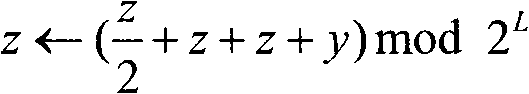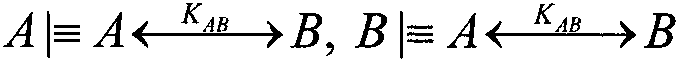Patents
Literature
121 results about "Key signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
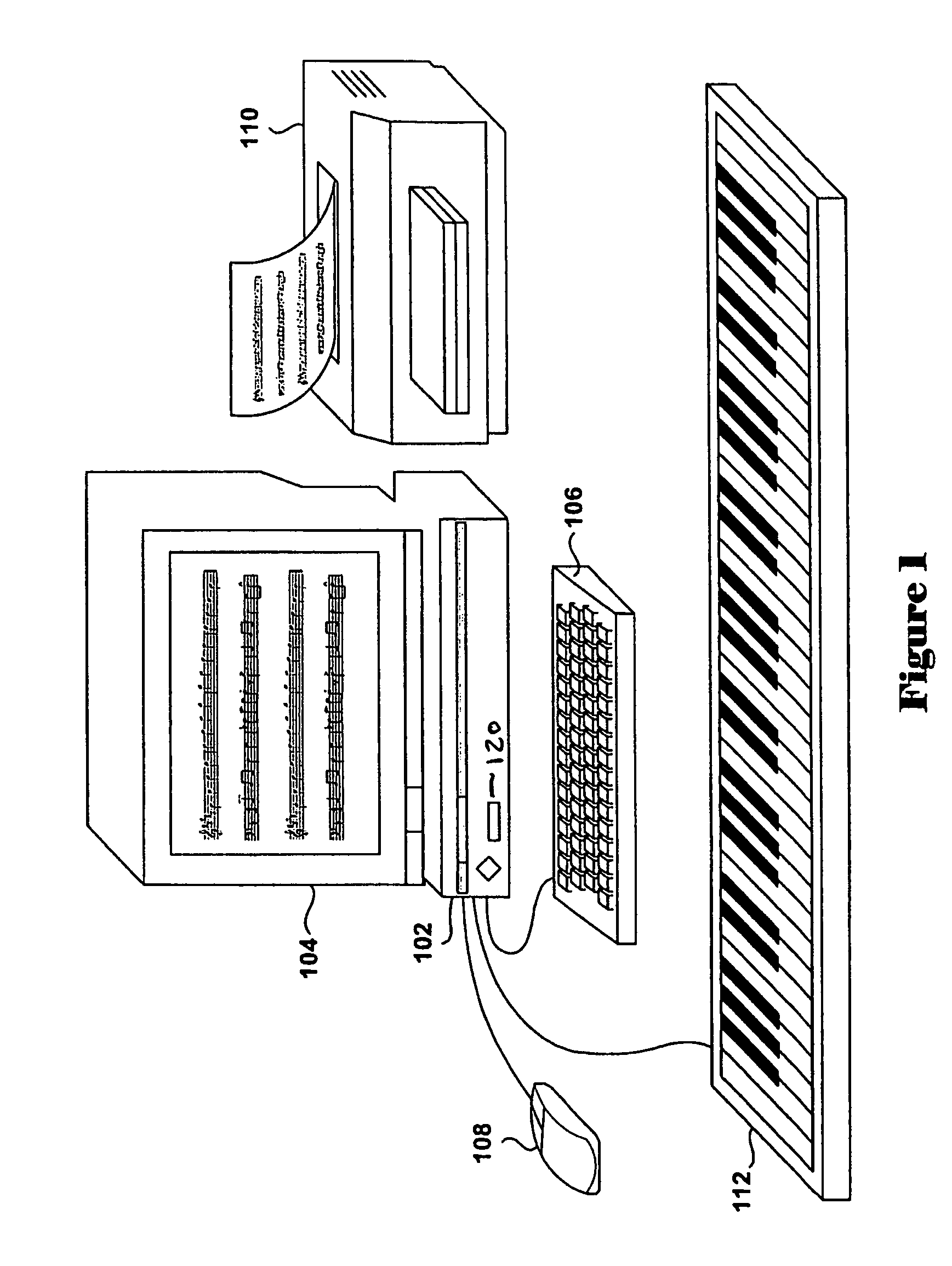
In musical notation, a key signature is a set of sharp (♯), flat (♭), and rarely, natural (♮) symbols placed together on the staff. Key signatures are generally written immediately after the clef at the beginning of a line of musical notation, although they can appear in other parts of a score, notably after a double barline.
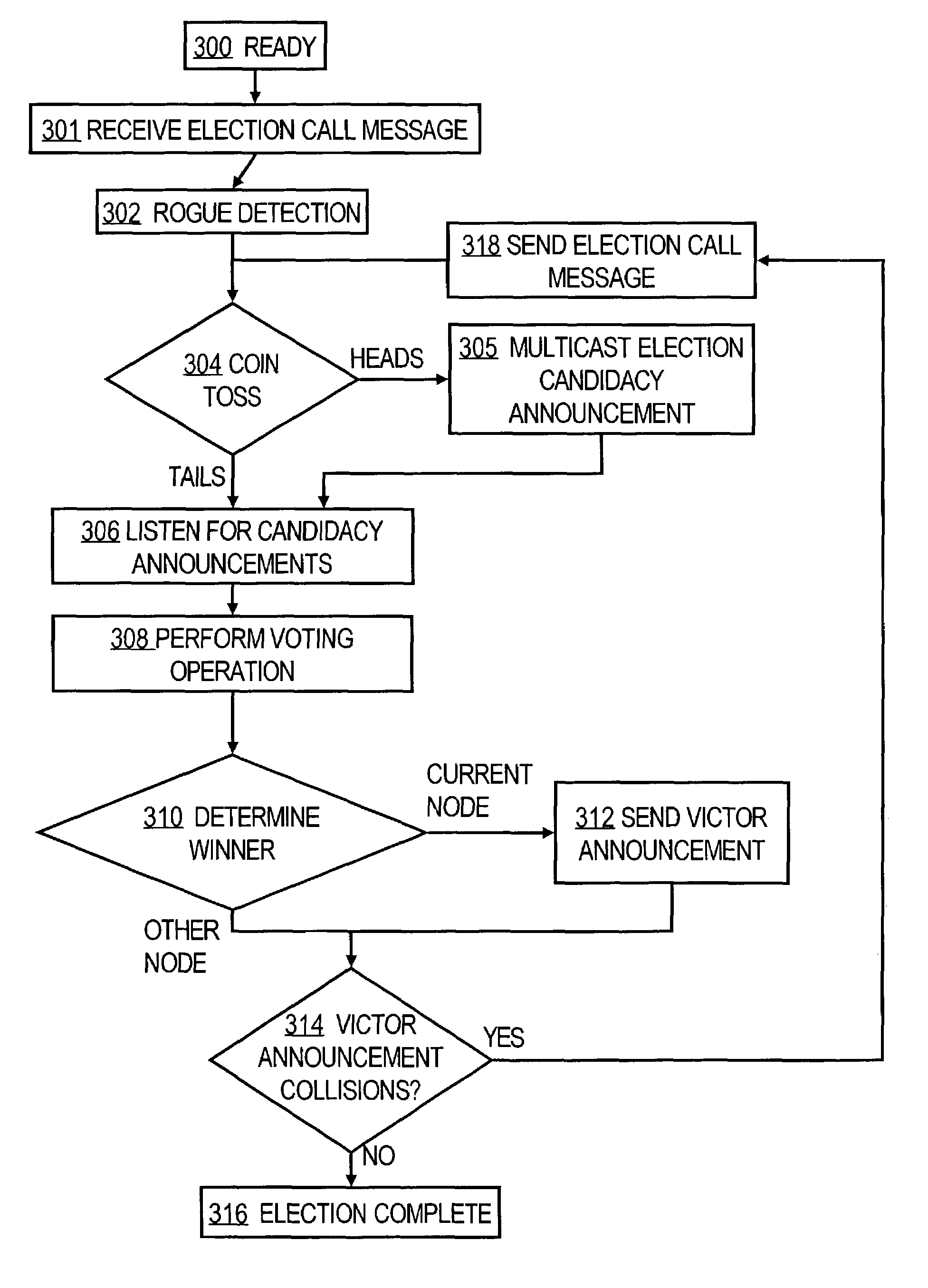
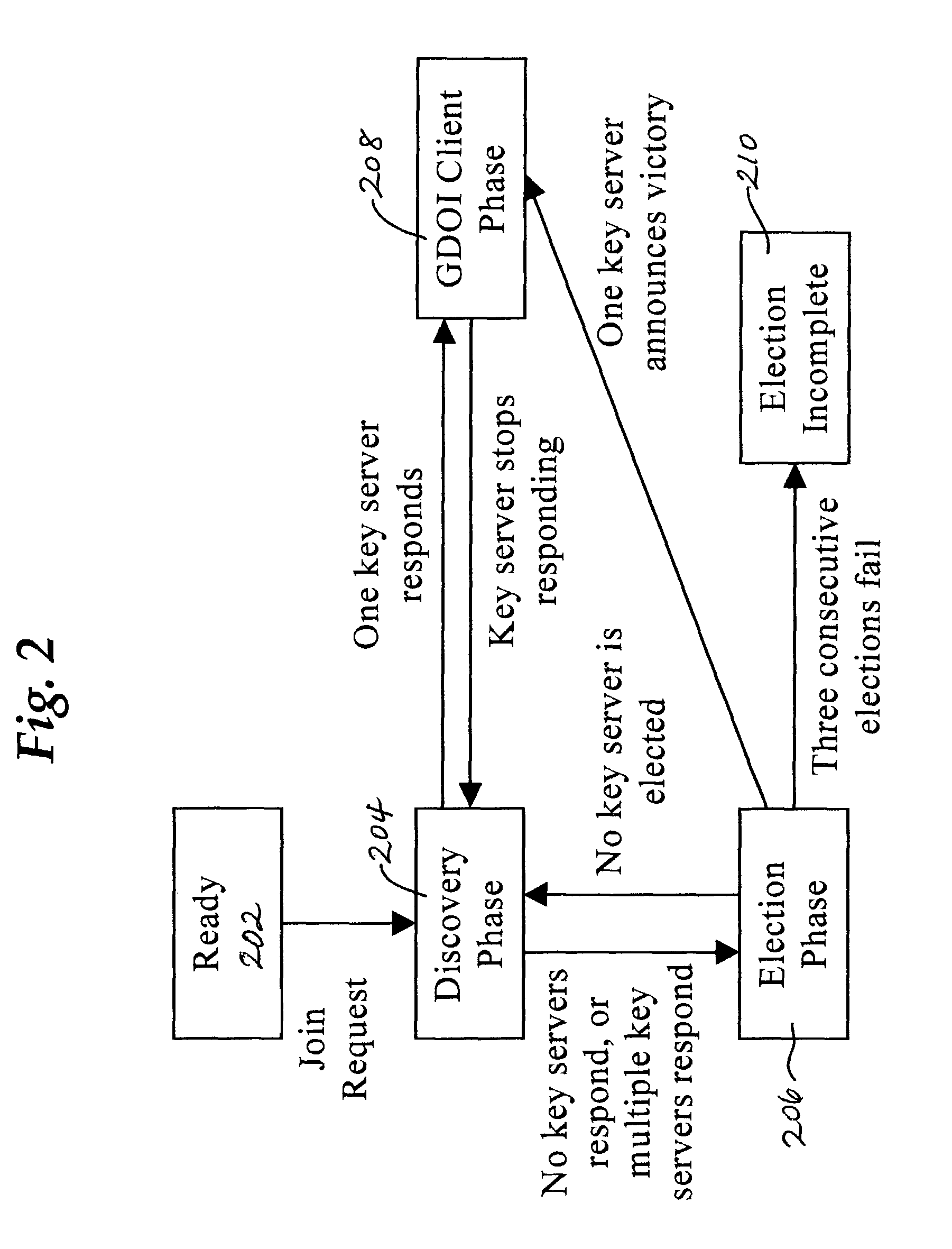
Method and apparatus for electing a leader node in a computer network
InactiveUS7421578B1Data switching by path configurationSecuring communicationTime segmentKey signature
A method performed by a first computer node for selecting a leader node to provide service to a plurality of other nodes in a multicast group, wherein each of the nodes communicates using multicast messages, comprises issuing a first election call message; receiving candidacy announcement messages from one or more leader candidate nodes in a specified time period; selecting a victor from among all leader candidate nodes from which candidacy announcement messages are received; receiving one or more victor announcement messages from one or more leader victor nodes for a second specified time period; resolving zero or more collisions among the victor announcement messages to result in selecting the leader node. One embodiment provides a dynamic secure protocol for electing a key server, such as a key server that is suited for use with a group key exchange protocol such as the Group Domain of Interpretation (GDOI). Public key signatures may be used to secure message exchanges and to provide for authentication of network nodes in a multicast group.
Owner:CISCO TECH INC
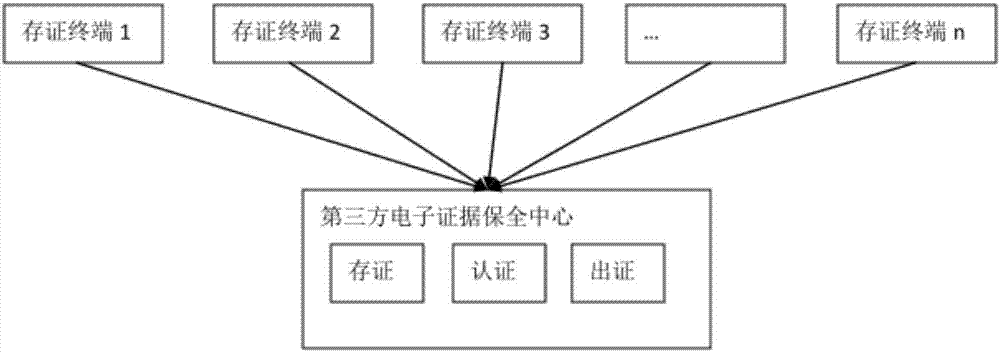
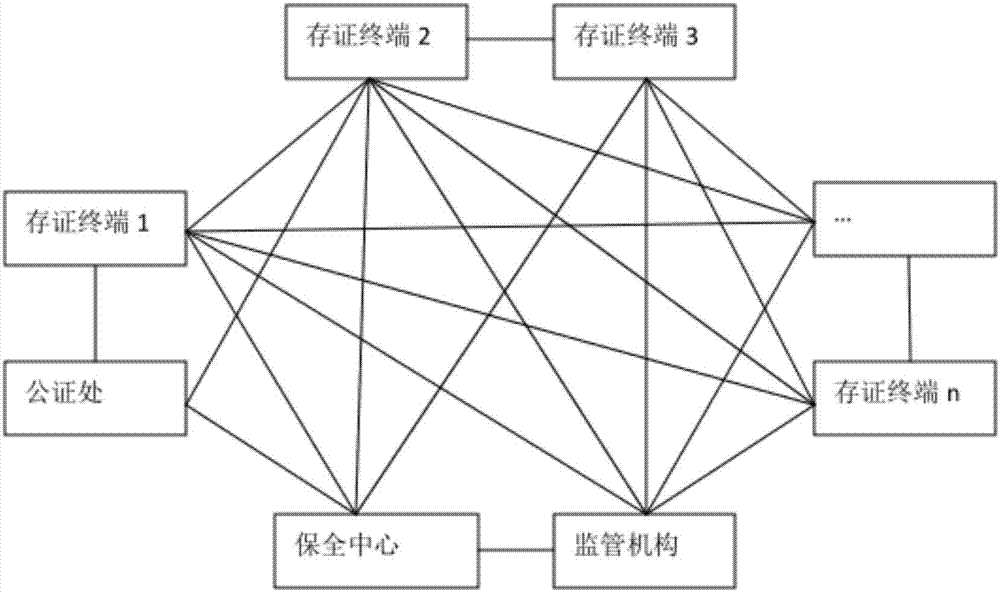
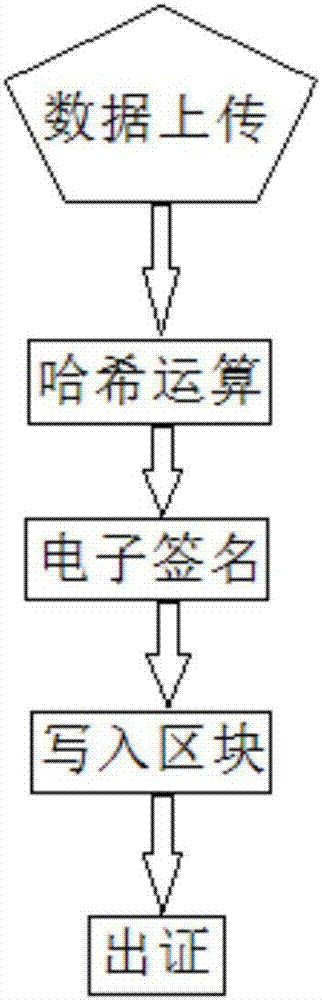
Electronic evidence preservation system and method based on block chain technology
InactiveCN107888375ASolve pain pointsFix bugsEncryption apparatus with shift registers/memoriesDigital data protectionOriginal dataComputer module
The invention discloses an electronic evidence preservation system and method based on the block chain technology. The preservation system comprises an evidence storage terminal and a block chain network. The evidence storage terminal comprises a hash operation module and an electronic signature module. The electronic data are uploaded to the evidence storage terminal, the evidence storage terminal performs hash operation on the uploaded electronic data to generate unique feature data of a fixed length of original data; then private key signature is performed on the generated data by using theasymmetric encryption technology, and the generated data are sent to the block chain network; and the block chain network performs primary consensus on the uploaded data and packs the uploaded data into blocks, and synchronously sends the blocks to nodes in the network for distributed storage. By establishing an evidence storage alliance by using the block chain technology, the electronic evidence preservation system has the characteristics of digitalized encryption, centralized grading, anti-tampering, data zero loss and so on. Each node in the block chain can preserve a complete block chaindata copy and witness the chain status of the blocks, so that the centralization risk can be effectively avoided.
Owner:SHENZHEN XIEWANG TECH CO LTD
System and Method for Producing a More Harmonious Musical Accompaniment
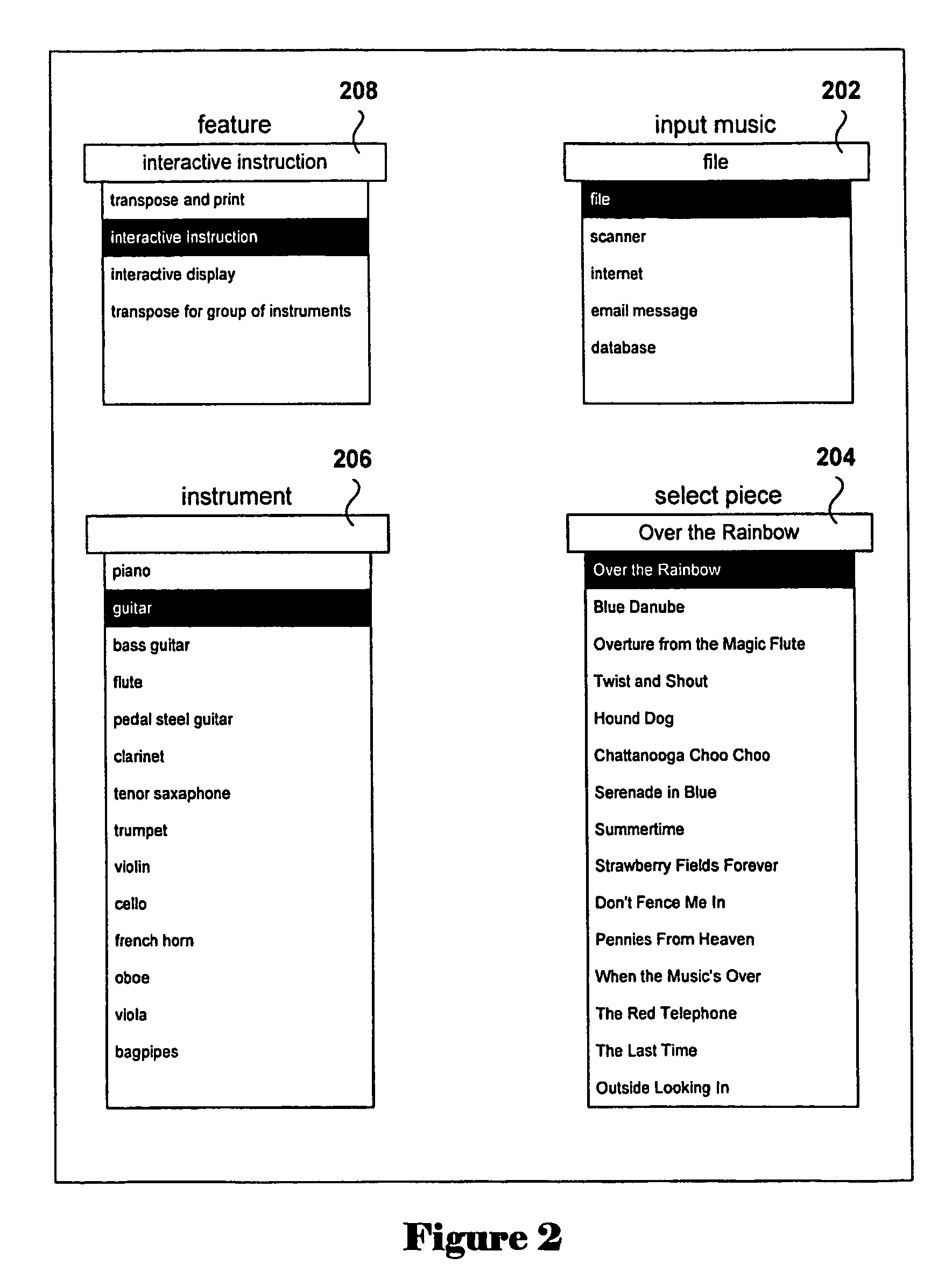
A system and process for producing a more harmonious musical accompaniment for a musical compilation, the process comprising determining a plurality of probable key signatures for the musical compilation, creating an interval profiling matrix for each of the probable key signatures, finding products of a major key interval profile matrix with each of the interval profiling matrices, summing each of the major key interval products into a running major key sum, finding a product of a minor key interval profile with each of the interval profiling matrices, summing each of the minor key interval products into a running minor key sum, and selecting the most probable key signature from the plurality of probable key signatures by comparing the minor key sum and the major key sum.
Owner:MUSIC MASTERMIND
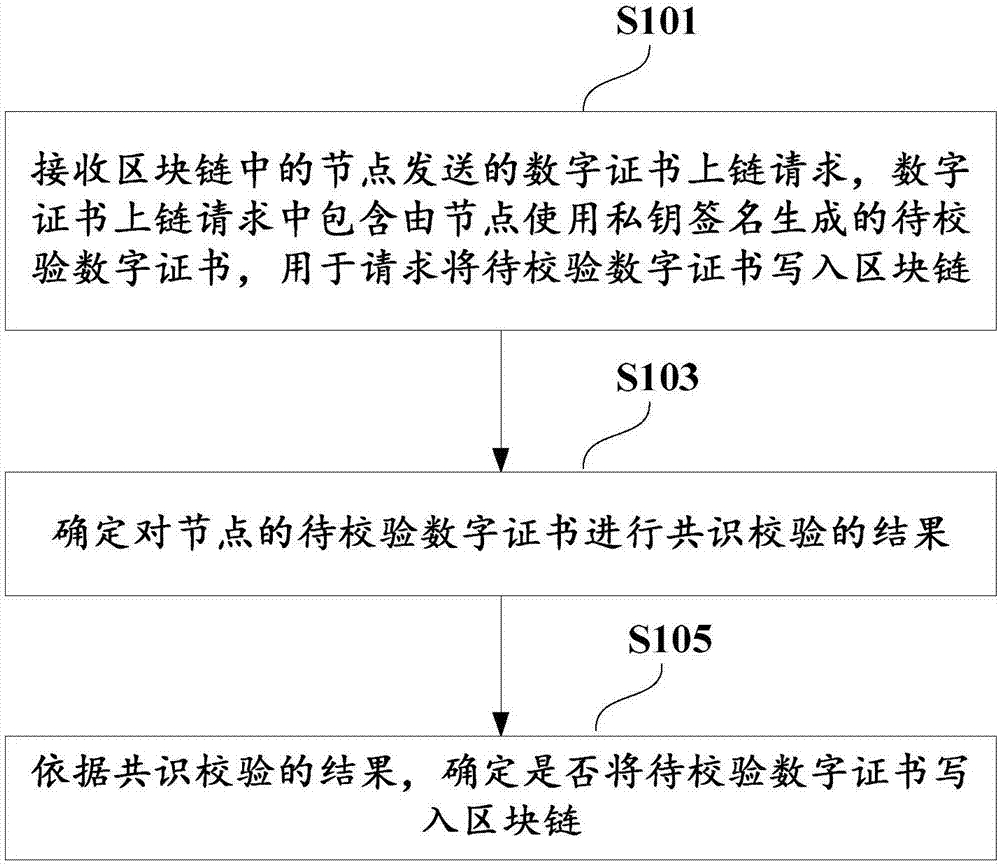
Digital certificate management method and device and electronic equipment
ActiveCN107508680AImprove securityCannot be tampered withCryptography processingUser identity/authority verificationKey signatureBlockchain
The application discloses a digital certificate management method which comprises the steps of: receiving a digital certificate uplink request sent by a node in a block chain, wherein the digital certificate uplink request comprises a to-be-checked digital certificate generated by the node by using a private key signature and is used for requesting to write the to-be-checked digital certificate into the block chain; determining a result of carrying out consensus checking on the to-be-checked digital certificate of the node; and according to the result of consensus checking, determining whether to write the to-be-checked digital certificate into the block chain. The application further discloses a corresponding device, electronic equipment and the like.
Owner:ADVANCED NEW TECH CO LTD
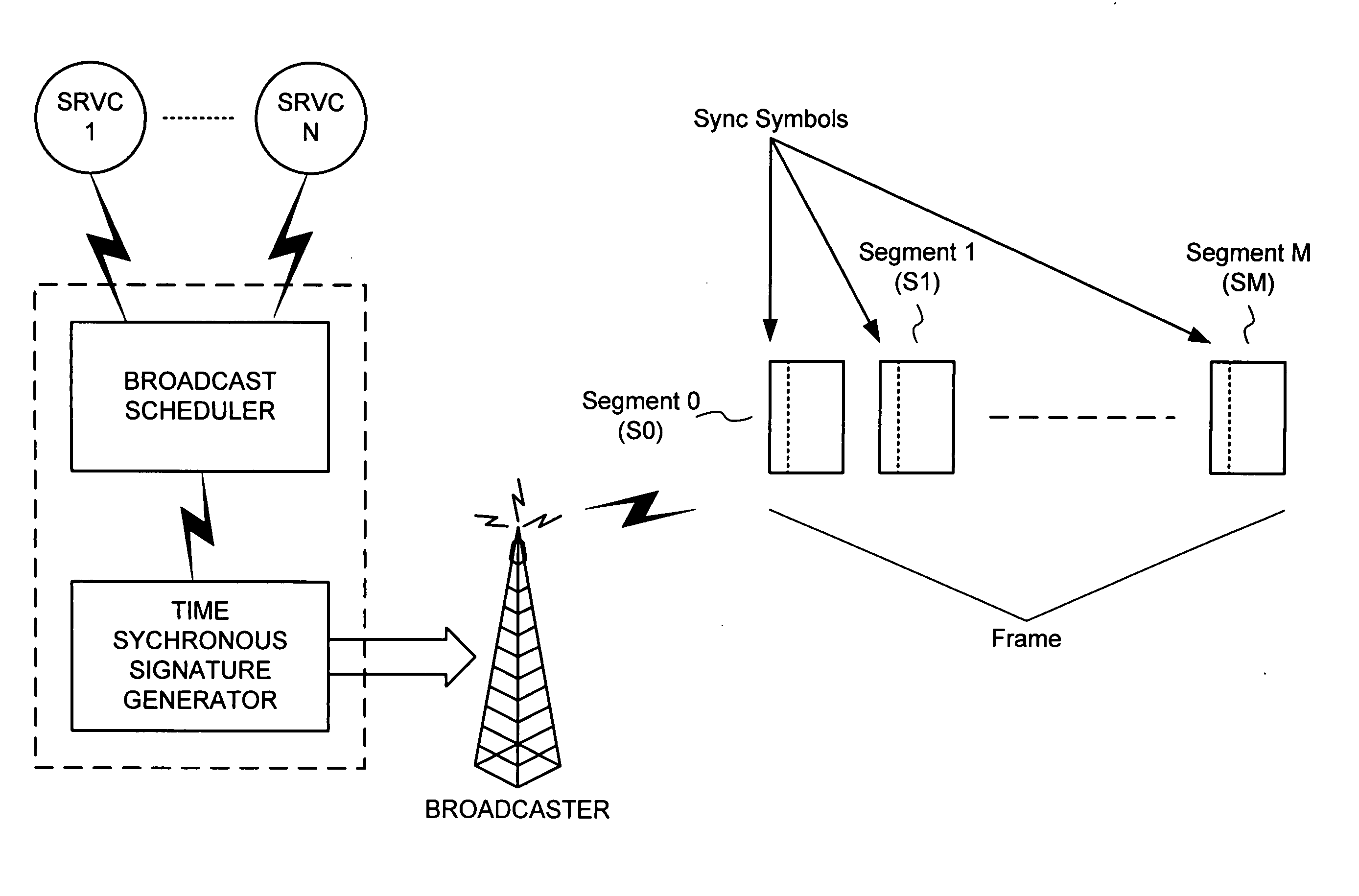
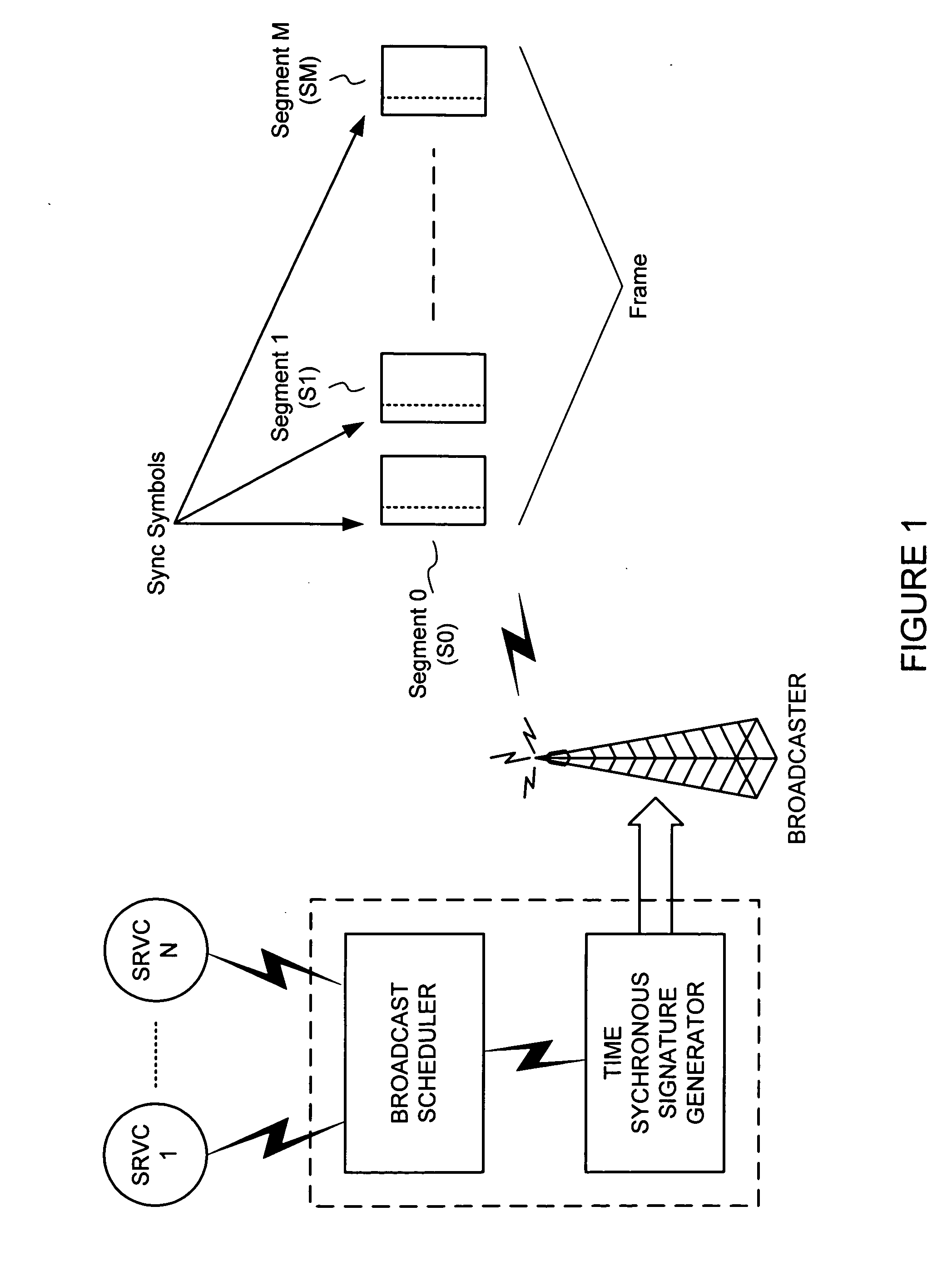
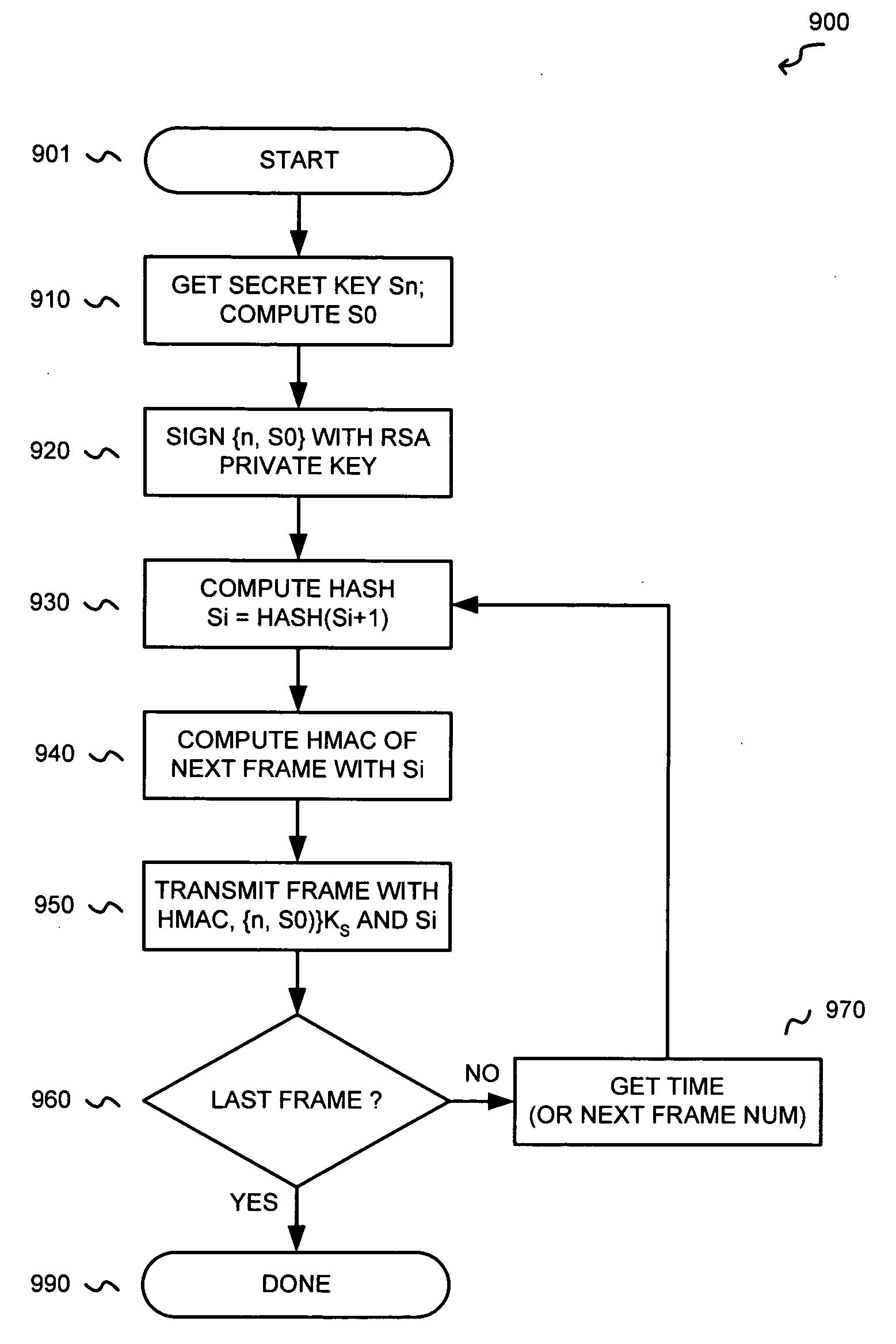
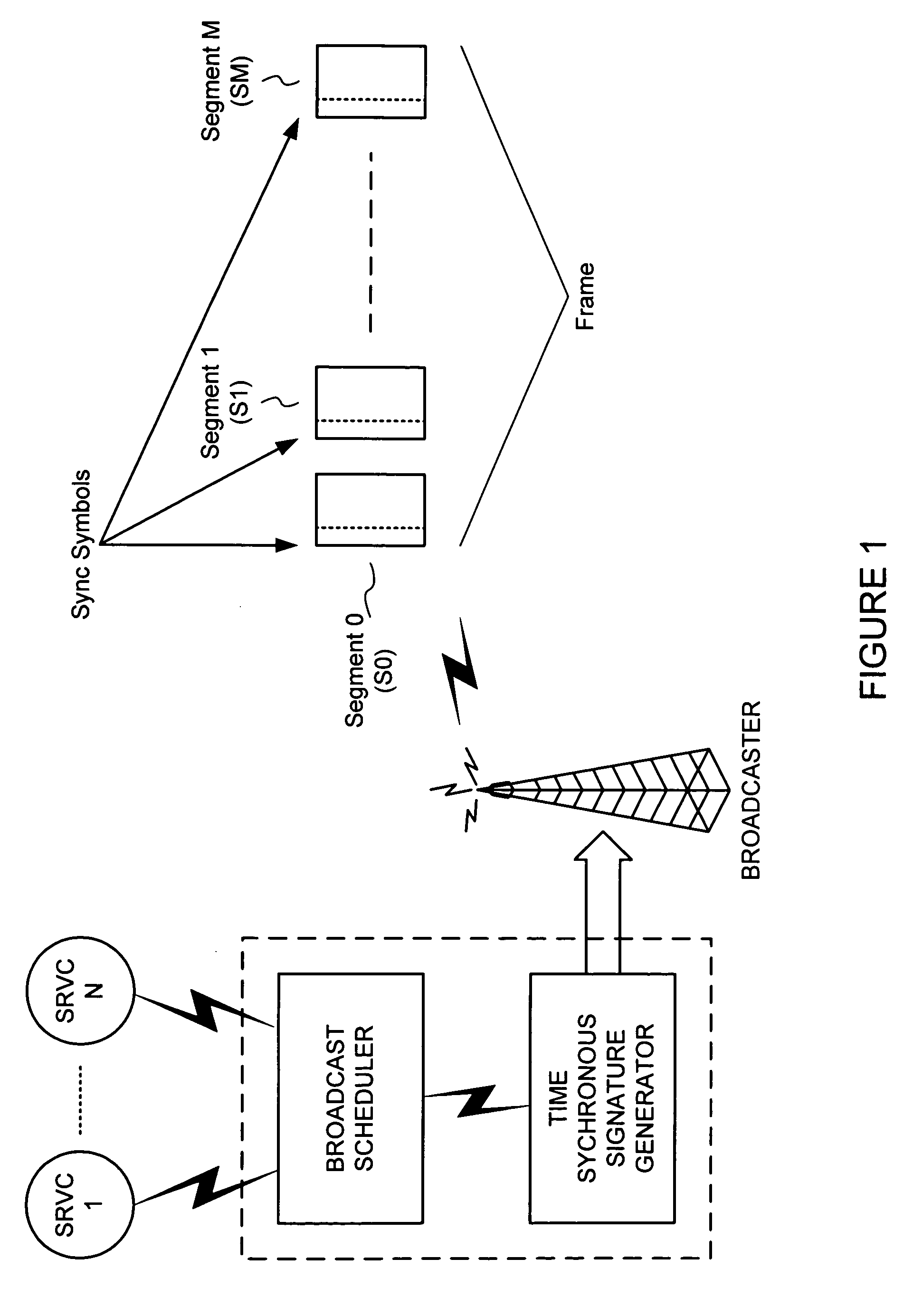
Cheap signatures for synchronous broadcast communication
InactiveUS20050182932A1Keep in syncSynchronising transmission/receiving encryption devicesUser identity/authority verificationHash functionClient-side
A method and system are configured for synchronous broadcast communications by applying signature keys using hashing functions. Each subsequent transmission in a sequence includes a signature key that can be verified by hashing to a preceding signature key from a previous portion of the sequence. The first transmission in the sequence is signed using a signature key that is known by the client device, typically verified using some other mechanism such as asymmetric key signatures. Each client device can utilize an internal counter for the current time or the block number in the transmission sequence to maintain synchronized transmissions in the even that a particular portion of the sequence is missed, and to validate signature keys. Since the signature keys can be validated when they are received but not predicted before they are received, the transmission is difficult to attack while synchronization is maintained.
Owner:MICROSOFT TECH LICENSING LLC
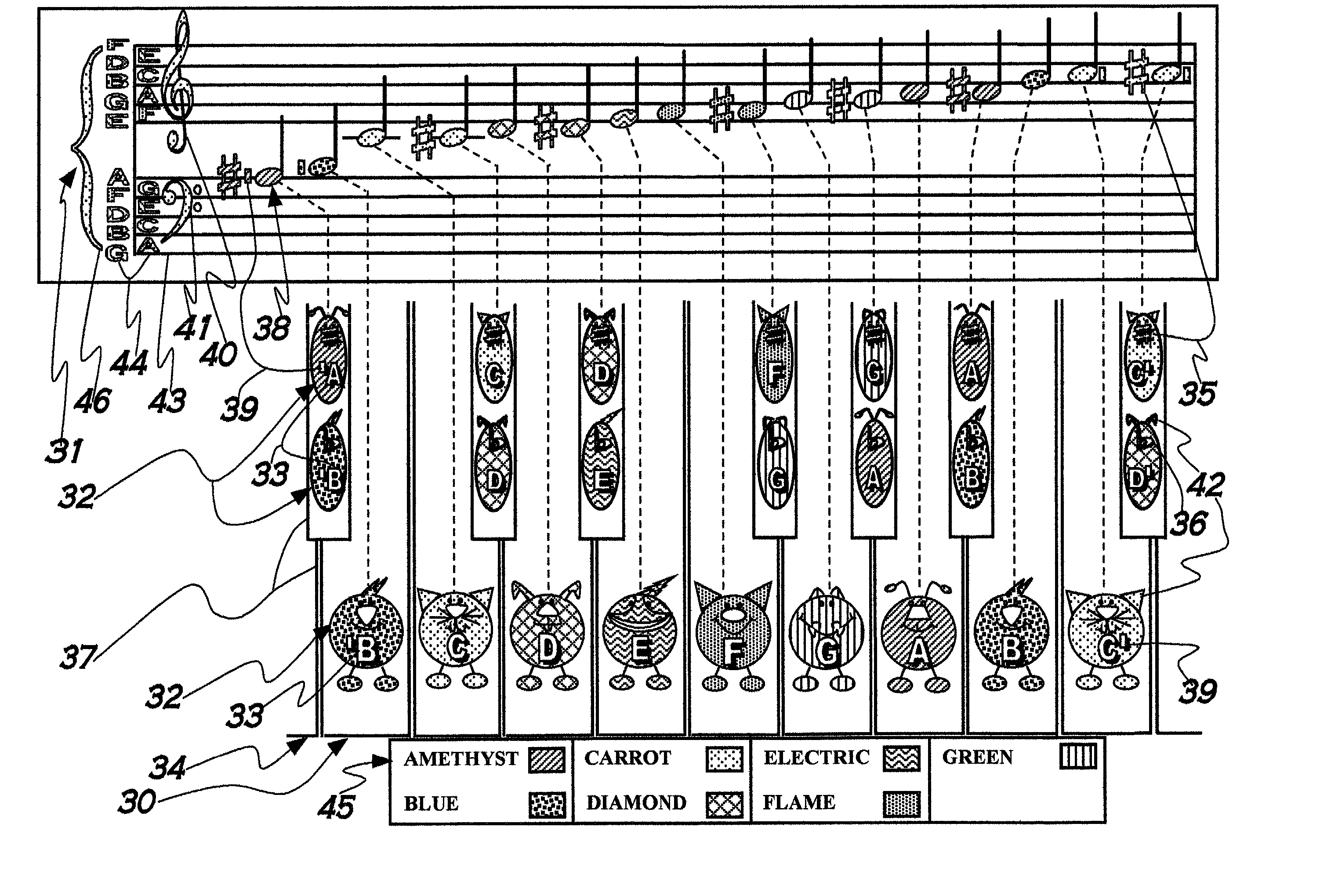
Music teaching system and method
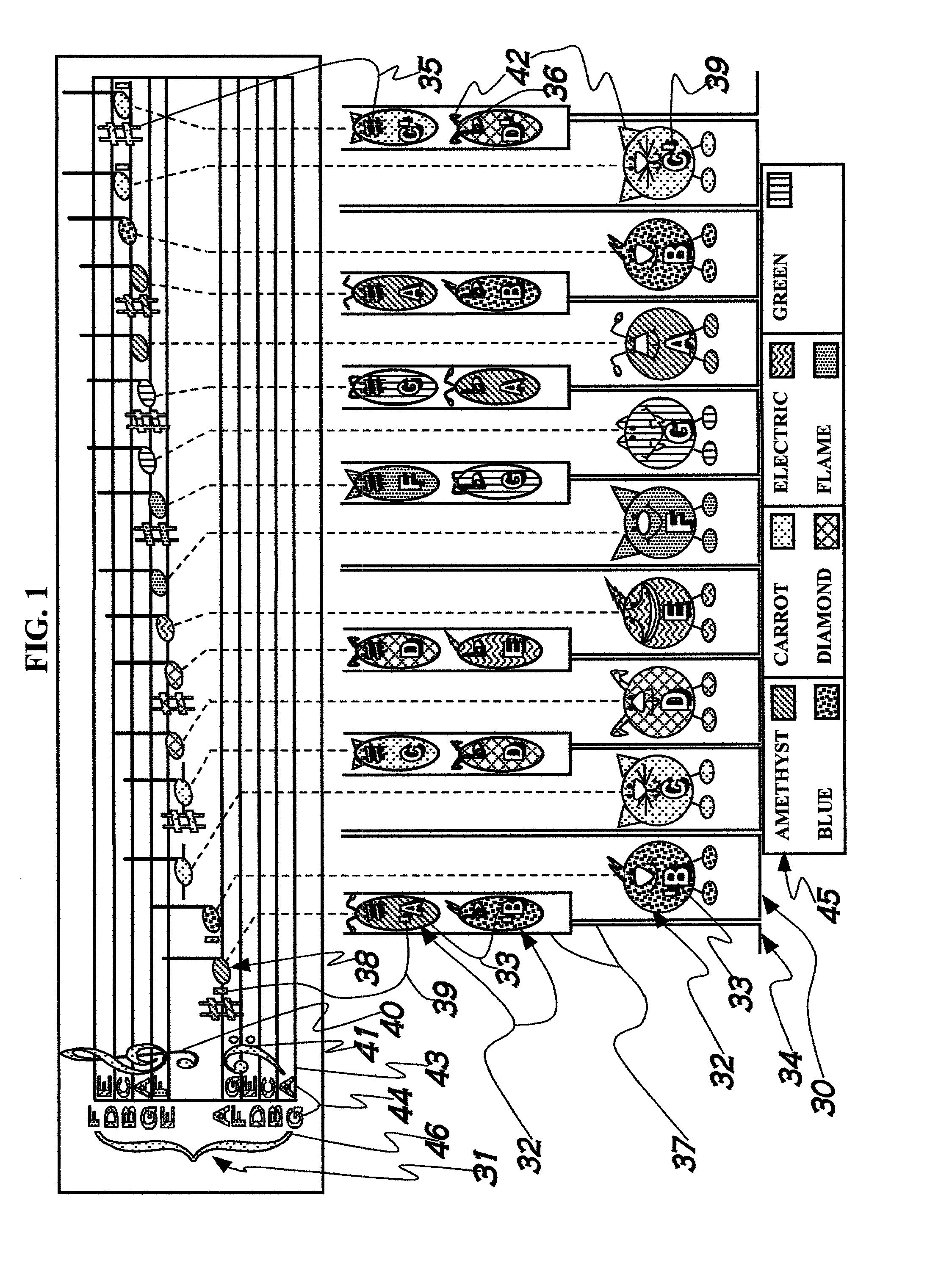
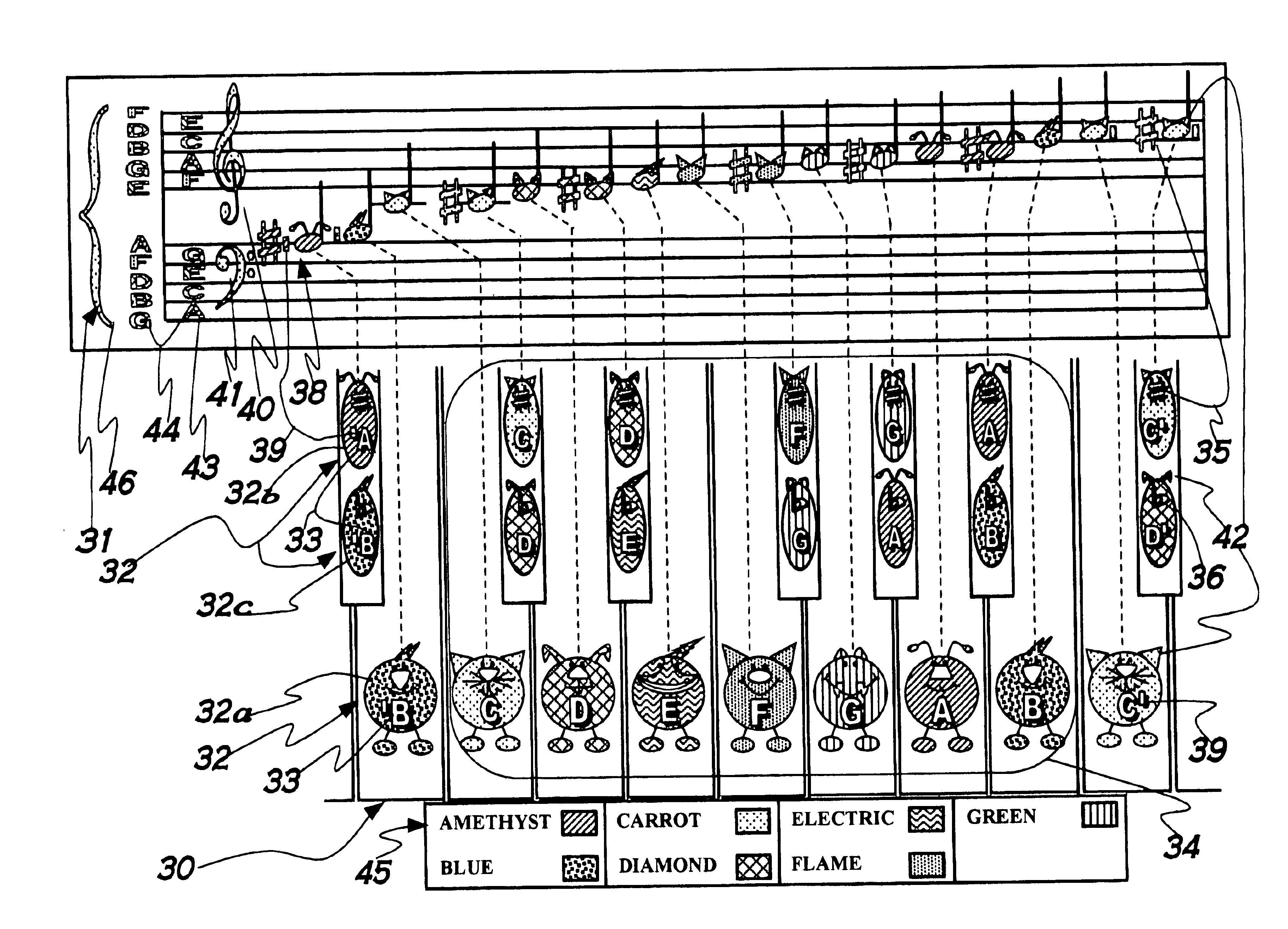
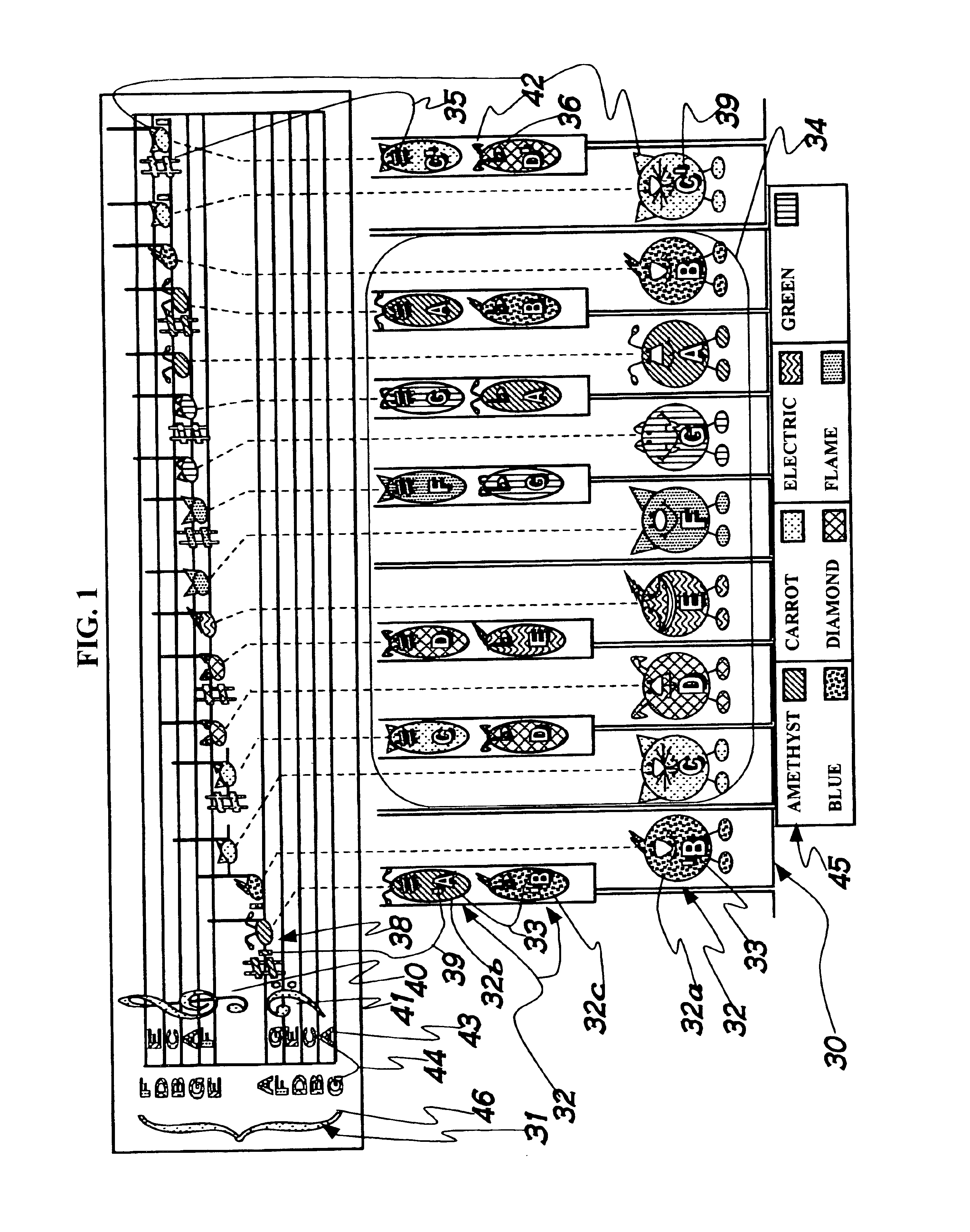
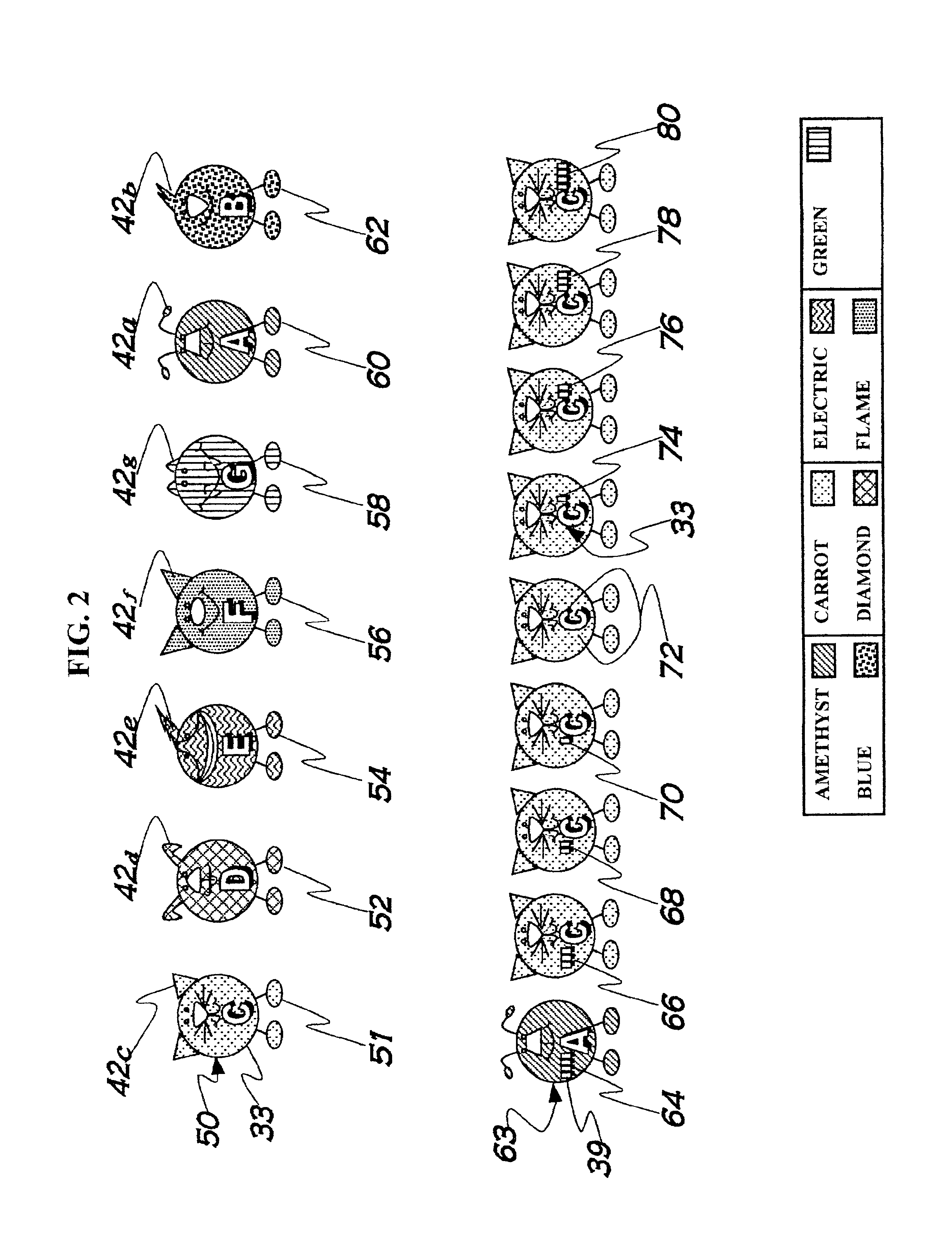
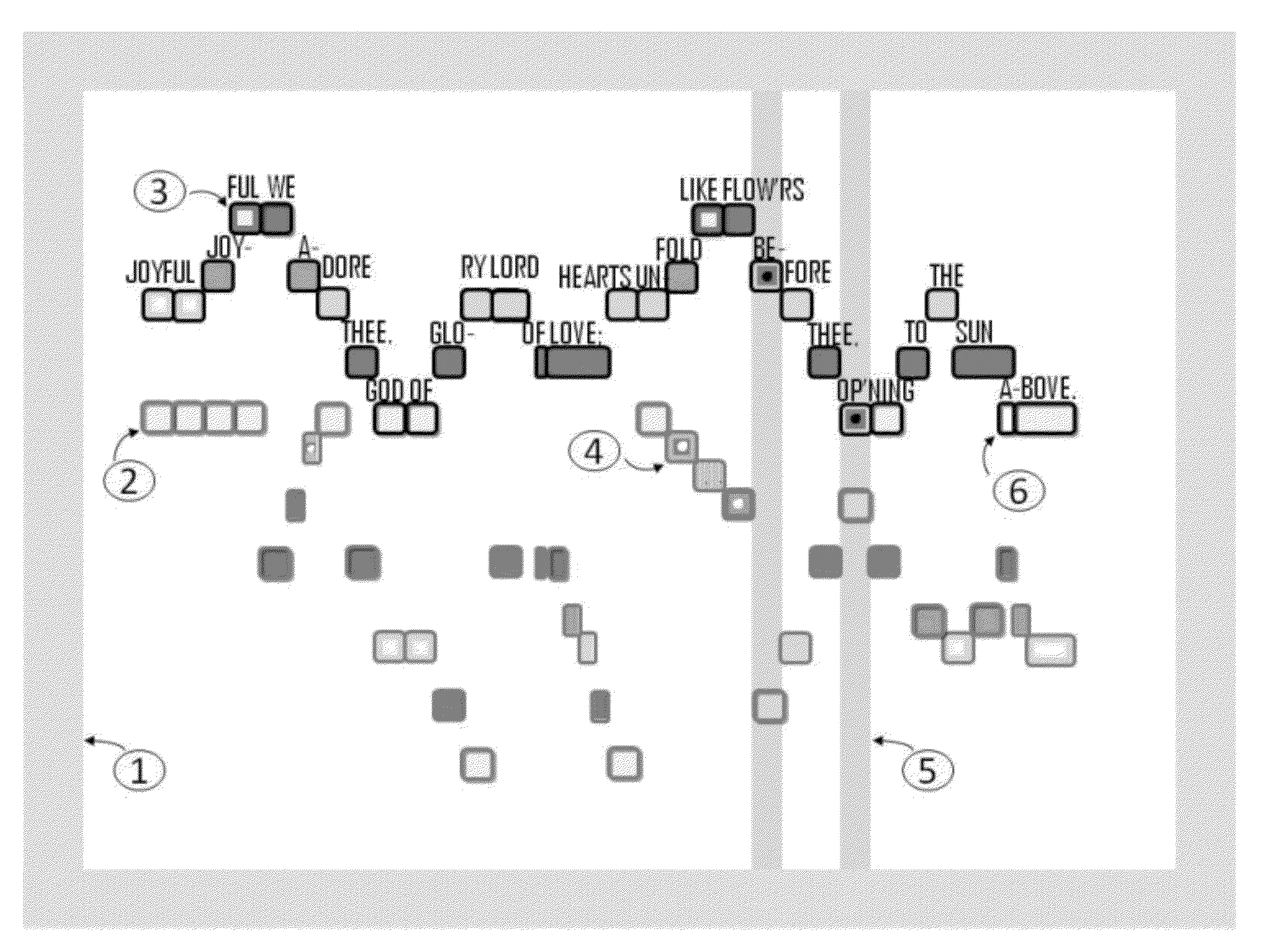
A method facilitating the learning of music by matching coded note symbols (38) of musical compositions to coded note location and formation identifiers (32) of instruments. Colors, each having a name beginning with one of the letter names of the musical alphabet (45), are combined with pitch marks (39), enabling the coding of musical notes. In the preferred embodiment of the invention, the colors are paired with stylized animal images (50, 52, 54, 56, 58, 60, 62). These animal images' names are coupled with the color names of the invention via reiteration of the first letter of the names (50, 52, 54, 56, 58, 60, 62) to enhance the remembering of the relationship between color and note. The invention's color coding system is also applied to musical composition structures (31, 40, 41, 43, 44, 46, 92, 93, 94, 95) for easy identification of musical elements such as compositional keys and key signature (92).
Owner:MACCUTCHEON JANE S
Method and apparatus for producing duplication- and imitation-resistant identifying marks on objects, and duplication- and duplication- and imitation-resistant objects
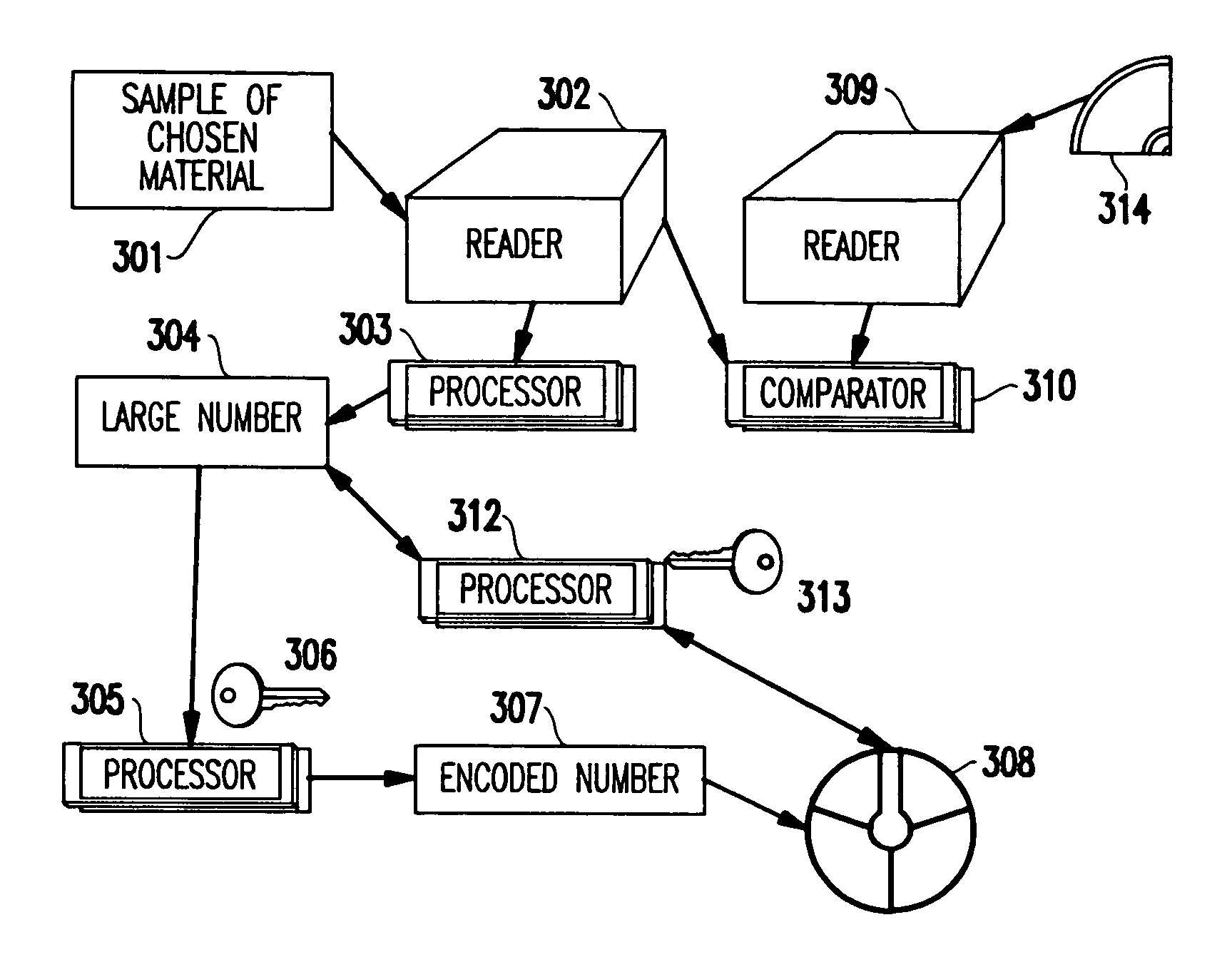
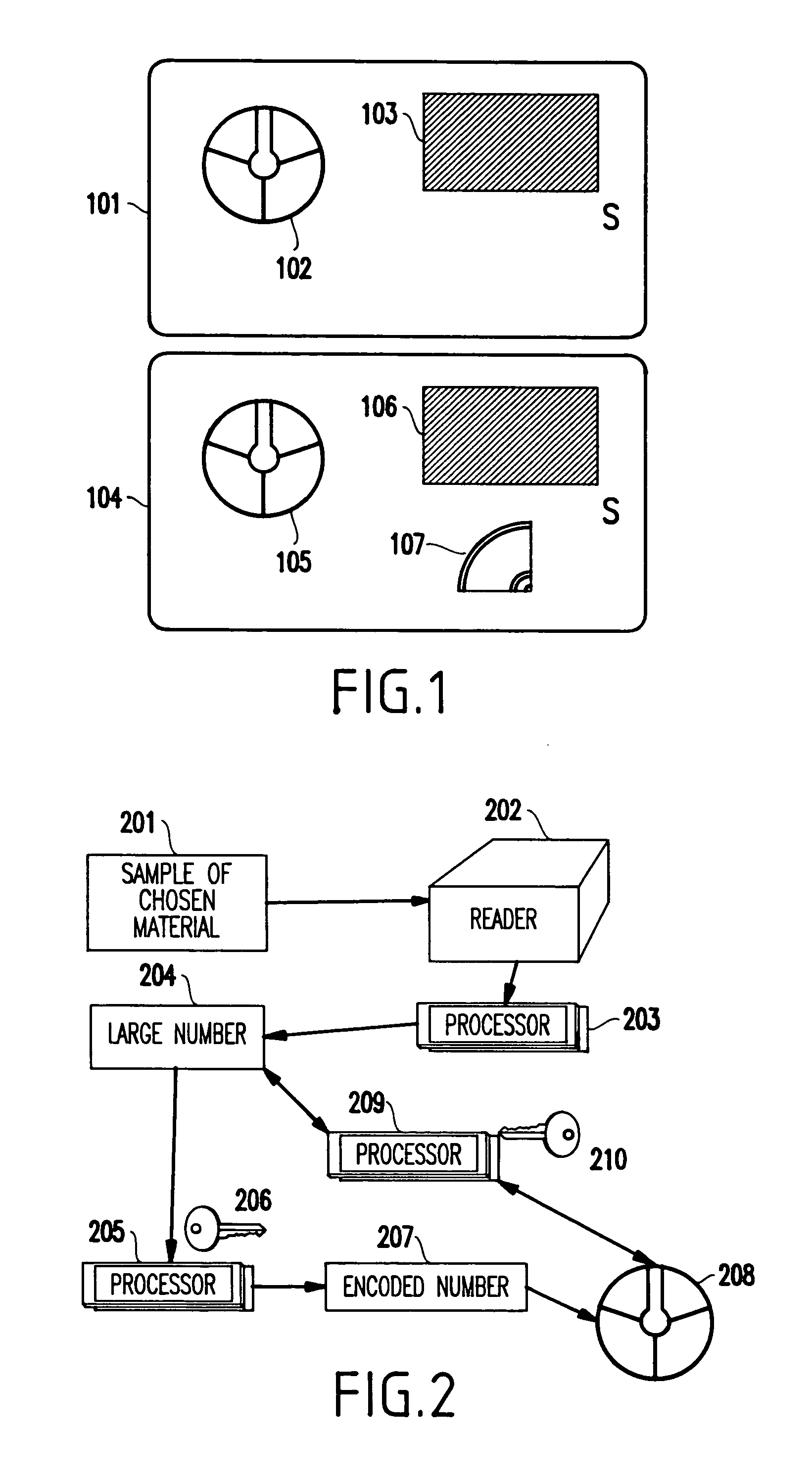
InactiveUS7188258B1Easy to detectConfidence in content-carrying-device-technologyUser identity/authority verificationUnauthorized memory use protectionKey signatureImitation
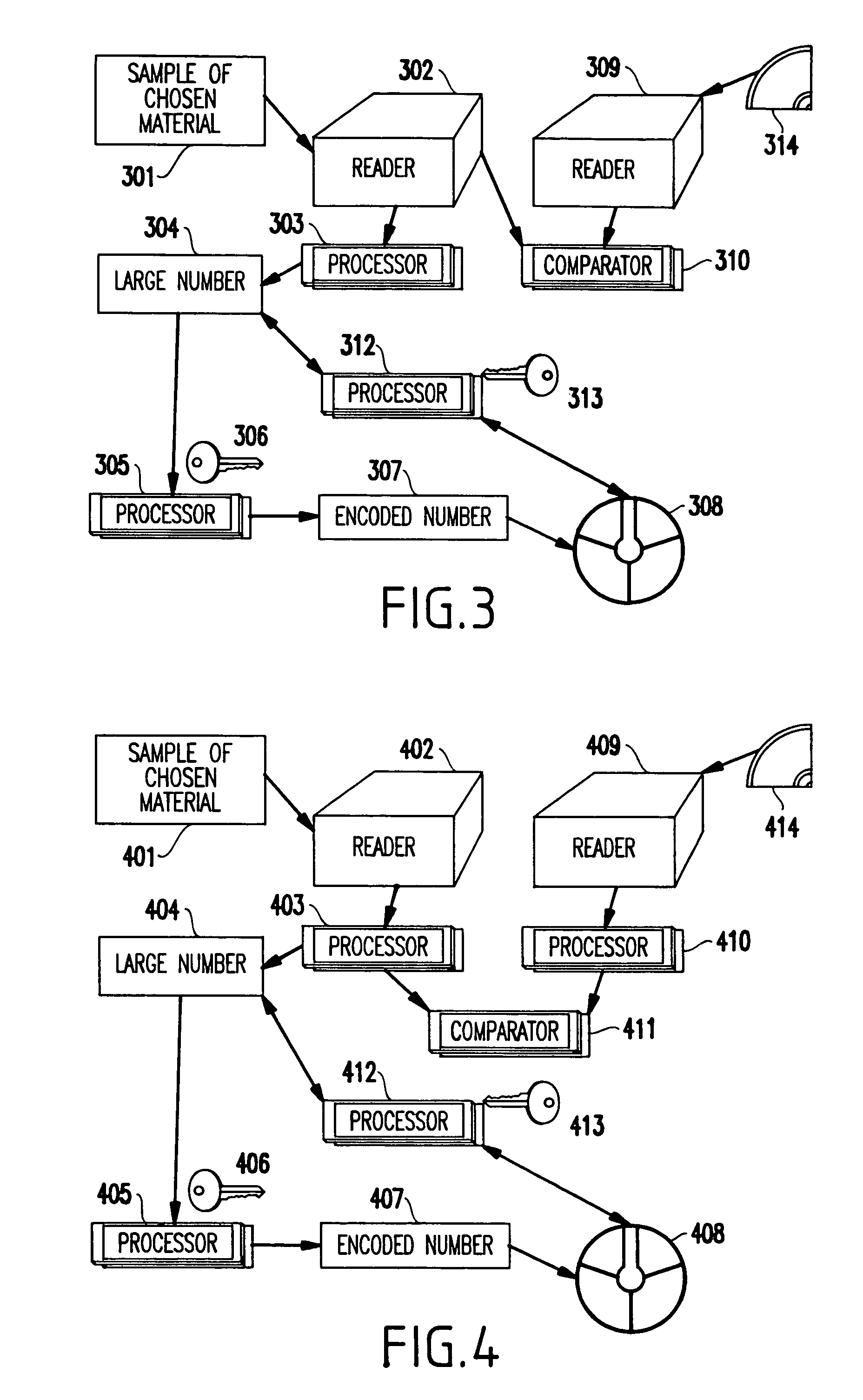
A method (and system) for guaranteeing authenticity of an object, includes providing a sample of material obtainable only by at least one of chemical and physical processes such that the sample is random and not reproducible, associating a number reproducibly to the sample by using a specific reader, and forming at least one coded version of the number, the at least one coded version being obtained by a key signature, and the version being recorded into an area of the object.
Owner:IBM CORP
Music teaching system and method
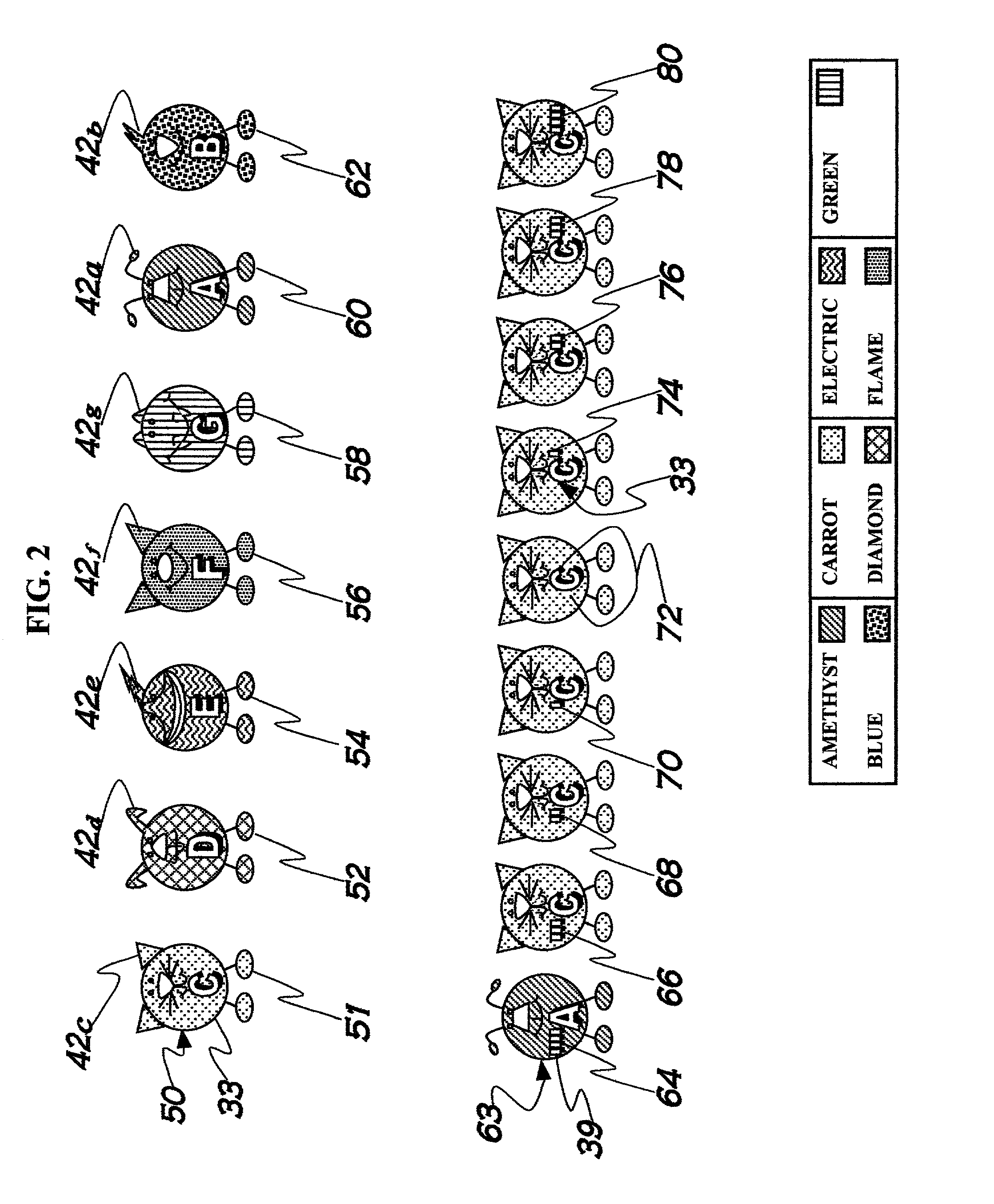
InactiveUS6870085B2Facilitating learning and playingEnhance recognition and learningElectrophonic musical instrumentsMusicMusical toneOctave
A method facilitating the learning of music by matching coded note symbols of musical compositions to coded note location and formation identifiers of instruments. Colors, in the preferred embodiment each having a name beginning with one of the letters names of the musical alphabet, are combined with octave group pitch marks, enabling the coding of musical notes. In the preferred embodiment of the invention, the colors are paired with stylized animal images. These animal images' names are coupled with the color names of the invention via reiteration of the first letter of the names to enhance the remembering of the relationship between color and note. The invention's color coding system is also applied to musical composition structures for easy identification of musical elements such as compositional keys and key signature.
Owner:MACCUTCHEON JANE S
Deterministic search algorithm
InactiveUS6625612B1Digital data information retrievalData processing applicationsDeterministic algorithmTheoretical computer science
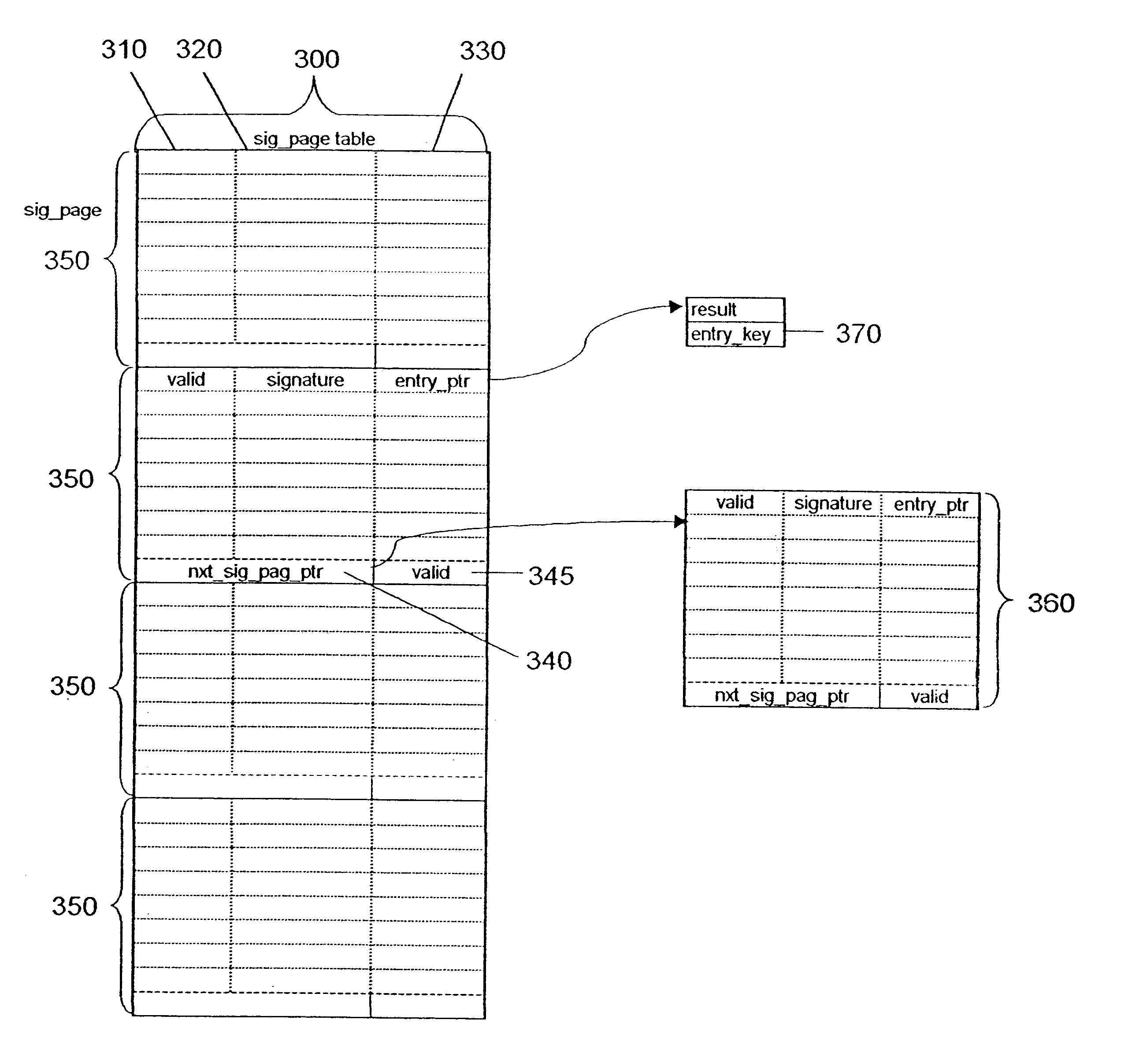
A method for storing and retrieving a key using a hash table, the method comprising the steps of: (a) hashing the key using a first hash function, thereby transforming the key into a table address in the hash table; (b) hashing the key using a second hash function, distinct from the first hash function, thereby transforming the key into a key signature; and (c) entering the key signature in a signature page located at the table address.
Owner:PLENUS TECH LTD +1
Systems and Methods for Identity-Based Secure Communications
InactiveUS20080031459A1Communication securityKey distribution for secure communicationPublic key for secure communicationSecure communicationTrusted third party
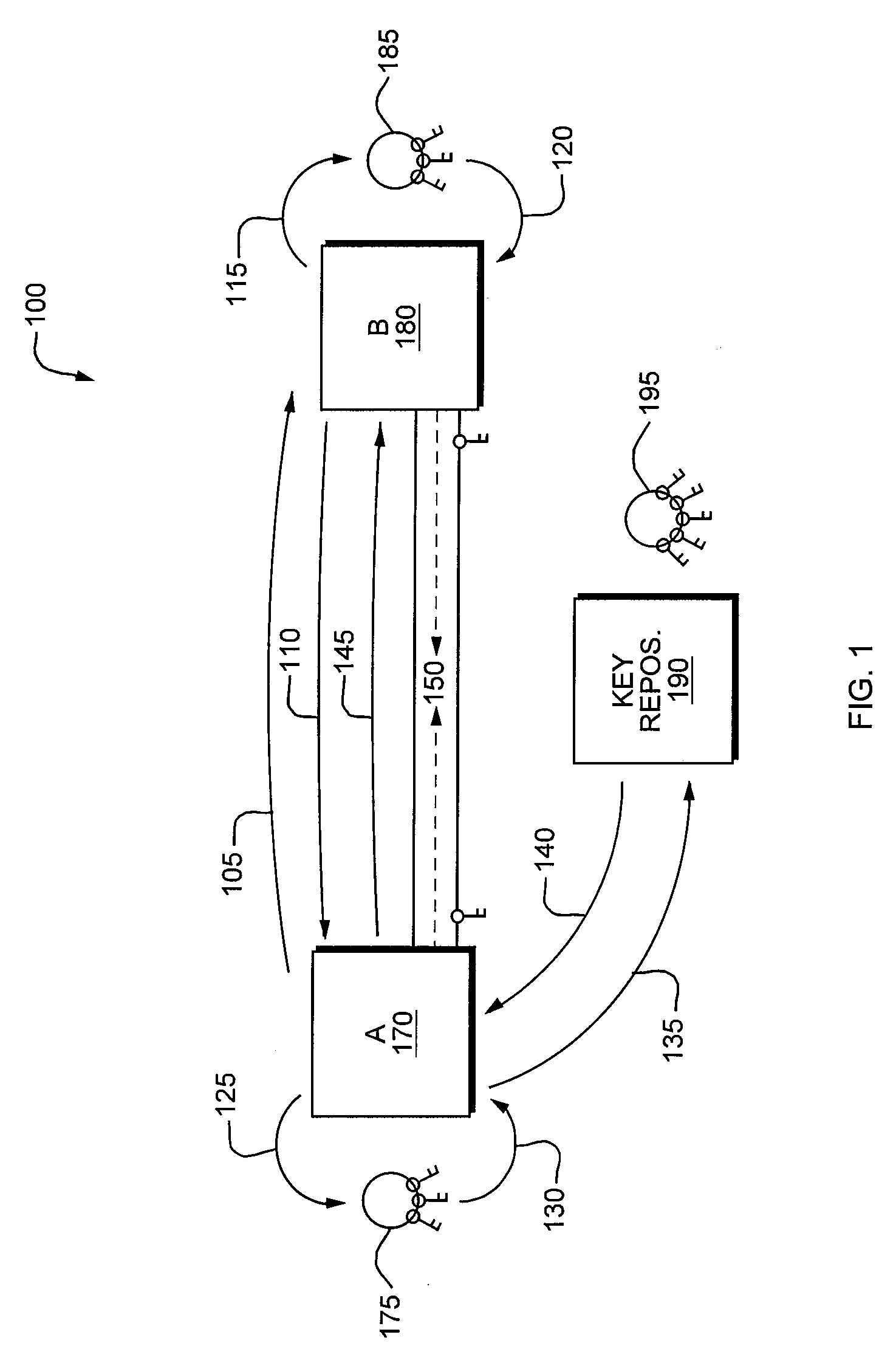
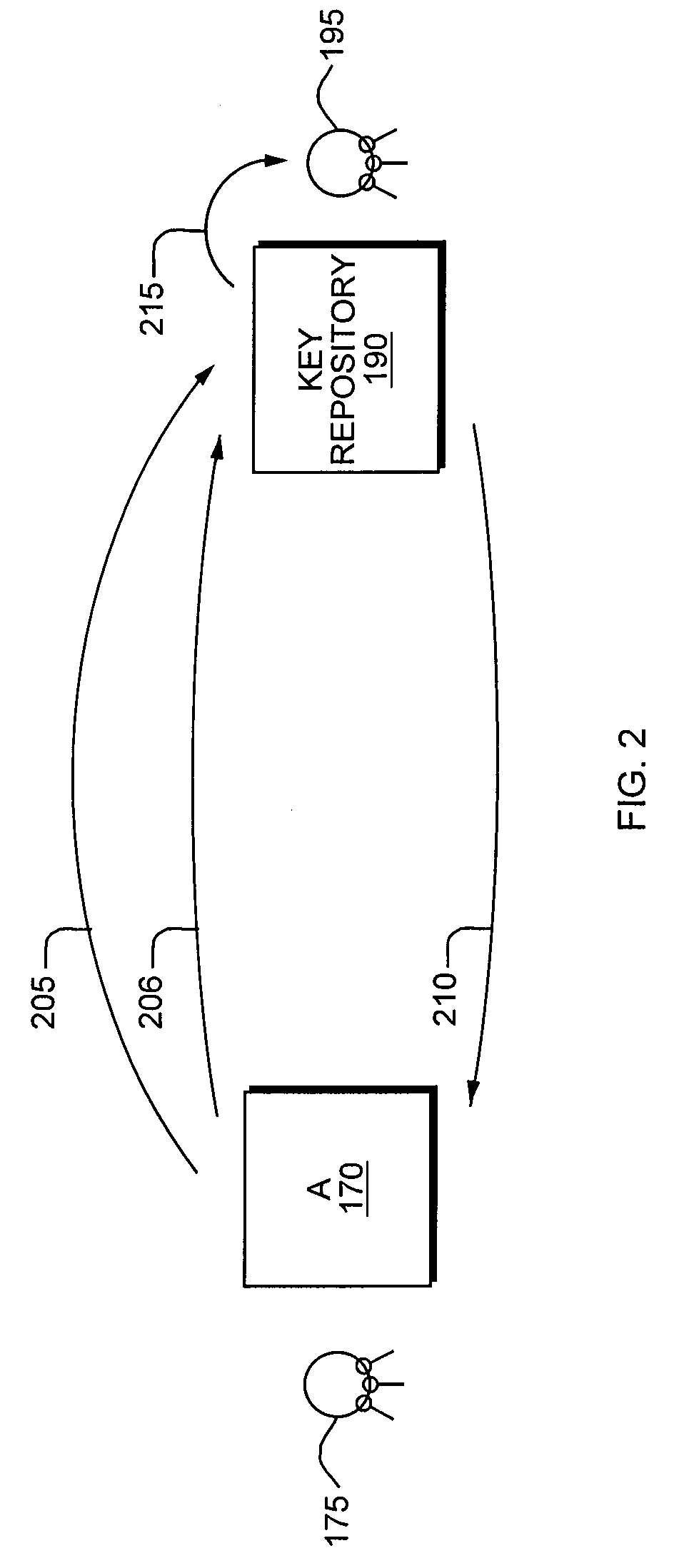
Methods and systems for securing communications between networked computer agents in a positively identifiable manner, using a centralized arbitration computer agent that acts as a trusted third party to store and manage user agent identities. Each user agent has a unique identity, which may be represented by at least a unique key identifier and an associated key. The computer agents use the key identifiers to retrieve the associated keys prior to exchanging messages, and the retrieved keys are used to encrypt the messages. The centralized arbitration agent serves as a key manager and repository by creating and storing the key identifiers, and by storing the associated keys. The centralized arbitration agent also records transactions and state changes for the keys, and handles key expiration, revocation and replacement. The centralized arbitration agent performs similar functions for key signatures.
Owner:ANAMORPHIC SYST
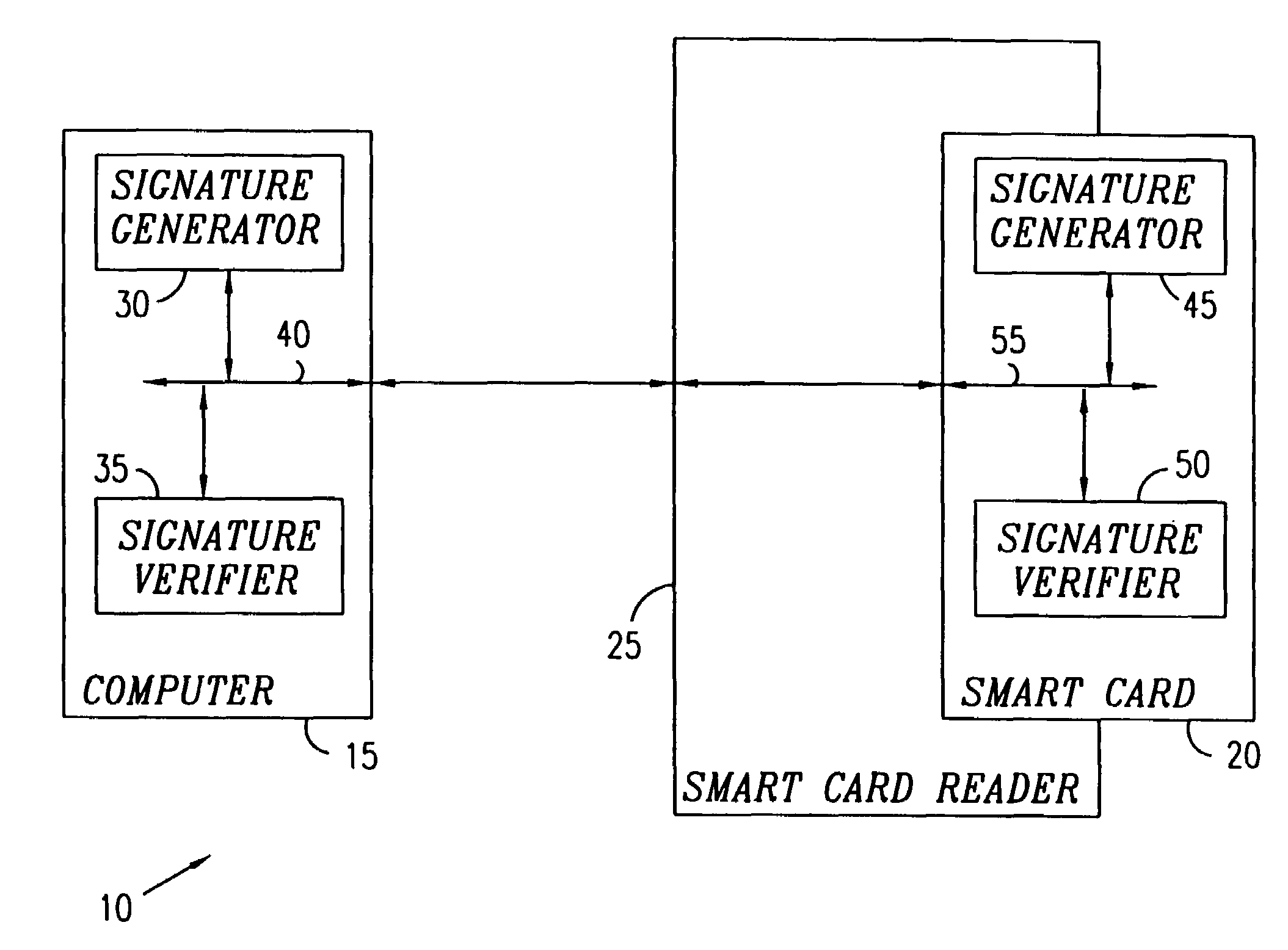
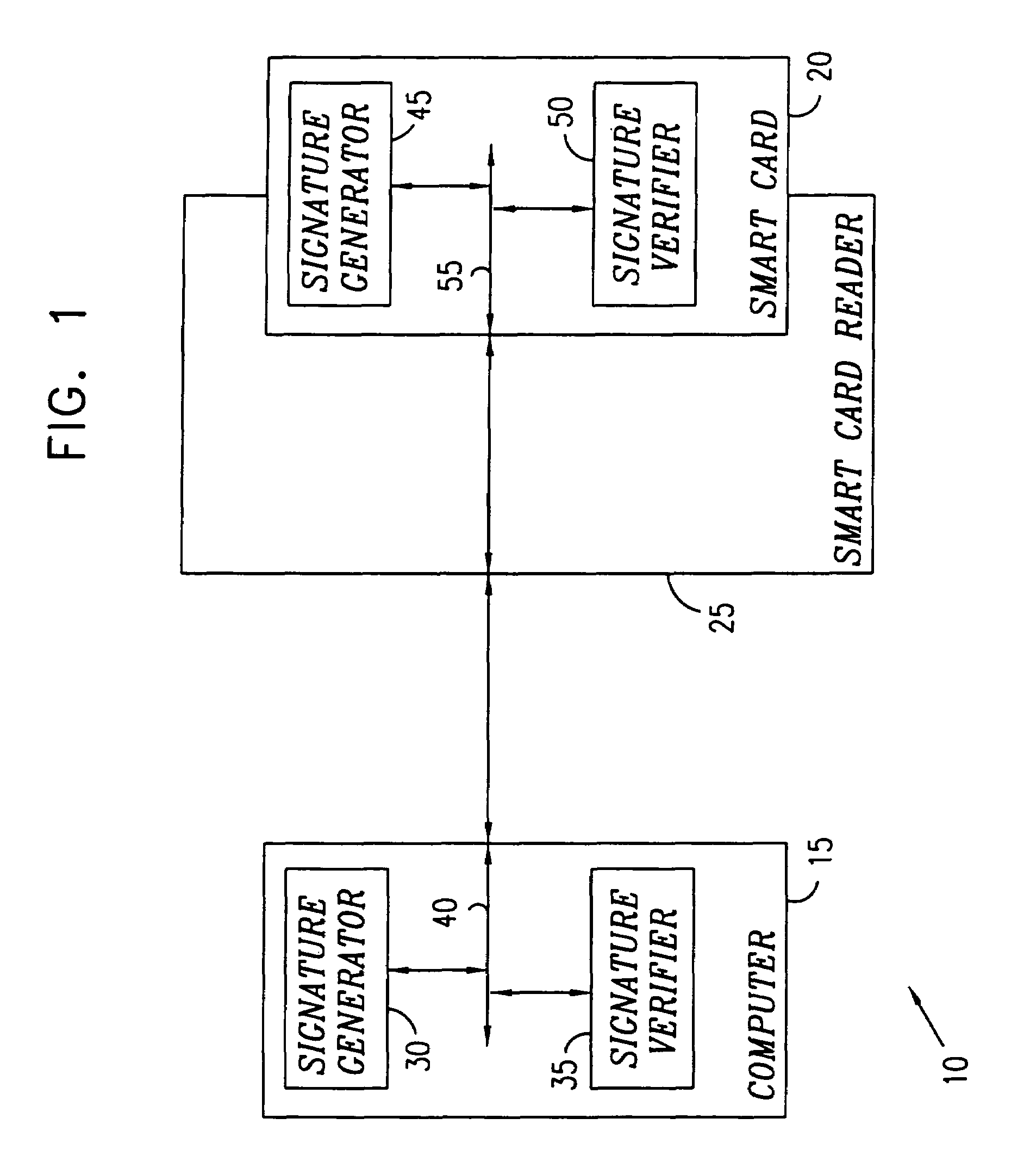
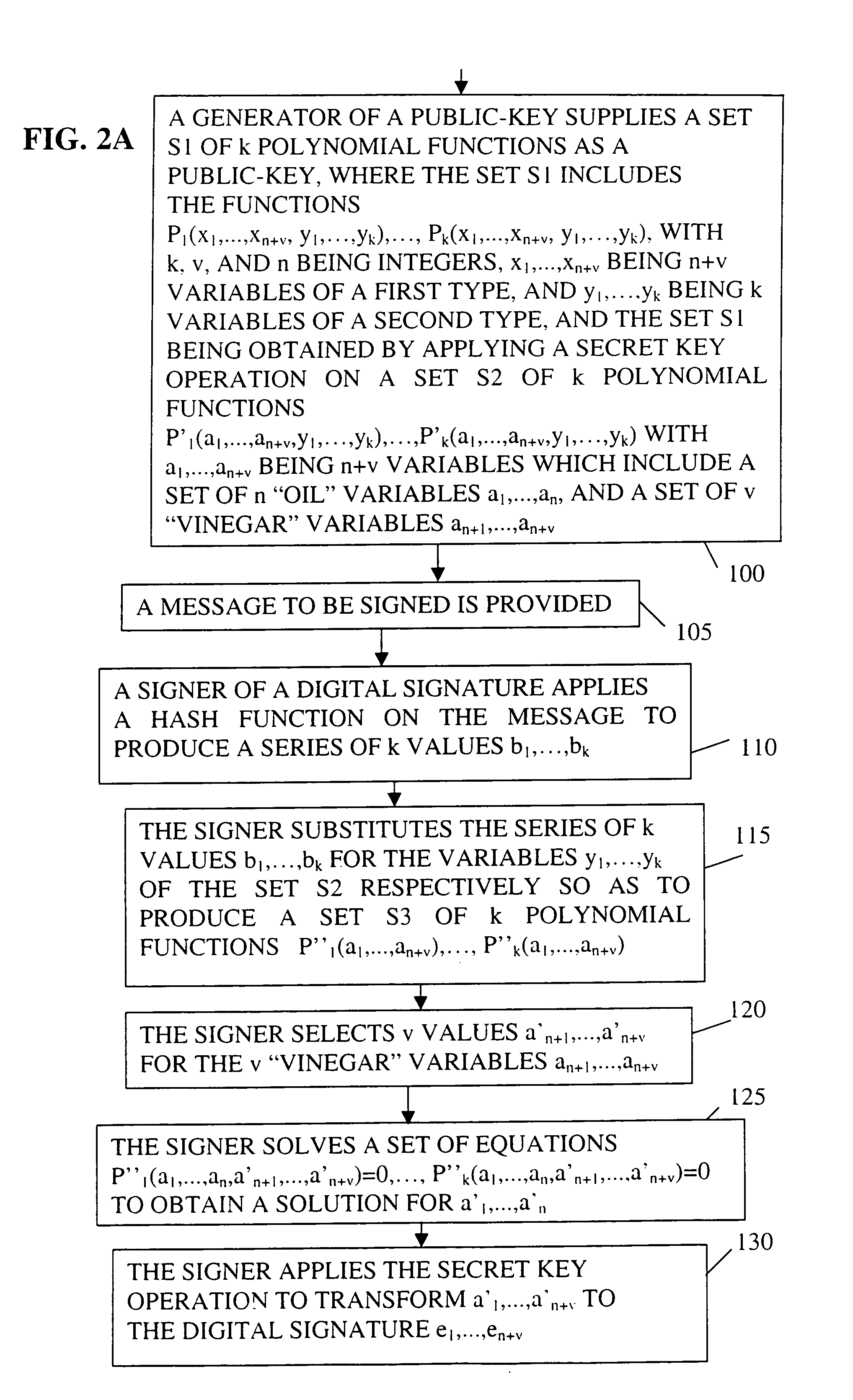
Public-key signature methods and systems
InactiveUS7100051B1Public key for secure communicationUser identity/authority verificationHash functionDigital signature
The invention provides for a cryptographic method for digital signature.A set S1 of k polynomial functions Pk(x1, . . . , xn+v, y1, . . . , yk) are supplied as a public key, where k, v, and n are integers, x1, . . . , xn+v are n+v variables of a first type, and y1, . . . , yk are k variables of a second type, the set S1 being obtained by applying a secret key operation on a given set S2 of k polynomial functions P′k(a1, . . . , an+v, y1, . . . , yk), a1, . . . , an+v designating n+v variables including a set of n “oil” and v “vinegar” variables.A message to be signed is provided and submitted to a hash function to produce a series of k values b1, . . . , bk. These k values are substituted for the k variables y1, . . . . , yk of the set S2 to produce a set S3 of k polynomial functions P″k(a1, . . . , an+v), and v values a′n+1, . . . , a′n+1, are selected for the v “vinegar” variables. A set of equations P″k(a1, . . . , a′n+v)=0 is solved to obtain a solution for a′1, . . . , a′n and the secret key operation is applied to transform the solution to the digital signature.
Owner:CP8 TECH SA +1
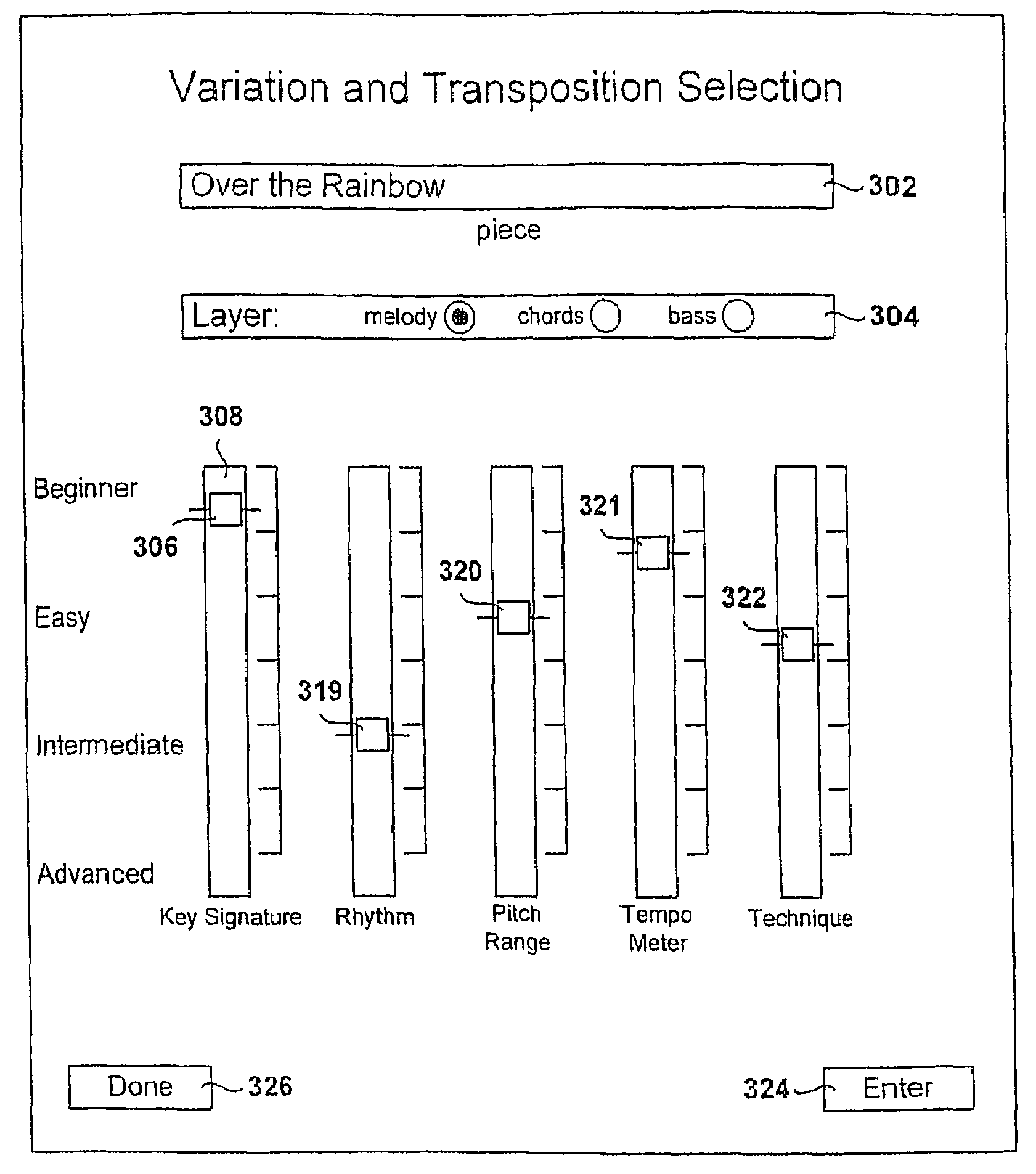
Method and system for generating musical variations directed to particular skill levels
Various embodiments of the present invention are directed to an automated method and system component for generating variations of one or more musical selections directed to particular students or to particular skill levels into which students may be classified. The method and system component may be included in a wide variety of different music rendering, music display, and music instruction systems. In one embodiment of the present invention, variations are generated by filtering each layer of a musical selection with respect to a number of common, musical components, with the filtering chosen to reflect a selected or desired skill level. In the embodiment of the present invention, the layers of a musical selection include a melody line, a chord progression, and a bass line, and musical components include key signature, rhythm, pitch range, tempo and meter, and technique. Skill level may be based on a numerically-encoded range of skill levels, or may include a number of fixed skill levels, such as beginning, easy, intermediate, and advanced levels.
Owner:PERLA JAMES C
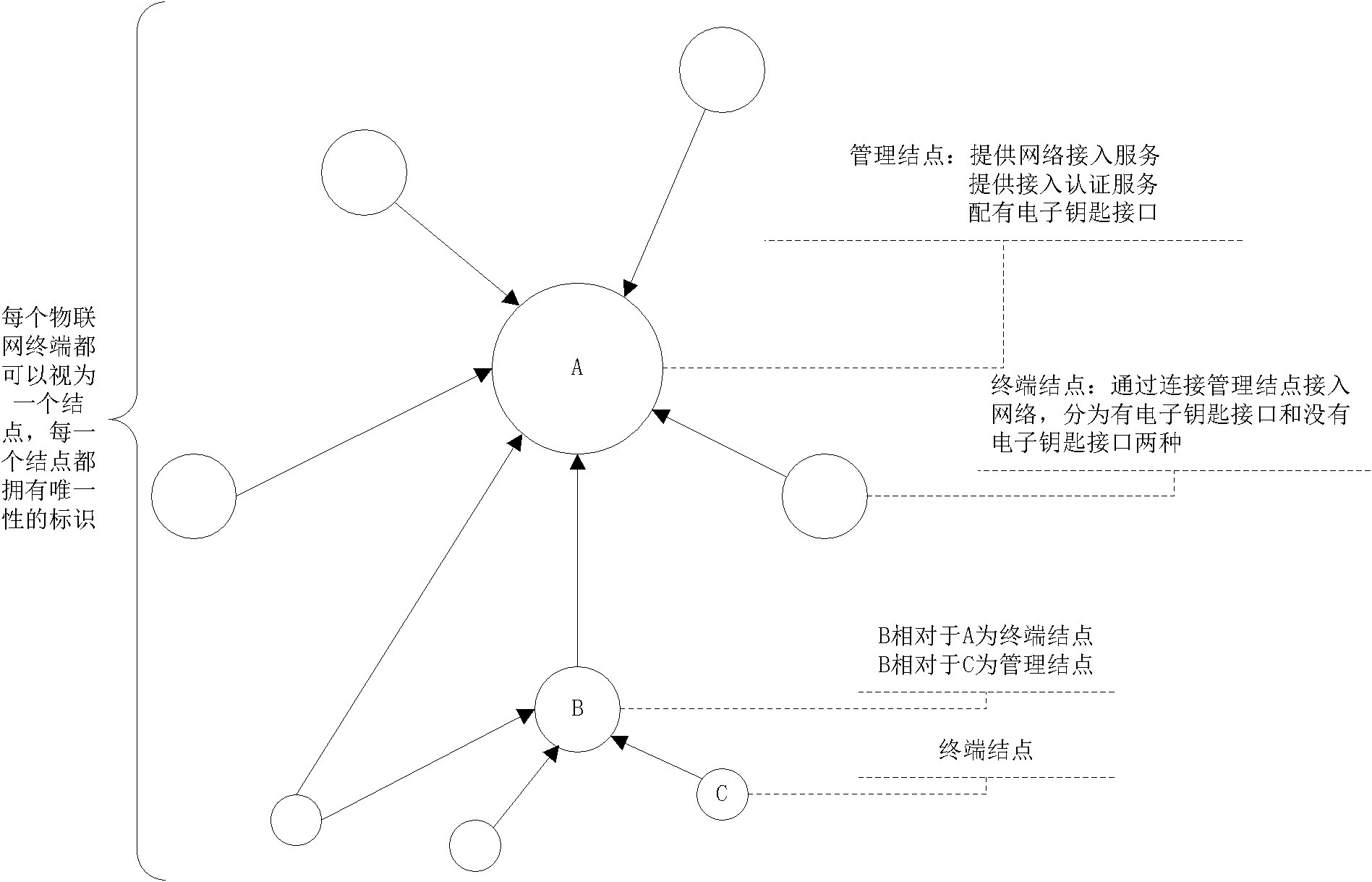
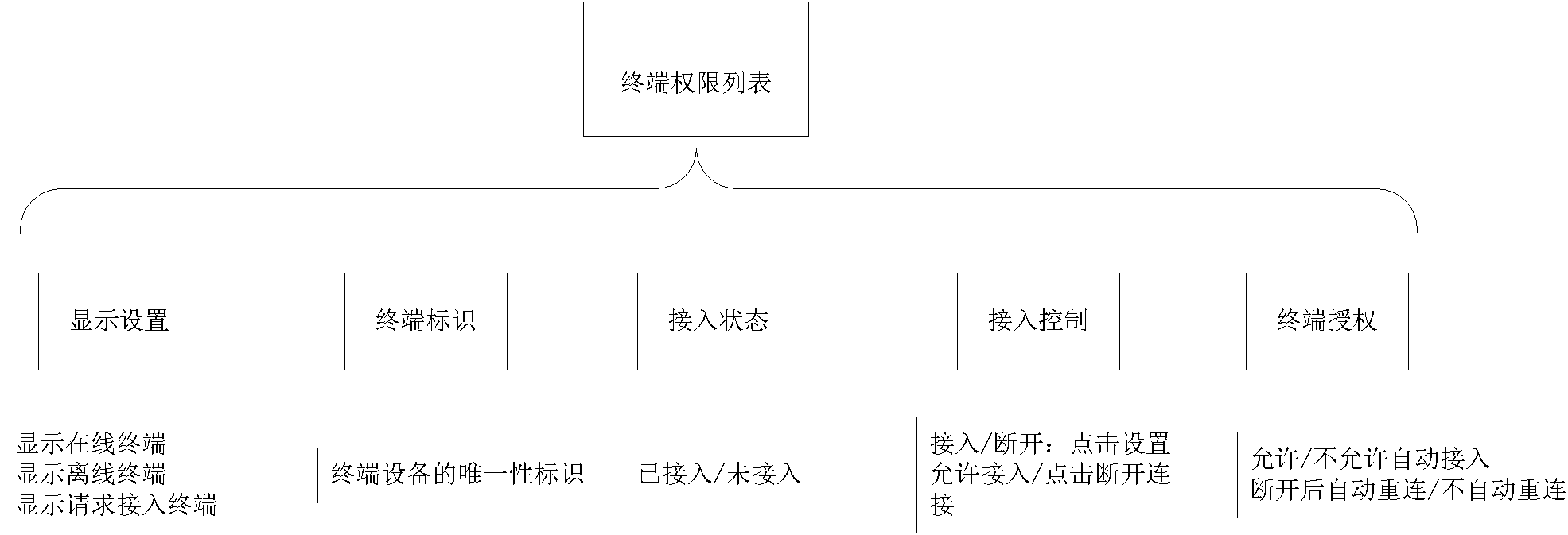
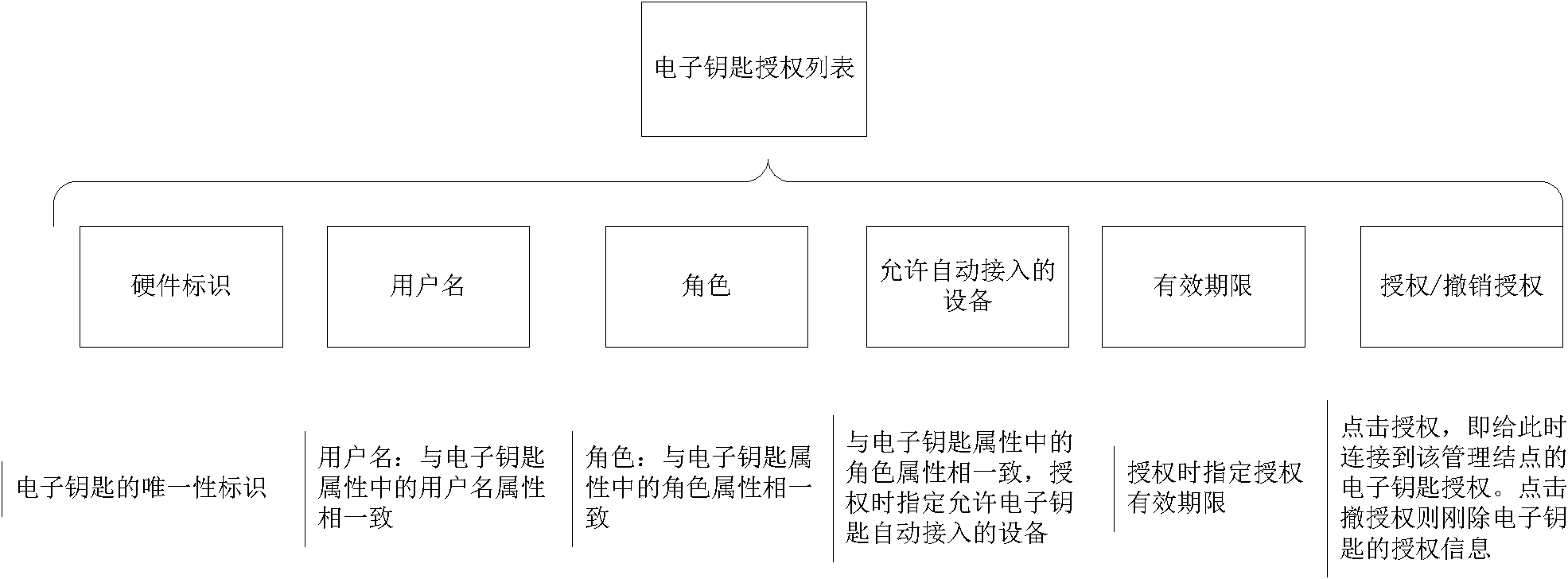
Method for realizing safe access of terminal of internet of thing
ActiveCN102065430ARealize managementSecure AccessNetwork topologiesSecurity arrangementThe InternetComputer terminal
The invention discloses a method for realizing safe access of a terminal of internet of thing, which comprises the steps of: storing an authorization message in an electronic key, and using the authorization message as an identity identification, wherein the authorization message is used as a private key signature by an authorized management node and stored in the authorized management node; writing the authorization message into the electronic key in an electronic key authorization list of the management node; when no terminal node connected with the electronic key applies to accessing the internet, searching a terminal authorization list by the management node to judge whether the access of the terminal node is allowed; and when the terminal node connected with the electronic key applies to accessing the internet, firstly executing the operation without the electronic key by the management node, and if the terminal is failed to access, searching the electronic key authorization listto judge whether the access of the terminal node is allowed. According to the method realizing the safe access of the terminal of the internet of thing, disclosed in the invention, the problem of safe access of the terminal can be effectively solved, a great amount of terminals of the internet of thing can be effectively managed, and the rapid automatic access of the terminals of the internet of thing can be realized.
Owner:无锡鼎驰信息科技有限公司
Method and system for generating musical variations directed to particular skill-levels
Various embodiments are directed to an automated method and system component for generating variations of one or more musical selections directed to particular students or to particular skill-levels into which students may be classified. The method and system component may be included in a wide variety of different music rendering, music display, and music instruction systems. In one embodiment, variations are generated by filtering each layer of a musical selection with respect to a number of common, musical elements, with the filtering chosen to reflect a selected or desired skill-level. In this embodiment, the layers of a musical selection include a melody line, a chord progression, and a bass line, and musical elements include key-signature, rhythm, pitch range, tempo and meter, and technique. Skill-level may be based on a numerically-encoded range of skill-levels, or may include a number of fixed skill-levels, such as beginning, easy, intermediate, and advanced levels.
Owner:PERLA JAMES C
Visual, tactile and motion-sensation system for representing music for an audience
ActiveUS20120216666A1Convenient to accommodateBroad freedomMusicDocumentation procedureTouch Perception
System of translation between written or performed music and visual, tactile and motion sensation experiences. Specific metaphors for most aspects of music among these non-audio media are described. Examples include rules for color assignment to pitches in a scale; positioning visual representations of notes; visualizing notes between pitches; arranging tactile stimuli to represent pitches; and rendering stages of cadence with motion sensing experiences such as movement within space, or changes in one's tilt, pitch, etc. The system includes documentation of theoretical / interpretive elements such as key signature, current chord, association of notes with melody, as they occur in a piece, along with metaphors for their translation in these non-audible media. The metaphors are strictly prescribed, yet accommodating large variations and freedoms in visual, tactile and motion renderings by producers / artists, allowing for visual, tactile or motor metaphors for non-musical instrument sounds such as finger sliding across windings of a guitar string.
Owner:FRESOLONE MARK
Bilateral authentication and data interaction security protection method based on CPK (Combined Public Key Cryptosystem)
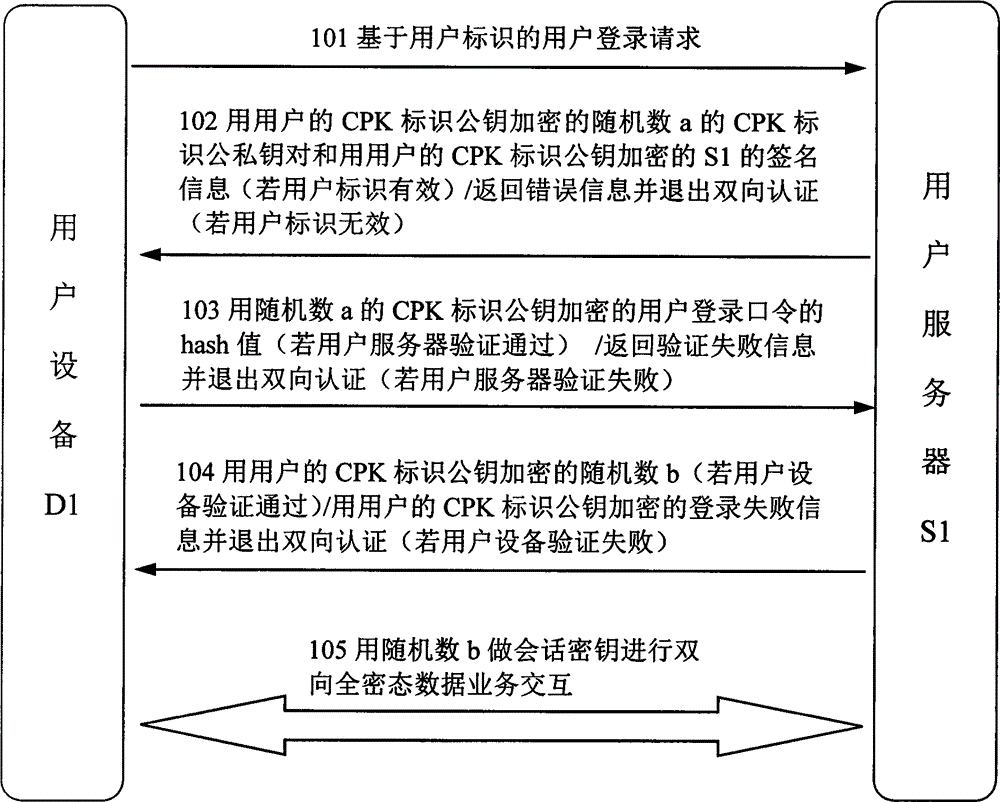
InactiveCN104901935AConvenient offline authenticationImplement offline authenticationUser identity/authority verificationPasswordPublic key cryptosystem
The invention provides a bilateral authentication and data interaction security protection method based on a CPK (Combined Public Key Cryptosystem). The method is applied to bilateral authentication between a user server (S1) and user equipment (D1) and interaction protection of all data. The method comprises the following steps that: the S1 receives a user login request transmitted by the D1, generates a random number a, a CPK identification public-private key pair of the random number and identification private key signature information of the S1, encrypts the random number a, the CPK identification public-private key pair and the identification private key signature information, and downloads the encrypted random number a, CPK identification public-private key pair and identification private key signature information to the D1; the D1 verifies whether or not the signature information of the S1 is legal with an identification public key of the S1 to finish authentication of the S1; the S1 performs comparative verification with the hash value of the received user login password and a saved value to finish authentication of the D1; if bilateral authentication is passed, the S1 generates a random number b, encrypts the random number b, and transmits the encrypted random number b to the D1; otherwise the S1 returns bilateral authentication failure information; and after the success of bilateral authentication of a user, the random number b is taken as a session key for all data between the D1 and the S1 in order to perform bilateral all-homomorphism data interaction.
Owner:成都腾甲数据服务有限公司
Method And Apparatus For Secure Cryptographic Key Generation, Certification And Use
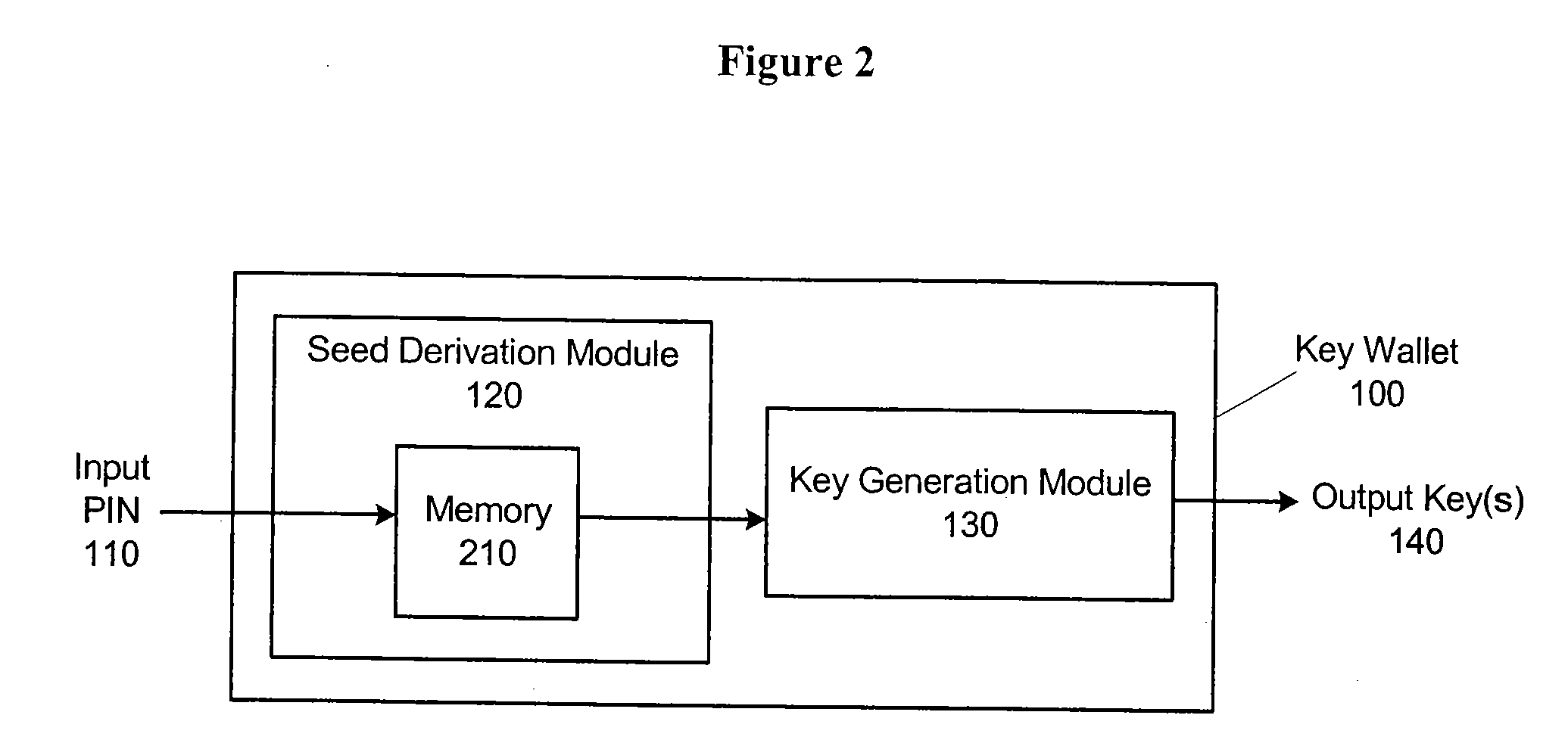
InactiveUS20080181408A1Good flexibilityNo Undue Burden on UserKey distribution for secure communicationMultiple keys/algorithms usageCryptographic key generationUser input
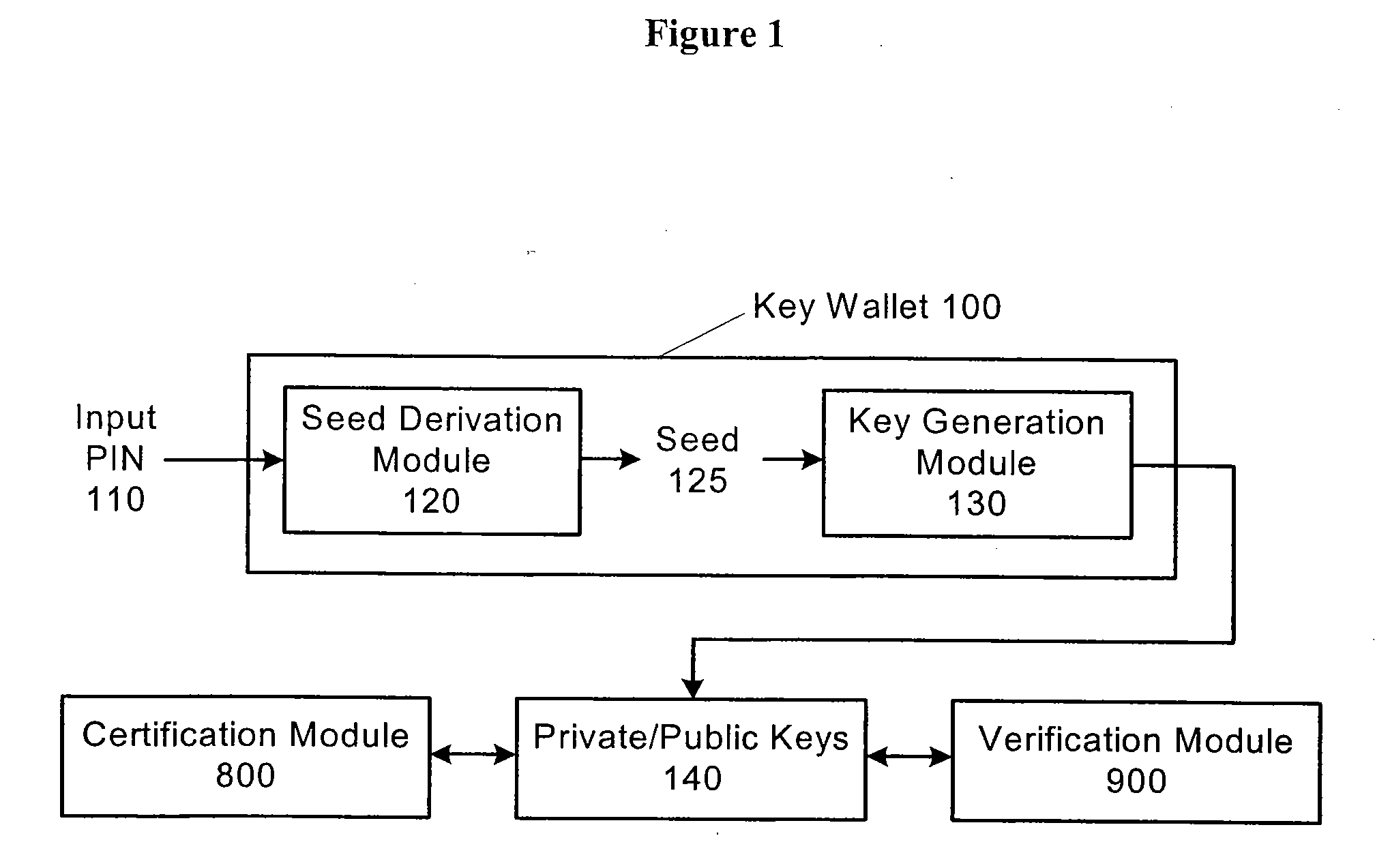
A confidential datum, such as a private key used in public key signature systems, is secured in a digital wallet using a “generation camouflaging” technique. With this technique, the private key is not necessarily stored in the digital wallet, not even in an encrypted form. Instead, the wallet contains a private key generation function that reproduces the correct private key when the user inputs his or her pre-selected PIN. If the user inputs an incorrect PIN, an incorrect private key is outputted. Such private key can be configured so that it cannot be readily distinguished from the correct private key through the use of private key formatting, and / or the use of pseudo-public keys corresponding to the private key. The techniques described herein are also applicable to other forms of regeneratable confidential data besides private keys.
Owner:CA TECH INC
Third-party digital signature method and data transmission system
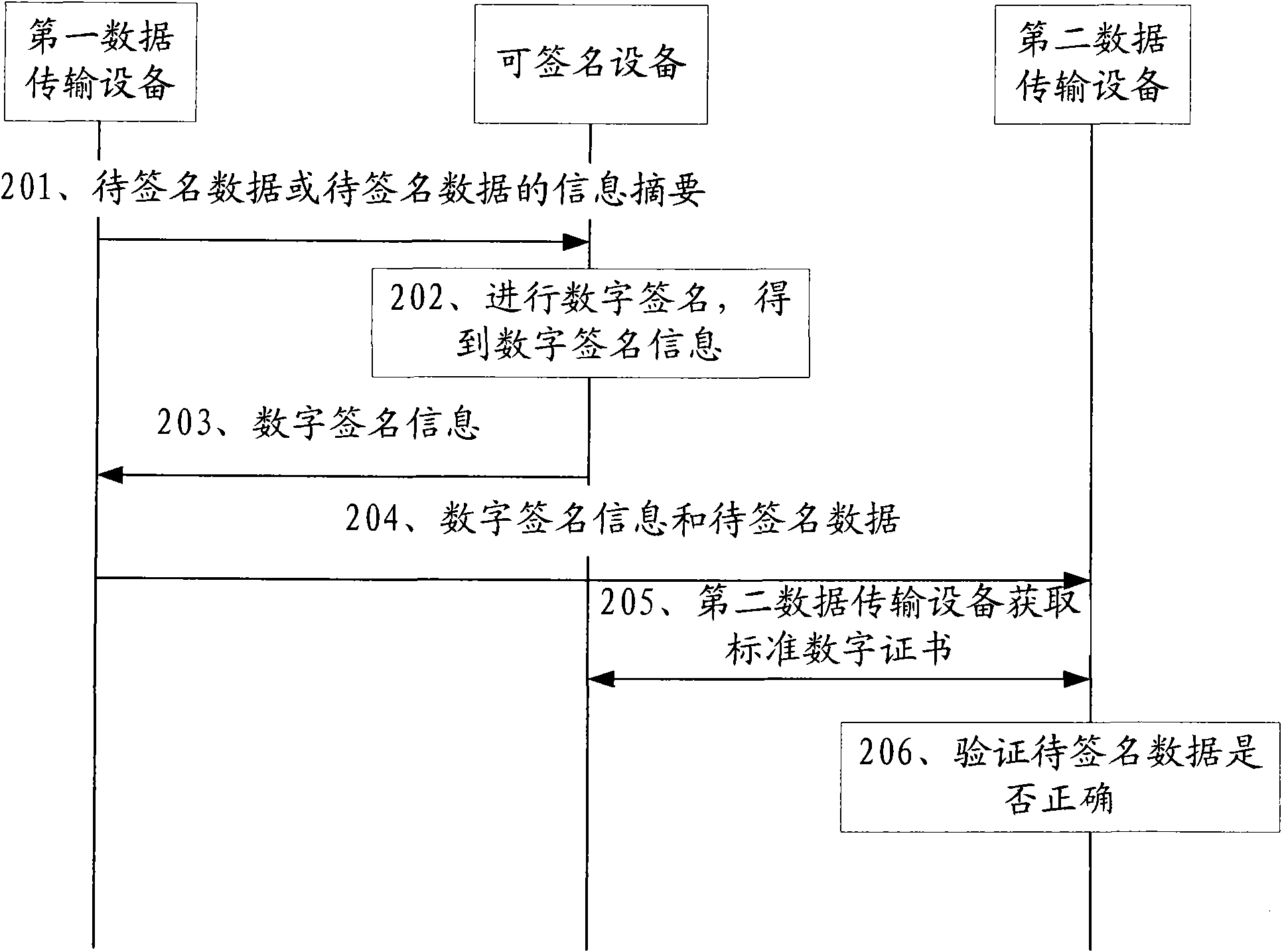
ActiveCN101610150AEnsure safetyReduce complexityPublic key for secure communicationUser identity/authority verificationThird partyDigital signature
The invention discloses a third-party digital signature method and a data transmission system, relates to the field of information security, realizes the control on the security of data transmission and enhances the safety of system. The third-party digital signature method includes the following steps: a first data transmission device sends a signature request to a signable device, and the signature request carries data to be signed or information abstract of data to be signed and requests the signable device to digitally sign the data to be signed; the signable device digitally signs the data to be signed or information abstract of data to be signed, obtains the digital signature information of the data to be signed or information abstract of data to be signed and transmits the digital signature information to the first data transmission device; and the first data transmission device receives the digital signature information and transmits the information as well as the data to be signed to a second data transmission device. The invention is applicable to data transmission based on public key signature.
Owner:HUAWEI TEHCHNOLOGIES CO LTD
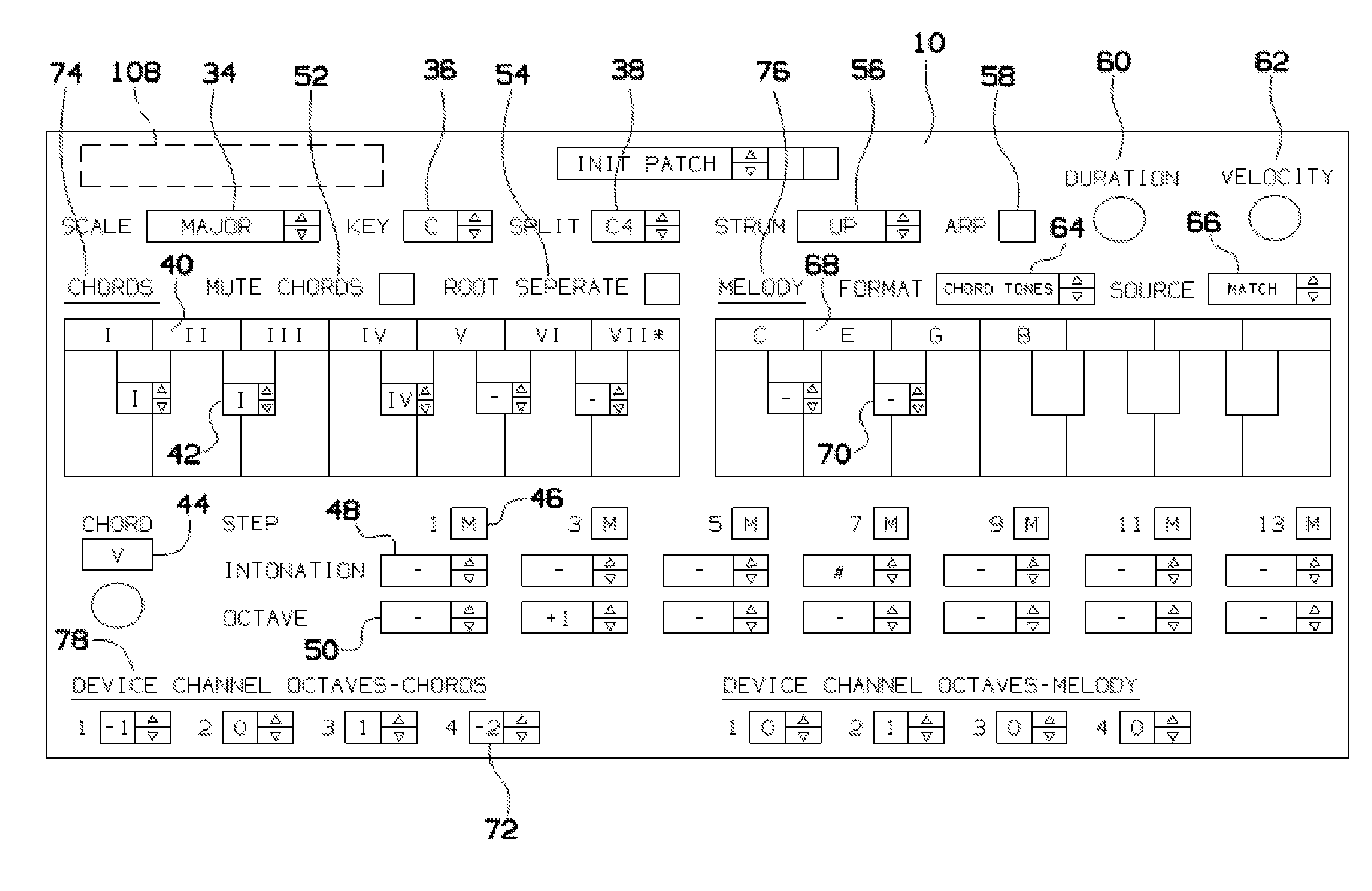
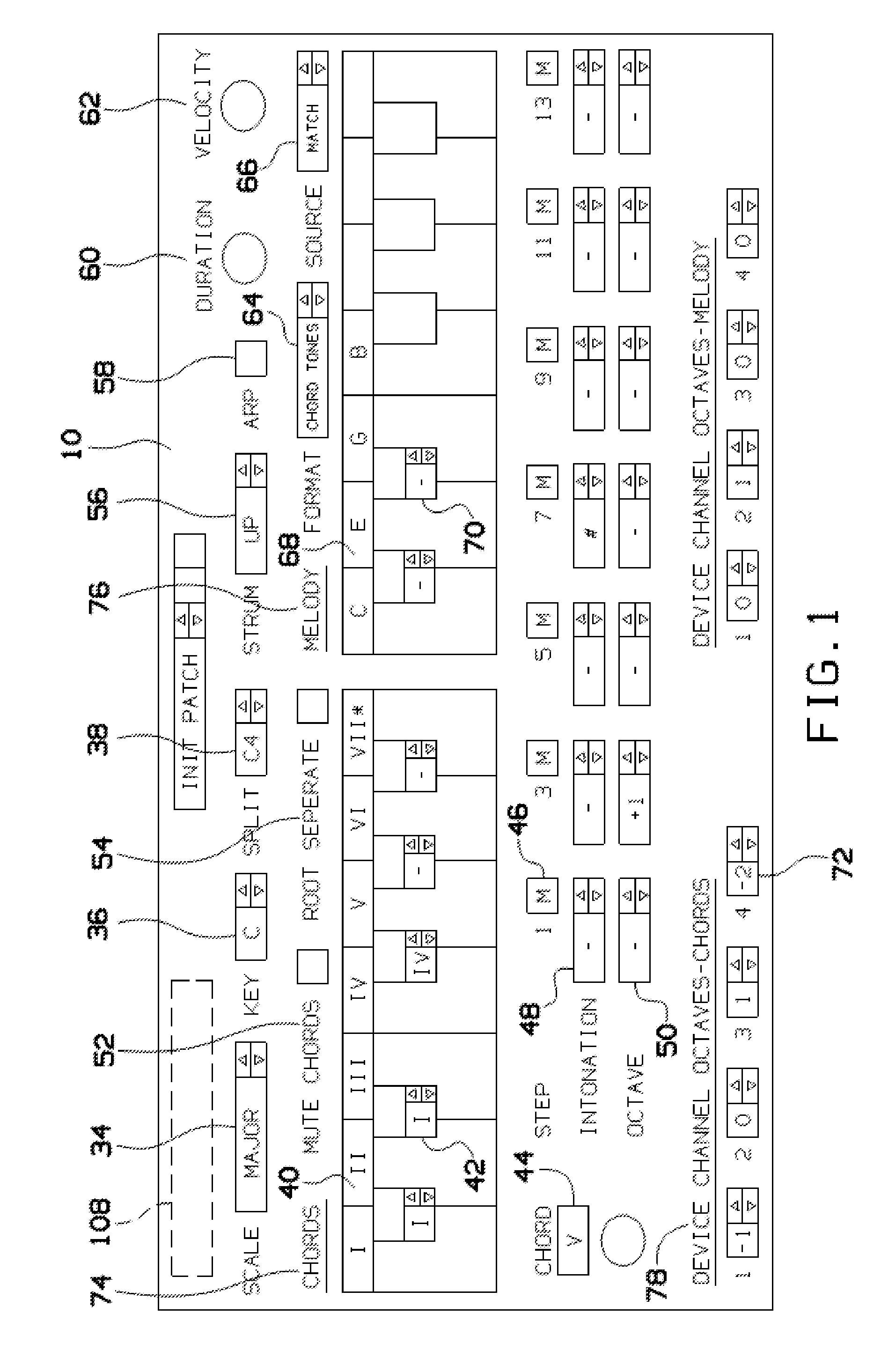
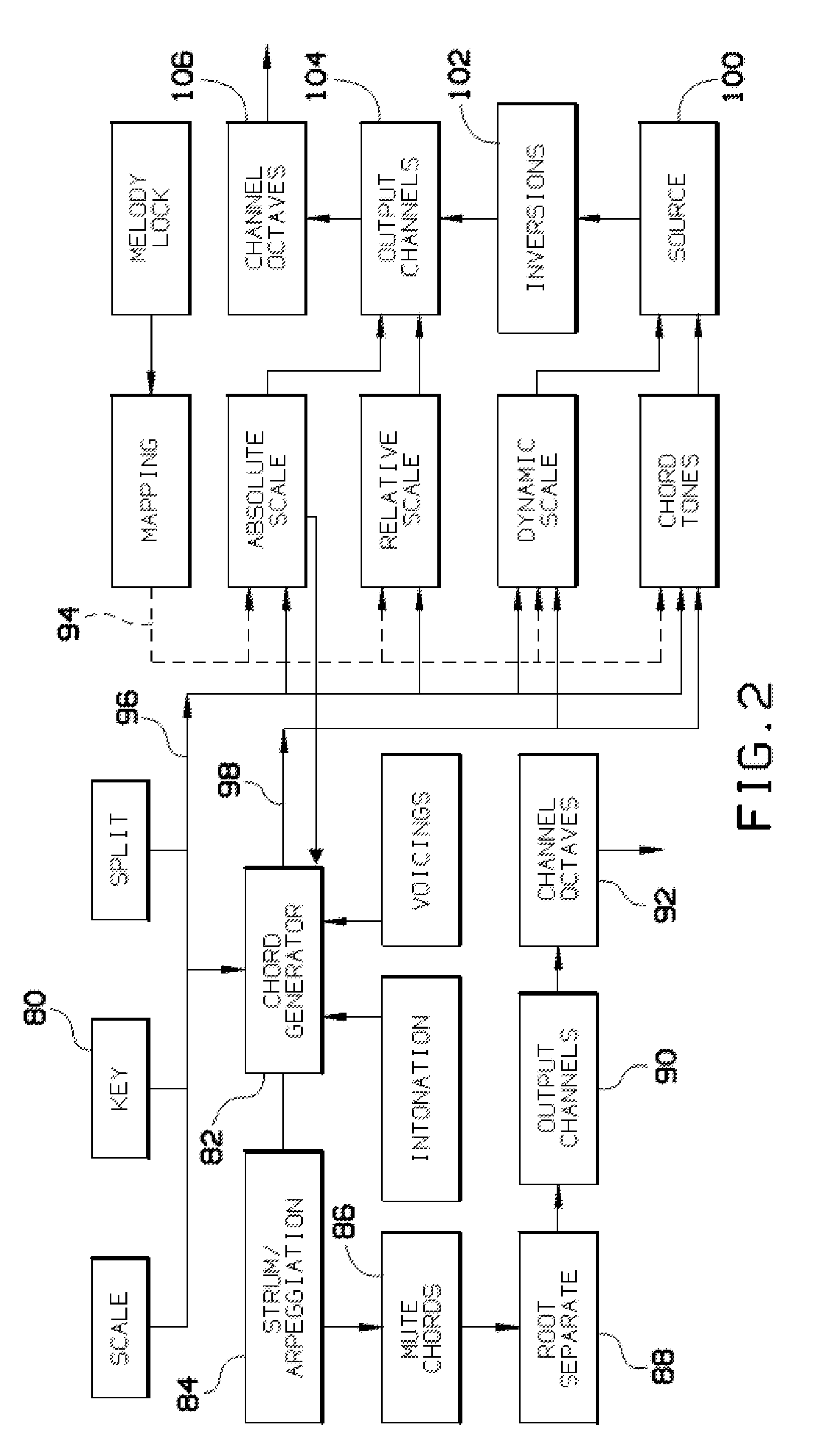
Midi re-mapping process for utilizing proper music theory when playing a keyboard
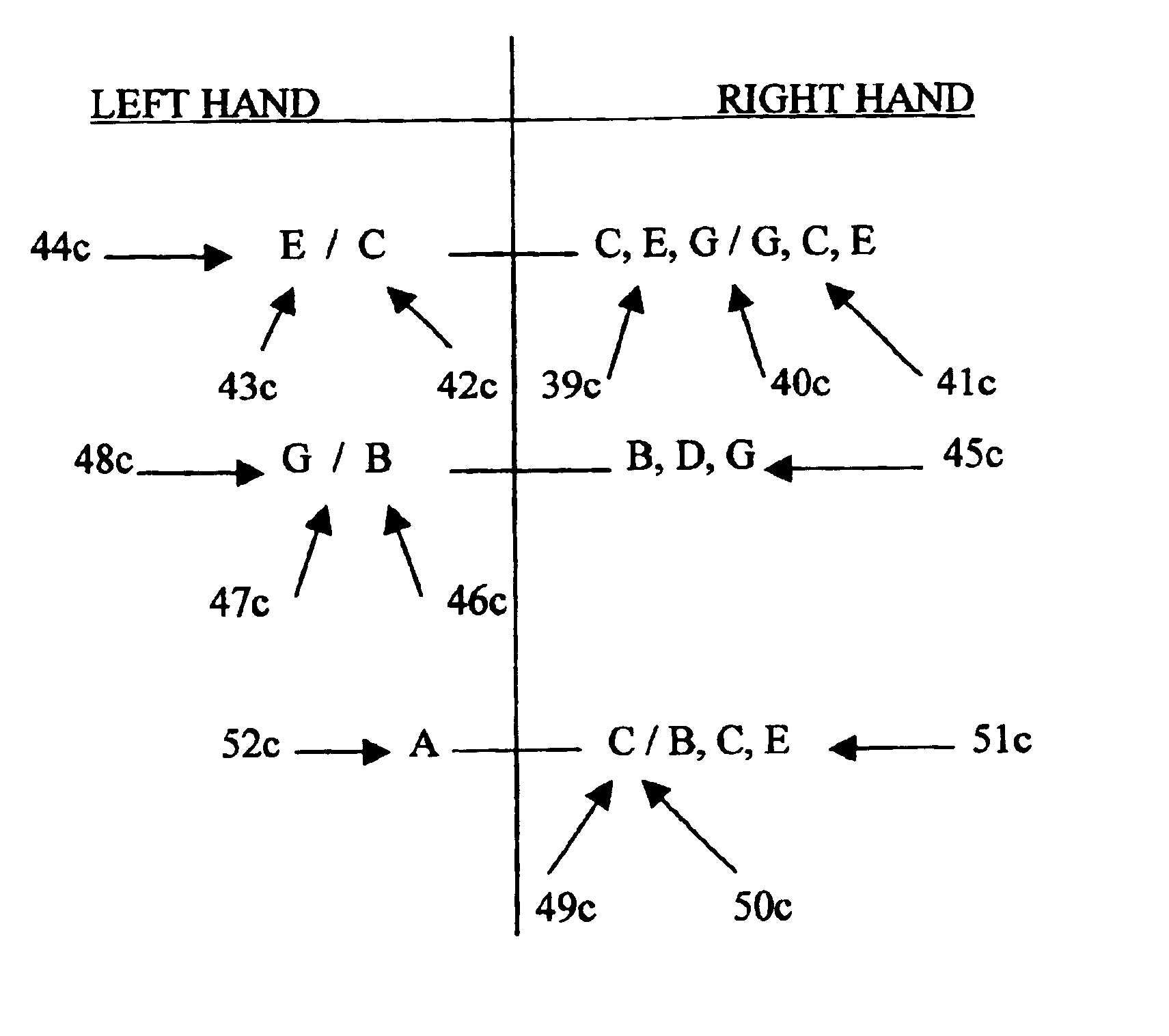
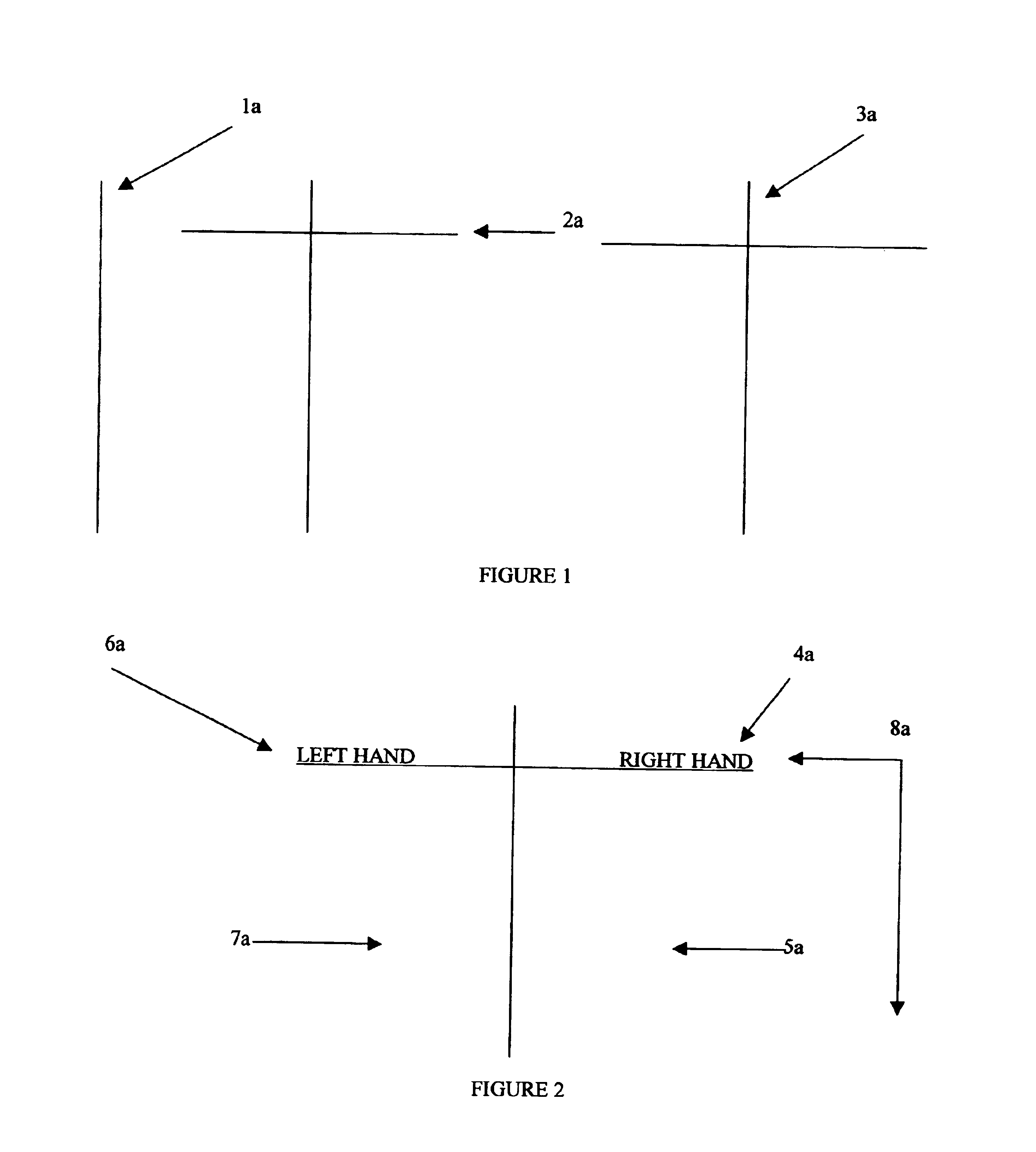
A process and a system are disclosed for some embodiments of the invention that map MIDI signals in a manner which always puts the harmony and melody octaves of an electronic MIDI keyboard in perfect pitch for a user of the keyboard. The process of some embodiments includes (i) receiving a selection of a key signature, (ii) receiving a selection of a scale, (iii) organizing the left side octave(s) (“chord” side) into a chord generator that places all scale tones on white keys and applies a chord effect to each white key, relative to the scale tone position, and (iv) organizing the right side octave(s) (“melody” side) into a melody lock that provides multiple settings for mapping the seven scale tones onto white keys.
Owner:KINTER ZACHARY CHARLES
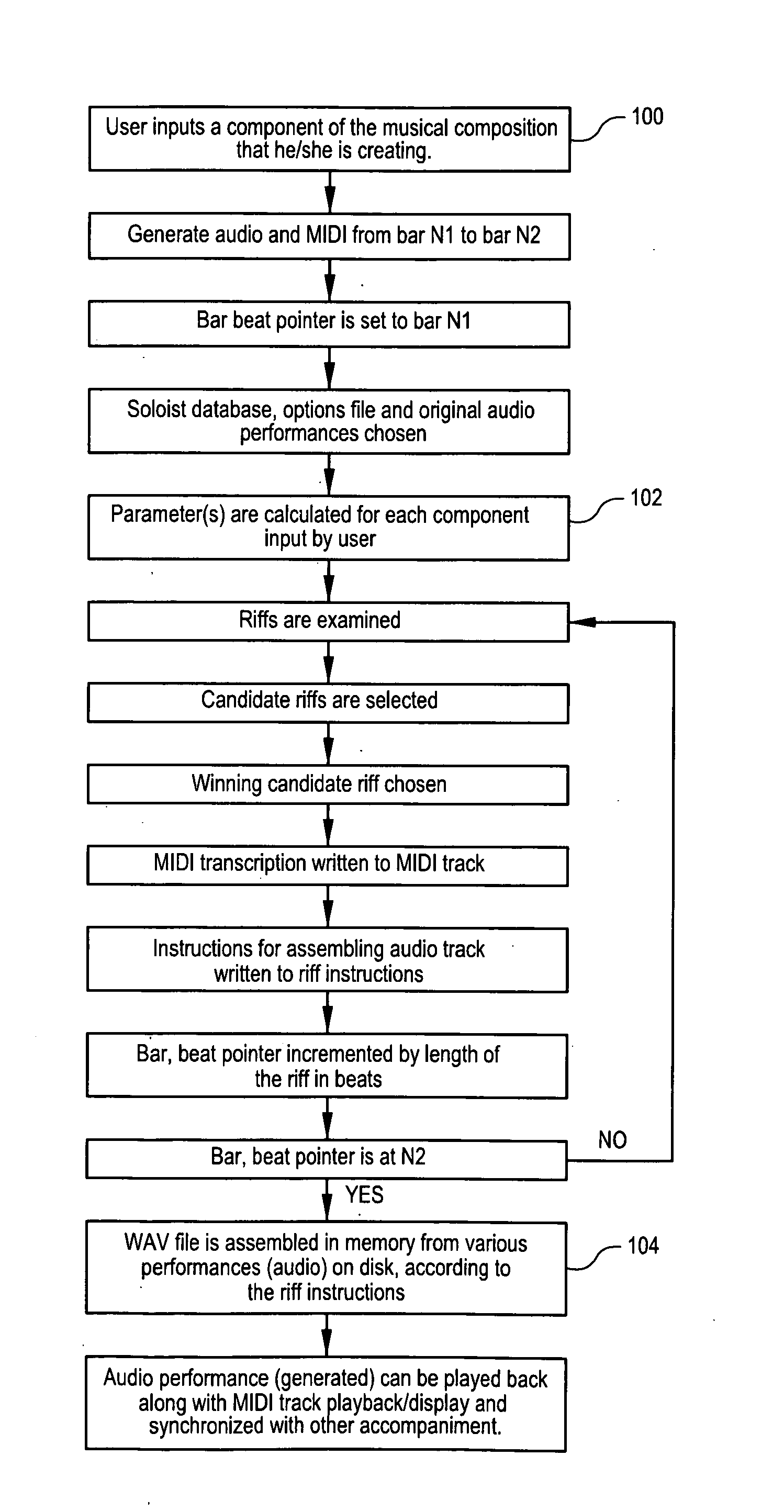
Systems and methods for composing music
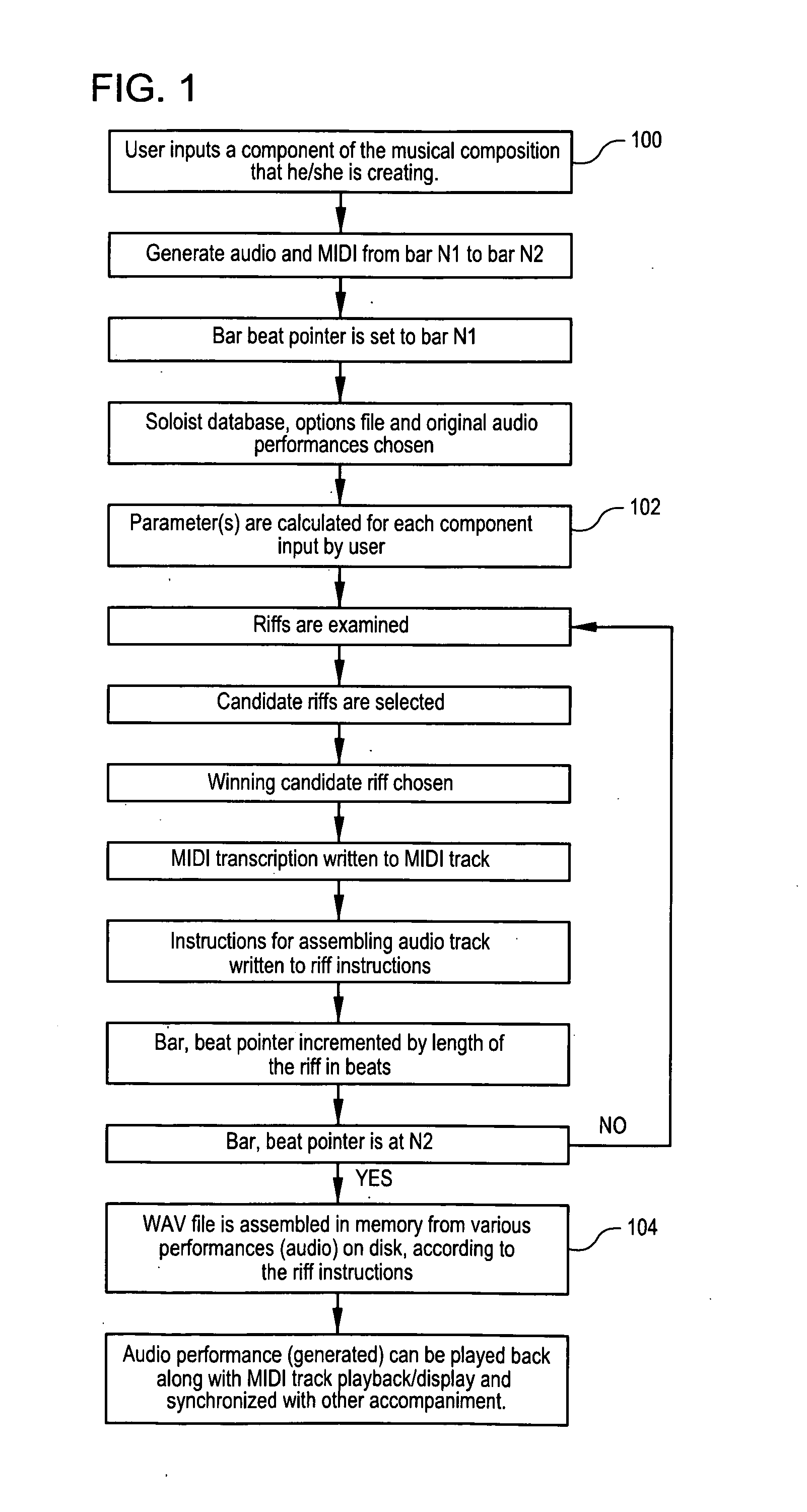
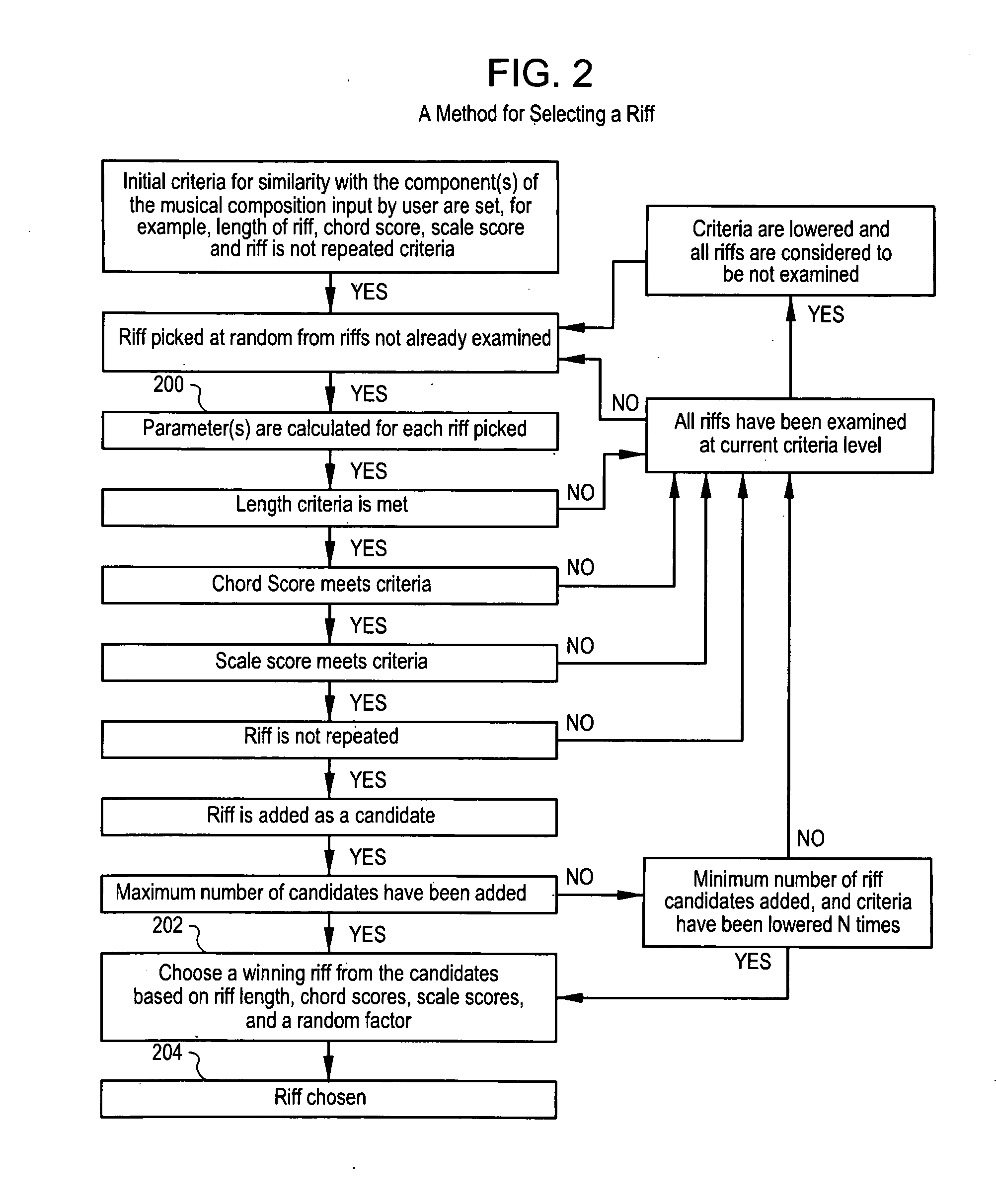
A system and method for generating a new composition based on a database of pre-recorded performances of existing compositions. A system and method for generating an automated method for converting existing performances and associated MIDI transcriptions to a database and generating a new composition from the database. Musical improvisations are performed by musicians, in digital audio format. The digital audio data is transcribed to MIDI data and stored in a song file. The tempo, chord symbols used and key signature are input, and added to the song file. The digital audio file is analyzed and markers for the start and the end of phrases are added in a phrase marker text file. The system analyzes the MIDI transcriptions, chords, and phrase marker text. Information about sections and phrases of the solo from the phrase market text are stored in a “Riffs” file. The MIDI data transcriptions, the chord symbols and the Riffs files are combined into a Soloist Database File, consisting of one or more MIDI transcriptions of the audio improvisations. The musician's performances are stored as digital audio files such as WAV format files. An Options file is created by the user to control parameters about the solo to be generated. The system then generates a new improvisation based on any input chord progression and key, and the Options file, by choosing portions of the Soloist Database and corresponding portions of the digital audio files to construct the new improvisation. MIDI transcriptions corresponding to the digital audio performance are displayable as notation, piano roll, and on-screen instrument keyboard or fretboard.
Owner:GANNON PETER
Method of writing keyboard music
Owner:KIMBROUGH TIMOTHY
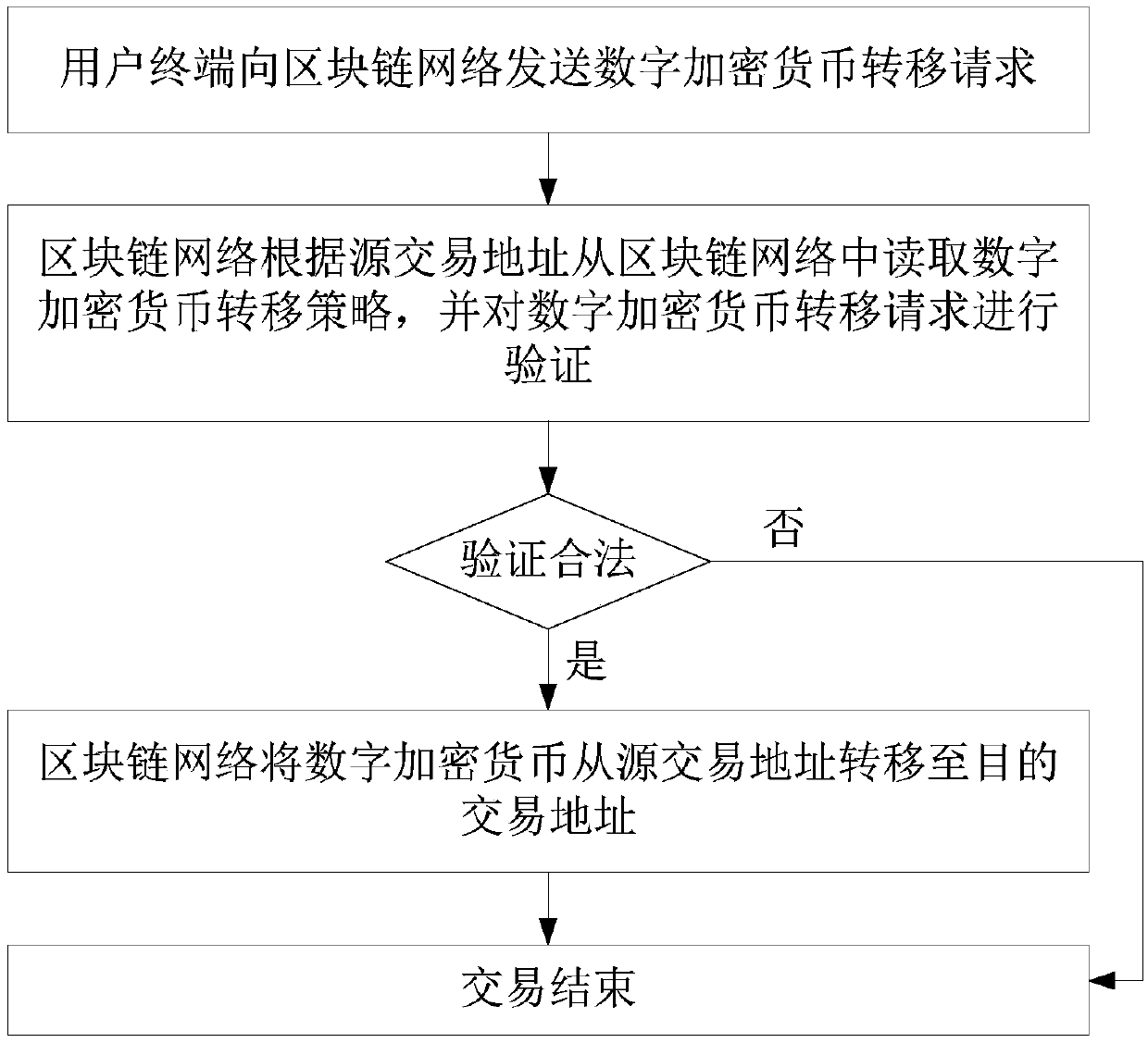
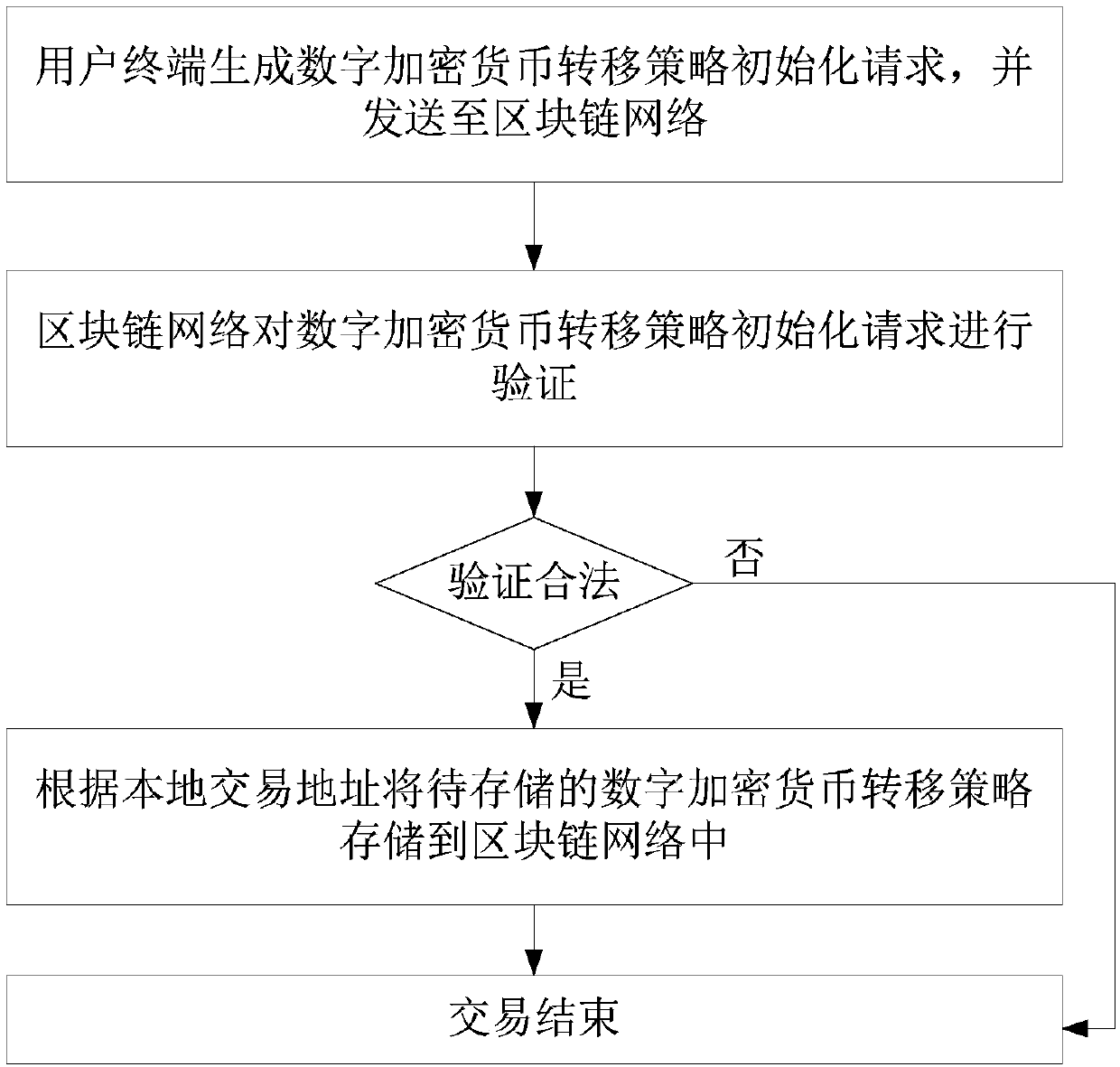
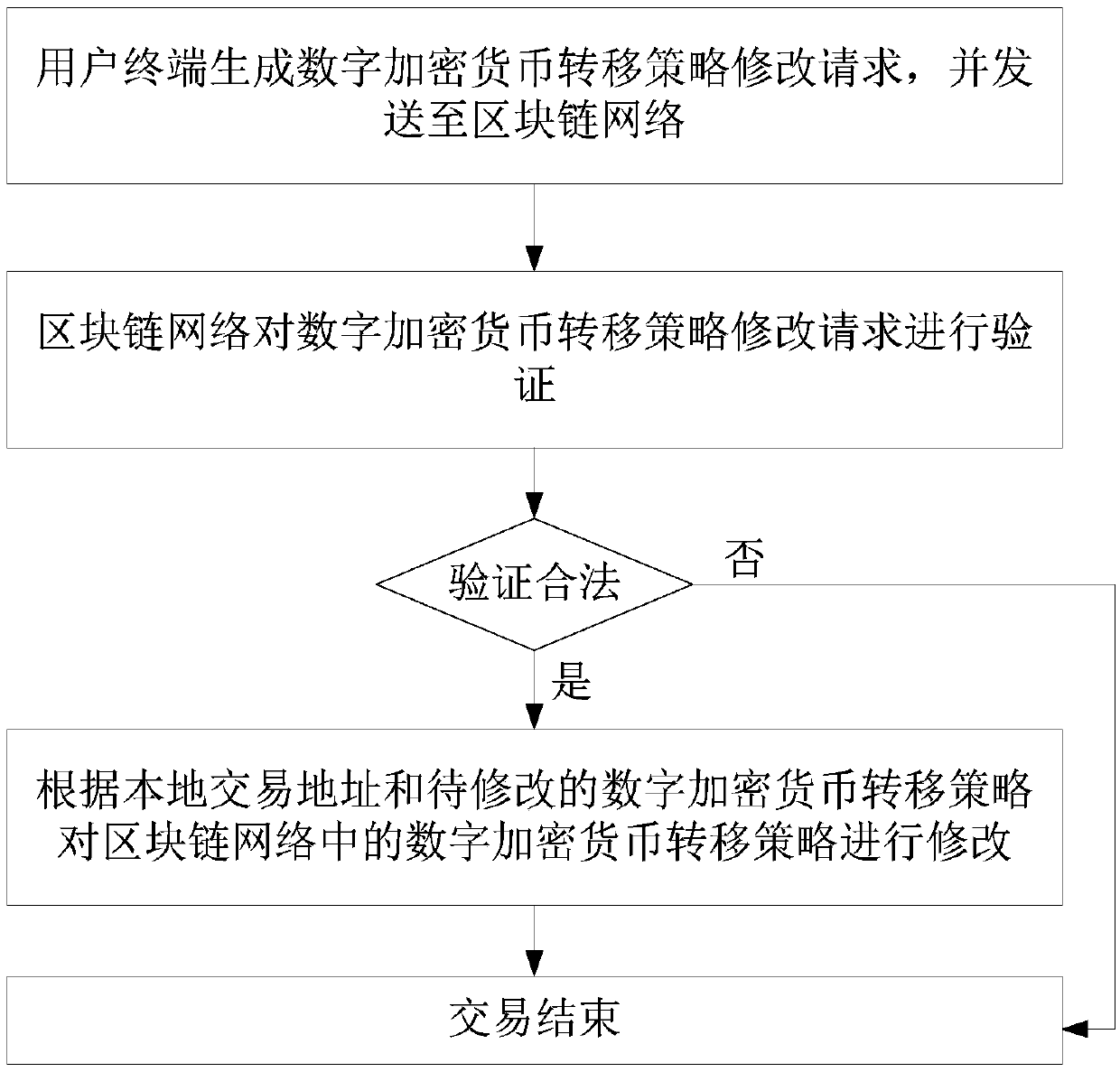
A digital encrypted currency transfer method for a block chain
ActiveCN109670801AEnsure safetyImprove securityPayment circuitsProtocol authorisationThird partyTimestamp
The invention discloses a digital encrypted currency transfer method for a block chain, and the method comprises the steps that a user terminal sends a digital encrypted currency transfer request to ablock chain network, and the request comprises a first timestamp, one or more first private key signatures, a source transaction address, and a destination transaction address, wherein the first private key signature is a private key signature of other user terminals; the block chain network reads the digital encrypted currency transfer strategy according to the source transaction address and verifies the digital encrypted currency transfer request, wherein the digital encrypted currency transfer strategy comprises one or more first public keys and a transfer condition, wherein the first public key is a public key of other user terminals; if the digital encrypted currency is verified to be legal, the digital encrypted currency is transferred from the source transaction address to the destination transaction address, transaction behaviors are recorded, and transaction is finished; otherwise, the transaction is ended. According to the method and the system, the user can still use the digital encryption currency under the condition that the private key is lost, and the user is prevented from hosting the digital asset on the third-party platform, so that the security is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Safe data information transmission method
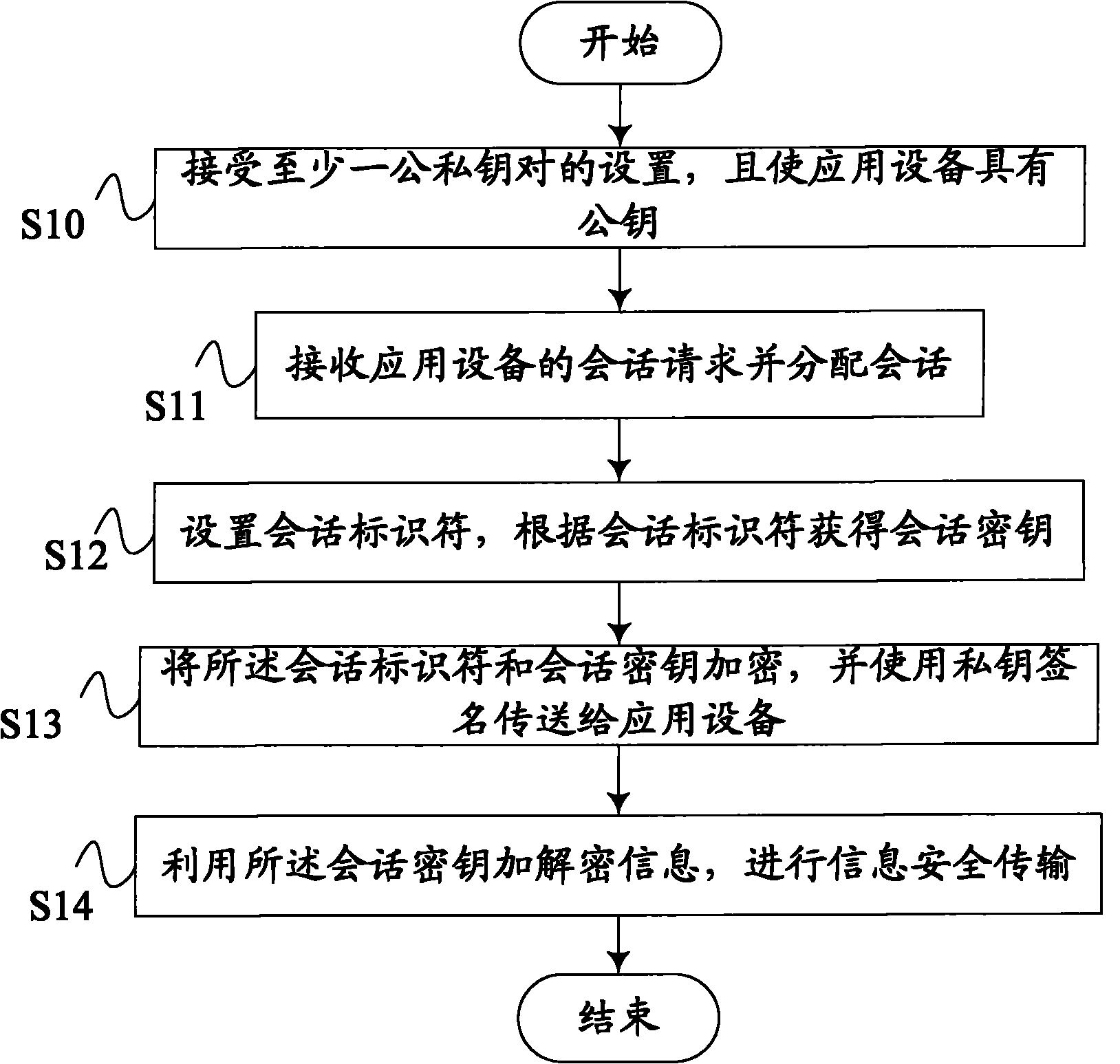
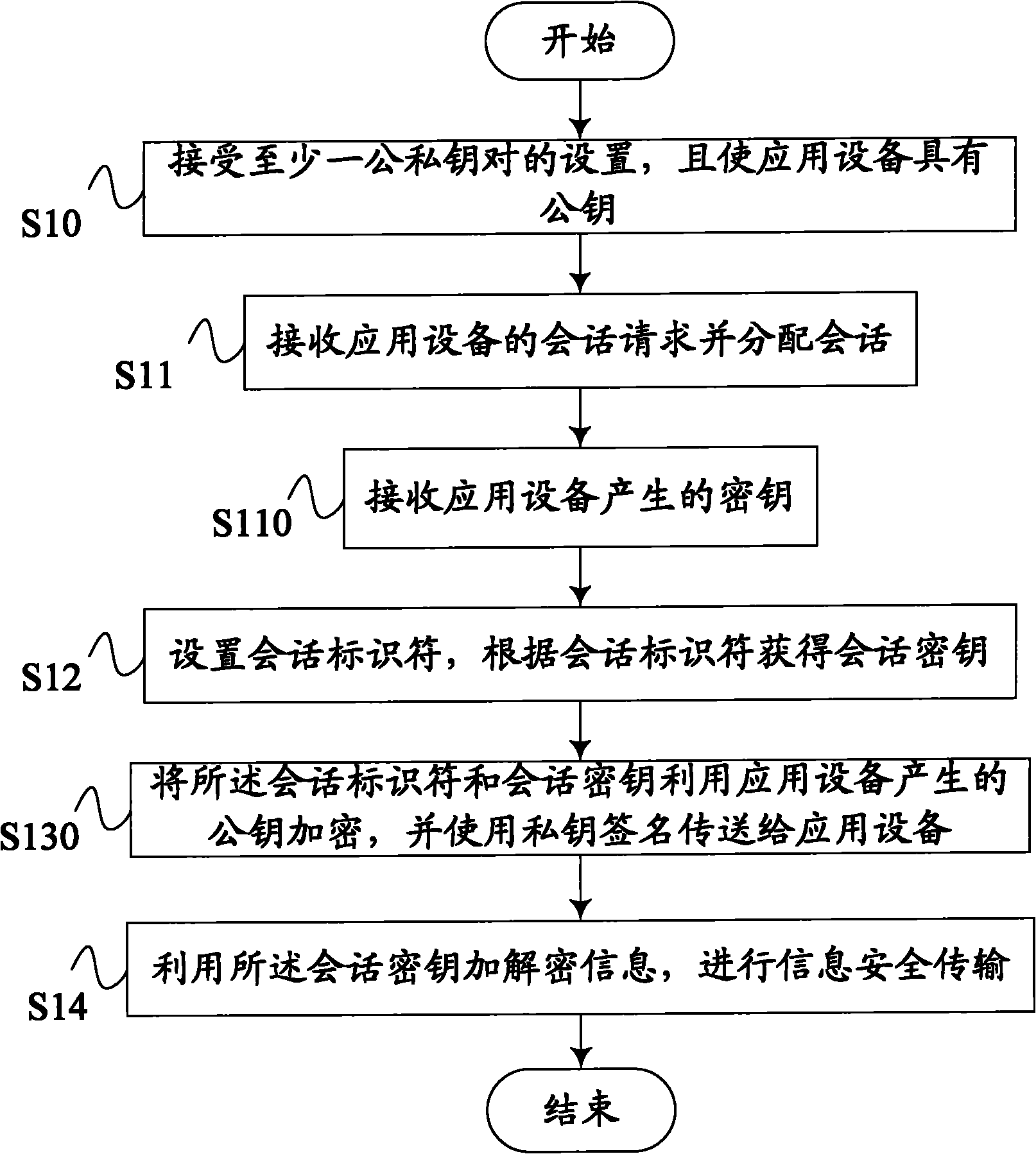
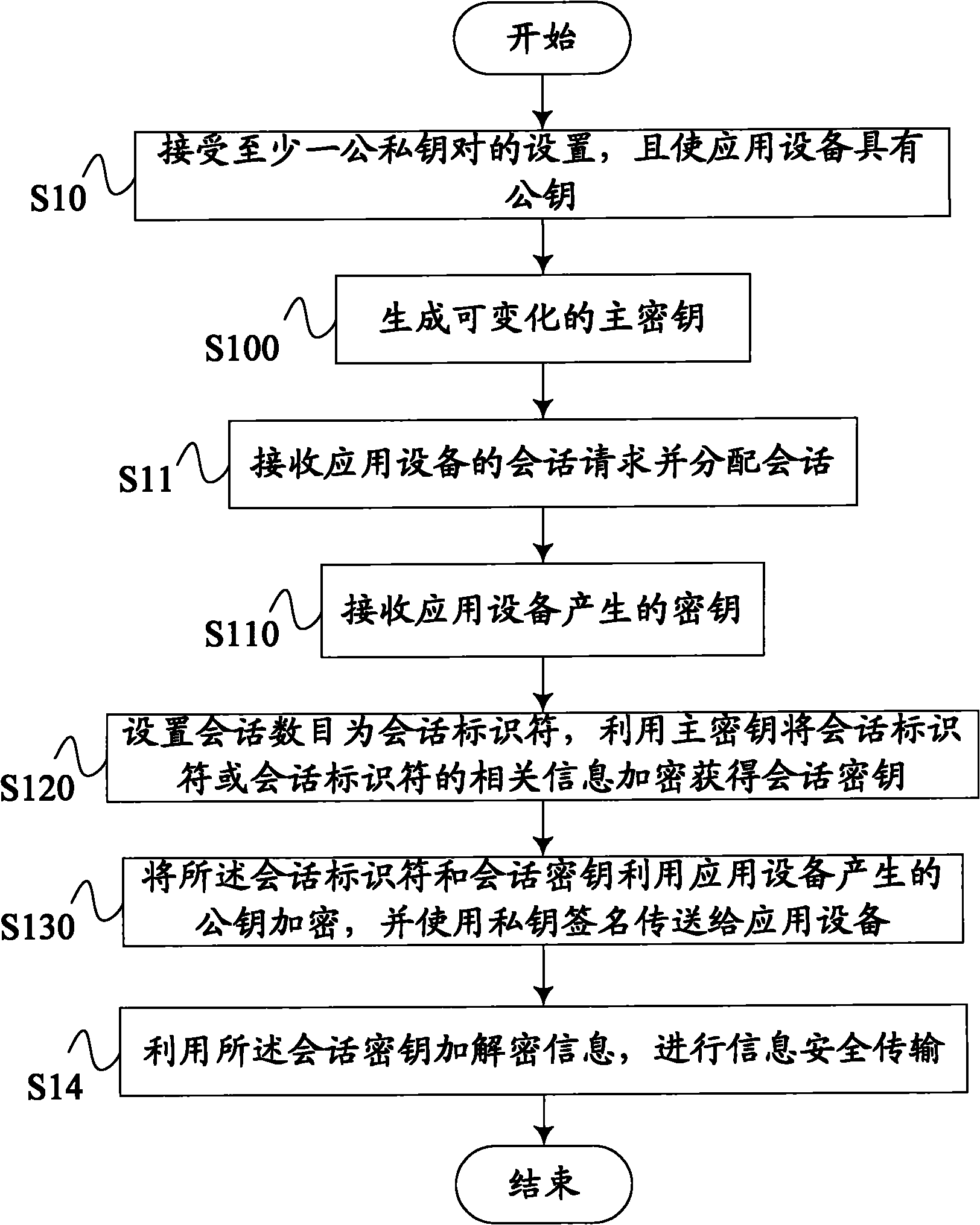
ActiveCN101789863AImprove confidentialitySecure transmissionPublic key for secure communicationUser identity/authority verificationData informationData transmission
The invention discloses a safe data information transmission method which makes data transmission between an information safety device and an application device safer. The method comprises the following steps: receiving setting of at least one pair of public and private keys by the information safety device and providing the public key for the application device; receiving a session request of the application device and allocating a session; setting a session identifier and acquiring a session key according to the session identifier; encrypting the session identifier and the session key and transmitting the encrypted session identifier and the encrypted session key to the application device by using a private key signature; and encrypting and decrypting the data information by using the session key to perform safe data information transmission. The safe data information transmission method makes the data transmission safer by generating variable session key and encrypting the session.
Owner:SHENZHEN EXCELSECU DATA TECH
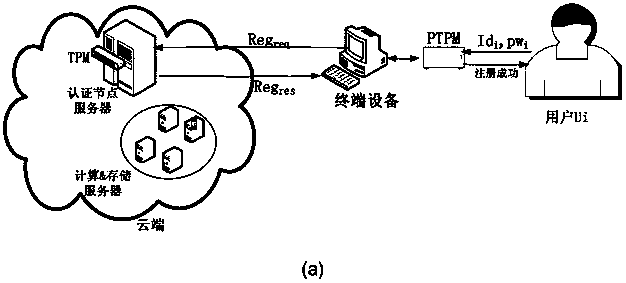
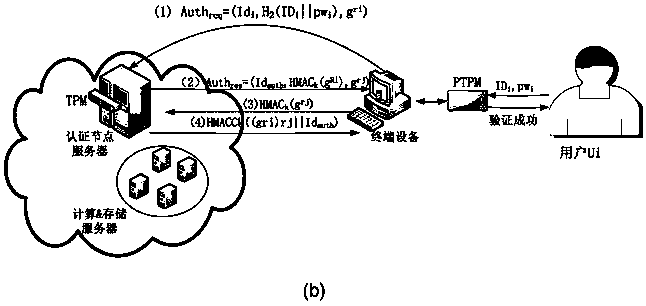
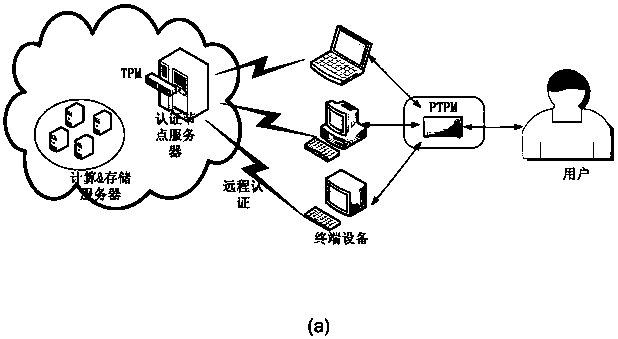
Two-factor authentication method based on portable TPM (PTPM) and certificateless public key signature for cloud
InactiveCN107733657AImprove computing efficiencyMake sure it's trueKey distribution for secure communicationPublic key for secure communicationPasswordTerminal equipment
The invention discloses a scheme for implementing two-way identity authentication between a user and cloud by applying a portable TPM (PTPM) and certificateless public key cryptography to a cloud environment, aiming at solving the security problems and deficiencies existing in identity authentication between the user and the cloud in a current cloud environment in a cloud computing mode. Comparedwith existing schemes, a new scheme has the following advantages: on the basis of realizing the uniqueness of user and cloud identities through the establishment of an identity management mechanism, firstly, the PTPM is adopted to ensure the security and credibility of a terminal platform and ensure the authenticity and correctness of authentication results between the cloud and the user, and moreover, the user is supported to use any terminal equipment to complete an identity authentication process with the cloud; secondly, the new scheme implements a 'password + key' two-factor authentication process based on a certificateless public key signature algorithm; and finally, the proposed scheme can significantly improve the computing efficiency of identity authentication between the user andthe cloud while ensuring the security of EUF-CMA.
Owner:SHENYANG NORMAL UNIV
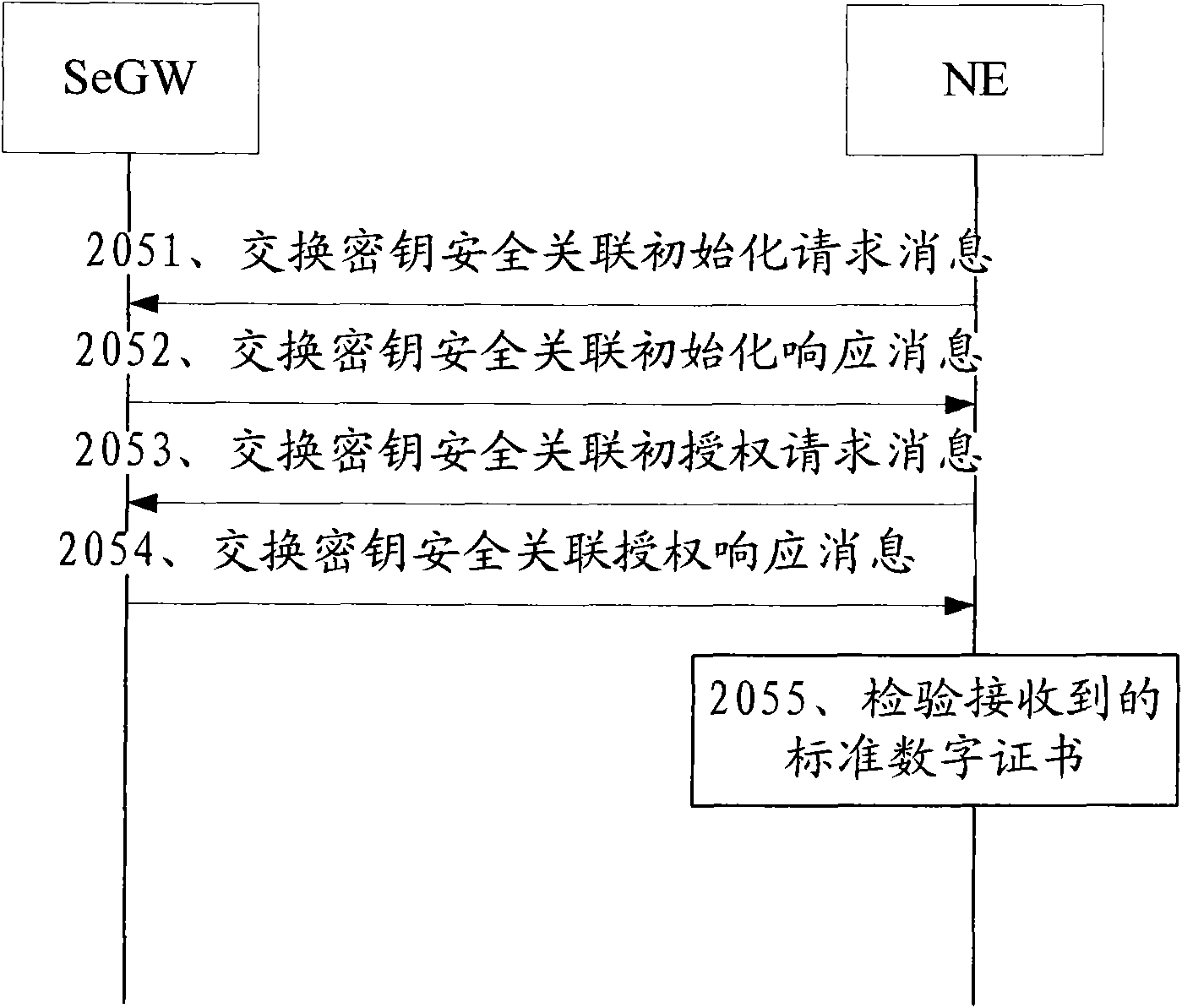
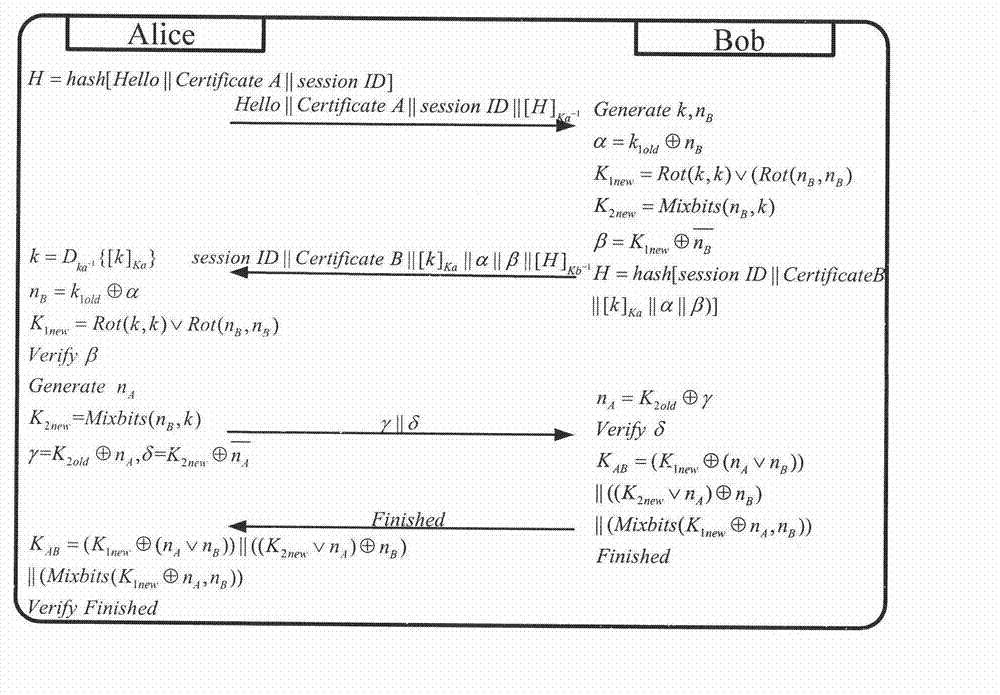
Wireless network lightweight class authentication key negotiation protocol based on digital certificate
InactiveCN102833748AReduce the number of communicationsSmall amount of calculationSecurity arrangementKey-agreement protocolPassword
The invention relates to a wireless network lightweight class authentication key negotiation protocol based on a digital certificate. A user identity is subjected to dual authentication through a 'certificate private key and protection key' dual authentication system and a 'protection key' dynamic negotiation mechanism by sharing a dynamic protection key according to a public key password; a user proves the session holdness and the private key owning property by exchanging the certificate according to a private key signature, so that primary authentication is executed; and due to protection key sharing, secondary authentication is executed. Important parameters are protected by two parties through the protection key after the last session is finished; the correctness of the key is confirmed through a new protection key calculated at the session; during each communication, when the parameters are exchanged, the correctness can be checked. Negotiation for key groups and parameter exchange adopt simple bit computation; and the key updating is confirmed by Finished messages. According to the protocol, a dynamic ID is set to dynamically select whether the shared old parameters are used for calculating the key of the session; and safety and high efficiency are guaranteed, and the flexibility of the protocol is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
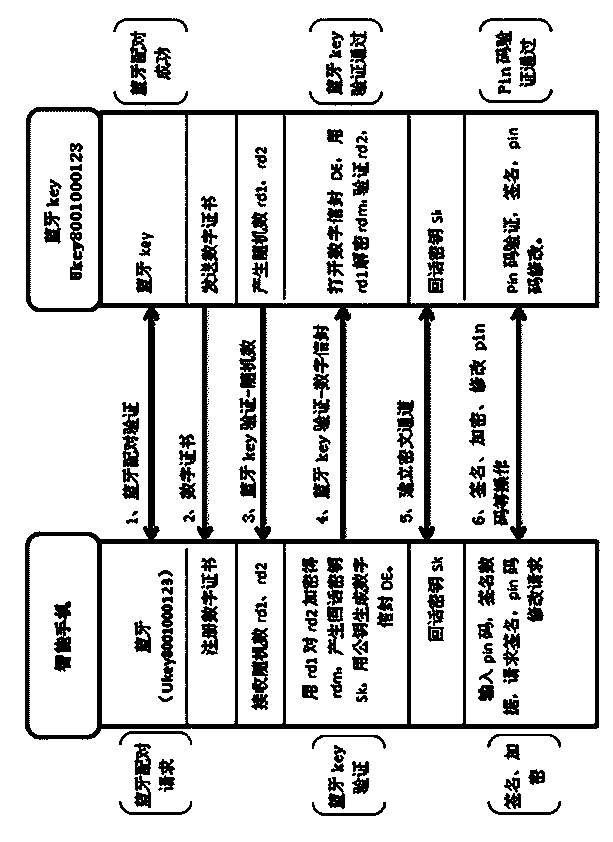
Mobile phone and Bluetooth key signature verification ciphertext communication method
ActiveCN104301115ATroubleshooting Service Security ChallengesMake sure to use the identityUser identity/authority verificationThird partyCiphertext
The invention provides a mobile phone and Bluetooth key signature verification ciphertext communication method. Mutual authentication is conducted on a mobile phone user and a Bluetooth key, the using identity of a Bluetooth key holder can be guaranteed, an established Bluetooth ciphertext channel is used for communication, so that Bluetooth communication is safe and reliable, the functions of ciphertext communication, encryption and decryption, electronic signature, signature verification and the like are achieved by signature authentication service on the mobile phone, safe and credible third party certification service is provided for the mobile phone user, and the difficult problem on the aspect of mobile phone service safety is truly solved.
Owner:浪潮(青岛)科技集团有限公司
Cheap signatures for synchronous broadcast communication
InactiveUS7464266B2Synchronising transmission/receiving encryption devicesUser identity/authority verificationHash functionClient-side
A method and system are configured for synchronous broadcast communications by applying signature keys using hashing functions. Each subsequent transmission in a sequence includes a signature key that can be verified by hashing to a preceding signature key from a previous portion of the sequence. The first transmission in the sequence is signed using a signature key that is known by the client device, typically verified using some other mechanism such as asymmetric key signatures. Each client device can utilize an internal counter for the current time or the block number in the transmission sequence to maintain synchronized transmissions in the even that a particular portion of the sequence is missed, and to validate signature keys. Since the signature keys can be validated when they are received but not predicted before they are received, the transmission is difficult to attack while synchronization is maintained.
Owner:MICROSOFT TECH LICENSING LLC
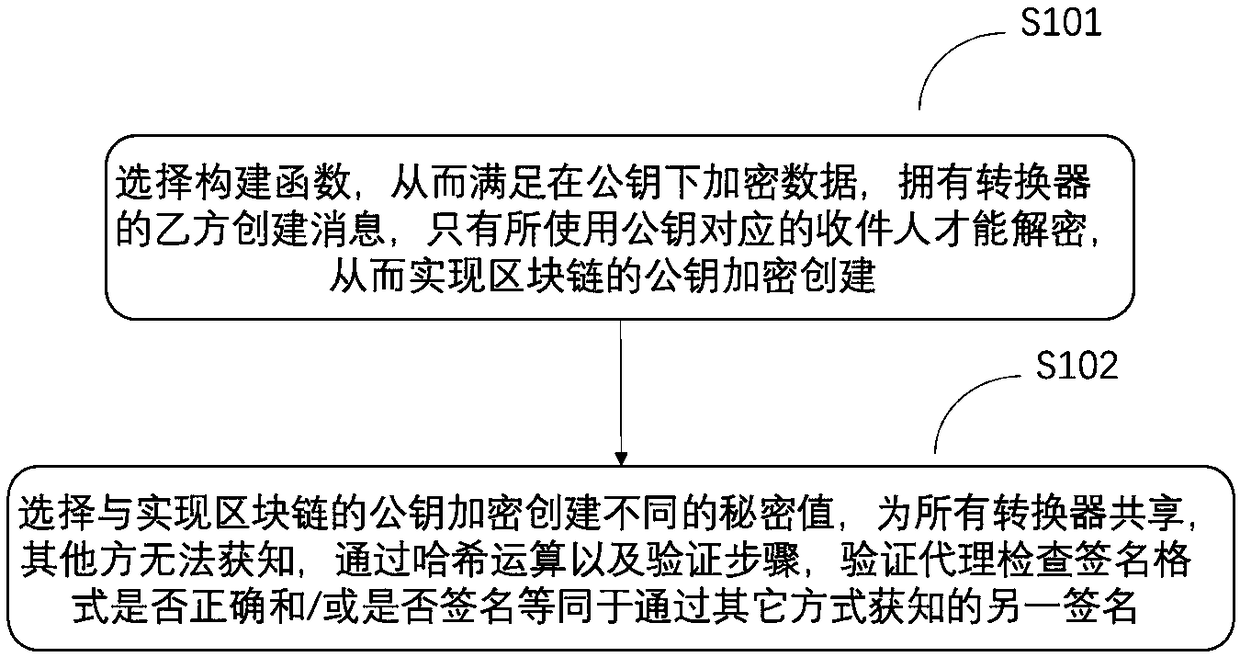
Method for creating public key encryption and key signature, apparatus, and readable storage medium
ActiveCN109274502AKey distribution for secure communicationPublic key for secure communicationHash functionKey signature
The invention discloses a method for creating a public key encryption and key signature of a block chain, comprises: step S101, constructing a function so as to encrypt data under a public key, creating a message by the party owning the converter, decrypting only the recipient using the public key, and decrypting only the corresponding secret key which cannot be obtained from the calculation of the public key, thereby realizing the public key encryption creation of a block chain; step S102, selecting a secret value different from the of the public key encryption of the block chain, and sharingthe secret value for all the converters, so that the other parties can not know, and verifying whether the proxy checks whether the signature format is correct and / or whether the signature is equal to another signature obtained by other means through the hashing operation and verification steps. Also disclosed are corresponding devices and readable storage media. The technical proposal of the present disclosure uses only symmetric encryption and a hash function to securely exchange keys, thereby creating cryptographic proof of authenticity, integrity, and non-repudiation in a basic and efficient manner, which cannot be reverse engineered.
Owner:CROSBIL LTD
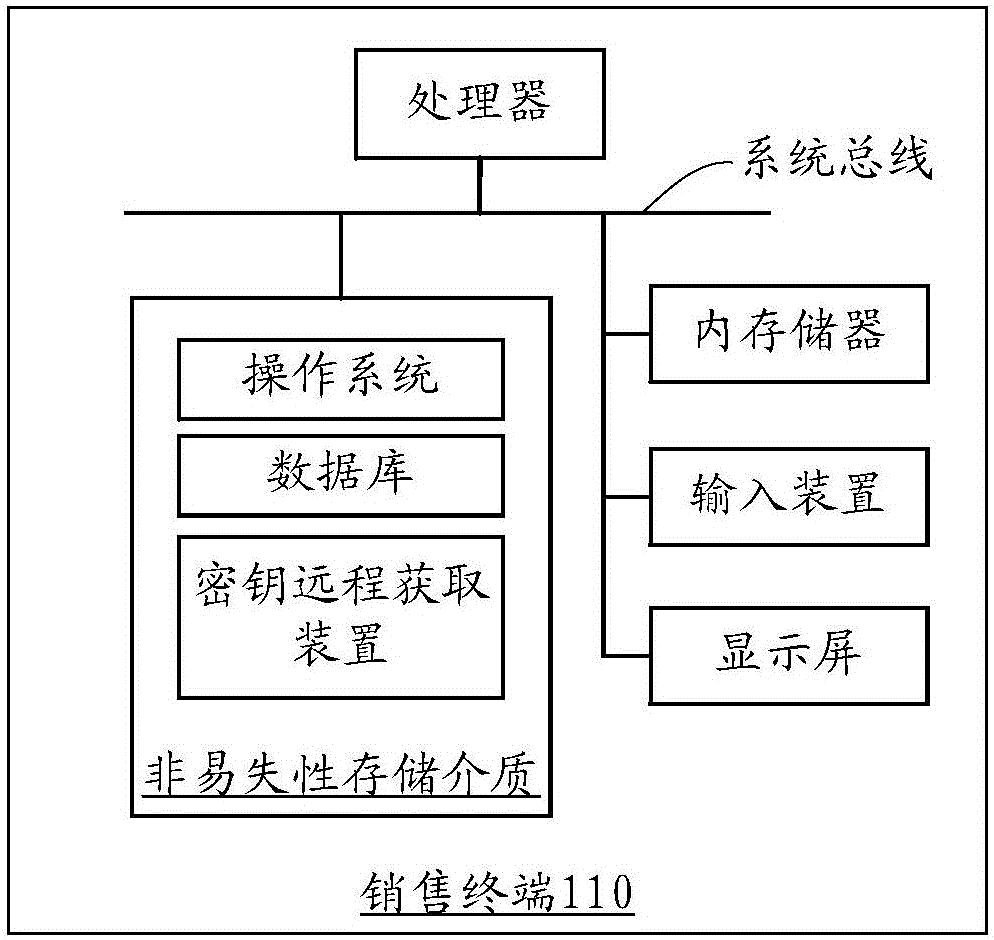
Secret key remote acquisition method and device
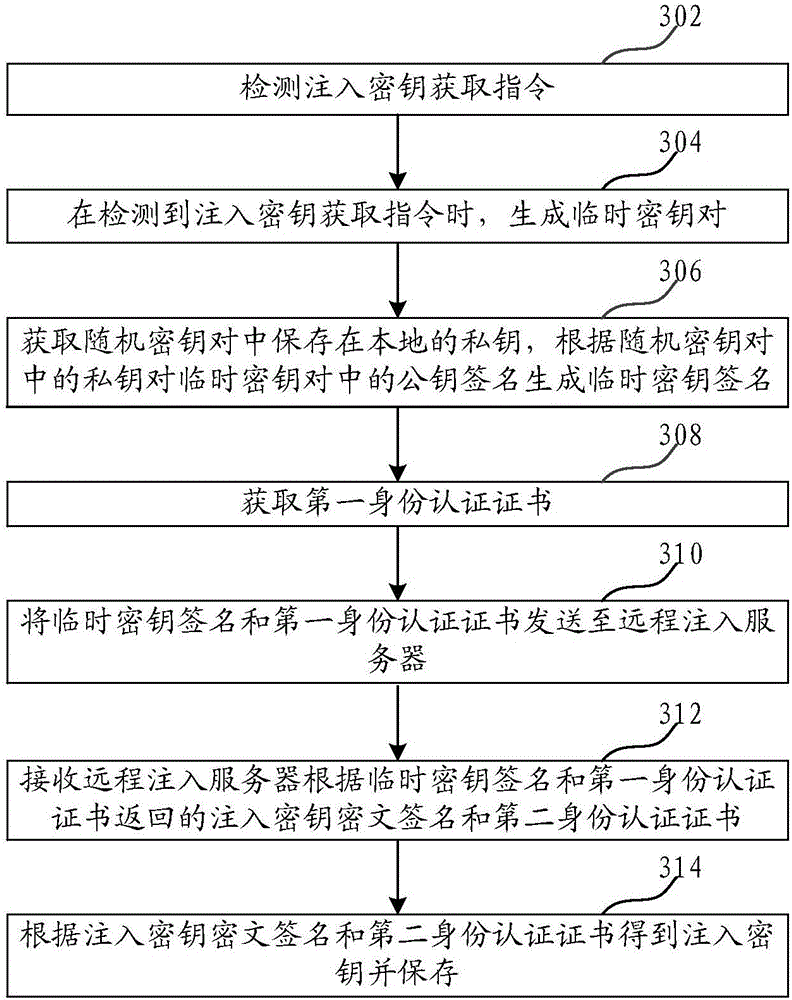
ActiveCN106789018ASecure transmissionSimplify the acquisition processKey distribution for secure communicationMultiple keys/algorithms usageCiphertextKey signature
The invention relates to a secret key remote acquisition method and device. The method includes the steps: detecting injected secret key acquisition instructions; generating temporary secret key pairs when the injected secret key acquisition instructions are detected; acquiring private keys saved in the locality in the random secret key pairs, and enabling public key signatures in the temporary secret key pairs to generate temporary secret key signatures according to private key pairs in the random secret key pairs; acquiring first identity authentication credentials; transmitting the temporary secret key signatures and the first identity authentication credentials to a random injection server; receiving injected secret key cipher text signatures and second identity authentication credentials returned by the random injection server according to the temporary secret key signatures and the first identity authentication credentials; acquiring and saving injection secret keys according to the injected secret key cipher text signatures and the second identity authentication credentials. According to the secret key remote acquisition method and device, the steps acquiring the secret keys to a fixed place are avoided, acquiring processes of the secret keys are simplified, consumed time for acquiring the secret keys is shortened, and the acquisition efficiency of the secret keys is improved.
Owner:PAX COMP TECH SHENZHEN
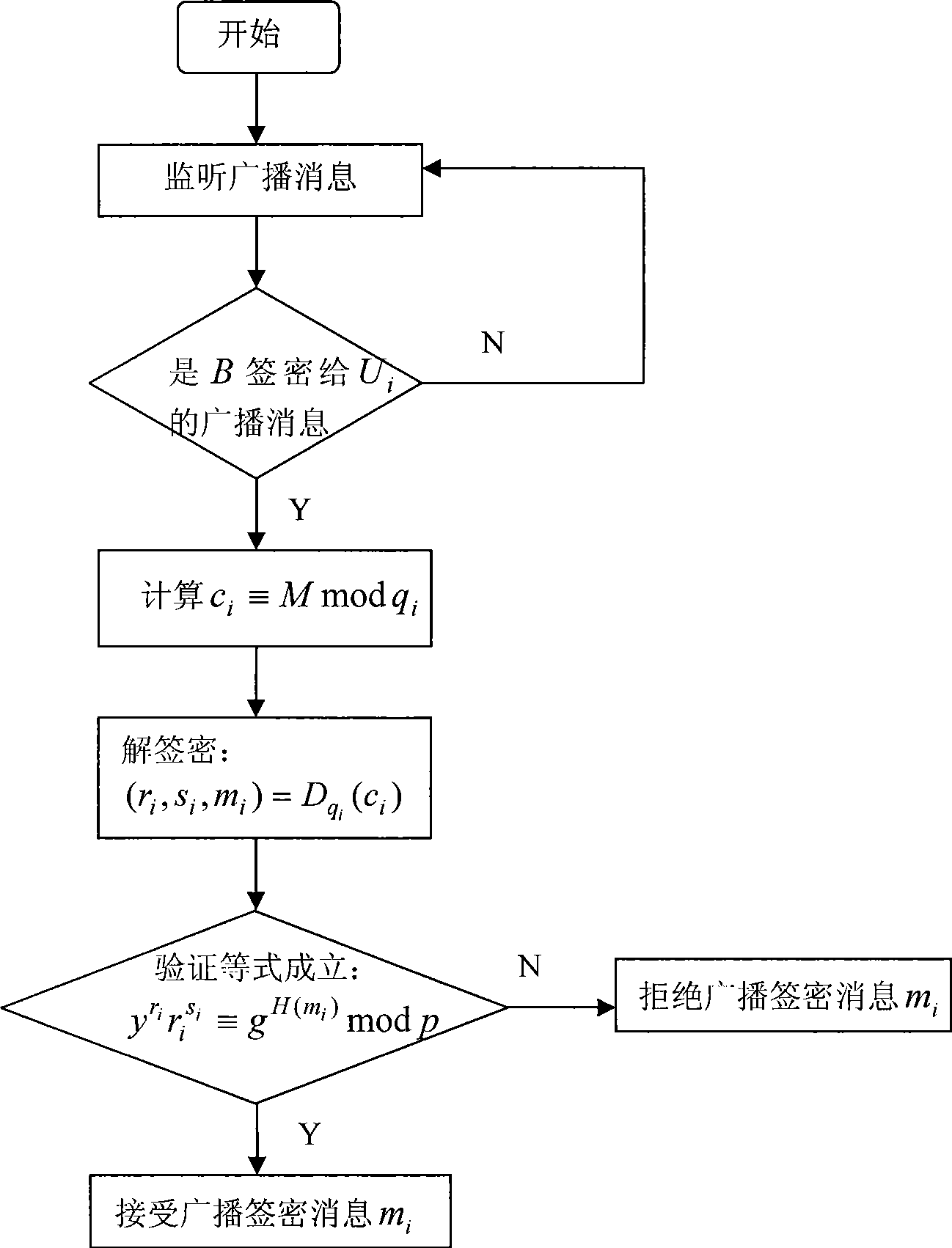
Authentication method by broadcast signature and ciphering
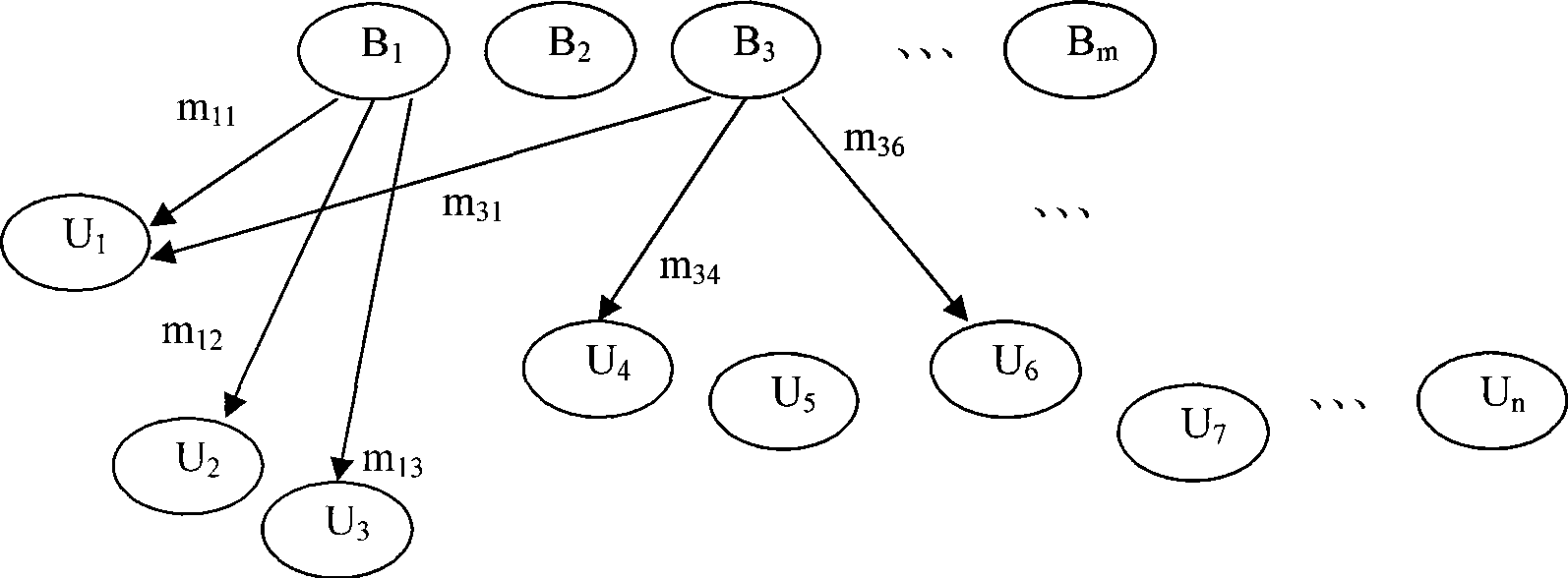
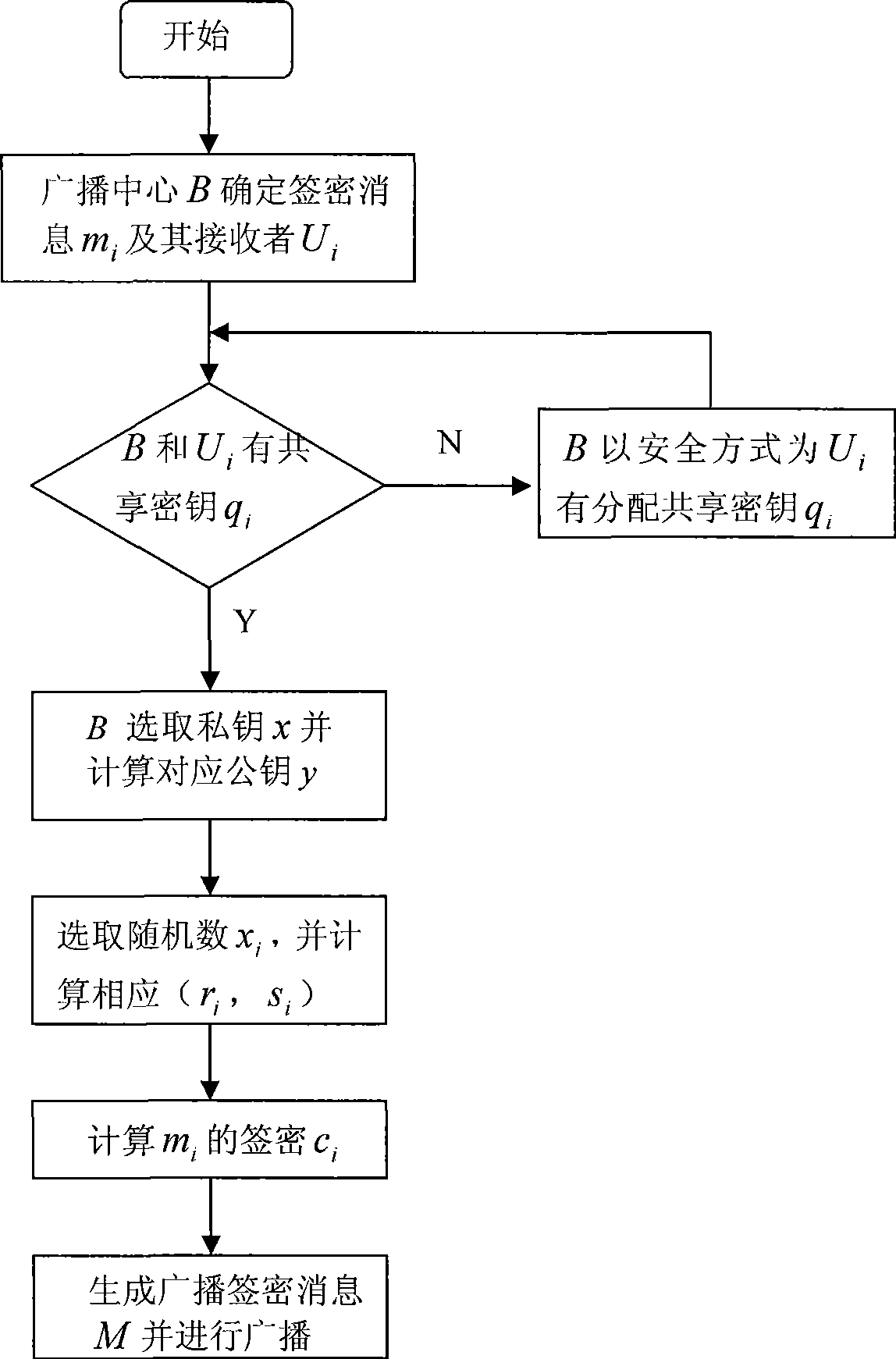
InactiveCN101505301AHigh strengthUnforgeableSpecial service provision for substationPublic key for secure communicationSigncryptionHigh intensity
The invention discloses a broadcast signcryption authentication method, which comprises the following steps that: 1) system parameters are set; 2) a broadcast center calculates public key signature according to the parameters, and uses a user secret key to encrypt message to be broadcasted; 3) the broadcast center broadcasts the encrypted message acquired in step 2) to a user group; and 4) the user receives the encrypted message broadcasted in the broadcast center, uses a private key to decrypt the signature and verifies the validity of the signature. The method carries out two-layer confidential encapsulation of signature and encryption for the message, and broadcasts and mass-sends different messages to a group of users in once broadcast; and only specific authorized users can receive the designated message; therefore, the method has high-strength information confidentiality, signcryption information unforgeability and signcryption information non-repudiation. The method can regulate legal user groups at any time according to actual demand, but does not need to newly distribute new shared secret keys, has high flexibility, can make full use of communication bandwidth, saves cost, and greatly improves the communication efficiency.
Owner:SHIJIAZHUANG RAILWAY INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com