Safe data information transmission method
A technology for secure transmission and data information, applied in the field of information security, to achieve the effect of transmission security and improving confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
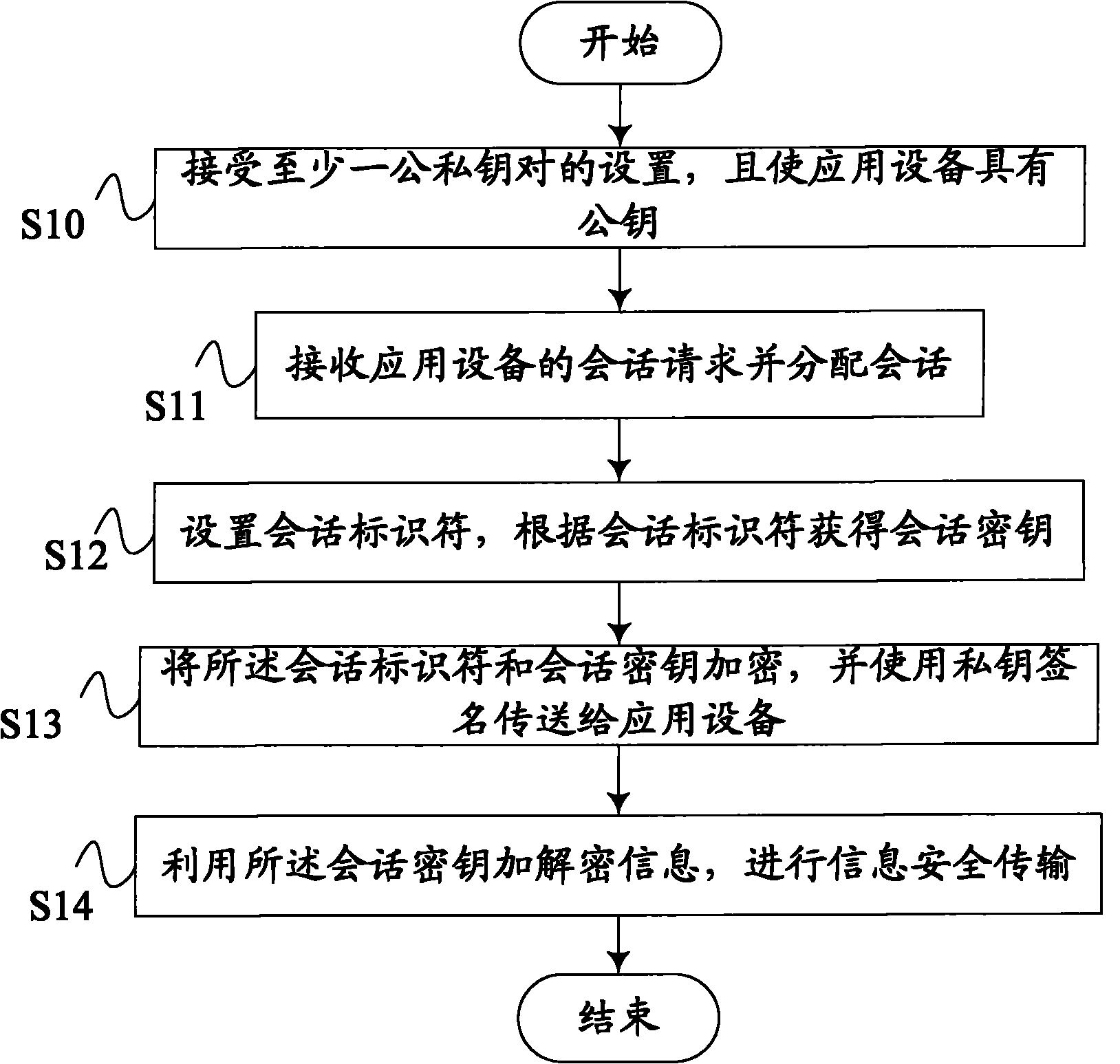
[0026] refer to figure 1 , the present invention proposes a method for secure transmission of data information in the first embodiment to make the data transmission between the information security device and the application device more secure, and the method includes the steps of:
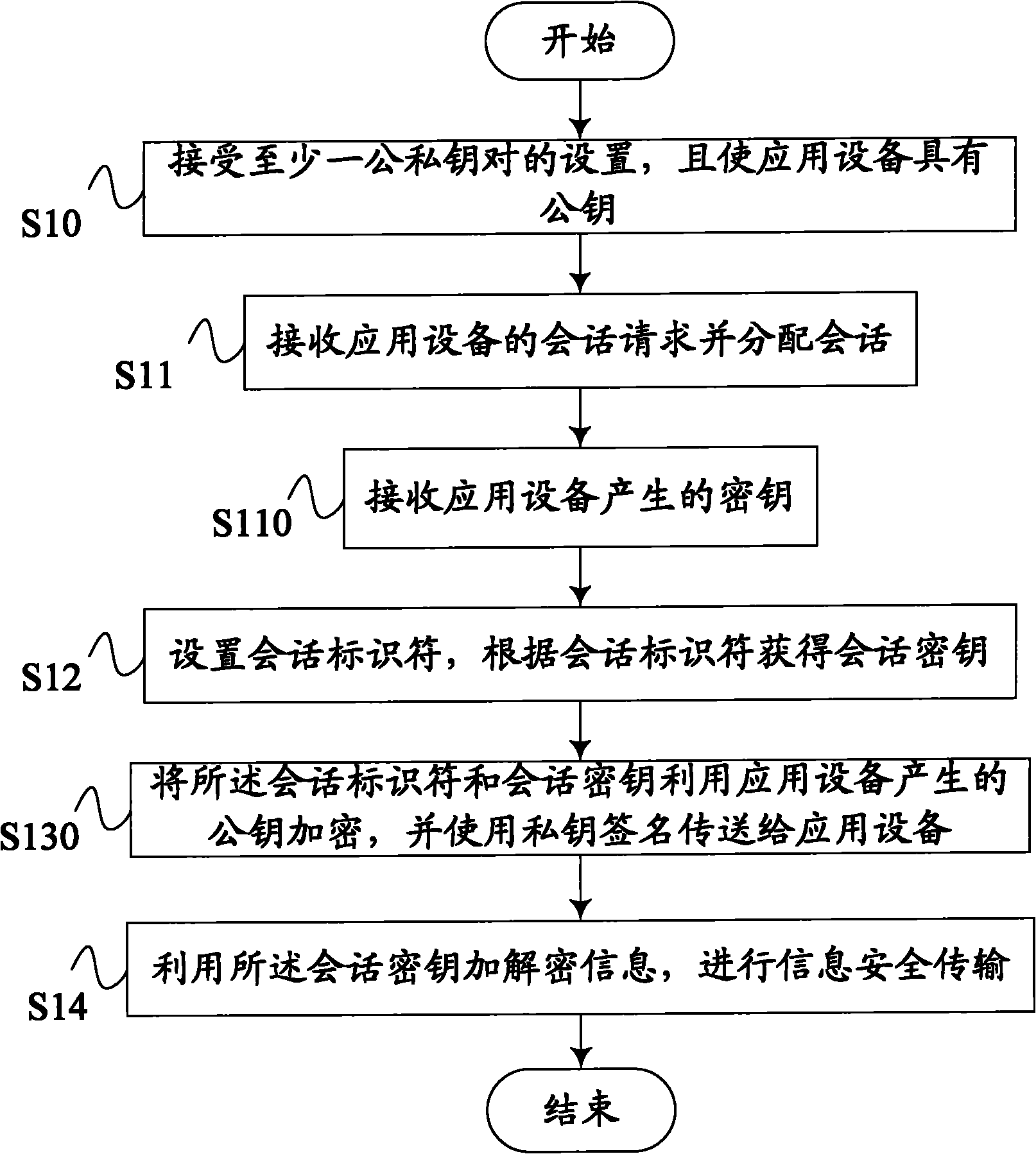
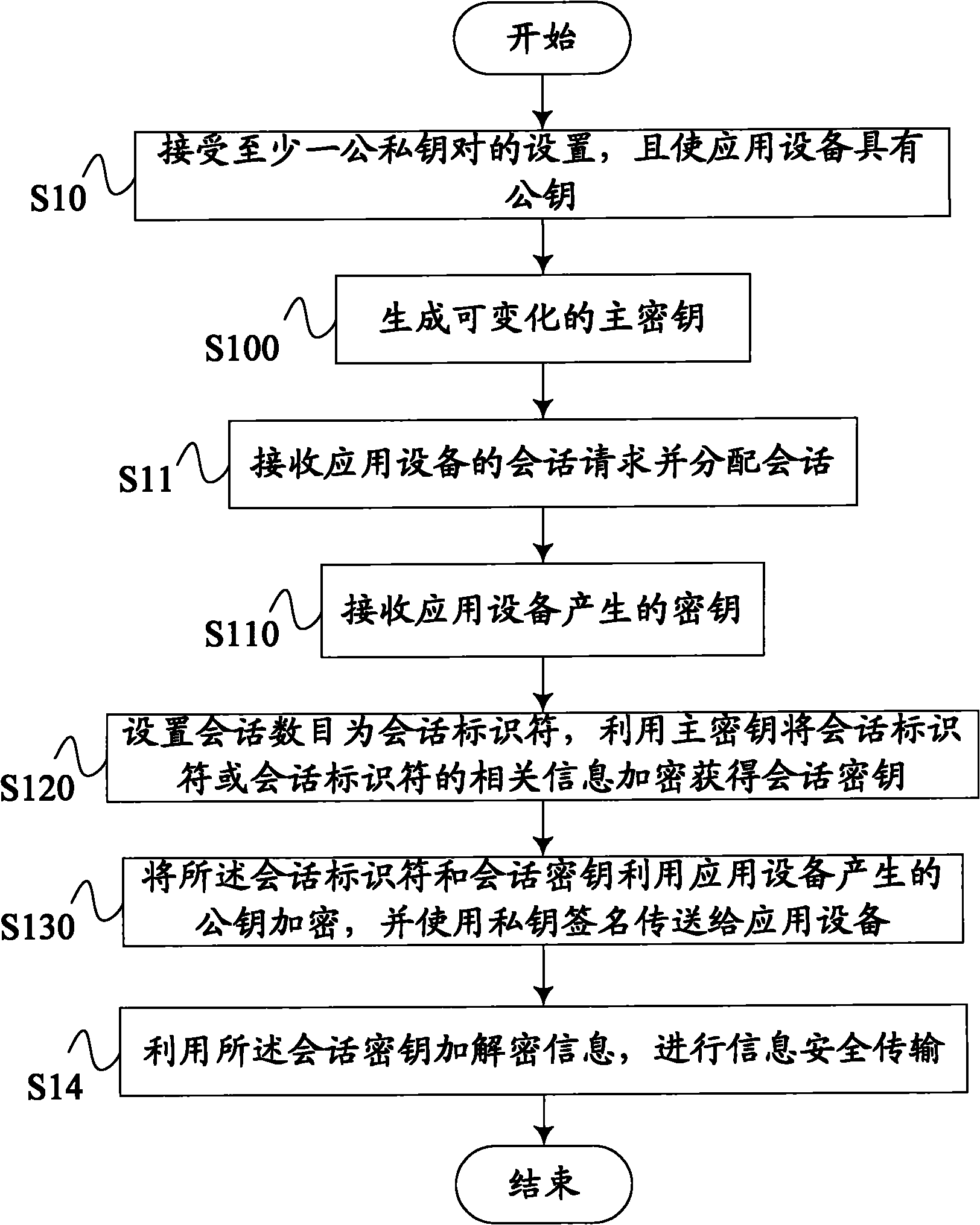
[0027] S10. Accept the setting of at least one public-private key pair, and enable the application device to have the public key;
[0028] S11. Receive a session request from the application device and allocate the session;
[0029] S12. Set a session identifier, and obtain a session key according to the session identifier;
[0030] S13. Encrypt the session identifier and session key, and use the private key to sign and transmit them to the application device;
[0031] S14. Use the session key to encrypt and decrypt data information, and perform secure transmission of data information.
[0032] In this embodiment, the information security device may be a device with a cryptographic operation fu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com