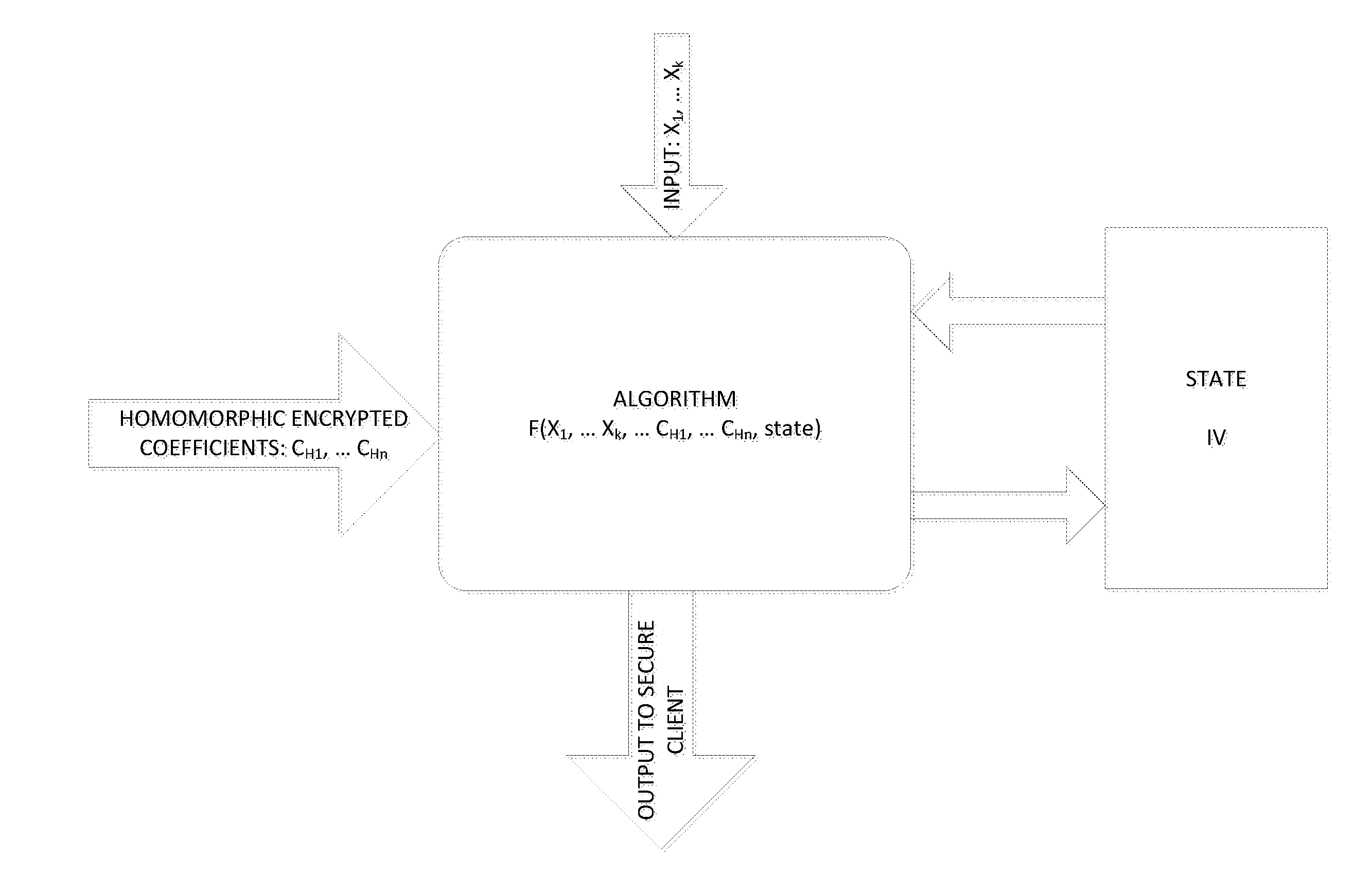Patents
Literature
92results about How to "Ensure confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for mapping at least two authentication devices to a user account using an authentication server
ActiveUS20180198614A1Improve securityReduce security risksSynchronising transmission/receiving encryption devicesUser identity/authority verificationSecure communicationAuthentication server
The invention provides a method for mapping at least two authentication devices to a user account using an authentication server, where each authentication device connects to the authentication server using a secured communication channel; their mapping to the user account is recorded on the authentication server, and, when a transfer of data between the authentication devices mapped to the user account occurs, the data is passed over from the first authentication device to the authentication server using a secured communication channel and from the authentication server to another authentication device mapped to the account of said user using a secured communication channel, where the aforesaid secured communication channel is created by the second authentication device. This procedure allows the use of a single personal local authentication factor for multiple authentication devices and increases the security of authentication of devices with authentication servers.
Owner:ADUCID
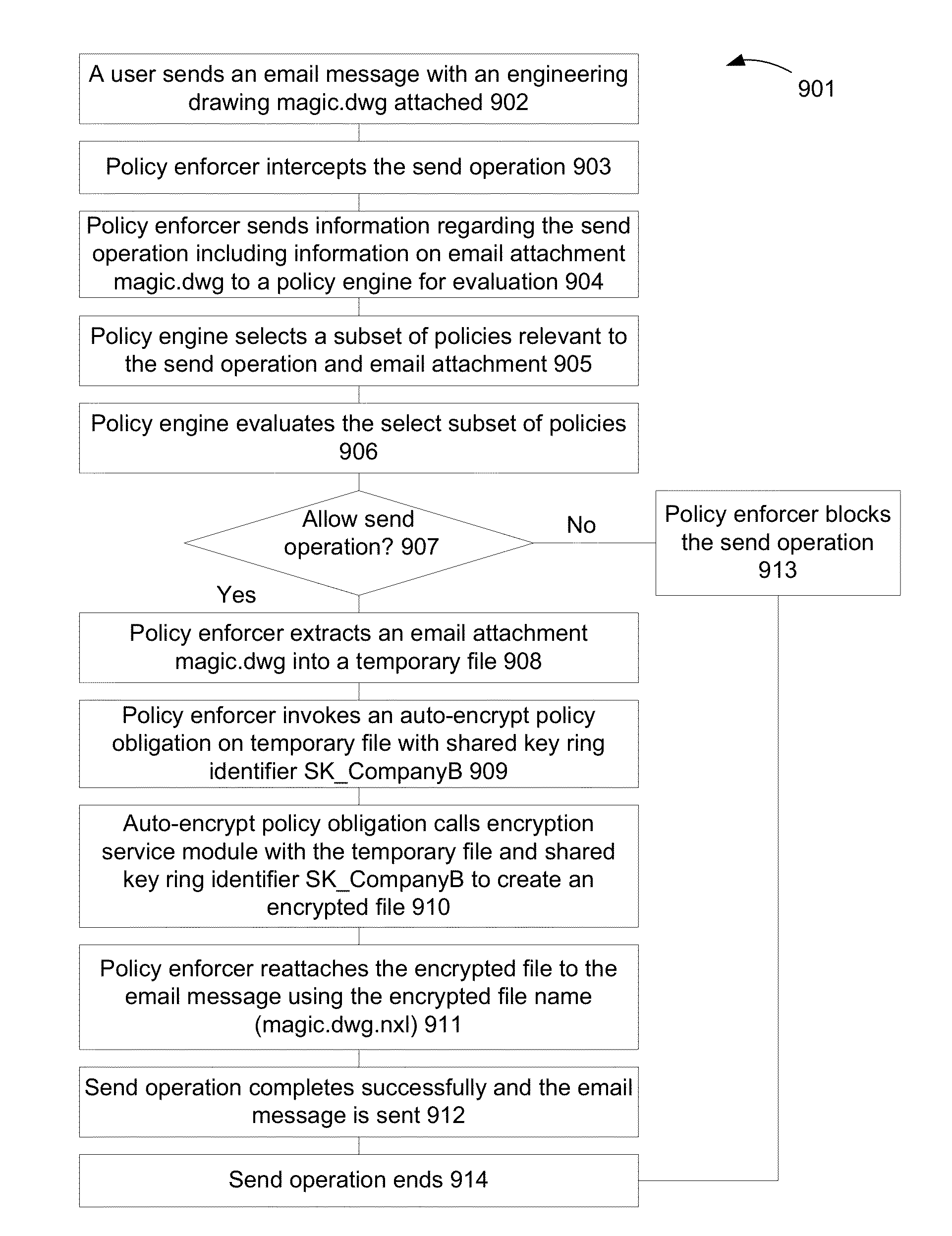
Protecting Information Using Policies and Encryption
ActiveUS20130097421A1Ensure confidentialityAvoid data lossDigital data protectionSecuring communicationDocumentation procedureConfidentiality
A technique and system protects documents at rest and in motion using declarative policies and encryption. Encryption in the system is provided transparently and can work in conjunction with policy enforcers installed at a system. A system can protect information or documents from: (i) insider theft; (ii) ensure confidentiality; and (iii) prevent data loss, while enabling collaboration both inside and outside of a company.
Owner:NEXTLABS
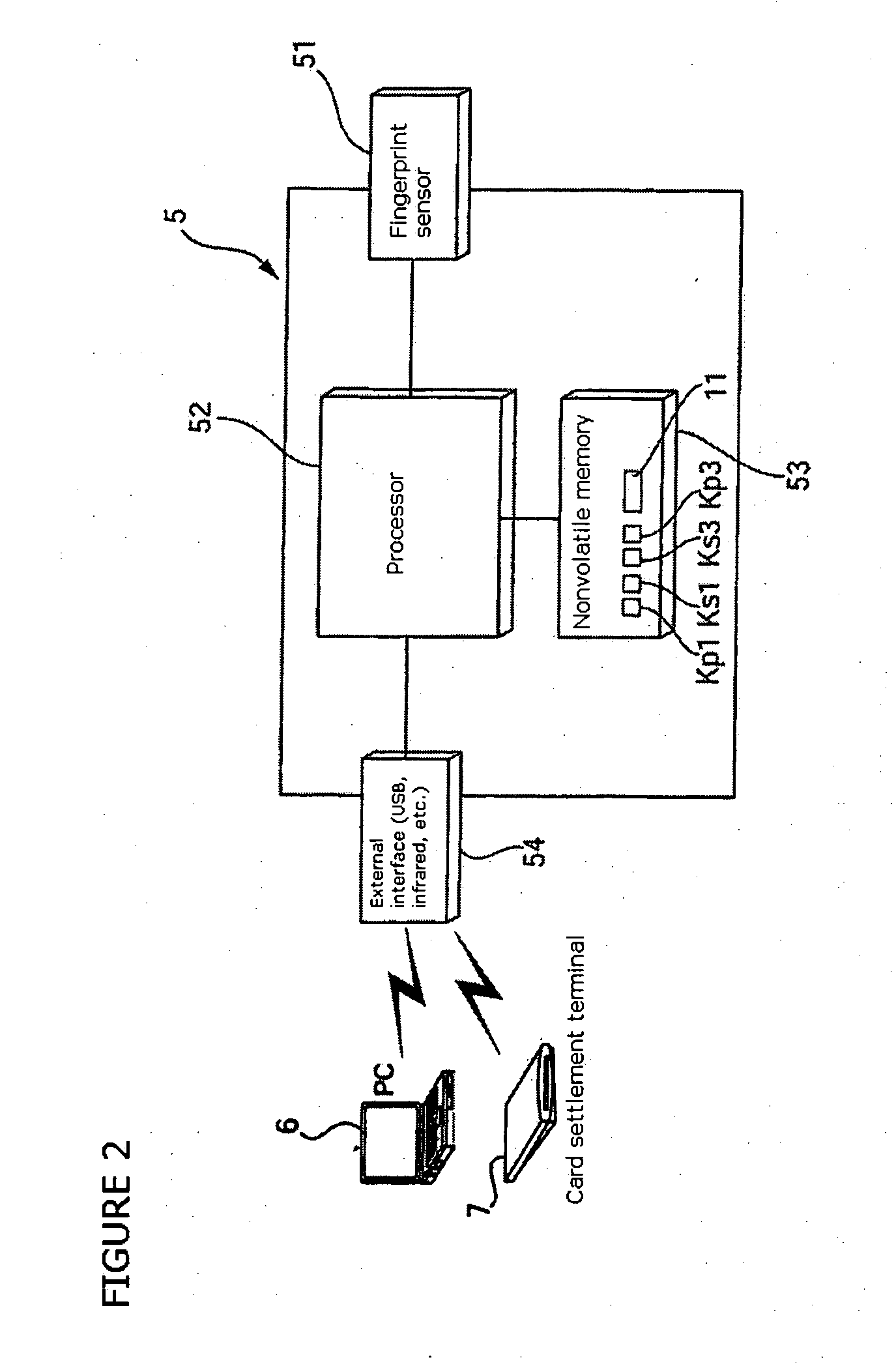
Card settlement method using portable electronic device having fingerprint sensor
InactiveUS20060229988A1Improper useEnsure confidentialityComputer security arrangementsIndividual entry/exit registersFingerprintComputer hardware
In a card settlement system using a portable electronic device having a fingerprint sensor, a credit card and a portable electronic device (5) having a fingerprint sensor are issued to a person who has made application. To this electronic device (5), card information (12), a storage public key Kp1, and
Owner:PARA3
Protecting information using policies and encryption
ActiveUS8843734B2Ensure confidentialityAvoid data lossUnauthorized memory use protectionHardware monitoringConfidentialityDocumentation
A technique and system protects documents at rest and in motion using declarative policies and encryption. Encryption in the system is provided transparently and can work in conjunction with policy enforcers installed at a system. A system can protect information or documents from: (i) insider theft; (ii) ensure confidentiality; and (iii) prevent data loss, while enabling collaboration both inside and outside of a company.
Owner:NEXTLABS INC
Security protection method of communication data of special electricity public network
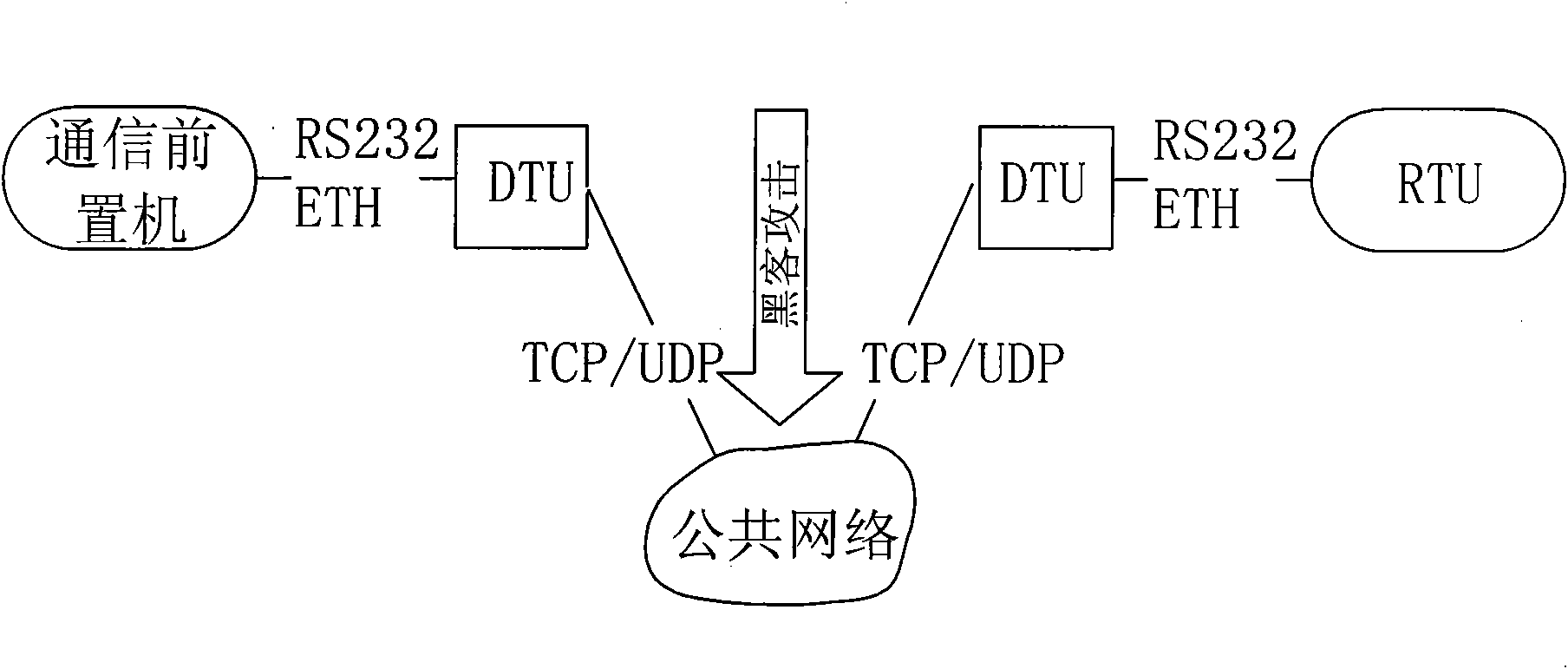
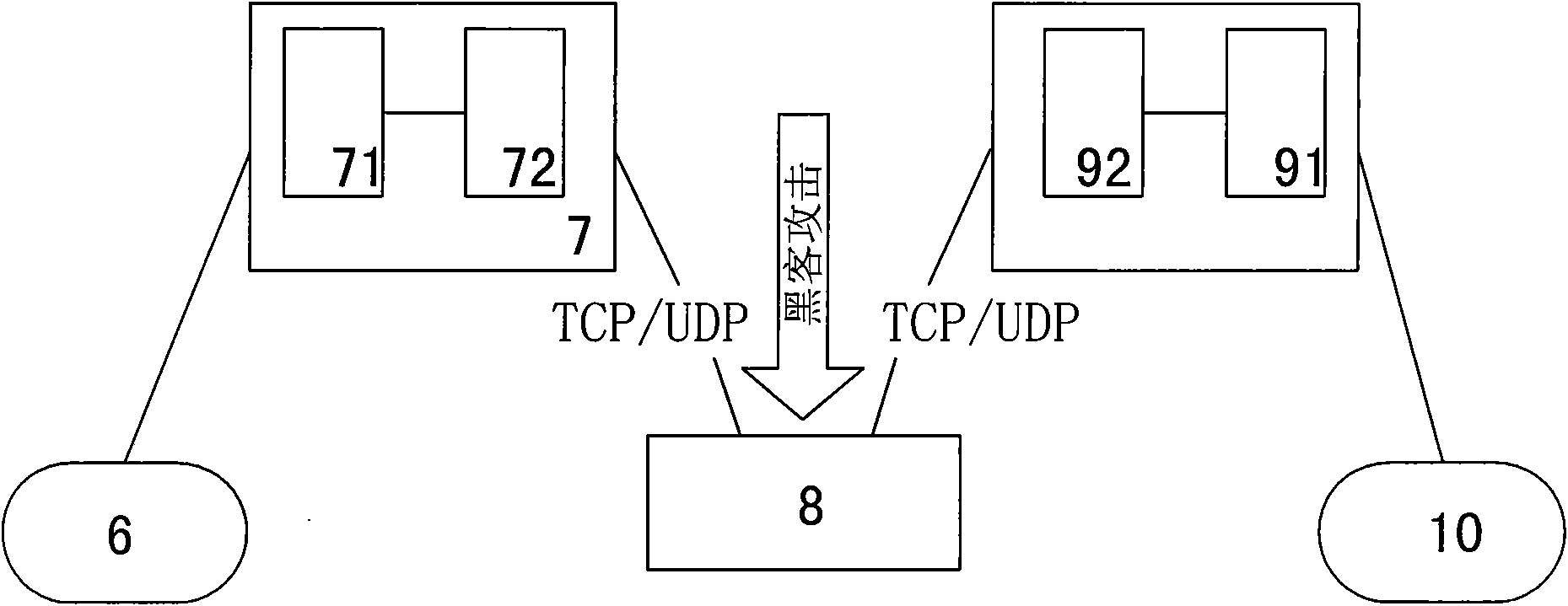
ActiveCN101662359AReal-time uninterruptible productionControl securityNetwork connectionsSecuring communicationCommunications securityElectricity
The invention discloses a security protection method of communication data of a special electricity public network, which provides secure and reliable data communication for the data communication ofthe special electricity public network by adopting the technical means of network isolation, right control, identity authentication and transmission encryption, realizes the purpose of securely usingthe public network for communication at any time and in any places without making any change to the application environment or software. In the process of application, a calling telecontrol communication security gateway (7) and a called telecontrol communication security gateway (9) are connected to a public network (8) by dialing; an encrypted public network communication channel is establishedfor the communication between a communication front-end processor (6) and a remote RTU (10); and the data is connected with the telecontrol communication security gateway (7) from the communication front-end processor (6) through a serial port or network, connected with the public network (8) through the calling telecontrol communication security gateway (7), connected with the called telecontrolcommunication security gateway (9) from the public network (8), and then connected with the remote RTU (10) through the serial port or the network. The invention can be widely applied to the field ofsecurity protection of the communication data of the public network.
Owner:CHINA SOUTHERN POWER GRID COMPANY +1
Method and system for controlling communication between an uicc and an external application
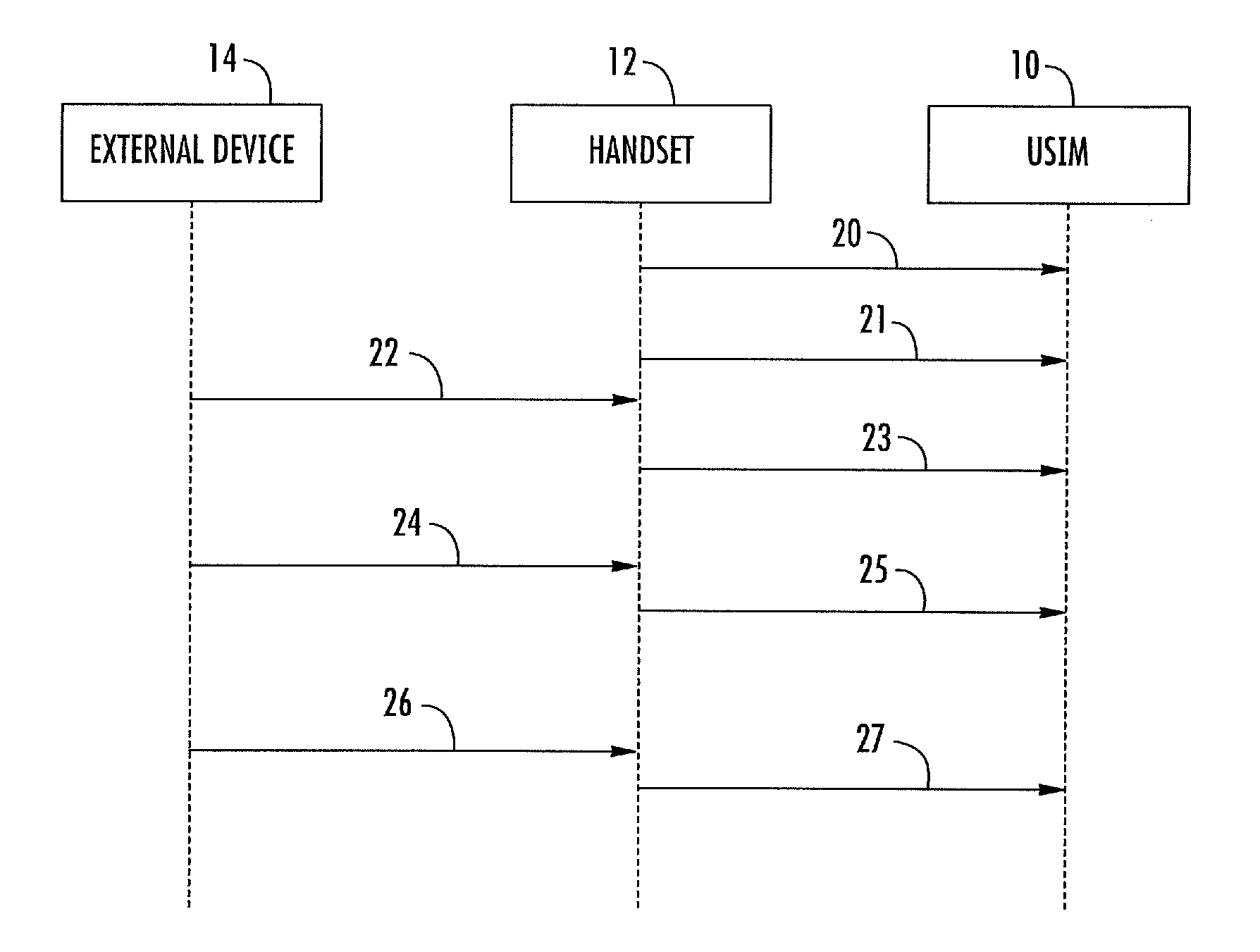
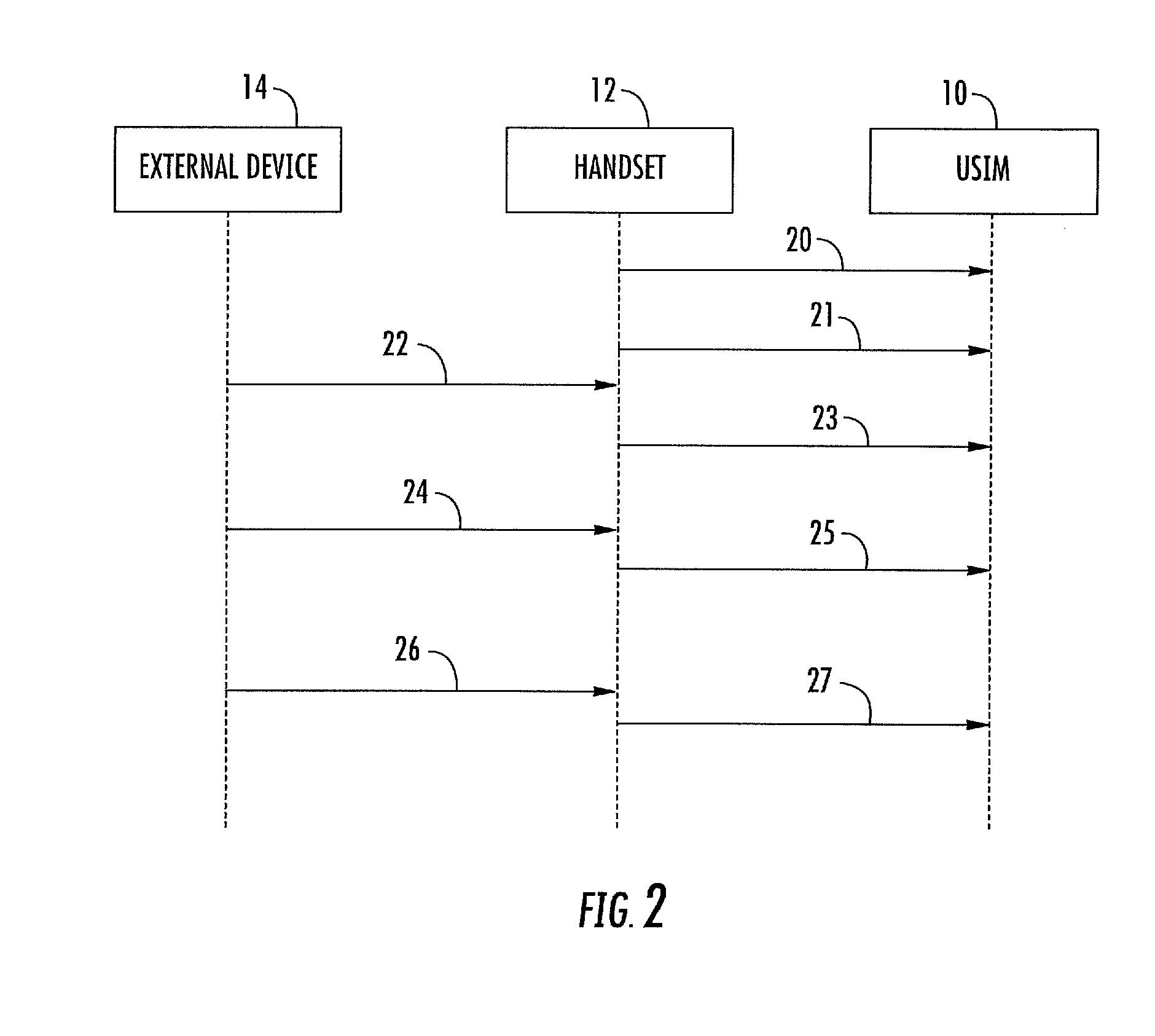
ActiveUS20120172016A1Ensure confidentialityDifficult to eavesdropSpecial service for subscribersConnection managementExternal applicationComputer network
A method may be for controlling communication between a UICC, a handset including the UICC, and an external device associated with an external application running outside the handset. The method may include switching on the UICC by the handset, executing a first initialization procedure by the handset to establish a first communication session between the handset and the UICC, establishing a second communication session between the UICC and the external device, and executing a second initialization procedure between the external device and the UICC. The method may include retrieving an attribute of the handset by the UICC after completing the first initialization procedure, retrieving an attribute of the external device via the handset by the UICC after the completing the second initialization procedure, and comparing the attribute of the handset with the attribute of the external device to distinguish the second communication session from the first communication session.
Owner:STMICROELECTRONICS INT NV
Method and system for homomorphicly randomizing an input
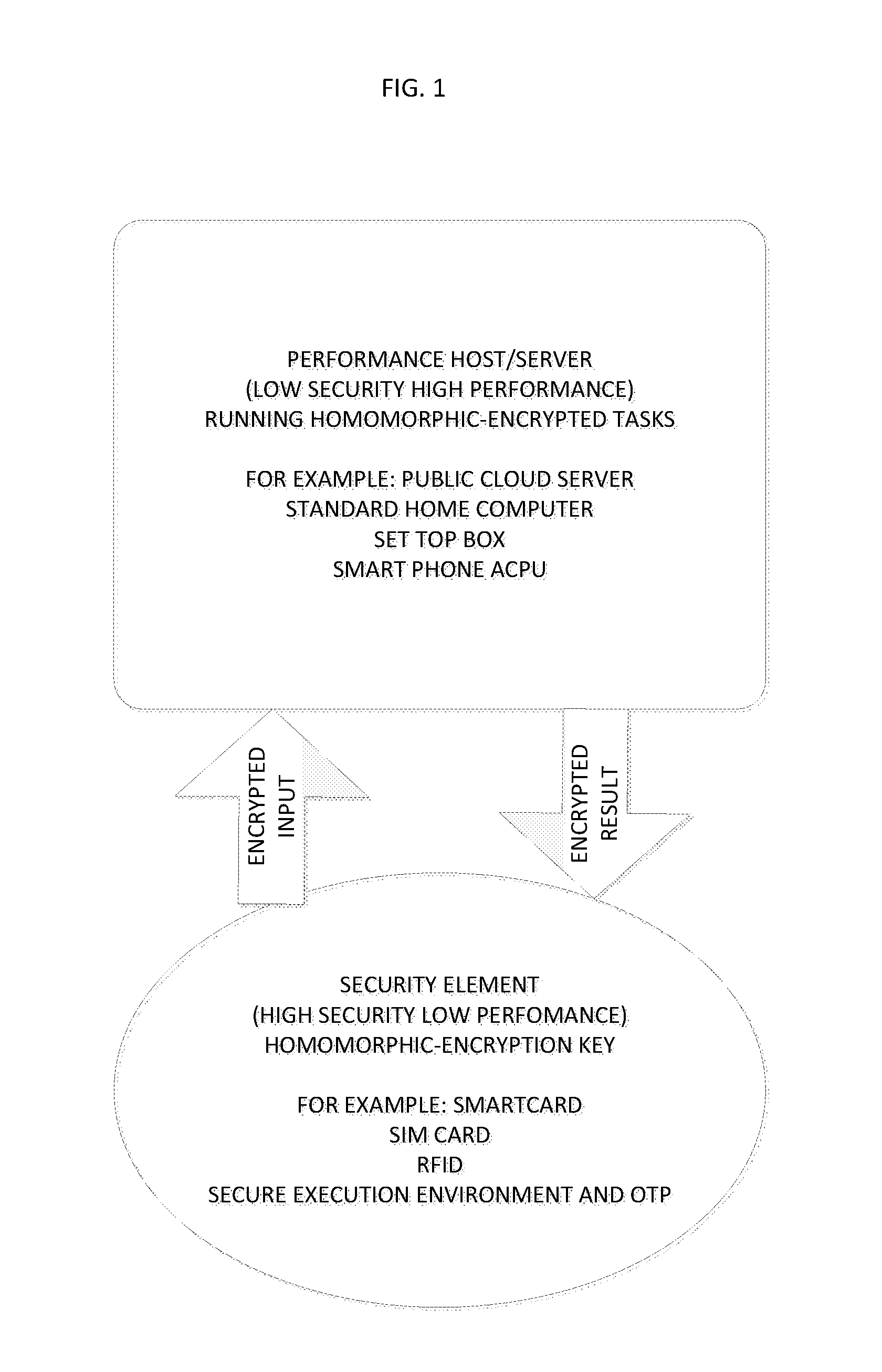
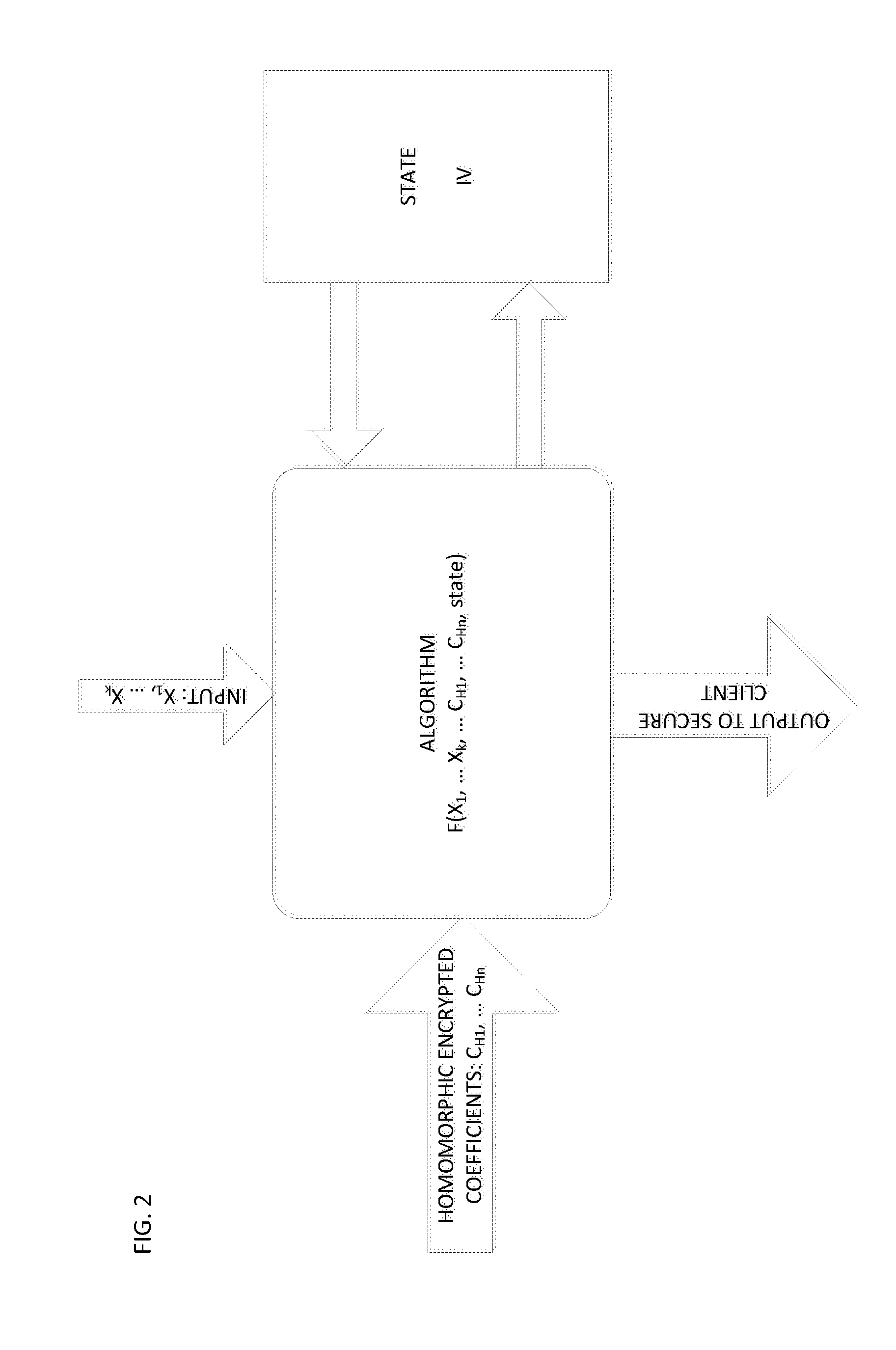
ActiveUS20150215123A1Easy to useEnsure confidentialityKey distribution for secure communicationRandom number generatorsThird partyAlgorithm
A fully homomorphic method and system for randomizing an input, wherein all computations are over a commutative ring is described. Equivalent methods for performing the randomization using matrices and polynomials are detailed, as well as ways to mix the matrix and polynomial functions. Addition, multiplication, and division of the matrix and polynomial functions is further described. By performing computations of the functions modulo N over a ring ZN, the functions are usable as encryption functions. The method and system can also be used for verifying that a returned result of a calculation performed by a third party is valid for any of the calculations described herein. Related methods, systems, and apparatus are also described.
Owner:CISCO TECH INC
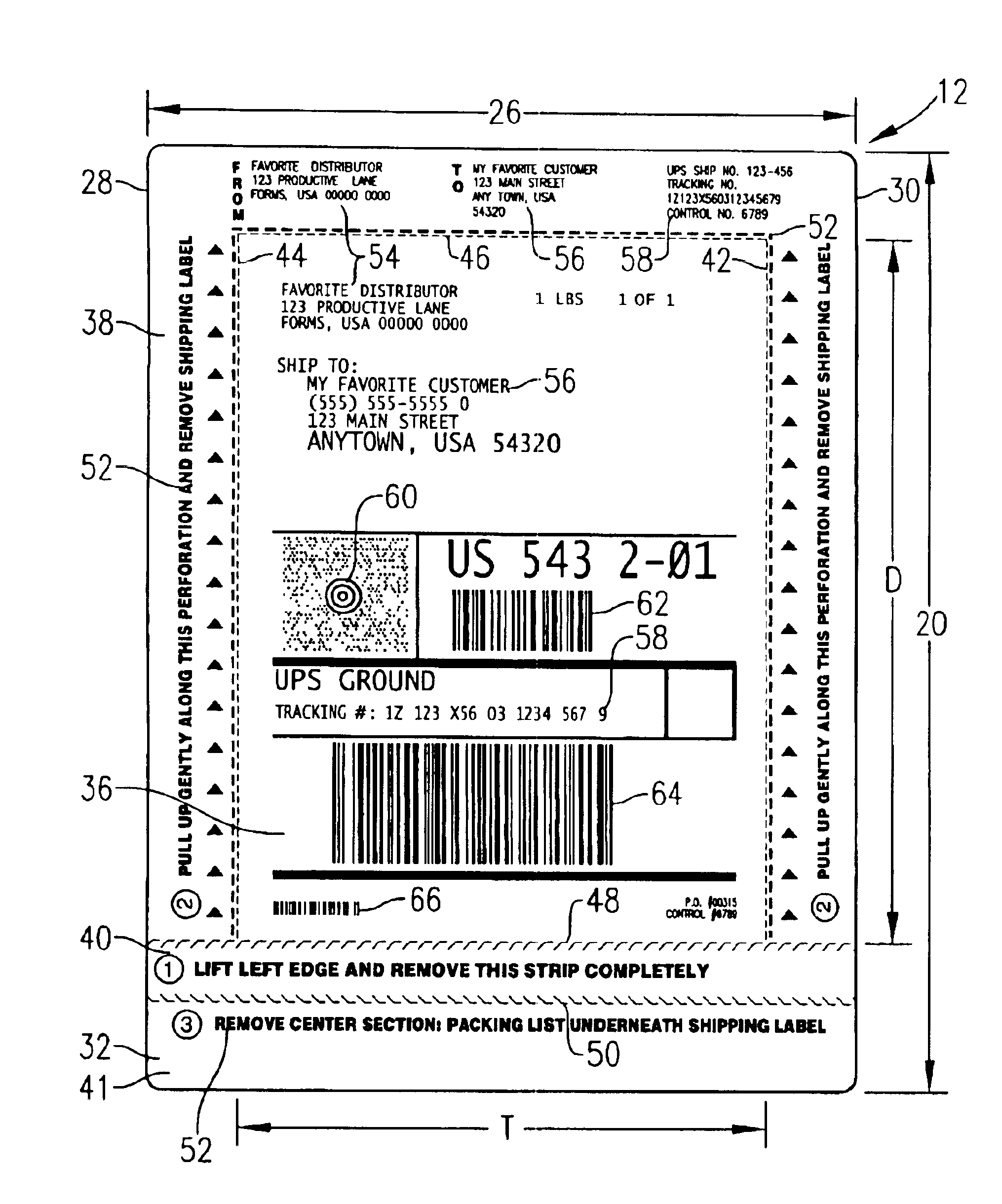
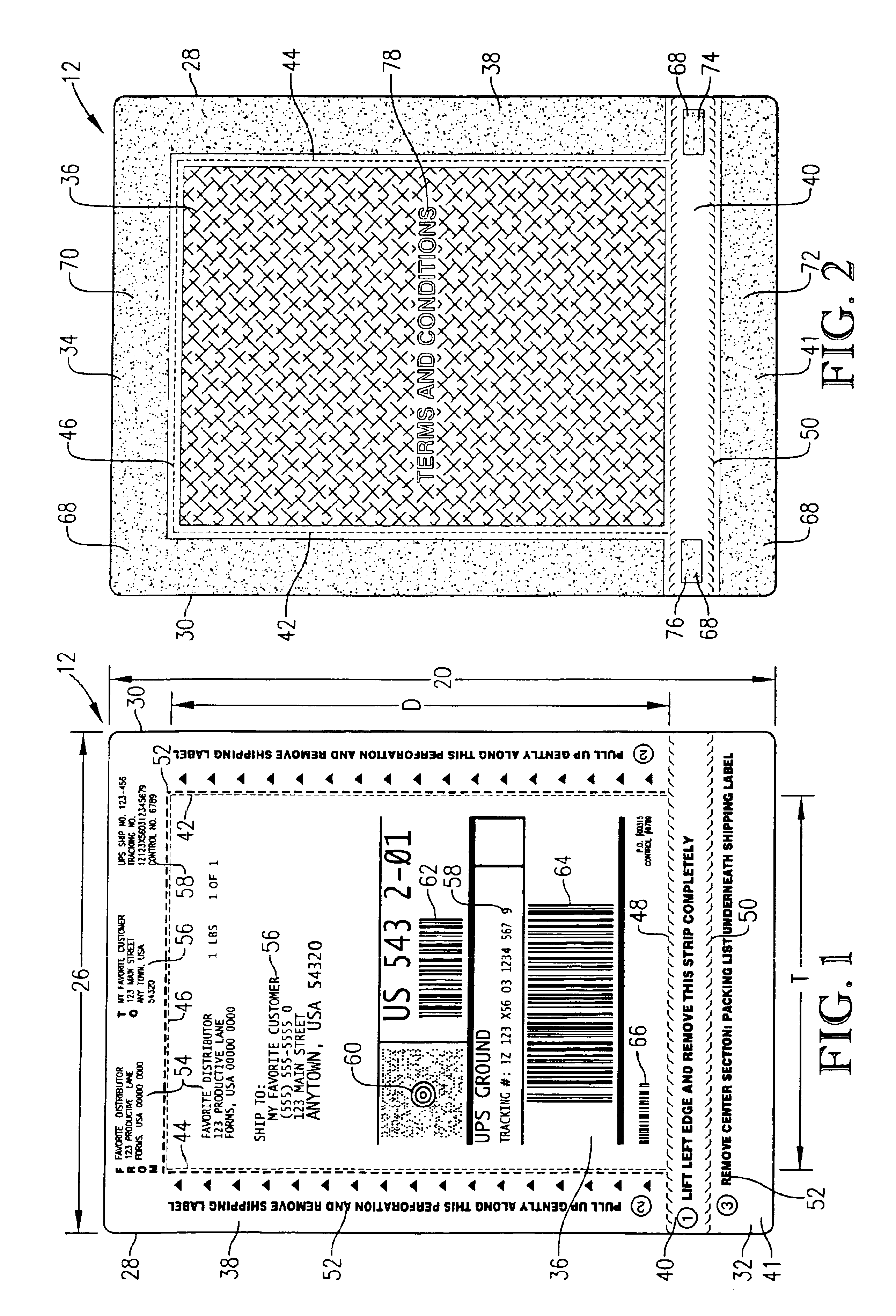
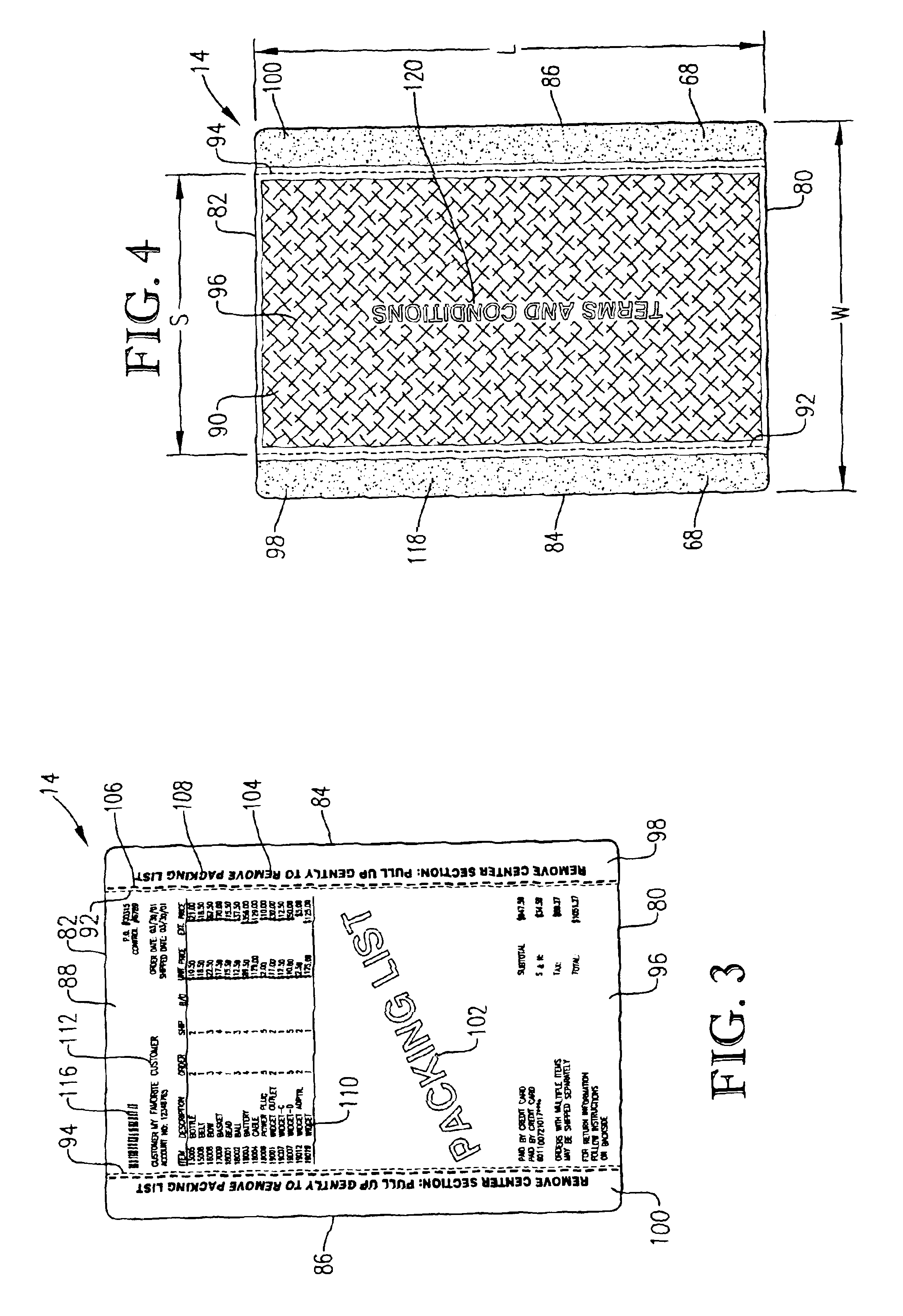
Sequentially placed shipping and packing label system
A system for providing a shipping label and a packing list on a container is provided which enables rapid and automated sequential application of a packing list and a shipping label to the container. The shipping label is configured complemental to the packing list whereby the packing list may first be adhered directly to the container and then the shipping label may be placed thereover. The shipping label may be applied over the packing list while the container moves continuously down a conveyor. The invention further includes an apparatus for sequentially applying the packing list and then the shipping label, and a method for applying the packing list and shipping label in registry.
Owner:PREMIER PRINT & SERVICES GROUP
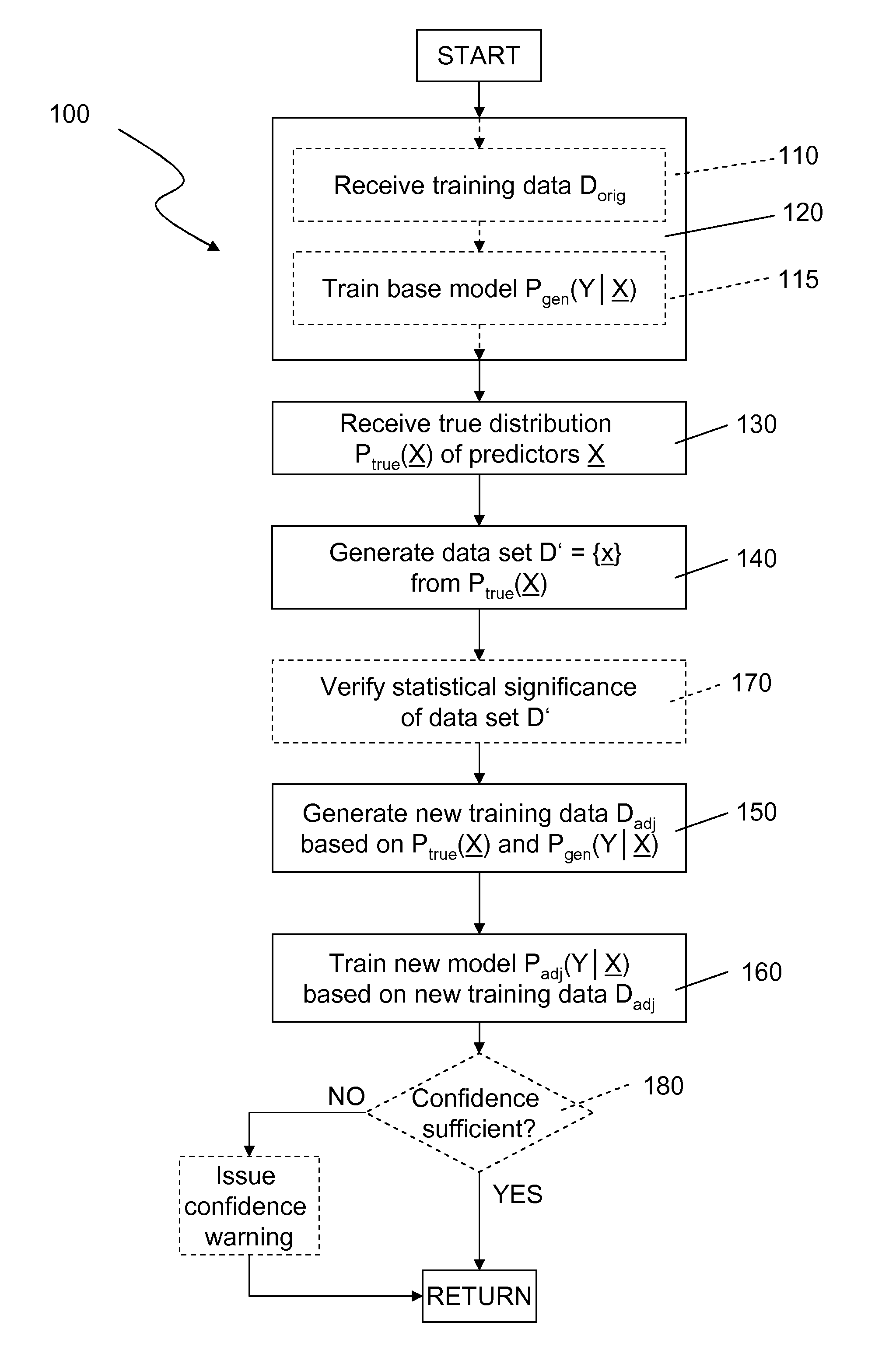
Predictive modeling
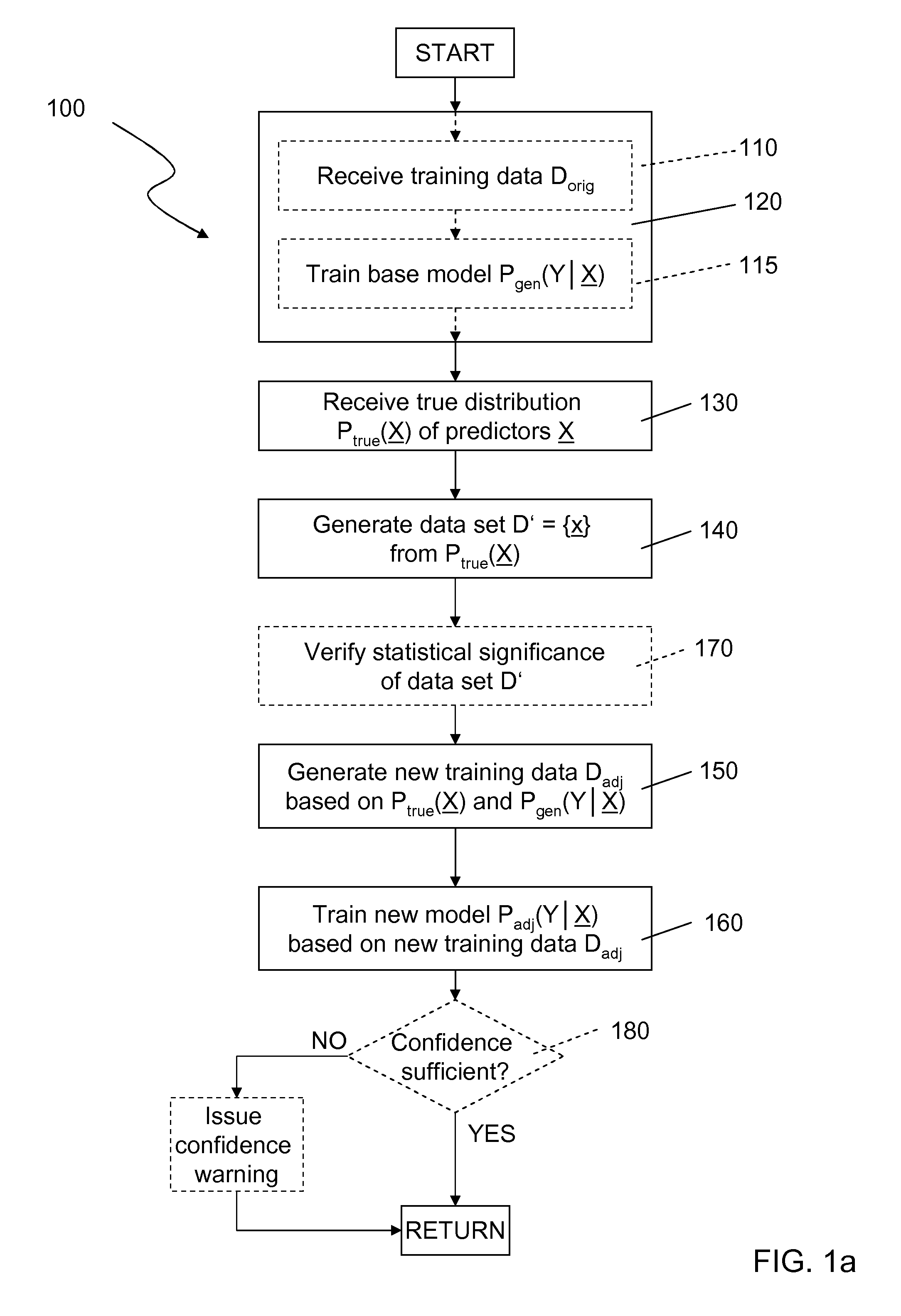
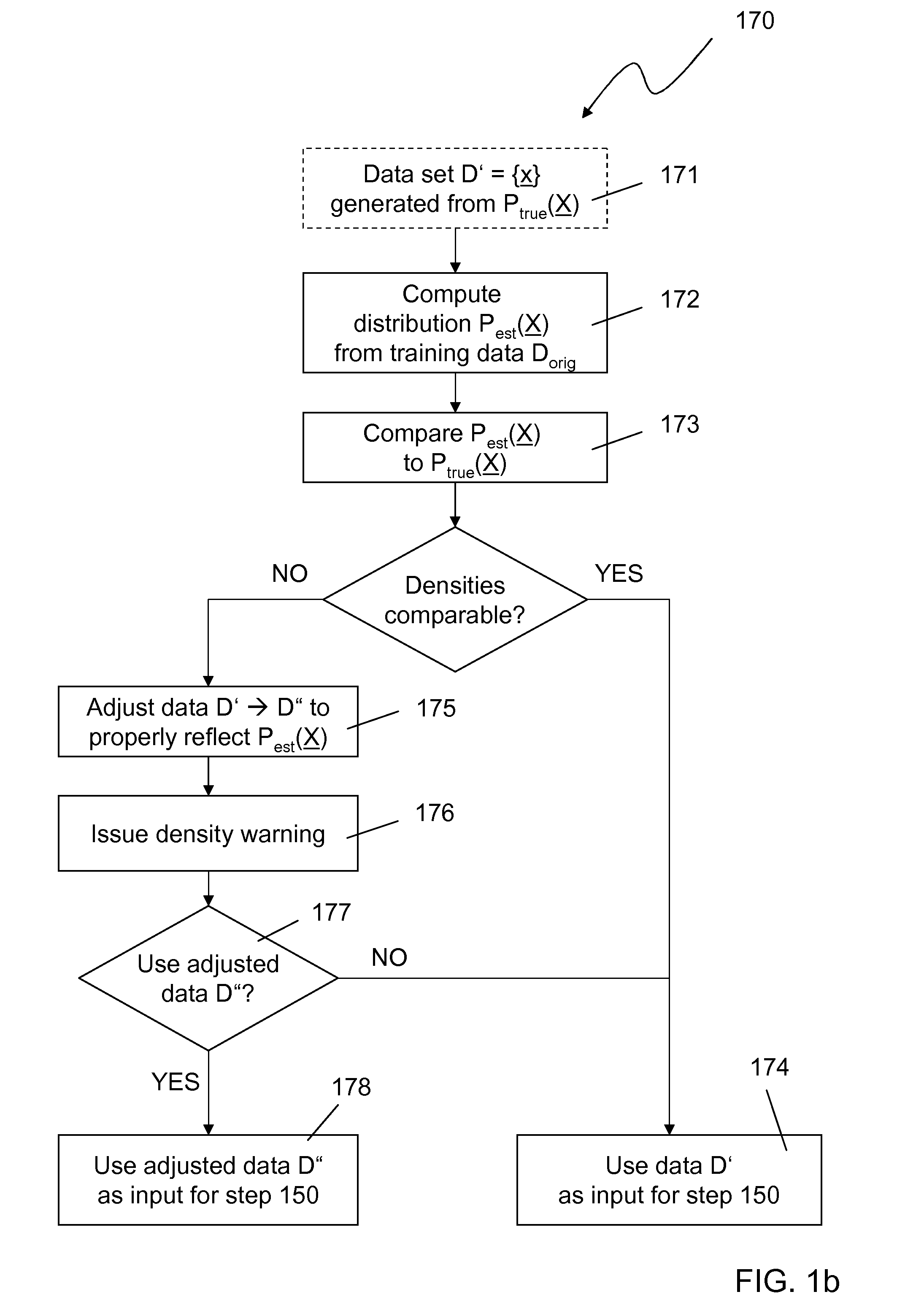
InactiveUS20120158624A1Computationally efficientImprove distributionDigital computer detailsCharacter and pattern recognitionPredictive modellingData set
A predictive analysis generates a predictive model (Padj(Y|X)) based on two separate pieces of information,a set of original training data (Dorig), anda “true” distribution of indicators (Ptrue(X)).The predictive analysis begins by generating a base model distribution (Pgen(Y|X)) from the original training data set (Dorig) containing tuples (x,y) of indicators (x) and corresponding labels (y). Using the “true” distribution (Ptrue(X)) of indicators, a random data set (D′) of indicator records (x) is generated reflecting this “true” distribution (Ptrue(X)). Subsequently, the base model (Pgen(Y|X)) is applied to said random data set (D′), thus assigning a label (y) or a distribution of labels to each indicator record (x) in said random data set (D′) and generating an adjusted training set (Dadj). Finally, an adjusted predictive model (Padj(Y|X)) is trained based on said adjusted training set (Dadj).
Owner:IBM CORP
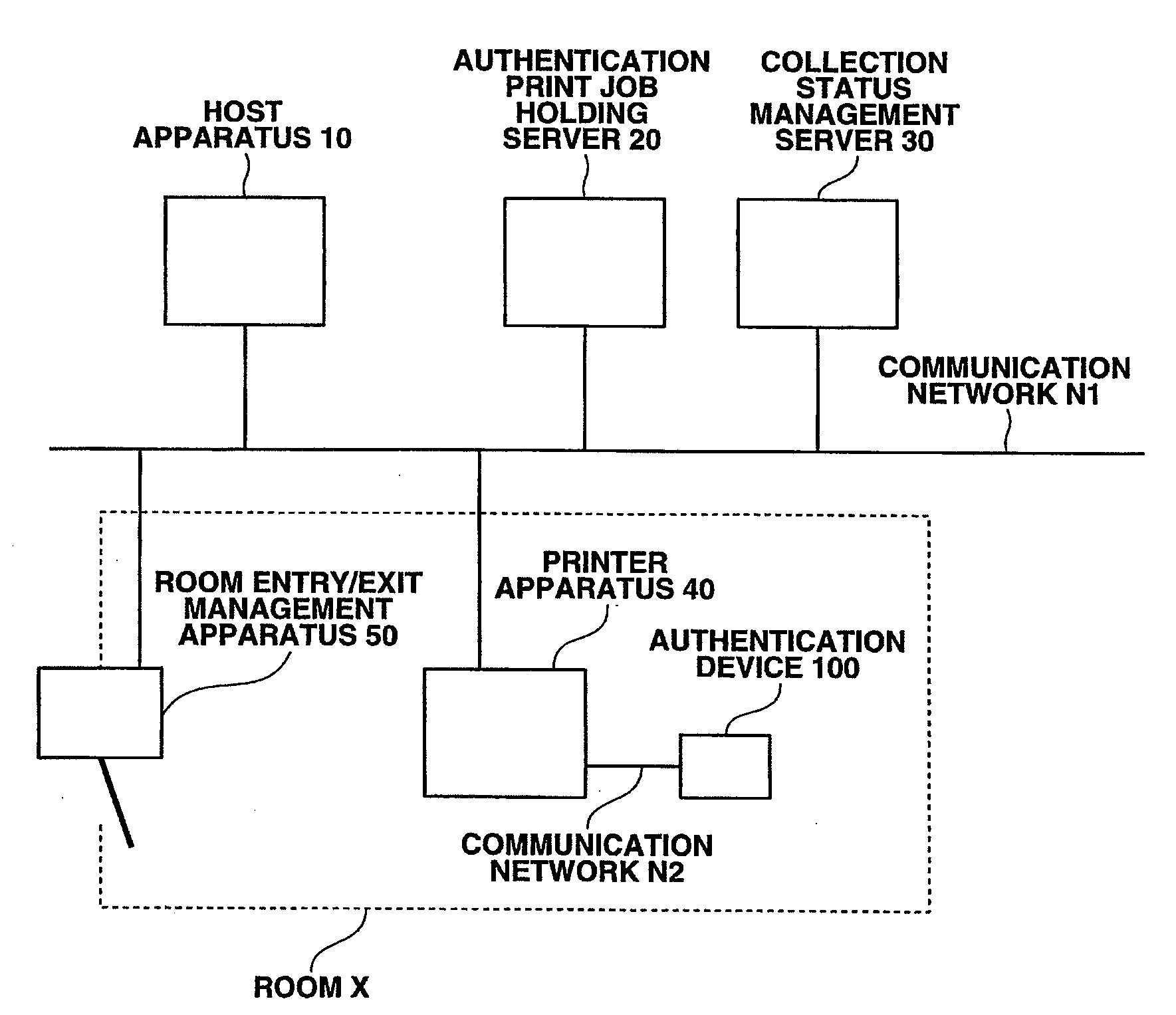
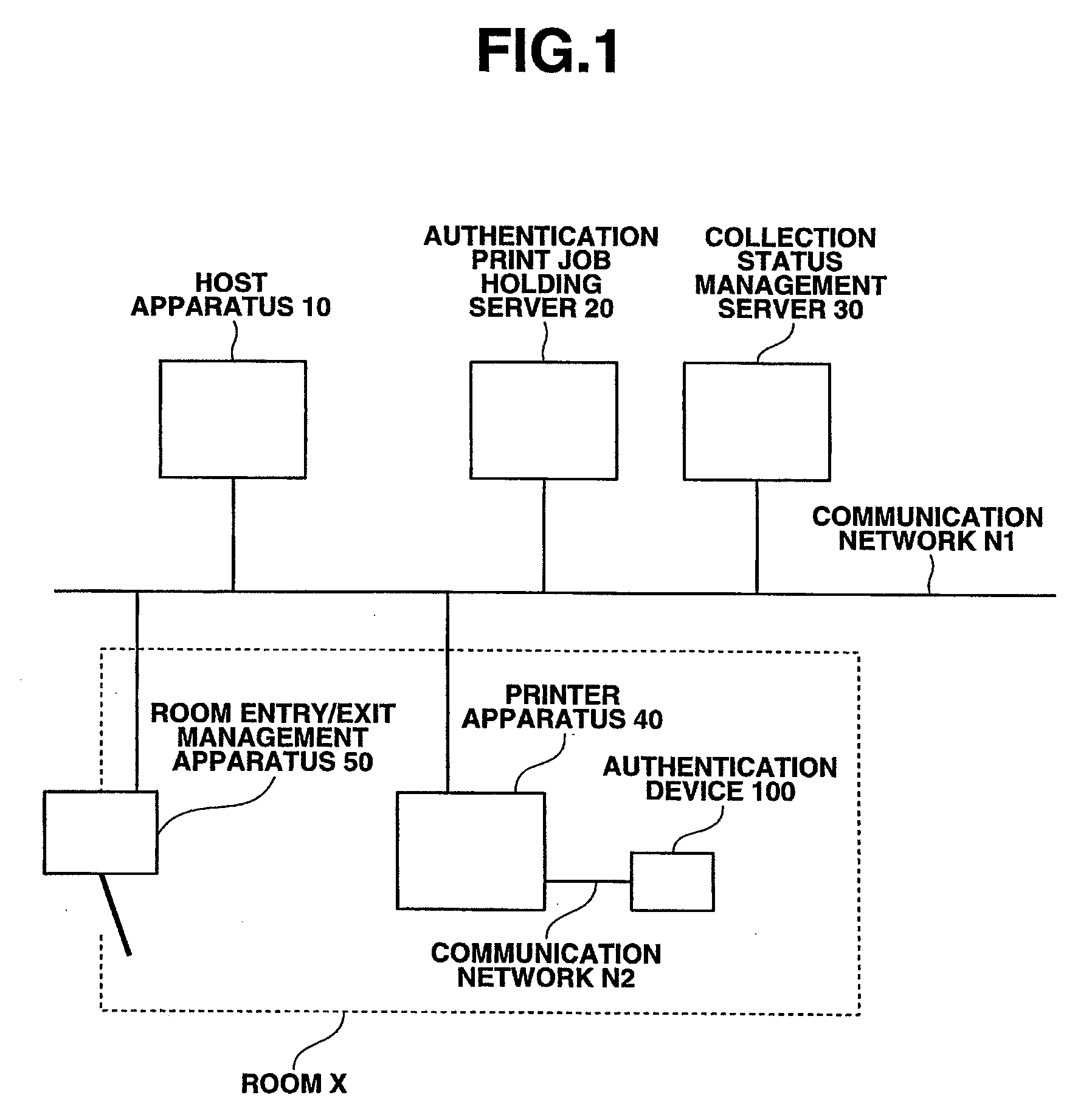
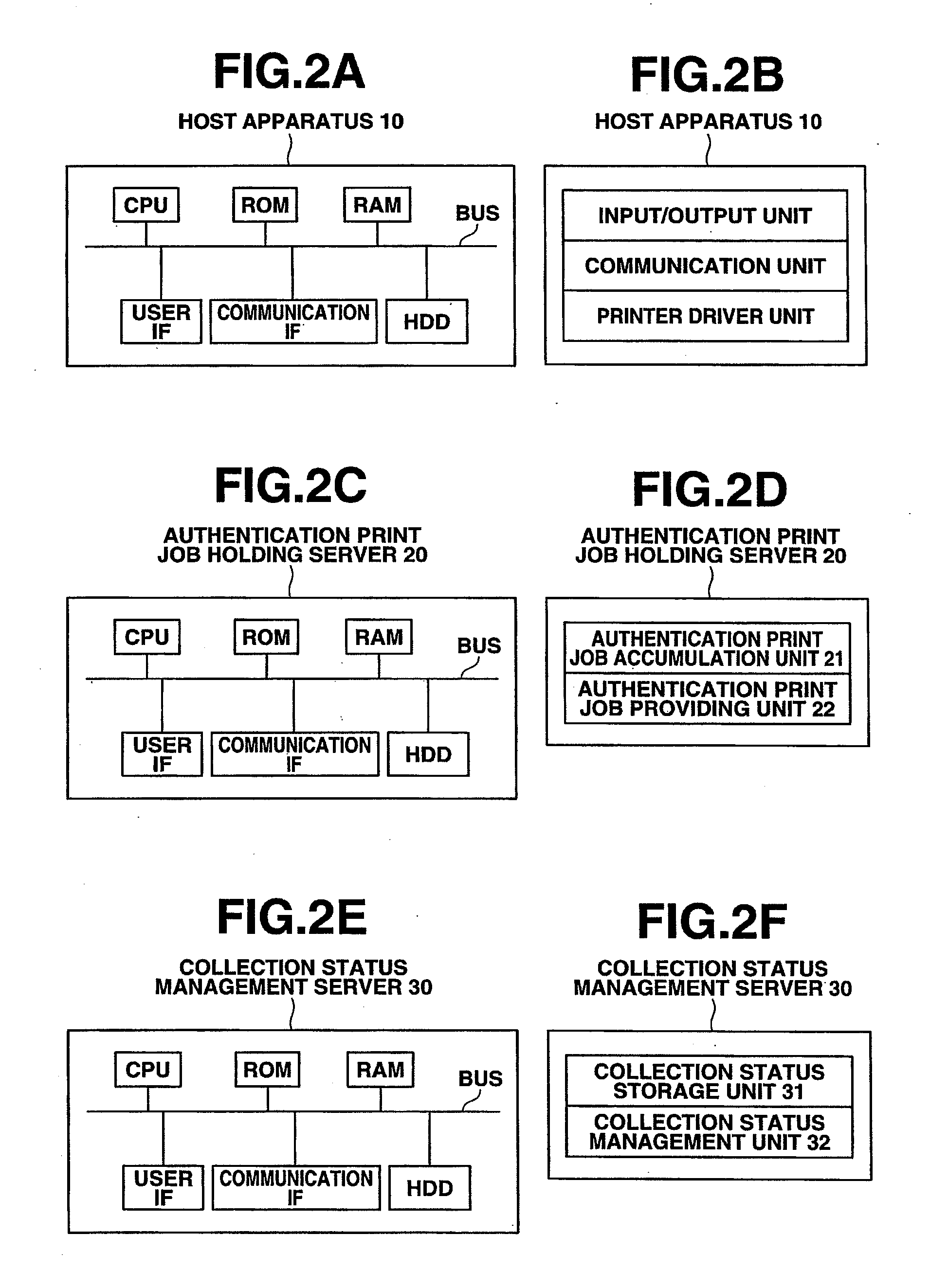
Authentication printing system and authentication printing method
ActiveUS20080115207A1Ensure confidentialityAvoid forgettingDigital data processing detailsUser identity/authority verificationComputer engineeringAuthentication information
An authentication printing system, comprising: an authentication unit that acquires authentication information from a user and authenticates based on the authentication information that the user possesses the authority to execute authentication printing (referred to as “authorized user”); a printing unit that acquires a print job corresponding to the authorized user from a printing job holding unit, and executes the authentication printing based on the print job (referred to as “print execution job”); a re-authentication unit that acquires the authentication information from a user upon completion of print processing, with regard to the print execution job, and authenticates based on the authentication information that the user is the authorized user of the print execution job; and a determination unit that determines that a printed matter is collected by the authorized user with regard to the print execution job, when re-authentication is completed with regard to the print execution job.
Owner:SEIKO EPSON CORP
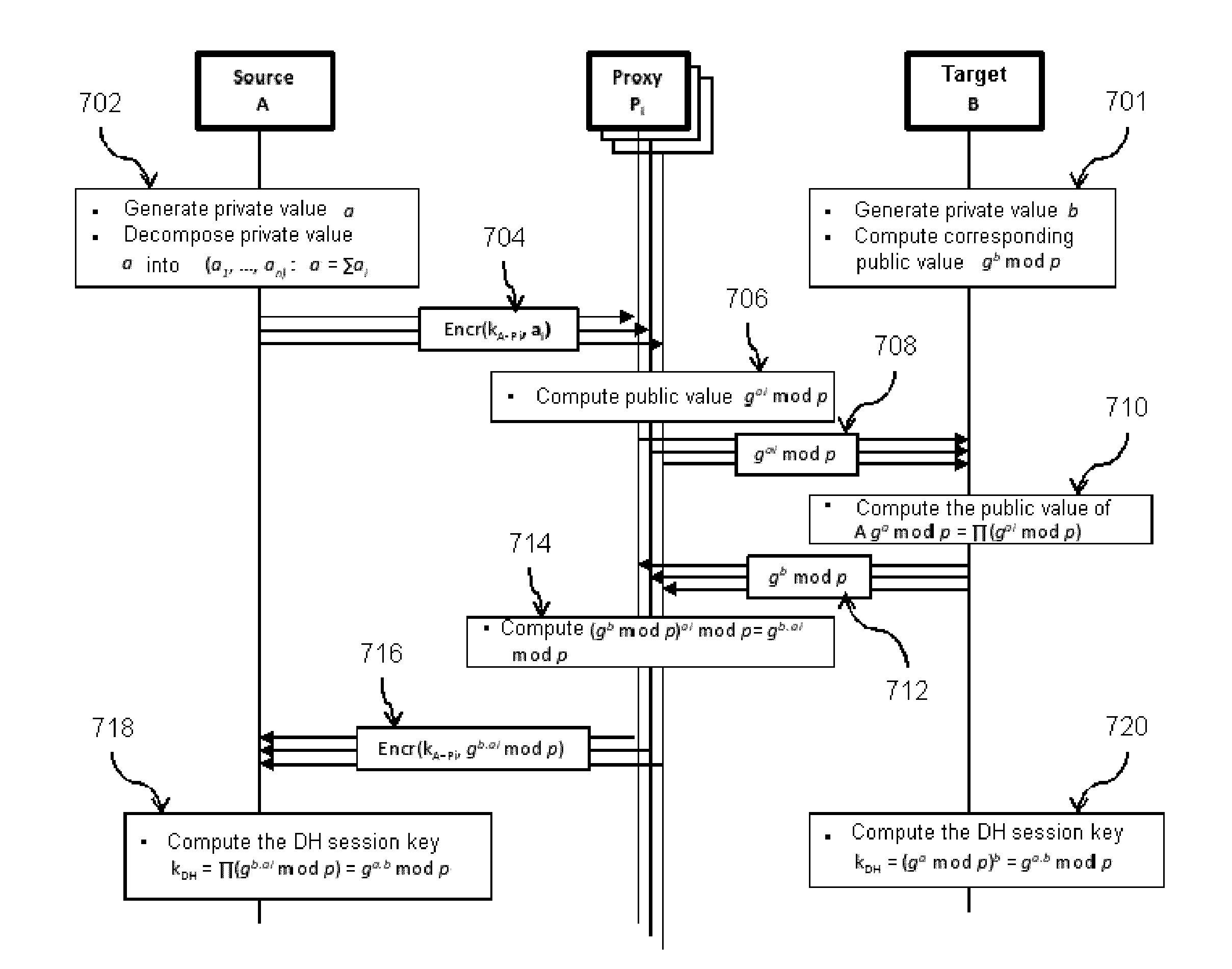
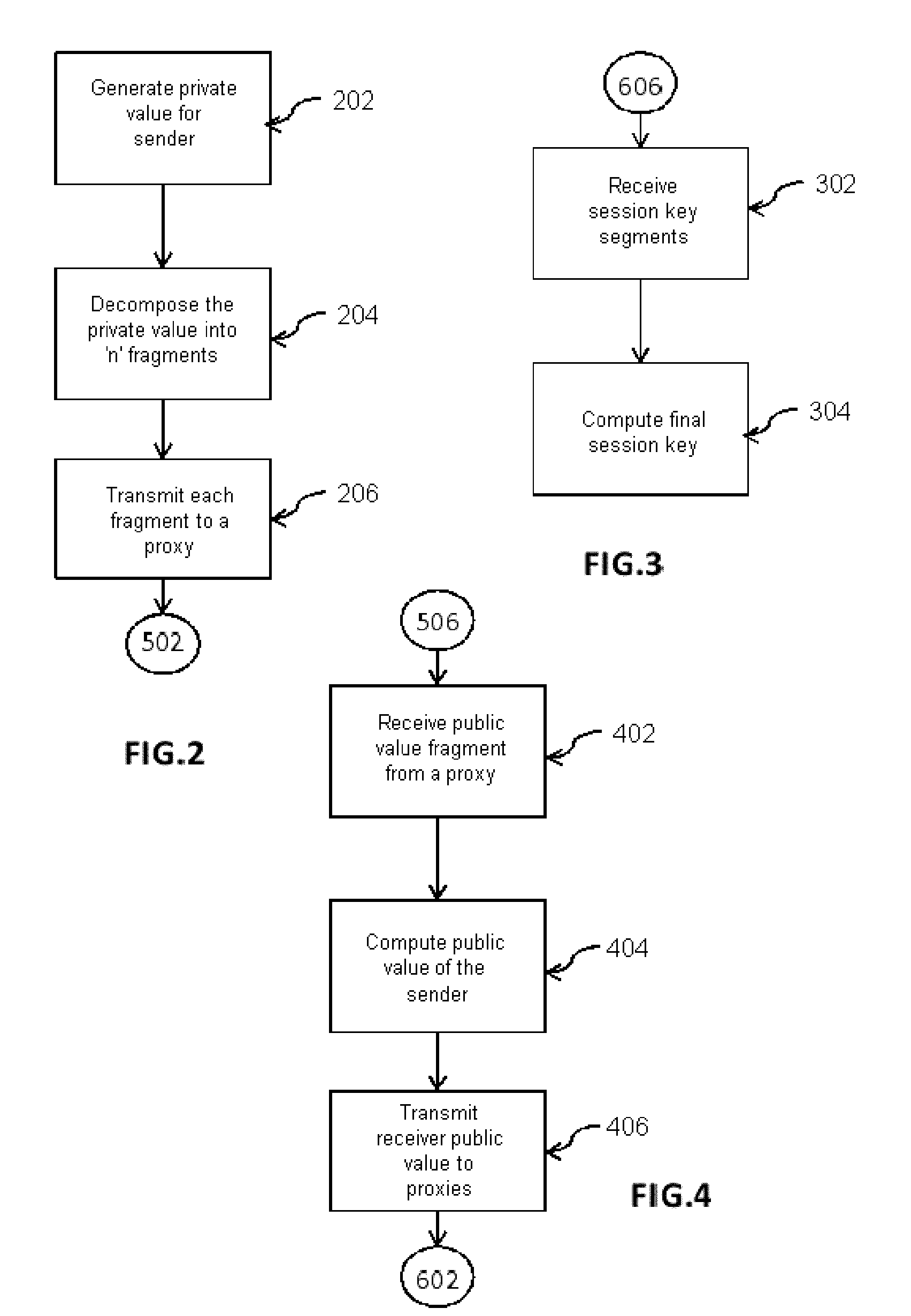
Device and method for generating a session key
InactiveUS20150188700A1Reduce operating costsEnsure confidentialityKey distribution for secure communicationComputer securitySession key
A device and method are provided for establishing a session key between two entities of a communication network that may be highly heterogeneous in terms of resources. The method, based on the Diffie-Hellman (DH) algorithm, provides for the delegation to assistant nodes of the network of the cryptographic operations required for the computations of the DH public value and of the DH session key for the node which is constrained in terms of resources.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
Method and apparatus for broadcasting and receiving entitlement management messages
InactiveUS7092729B1Simple wayEnsure confidentialitySpecial service provision for substationPicture reproducers using cathode ray tubesBroadcasting
The present invention provides a method of broadcasting a message having a text portion to be communicated to a user, the method including broadcasting the message in the form of an entitlement management message for reception by the user.
Owner:INTERDIGITAL CE PATENT HLDG
Electronic license information interaction system and method
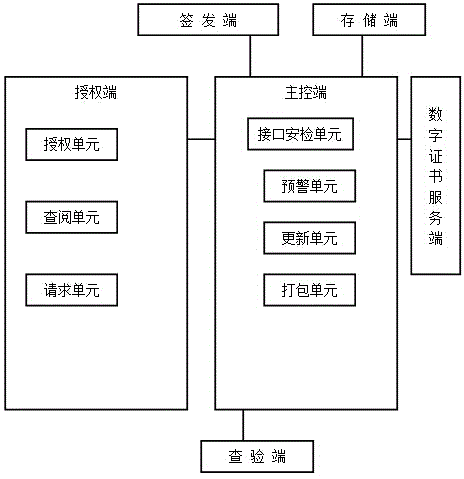
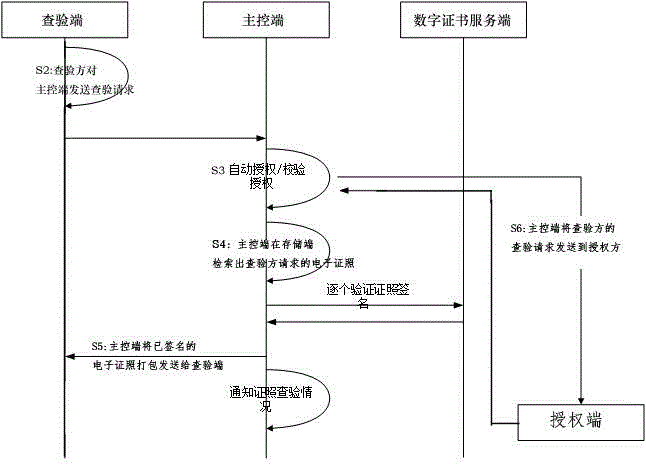
ActiveCN104951928AEasy to useImprove directionalityUser identity/authority verificationOffice automationInteraction systemsConfidentiality
The invention discloses an electronic license information interaction system. The system comprises a master control terminal for coordinating calling of ports, a storage terminal for storing an electronic license, an issuing terminal called by an electronic license issuing department, an authorization terminal called by an electronic license holder, an inspection terminal called by an electronic license inspection institution and a digital certificate server for calling a digital certificate service agency. The electronic license information interaction system has the advantages as follows: the license holder can authorize different administrative agencies to inspect electronic licenses according to different working procedures, accordingly, the directionality of license circulation is greatly increased, and institutions with no need for inspection are shielded; the master control terminal can compare licenses provided by the license holder with licenses in a license list required to be inspected by the administrative agencies, so that the license holder can know which licenses required to be supplemented by an issuing institution in the procedure handling process are lacked and through comparison; confidentiality and safety of information are ensured while the licenses are effectively used.
Owner:梅卓军
Information communication system, information communication device and information communication method, and computer program
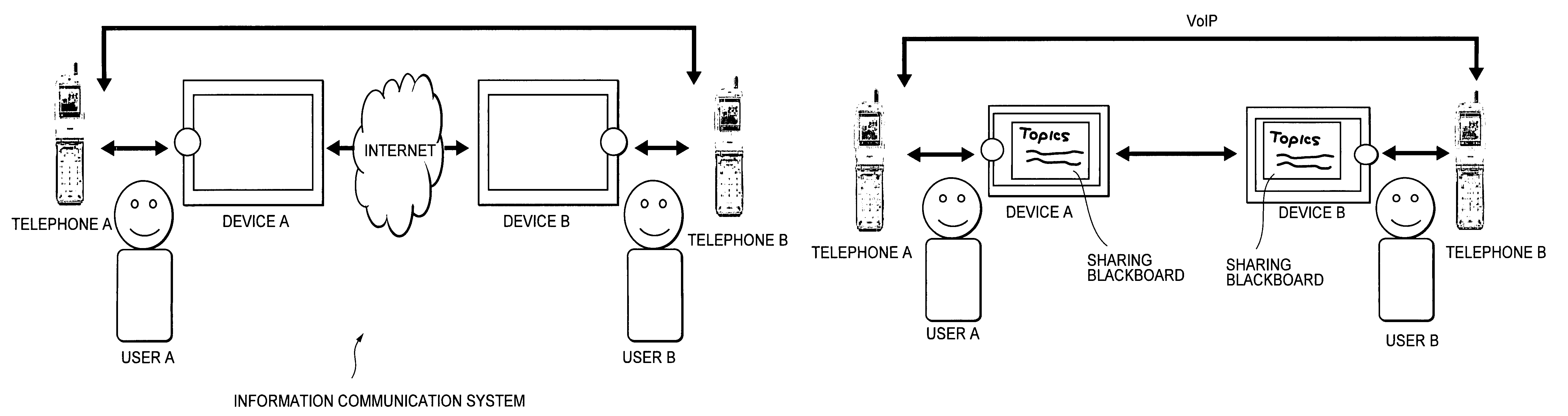
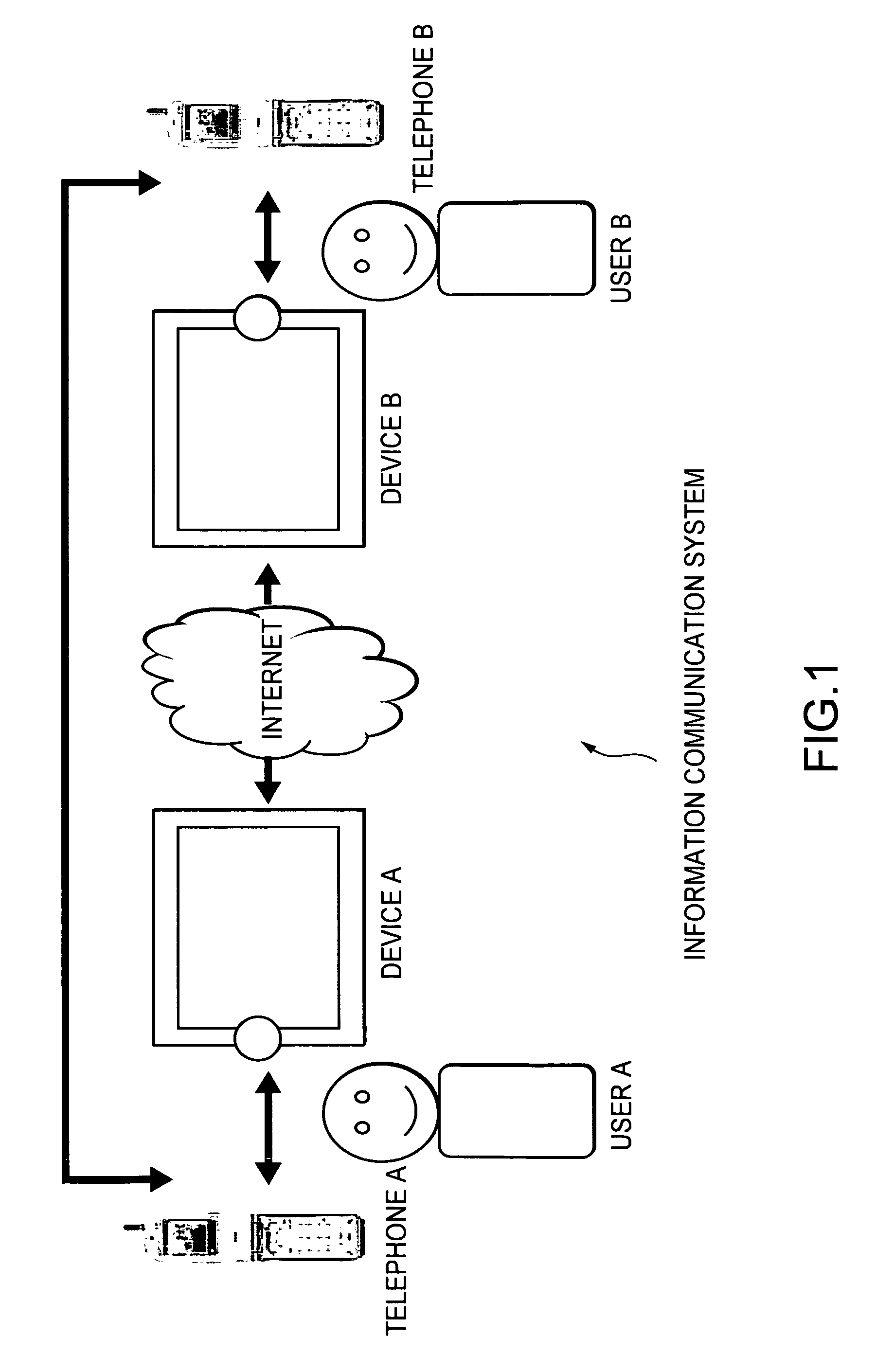
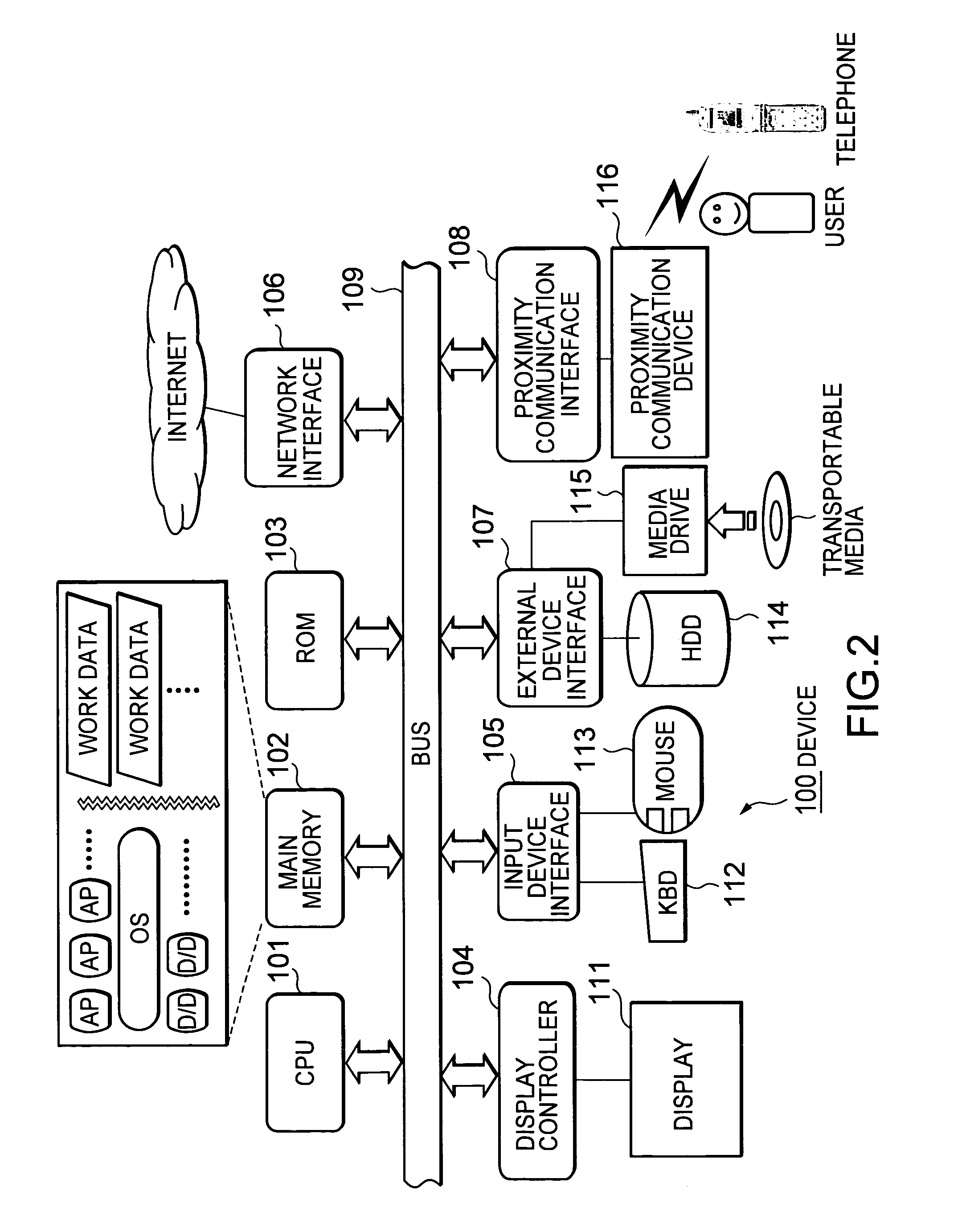
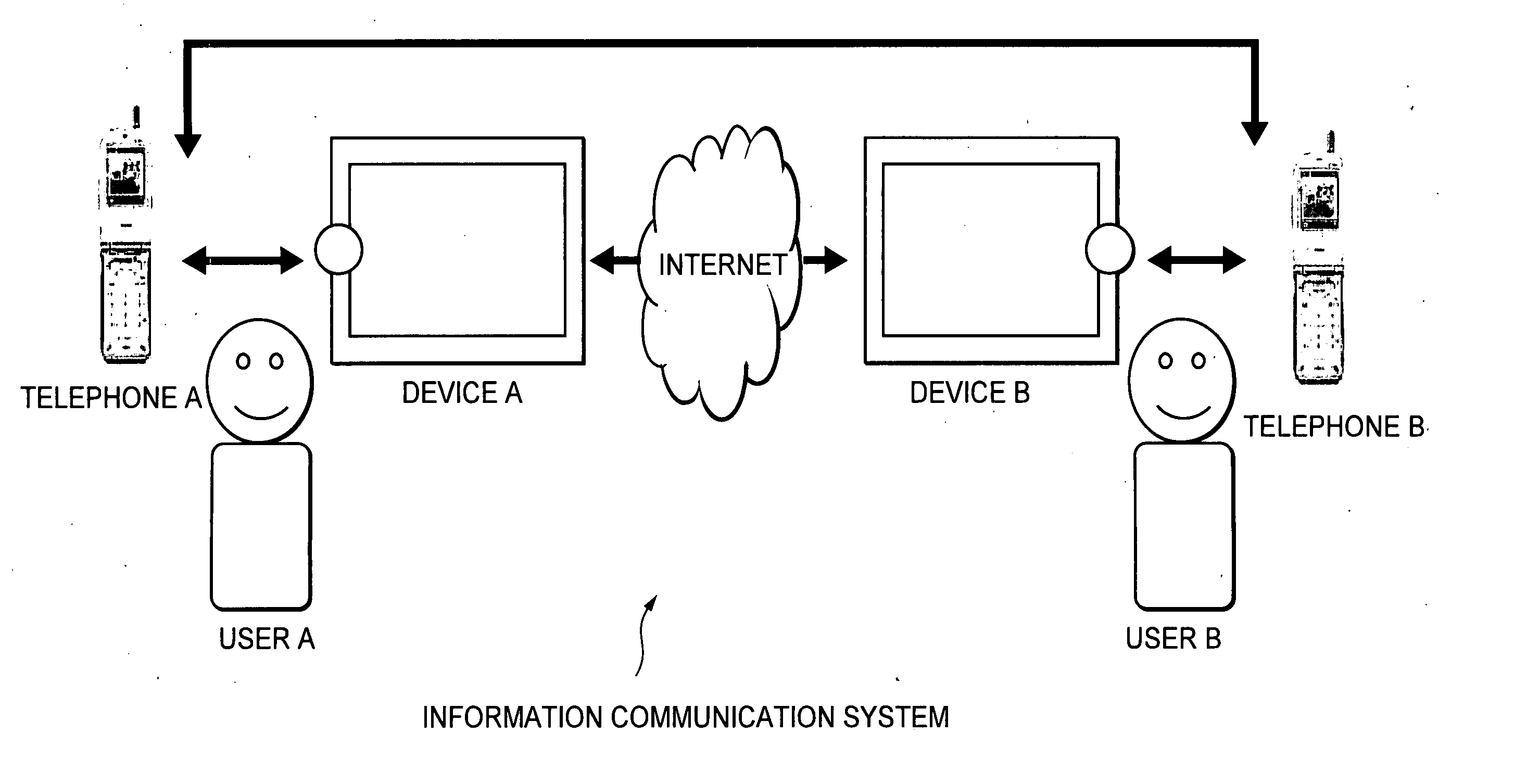
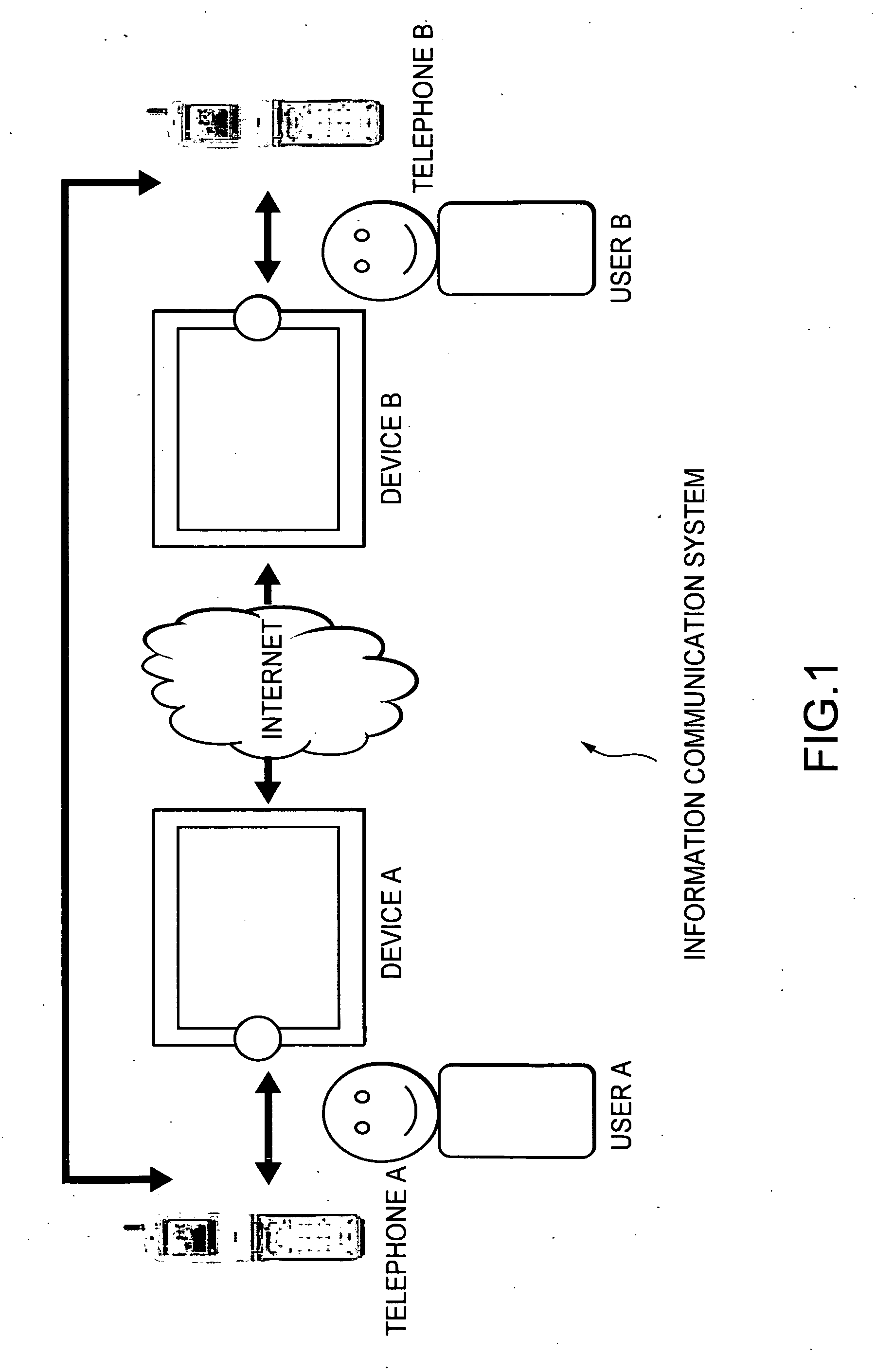
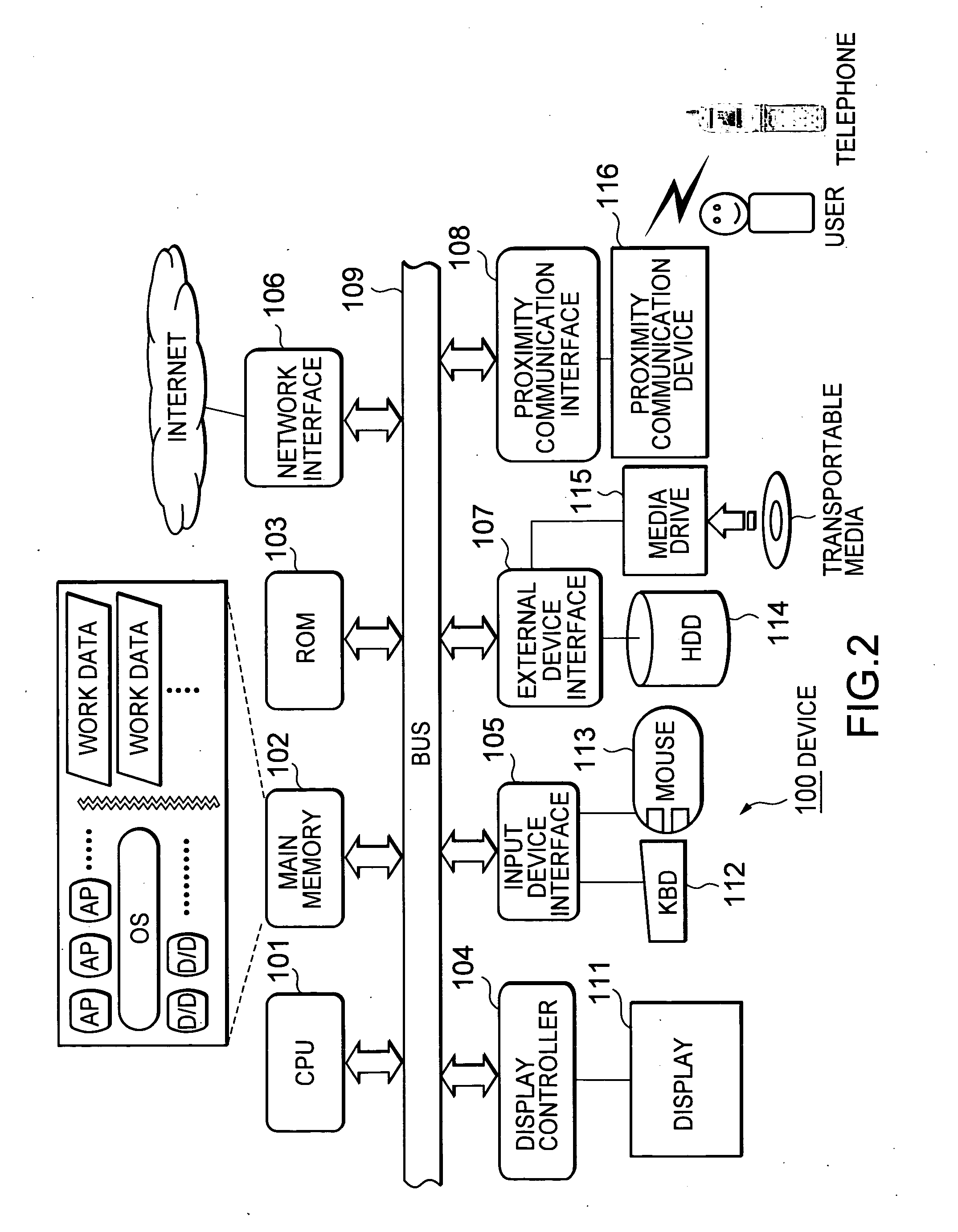
ActiveUS7526252B2Ensure confidentialitySecure transmissionTelephone data network interconnectionsNetwork traffic/resource managementCommunications systemIp address
An information communication system includes a first telephone operated by a first user, first proximity communication means operated when a first device comes into its vicinity so as to connect the both, a second telephone operated by a second user, and second proximity communication means operated when a second device comes into its vicinity so as to connect the both. The first telephone reads an IP address of the first device via the first proximity communication means, transmits it to the second telephone via a telephone network, and notifies it to the second device via the second proximity communication means. By link operation between a telephone and an electronic device in its vicinity, it is possible to share information and exchange information with a conversation partner via the telephone.
Owner:SONY CORP
Information communication system, information communication device and information communication method, and computer program
ActiveUS20050114646A1Ensure confidentialitySecure transmissionTelephone data network interconnectionsNetwork traffic/resource managementIp addressProximity communication
An information communication system includes a first telephone operated by a first user, first proximity communication means operated when a first device comes into its vicinity so as to connect the both, a second telephone operated by a second user, and second proximity communication means operated when a second device comes into its vicinity so as to connect the both. The first telephone reads an IP address of the first device via the first proximity communication means, transmits it to the second telephone via a telephone network, and notifies it to the second device via the second proximity communication means. By link operation between a telephone and an electronic device in its vicinity, it is possible to share information and exchange information with a conversation partner via the telephone.
Owner:SONY CORP
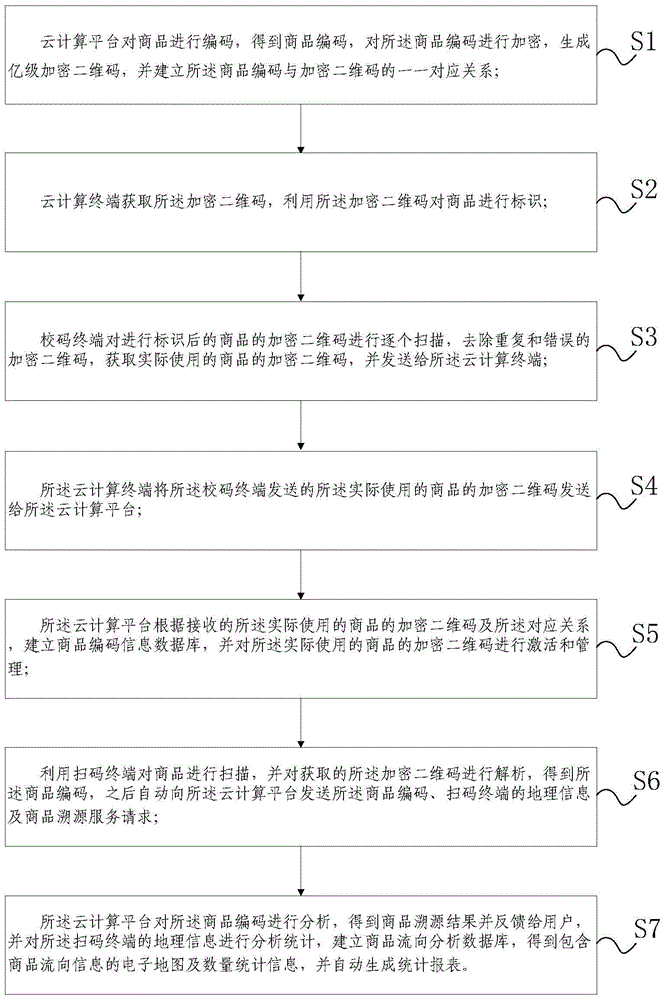
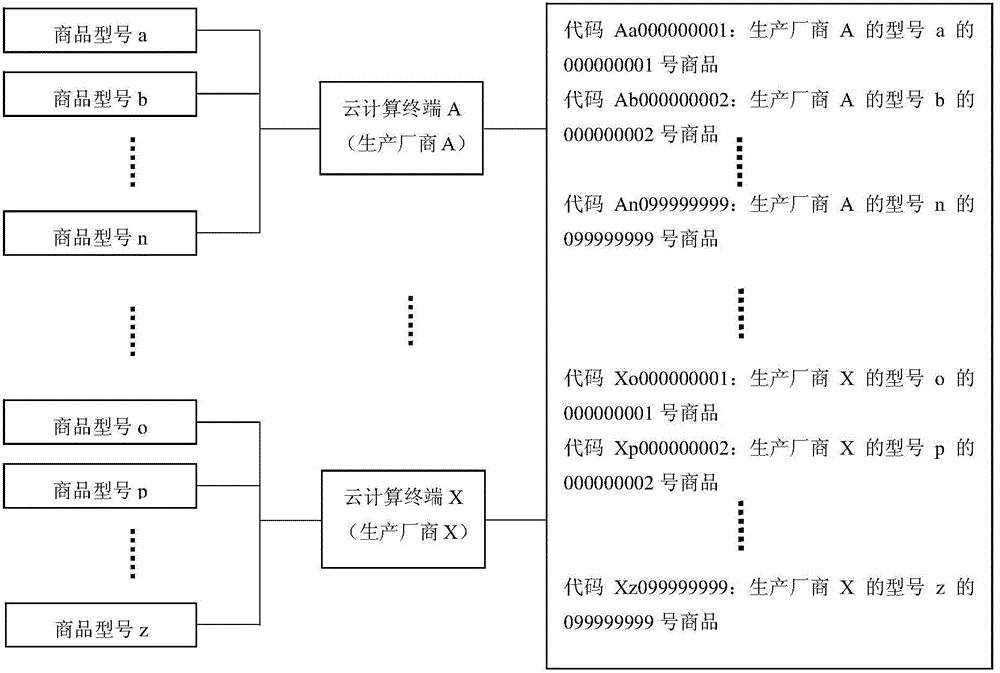
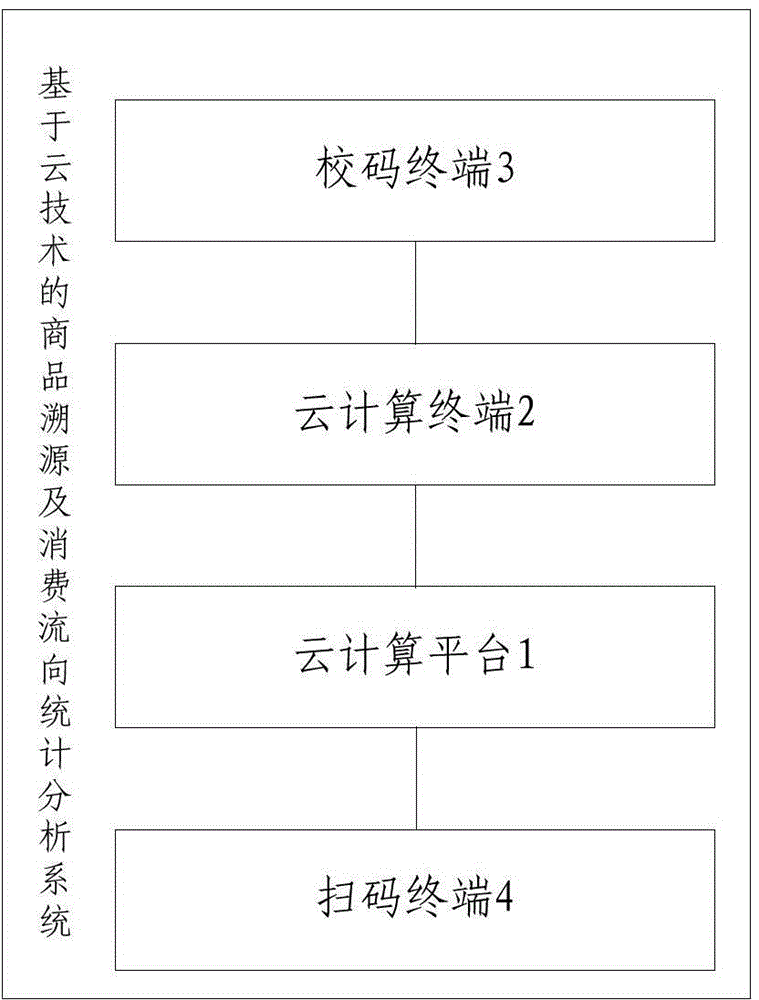
Cloud technology-based commodity traceability and consumption flow statistical analysis method and system
ActiveCN104834999AStrong computing powerImprove performanceResourcesCommerceStatistical analysisBiological activation
The invention discloses a cloud technology-based commodity traceability and consumption flow statistical analysis method and system. According to the cloud technology-based commodity traceability and consumption flow statistical analysis method and system, a cloud technology architecture in which a cloud computing platform and a cloud computing terminal coordinate with each other is adopted, wherein the cloud computing platform is responsible for coding, compression, encryption, generation and activation, assignment and management of hundred-million-level encrypted two-dimension codes and providing traceability services for consumers and providing consumption flow statistical analysis services for enterprises, and the cloud computing terminal is responsible for assigning identifiers for the encrypted two-dimension codes of commodities; since the powerful computing ability and performance of cloud technologies are utilized, and a convenient automated centralized management mode is adopted, the operational efficiency, reliability, flexibility and robustness of the system can be ensured.
Owner:NANJING DASHU INTELLIGENT SCI & TECH CO LTD
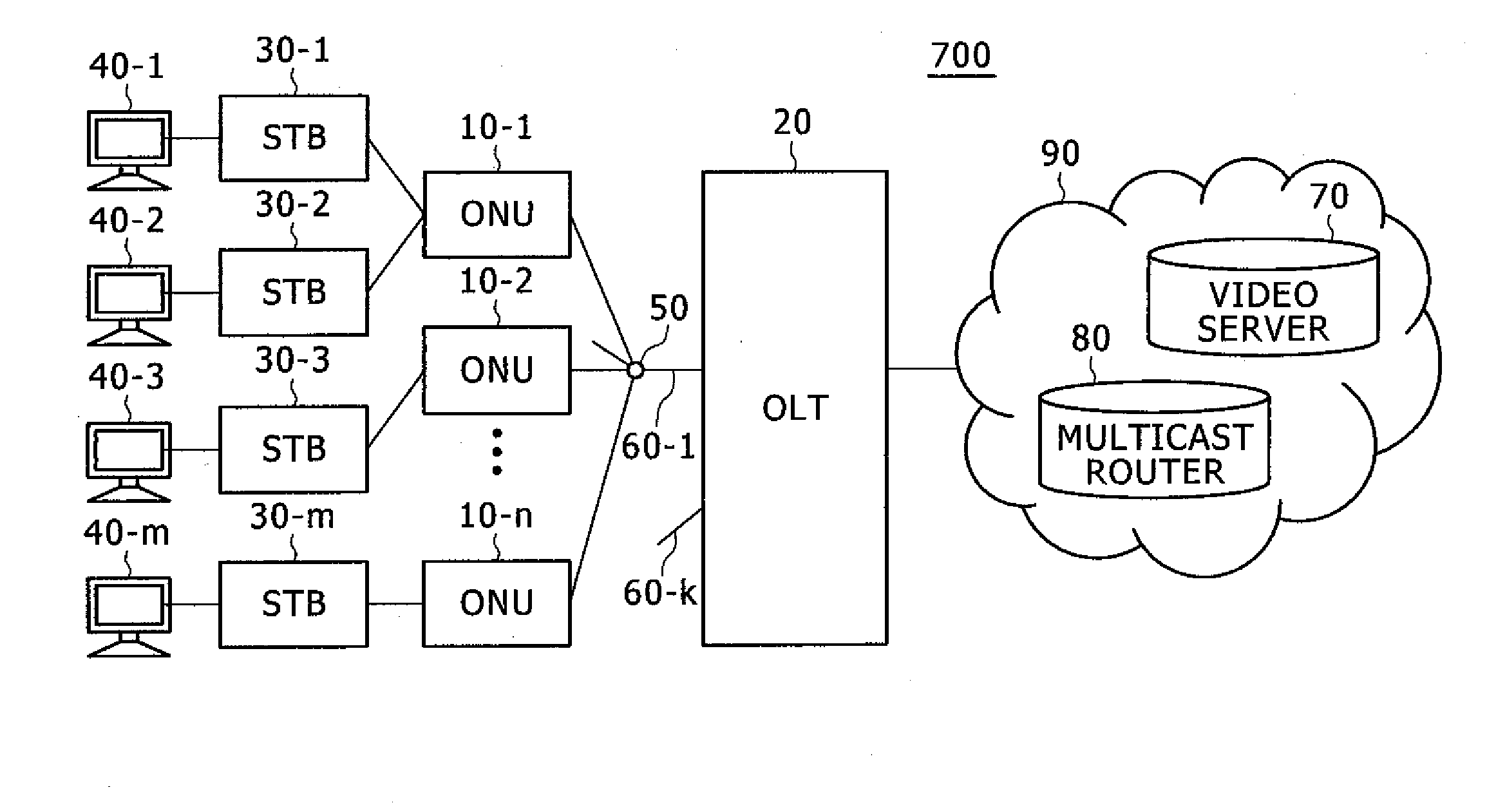
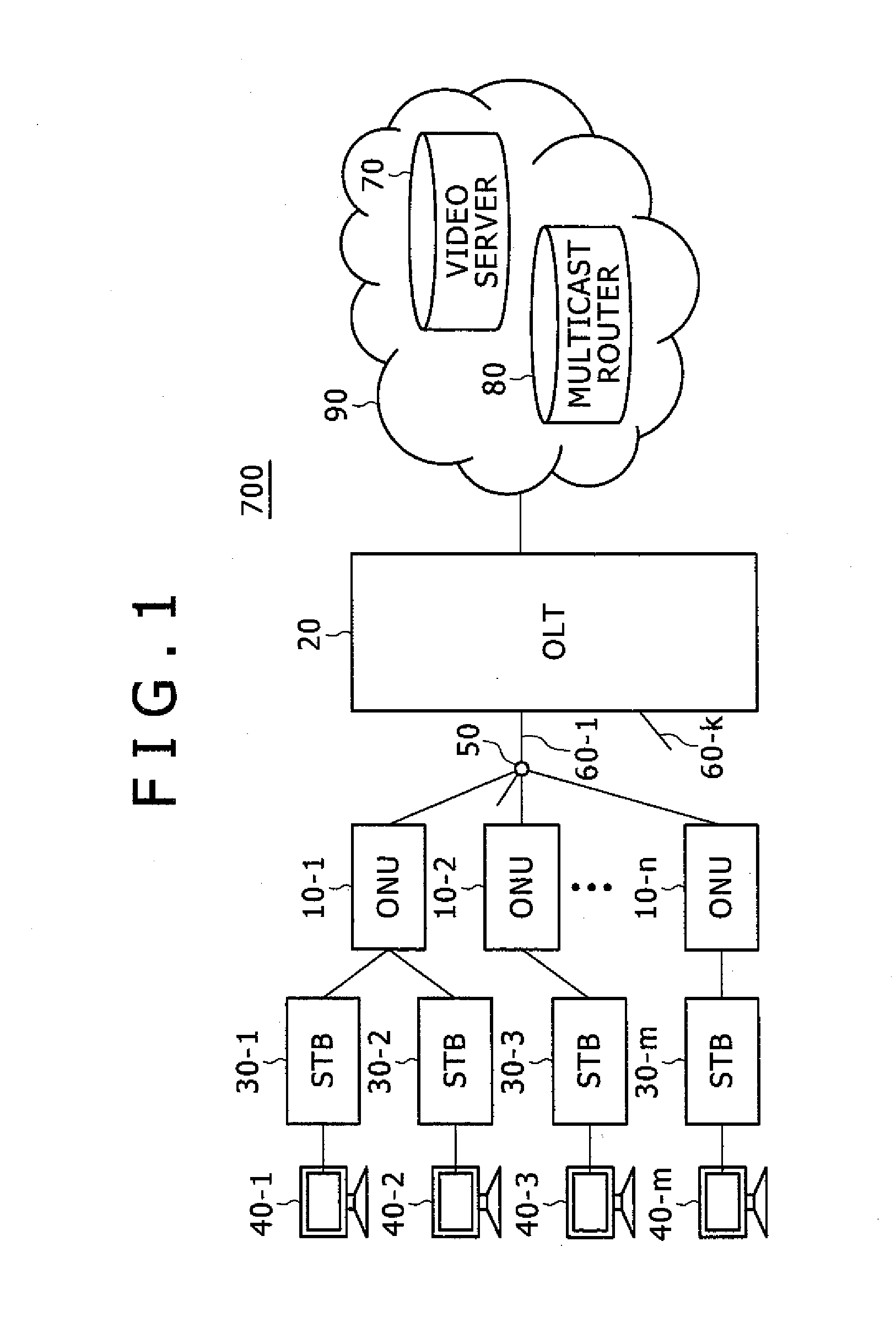
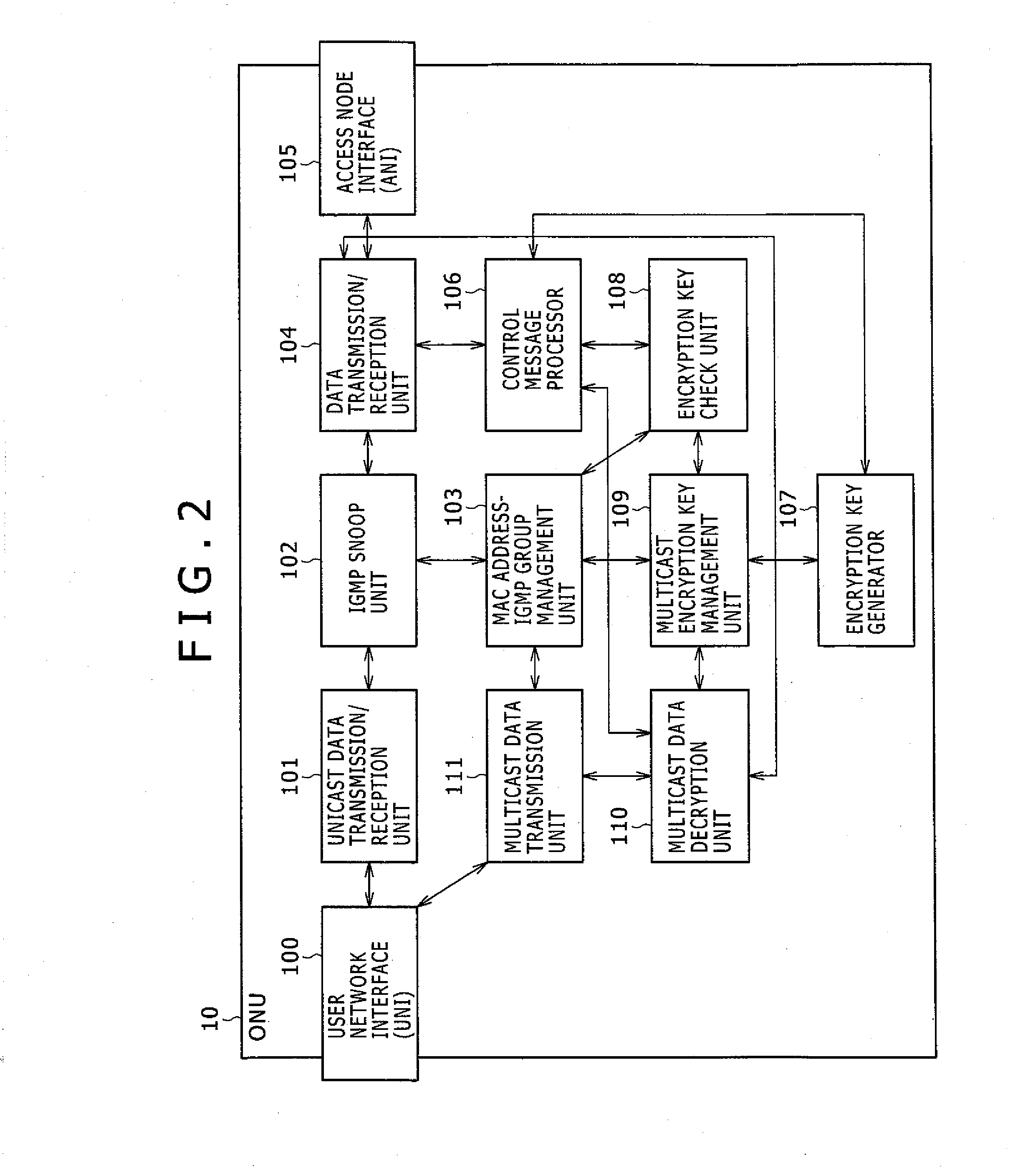
Optical network system and method of changing encryption keys
InactiveUS20100202612A1Ensure confidentialityMultiplex system selection arrangementsSpecial service provision for substationComputer hardwareCryptographic key generation
An optical network system including an OLT and ONUs is provided that can prevent the loss of a multicast signal. When receiving an encryption key generation request from the OLT, the ONU generates an encryption key, and transmits the generated encryption key to the OLT. When receiving a notice of timing from the OLT, the ONU updates the encryption key of a belonging group. When receiving a report message from a STB through the ONU, the OLT analyzes the report message, stores a group that the STB belongs to as well as the ONU in a second table, and transmits the encryption key generation request to the ONU. When receiving the encryption key from the ONU, the OLT further stores the encryption key in the second table, and transmits to the ONU a notice of the timing in which the encryption key is valid.
Owner:HITACHI LTD
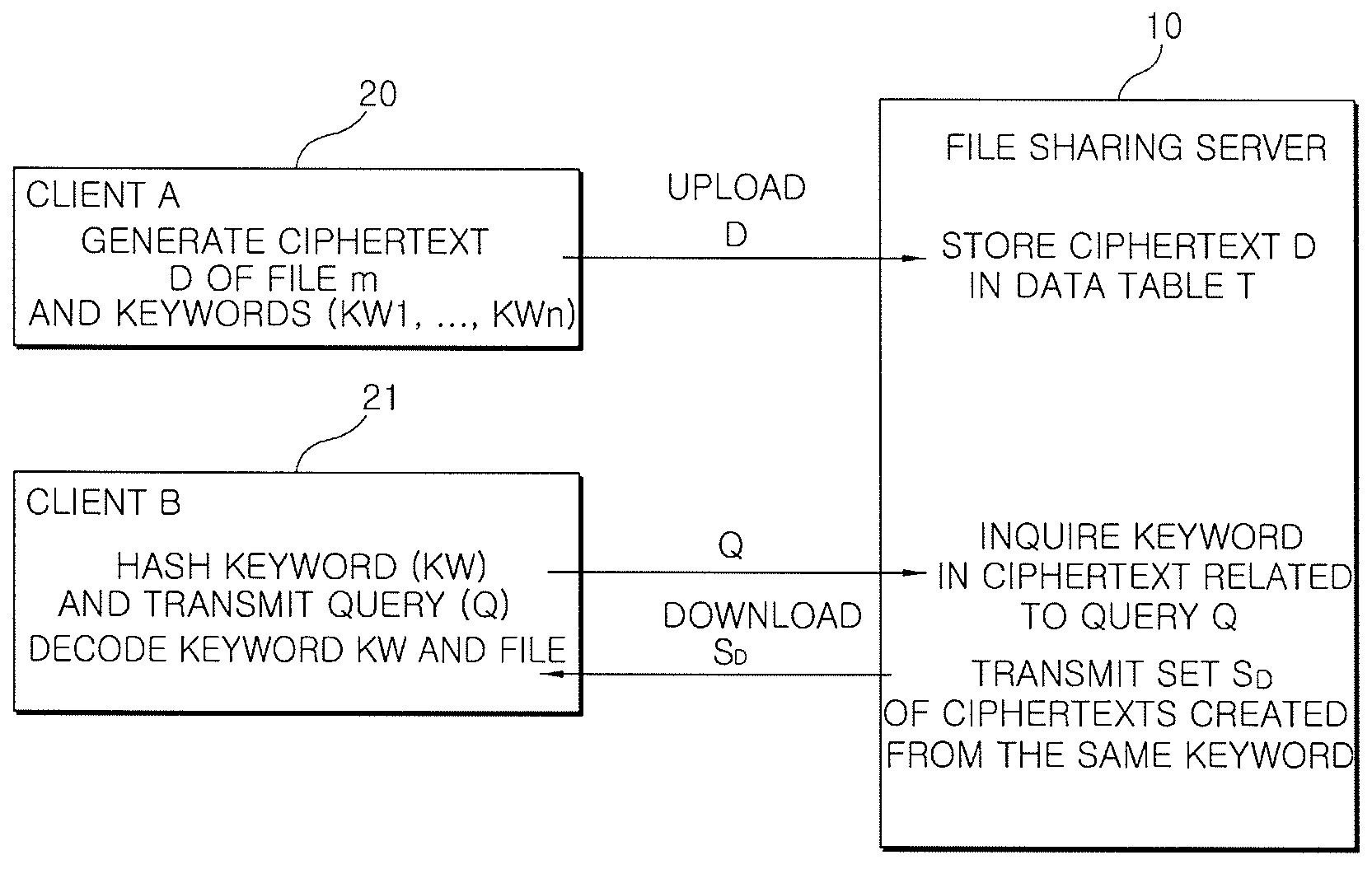
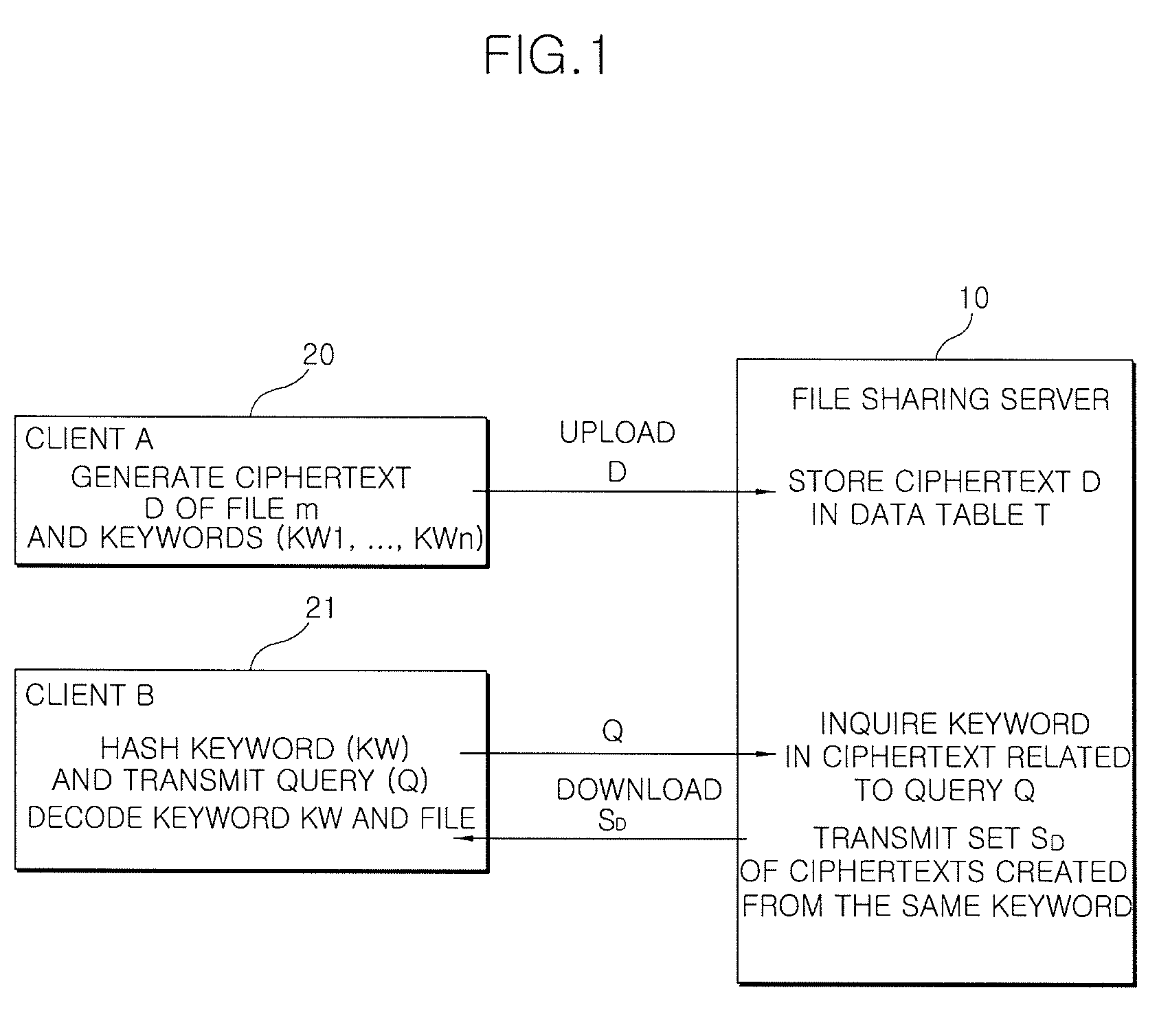
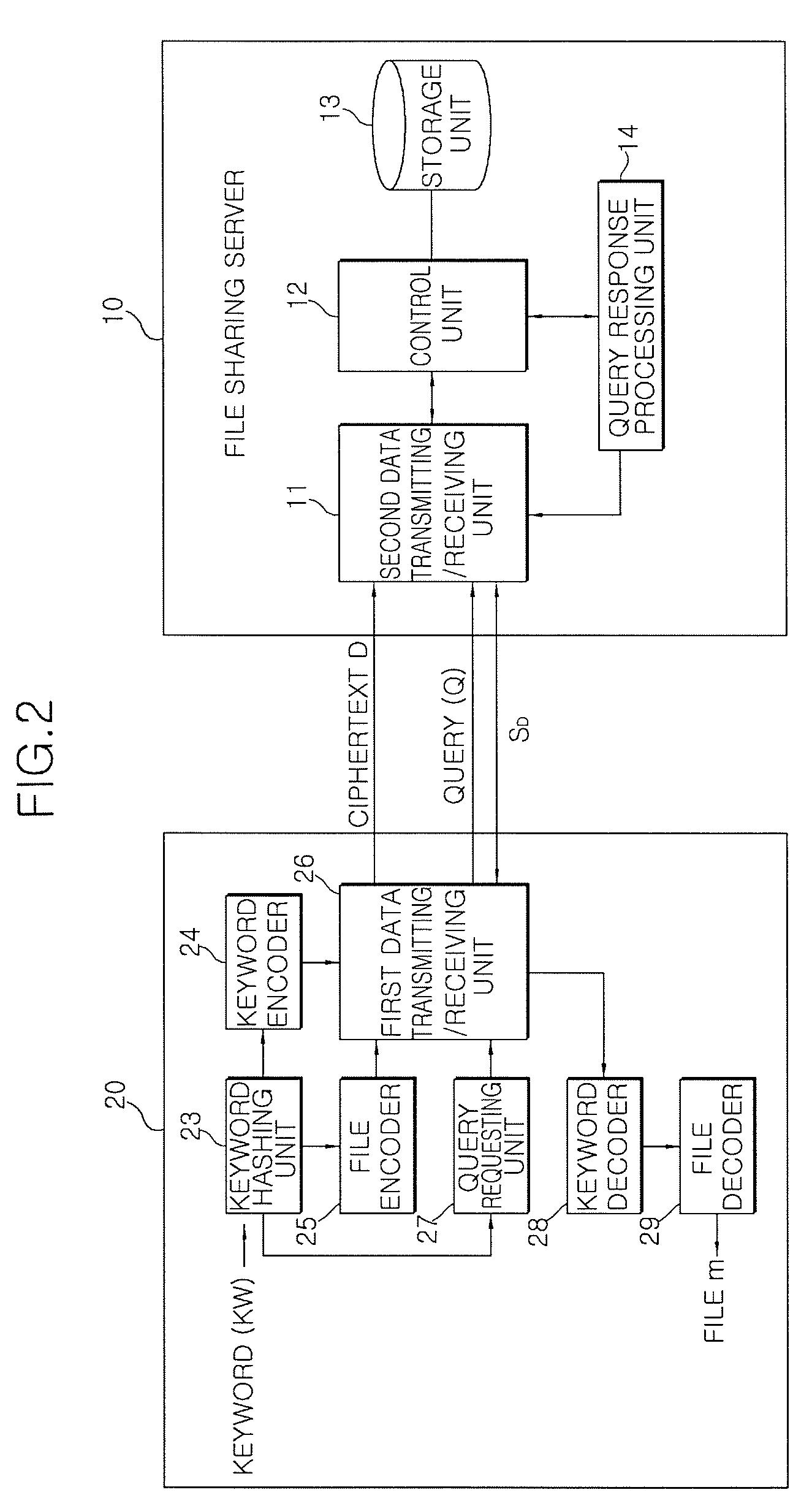
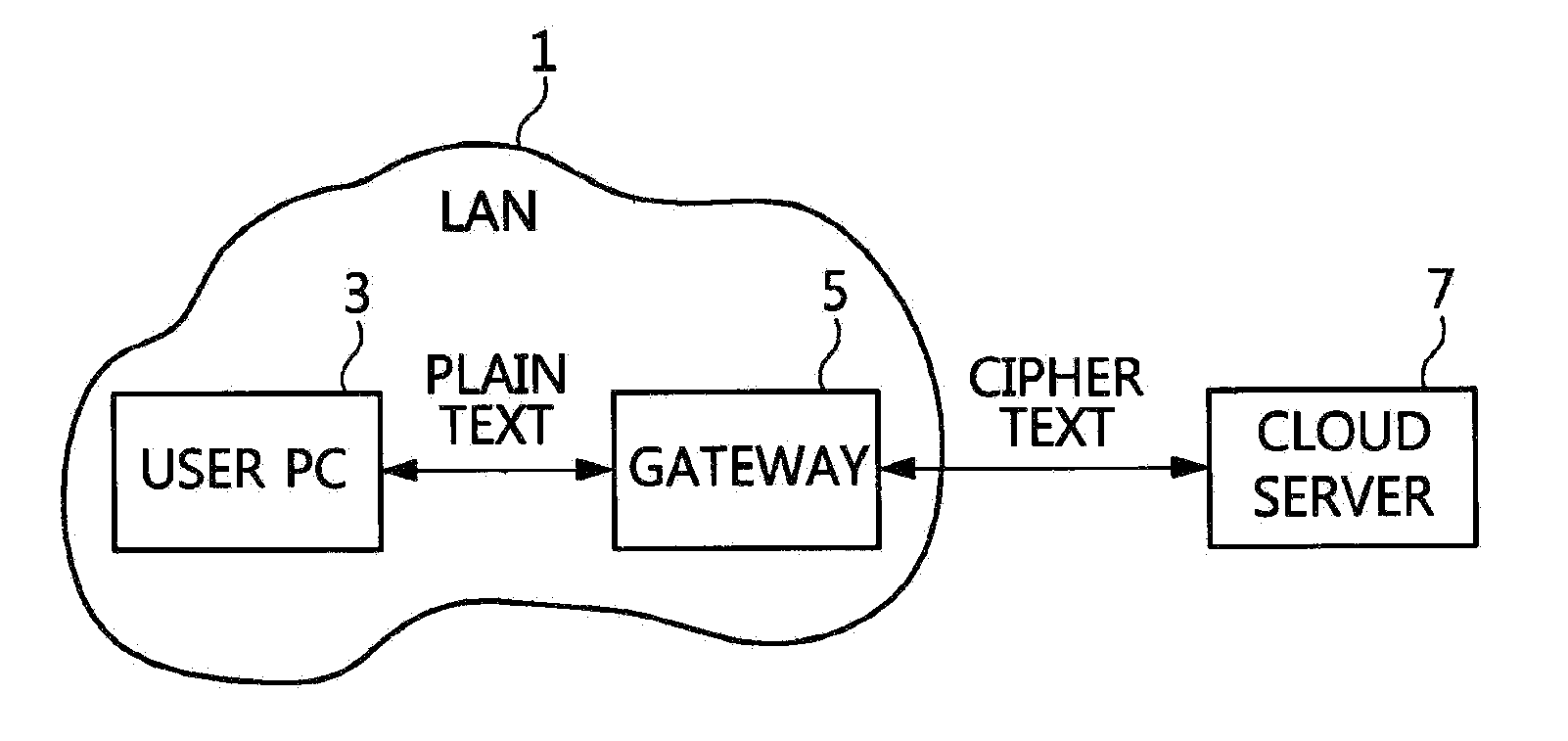
File sharing method and system using encryption and decryption
InactiveUS20090116645A1Improve privacyEnsure confidentialitySynchronising transmission/receiving encryption devicesPublic key for secure communicationCiphertextClient-side
Disclosed is a file sharing method and system using encryption and decryption. A client hashes keywords related to files using a symmetric key algorithm, and encodes the hashed keywords. Then, the client encodes the files using the hashed keywords, and uploads to a file sharing server a ciphertext D including an encoded file m and the encoded keywords KW1, . . . , KWn. In order to download a desired file, the client transmits to the file sharing server a query Q derived from the hashed keyword KW related to the desired file. The client receives from the file sharing server a set SD of ciphertexts created from the same keyword as that queried, decodes the keyword, and decodes the file m using the decoded keyword KW.
Owner:ELECTRONICS & TELECOMM RES INST
Print system
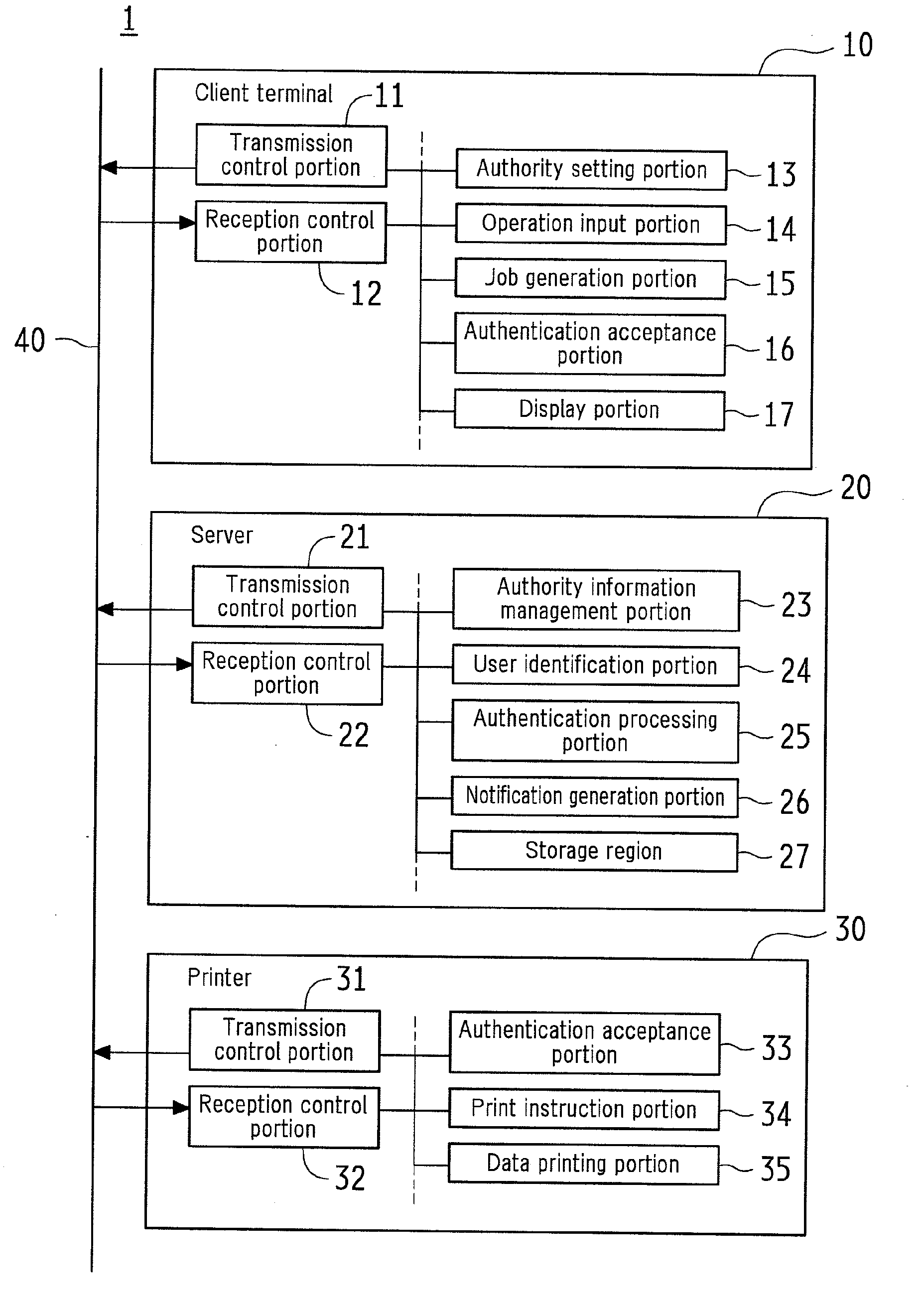
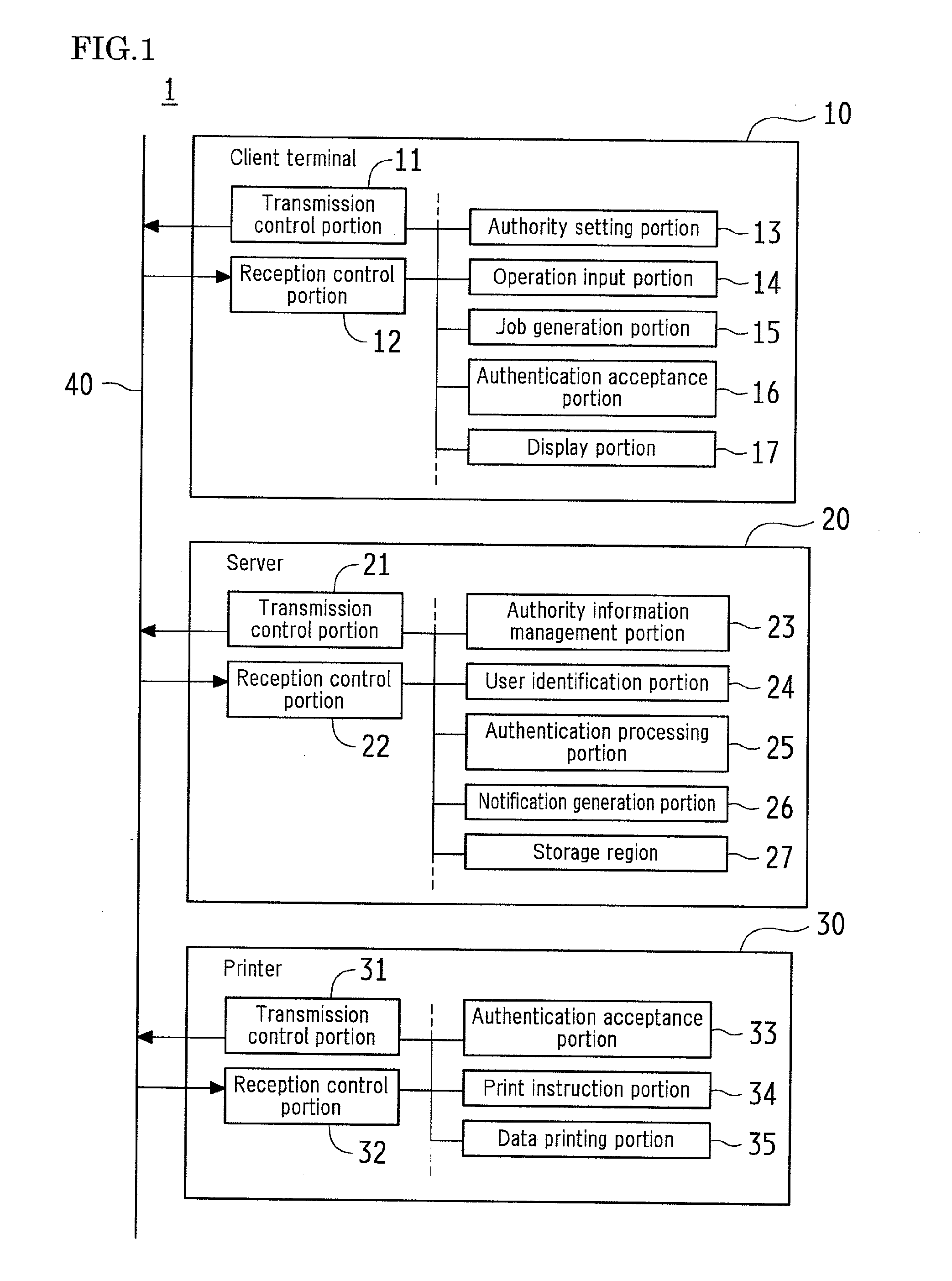
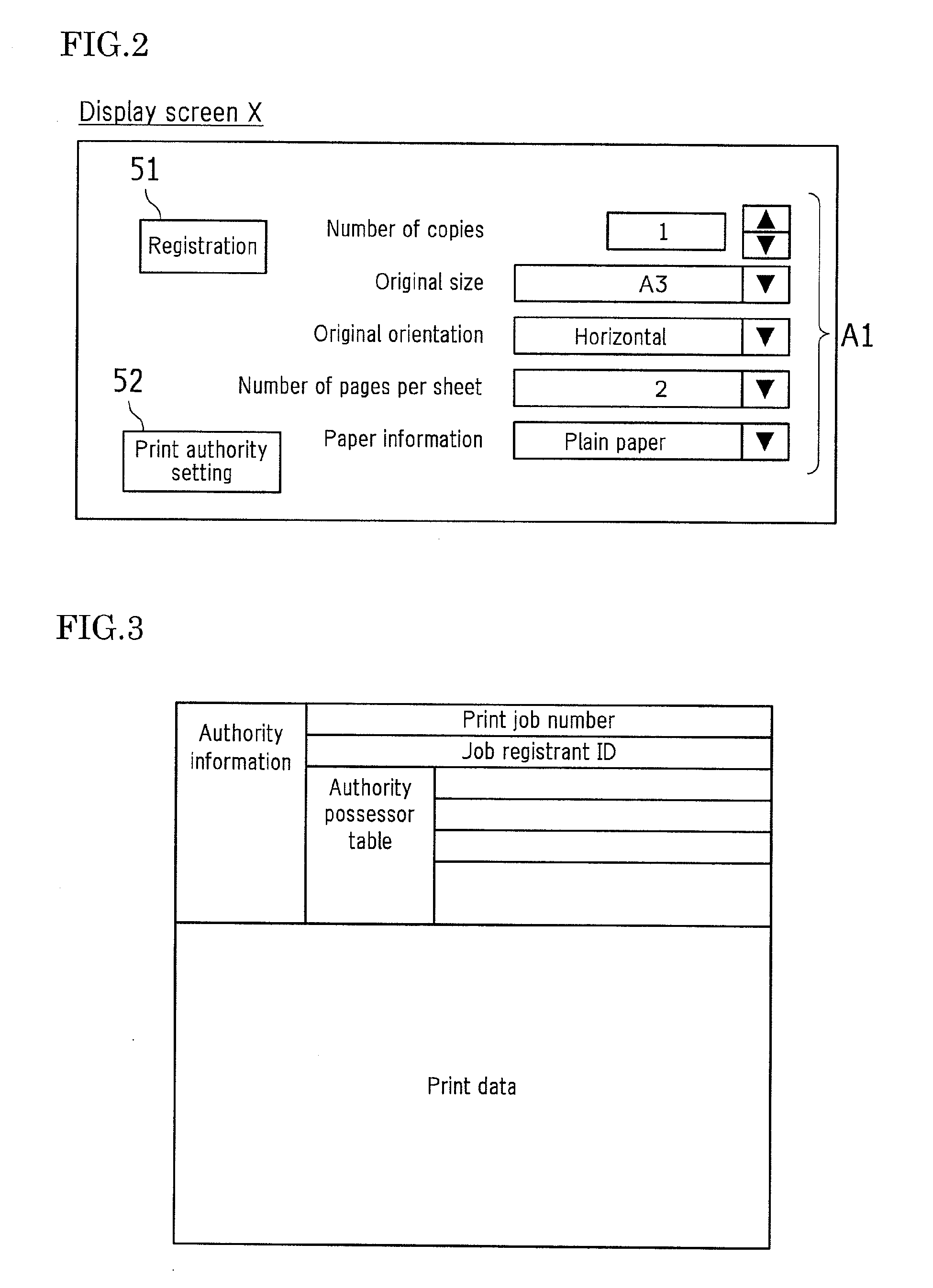
ActiveUS20110261402A1Reduce dataShorten the time periodComputer security arrangementsDigital output to print unitsIdentification deviceUser information
In one embodiment of a print system, a client terminal (10) that generates a print job, a server function portion that stores the print job, a printer (30) that performs pull printing of the print job are connected via the network (40). The print job holds print data and authority information including user information for specifying a user having print authority over the print data. The client terminal (10) is provided with an authority setting means for setting authority information. A server (20) is provided with the server function portion, and is configured to update authority information, identify a user, authenticate whether or not to permit printing based on the authority information and the identification result obtained by a user identification means, and transmit print data.
Owner:SHARP KK
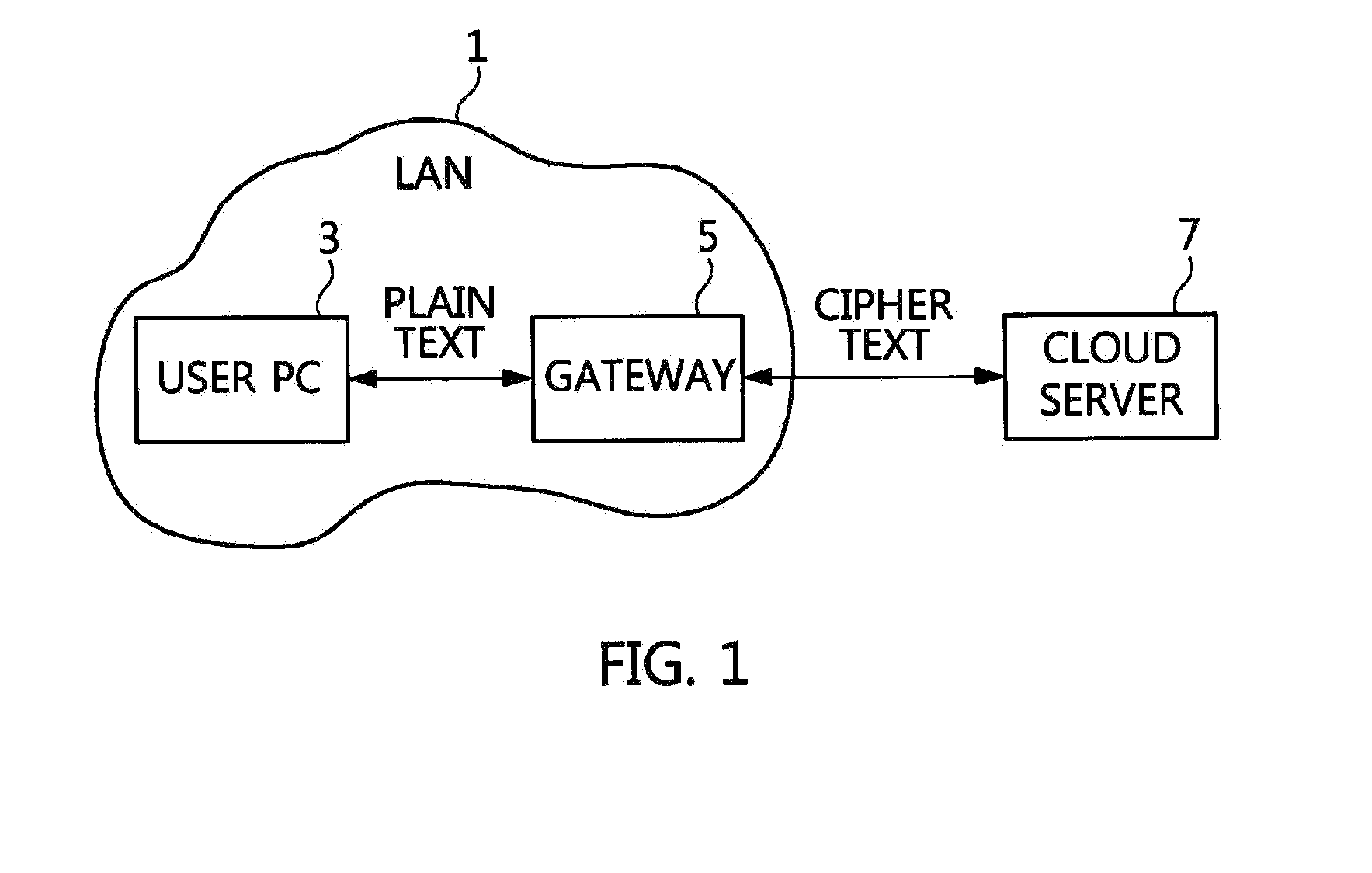
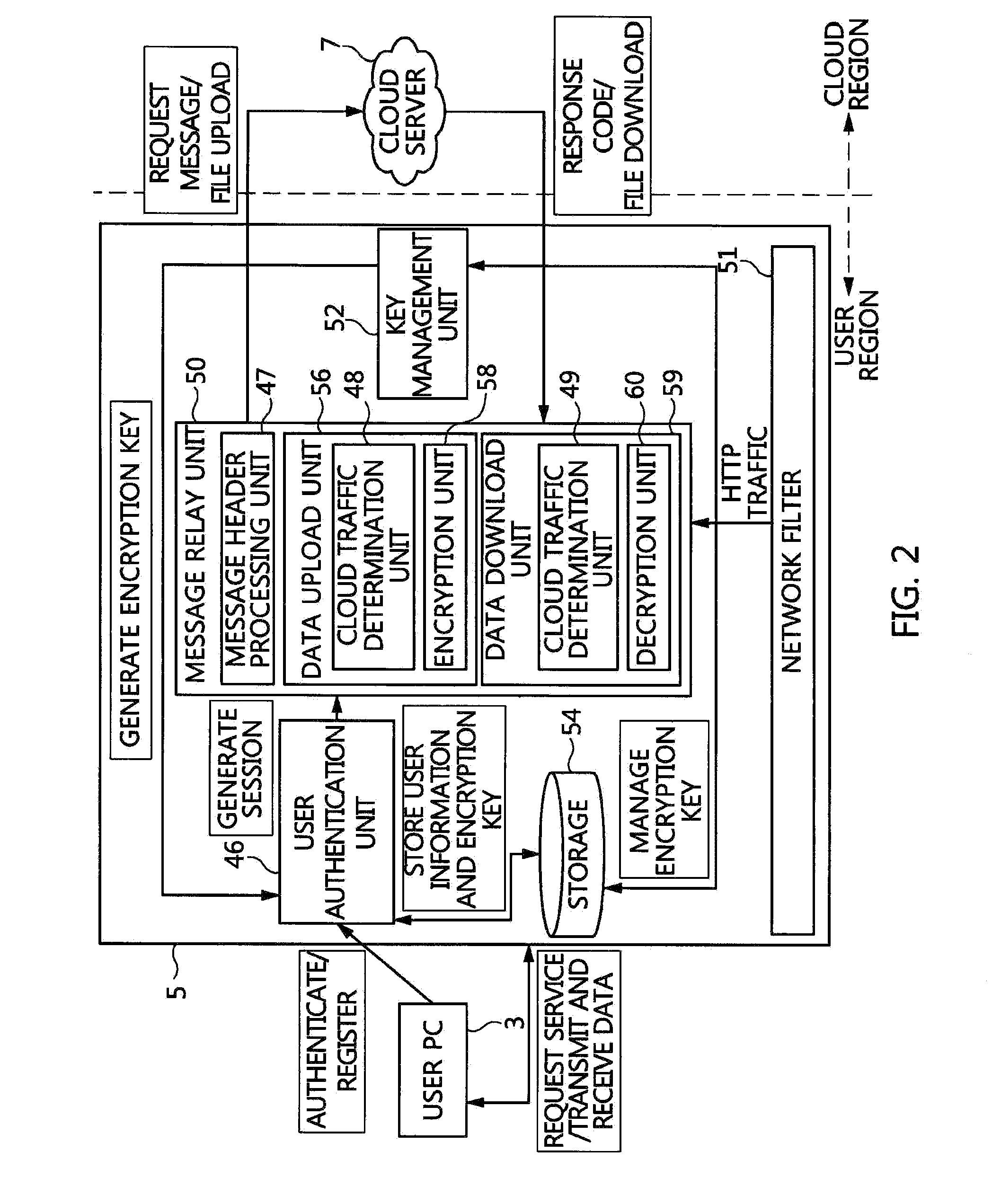
Apparatus and method for protecting user data in cloud computing environment
InactiveUS20160226831A1Support mobilityEnsure confidentialityUser identity/authority verificationTraffic capacityUser authentication
An apparatus and method for protecting user data are disclosed herein. The apparatus for protecting user data includes a network filter, a user authentication unit, a message relay unit, and a key management unit. The network filter filters traffic between a user and a cloud server. The user authentication unit registers and authenticates the user. The message relay unit relays a message and data included in the traffic between the user and the cloud server. The key management unit generates and manages a key required to encrypt the data.
Owner:ELECTRONICS & TELECOMM RES INST
Mobile terminal safety access authentication method in combination with fingerprint
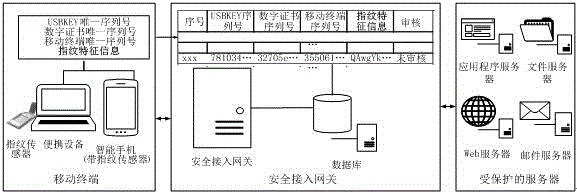
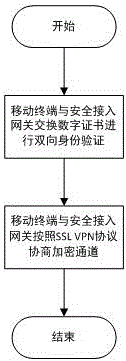
ActiveCN106488452APrevent unauthorized accessEnsure safetyDigital data authenticationSecurity arrangementIdentity recognitionInformation access
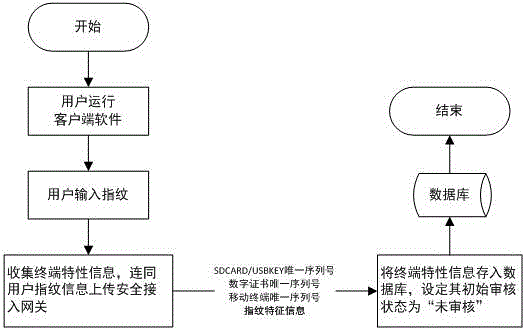
The invention provides a mobile terminal safety access authentication method in combination with fingerprint. The method comprises the four steps of establishing an encryption channel, user registering, user information checking and user business accessing. A client collects terminal feature information which comprises a USBKEY sequence number, a digital certificate sequence number, a mobile terminal sequence number and user fingerprint feature information, and the terminal feature information is uploaded to a safety access gateway through the encryption channel; the safety access gateway verifies the integrity and validity of the terminal information, and decides whether the terminal can access a protected server according to a verification result. The fingerprint recognition technology is combined with the traditional identity recognition mode, so that the medium for marking the identity is directly related to the natural person, the identity recognition and the recognized person are really corresponding to each other, the security level of the mobile terminal information access is effectively improved, and the convenient mobile technology can be facilitated to play effect in the information application.
Owner:JIANGSU ELECTRIC POWER CO +1
Intelligent power grid security data aggregation method and system based on block chain technology
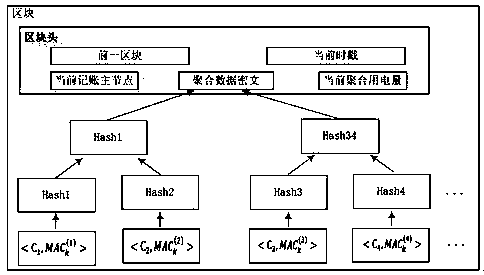
ActiveCN110120868AIntegrity guaranteedProtect power consumption privacy informationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesConfidentialityData aggregator
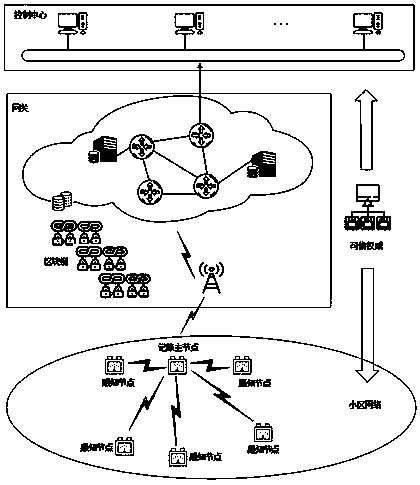
The invention discloses an intelligent power grid security data aggregation method and system based on a block chain technology. A credible authority is responsible for managing and distributing secret information of all other entities; a control center is responsible for integrating, processing and analyzing periodic time sequence data of the cell network nodes and providing comprehensive and reliable intelligent services; agateway is responsible for aggregating the data submitted by the user; a sensing nodes are responsible for collecting data in real time and forwarding the data to the control center. The method includes a system initialization stage; a data collection stage; a security data aggregation stage; an accounting node selection stage; a new block generation stage; a block verification stage; and a decision support stage. On the basis of deeply researching and analyzing the existing application achievements of the block chain technology in the field of smart power grid application, the smart power grid security data aggregation method and system based on the block chain technology are realized, and meanwhile, the user privacy is protected and the confidentiality and integrity of communication data are ensured.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
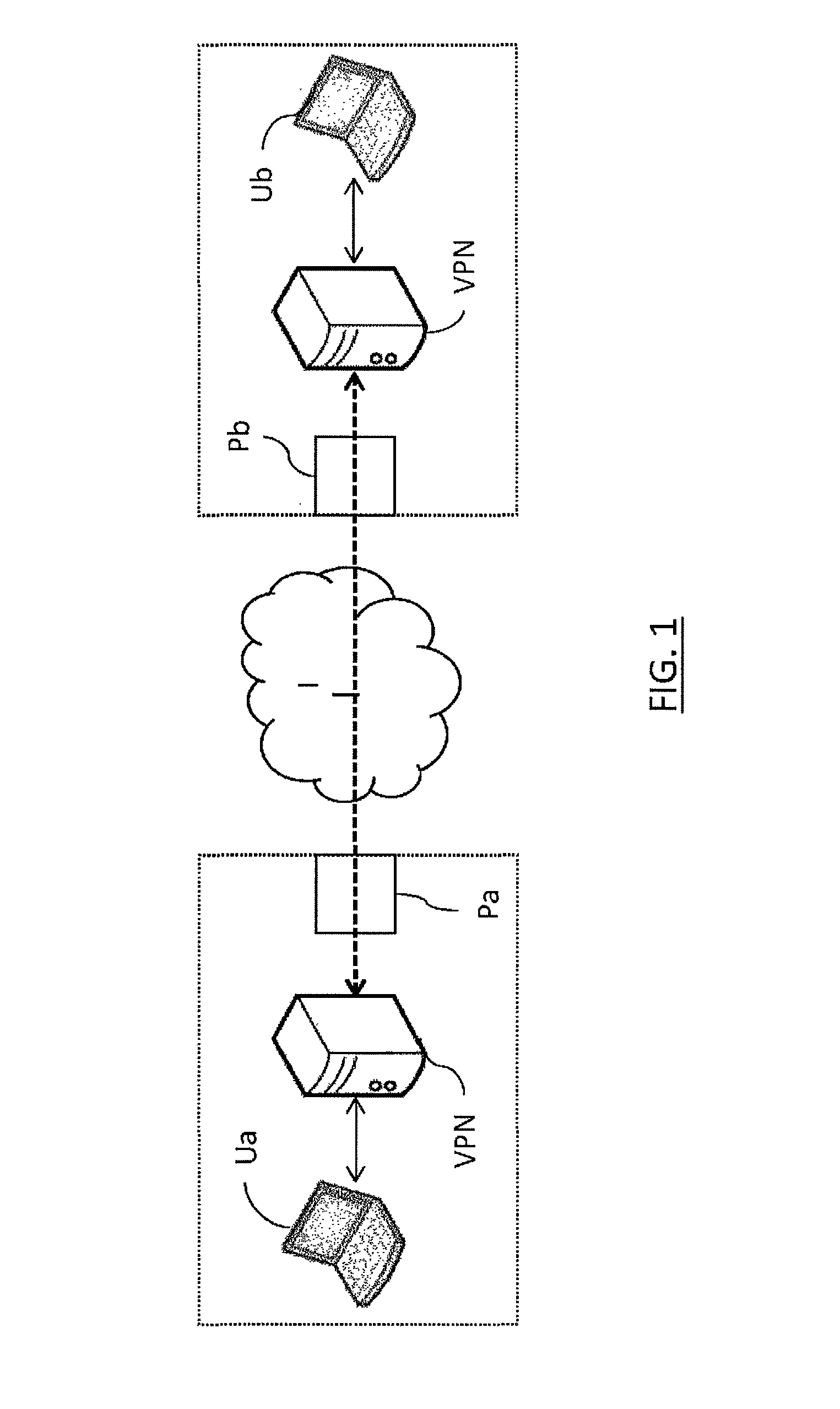
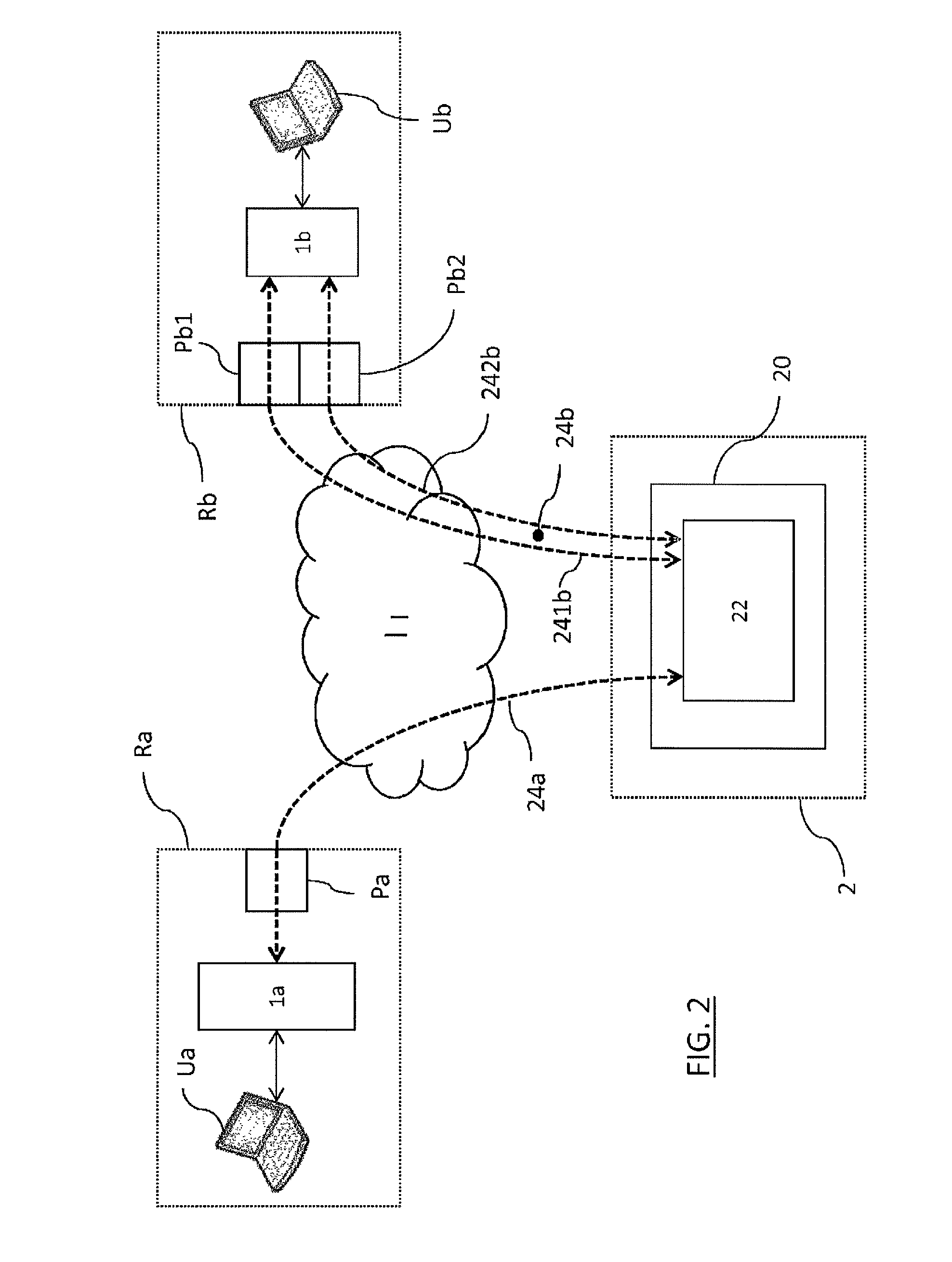
Method and system for establishing virtual private networks between local area networks
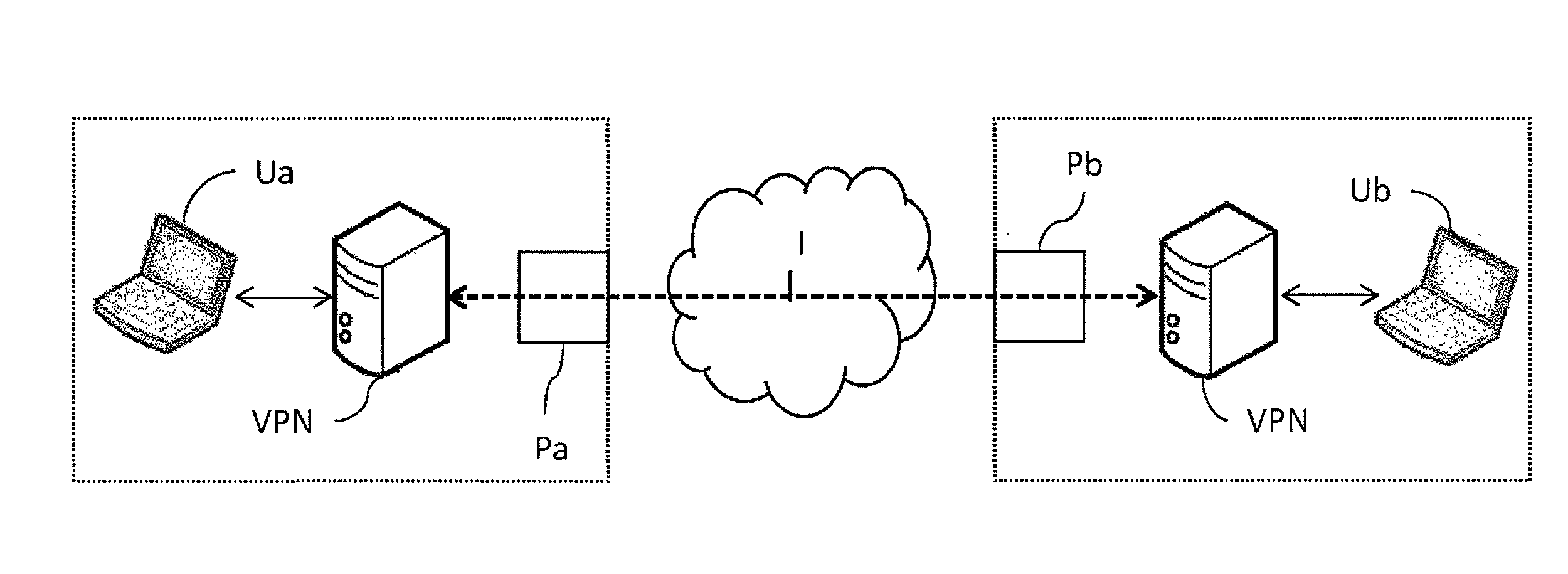
ActiveUS20160294777A1Ensure confidentialityUser identity/authority verificationStore-and-forward switching systemsPrivate networkPublic network
The invention relates to a method for establishing a virtual private network between local area networks, each local area network comprising at least one access gateway to a public network and a unit comprising a VPN client, the method comprising the following steps carried out each time a unit is powered on: sending, by the unit, of at least one connection message to an infrastructure connected to the public network and comprising at least one intermediate server, each connection message passing through a respective gateway of the local area network; reception, by the infrastructure, of each connection message; and determination of topology data identifying each bridge of the local area network in which the unit is placed, the method further comprising the following steps carried out for a plurality of units: instancing, by a predetermined intermediate server of the infrastructure, of a VPN server associated with the plurality of units; establishing an encryption tunnel between the VPN server and the VPN client of each unit from the corresponding topology data; and creating and storing routing data representative of a data routing rule between the established encryption tunnels.
Owner:CITYPASSENGER
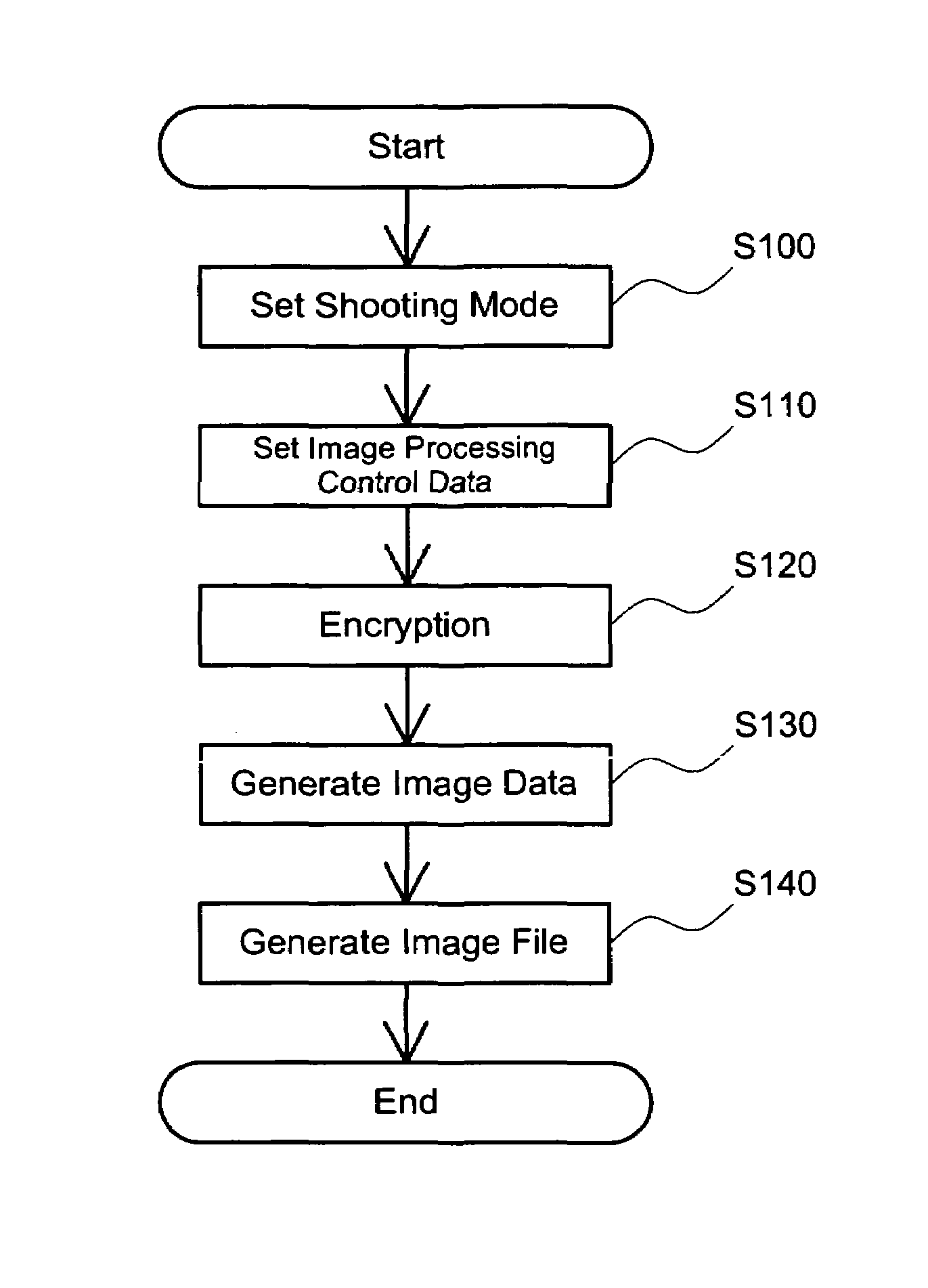
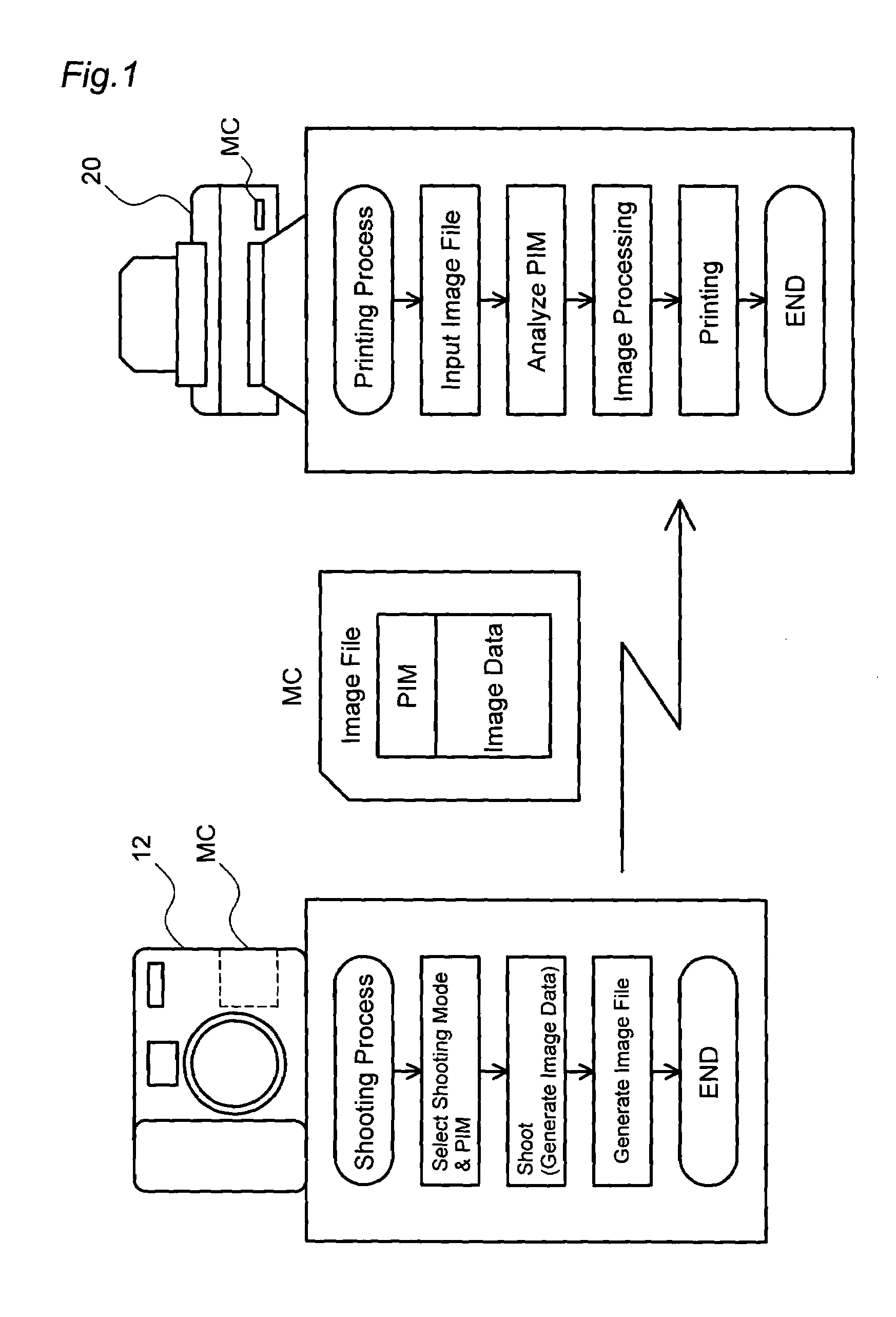
Creation of image file
ActiveUS7350086B2Ensure confidentialityTelevision system detailsKey distribution for secure communicationImaging processingComputer graphics (images)
The technique of the present invention ensures generation of an image file, in which image data and additional data are included, with the confidentiality of specific data kept.An image output system outputs the image data, which is generated in a digital still camera DSC 12, with a color printer 20. The DSC 12 encrypts image processing control data, which is preset by the manufacturer, and generates the image file, in which the image data and the encrypted image processing control data are included. The color printer 20 decodes the image processing control data included in the image file, performs image processing based on the image processing control data, and thereby outputs an image.
Owner:138 EAST LCD ADVANCEMENTS LTD
Information security method of industrial control network and security function block
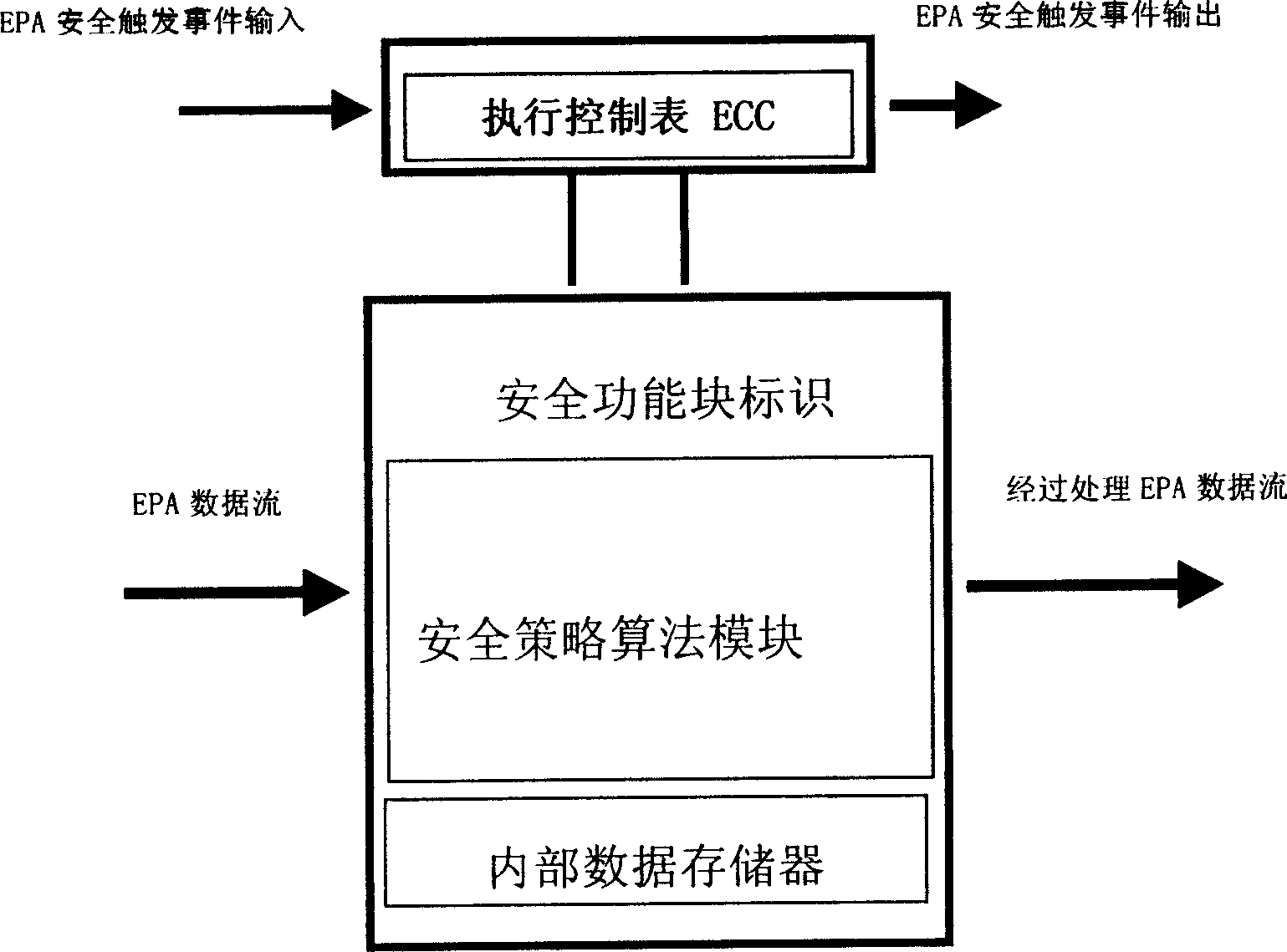
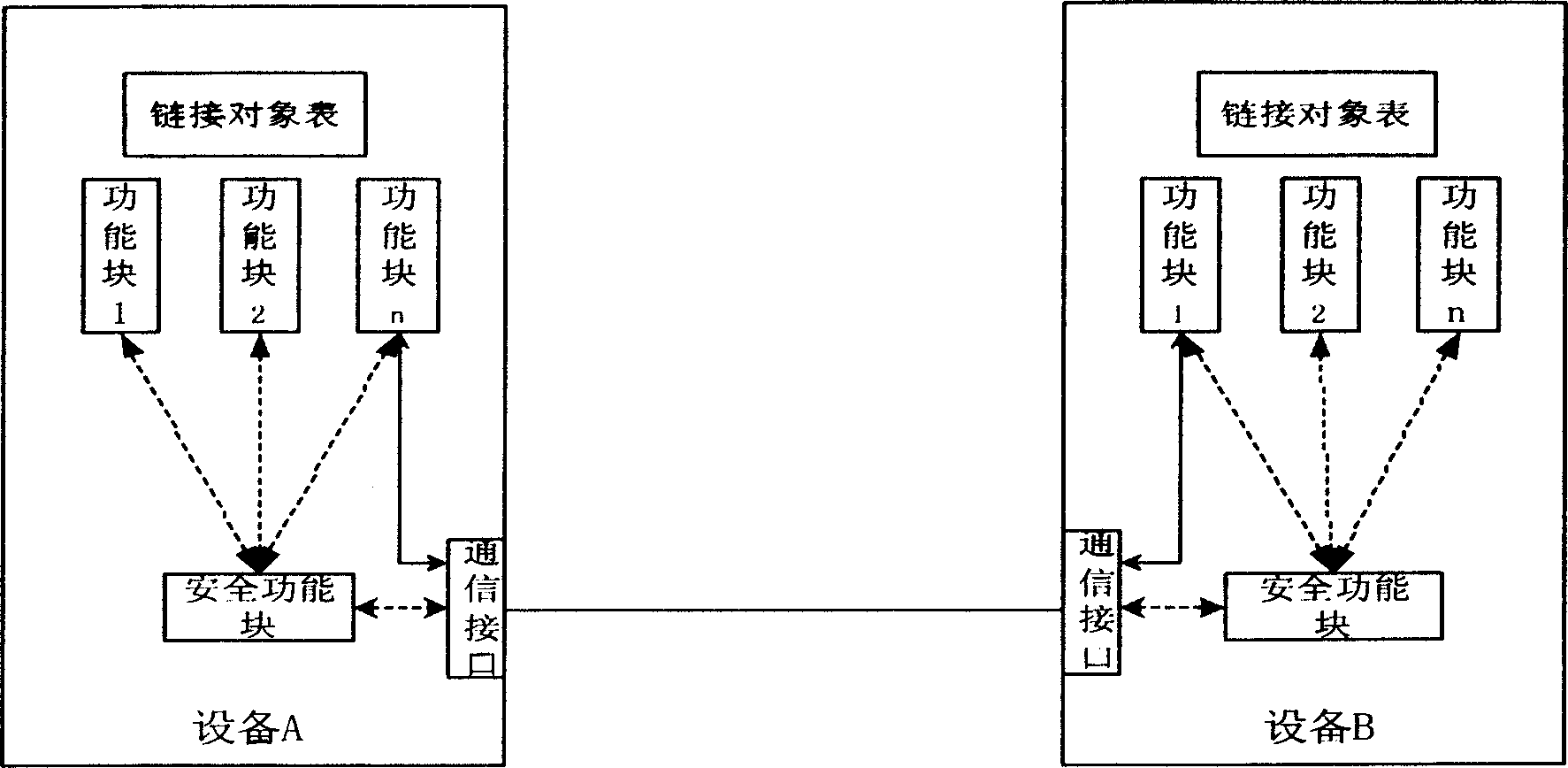
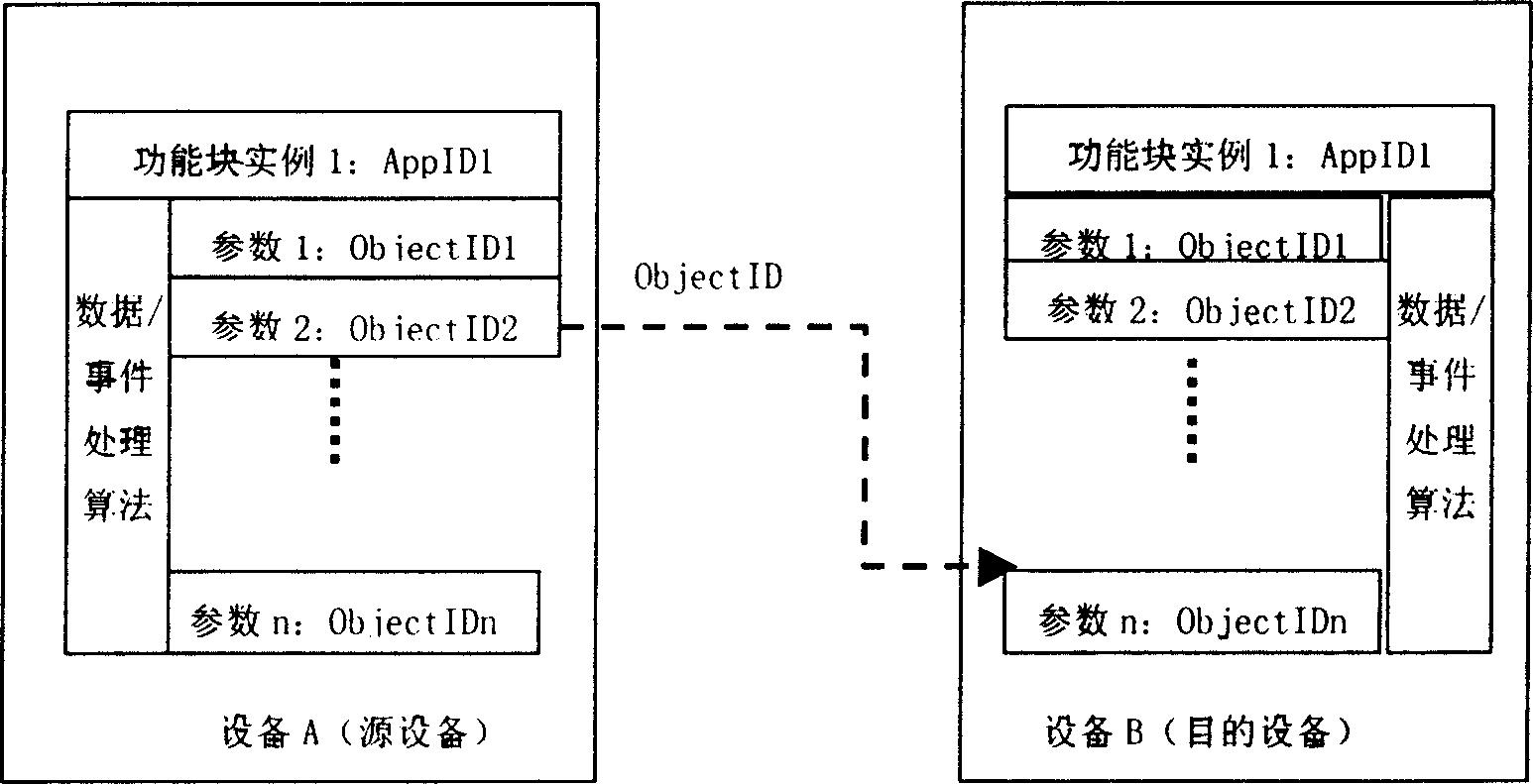
InactiveCN1703046AEnsure confidentialityEnsure integrityData switching networksSecuring communicationExecution controlInformation security
This invention relates to one information safety method and its function module based on industry controlled network and to the safety management method, which comprises the following steps: establishing safety function module in the net; defining safety function module input interface and outputting interface and safety affairs and executing control form dispatching formula when the affairs arrive; processing the input unsigned char to fulfill the data coding and buffer the results in the output interface; finally executing the control form to send one affair signal and completing the coding formula in the key dispatching system.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
System and Method for Evaluating Supplier Quality
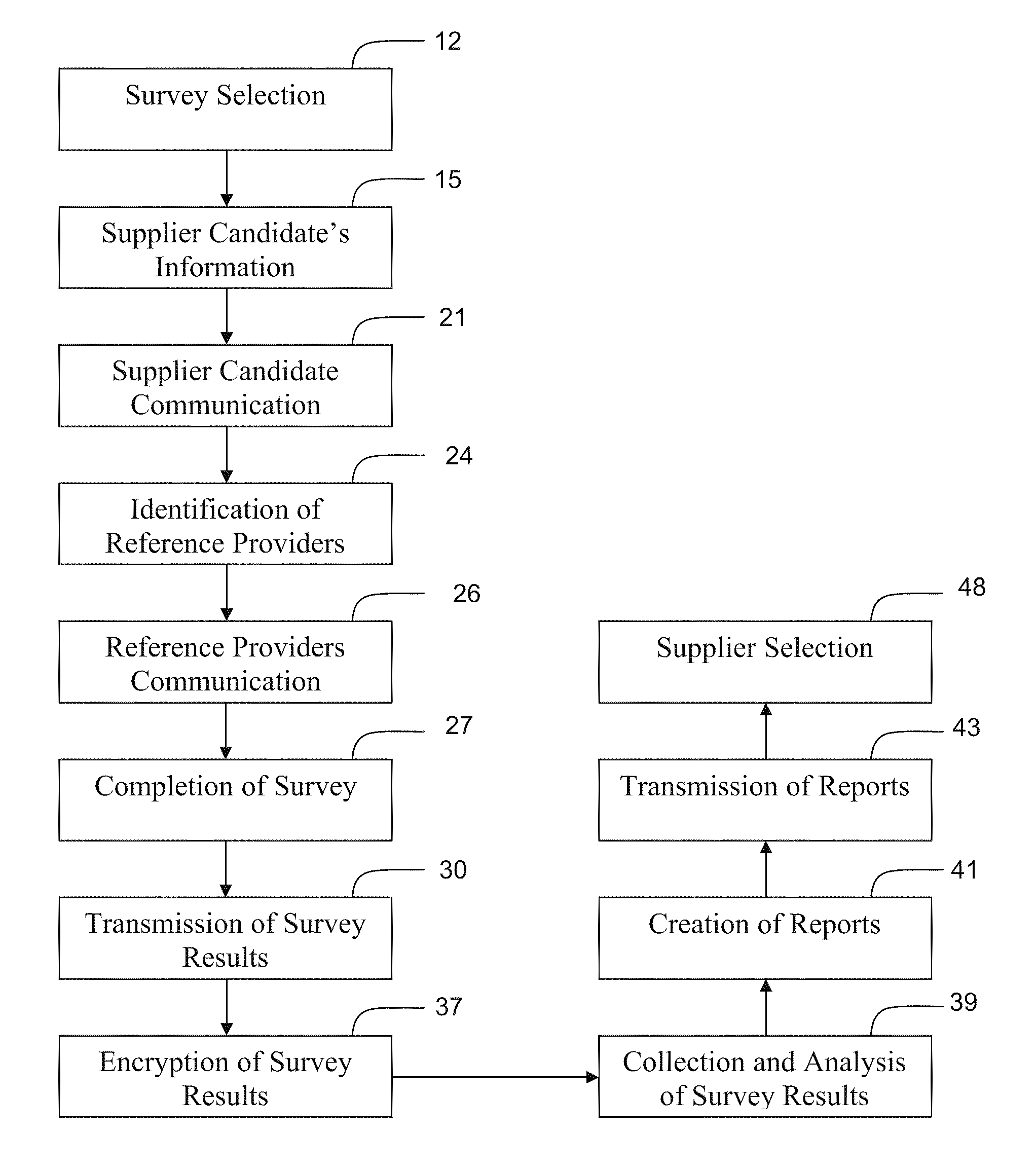
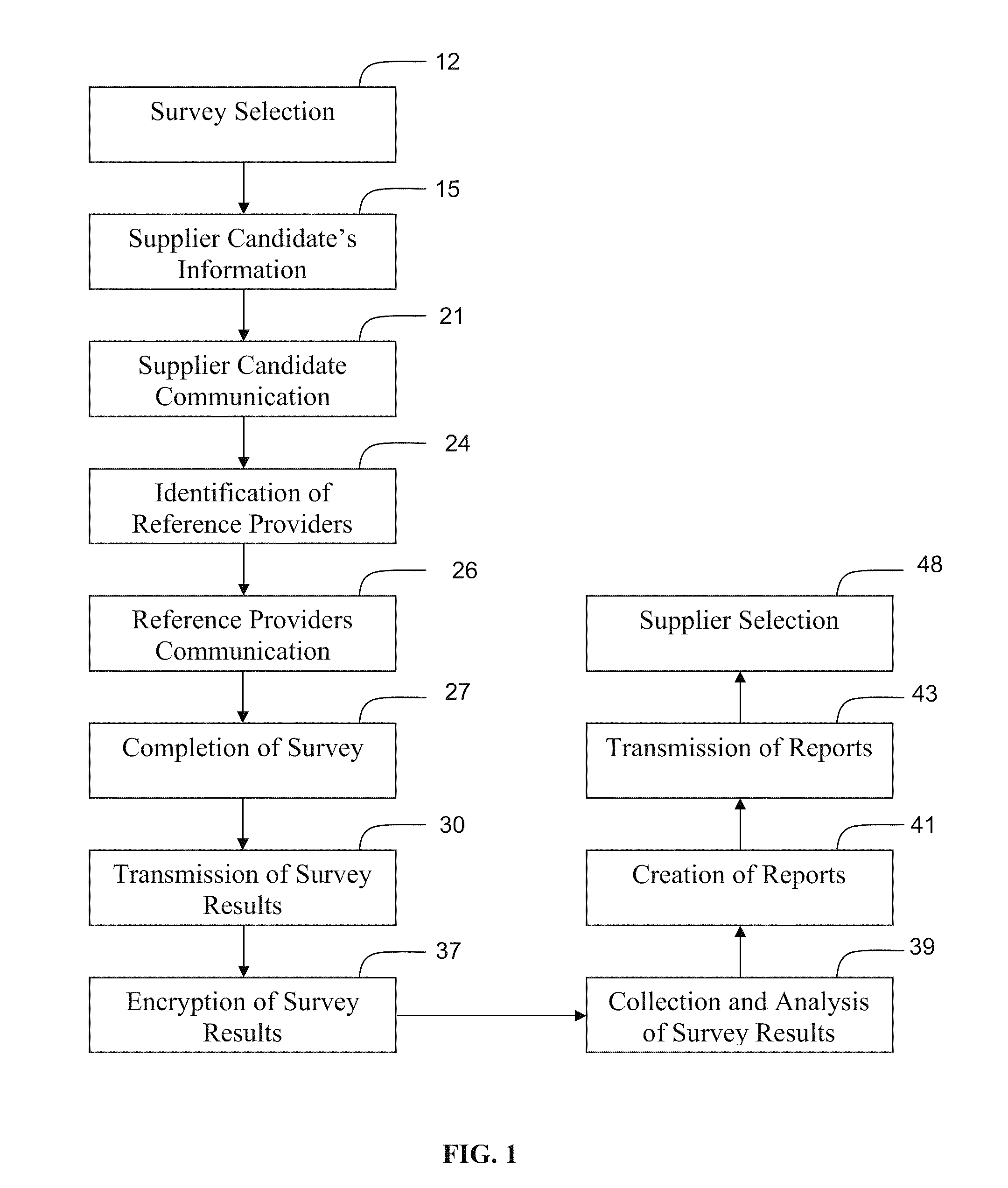
InactiveUS20110087613A1Ensure confidentialityOffice automationResourcesManagement systemUser interface
Supplier evaluation system for selecting a supplier for a project and / or monitoring a current supplier's performance. A supplier evaluation system first comprises a first database storing a plurality of inquiries and supplier contact information. The supplier candidates identify raters and those raters receive the inquiries over a computer network. The system provides a user interface for the rater to confidentially respond to the inquiries. The raters' responses are then electronically sent to one or more databases in the system and the system's database management system analyses the responses and makes them available to purchasing agents in a plurality of formats.
Owner:EVENDOR CHECK
Safe payment system based on wireless fidelity (wifi)
InactiveCN103093344AEnsure safetyEnsure confidentialityProtocol authorisationWireless routerConfidentiality
The invention relates to a mobile payment system, in particular to a safe payment system based on wireless fidelity (wifi). According to the system, after a purchasing side is connected with a network through wifi sending equipment of a selling side, a wireless router mark of the wifi sending equipment is acquired and sent to a wifi sending equipment management and authentication server of the selling side through a wireless router network channel, authentication is carried out from two parts, namely a hardware wireless router and the wireless router network channel, safety and confidentiality of selling side information are guaranteed, one wireless router mark is acquired at one time, the purchasing side and the selling side do not need to interact to carry out screening and selecting, and accordingly payment can be smooth and convenient.
Owner:沈志松 +1
System for analysing genomic data comprising a plurality of application nodes and a knowledge database
ActiveUS11424009B2Efficient use ofEnsure confidentialityProteomicsGenomicsHuman–machine interfaceEngineering
A genomic data analysis architecture includes a plurality of application nodes, each application node including a calculation system including at least one calculation node, the calculation system being constructed and arranged so as to carry out genomic calculations, a human-machine interface constructed and arranged so as to communicate with the calculation system, and a knowledge base access interface, and including a knowledge base constructed and arranged so as to communicate with the plurality of application nodes. The knowledge base contains genomic data.
Owner:SEQONE
Information distributing apparatus and method, receiving apparatus and method, distribution system, and computer program
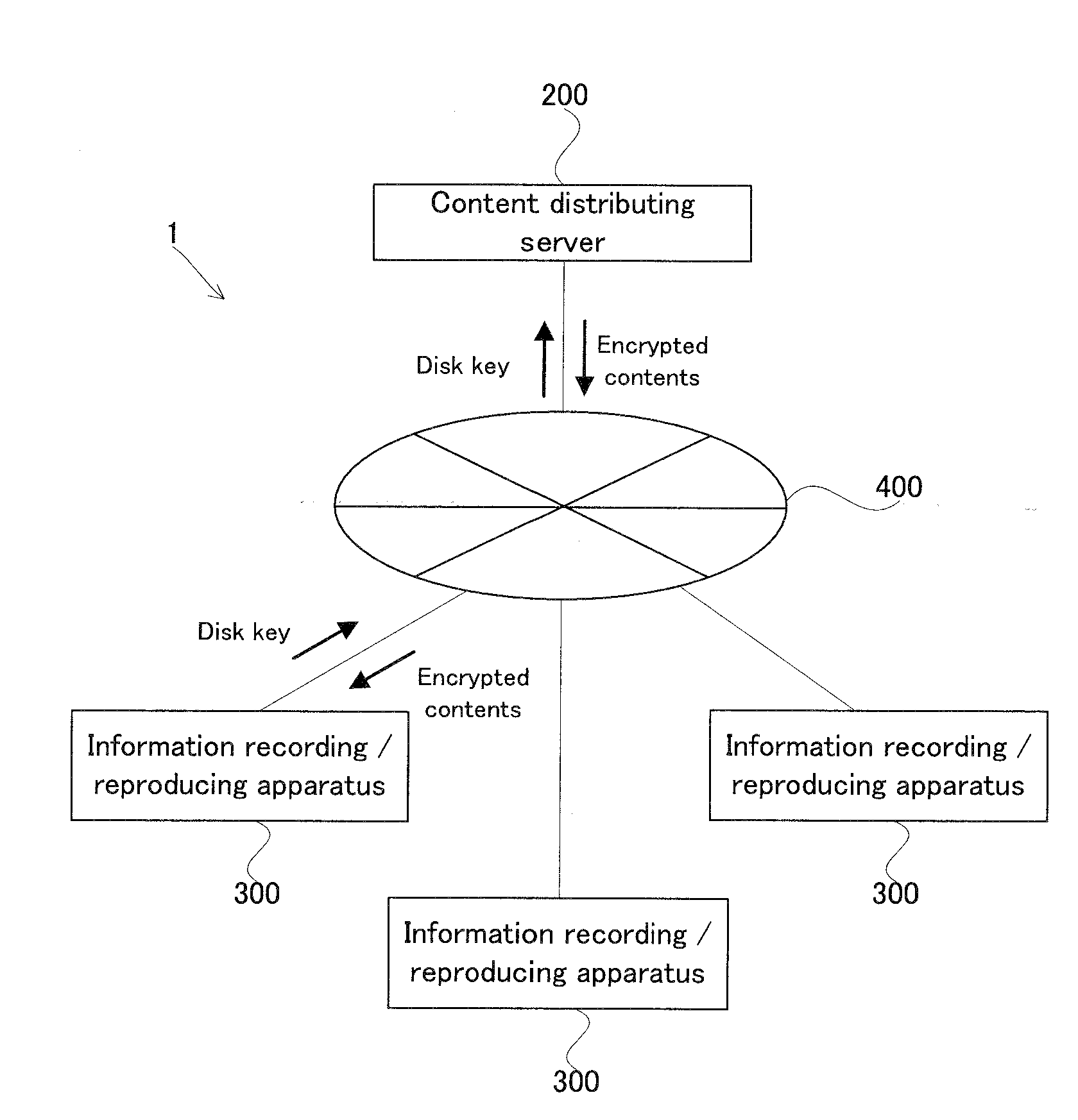
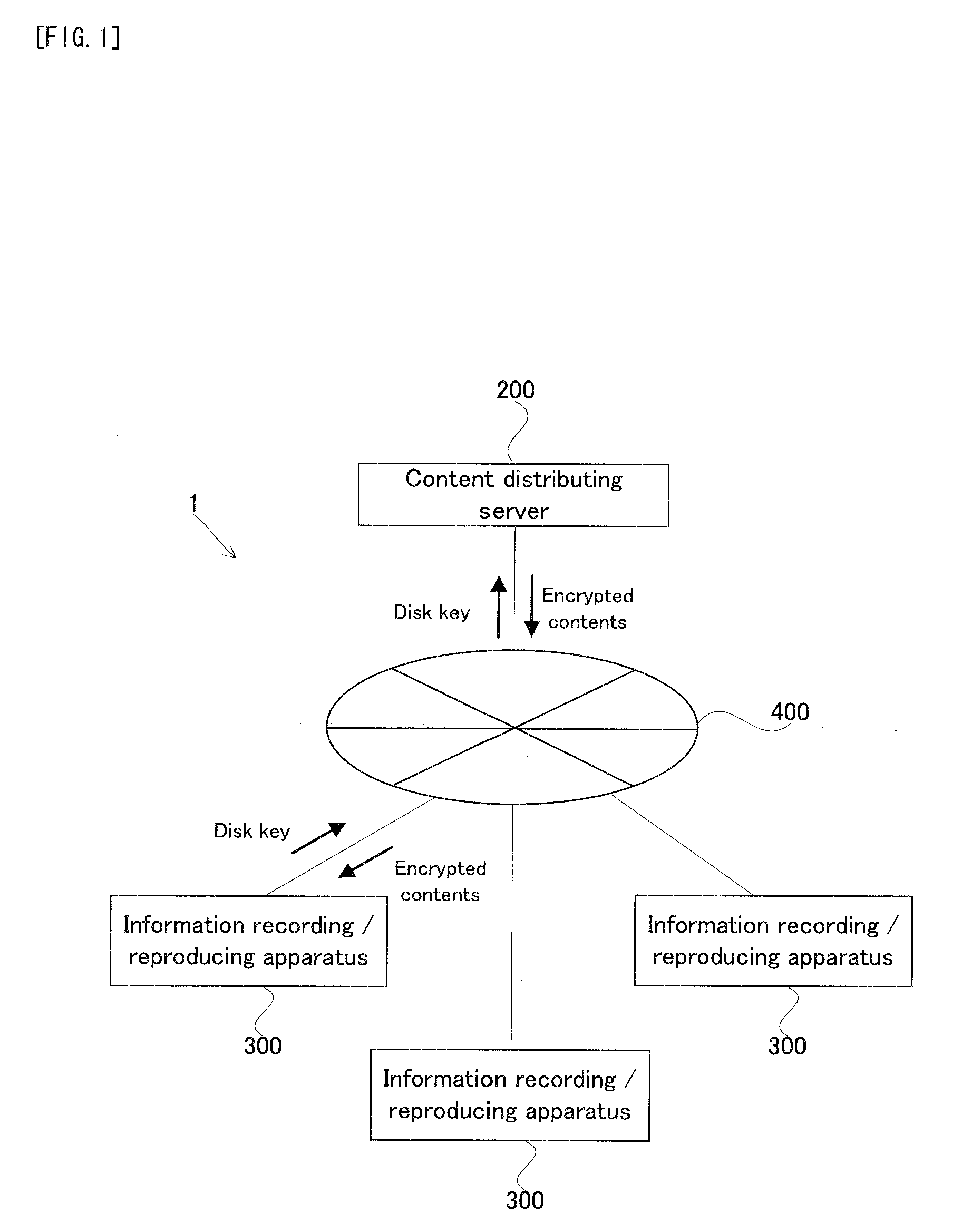
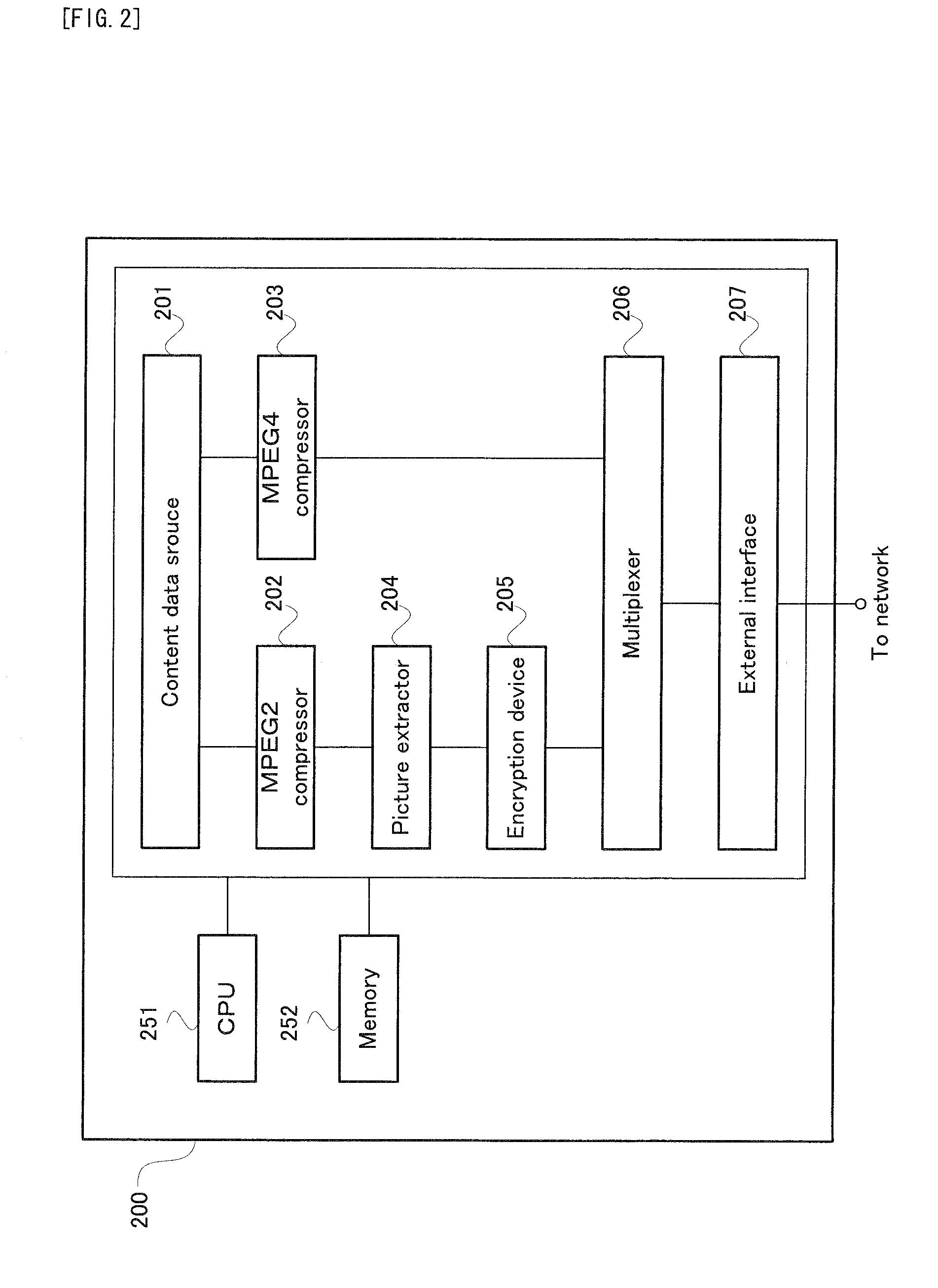
InactiveUS20090055932A1Improve transmission efficiencyShorten the length of timeTelevision system detailsDigital data processing detailsComputer hardwareDistribution system
A distribution system is provided with: a distributing apparatus being provided with: a first compressing device (202) for compressing first data, which is a reproduction reference in a first compression method (MPEG2); a second compressing device (203) for compressing second data other than the first data in a second compression method (MPEG4); an encrypting device (205) for encrypting at least one portion of the compressed first data; and a distributing device (207) for distributing each of the encrypted first data and the compressed second data to a receiving apparatus, and a receiving apparatus being provided with: a receiving device (307) for receiving each of the encrypted first data and the compressed second data; a converting device (304) for converting the compression method for the compressed second data to the first compression method; and a generating device for generating the content data by combining the encrypted first data with the second data whose compression method is converted.
Owner:PIONEER CORP
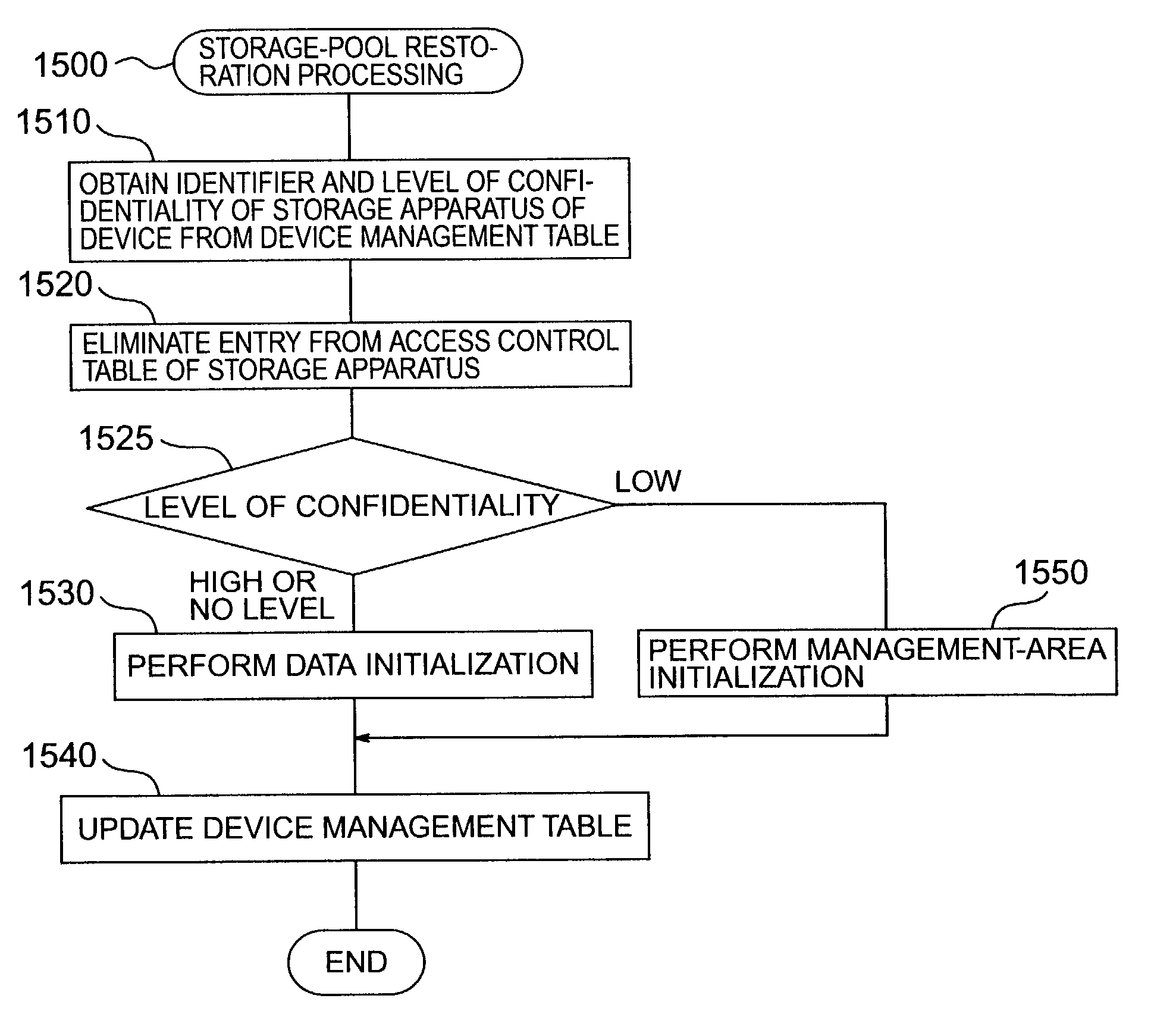
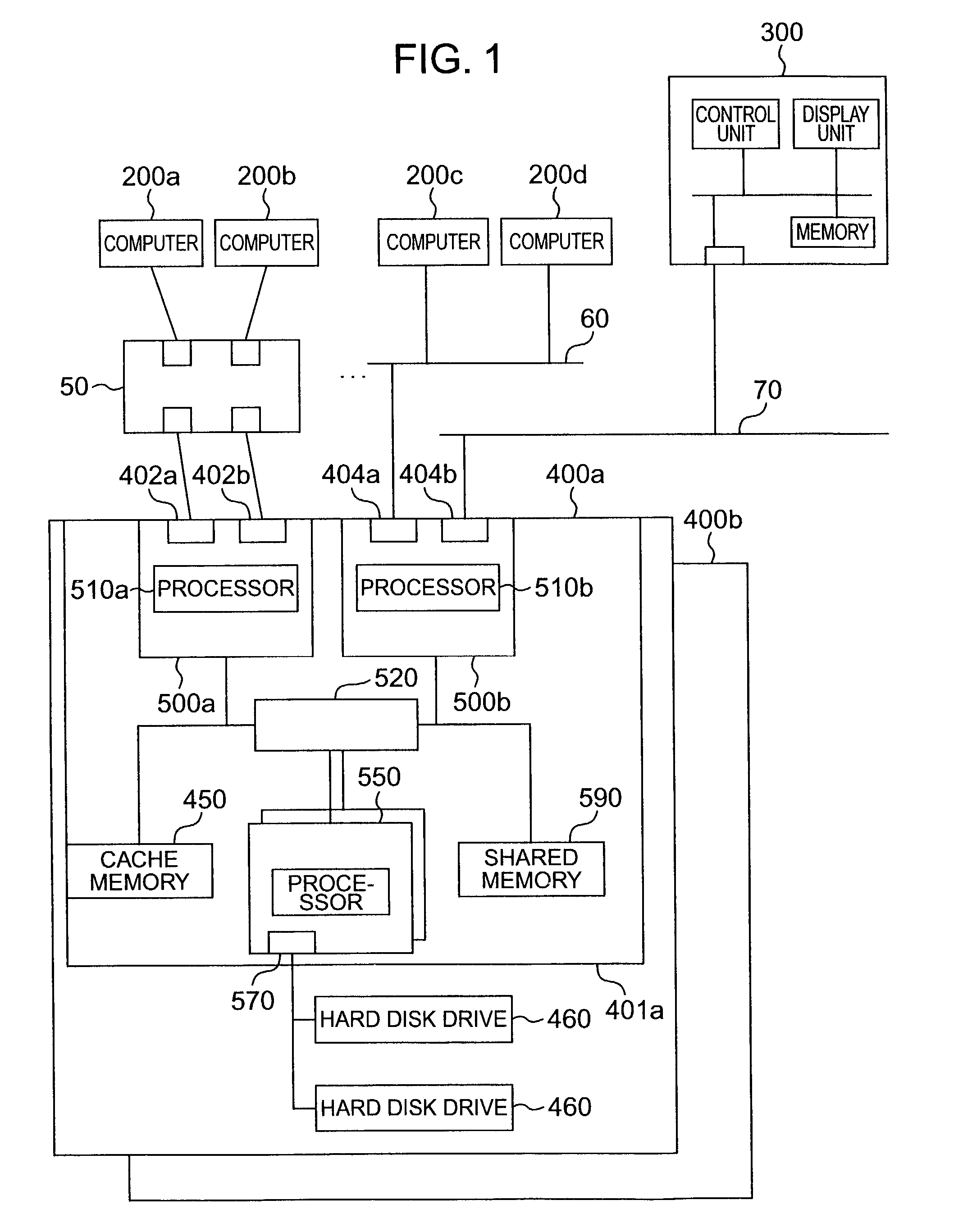
Centralized storage management method
InactiveUS7152144B2Ensure confidentialityInput/output to record carriersMemory adressing/allocation/relocationControl storeStorage management
A storage system includes plural storage apparatuses storing data, and a storage controller which transmits and receives data between an external computer and the plural storage apparatuses, and further controls the plural storage apparatuses. Logical devices each representing a logical storage area are defined on the storage apparatuses. When one logical device is in a state of allocation to the external computer and stores data used by the external computer, and the logical device is deallocated from the external computer, the storage controller performs a processing such as erasing data from the logical device to be deallocated. The processing is performed according to the logical device being deallocated.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com