Mobile terminal safety access authentication method in combination with fingerprint
A mobile terminal and secure access technology, applied in security devices, digital data authentication, electrical components, etc., can solve problems such as identity verification of people who cannot use the device, to ensure timeliness, solve security defects, and prevent illegal access Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
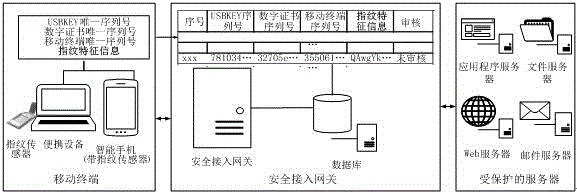
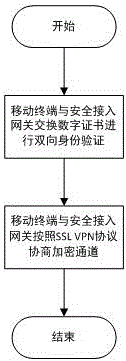
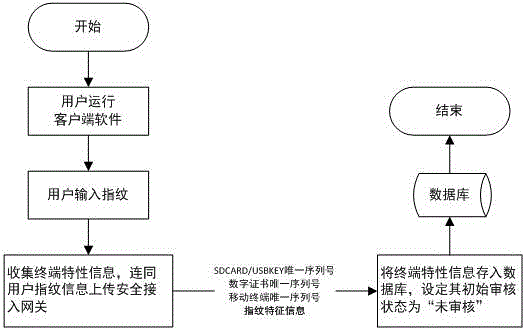
[0029] Such as Figure 1-5 As shown, the mobile terminal secure access authentication method combined with fingerprints disclosed in the present invention adopts the client / server mode, and the mobile terminal installs client software, and the software first uses USBKEY and digital certificate to negotiate with the secure access gateway to complete certificate-based identity authentication Establish an encrypted channel based on the national secret algorithm, and then collect terminal characteristic information, including USBKEY serial number, digital certificate serial number, mobile terminal serial number and user fingerprint characteristic information, and upload it to the secure access gateway through the encrypted channel. The secure access gateway verifies the integrity and validity of the terminal information, and determines whether the terminal can access the protected server according to the verification result. Specifically include the following steps:
[0030] Step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com