Patents
Literature
3494results about How to "Guaranteed timeliness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
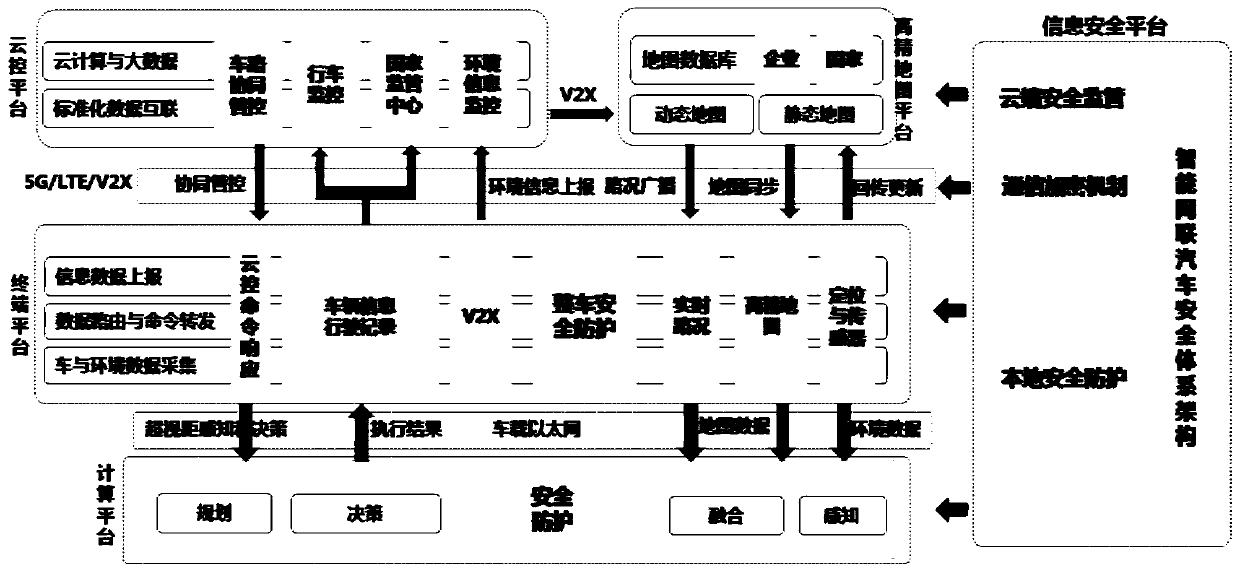
An intelligent network-connected automobile operation system based on vehicle-road collaboration
ActiveCN109714421ARealize data standardization and interconnectionMeet different applicationsParticular environment based servicesDetection of traffic movementHorizonVehicle driving
The invention discloses an intelligent network-connected automobile operation system based on vehicle-road collaboration. The intelligent networked automobile operation system comprises a high-precision map platform, a cloud control platform, a vehicle-mounted terminal platform, a vehicle-mounted computing platform and an information security platform. The high-precision map platform provides a real-time dynamic high-precision map; the cloud control platform and the vehicle-mounted terminal platform are subjected to cooperative management and control through a communication network; the cloudcontrol platform executes data storage, cloud computing and standardized data interconnection; the vehicle-mounted terminal platform executes information reporting; wherein the vehicle-mounted computing platform is connected with the vehicle-mounted terminal platform through the vehicle-mounted Ethernet, over-the-horizon perception data, map data, environment data and the like are obtained, a vehicle driving scheme is formulated through fusion calculation, and the cloud control platform, the vehicle-mounted terminal platform, the vehicle-mounted computing platform and the map platform are allprovided with safety monitors. Common basic services are provided for operation of the intelligent network connection automobile, and national and industrial development requirements are met.
Owner:CHINA INTELLIGENT & CONNECTED VEHICLES (BEIJING) RES INST CO LTD +1
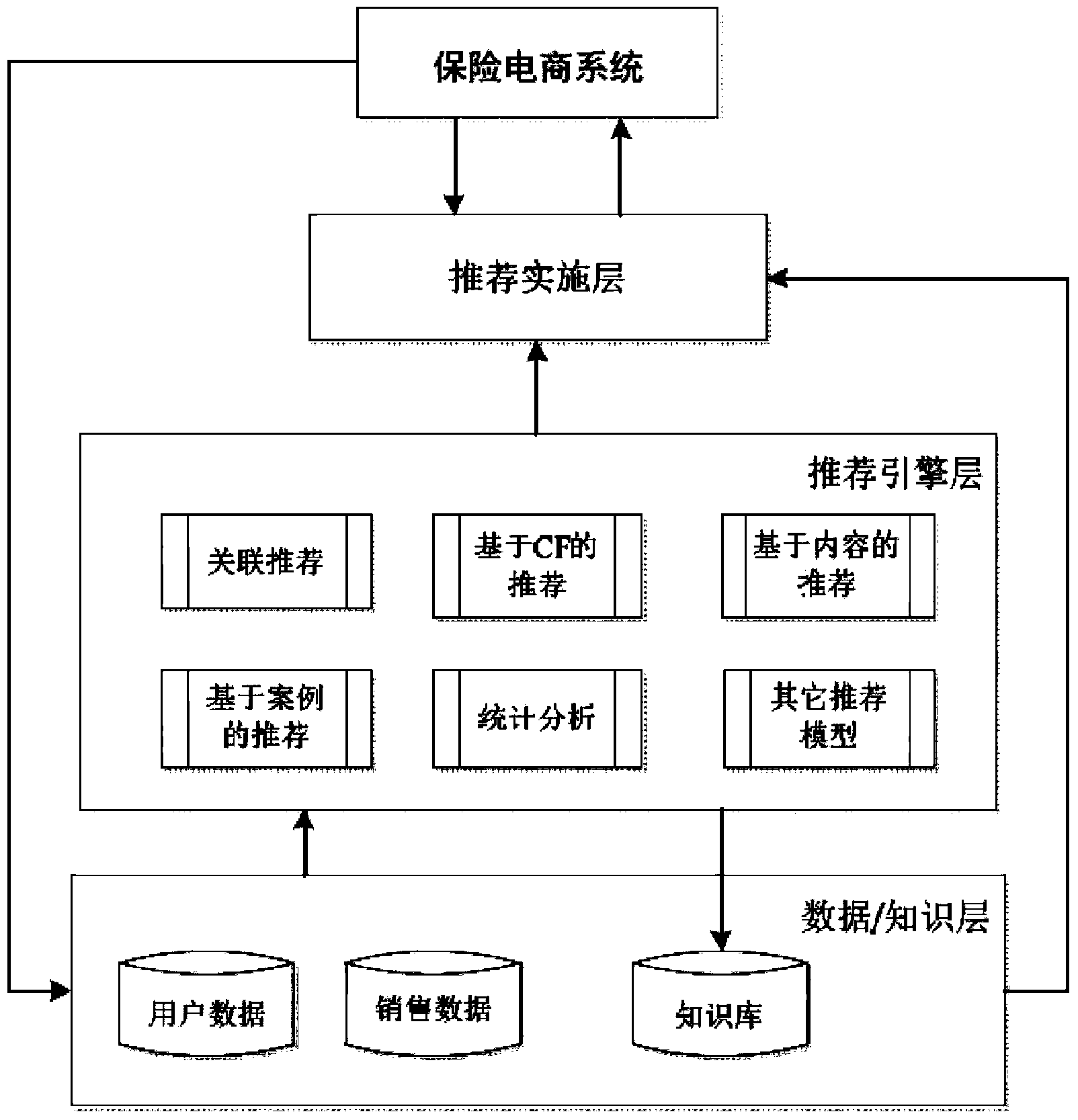
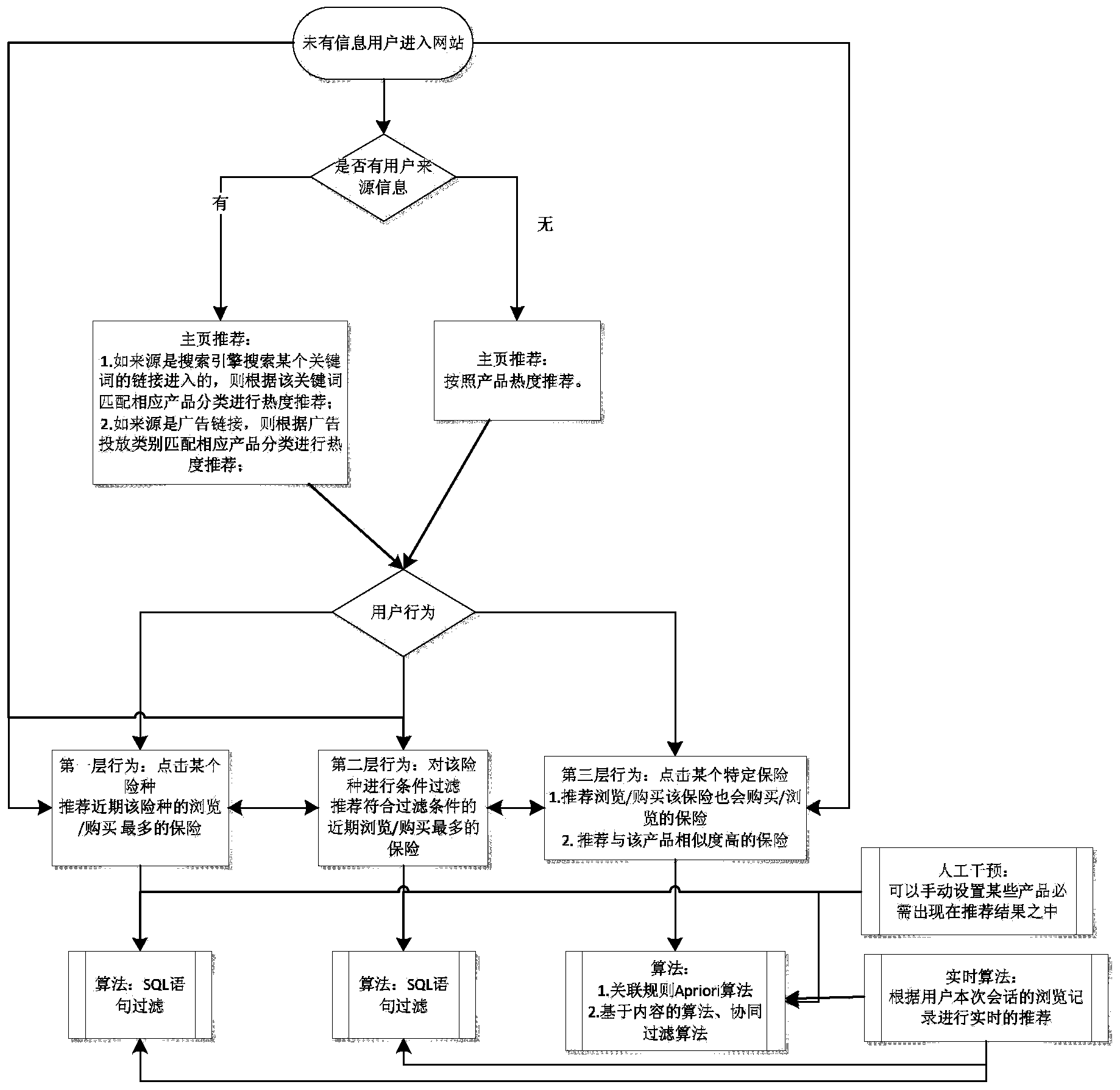
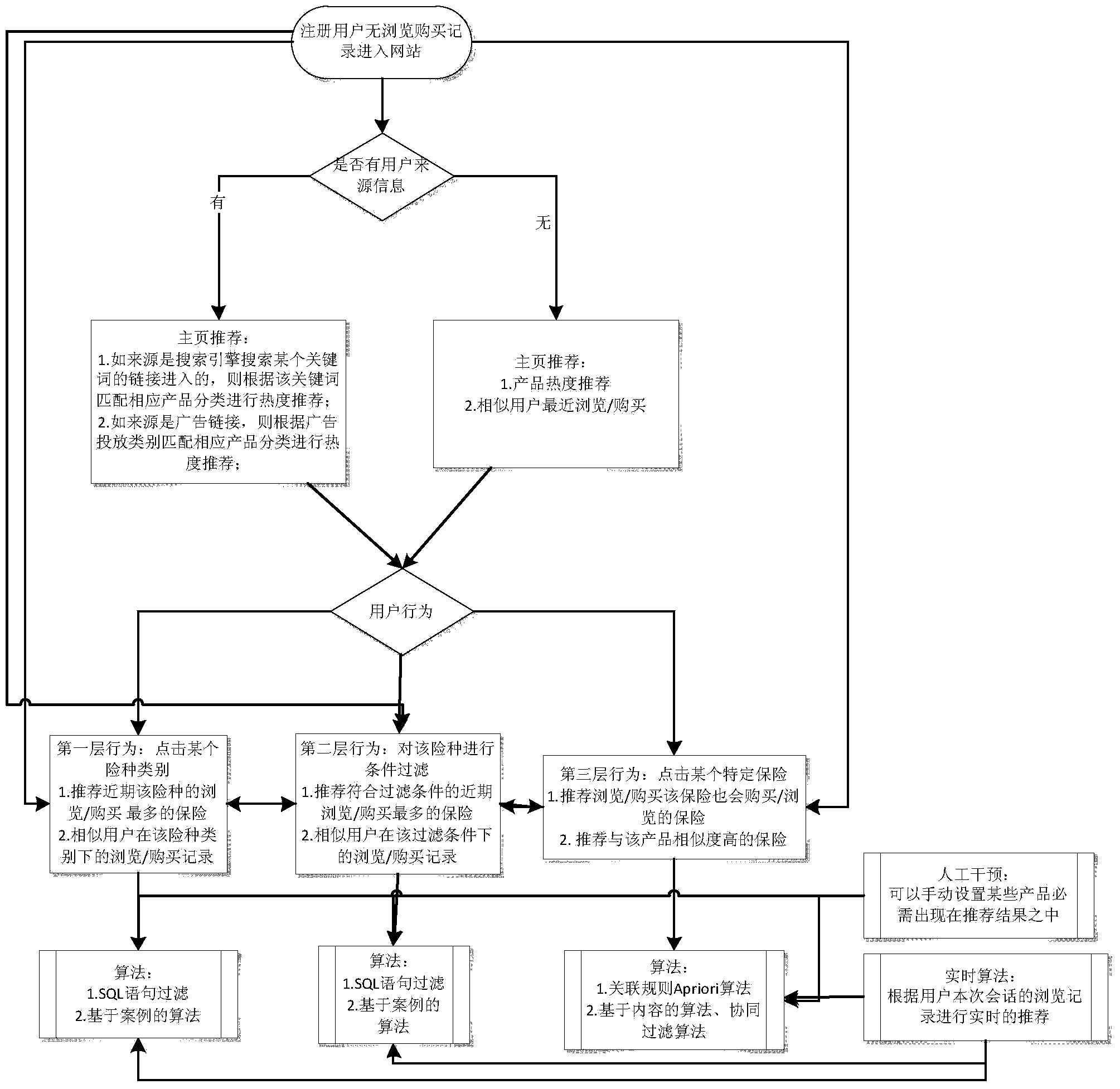
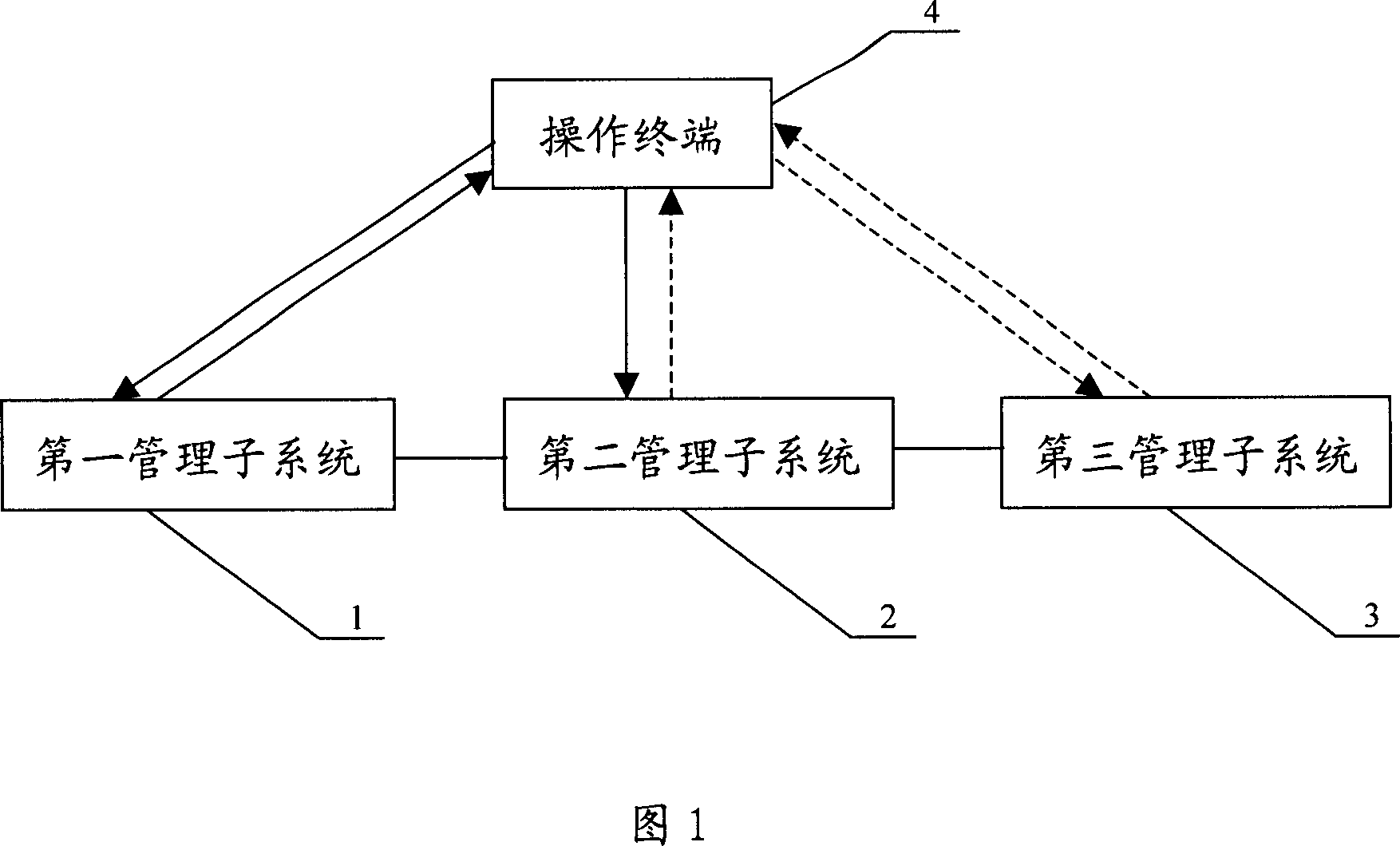
Insurance recommendation system framework and insurance recommendation method based on e-commerce platform
InactiveCN103473354AAccurate and personalized insurance recommendationGuaranteed timelinessFinanceSpecial data processing applicationsPersonalizationThe Internet
The invention belongs to the technical field of recommendation systems in the information technology and relates to an insurance recommendation system framework and an insurance recommendation method based on an e-commerce platform. The insurance recommendation system framework and the insurance recommendation method are particularly suitable for insurance recommendation application under the Internet environment and also have reference significance to the recommendation of other commodities based on the e-commerce. Aiming at the characteristic of being based on an insurance e-commerce platform, a generalized system framework for an individualized insurance recommendation system is disclosed; in consideration of the specific scene of the insurance e-commerce platform, an insurance individualized recommendation process based on the e-commerce platform is designed; all recommendation methods are integrated in one recommendation framework, the advantages of all recommendation methods are fully utilized and the goal of accurate and reliable individualized insurance recommendation is realized; two modes, i.e. an offline recommendation mode and an online recommendation mode are jointly used to guarantee the timeliness of the recommendation; recommendation results are explained and the behaviors of users on which each recommendation result is given are pointed out; due to the specificity of insurance recommendation, a reasonable recommendation result display interface is designed.
Owner:FOCUS TECH
Traffic information processing method based on vehicle mounted wireless sensor network
InactiveCN101286266AReduce data redundancyReduce data transfer burdenDetection of traffic movementInformation processingLine sensor
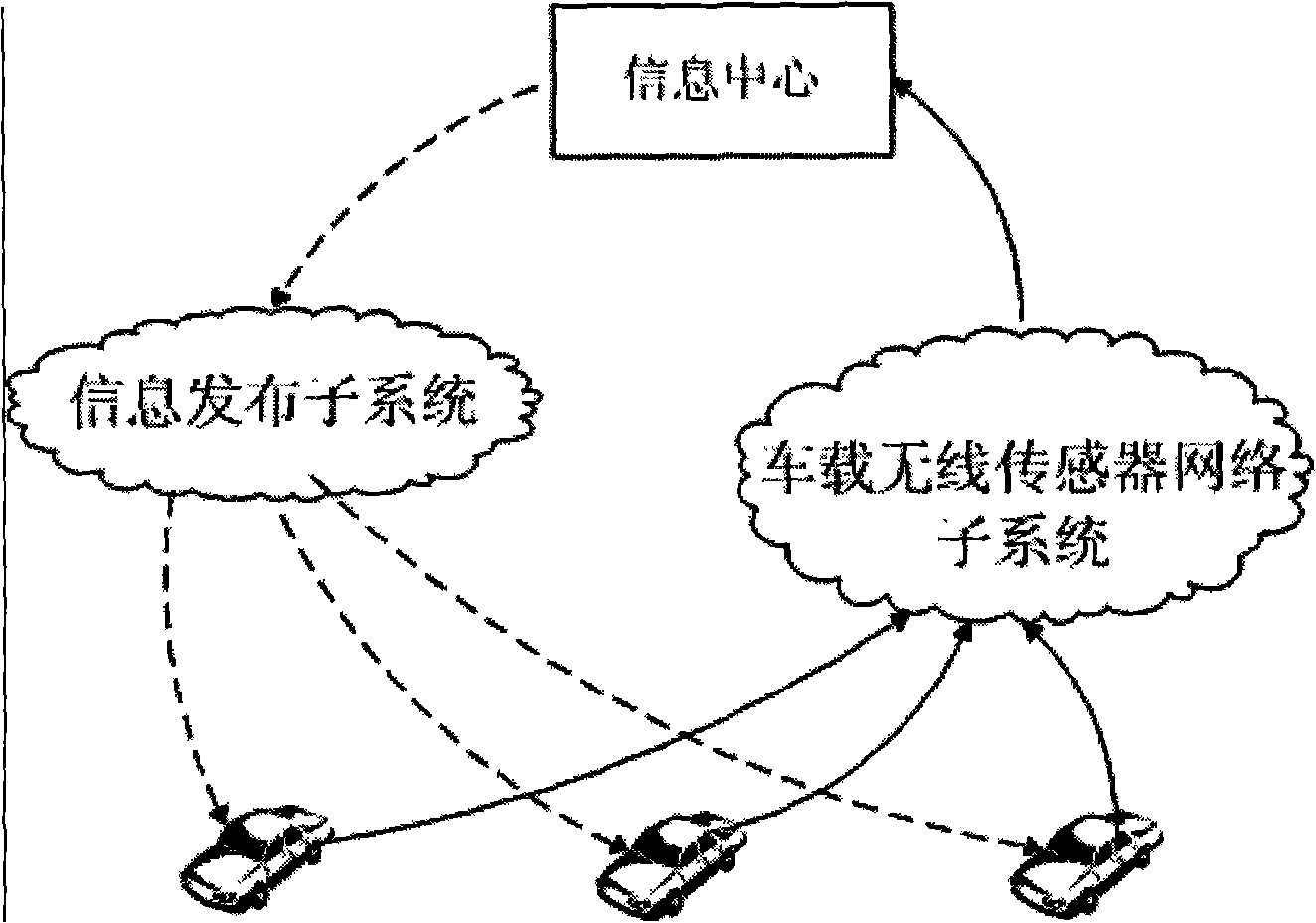
The invention discloses a traffic-road condition information processing method based on a vehicle wireless sensor network. The method is characterized in that: firstly, a wireless communication network is established and the network includes an information center, a vehicle wireless sensor network sub-system formed by limited vehicle mobile knots and an information publishing sub-system based on a broadcasting network; the information center is fixed in a traffic hub in a city as the center of the wireless communication network; secondly, each vehicle mobile knot collects the timely road condition information and integrates data through the vehicle wireless sensor network sub-system according to the instruction of the information center; then the timely road condition information from the information collection and data integration of each road section is reported to the information center through the vehicle wireless sensor network sub-system; finally, the processed traffic road condition information and network control instructions are published by the information center through the information issuing sub-system to each vehicle mobile knot for the road choosing by drivers.
Owner:XI AN JIAOTONG UNIV
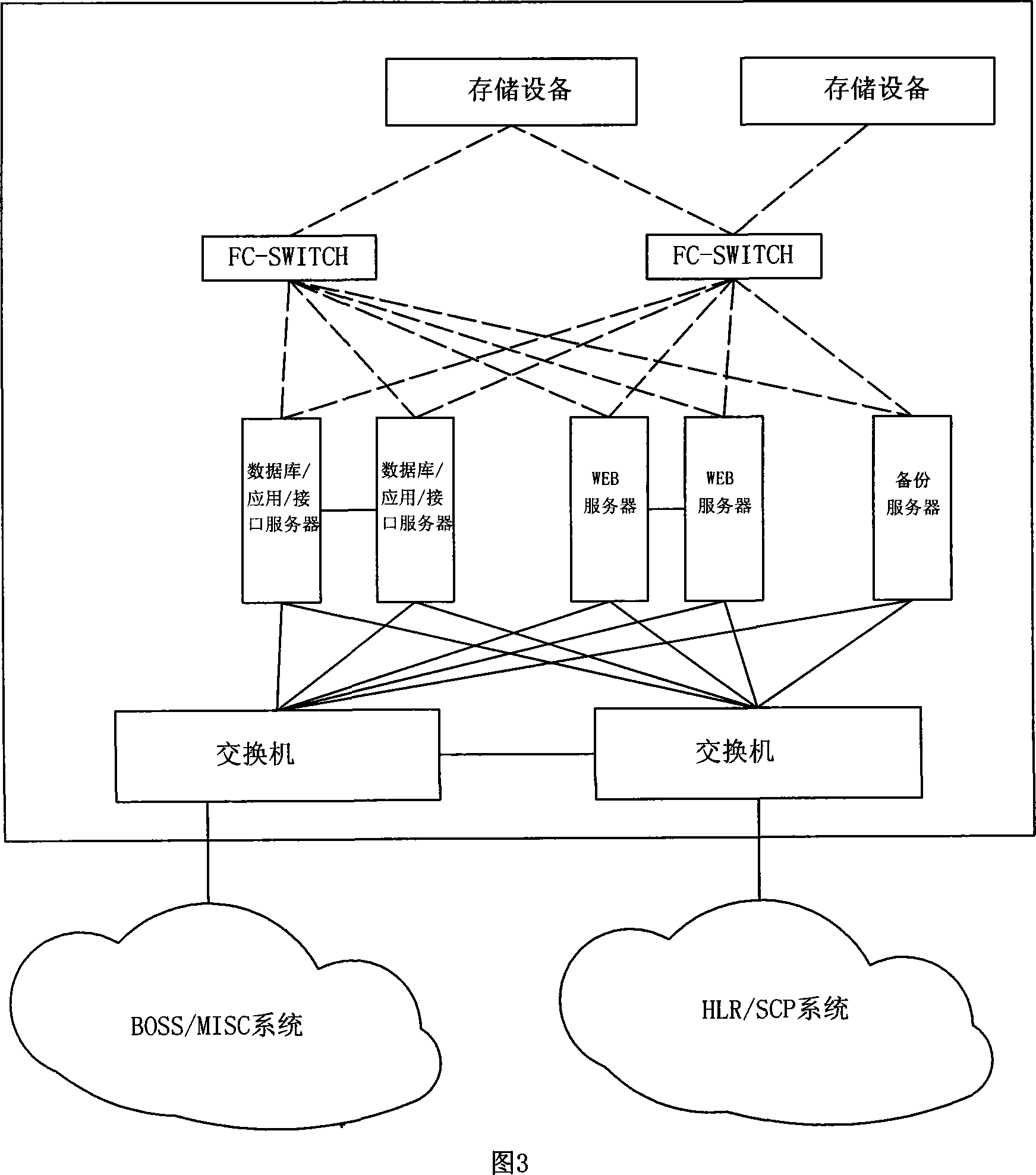
Server cluster system and load balancing implementation method thereof
ActiveCN104283948AImprove service stabilityGuarantee the best electionTransmissionCluster systemsComputer science
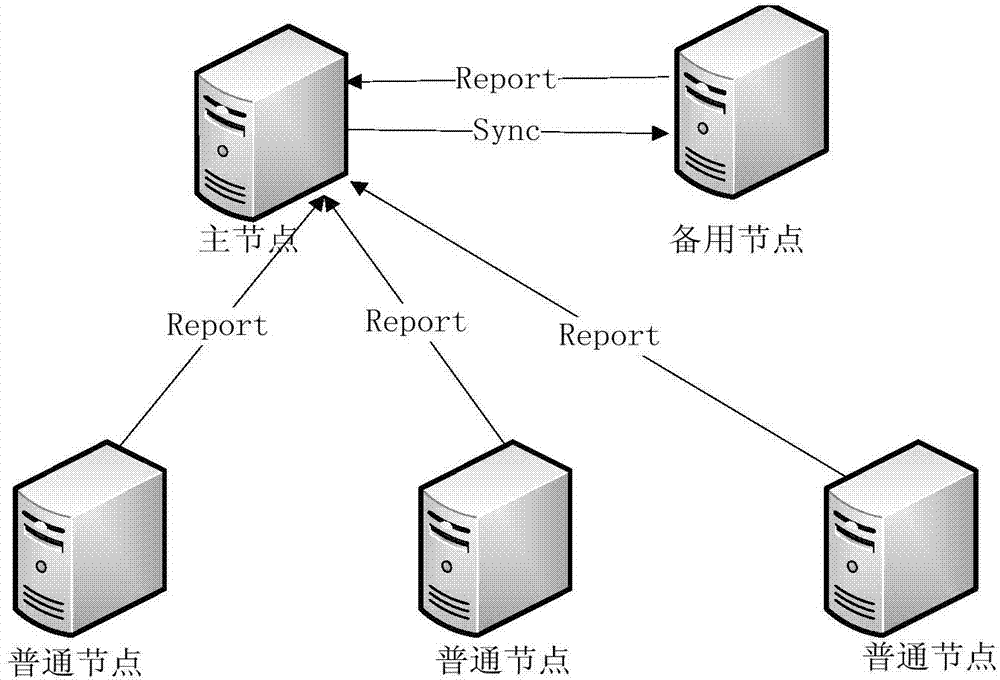
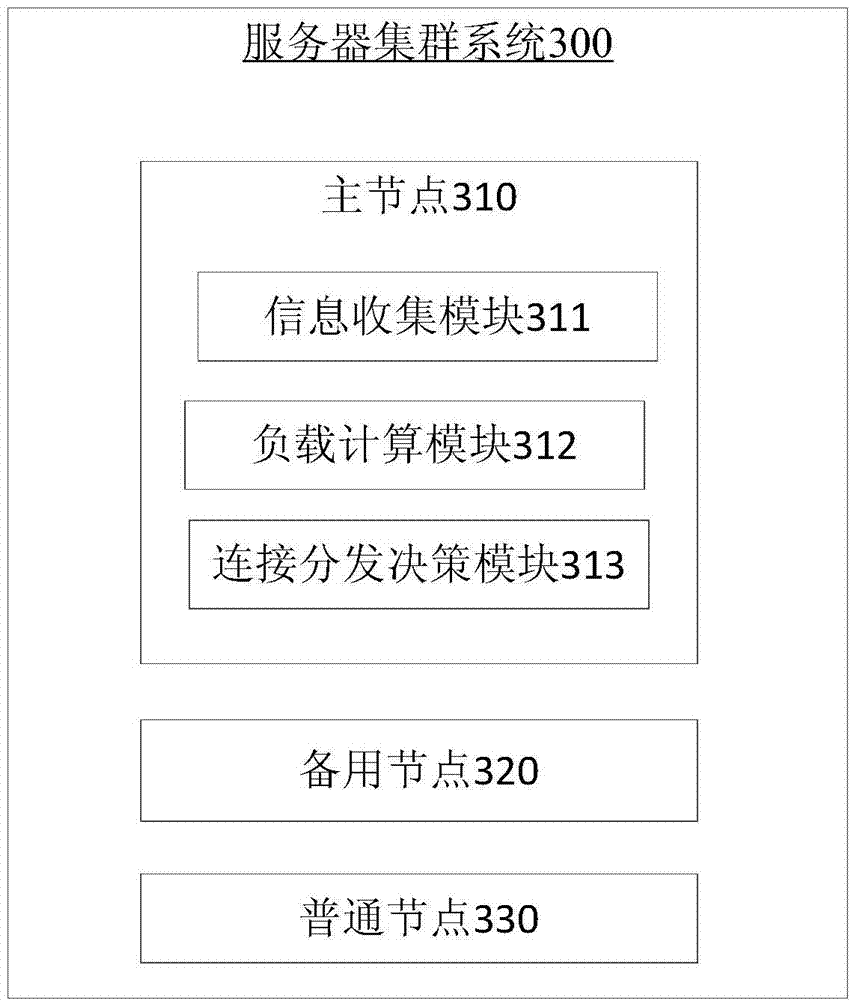
The invention provides a server cluster system and a load balancing implementation method of the server cluster system. The system comprises a main node, a standby node and common nodes. The main node comprises an information collecting module, a load calculating module and a connecting and distribution deciding module. The standby node is used for reporting the information of the standby node to the main node, and synchronizes with the information of the main node, and the common nodes are screened, so that the selected common node is adopted as a new standby node after the common node becomes the main node. The common nodes are used for reporting the information of the common nodes to the main node, and when one common node becomes the standby node, standby node switching is carried out. Through the server cluster system and the load balancing implementation method, the server cluster system with the main node and the standby node of a mesh network is adopted, the structure of the main node and the standby node is utilized for achieving connection and distribution, the function of sharing connection is achieved, and the problems that connection and distribution delay, and connection is unstable and unreliable can be solved.
Owner:NEUSOFT CORP
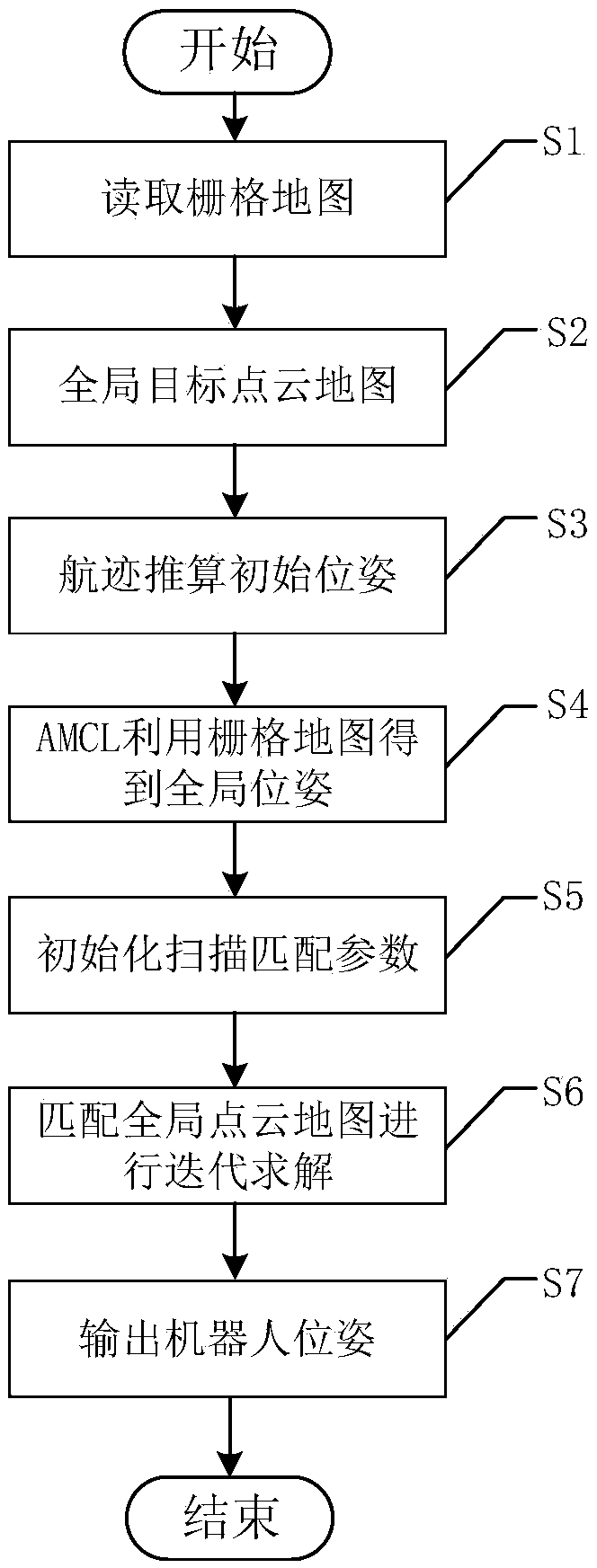
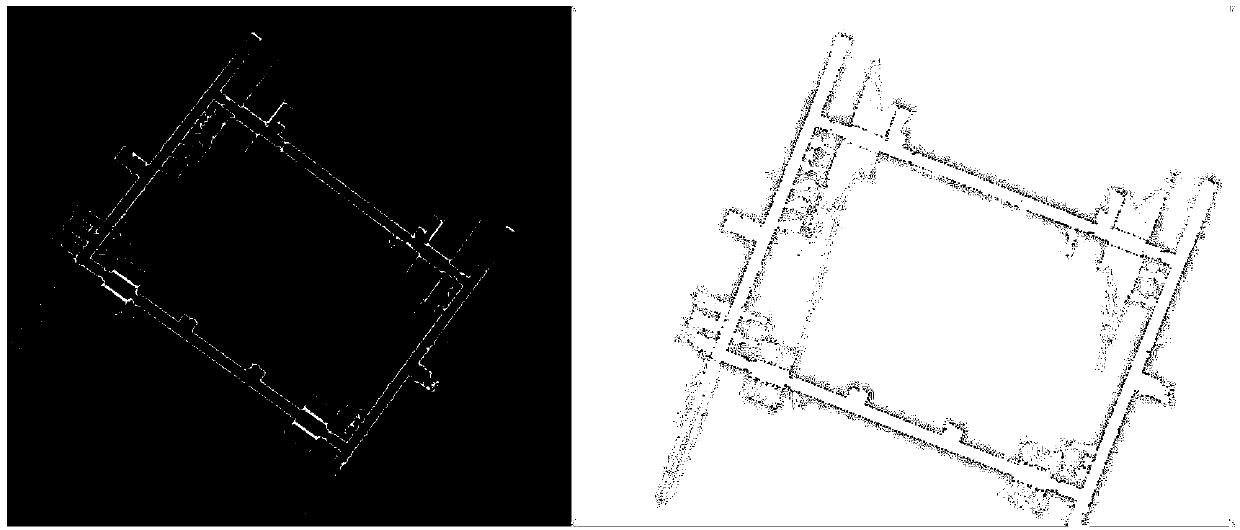
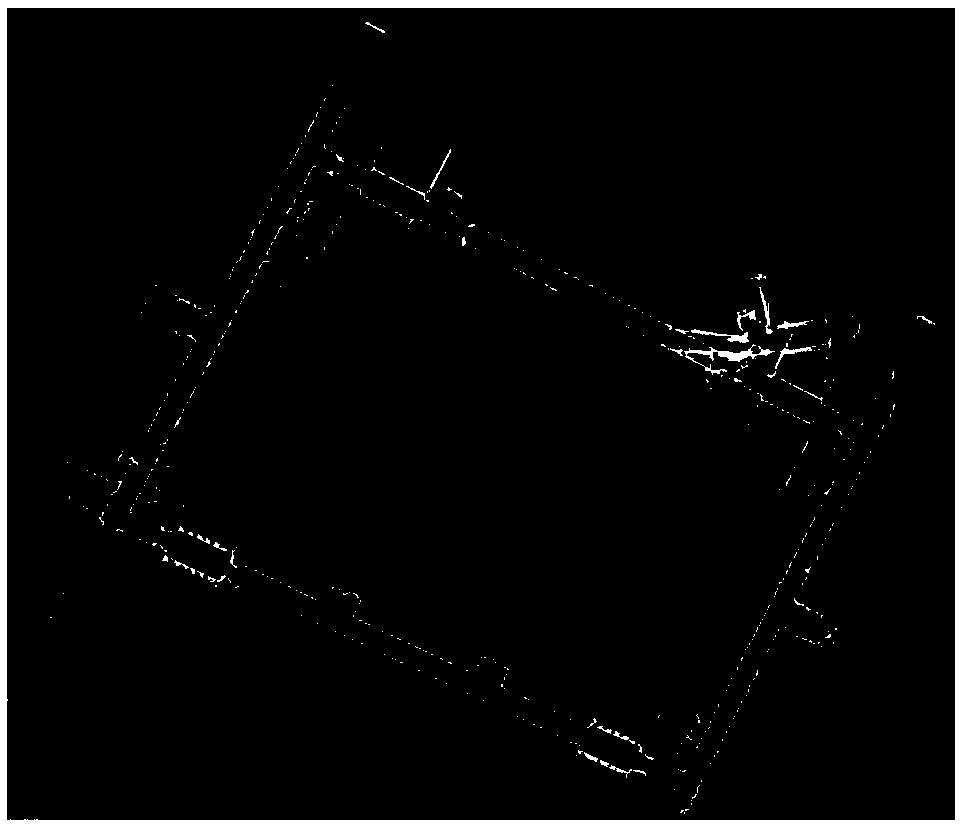
Mobile robot pose correction algorithm based on multi-level map matching
InactiveCN108917759AImprove global pose accuracyHigh positioning accuracyNavigational calculation instrumentsNavigation by speed/acceleration measurementsRoboticsCorrection algorithm
The invention discloses a mobile robot pose correction algorithm based on multi-level map matching, which belongs to the technical fields of robotics and computer graphics. The algorithm of the invention uses a synchronous positioning and a composition algorithm to establish a global raster map, and combines a matching relationship between the current observation and the raster map to correct thetrack calculated by the track using an AMCL algorithm for reckoning the pose, so that the relatively accurate global pose information can be obtained, at the same time, the raster map is converted toa corresponding global target point cloud map, and the laser point cloud observed by the robot in real time is registered with the target point cloud map to further correct the global pose. The methodof the invention can obtain accurate global pose information and reduce the accumulation of long-distance positioning errors, and avoids the shortcomings of an existing particle filter technology that the pose solution is not accurate due to a limited particle space, the accuracy and efficiency of an ICP algorithm are too dependent on the initial pose, and efficient and accurate pose solution canbe realized.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
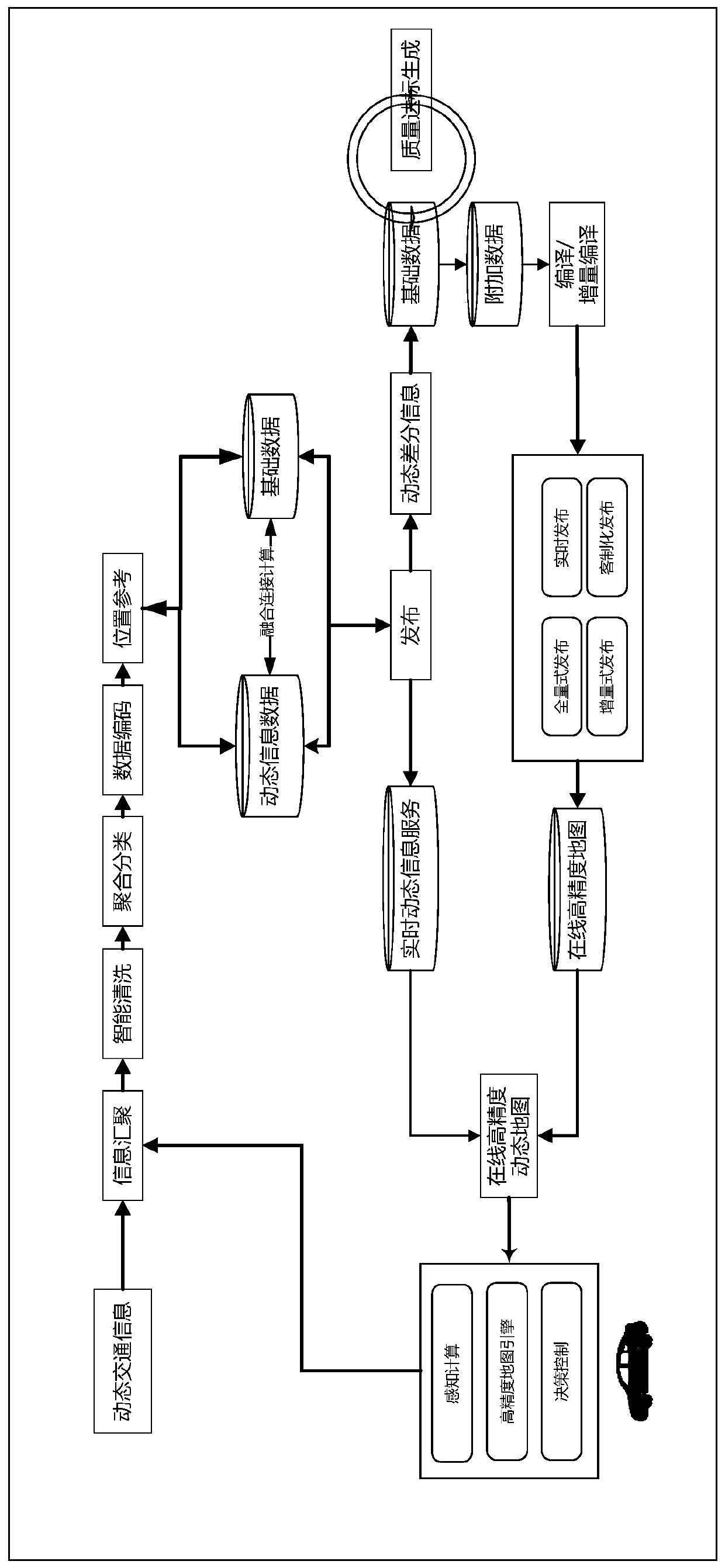
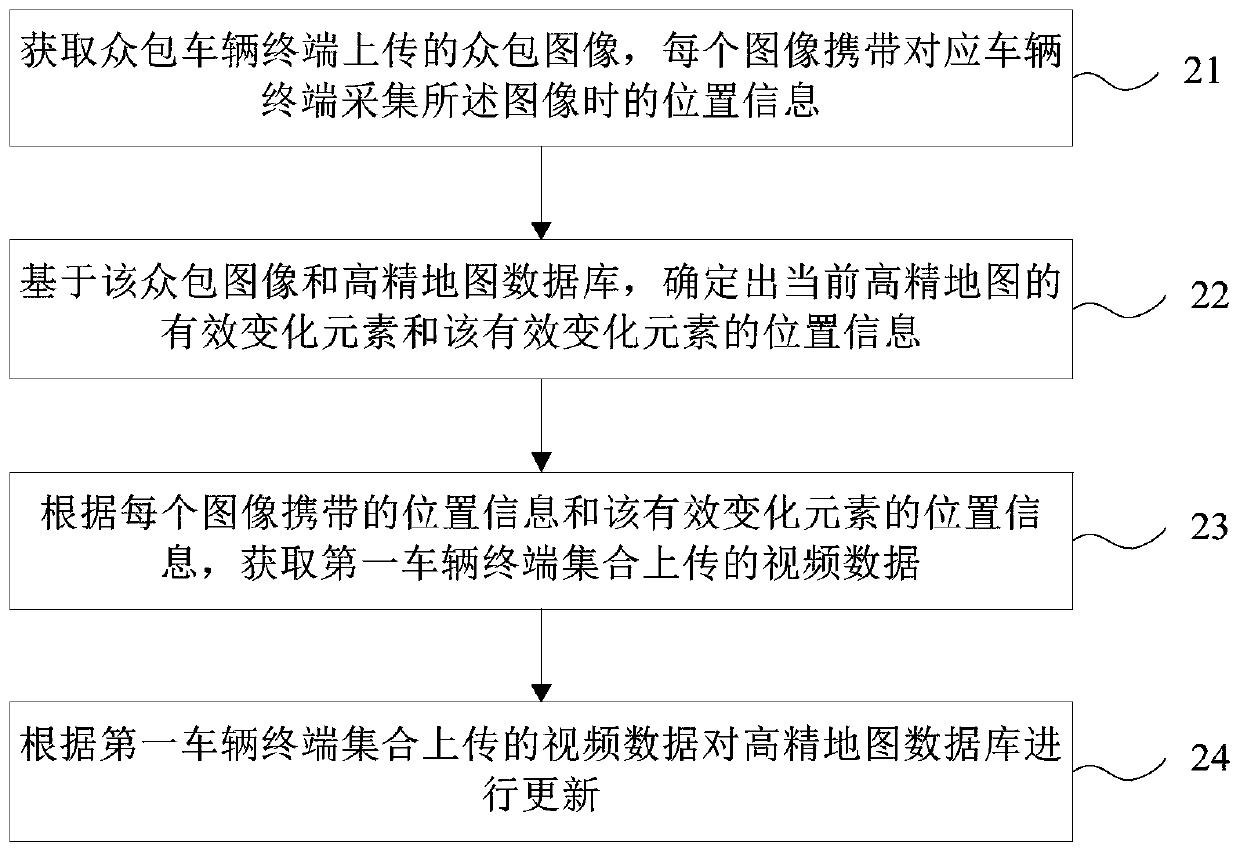
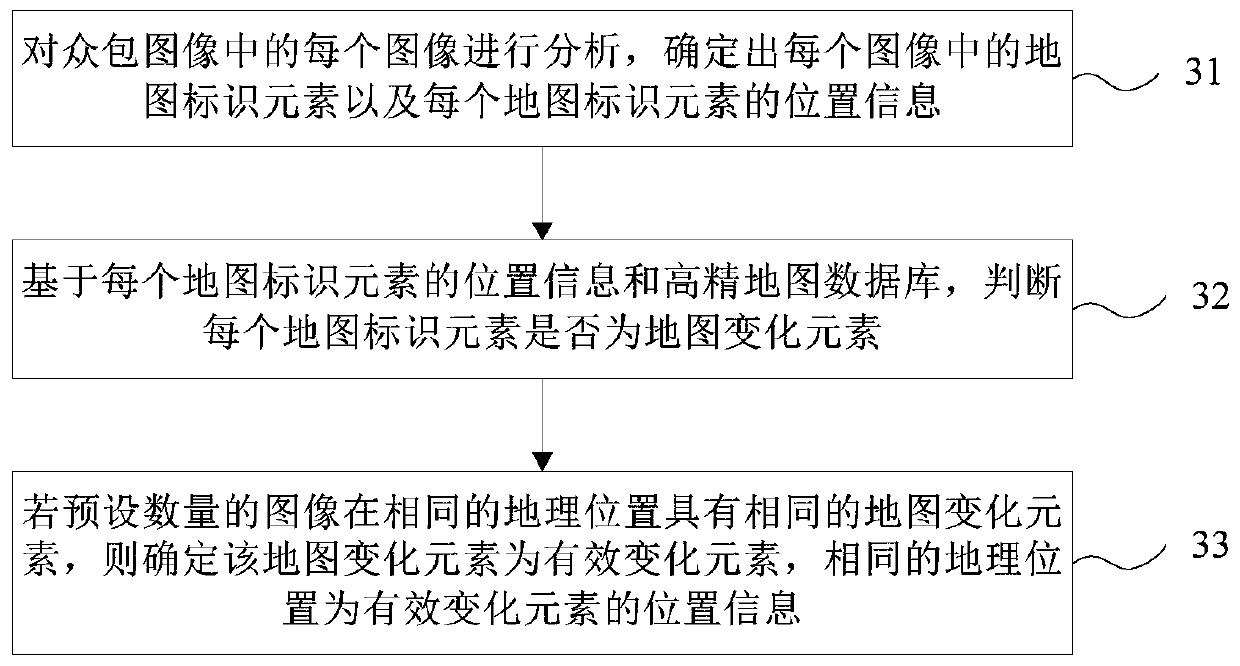
High-precision map updating method and device and storage medium
ActiveCN110287276AGuaranteed timelinessAvoid Driving Safety IssuesGeographical information databasesSpecial data processing applicationsComputer scienceDriving safety
The invention provides a high-precision map updating method and device and a storage medium. The method comprises the following steps of obtaining a crowdsourcing image uploaded by a crowdsourcing vehicle terminal, wherein each image carries the position information when the corresponding vehicle terminal collects the image; based on the crowdsourcing images and a high-precision map database, determining the effective change elements of the current high-precision map and the position information of the effective change elements; and obtaining the video data uploaded by the first vehicle terminal set according to the position information carried by each image and the position information of the effective change elements, and updating the high-precision map database according to the video data uploaded by the first vehicle terminal set. According to the technical scheme, the updating of the high-precision map database is based on the image and video information uploaded by a crowdsourcing vehicle terminal, the collection by using an expensive collection vehicle is not needed, the updating speed is high, the timeliness of map updating can be ensured, and the driving safety problem of an automatic driving vehicle is avoided.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
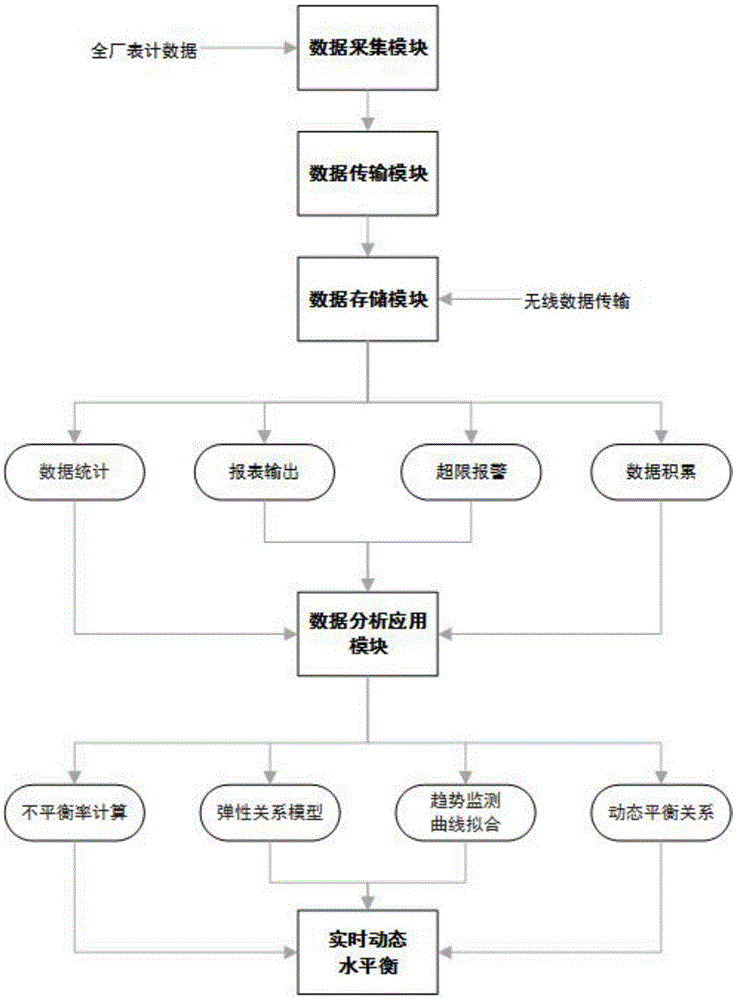
Real-time dynamic 3D water balance monitoring system of power plant and working method of system
InactiveCN105549557AEffective monitoringEfficient managementTotal factory controlProgramme total factory controlWater balanceApplication module
The invention relates to a real-time dynamic 3D water balance monitoring system of a power plant and a working method of the system. The system is characterized by comprising a data collection module, a data transmission module, a data storage module, a monitoring center and a data analysis and application module, wherein the data collection module collects flow data, and the data transmission module returns data collected by the data collection module in real time. Water volume data of different collection points is collected by the data collection module, transmitted to the data storage module by the data transmission module, and further transmitted to the data analysis and application module by the data storage module. The system and method have the advantages that the relation between water volume change and generating load is found via data analysis, the imbalance rate is calculated, and thus, scientific basis is provided for planning water-saving measures of the power plant.
Owner:TIANJIN AOLANG NEW ENERGY RESOURCES & TECH CORP
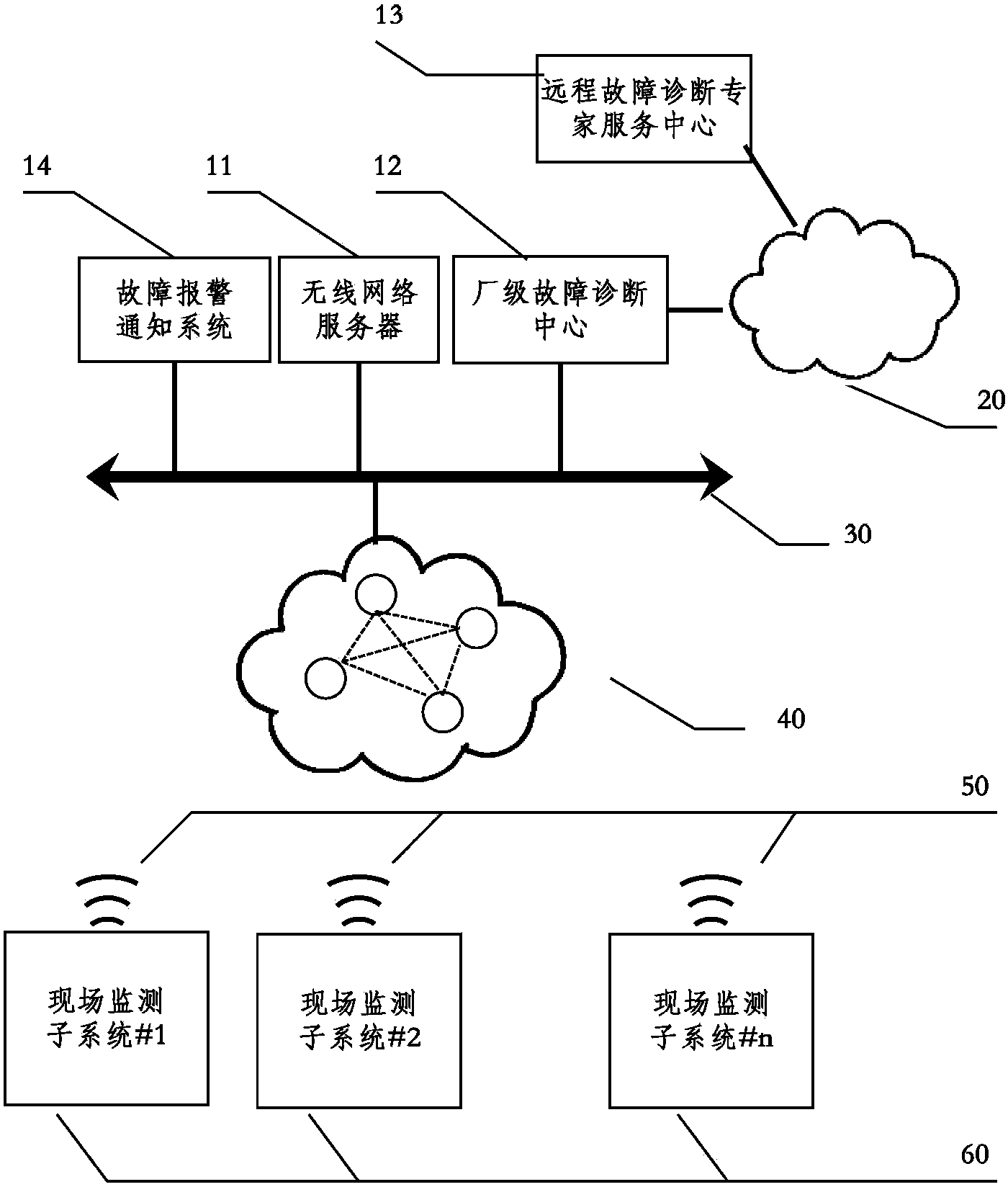
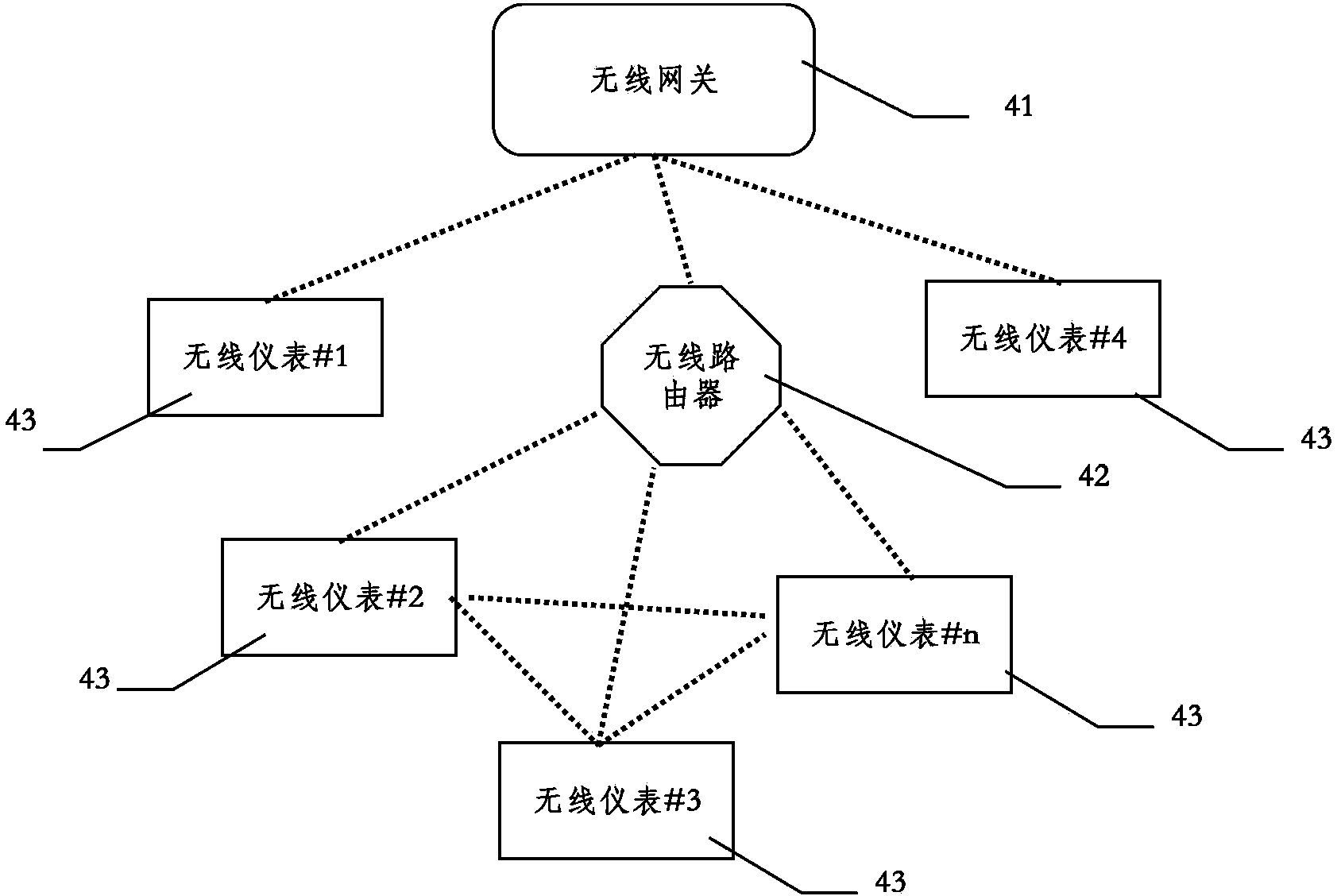
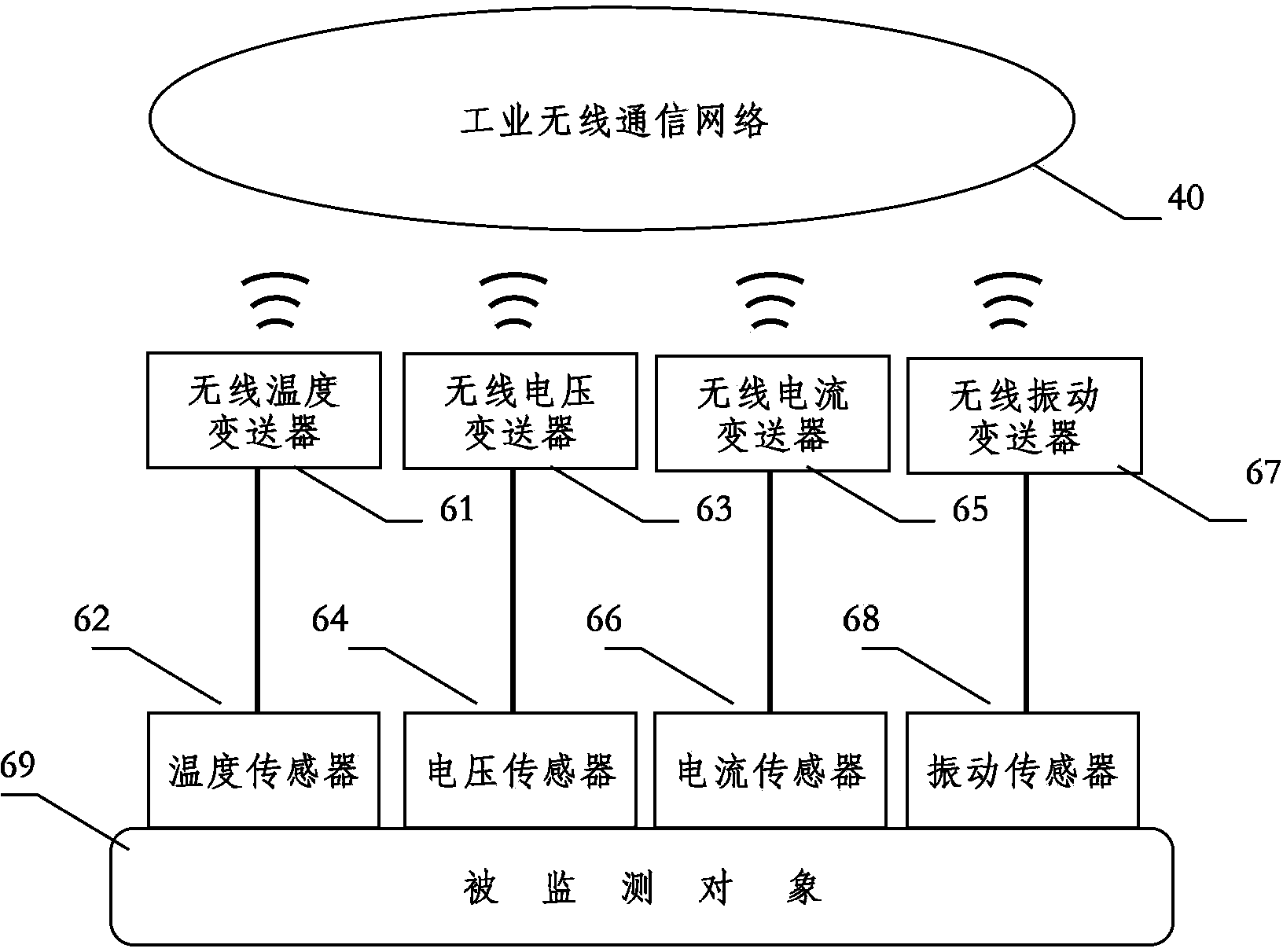
Device fault pre-maintenance method based on industrial wireless technology
InactiveCN103913193AEliminate dead endsIncrease flexibilityMeasurement devicesTransmission systemsIndustrial EthernetMonitor equipment
The invention relates to a device fault pre-maintenance method based on an industrial wireless technology. In the method, through data communication of an industrial wireless network and an industrial Ethernet, real-time monitoring and fault pre-maintenance are performed on an on-site device. The method includes the following steps: an upper computer performs parameter configuration on on-site instruments, which are used for monitoring the device, through the industrial Ethernet and the industrial wireless network; the instruments acquire sensor information of the on-site device according to the parameter configuration and upload result data, which is obtained after local processing of the sensor information, to the upper computer through the industrial wireless network and the industrial Ethernet; the upper computer performs fault diagnosis according to the result data and judges the operation state of the device; and if the fault diagnosis result is obtained, on-site maintenance personnel are notified through a fault alarm so as to maintain the device.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Metro ticket buying and checking method based on two-dimension code recognition
ActiveCN104134142AImprove comfortReduced comfortTicket-issuing apparatusUser identity/authority verificationKey issuesPublic key certificate
The invention discloses a metro ticket buying system and an entrance and exit ticket checking system based on the two-dimension code recognition technology. Smartphone terminals, smartphone application programs, a metro ticket selling and checking system background recharging server, automatic metro entrance and exit ticket checking systems and a CA center are included. The metro ticket selling and checking system background recharging server, each smartphone application program and each automatic metro entrance and exit ticket checking system respectively have a unified center public key issued by the CA center, a public key and a private key which are independent of each other and issued by the CA center and a public key certificate issued by the CA center. A user buys a ticket and has the ticket checked through the mobile phone program and two-dimension codes. The ticket buying efficiency is improved, the ticket buying time is saved, ticket card cost is reduced, paper is saved, timeliness and uniqueness of ticket cards are guaranteed, and metro tickets can be bought and checked fast, efficiently and safely.
Owner:SOUTHEAST UNIV
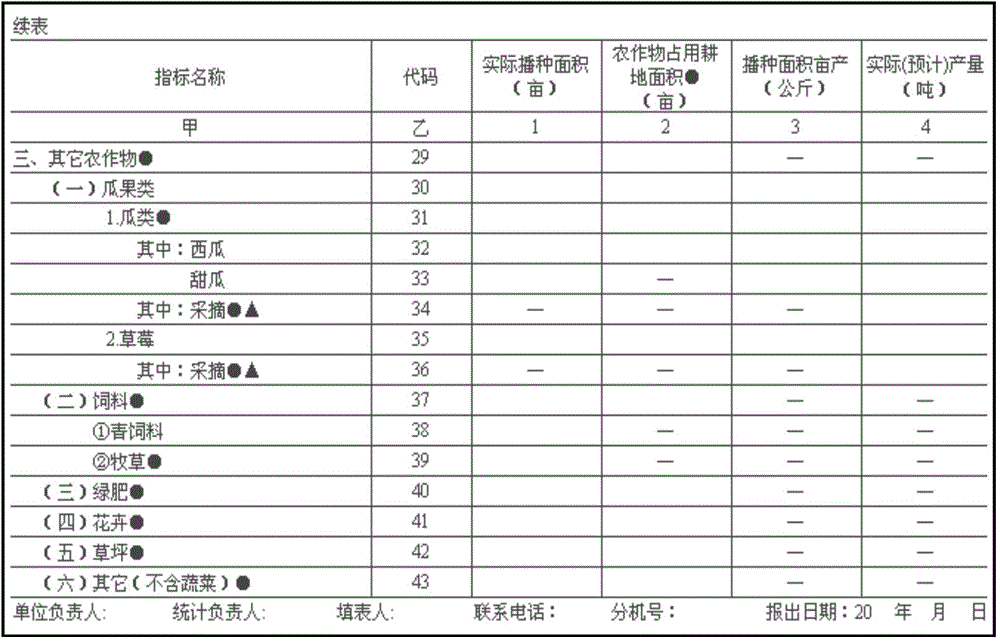
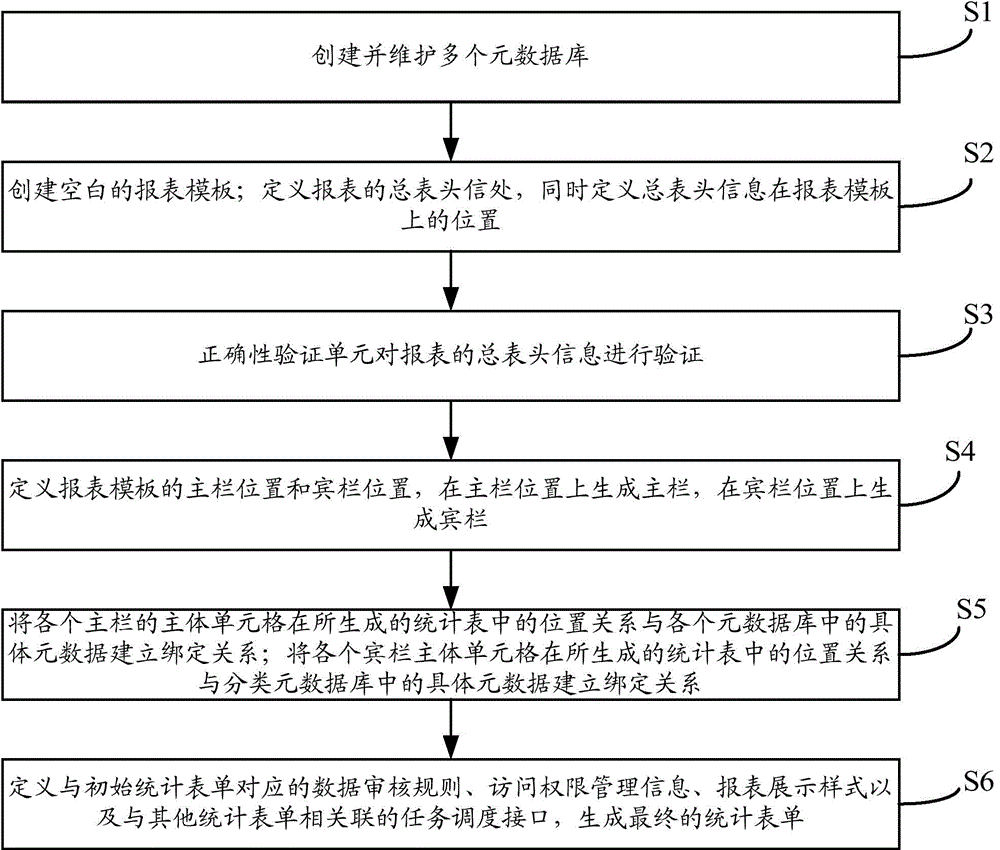
Metadata based rapid statistic form generation method and system
ActiveCN105320690ASimplify how survey indicators are customizedConvenient management of indicator library informationSpecial data processing applicationsMetadata managementForm generation
The invention provides a metadata based rapid statistic form generation method and system. The system comprises a metadata base management module and a report customization module, wherein the metadata base management module comprises an attribute metadata base definition unit, a measurement unit metadata base definition unit, a classified metadata base definition unit and a shared index metadata base definition unit; the report customization module comprises a report attribute definition unit, a template definition unit, an index definition unit, a report style definition unit, a management authority definition unit, an access definition unit and a preview definition unit. Through configuration of report structure rules, when a report structure changes, a report engine adjusts a report structure automatically according to changes, a new report is generated, and the flexibility of report customization is improved; a metadata management mode is adopted for managing index names and index attributes; when index names and index attributes change, all that is required is to modify metadata in the metadata base, and the surveying index customization mode is simplified.
Owner:BEIJING ZHONGHAIJIYUAN DIGITAL TECH DEV CO LTD
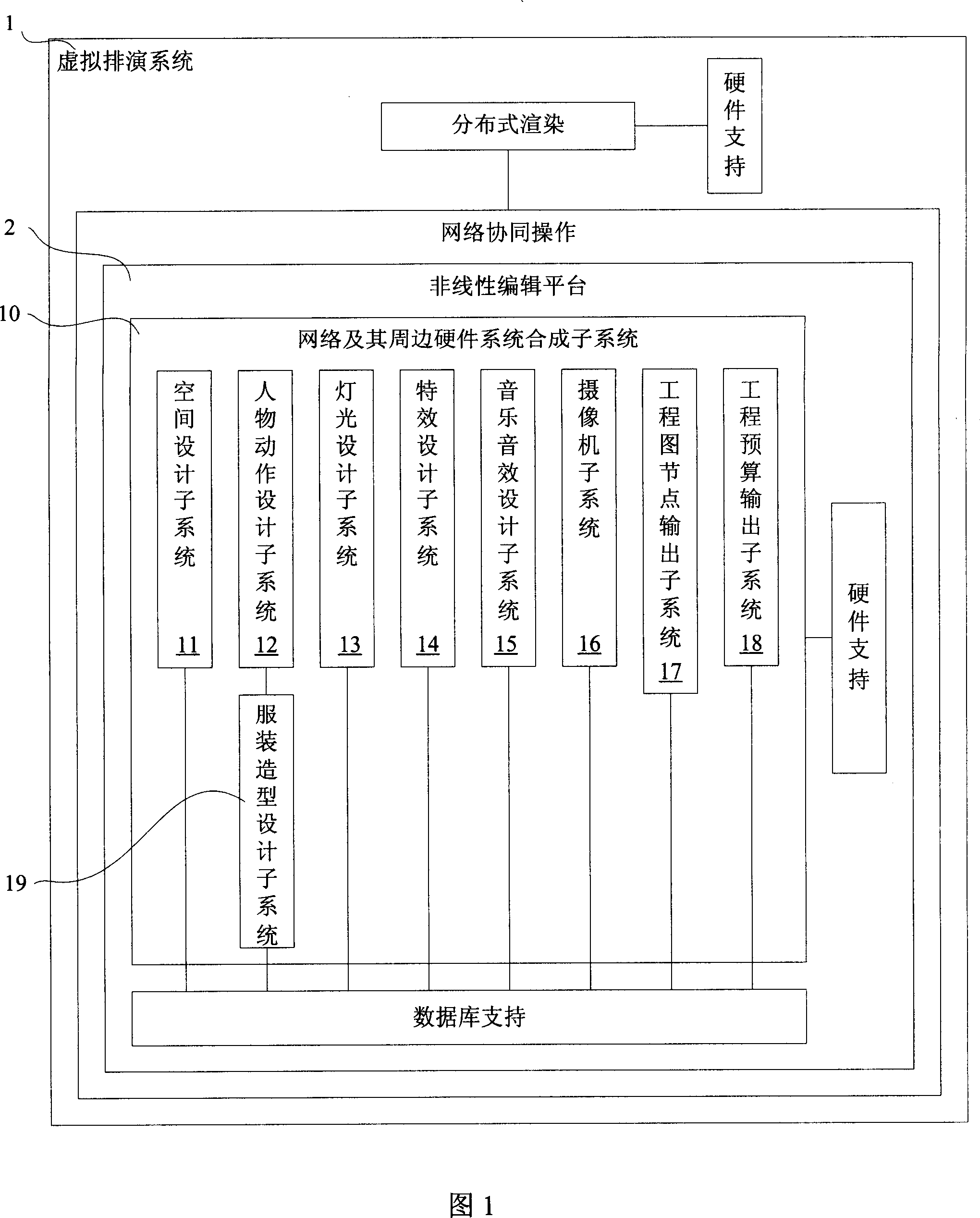
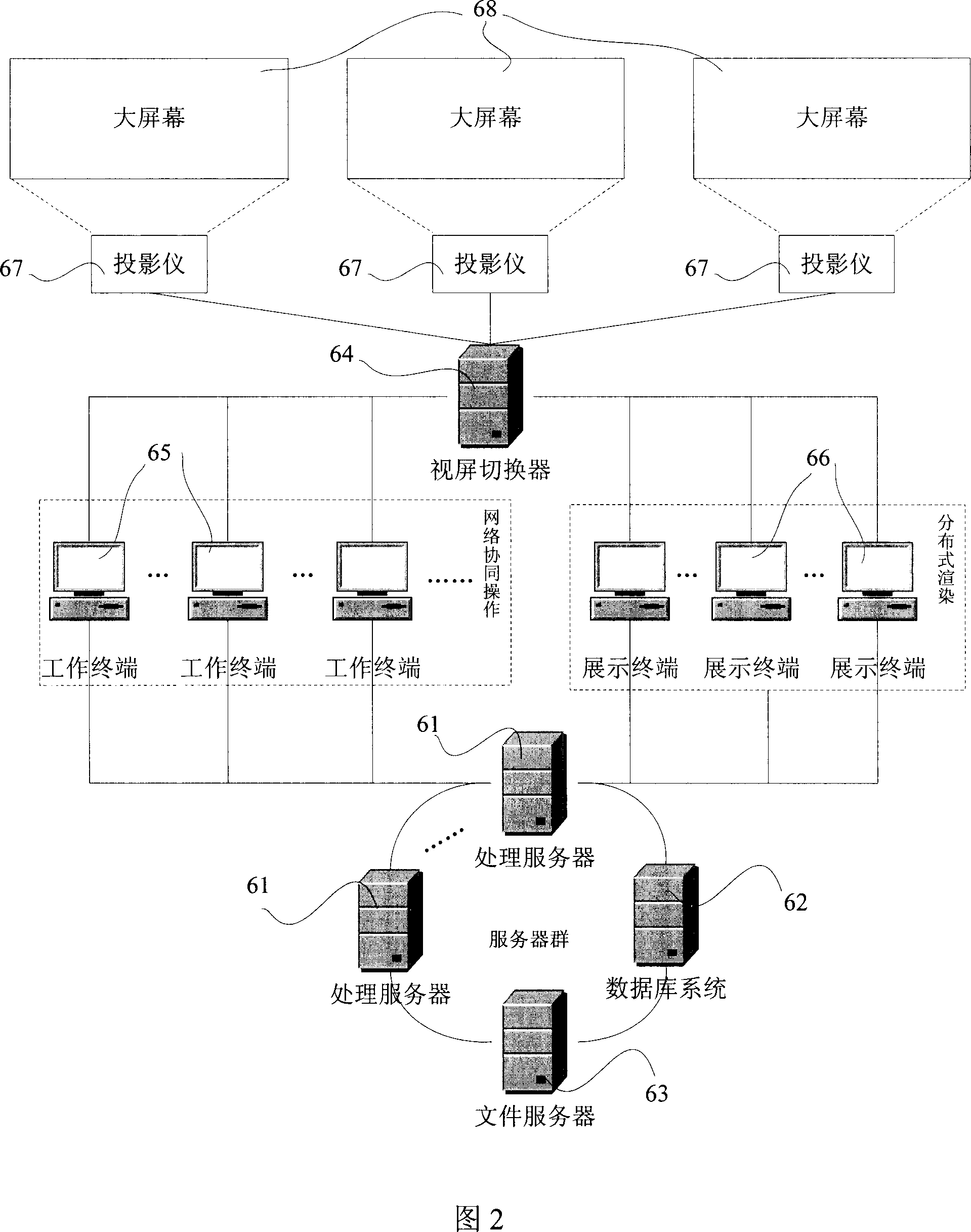
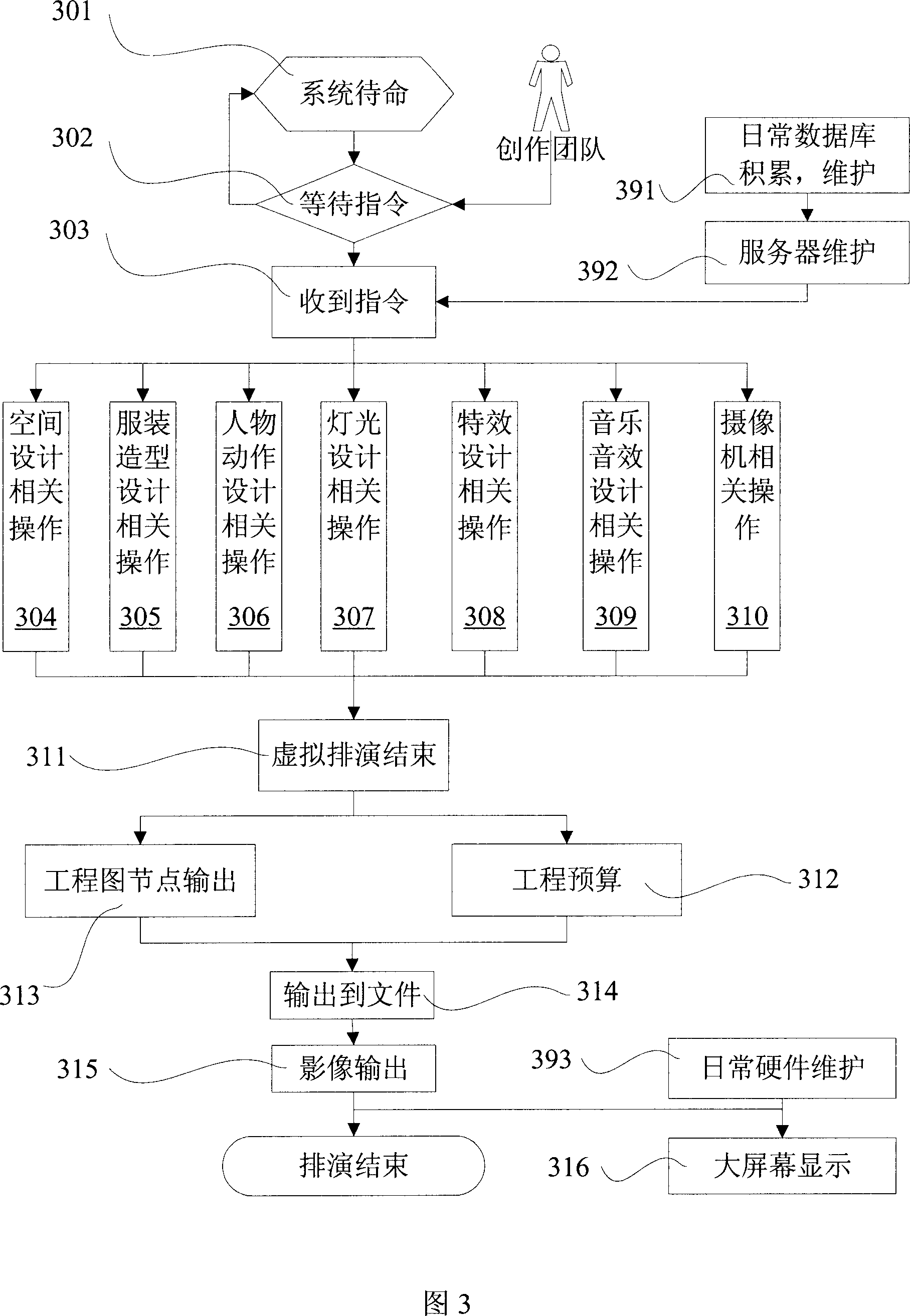
Virtual rehearsing system
ActiveCN101082901AAdd artistryGuaranteed reliabilitySpecial data processing applicationsAcoustic effectSpatial design
The invention discloses a virtual performing system, which comprises the following subsystems: space designing subsystem, garment modeling designing subsystem, figure movement designing subsystem, light designing subsystem, specially good effect designing subsystem, acoustic effect designing subsystem, wherein these subsystems are mated to analog and set and replay project or performance, which display entire effect with less labor and cost. The invention is convenient to operate for multiple users simultaneously, which can rapidly finish analoging.
Owner:SHANGHAI THEATRE ACADEMY
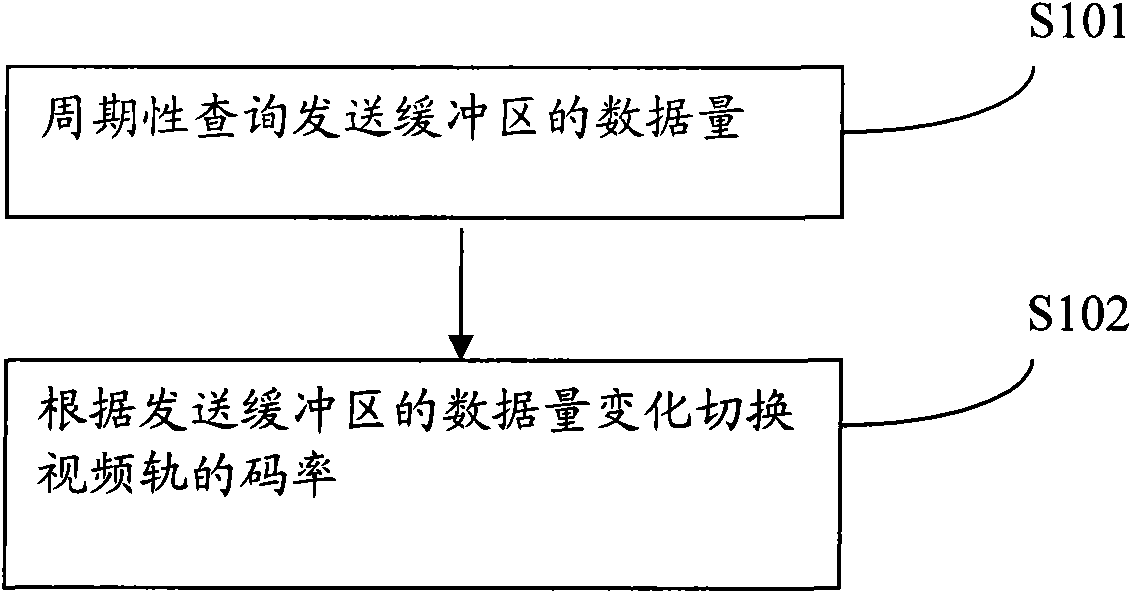
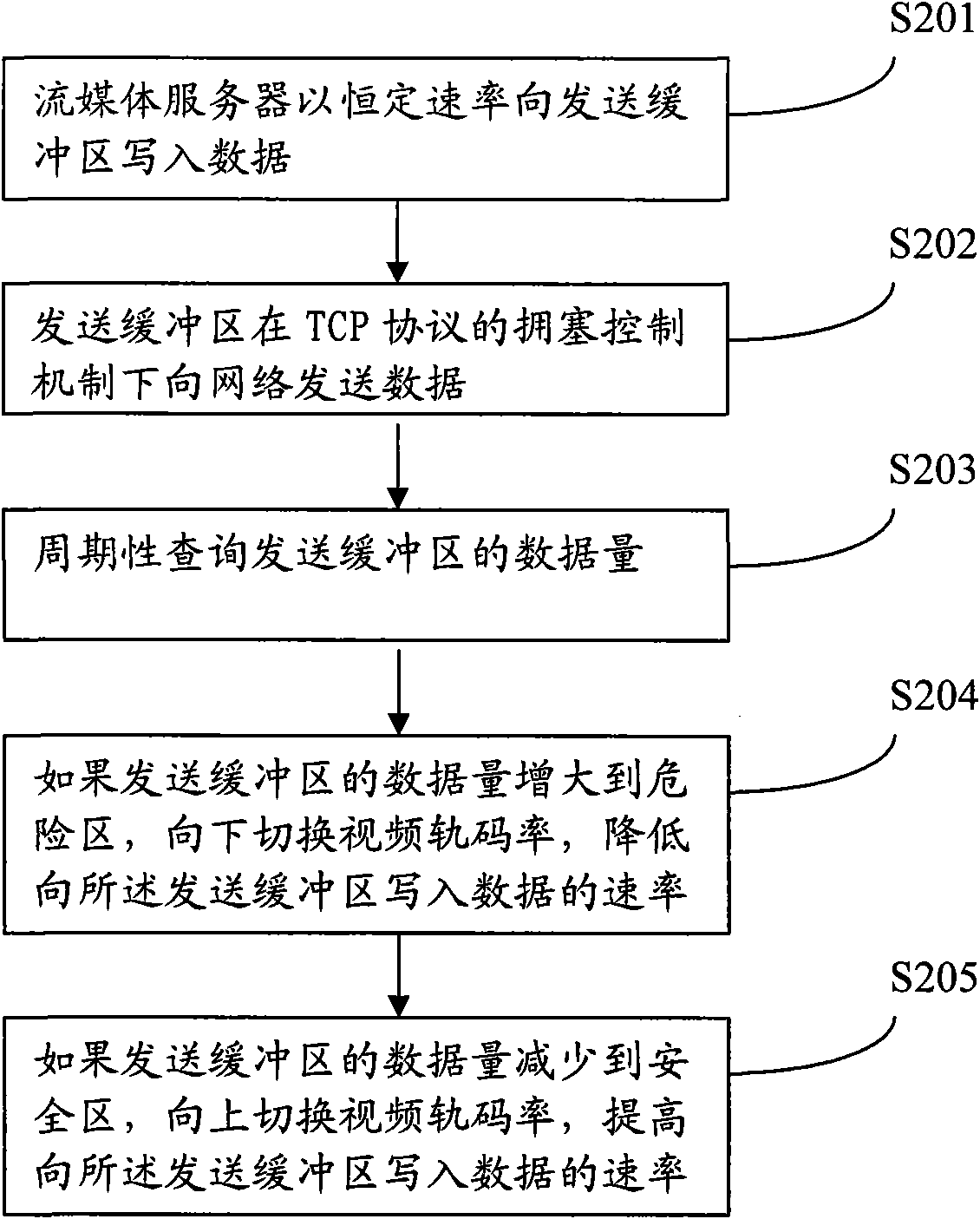
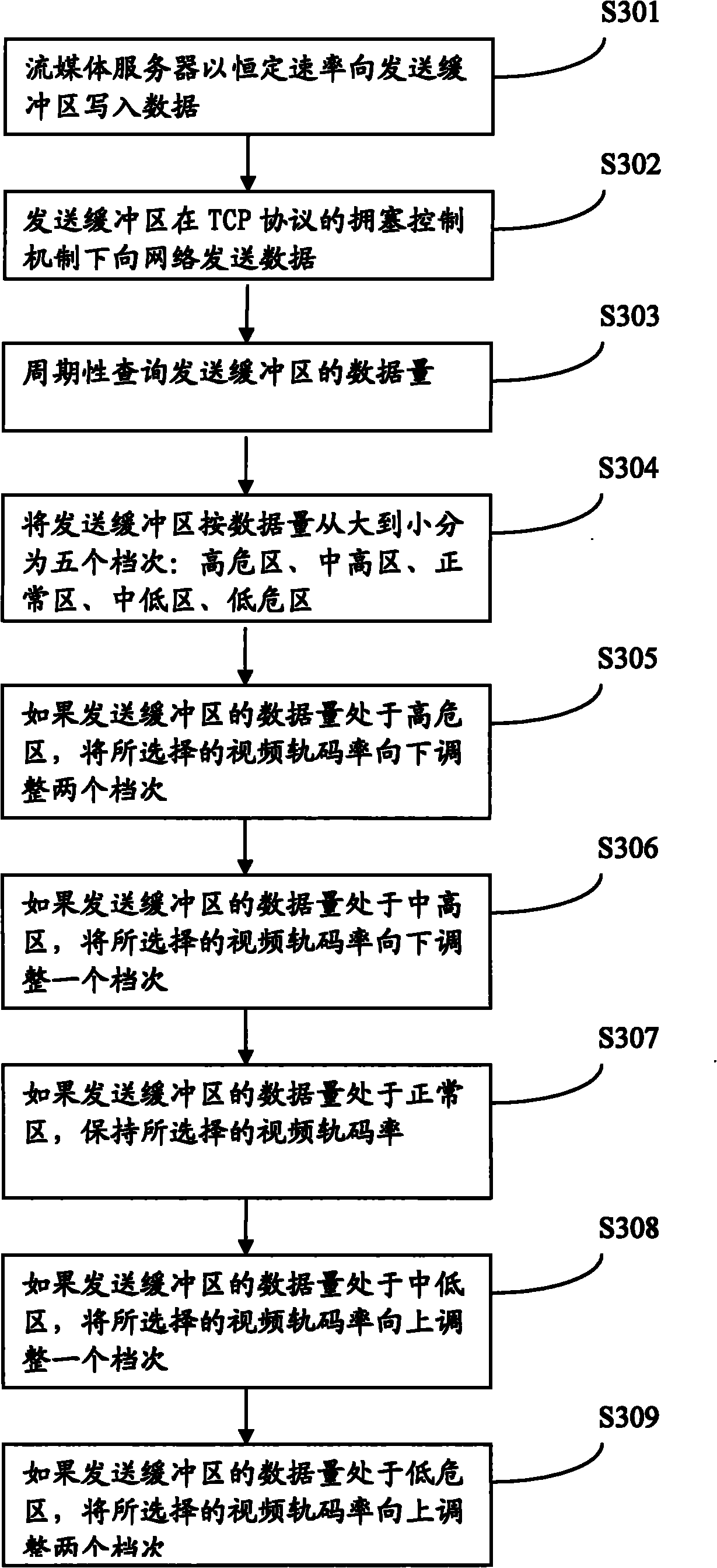
Method and device for adjusting streaming media bit rate
InactiveCN101771492AGuaranteed timelinessSpecial service provision for substationError preventionReal-time computingWeb transport
The invention discloses a method and a device for adjusting the streaming media bit rate, relating to the field of communication. The invention is invented for solving the problem of poor efficiency in the process of adjusting the streaming media bit rate in the prior art in real time. The method provided by the embodiment of the invention comprises the following steps of: periodically inquiring data amount of a sending buffer area, and switching the bit rate of a video track according to the change of the data amount of the sending buffer area, thereby changing the rate of writing data to the buffer area, enhancing the quality of network transmission, and enhancing the audio and the video experience effect. The invention is suitable for communication systems.
Owner:HUAWEI TECH CO LTD
Method for detecting, recovering and controlling for independence trouble during orbital transfer course
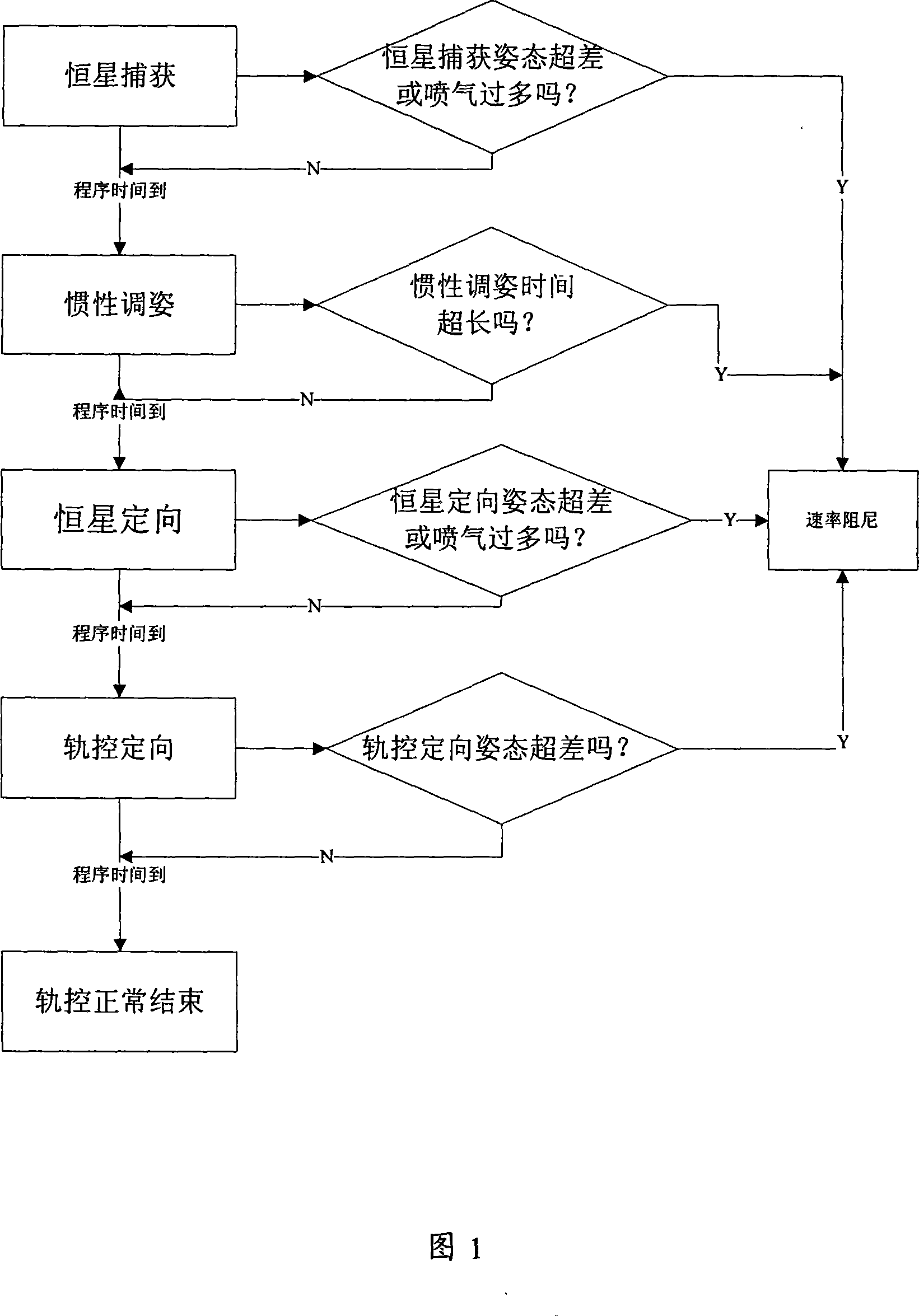
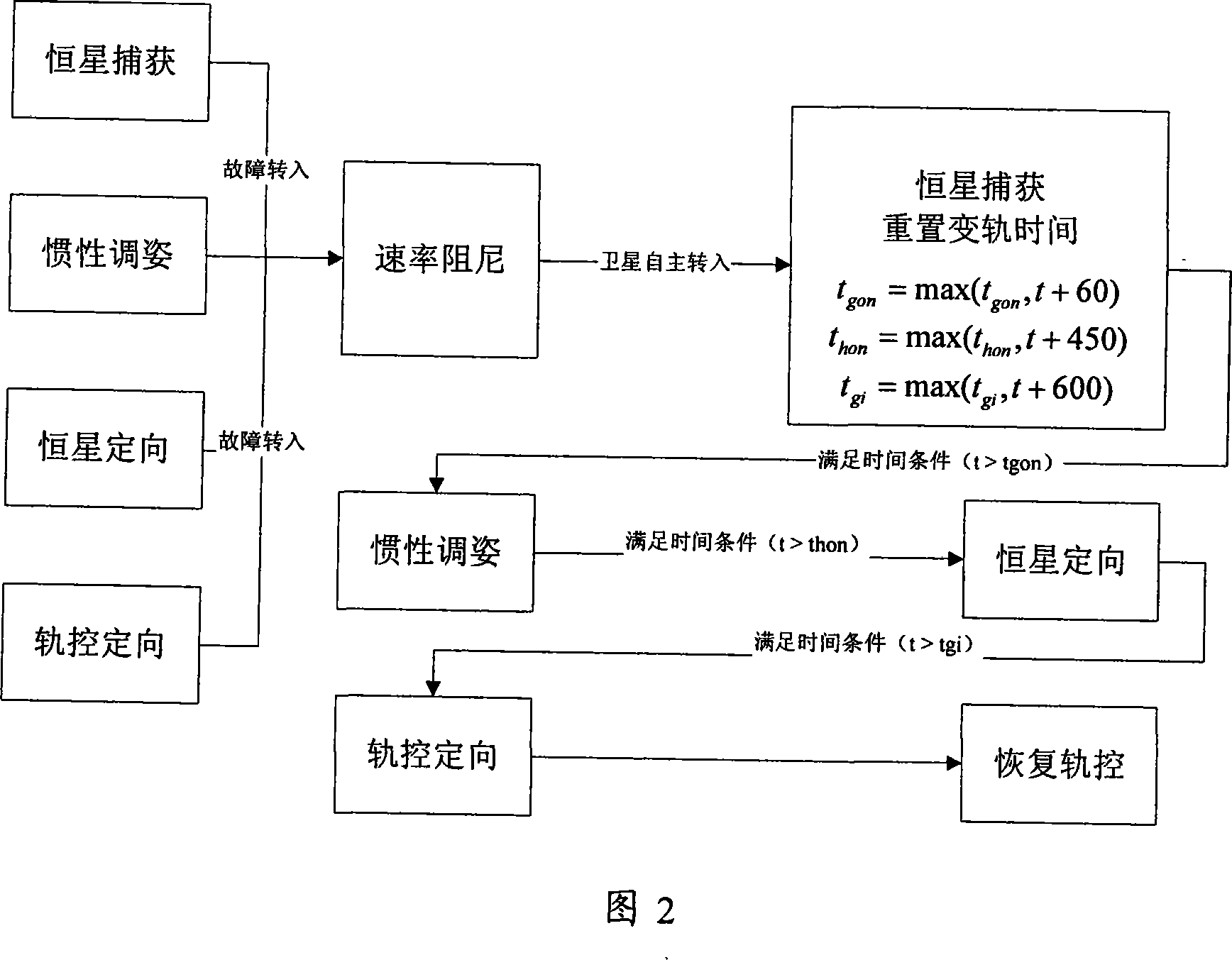
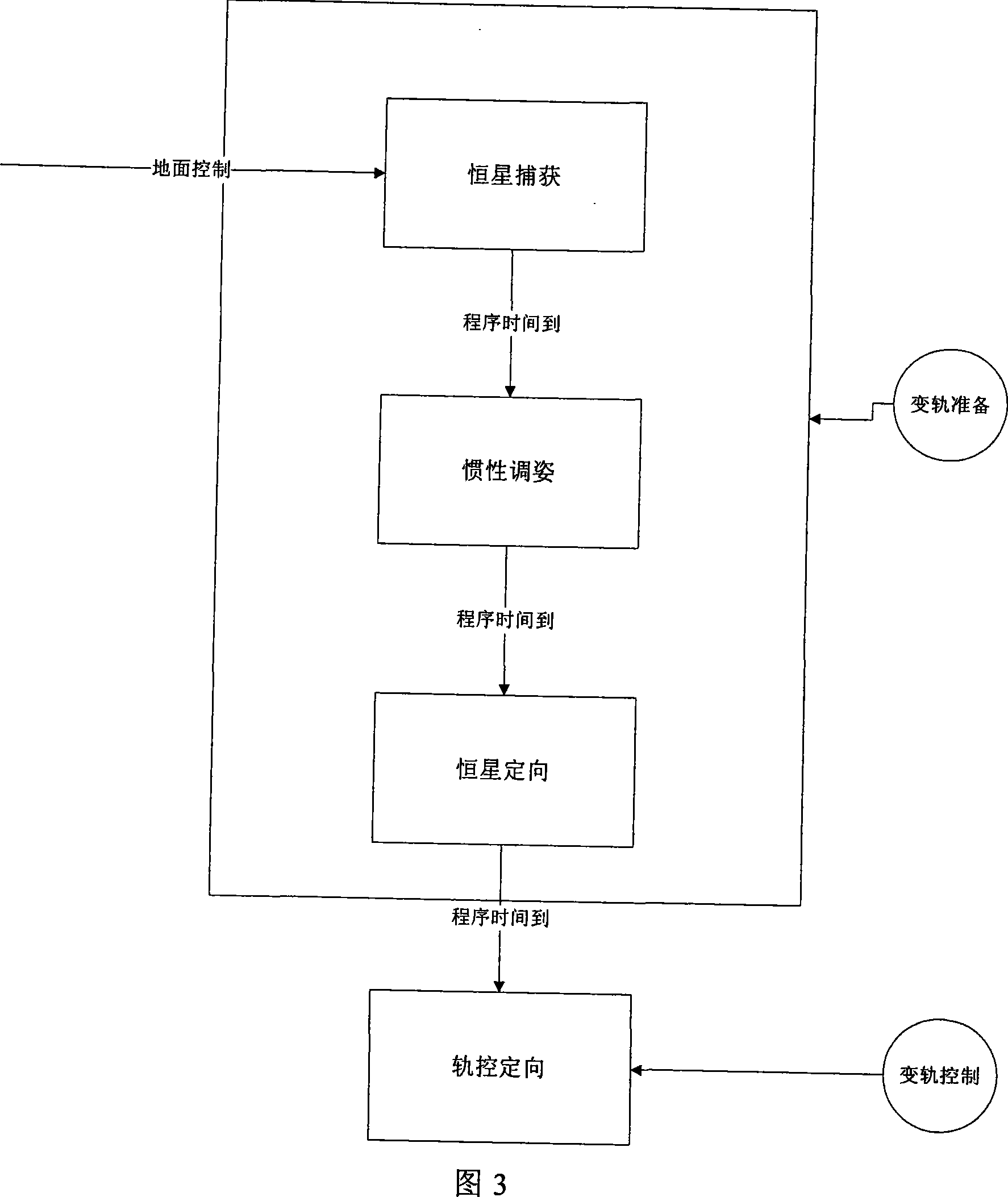
InactiveCN101214859AGuaranteed timelinessSimplify ground operationsSpacecraft guiding apparatusStart timeAngular velocity
An autonomous fault detection recovery control method during the orbital transfer includes (1) the autonomous fault detection: firstly, setting fault judgment conditions at a star acquisition stage, an inertia attitude adjusting stage, a star directional stage and a rail control directional stage of an autonomous orbital transfer method; introducing judgment conditions during the orbital transfer process; (2) the autonomous recovery control: when a satellite autonomously detects out faults and enters the recovery control, the autonomous control satellite on the star enters a velocity damping stage; when the attitude angular velocity damping of the satellite is successful, the satellite autonomously enters the star acquisition stage; the rail control process is reinstalled, which means that the starting time of every stage during the subsequent orbital transfer process; the satellite transfers into the corresponding working stage to recover the orbital control according to the reinstalled time. The method of the invention improves the reliability of the orbital transfer, ensures the accurate implementation of the orbital control in time and can better ensure the realization of the only window for the orbital control.
Owner:BEIJING INST OF CONTROL ENG
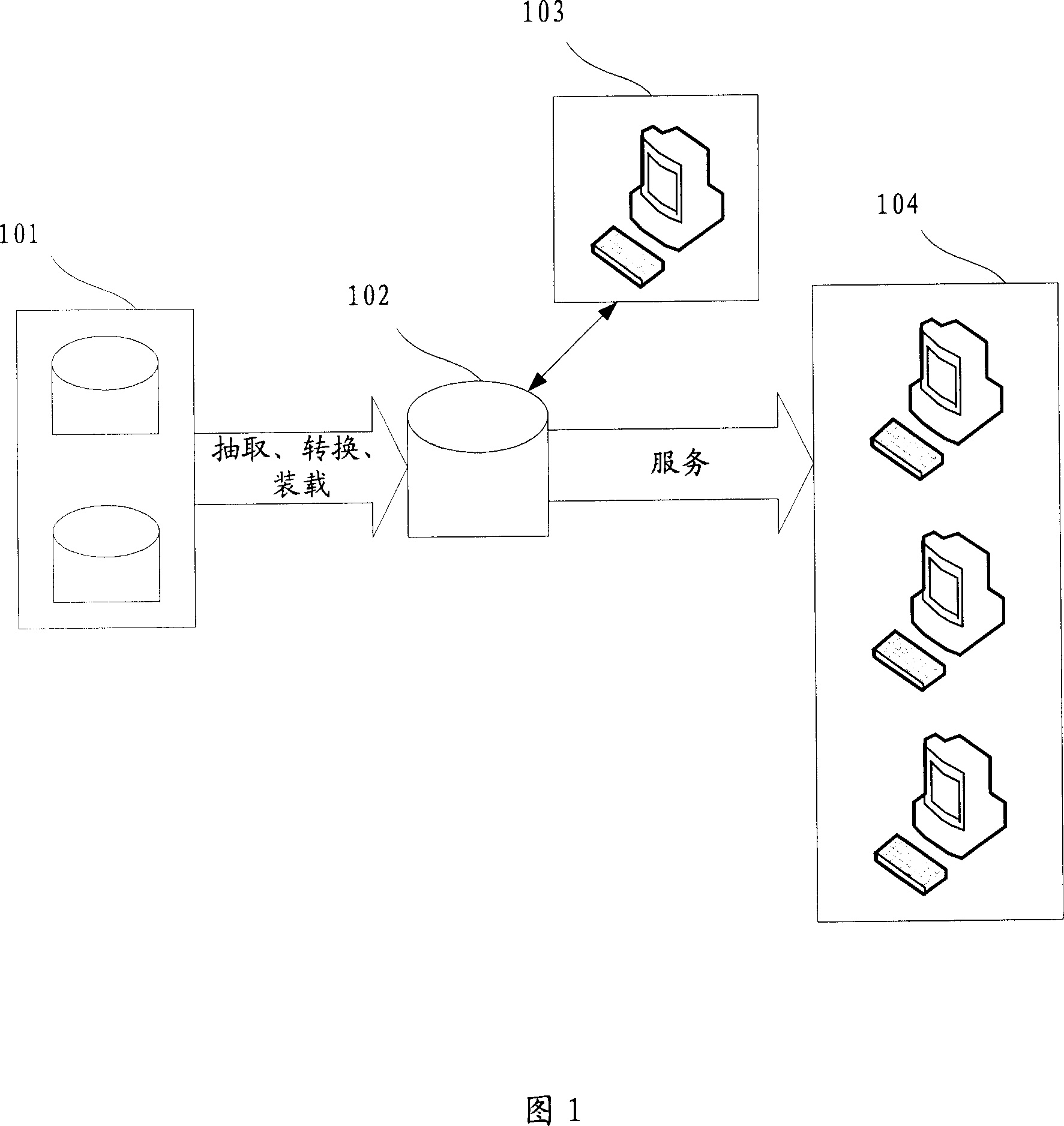
Data processing method and system of data library
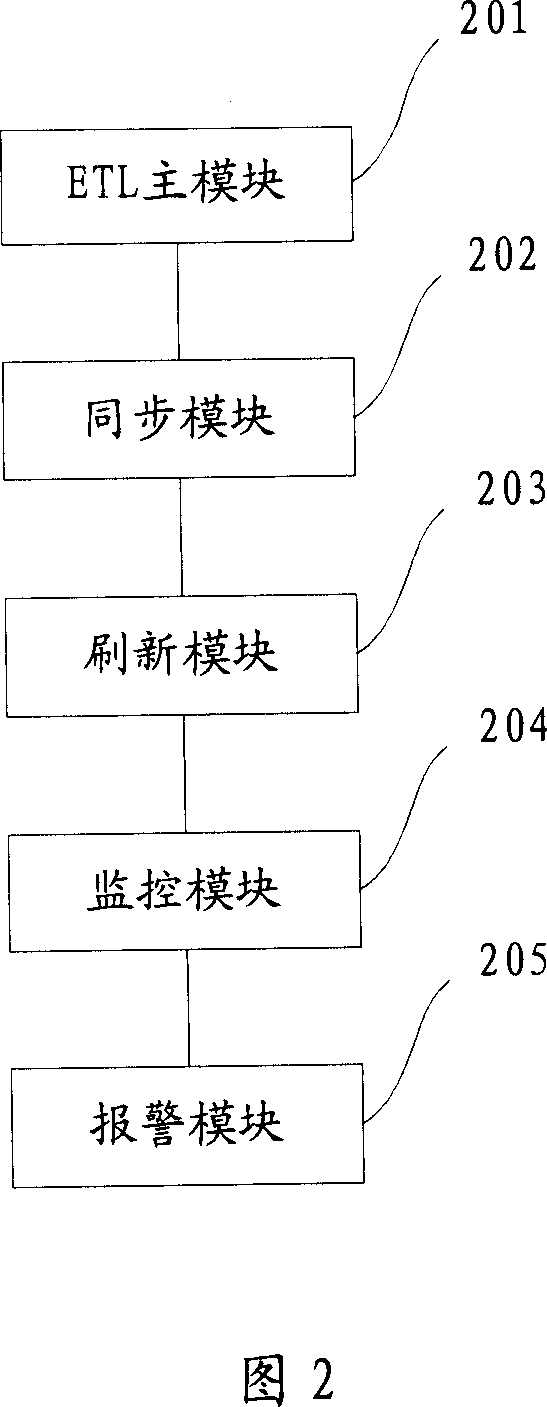
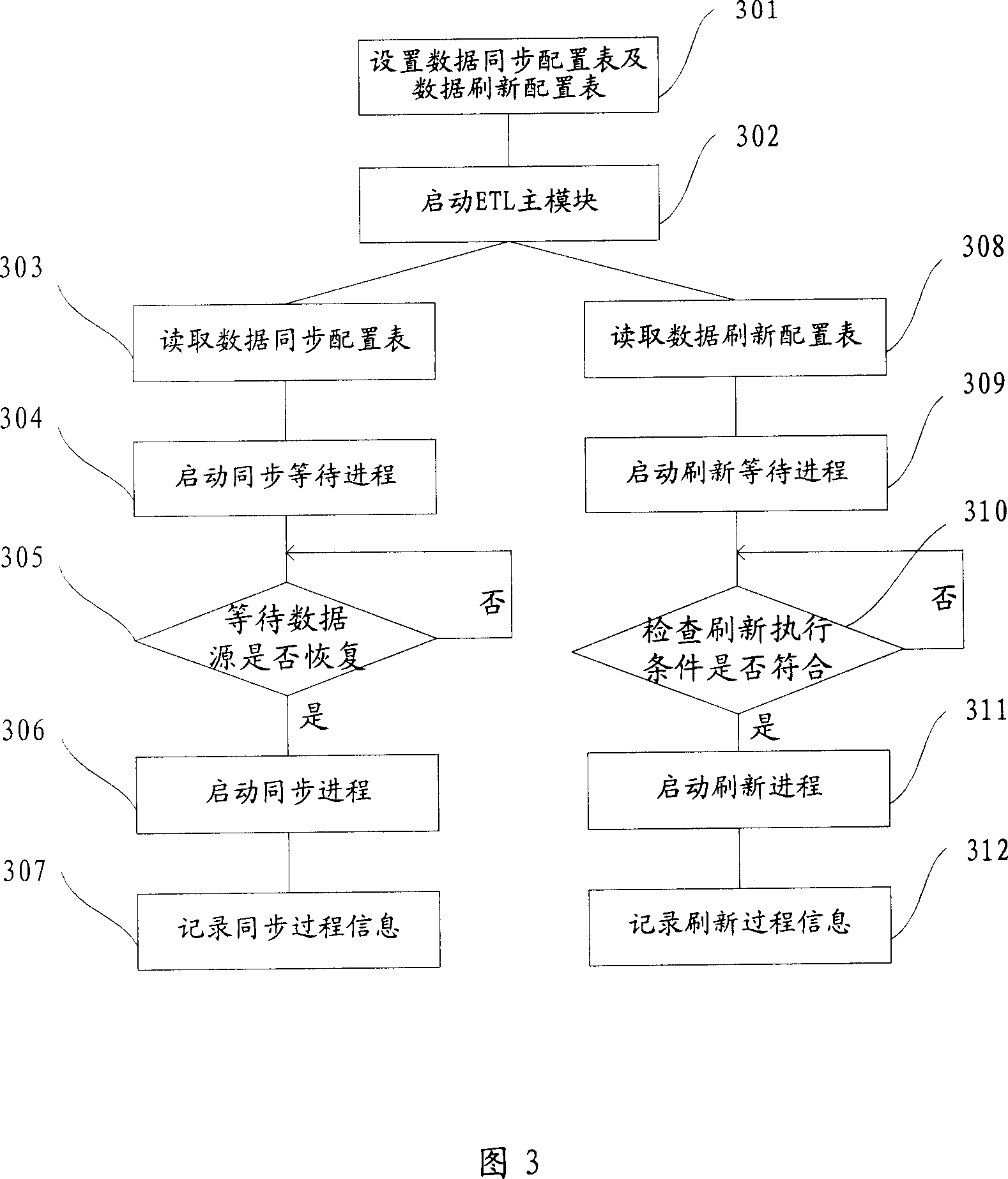
InactiveCN101105793ASolve the problem of inconsistent synchronization timeGuaranteed processing timeMultiprogramming arrangementsSpecial data processing applicationsData synchronizationData warehouse
The invention discloses a data handling method and a system in database to solve the problem that the single course treatment requires great amount of time and manpower cost and can not handle abnormities in ETL process. The method includes: arrange data synchronous configuration table and data refreshing configuration table; configuration information of the corresponding data source, start up a plurality of synchronous courses in parallel; refreshing grades, and start up a plurality of refreshing courses to make sequential synchronous and refreshing treatment on a plurality of data sources. The invention also includes parallel monitoring treatment; periodically checking synchronous refreshing information table; any abnormity discovered should be recorded in the alarm information table; the invention also includes parallel alarm treatment: Periodically checking alarm information table; alarm information should be sent immediately for new abnormities. The invention enhances the efficiency of synchronization and refreshing and saves a great deal of time and manpower cost. Real-time monitoring ensures timely handling of problems and safe, reasonable, and stable operation of database.
Owner:ALIBABA GRP HLDG LTD
System and method for synchronizing comparison of data consistency
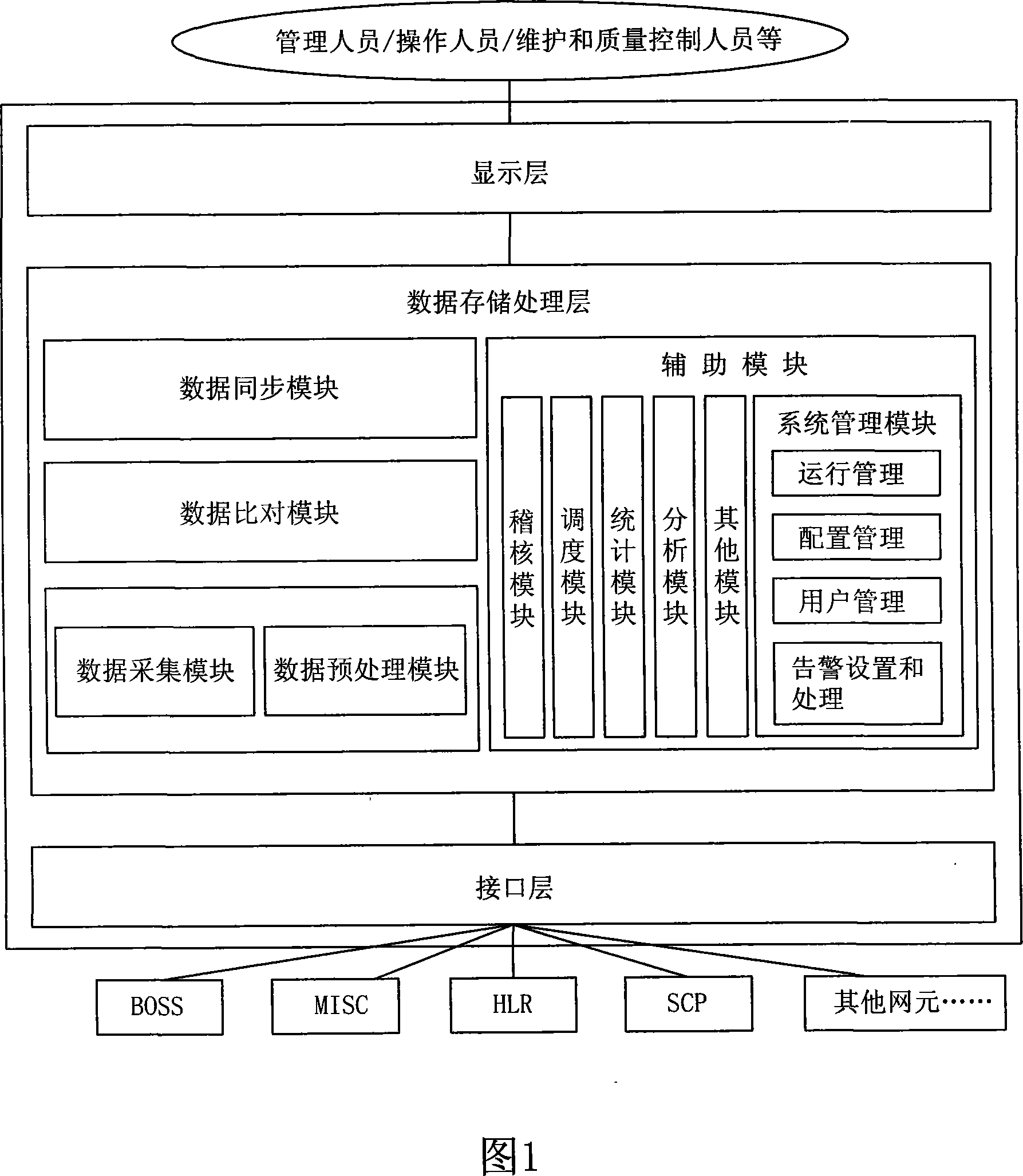
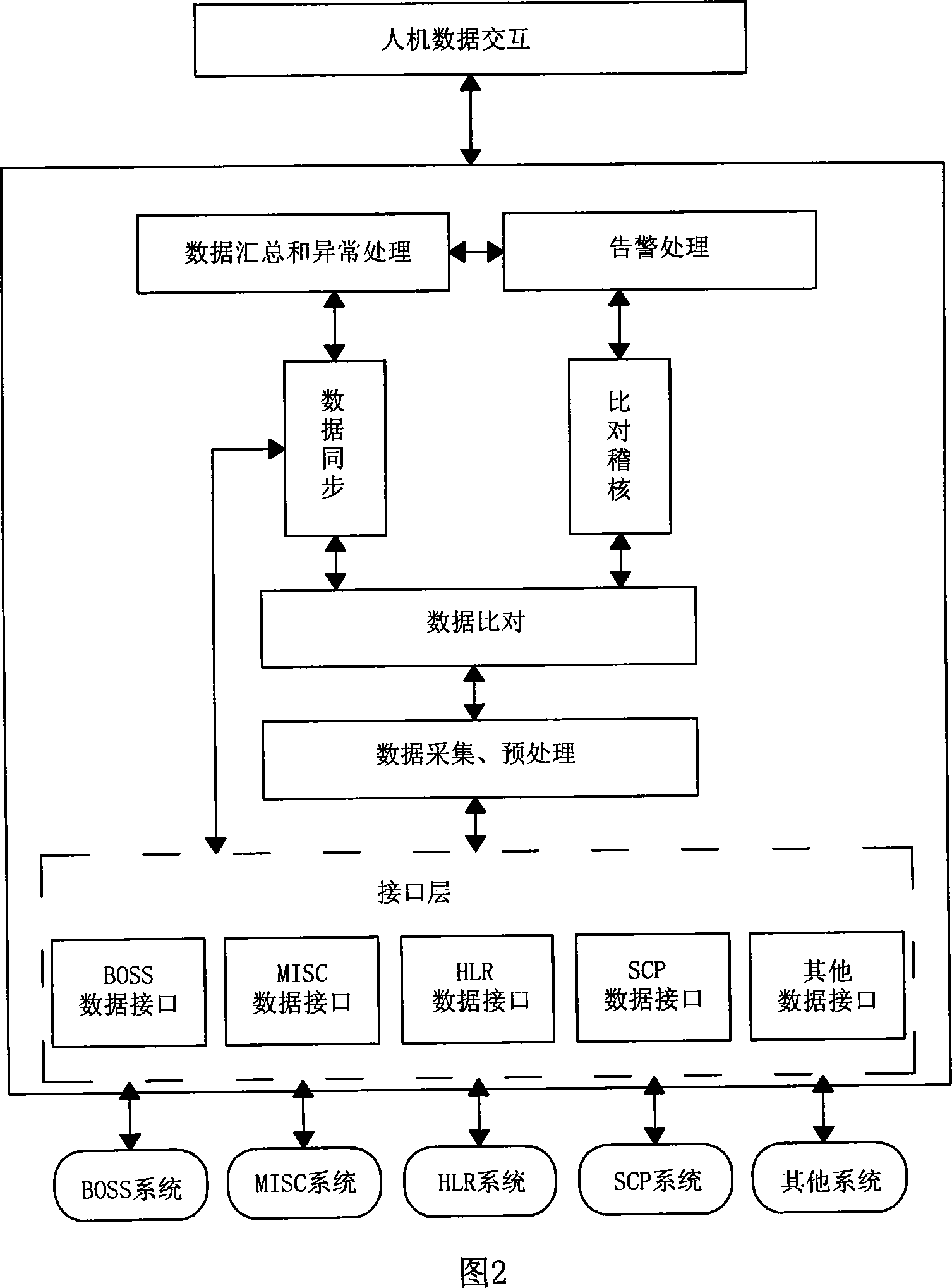
ActiveCN101094051AAvoid complaintsImprove effectivenessSynchronisation signal speed/phase controlData switching networksData synchronizationDifference list
It includes display layer, data storage / procession layer (SP) and system interface layer (SI). SP includes data collect module (DL), data pre-processing module (DP), data comparison module (DM), data sync, module (DS) and assistant module. Via SI, the business backup and bearing nets (BBB) realize mutual comm. between net elements (NE). From BBB, DL collects NE data requiring keeping coincident. DP / DM pre-processes and compares these data. Non-coincident data are recorded in the error list. According to availability test rule, DS verifies availability of data difference, generates corresponding synchronization data against valid data difference base on sync. rule and sends to related NE to keep coincidence of data between NEs. This invention raises data comparison synchronization level, system running efficiency and resource utilization. It ensures accuracy and coincidence of system data. It extensively is applied in multi-NE cooperation fields, such as comm., insurance and banking.
Owner:CHINA MOBILE GROUP SICHUAN
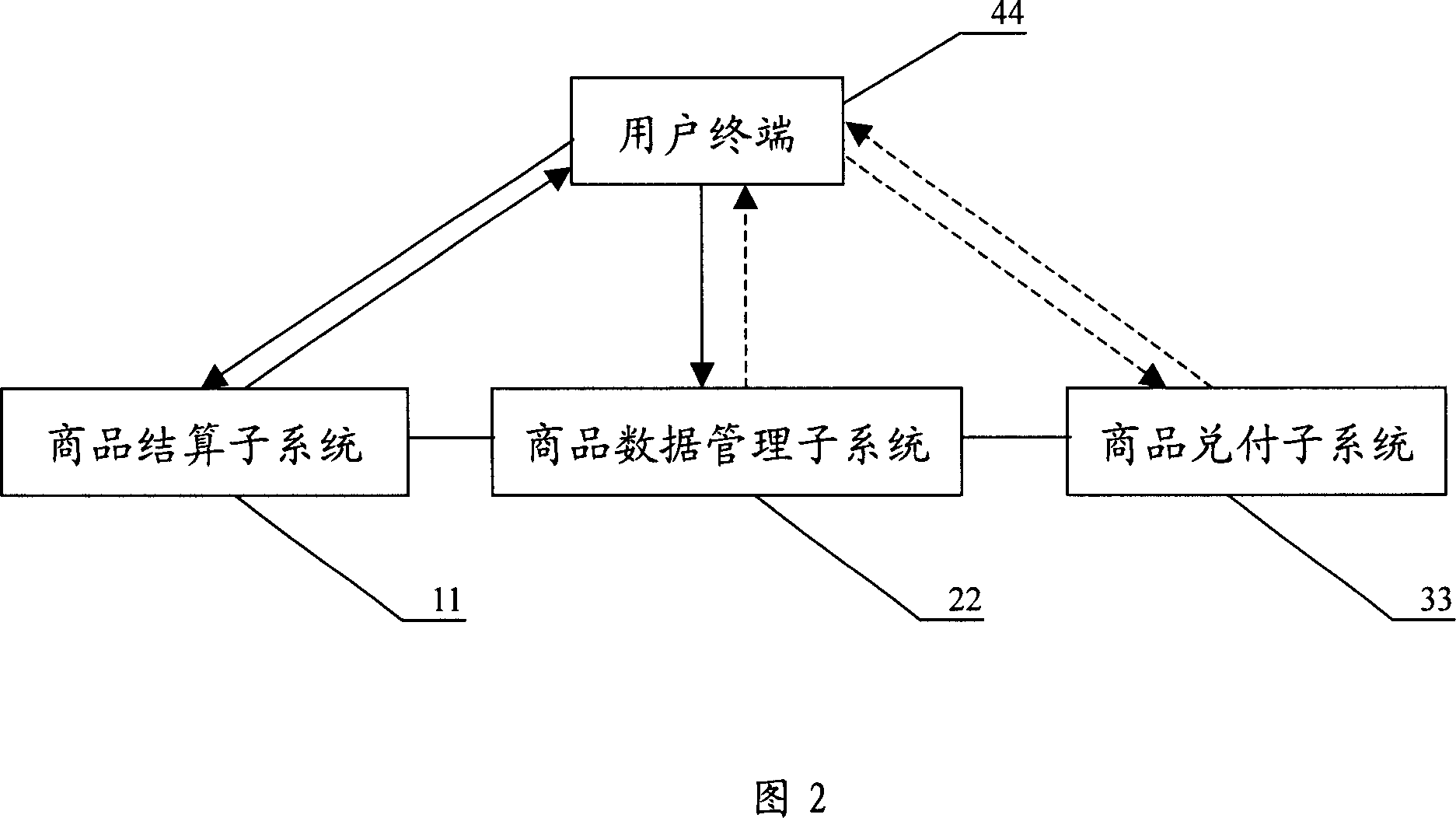
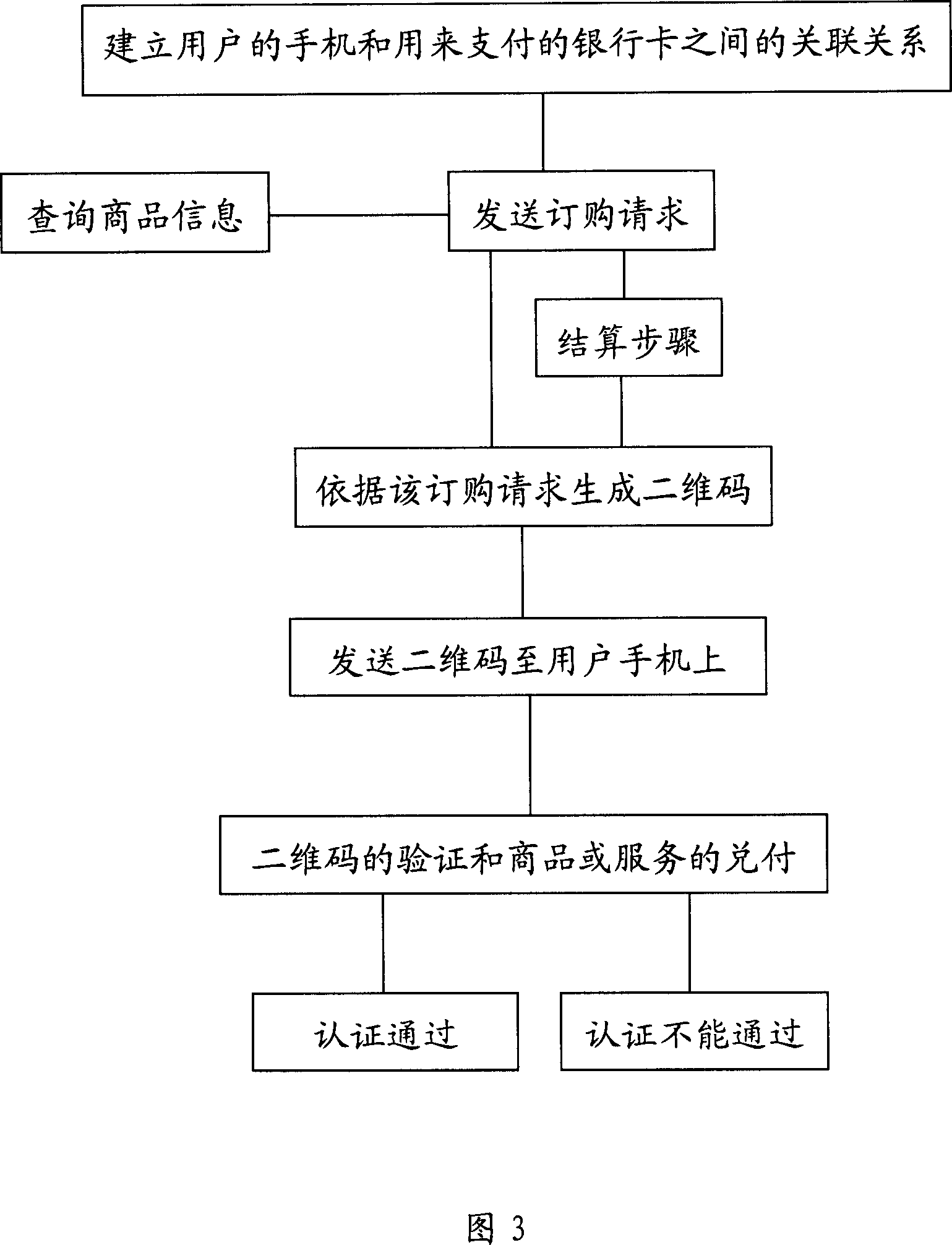
Shopping method and system by using handset based on technique of 3D codes
InactiveCN1959727AImprove securityUniqueness guaranteedPayment architectureRadio/inductive link selection arrangementsComputer terminalData management
A mobile phone purchasing method based on 2-D code technique includes setting up correlation relation of user mobile phone to bank card, issuing purchase request and generating 2-D code according to said purchase request then sending generated 2-D code to user mobile phone, cashing relevant commodity or service if certification is passed. The mobile phone purchasing system used for realizing said method is also disclosed.
Owner:CHINA UNIONPAY
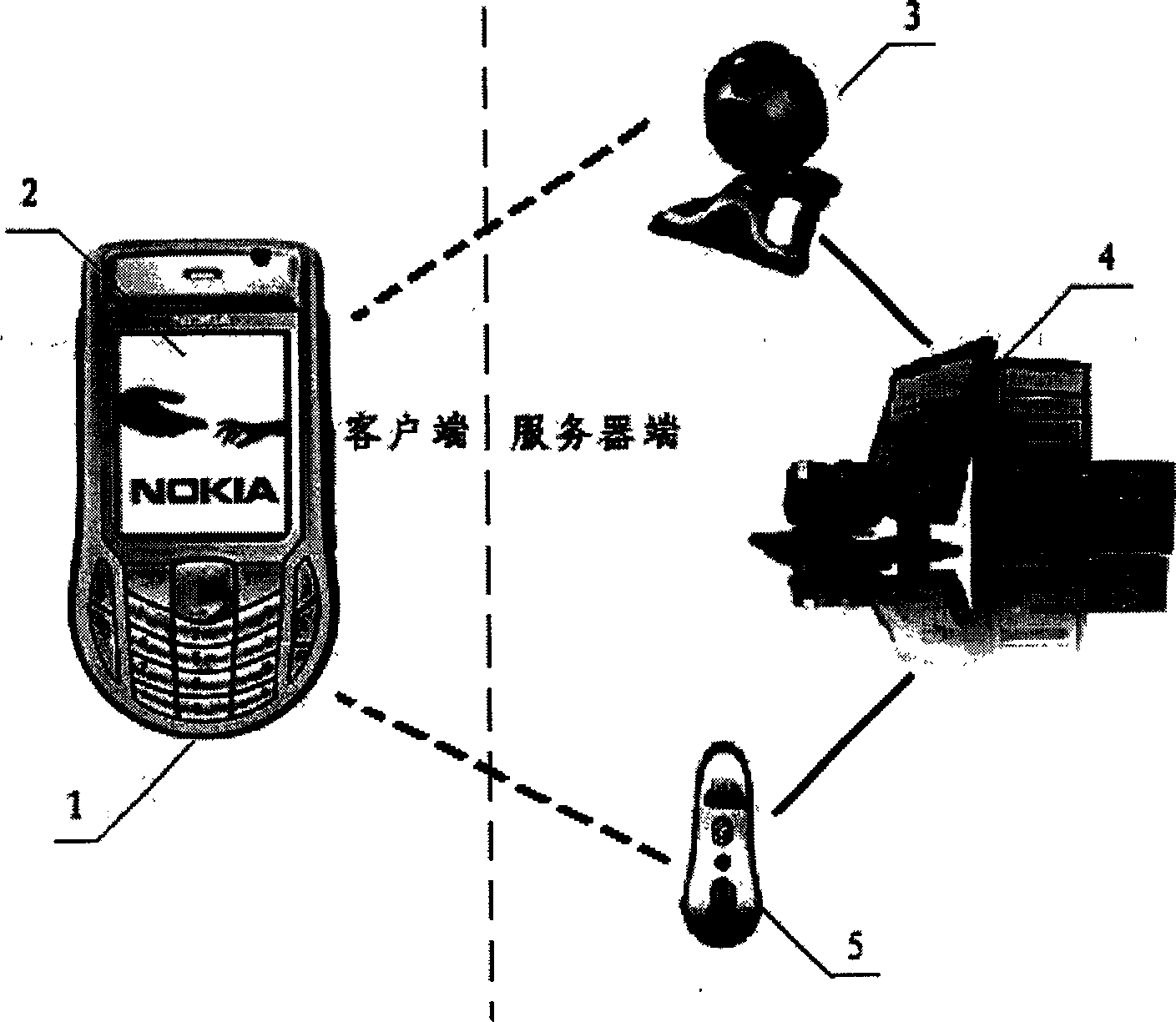
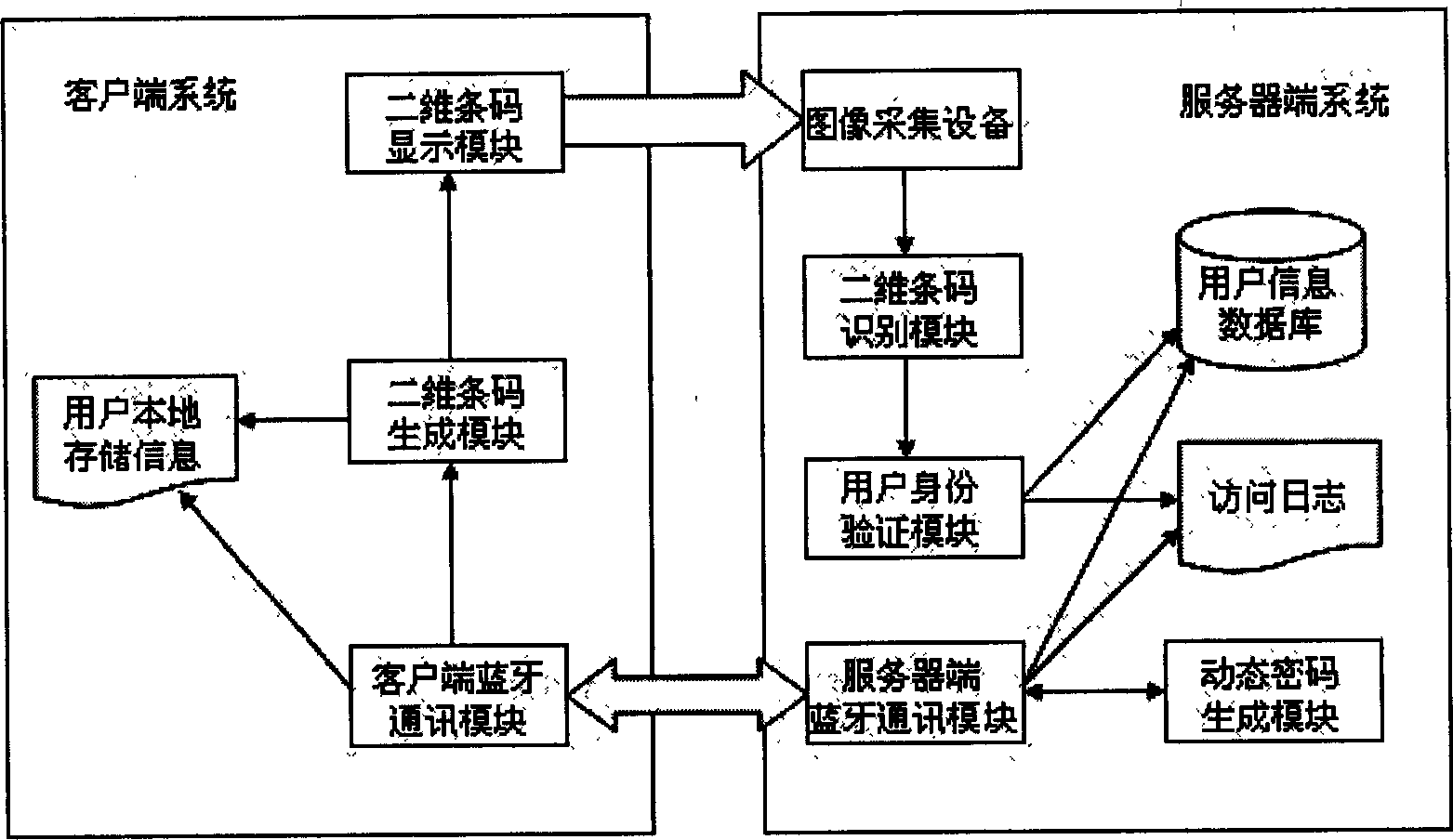
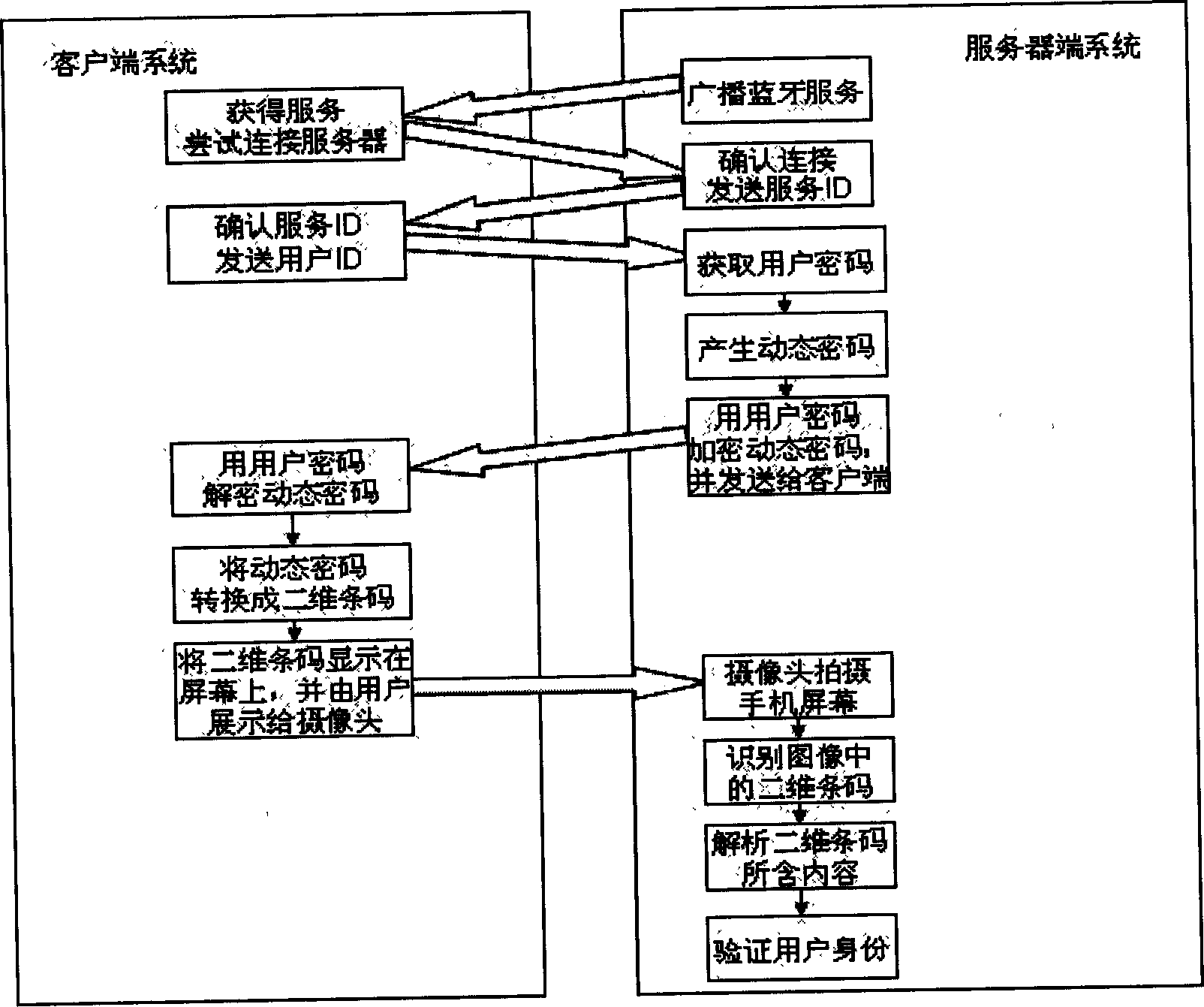
Real-time identity authentication method based on mobile phone, bluetooth and two-dimensional barcode
InactiveCN1777101AReduce the likelihood of gettingReduce the possibilityNear-field transmissionUser identity/authority verificationComputer hardwareBarcode
The method for authenticating ID is related to handset, blue teeth communication technique and 2D bar code technique synthetically. Characters are that using blue teeth function of handset builds connection with server; using cipher key agreed on user in advance encrypts dynamic cipher generated by server, and transfers the encrypted dynamic cipher to handset; handset converts the decrypted dynamic cipher to information of 2D bar code, and displays the bar code on screen of the handset; server end uses camera header to take image of handset screen so as to recognize information of 2D bar code, and interpret the dynamic cipher contained; matching dynamic cipher from screen with dynamic cipher created before to authenticate userí»s ID. Advantages are: without need of carrying certificate, not easy of imitating features of authentication, solving issue of capturing and stealing information of authentication.
Owner:DALIAN UNIV OF TECH
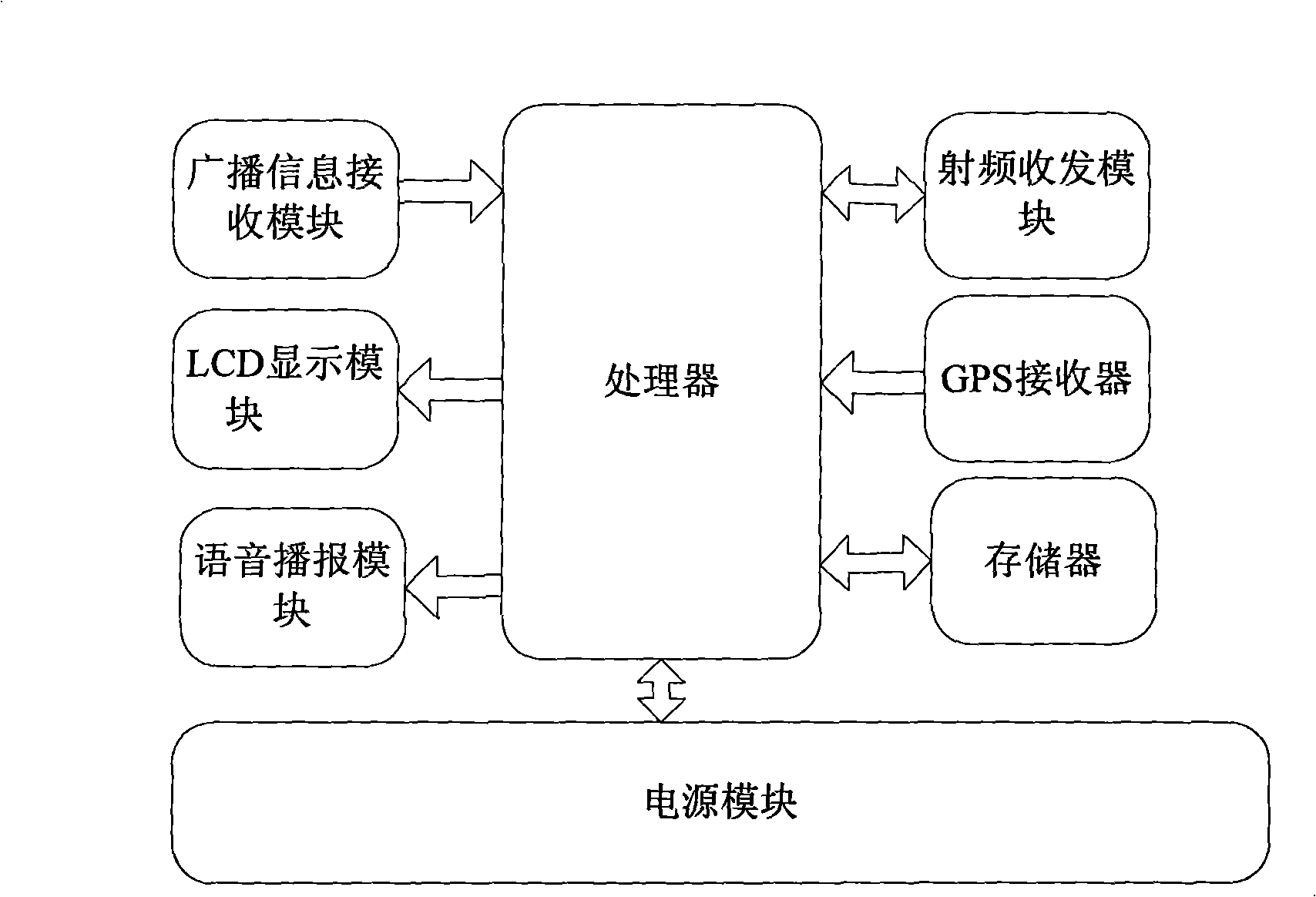
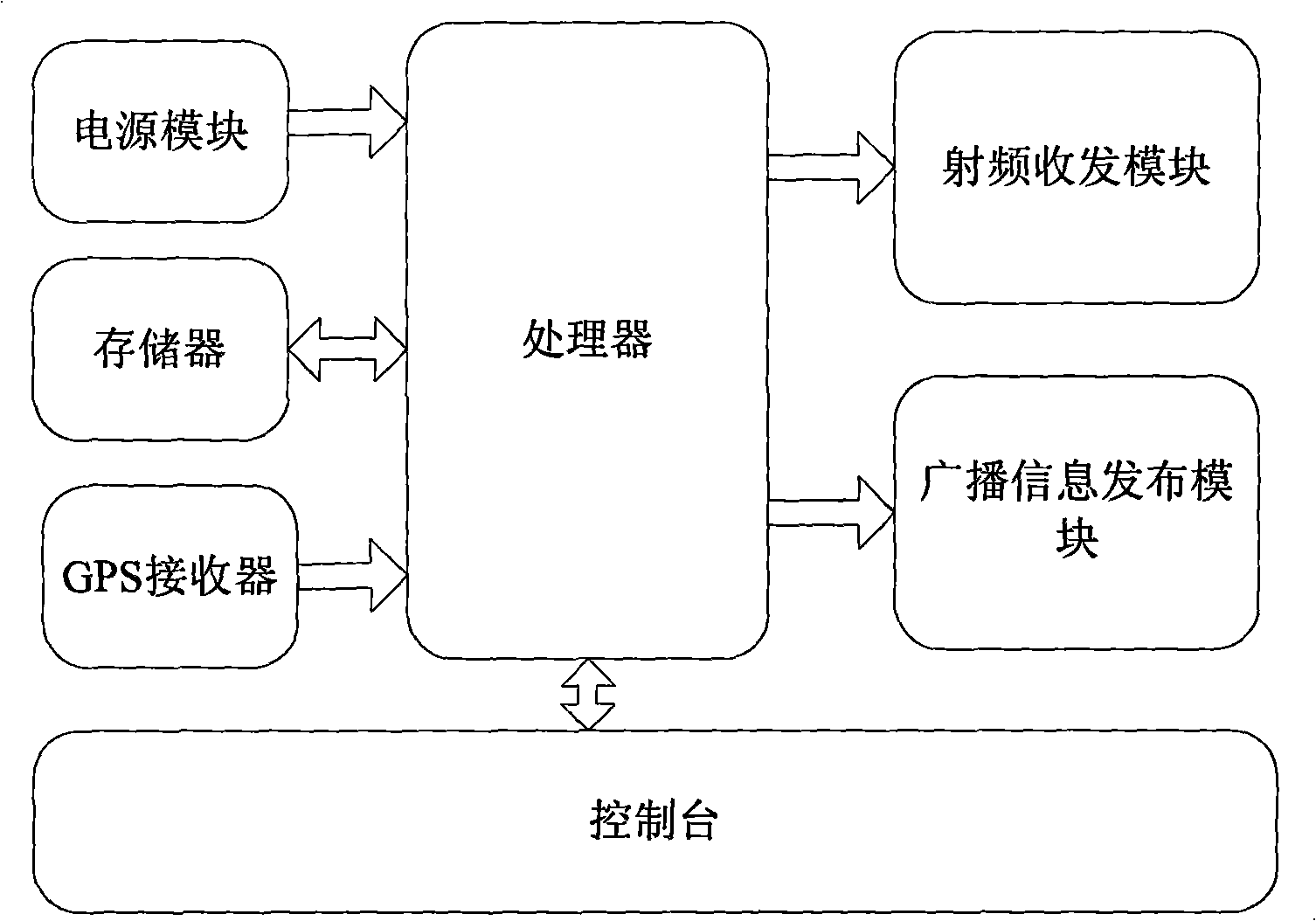
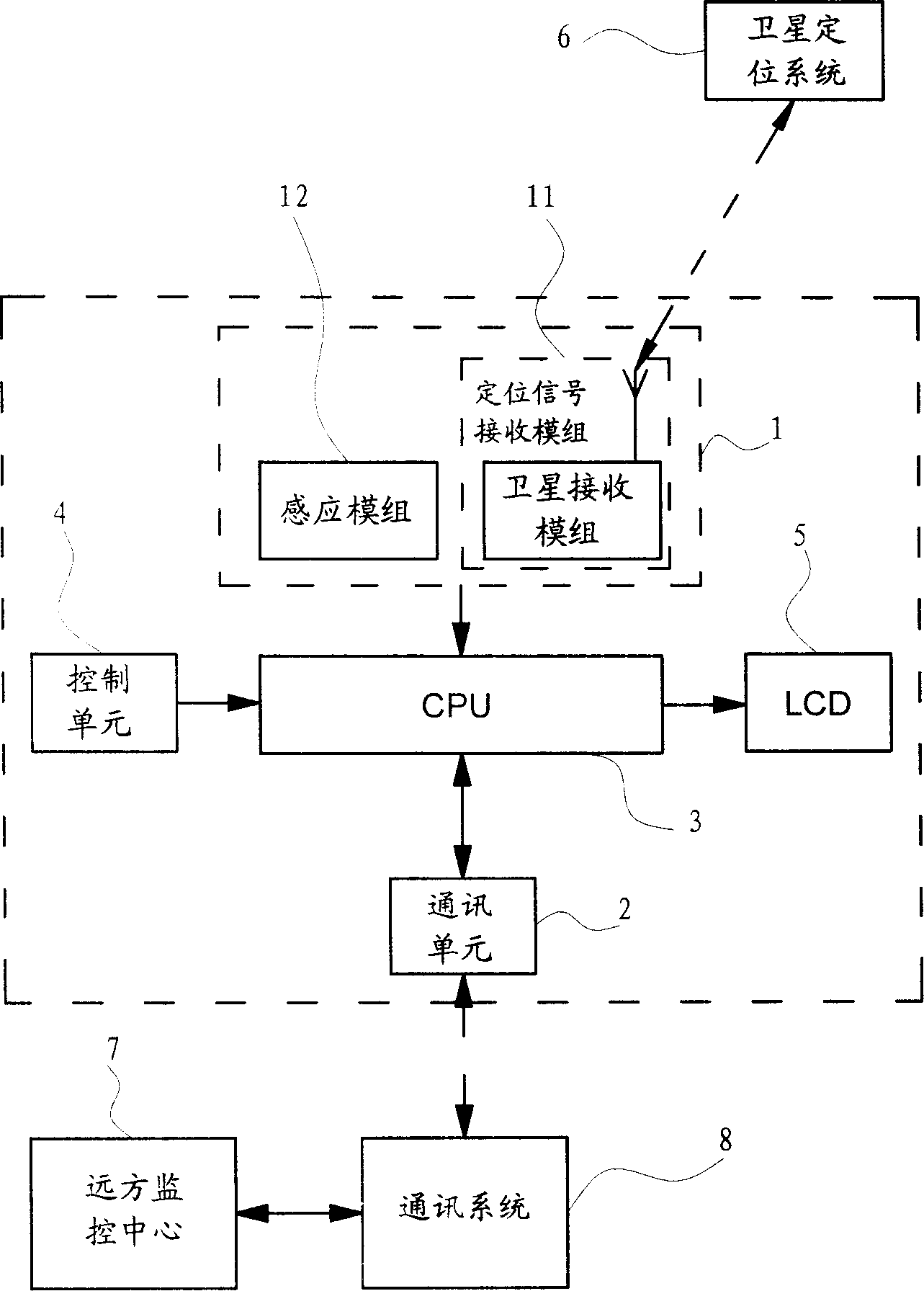
Structure of multifunctional monitoring and tracing device worn on human body, and its monitoring and tracing method
ActiveCN1801236AGuaranteed timelinessAvoid blind spotsElectric signal transmission systemsPosition fixationHuman bodyCommunications system
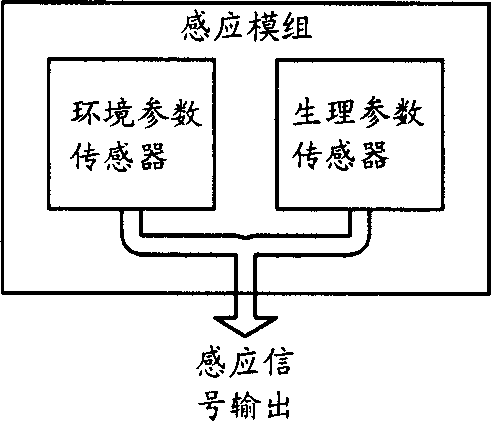
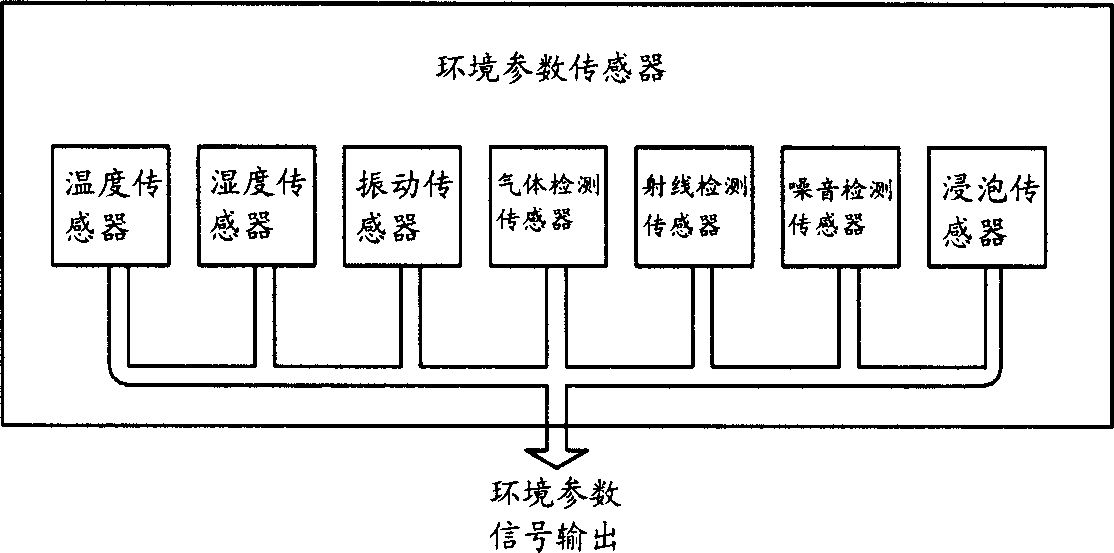
The invention relates to a multi-function monitoring tracking device and the method for realizing this. The inventive device comprises: signal collecting unit which includes a positioning signal receiving module group and a sensing module group; a communication unit for emitting wireless signal; a central processing unit with an input terminal connected with the signal collecting unit and an output terminal connected with the communication unit; the central processing unit convert the signal from the collecting unit into communication signal used for the communication system; the sensing module group comprises sensor for monitoring the ambient parameter of the life body.
Owner:朱水林
Method for purifying error matching of visual image characteristic points based on ORB (Oriented FAST and Rotated BRIEF)
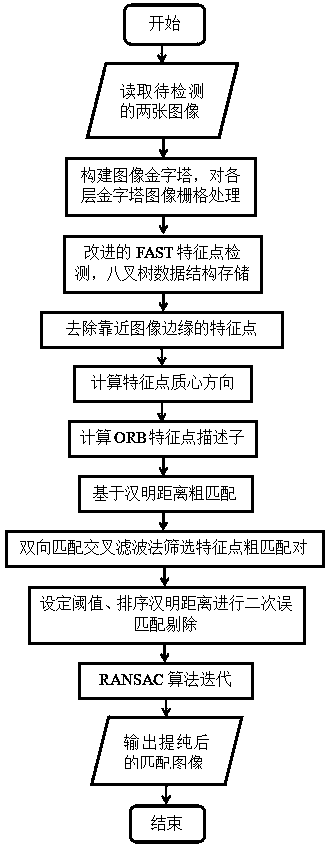
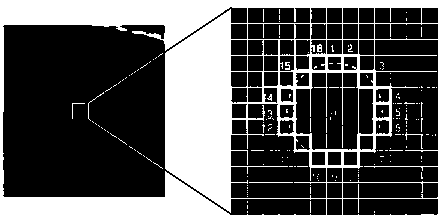
InactiveCN108010045AImprove matching accuracyGuaranteed timelinessImage enhancementImage analysisPattern recognitionImage edge
The invention relates to a method for purifying error matching of visual image characteristic points based on ORB (Oriented FAST and Rotated BRIEF). The method comprises the following steps of readingtwo to-be-detected left and right images shot under different viewing angles, constructing scale image pyramids for the images and performing grid processing; detecting characteristic points in eachsmall grid of each layer of pyramid images, extracting the characteristic points and determining a characteristic point coordinate; removing the characteristic points close to edges of the images, andcalculating the direction of a barycenter of the remaining characteristic points; calculating descriptors of ORB characteristic points; performing rough matching on the characteristic points of the two images; screening rough matching pairs of the characteristic points; removing error matching pairs again; and performing an RANSAC (Random Sample Consensus) algorithm iteration on the remaining characteristic points, and outputting the purified matching images. According to the method for purifying error matching of the visual image characteristic points based on the ORB, the detected characteristic points are uniformly distributed, the characteristic point clustering effect caused by easy huddle of multiple characteristic points is avoided, and the matching speed is accelerated while improving the matching accuracy.
Owner:FUZHOU UNIV
System and method for providing network service relating to four parties
ActiveCN101272281AEasy to useRich service resourcesData switching networksThird partyNetwork service
The invention provides a system of providing network service involving four parties, which comprises: a plurality of operation information subsystems, a plurality of third party service-providing subsystems, and a fourth party service platform; the operation information subsystems are used for providing a detailed operation network service of a certain field for each user; the third party service-providing subsystems are used for providing a certain generality service to at least one operation information subsystem and the generality service points at generality requirement of each operation information system; the fourth party service platform is located between each operation information system and each third party service-providing subsystem, so as to adapt to each operation information system and each third party service-providing subsystem; the fourth service platform is used for providing unified interfaces for each operation information system, and for respectively providing unified interface for the third party service-providing subsystem, dispatching the required service and returning results and providing service operation support. The system of the invention can remarkably reduce the difficulty of using generality services of a third party for the operation information system.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Video broadcast monitoring method and device
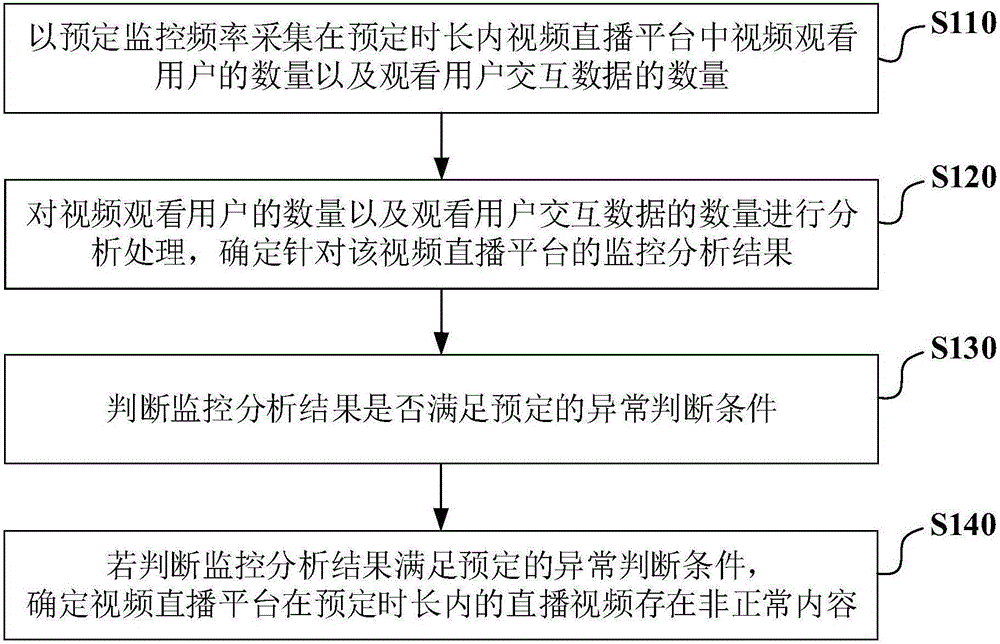
ActiveCN105872773AGuaranteed timelinessQuick and timely judgmentSelective content distributionReal-time computingVideo broadcast
The invention provides a video broadcast monitoring method and device. The monitoring method includes the steps that the number of video watching users and the number of watching user interactive data in a video broadcast platform in preset time are acquired at preset monitoring frequency; the number of video watching users and the number of watching user interactive data are analyzed, and a monitoring analysis result targeted to the video broadcast platform is determined; whether the monitoring analysis result meets the preset abnormity judgment condition or not is judged; if the monitoring analysis result meets the preset abnormity judgment condition, it is determined that abnormal contents exist in the broadcast video of the video broadcast platform in preset time. According to the video broadcast monitoring method and device, data changes under various situations in the video platform are analyzed, the purpose that whether abnormal contents exist in the broadcast video of the video broadcast platform in preset time or not is judged rapidly and timely is achieved, and reliable guarantee is provided for healthy and legal operation of the video broadcast platform.
Owner:北京鸿享技术服务有限公司
BIM-based water conservancy and hydropower project management cloud platform and application method thereof
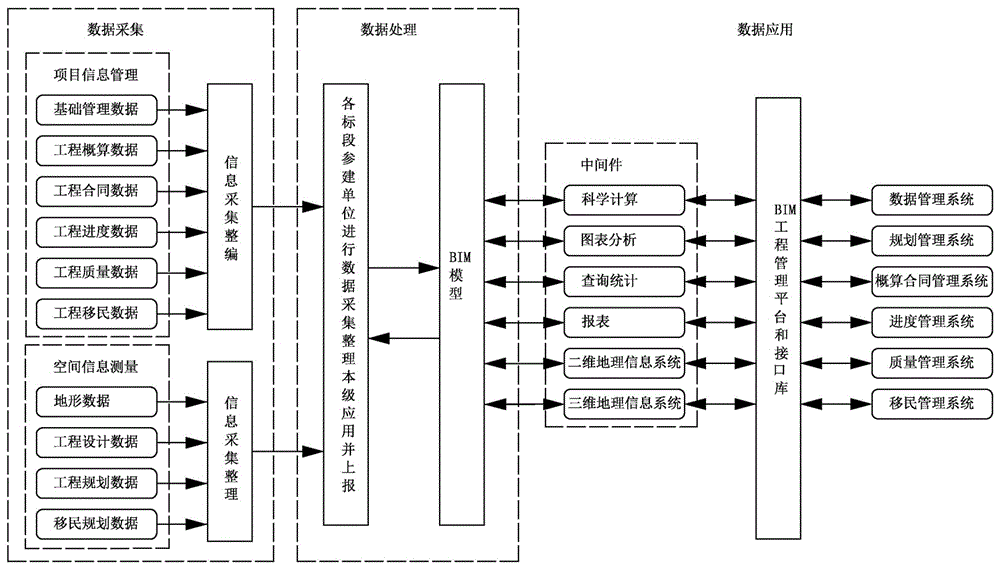
InactiveCN106022979AGuaranteed clarityEnsure consistencyData processing applicationsPrivate networkData acquisition
A BIM (Building Information Modeling)-based water conservancy and hydropower project management cloud platform comprises a data acquisition layer, a communication network layer, a data resource layer, an application support layer, and a service application layer. The data acquisition layer includes project information management and spatial information measurement; the communication network layer includes a local area network, a VPN (Virtual Private Network) or a public network; the data resource layer includes a BIM model which is stored in a public cloud, in a private cloud or in a hybrid cloud and includes a BIM integrated database; the application support layer includes a BIM project management platform and a data exchange platform; and the service application layer includes BIM information query, construction process BIM management and BIM information output. The BIM integrated database is connected with different project object data, processes and resources, is a digital expression of construction facilities which contains rich data, is object-oriented and has intelligent and parametric characteristics, and supports dynamic information creating, sharing, updating and managing in the life cycle of a project.
Owner:ZHENGZHOU SHUANGJIE TECH CO LTD
Event warning method based on Internet information
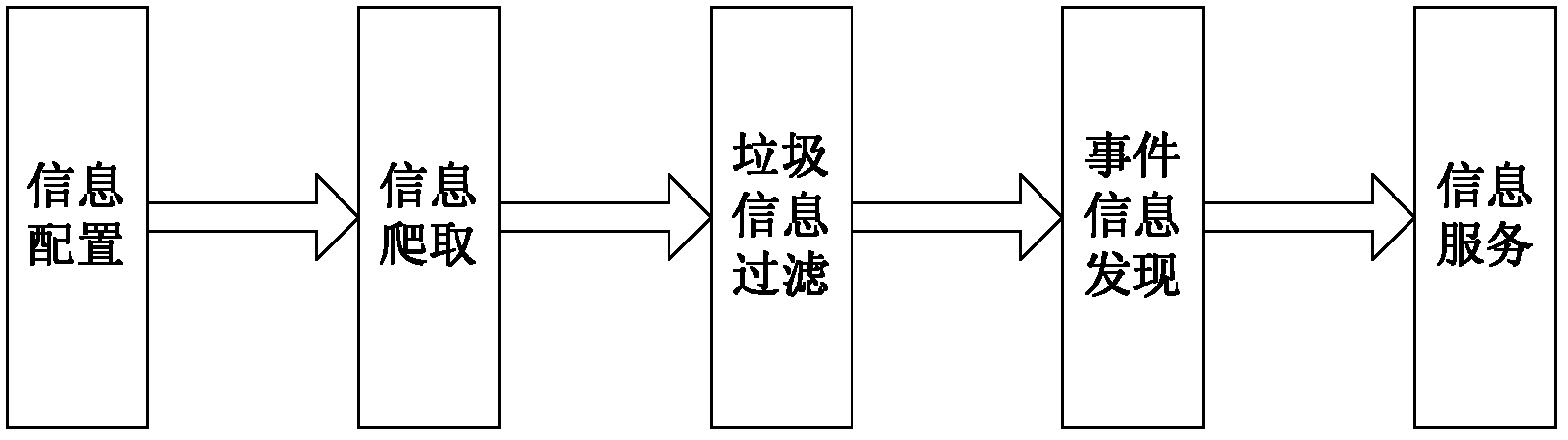
ActiveCN103176983AGuaranteed timelinessGuaranteed accuracySpecial data processing applicationsFood safetyThe Internet
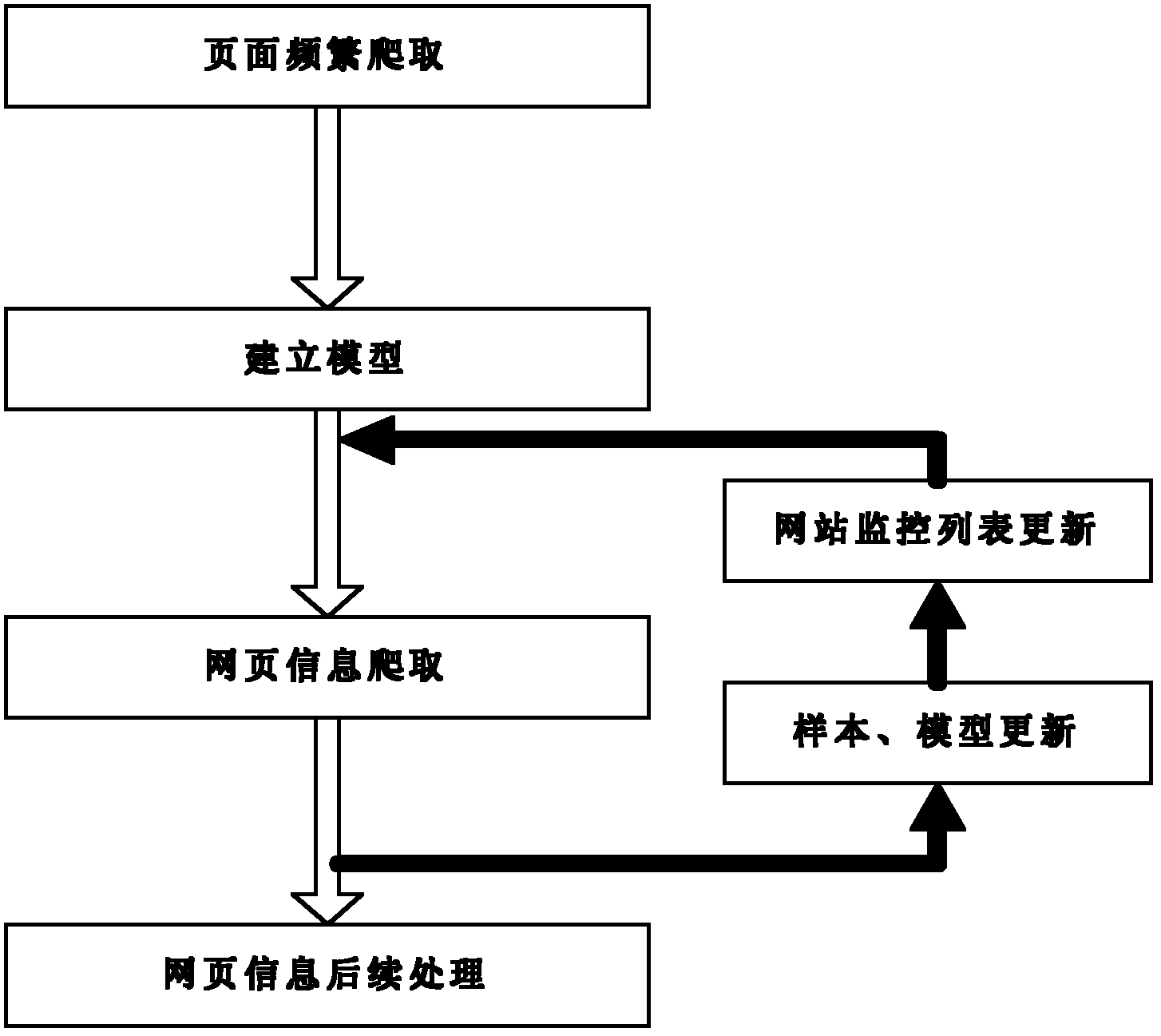
The invention discloses an event warning method based on Internet information and belongs to the technical field of information. The method comprises the following steps. Firstly, crawling of webpage information on each set website is performed, the webpage information is stored, and information relevant to an event is obtained. Secondly, junk information filtering is performed on the information which is relevant to the event and obtained by crawling. Thirdly, an event information main body is set up, the information after filtering is sorted based on example names and attributes in the event information main body by utilizing a mode matching method. Fourthly, the sorted information is clustered according to set characteristics, and events in each kind of information are obtained. Fifthly, all the characteristic parameter values of each event are obtained regularly, and if a difference value of all the characteristic parameter values of one event and an average value of the event in a given previous period exceeds a preset threshold, warning on the event is performed. The event warning method based on the internet information ensures timeliness, accuracy and comprehensiveness of information identification and warning of food safety events, and improves efficiency of risk warning of food safety.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Message pushing method and pushing server
ActiveCN103501486AGuaranteed reliabilityGuaranteed timelinessMessaging/mailboxes/announcementsApplication serverComputer terminal
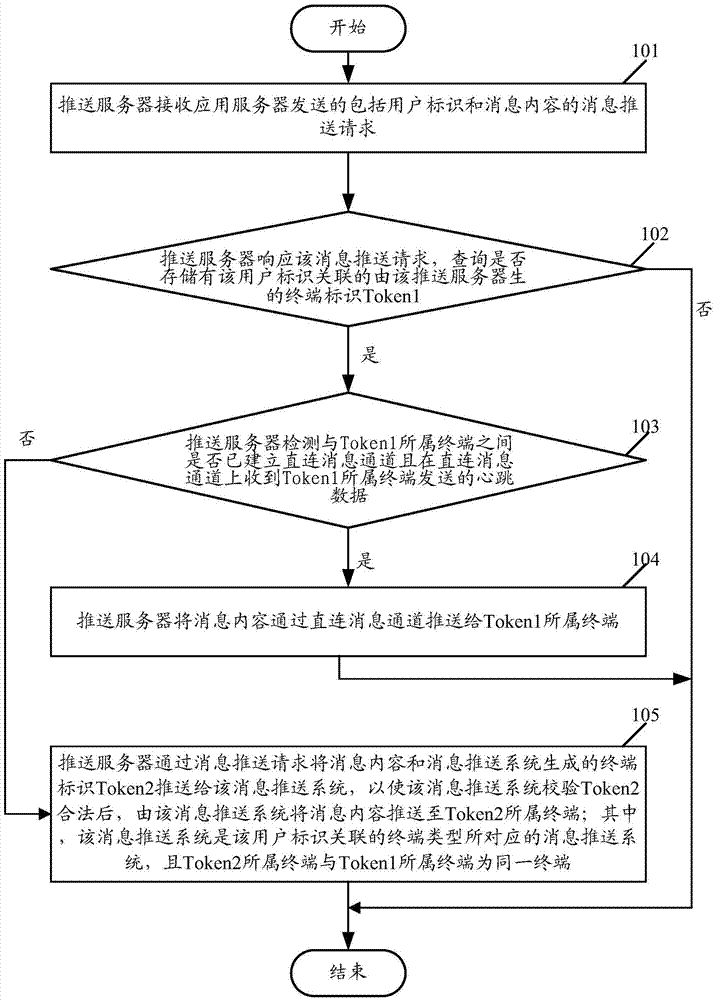
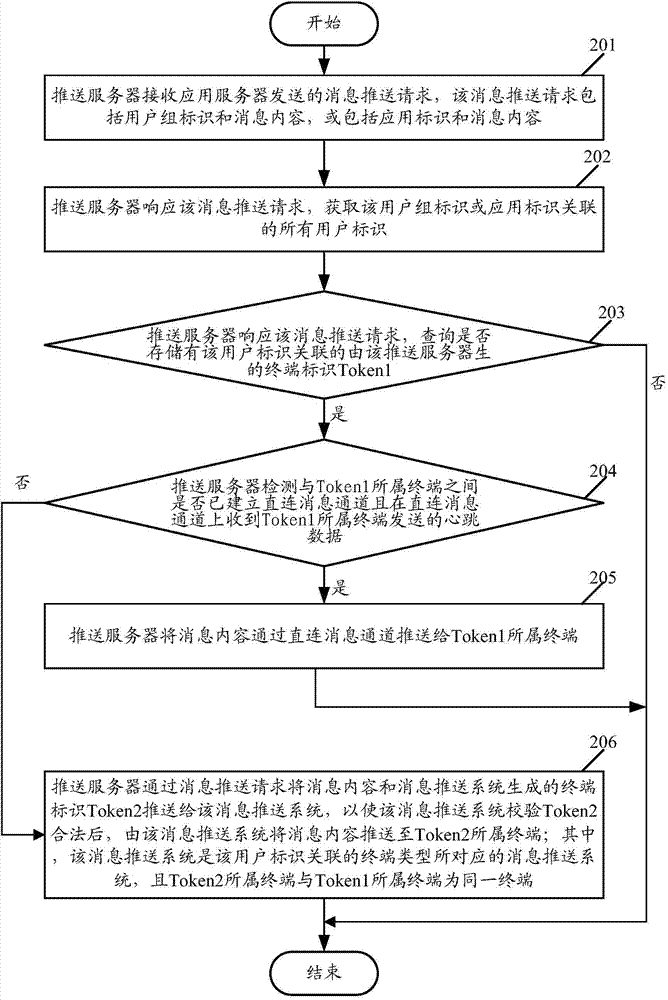
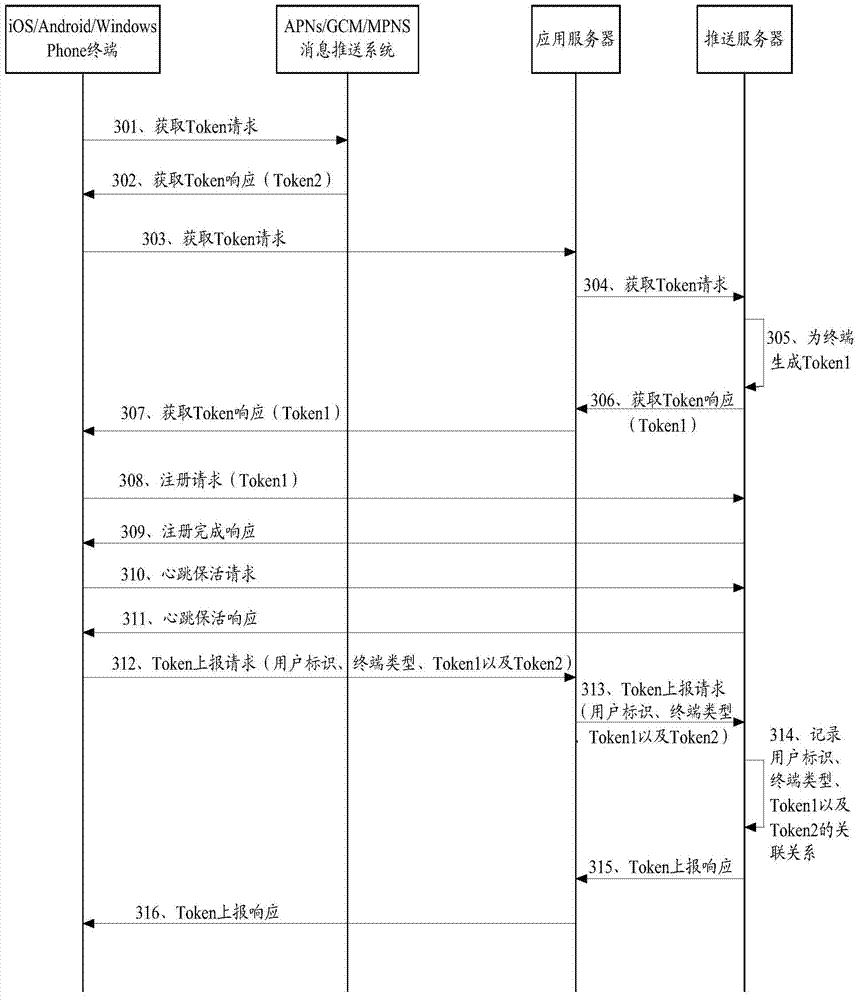
The invention relates to a message pushing method and a pushing server. According to the method, the pushing server receives message pushing requests, including user identifications and message content, sent by an application server, when the storage of Token1 which is associated with the user identifications and is generated by the pushing server is inquired, in addition, the building of a direct connection message passage among affiliated terminals of the Token1 is detected, and in addition, the heartbeat data is received on the passage, message content is pushed to the affiliated terminals of the Token1 through the passage, otherwise, the message content and Token2 generated by the message pushing system are pushed to the message pushing system, and the message content is pushed to affiliated terminals of the Token2 after the message pushing system checks the legality of the Token2; the message pushing system is a message pushing system corresponding to the terminal type associated with the user identifications, and the affiliated terminals of Token2 and the affiliated terminals of Token1 are the same terminals. The reliability and the timeliness of the message pushing are ensured, and an application server interface is simplified.
Owner:HUAWEI TECH CO LTD
Method and device for editing video file
InactiveCN101635848AEdit real timeGuaranteed normal playbackElectronic editing digitised analogue information signalsTelevision systemsStart timeKey frame
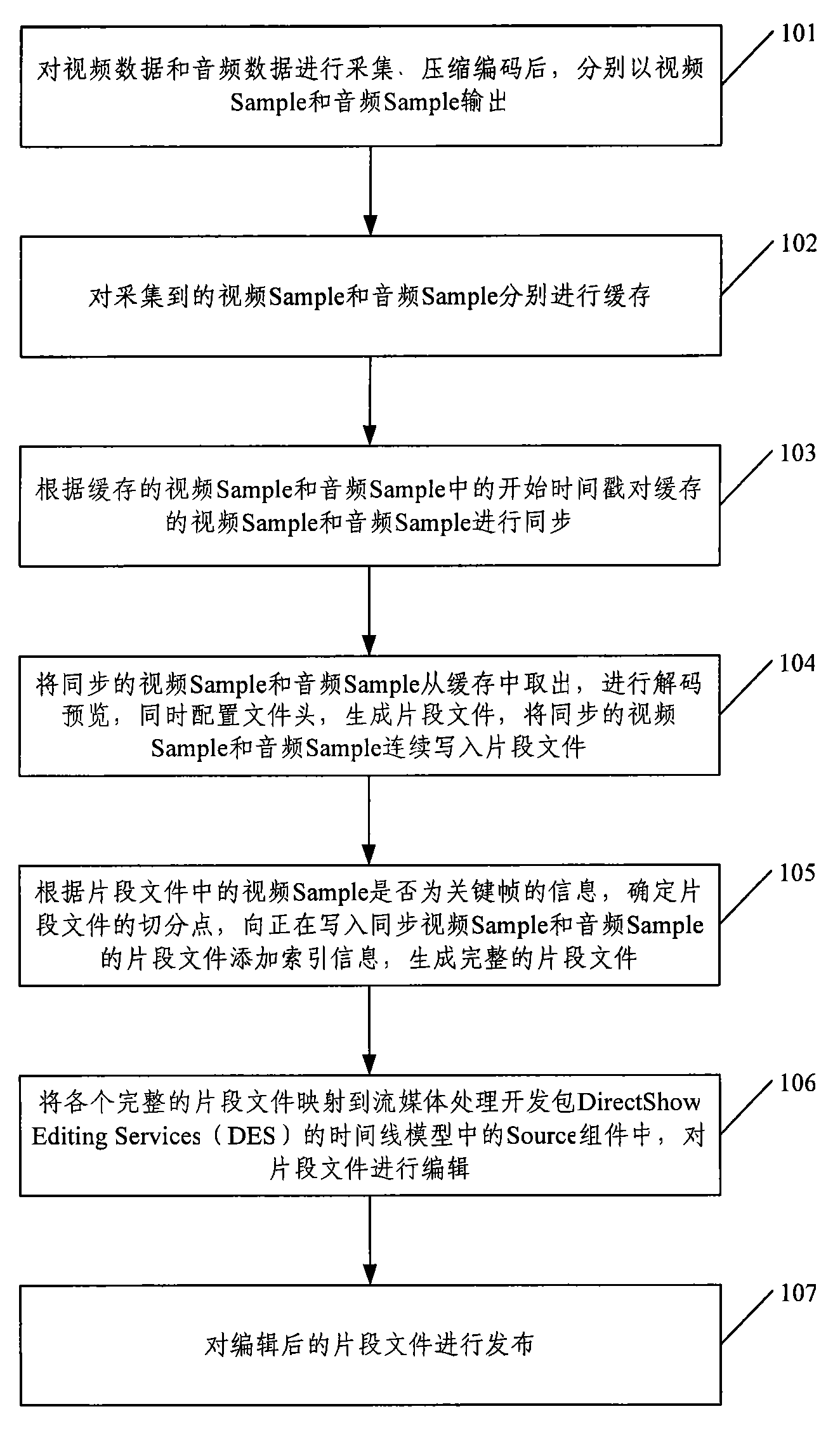
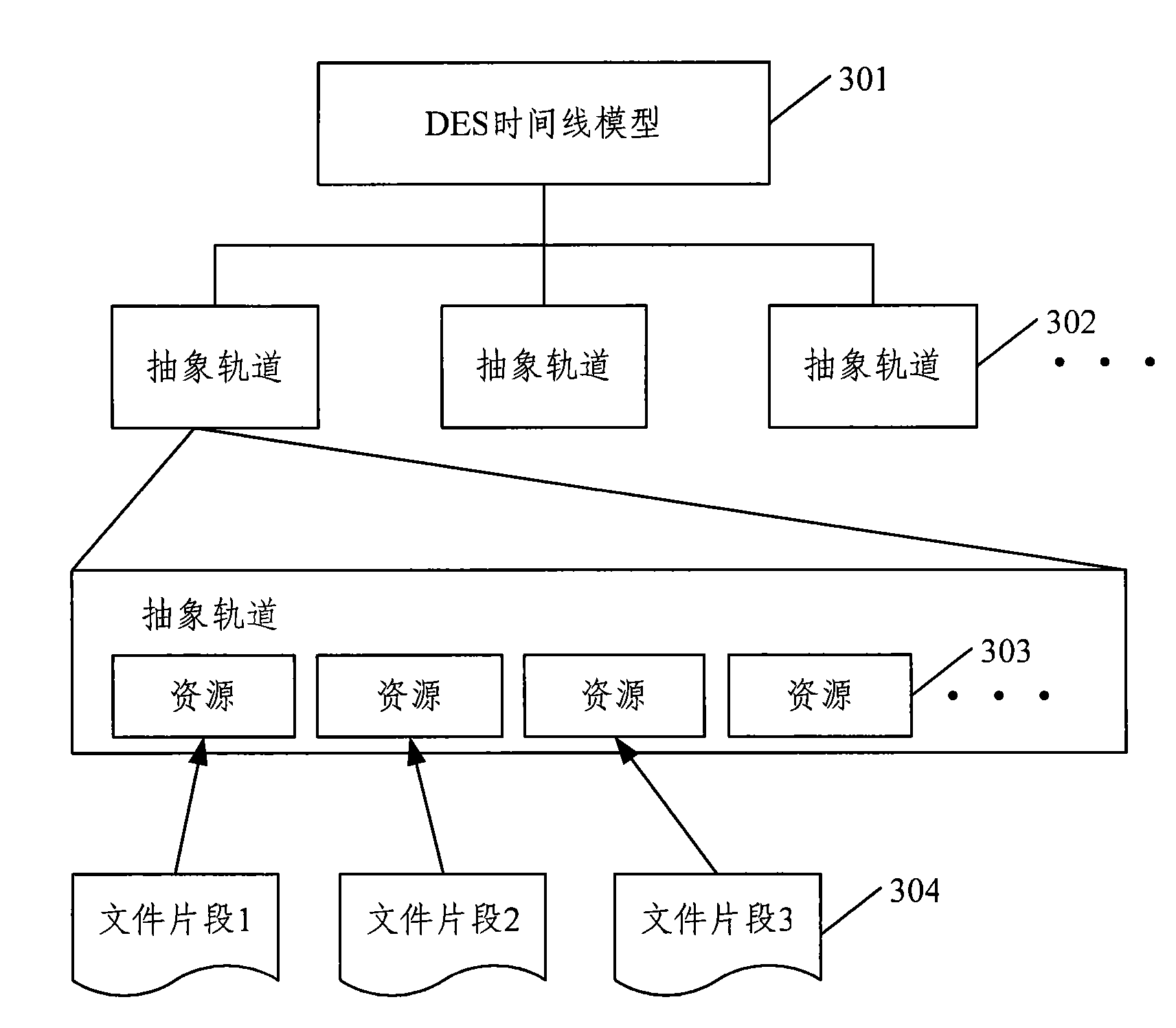
The invention discloses a method for editing a video file. The method comprises the following steps of: buffering acquired video sample and audio sample respectively; according to starting time sample and sample; picking up and decoding the video audio samples which are synchronized for previewing, simultaneously configuring a file header, generating a fragment file, continuously writing the video audio samples which are synchronized in the fragment file; and according to the information on whether the video sample in the fragment file is a key frame, determining a dividing point of the fragment file, adding the index information to the fragment file in which the video audio samples which are synchronized are written, and generating the whole fragment file. The invention also provides a device for editing the video file. Based on the method and the device, the video fragment file which is finally released can be generated when the video fragment file is being edited in real time, so that the release flow is shortened, and the editing efficiency is improved.
Owner:NEW FOUNDER HLDG DEV LLC +2
Network protocol conversion method for power grid system and intercommunication method of power grid system
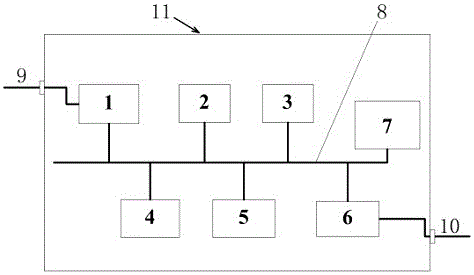
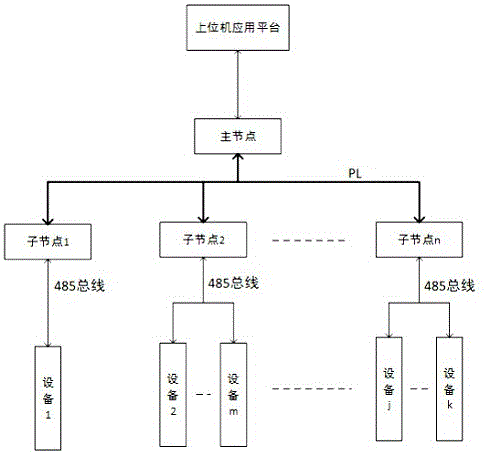
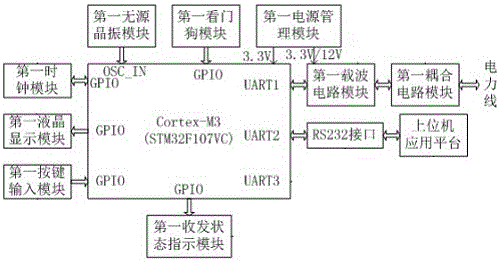
The invention discloses a network protocol conversion in a power grid system and a mutual communication method thereof. The protocol conversion is connected to a host running a virtualization concentrator through an Ethernet interface through an Ethernet; it receives and processes the protocol sent from the virtual concentrator Ethernet meter reading message; send the DL645 protocol message through the 485 bus; send back according to the Ethernet meter reading protocol. The power line network system includes a main node and several sub-nodes, and the main node and each sub-node are interactively connected through power lines. The master node is interactively connected with the upper computer application platform terminal through the RS232 interface. The several sub-nodes are interactively connected with the field application equipment through the RS485 interface. The electric network system and its protocol conversion and communication method described in the present invention can solve the deficiencies in the prior art, improve the speed of sending and receiving data at each node of the power line network system, ensure the timeliness of data message transmission in the PLC networking, and make the PLC Networking applications are more flexible and reliable.
Owner:汤亮
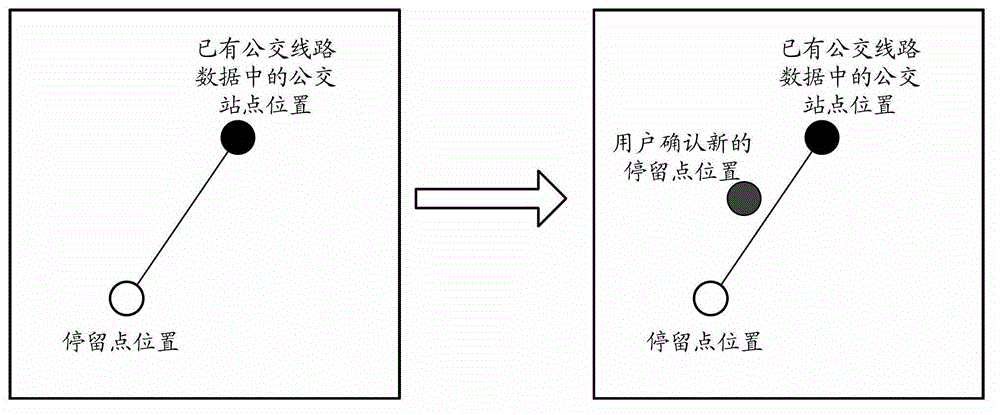
Method, device and system for updating bus route data
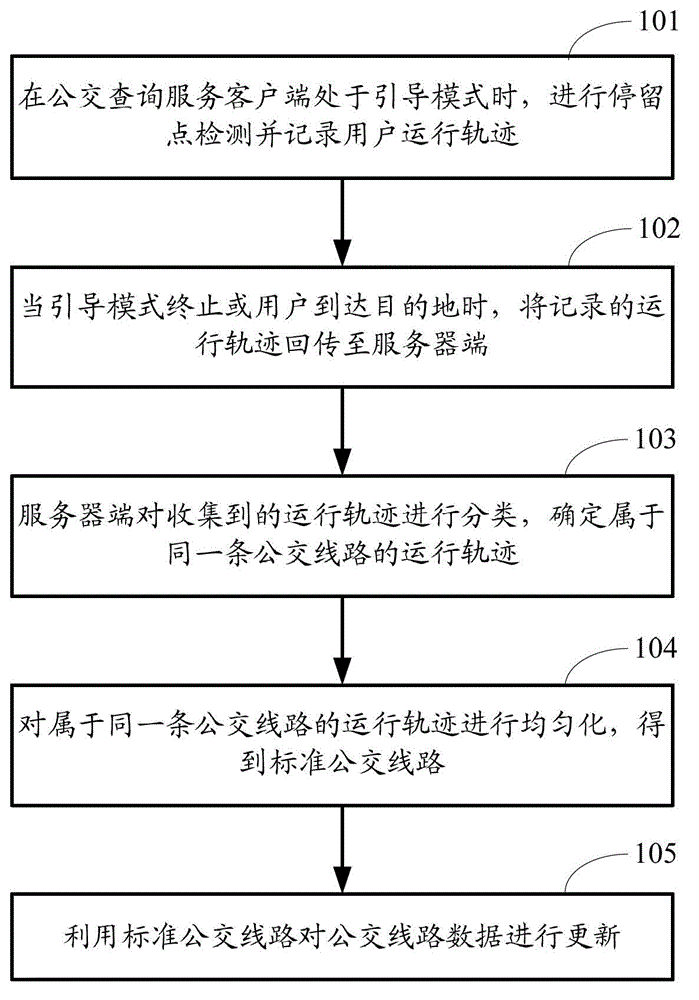
ActiveCN103150177AGuaranteed timelinessReduce replacement costsProgram loading/initiatingTransmissionData acquisitionData profiling
The invention provides a method, a device and a system for updating bus route data, wherein the method comprises the steps of: in a data acquiring stage: when a bus inquiring service client end is in a guide mode, recording a moving trajectory of a user; when a navigation mode is ended or the user arrives at a destination, re-transmitting the moving trajectory to a server end; in a data analyzing stage: classifying the collected moving trajectory by the server end, determining moving trajectories belonging to the same bus route; homogenizing the moving trajectories belonging to the same bus route to obtain a standard bus route; and updating the bus route data by using the standard bus route. According to the invention, data is acquired in real time without using an unprofessional person so that the updating cost is lowered, and the timeliness of updating the bus route data is ensured.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
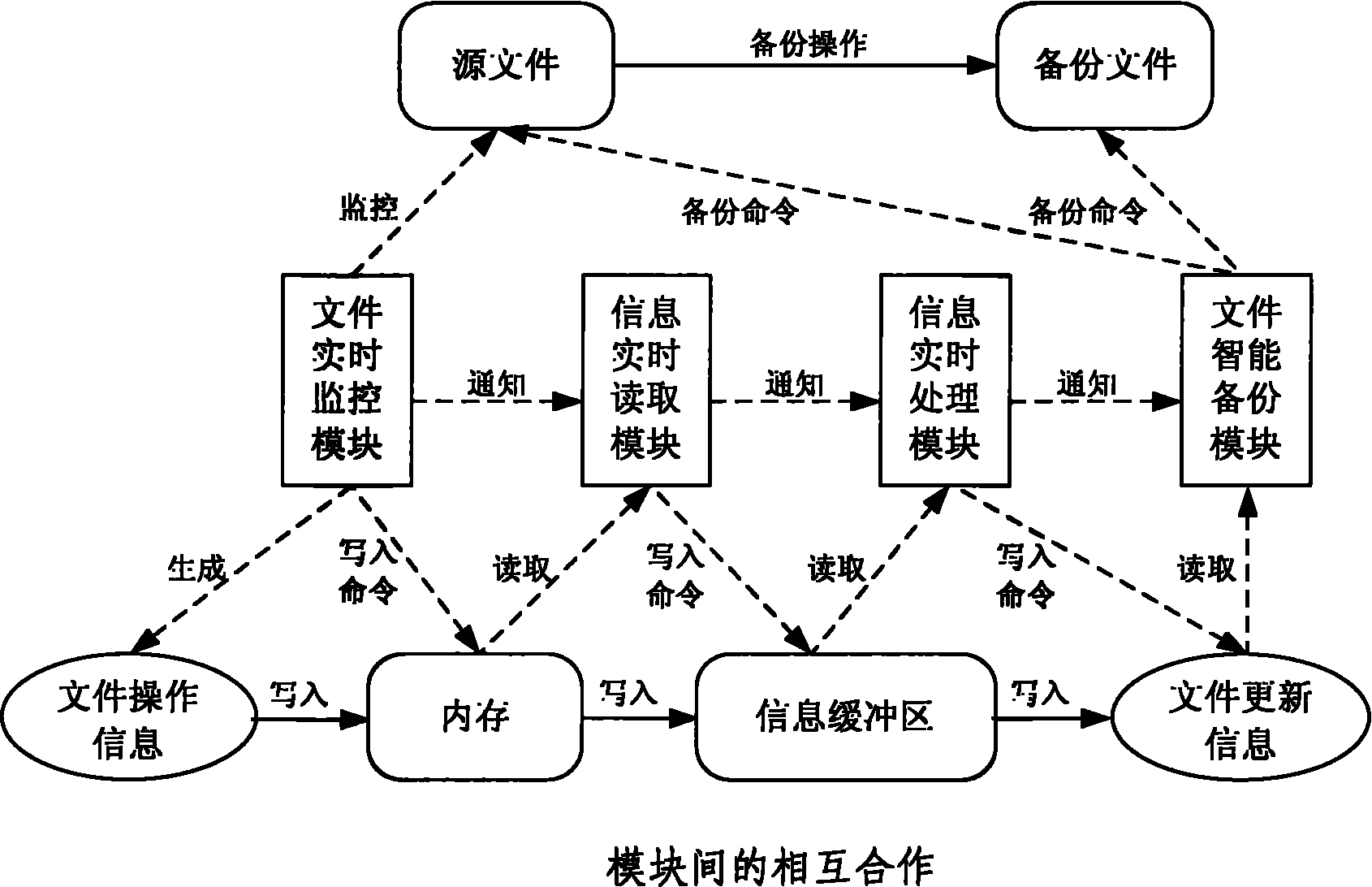
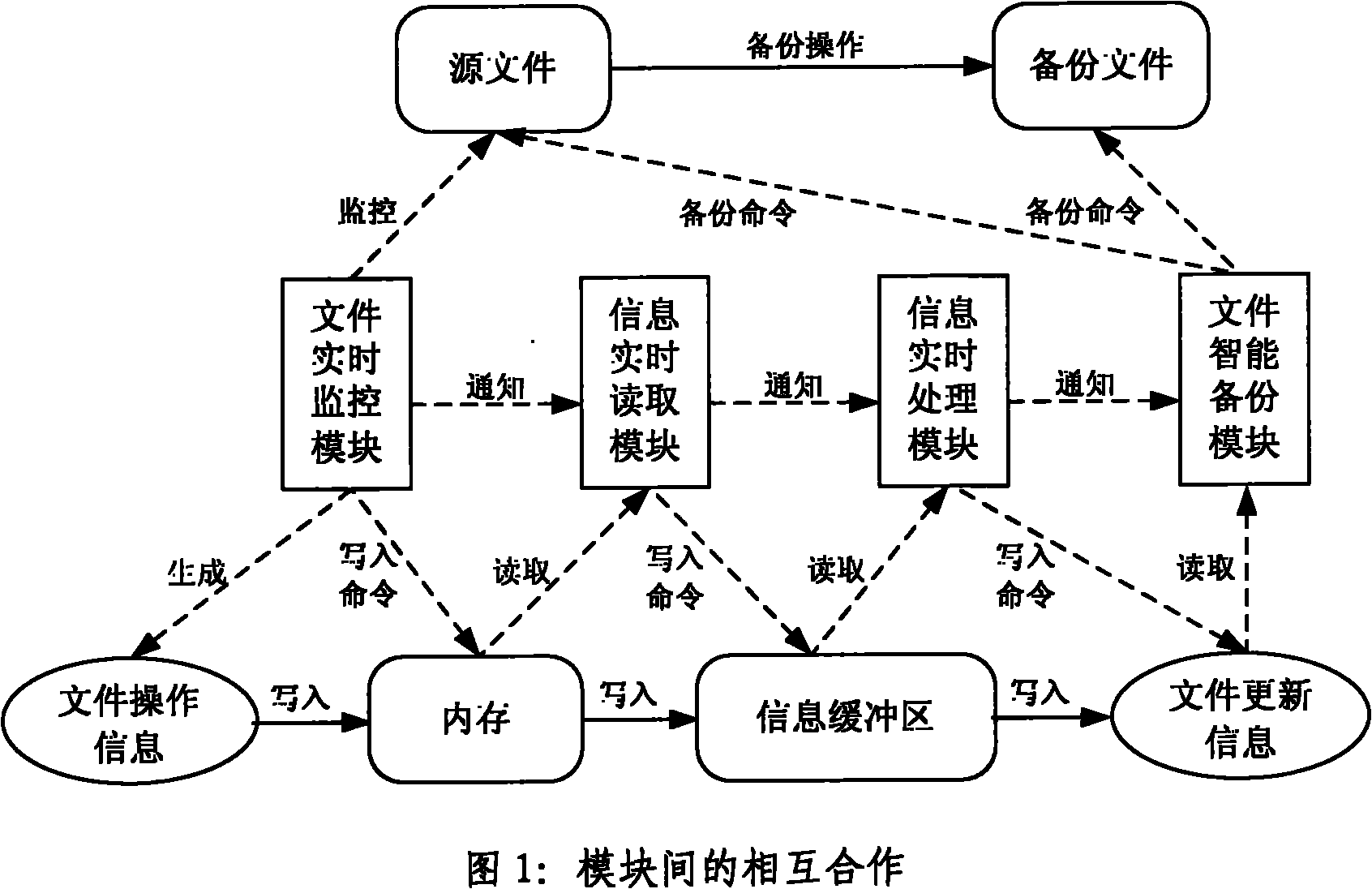
Method for file real-time monitoring and intelligent backup
InactiveCN101833489AMonitor changes in real timeImprove real-time performanceSpecial data processing applicationsRedundant operation error correctionProcess moduleTime processing
The invention provides a method for real-time monitoring and intelligent backup of file operation. The method implementing device consists of a file real-time monitoring module, an information real-time reading module, an information real-time processing module and a file intelligent backup module. Each module has the following function: the file real-time monitoring module is used for monitoringuser operation on the specified file and can acquire all user operation information on the file under multiple specified directories; the information real-time reading module is used for reading the file operation information acquired from the file monitoring module, and notifying the information real-time processing module to process the file operation information; the information real-time processing module is used for processing the file operation information and notifying the file intelligent backup module to perform file backup operation; and the file intelligent backup module is used for performing backup on the file, wherein the backup mode can select real-time backup or perform intellectualized backup according to the file operation frequency. The four modules execute the functions concurrently. The method can timely and accurately record the user operation information on the file under the monitoring directory and perform real-time or intelligent backup, and provides support for continuous data protection of the file.
Owner:BEIJING UNIV OF POSTS & TELECOMM
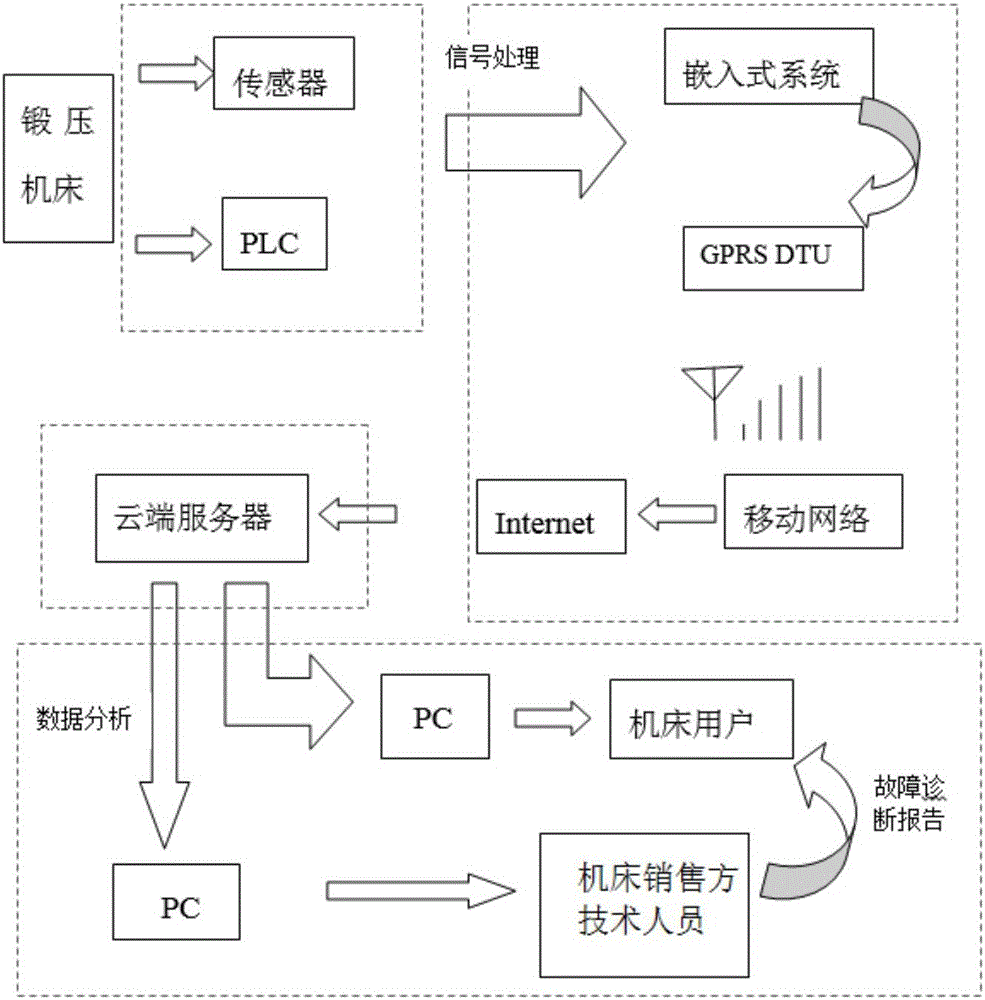
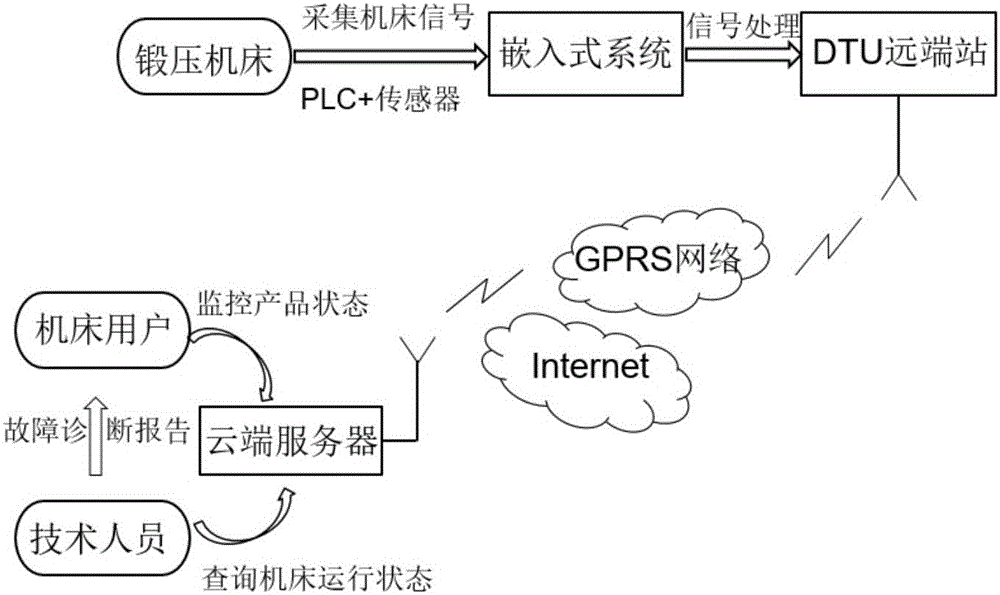
Forging press machine operation condition information acquisition and analysis system based on the internet of things technology
ActiveCN105785961AStrong real-timeReduce volumeTotal factory controlProgramme total factory controlGeneral Packet Radio ServiceReal time analysis
The invention discloses a forging press machine operation condition information acquisition and analysis system based on the internet of things technology. According to the system, the operation condition analog quantity is obtained through a sensor; the forging press machine operation condition switching values are obtained through acquiring the PLC signal points; the information contents are processed by a data acquisition terminal interface circuit and then transmitted to processor chips of the data acquisition terminal; then the information contents are transmitted to a cloud server through a GPRS (General Packet Radio Service) communication module for the convenience of data sharing. By means of the server built-in software, the cloud data is analyzed in real time; on one hand, machine tool users can obtain the machine tool operation reports or pre-warning information through PC so that they can monitor the machine tool condition at any time, and obtain fault diagnosis reports from machine tool seller technical staff; on the other hand, the seller technical staff can inquire the machine tool operational efficiency and working curves through PC at any time to acquire the machine tool physical condition in real time and to estimate faults in time.
Owner:UNIV OF SCI & TECH OF CHINA
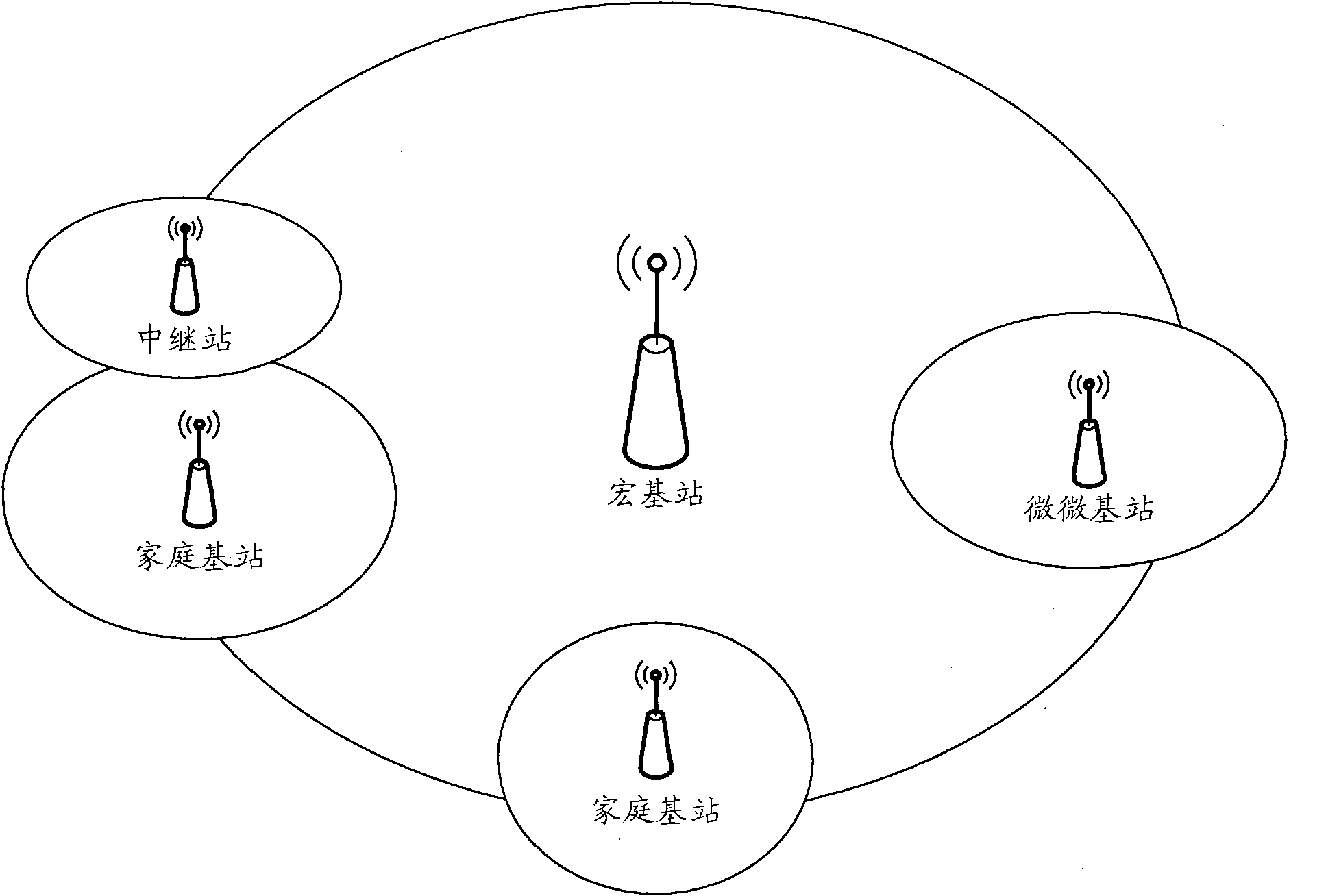
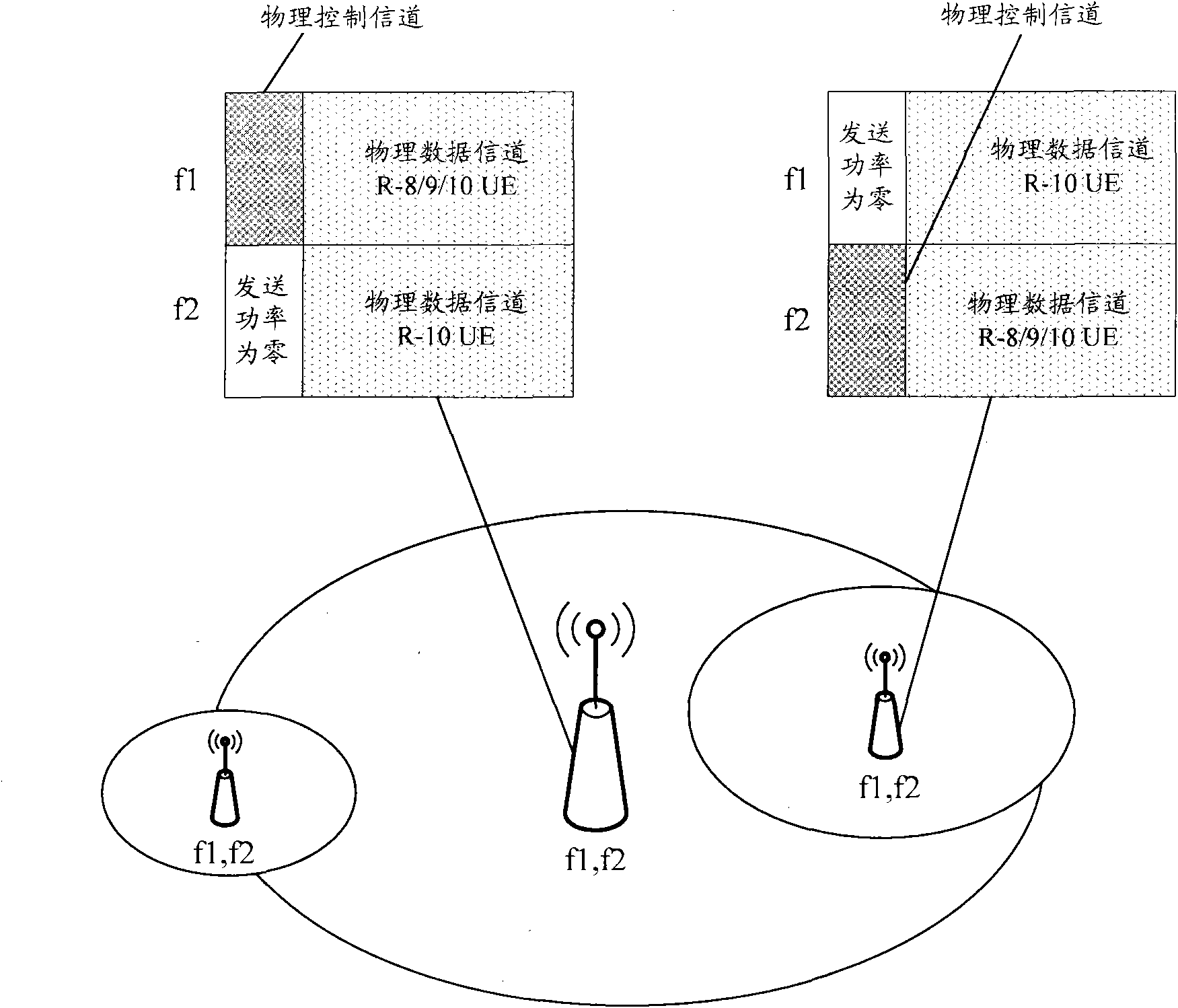
Heterogeneous network switching control method, signal transmission method, equipment and communication system
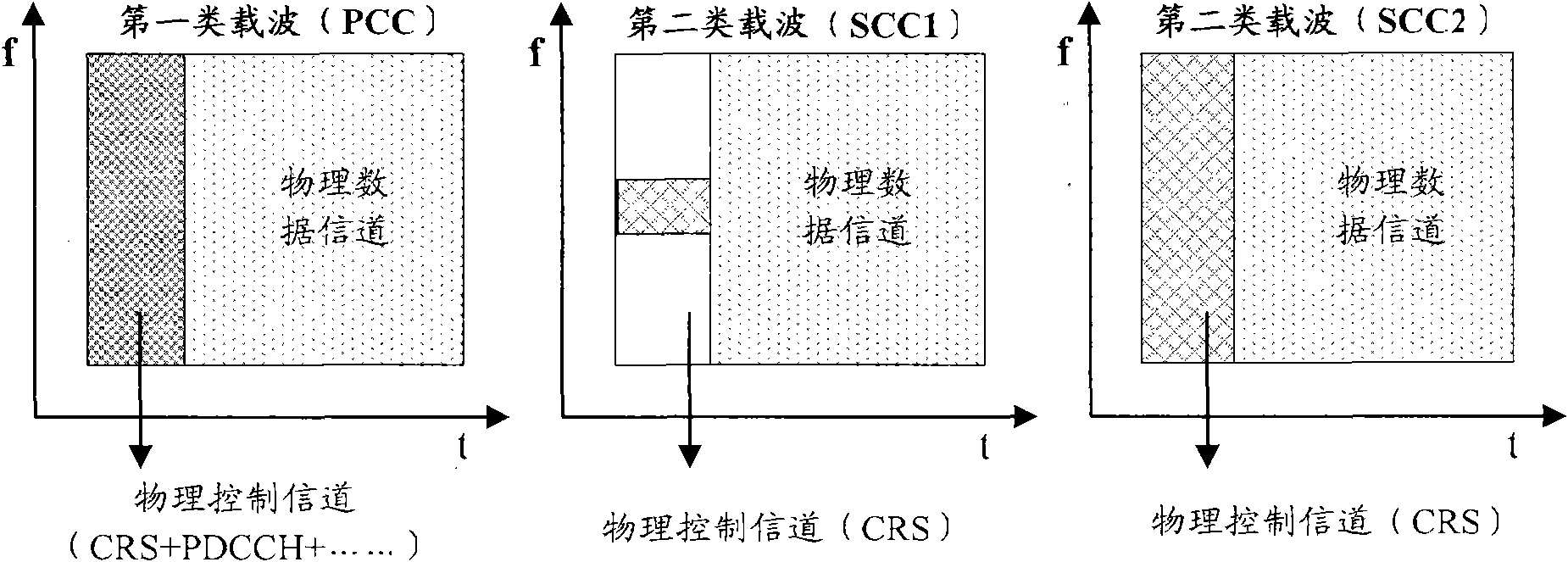
ActiveCN102238680AGuaranteed accuracyGuaranteed service continuityWireless communicationCommunications systemFrequency measurements
The embodiment of the invention discloses a heterogeneous network switching control method, a signal transmission method, signal transmission equipment and a communication system. In the embodiment of the invention, adjacent / covered overlapped base stations all adopt the combination design of first-type and second-type carriers, and at least a pair of the first-type and second-type carriers of the adjacent / covered overlapped base stations are identical in frequency; and the adjacent / covered overlapped base stations transmit physical downlink control channel (PDCCH) signaling, physical control format indicator channel (PCFICH) signaling, physical hybrid automatic repeat request indicator channel (PHICH) signaling and cell-specific reference symbols (CRS) in physical control channels of the first-type carriers, and transmit the CRSs on the second-type carriers. Therefore, user equipment (UE) can be ensured to obtain accurate physical control channel mobility measurement results of cells of the adjacent / covered overlapped base stations and timely trigger measurement reporting in same-frequency measurement; moreover, the service continuity of a user can be relatively better ensured, and unnecessary uplink / downlink data channel interference between neighbor cells can be avoided.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com