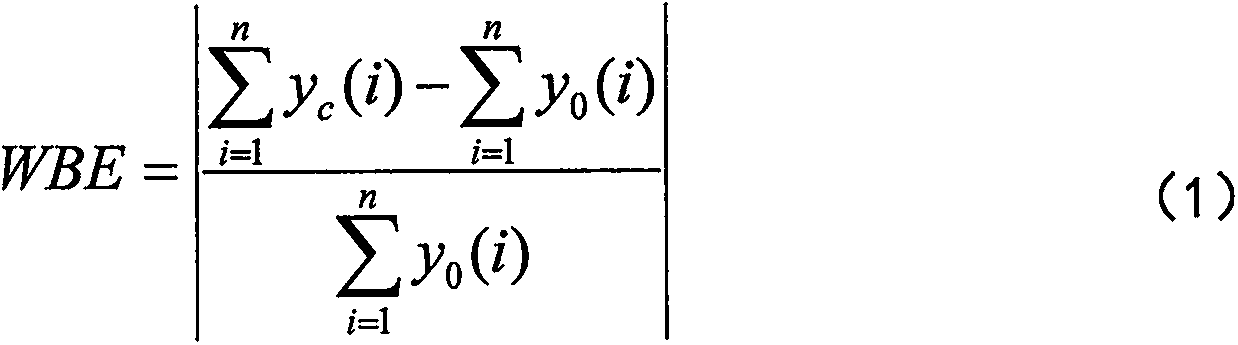Patents
Literature
211 results about "Key issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Key Issues. Leaders in healthcare are committed to a healthcare system focused on meeting needs of consumers. Information will empower patients and consumers to make sound healthcare and lifestyle choices, leading to cost-effective healthcare and significantly reduced chronic disease.
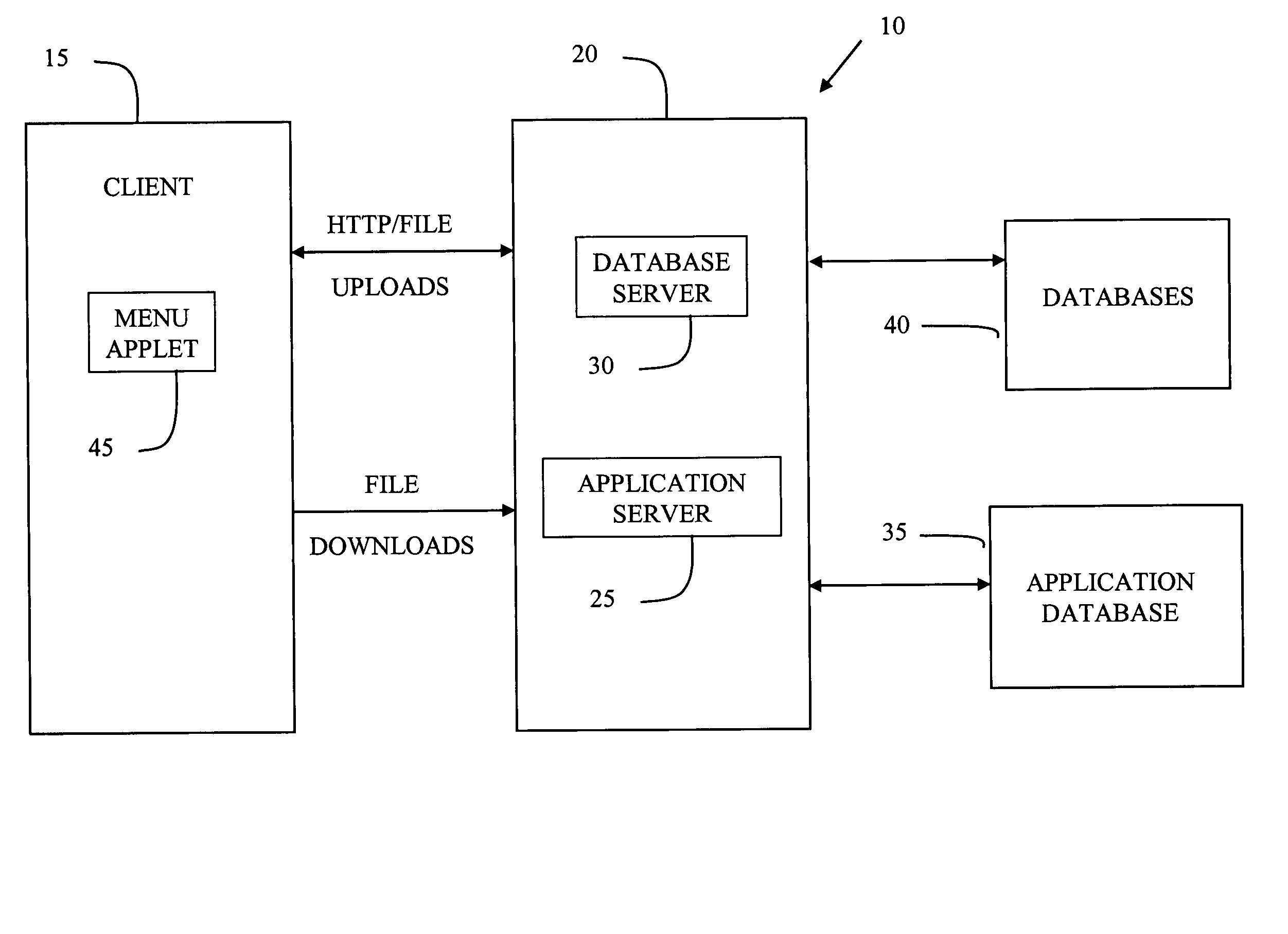
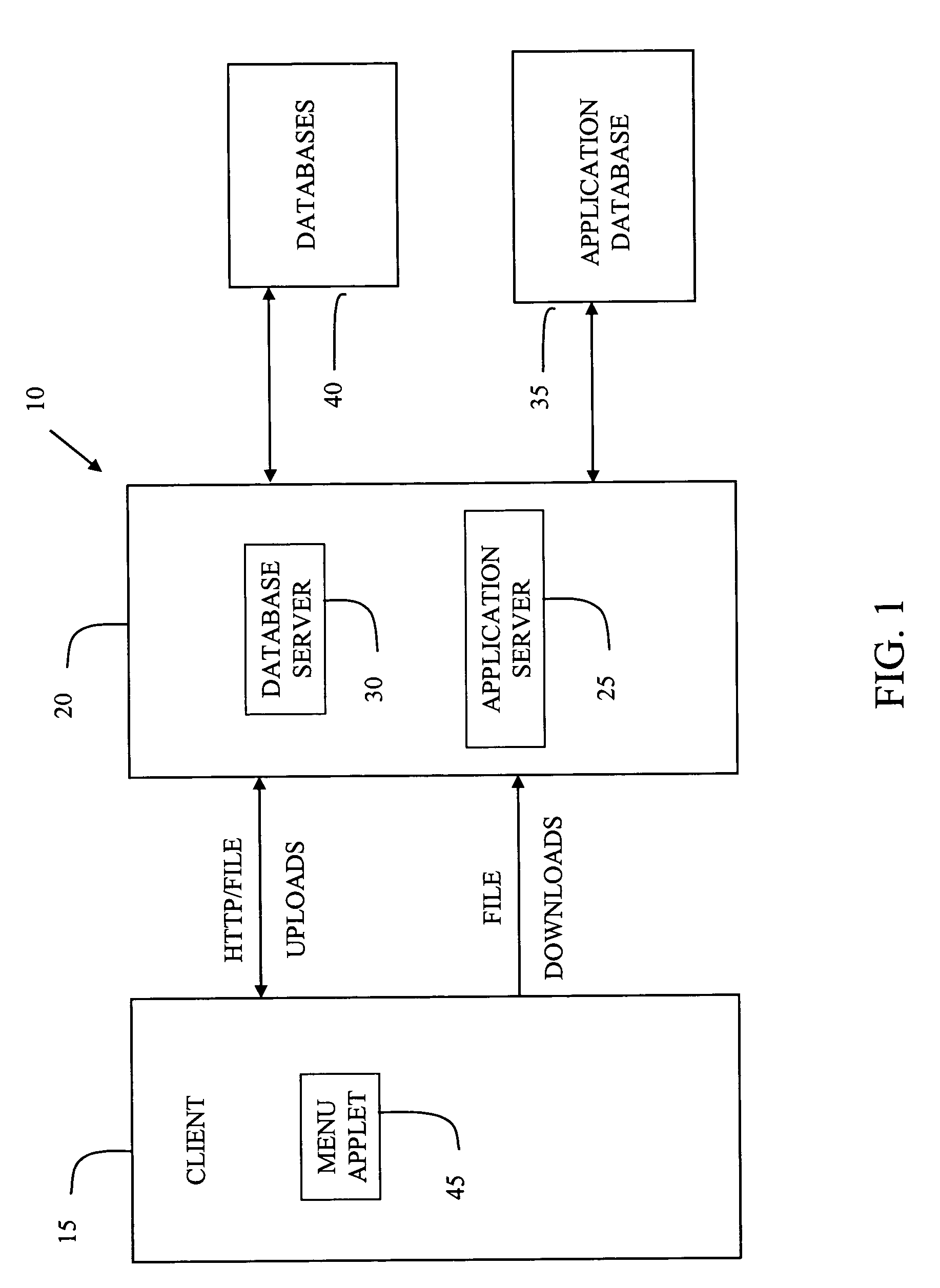
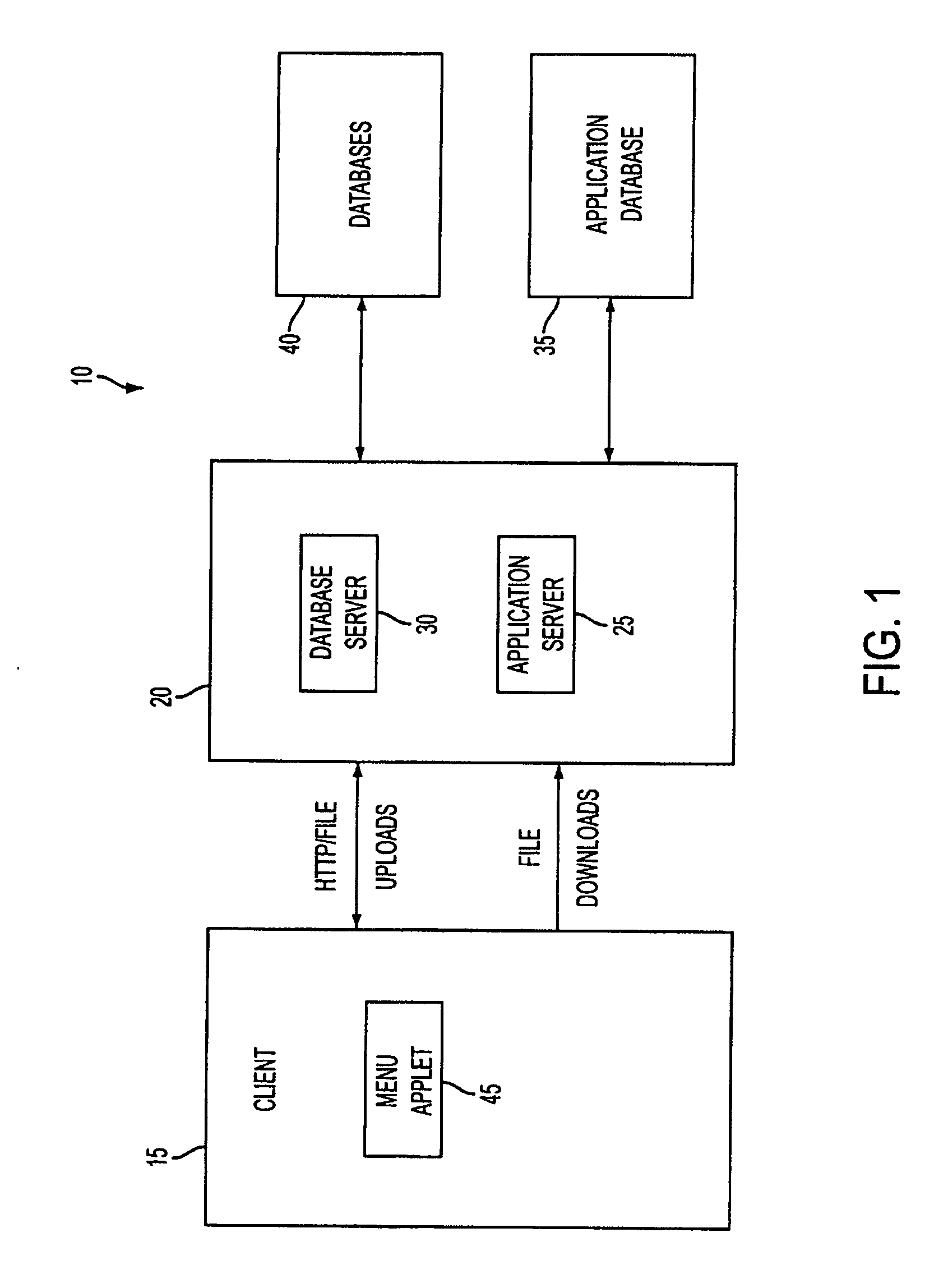
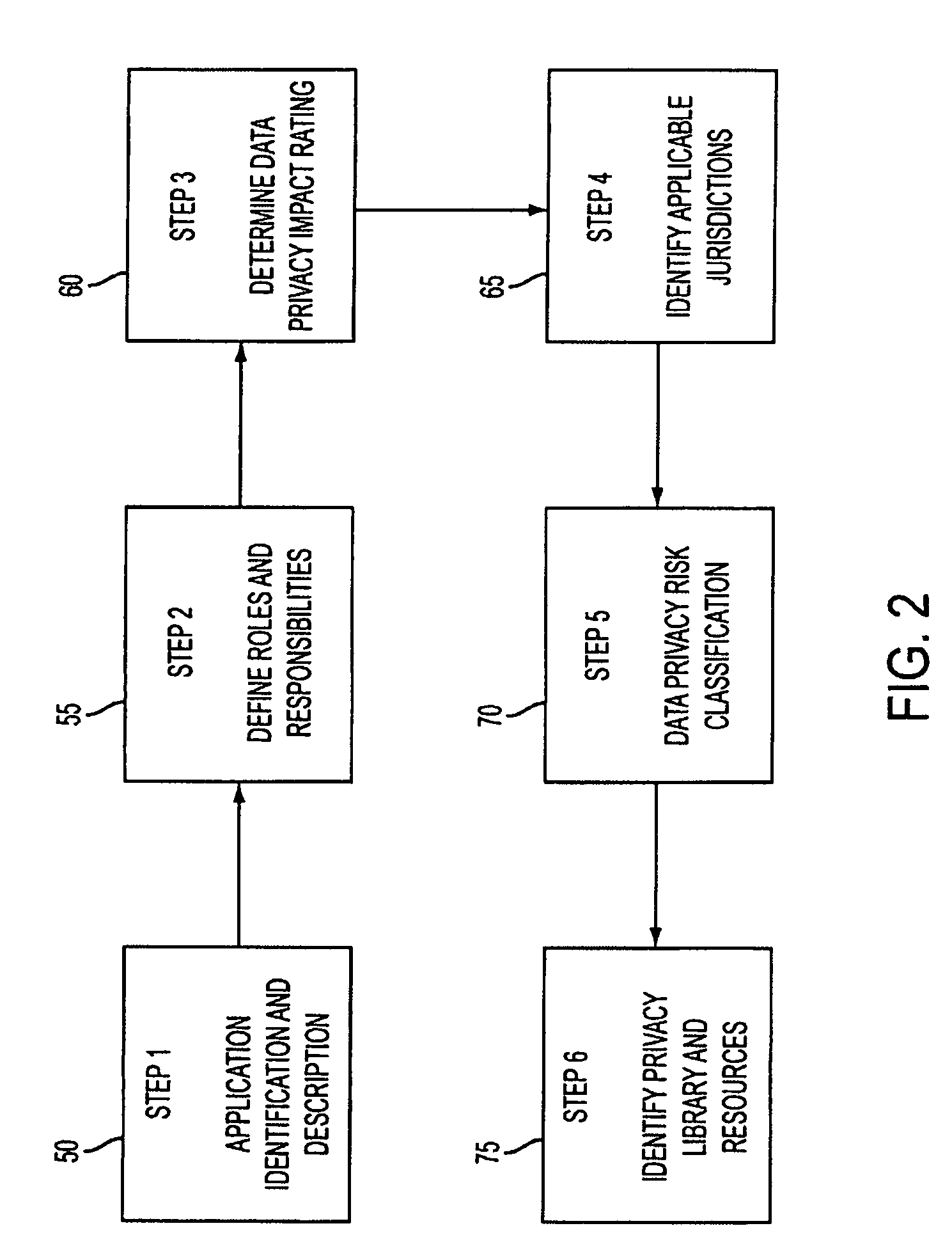
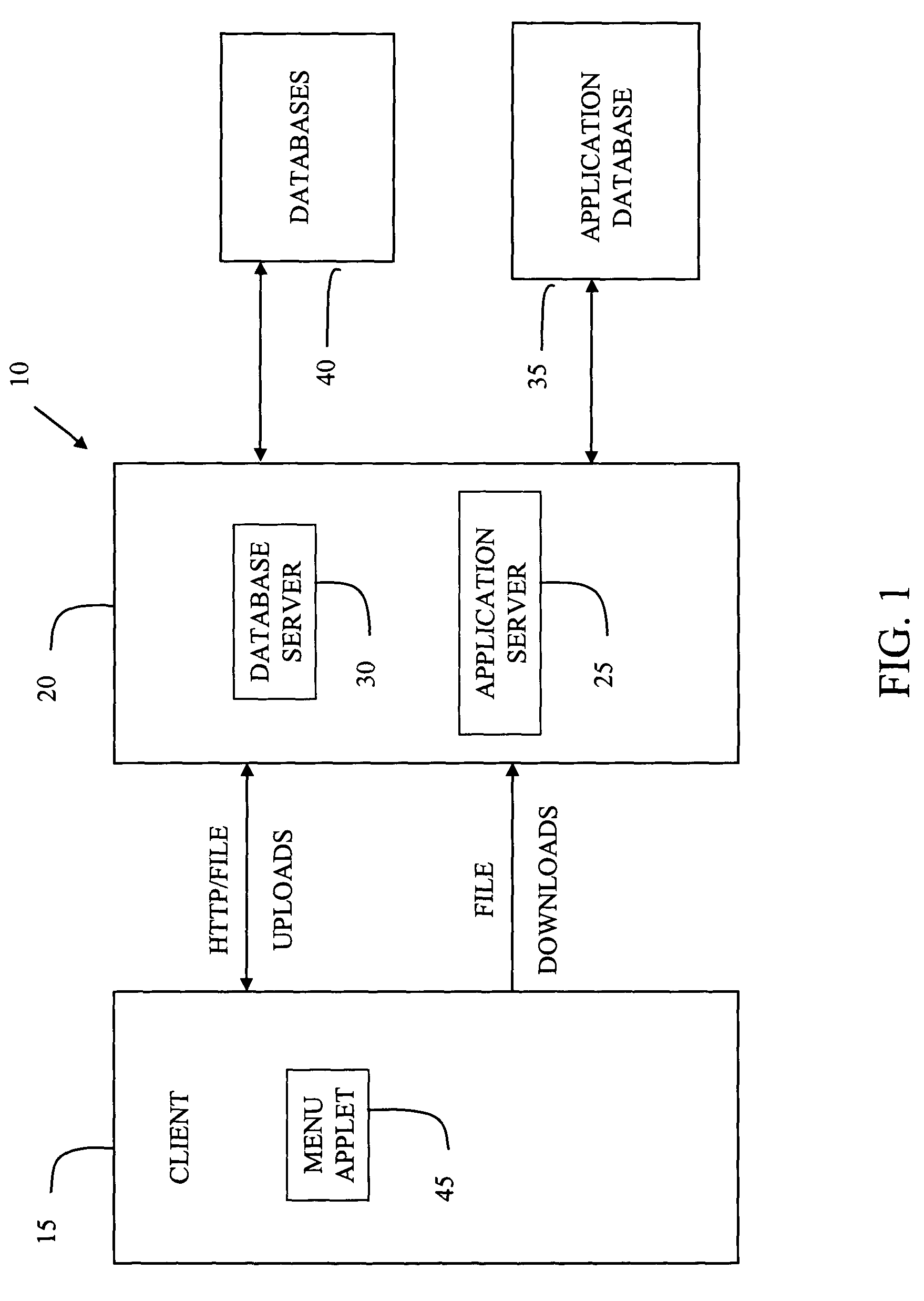
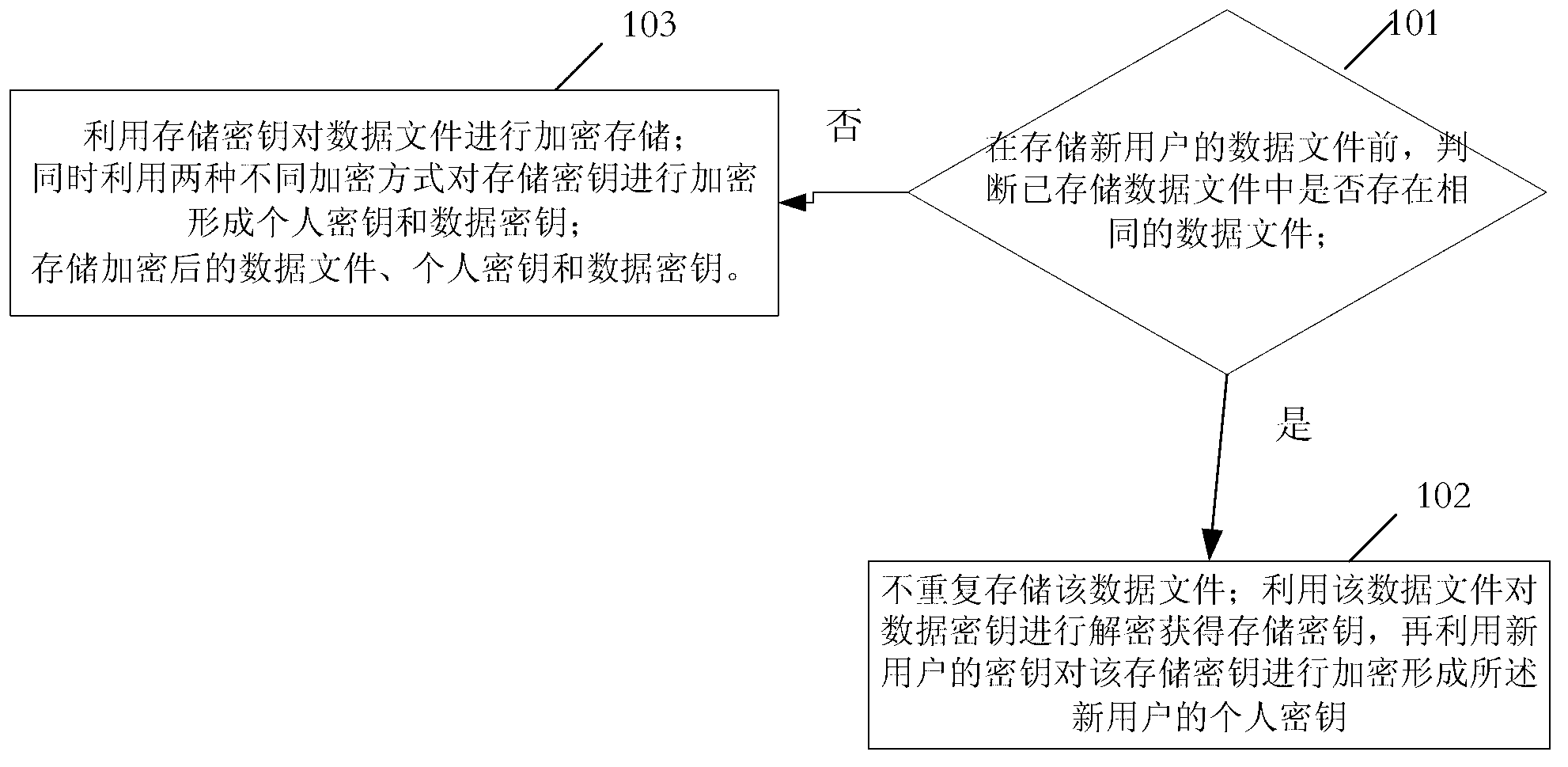
System and method for managing data privacy
ActiveUS7234065B2Easy to manageSpeed up the processUser identity/authority verificationUnauthorized memory use protectionInternet privacyKey issues
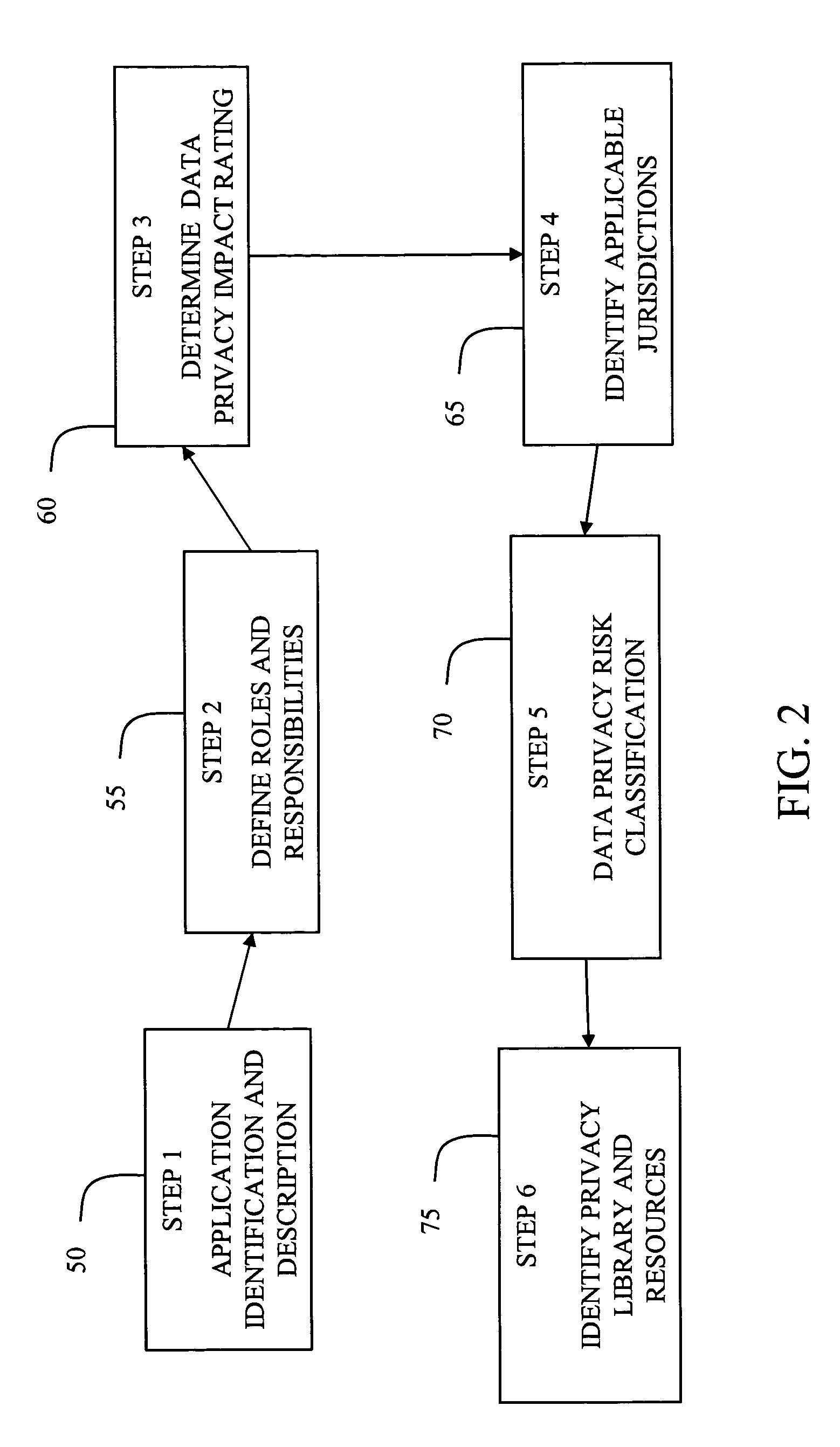
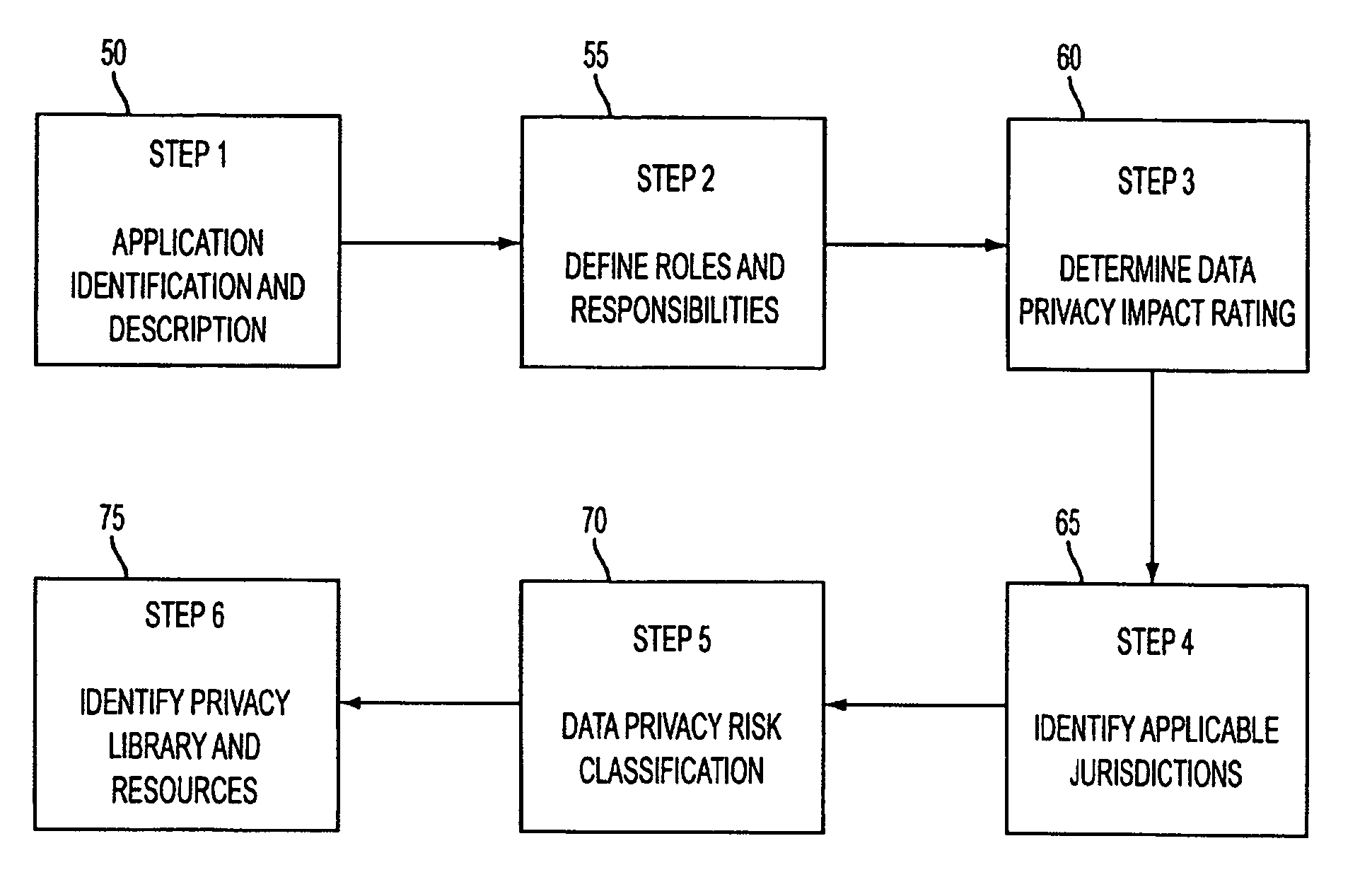
A system and method for assessing the risk associated with the protection of data privacy by software application. A decision engine is provided to assess monitor and manage key issues around the risk management of data privacy. The system creates a core repository that manages, monitors and measures the data privacy assessments of applications across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager responsible for the application). The responses are tracked in order to evaluate the progress of the assessment and the status of the applications with respect to compliance with the enterprise's data privacy policies and procedures as well as the regulations and laws of the jurisdictions in which the application is operated. Once a questionnaire has been completed, the application is given ratings both with respect to the data privacy impact of the application and the application's compliance with the data privacy requirements. If a risk exists, a plan for reducing the risk or bringing the application into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be acknowledged through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
System and method for managing data privacy
InactiveUS20070283171A1Easy to manageSpeed up the processUnauthorized memory use protectionHardware monitoringInternet privacyKey issues
A system and method for assessing the risk associated with the protection of data privacy by software application. A decision engine is provided to assess monitor and manage key issues around the risk management of data privacy. The system creates a core repository that manages, monitors and measures the data privacy assessments of applications across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager responsible for the application). The responses are tracked in order to evaluate the progress of the assessment and the status of the applications with respect to compliance with the enterprise's data privacy policies and procedures as well as the regulations and laws of the jurisdictions in which the application is operated. Once a questionnaire has been completed, the application is given ratings both with respect to the data privacy impact of the application and the application's compliance with the data privacy requirements. If a risk exists, a plan for reducing the risk or bringing the application into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be acknowledged through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
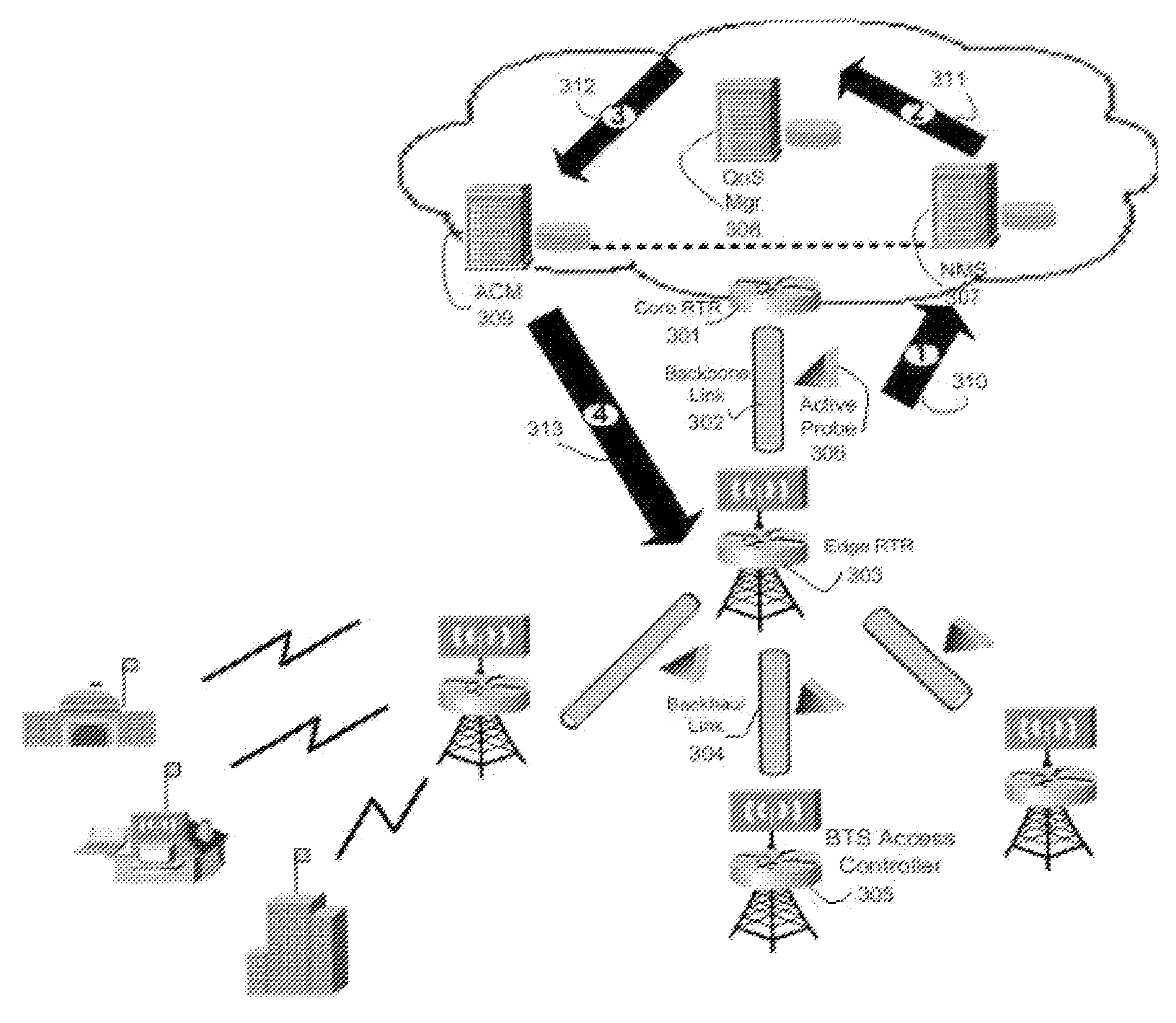
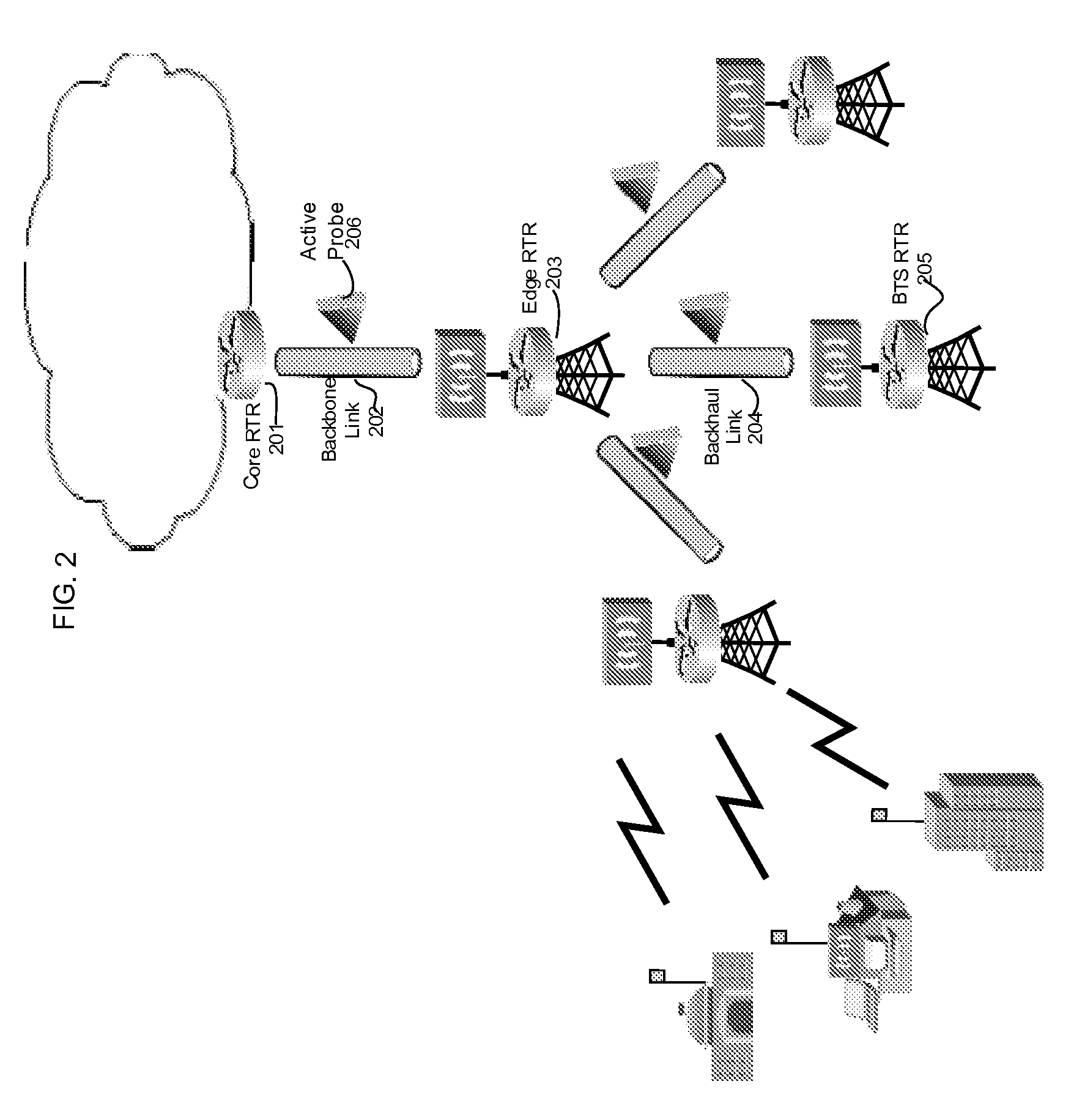
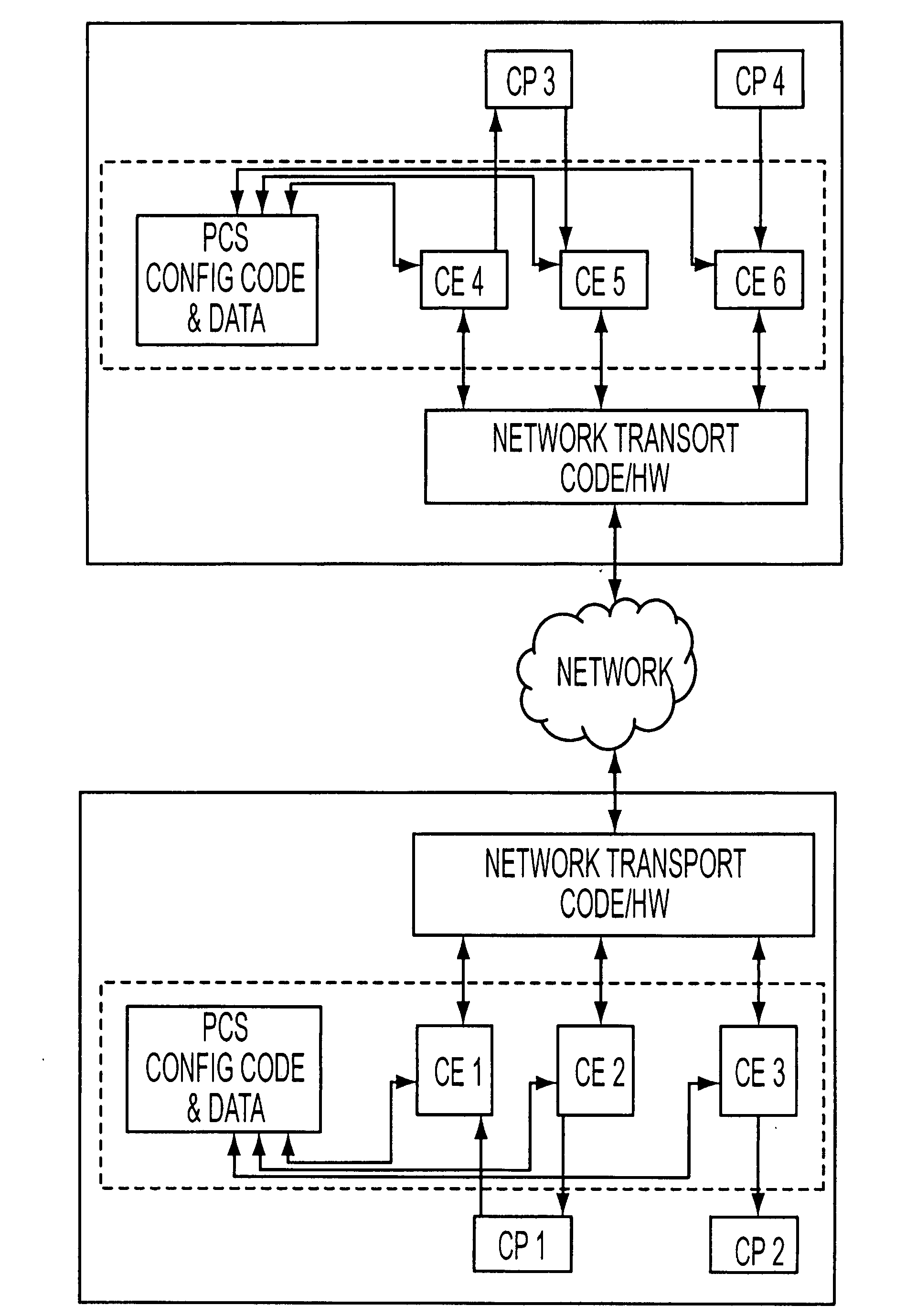
Methods And Systems For Dynamic Bandwidth Management For Quality Of Service In IP Core And Access Networks
InactiveUS20080130495A1Easy to useStringent qualityError preventionTransmission systemsPresent methodKey issues
Proper allocation of network bandwidth is a crucial issue in rendering certain performance guarantees to meet the growing customer demands. Hence, allocation methodologies must explicitly be carried out for these guarantees to be given as efficiently as possible since the shared resources are limited. This invention presents methods and systems for Dynamic Bandwidth Management (DBM) and Quality of Service (QoS) in packet-based networks. DBM is an algorithm that dynamically adjusts the resource allocation in the IP Access Networks based upon measured QoS at the IP Core Network through an implementation of a Feedback Control Mechanism to manage available core transport bandwidth. Such a Feedback Control Mechanism is capable of maintaining a condition of non-congestion, a sufficient and necessary condition to meet end-to-end QoS requirements in a Next Generation Network (NGN). The emphasis is given on the system implementation of QoS policies for the fair distribution of network resources through a scalable architecture comprising key Resource and Admission Control Functional (RACF) entities, namely: a Network Management System (NMS), a QoS Manager, an Access Controller Manager (ACM), the Access Controllers, and the active probes.
Owner:LATITUDE BROADBAND
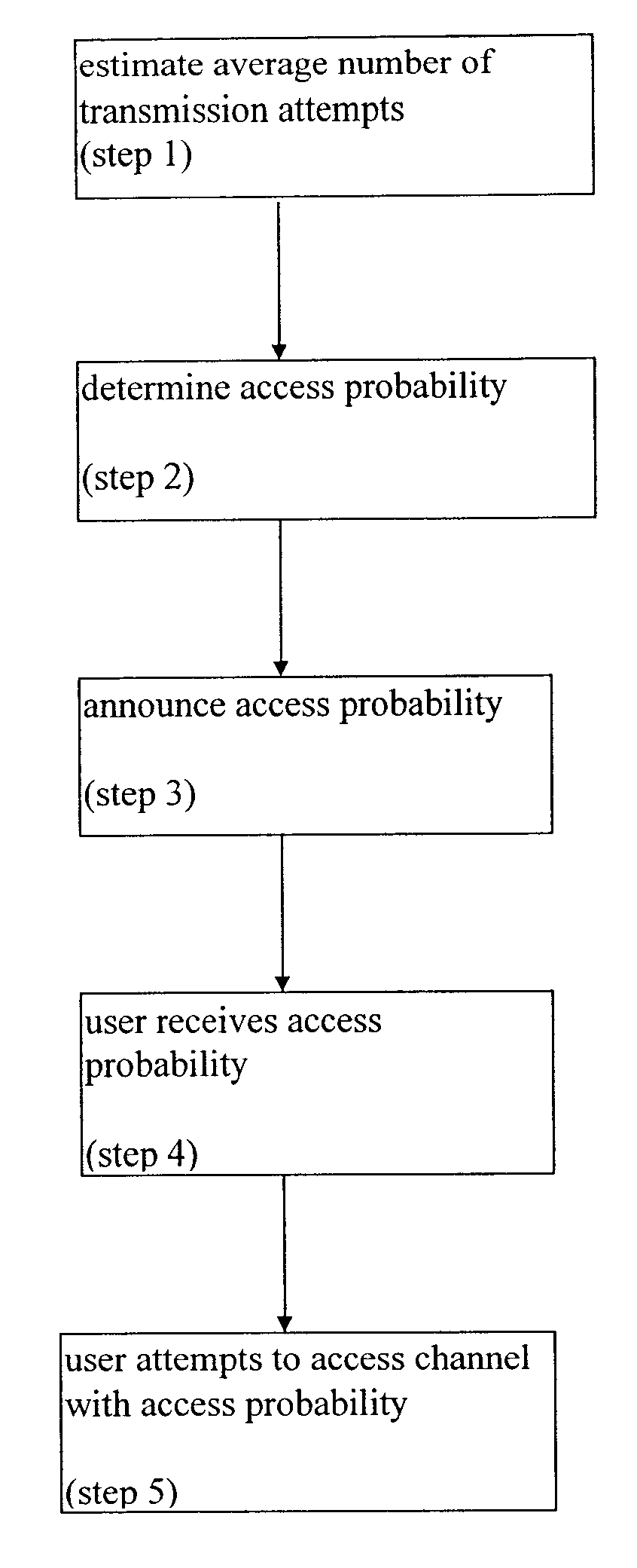
Announced dynamic access probability protocol for shared bandwidth networks
InactiveUS6418136B1Network traffic/resource managementRadio transmissionWireless mesh networkLow load
A system and a method for a dynamic probability access protocol for determining access to shared channels. Some networks have a common channel which is shared by many users. A key issue in such networks is the allocation of the shared channel among many competing users. The system and method of the present invention enable media access control in shared bandwidth networks. When the user wishes to send a message, the user transmits with a probability p, which depends on the load on the channel. The probability p is announced by the network, and transmitted to the users as a broadcast message. Under conditions of low load, the probability p approaches 1, while at high load p is relatively low. This media access control protocol guarantees high channel utilization at high load, as well as low delay at low load periods. The proposed method is applicable on wireless networks, such as cellular networks and satellite-based networks. In addition, the method and system of the present invention can be used in wired networks, for other applications such as local area networks (LAN), client / server networks, and accessing a Web site through the Internet. The method and system of the present invention are able to reduce the likelihood of collisions, without increasing the access delay at low load periods.
Owner:RAMOT UNIV AUTHORITY FOR APPLIED RES & INDAL DEVMENT
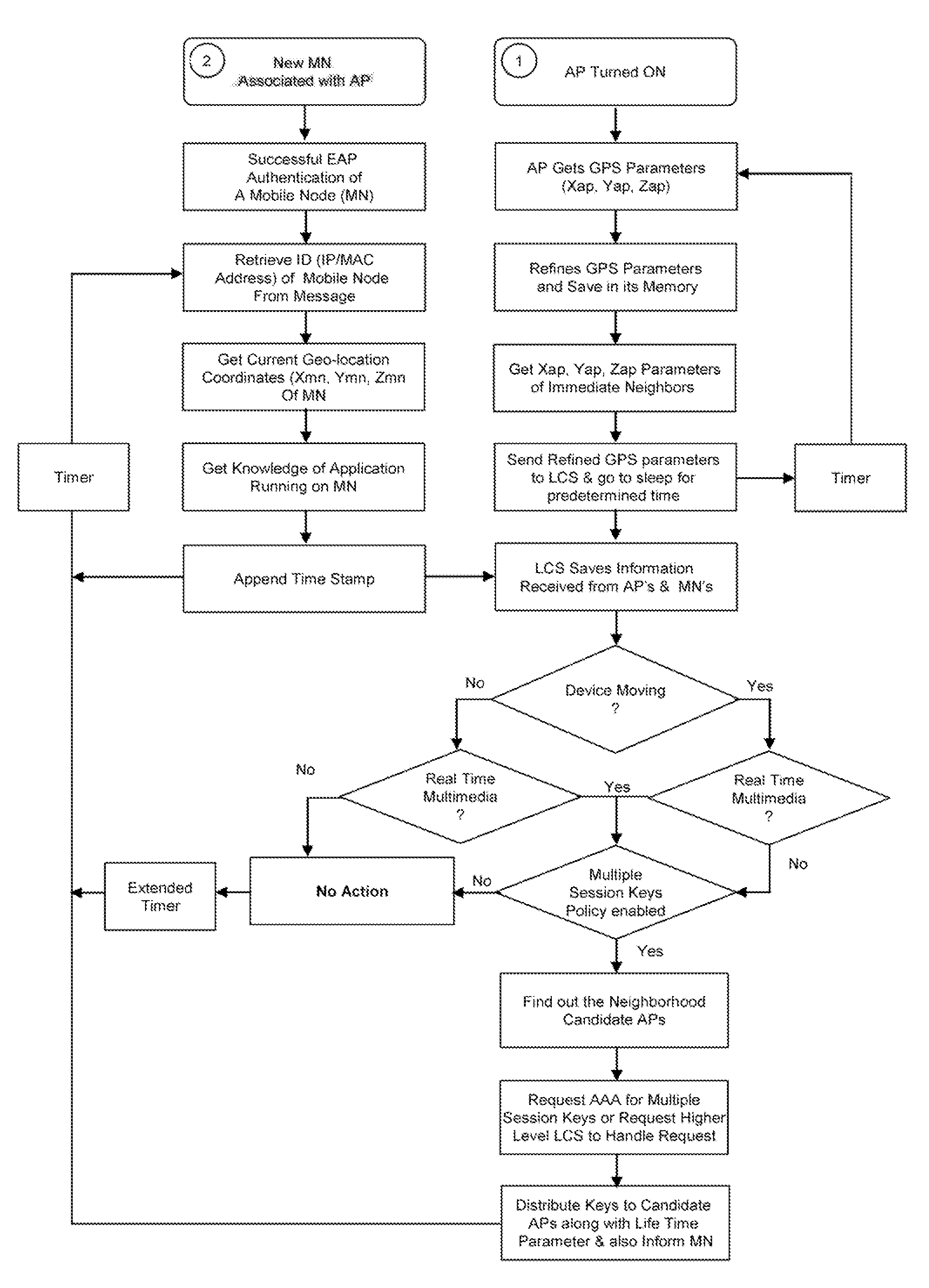
Distribution of Session Keys to the Selected Multiple Access Points Based on Geo-Location of APs
ActiveUS20080031194A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsKey issuesGeolocation
In the public WLAN systems, reliable user re-authentication for mobility support is an essential step. However, re-authentication during handoff procedures causes long handoff latency which deteriorates the quality of service specifically for real-time multimedia applications. One possible solution is to authenticate the Mobile Node (MN) in advance with all the neighboring Access Points (APs) and distribute the Session Keys to them. However, the key issue is how to optimally and efficiently select the neighboring APs. In the preferred embodiments, we propose a system that takes into account the user current “Geo-Location”, “Mobility Pattern” and “Application Running on MN”; estimates the “Expected Mobility Zone” (EMZ) and selects an appropriate set of candidate APs corresponding to the MN's geo-location. The EMZ may comprise of APs belonging to “Intra-domain”, “Inter-domain” or “Inter-technology Networks” (e.g., WLAN, WiMAX, and Cellular etc). The system assumes that not only the Mobile Nodes but also the Fixed Nodes (APs or Base Stations) are capable of knowing their Geo-Location Coordinates X, Y, Z. This capability may come either by integrating GPS receiver or through any other alternate, state of the art or future positioning technologies in the APs.
Owner:FOUR BATONS WIRELESS LLC +1
Domain manager and domain device
InactiveUS20070180497A1Efficient revocation mechanismAvoid disadvantagesKey distribution for secure communicationDigital data processing detailsKey issuesA domain
A domain manager device for managing a network. The manager issues to a new device joining the network a number of symmetric authentication keys, and preferably a number of authentication tickets. Each respective authentication key allows the new device to communicate securely with one respective other device comprised in the network. Each respective authentication ticket allows a device with a first identifier to authenticate itself to a device with a second identifier. The new device receives those authentication tickets whose first identifier matches its identifier. The new device presents the ticket with second identifier ‘B’ to device ‘B’ to authenticate itself to ‘B’. Preferably the domain manager generates a number of master device keys and issues one to the new device. Then the authentication tickets can be encrypted with the master device key issued to device with the second identifier.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
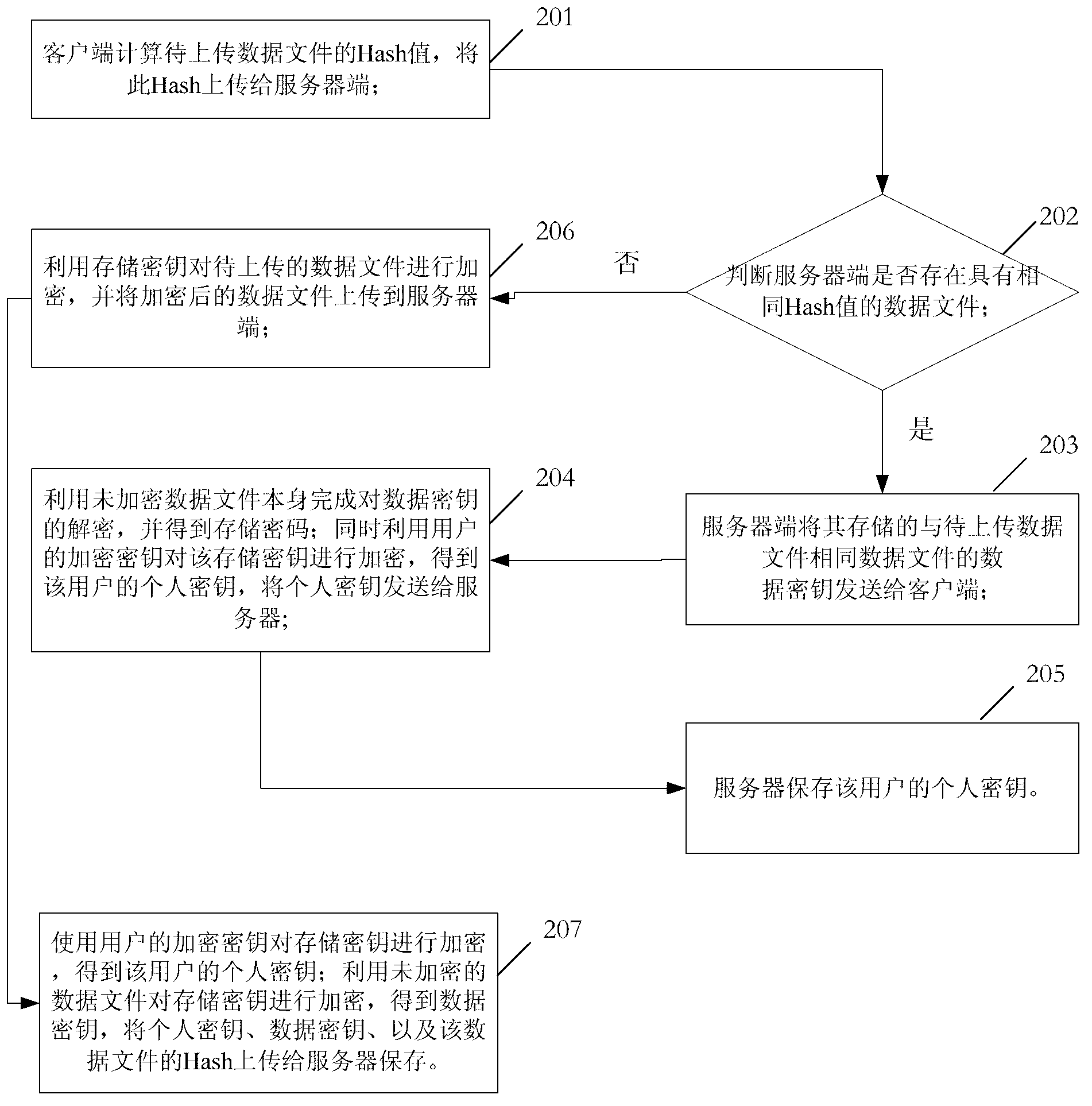
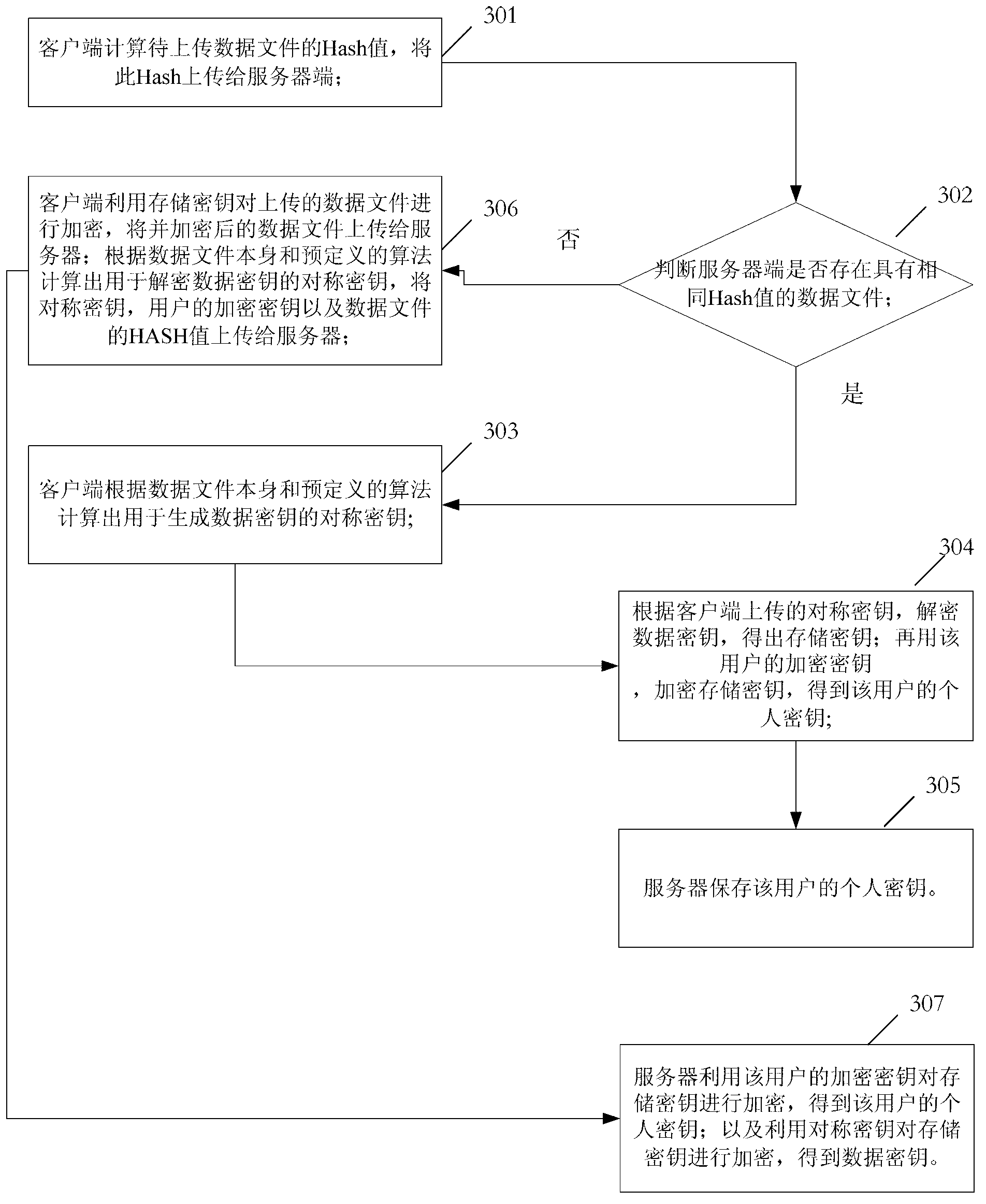
Metro ticket buying and checking method based on two-dimension code recognition
ActiveCN104134142AImprove comfortReduced comfortTicket-issuing apparatusUser identity/authority verificationKey issuesPublic key certificate
The invention discloses a metro ticket buying system and an entrance and exit ticket checking system based on the two-dimension code recognition technology. Smartphone terminals, smartphone application programs, a metro ticket selling and checking system background recharging server, automatic metro entrance and exit ticket checking systems and a CA center are included. The metro ticket selling and checking system background recharging server, each smartphone application program and each automatic metro entrance and exit ticket checking system respectively have a unified center public key issued by the CA center, a public key and a private key which are independent of each other and issued by the CA center and a public key certificate issued by the CA center. A user buys a ticket and has the ticket checked through the mobile phone program and two-dimension codes. The ticket buying efficiency is improved, the ticket buying time is saved, ticket card cost is reduced, paper is saved, timeliness and uniqueness of ticket cards are guaranteed, and metro tickets can be bought and checked fast, efficiently and safely.
Owner:SOUTHEAST UNIV
Method for executing structured symbolic machine code on a microprocessor
InactiveUS20060090063A1Software engineeringInstruction analysisScheduling instructionsHigh probability
The invention describes a method for executing structured symbolic machine code on a microprocessor. Said structured symbolic machine code contains a set of one or more regions, where each of said regions contains symbolic machine code containing, in addition to the proper instructions, information about the symbolic variables, the symbolic constants, the branch tree, pointers and functions arguments used within each of said regions. This information is fetched by the microprocessor from the instruction cache and stored into dedicated memories before the proper instructions of each region are fetched and executed. Said information is used by the microprocessor in order to improve the degree of parallelism achieved during instruction scheduling and execution. Among other purposes, said information allows the microprocessor to perform so-called speculative branch prediction. Speculative branch prediction does branch prediction along a branch path containing several dependent branches in the shortest time possible (in only a few clock cycles) without having to wait for branches to resolve. This is a key issue which allows to apply region scheduling in practice, e.g. treegion scheduling, where machine code must be fetched and speculatively executed from the trace having highest probability or confidence among several traces. This allows to use the computation resources (e.g. the FUs) of the microprocessor in the most efficient way. Finally, said information allows to re-execute instructions in the right order and to overwrite wrong data with the correct ones when miss-predictions occur.
Owner:THEIS JEAN PAUL
Access control for rental cars
InactiveUS7366677B1Reduce usageSufficient protectionElectric signal transmission systemsMultiple keys/algorithms usagePersonal identification numberKey issues
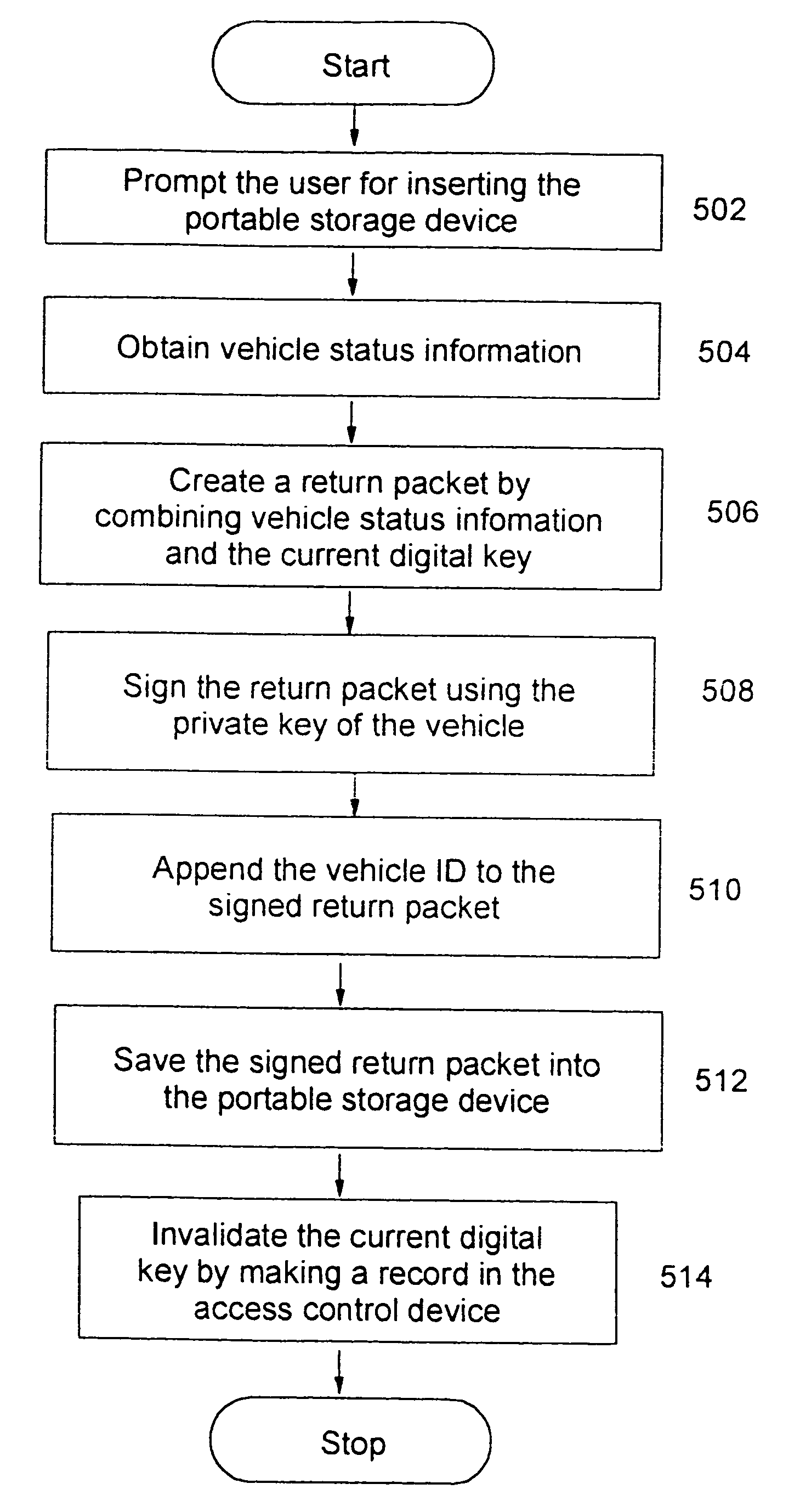
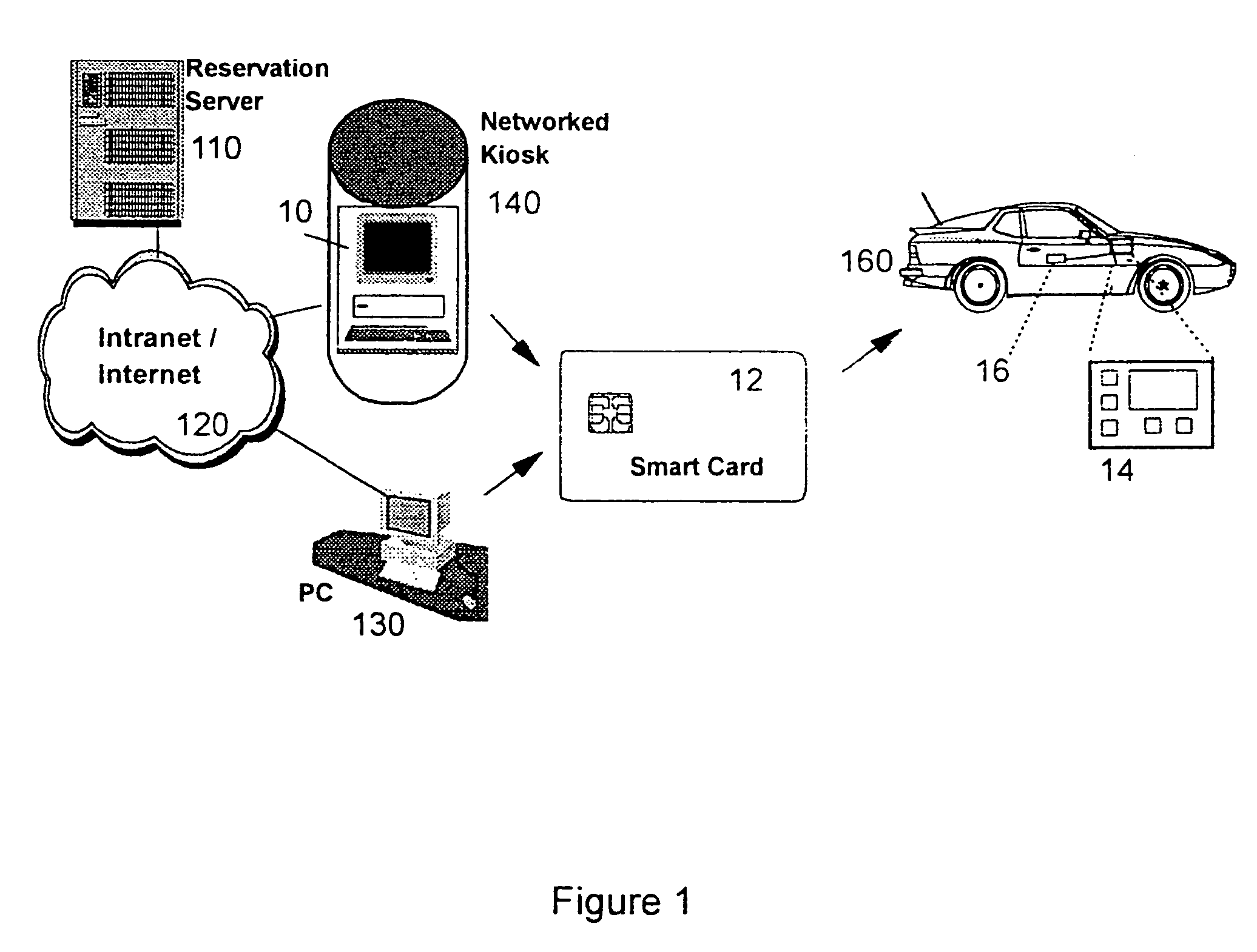
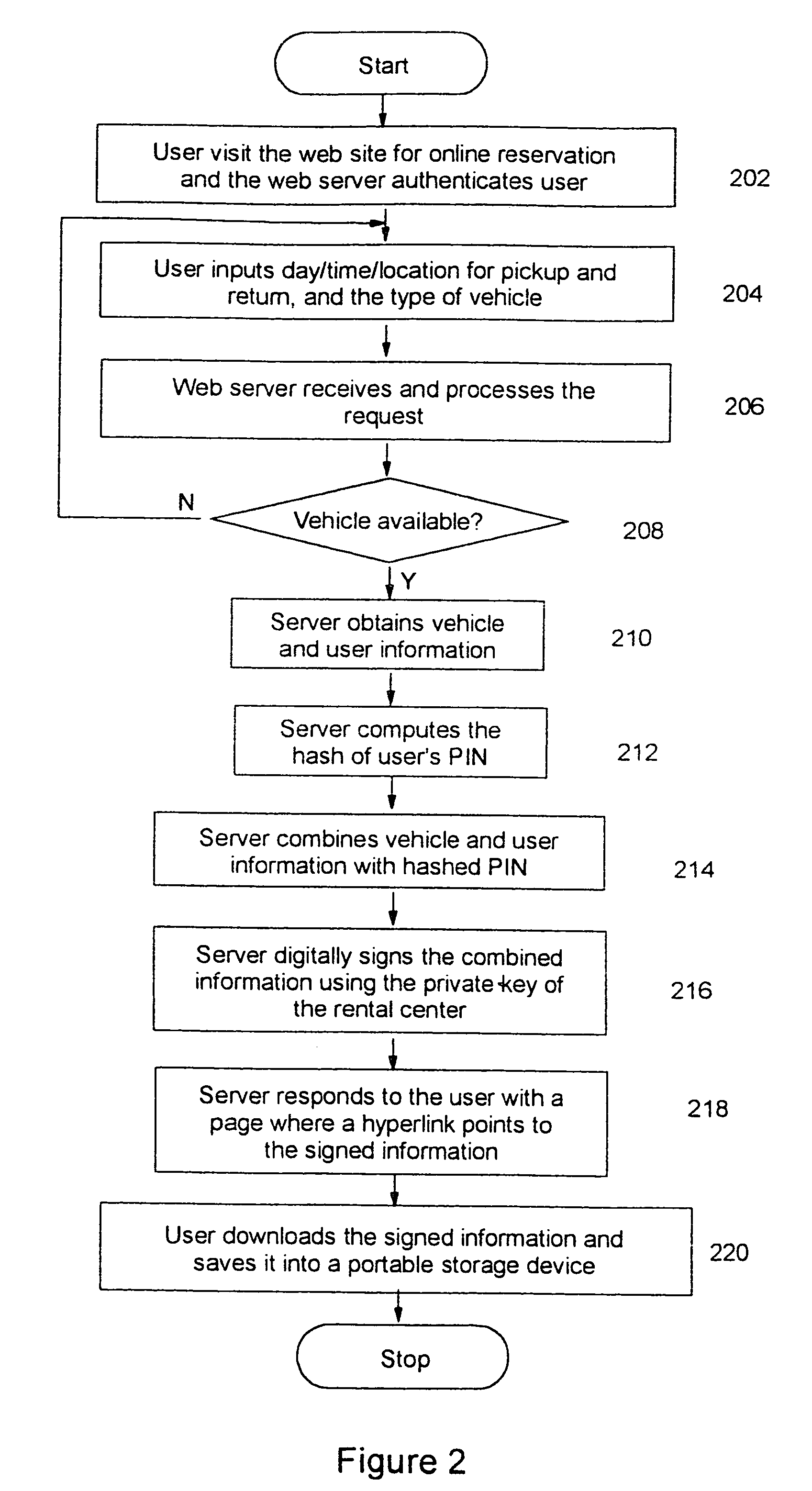
Cars of a car rental system are made operable by having a renter present a digital key issued from the car rental system. The digital key specifies the starting date and time of a given rental transaction, and the identification of the car the key is for. The digital key is further signed by the car rental system for authenticity. A prospective renter makes online reservation over the Web and downloads into a portable storage device a digital key which can be used to operate the reserved car on the day the reservation is made for. On the pickup day, the renter goes to the car and inserts the portable storage device into a slot on the car. Upon successful verification of the digital key, the car is enabled and the renter can keep the car until he or she wants to return the car. The return process starts by having the renter obtain a invalidated digital key from the car. Once the rental car invalidates the digital key provided by the renter, the renter can no longer operate the rental car. Since the in-car controller is able to decipher the given authorization information, there is no need to re-program the in-car controller for each renter. The renter will be held liable for the rental car until he or she presents the invalidated digital key to the central station of the car rental system. To prevent a lost digital key from being used by unauthorized parties, a digital key can contain information such as a personal identification number (PIN) or a hash of the PIN of the authorized renter. For extra protection, the renter can opt to include his or her PIN in the digital key when the key is created by the car rental system. The parking lot of the car rental system can be operated without security personnel checking for proper authorization.
Owner:WAYMO LLC
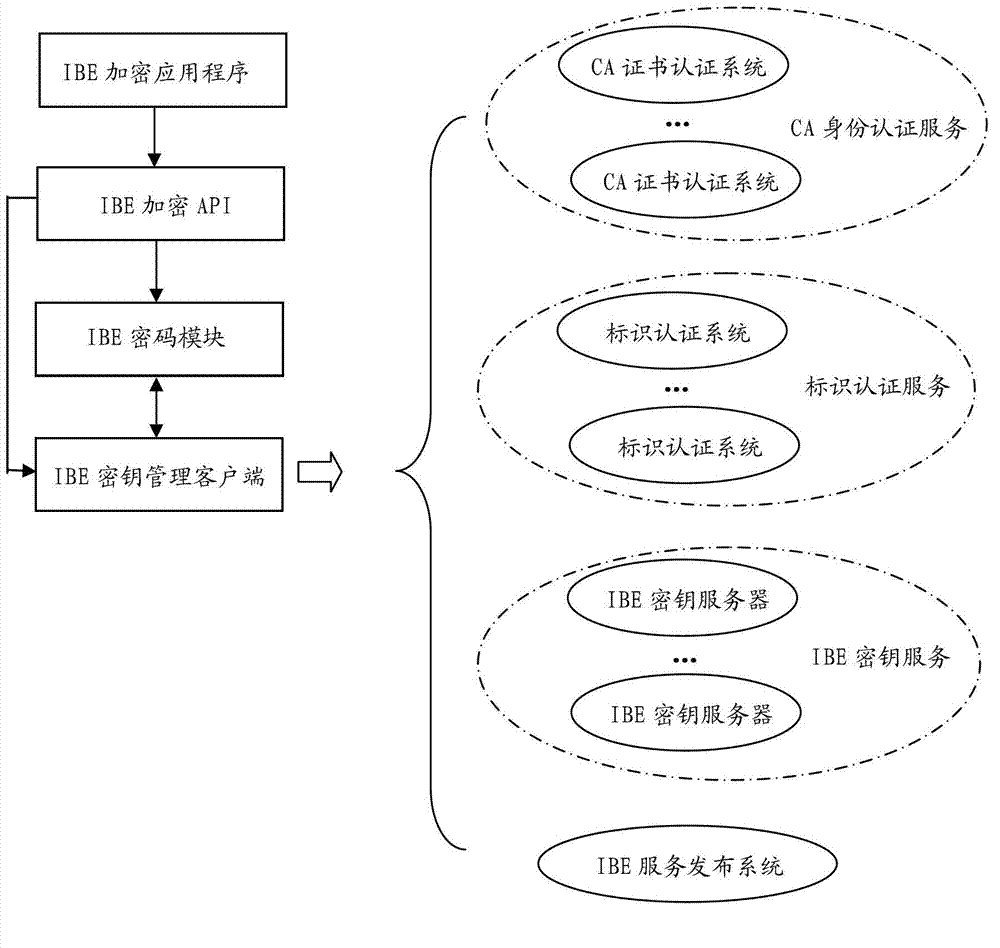
Integrated identity based encryption (IBE) data encryption system
InactiveCN102932149AEasy accessSolve the convenienceUser identity/authority verificationService systemKey issues
The invention relates to an integrated IBE data encryption system. The system comprises an IBE key server, a certification authority (CA) system, an identification authority system, an IBE service publication system, an IBE encryption application program, an IBE encryption application program interface (API), an IBE crypto module and an IBE key management client. The IBE service publication system publishes related service system information on line, and the encryption application program calls the IBE crypto module through the IBE encryption API to complete IBE data encryption and decryption functions; the IBE crypto module is connected with the IBE key server through the IBE key management client to obtain IBE public parameters and IBE private keys needed for the encryption and decryption; when the private keys are obtained, the IBE key management client obtains identification certifications from the CA system; and in an online interaction process, the key management client proves identities of users by using the identification certifications signed by the CA system. The system solves the key problems of identification safety, identification attribution confirmation, obtaining convenience of the public parameters and the like in IBE encryption.
Owner:WUHAN UNIV OF TECH +1
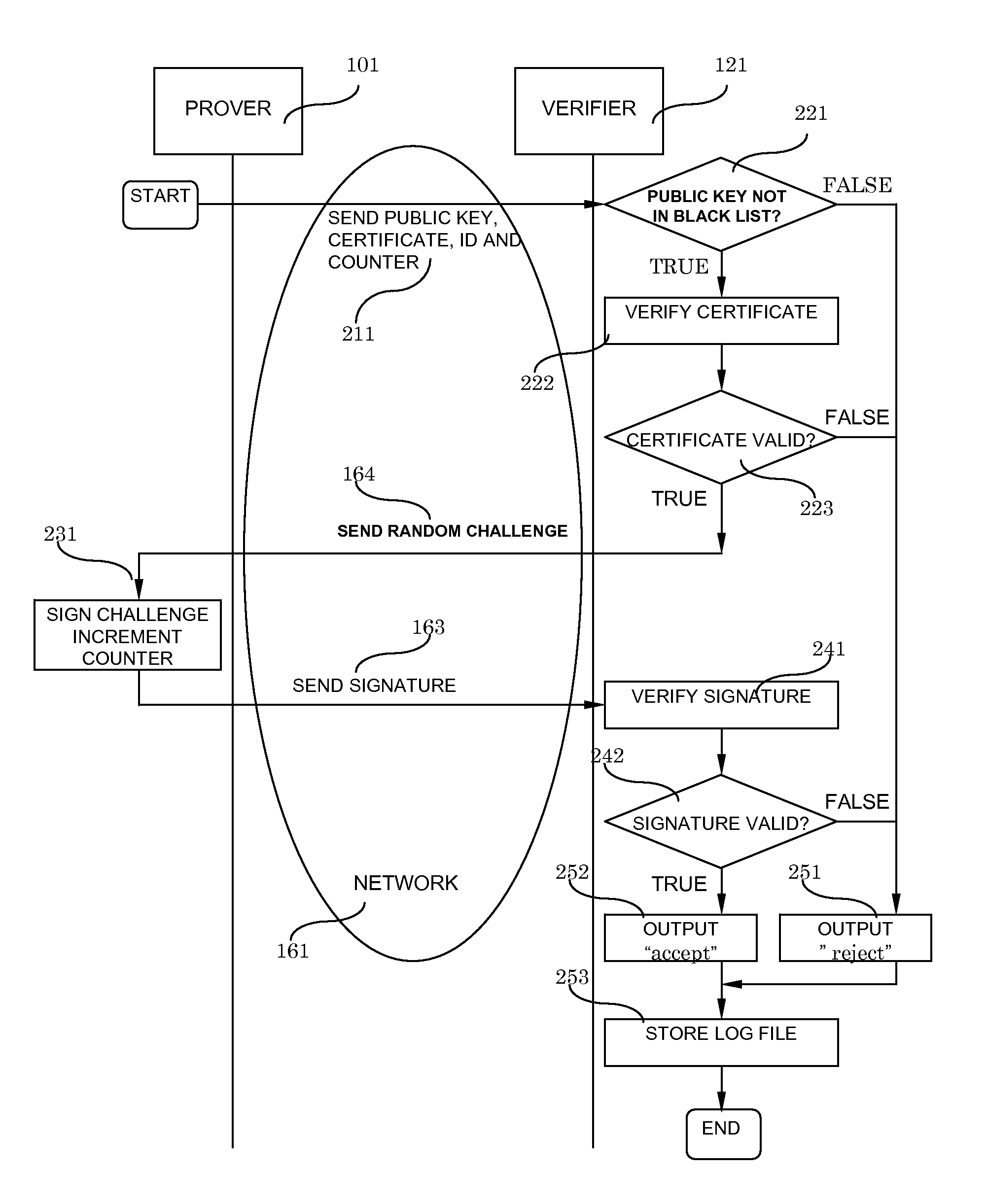
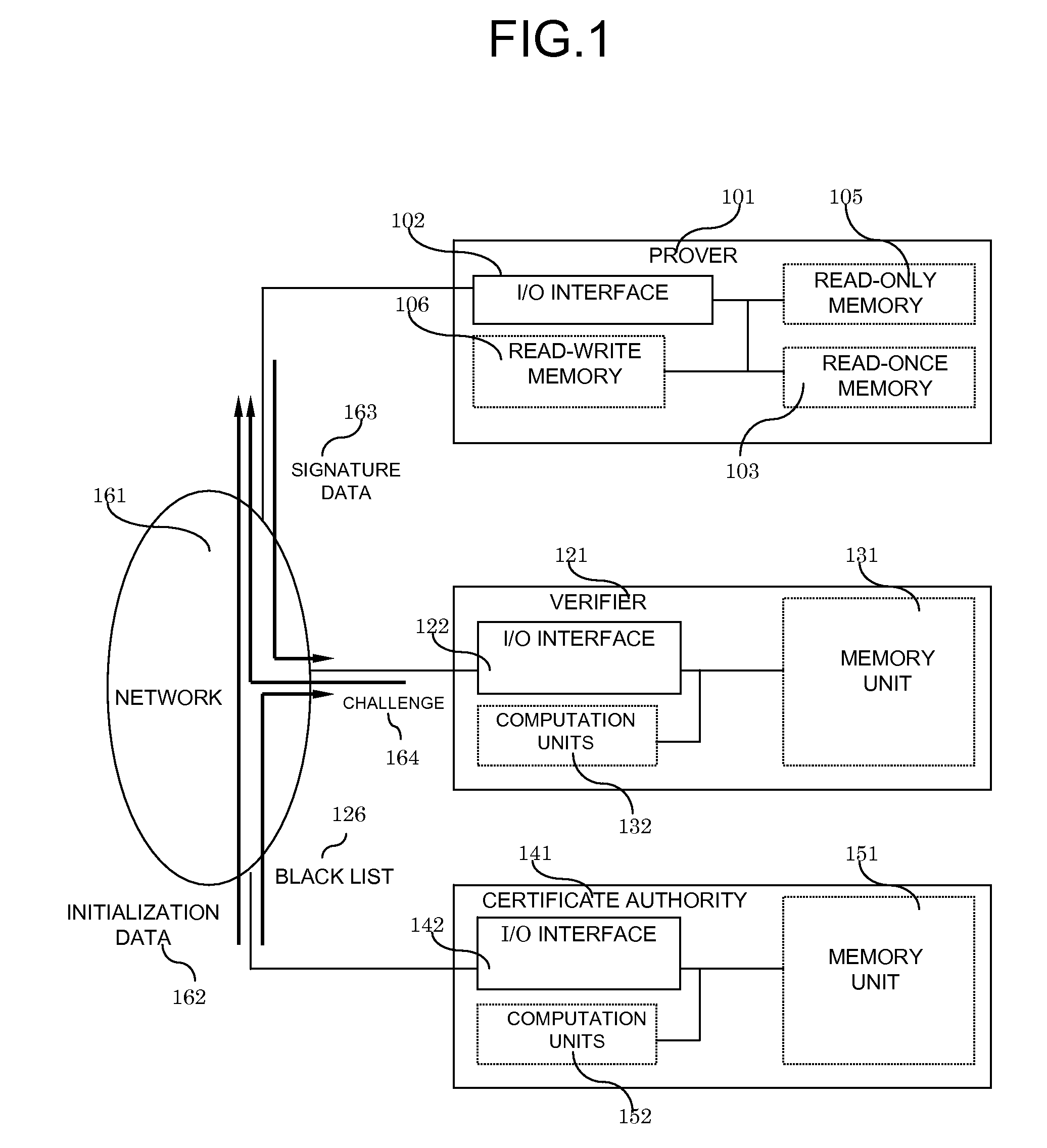
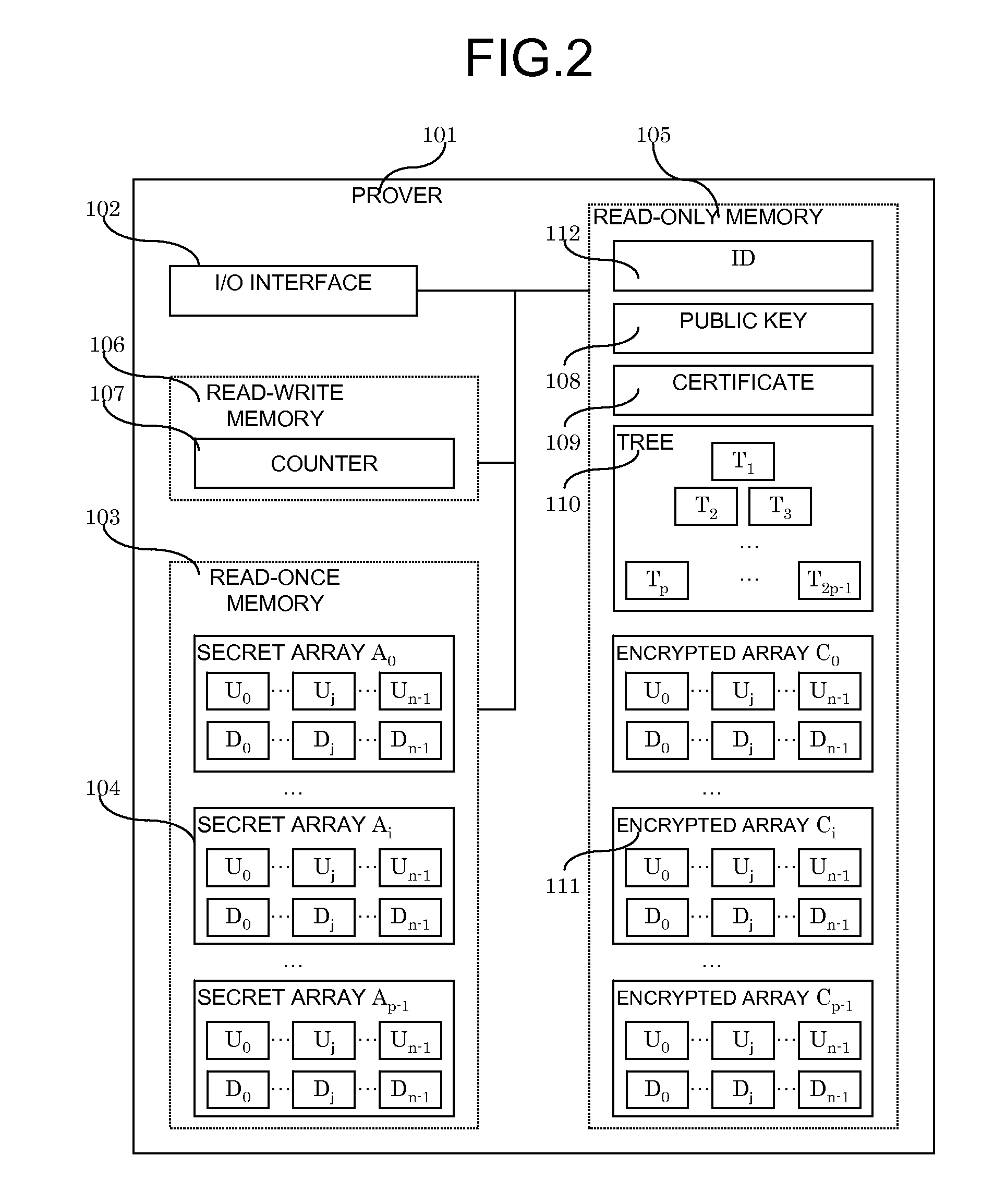
System and Method for Digital Signatures and Authentication
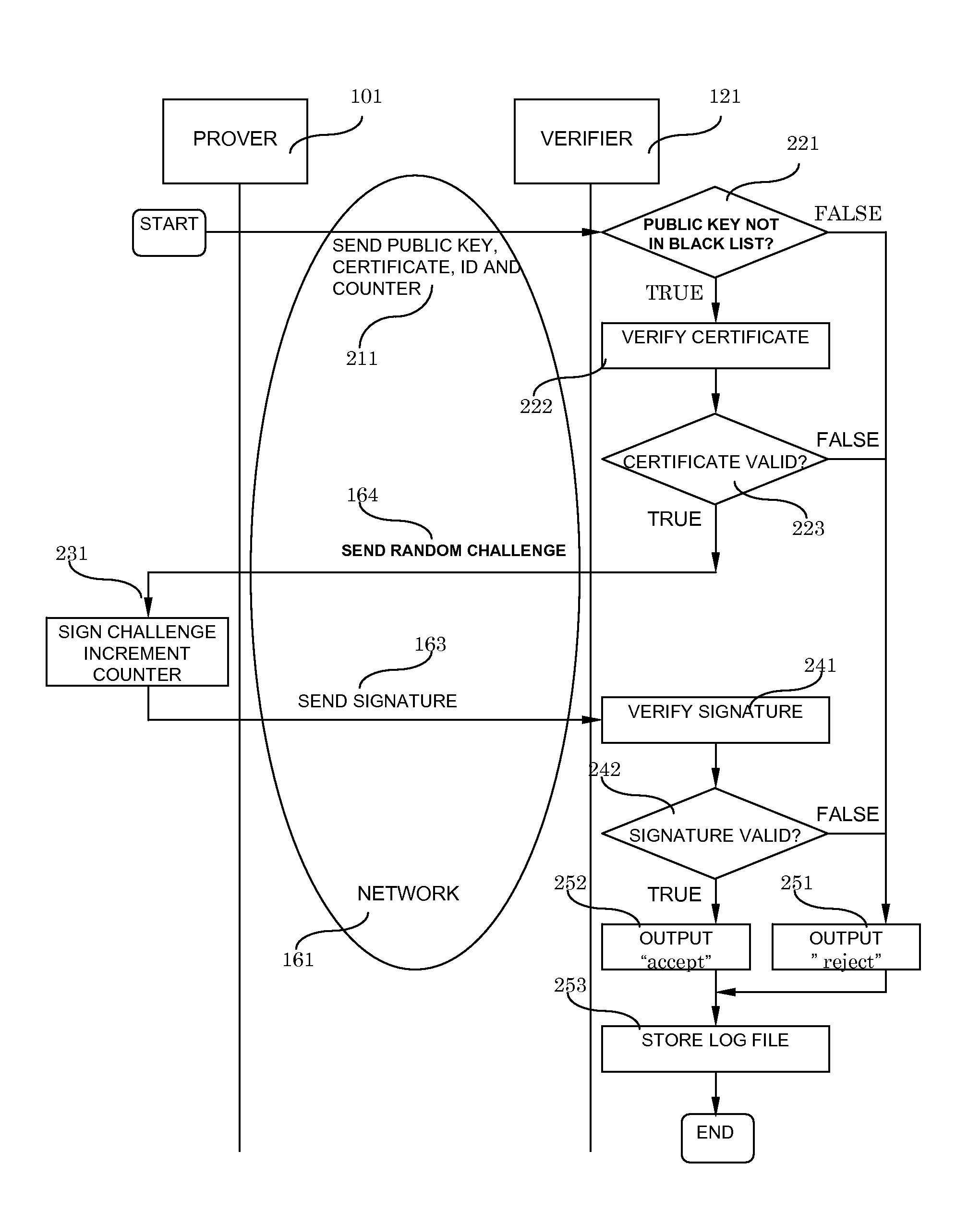
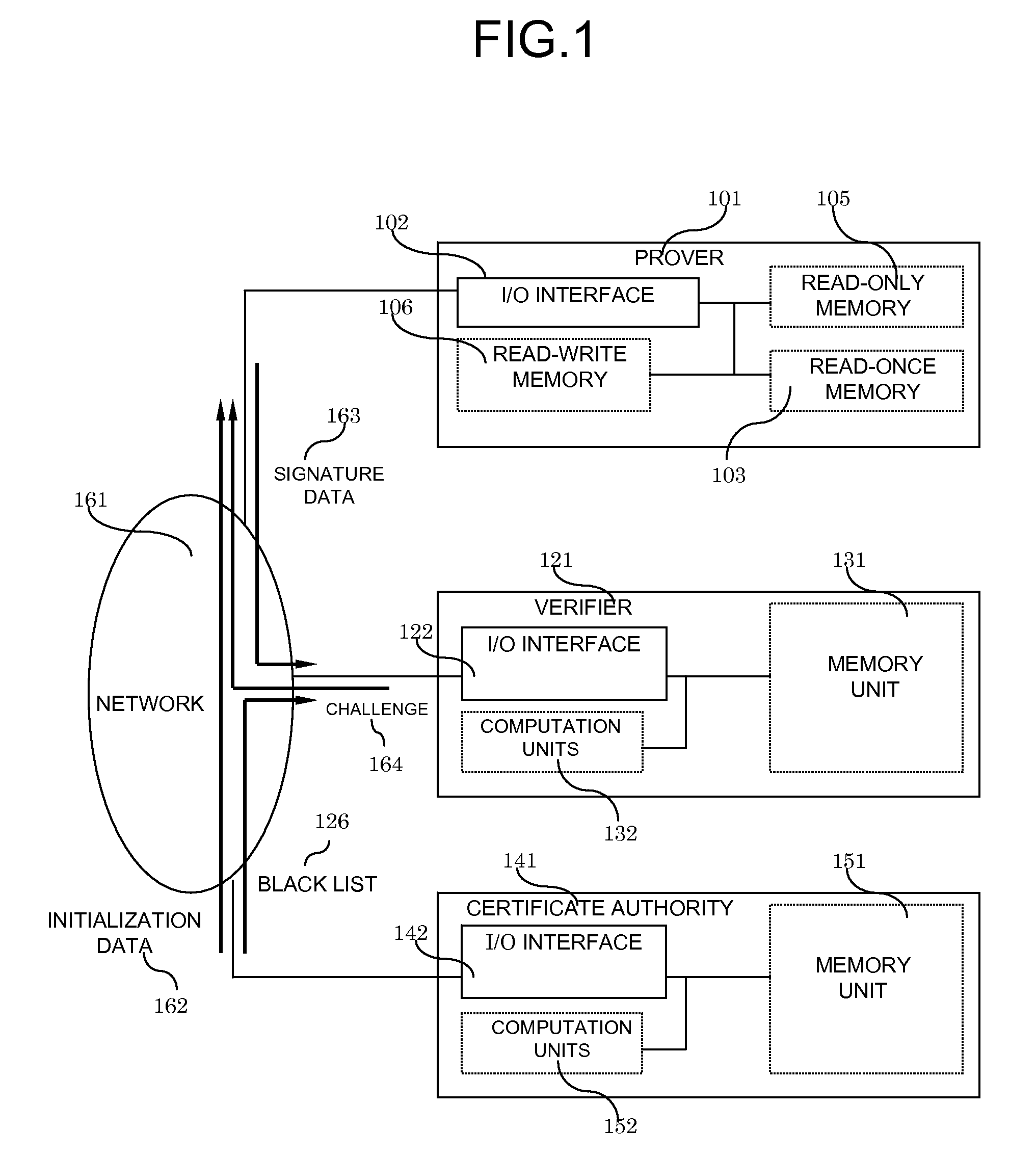
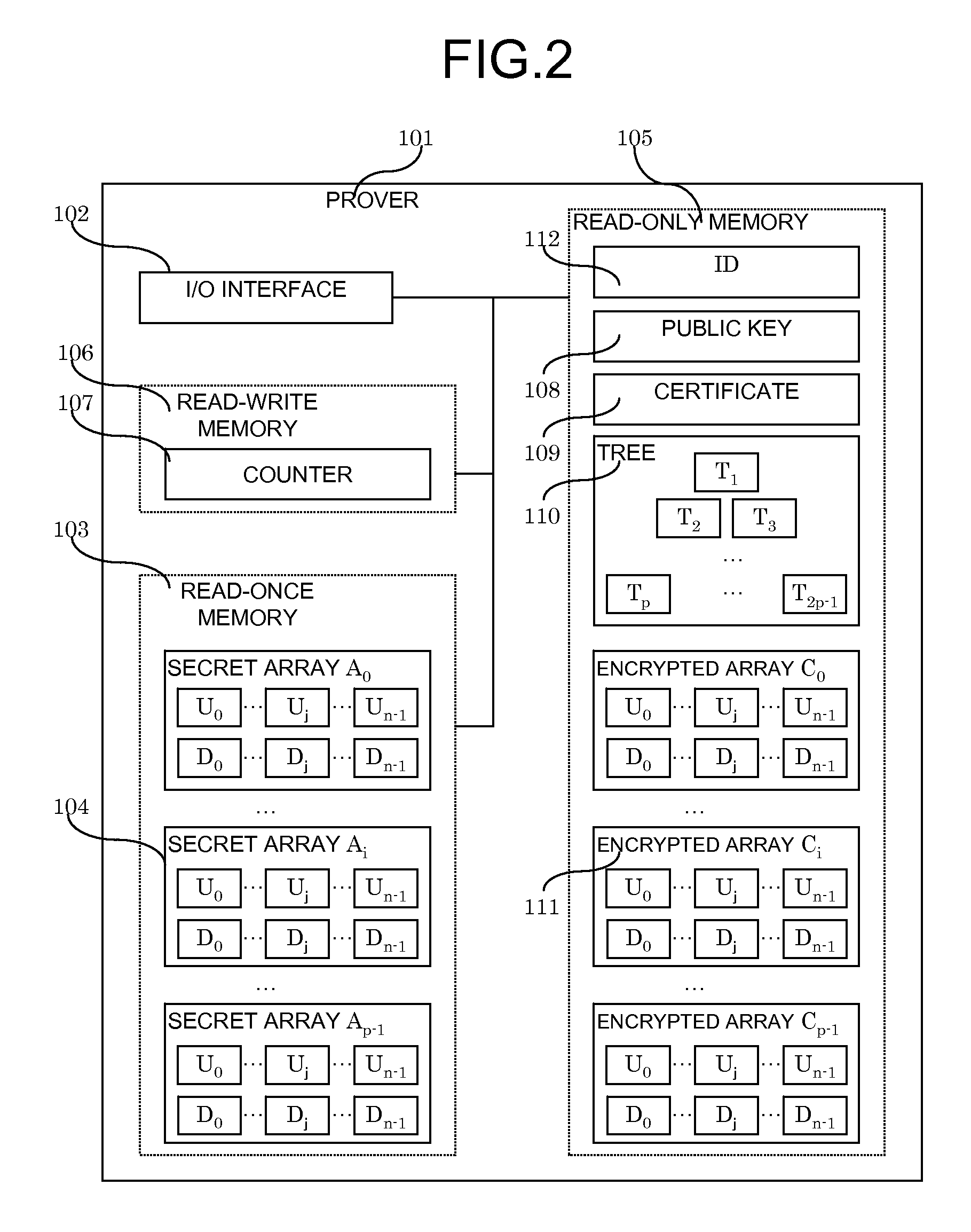
InactiveUS20090187766A1Required computational ability is significantSimple memory controllerPublic key for secure communicationUser identity/authority verificationDigital signatureKey issues
A system and method for authentication and digital signatures on memory-only supports, comprising a read-once memory unit storing secret arrays, whose contents are destroyed upon reading, a standard memory unit storing encrypted arrays, tree data authenticating the encrypted arrays to one single public key, and a certificate of the public key issued by a certificate authority. The memory support sends its public key and certificate to a verifier, receives a challenge which is signed by elements from secret arrays in the read-once memory. The verifier system checks the authenticity of the data revealed from the read-once memory by encrypting it and comparing the result to one of the encrypted arrays, and verifies that the encrypted array authenticates to the public key using tree data. Finally, the verifier checks the authenticity of the public key using the certificate.
Owner:HITACHI LTD
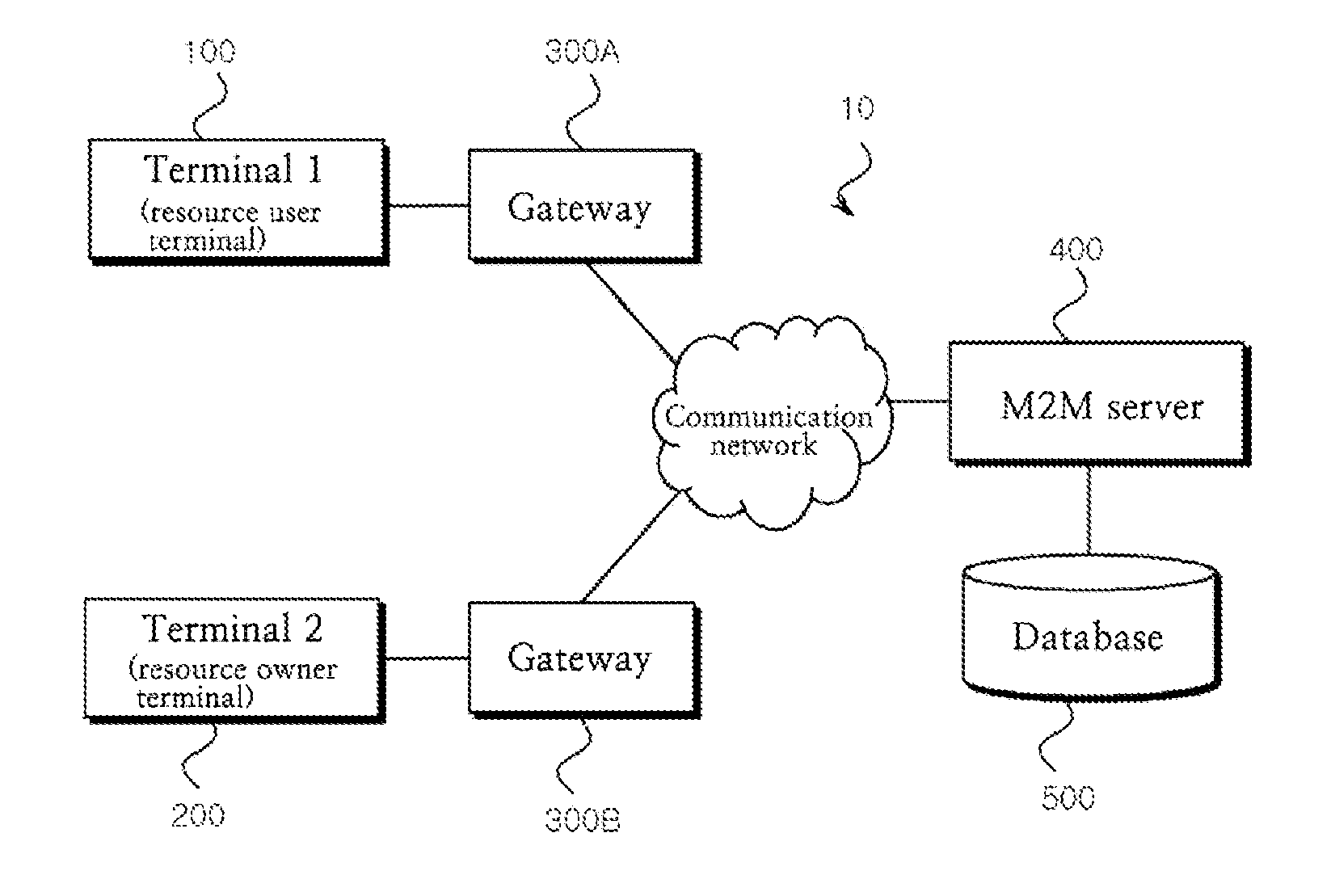
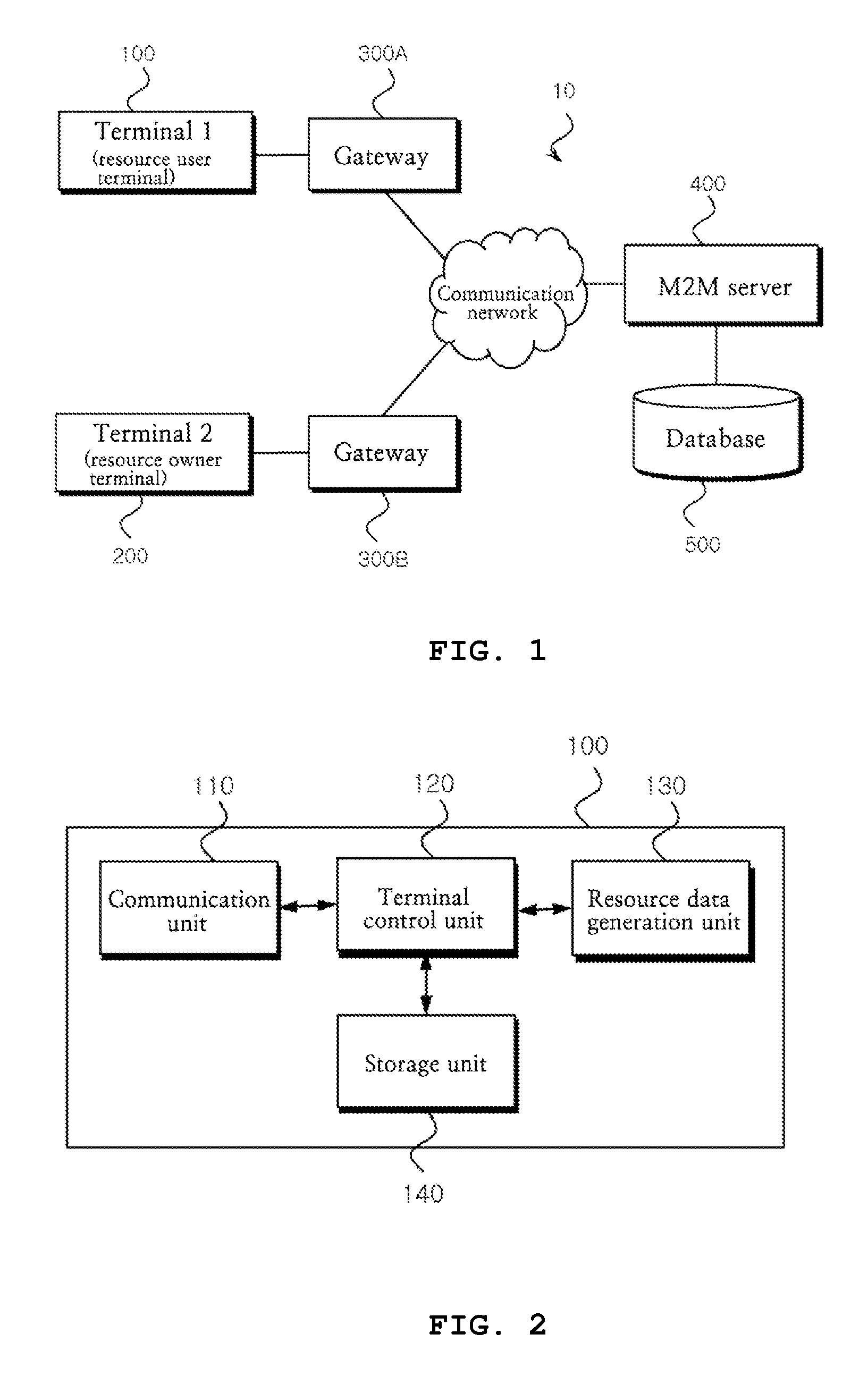
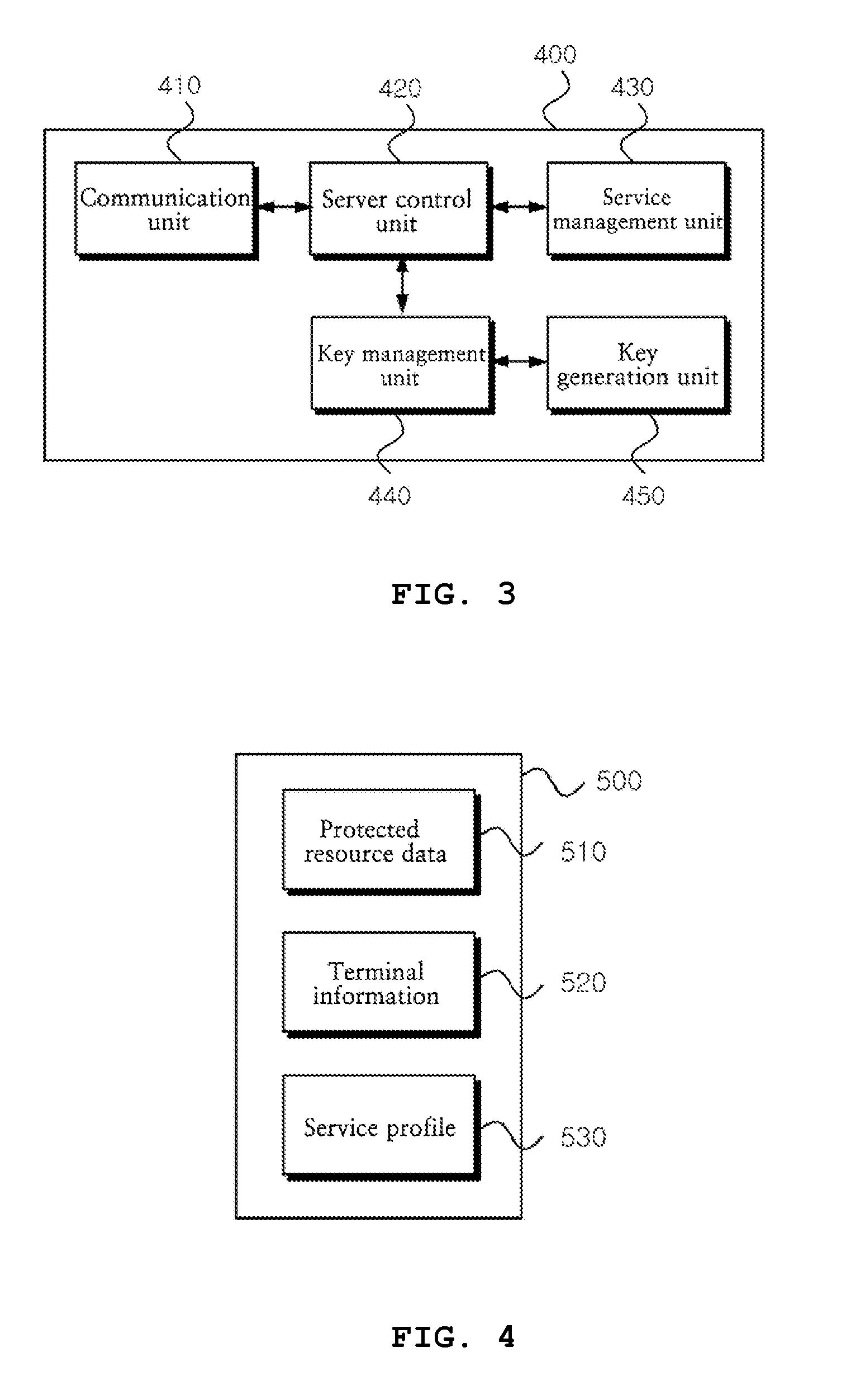
Method for sharing data of device in m2m communication and system therefor
ActiveUS20140317707A1Data taking preventionDigital data processing detailsKey issuesComputer terminal
The present invention relates to a method for sharing data of a device in M2M communication and a system therefor. The invention comprises: a step of allowing a resource user terminal to request access authority of protected resource data to a resource owner terminal, in order to prevent a security threat; a verification step of allowing the resource owner terminal to verify the resource user terminal to request the setting of the access authority to an M2M server, and to transmit a verification key issued from the M2M server to the resource user terminal; an access authority setting step of allowing the M2M server to generate an access authentication key based on the verification key, and to transmit the access authentication key to the resource user terminal; and a using step of allowing the resource user terminal to inquire about the protected resource data from the M2M server based on the access authentication key, and to use the protected resource data.
Owner:MODACOM
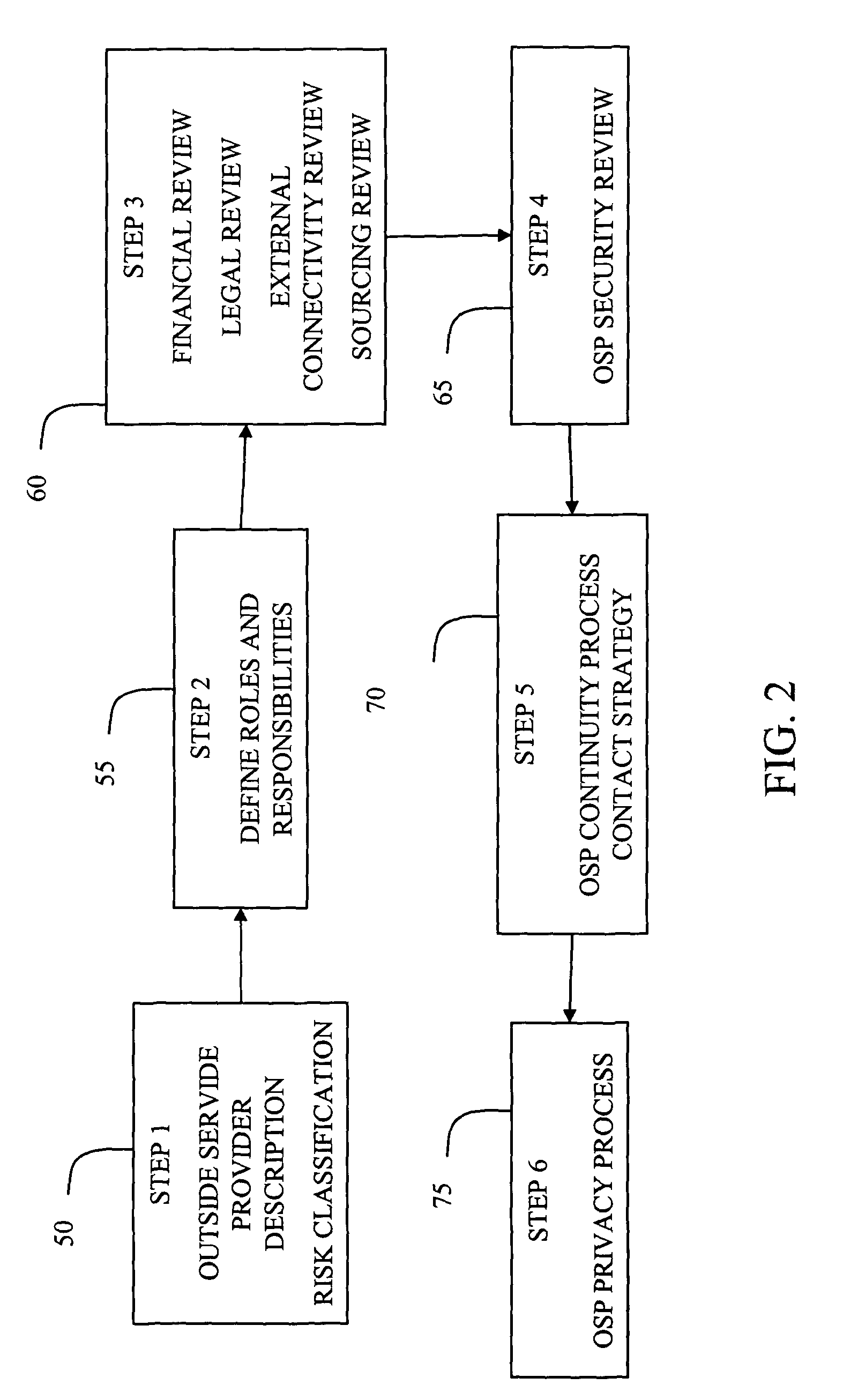
System and method for managing risks associated with outside service providers
A system and method for assessing the risk associated with Outside Service Providers. A decision engine is provided to assess monitor and manage key issues around the risk management capabilities of the OSP. The system creates a core repository that manages, monitors and measures all OSP assessments across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager of the OSP relationship). The responses are tracked in order to evaluate the progress of the assessment and the status of the OSP with respect to compliance with the enterprise's requirements for OSPs. Once a questionnaire has been completed, the OSP can be given an overall rating of exposure to various forms of risk. Areas of risk can be acknowledged, prompting a sensitivity rating, such as severe, negligible and so forth. Once risk is acknowledged, a plan for reducing the risk or bringing the OSP into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be disclaimed through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
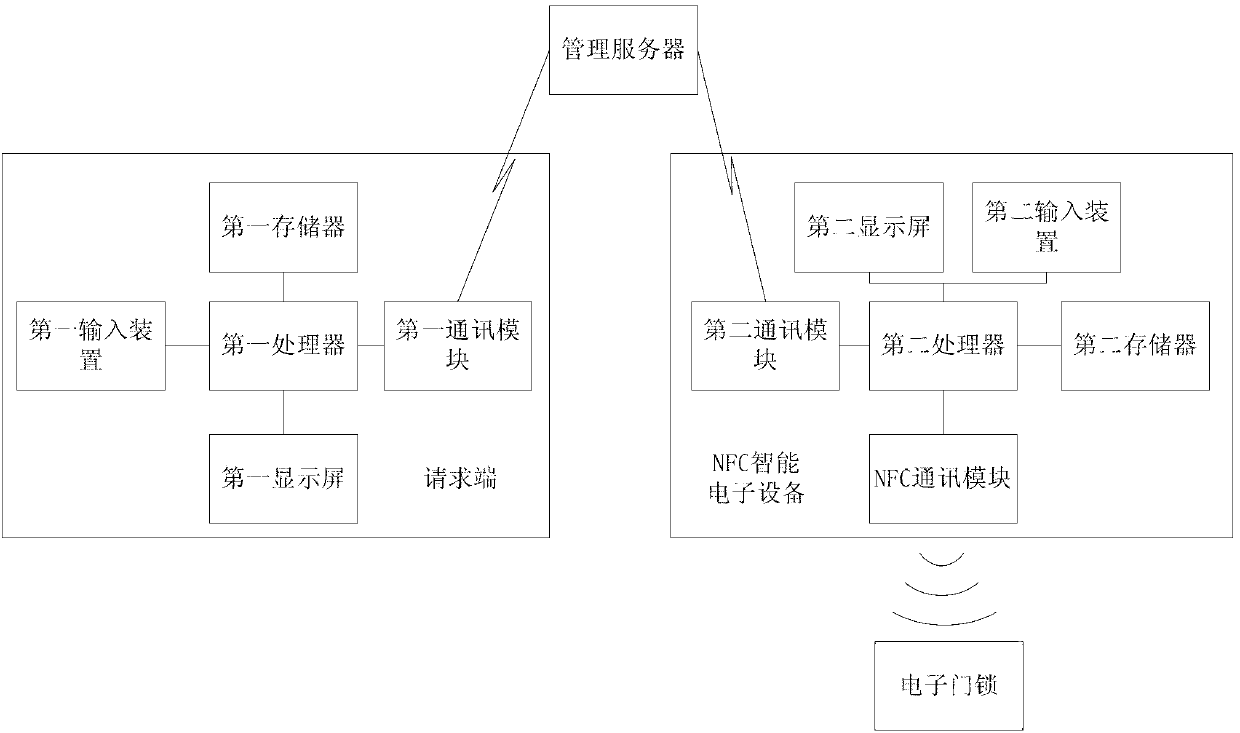
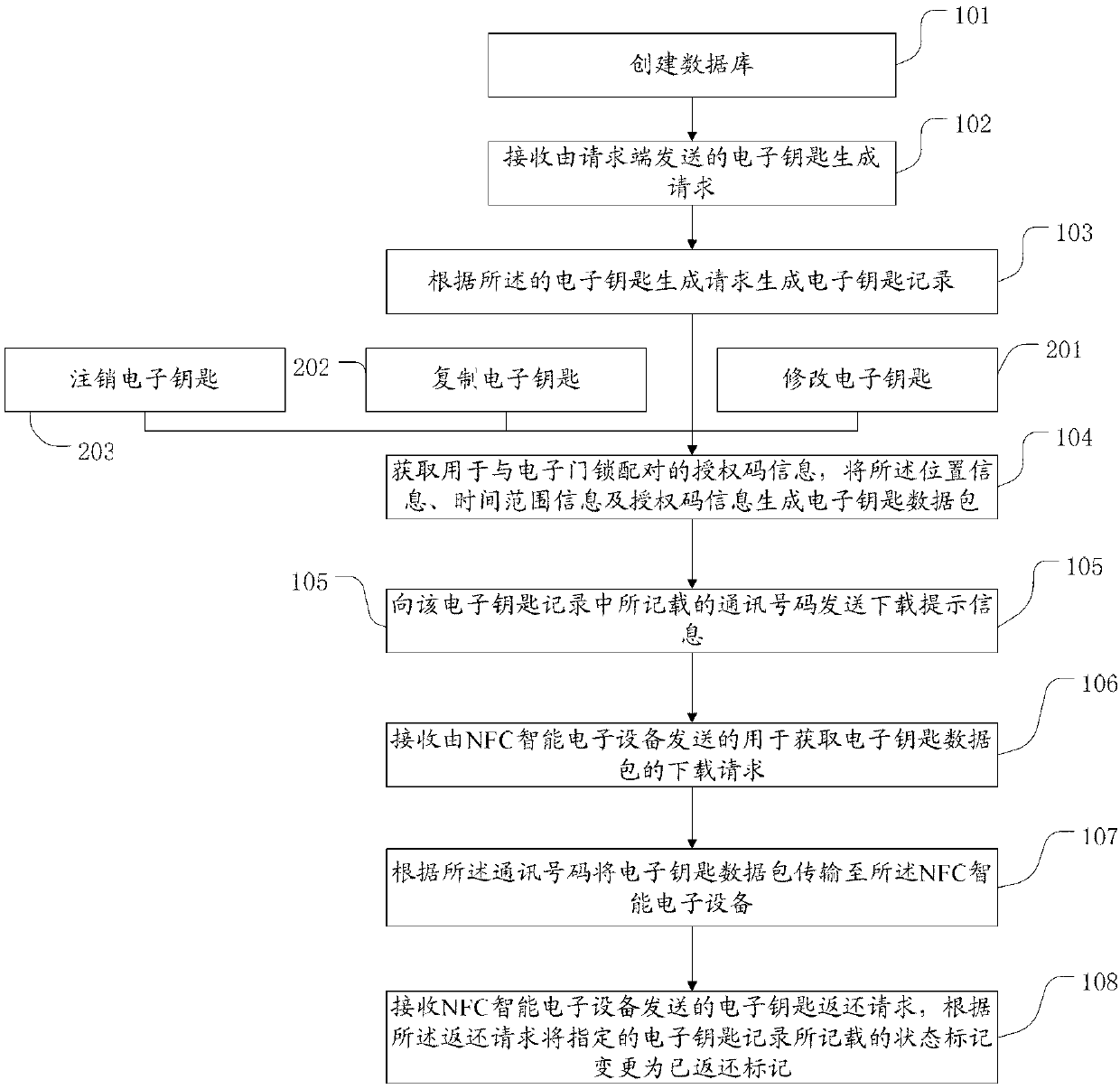
Electronic door lock management method and system based on NFC (near field communication) intelligent electronic equipment
ActiveCN103345790AReduce manufacturing costEasy to manageIndividual entry/exit registersKey issuesE communication
The invention discloses an electronic door lock management method and system based on NFC (near field communication) intelligent electronic equipment. The method comprises the following steps of: receiving an electronic key generation request sent by a request end, generating an electronic key record comprising electronic door lock opening information and an NFC intelligent electronic equipment communication number, receiving an electronic key query request sent by the NFC intelligent electronic equipment, and pushing the electronic key record to the NFC intelligent electronic equipment. An electronic key issuing request is initiated to a management server by the request end, electronic key data is transmitted to the NFC intelligent electronic equipment by the management server, and a corresponding electronic door lock is opened by taking the NFC intelligent electronic equipment as an electronic key, so that the effects of remote management and electronic key issuing are achieved, the manufacturing cost of the electronic key is saved, when a problem occurs, the problem can be solved under the circumstance that an electronic key possessor does not need to arrive on the scene of the request end, and the management is convenient; further, the wide-range electronic key management is conveniently achieved under low management cost.
Owner:SHENZHEN LOCSTAR TECH
Method and system for controlling data traffic in a network
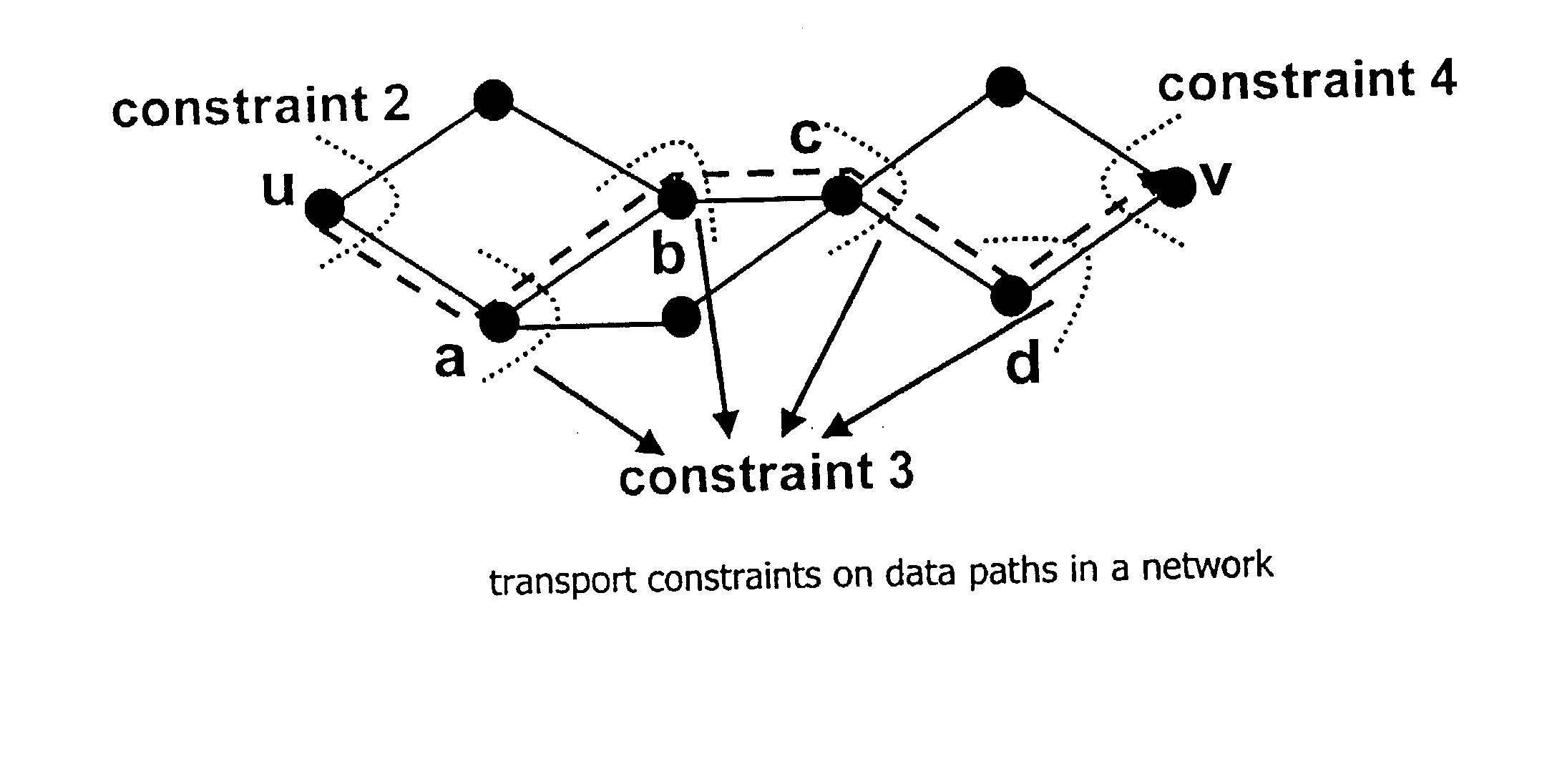
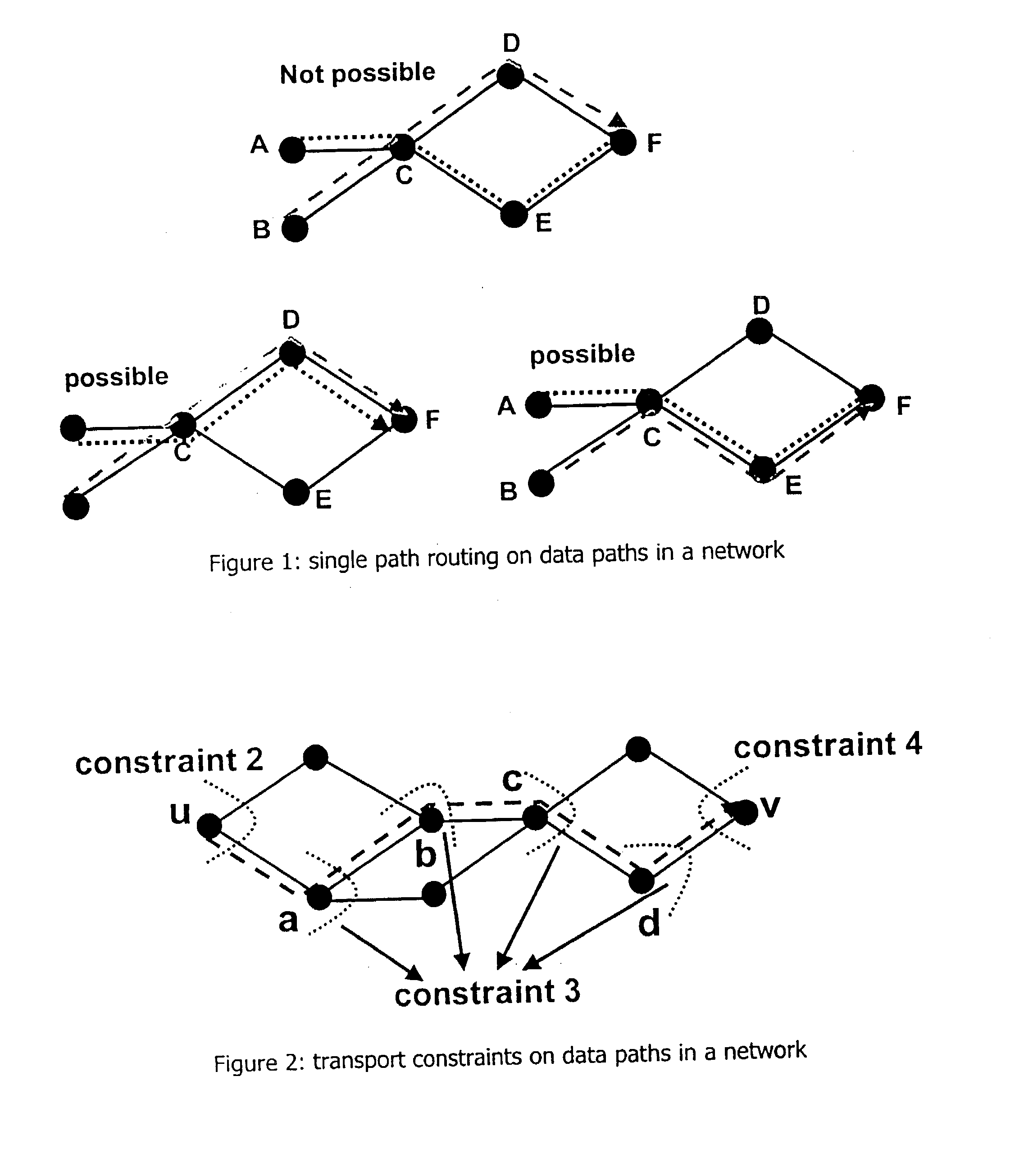
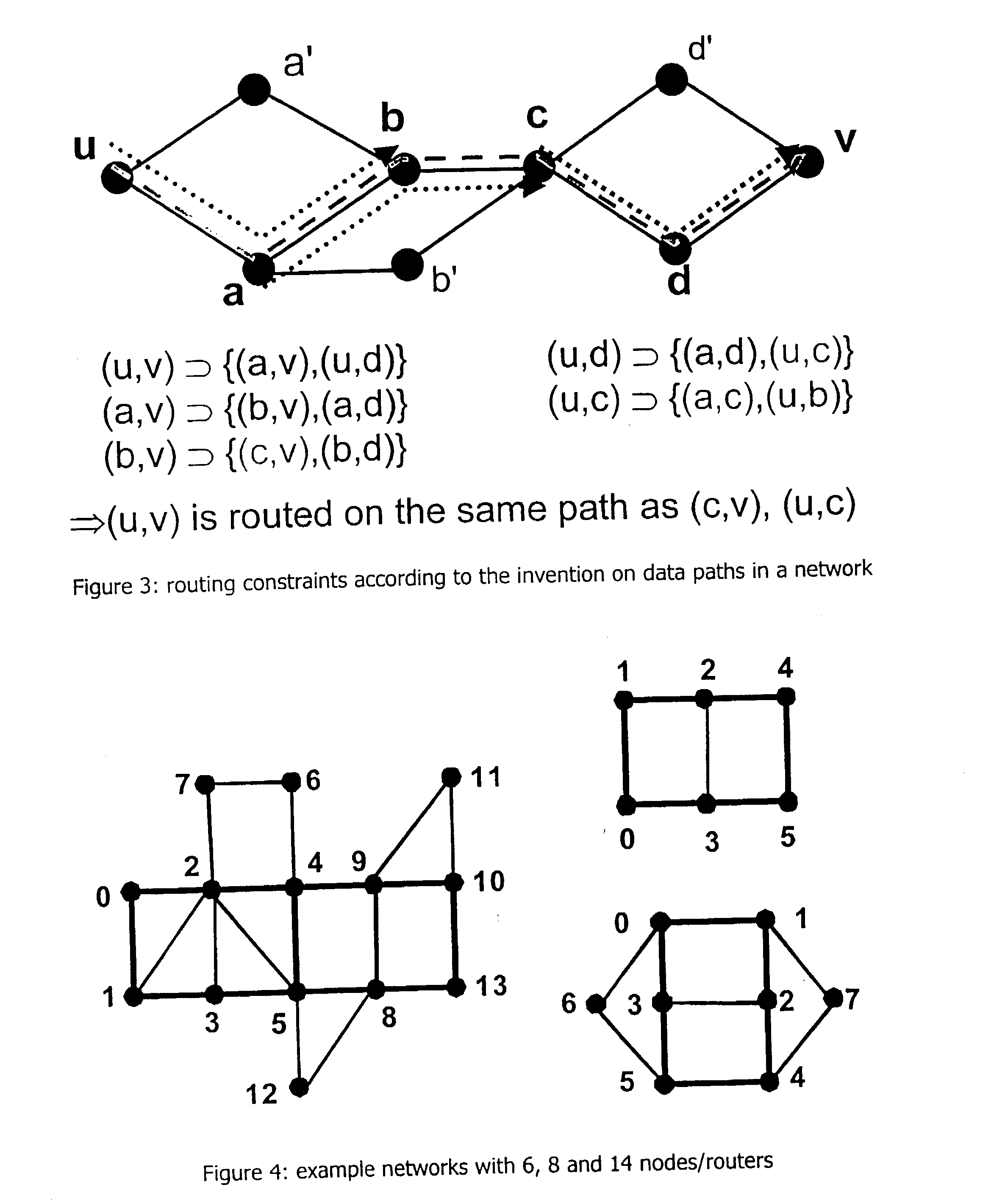
Routing is one of the key issues in networks for communication of data. Conventionally, the optimization of the routing for a particular network is achieved by improving / changing / expanding the routing protocol. In order to optimize the routing of data networks without varying existing routing protocols, the present invention provides a method and a system for optimizing the routing of data to be communicated in a network. In particular, the invention achieves an improved control for routing data traffic in a network by a minimization of link costs between nodes of the network.
Owner:XYLON LLC
Method for cloud storage security control
ActiveCN103236934AUser identity/authority verificationComputer security arrangementsPlaintextPassword
The embodiment of the invention discloses a method for cloud storage security control, which is used for solving the problems that since shared storage is commonly adopted during the storage in the prior art, and service providers need to control private keys, the security of private keys is low. The method comprises the steps of encrypting a private key issued to each user through two different encryption modes, so as to form a first cryptographic key and a second cryptographic key, storing the first cryptographic key and the second cryptographic key, receiving answers to security problems input by the user after decryption failure of the first cryptographic key through user passwords, deciphering the second cryptographic key through the answers to the security problems, so as to obtain a clear cryptographic key, resetting the user passwords, and encrypting the clear cryptographic key obtained by deciphering the answers to the security problems, so as to form a new first cryptographic key to be stored.
Owner:北京书生信息技术有限公司
Method and apparatus for designing and planning of workforce evolution
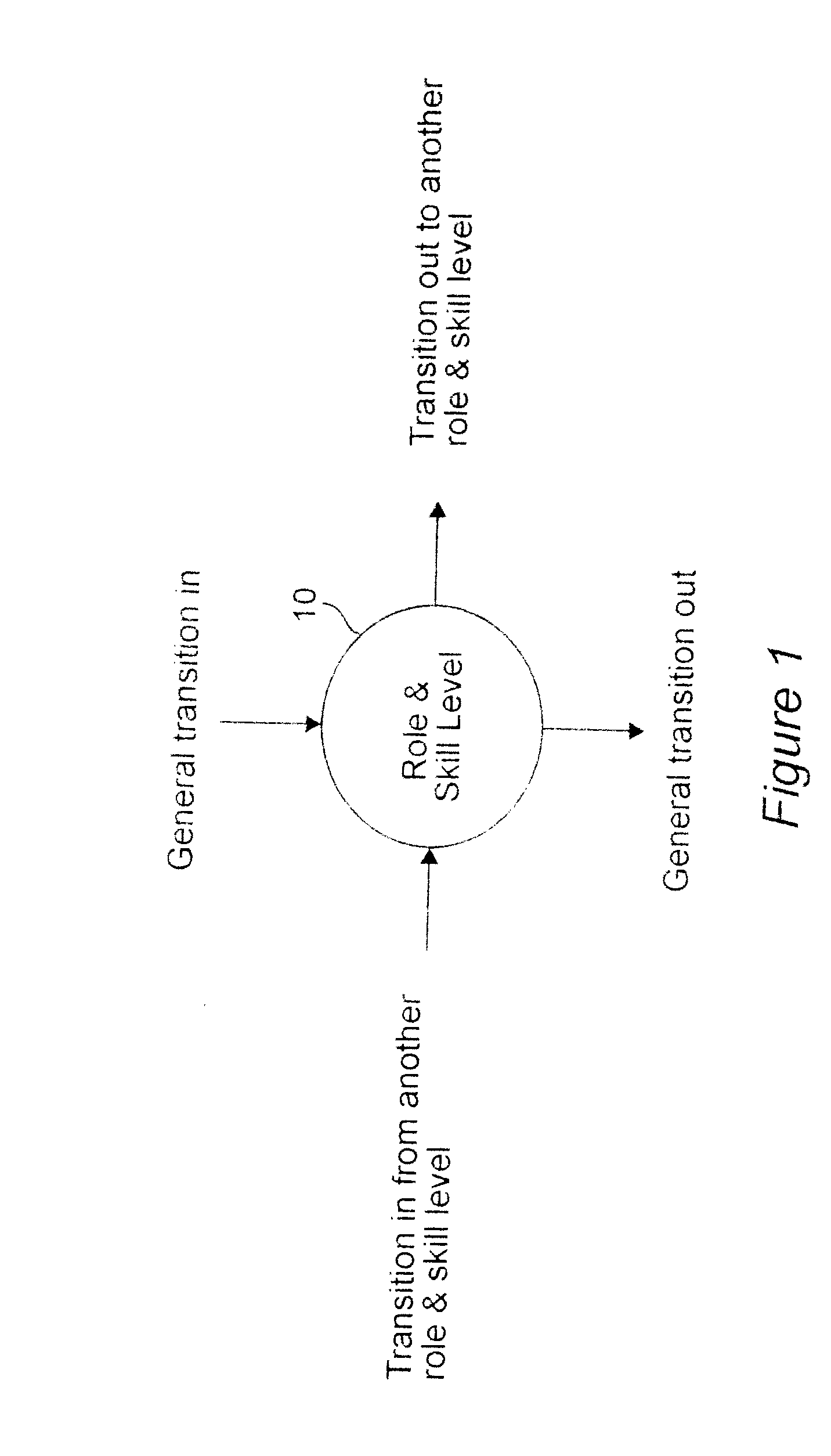
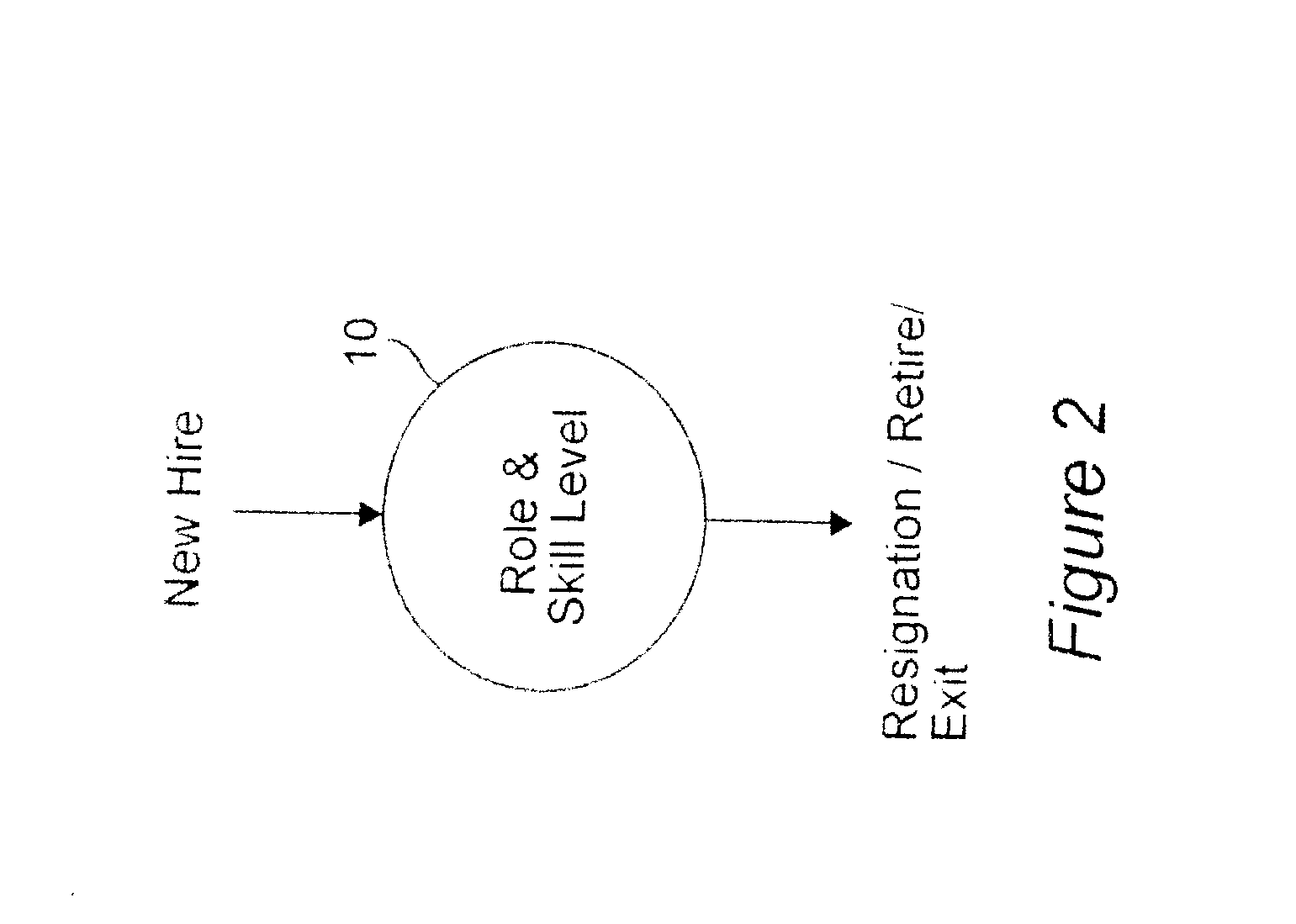
Mathematical means and methods are used within the context of mathematical models of a workforce evolution to address key issues in workforce design and planning. Examples of such mathematical means and methods are (but not limited to) fluid-flow models and diffusion-process models. In each case, these mathematical models characterize the workforce evolution over time as a function of dynamic workforce events, such as new hires, terminations, resignations, retirements, promotions and transfers, and dynamic workforce topology, policy, or scenario, such as the viable paths from one workforce resource state to another workforce resource state.
Owner:DEITRICH BRENDA LYNN +3
System and method for digital signatures and authentication
InactiveUS8291229B2Simple memory controllerPublic key for secure communicationUser identity/authority verificationDigital signatureKey issues
A system and method for authentication and digital signatures on memory-only supports, comprising a read-once memory unit storing secret arrays, whose contents are destroyed upon reading, a standard memory unit storing encrypted arrays, tree data authenticating the encrypted arrays to one single public key, and a certificate of the public key issued by a certificate authority. The memory support sends its public key and certificate to a verifier, receives a challenge which is signed by elements from secret arrays in the read-once memory. The verifier system checks the authenticity of the data revealed from the read-once memory by encrypting it and comparing the result to one of the encrypted arrays, and verifies that the encrypted array authenticates to the public key using tree data. Finally, the verifier checks the authenticity of the public key using the certificate.
Owner:HITACHI LTD
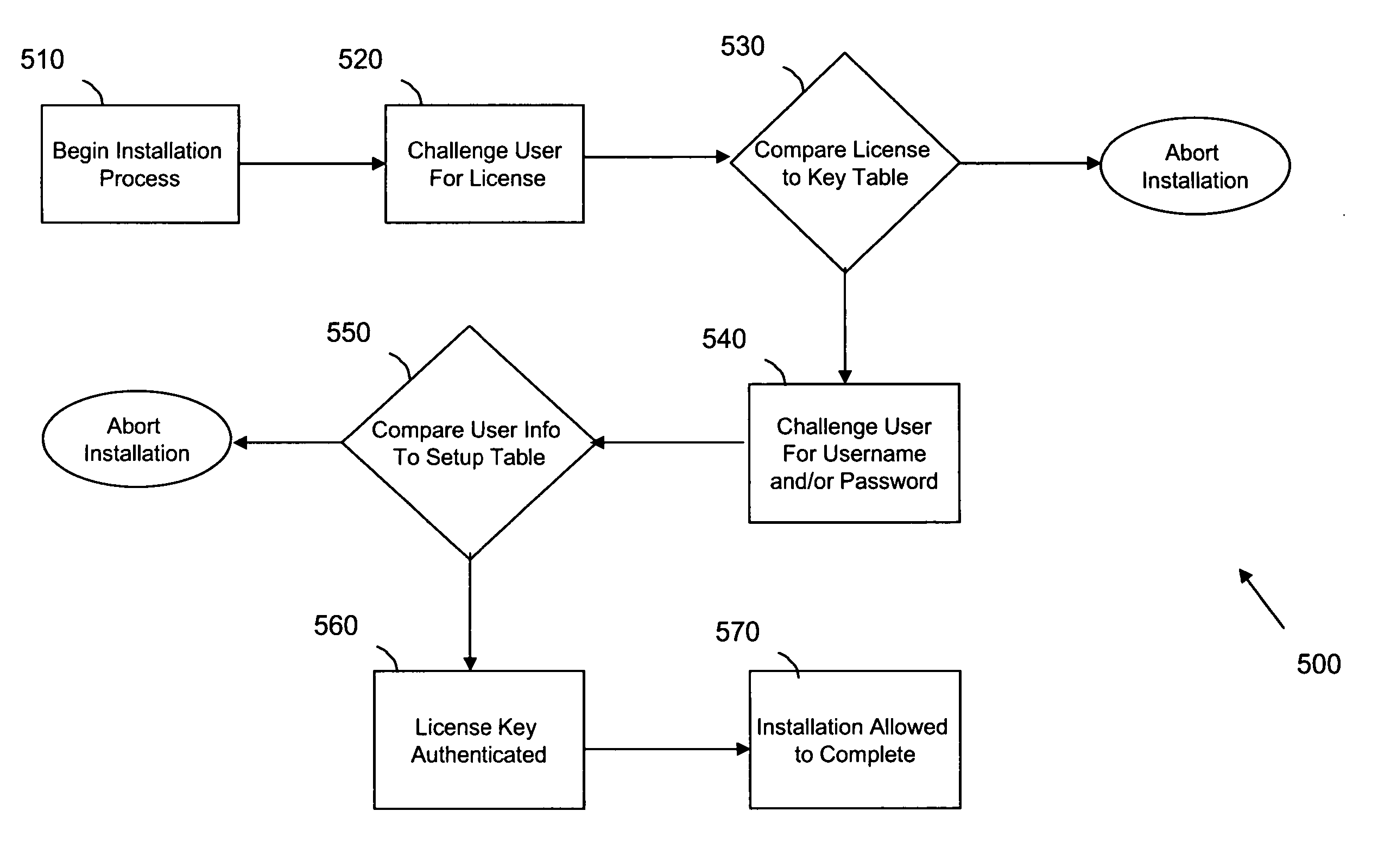
System and method for providing peer-to-peer communication
User identity is verified using license keys issued during a pre-registration process. In one embodiment, members of a defined community communicate with other members of the community using uniquely identifying PKI keys. In one embodiment, the identity of a user is assured by having a system-level administrator issue license keys and pre-register the user. In one embodiment, during a pre-registration process, a setup server may be accessed to generate a private license key that will be used to secure and encrypt all communication from one user to another.
Owner:SEAMLESS GLOBAL
Electronic intelligent auxiliary writing training and analysis evaluation system
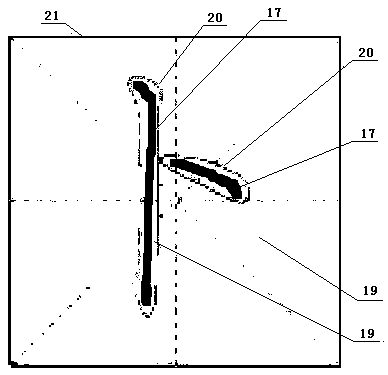
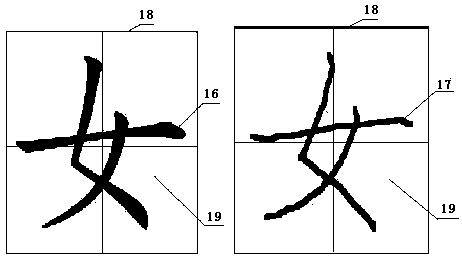
PendingCN108399821AIntuitive evaluationIntuitive Quantitative EvaluationTeaching apparatusVisual comparisonKey issues
The invention provides an electronic intelligent auxiliary writing training and analysis evaluation system, and belongs to the field of electronic auxiliary writing training. Aiming to solve the key problem of good character writing in the writing training, the technical feedback about the writing quality is given in time by using an intelligent electronic or computer auxiliary means to answer thequestions of 'how about the writing'or what's the difference', so that the psychological doubts are resolved and the lack of skills is pointed out. The character image or the information is acquiredby the aid of a sensing device. The device is characterized in that quantitative or visual comparison is conducted on the writing words acquired by the sensing device and the corresponding standard copybook words called out from the system, the consistency quantitative evaluation and / or visual comparison image can be given as the feedback to guide the writing training, so that the writing skills and levels can be improved. The interactive and gain cycling of the writing training process can be realized, the effect is remarkable, the cost is low, the on-purpose, guiding, and assisting properties are achieved. The system makes the user feel it like a good teacher and student, and the writing level is stably improved by means of the aiding.
Owner:常涛涛
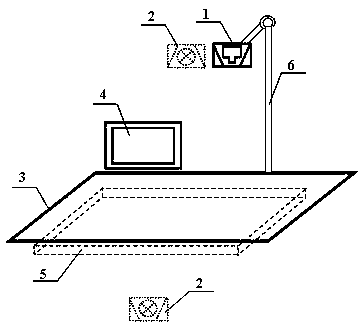
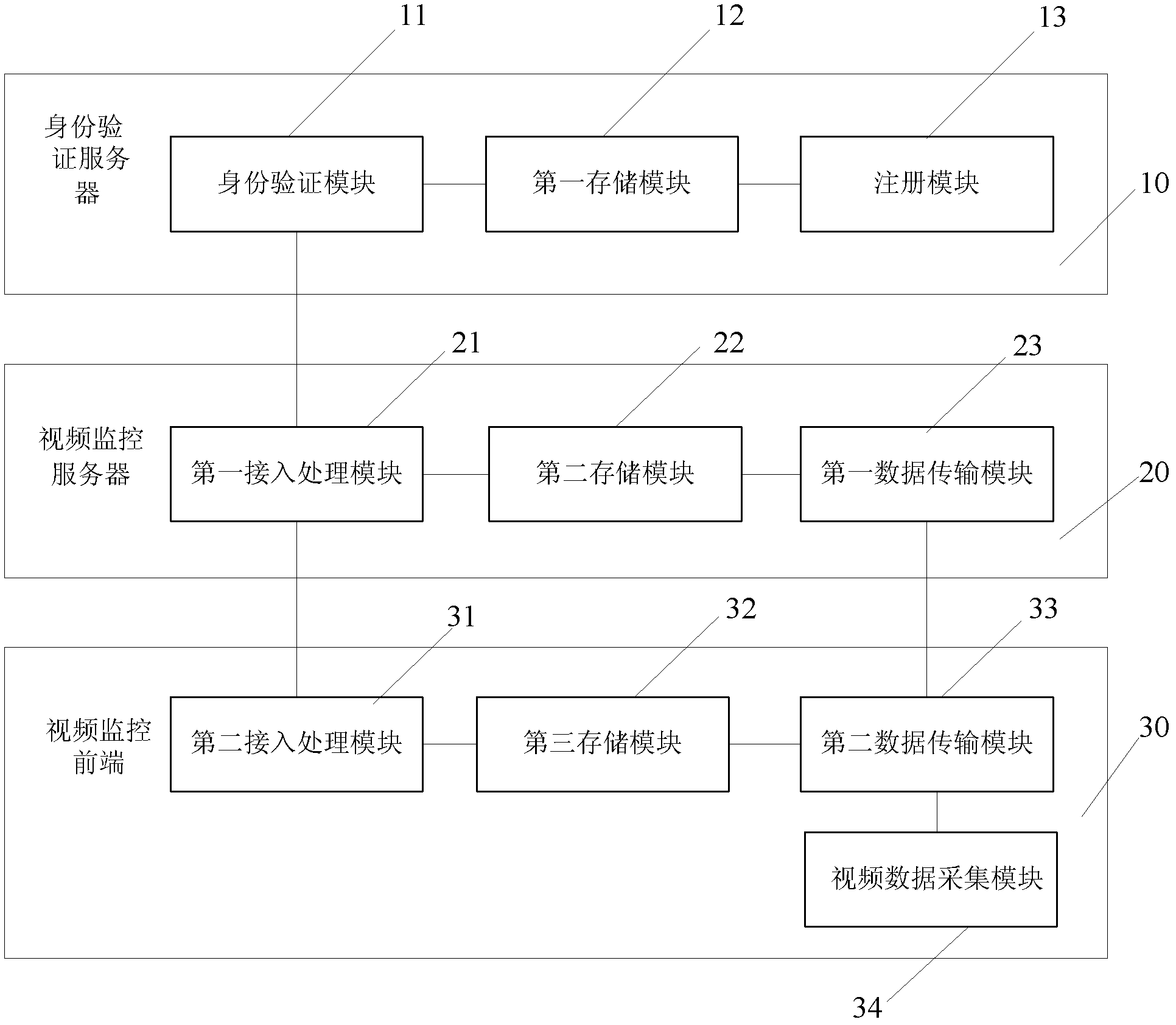
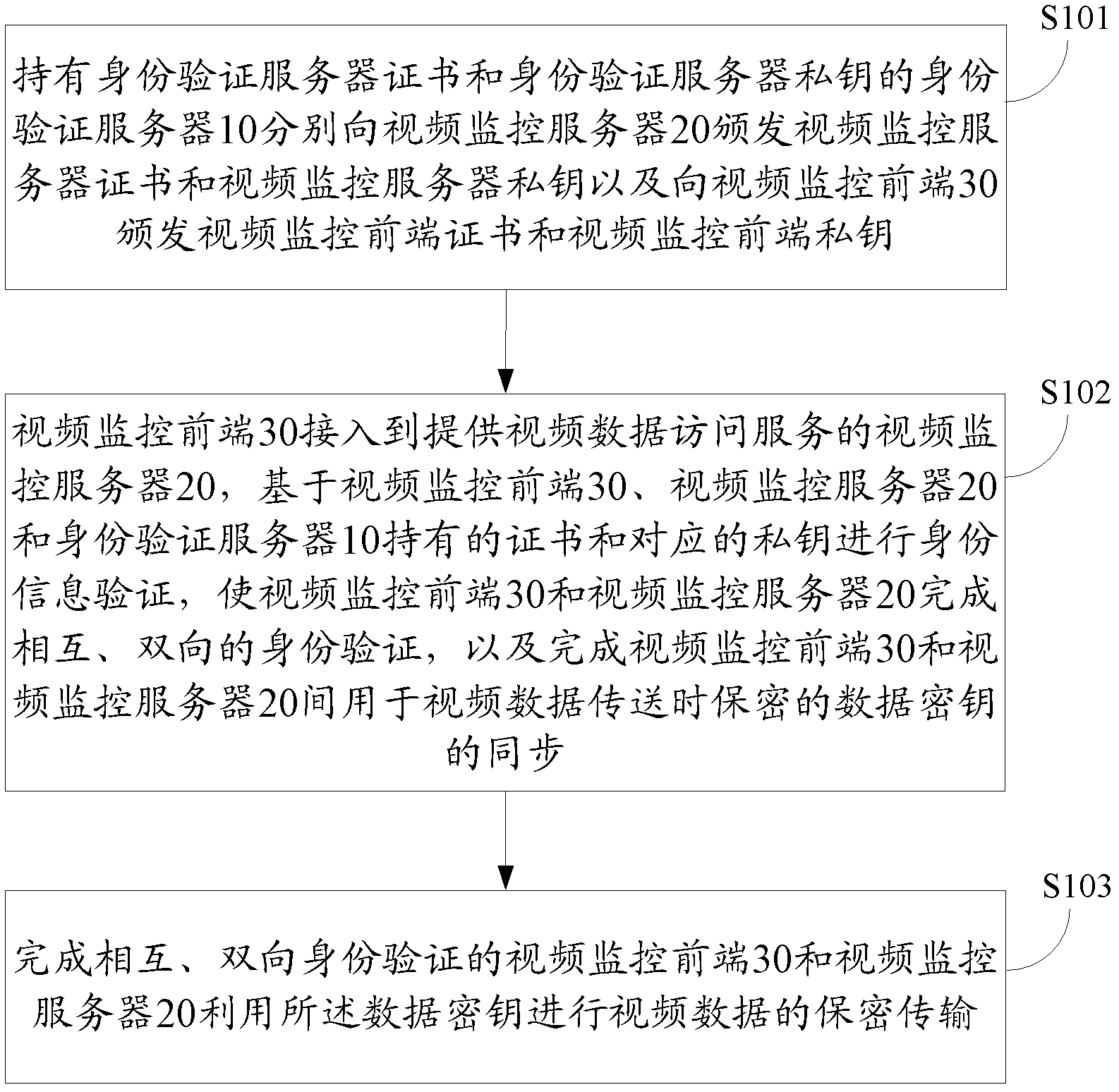
Digital-certificate-based video monitoring data transmission method and system
ActiveCN102497581AAvoid intercepting data and usingEasy to superviseSelective content distributionComputer hardwareVideo monitoring
The invention discloses a digital-certificate-based video monitoring data transmission method, which comprises the following steps that: A, an authentication server with an authentication server certificate and an authentication server private key issues a video monitoring server certificate and a video monitoring server private key to a video monitoring server, and issues a video monitoring front end certificate and a video monitoring front end private key to a video monitoring front end; B, the video monitoring front end accesses the video monitoring server, and the video monitoring front end and the video monitoring server finish mutual authentication and the synchronization of data keys for the secure transmission of video data between the video monitoring front end and the video monitoring server based on the certificates and corresponding private keys of the video monitoring front end, the video monitoring server and the authentication server; and C, after finishing the mutual authentication, the video monitoring front end and the video monitoring server securely transmit the video data by utilizing the data keys. The invention also discloses a digital-certificate-based video monitoring data transmission system.
Owner:GCI SCI & TECH
Device access authentication method of distribution network automated communication system based on ID
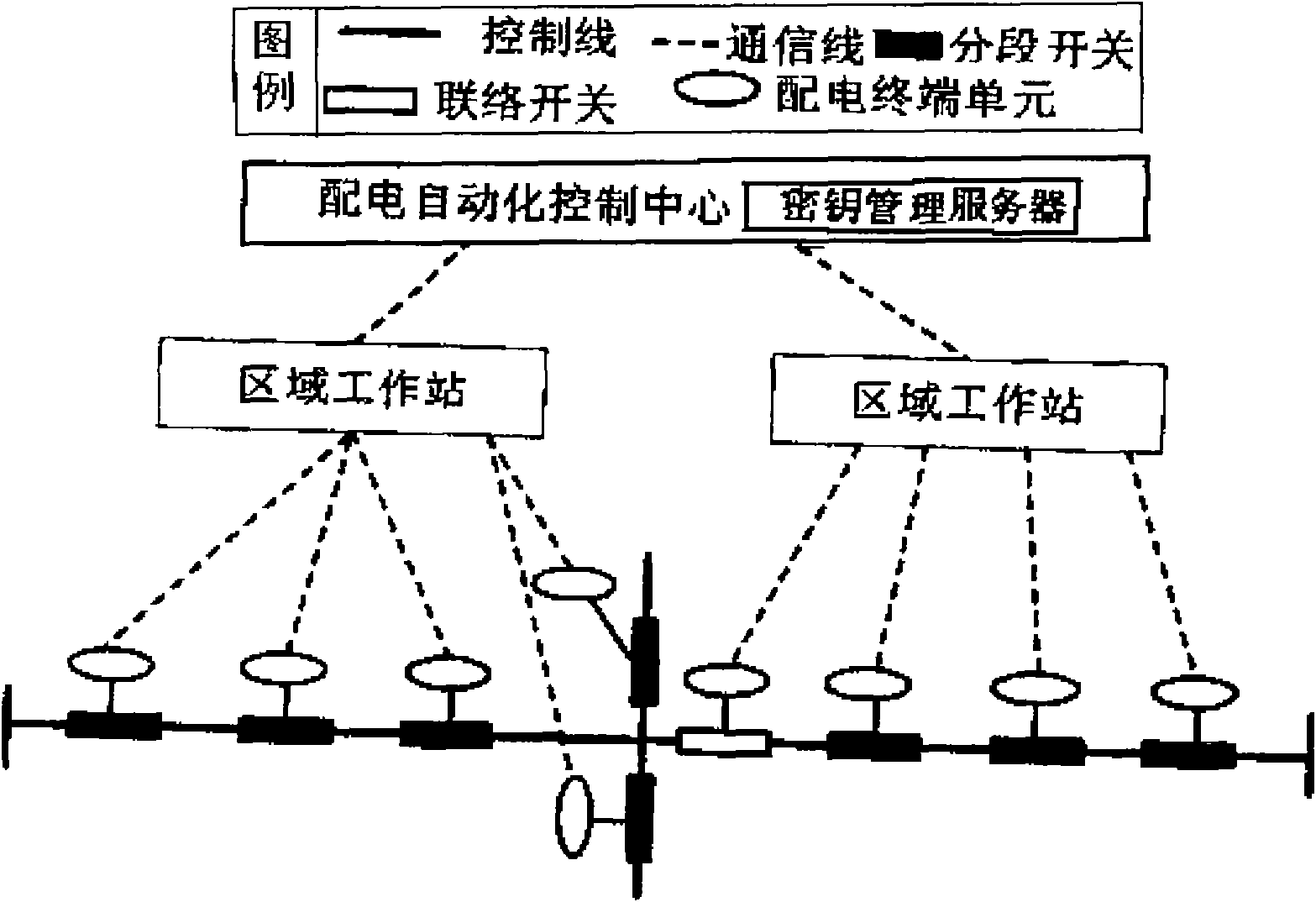
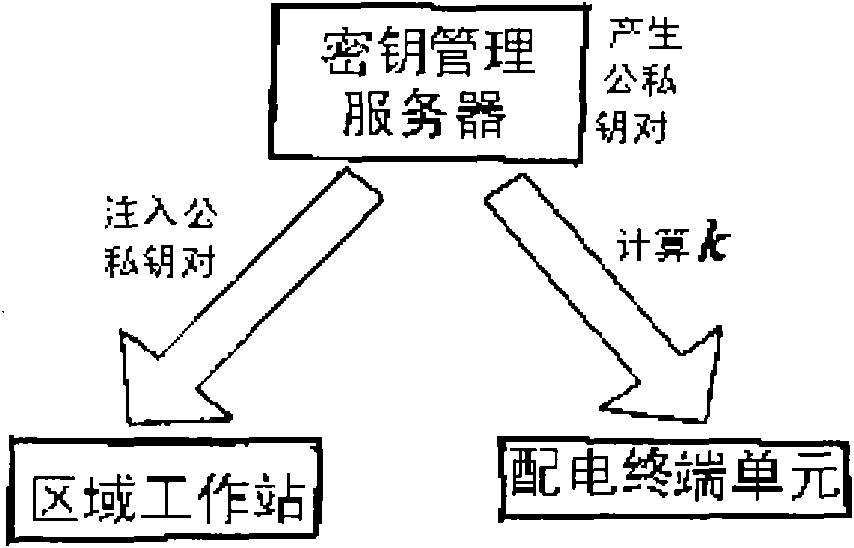
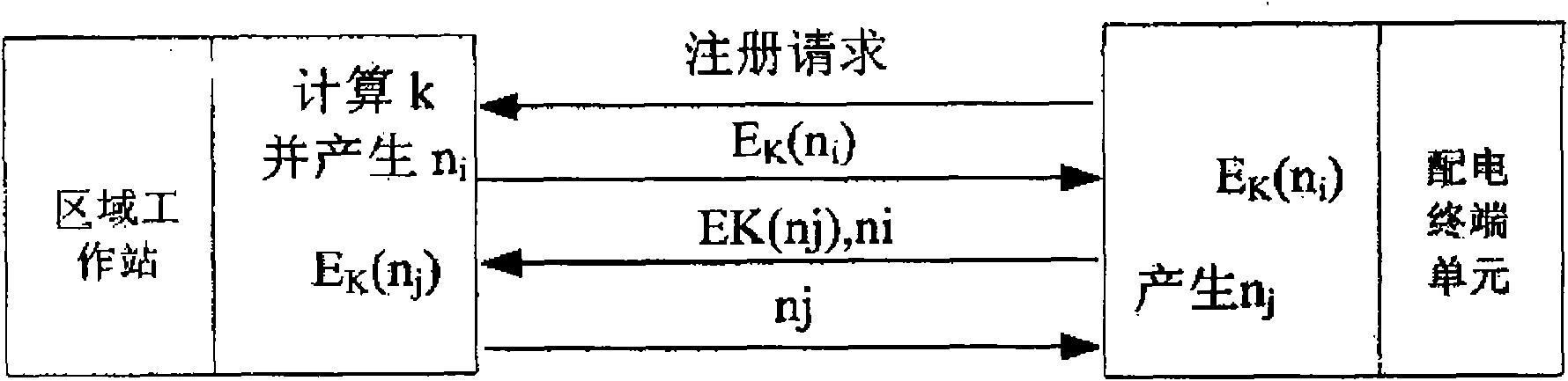
InactiveCN101807818AEasy to manageSolve computing problemsKey distribution for secure communicationCircuit arrangementsAutomatic controlCommunications system
The invention discloses an access authentication method of a distribution network automated communication device based on an ID, belonging to the field of distribution network automated communication systems. The method comprises the following steps that: a distribution automated control center, a regional workstation, a distribution terminal unit and a distribution automated communication network in a centralized control mode are established; and a key management server of the distribution automated control center conducts the key allocation, and the regional workstation and the distribution terminal unit compare whether deciphered data are the same to realize the access authentication, thereby realizing the function that any device can be installed in the distribution network automated communication system only by acquiring the key issued by the key management server. The invention is applicable to the large-scale distribution network, simplifies the key management, utilizes the communication and calculation processing capacities of the regional workstation, and solves the problems of the limited calculation and communication capabilities of the distribution terminal unit. Besides, the invention realizes the mutual authentication of the devices, thereby increasing the safety and improving the access safety of the distribution network device.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
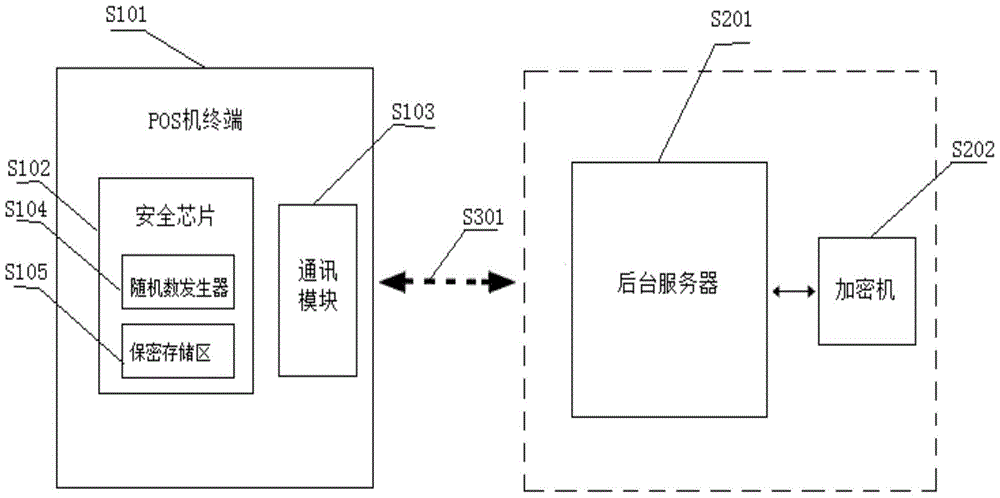
POS machine secret key remote downloading service system and secret key downloading method
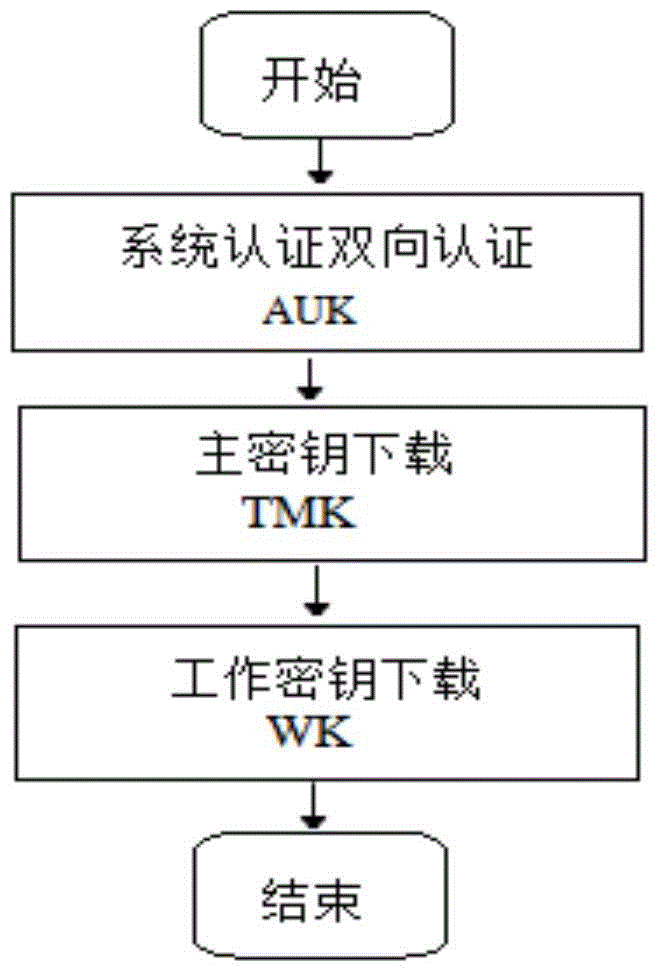
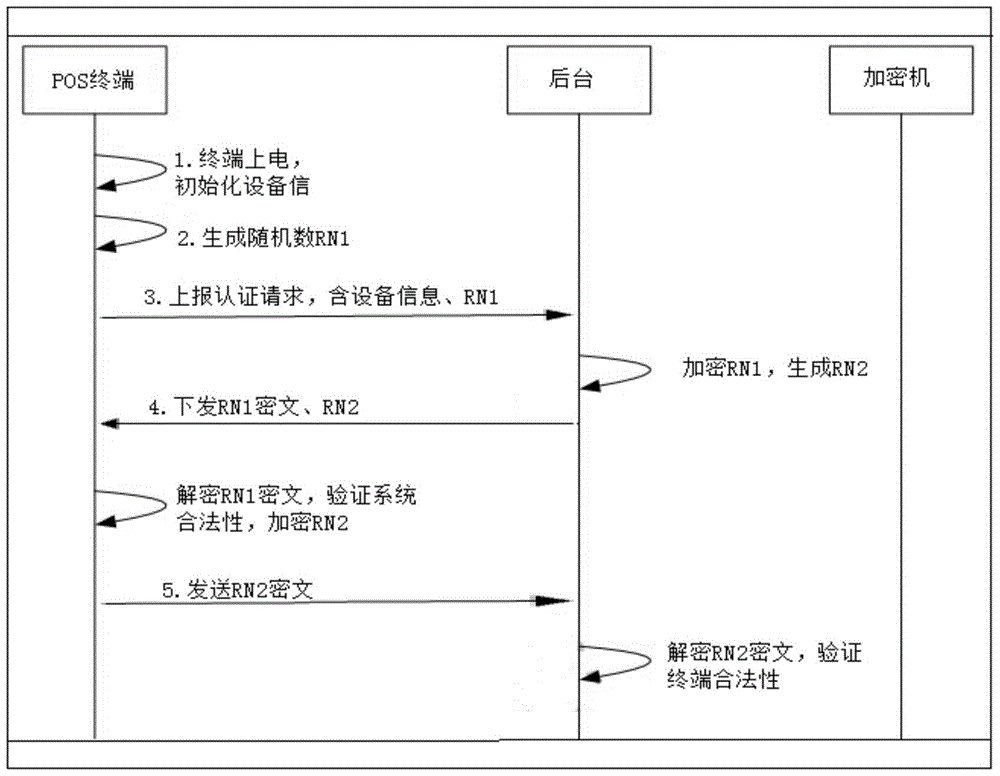
InactiveCN105743654ARealize dynamic updateSuitable for remote useKey distribution for secure communicationUser identity/authority verificationThree stageComputer module
The invention discloses a POS machine secret key remote downloading service system and secret key downloading method, and relates to the technique of POS machine information security. The whole scheme comprises seven components of a POS machine terminal, a security chip, a communication module, a random number generator, a secret storage region, a background server and an encryptor; wherein the security chip, the communication module, the random number generator and the secret storage region are contained in the POS machine terminal; the background server is directly connected with the encryptor; the POS machine terminal builds a remote communication channel with the background server through the communication module; and three stages of bidirectional authentication, master secret key issuing and working secret key issuing are successively finished. According to the system and the method, the features that the conventional POS machine secret key downloading method is low in efficiency, low in flexibility and difficult in secondary updating are overcome; the security demand is taken into consideration; high secret demands of one machine one key and one day one key are satisfied; the POS machine secret keys are dynamically updated; and the system and the method are applicable to remote use and rapid deployment of the POS machine.
Owner:DYNAMICODE
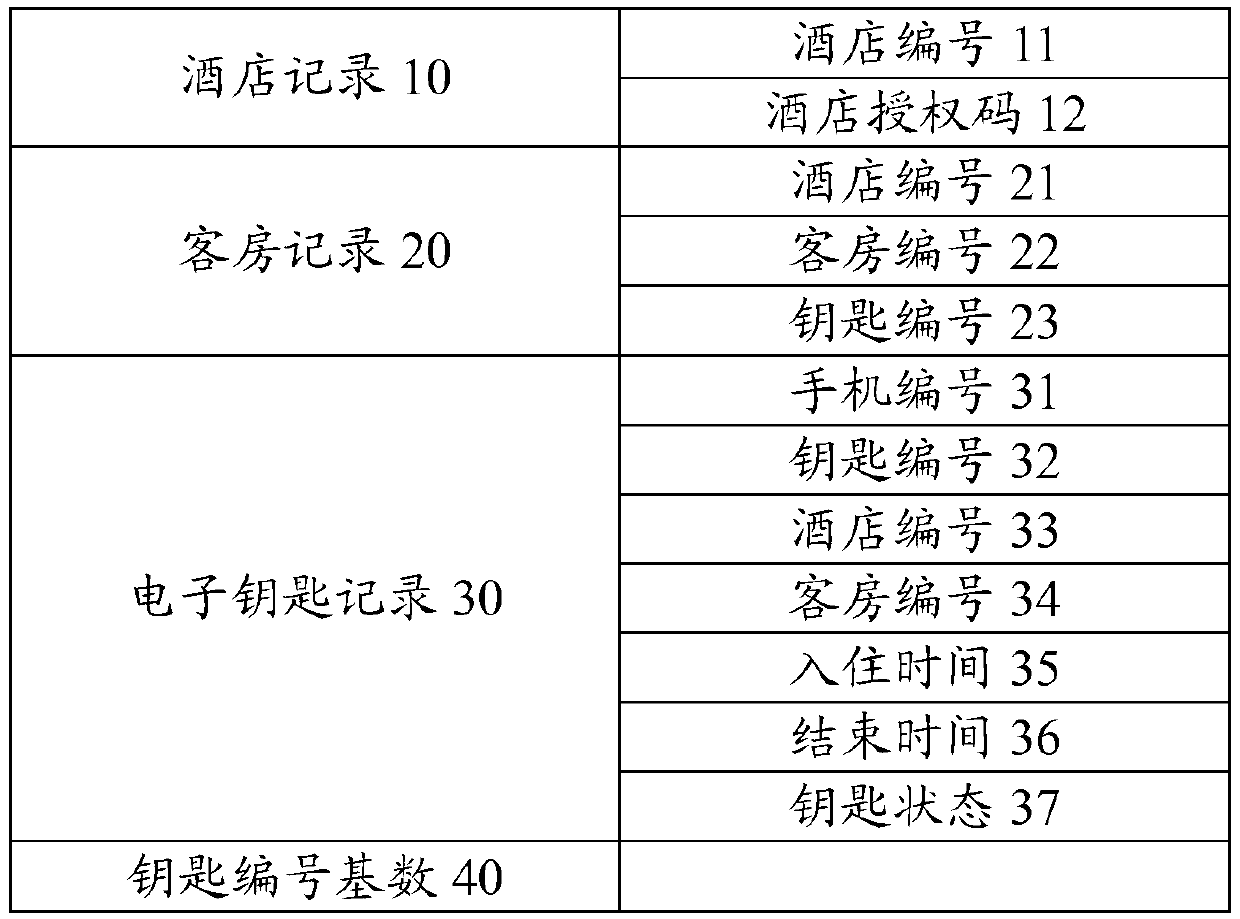
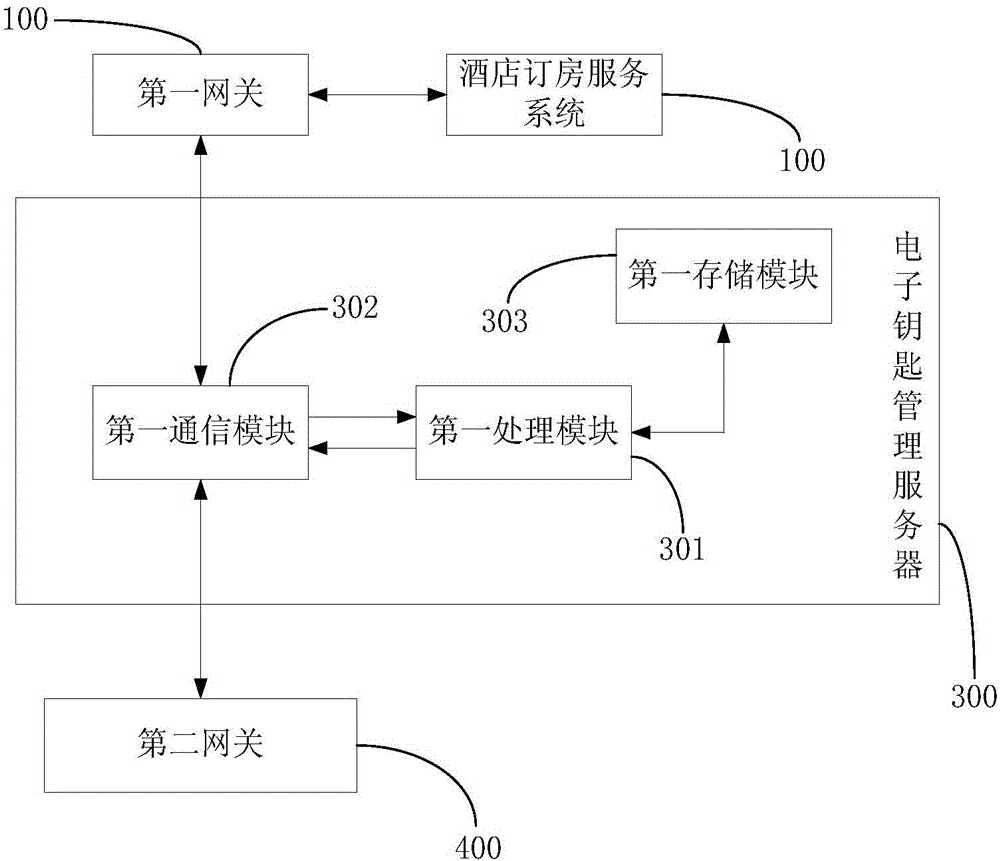
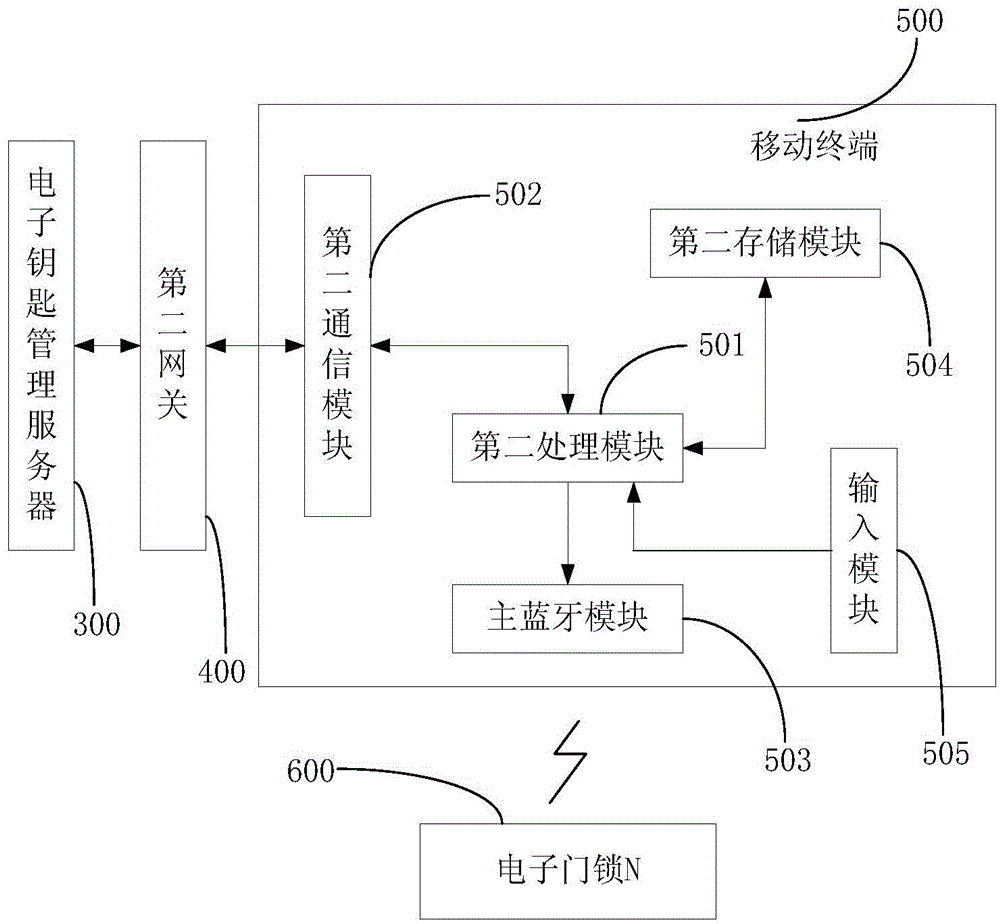
Hotel room management method and system based on electronic key management server
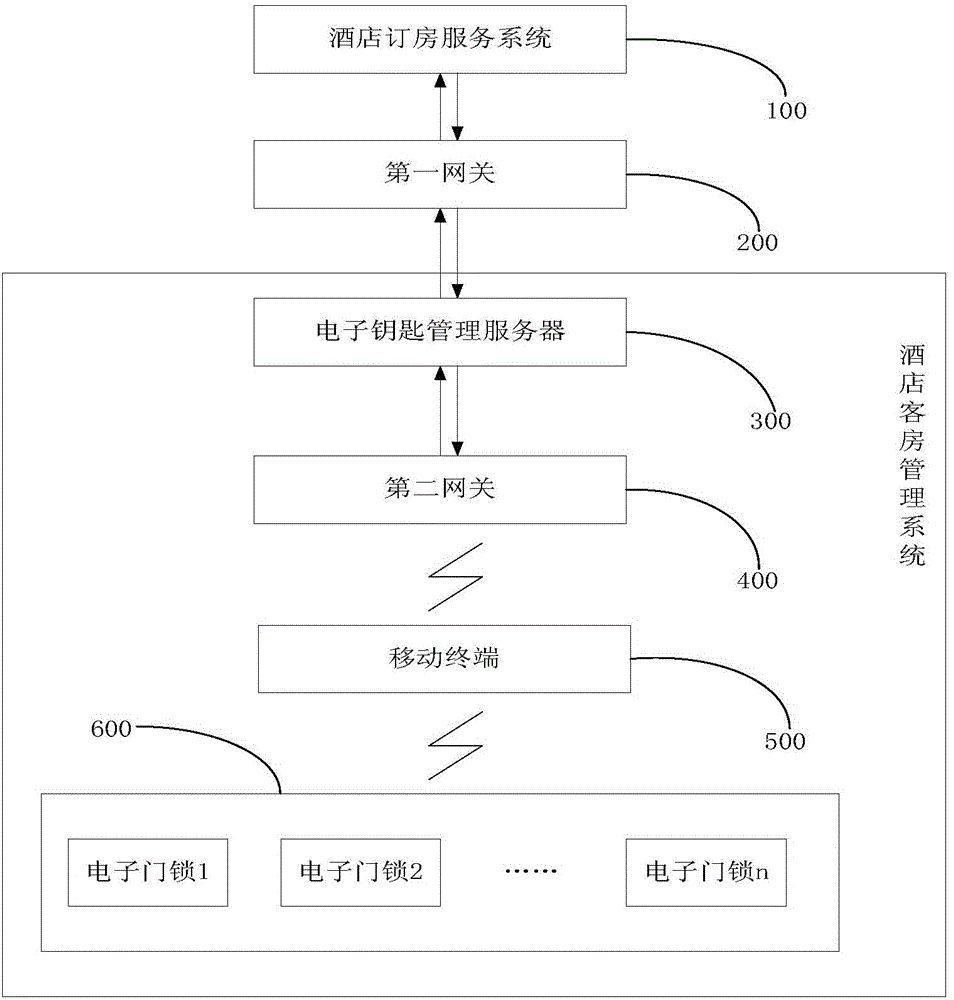
InactiveCN104063817AImprove management efficiencyNovelty processing experienceData processing applicationsLocking mechanismComputer module
The invention discloses a hotel room management method and system based on an electronic key management server. The system comprises the electronic key management server, a mobile terminal and a plurality of electronic door locks, wherein electronic key management server is used for generating an electronic key according to the electronic key issuing request of a hotel room booking service system; the mobile terminal is used for downloading the electronic key from the hotel electronic key management system, and setting the name of master Bluetooth module equipment according to the electronic key; the mobile terminal is further used for searching for a slave Bluetooth module having the same name as the master Bluetooth module equipment, issuing a pairing request to an electronic door lock into which the slave Bluetooth module is embedded in the door locks, and establishing Bluetooth connection with the electronic door lock when pairing is successful; the electronic door locks are used for receiving the electronic key of the mobile terminal through Bluetooth, and controlling a locking mechanism to perform unlocking operation when key recording information in the electronic key is valid key recording information.
Owner:SHENZHEN LOCSTAR TECH
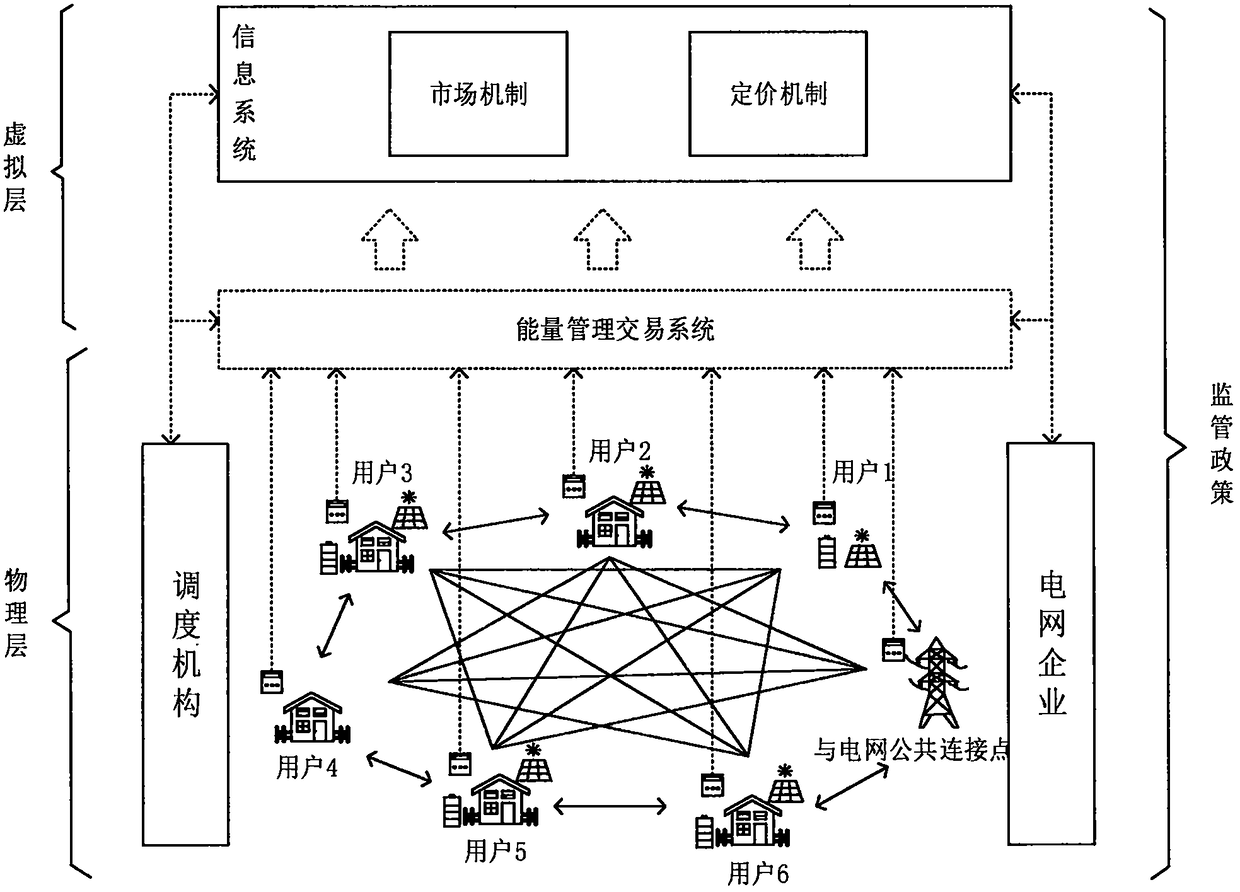
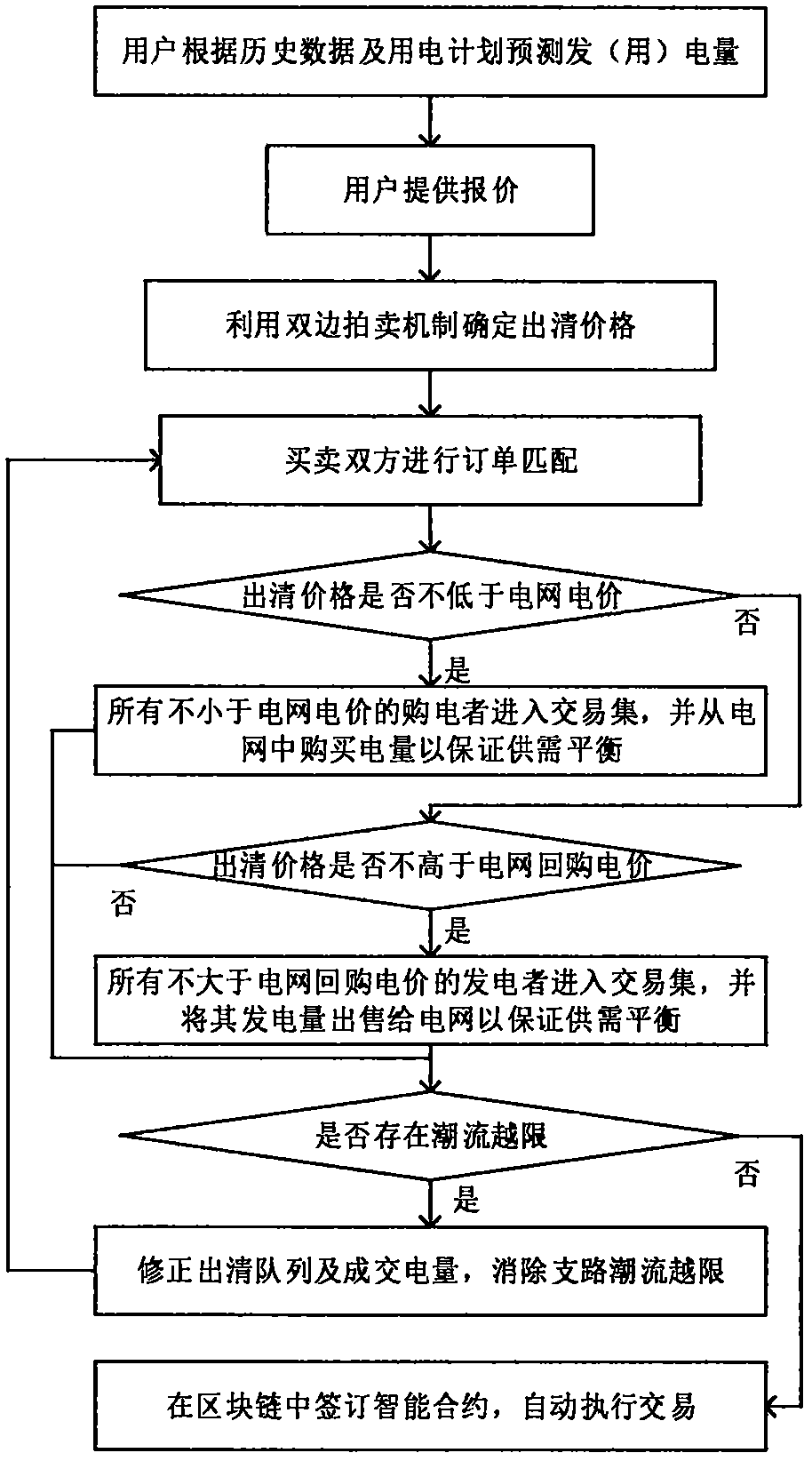
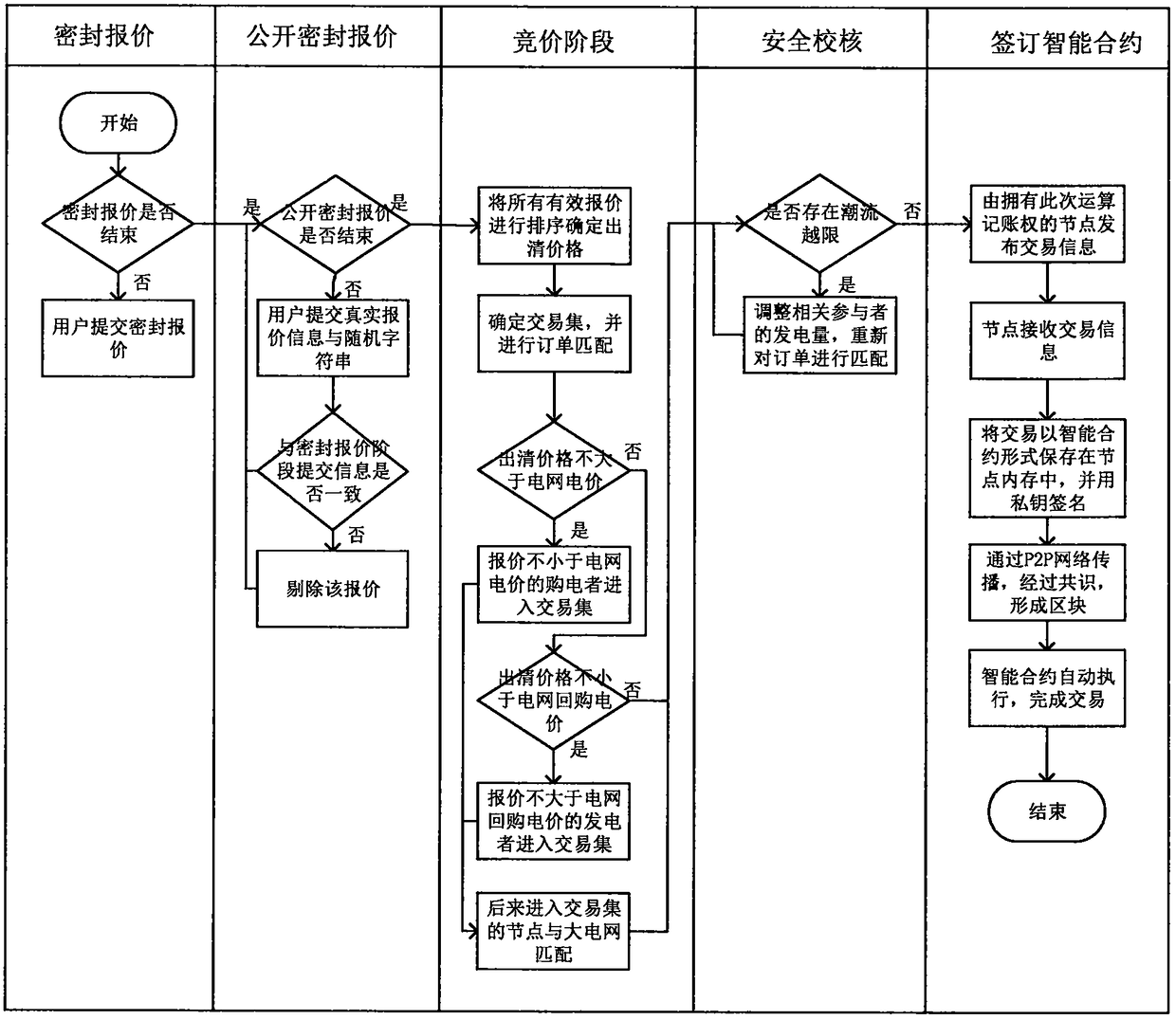
Microgrid power market decentralized transaction mechanism based on smart contract
The microgrid, which serves as an effective means for accessing distributed generation to the power grid, has gradually attracted wide attention. How to design an effective microgrid transaction mechanism and realize effective allocation of electric power resources is a key issue in the reformation of the electric power market. The invention designs a decentralized microgrid transaction mechanismand model. Both producers and consumers in the microgrid can initiate a real-time transaction request, and users are motivated to make rational bids by adopting bilateral auction rules; secondly, a microgrid operation method based on an Ethereum blockchain technology is proposed so as to ensure the transparency, openness and information symmetry of decentralized transactions, and the generation process and transaction settlement method of a smart contract for power transactions are described in detail.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
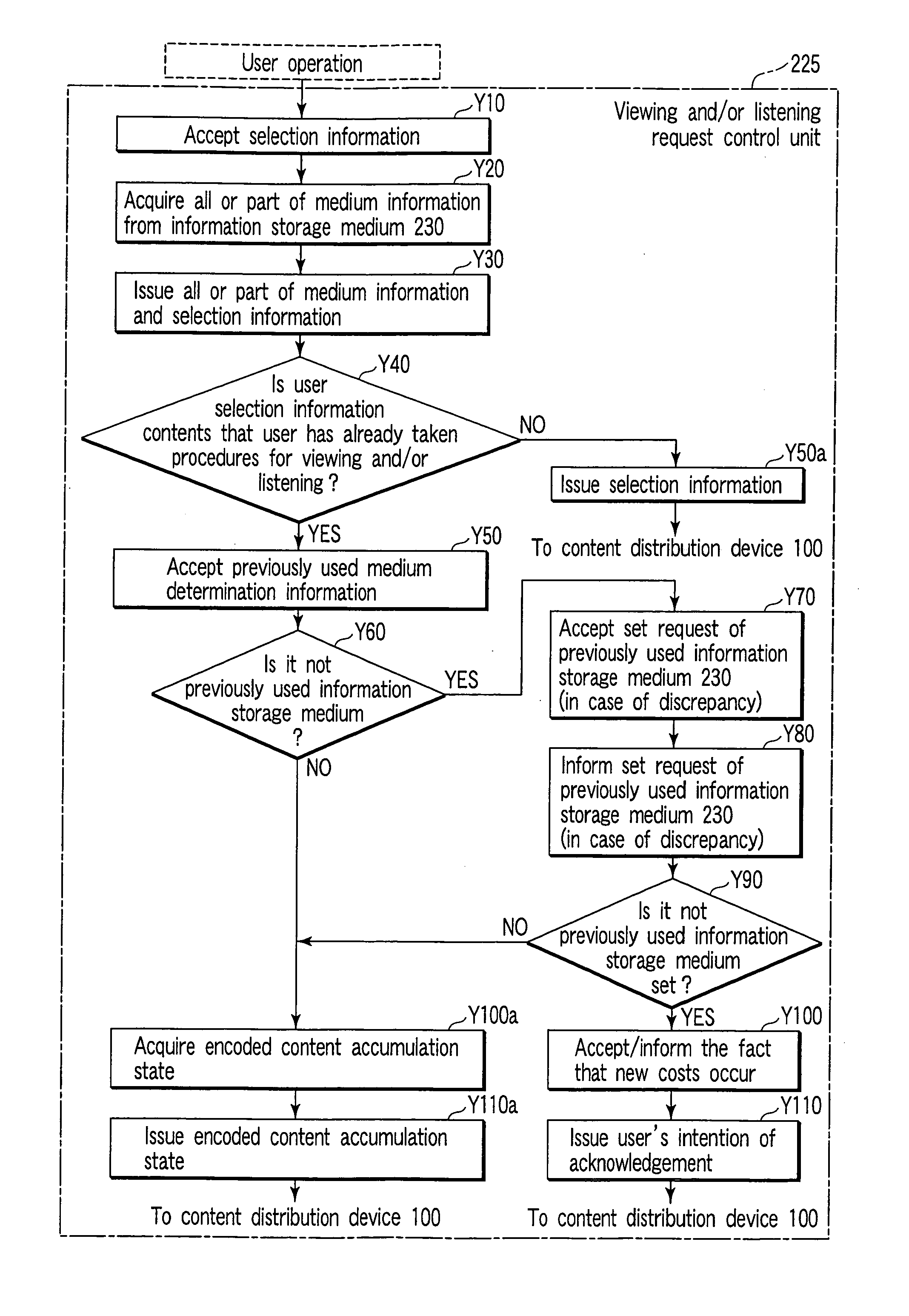
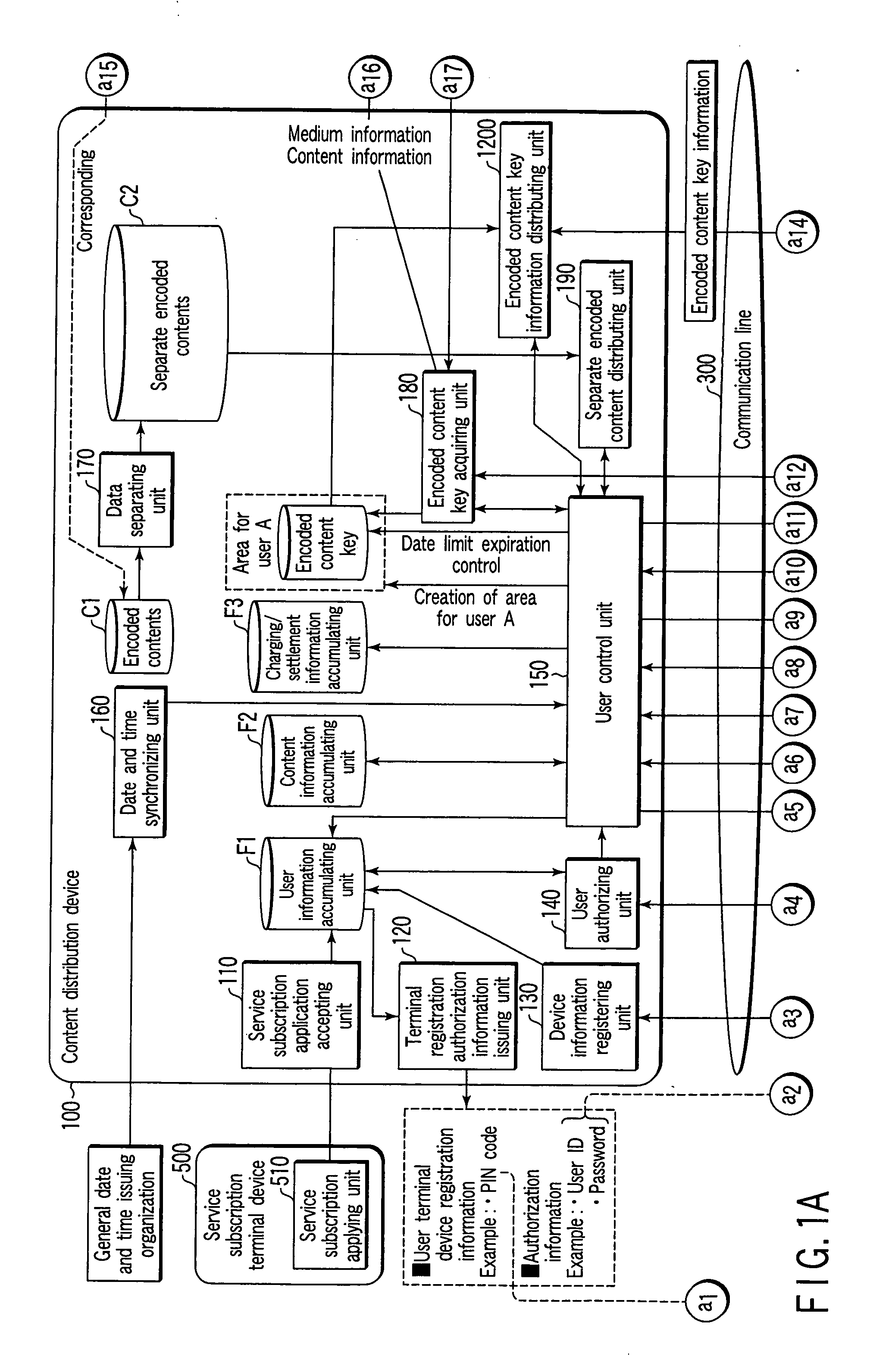
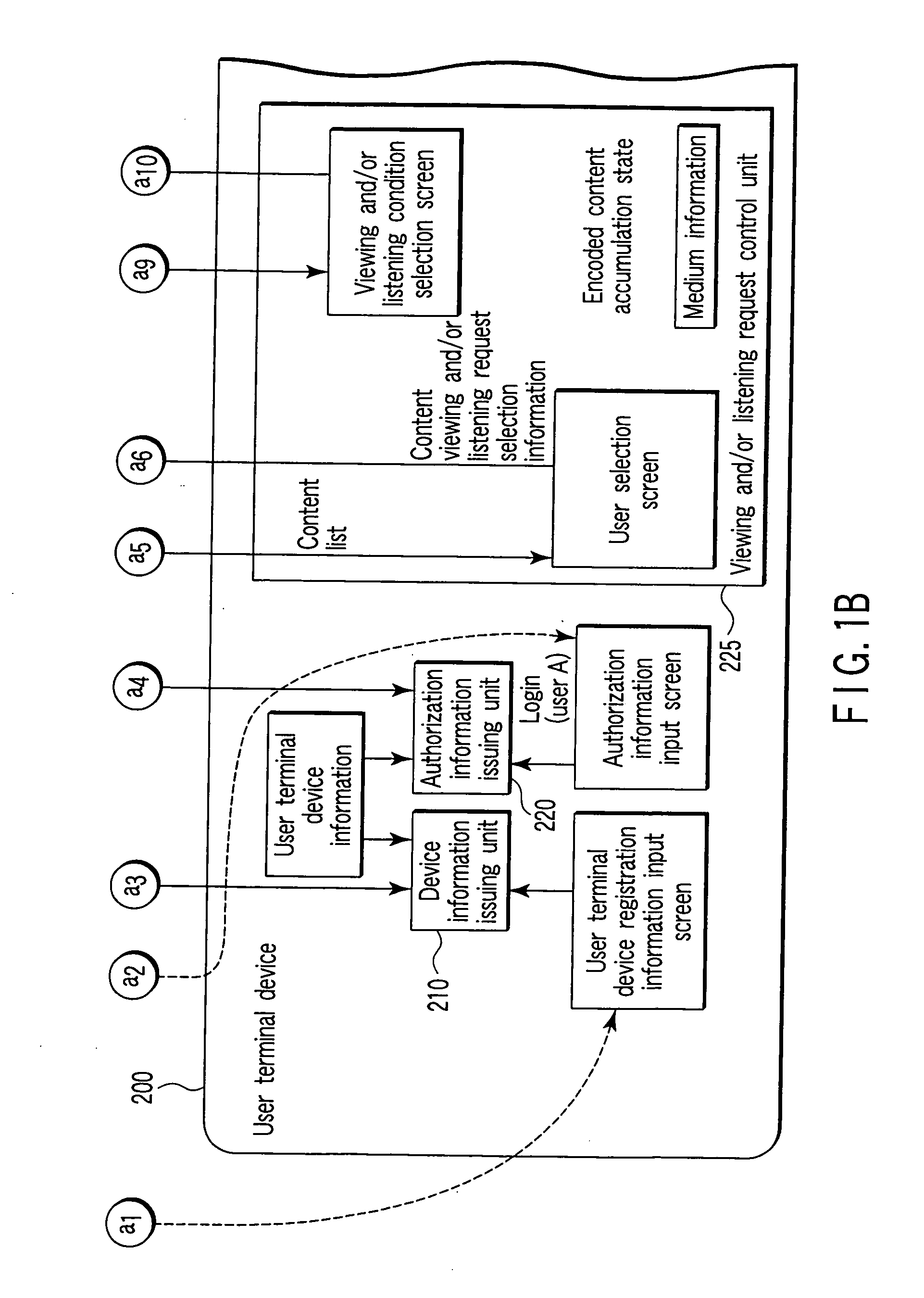
Content distribution service providing system and content distribution device and user terminal device thereof
InactiveUS20050171913A1Improve reliabilityStable viewingSpecial service provision for substationKey distribution for secure communicationContent distributionTerminal equipment
A content distribution device carries out distribution services of contents whose copyright protection is required via a communication line, to a user terminal device that enables to record contents to an information storage medium in which medium information is written, when receiving a content distribution request from the user terminal device, distributes a content list, and receives content selection information. At that moment, the content distribution device acquires the medium information from the user terminal device, sends this medium information to an encoded content key issuing device and receives an encoded content key based on the medium information concerned, and encodes contents by this encoded content key and distributes them to the user terminal device as distribution request source. The encoded content key is to be distributed at every viewing and / or listening request from the user terminal device, and when viewing and / or listening valid period expires, key distribution is stopped.
Owner:KK TOSHIBA
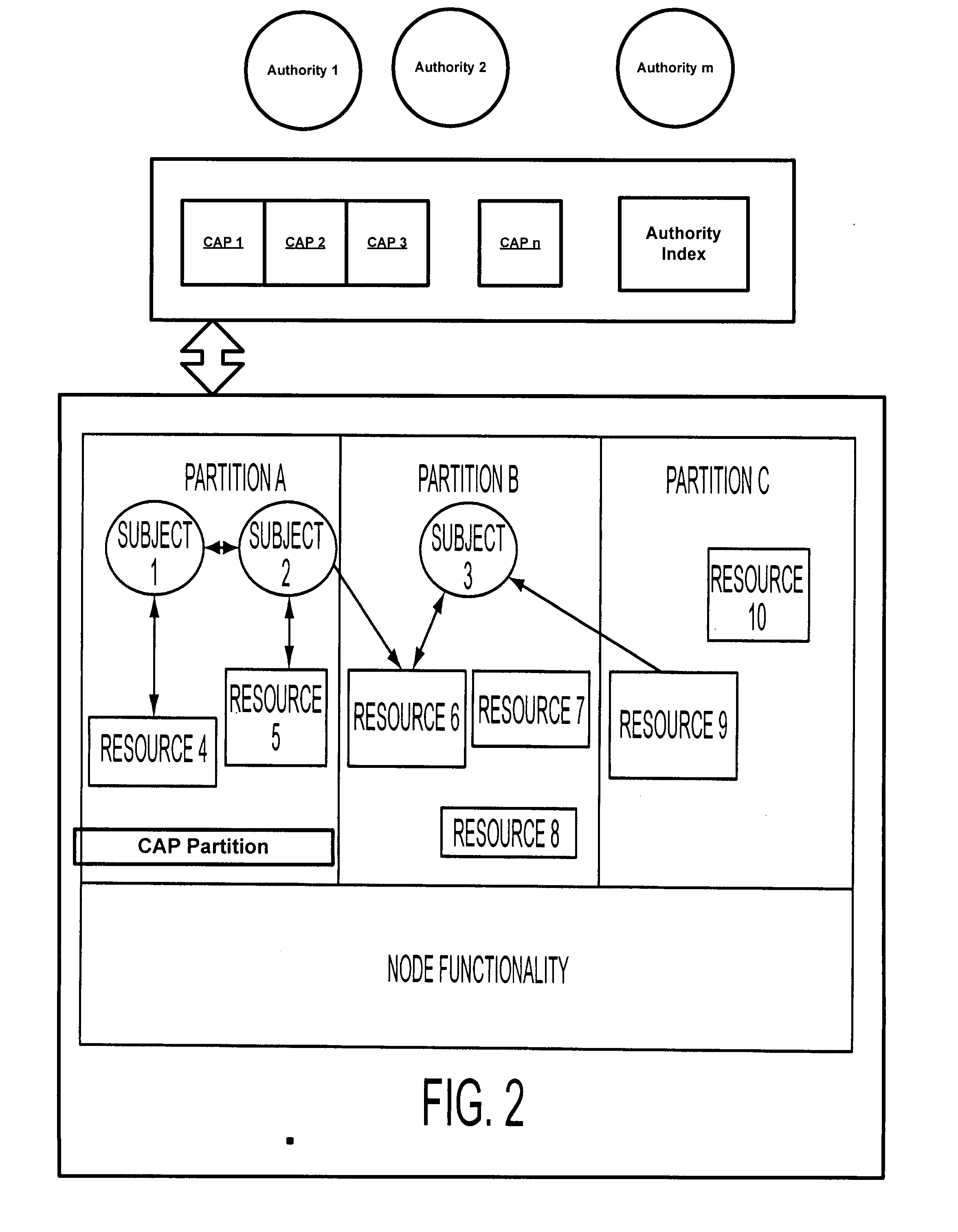
System and method for accessing information resources using cryptographic authorization permits
ActiveUS20080250253A1Digital data processing detailsUser identity/authority verificationDigital signatureInformation resource
A system and method for securing information associates a party with a node that communicates messages over one or more channels based on a channel access privilege. One or more authorities sign a cryptographic authorization permit (CAP) to authorize the channel access privilege, which can be a write privilege or a read privilege. In one embodiment, the authorization for the channel access privilege is based on a public key issued by an authority and the CAP comprises a cryptographic certificate digitally signed by the authority.
Owner:OBJECTIVE INTERFACE SYSTEMS
Distribution of session keys to the selected multiple access points based on geo-location of APs
ActiveUS8218512B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsGeolocationKey issues
In the public WLAN systems, reliable user re-authentication for mobility support is an essential step. However, re-authentication during handoff procedures causes long handoff latency which deteriorates the quality of service specifically for real-time multimedia applications. One possible solution is to authenticate the Mobile Node (MN) in advance with all the neighboring Access Points (APs) and distribute the Session Keys to them. However, the key issue is how to optimally and efficiently select the neighboring APs. In the preferred embodiments, we propose a system that takes into account the user current “Geo-Location”, “Mobility Pattern” and “Application Running on MN”; estimates the “Expected Mobility Zone” (EMZ) and selects an appropriate set of candidate APs corresponding to the MN's geo-location. The EMZ may comprise of APs belonging to “Intra-domain”, “Inter-domain” or “Inter-technology Networks” (e.g., WLAN, WiMAX, and Cellular etc). The system assumes that not only the Mobile Nodes but also the Fixed Nodes (APs or Base Stations) are capable of knowing their Geo-Location Coordinates X, Y, Z. This capability may come either by integrating GPS receiver or through any other alternate, state of the art or future positioning technologies in the APs.
Owner:FOUR BATONS WIRELESS LLC +1
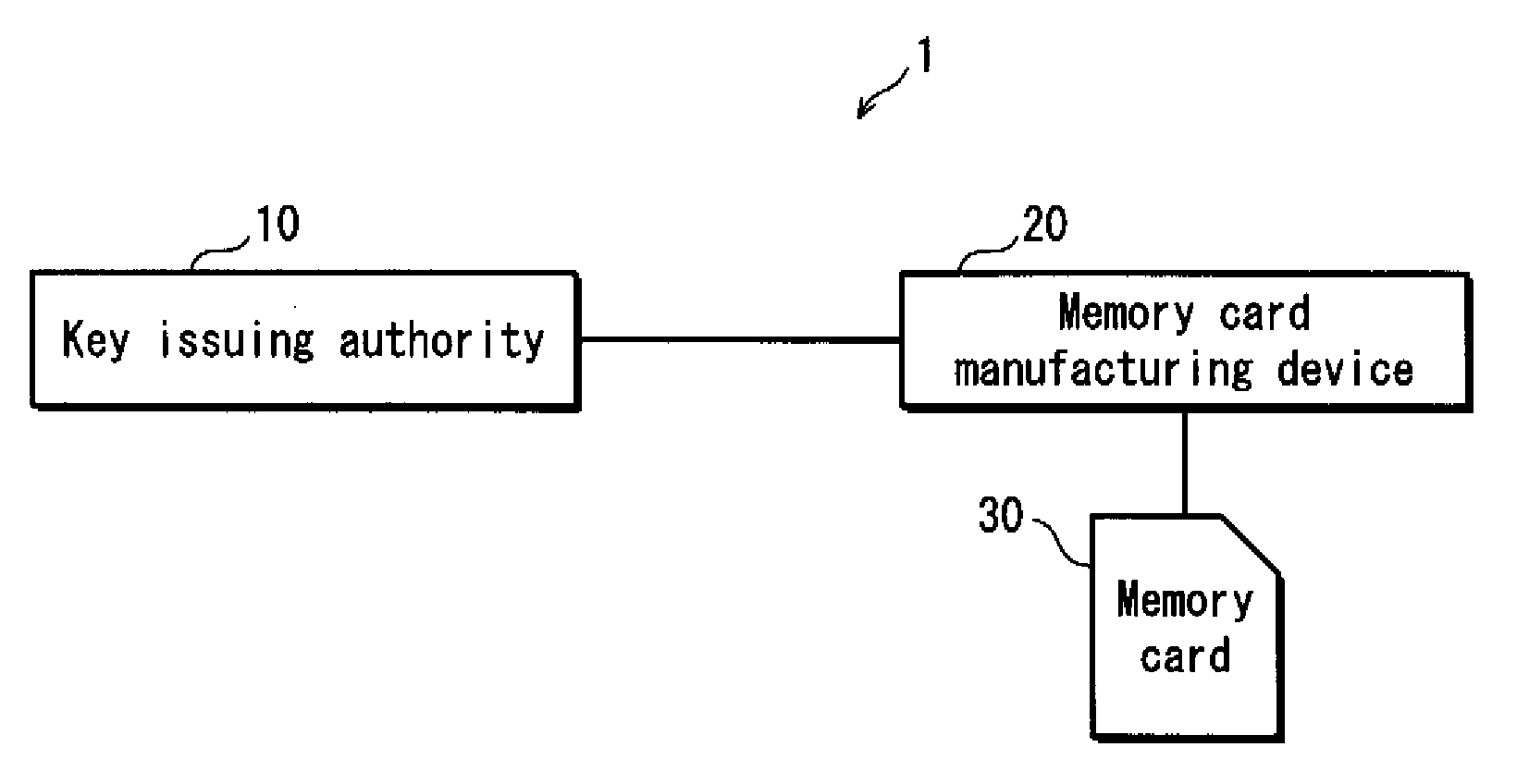
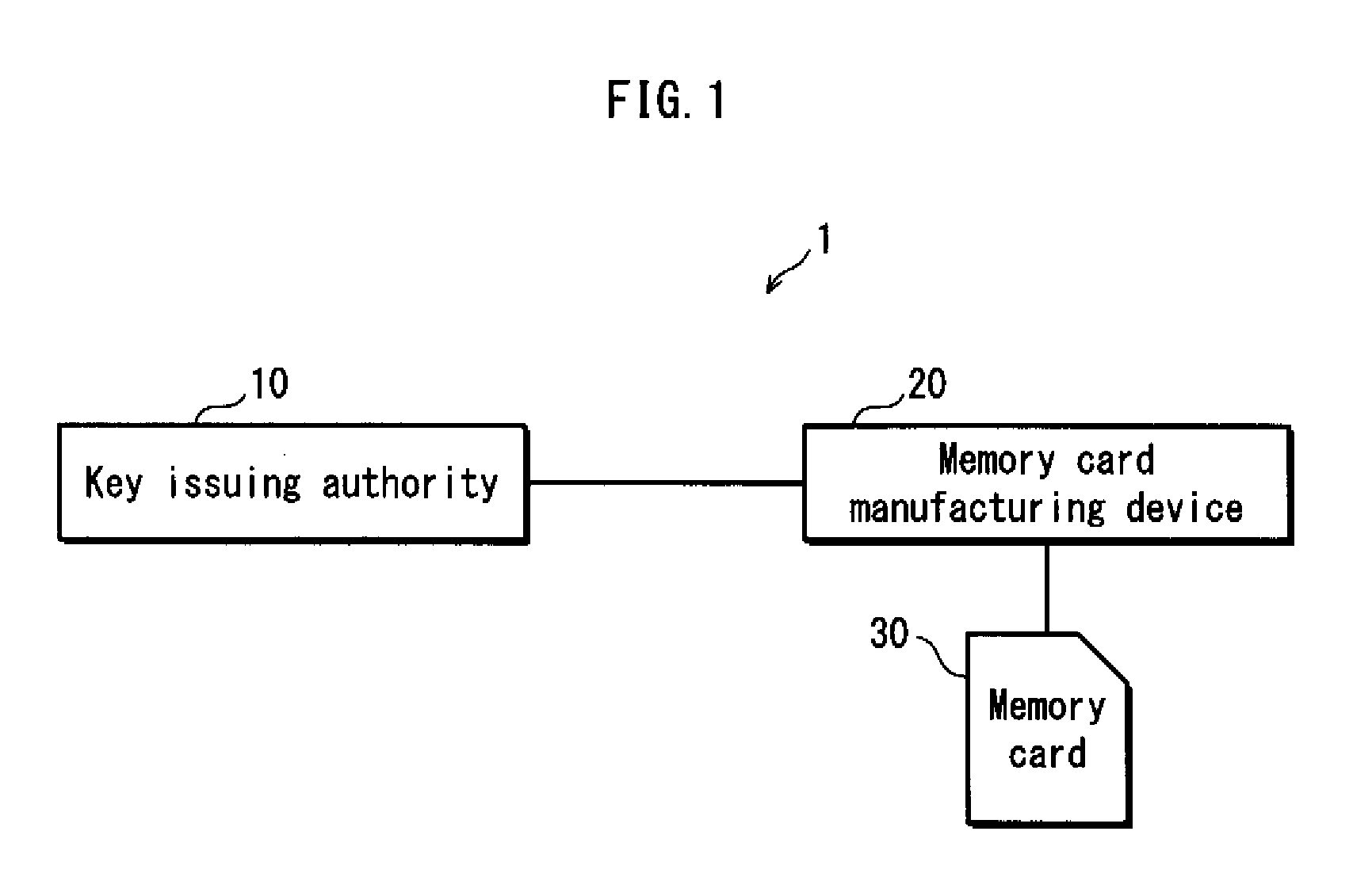
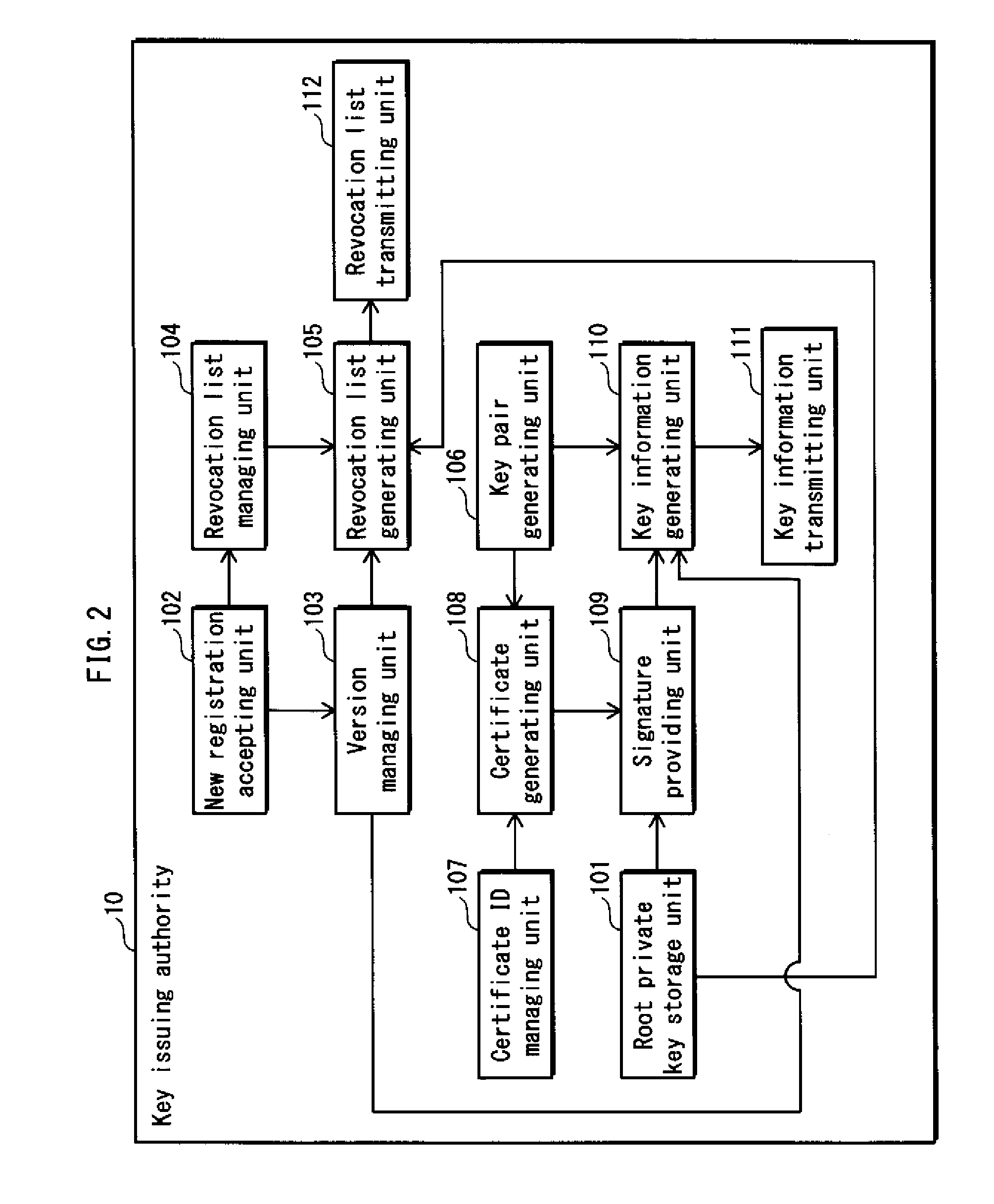
Information processing device, controller, key issuing authority, method for judging revocation list validity, and key issuing method
ActiveUS20120023329A1Avoid makingUser identity/authority verificationDigital data protectionInformation processingKey issues
A memory card 30 includes a storage unit 302 storing key information and version information in association with the key information, the key information and the version information being issued by a key issuing authority, and the version information indicating a version of the latest revocation list that has been issued when the key information is generated; a revocation list receiving unit 304 that receives a revocation list having a version; a version verification unit 308 operable to compare the version of the revocation list received by the revocation list receiving unit 304 and the version information; and a revocation list writing unit 309. When the version of the revocation list is older than version information, processing by the revocation list writing unit 309 is prohibited.
Owner:PANASONIC CORP
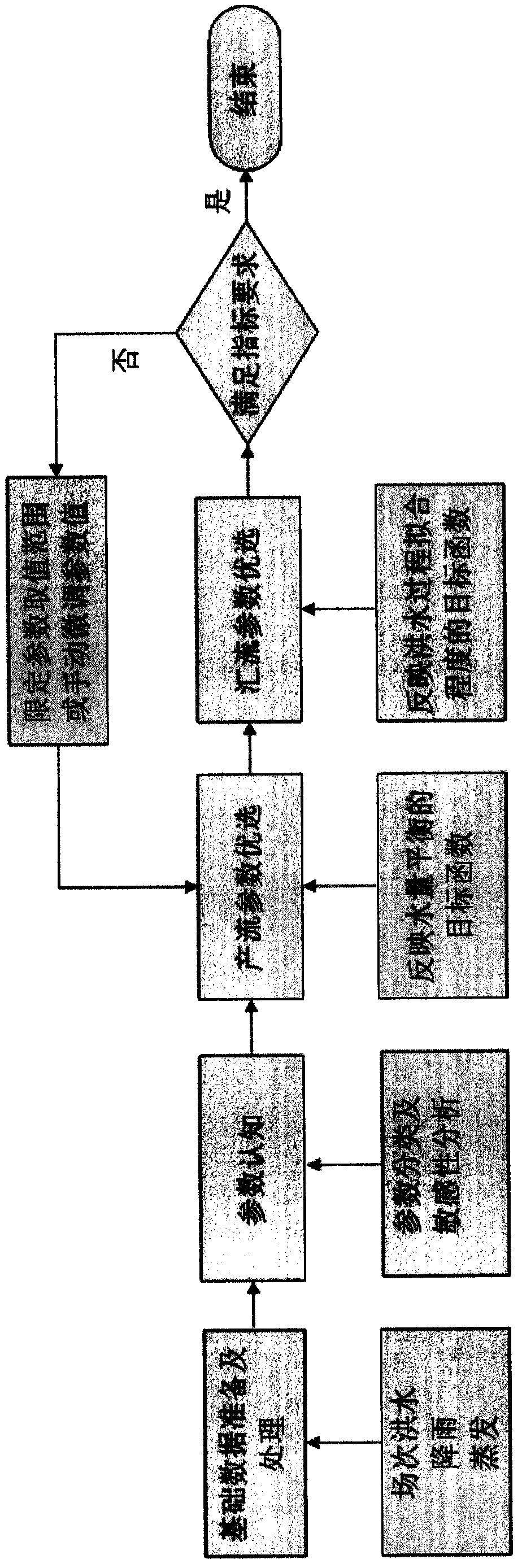
Basin hydrologic model parameter calibration method
InactiveCN108345735AImprove forecast accuracyClimate change adaptationDesign optimisation/simulationKey issuesData preparation
The invention provides a basin hydrologic model parameter calibration method. The method is characterized in that focusing on the key issue of conceptual model parameter calibration, the process is divided into the three steps of basic data preparation and processing, parameter cognition and parameter optimization, wherein during basic data preparation and processing, for a lumped hydrologic model, special attention needs to be paid to analysis of periodical floods, and the floods need to be classified according to different rainfall central positions and flood magnitudes to be selectively used for parameter optimization; parameter cognition aims to clarify the influence of a value change of each parameter on the hydrologic process, which is the most basic to model application; and duringparameter optimization, parameters are divided into runoff producing parameters and converging parameters for step-by-step optimization, and an appropriate objective function needs to be selected according to an expected goal at each optimization stage, which can ensure that an optimization result meets water balance while meeting flood process similarity, and optimization efficiency is improved.
Owner:YUNFENG POWER PLANT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com