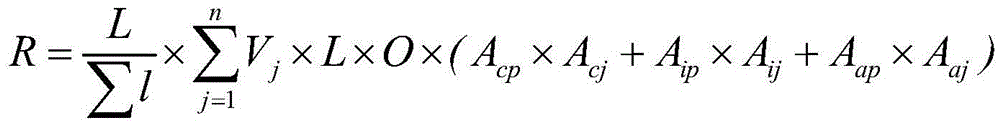Patents
Literature
156 results about "Assessment evaluation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
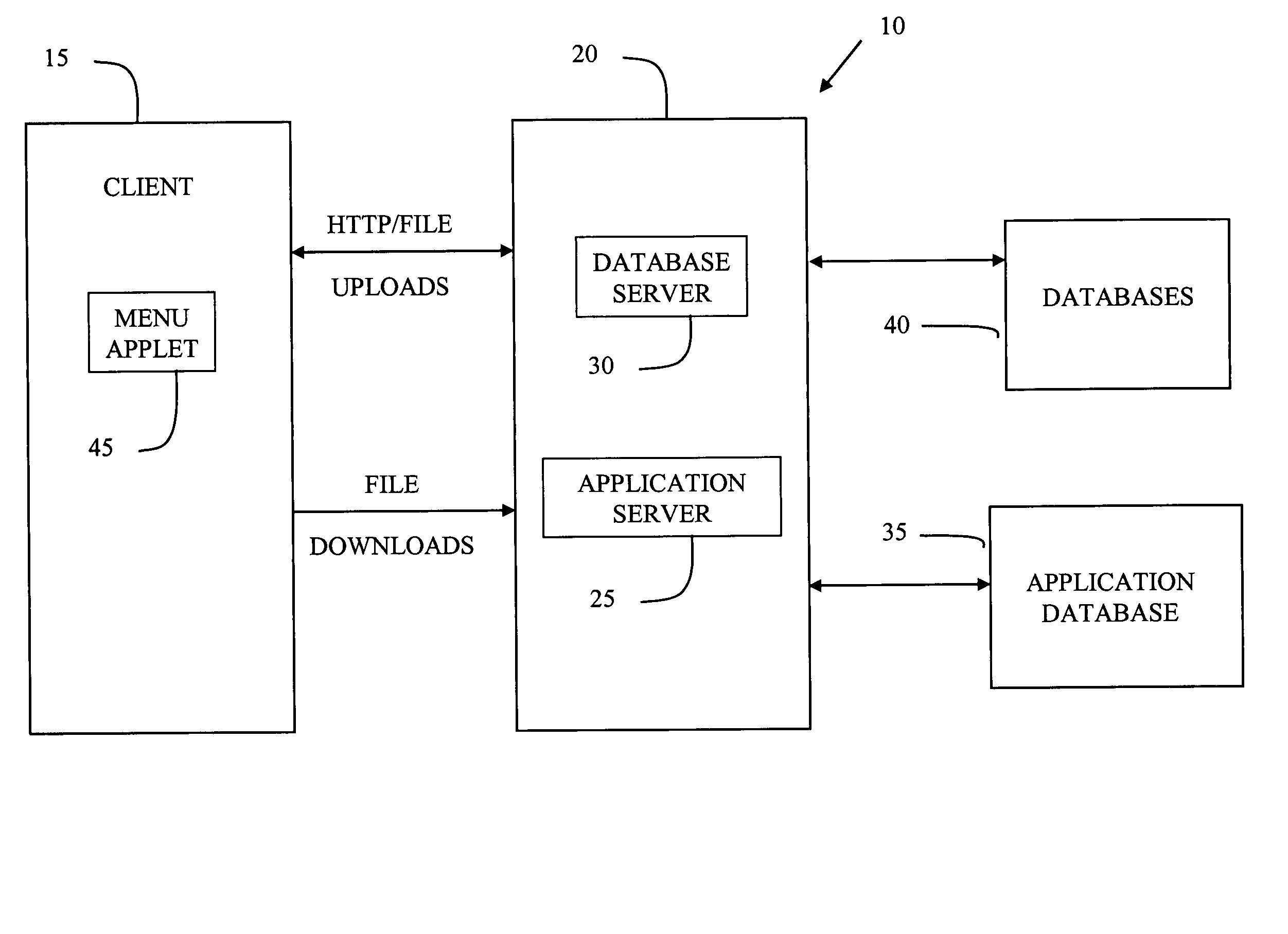
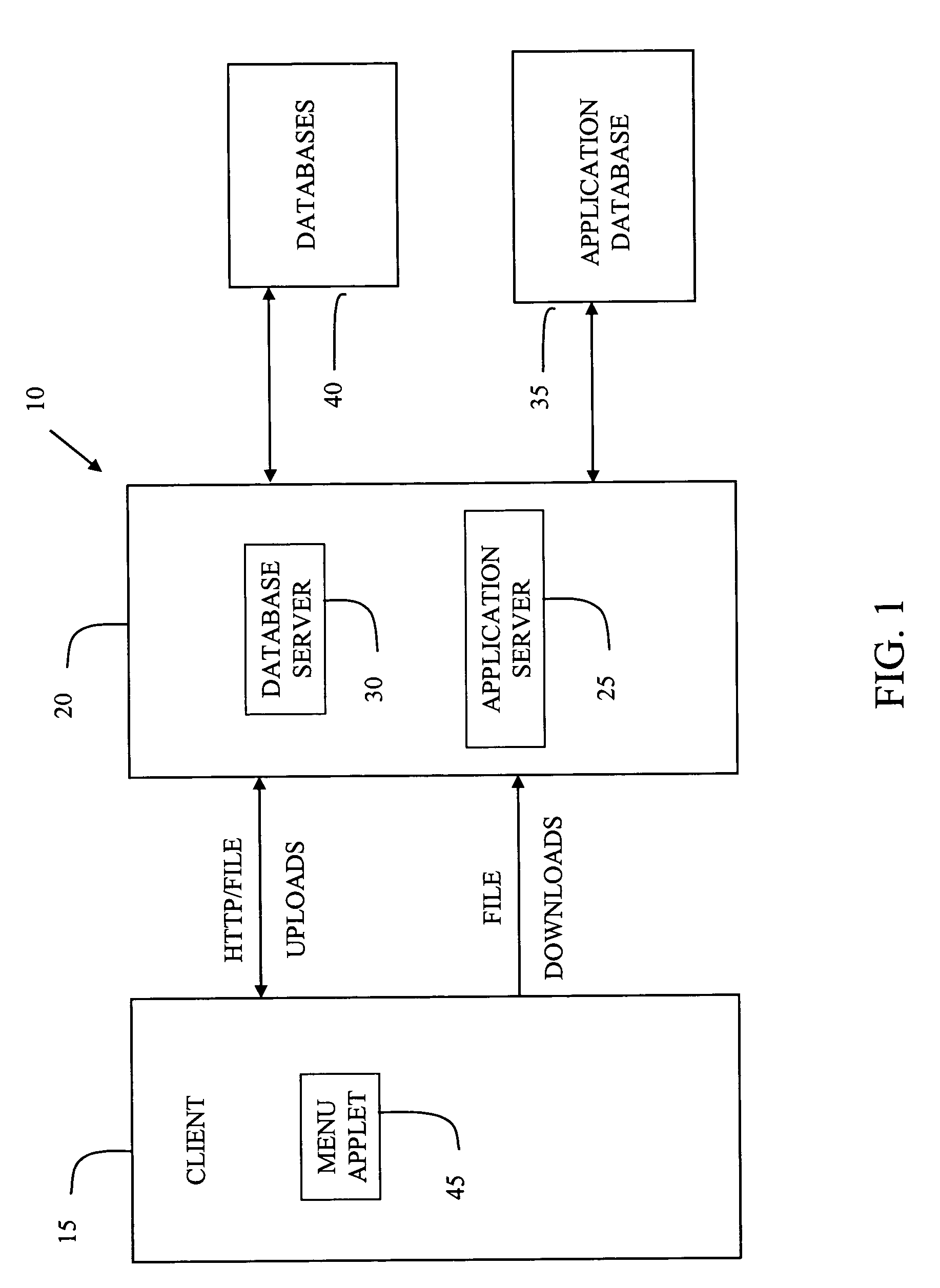
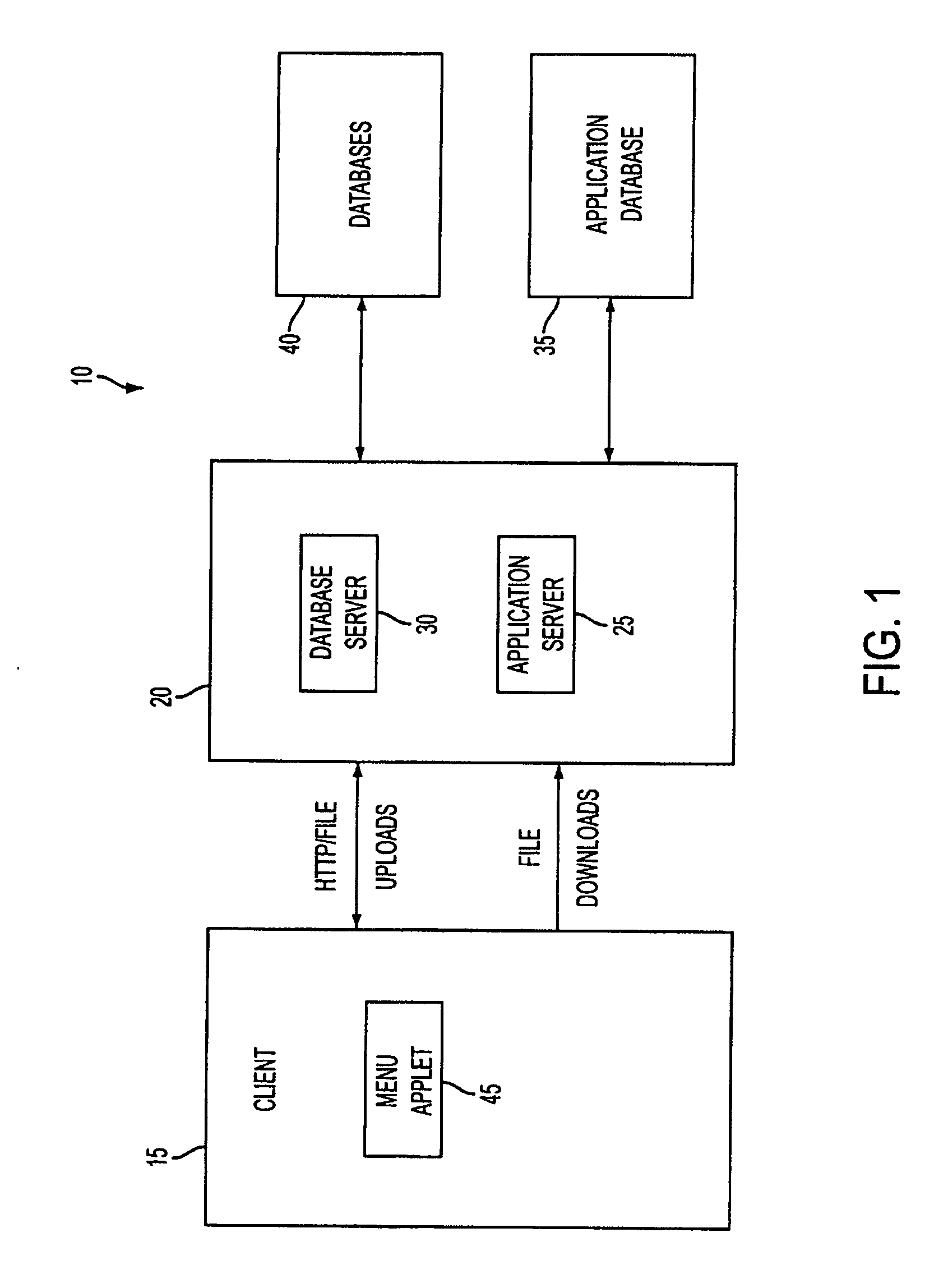
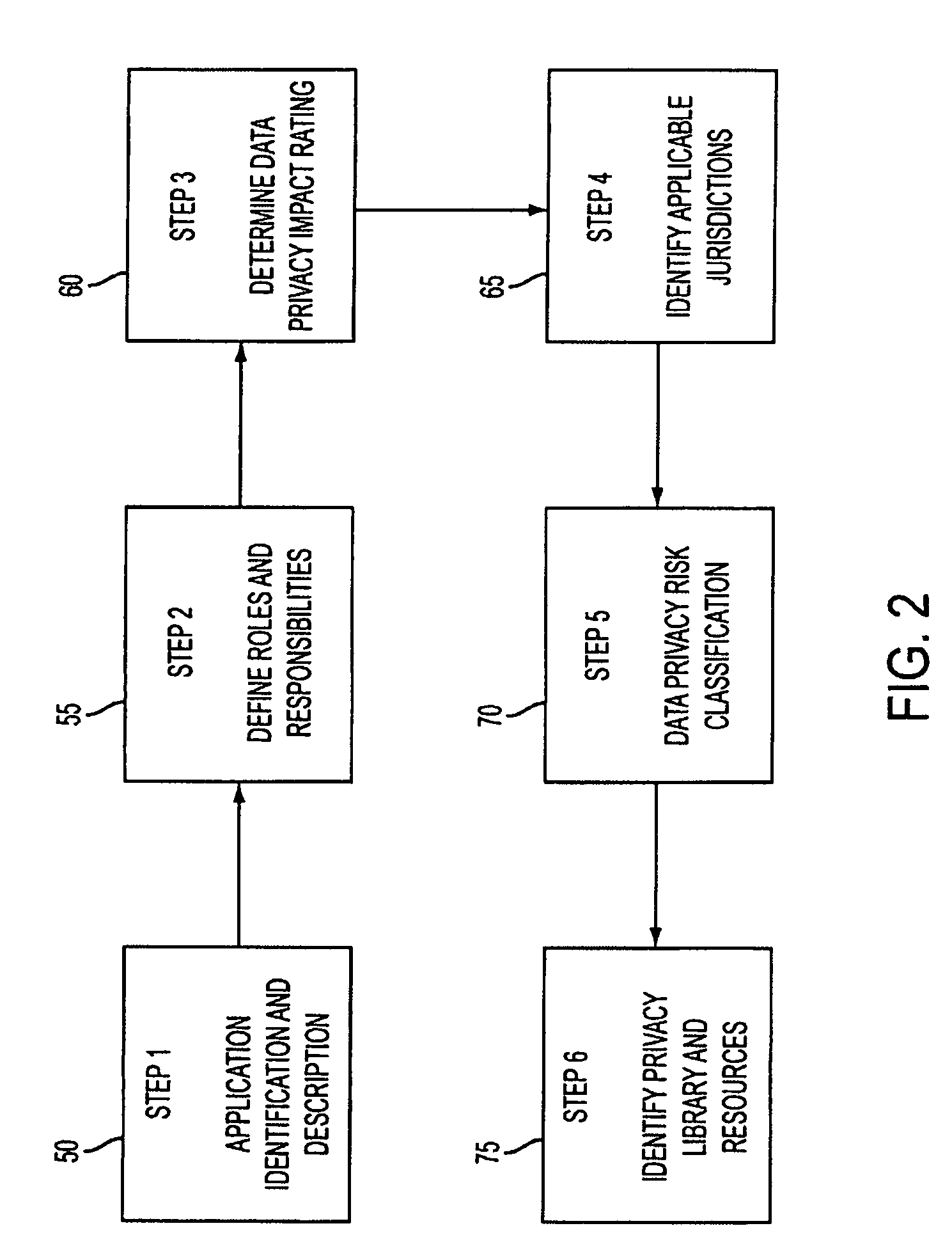
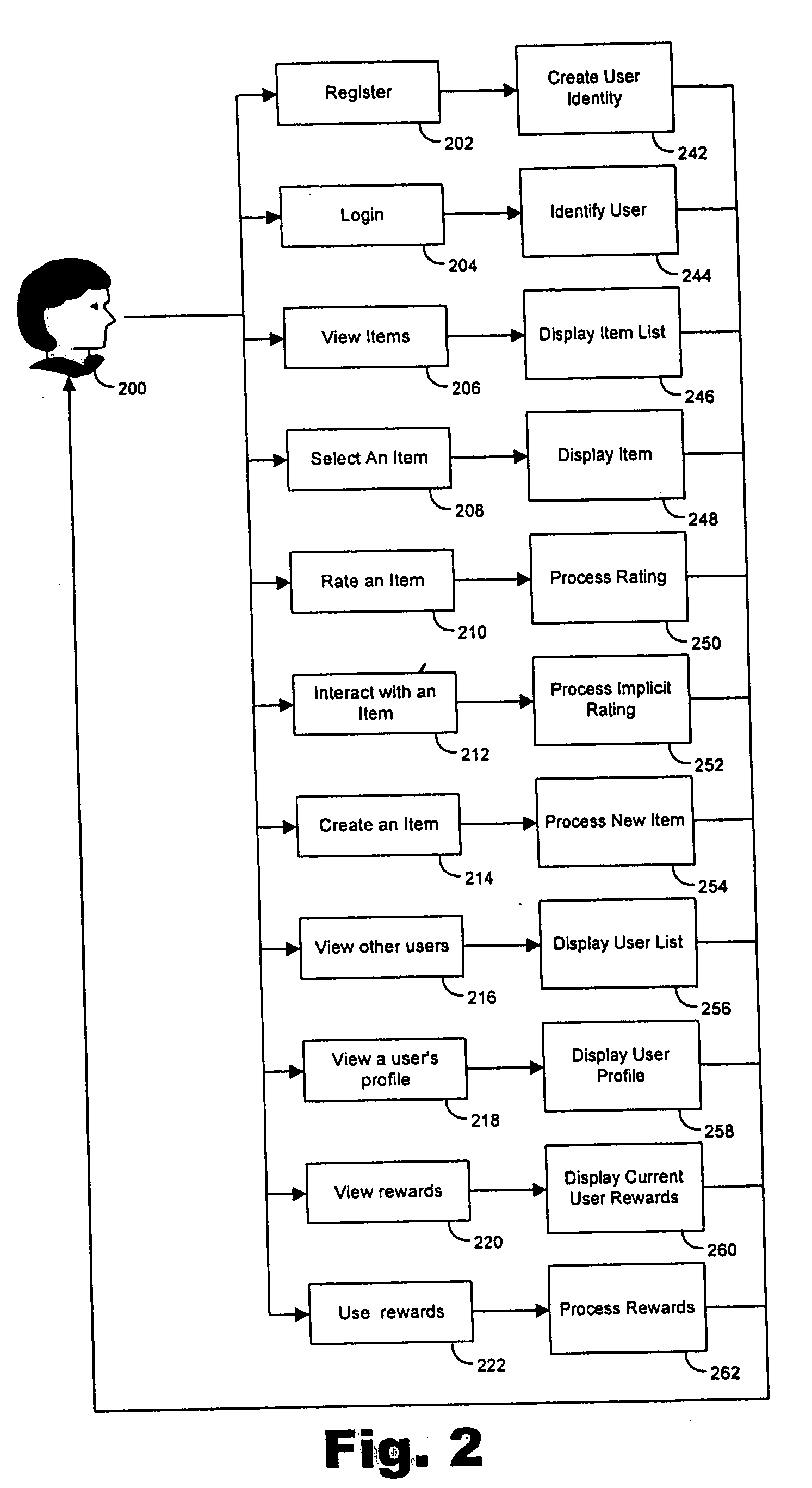
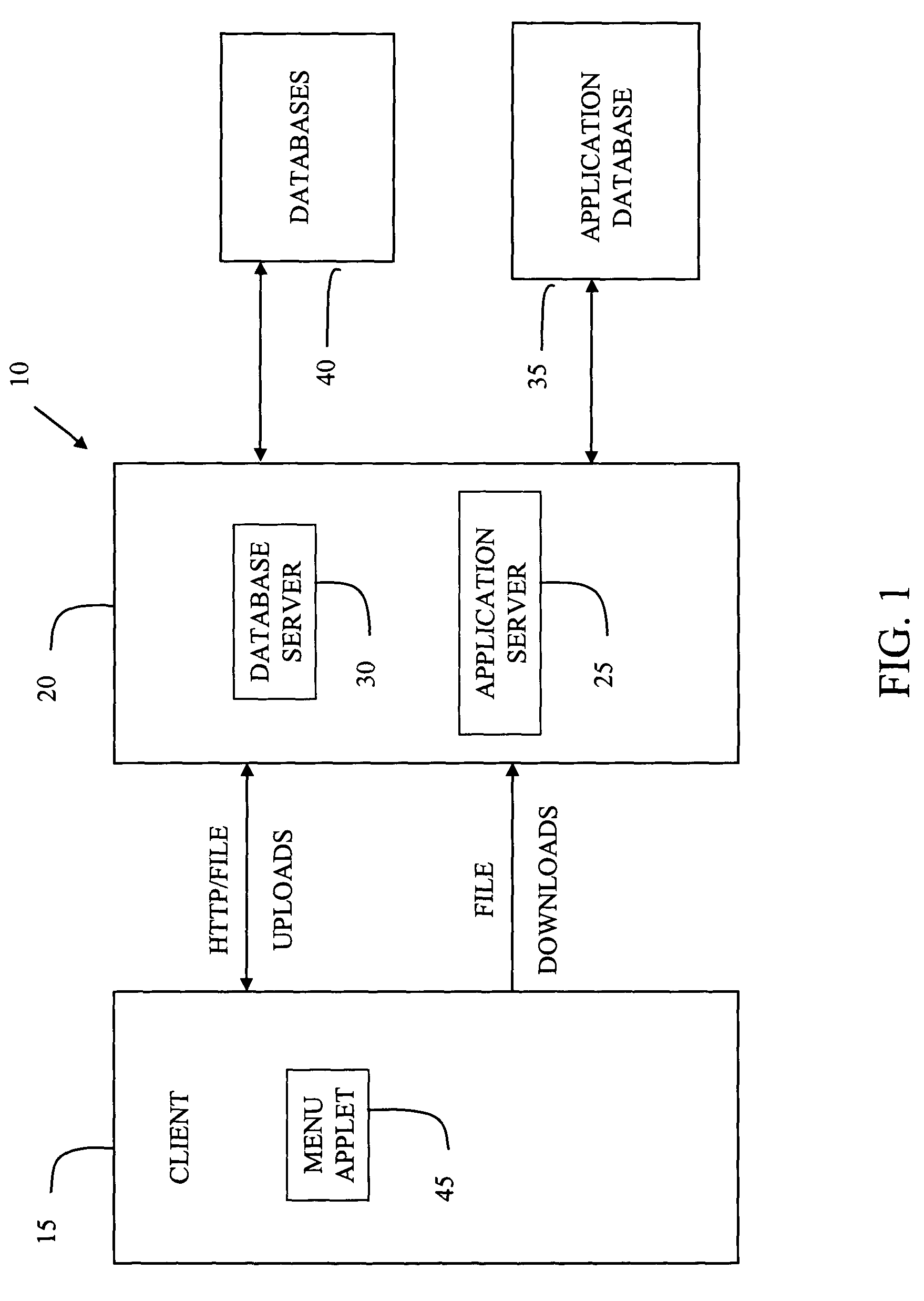
System and method for managing data privacy
ActiveUS7234065B2Easy to manageSpeed up the processUser identity/authority verificationUnauthorized memory use protectionInternet privacyKey issues
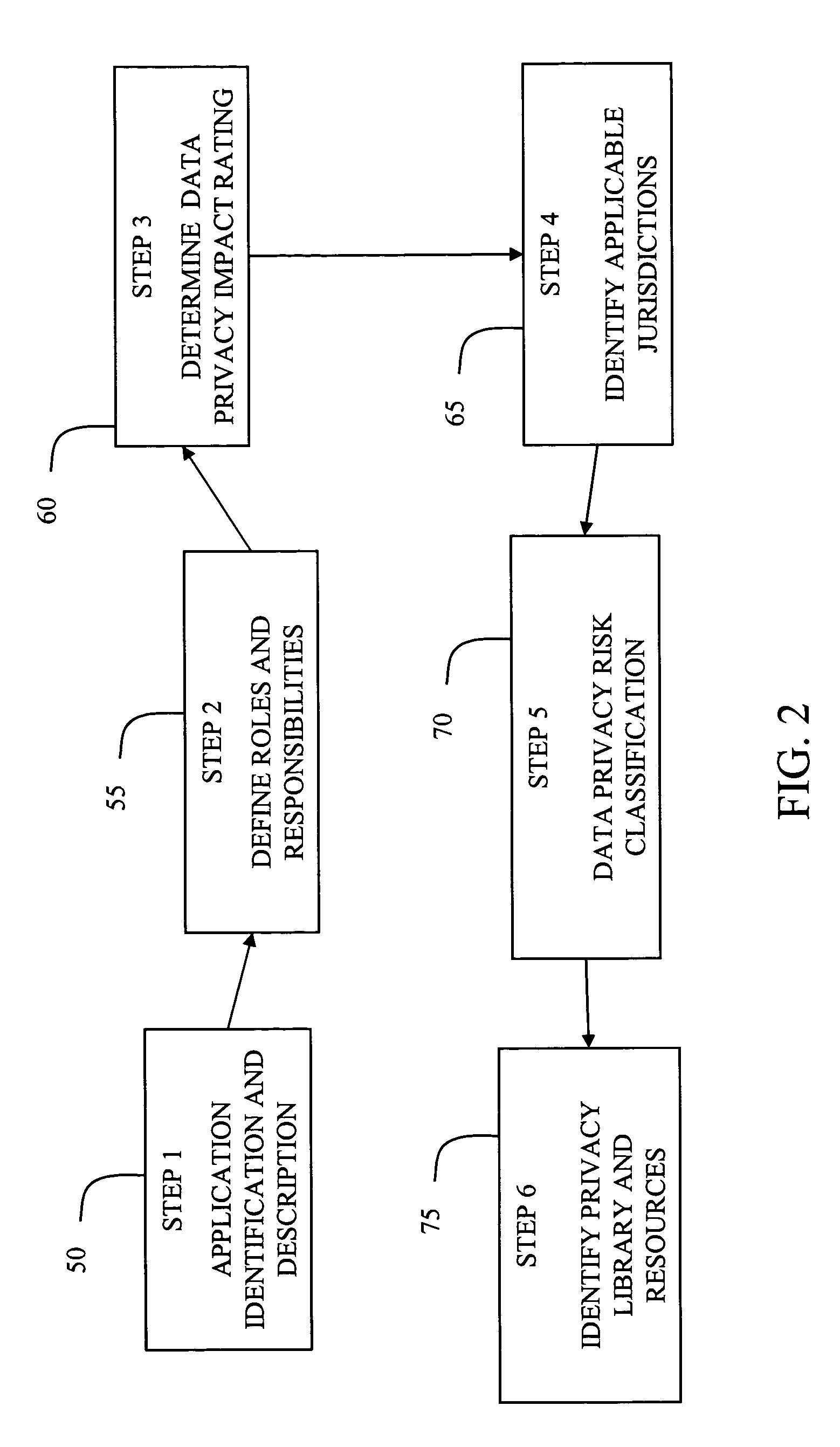
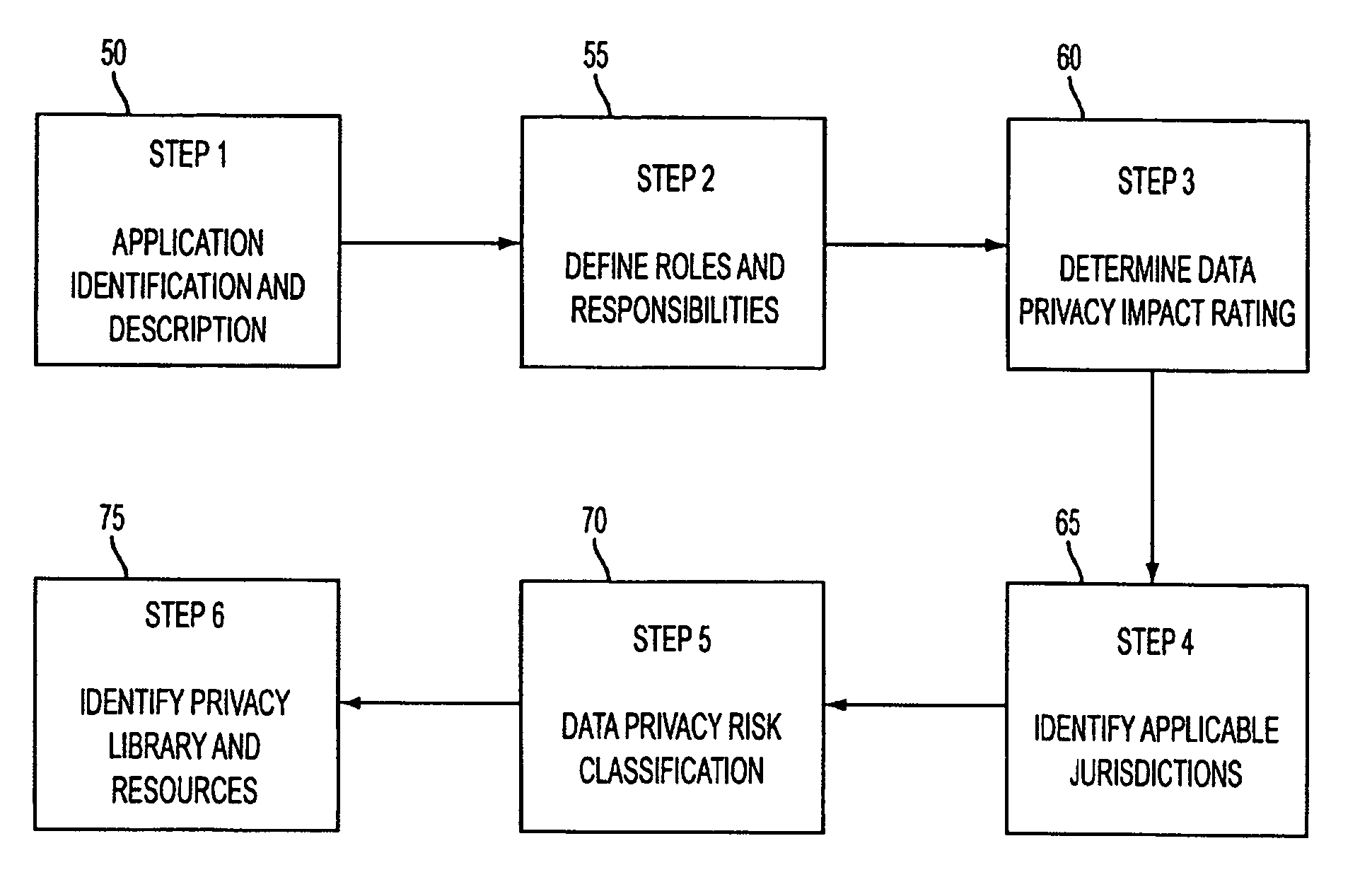
A system and method for assessing the risk associated with the protection of data privacy by software application. A decision engine is provided to assess monitor and manage key issues around the risk management of data privacy. The system creates a core repository that manages, monitors and measures the data privacy assessments of applications across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager responsible for the application). The responses are tracked in order to evaluate the progress of the assessment and the status of the applications with respect to compliance with the enterprise's data privacy policies and procedures as well as the regulations and laws of the jurisdictions in which the application is operated. Once a questionnaire has been completed, the application is given ratings both with respect to the data privacy impact of the application and the application's compliance with the data privacy requirements. If a risk exists, a plan for reducing the risk or bringing the application into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be acknowledged through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
System and method for managing data privacy
InactiveUS20070283171A1Easy to manageSpeed up the processUnauthorized memory use protectionHardware monitoringInternet privacyKey issues
A system and method for assessing the risk associated with the protection of data privacy by software application. A decision engine is provided to assess monitor and manage key issues around the risk management of data privacy. The system creates a core repository that manages, monitors and measures the data privacy assessments of applications across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager responsible for the application). The responses are tracked in order to evaluate the progress of the assessment and the status of the applications with respect to compliance with the enterprise's data privacy policies and procedures as well as the regulations and laws of the jurisdictions in which the application is operated. Once a questionnaire has been completed, the application is given ratings both with respect to the data privacy impact of the application and the application's compliance with the data privacy requirements. If a risk exists, a plan for reducing the risk or bringing the application into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be acknowledged through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
System and method for measuring rating reliability through rater prescience
InactiveUS20040225577A1Discounts/incentivesSpecial data processing applicationsDependabilityData mining
Owner:TRANSPOSE
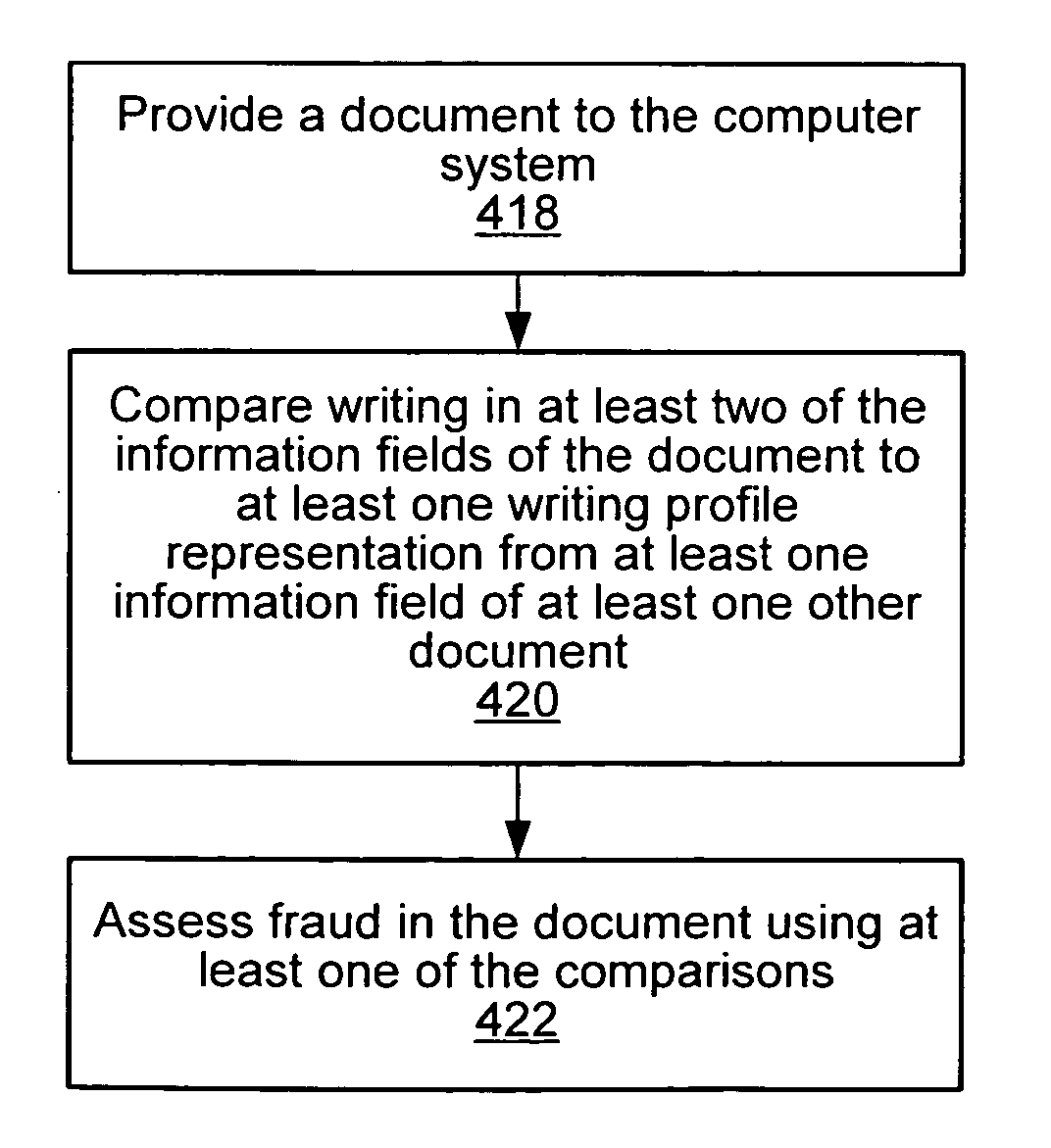
Systems and methods for handwriting analysis in documents
InactiveUS20040218801A1Character recognitionSignature reading/verifyingNatural language processingHandwriting
Methods and systems are provided for analyzing and assessing documents using a handwriting profile for documents, such as a payment instrument. A method may include providing one or more documents to a computer system. In one embodiment, handwriting profile representations may be determined for information fields of the document. The determination may use handwriting from at least one of the information fields of the documents. In some embodiments, handwriting profile representations may be updated from one or more additional documents. In certain embodiments, a document may be provided to a computer system for assessment. Assessment may include comparing handwriting in the information fields of the document to handwriting profile representations from information fields of at least one other document. In an embodiment, the method may include assessing fraud in the document using at least one of the comparisons.
Owner:COMP SCI A OF NV
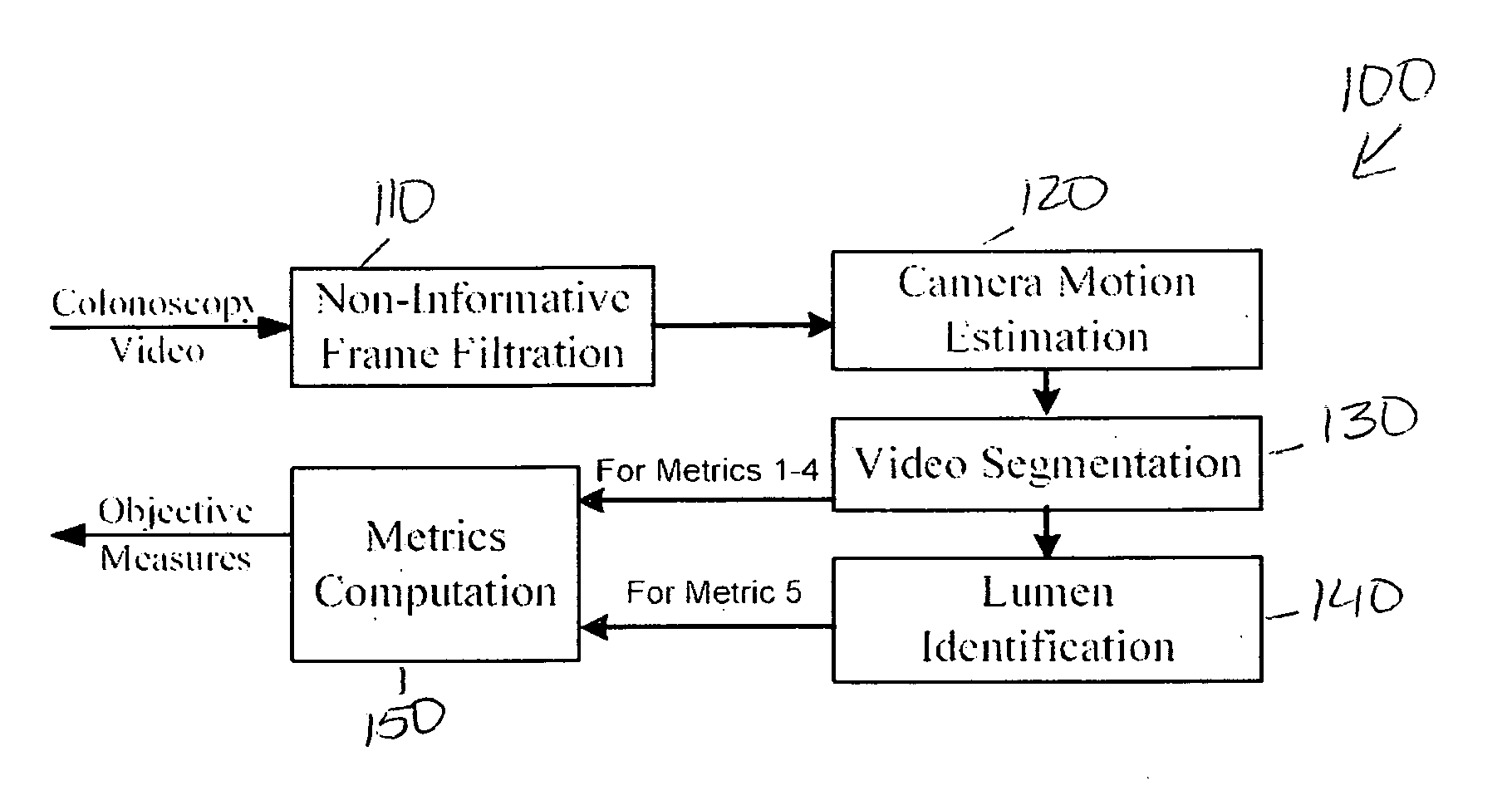
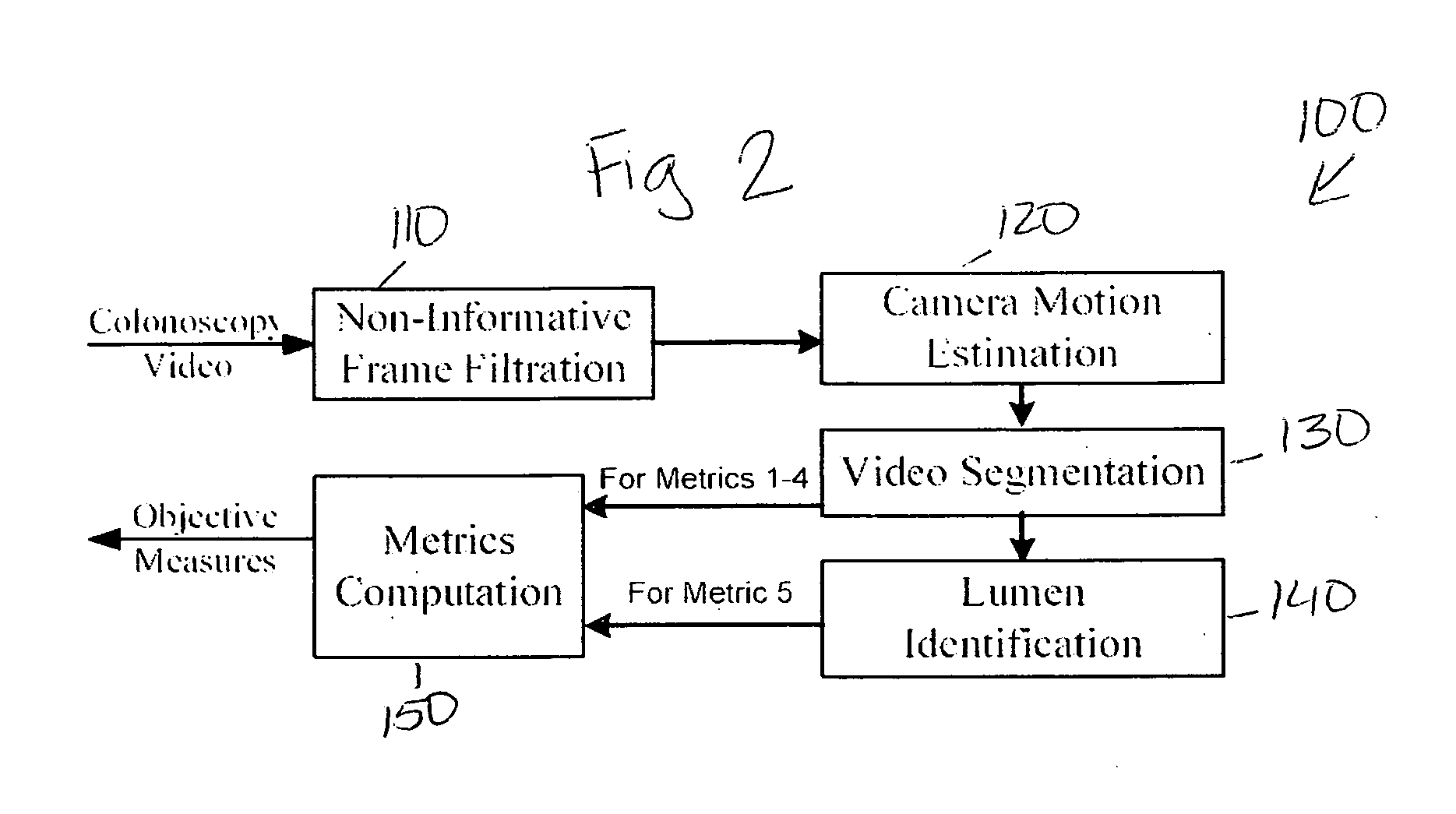
Colonoscopy video processing for quality metrics determination
A computer-based method that allows automated measurement of a number of metrics that likely reflect the quality of a colonoscopic procedure. The method is based on analysis of a digitized video file created during colonoscopy, and produces information regarding insertion time, withdrawal time, images at the time of maximal intubation, the time and ratio of clear versus blurred or non-informative images, and a first estimate of effort performed by the endoscopist. As these metrics can be obtained automatically, the method allows future quality control in the day-to-day medical practice setting on a large scale. In addition, the method can be adapted to other healthcare procedures. The method may be useful to assess progress during colonoscopy training, or as part of endoscopic skills assessment evaluations.
Owner:MAYO FOUND FOR MEDICAL EDUCATION & RES +2
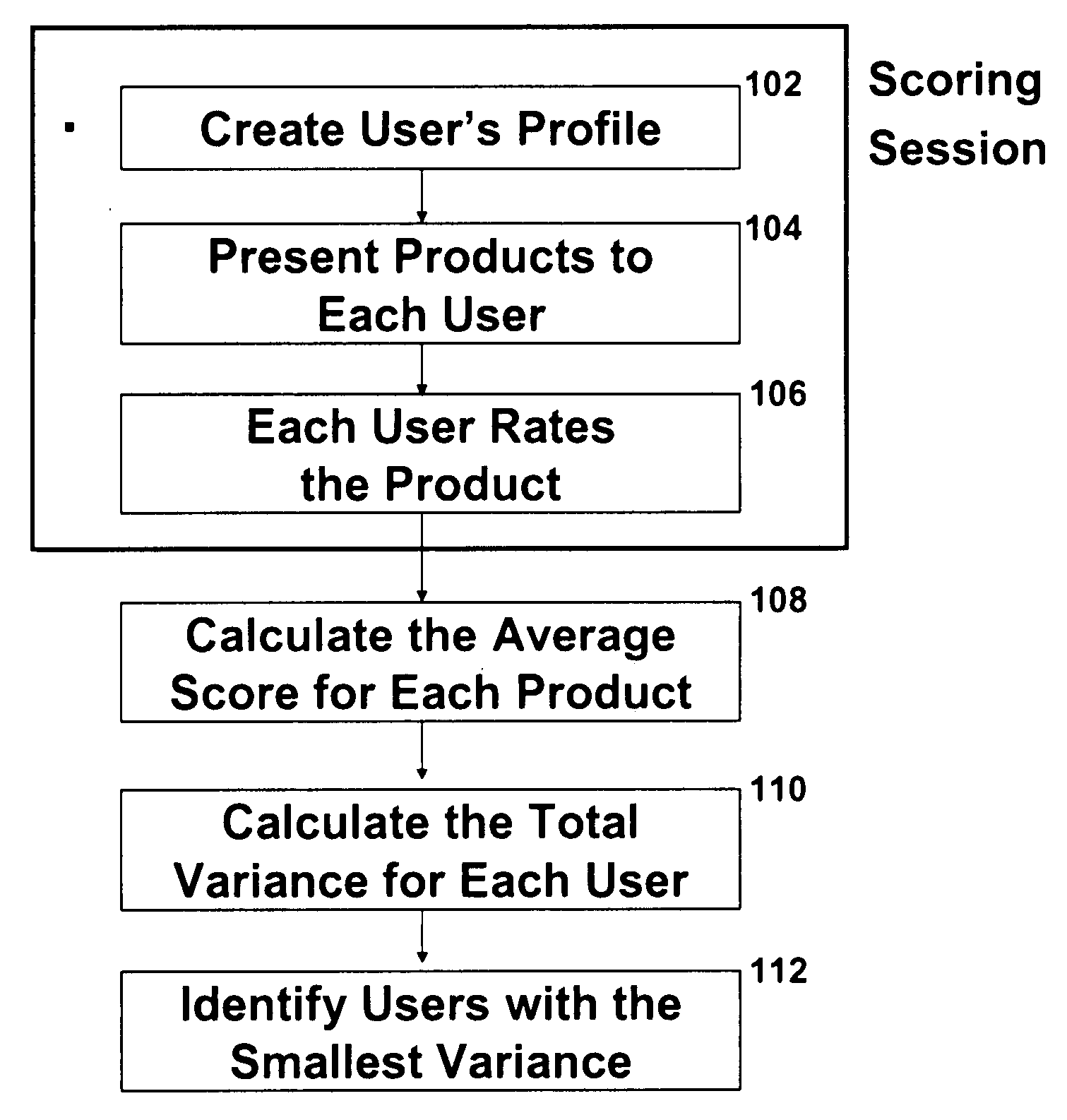
Method and system for evaluating evaluators
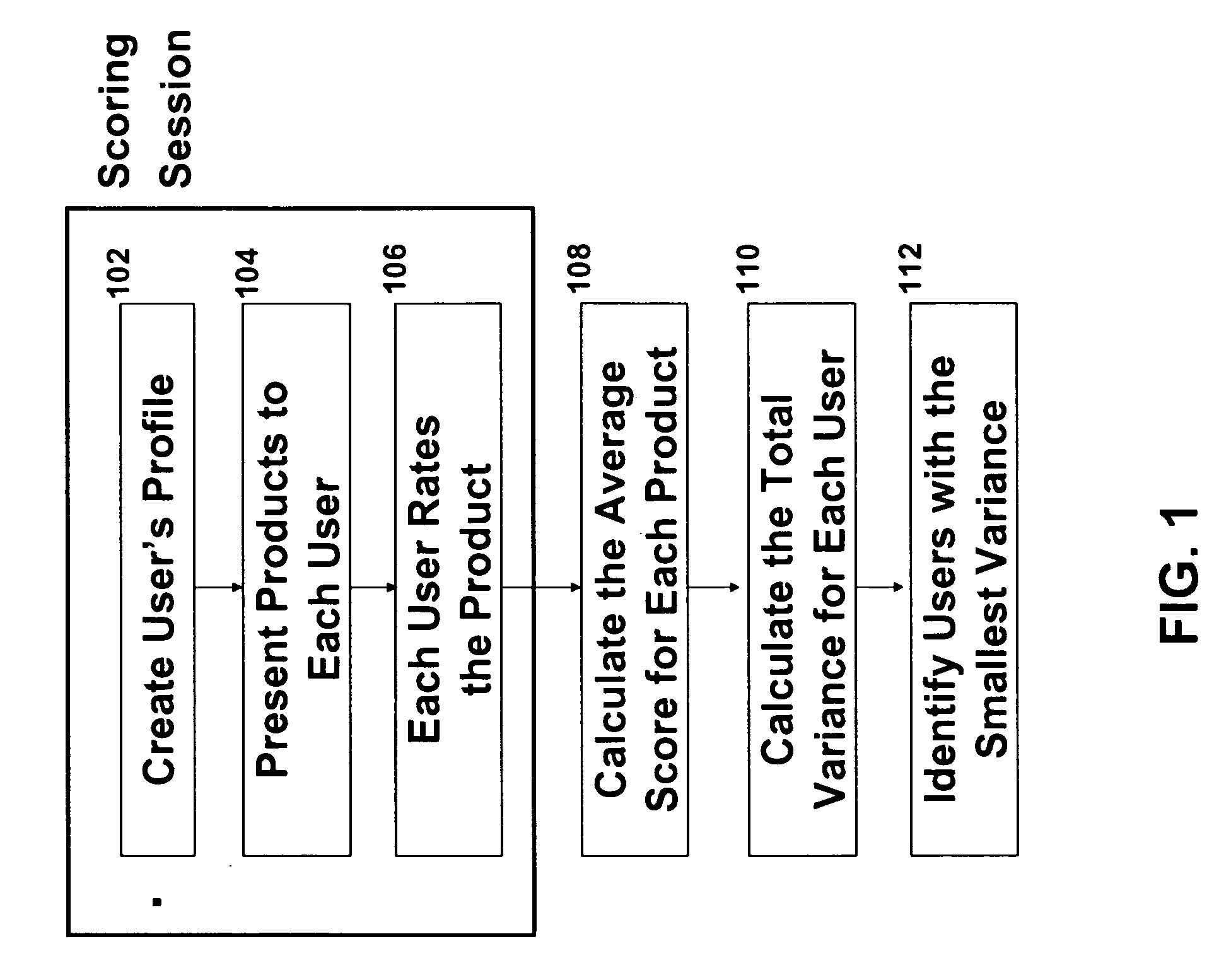
A system or method presents a plurality of content items to each of a plurality of users and receives an evaluation score for each item from each user. An average score for each item is calculated and then, for each user, a composite variance score is calculated. The composite variance score is the sum of the absolute value of the difference between a user's score for an item and the population's average score for that item. The evaluators' performance and the items' rankings can be used for additional information and purposes.
Owner:ALLEN CHRIS
Performance assessment system
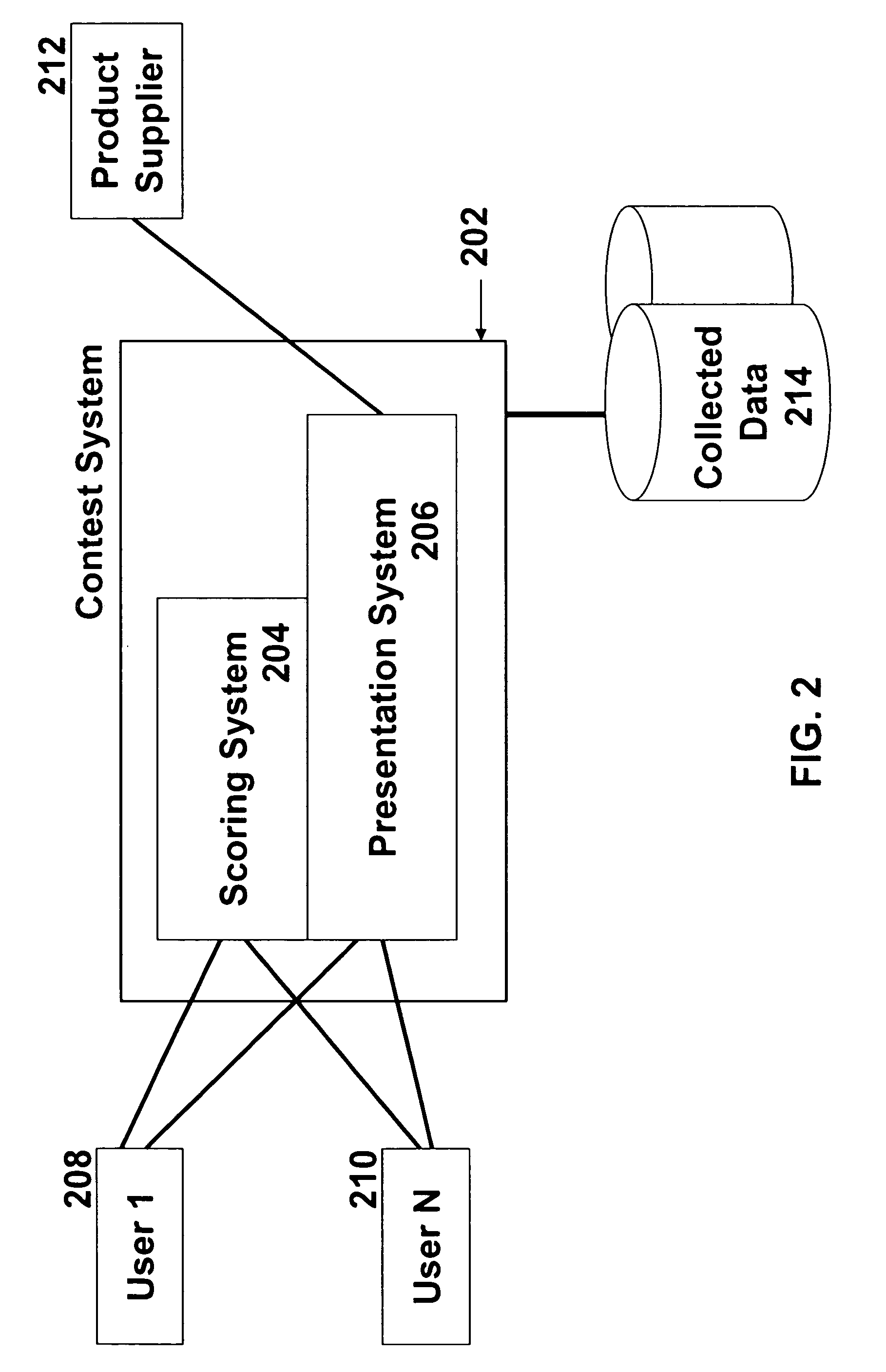
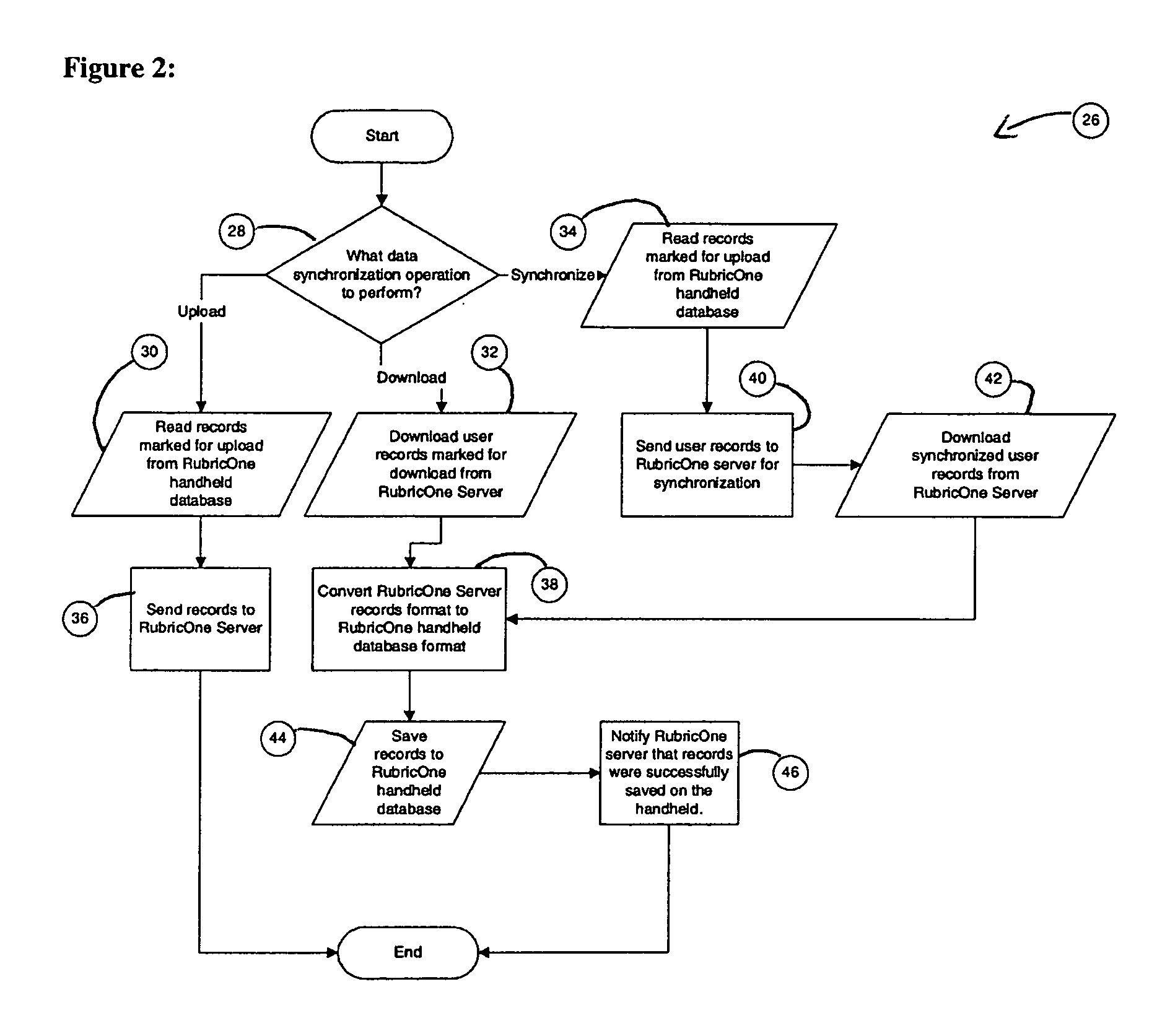
A data collection and scoring system for performance assessments wherein the system has the facility for creating, editing, and scoring various rubrics and checklists, for maintaining a library of rubrics and checklists to download and use or edit, for utilizing either a PC or a mobile handheld computer to create, edit, or score the assessments, for uploading and downloading data between the PC and the handheld computer, and for creating customizable, objective scoring systems for subjective assessments. The system may be used for any performance or observable assessment including but not limited to, writing exams, listening exams, speaking exams, judging contests, driver's exams, physical education skills, music skills, votech course skills, employee reviews, and / or any type of inspection whether it's inspecting a person, a building, a mechanism, a component, a process, or anything that can potentially be inspected.
Owner:ZEECH
Evaluating risk of insuring an individual based on timely assessment of motor vehicle records
InactiveUS20060095304A1Effective assessmentContinuous monitoringFinanceSpecial data processing applicationsEngineeringMotorized vehicle
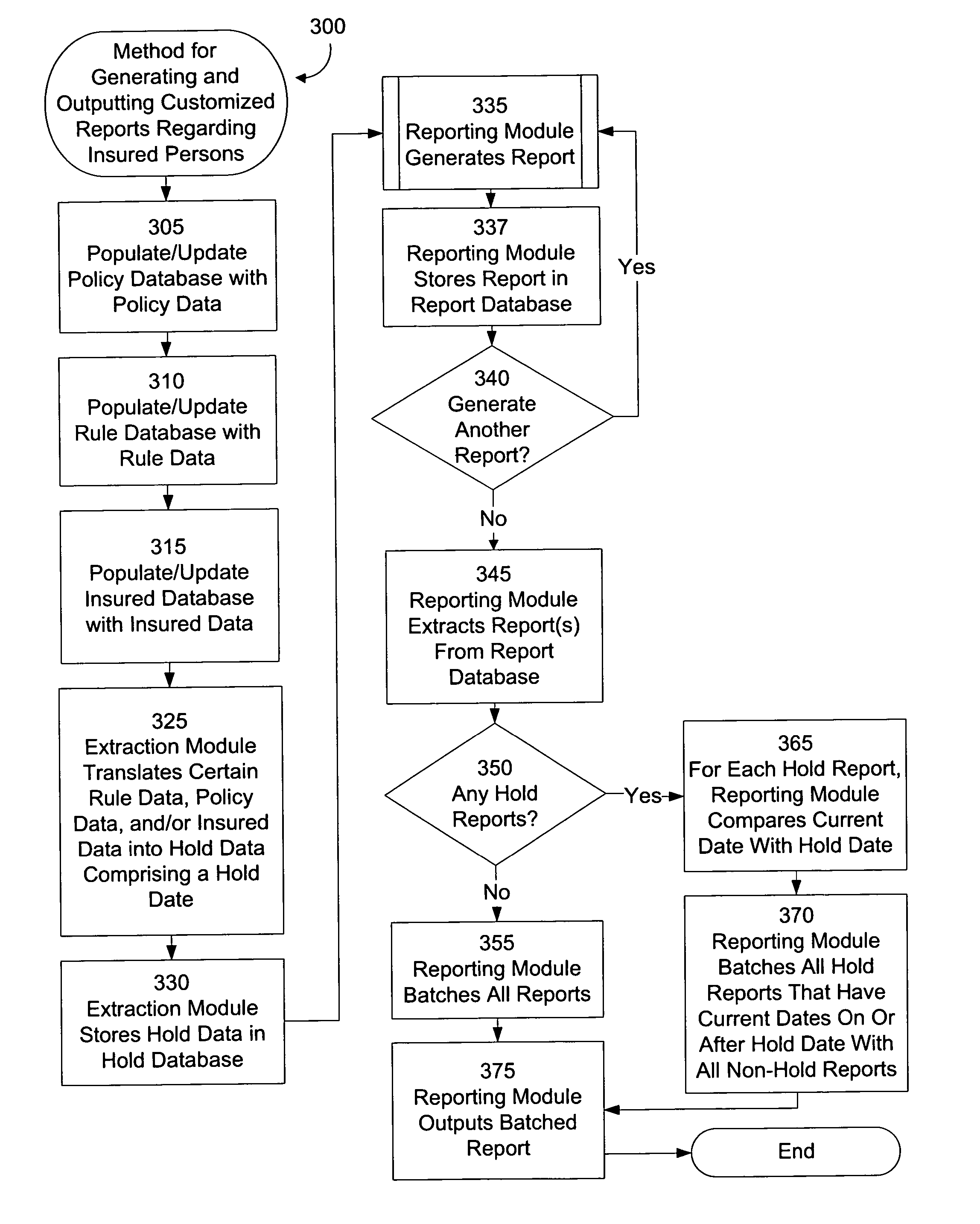
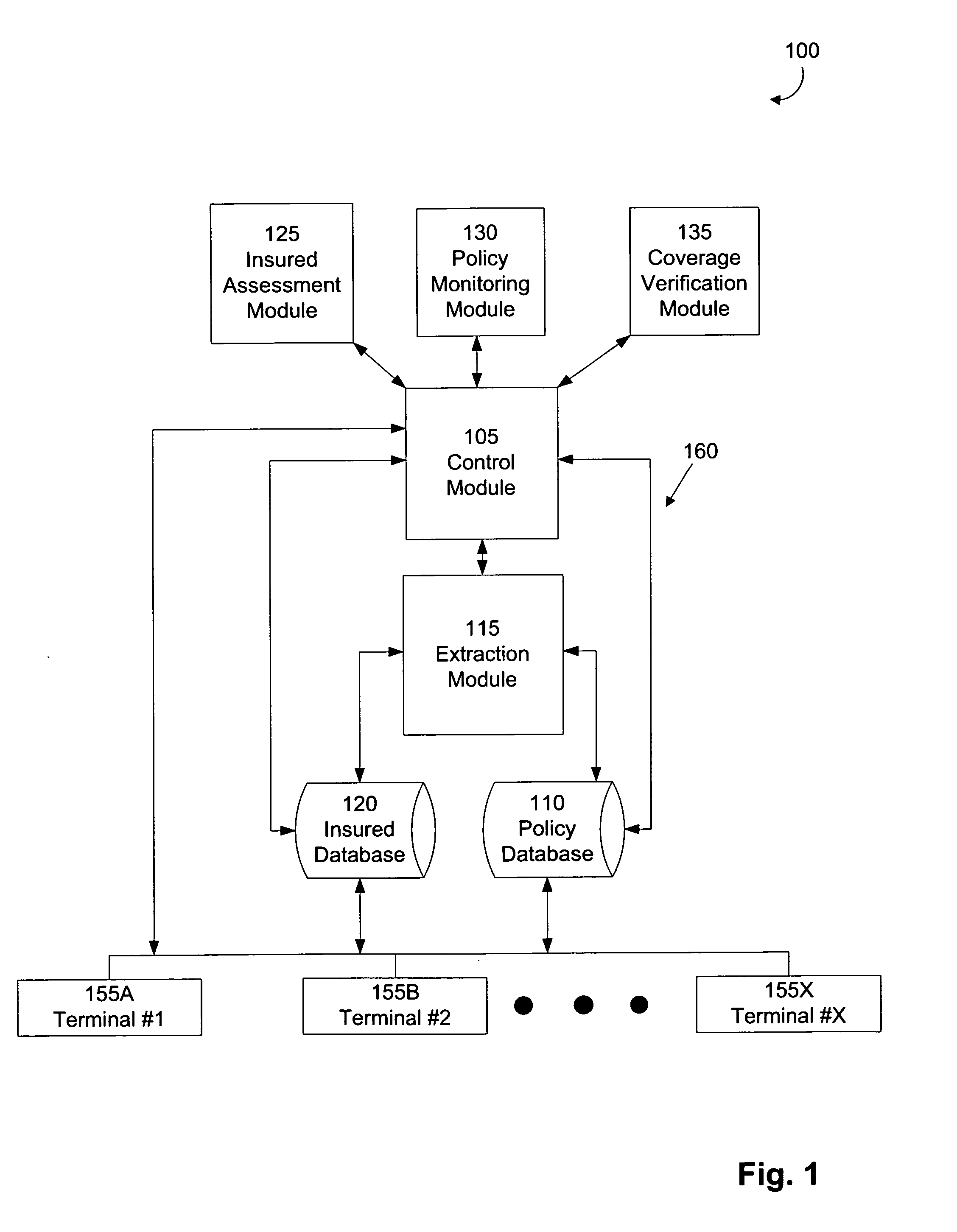
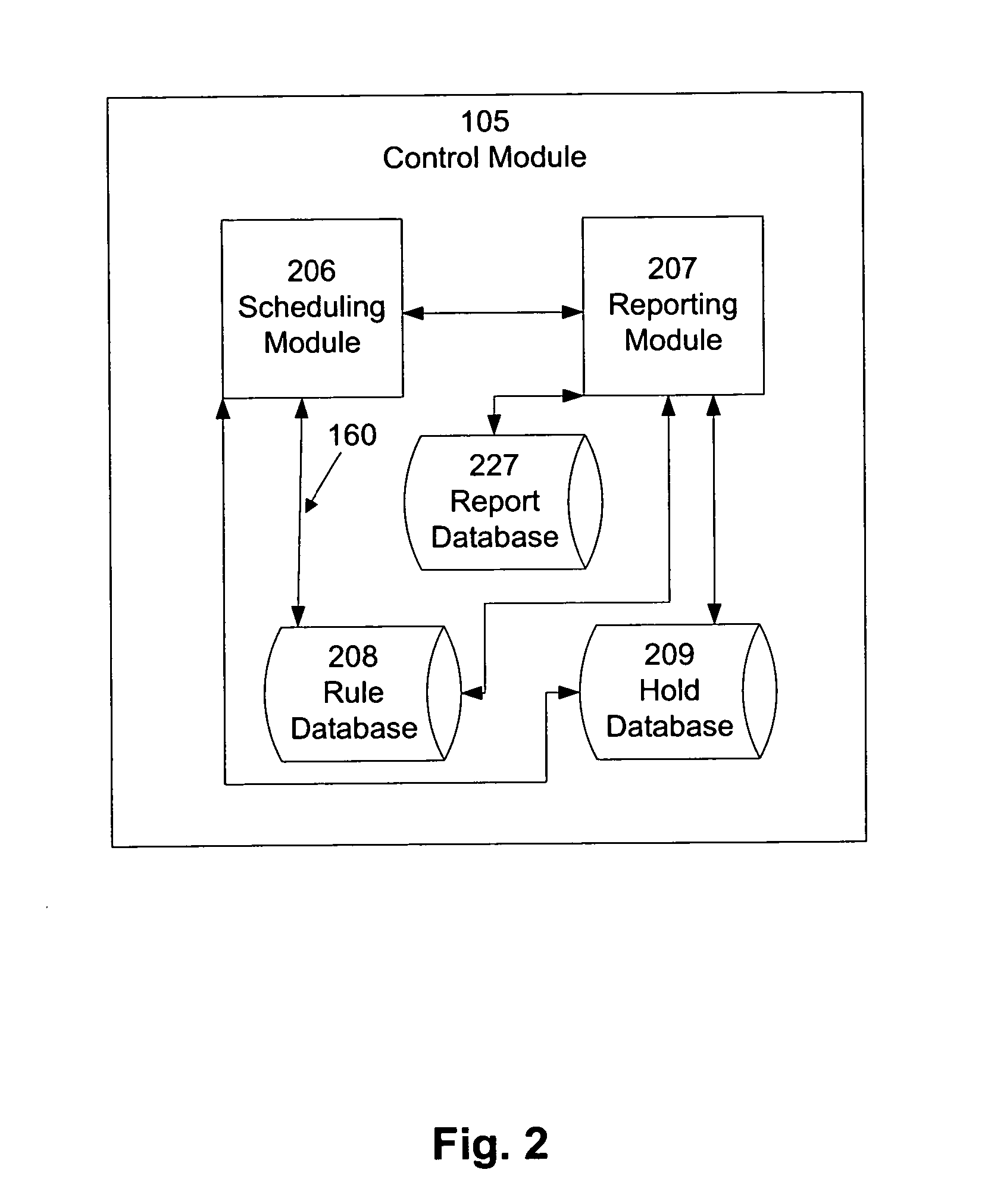
Automated generation of reports based on insured persons' motor vehicle records. Insurance carriers can automatically obtain, at appropriate times, customized reports for use in monitoring and assessing insured persons. Incident data regarding the insured persons' motor vehicle records is received and translated, according to the insurance carriers' pre-set designations, into a customized report. For example, the insurance carriers can designate the reports' format, content, generation times, and output times. Such designations can depend upon other insurance-carrier-specific designations. For example, the designations can depend upon whether certain incident data is deemed “selective” or “non-selective.” For example, selective information can be more urgent to the insurance carrier than non-selective information. Allowing insurance carriers to designate when, how, and in what format, they wish to receive each of various types of information permits for more effective, more efficient, continuous monitoring and assessment of insured persons.
Owner:LEXISNEXIS RISK SOLUTIONS
Method And Apparatus For Processing Assertions In Assertion-Based Verification of A Logic Design
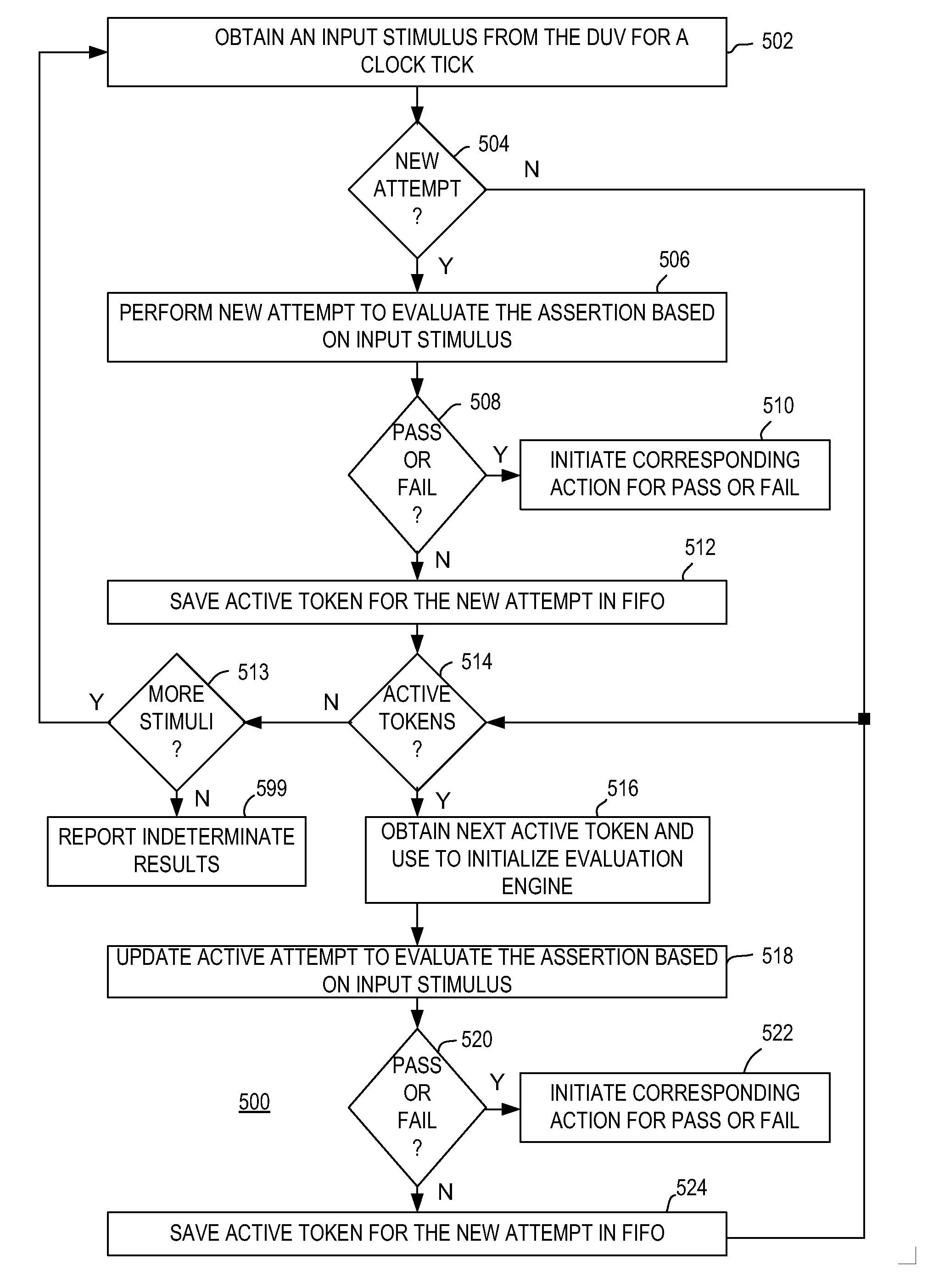
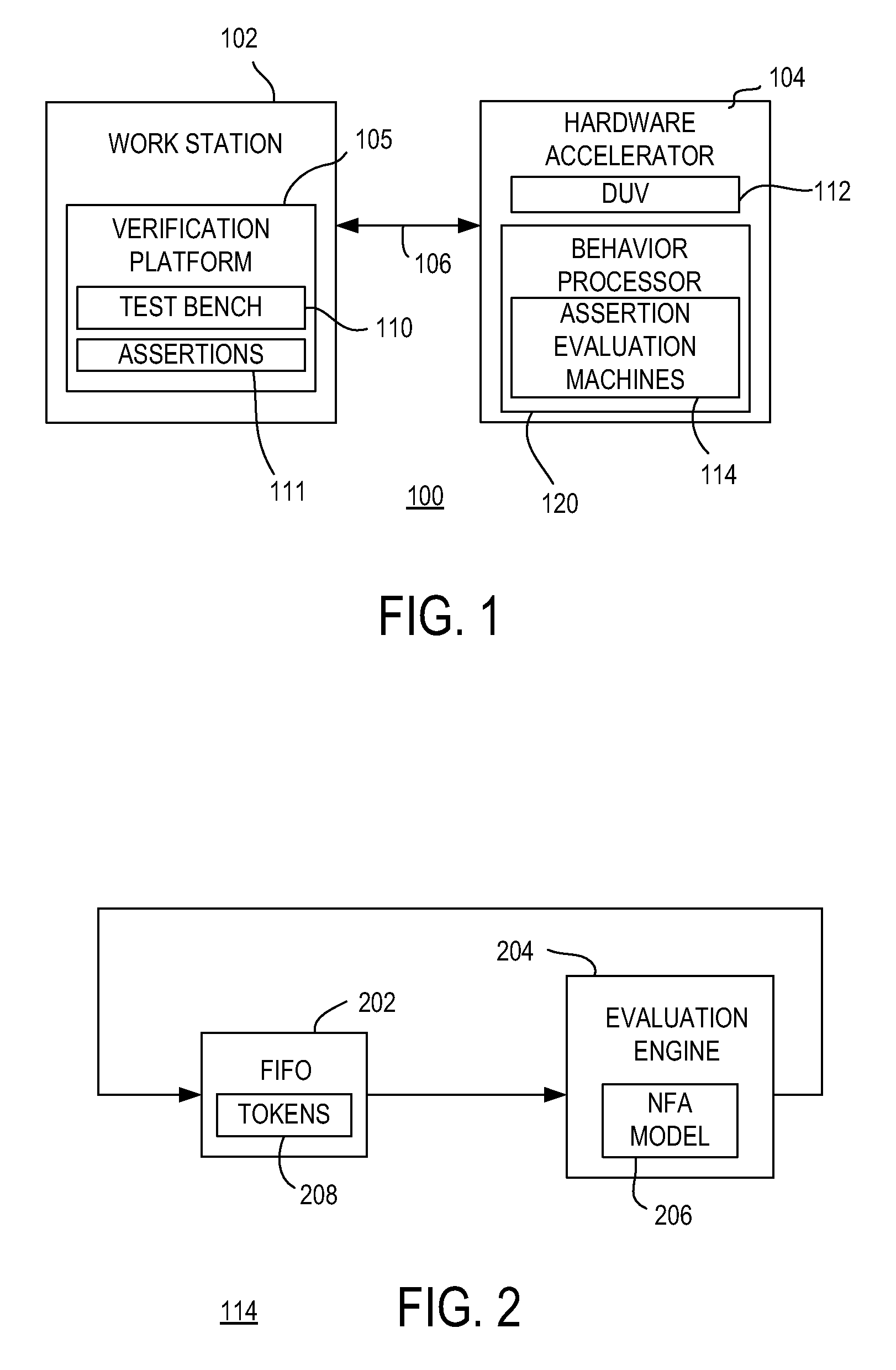
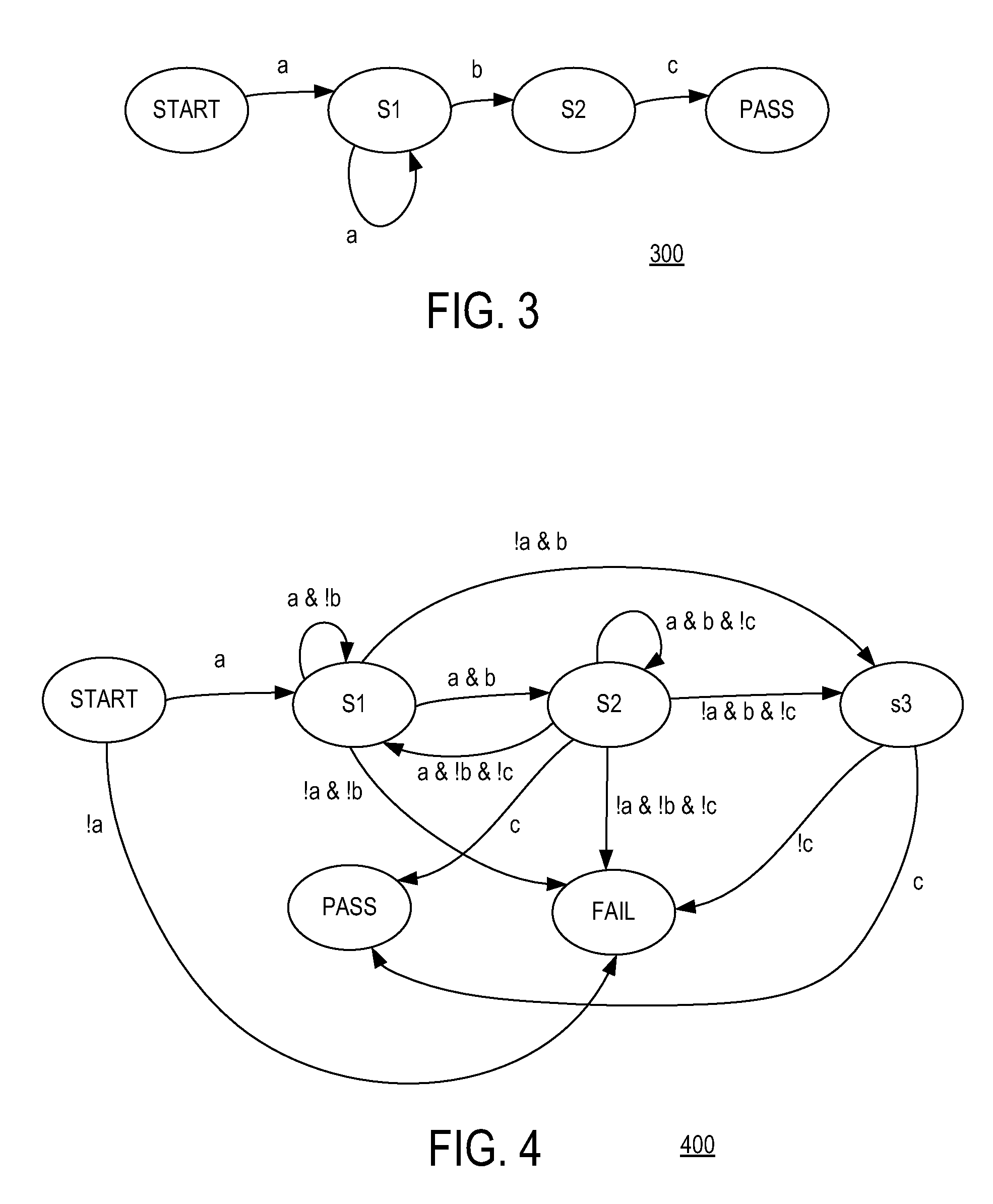
ActiveUS20090204931A1Computer aided designSoftware simulation/interpretation/emulationTheoretical computer scienceENCODE
Method and apparatus for processing assertions in assertion-based verification of a logic design are described. One example relates to processing an assertion during verification of a logic design. An evaluation engine is generated that encodes, using a non-deterministic finite automata (NFA) model, temporal behavior of the logic design required by the assertion for a single attempt to evaluate the assertion. The evaluation engine is implemented in first reconfigurable hardware. The logic design is simulated over a plurality of clock events. Attempts to evaluate the assertion by the evaluation engine are preformed sequentially based on input stimuli obtained from the logic design during simulation thereof. Each of the attempts results in one of the assertion passing, the assertion failing, or the assertion requiring further evaluation.
Owner:CADENCE DESIGN SYST INC
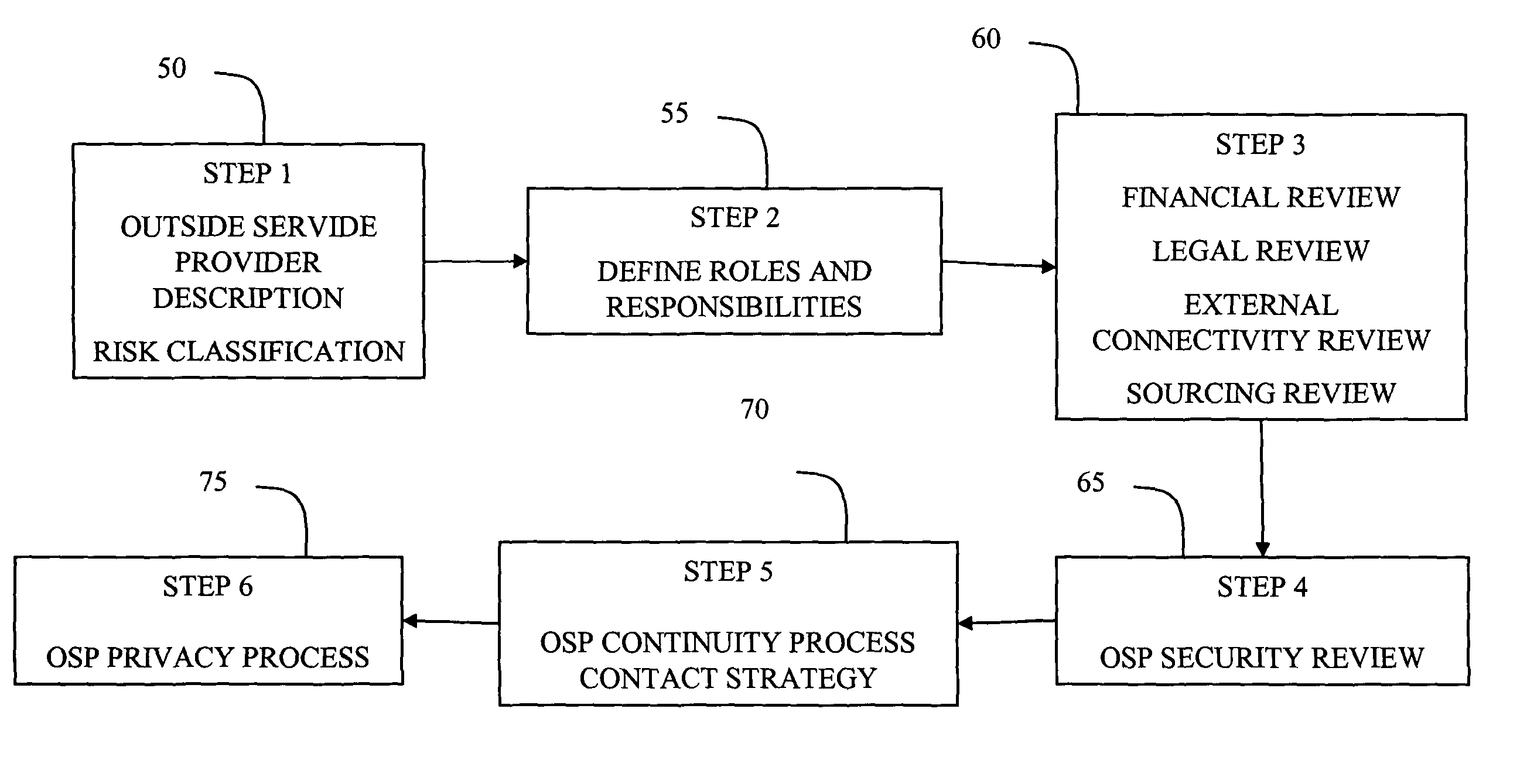
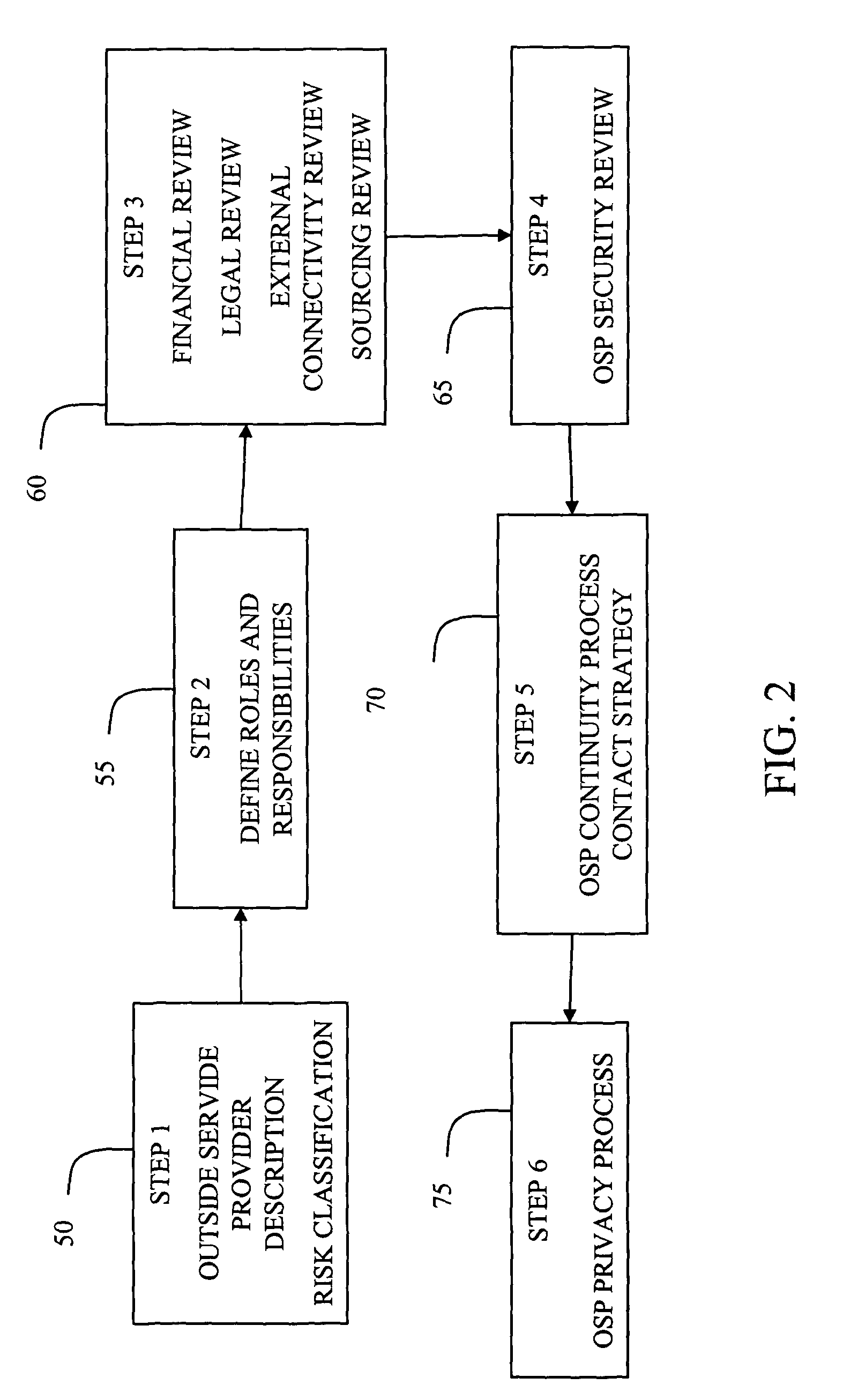
System and method for managing risks associated with outside service providers
A system and method for assessing the risk associated with Outside Service Providers. A decision engine is provided to assess monitor and manage key issues around the risk management capabilities of the OSP. The system creates a core repository that manages, monitors and measures all OSP assessments across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager of the OSP relationship). The responses are tracked in order to evaluate the progress of the assessment and the status of the OSP with respect to compliance with the enterprise's requirements for OSPs. Once a questionnaire has been completed, the OSP can be given an overall rating of exposure to various forms of risk. Areas of risk can be acknowledged, prompting a sensitivity rating, such as severe, negligible and so forth. Once risk is acknowledged, a plan for reducing the risk or bringing the OSP into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be disclaimed through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
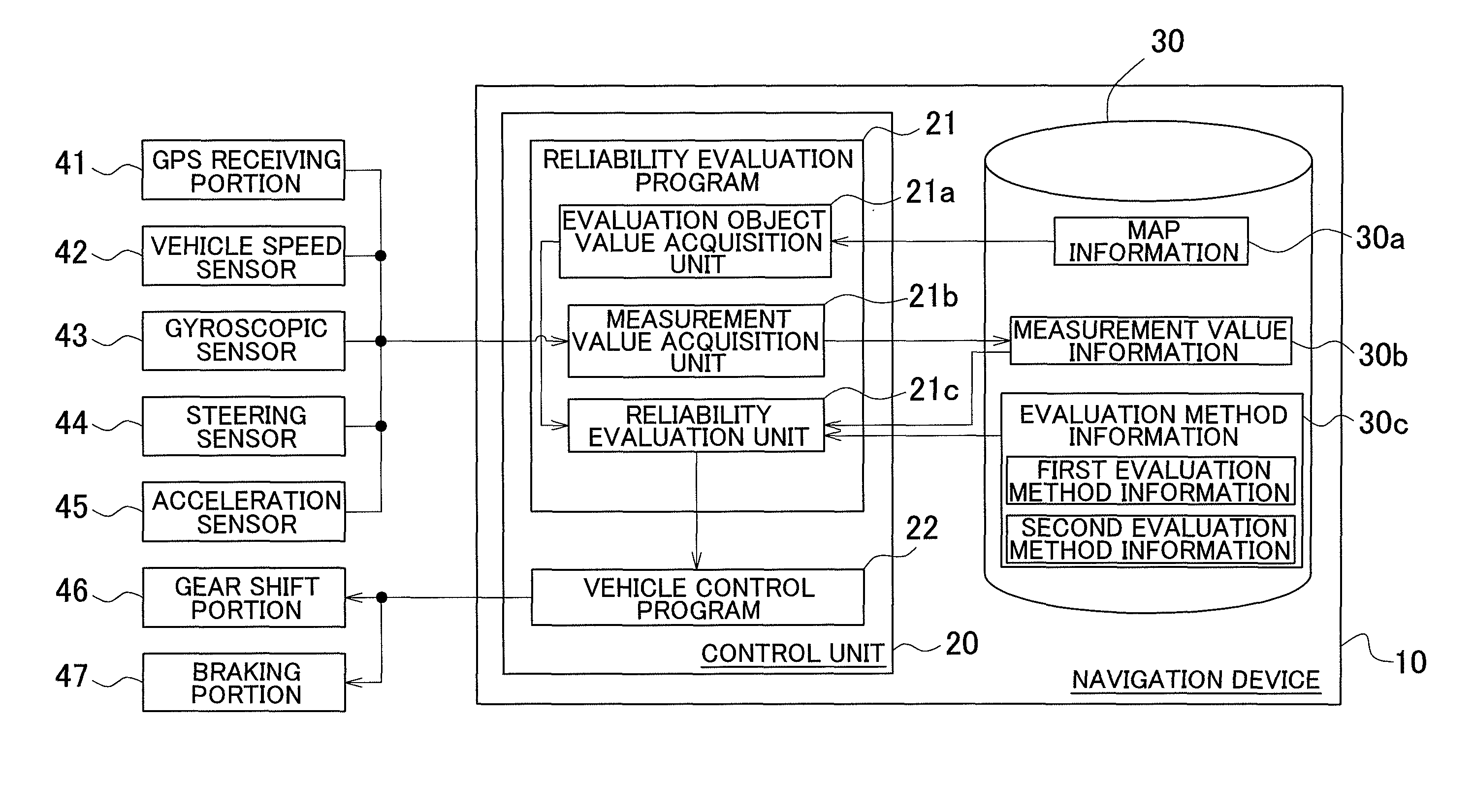
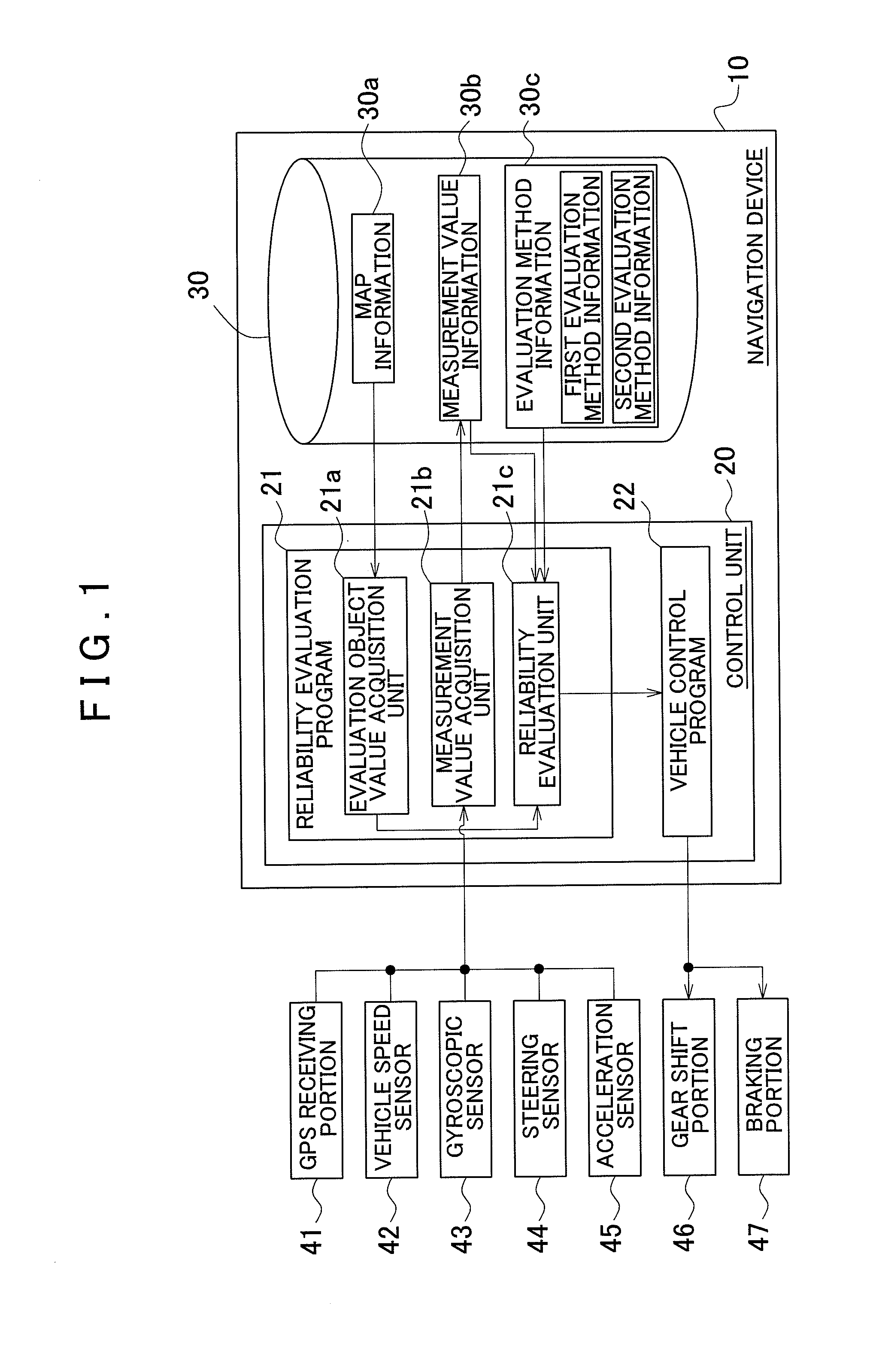
Reliability evaluation device, reliability evaluation method, and reliability evaluation program
InactiveUS20110010131A1Reliability of map informationLow reliabilityInstruments for road network navigationDigital computer detailsAssessment evaluationDependability
Owner:AISIN AW CO LTD
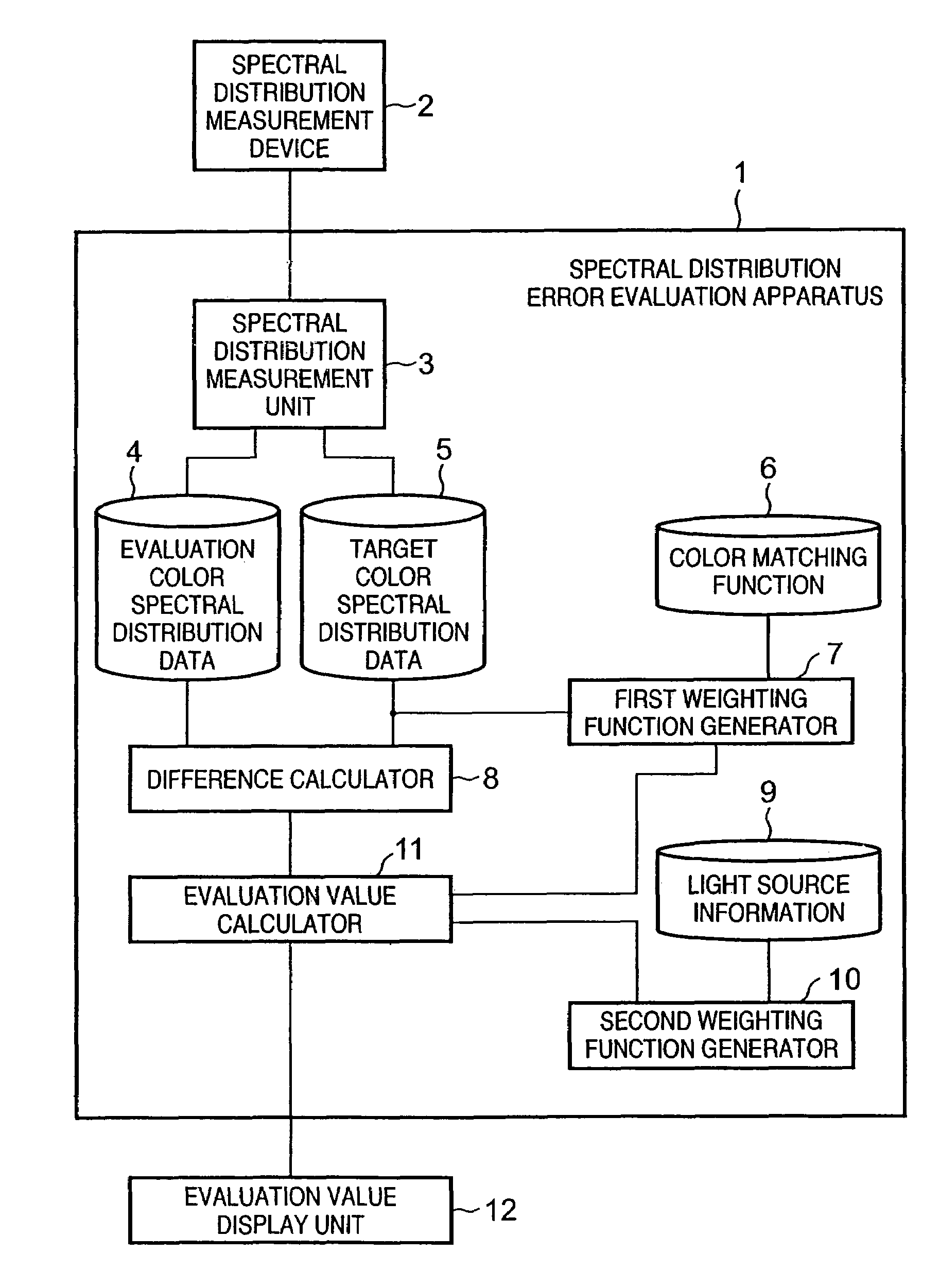
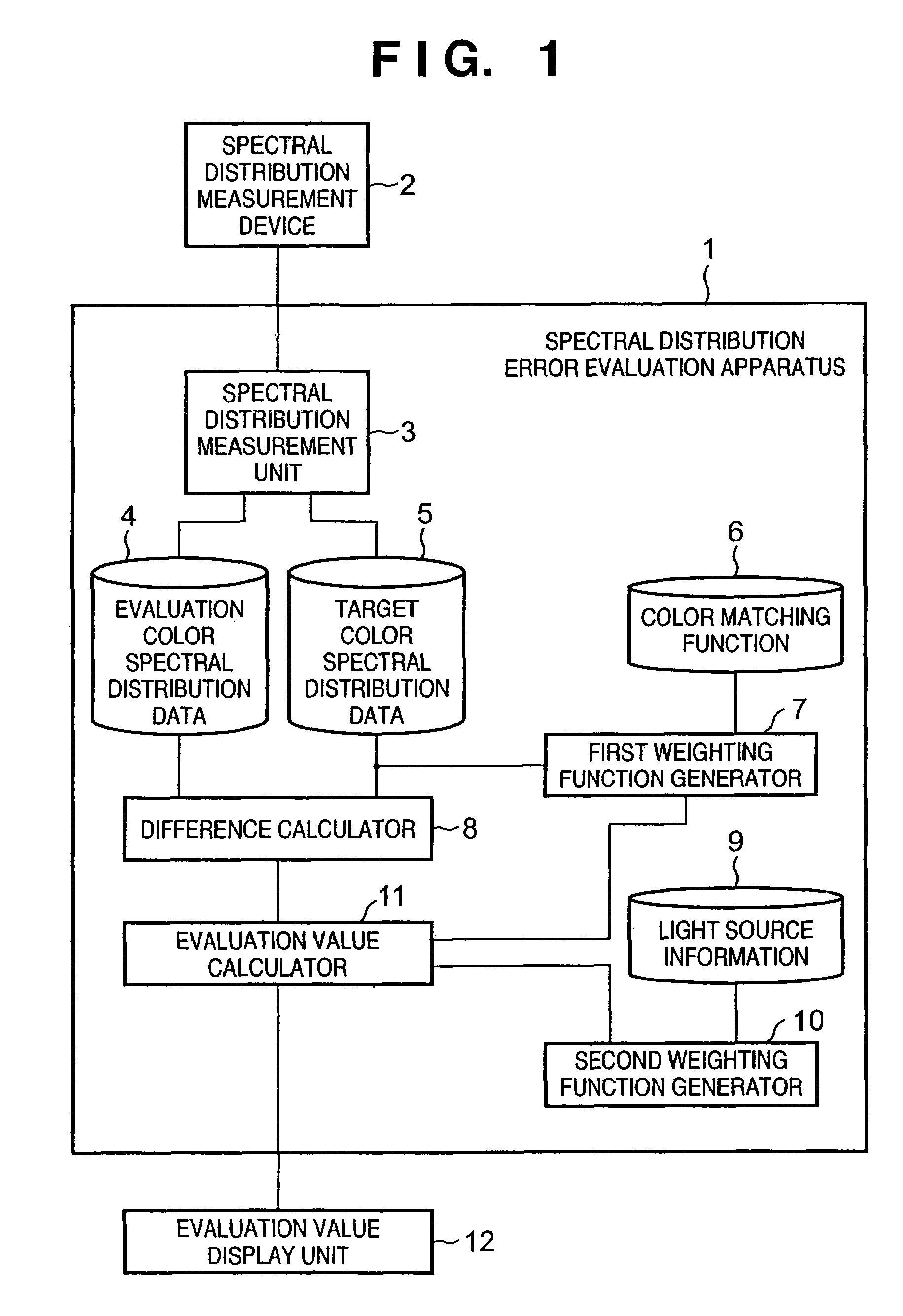
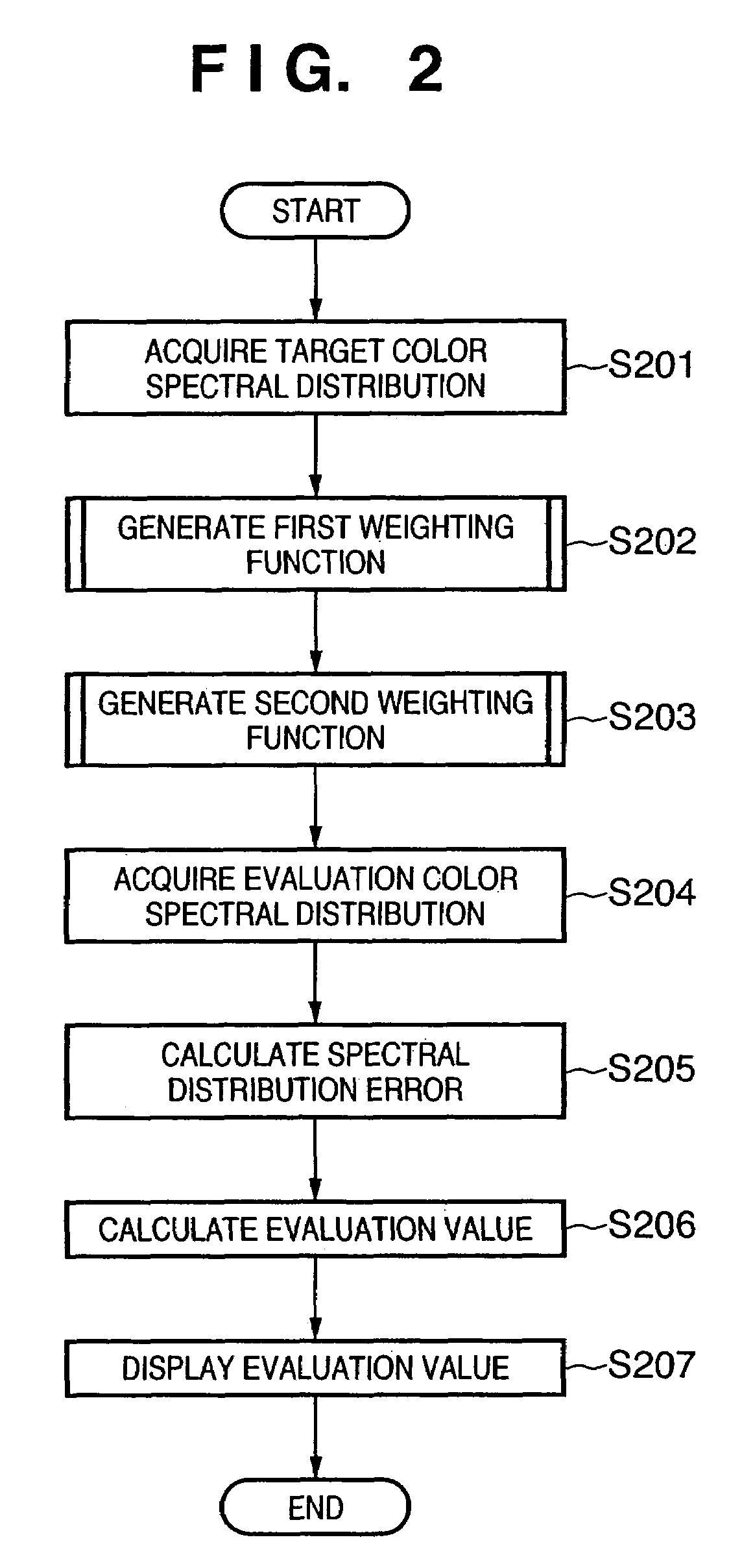
Color evaluation apparatus and method
InactiveUS6987567B2High appearance requirementsGood colorColor/spectral properties measurementsImage data processing detailsCalculation errorLength wave
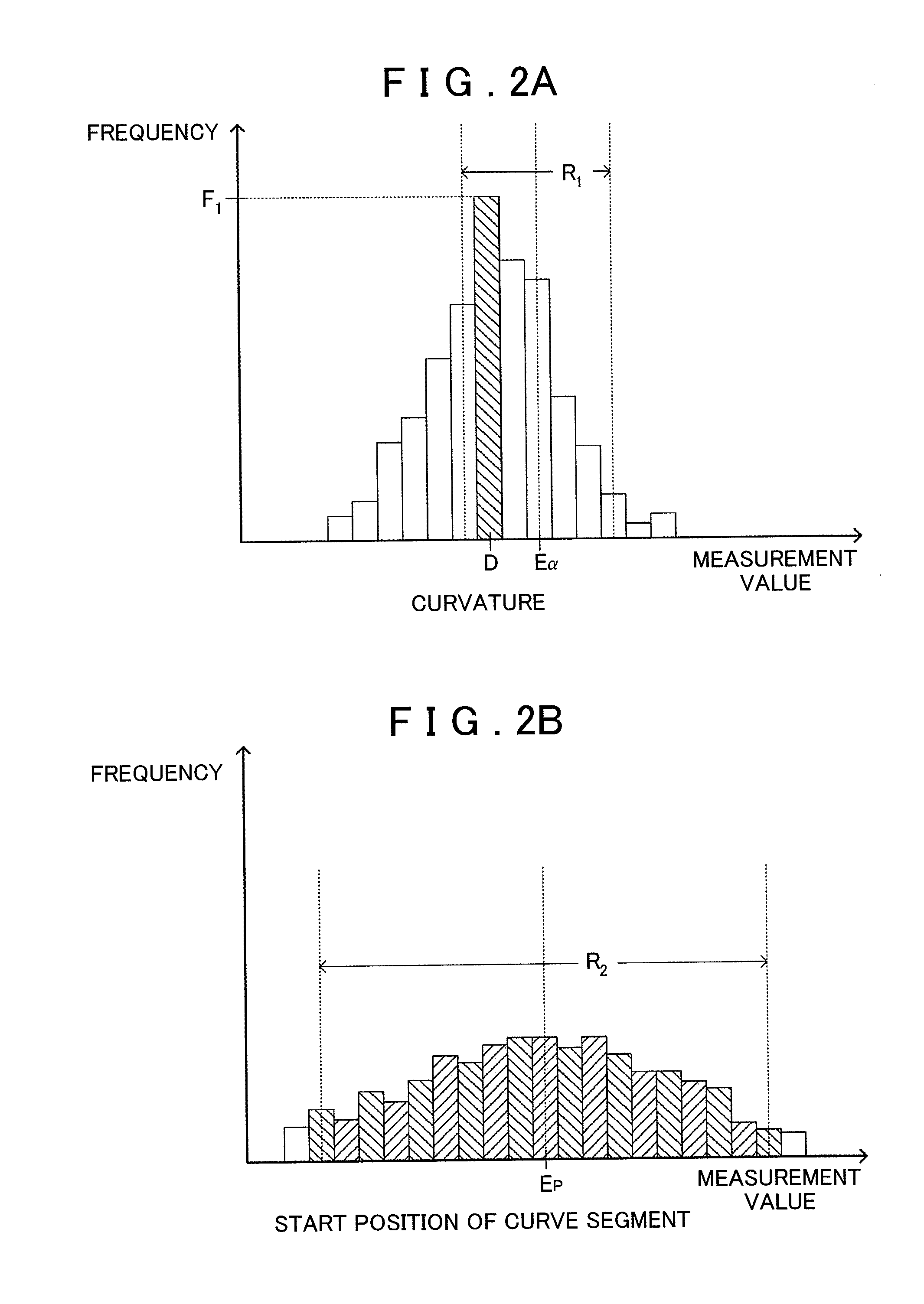
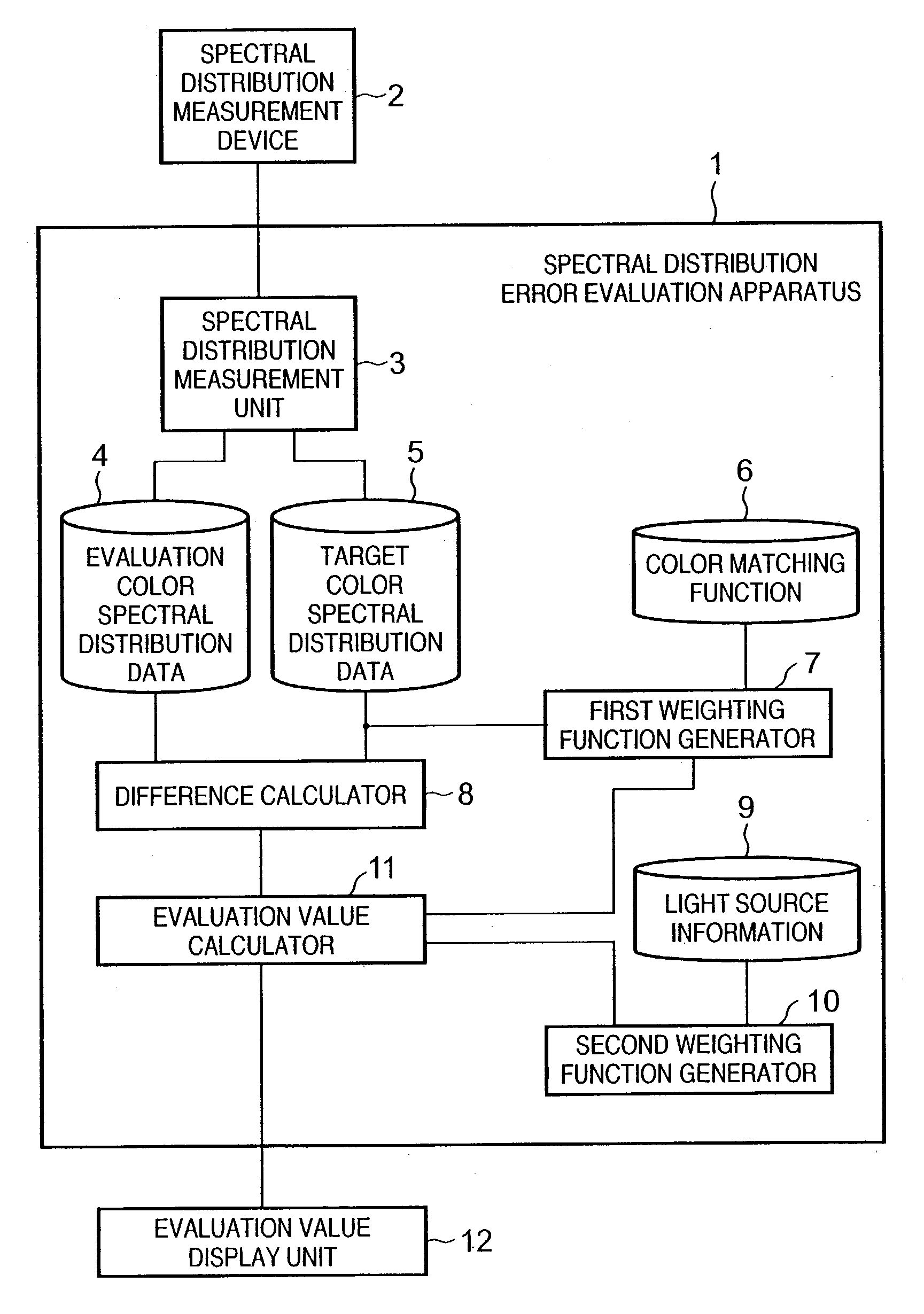
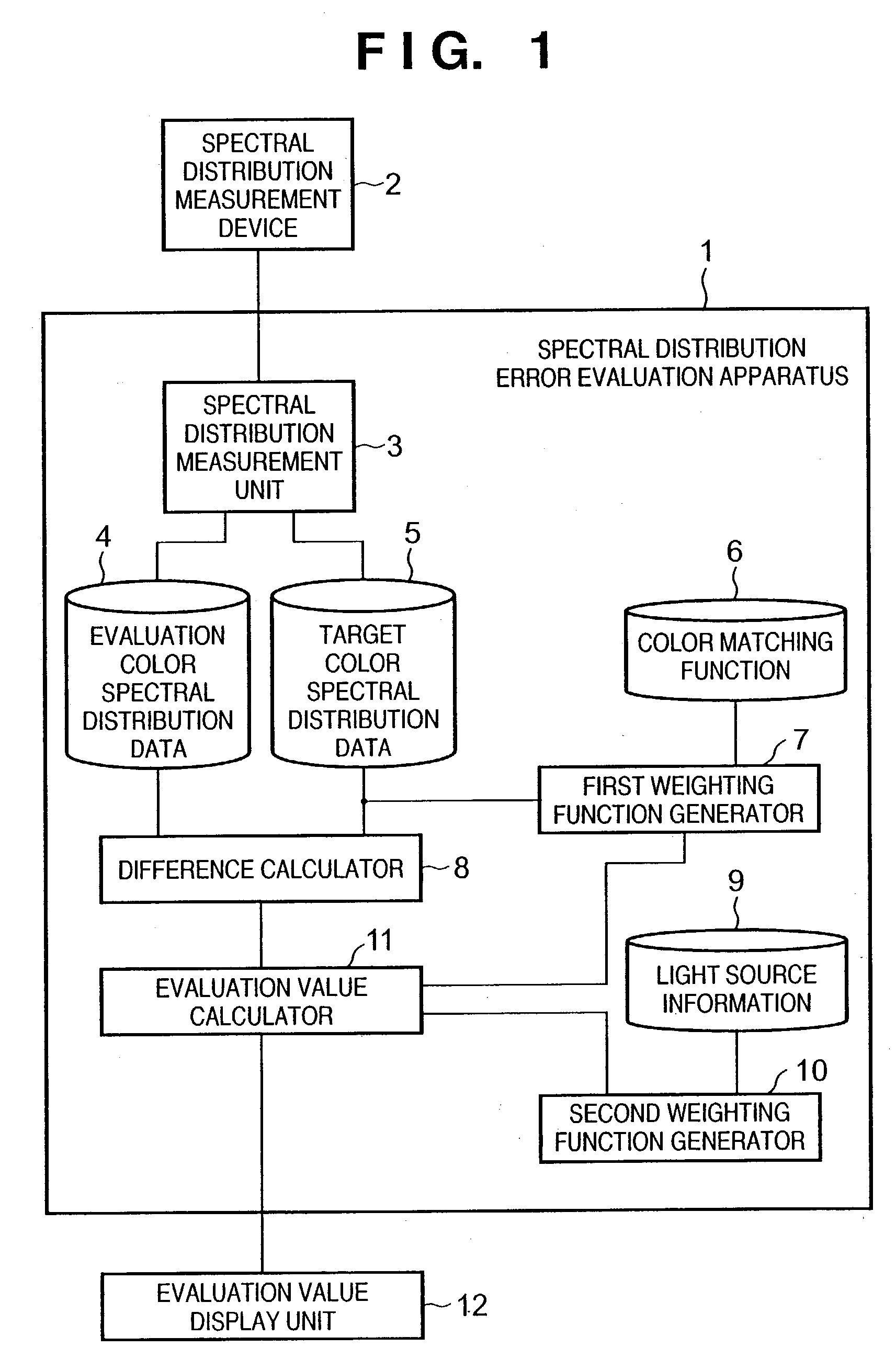
A spectral distribution error evaluation apparatus is used to evaluate precision of color matching between evaluation and target colors. A first weighting function generator generates a first weighting function on the basis of color matching functions, wavelength characteristics which are independent of a light source of the target color, and visual characteristics which depend on wavelengths. A second weighting function generator generates a second weighting function on the basis of light source information of selected light sources. A difference calculator calculates error values between the evaluation and target colors for respective frequencies. An evaluation value calculator applies the first and second weighting functions to the error values, and calculates the sum total of the error values as an evaluation value. In this way, a precision evaluation value which has high correlation with actual color appearance and is used to improve the color matching precision can be calculated independently of a change in condition such as a light source or the like.
Owner:CANON KK
Information system security performance assessment method
ActiveCN105635112AEvaluation results are intuitive and reliableCalculation method is simple and scientificData switching networksAssessment methodsSecurity assessment
The invention discloses an information system security performance assessment method. The method comprises following steps: carrying out leveled scoring to the security level, the operating maintenance level, the confidentiality, the integrity and the availability of an information system; classifying the assets subordinate to the information system; carrying out leveled scoring to the confidentiality, the integrity and the availability of the assets; discovering the vulnerabilities of the information system; obtaining the asset classes to which the vulnerabilities belong; carrying out vulnerability scoring to the vulnerabilities; calculating the security risk values of all vulnerabilities of the information system; and finishing assessing the information system security performance. According to the method of the invention, the information system and the assets subordinate to the information system are classified and scored; the security assessment is carried out to the information system through combining the vulnerability of the vulnerabilities and the assets to which the vulnerabilities belong; the security of the information system can be reacted visually in real time; the information system is assessed by a quantitative calculation method; the assessment result is visual and reliable; and the calculation method is simple and scientific.
Owner:STATE GRID CORP OF CHINA +2
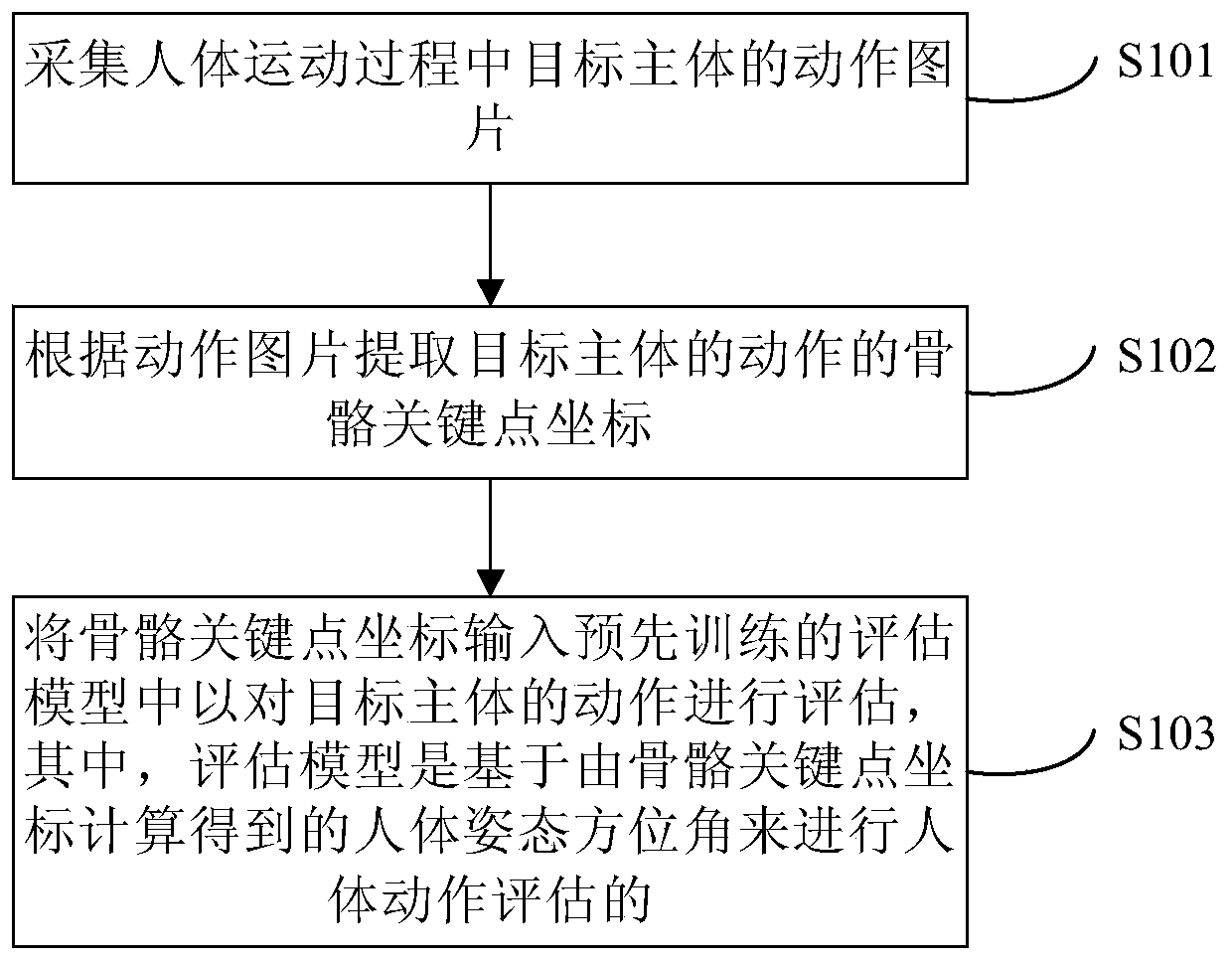
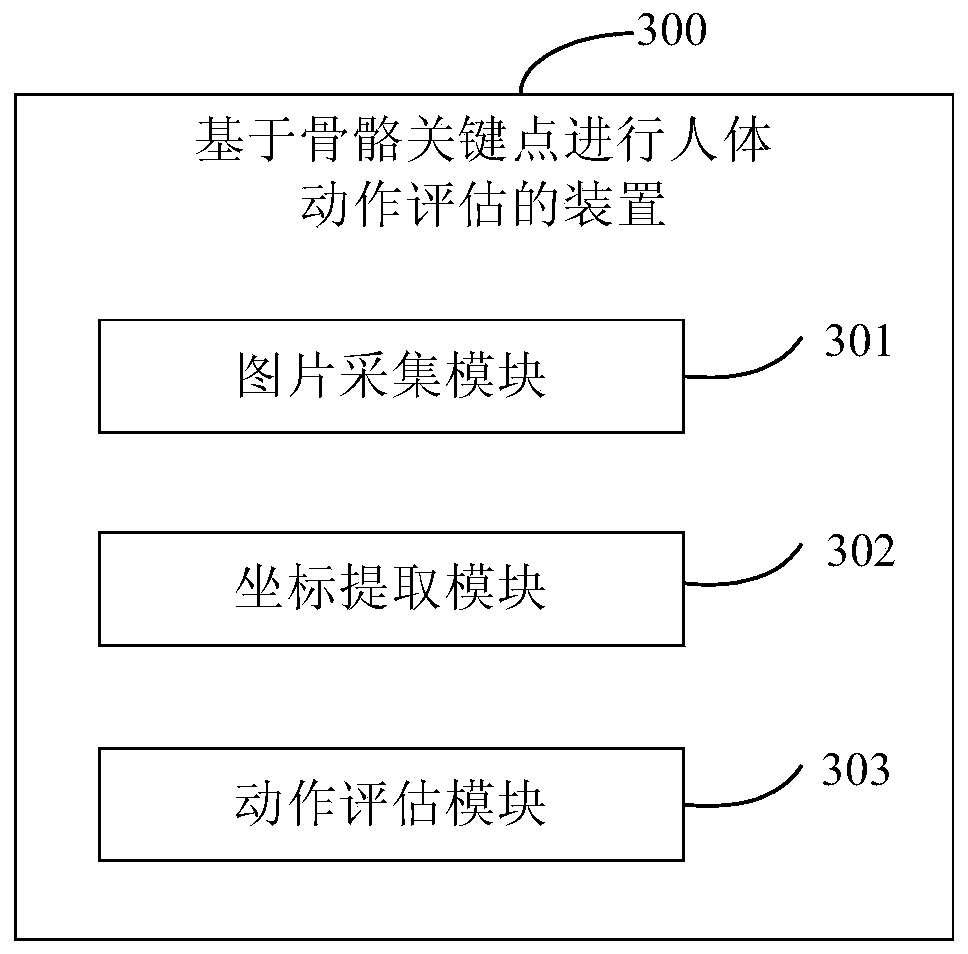
Method and device for evaluating human body actions based on skeleton key points
ActiveCN110941990AImprove experienceThe evaluation method is simpleCharacter and pattern recognitionManufacturing computing systemsHuman bodyEvaluation result
The invention discloses a method and a device for evaluating human body actions based on skeleton key points, and relates to the technical field of computers. A specific embodiment of the method comprises the steps of collecting an action picture of a target main body in a human body movement process; extracting skeleton key point coordinates of the action of the target main body according to theaction picture; and inputting the skeleton key point coordinates into a pre-trained evaluation model to evaluate the action of the target main body, the evaluation model being used for evaluating theaction of the human body on the basis of a human body posture azimuth angle calculated by the skeleton key point coordinates. According to the method, human body action evaluation can be performed based on the skeleton key points and the human body posture azimuth angle, and the evaluation method is simple, high in efficiency and accuracy and good in user experience; and meanwhile, the problem that the evaluation result is not objective and accurate enough due to artificial subjective judgment of an evaluator is solved.
Owner:TAIKANG LIFE INSURANCE CO LTD +1
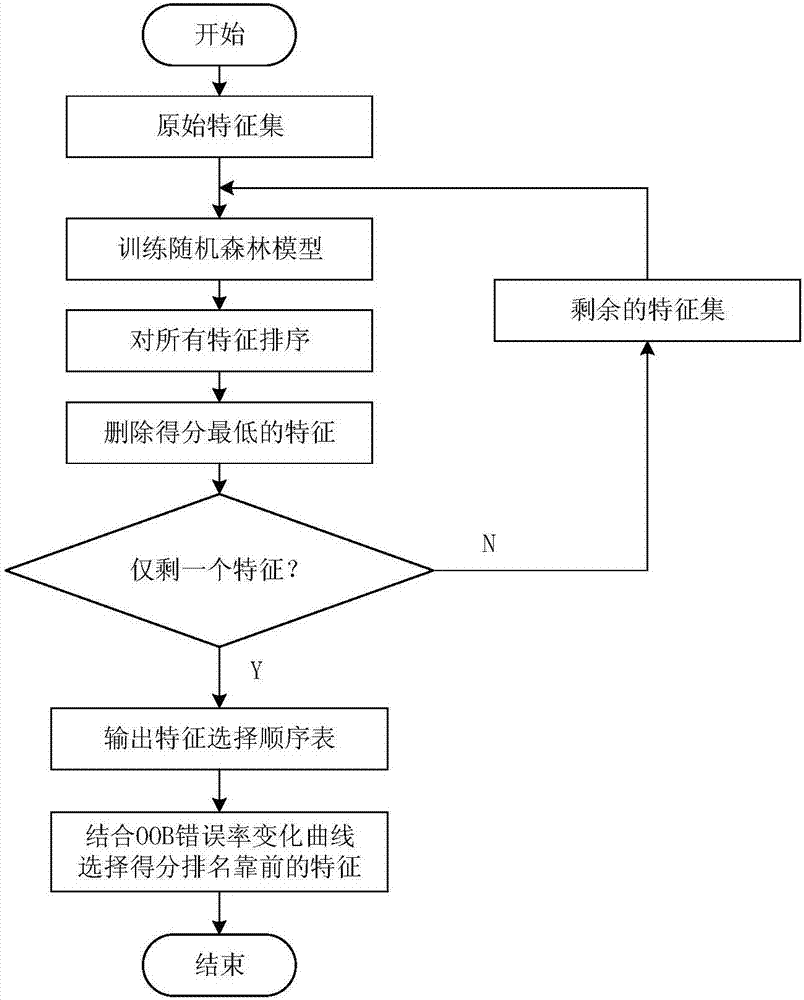
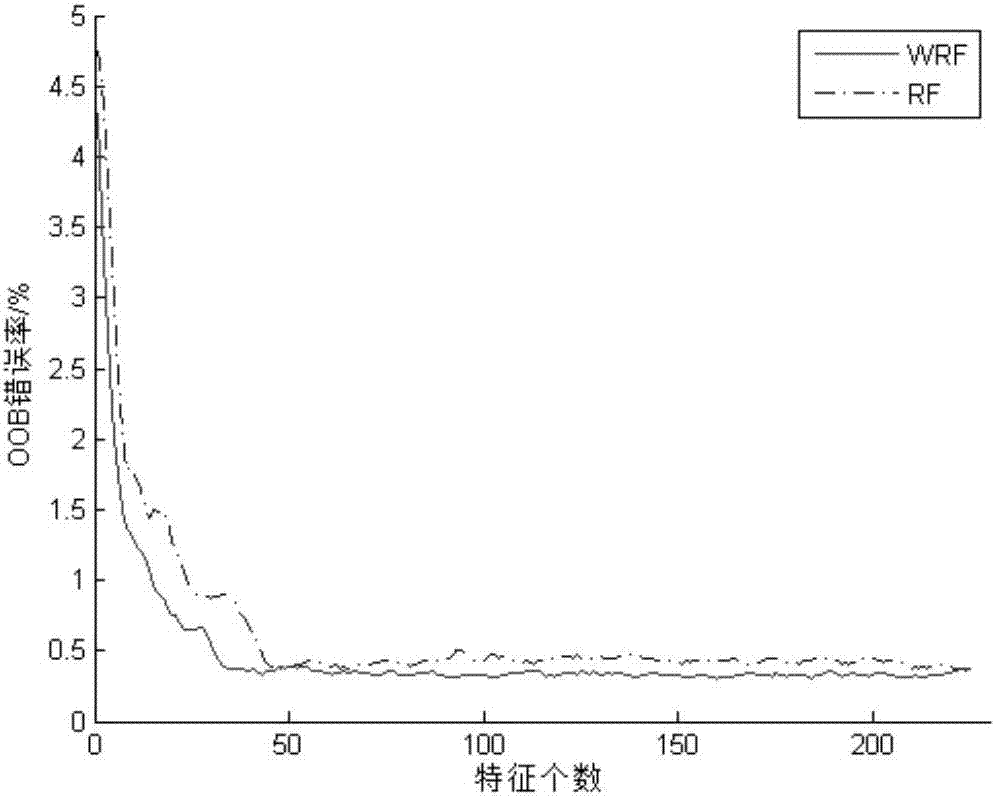
Transient assessment evaluation feature selection method and device
PendingCN106897821AImprove performanceReduce the impact of feature selectionResourcesInformation technology support systemTransient stateRanking
The present invention provides a transient assessment evaluation feature selection method and device. The method comprises the following steps that: a weighted random forest model is constructed; features with the lowest importance are deleted from calculated feature importance; final feature sequencing is performed on the retained technical features; and features which are high in ranking are retained according to OOB (Out-Of-Bag) error rate curve changes. According to the transient assessment evaluation feature selection method and device provided by the technical schemes of the invention, few unstable sample data weight factors are introduced into the weighted random forest, so that the influence of unbalanced data on feature selection can be decreased, feature subsets of which the performance can be better than that of feature subsets selected by an ordinary random forest algorithm can be selected; and threshold values are not required to be set manually, and the rationality of the selected feature subsets can be ensured.
Owner:CHINA ELECTRIC POWER RES INST +3
Universal three-dimensional simulation system for hydropower station
InactiveCN107369347AMeeting skills training needsReasonable designCosmonautic condition simulationsSimulatorsThree dimensional simulationSoftware system
Owner:HUANENG LANCANG RIVER HYDROPOWER
Resident customer value grading model construction method based on analytic hierarchy process
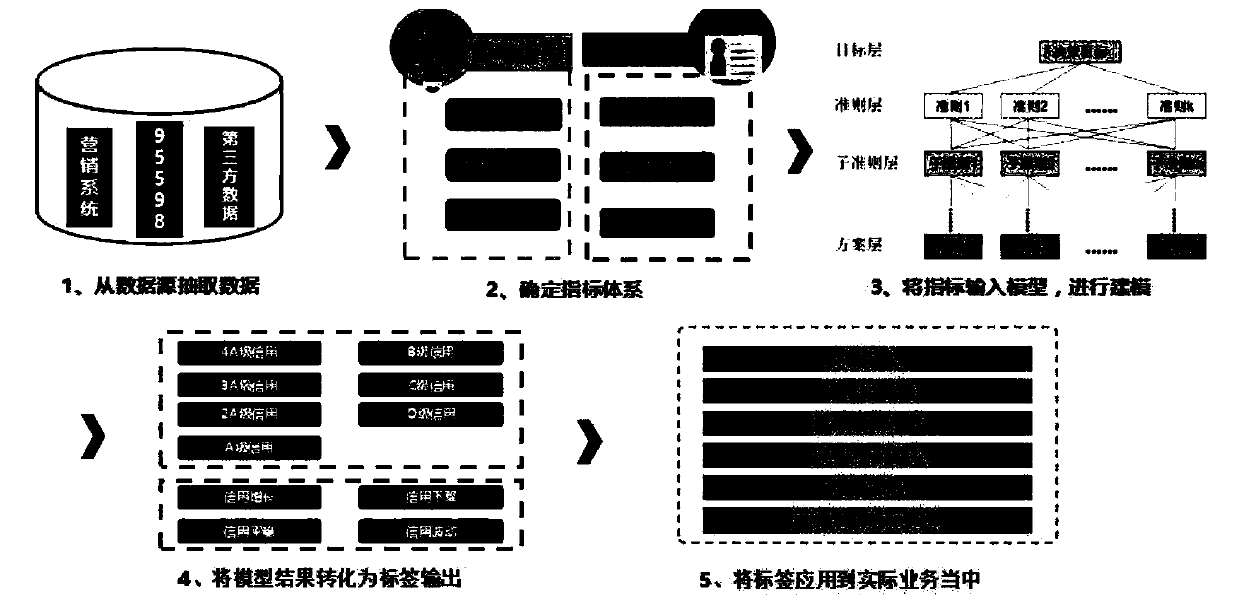
The invention discloses a resident customer value grading model construction method based on an analytic hierarchy process, and belongs to the technical field of electric power. An existing evaluationscheme directly uses a formula to carry out credit evaluation calculation, deeper influence factor identification and evaluation cannot be carried out according to actual conditions, and an evaluation grading scheme is not scientific and reasonable enough. According to the invention, the AHP analytic hierarchy process is adopted to calculate the comprehensive rating score of the customer, and qualitative and quantitative analysis is carried out on the value of the customer in a multi-objective and hierarchical manner; customer value characteristics can be fully mined, and an evaluation grading scheme is more scientific and reasonable. In combination with customer marketing service guidance at the present stage and based on customer power consumption historical data such as information conditions, payment conditions, power consumption conditions, interaction conditions and growth conditions, customer model scores are comprehensively evaluated from five dimensions such as the customer information conditions, the payment conditions, the power consumption conditions, the interaction conditions and the growth conditions through research methods such as business research, expert interview and mining modeling.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO MARKETING SERVICE CENT
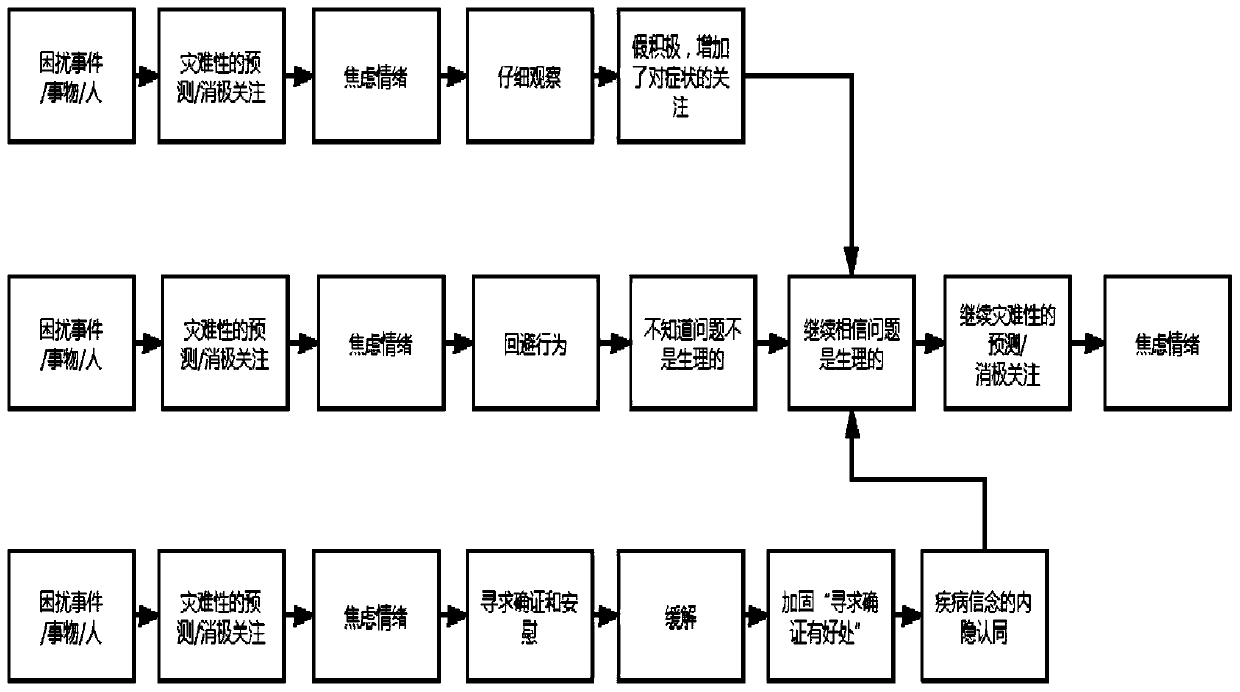
Psychological assessment method based on human-machine interaction and electronic equipment
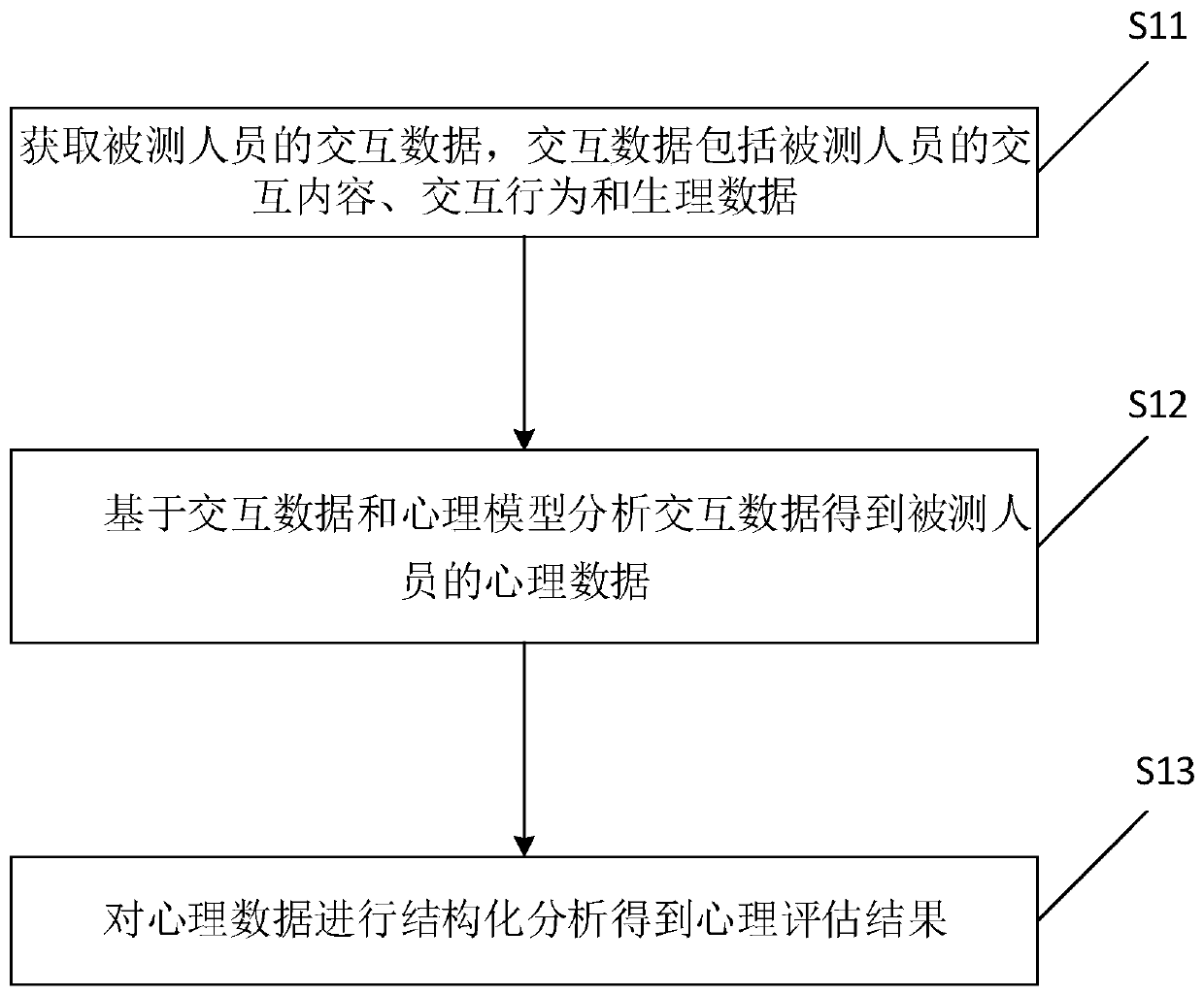
InactiveCN111430033AMitigate the lack of professionalismEase of convenienceMedical simulationHealth-index calculationPsychological ModelsEngineering
The invention discloses a psychological assessment method based on human-machine interaction and electronic equipment. The method includes: acquiring the interaction data of a subject, wherein the interaction data includes: interaction content, interaction behavior and psychological data of the subject; on the basis of the interaction data and the psychological model, analyzing the interaction data to obtain the psychological data of the subject, and performing structural analysis on the psychological data to obtain the psychological assessment result. The psychological assessment method integrates artificial intelligence, psychological principle, psychological counseling and evaluation technology, so that scientific, standard, systemic and convenient psychological assessment service is supplied to population. On the basis of offline mature psychological researching, psychological assessment evaluation conversation and professional psychological evaluation, human-machine interaction content is designed to ensure the standardization, structuralization and systematization of collection of the psychological health data, so that the defects that the psychological assessment service islack in professionality and convenience can be solved.
Owner:浙江连信科技有限公司
Autonomous vehicle component damage and salvage assessment
ActiveUS20210116256A1Registering/indicating working of vehiclesAnti-collision systemsAutopilotReliability engineering
Methods and systems for assessing, detecting, and responding to malfunctions involving components of autonomous vehicle and / or smart homes are described herein. Autonomous operation features and related components can be assessed using direct or indirect data regarding operation. Such assessment may be performed to determine the condition of components for salvage following a collision or other loss-event. To this end, the information regarding a plurality of components may be received. A component of the plurality of components may be identified for assessment. Assessment may including causing test signals to be sent to the identified component. In response to the test signal, one or more responses may be received. The received response may be compared to an expected response to determine whether the identified component is salvageable.
Owner:HYUNDAI MOTOR CO LTD +1
Device for Monitoring the State of Roads, Infrastructure and Traffic
InactiveUS20210027624A1High precisionEffectively scare awayDetection of traffic movementParticular environment based servicesSimulationTraffic conditions
Owner:SWAREFLEX
Non-intrusive assessment of fatigue in drivers using eye tracking
InactiveUS20200151474A1Improve road safetyImprove correspondenceInput/output for user-computer interactionAcquiring/recognising eyesDriver/operatorFeature extraction
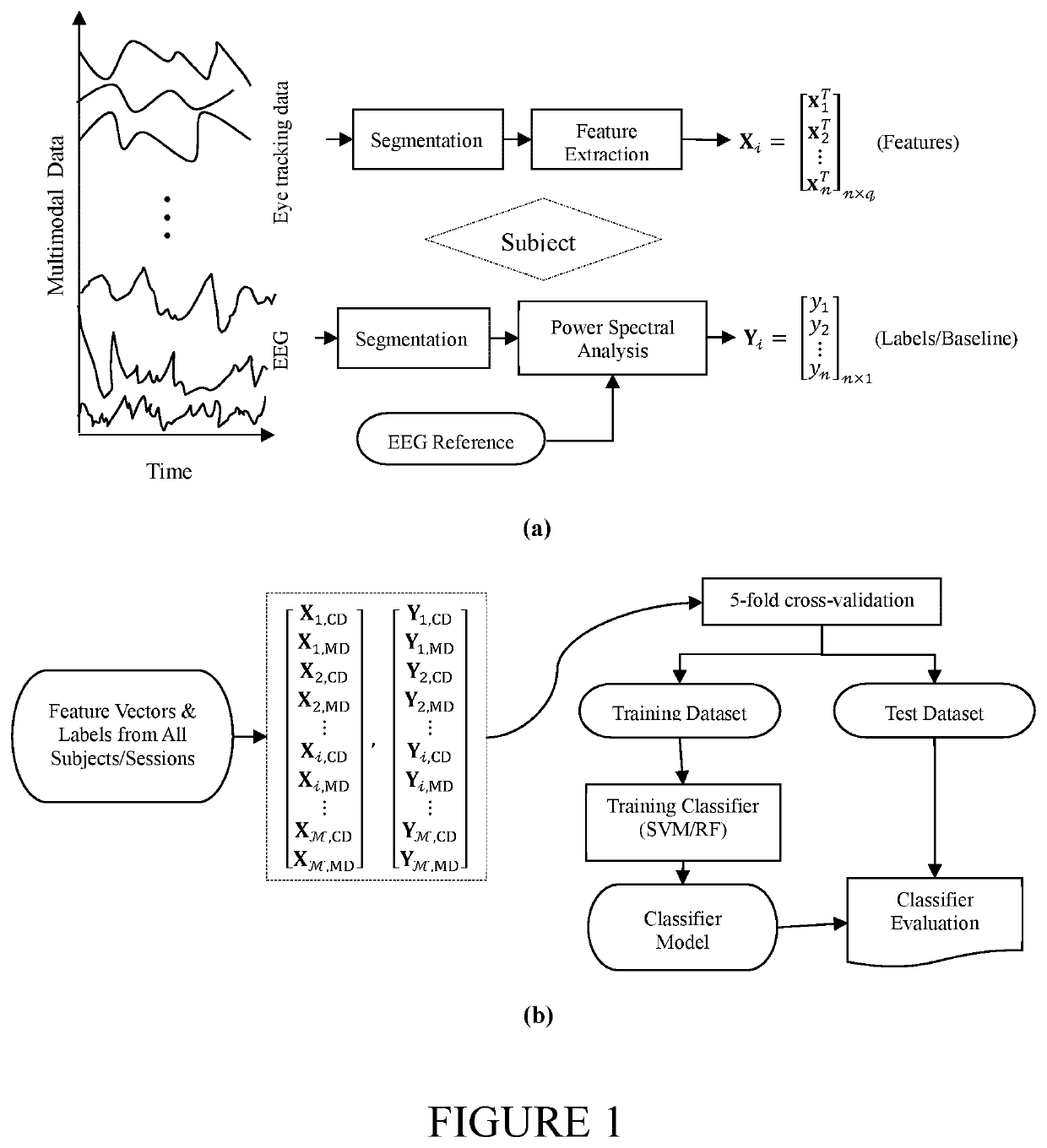
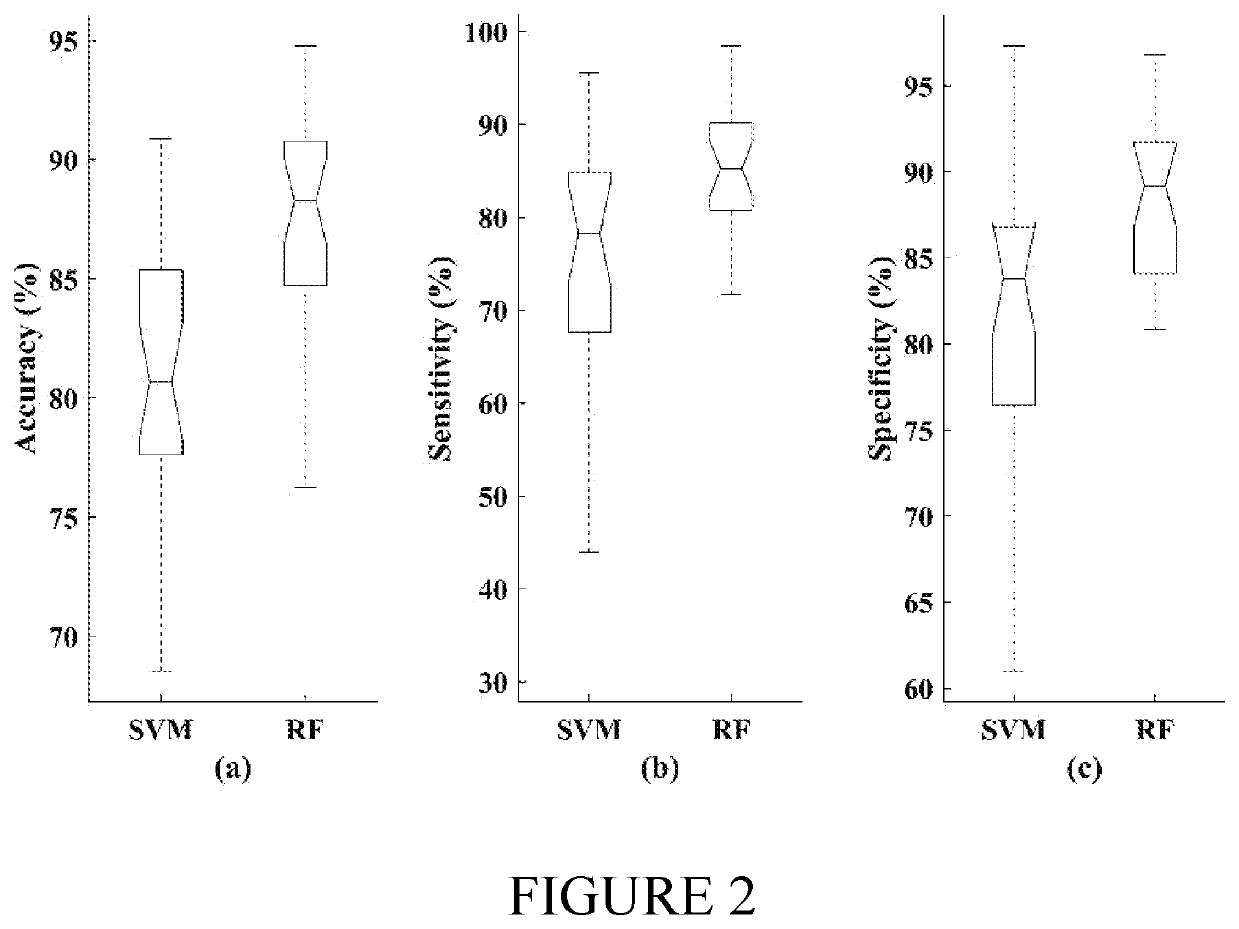
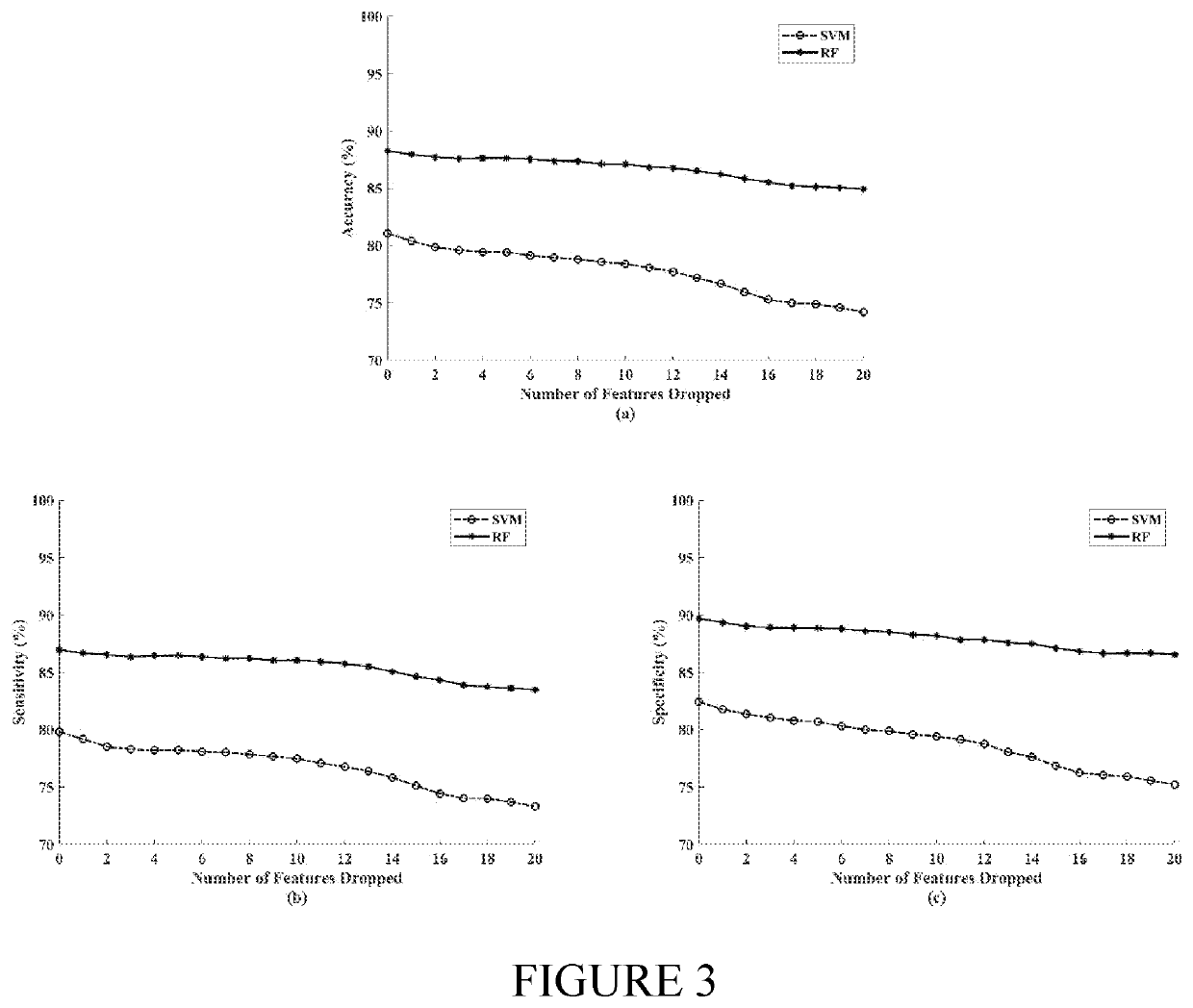
Non-intrusive assessment of fatigue in drivers using eye tracking. In a simulated driving experiment, vigilance was assessed by power spectral analysis of multichannel electroencephalogram (EEG) signals, recorded simultaneously, and binary labels of alert and drowsy (baseline) were generated for each epoch of the eye tracking data. A classifier and a non-linear support vector machine were employed for vigilance assessment. Evaluation results revealed a high accuracy of 88% for the RF classifier, which significantly outperformed the SVM with 81% accuracy (p<0.001). In a simulated driving experiment, the simultaneously recorded multichannel electroencephalogram (EEG) signals were used as the baseline. A random forest (RF) and a non-linear support vector machine (SVM) were employed for binary classification of the state of vigilance. Different lengths of eye tracking epoch were selected for feature extraction, and the performance of each classifier was investigated for every epoch length. Results revealed a high accuracy for the RF classifier in the range of 88.37%-91.18% across all epoch lengths, outperforming the SVM with 77.12%-82.62% accuracy. A feature analysis approach was presented and top eye tracking features for drowsiness detection were identified. A high correspondence was identified between the extracted eye tracking features and EEG as a physiological measure of vigilance and verified the potential of these features along with a proper classification technique, such as the RF, for non-intrusive long-term assessment of drowsiness in drivers.
Owner:ALCOHOL COUNTERMEASURE SYST INT
T.E.S.S. Teacher Evaluation Systems Software
InactiveUS20100145870A1Enhancing their self-conceptData processing applicationsDocument preparationEvaluation system
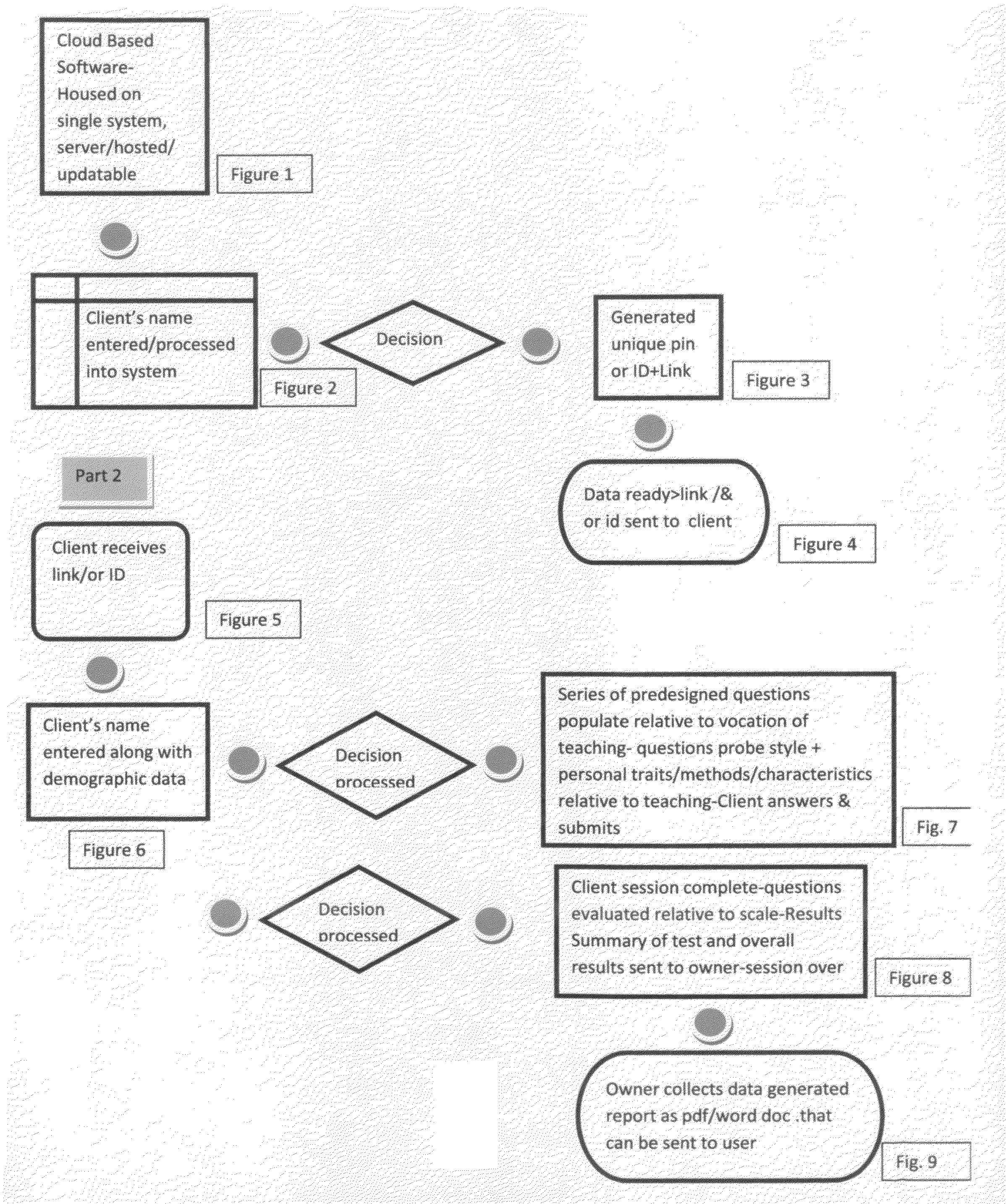
T.E.S.S. is a Teacher Evaluation Assessment Software which evaluates the teacher / candidate based on a series of pre-designed questions that probe teaching styles, traits, strengths & weaknesses as related to the vocation of teaching. Results determine teaching styles / archetypes (The Discoverer, The Sage, The Counselor and The Motivator), in addition to learning styles associated, methods to assist the client, qualities & characteristics adaptable to the profession, a movie reference that fits learner style, tools for teachers, need to knows and a supervisory portion if requested by administrator for client to assist in supervising to their preferred teaching style. Employers / Clients are provided pdf / word document of results. Used for development of faculty / staff and as a screening tool for schools and universities for teacher candidates.
Owner:RODNEY LUSTER RODNEY LUSTER JAMES
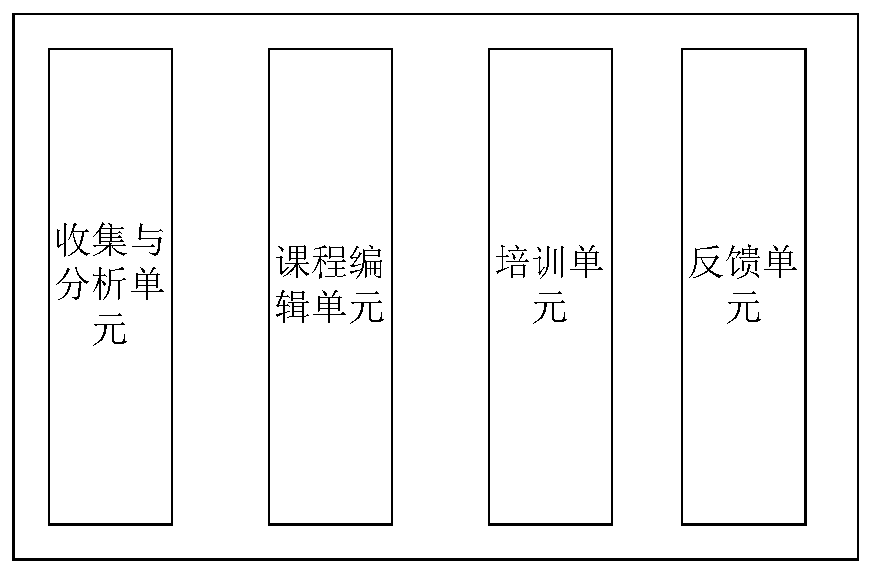
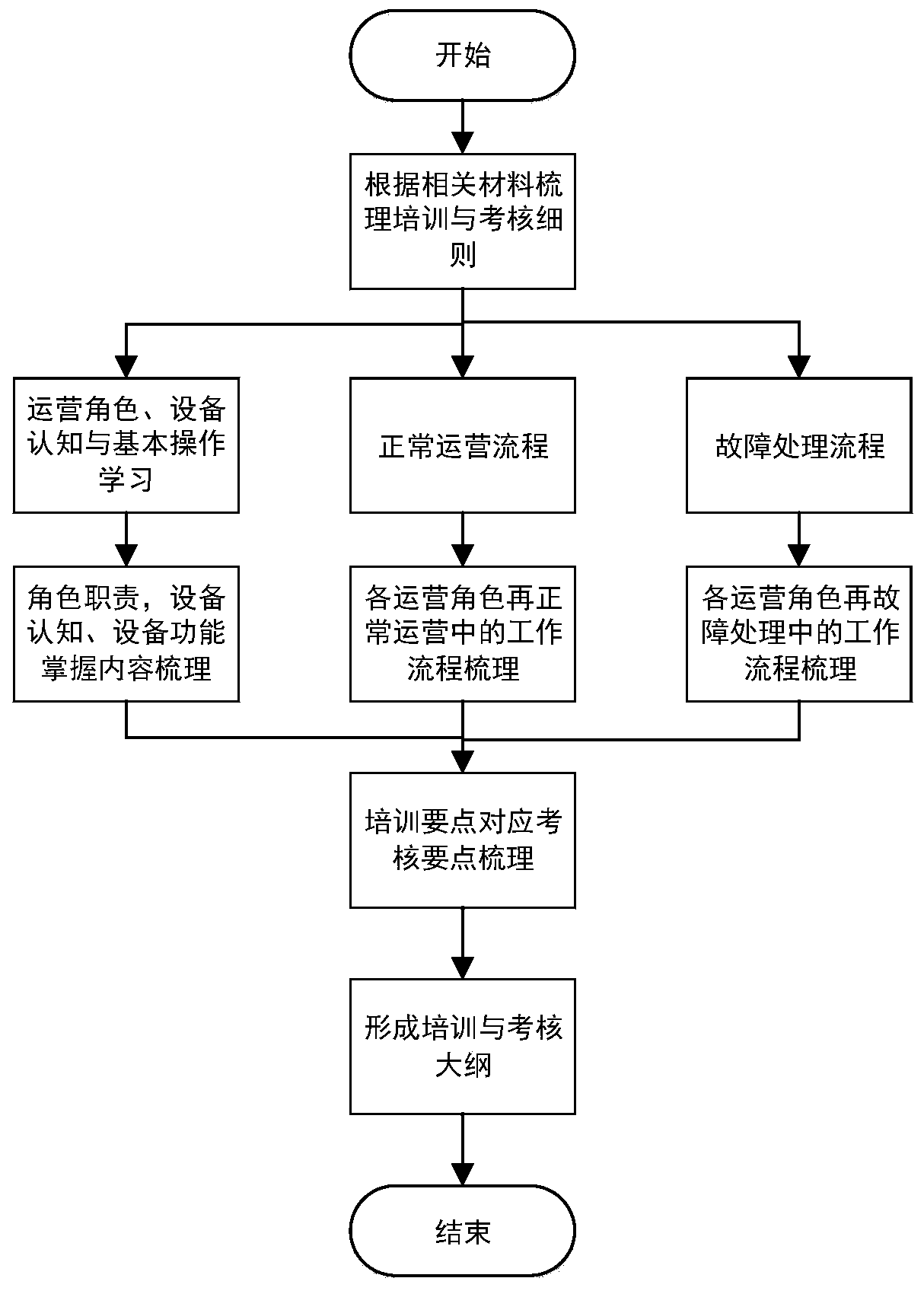
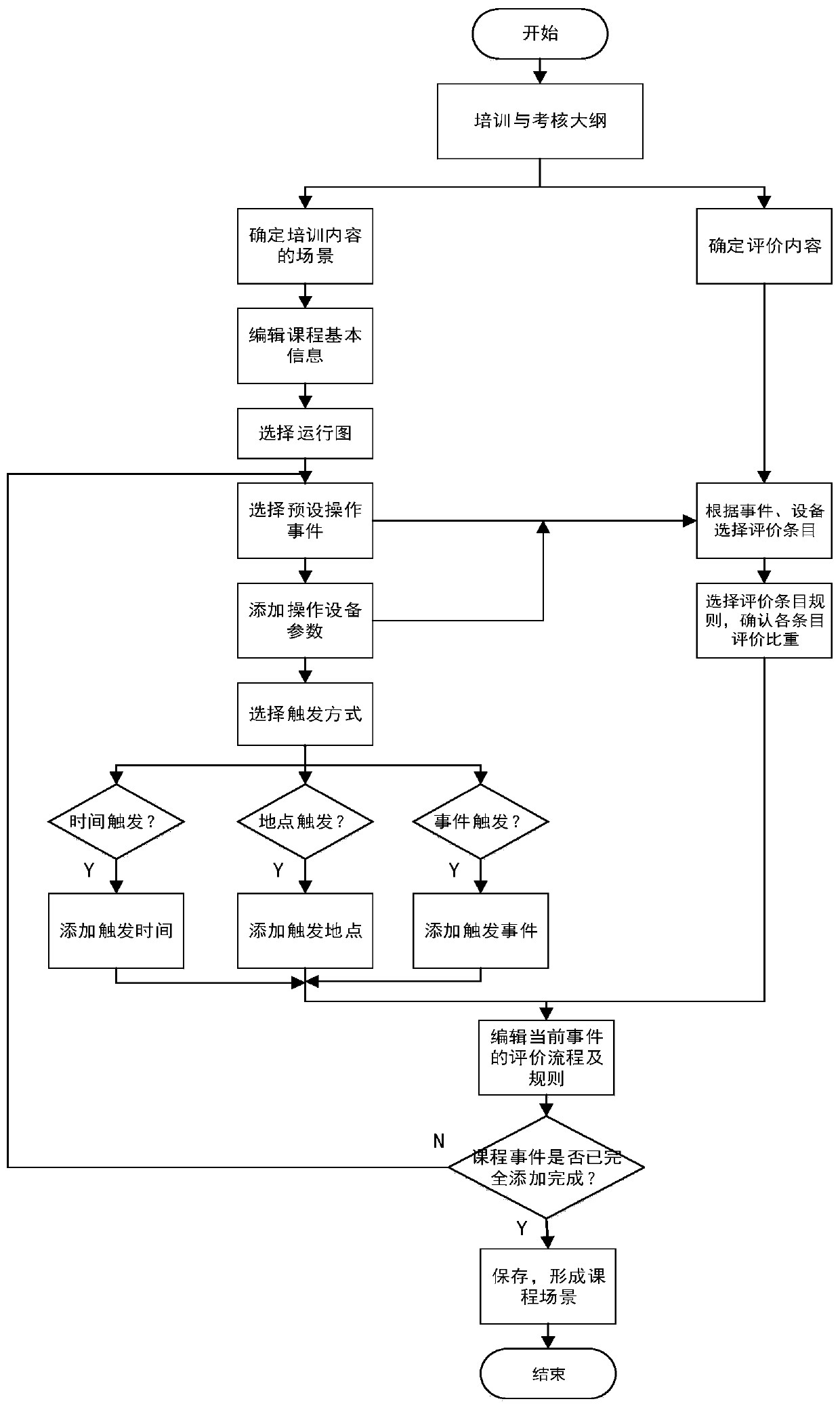
CTC scheduling simulation assessment evaluation system based on scene control
InactiveCN110807970AImprove realismDeepen cognitionCosmonautic condition simulationsResourcesArtificial intelligenceCoursework
The invention discloses a CTC scheduling simulation assessment evaluation system based on scene control. The scheduling simulation assessment evaluation system is applicable to learning, practice, assessment and skill evaluation and capability analysis on professional theoretical knowledge and real operation skills of different-level operators of different types of work and different positions ofthe universal and high-speed railways; the operation flow of the system is that firstly, CTC scheduling operator training and assessment outline and assessment details are constructed; then, an application scene editing tool edits course scene and an evaluation rule according to the training requirement, loads the course scene and the evaluation rule into a CTC scheduling simulation system in theimplementation process of a teaching plan, and combines with an application scene driving control module to realize scene reproduction; and next, the scene maneuvering process data is input into an evaluation assessment system to realize autonomy assessment and analysis statistics. The scheduling simulation assessment evaluation system can carry out cognitive and different levels of skill trainingand assessment identification on CTC scheduling related operators efficiently, quickly and conveniently, and has a wide application prospect in the aspects of railway service organization and railwaycomprehensive operation.
Owner:CHENGDU YUNDA TECH CO LTD
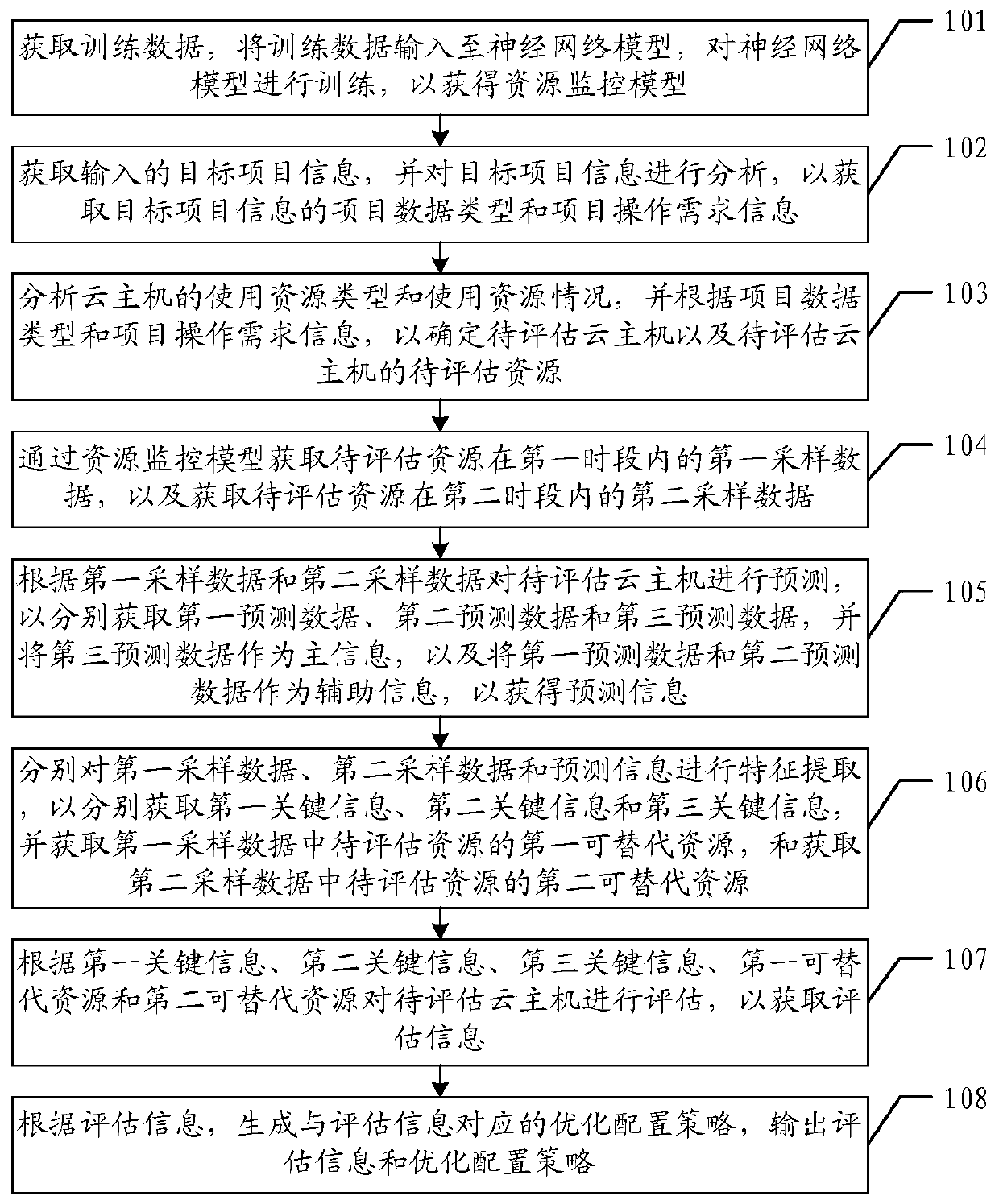
Method, device and equipment for evaluating cloud host resources and storage medium
ActiveCN110806954AMeet assessment needsImprove resource utilizationDetecting faulty hardware by configuration testFunctional testingService domainEngineering
The invention relates to the field of cloud services. The invention provides a method, device and equipment for evaluating cloud host resources and a storage medium. The method comprises the followingsteps: analyzing the target project information, and the use resource types and use resource conditions of the plurality of cloud hosts through the trained resource monitoring model to obtain a to-be-assessed cloud host and to-be-assessed resources of the to-be-assessed cloud host; obtaining first sampling data and second sampling data of the to-be-evaluated resource, and obtaining prediction information according to the first sampling data and the second sampling data, obtaining evaluation information according to the first sampling data, the second sampling data and the prediction information, and generating an optimal configuration strategy corresponding to the evaluation information according to the evaluation information. By adopting the scheme, the resource utilization rate of the cloud host can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
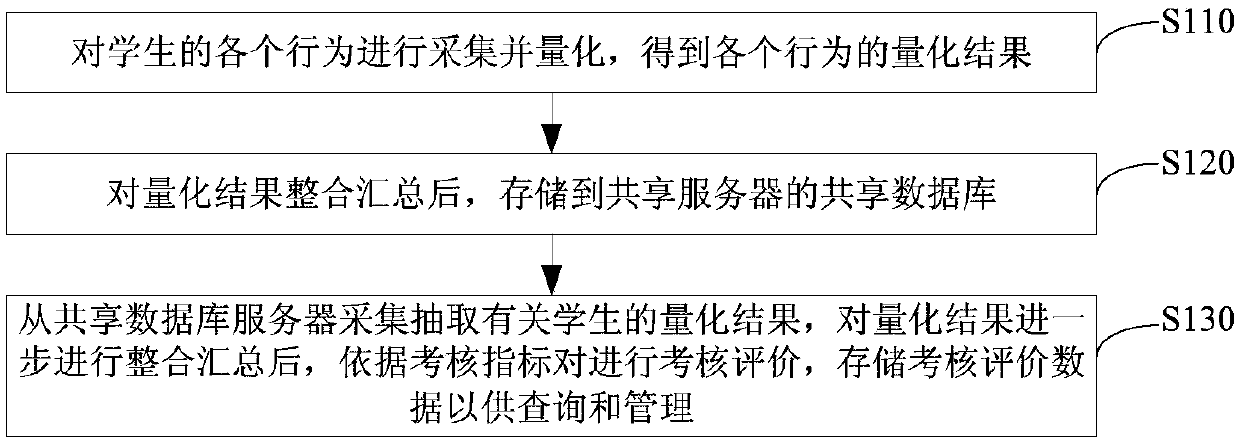
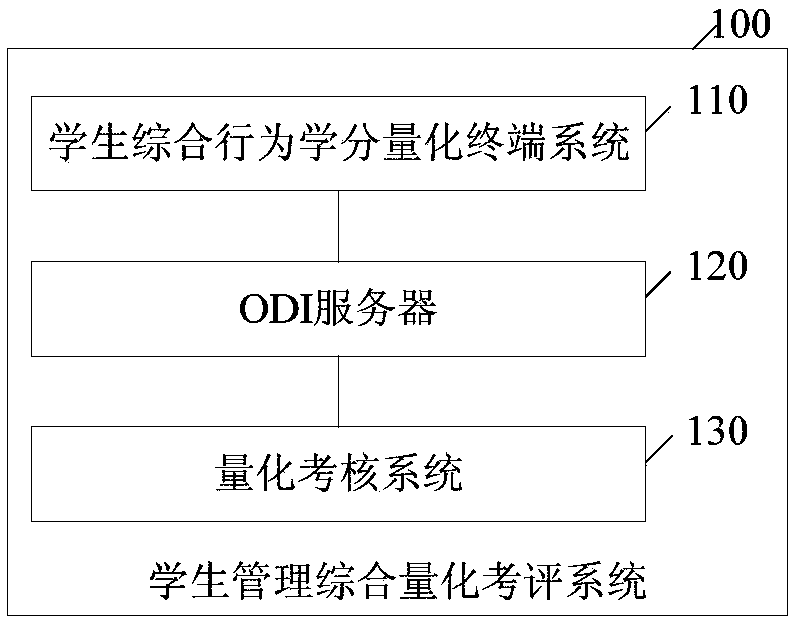
A comprehensive quantitative evaluation method and system for student management
PendingCN109670677AQuick and efficient rollup integrationOvercome the shortcomings of less content and difficulty in judging differencesResourcesDatabase design/maintainanceComputer scienceManagement system
The invention relates to the technical field of management systems, and particularly discloses a comprehensive quantitative evaluation method for student management. The method comprises the steps ofcarrying out the collection and quantification of each behavior of a student, and obtaining a quantification result of each behavior; integrating and summarizing the quantification results, and storing the quantification results in a shared database of a shared server; collecting and extracting quantization results related to students from a shared database server, further integrating and summarizing the quantization results, carrying out assessment evaluation according to assessment index pairs, and storing assessment evaluation data for query and management. The invention also discloses a comprehensive quantitative evaluation system for student management. According to the student management comprehensive quantitative evaluation method provided by the invention, the subjectivity and theobjectivity can be distinguished, so that the evaluation can be refined and quantized to achieve comprehensive evaluation. In addition, during evaluation, all evaluation reference data can be rapidlyand effectively gathered and integrated through tools, and the interference of factors such as manual statistics is avoided.
Owner:WENZHENG COLLEGE OF SOOCHOW UNIV
Color evaluation apparatus and method
InactiveUS7667845B2High appearance requirementsGood colorDigitally marking record carriersRadiation pyrometryCalculation errorLength wave
A spectral distribution error evaluation apparatus is used to evaluate precision of color matching between evaluation and target colors. A first weighting function generator generates a first weighting function on the basis of color matching functions, wavelength characteristics which are independent of a light source of the target color, and visual characteristics which depend on wavelengths. A second weighting function generator generates a second weighting function on the basis of light source information of selected light sources. A difference calculator calculates error values between the evaluation and target colors for respective frequencies. An evaluation value calculator applies the first and second weighting functions to the error values, and calculates the sum total of the error values as an evaluation value. In this way, a precision evaluation value which has high correlation with actual color appearance and is used to improve the color matching precision can be calculated independently of a change in condition such as a light source or the like.
Owner:CANON KK
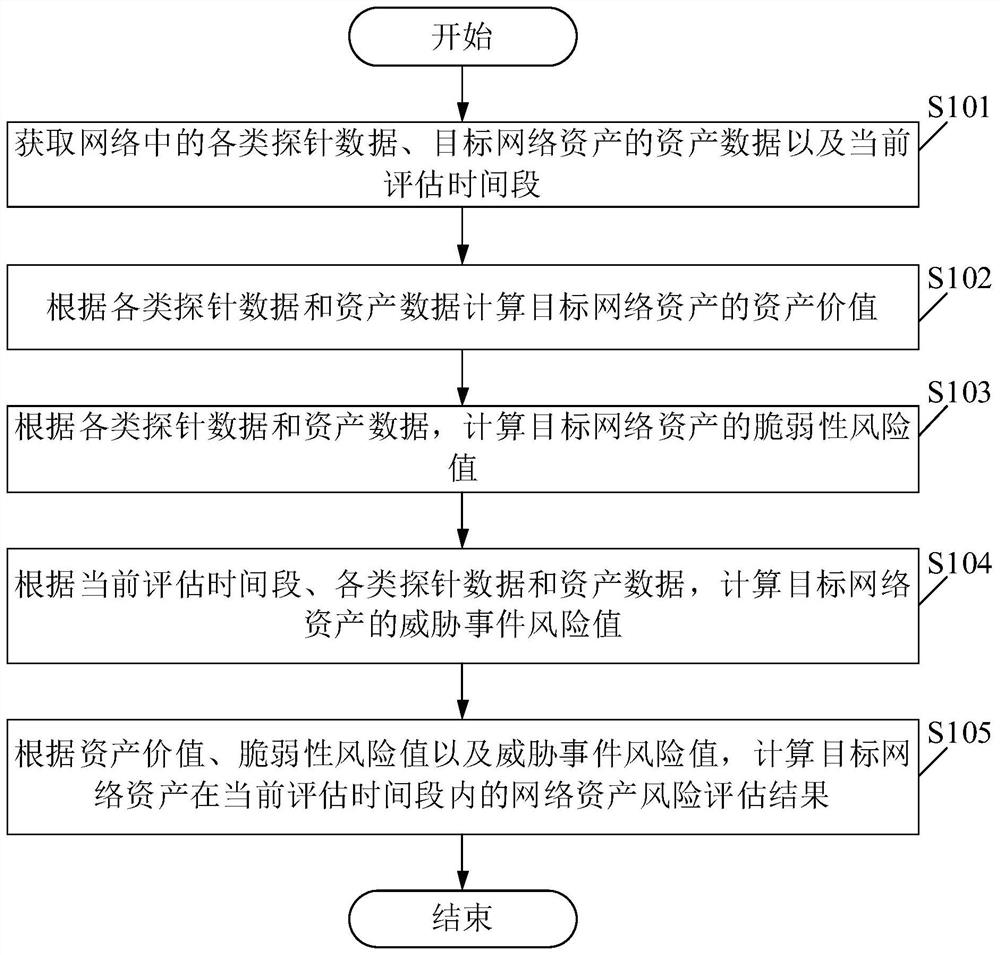
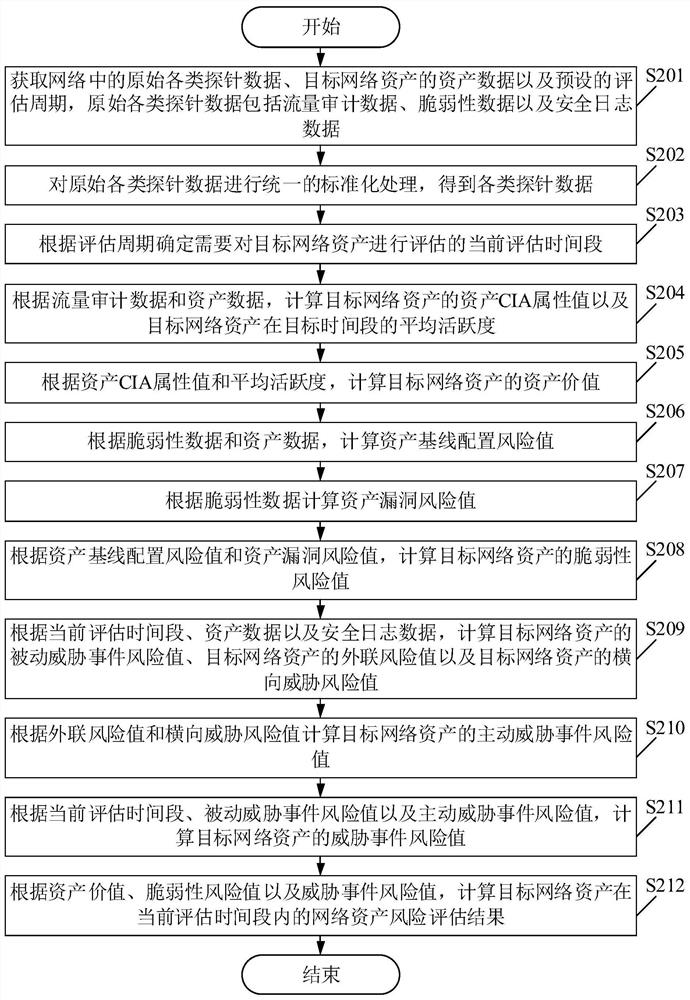
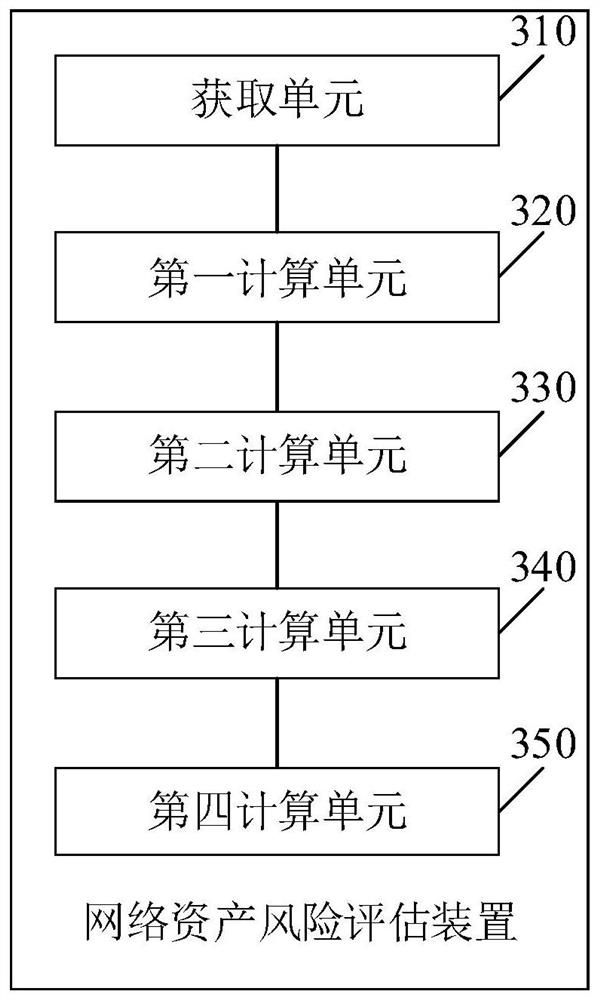
Network asset risk assessment method, device and system
The embodiment of the invention provides a network asset risk assessment method, device and system, and relates to the technical field of Internet. The network asset risk assessment method comprises the following steps: firstly, obtaining various kinds of probe data in a network, asset data of target network assets and a current assessment time period; calculating an asset value of the target network assets according to the various kinds of probe data and the asset data; calculating a vulnerability risk value of the target network assets according to the various probe data and the asset data; further calculating a threat event risk value of the target network assets according to the current assessment time period, the various probe data and the asset data; and finally, according to the asset value, the vulnerability risk value and the threat event risk value, calculating a network asset risk assessment result of the target network assets in the current assessment time period. Therefore, comprehensive assessment of network asset risks can be realized, artificial participation in assessment is not needed, and an assessment result is accurate, objective and highly professional.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Risk assessment method and device, storage medium and electronic device
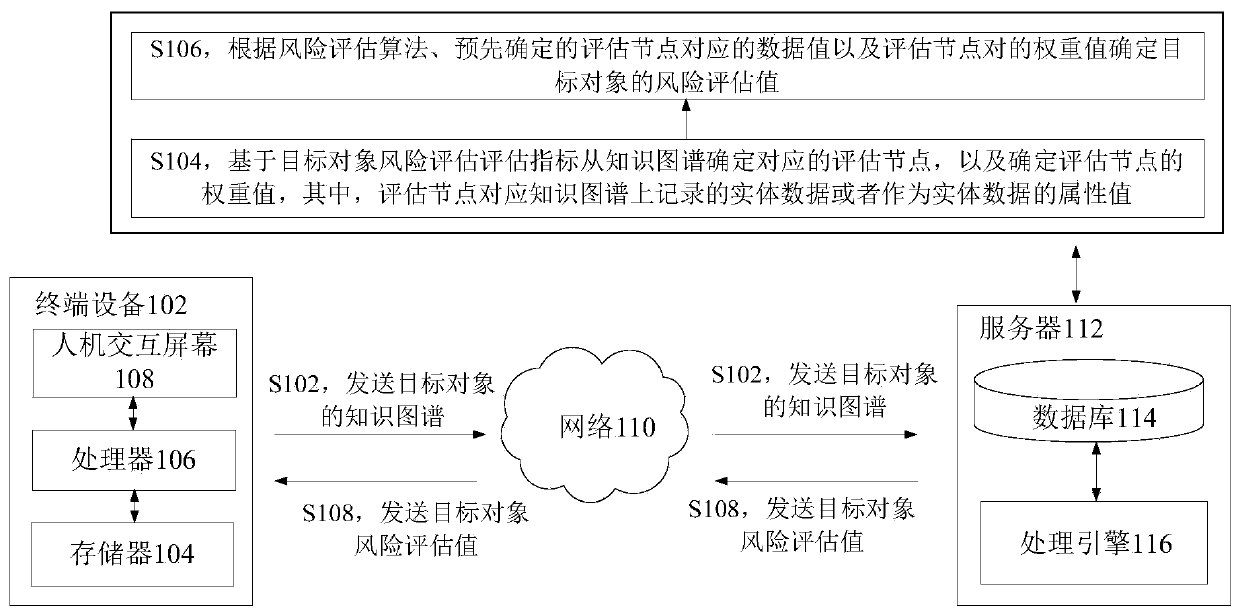
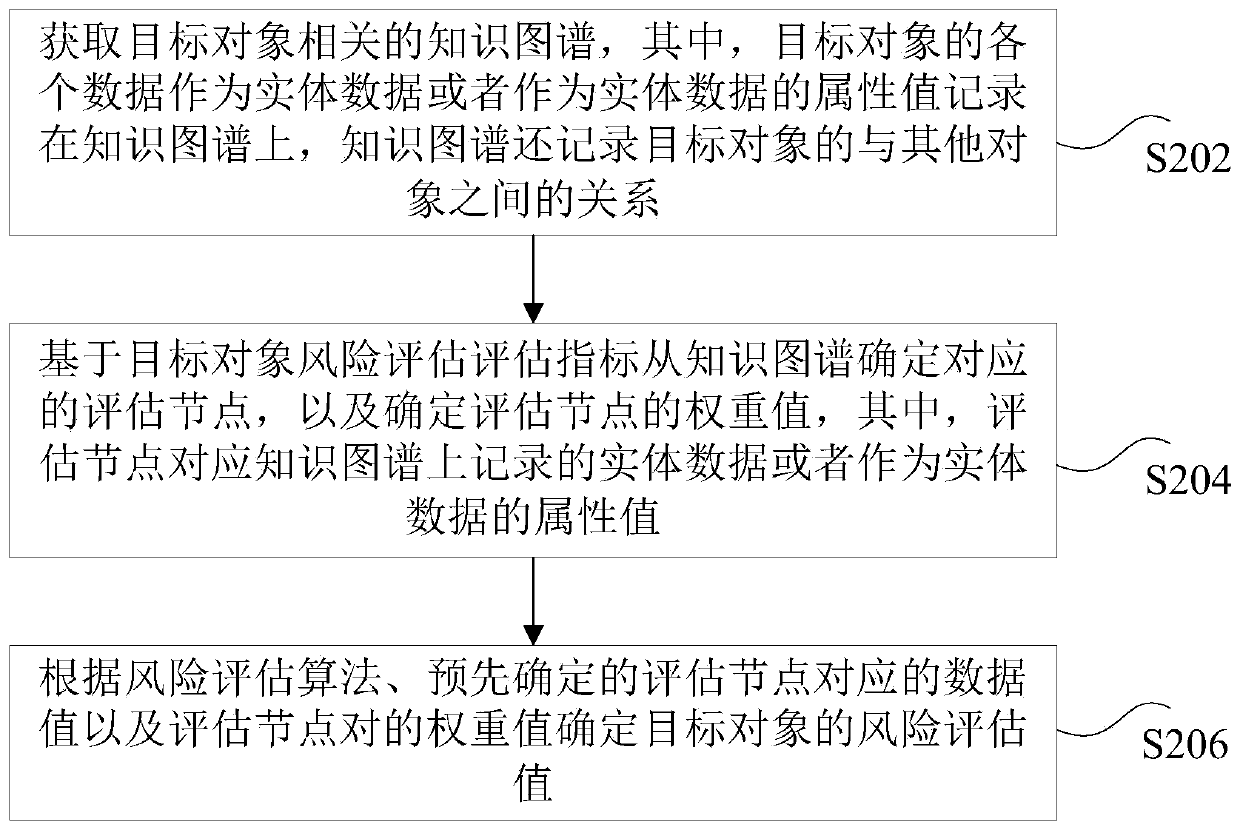
InactiveCN111445121AAccurate risk assessmentRisk assessment assessment is accurateResourcesSpecial data processing applicationsRelevant informationKnowledge graph
The invention discloses a risk assessment method and device, a storage medium and an electronic device. The method comprises the steps that a knowledge graph related to a target object is acquired, all data of the target object serve as entity data or serve as attribute values of the entity data to be recorded on the knowledge graph, and the knowledge graph further records the relation between thetarget object and other objects; a corresponding evaluation node is determined from the knowledge graph based on the target object risk evaluation index, and a weight value of the evaluation node isdetermined; and a risk assessment value of the target object is determined according to a risk assessment algorithm, a predetermined data value corresponding to the assessment node and the weight value of the assessment node pair. The technical effects of obtaining more comprehensive related information from the knowledge graph and carrying out accurate risk assessment on the target object are achieved, and the technical problem that in the prior art, the risk assessment accuracy of the target object is low due to the fact that the related information of the target object cannot be comprehensively obtained is solved.
Owner:SHANGHAI MININGLAMP ARTIFICIAL INTELLIGENCE GRP CO LTD
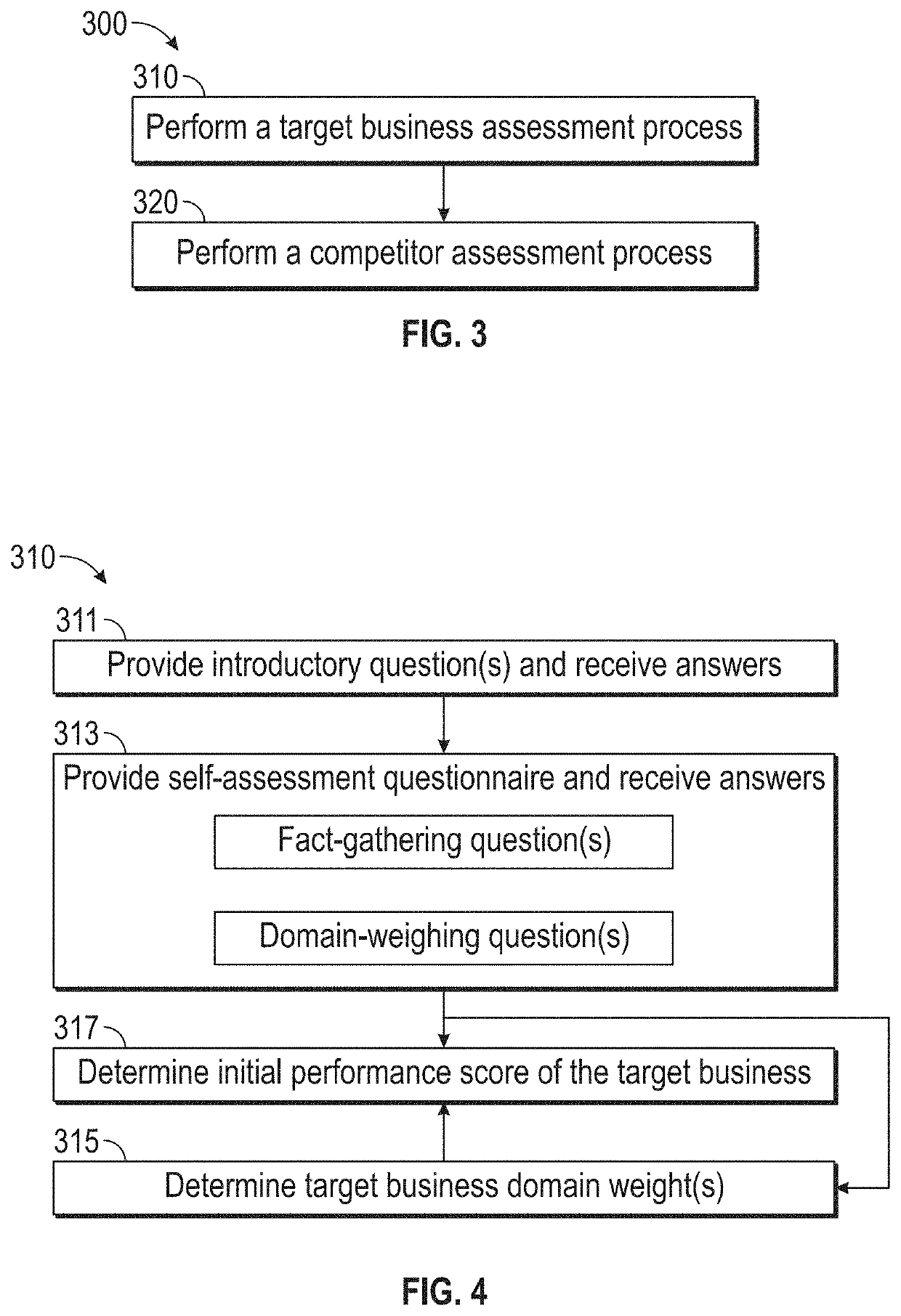
Data driven systems and methods for optimization of a target business
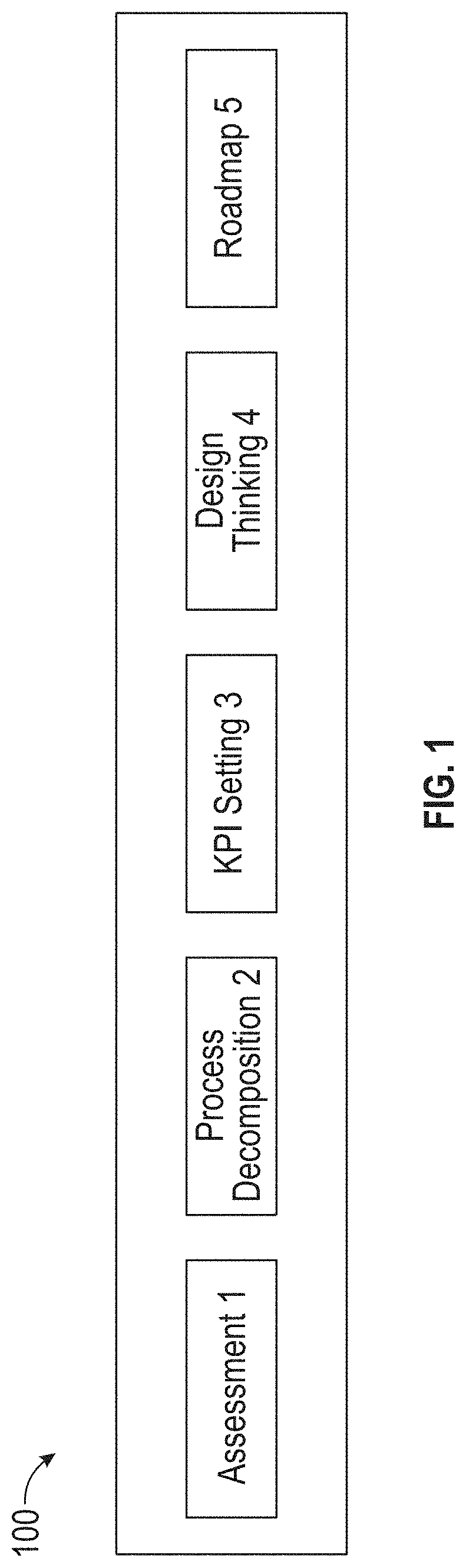
The present disclosure is directed to a system and associated methods for assessing, evaluating a target business, and leveraging insights from the assessment and evaluation to provide strategy recommendations to optimize the performance of the target business. In some embodiments, the system may identify a benchmark competitor and determine a performance score for the benchmark competitor. In some embodiments, the system may determine a domain score of an identified benchmark competitor. In some embodiments, the system determines an updated performance score based on provided capability process data. In some embodiments, the system recommends solutions and / or key performance indicators (KPI) to solve a provided problem. In some embodiments, the system provides a platform to enable stakeholders, (e.g., users) in the target business to perform a design thinking process.
Owner:AMPLO GLOBAL INC
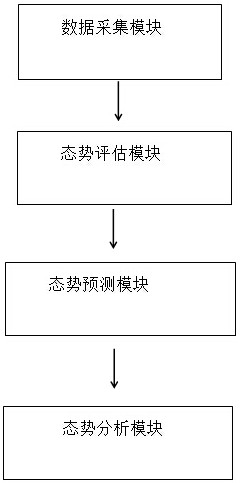
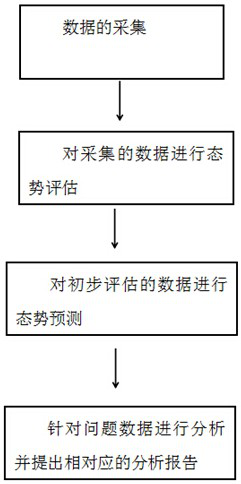
Network security situation awareness system and method
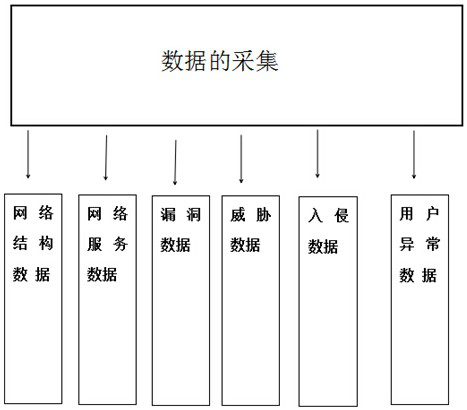
The invention relates to a network security situation awareness system and a network security situation awareness method. The network security situation awareness method comprises the steps of 1, acquiring data, and widely acquiring network security data; 2, carrying out situation assessment on the collected data, establishing assessment of multiple levels and multiple angles during situation assessment, assessing service security, data security, infrastructure security and overall security conditions of the network, and selecting different assessment methods for different application backgrounds and different network scales; 3, carrying out situation prediction on the preliminarily evaluated data to prevent large-scale security events; and 4, analyzing the problem data and proposing a corresponding analysis report. The method is high in pertinence and wide in data acquisition range, and can perform comprehensive acquisition and subsequent perception on network structure data, networkservice data, vulnerability data, threat data, intrusion data and user abnormal data.
Owner:黑龙江省网络空间研究中心 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com