Patents
Literature
9313results about "Database design/maintainance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
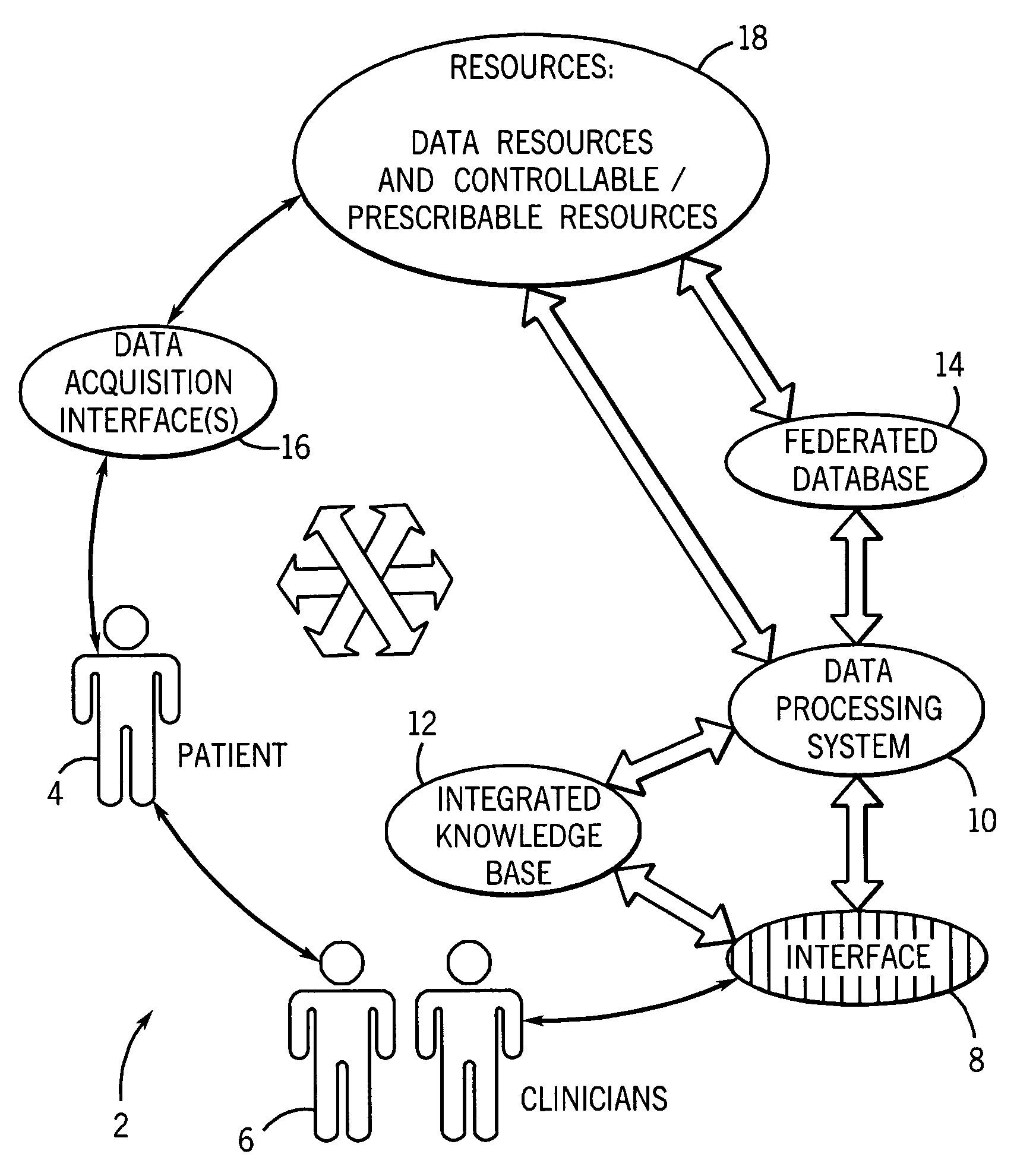
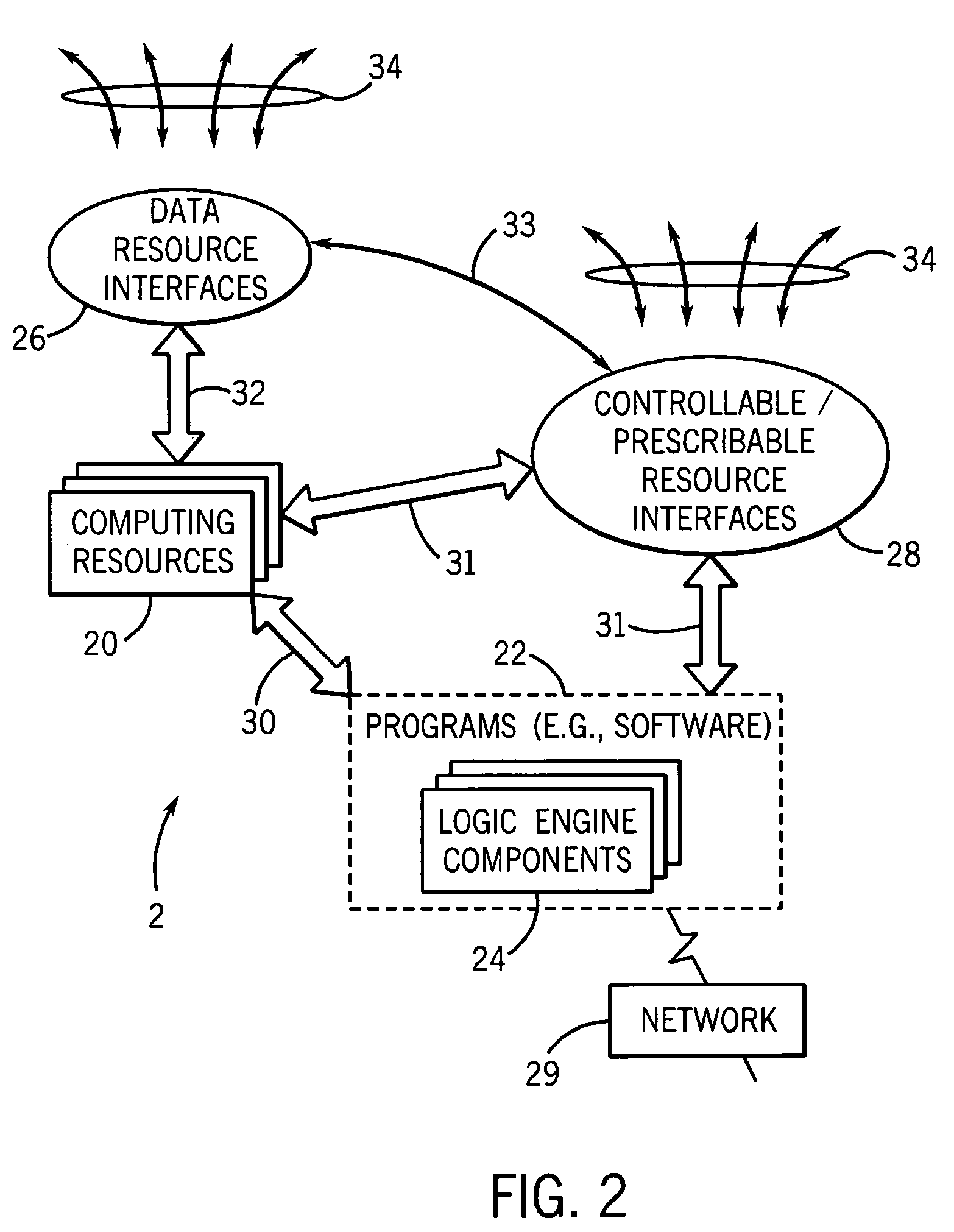
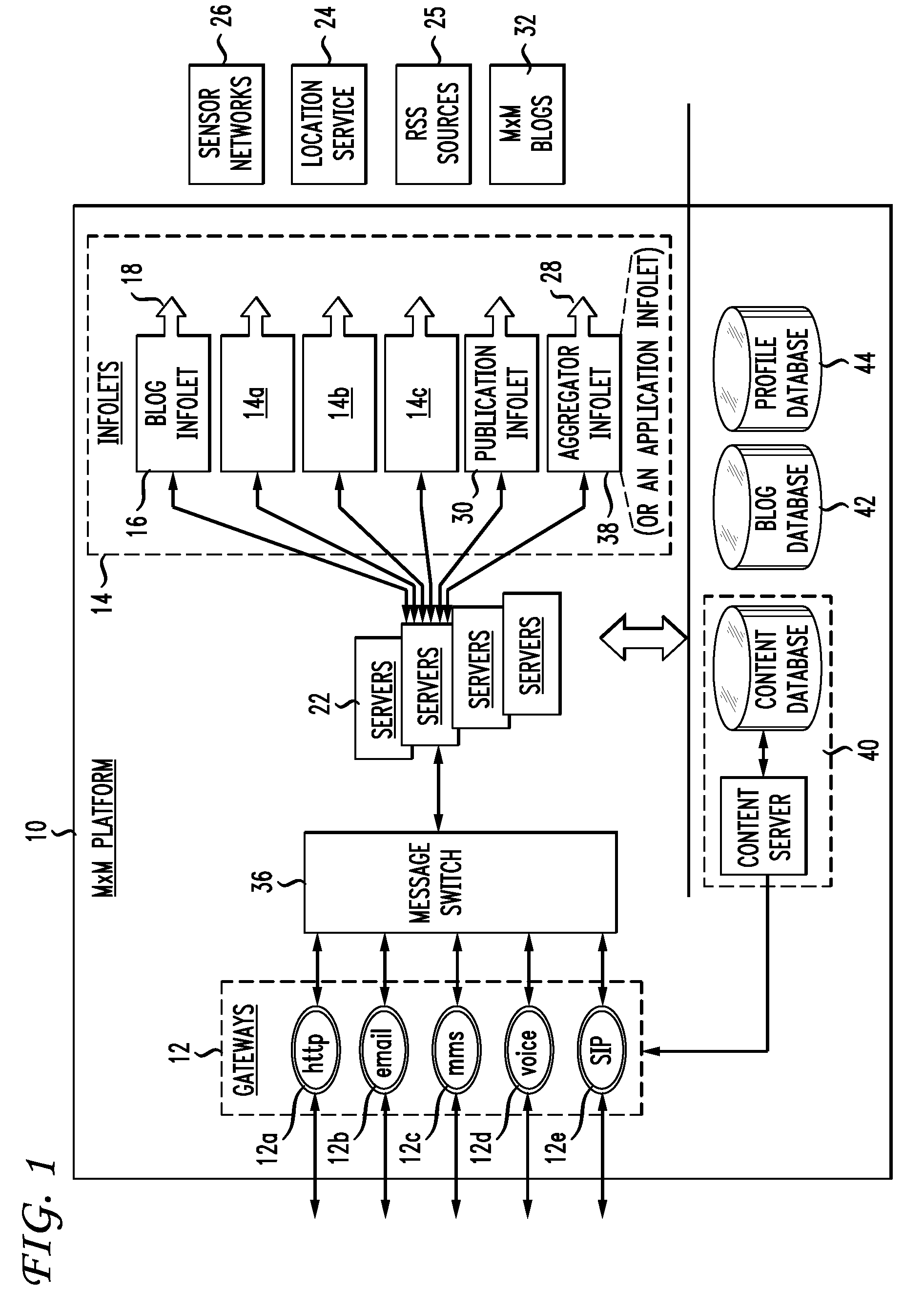
System and method for integrated learning and understanding of healthcare informatics
InactiveUS20070118399A1Data processing applicationsPatient personal data managementCrowdsData entity
An informatics system permits data entities from a wide range of data sources to be accessed and evaluated. The sources of the data entities may be simply data sources, such as for articles and other non-patient or population specific information, as well as controllable and prescribable sources, such diagnostic imaging, clinical and other sources forming part of the patient care path. The entities are organized, analyzed in accordance with a domain framework, which may be altered by a user to focus on factors and informational components of interest. Holistic and integrated understanding of such factors are there fore available, and refinement of healthcare processes can be made to provide improved care in a more time and cost effective manner.
Owner:GENERAL ELECTRIC CO
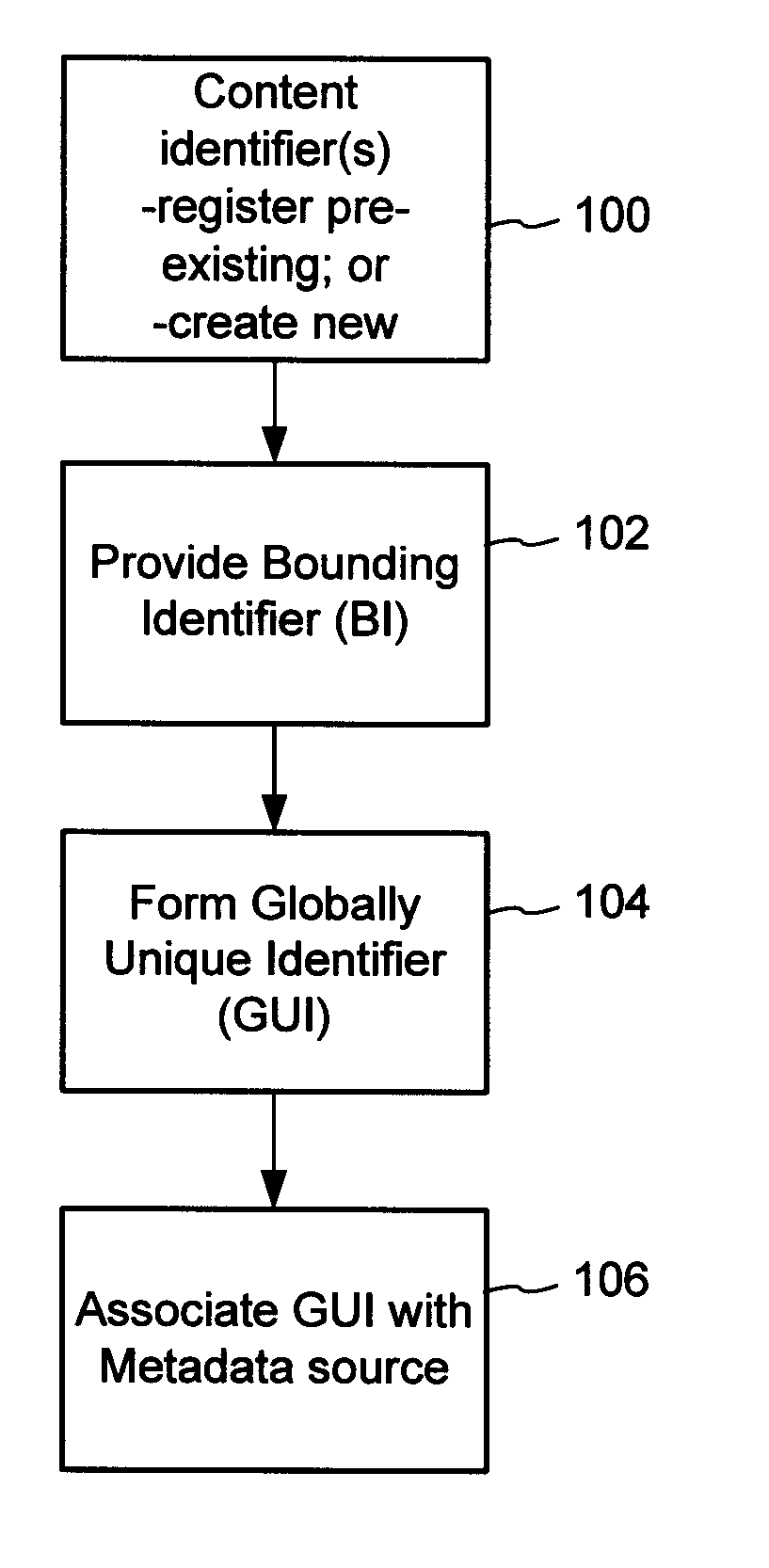
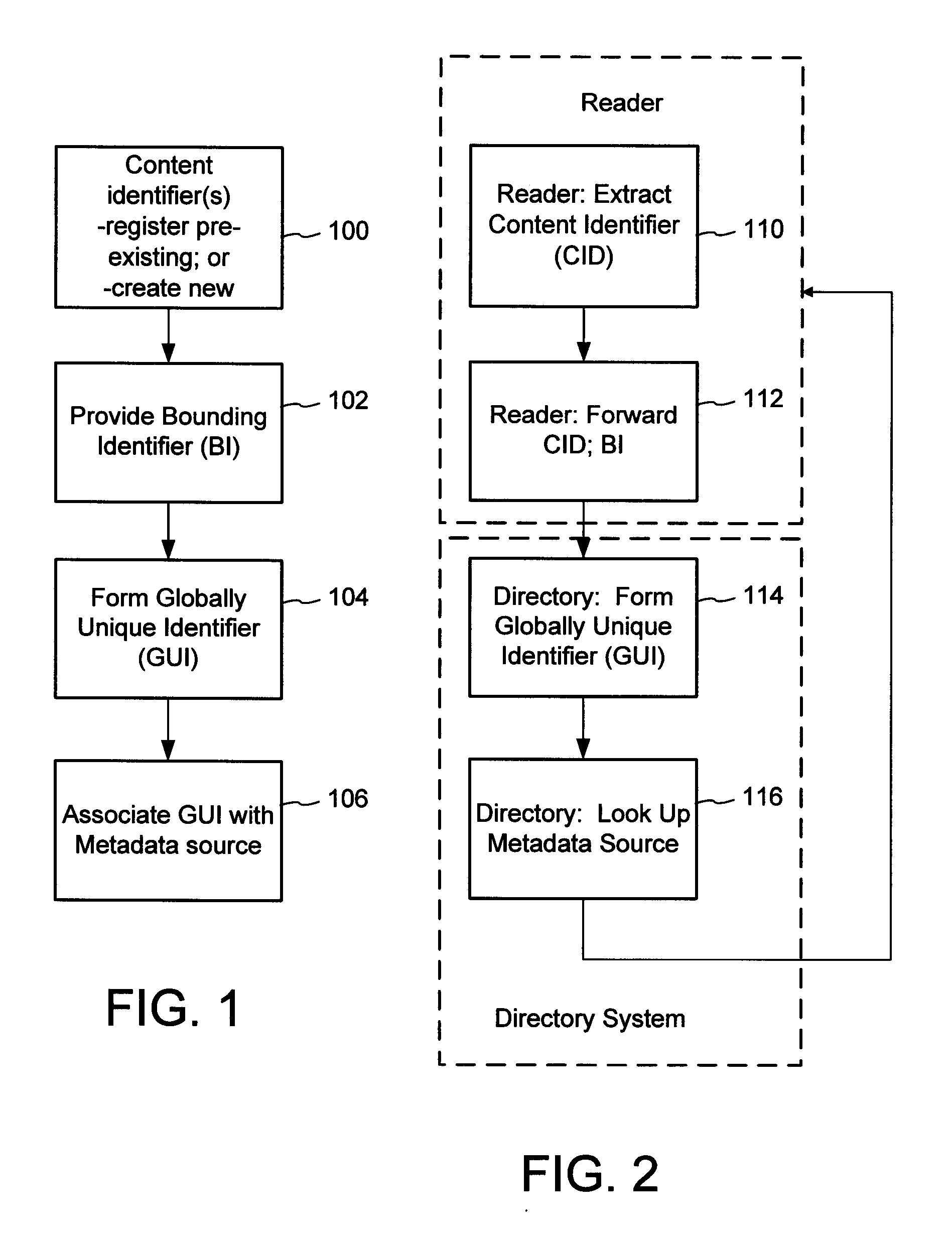
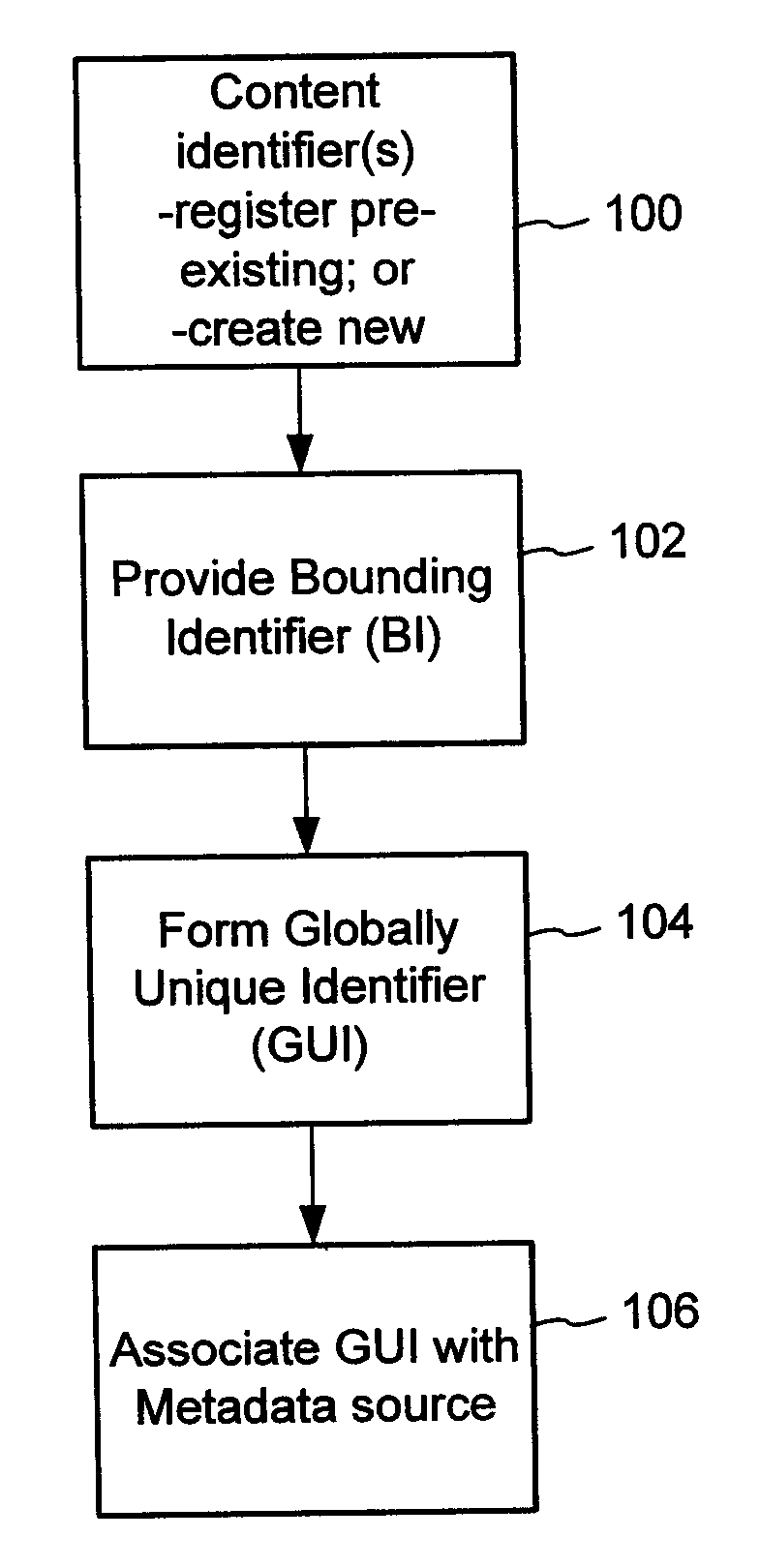
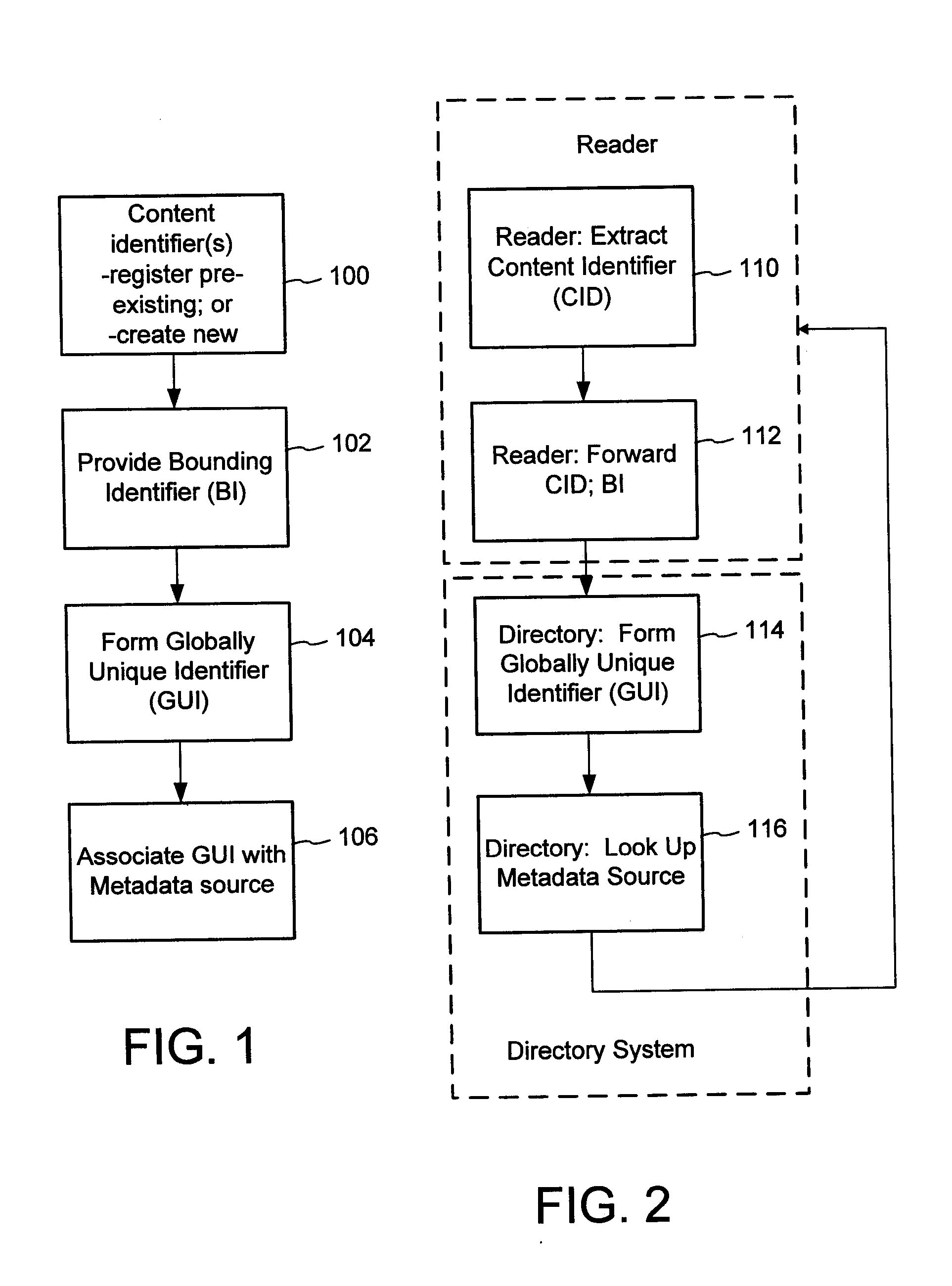
Content Metadata Directory Services
ActiveUS20070156726A1Improve interoperabilityIncrease the number ofMultimedia data indexingDigital data processing detailsContent IdentifierSystems management
The content metadata directory system connects consumers of identified content to managed metadata databases and other digital resources. The system manages links between identifiers in content objects and metadata sources. It supports a variety of different type of content identifiers and allows for overlap among different content identification schemes. One method of associating a content object with metadata uses a combination of a content identifier and a bounding identifier to enable handling of disparate sets of content identifiers for content objects with potentially conflicting content identifiers. The method receives a content identifier for a content object from among a set of content identifiers and provides a unique bounding identifier for the set of content identifiers. This unique bounding identifier is used in combination with the content identifier to form a globally unique identifier for the content object. This globally unique identifier is associated with a metadata source, which enables routing of a user to the metadata source.
Owner:DIGIMARC CORP
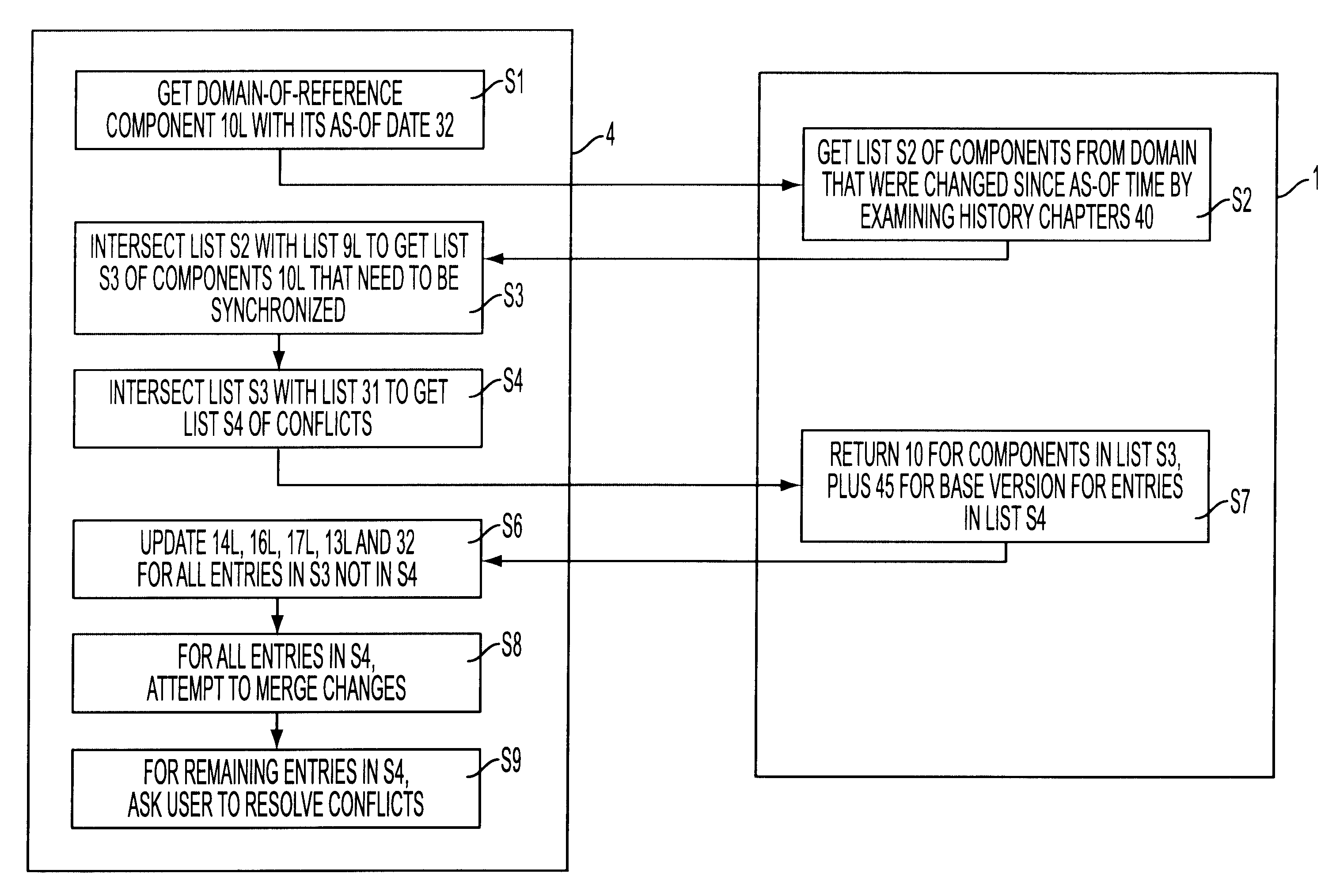
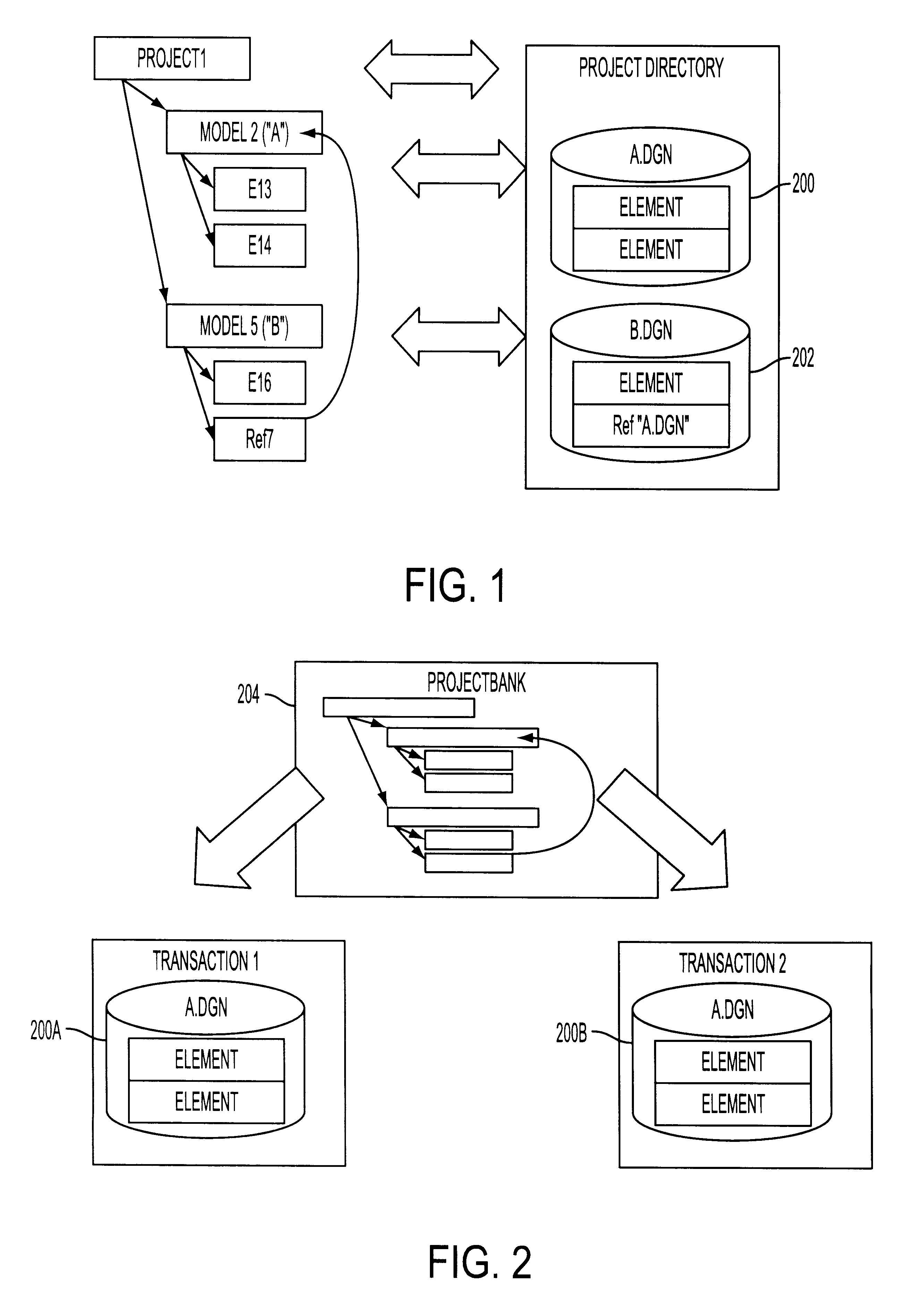
System for collaborative engineering using component and file-oriented tools
InactiveUS6341291B1Improve the level ofHigh currentData processing applicationsCAD network environmentSoftware engineeringIdenticon
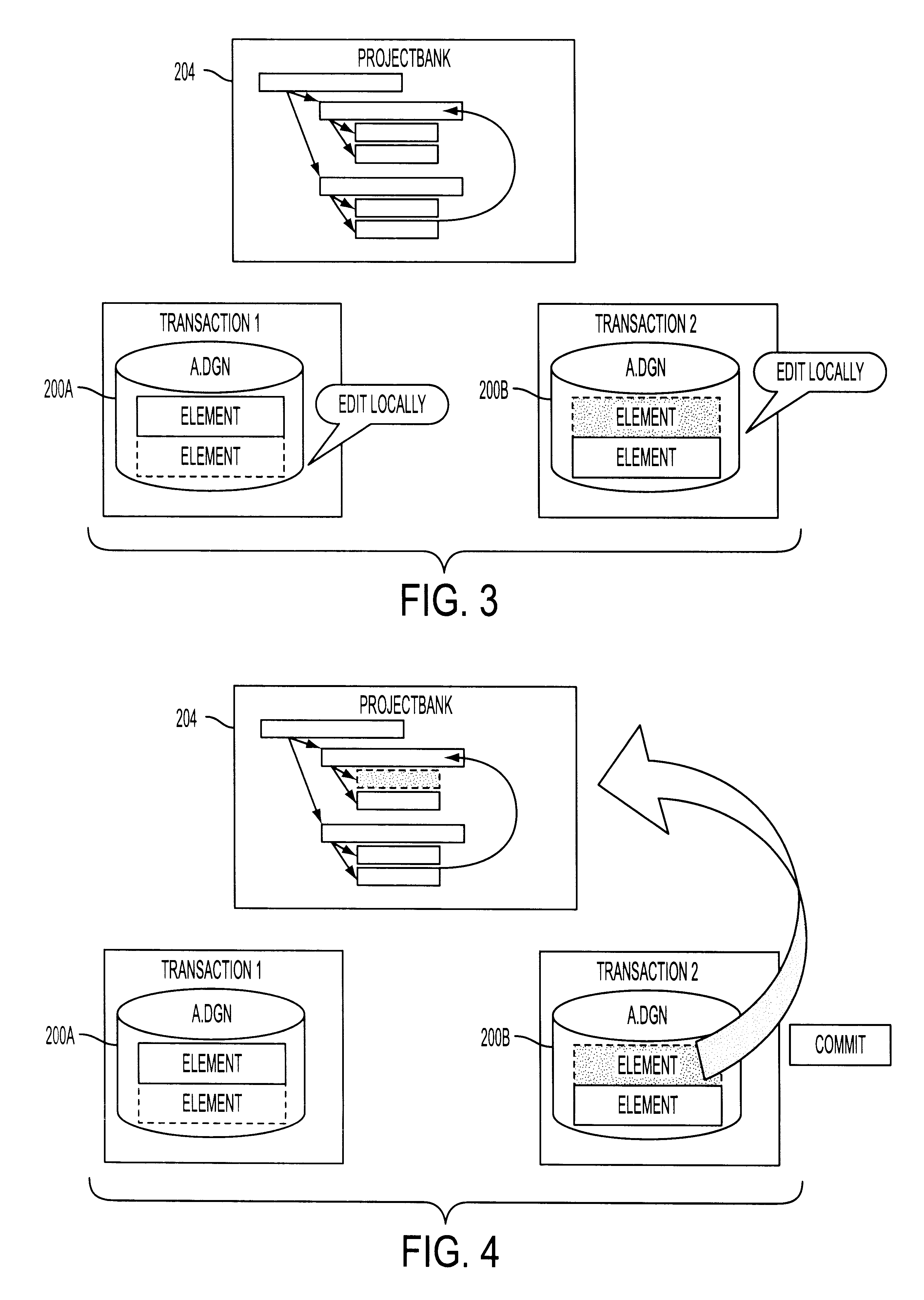
Conventional file-based engineering design data for an engineering model are represented by a plurality of components. Each component has a unique identifier, a set of fields, each field having a data type and a data value, and a program which interprets and modifies the fields. The plurality of components are stored in a repository of a server. The repository also stores a history of any changes made to the components. A plurality of client computers are bidirectionally connected to the server. Each client computer may obtain the current version of the components and may send locally edited versions of the components back to the server to replace the current versions in the repository. At the client computer, the user interacts with the components using conventional file-based software. Before locally edited versions of the components are committed to the server to replace the current versions, a synchronization and merging process occurs whereby the latest version of the components are downloaded to the client computer and are compared to the locally edited version of the components to detect resolvable (compatible) and unresolvable (incompatible) conflicts therebetween. The commit process is performed only if no unresolvable conflicts exist between the two versions of the components. To facilitate translation between file-based data and components, a schema is written to "wrap" each of the engineering file formats. Each schema is a set of classes that capture all of the information in the file-based data.
Owner:BENTLEY SYST INC
System and method for creating a point-in-time restoration of a database file
InactiveUS7373364B1Overcome disadvantagesAvoid data lossData processing applicationsError detection/correctionFile systemDatabase file
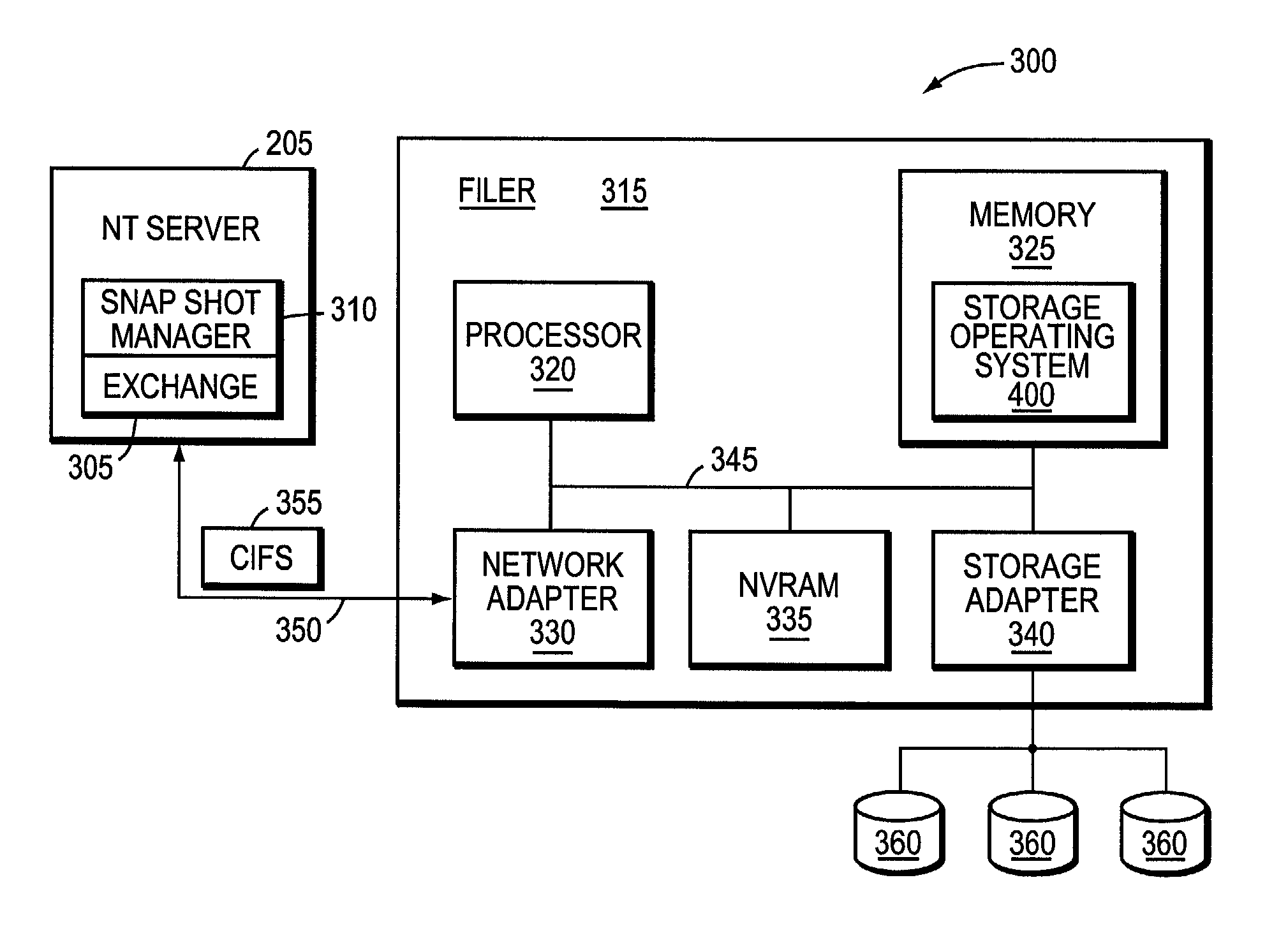
The present invention provides a method for generating a point-in-time restoration of database files and associated log files by utilizing a snapshot feature of the file system storing the files. At regular intervals, snapshots, which produce read-only copies of the files, are taken along with backups of the associated log files. To restore to a given point-in-time, the snapshot and stored log files are transferred to the active file system. In a second embodiment, all log files associated with snapshots taken after the selected snapshot are also restored.
Owner:NETWORK APPLIANCE INC
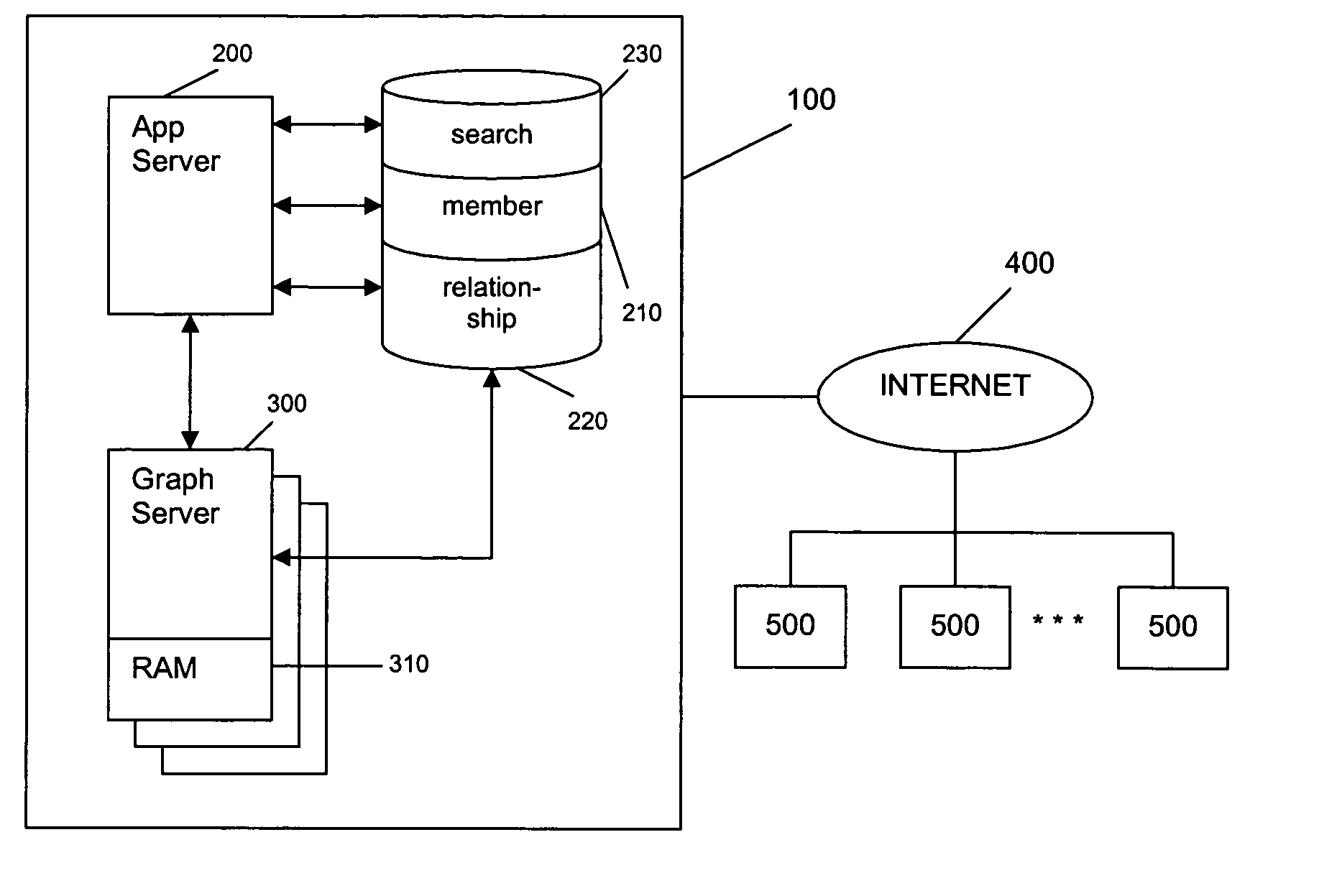
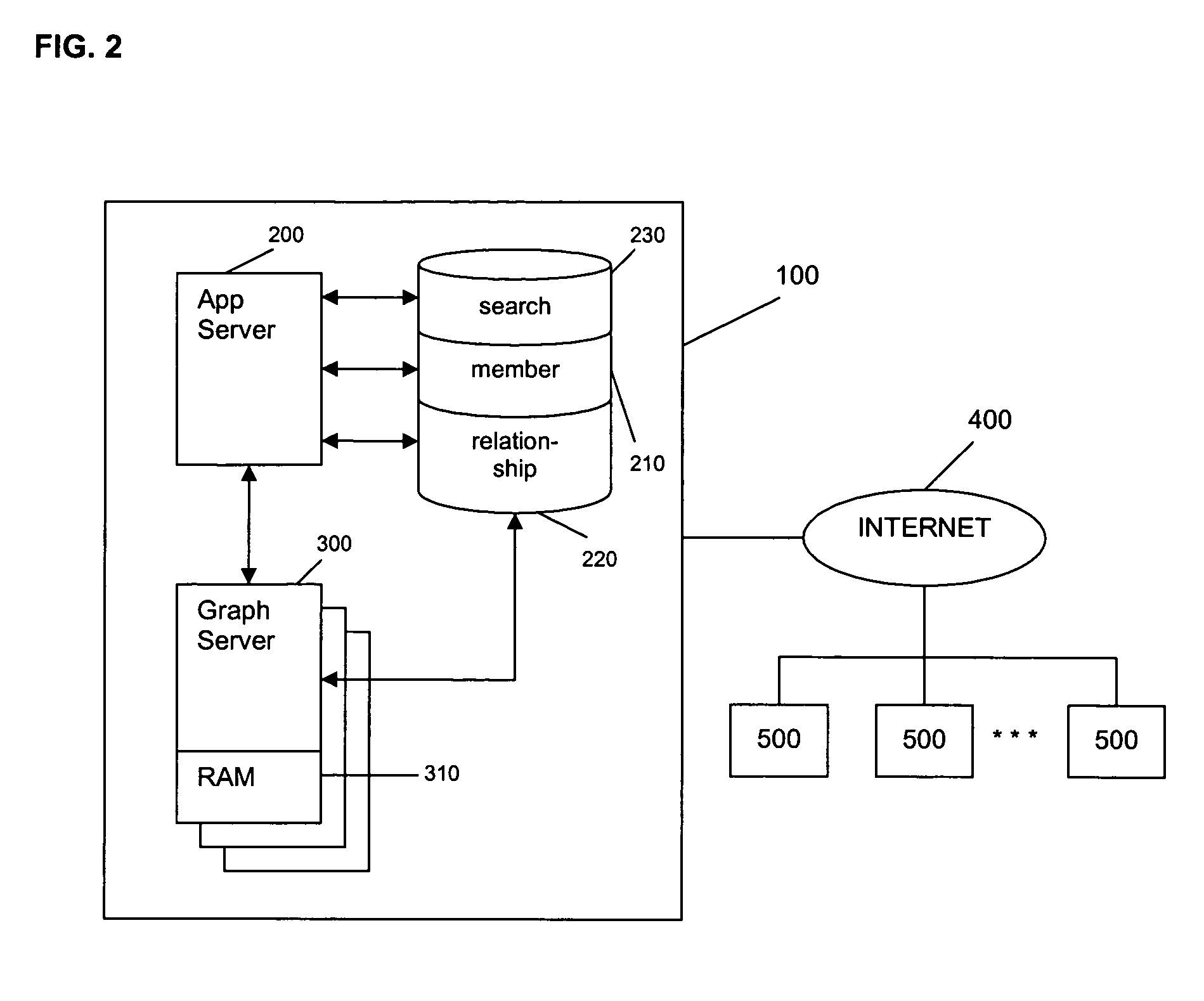
System and method for managing information flow between members of an online social network
An online social network is provided in which members of the online social network control who may view their personal information and who may communicate with them. The members control who may view their personal information by setting a visibility preference. A member may not view another member's full personal profile if the measure of relatedness between the two is greater than the visibility preference of the other member. The members also control who may communicate with them by setting a contactability preference. A member may not communicate with another member if the measure of relatedness between the two is greater than the contactability preference of the other member.
Owner:META PLATFORMS INC
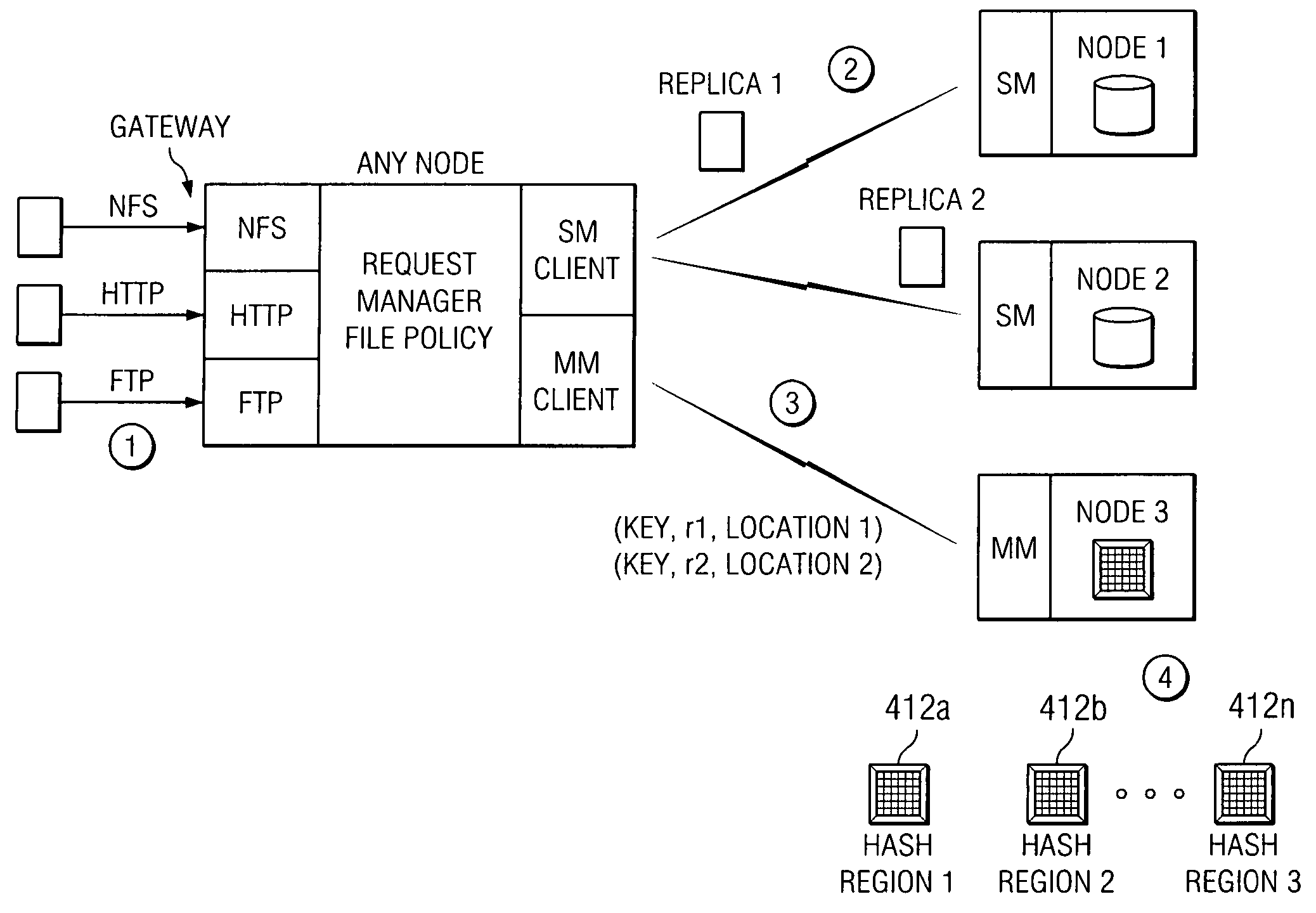
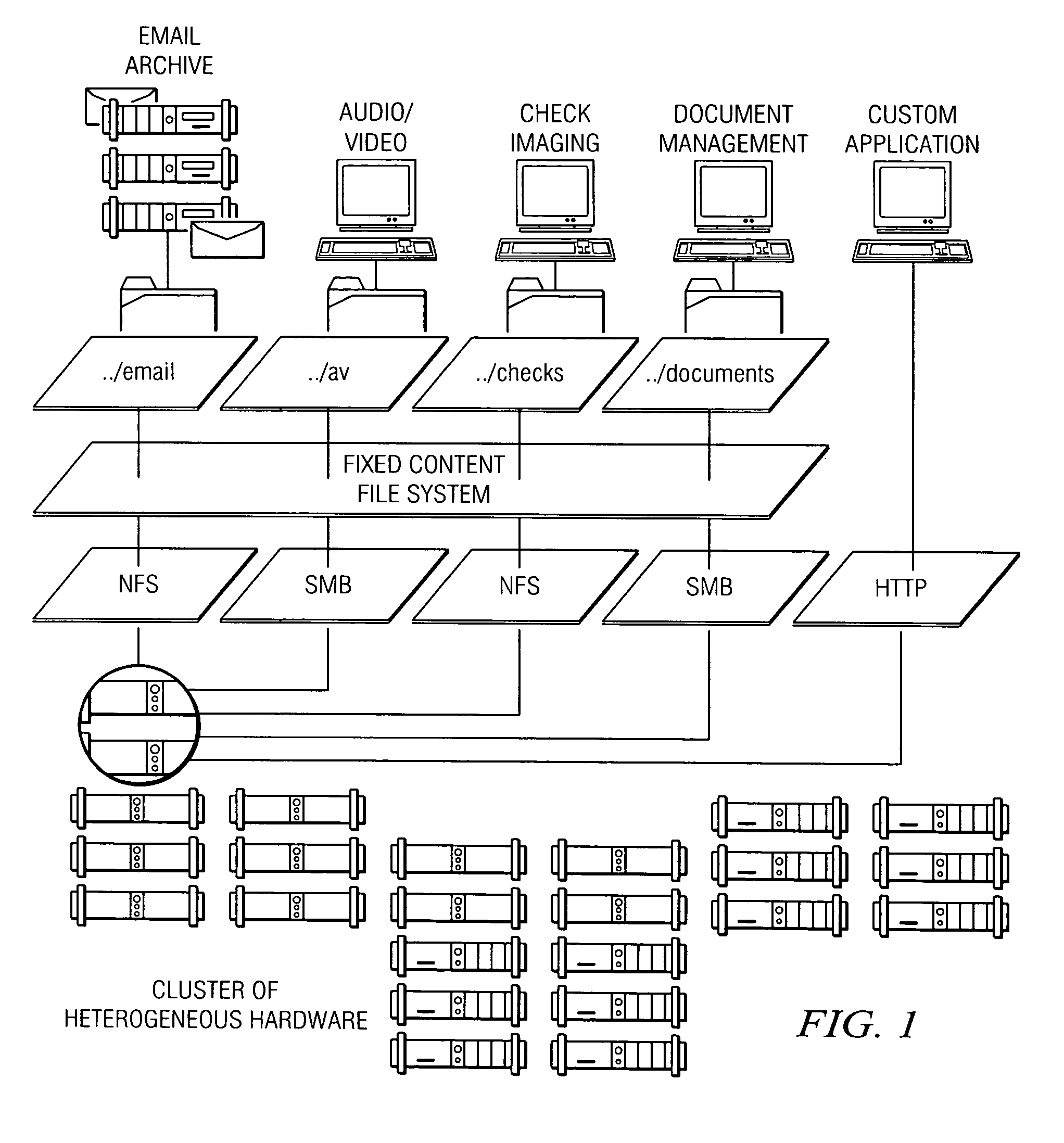
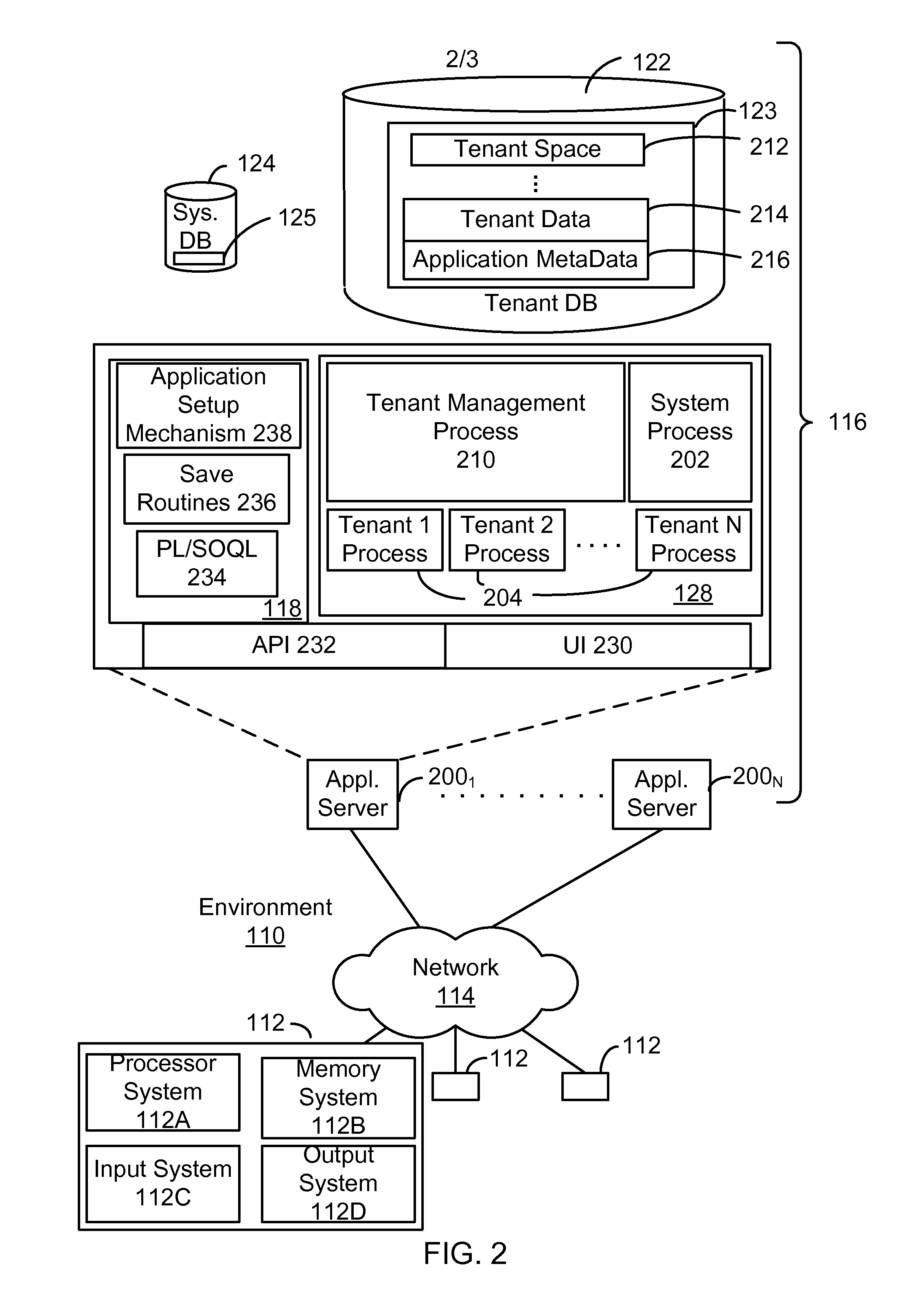
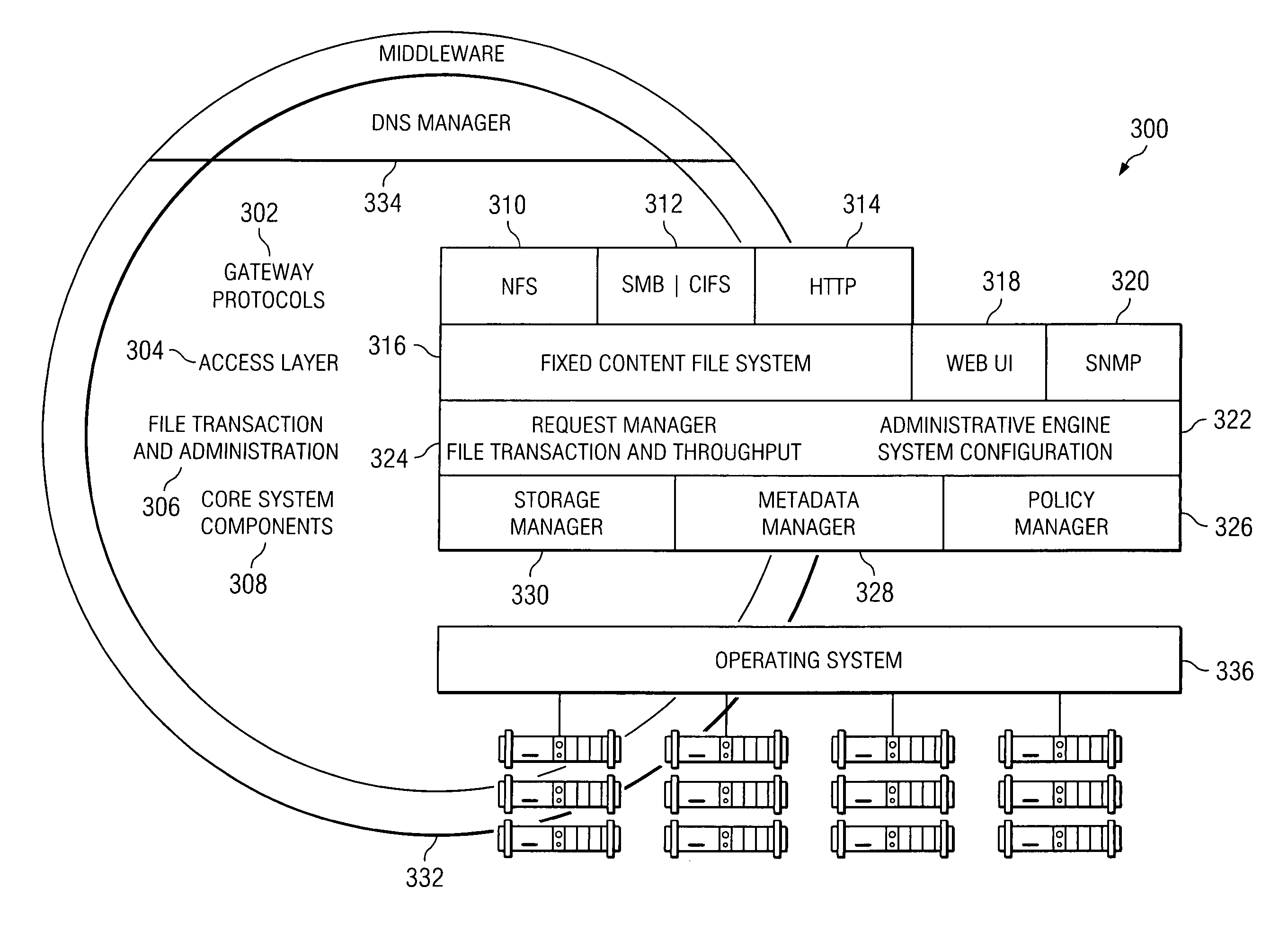
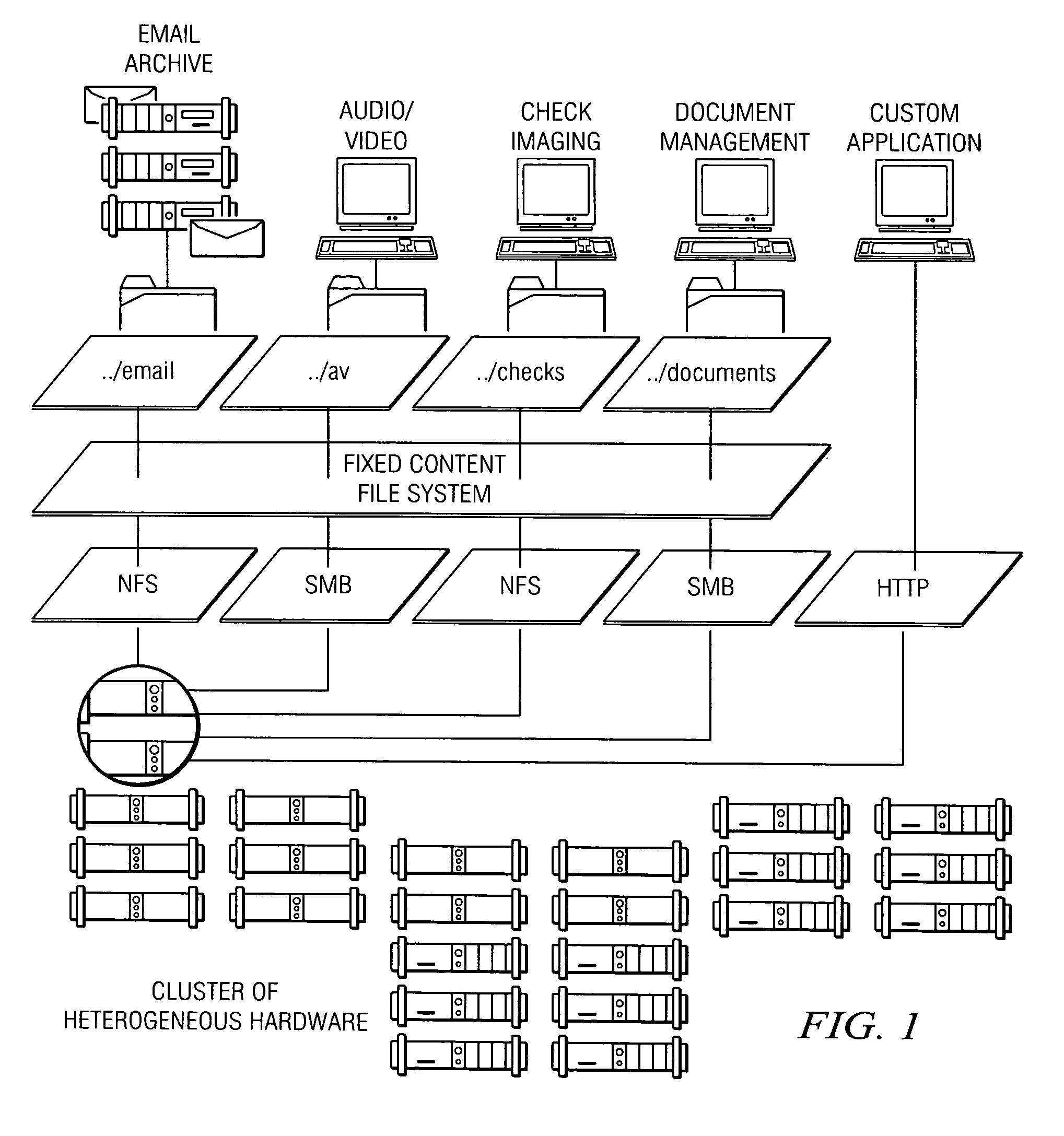
Policy-based management of a redundant array of independent nodes
ActiveUS20050120025A1Reduce complexityData processing applicationsDigital data processing detailsObject basedMetadata management
An archive cluster application runs in a distributed manner across a redundant array of independent nodes. Each node preferably runs a complete archive cluster application instance. A given nodes provides a data repository, which stores up to a large amount (e.g., a terabyte) of data, while also acting as a portal that enables access to archive files. Each symmetric node has a set of software processes, e.g., a request manager, a storage manager, a metadata manager, and a policy manager. The request manager manages requests to the node for data (i.e., file data), the storage manager manages data read / write functions from a disk associated with the node, and the metadata manager facilitates metadata transactions and recovery across the distributed database. The policy manager implements one or more policies, which are operations that determine the behavior of an “archive object” within the cluster. The archive cluster application provides object-based storage. Preferably, the application permanently associates metadata and policies with the raw archived data, which together comprise an archive object. Object policies govern the object's behavior in the archive. As a result, the archive manages itself independently of client applications, acting automatically to ensure that all object policies are valid.
Owner:HITACHI VANTARA LLC
Generating performance alerts
A method for generating performance alerts in a database system. The method includes collecting a predefined set of performance data, and comparing the performance data to one or more predefined thresholds. The method also includes determining if any of the performance data exceeds the one or more predefined thresholds, and generating an alert if any of the data exceeds one of the predefined thresholds.
Owner:SALESFORCE COM INC
Policy-based management of a redundant array of independent nodes
ActiveUS7155466B2Reduce complexityData processing applicationsDigital data processing detailsObject basedMetadata management
An archive cluster application runs in a distributed manner across a redundant array of independent nodes. Each node preferably runs a complete archive cluster application instance. A given nodes provides a data repository, which stores up to a large amount (e.g., a terabyte) of data, while also acting as a portal that enables access to archive files. Each symmetric node has a set of software processes, e.g., a request manager, a storage manager, a metadata manager, and a policy manager. The request manager manages requests to the node for data (i.e., file data), the storage manager manages data read / write functions from a disk associated with the node, and the metadata manager facilitates metadata transactions and recovery across the distributed database. The policy manager implements one or more policies, which are operations that determine the behavior of an “archive object” within the cluster. The archive cluster application provides object-based storage. Preferably, the application permanently associates metadata and policies with the raw archived data, which together comprise an archive object. Object policies govern the object's behavior in the archive. As a result, the archive manages itself independently of client applications, acting automatically to ensure that all object policies are valid.
Owner:HITACHI VANTARA LLC
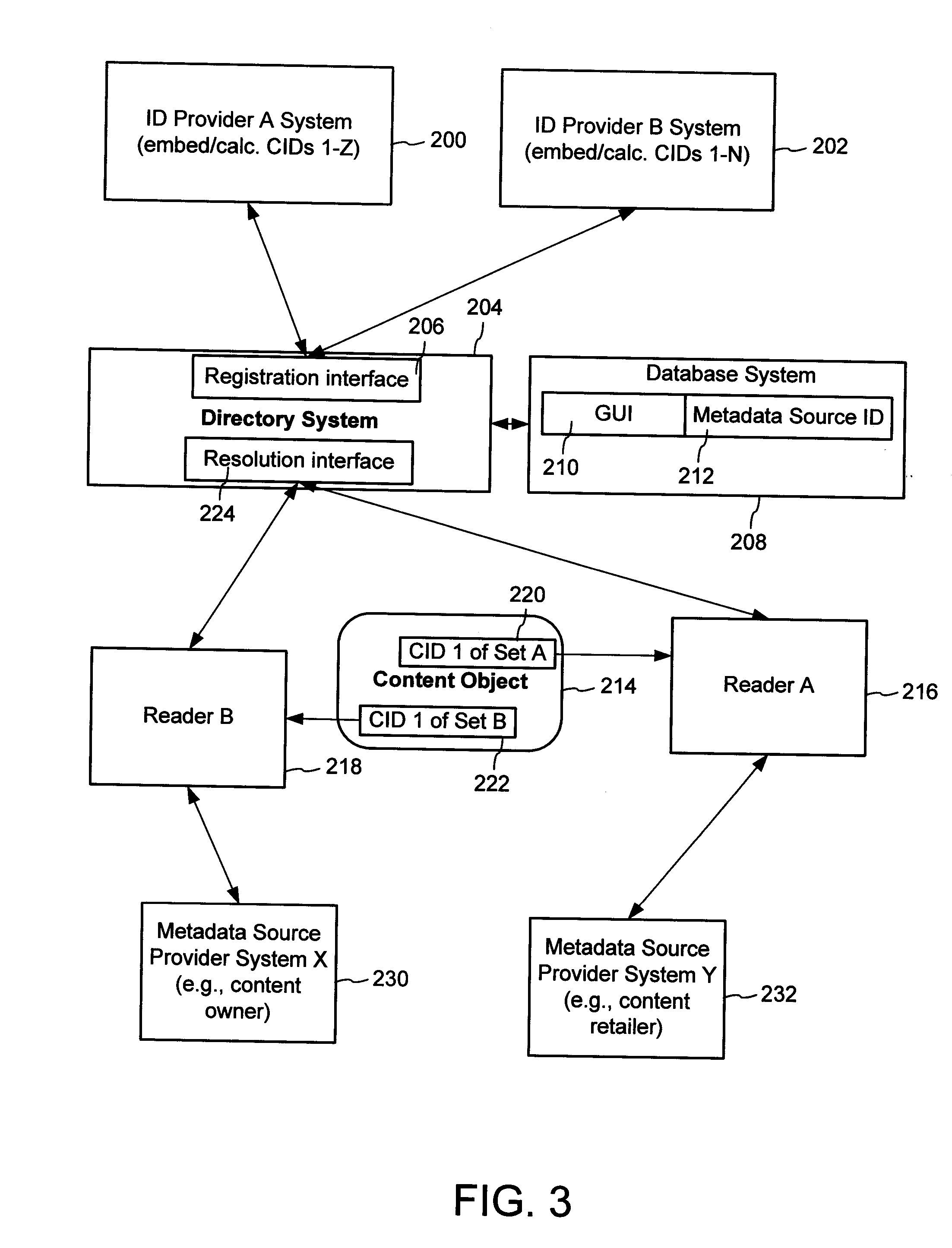
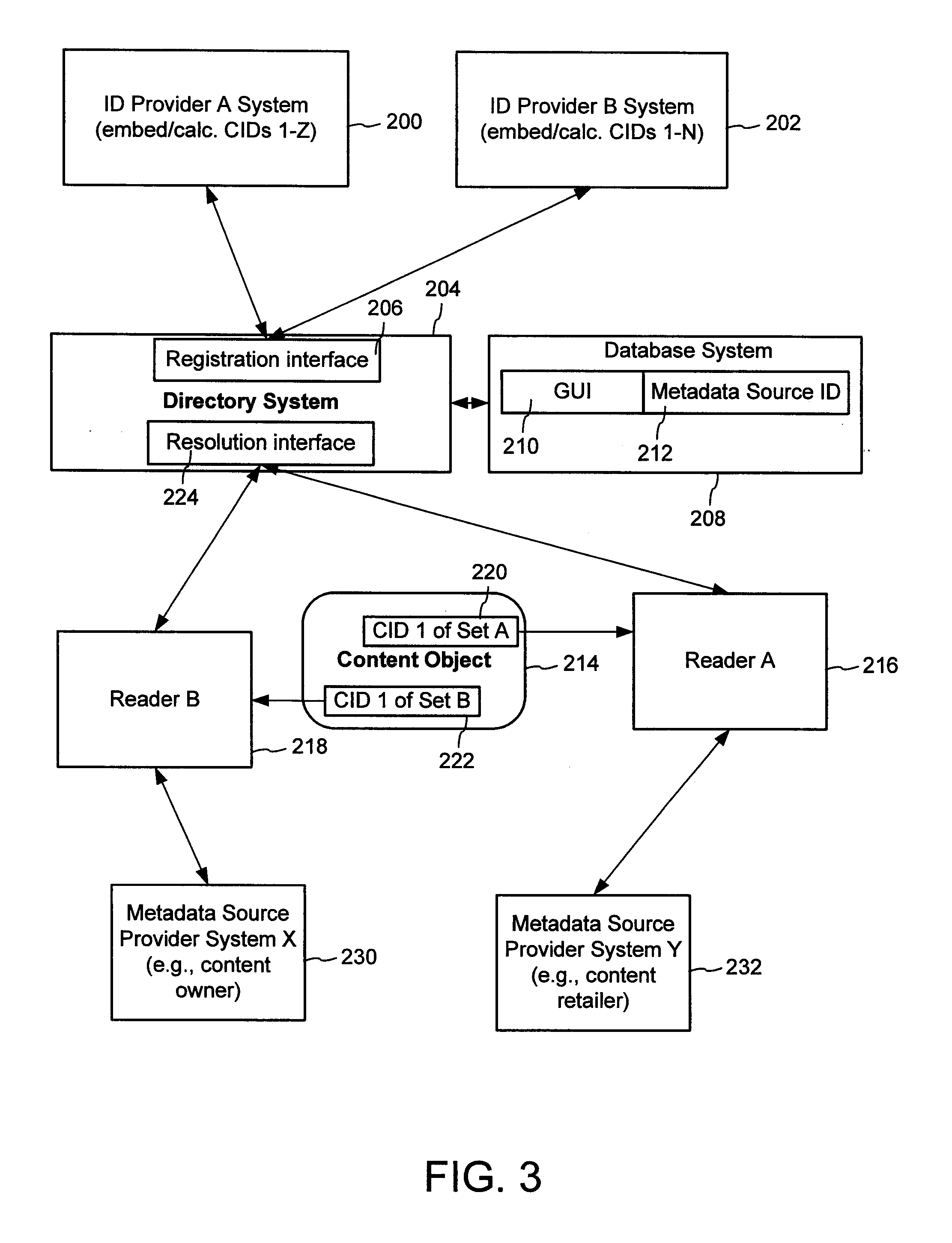
Content Metadata Directory Services
ActiveUS20070192352A1Increase the number ofComplicate to identifyMultimedia data indexingDigital data processing detailsContent IdentifierWeb site
A method of associating a content object with metadata uses a combination of a content identifier and a bounding identifier to enable handling of disparate sets of content identifiers for content objects with potentially conflicting content identifiers. The method receives a content identifier for a content object from among a set of content identifiers. It provides a unique bounding identifier for the set of content identifiers. This unique bounding identifier is used in combination with the content identifier to form a globally unique identifier for the content object. This globally unique identifier is associated with a metadata source, which enables routing of a user to the metadata source. Another novel method addresses content objects with two or more content identifiers, potentially referencing different metadata sources. This method registers different globally unique identifiers for a content object. These globally unique identifiers each comprise a content identifier provided with the content object and a bounding identifier identifying a set of content identifiers of which the content identifier is a member. For each of the globally unique identifiers, information is maintained about a metadata source. The method receives a first content identifier for the content object, and uses a bounding identifier associated with the set of the first content identifier to determine the globally unique identifier for the first content identifier. The user is routed to the metadata source associated with globally unique identifier. This document describes a novel system that enables multiple identity providers (ID Providers) to register and use the system. The ID Provider registers with a metadata directory system, receives a unique bounding identifier, and uses this bounding ID (e.g., an ID provider ID) with subsequent interactions with the metadata directory system. Separately, metadata source providers register metadata sources with the metadata directory system. This enables many different participants to associate content objects with metadata sources using one or more identify providers. Examples of metadata source providers include content providers, like content owners or retailers that have the flexibility of working with different ID providers to associate content objects with metadata. Both content providers and ID providers can register and use the system. The metadata source is the system or device that provides the metadata, like a web site. The directory system uses an identifier for the metadata source, which enables it to maintain an association between a content object and its corresponding metadata source. For example, in some embodiments, a URL serves to identify the location of the source. The Content Metadata Directory Services (CMDS) is a global trusted directory service that connects consumers of identified content to content-provider authorized and managed metadata databases and other digital resources. It includes mostly links to metadata, forms globally unique IDs based upon overlapping content identifiers and unique bounding identifiers, enables multiple content identifiers within a content object, and enables multiple content identity technology providers, even when they are using different technology.
Owner:DIGIMARC CORP
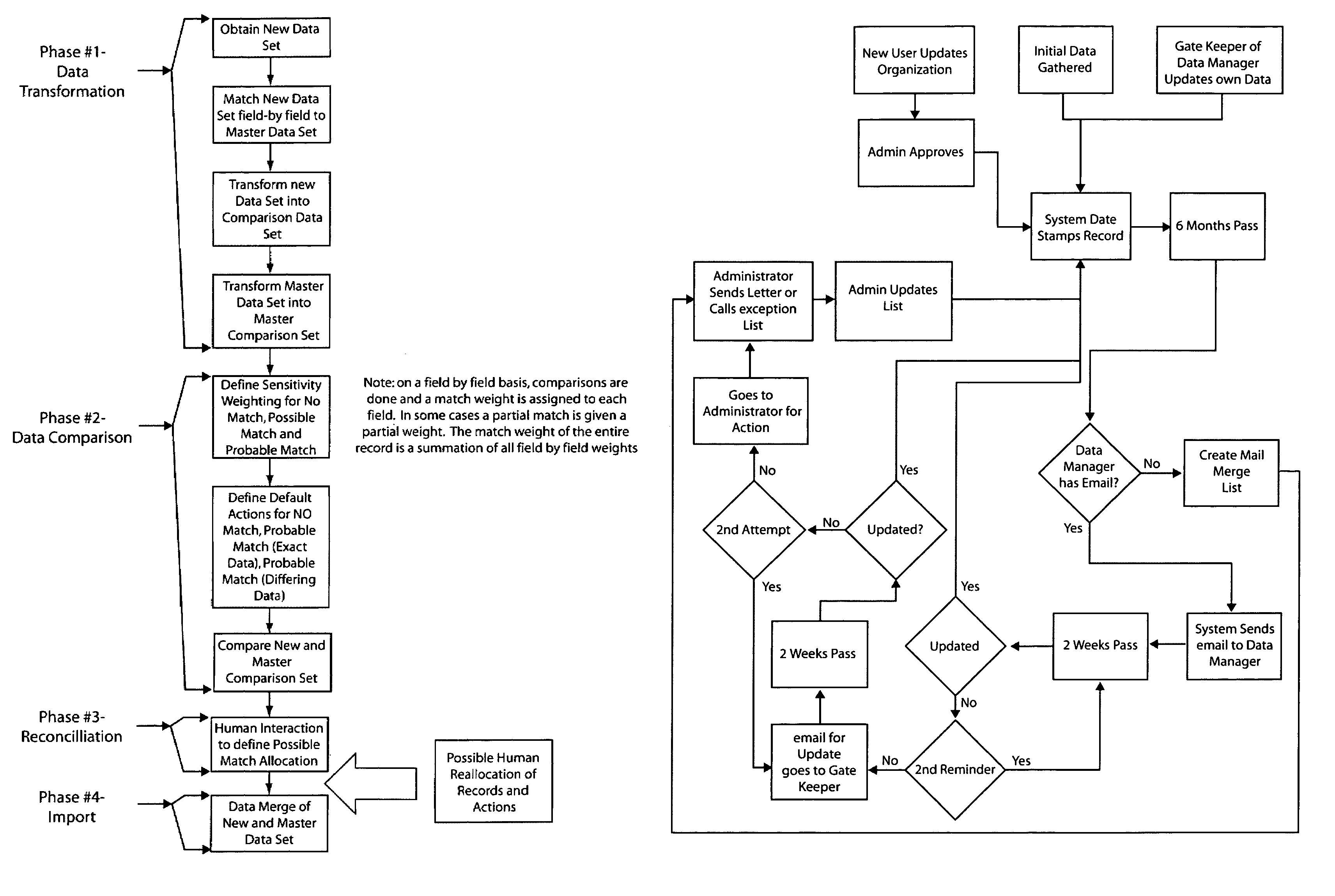
Database management system
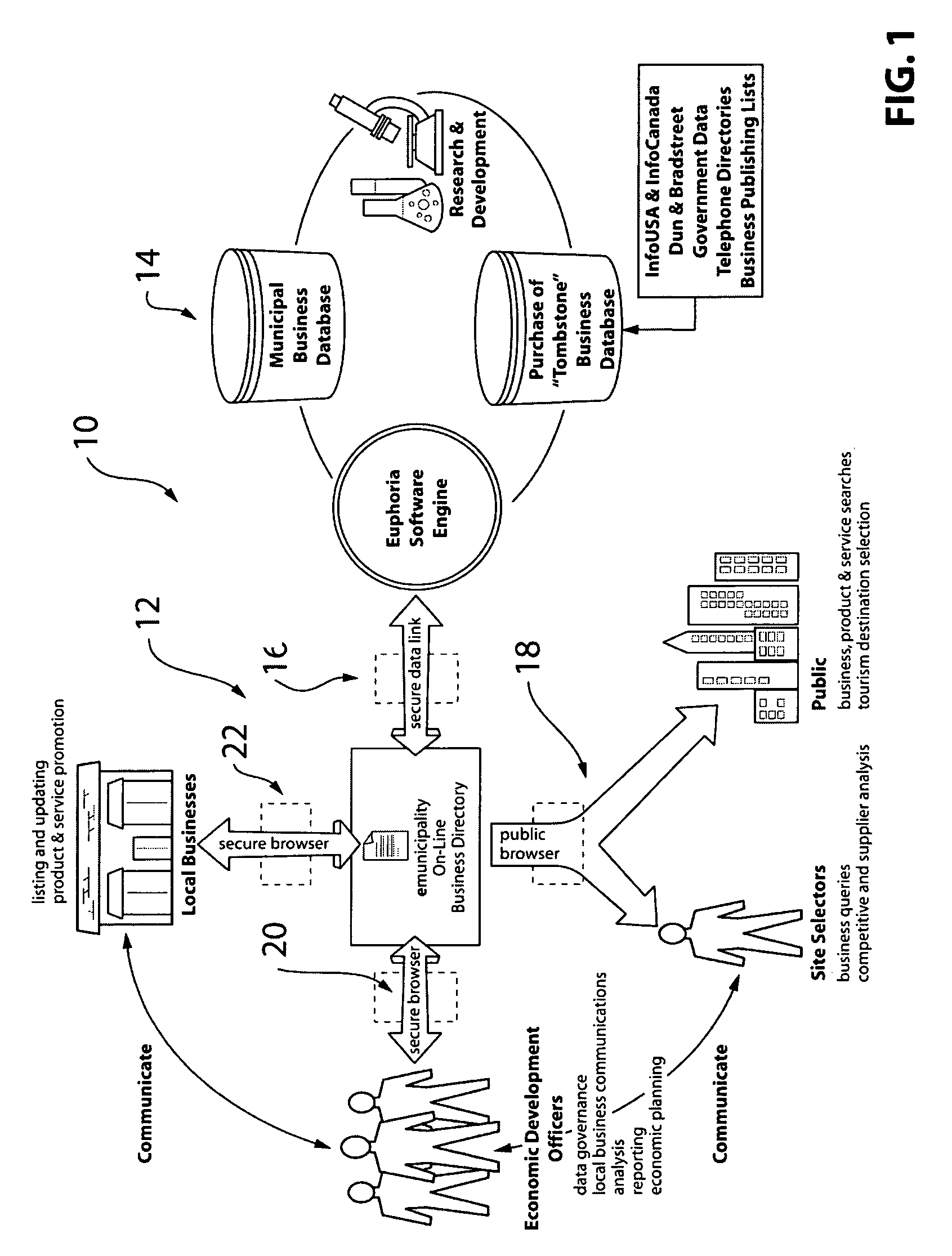
A method of creating a database and of providing results from a database, for use by a municipality, and operating a community database, comprises the steps of: providing first and second source databases addressable under first and second data protocols respectively, which protocols are incompatible one with the other; transforming, comparing and reconciling the data in the first and second source databases in order to optimize each field of data in each record; and storing the optimized data for each record as a record in a resulting master database. Records from searches are presented in order of recency. The present invention also provides a method of generating revenue from activities associated with a community.
Owner:BREKEN TECH GROUP
Method and system for pushing data to a plurality of devices in an on-demand service environment
ActiveUS20080010243A1Reduce workloadEfficient and transparent transferDatabase distribution/replicationSpecial data processing applicationsUser deviceData shipping
Mechanisms and methods for pushing data to a plurality of devices of a plurality of organizations are provided. Queries are handled in bulk for a group of users of an organization or the entire organization, and limited results are sent to a middle tier server between the database system and the user devices. These mechanisms and methods for pushing data to a plurality of devices enable an efficient and transparent transfer of data to user devices. This efficient and transparent transfer of data can enable mobile devices of many organizations to seamlessly have the data that is required to perform business.
Owner:SALESFORCE COM INC
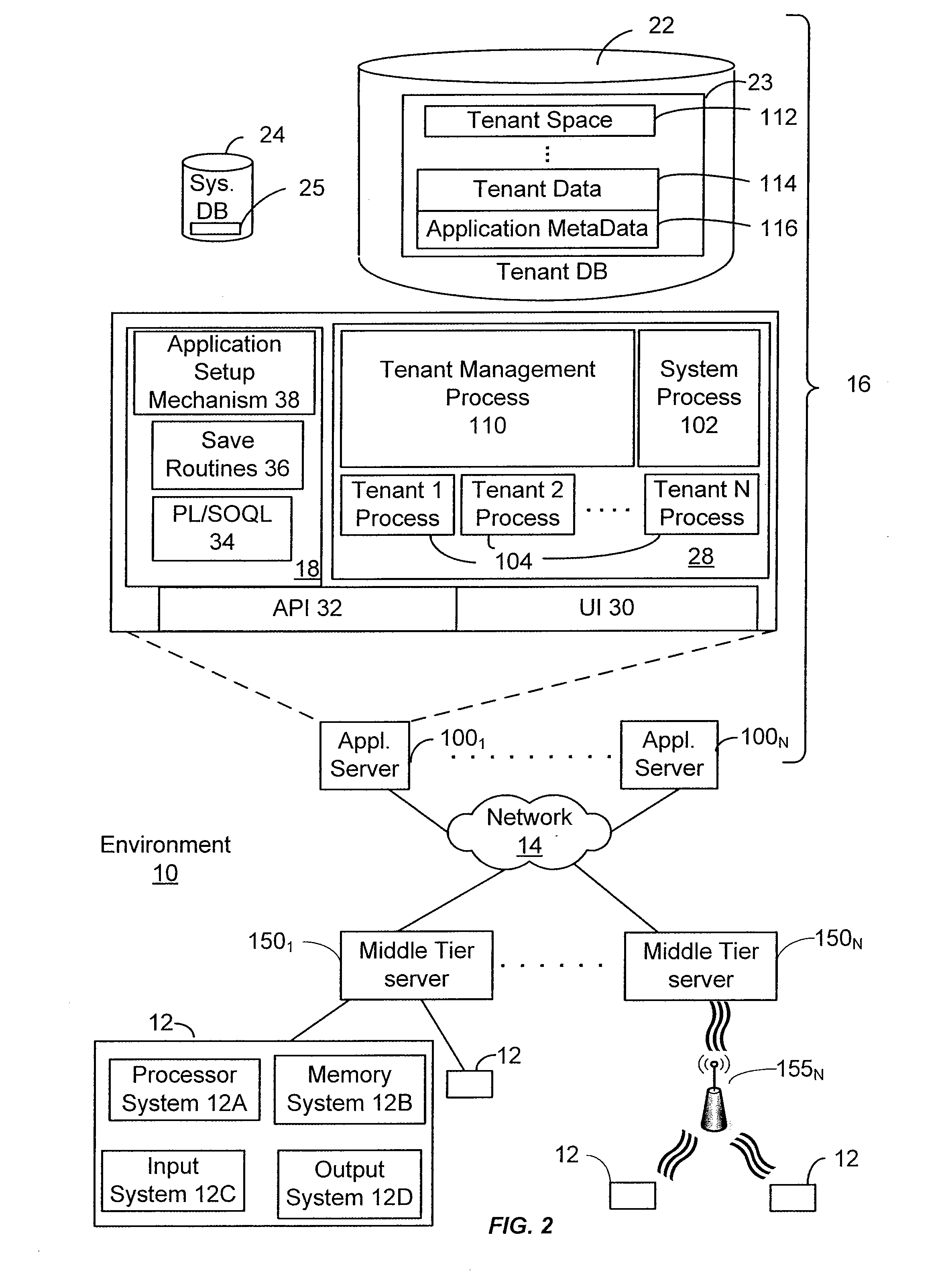
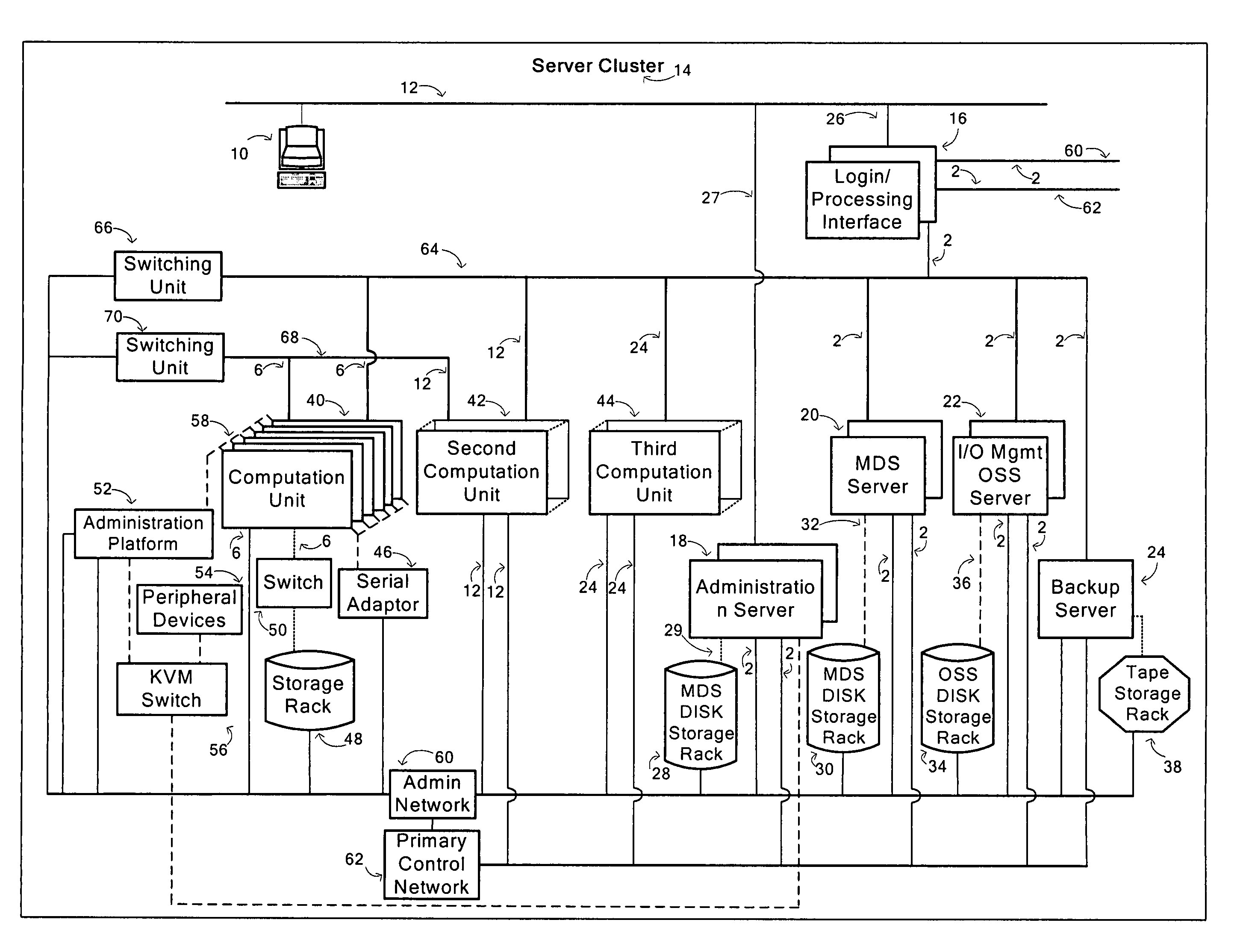
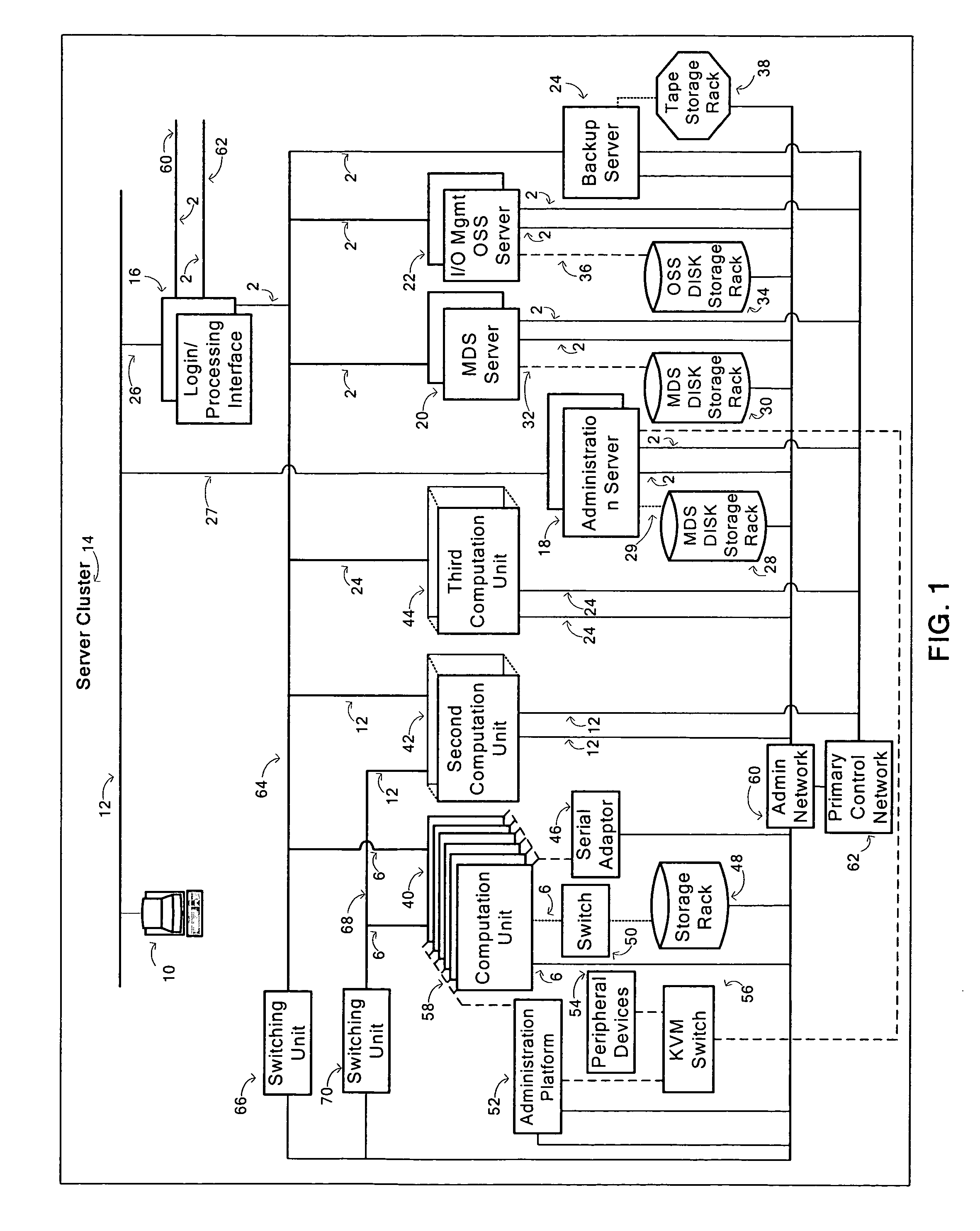
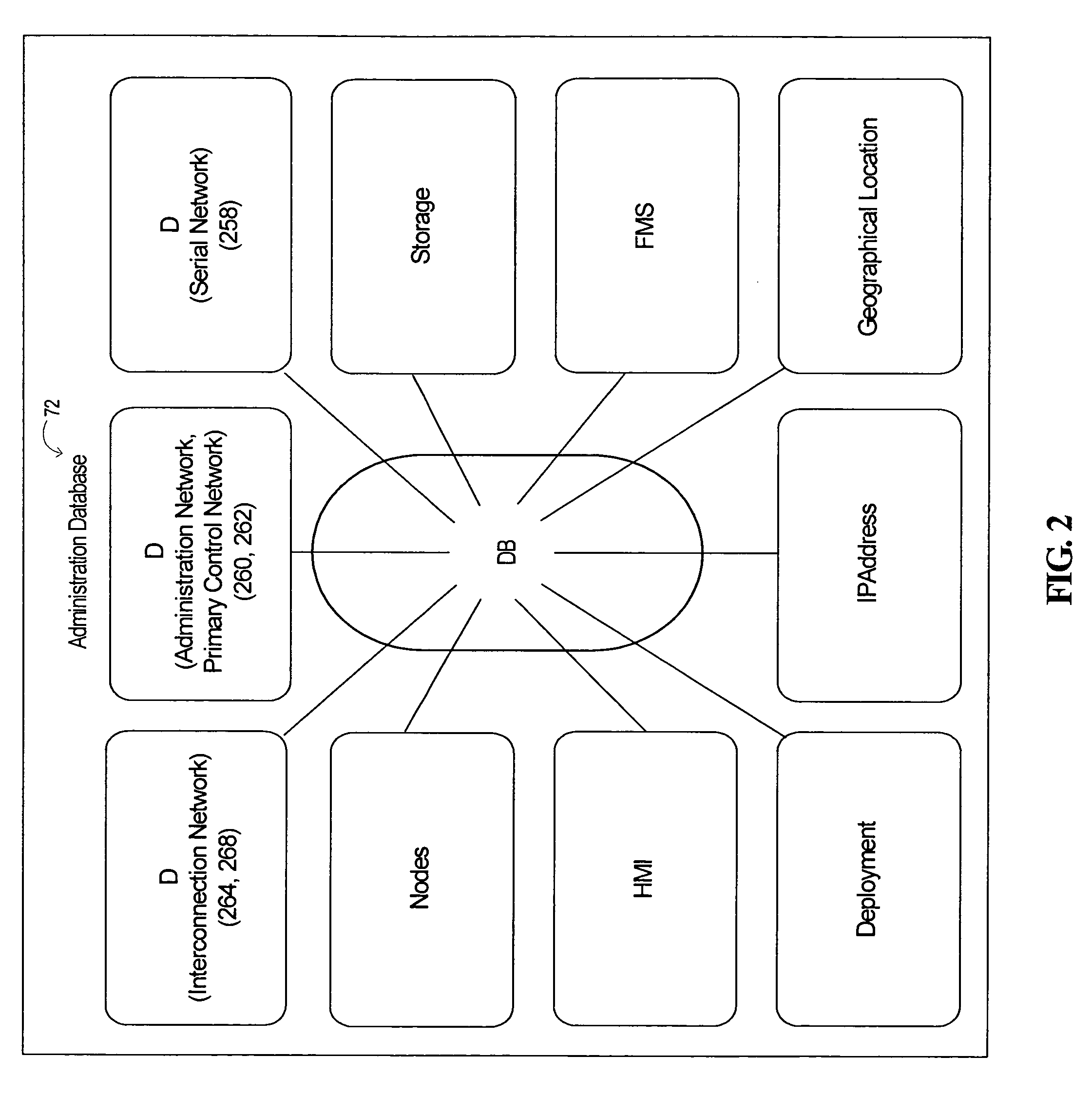
Method for generating manipulation requests of an initialization and administration database of server cluster, data medium and corresponding a server cluster, data medium and corresponding service cluster
InactiveUS20100115070A1Facilitated and even and generationDigital data processing detailsDigital computer detailsData transmissionDistributed computing
This method relates to the generation of manipulation requests of an initialization and administration database of a server cluster comprising several nodes interconnected between each other by at least one data transmission network. It comprises steps of generating from a logical distribution of the nodes of the cluster, from a geographical distribution and from a hardware definition of the nodes of the cluster at least one set of profiles of the nodes and of the data transmission network; defining an addressing policy of the nodes of the cluster; allocating from the set of profiles and according to the addressing policy, at least one address to each node of the server cluster and generating a set of parameters of the cluster; and generating from the set of parameters of the cluster and of the addresses of its nodes, at least one file of manipulation requests of the database.
Owner:BULL SA
Smart containers
Owner:EMC IP HLDG CO LLC
Database System with Methodology for Automated Determination and Selection of Optimal Indexes
ActiveUS20050203940A1Superior cost benefitImprove performanceData processing applicationsSpecial data processing applicationsDatabase queryCost effectiveness
A database system with methodology for automated determination and selection of optimal indexes is described. In one embodiment, for example, in a database system, a method of the present invention is described for recommending database indexes to be created for optimizing system performance, the method comprises steps of: capturing a workload representative of database queries employed during system use; creating virtual indexes for optimizing system performance during execution of the database queries captured in the workload; computing cost benefits for different combinations of the virtual indexes; and recommending physical indexes to be created based on virtual indexes that have favorable cost benefits for the captured workload.
Owner:IANYWHERE SOLUTIONS
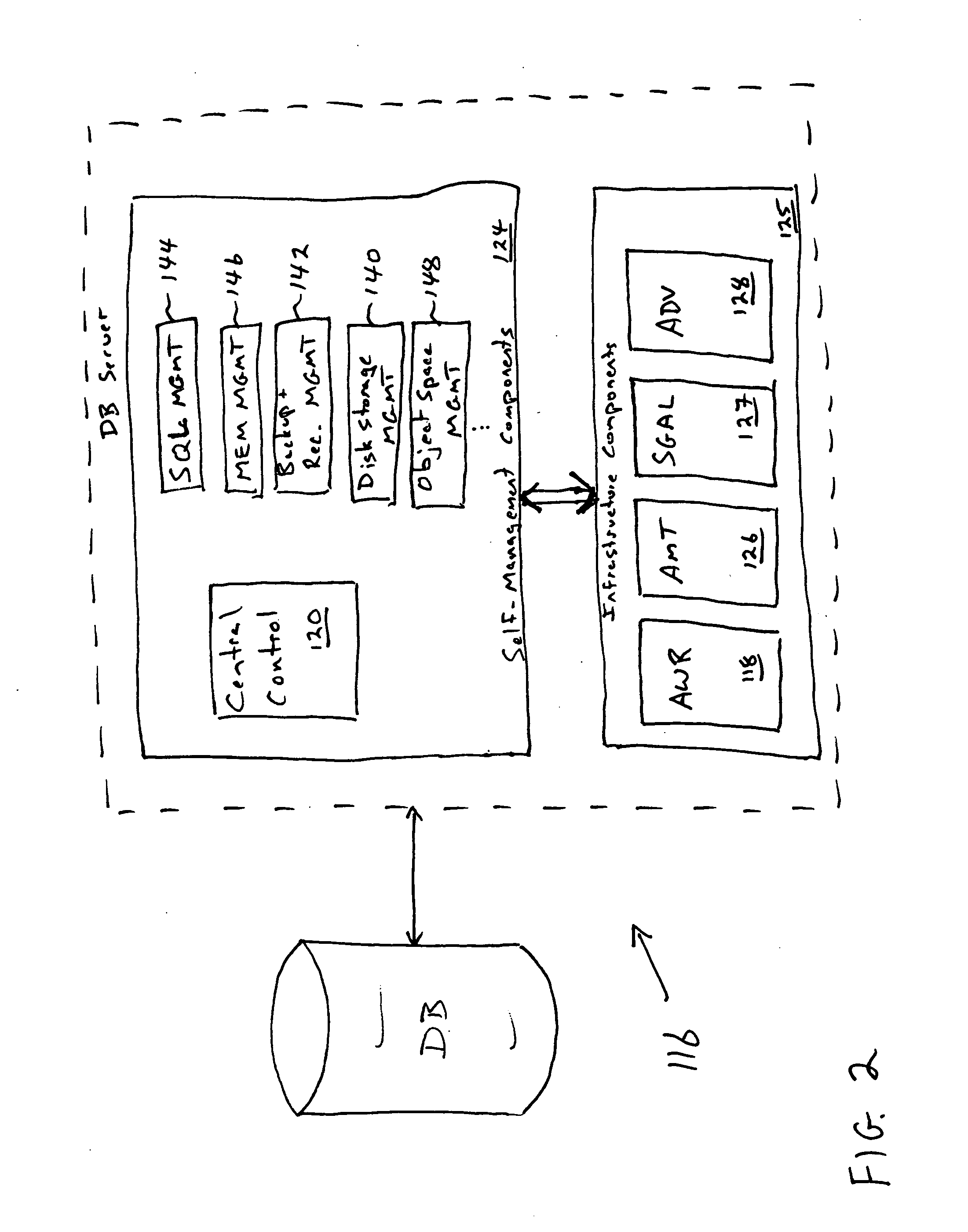
Self-managing database architecture
ActiveUS20050086195A1Improve system performanceExpand databaseData processing applicationsDigital data processing detailsWorkloadDatabase
An intelligent database infrastructure wherein the management of all database components is performed by and within the database itself by integrating management of various components with a central management control. Each individual database component, as well as the central management control, is self-managing. A central management control module integrates and interacts with the various database components. The database is configured to automatically tune to varying workloads and configurations, correct or alert about bad conditions, and advise on ways to improve overall system performance.
Owner:ORACLE INT CORP
Remote backup and restore
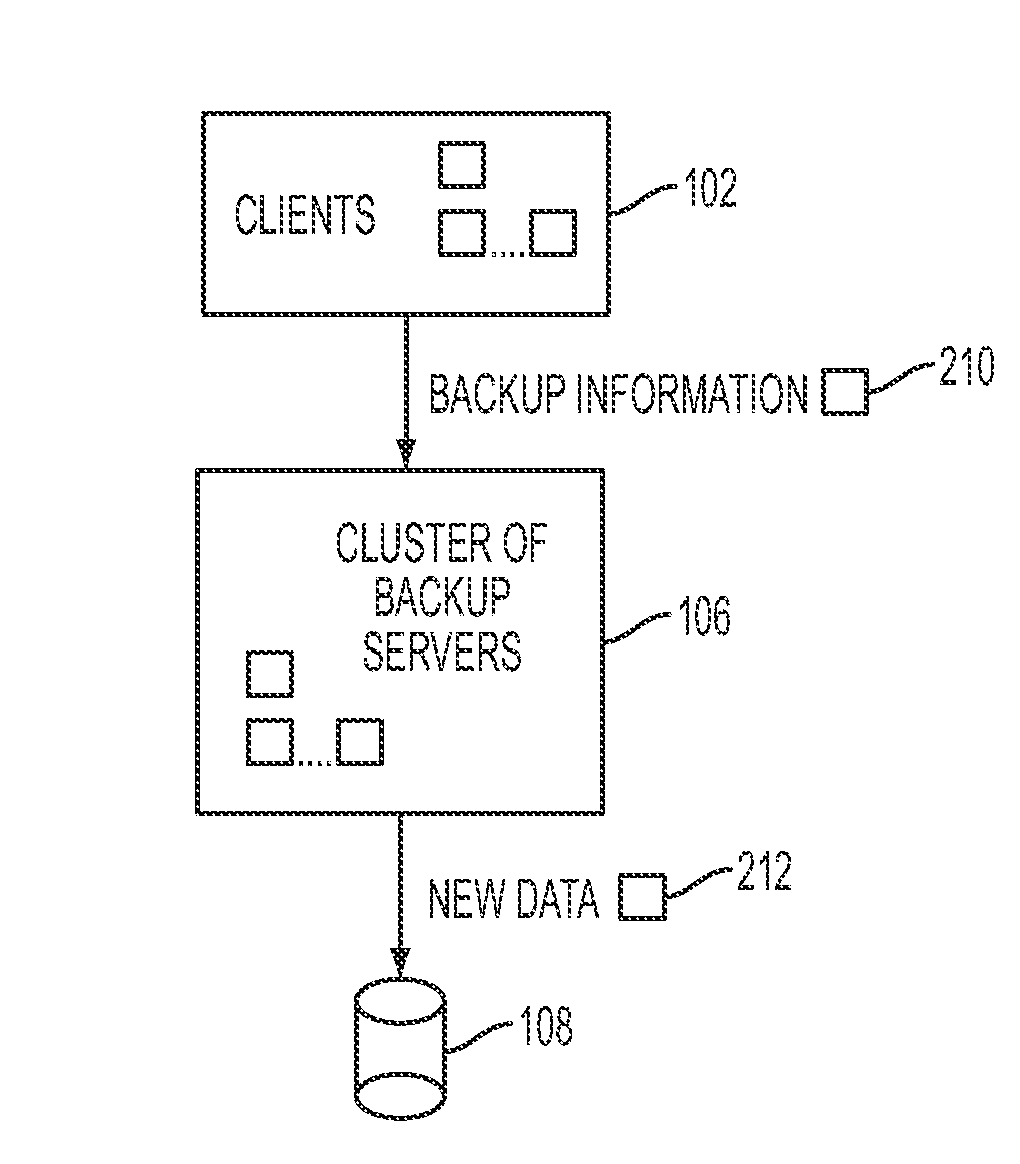
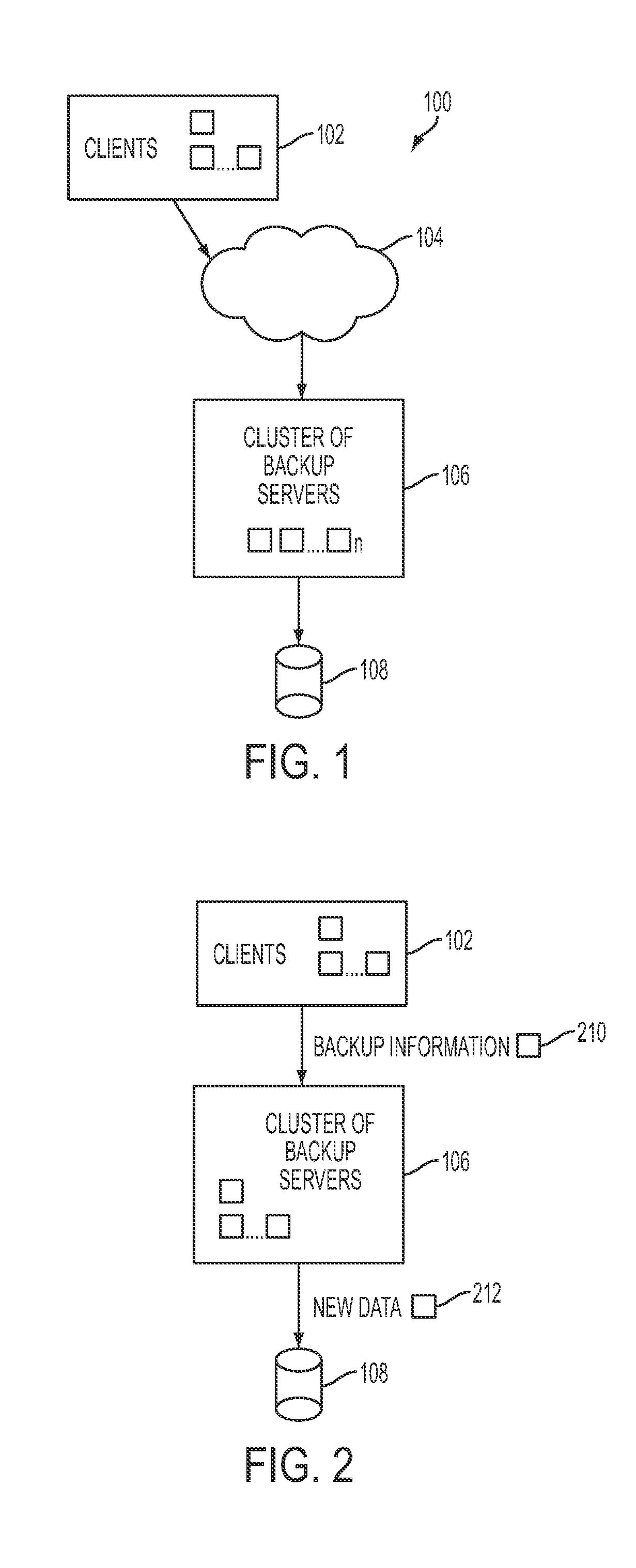
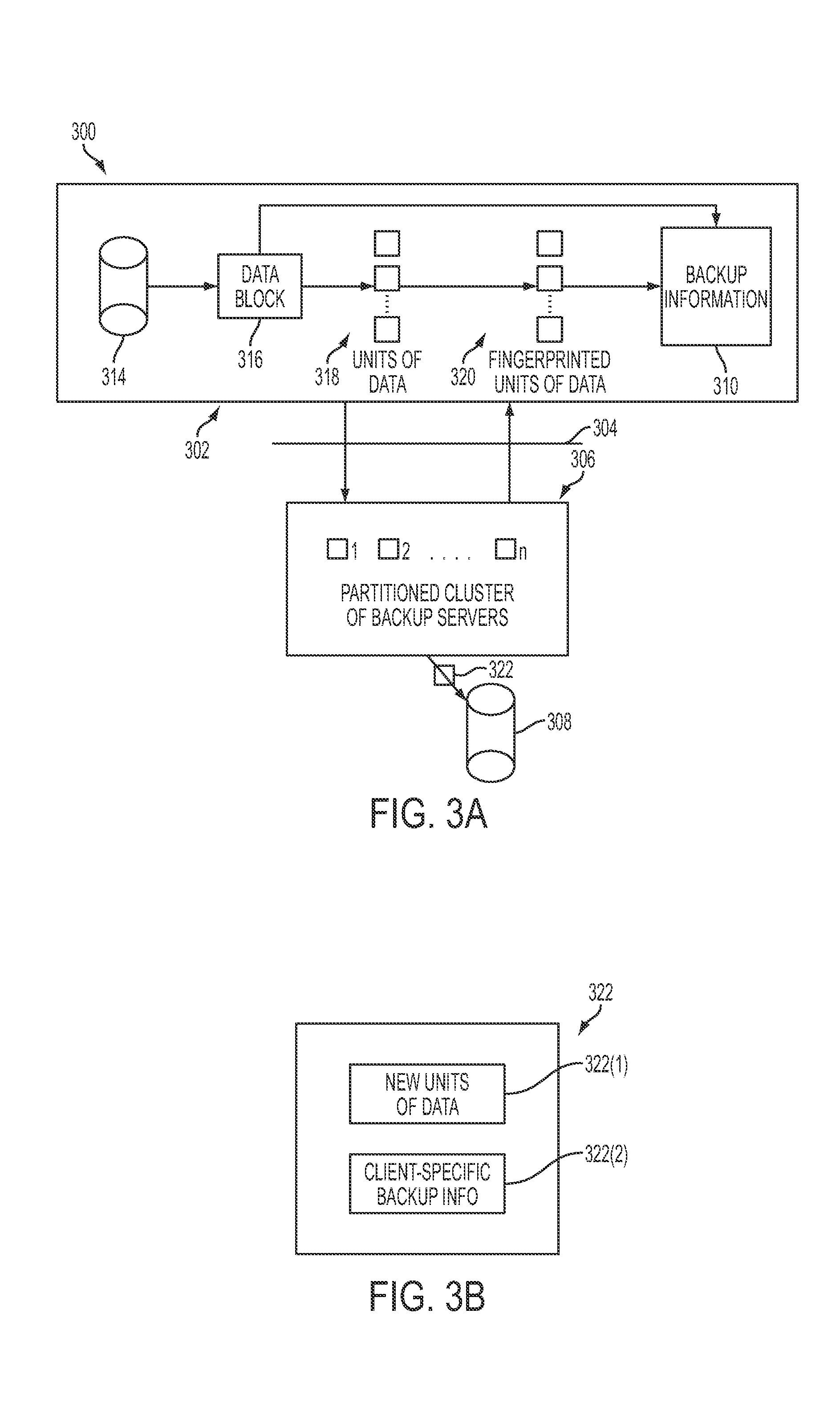
ActiveUS20100106691A1Memory loss protectionDigital data processing detailsNamespaceData deduplication
In one embodiment of the present invention, a data-backup method includes partitioning a fingerprint namespace among a cluster of backup servers, the fingerprint namespace comprising fingerprints for representing units of data, each backup server of the cluster of backup servers managing units of data having fingerprints corresponding to an assigned partition of the fingerprint namespace. The method further includes receiving backup information from a client computing device for a block of data comprising units of data, the backup information including at least a fingerprint for each of the units of data and client-specific backup information. In addition, the method includes, utilizing the fingerprint for each of the units of data, deduplicating the units of data in parallel at the cluster of backup servers in accordance with the partitioning step, the deduplicating step comprising identifying ones of the units data already stored by the cluster of backup servers.
Owner:QUEST SOFTWARE INC
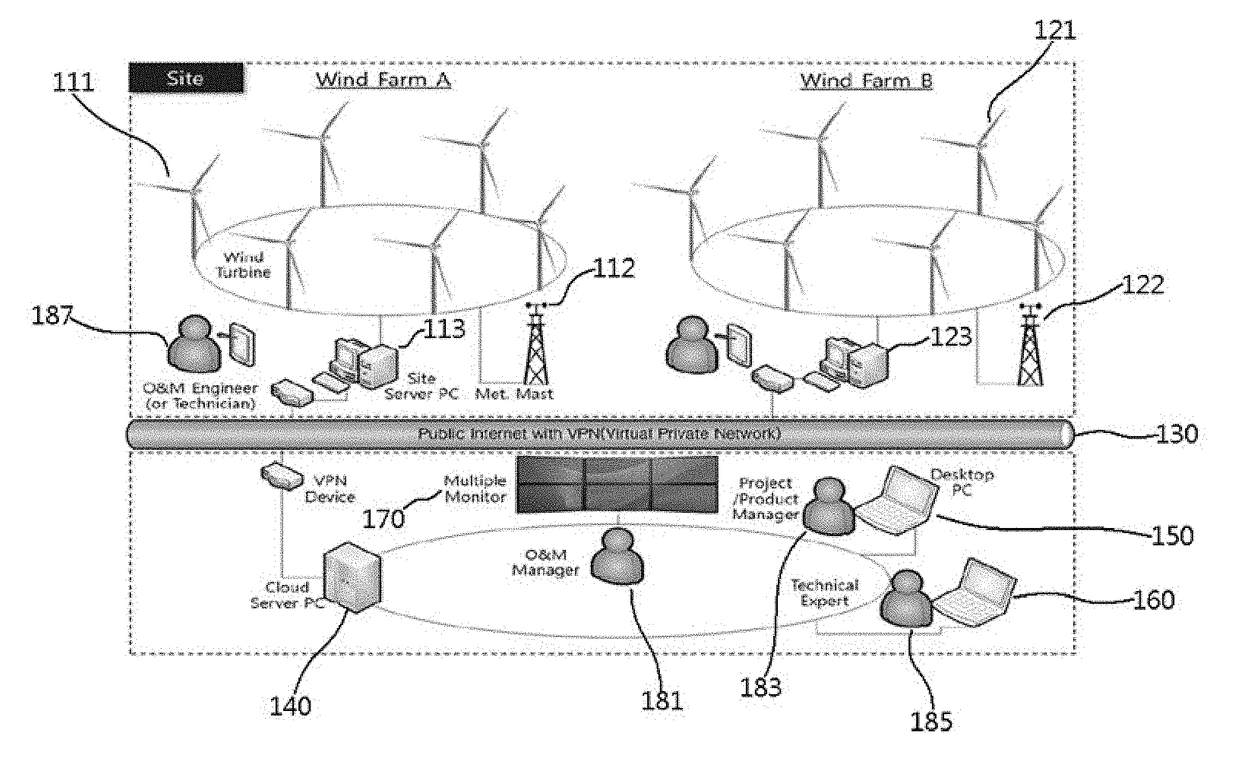
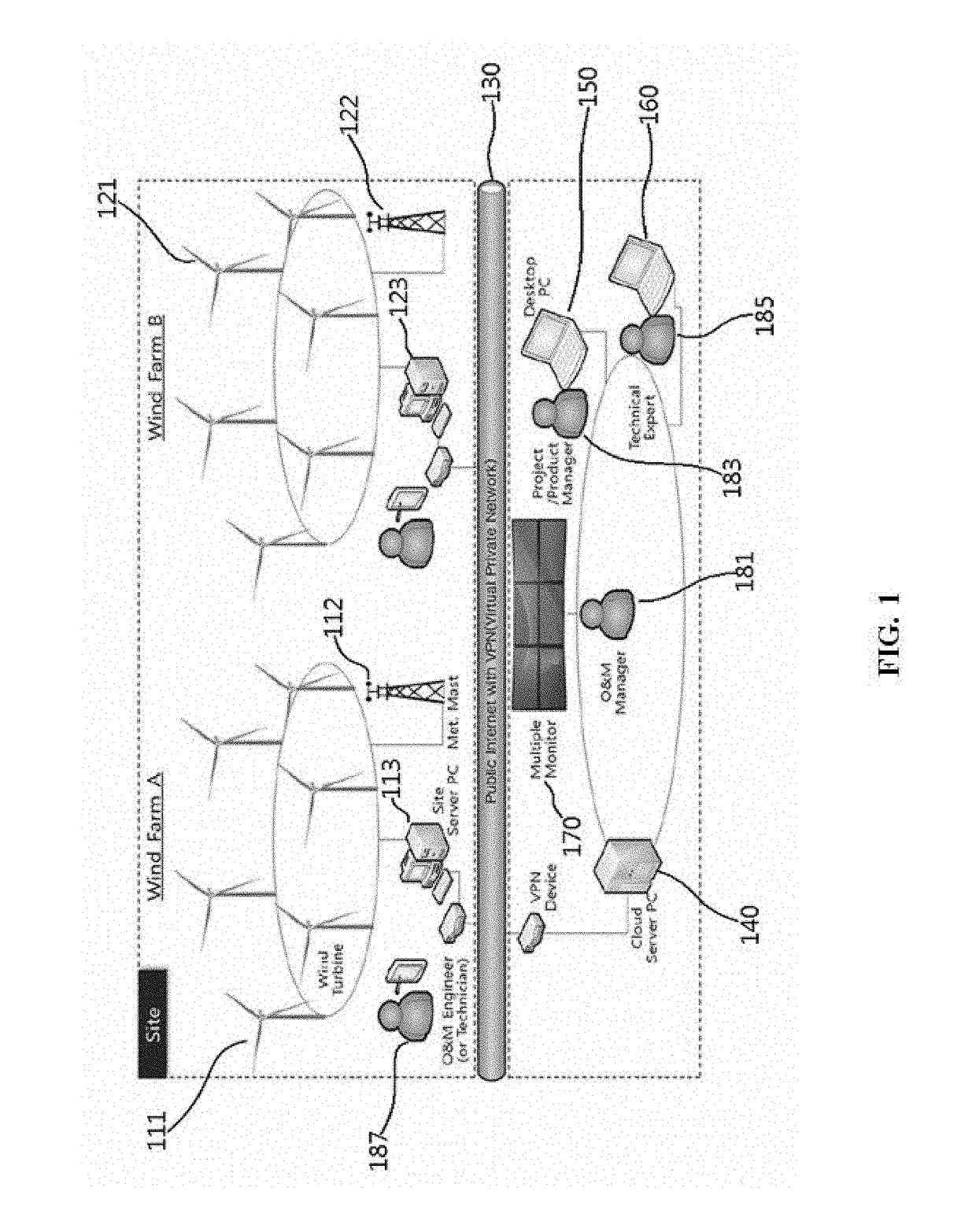
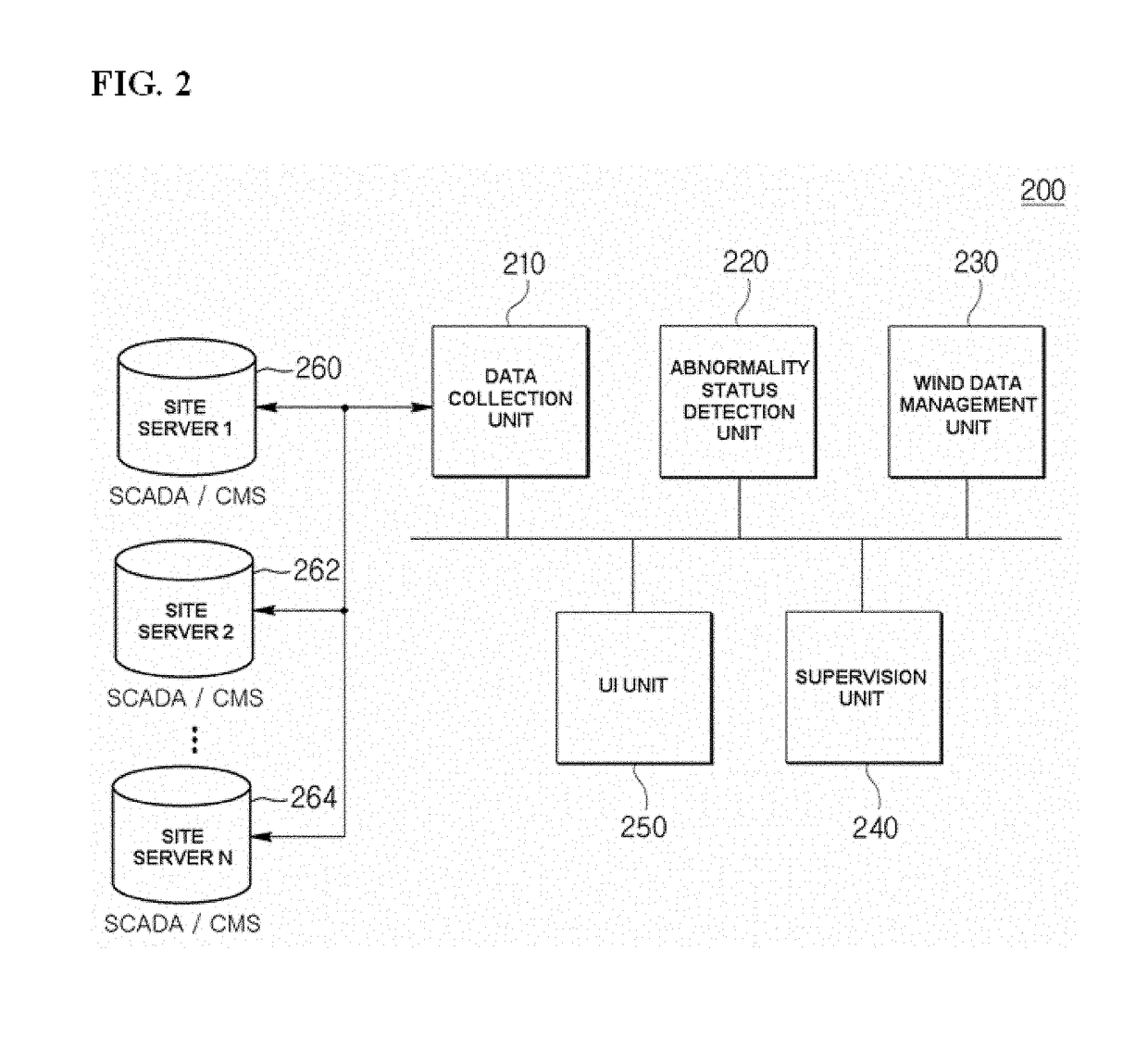
Wind farm supervision monitoring system
ActiveUS20170352010A1Minimize impactEarly detectionWind motor controlElectric testing/monitoringManagement unitMonitoring system
A wind farm supervision monitoring system includes: a data collection unit configured to collect data about a status monitoring of each wind turbine from at least one site server; an abnormality status detection unit configured to detect an abnormality status of each wind turbine based on the collected data about the status monitoring and issue an alarm; a wind data management unit configured to early detect a fault of each wind turbine and or monitor performance of each wind turbine based on the data about the status monitoring or the data about the abnormality status; and a supervision unit configured to manage a turbine operation status and operation and maintenance of each wind turbine and provide information for establishing an operation and maintenance plan for the detected abnormality status of the wind turbine.
Owner:DOOSAN HEAVY IND & CONSTR CO LTD
System and method of collecting, correlating, and aggregating structured edited content and non-edited content
ActiveUS7581166B2Easy searchEasy to storeData processing applicationsMultimedia data browsing/visualisationStructured contentData source
Owner:META PLATFORMS INC
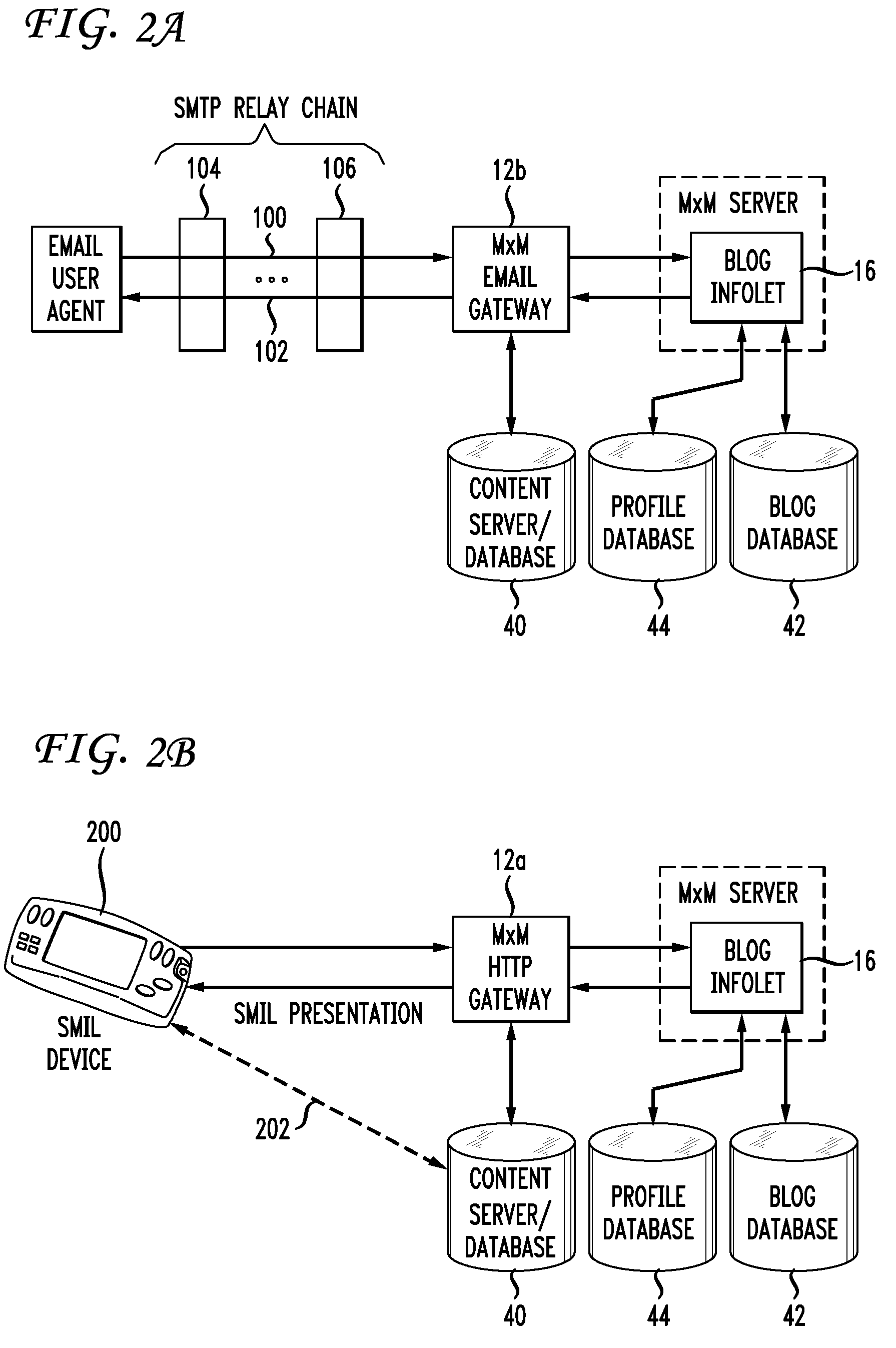
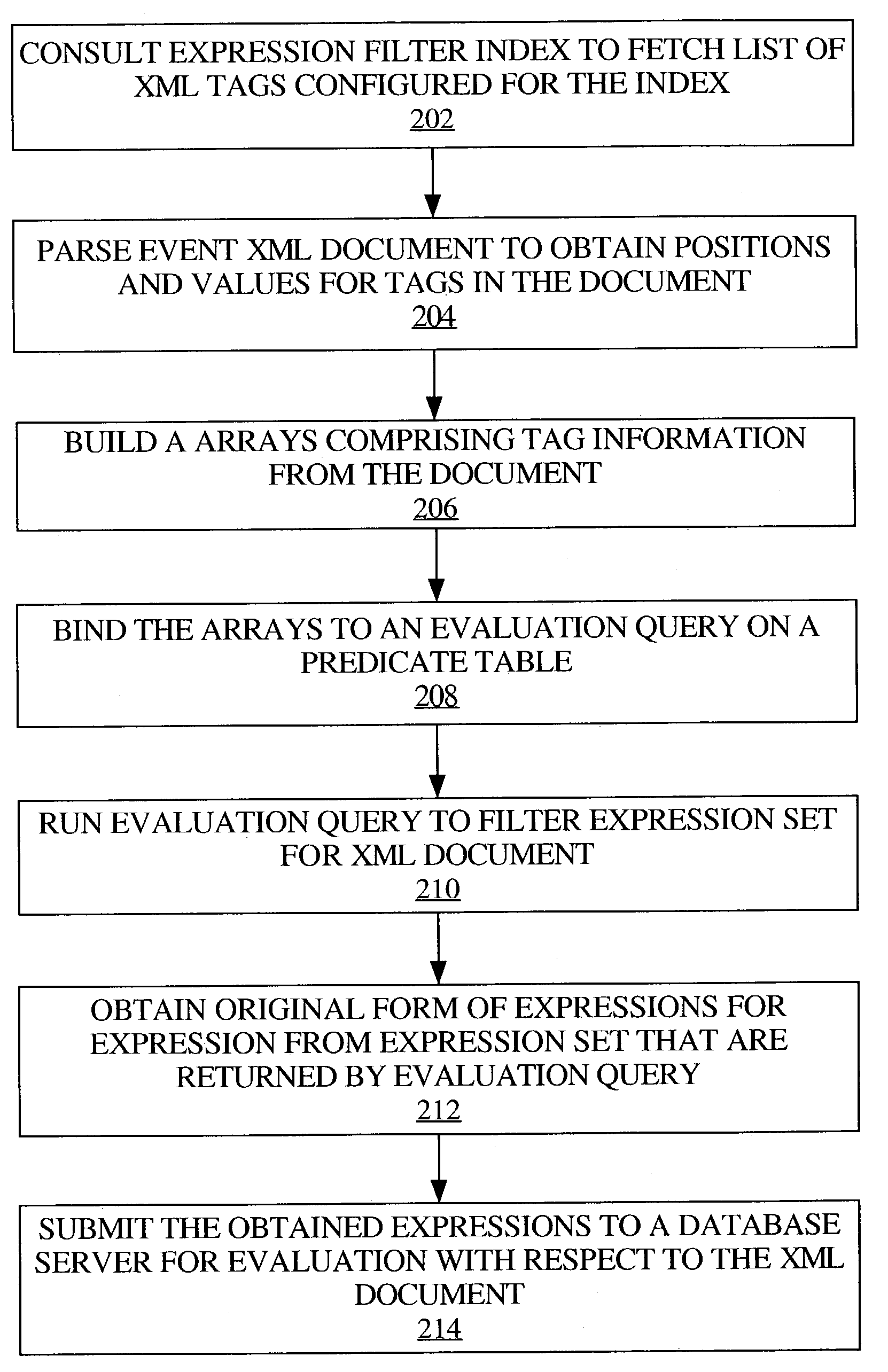
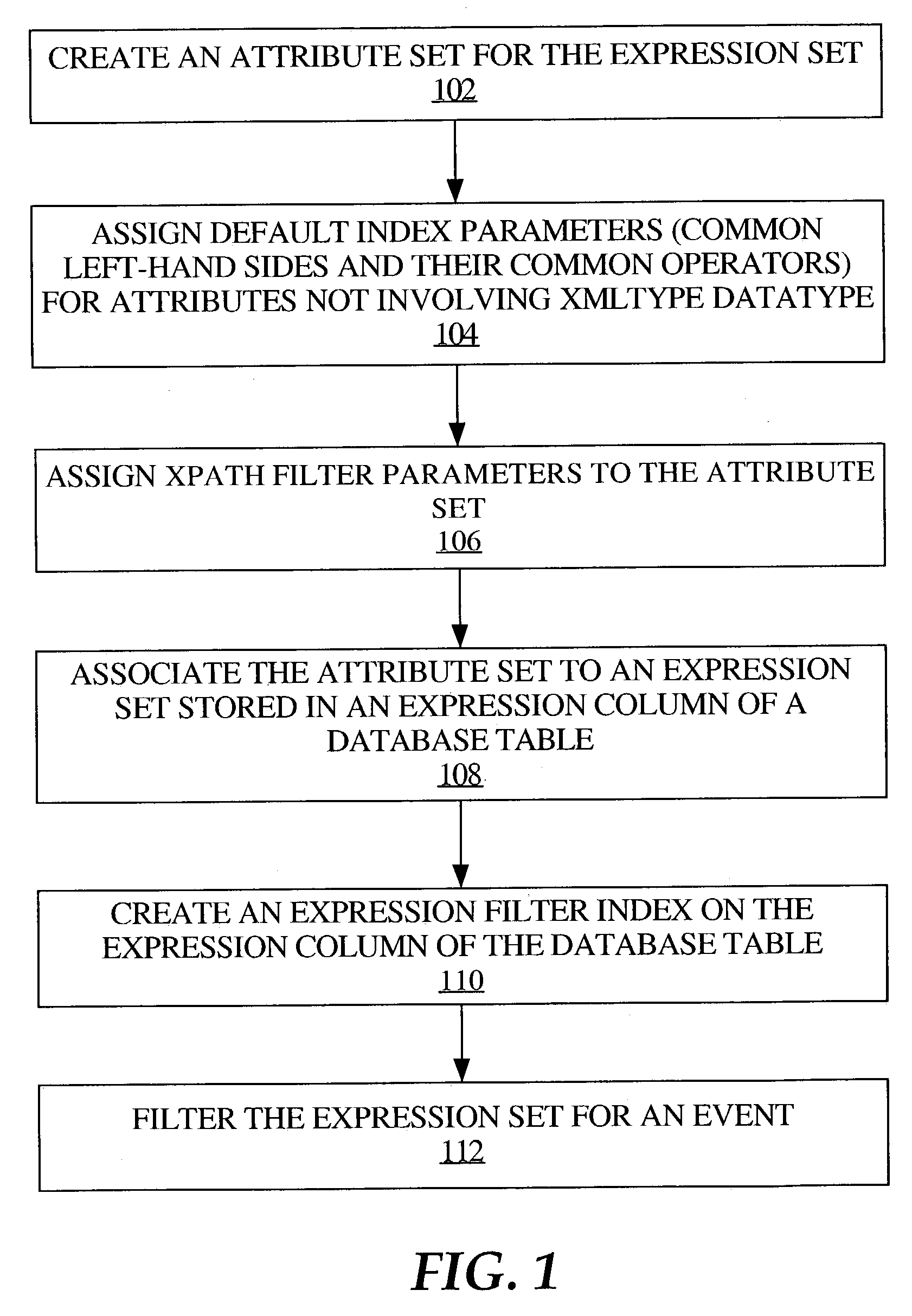
Managing XPath expressions in a database system
First data that represents a level associated with an element within an expression, such as an XPath expression, is generated from the expression, and stored in one or more columns of a table. Second data that represents a condition on an attribute of the element is generated from the expression, and stored in one or more columns of the same or a different table. A plurality of expressions can be processed as such, and a determination made whether any of the expressions match with a given hierarchical data item, such as an XML document, that includes a value that corresponds to an attribute that is associated with an element that resides at a particular level within the data item. Such determination is made based on whether the particular level matches the first data and the value satisfies the second data associated with a given expression.
Owner:ORACLE INT CORP
Data capture and identification system and process
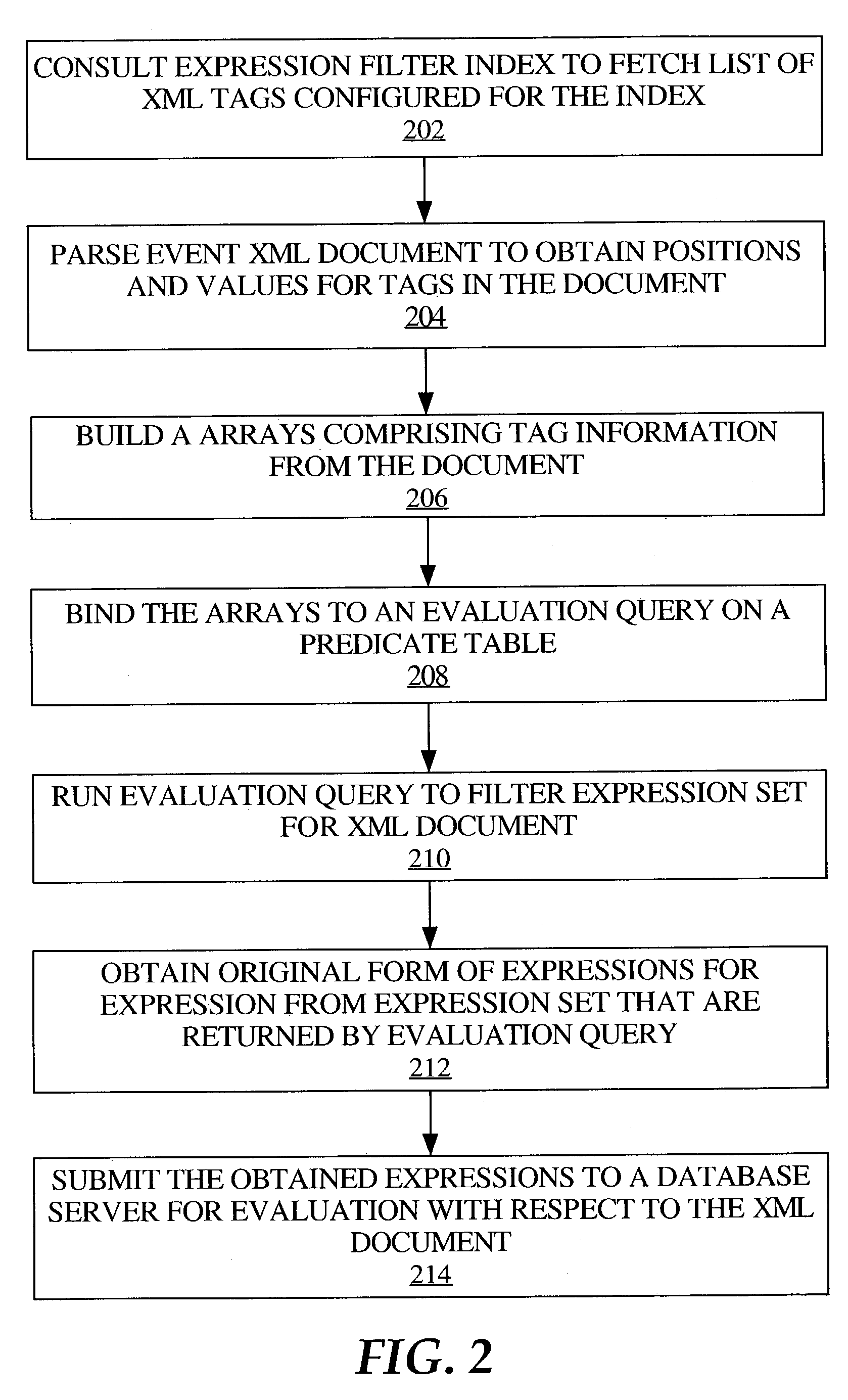
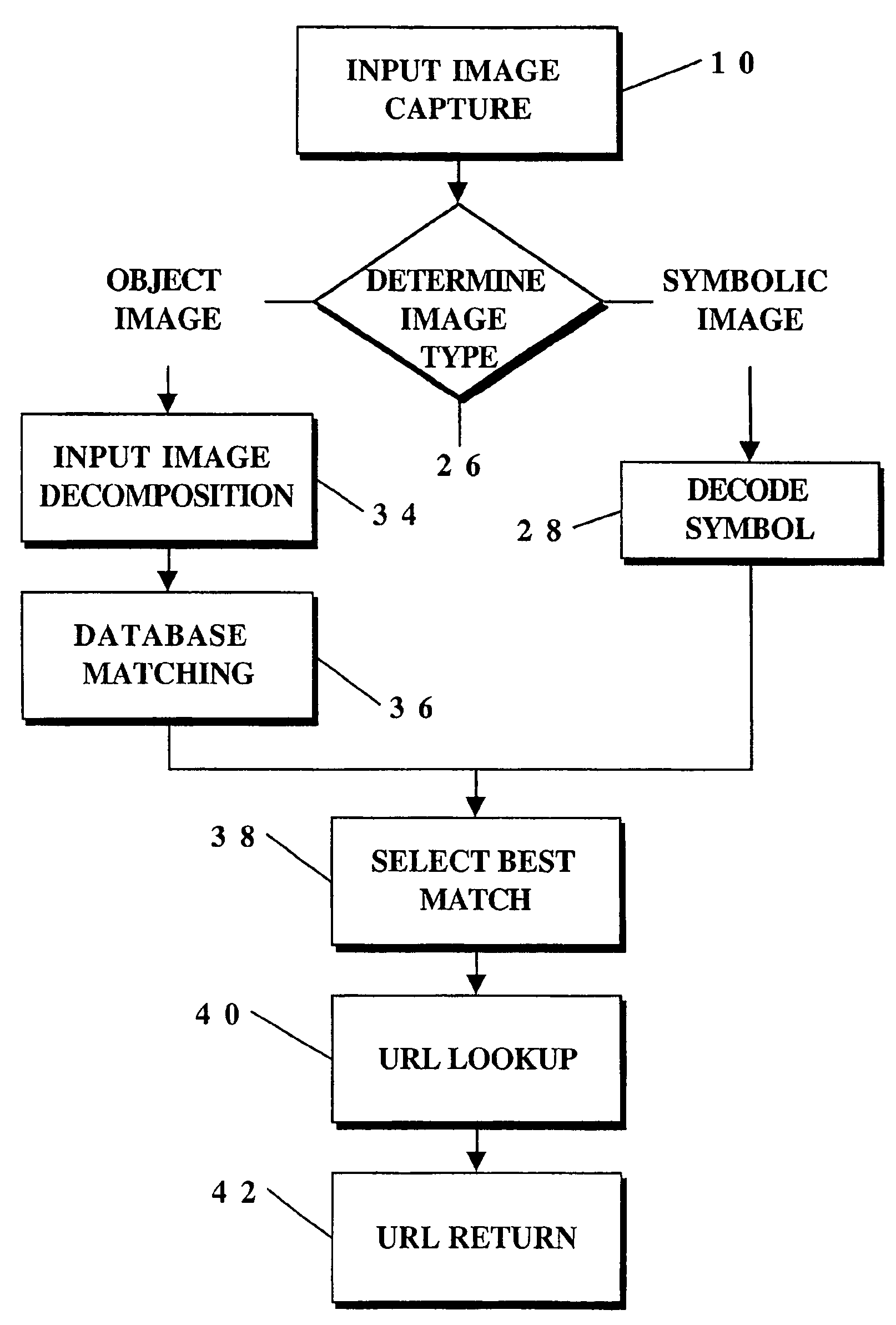
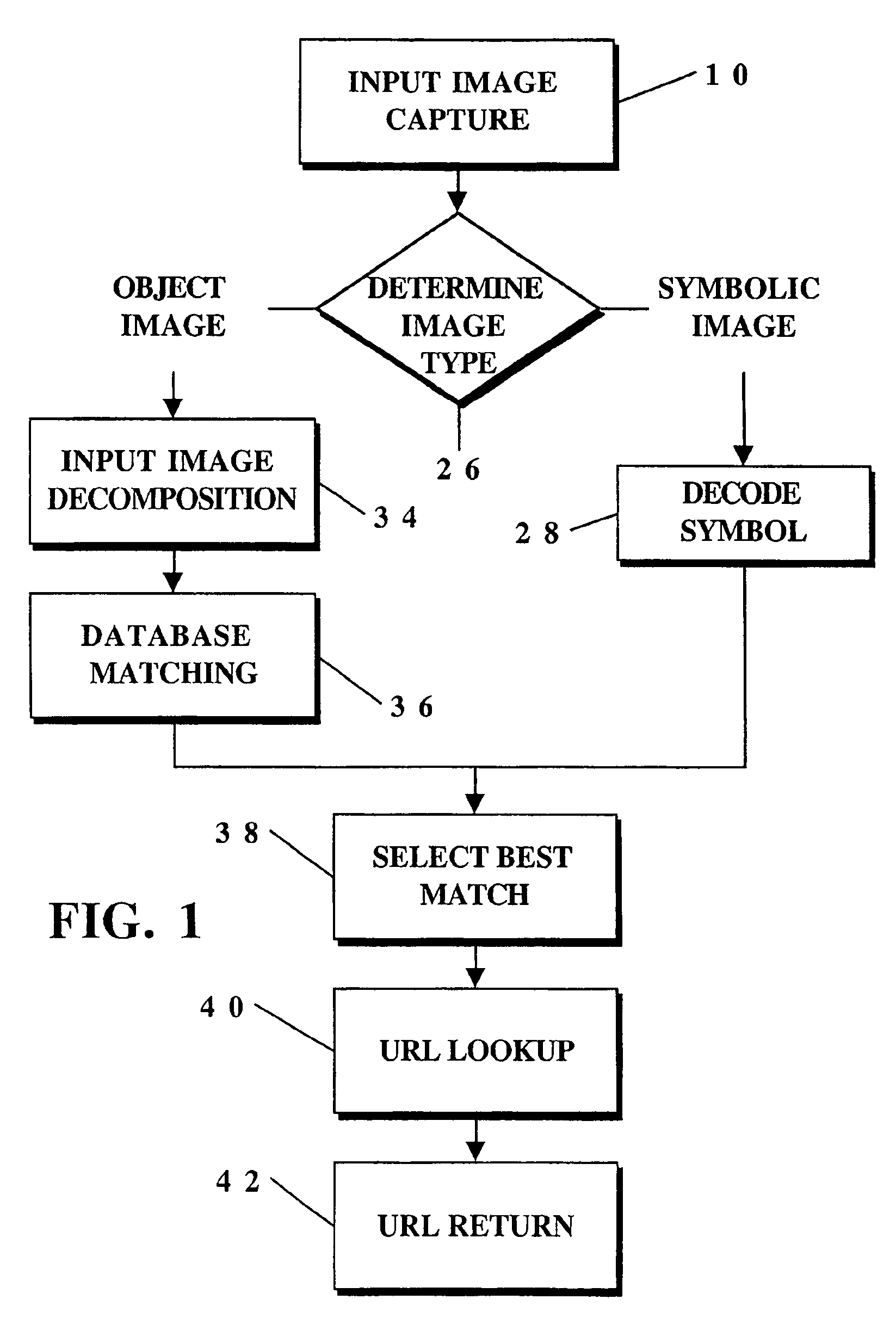
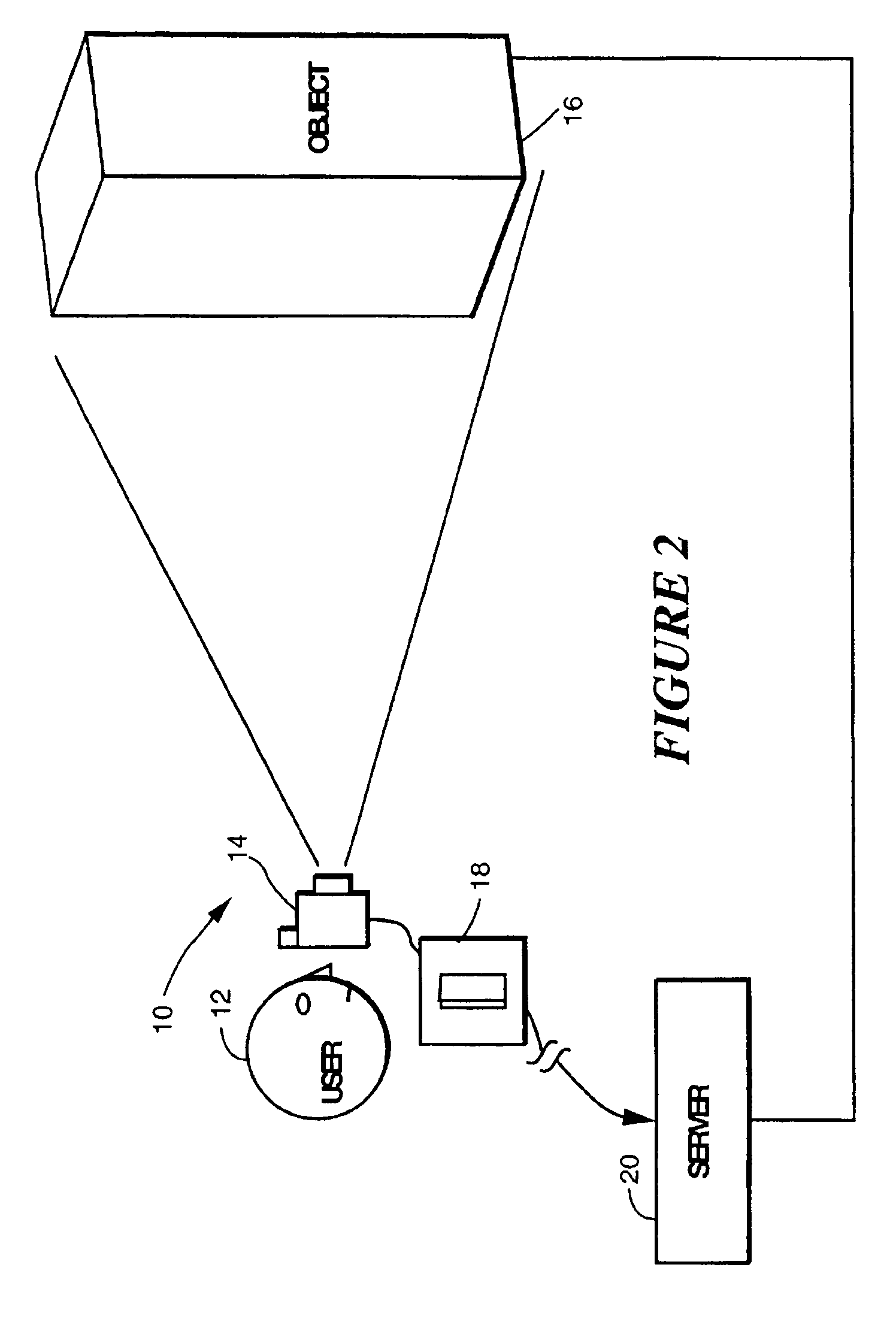
InactiveUS7565008B2Fast and reliable detection and recognitionReduce sizeStill image data indexingCharacter and pattern recognitionRadiologyData acquisition
An identification method and process for objects from digitally captured images thereof that uses data characteristics to identify an object from a plurality of objects in a database. The data is broken down into parameters such as a Shape Comparison, Grayscale Comparison, Wavelet Comparison, and Color Cube Comparison with object data in one or more databases to identify the actual object of a digital image.
Owner:NANT HLDG IP LLC
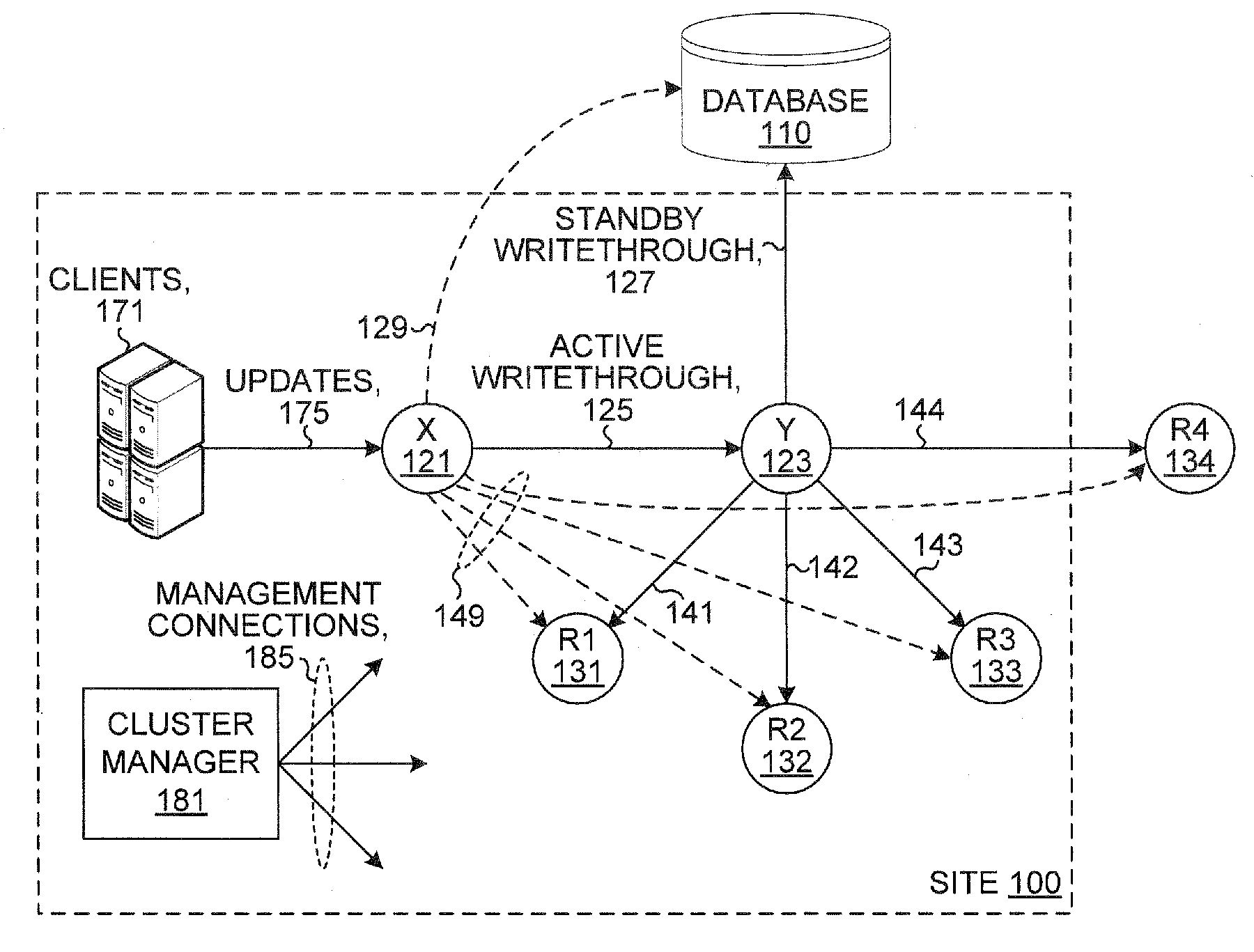
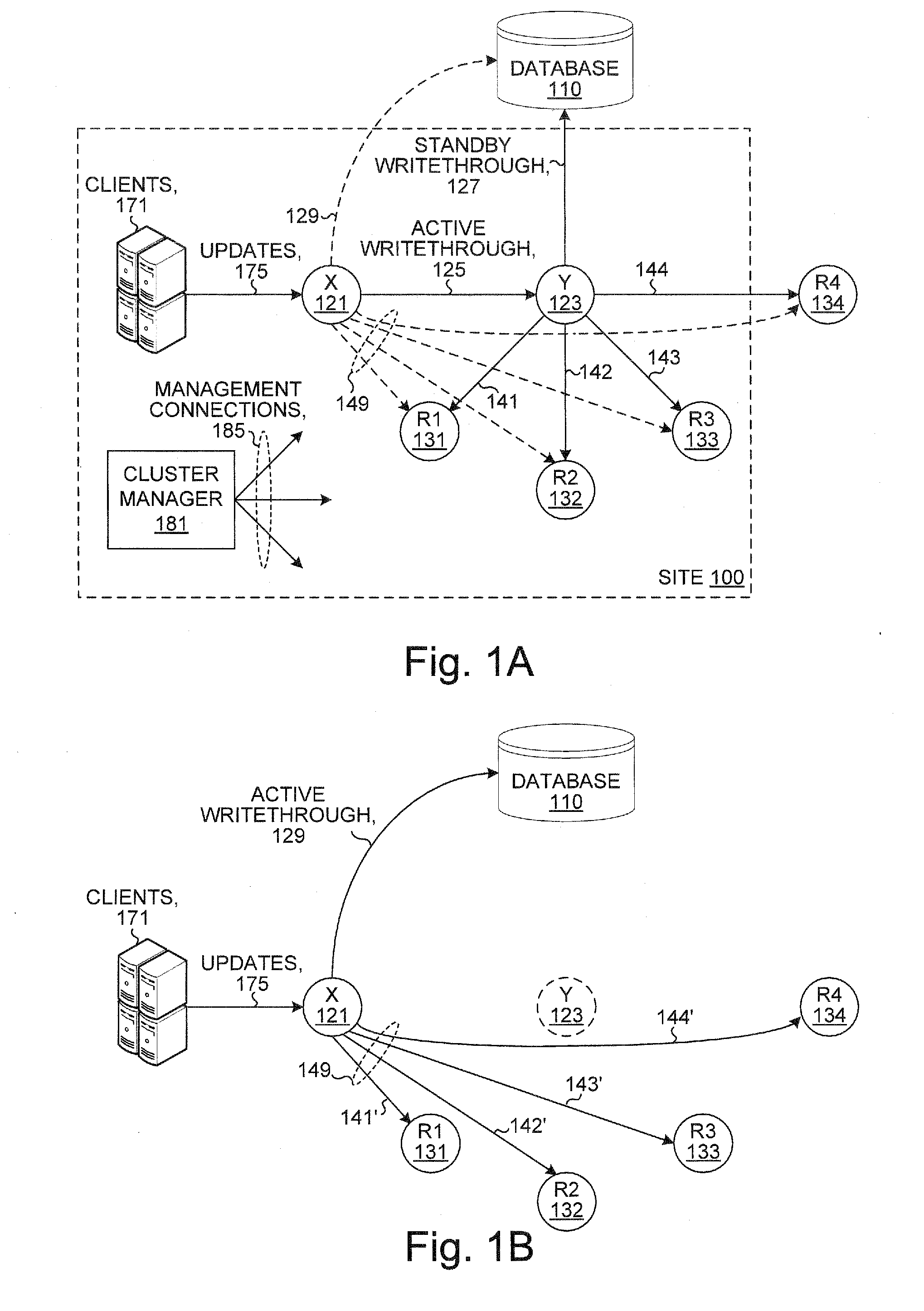
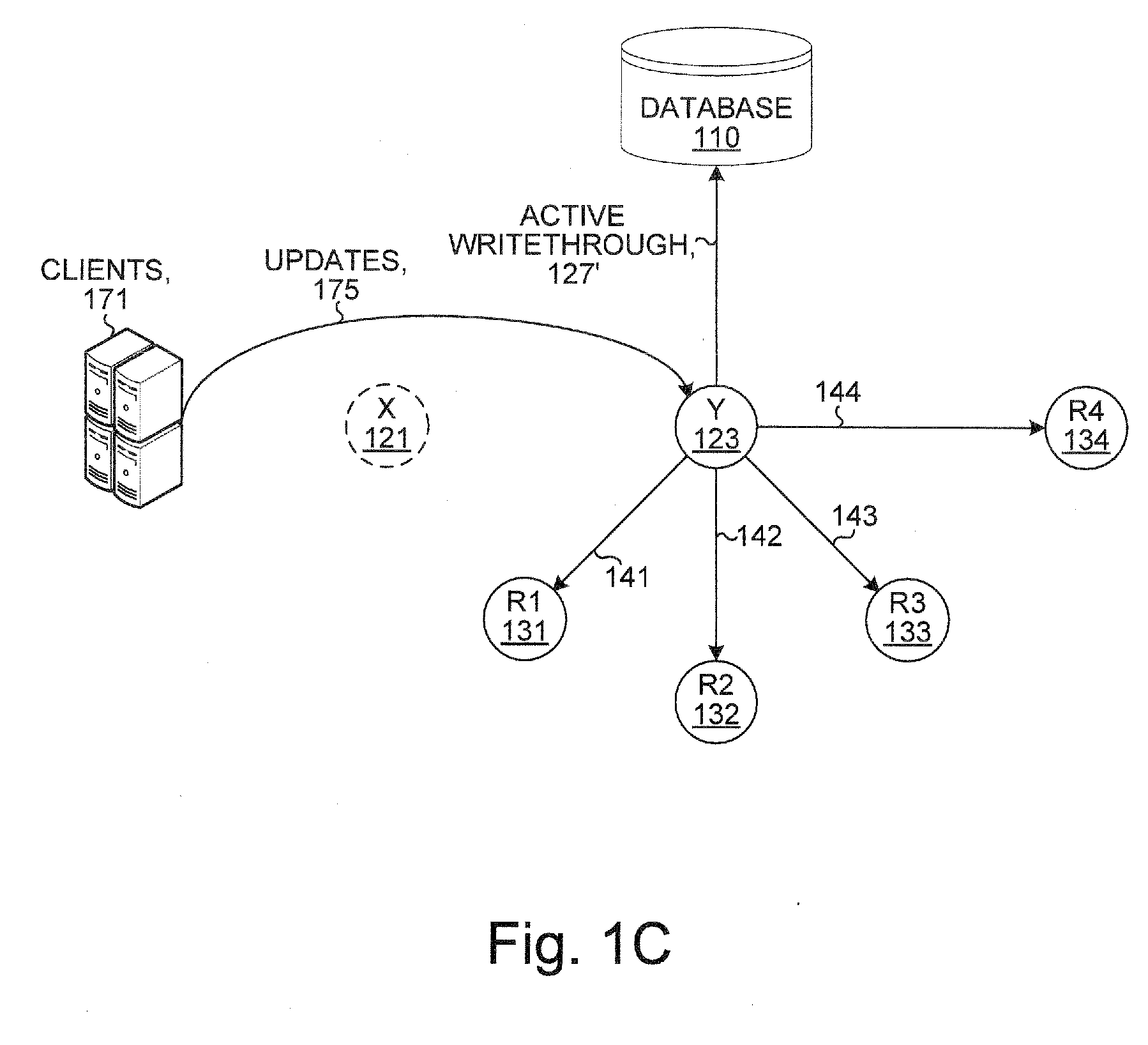
Database system with active standby and nodes
ActiveUS20080222159A1Special data processing applicationsDatabase design/maintainanceIn-memory databaseTransaction log
A system includes an active node and a standby node and zero or more replica nodes. Each of the nodes includes a database system, such as an in-memory database system. Client updates applied to the active node are written through to the standby node, and the standby node writes the updates through to a primary database and updates the replica nodes. Commit ticket numbers tag entries in transaction logs and are used to facilitate recovery if either of the active node or the standby node fails. Updates applied to the primary database are autorefreshed to the active node and written through by the active node to the standby node which propagates the updates to the replica nodes. Bookmarks are used to track updated records of the primary database and are used to facilitate recovery if either of the active node or the standby node fails.
Owner:ORACLE INT CORP
Systems and methods for rule-based virtual machine data protection
InactiveUS20140201157A1None of data be protected effectivelyDigital data processing detailsSpecial data processing applicationsSystem identificationUser interface
A data storage system backs up or protects virtual machines. For instance, the system identifies the different virtual machines executing in the system and provides a number of factors that can be used to create a backup policy. The system further creates specific rules for virtual machine backup policies using a user interface with drop down boxes of relevant criteria and Boolean operators. A preview of included virtual machines allows the rule to be refined. Particular virtual machines can be excluded during the preview. The system further dynamically updates the list of virtual machines satisfying the rules at time of backup.
Owner:COMMVAULT SYST INC
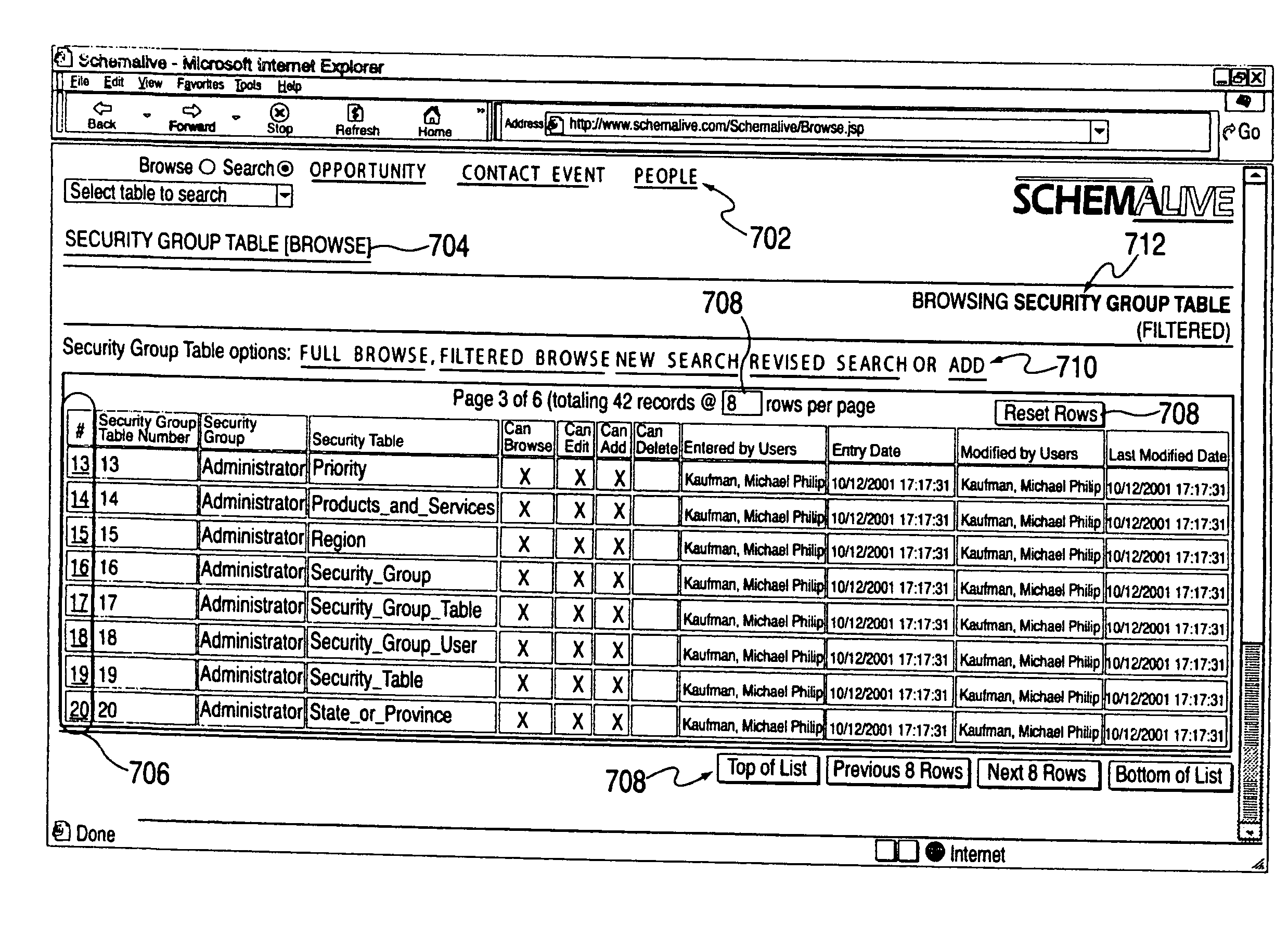
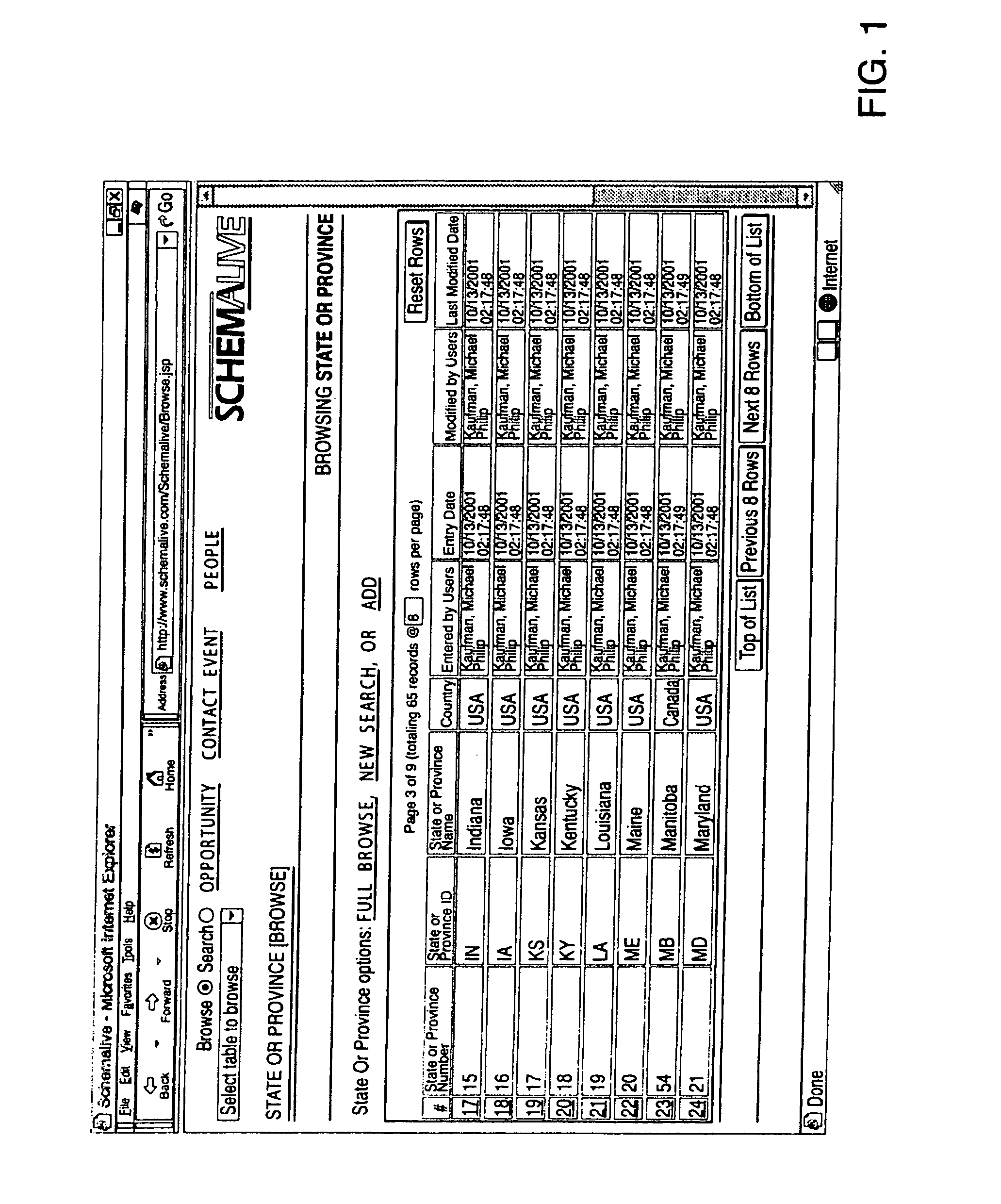
System and method for generating automatic user interface for arbitrarily complex or large databases
InactiveUS20110191303A1Natural, powerful, and easy-to-useData processing applicationsWeb data indexingDrill downSoftware system
A software system automatically and dynamically generates a fully functional user interface (UI) based upon, and connected directly to, an underlying data model (as instantiated within a relational database management system (RDBMS)). The UI derives from an automated interrogation of the RDBMS, and comprises all mode displays (e.g., browse, search, edit, add) for all tables, and a full complement of mechanisms—integrated directly into the mode displays—for representing, navigating, and managing relationships across tables, regardless of the complexity of the underlying RDBMS schema. It utilizes a hierarchical “context stack” for suspending the working state of a particular table while “drilling down” to work with related-table information and return relevant changes to the base table. The embodiment further provides methods to enhance and extend the internal representation of table structures, constraints, relationships, and—special requirements (“business rules”) for improved revelation of the schema structure through external interrogation.
Owner:KAUFMAN MICHAEL PHILIP
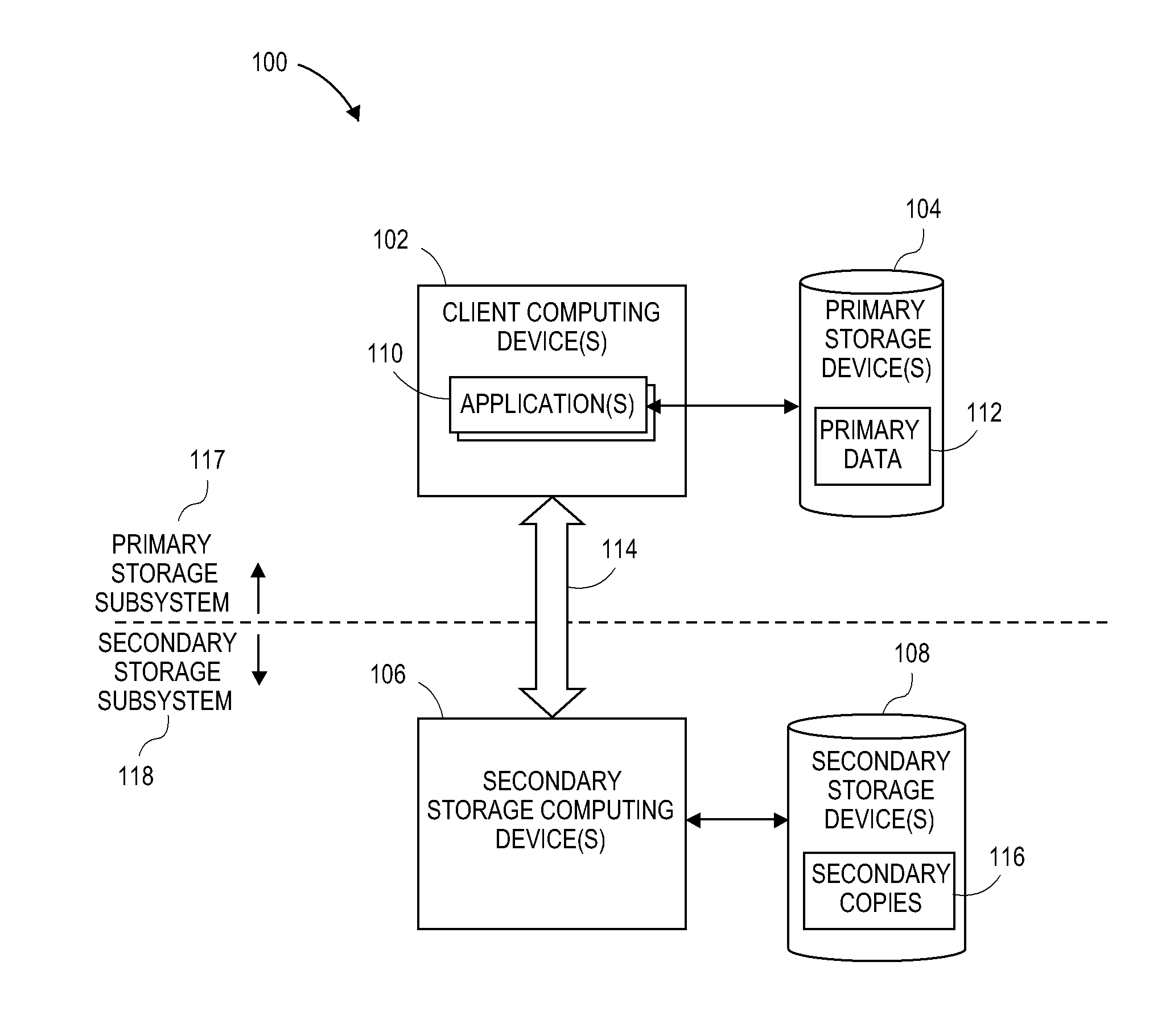
Virtual data store creation and use
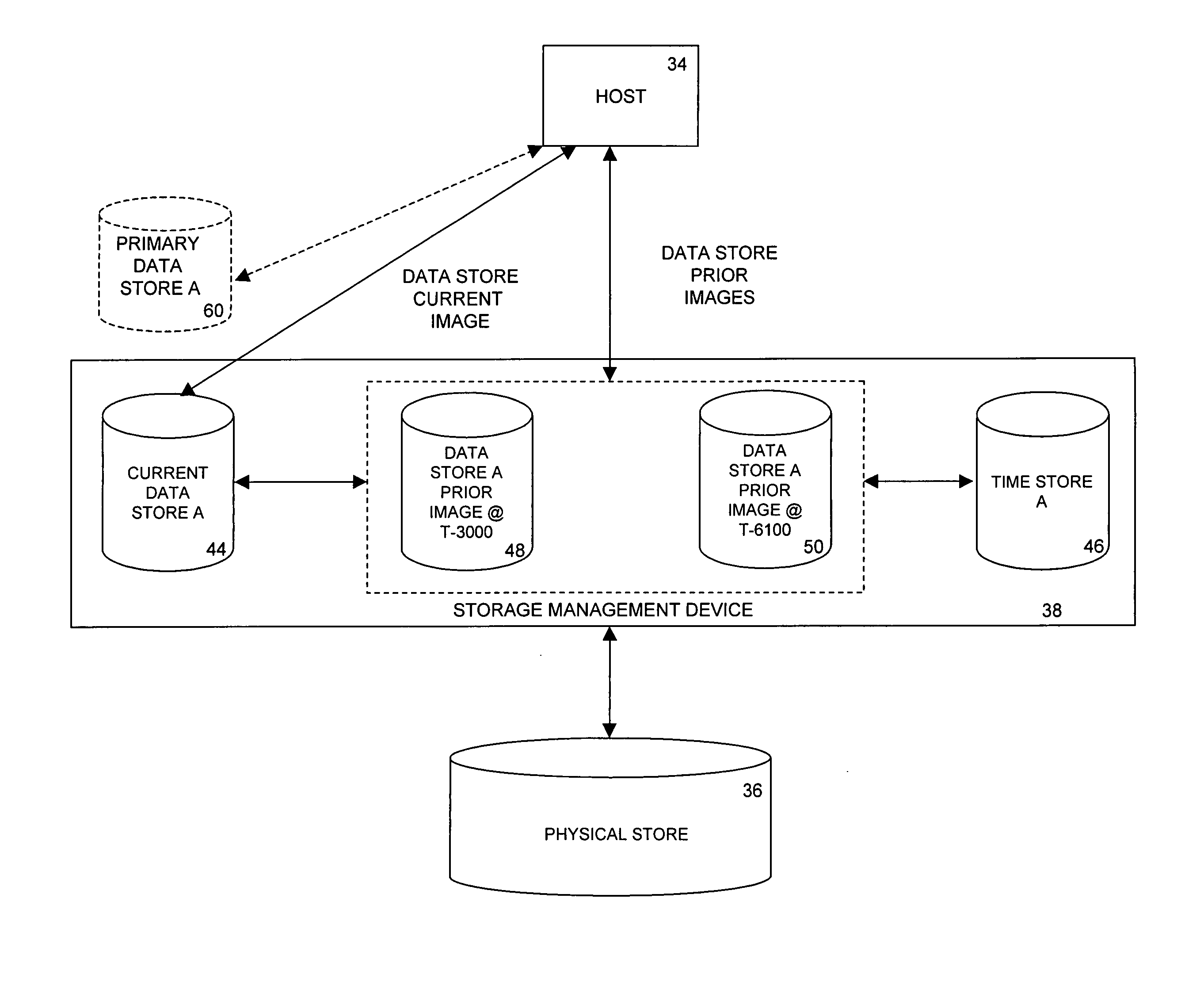
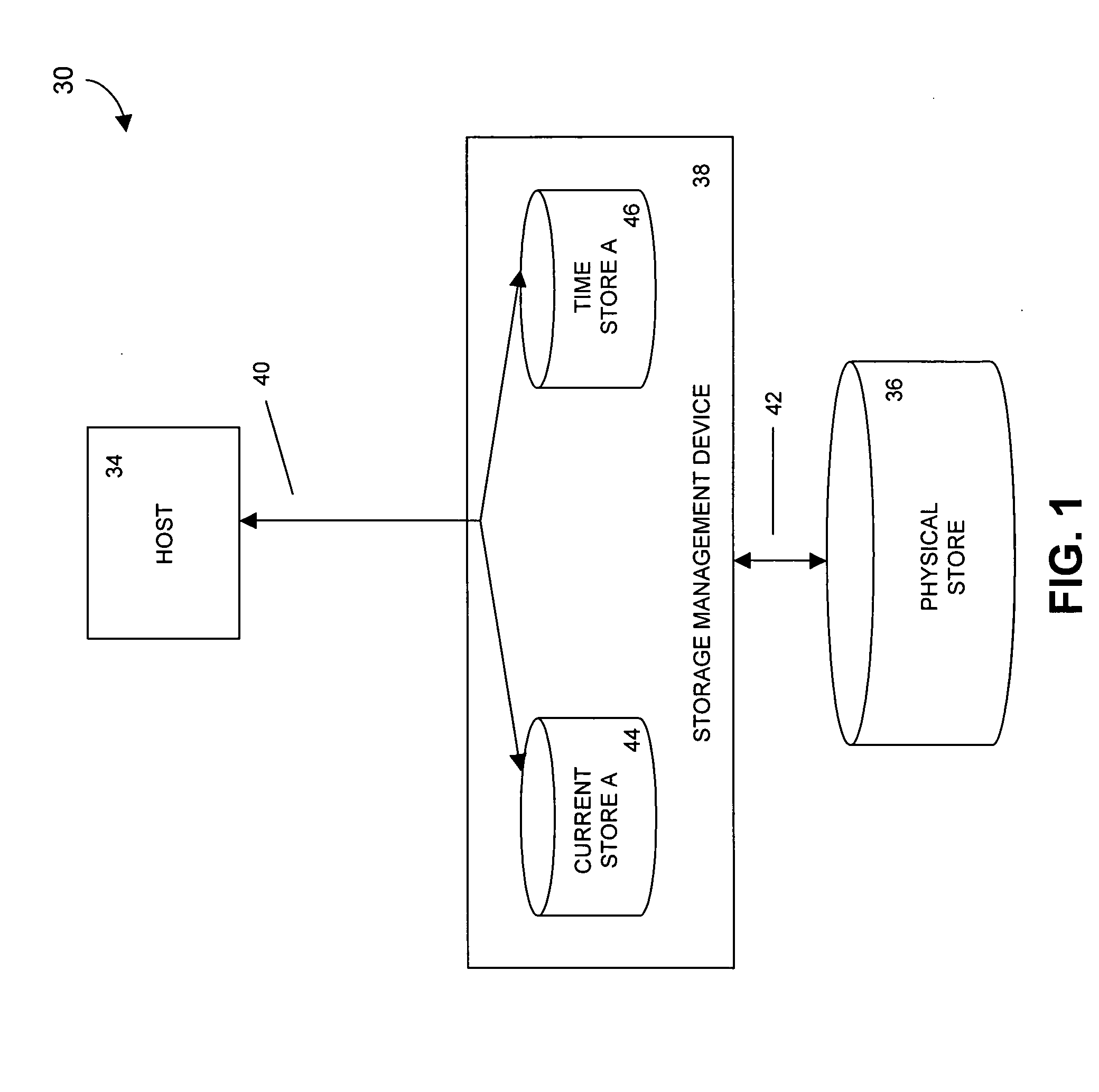
ActiveUS20050065962A1Promote recoveryEasy to storeMemory loss protectionError detection/correctionData storeStorage cell
A method, apparatus, and system for accessing units of storage that depends at least in part on an address of the unit of storage and the time that data was written to the unit of storage. By accessing units of storage in response to a time, prior images of a data store can be generated substantially instantaneously.
Owner:SYMANTEC OPERATING CORP
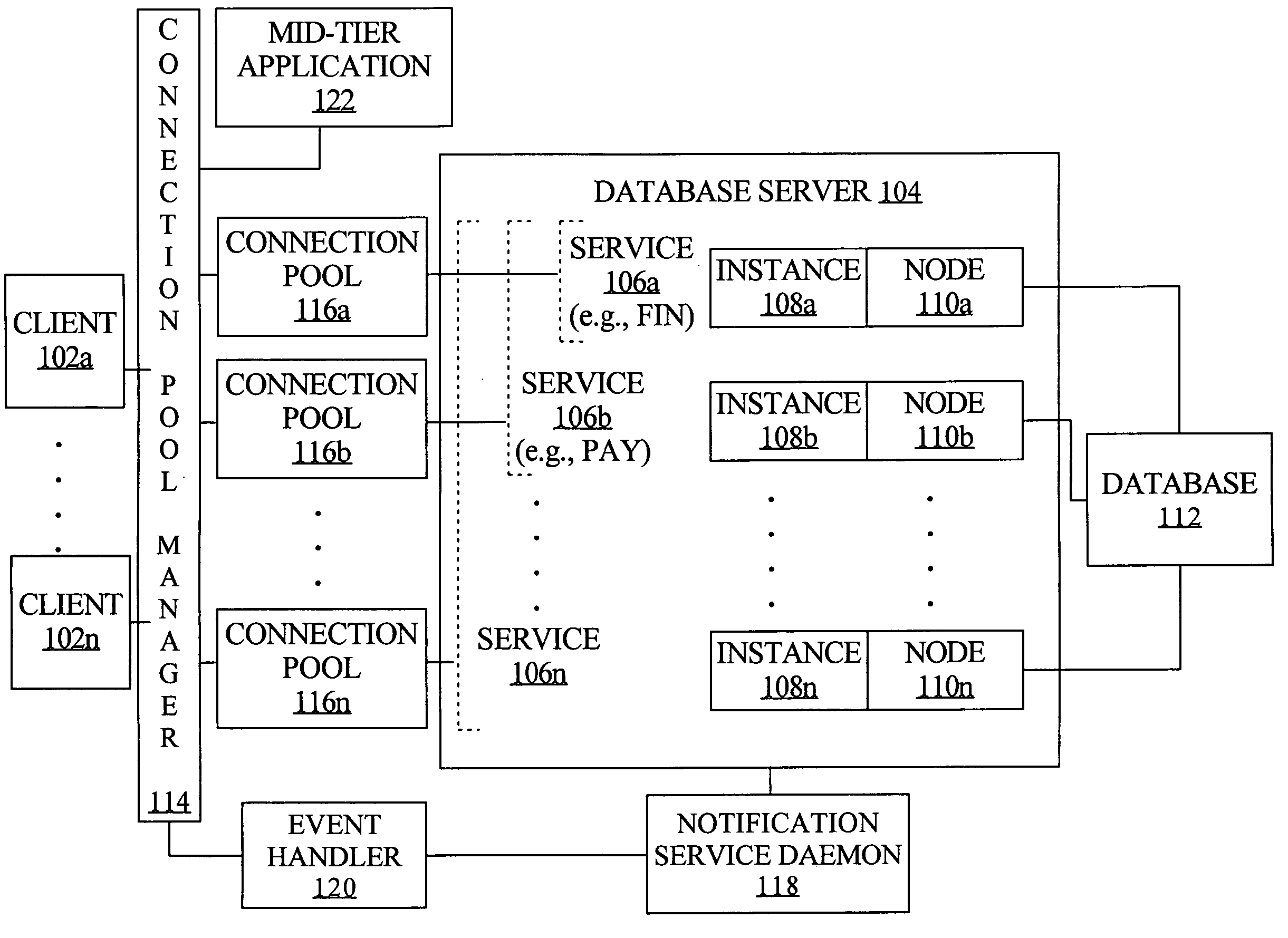
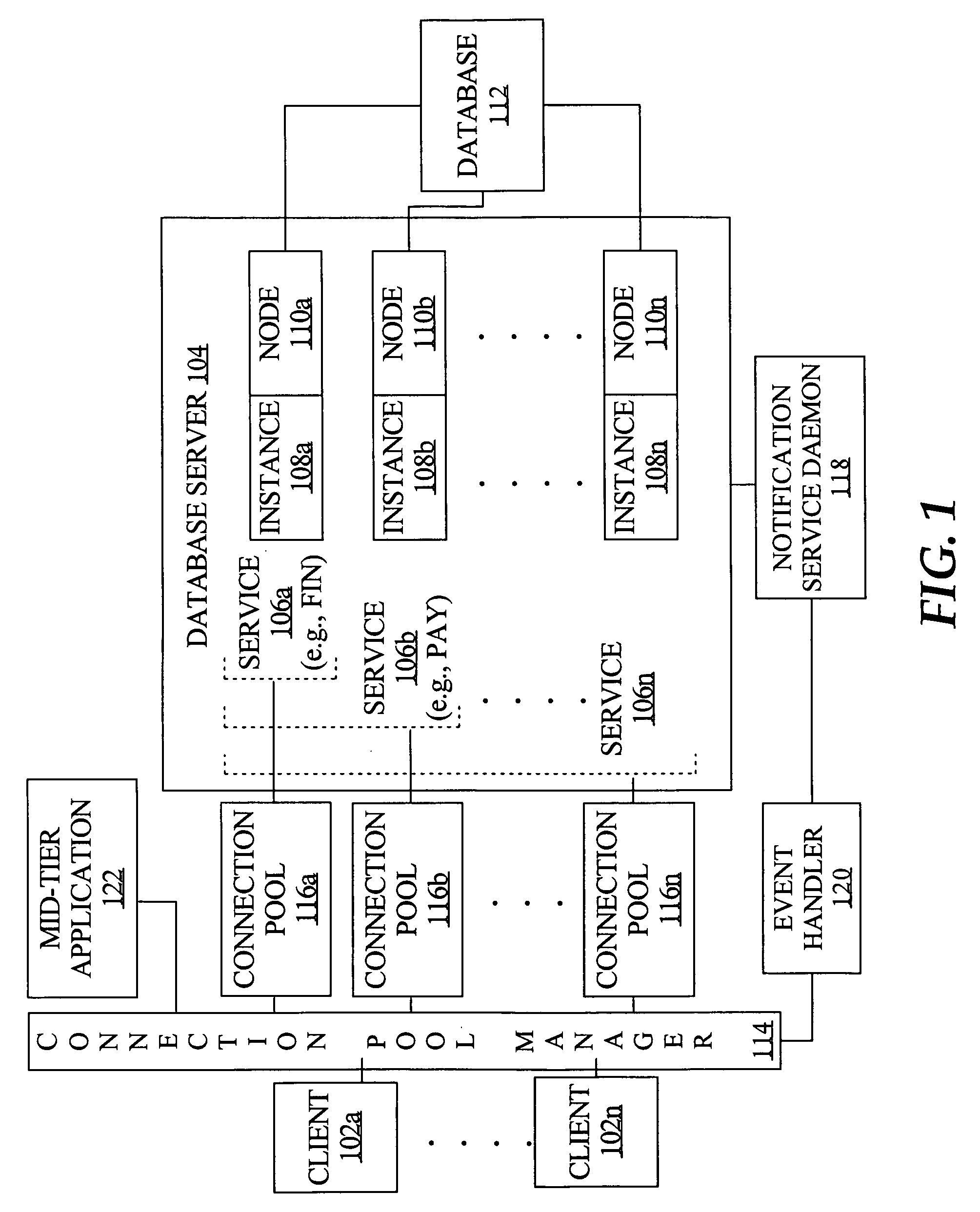
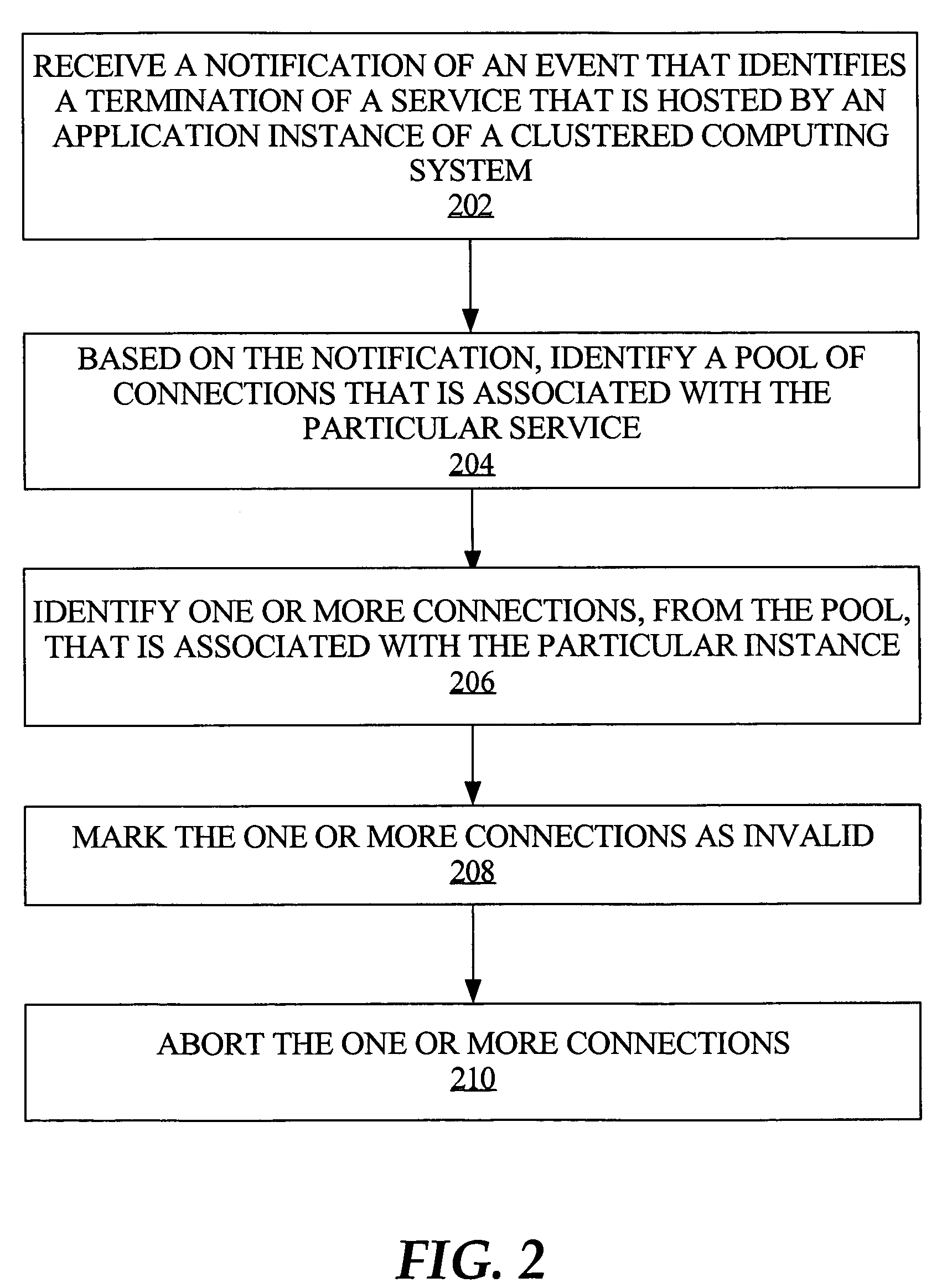
Fast reorganization of connections in response to an event in a clustered computing system
ActiveUS20050038801A1Easy to handleRapid positioningError detection/correctionDigital data processing detailsParallel computingConnection pool
Techniques for fast recovery and / or balancing of connections to a clustered computing system provide management of such connections by determining a number of connections to load balance across nodes and by triggering creation of such connections. In one aspect, a notification of an event regarding the clustered computing system is received by a connection pool manager, a pool of connections to the system is identified based on the notification, and one or more connections from the pool are processed in response to the event. According to an embodiment, the notification comprises the identities of the service, database, server instance and machine that correspond to the event.
Owner:ORACLE INT CORP
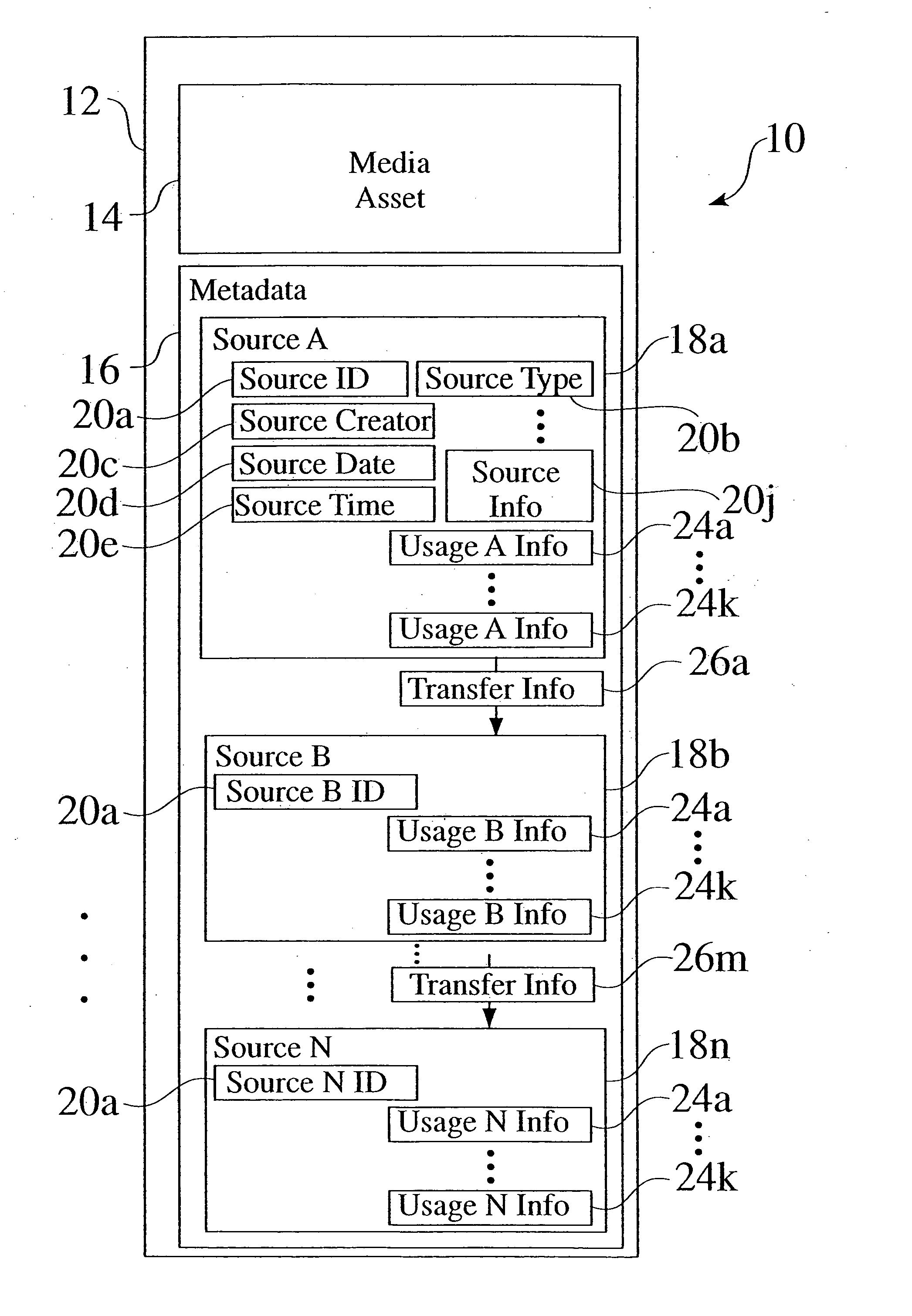
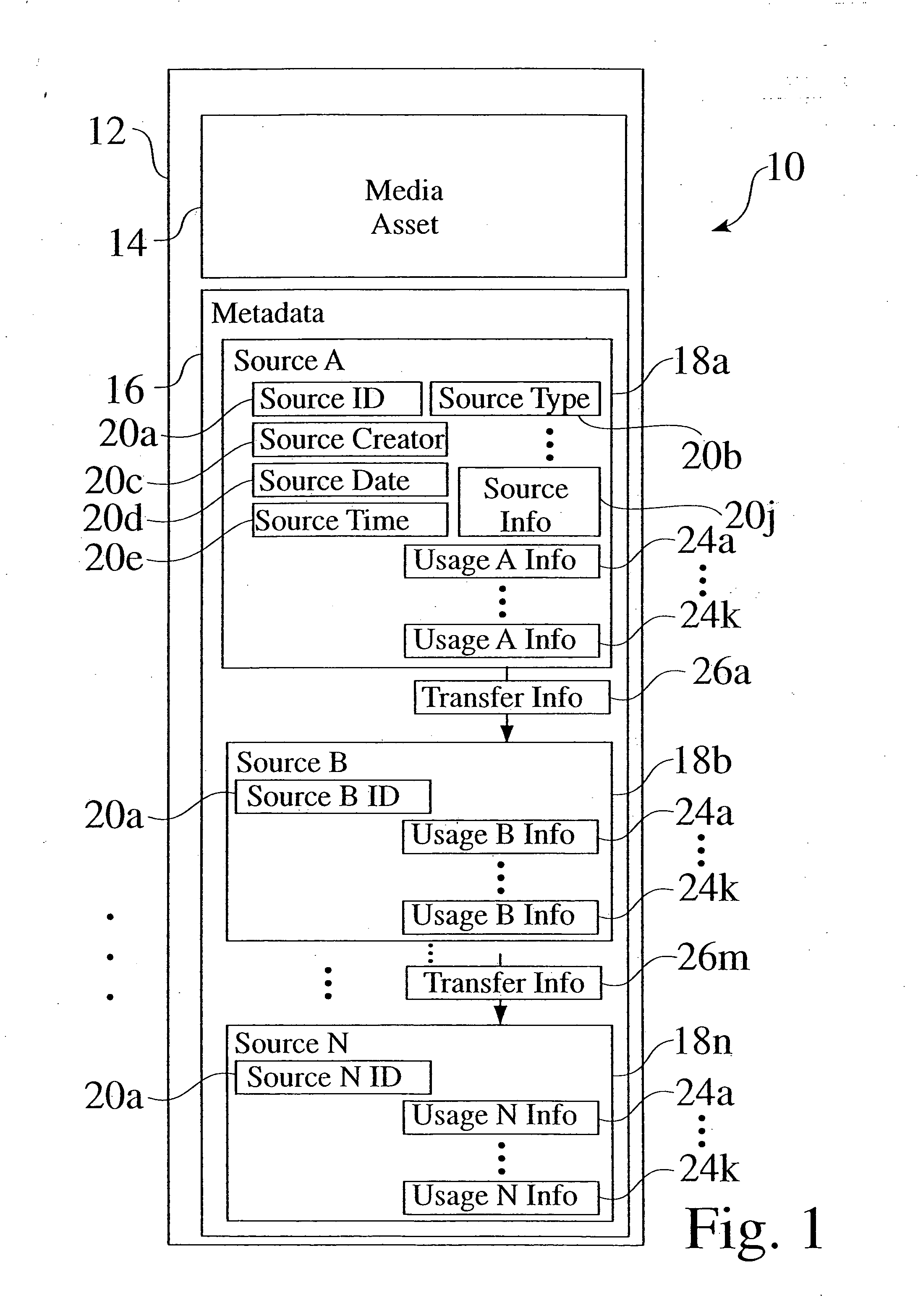
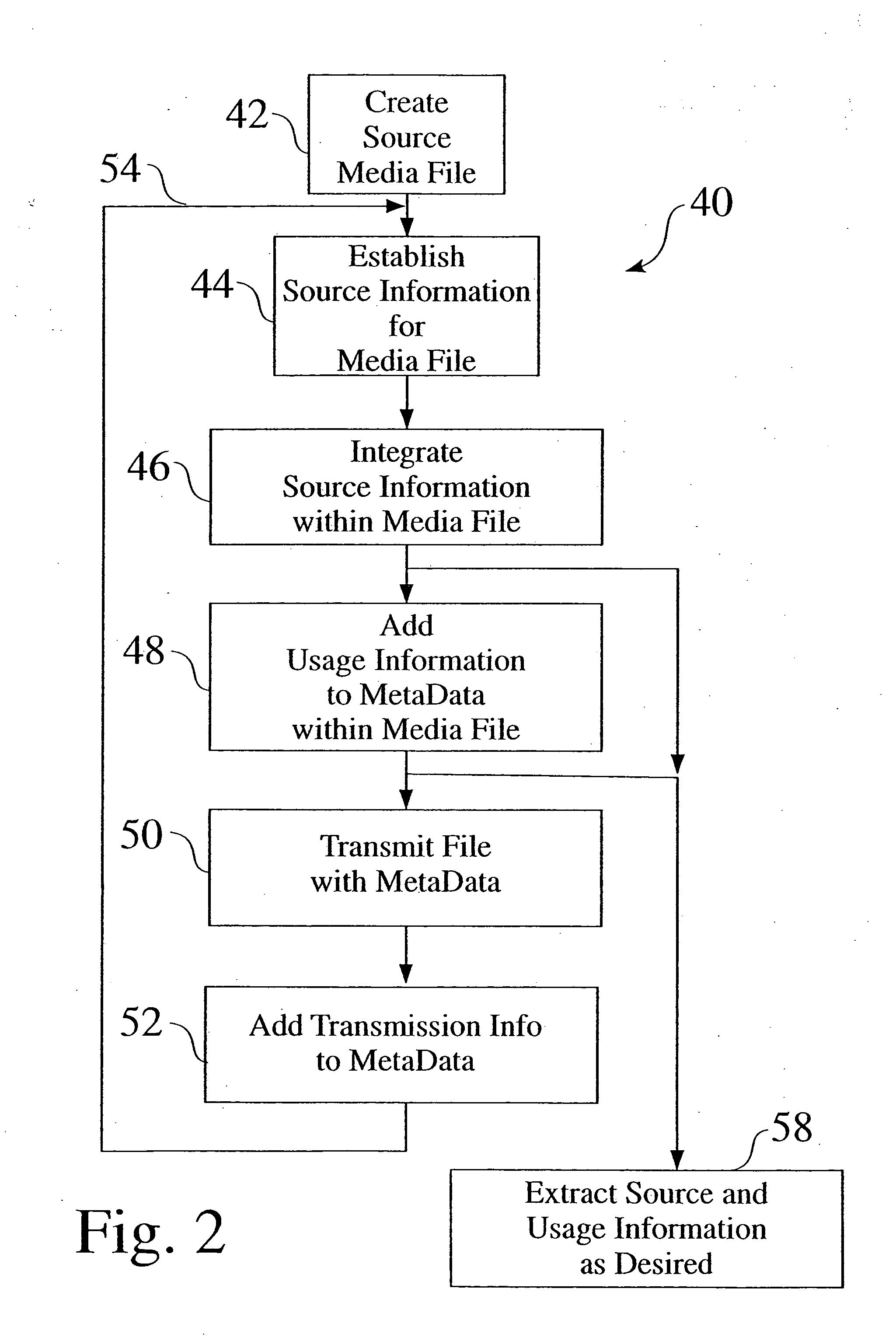
System for incorporating information about a source and usage of a media asset into the asset itself
ActiveUS20050038813A1Data processing applicationsDigital data processing detailsComputerized systemDatabase
An enhanced metadata structure and associated process is provided which captures and stores metadata gathered about the source and usage of a media asset or file. The source and usage metadata is integrated, such as by encoding within the enhanced media file, as the media asset is transferred and used. The integrated metadata accumulates, as a trail of source information and usage information in the enhanced media asset, and can be extracted upon arrival at a target computer system.
Owner:META PLATFORMS INC
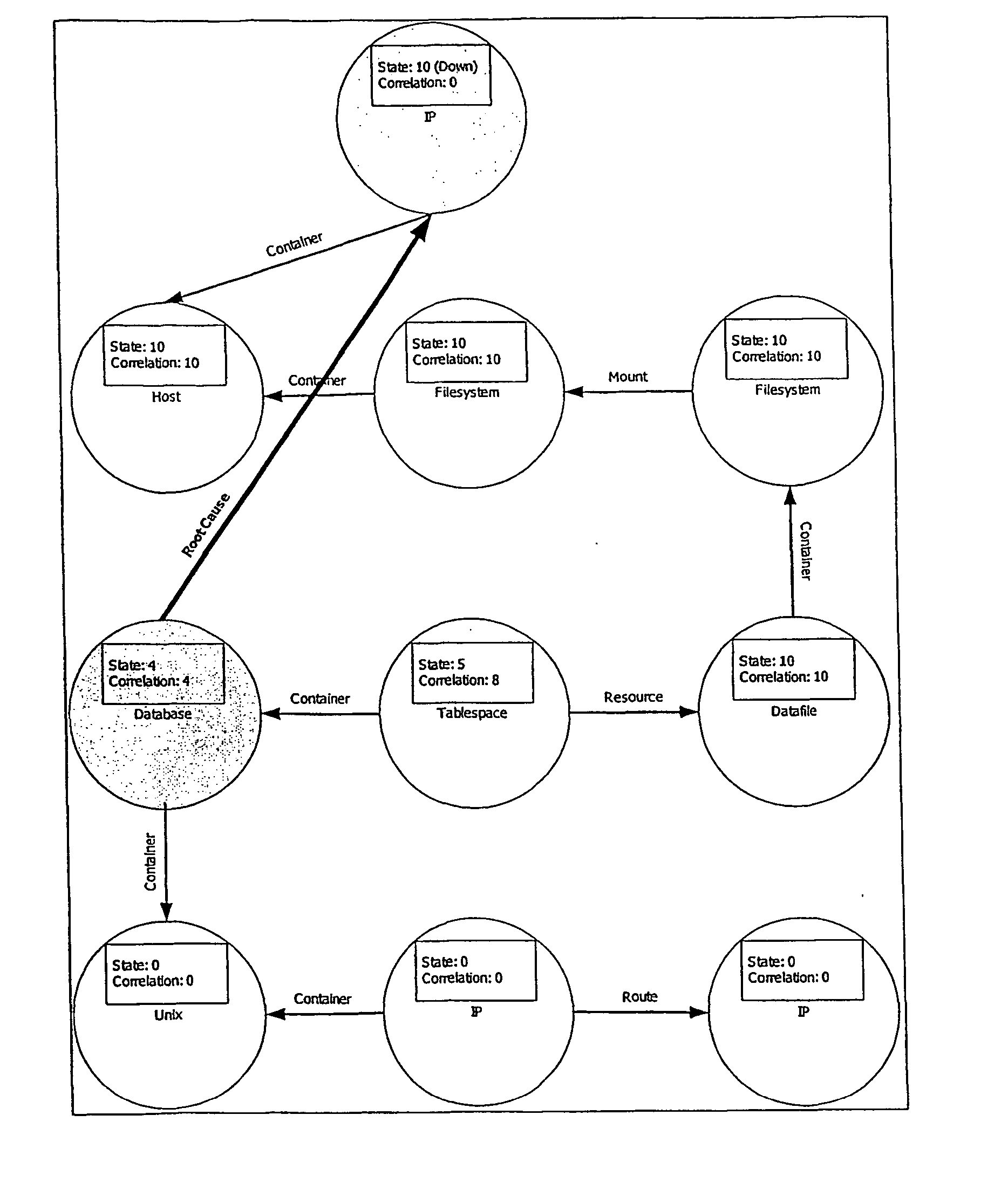
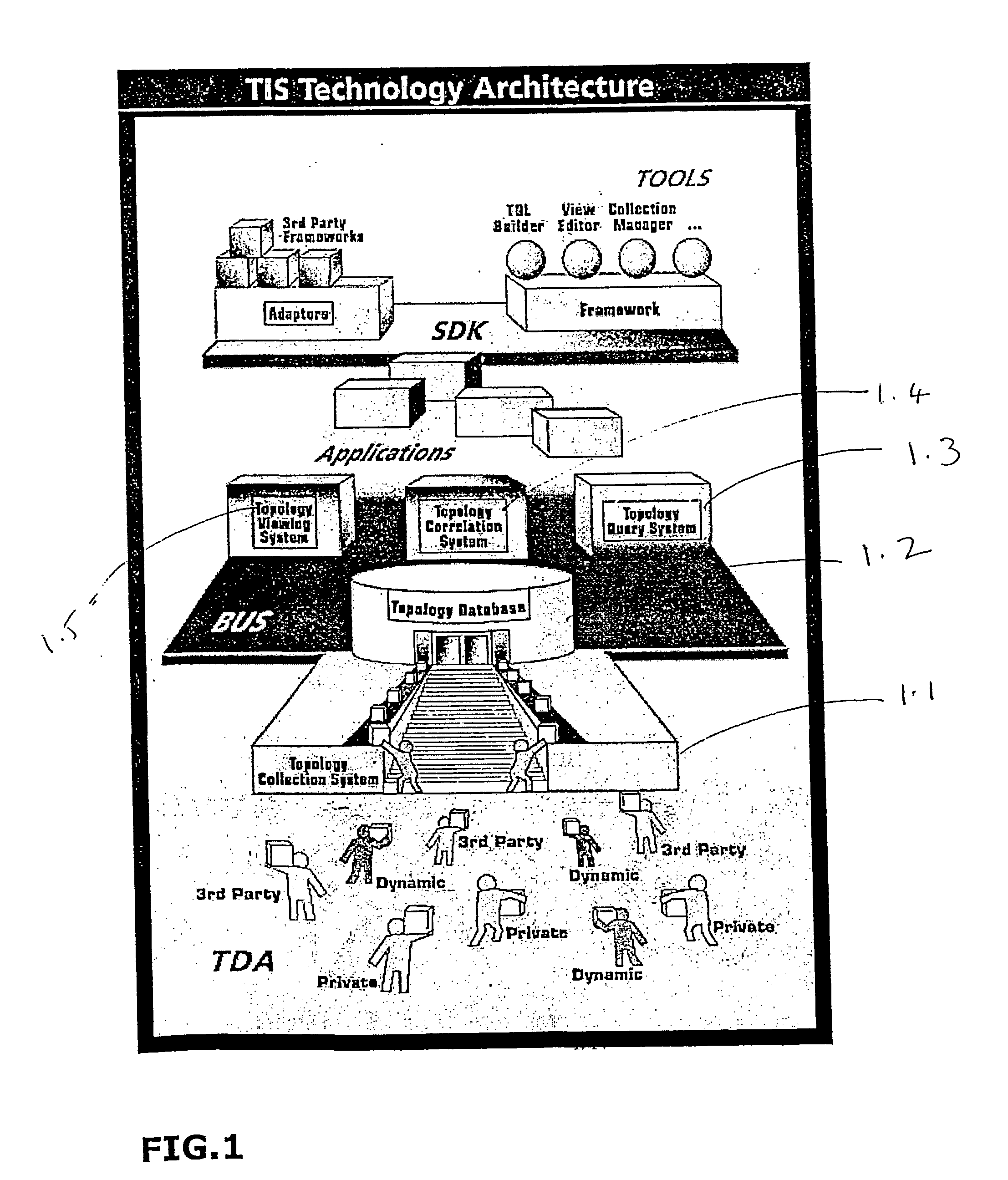
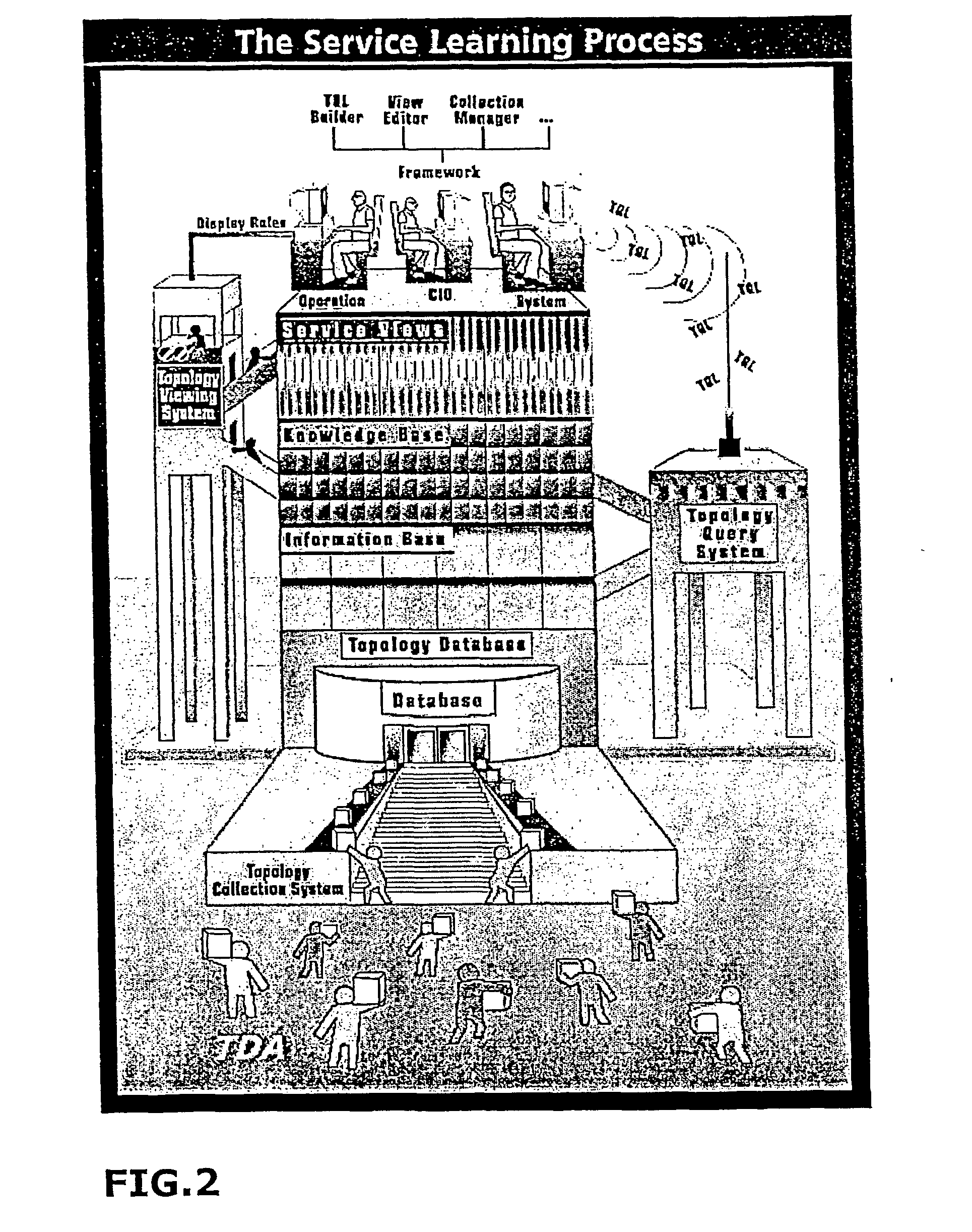
Topology information system for a managed world
ActiveUS20040059812A1Digital computer detailsSpecial data processing applicationsInformation repositoryTopology information
A topology information system, comprising a topology collection sub-system, a topology database, a topology query sub-system and a topology correlation sub-system. The topology collection sub-system includes at least one topology discovery agent. The topology collection sub-system automatically collects topology information from at least one topology layer of at least one managed world. The topology database is adapted to store the topology information collected by the topology collection sub-system. The topology query sub-system is adapted to query the topology information stored in the topology database using a topology pattern query created by a user. The topology correlation sub-system operates in parallel to the topology query sub-system, constantly monitoring the managed world for events and updating the Information Base accordingly.
Owner:MERCURY INTERACTIVE +1
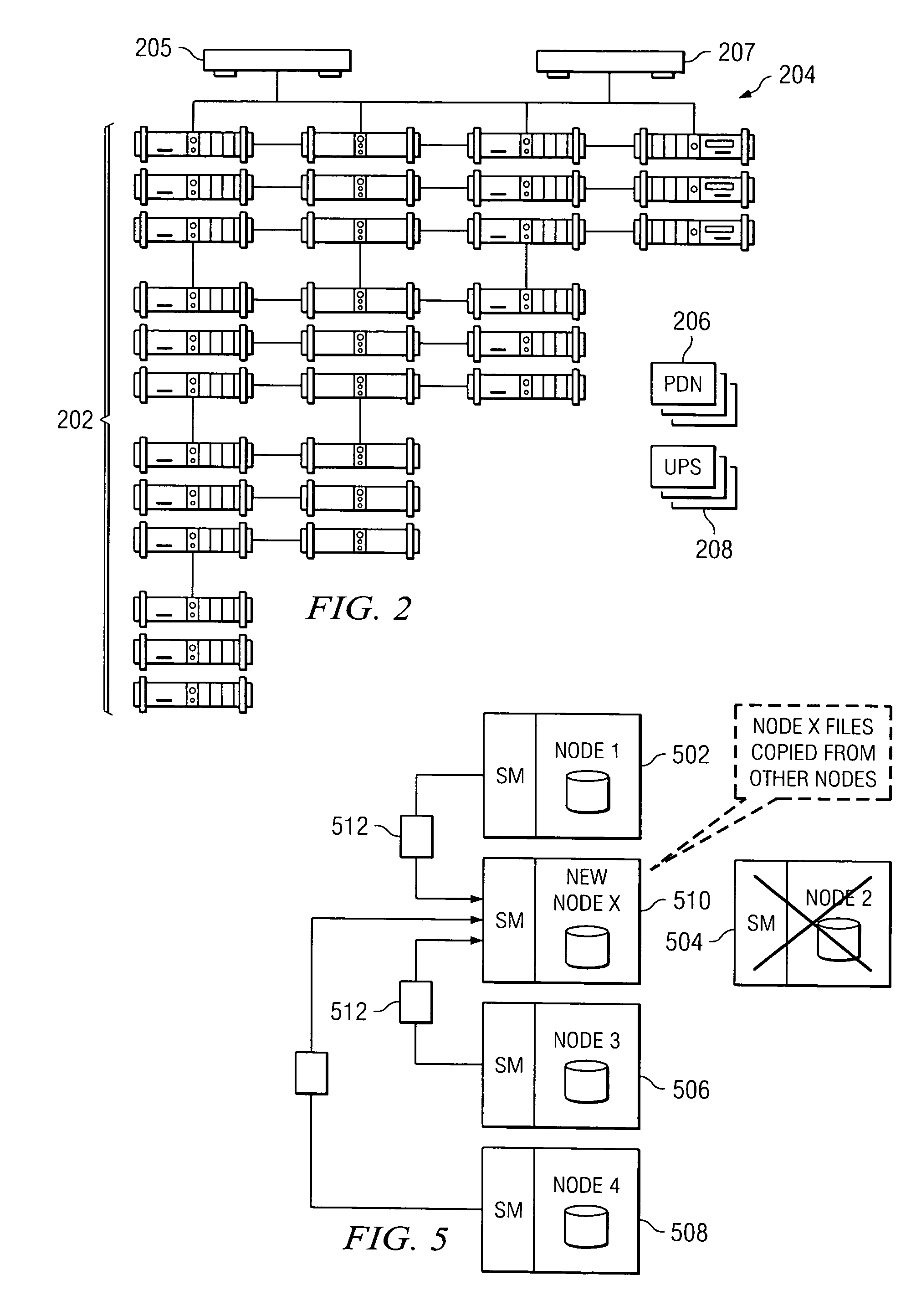
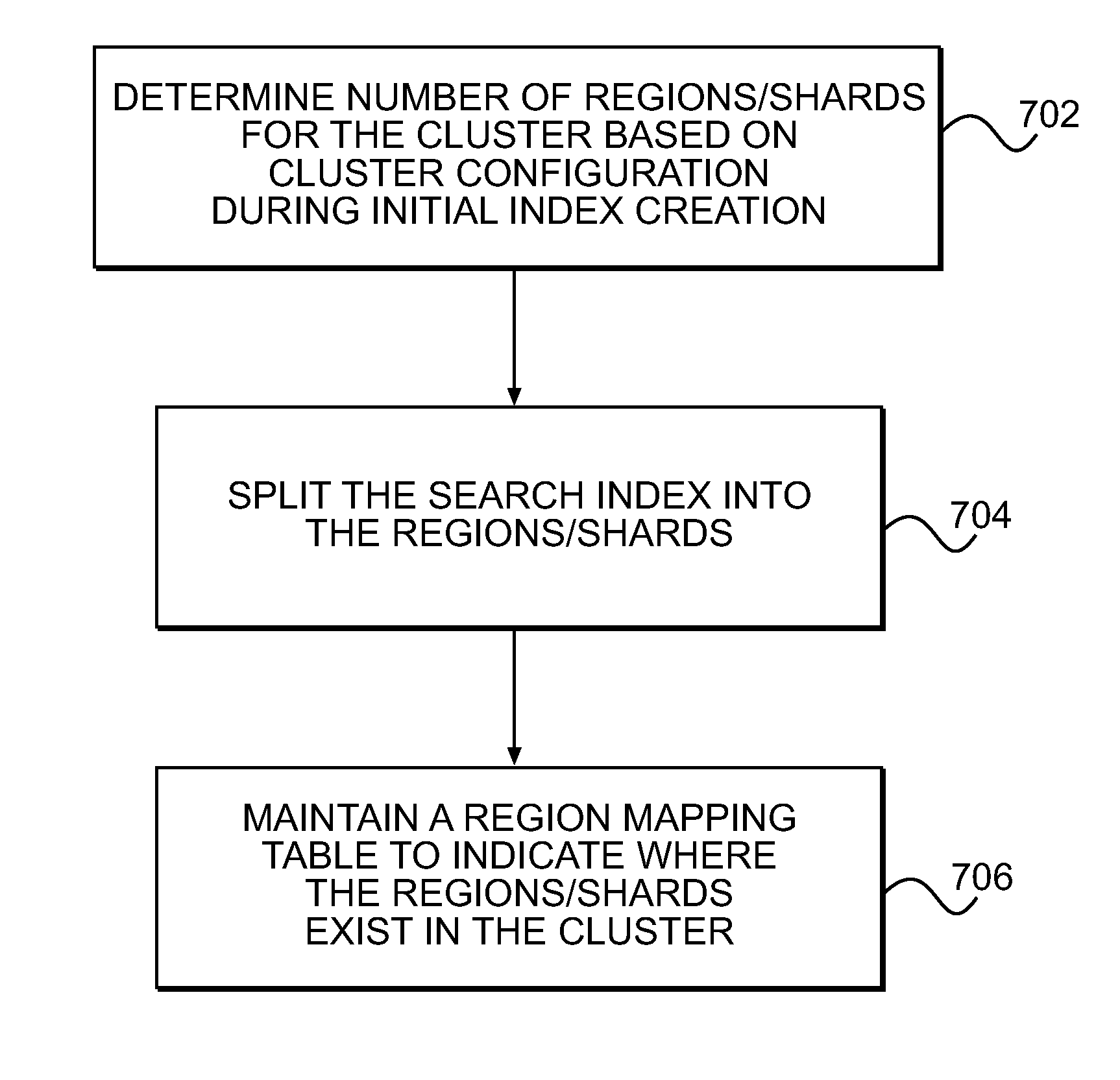
Highly available search index with storage node addition and removal
ActiveUS20140330785A1Facilitate new region distributionAddressing slow performanceDigital data processing detailsTransmissionObject basedTheoretical computer science
A redundant array of independent nodes are networked together. Each node executes an instance of an application that provides object-based storage. The nodes are grouped into systems each having multiple nodes. A search index is provided in each system for locating objects within the system. A method of managing the search index comprises splitting the search index into shards to be divided among a plurality of regions (704). The regions are larger in number than the nodes in the system. Each region has a master and at least one backup copy of one of the shards. A shard core is a master or backup copy of a shard. The method further comprises distributing the shard cores to the nodes, and providing a region mapping table in each node in the system to map the shard cores to the nodes in which the shard cores are stored (706).
Owner:HITACHI VANTARA LLC
Method and System for Managing Entities
InactiveUS20080243885A1Digital data processing detailsDigital computer detailsGroup entityIndex system
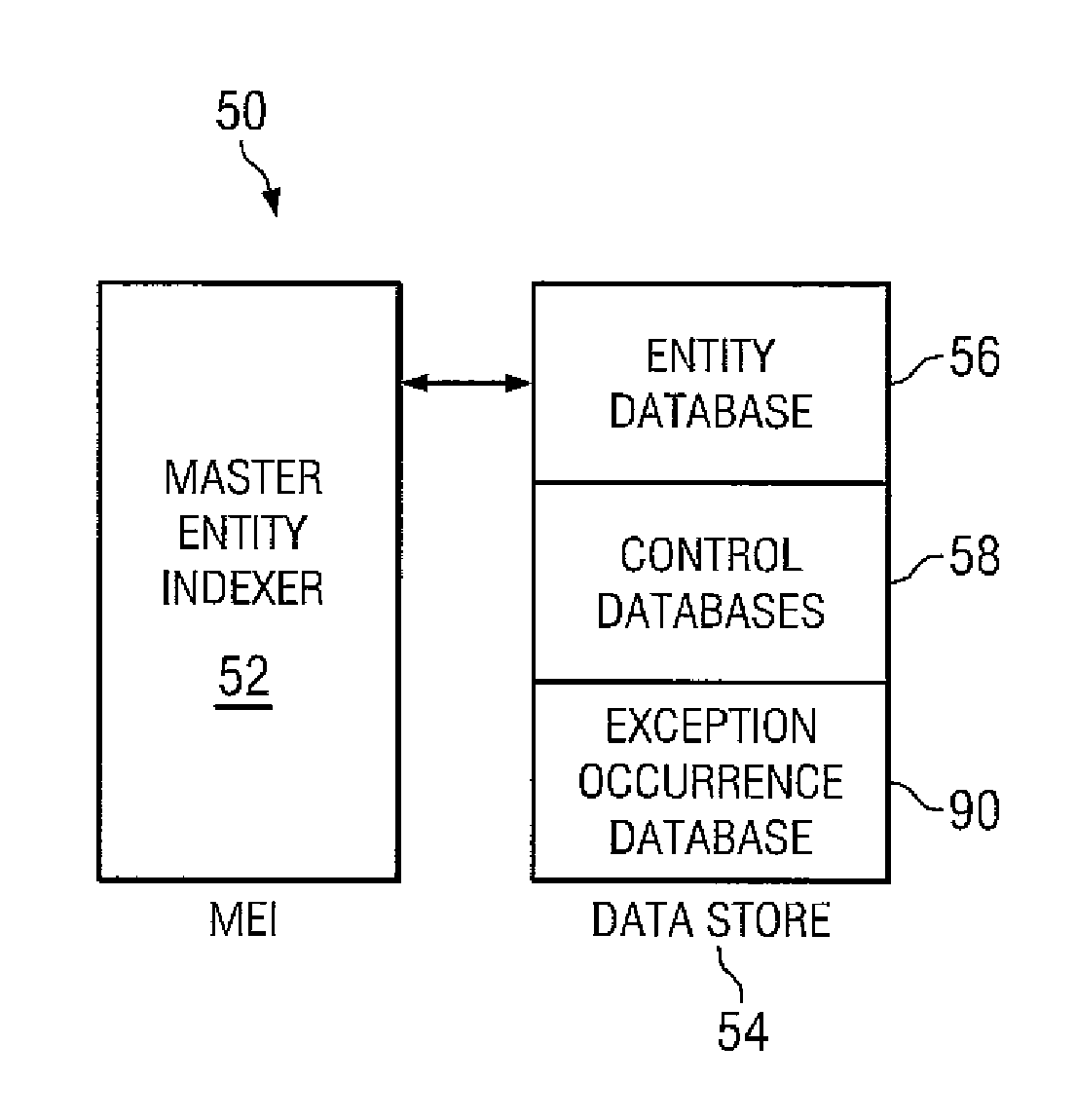
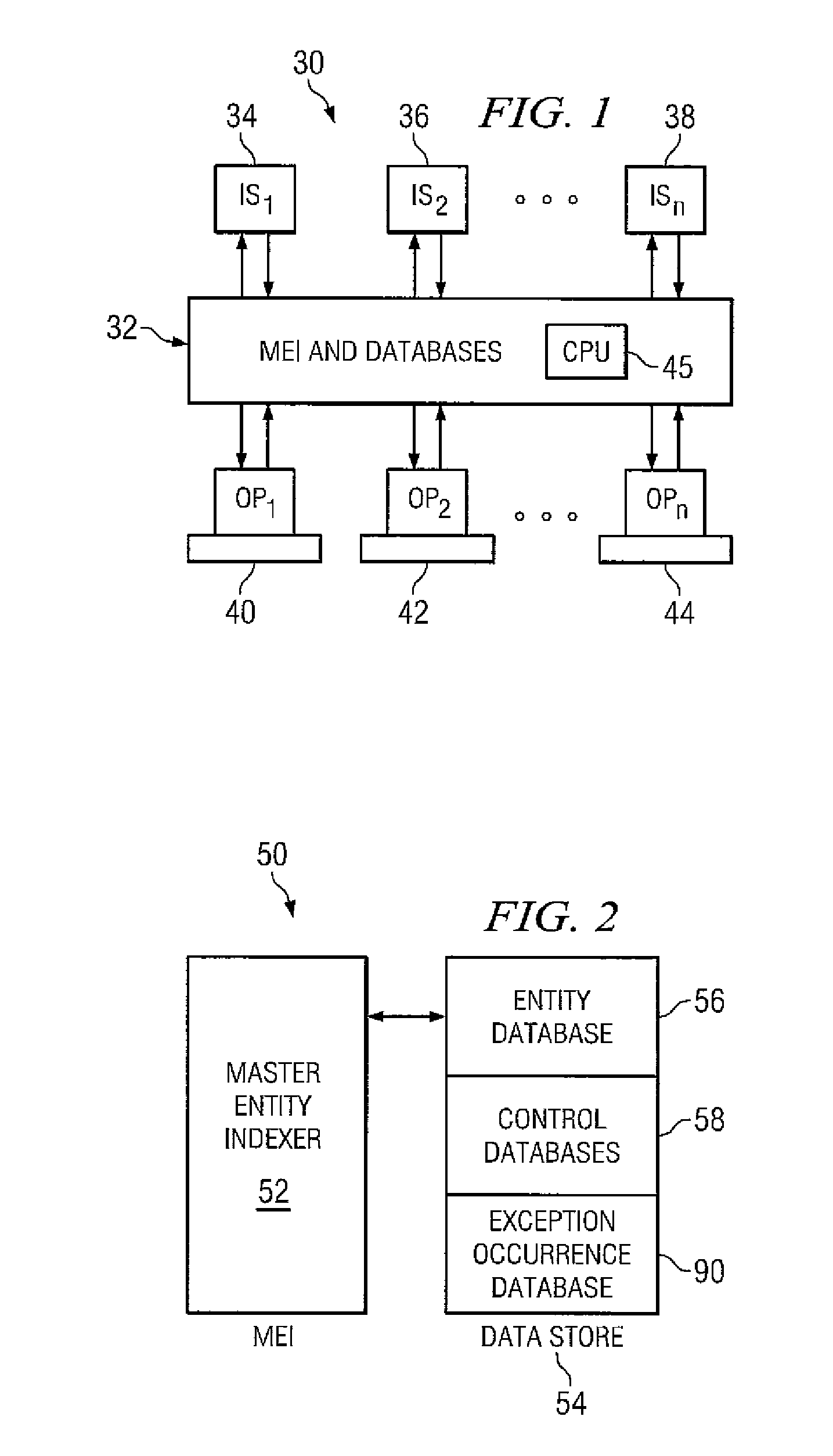
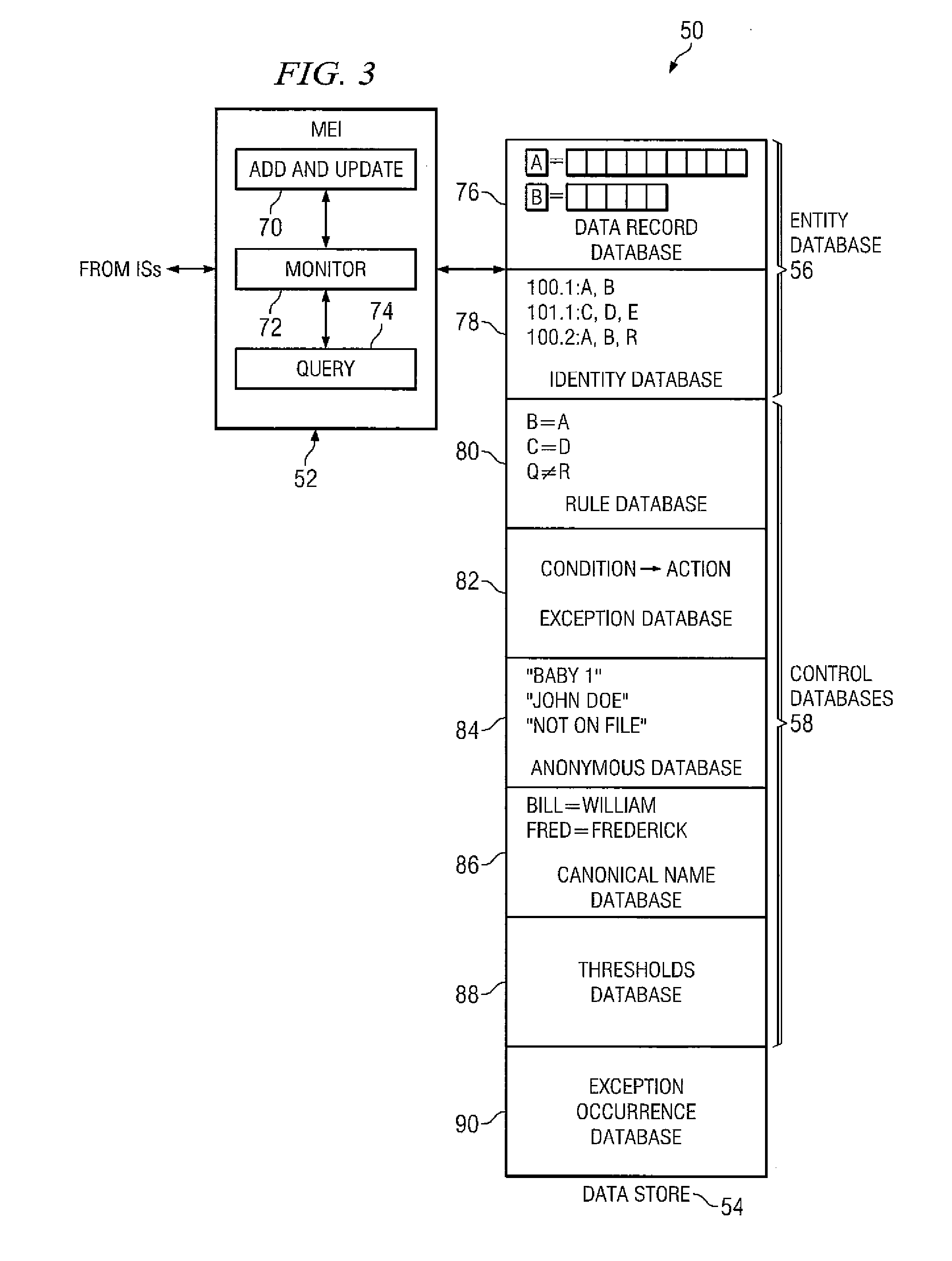
Embodiments of a method for managing entities include candidate selection by a transitive bucketing process where at least one attribute of an initial data record is used to determine a set of candidate data records corresponding to the initial data record. For each candidate data record thus determined, additional candidate data record(s) may be determined using attribute(s) not used in linking the candidate data record to the initial data record. This process may be repeated until no more candidate data records are returned. The initial data record and related candidates thus determined are then resolved into group entities, each having member records that match one another above a certain threshold. If no match is found, a group entity comprising a single data record may be created. These group entities are then reconciled with other entities in a master entity index system.
Owner:AIRBNB
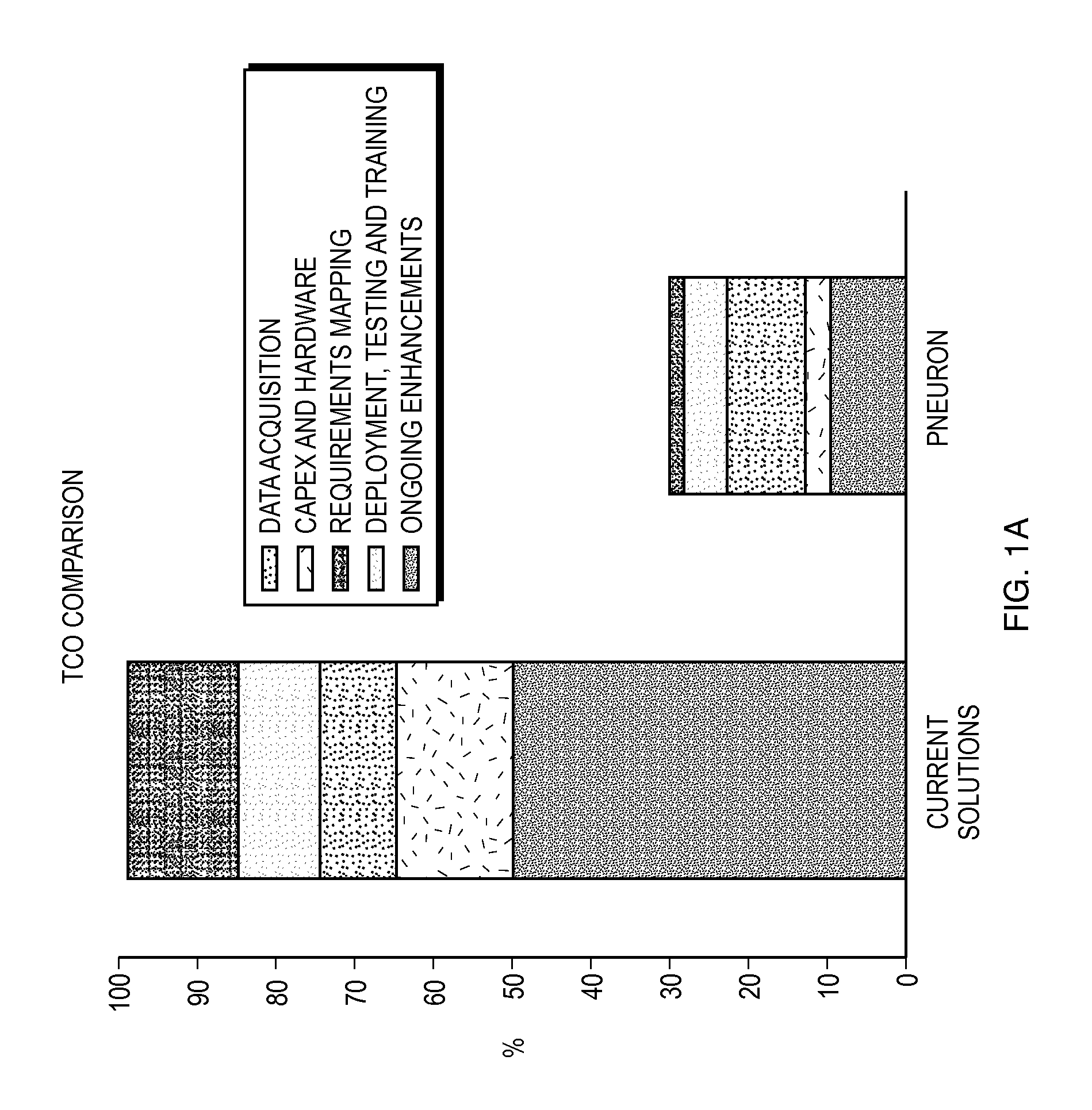
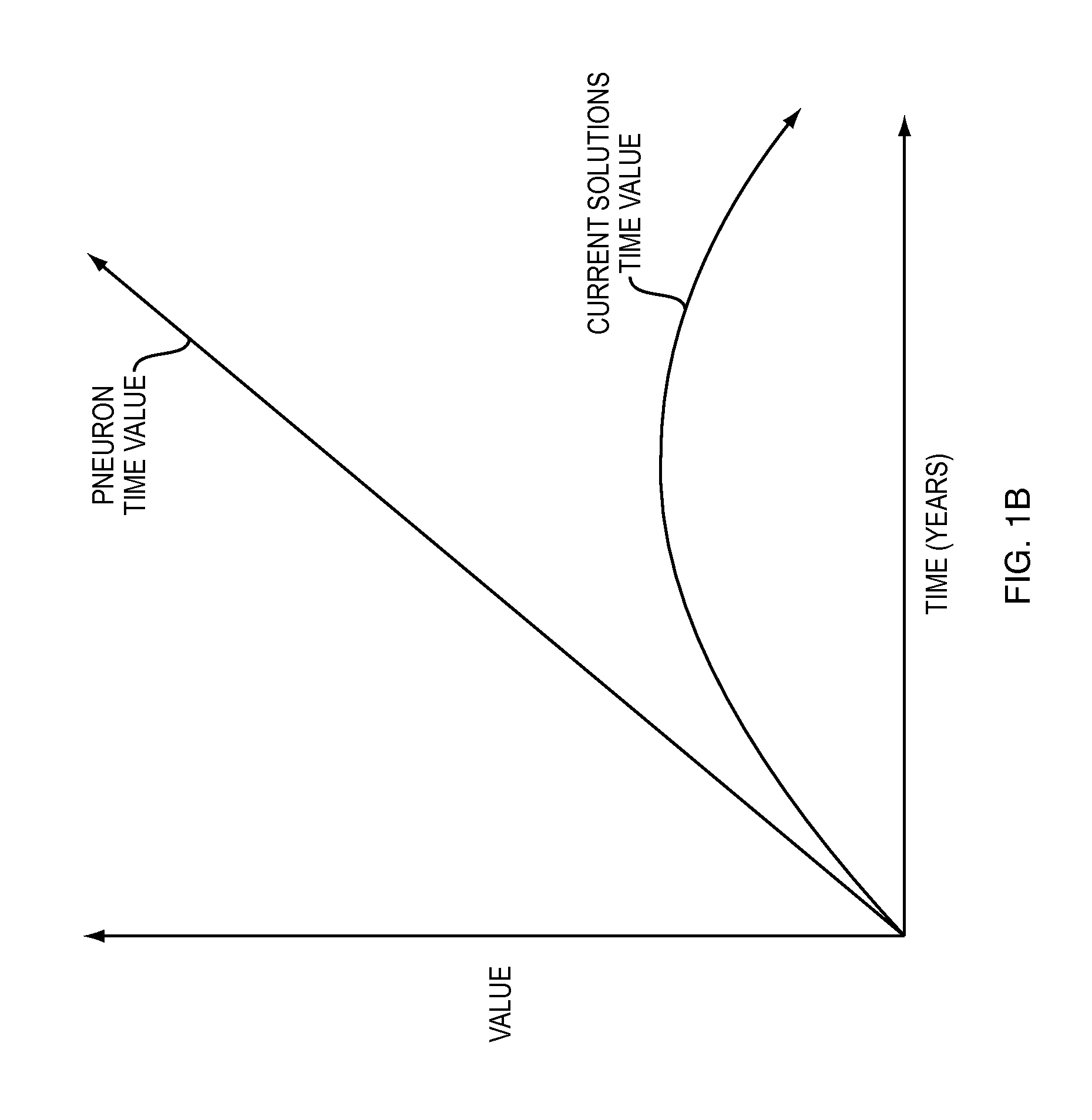
Pneuron distributed analytics
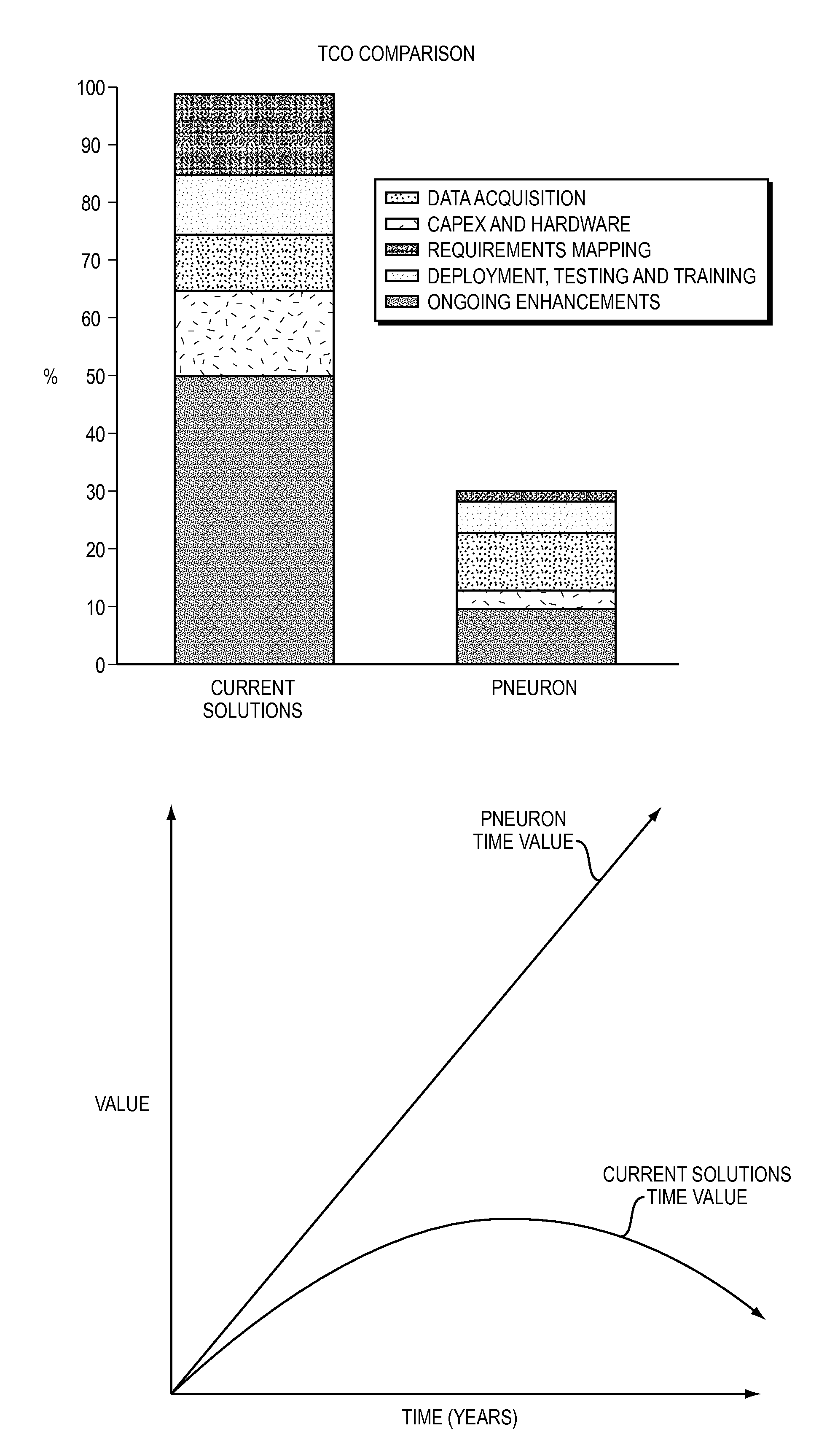
A method and system for the integration of disparate data stored within an Information Technology infrastructure of a company is provided. The system and method enables holistic, real time control of data discovery, retrieval and analysis. The system combines data mining, retrieval and analytics at the source of the data, thereby solving traditional problems with disparate and distributed data, systems, business processes and analytics across an organization. The system enables a user to configure and target data, then apply rules, workflows and analytics from one central source. This process is accomplished by distributing functions in the form of software pneurons against the existing infrastructure for maximum processing while preserving a robust and extendable suite of definitions. The system uses the existing application, network and hardware assets and enables connection to the native data, maps only the data fields that need to be mapped to carry out the desired analysis, runs the analysis and then returns the data to a central location to be assembled, analyzed, organized and / or reported.
Owner:UST GLOBAL (SINGAPORE) PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com