Patents
Literature
703 results about "Middle tier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
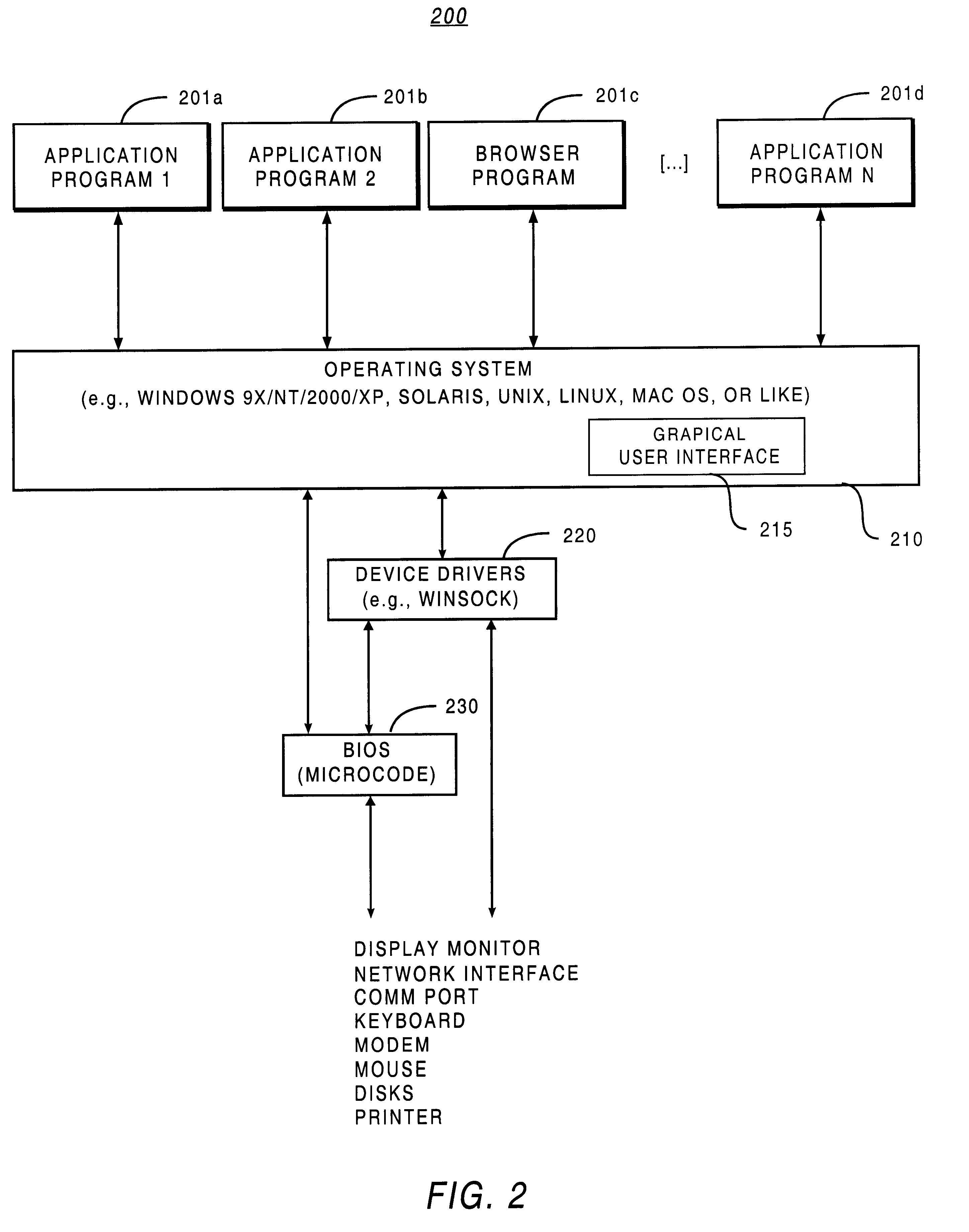
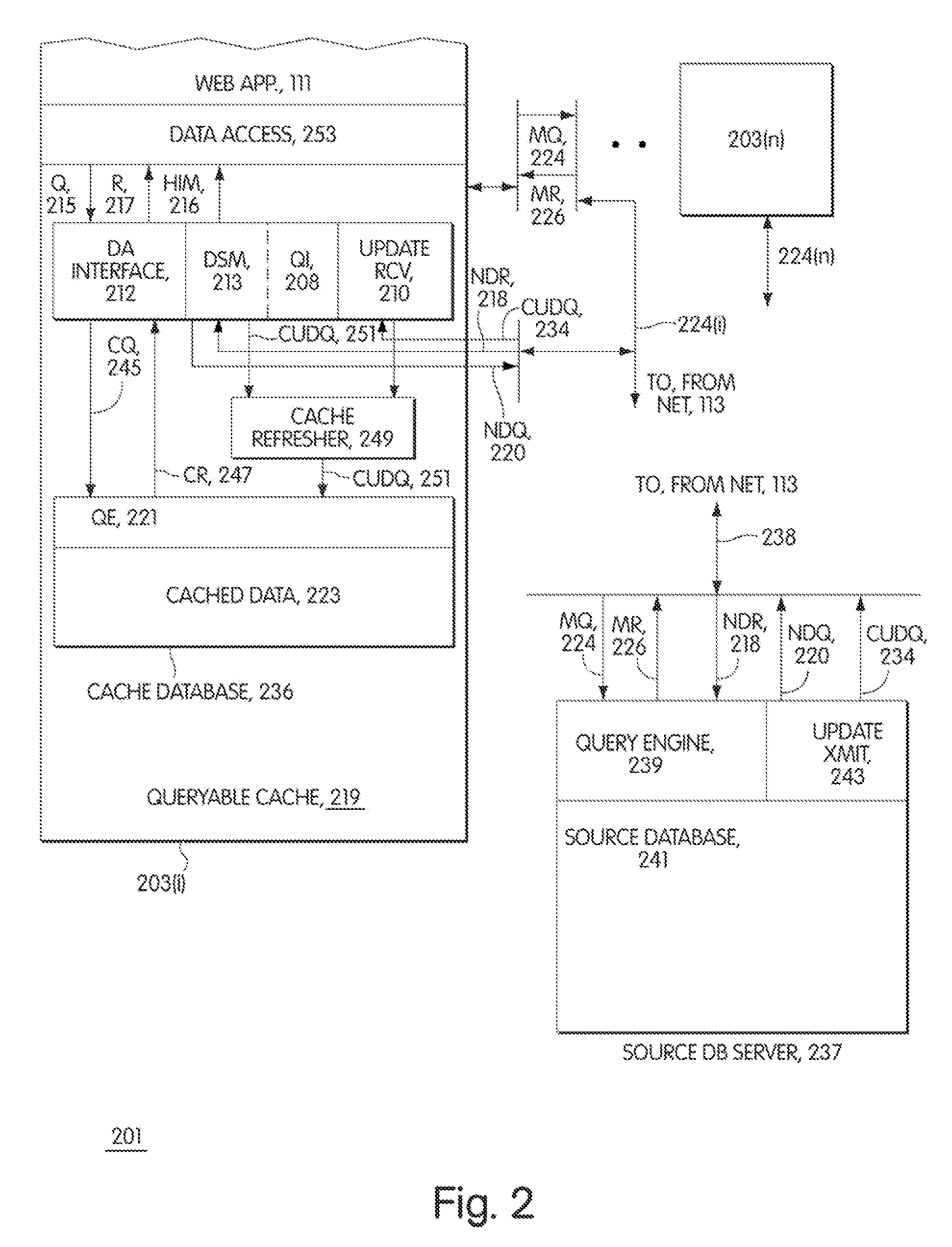
Definition of: middle tier (1) Generally refers to the processing that takes place in an application server that sits between the user's machine and the database server. The middle tier server performs the business logic. See application server and client/server. (2) A level or step between two others. May refer to an infinite variety of situations.
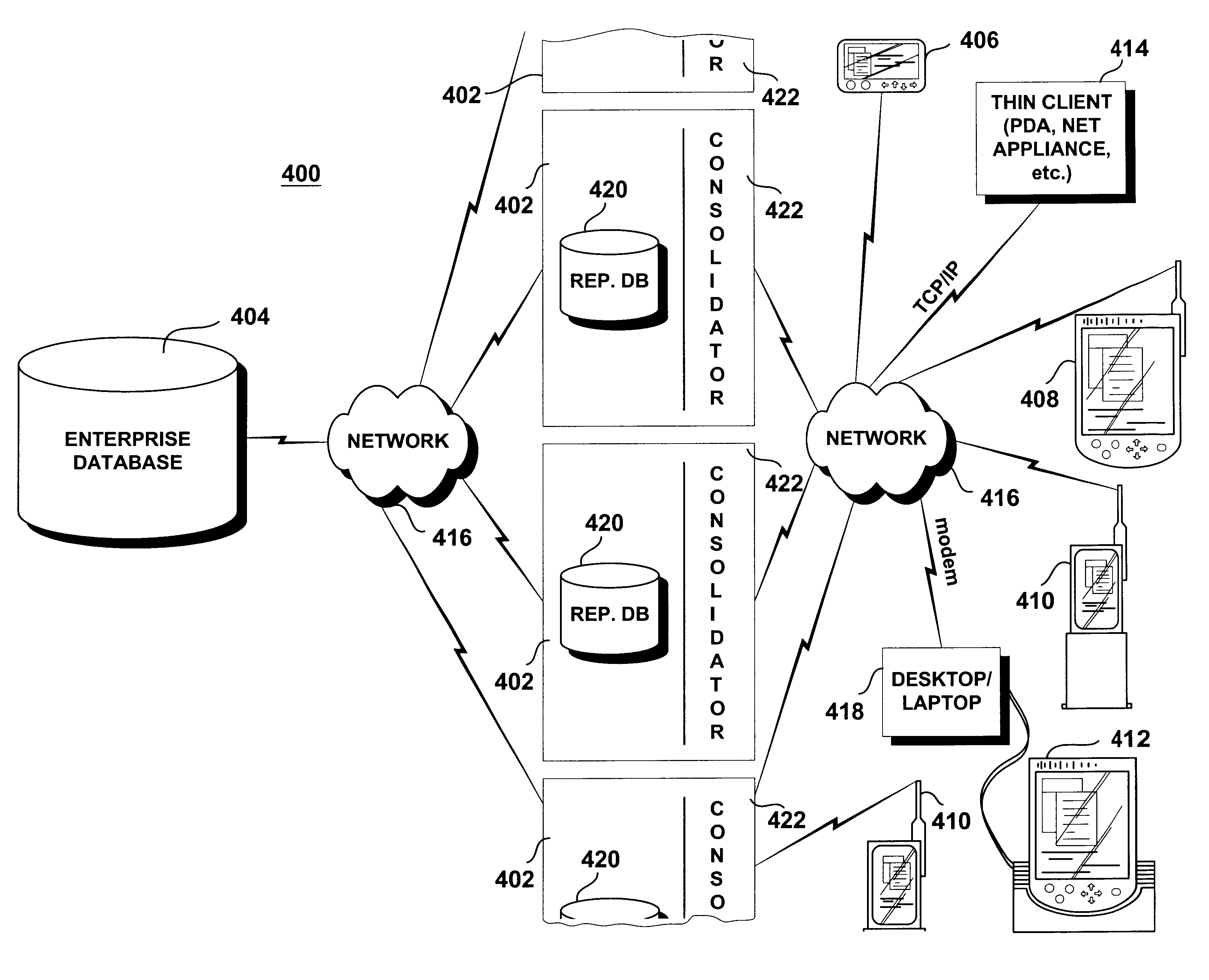
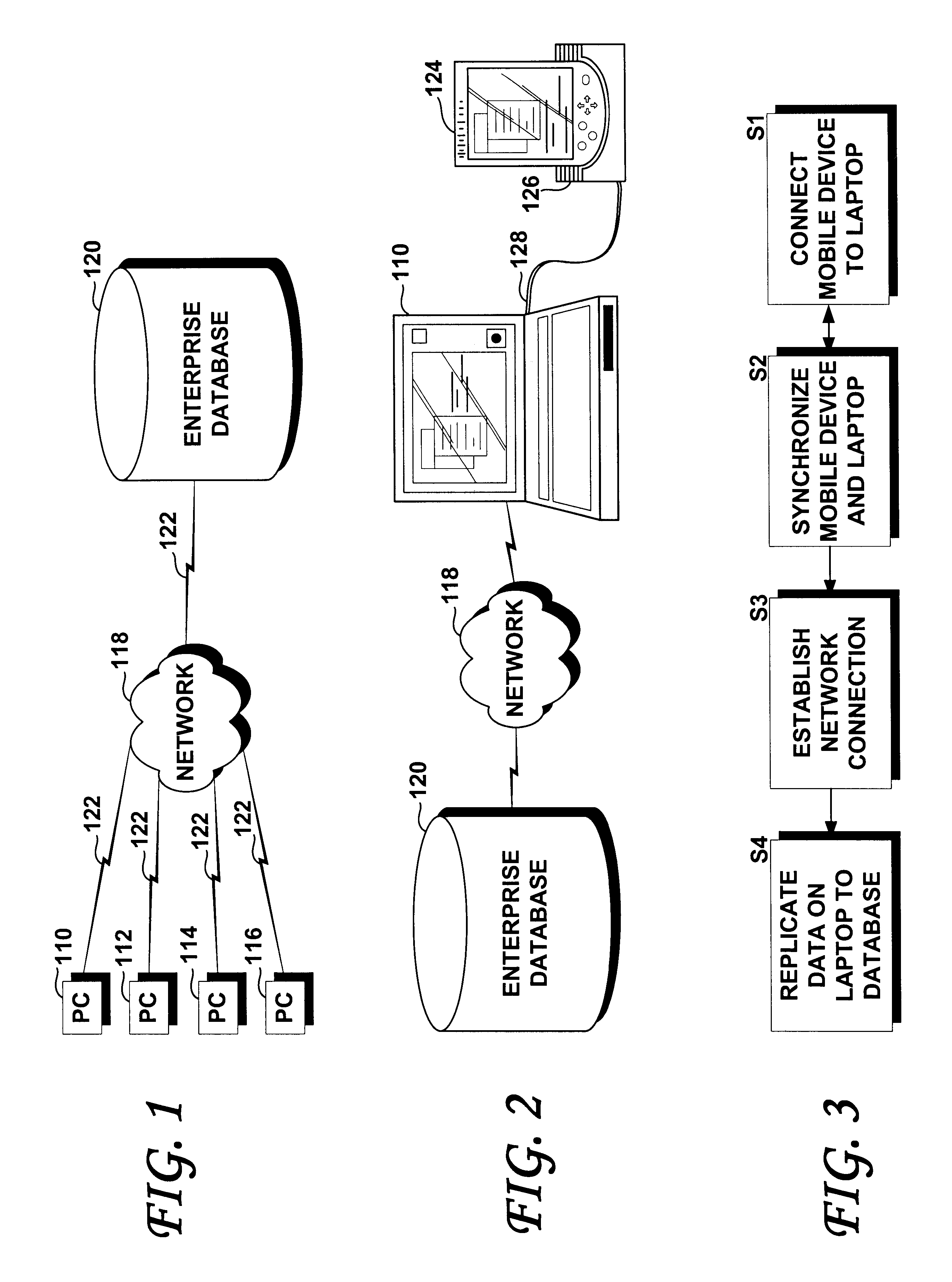
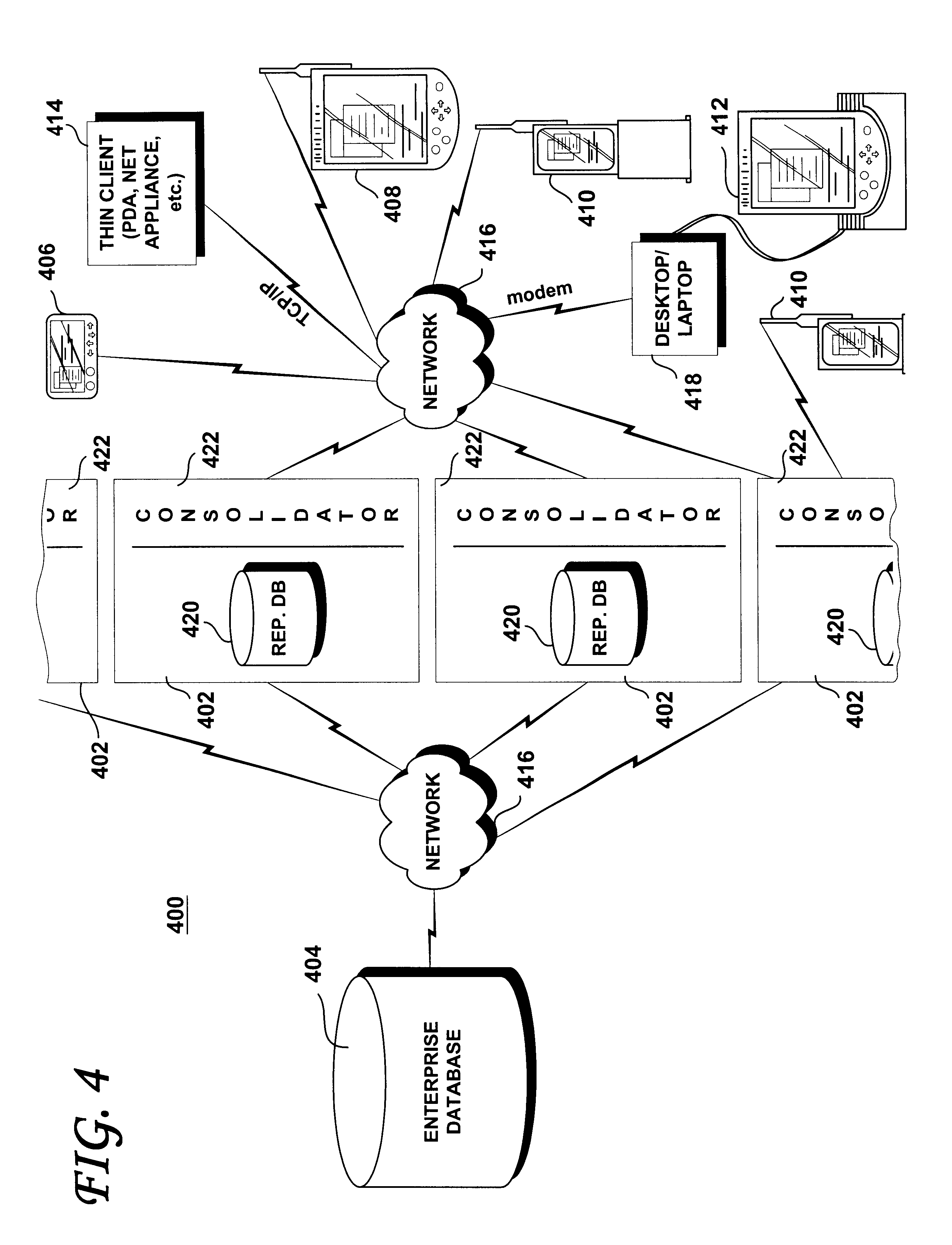
Methods and systems for synchronization of mobile devices with a remote database
InactiveUS6636873B1Data processing applicationsDigital data information retrievalComputerized systemClient-side
A computer system for synchronizing a mobile device with a remote enterprise database includes a replication database. The replication database is mapped to and maintained as a subset image of the remote enterprise database through a bi-directional replication process. A mobile device gateway server is coupled to the replication database. The mobile device gateway includes a concentrator, which is configured to selectively receive replication data from the replication database, transform the received replication data into a format native to the mobile device and to selectively send the received and transformed replication data to the mobile device. The concentrator is also configured to receive mobile device data, transform and to send the received mobile device data to the replication database. The mobile device gateway server acts as a middle tier between one or more enterprise databases and one or more mobile devices or any network-enabled thin client.
Owner:ORACLE INT CORP
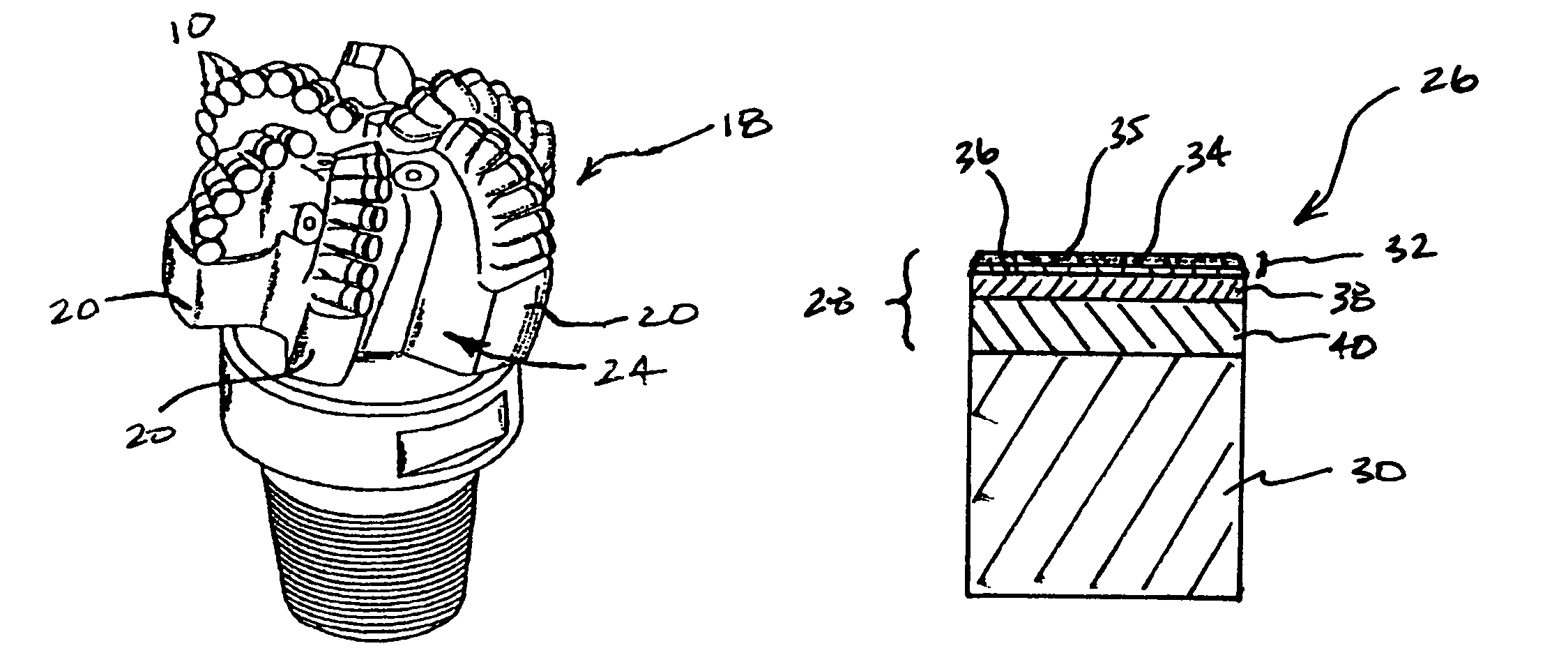
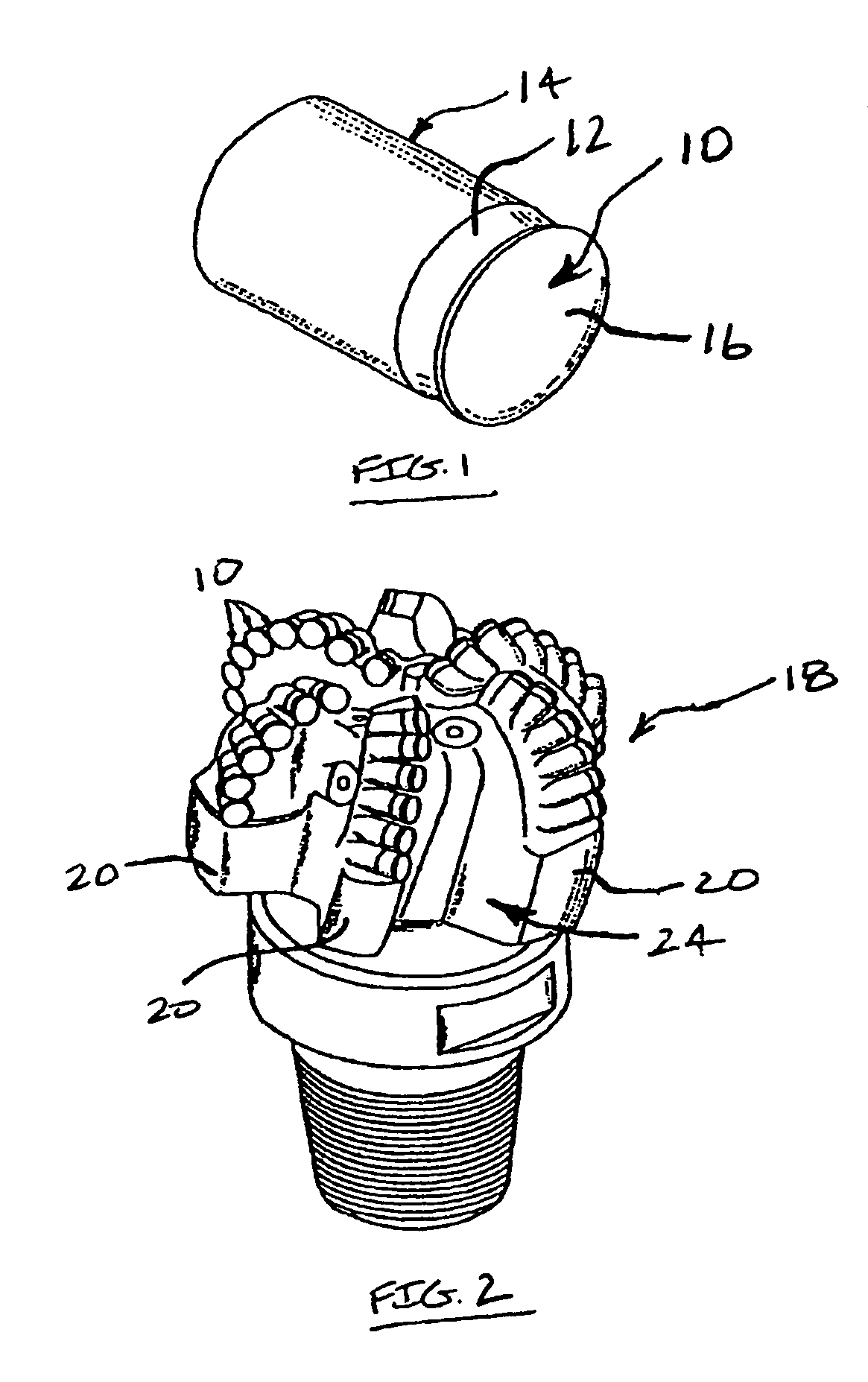
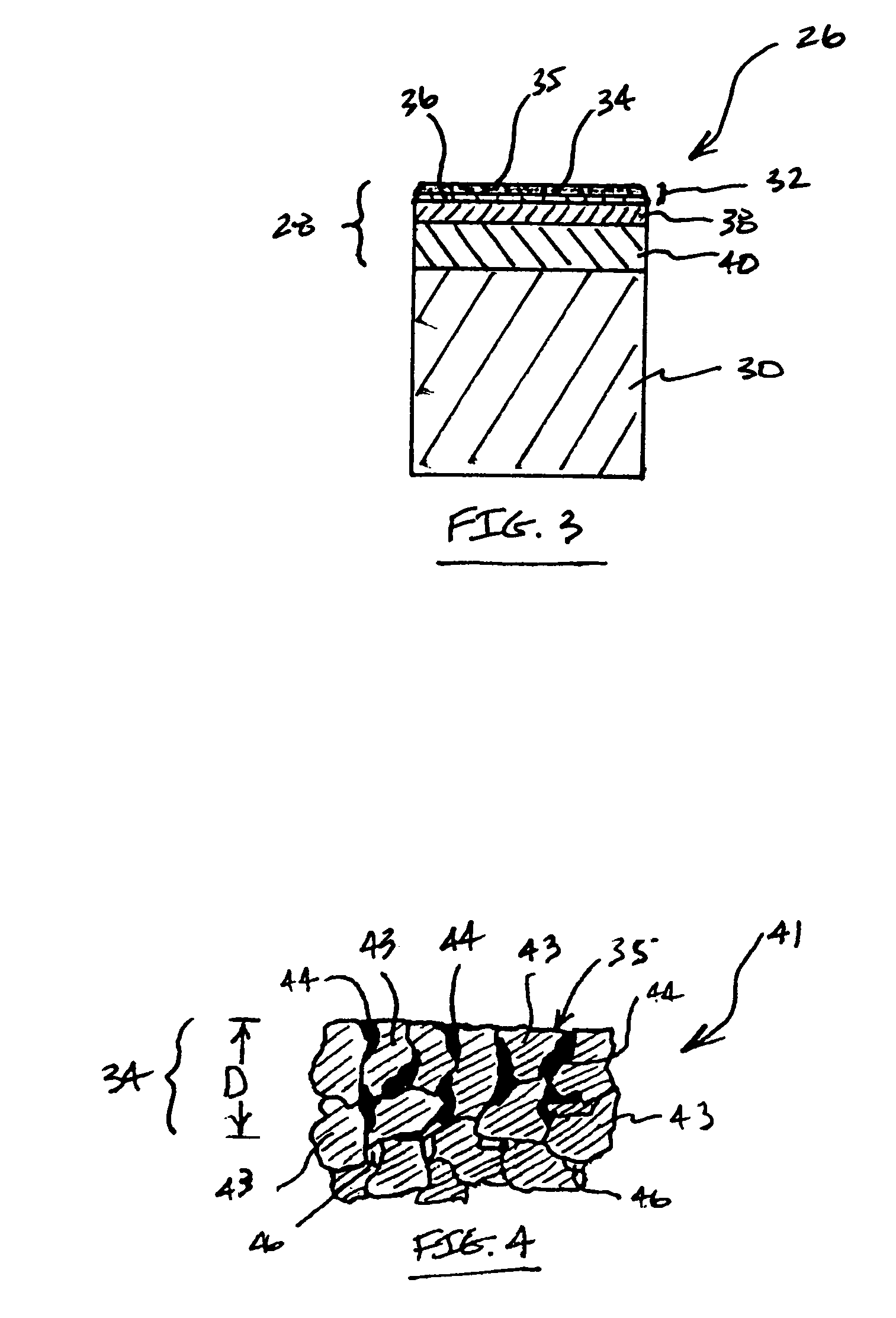
Cutting elements formed from ultra hard materials having an enhanced construction
InactiveUS7350601B2Eliminate or resist any cracking during useDifferential wear resistanceDrill bitsConstructionsSuperhard materialWear resistance
Cutting elements of this invention include an ultra hard body joined with a metallic substrate. The body includes an uppermost layer comprising a plurality of bonded ultra hard crystals and interstitial regions, and that defines a body working surface. The uppermost layer includes an outer region that is relatively more thermally stable than a remaining portion of the uppermost layer. The body further includes an intermediate layer joined to the uppermost layer, comprising a plurality of bonded ultra hard crystals, and having a wear resistance less than that of the uppermost layer remaining region. The body may additionally include a lowermost PCD layer that is interposed between and attached to the intermediate layer and the substrate.
Owner:SMITH INT INC
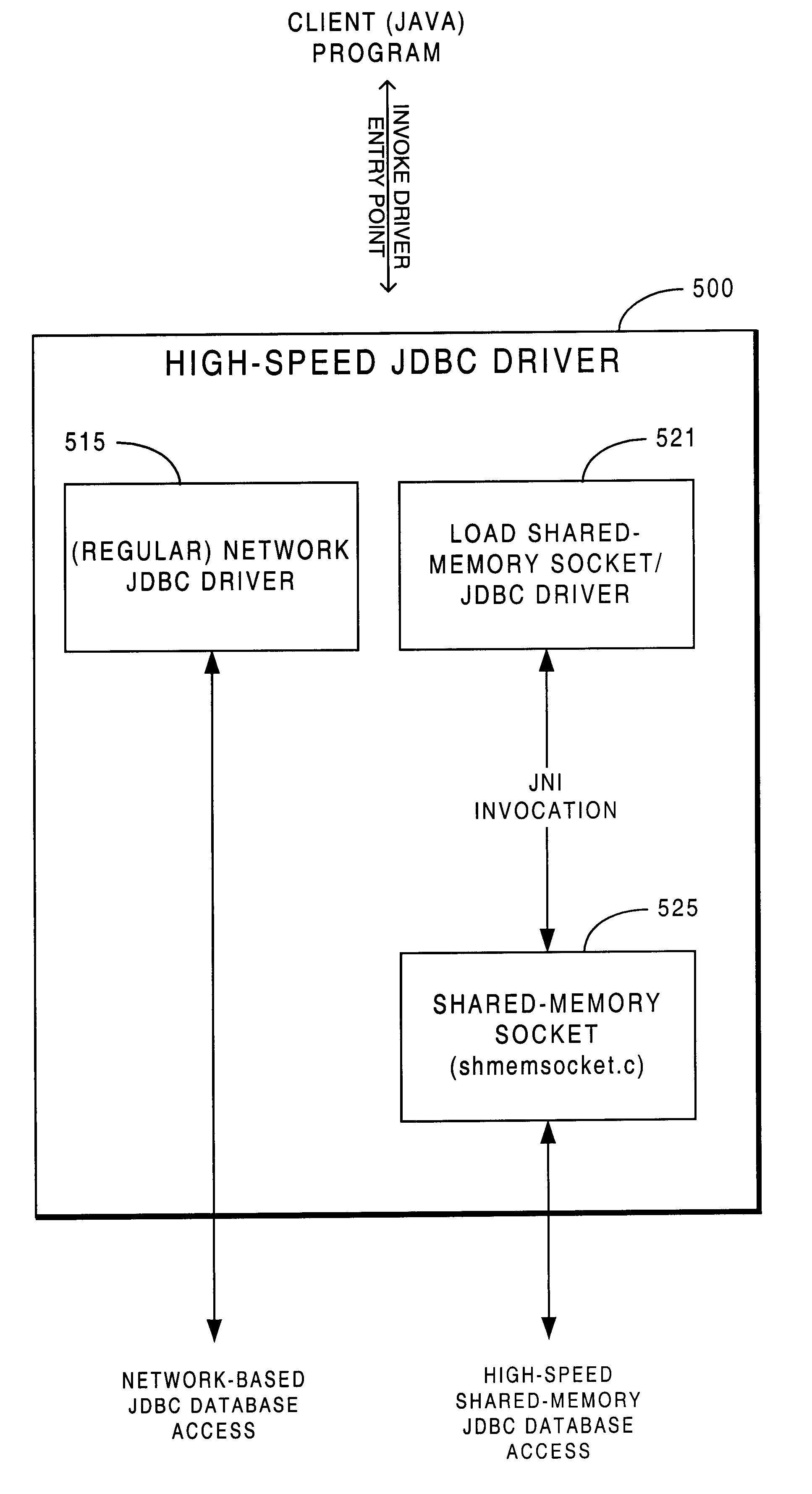
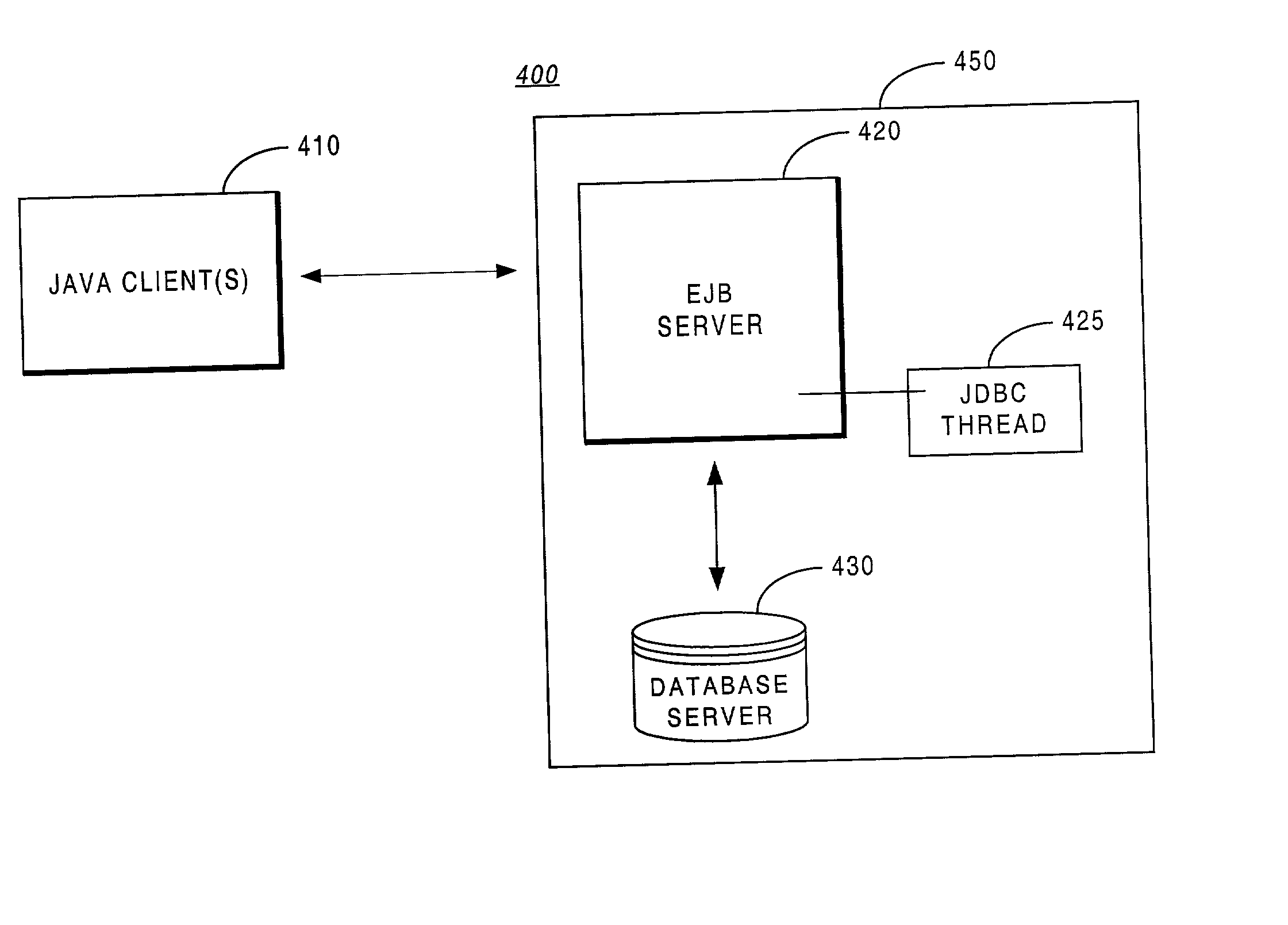
Methodology providing high-speed shared memory access between database middle tier and database server
InactiveUS6687702B2Data processing applicationsInterprogram communicationApplication serverDatabase server
A multi-tier database system is modified such that a middle-tier application server (EJB server) and a database server run on the same host computer and communicate via shared-memory interprocess communication. The system includes a database (e.g., JDBC) driver thread that attaches to the database server, specifically by attaching to the database server's shared memory segment. Operation of the JDBC driver is modified to provide direct access between the middle tier (i.e., EJB server) and the database server, when the two are operating on the same host computer.
Owner:SYBASE INC
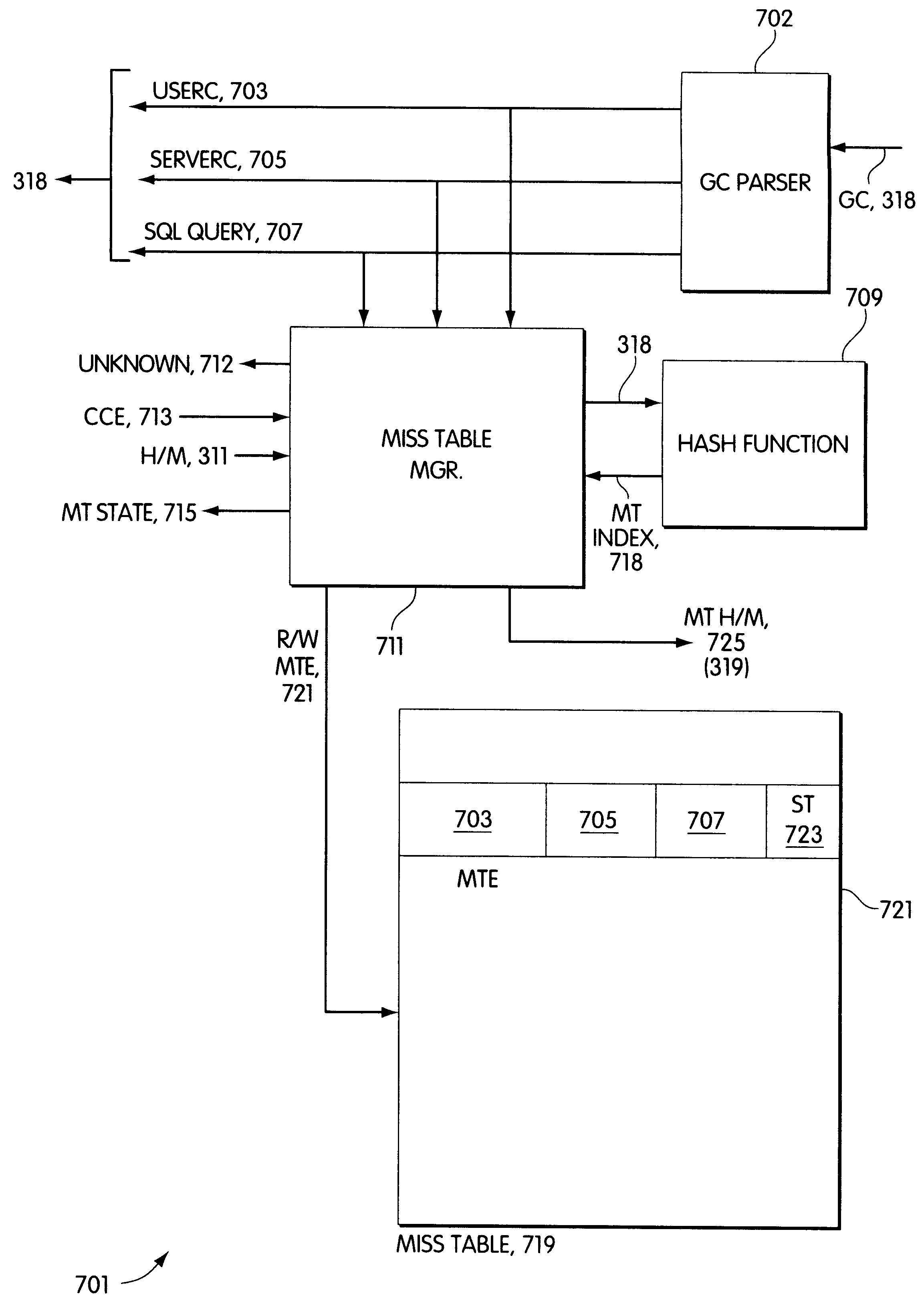
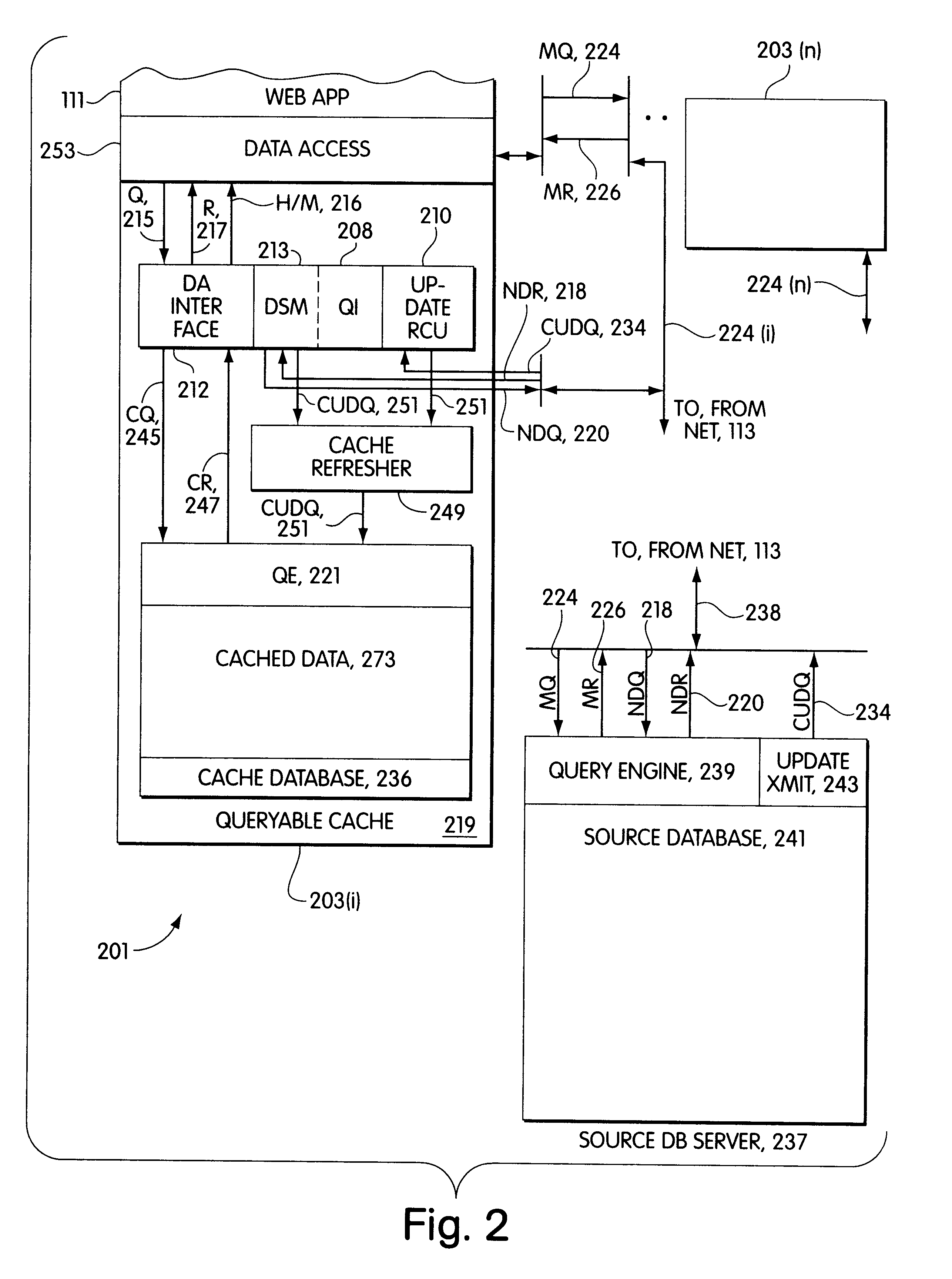
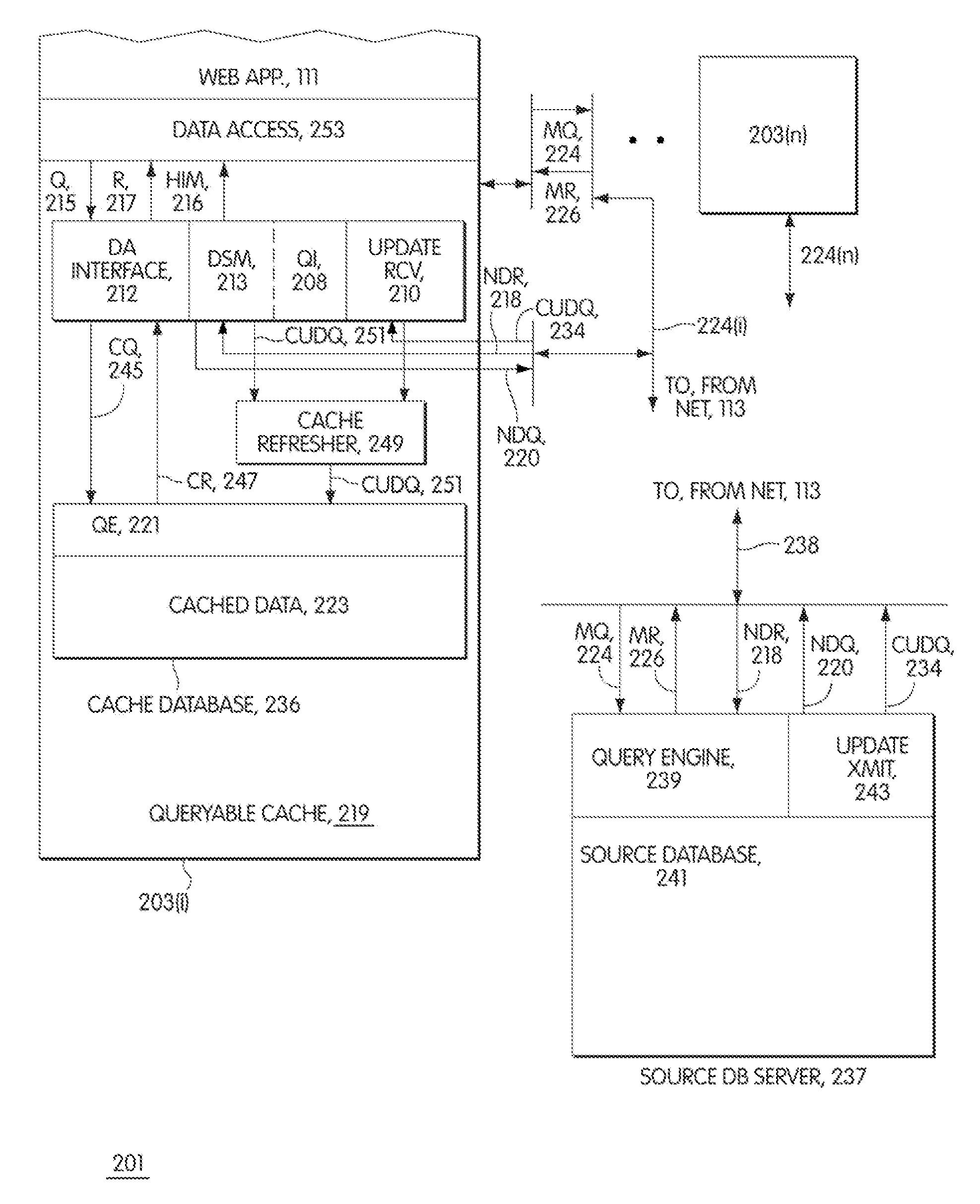
Dynamic caches with miss tables
InactiveUS6487641B1Digital data information retrievalMemory adressing/allocation/relocationWeb serviceData source
A middle-tier Web server with a queryable cache that contains items from one or more data sources. Items are included in the cache on the basis of the probability of future hits on the items. When the data source determines that an item that has been included in the cache has changed, it sends an update message to the server, which updates the item if it is still included in the cache. In a preferred embodiment, the data source is a database system and triggers in the database system are used to generate update messages. In a preferred embodiment, the data access layer determines whether a data item required by an application program is in the cache. If it is, the data access layer obtains the item from the cache; otherwise, it obtains the item from the data source. The queryable cache includes a miss table that accelerates the determination of whether a data item is in the cache. The miss table is made up of miss table entries that relate the status of a data item to the query used to access the data item. There are three statuses: miss, indicating that the item is not in the cache, hit, indicating that it is, and unknown, indicating that it is not known whether the item is in the cache. When an item is referenced, the query used to access it is presented to the table. If the entry for the query has the status miss, the data access layer obtains the item from the data source instead of attempting to obtain it from the cache. If the entry has the status unknown, the data access layer attempts to obtain it from the cache and the miss table entry for the item is updated in accordance with the result. When a copy of an item is added to the cache, miss table entries with the status miss are set to indicate unknown.
Owner:ORACLE INT CORP
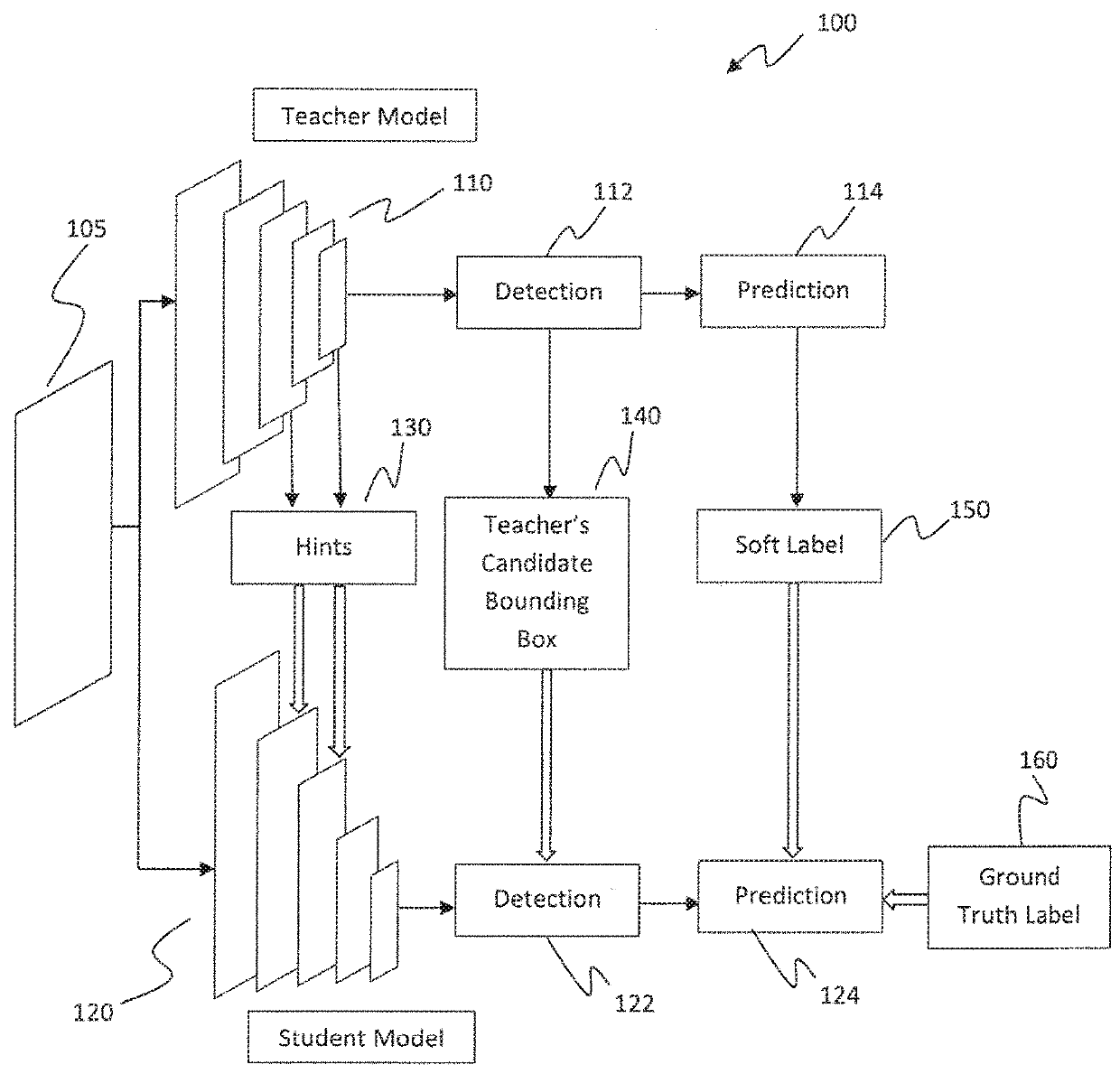
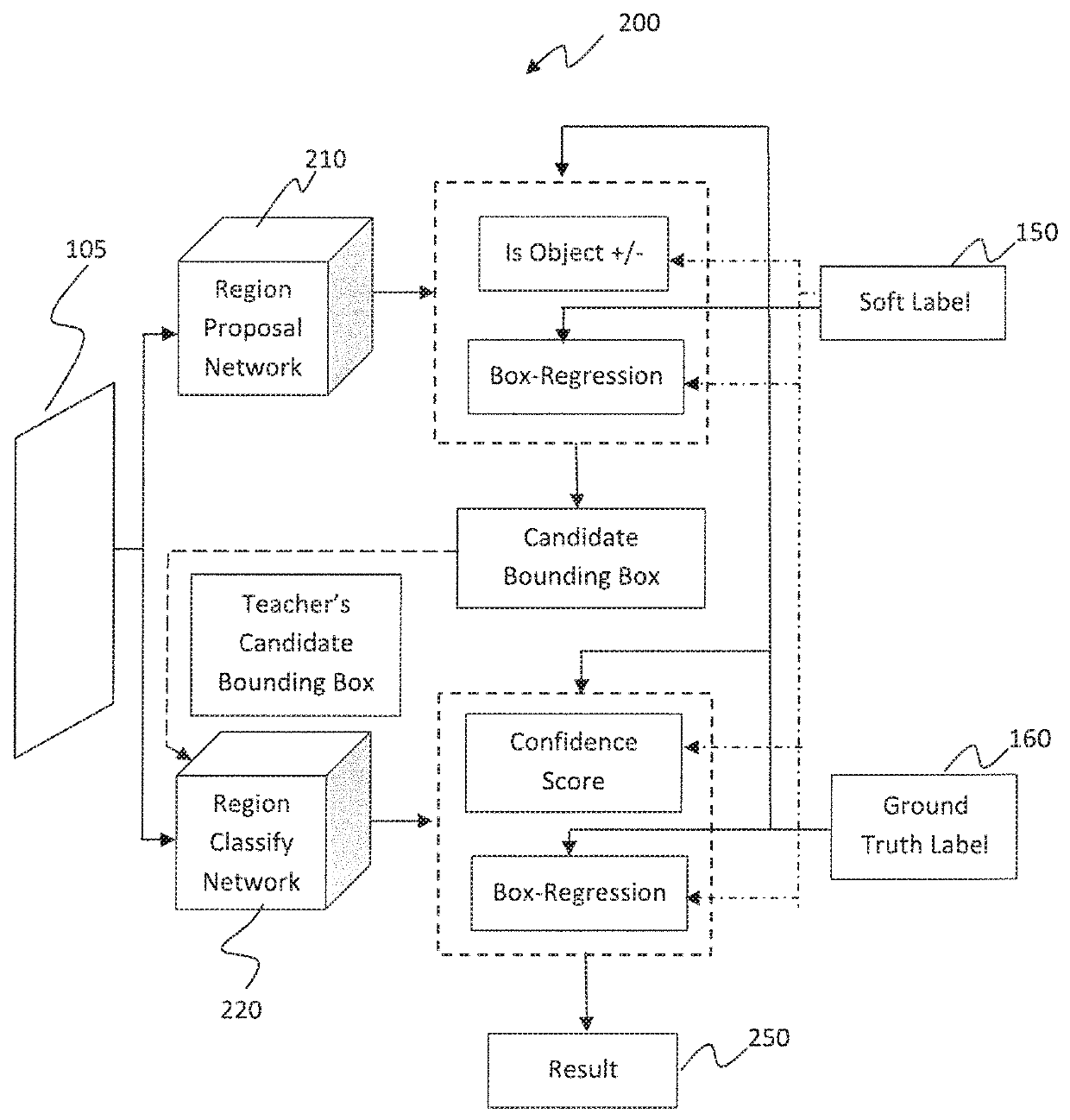
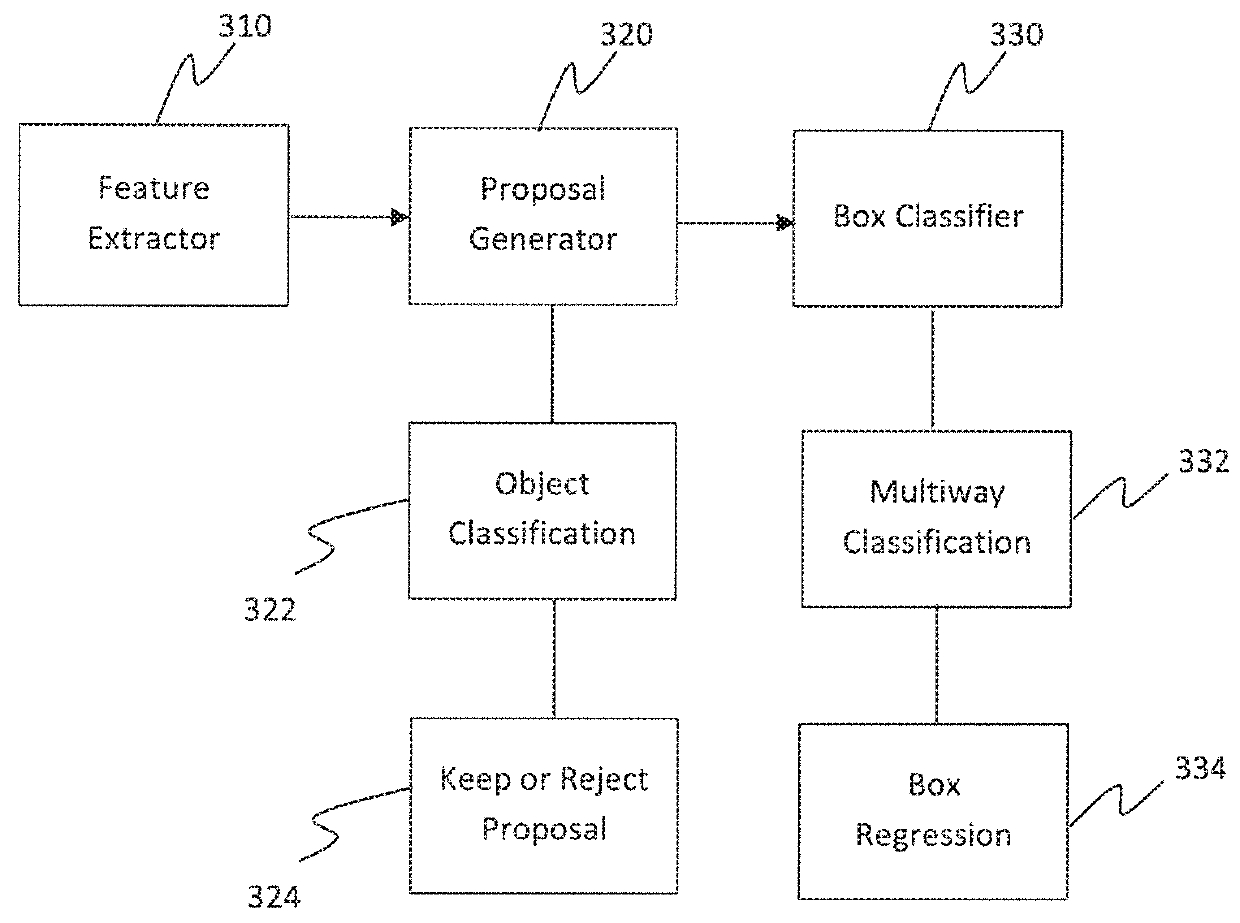
Learning efficient object detection models with knowledge distillation
InactiveUS20180268292A1Character and pattern recognitionNeural learning methodsObject ClassDistillation
A computer-implemented method executed by at least one processor for training fast models for real-time object detection with knowledge transfer is presented. The method includes employing a Faster Region-based Convolutional Neural Network (R-CNN) as an objection detection framework for performing the real-time object detection, inputting a plurality of images into the Faster R-CNN, and training the Faster R-CNN by learning a student model from a teacher model by employing a weighted cross-entropy loss layer for classification accounting for an imbalance between background classes and object classes, employing a boundary loss layer to enable transfer of knowledge of bounding box regression from the teacher model to the student model, and employing a confidence-weighted binary activation loss layer to train intermediate layers of the student model to achieve similar distribution of neurons as achieved by the teacher model.
Owner:NEC LAB AMERICA
Method and system for pushing data to a plurality of devices in an on-demand service environment
ActiveUS20080010243A1Reduce workloadEfficient and transparent transferDatabase distribution/replicationSpecial data processing applicationsUser deviceData shipping
Mechanisms and methods for pushing data to a plurality of devices of a plurality of organizations are provided. Queries are handled in bulk for a group of users of an organization or the entire organization, and limited results are sent to a middle tier server between the database system and the user devices. These mechanisms and methods for pushing data to a plurality of devices enable an efficient and transparent transfer of data to user devices. This efficient and transparent transfer of data can enable mobile devices of many organizations to seamlessly have the data that is required to perform business.
Owner:SALESFORCE COM INC
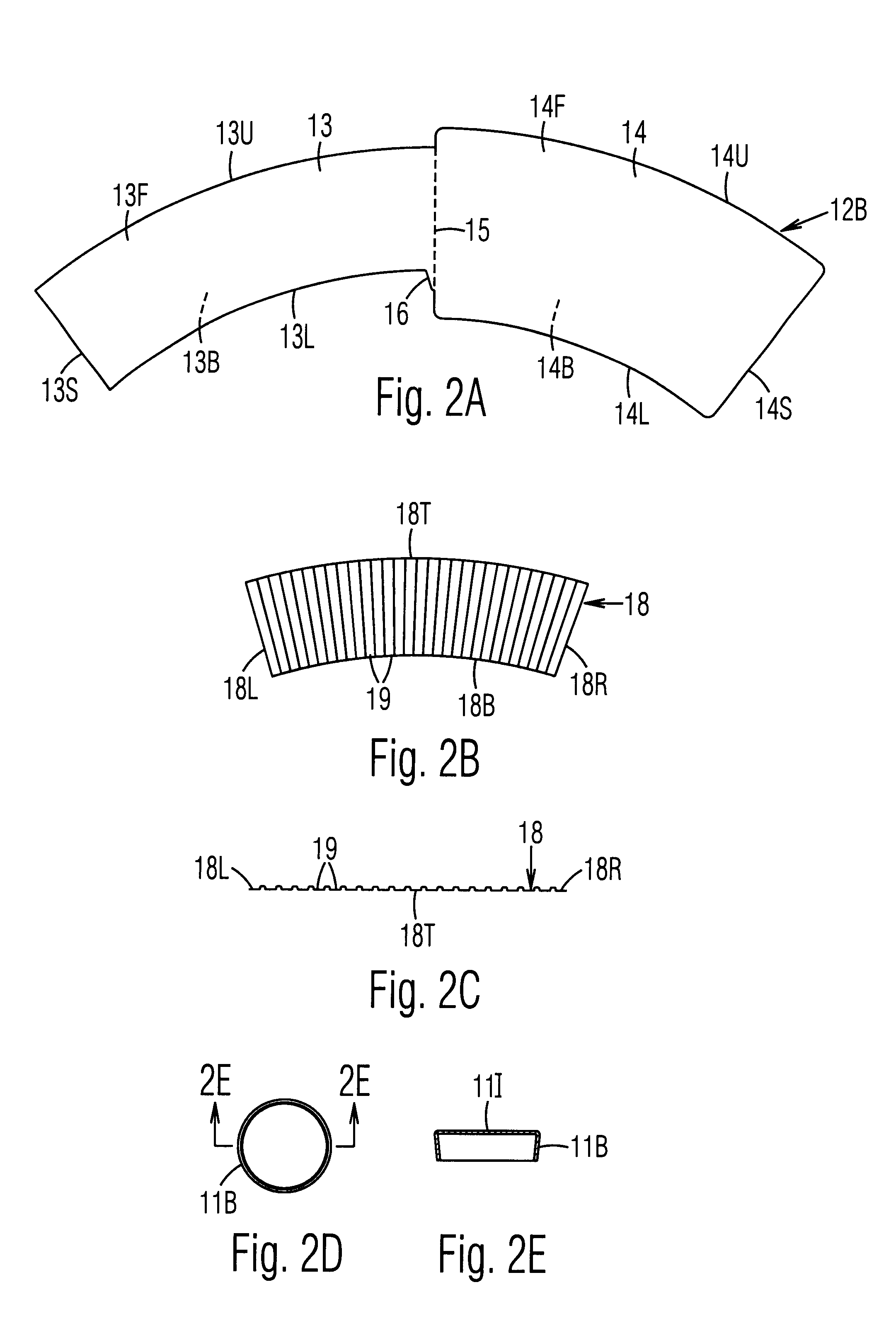
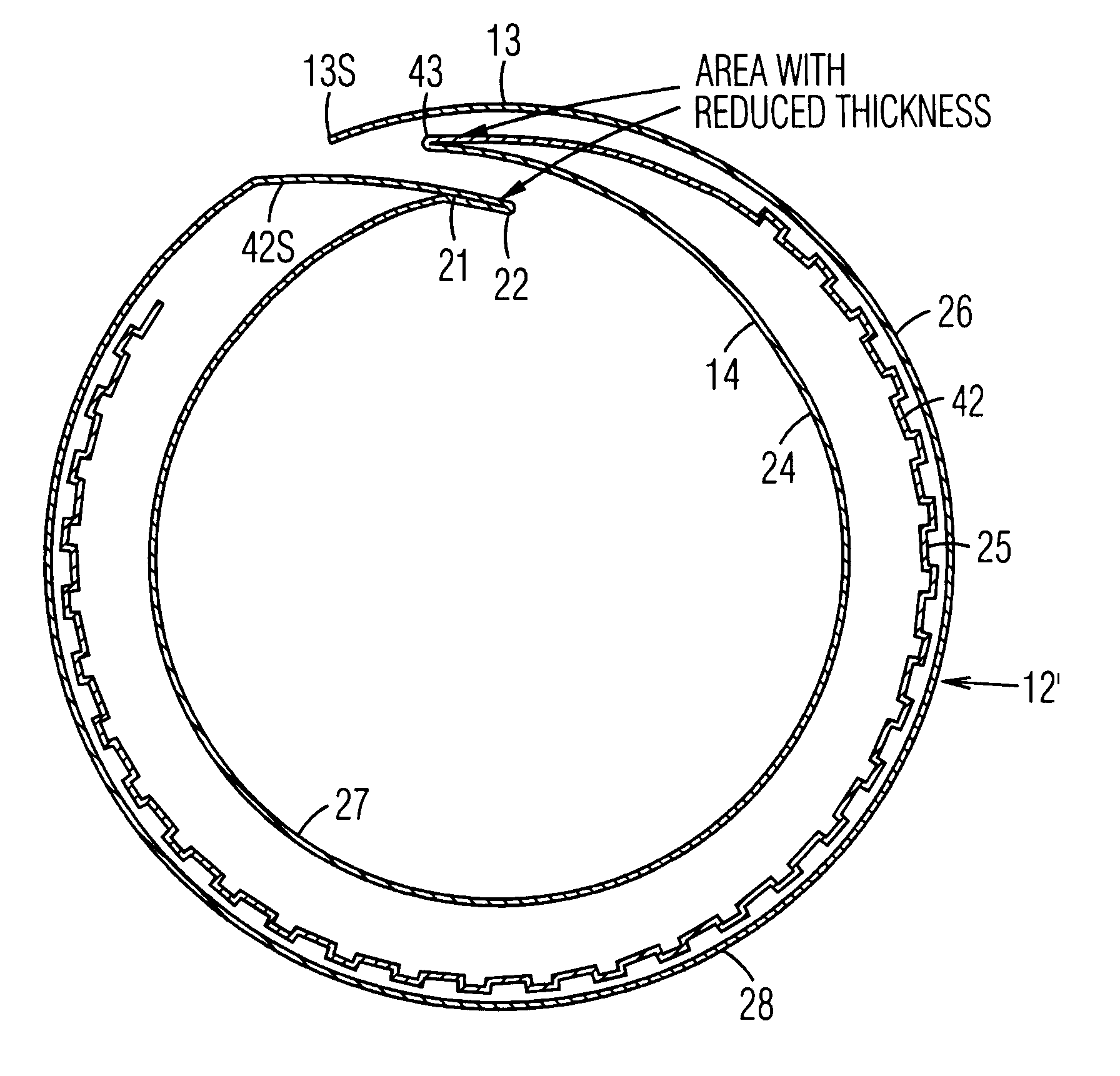
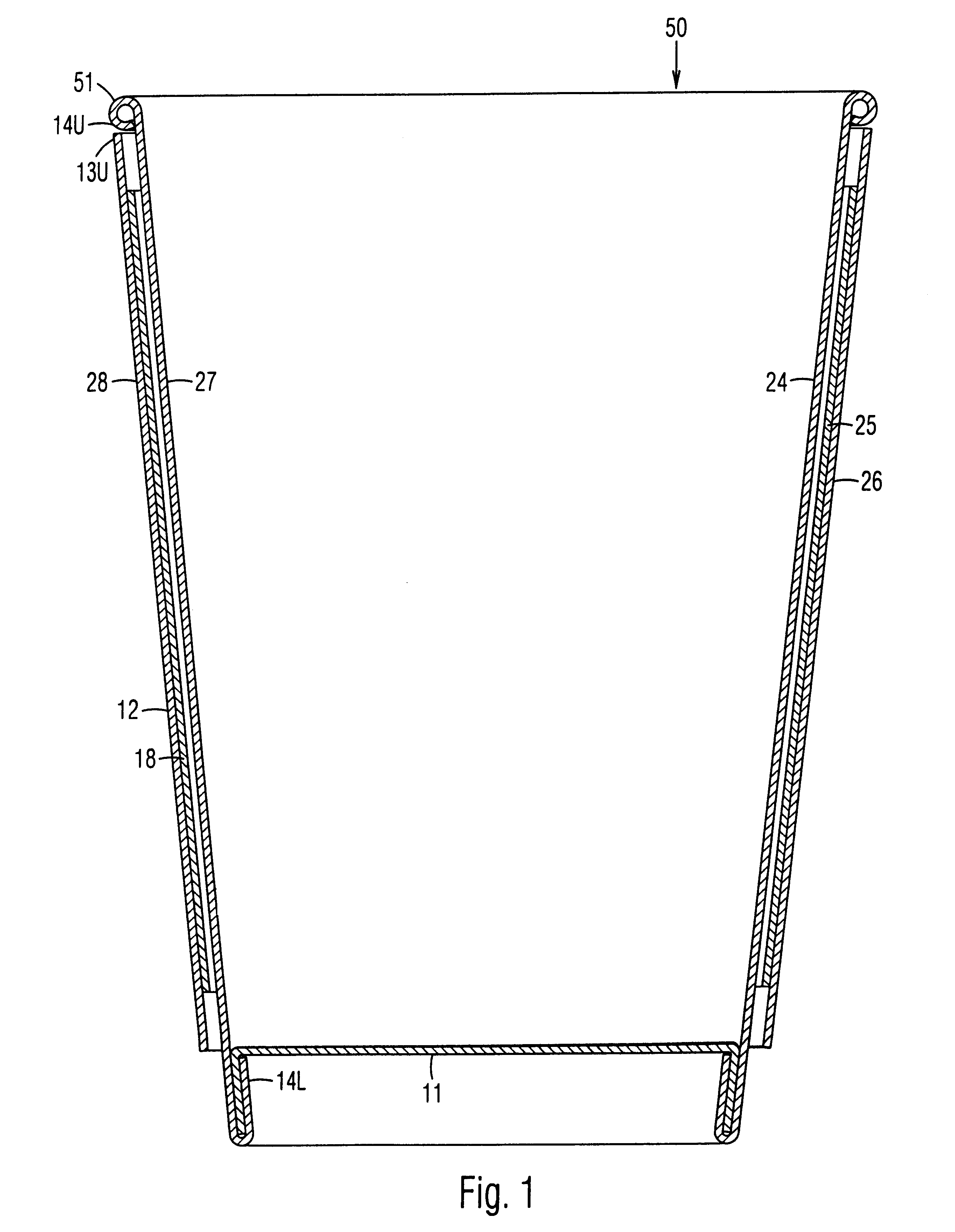
Insulated cup and method of manufacture
InactiveUS6257485B1Boxes/cartons making machineryDomestic cooling apparatusEngineeringMechanical engineering
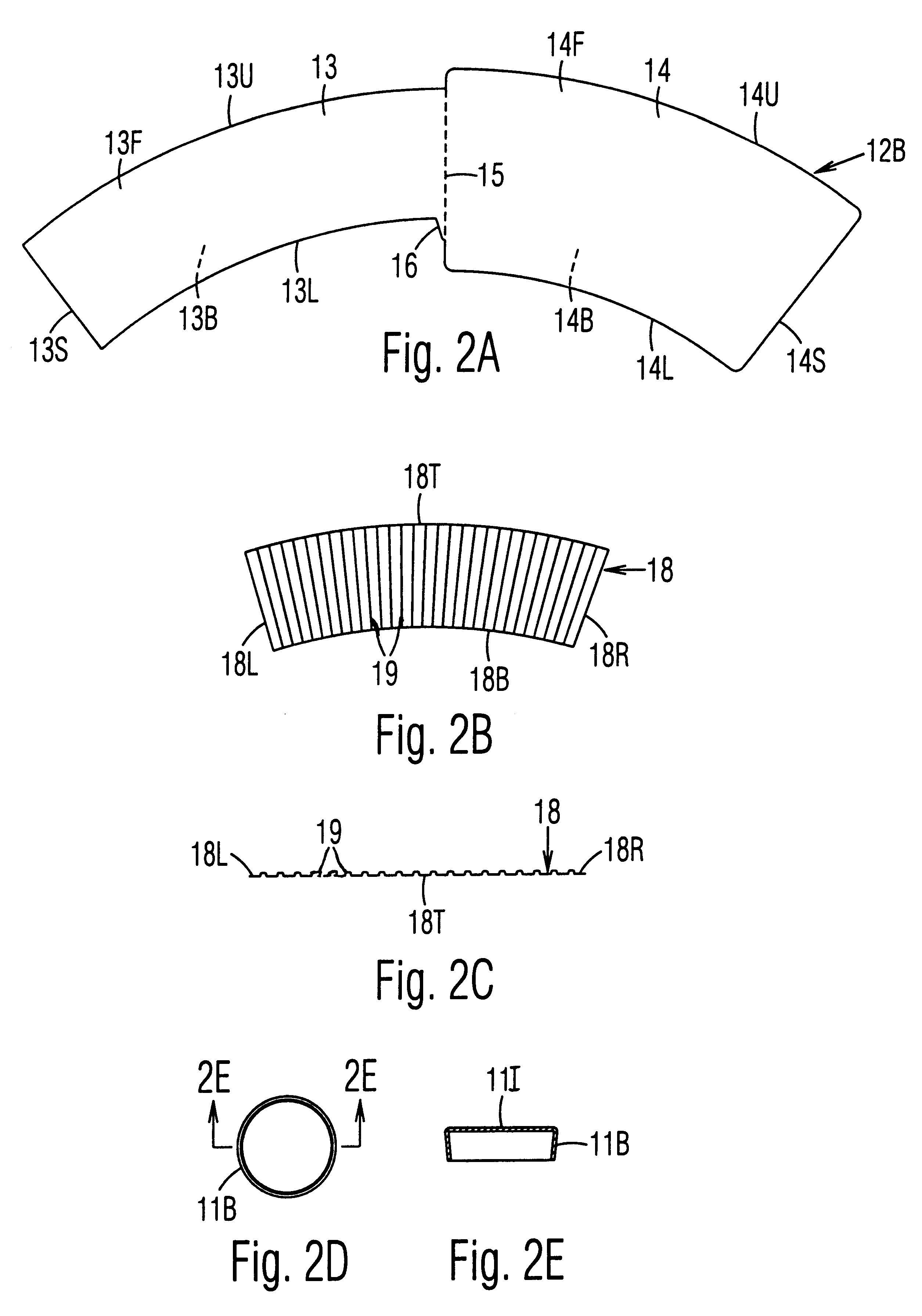
An insulating cup or container (50) and a method of manufacturing it comprises (first embodiment) providing a sidewall blank (12B) having two sections separated by a fold score (15), and a separate insulating sheet (18) (corrugated, ribbed, embossed, foamed, perforated, etc.) which is adhesively fastened to one of the sections. The blank is folded in half along the fold score, to form a three-layered assembly with the insulating sheet in the middle. To reduce the thickness of the seam, the blank is thinned in the area adjacent a fold score prior to folding. The assembly is wrapped around a mandrel to bring the outer edges together at a side seam (22S) to form a sidewall 12. The side seam is sealed, the bottom is added, and the rim is formed. In a second embodiment, the insulating layer can be a coating on one or both of the sections of the two-section starting blank. In a third embodiment, the insulating section (40) is integral with, and extends from, one edge of the starting blank. It is folded over first to form the middle layer of the wrappable assembly. The width of the seam is reduced while being reinforced at the top by using edge tabs, thereby providing a rounder cup and one which is less susceptible to top leakage due to an unsealed top curl. One tab extends at the fold line from the top edge of one section, which is shorter, to the top edge of the adjacent and higher section. A second tab extends out from the top of the side edge of the higher section so that it overlaps and seals the other tab when the cup is formed.
Owner:GPCP IP HLDG LLC
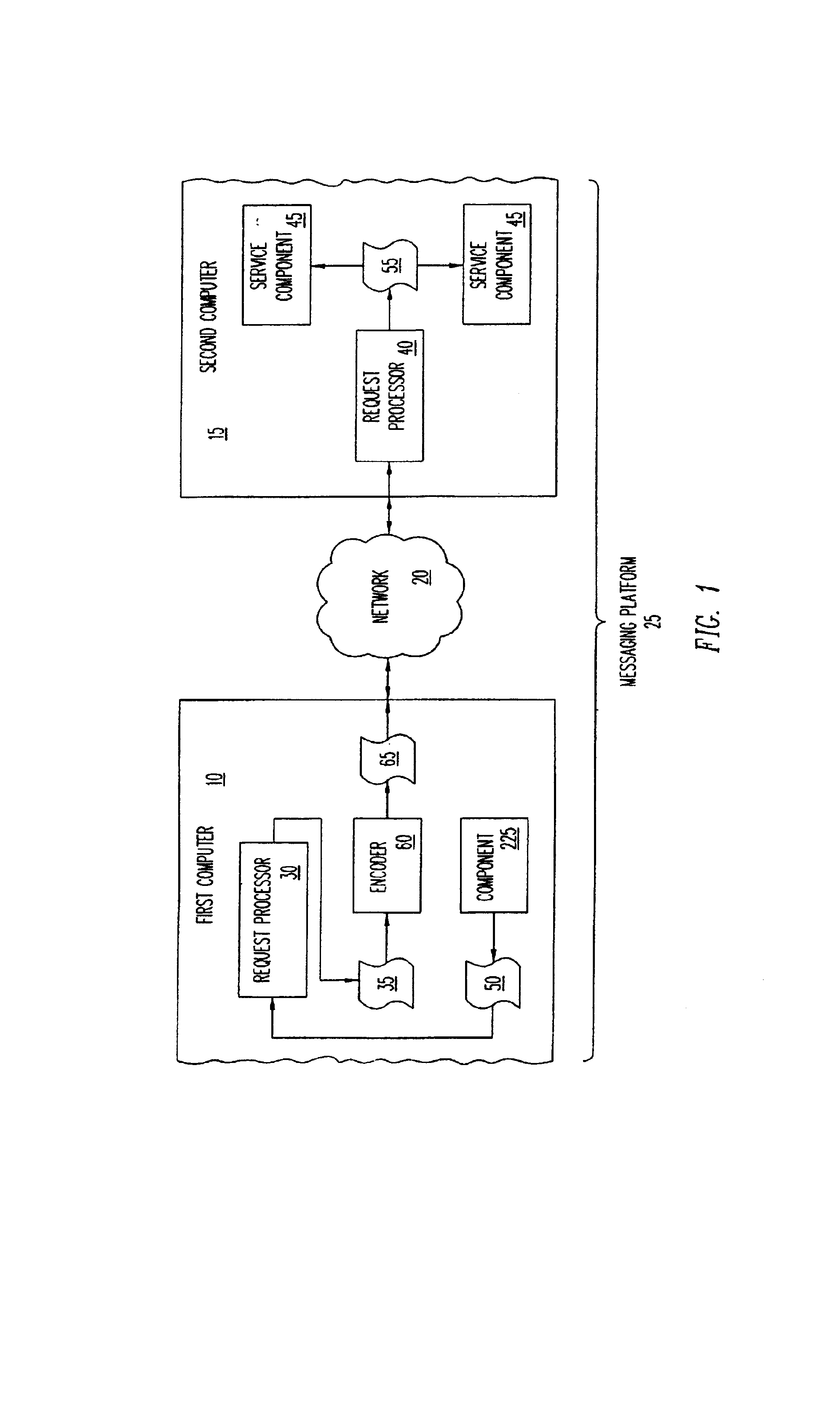
System and method for component-based software development
InactiveUS7188158B1Low costShorten the time to marketDigital computer detailsSoftware designSoftware development processThe Internet
An enterprise component-based software development system includes a component platform with a number of development tools and services that enable rapid and straightforward development of component-based systems. The component platform describes a middle tier architecture for a multi-tier, multi-user application. It defines the services and facilities as well as the structure in which components can execute. It helps to provide an extensible platform for the construction, management and execution of component-based software. A messaging platform facilitates communication between different computers. When a component requests a service from another component, the request is serialized and encoded into a platform-independent language such as XML. The XML-encoded message is transmitted over the Internet using an HTTP protocol to a receiving computer, which validates the message and delivers it to the component providing the requested service. Since XML is a platform and architecture independent language, requests processed in this way can be used by a wide variety of disparate systems.
Owner:HEWLETT PACKARD DEV CO LP +1
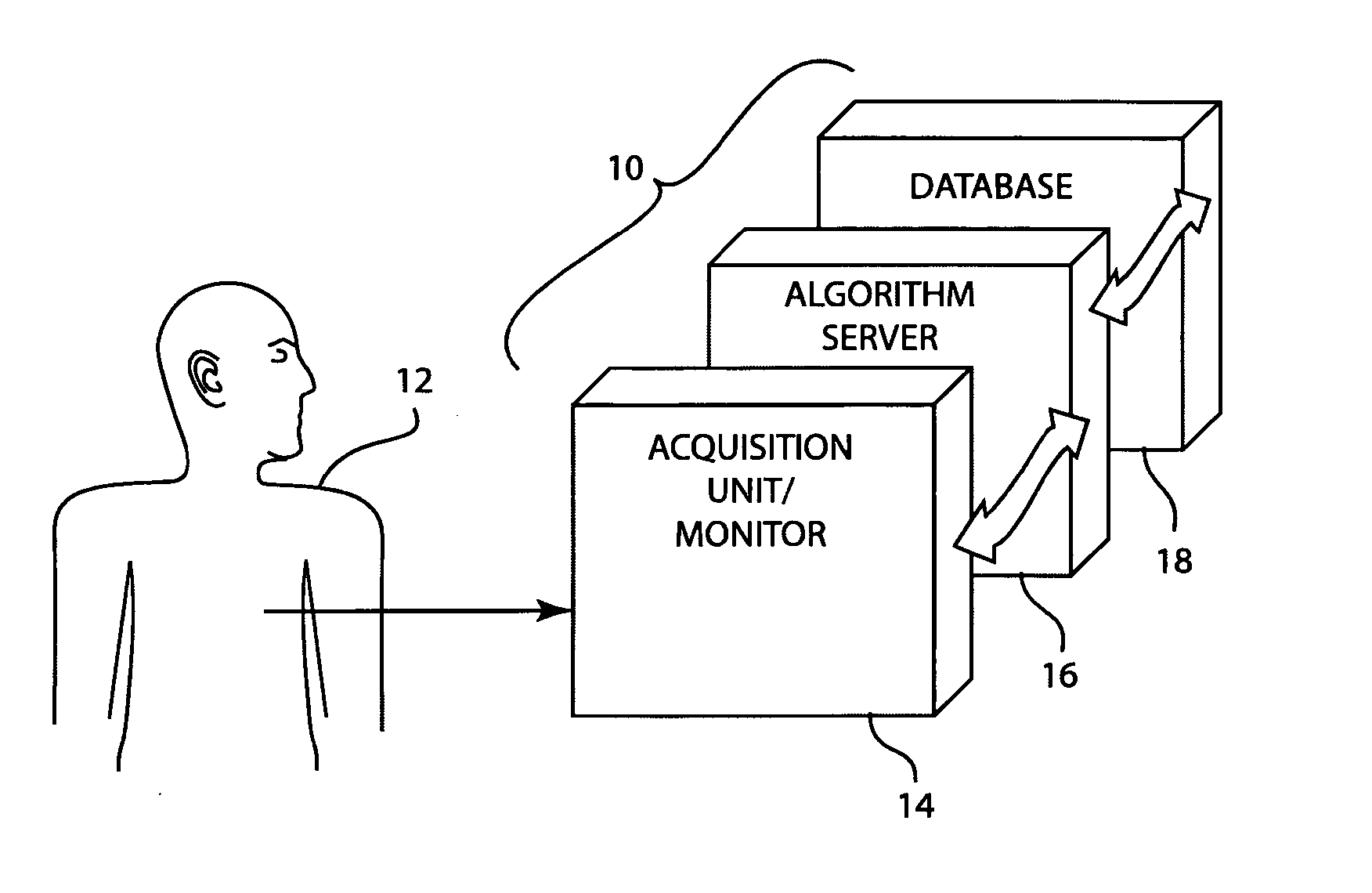
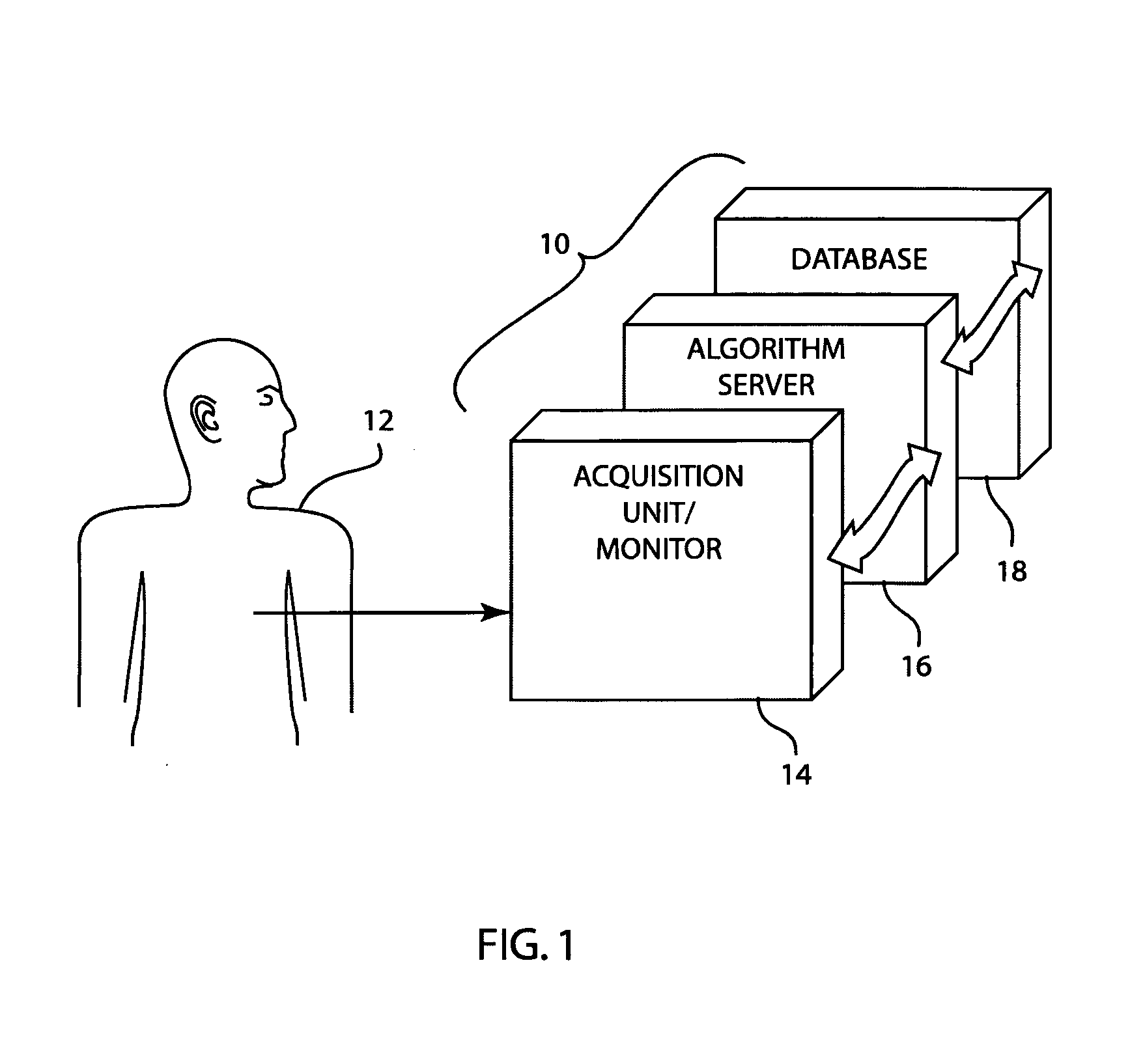
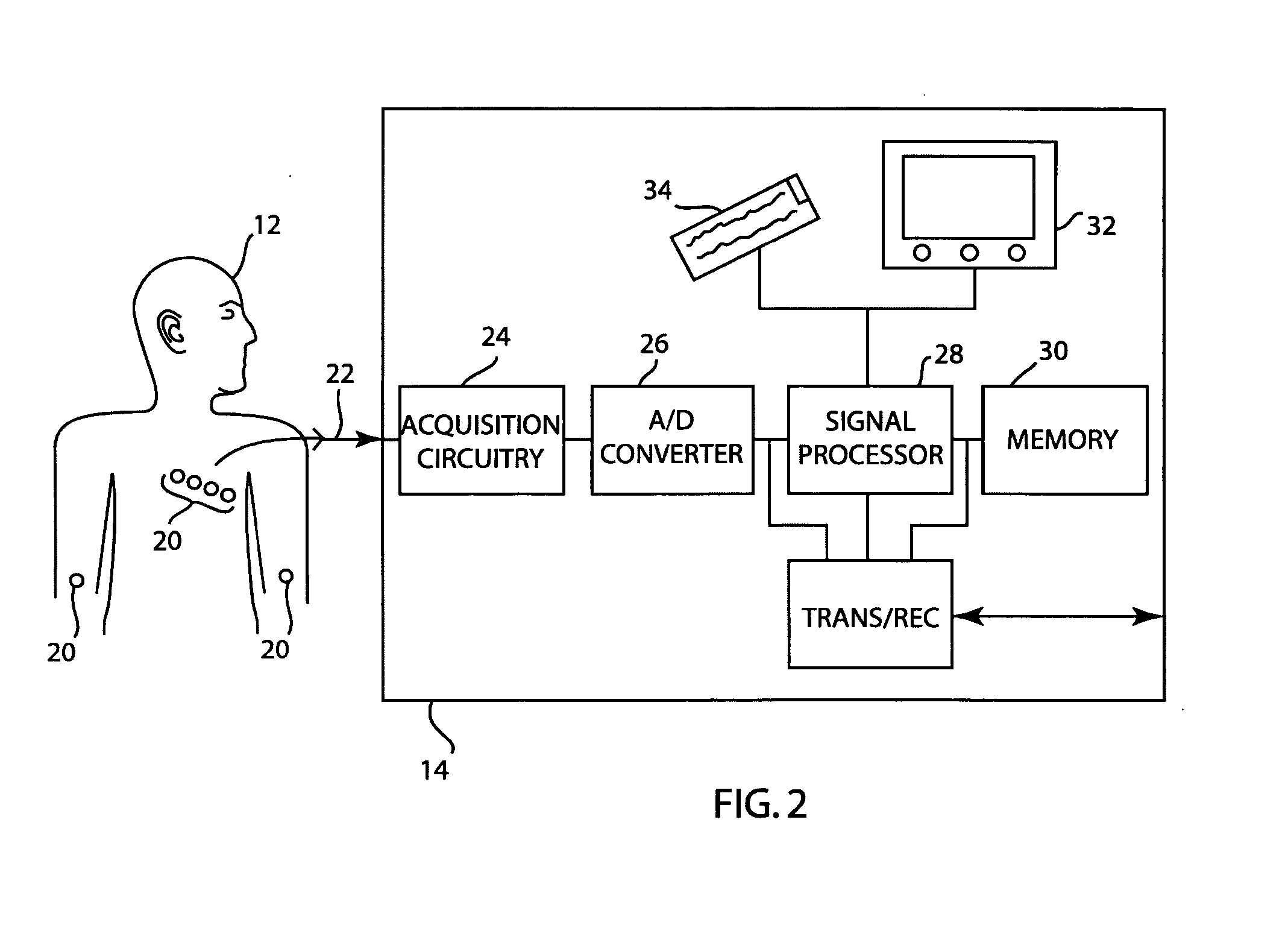
Multi-tier system for cardiology and patient monitoring data analysis
ActiveUS20070244405A1Improve good performanceMinimal disruptionElectrocardiographyComputer-assisted medical data acquisitionEcg signalPatient monitor
In a multi-tier patient monitoring data analysis system, an algorithm server is positioned as a middle tier between an acquisition device, such as a cardiograph or patient monitor that can be seen as a lower tier, and a storage device for a database, such as that of a central computer for a hospital or clinic that can be seen as an upper tier. The algorithm server gathers current data from the real time acquisition device and obtains previously stored ECG signal data from the database. The algorithm server contains ECG analysis algorithm(s) and runs one or more algorithms using the current and previously acquired ECG signal data. Analysis algorithms may also be run on the acquisition device. The system provides the rapid, extensive, and thorough ECG analysis that is critical to patient welfare.
Owner:GENERAL ELECTRIC CO
Insulated cup and method of manufacture
InactiveUS6196454B1Boxes/cartons making machineryDomestic cooling apparatusEngineeringMechanical engineering
An insulating cup or container (50) and a method of manufacturing it comprises (first embodiment) providing a sidewall blank (12B) having two sections separated by a fold score (15), and a separate insulating sheet (18)(corrugated, ribbed, embossed, foamed, perforated, etc.) which is adhesively fastened to one of the sections. The blank is folded in half along the fold score, to form a three-layered assembly with the insulating sheet in the middle. To reduce the thickness of the seam, the blank is thinned in the area adjacent a fold score prior to folding. The assembly is wrapped around a mandrel to bring the outer edges together at a side seam (22S) to form a sidewall 12. The side seam is sealed, the bottom is added, and the rim is formed. In a second embodiment, the insulating layer can be a coating on one or both of the sections of the two-section starting blank. In a third embodiment, the insulating section (40) can be integral with, and extend from, one edge of the starting blank. It is folded over first to form the middle layer of the wrappable assembly.
Owner:GPCP IP HLDG LLC
Neural network training method and device
ActiveCN107247989AImprove performanceImprove accuracyKernel methodsNeural architecturesApplicability domainLarge applications
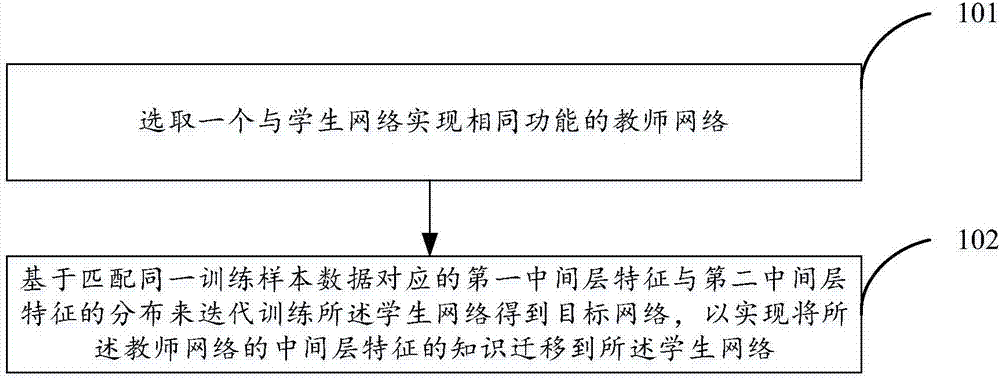
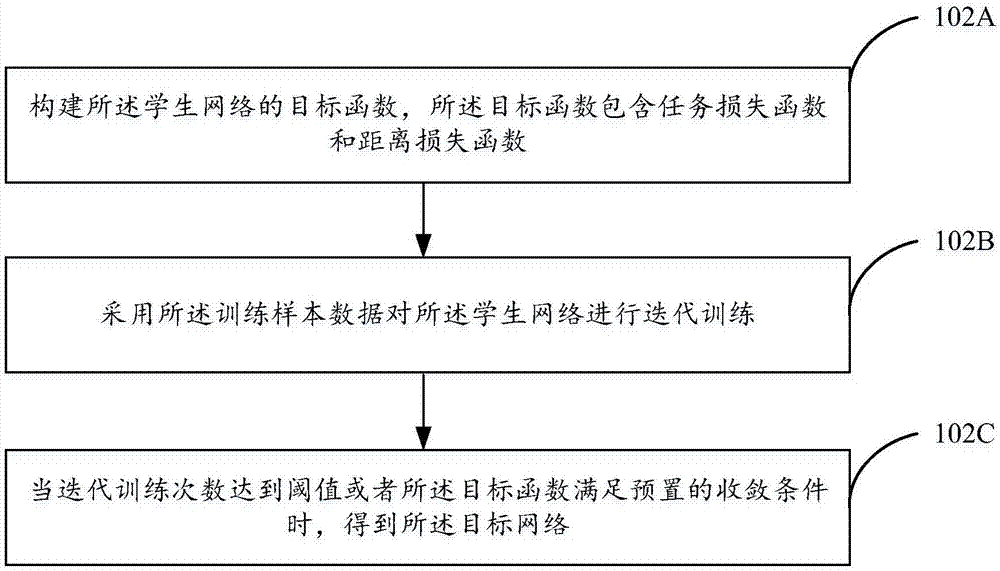
The invention discloses a neural network training method and device so as to solve a technical problem that a student network trained by the existing knowledge transfer mode cannot give consideration to a large application range and accuracy. The neural network training method comprises the steps of selecting a teacher network which realizes the same functions as the student network; and iteratively training the student network based on distribution of first intermediate layer features and second intermediate layer features corresponding to matching with the same training sample data so as to acquire a target network, and thus transferring knowledge of intermediate layer features of the teacher network to the student network, wherein the first intermediate layer features are a feature map outputted from a first specific network layer of the teacher network after inputting the training sample into the teacher network, and the second intermediate layer features are a feature map outputted from a second specific network of the student network after inputting the training sample data into the student network. The neural network acquired by adopting the technical scheme disclosed by the invention is not only wide in application range but also excellent in performance.
Owner:BEIJING TUSEN ZHITU TECH CO LTD
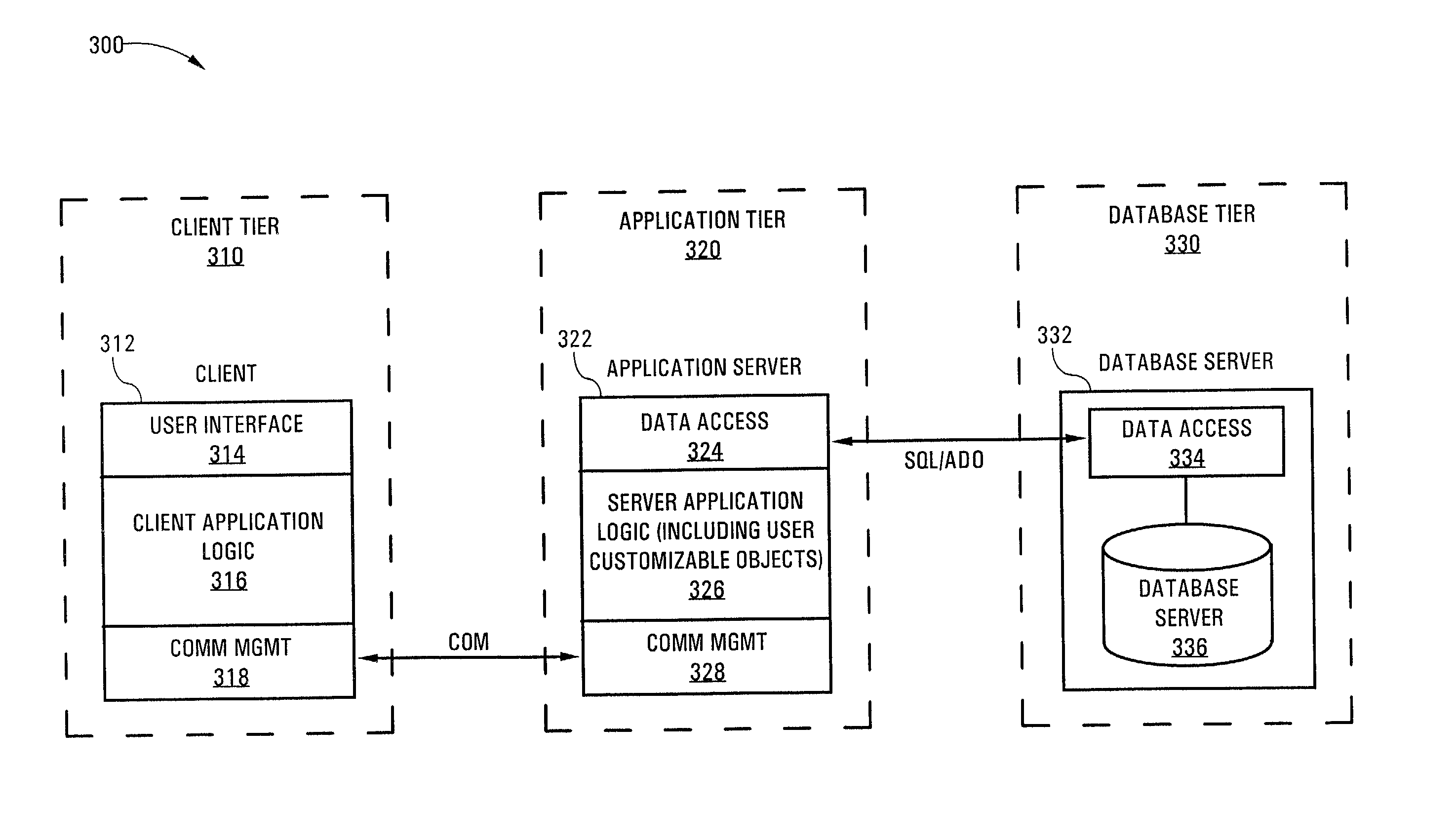
Customizable remote order entry system and method
InactiveUS20020099796A1Multiple digital computer combinationsTransmissionNetwork connectionApplication software
A system for generating a requisition comprises a client computer system and a server computer system connected via a network. The client computer is configured to allow a plurality of users to access the server computer system. The system further includes a server application comprising a user interface running on the server computer system and having a multi-tier architecture. The multi-tier architecture includes a first tier of client application code for initiating processing by the server application in response to input by a user of the client computer system, a middle tier of object-oriented server application code, and a third tier of shared access and data code. An application programming interface is configured to allow a user, such as a system administrator or the like, to customize the user interface. In a further aspect, a method of customizing a server application is also provided.
Owner:MAJANDRO LLC
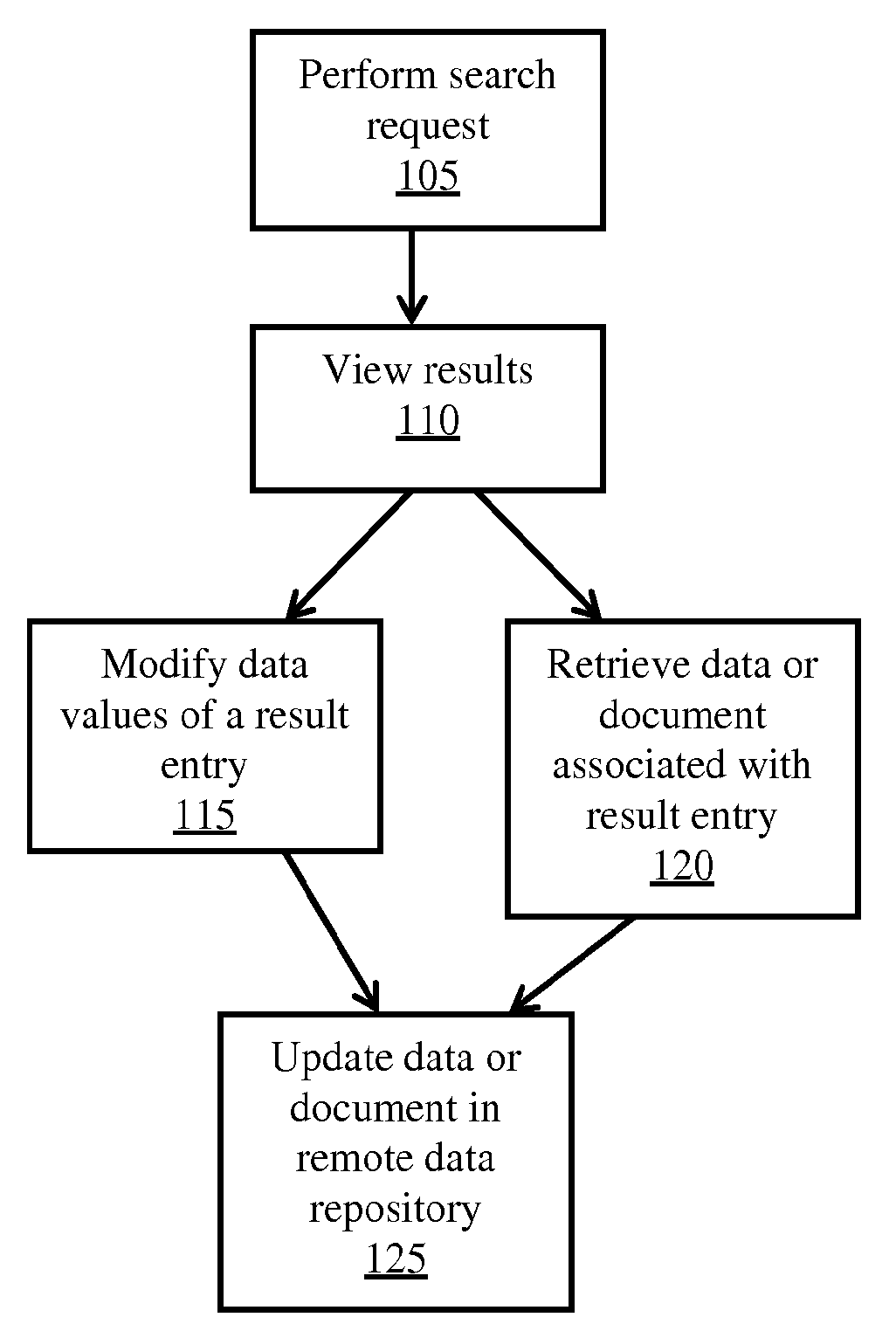
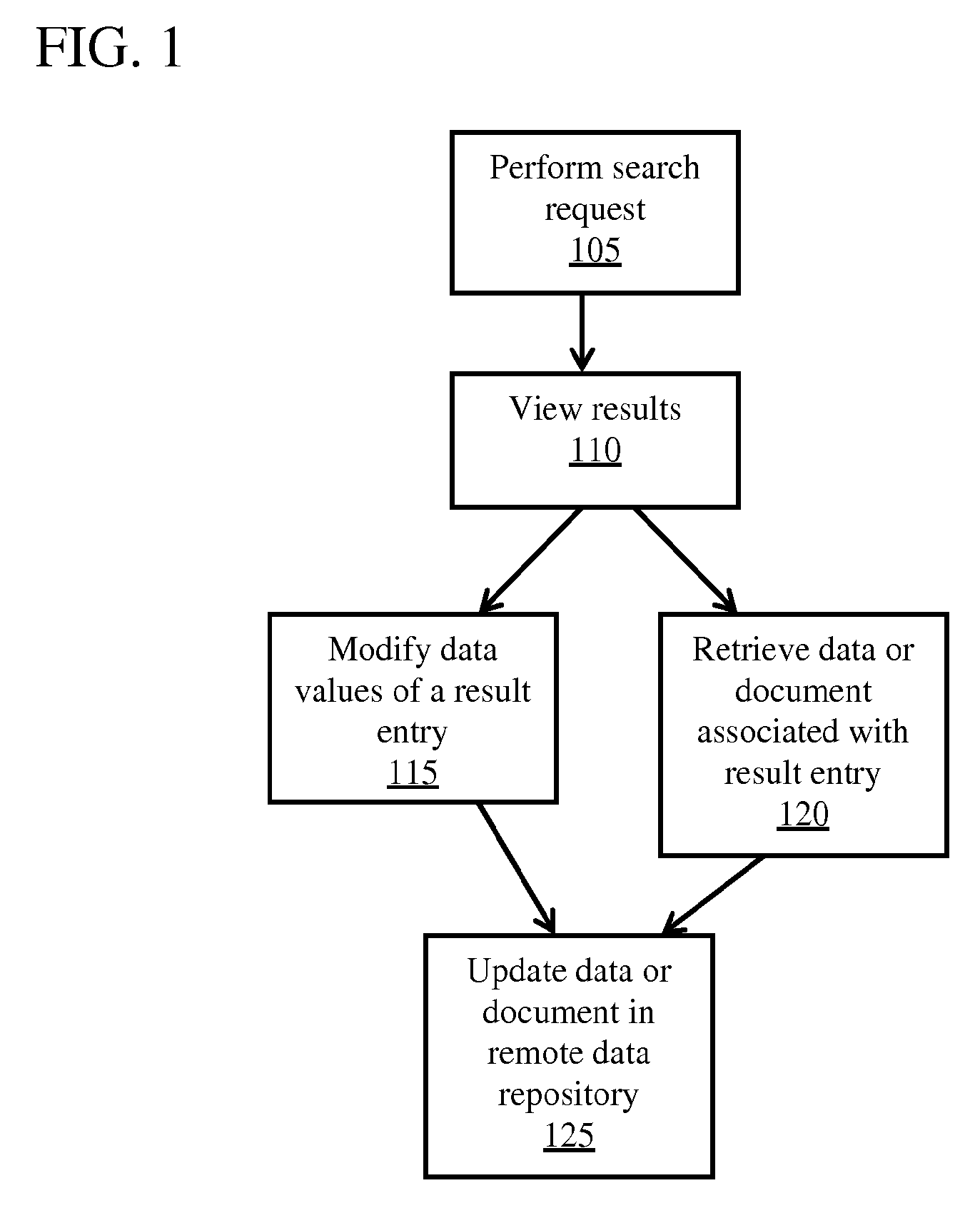
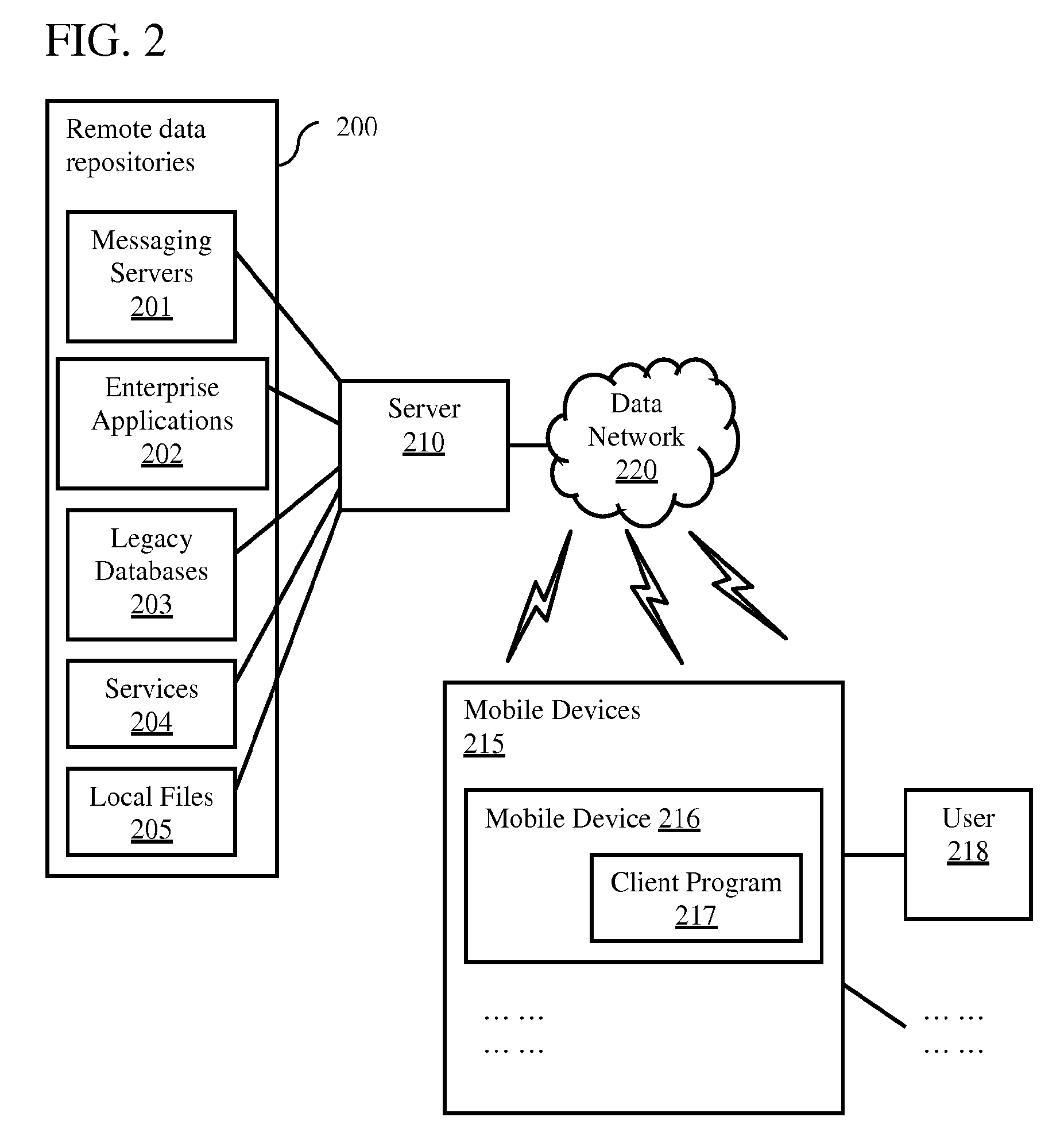
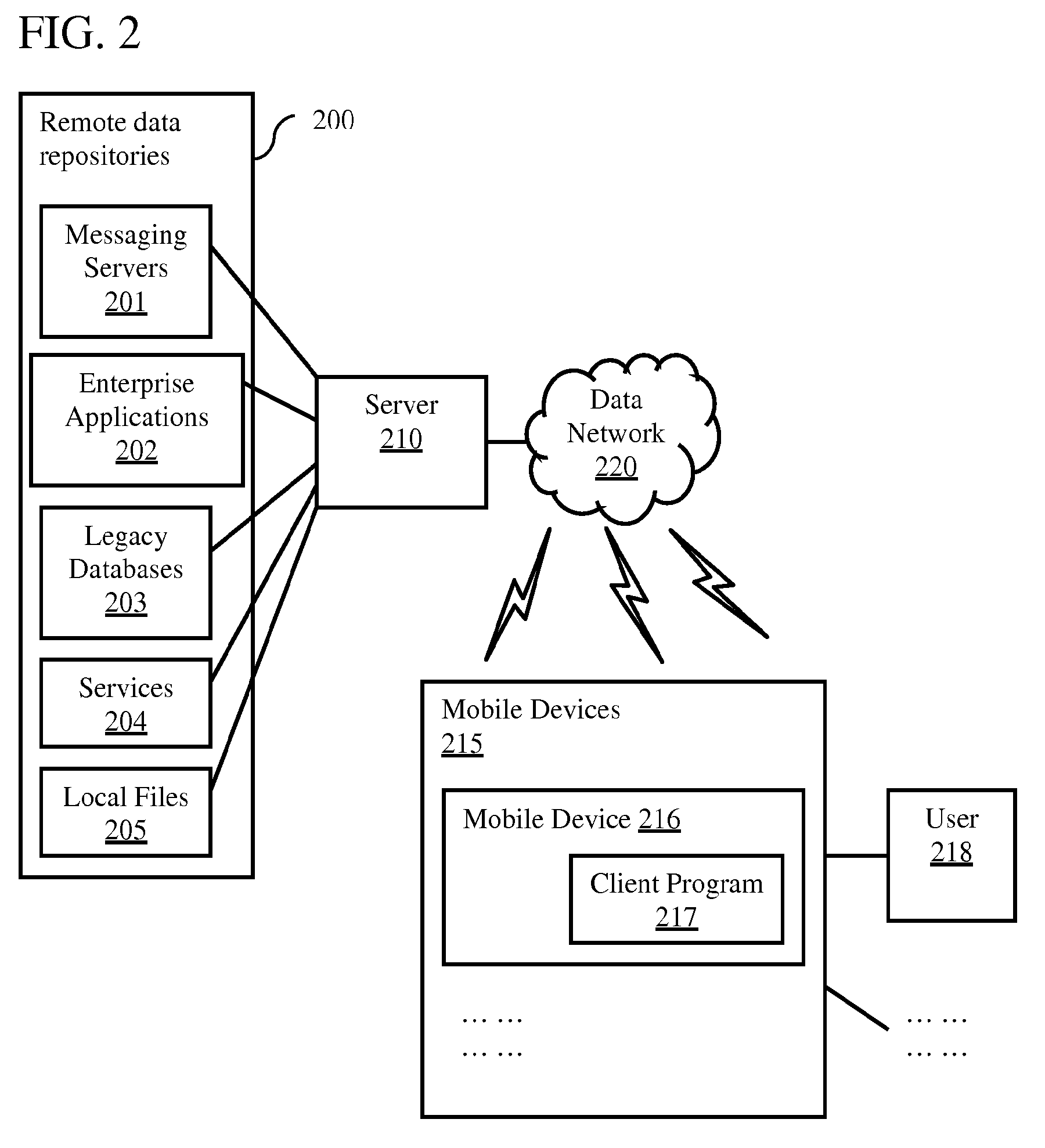
Remote Access of Heterogeneous Data
InactiveUS20090234823A1The process is convenient and fastConvenient and efficient accessDigital data information retrievalDigital data processing detailsDocument preparationCellular telephone
A method and system for providing remote access to heterogeneous information sources from computing devices including but not limited to personal computers, laptop computers, PDAs, cellular telephones is presented. A middle-tier server is provided in a multi-tier environment for allowing a data-centric approach to accessing, modifying and updating content located at remote data sources. The middle-tier server provides functionality for a mobile (or similar) user to perform a search query, request for document and / or data, update remote data, and perform commands on remote data sources. In addition, the middle-tier server manages the authentication of the user in sessioned or sessionless mode. In particular, search query results are processed such that the results answer a search query. That is, rather than simply providing a list of document matches, the middle-tier server extracts information from the document that answers the search query most appropriately. Finally, the middle-tier server, using user preferences, device capabilities and settings, transforms the result, document or data into an appropriate format that is suitable for the device, user and communication network. This allows the user to easily process and view the document on a (possibly limited capacity / functionality) device.
Owner:STATE CAPITAL RESOURCES
Methodology providing high-speed shared memory access between database middle tier and database server
InactiveUS20030014552A1Data processing applicationsInterprogram communicationApplication serverDatabase server
A multi-tier database system is modified such that a middle-tier application server (EJB server) and a database server run on the same host computer and communicate via shared-memory interprocess communication. The system includes a database (e.g., JDBC) driver thread that attaches to the database server, specifically by attaching to the database server's shared memory segment. Operation of the JDBC driver is modified to provide direct access between the middle tier (i.e., EJB server) and the database server, when the two are operating on the same host computer.
Owner:SYBASE INC
Cloud computing implementation method and system
ActiveCN102325192AAvoid pauseGuaranteed unobstructedTransmissionSoftware simulation/interpretation/emulationFile systemComputer module
The invention discloses a cloud computing implementation method. By multilayer load balancing architecture design, a plurality of virtual machines with totally same functions are deployed in an application layer, a middle layer and a database layer, and fault monitoring modules are respectively deployed on the virtual machines; when one virtual machine has a file system read-only fault and the like, the fault monitoring module automatically turns off the virtual machine to realize automatic isolation of a virtual machine node, and reports the fault information to a management center; the management center migrates the access request of the virtual machine having the fault to the other corresponding virtual machine; and the fault or the deletion of any main virtual machine does not cause pause on the current service system, so that the fault of a single main virtual machine can be prevented from affecting the whole cloud computing platform, the smoothness of services is ensured, and the user experience and the performance of the whole system are improved. The invention also discloses a cloud computing system.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD +1
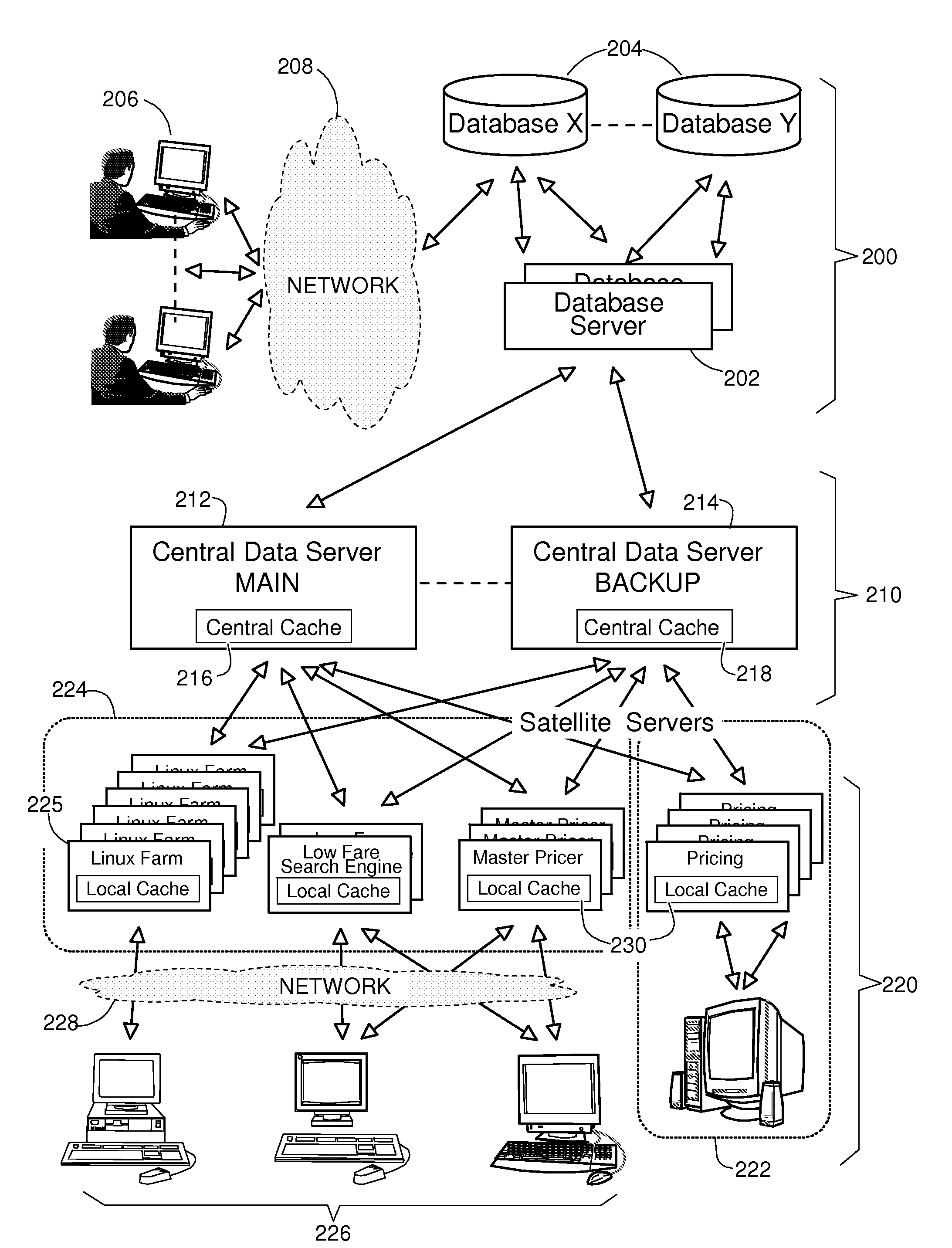
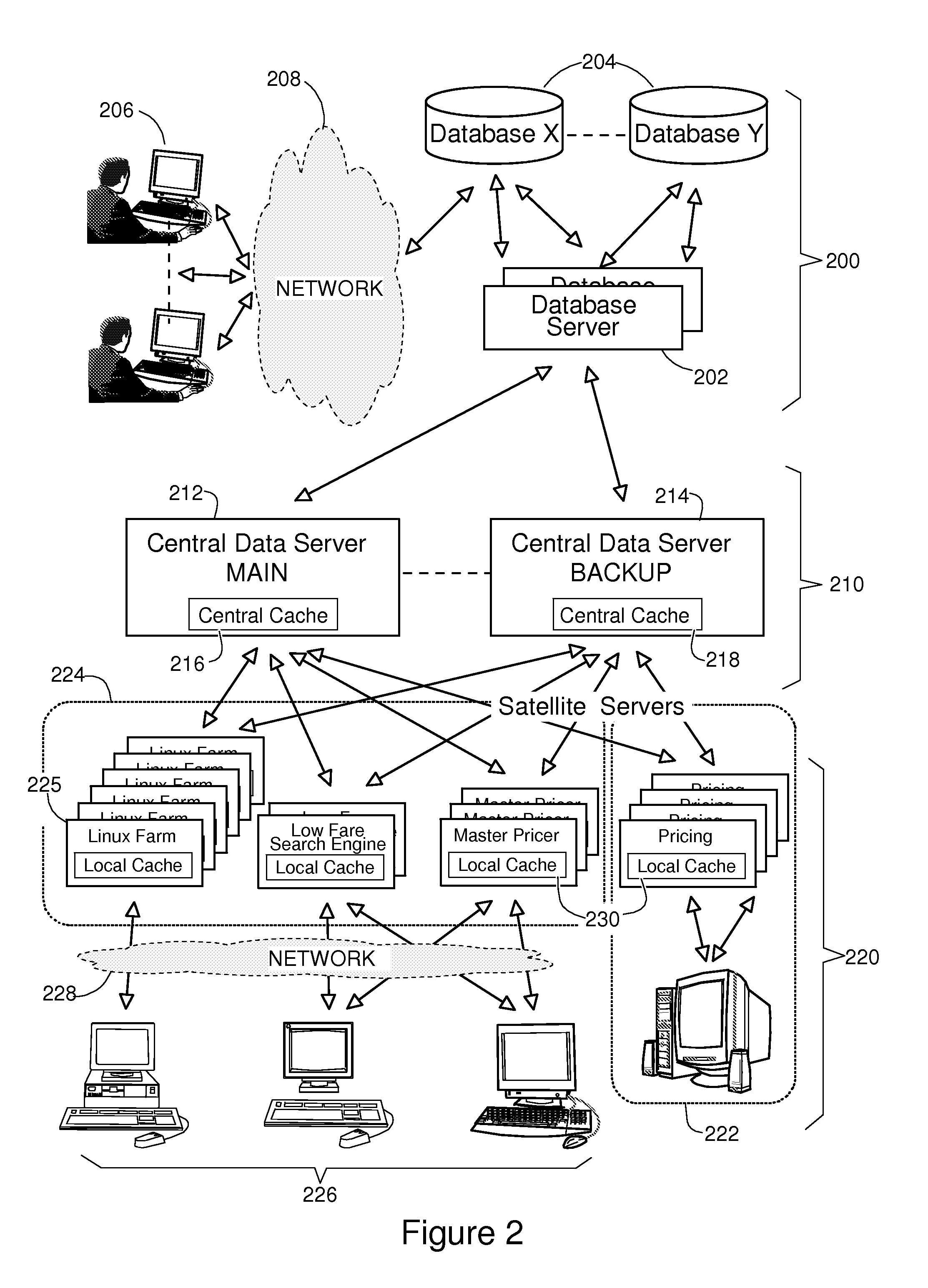
System and Method to Maintain Coherence of Cache Contents in a Multi-Tier System Aimed at Interfacing Large Databases
ActiveUS20080235292A1Improve the level ofFrequent updateDigital data processing detailsDatabase distribution/replicationDatabase serverApplication software
A method and a system for maintaining coherence of cache contents in a multi-tiered architecture of servers are described. This includes a front tier of satellite servers, each operating a local cache, and a middle tier of central servers each operating a central cache. Central servers interface with databases through database servers to retrieve the data elements used to construct objects and store them in central caches. Once constructed, objects are attributed a time-to-live (TTL) and stored in central caches then, forwarded to the satellite servers where they are stored in local caches before being delivered to the software applications that have requested them. They are invalidated when outdated and reconstructed from a central server from where they are forwarded to all central caches and to the local caches where they are needed.
Owner:AMADEUS S
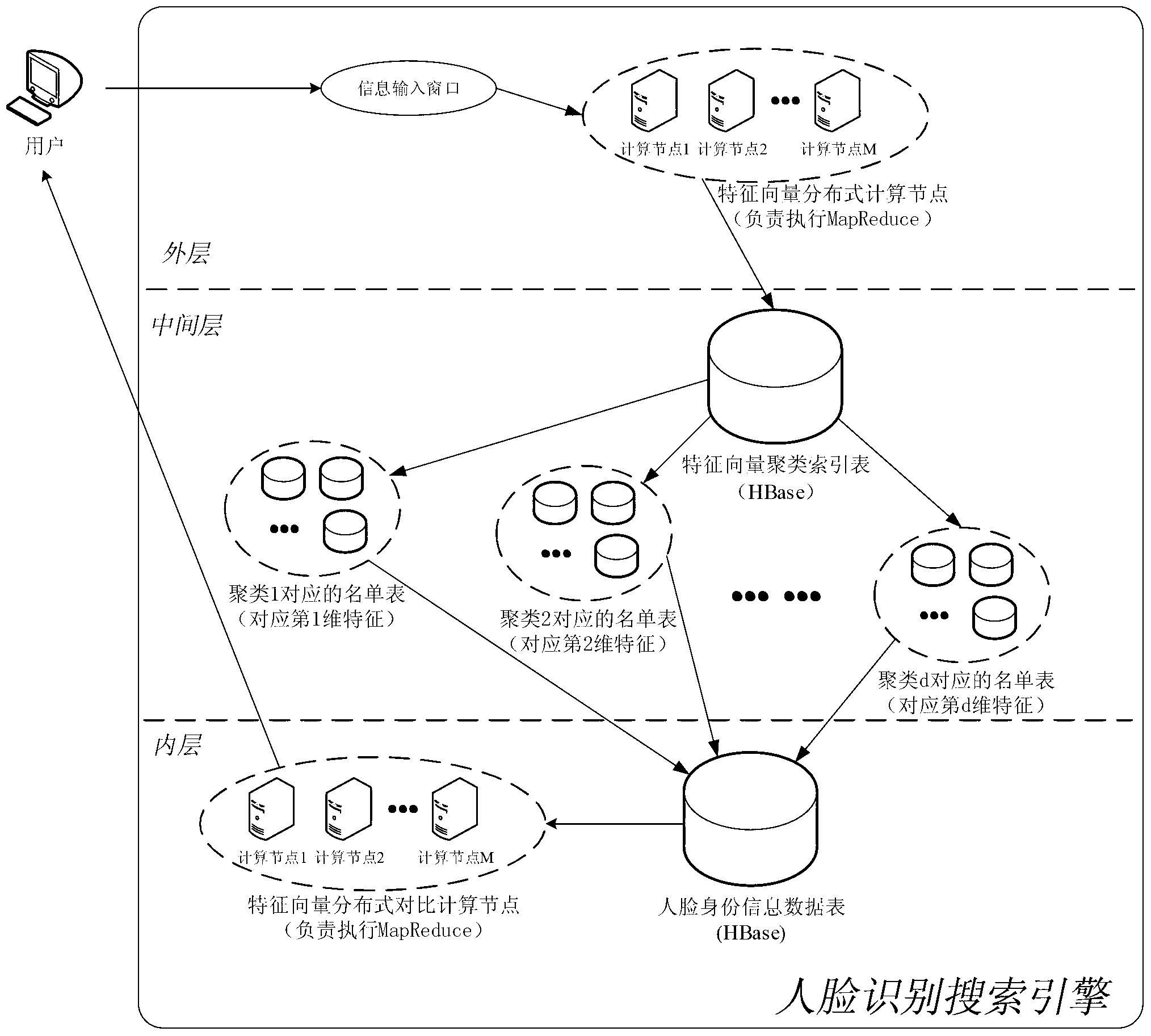
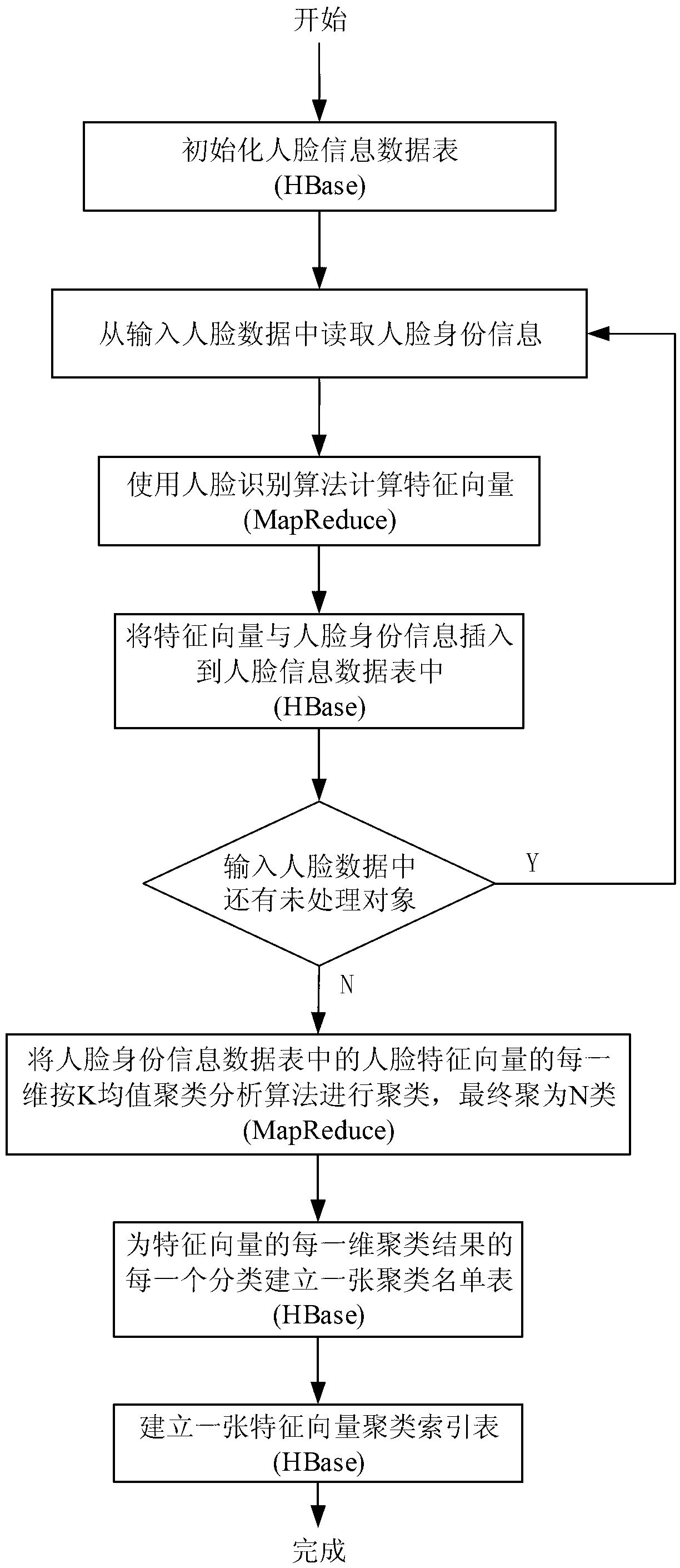
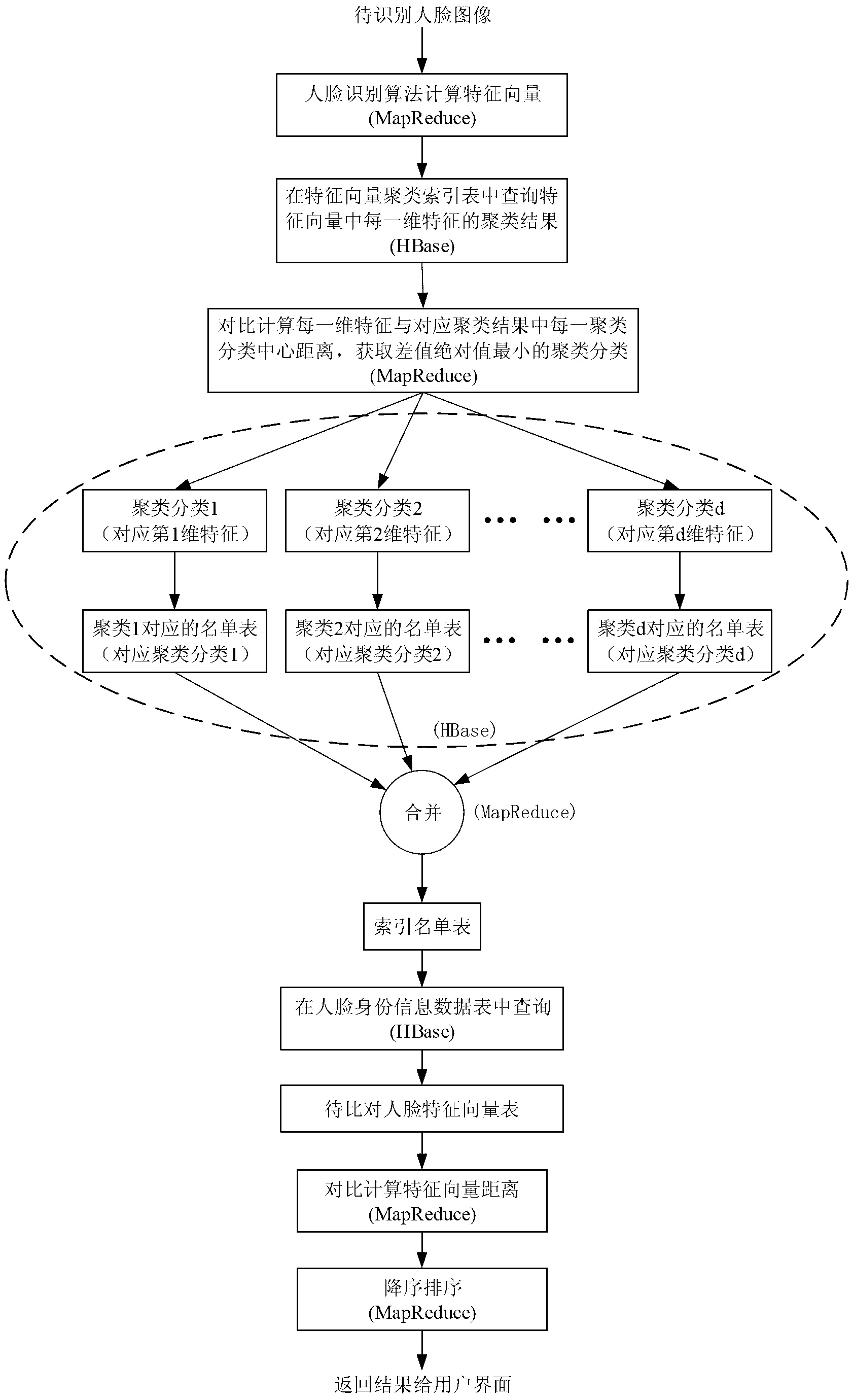
Method used for designing large-quantity face recognition search engine and based on Hadoop cloud computing frame
ActiveCN103235825AGuaranteed real-timeGuaranteed reliabilityCharacter and pattern recognitionSpecial data processing applicationsFeature vectorMachine learning
A method used for designing a large-quantity face recognition search engine and based on a Hadoop cloud computing frame belongs to the field of cloud computing and mode recognition. Based on the Hadoop cloud computing frame, the search engineis formed by an inner layer, a middle layer and an outer layer. The inner layer is used for storing a large quantity of face images and identity information and providing distributed computing resources. The middle layer is used for building and maintaining an index table of the search engine, and the outer layer is used for receiving tasks and distributing tasks. In order to increase searching speed of the face images in a data base while the precision is guaranteed, a K-means clustering algorithm is used in the middle layer to build a face feature vector cluster index table to be combined with a clustering list table. By means of the method, cheap common server groups can be used for building the large-quantity face recognition search engine, and the method is achieved based on the Hadoop cloud computing frame proved by a large amount of practice, has good stability and is simple and easy to implement.
Owner:CHONGQING UNIV
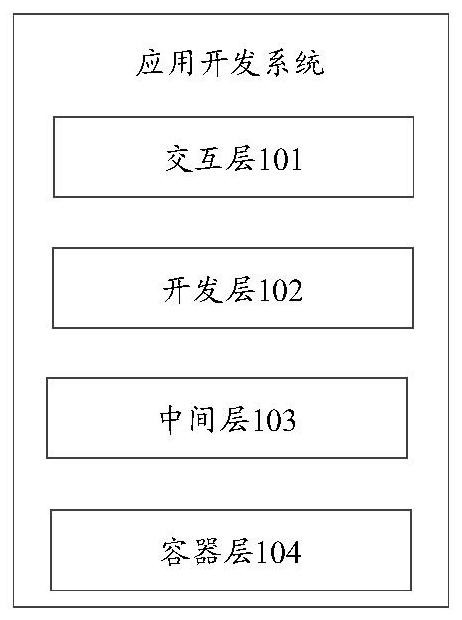
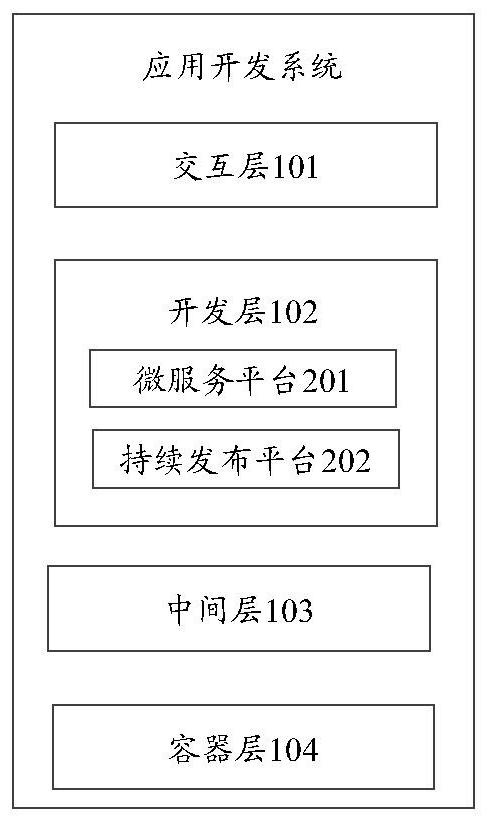
Application development system, operation method, equipment and storage medium
PendingCN111831269AShorten the timeImprove R&D efficiencyData switching networksSoftware simulation/interpretation/emulationInteraction layerEngineering
The embodiment of the invention provides an application development system, an operation method, equipment and a storage medium, and the system comprises: an interaction layer which is used for providing an operation interface, transmitting a creation request triggered on the operation interface to a development layer, and receiving and displaying a completed micro-service, wherein the creation request is used for requesting to create a micro-service of a to-be-developed business item; the development layer that is used for generating a calling request according to the microservice and sendingthe calling request to the intermediate layer so as to call the target intermediate component, and further, in the micro-service framework, a completed micro-service of the business item is created by utilizing the target intermediate component; the middle layer that is used for sending a calling request to the container layer to call the target container and creating a target middle component byutilizing the target container; the container layer that is used for providing at least two containers for setting up different intermediate components and feeding back a target container to the intermediate layer in response to the calling request; in this way, developers can focus on business development, and therefore the research and development efficiency is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
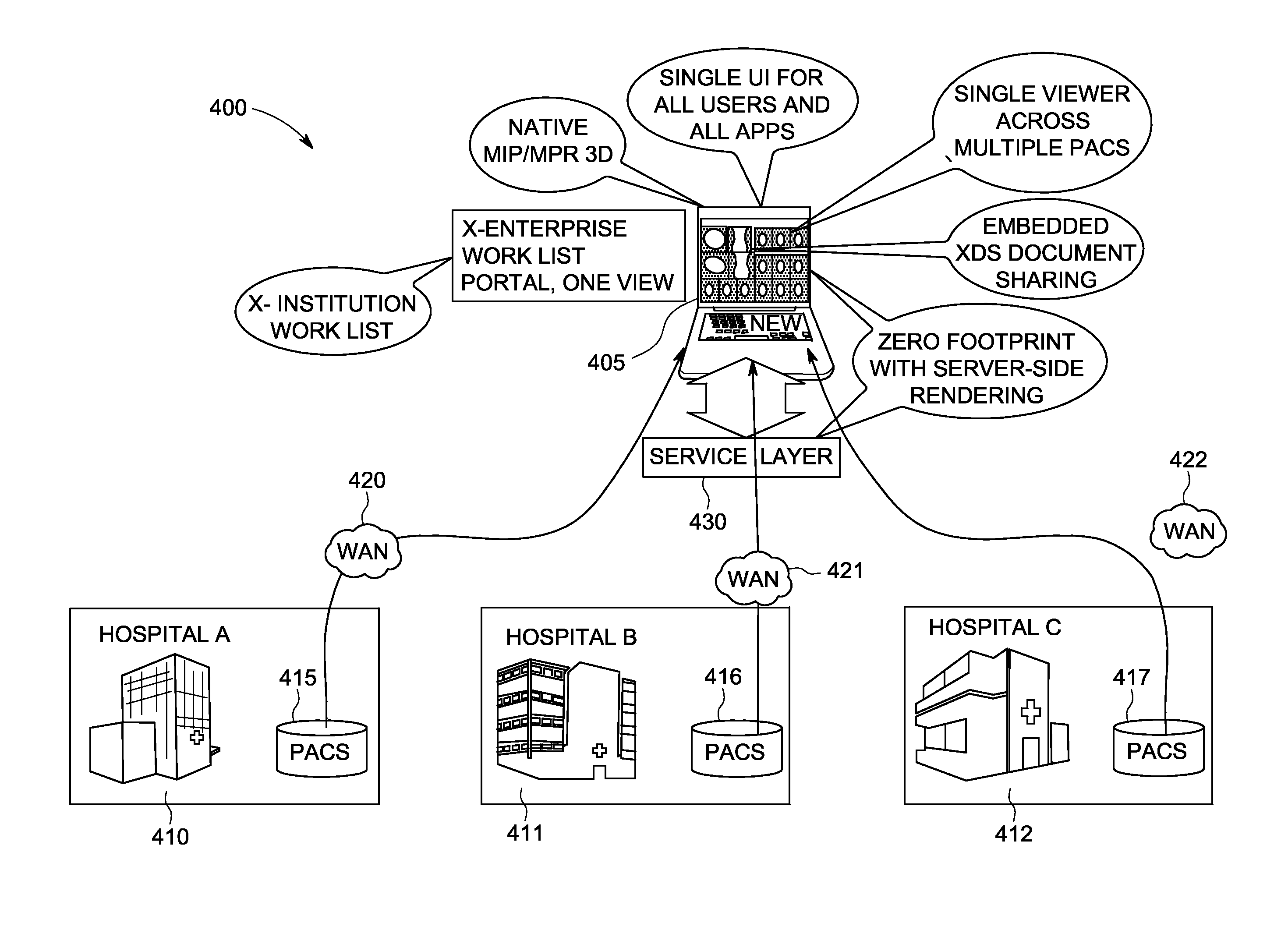
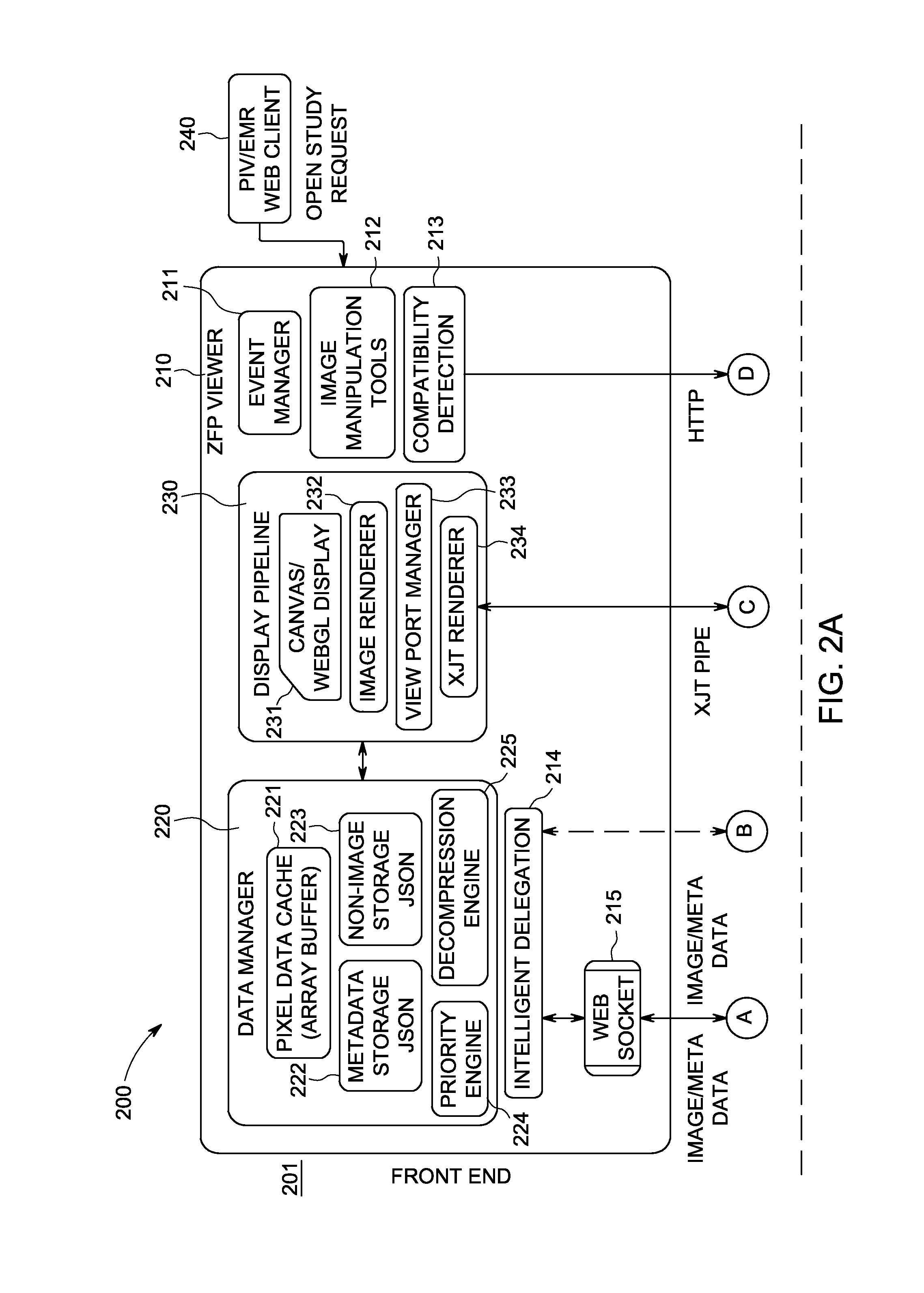
Zero footprint dicom image viewer
InactiveUS20140143298A1Facilitate of image contentFacilitates transfer of imageTransmissionSpecial data processing applicationsDICOMImage View
Certain examples provide systems and methods for zero footprint medical image viewing. An example system includes a zero footprint viewer including a display pipeline to render and provide image content to a client device without particular configuration of the client device to display and facilitate manipulation of the image content via a client browser. The example system also includes a middle-tier server to retrieve the image content from storage and to convert the image content from a stored format to a browser-convenient format. The example zero footprint viewer includes a first data manager to gather image content from the middle-tier server, and the example middle-tier server includes a second data manager to retrieve the image content and format the image content from the stored format to the browser-convenient format, the second data manager to communicate with the first data manager to facilitate transfer of the image content for display.
Owner:GENERAL ELECTRIC CO
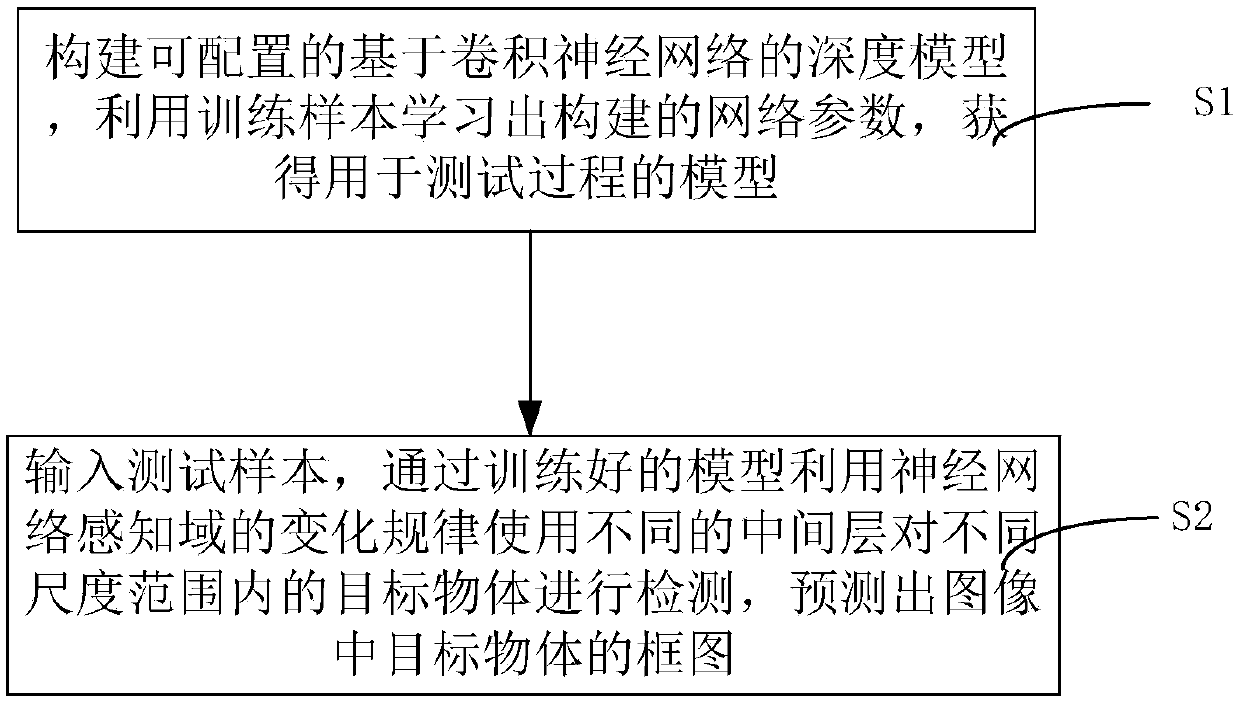
Fast pedestrian detection method and device
ActiveCN108399362AReduce the amount of parametersImprove computing efficiencyBiometric pattern recognitionNeural architecturesTest sampleAlgorithm
The invention discloses a fast pedestrian detection method and device. The method comprises the following steps: step S1, constructing a configurable deep model based on a convolutional neural network, and utilizing training samples to obtain parameters of a constructed network by learning to obtain a model used for a test process; and step S2, inputting test samples, utilizing a variation law ofneural-network perception domains, using different intermediate layers to detect target objects in different scale ranges through the trained model, and obtaining box graphs of the target objects in images by prediction. The method uses the different intermediate layers to detect the target objects in the certain scale ranges through utilizing the variation law of the neural-network perception domains, better adapts to relationships of the perception domains and object sizes, and effectively improves a detection result.
Owner:SUN YAT SEN UNIV
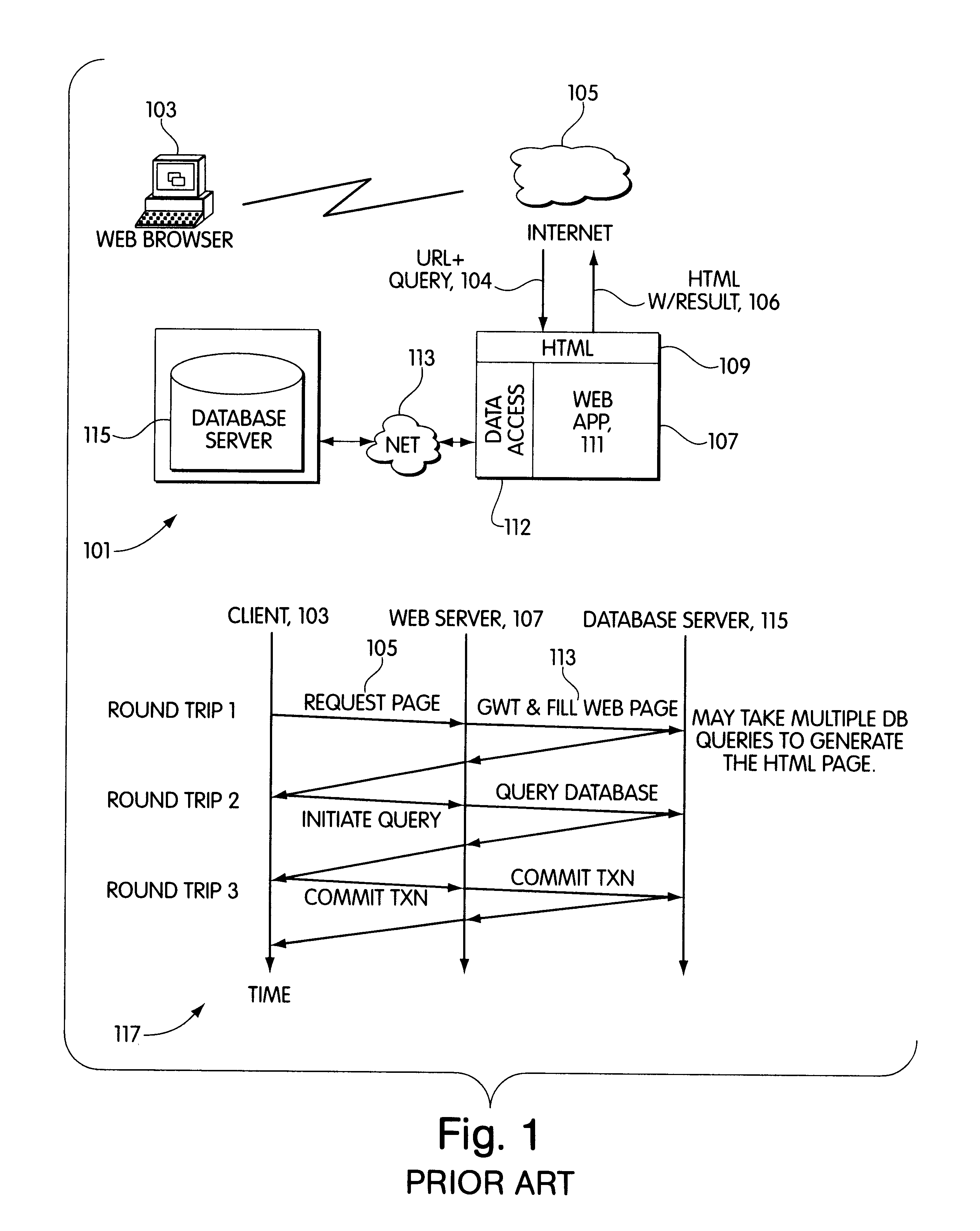
Web servers with queryable dynamic caches
InactiveUS7526481B1Digital data information retrievalData processing applicationsData setWeb application
A middle-tier Web server with a queryable cache that contains items from one or more data sources. Items are included in the cache on the basis of the probability of future hits on the items. When the data source determines that an item that has been included in the cache has changed, it sends an update message to the server, which updates the item if it is still included in the cache. As disclosed, the data source is a database system and triggers in the database system are used to generate update messages. The data access layer determines whether a data item required by an application program is in the cache. If it is, the data access layer obtains the data item from the cache; otherwise, it obtains it from the data source. The Web application programs use global data set identifiers to identify data sets, while the cached data sets are identified by local data set identifiers. The cache receives a query context of global data set identifiers, determines whether the data sets of the query context are cached, and if they are, provides the local data set identifiers for the query context to the access layer, which then uses the local data set identifiers to query the cache.
Owner:ORACLE INT CORP
Remote access of heterogeneous data
InactiveUS7882122B2The process is convenient and fastConvenient and efficient accessDigital data information retrievalDigital data processing detailsDocument preparationCellular telephone
A method and system for providing remote access to heterogeneous information sources from computing devices including but not limited to personal computers, laptop computers, PDAs, cellular telephones is presented. A middle-tier server is provided in a multi-tier environment for allowing a data-centric approach to accessing, modifying and updating content located at remote data sources. The middle-tier server provides functionality for a mobile (or similar) user to perform a search query, request for document and / or data, update remote data, and perform commands on remote data sources. In addition, the middle-tier server manages the authentication of the user in sessioned or sessionless mode. In particular, search query results are processed such that the results answer a search query. That is, rather than simply providing a list of document matches, the middle-tier server extracts information from the document that answers the search query most appropriately. Finally, the middle-tier server, using user preferences, device capabilities and settings, transforms the result, document or data into an appropriate format that is suitable for the device, user and communication network. This allows the user to easily process and view the document on a (possibly limited capacity / functionality) device.
Owner:STATE CAPITAL RESOURCES
Multiple-tier distributed cluster system
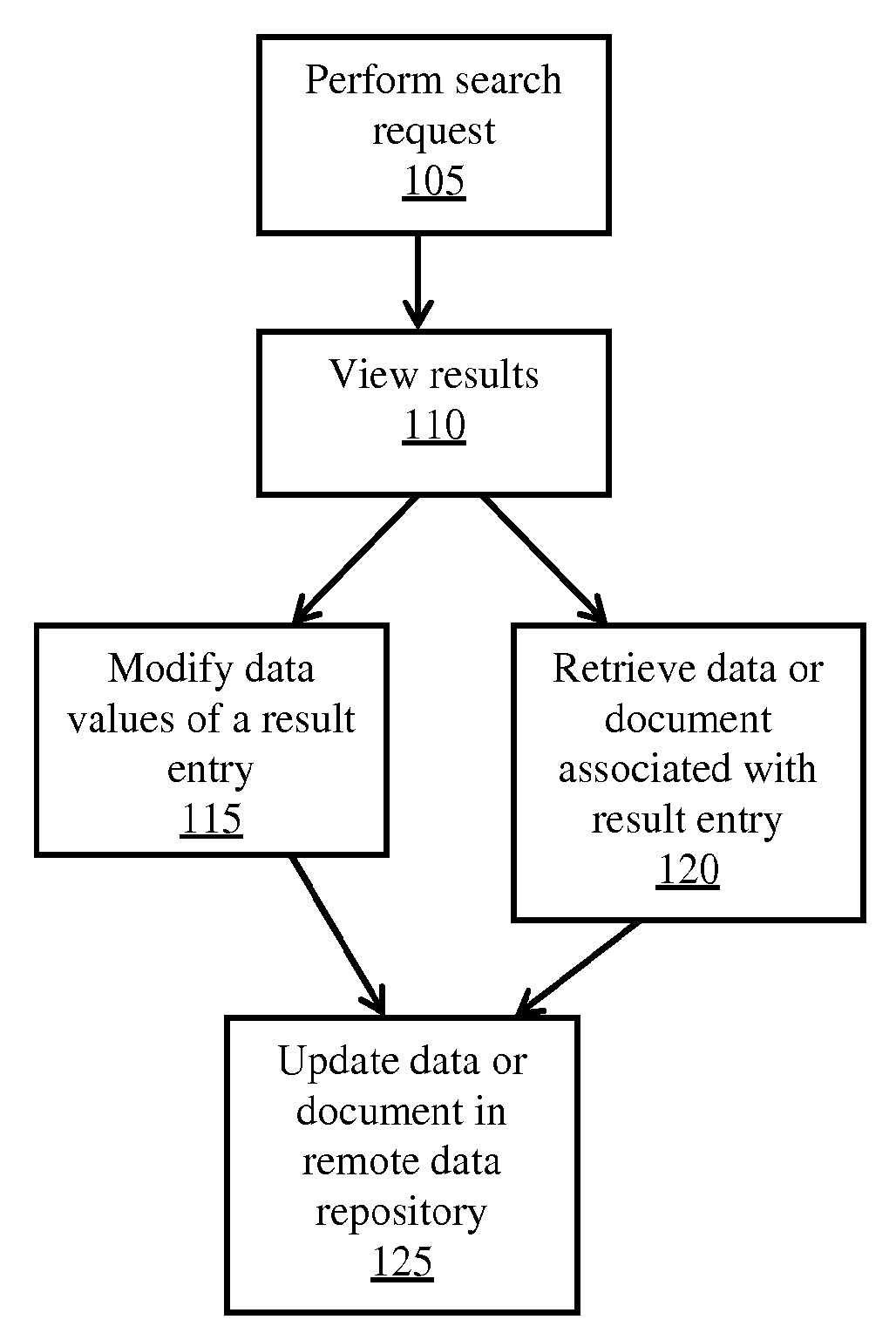
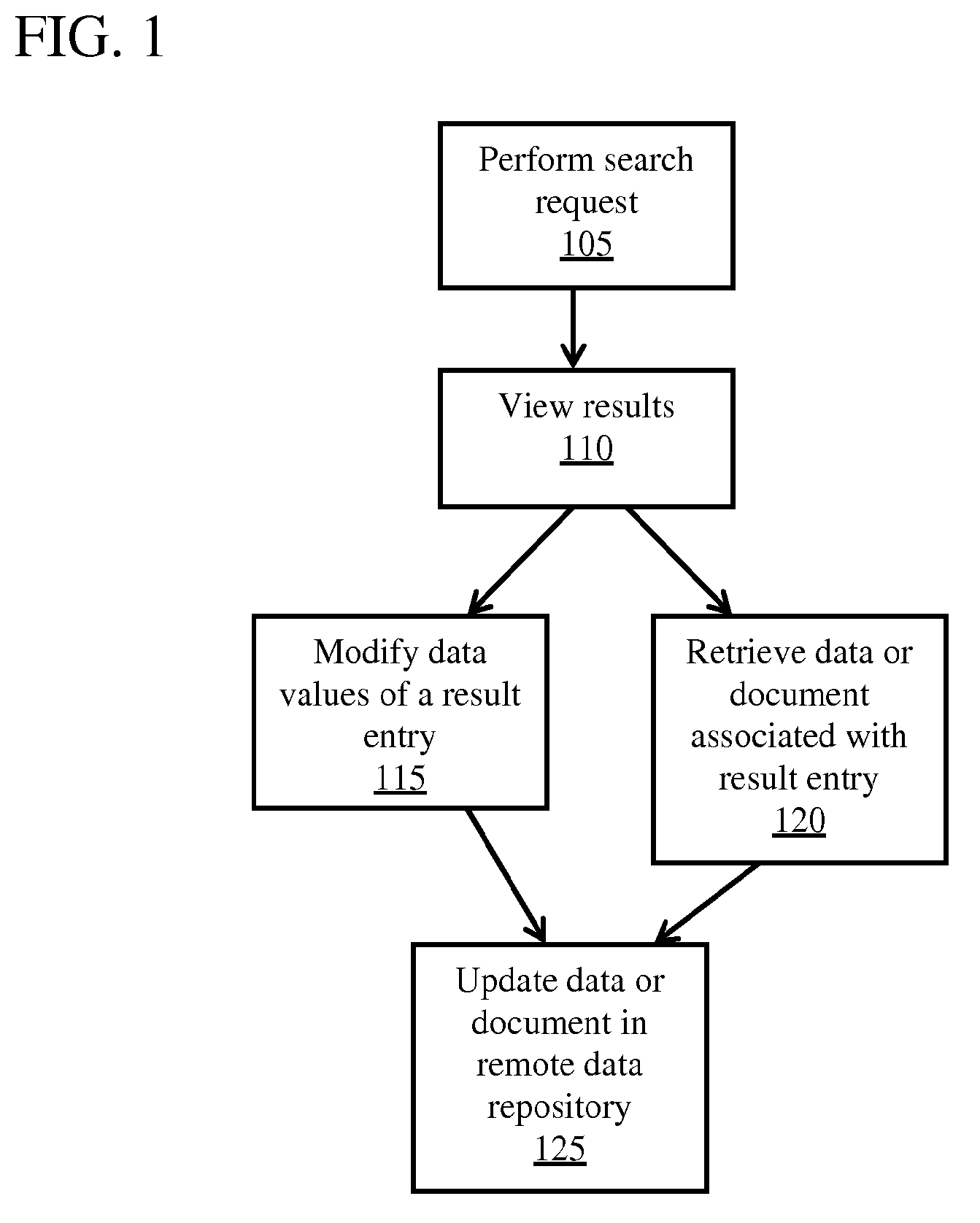
InactiveCN102118433AImprove scalabilityPromote migrationTransmissionCluster systemsConsistent hashing
The invention discloses a multiple-tier distributed cluster system and solves the possible content transfer of common load balance technology that is based on a polling strategy or content hash. The system solves the problems of cluster expansibility, content transfer and the like by adopting tiered load balance technology and combining the polling strategy and consistent hashing algorithm. The technical scheme of the system is as follows: the system comprises a transport tier load balancer at the front end of the system, a URL (Uniform Resource Locator) consistent hashing balancer at the middle tier of the system, and a real server at the rear end of the system, wherein the transport tier load balancer receives request data transmitted by a client side and conducts load balance; requests of the client side are distributed to the URL consistent hashing balancer at the middle tier; the URL consistent hashing balancer receives the request data of the client side distributed by the transport tier load balancer and distributes the same URL to the same real balancer for service through the consistent hashing algorithm; and the real server stores the data.
Owner:CHINANETCENT TECH
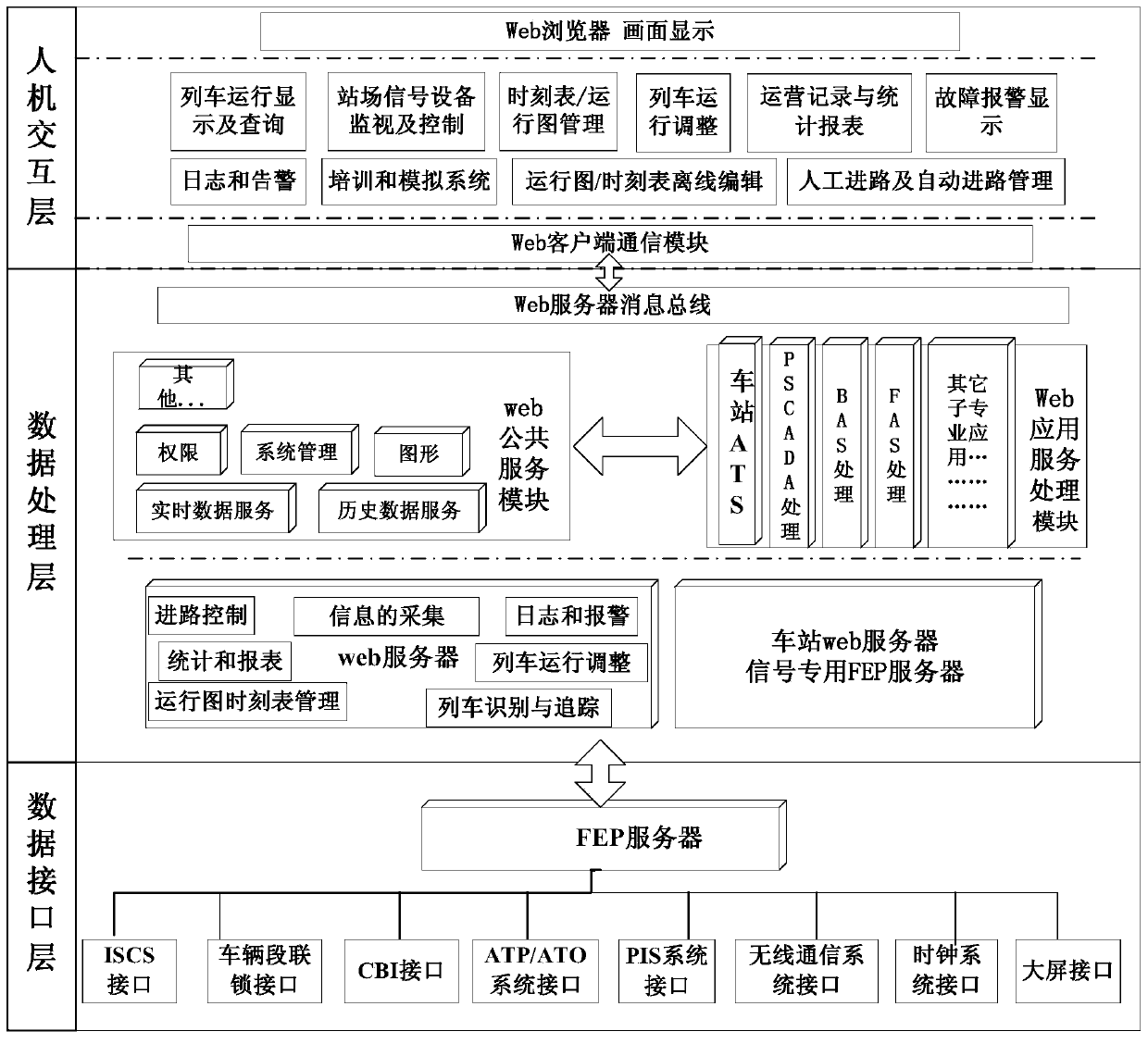
Train real-time monitoring system based on B/S architecture
InactiveCN103442055ARealize real-time monitoringEasy to useSignalling indicators on vehicleTransmissionMonitoring systemThe Internet
The invention discloses a train real-time monitoring system based on a B / S architecture. The train real-time monitoring system comprises a three-layer mode architecture based on the B / S architecture, and the three-layer mode architecture comprises an uppermost man-machine interaction layer, a middle data processing layer and a lowermost data interface layer. The train real-time monitoring system has the advantages of adaptability and extendibility of the B / S architecture, convenient maintenance and low total cost; the train real-time monitoring system also has real-time communication capacity of an application system under a C / S architecture, operates on the internet, overcomes space and regional limits and can have access to the system through a browser anywhere, a train can be monitored in time whenever and wherever possible, a communication method is simple, network resources are saved, network distribution is convenient to achieve, and the train real-time monitoring system is convenient to use and has good application prospects.
Owner:NARI TECH CO LTD +1
Interlayer system used for searching database information and information searching method
ActiveCN102426589AAdd fieldEfficient searchTransmissionSpecial data processing applicationsApplication serverInformation searching
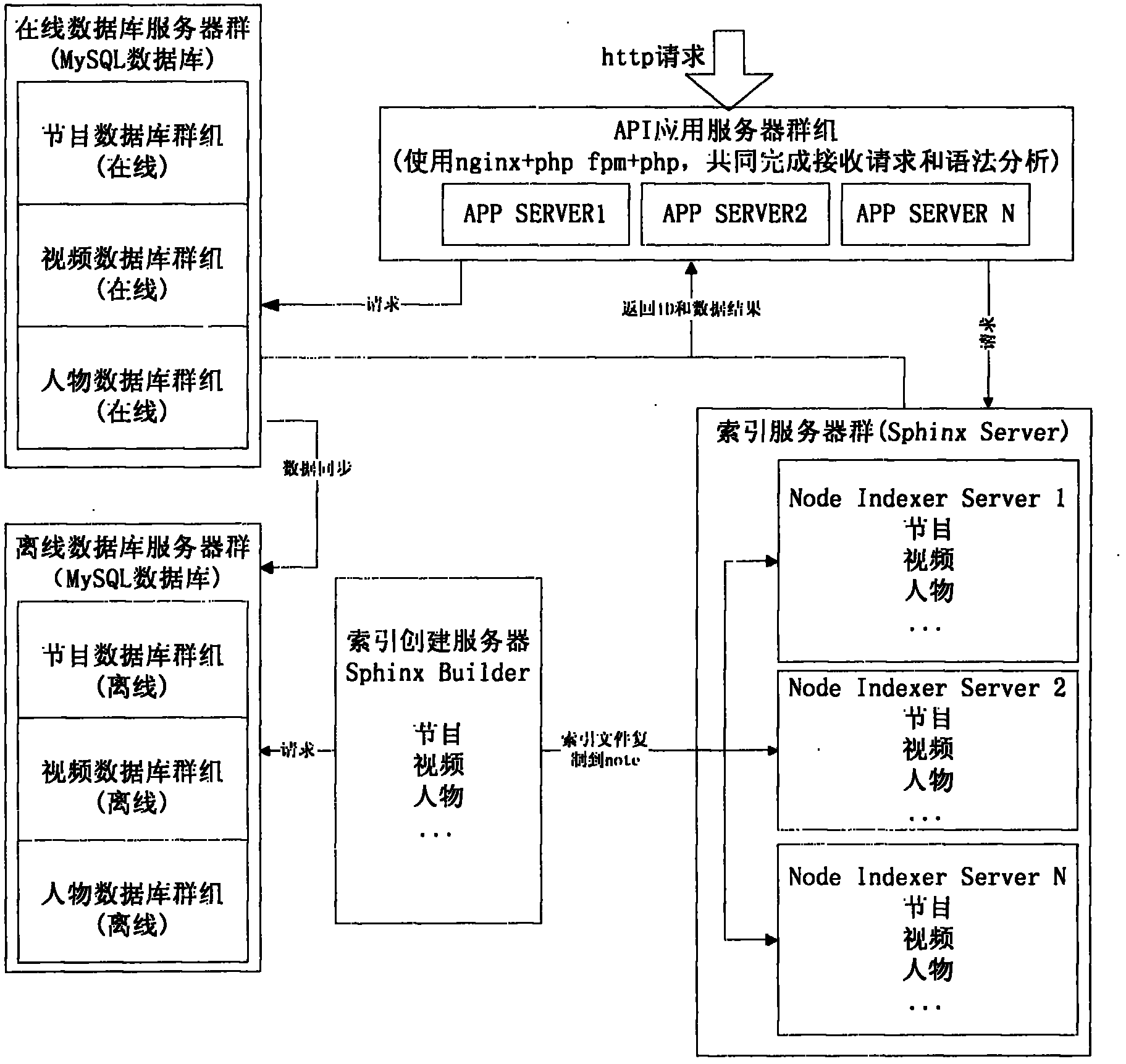
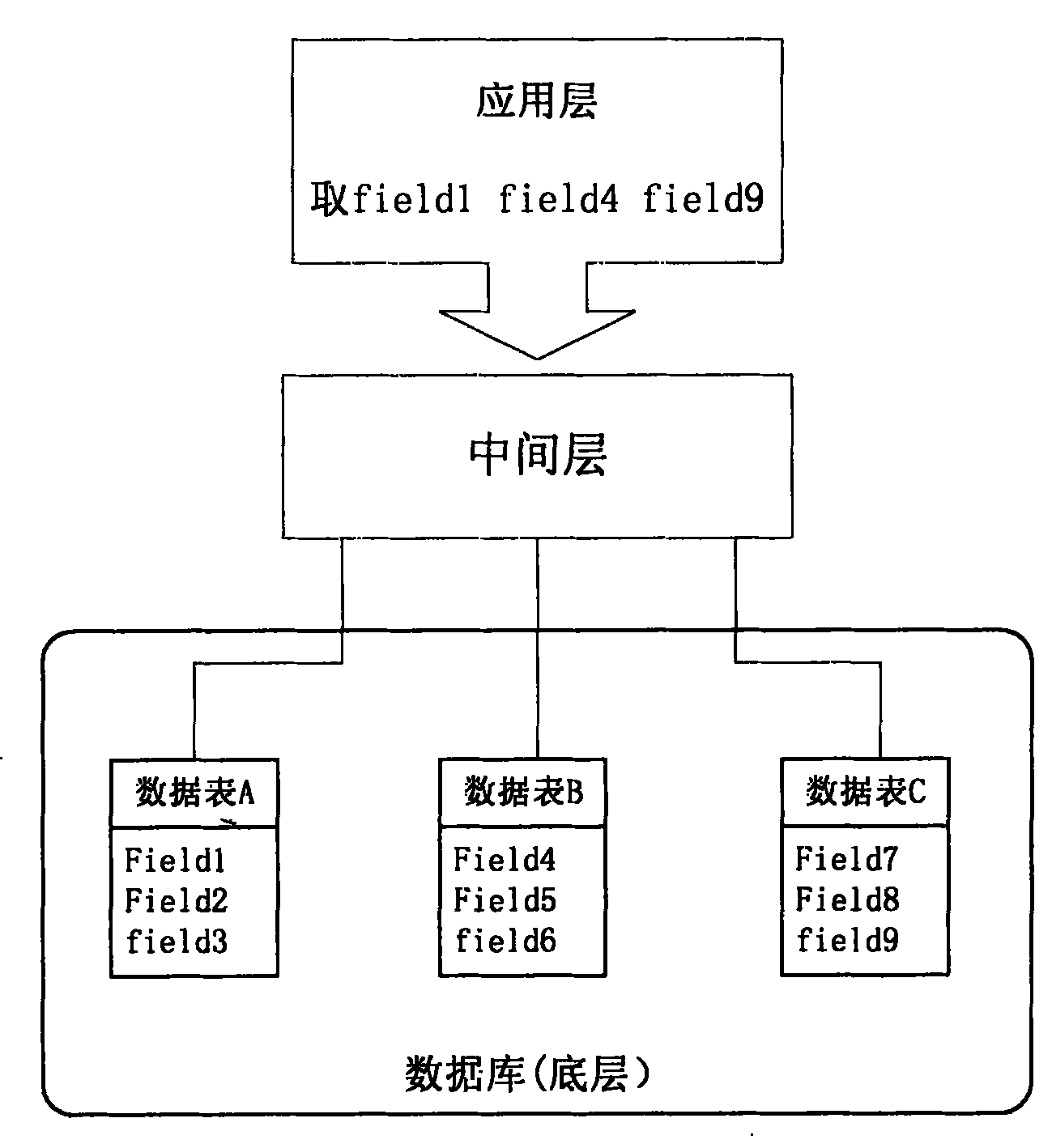
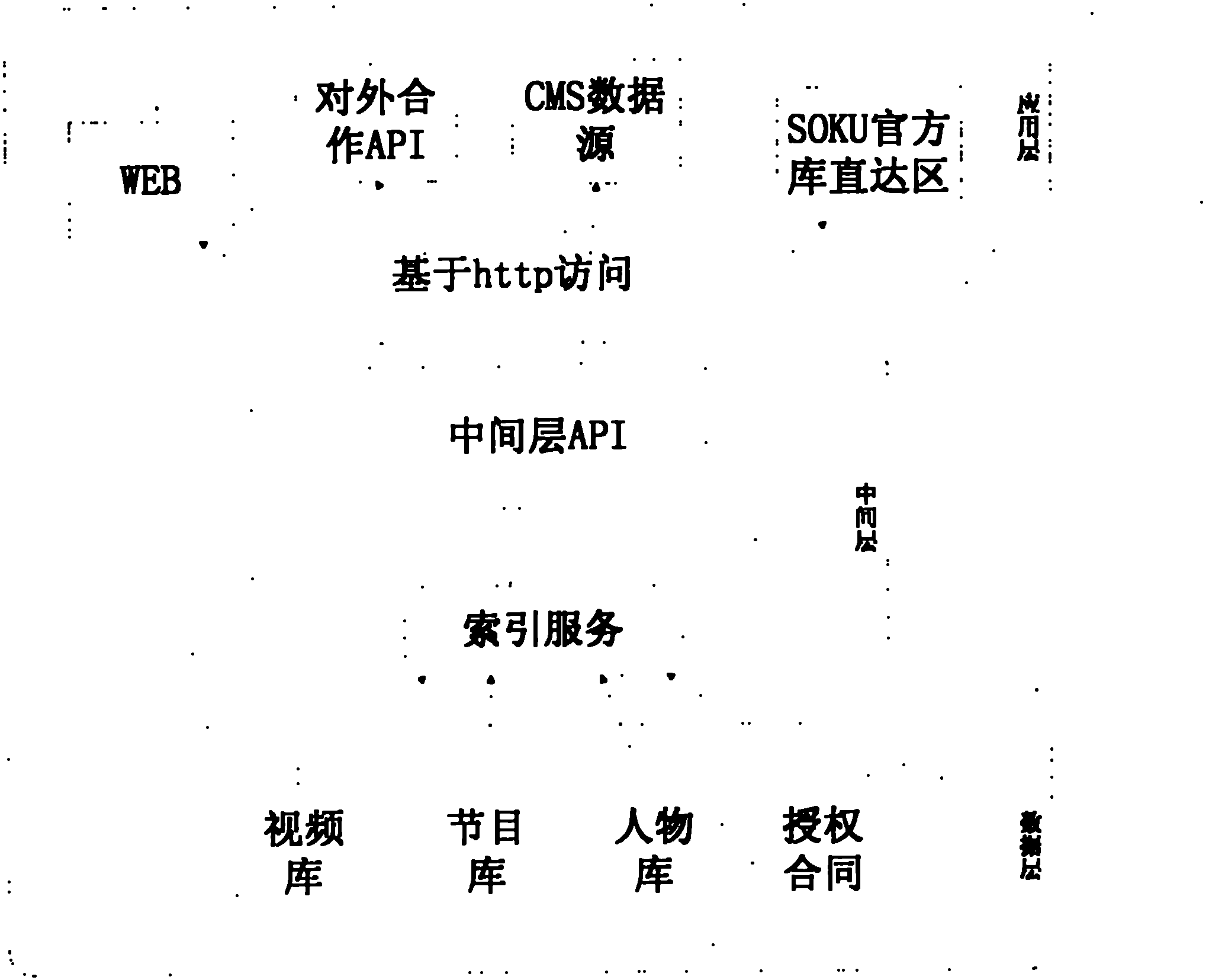
The invention relates to an interlayer system used for searching database information and an information searching method. The interlayer system comprises an API (Application Program Interface) application server group used for receiving a searching request sent by an application layer, wherein the API application server group is used for acquiring an ID of a searched video from an index server and acquiring the video from an on-line database according to the ID of the video. After the information of the on-line database is synchronized by an off-line database, an index is created and stored in an index server group by an index creating server. In the interlayer system used for searching the database information and the information searching method provided by the invention, the interlayer system can be used for receiving the searching request based on an http protocol, and after syntax analysis and engine analysis are performed, the data can be accurately acquired. The searching for the combination of any field with a large data volume is achieved, the searching time of the database is short, a data layer is separated from the application layer, and the development of the data layer and the application layer are free from being influenced by each other.
Owner:ALIBABA (CHINA) CO LTD
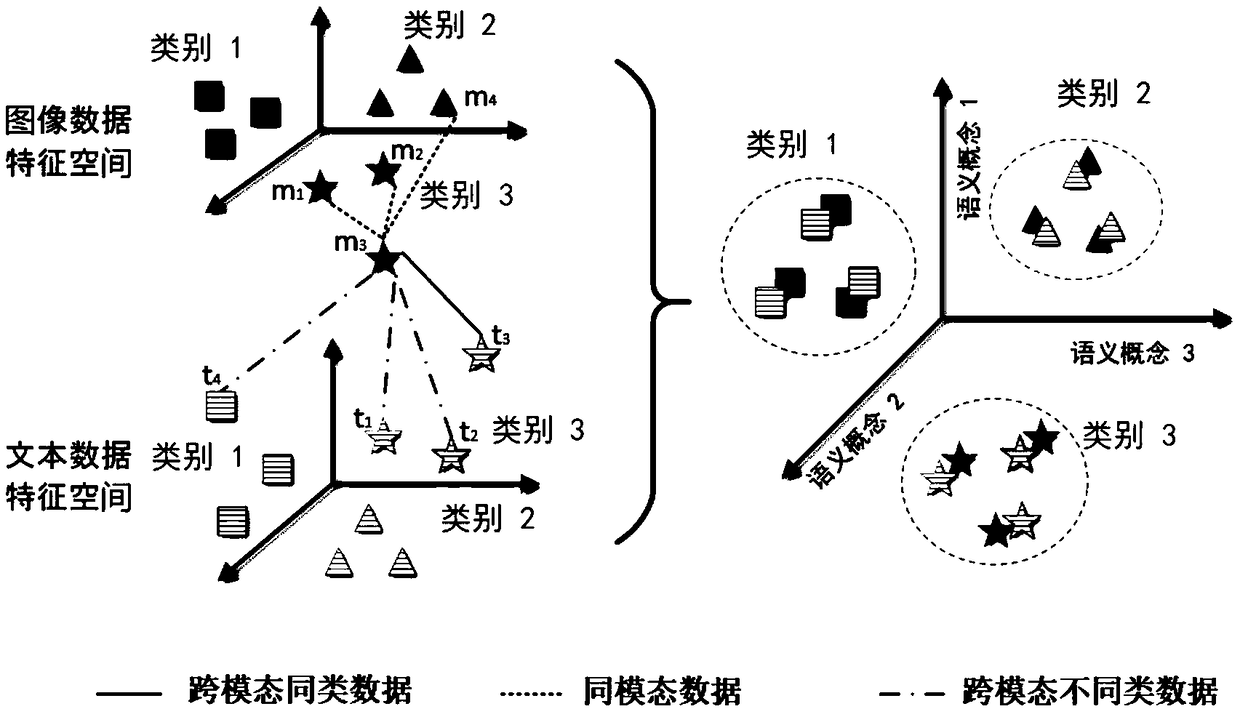
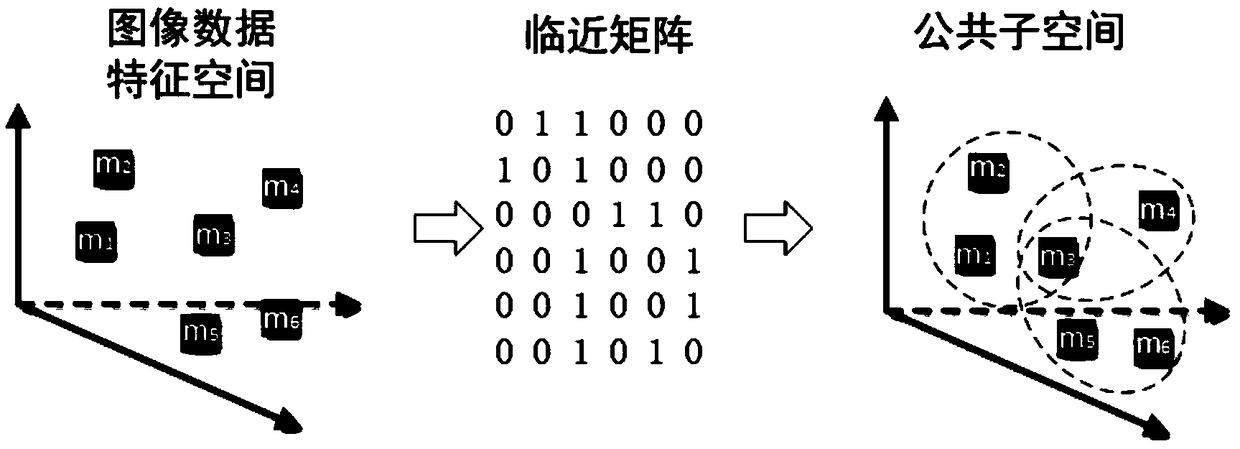
A cross-modal retrieval method based on cyclic generation antagonistic network
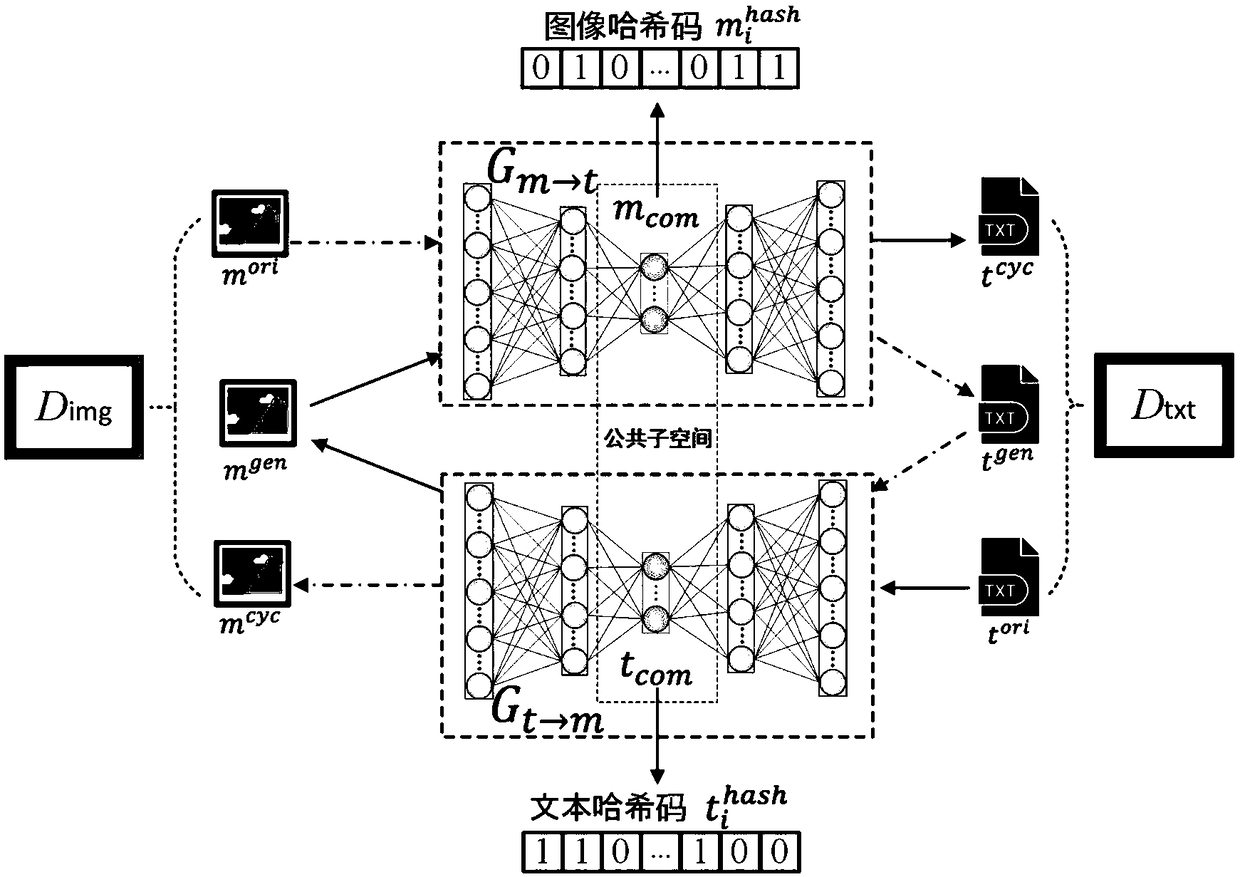
ActiveCN109299342AEstablish semantic relationshipImprove accuracyCharacter and pattern recognitionOther databases queryingModal dataApproximation function
The invention discloses a cross-modal retrieval method based on a cyclic generation antagonistic network. The method designs a novel dual-channel cyclic generation antagonistic neural network and establishes semantic correlation of cross-modal data by training the neural network. Given different modal data can flow bi-directionally in the network, each modal data can generate another modal data through a group of generative antagonistic networks, and the generated data can be used as the input of the next group of generative antagonistic networks, so that the bi-directional loop generation ofdata can be realized, and the network continuously learns the semantic relationship among the cross-modal data. In order to improve the efficiency of retrieval, The method also uses threshold functionand approximation function to approximate the result of the middle layer of the generator to the corresponding binary hash code, and designs a variety of constraints to ensure the same mode, the similarity and cross-mode of the same kind of data, and the difference of data between classes, thus further improving the accuracy and stability of retrieval.
Owner:WUHAN UNIV
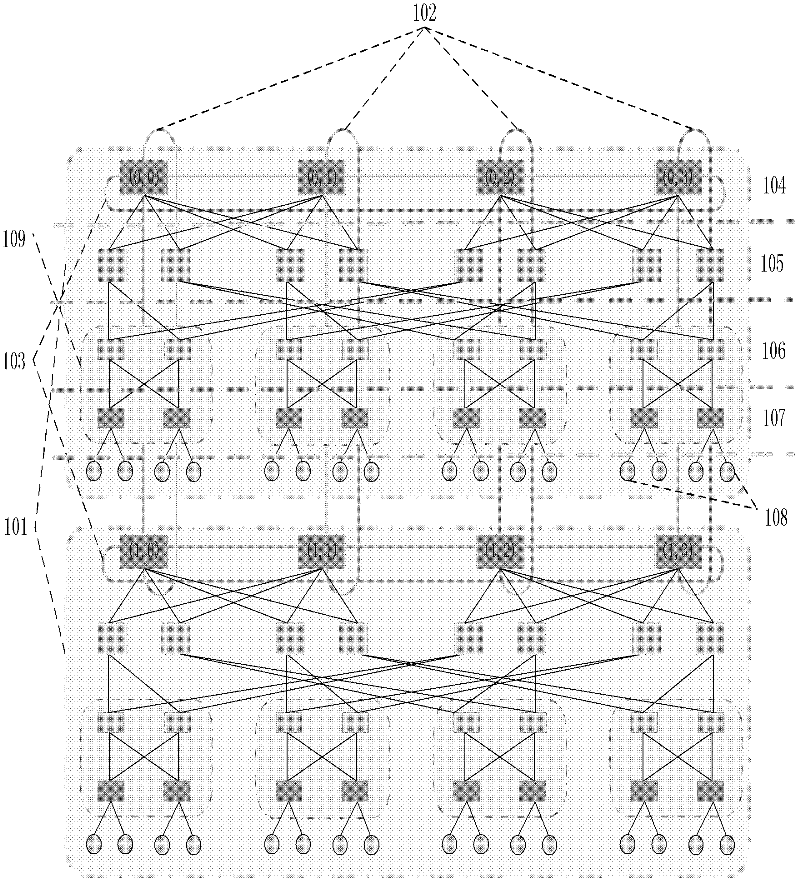
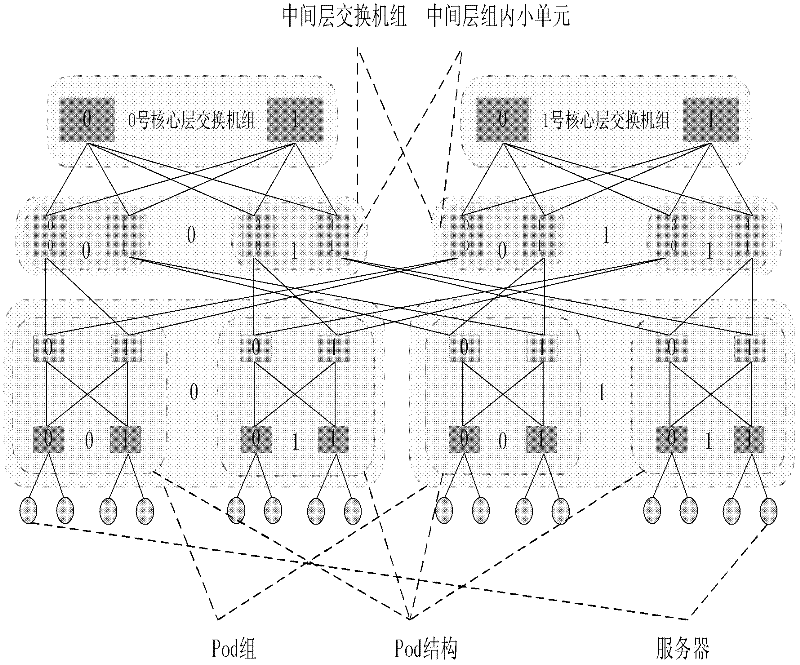
Data center network topology system based on module expansion
InactiveCN102394782AMeet application development needsAchieving dynamic selectivityData switching networksFault toleranceNetwork size
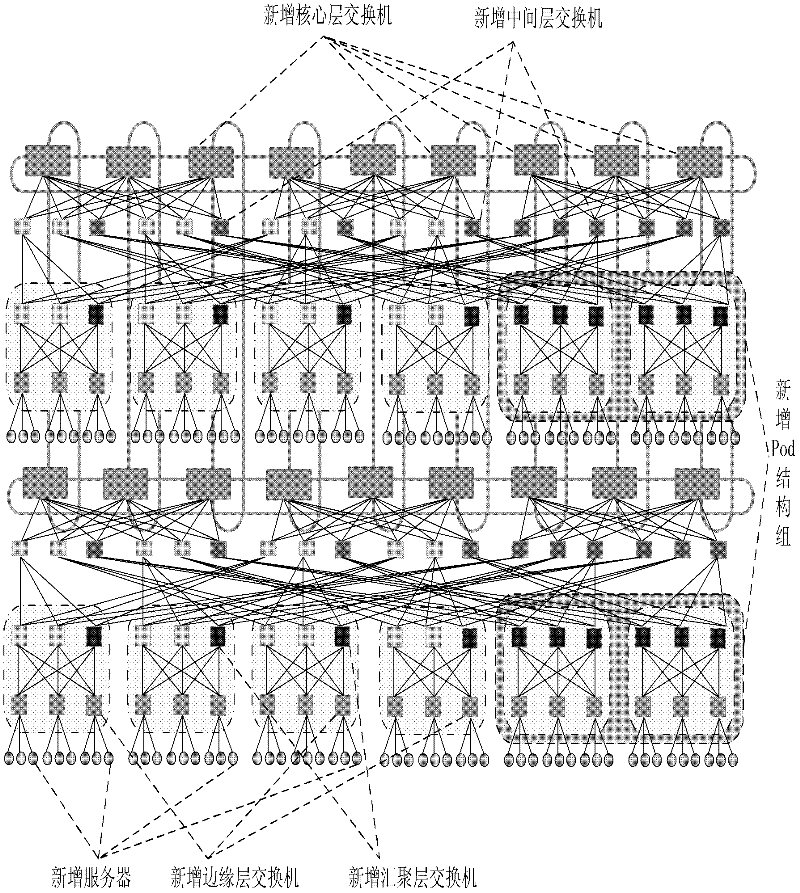
The invention discloses a data center network topology system based on module expansion. And therefore, a problem that an expansion capability of tree topology of a data center is limited to the number of ports of a switch device and insufficiency of dynamic selectivity of a downlink can be solved. The implementation steps of system are as follows: an intermediate layer is introduced between a core layer and a convergence layer of a fat tree structure; a small network that is formed by connection of switches and servers of each of the layer is recorded as a basic module, so that a plurality of basic modules are constructed; four additional ports of switches of the core layer are utilized to connect all the basic modules to form a large whole network, so that a demand of construction of a data center network can be met and dynamic selection of a down link can be satisfied as well as a high halving bandwidth is provided; and lateral expanding, vertical expanding or mixing expanding is carried out on the network topology system as well as expansion of the network scale is supported flexibly. According to the invention, the system has a high network fault tolerance performance; more server devices can be accommodated; and a demand of application expansion in the future can be met; therefore, the system can be applied to construction of a data center network and high bandwidth data transmission can be provided.
Owner:XIDIAN UNIV
Receive processing with network protocol bypass
InactiveUS6956853B1Reducing number of time payloadPerformanceDigital computer detailsData switching by path configurationNetwork interface deviceNetworking protocol
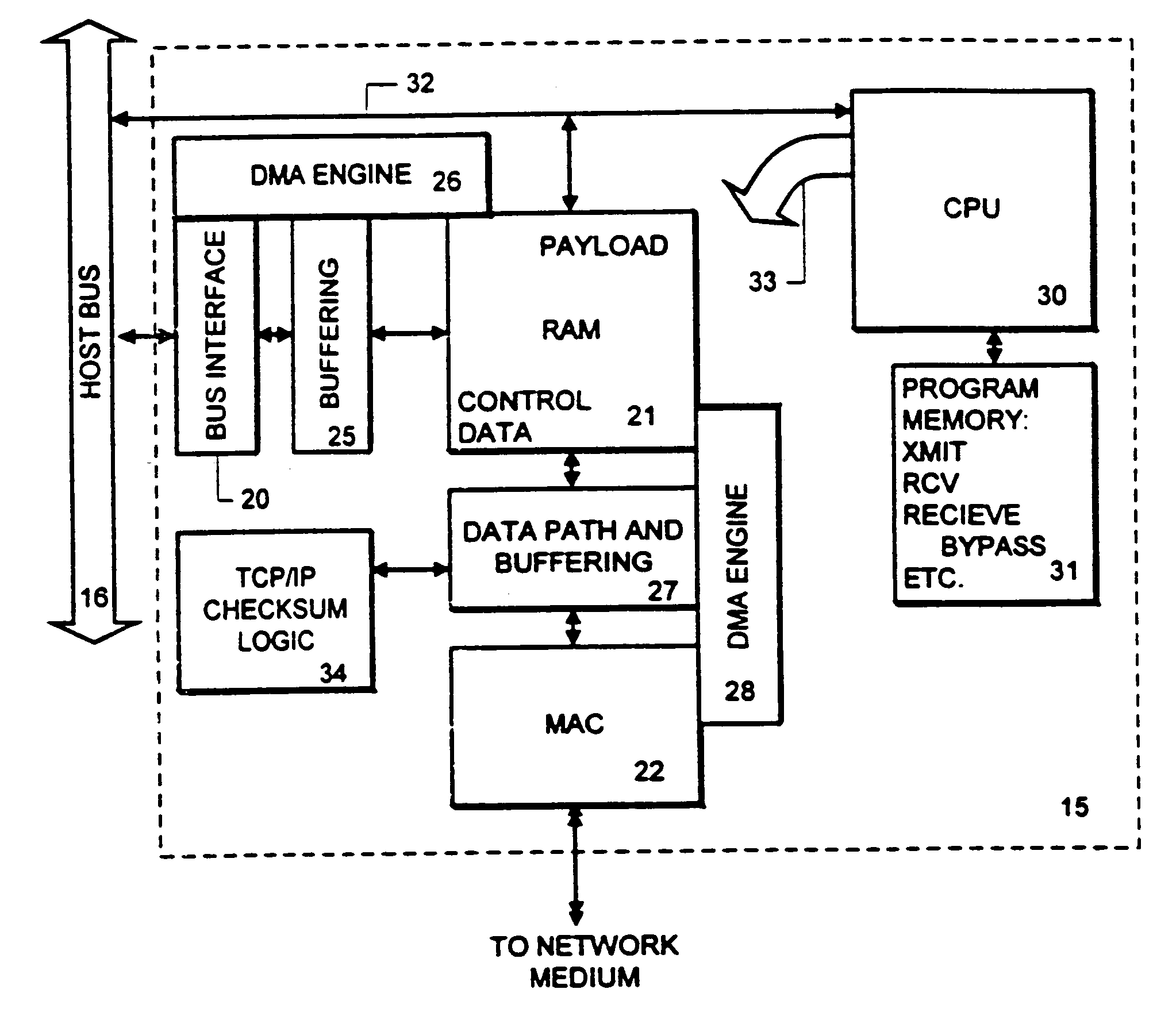
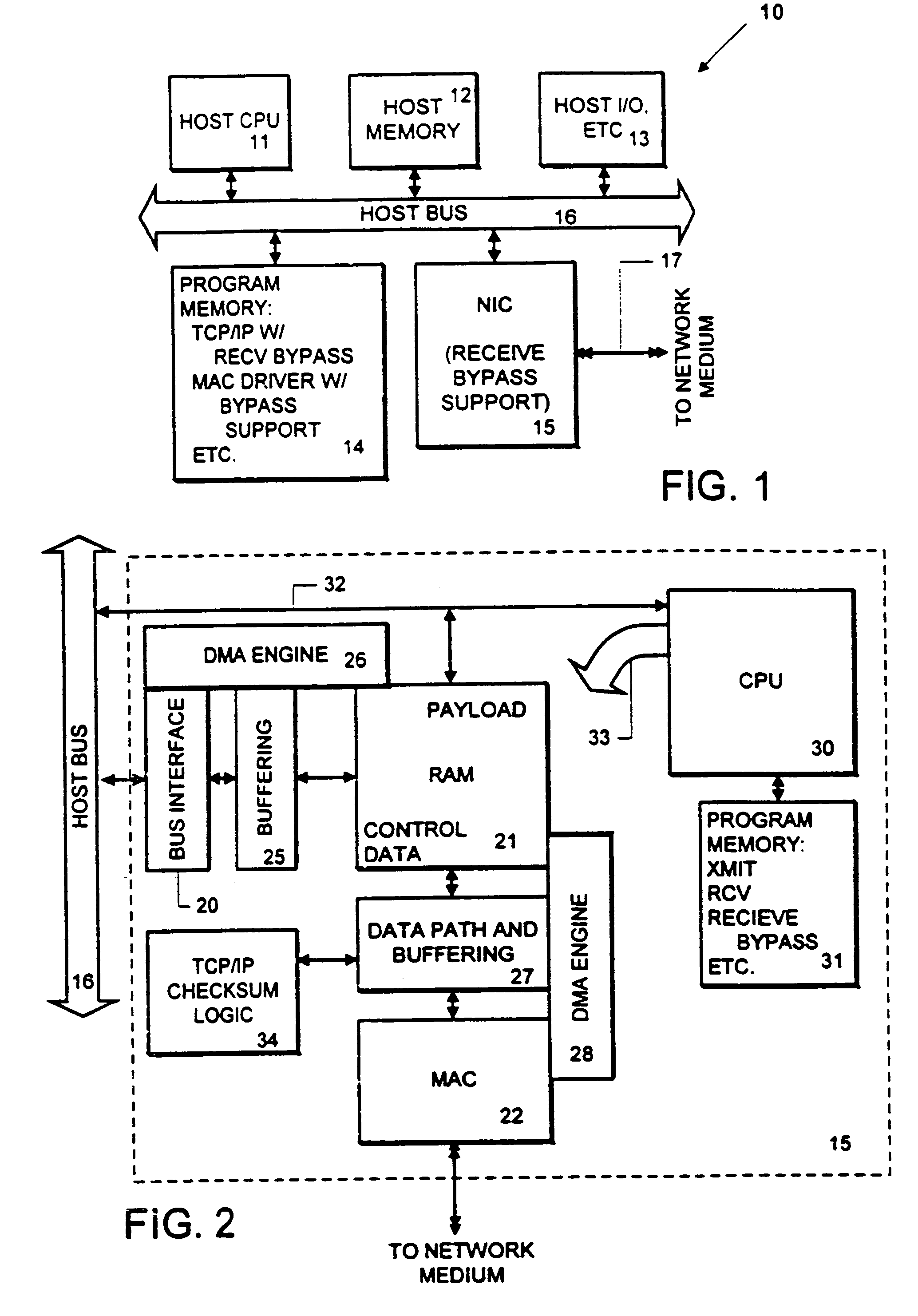
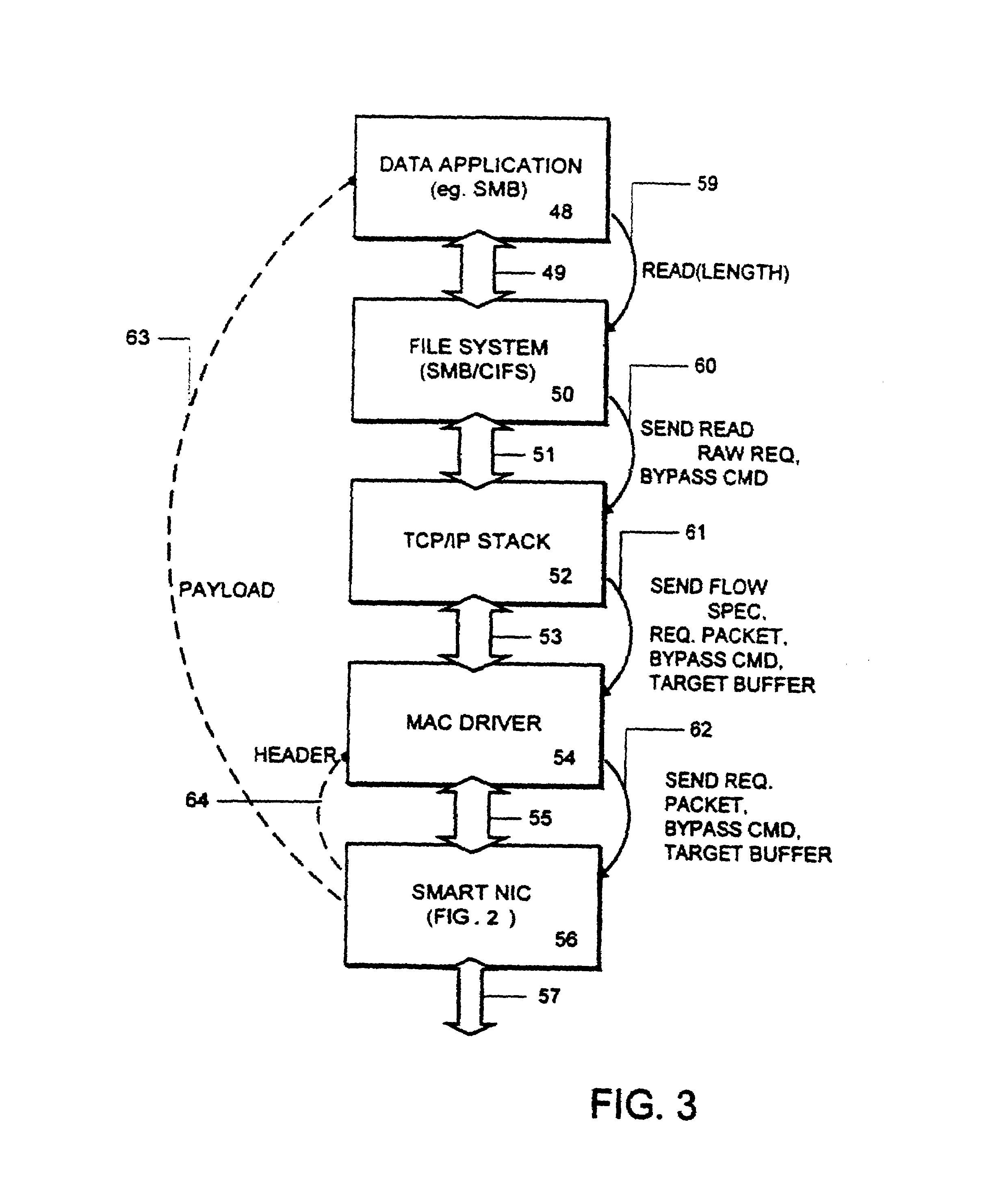
An adapter is provided with intelligence that allows it to separate the header parts of a packet being received from the payload it carries, and in most cases move the payload directly into a destination buffer at the application layer or file system layer. Copies by the intermediate layers of the protocol stack are bypassed, reducing the number of times that the payload of a communication must be copied by the host system. At the network interface, a plurality of packets is received, and the payload of each is bypassed directly into the target destination buffer. The network interface device identifies the packets which are in the sequence of packets carrying payload to be stored in the target buffer by the flow specification carried with such packets. Also, the packets carrying data payload for the file include a sequence number or other identifier by which the network interface is able to determine the offset within the target buffer to which the packet is to be stored.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Drainage internet-of-things system
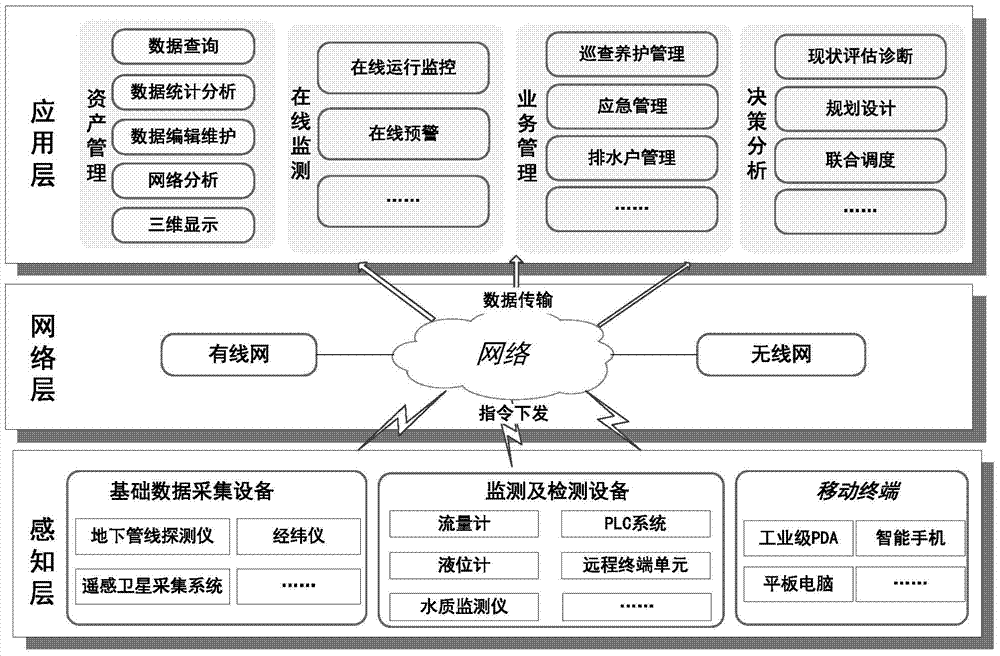
ActiveCN103543706ARealize visualizationRealize the integration of management and controlData processing applicationsTransmissionCorrelation analysisDigitization
The invention provides a drainage internet-of-things system comprising a sensing layer, a network layer and an application layer. The sensing layer is located at the bottommost layer of the drainage internet-of-things system and composed of various transmission units; the network layer is located in the intermediate layer of the drainage internet-of-things system, and is a link for linking a monitoring center and each field site. The network layer realizes bidirectional information transmission between the application layer and the sensing layer through an existing wired network, a wireless network and the like; the application layer is located in the topmost layer of the drainage internet-of-things system, acquires the sensing layer mainly based on data analysis methods such as correlation analysis and cluster analysis or a hydrodynamic model, and performs summary analysis and deep mining through data transmitted by the network layer so as to guide management and operation maintenance of a drainage system. By the application of the drainage internet-of-things system, a traditional drainage management mode is changed, running supervision, scientific warning and unified scheduling of the drainage system are realized, and intelligent and digital management level of the drainage system is increased effectively.
Owner:北京清控人居环境研究院有限公司
Three-dimensional scene real-time drafting framework and drafting method
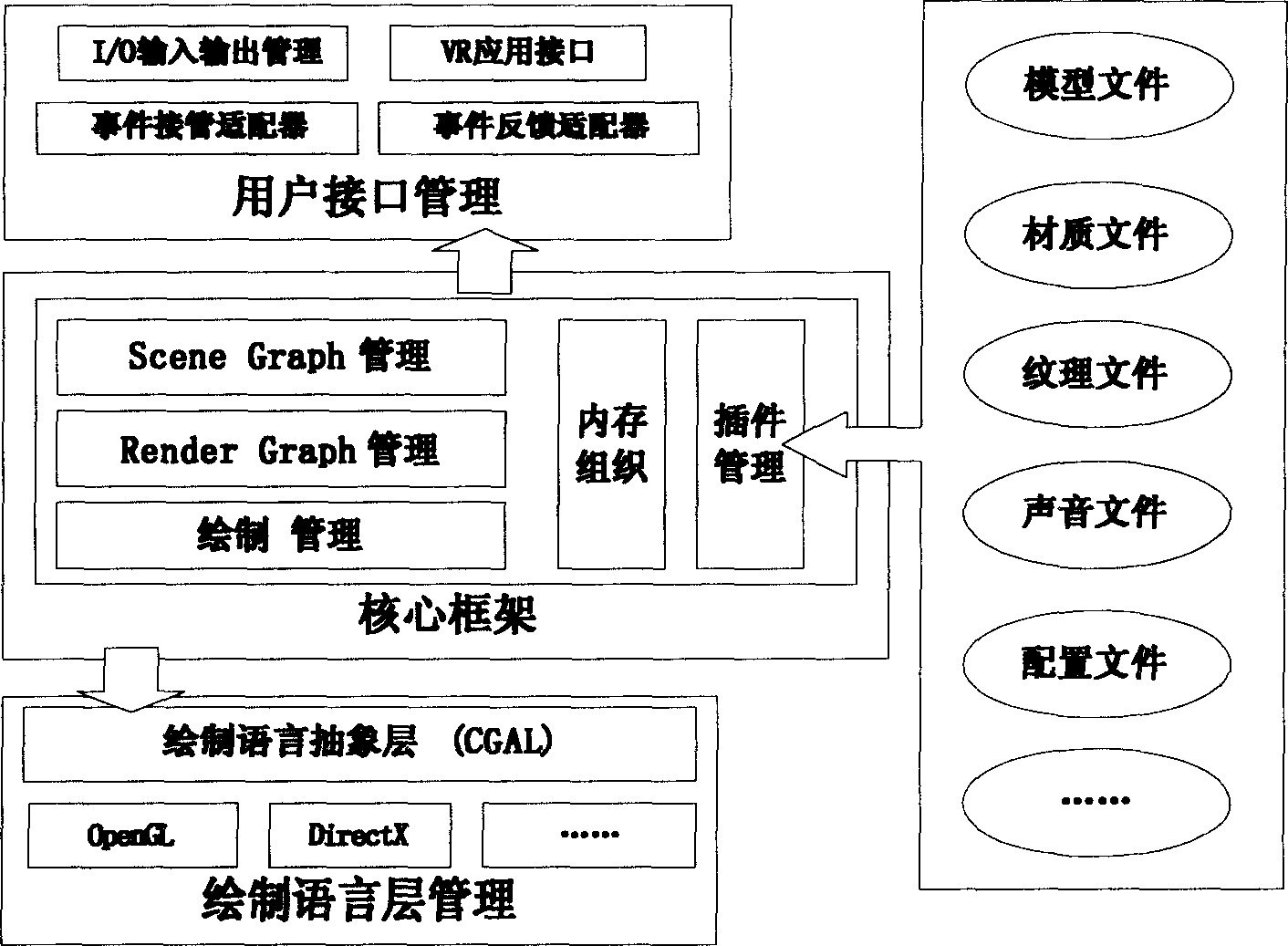
InactiveCN1763784AUser-friendly calling mechanismConvenient message processing mechanism3D-image renderingProcess mechanismInterface layer
The invention discloses a three-dimensional scene real-time drafting frame of three-layer system, which is characterized by the following: the bottom layer is drafting language administration layer to call all states and drafting properties of different edition format drafting language; the medium layer contains slot administration, scenegraph administration, drafting graph administration and drafting administration mode; when the top layer displays the call requirement; the slot administration mode reads the model file to form scene image through scenegraph administration mode, which finishes App, Cull and Draw operation of scenegraph through drafting administration mode; the top layer provides interface layer for user, which provides convenient user call mechanism and message disposal mechanism.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com