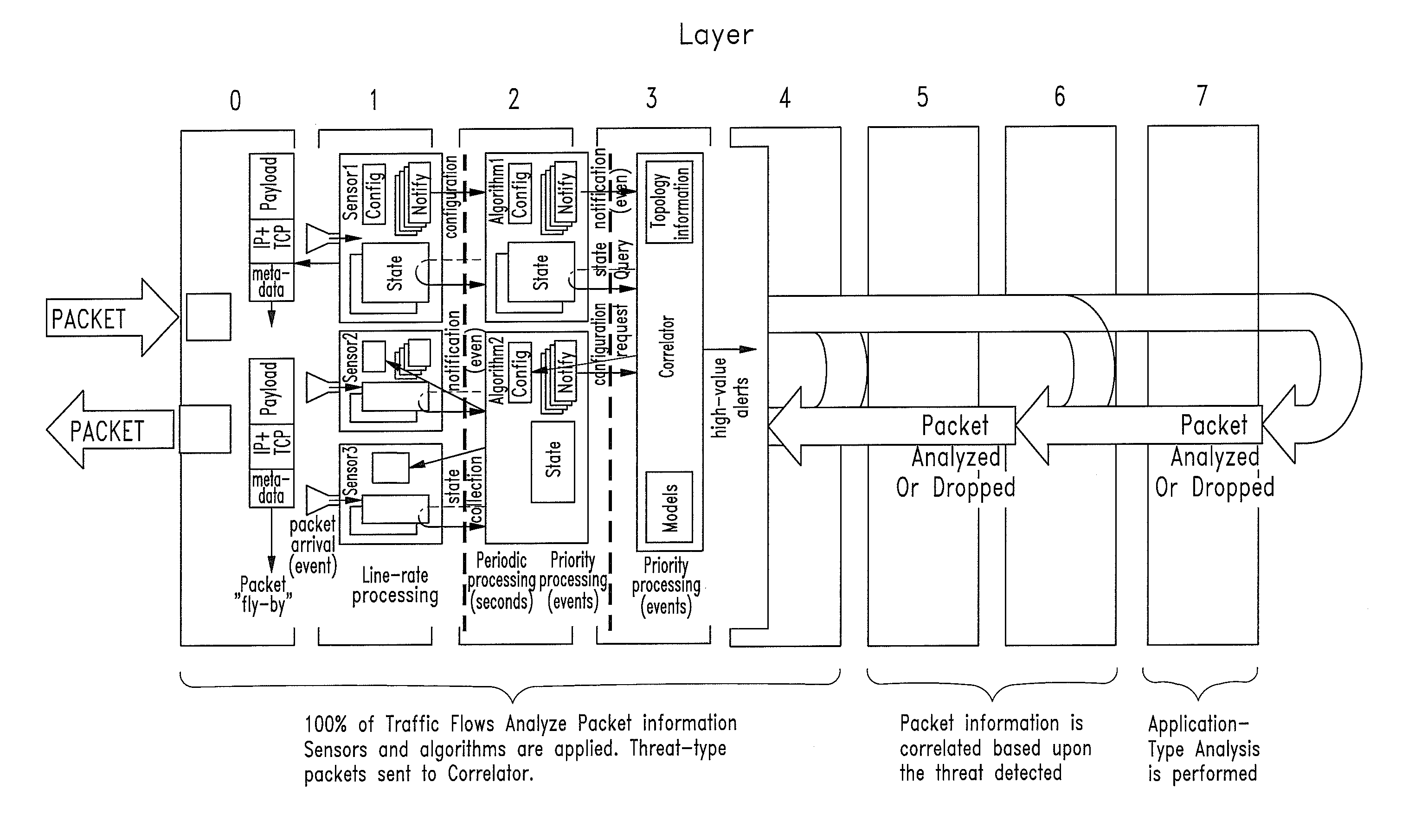
Patents
Literature
5359 results about "Network layer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
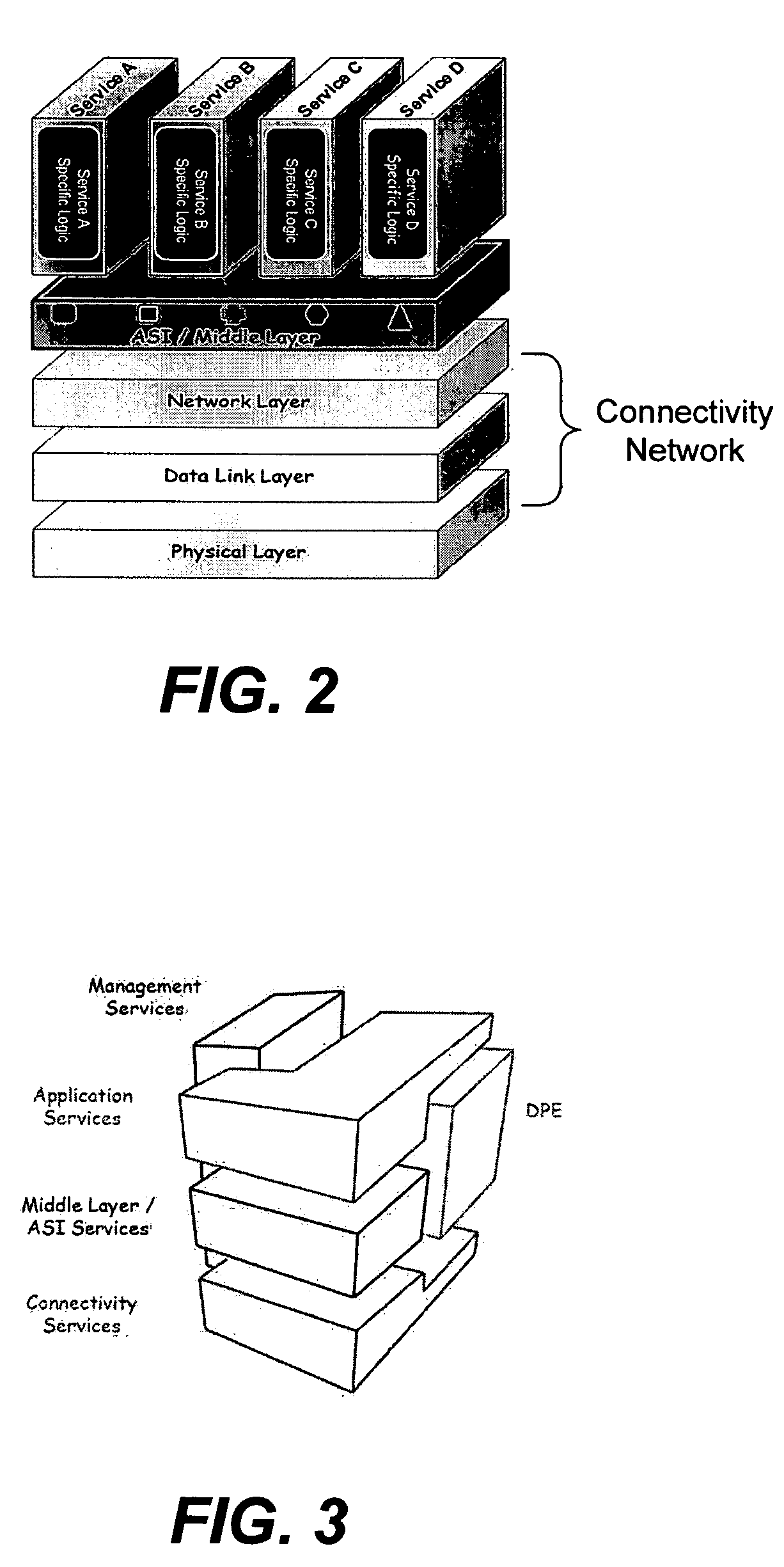
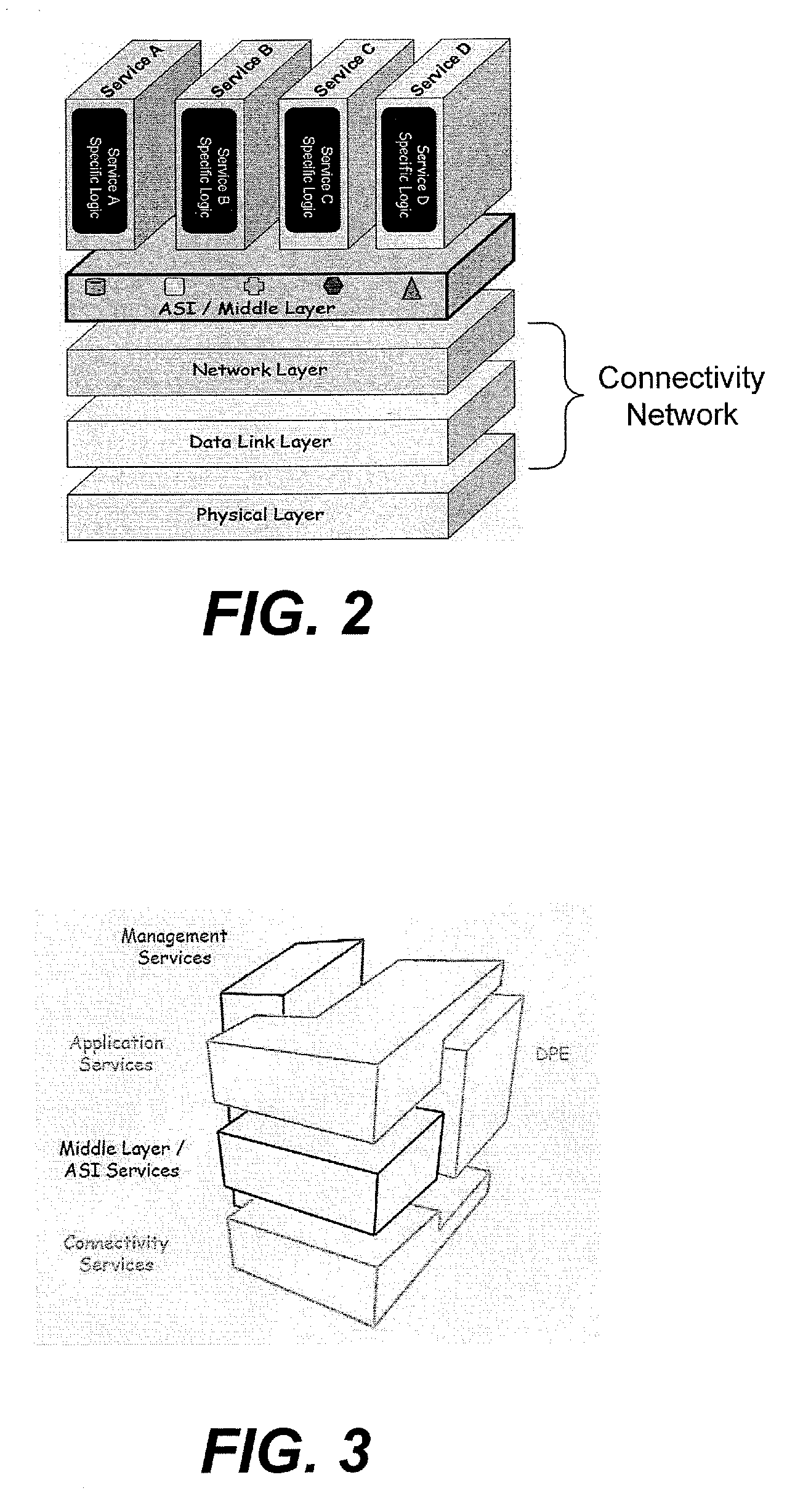
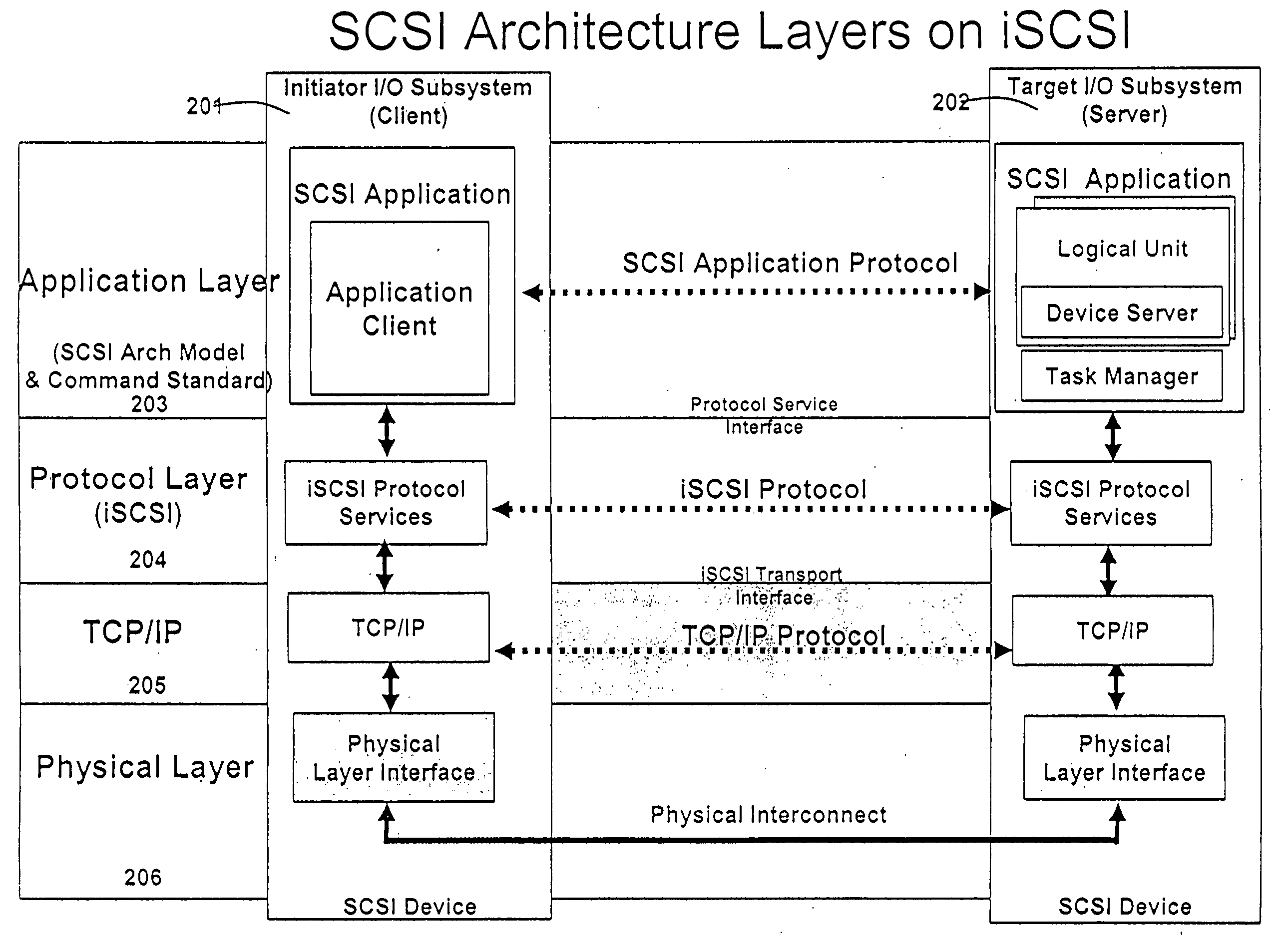
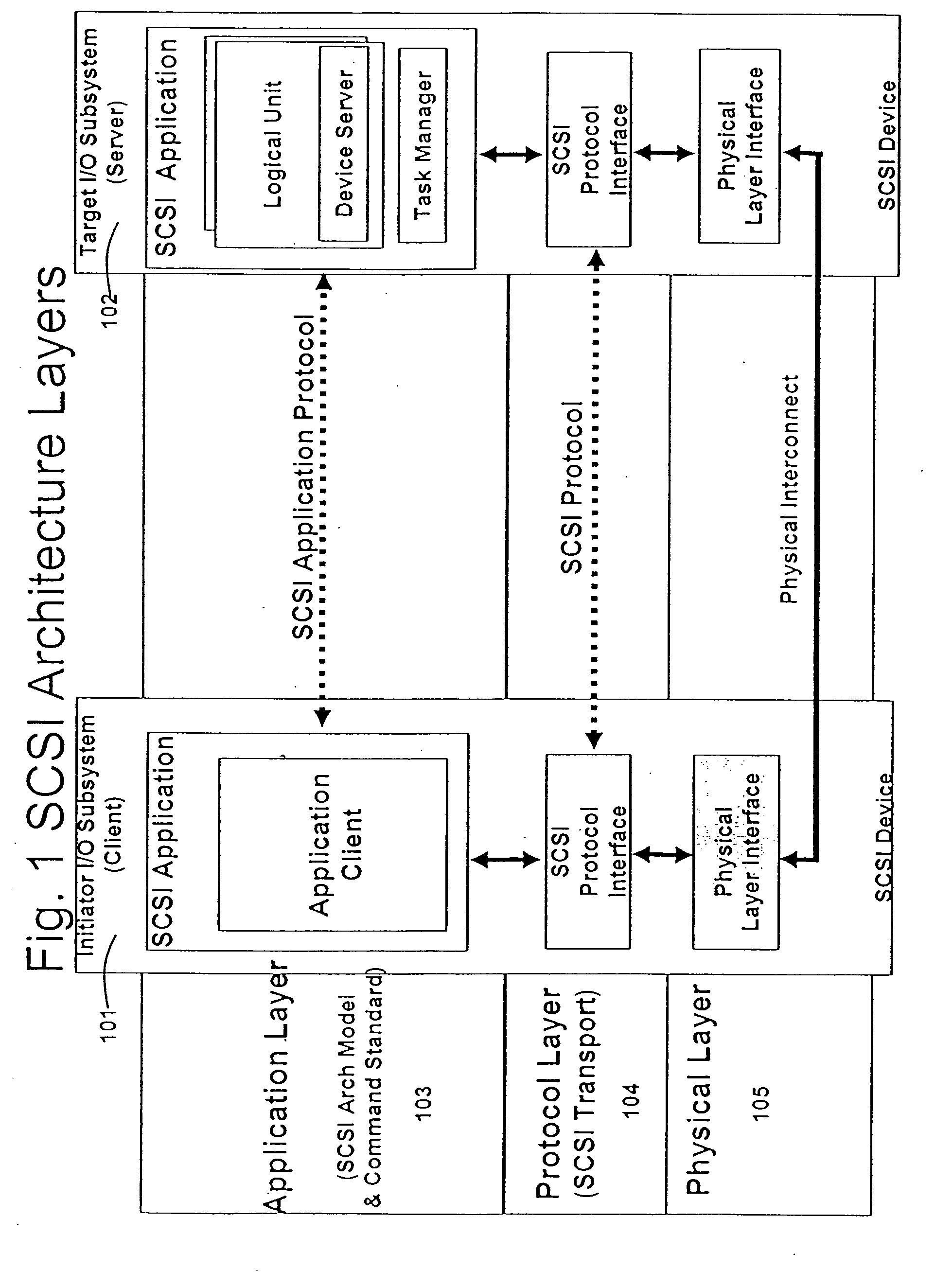
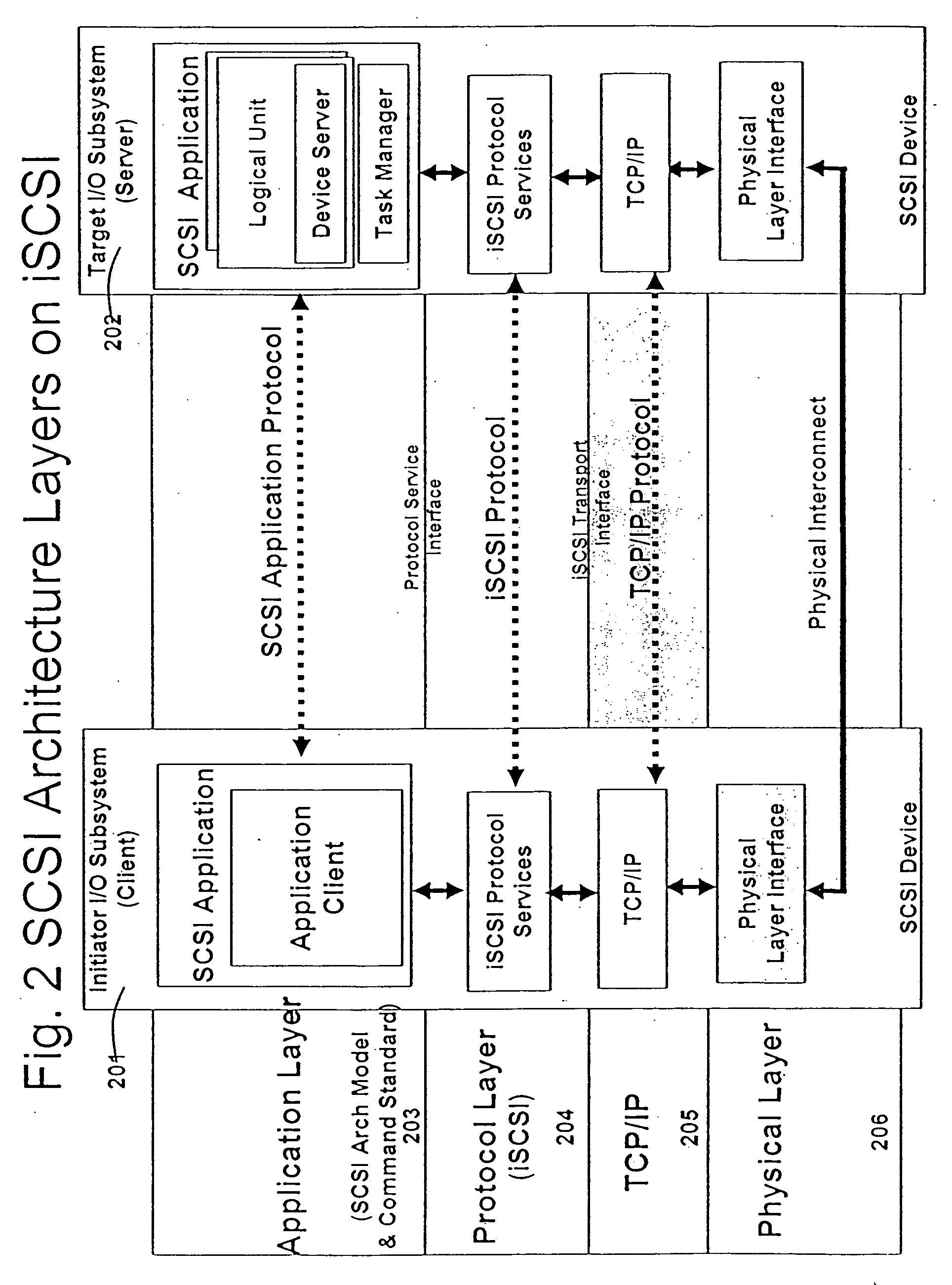
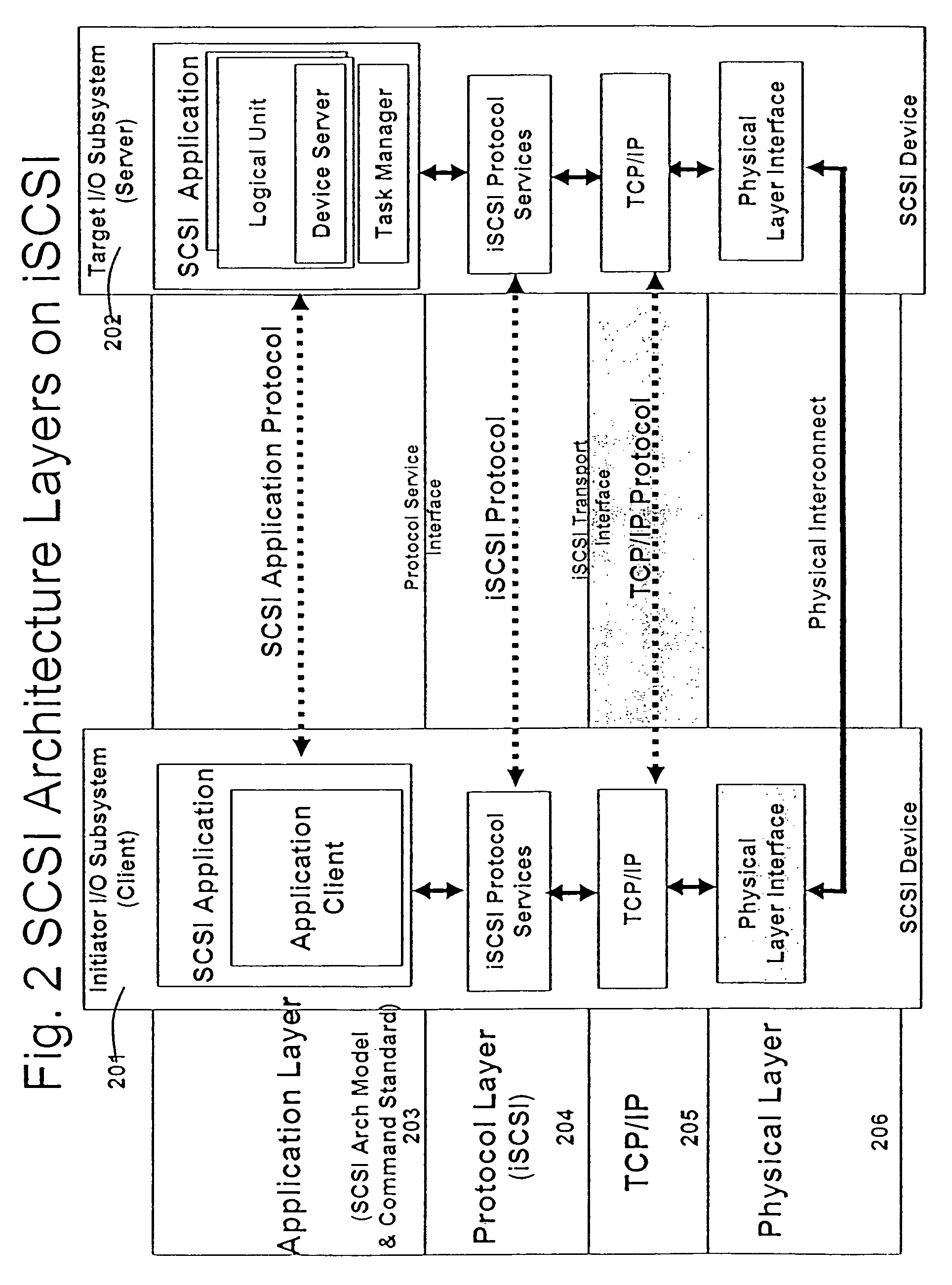
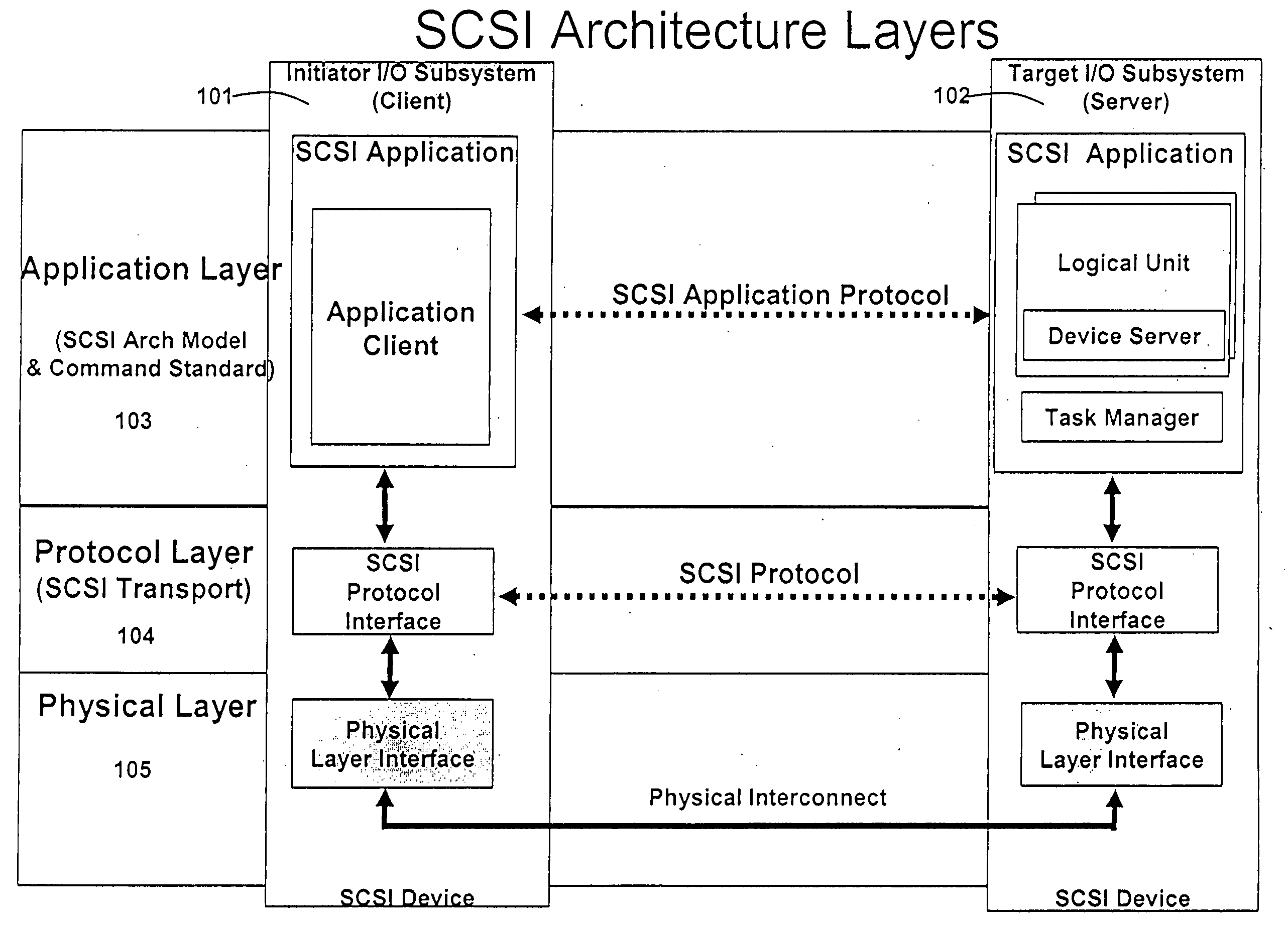
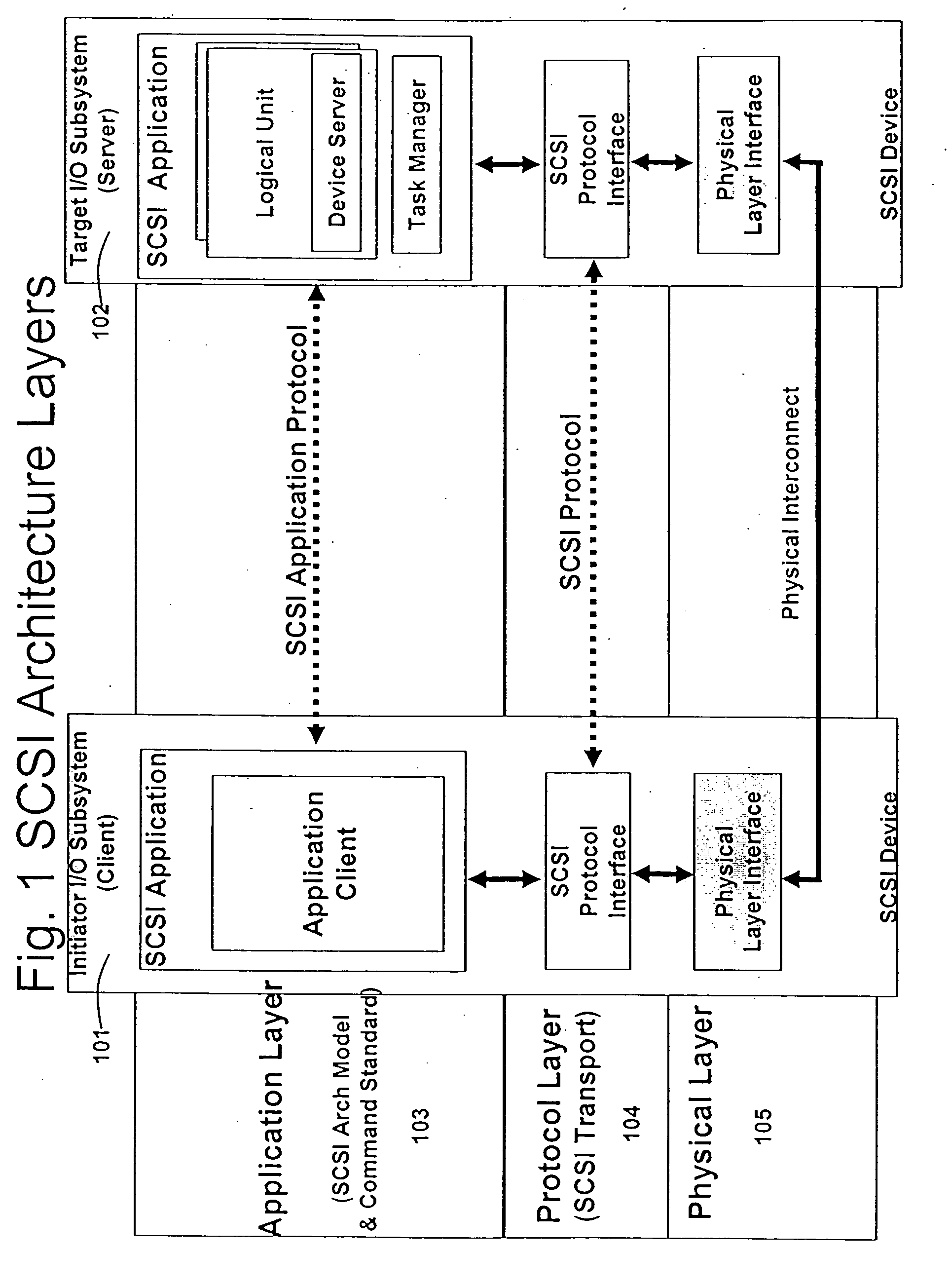
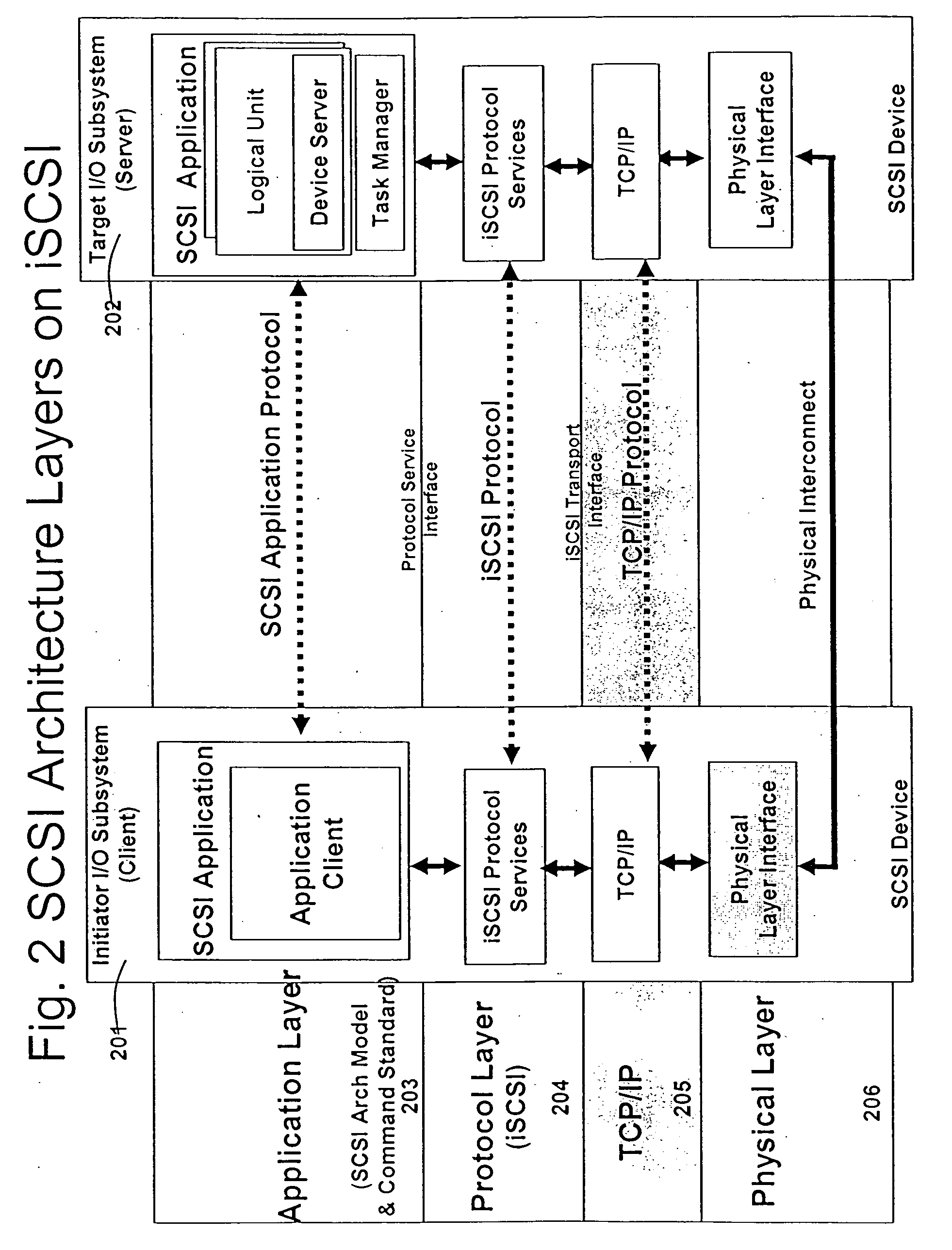
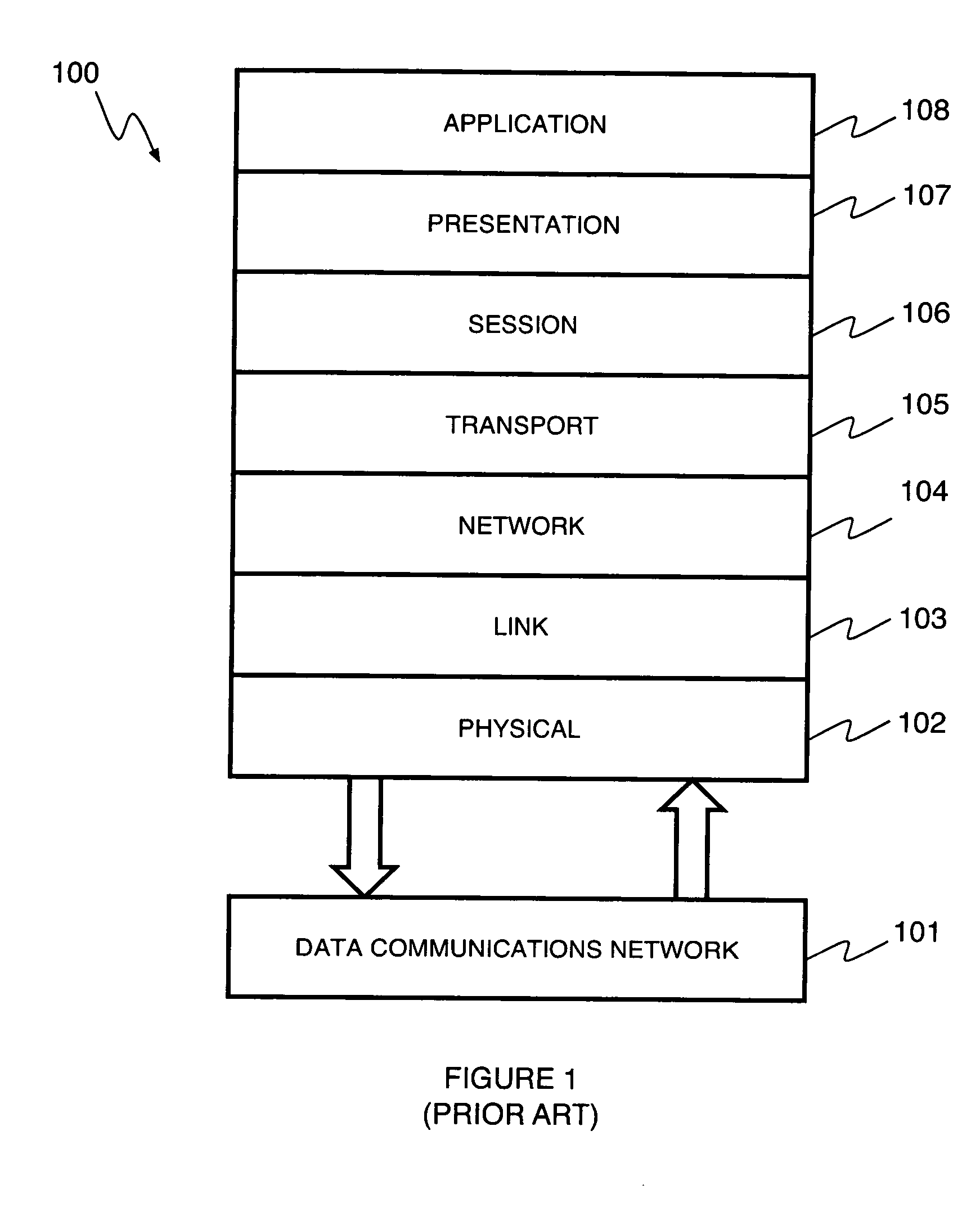
In the seven-layer OSI model of computer networking, the network layer is layer 3. The network layer is responsible for packet forwarding including routing through intermediate routers.
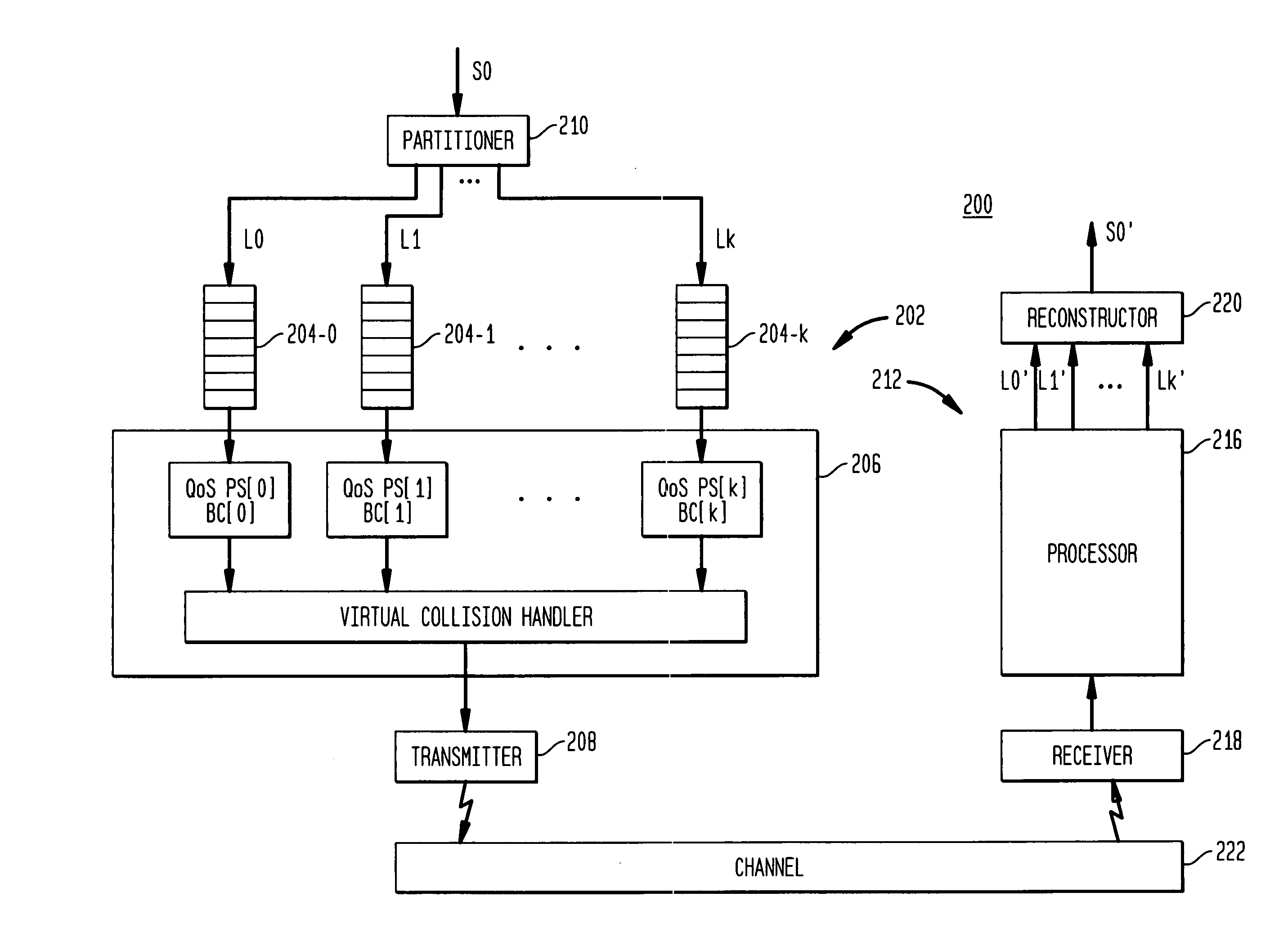
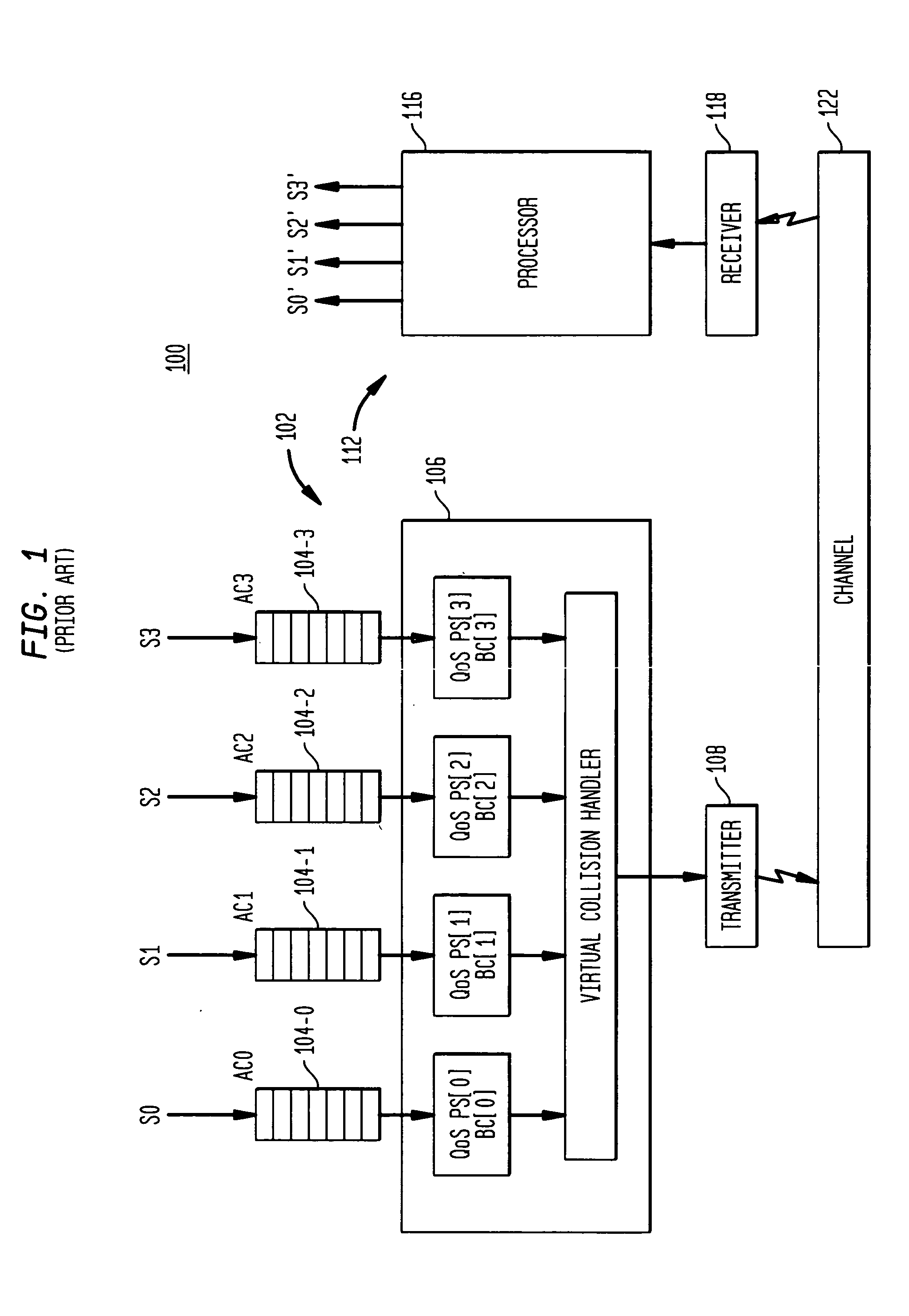
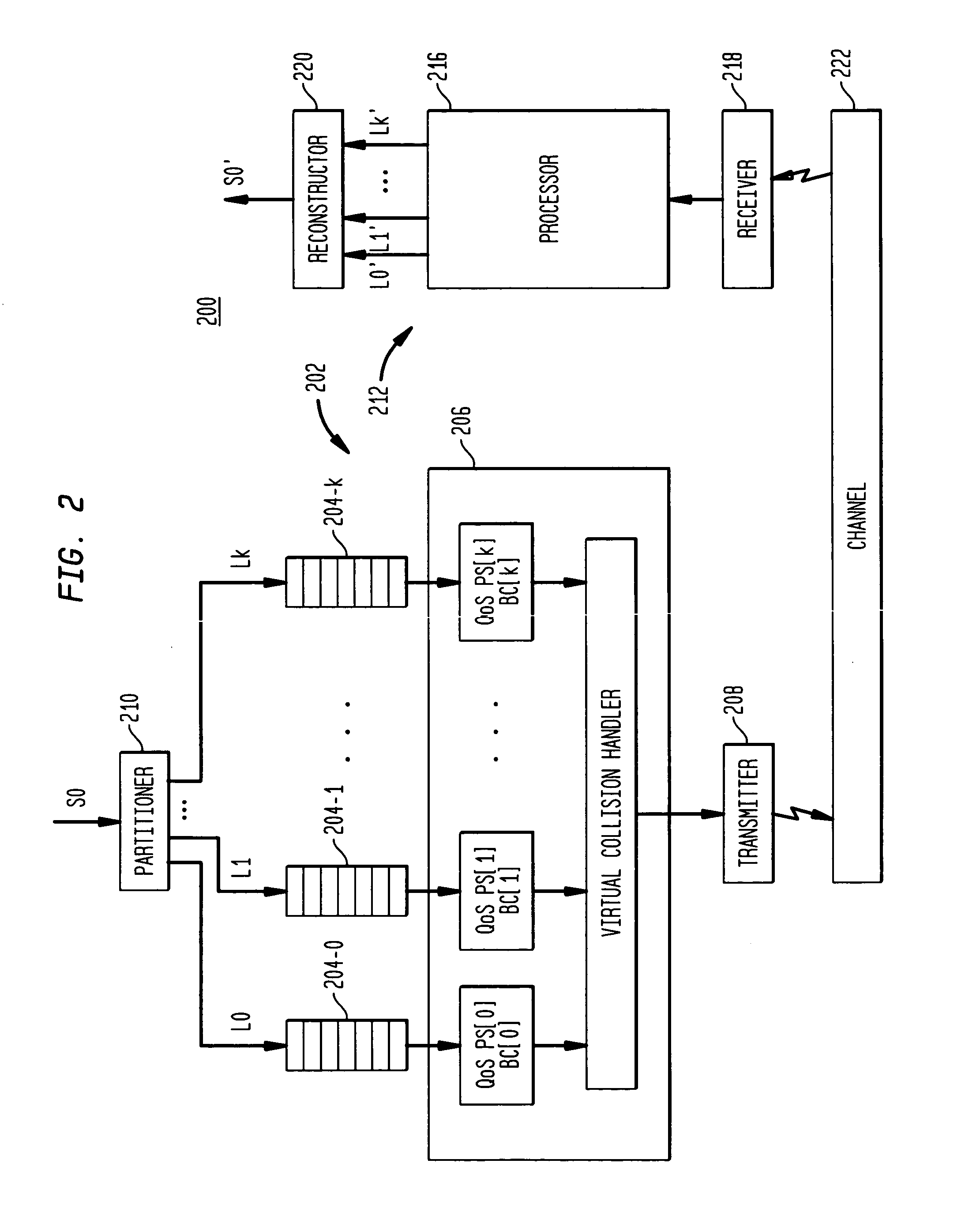
Media delivery using quality of service differentiation within a media stream
ActiveUS20050100022A1Equal qualityError preventionNetwork traffic/resource managementQos quality of serviceStation
A WLAN system adapted to apply QoS differentiation to a media stream to be transmitted from a transmitting station (STA) to a receiving STA of that system. The transmitting STA processes the media stream to generate a base sub-stream and one or more enhancement sub-streams for subsequent transmission over a wireless communication channel and assigns different priorities to different sub-streams. Depending on the channel conditions, the transmitting STA may select to discard, without transmission, portions of data from enhancement sub-streams. The selection process is based on the assigned priority and operates to preserve as much of relatively high-priority data as possible. The receiving STA then processes the received data to generate a reconstructed media stream, which provides signal quality equal to or better than the signal quality supported by the base sub-stream. Advantageously, a WLAN system of the invention is adapted to change signal quality dynamically and incrementally in a manner commensurate with current channel conditions without the need for communication between the higher and lower network layers. In addition, it provides gradual and graceful degradation of signal quality when channel conditions deteriorate as opposed to abrupt degradation inherent in analogous prior art systems.
Owner:AVAGO TECH INT SALES PTE LTD
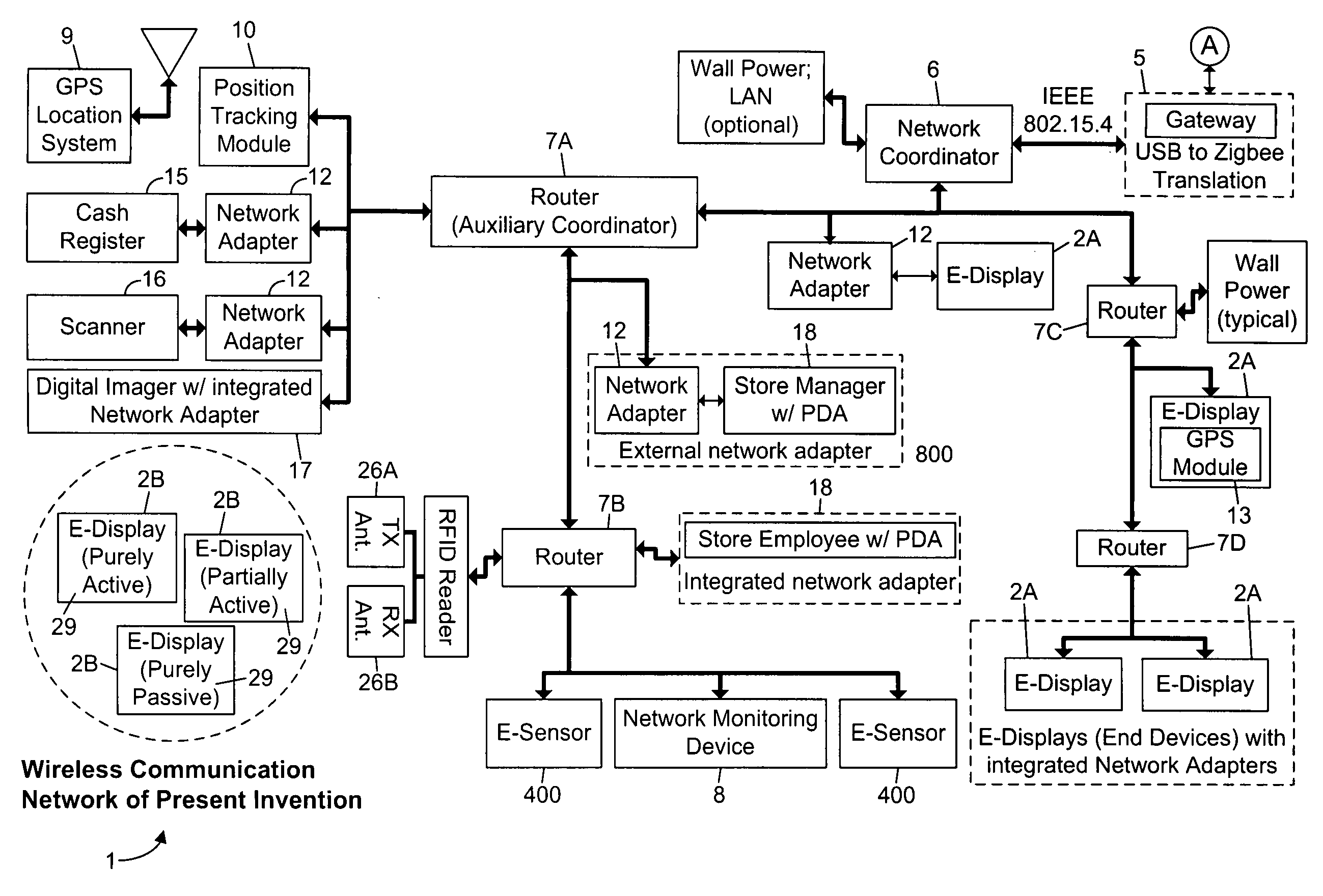
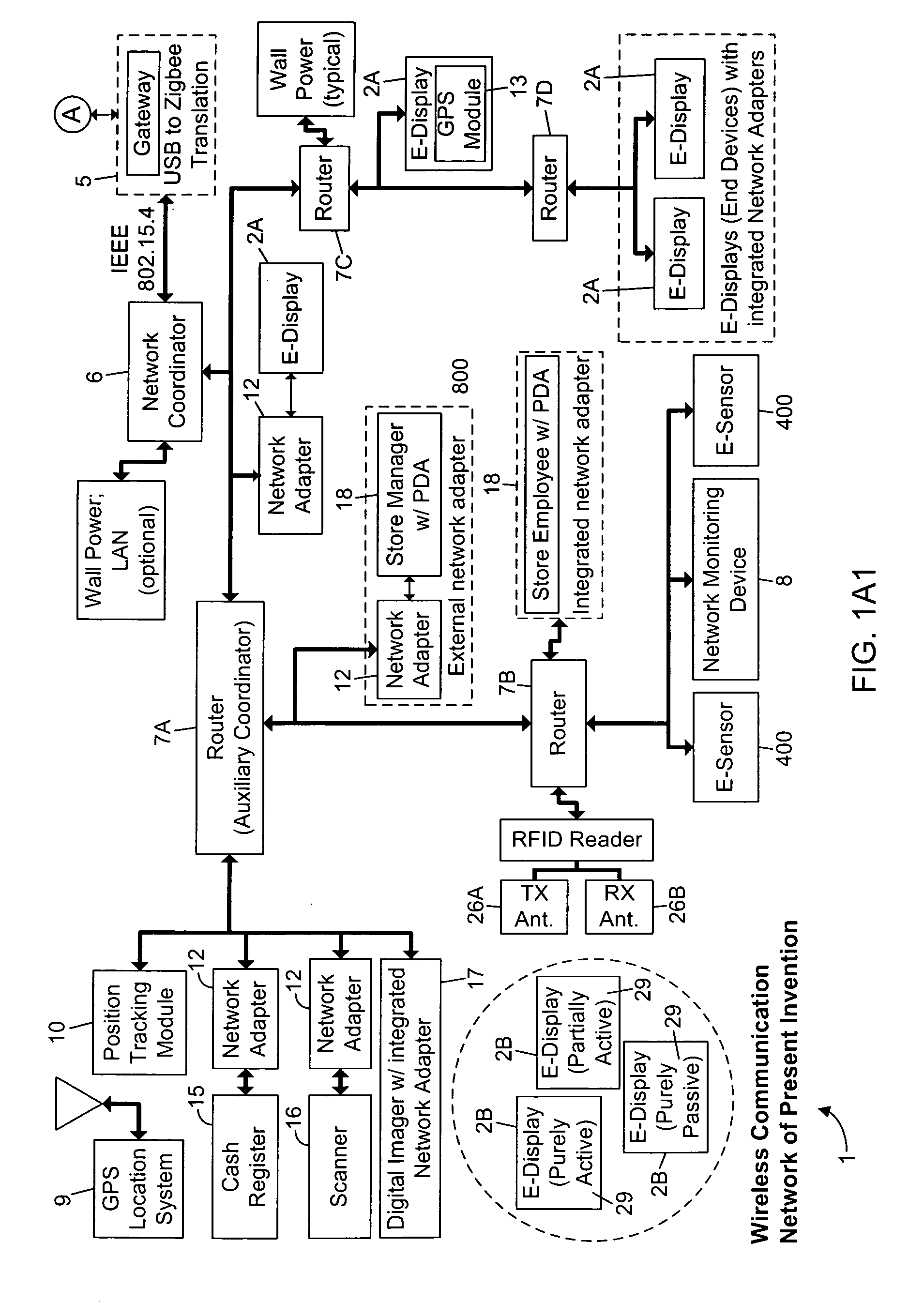
Methods of and apparatus for programming and managing diverse network components, including electronic-ink based display devices, in a mesh-type wireless communication network
InactiveUS20100177749A1Static indicating devicesDigital data processing detailsLogistics managementDisplay device
A wireless communication network for programming and monitoring a plurality of network-managed devices, including electronic-ink based display devices, comprising a network management computer system, a network gateway device, one or more wireless network routers, a plurality of network-managed devices, and a network coordinator. The wireless communication network of the present invention bridges the gap between wireless display networks, wireless sensor networks, and the worlds of passive, active and partially-active RFID and real-time locating systems. The wireless communication network of the present invention allows conventional communication network protocols to operate in more flexible ways in dynamic, diverse, and heterogeneous application environments, in fields including retail, healthcare, transport, logistics, manufacturing, education, etc. At the same time, the wireless communication network of the present invention is preferably based on the IEEE 802.15.4 network layer standard, which offers low-cost wireless network communication between a large number of wireless network end-devices.
Owner:METROLOGIC INSTR
Application services infrastructure for next generation networks including one or more IP multimedia subsystem elements and methods of providing the same
A system for supporting a plurality of different applications utilizing a next generation network having a network layer includes an application services middleware between the applications and the network layer that includes a plurality of common infrastructure elements usable by the different applications. The common infrastructure elements provide both services associated with use of the network and services that are not associated with use of the network. At least one of the common infrastructure elements is an Internet Protocol (IP) Multimedia Subsystem (IMS) element.
Owner:BELLSOUTH INTPROP COR
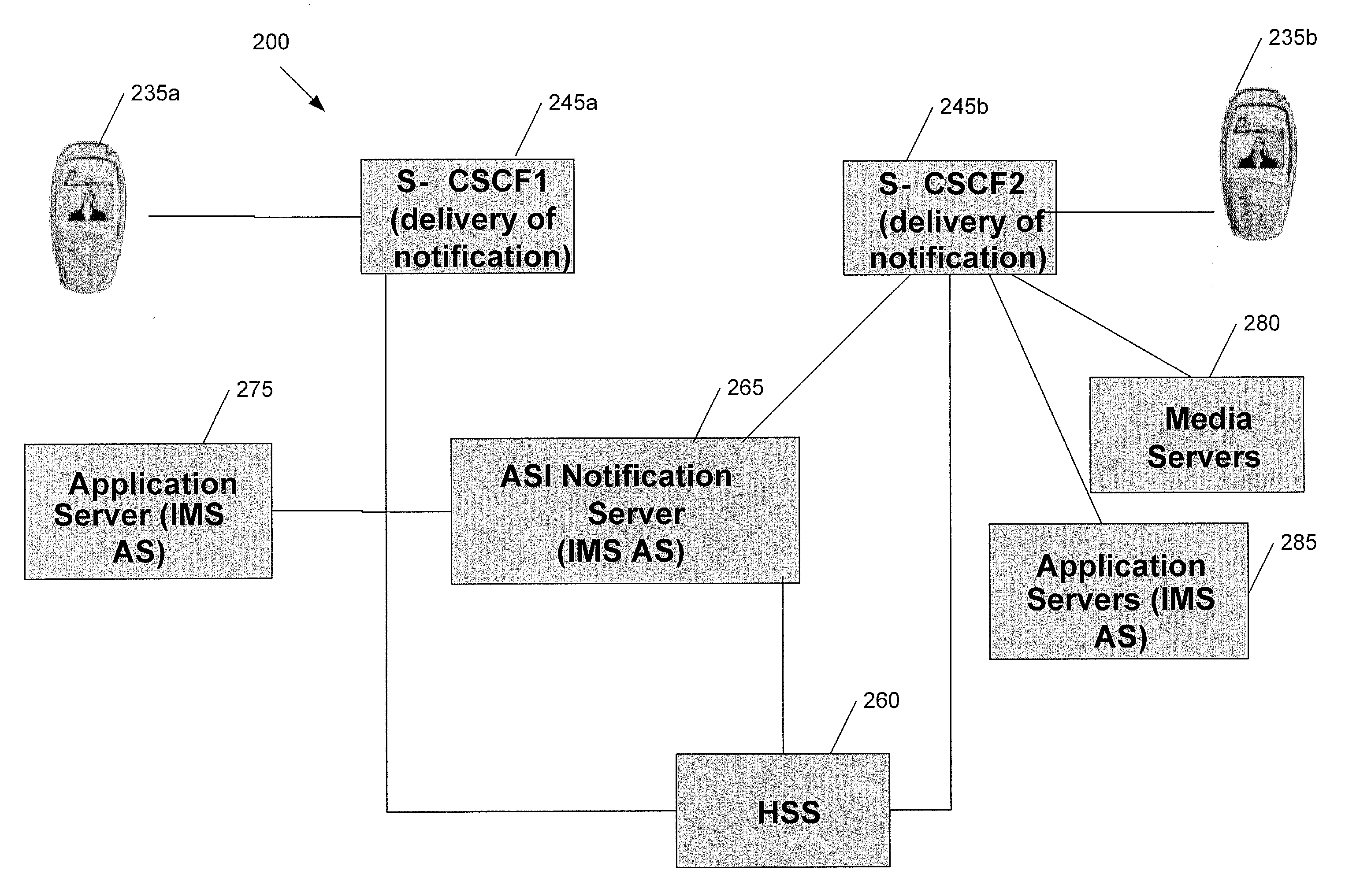
Application services infrastructure for next generation networks including a notification capability and related methods and computer program products
ActiveUS20080162637A1Facilitate sending of messageMultiple digital computer combinationsData switching networksService infrastructureNetwork layer
A system for supporting a notification capability for a plurality of applications utilizing a next generation network having a network layer includes an application services middleware between the applications and the network layer comprising a plurality of common infrastructure elements usable by the applications. The common infrastructure elements provide both services associated with use of the network and services that are not associated with use of the network. The plurality of common infrastructure elements includes a notification service that is configured to facilitate the sending of messages from authorized services to recipients.
Owner:AT&T INTPROP I L P
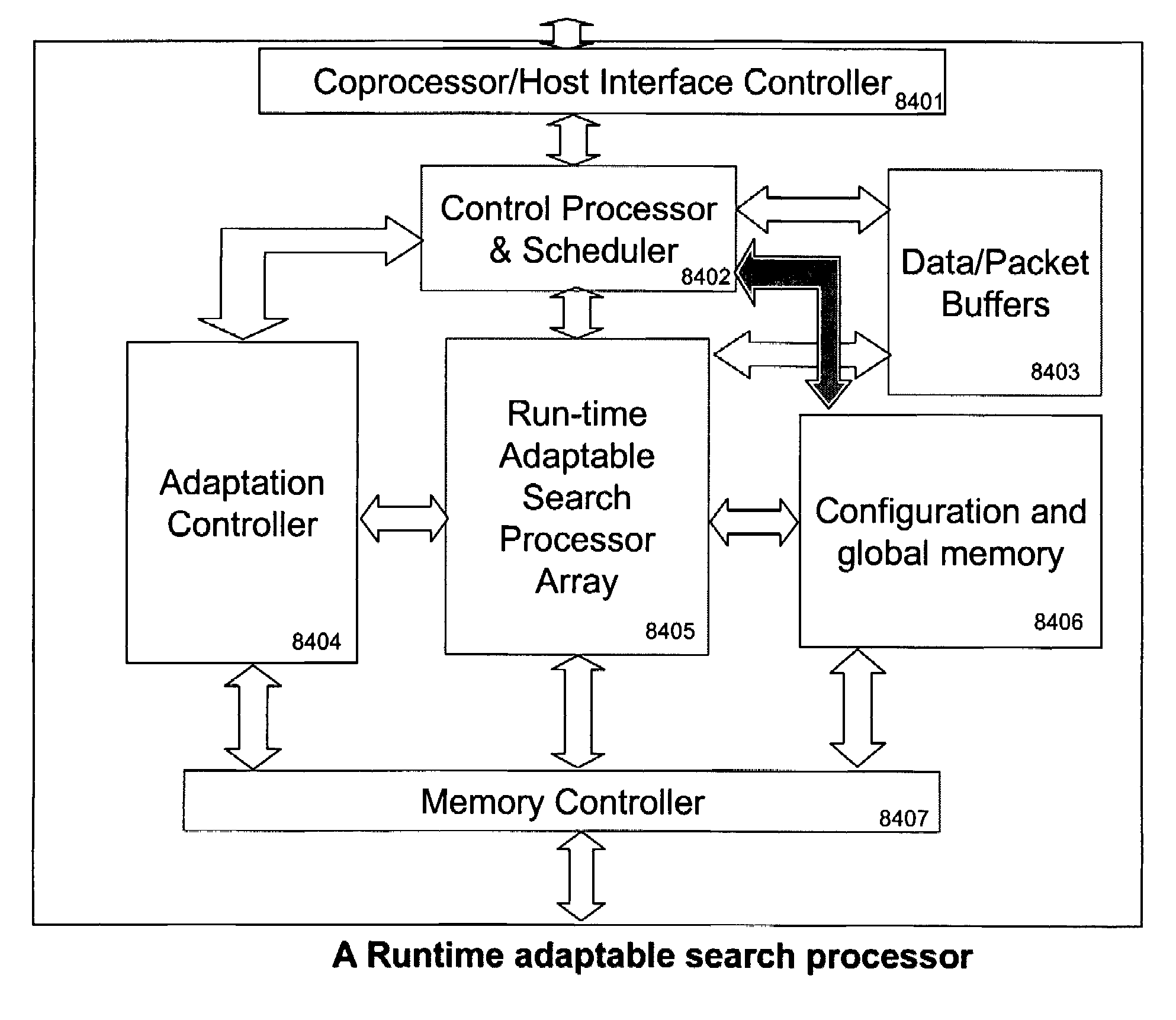
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
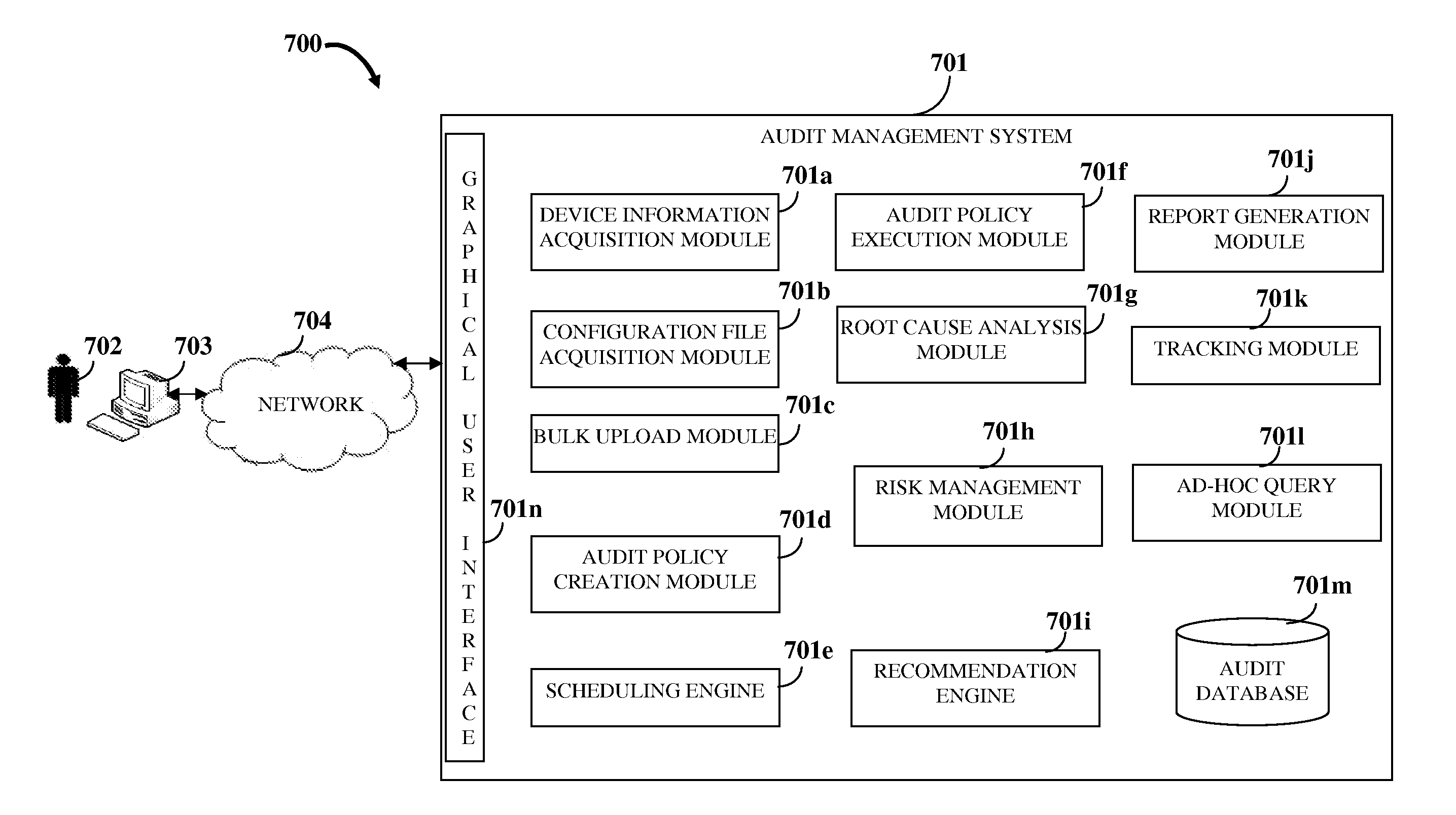
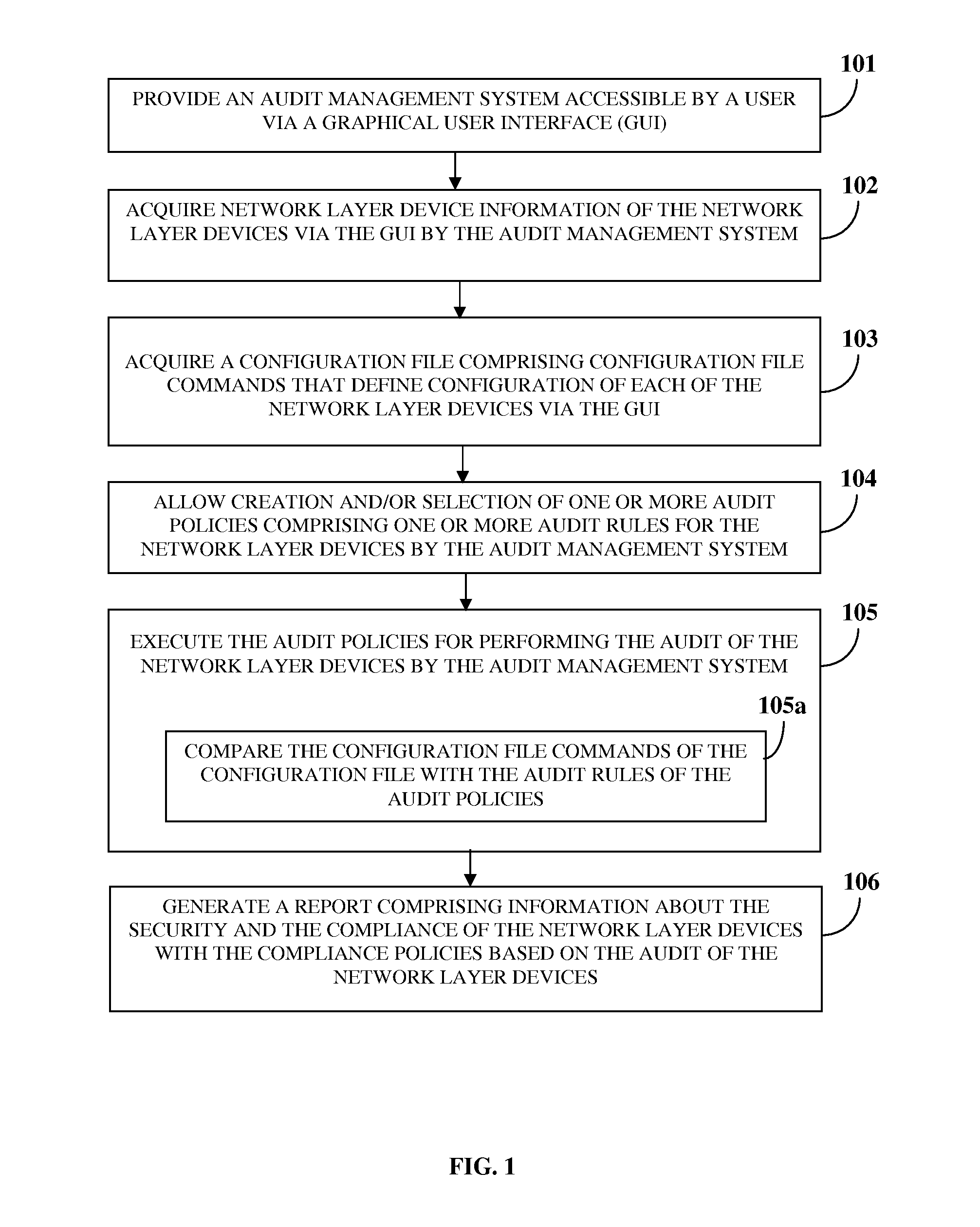
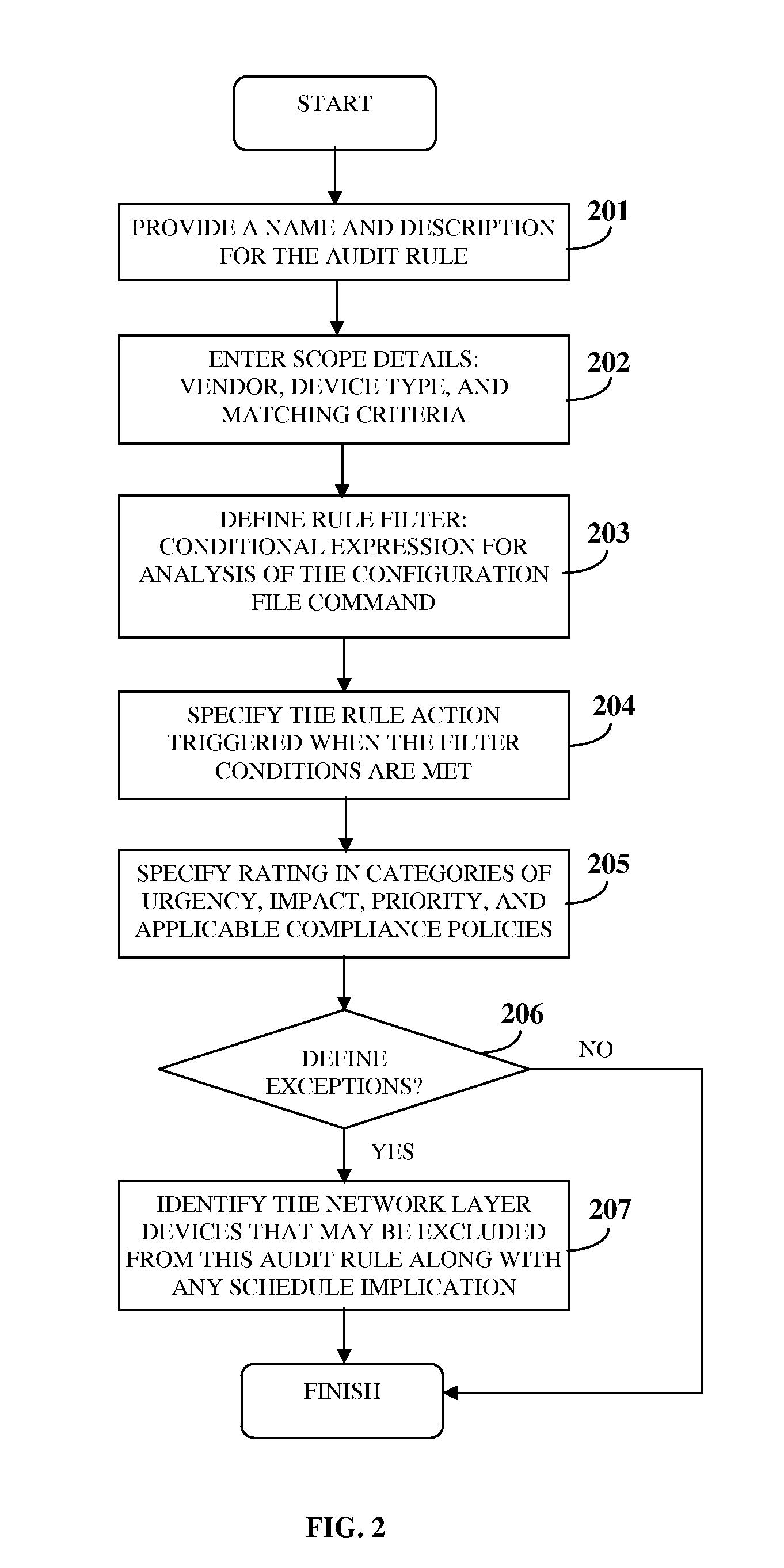
Audit Management System
InactiveUS20120102543A1Increase flexibilityIncrease speedComputer security arrangementsTransmissionGraphicsGraphical user interface
A computer implemented method and system for managing an audit of one or more network layer devices is provided. An audit management system accessible by a user via a graphical user interface acquires network layer device information of the network layer devices and a configuration file comprising configuration file commands. The audit management system allows creation and / or selection of one or more audit policies for the network layer devices. The audit policies comprise one or more audit rules that define functioning of the network layer devices for one or more compliance policies. The audit management system executes the audit policies for performing the audit of the network layer devices by comparing the configuration file commands of the configuration file with the audit rules of the audit policies, and generates a report comprising information about security and compliance of the network layer devices with the compliance policies based on the audit.
Owner:360 GRC
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Runtime adaptable security processor
InactiveUS20050108518A1Improve performanceReduce overheadSecuring communicationInternal memoryPacket scheduling
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
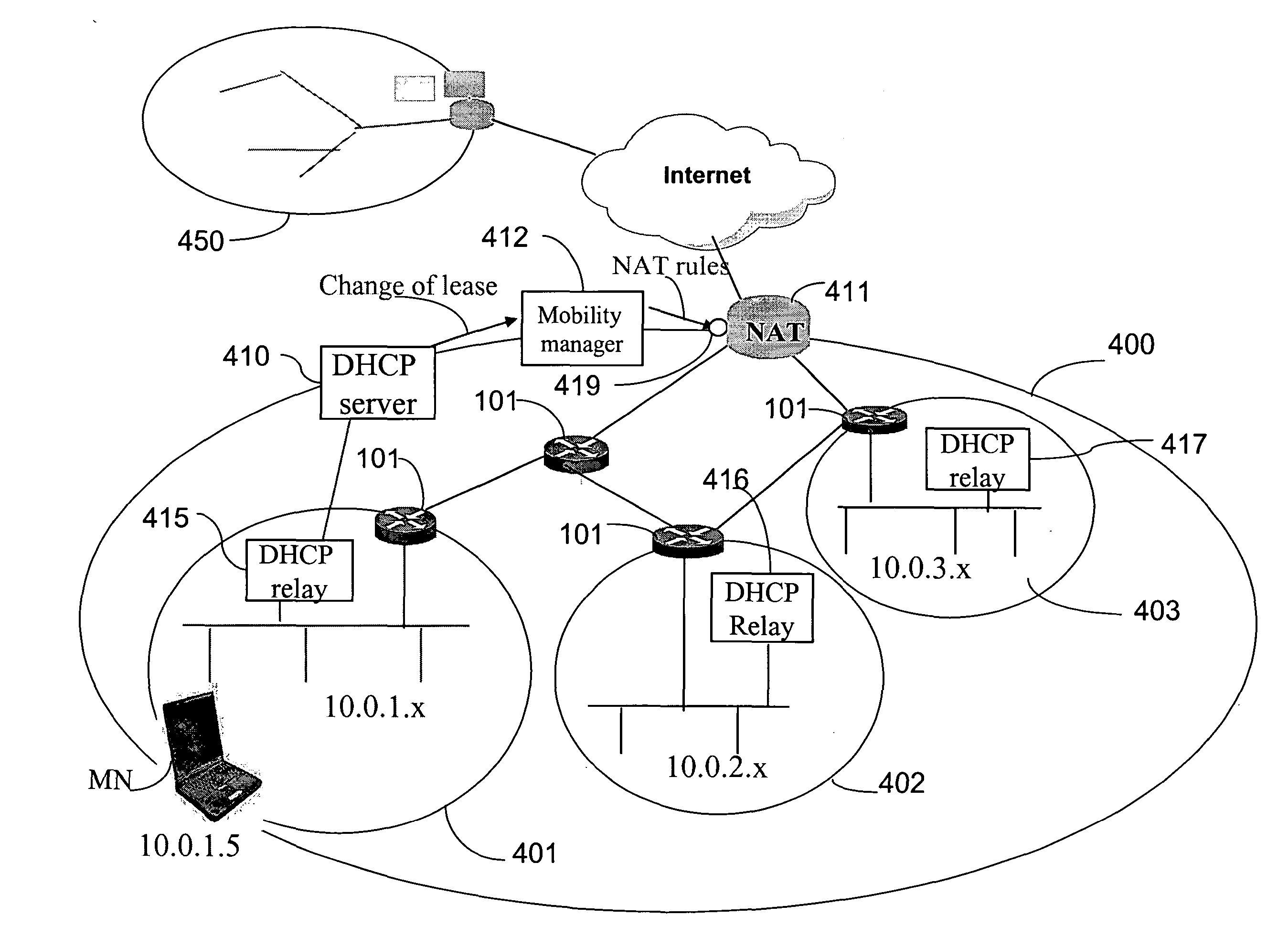
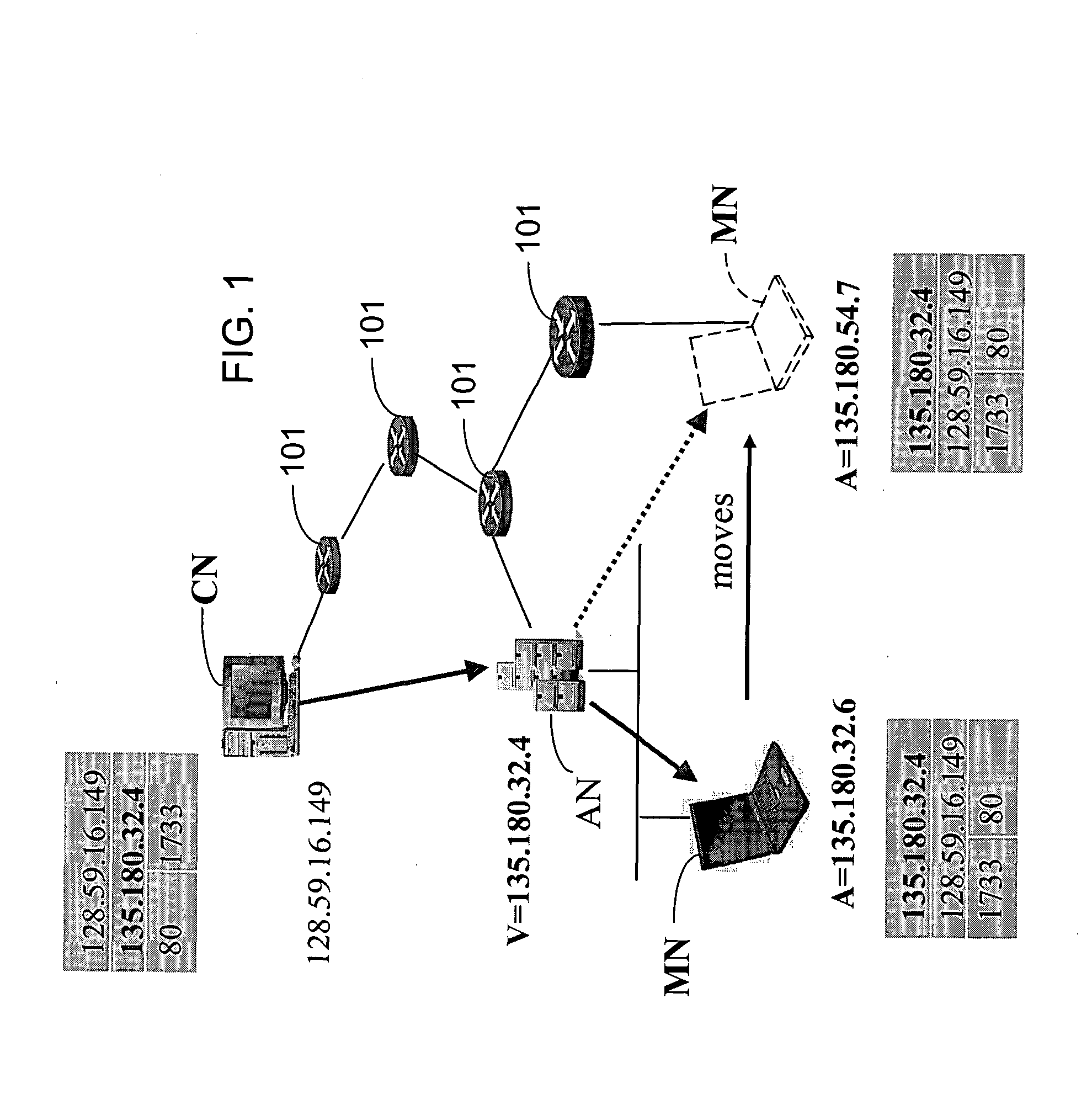
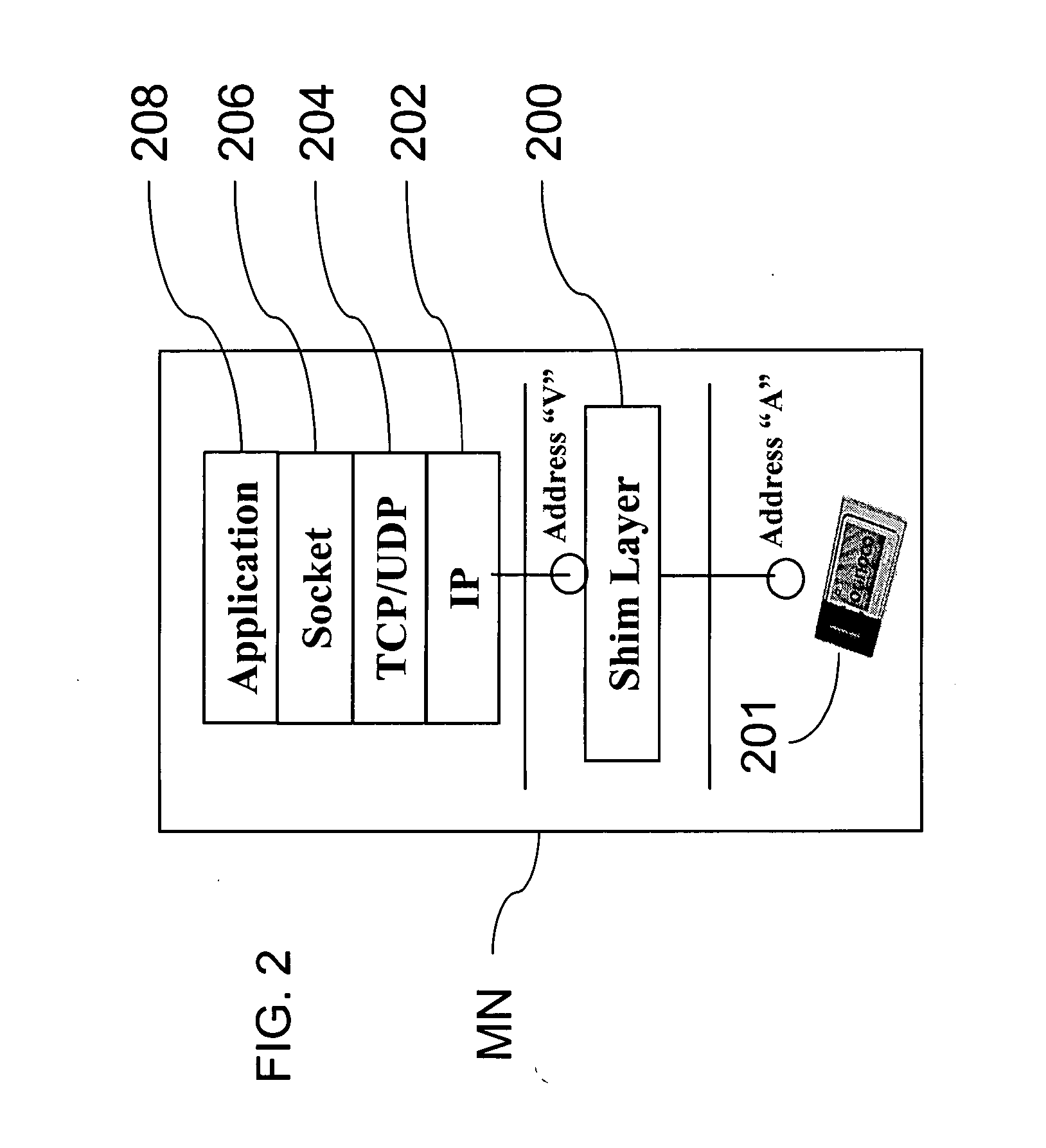
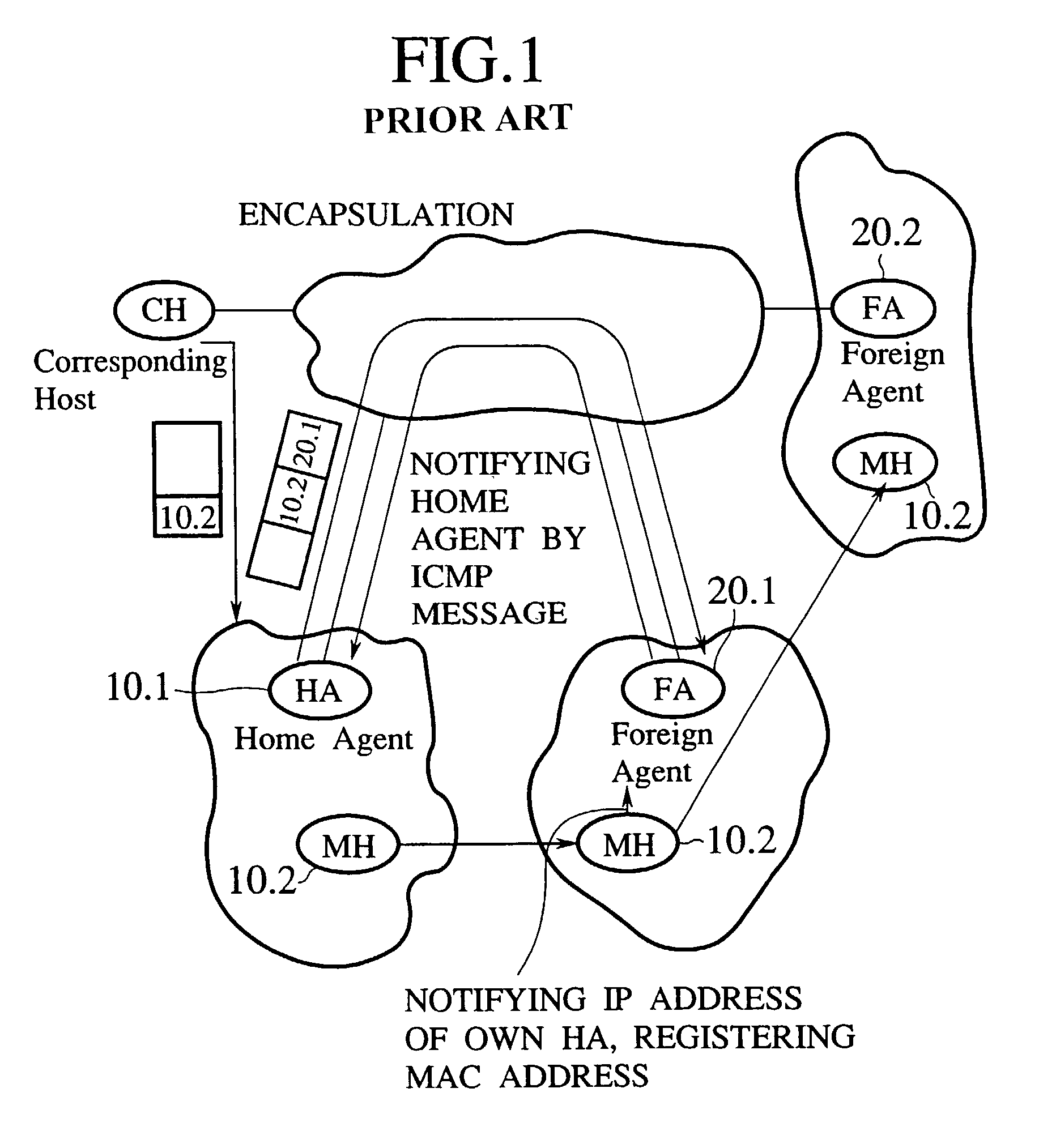
Method and system for mobility across heterogeneous address spaces
ActiveUS20050013280A1Time-division multiplexData switching by path configurationAddress spaceInternet Protocol
A mobile node includes a processor, a network interface, and a storage device having computer program code for execution by the processor. The computer program code includes a network layer for transmitting and receiving packets and an intermediate driver that transmits packets to the network layer and receives packets from the network layer using a virtual internet protocol (IP) address to identify the mobile node. The intermediate driver transmits packets to the network interface and receives packets from the network interface using a routable actual IP address to identify the mobile node. The intermediate driver permits the actual IP address to change when the mobile node moves from a first subnet to a second subnet without a corresponding change in the virtual IP address. A corresponding NAT associates the virtual IP address with a second actual IP address when the NAT is notified that the mobile node is in the second subnet.
Owner:ALCATEL LUCENT SAS
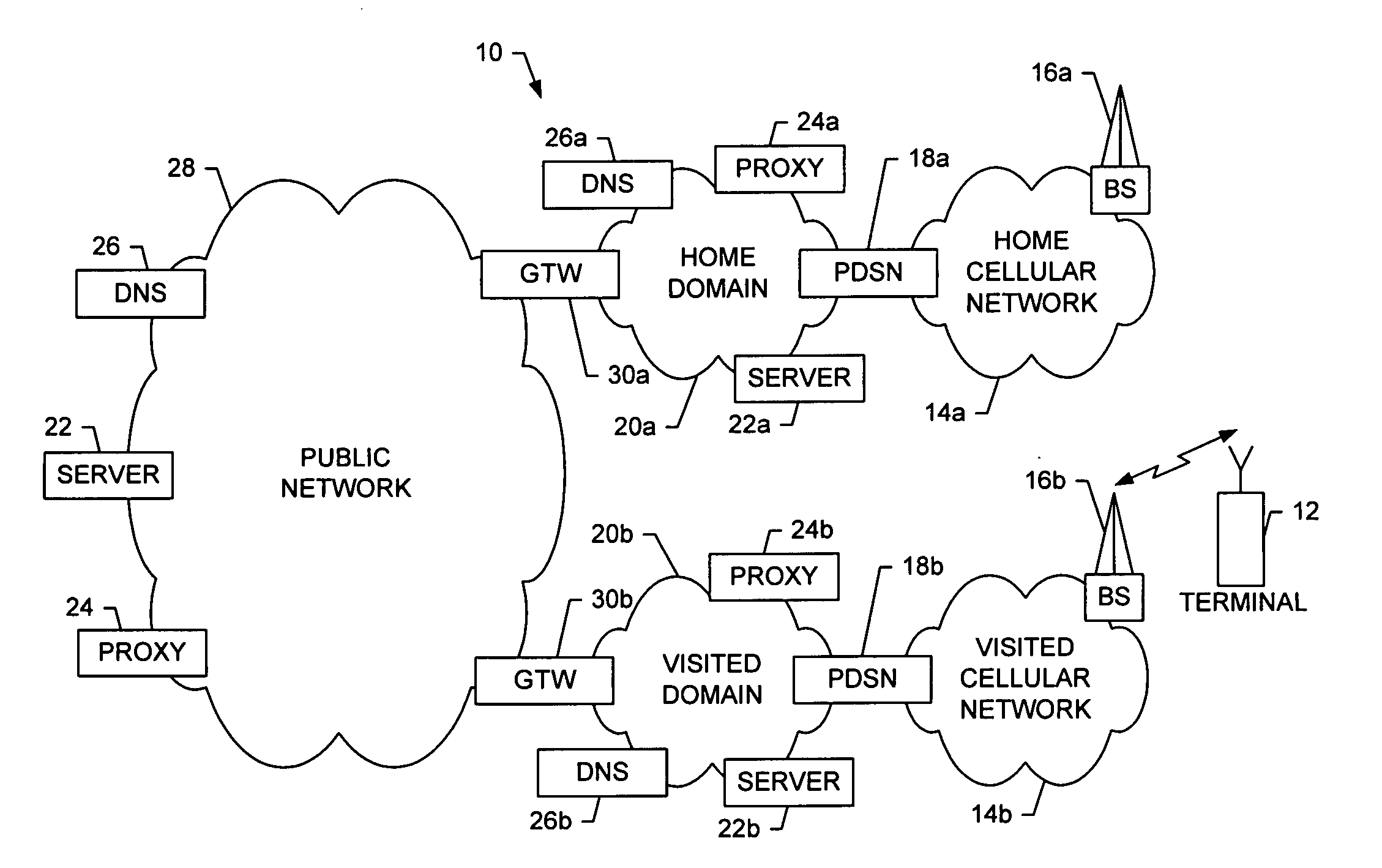
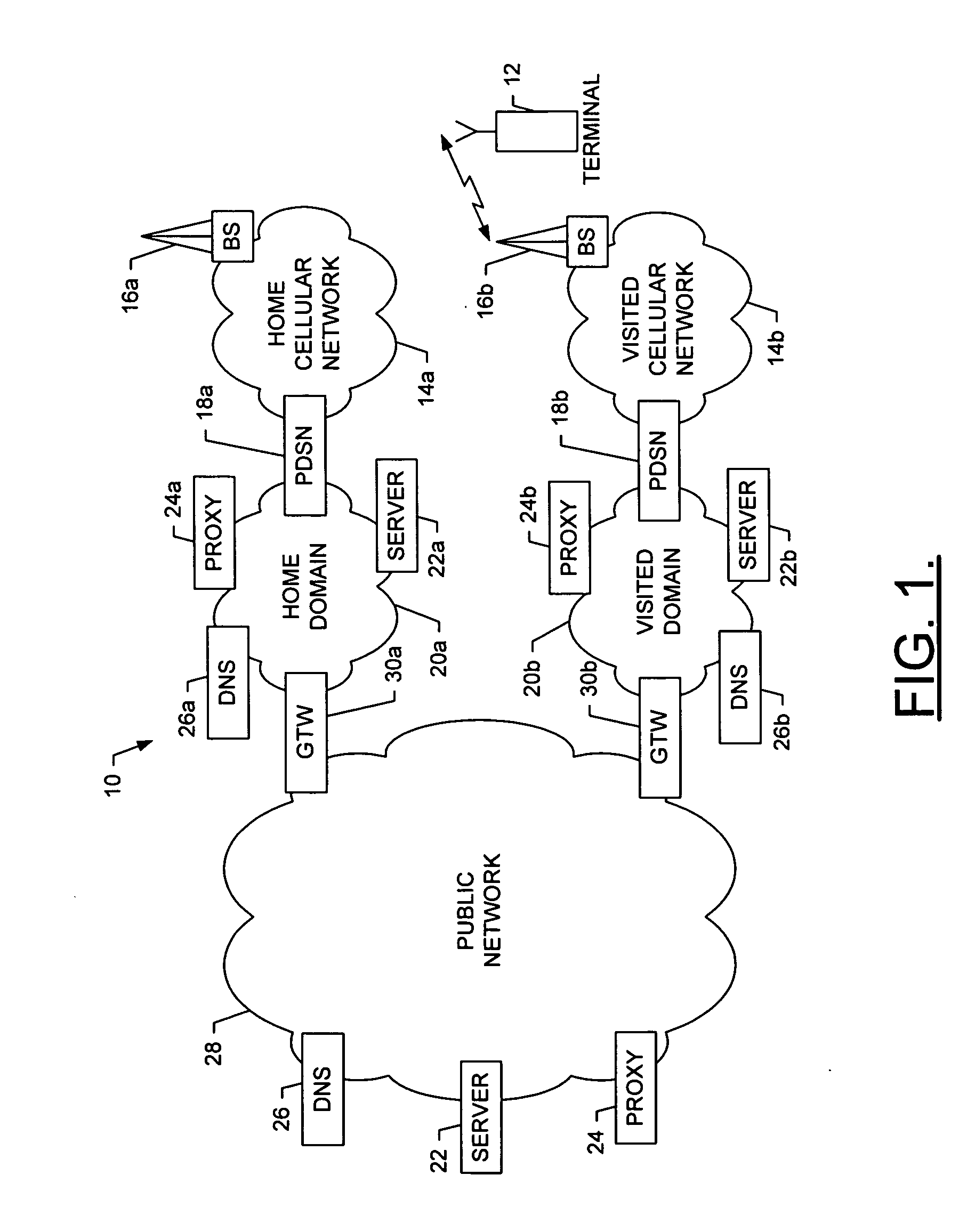
System and method for service discovery during connection setup in a wireless environment
InactiveUS20060034256A1Reduce traffic problemsSave response timeAssess restrictionConnection managementPhysical layerData format
A system is provided that includes a network entity, such as a packet data switching node (PDSN), and a terminal capable of establishing a data-link connection with the network entity, such as after setting up a physical-layer connection with the network entity. After the data-link connection is established, the network entity and the terminal can configure a network-layer protocol such that data formatted in accordance with the network-layer protocol can thereafter be sent between the terminal and the network entity over the data-link connection. Then, during configuration of the network-layer protocol, the terminal can discover at least one service available to the terminal by receiving, from the network entity, a listing of the at least one available service. The listing of each available service includes an address of a provider of the available service and a port number and / or pathname for accessing the service at the provider.
Owner:NOKIA CORP
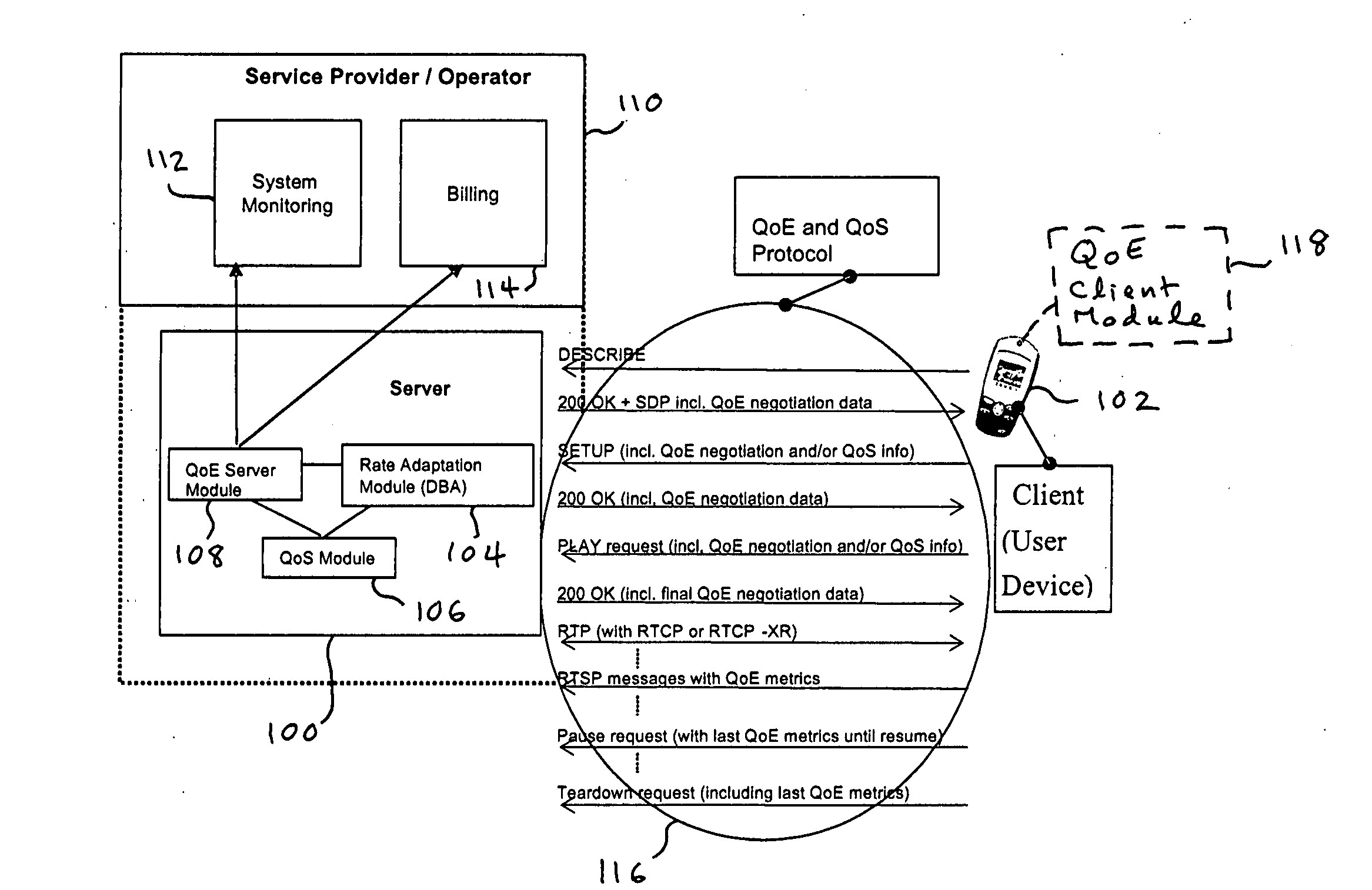
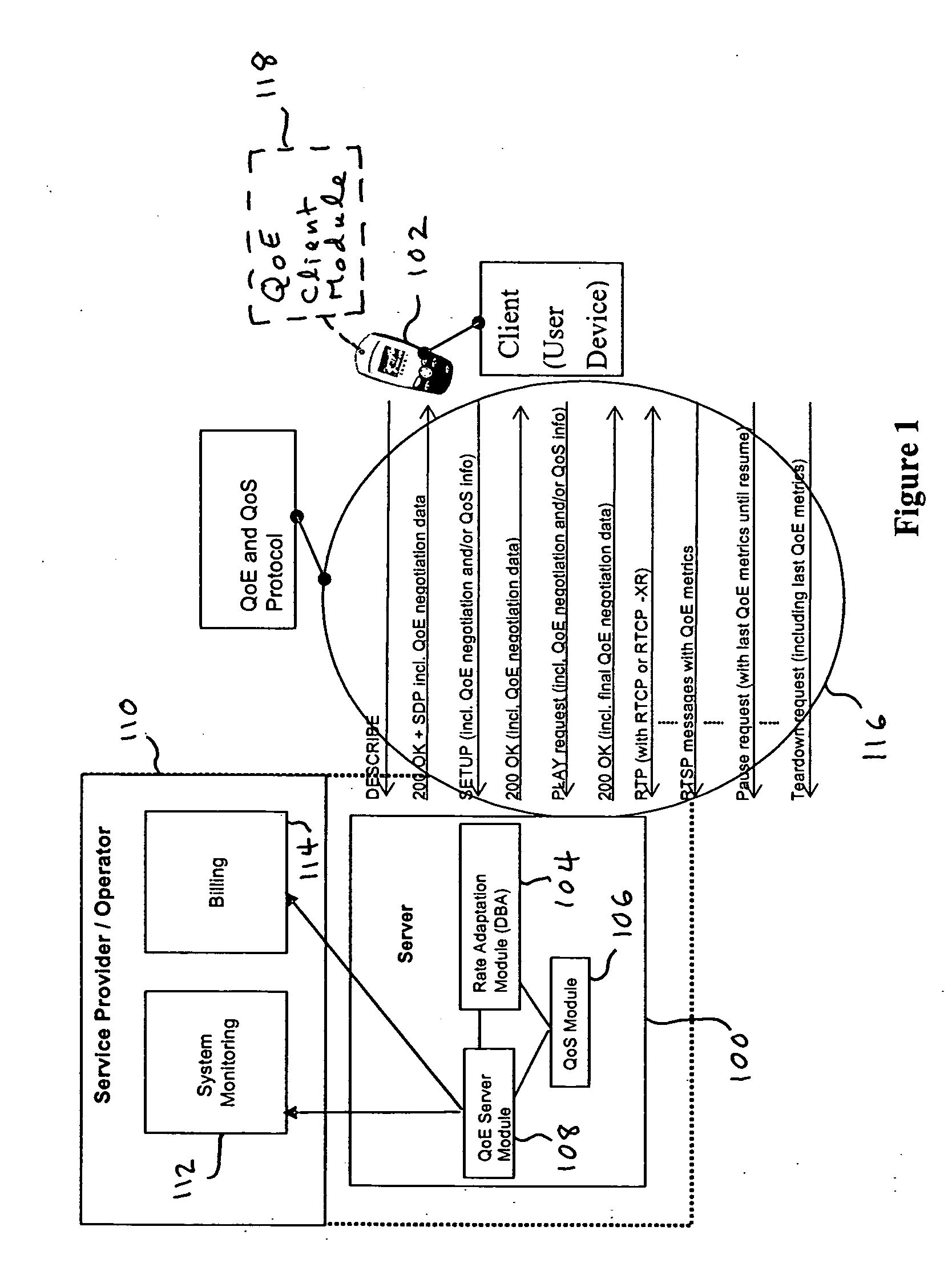
Quality of experience (QOE) method and apparatus for wireless communication networks
A Quality of Experience (QoE) framework provides a technique to assess the end user experience in a mobile wireless communication environment, such as 2.5G or 3G networks, or in any other wireless or hardwired communication environment. The framework is usable in conjunction with media streaming applications and enables a combination of network layer, transport layer, codec layer, and application layer measurements in extracting results. The extracted results can be used to monitor and improve, if necessary, the end user experience over severely variable network conditions.
Owner:VIDIATOR ENTERPRISES INC
Integrated system for network layer security and fine-grained identity-based access control
ActiveUS6986061B1Simple technologyUser identity/authority verificationDigital computer detailsKey exchangeMedia access control
Owner:TREND MICRO INC
Cyber Behavior Analysis and Detection Method, System and Architecture
A scalable cyber-security system, method and architecture for the identification of malware and malicious behavior in a computer network. Host flow, host port usage, host information and network data at the application, transport and network layers are aggregated from within the network and correlated to identify a network behavior such as the presence of malicious code.
Owner:CYBER ADAPT INC
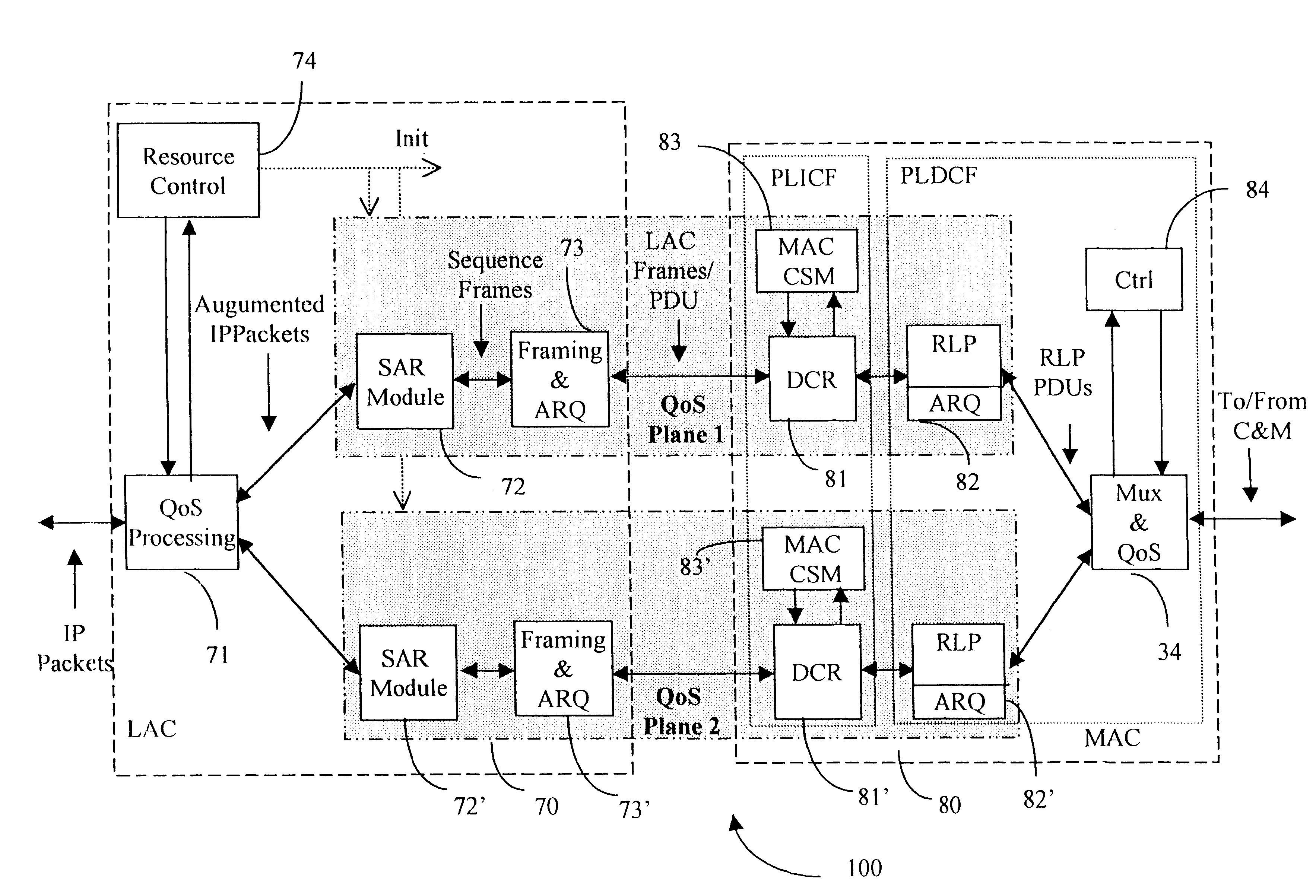
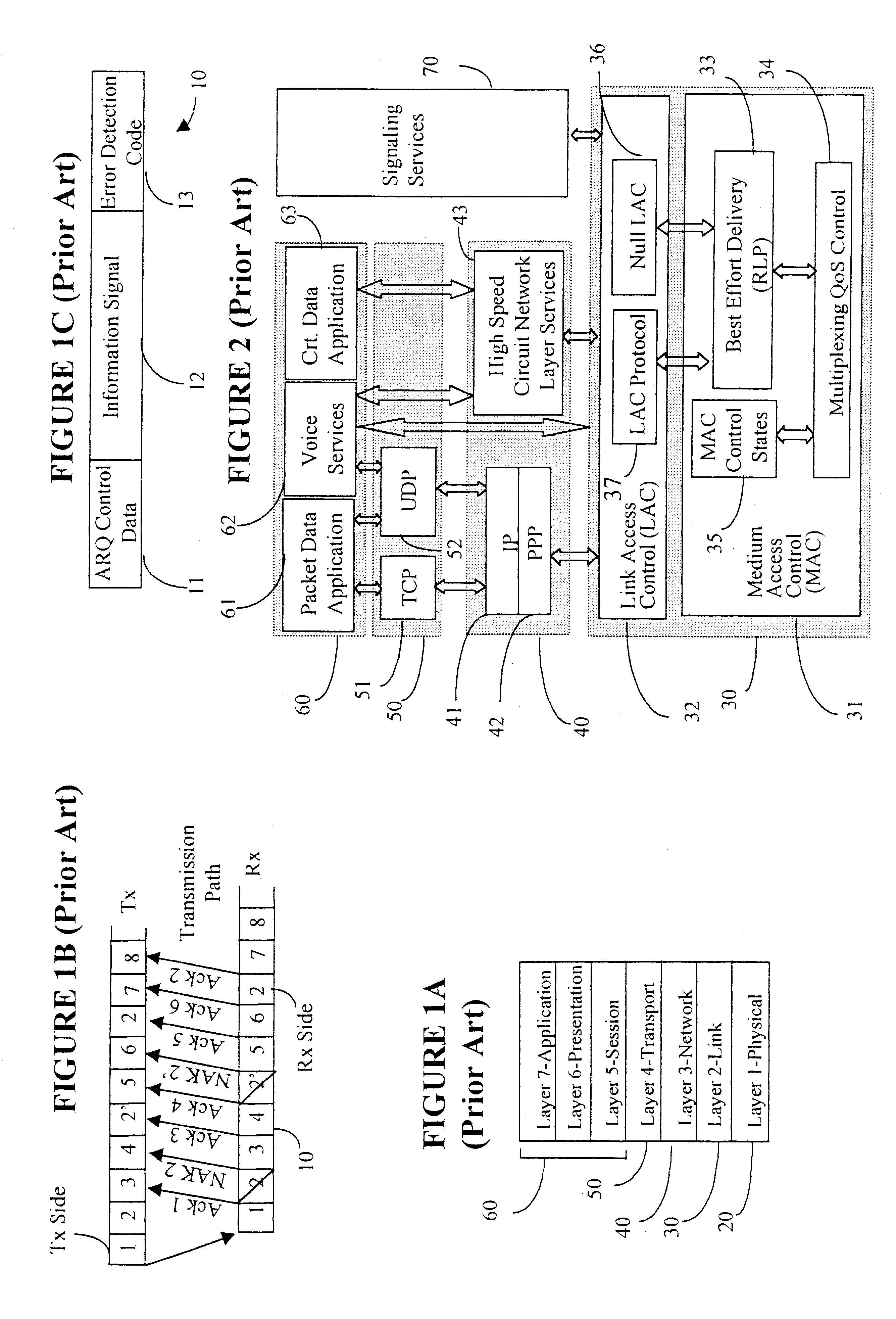
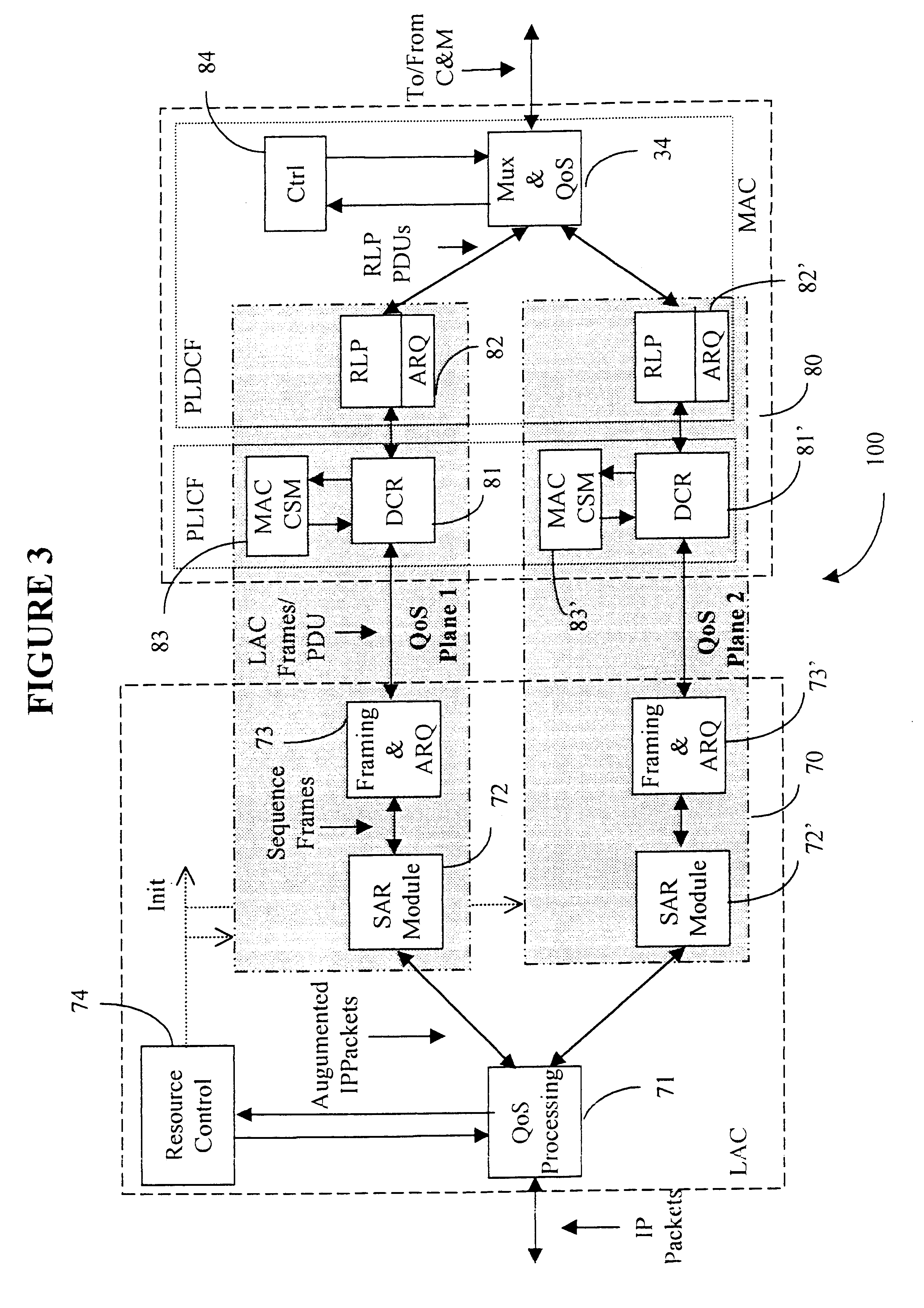
Data link control proctocol for 3G wireless system
InactiveUS6542490B1Error prevention/detection by using return channelElectronic circuit testingTelecommunications linkDual mode
A Data Link Control protocol for 3G wireless communication system for direct support for network layer protocols, e.g. the Internet Protocol (IP), is provided. The Link Layer disclosed comprises a Link Access Control (LAC) sublayer and a Medium Access Control (MAC) sublayer. At a transmit end of the wireless system, a plurality of Quality of Service (QoS) data planes are created to directly support the IP QoS. Each QoS data plane is optimized to handle QoS requirements for a corresponding Class of Service (CoS). Data packets received at the LAC sublayer are directed to a QoS data plane according to the particular QoS information they contain and processed according to the particular QoS requirement to generate variable size LAC frames. The variable size LAC frames are transmitted to the MAC sublayer for generating radio link protocol data units (RLP PDUs) to be transmitted to a receiving end. A new level of error correction is provided at the LAC sublayer as the size of the LAC PDUs can be dynamically adjusted in response to the conditions of the communication link. A dual mode ARQ is provided at the MAC sublayer to improve the quality of the air transmission for bursty as well as non-bursty traffic conditions.
Owner:ALCATEL LUCENT SAS
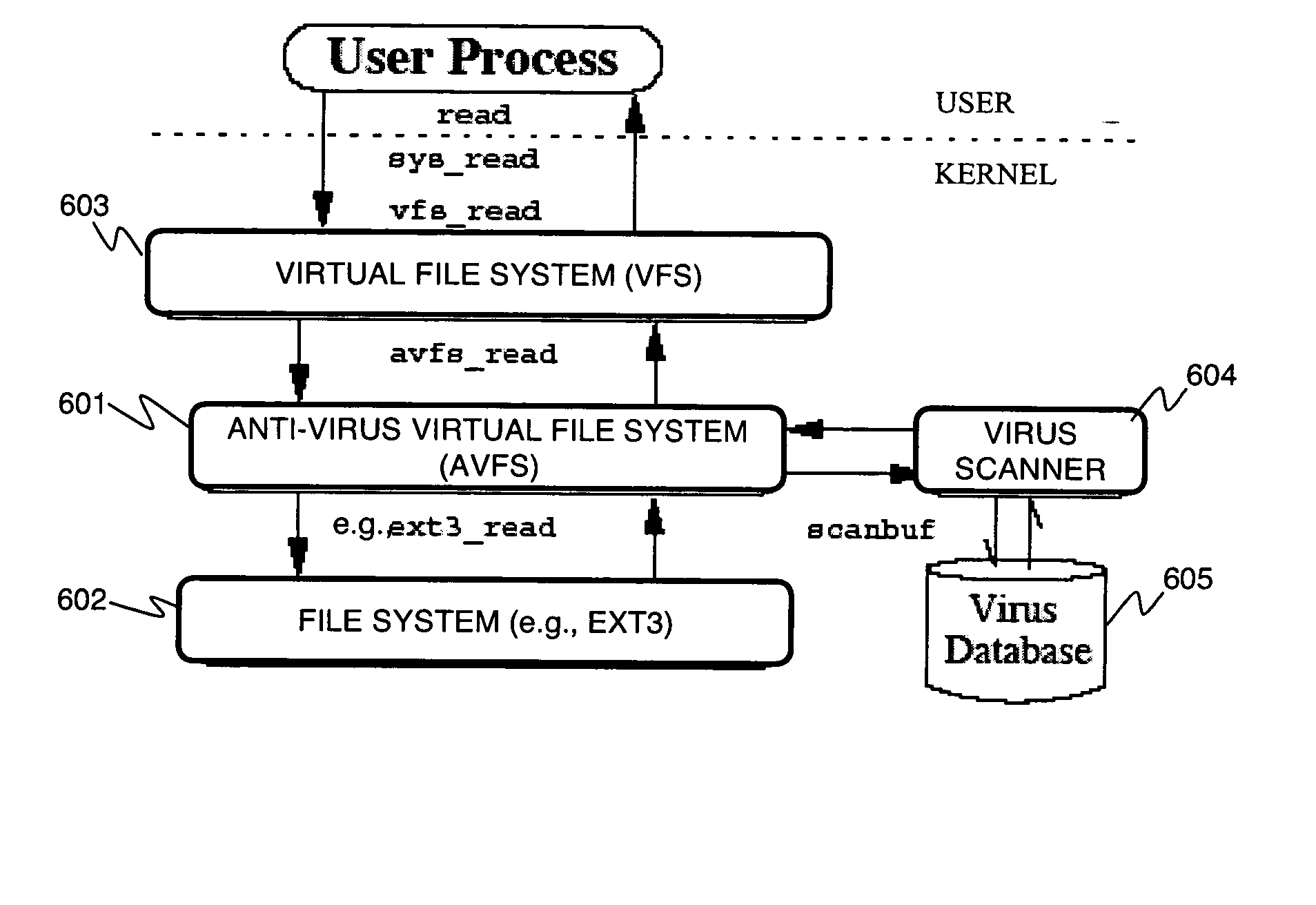
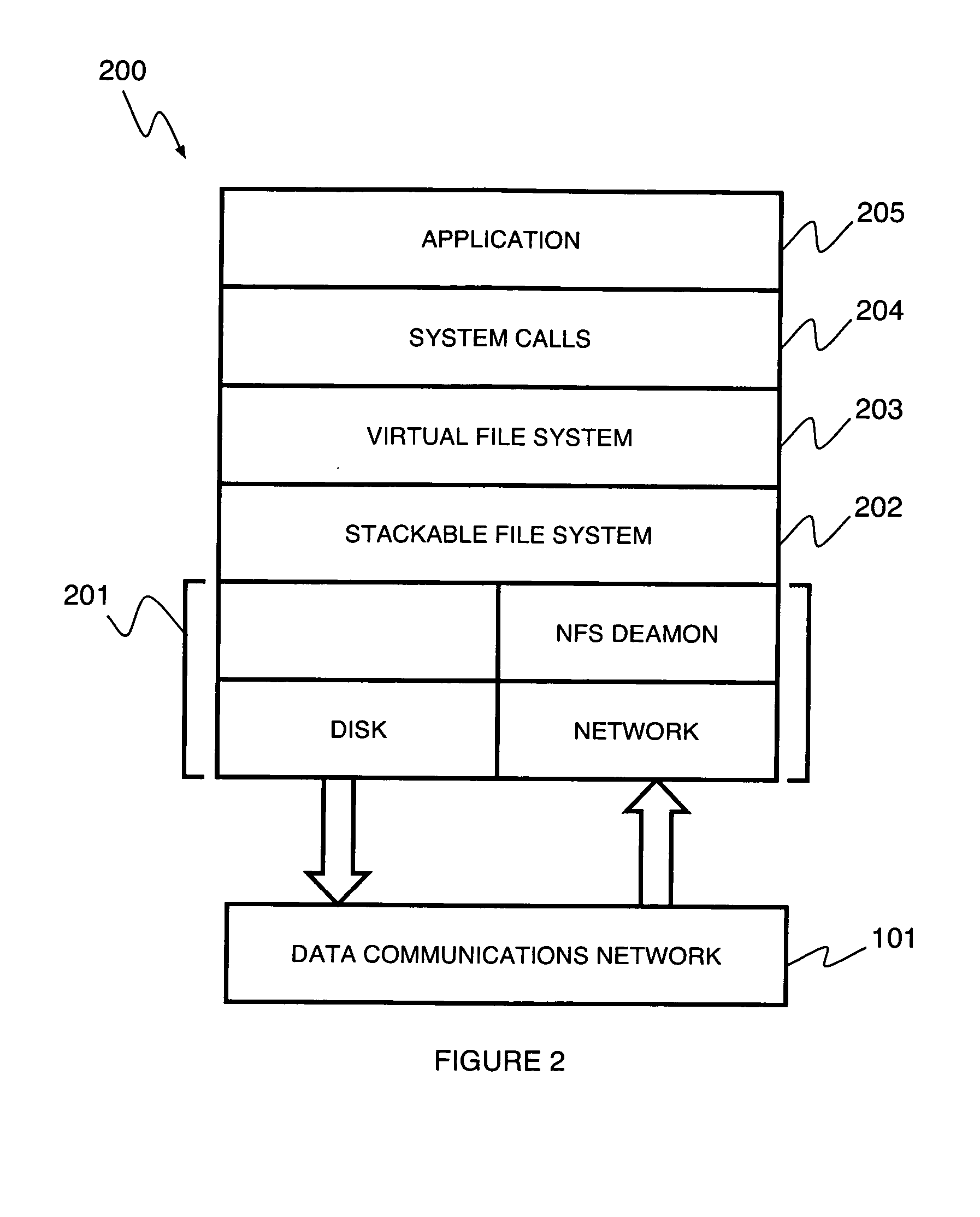
Stackable file systems and methods thereof
InactiveUS20050273858A1Memory loss protectionError detection/correctionOperational systemFile system
An operating system kernel, including a protocol stack, includes a network layer for receiving a message from a data network, a stackable file system layer coupled to the network layer for inspecting the message, wherein the stackable file system layer is coupled to a storage device, the stackable file system determining and storing file system level information determined from the message, and a wrapped file system comprising a file targeted by the message coupled to the stackable file system layer for receiving the message inspected by the stackable file system.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK +1
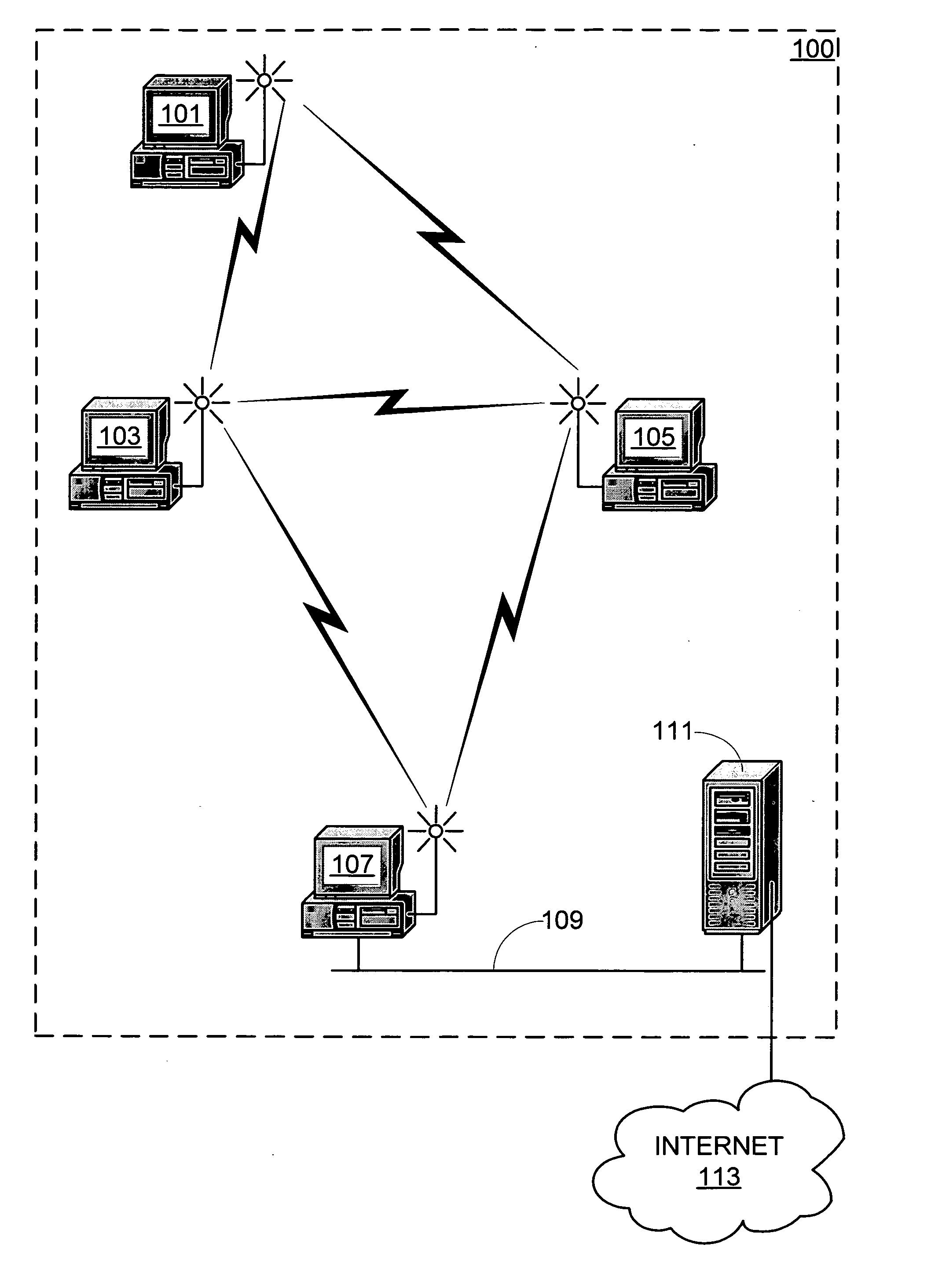
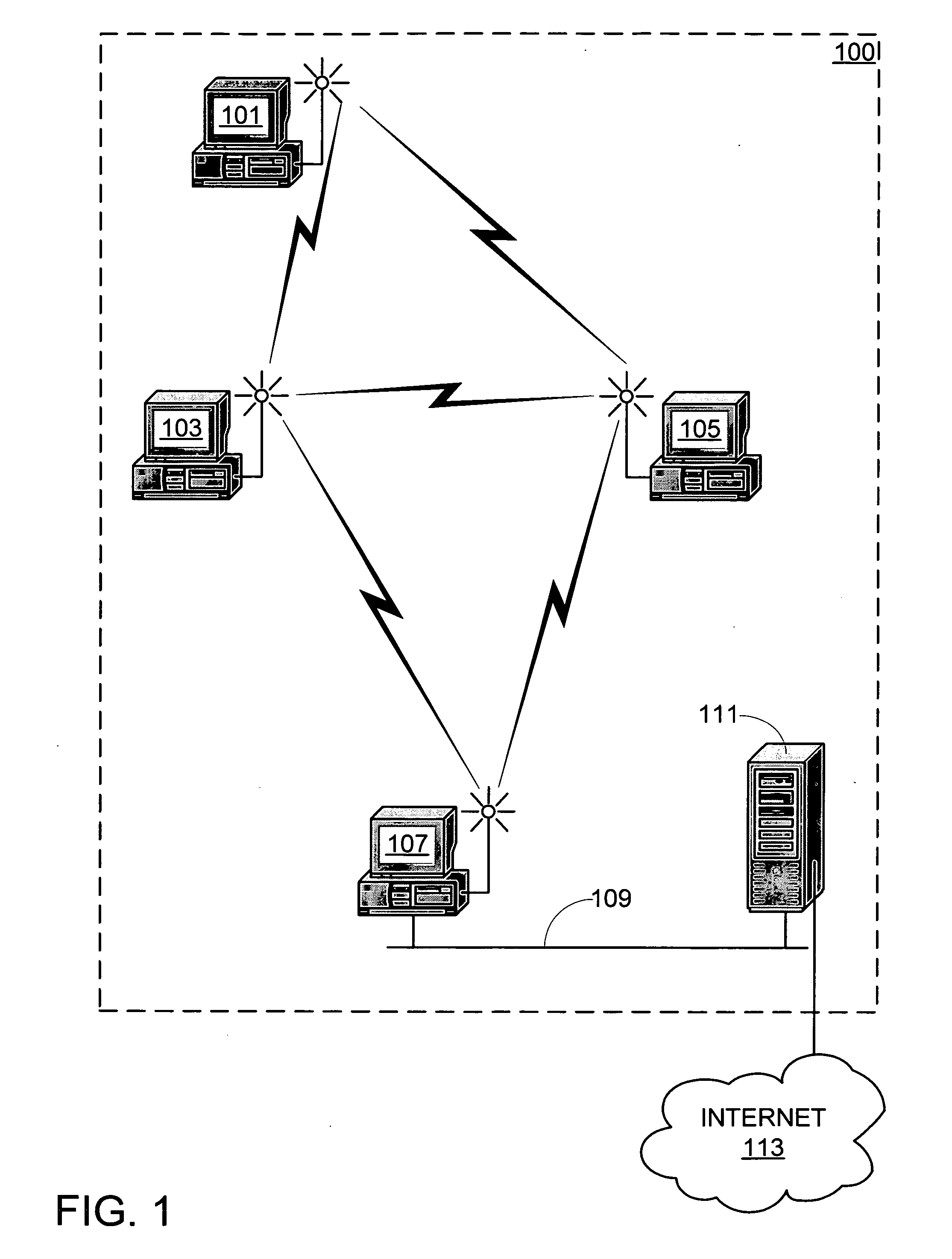
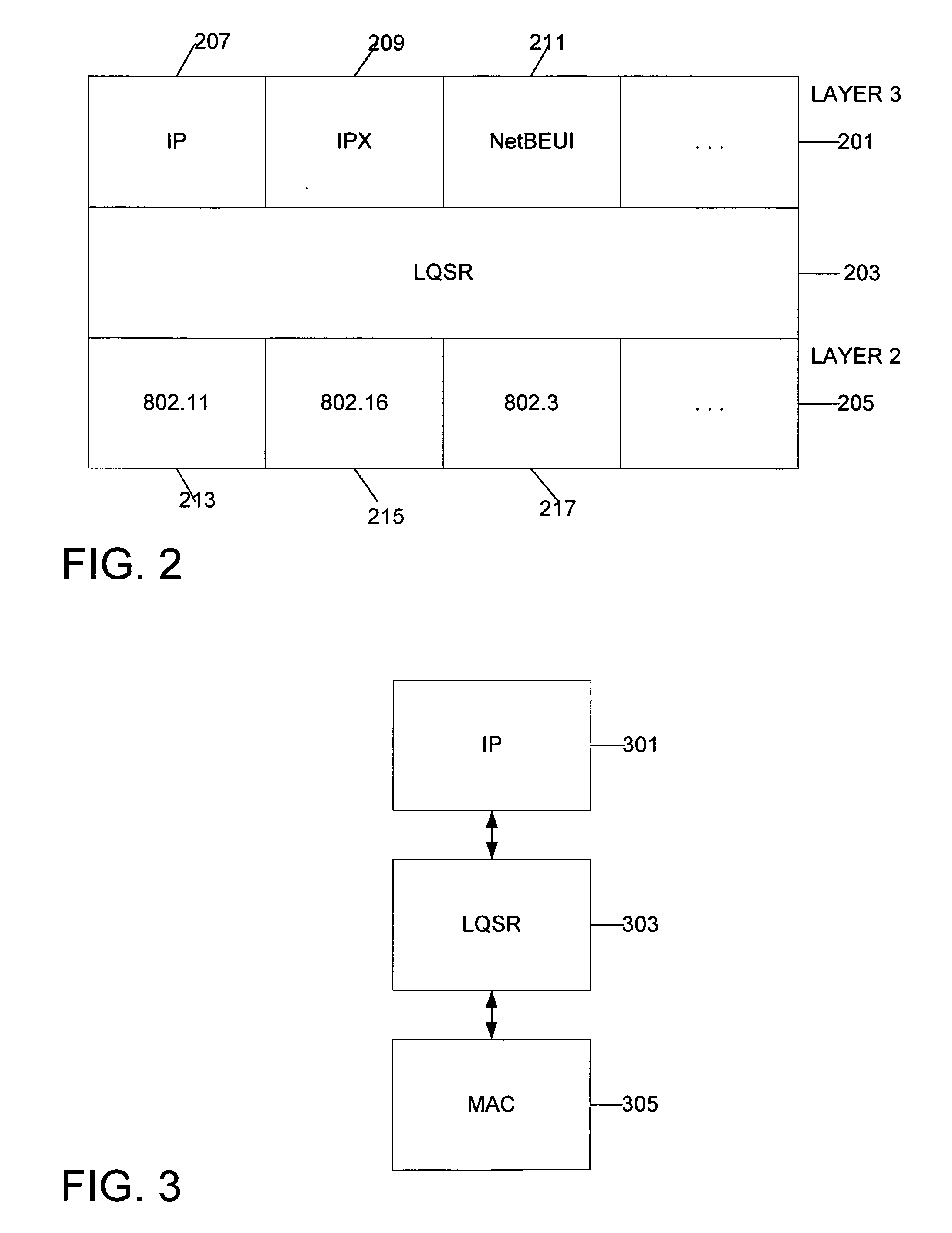
System and method for link quality source routing
InactiveUS20050185632A1Data switching by path configurationWireless communicationKnowledge gainNetwork packet
Systems and methods for routing packets by nodes in an ad hoc network in accordance with a link quality source routing protocol are disclosed. Route discovery, route maintenance, and metric maintenance are designed to propagate and keep current link quality measurements. Metric maintenance includes a reactive approach for links that a node is currently using to route packets, and a proactive mechanism for all links. Nodes are configured to include a send buffer, a maintenance buffer, a request table, link quality metric modules, and preferably a neighbor cache and a link cache. The invention allows for asymmetric links in the network. The invention may be implemented within a virtual protocol interlayer between the link and network layers. The invention may employ any particular link quality metrics, including metrics based on probing techniques as well as metrics based on knowledge gained in other ways.
Owner:MICROSOFT TECH LICENSING LLC
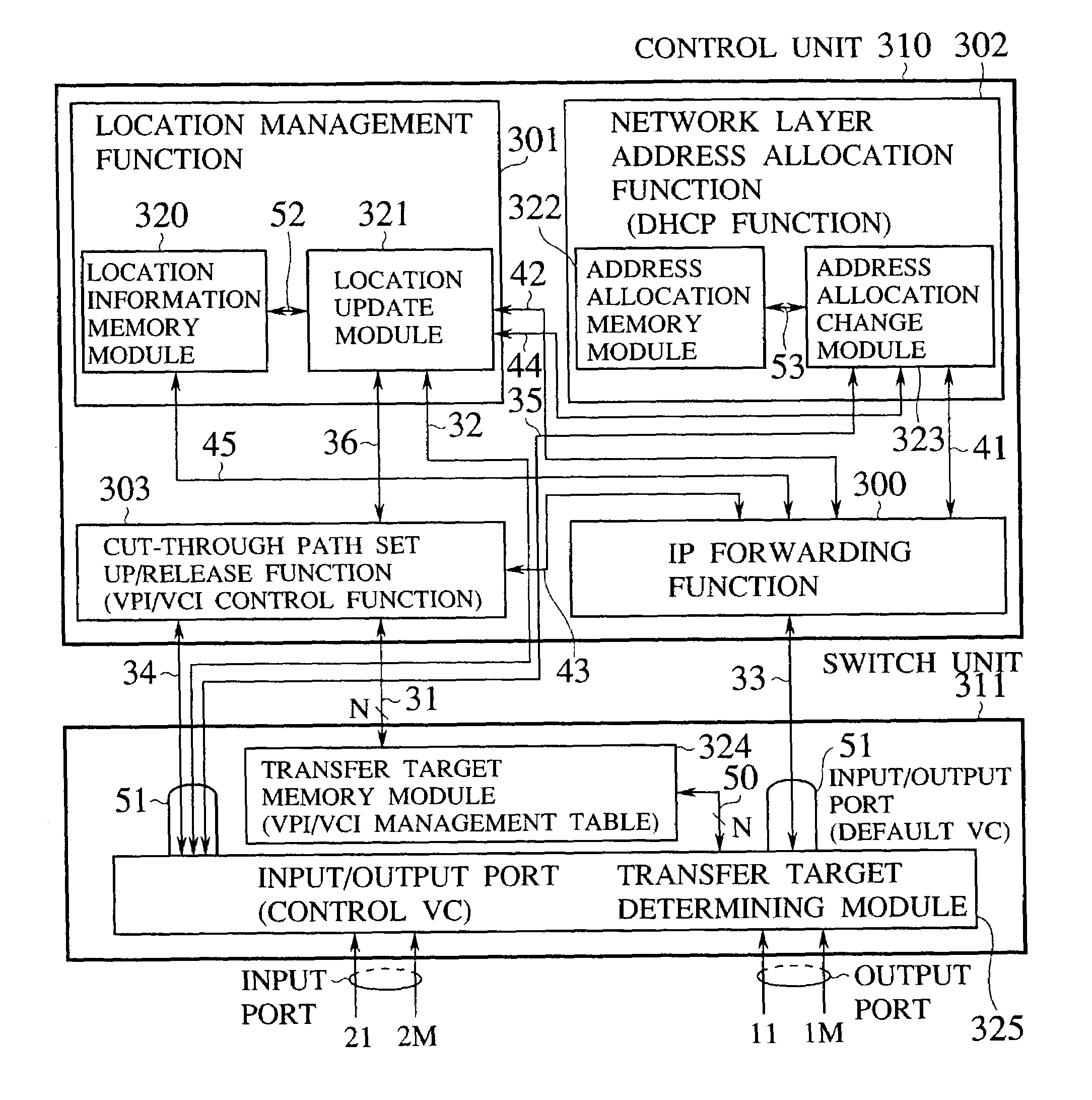
Router device, datagram transfer method and communication system realizing handoff control for mobile terminals
InactiveUS7151758B2Increase speedEasy to controlData switching by path configurationWireless network protocolsCommunications systemHandoff control
A mobile supporting router device for realizing the handoff control associated with the moving in high speed is forms by at least one first interface connected with radio base stations, each capable of accommodating at least one mobile terminal; at least one second interface connected with a wire network; an information exchanging unit for exchanging a routing protocol on a network layer, through the second interface; a memory unit for storing information regarding a routing on the network layer based on the routing protocol exchanged by the information exchanging unit; a transfer unit for transferring datagram through the first interface according to the information regarding the routing on the network layer stored in the memory unit; a moving detection unit for detecting a moving of the mobile terminal among the radio base stations; and an information updating unit for updating the information regarding the routing on the network layer stored in the memory unit when the moving of the mobile terminal is detected by the moving detection unit.
Owner:KK TOSHIBA
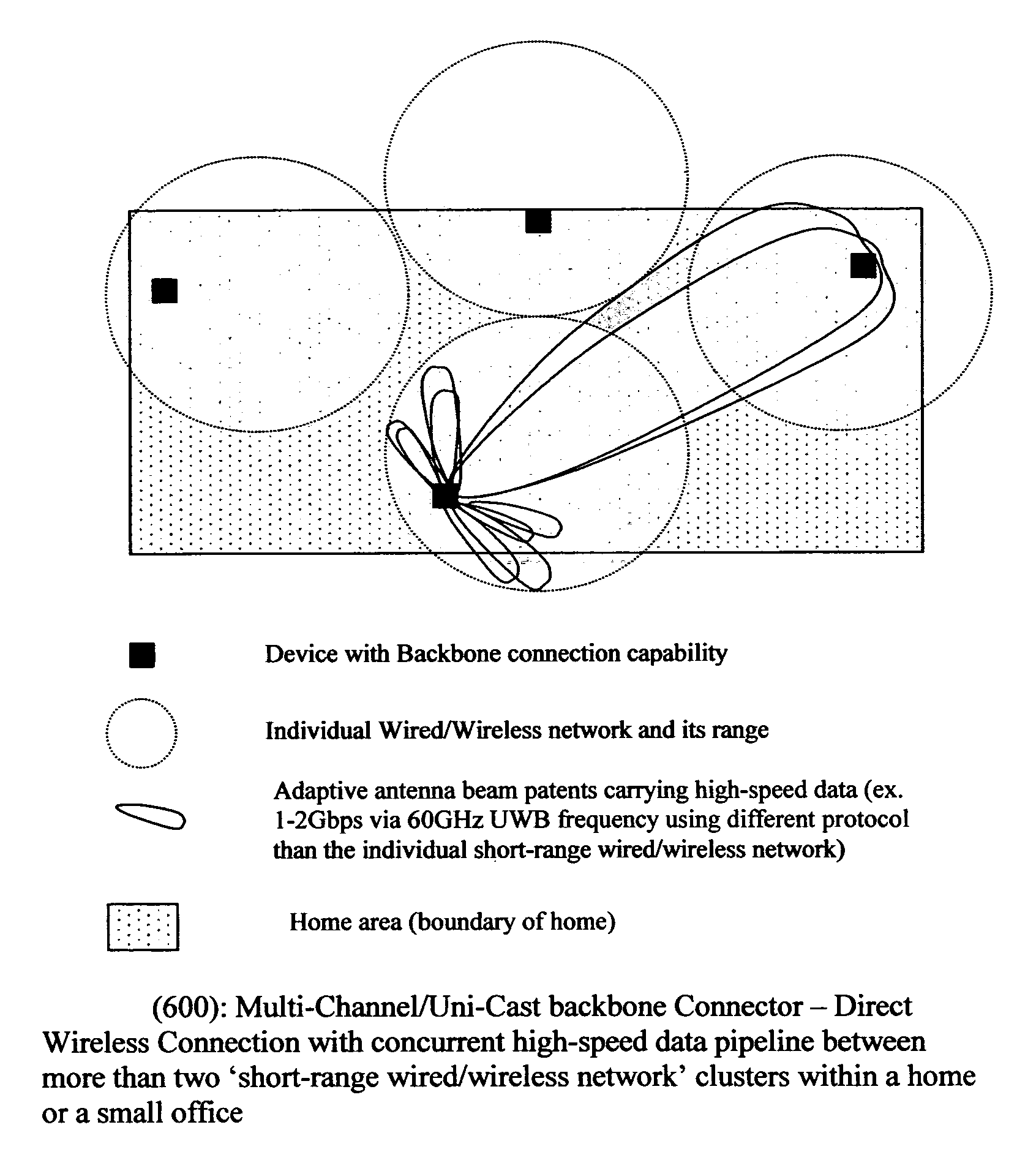
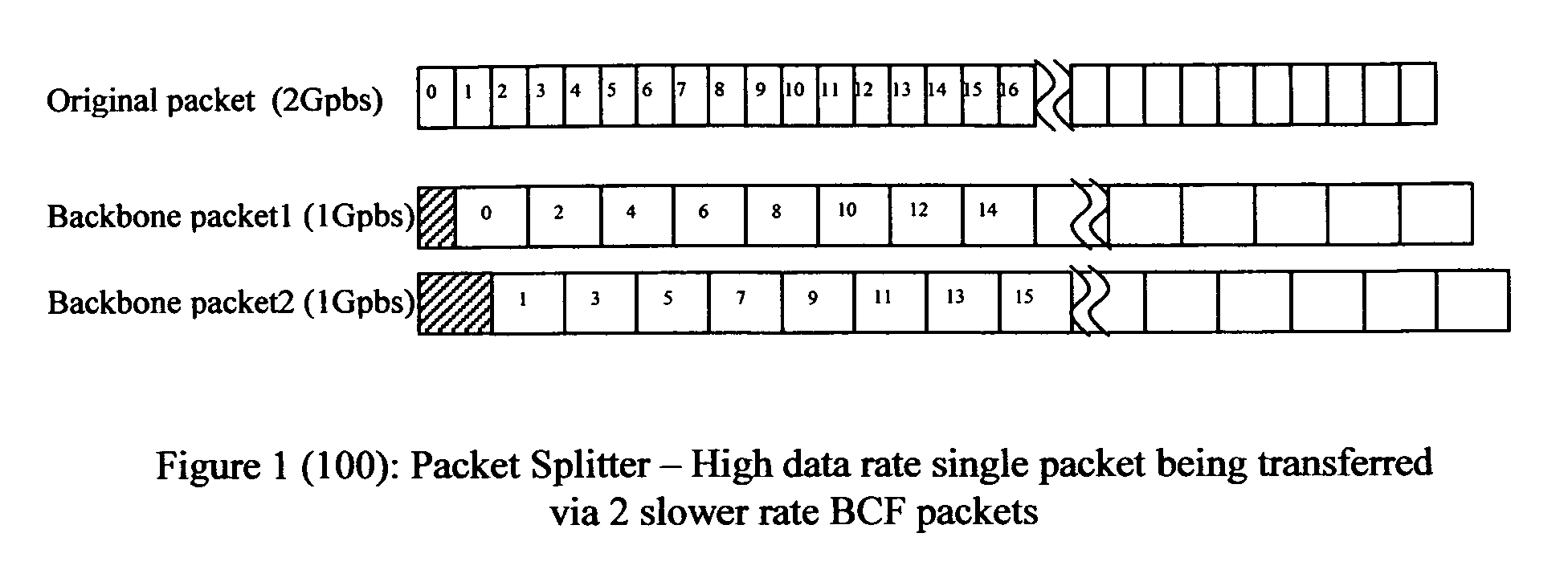
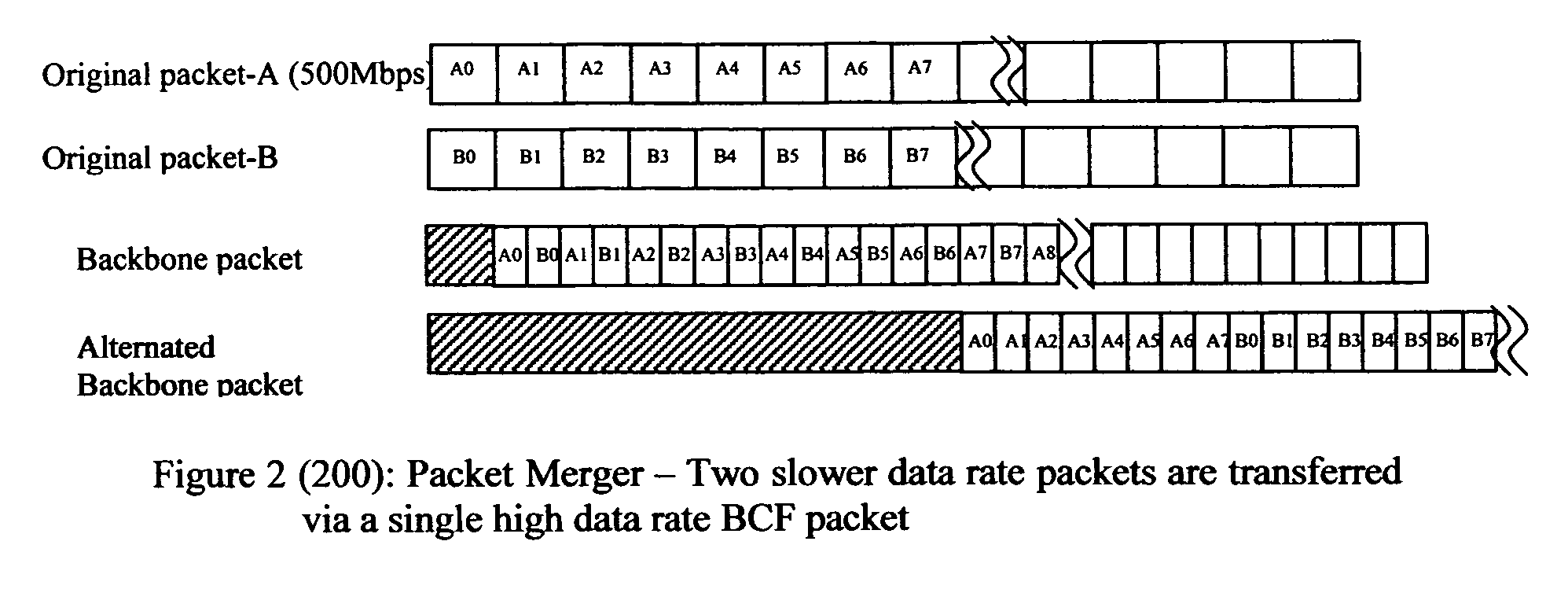
Method of constructing wireless high speed backbone connection that unifies various wired/wireless network clusters by means of employing the smart/adaptive antenna technique and dynamically creating concurrent data pipelines
InactiveUS7672271B2Reduce distractionsMinimize powerMultiplex system selection arrangementsEnergy efficient ICTTransmitted powerData link layer
In accordance with the present invention, there is provided a high-speed wireless backbone connection, Backbone Connection Facilitator (BCF), to create a wireless home network, which may consist of many short-range wired / wireless networks. BCF dynamically creates concurrent data pipelines to meet the data bandwidth demand to transfer packets from one short-range wired / wireless network to another. BCF employs the newly developed antenna technologies (ex. MIMO, SDMA) to minimize the transmit power, to reduce the interferences, and to support the real time communication.BCF contains the BCF-PHY layer, the BCF-Data-Link-Layer, and the BCF-Network-Layer. The BCF-PHY layer consists of antenna array, a PHY Base Band controller, and a digital beam former. The BCF-Data-Link-Layer provides the MAC functionality. The BCF-Network-Layer assembles the packet, provides the source and destination address, and provides the BCF-PHY beam forming information. The BCF-Network-Layer is also responsible for parsing and assembling the packet payloads for the high-speed backbone connection.
Owner:LEE HYUN
Boarder Gateway Protocol Signaling to Support a Very Large Number of Virtual Private Networks
InactiveUS20150003458A1Data switching switchboardsNetworks interconnectionBorder Gateway Protocol24-bit
Disclosed herein are example embodiments for Boarder Gateway Protocol (BGP) signaling in virtual private network (VPN) communications. For example, a first network element may encode Multiprotocol Label Switching (MPLS) information in a Network Layer Reachability Information (NLRI) label field that is longer than 24 bits, and transmit a BGP update message comprising a BGP attribute to a second network element. The BGP attribute comprises the NLRI and a specific Subsequent Address Family Identifier (SAFI) value. The specific SAFI value signals to the second network element, upon reception of the BGP update message by the second network element, that the NLRI label field is more than 24 bits long.
Owner:FUTUREWEI TECH INC
Method for wireless access system supporting multiple frame types
InactiveUS20060062250A1Error prevention/detection by using return channelNetwork traffic/resource managementWireless routerMultiple frame
A wireless access system having a subscriber subsystem gateway (20) and a wireless router (30) in communication with the gateway via a two-way radio channel (25) according to a communication protocol. The communication protocol has a medium access control (MAC) layer (602, 603, 604, 605) capable of supporting several different network layer frame types (610-612 and 613-615) and includes a MAC layer header (800) having a frame type indicator (801), so that multiple frames of differing frame types are communicated contiguously over the radio channel separated by MAC layer headers.
Owner:PAYNE WILLIAM A III
Multiplexed Client Server (MCS) Communications and Systems
ActiveUS20100009758A1Multiple digital computer combinationsStore-and-forward switching systemsNetwork connectionComputer terminal
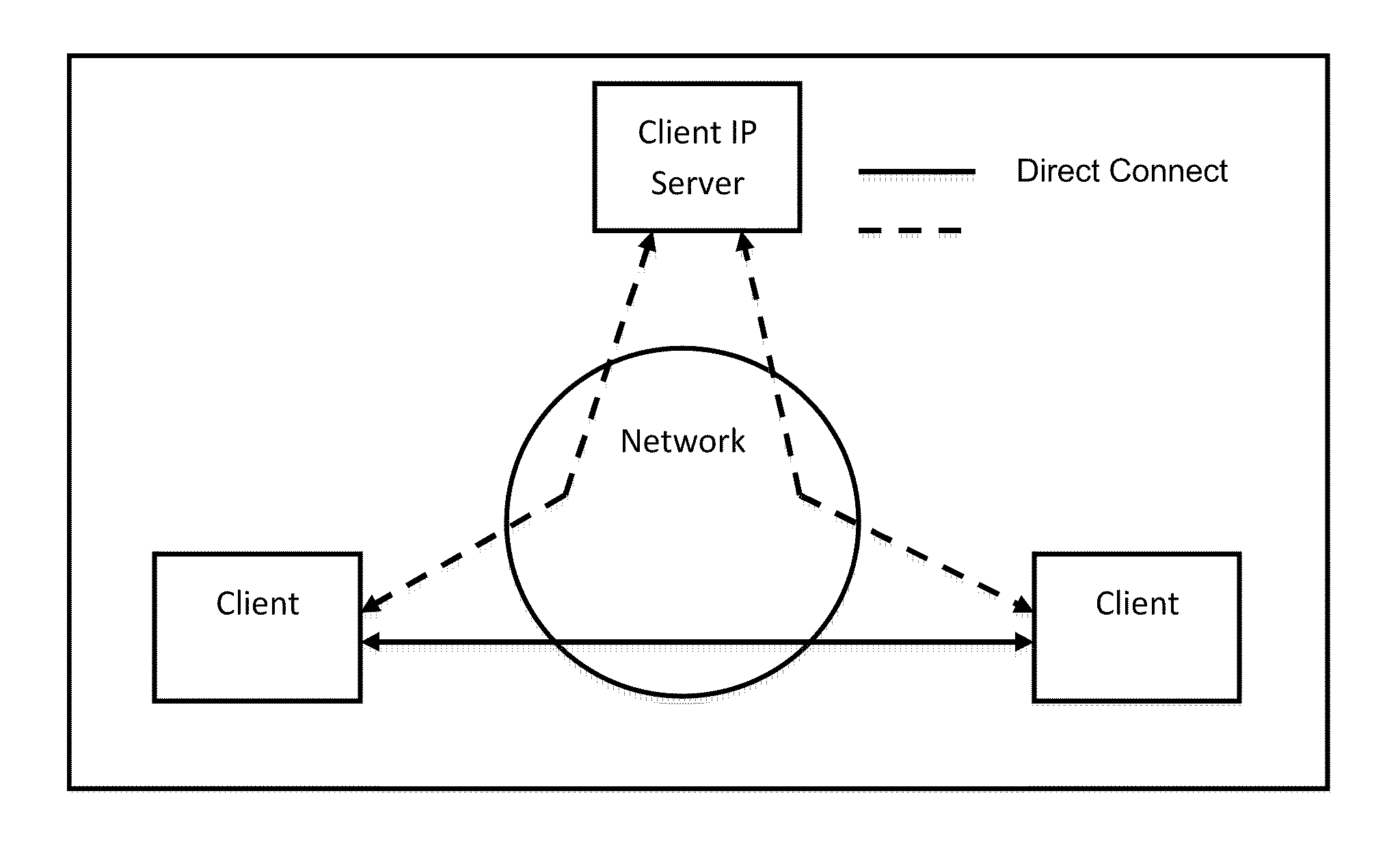
A method of transferring a file between first and second end-user devices via network communications includes: communicating by the first end-user device network contact information of the first end-user device; communicating by the second end-user device network contact information of the second end-user device; establishing an open network connection between the first end-user device and the second-end user device based on the communicated network contact information of each of the end-user devices; and transferring the file from the first end-user device to the second end-user via the open network connection between the first end-user device and the second-end user device. A single encryption key may be used between the application and network layers on each end-user device, each of which may include virtualized routing capabilities.
Owner:ASSET RECOVERY ASSOC +1
System, device, and method for establishing and removing a label switched path in a communication network
InactiveUS7023846B1Data switching by path configurationStore-and-forward switching systemsSignaling protocolLabel switching
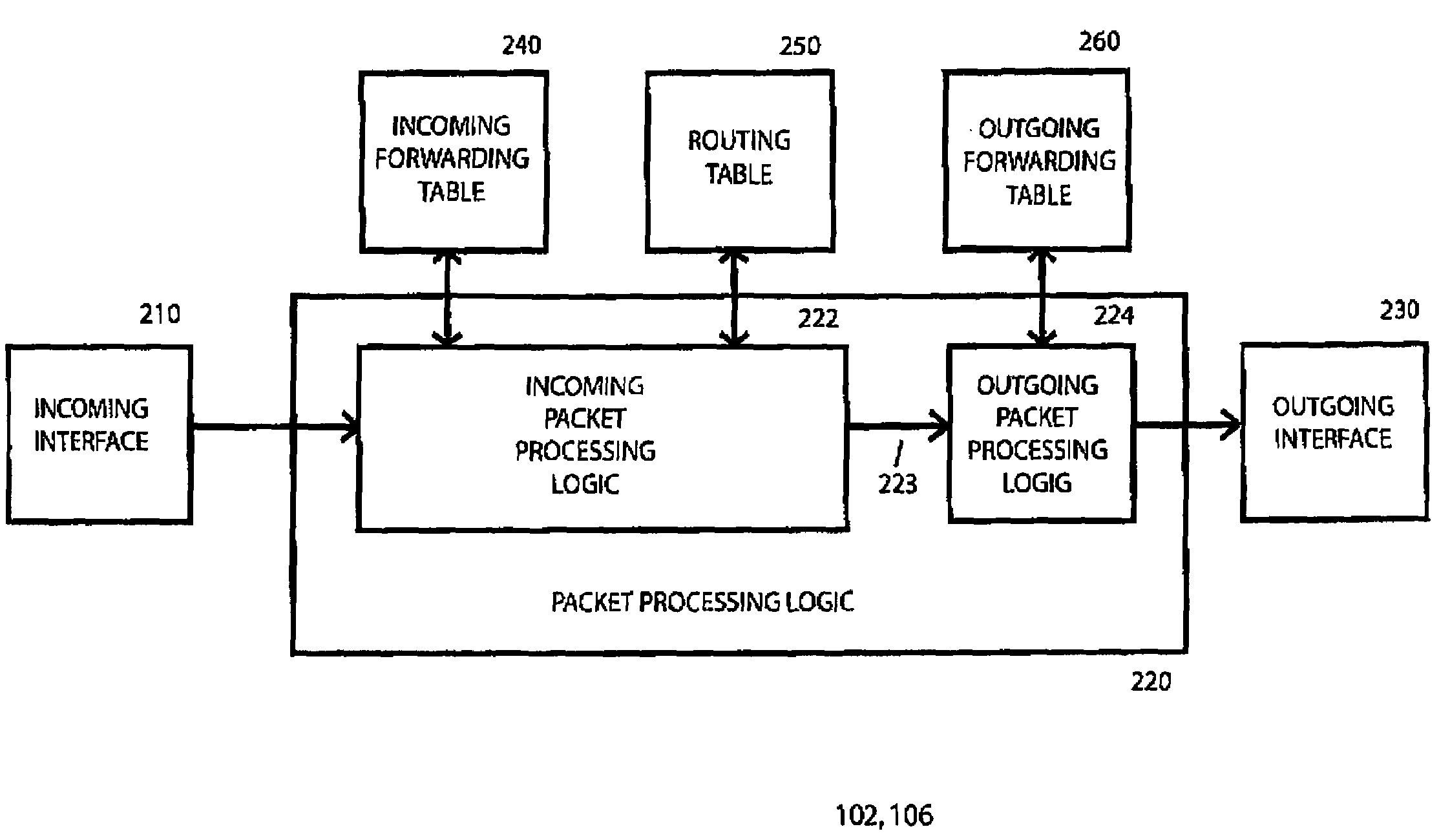
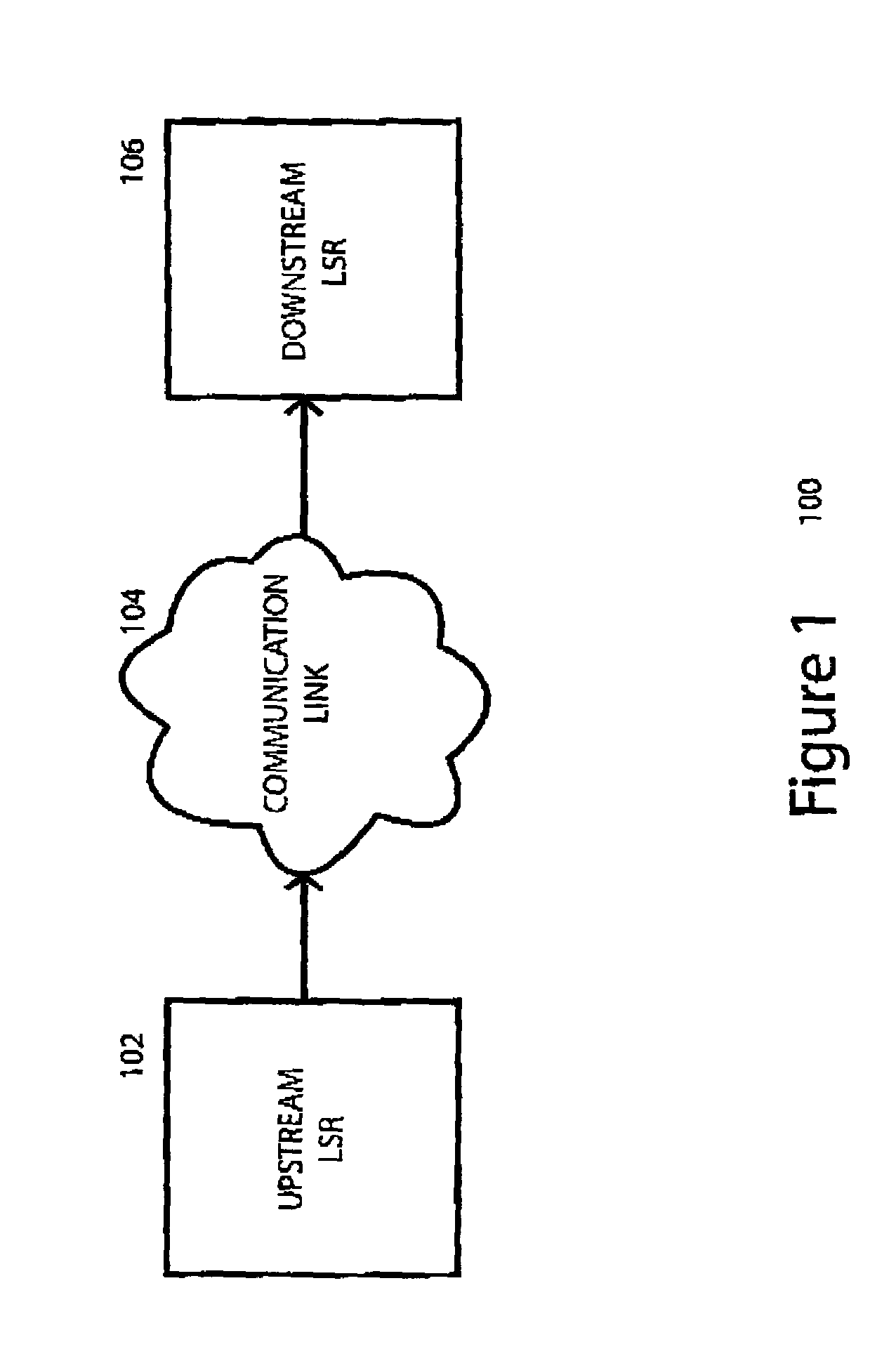
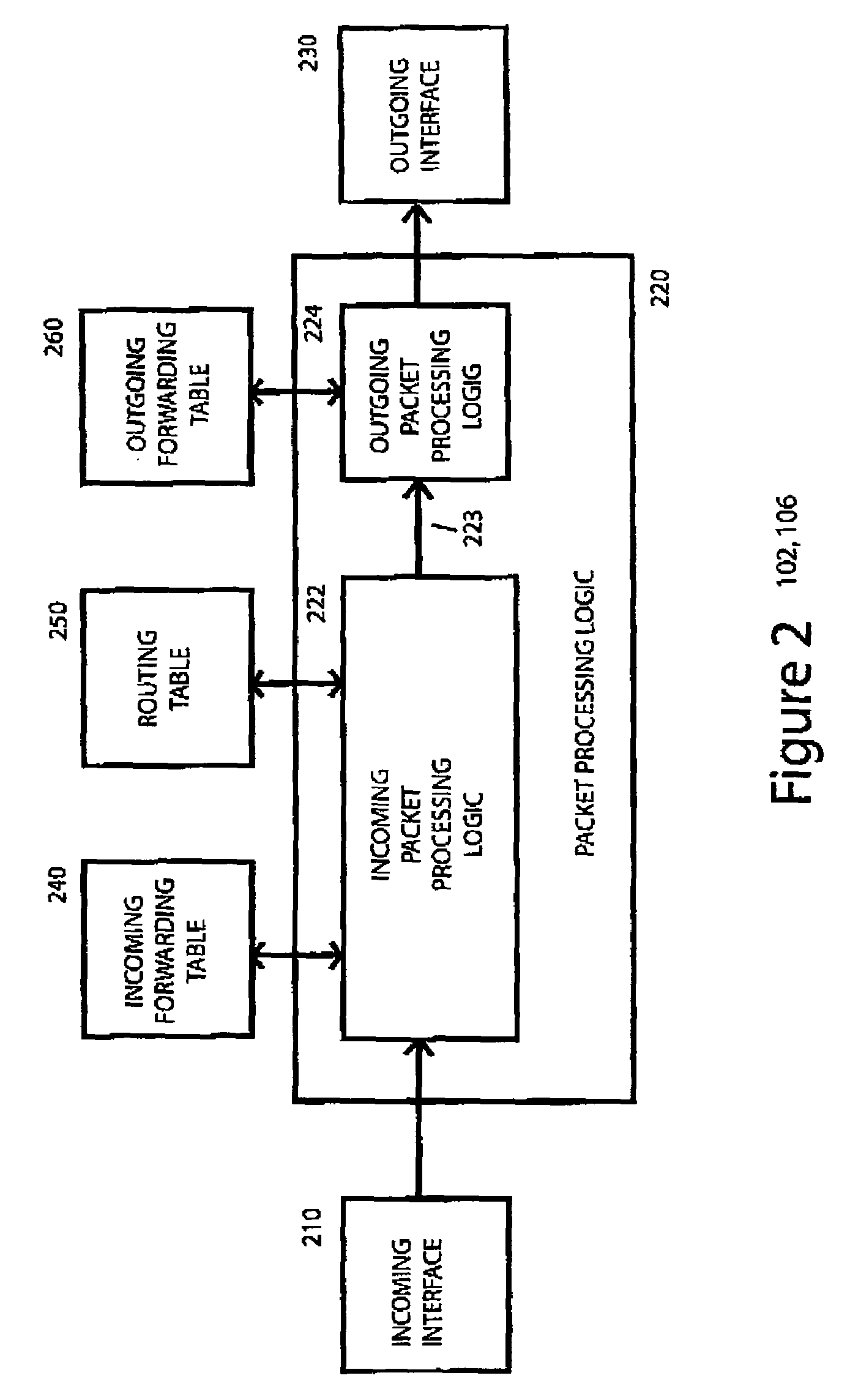
A system, device, and method for establishing and removing a label switched path in a communication network uses a packet-driven mechanism rather than using an explicit signaling protocol to exchange label switching information from an upstream label switching device to a downstream label switching device. In order to establish a label switched path from the upstream label switching device to the downstream label switching device, the upstream label switching device allocates a new label for the label switched path, sets up the label switched path by adding the new label to its forwarding table, and forwards a labeled packet including the new label and an indicator indicating that the packet is labeled. Upon receiving the labeled packet from the upstream label switching device, the downstream label switching device sets up the label switched path by adding the new label to its forwarding table, and forwards the packet based upon network layer addressing information in the packet. In order to remove the label switched path, the upstream label switching device forwards unlabeled packets to the downstream label switching device, and both devices remove the label from its respective forwarding table.
Owner:RPX CLEARINGHOUSE
Bidirectional communication system
InactiveUS6188684B1Broadcast transmission systemsTelephonic communicationTelecommunicationsTelecommunications link
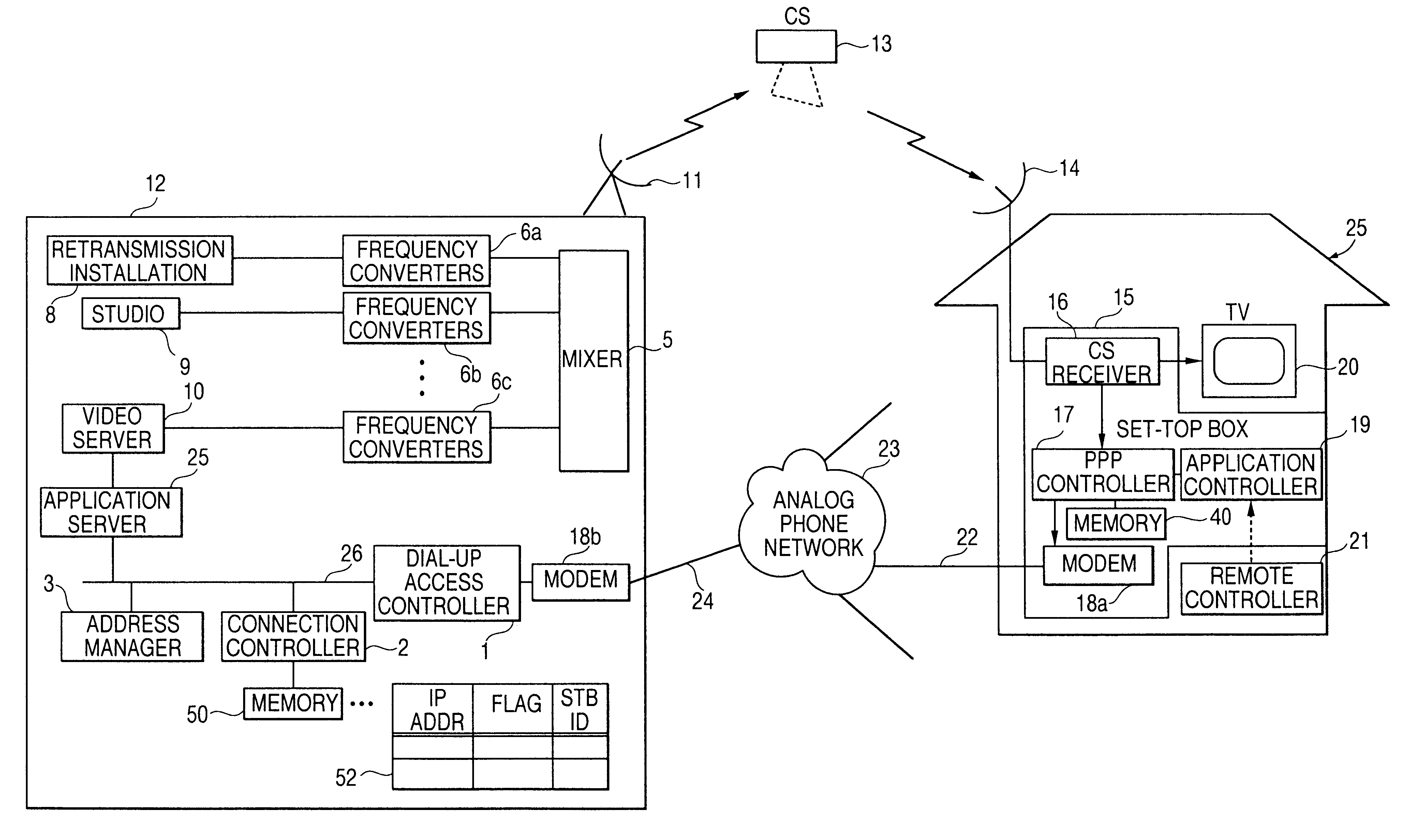
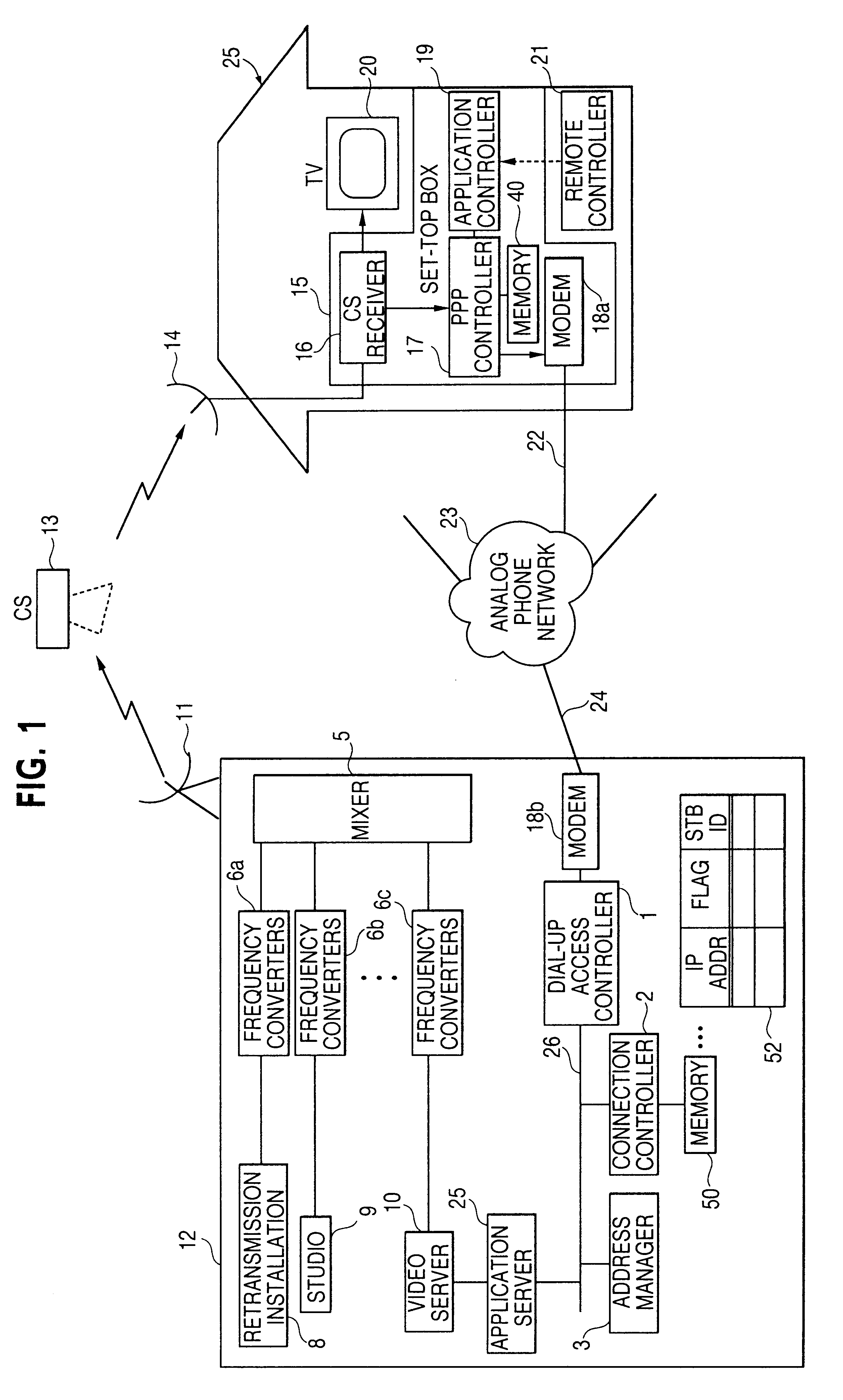
A bidirectional communication system in which dial-up connection for transmitting communication data may be disconnected when not used, and may be insured to be reconnected when needed. Also, the system includes an arrangement in which availability of connection with dial-up may be notified / determined in advance. The bidirectional communication system includes a first communication station and one or more second communication stations, the second communication stations receiving information delivery service from the first communication station, and the second communication stations performing data communication with the first communication station by means of dial-up link. The first communication station includes: an assignor assigning to the second communication station a protocol identifier of a network layer; a connector / disconnector for connecting / disconnecting the communication link according to respectively the presence and absence of communication data from the second communication station; and a storage holding the protocol identifier of the network layer assigned to the second communication station during the information delivery service from the second communication station.
Owner:HITACHI LTD
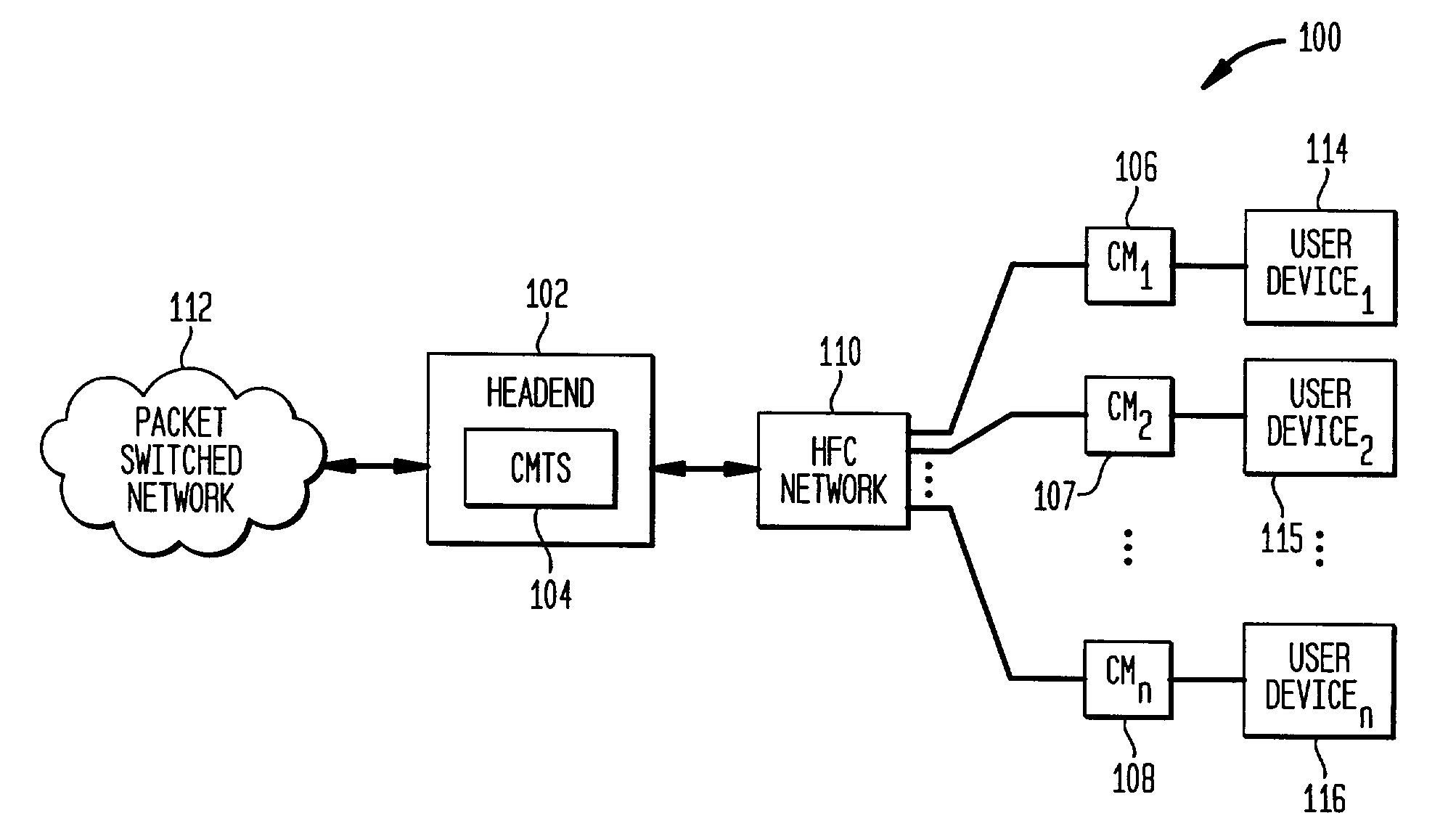
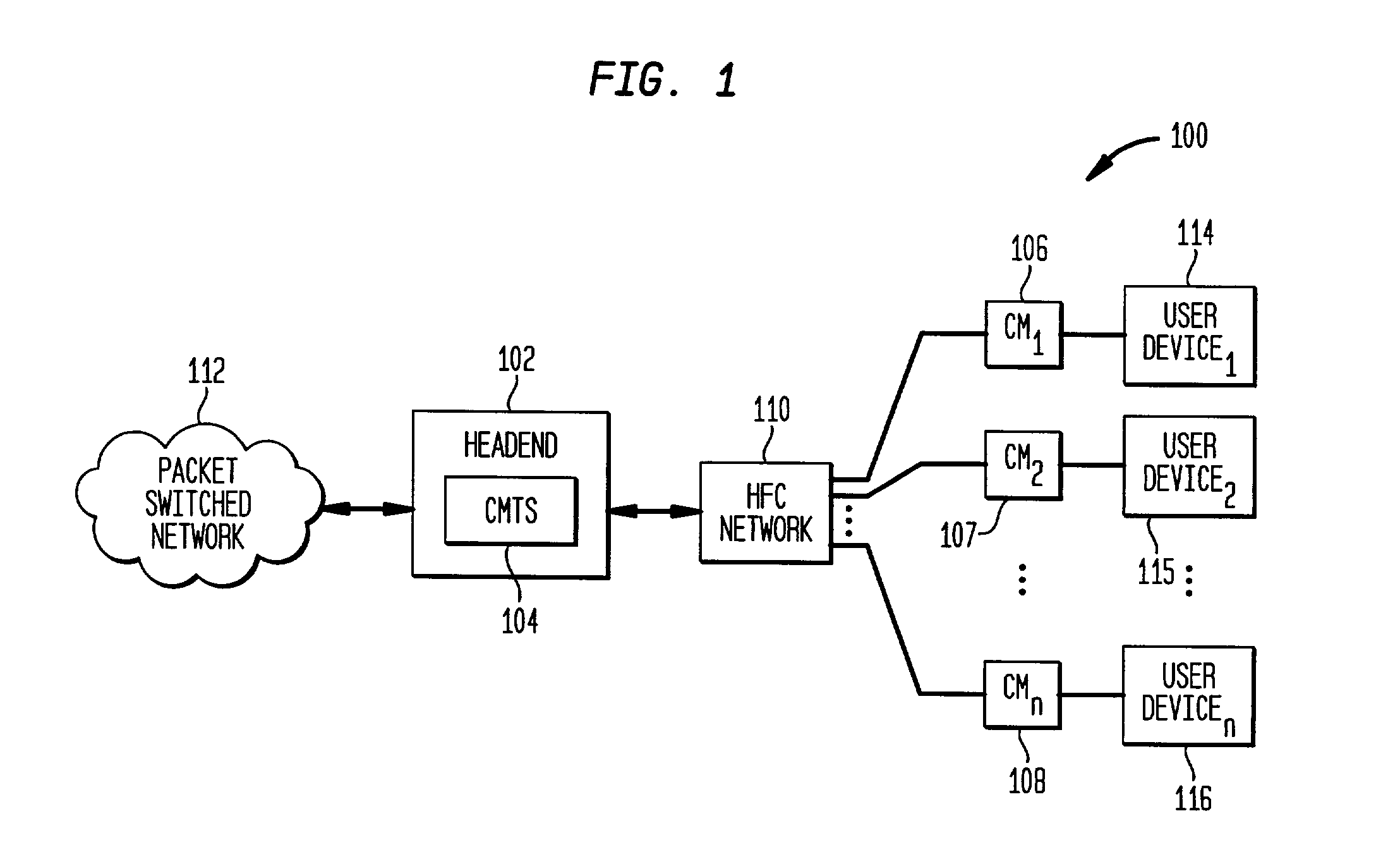
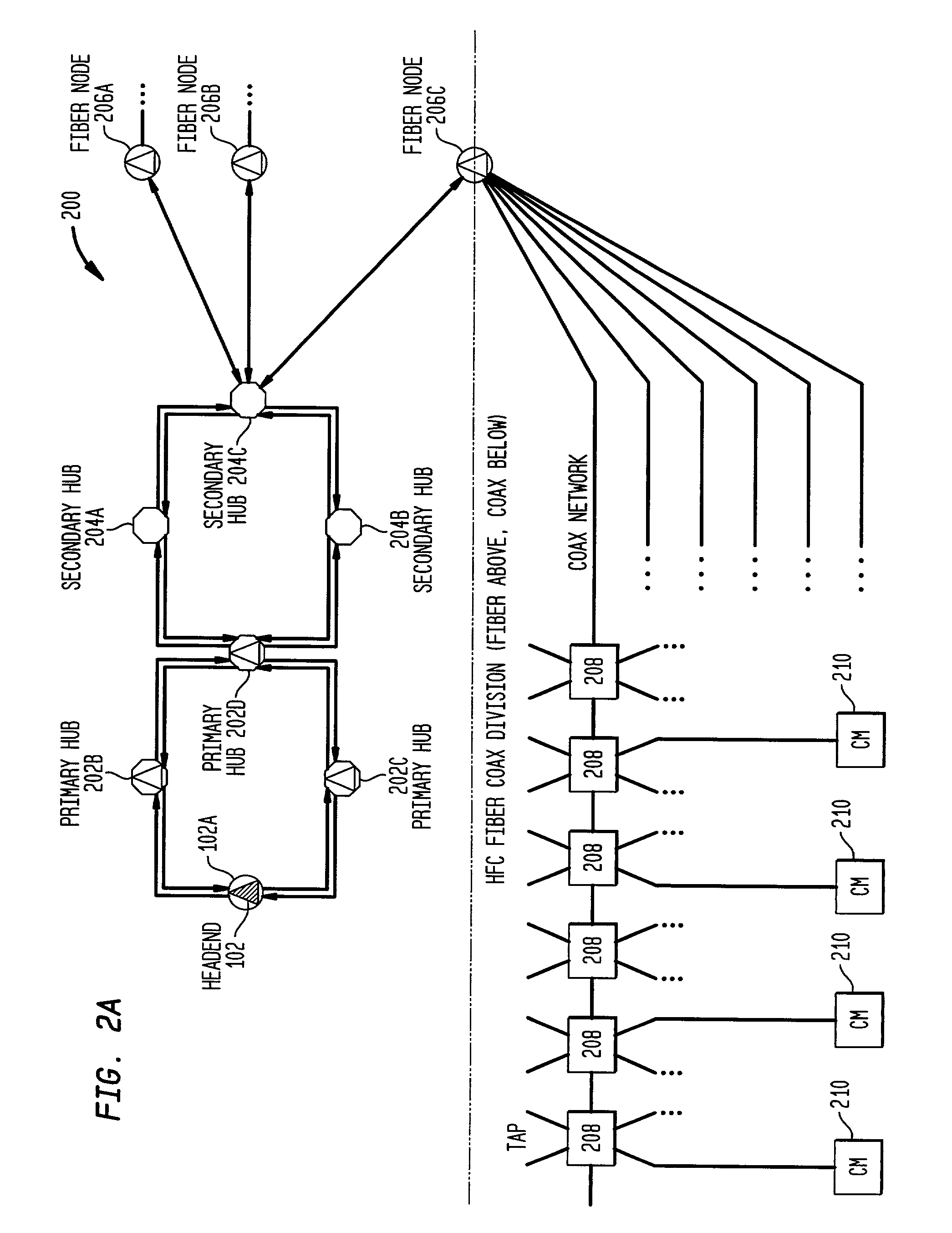
Distributed cable modem termination system (CMTS) architecture
A distributed CMTS in a hybrid fiber / coaxial (HFC) plant. The distributed CMTS comprises at least one network layer, at least one media access control layer, and one or more physical layers. The at least one network layer, at least one media access control layer and one or more physical layers each function as separate modules, enabling them to be in separate locations, yet physically connected, throughout the HFC plant.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Multi-layer based method for implementing network firewalls
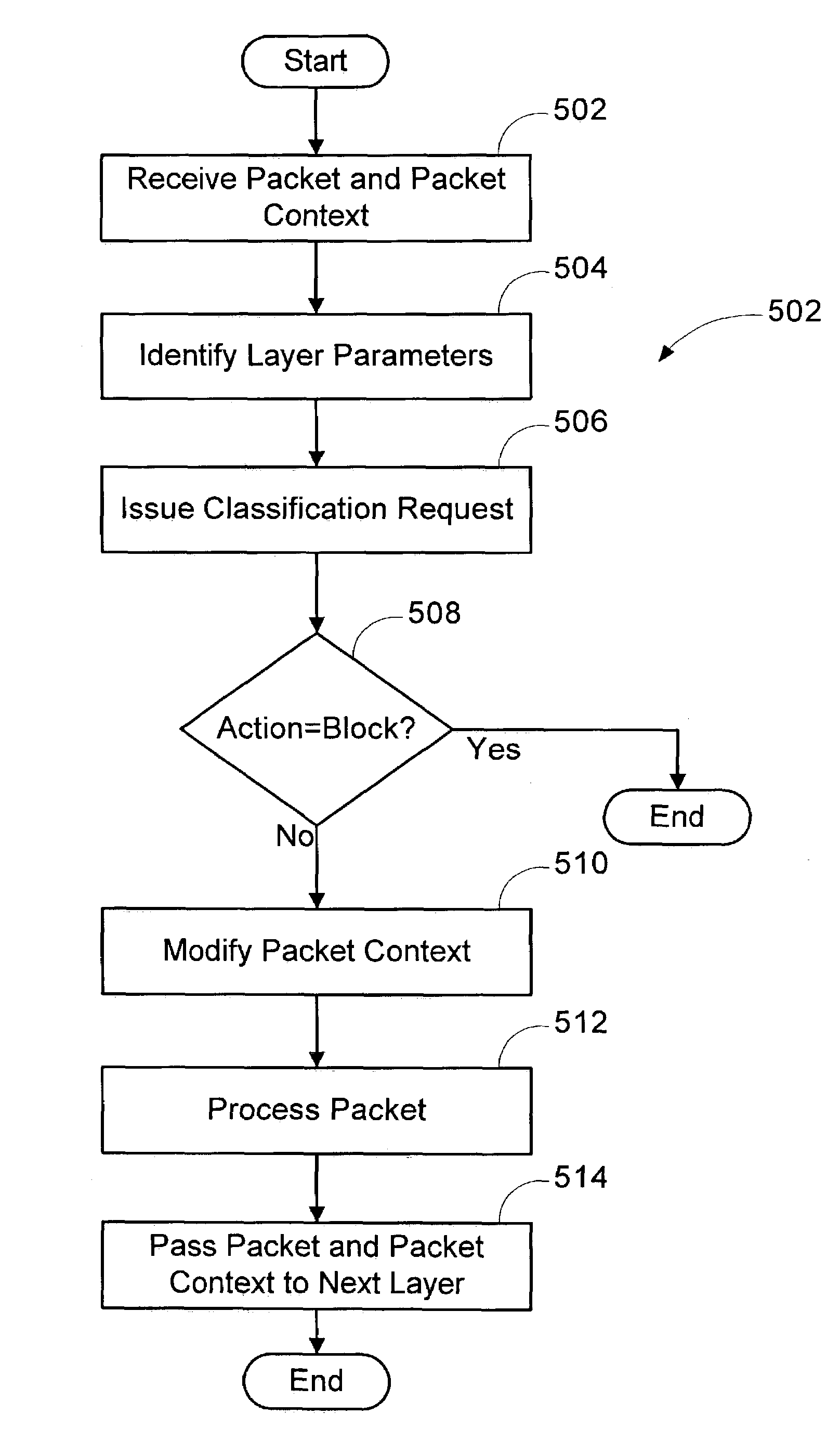
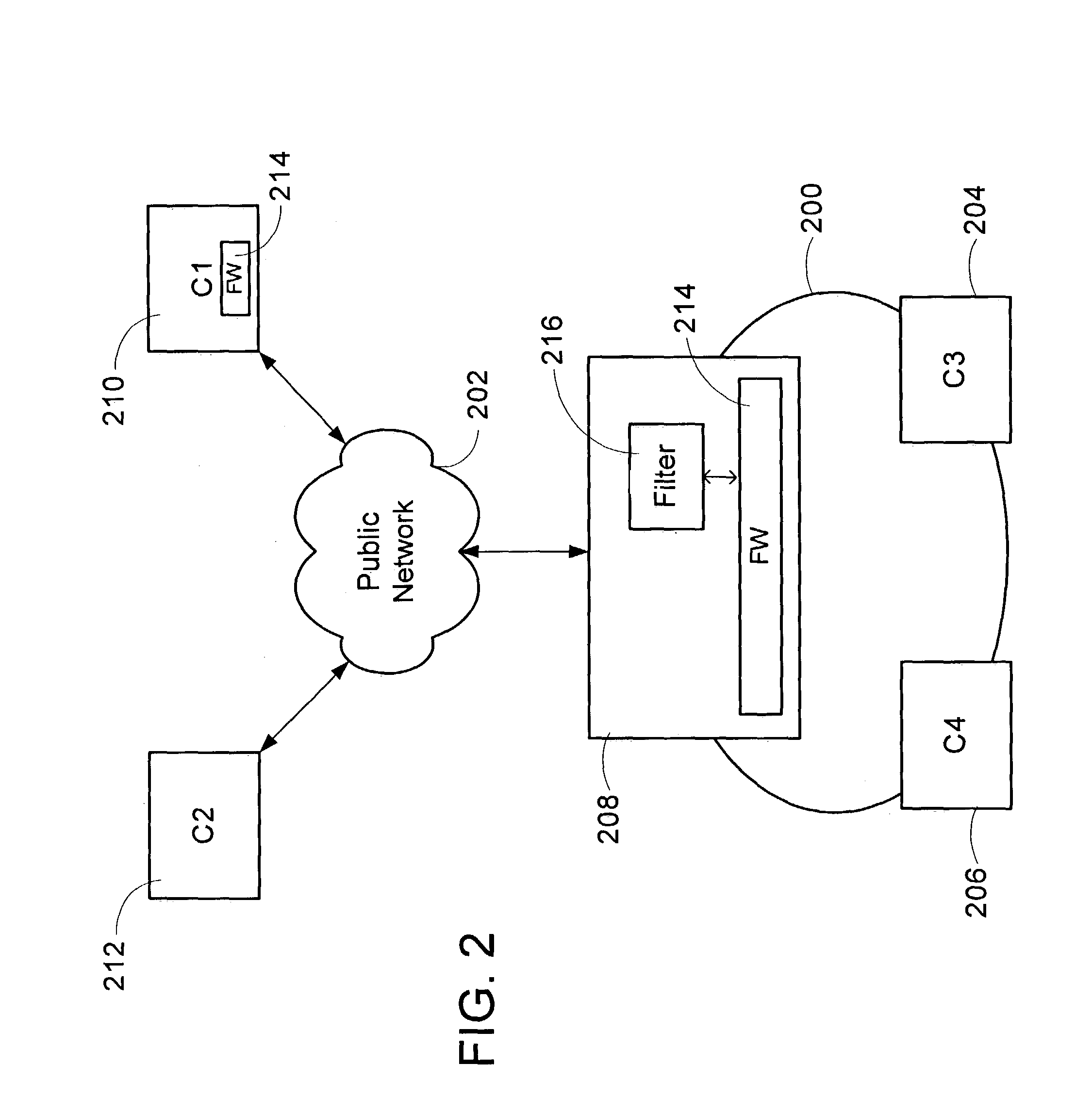
A method is provided for implementing a firewall in a firewall architecture. The firewall architecture includes a plurality of network layers and a first firewall engine. The layers send packets and packet information to the first firewall engine, maintain and pass packet context to subsequent layers, and process the packets. The first firewall engine compares the packet information to one or more installed filters and returns an action to the layers indicating how to treat the packet.
Owner:MICROSOFT TECH LICENSING LLC
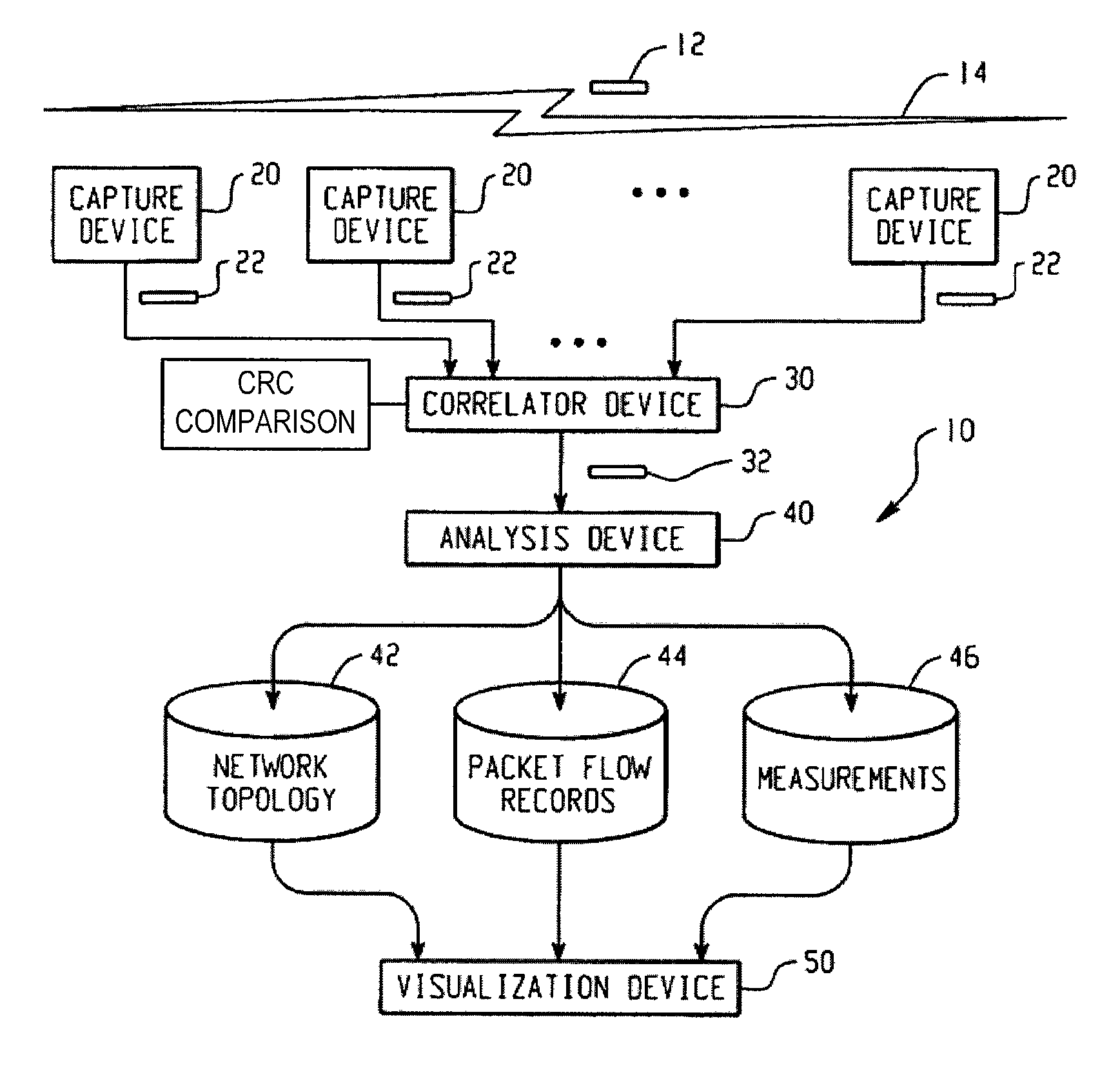
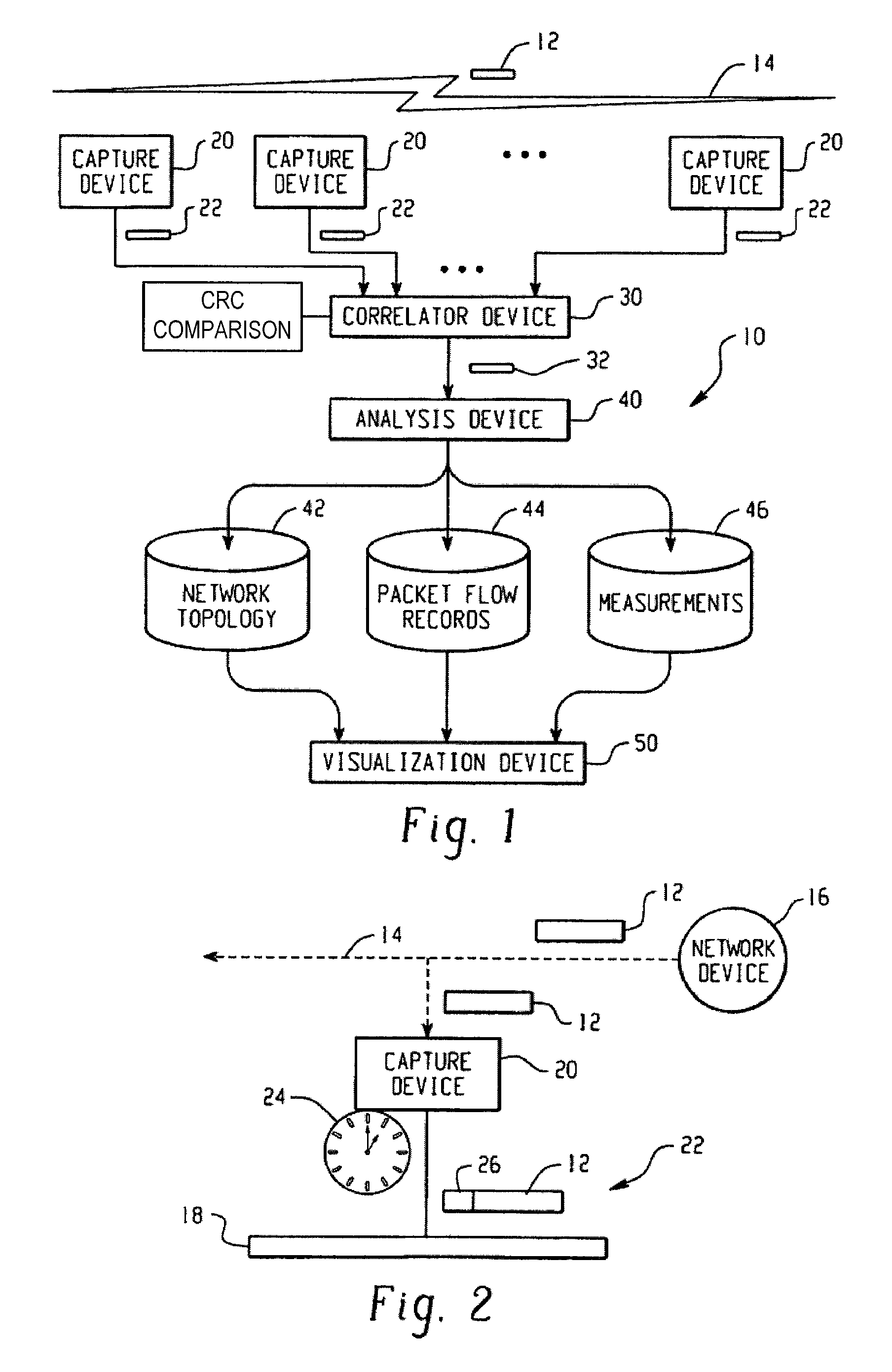
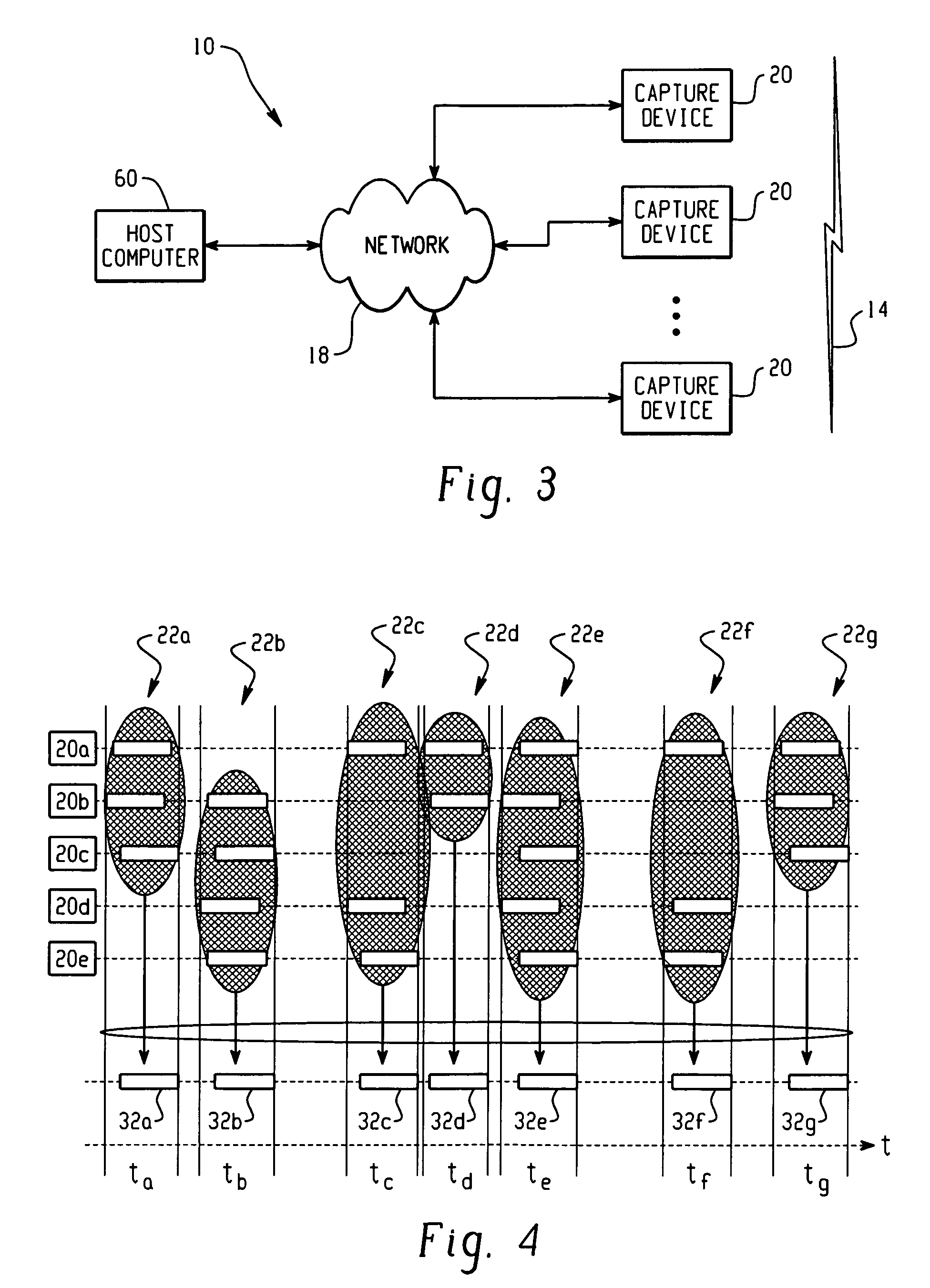
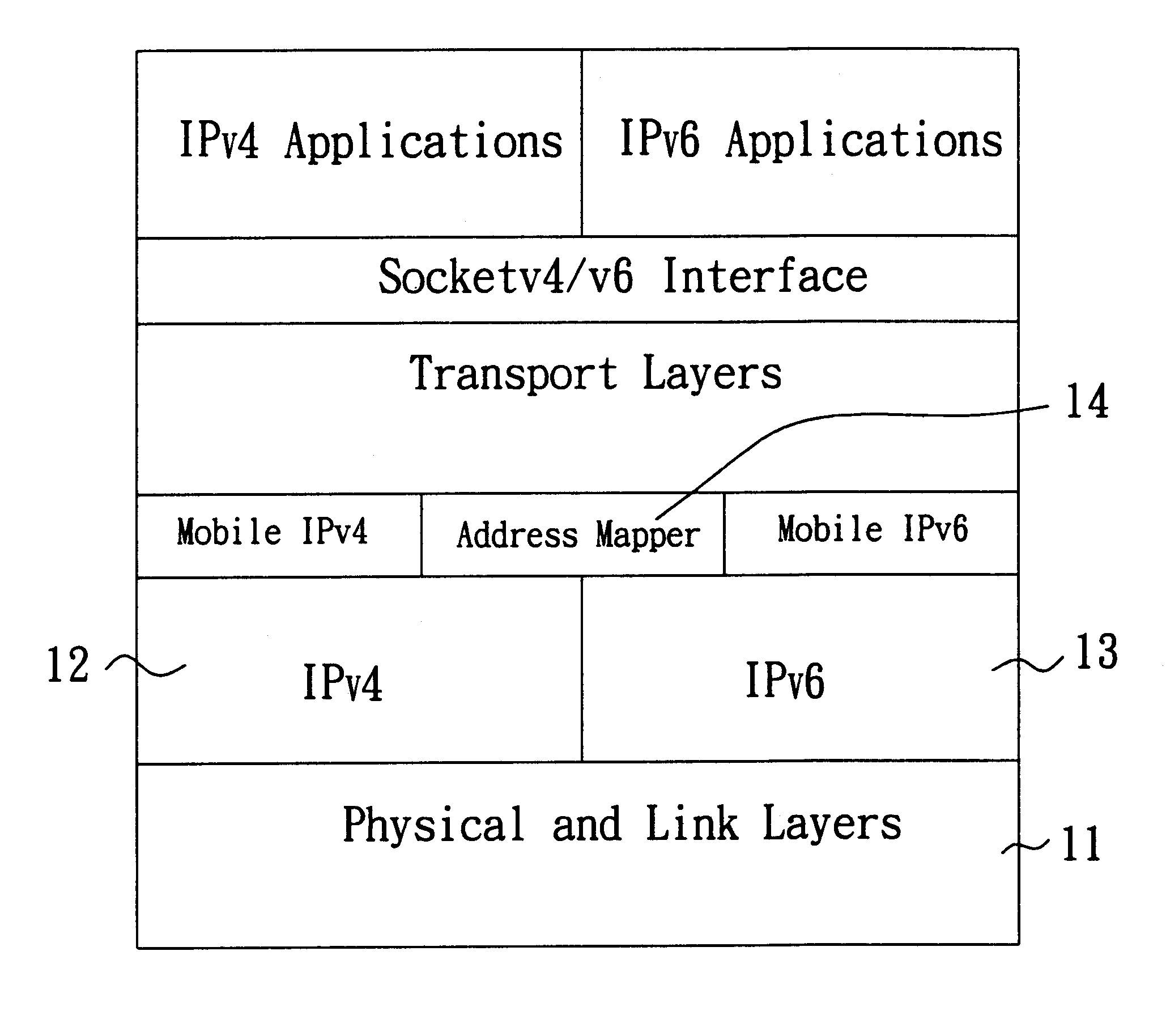
Network analysis system and method
ActiveUS7660892B2Easy to captureError preventionFrequency-division multiplex detailsNetwork packetMedia access control
A system for analyzing a packet-based network includes a wireless network analysis processing device that is configured to receive correlated packet records representative of the order in which corresponding packets are transmitted in a wireless network. The correlated packet records include media access control (MAC) layer data and network layer data for each corresponding packet. The MAC layer data and network layer data are processed to generate network topology data representative of the network topology, generate packet flow data representative of the flow of packets between devices at the MAC layer and across the network at the network layer, and measurement data relating to the packet flow data.
Owner:DAINTREE NETWORKS
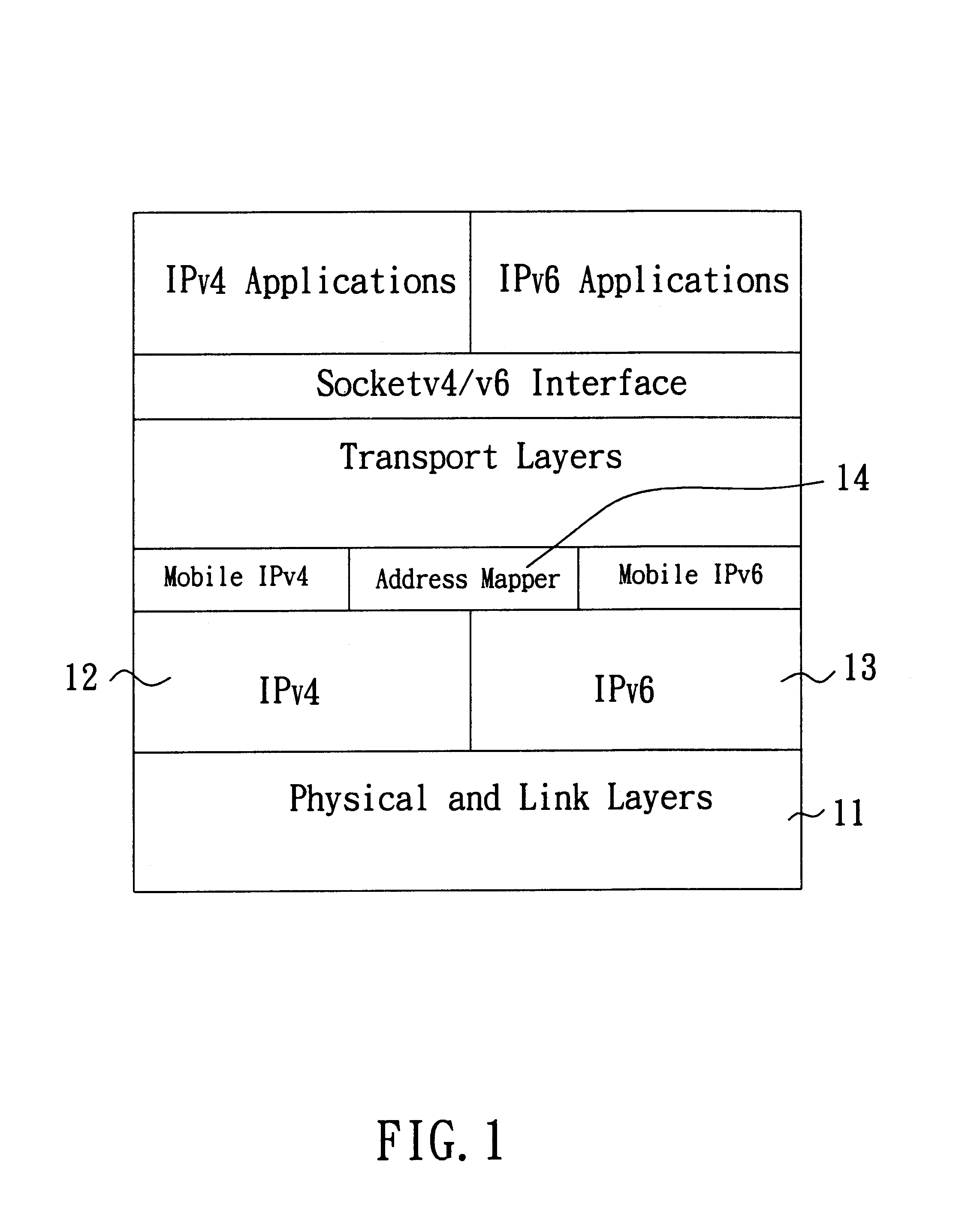
Method and system capable of providing mobility support for IPv4/IPv6 inter-networking
InactiveUS6862274B1Time-division multiplexData switching by path configurationNetwork packetForeign agent
A method and system capable of providing mobility support for IPv4 / IPv6 inter-networking to a mobile node is disclosed. The mobile node in the system has an address mapper, an IPv4 protocol stack and an IPv6 protocol stack in the network layer. When moving from IPv4 to IPv6 networks, the mobile node registered an IPv4 address receives router advertisement packets from an IPv6 router, so as to obtain a IPv6 care-of-address, and resolve the IPv6 care-of-address by an IPv4 care-of-address. The address mapper issues an IPv4 message to register the IPv4 care-of-address. When moving from IPv6 to IPv4 networks, the mobile node registered an IPv6 address receives agent advertisement messages from a foreign agent, so as to obtain an IPv4 care-of-address, resolve the IPv4 care-of-address by an IPv6 care-of-address. The address mapper issues an IPv6 message to register and update binding information by the IPv6 care-of-address.
Owner:IND TECH RES INST
Method for performing inter system handovers in mobile telecommunication system
ActiveUS6963745B2Radio/inductive link selection arrangementsWireless communicationDual modeData link layer
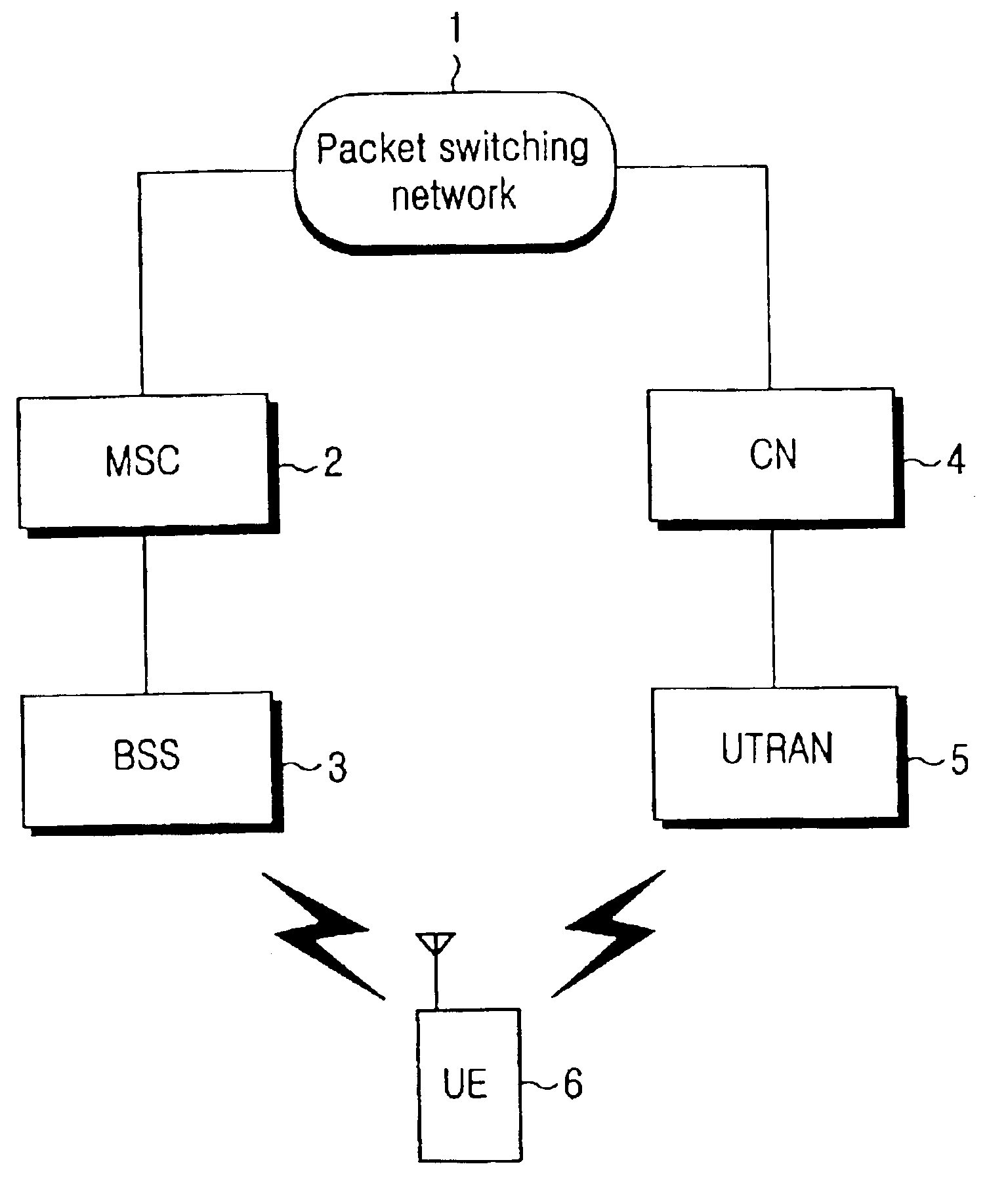
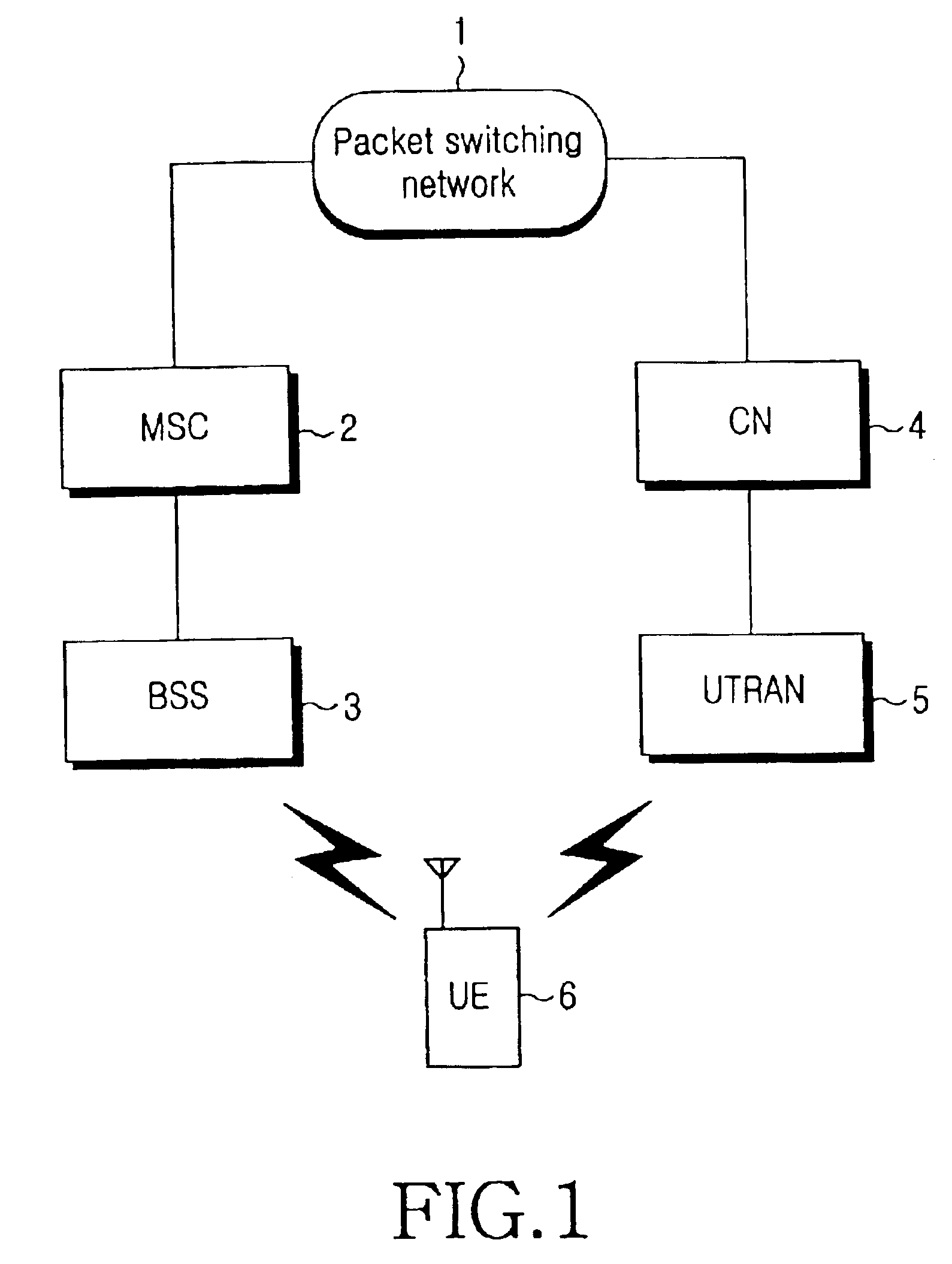
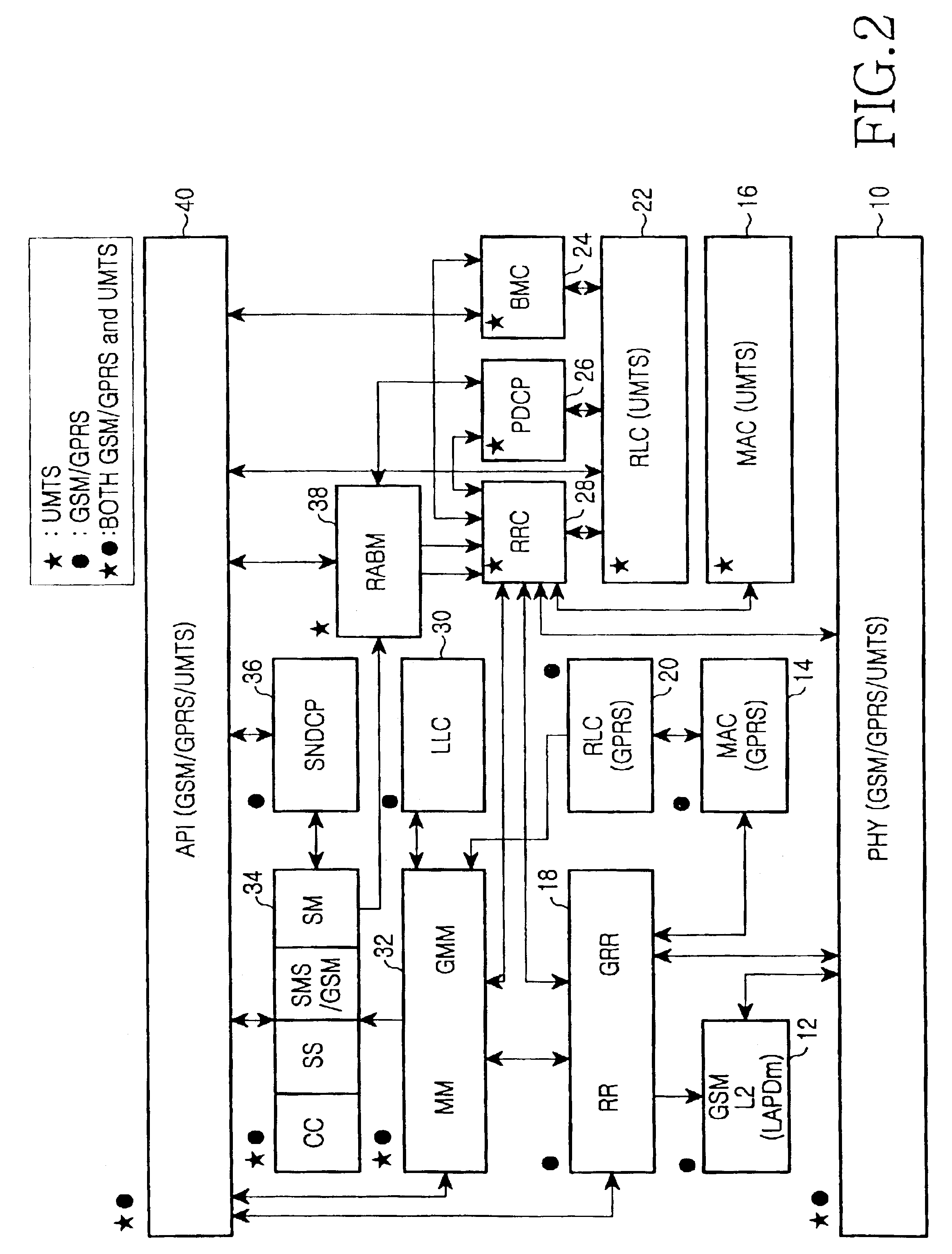
An inter system handovers in a mobile telecommunication system is performed when a dual mode user equipment (UE) covered by both GSM / GPRS network and UMTS network connects a dedicated channel and sets up a call in a BSS region where the GSM / GPRS provides coverage, and then moves to a UTRAN (UMTS Terrestrial Radio Access Network) where the UMTS provides coverage, wherein the method includes the steps of: if the dual mode UE receives an inter system handover command, i.e. from the BSS to the UTRAN, requesting GSM / GPRS data link layer to suspend a GSM / GPRS data link by a sublayer RR of GSM / GPRS network layer in the UE, requesting a GSM / GPRS physical layer to release a physical channel of the GSM / GPRS, and sending the inter system handover command to the UTRAN for authorizing a sublayer RRC of UMTS network layer in the UE to continue a call; requesting, at the RRC in the UE, a UMTS physical channel to be configured as a UMTS physical channel, and monitoring if the UMTS physical layer succeeds to have the configuration of the UMTS physical channel as requested; if the UMTS physical layer succeeds to have the configuration of the UMTS physical channel, requesting, at the RRC in the UE, a UMTS data link layer to configure a UMTS data link, and conveying information to the UTRAN through a UMTS channel that the handover between systems from the BSS to the UTRAN has been successfully performed; and sending, at the RRC, a GSM / GPRS resource release message to RR / GRR, thereby resetting the GSM / GPRS physical layer and the GSM / GPRS data link layer.
Owner:SAMSUNG ELECTRONICS CO LTD
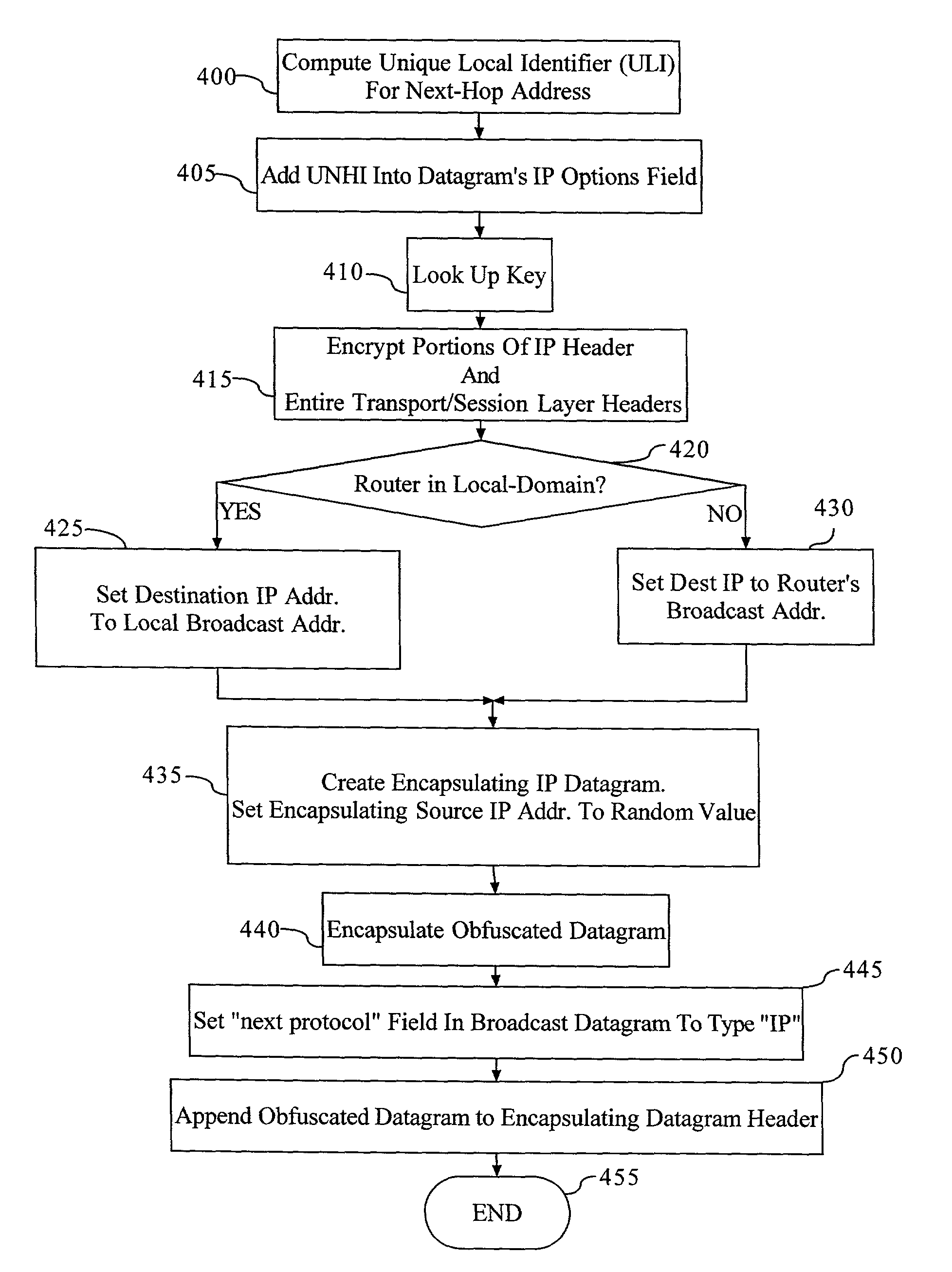
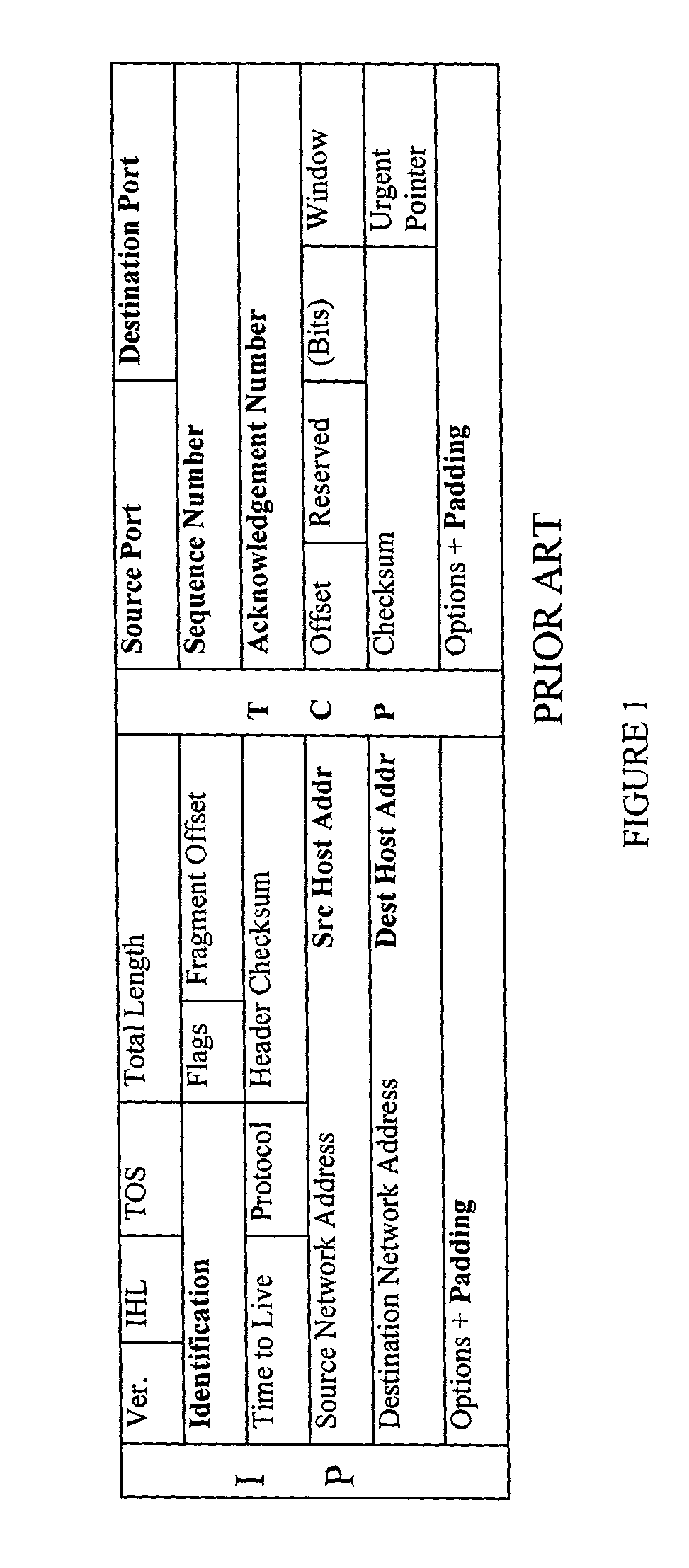
Method and apparatus for anonymous IP datagram exchange using dynamic network address translation
Methods, apparatus, system and computer program are provided for concealing the identity of a network device transmitting a datagram having a network layer header. A unique local identifier and broadcast address are determined in accordance with a next-hop address. A partially encrypted network layer header is determined by encrypting a plurality of identifying portions of the network layer header, where one portion of the network layer header is the unique local identifier. The datagram is encapsulated with another network layer header whose address is set to the broadcast address. The encapsulated datagram can be received and detunneled, and an address of a recipient can be extracted from the network layer header. The datagram is then admitted into a network domain.
Owner:VERIZON PATENT & LICENSING INC +1
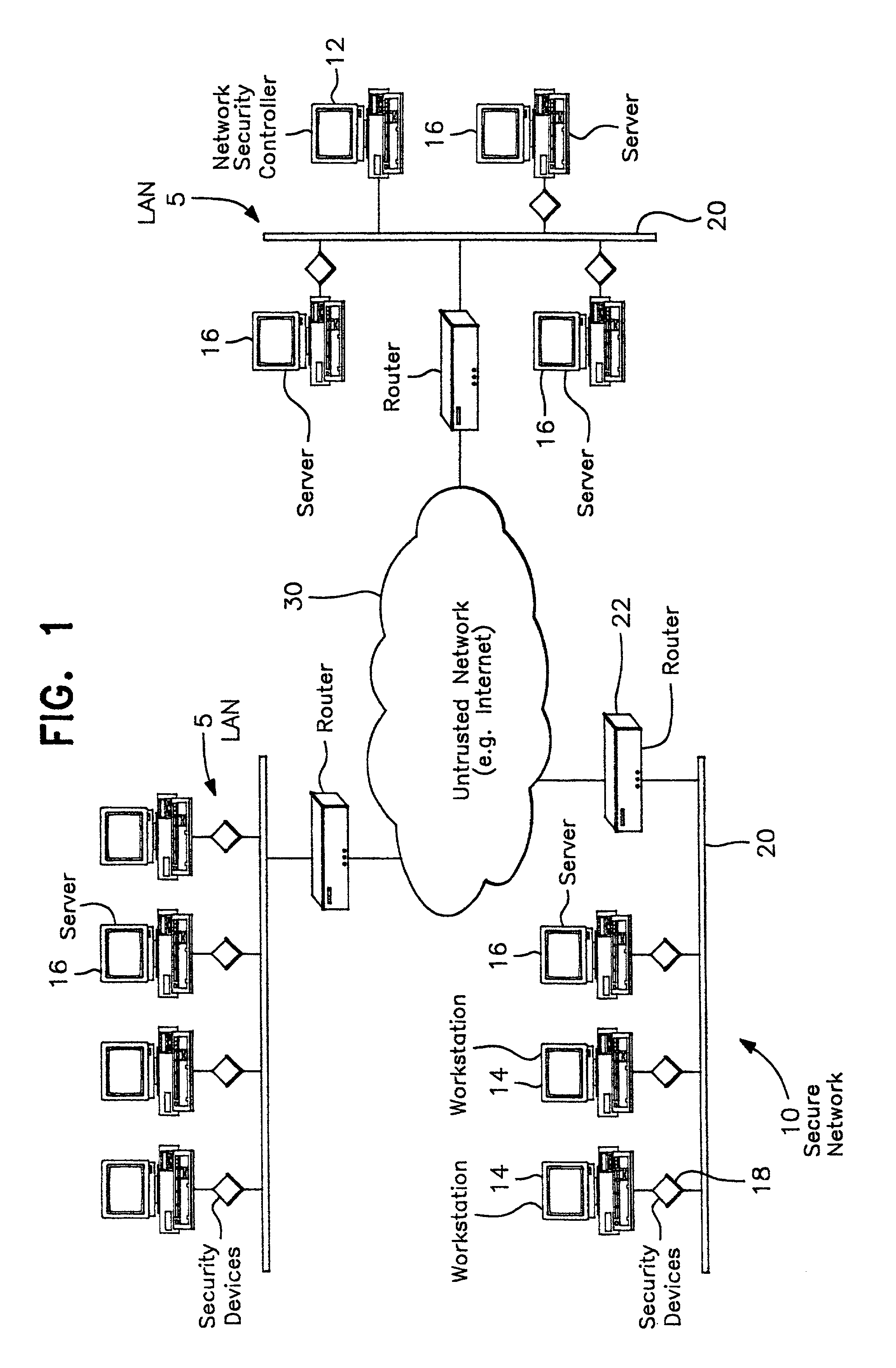
Multi-level security network system
InactiveUS7069437B2Ensure integrityDigital data processing detailsComputer security arrangementsPrivate networkThe Internet
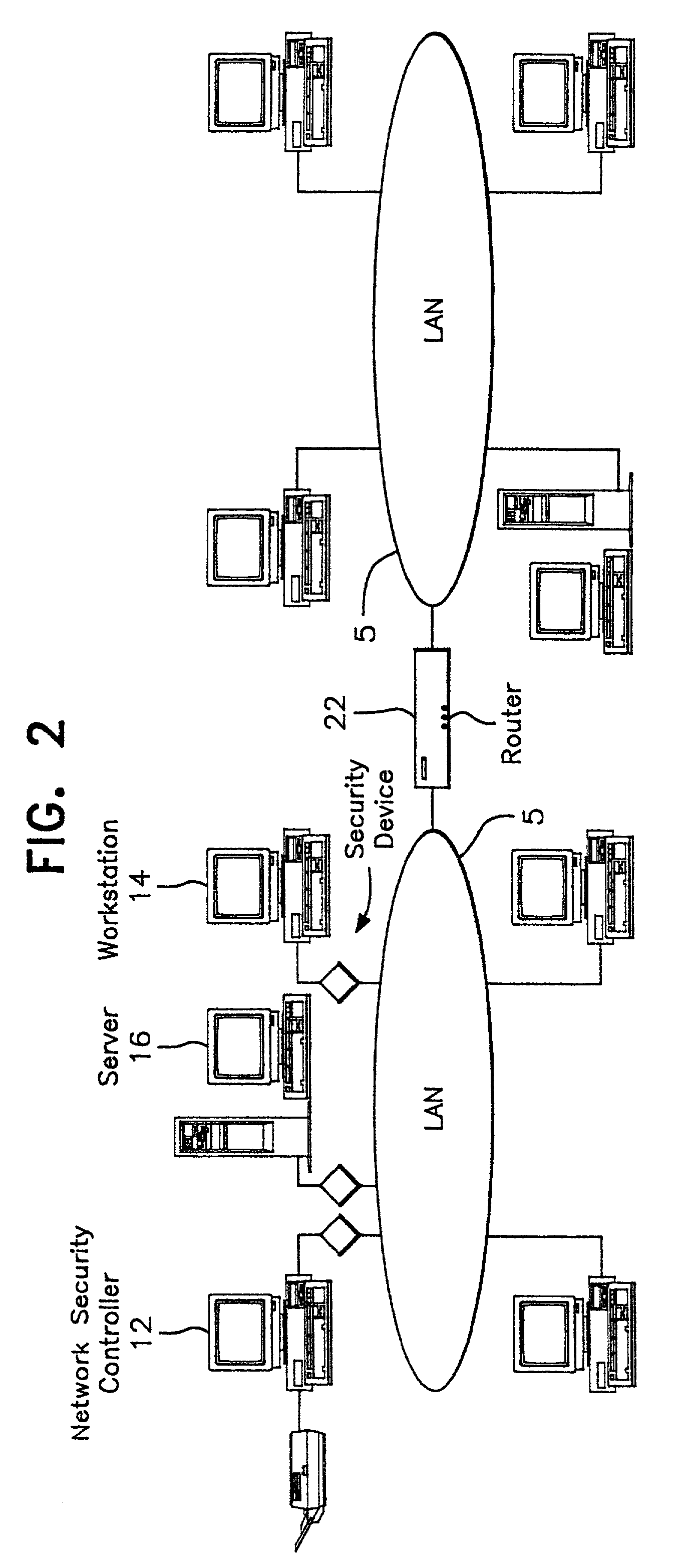
A network prevents unauthorized users from gaining access to confidential information. The network has various workstations and servers connected by a common medium and through a router to the Internet. The network has two major components, a Network Security Center (NSC) and security network interface cards or devices. The NSC is an administrative workstation through which the network security officer manages the network as a whole as well as the individual security devices. The security devices are interposed between each of workstation, including the NSC, and the common medium and operate at a network layer (layer 3) of the protocol hierarchy. The network allows trusted users to access outside information, including the Internet, while stopping outside attackers at their point of entry. At the same time, the network limits an unauthorized insider to information defined in their particular security profile. The user may select which virtual network to access at any given time. The result is trusted access to multiple secure Virtual Private Networks (VPN), all from a single desktop machine.
Owner:CRYPTEK INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com