Patents
Literature
534 results about "Border Gateway Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
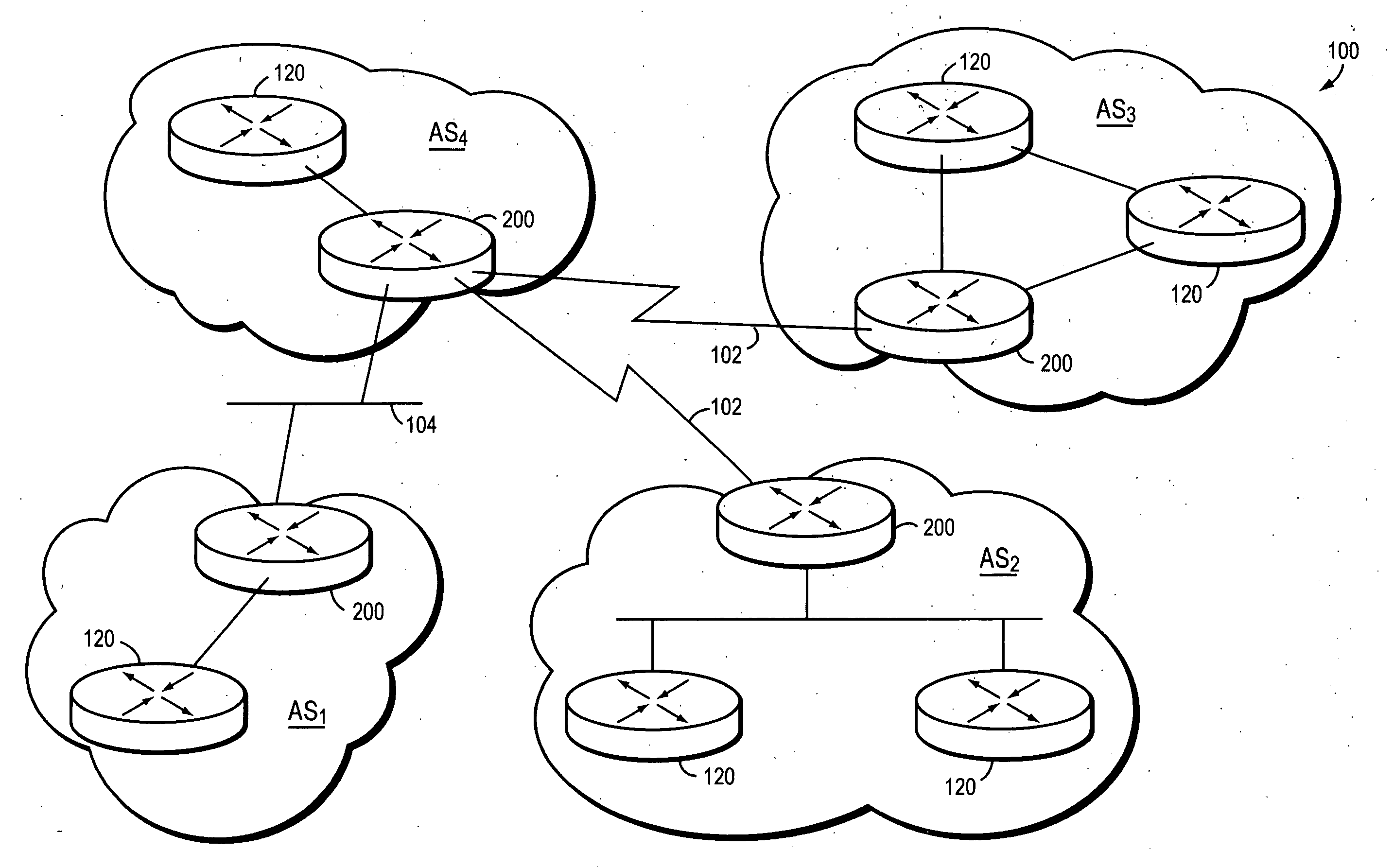
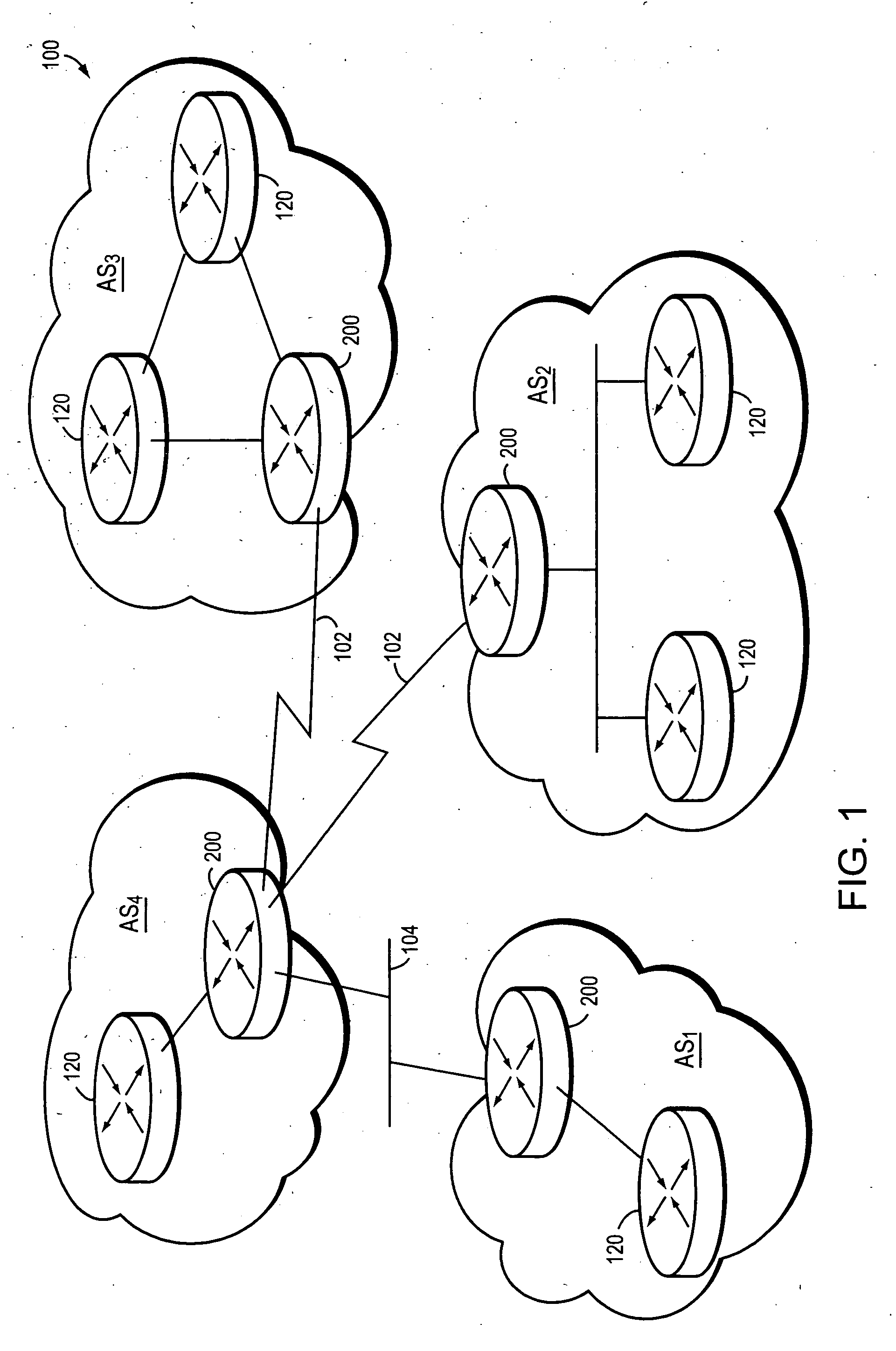
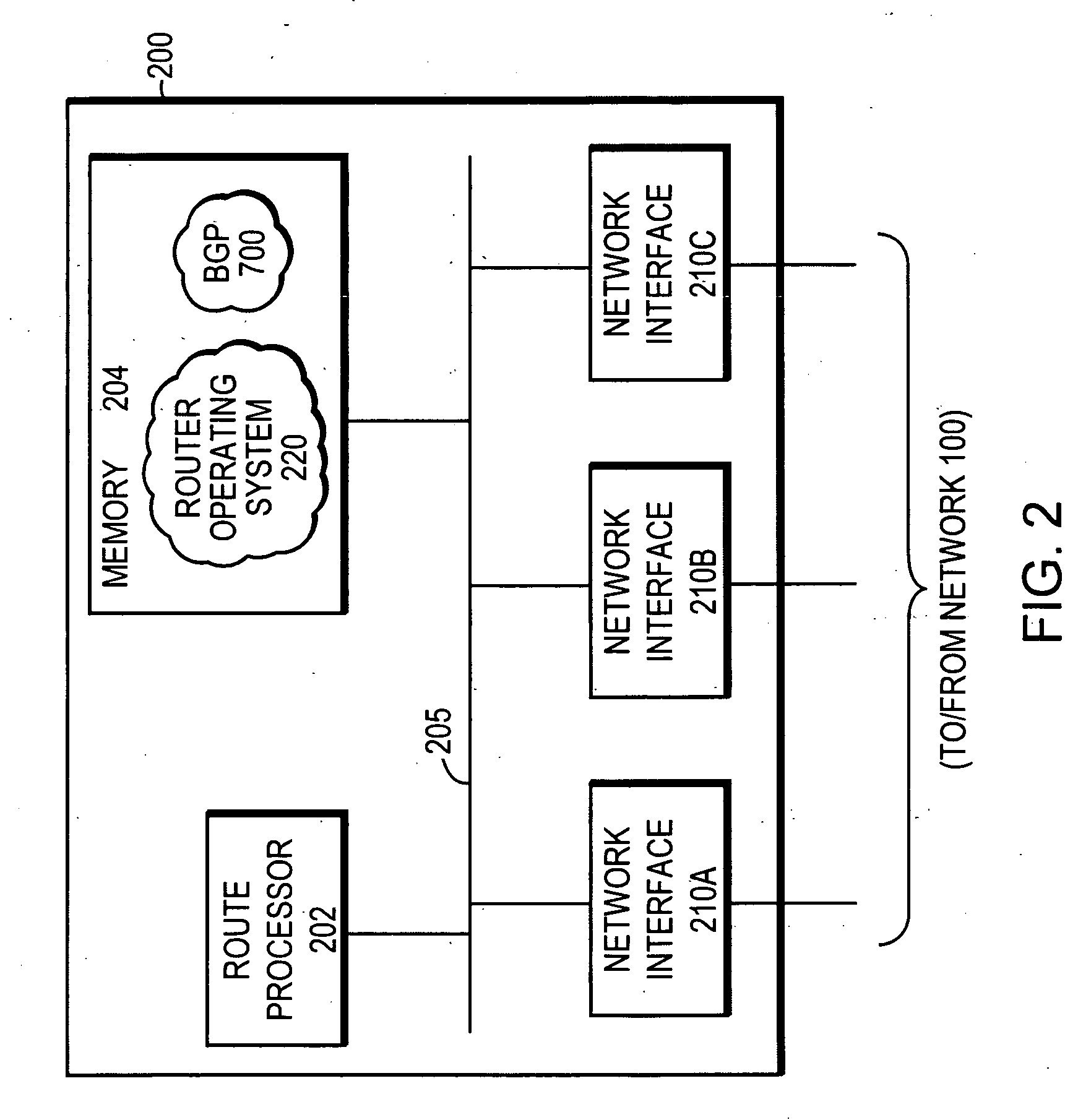
Border Gateway Protocol (BGP) is a standardized exterior gateway protocol designed to exchange routing and reachability information among autonomous systems (AS) on the Internet. The protocol is classified as a path vector protocol. The Border Gateway Protocol makes routing decisions based on paths, network policies, or rule-sets configured by a network administrator and is involved in making core routing decisions.
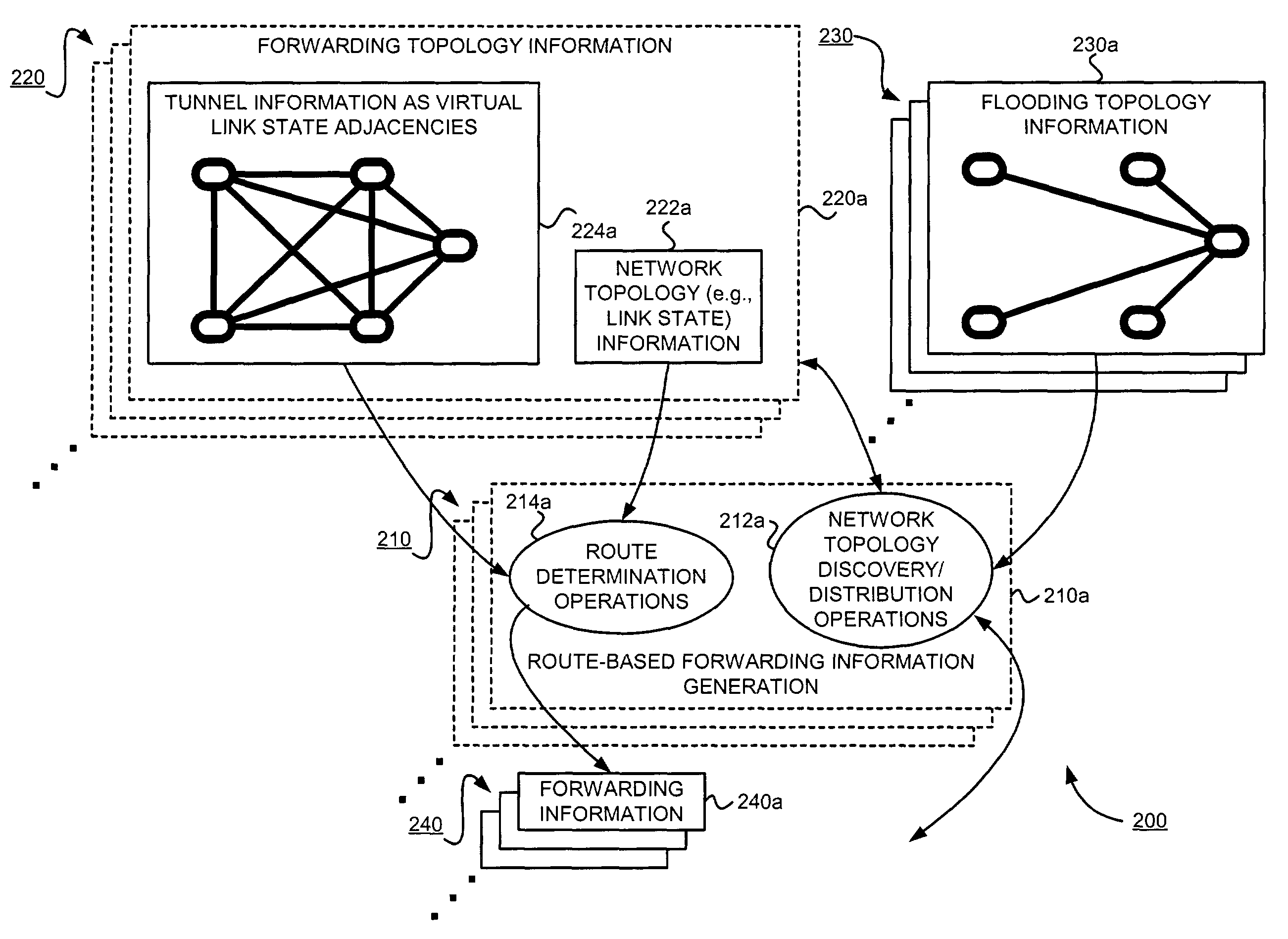
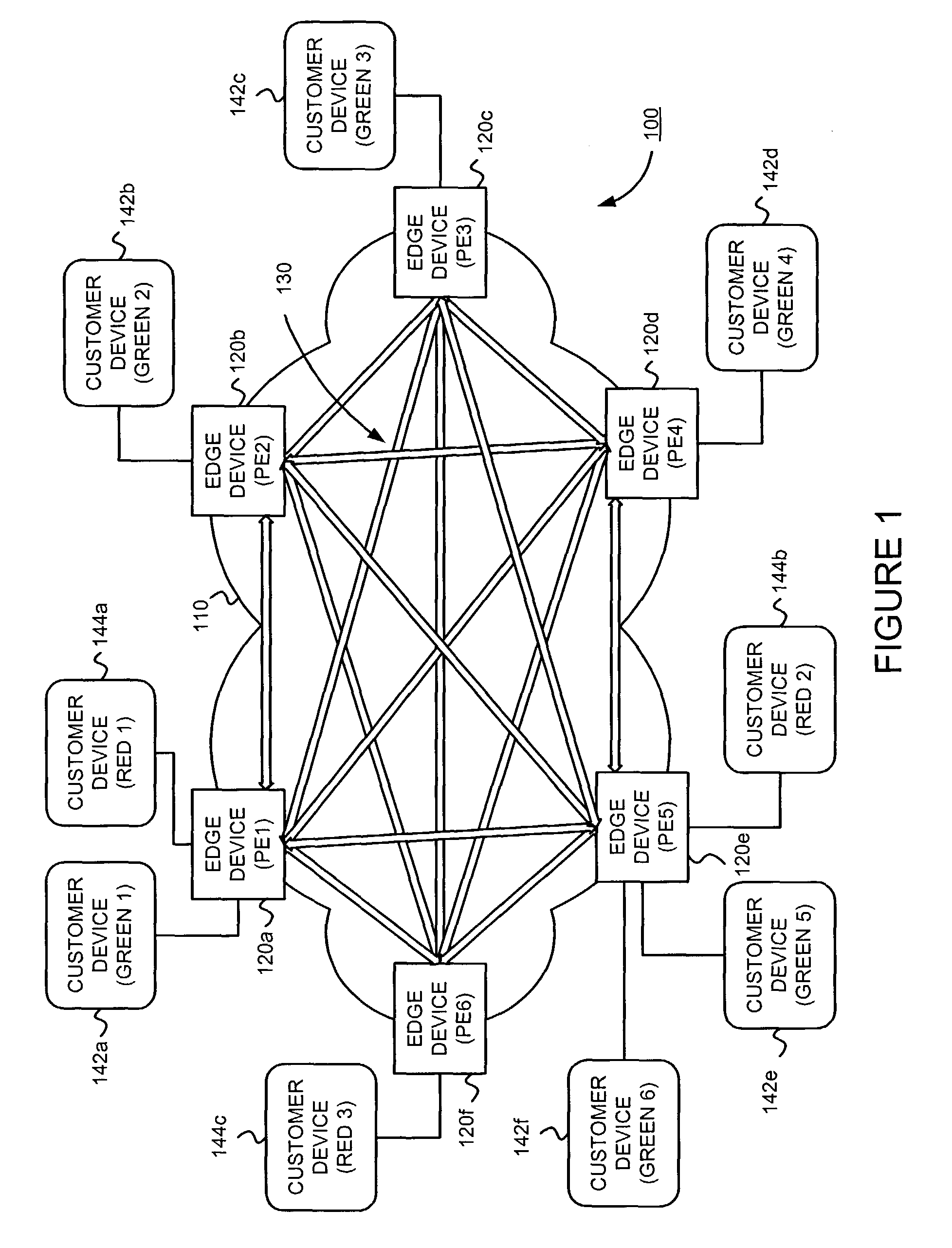
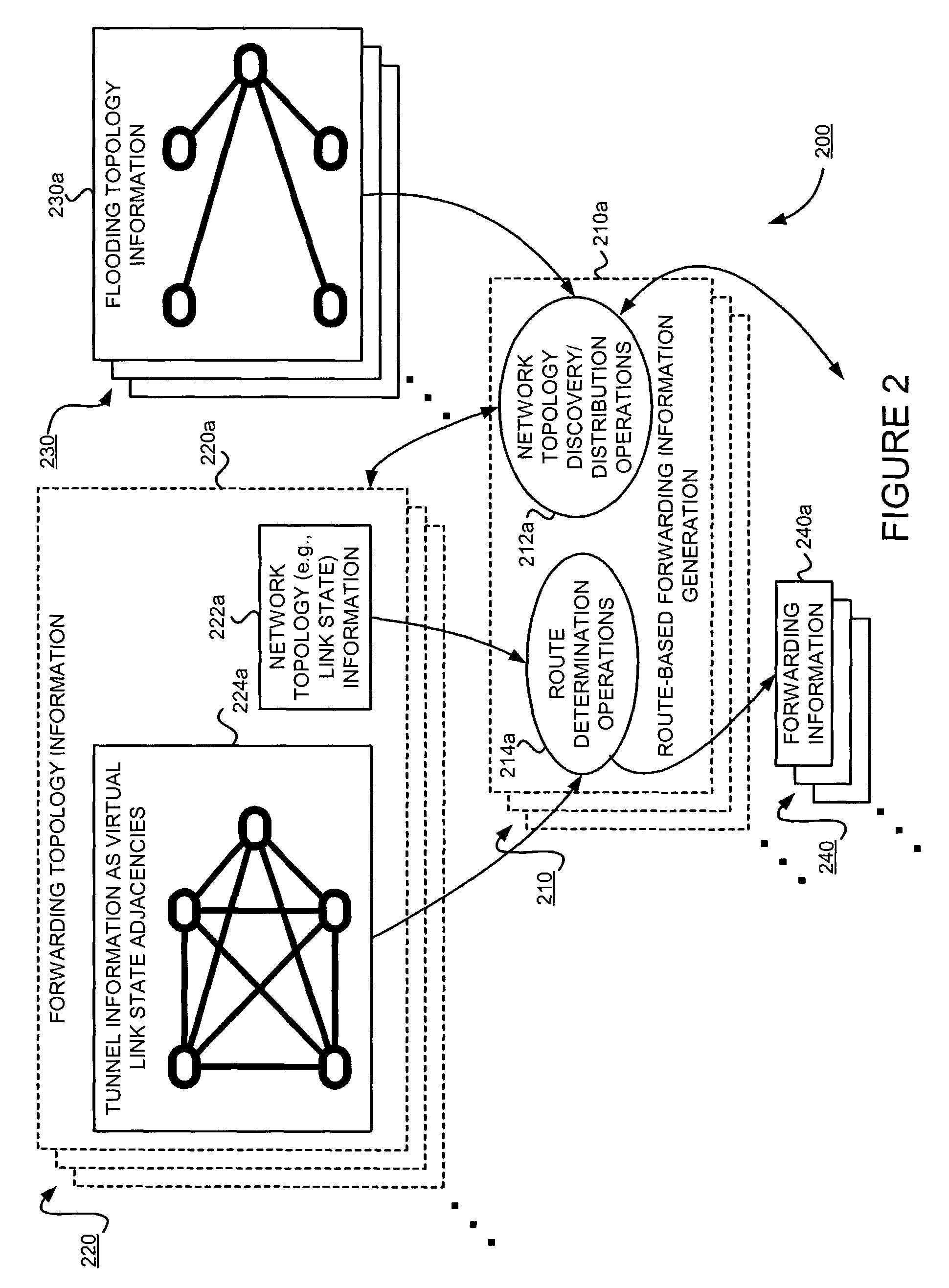
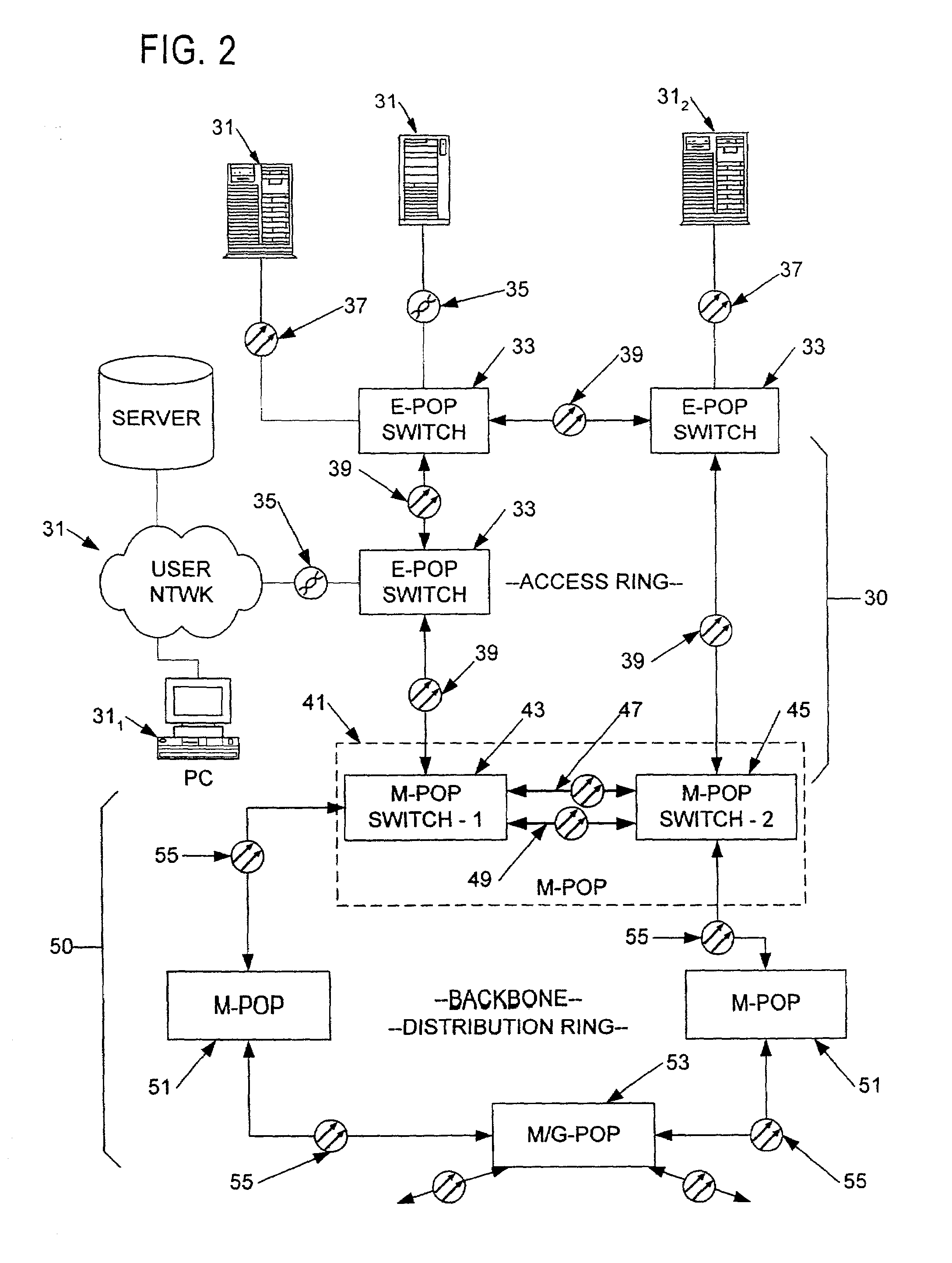
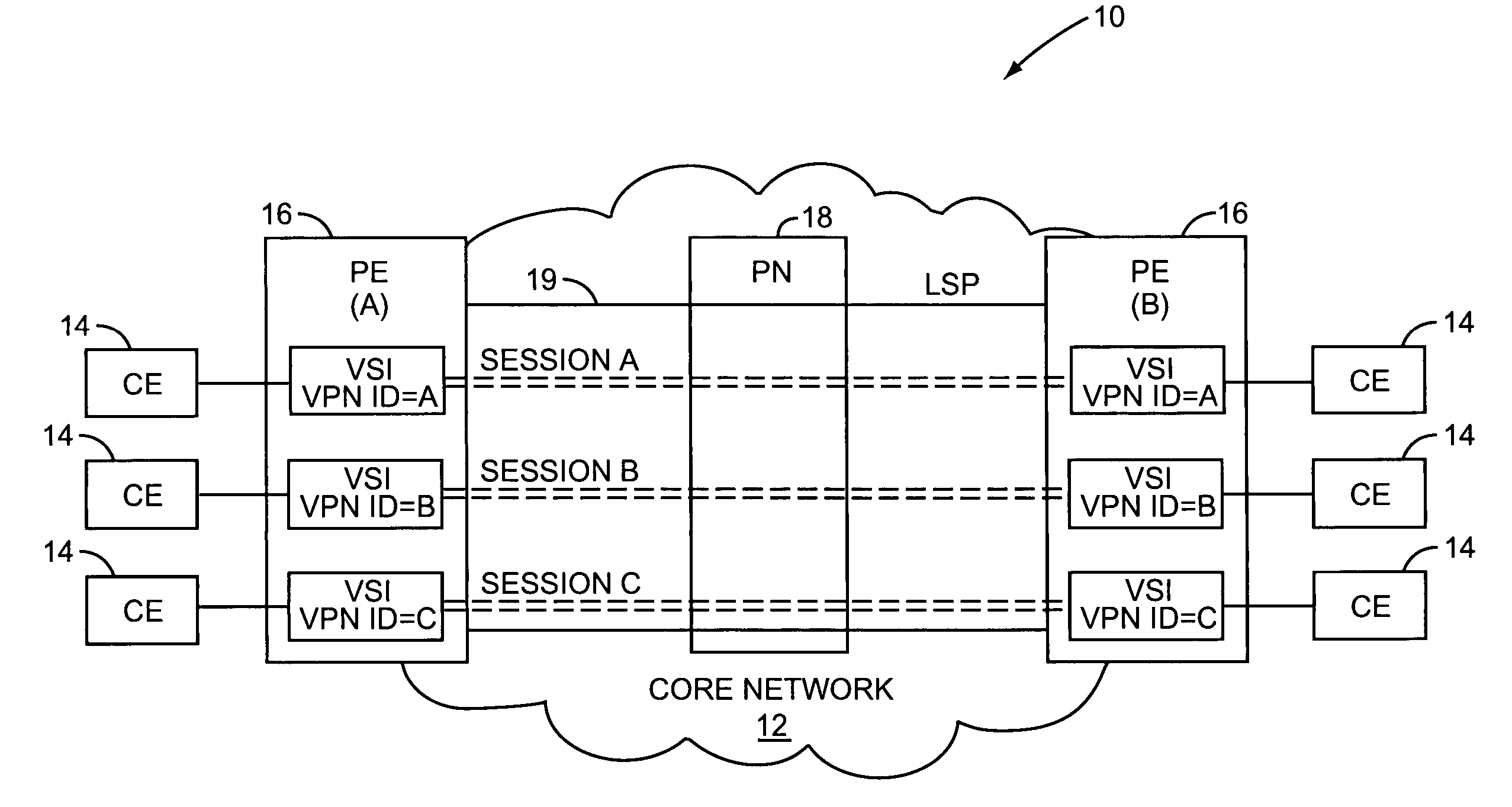
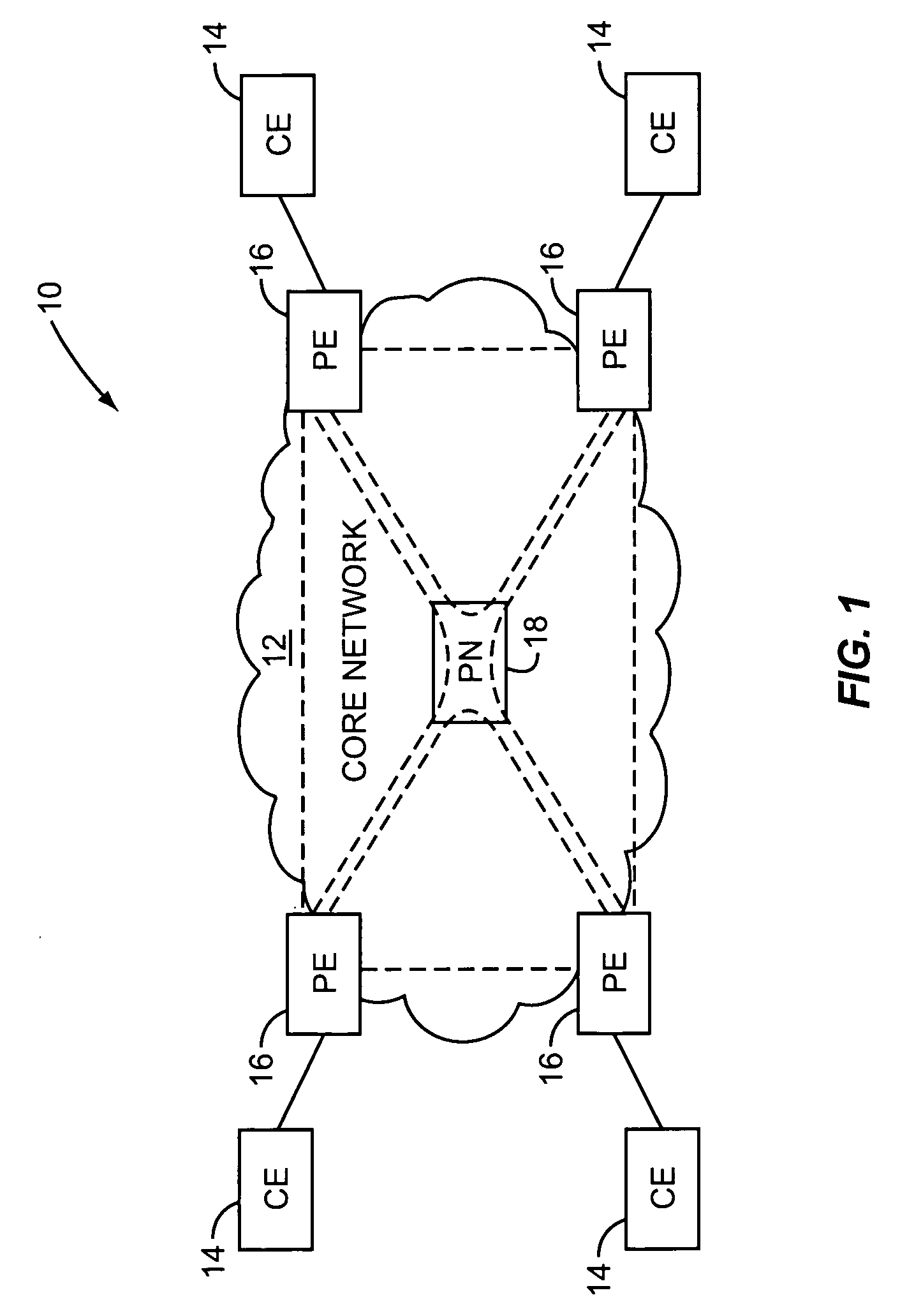
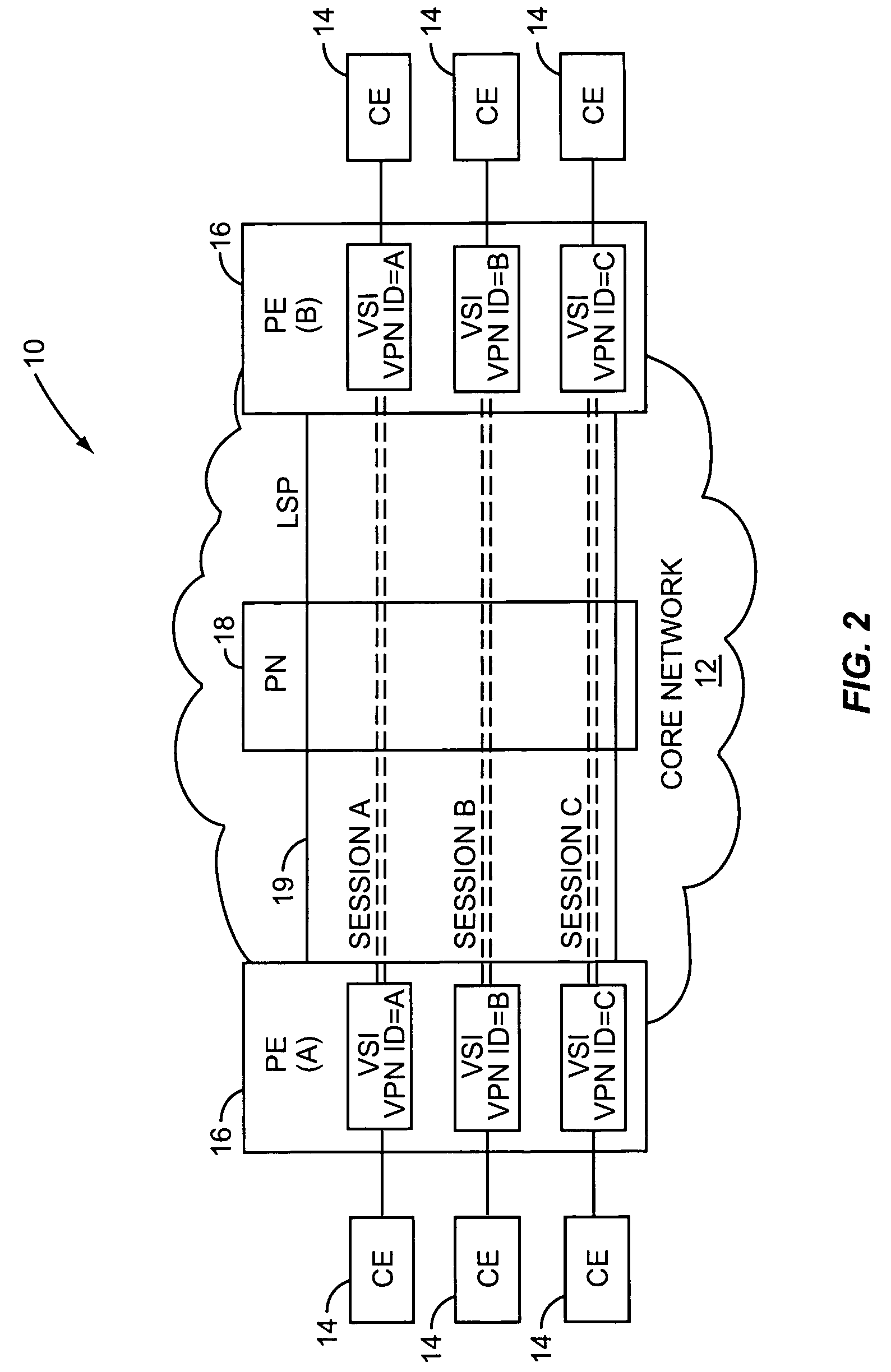
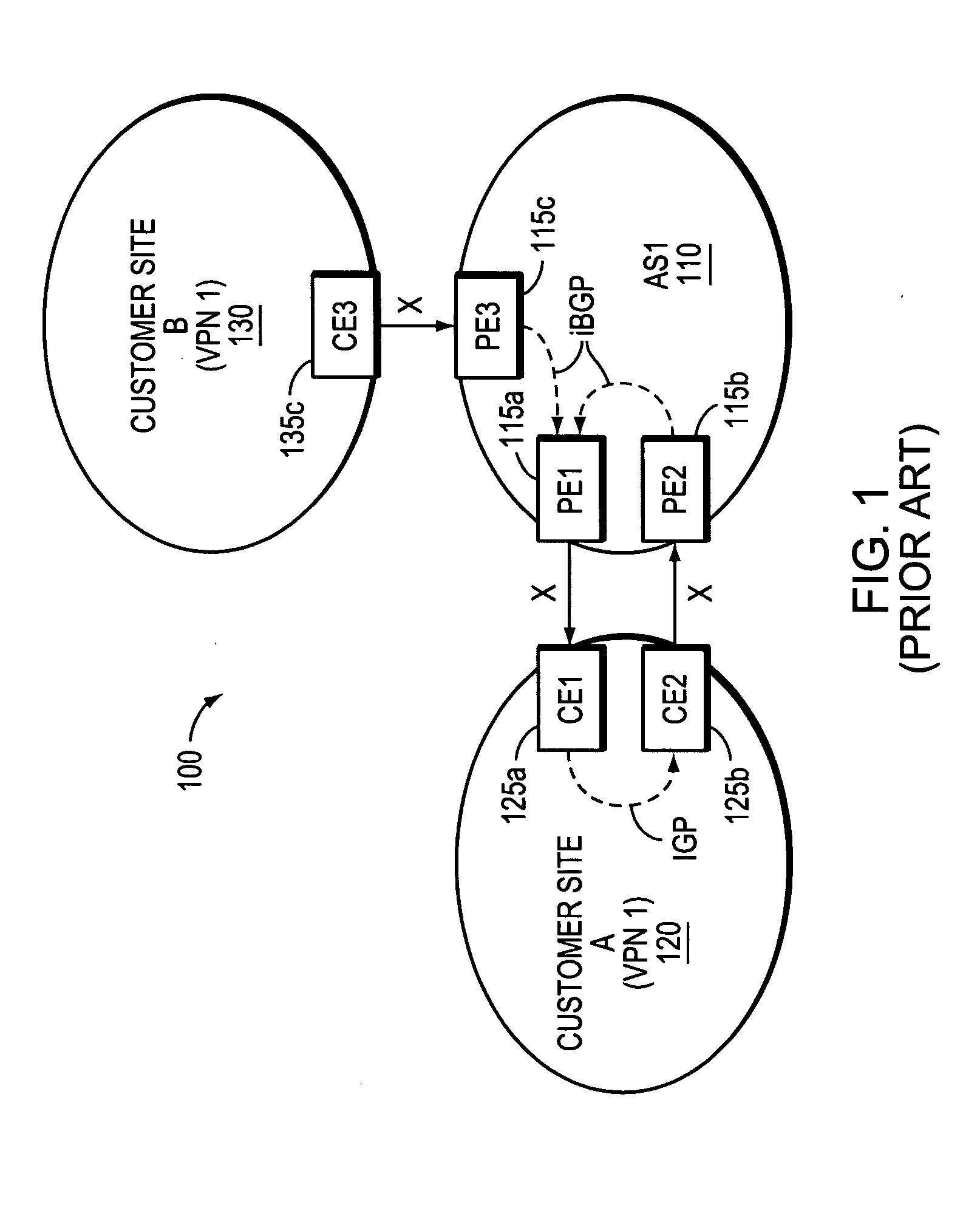
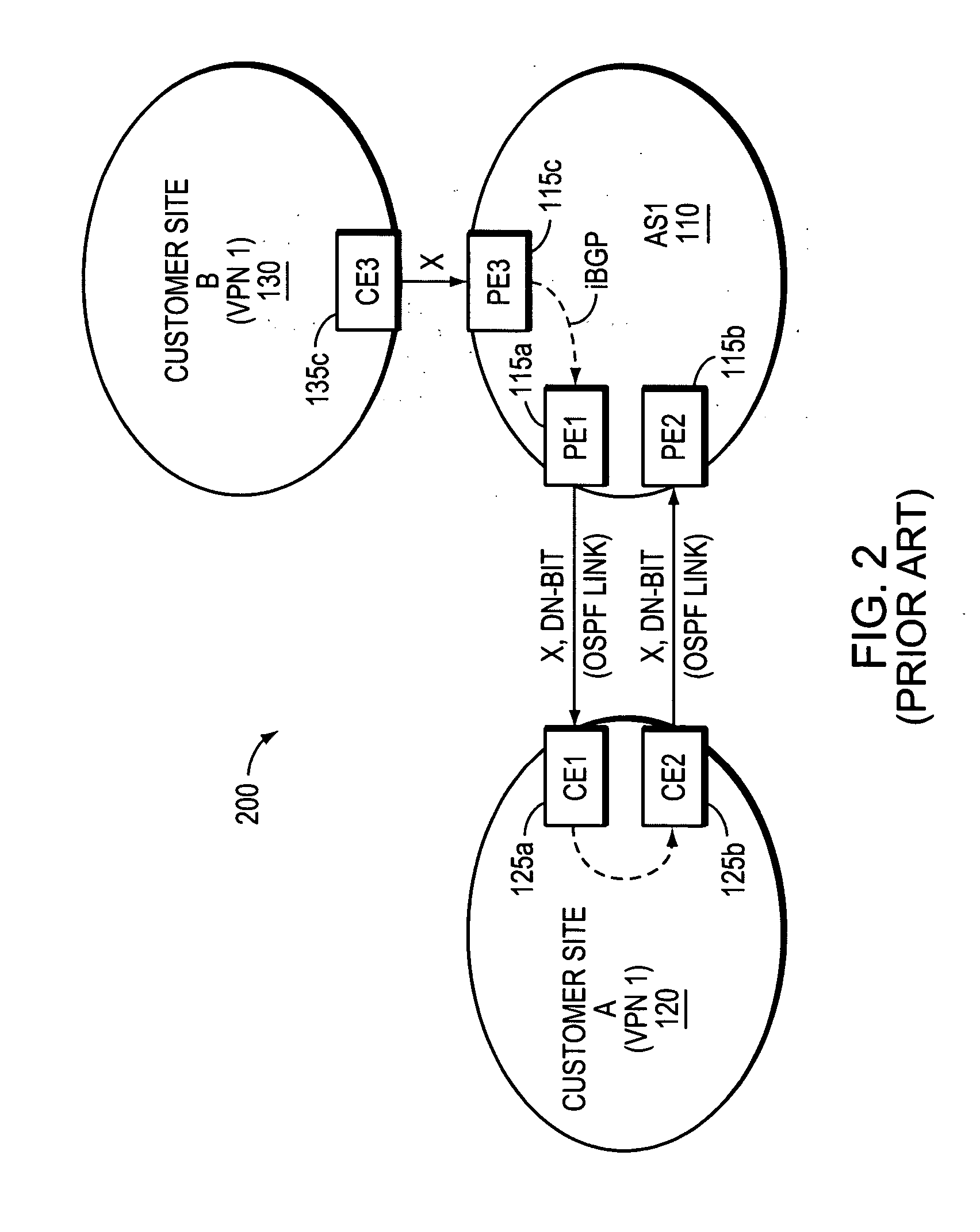
Supporting virtual private networks using a first network topology for forwarding and a subset of the first network topology or a smaller topology for signaling
InactiveUS7792987B1Avoid problemsError preventionTransmission systemsBorder Gateway ProtocolTTEthernet
Virtual Private Networks (VPNs) are supported in which customers may use popular internet gateway protocol (IGPs) without the need to convert such IGPs, running on customer devices to a single protocol, such as the border gateway protocol (BGP). Scaling problems, which might otherwise occur when multiple instances of an IGP flood link state information, are avoided by using a flooding topology which is smaller than a forwarding topology. The flooding topology may be a fully connected sub-set of the forwarding topology.
Owner:JUMIPER NETWORKS INC
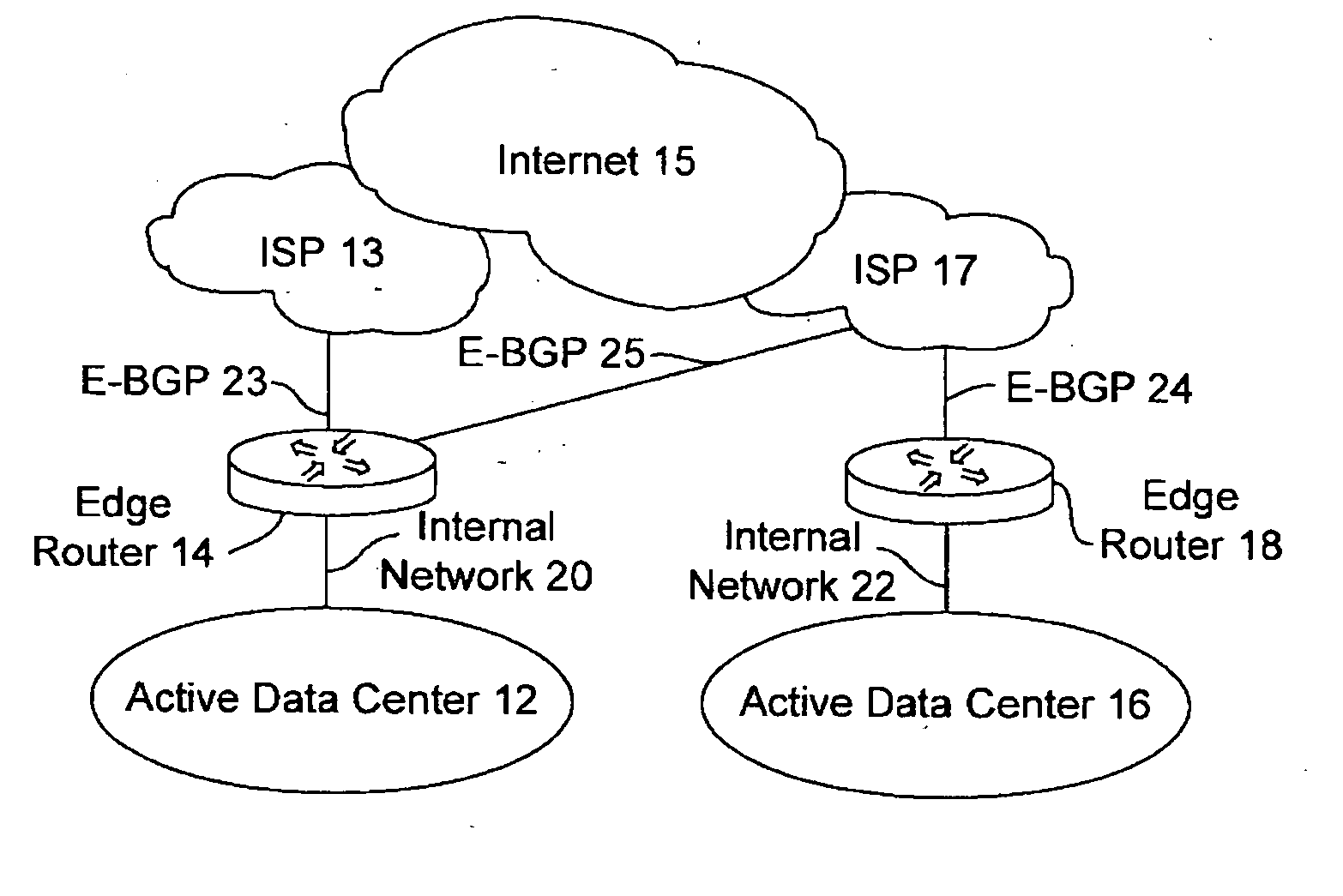
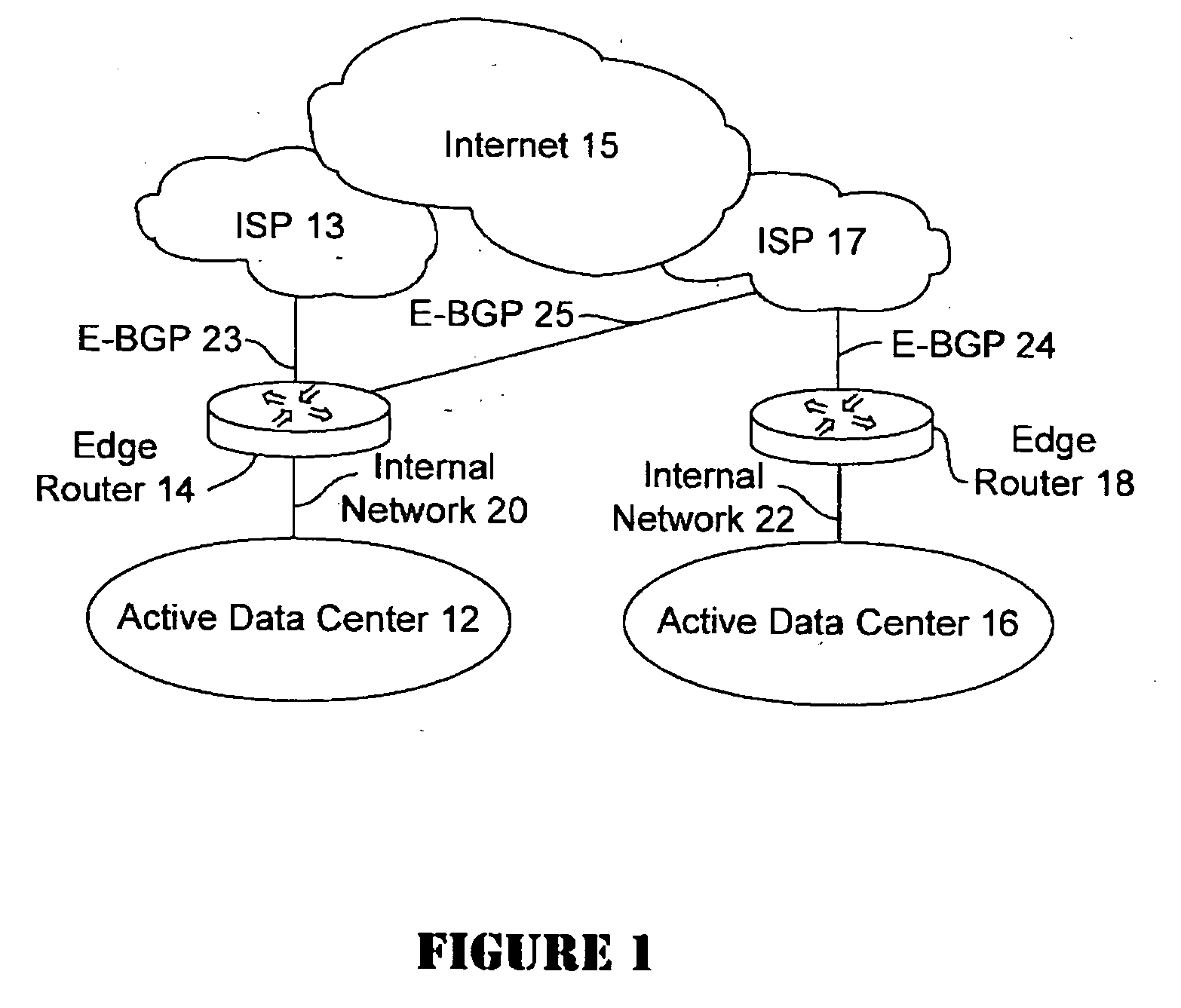
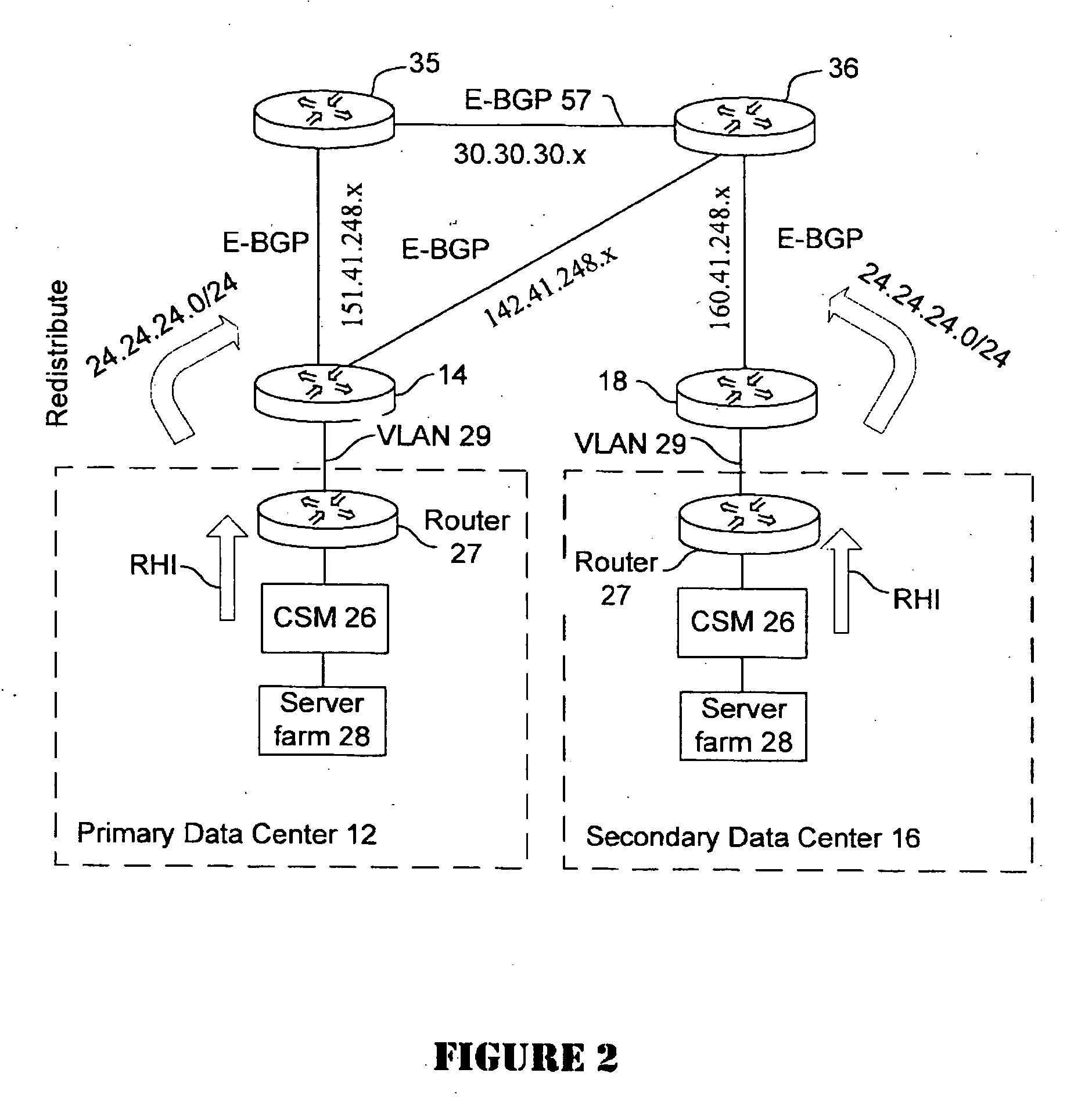
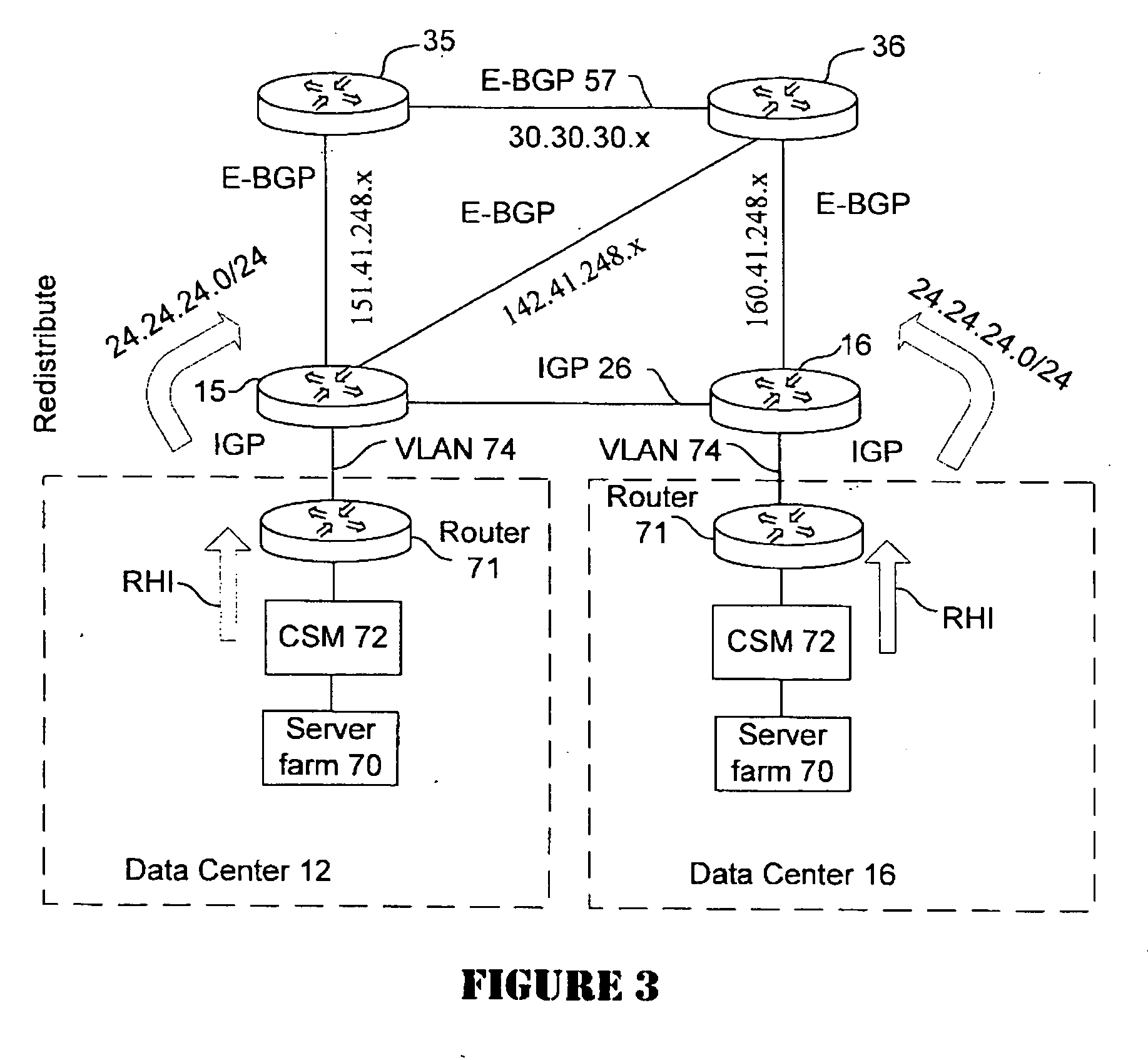
Active-active data center using RHI, BGP, and IGP anycast for disaster recovery and load distribution
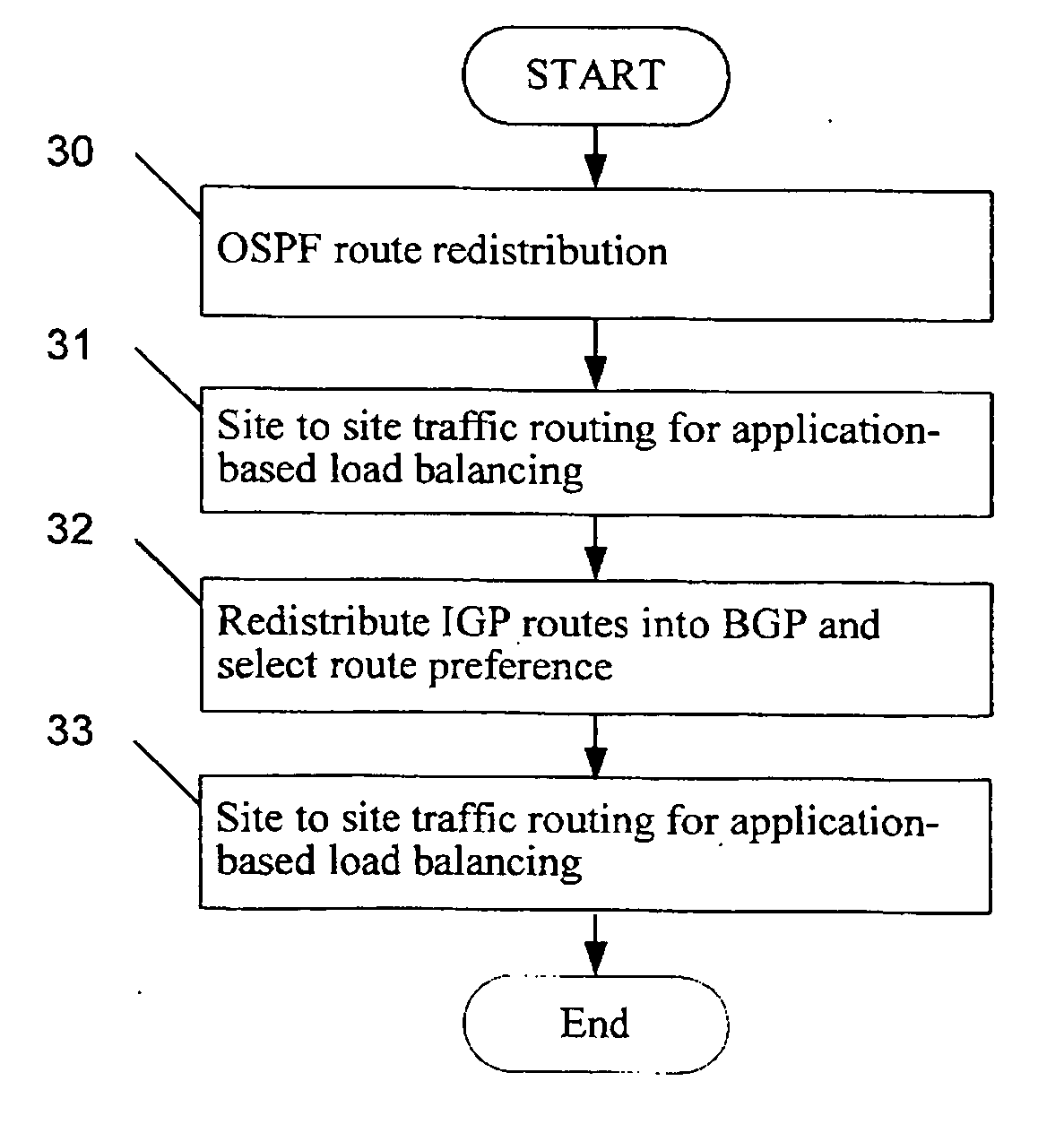
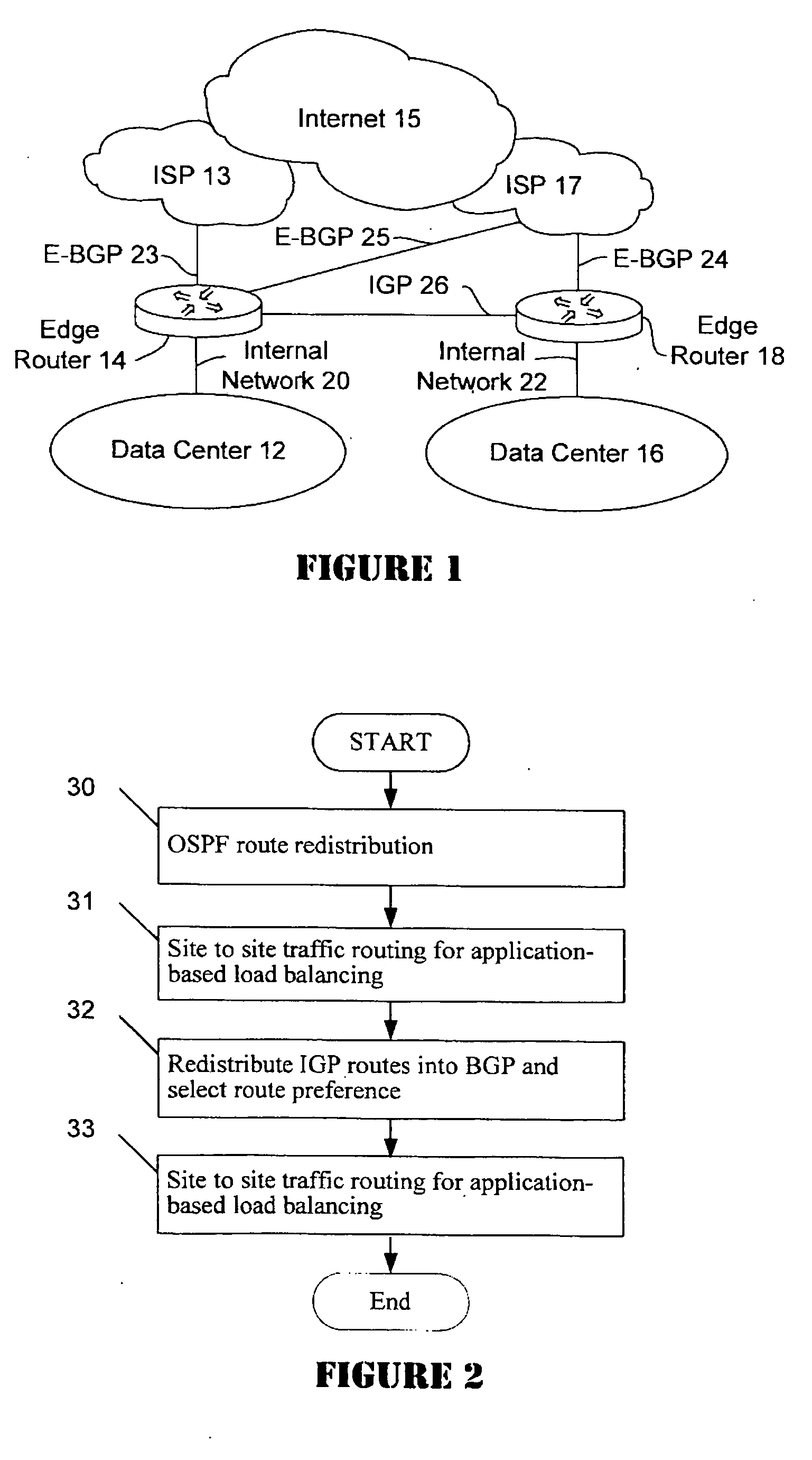
A distributed data center topology having at least a pair of active data centers that can recover from a disaster at one of the data centers and achieves load balancing using IGP (Interior Gateway Protocol) between data centers. The distributed data centers use virtual IP addresses, route health injection and Border Gateway Protocol (BGP) for business continuance, disaster recovery and load balancing. The active / active topology supports load balancing where each site concurrently hosts active applications or applications can be hosted in a logical active / standby mode. IGP and RHI (Route Health Injection) are used to propagate routes to an edge router and BGP (Border Gateway Protocol) and IP Anycast are used for site-to-site recovery and load balancing between data center sites.
Owner:CISCO TECH INC
Enhanced data switching/routing for multi-regional IP over fiber network
InactiveUS6963575B1Multiplex system selection arrangementsNetworks interconnectionWide areaBorder Gateway Protocol
Wide-area data communications utilize regional networks transporting IP-over-Ethernet on fiber. For certain Layer 2 services, a regional implementation of the network makes limited use of spanning tree protocol on a backbone ring. Learning bridge operations in switches on associated access rings involve a short default for an aging timer. For use of Open Shortest Path First (OSPF), the connection of each access ring to the backbone ring uses a pair of routers with dual links therebetween. One of these links is bonded to the backbone (OSPF Area 0), whereas the other link is bonded to the Area of the respective access ring. Also, certain routers within each regional network form a mini-autonomous system, for boundary gateway protocol (BGP). The mini-autonomous systems of the regional networks form a confederation. The network utilizes route reflectors in the mini-autonomous systems. The Internet carries confederation commands to and from a designated hub.
Owner:YIPES ENTERPRISE SERVICES
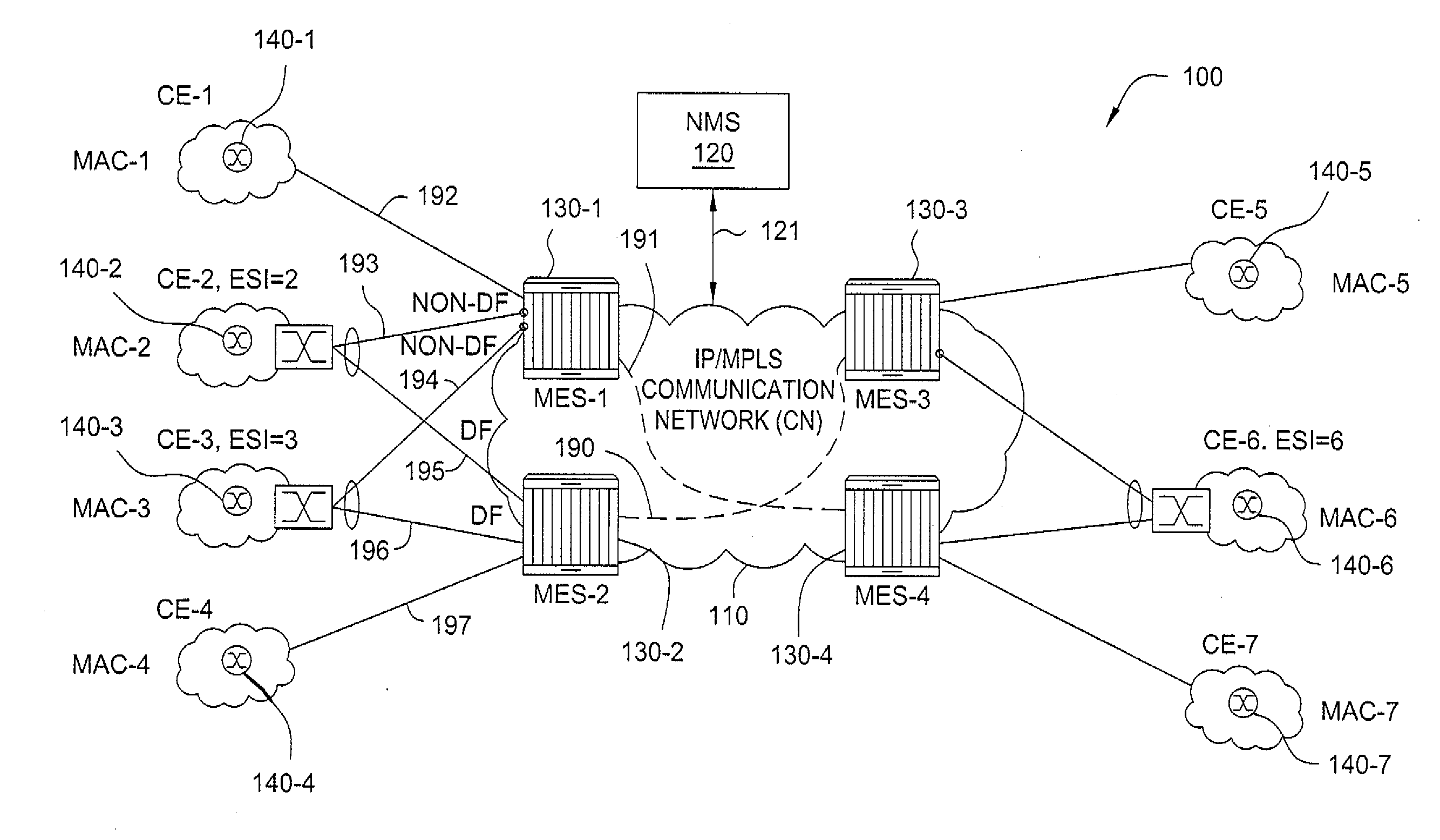
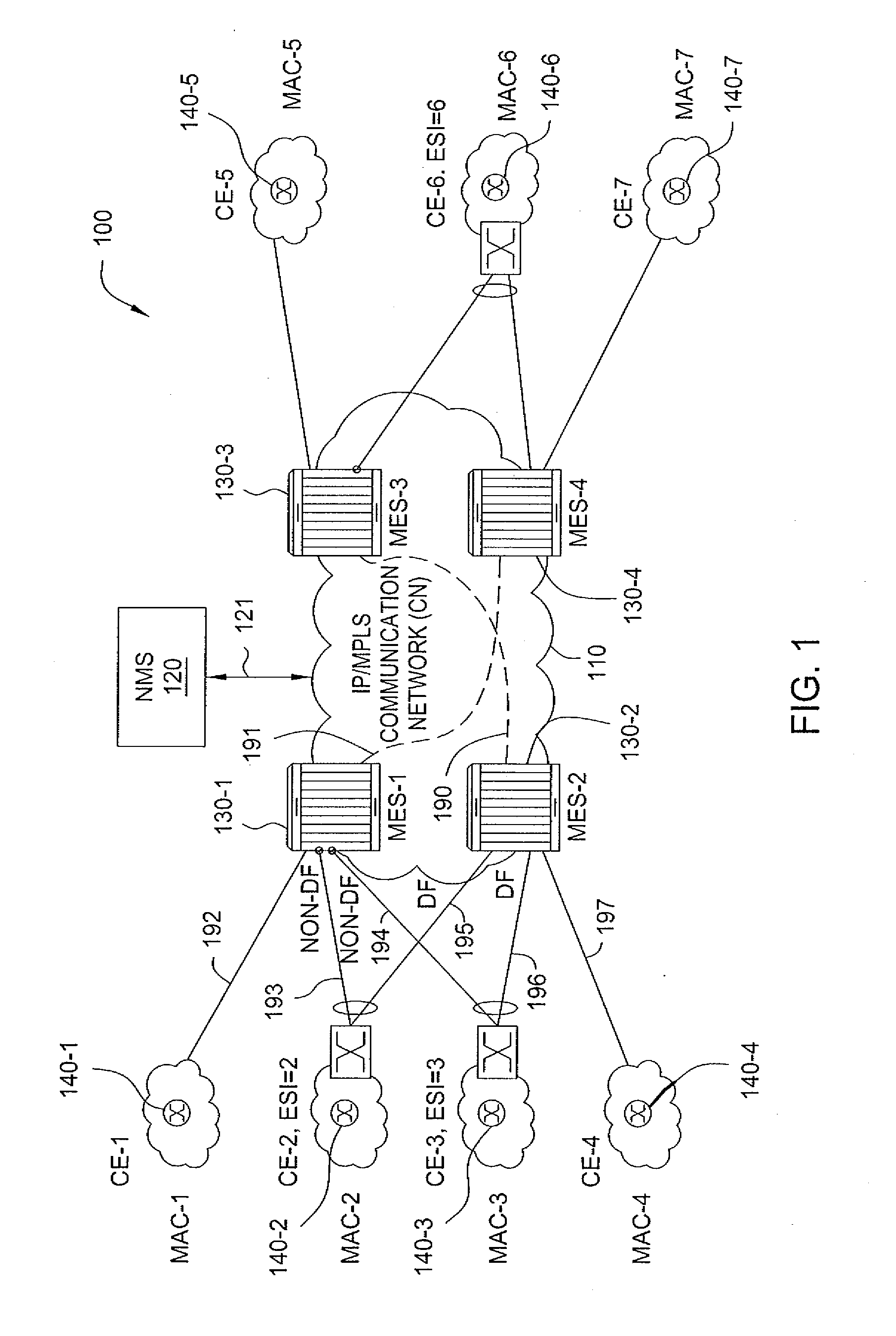
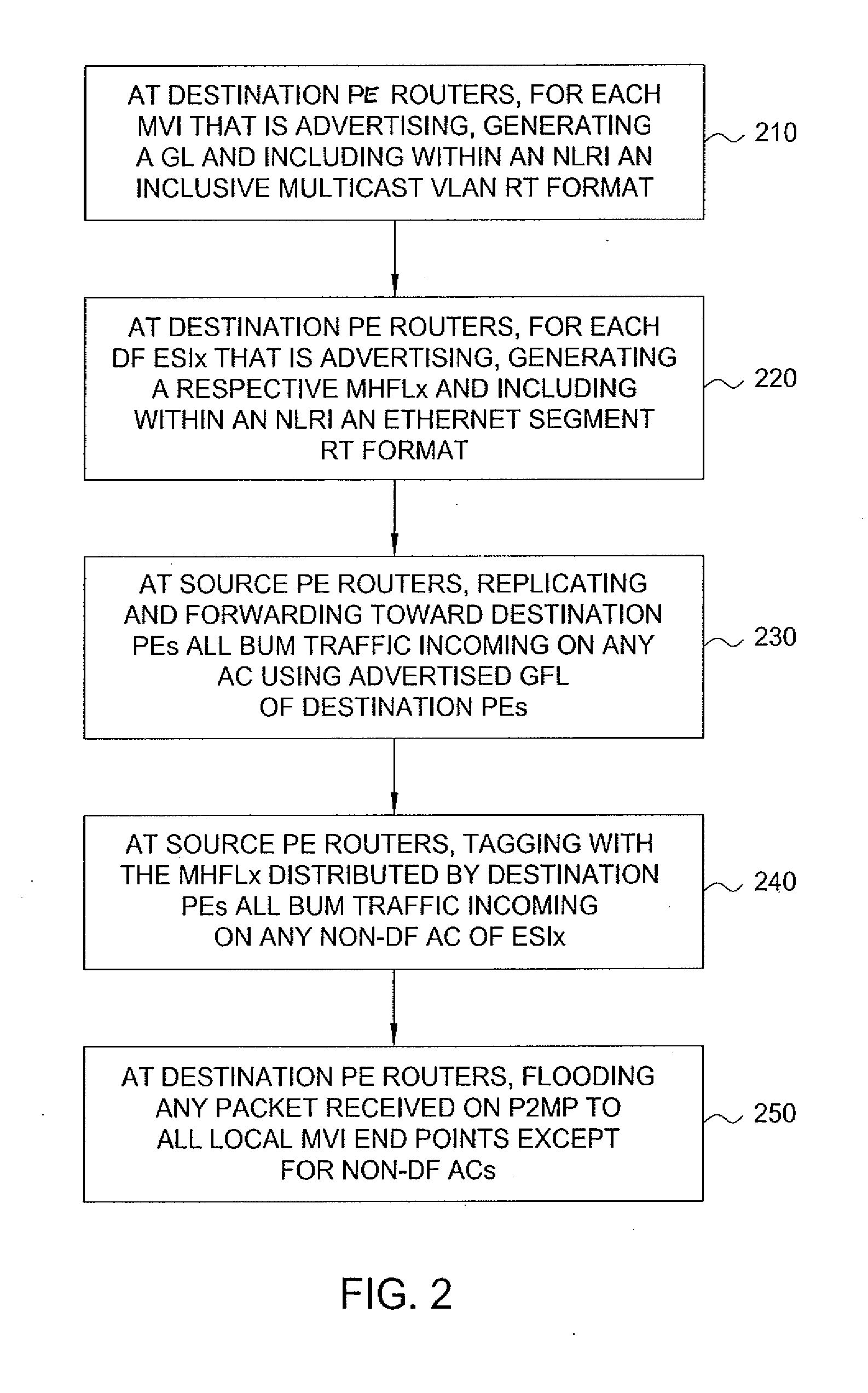
Method and apparatus for mpls label allocation for a bgp mac-vpn
ActiveUS20110286452A1Data switching by path configurationBorder Gateway ProtocolMultiprotocol Label Switching
The invention includes a method and apparatus for distributing flooding labels within a Multiprotocol Label Switching (MPLS) infrastructure supporting Border Gateway Protocol (BGP) Media Access Control (MAC) Virtual Private Networking (VPN).
Owner:ALCATEL LUCENT SAS
Boarder Gateway Protocol Signaling to Support a Very Large Number of Virtual Private Networks
InactiveUS20150003458A1Data switching switchboardsNetworks interconnectionBorder Gateway Protocol24-bit
Disclosed herein are example embodiments for Boarder Gateway Protocol (BGP) signaling in virtual private network (VPN) communications. For example, a first network element may encode Multiprotocol Label Switching (MPLS) information in a Network Layer Reachability Information (NLRI) label field that is longer than 24 bits, and transmit a BGP update message comprising a BGP attribute to a second network element. The BGP attribute comprises the NLRI and a specific Subsequent Address Family Identifier (SAFI) value. The specific SAFI value signals to the second network element, upon reception of the BGP update message by the second network element, that the NLRI label field is more than 24 bits long.
Owner:FUTUREWEI TECH INC
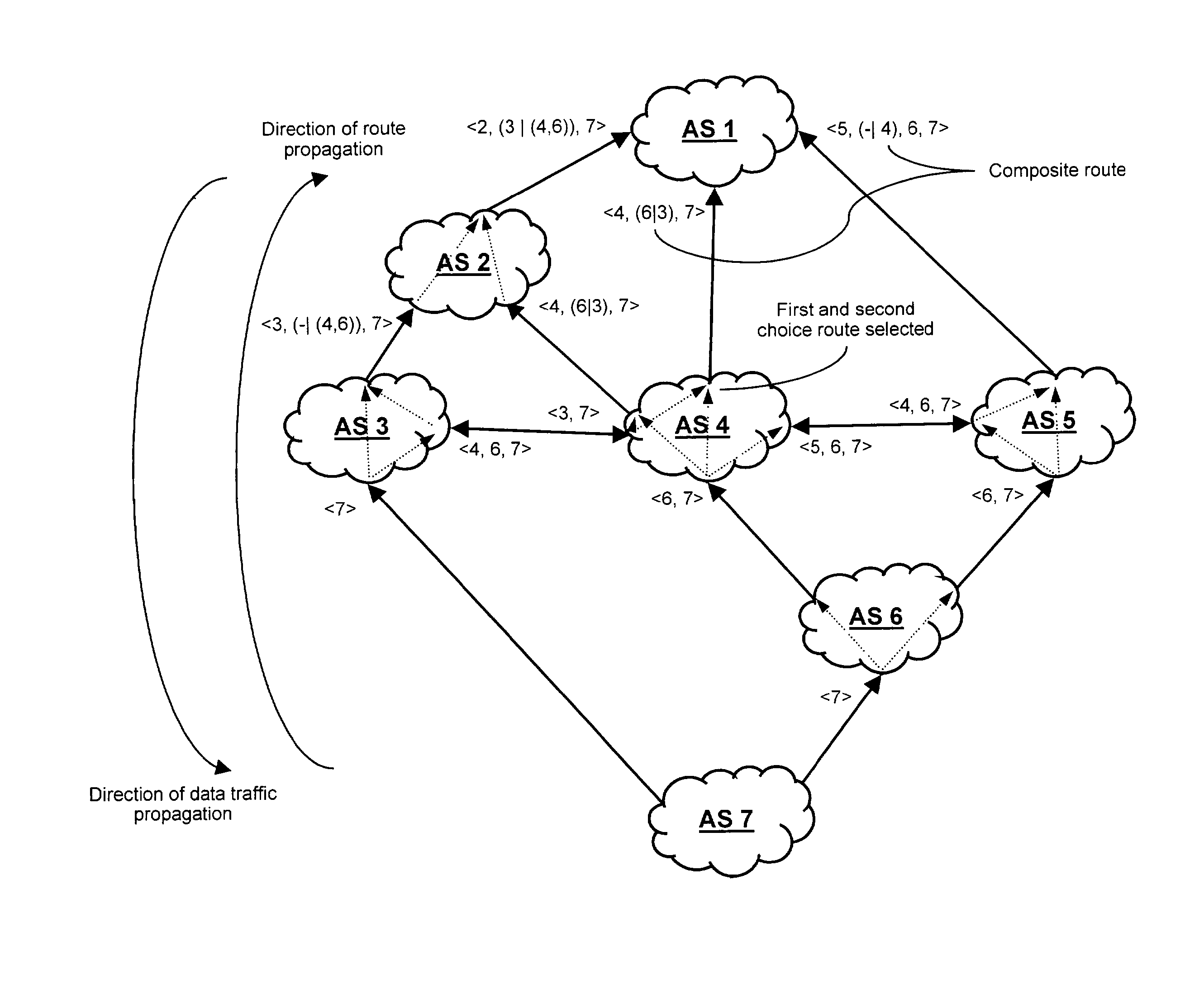
Routing for a communications network
InactiveUS7286479B2Improve response speedError preventionTransmission systemsVisibilityBorder Gateway Protocol
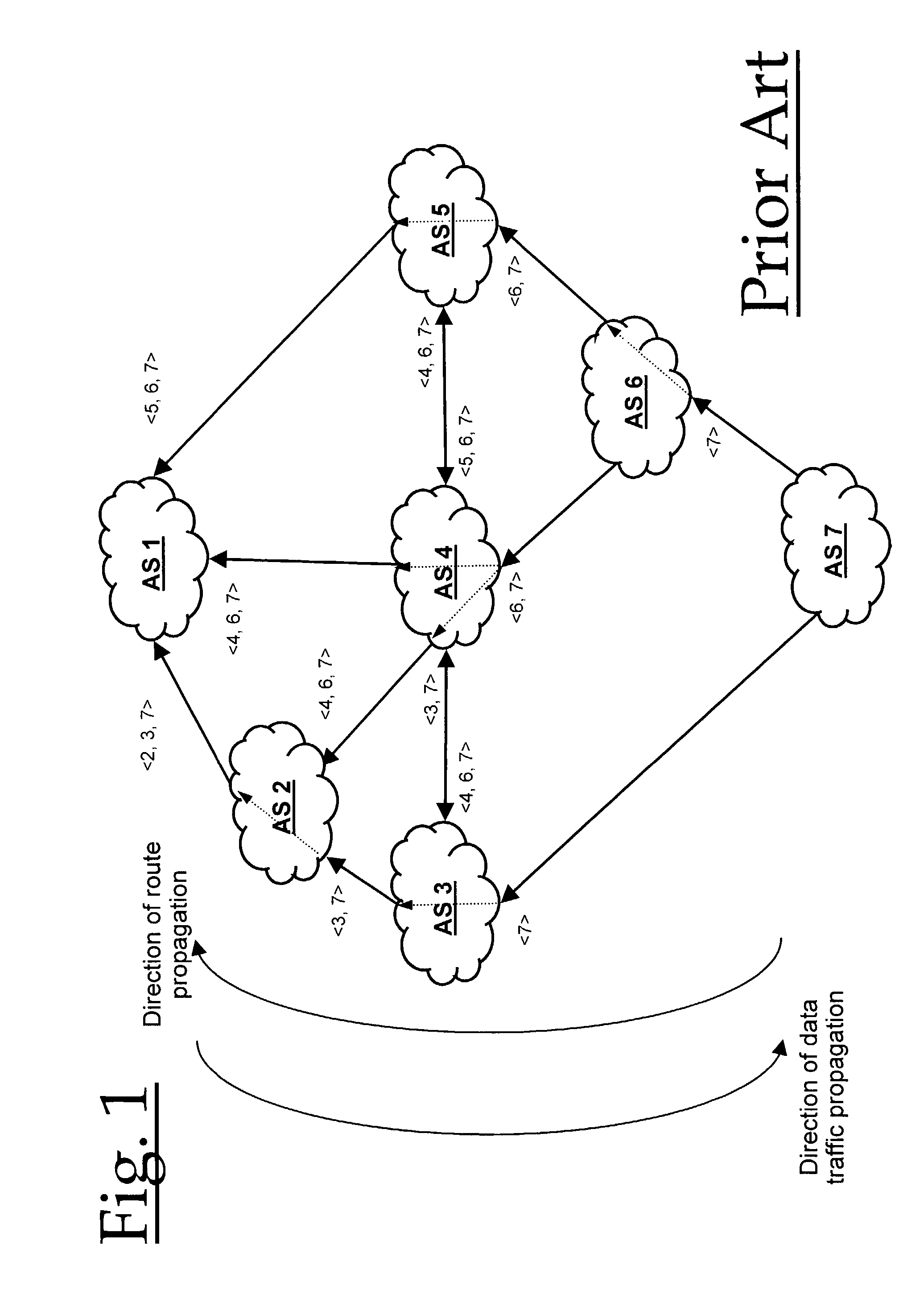
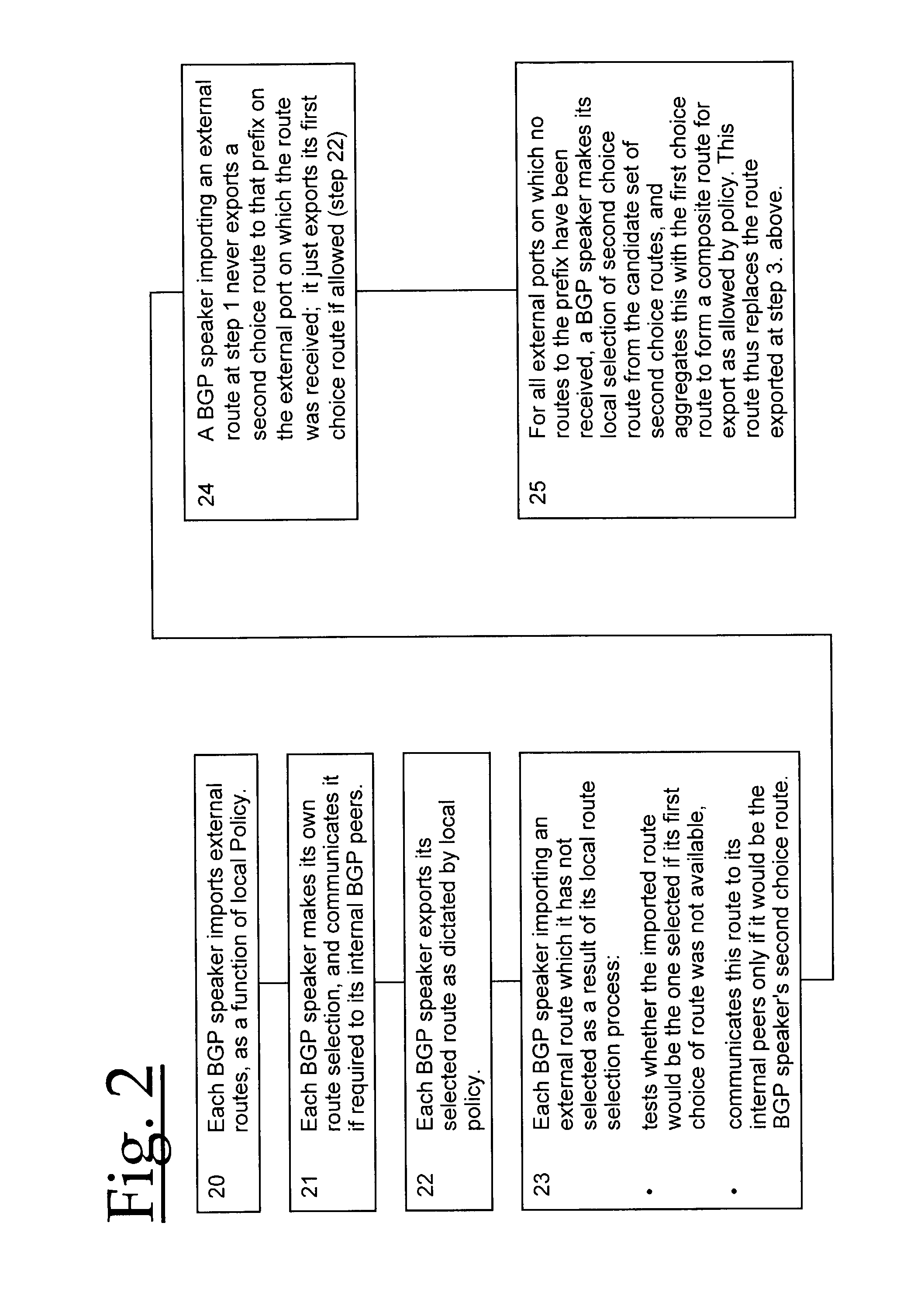
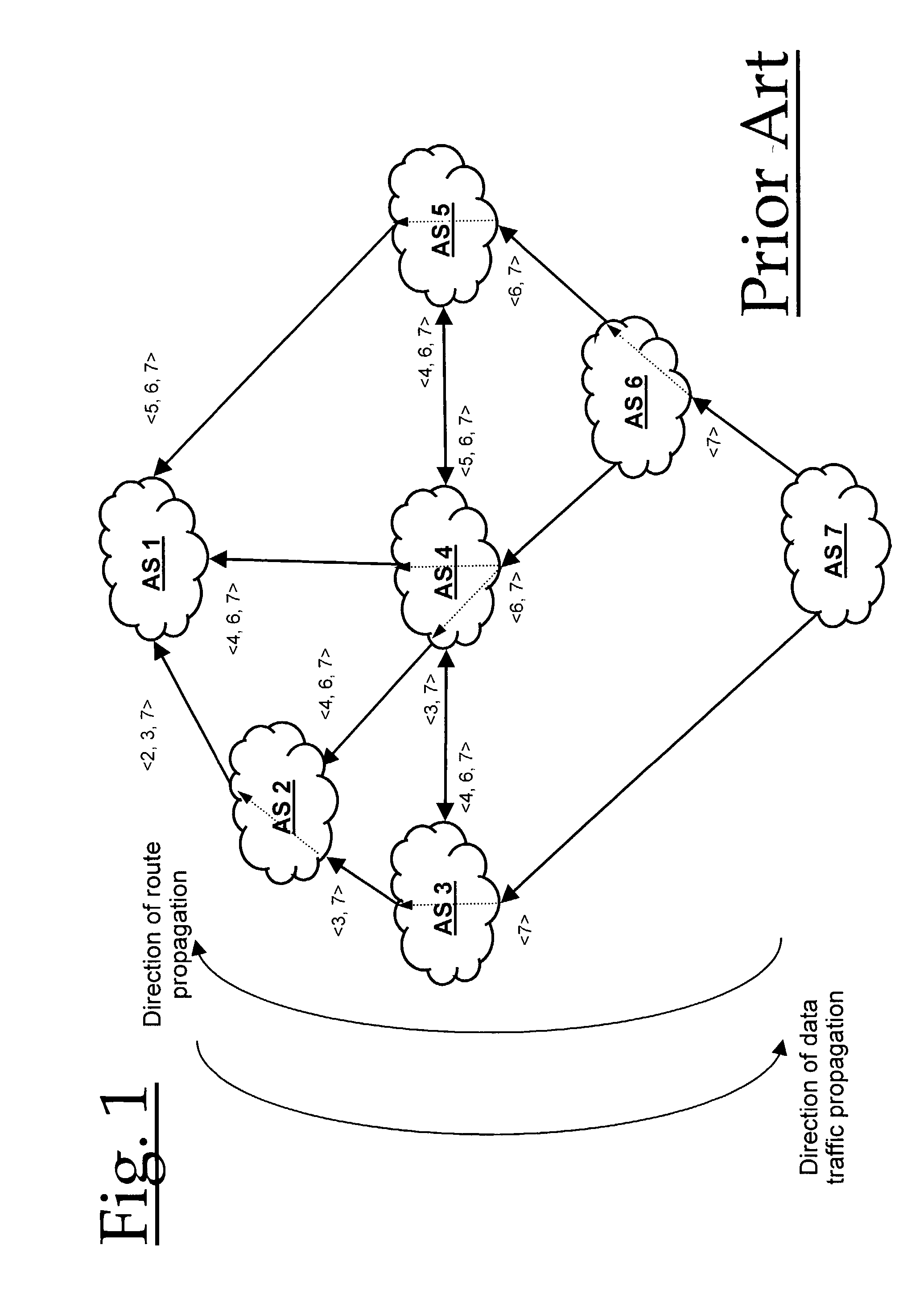
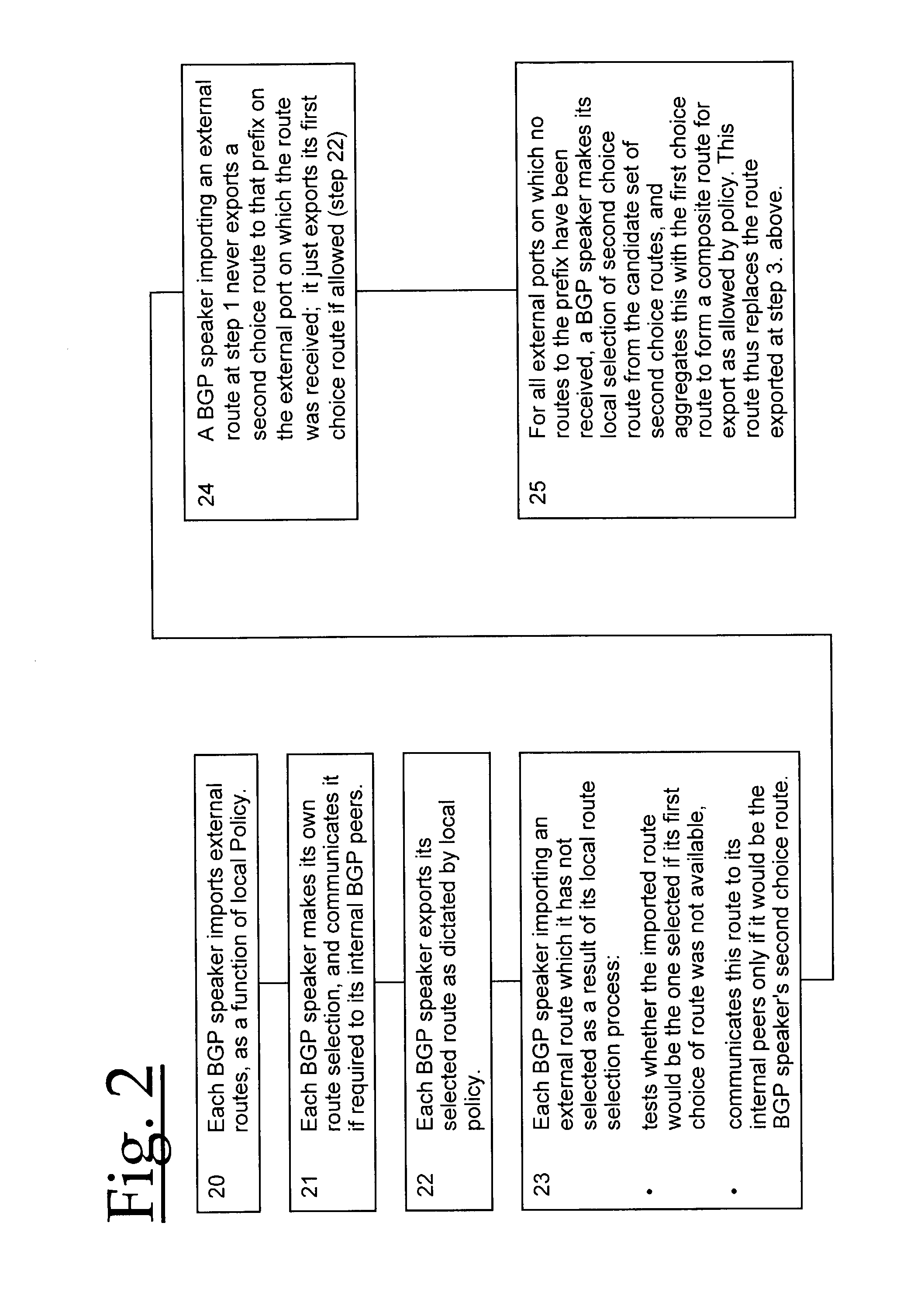
For routing in a communications network, alternate paths to a destination are aggregated into a single composite route, prior to onward propagation of the route. Ideally, aggregation is performed at each point of route convergence in the network. Consequently, failure in only one of the paths does not then require that the composite route be withdrawn, and thus visibility of and reaction to the fault is restricted to parts of the network directly affected. The method is particularly applicable to border gateway protocols employed between Autonomous Systems as in, for example, the Internet.
Owner:RPX CLEARINGHOUSE
Application based active-active data center network using route health injection and IGP
A distributed data center topology having at least a pair of active data centers that can recover from a disaster at one of the data centers and achieves load balancing using IGP (Interior Gateway Protocol) between data centers. The distributed data centers use virtual IP addresses, route health injection and Border Gateway Protocol (BGP) for business continuance, disaster recovery and load balancing. Active applications are deployed at each data center to provide a logical active / standby configuration for certain applications. Alternatively, active applications are deployed at both sites and BGP routes traffic to the closest data center edge router. Load balancing occurs over an internal IGP link between sites.
Owner:CISCO TECH INC
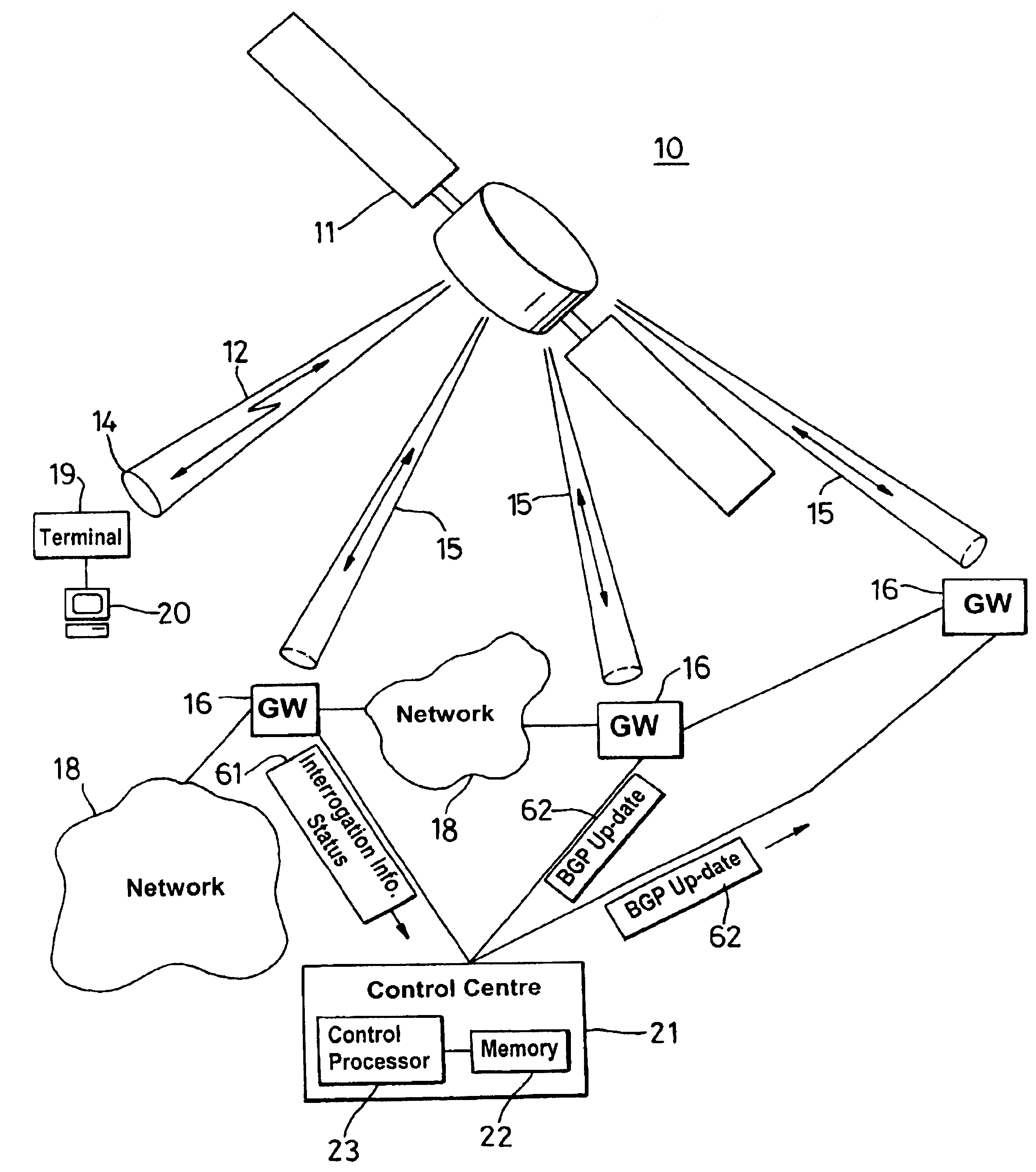
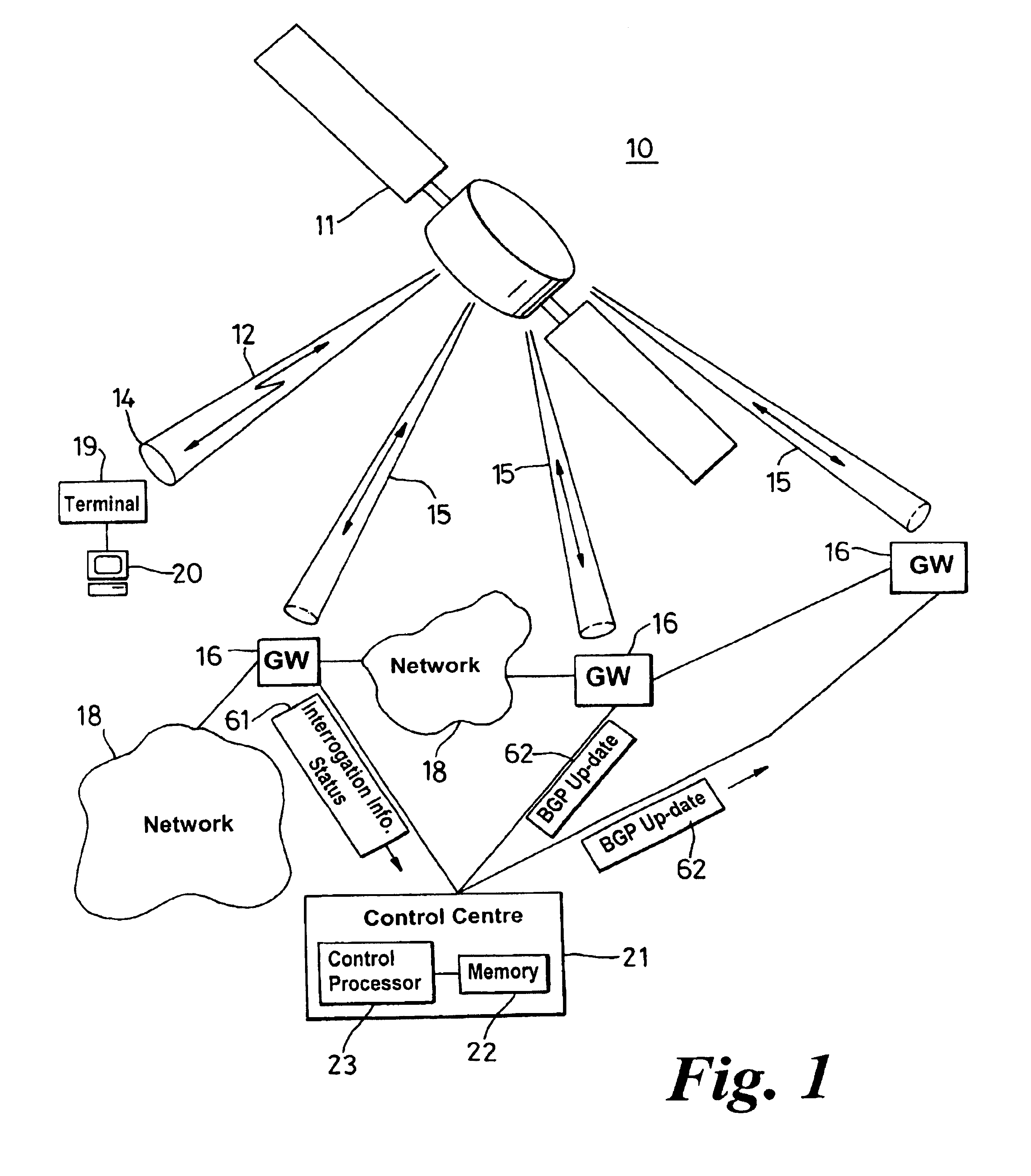
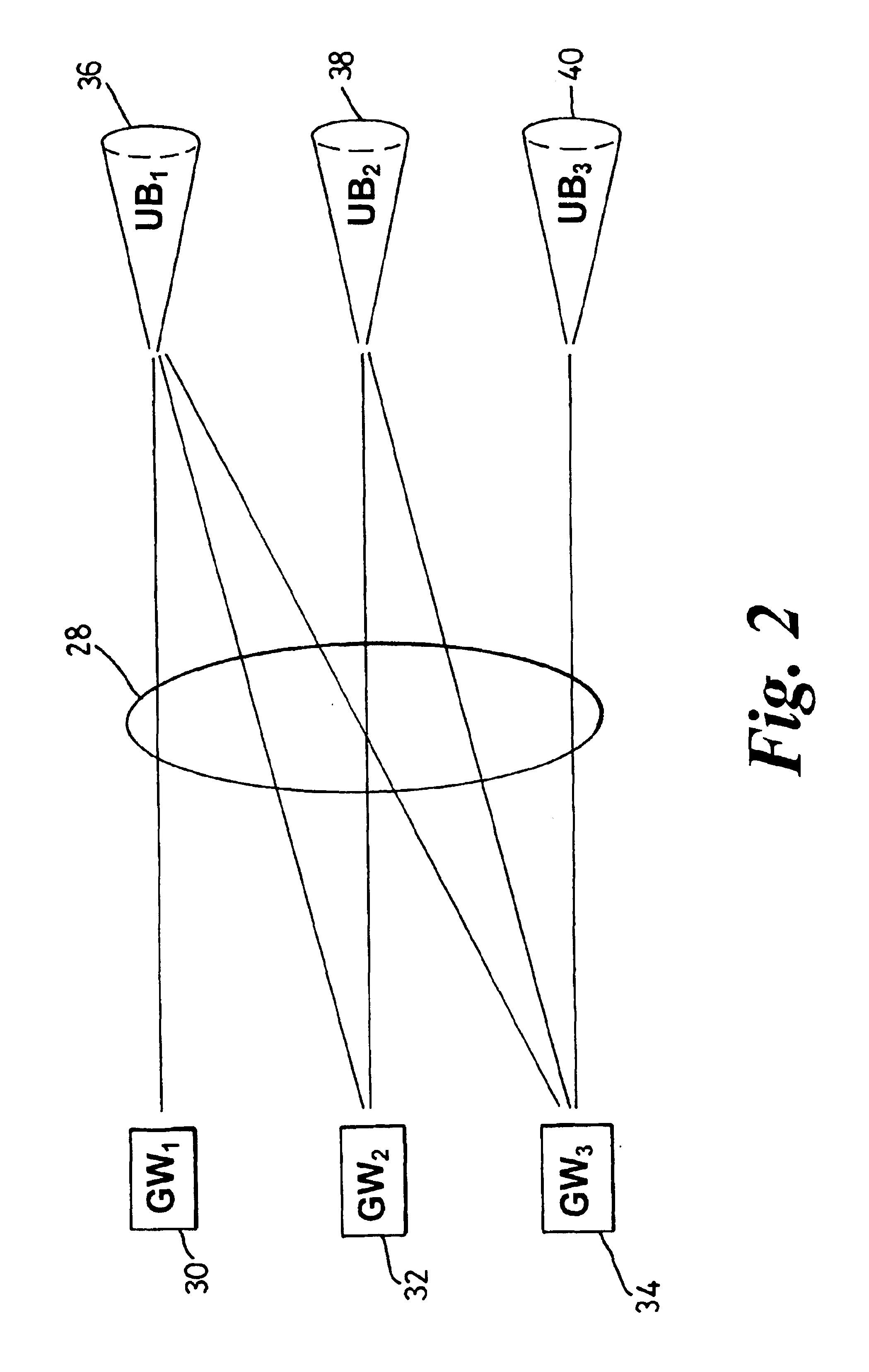
Border gateway protocol manager and method of managing the selection of communication links
InactiveUS6829221B1Avoid congestionLeast costError preventionTransmission systemsBorder Gateway ProtocolCommunication link
A border gateway protocol (BGP) management system (10) dynamically determines an optimum or preferred data route (12) from wireline networks (18) into a satellite communication system (11). Multiple gateways (16, 30-34) provide access points to the wireline networks. The management system includes a connectivity matrix which processes (74) information, such as bandwidth availability and route congestion, and then generate a BGP update that is communicated (80) into at least one of the gateways. The BGP update promotes preferred gateways and so identifies a preferred access path to the satellite system. Specifically, the BGP update instruction contains a metric altering a weighting of an identified route data route, which metric effects path selection at a gateway receiving IP datagrams. The metric is derived from information pertaining to a connectivity matrix associated with the satellite system.
Owner:NORTEL NETWORKS LTD
Autodiscovery for virtual networks
InactiveUS20050097203A1Facilitates automatic discoveryFacilitate signaling over LDP sessionsMultiplex system selection arrangementsDigital computer detailsBorder Gateway ProtocolProtocol for Carrying Authentication for Network Access
The present invention facilitates automatic discovery of VPN-related information, which relates to the existence or association of VPNs as supported by provider edge devices in a core network. In particular, the Border Gateway Protocol (BGP) is used to facilitate the automatic discovery, and the provider edge devices are capable of subsequently and automatically triggering Label Distribution Protocol (LDP) processes to facilitate signaling over LDP sessions within the core network.
Owner:RPX CLEARINGHOUSE
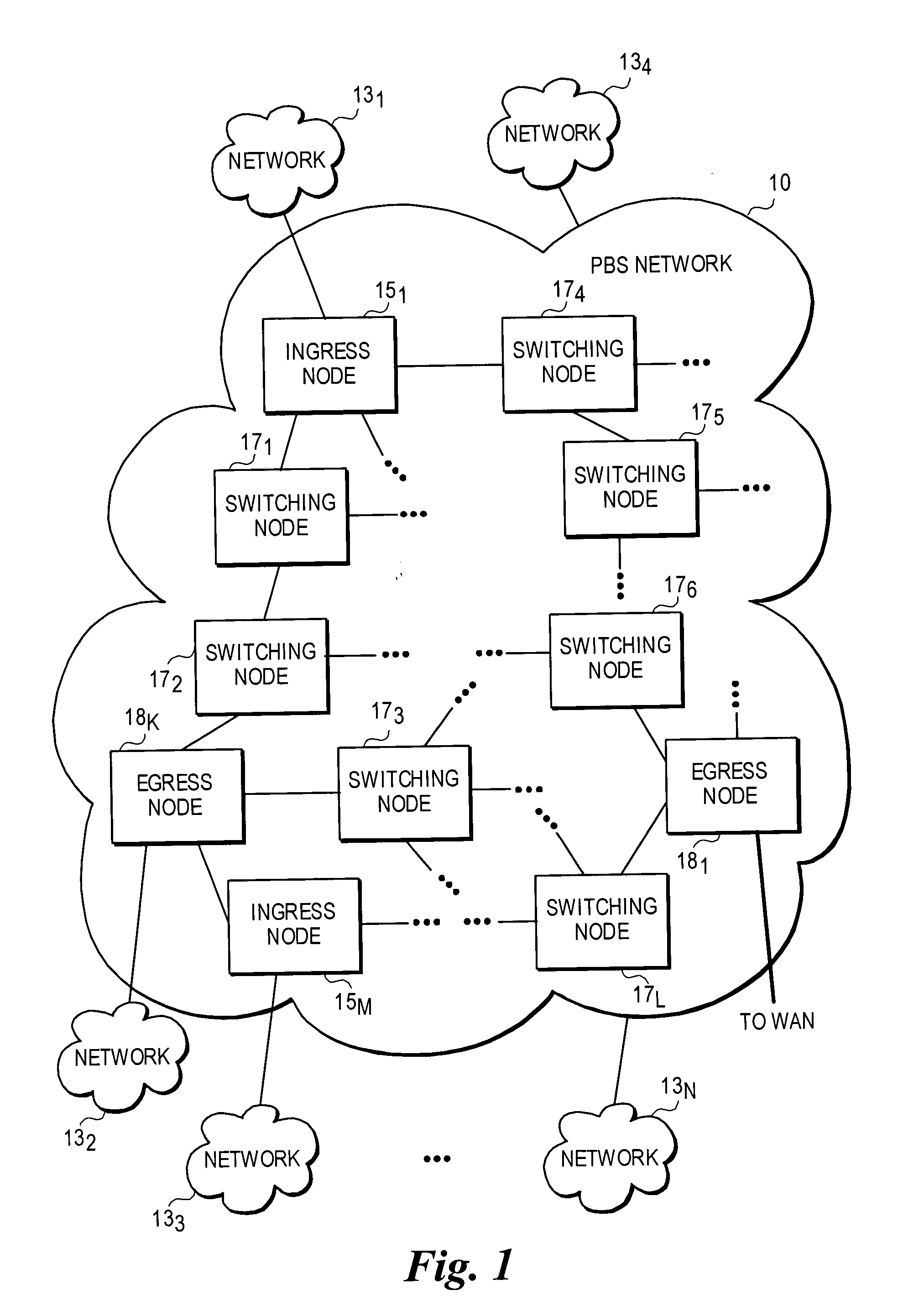
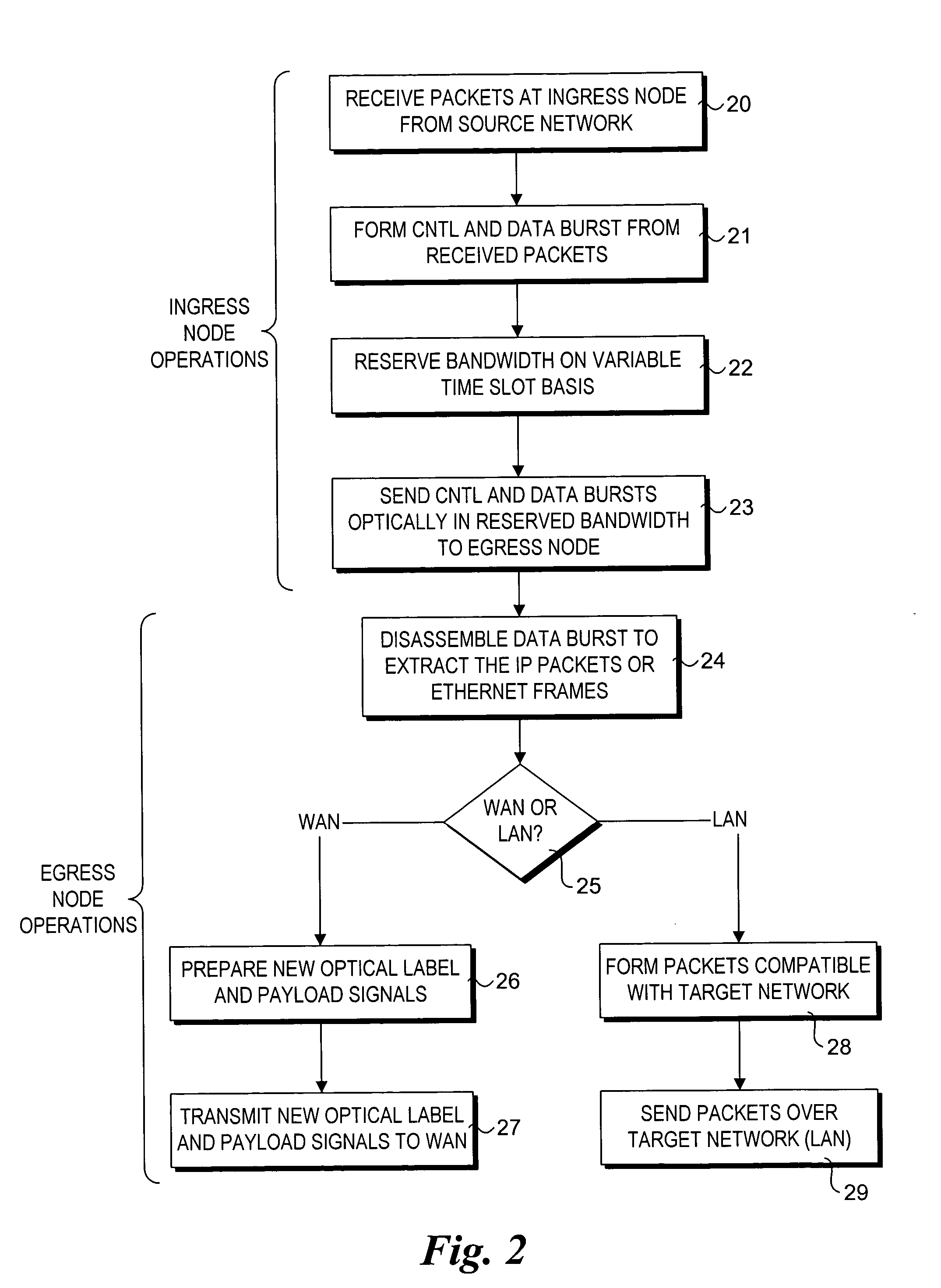
Optical-switched (OS) network to OS network routing using extended border gateway protocol
InactiveUS20050068968A1Multiplex system selection arrangementsData switching by path configurationBorder Gateway ProtocolRouting table
Routing mechanisms for routing data via a plurality of optical switched (OS) networks, such as optical burst-switched (OBS) networks. A plurality of OBS networks are connected to form an enterprise network, which may further include non-OBS networks such as LANs and the like. Each of the OBS networks is modeled as an autonomous system (AS), and one or more edge nodes of each OBS network are designated as external gateway protocol (EGP) routers. Each EGP router maintains a routing table identifying routes that may be used to reach destination networks. The routing table is dynamically updated via update messages that comprise an extension to the Border Gateway Protocol (BGP) and account for optical routing considerations particular to OBS networks. In response to a routing request, data is sent from an internal node using an internal routing protocol to a BGP router edge node. The BGP router edge node then determines a next network hop based on current routing information in its routing table, and the data is routed using an external routing protocol. At the same time, data is routed within an individual OBS network using an internal routing protocol under which data are sent as data bursts via reserved lightpaths.
Owner:INTEL CORP
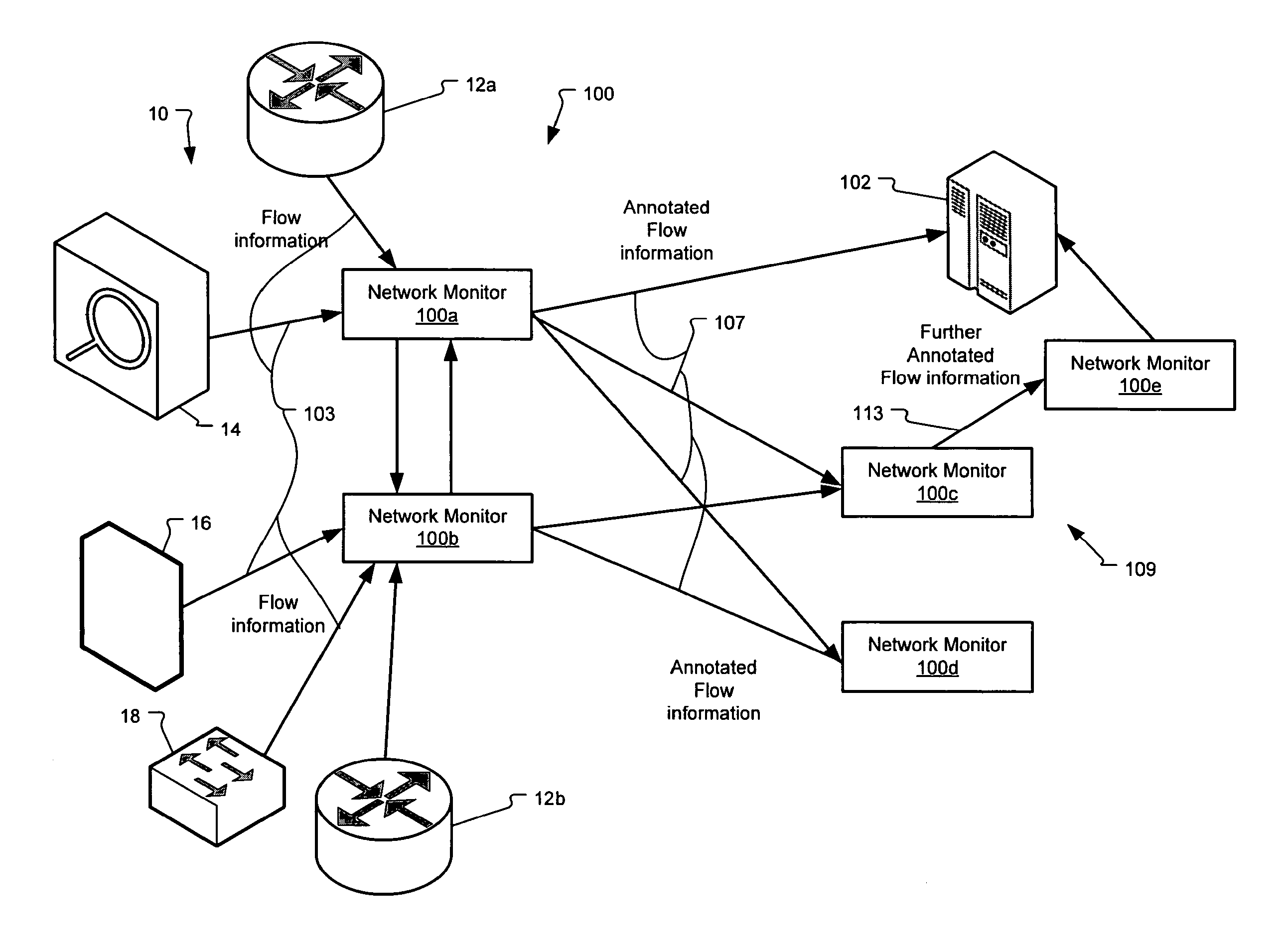
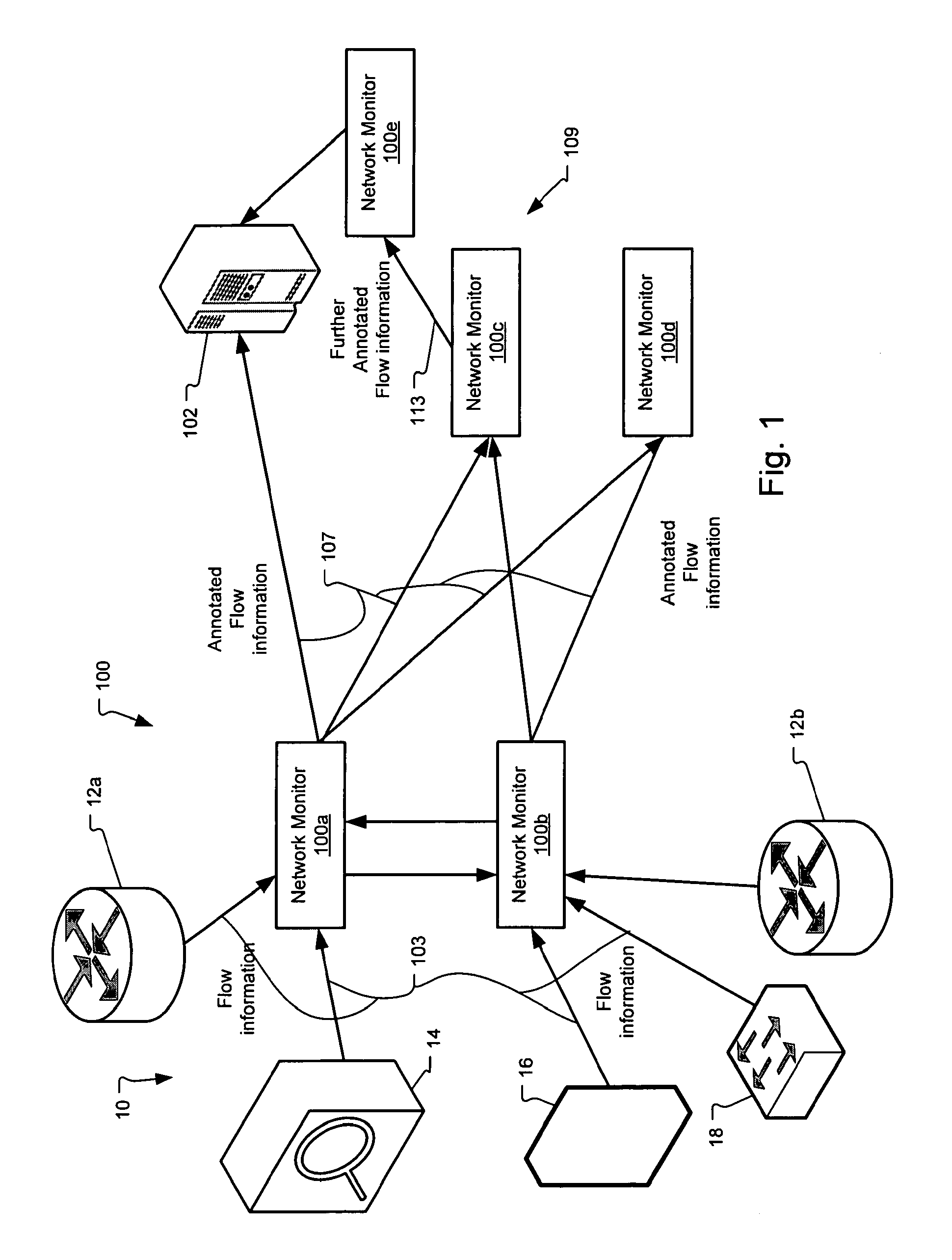
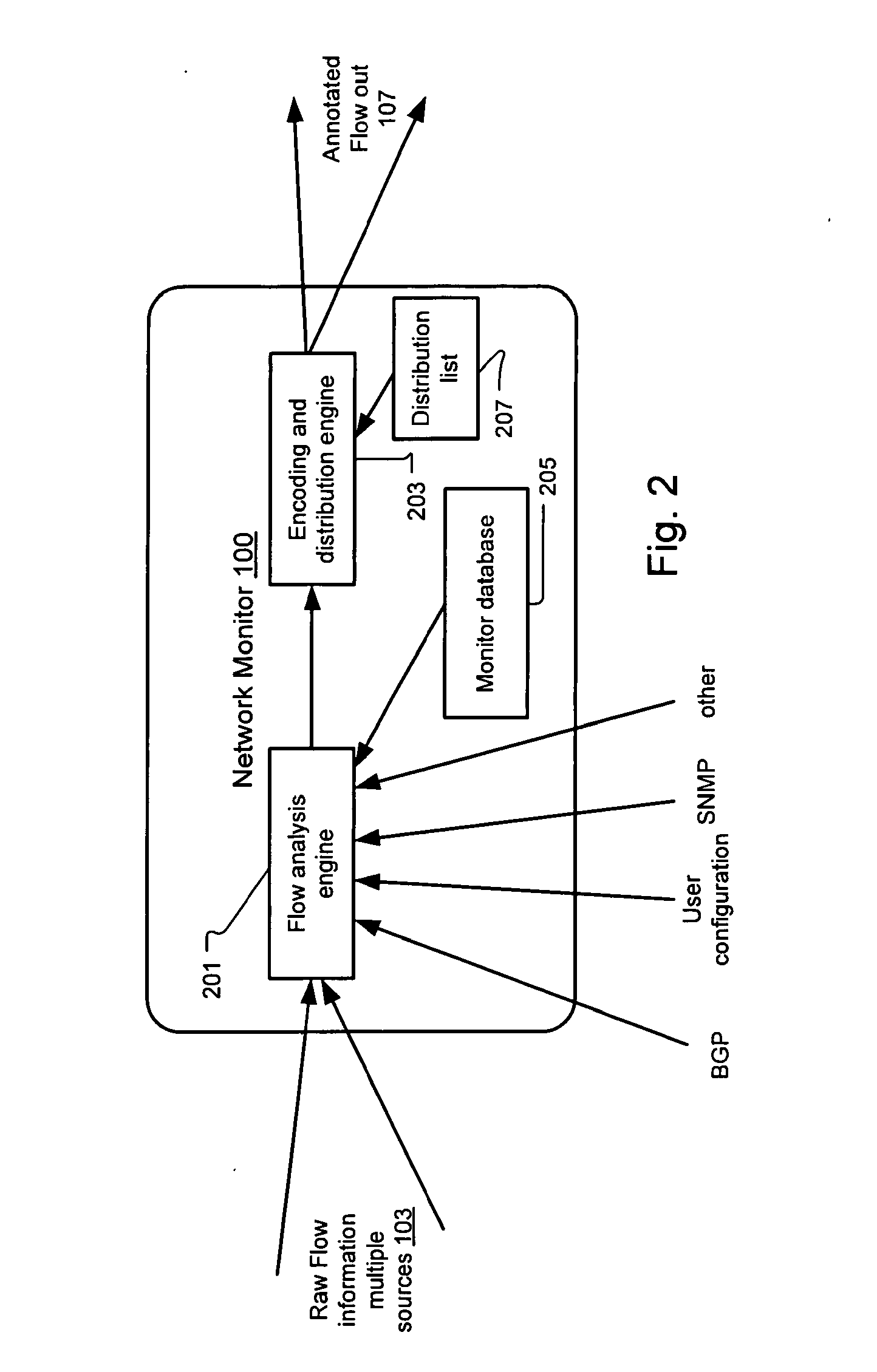
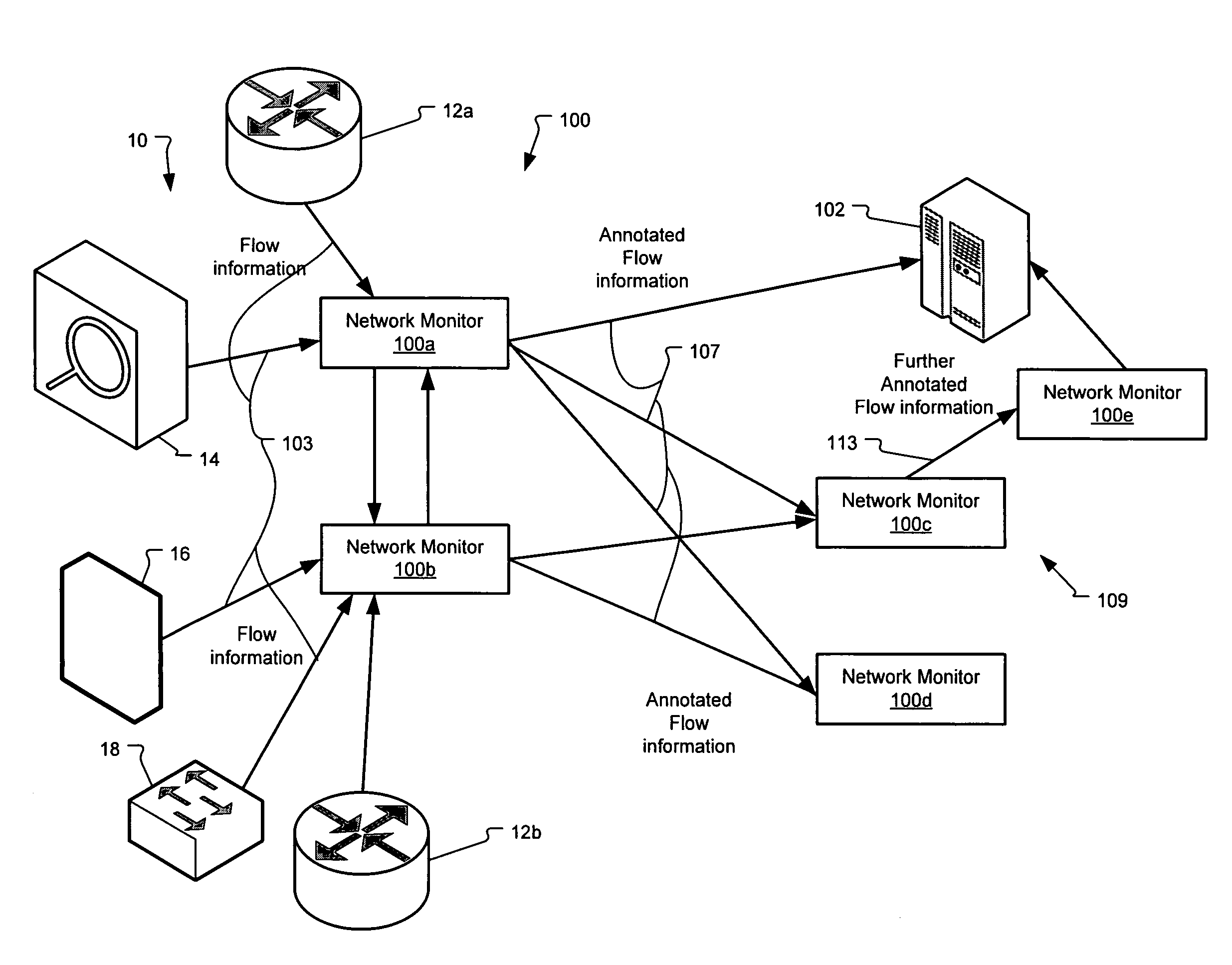
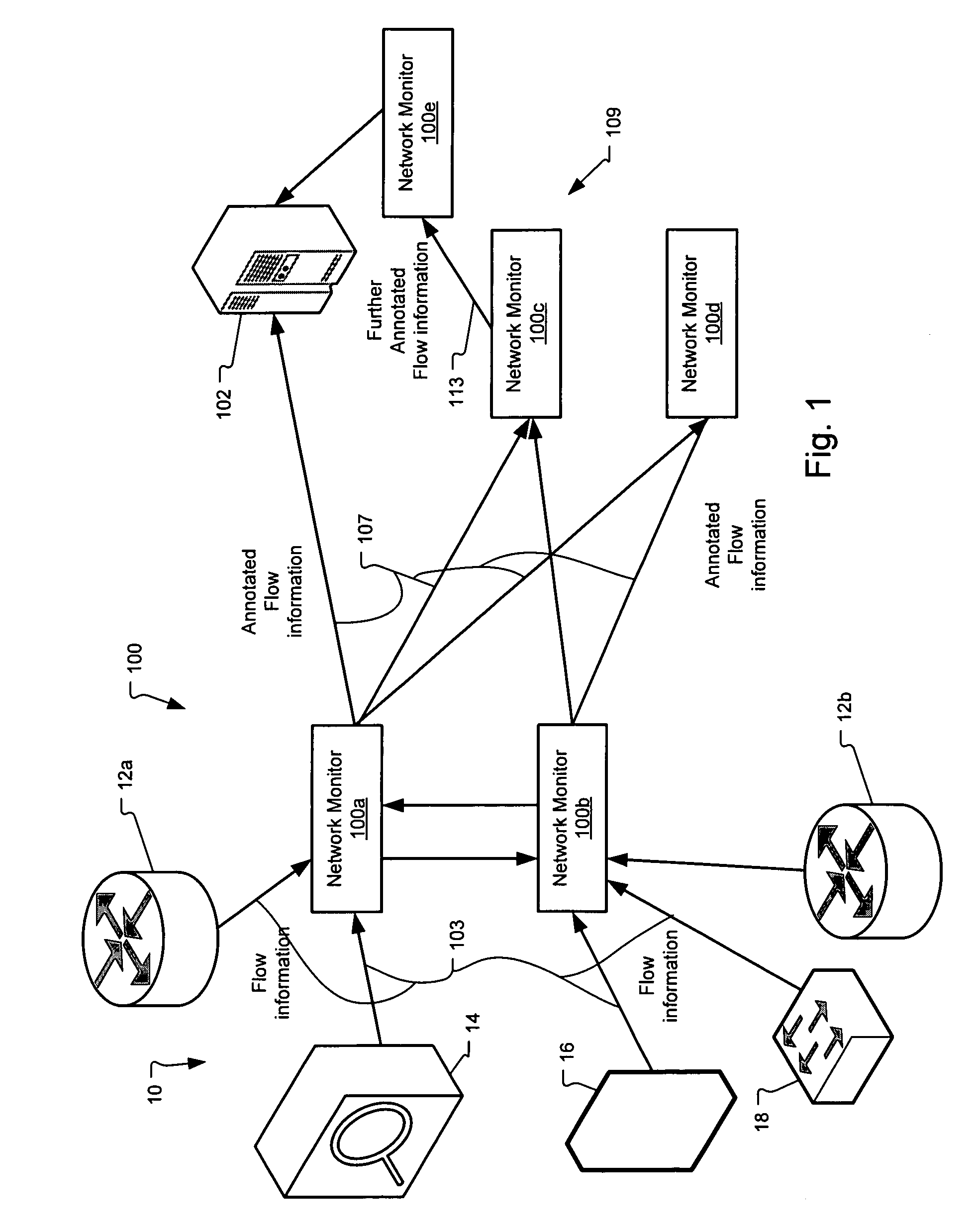
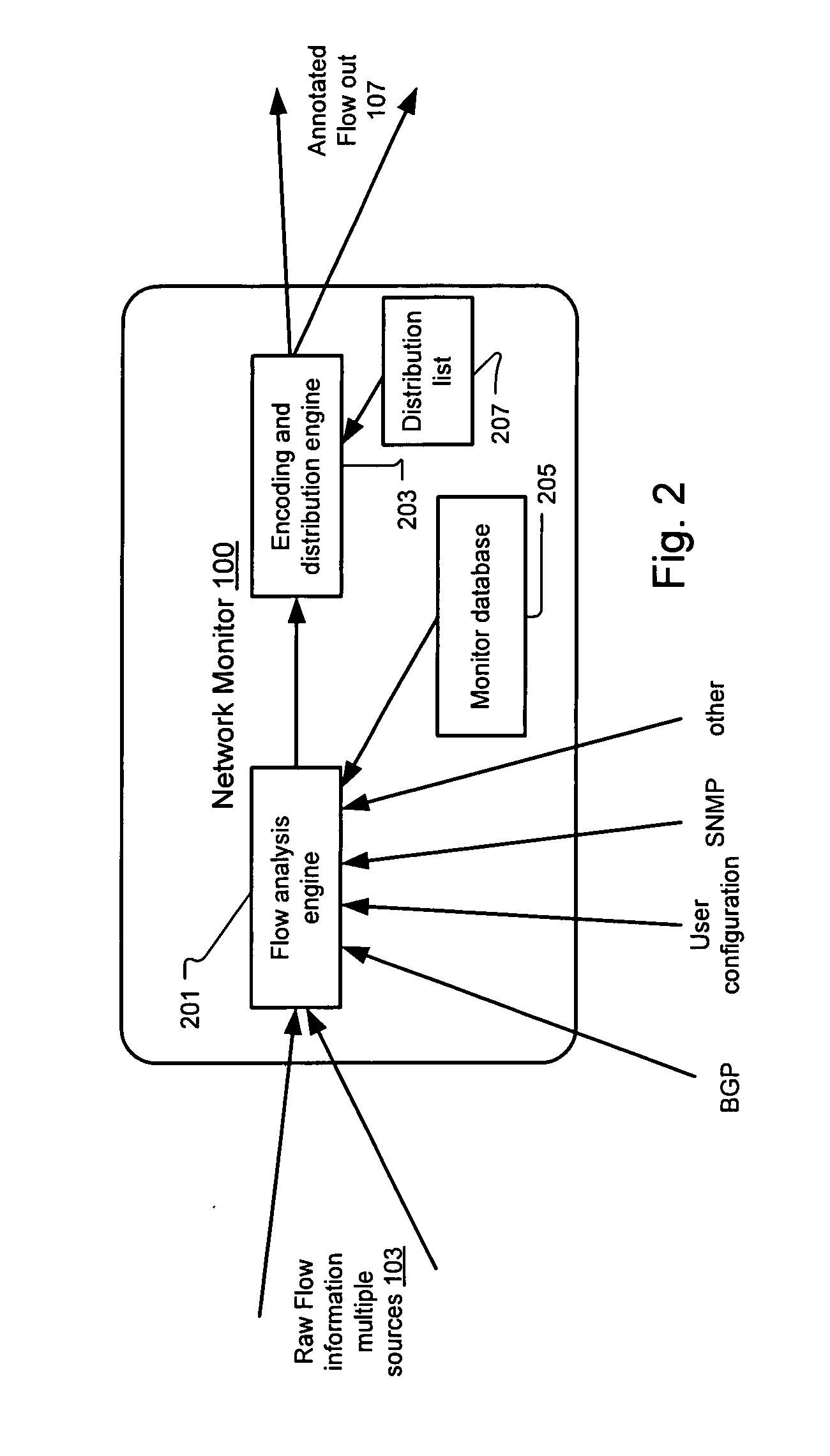
Method and system for annotating network flow information
ActiveUS20130290521A1Easy to createReduce overheadDigital computer detailsData switching networksBorder Gateway ProtocolStructure of Management Information
A scalable flow monitoring solution takes in standard flow records exported from network devices such as routers, switches, firewalls, hubs, etc., and annotates the flow with additional information. This information is derived from a number of sources, including Border Gateway Protocol (BGP), Simple Network Management Protocol (SNMP), user configuration, and other, intelligent flow analysis. These annotations add information to the flow data, and can be used to perform value-added flow analysis. The annotated flow is then resent to a configurable set of destinations using standard flow formatting, e.g., Cisco System Inc.'s NetFlow, in one implementation. This allows the annotated flow to be processed and the enhanced information to be used by other flow analysis tools and existing flow analysis infrastructure.
Owner:ARBOR NETWORKS
Network routing apparatus that performs soft graceful restart
ActiveUS20060171404A1Data switching by path configurationStore-and-forward switching systemsBorder Gateway ProtocolNetwork data
A network data packet routing apparatus with BGP is configured to soft reset an AFI or SAFI, so that forwarding on routes associated with the AFI or SAFI can continue even after an event or error. One approach involves establishing a Border Gateway Protocol (BGP) peering session between a first node and a second node in a packet-switched network; detecting a BGP condition requiring a reset of a BGP address family indicator (AFI) data structure or a sub-address family indicator (SAFI) data structure, wherein the BGP condition does not affect states of routes in the AFI or SAFI; preserving a BGP state and a forwarding state of the AFI or SAFI; and forwarding data on routes represented in the AFI or SAFI. Soft notification messaging and marking routes as stale facilitates the approach.
Owner:CISCO TECH INC
Dynamic retrieval of routing information for inter-AS TE-LSPs
A technique dynamically triggers an exchange of reachability information between a tail-end (remote) domain target node (e.g., a tail-end node) of a traffic engineering (TE) label switched path (LSP) and a local domain head-end node of the TE-LSP in a computer network. The inter-domain information retrieval technique is illustratively based on triggering a Border Gateway Protocol (BGP) session whereby at least a portion of the reachability, i.e., routing, information of the tail-end node is transmitted to the head-end node of the TE-LSP in accordance with BGP. Specifically, once a TE-LSP is established between the head-end node and the tail-end node, the head-end node triggers the tail-end node, e.g., through extensions to a request / response signaling exchange, to establish the BGP session. Establishment of the BGP session enables transmission of the routing information from the tail-end node to the head-end node. The head-end node uses the routing information to calculate routes, i.e., address prefixes and associated attributes, reachable from the tail-end node for insertion into its routing table.
Owner:CISCO TECH INC
Technique for preventing routing loops by disseminating BGP attribute information in an OSPF-configured network
ActiveUS20070214275A1Overcome disadvantagesAvoid developmentMultiple digital computer combinationsTransmissionBorder Gateway ProtocolType-length-value
A novel technique is provided for preventing routing loops by disseminating Border Gateway Protocol (BGP) attribute information in an Open Shortest Path First (OSPF) configured network. Specifically, a new OSPF sub-type-length-value (TLV) is introduced for transporting a conventional BGP autonomous system (AS) path attribute through the OSPF-configured network. Like the BGP AS-path attribute, the new OSPF AS-path sub-TLV is configured to store a set of AS numbers corresponding to the AS path of one or more advertised routes. Thus, when a network device receives an OSPF link-state advertisement (LSA) containing the novel AS-path sub-TLV, the network device determines whether it resides in an autonomous system whose AS number is stored in the sub-TLV. If so, the network device does not install the LSA's advertised routes in its link-state database since the routes, if installed, could result in routing loops.
Owner:CISCO TECH INC
Method and System for Annotating Network Flow Information
InactiveUS20090168648A1Easy to createReduce overheadError preventionFrequency-division multiplex detailsTraffic capacityBorder Gateway Protocol
A scalable flow monitoring solution takes in standard flow records exported from network devices such as routers, switches, firewalls, hubs, etc., and annotates the flow with additional information. This information is derived from a number of sources, including Border Gateway Protocol (BGP), Simple Network Management Protocol (SNMP), user configuration, and other, intelligent flow analysis. These annotations add information to the flow data, and can be used to perform value-added flow analysis. The annotated flow is then resent to a configurable set of destinations using standard flow formatting, e.g., Cisco System Inc.'s NetFlow, in one implementation. This allows the annotated flow to be processed and the enhanced information to be used by other flow analysis tools and existing flow analysis infrastructure.
Owner:ARBOR NETWORKS
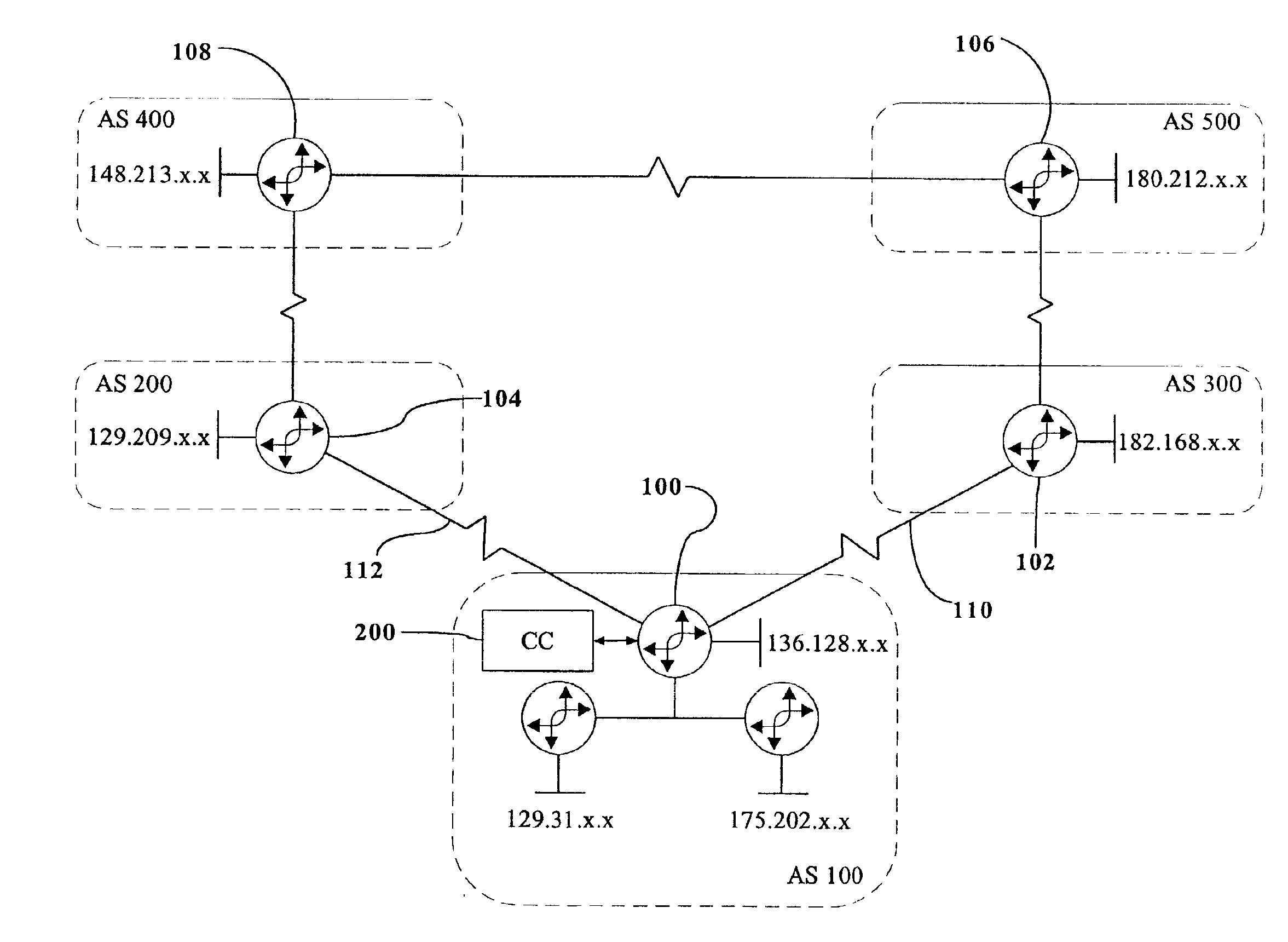
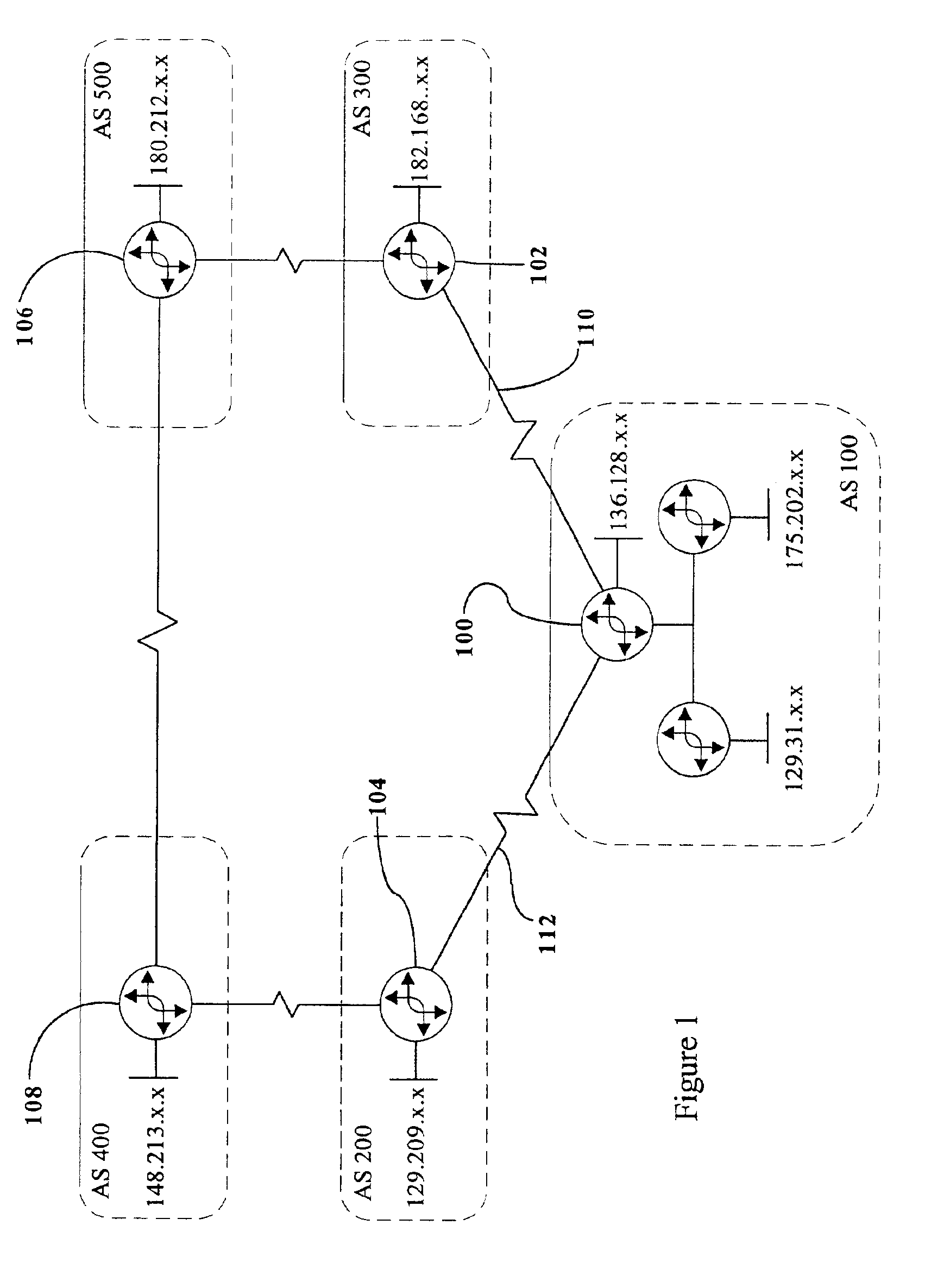
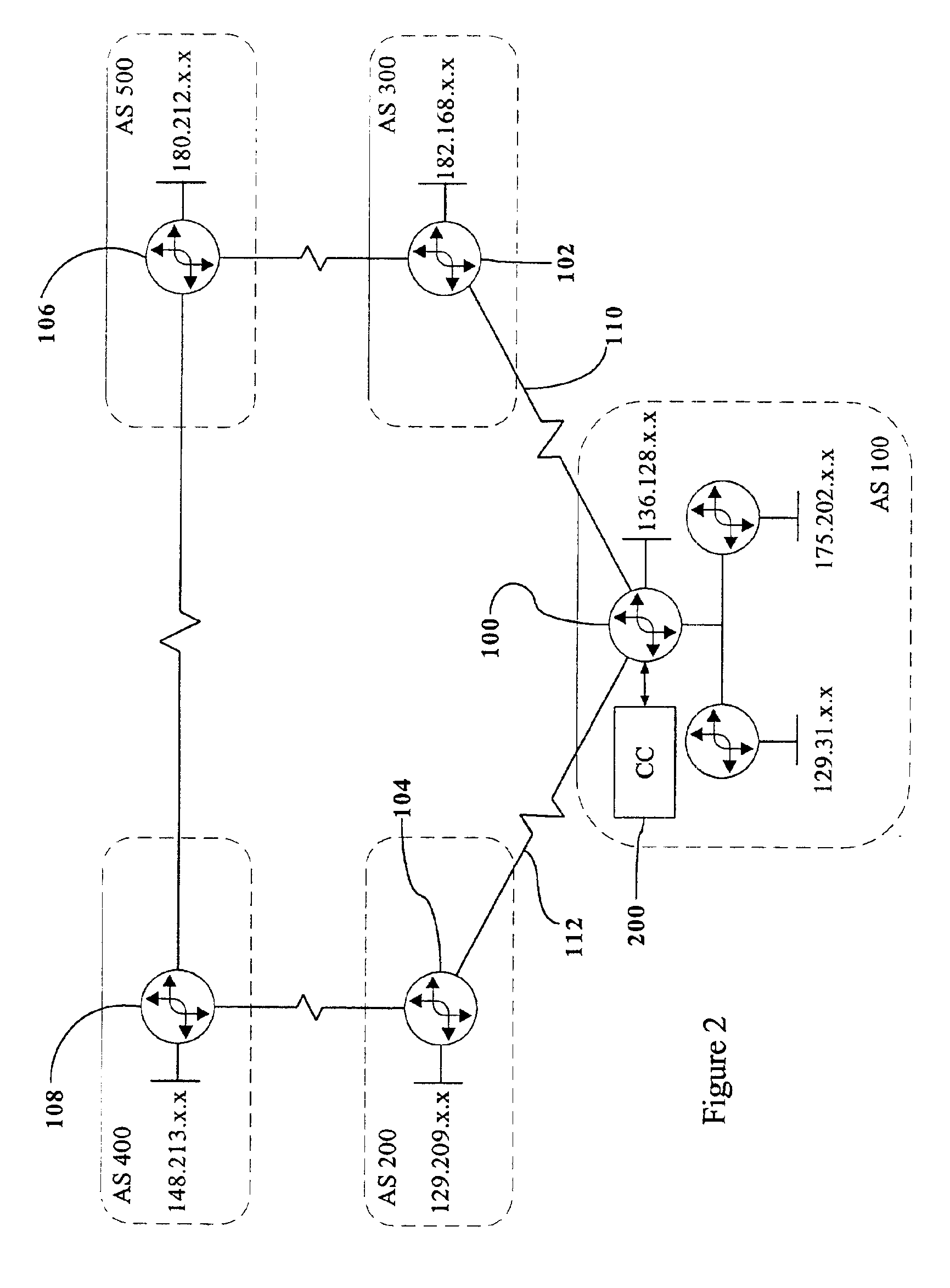
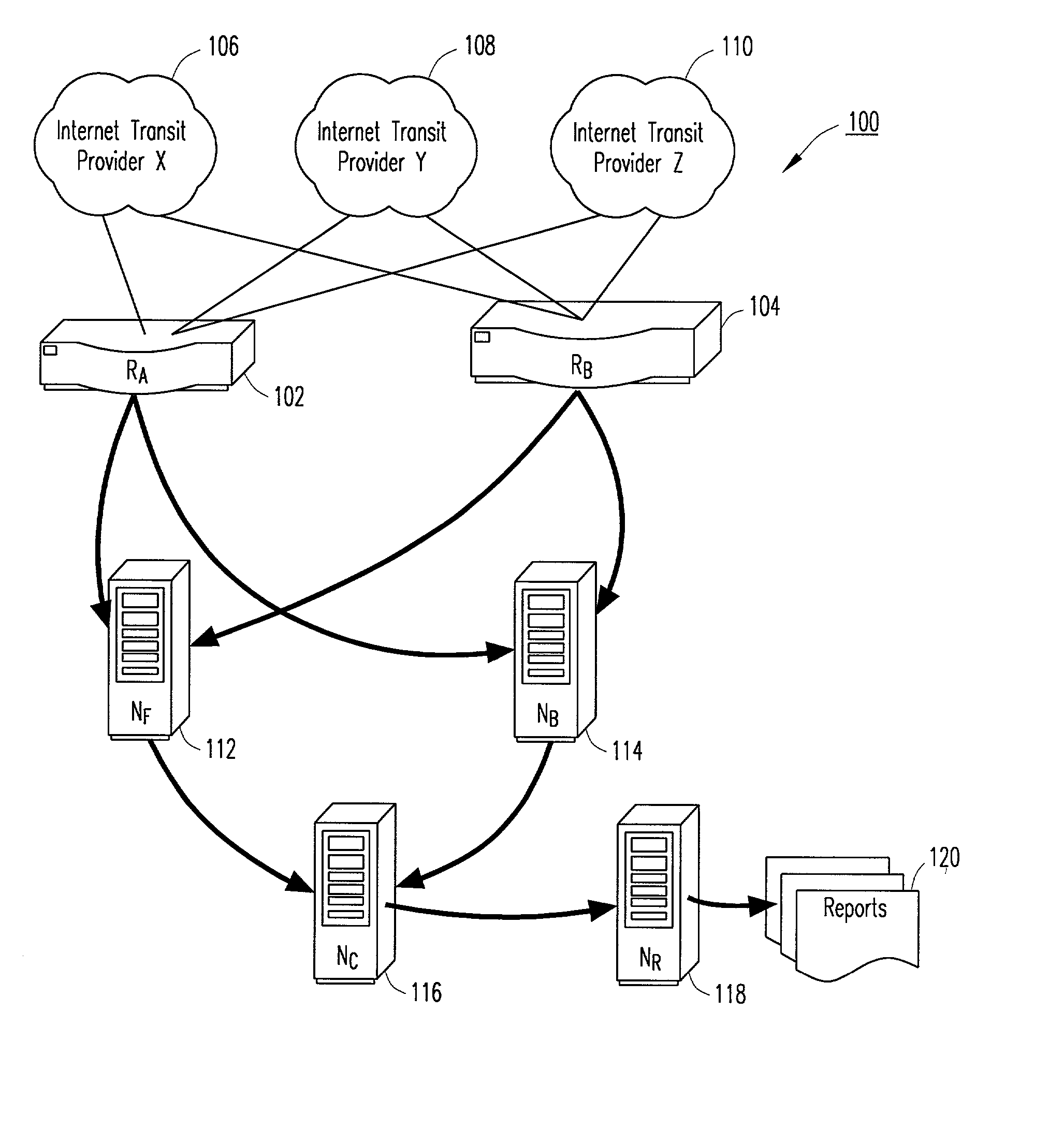
Controlling traffic on links between autonomous systems
The present invention provides for controlling incoming traffics on the links to an autonomous system. Incoming traffic usage for blocks of IP addresses within an autonomous system and load, congestion and capacity of the links for the incoming traffic is monitored to determine the optimal link for incoming traffic destined for a block of IP addresses. Incoming traffic for a block of IP addresses is biased towards the optimal link by configuring the border routers to announce the block of IP addresses via Border Gateway Protocol (BGP) across the non-optimal links with one or more local AS numbers pre-pended, causing the non-optimal links to look as if they are of a greater routing distance than the optimal link. In addition, outgoing traffic for a session is separately controlled by tagging the packets of the session for a specific link, causing the router to send the packet out the optimal link.
Owner:RADWARE
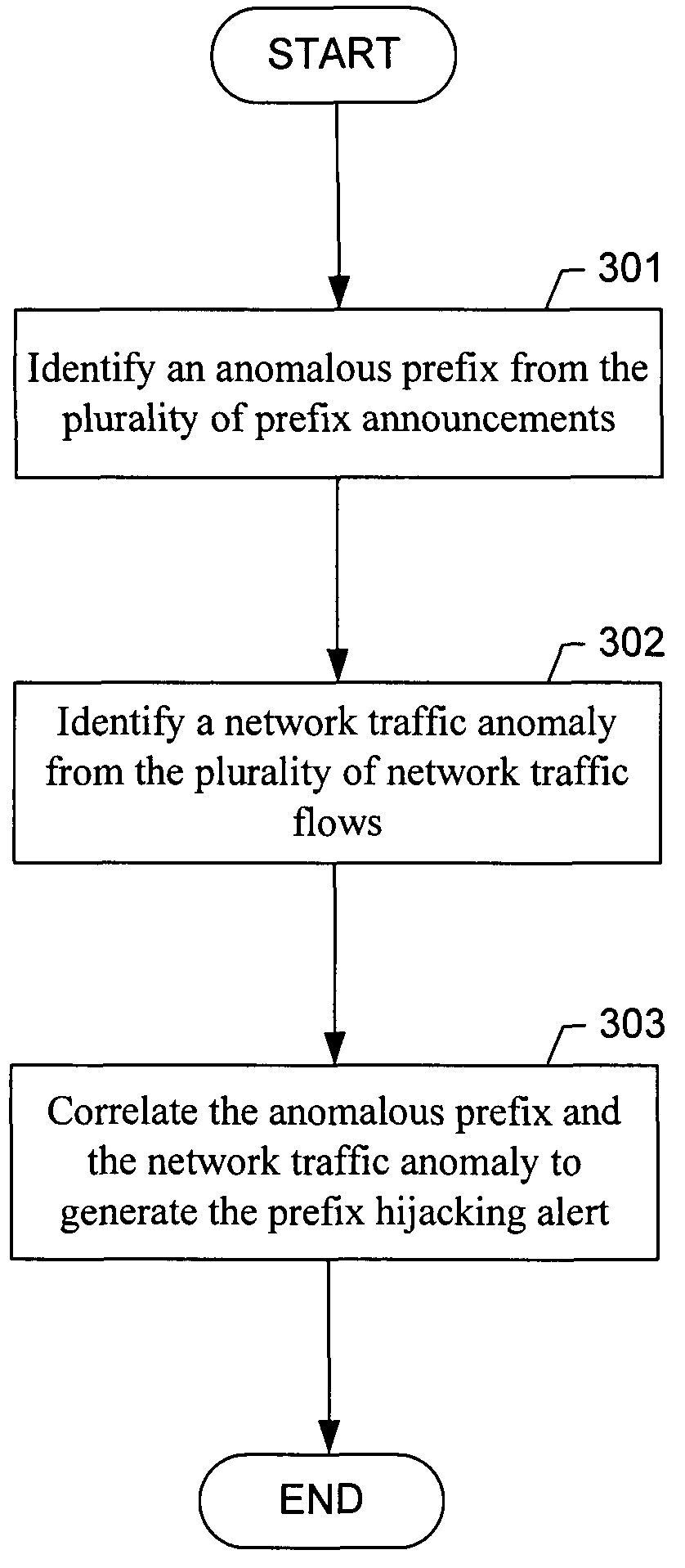
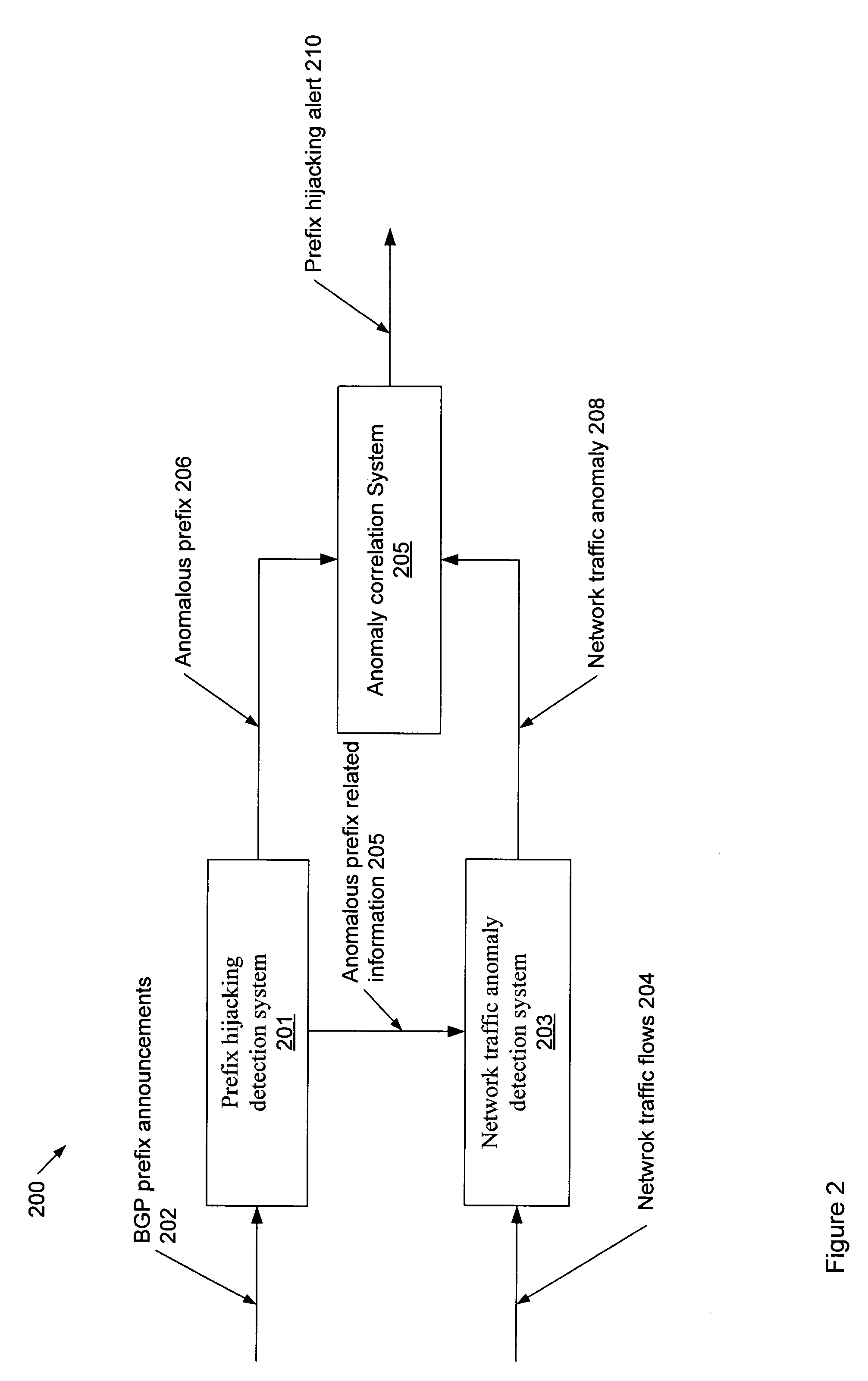
Method for detecting internet border gateway protocol prefix hijacking attacks
ActiveUS7823202B1Memory loss protectionError detection/correctionTraffic capacityBorder Gateway Protocol
The invention relates to a method for generating a prefix hijacking alert in a network, wherein a plurality of network traffic flows are routed based at least on a plurality of prefix announcements from one or more Border Gateway Protocol (BGP) router, the method comprises identifying an anomalous prefix from the plurality of prefix announcements, identifying a network traffic anomaly from the plurality of network traffic flows, and correlating the anomalous prefix and the network traffic anomaly to generate the prefix hijacking alert.
Owner:THE BOEING CO
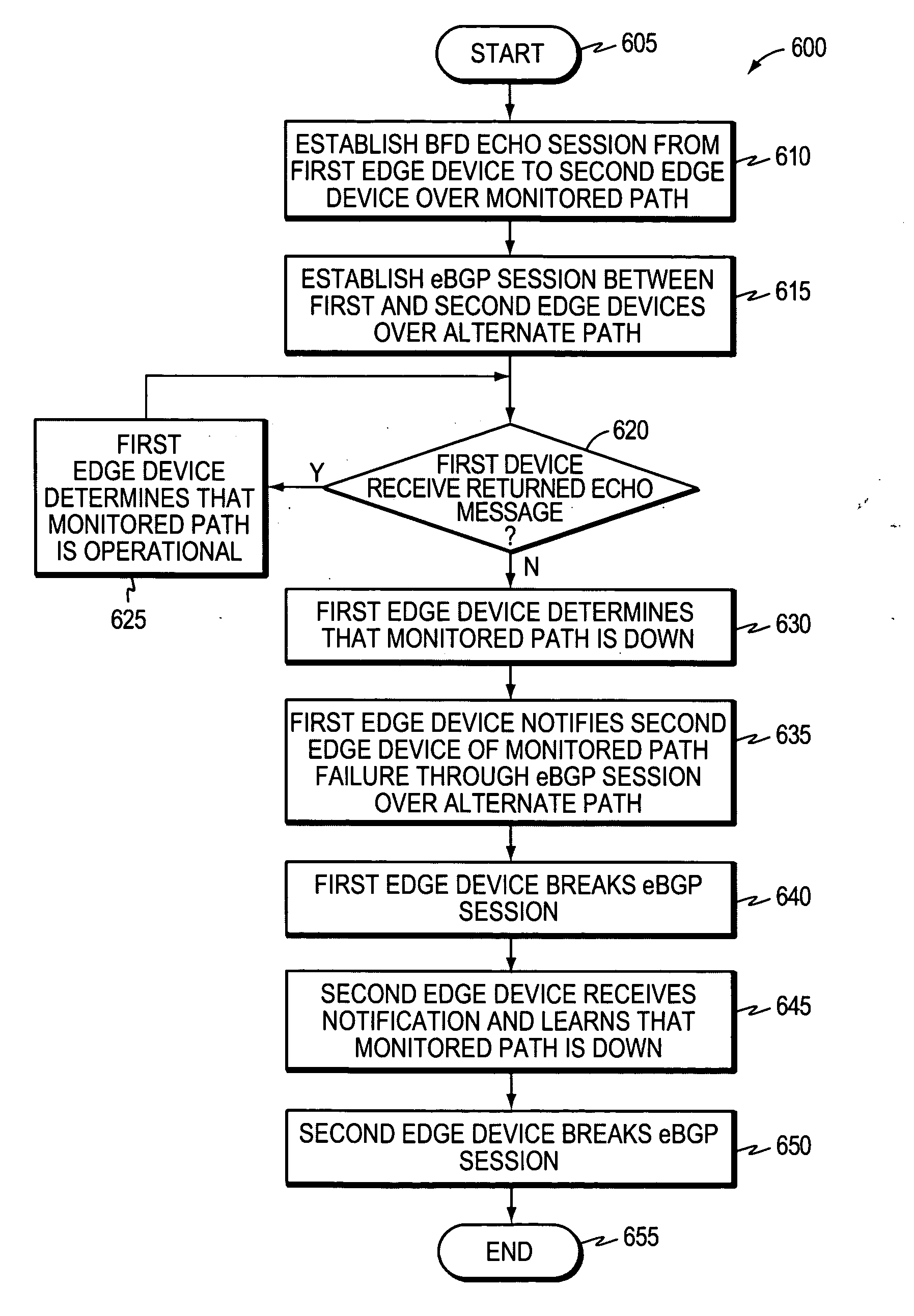
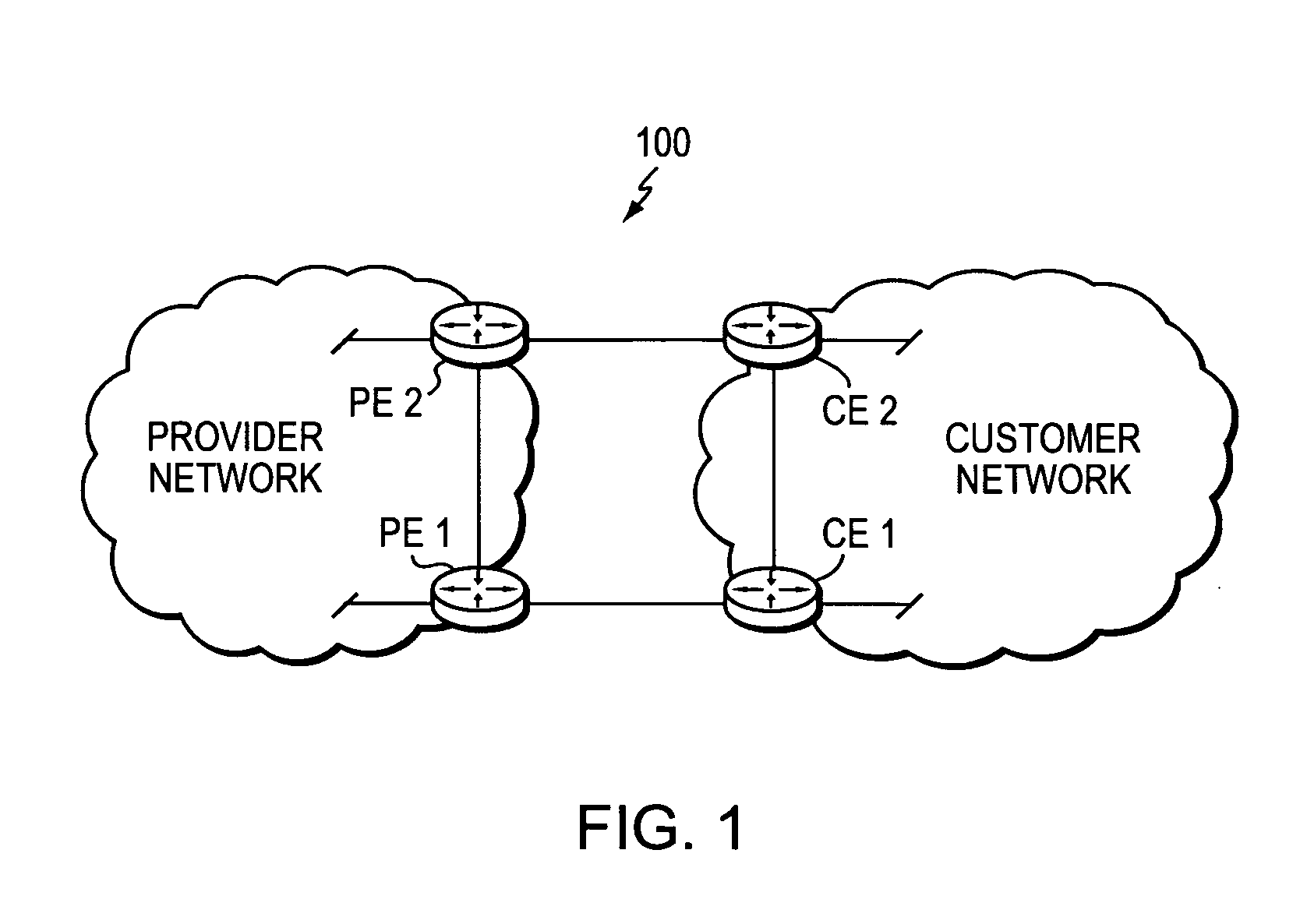
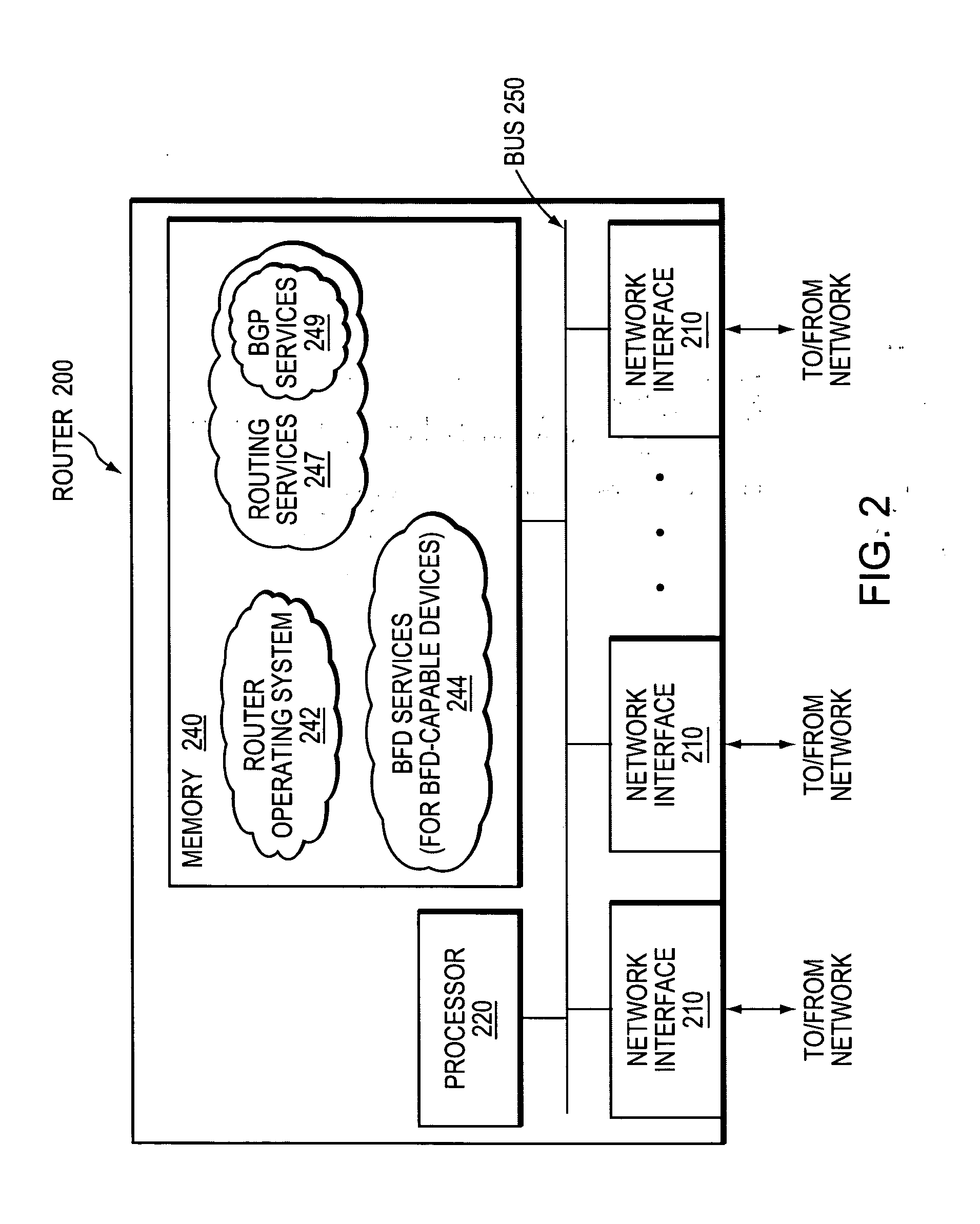
Technique for enabling bidirectional forwarding detection between edge devices in a computer network
ActiveUS20070180104A1Shorten the timeSave moneyMultiple digital computer combinationsTransmissionBorder Gateway ProtocolBidirectional Forwarding Detection
A technique enables bidirectional forwarding detection (BFD) between first and second edge devices in a computer network, wherein the second edge device is not configured for BFD. According to the novel technique, a BFD Echo session is established from the first edge device to the first edge device via the second edge device, i.e., along a monitored path (e.g., a single link). Also, an external border gateway protocol (eBGP) session is established between the first and second edge devices over an alternate path (e.g., an eBGP multi-hop session). The first edge device determines that the monitored path is down upon not receiving a returned BFD Echo message from the second edge device. In response, the first edge device notifies the second edge device that the monitored path is down through the eBGP session over the alternate path. Notably, upon notifying the second edge device that the monitored path is down, the first edge device breaks the eBGP session, and upon receiving the notification, the second edge device also breaks the eBGP session.
Owner:CISCO TECH INC
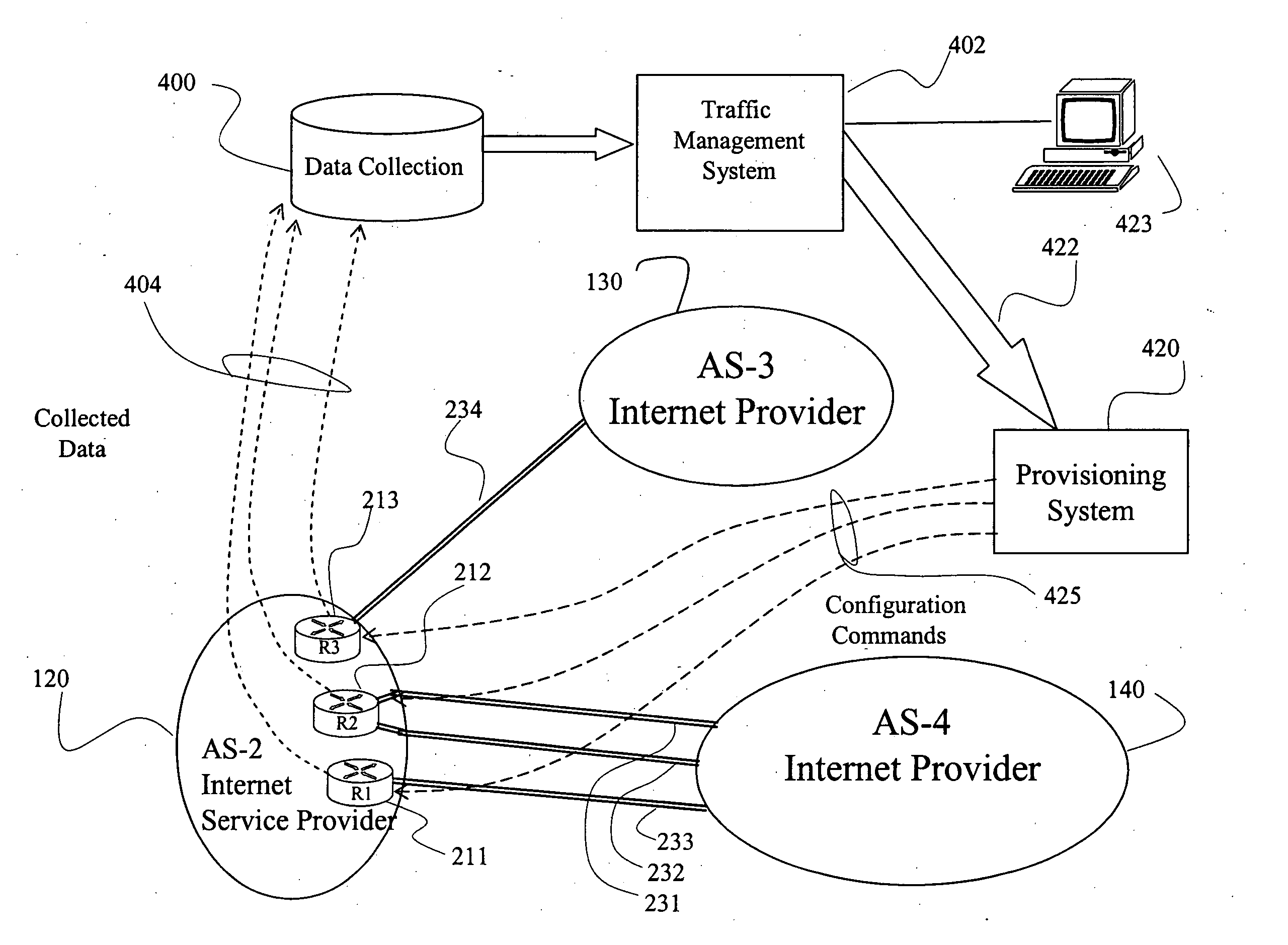
Systems and methods for traffic management between autonomous systems in the Internet
InactiveUS20060165009A1Error preventionFrequency-division multiplex detailsTraffic capacityBorder Gateway Protocol
Systems and methods are disclosed for managing the traffic between autonomous systems in the Internet. Data on links on border routers between autonomous systems is collected and analyzed at certain traffic times. Once determined, traffic on various customer facing interfaces at that time is associated with an Internet Prefix. Then, the aggregate traffic volume for each Internet Prefix is allocated to a first link on a primary routing basis and to a second link on a secondary routing basis. These routes are announced to a provisioning system that in turn, configures various border routers, which in turn announce the new routes using the Internet Border Gateway Protocol. In this manner, inter-autonomous traffic is managed to facilitate traffic distribution on the links according to criteria defined by network provider, allowing resources to be better utilized and network traffic to be maintained if a link fails.
Owner:ZVOLVE
High available method for border gateway protocol version 4
InactiveUS7236453B2Improve usabilityError preventionTransmission systemsBorder Gateway ProtocolRecovery period
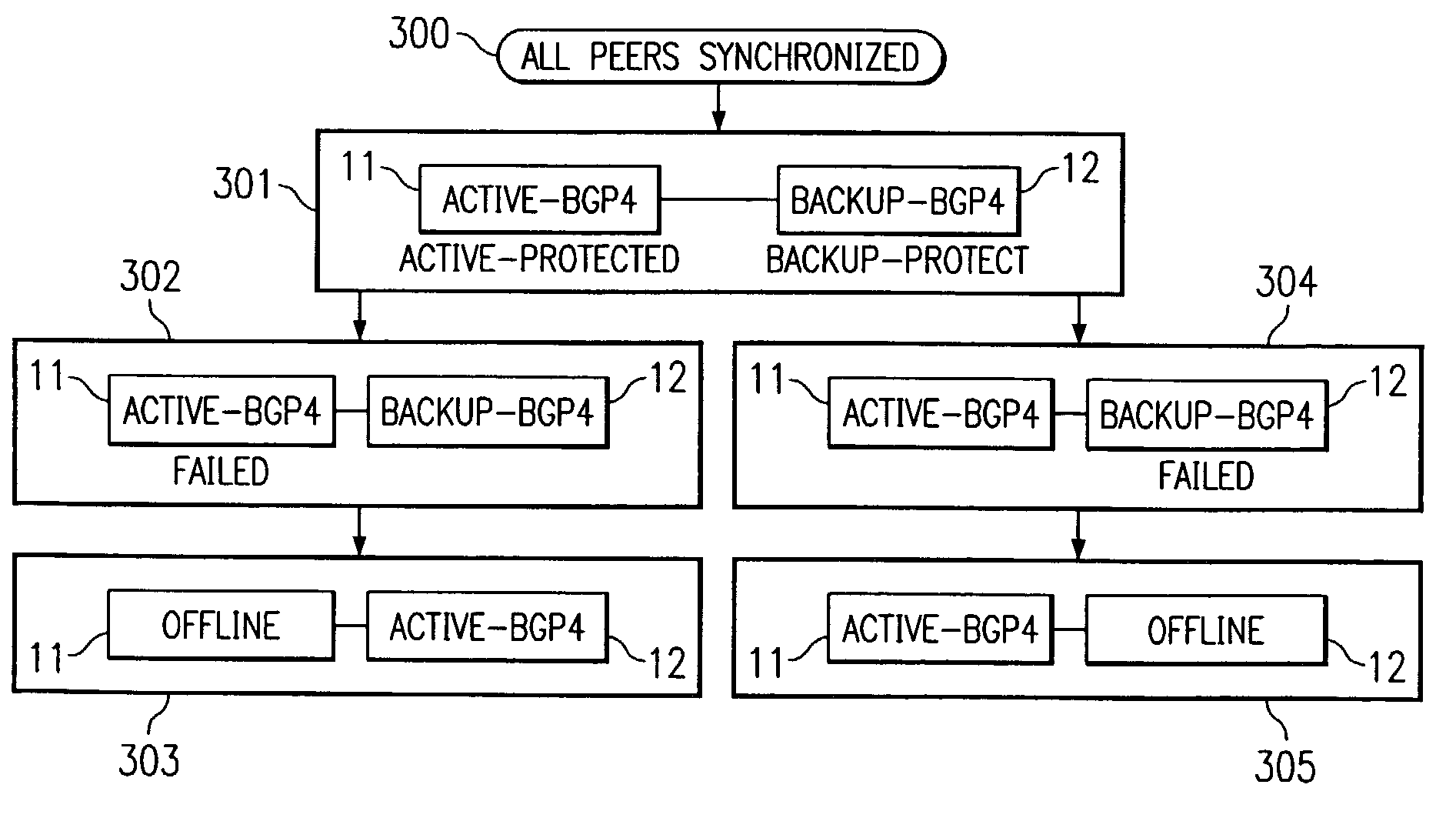
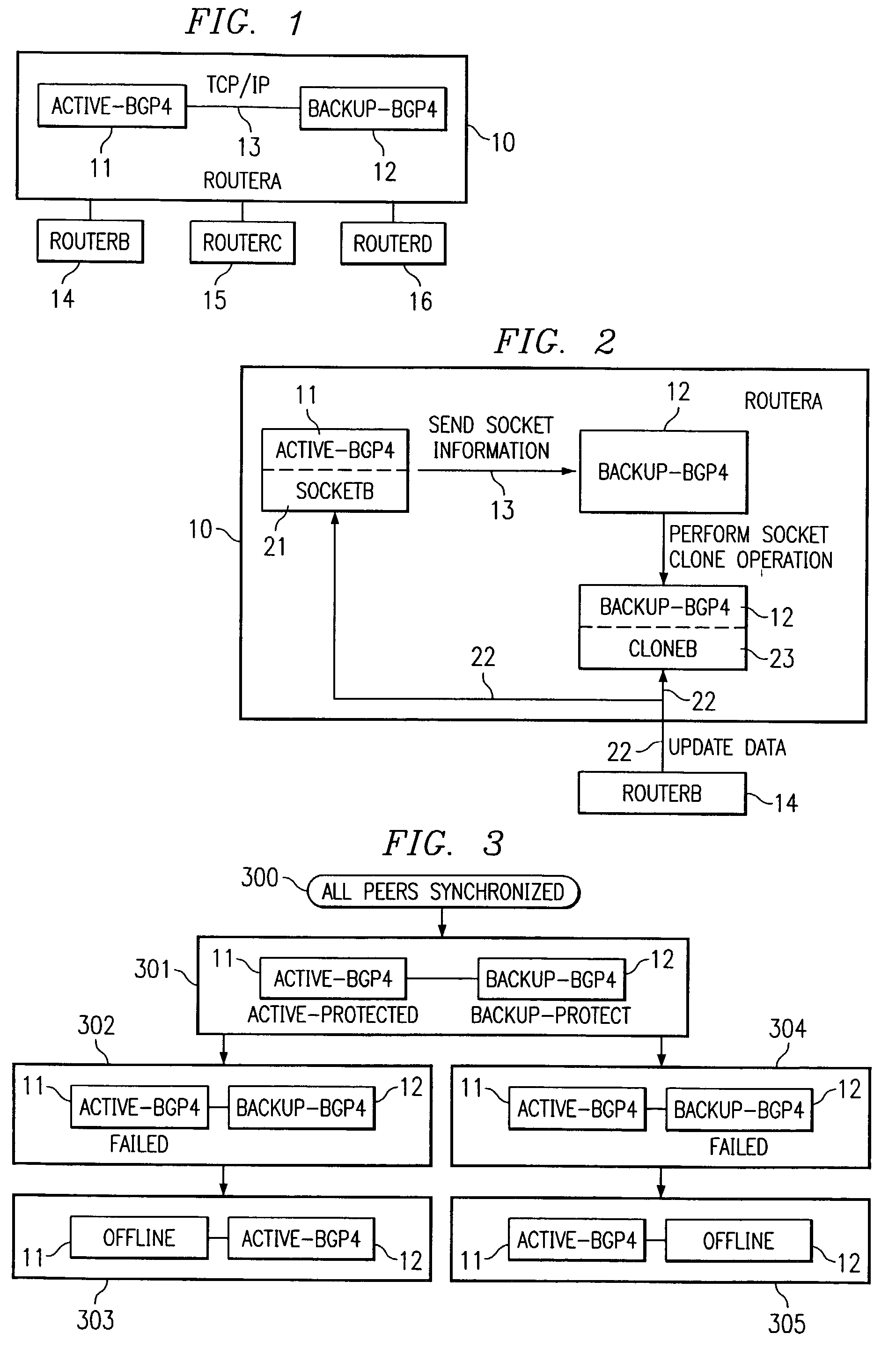
High availability BGP4 is based on redundant hardware as well as redundant software that replicates the RUN state of BGP4. There are two copies, respectively active and backup, of BGP4 running on two separate redundant hardware platforms. All BGP4 internal implementations apply various methods to replicate the running state of BGP4 independently of peer network routers. When this hardware or software fails on one redundant hardware platform, peer routers are unaware of the failure. Internally, based on duplicative states, the local router recovers from the failure and keeps the protocol running. During the recovery period, the local router can bring up a backup again. In the HA architecture, these activities are not detected by peer routers, such that there is no instability to the Internet backbone caused by BGP4 failure.
Owner:AVAGO TECH INT SALES PTE LTD
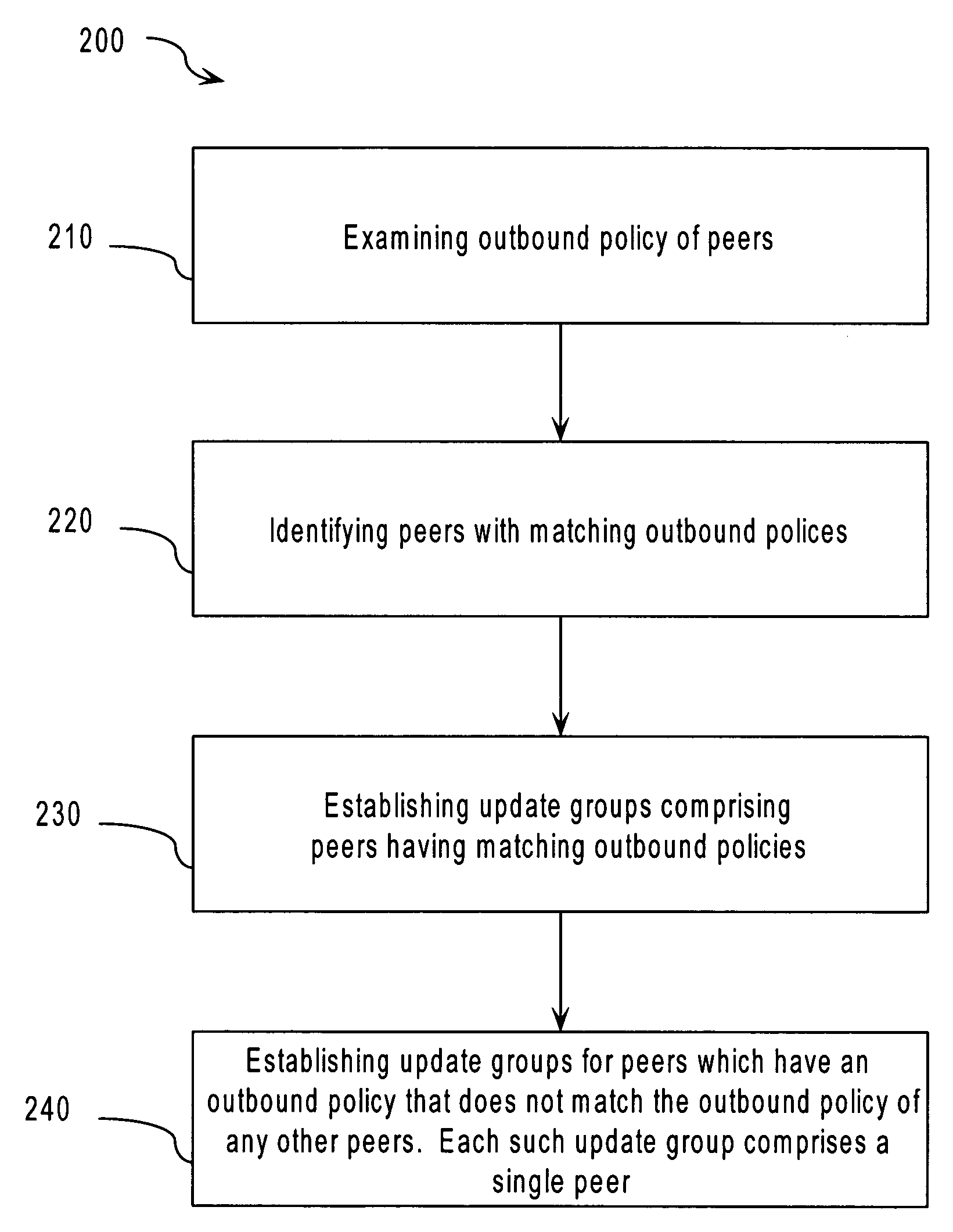
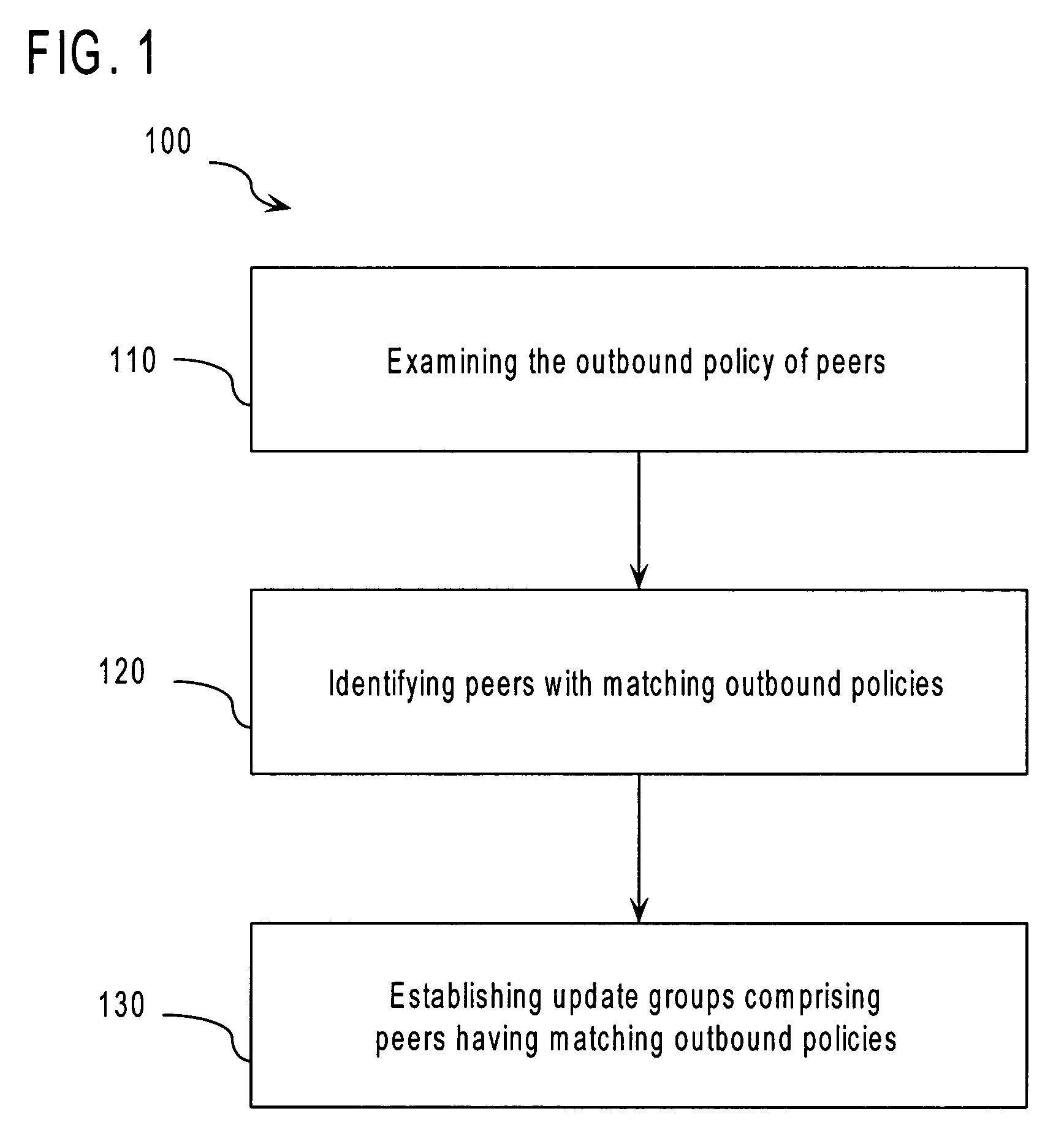
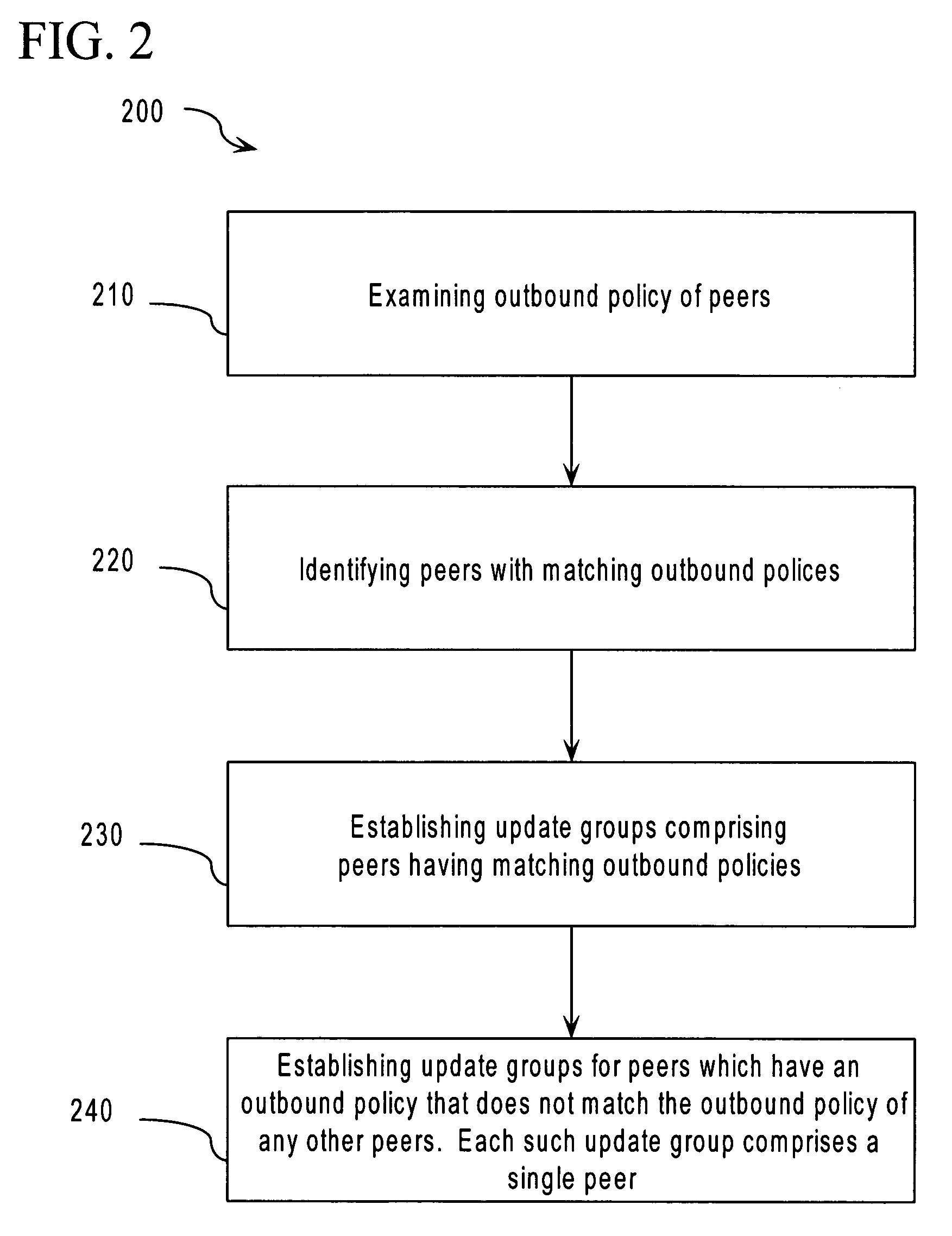
Method and apparatus for border gateway protocol convergence using update groups
ActiveUS7359393B1Data switching by path configurationSpeech recognitionBorder Gateway ProtocolComputer science
Owner:CISCO TECH INC
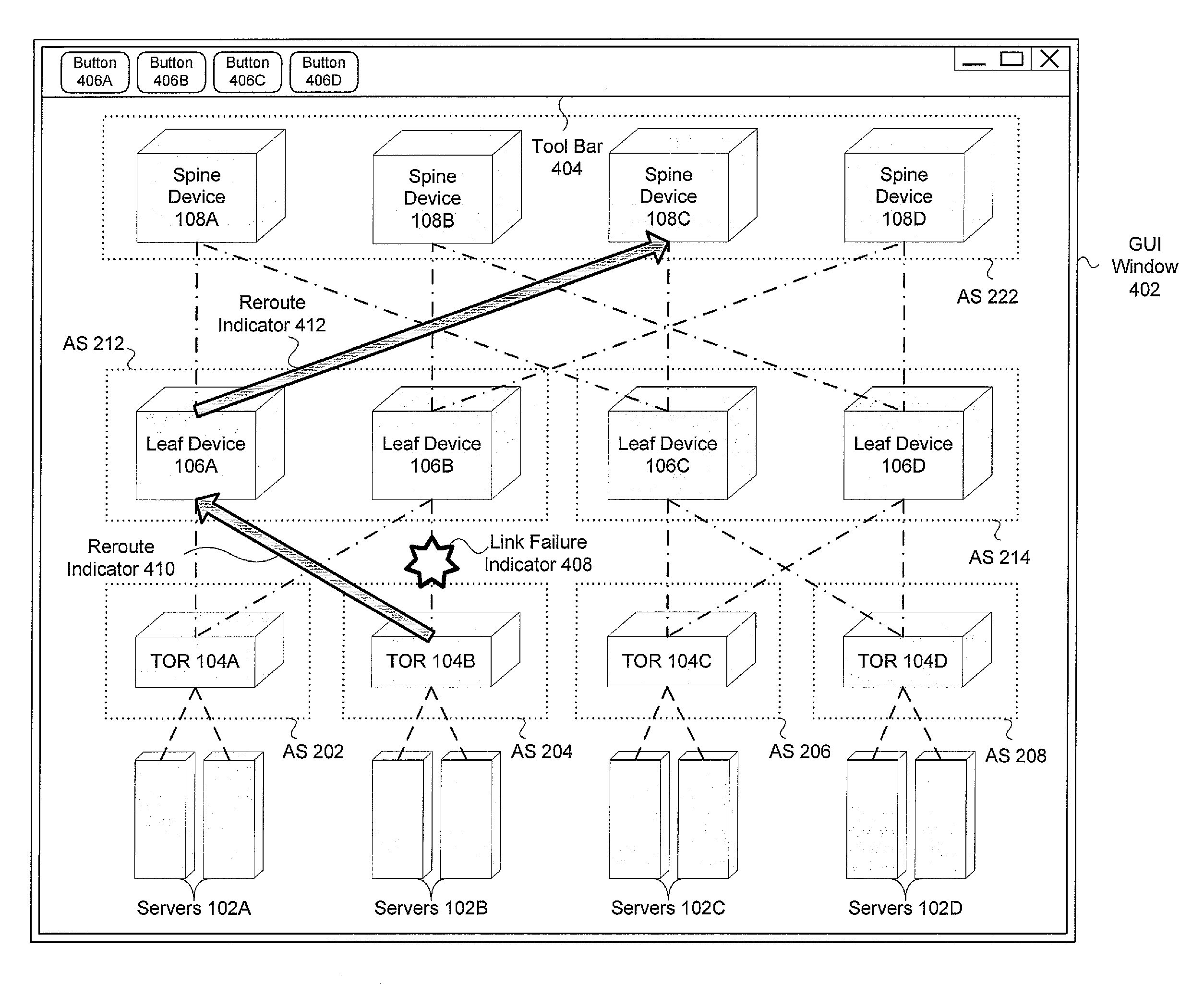
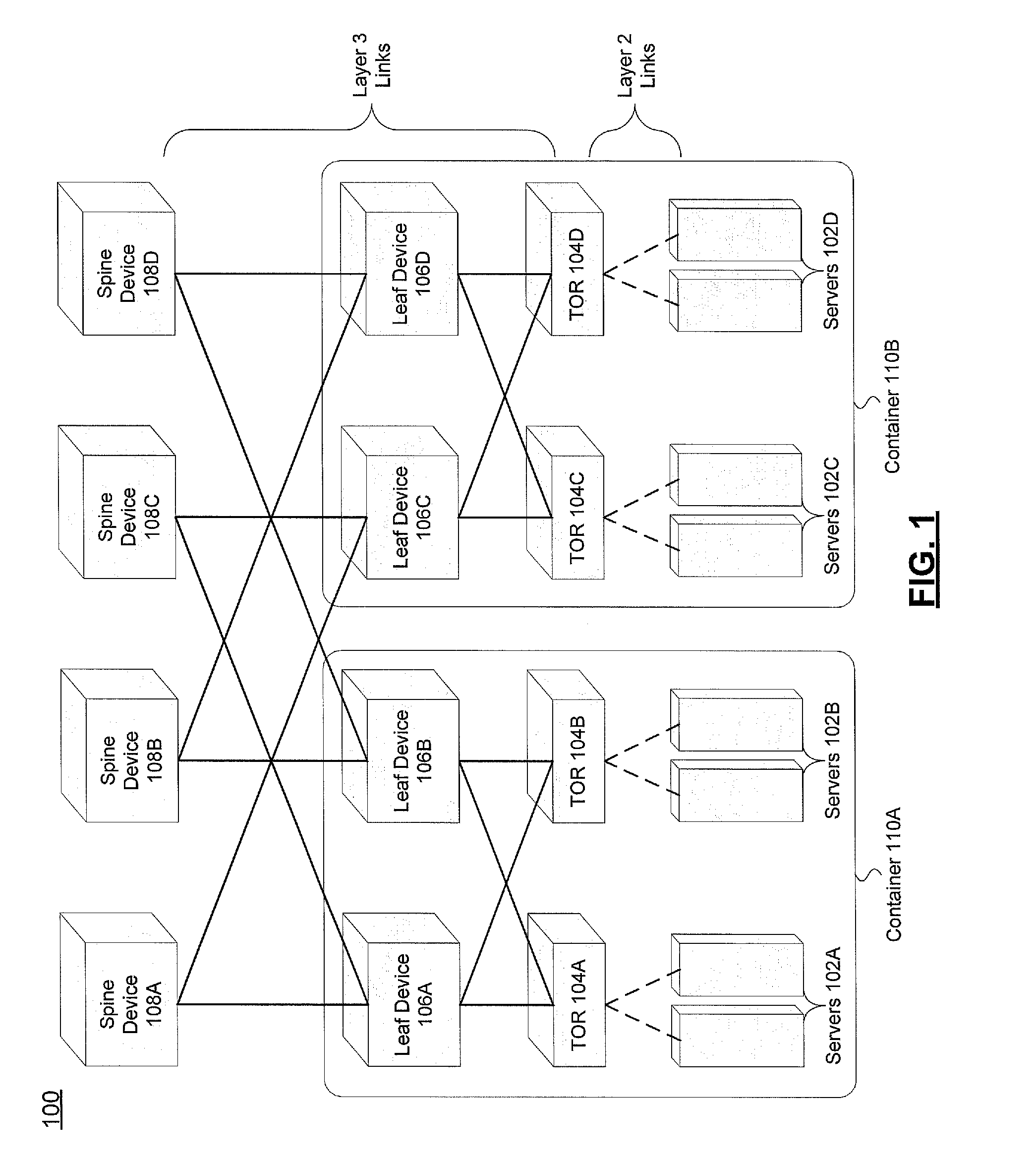
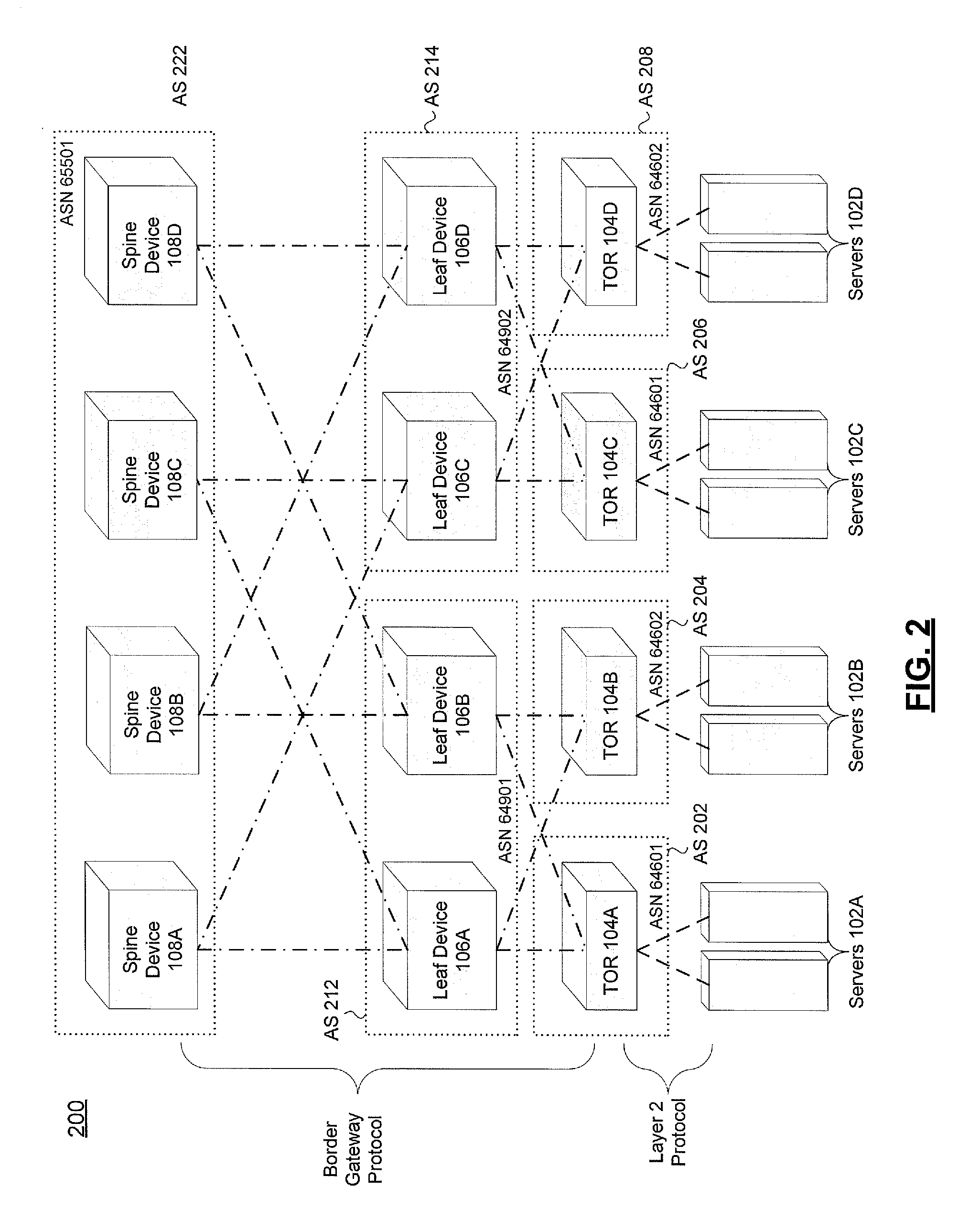
Systems and methods for topology discovery and application in a border gateway protocol based data center
ActiveUS20140181292A1Special service provision for substationDigital computer detailsBorder Gateway ProtocolNetwork orchestration
An information handling system is provided. The information handling system includes a network orchestration service running on a computer processor. The network orchestration service provides a Border Gateway Protocol (BGP) listener module and a topology builder module. The BGP listener module is configured to receive information from a plurality of spine devices configured as an autonomous system and the topology builder module is configured to use the information received by the BGP listener module to create a topology of a data center that includes the plurality of spine devices. Additionally, the network orchestration service is in communication with a memory that is used to store information received by the BGP listener module and the topology of the data center. Applications of the information handling system for better operating the data center are also provided.
Owner:DELL PROD LP
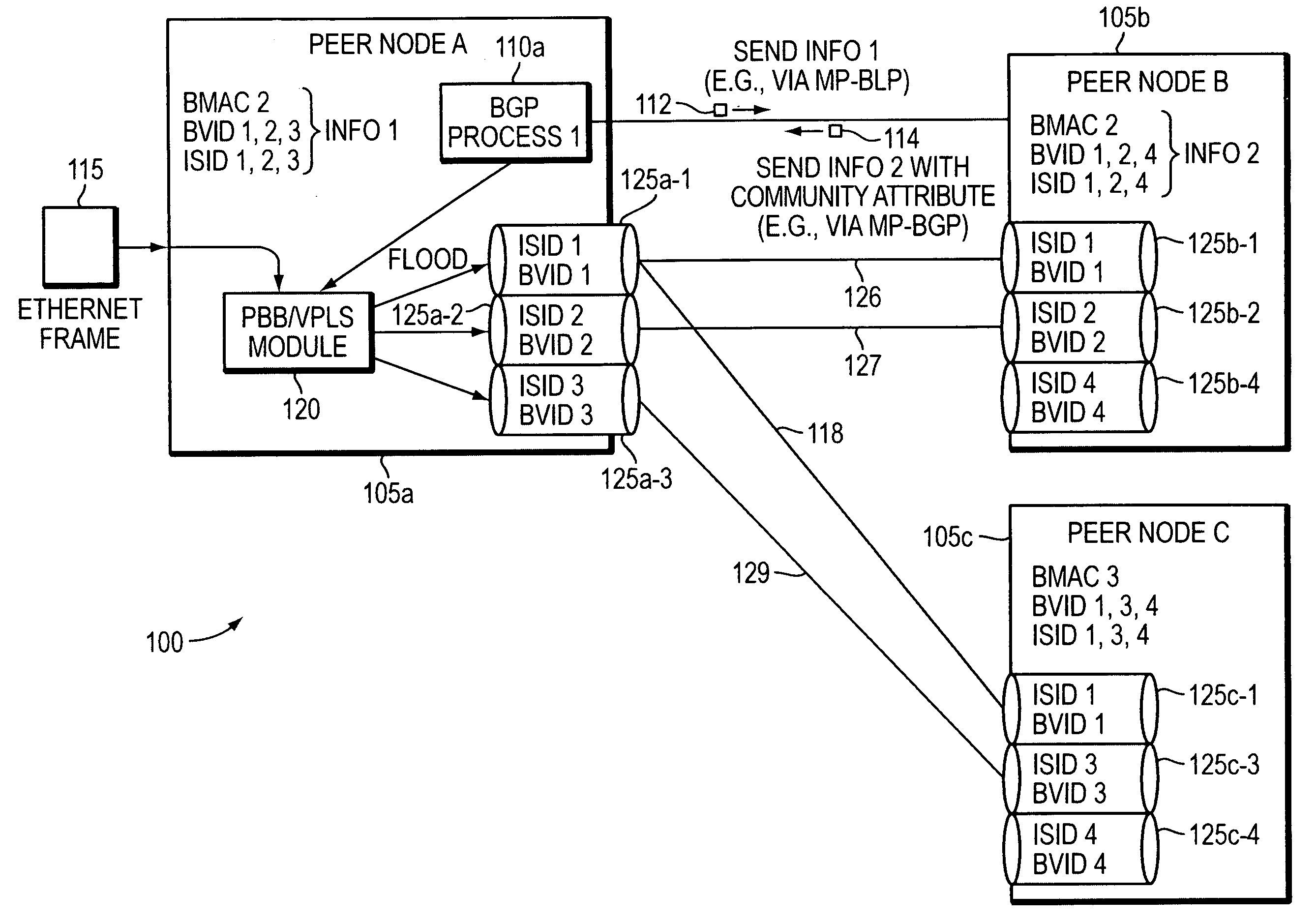
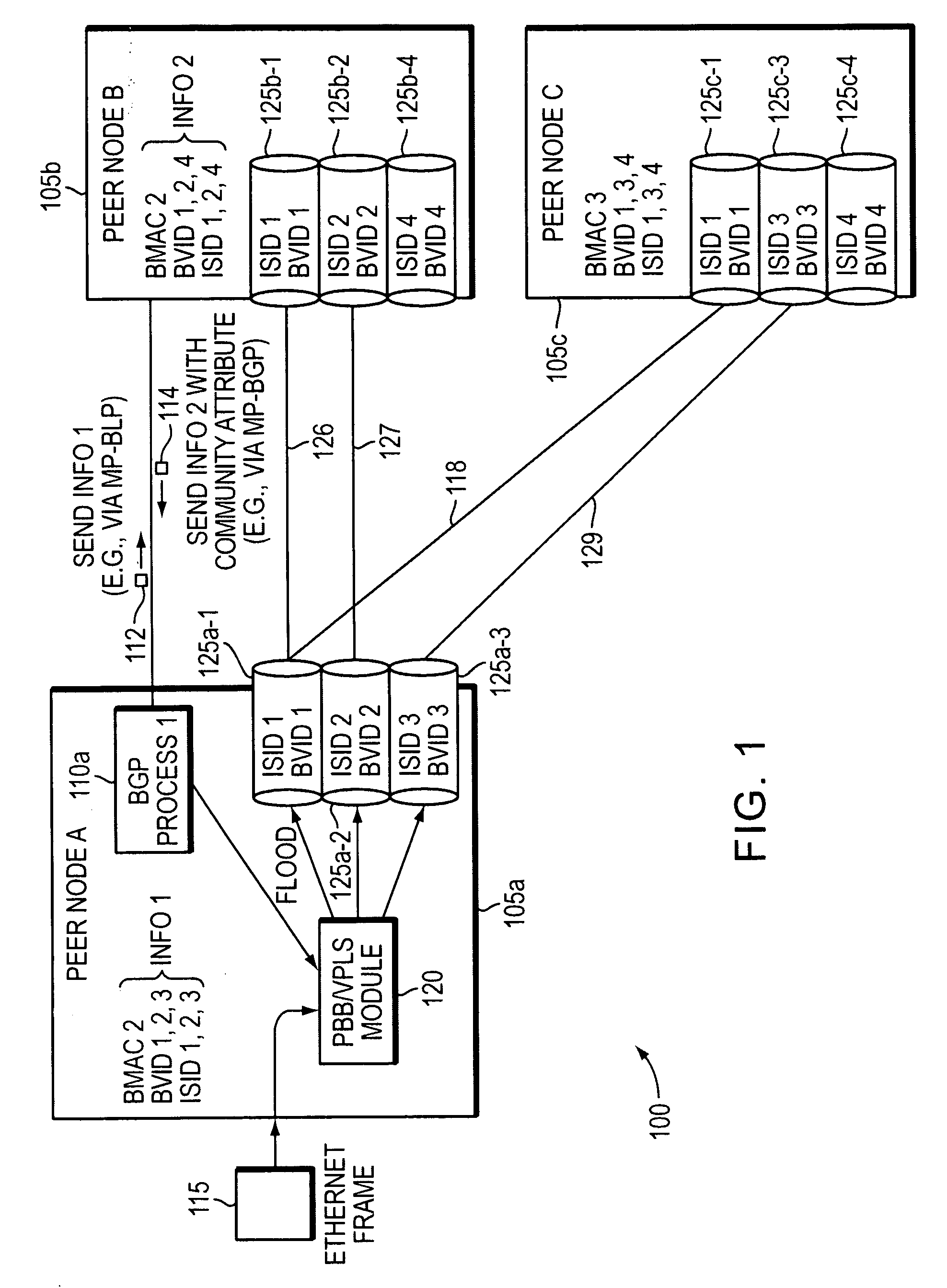
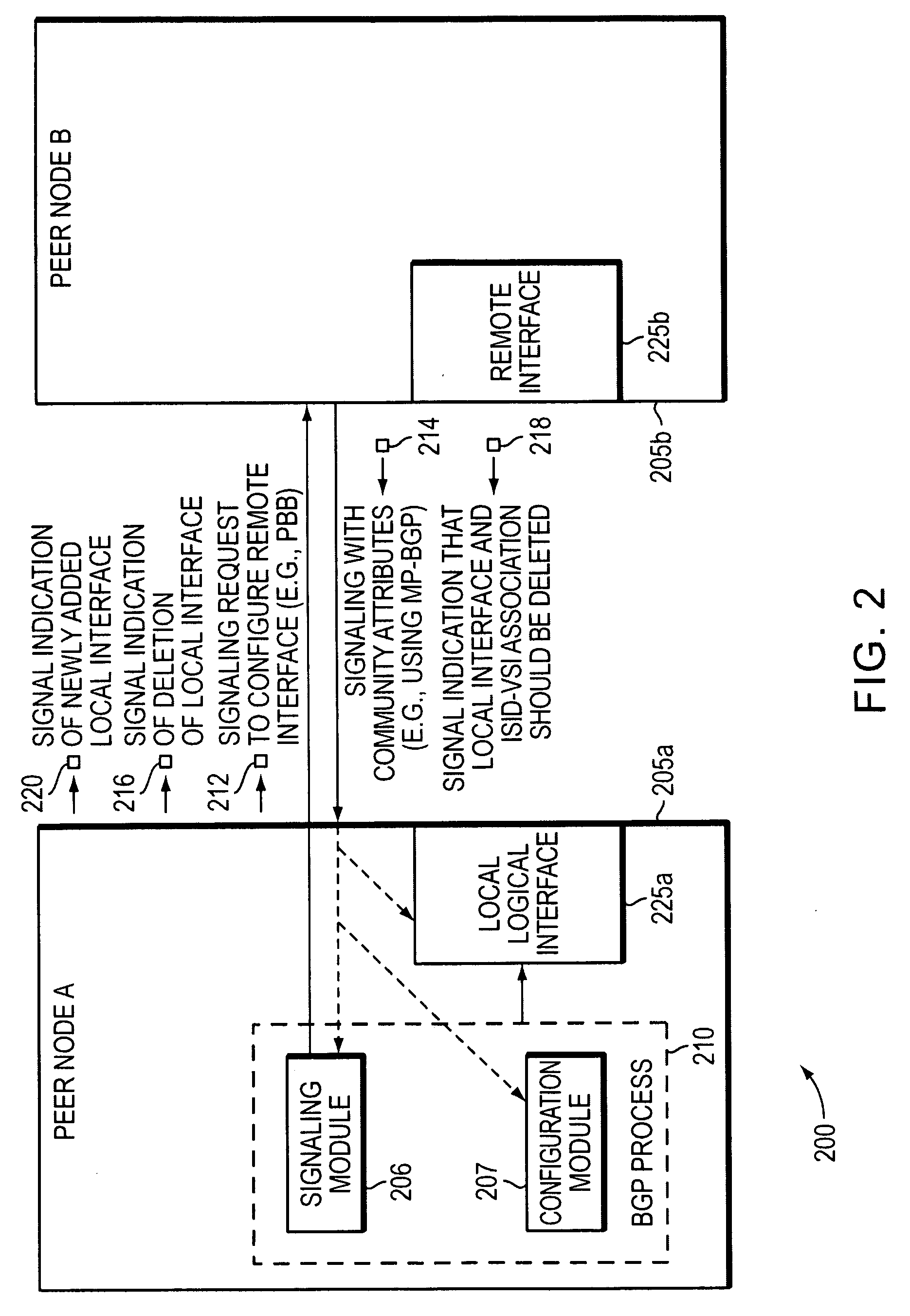
Method and apparatus for provisioning a network element
Methods and apparatuses are disclosed for configuring a Provider Backbone Bridge (PBB) interface within Virtual Private LAN Service using Multi-Protocol Border Gateway Protocol (MP-BGP). Previously, the only ways to enable PBB interfaces for transmission were by learning, which poses security and scalability concerns due to flooding, or by manual configuration, which is impractical for large networks. Embodiments of the present invention enable custom topologies to be built in a controlled manner, which has not previously been possible for PBB over VPLS. By using MP-BGP messages to exchange PBB interface information between nodes, peering relationships are established, and communities may be built with any desired topology. Previously, PBB has only been used as a connectionless bridge; embodiments of the present invention use PBB as a connection between edge nodes. Network designers are provided increased flexibility, and security and congestion are improved, benefiting end users.
Owner:TELLABS OPERATIONS
Routing traffic in a communications network
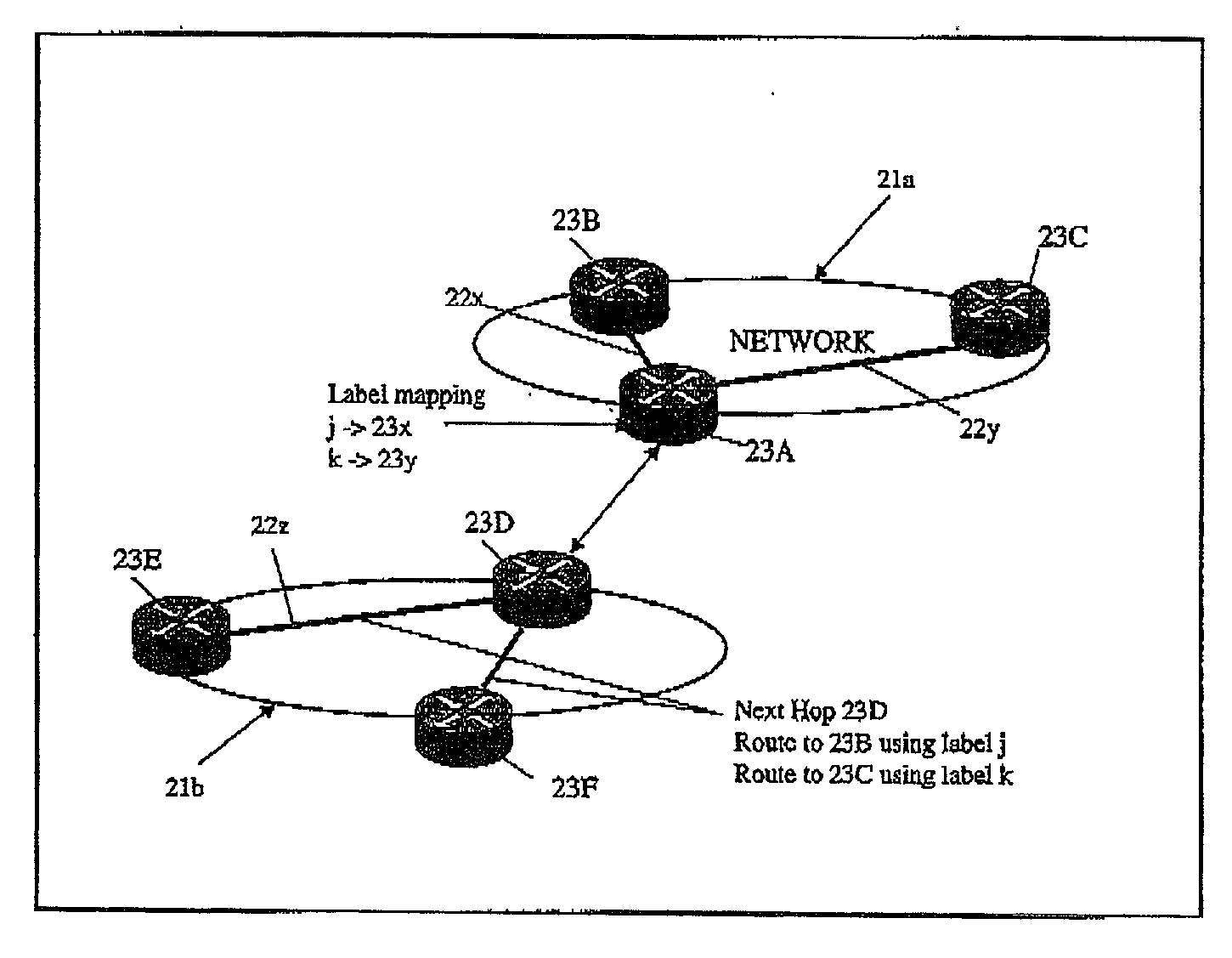
InactiveUS20030118036A1Data switching by path configurationPacket communicationBorder Gateway Protocol
In a packet communications network system, a border gateway protocol is employed to route an information packet from a source in a first autonomous system via a first label switched path to a destination in a second autonomous system via first and second border routers at an interface between the first and second autonomous systems. A label stack attached to the packet identifies both a forwarding interface for the packet and a forwarding behaviour at that interface. This provides a mapping from the first label switched path on to a second label switched path to the destination in the second autonomous system. Preferably, the destination router in the second autonomous system returns to the source router in the first autonomous system a two-label stack identifying first and second paths across the first and second autonomous systems respectively.
Owner:RPX CLEARINGHOUSE
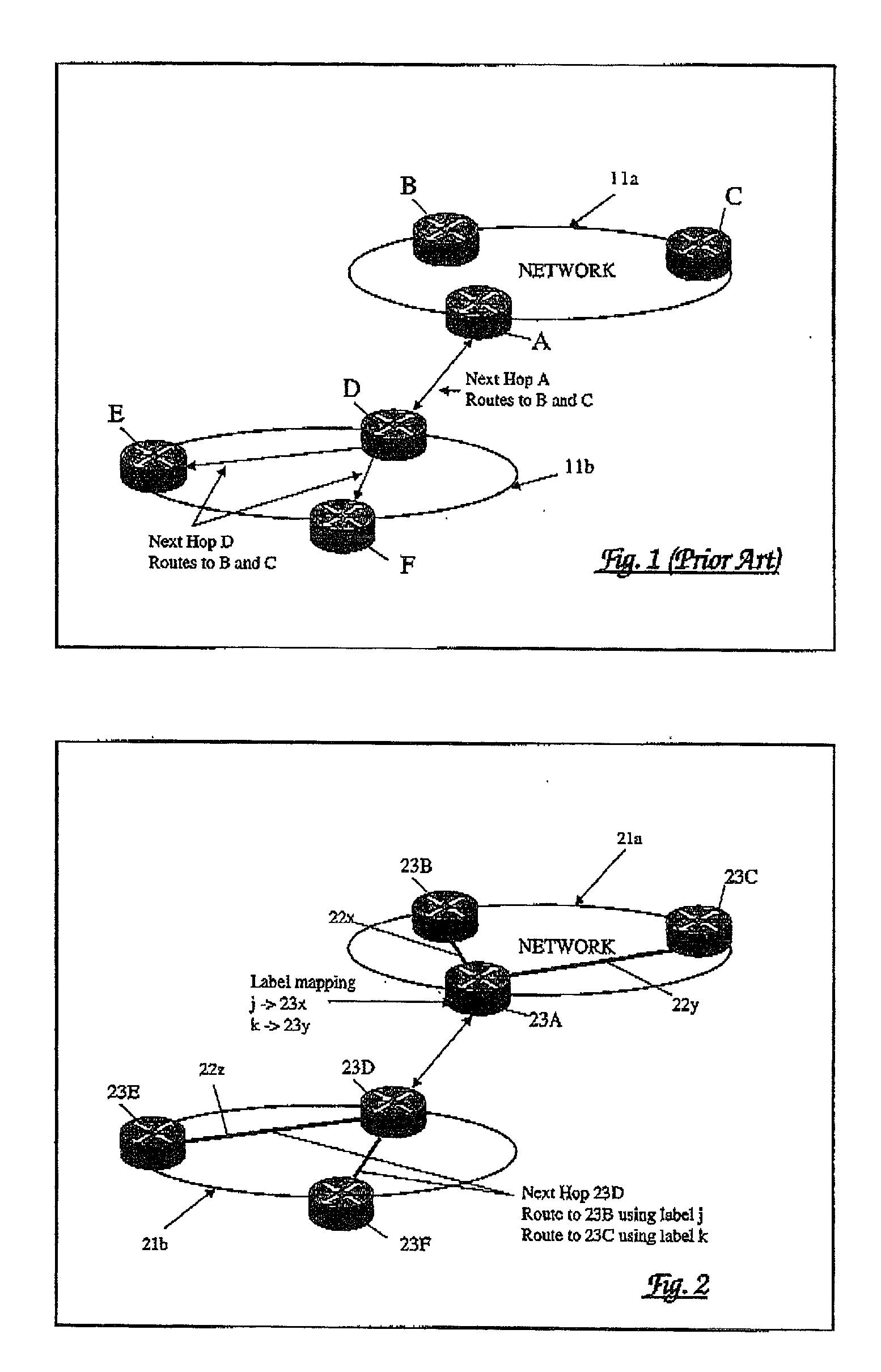
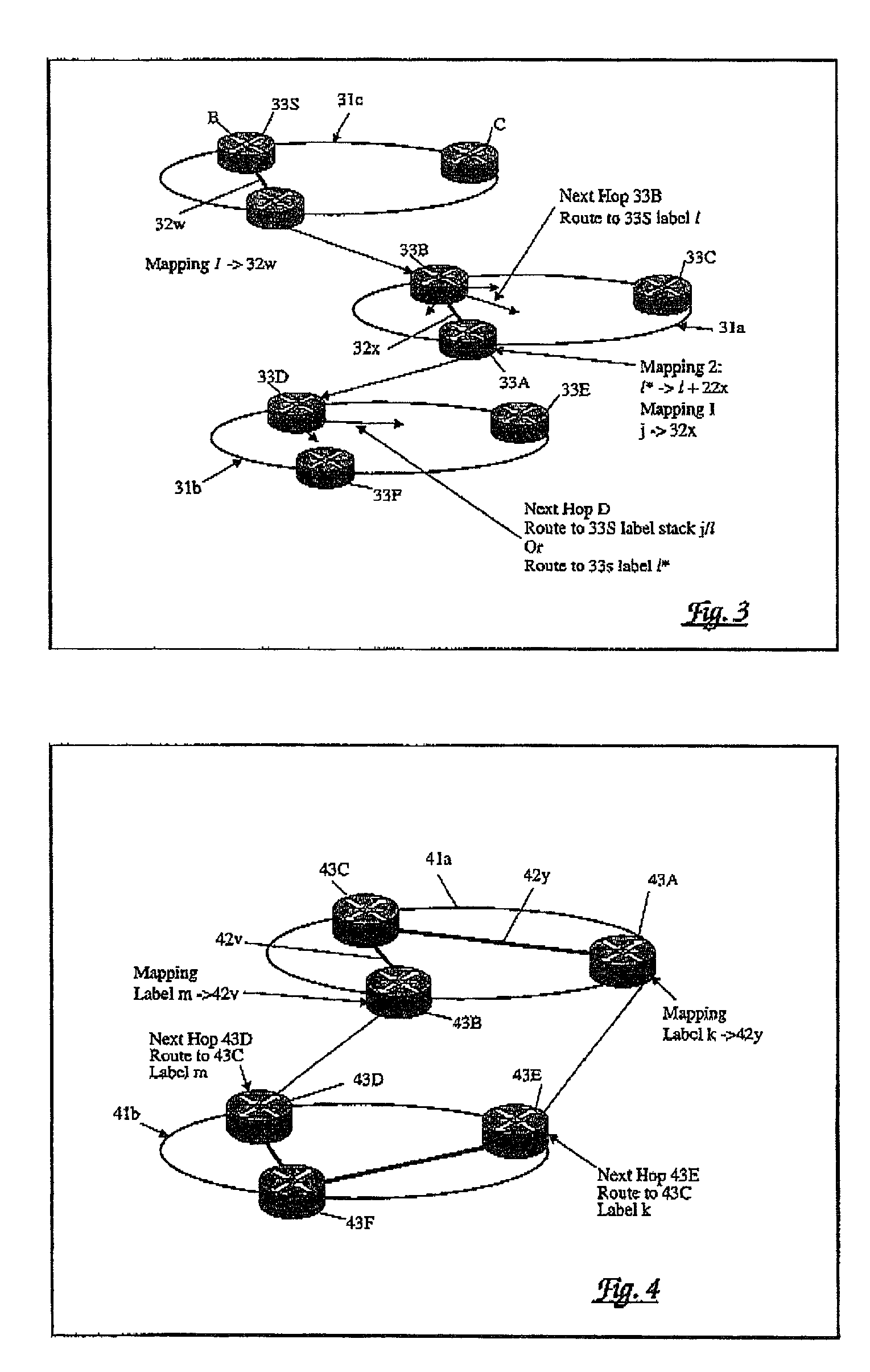
Routing for a communications network
InactiveUS20030012145A1Improves important aspectImprove visibilityError preventionFrequency-division multiplex detailsVisibilityBorder Gateway Protocol
For routing in a communications network, alternate paths to a destination are aggregated into a single composite route, prior to onward propagation of the route. Ideally, aggregation is performed at each point of route convergence in the network. Consequently, failure in only one of the paths does not then require that the composite route be withdrawn, and thus visibility of and reaction to the fault is restricted to parts of the network directly affected. The method is particularly applicable to border gateway protocols employed between Autonomous Systems as in, for example, the Internet.
Owner:RPX CLEARINGHOUSE
Discovery of border gateway protocol (BGP) multi-protocol label switching (MPLS) virtual private networks (VPNs)
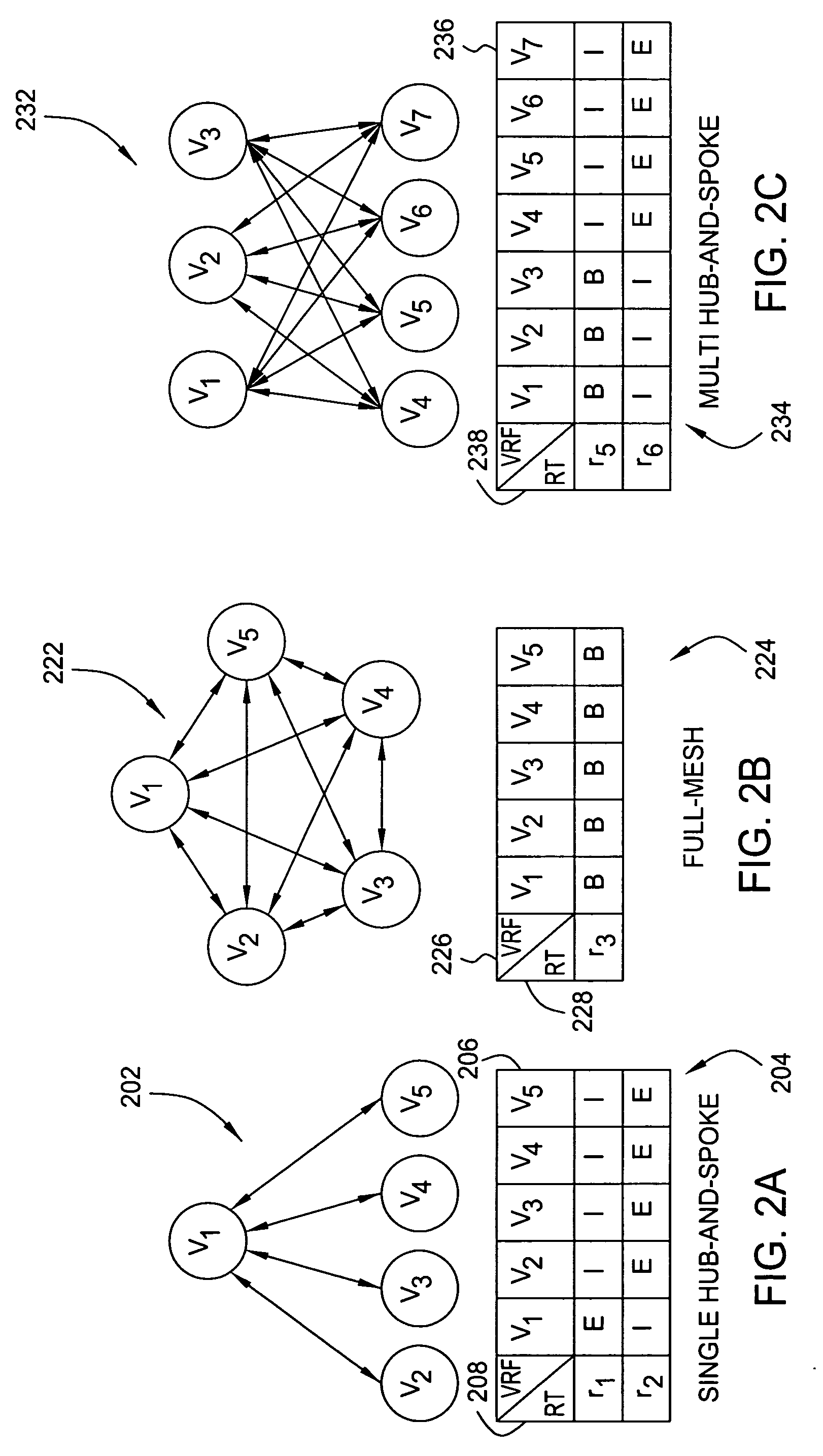
A method and apparatus for identifying virtual private networks (VPNs) in a network of a service provider. The method and apparatus includes generating a VPN routing forwarding—route target (VRF-RT) table for the network. From the VRF-RT table, at least one of a VRF-VRF table and a VRF connectivity graph is generated. From the VRF-RT table, a set of atomic full-mesh components are identified, and from the at least one of a VRF-VRF table and a VRF connectivity graph, at least one set of other types of VPN components are identified, such as atomic single hub-and-spoke components, molecular multi-hub-and-spoke components, composite full-mesh components, composite single hub-and-spoke components, and / or composite multi hub-and-spoke components.
Owner:ALCATEL-LUCENT USA INC +1
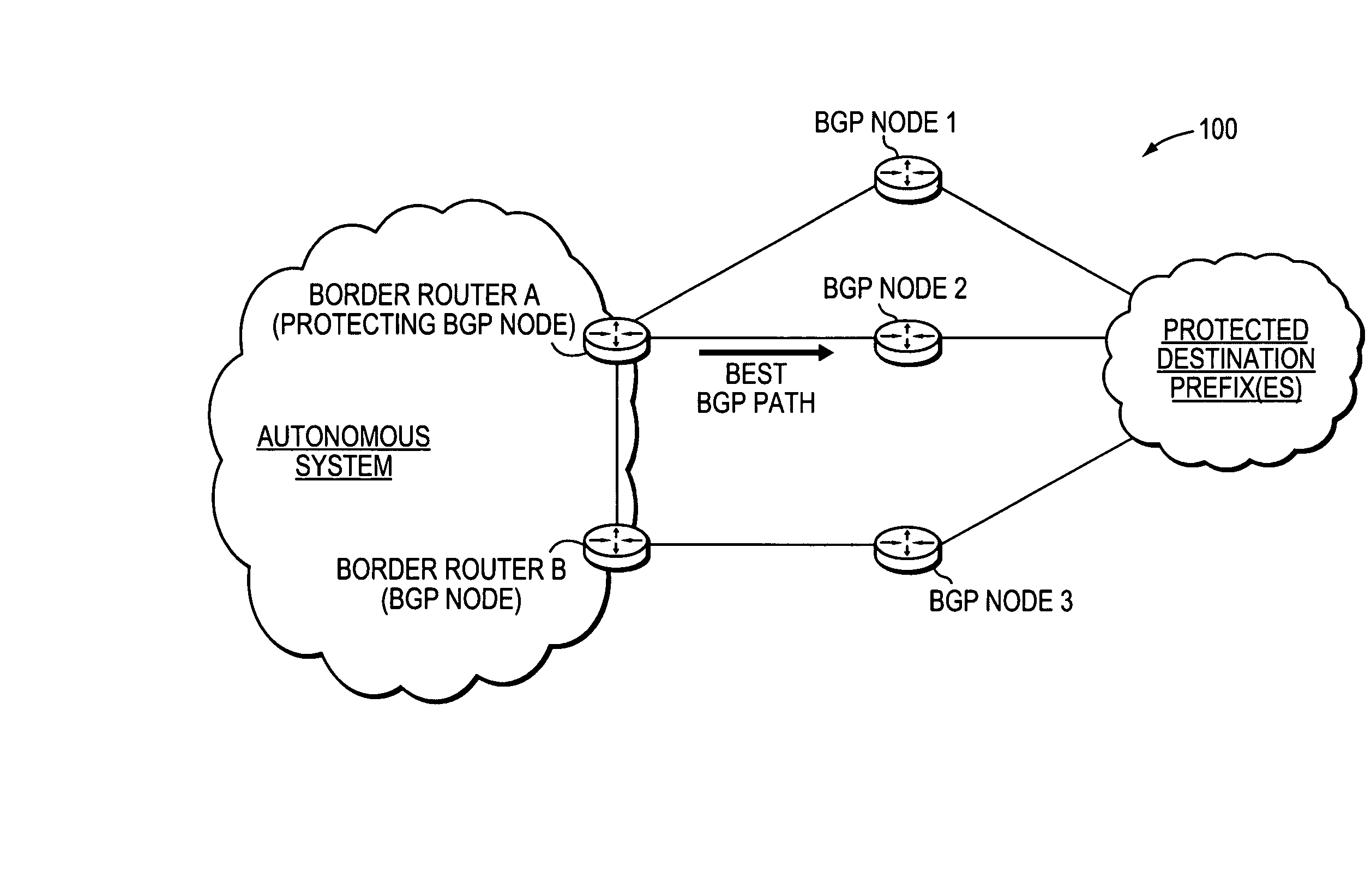
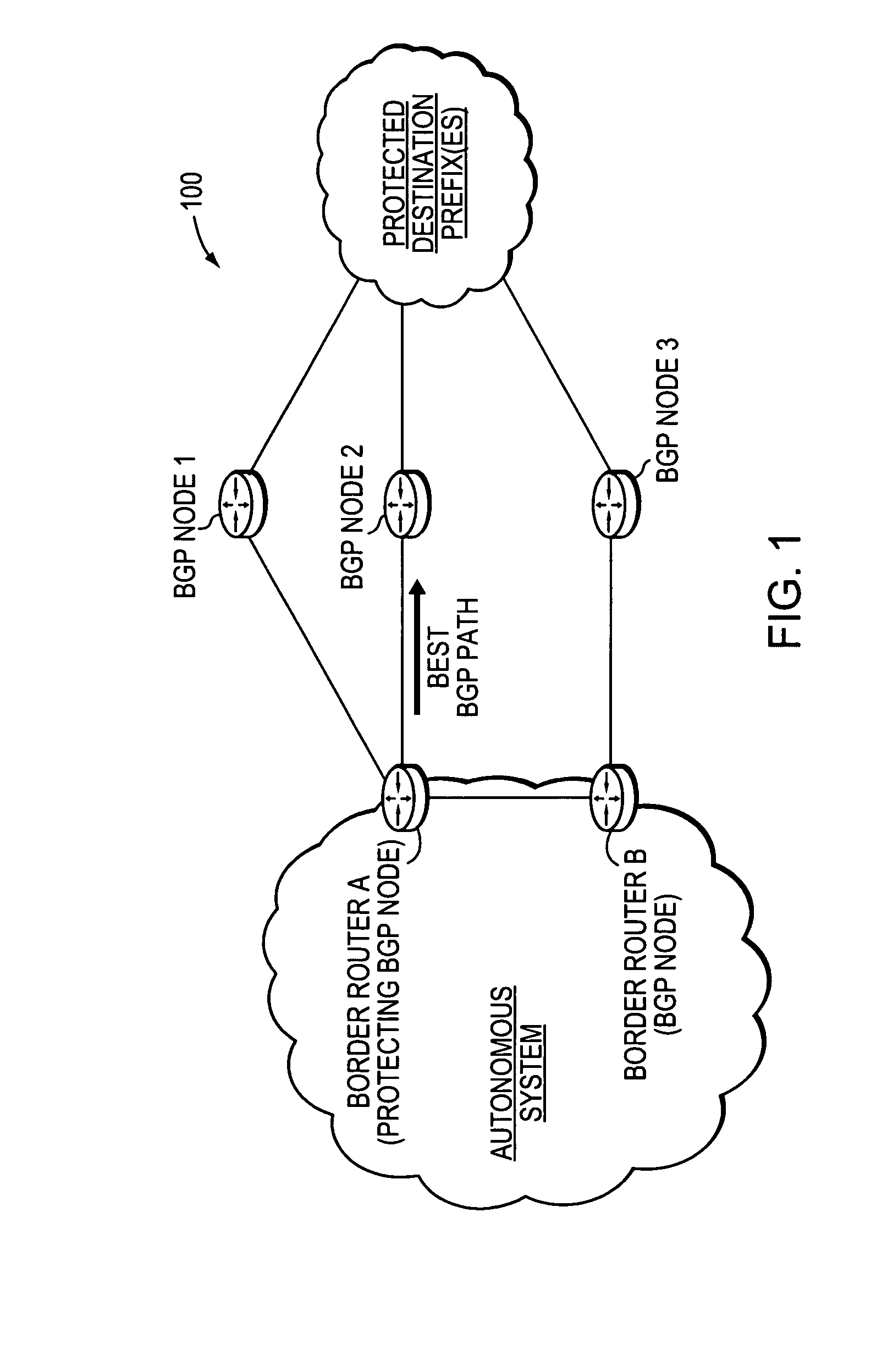
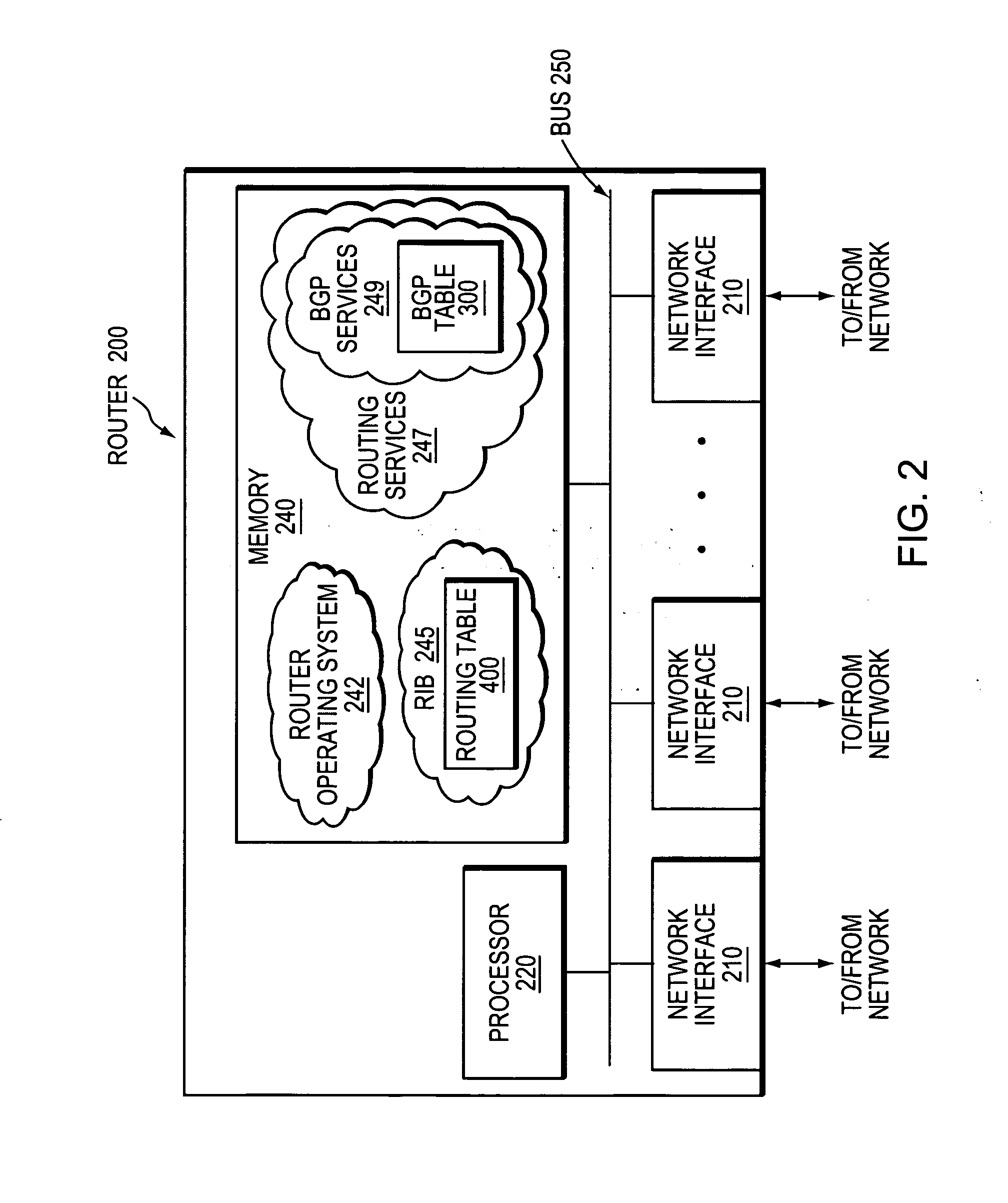
Backup BGP paths for non-multipath BGP fast convergence
ActiveUS20070214280A1Fast convergenceReduce needDigital computer detailsTransmissionTraffic capacityBorder Gateway Protocol
A technique institutes backup Border Gateway Protocol (BGP) paths for non-multipath BGP Fast Convergence in a computer network. According to the novel technique, a protecting node, e.g., a border router, calculates a best BGP path to a destination prefix, and also calculates one or more backup BGP paths (i.e., non-multipath paths) to the destination prefix. The best path is selected as a utilized path for the destination prefix, e.g., the path over which to send traffic destined for the prefix from the border router. Upon determining that the best BGP path has failed, one of the backup BGP paths is selected as the utilized path for the destination prefix.
Owner:CISCO TECH INC
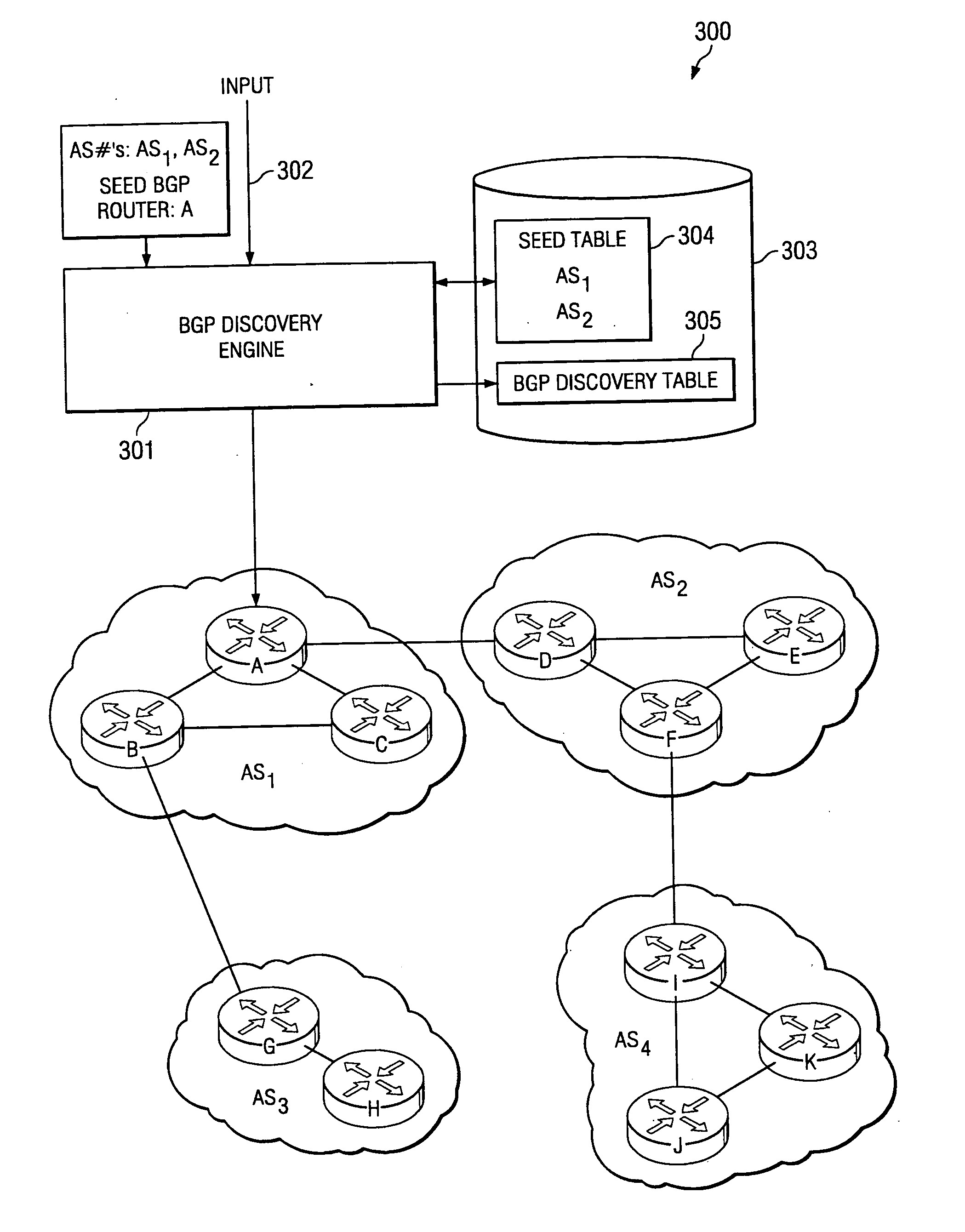
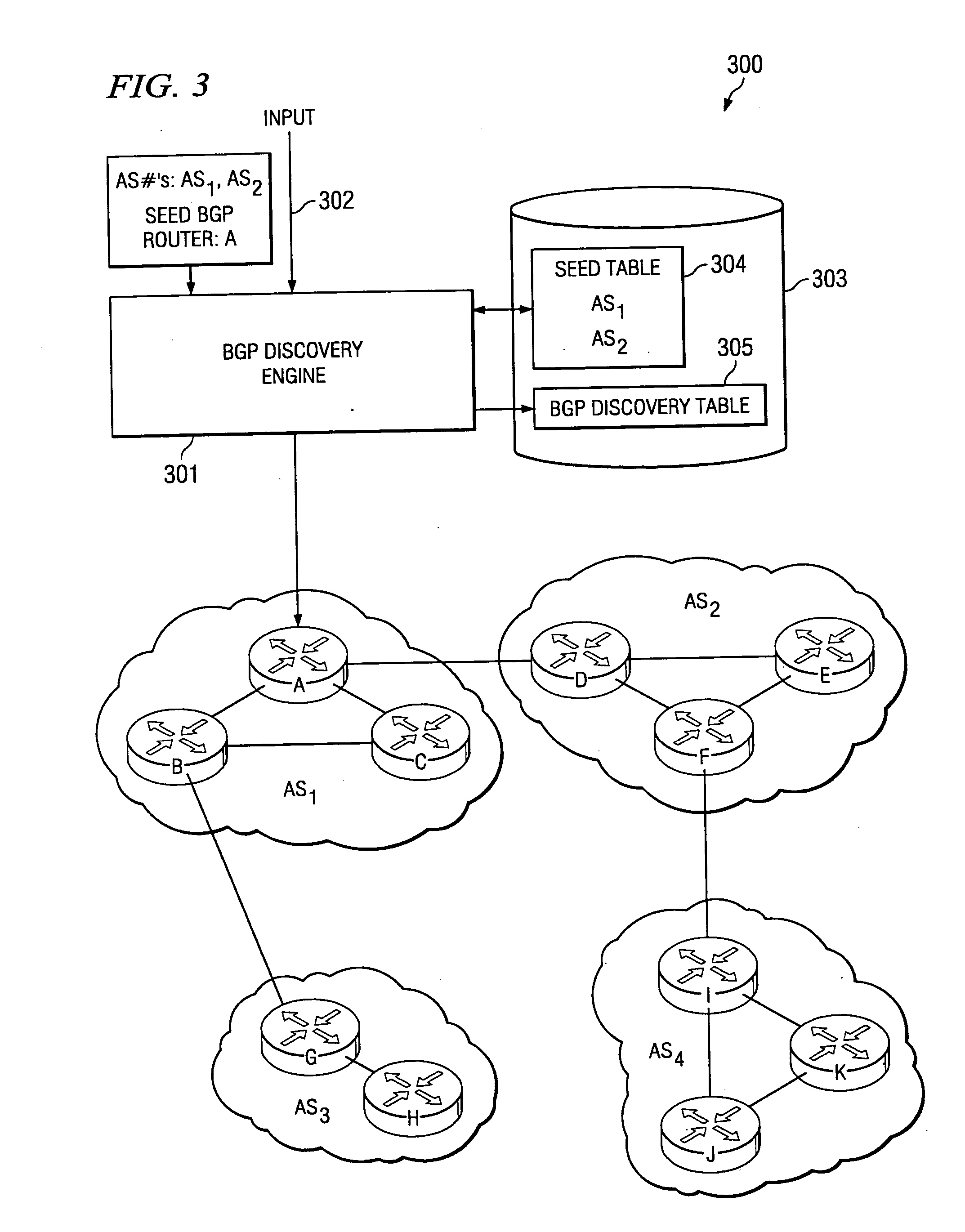
System and method for discovery of BGP router topology
InactiveUS20050050225A1Accurately and efficiently compiledMinimal effortDigital computer detailsData switching networksBorder Gateway ProtocolA domain
A system and method for discovering a routing topology within a domain of interest are disclosed. In accordance with certain embodiments, a Border Gateway Protocol (“BGP”) discovery engine is provided that enables auto-discovery of BGP routers in a specified domain of interest. For instance, such a BGP discovery engine may receive, as input, an identification of a domain of interest and a “seed” BGP router within such domain of interest, and may recursively query the BGP routers identified within the domain of interest for information to compile the topology of such BGP routers in such domain of interest.
Owner:AGILENT TECH INC
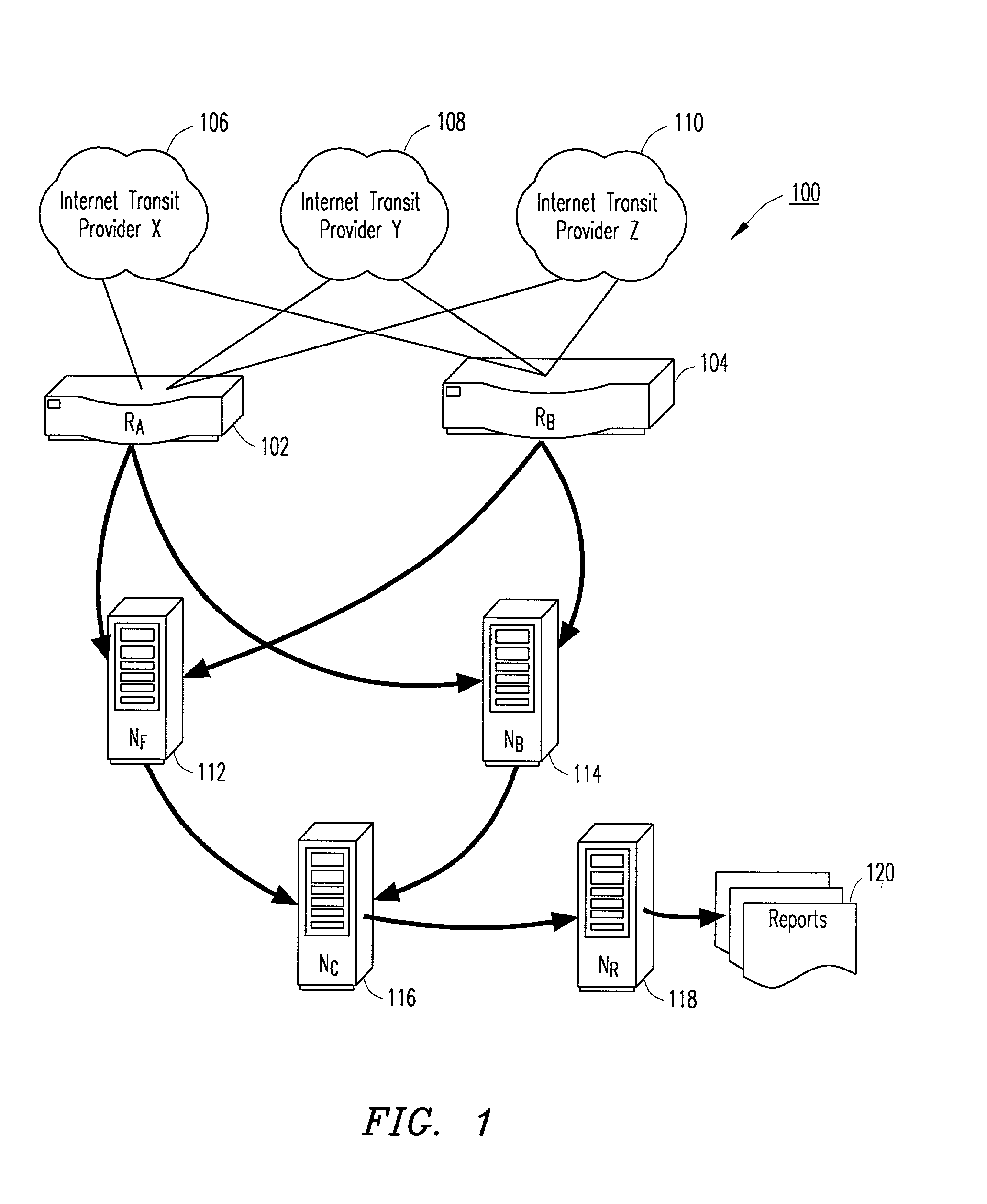
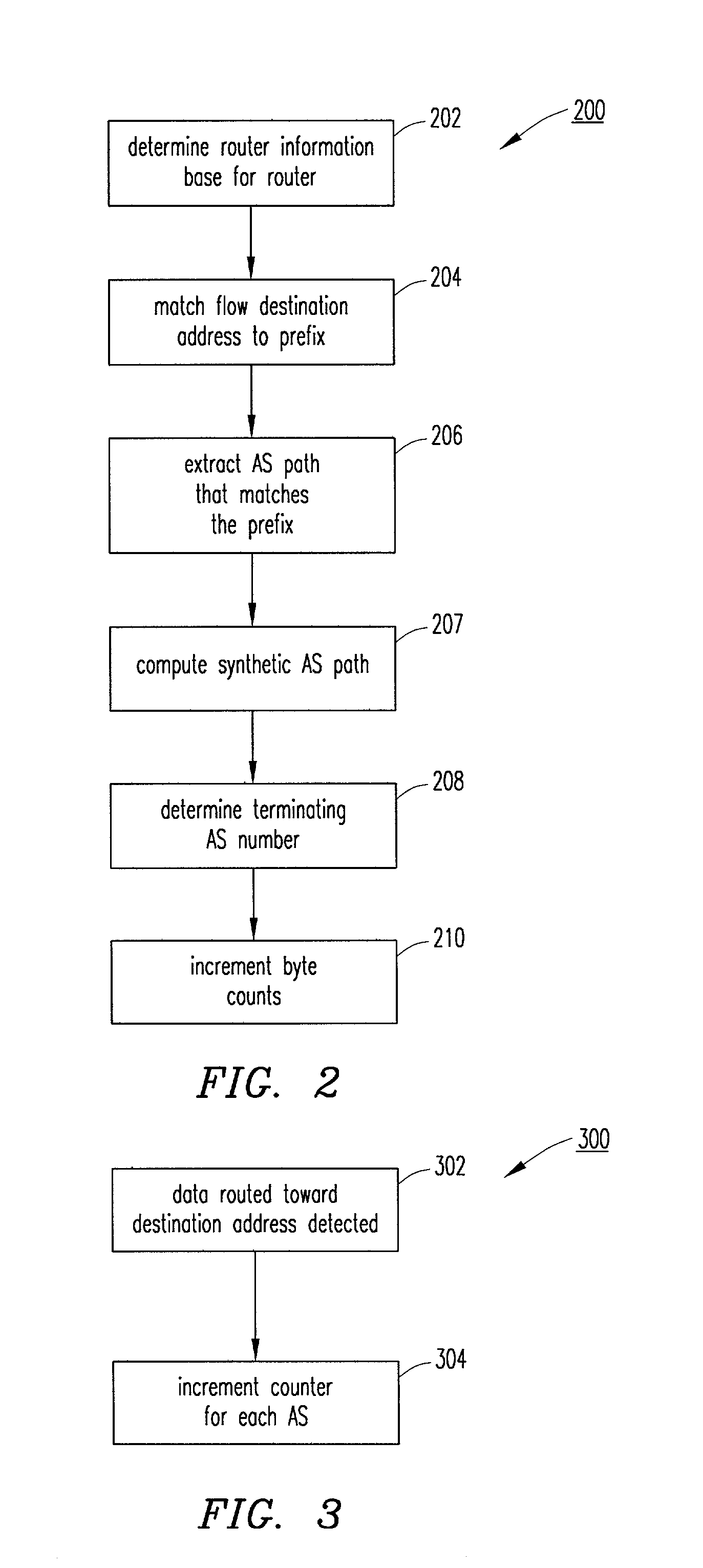
Method and system for determining autonomous system transit volumes
InactiveUS20030120769A1Digital computer detailsData switching networksBorder Gateway ProtocolData stream
Border gateway protocol (BGP) tables and data flow statistics sorted by destination address are collected from a plurality of routers. The BGP tables and the data flow statistics are aggregated and correlated by a correlation node. The correlation node produces autonomous system (AS) transit volumes and AS terminating volumes by AS number. The AS transit volumes and the AS terminating volumes can be used to evaluate the suitability of transit providers and potential peers.
Owner:AGILENT TECH INC
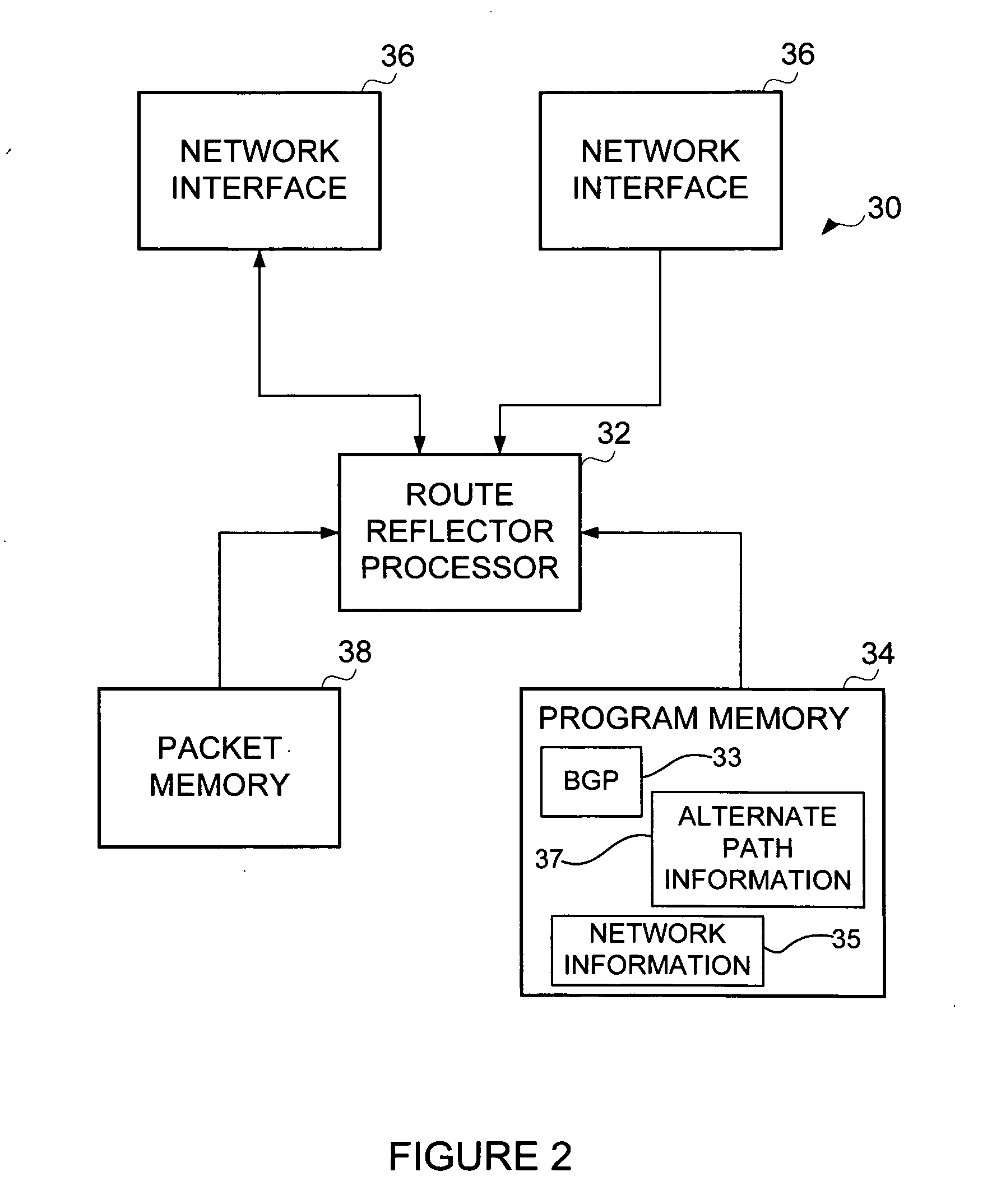
Advertising alternate paths at border gateway protocol route reflectors
ActiveUS20100220736A1Data switching by path configurationBorder Gateway ProtocolDistributed computing
In one embodiment, a method includes receiving routing information at an alternate route reflector in a network, identifying at the alternate route reflector, an alternate path different from a primary path selected and advertised at a primary route reflector in the network, and advertising at the alternate route reflector, the alternate path. The primary and alternate paths define paths for a destination and the alternate path is the only path advertised by the alternate route reflector for the destination.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com