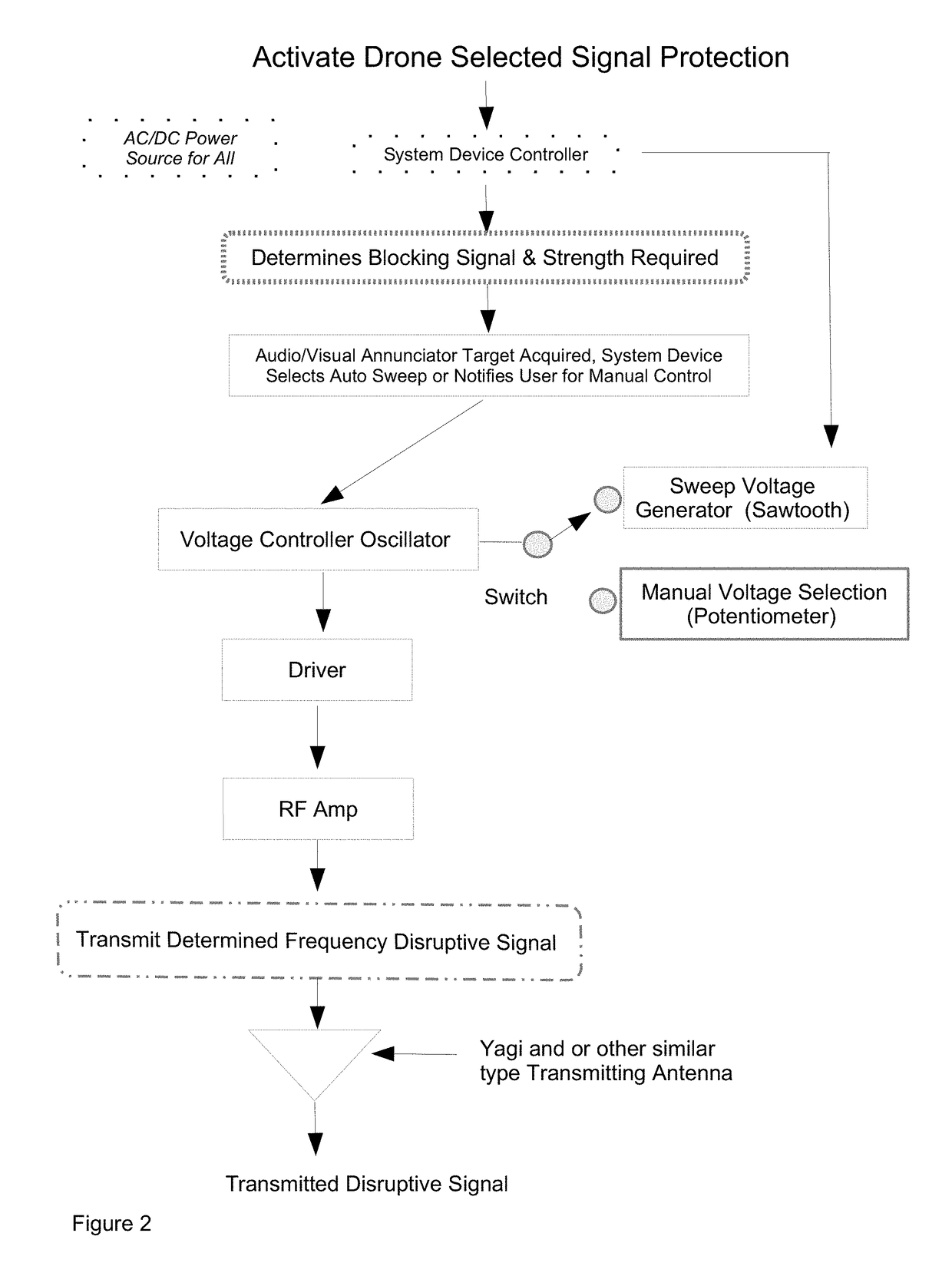
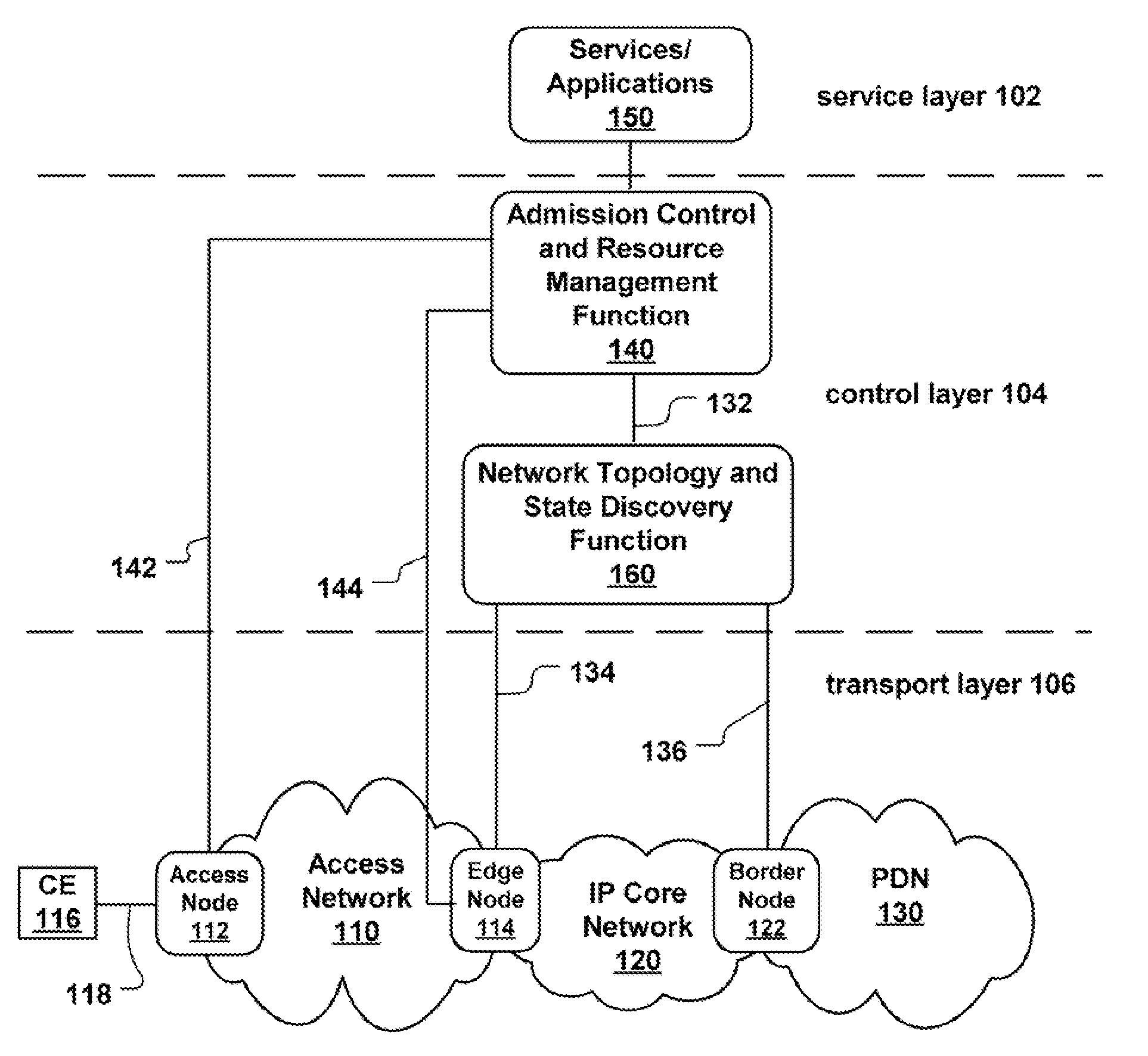
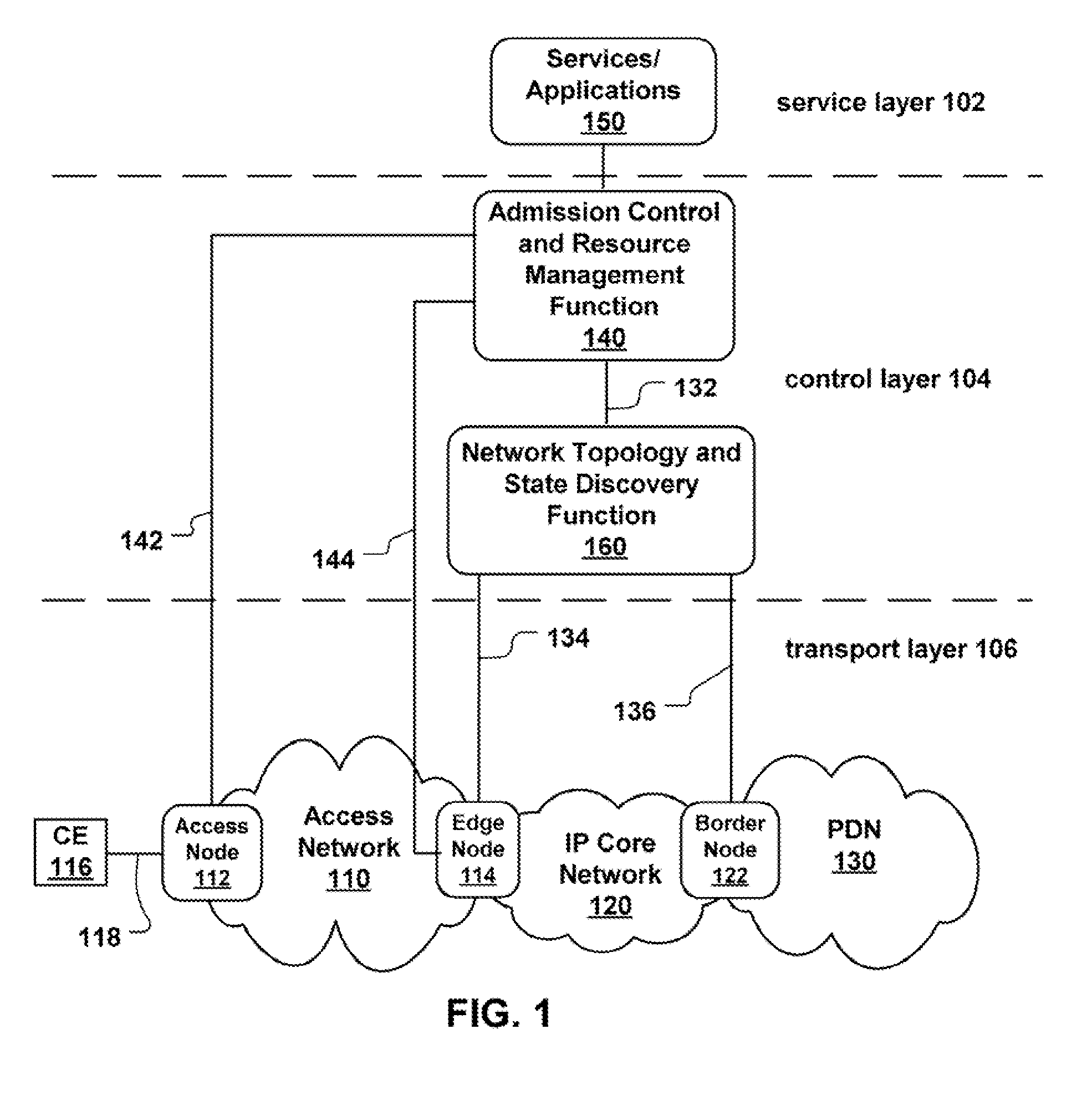
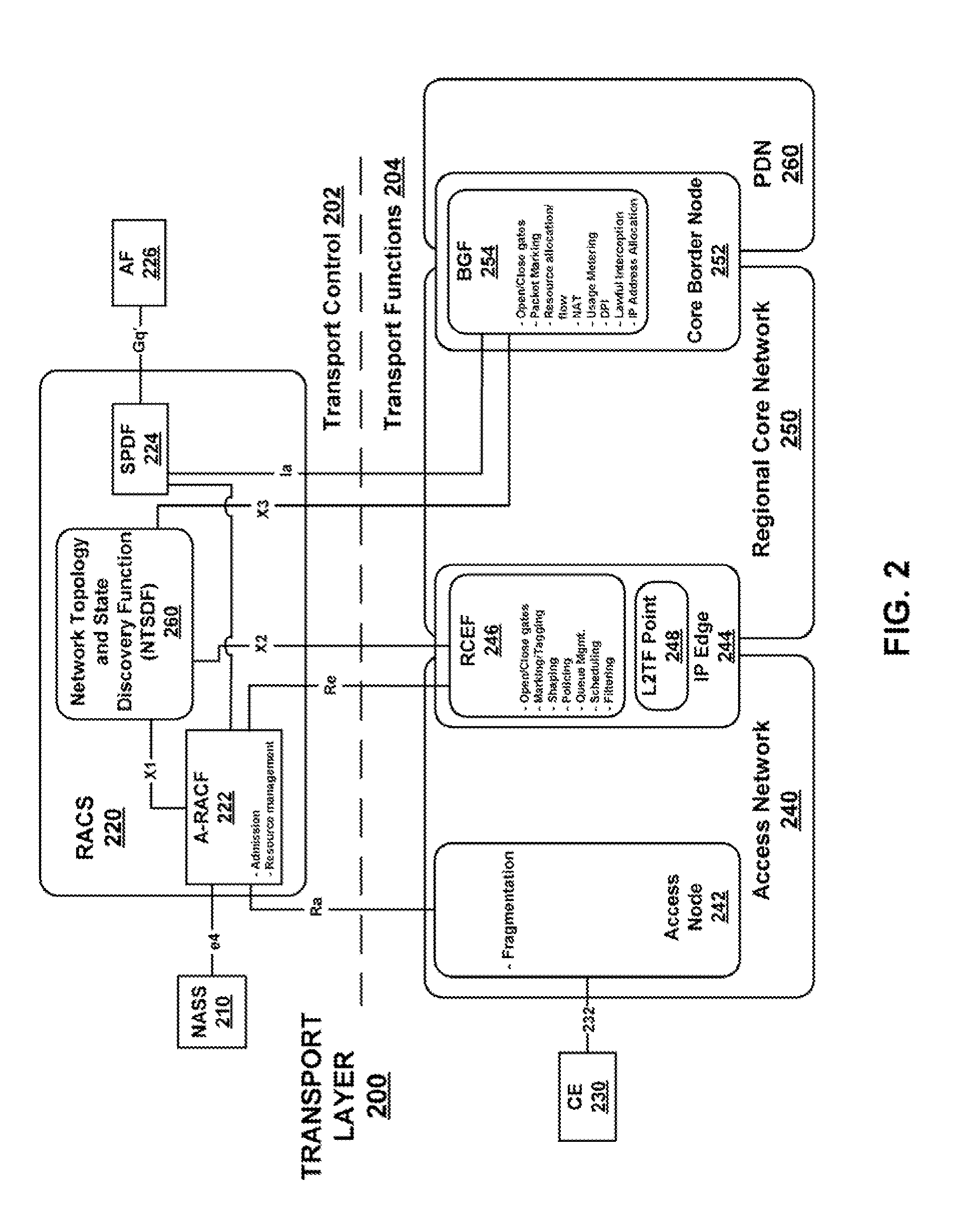
Patents
Literature
9668 results about "Network topology" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
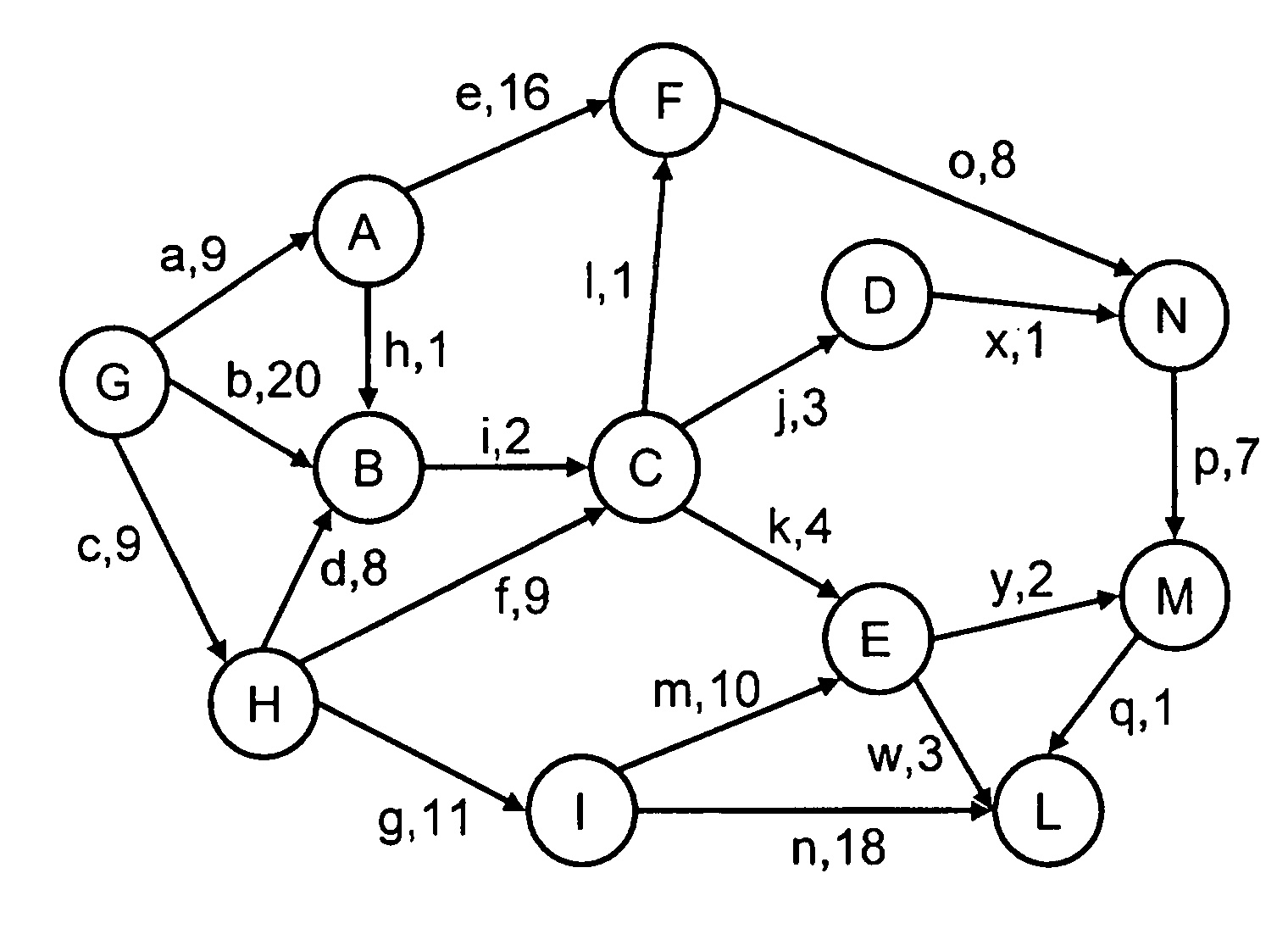
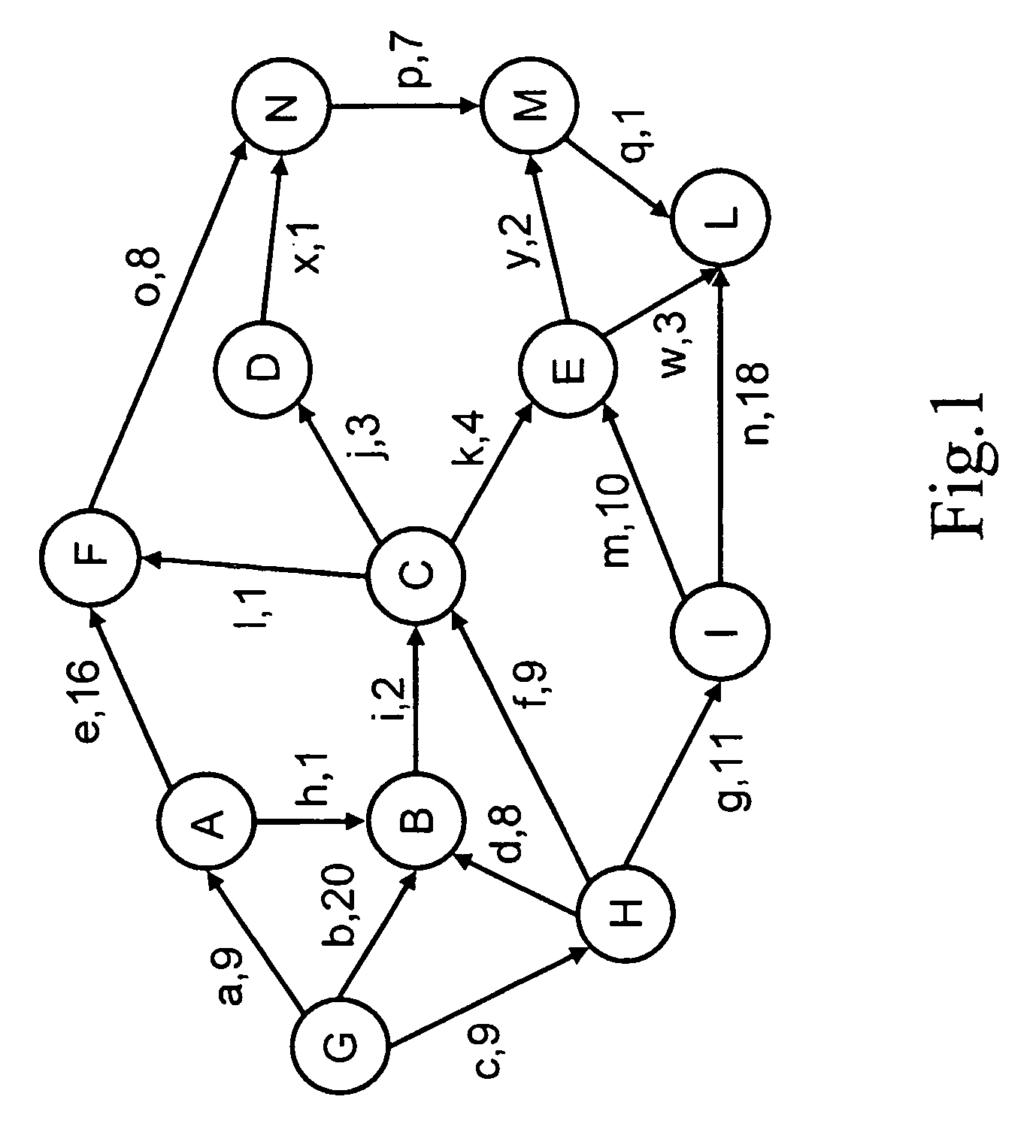
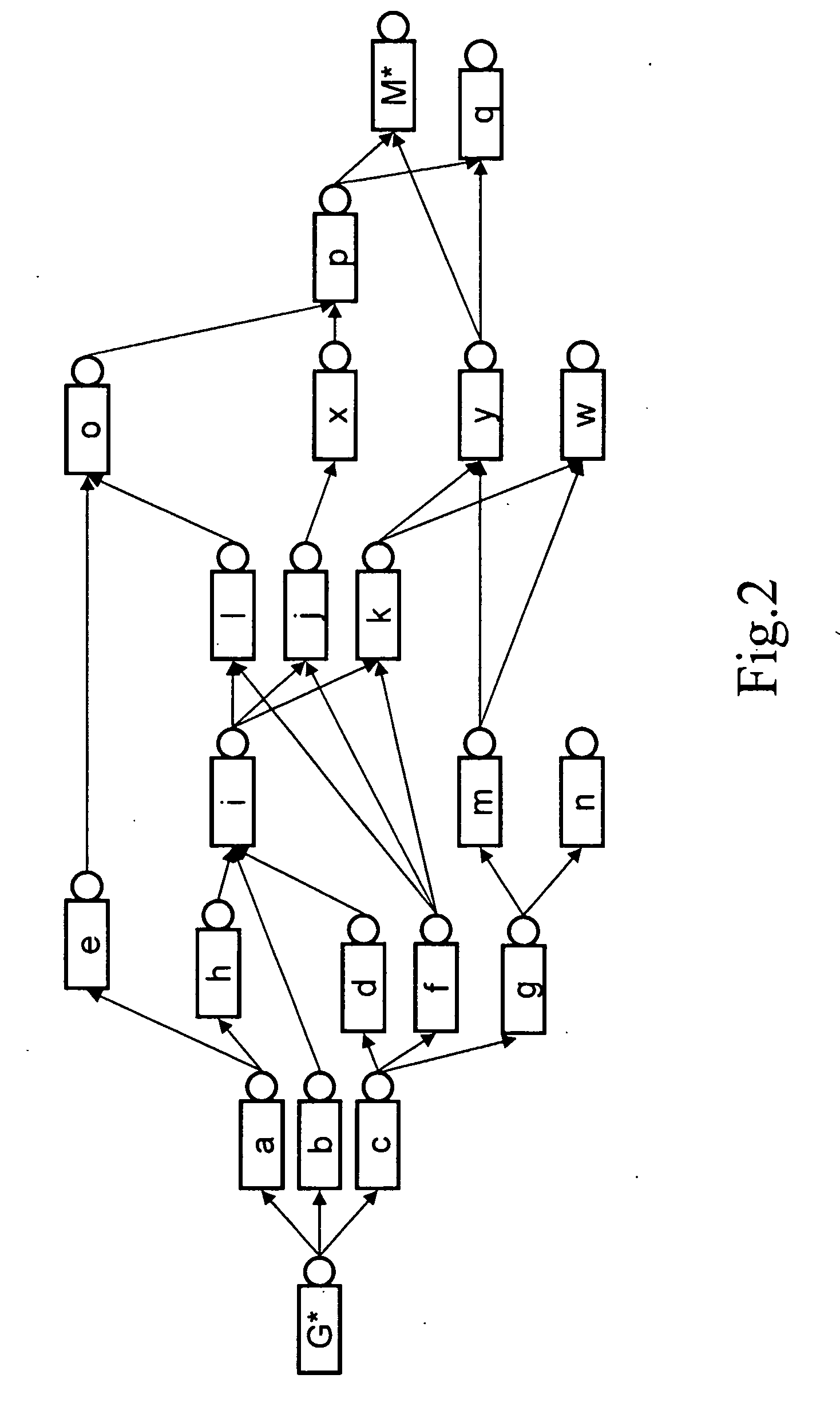
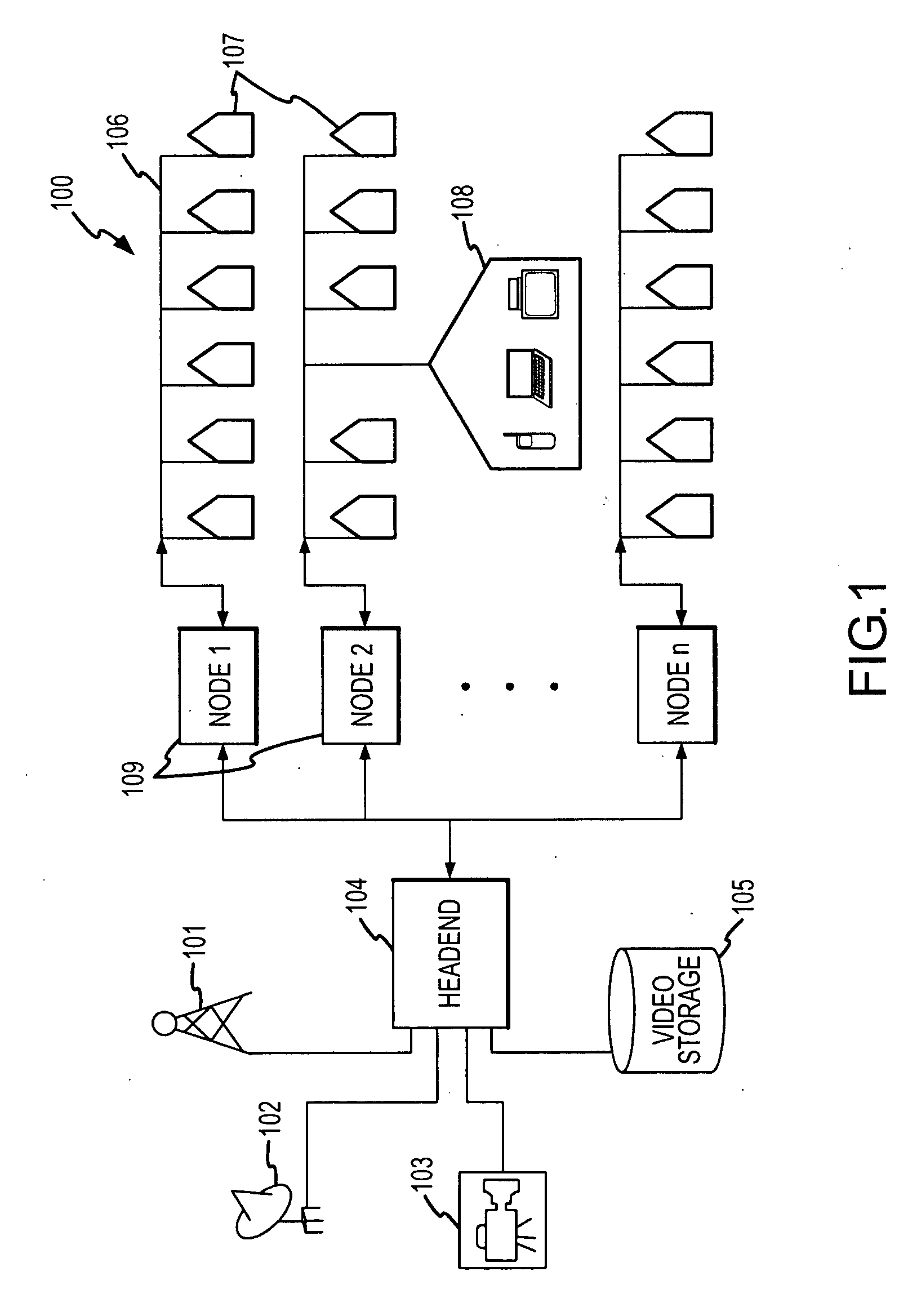
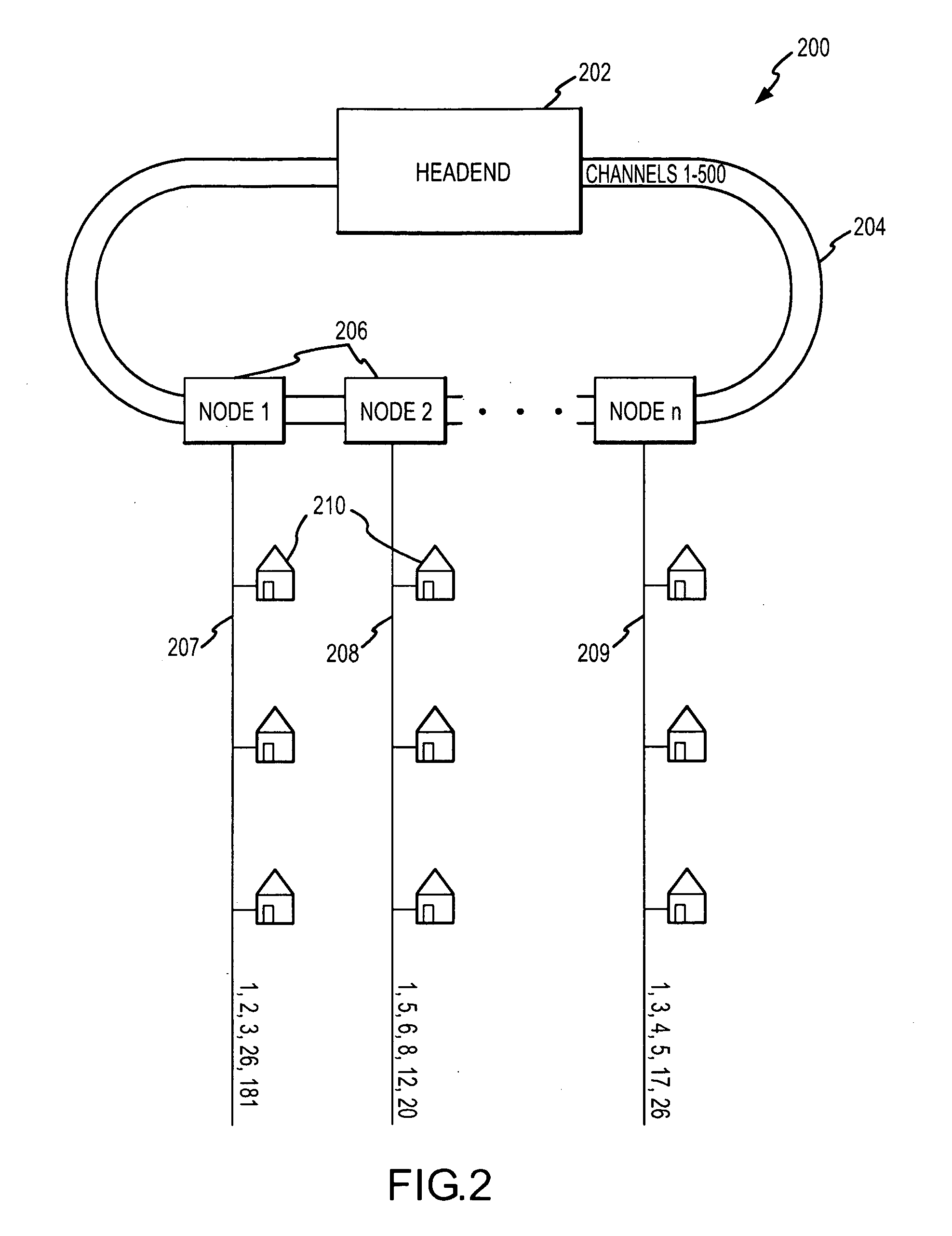
Network topology is the arrangement of the elements (links, nodes, etc.) of a communication network. Network topology can be used to define or describe the arrangement of various types of telecommunication networks, including command and control radio networks, industrial fieldbusses and computer networks.
Method and apparatus for product lifecycle management in a distributed environment enabled by dynamic business process composition and execution by rule inference
InactiveUS20040162741A1Detect and resolve conflictOffice automationResourcesDistributed servicesNetwork topology
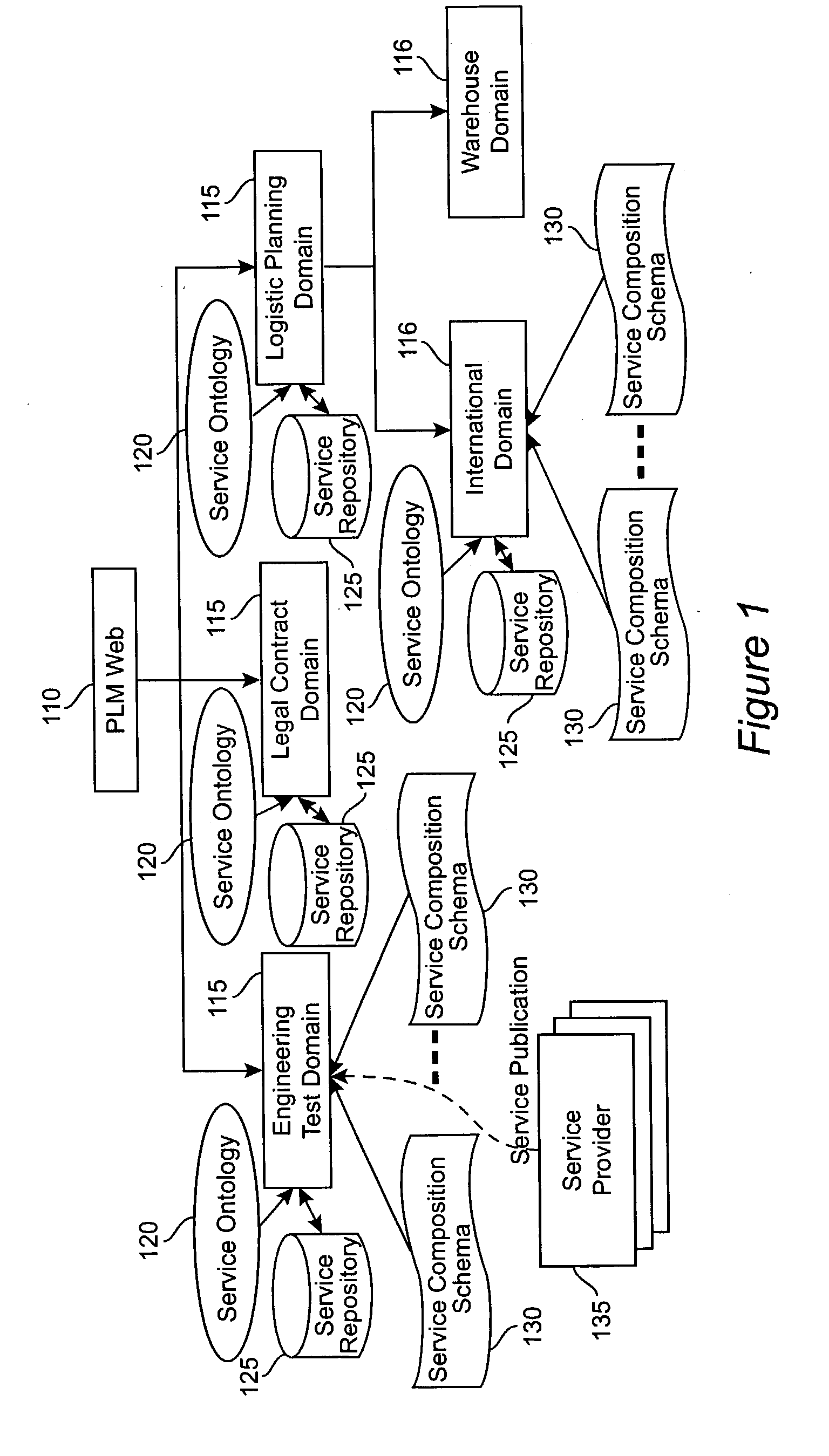
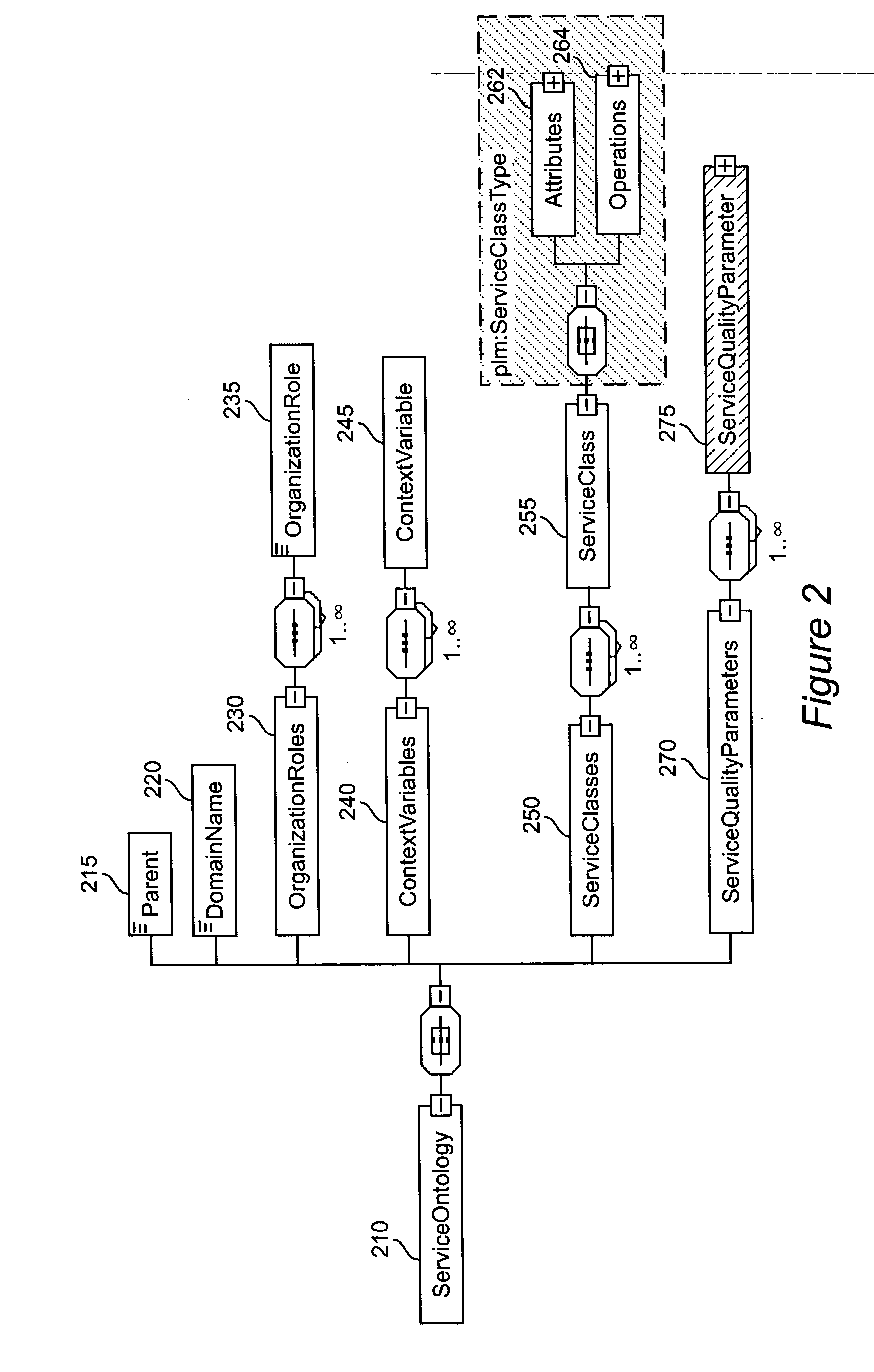
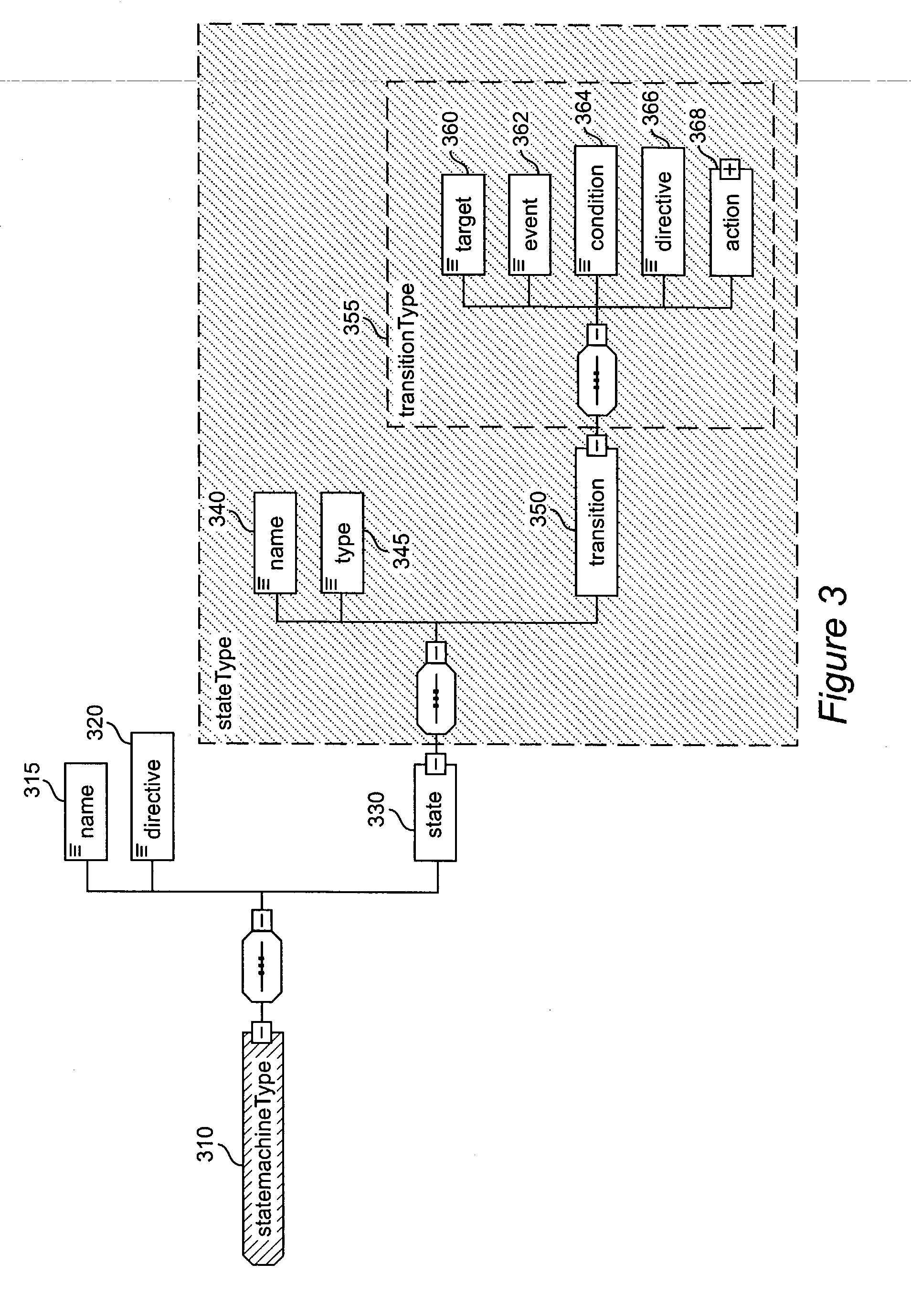
A system and method for supporting Product Lifecycle Management over a distributed service network topology that connects a hierarchy of functional domains, each domain having a service ontology and one or more service composition schemas defined by the service ontology. Each service composition schema models a business process in its domain. Descriptions of services provided to each domain are published to a service repository by providers of the services, in conformity with one of the service composition schemas. There is a business process proxy provided by the service provider for each service description, which encapsulates for public access the internal processes of the service provider. The invention makes use of an event messaging protocol that enables service collaboration and ad-hoc workflow composition. Each business process is implemented by an ad-hoc workflow comprised of one or more tasks connected by one or more business rules. For each business process there is a business flow manager that dynamically composes ad-hoc workflow prior to execution and dynamically modifies the ad-hoc workflow as the business process executes. The business flow manager uses backward-chain inferencing and then forward-chain inferencing to generate the ad-hoc workflows, based on user identification of a target task. The business flow manager is able to stop execution of the workflow and regenerate a workflow for remaining tasks in response to events received over the network from service providers, and is also able to detect conflicts in the workflows at composition time and at execution time.
Owner:IBM CORP
Method and apparatus for determining a network topology during network provisioning
Owner:JUMIPER NETWORKS INC
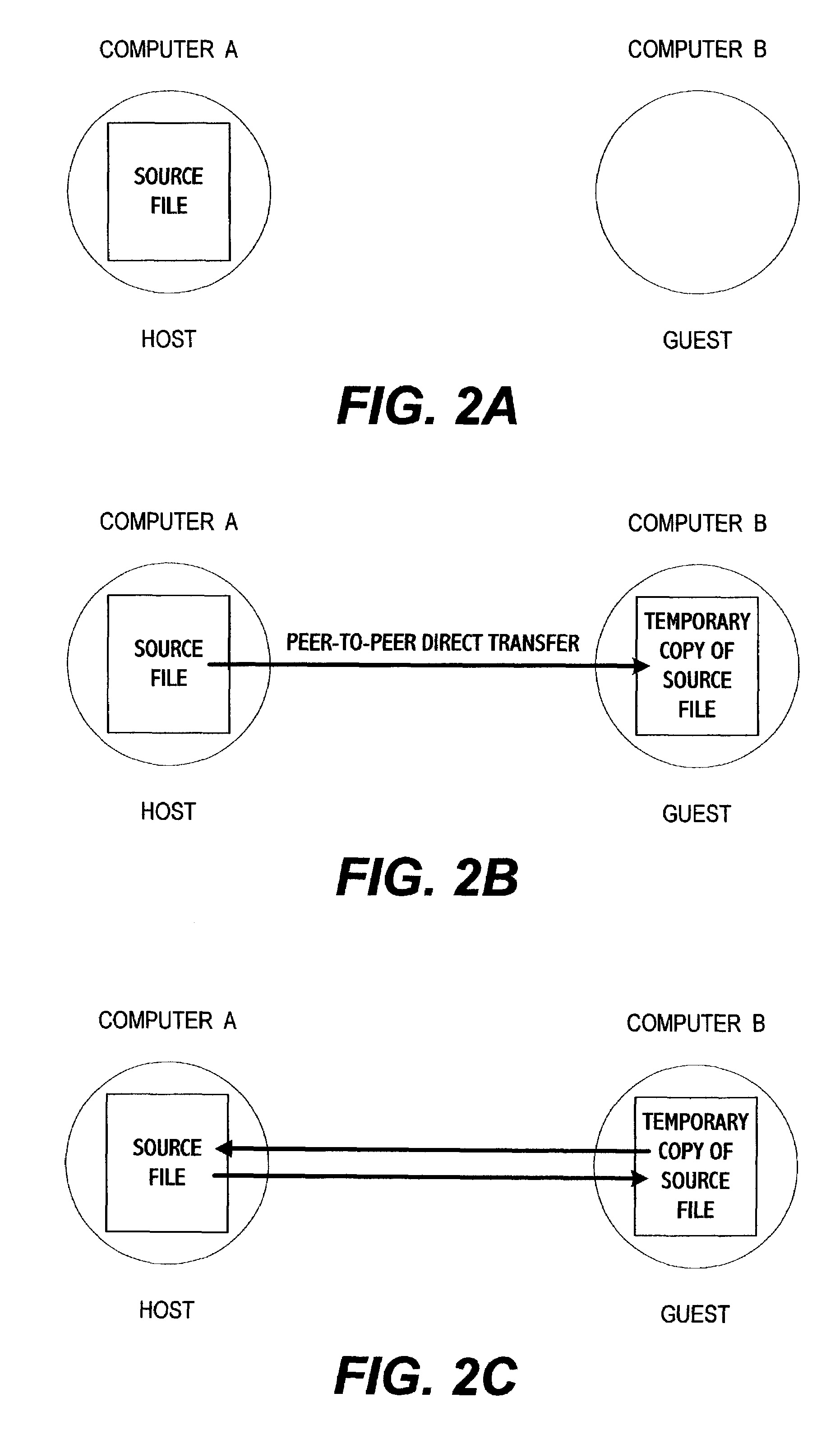
System for electronic file collaboration among multiple users using peer-to-peer network topology
InactiveUS7353252B1Avoid storage problemsMultiple digital computer combinationsOffice automationDocumentation procedurePrivate network
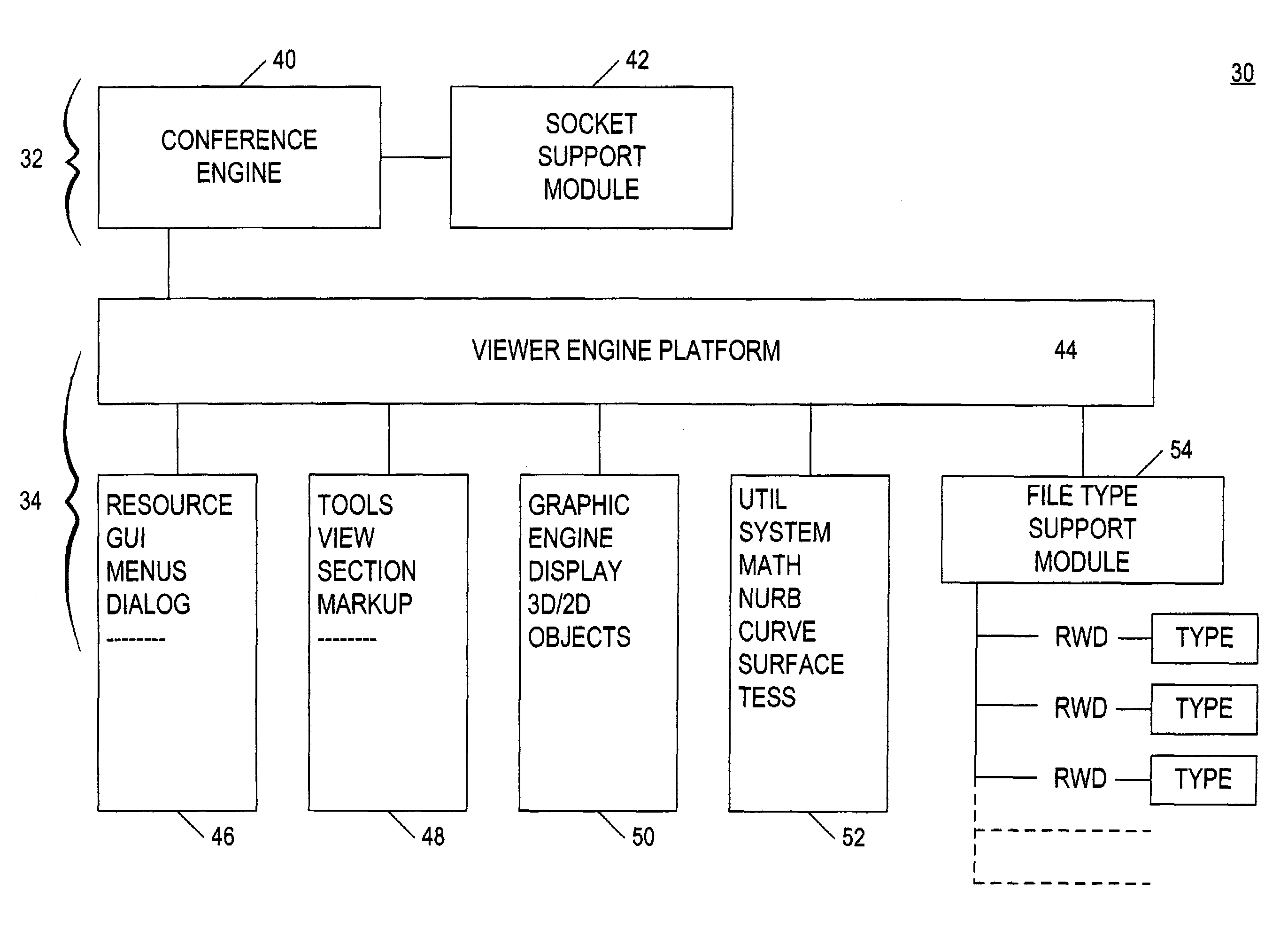
A system for electronic file collaboration among multiple users is implemented using command messages transmitted on dedicated network channels established between conference participants in a peer-to-peer architecture with total autonomy from a central server. The system employs owner-in-control methodology to allow direct transmission of copies of documents among participants by permission, and to prevent storage of copies of documents used in a conference by participants. Mark-ups, additions, and other actions occurring on a conference document can only be saved by the document owner. An advanced viewer engine is provided for reading, displaying and manipulating electronic data in texts, tables, vectors and 3D model formats, as well as common raster images. A proxy module allows data transmitted through IPFW routers or firewall devices with sufficient authentications and security measures.
Owner:SIGMA DESIGNS
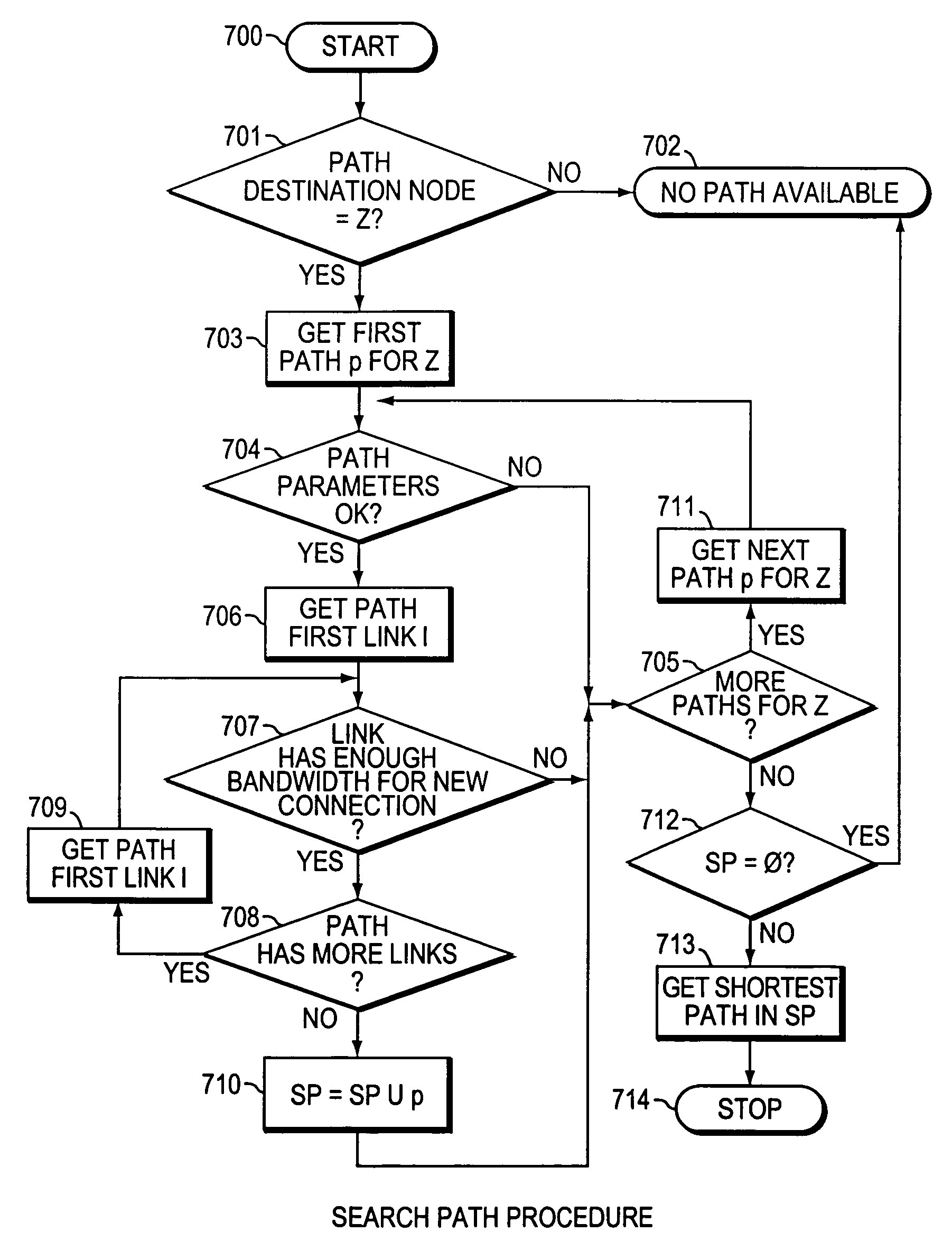
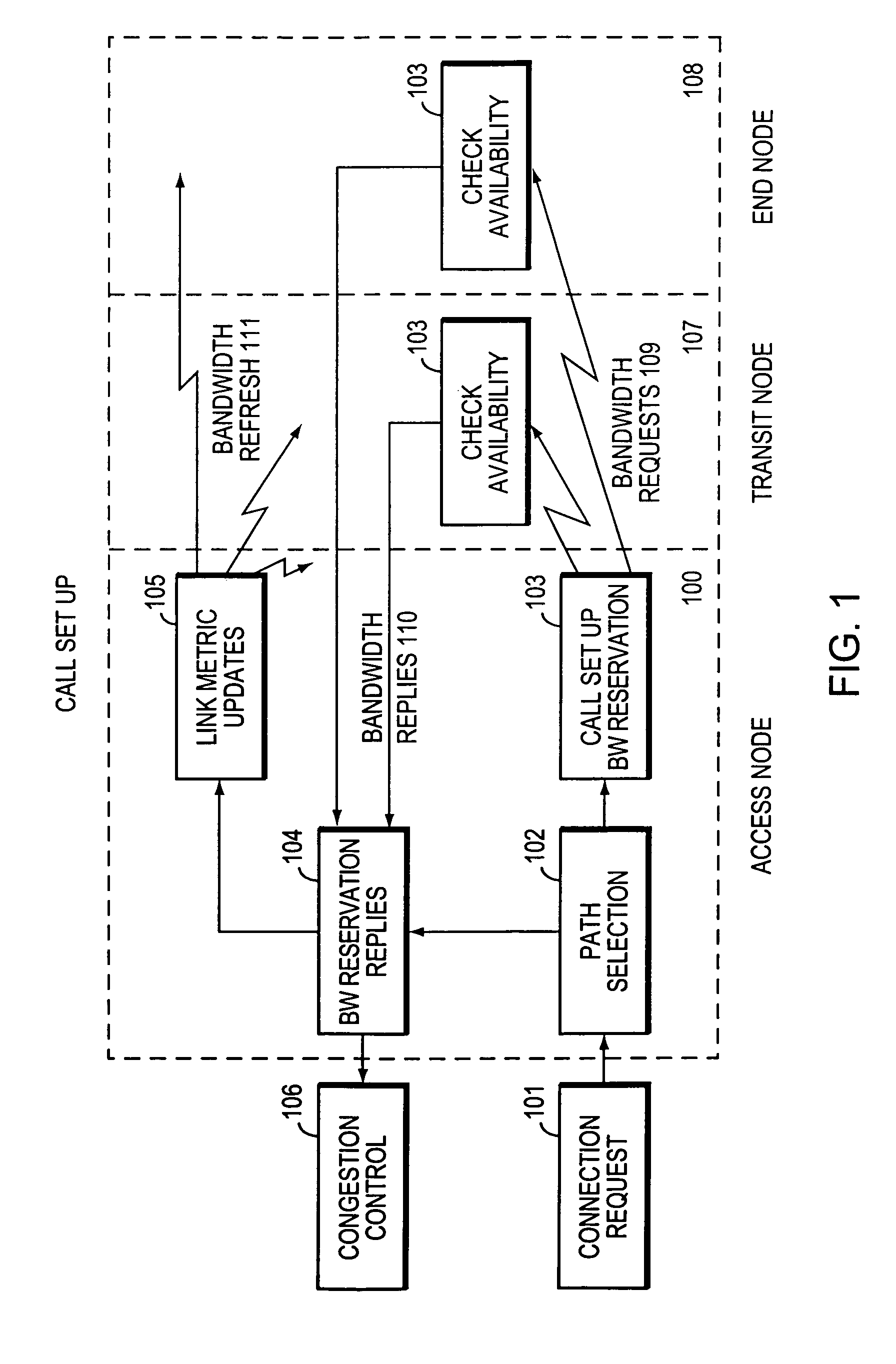
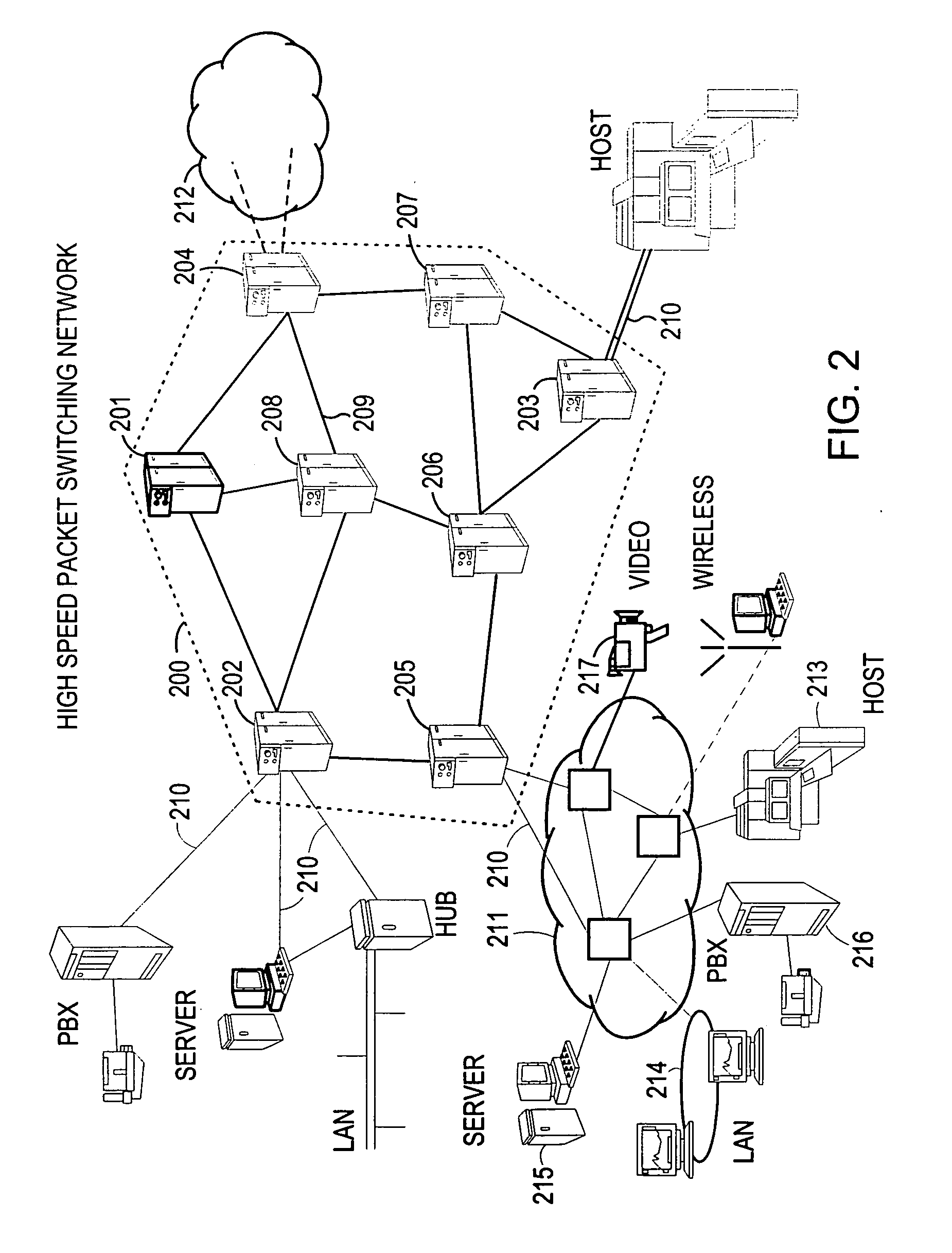
Method and system for minimizing the connection set up time in high speed packet switching networks
InactiveUS6934249B1Minimize delayMinimize in in to selectError preventionFrequency-division multiplex detailsTraffic capacityPacket switched
The present invention is directed to a high speed packet switching network and, in particular to a method and system for minimizing the time to establish a connection between an origin and a destination node. Due to high dynamicity of the traffic on transmission links, it is important to select a routing path according to a fully up-to-date information on all network resources. The simpler approach is to calculate a new path for each new connection request. This solution may be very time consuming because there are as many path selection operations as connection set up operations. On another hand, the calculation of paths based on an exhaustive exploration of the network topology, is a complex operation which may also take an inordinate amount of resources in large networks. Many of connections originated from a network node flow to the same destination network node. It is therefore possible to take a serious benefit in reusing the same already calculated paths for several connections towards the same node. The path calculated at the time the connection is requested is recorded in a Routing Database and updated each time a modification occurs in the network. Furthermore, alternate paths for supporting non-disruptive path switch on failure or preemption, and new paths towards potential destination nodes can be calculated and stored when the connection set up process is idle. These last operations are executed in background with a low processing priority and in absence of connection request.
Owner:CISCO TECH INC
System and method for configuring computer applications and devices using inheritance
InactiveUS20020091819A1Multiple digital computer combinationsData switching networksStructure of Management InformationNetwork topology
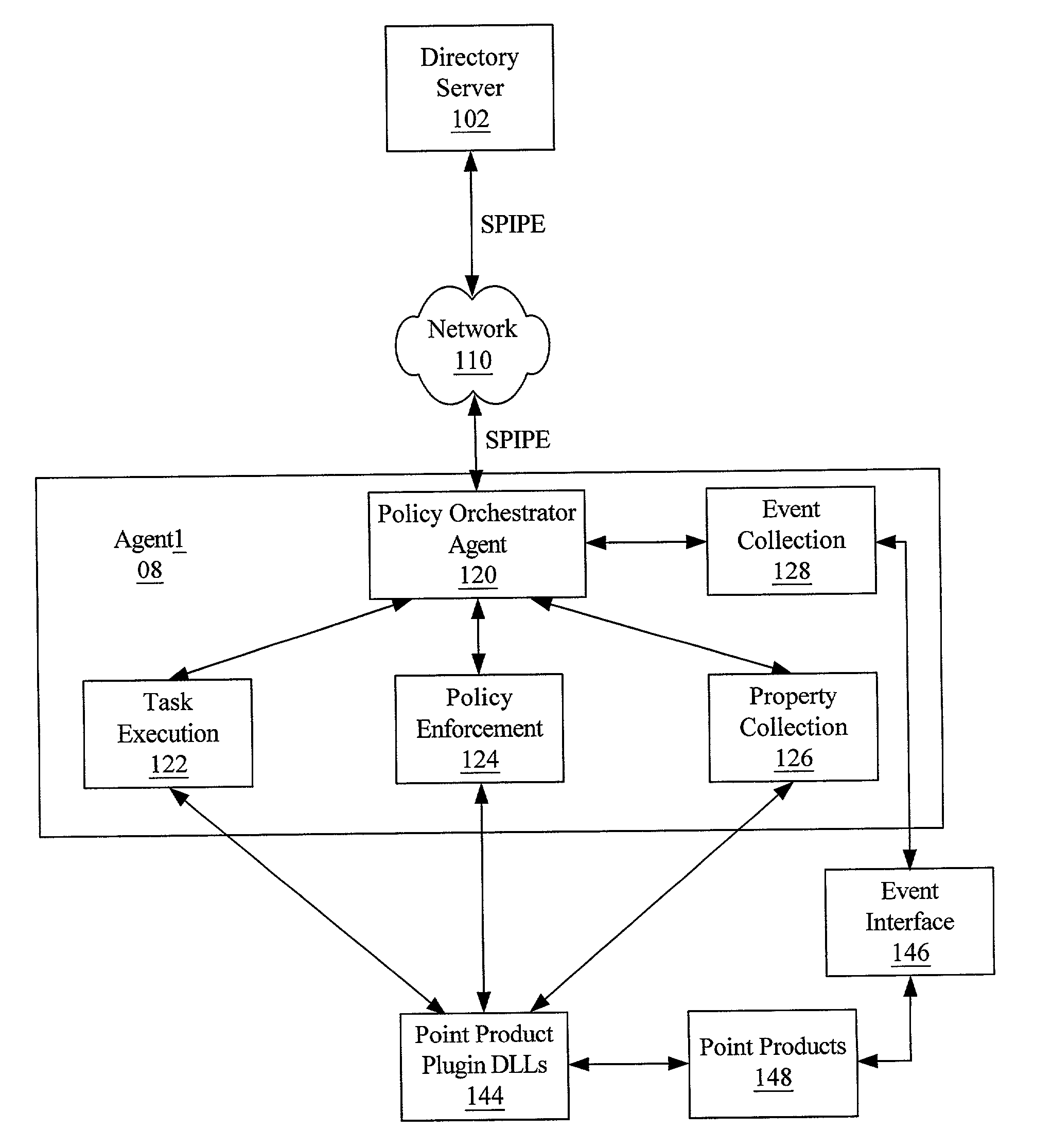
A system and method using inheritance for the configuration, management, and / or monitoring of computer applications and devices via a computer network are disclosed. The method generally comprises determining a hierarchical tree structure based upon locations of devices in a network topology, each device being a node in the hierarchical tree structure, determining policies for each node in the hierarchical tree structure to be enforced by an agent corresponding to each node, the agent being in communication with the device and the resources corresponding to the device, and communicating the policy to the corresponding agent, wherein the policies corresponding to the resources of each device are selectively inherited along the hierarchical tree structure of the network directory.
Owner:MCAFEE INC
Network operating system for managing and securing networks
ActiveUS20090138577A1Reduced power modeDigital computer detailsTransmissionTraffic capacityAuto-configuration
Systems and methods for managing a network are described. A view of current state of the network is maintained where the current state of the network characterizes network topology and network constituents, including network entities and network elements residing in or on the network. Events are announced that correspond to changes in the state of the network and one or more network elements can be configured accordingly. Methods for managing network traffic are described that ensure forwarding and other actions taken by network elements implement globally declared network policy and refer to high-level names, independently of network topology and the location of network constituents. Methods for discovering network constituents are described, whereby are automatically configured. Routing may be performed using ACL and packets can be intercepted to permit host to continue in sleep mode. The methods are applicable to virtual environments.
Owner:NICIRA
Method for optimal path selection in traversal of packets through network address translators
InactiveUS20050259637A1Reduce administrative overheadFast convergenceMultiplex system selection arrangementsError preventionNetwork addressNetwork address translation
Reduction of administrative overhead in maintaining network information, rapid convergence on an optimal routing path through the data network, and utilization of only required network resources are realized by a novel method for establishing a call path between network users. The method is based upon deployment of a network information server that stores network topology information and that is addressable by each end user. In this method, the network information server receives a request to establish a call path. The request identifies at least the calling party. In response to the request, the network information server determines a network traversal between the calling party and a root network wherein the network traversal includes call path information about the sub-networks between the calling party and the root network. The request for establishing a call path can also identify the called party. Based on the calling and called party identification, the network information server also determines a second network traversal between the called party and the root network. The second network traversal is sent to either the calling party or the called party or to both the calling and called parties. The server can determine an intersection of the traversals and send the intersection information to the parties. The intersection information is known as a merge point and represents an optimal call path between the parties.
Owner:ALCATEL-LUCENT USA INC
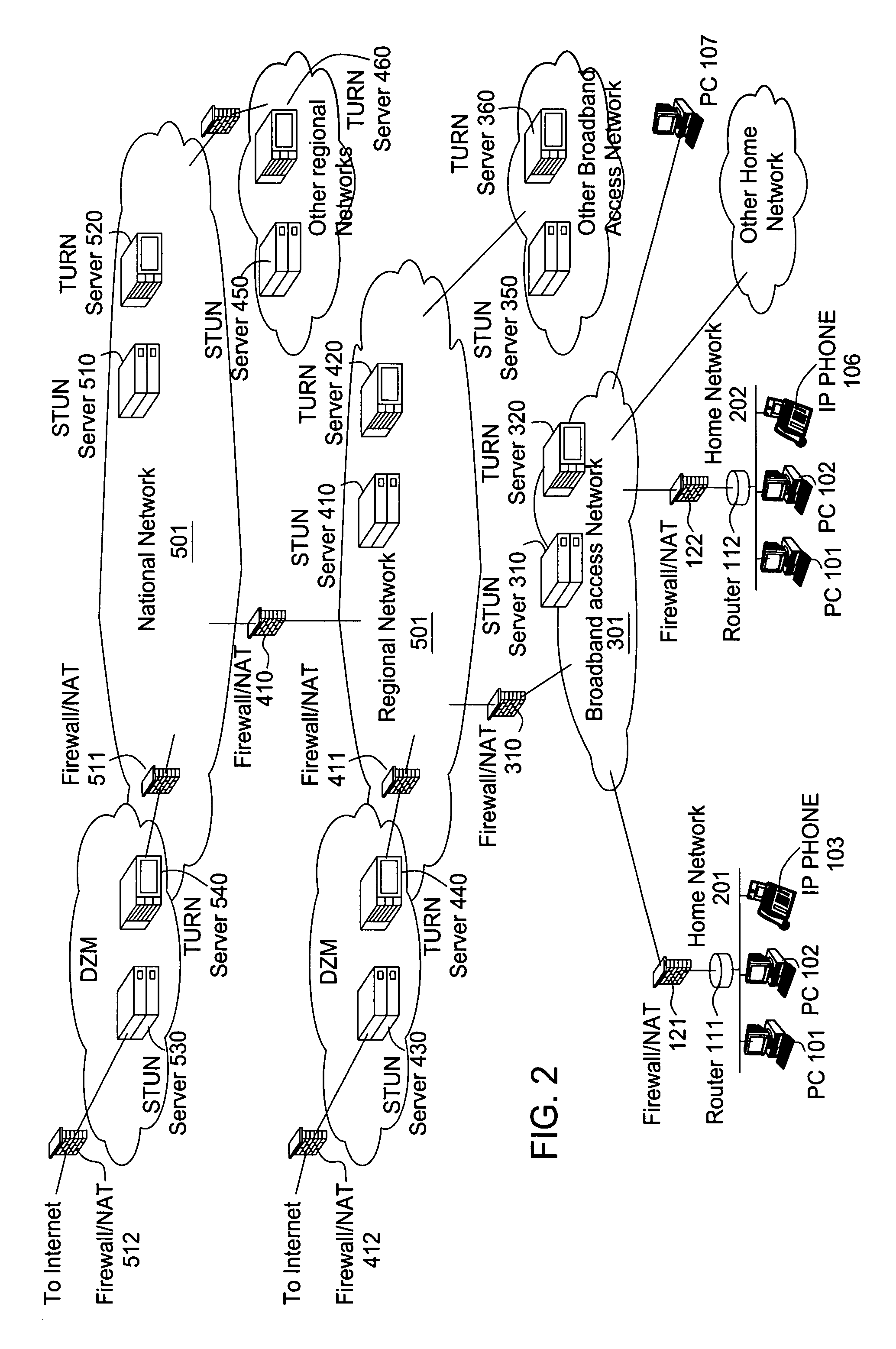
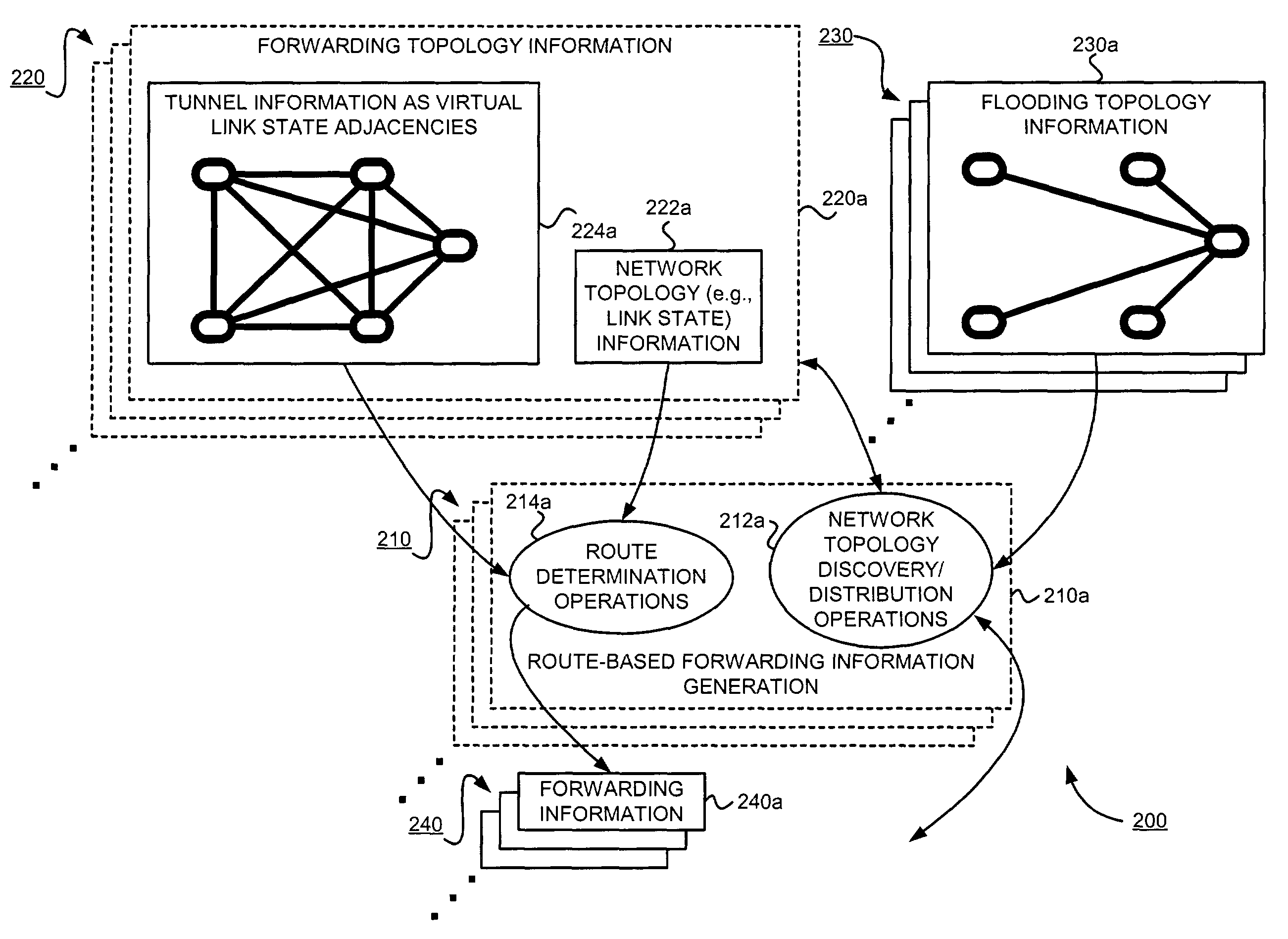
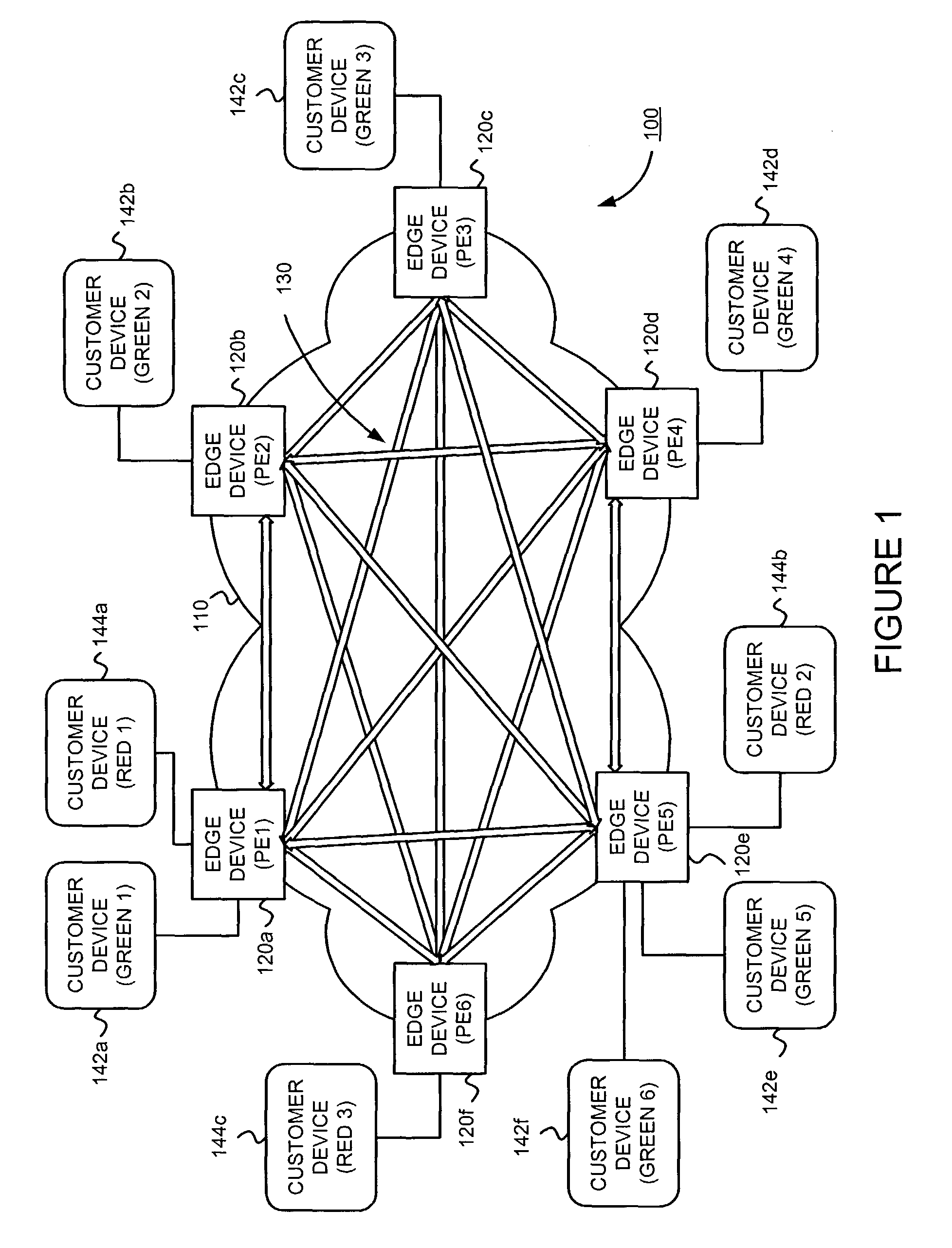
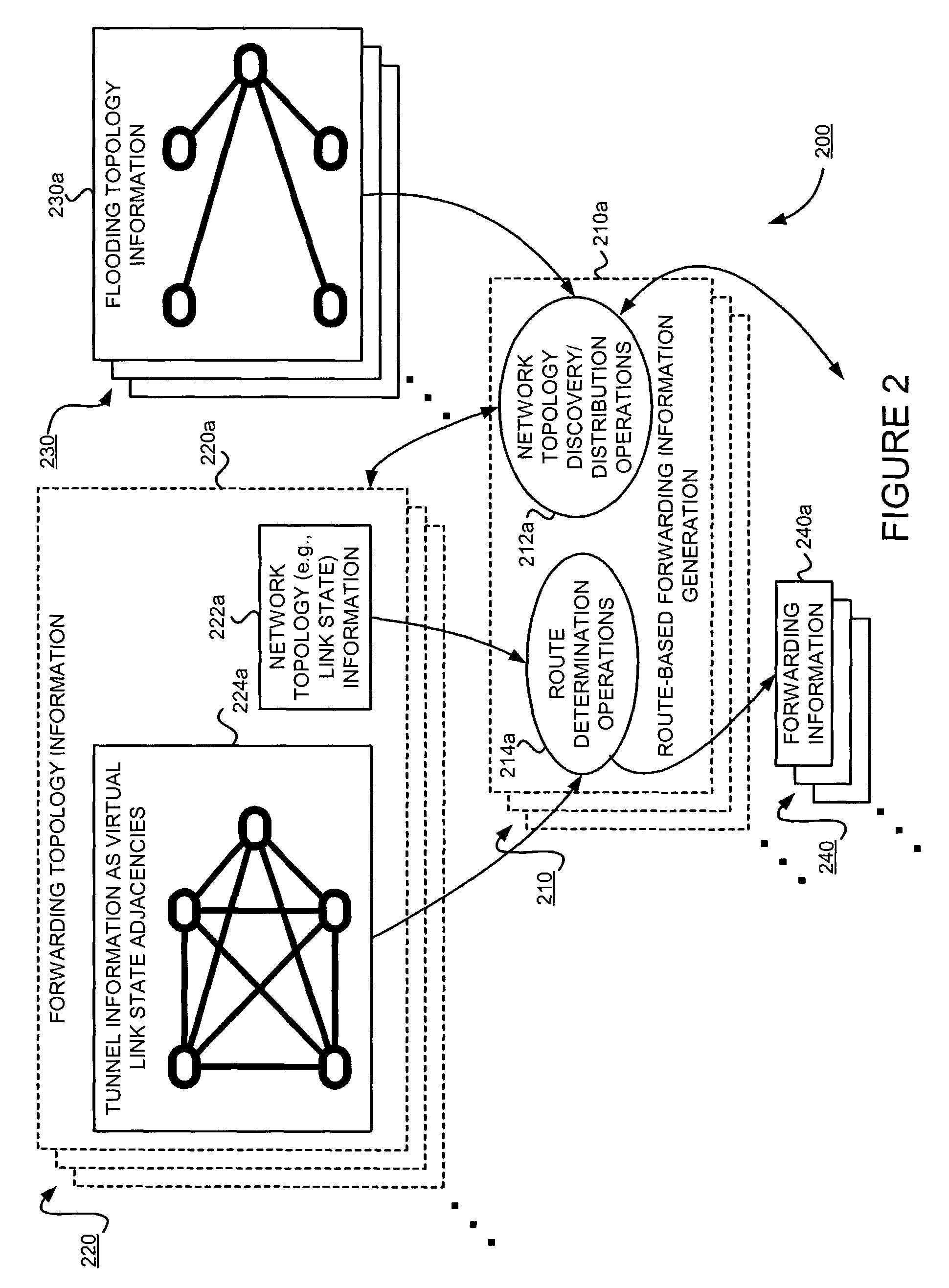
Supporting virtual private networks using a first network topology for forwarding and a subset of the first network topology or a smaller topology for signaling
InactiveUS7792987B1Avoid problemsError preventionTransmission systemsBorder Gateway ProtocolTTEthernet
Virtual Private Networks (VPNs) are supported in which customers may use popular internet gateway protocol (IGPs) without the need to convert such IGPs, running on customer devices to a single protocol, such as the border gateway protocol (BGP). Scaling problems, which might otherwise occur when multiple instances of an IGP flood link state information, are avoided by using a flooding topology which is smaller than a forwarding topology. The flooding topology may be a fully connected sub-set of the forwarding topology.
Owner:JUMIPER NETWORKS INC
Method and apparatus for on demand multicast and unicast using controlled flood multicast communications
ActiveUS7184421B1Efficient routingEasy to collectSpecial service provision for substationData switching by path configurationFlexible MechanismsTraffic capacity
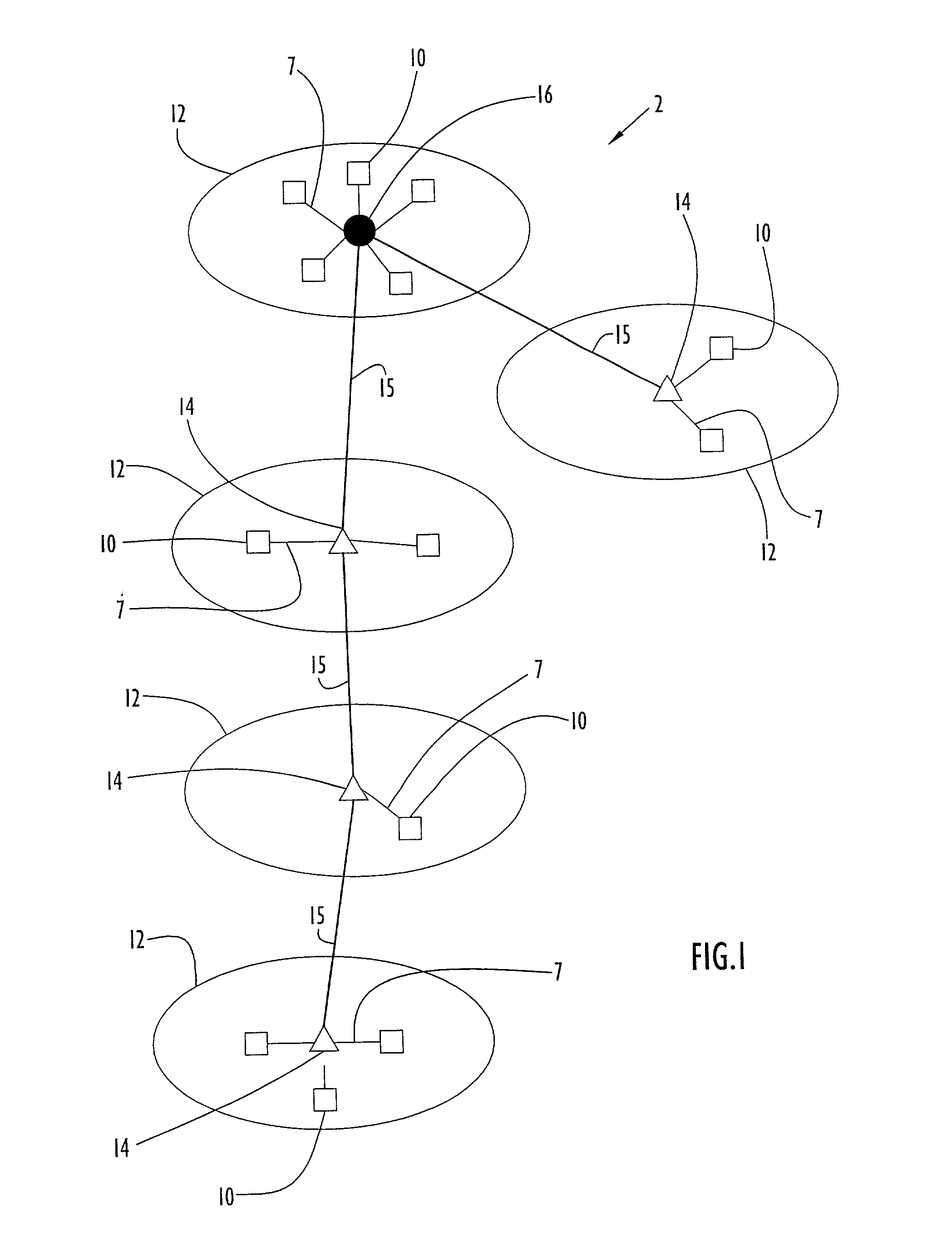
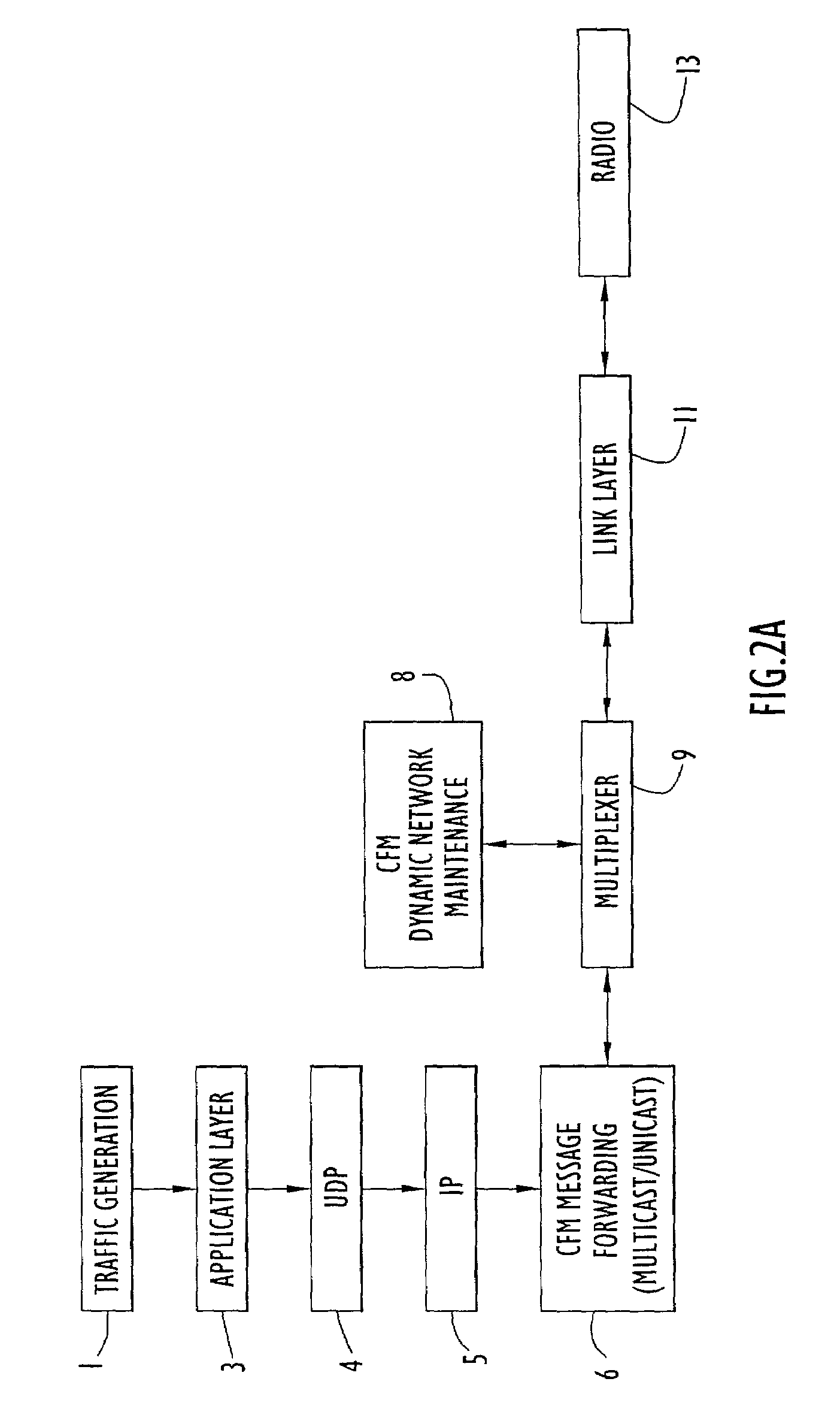
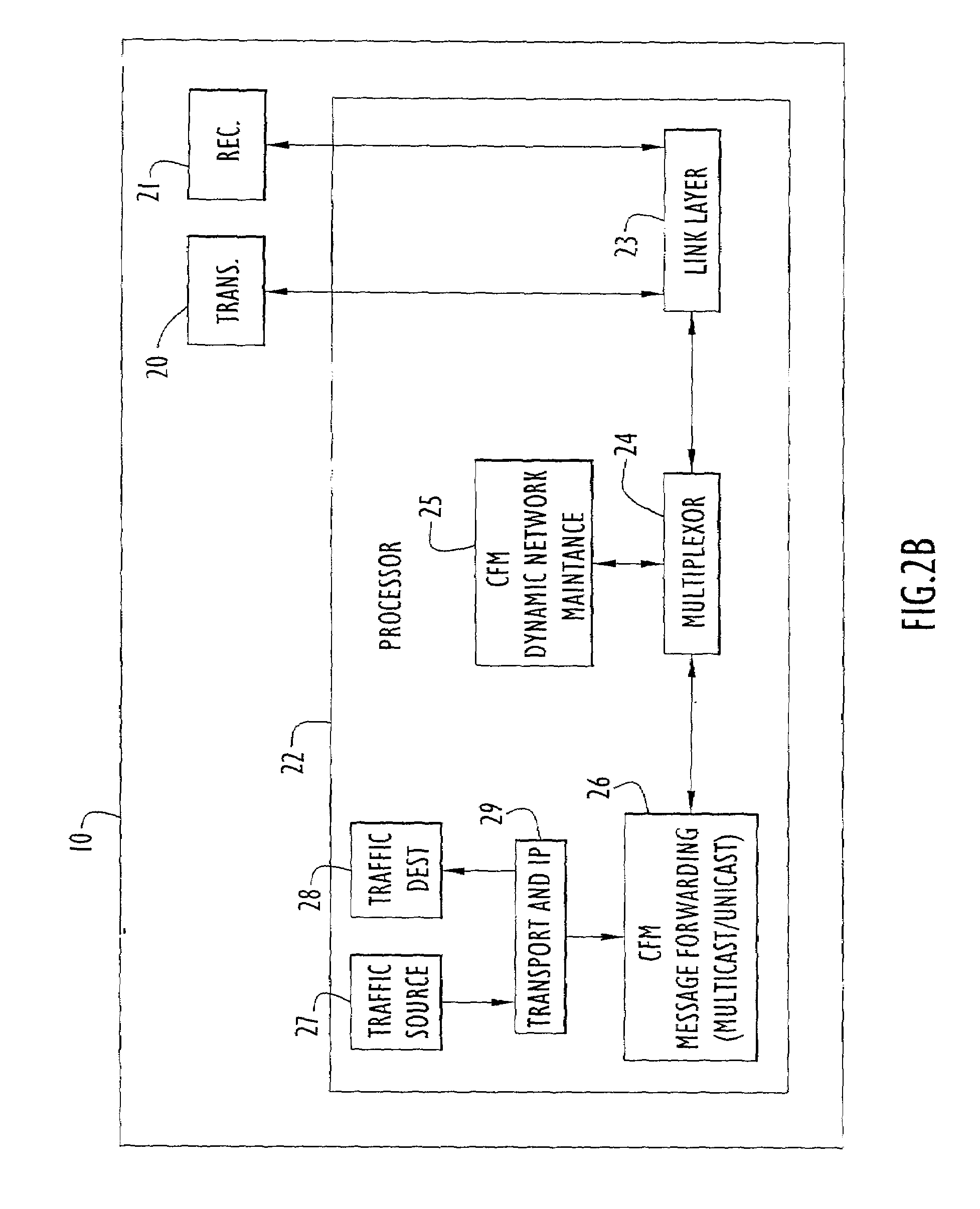
Network configuration hierarchy information is maintained using flexible mechanisms and methods for establishing routes and transferring information between nodes in ad-hoc data communication networks using on-demand multicast and unicast techniques. Communication nodes use network topology information to build and maintain a dynamically mobile, wireless, ad-hoc network capable of efficiently routing both unicast and multicast traffic. Network nodes that facilitate the collection and distribution of network topology and routing data are dynamically selected, configured, and maintained. Network traffic overhead necessary for maintaining and distributing network routing table information is held to a minimum and efficiently distributed across the network, thereby reducing the potential for network traffic bottlenecks due to network overhead processes.
Owner:STINGRAY IP SOLUTIONS LLC
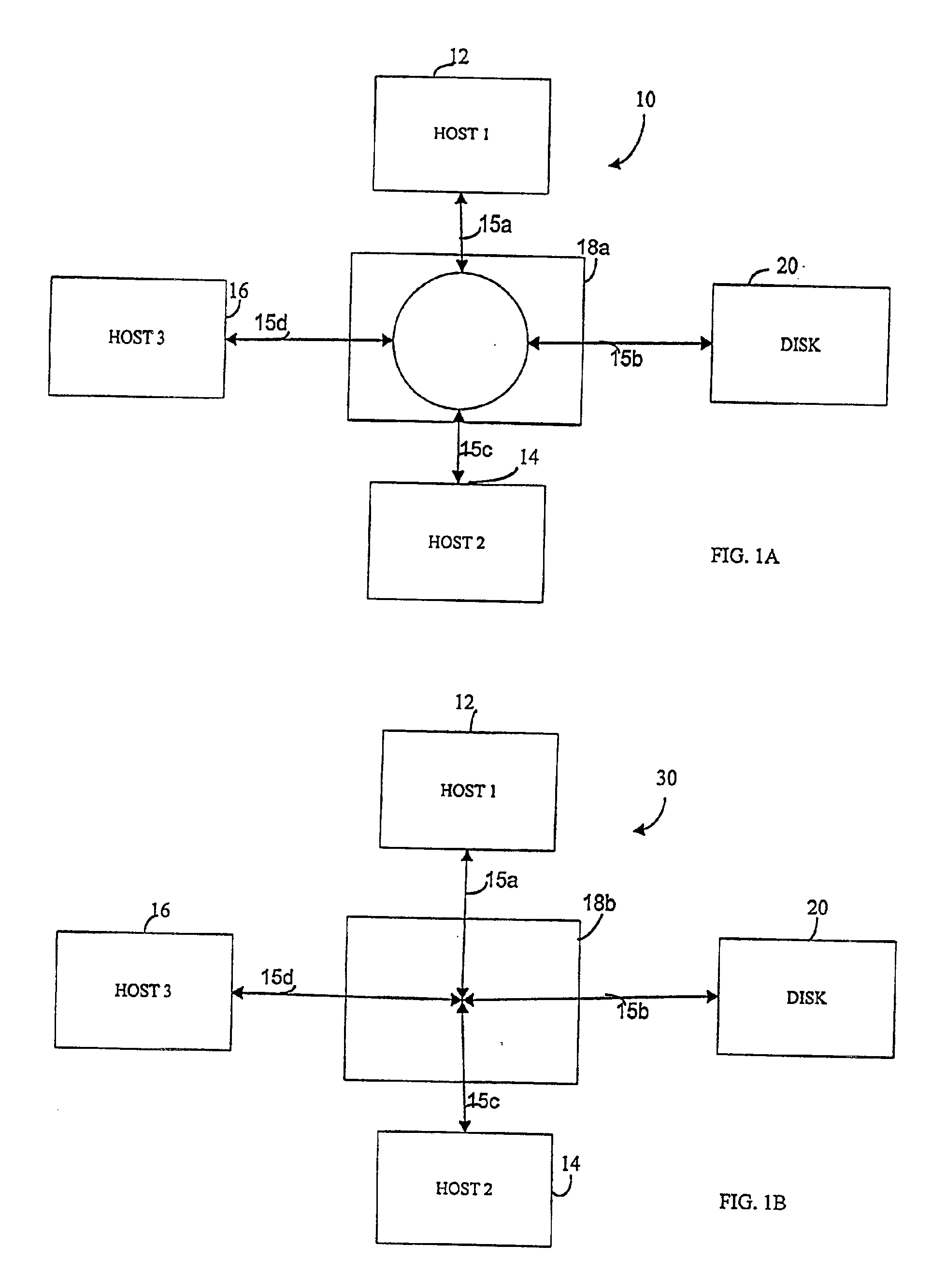
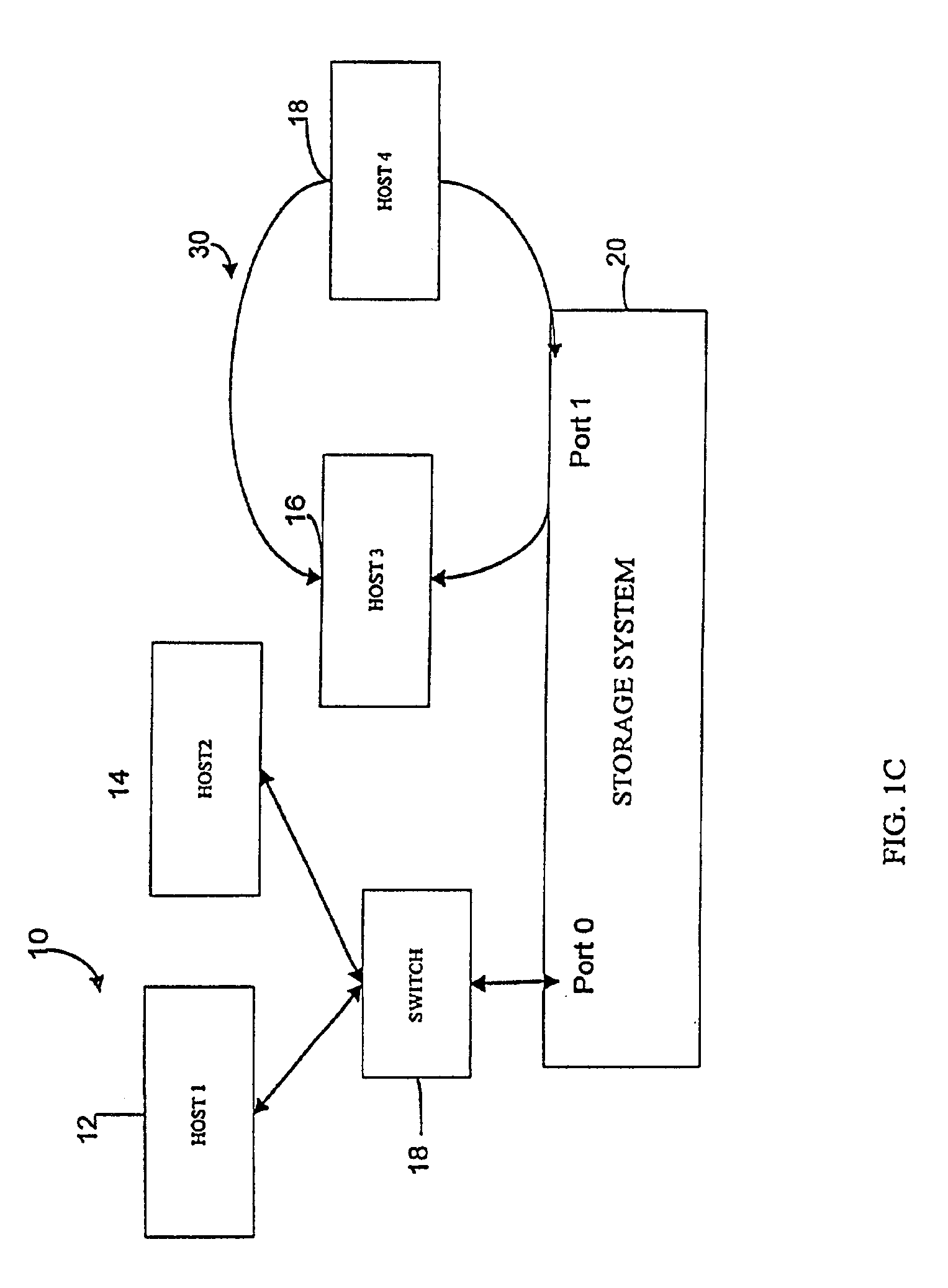
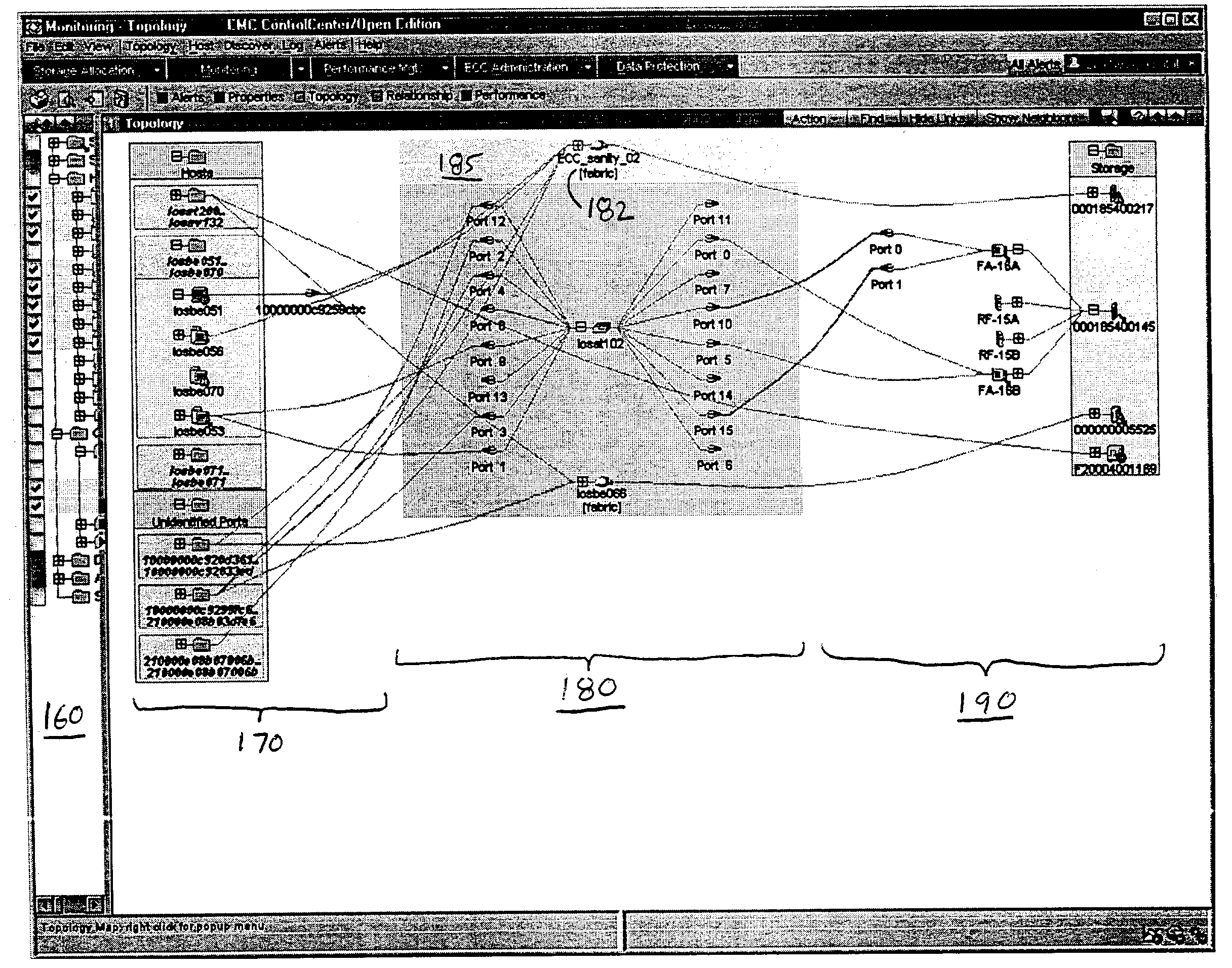
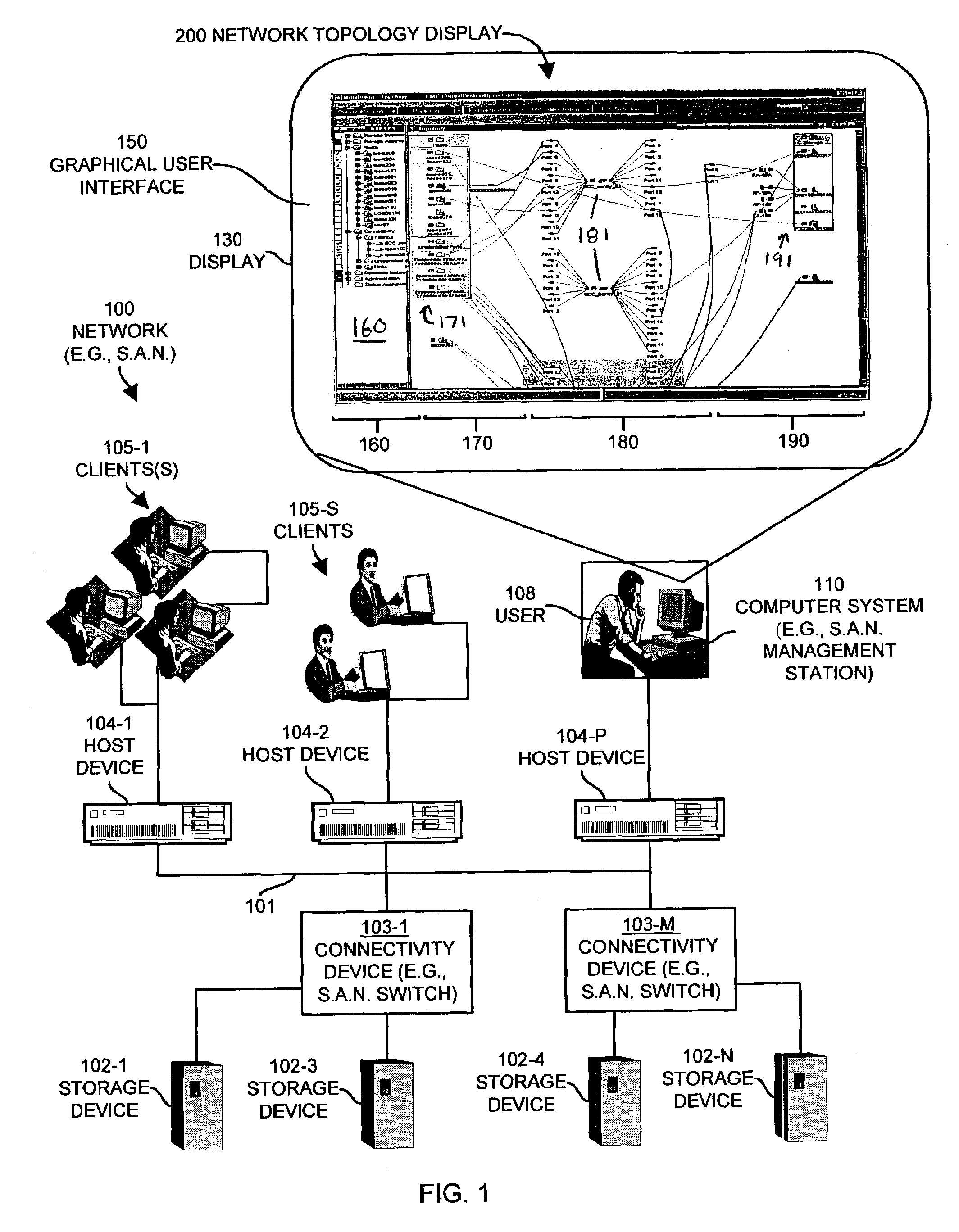
User interface for managing storage in a storage system coupled to a network
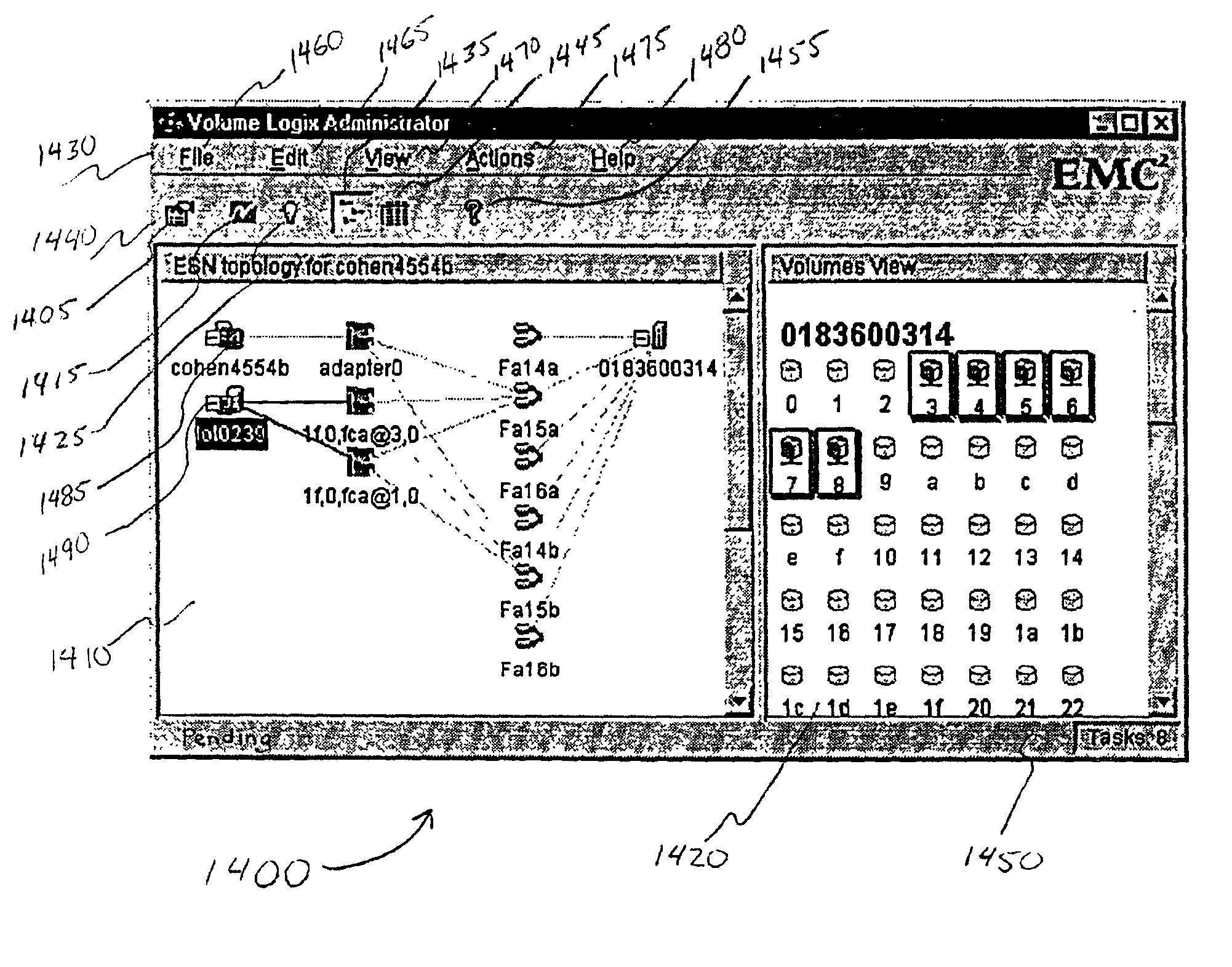
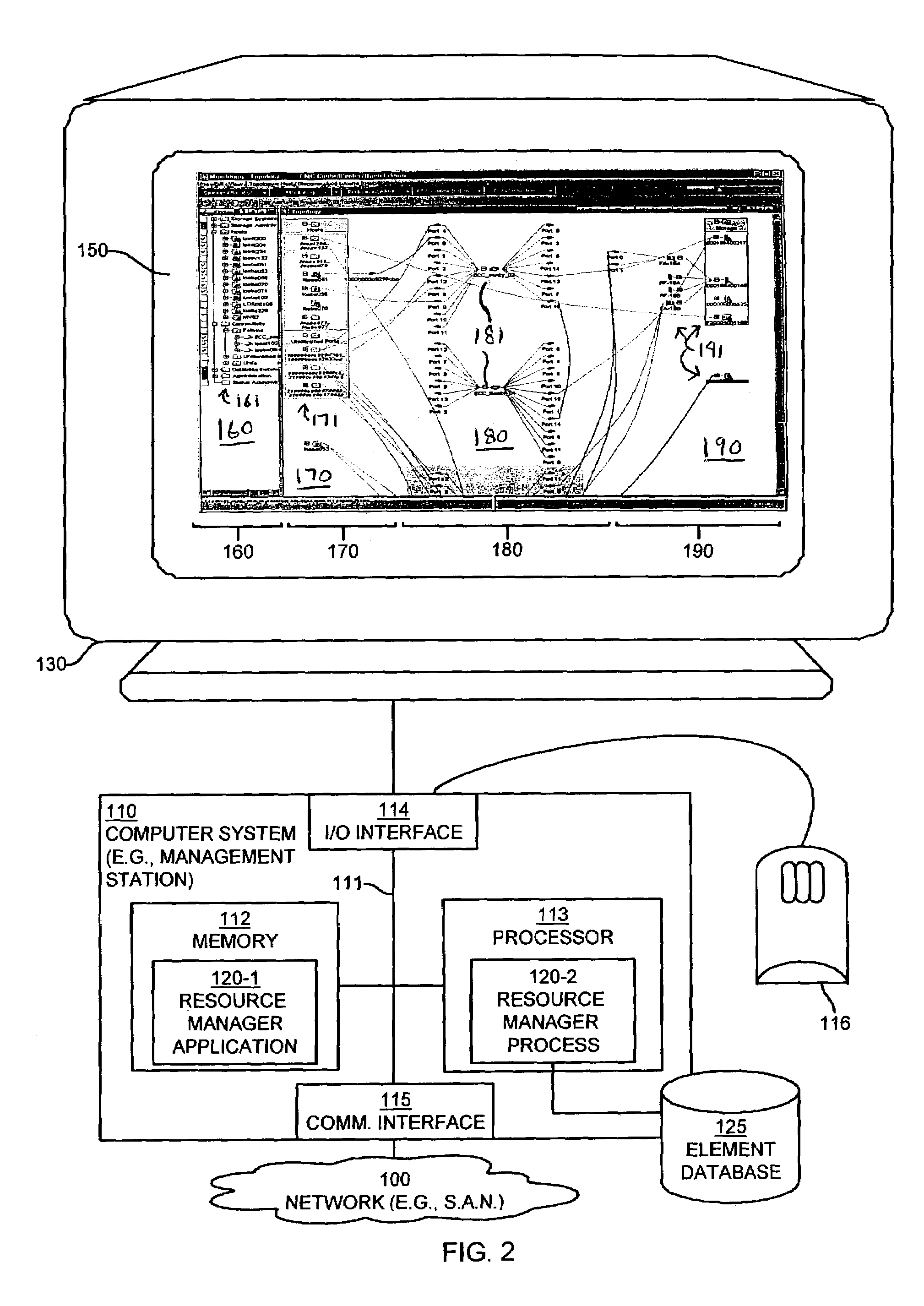
A method and apparatus for managing the availability and assignment of data in a storage system that is coupled to a network. A user interface is provided that executes on a host processor that is coupled to the storage system over the network. The user interface communicates with a configuration database in the storage system to identify host processors that are logged into the storage system over the network, to identify storage volumes on the storage system, to identify whether access to a particular storage volume on the storage system is permitted from a particular host processor, and to identify a network path by which host processors are logged into the storage system over the network. In one embodiment, a graphical user interface is provided that can be used to graphically represent host processors, host bus adapters, storage systems, and storage system adapters and storage volumes on the storage system. The graphical representation provided by the graphical user interface permits a user to graphically view a topology of the network at varying levels of detail, selectable by the user. The graphical user interface also permits a user to allow or deny access to storage systems or a particular storage volume on storage system from one or more of the host processors, host bus adapters, etc., by selecting and manipulating graphical representations thereof. In another embodiment, a command line user interface is provided with similar functionality.
Owner:EMC IP HLDG CO LLC
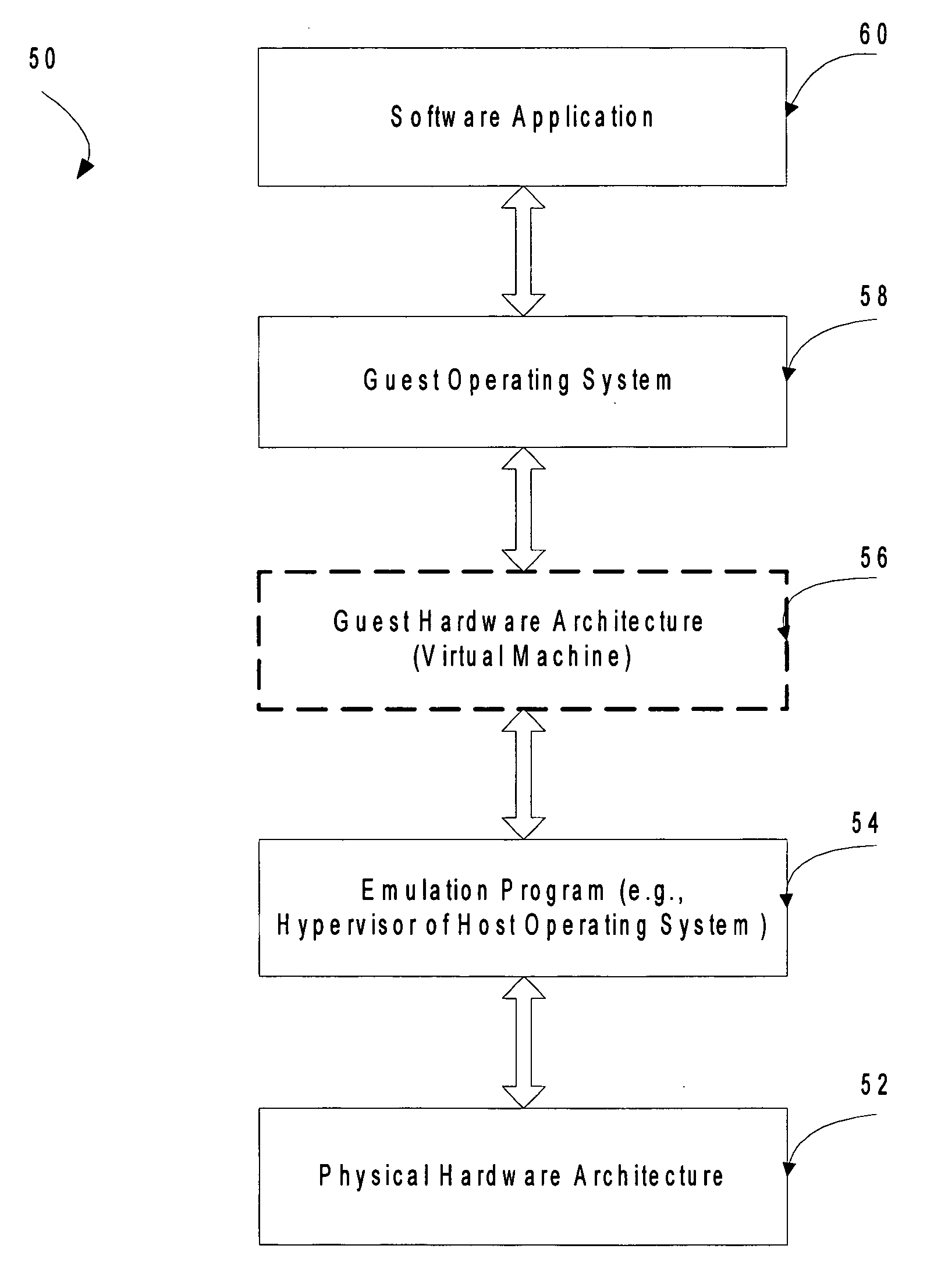
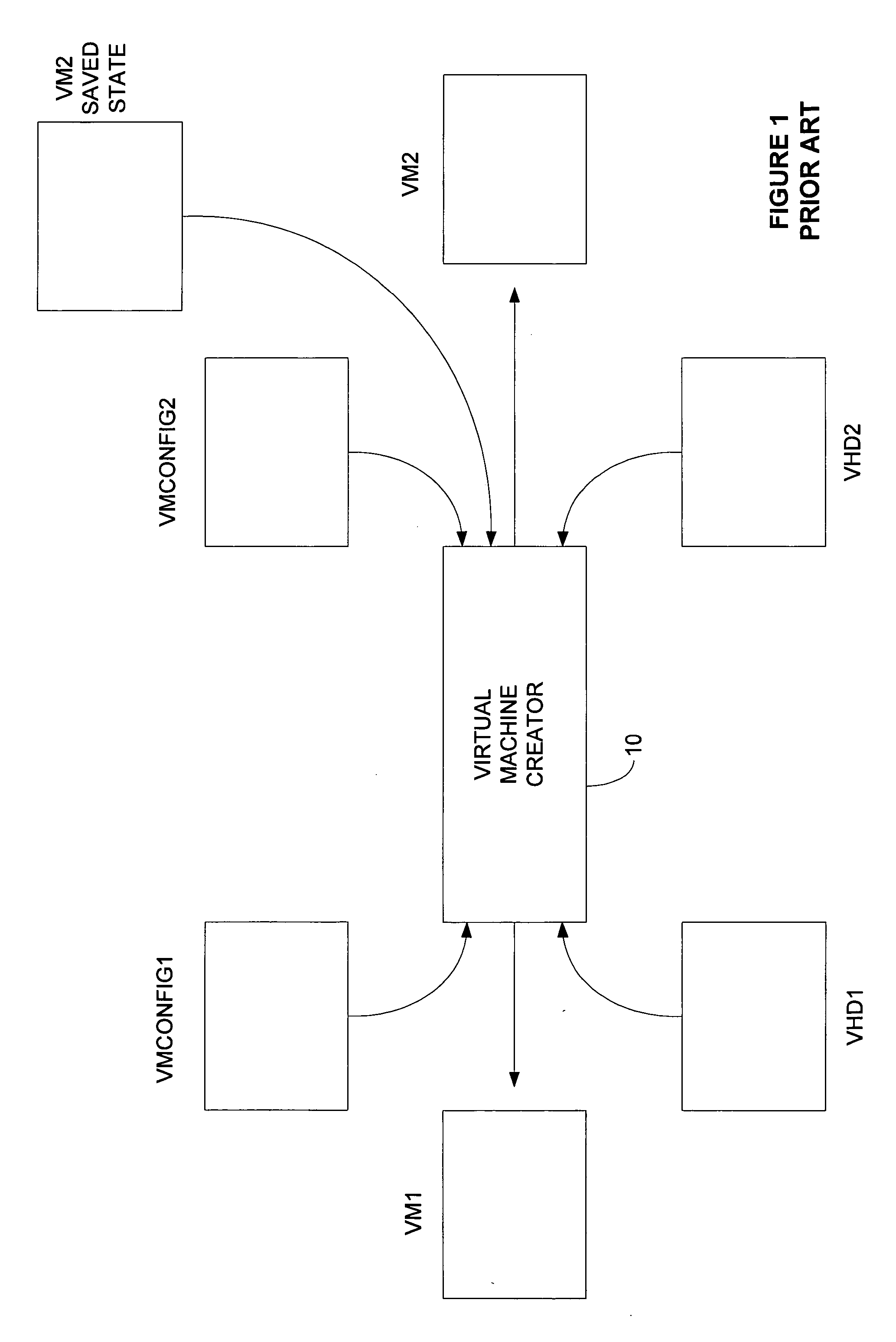
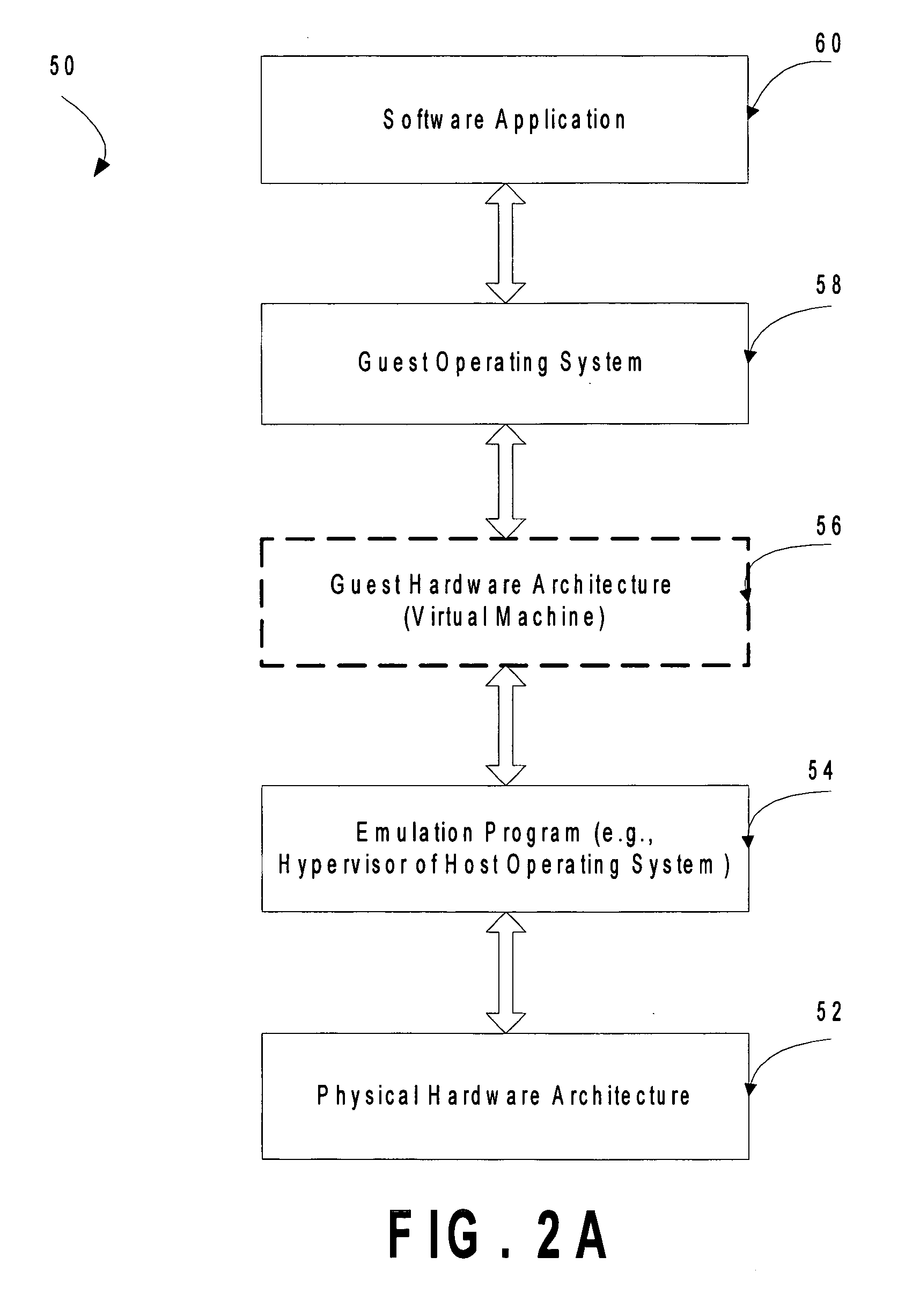
Mechanism to store information describing a virtual machine in a virtual disk image
ActiveUS20060218544A1Reduce in quantityTightly coupledSoftware simulation/interpretation/emulationMemory systemsExtensibilityOperational system
A mechanism is provided for making information about the virtual disk image file and / or its associated virtual image configuration file more readily available to a user. The virtual disk image file format is expanded to include fields in which information about the data in the file can be stored. Extensible information on file content, compatible HW configurations, compatible host OSes, timeout status, DRM status, patch state, and network topology, tag data for indexing, configuration files, saved state files, operation history data, and the like is stored in a location within a virtual disk image file that can be read without executing the virtual machine. This information can then be used to search the contents of the virtual disk image, to enforce usage policies, to provide extensibility for vendors, and the like.
Owner:MICROSOFT TECH LICENSING LLC
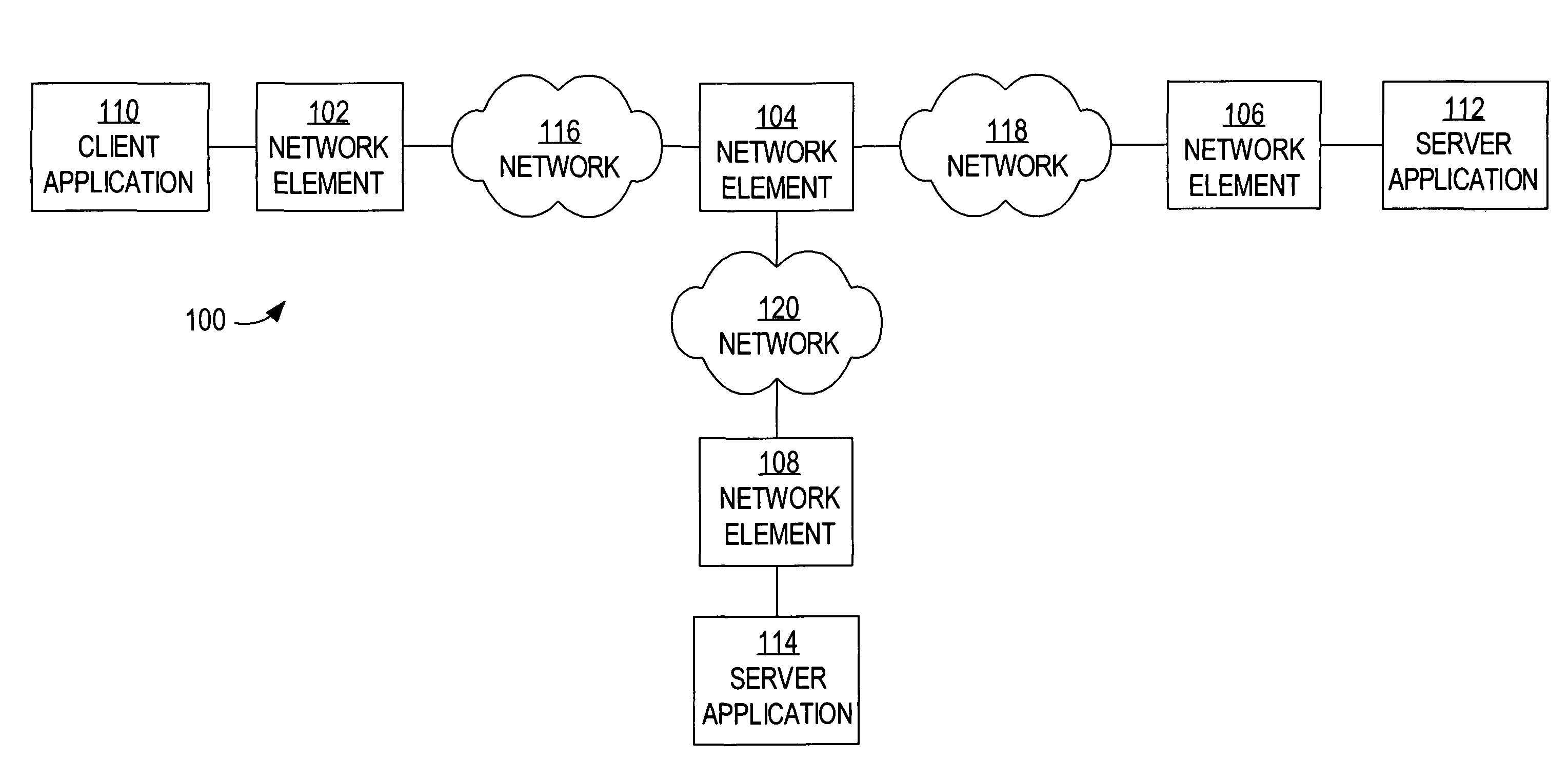
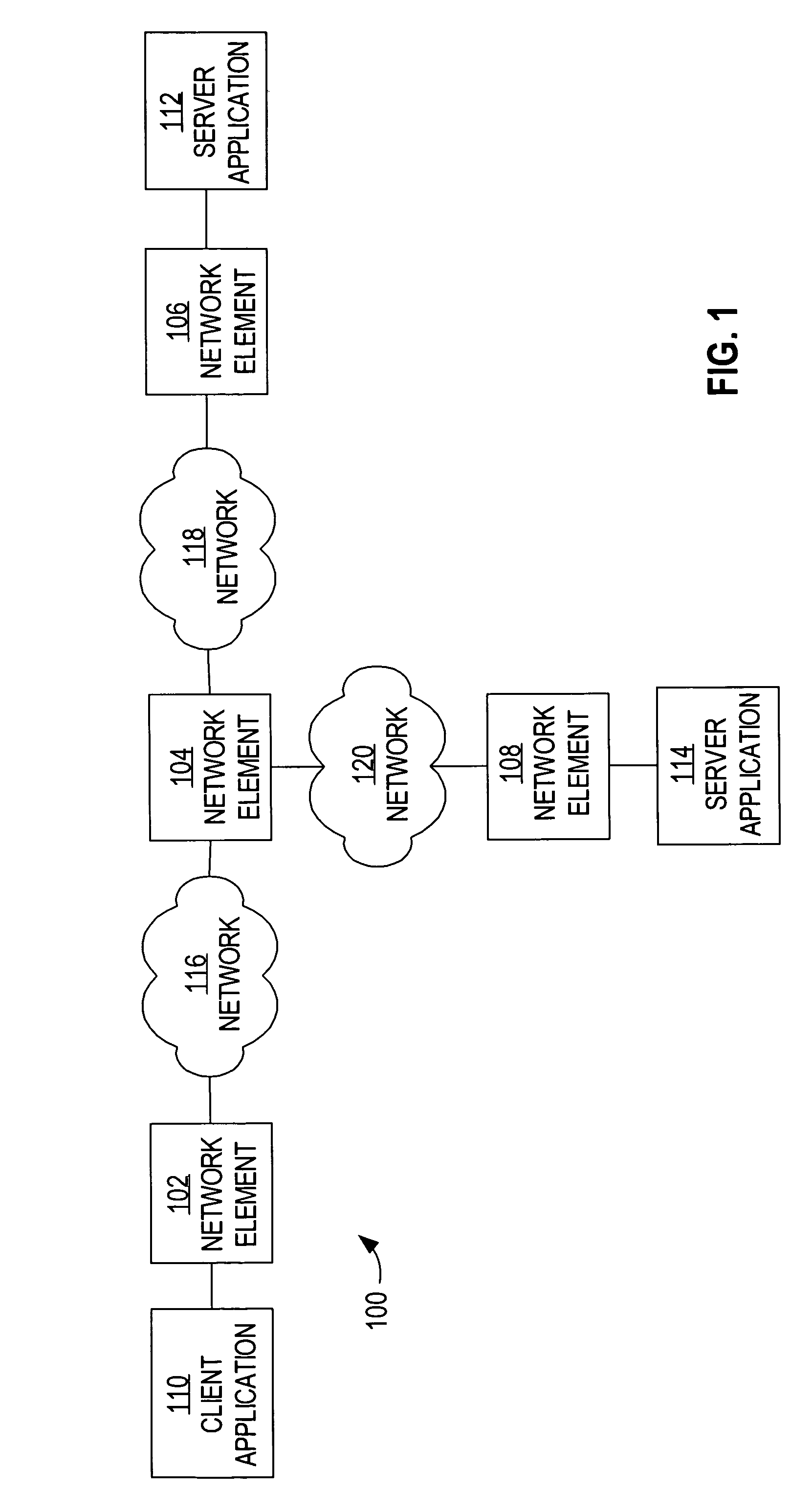
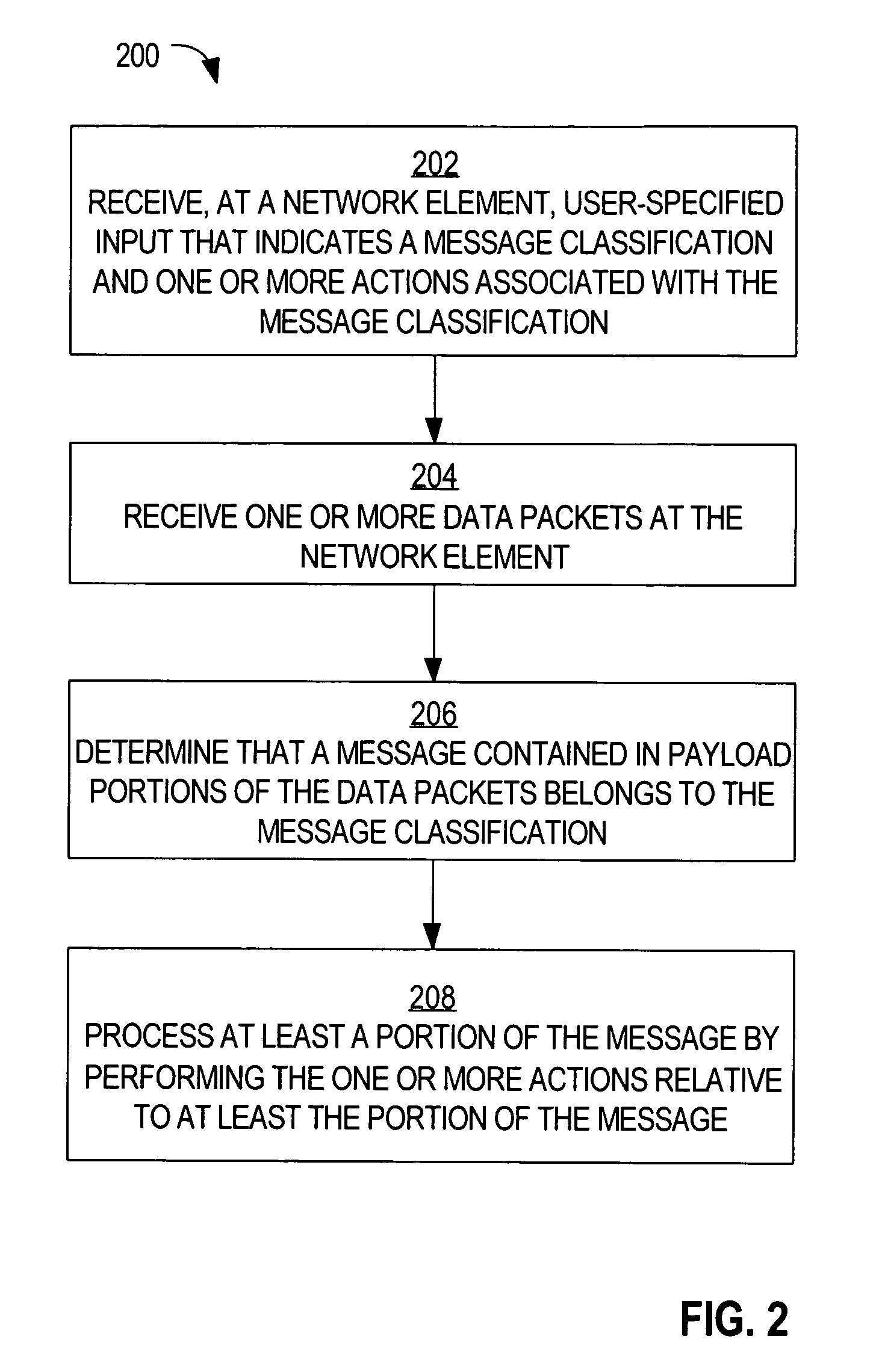
Method and apparatus for generating a network topology representation based on inspection of application messages at a network device
ActiveUS7996556B2Multiple digital computer combinationsProgram controlRelevant informationContext based
A method is disclosed for generating a network topology representation based on inspection of application messages at a network device. According to one aspect, a network device receives a request packet, routes the packet to the destination, and extracts and stores correlation information from a copy of the request packet. When the network device receives a response packet, it examines the contents of a copy of the response packet using context-based correlation rules and matches the response packet with the appropriate stored request packet correlation information. It analyzes recorded correlation information to determine application-to-application mapping and calculate application response times. Another embodiment inserts custom headers that contain information used to match a response packet with a request packet into request packets.
Owner:CISCO TECH INC
Method and apparatus for transmitting data in a peer-to-peer network
InactiveUS20080256175A1Improve download speedMultiple digital computer combinationsTransmissionManagement unitClient-side
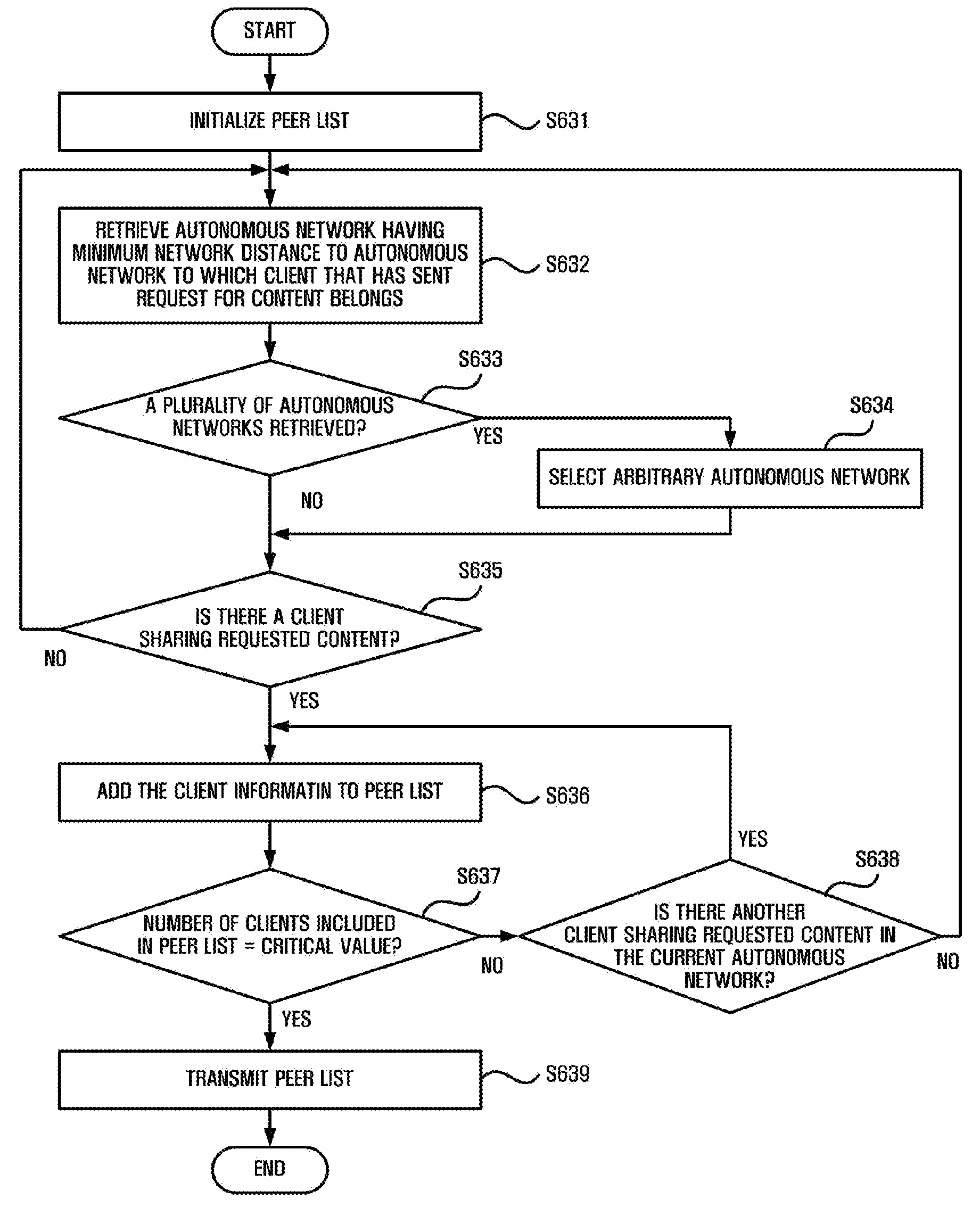
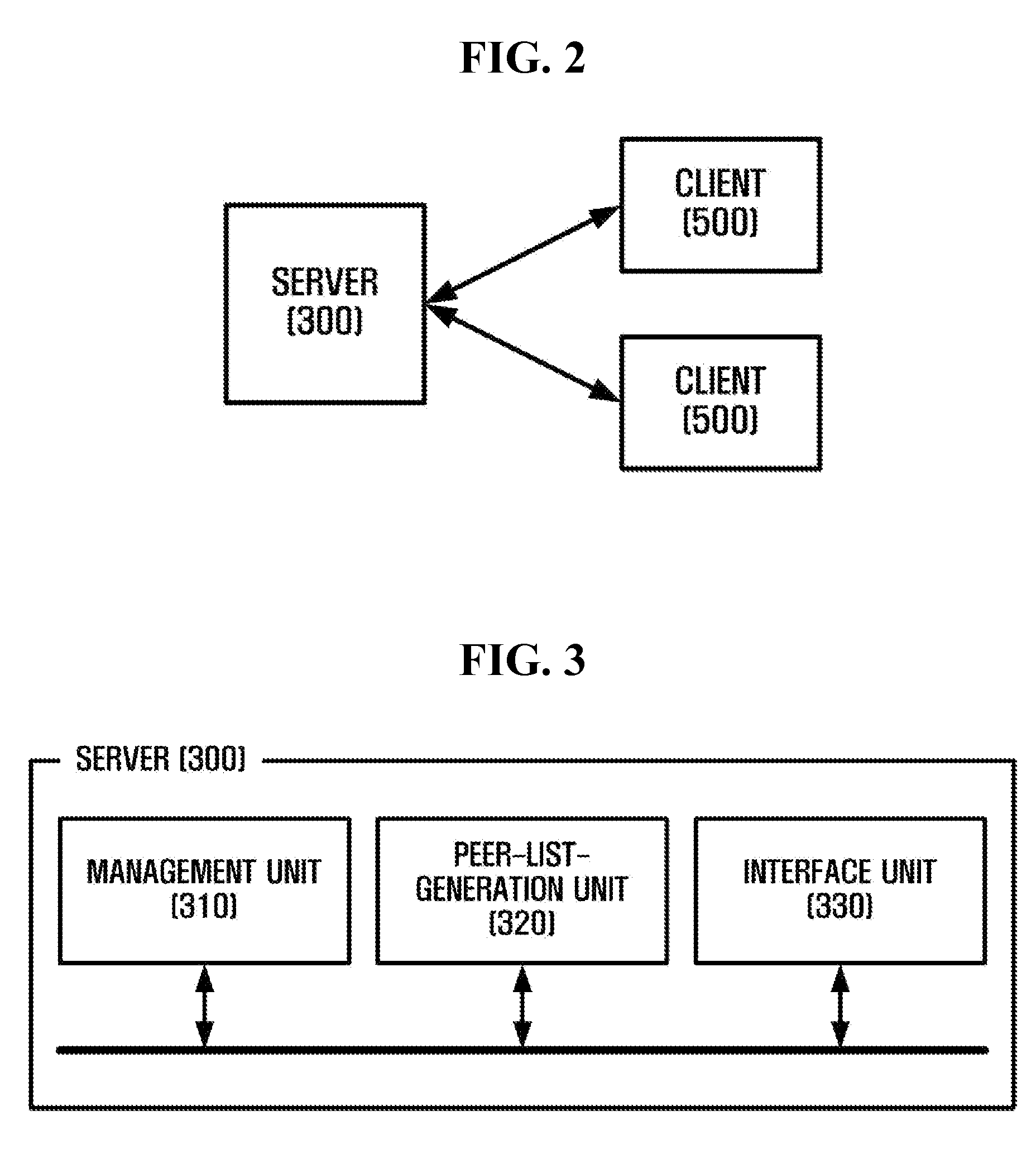
An apparatus for transmitting data which includes a management unit that manages network-topology information of clients participating in the P2P service, and an interface unit that provides to a first client a peer list including information of a client having the minimum network distance to the first client, based on the network topology information, when receiving a request for content from the first client.
Owner:SAMSUNG ELECTRONICS CO LTD
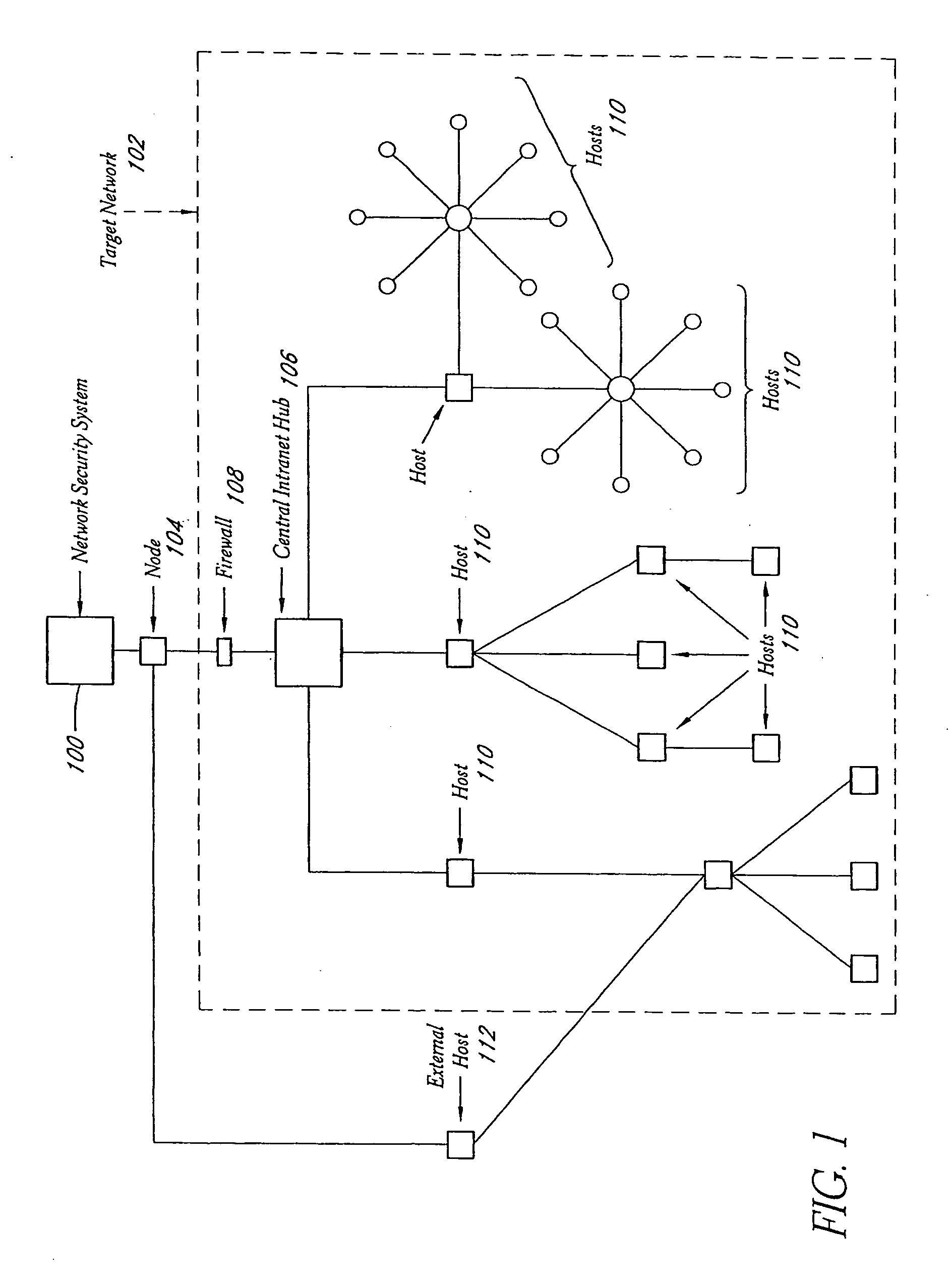
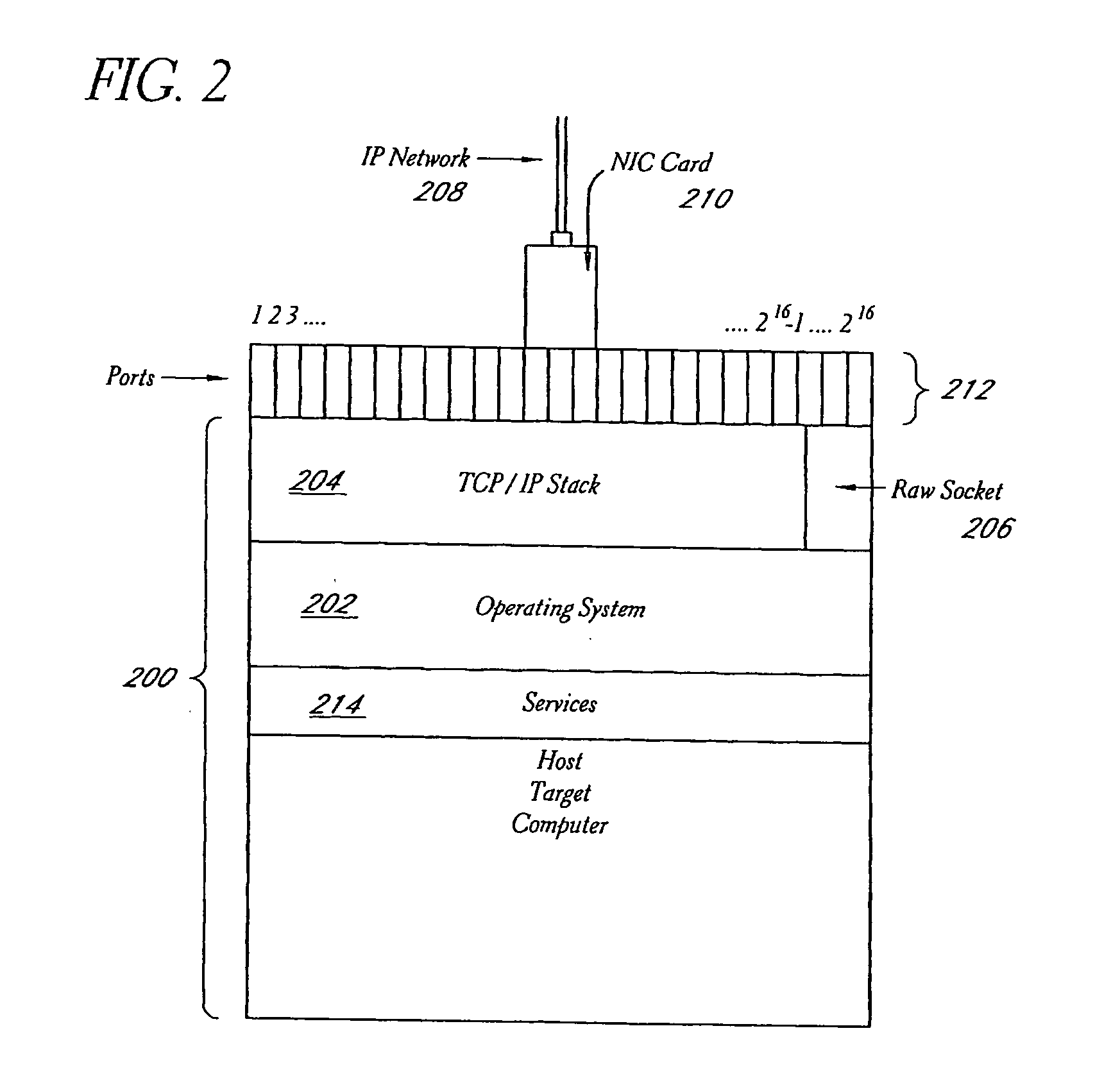
System and method for network vulnerability detection and reporting
ActiveUS7257630B2Reduce the possibilityReliably determinedMemory loss protectionError detection/correctionGraphicsOperational system
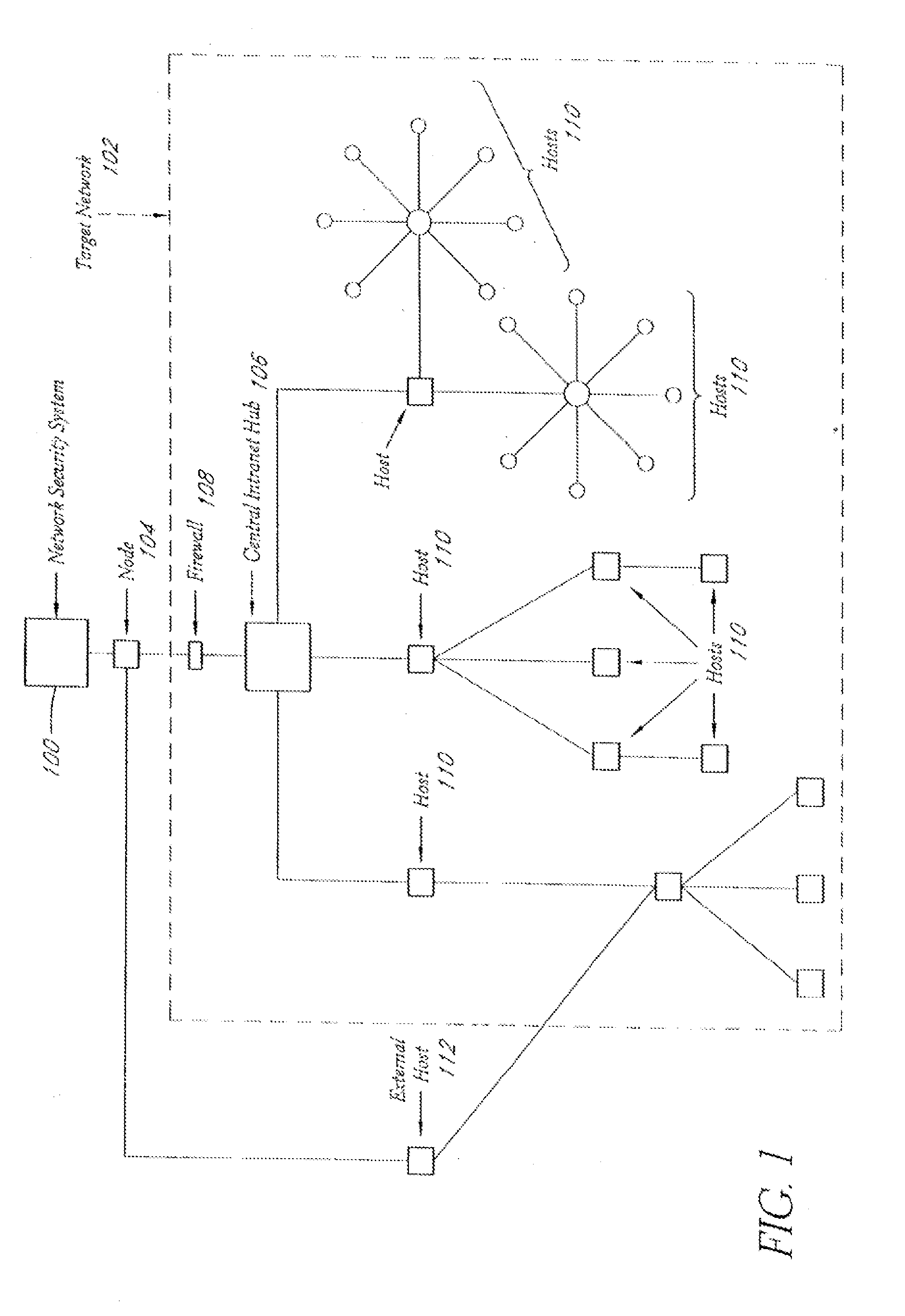
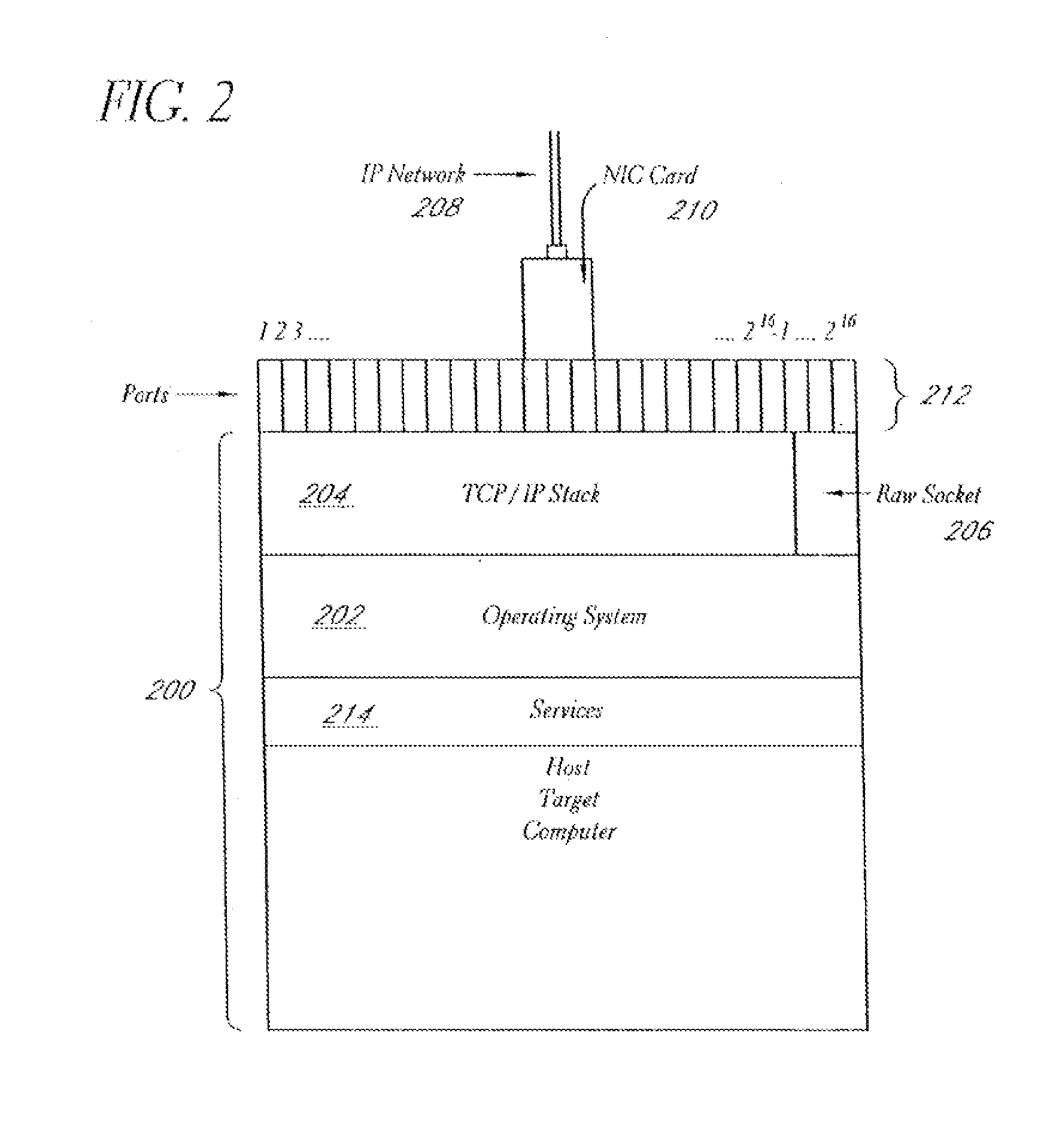
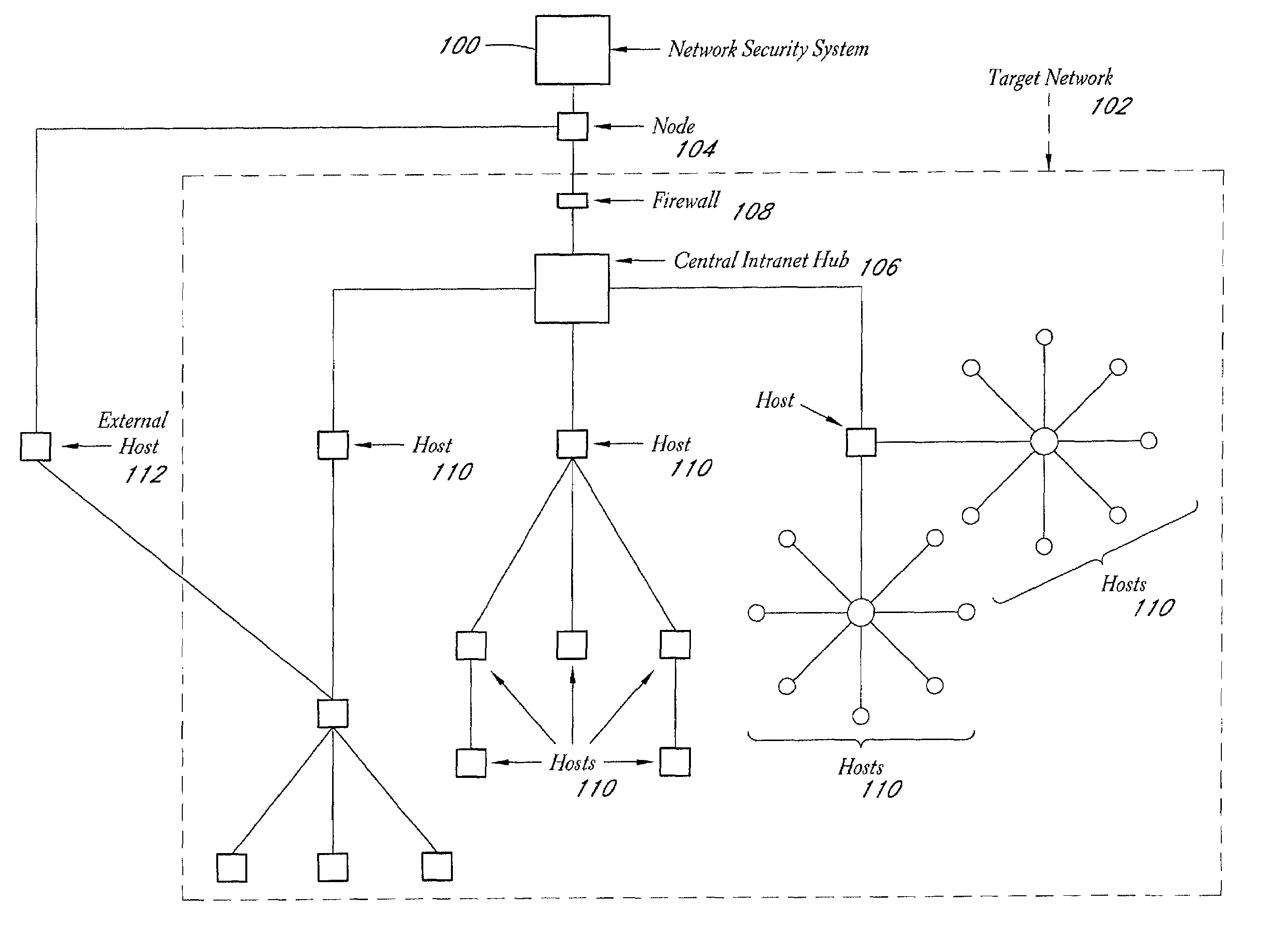
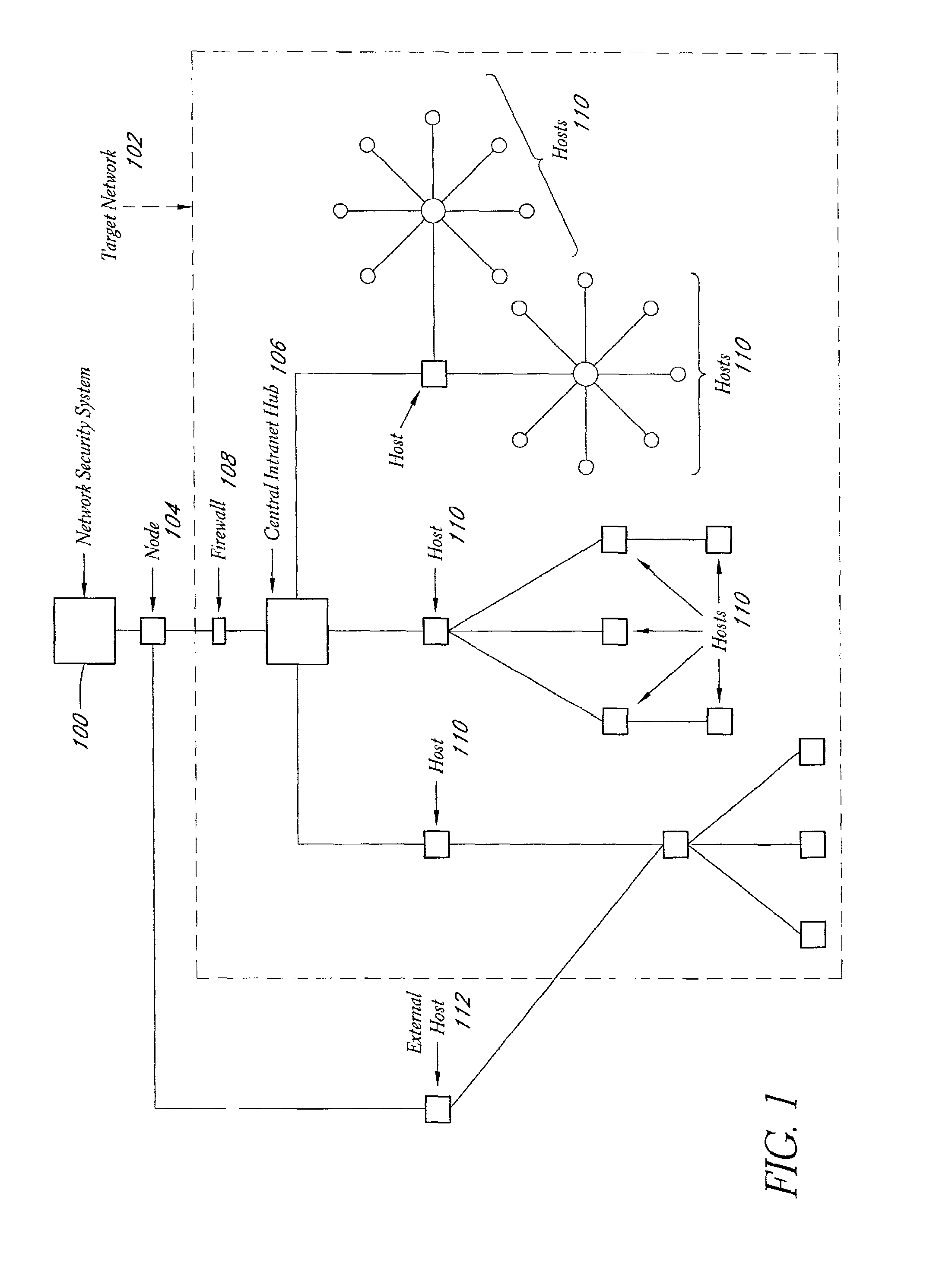
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
System and method for network vulnerability detection and reporting
ActiveUS7152105B2Easy to useReliably determinedElectric signal transmission systemsImage analysisGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
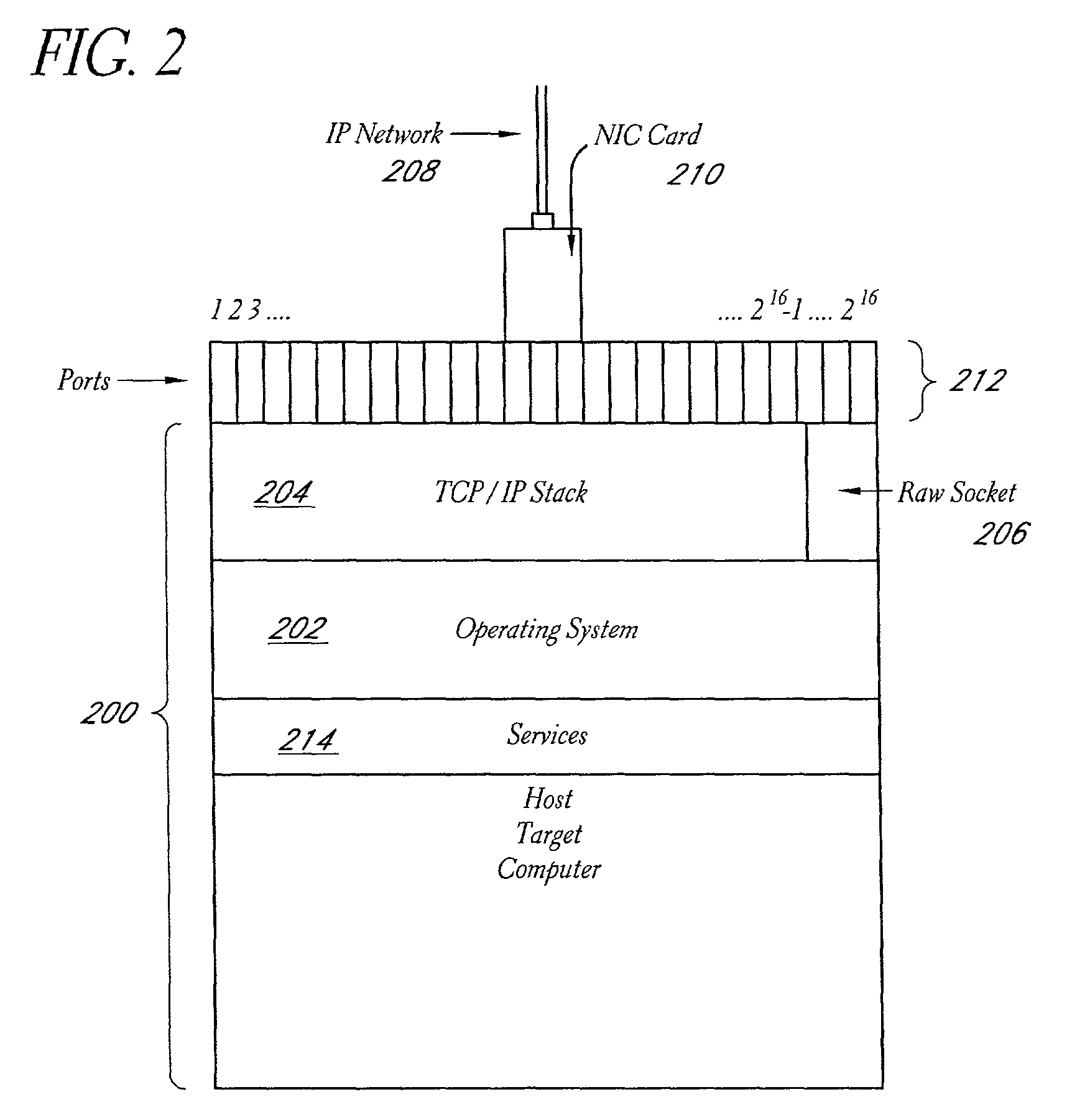
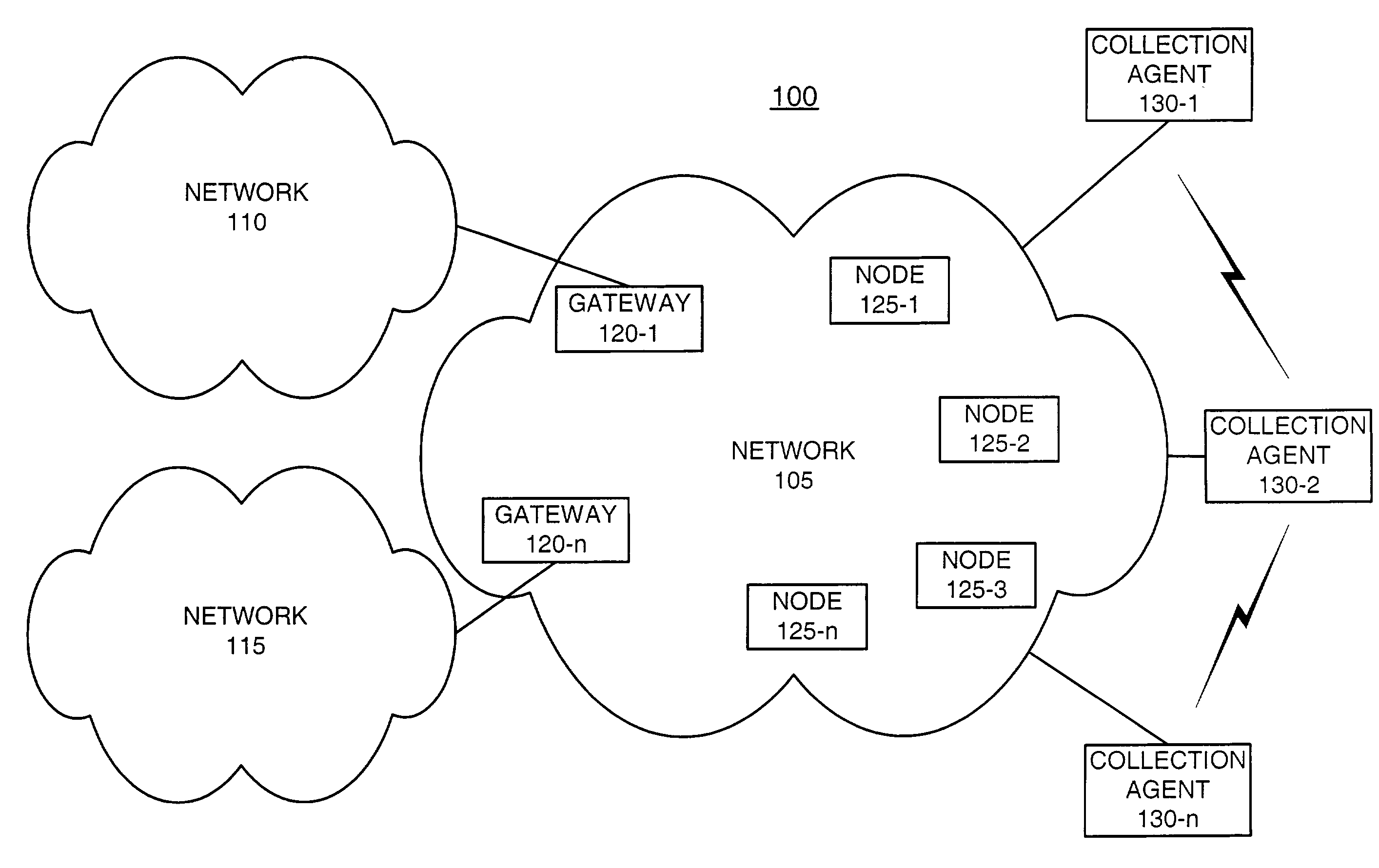
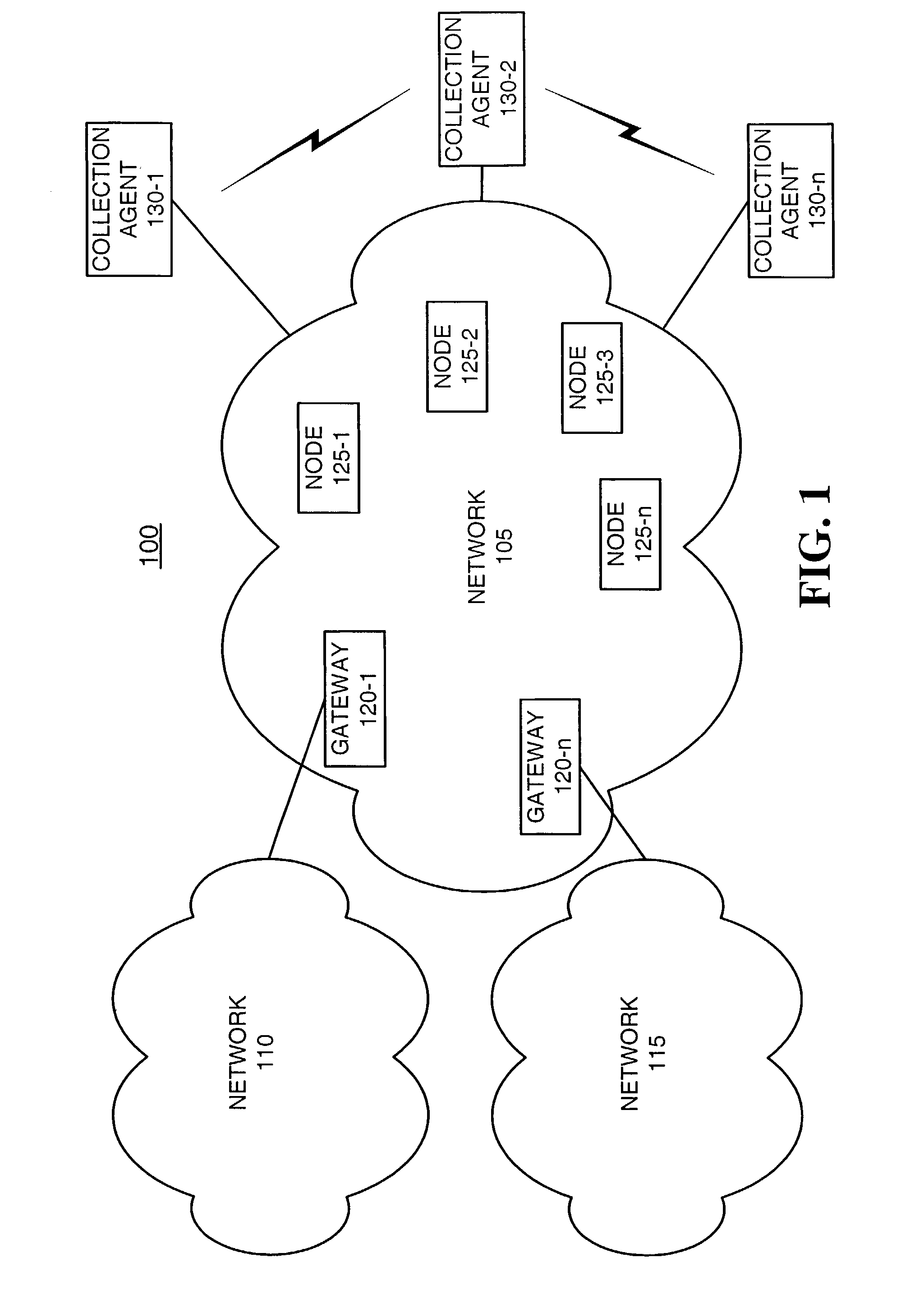
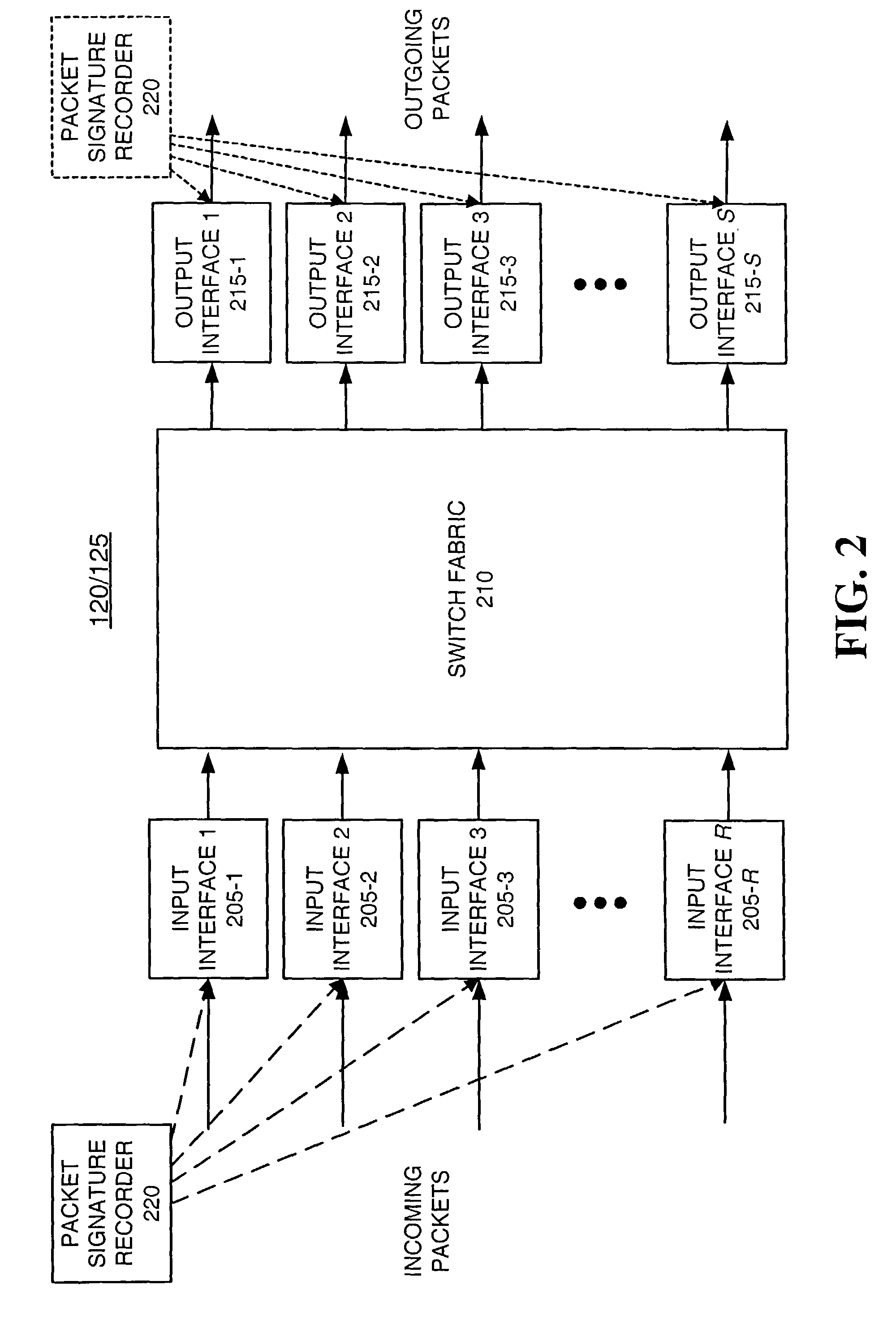
Systems and methods for network performance measurement using packet signature collection
InactiveUS6978223B2Amplifier modifications to reduce noise influenceNuclear monitoringNetwork topologyDistributed computing
A system for measuring network performance parameters includes multiple network nodes (125) and at least one collection agent (130). Each of the multiple network nodes (125) calculates signature values for received packets. Each of the signature values includes an identifier for a corresponding packet. The collection agent (130) collects the signature values from the multiple network nodes (125), and determines one or more network performance parameters based on the collected signature values and network topology information.
Owner:RAYTHEON BBN TECH CORP
Method and apparatus for network wide policy-based analysis of configurations of devices
ActiveUS7003562B2Traffic controlDigital computer detailsData switching networksNetwork strategyNetwork topology
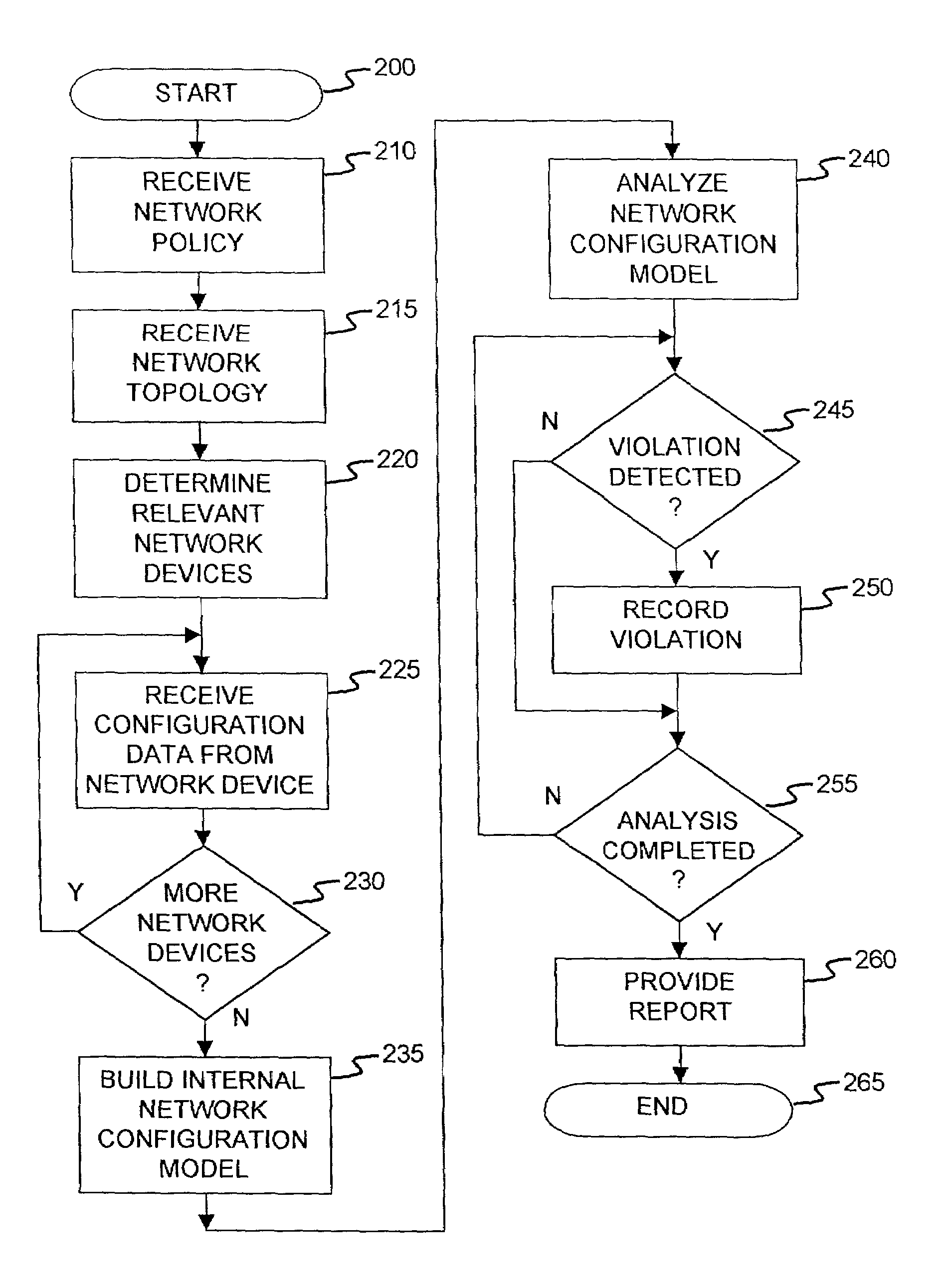
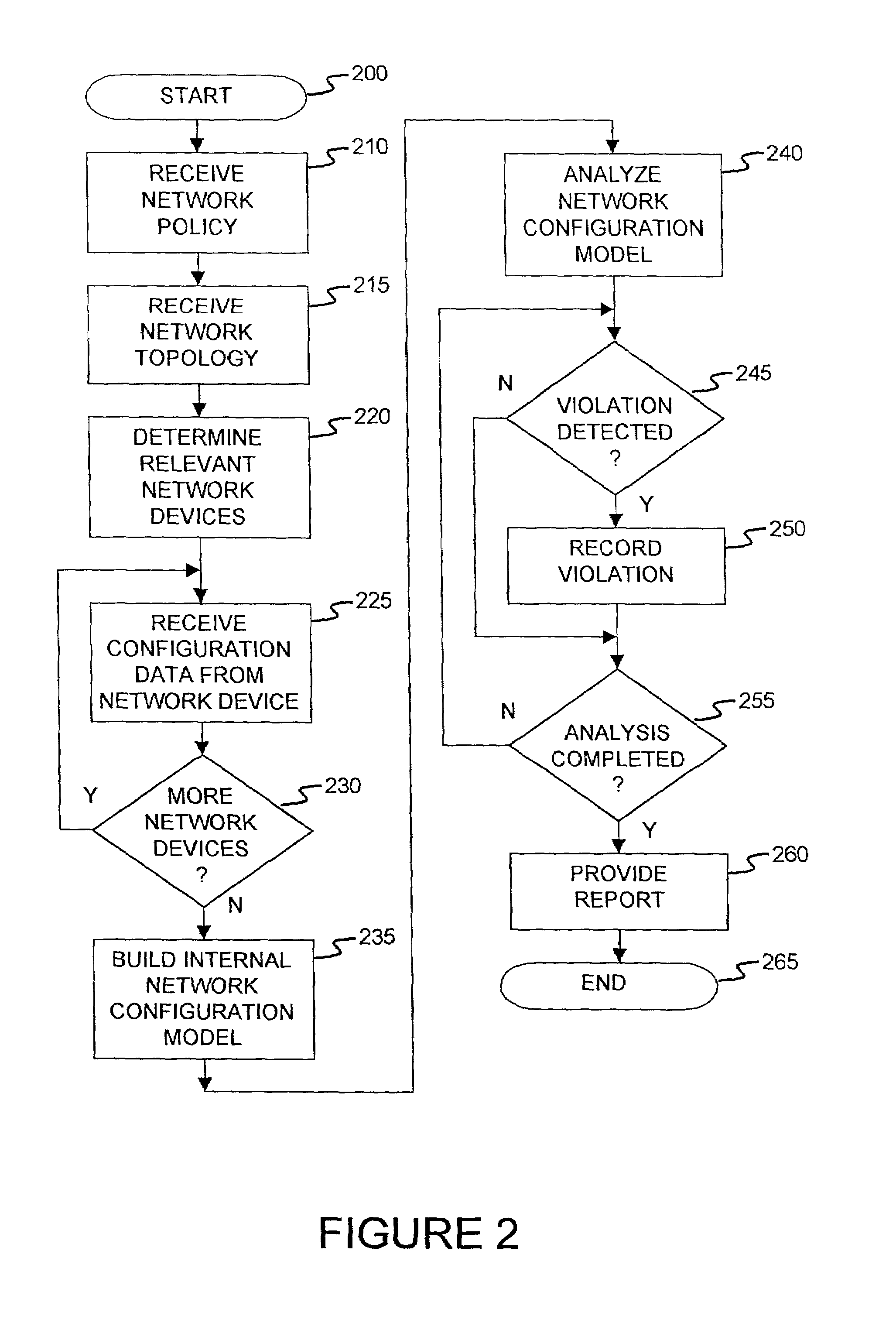
A method and an apparatus for analyzing a network configuration against a corporate network policy and determining violation(s) against the corporate network policy. A report indicating the violation(s) can be generated indicating instances of the violation(s). An analysis platform reads in a network policy. The analysis platform collects configuration files from the relevant network devices in the network and builds up an internal instance of a network configuration model based on the configuration files and the network topology. The analysis platform analyzes this network configuration model according to the network policy and adds an entry to its final report each time that it detects a violation against the network policy in the network configuration model. The data in the entries pinpoints the cause of the deviation(s) from the network policy.
Owner:REDSEAL
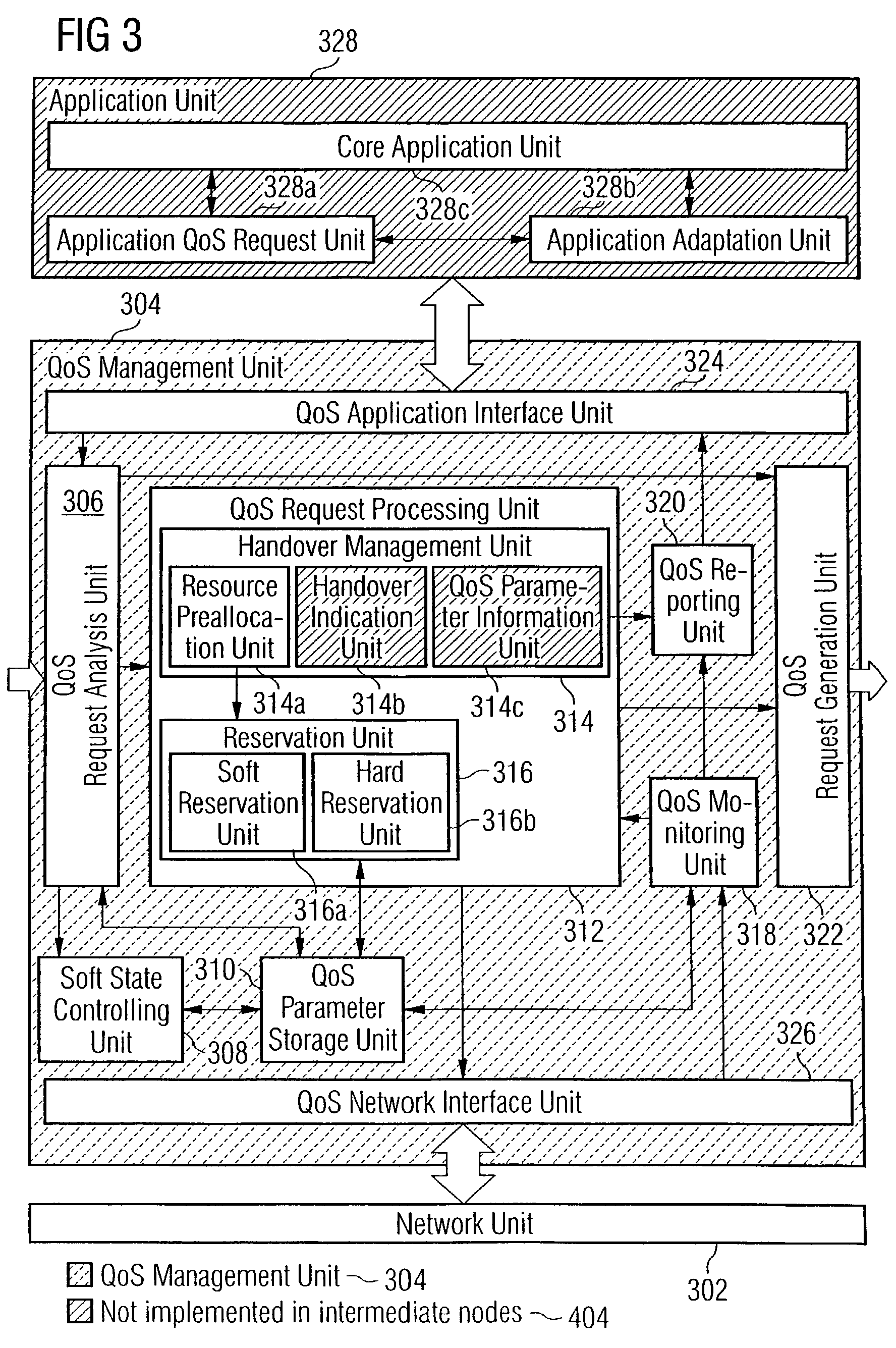
Adaptive quality-of-service reservation and pre-allocation for mobile systems
ActiveUS7289453B2Minimize impactDelay minimizationError preventionTransmission systemsAdaptive servicesQos management
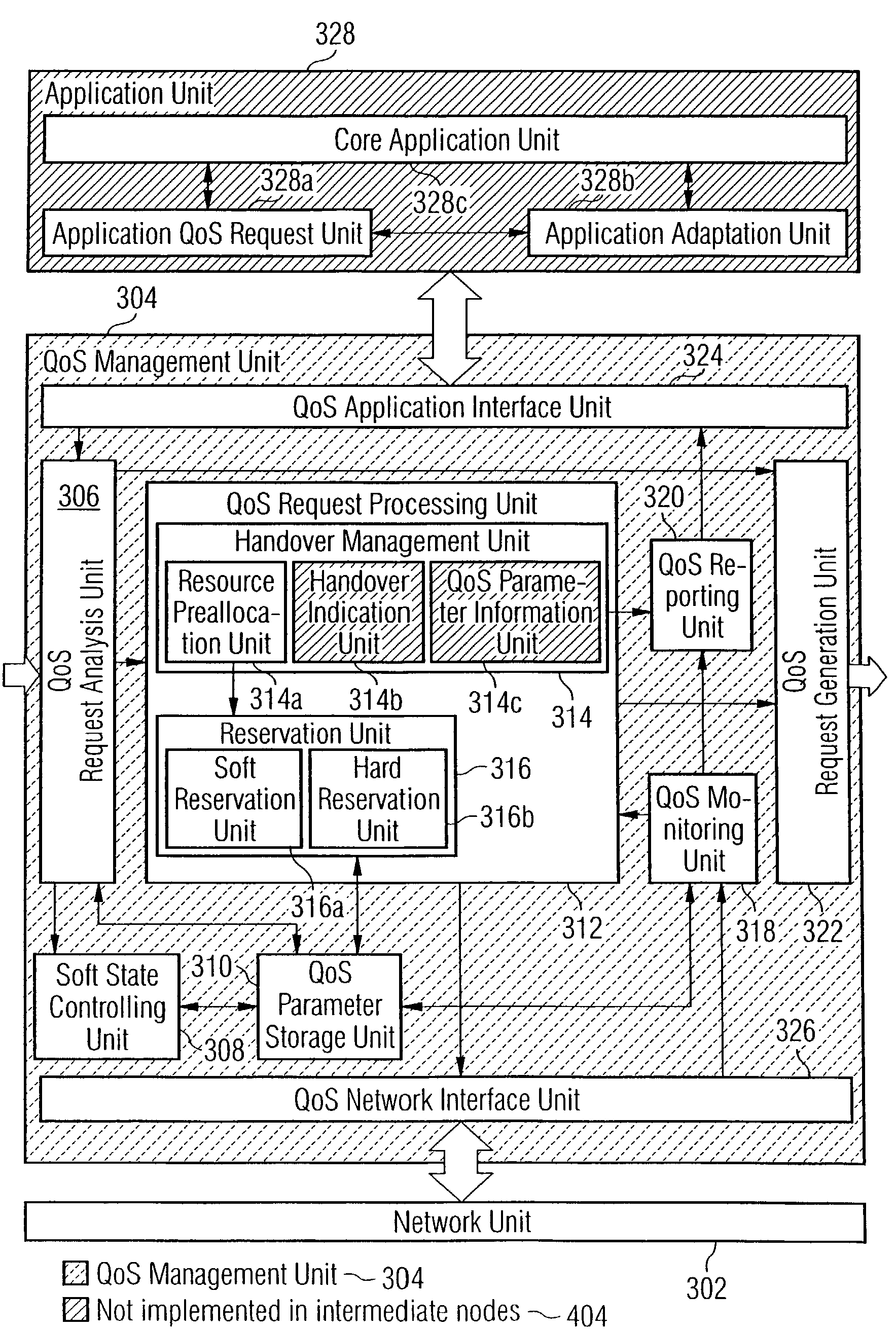
In the field of Quality-of-Service (QoS) management for adaptive real-time services running on mobile devices which support different access technologies in dynamic wireless Internet Protocol (IP) networks, the connectivity of the applied nodes is unpredictable time-varying. In this context, a QoS management unit (304) is proposed that allows adaptive applications with real-time requirements in typical mobile wireless scenarios—e.g. a radio link with a changing transmission quality and handover procedures (2900)—to adaptively and responsively react to a time-varying network topology and different radio link characteristics. Said QoS management unit (304) provides methods of pre-allocating, reserving, monitoring and adapting QoS-related parameters in a dynamic mobile environment.The QoS management unit (304) comprises at least one analysis unit (306) which evaluates QoS requests received from other nodes (402a / b, 404) to inform the application unit (328) of said mobile terminal (208) about the current QoS situation, at least one processing unit (312) that manages request messages (1200, 2000, 2400) for each type of QoS request, at least one monitoring unit (318) which monitors the current QoS situation within said mobile node (208) and initiates requests by activating the processing unit (312), and at least one generation unit (322) which is responsible for generating QoS requests or passing them on to the QoS management units (304) of other nodes (402a+b, 404).
Owner:SONY DEUT GMBH
Methods and apparatus for managing network resources using a network topology view
ActiveUS7315985B1Quick fixReduce usageDigital computer detailsProgram controlGraphicsGraphical user interface
Mechanisms and techniques provide a system for visualization of manageable network resources in a graphical user interface. The system displays a host element in a host display area, a storage element in a storage display area, and a connectivity element in a network display area of the network topology view on the display of the computerized device. The system displays the network display area in between the host display area and the storage display area. The system determines a coupling condition of the connectivity element in relation to at least one of the host element and the storage element and displays the coupling condition as a link on the display of the computerized device between the connectivity element and either or both of the host element and the storage element to which that coupling condition relates in order to visually convey the coupling condition to a user viewing the network topology view on the display of the computerized device.
Owner:EMC IP HLDG CO LLC
Secure cloud fabric to connect subnets in different network domains
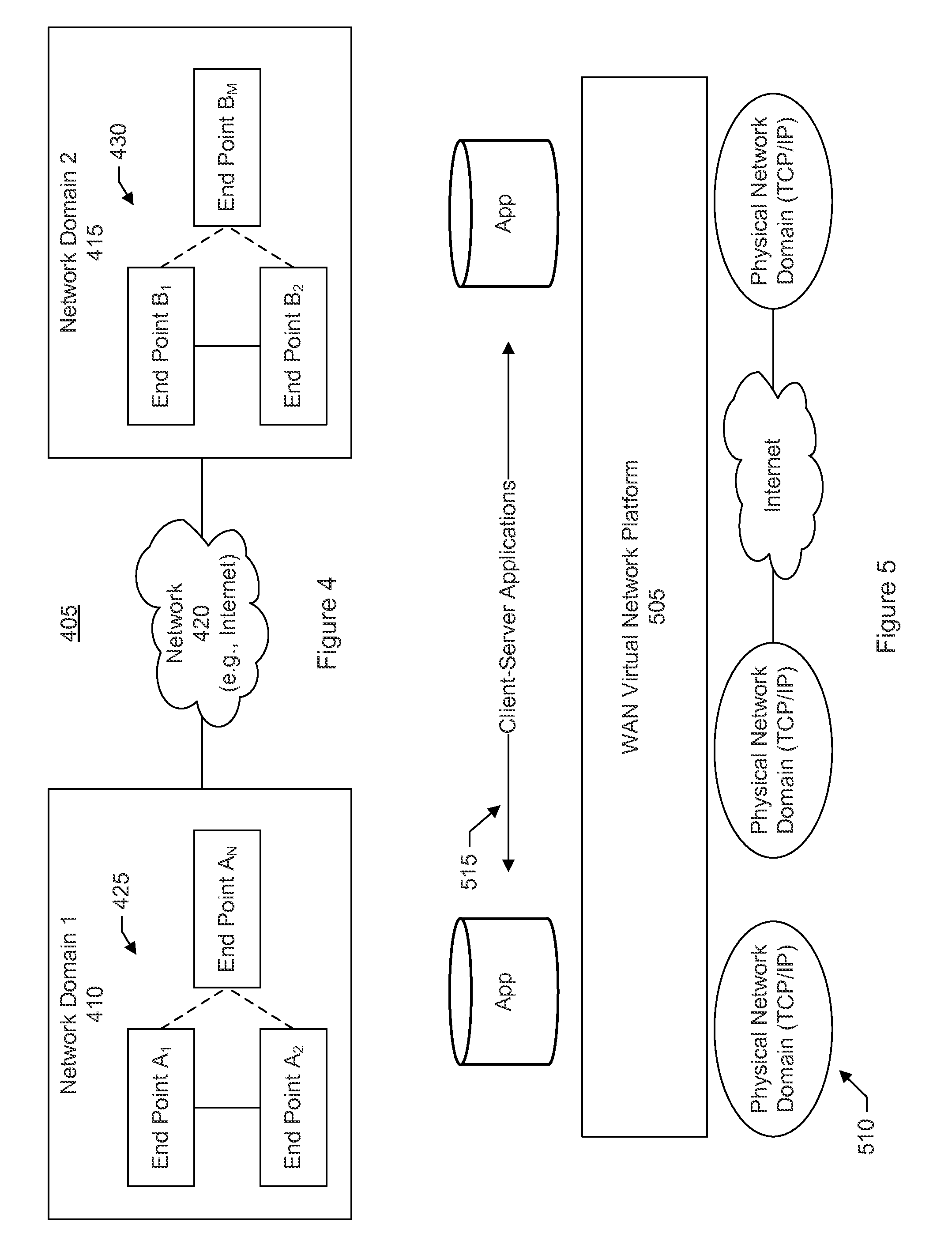
ActiveUS20140337500A1Digital computer detailsData switching networksStructure of Management InformationNetwork topology
A secure virtual network platform connects two or more subnets in different or separate network domains. The secure virtual network can use the under layer physical networks in various domains as an IP forwarding fabric without changing any existing firewalls, security settings, or network topology. A first type of connection across the virtual network involves connecting server groups. A second type of connection across the virtual network involves connecting a server group to a physical network. A third type of connection across the virtual network involves connecting a physical network to another physical network.
Owner:ZENTERA SYST
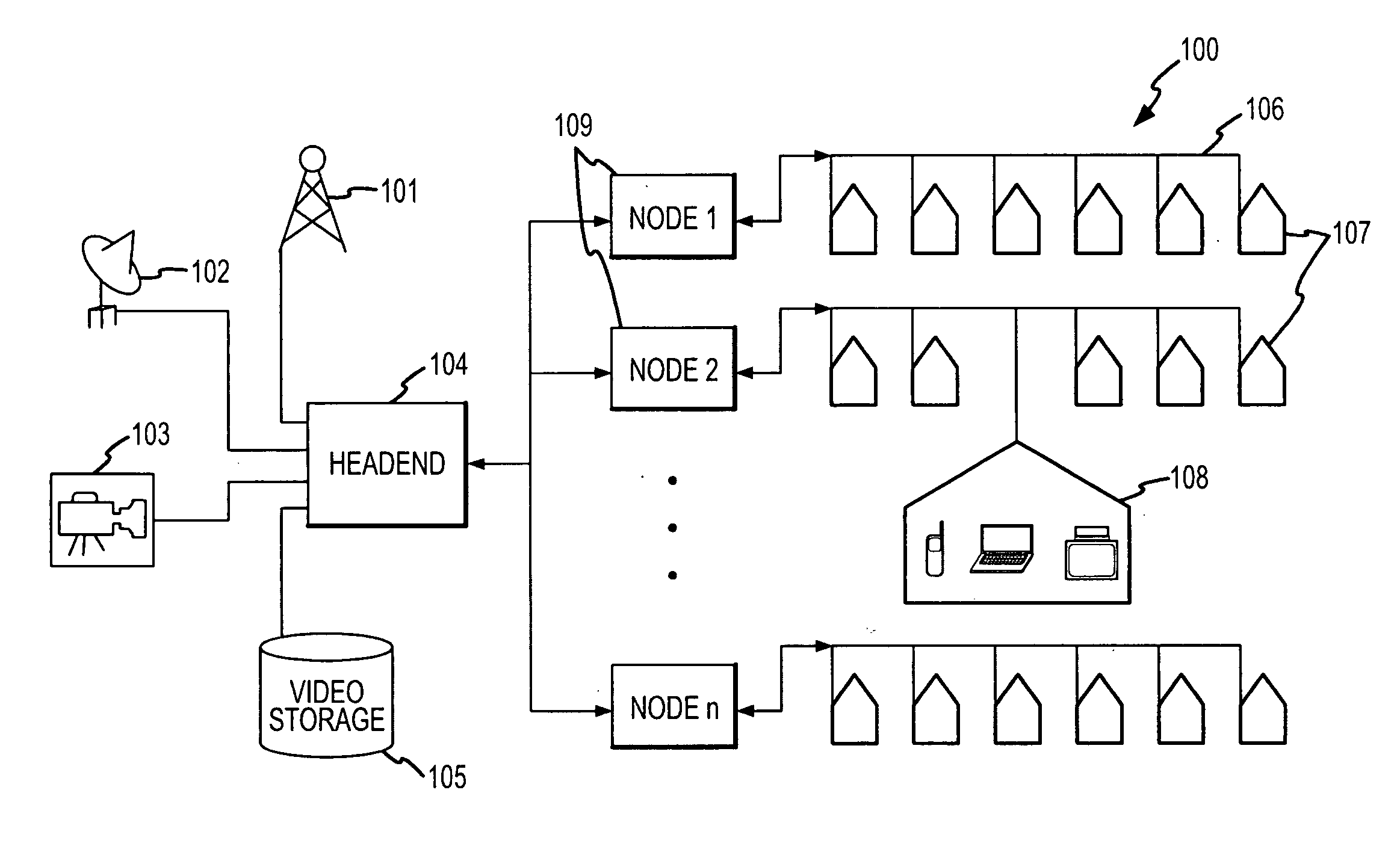
Dynamically distributed, portal-based application services network topology for cellular systems
InactiveUS20060111095A1Increase incomeEasily augment and/or customize the “look and feel”Network topologiesAutomatic exchangesHuman–machine interfaceData acquisition
Methods, apparatuses and systems directed to a portal-based, dynamically distributed application topology for cellular systems. The portal-based application topology, in one implementation, is an application architecture featuring strategic dynamic distribution of the man-machine interface (such as data acquisition and information presentation) and the backend processing aspects, of a particular application. In one implementation, all terminal interfacing aspects (such as data acquisition, data presentation) are formatted and handled by systems associated with a cellular system operator, as described below, while background processing is performed by a processing facility remote to the cellular system operator. In one implementation, the distributed application topology allows a mobile station, such as a cellular telephone, to simply act as a thin-client accessing an application server via a cellular systems operator's web portal for page-based interface screens.
Owner:GLENN PATENT GROUP
System and method for network vulnerability detection and reporting
InactiveUS20070011319A1Easy to useReliably determinedDigital computer detailsPolarising elementsGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
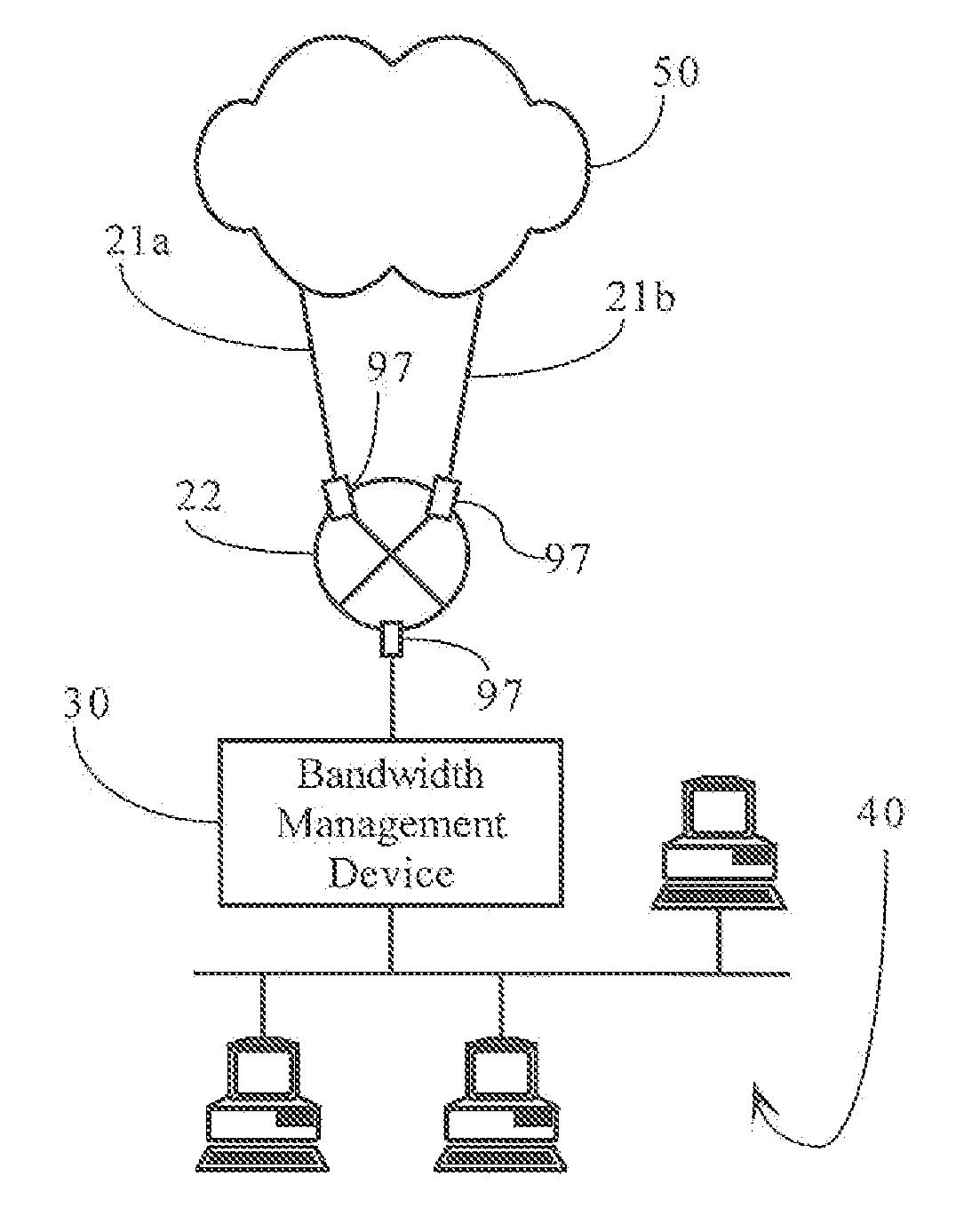
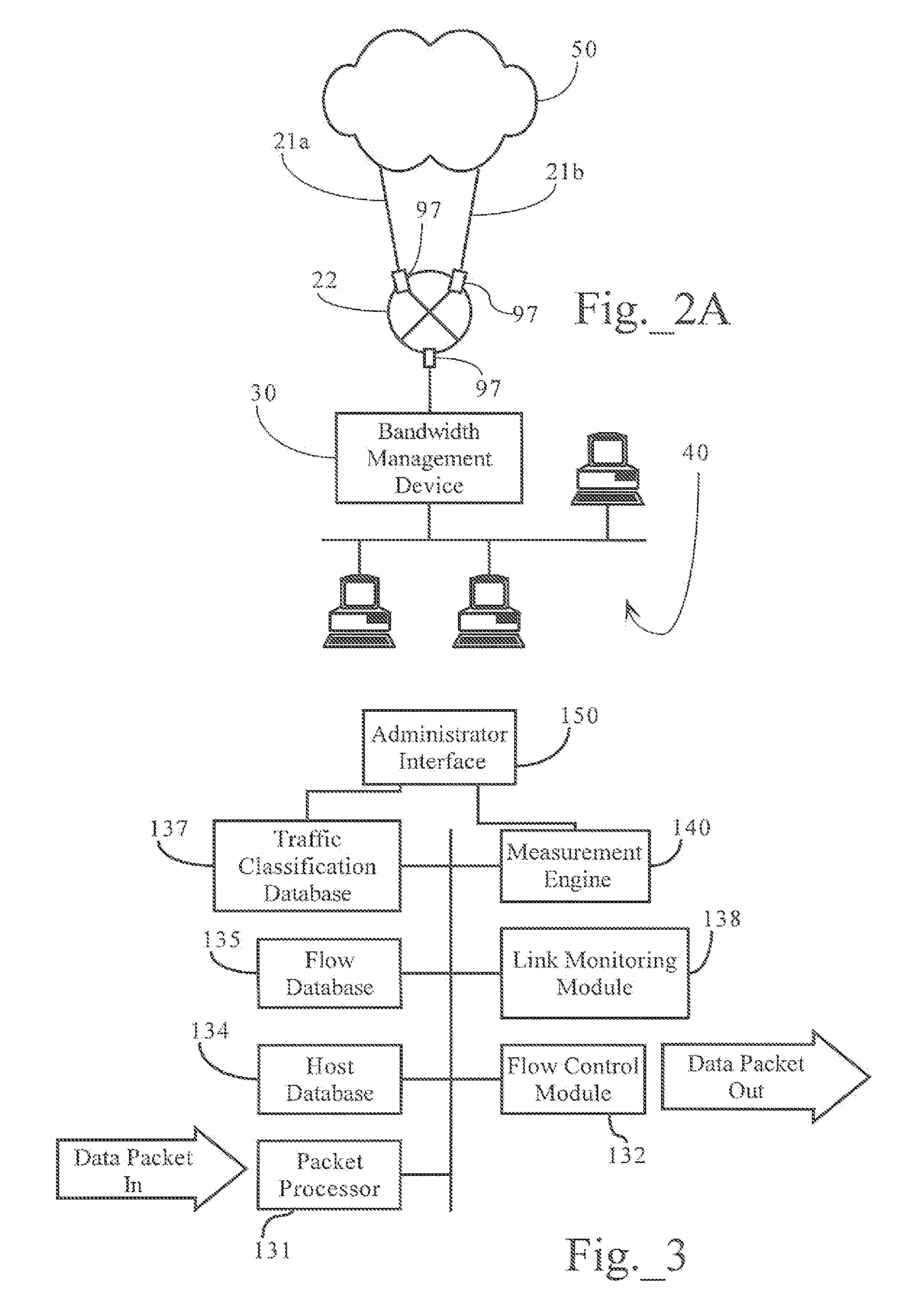
Dynamic bandwidth management responsive to access link state in redundant network topologies
ActiveUS7324553B1Improve network efficiencyEnsure smooth networkError preventionFrequency-division multiplex detailsTraffic capacityBandwidth management
Methods, apparatuses and systems allowing for dynamic bandwidth management schemes responsive to the state of a plurality of access links in redundant network topologies. In one embodiment, the present invention provides a bandwidth management device that periodically queries routing systems associated with access links, conceptually grouped into a virtual access link, to monitor that load of the access links and, depending on the detected load, adjust the configuration of the bandwidth management device to avoid overloading one or more of the access links. Embodiments of the present invention increases network efficiency and help network traffic to flow more smoothly with higher throughput. In one embodiment, the dynamic link control functionality is invoked when any given access link reaches a threshold capacity level. Assuming that network traffic will scale in the same ratio as presently observed, the present invention calculates the maximum traffic that can be let through so that no network interface or access link is overloaded.
Owner:CA TECH INC
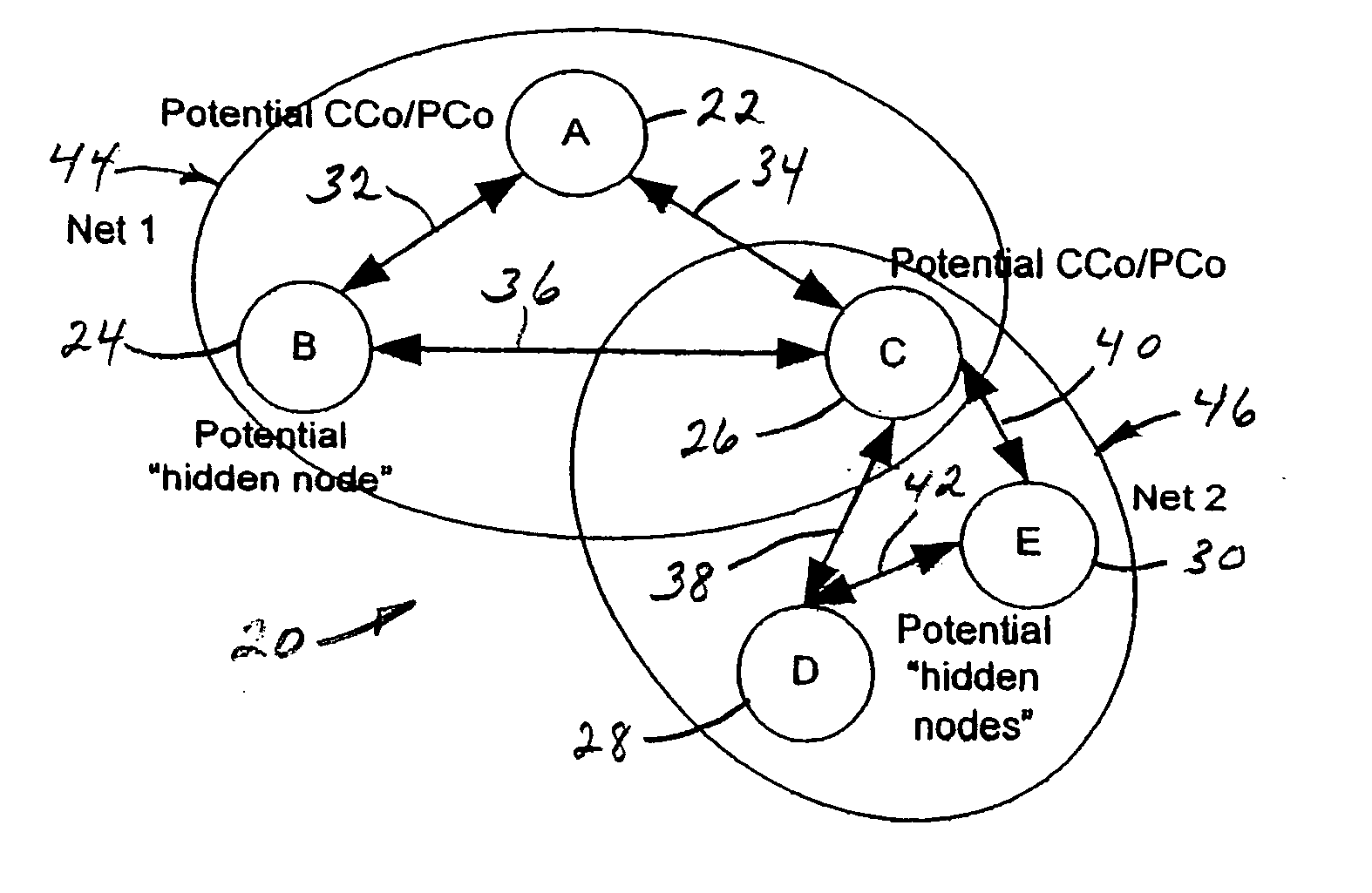
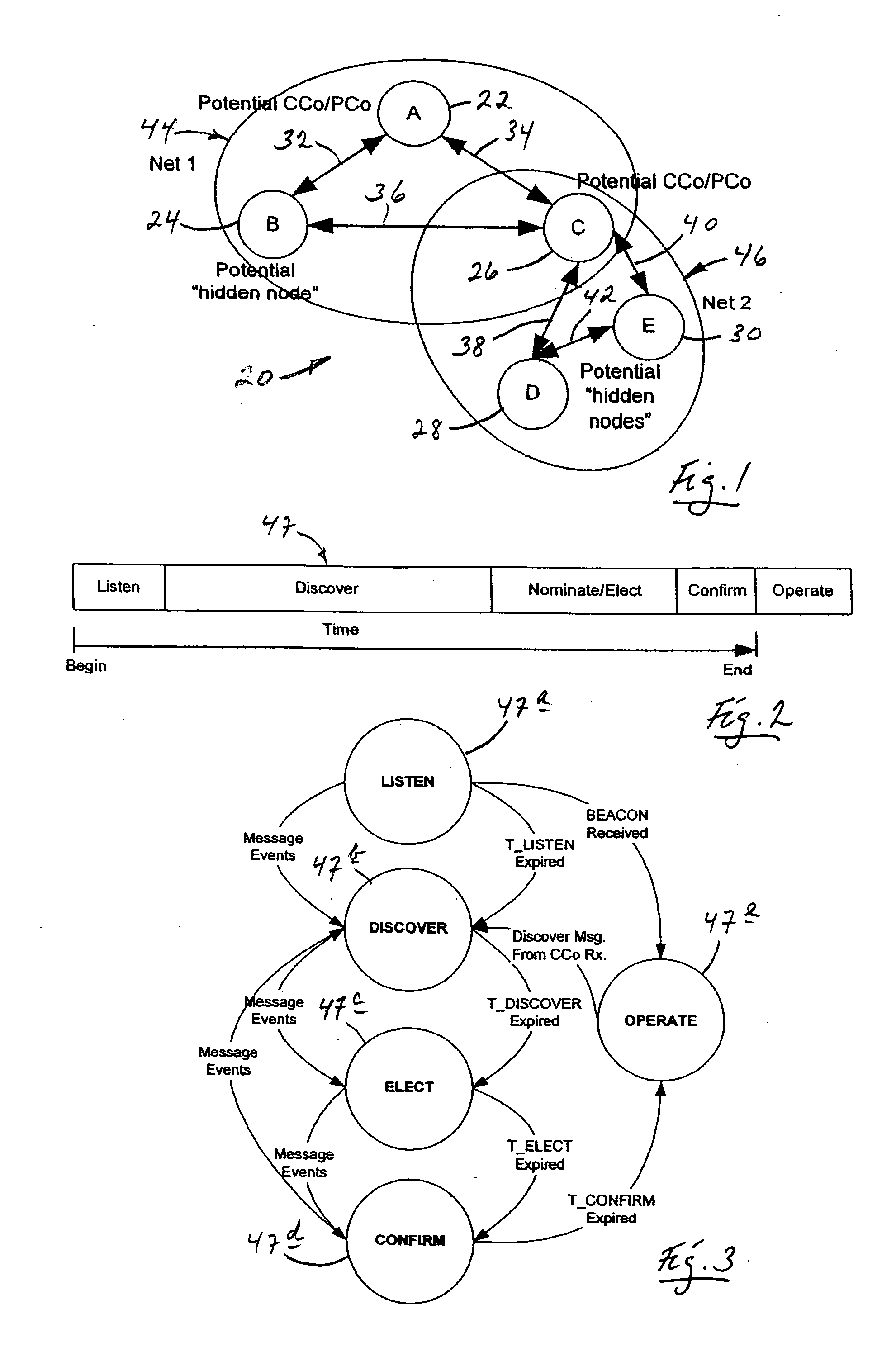
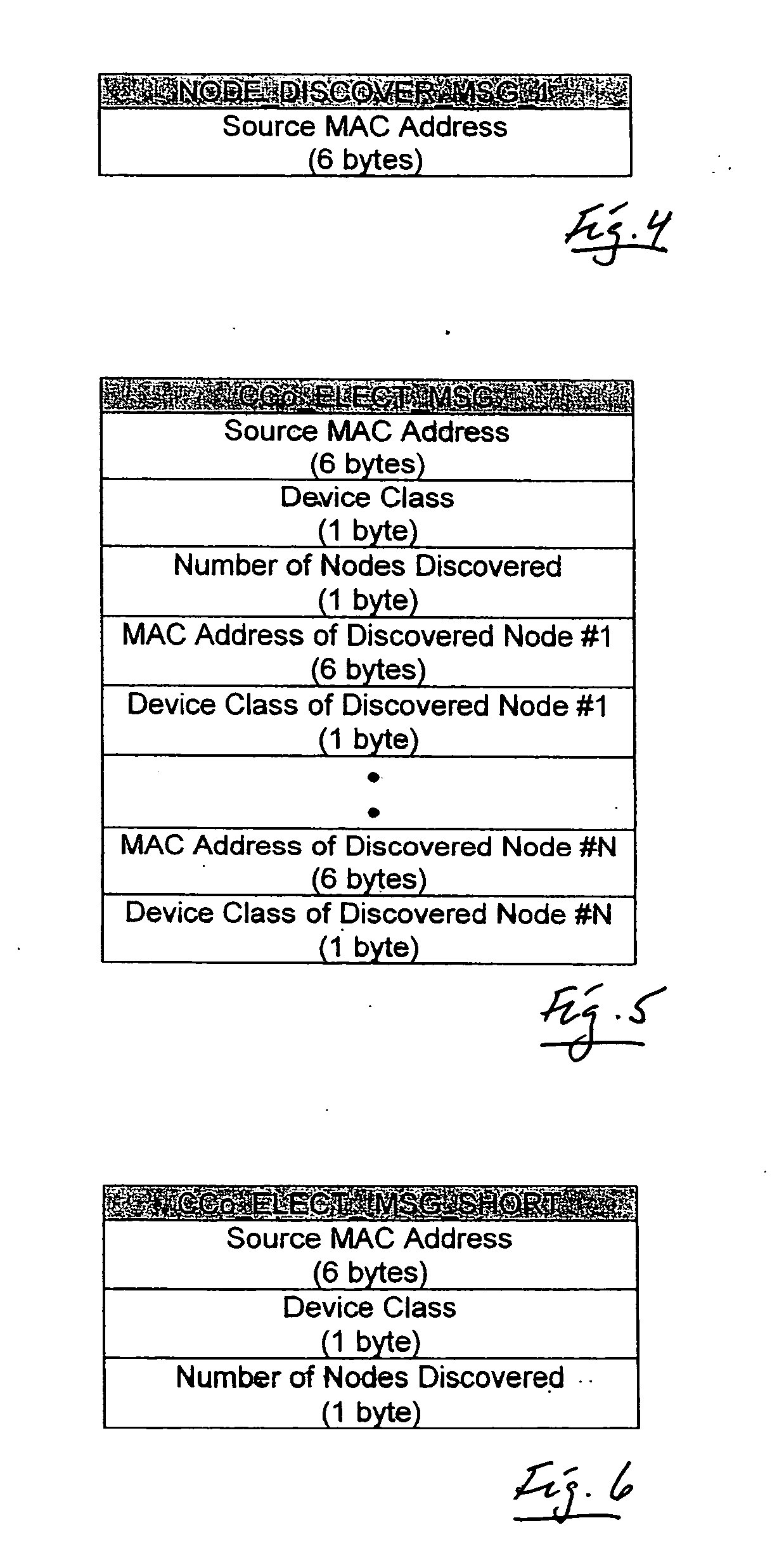
Distributed network organization and topology discovery in ad-hoc network
InactiveUS20050174950A1Reduce collisionImprove throughputData switching by path configurationNetwork topologyDistributed computing
A distributed network method for self-organizing a group of nodes into a bi-directional communication network where initially there is no central coordinator in the prospective network environment. The method involves engaging in the process of determining internodal communication capabilities en route to creating a network topology table, and then using that table as a guide (a) selecting, by nodal election, an appropriate central coordinator, and (b) establishing proxy nodes which enable full network bi-directional communication between all nodes, including otherwise communicatively-compromised hidden nodes.
Owner:SHARP LAB OF AMERICA INC
Method for Configuring an Optical Network
InactiveUS20090296719A1Huge complexityHuge timeData switching by path configurationOptical multiplexObject definitionNetwork model
A network model for the planning and / or the provisioning of traffic flows in a communication network includes nodes interconnected with each other by links according to a given network topology. The network model uses a graph defined by arc objects storing information related to both the links and adjacent nodes thereof.
Owner:TELECOM ITALIA SPA
Targeting content based on location
ActiveUS20090044246A1Enhanced location based targetingPrecise positioningAnalogue secracy/subscription systemsSelective content distributionGraphicsGraphical user interface
Assets of broadcast network content are targeted to network users of interest based on location information regarding user equipment devices. Asset providers can specify location targeting criteria via a graphical user interface displaying mapping information. This location targeting criteria can then be compared to location information regarding user equipment devices so that assets are delivered to appropriate devices. The comparison of the location targeting criteria to the device location information can be performed at the user equipment devices or at another location. In the latter case the assets can be addressed to appropriate user equipment devices or appropriate user equipment devices can be directed to select the asset, which is broadcast via the network. In this manner, assets can be targeted to individual network users on a basis independent of network topology.
Owner:INVIDI TECH
Sustained vehicle velocity via virtual private infrastructure
ActiveUS20170337813A1Controlling traffic signalsInstruments for road network navigationNavigational systemPhase change
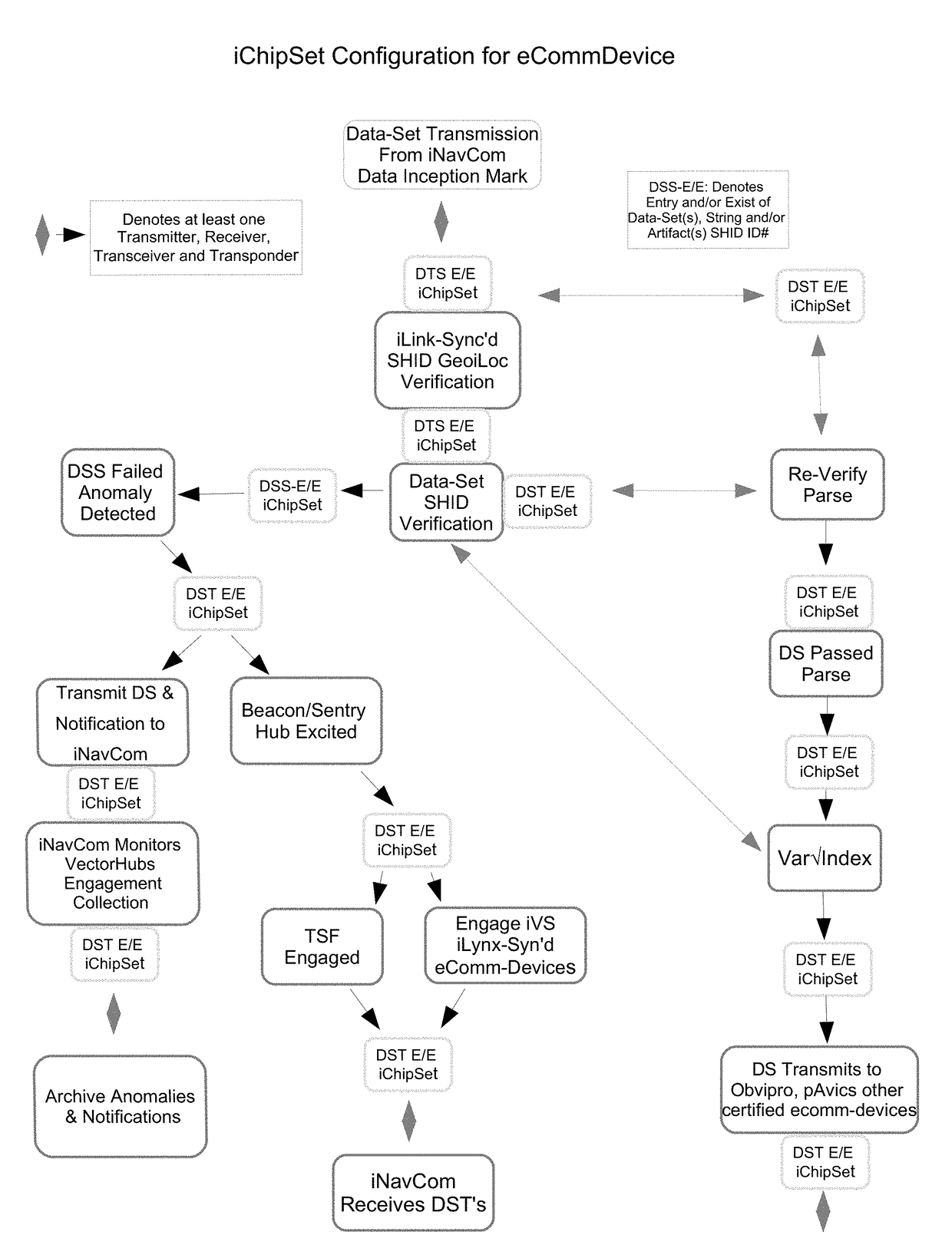
The navigational system comprises a plurality of mobile and stationary telemetry-devices, recording spatial data-artifacts, transmitting forecasted positional phase-changes, density point clustering schema that Maptrac's each transport imechanixm; providing calculated digital navigation directives transmitted to a plurality of devices equipped with pAvics, Obvipro and / or other certified compliant telemetry-devices, attached to and or carried by humans, motorcycles, bicycles, skis, snow boards and or a plurality of transport imechanixms; telematic-data of each transmits collected data-relics through a subnaysys network-topology provided by telemetry mobility, viewable and / or audibly heard on iNavX2 virtual interface and or iNavCom centers and / or a facilities interface.
Owner:TAYLOR DONALD WARREN
Topology discovery in heterogeneous networks
InactiveUS20090116404A1Data switching by path configurationResource Management SystemAdministrative domain
A Next Generation Network (NGN) resource management system and method includes a network topology discovery mechanism at the scale of an administrative domain. Information about nodes and links, such as bandwidth, delay, jitter, name and description of devices is collected and stored in a database by way of a protocol. The protocol is notifications-based, which involves each node device (e.g., a switch, router etc.) notifying its presence to its neighboring node.
Owner:TELEFON AB LM ERICSSON (PUBL)
Graphical models for cyber security analysis in enterprise networks
ActiveUS8881288B1Accurate and efficientReduce and compress redundancyMemory loss protectionError detection/correctionGraphicsGaussian network model
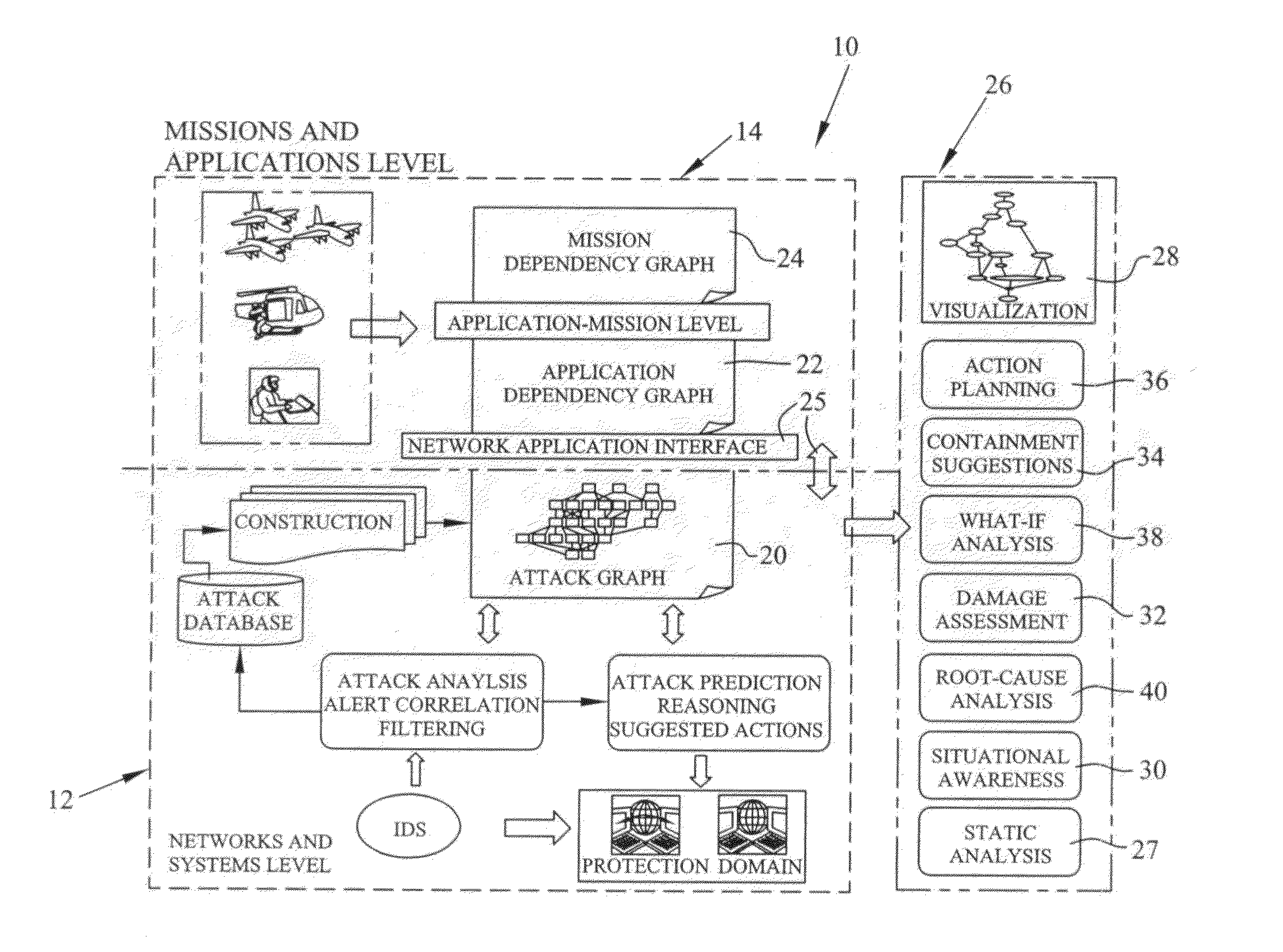
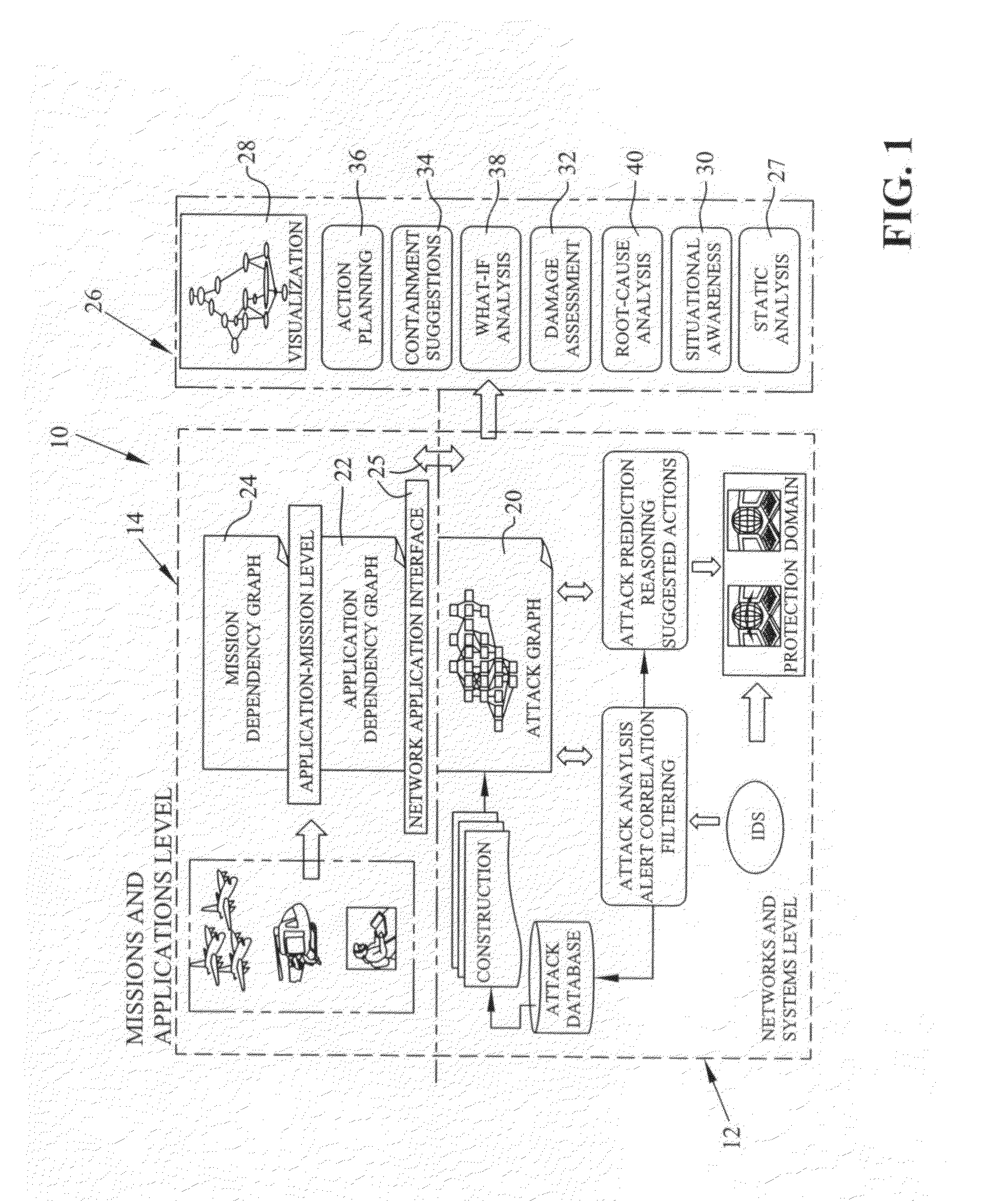
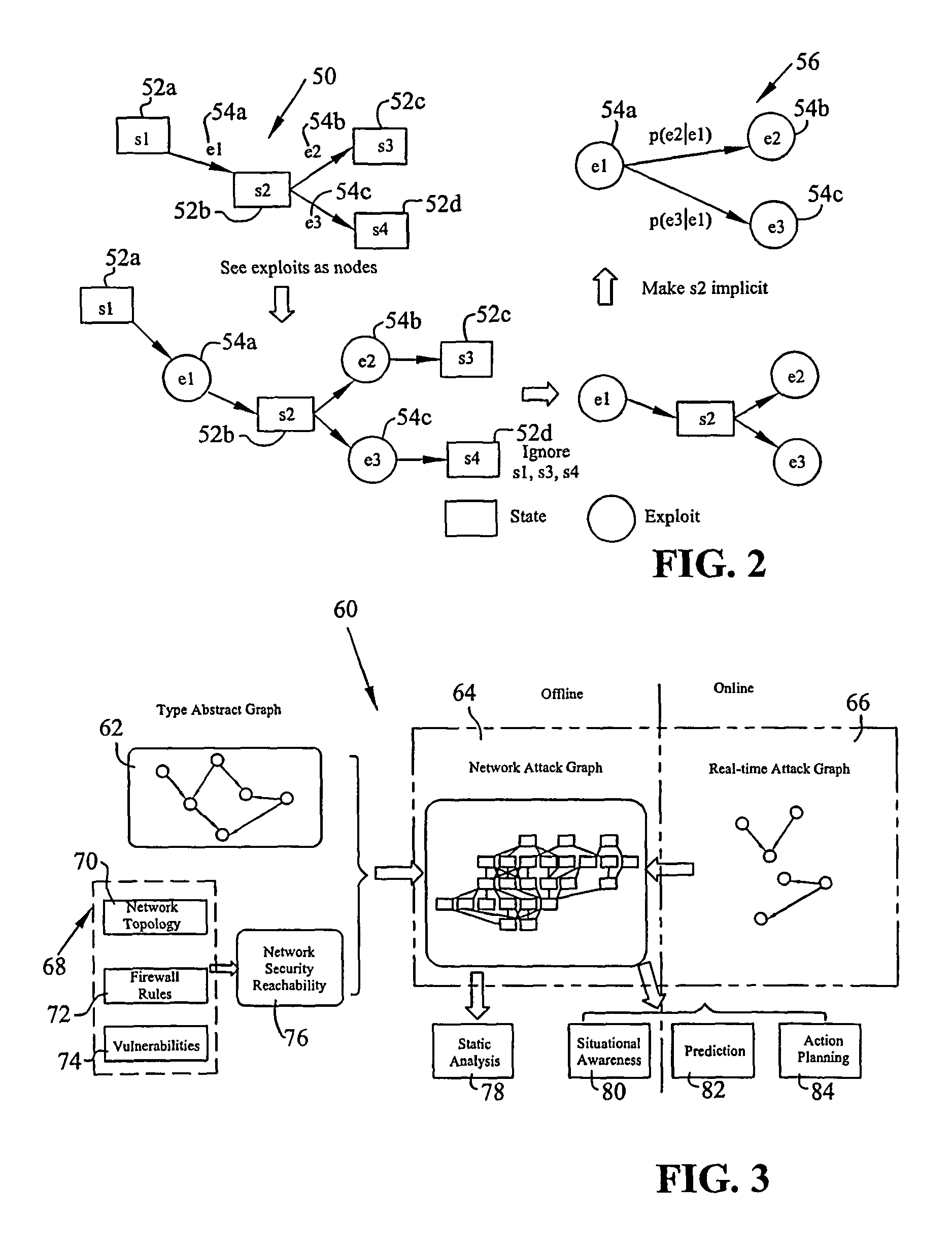
A method of generating graphical models for providing security analysis in computer networks that in one embodiment includes the steps of generating a type abstract graph independent of particular networks that models abstract dependency relationships among attributes and exploits; generating network-specific attack graphs by combining the type abstract graph with specific network information; monitoring an intruder alert; and generating a real-time attack graph by correlating the intruder alert with the network-specific attack graph. The real-time attack graph can be generated using reachability checking, bridging, and exploit prediction based on consequence alerts and may further include the step of calculating the likelihood of queries using a Bayesian network model. The method may also include the steps of inferring unobserved attacks that may have been missed by intrusion detection sensors, and projecting on which hosts and using what exploits additional intruder attacks may occur. The method may further include the step of comparing alternate actions by computation, wherein the alternate actions include the step of patching some vulnerabilities, and wherein the specific network information includes network topology. The specific network information may also include firewall rules.
Owner:INTELLIGENT AUTOMATION LLC
System and method for ad hoc network access employing the distributed election of a shared transmission schedule
InactiveUS20020067736A1Eliminate negotiationMore controlledNetwork topologiesTime-division multiplexTime division multiple accessTransmission schedule
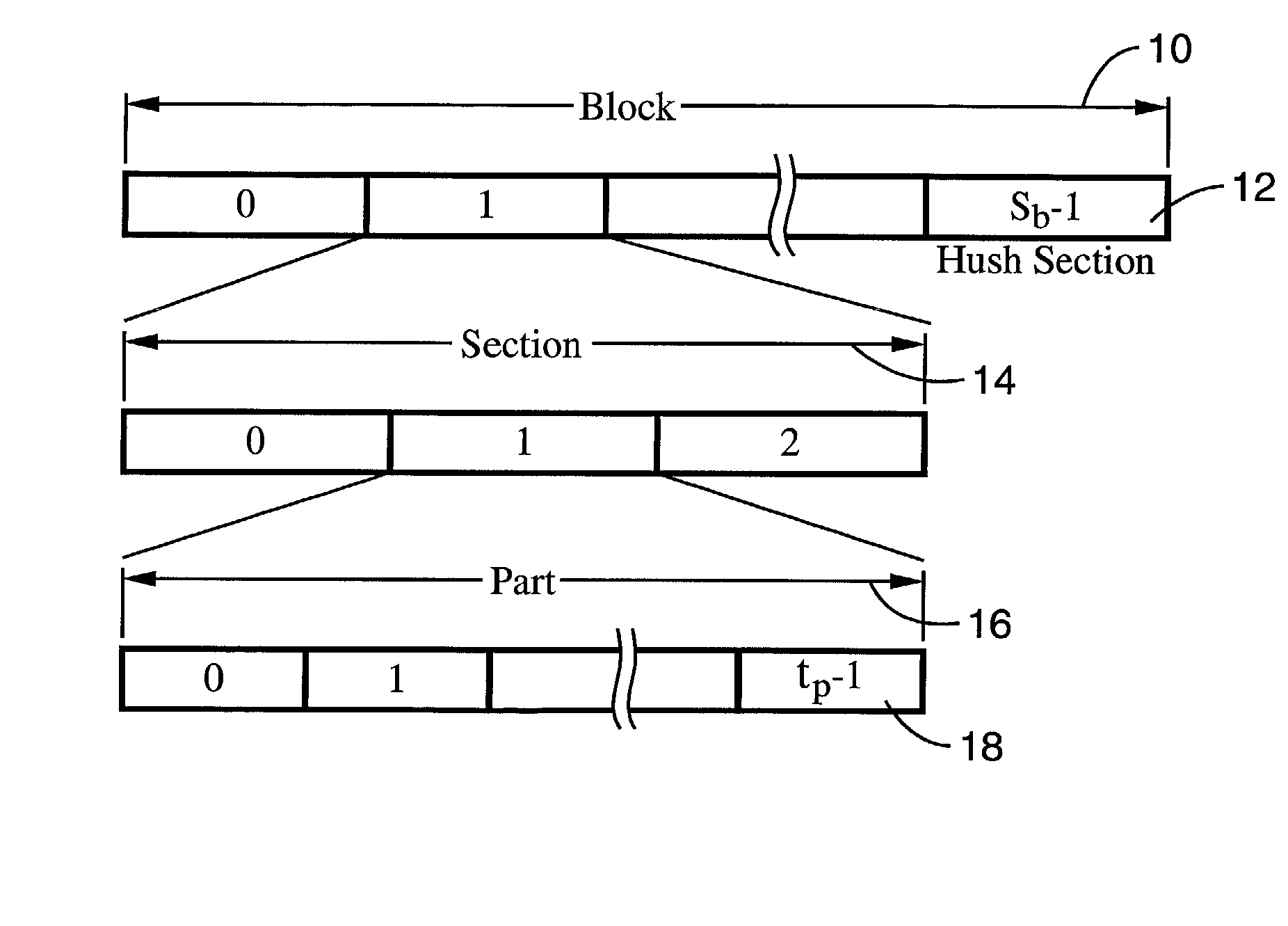
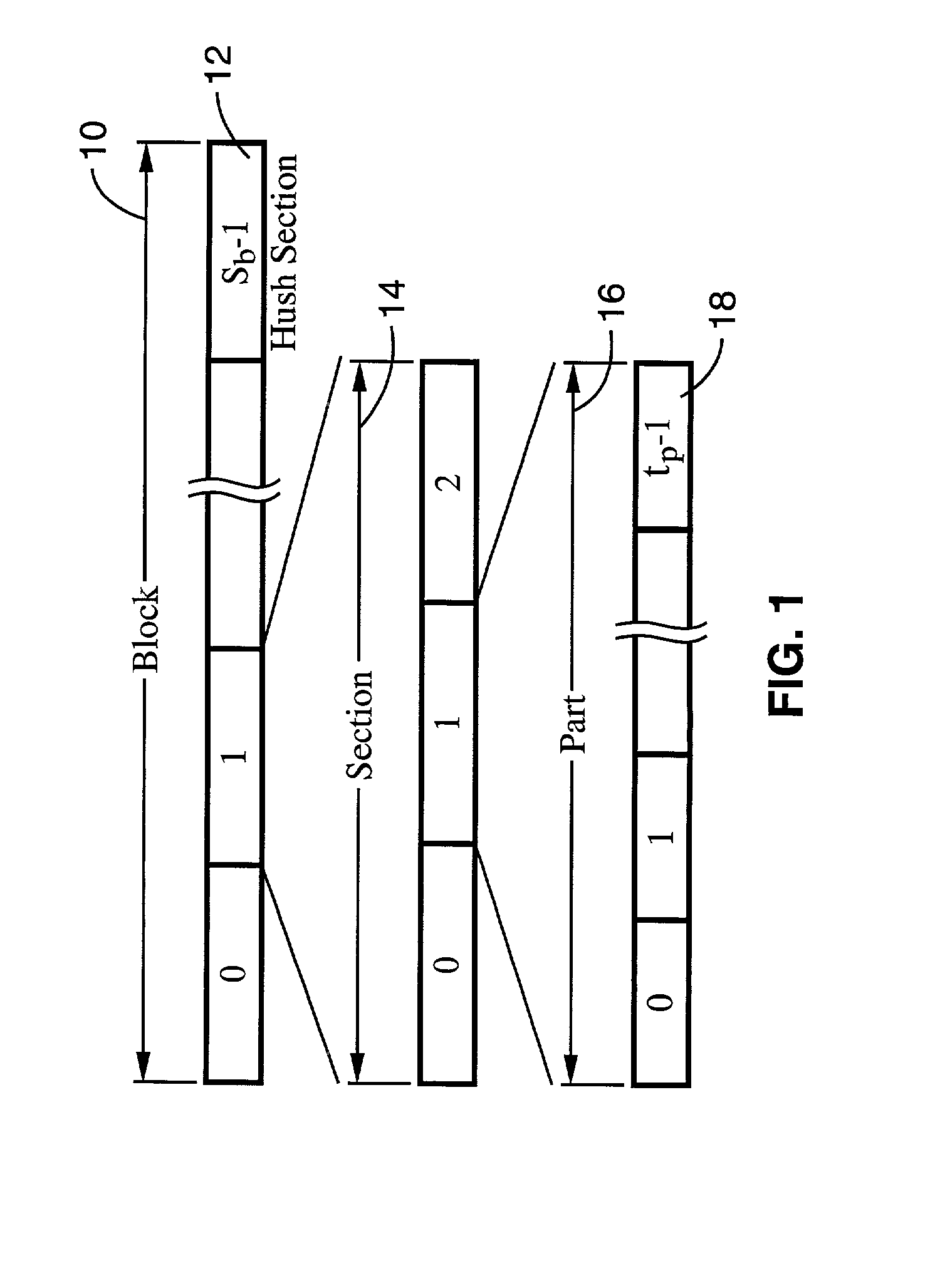
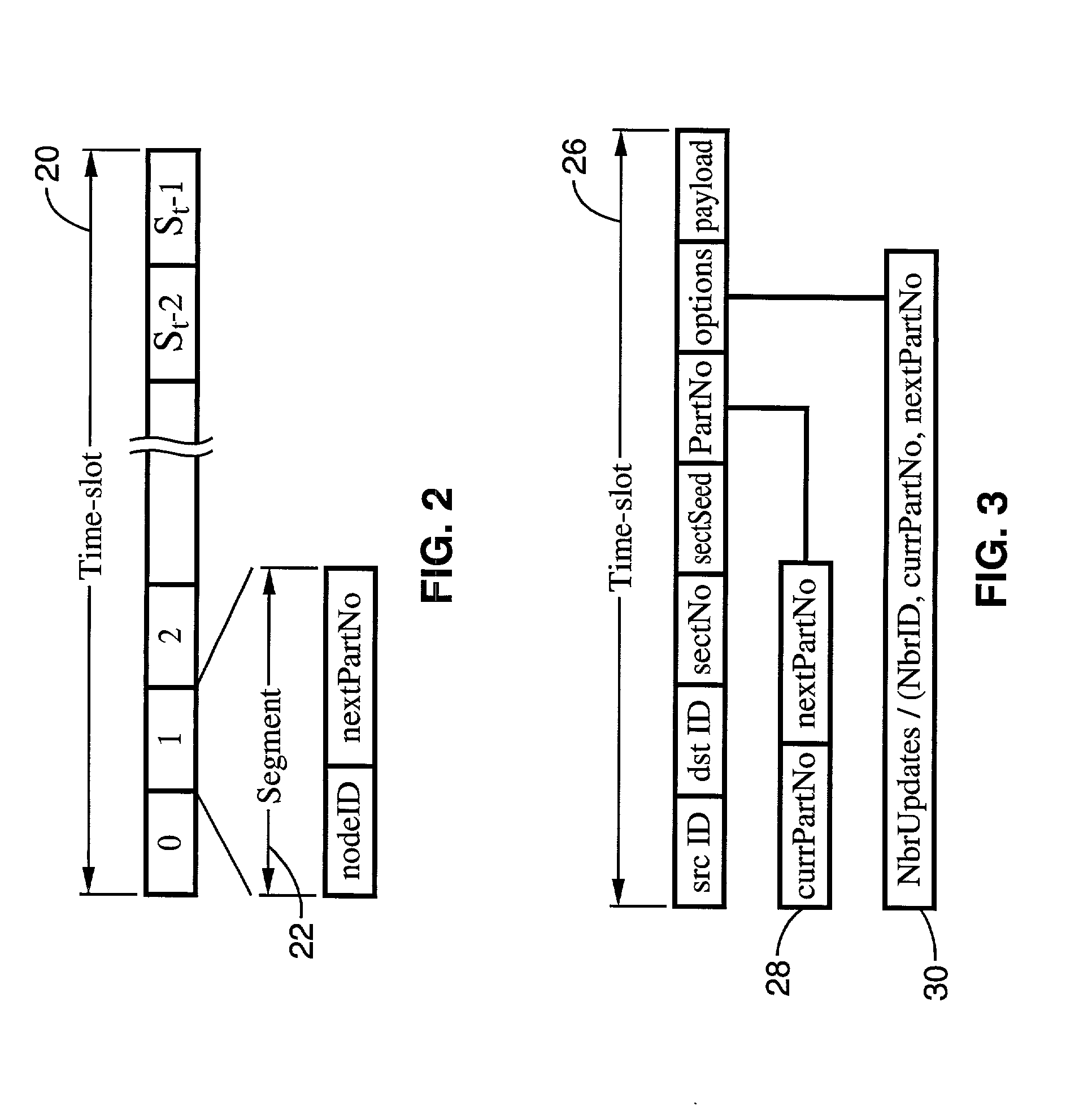
A system and method of providing distributed election of a shared transmission schedule within an ad hoc network. The invention includes a collision-free access protocol which resolves channel access contentions for time division multiple access (TDMA) of a single channel. Time-slots are organized into part numbers, which are included within sections, a sequence of which define a block. Each node is given a ring number according to its location within the network topology and maintains local neighbor information along with its own part number and message digest. Collision-free channel access is automatically scheduled and repetitious contention phases are resolved by a random permutation algorithm operating in message digests. An empty time-slot utilization method is also described and data packets may also be transmitted subject to a non-zero collision probability within a blind section of the block.
Owner:RGT UNIV OF CALIFORNIA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com