Patents
Literature
1939 results about "Network routing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Mitigating denial of service attacks
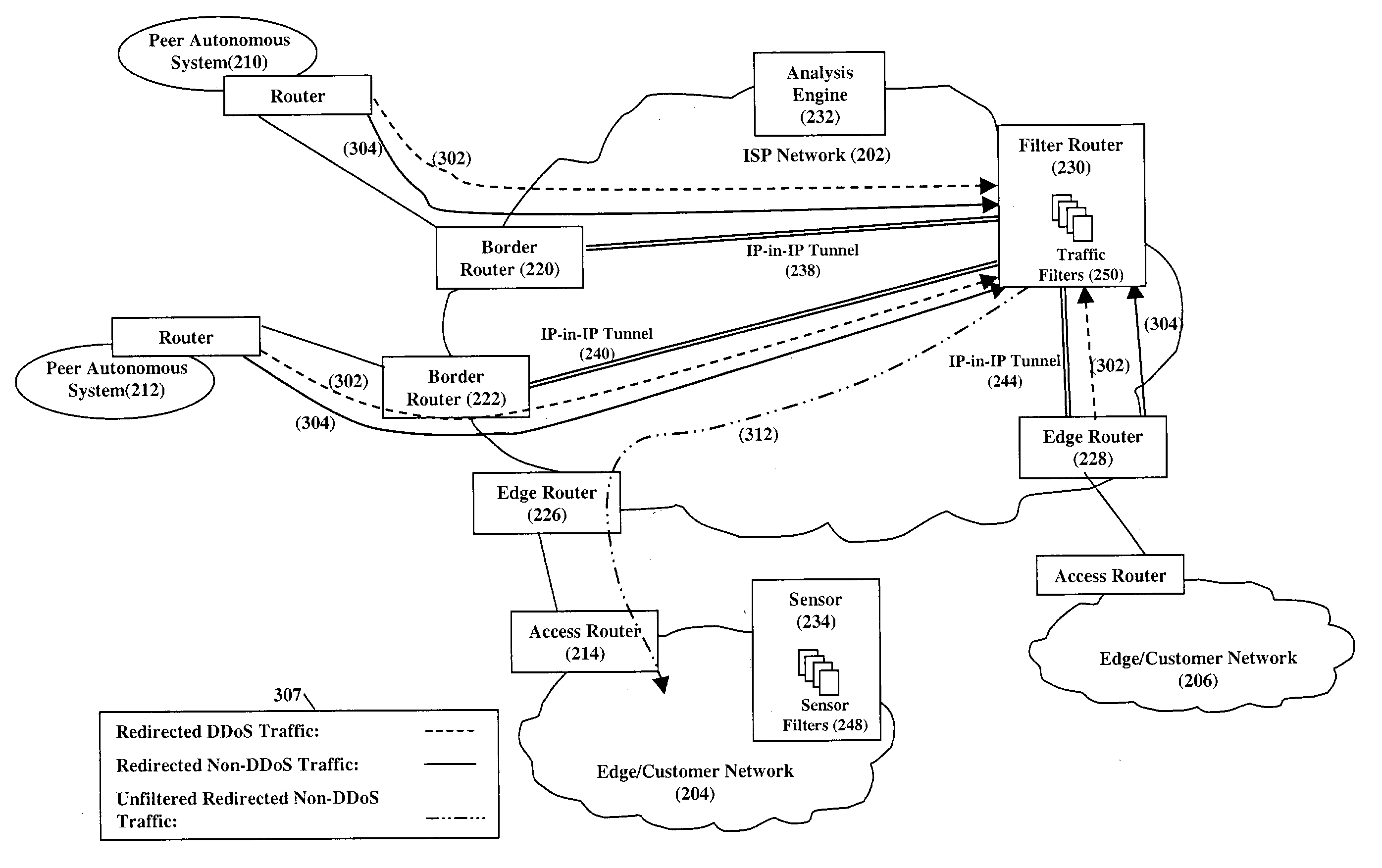
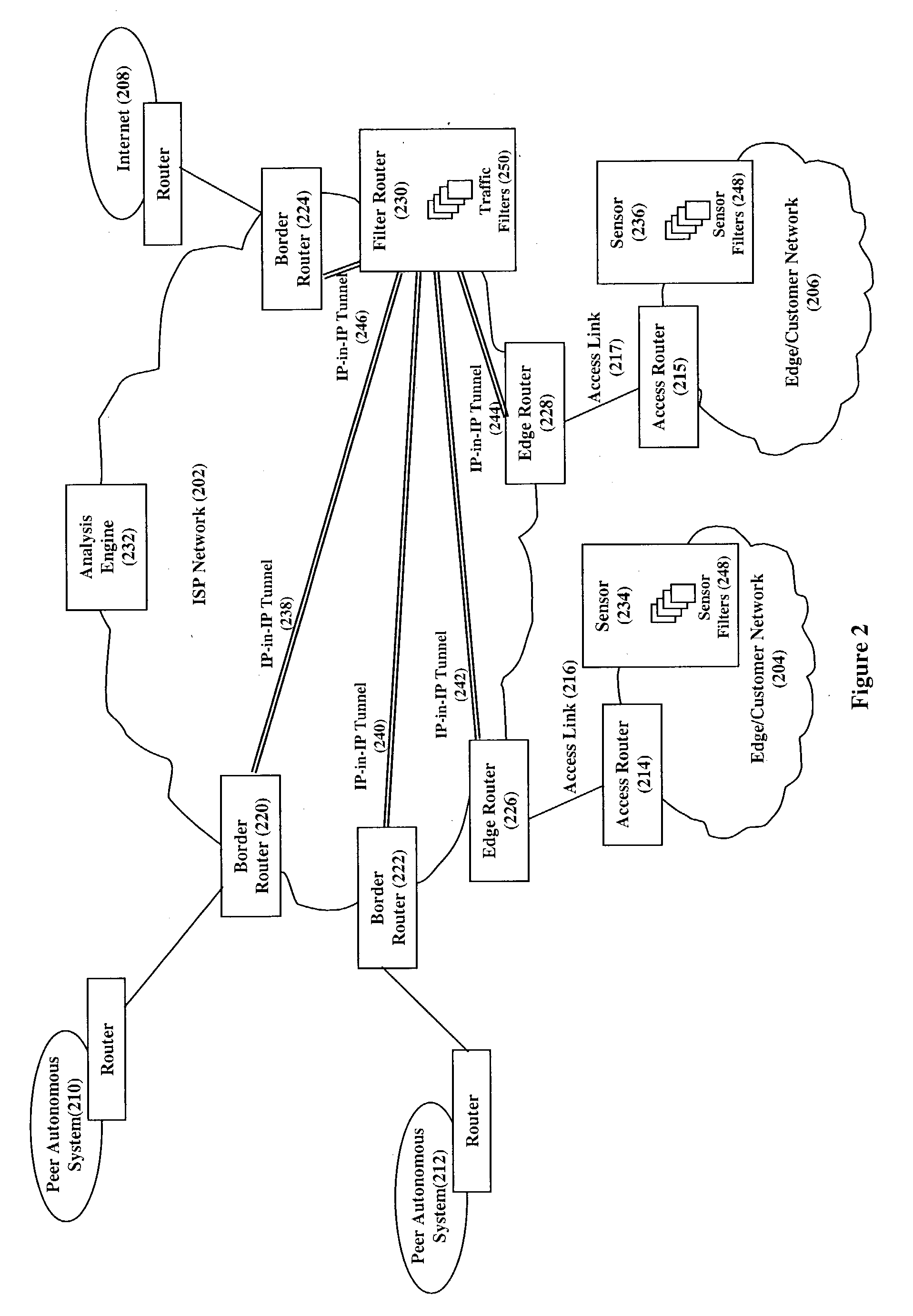
InactiveUS20040148520A1Easily scaledMemory loss protectionUnauthorized memory use protectionThe InternetNetwork routing
Service attacks, such as denial of service and distributed denial of service attacks, of a customer network are detected and subsequently mitigated by the Internet Service Provider (ISP) that services the customer network. A sensor examines the traffic entering the customer network for attack traffic. When an attack is detected, the sensor notifies an analysis engine within the ISP network to mitigate the attack. The analysis engine configures a filter router to advertise new routing information to the border and edge routers of the ISP network. The new routing information instructs the border and edge routers to reroute attack traffic and non-attack traffic destined for the customer network to the filter router. At the filter router, the attack traffic and non-attack traffic are automatically filtered to remove the attack traffic. The non-attack traffic is passed back onto the ISP network for routing towards the customer network.
Owner:TELCORDIA TECHNOLOGIES INC
Method and apparatus for on demand multicast and unicast using controlled flood multicast communications
ActiveUS7184421B1Efficient routingEasy to collectSpecial service provision for substationData switching by path configurationFlexible MechanismsTraffic capacity
Network configuration hierarchy information is maintained using flexible mechanisms and methods for establishing routes and transferring information between nodes in ad-hoc data communication networks using on-demand multicast and unicast techniques. Communication nodes use network topology information to build and maintain a dynamically mobile, wireless, ad-hoc network capable of efficiently routing both unicast and multicast traffic. Network nodes that facilitate the collection and distribution of network topology and routing data are dynamically selected, configured, and maintained. Network traffic overhead necessary for maintaining and distributing network routing table information is held to a minimum and efficiently distributed across the network, thereby reducing the potential for network traffic bottlenecks due to network overhead processes.
Owner:STINGRAY IP SOLUTIONS LLC
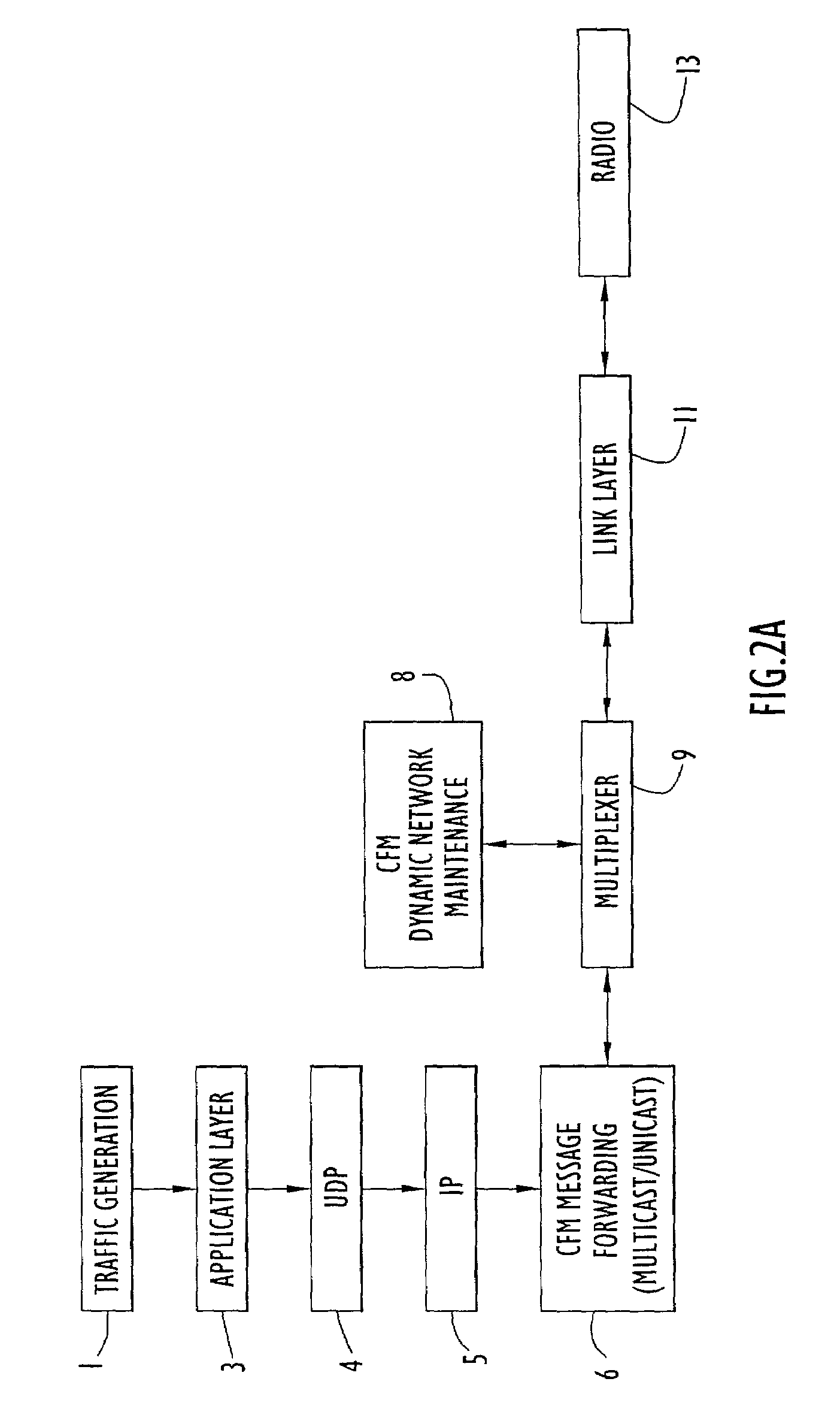
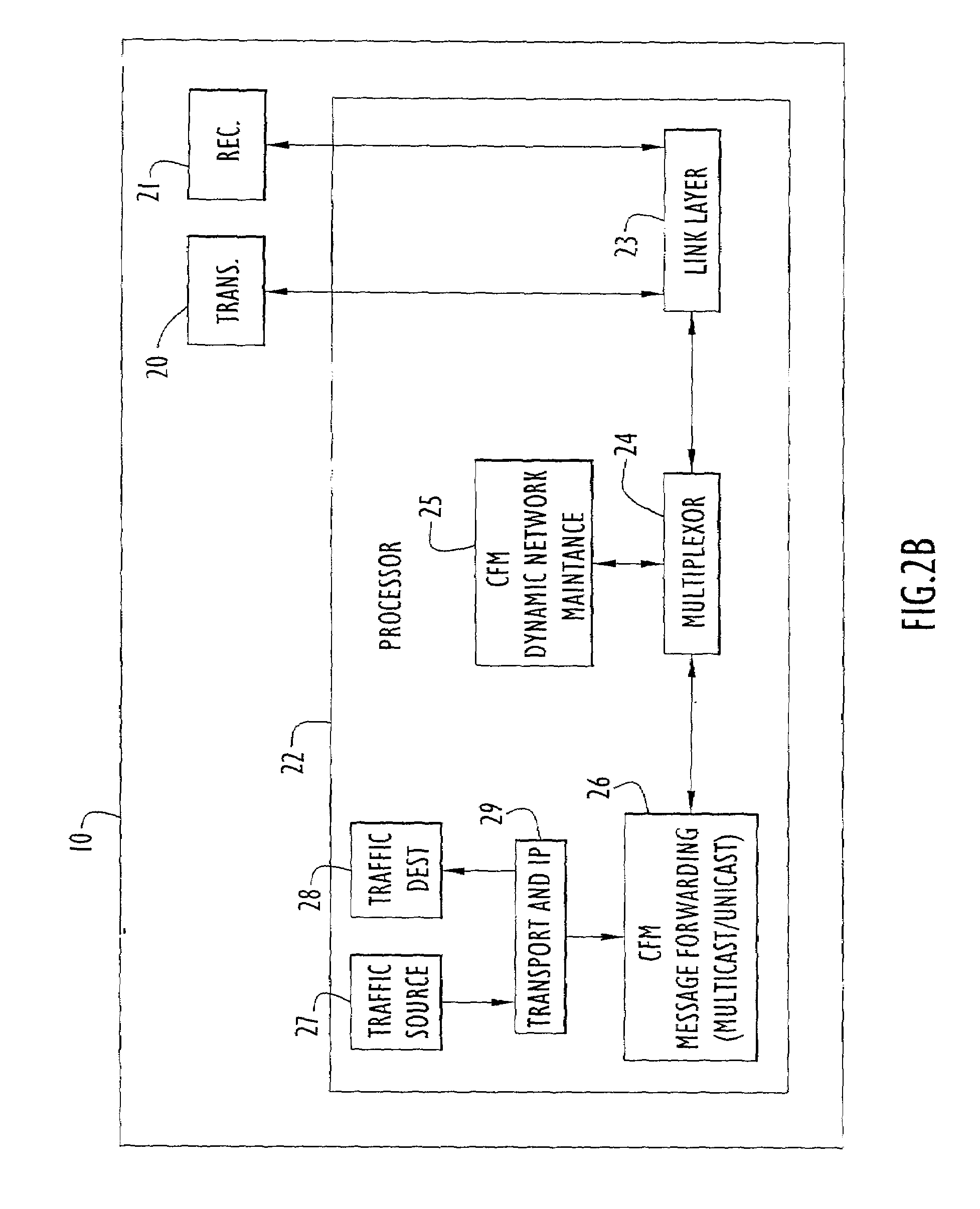
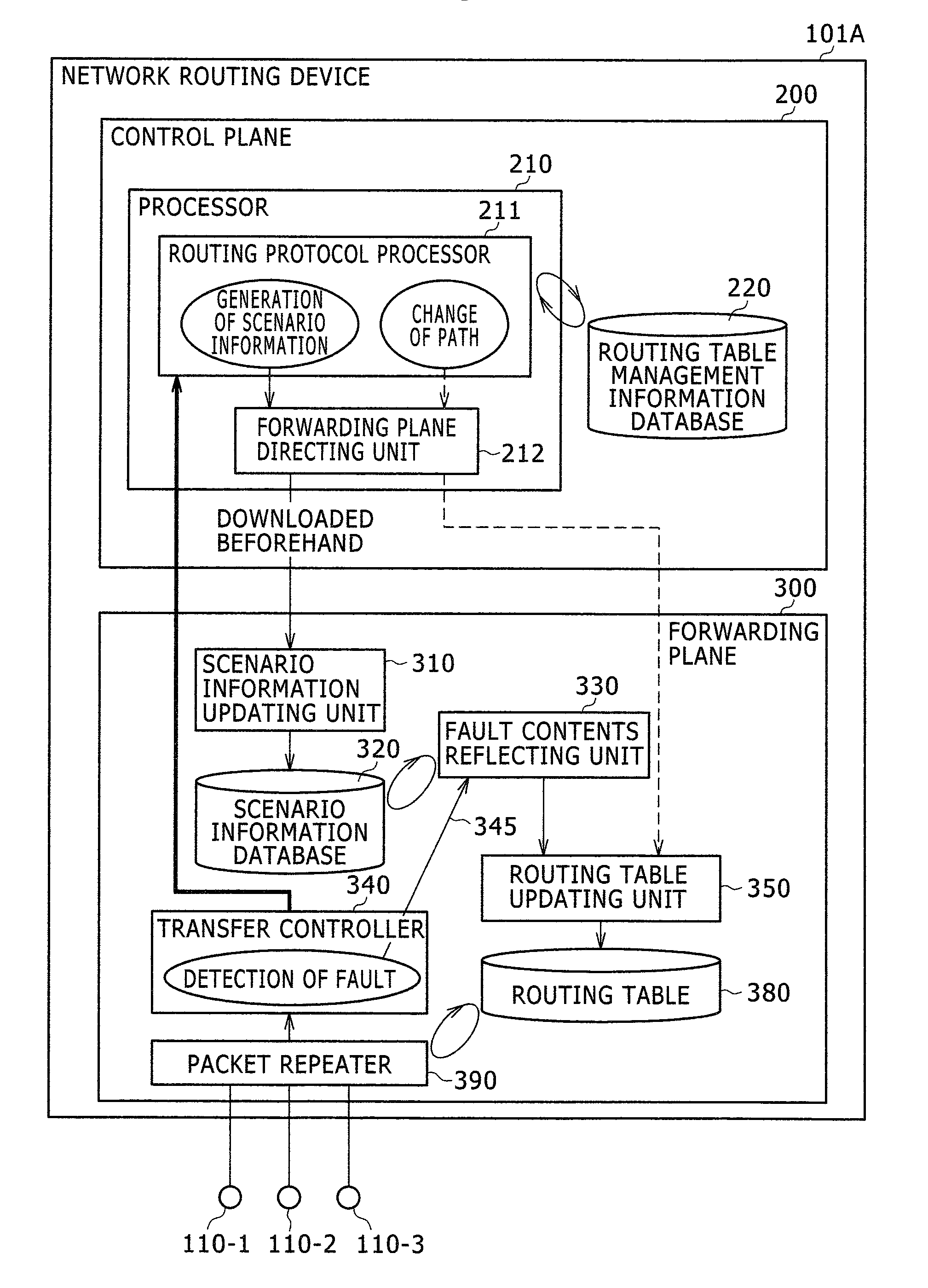
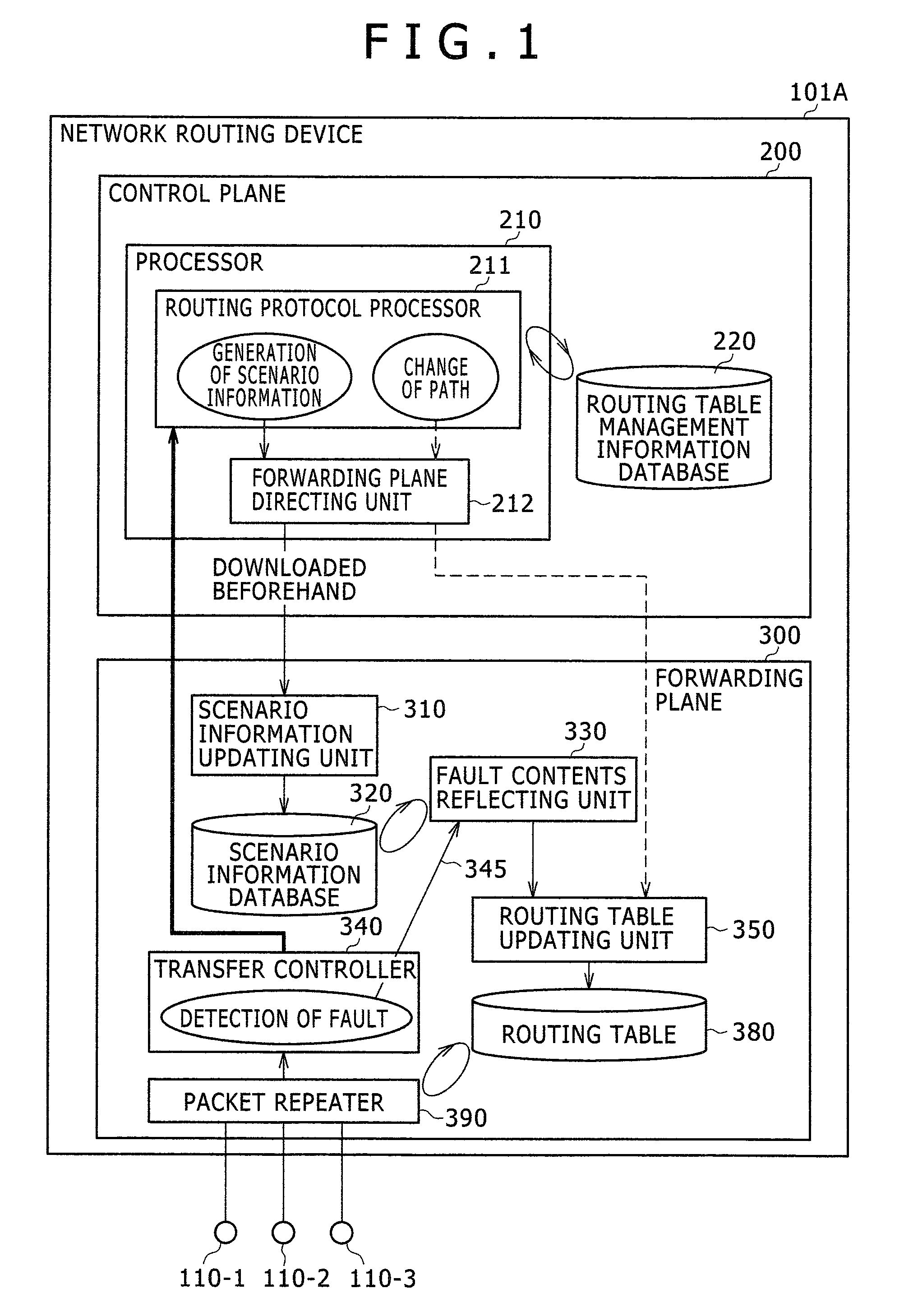
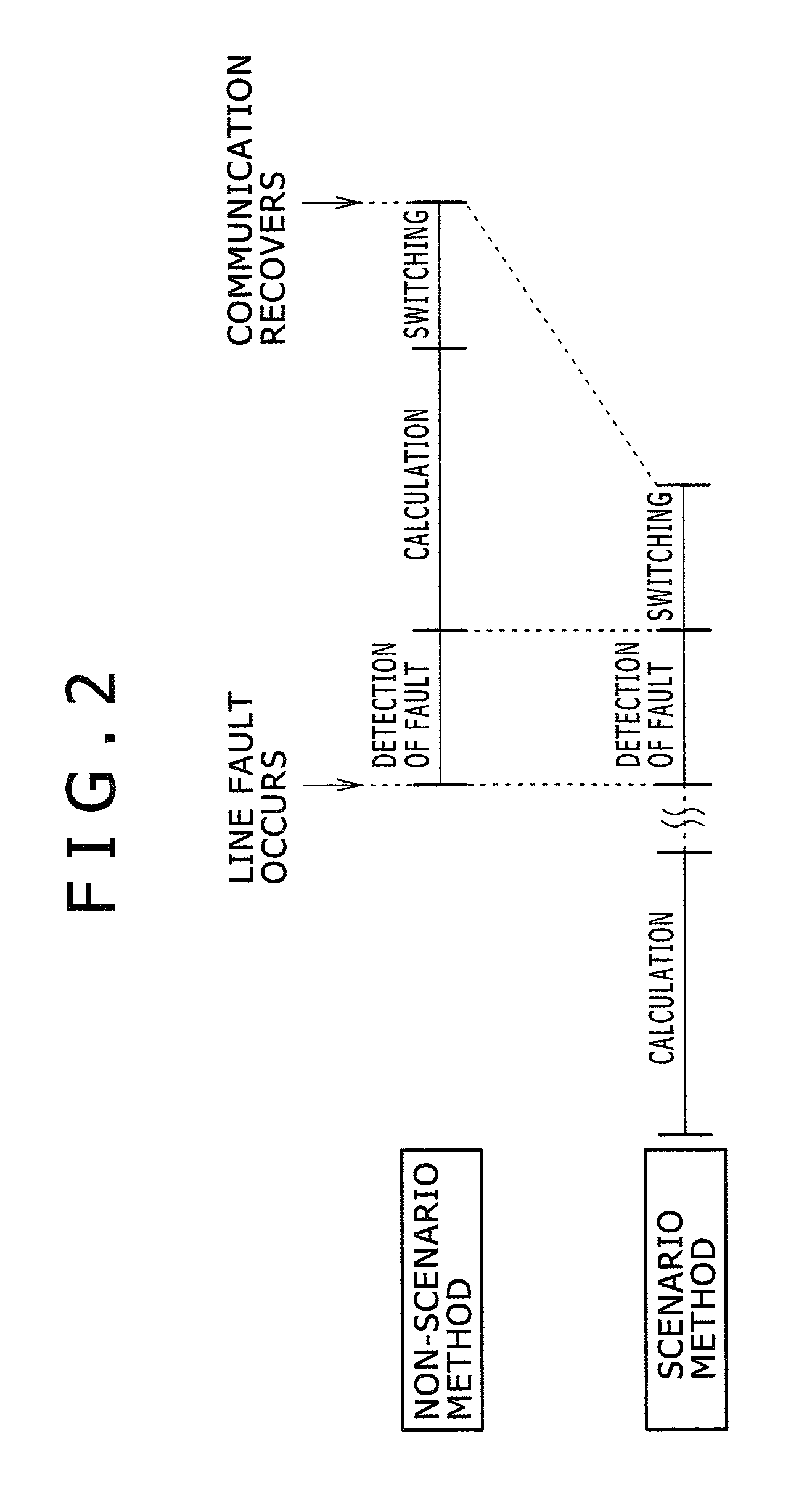
Network routing device and network routing method
A network routing device according to the invention transmits a packet via a second port based upon destination information included in the packet received via a first port referring to a routing table. In addition, the network routing device calculates beforehand a third port which is a transfer destination when a fault occurs in a destination connected to the second port. Further, the network routing device holds scenario information including a combination of the second port and the third port and updates the routing table based upon the scenario information when a fault is detected in either of the ports.
Owner:ALAXALA NETWORKS
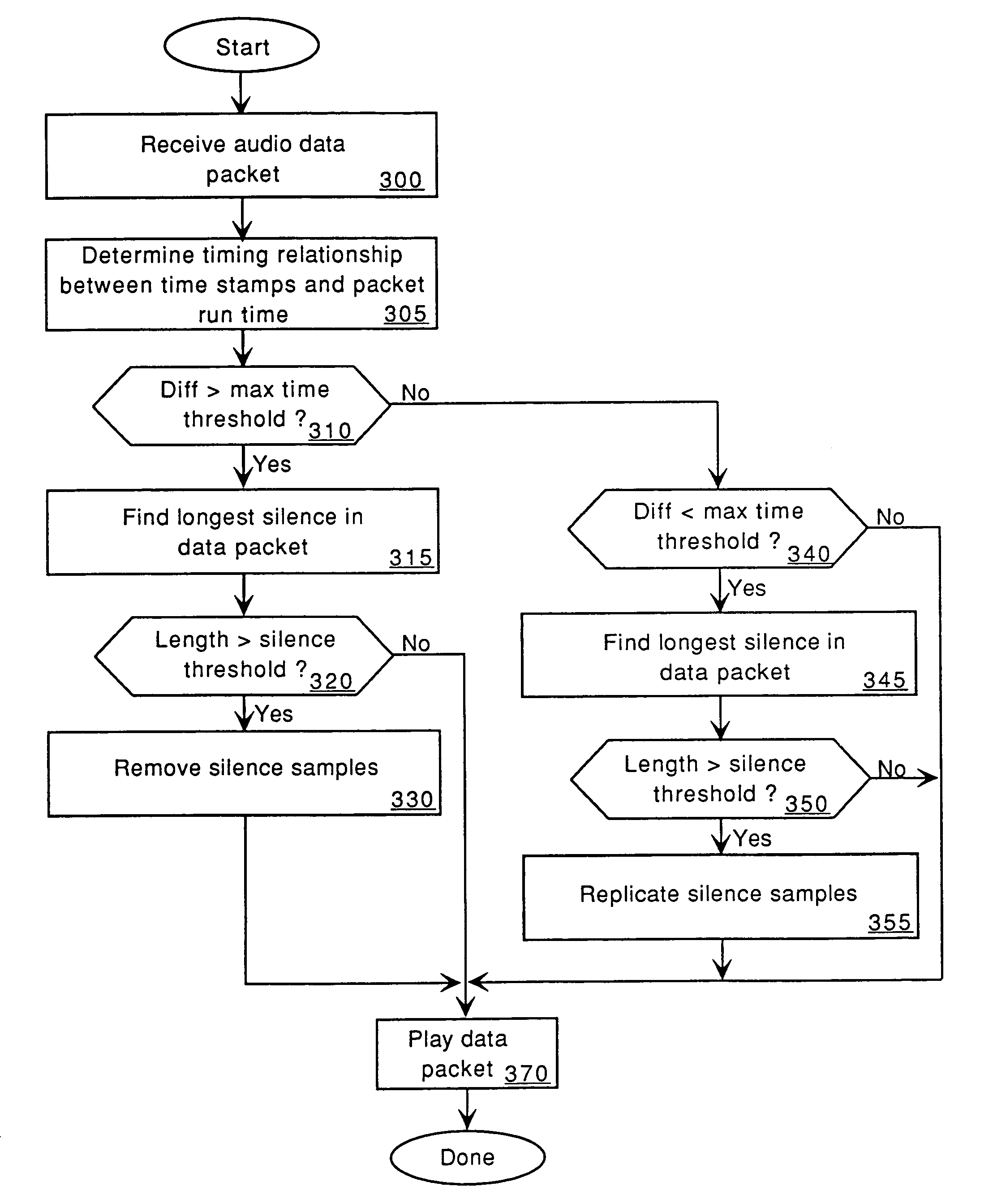
Digital audio compensation
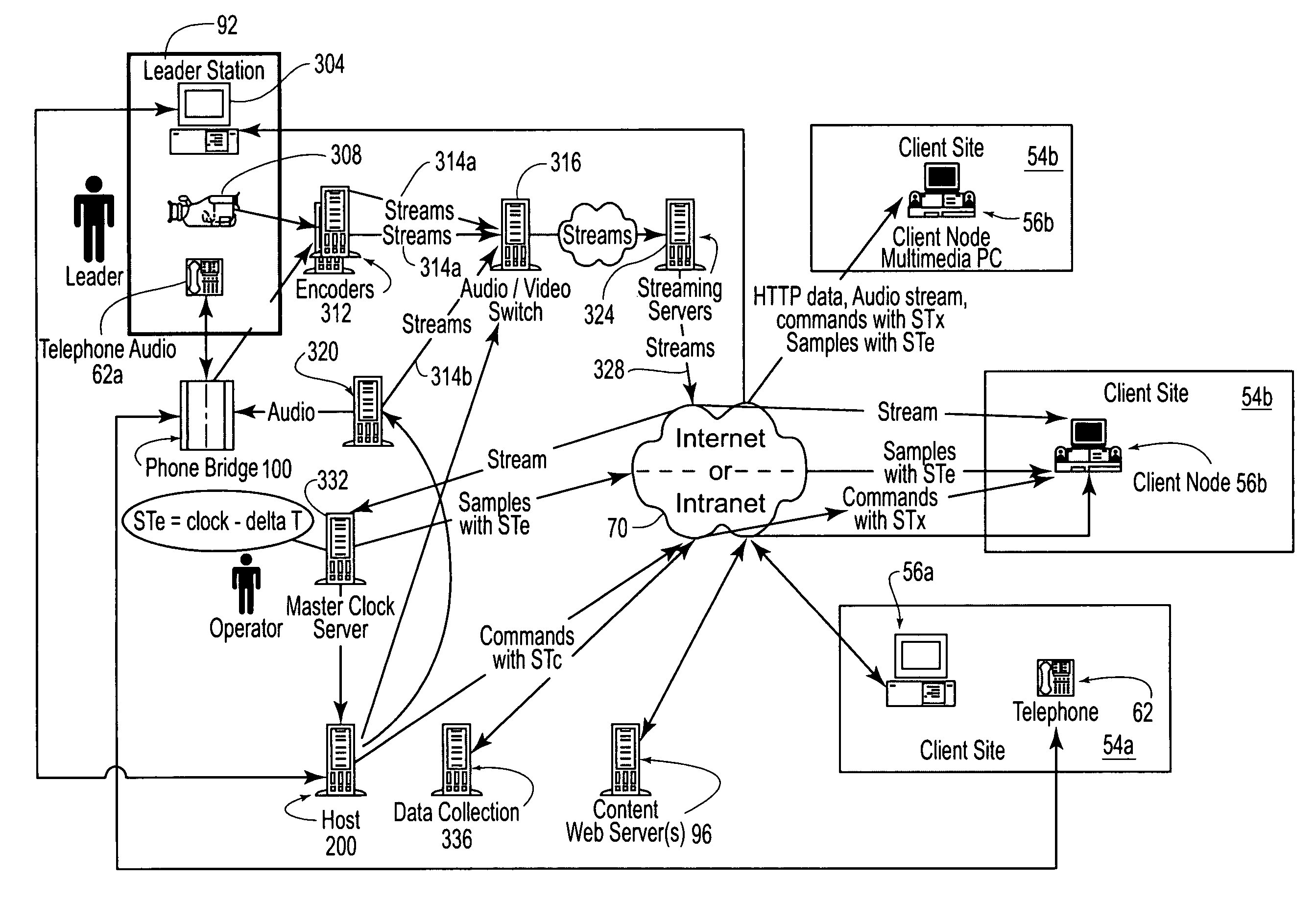
A method and apparatus for audio compensation is disclosed. If audio input components and audio output components are not driven by a common clock (e.g., input and output systems are separated by a network, different clock signals in a single computer system), input and output sampling rates may differ. Also, network routing of the digital audio data may not be consistent. Both clock synchronization and routing considerations can affect the digital audio output. To compensate for the timing irregularities caused by clock synchronization differences and / or routing changes, the present invention adjusts periods of silence in the digital audio data being output. The present invention thereby provides an improved digital audio output.
Owner:MICROSOFT TECH LICENSING LLC
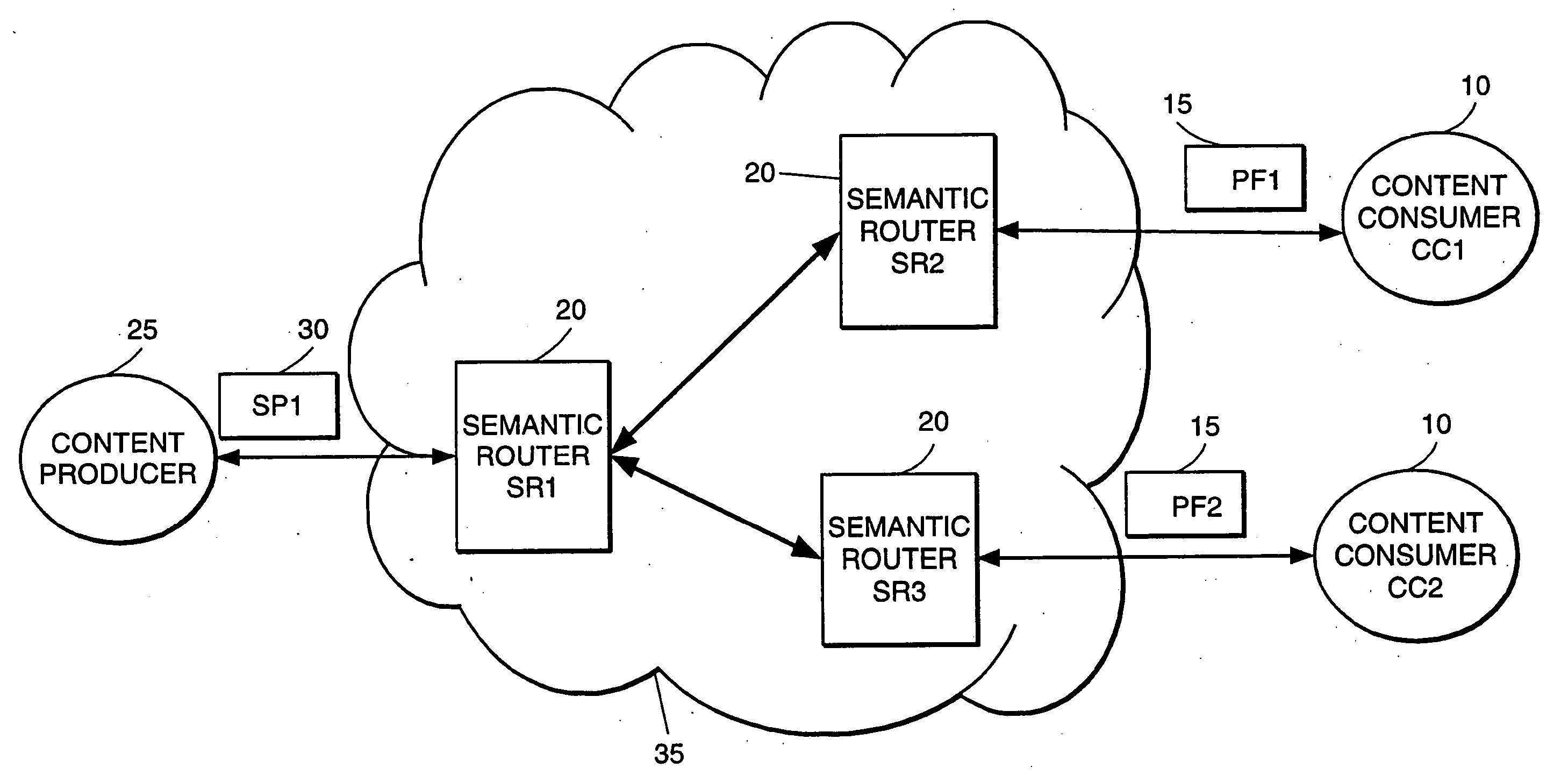
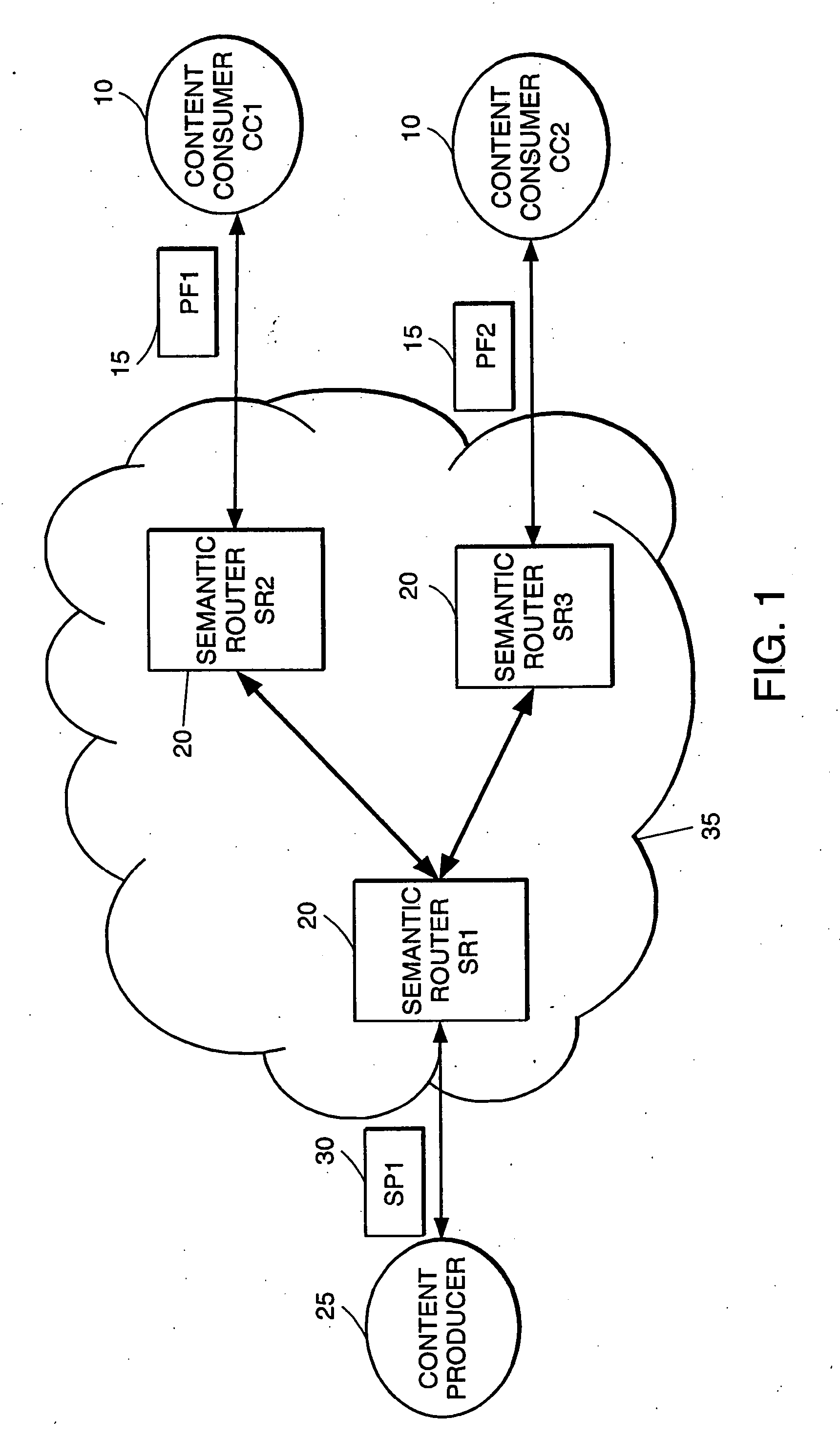
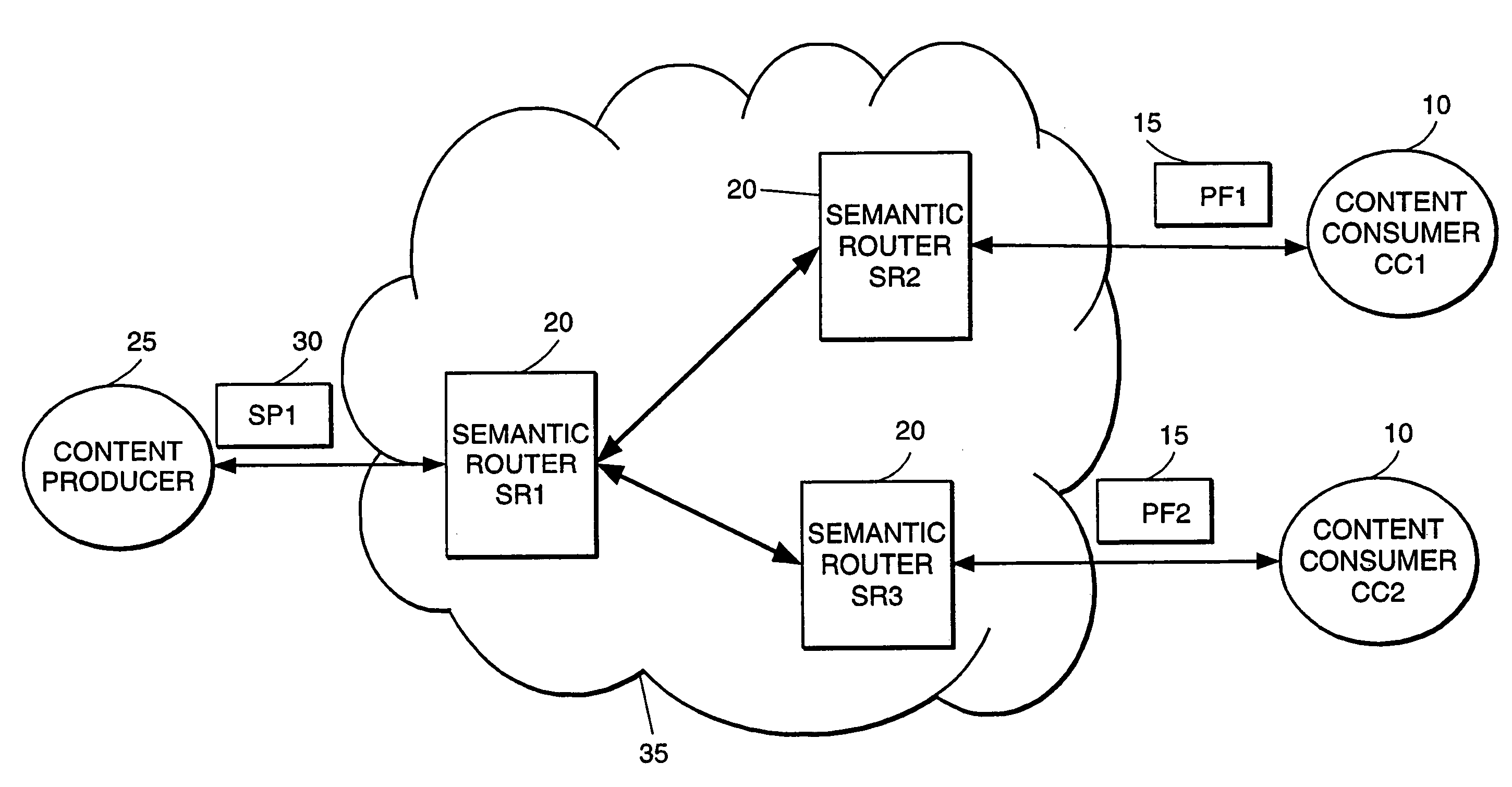
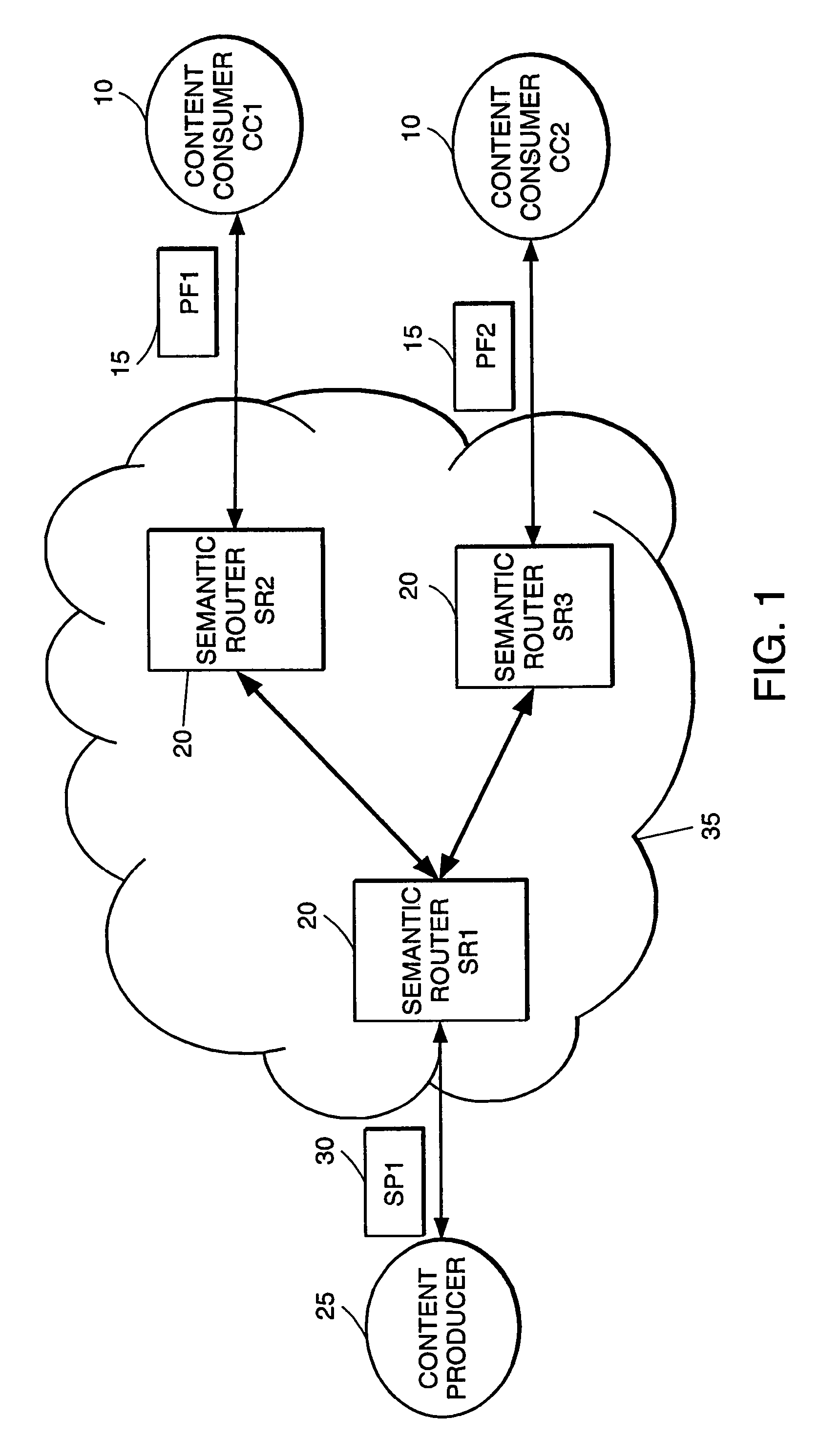
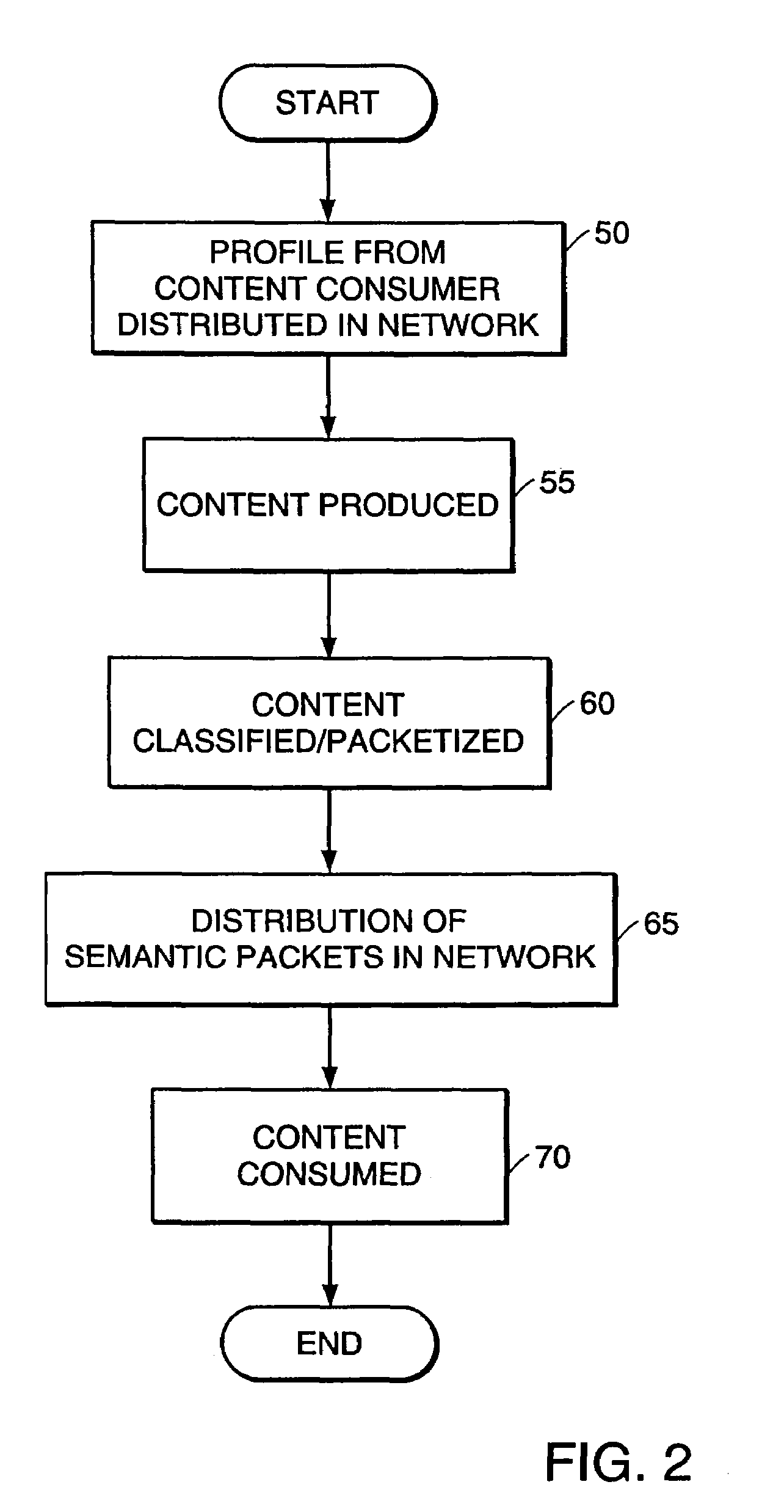
High-performance addressing and routing of data packets with semantically descriptive labels in a computer network
InactiveUS20070239892A1Reduce storageEasy to operateDigital computer detailsData switching networksRouting tableNetwork packet
A method, system and apparatus for routing data through a network based on the content or semantics of the data. Semantic routing engines route the data through the network based upon information maintained in routing tables. The routing tables used to route the content through the network are derived by aggregating information about either content consumers or content producers into ontological
Owner:SEMANDEX NETWORKS
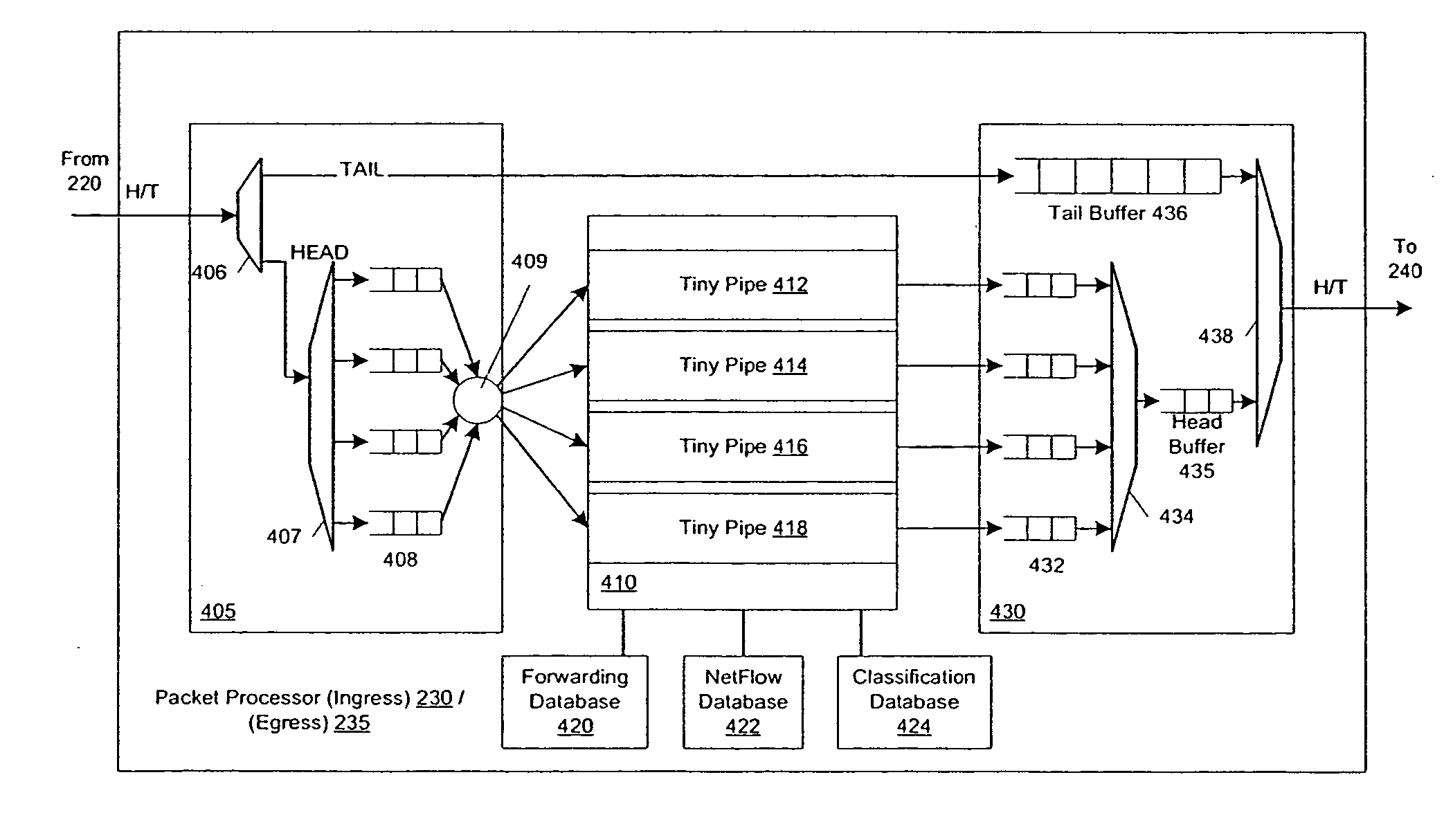
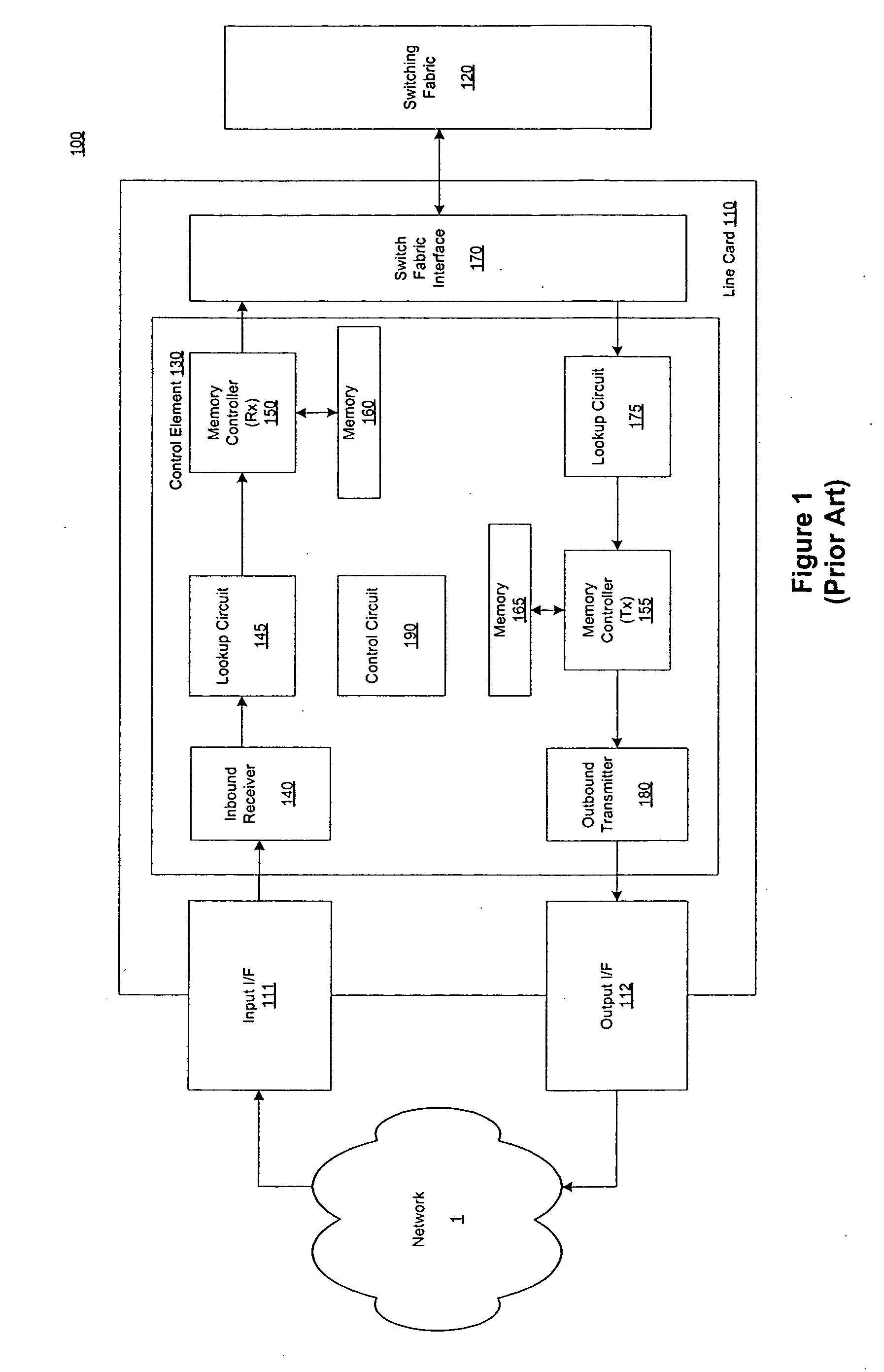
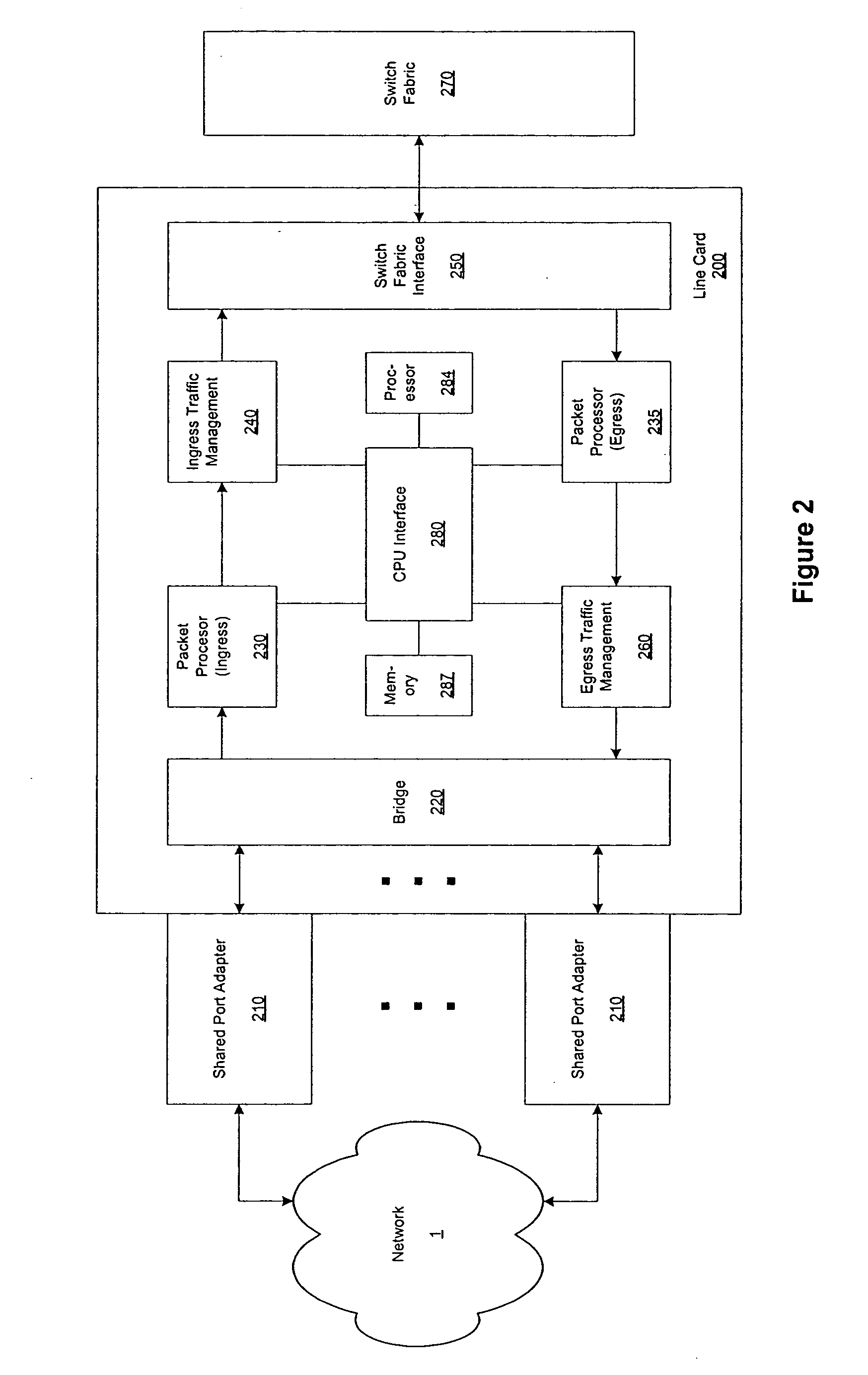
Pipelined packet switching and queuing architecture
An architecture for a line card in a network routing device is provided. The line card architecture provides a bi-directional interface between the routing device and a network, both receiving packets from the network and transmitting the packets to the network through one or more connecting ports. In both the receive and transmit path, packets processing and routing in a multi-stage, parallel pipeline that can operate on several packets at the same time to determine each packet's routing destination is provided. Once a routing destination determination is made, the line card architecture provides for each received packet to be modified to contain new routing information and additional header data to facilitate packet transmission through the switching fabric. The line card architecture further provides for the use of bandwidth management techniques in order to buffer and enqueue each packet for transmission through the switching fabric to a corresponding destination port. The transmit path of the line card architecture further incorporates additional features for treatment and replication of multicast packets.
Owner:CISCO TECH INC
Methods and systems for generating, distributing, and screening commercial content
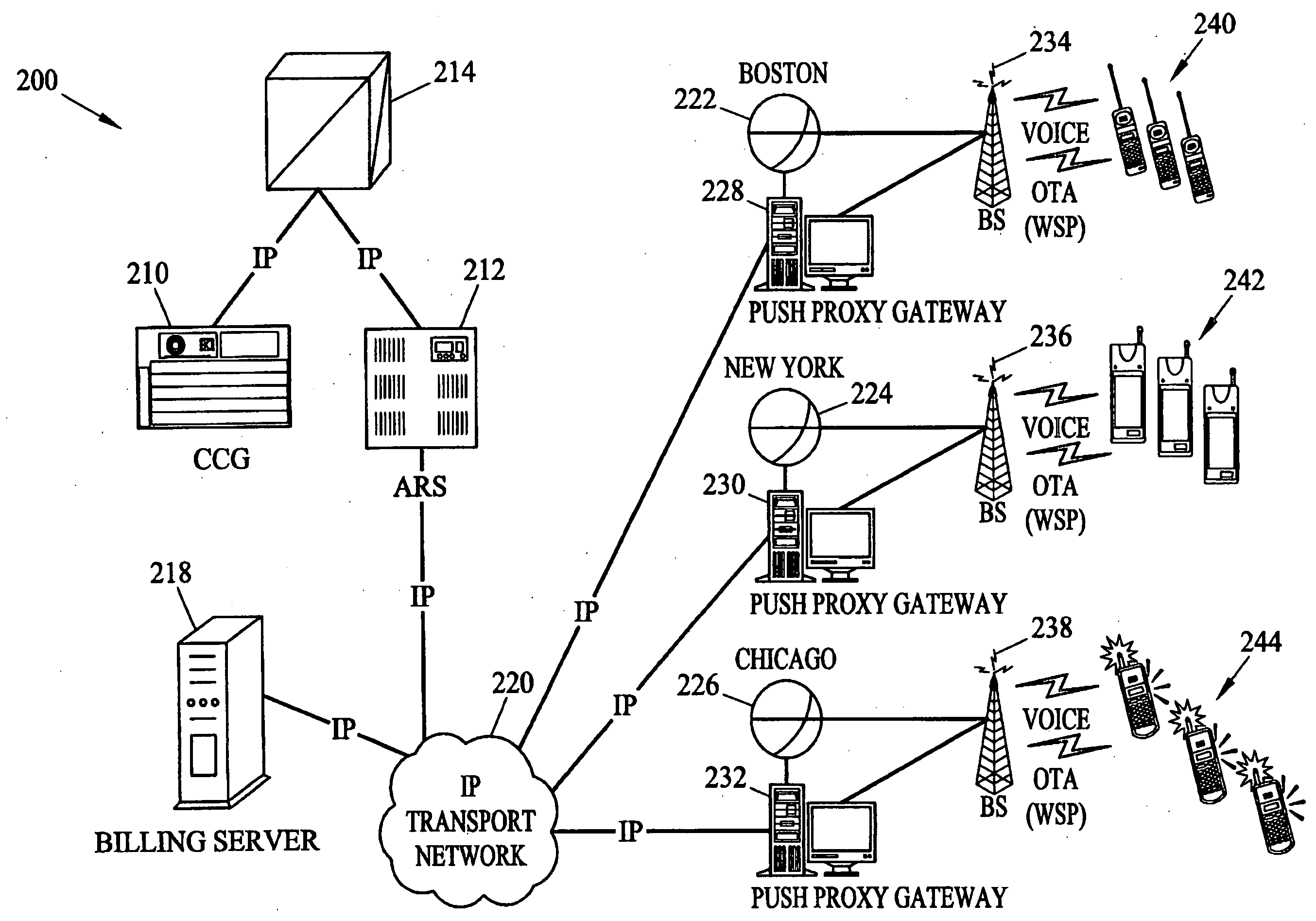
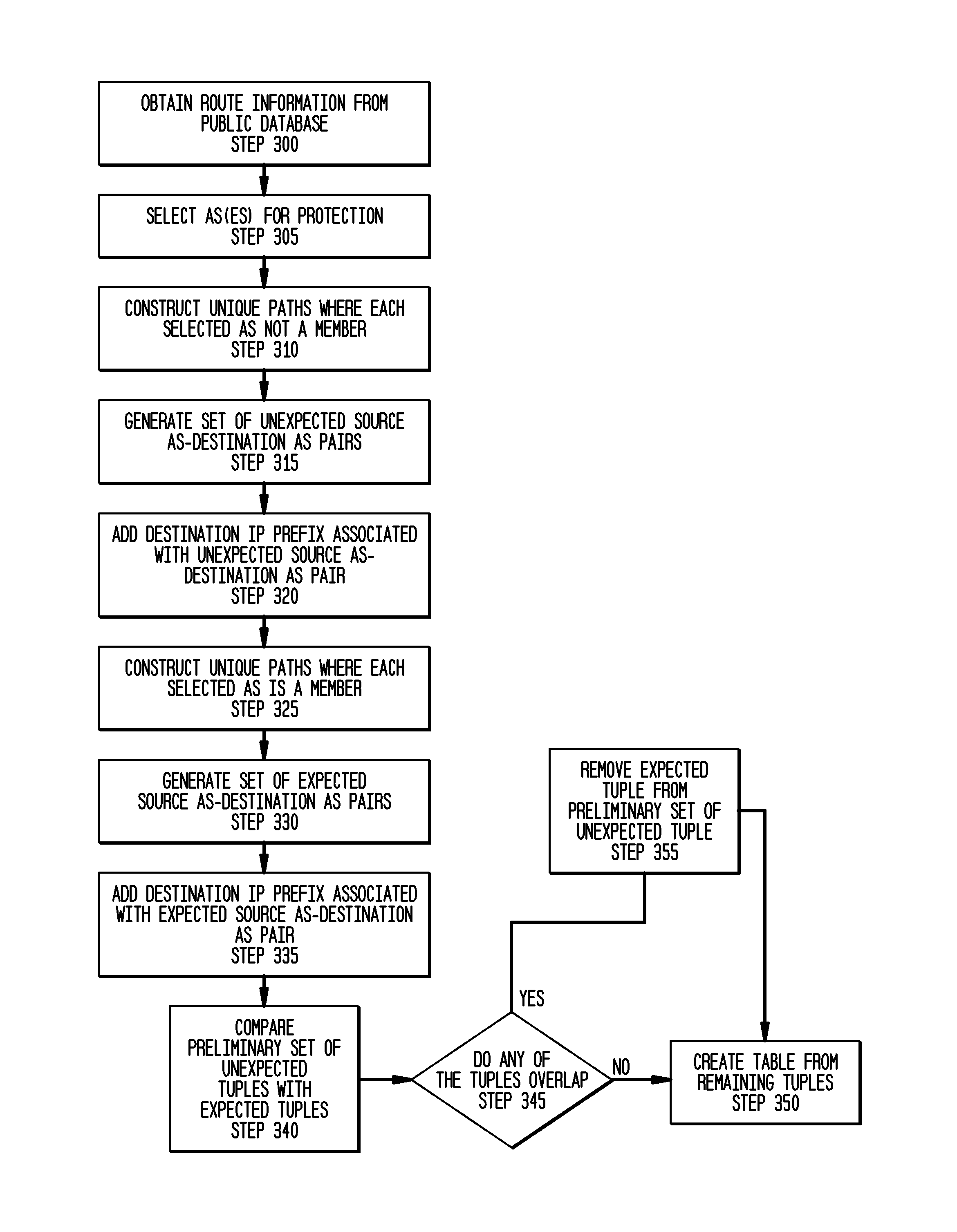
ActiveUS20040259553A1Broadcast systems characterised by addressed receiversBroadcast transmission systemsProcessor registerAddress resolution
Methods and systems for generating, distributing, and screening commercial content are disclosed. A commercial content generator (CCG) generates commercial content message and obtains from a push proxy agent address resolution server the network routing address of each push proxy agent that is required for distribution of the message to the target mobile subscriber audience. A push proxy agent receives a message containing commercial content and resolves a mobile subscriber identifier for each mobile subscriber who is to receive the commercial content information using subscriber information obtained from a subscriber location register, such as a visitor location register (VLR). The push proxy agent may also negotiate media format characteristics for each member of the target mobile subscriber audience and facilitate delivery of the commercial content to each member of the target mobile subscriber audience.
Owner:TEKELEC
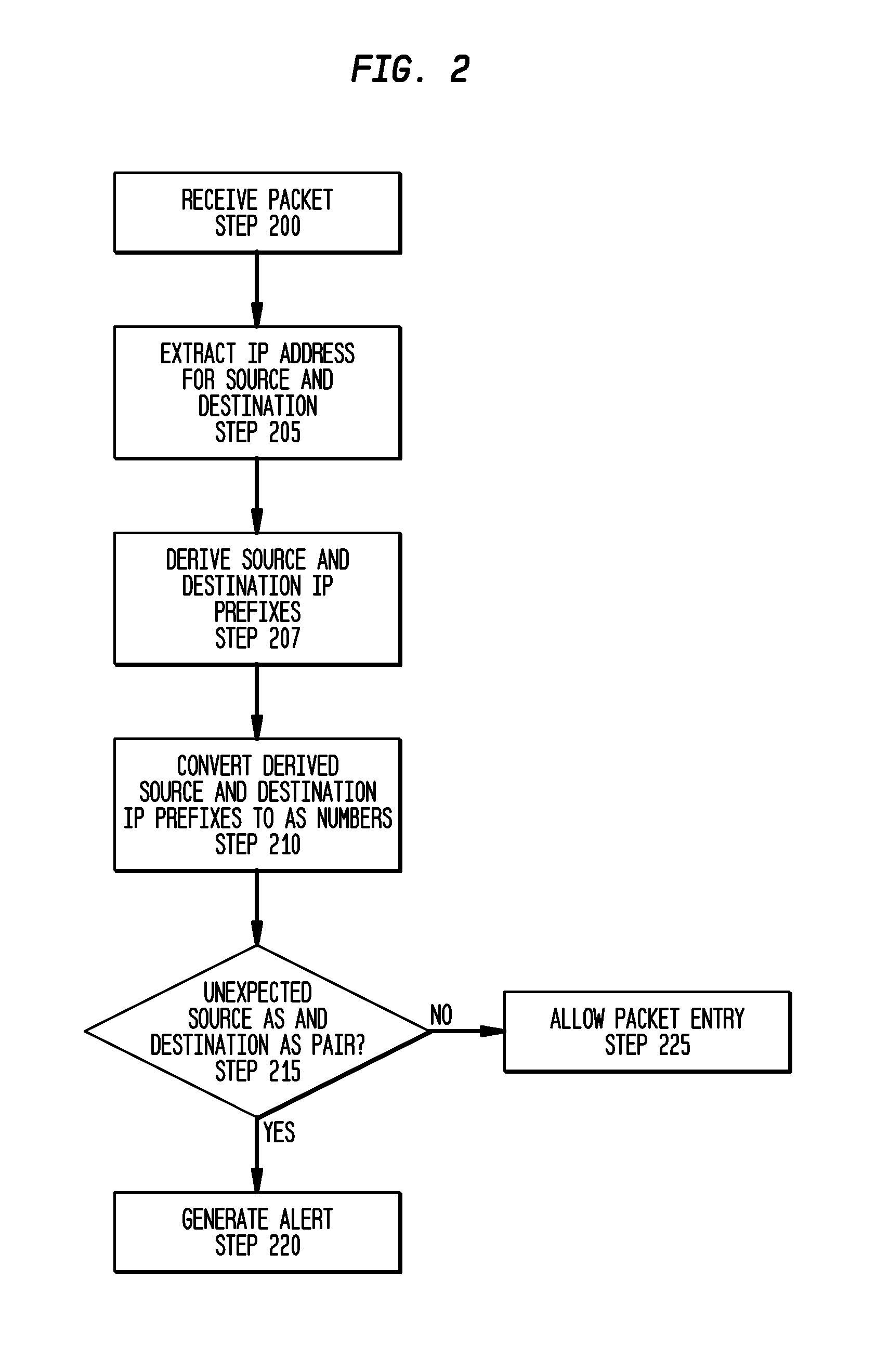
Method, apparatus and program for detecting spoofed network traffic
A method, an apparatus and a program for detecting spoofed Internet Protocol (IP) traffic directed to a network having a plurality of autonomous systems (AS) is provided. The method comprises receiving an incoming packet through an AS, the incoming packet containing a source IP address and a destination IP address, acquiring a corresponding source and destination IP address prefixes, converting the corresponding source and destination IP address prefixes into a source AS number and a destination AS number, determining if the incoming packet arrived from an unexpected source based upon the corresponding destination IP address prefix and the converted source and destination AS number using an unexpected pair tuple table generated from network routing information and generating an alert indicating that the incoming packet is not allowed to enter the network.
Owner:TELCORDIA TECHNOLOGIES INC +1
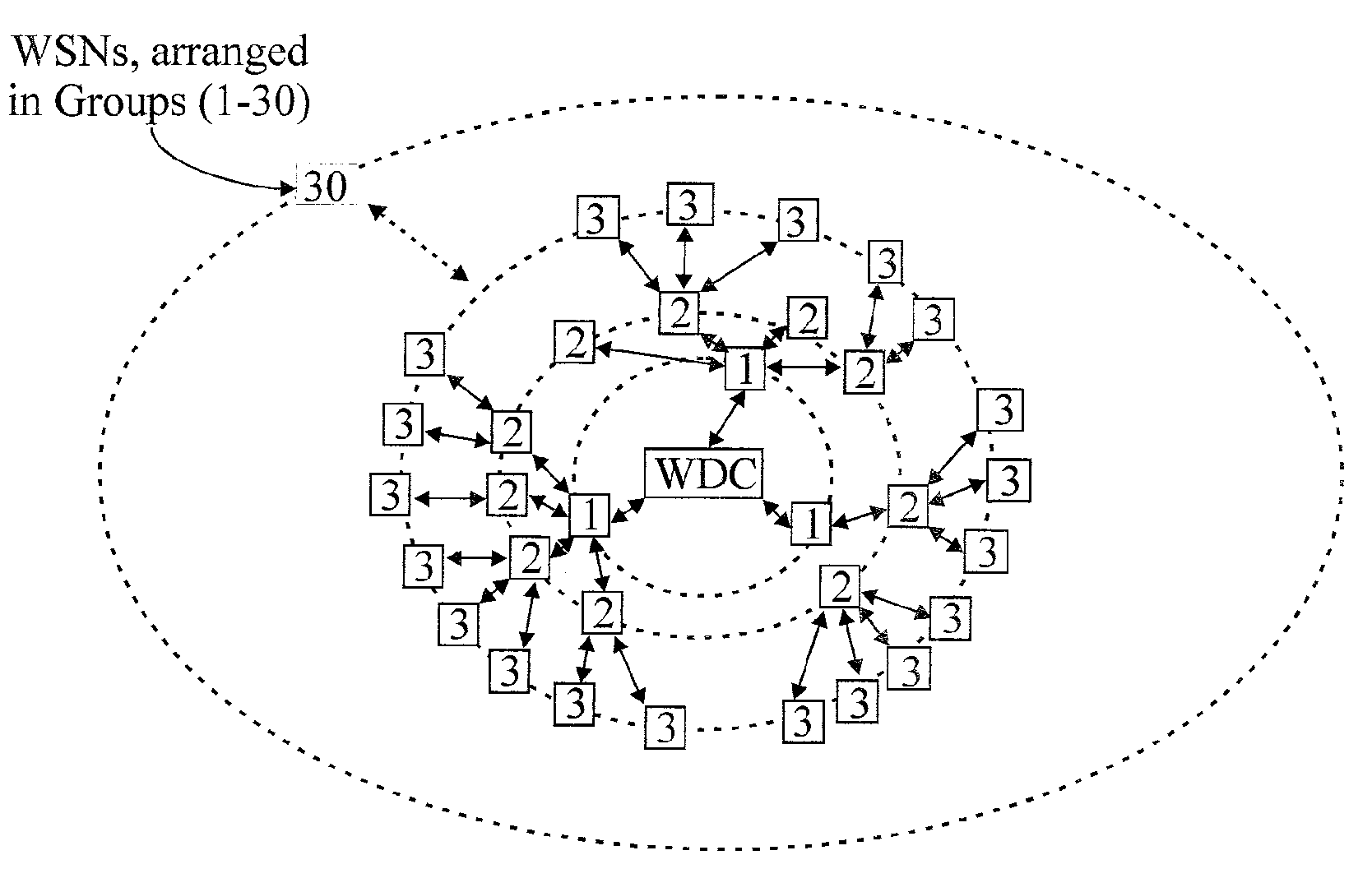
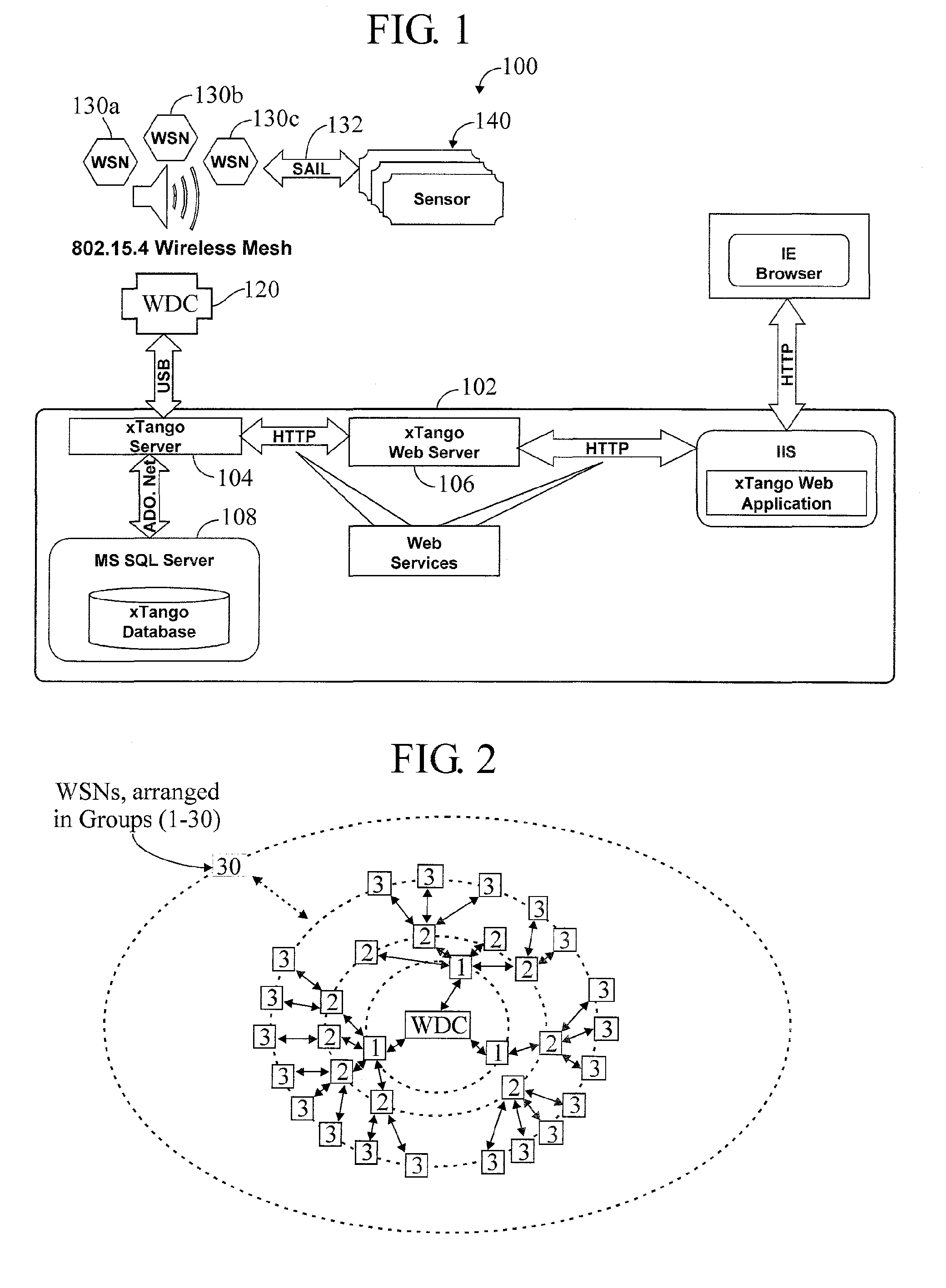
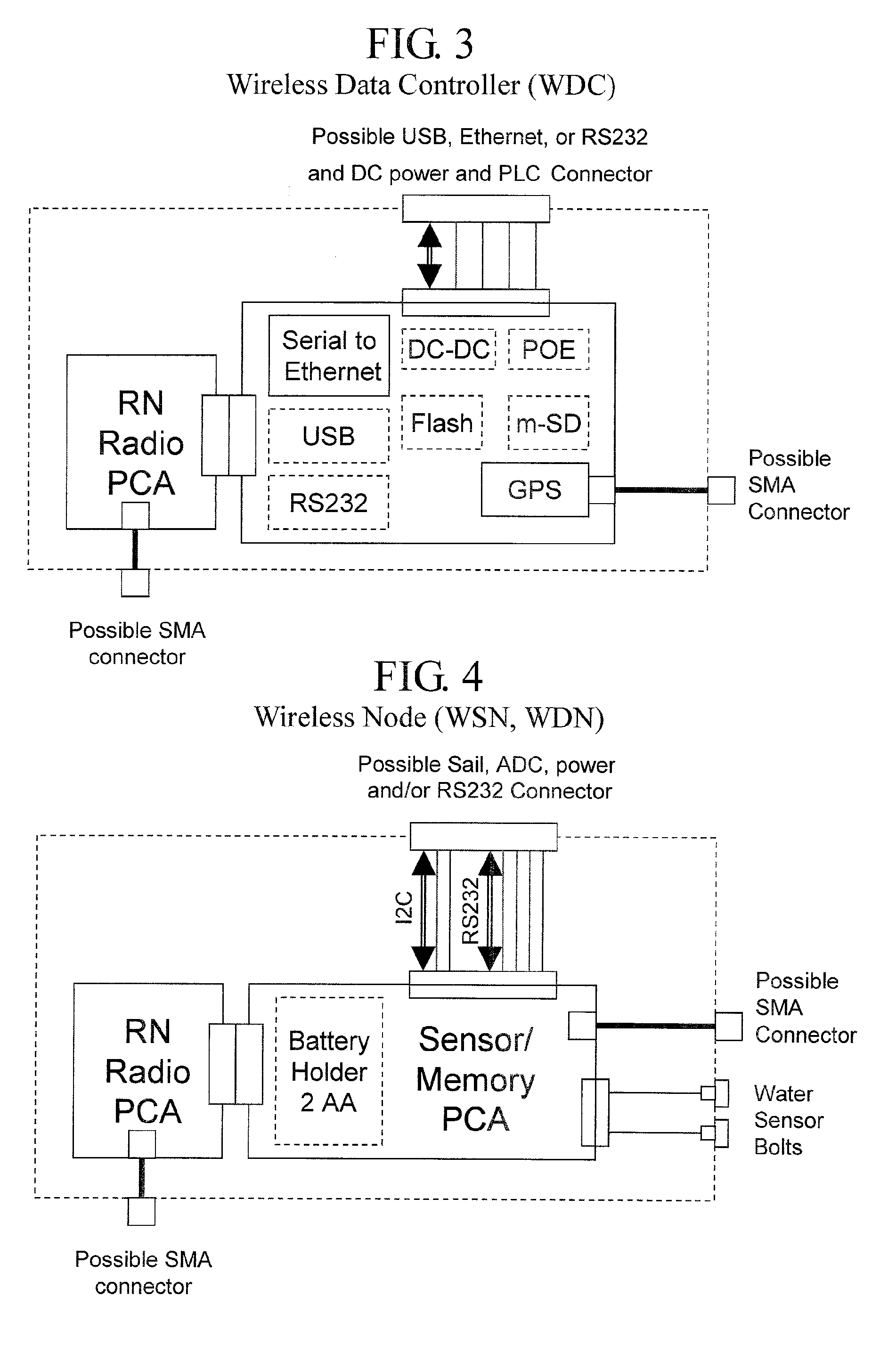
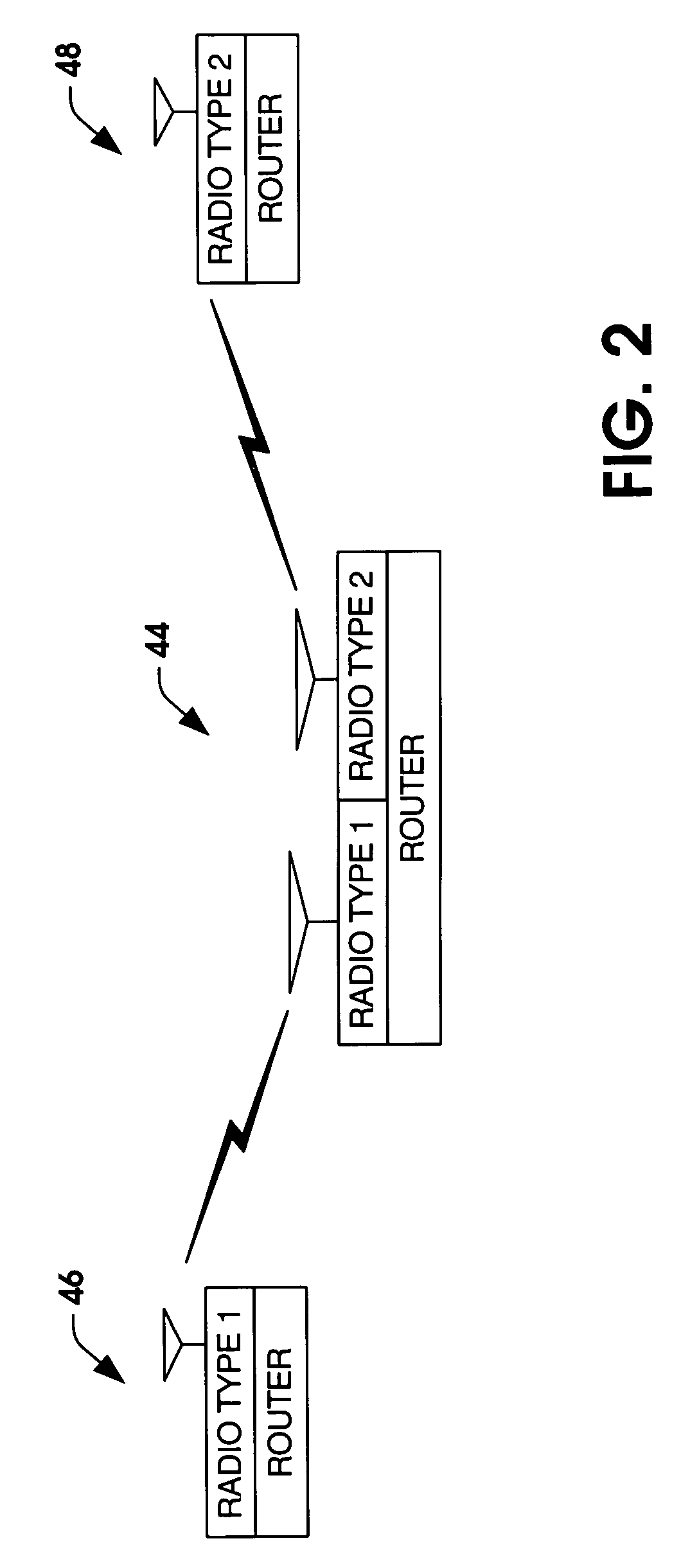
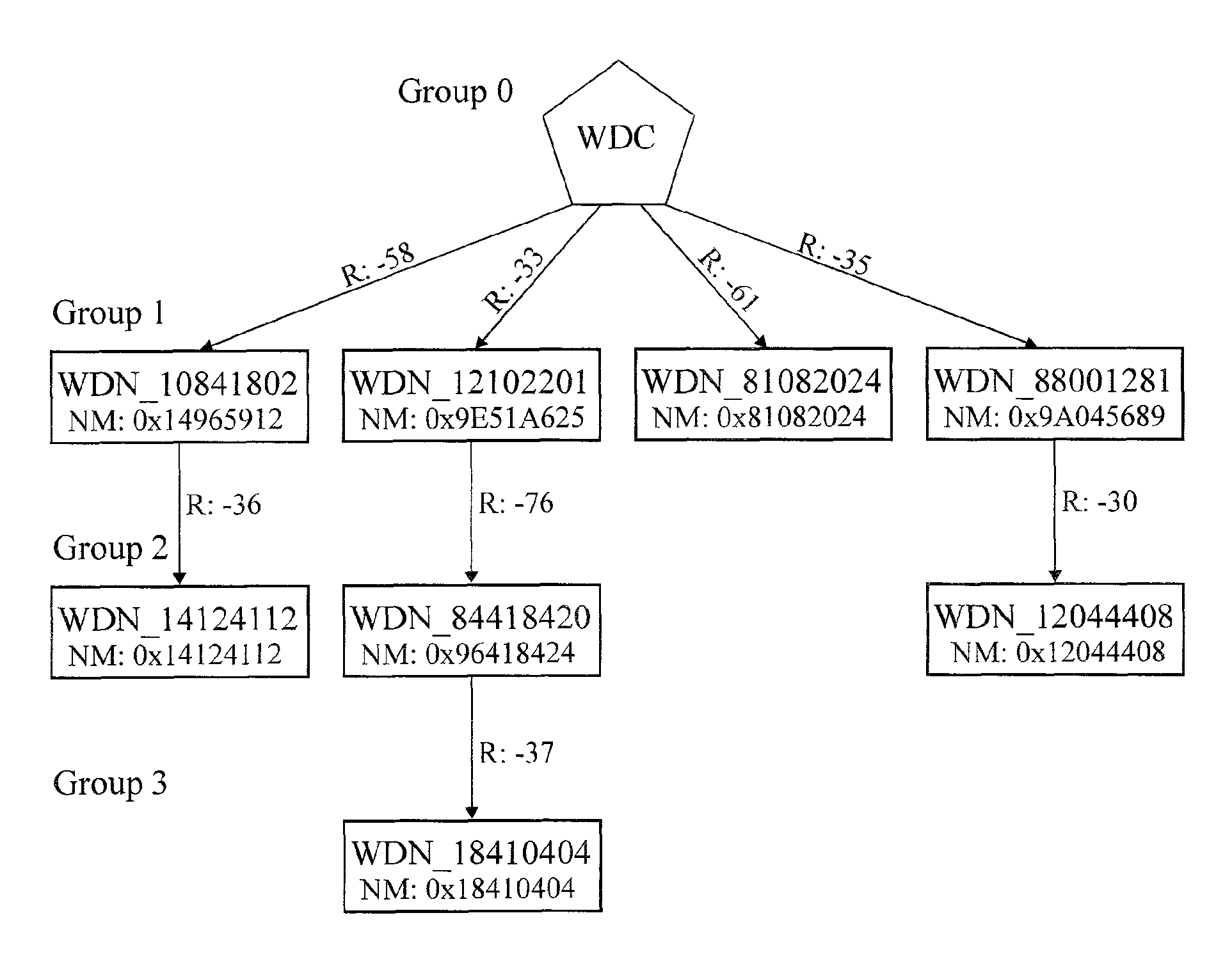
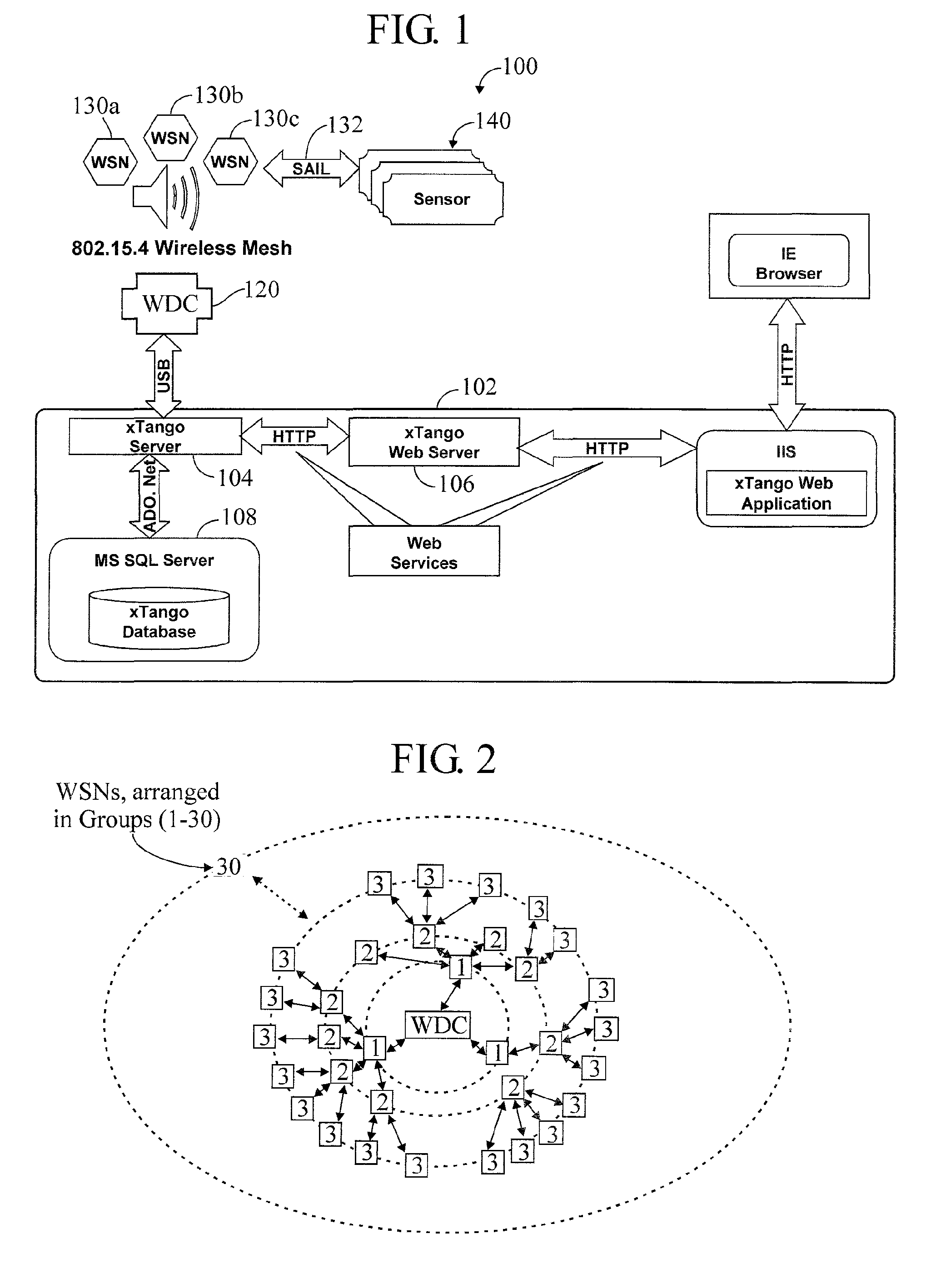
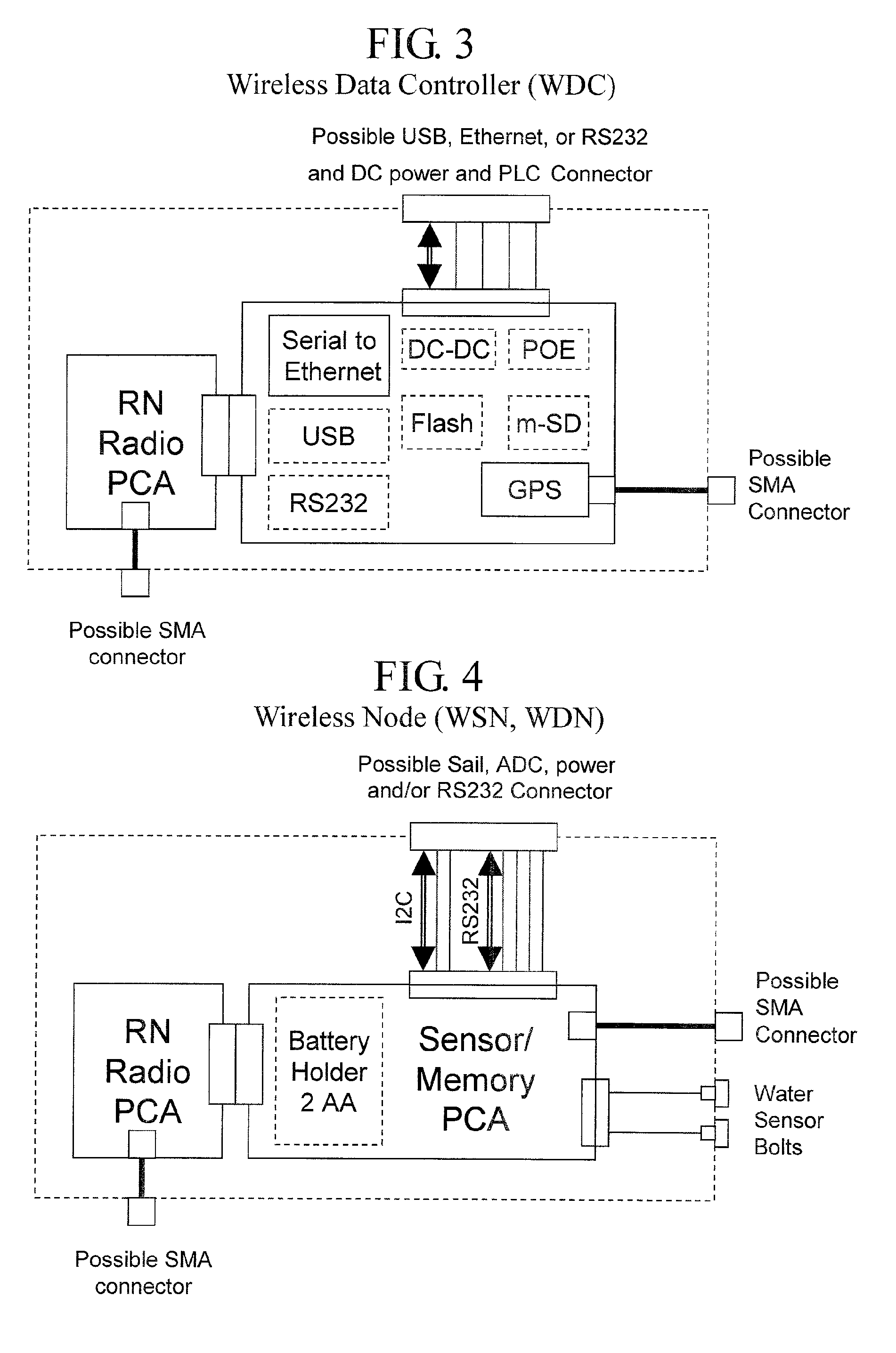
Wireless Data Networking
ActiveUS20080291855A1Low powerBetter read rateEnergy efficient ICTPower managementWireless dataNetwork mapping
A meshing network comprising one full function controller (WDC) and a plurality of nodes (WDN, WSN), that is RF quiet capable with very low power consumption and the ability to quickly heal itself and create new network paths. The network uses an addressing scheme that allows for each node to not have a network map but still be able to route messages. A piping scheme allows a mesh to become a high throughput network. A sensor rail protocol definition allows sensor devices to connect to nodes and route messages through the network.
Owner:RAYTHEON CO
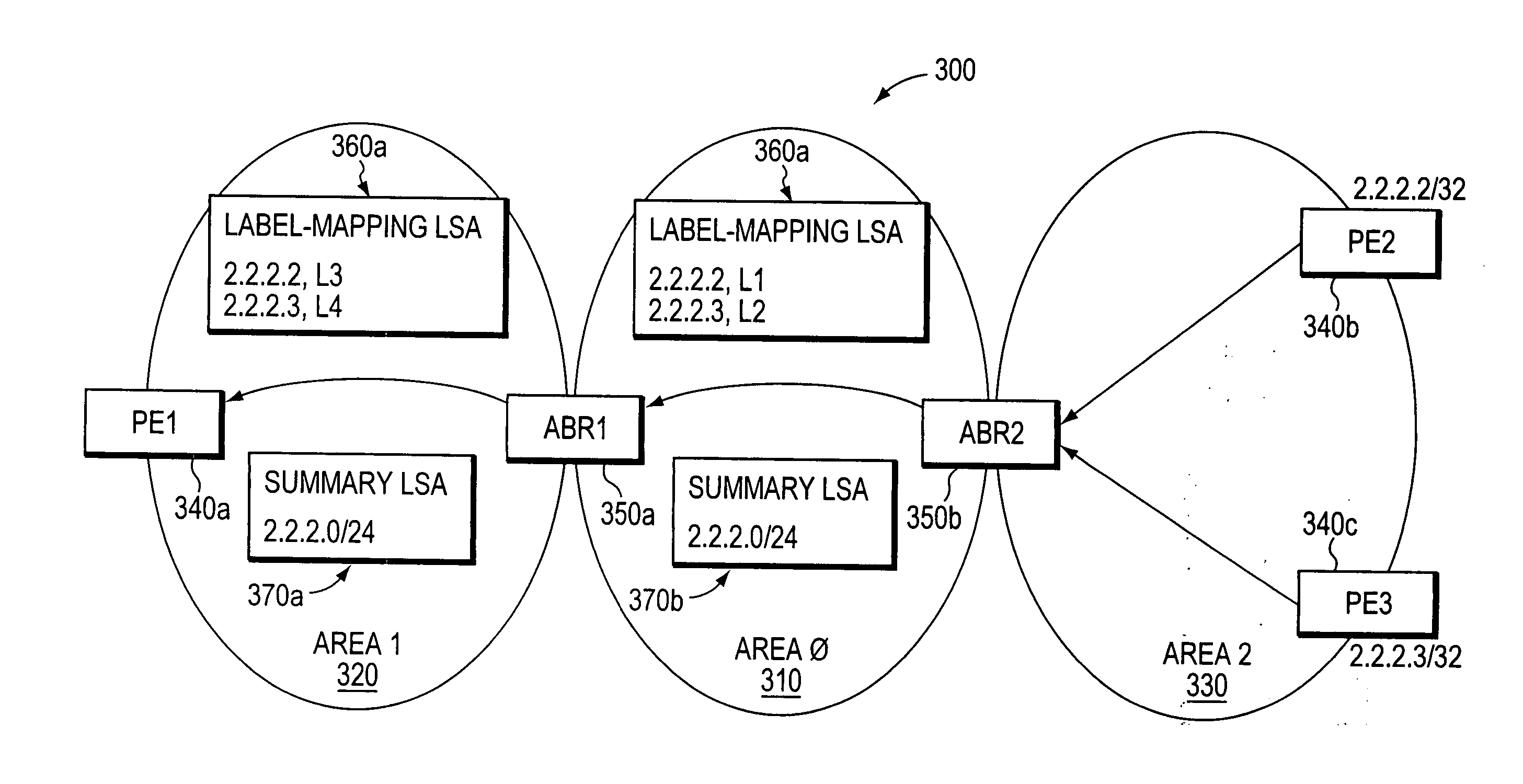
Hierarchical label distribution for inter-area summarization of edge-device addresses
ActiveUS20060262735A1Less memoryFaster FIB lookupError preventionFrequency-division multiplex detailsDistributed computingEdge device
A system and method are provided for separately distributing edge-device labels and routing information across routing areas of a computer network. Because the edge-device labels are distributed separately from network routing information, the process of distributing the edge-device labels does not preclude conventional edge-device address summarizations. Illustratively, a novel “label mapping” LSA is employed for distributing the edge-device labels across routing areas. The label-mapping LSA may be embodied as an area-scope OSPF opaque LSA (type 10) or an IS-IS LSP containing TLVs of area scope. Advantageously, the present invention is generally applicable whenever label values are allocated to edge devices in a multi-area computer network and data is “tunneled” through the network from one edge device to another.
Owner:CISCO TECH INC
Secure network-routed voice multicast dissemination
InactiveUS20040095900A1Efficient processTime-division multiplexData switching by path configurationVoice communicationMobile communication systems
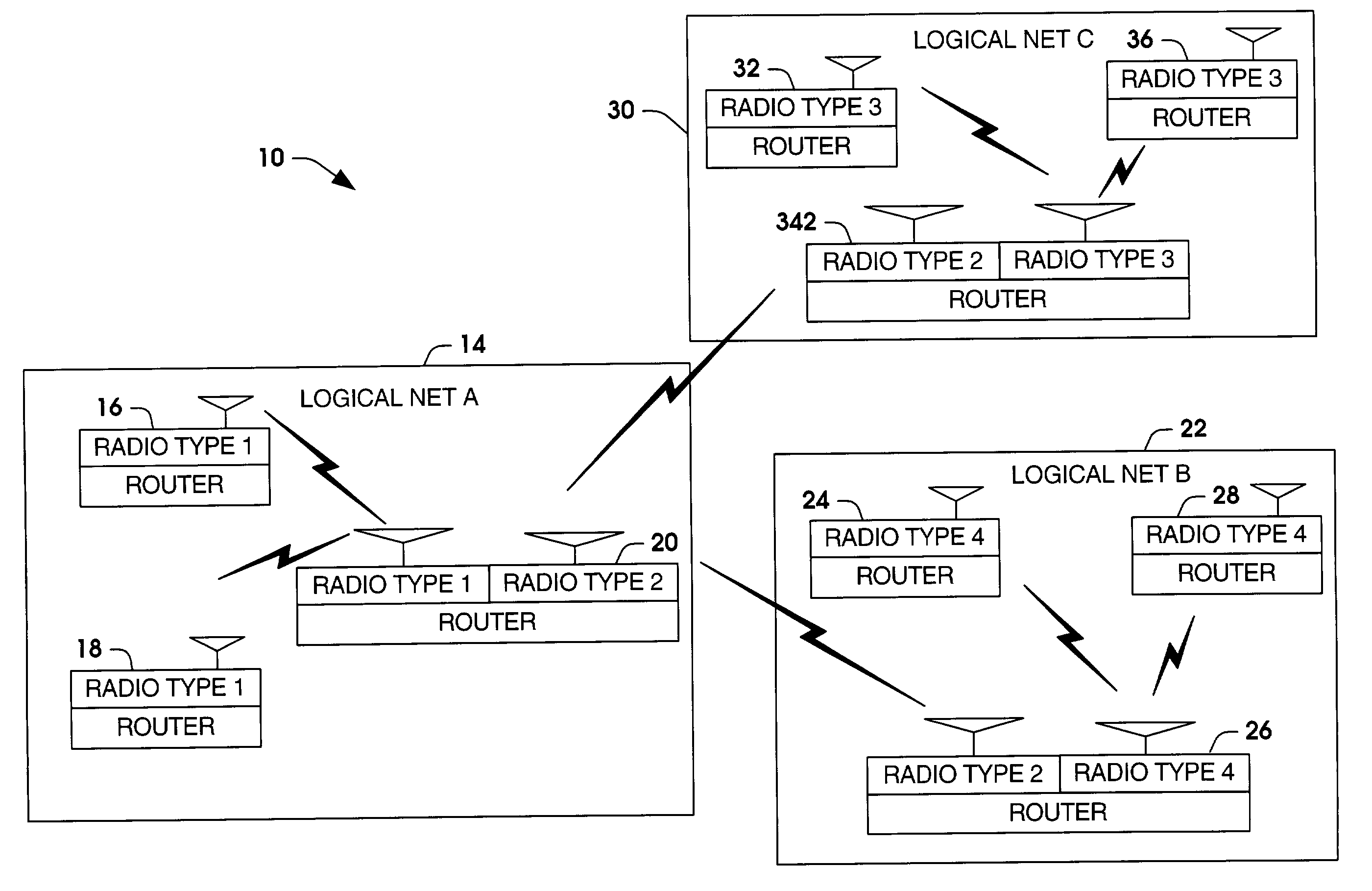
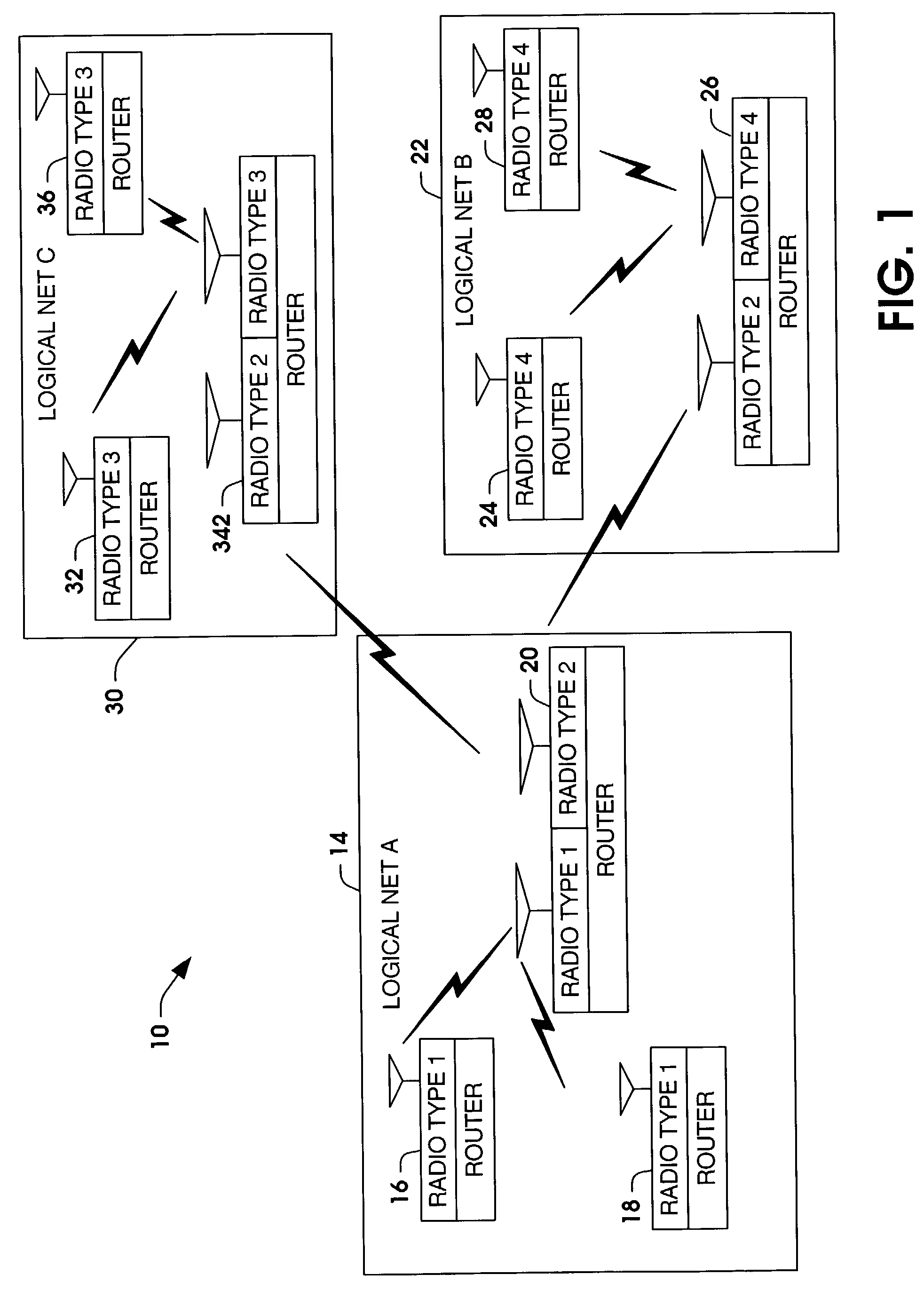
Systems and methods are provided for routing voice communications to groups in a voice communication system. The voice communication system can be a mobile communication system having a plurality of members grouped as logical networks and / or unit task organizations. One or more routers are provided in the system. The one or more routers extract routing information from received voice messages. The routing information is used with a router database to determine which identified group to route the digitized voice packets. The one or more routers can be adapted to receive and route voice communications to different radio types across different logical networks.
Owner:NORTHROP GRUMMAN SYST CORP
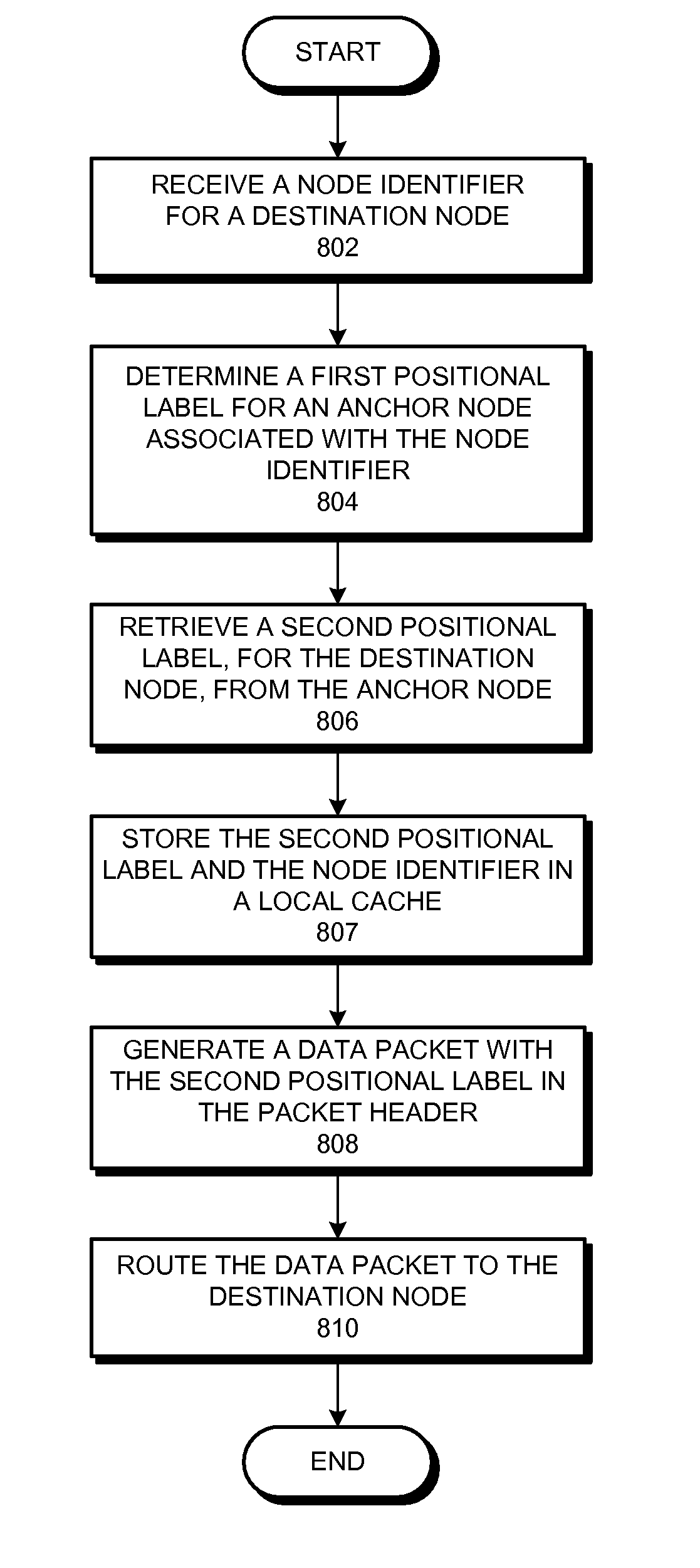
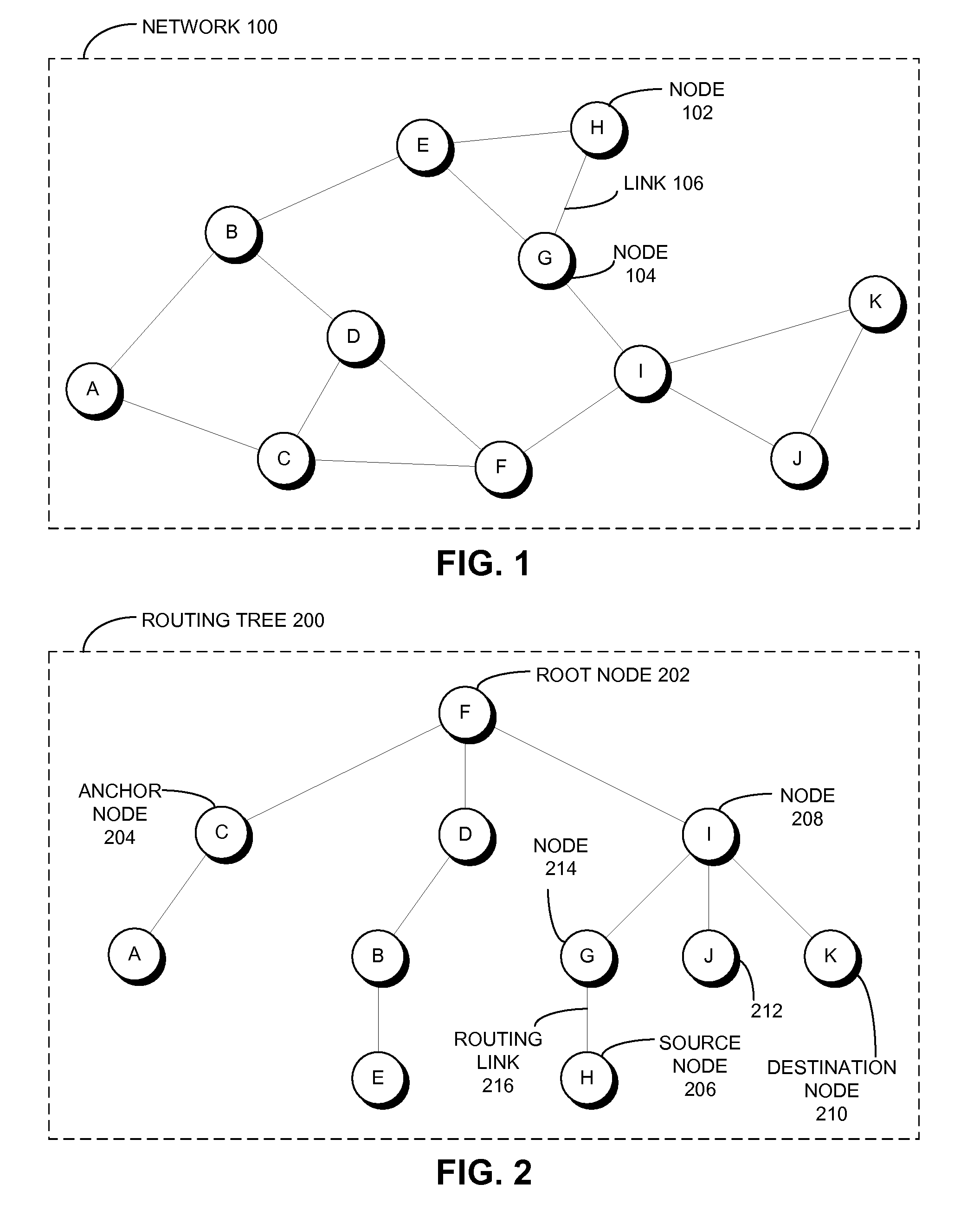
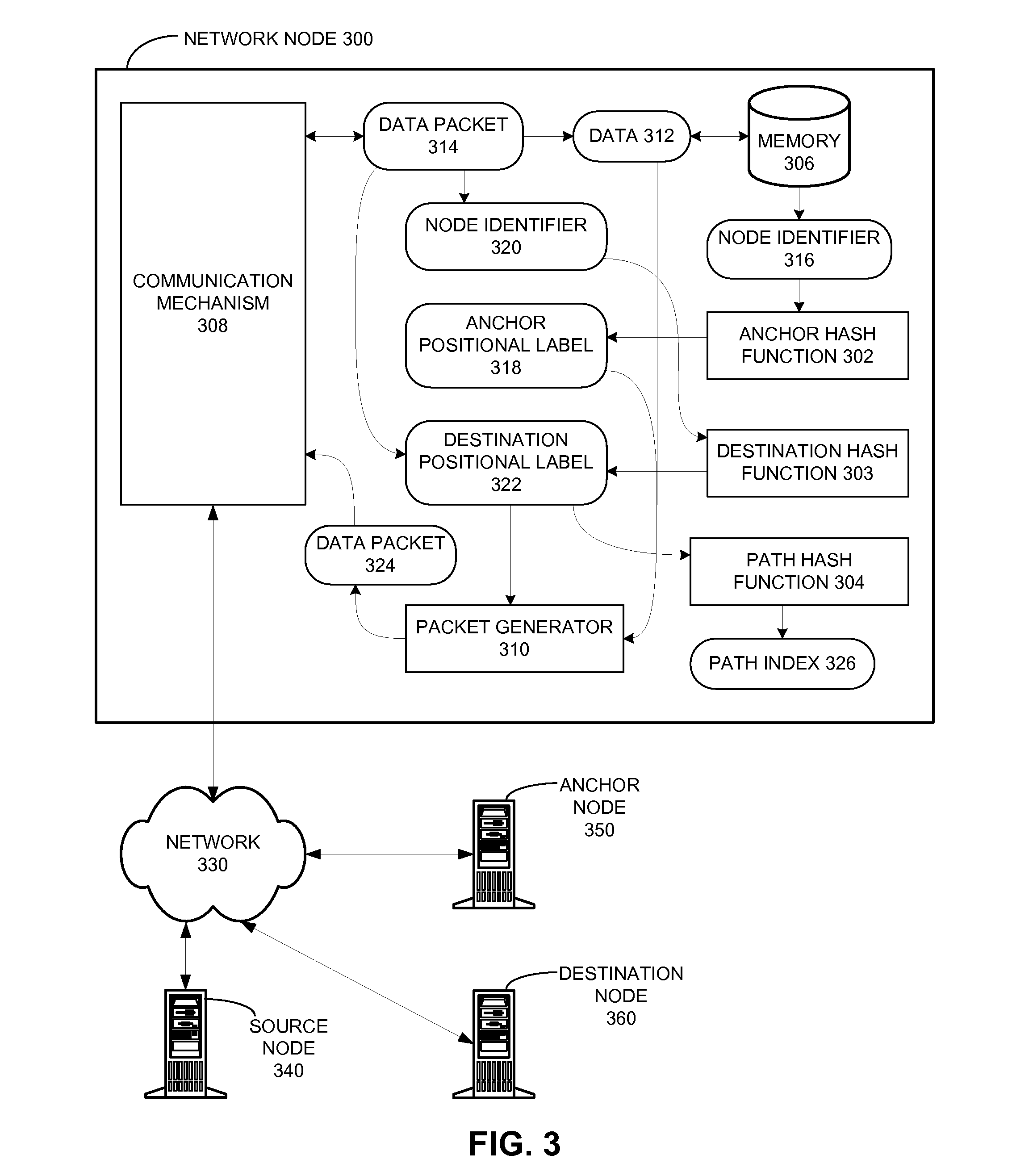
Network routing with path identifiers
One embodiment of the present invention provides a system that communicates a data packet in a network to a target node. In doing so, the system receives a node identifier for the target node, and determines a first positional label, based in part on the node identifier, for reaching a first anchor node from a root node in the network. The first anchor node stores a second positional label for reaching the target node from the root node in the network, which comprises a number of nodes coupled to the root node in a tree topology. The system then retrieves the second positional label from the first anchor node, and communicates the data packet to the target node based in part on the second positional label.
Owner:CISCO TECH INC
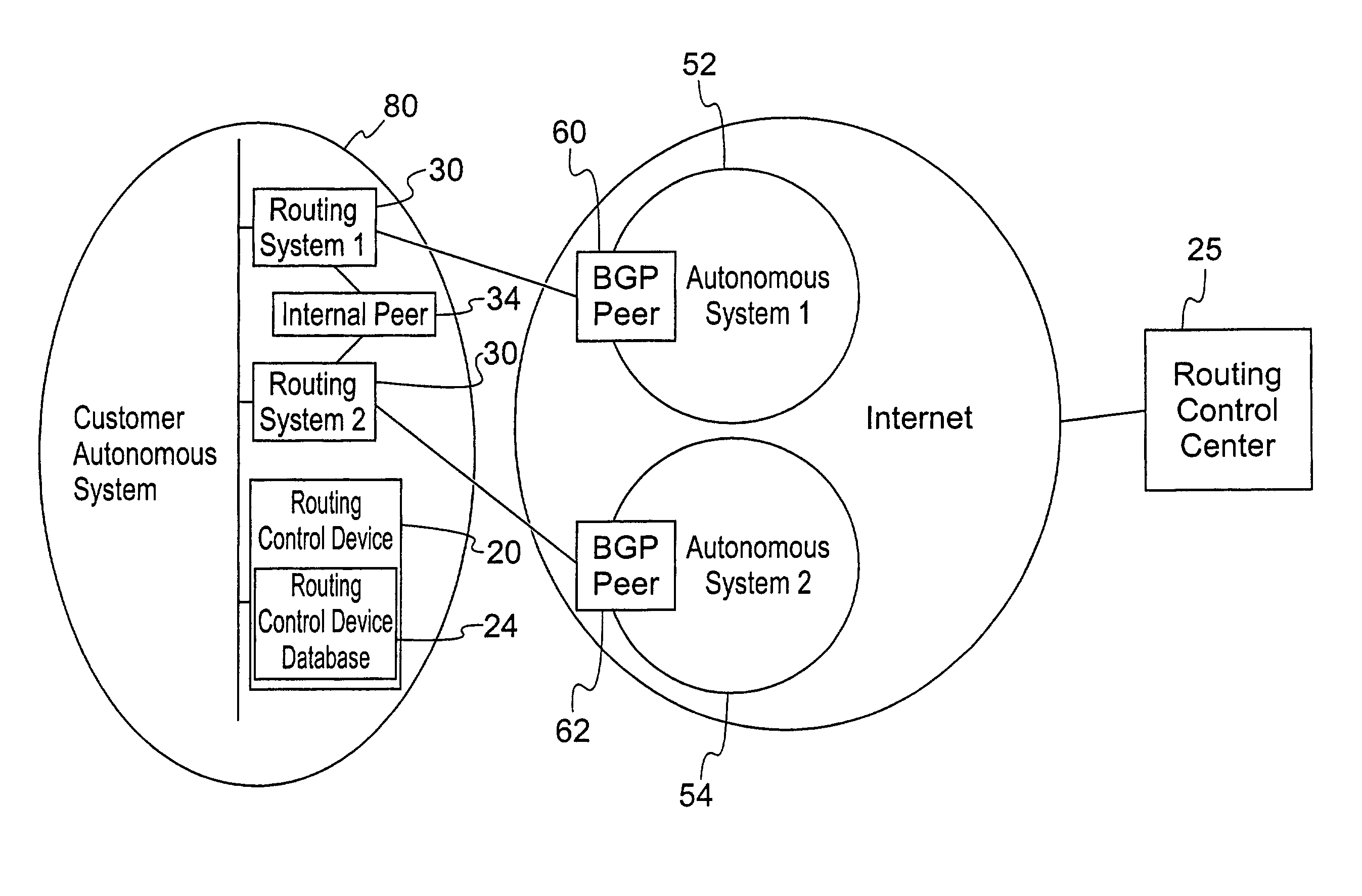
Methods, apparatuses and systems facilitating deployment, support and configuration of network routing policies
InactiveUS7139242B2Routing decisionIncrease currentError preventionTransmission systemsThe InternetDistributed computing
Methods, apparatuses and systems relating to the control and application of policies for routing data over a computer network, such as the Internet. Some implementations of the invention facilitate the configuration, deployment and / or maintenance of network routing policies. Some implementations of the invention are particularly useful for controlling the routing of data among autonomous systems or organizations. Certain implementations allow for dynamic modification of routing policy based on such factors as current Internet performance, load sharing, user-defined parameters, and time of day.
Owner:TRANSACTION NETWORK SERVICES +1
Client device method and apparatus for routing a call
ActiveUS20080139210A1Commmunication supplementary servicesRadio/inductive link selection arrangementsClient-sideTelephone communication
A telecommunication method, server and system that route an outbound telephone communication initiated by a wireless remote device through an enterprise communication network. The system also routes an incoming call to a device associated with an enterprise communication network to a plurality of telephony devices including wireless devices and other remote devices.
Owner:MALIKIE INNOVATIONS LTD
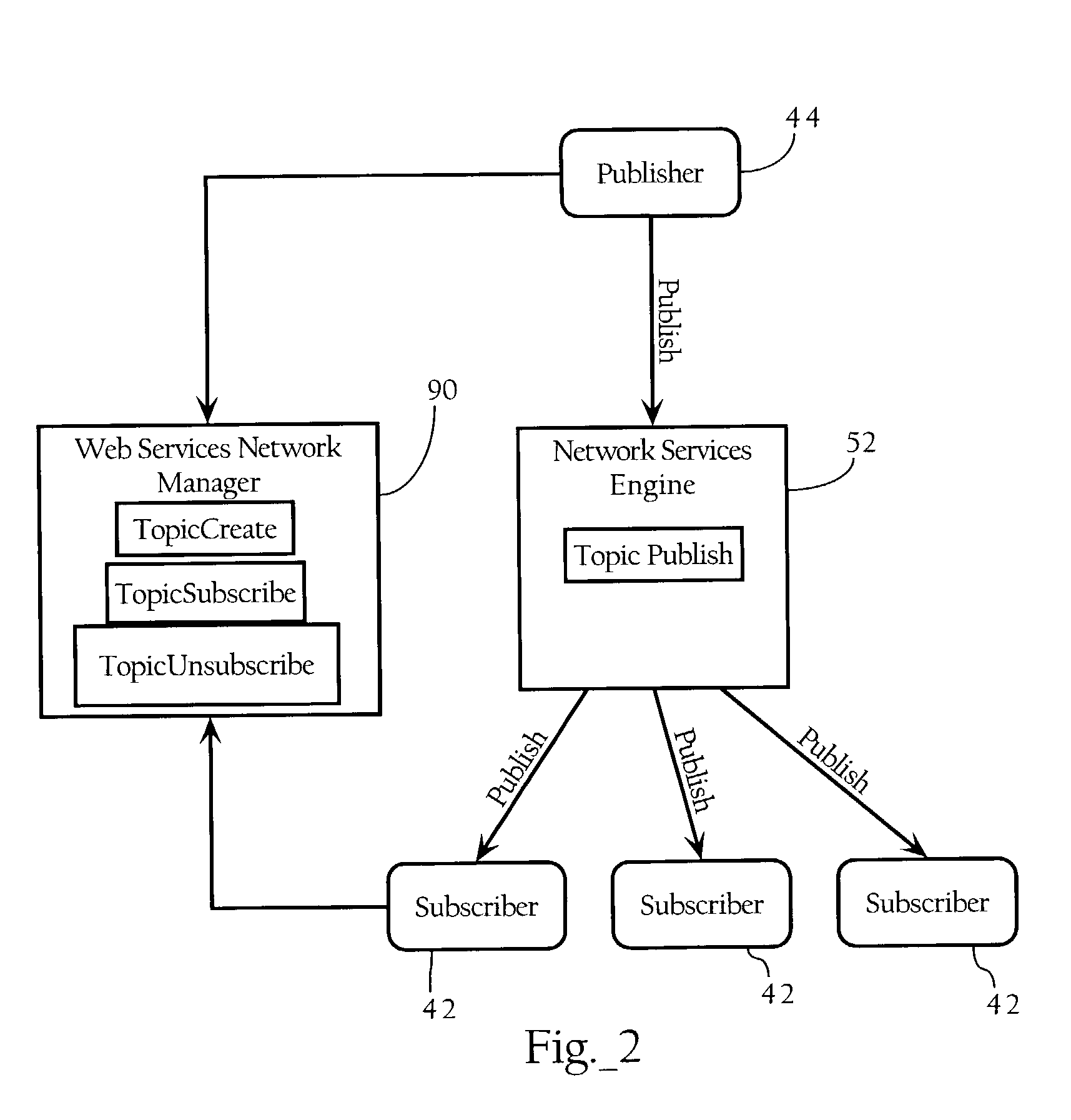
Network publish/subscribe system incorporating Web services network routing architecture
ActiveUS7349980B1Facilitating deployment and configuration and maintenanceMultiple digital computer combinationsWebsite content managementWeb serviceNetwork architecture
Methods, apparatuses, and systems facilitating the deployment, configuration and maintenance of publication / subscription systems within the context of Web service networks. In one embodiment, the present invention provides Web services network system that presents a topic as a routing entity and includes functionality facilitating topic creation, subscription and publication in a manner consistent with the basic modes of Web services development and deployment, allowing such tasks to be approached in an intuitive, cost-effective and manageable manner. In a preferred embodiment, the publication / subscription system functionality according to the present invention is integrated into a distributed Web services network architecture as more fully described below. The Web services network architecture and integrated publication / subscription system according to the present invention can be implemented across any suitable computer network, including a local area network, an intranet or the Internet.
Owner:AKANA
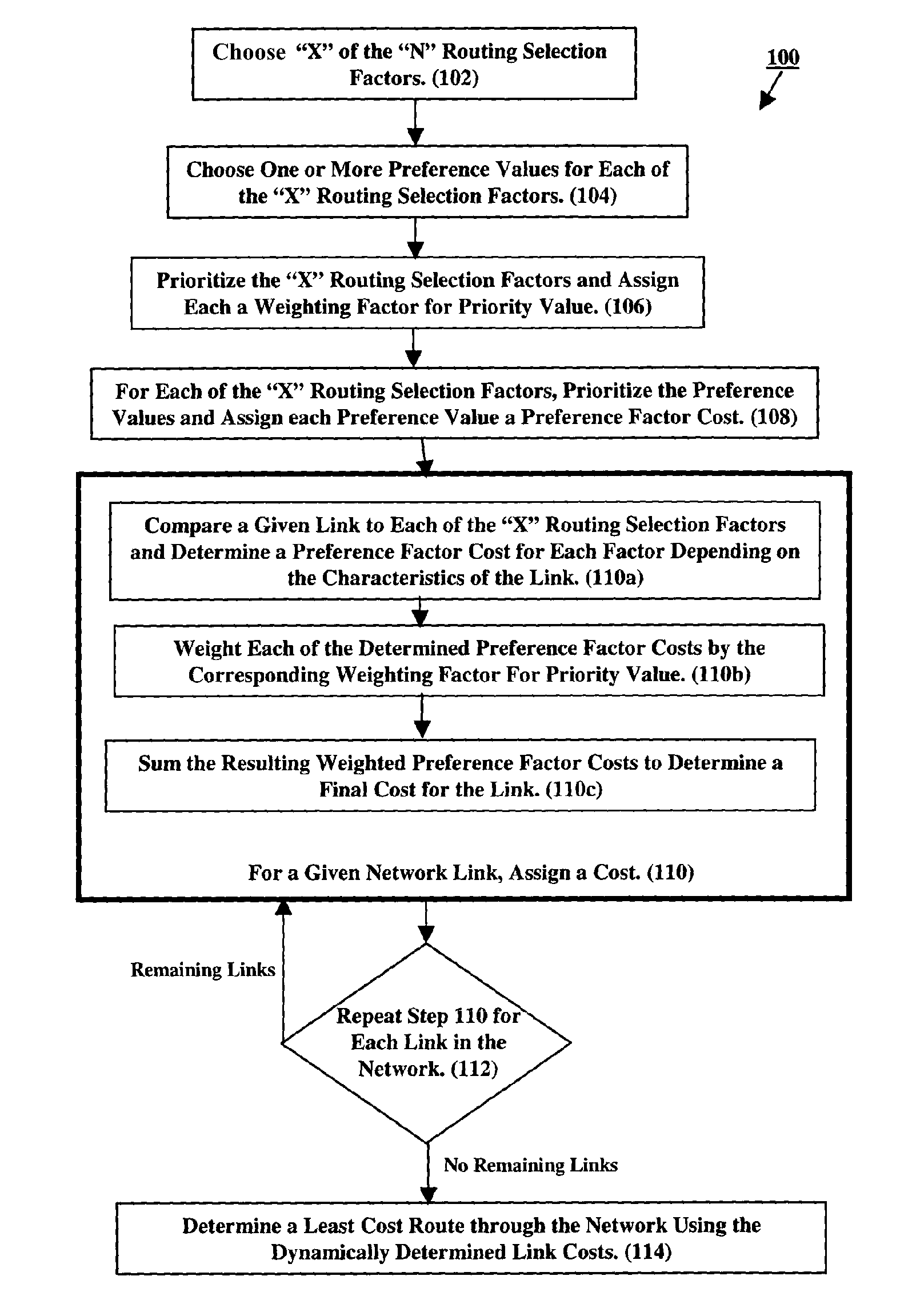
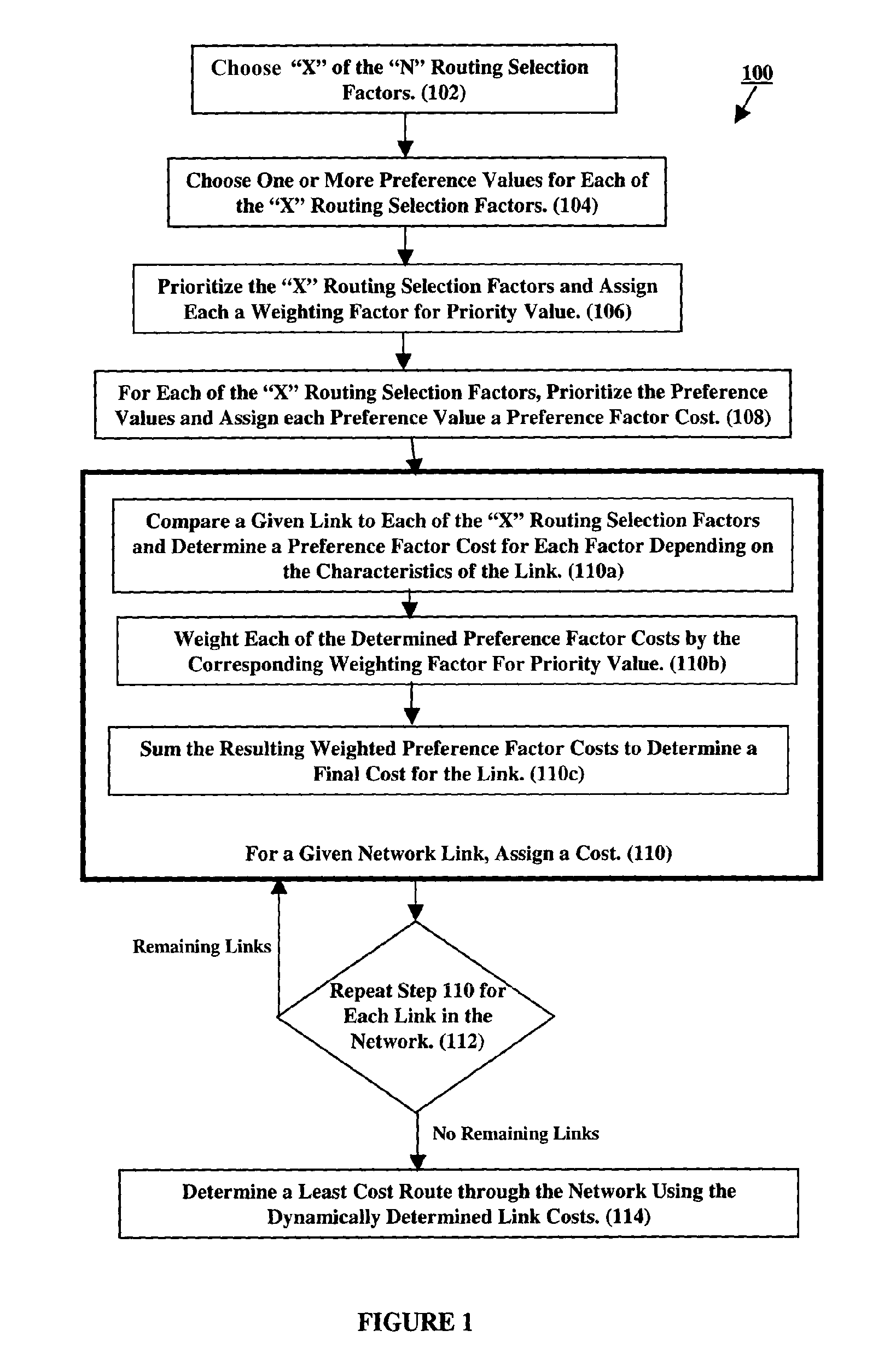
Dynamic cost network routing
ActiveUS7779065B2Digital data processing detailsDigital computer detailsUser needsDistributed computing
To determine a network route corresponding to user needs, costs are dynamically defined for each link of a network. Specifically, based on link characteristics, routing factors are defined and for each factor, allowable values are defined. When determining a route, one or more routing factors and one or more allowable values for each factor are selected. Based on user prioritization of these factors and prioritization of the allowable values for each factor, weights are assigned to the factors and costs are assigned to the values. Link costs are determined by comparing a given link to each selected factor and determining for each factor which allowable value matches the link's characteristics. The cost of each matching value is then weighted by its corresponding factor. The weighted costs are summed to determine a link cost. The link costs are subsequently used to determine a route through the network.
Owner:NYTELL SOFTWARE LLC
High-performance addressing and routing of data packets with semantically descriptive labels in a computer network
InactiveUS7555563B2Reduce storageEasy to operateDigital computer detailsData switching networksRouting tableNetwork packet
A method, system and apparatus for routing data through a network based on the content or semantics of the data. Semantic routing engines route the data through the network based upon information maintained in routing tables. The routing tables used to route the content through the network are derived by aggregating information about either content consumers or content producers into ontological.
Owner:SEMANDEX NETWORKS
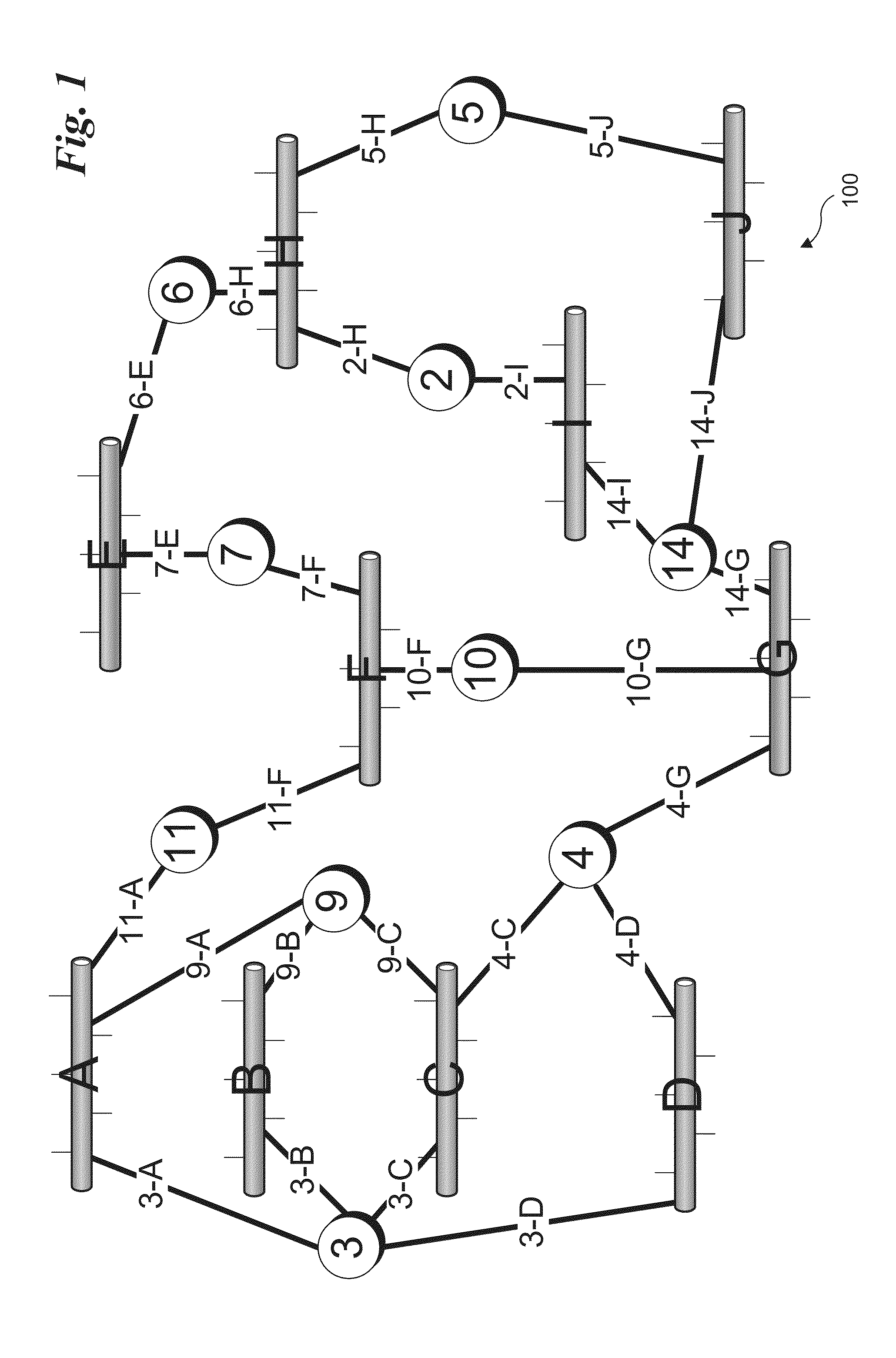
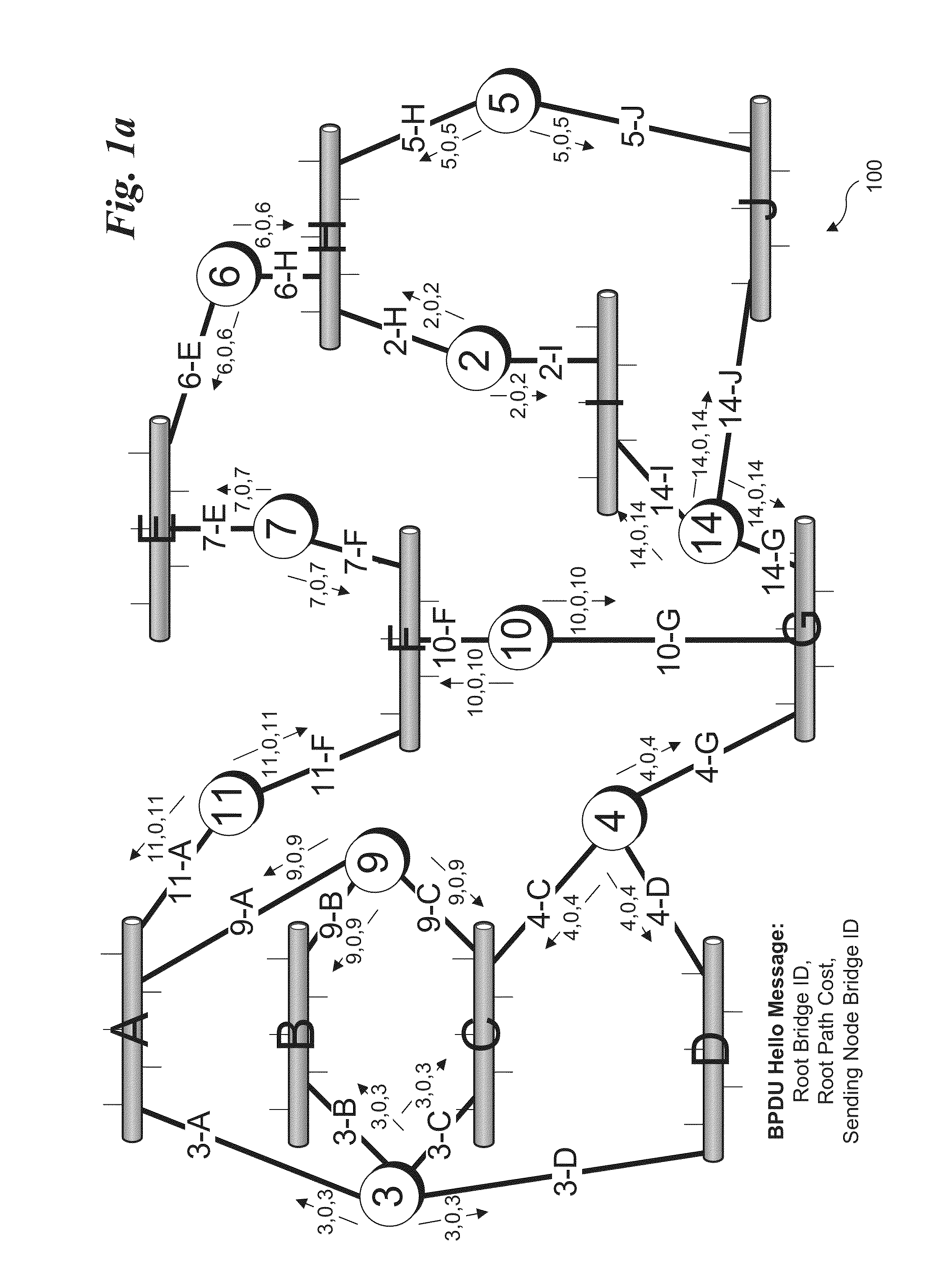
Network routing protocol power saving method for network elements
ActiveUS20140192677A1Energy efficient ICTData switching by path configurationDistance-vector routing protocolPath network
Methods and apparatus relating to network routing protocols to support power savings in network elements. A most utilized link path network topology for a computer network is discovered using a routing protocol such as a Spanning Tree, link-state, or distance vector routing protocol. In view of the most utilized link path network topology, links are identified as candidates for power management under which a power state of the link and associated network ports are managed to save power under applicable link conditions, such as low utilization. Link power-state change conditions are detected, and in response a corresponding change to the power state of a link is effected by changing the power-state of the network ports at the ends of the link. Power state changes include putting a link into a reduced power state, taking a link offline, and powering a link back up.
Owner:INTEL CORP
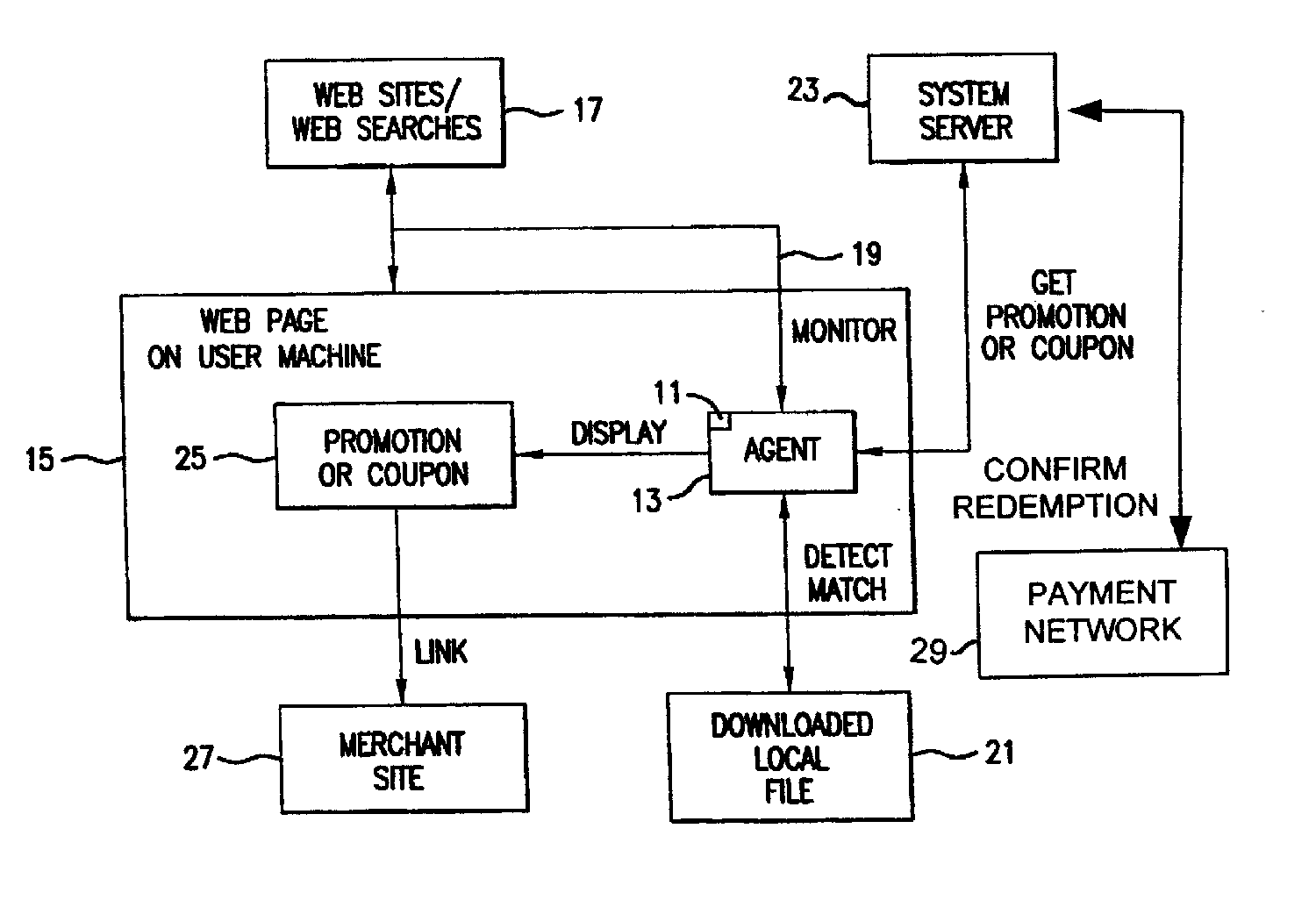
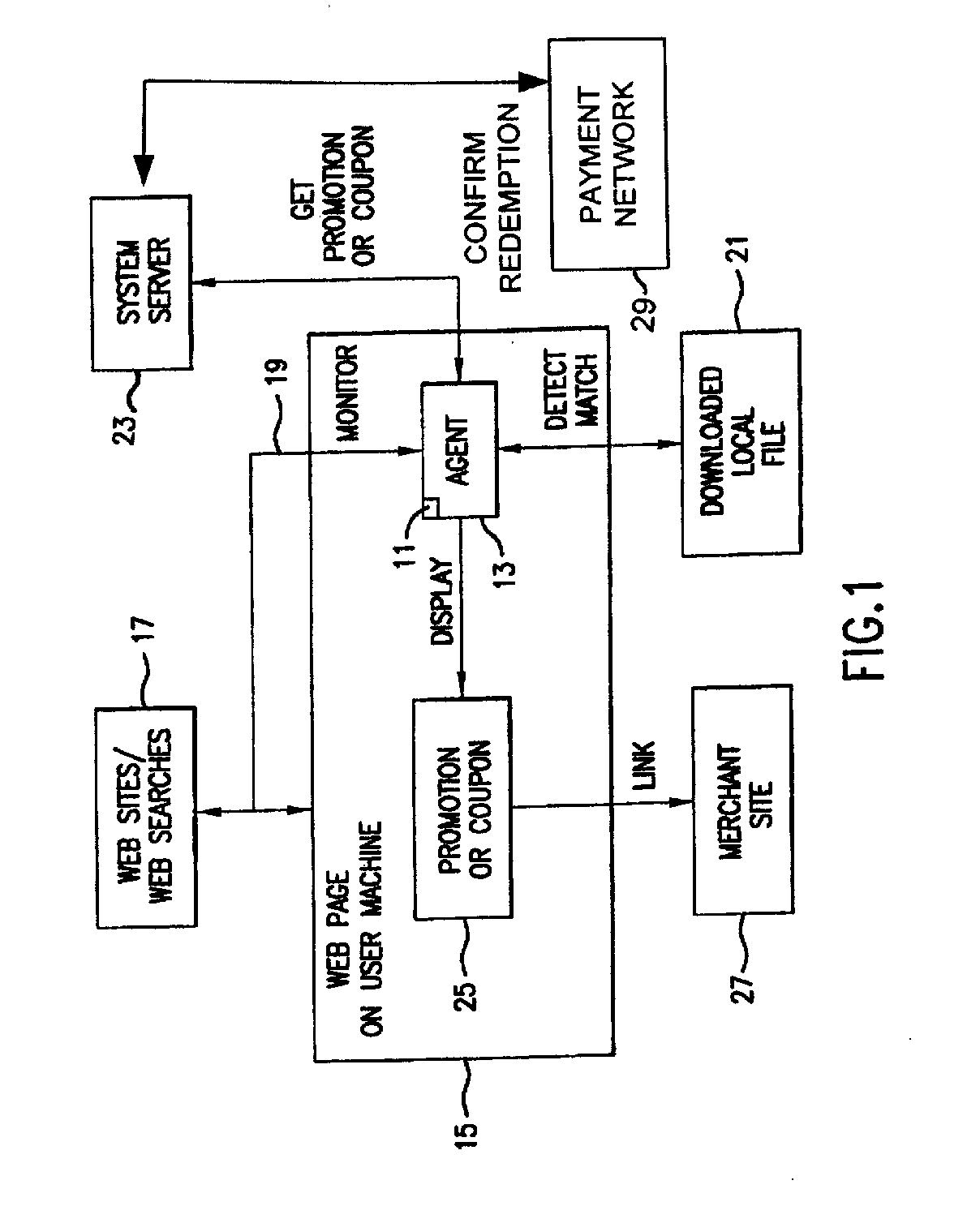
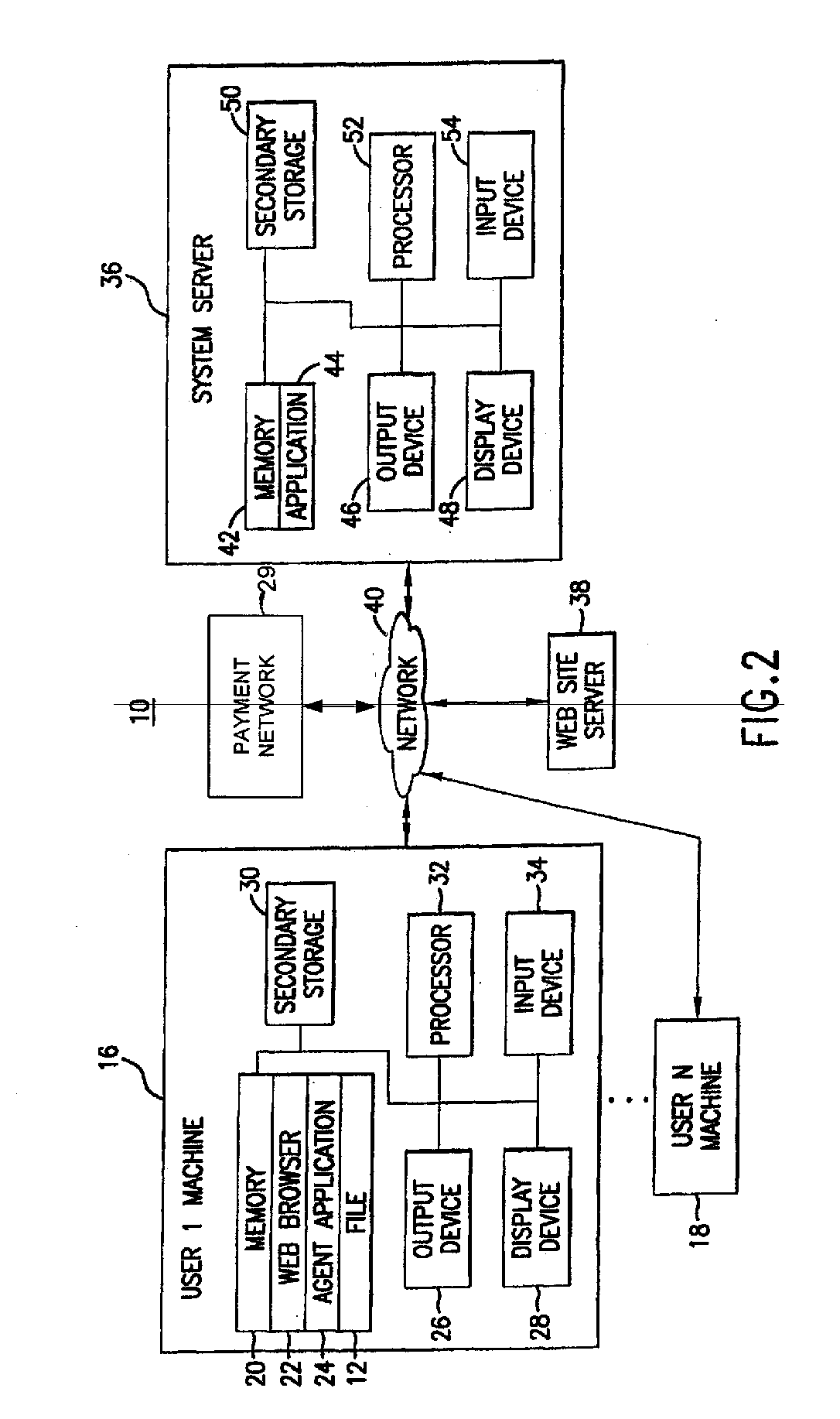
Software agent for facilitating electronic commerce transactions through display of targeted promotions or coupons
InactiveUS20060015405A1Easy to confirmAdvertisementsBroadcast information monitoringNetwork addressSoftware
A software agent for locally tracking a user's network interaction, such as web browsing, and providing targeted promotions with optional coupons to the user. The monitoring involves use of a downloaded file of network addresses and words potentially tailored to each individual user. The software agent locally compares network addresses and content of web sites accessed and search terms entered against the stored addresses and key words in the file. Upon detecting a match, the software agent contacts a system server to obtain a promotion with an optional coupon for the match, and displays an indication of the promotion or coupon to the user, providing the user with the option to view, decline, save, or defer the promotion. The user is provided with redeemable credits for viewing promotions, visiting the site of a merchant offering the promotion, completing a transaction, and spending at least a threshold dollar amount. The coupons can include coupons targeted to users geographically close to particular merchants so that the coupons can be printed and redeemed at the merchant's establishment. Transactions related to the promotions, whether completed online or in-store, are confirmed to demonstrate the efficacy of the promotions, award additional loyalty rewards to a user's account, or to compensate an advertiser or affiliate. Confirmation of in-store transactions may be accomplished by accessing transaction data routed through third-party payment networks used for credit and debit card transactions and cellular phone transactions and the like.
Owner:KNOWLEDGEFLOW
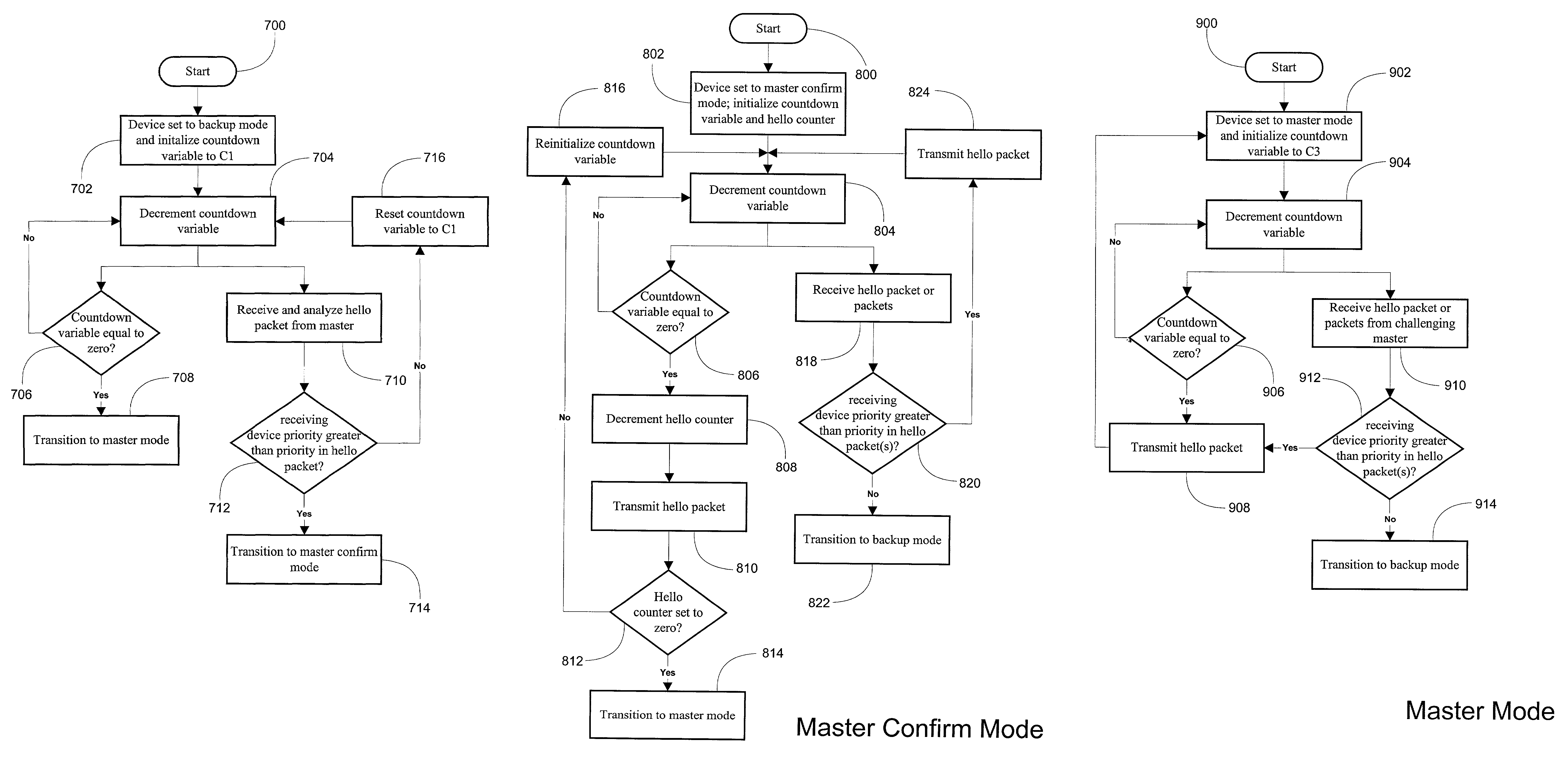
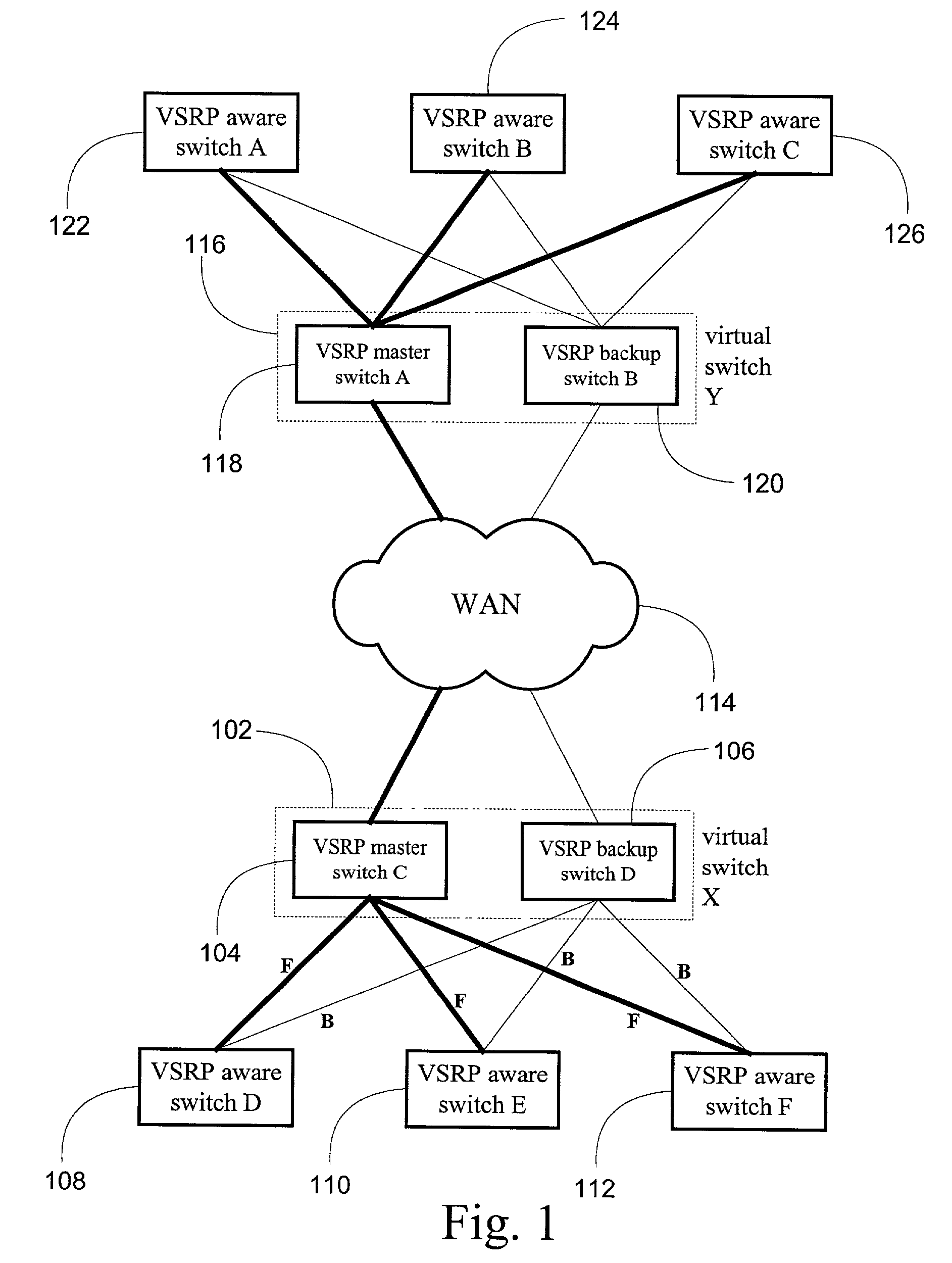
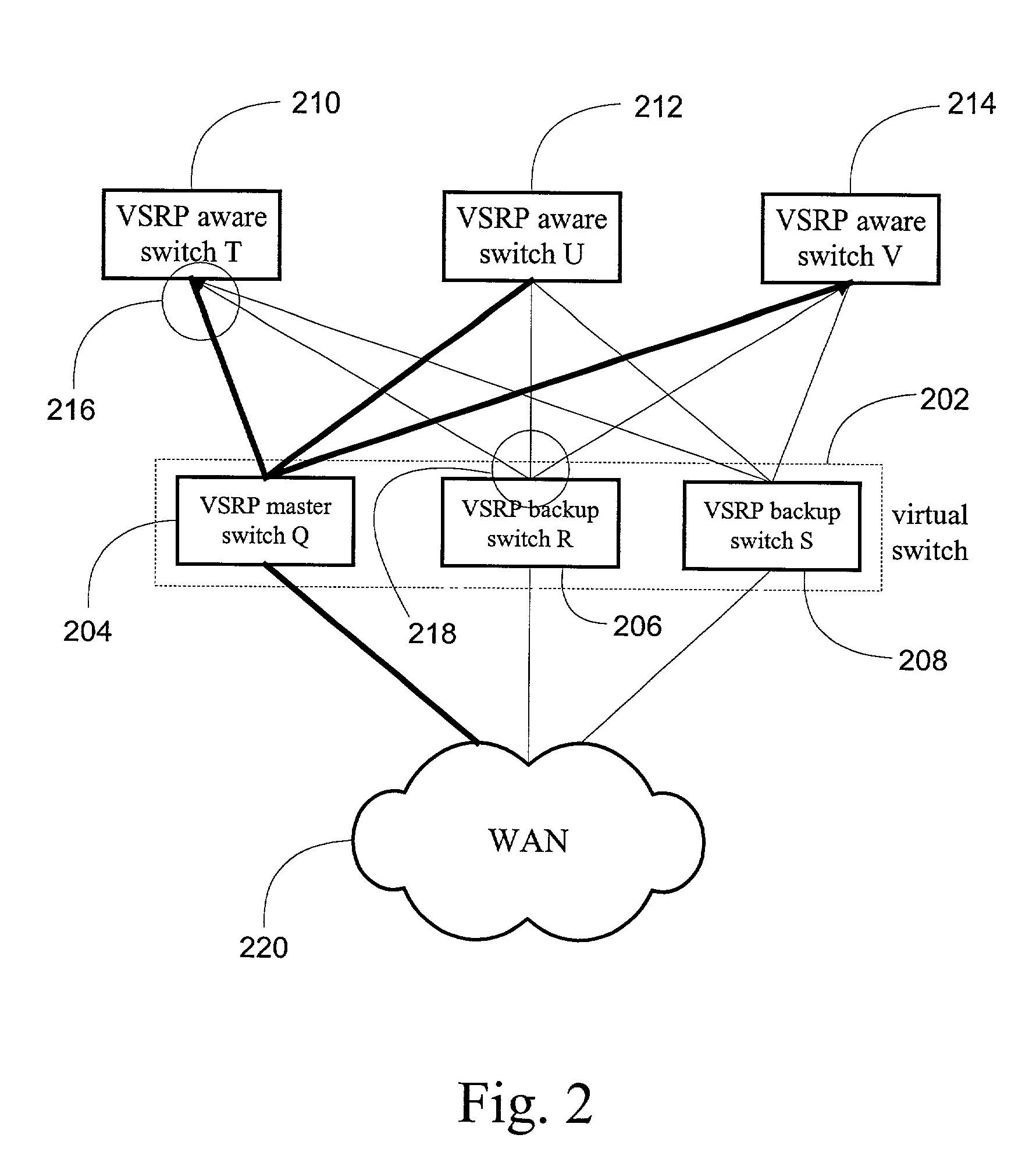
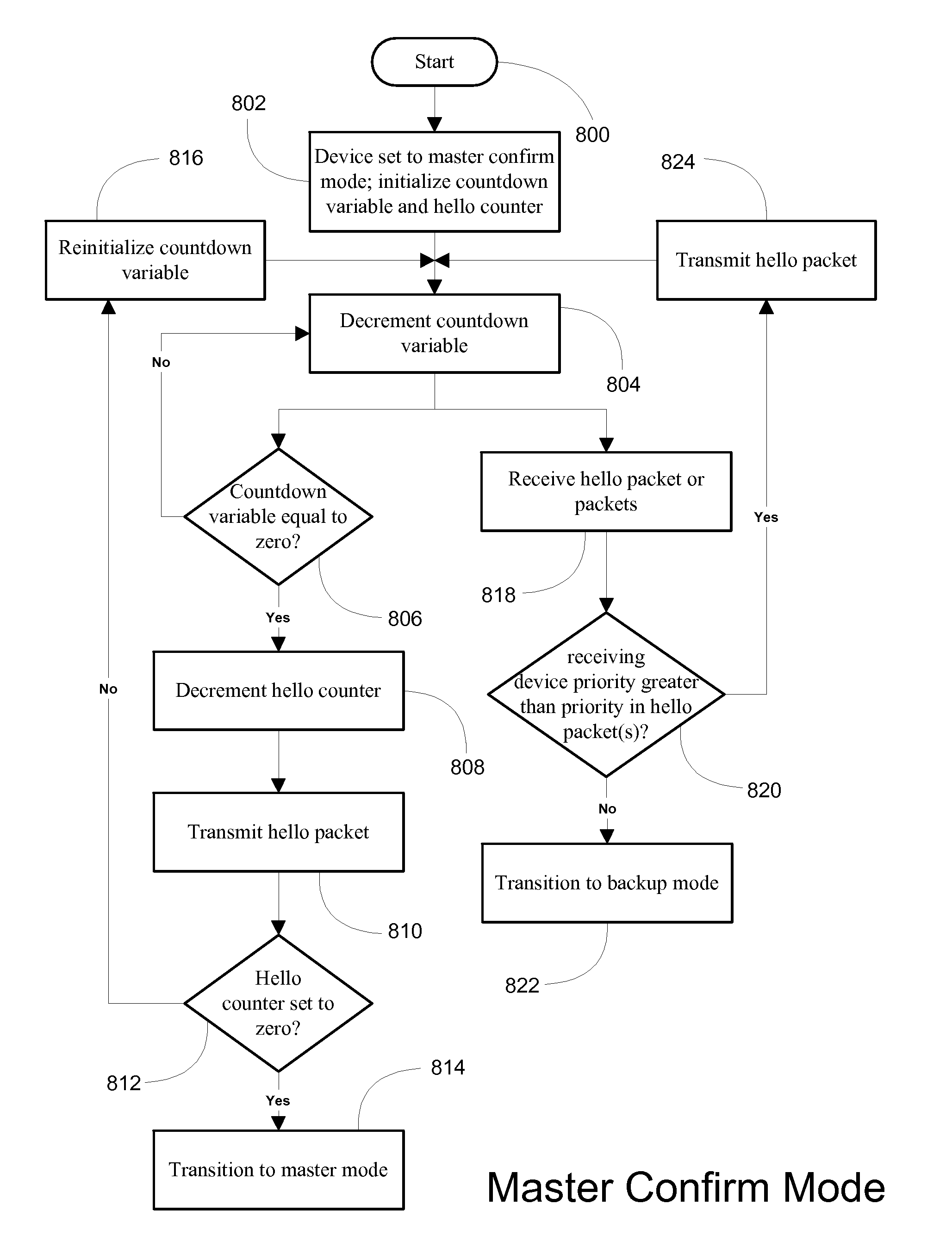
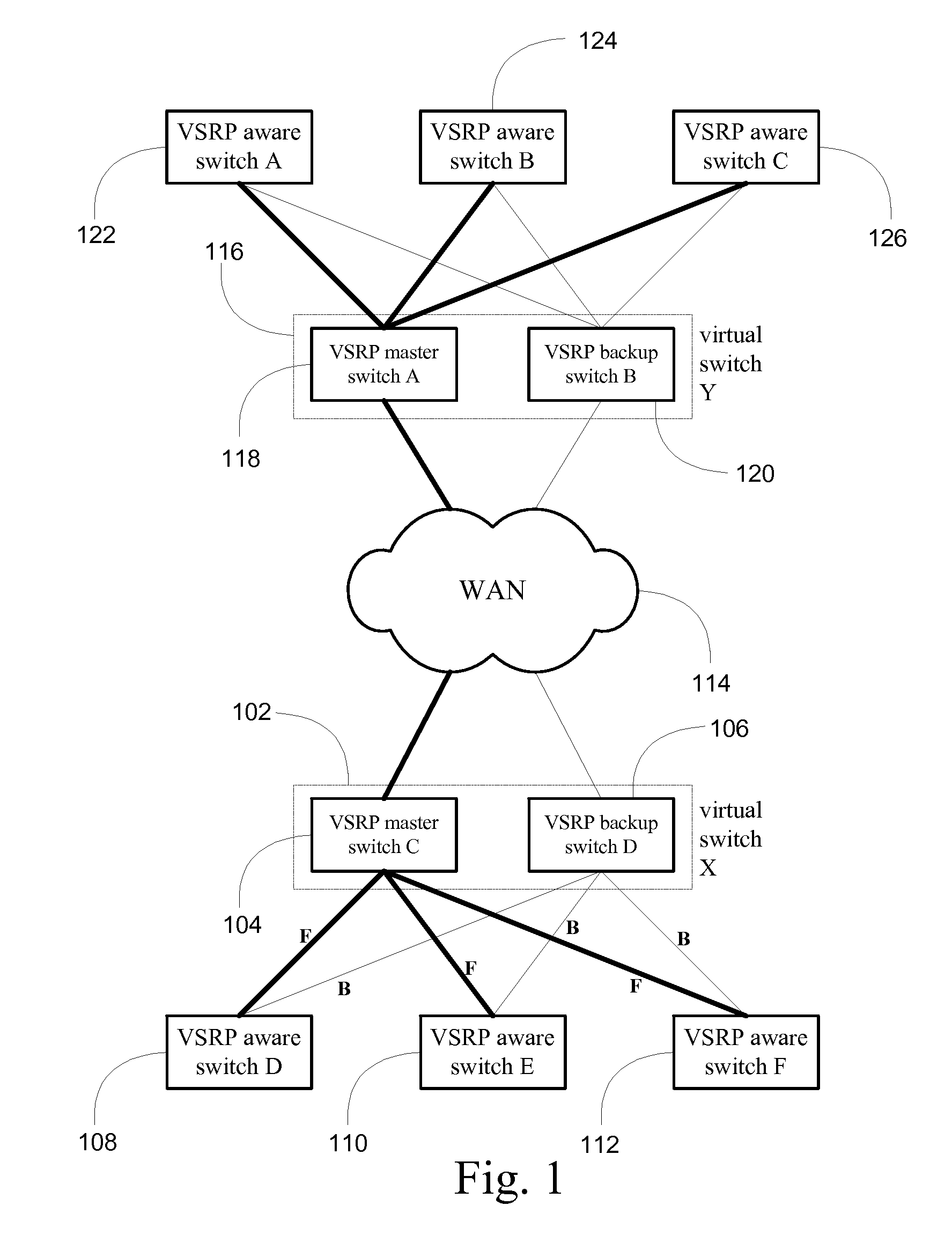
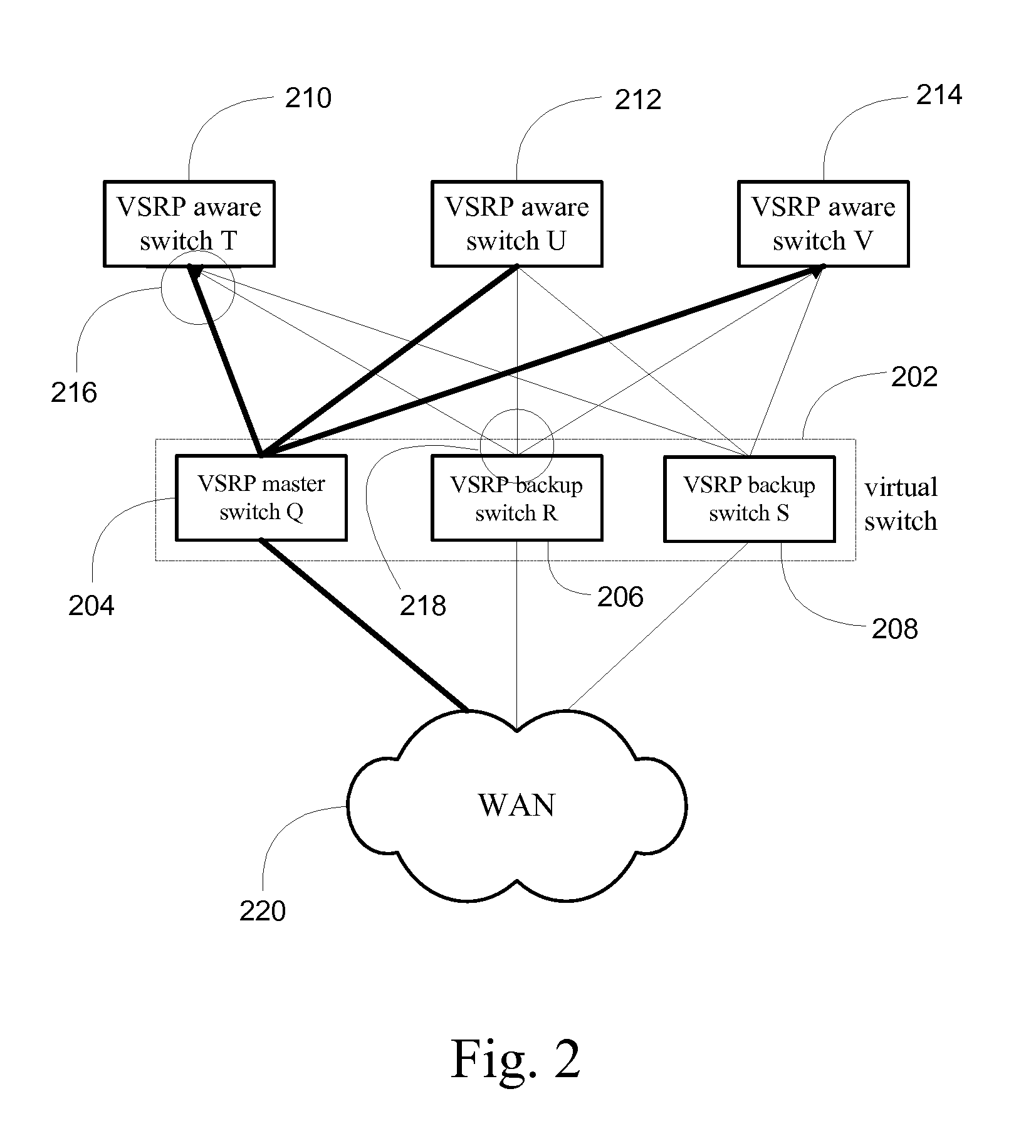
System and method for providing network route redundancy across Layer 2 devices
ActiveUS7209435B1Provides redundancyMultiplex system selection arrangementsError preventionTier 2 networkVirtual switch
Systems and methods are described for providing network route redundancy through Layer 2 devices, such as a loop free Layer 2 network having a plurality of switching devices. A virtual switch is coupled to the loop free Layer 2 network, the virtual switch having two or more switches configured to transition between master and backup modes to provide redundant support for the loop free Layer 2 network, the switches communicating their status through use of a plurality of redundancy control packets. The system also includes means for allowing the redundancy control packets to be flooded through the Layer 2 network. The means may include time-to-live data attached to the redundancy control packet which is decremented only when the packets are transferred through devices which are configured to recognize the protocol used in redundancy control packets.
Owner:AVAGO TECH INT SALES PTE LTD
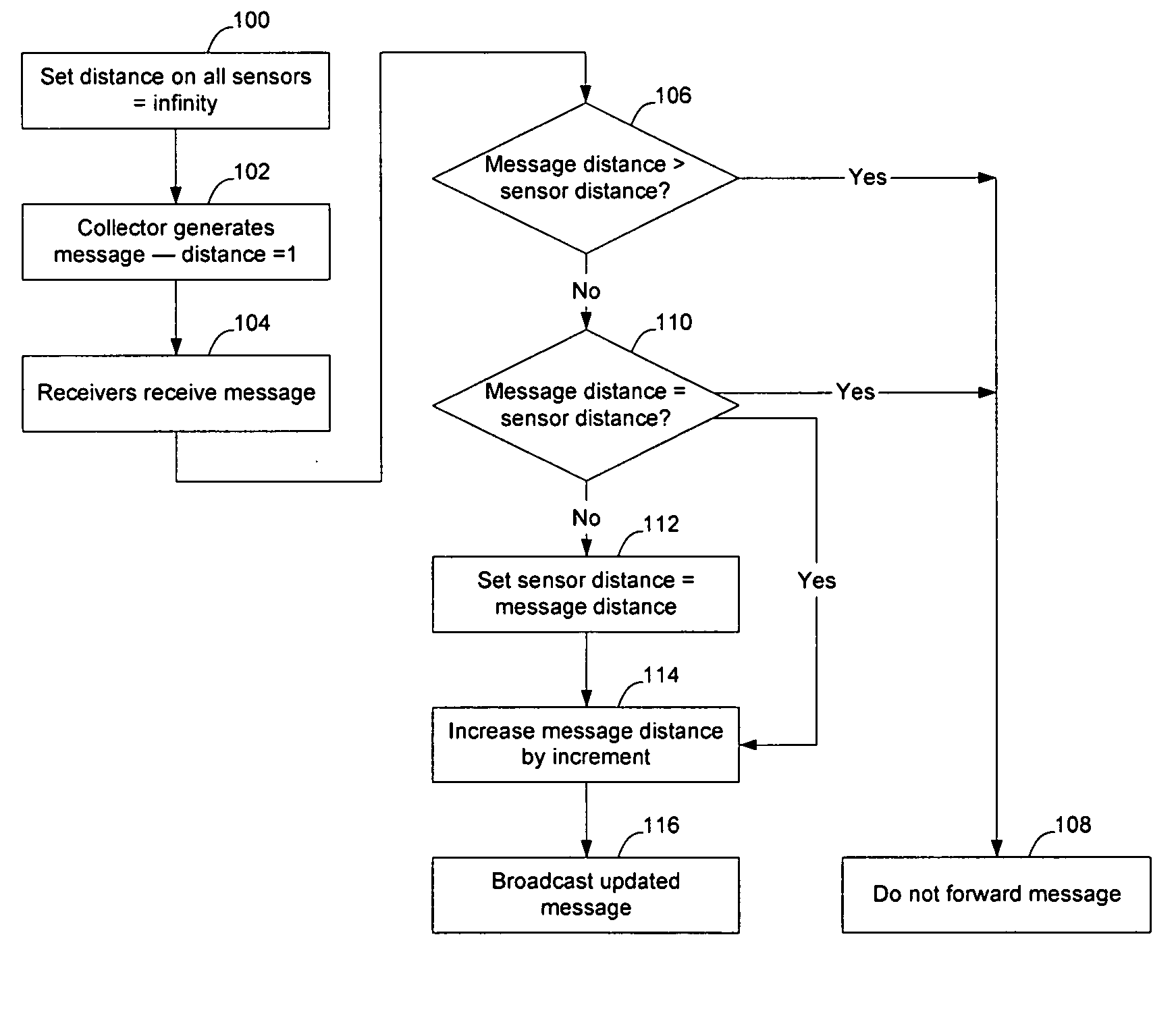
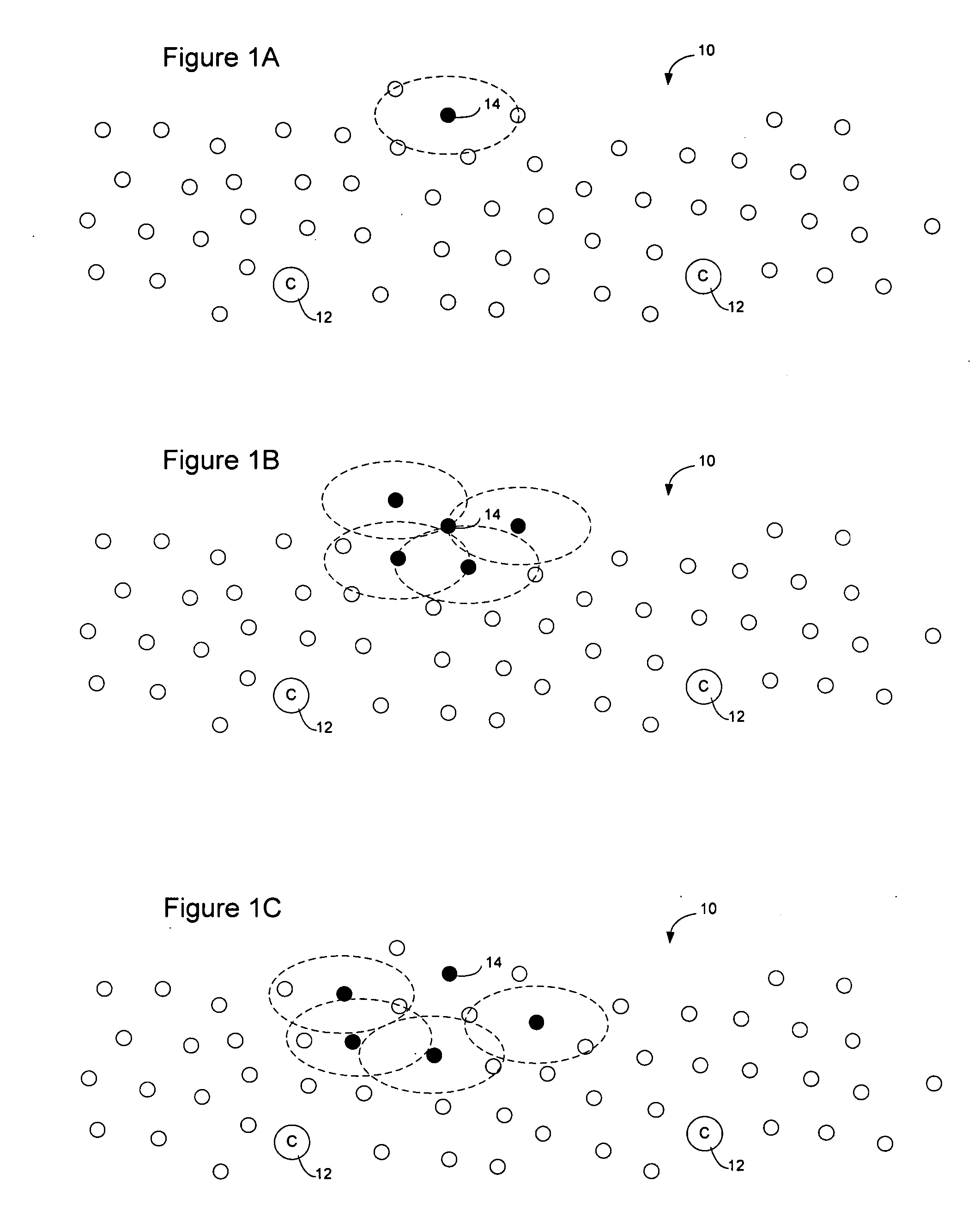
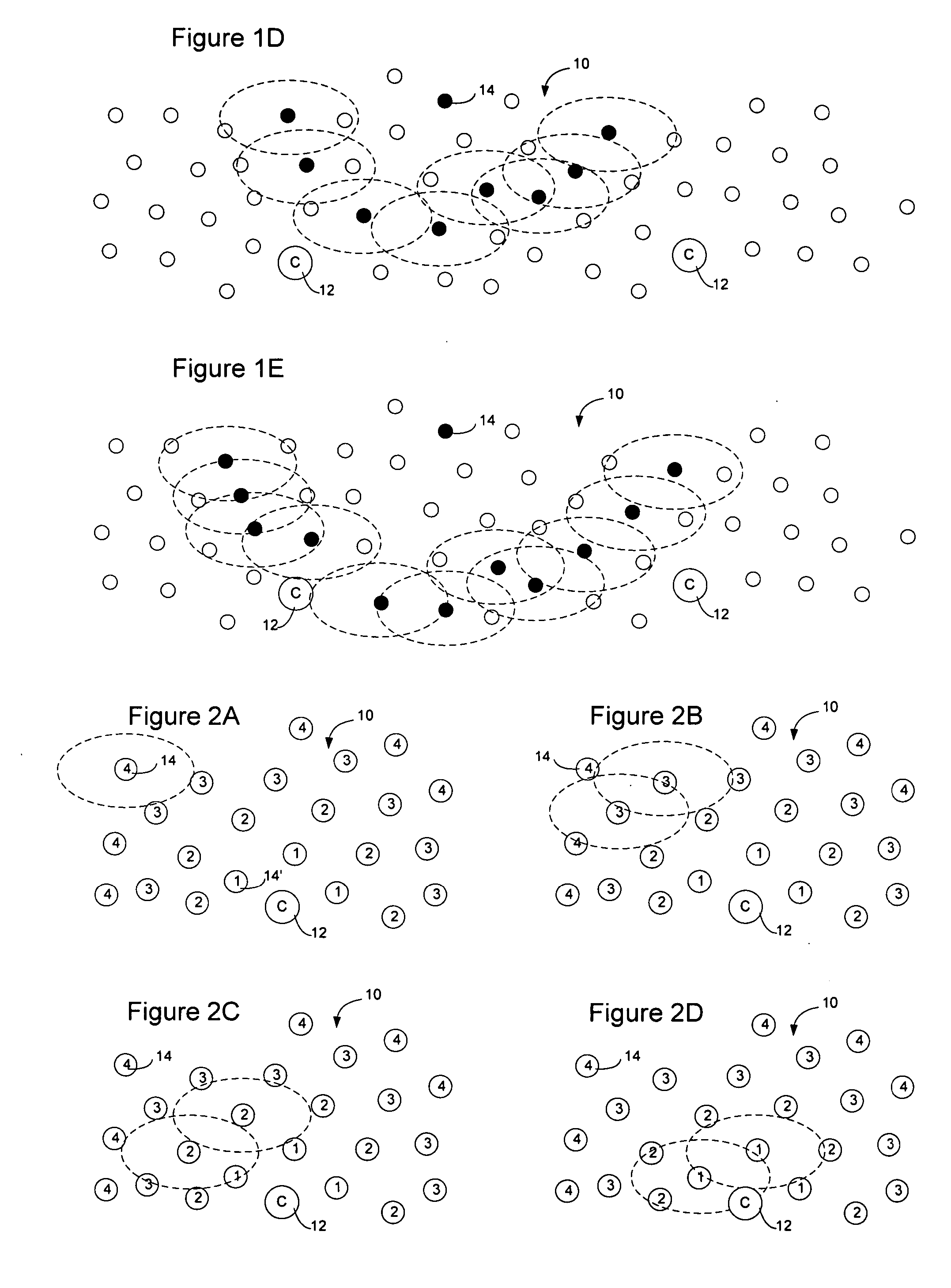
Method and apparatus for sensor network routing
InactiveUS20050207376A1Reduce multiplicityOvercome limitationsNetwork topologiesData switching by path configurationBroadcastingTraffic conditions
Sensor network routing uses distance information of sensors relative to a collector node, optionally along with non-unique key information, to route broadcasts from addressless sensors to a selected addressless collector. Distance calculation messages (DCMs) are used to set distance values on sensors relative to collectors. The distance values enable messages to propagate toward collectors to reduce the number of broadcasts. Self-assigned key information may be added to DCMs propagating in the network to enable routes to be determined through the network without assigning addresses to the participants. By storing the key information associated with the route, and causing sensors to only rebroadcast a message if the message contains a matching key at the matching distance position, broadcast paths may be created on the network. Optionally, diverse collectors and paths may be selected on the network by exchanging traffic condition indications and preferentially selecting paths with better traffic conditions.
Owner:RPX CLEARINGHOUSE
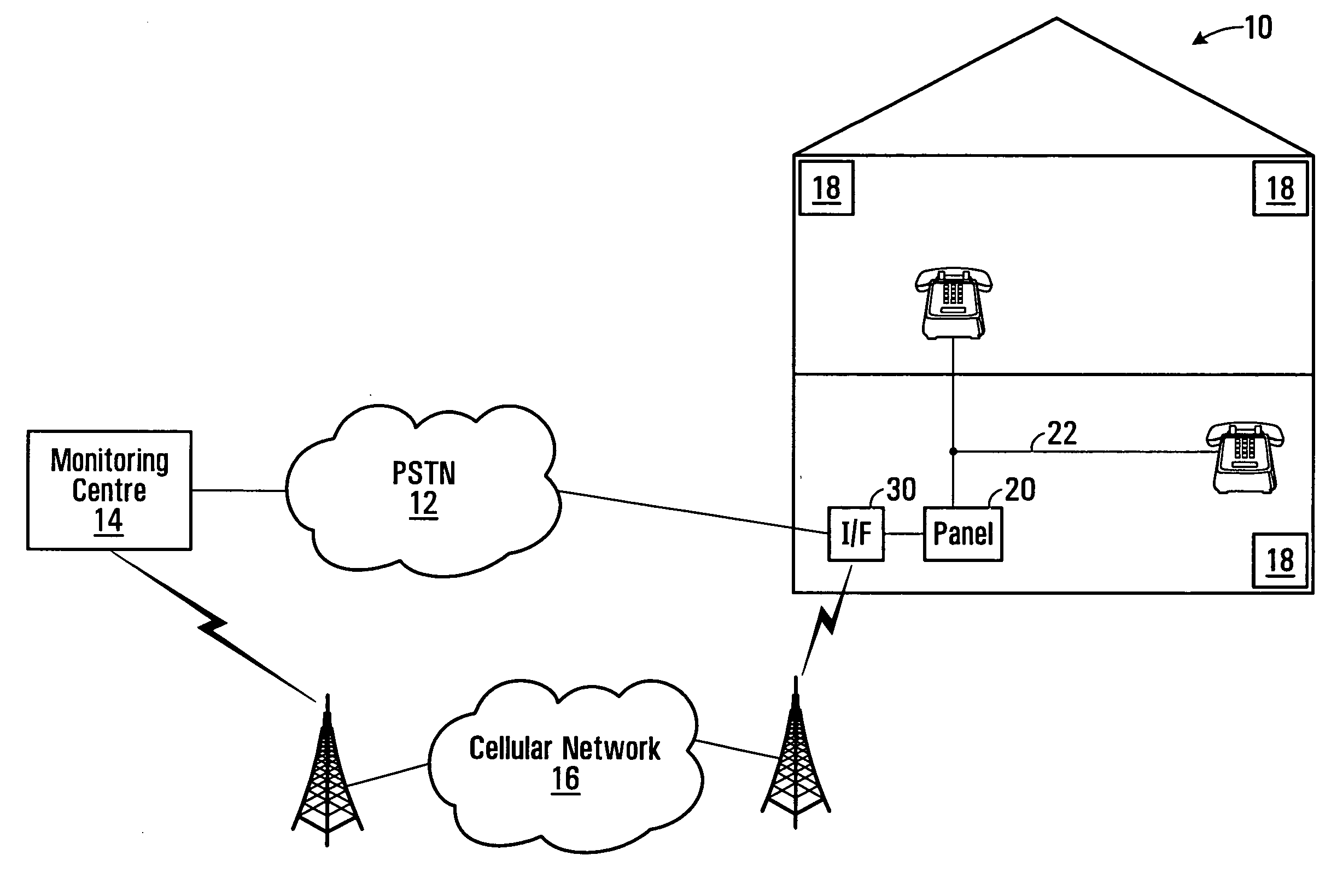
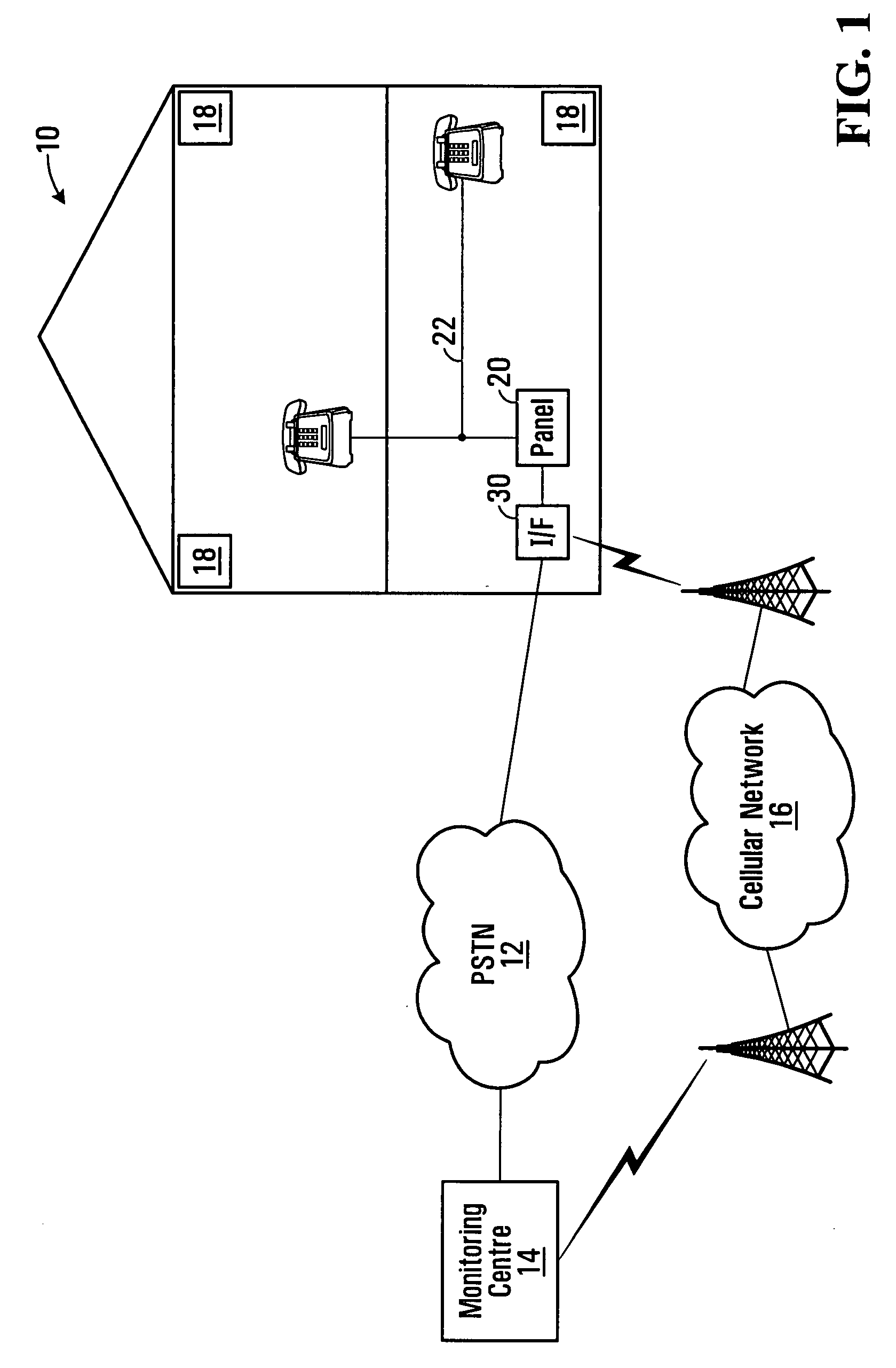
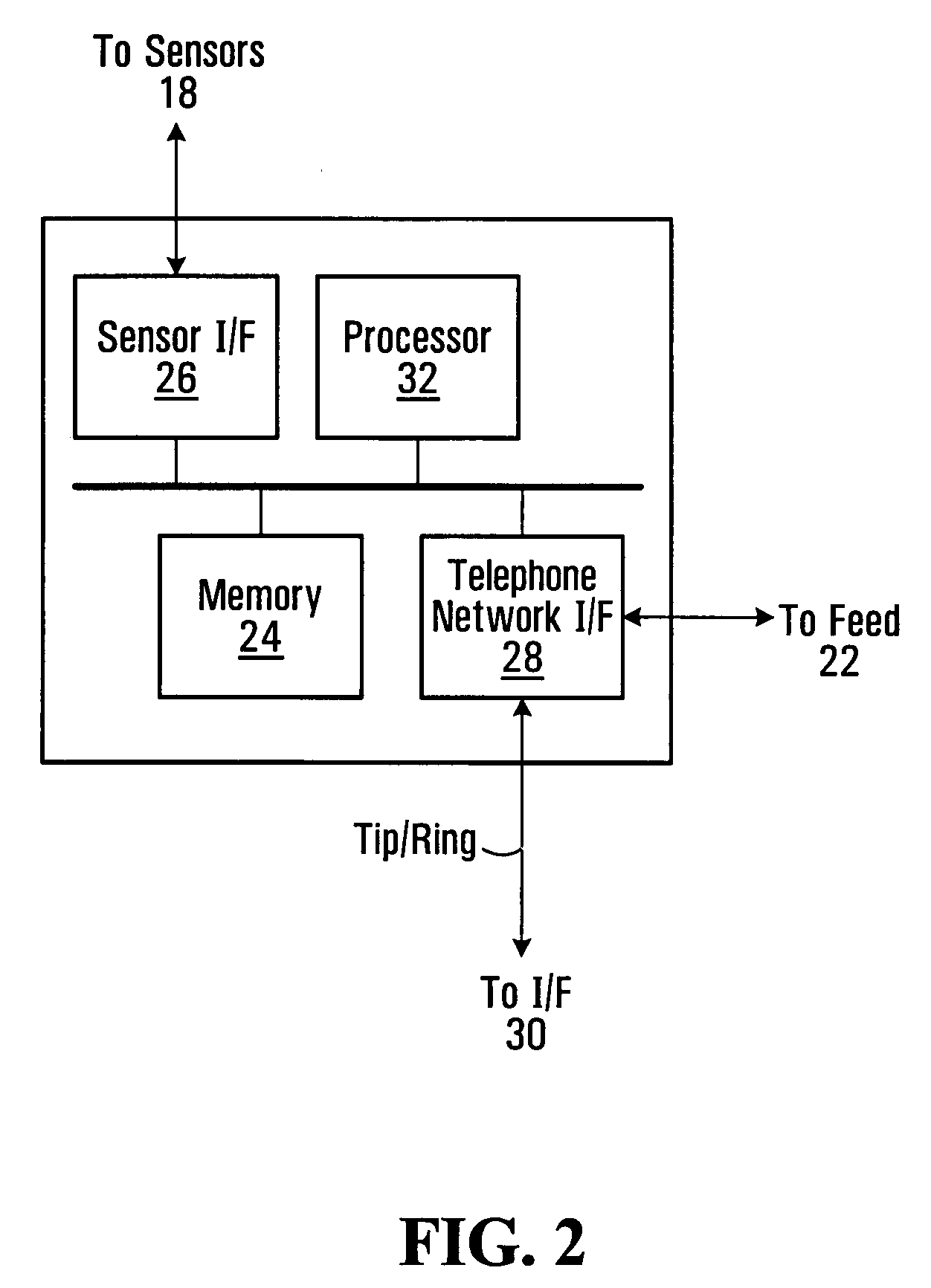
Alarm system providing multiple network routing, interface module and method
In an alarm system, outgoing calls representing a sensed alarm condition are routed to one of several communications networks. The calls are routed by first initiating a telephone call to a defined number, in response to sensing the alarm condition, and then selecting one of plurality a plurality of available networks based on called number information. A communication over the chosen network is placed to signal the alarm condition. Routing may be performed at an interface module in communication with a conventional alarm panel.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
System and method for providing network route redundancy across layer 2 devices
InactiveUS7558195B1Multiplex system selection arrangementsError preventionTier 2 networkVirtual switch
Systems and methods are described for providing network route redundancy through Layer 2 devices, such as a loop free Layer 2 network having a plurality of switching devices. A virtual switch is coupled to the loop free Layer 2 network, the virtual switch having two or more switches configured to transition between master and backup modes to provide redundant support for the loop free Layer 2 network, the switches communicating their status through use of a plurality of redundancy control packets. The system also includes means for allowing the redundancy control packets to be flooded through the Layer 2 network. The means may include time-to-live data attached to the redundancy control packet which is decremented only when the packets are transferred through devices which are configured to recognize the protocol used in redundancy control packets.
Owner:AVAGO TECH INT SALES PTE LTD
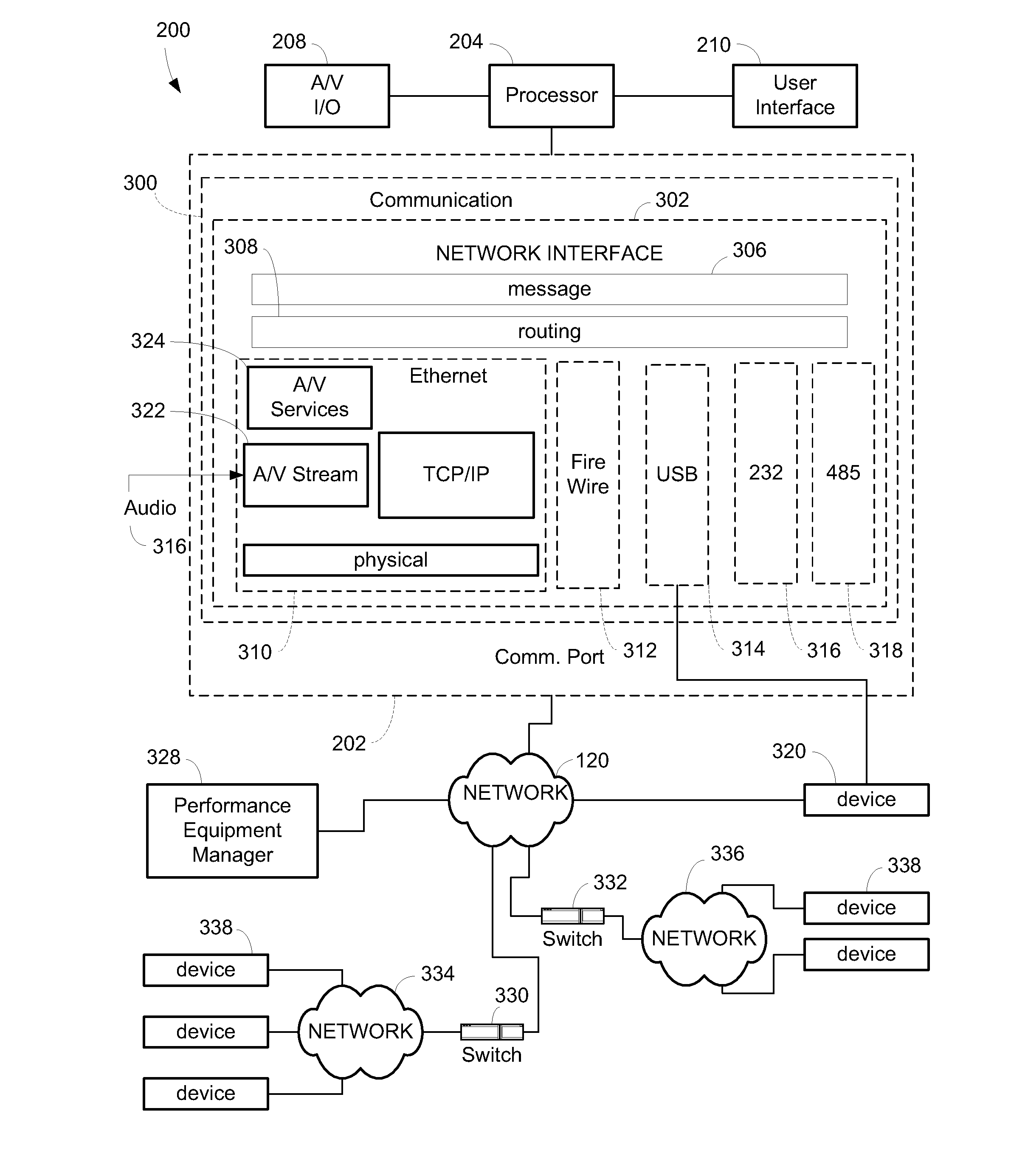
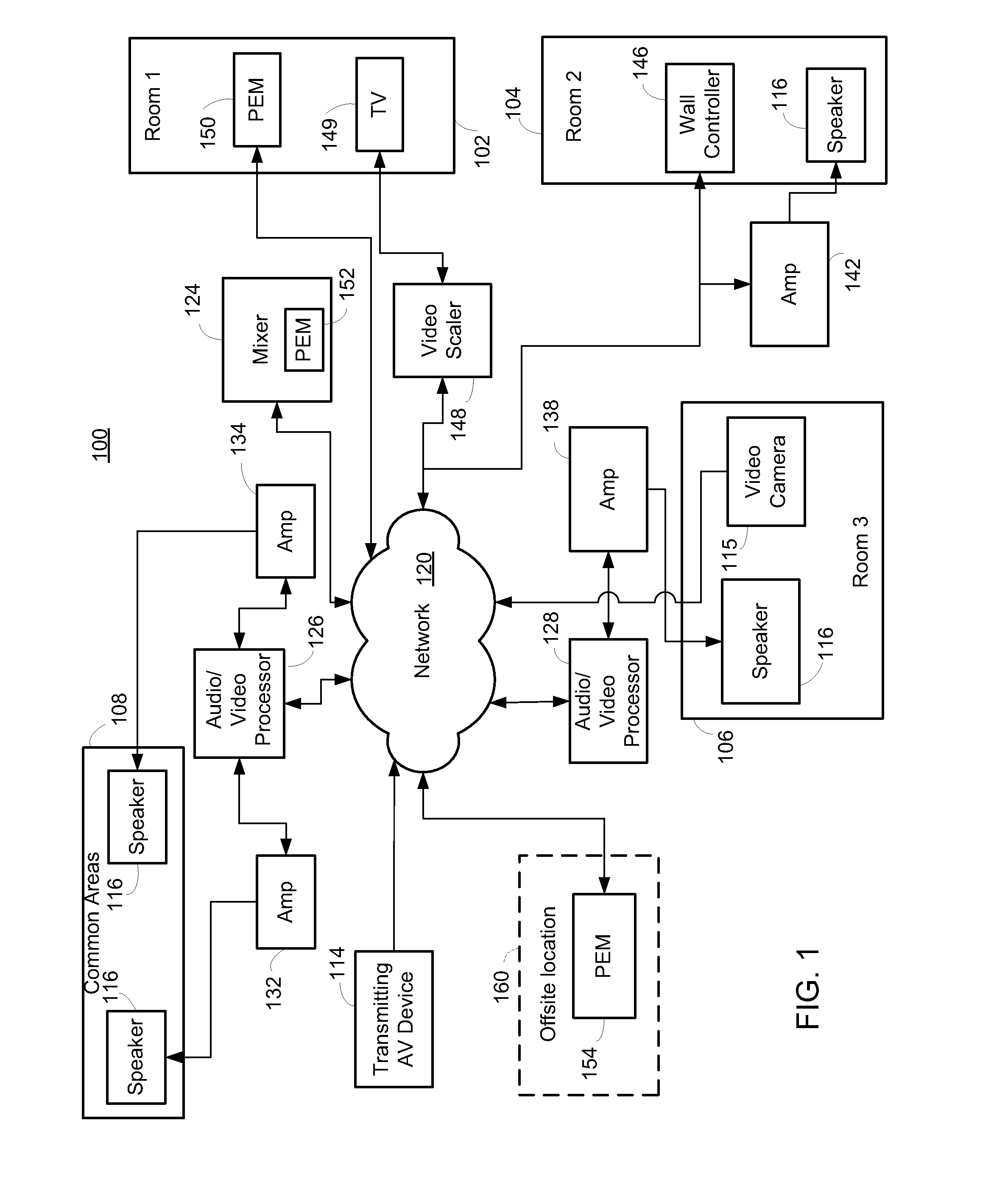
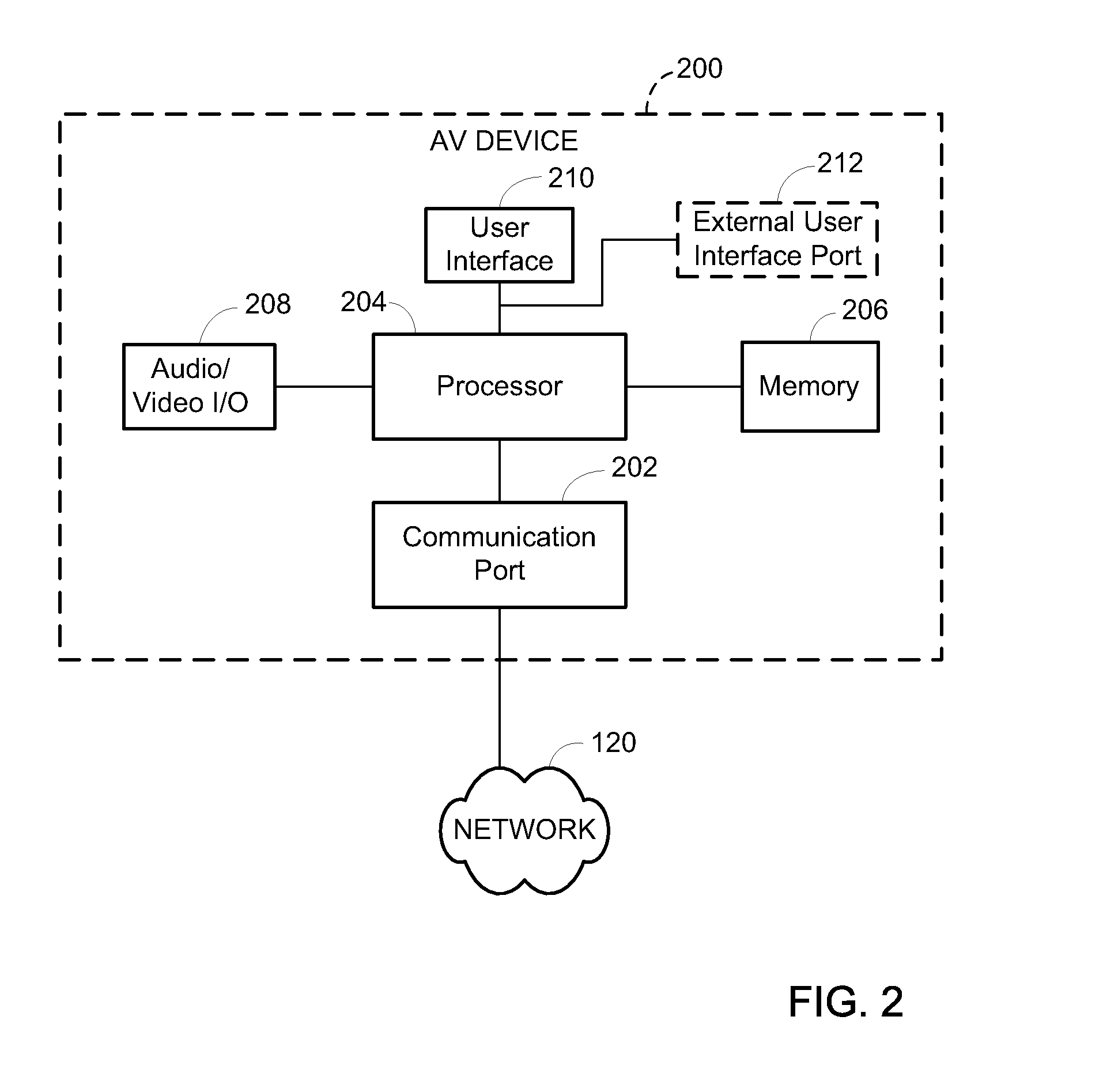
Networked audio/video system
ActiveUS20100318917A1Facilitate AV-related routing and controlDigital computer detailsTransmissionComputer hardwareEmbedded system
A system for configuring an audio / video (AV) system includes a computing device having a processor to enable a user, with a user interface of the computing device, to configure the AV system. The processor may enable the user to draw output zones to create a representation of a geographical layout of a venue in which the AV system is located. The processor may enable the user to place transmitting and receiving AV devices within the output zones that substantially represent physical locations thereof within the venue. The processor may enable the user to logically associate receiving AV device channels of one or more receiving AV devices within an output zone. The processor may also enable the user to select which of a number of source AV signals from transmitting AV devices the user wants to route to the associated output zone. The processor routes the source AV signals from one or more transmitting AV devices over a network to the one or more receiving AV device channels, such that the one or more receiving AV device channels are processed according to the output zone as configured by the user in the user interface.
Owner:HARMAN INT IND INC
Providing a presentation on a network having a plurality of synchronized media types
InactiveUS7143177B1Dynamic control of paceMaintain continuitySpecial service provision for substationPulse modulation television signal transmissionMedia typeThe Internet
A presentation system is disclosed for synchronizing a performance of a plurality of presentation content portions at a network node, wherein, when two such content portions are to be presented concurrently at the network node, at least one is delayed until the other such portion can be presented concurrently therewith. In one embodiment, the content portions are transmitted via at least a portion of the Internet to a plurality of network nodes, wherein the presentation system can distribute the presentation content data to the network nodes via a plurality of network routes and presentation formats. Additionally, the present invention can provide various portions of the content data from a plurality of network server nodes, and during a performance of the presentation, the presentation receiving network nodes can determine a particular variation of the presentation to retrieve from the network server nodes. In particular, the retrieval of presentation data depends upon the transmission characteristics of the network such as data transmission rate. Thus, if a low transmission data rate is detected at a first network node, presentation elements of a reduced size can be retrieved.
Owner:RED HAT +1
Methods, apparatuses and systems facilitating determination of network path metrics
InactiveUS7260645B2Easy to configureEasy to deployMultiple digital computer combinationsData switching networksThe InternetTime of day
Methods, apparatuses and systems relating to the control and application of policies for routing data over a computer network, such as the Internet. Some implementations of the invention facilitate the configuration, deployment and / or maintenance of network routing policies. Some implementations of the invention are particularly useful for controlling the routing of data among autonomous systems or organizations. Certain implementations allow for dynamic modification of routing policy based on such factors as current Internet performance, load sharing, user-defined parameters, and time of day. In one embodiment, the present invention provides methods, apparatuses and systems implementing enhanced network path testing methodologies that enhance the efficiency of processes associated with testing of a network path, while reducing the perceived intrusiveness of test packets associated with such metrics tests.
Owner:SUNTRUST BANK AS SUCCESSOR AGENT +1
Secure network-routed voice processing
InactiveUS7187941B2Well formedNetwork topologiesActive radio relay systemsCommunications systemVoice communication
Systems and methods are provided for routing voice communications through a mobile communication system having a self-contained infrastructure, such as a two-way radio communication system. The voice communications are transmitted as digitized voice packets over radio frequency links. The digitized voice packets contain one or more destination addresses in addition to other routing information. Routers receive the digitized voice packet and extract the routing information. The routing information is used in conjunction with a member router database to determine where to route the digitized voice packets.
Owner:NORTHROP GRUMMAN SYST CORP
Wireless data networking
ActiveUS8149748B2Small batteryReduce power consumptionEnergy efficient ICTPower managementWireless dataDistributed computing
A meshing network comprising one full function controller (WDC) and a plurality of nodes (WDN, WSN), that is RF quiet capable with very low power consumption and the ability to quickly heal itself and create new network paths. The network uses an addressing scheme that allows for each node to not have a network map but still be able to route messages. A piping scheme allows a mesh to become a high throughput network. A sensor rail protocol definition allows sensor devices to connect to nodes and route messages through the network.
Owner:RAYTHEON CO
Virtual private networks and methods for their operation
InactiveUS6937574B1Economically feasibleLower acquisition costsNetworks interconnectionPrivate networkPhysical address
In methods and apparatus for routing packets through a communications network, a respective distinct broadcast address is assigned to each of a plurality of distinct sets of virtual ports. No virtual port belongs to more than one of the distinct sets. A respective egress address is assigned to each packet entering the network via an ingress virtual port. The respective egress address corresponds to a respective destination address of the entering packet when a correspondence between the destination address and an egress address is known. When no correspondence between the destination address and an egress address is known, the respective egress address is a broadcast egress address corresponding to the set comprising the ingress virtual port. The packet is routed according to the respective egress address. The routing is restricted to virtual ports belonging to the distinct set of virtual ports that includes the ingress virtual port. The distinct sets of virtual ports and their associated broadcast addresses define isolated virtual private networks within the network. Each physical port of the network may map one-to-one onto a corresponding virtual port, or may map onto a corresponding plurality of virtual ports, in which case the each virtual port of the plurality is associated with a respective distinct combination of a physical address of the physical port and a respective virtual network identifier.
Owner:RPX CLEARINGHOUSE
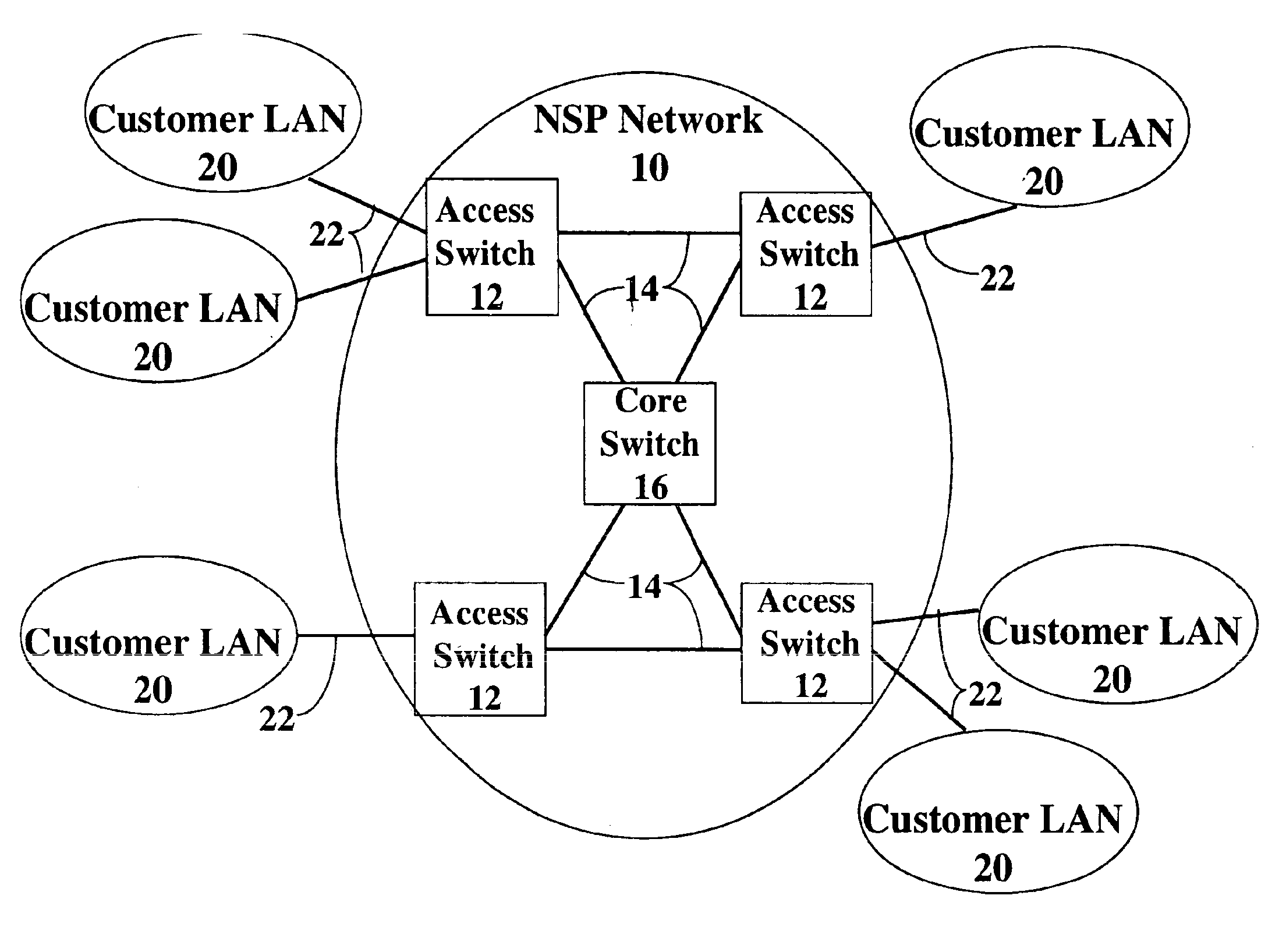
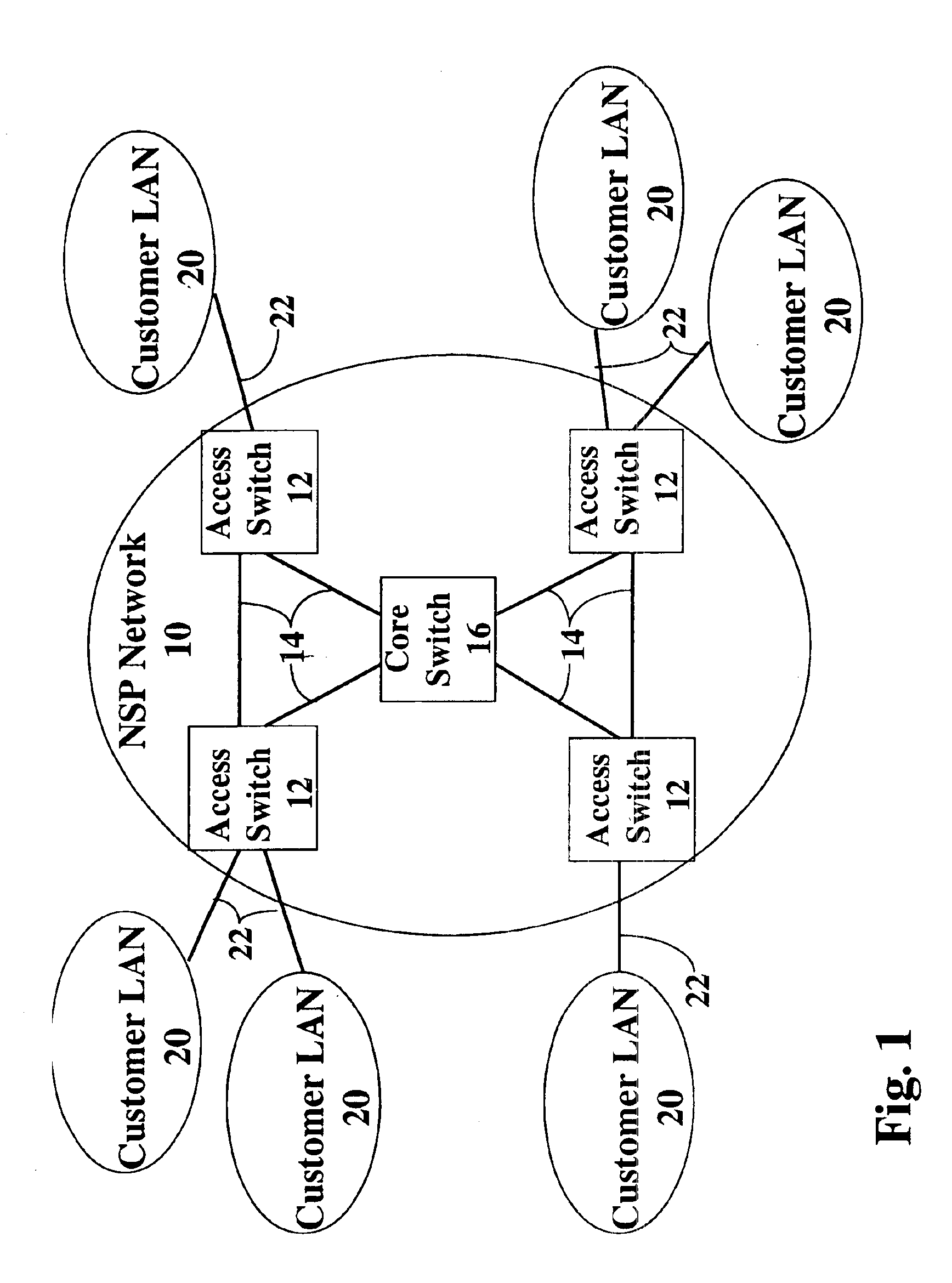
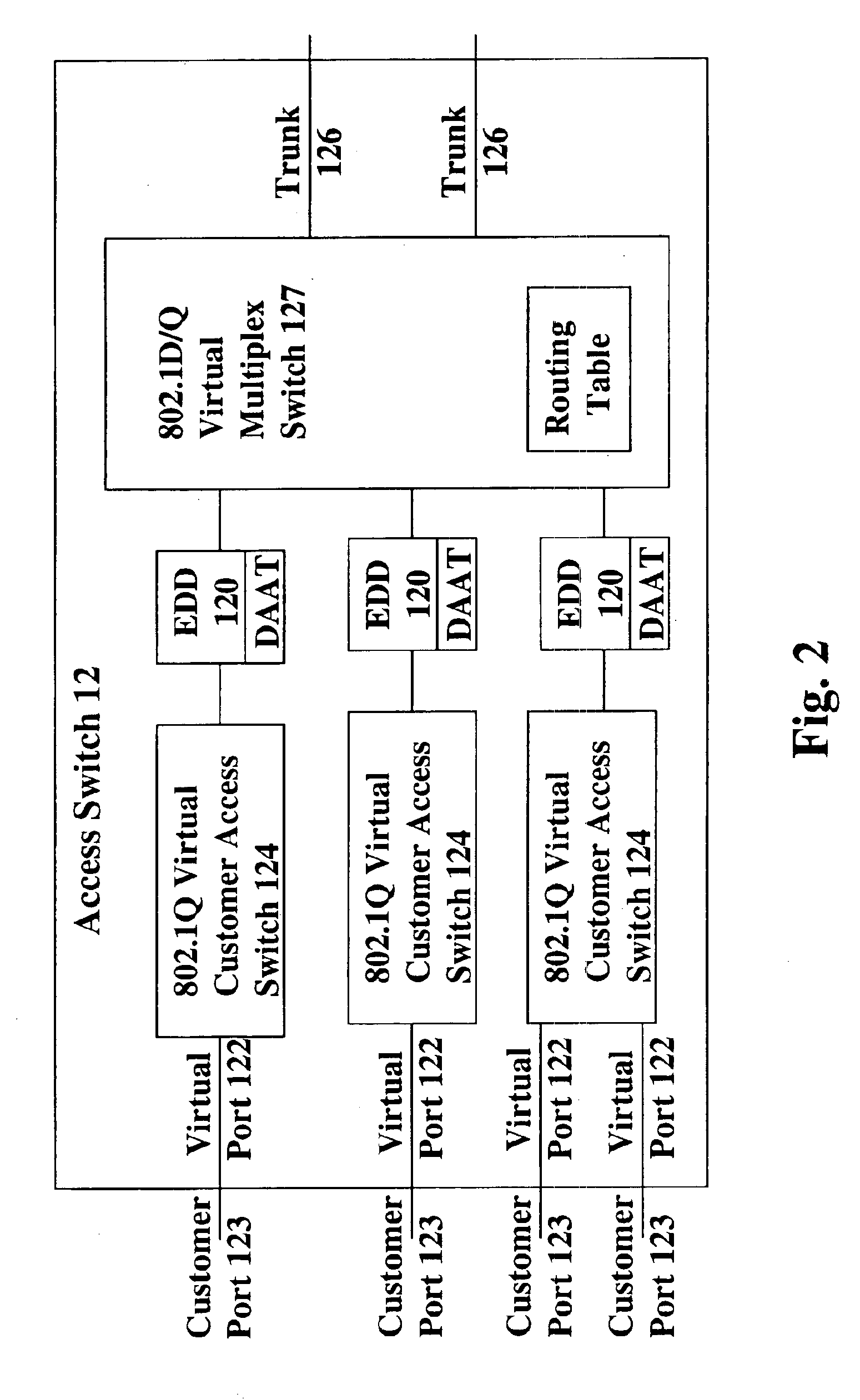
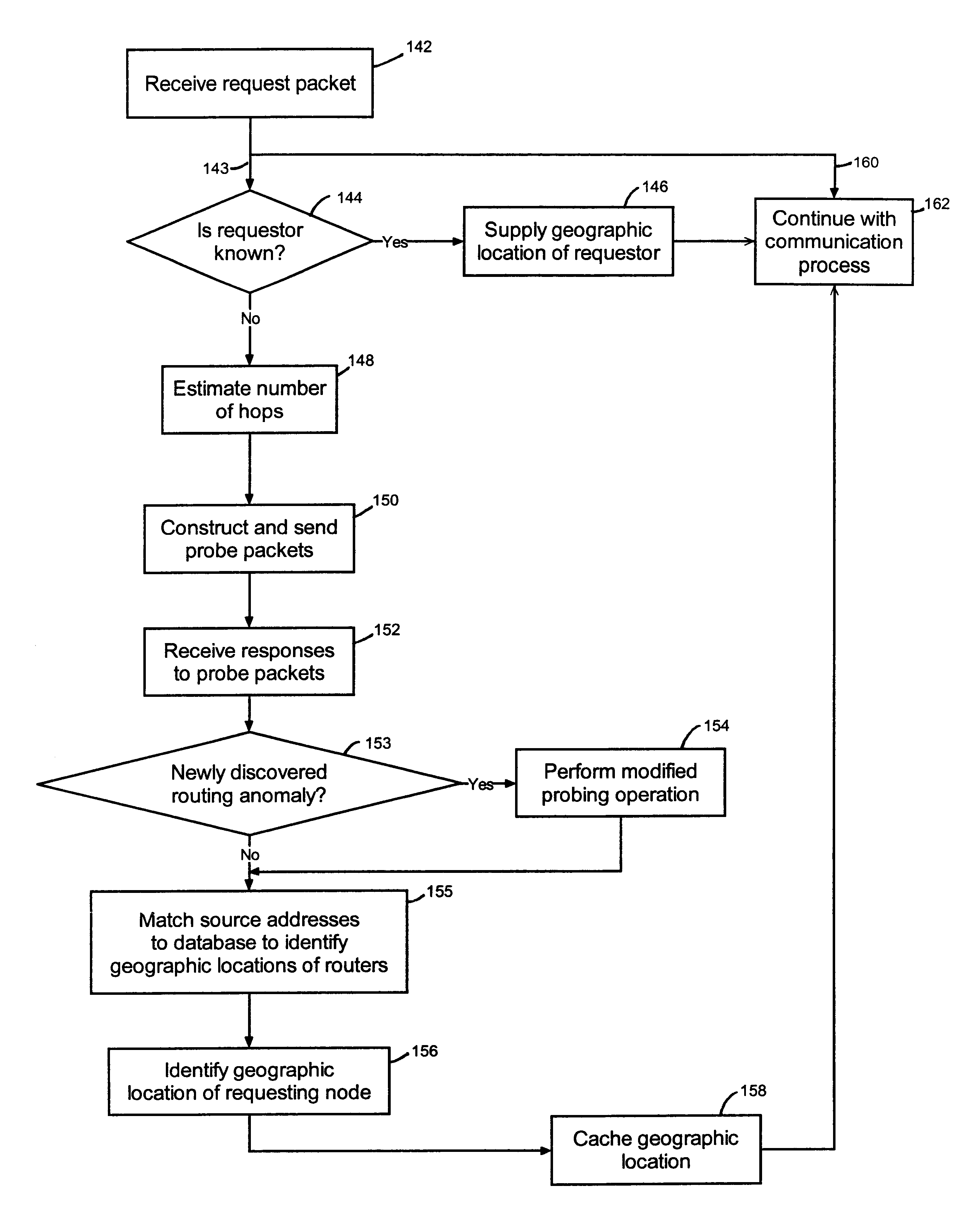
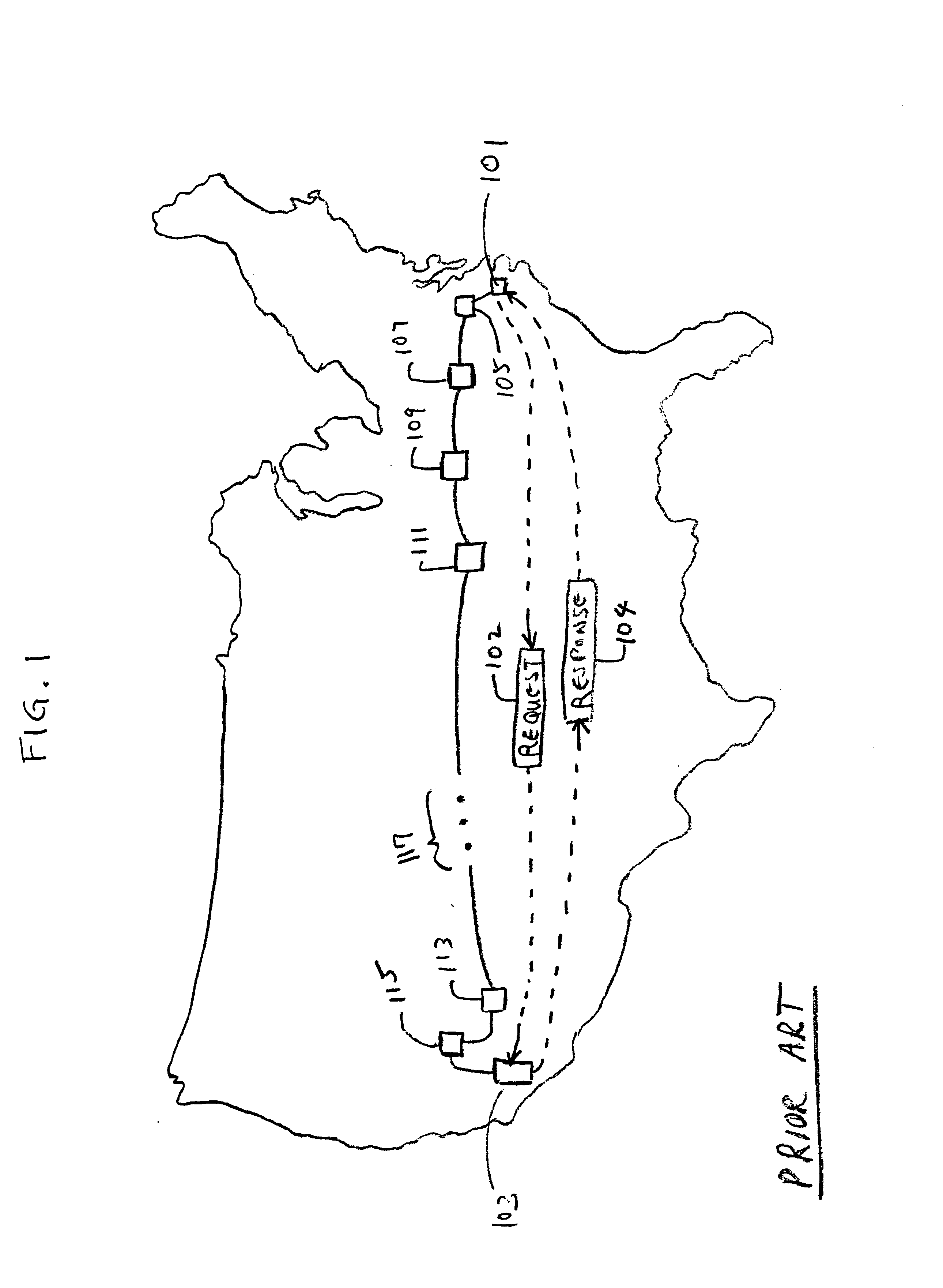
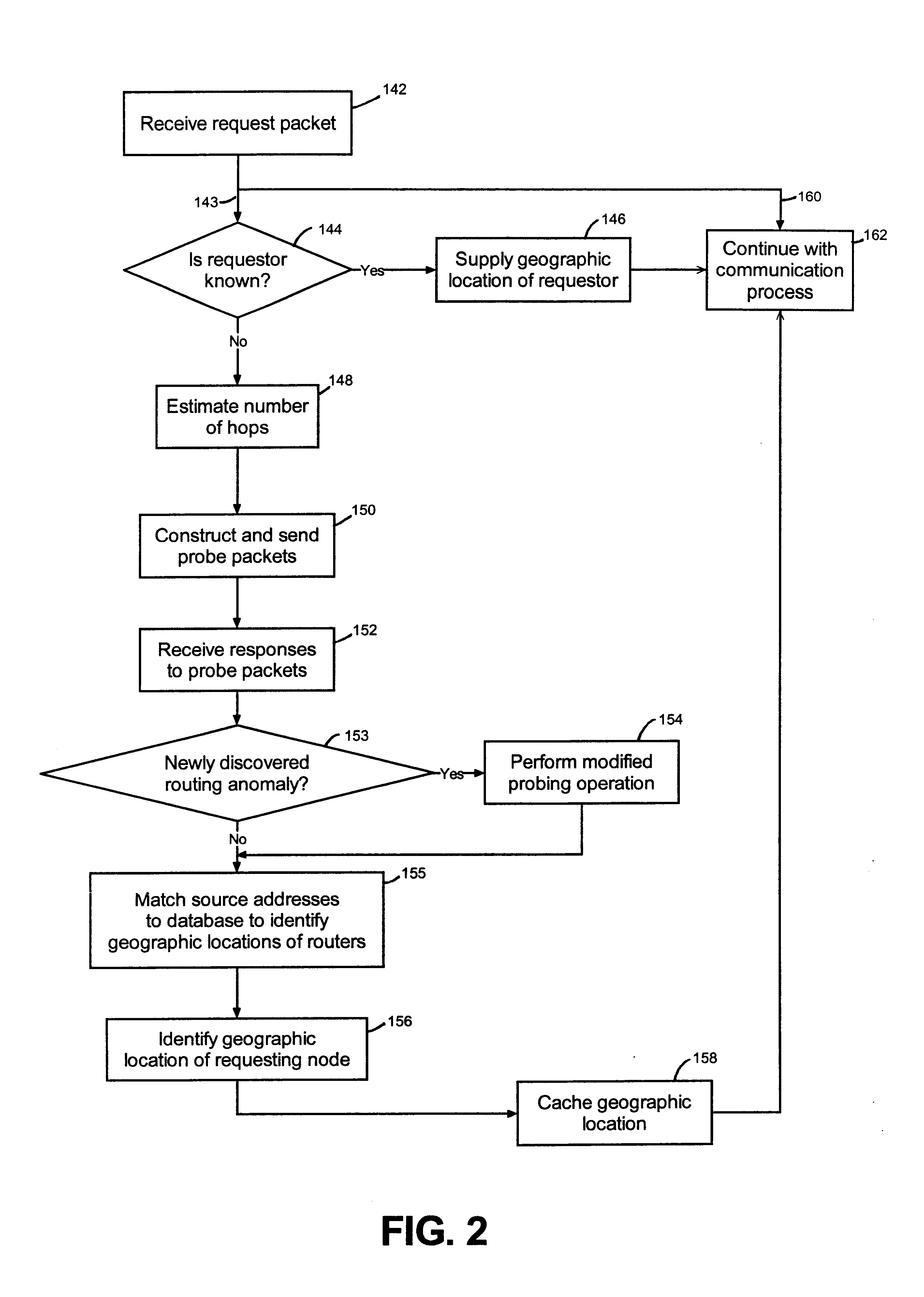
Creating a geographic database for network devices
InactiveUS6778524B1Error preventionFrequency-division multiplex detailsNetwork connectionGeolocation
A database is populated with geographic locations for network devices by providing a node on a network and making a connection into a network service provider (NSP) point of presence (POP) to obtain a connection to the network via the NSP. A message is then transmitted to the node over the network connection obtained from the NSP. The message is received at the node and a source network identifier is extracted from the message. The source network identifier is then associated with a known geographic location for the POP in a database. The foregoing steps are then repeated for multiple different POPs. Also, a database is populated with geographic locations for network devices by providing a node on a network and making a connection into a network service provider (NSP) point of presence (POP) to obtain a connection to the network via the NSP. A message is then transmitted to the node over the network connection obtained from the NSP. The message is received at the node and a source network identifier is extracted from the message. The route over the network between the node and the POP is then probed to obtain network identifiers for routers along the route. The foregoing steps are then repeated for multiple different POPs.
Owner:RESOURCE CONSORTIUM LTD LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com