Patents
Literature
7314 results about "Attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer and computer networks an attack is any attempt to destroy, expose, alter, disable, steal or gain unauthorized access to or make unauthorized use of an asset.
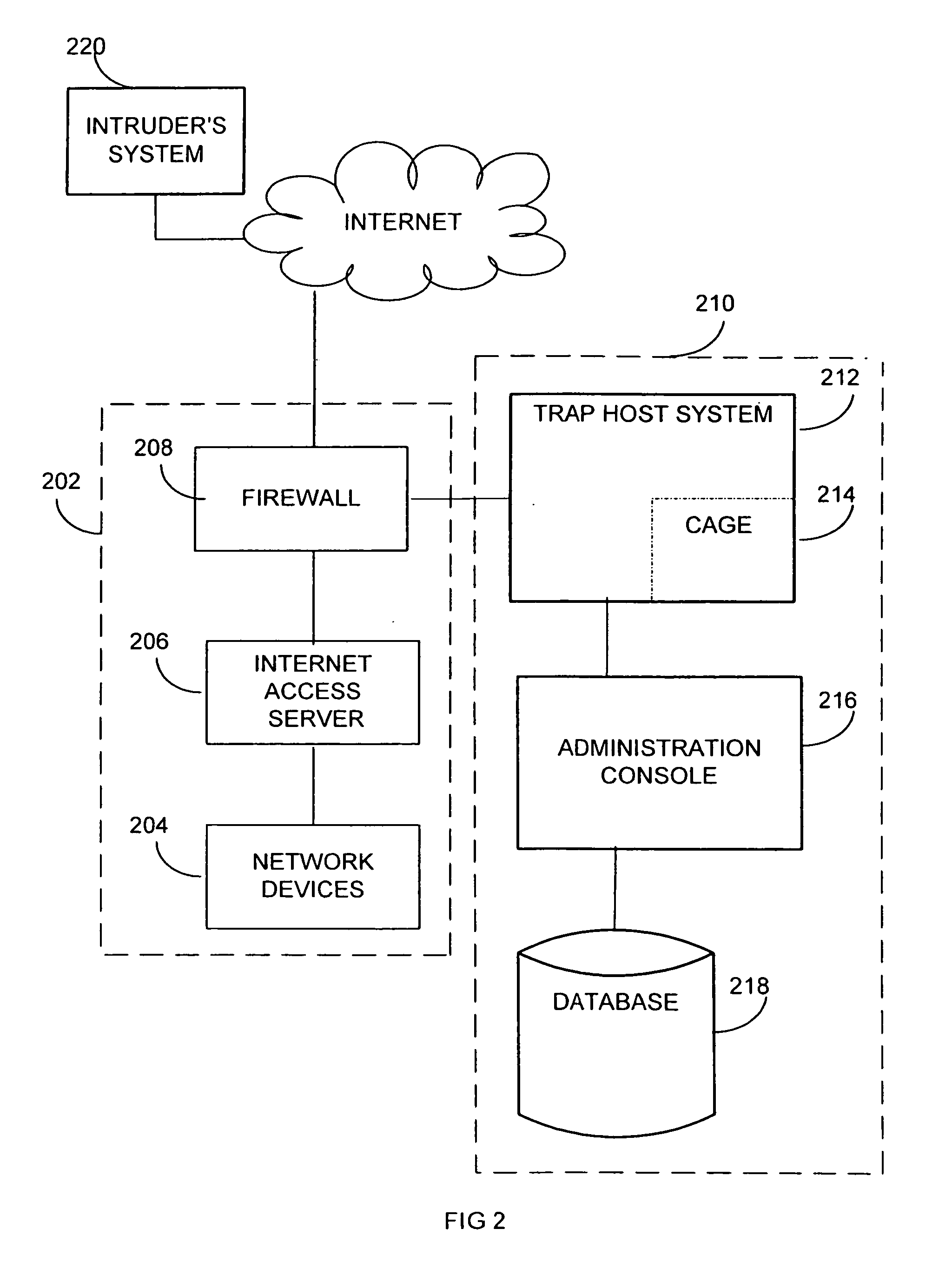
System and method of identifying the source of an attack on a computer network
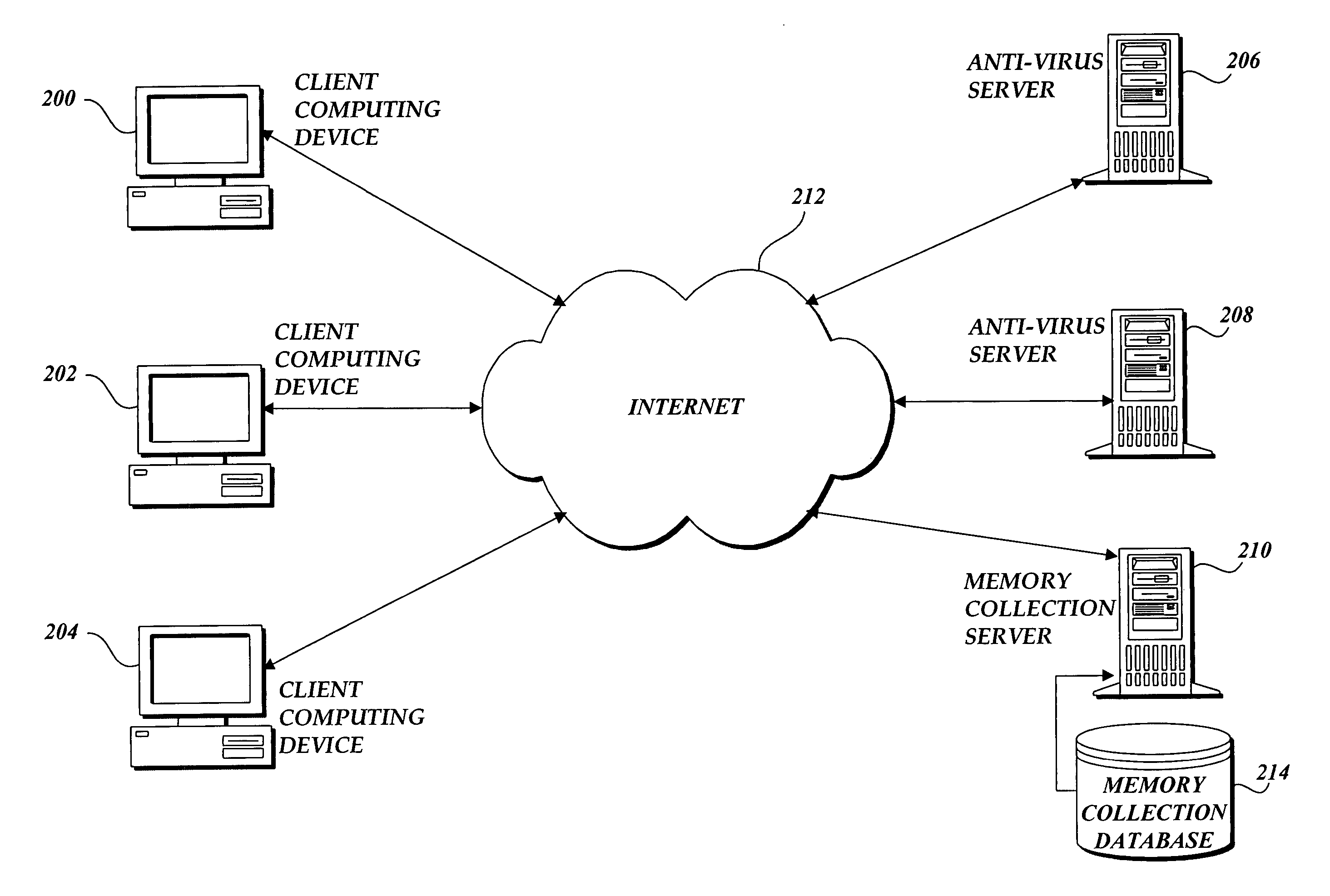
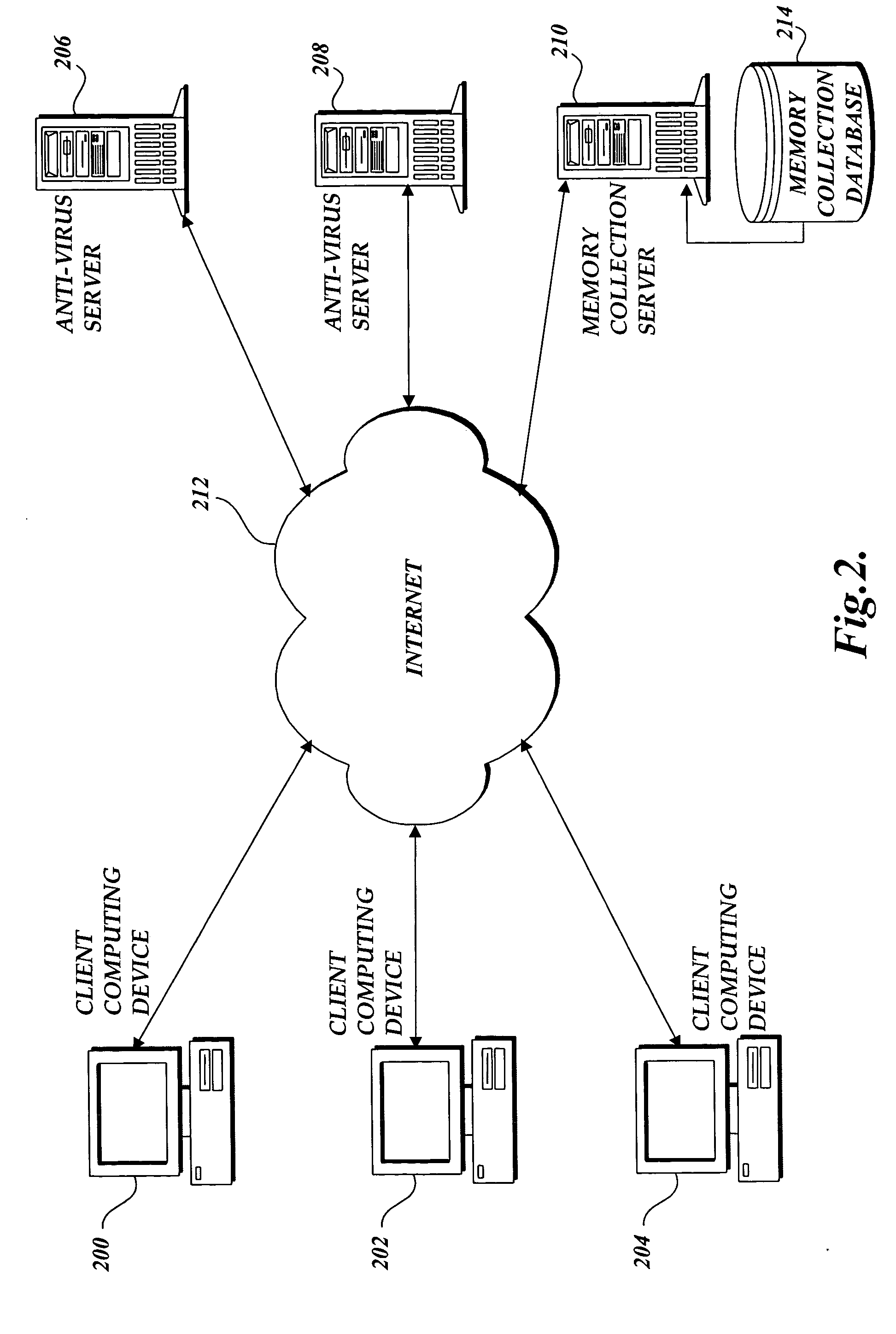
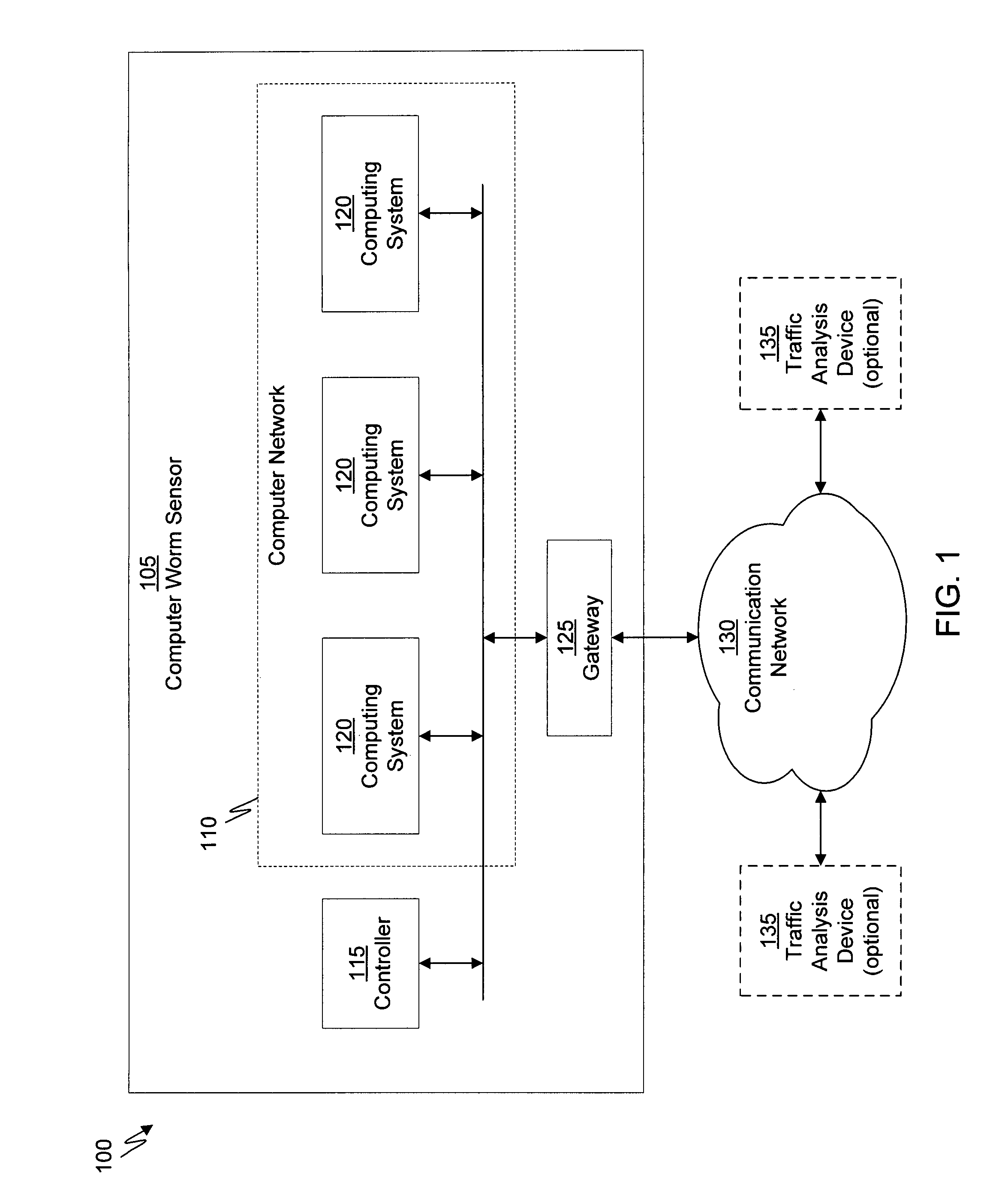
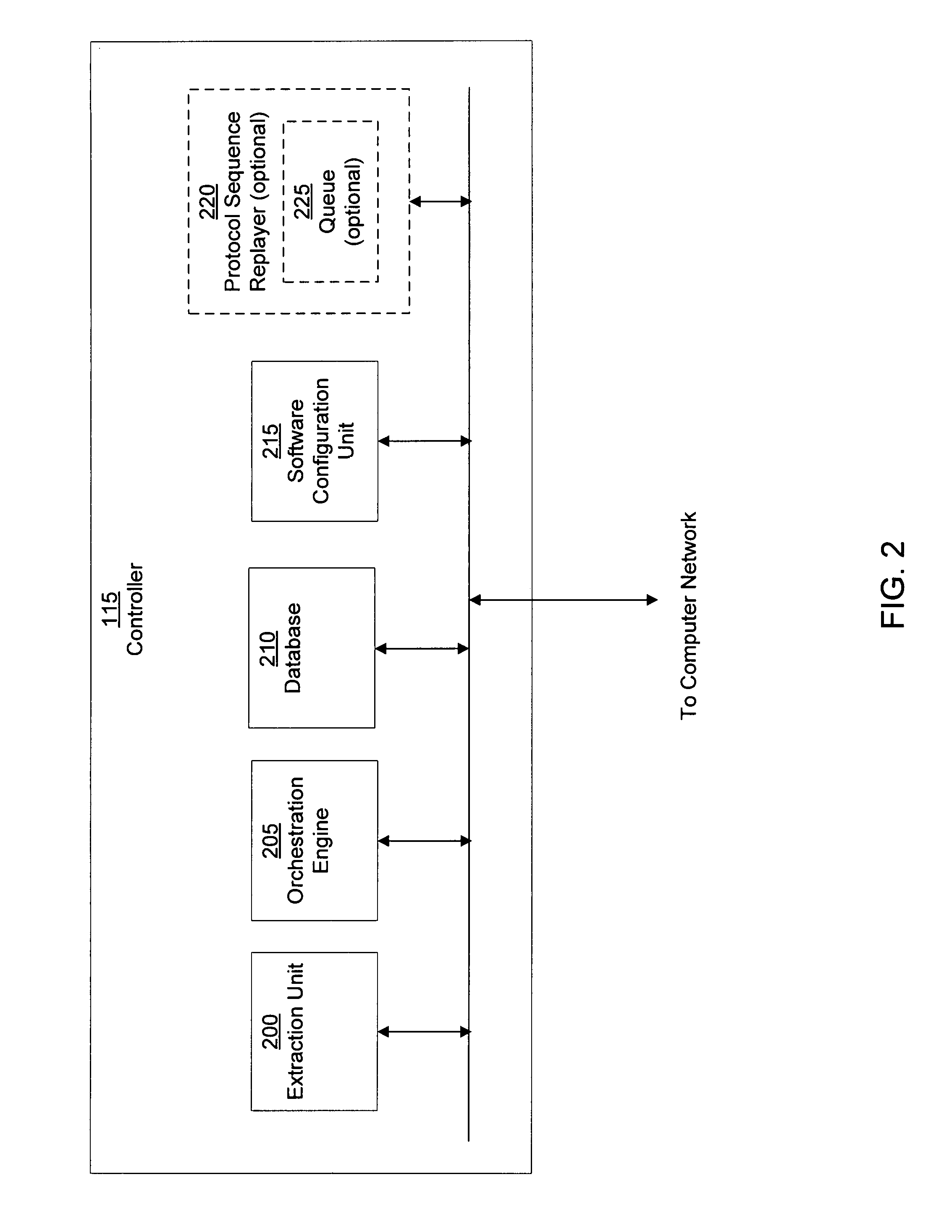
The present invention provides a system and method of tracing the spread of computer malware in a communication network. One aspect of the present invention is a method that traces the spread of computer malware in a communication network. When suspicious data characteristic of malware is identified in a computing device connected to the communication network, the method causes data that describes the state of the computing device to be stored in a database. After a specific attack against the communication network is confirmed, computing devices that are infected with the malware are identified. Then, the spread of the malware between computing devices in the communication network is traced back to a source.
Owner:MICROSOFT TECH LICENSING LLC
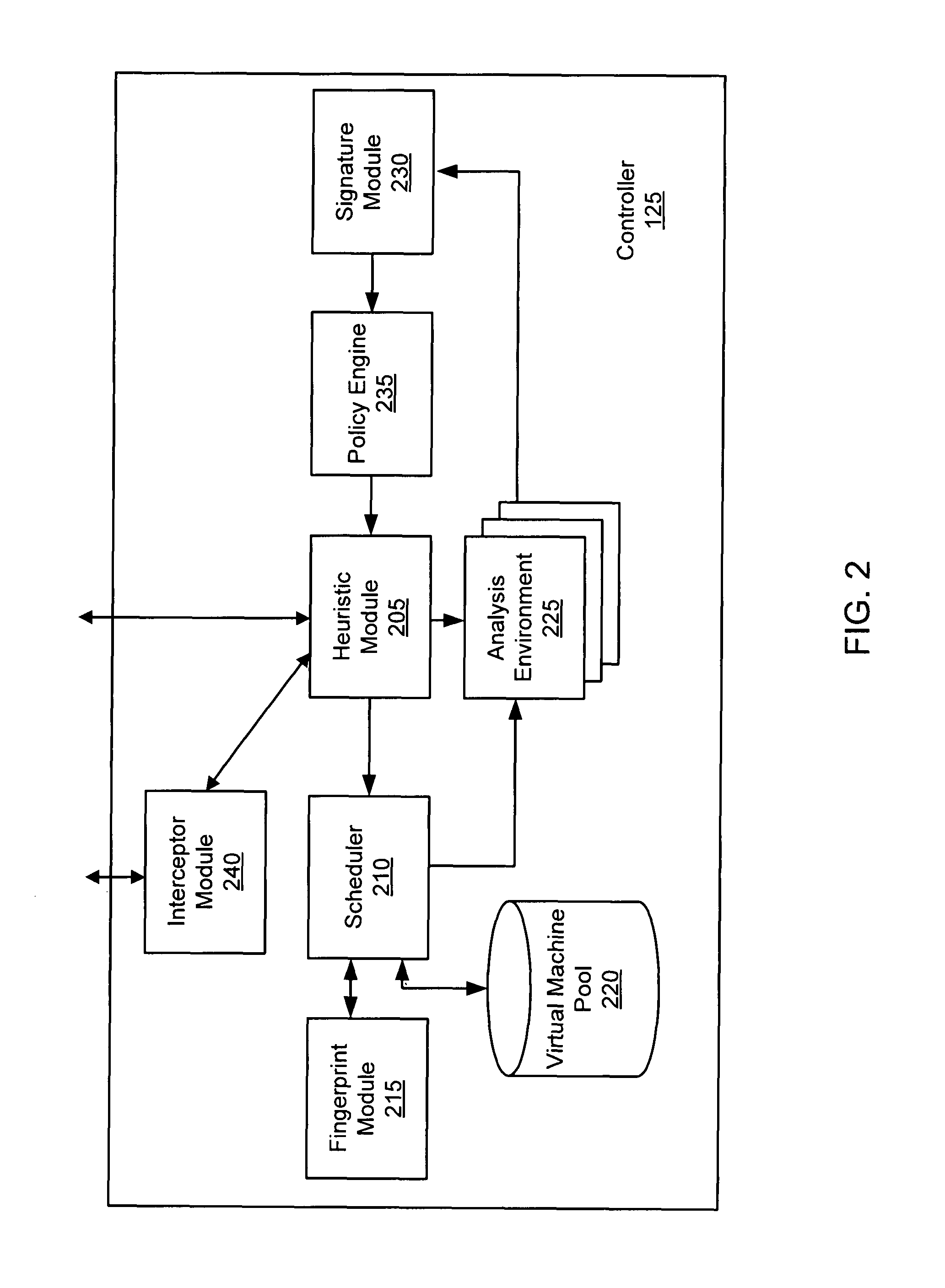
Systems and methods for malware attack detection and identification
Exemplary systems and methods for malware attack detection and identification are provided. A malware detection and identification system can comprise a controller. The controller can comprise an analysis environment configured to transmit network data to a virtual machine, flag input values associated with the network data from untrusted sources, monitor the flagged input values within the virtual machine, identify an outcome of one or more instructions that manipulate the flagged input values, and determine if the outcome of the one or more instructions comprise an unauthorized activity.
Owner:FIREEYE SECURITY HLDG US LLC
Prospective client identification using malware attack detection
Systems and methods for prospective client identification using malware attack detection are provided. A malware device is identified. The entity with the responsibility for the malware device or a potentially compromised device in communication with the malware device is determined. A message is communicated to the entity based on the determination. In various embodiments, the message comprises an offer for security related products and / or services.
Owner:FIREEYE SECURITY HLDG US LLC
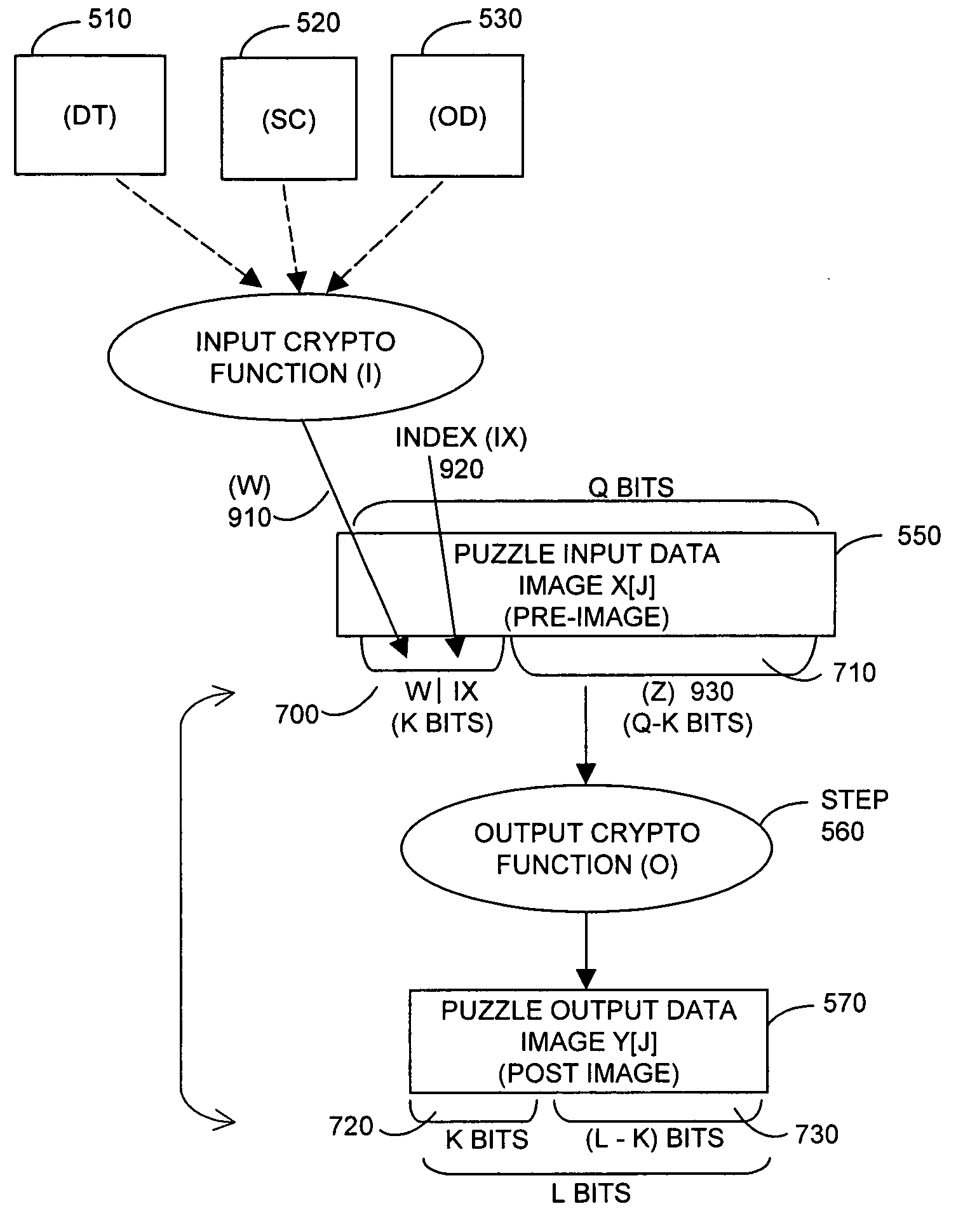
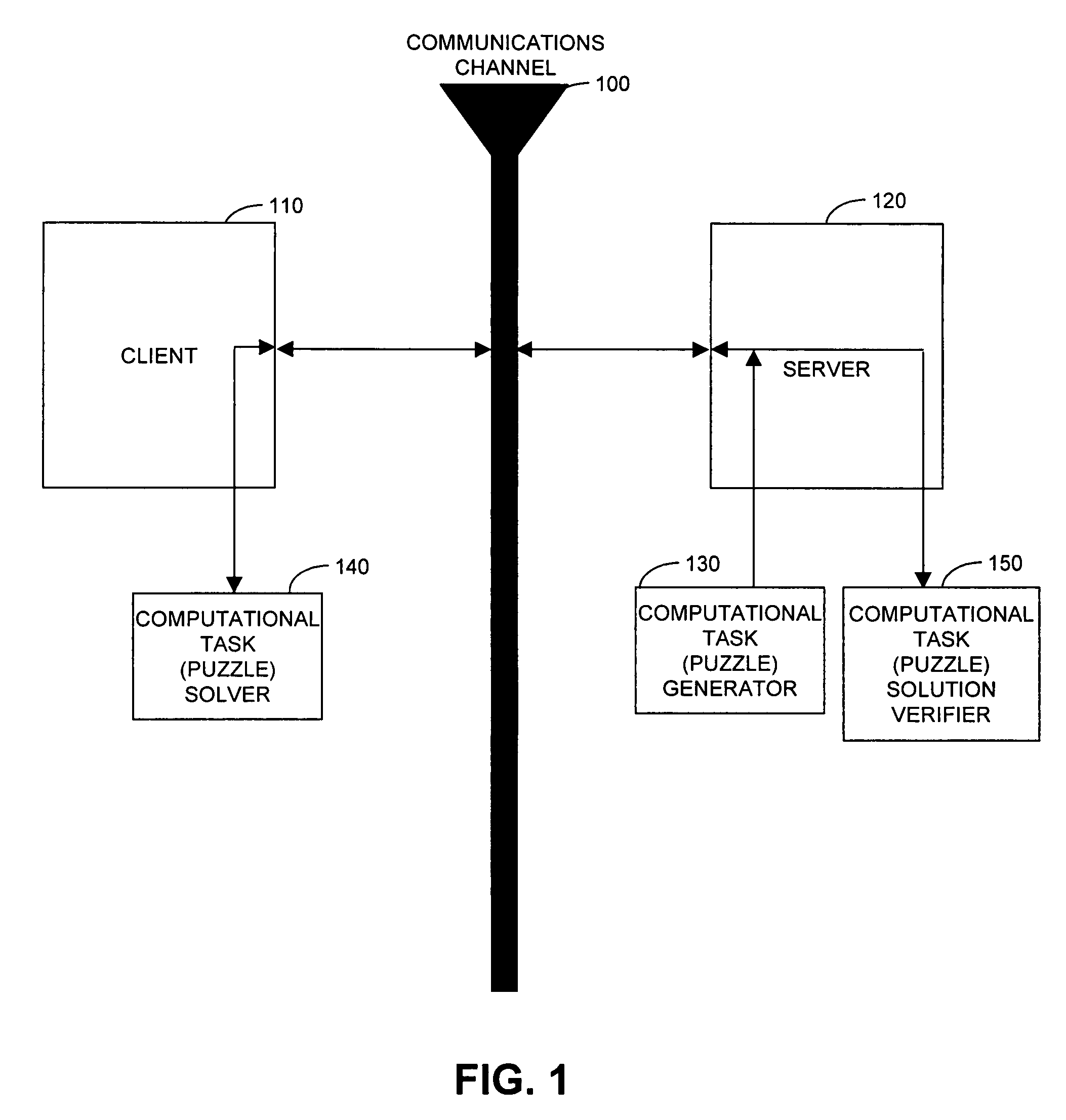
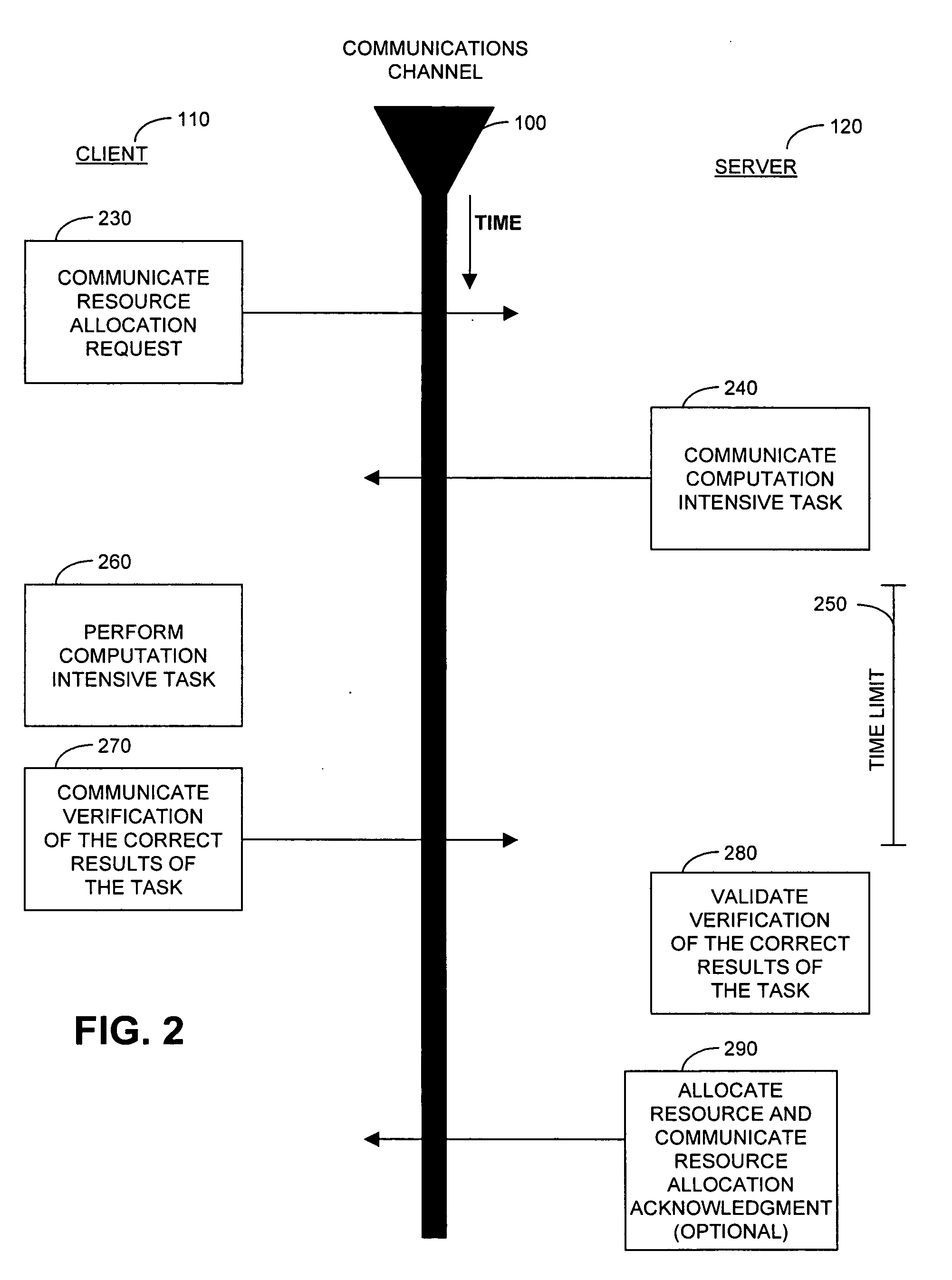
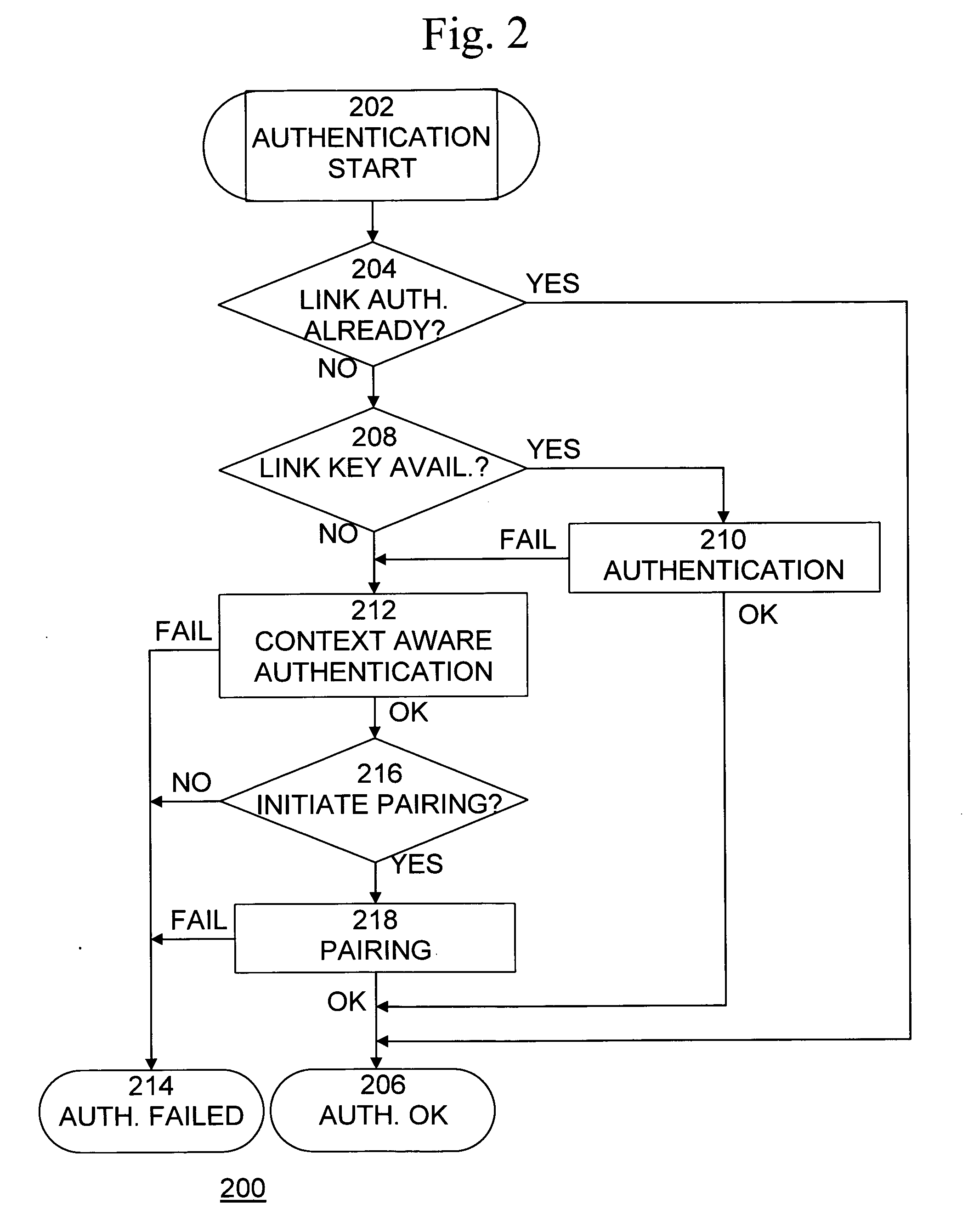
Cryptographic countermeasures against connection depletion attacks
InactiveUS7197639B1Ensure correct executionDigital data processing detailsUser identity/authority verificationCountermeasureTime limit
This invention relates to cryptographic communications methods and systems that protect a server from a connection depletion attack. Specifically, the invention presents a method for allocating a resource comprising the steps of receiving a resource allocation request from a client, imposing a computational task and a time limit for correct completion of the task upon the client, verifying that the task was performed correctly within the time limit, and allocating the resource if the task was correctly performed within the time limit.
Owner:EMC IP HLDG CO LLC
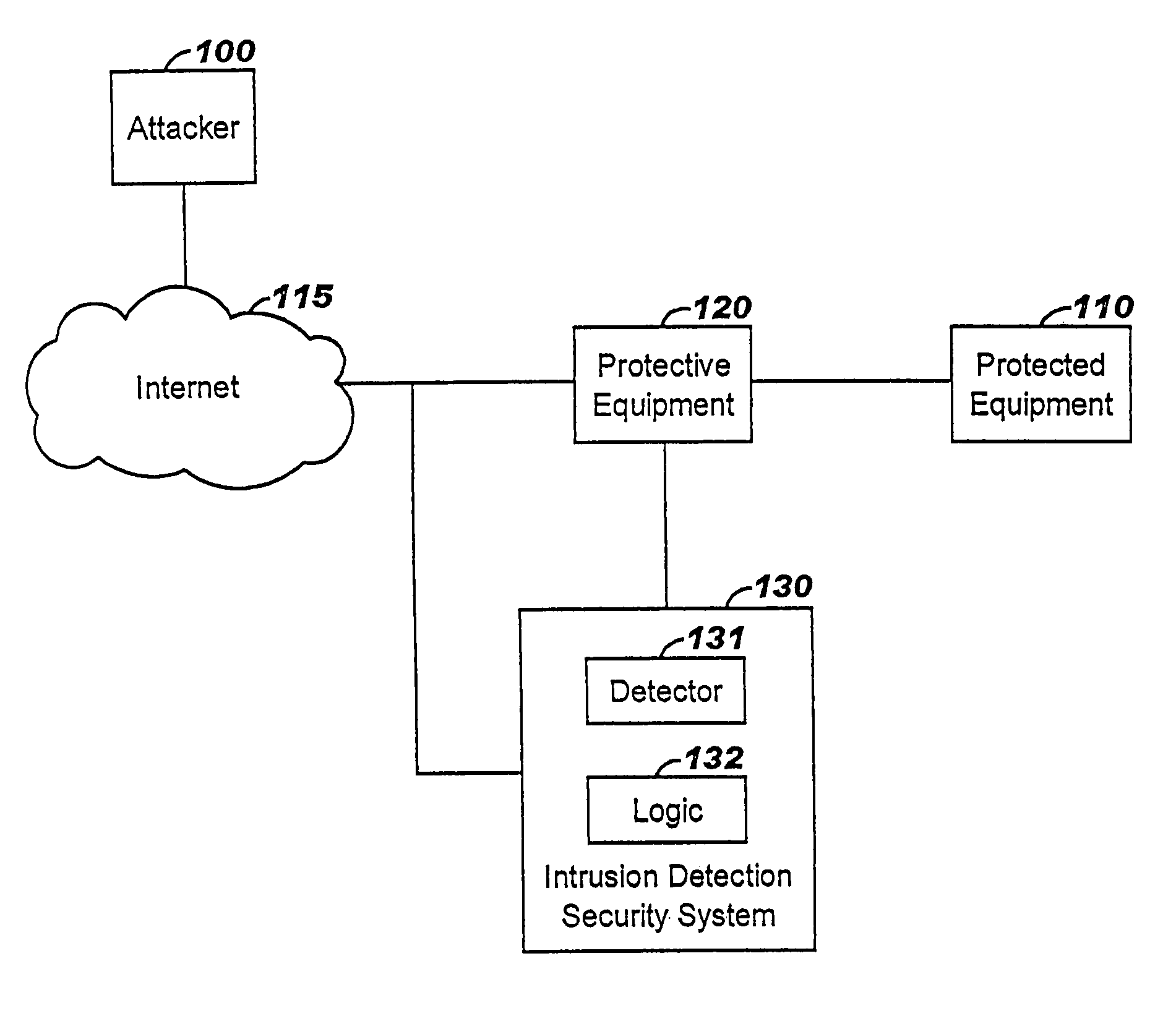
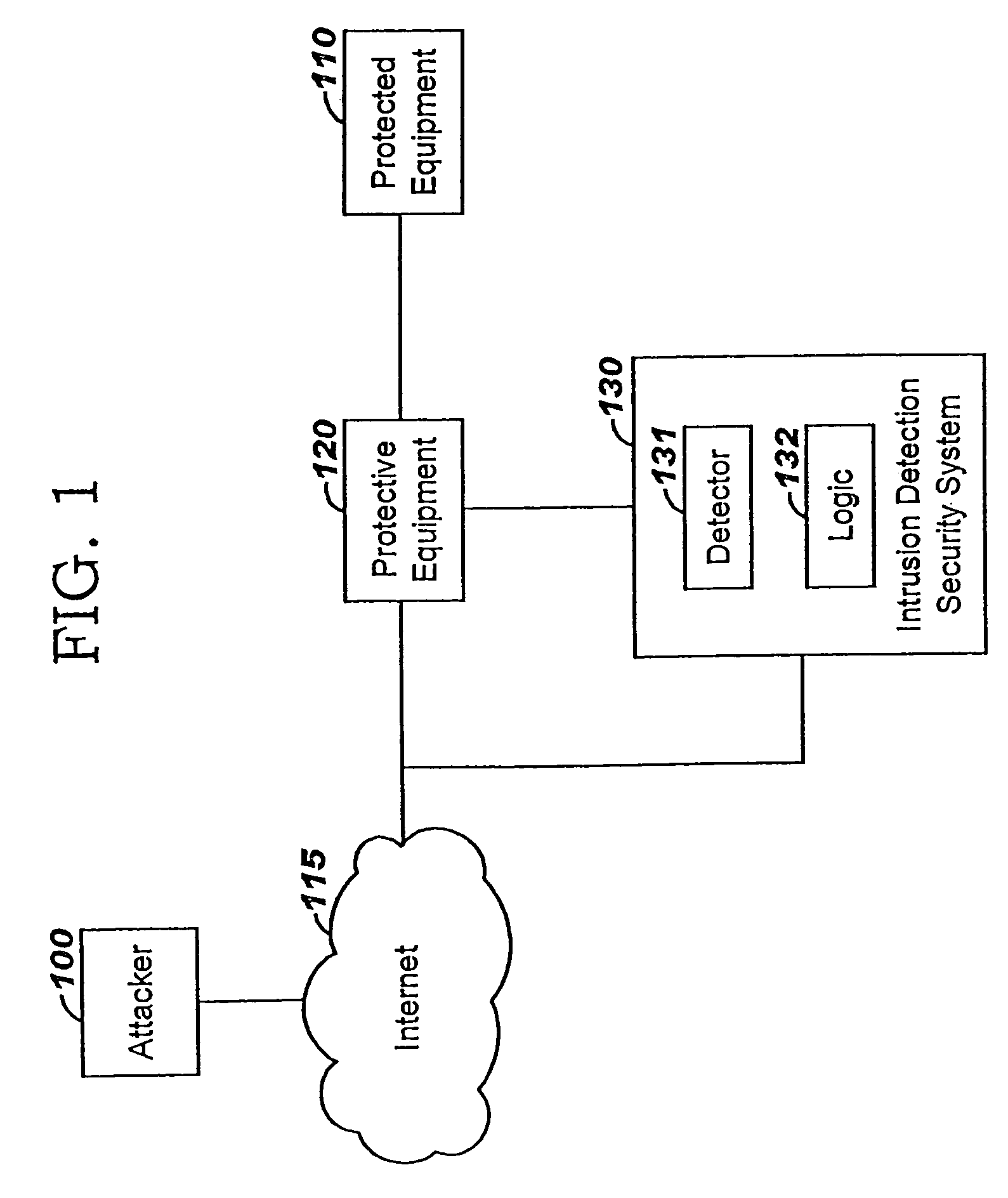
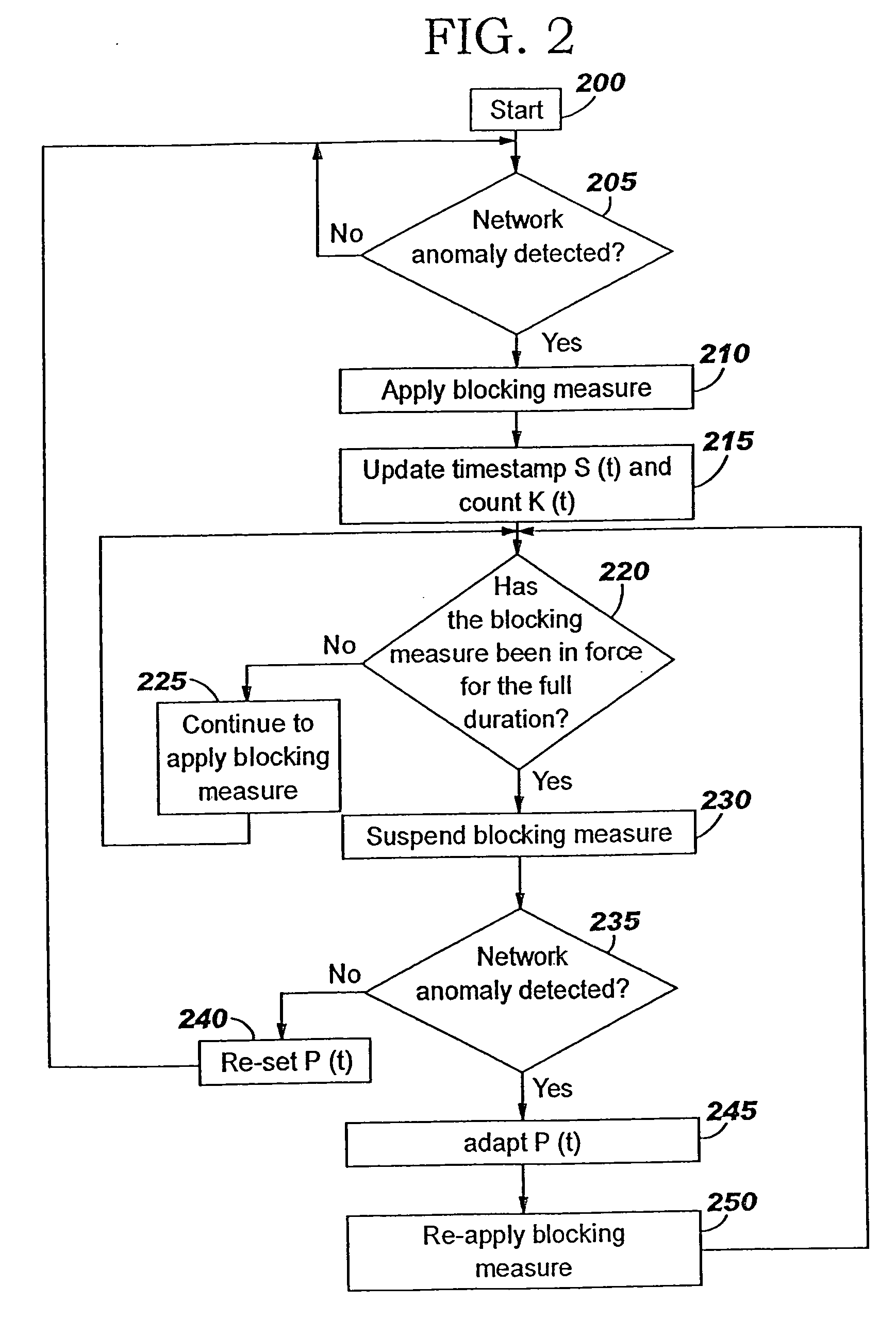
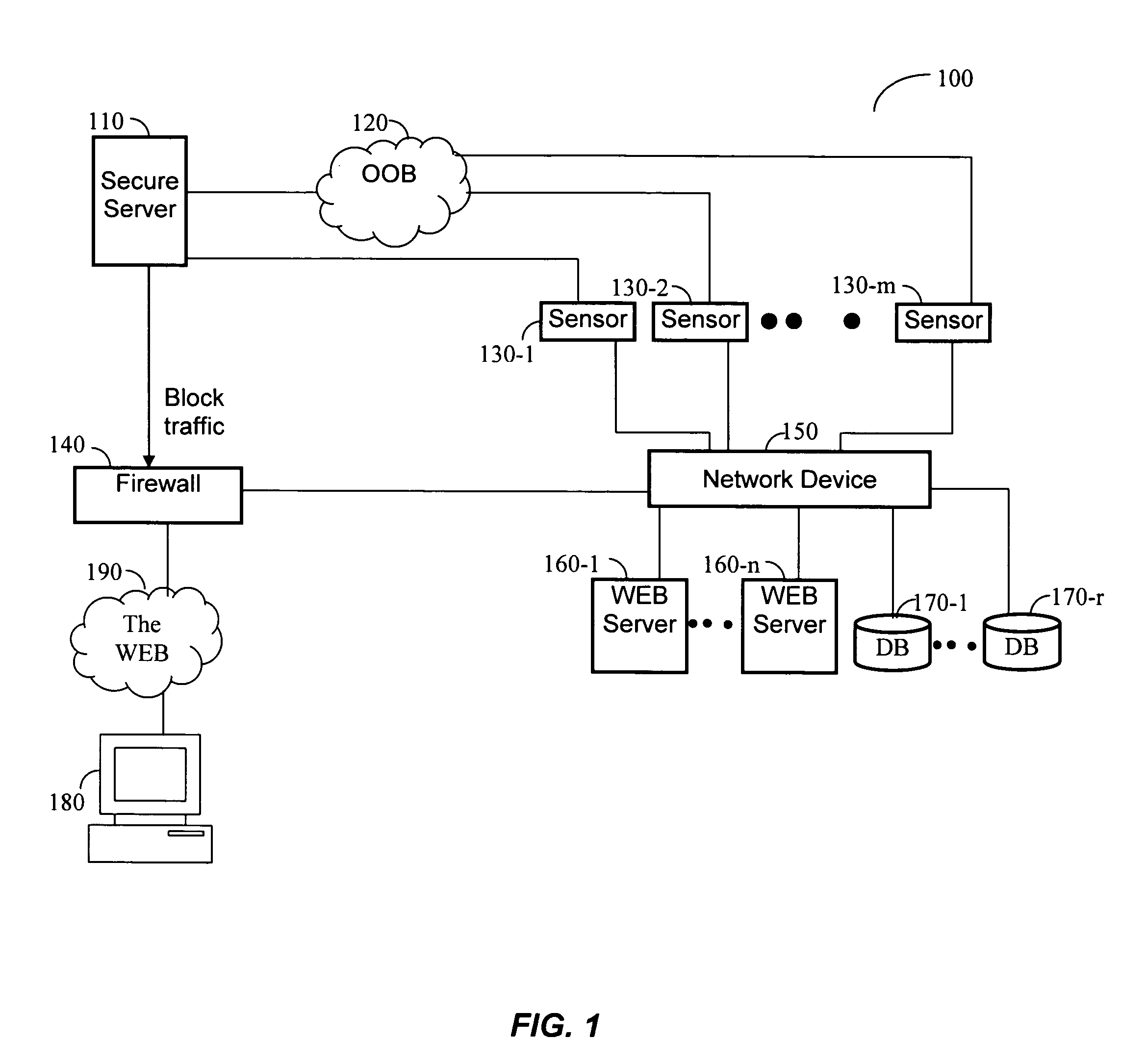
Applying blocking measures progressively to malicious network traffic
InactiveUS20060075496A1Minimizing adverse consequenceMinimize consequencesMemory loss protectionUnauthorized memory use protectionResponse methodFalse positives and false negatives
A method of progressive response for invoking and suspending blocking measures that defend against network anomalies such as malicious network traffic so that false positives and false negatives are minimized. When a truncated secure session attack is detected, the detector notifies protective equipment such as a firewall or a router to invoke a blocking measure. The blocking measure is maintained for an initial duration, after which it is suspended while another test for the anomaly is made. If the attack is no longer evident, the method returns to the state of readiness. Otherwise, a loop is executed to re-applying the blocking measure for a specified duration, then suspend the blocking measure and test again for the attack. If the attack is detected, the blocking measure is re-applied, and its duration is adapted. If the attack is no longer detected, the method returns to the state of readiness.
Owner:TREND MICRO INC
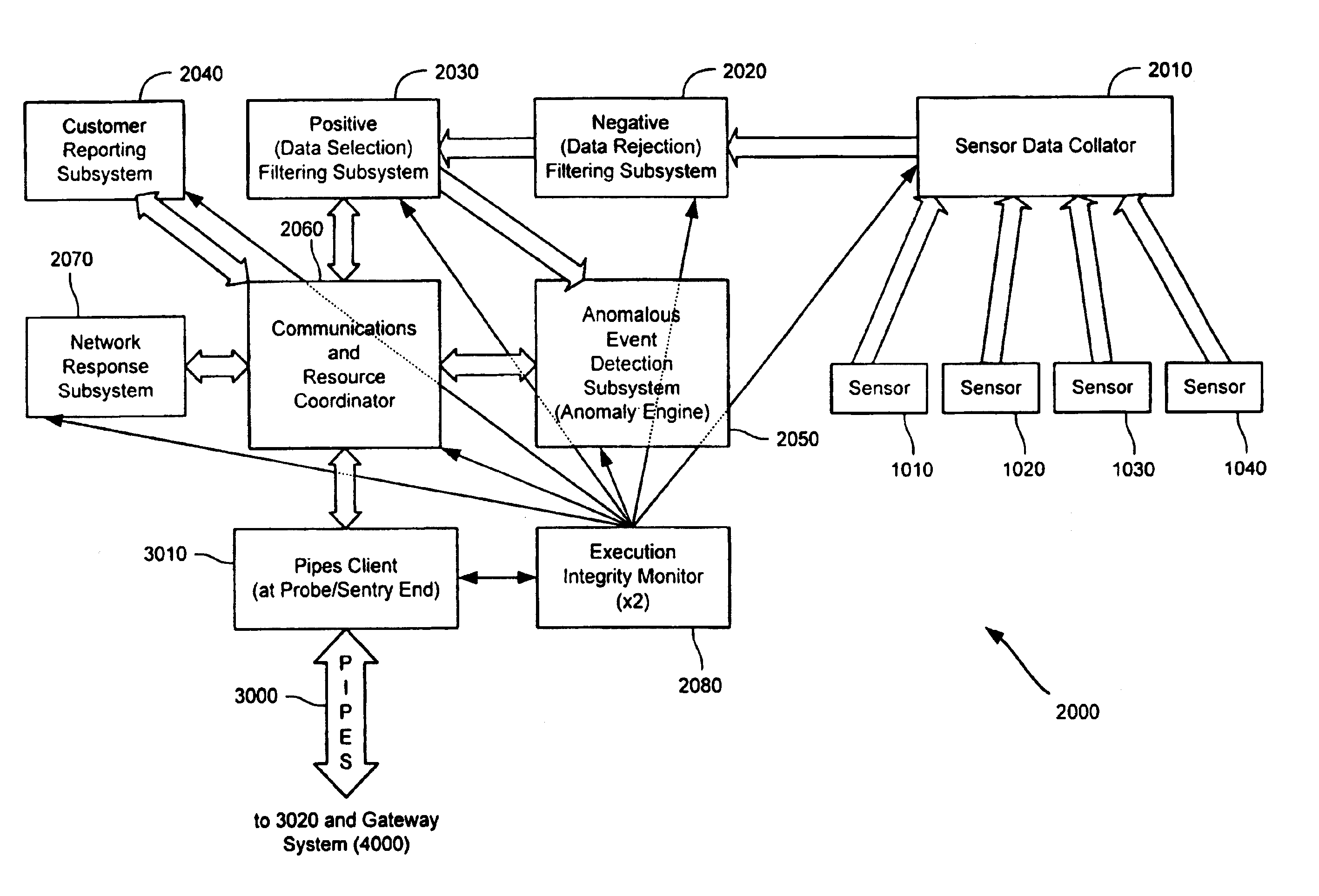
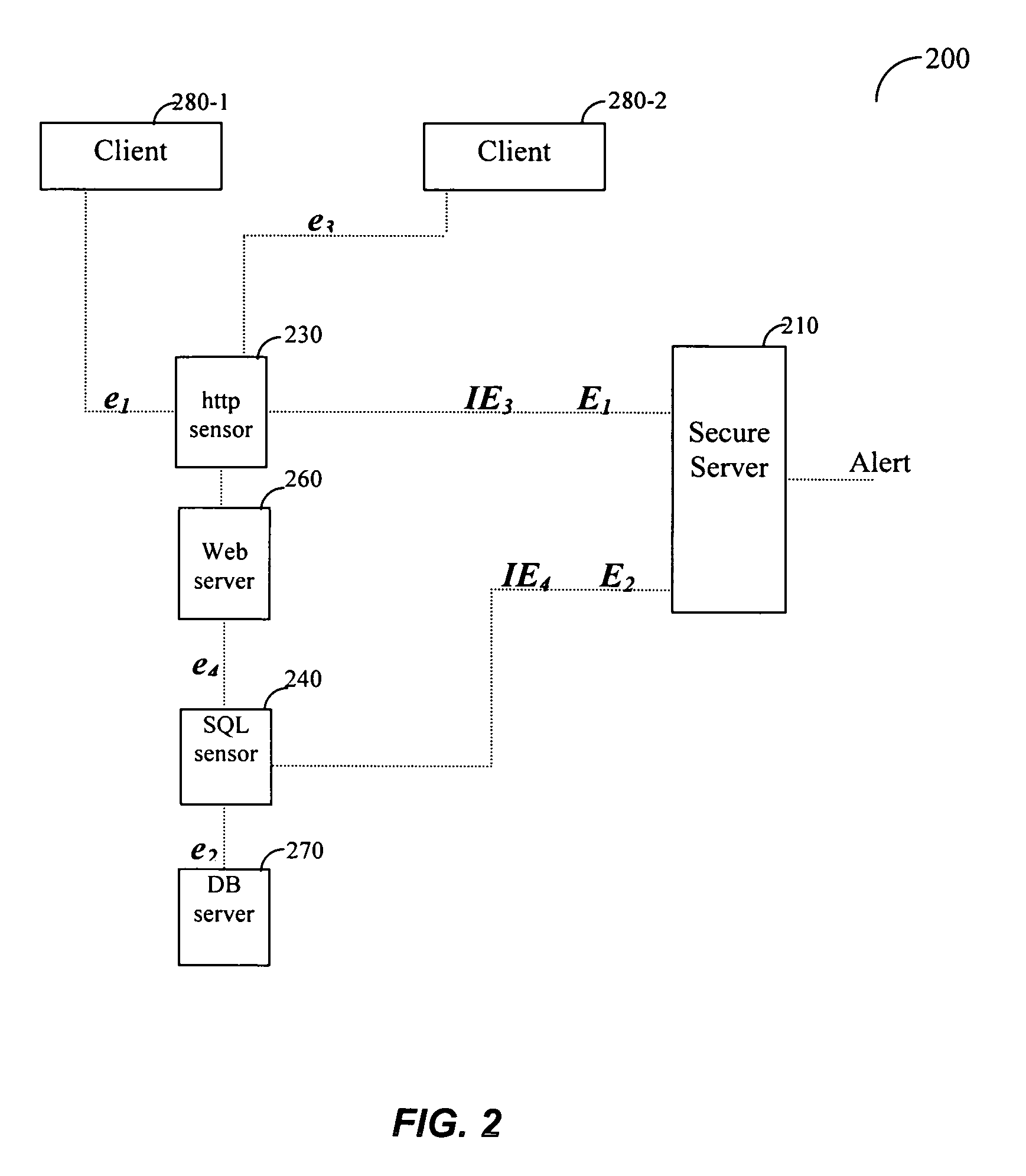
Method and system for dynamic network intrusion monitoring, detection and response
InactiveUS7159237B2Eliminate false positivesIncrease in sizeMemory loss protectionDigital data processing detailsProblem resolutionVulnerability
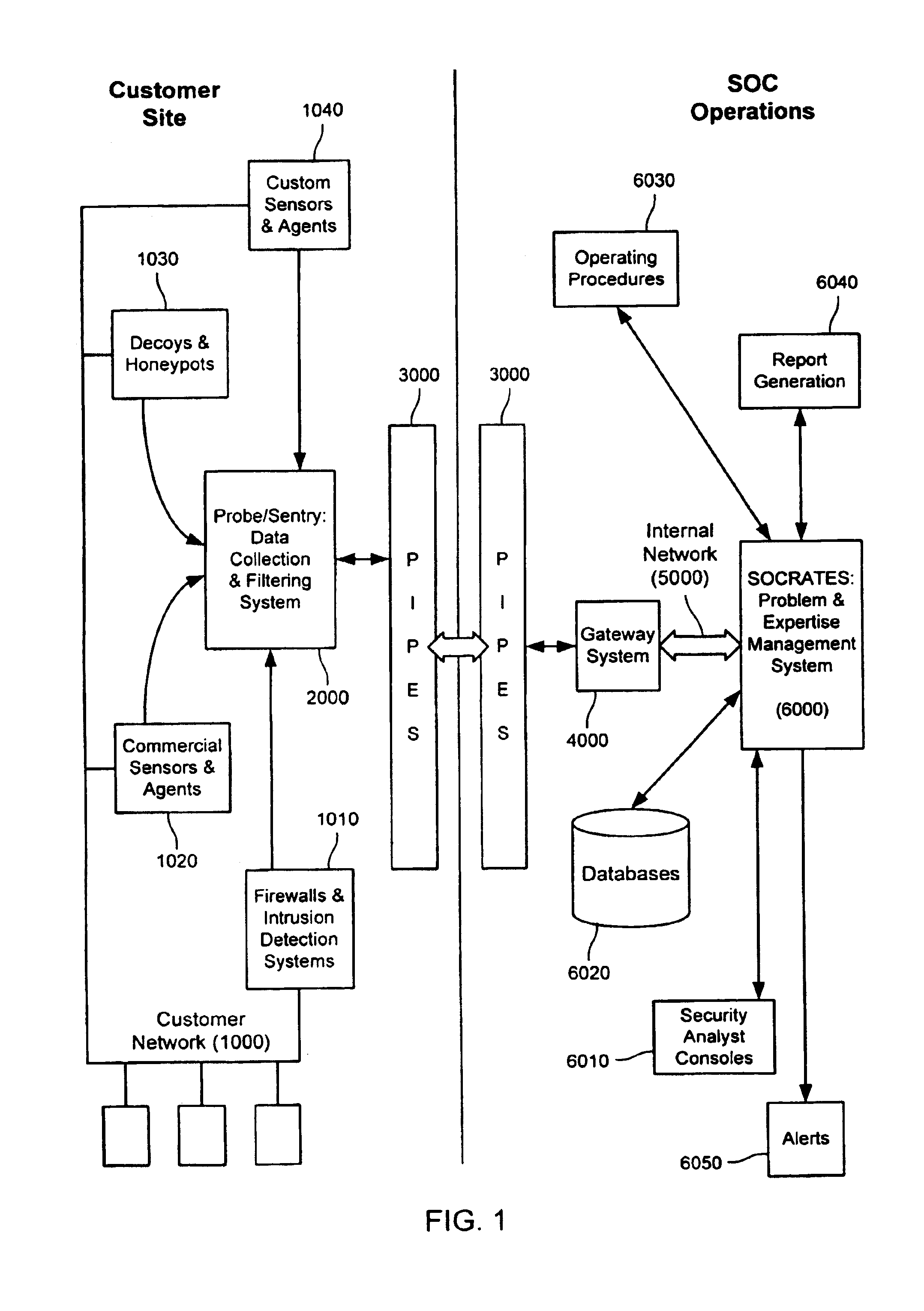
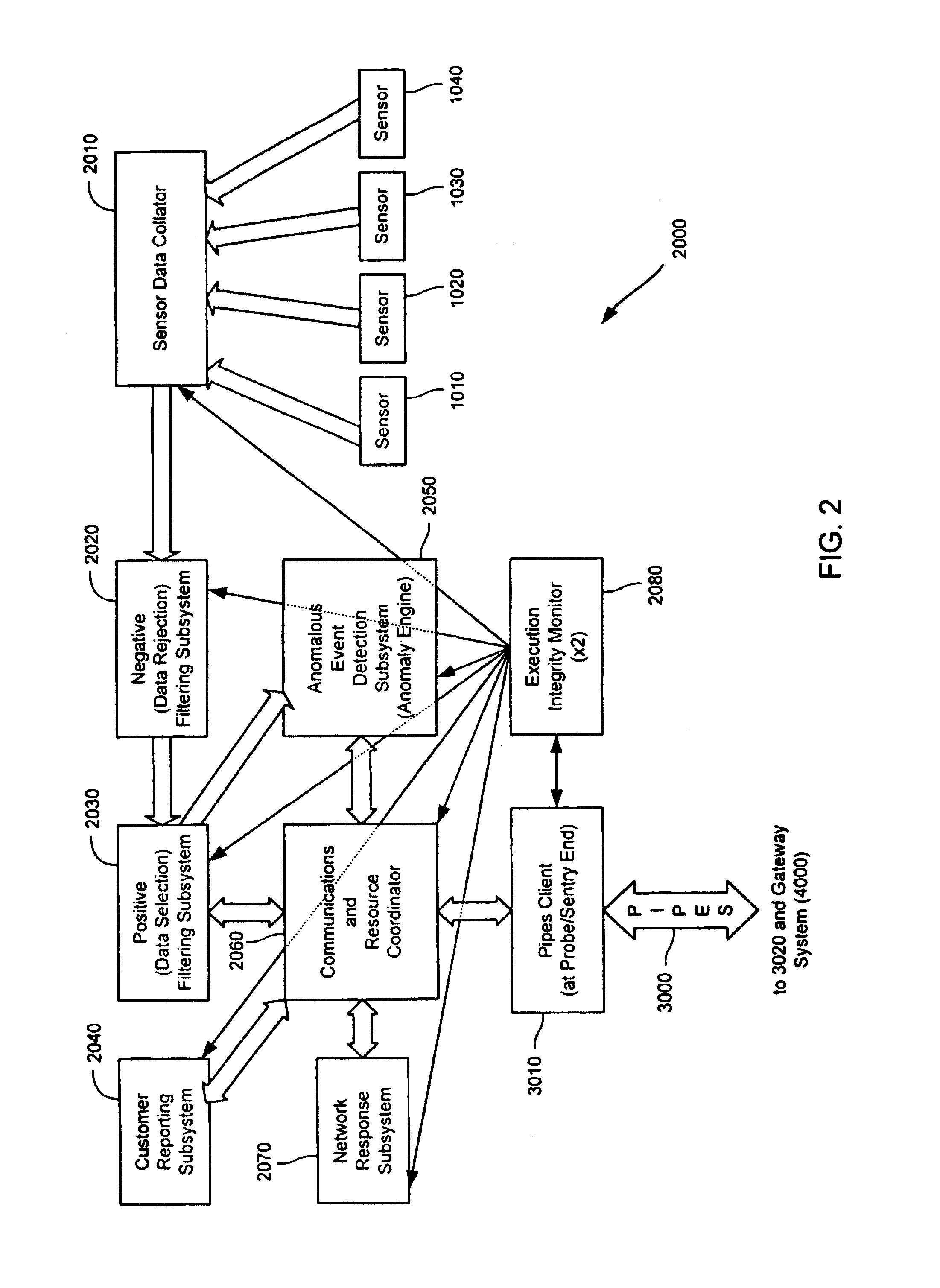
A probe attached to a customer's network collects status data and other audit information from monitored components of the network, looking for footprints or evidence of unauthorized intrusions or attacks. The probe filters and analyzes the collected data to identify potentially security-related events happening on the network. Identified events are transmitted to a human analyst for problem resolution. The analyst has access to a variety of databases (including security intelligence databases containing information about known vulnerabilities of particular network products and characteristics of various hacker tools, and problem resolution databases containing information relevant to possible approaches or solutions) to aid in problem resolution. The analyst may follow a predetermined escalation procedure in the event he or she is unable to resolve the problem without assistance from others. Various customer personnel can be alerted in a variety of ways depending on the nature of the problem and the status of its resolution. Feedback from problem resolution efforts can be used to update the knowledge base available to analysts for future attacks and to update the filtering and analysis capabilities of the probe and other systems.
Owner:BT AMERICAS
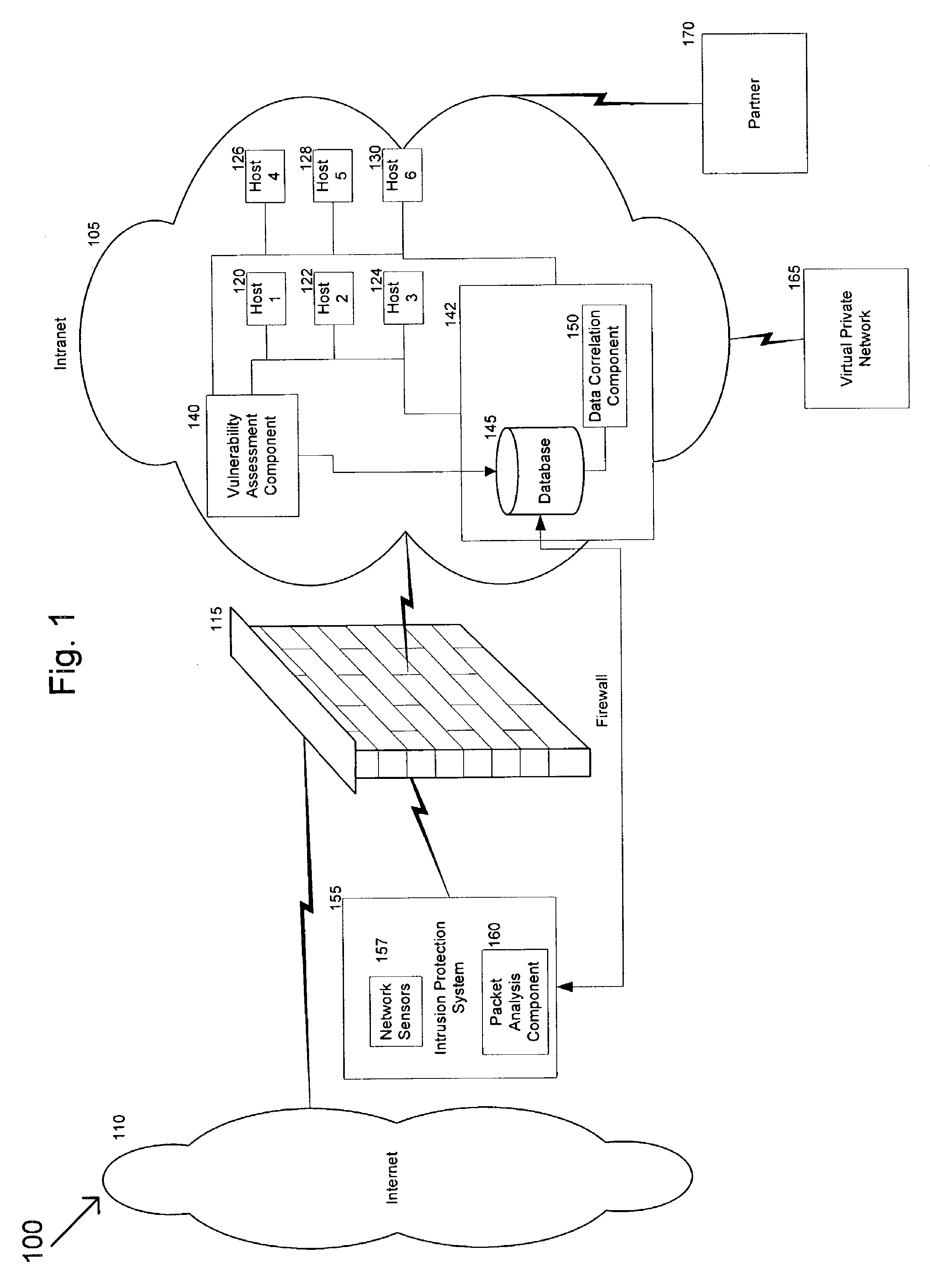
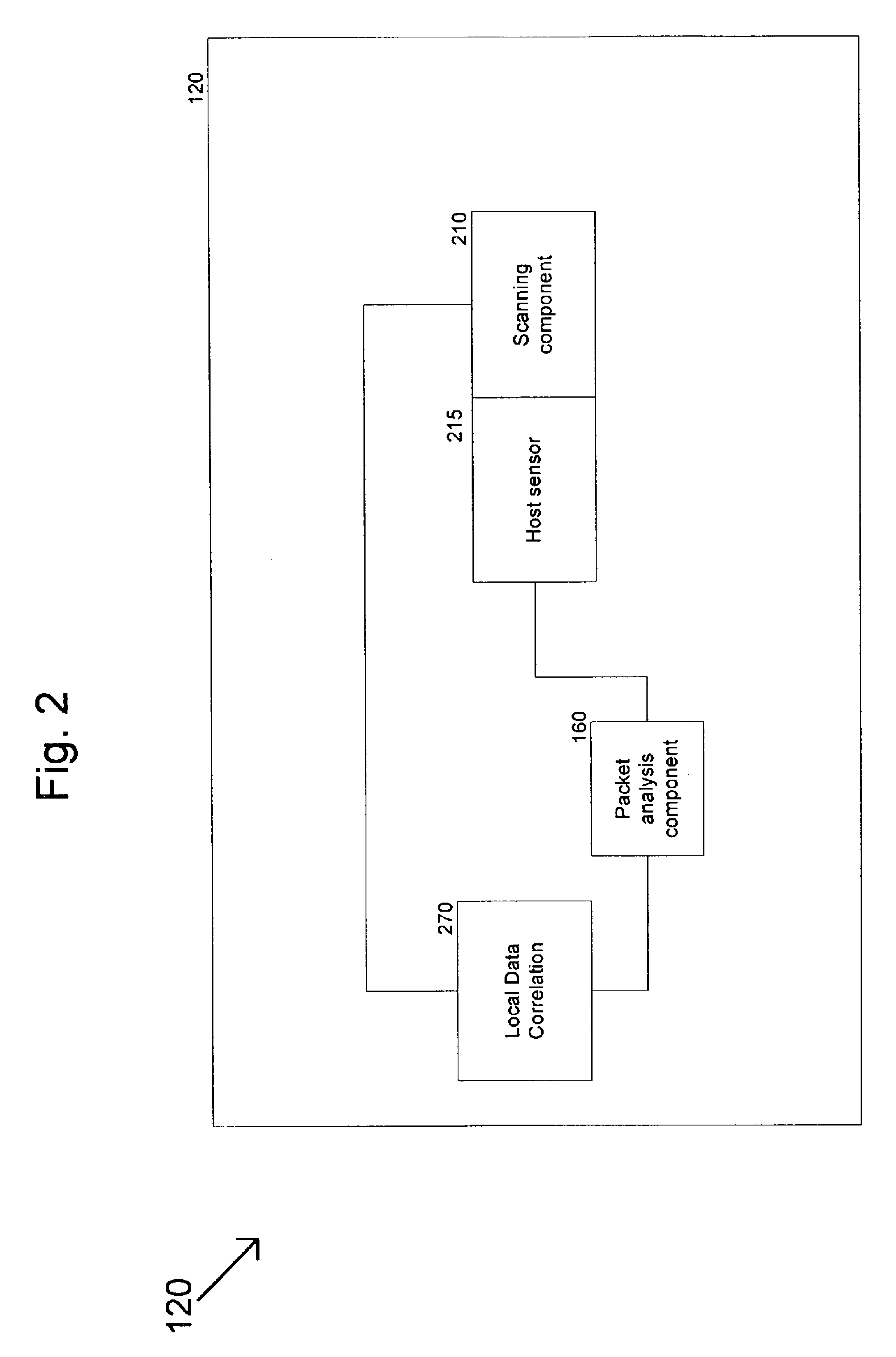
System and method for risk detection and analysis in a computer network
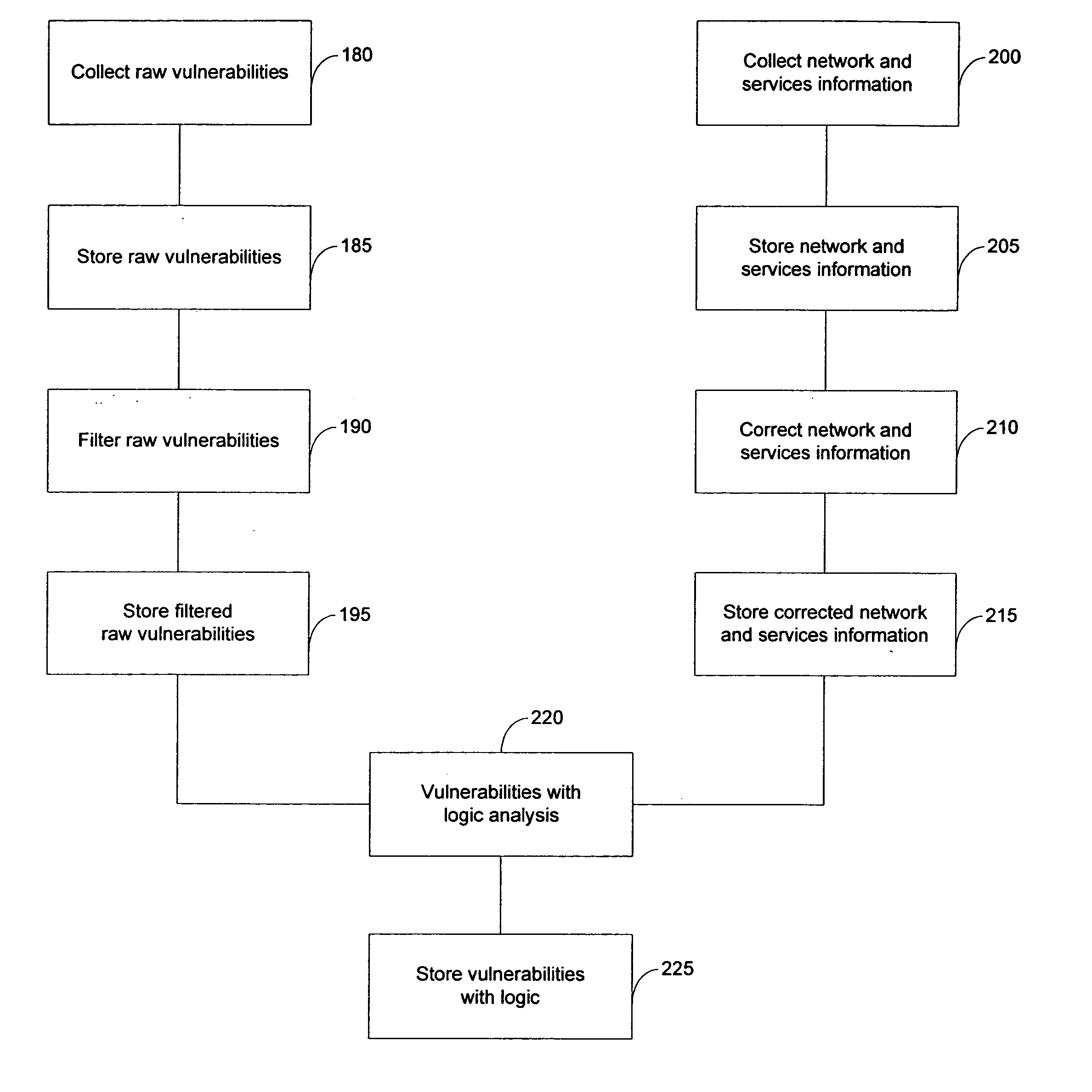
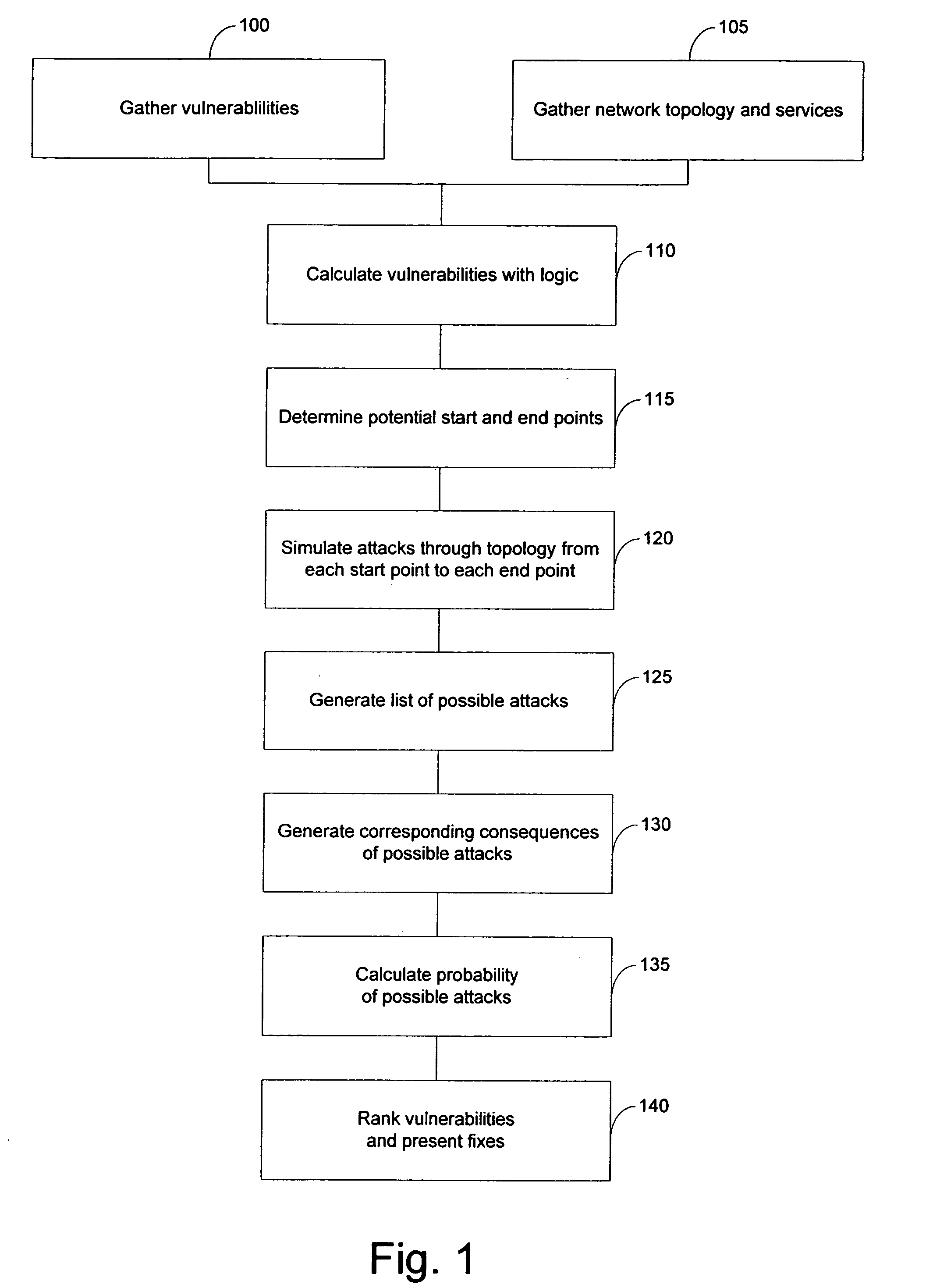
ActiveUS20050193430A1Reduce riskAnalysis can be performedMemory loss protectionDigital data processing detailsAttackEngineering
The present invention provides systems and methods for risk detection and analysis in a computer network. Computerized, automated systems and methods can be provided. Raw vulnerability information and network information can be utilized in determining actual vulnerability information associated with network nodes. Methods are provided in which computer networks are modeled, and the models utilized in performing attack simulations and determining risks associated with vulnerabilities. Risks can be evaluated and prioritized, and fix information can be provided.
Owner:SKYBOX SECURITY
Content security layer providing long-term renewable security
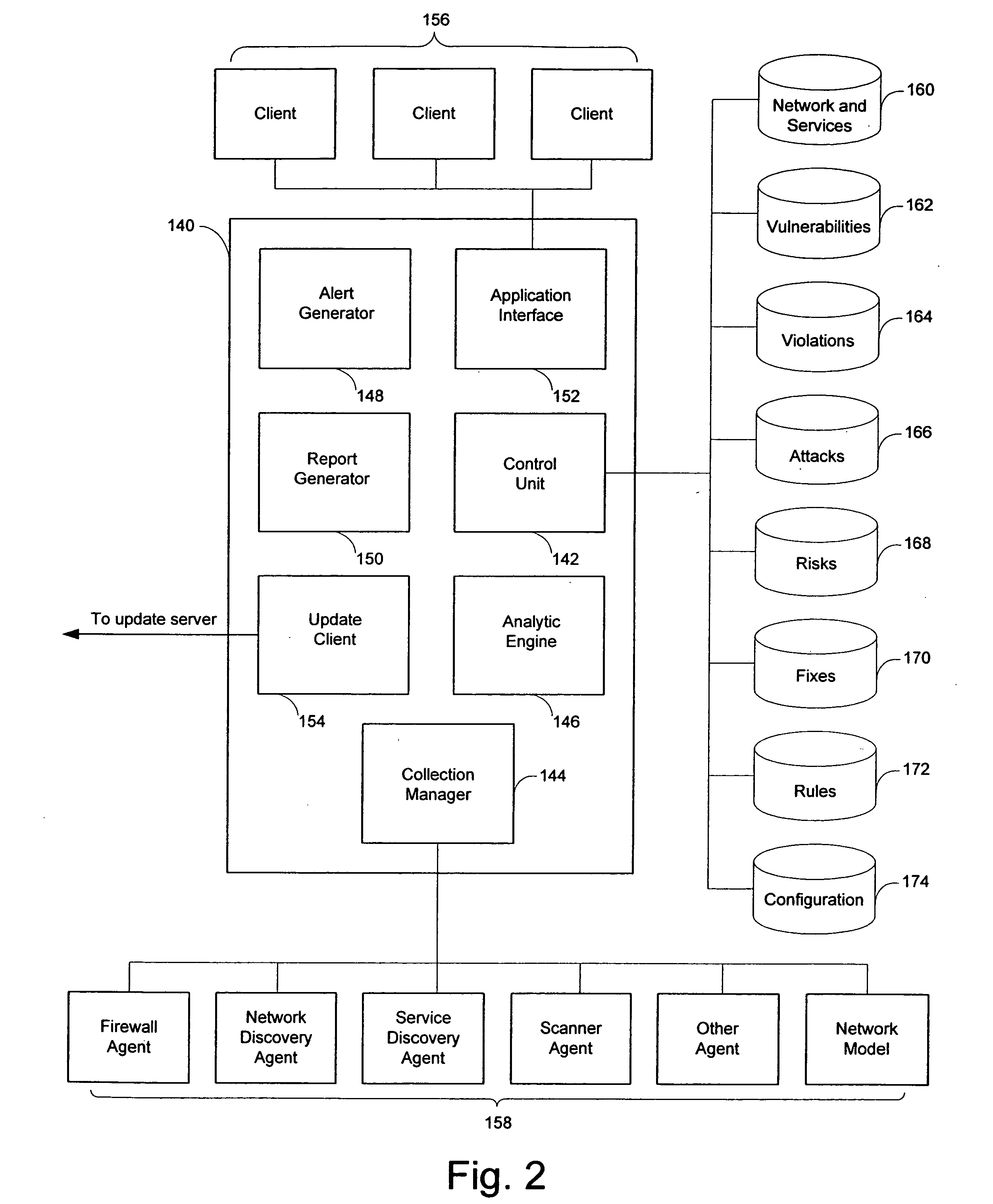
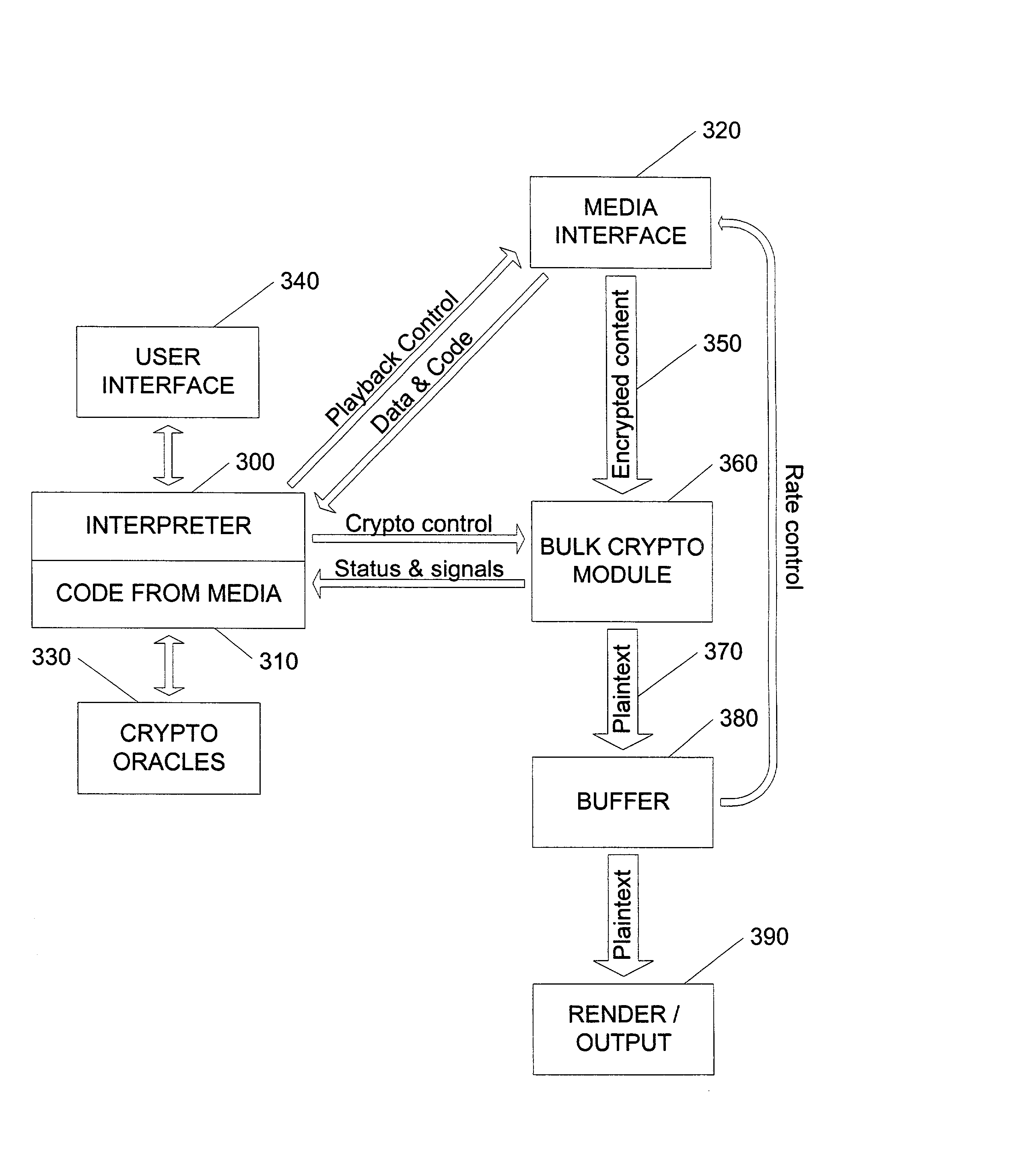
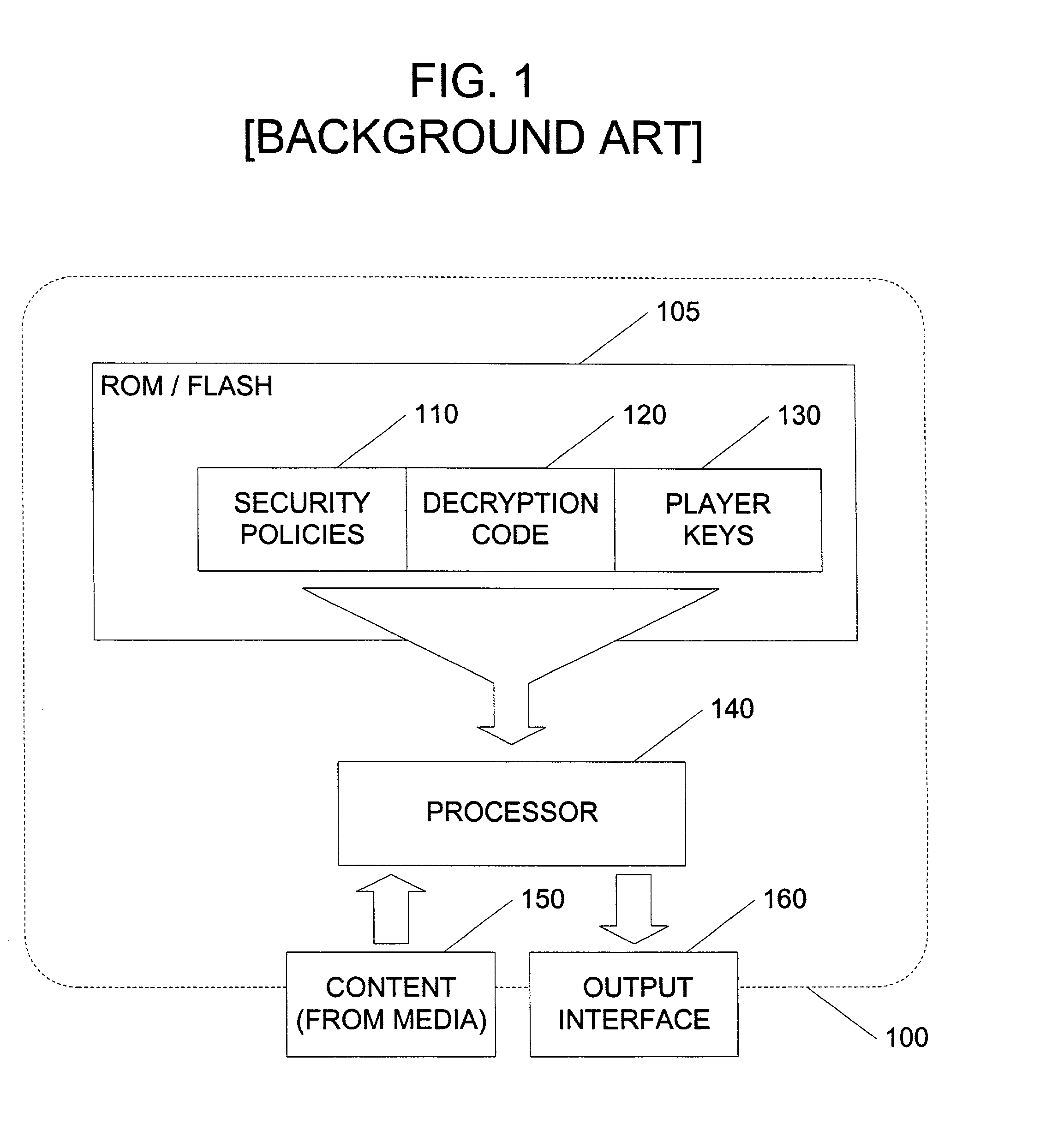
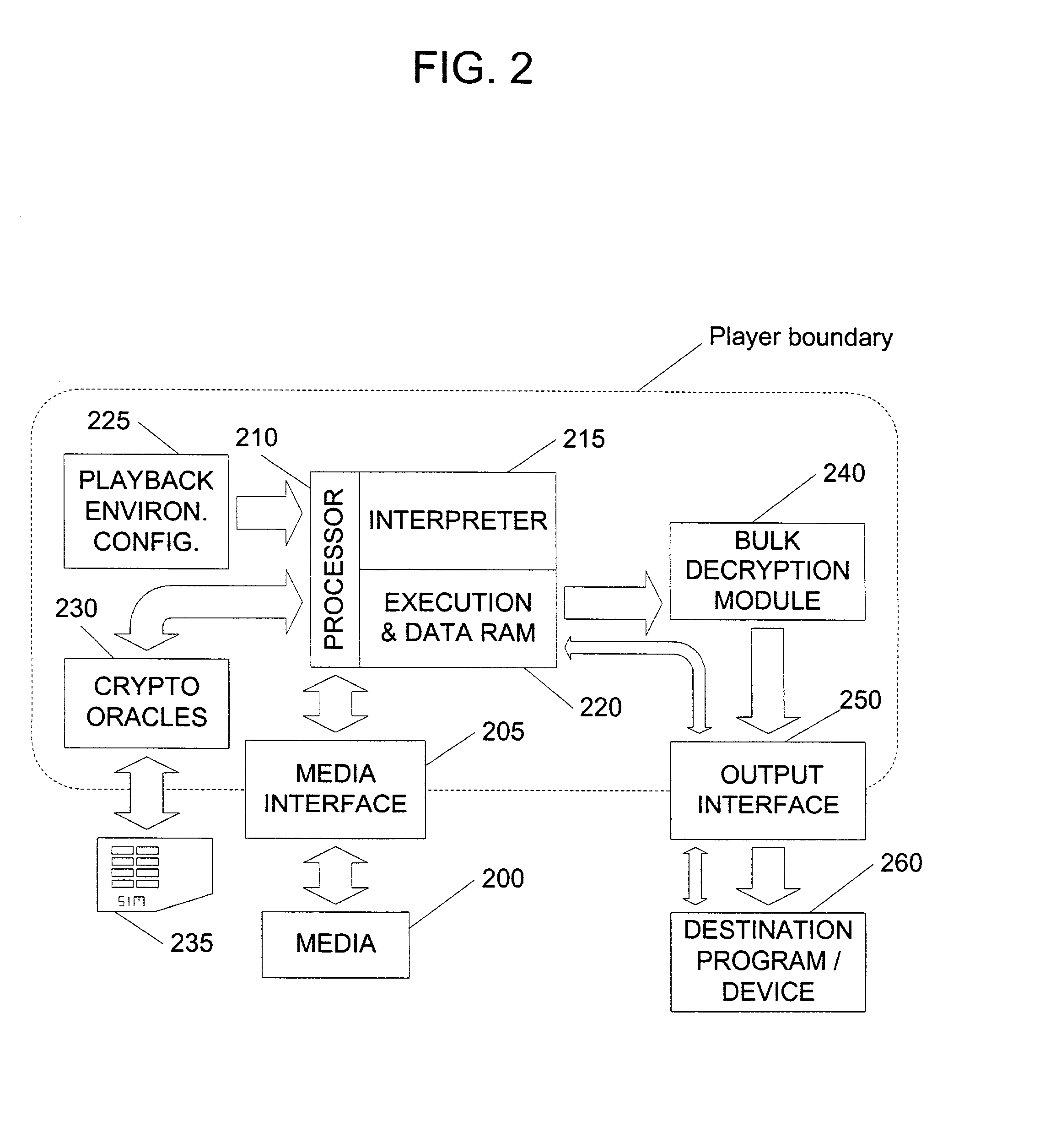
InactiveUS20020141582A1Unparalleled flexibilityIncrease sampling rateTelevision system detailsKey distribution for secure communicationAttackMediaFLO
In an exemplary embodiment, digital content is mastered as a combination of encrypted data and data processing operations that enable use in approved playback environments. Player devices having a processing environment compatible with the content's data processing operations are able to decrypt and play the content. Players can also provide content with basic functions, such as loading data from media, performing network communications, determining playback environment configuration, controlling decryption / playback, and / or performing cryptographic operations using the player's keys. These functions allow the content to implement and enforce its own security policies. If pirates compromise individual players or content titles, new content can be mastered with new security features that block the old attacks. A selective decryption capability can also be provided, enabling on-the-fly watermark insertion so that attacks can be traced back to a particular player. Features to enable migration from legacy formats are also provided.
Owner:ROVI SOLUTIONS CORP
Systems and methods for detection of session tampering and fraud prevention
ActiveUS20070234409A1Secure performanceIdentify theftMemory loss protectionError detection/correctionMan-in-the-middle attackOperating system
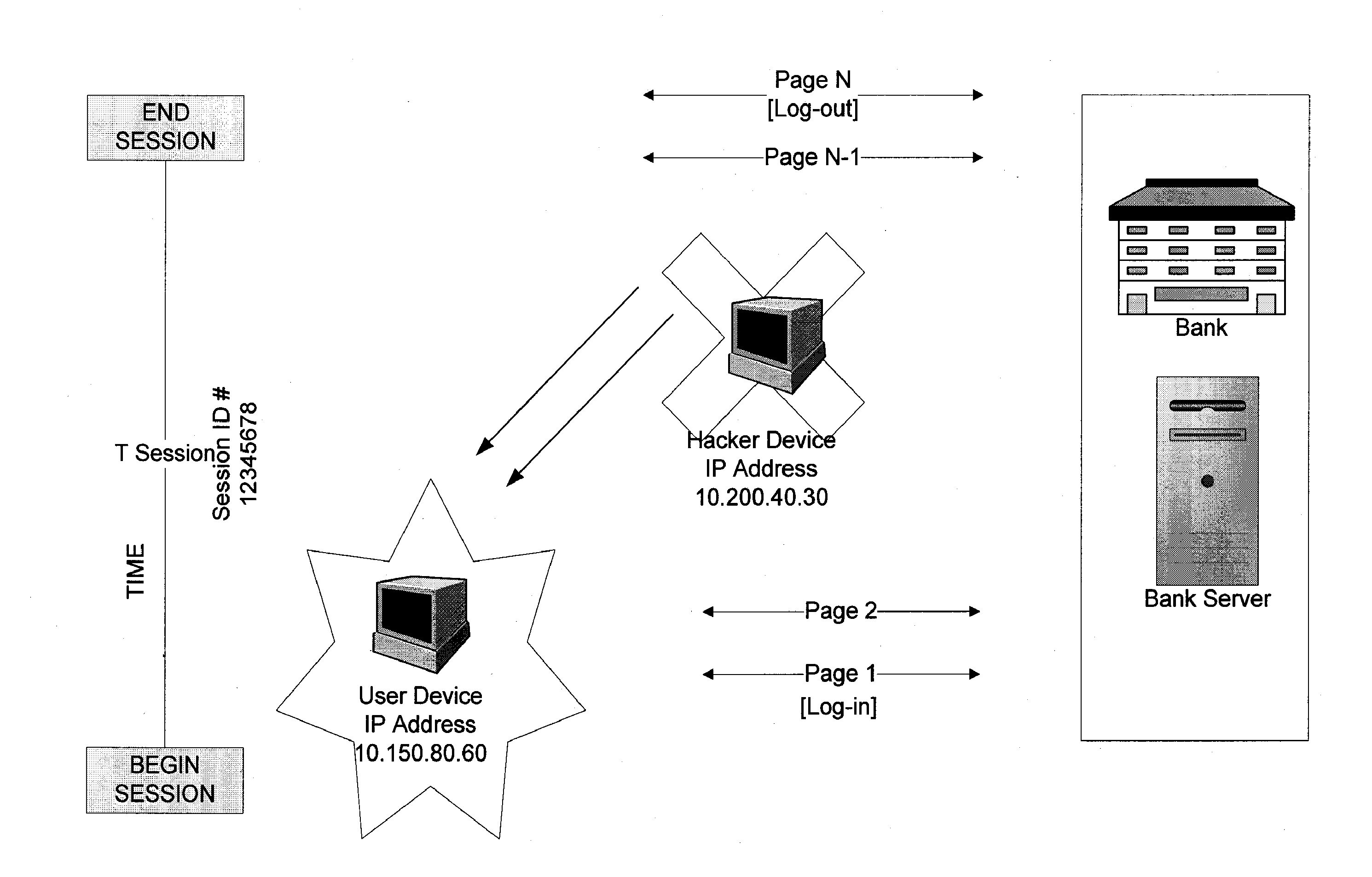
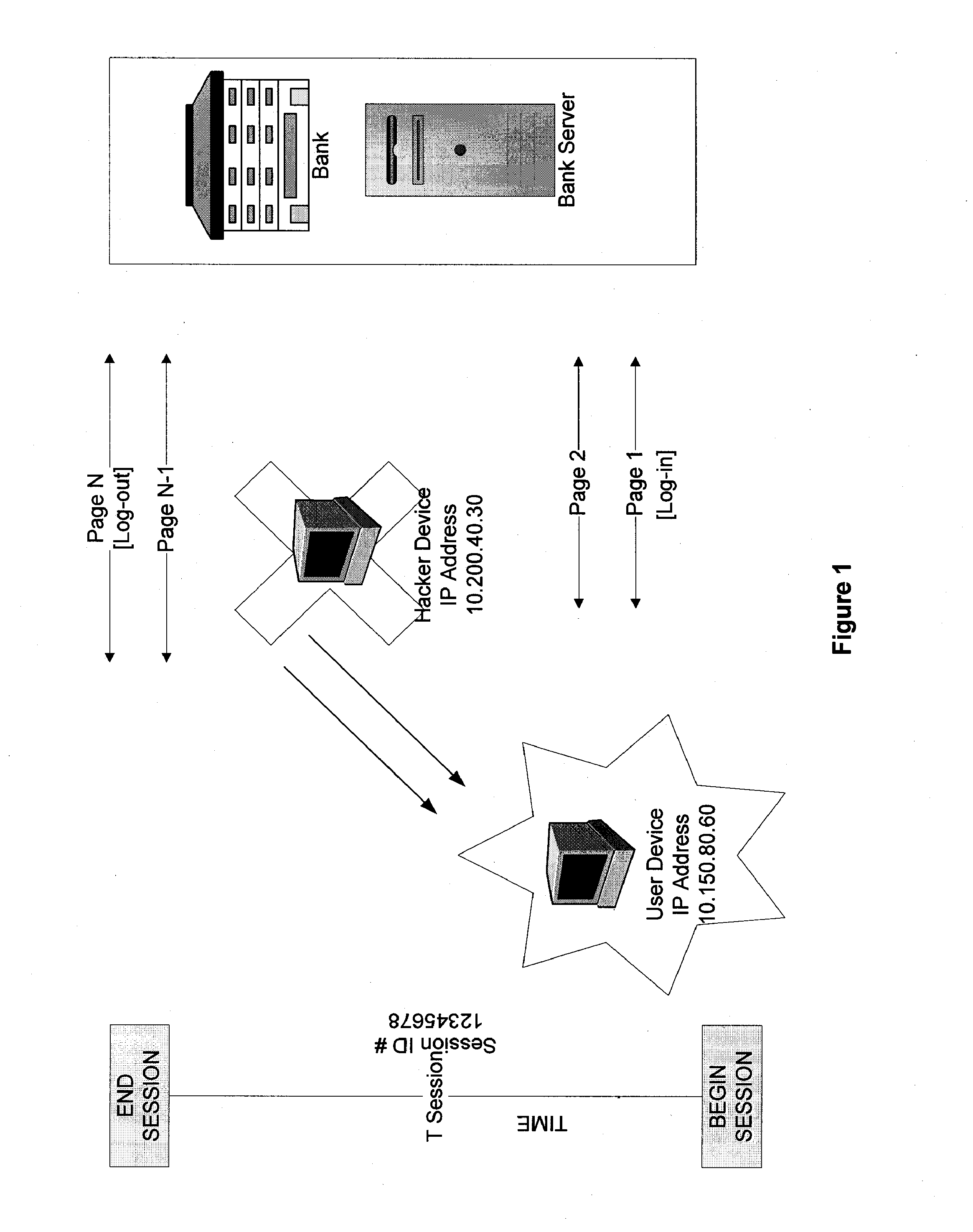
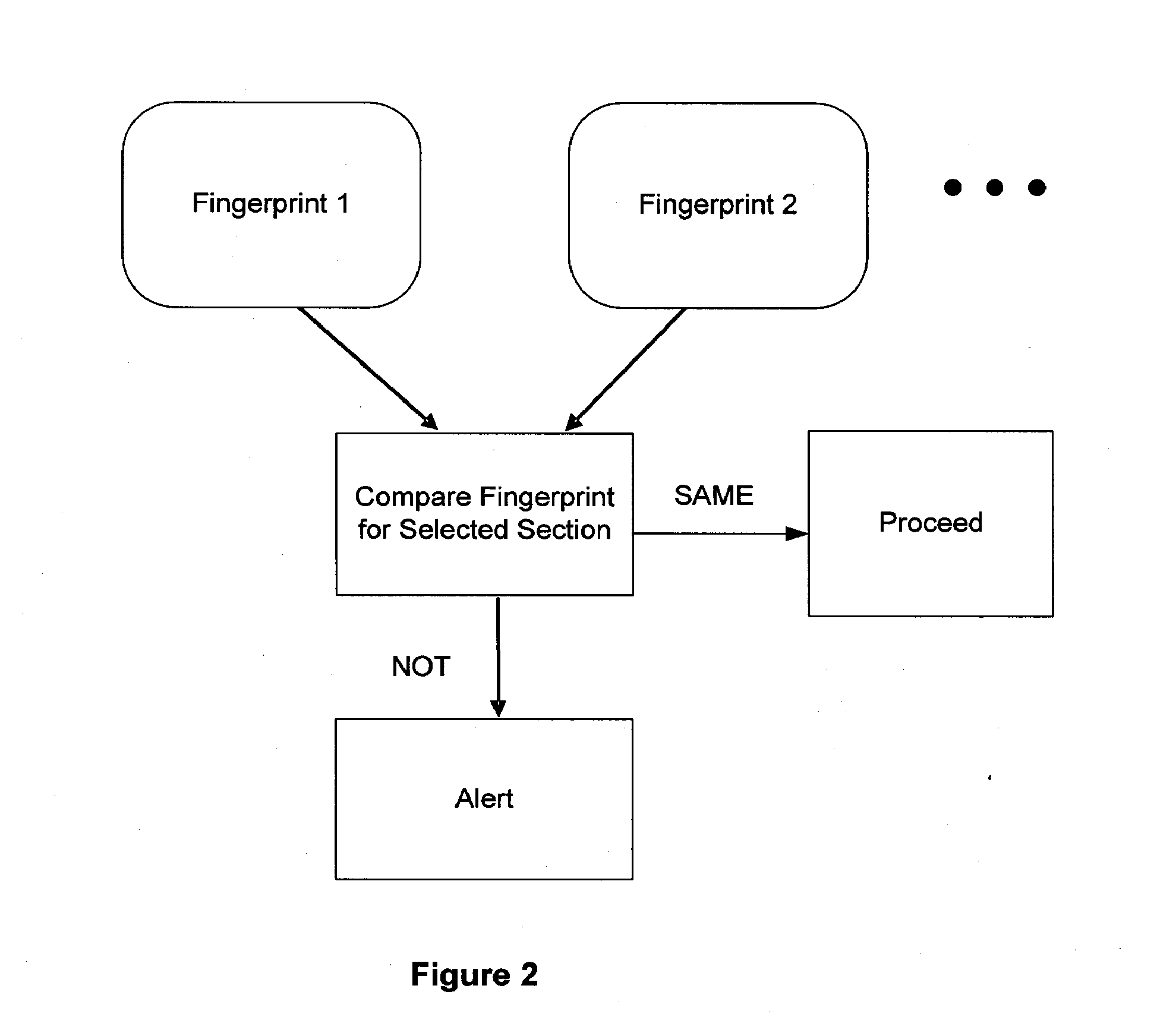
The invention provides methods and apparatus for detecting when an online session is compromised. A plurality of device fingerprints may be collected from a user computer that is associated with a designated Session ID. A server may include pages that are delivered to a user for viewing in a browser at which time device fingerprints and Session ID information are collected. By collecting device fingerprints and session information at several locations among the pages delivered by the server throughout an online session, and not only one time or at log-in, a comparison between the fingerprints in association with a Session ID can identify the likelihood of session tampering and man-in-the middle attacks.
Owner:THE 41ST PARAMETER
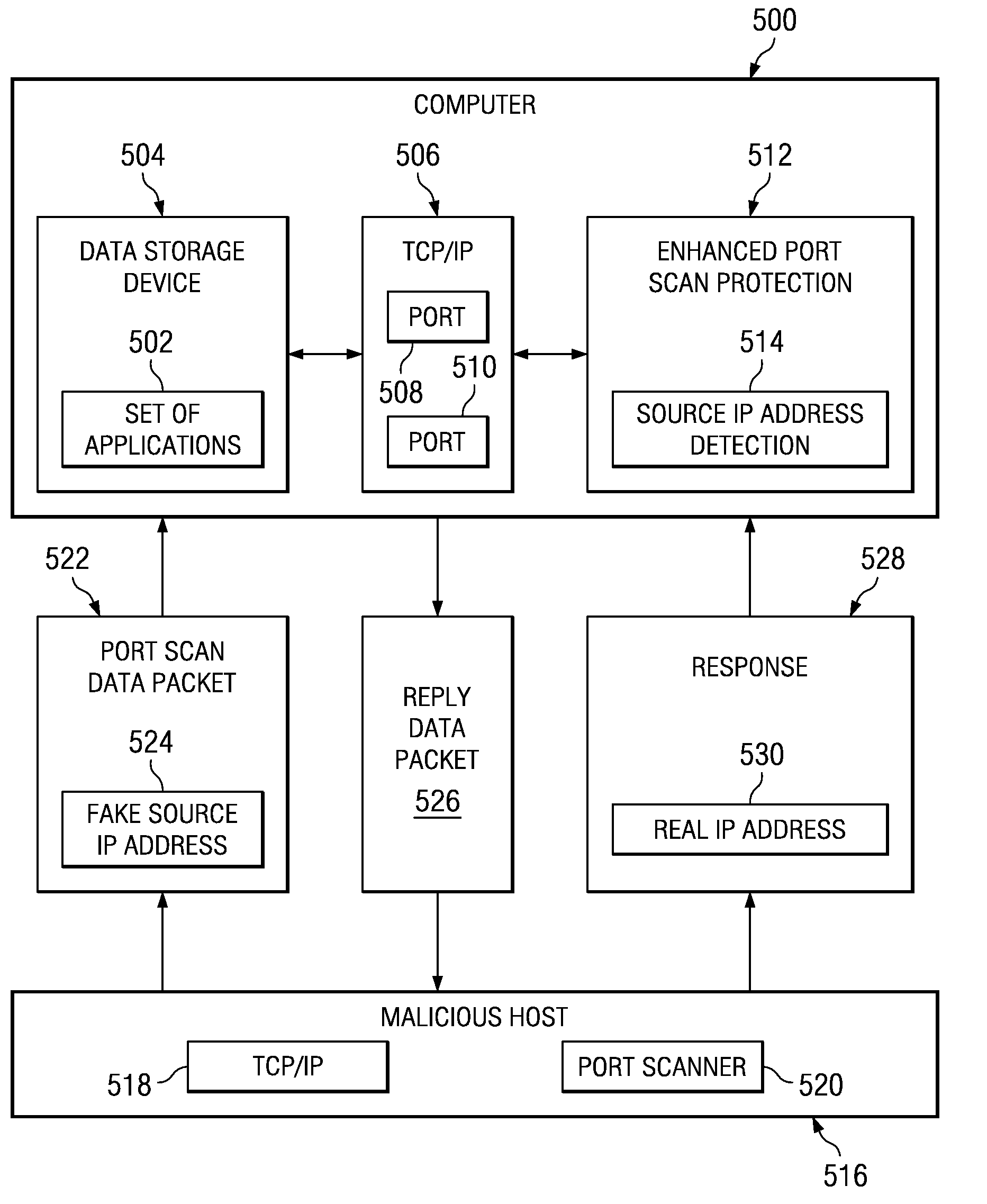
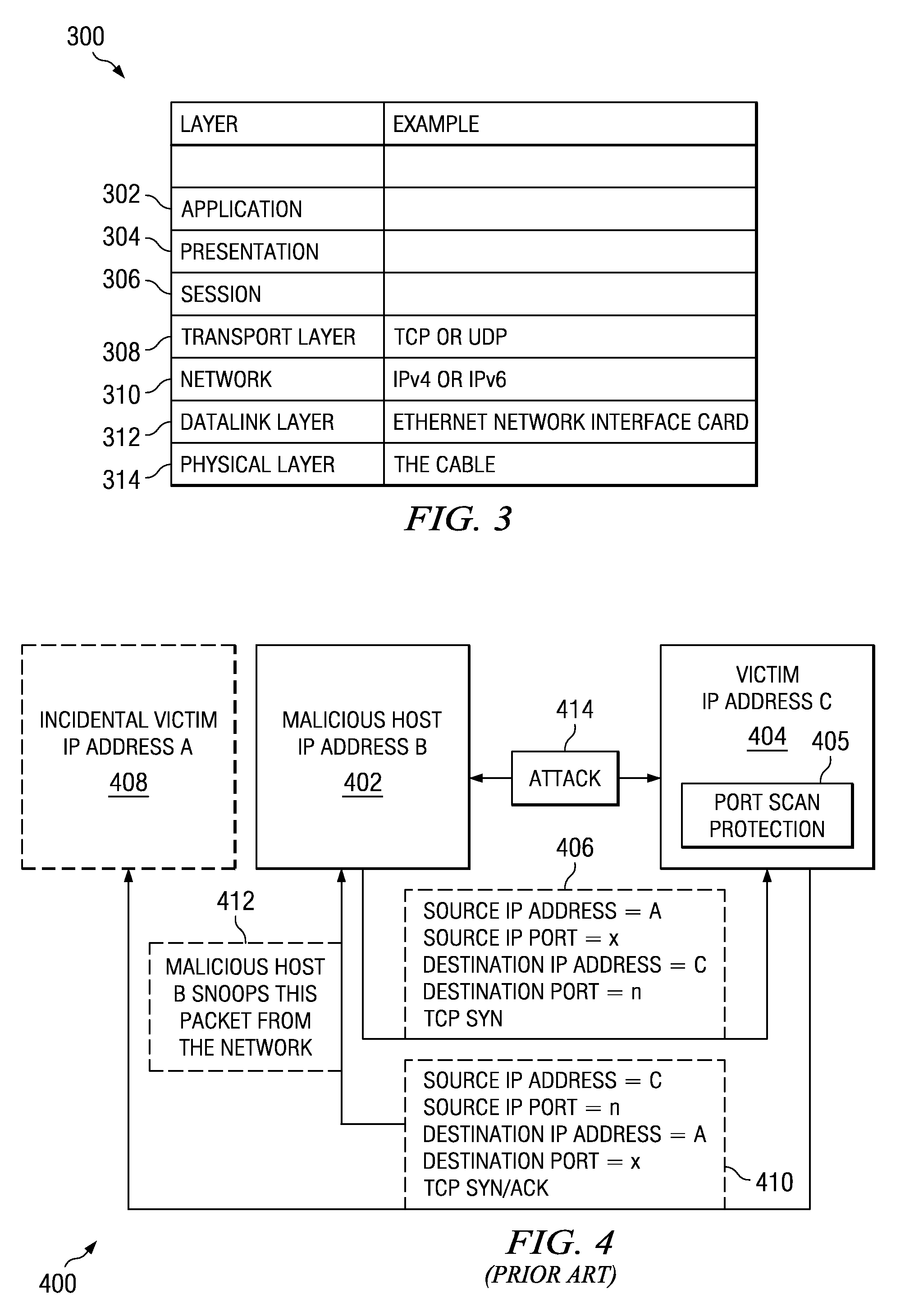
Method and apparatus for detecting port scans with fake source address
Owner:INT BUSINESS MASCH CORP
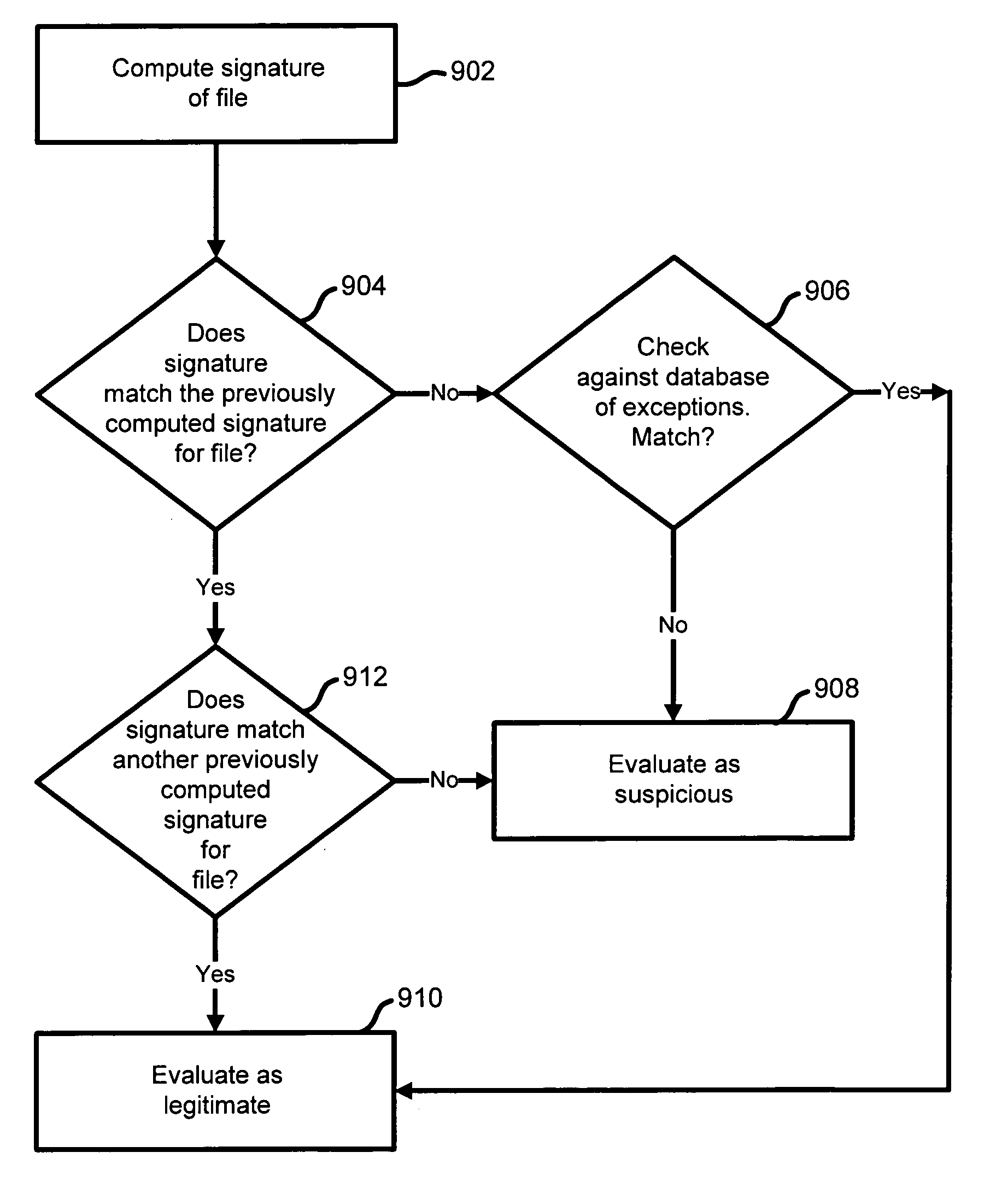
System and method for using signatures to detect computer intrusions
InactiveUS7032114B1Problem can be overcomeEnabling detectionMemory loss protectionUser identity/authority verificationIntrusion detection systemContinuation
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
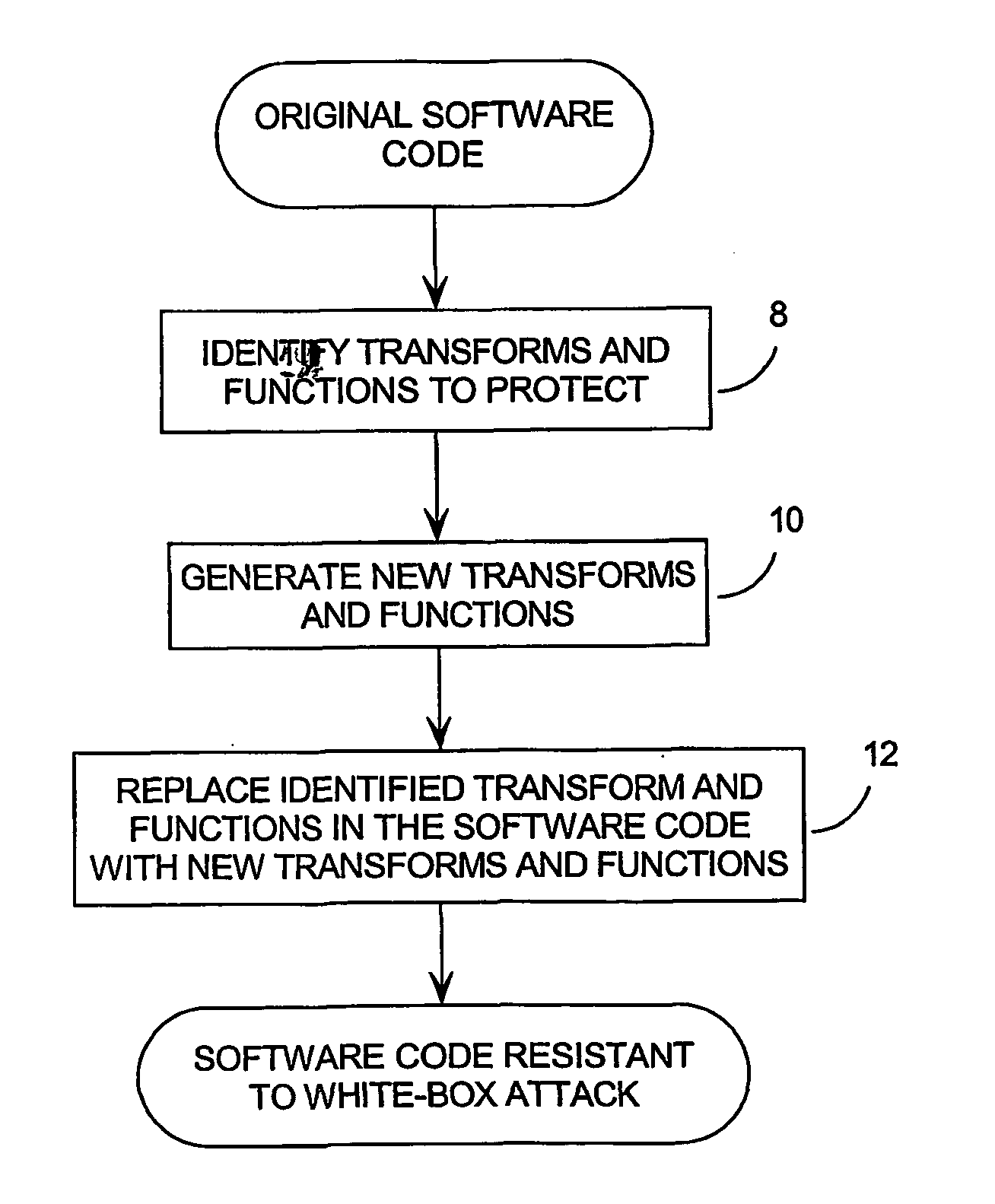
System and method for protecting computer software from a white box attack
InactiveUS20040139340A1Small costLow costUnauthorized memory use protectionHardware monitoringEncryption systemVisibility
Existing encryption systems are designed to protect secret keys or other data under a "black box attack," where the attacker may examine the algorithm, and various inputs and outputs, but has no visibility into the execution of the algotitm itself. However, it has been shown that the black box model is generally unrealistic, and that attack efficiency rises dramatically if the attacker can observe even minor aspects of the algorithm's execution. The invention protects software from a "white-box attack", where the attacker has total visibility into software implementation and execution. In general, this is done by encoding the software and widely diffusing sites of information transfer and / or combination and / or loss. Other embodiments of the invention include: the introduction of lossy subcomponents, processing inputs and outputs with random cryptographic functions, and representing algorithmic steps or components as tables, which permits encoding to be represented with arbitrary nonlinear bijections.
Owner:CLOAKWARE CORP
Malicious attack detection and analysis
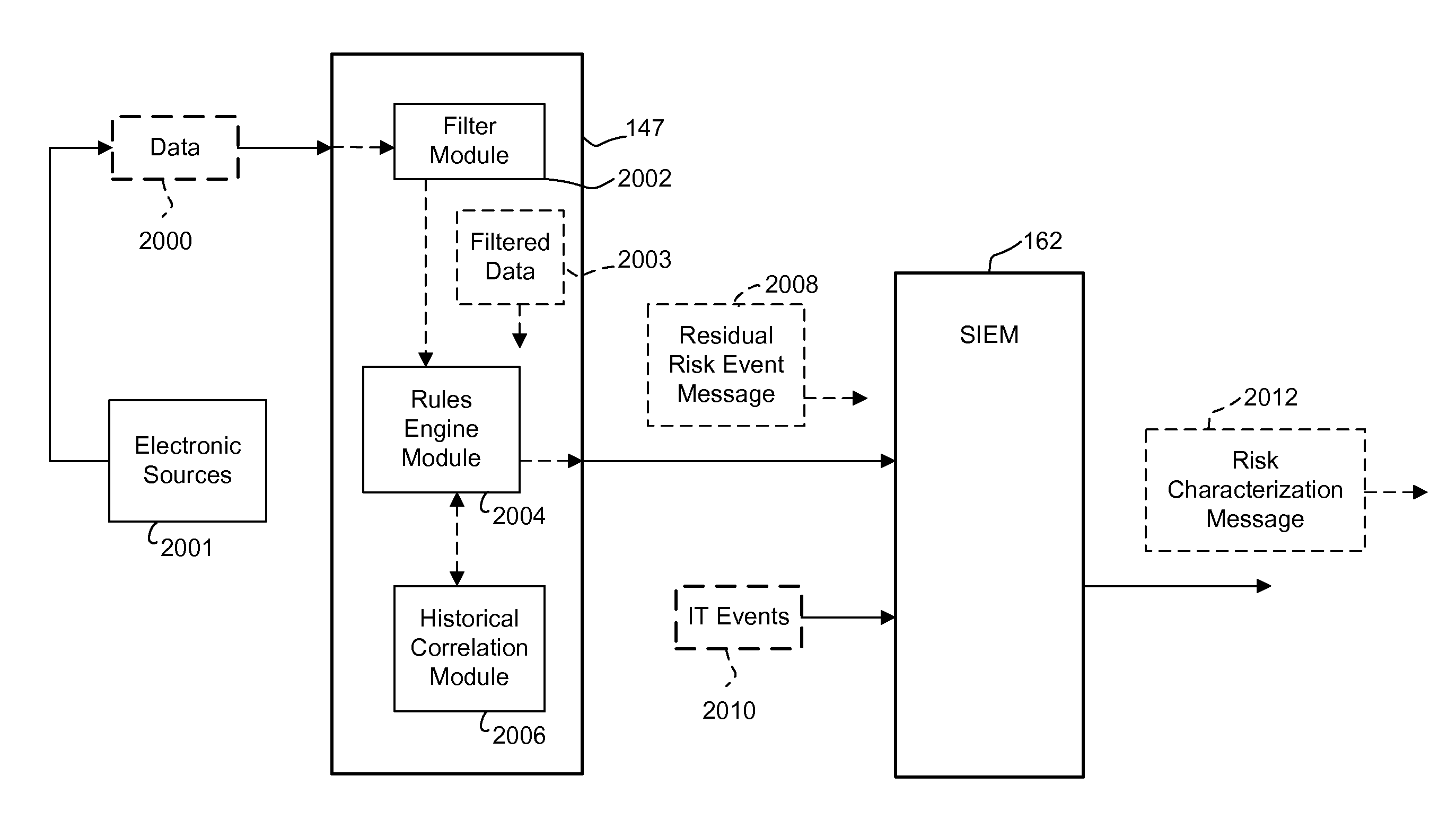
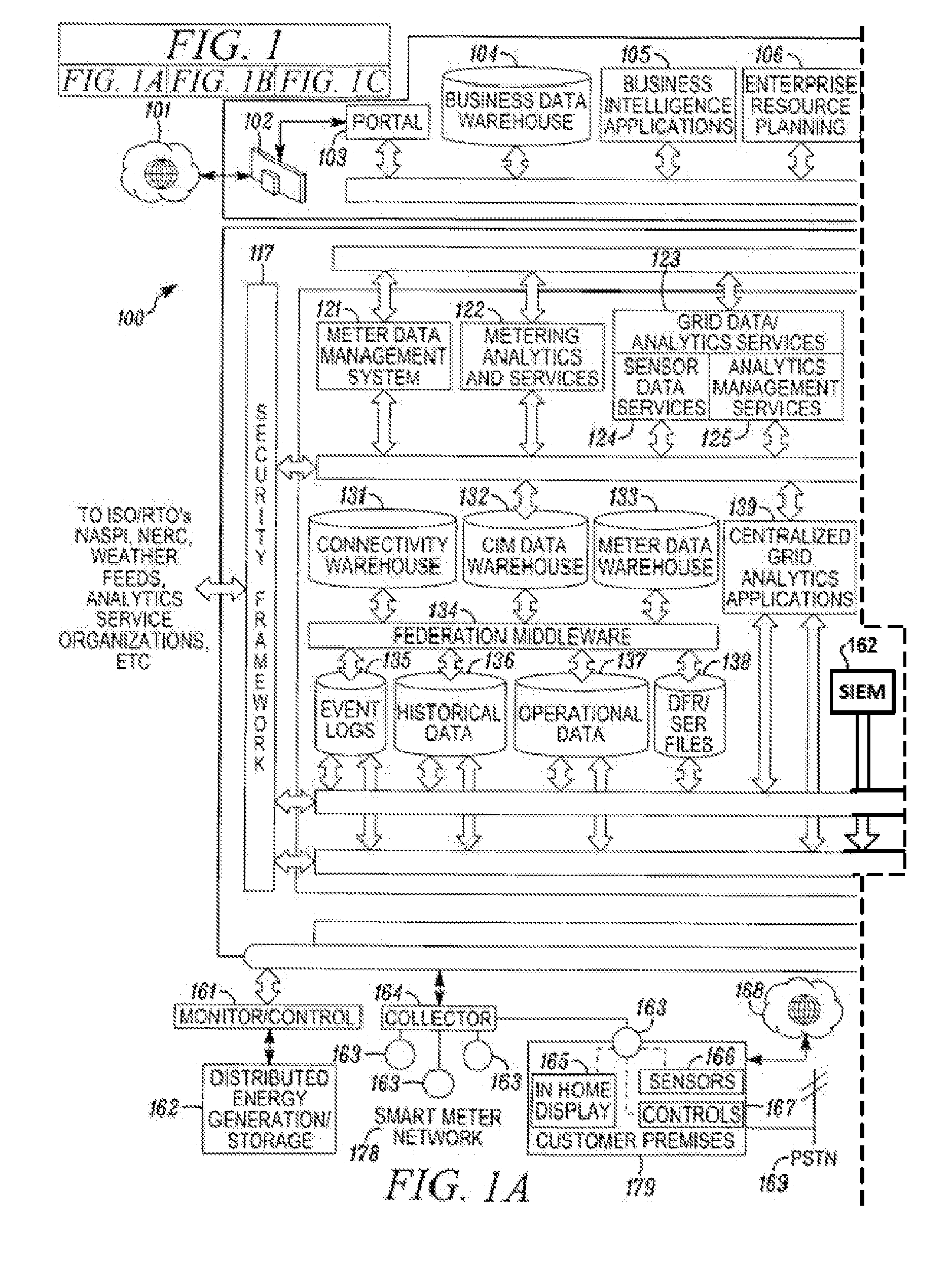
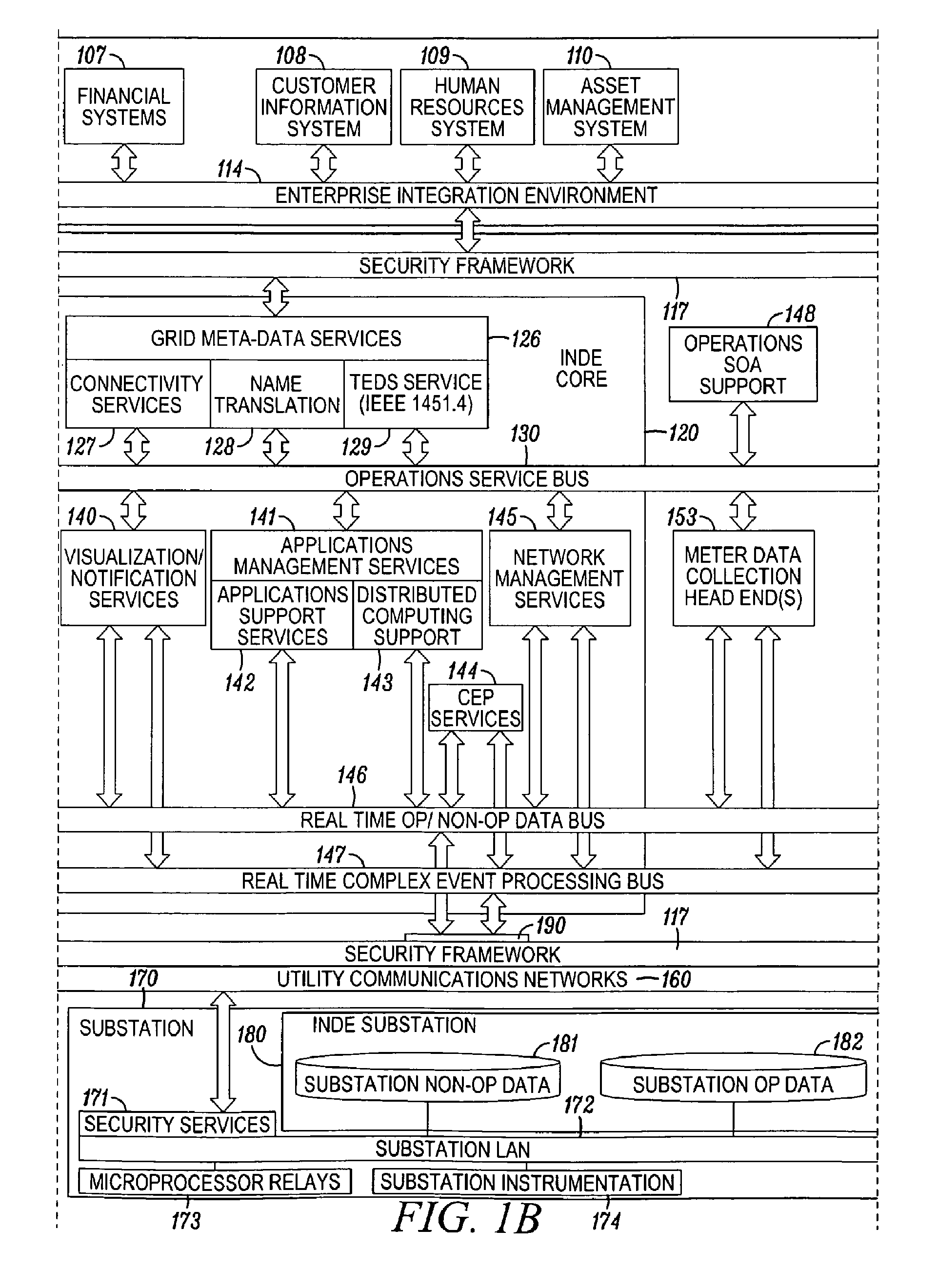
A system for characterizing malicious activity in an intelligent utility grid system includes a system storage in which to store a database including a plurality of rules. A collector is operable to collect and store in the system storage information-technology (IT) data including IT-related activity from the intelligent grid system. A complex event processing (CEP) bus is operable to receive non-IT data including location-specific event data from a plurality of electronic sources, the CEP bus further operable to disregard the non-IT data failing to meet a predetermined level of relevance to one of a plurality of risk-related events. A processor is operable to apply the plurality of rules to the relevant non-IT data to: associate an undesired event with reference to the IT-related activity; and determine a probability that the undesired event is indicative of malicious activity. The processor further applies a risk characterization to the undesired event based on the probability and the IT-related activity.
Owner:ACCENTURE GLOBAL SERVICES LTD
Stateful attack protection
ActiveUS20060137009A1Reduces false positiveExtended durationMemory loss protectionError detection/correctionApplication protocolTraffic volume
A method for detecting an attack in a computer network includes monitoring communication traffic transmitted over connections on the network that are associated with a stateful application protocol so as to detect respective states of the connections, and analyzing a distribution of the states so as to detect the attack.
Owner:RADWARE
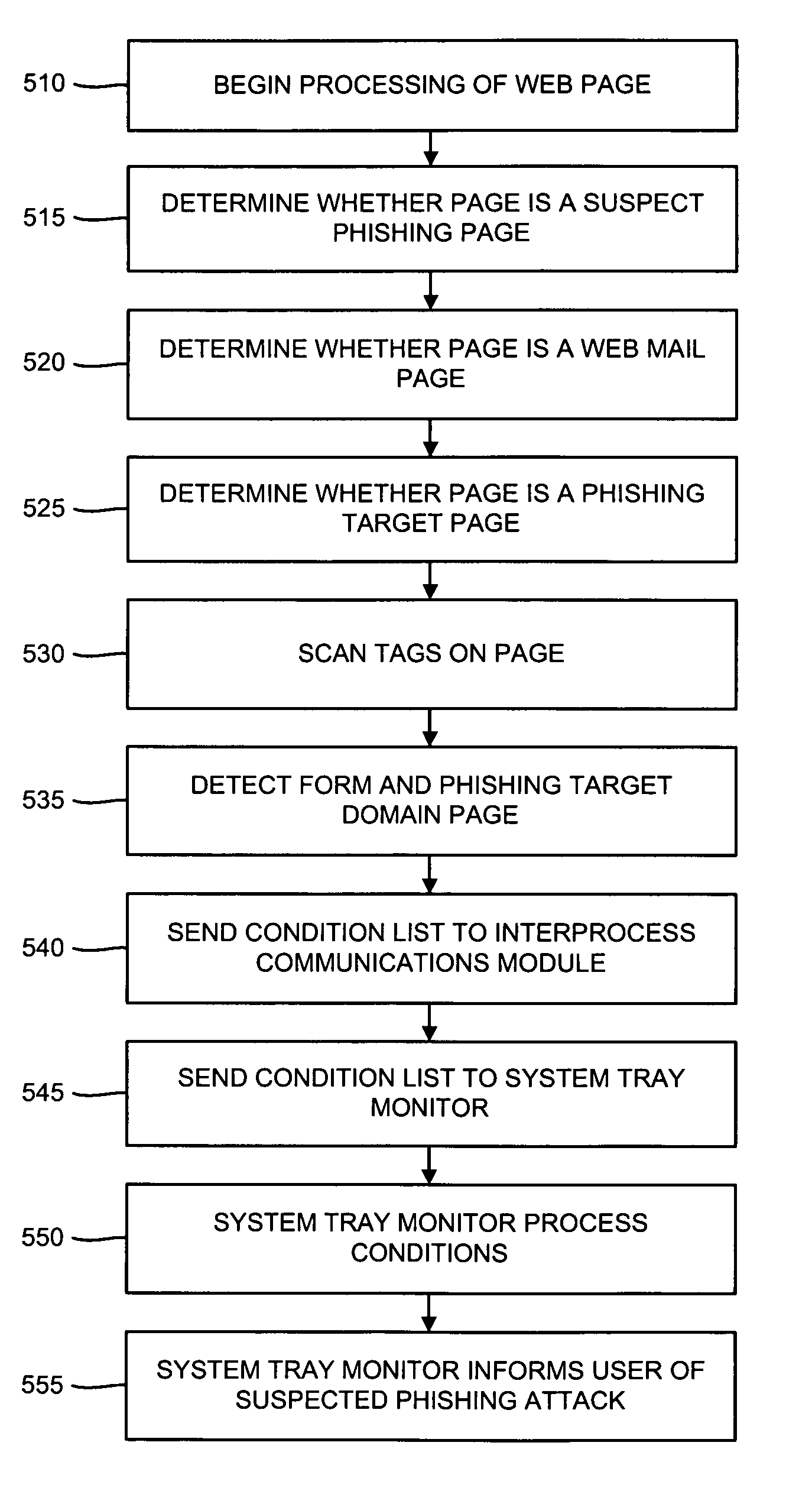
Methods and systems for phishing detection and notification
Various techniques are provided for detecting phishing attacks and notifying users of such attacks. In one example, a machine-implemented method can be provided for detecting a phishing attack over a computer network. A web page can be accessed and information associated with the web page can be processed. One or more conditions can be set in response to the processing. The conditions can be compared to a set of conditions indicative of a phishing attack. A user can then be informed of a potential phishing attack corresponding to the conditions through the display of an alert window and / or an icon. Such actions can also be performed in response to a user's selection of a link appearing in an email message. Appropriate systems and / or computer readable media incorporating these features can also be provided.
Owner:SEARCH INITIATIVES LLC
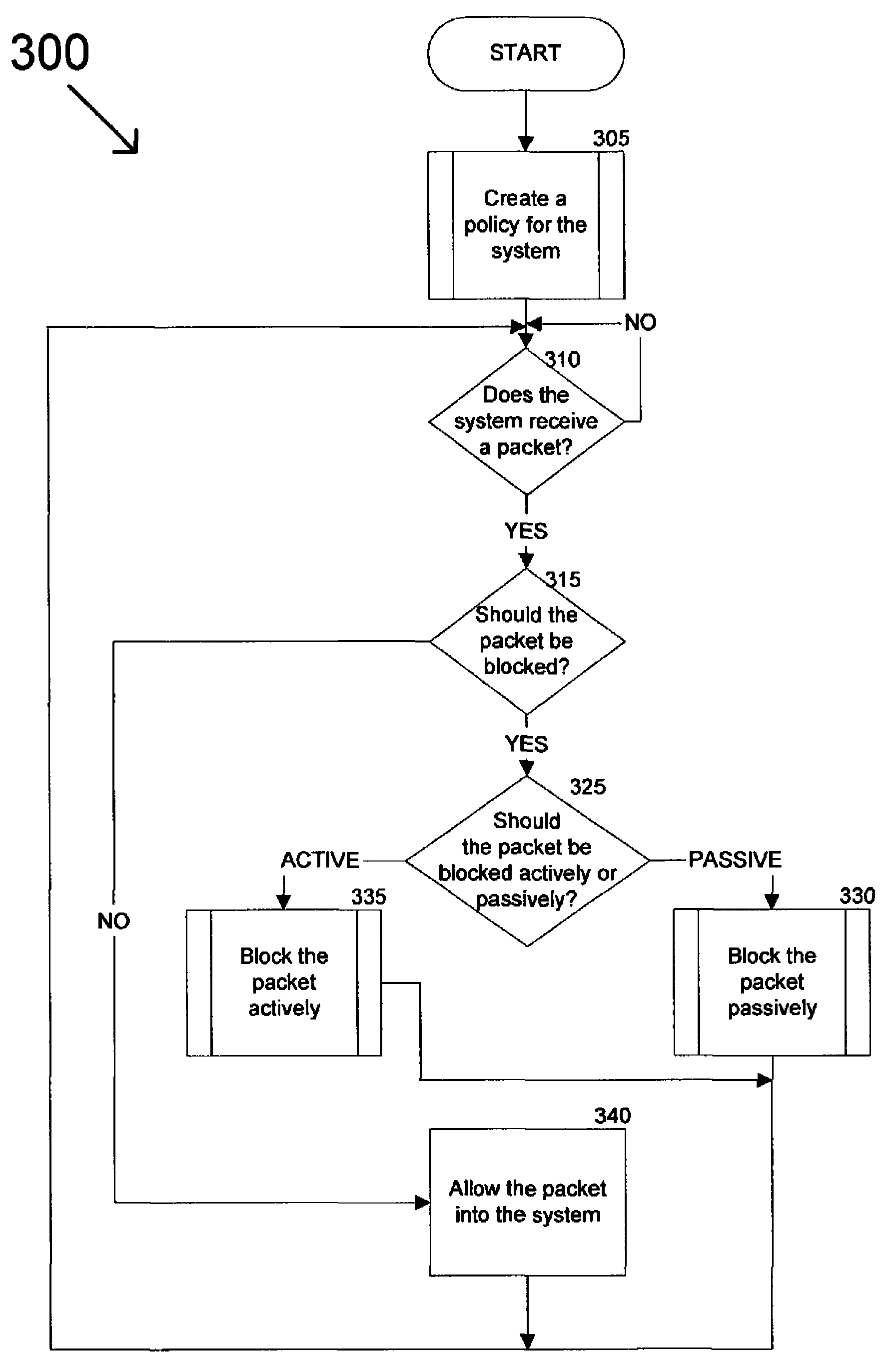
Method and system for dynamically protecting a computer system from attack
ActiveUS7913303B1Protection attackMemory loss protectionUnauthorized memory use protectionProtection systemVulnerability
A dynamic protection system can analyze a computer system to determine its vulnerabilities to attack and generate a policy for protecting the computer system based on the identified vulnerabilities. Data received by the computer system can be analyzed to determine if it poses a threat to the system. This can prevent the data from entering the system or host based on a determination that the data poses a threat. Also, the dynamic protection system can receive policy updates to allow it to protect the system more efficiently and effectively. In other words, the dynamic protection system can protect an evolving computer system operating in an environment that is characterized by constantly changing methods of attack. Furthermore, by minimizing a need for manual intervention, attacks can be rapidly and accurately detected with a minimization of false positives, thereby lowering the cost of operation.
Owner:ALIBABA GRP HLDG LTD
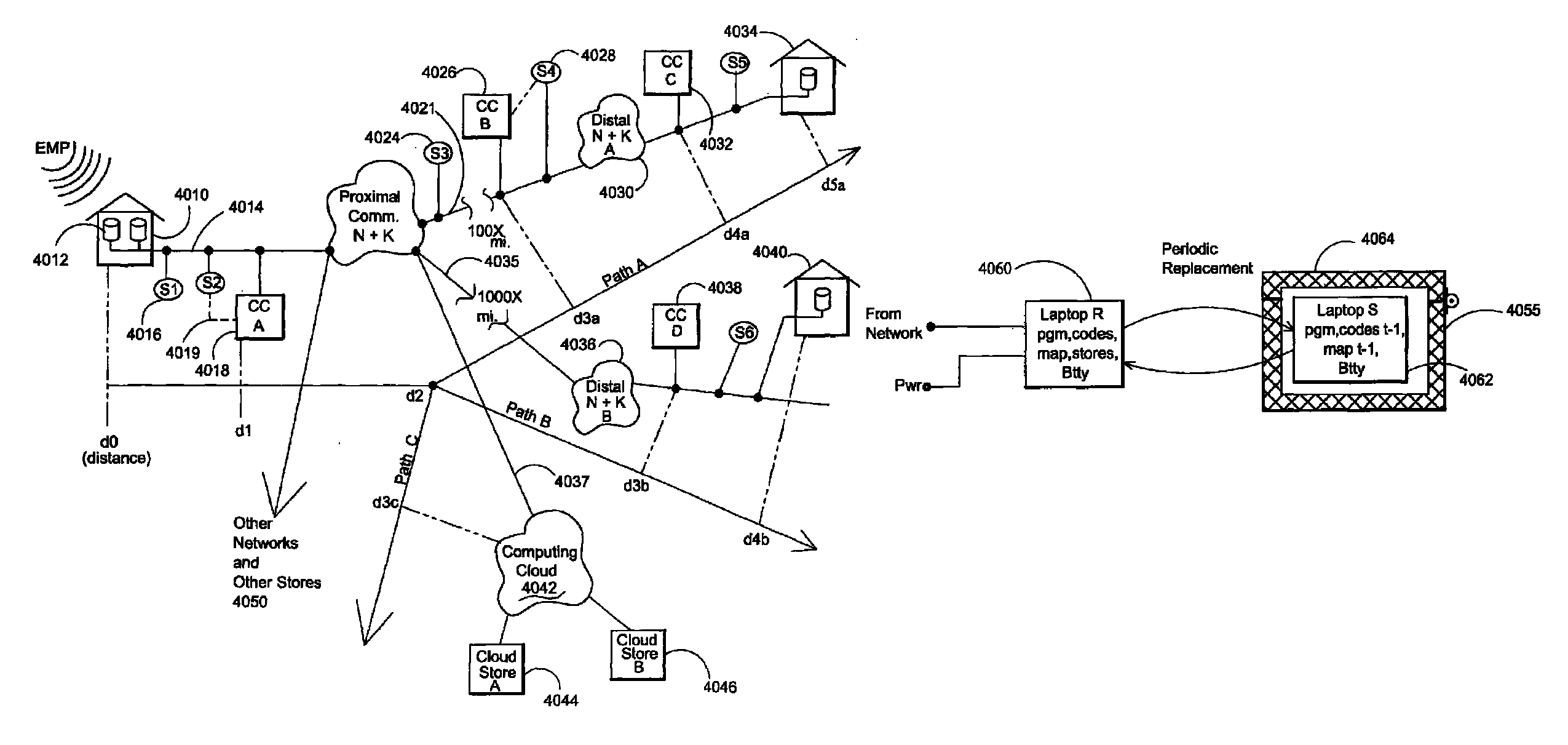
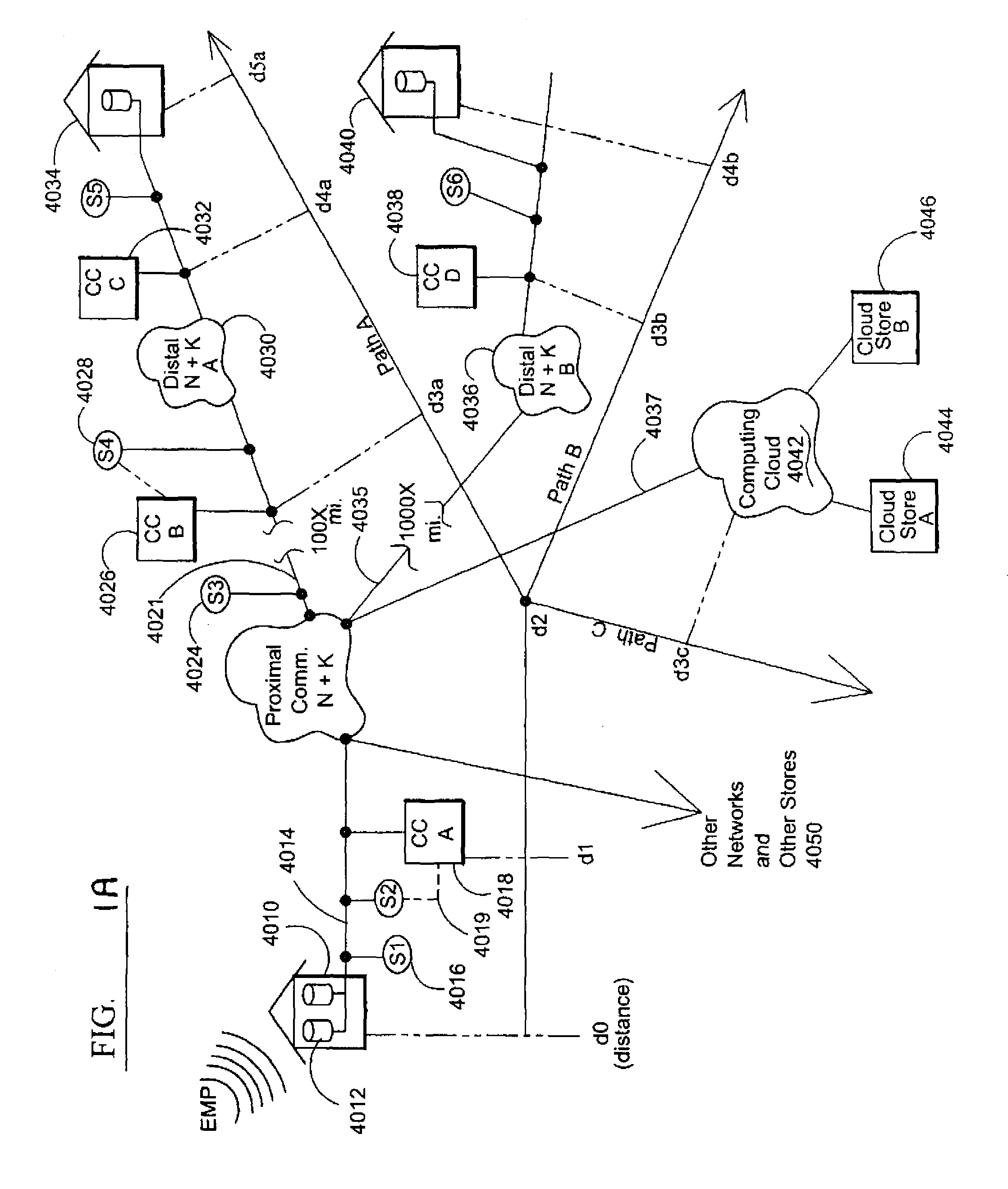
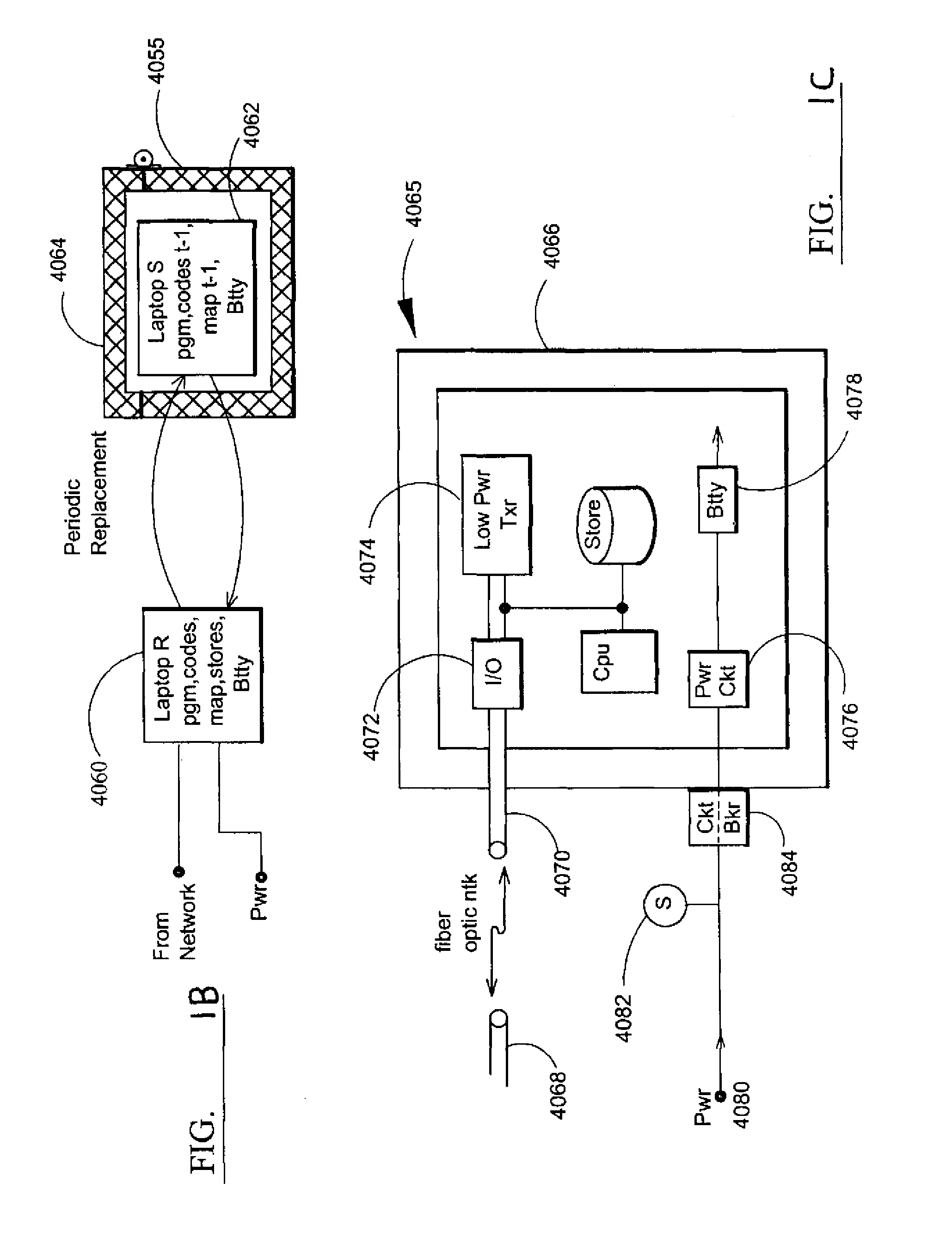
Electromagnetic pulse (EMP) hardened information infrastructure with extractor, cloud dispersal, secure storage, content analysis and classification and method therefor
ActiveUS8655939B2Improve the level ofImprove security levelDigital data processing detailsError detection/correctionElectromagnetic pulseContent analytics
A method and system processes data in a distributed computing system to survive an electromagnetic pulse (EMP) attack. The computing system has proximal select content (SC) data stores and geographically distributed distal data stores, all with respective access controls. The data input or put through the computing system is processed to obtain the SC and other associated content. The process then extracts and stores such content in the proximal SC data stores and geographically distributed distal SC data stores. The system further processes data to geographically distribute the data with data processes including: copy, extract, archive, distribute, and a copy-extract-archive and distribute process with a sequential and supplemental data destruction process. In this manner, the data input is distributed or spread out over the geographically distributed distal SC data stores. The system and method permits reconstruction of the processed data only in the presence of a respective access control.
Owner:DIGITAL DOORS
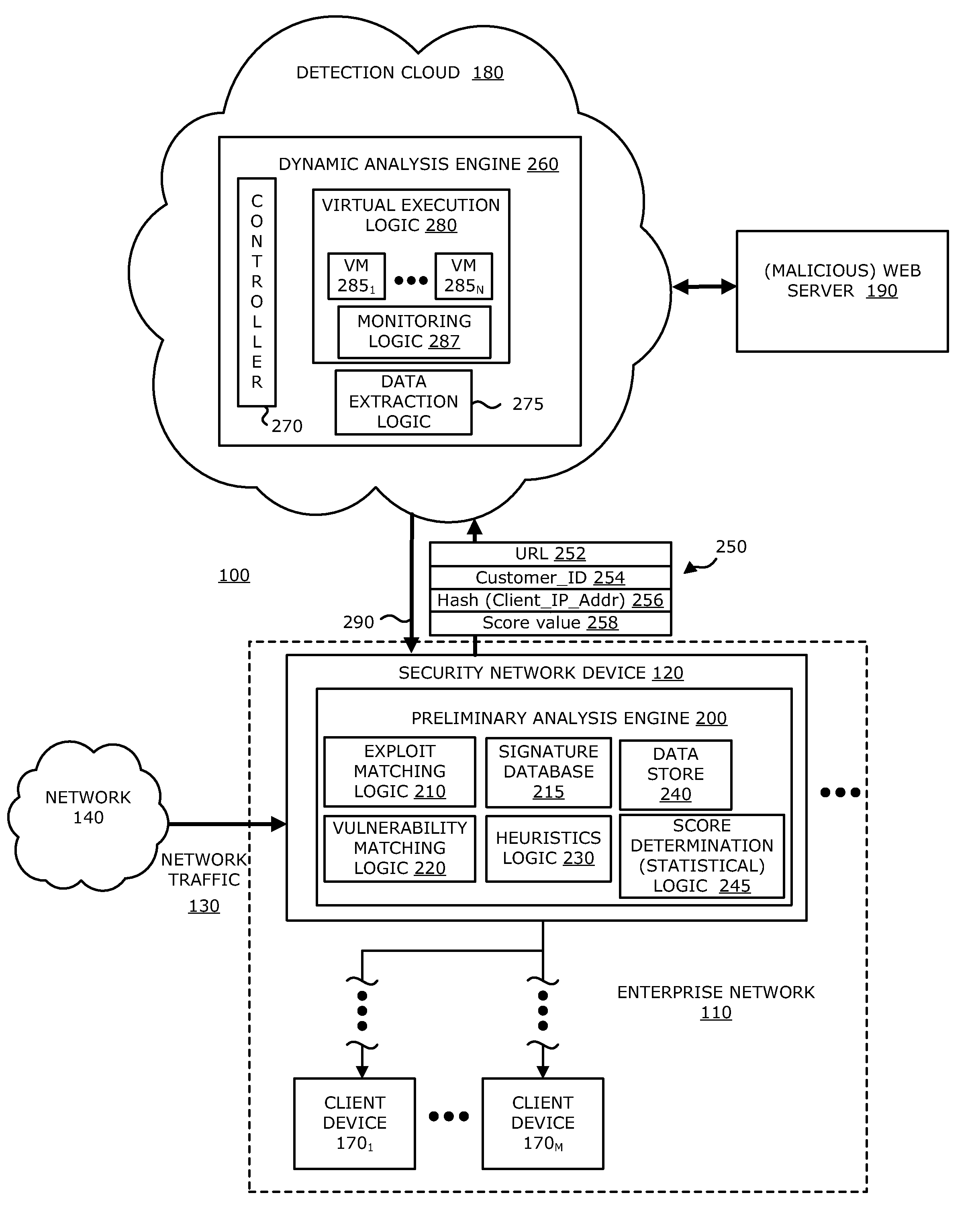
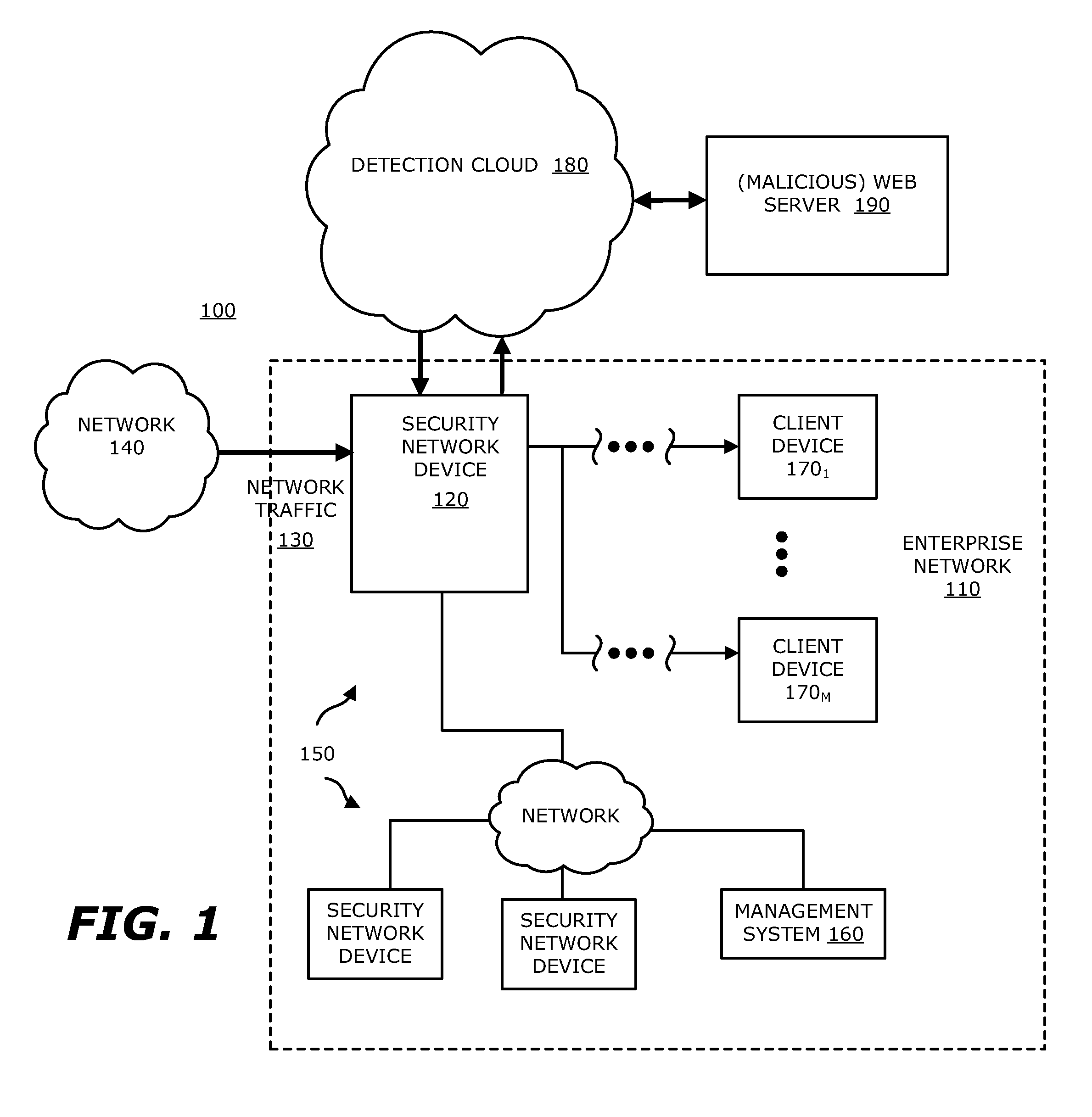
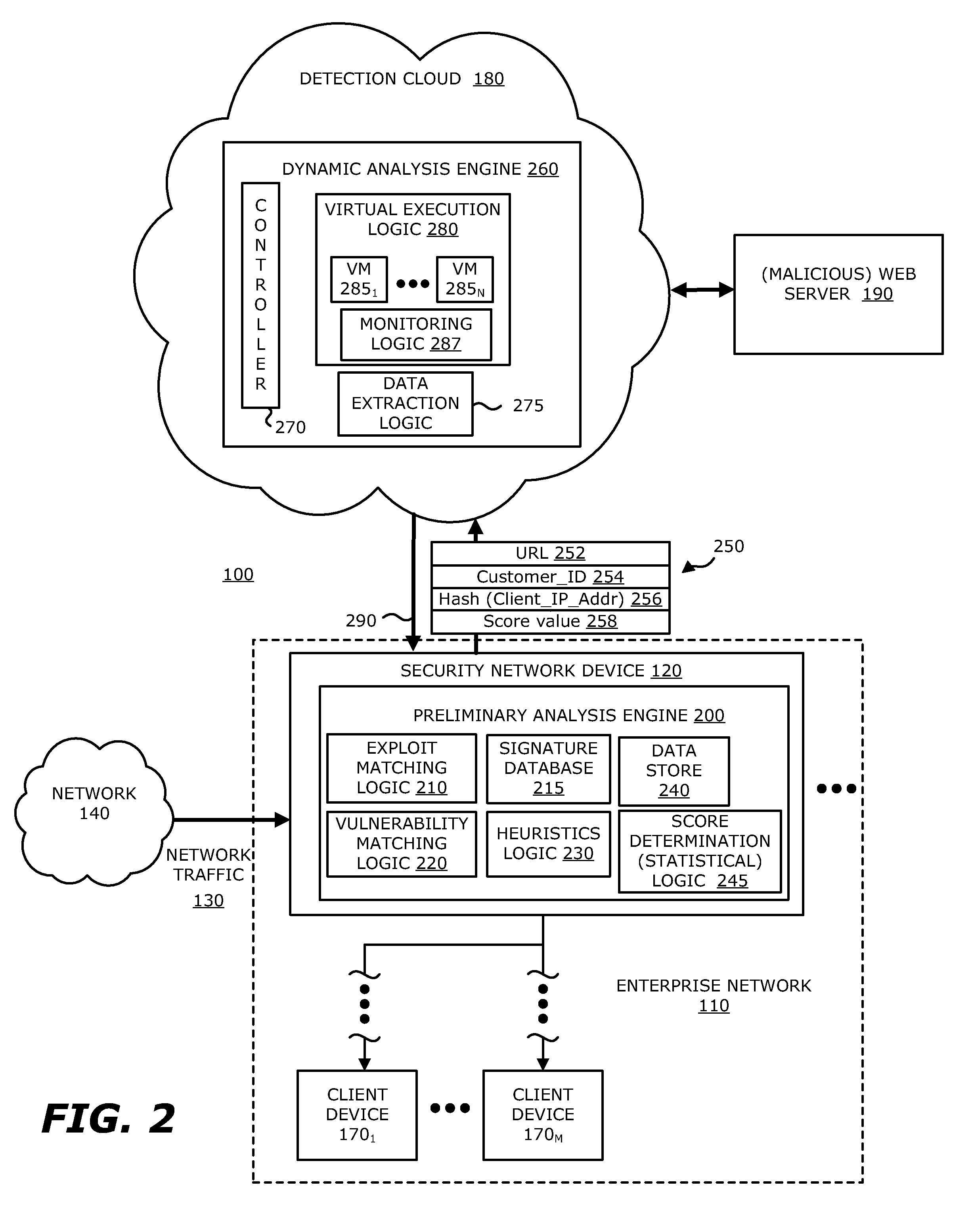
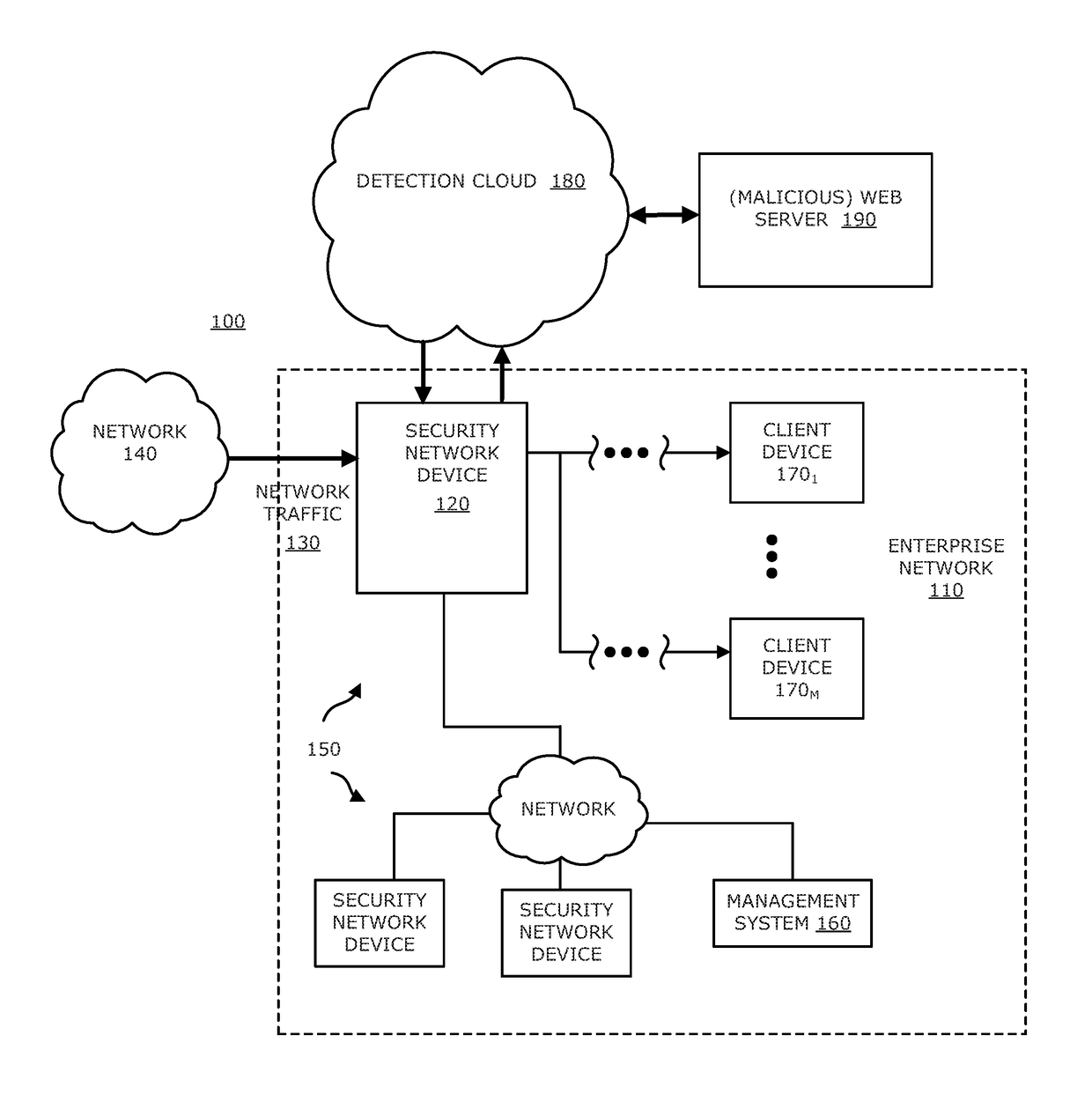
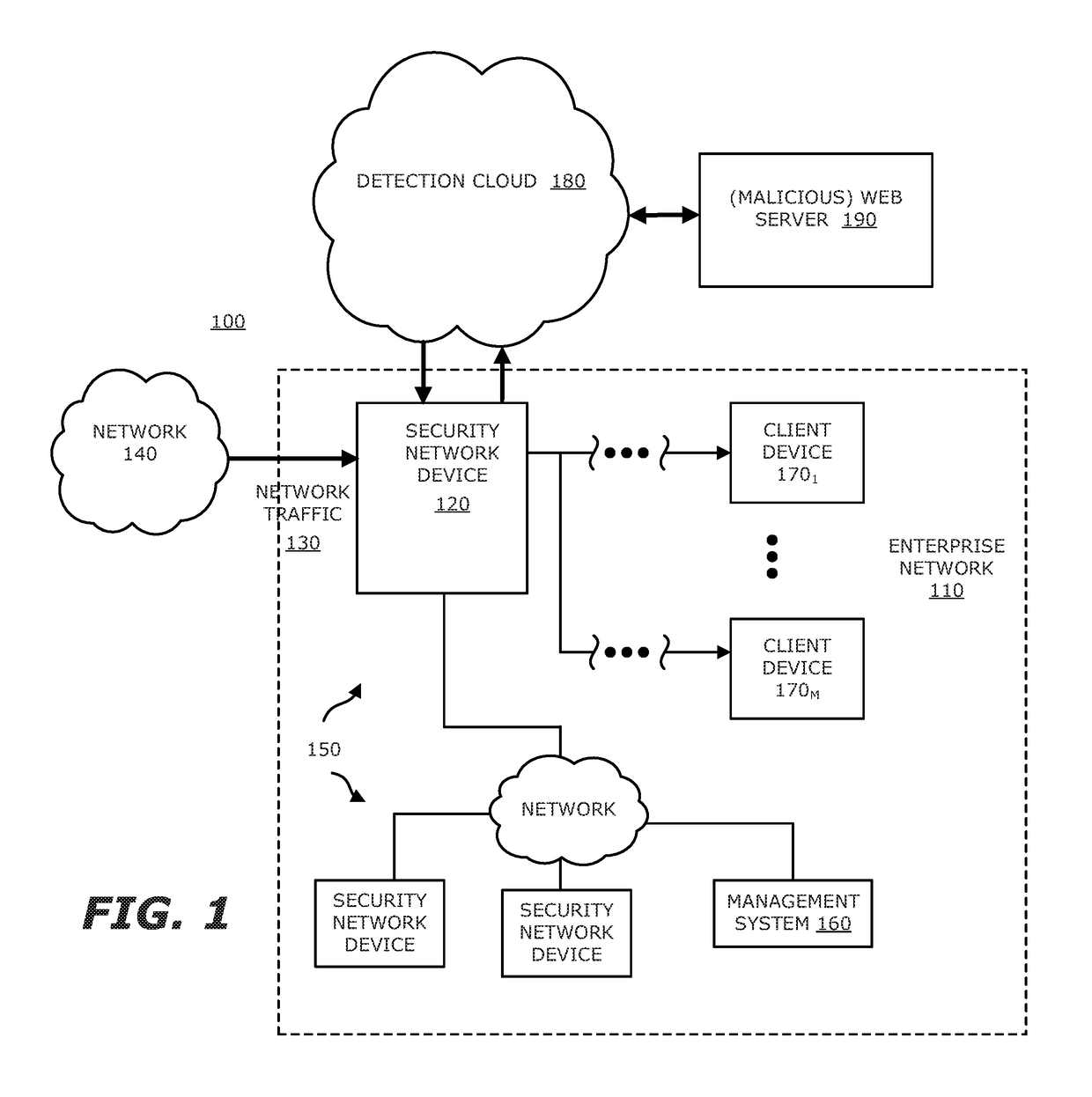
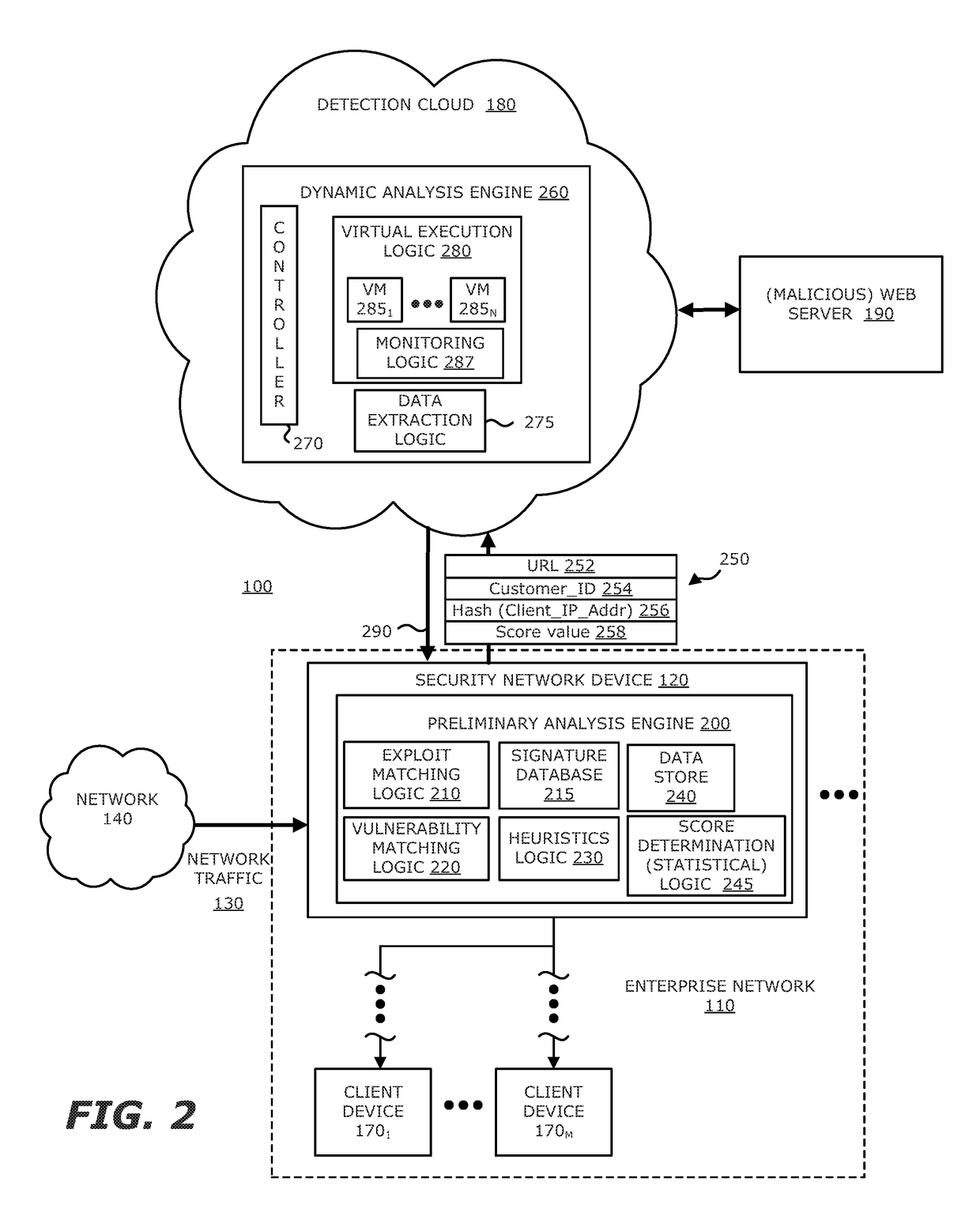
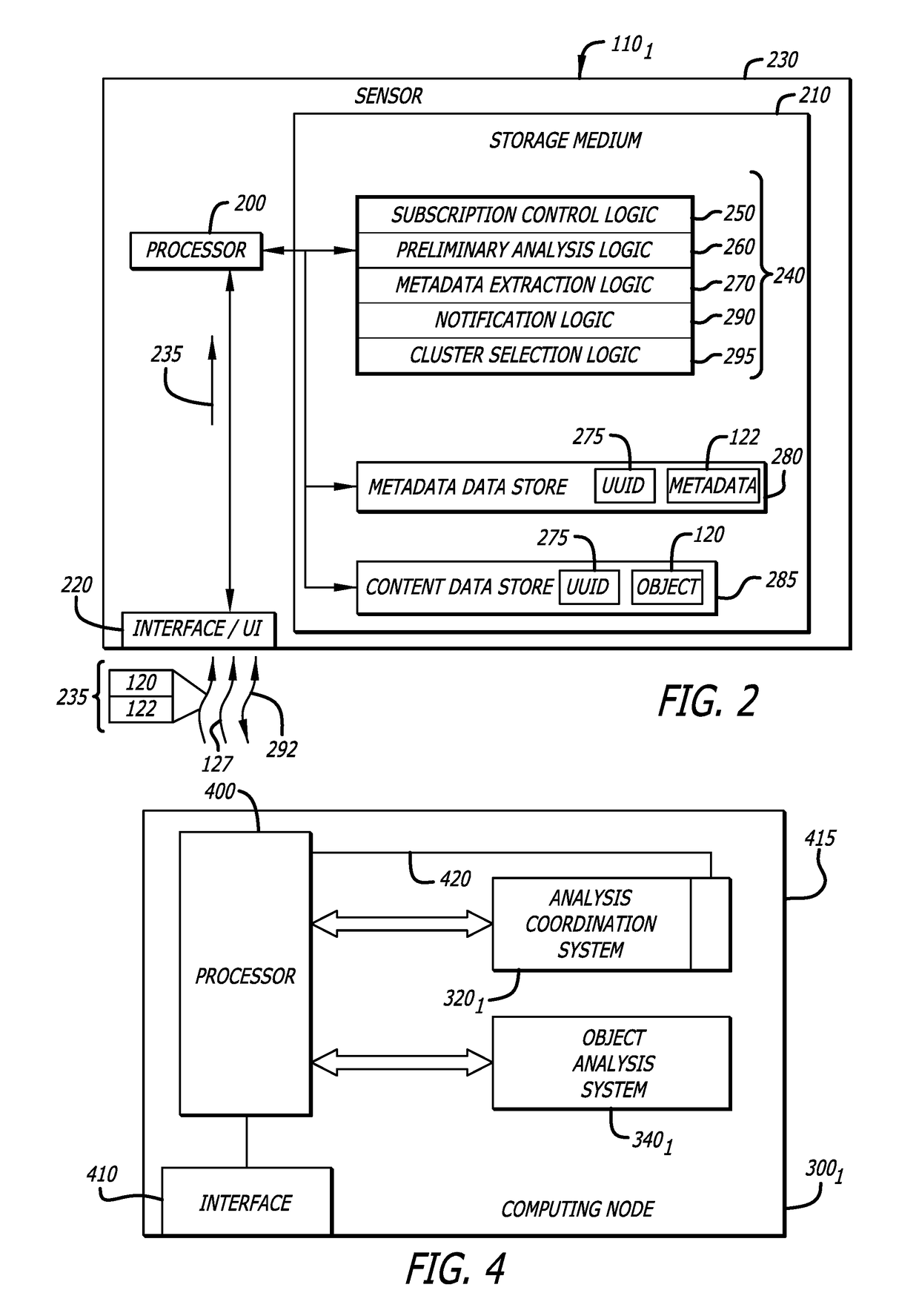
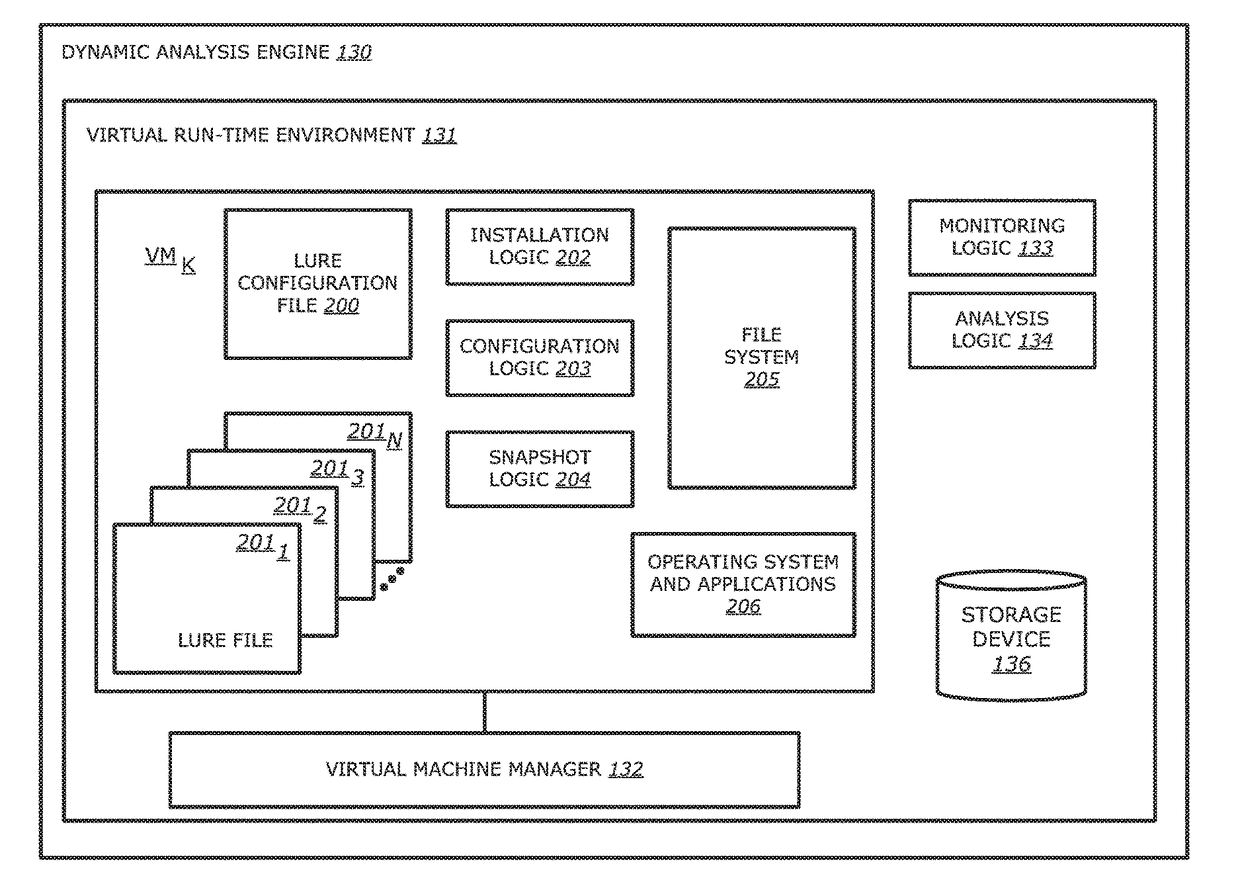
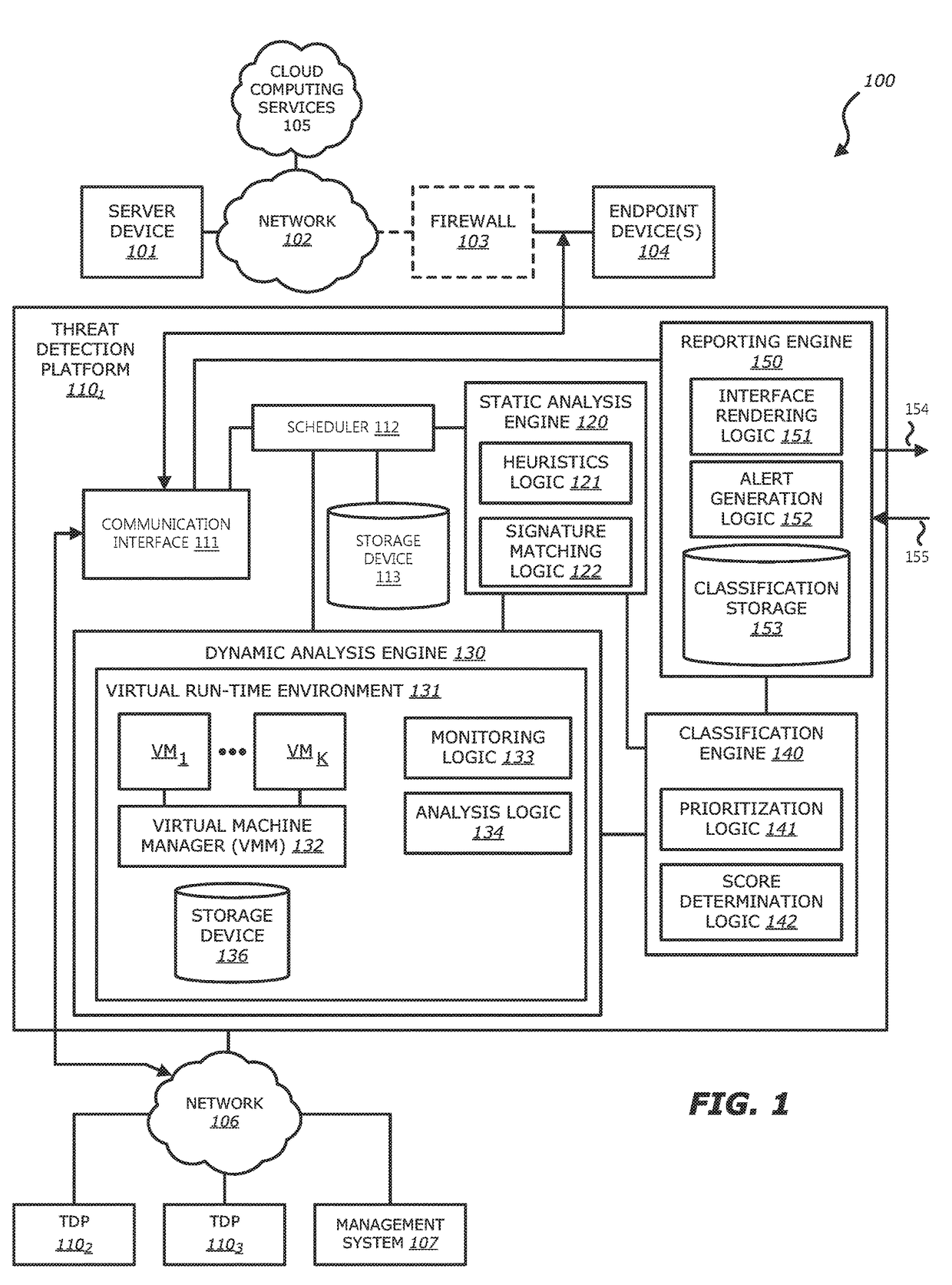
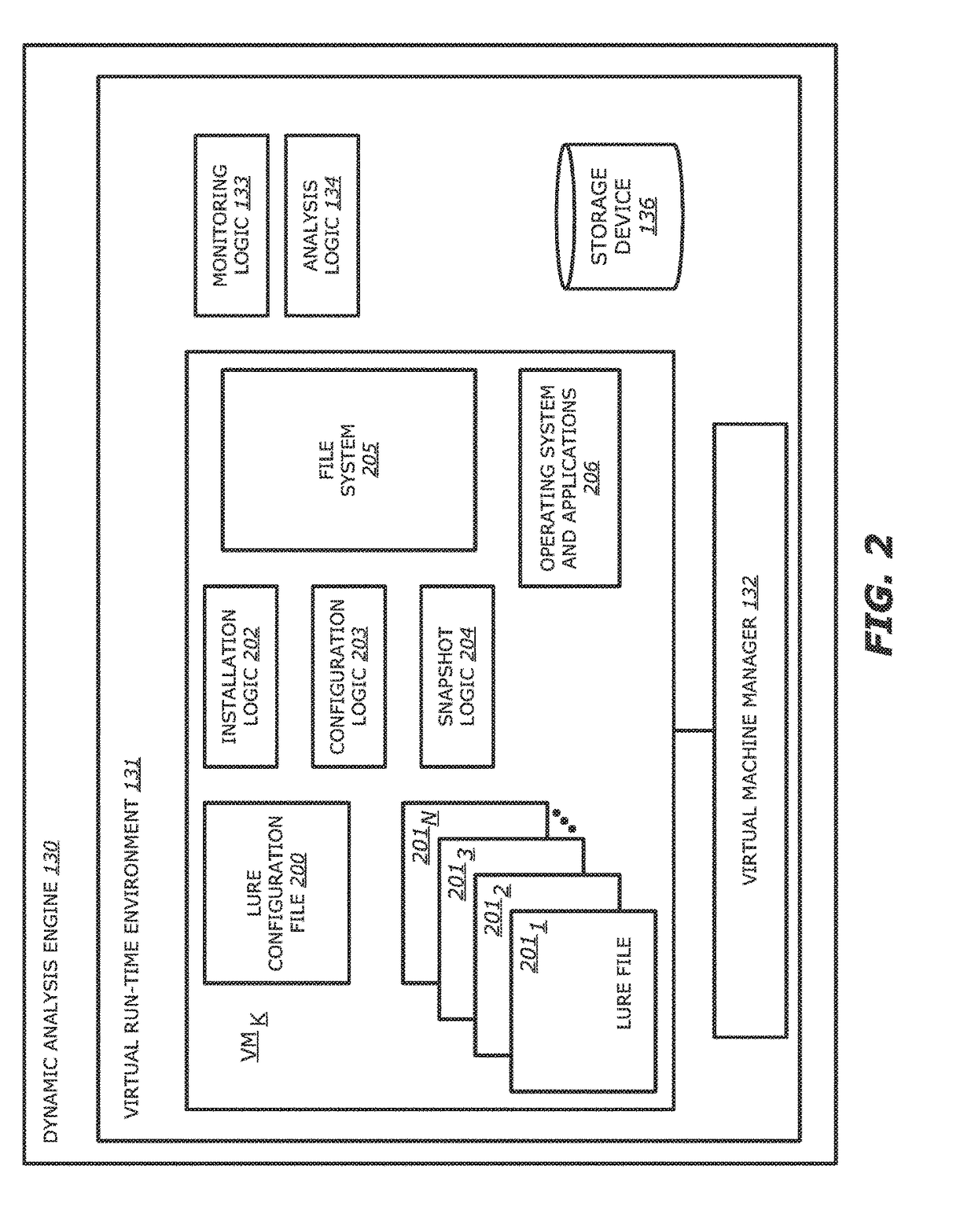
System, device and method for detecting a malicious attack based on communcations between remotely hosted virtual machines and malicious web servers
In an embodiment, a dynamic analysis engine is configured to receive an identifier associated with a source for network traffic including at least one object having at least a prescribed probability of being associated with an exploit. Deployed within a detection cloud, the dynamic analysis engine comprises one or more virtual machines and monitoring logic. The virtual machines are adapted to virtually process the identifier by establishing a communication session with a server hosting a website accessible by the identifier. In communication with the virtual machines, the monitoring logic is adapted to detect anomalous behaviors by the virtual machines during the communication session with the server.
Owner:FIREEYE SECURITY HLDG US LLC +1
Network-based malware detection
In an embodiment, a system, device and method for detecting a malicious attack is described. Herein, the system includes a security network device that conducts an analysis on received network traffic to detect a suspicious object associated with the network traffic and determine an identifier associated with a source of the suspicious object. Both information associated with the suspicious object and ancillary data, including information that identifies a return path for analysis results to a customer, are uploaded to a detection cloud. The detection cloud includes provisioning logic and one or more virtual machines that are provisioned by the provisioning logic in accordance with at least a portion of the ancillary data. The provisioning logic to customize functionality of the detection cloud for a specific customer.
Owner:FIREEYE SECURITY HLDG US LLC +1
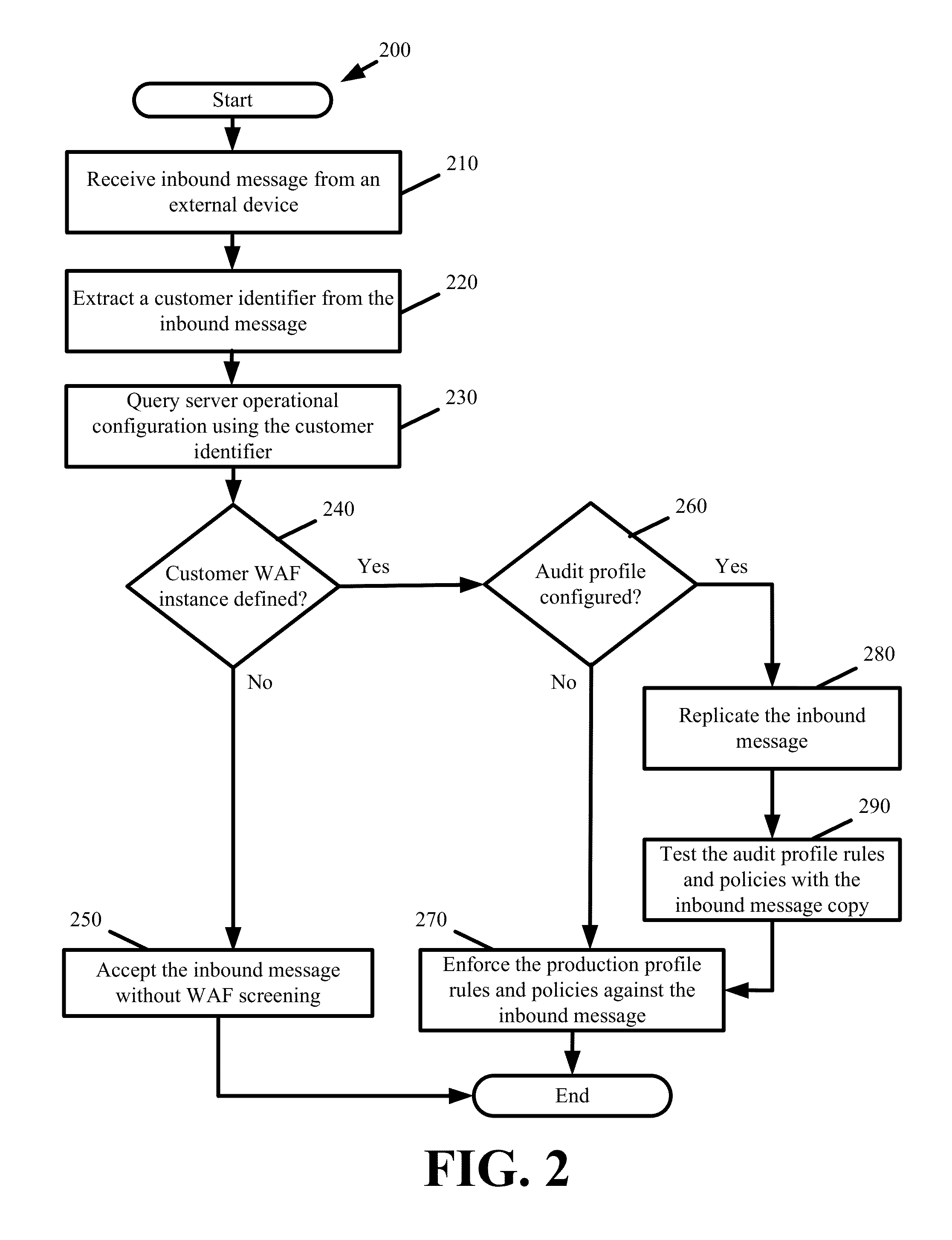
Real-Time Reconfigurable Web Application Firewall For a Distributed Platform
Some embodiments provide reconfigurable web application firewall (WAF) functionality across a distributed platform. Specifically, the WAF function at each distributed platform server is customizable on a per customer and per inbound message basis. When a server receives an inbound message, the server identities the content or services of which specific customer are implicated by the inbound message. The server screens the inbound message for attacks using a first set of rules and policies defined as part of a production profile from a WAF instance defined by the specific customer while contemporaneously testing the inbound message against a second set of rules and polices defined as part of an audit profile from the same WAF instance. In this manner, the specific customer tests the audit profile rules and policies while still receiving the protections of the production profile rules and policies.
Owner:EDGIO INC
Transaction authentication over independent network
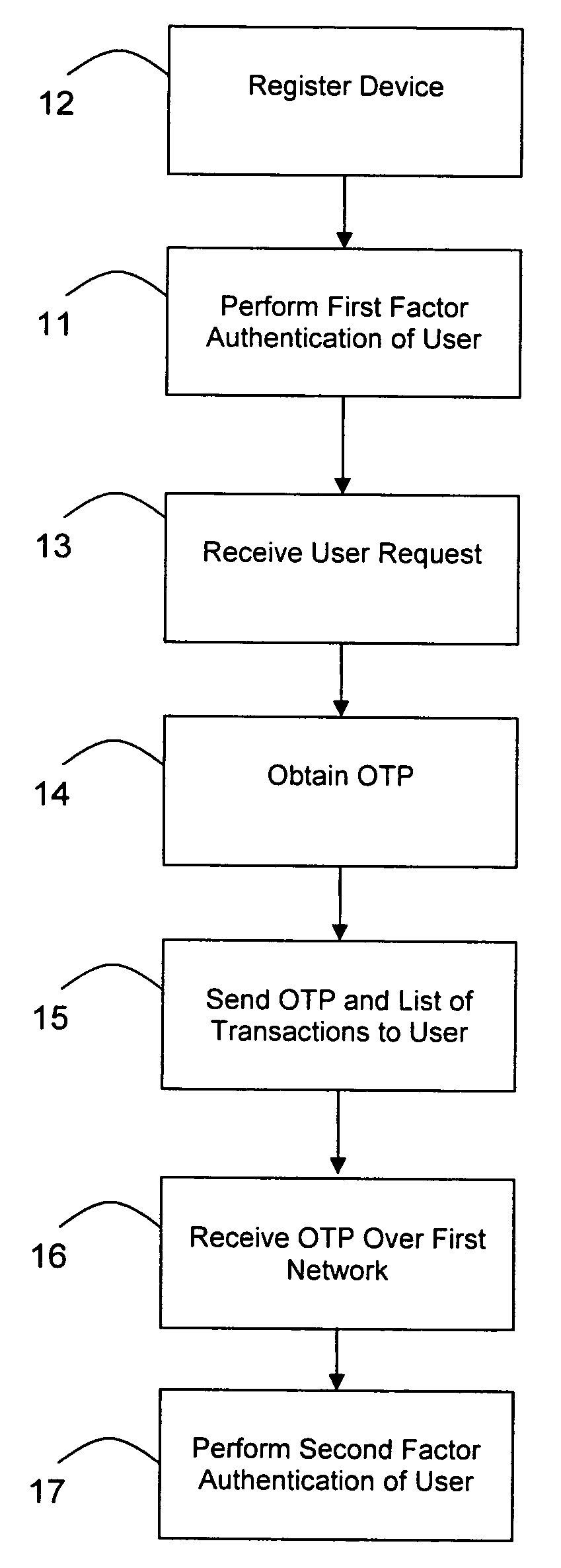
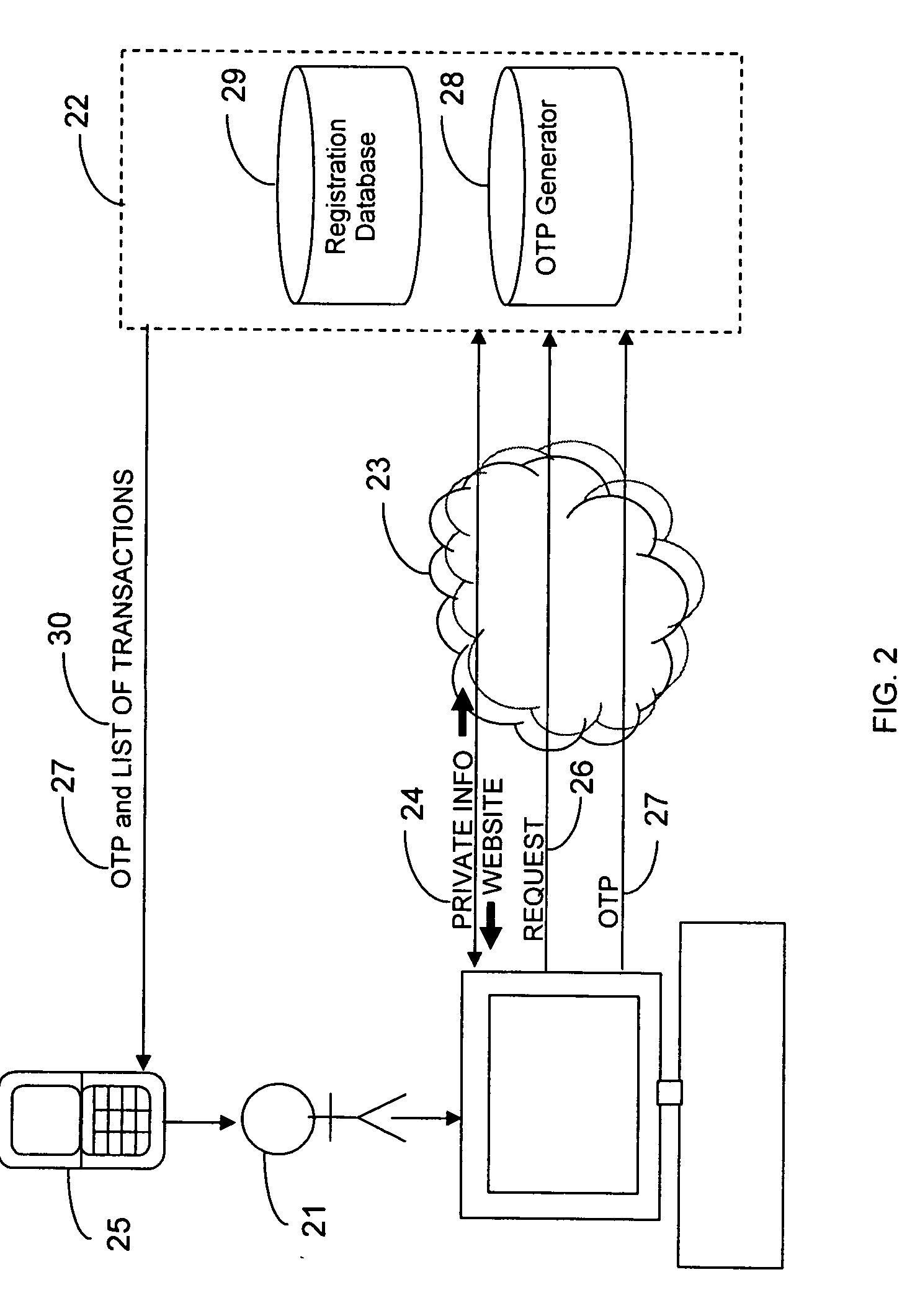
InactiveUS20090106138A1Accelerating transactionFinanceProtocol authorisationOne-time passwordCommunication device
A method of authenticating an online transaction over a first network uses 2-factor authentication of the user to defeat hacker attacks. A communication device is registered for use with the method. The communication device is configured to receive messages over a second network independent of the first network. The user is authenticated over the first network using a first factor, such as a username and password, and then initiates the transaction. A request to execute the transaction is received and a one-time password is obtained to be used as a second factor of authentication. The one-time password and details describing the transaction are sent to the communication device over the second network. The one-time password is received from the user over the first network to complete the second factor of authentication.
Owner:CLAREITY VENTURES INC
Using flow metric events to control network operation
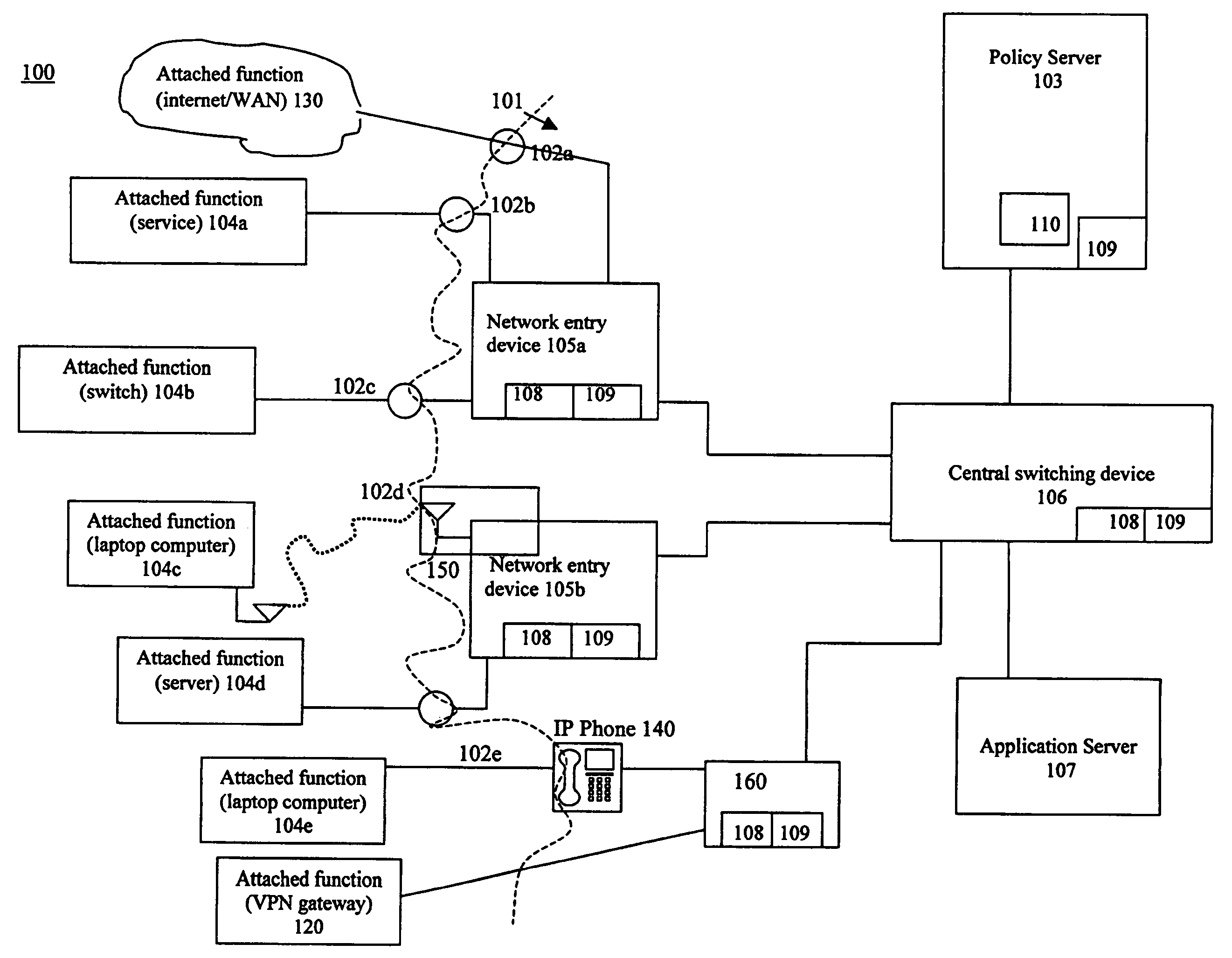
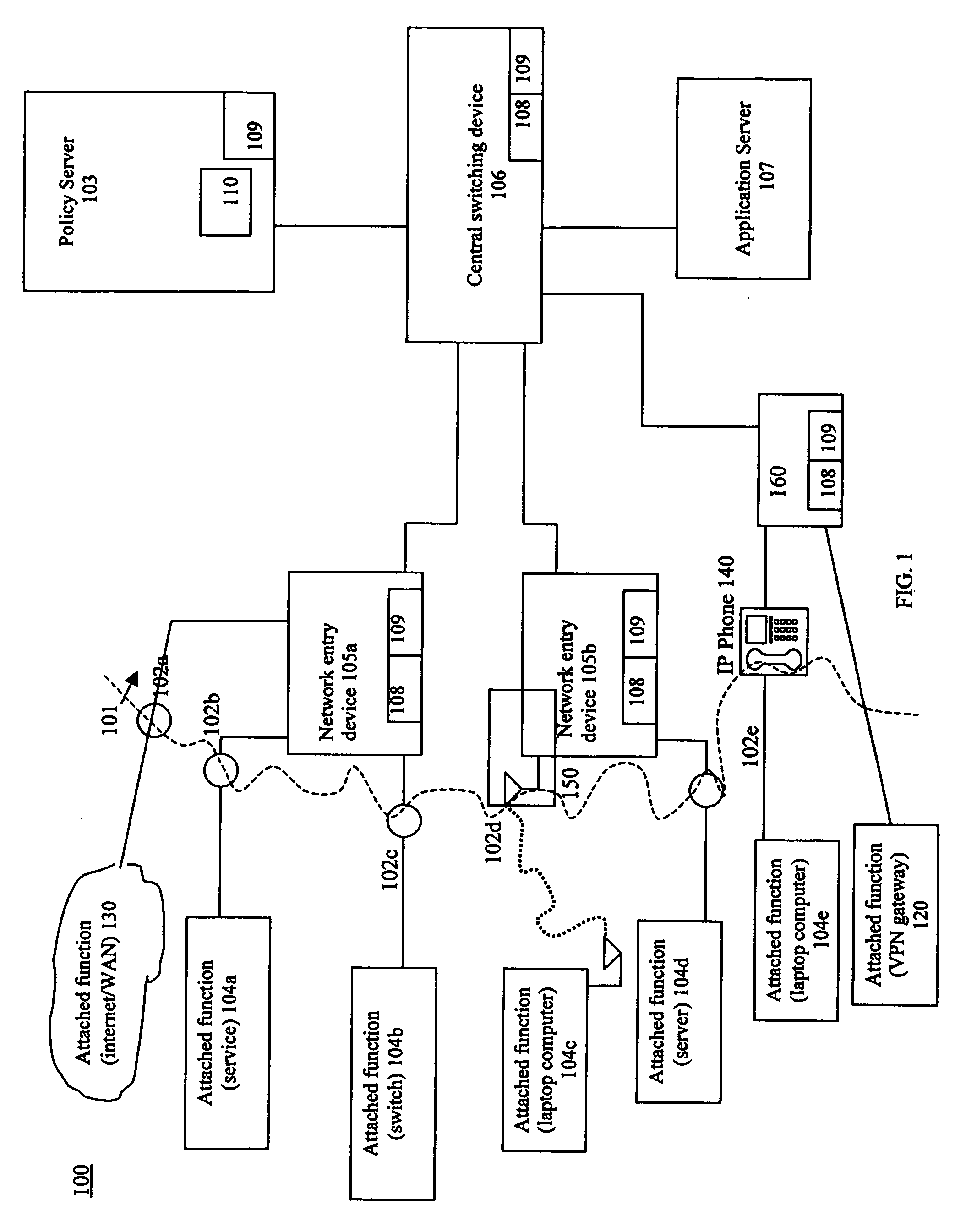
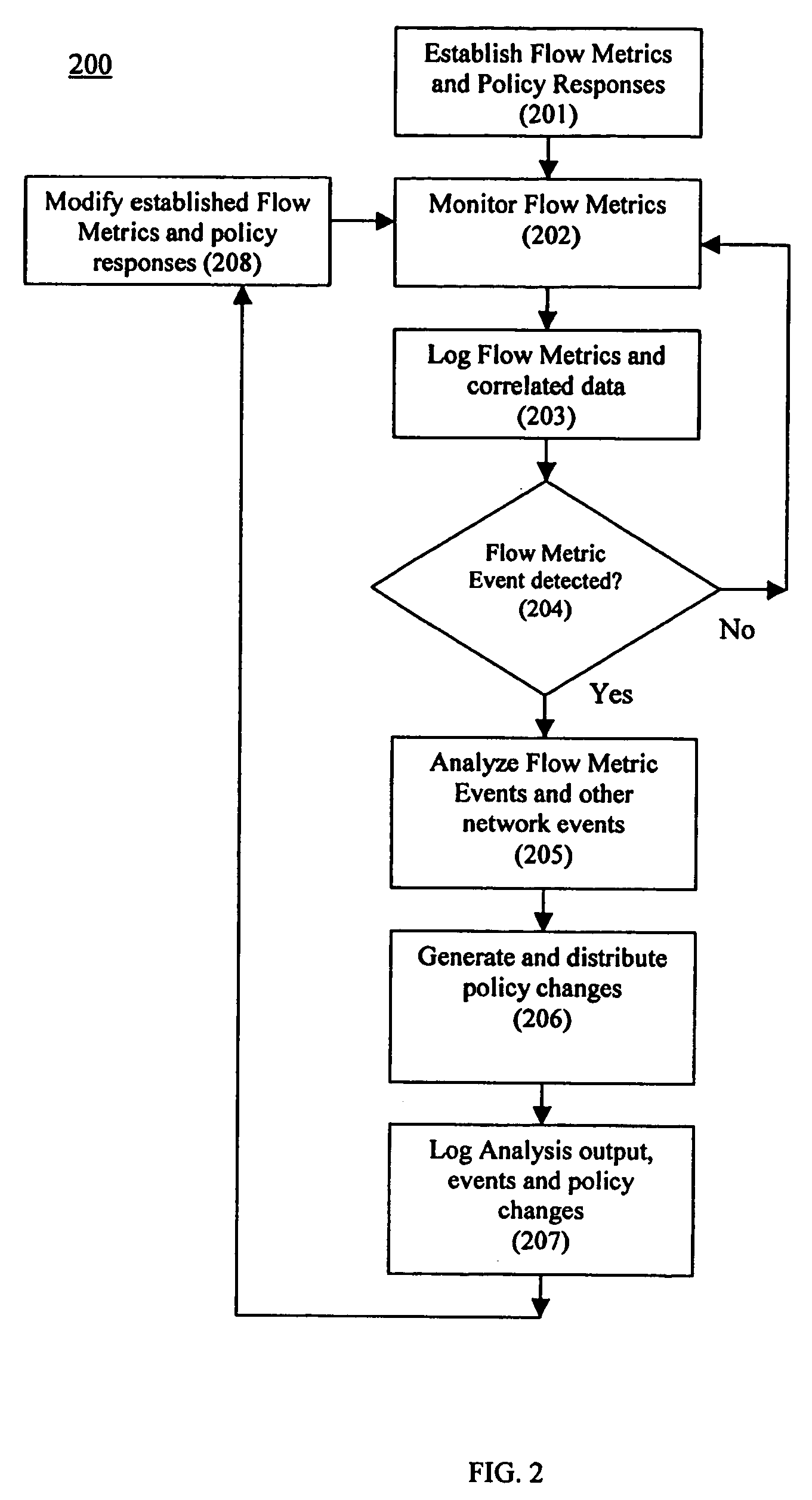
InactiveUS20060075093A1Minimize impactSlow changeDigital computer detailsTransmissionNetworked systemTraffic flow
A system and method to monitor, detect, analyze and respond to, triggering conditions associated with packet and signal flows in a network system including attached functions and a network infrastructure. The system includes a detection function, an analysis function, and a response function. The detection function includes a monitoring sub-function, a flow definition sub-function, and a monitor counter sub-function. The flow definition sub-function defines the types of activities associated with the traffic flow that may indicate a triggering condition requiring analysis and potentially a response. The monitor sub-function observes traffic flows. The monitor counter sub-function counts the defined types of activities occurring in the device. The analysis function analyzes the event from the monitored flows, flow counters, status and other network information and determines whether a response is required. The response function initiates a response to a perceived event or attack based on the events detected in the flow metrics and other data. The response function further includes a sub-function for activating changes throughout the network system based on receiving and sending event notifications. Responses generated by the response function include dynamic policy changes.
Owner:ENTERASYS NETWORKS
Method and system for enhanced wireless network security
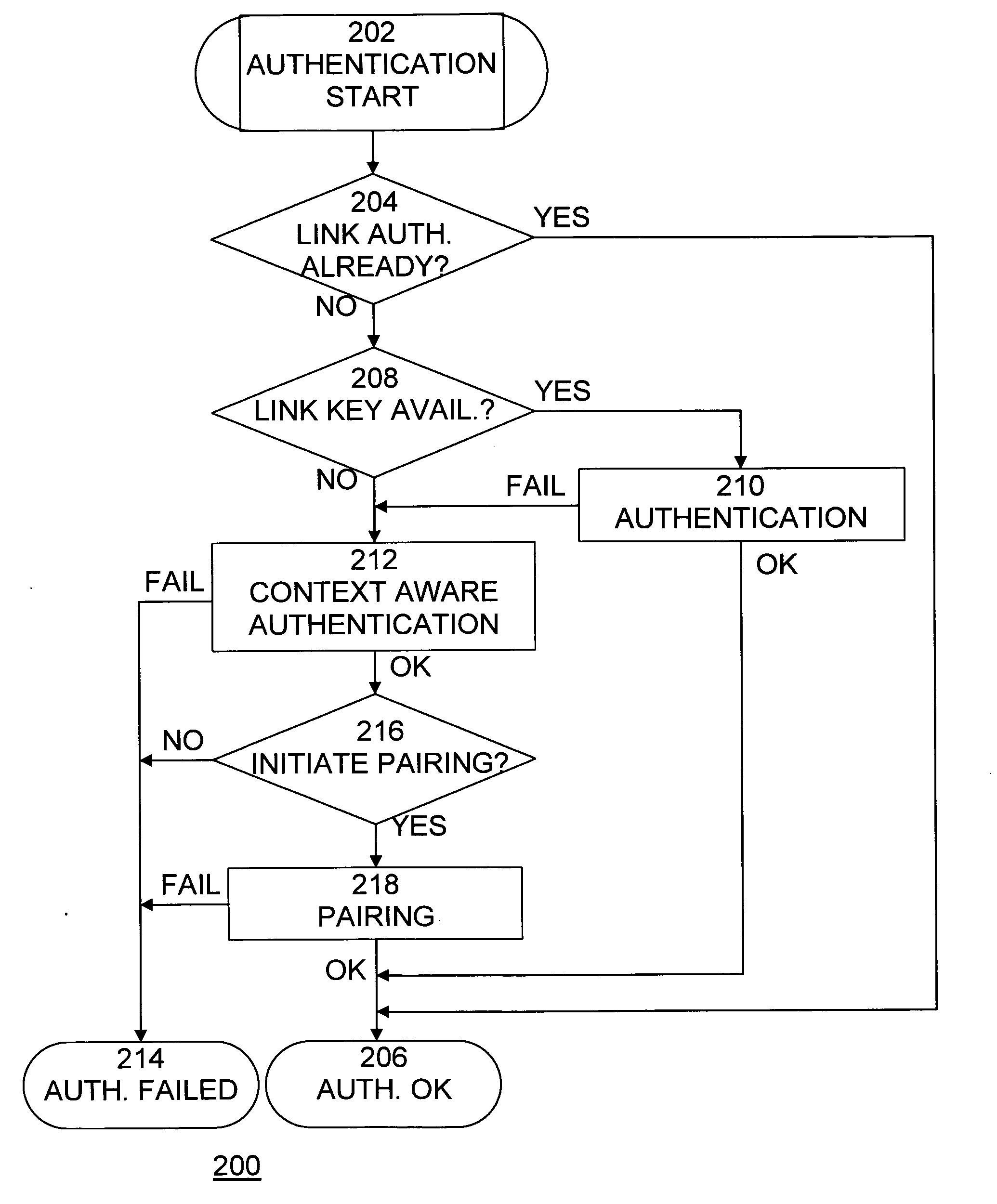
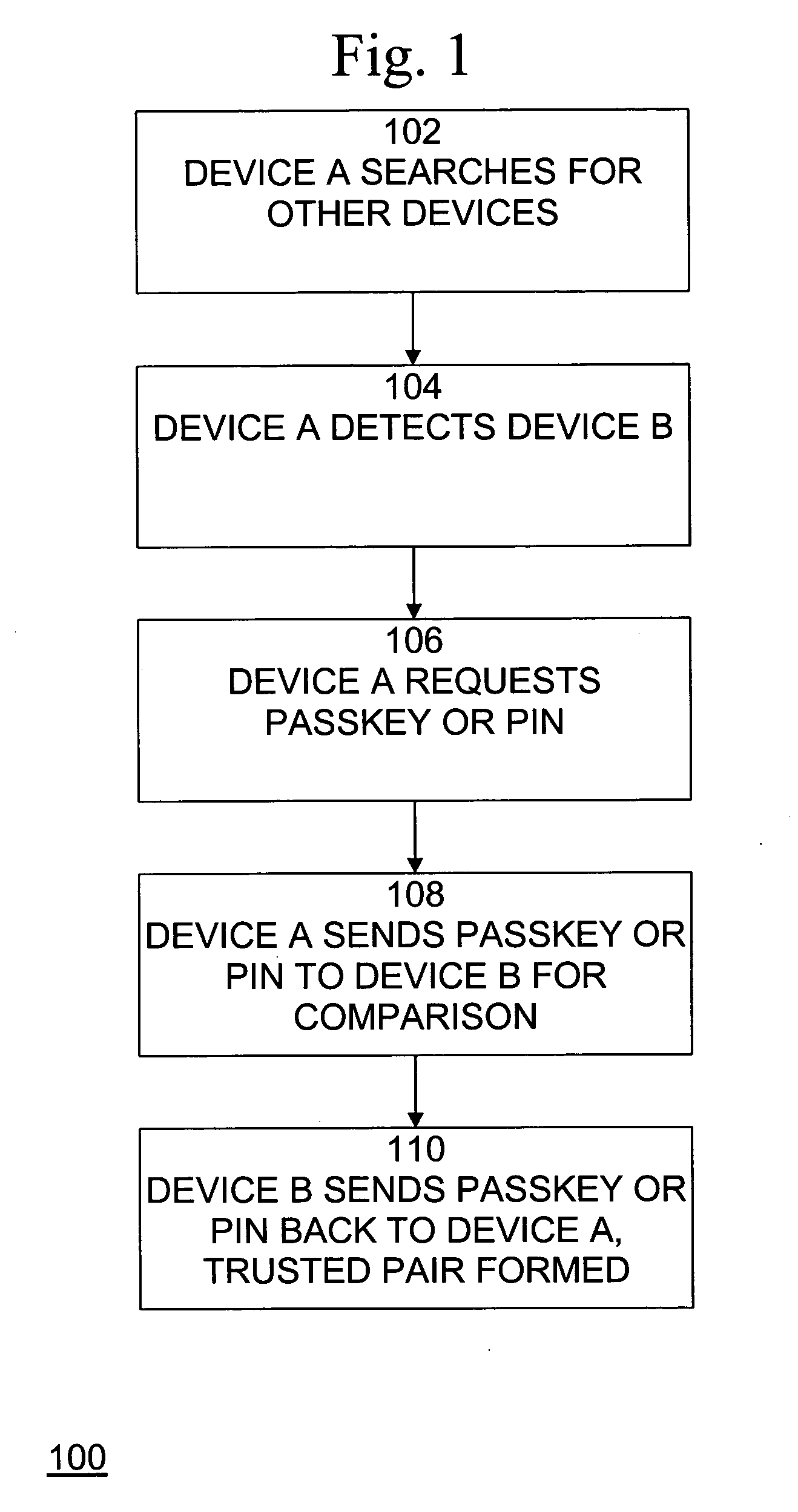
ActiveUS20080134281A1Improve safetyPrevent attackNetwork topologiesDigital data authenticationBluetooth networksSecurity policy
A method, system, and computer program product for securing wireless network devices improves the security of wireless networks and devices, such as Bluetooth networks and devices, to prevent security attacks on and hacking of such networks and devices. A method for secure wireless communications, comprises the steps of requesting a connection with a wireless device, determining whether the wireless device is trusted, determining a security policy of the wireless device, and establishing a connection with the wireless device if the wireless device is trusted and if the security policy of the wireless device is as expected.
Owner:MCAFEE LLC
Dynamic learning method and adaptive normal behavior profile (NBP) architecture for providing fast protection of enterprise applications
ActiveUS20050120054A1Quick protectionDigital data information retrievalMemory loss protectionDynamic learningStudy methods
A dynamic learning method and an adaptive normal behavior profile (NBP) architecture for providing fast protection of enterprise applications are disclosed. The adaptive NBP architecture includes a plurality of profile items. Each profile item includes a plurality of profile properties holding the descriptive values of the respective item. An application-level security system can identify and prevent attacks targeted at enterprise applications by matching application events against at least a single profile item in the adaptive NBP.
Owner:IMPERVA
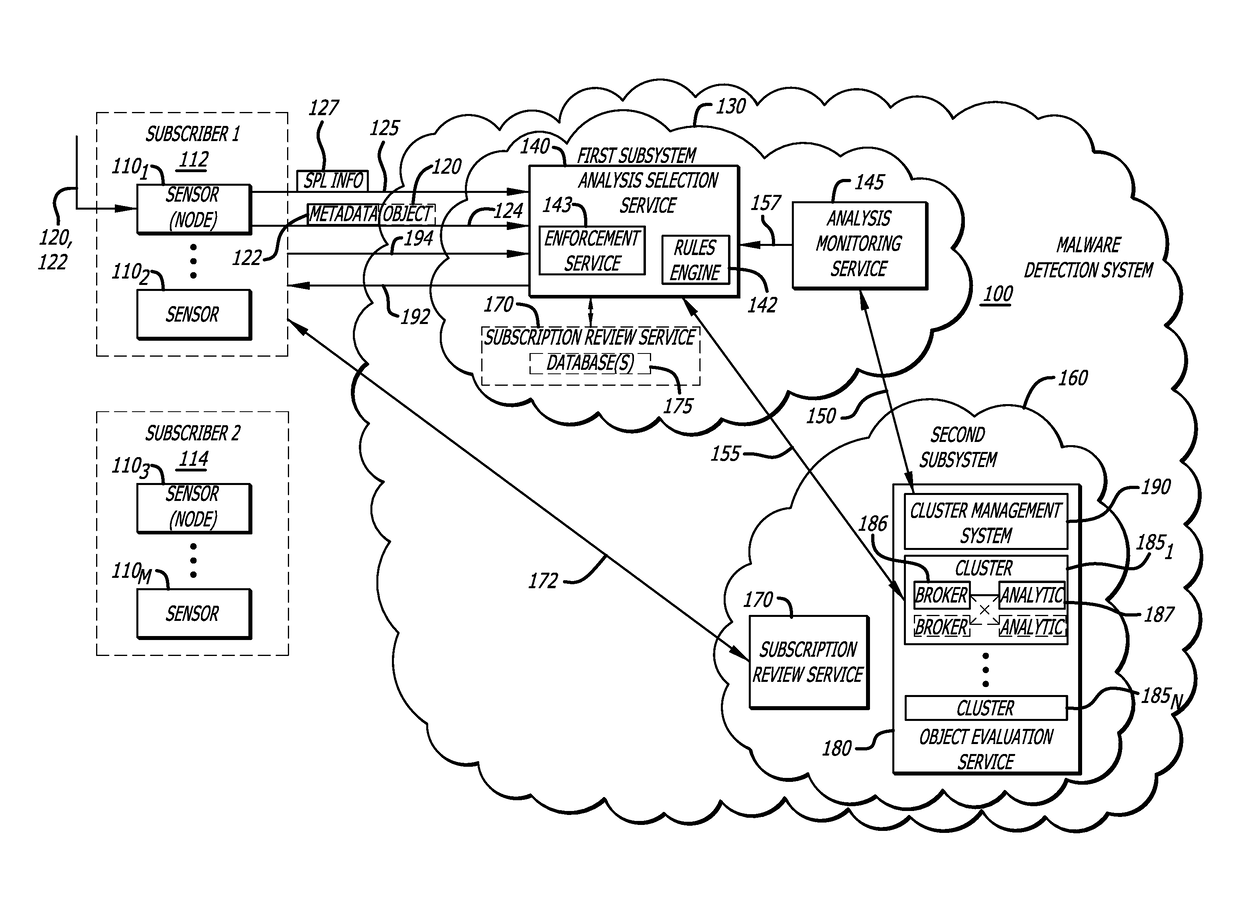
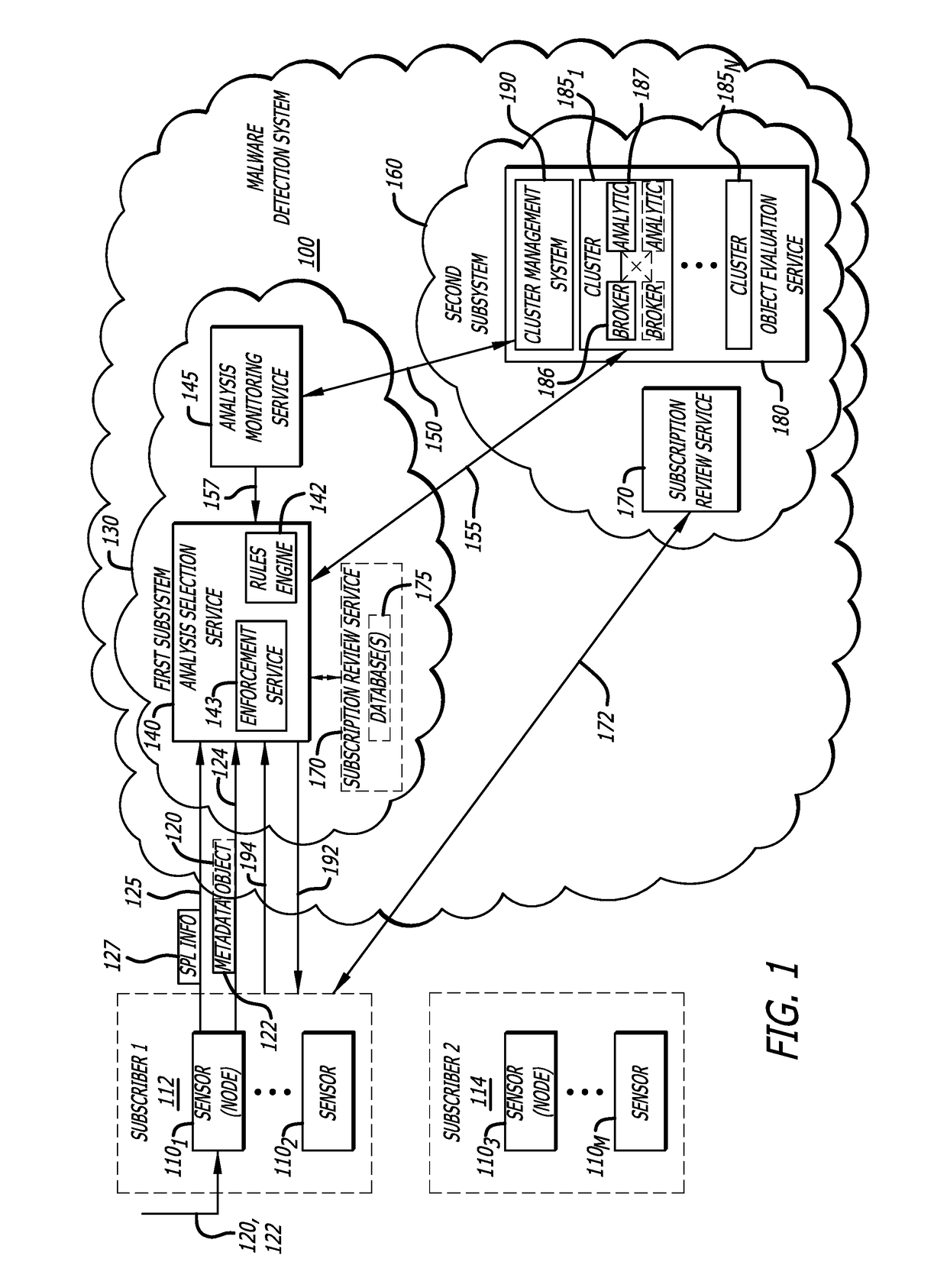
Attribute-controlled malware detection
A computerized method for authenticating access to a subscription-based service to detect an attempted cyber-attack. The method features operations by the cloud broker that include receiving service policy level information and information based on operational metadata. The service policy level information includes at least subscription attributes to identify one or more performance criterion in analyses conducted on one or more objects submitted by a sensor for malware representing an attempted cyber-attack. The operational metadata includes metadata that pertains to an operating state of one or more clusters of a plurality of clusters of the subscription-based service. The cloud broker, using both the service policy level information and the information based on the operational metadata, selecting a cluster of the plurality of clusters to analyze the one or more objects submitted by the sensor and establishes a communication session between the sensor and the cluster via the cloud broker.
Owner:FIREEYE SECURITY HLDG US LLC
Method for preventing malicious software installation on an internet-connected computer
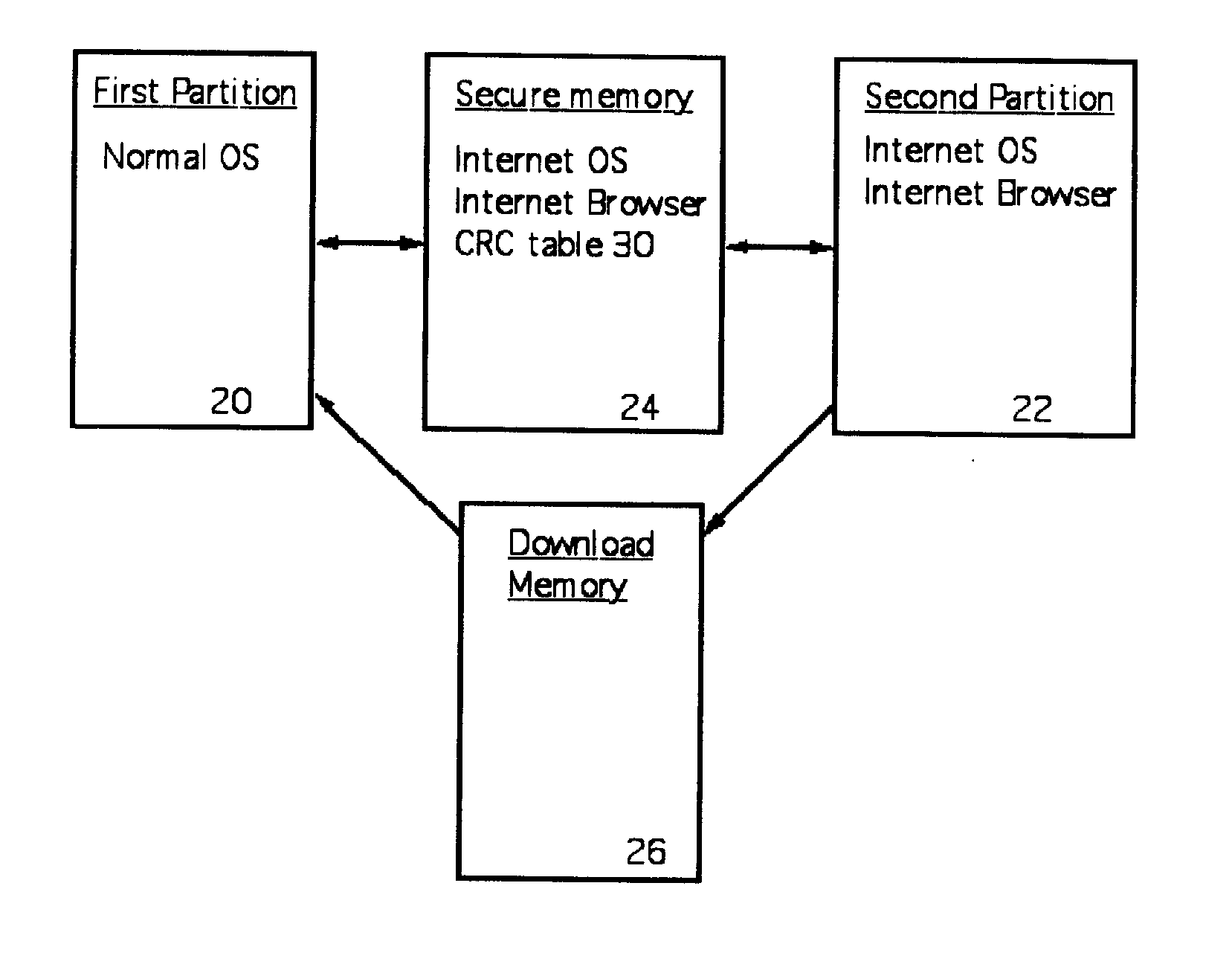
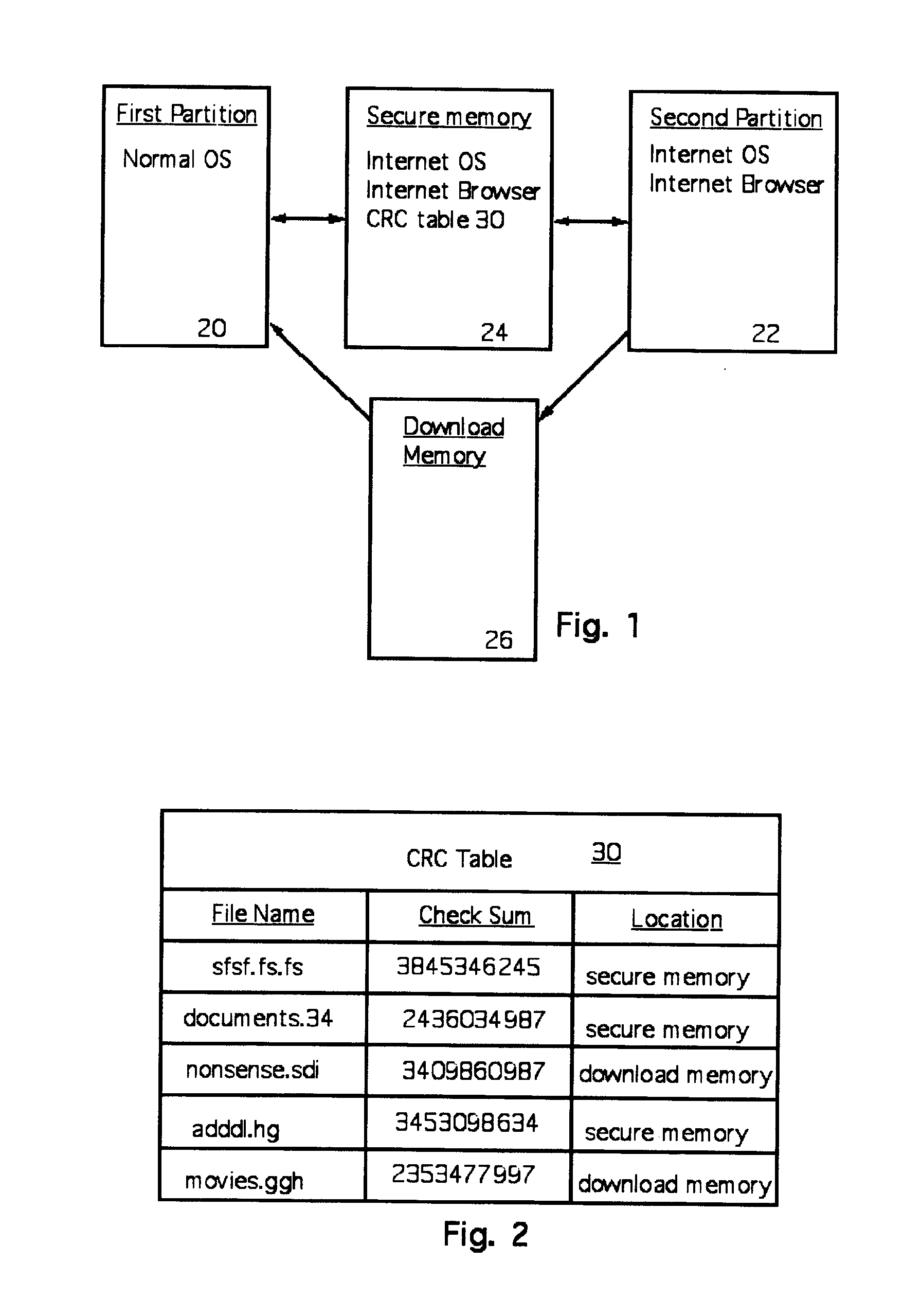
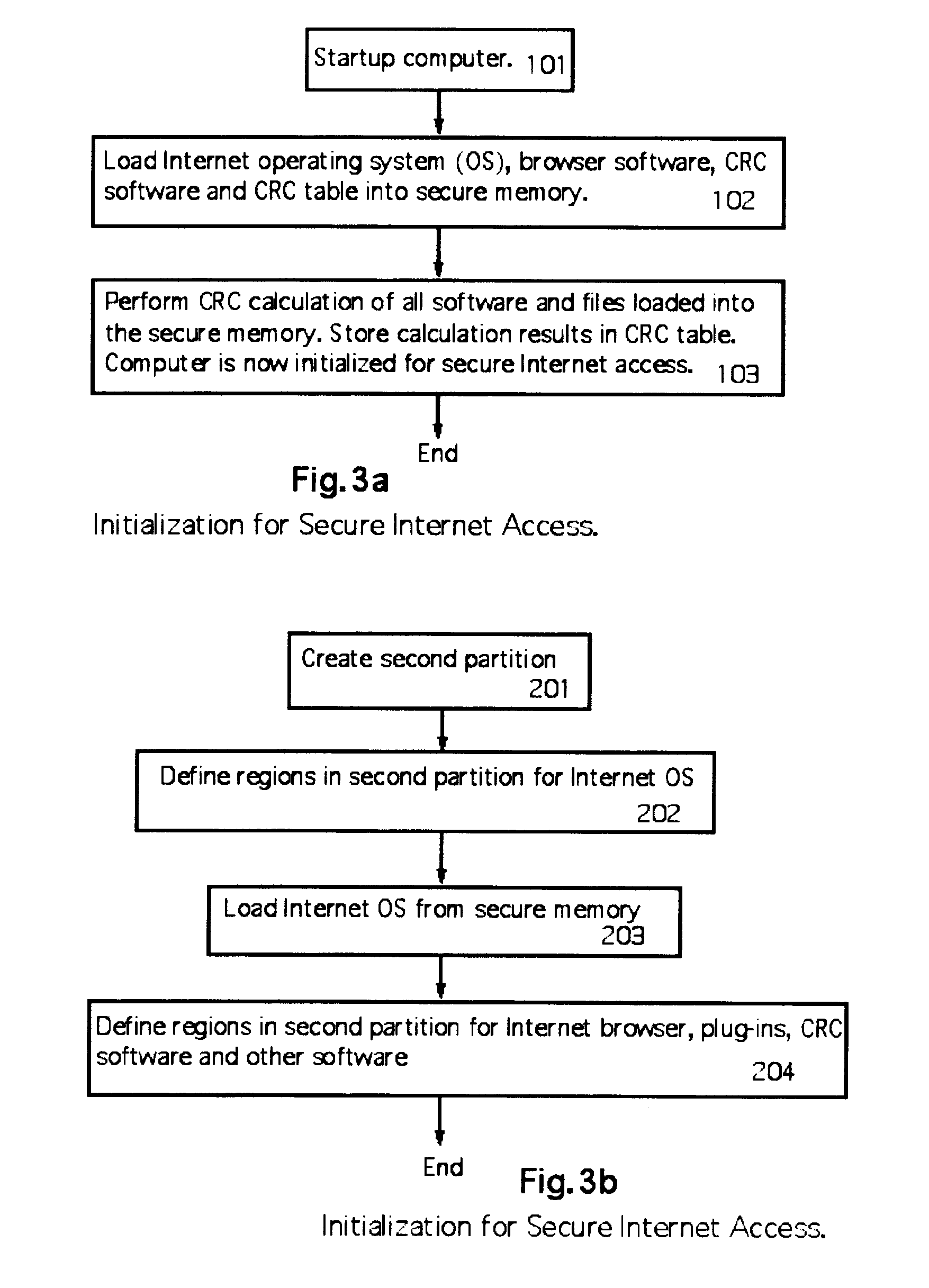
ActiveUS20070192854A1Prevents gaining accessAvoid accessMemory loss protectionDigital data processing detailsOperational systemTerm memory
A computer random access memory is divided into first and second partitions. Each partition has its own operating system (OS). The first partition has a conventional OS and is designated for non-Internet use. The second partition is designated for secure Internet access, and has an OS specific for Internet usage. Software in the second partition cannot write or copy files in the second partition. The size of the second partition is fixed and unchangeable while said second partition is open. Each software application in the second partition is allocated a memory region that cannot be changed, thereby preventing memory overflow attacks. A secure memory is designated for temporary storage of software used in the second partition. Cyclic redundancy check (CRC) values are calculated for all files in the secure memory. To detect unauthorized file changes, CRC values are calculated for all files used in the second partition, and checked against values stored in the secure memory. The second partition can write only to a secure memory using a security arrangement such as password protection or a download memory separate from the first partition to allow files stored in the download memory to be examined by scanning and testing from the first partition prior to being stored elsewhere in the computer.
Owner:KYNDRYL INC
System and method for network security including detection of man-in-the-browser attacks
ActiveUS20110185421A1Memory loss protectionError detection/correctionElectronic equipmentNetwork security
A method is performed in a network security system implemented in a computer or electronic device that is coupled to secured online resources for detecting unauthorized accesses of those secured online resources. The method includes monitoring a user activity session. It is determined whether the user activity session is indicative of a hidden session by an attacker, where the determination includes comparing the user activity session to an average user activity session.
Owner:EMC IP HLDG CO LLC
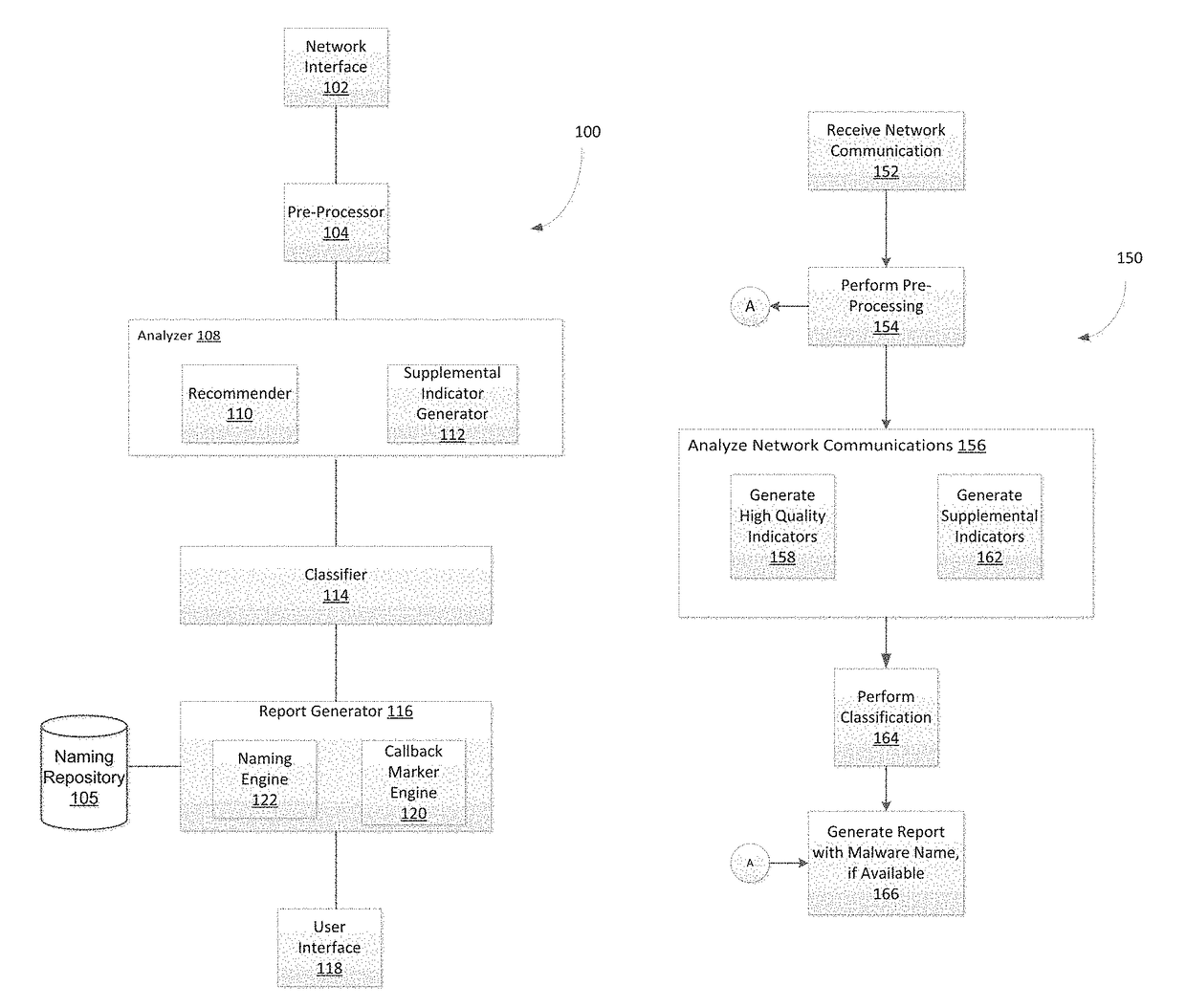
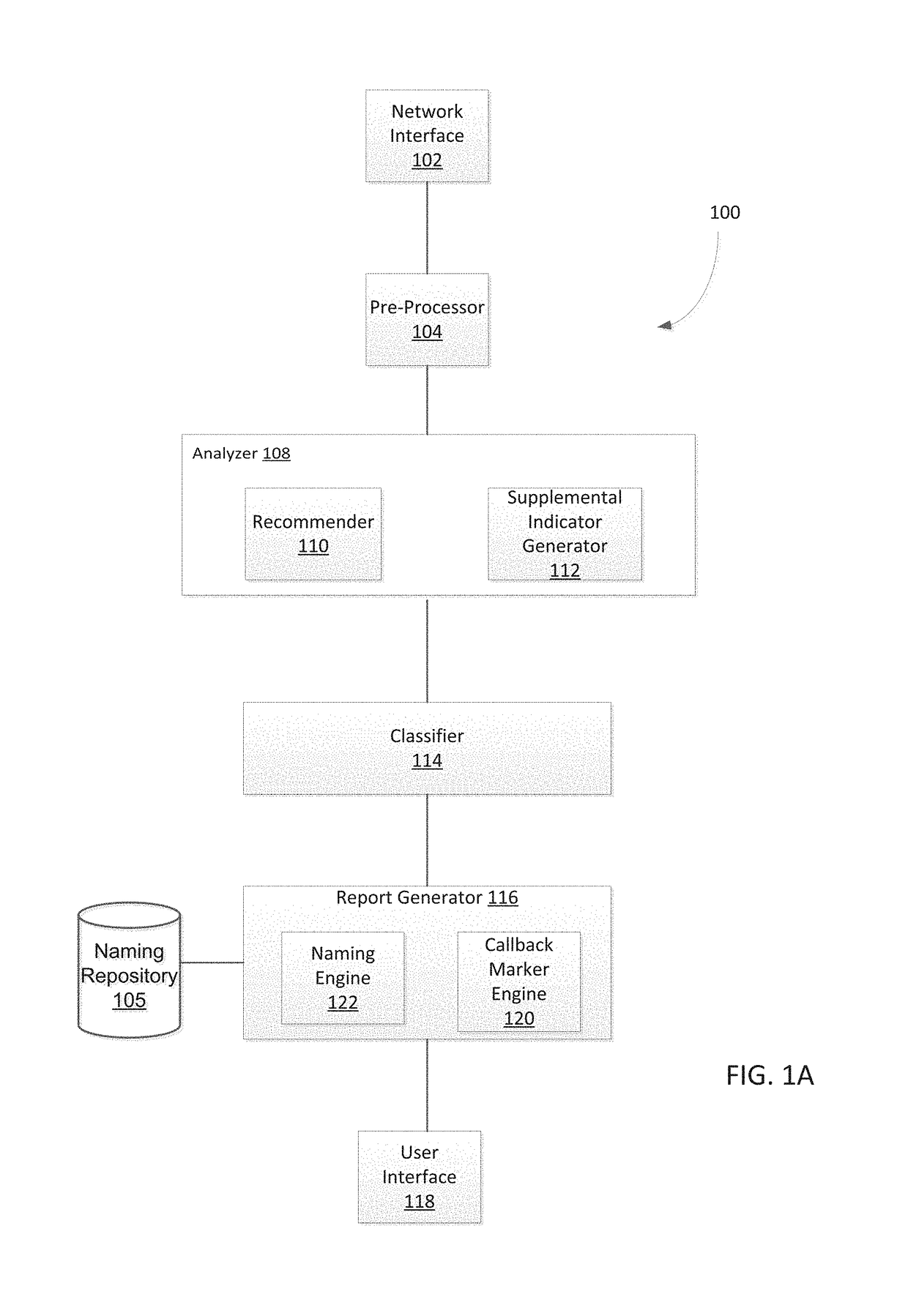
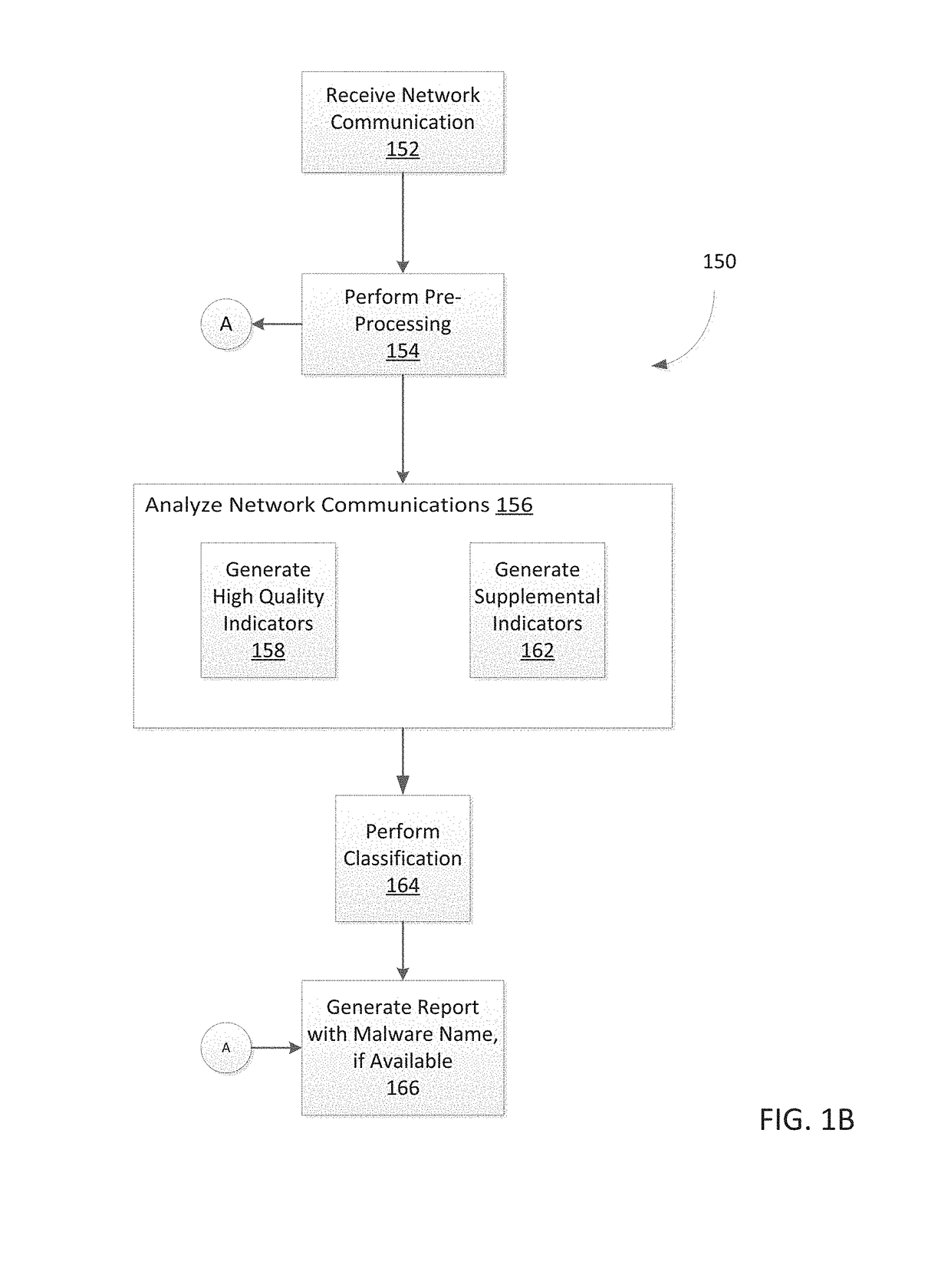
System and method for detecting malicious activity and classifying a network communication based on different indicator types
Owner:FIREEYE SECURITY HLDG US LLC +1
System and method for detecting file altering behaviors pertaining to a malicious attack
ActiveUS9846776B1Digital data information retrievalPlatform integrity maintainanceData informationAttack
Owner:FIREEYE SECURITY HLDG US LLC
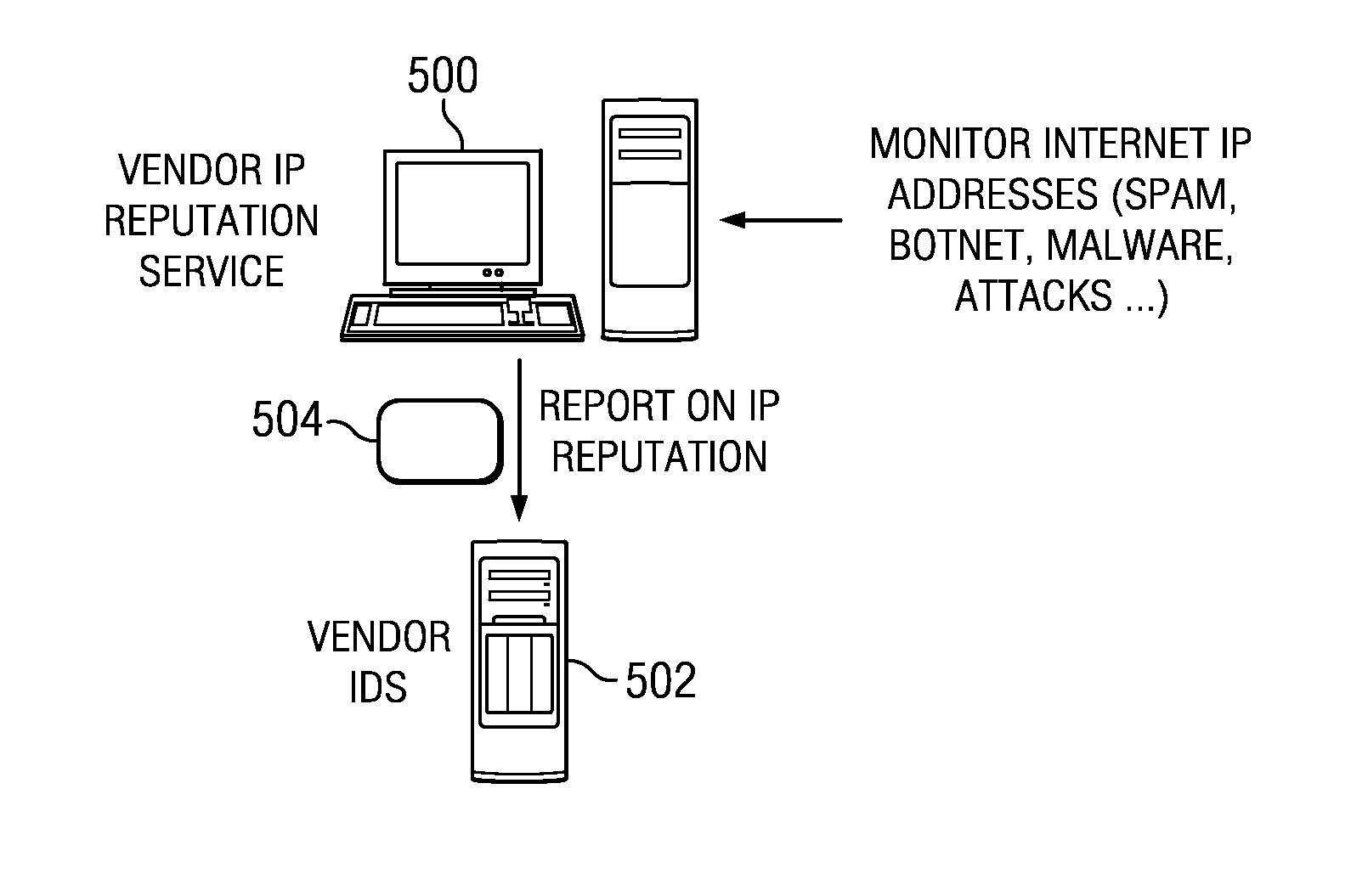
Cooperative intrusion detection ecosystem for IP reputation-based security
ActiveUS20140059683A1Easy to operateImprove system response timeMemory loss protectionError detection/correctionPattern matchingContinuous data
An intrusion detection system (IDS) is enhanced to operate in a cluster of such systems, and IDSs organized into a cluster cooperate to exchange IP reputation influencing events information between or among the cooperating systems in real-time to enhance overall system response time and to prevent otherwise hidden attacks from damaging network resources. An IDS includes an IP reputation analytics engine to analyze new and existing events, correlate information, and to raise potential alerts. The IP reputation analytics engines may implement an algorithm, such as a pattern matching algorithm, a continuous data mining algorithm, or the like, to facilitate this operation. Clustering IDS endpoints to share IP reputation influencing events, using the cluster-wide view to determine IP reputation, and feeding the cluster-wide view back to the IDS endpoints, provides for enhanced and early detection of threats that is much more reliable and scalable as compared to prior art techniques.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com