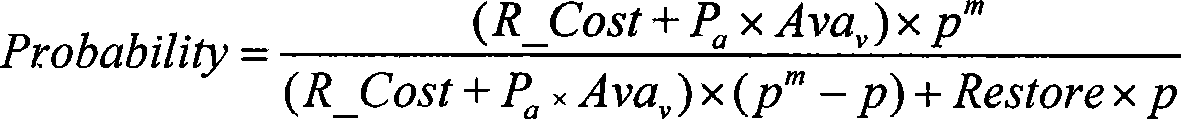Patents
Literature
219 results about "Open port" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
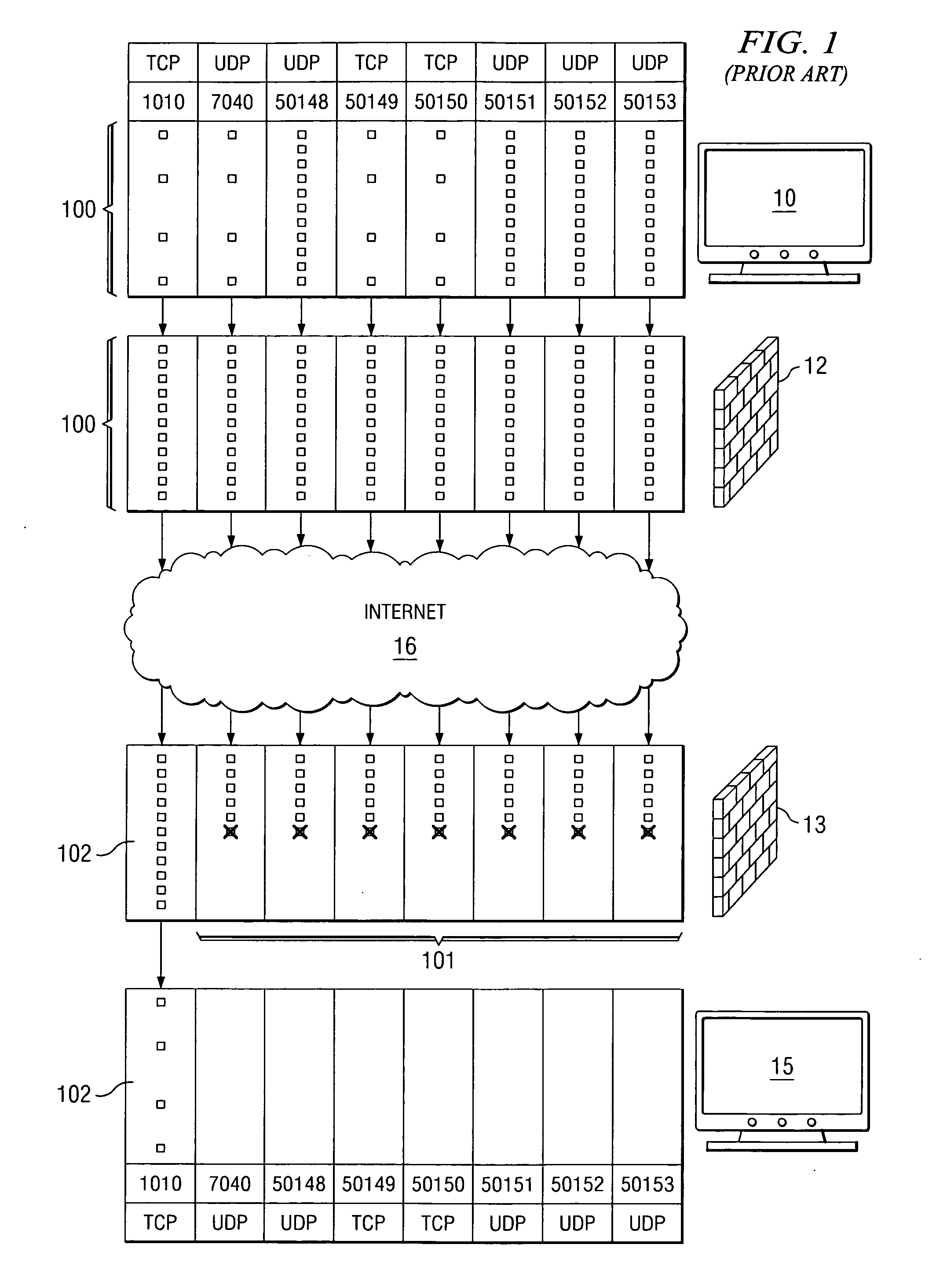
In security parlance, the term open port is used to mean a TCP or UDP port number that is configured to accept packets. In contrast, a port which rejects connections or ignores all packets directed at it is called a closed port.
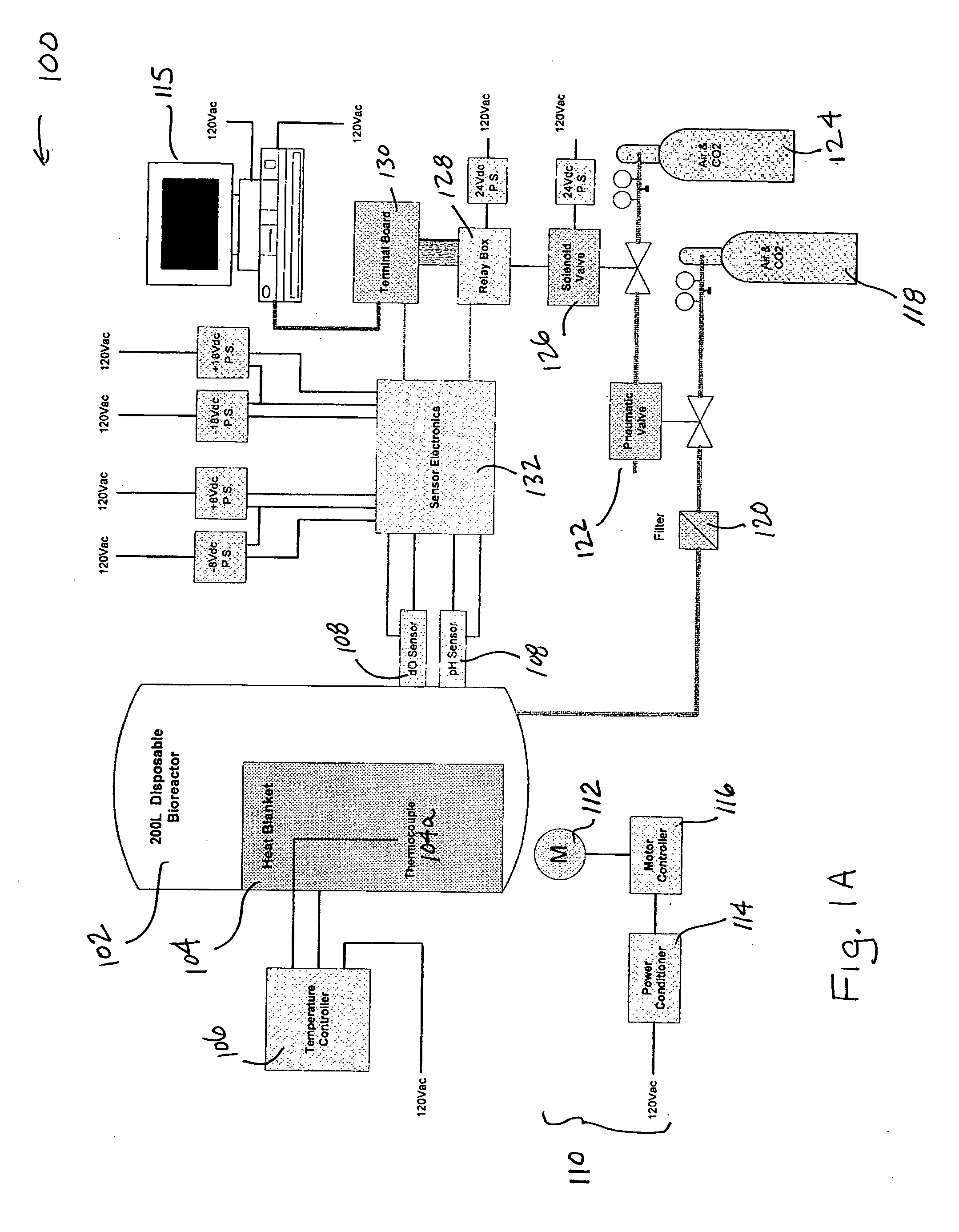
Disposable bioreactor systems and methods
ActiveUS20050272146A1Reduce wearReduce tearingBioreactor/fermenter combinationsBiological substance pretreatmentsOpen portSterile environment
Accordingly, in one embodiment of the invention, a bioreactor system is presented and includes a disposable container for housing biomaterials for processing, the disposable container including at least one input port, at least one exhaust port, at least one harvest port, and the integrity of the sterile environment is protected with sterile filters attached to all external open ports a structure for supporting the disposable container, one or more sensors for sensing one or more parameters of the biomaterials in the container, a heater for heating the contents of the container, the heater having a thermostat and mixing system arranged with the system such that biomaterials contained in the disposable container are mixed.
Owner:GLOBAL LIFE SCI SOLUTIONS USA LLC
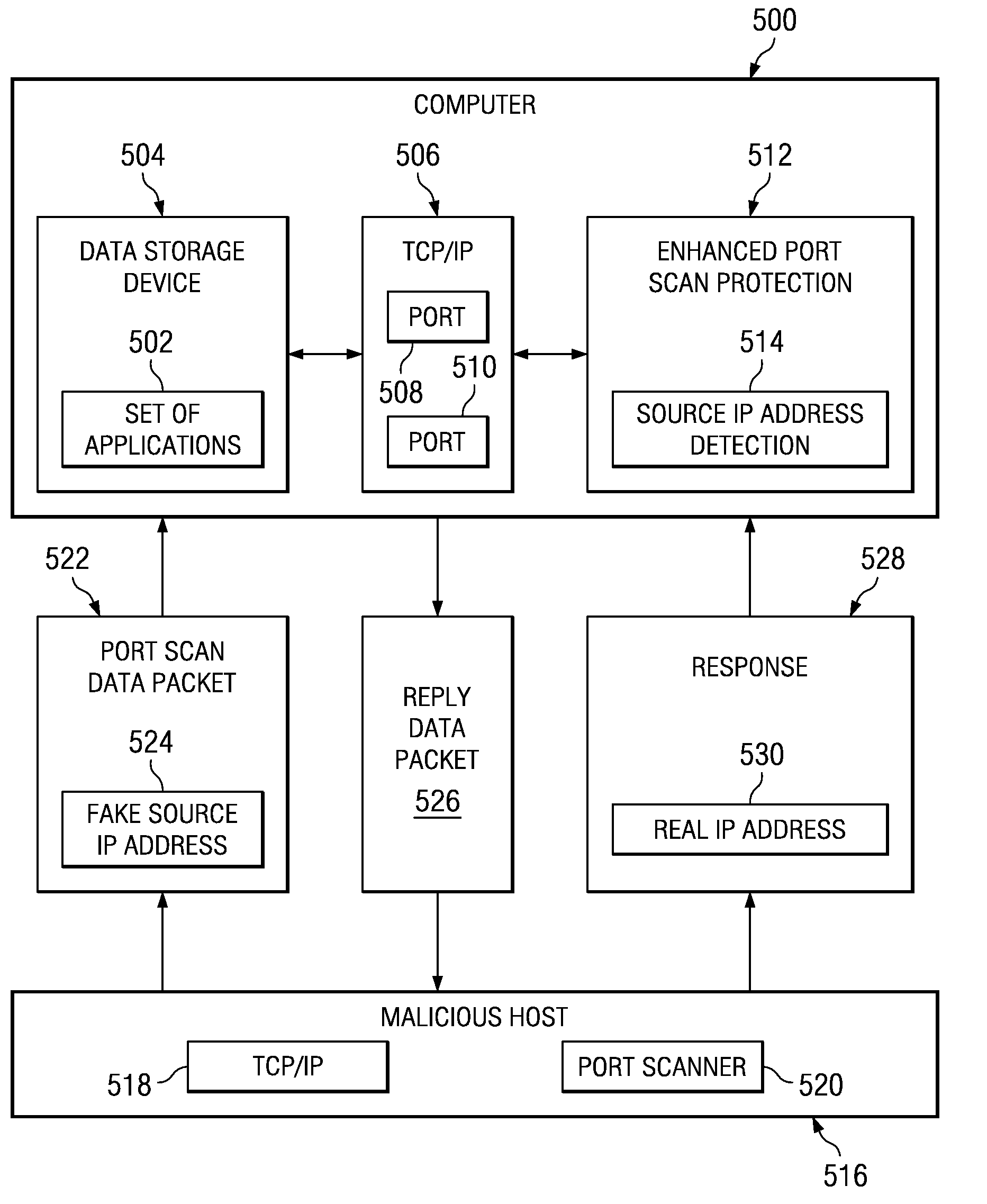
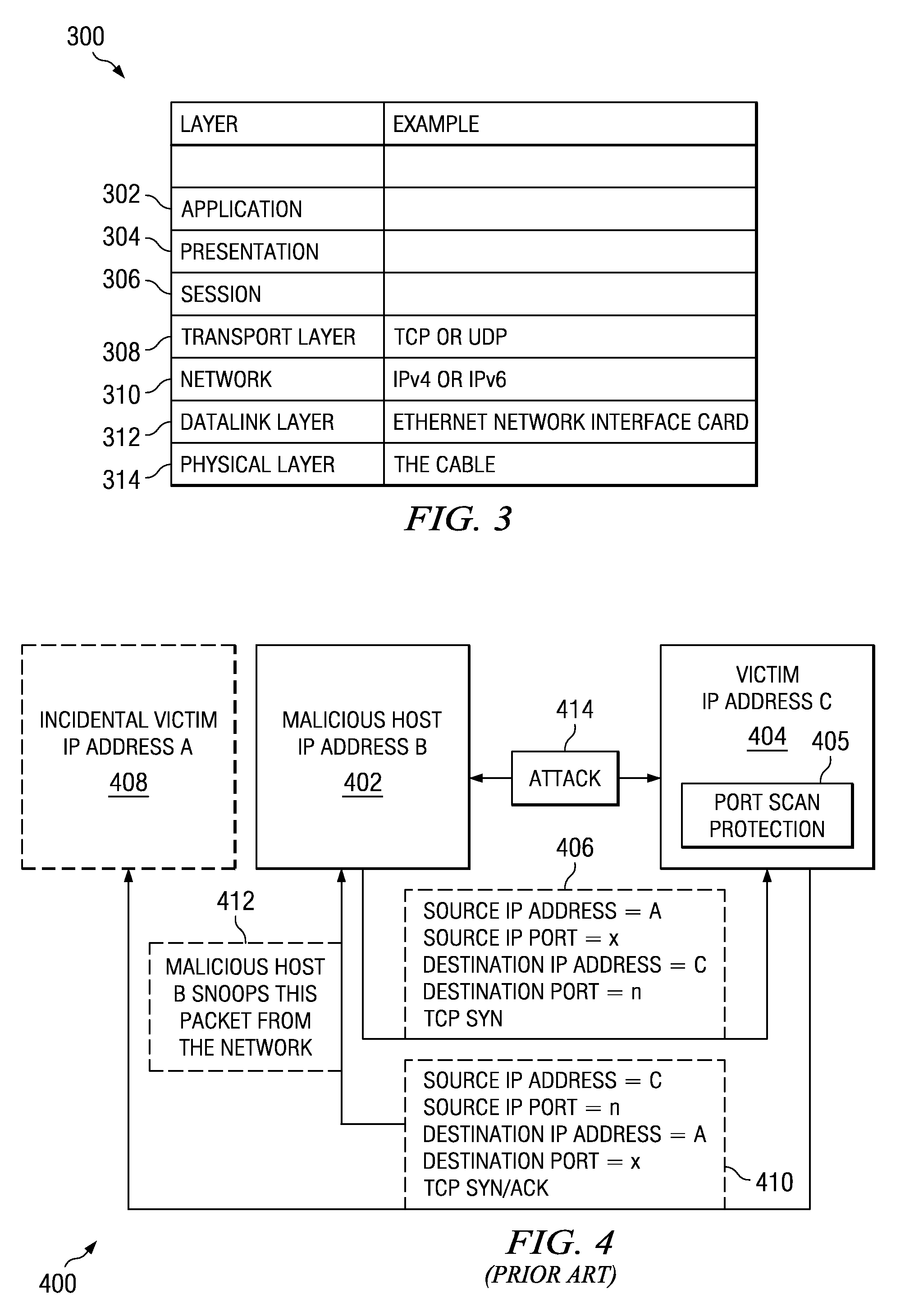
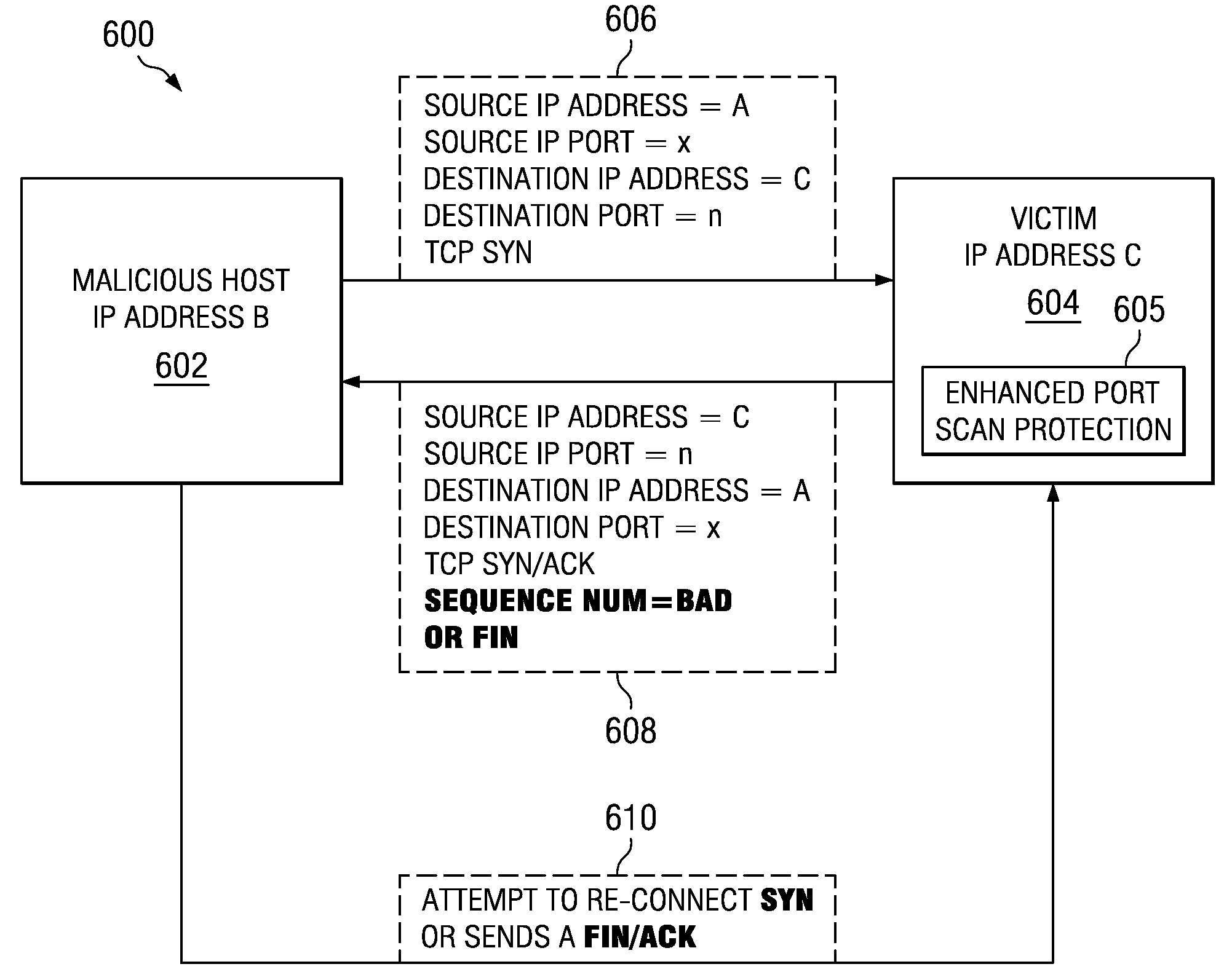
Method and apparatus for detecting port scans with fake source address
Owner:INT BUSINESS MASCH CORP
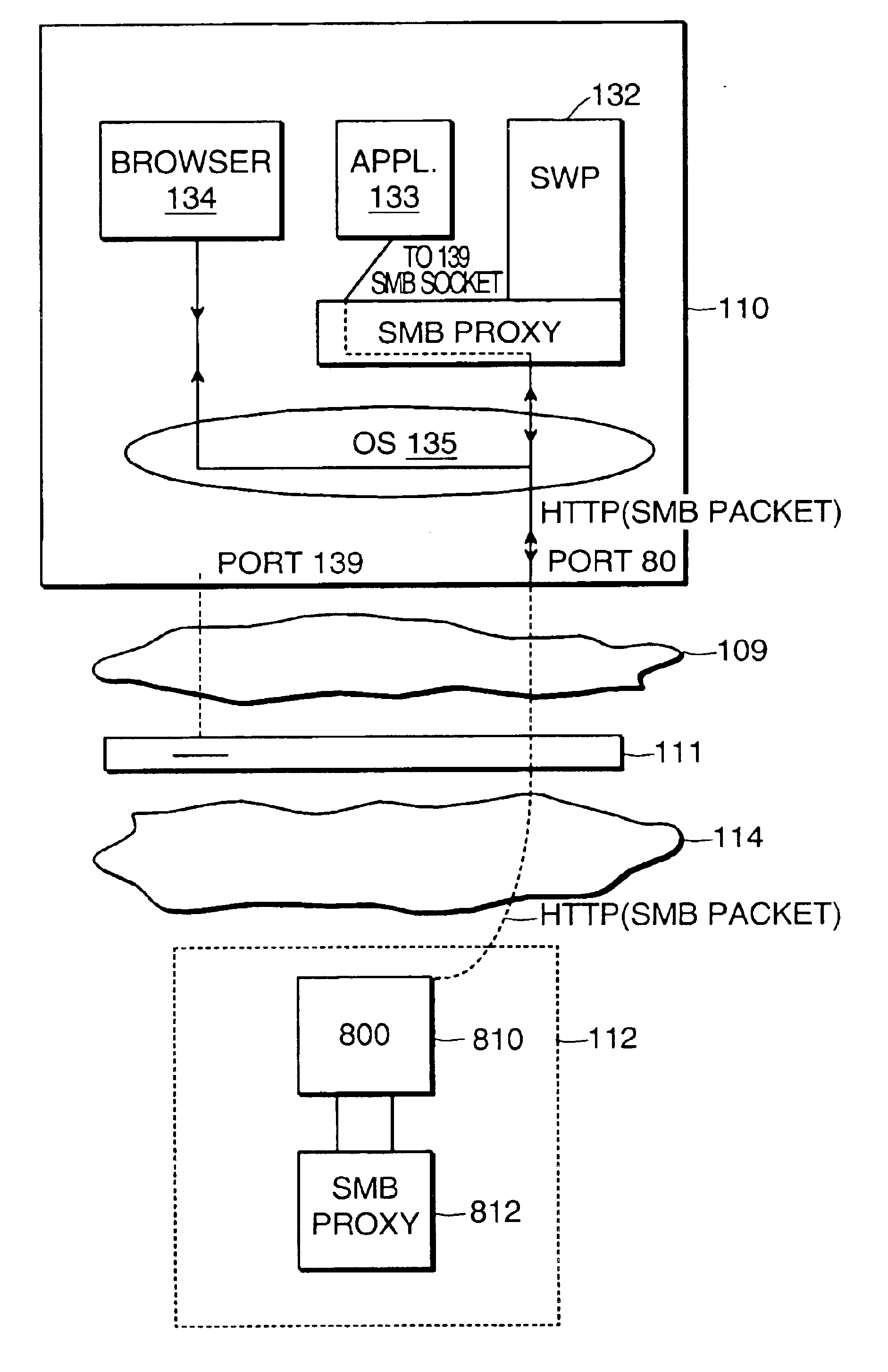
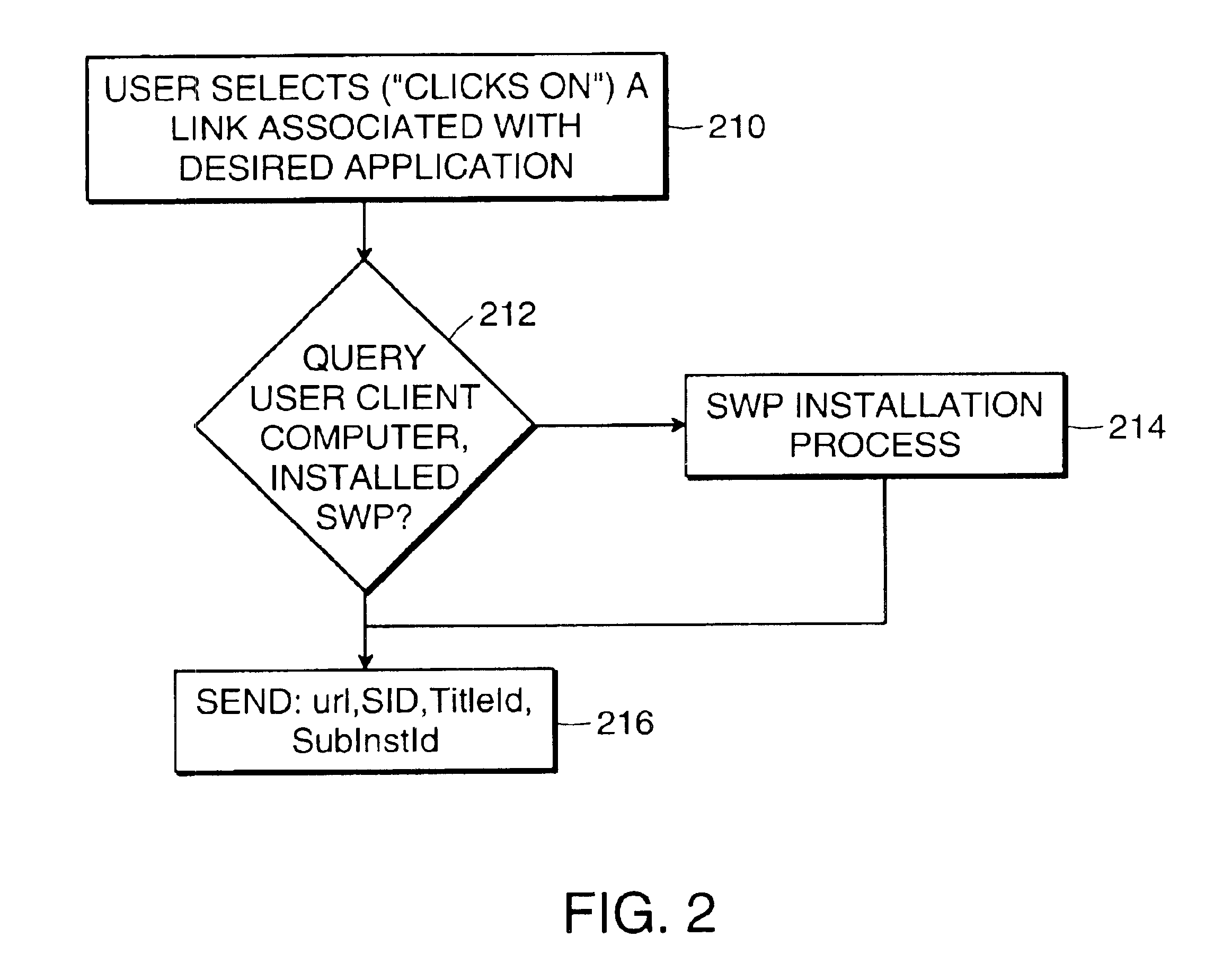
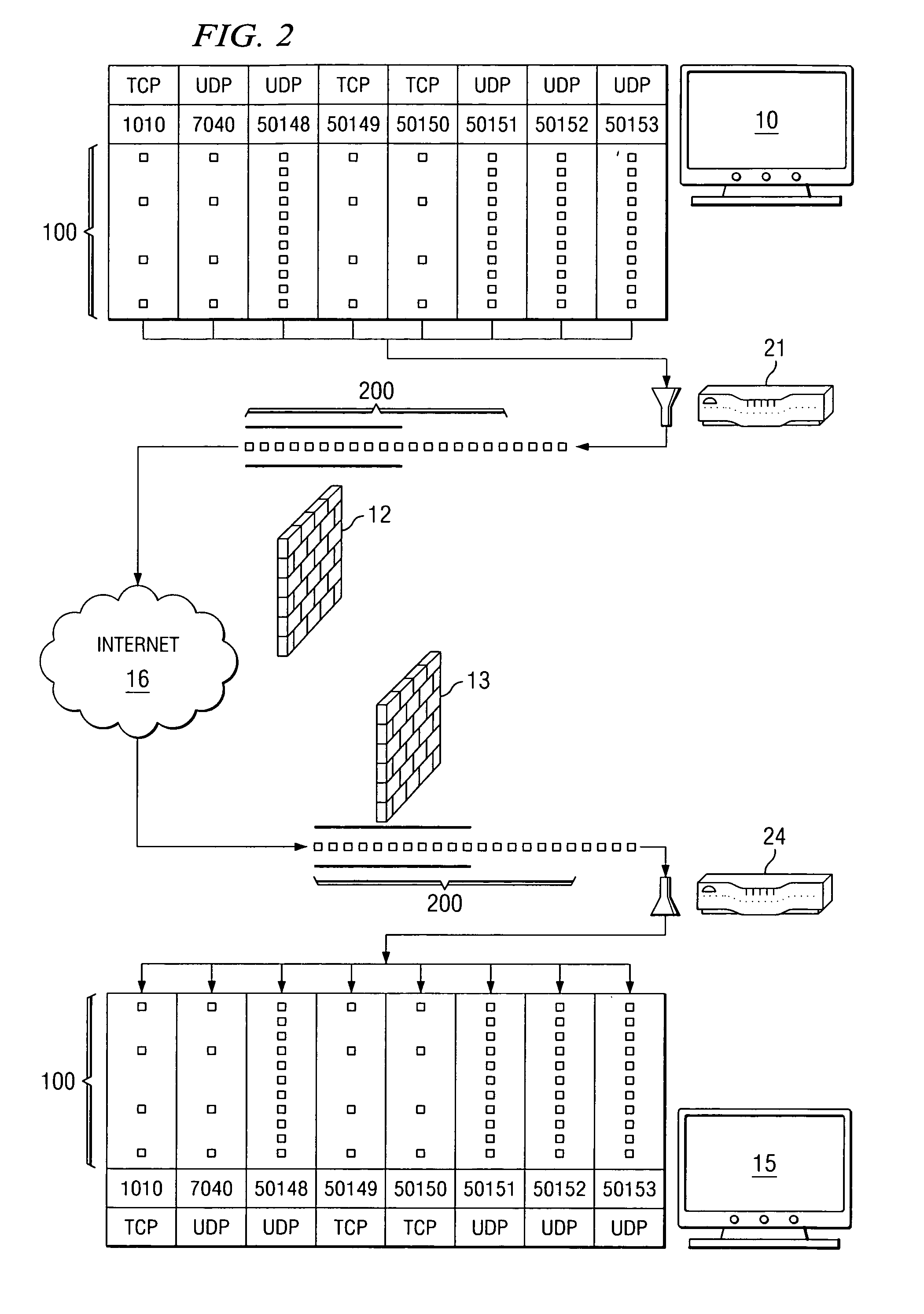
Method and system for remote networking using port proxying by detecting if the designated port on a client computer is blocked, then encapsulating the communications in a different format and redirecting to an open port
InactiveUS6938096B1Multiple digital computer combinationsProgram loading/initiatingOpen portThird party
A method and system for serving software applications to remote clients across the internet, for example, is disclosed that preferably utilizes standard, SMB (server message block), protocols, which are available in commercial operating systems. Further, an associated business method is described in which subscribing institutions can out-source the application serving to a third party institution, transparently. Finally, a port proxy system is provided that enables tunneling through firewalls that are configured to block communications from SMB ports.
Owner:MICROSOFT TECH LICENSING LLC
Air seeder/fertilizer apparatus having metering means and distribution manifold with selectively openable ports
A seeding apparatus having a distribution manifold with selectively openable outlet ports thereon, to permit or stop delivery of seed or fertilizer to soil A meter device, responsive to both the number of selected open ports and the speed of the apparatus over the ground, is provided to regulate supply of seed / fertilizer to a distribution manifold. The distribution manifold has a plurality of outlet ports spaced about a periphery of such manifold, each outlet port having a valve to allow opening and closing of individual outlet ports. Soil engaging members on such apparatus are individually raisable from an lowered operative position to a raised inoperative position, and when moved to such inoperative position, valve associated with an outlet port for providing seed and / or fertilizer to such soil engaging member is closed to prevent supply to the associated soil engaging member.
Owner:ONE PASS IMPLEMENTS
Personal network security token
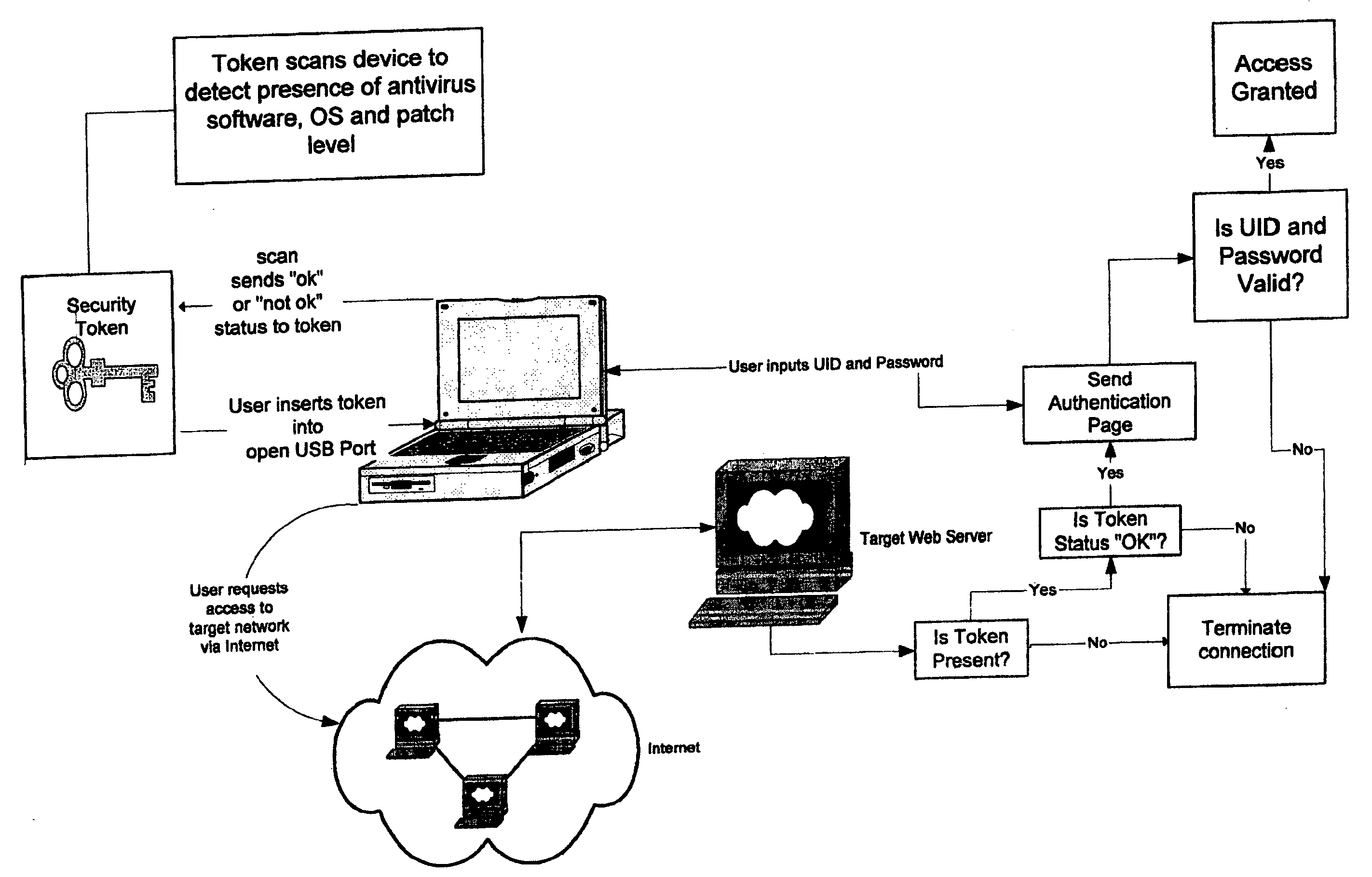
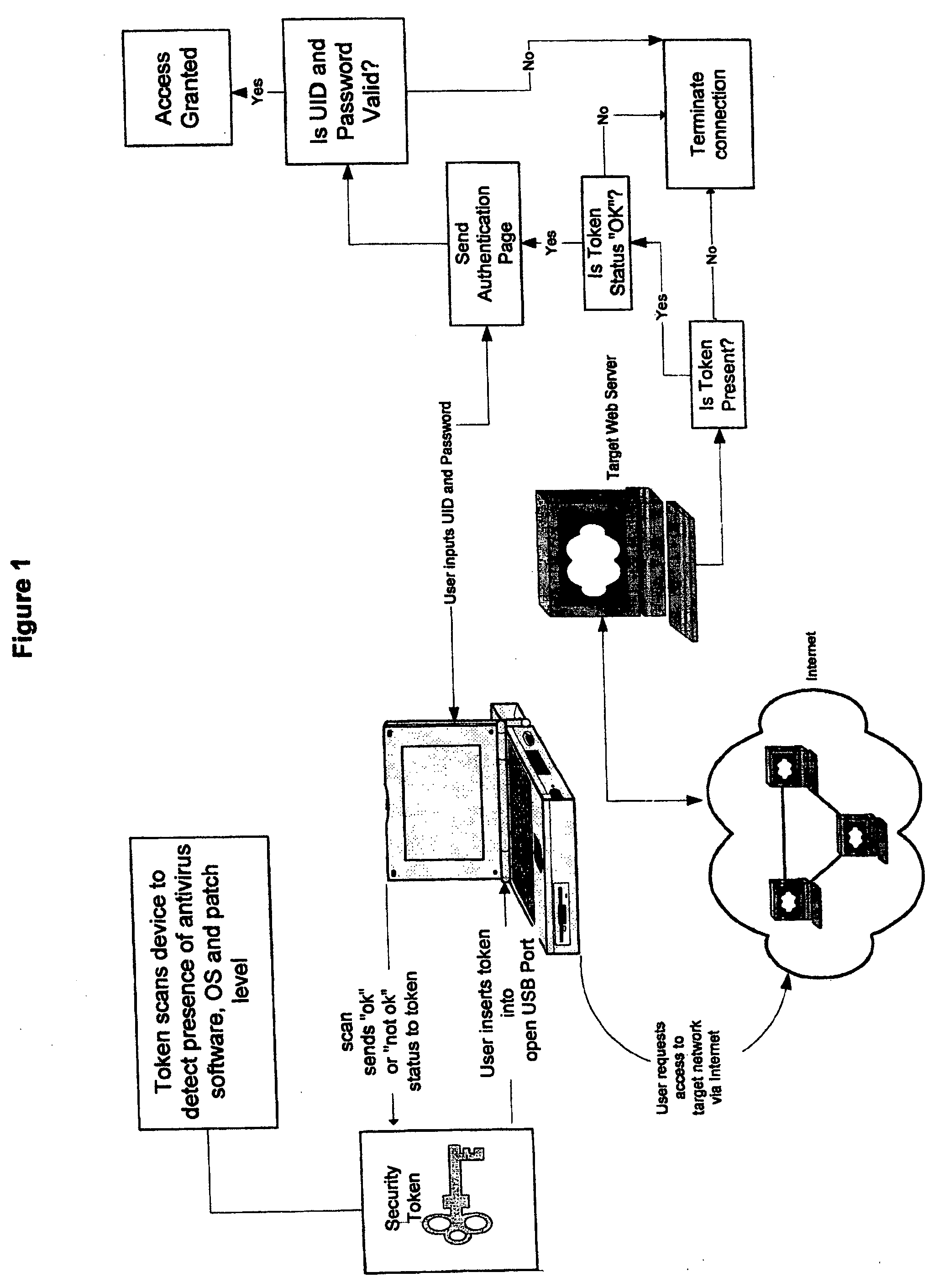
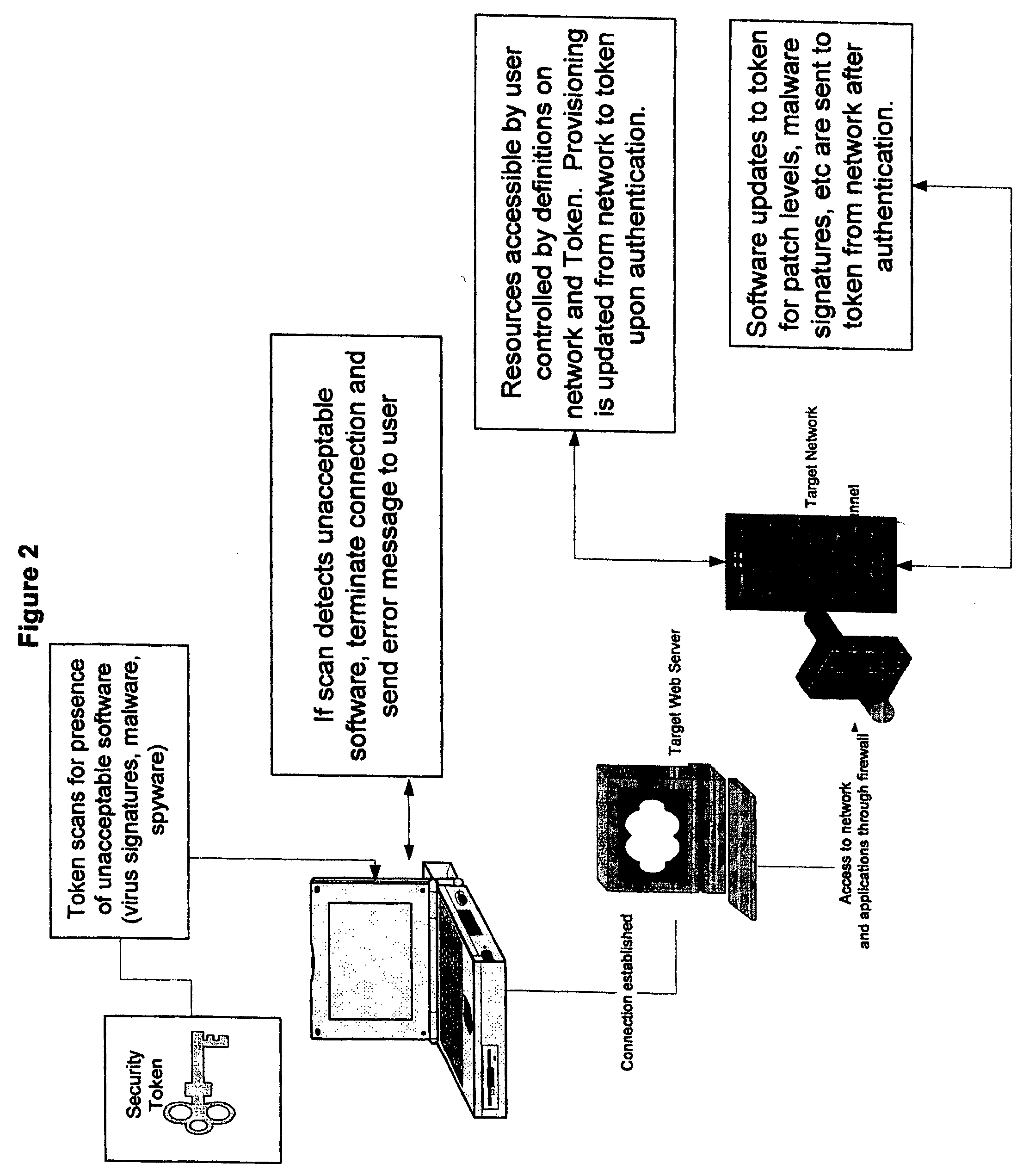
InactiveUS20060168653A1Satisfies needDigital data processing detailsUser identity/authority verificationAnti virusOperational system
In general the present invention provides for a small hand held size device that is easily kept in a pocket or purse or on a key chain. The security token will contain a microprocessor having memory function and will connect to a PC or other computing device or workstation via a USB port. Upon insertion into the open USB port of the user's remote computer, the personal network security token scans the remote computer to detect the presence of at least one or more operating applications, such as the type of anti-virus software and patch level and / or the type of operating system (OS) the remote computer is running and the patch level. Upon contacting the target network, the network will send an inquiry to the user's remote computer to determine if the personal network security token is present as well as other parameters. If the condition status of the token is “OK” then the network sends an authentication page to the user for the user to enter his or her user ID and password. If the ID and password are valid, then the user is allowed access to the network.
Owner:CONTRERA SUZANNE HALL
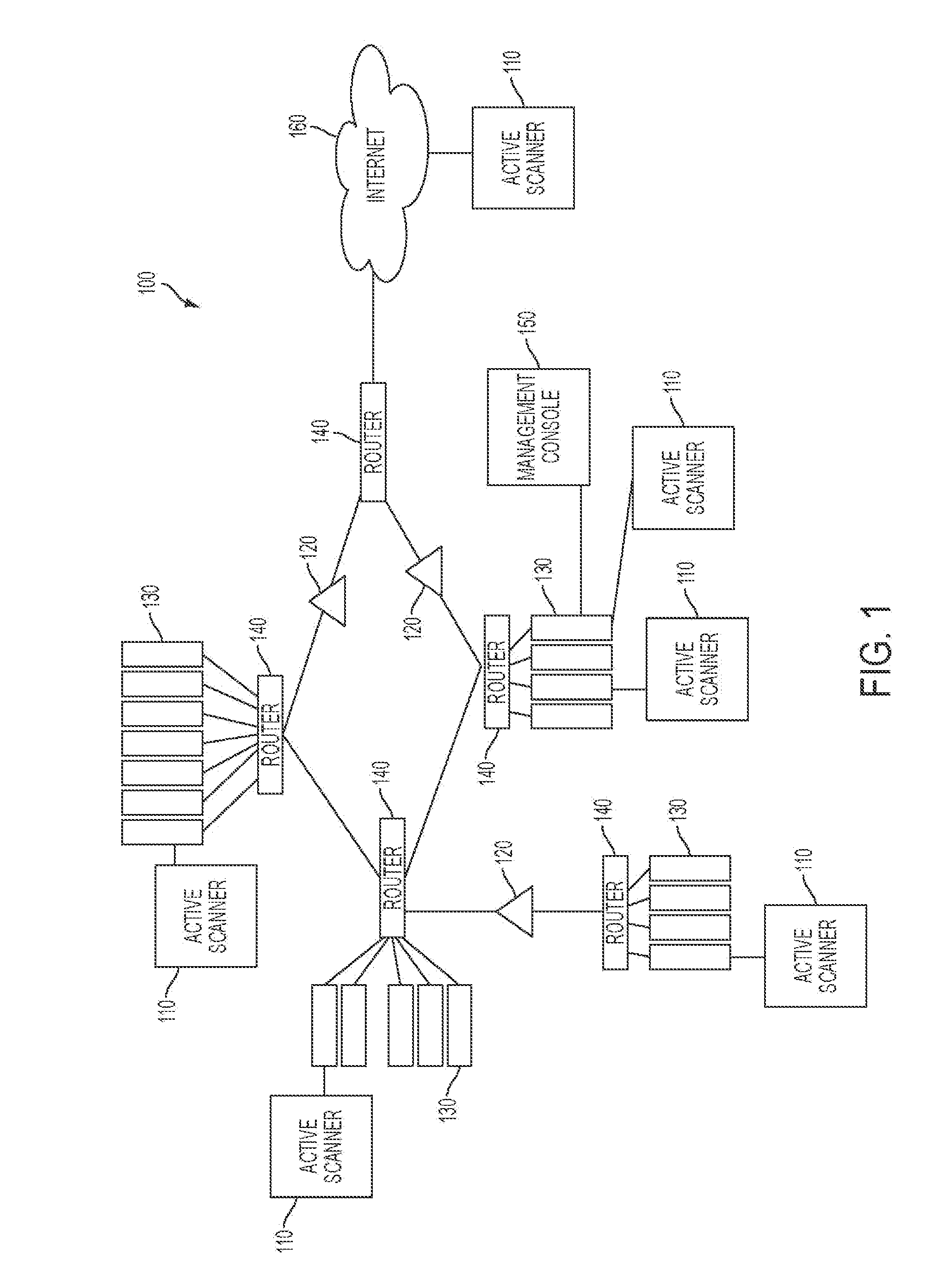
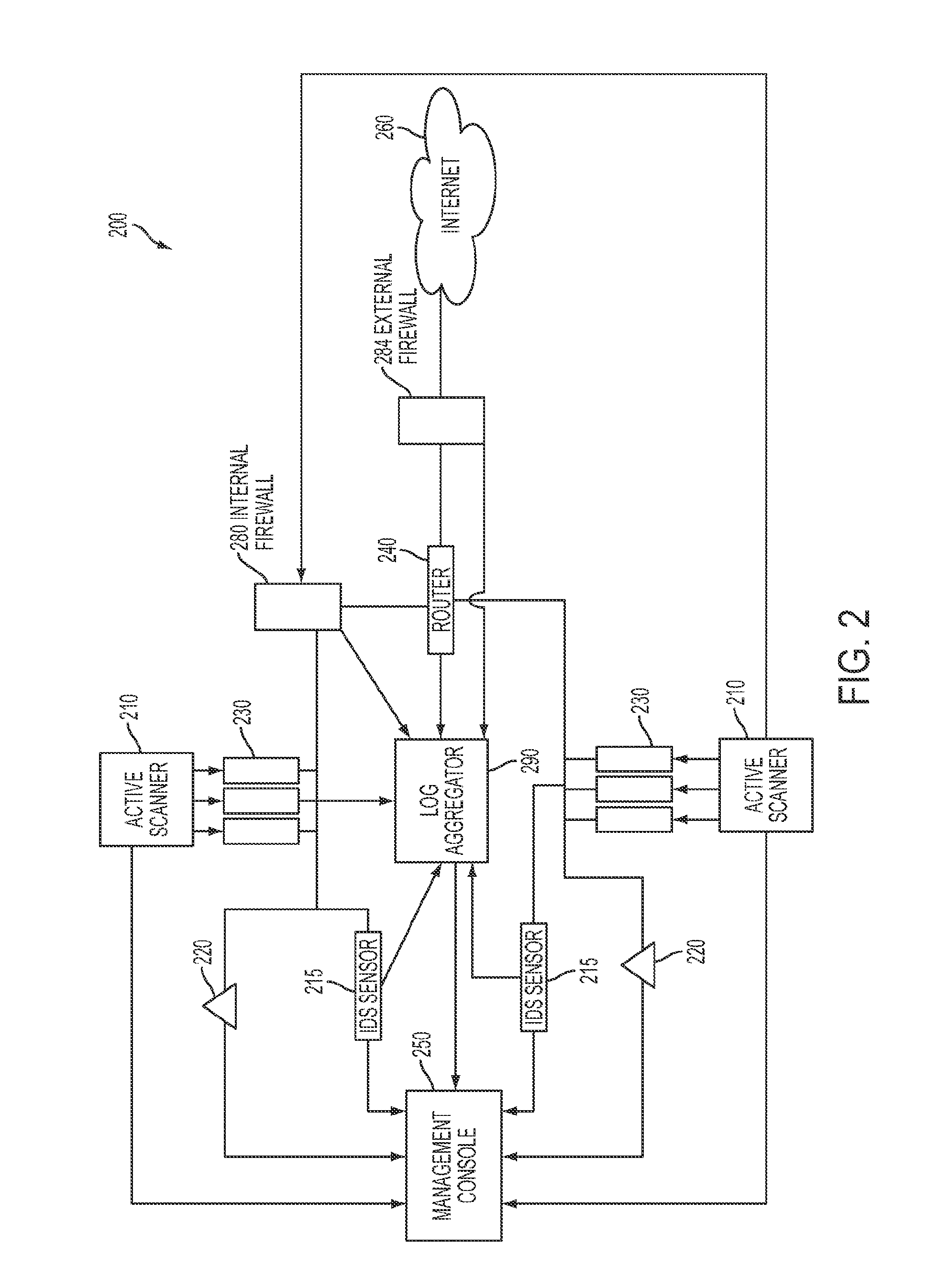
System and method for identifying exploitable weak points in a network
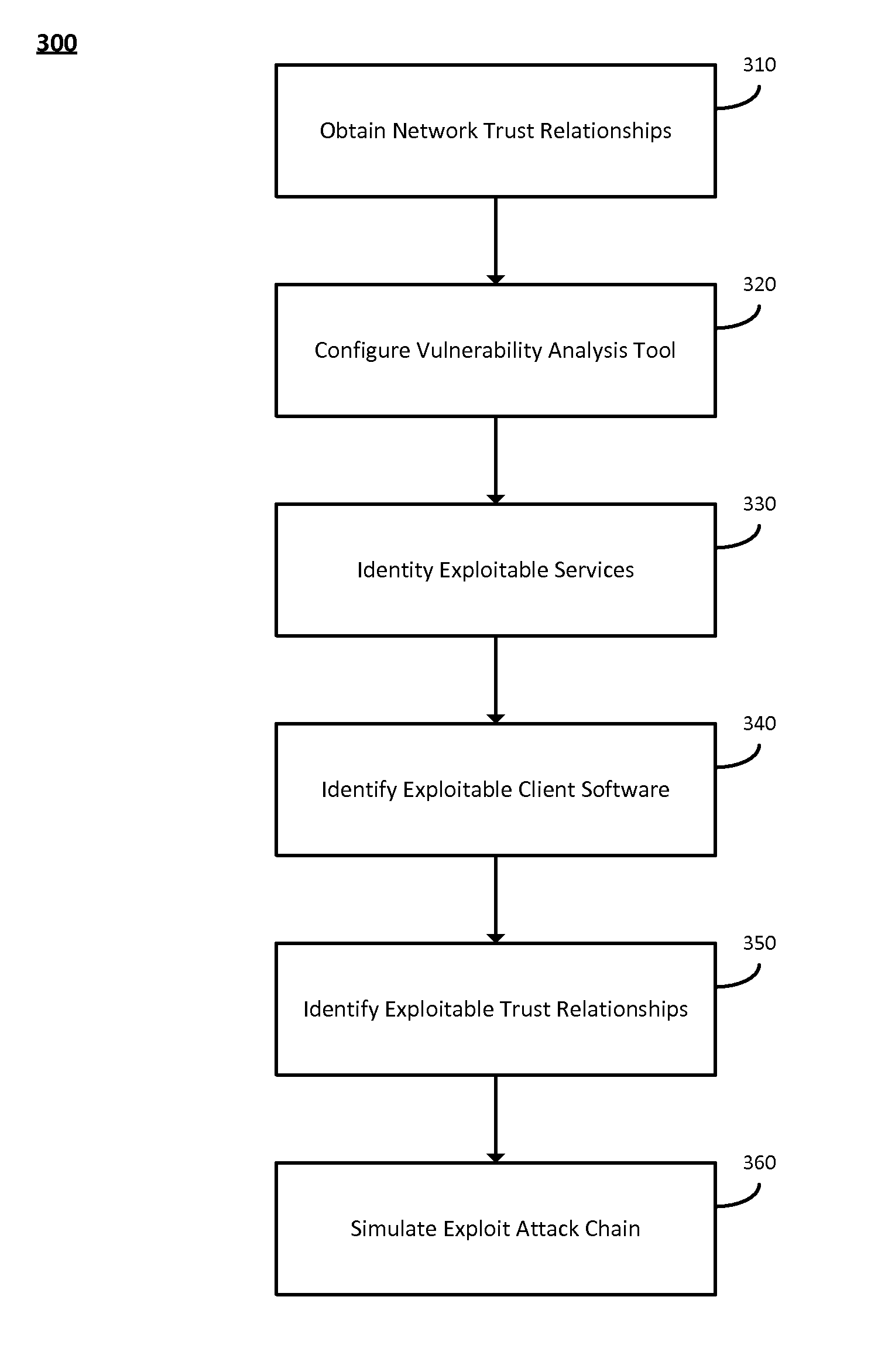
ActiveUS20140007241A1Low rateMemory loss protectionError detection/correctionOpen portTrust relationship
The system and method described herein may leverage passive and active vulnerability discovery to identify network addresses and open ports associated with connections that one or more passive scanners observed in a network and current connections that one or more active scanners enumerated in the network. The observed and enumerated current connections may be used to model trust relationships and identify exploitable weak points in the network, wherein the exploitable weak points may include hosts that have exploitable services, exploitable client software, and / or exploitable trust relationships. Furthermore, an attack that uses the modeled trust relationships to target the exploitable weak points on a selected host in the network may be simulated to enumerate remote network addresses that could compromise the network and determine an exploitation path that the enumerated remote network addresses could use to compromise the network.
Owner:TENABLE INC
High-fidelity earpiece with adjustable frequency response
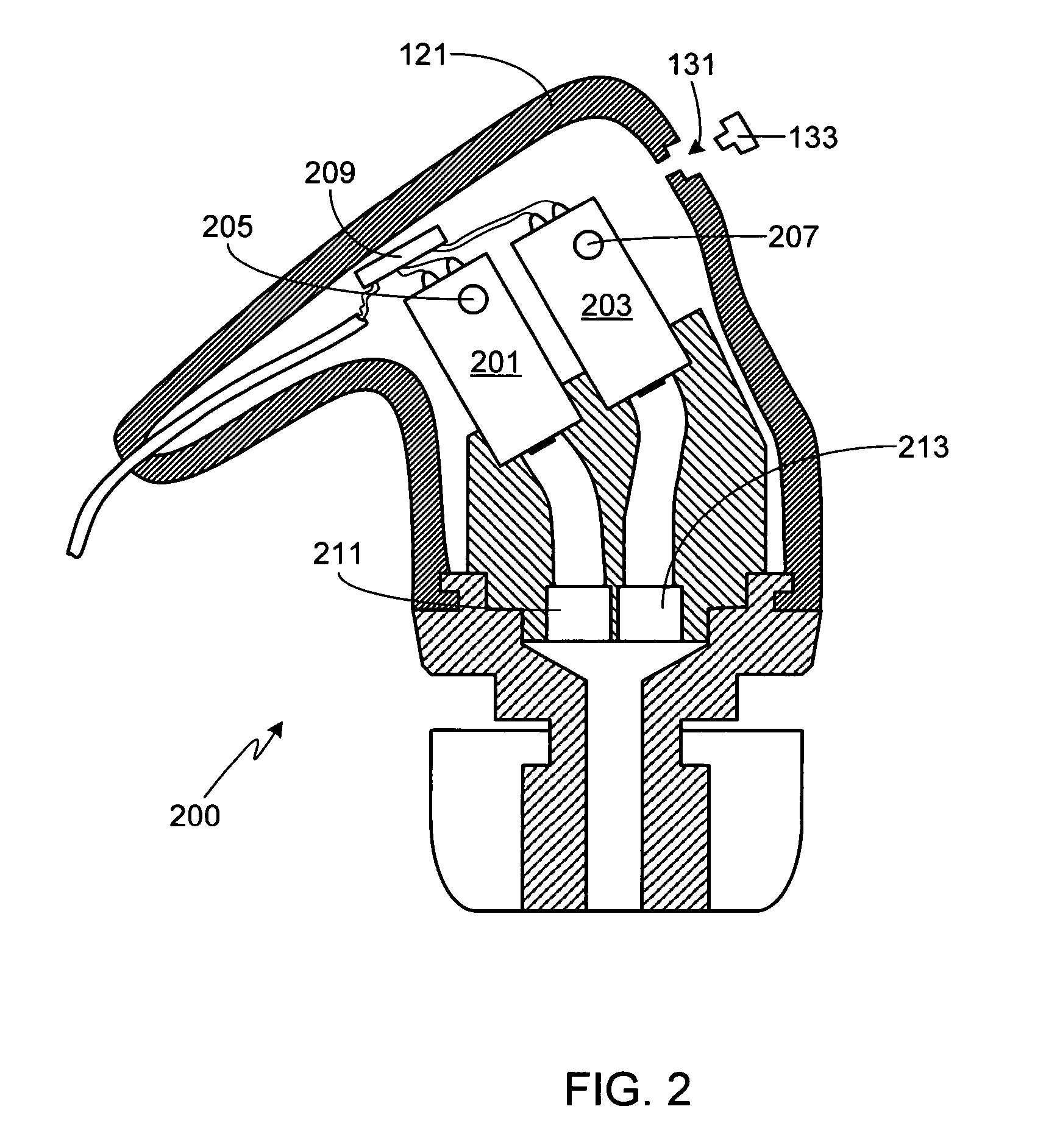
ActiveUS7634099B2Intra aural earpiecesEarpiece/earphone mechanical/electrical switchesOpen portHeadphones
Owner:LOGITECH INT
Air seeder/fertilizer apparatus having metering means and distribution manifold with selectively openable ports
An seeding apparatus having a distribution manifold with selectively openable outlet ports thereon, to permit or stop delivery of seed or fertilizer to selected soil engaging means on the apparatus. A metering means, responsive to both the number of selected open ports and the speed of the apparatus over the ground, is provided to regulate supply of seed / fertilizer to the distribution manifold. The distribution manifold has a plurality of outlet ports spaced about a periphery of such manifold, each outlet port having a valve means to allow opening and closing of individual outlet ports. Soil engaging means on such apparatus are individually raisable from an lowered operative position to a raised inoperative position, and when moved to such inoperative position, valve means associated with an outlet port for providing seed and / or fertilizer to such soil engaging member are closed to prevent supply to the associated soil engaging member.
Owner:ONE PASS IMPLEMENTS
High-fidelity earpiece with adjustable frequency response
ActiveUS20070036385A1Intra aural earpiecesEarpiece/earphone mechanical/electrical switchesOpen portHeadphones
An earpiece is provided that includes an earpiece enclosure, a sound delivery member that contains a sound delivery tube, and one or more drivers. The earpiece enclosure includes one or more enclosure ports that couple the internal enclosure volume to the volume outside of the earpiece. Corresponding to each enclosure port is a port cover that has at least a fully open port position and a fully closed port position. Preferably the port covering means is capable of multiple positions between the fully open port position and the fully closed port position. The port cover can be a plug, a rotating earpiece collar, a sliding cover, or other means. In at least one embodiment, separate drivers and / or separate volumes within the earpiece enclosure are coupled to separate enclosure ports.
Owner:LOGITECH INT
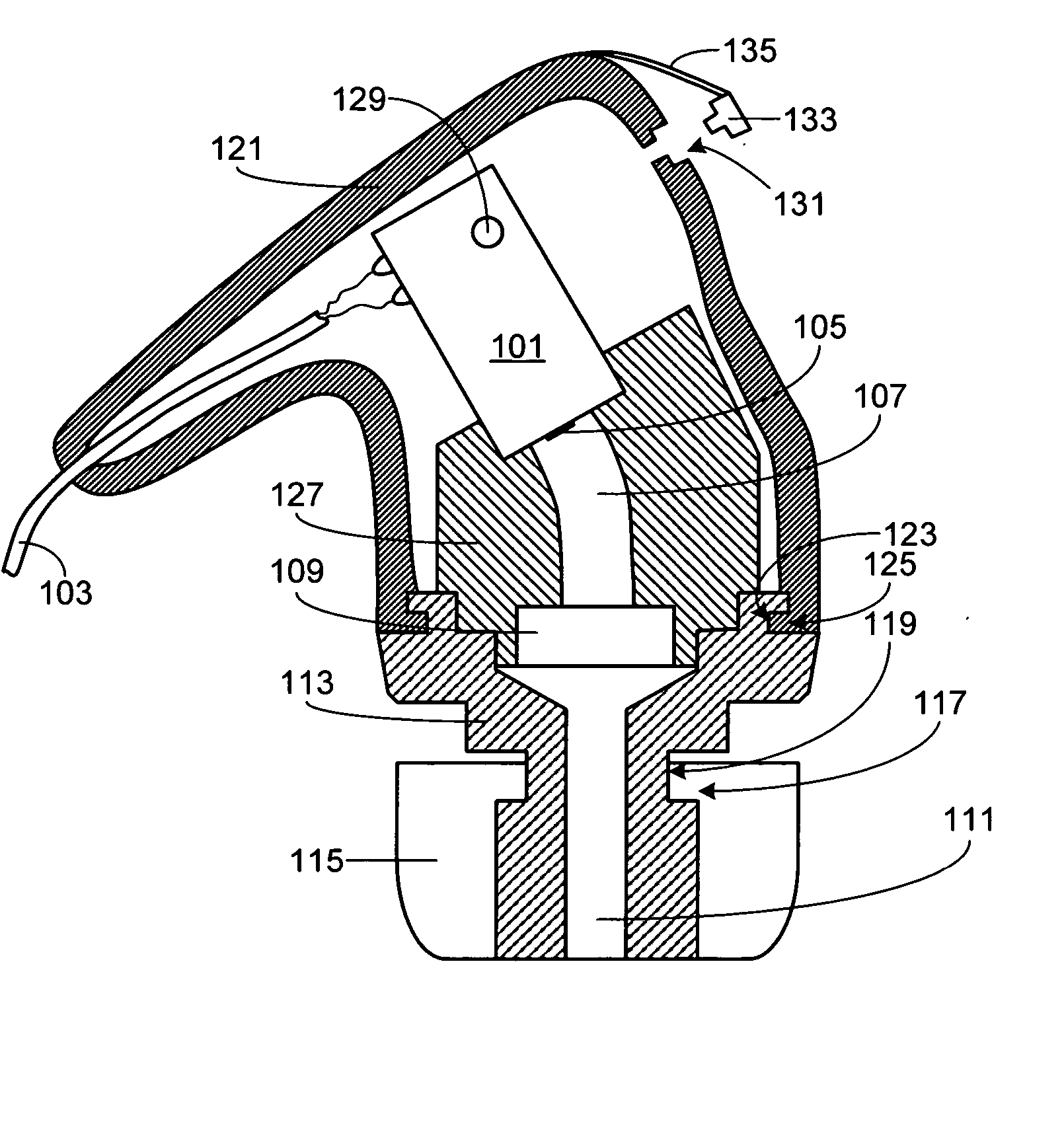
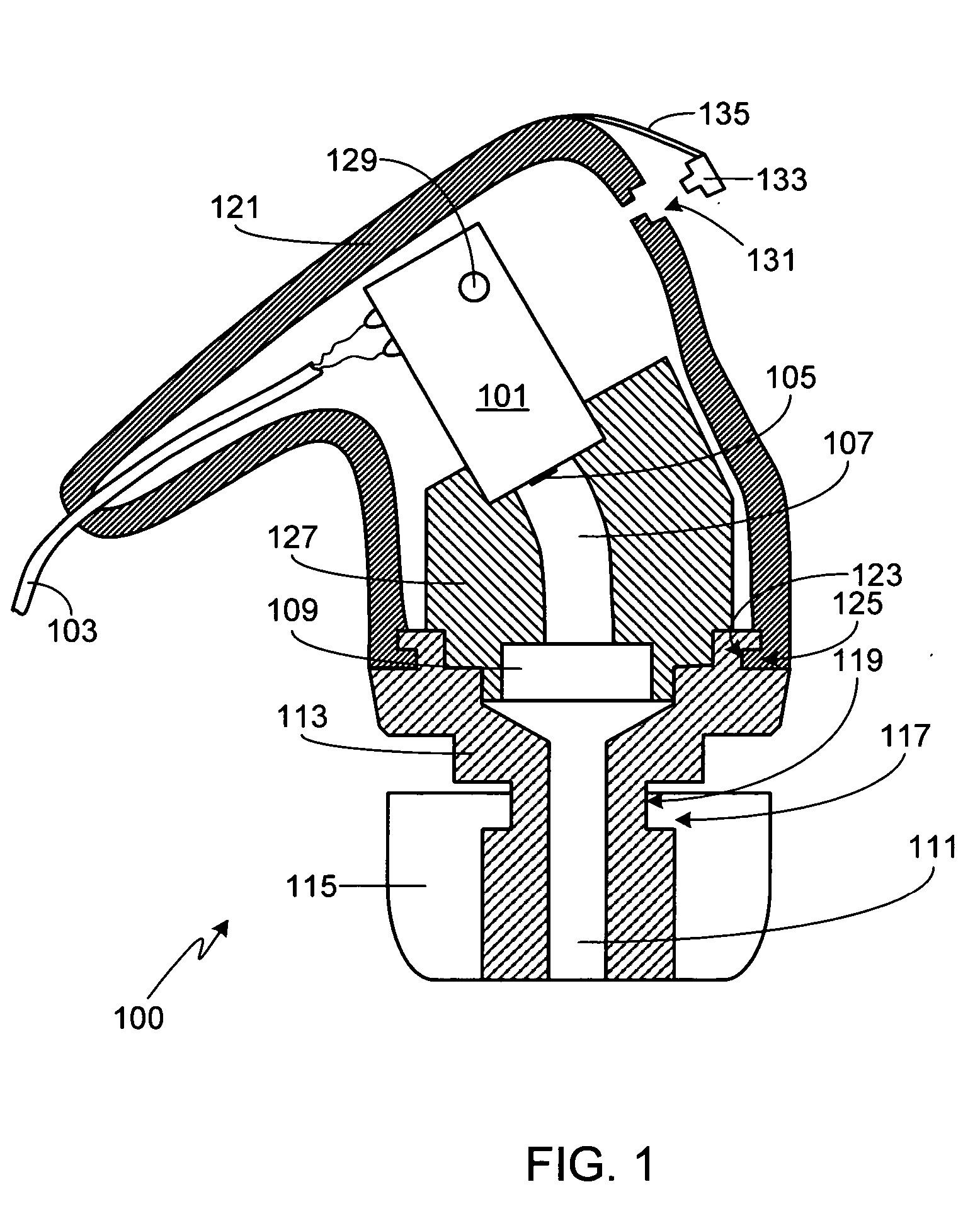
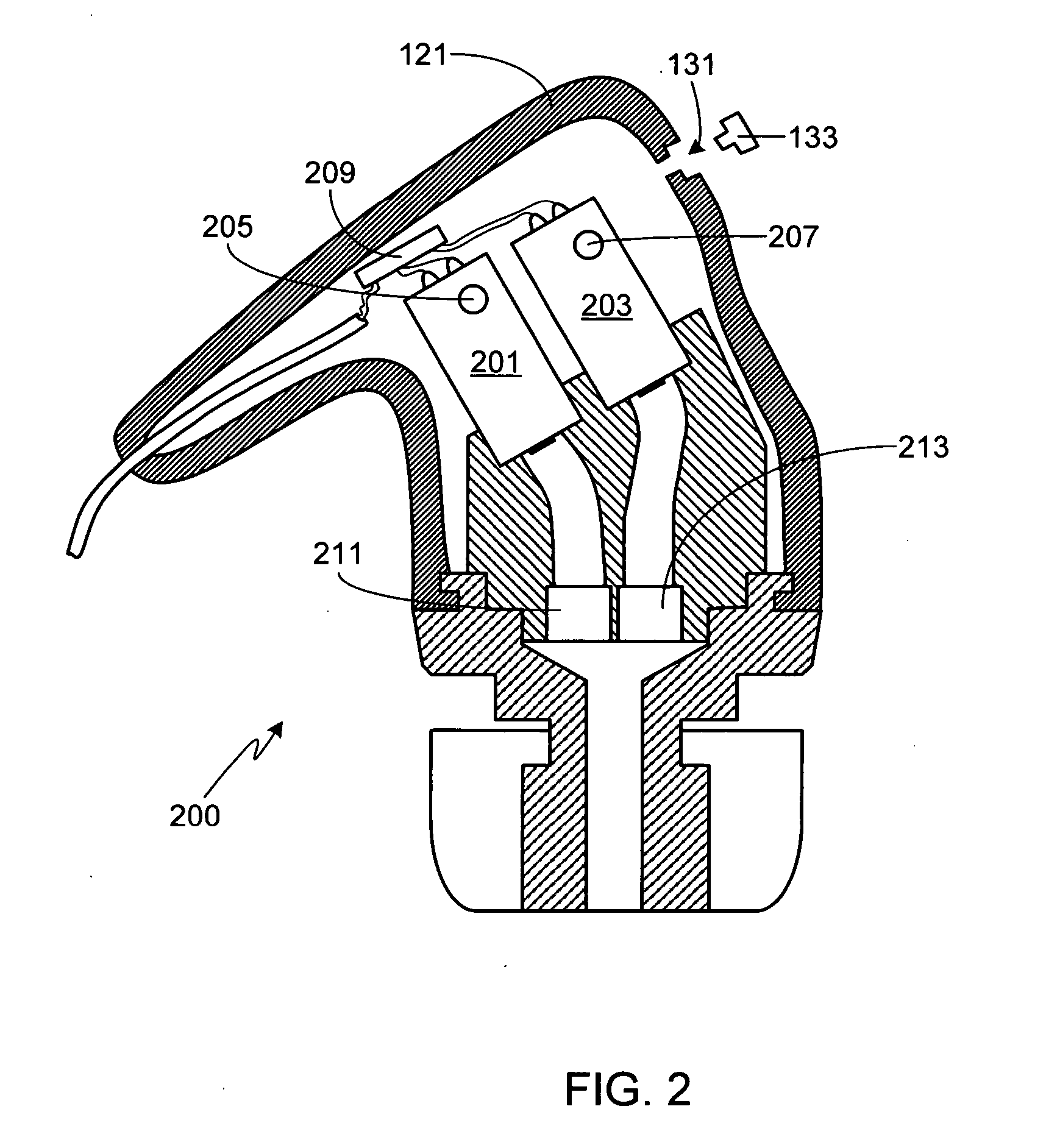
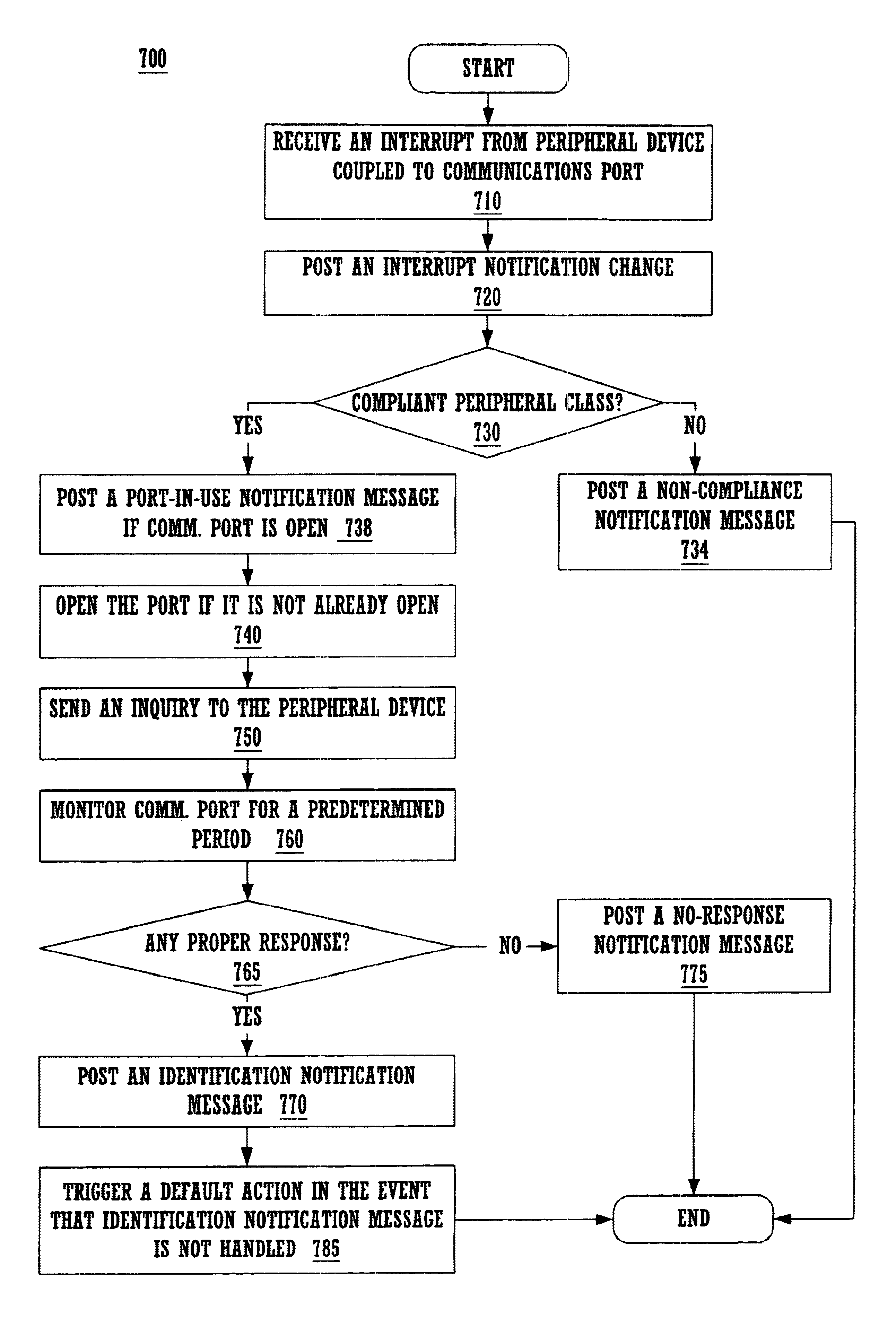
System for indentifying a peripheral device by sending an inquiry thereto after receiving an interrupt notification message if the interrupt and communication port meet predetermined conditions
Method and system for latency-independent peripheral device identification. In one embodiment, a computer system receives an interrupt from a peripheral device coupled to a computer system communications port. In response, an interrupt notification message is posted alerting a notification handler running on the system. It is determined whether the interrupt is indicates peripheral class compliance. In one embodiment, communications port device sense pin voltage is determinative. If the interrupt indicates peripheral class compliance and the communications port is inactive, the port is opened, and inquiry sent to the peripheral device via the open port. The computer system then waits for response from the peripheral device. If response is received within a predetermined time, identification is posted based on the response, including peripheral device classification information, so that a software handler registered with the operating system can handle the identification message when received. Thus, this embodiment imposes no time-critical interrupt response.
Owner:QUALCOMM INC
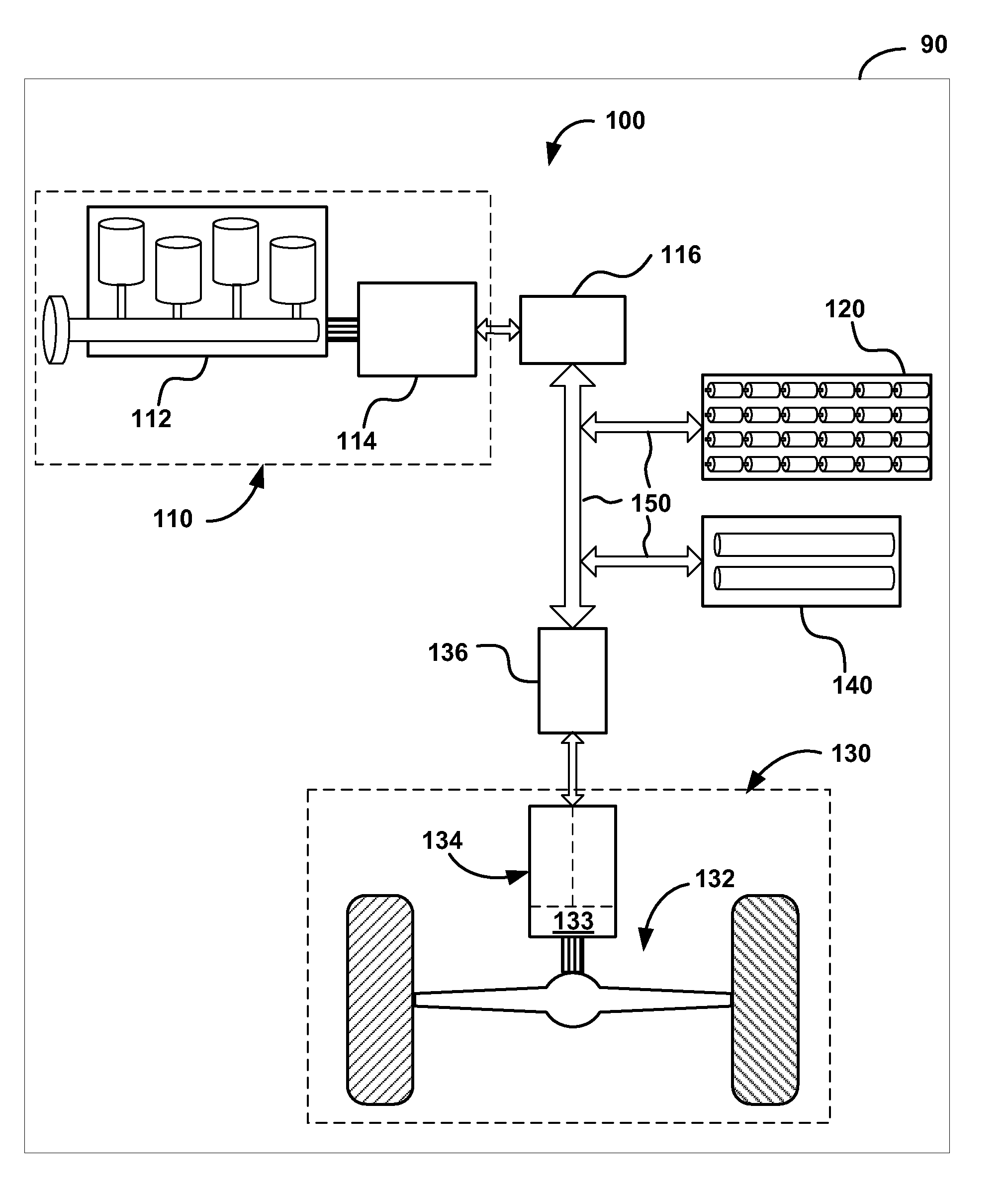
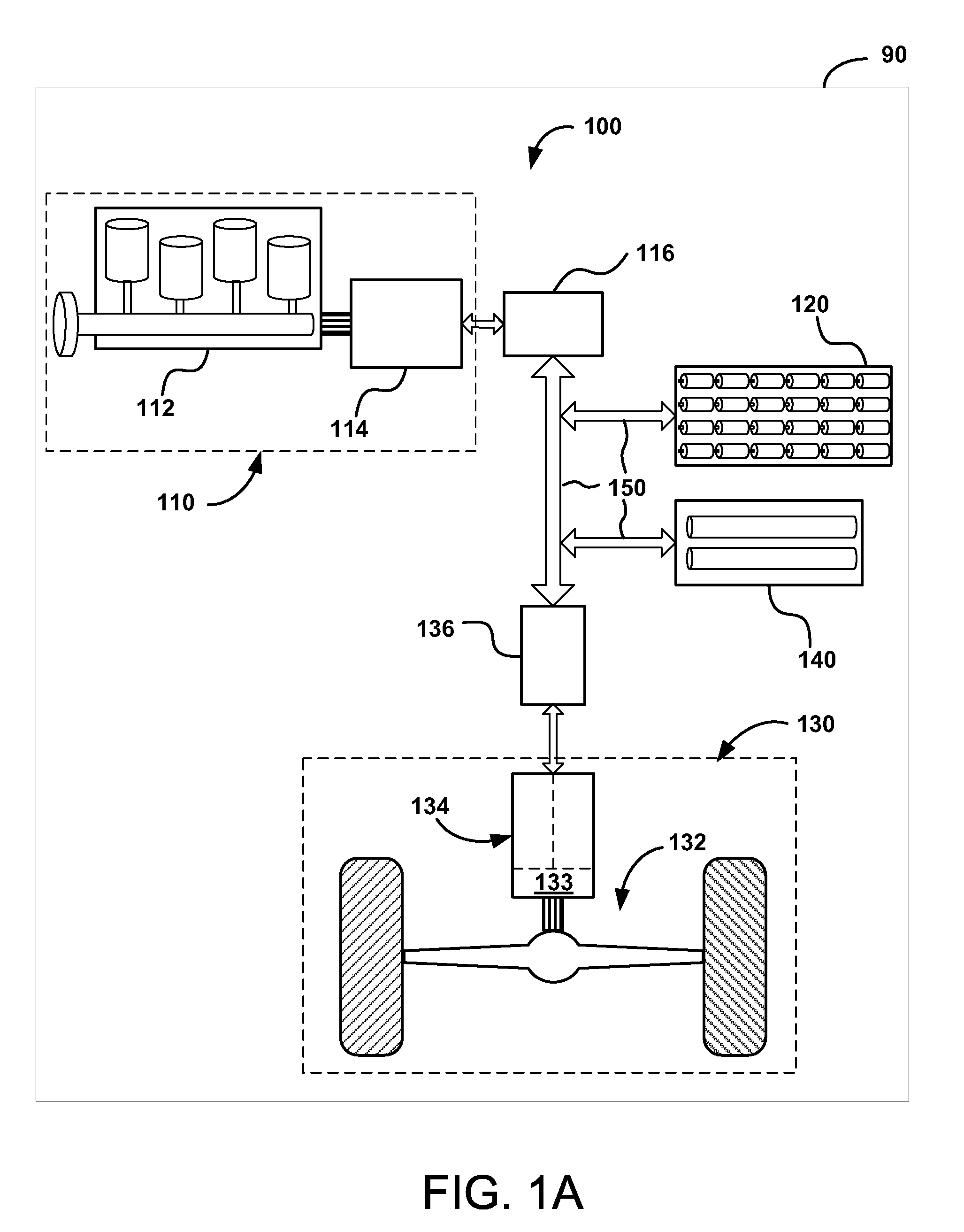
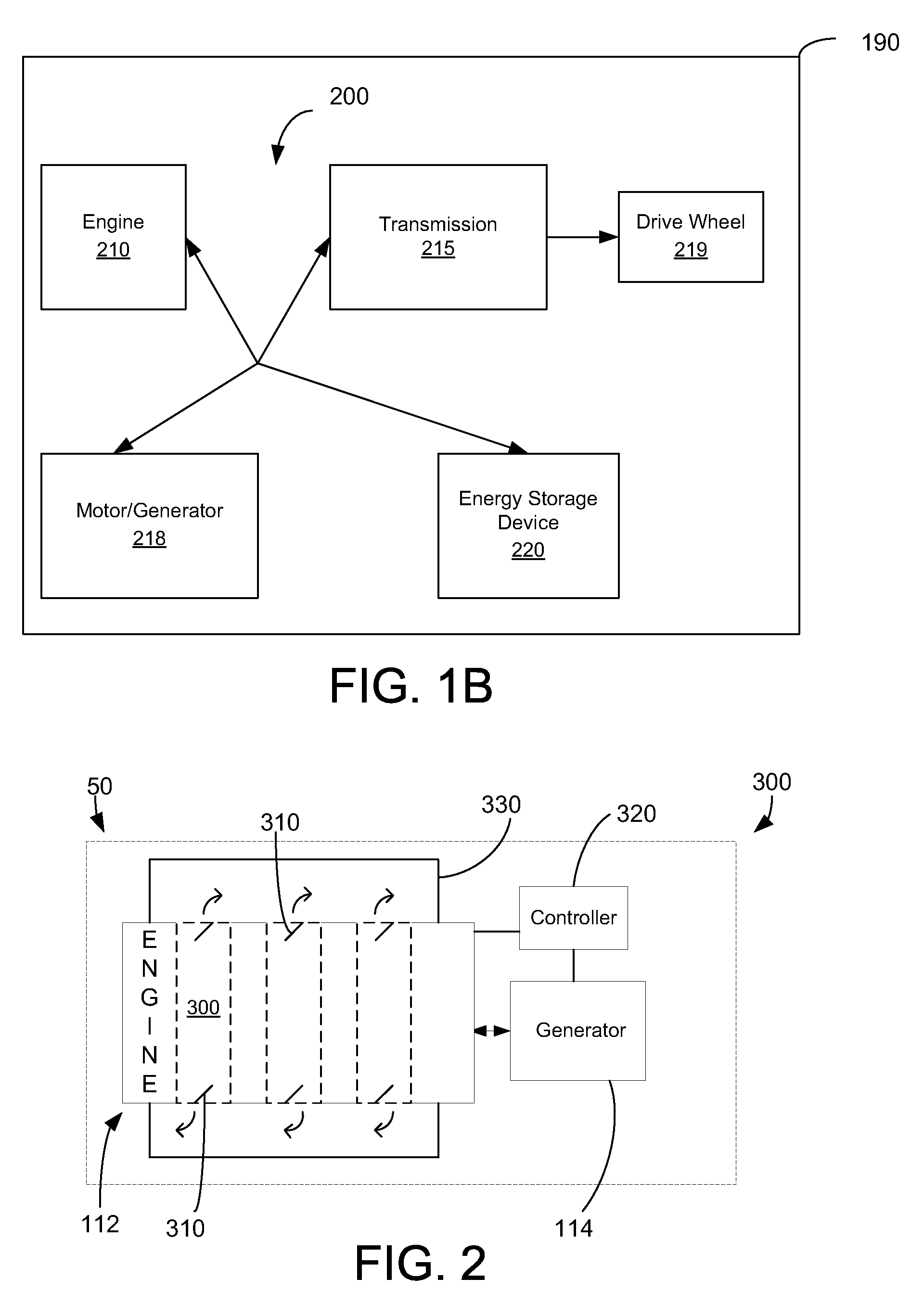
Hybrid Vehicle Vibration Reduction System and Method
InactiveUS20090271057A1Reduce vibrationReduce NVH resonanceElectrical controlInternal combustion piston enginesOpen portCombustion chamber
Owner:SHEPPARD MULLIN RICHTER & HAMPTON
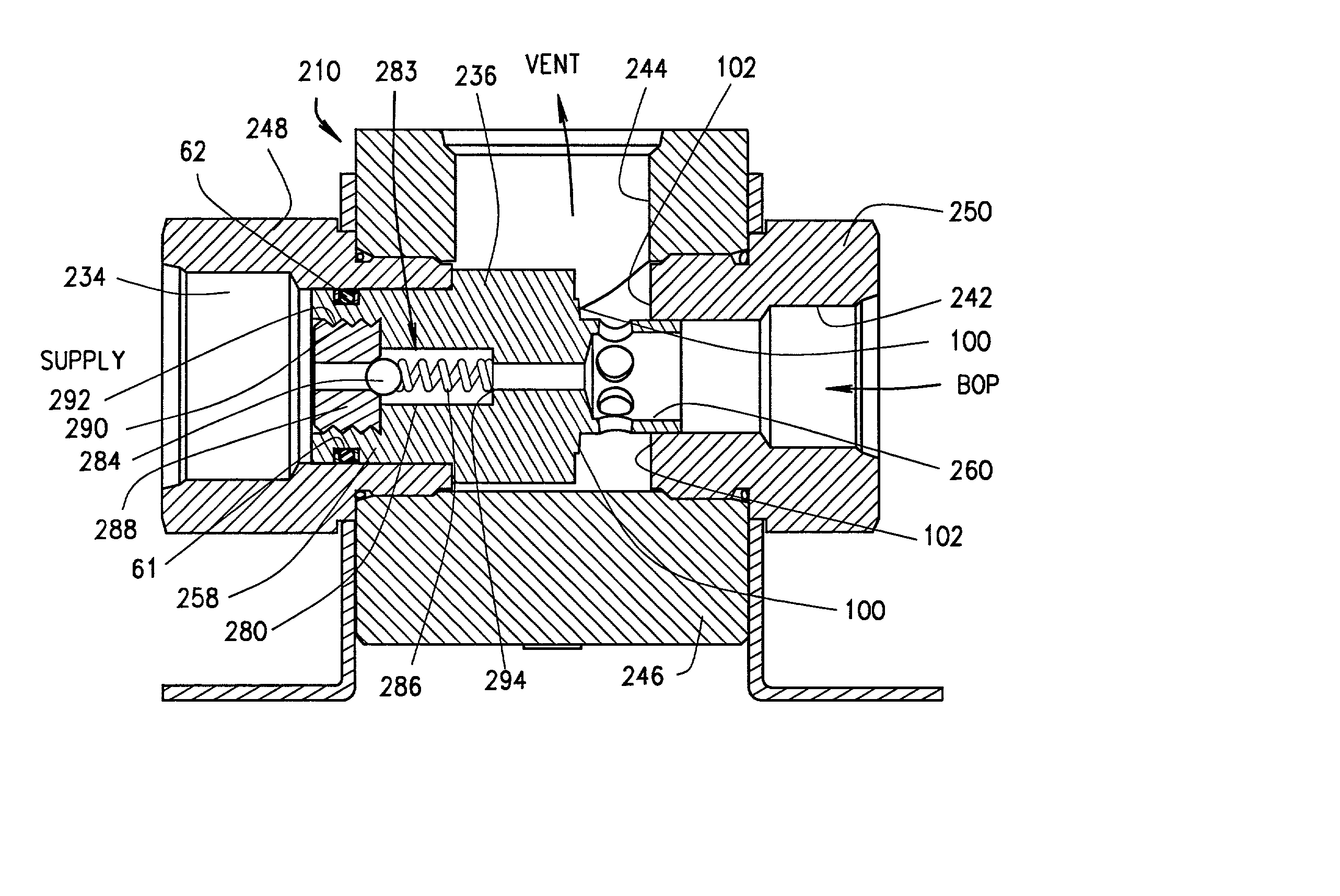
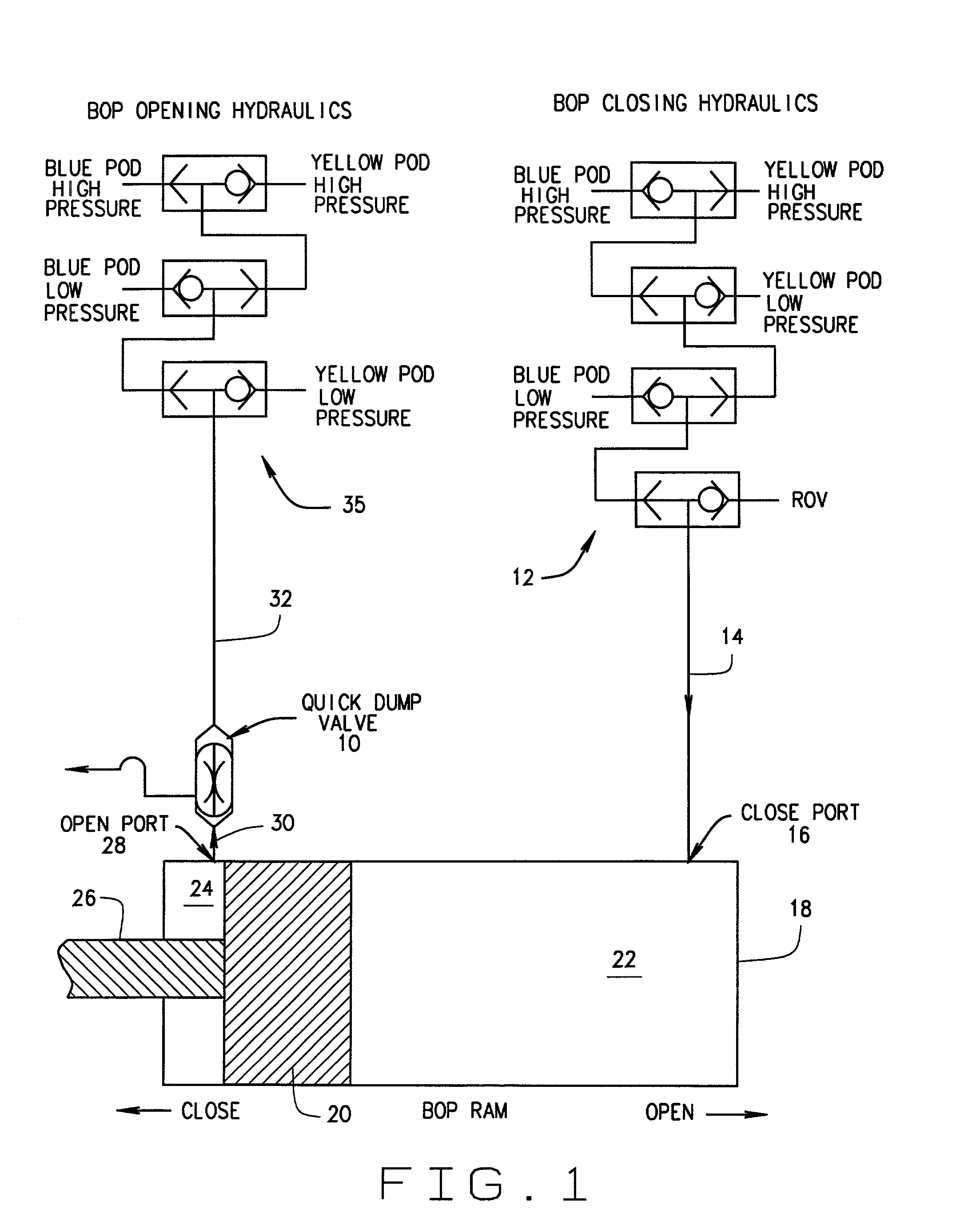
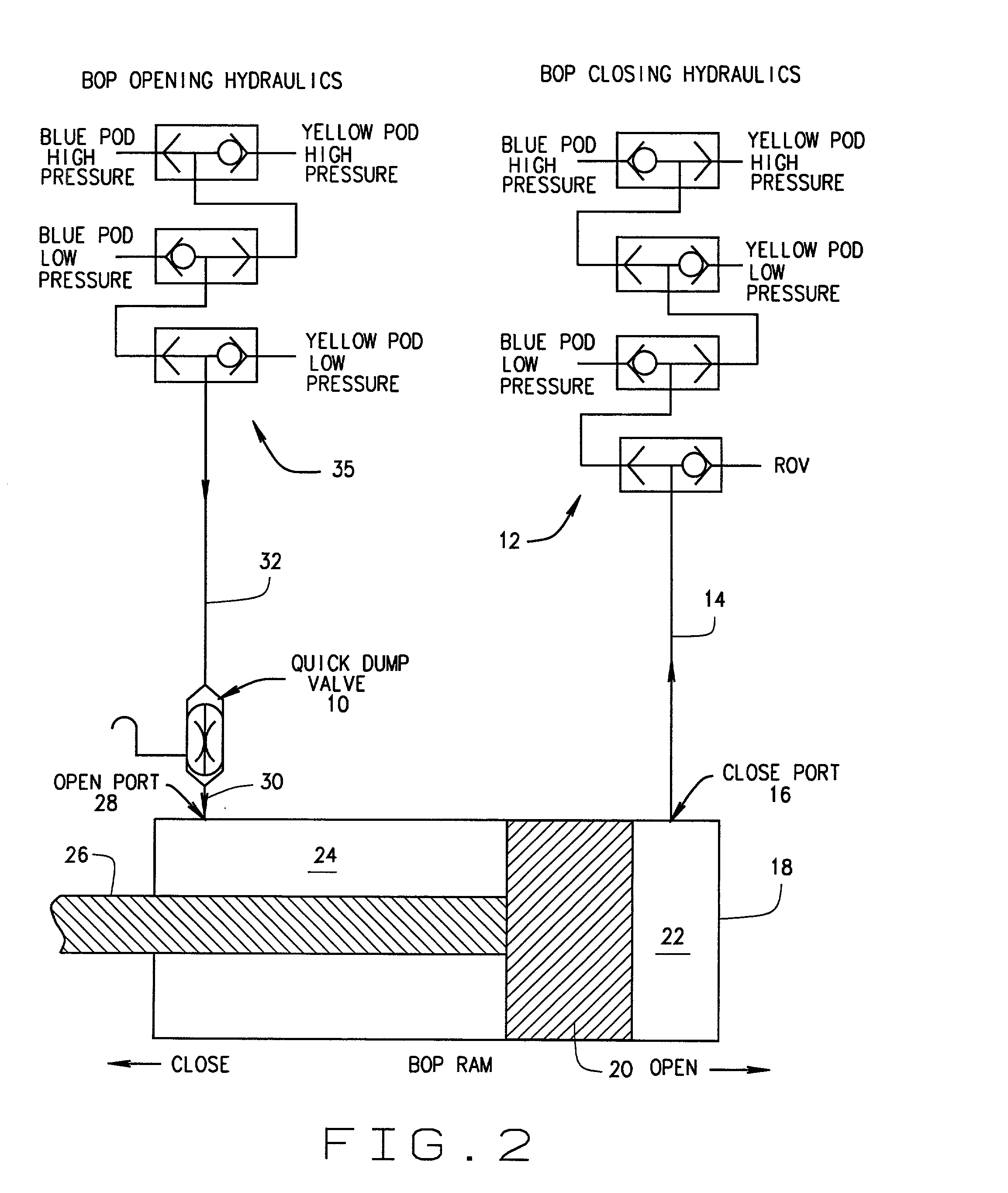
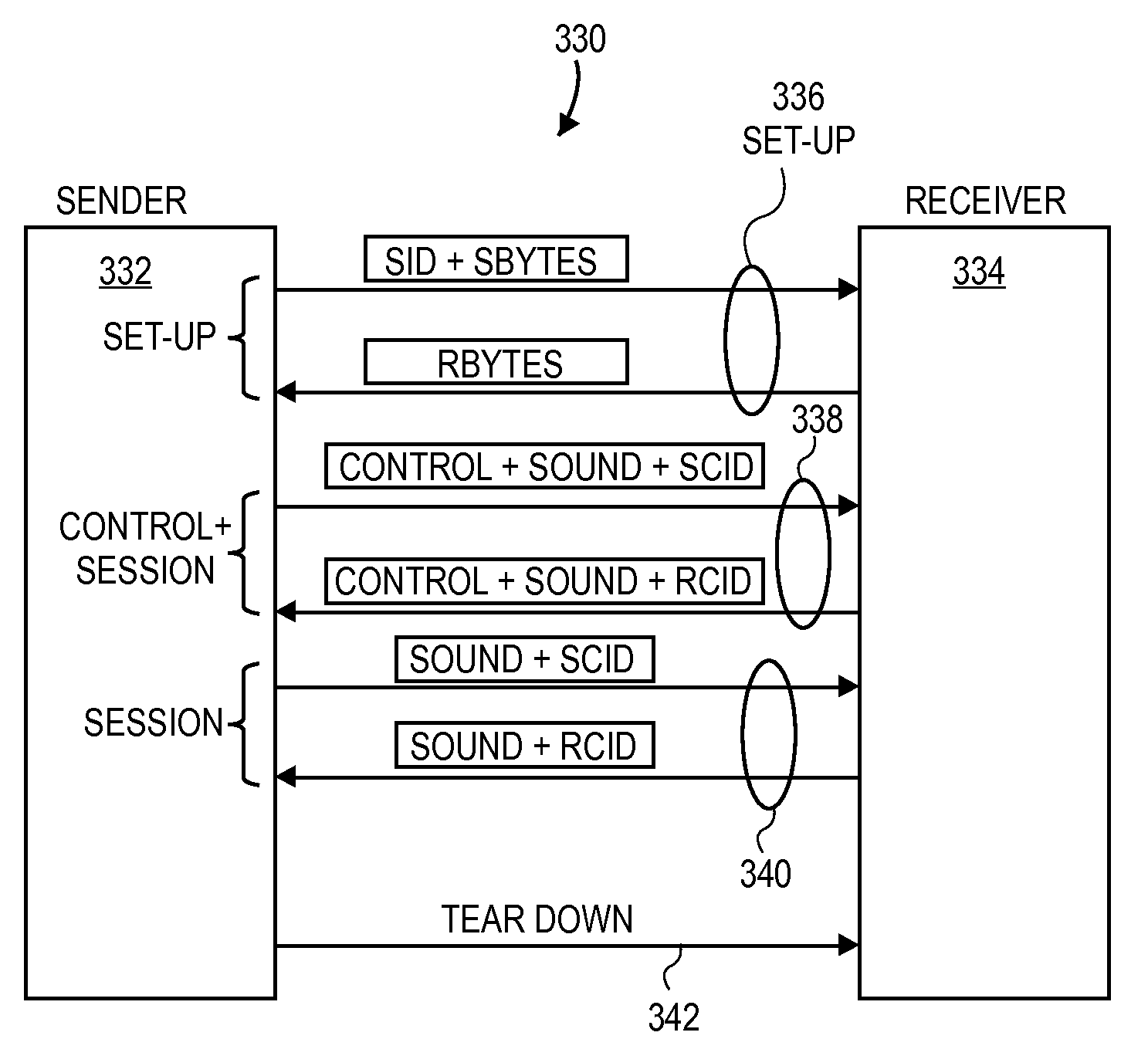
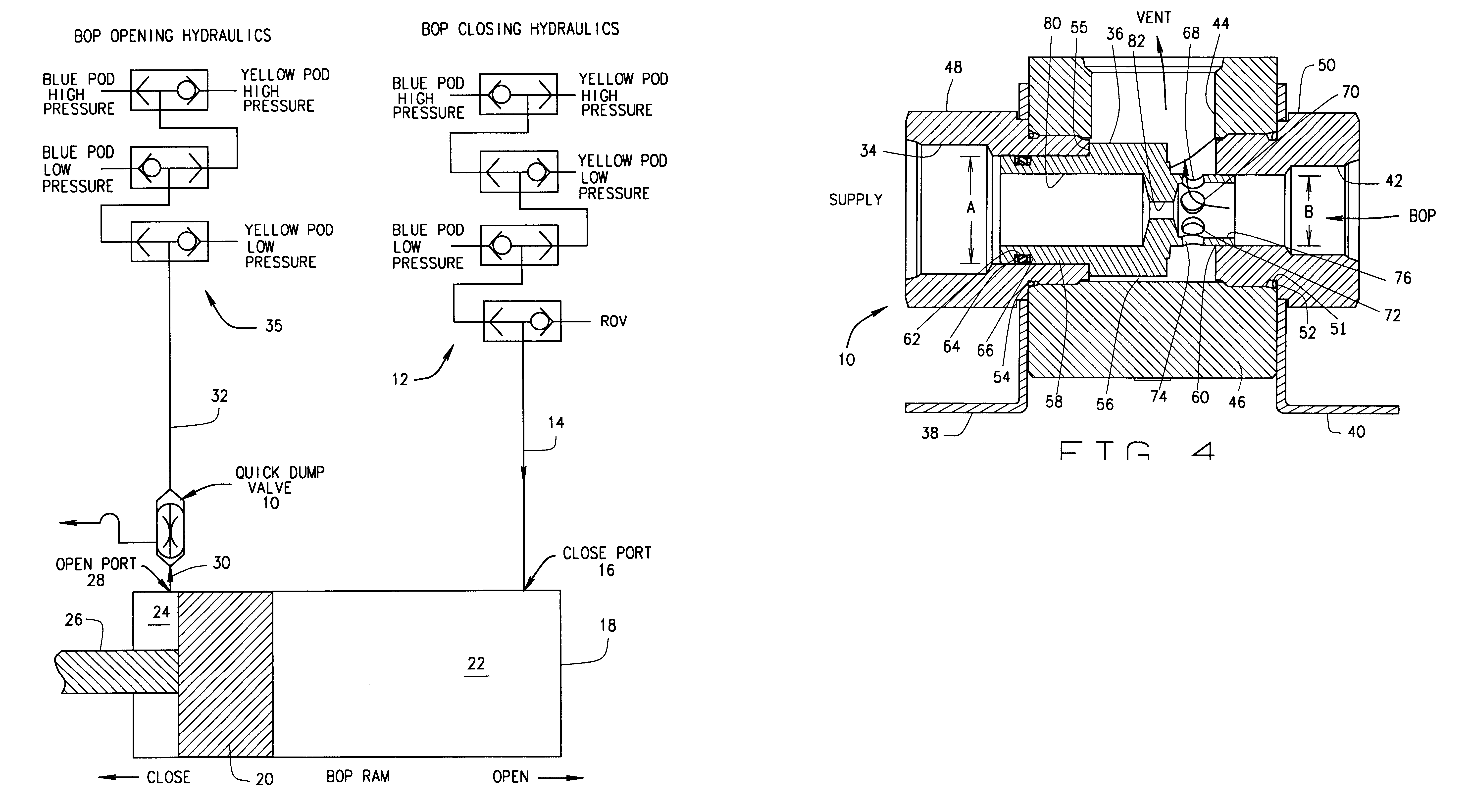
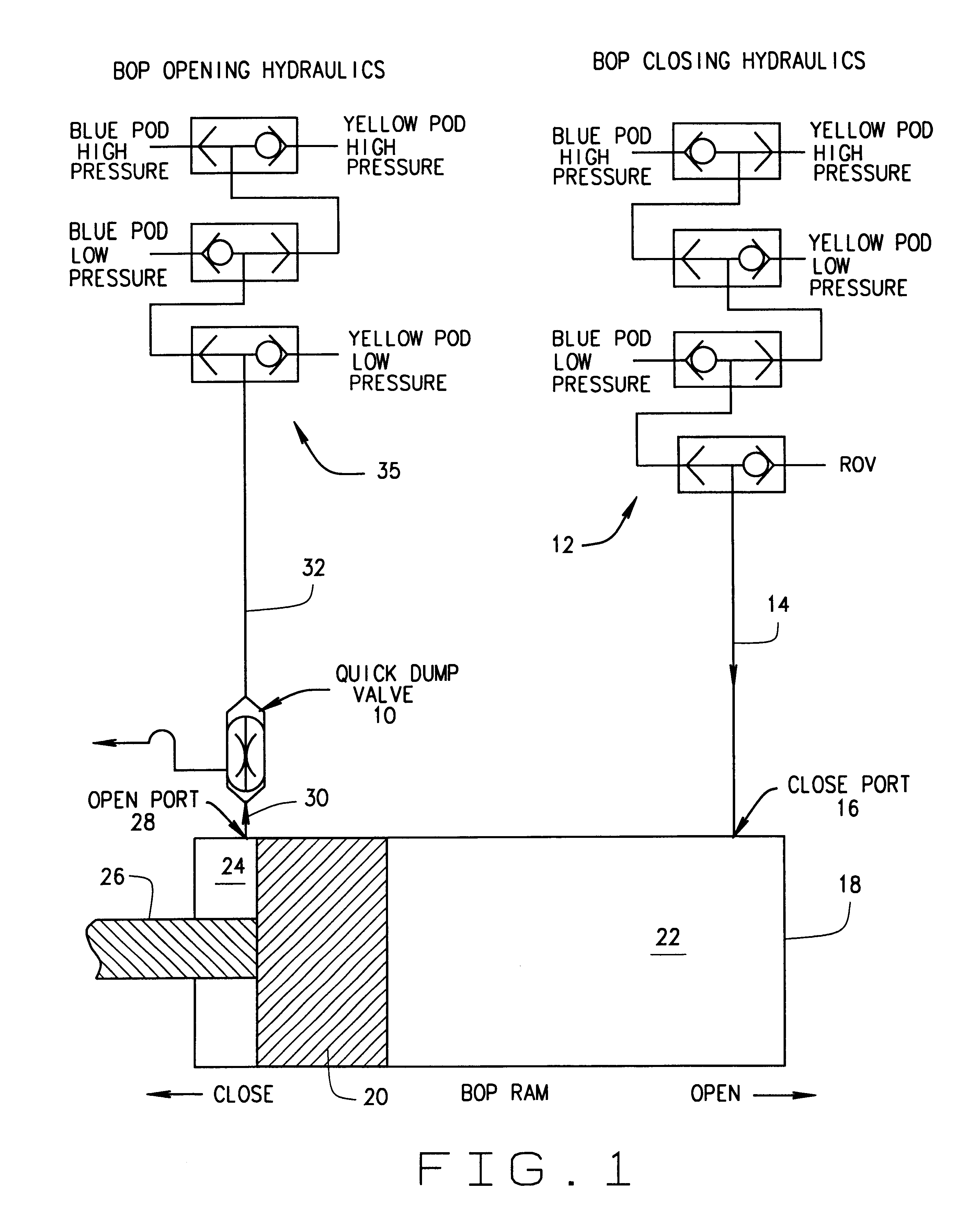
BOP operating system with quick dump valve
In some prior art Blowout Preventer (BOP) operating systems, high velocity fluid flows and low differential pressures induced vibration in the system. This vibration may result in collapse and failure of hydraulic hoses in the system. A quick dump valve has been added at or near the open port on the BOP assembly to reduce vibration and other problems. The dump valve has a vent position and an open position. Several alternative embodiments add a ball check valve assembly to the shuttle in the quick dump valve.
Owner:PROSERV GILMORE VALVE LLC +1
Globally unique identification in communications protocols and databases
InactiveUS20100325430A1Reduces overhead bitMultiplex system selection arrangementsSpecial service provision for substationOpen portNetwork Communication Protocols
A globally unique identification system for a communications protocol and database is disclosed. A method for generating the globally unique identification code and for generating a compressed globally unique identification code is also described. The communications protocol permits multiple communications sessions to be sent through a single open port of a firewall.
Owner:INTEL CORP
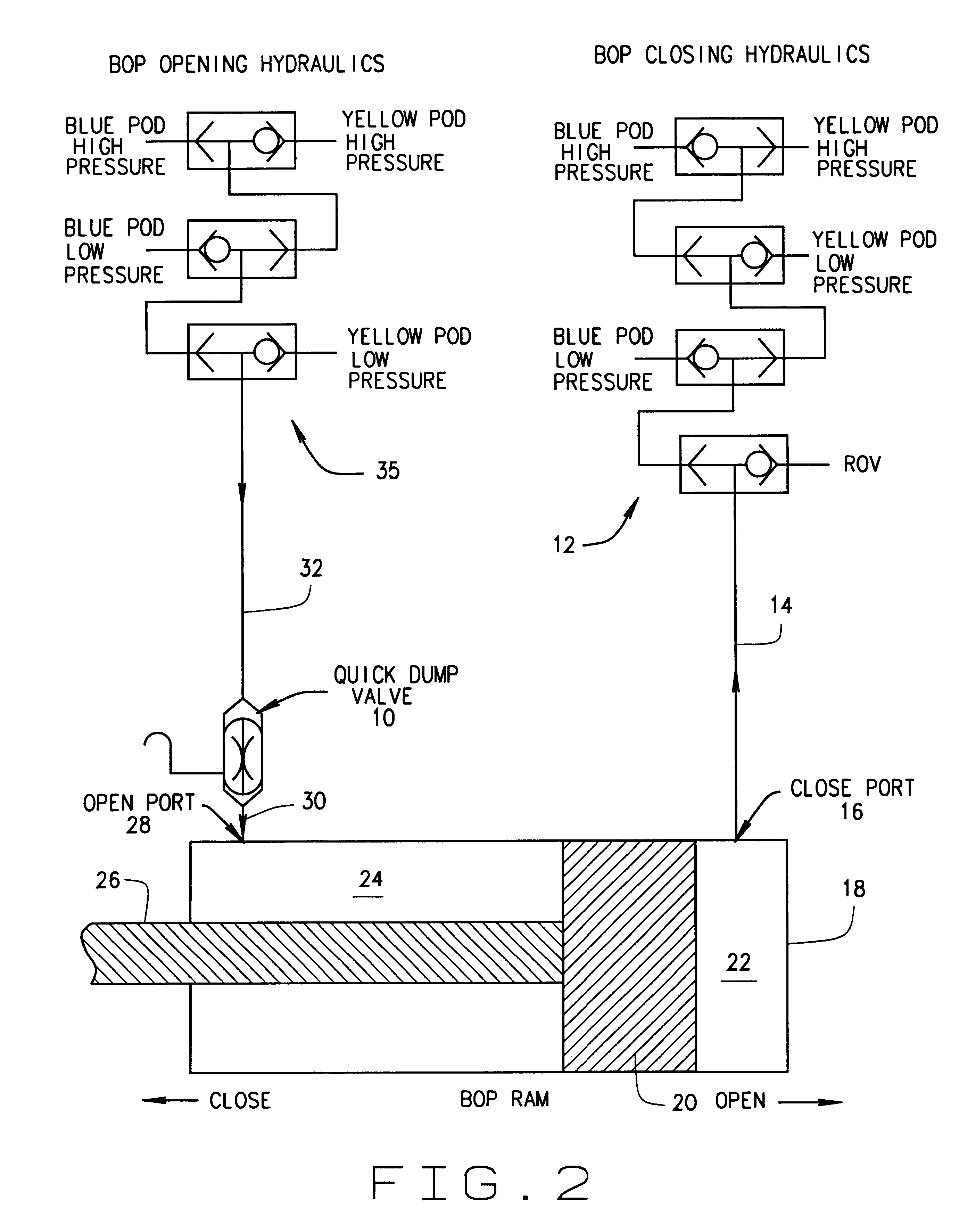
BOP operating system with quick dump valve
In some prior art Blowout Preventer (BOP) operating systems, high velocity fluid flows and low differential pressures induced vibration in the system. This vibration may result in collapse and failure of hydraulic hoses in the system. A quick dump valve has been added at or near the open port on the BOP assembly to reduce vibration and other problems. The dump valve has a vent position and an open position. Several alternative embodiments add a ball check valve assembly to the shuttle in the quick dump valve.
Owner:PROSERV GILMORE VALVE LLC +1
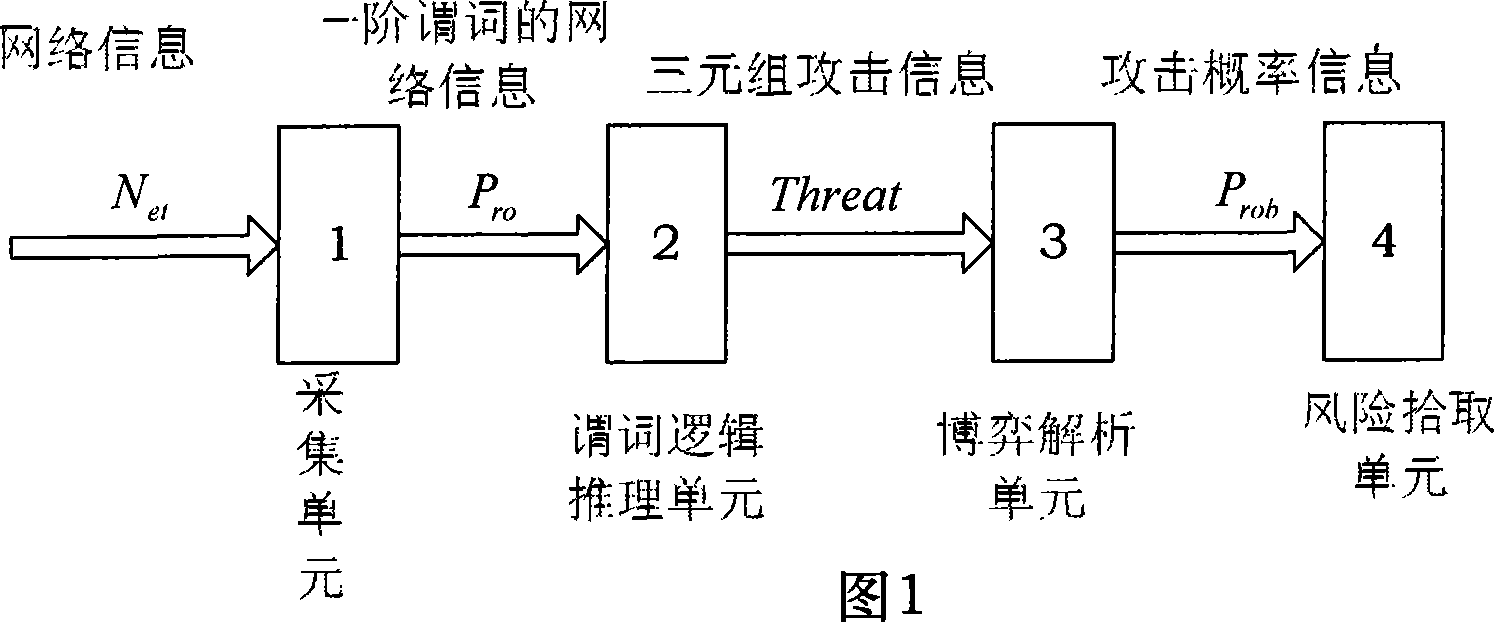
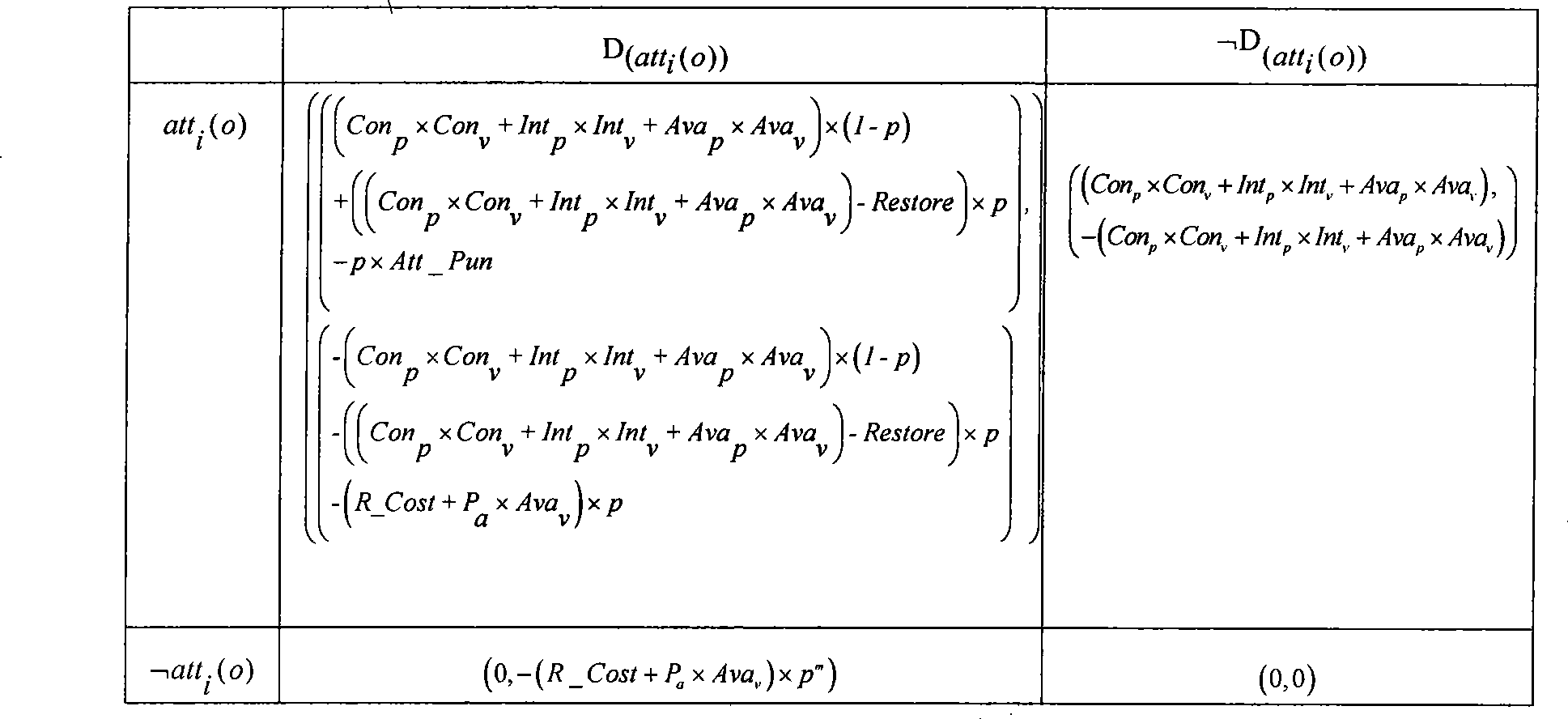
Network security risk evaluation system based on game theory
The present invention discloses a network safety risk evaluating system based on game theory. The system firstly collects network property data which comprises information of node address, service, application program, software leak, etc. from an evaluated network, describes with a first-order predicate logic, reasons with an XSB reasoning engine based on the description of first-order predicate logic, and obtaining the leak which is on the evaluated network system and can be used by an attacker, and a corresponding attack threat. Aiming at each attack threat, the system according to the invention establishes a game theoretical attack-defense model GTADM and calculates the game equilibrium point. The obtained attack probability is multiplied to the expected damage value of the attack to the attack target for obtaining the attack risk to the system. Thereby the risk level of nodes in the evaluated system is obtained and the security evaluating to the network is realized.
Owner:BEIHANG UNIV
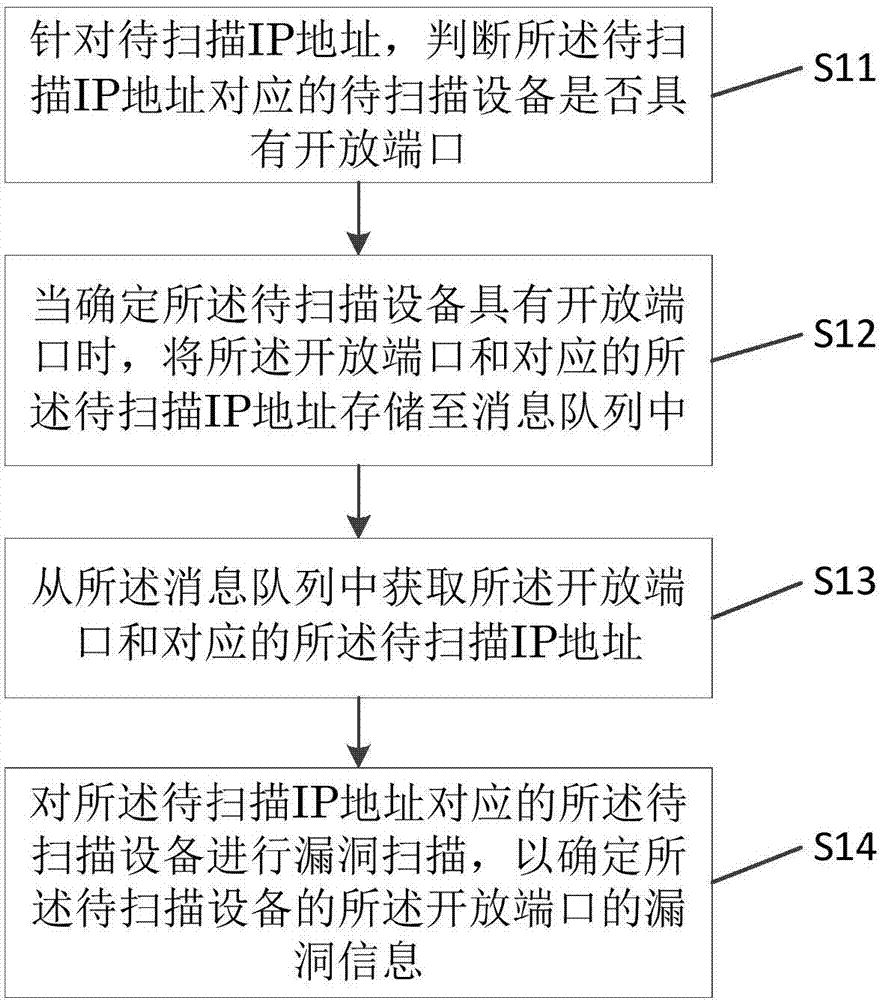
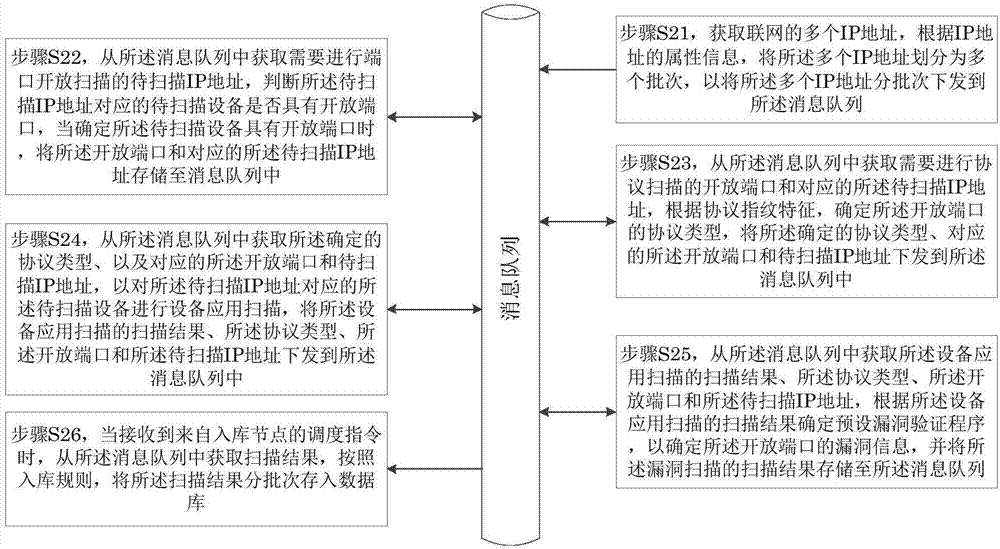
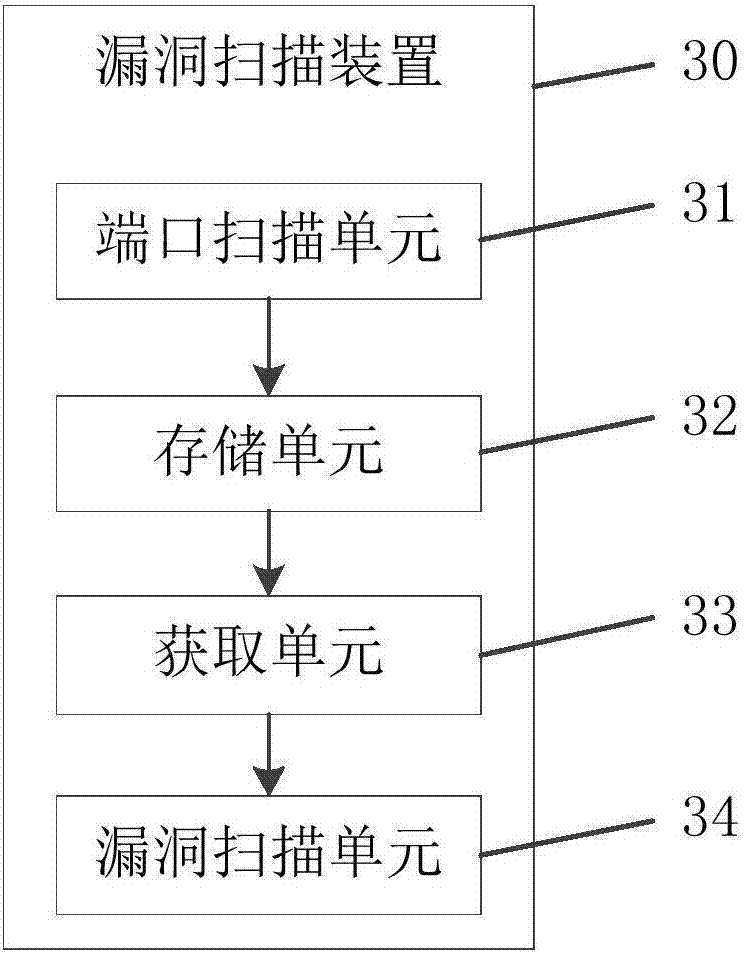
Vulnerability scanning method and device
The invention provides a vulnerability scanning method and device. The method comprises a step of judging whether equipment to be scanned corresponding to an IP address to be scanned has an open port for the IP address to be scanned, a step of storing the open port and the corresponding IP address to be scanned into a message queue when a condition that the equipment to be scanned has the open port is determined, a step of obtaining the open port and the corresponding IP address to be scanned from the message queue, and a step of carrying out vulnerability scanning on the equipment to be scanned corresponding to an IP address to be scanned so as to determine the vulnerability information of the open port of the equipment to be scanned. Through the vulnerability scanning method and device, by using a message queue mechanism, the vulnerability discovery efficiency of online equipment corresponding to massive IP addresses is improved.
Owner:BEIJING KUANGEN NETWORK TECH
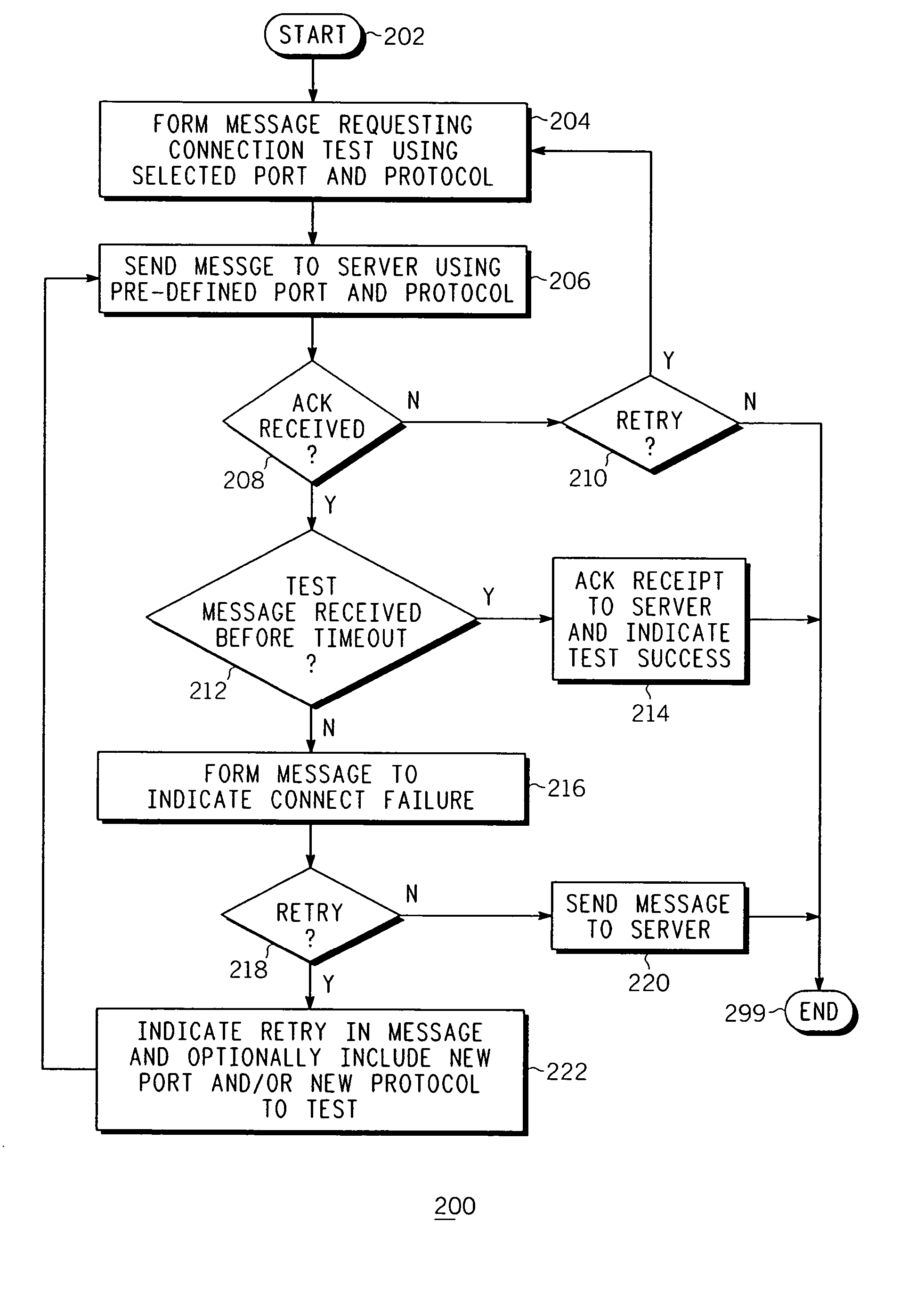
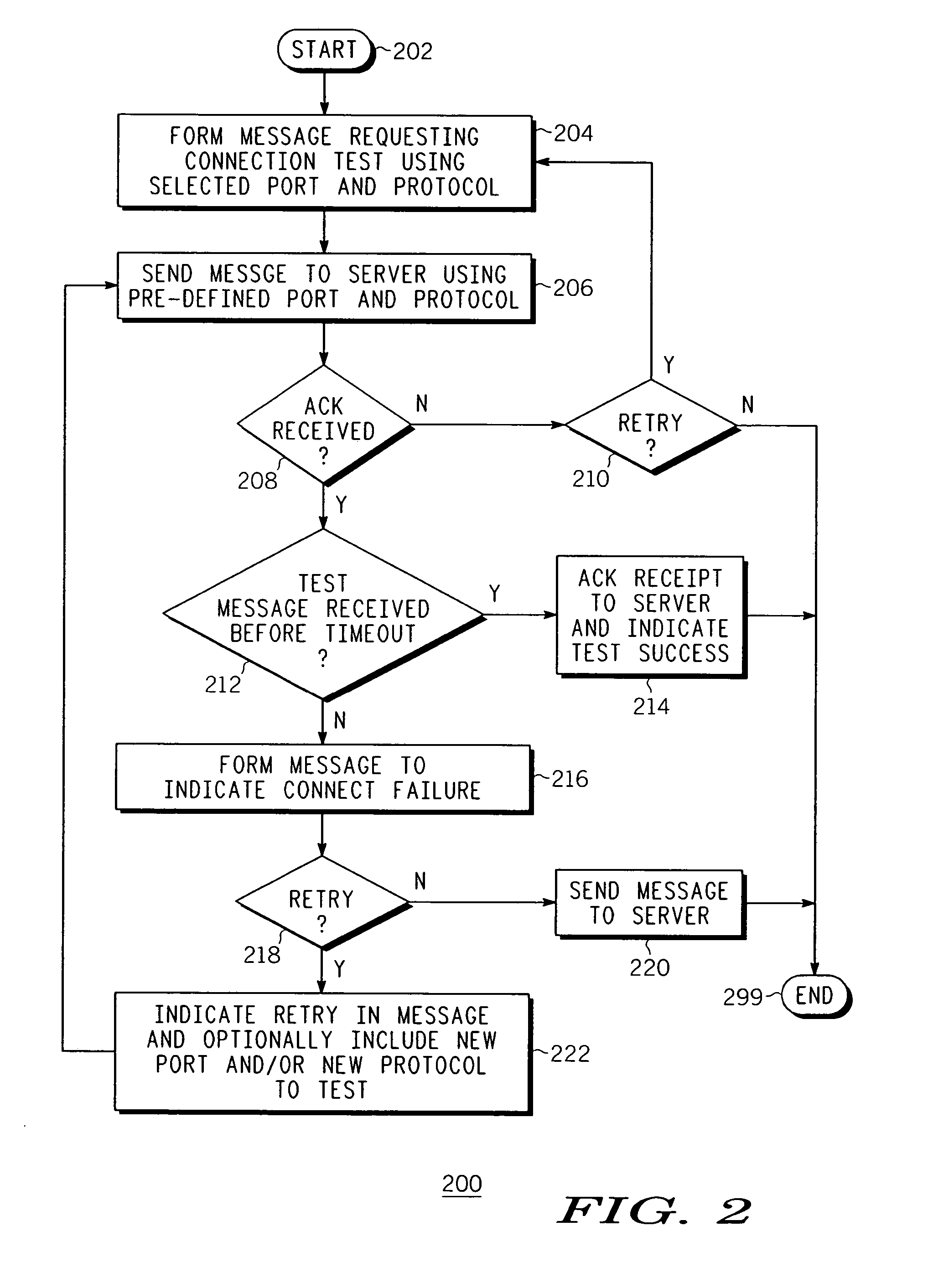
Method and apparatus for testing for open ports of an endpoint device in a packet network
Method, apparatus, and computer readable medium for testing for an open port of an endpoint device in a communication network is described. A test request message is sent from the endpoint device to a server. The test request message is configured to request the server to send a test message to a port of the endpoint device using a protocol. The port is polled for the test message during a time period. The port is indicated as being open if the test message is received by the endpoint device at the port before expiration of the time period. A connect failure message is sent to the server if the test message is not received by the endpoint device at the port before expiration of the time period. The connect failure message may be configured to request the server to send another test message to the endpoint device.
Owner:GENERAL INSTR CORP
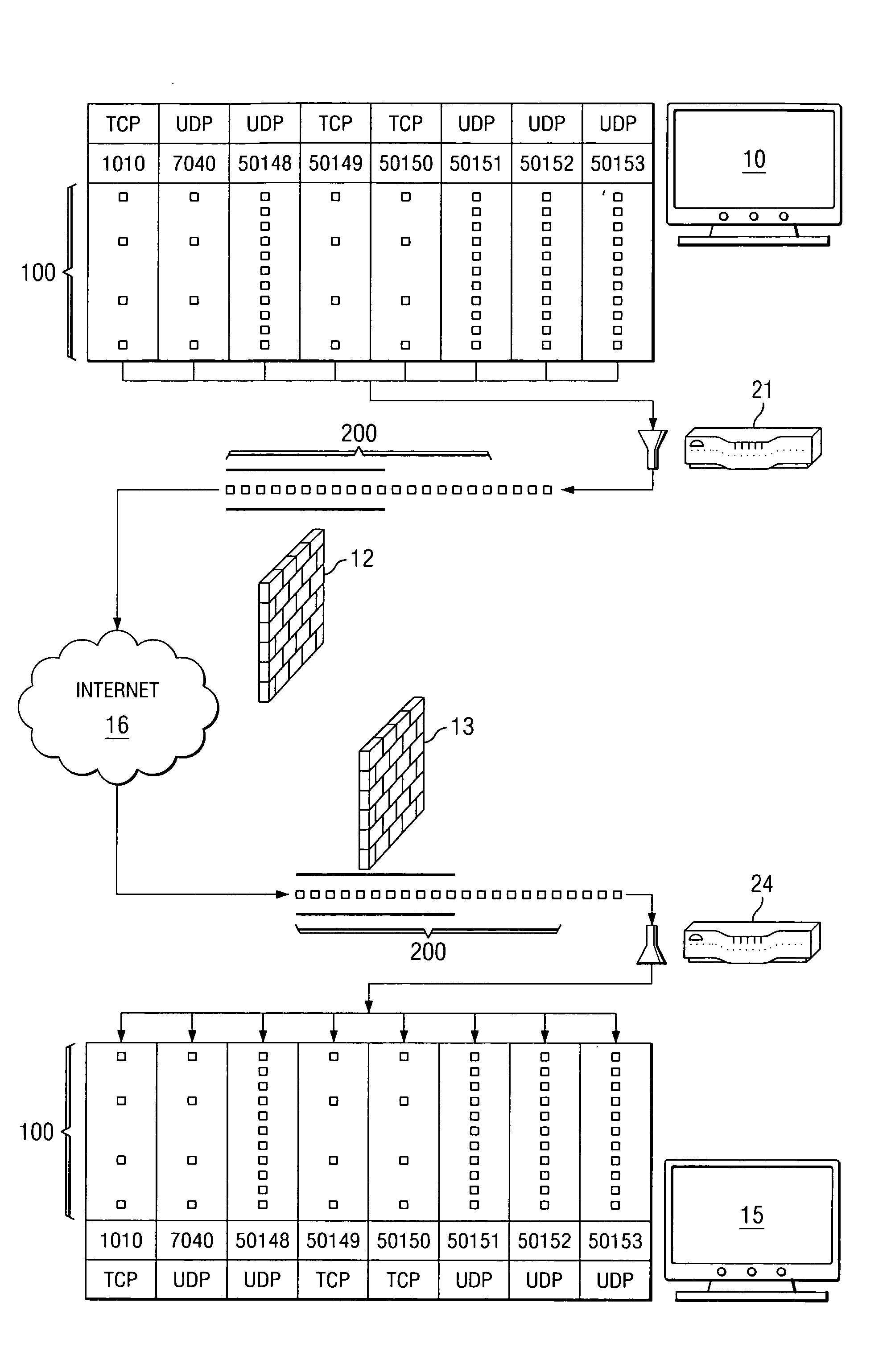
System and method for traversing a firewall with multimedia communication
Systems and methods are disclosed for transporting multiport protocol traffic using a single-port protocol. Multiport protocol traffic from a first endpoint is converted into a single-port protocol for transport across a network. The traffic is sent over a commonly-open port and received at a second endpoint before being dispersed to the appropriate ports of the second endpoint. By converting the traffic to a single-port protocol and choosing which commonly open port to communicate the traffic through, firewalls between each endpoint may be traversed without changing any of their settings.
Owner:DIRECTPACKET RES
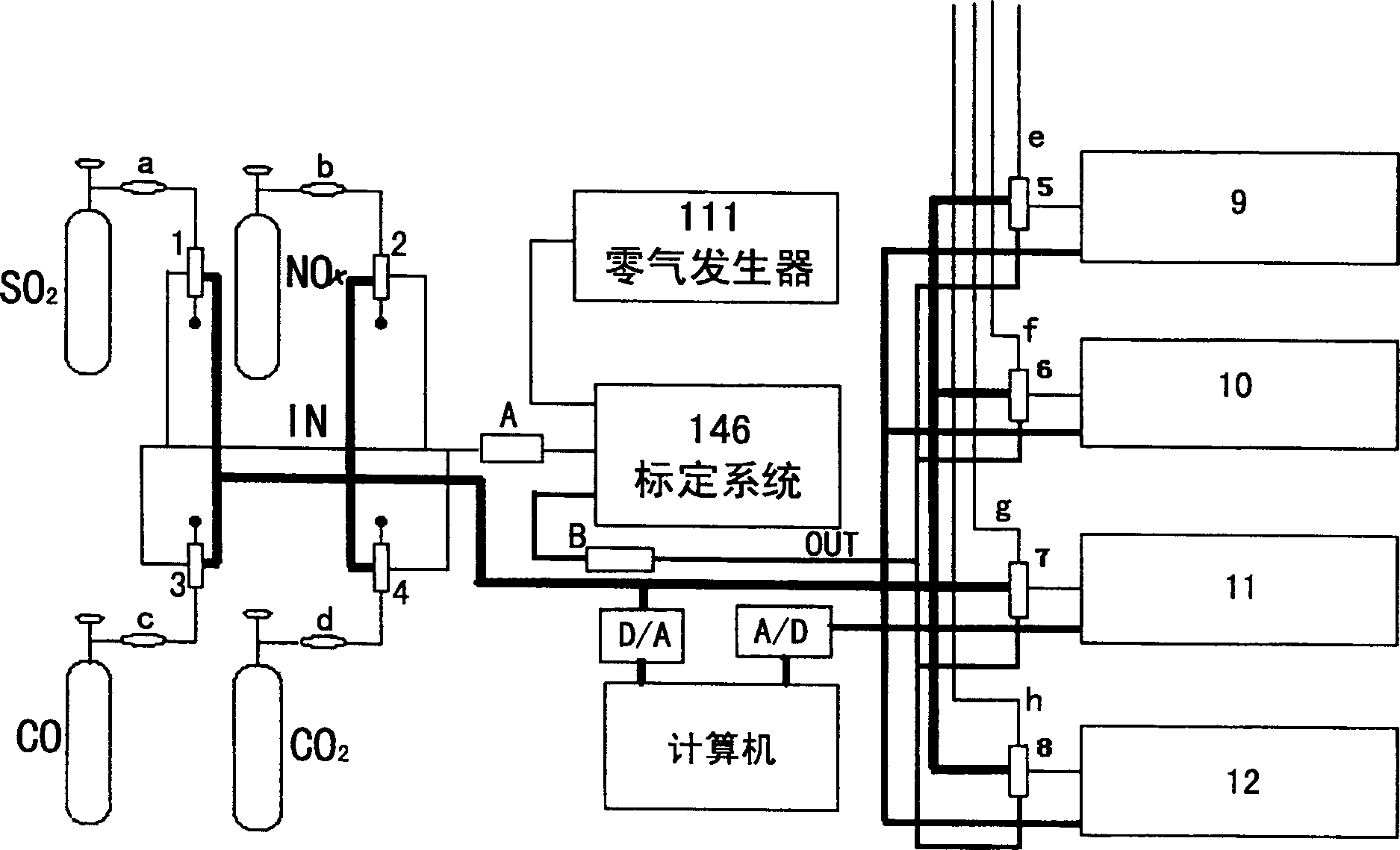
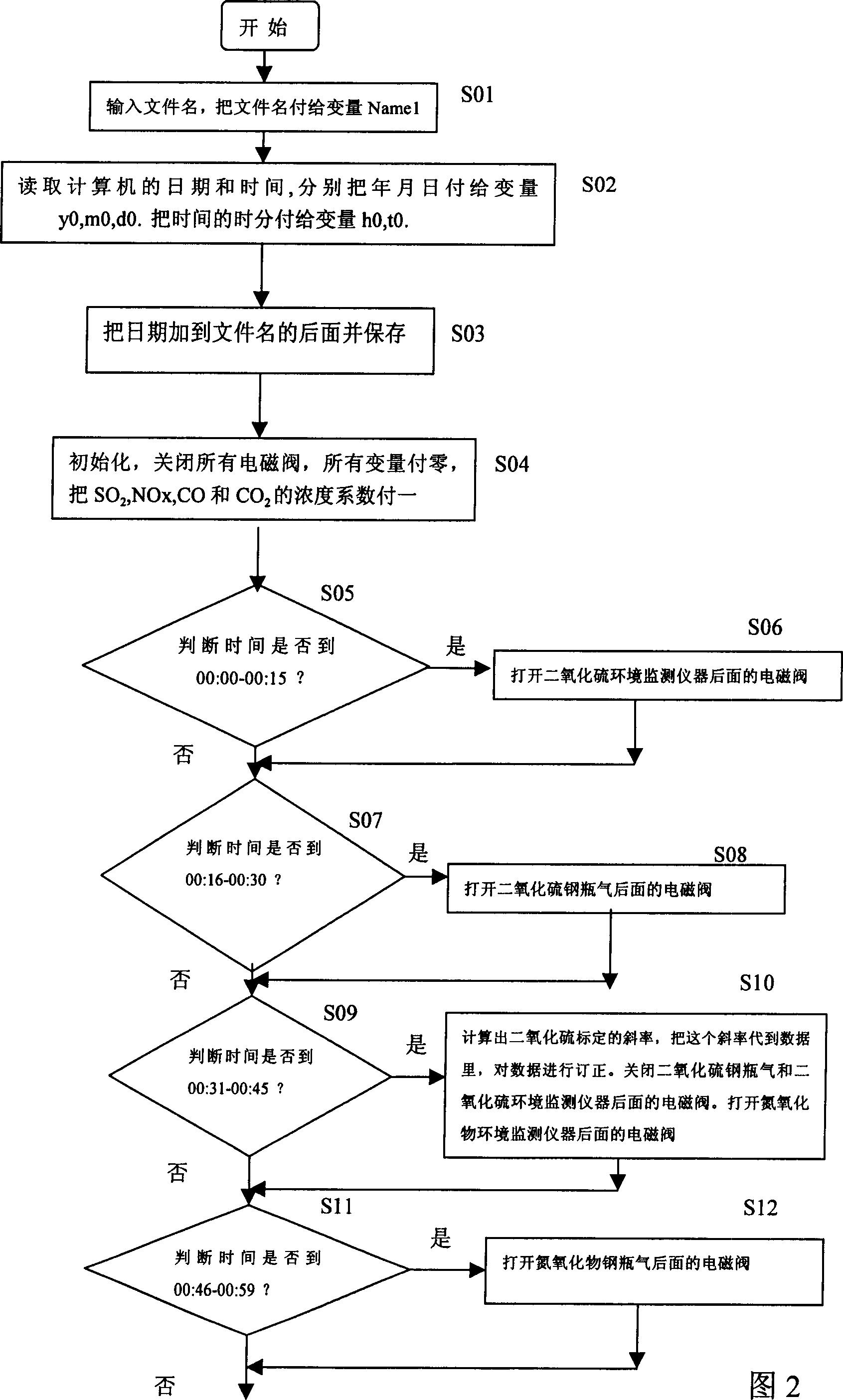
A gas analyser calibrating device and calibrating method
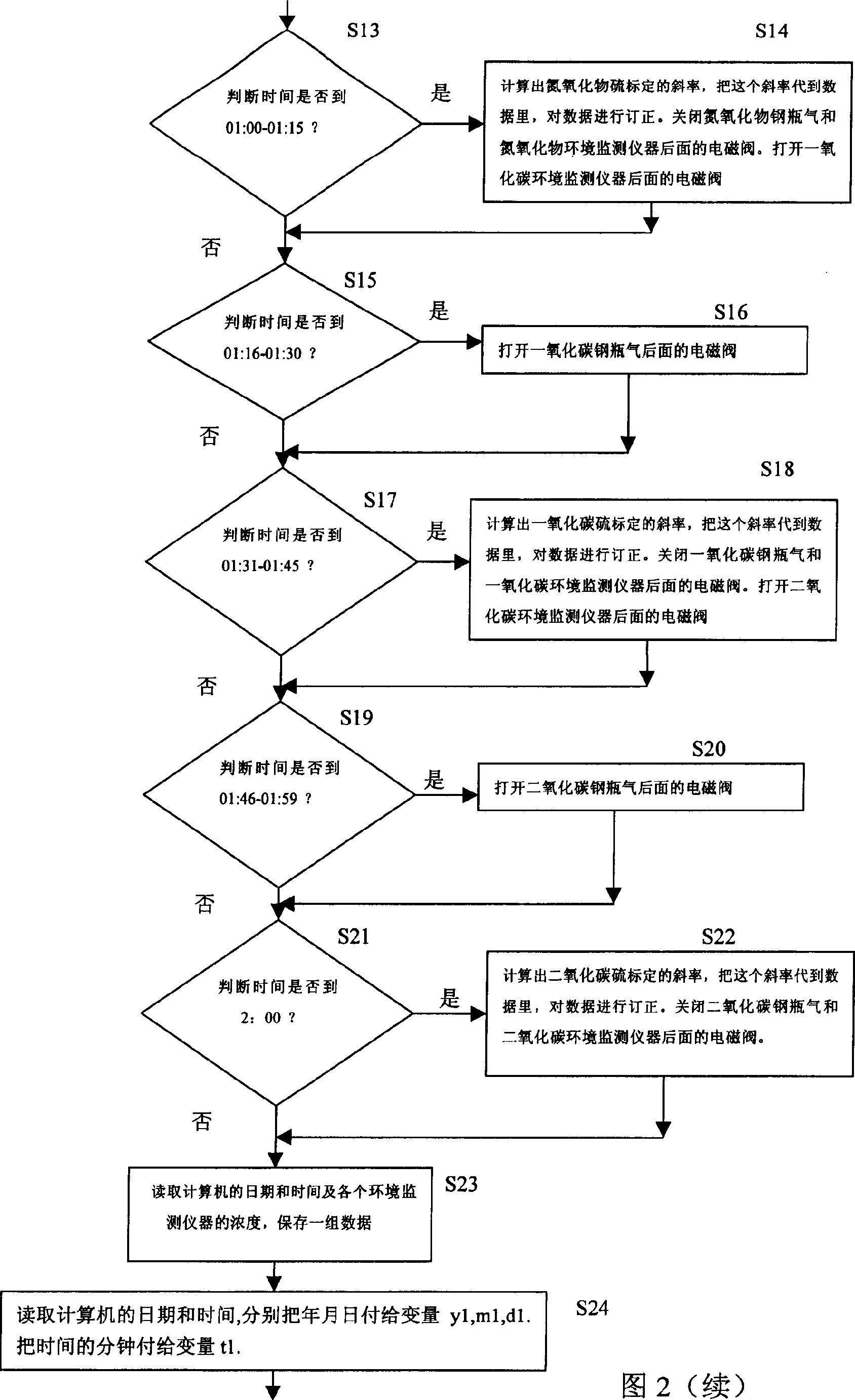
The gas analyzer calibrating equipment includes zero gas generator, calibration system and various kinds of gas analyzers. One gas inlet of the calibration system has one total gas intake pipe connected and the total gas intake pipe is connected to several standard gas cylinders via solenoid valve; and the gas outlet of the calibration system has one total gas outlet pipe connected and the total gas outlet pipe has the other end connected to analyzer via one three-way solenoid valve, which has normally closed port connected to the total gas outlet pipe, the normally opened port connected to atmosphere, and common port connected to the air intake port of the analyzer. The computer controls these solenoid valves via D / A converter. The equipment may be used to obtain the output slope of the analyzer data for correcting the data the analyzer obtains and obtaining the practical value of the gas component in atmosphere, solving the drift problem of analyzer.
Owner:INST OF ATMOSPHERIC PHYSICS CHINESE ACADEMY SCI
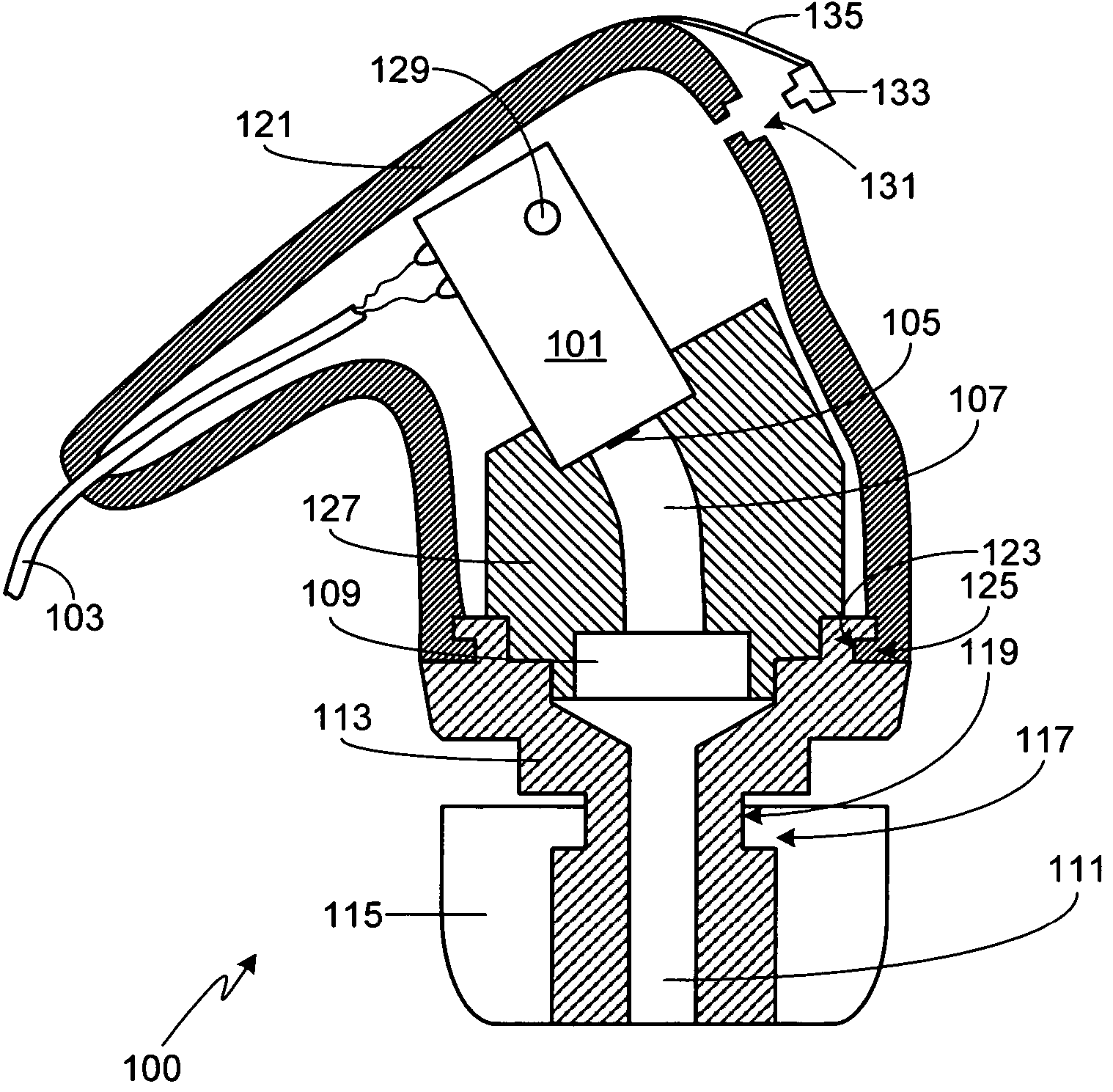
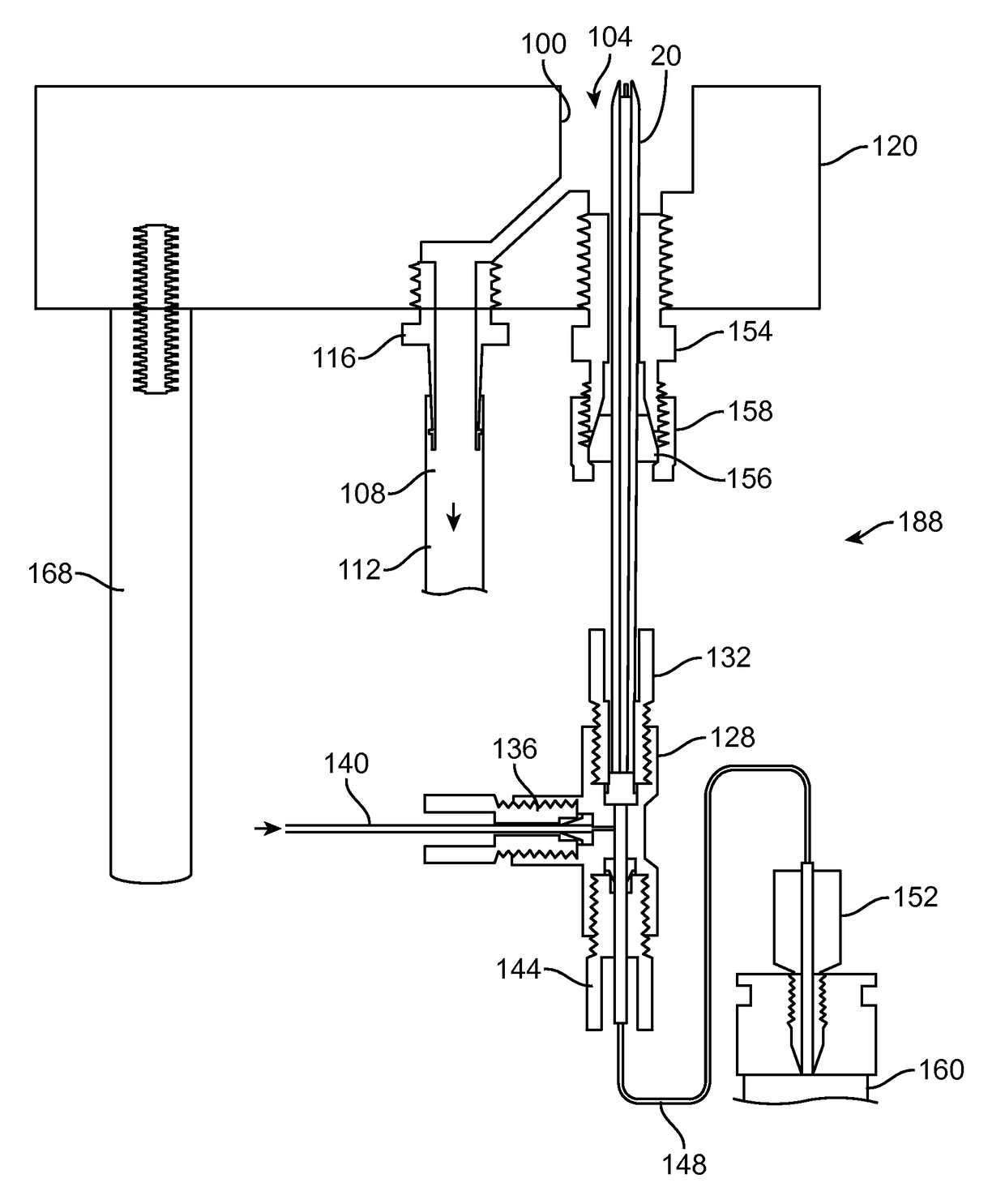
Open port sampling interface
A system for sampling a sample material includes a probe which can have an outer probe housing with an open end. A liquid supply conduit within the housing has an outlet positioned to deliver liquid to the open end of the housing. The liquid supply conduit can be connectable to a liquid supply for delivering liquid at a first volumetric flow rate to the open end of the housing. A liquid exhaust conduit within the housing is provided for removing liquid from the open end of the housing. A liquid exhaust system can be provided for removing liquid from the liquid exhaust conduit at a second volumetric flow rate, the first volumetric flow rate exceeding the second volumetric flow rate, wherein liquid at the open end will receive sample, liquid containing sample material will be drawn into and through the liquid exhaust conduit, and liquid will overflow from the open end.
Owner:UT BATTELLE LLC
Method and apparatus for detecting port scans with fake source address
A computer implemented method, apparatus, and computer program product for port scan protection. A reply data packet having a modified transmission control protocol header is generated to form a modified reply data packet, in response to detecting a port scan. The modified reply data packet will illicit a response from a recipient of the modified data packet. The reply data packet is sent to a first Internet protocol address associated with the port scan. A second Internet protocol address is identified from a header of the response to the modified reply data packet. The second Internet protocol address is an actual Internet protocol address of a source of the port scan. All network traffic from the second Internet protocol address may be blocked to prevent an attack on any open ports from the source of the port scan.
Owner:IBM CORP
Toner container
InactiveUS20090285604A1Reducing toner leakageReduce leakageElectrographic process apparatusOpen portReciprocating motion
A toner cartridge includes a cylindrical supplying pipe having a toner opening port arranged on a side surface thereof; a cylindrical cover that is attached to the supplying pipe and has a cover opening port arranged on a side surface thereof, and a cam mechanism that is provided to the supplying pipe and the cover, and that reciprocates the cover between an opening position where the toner opening port and the cover opening port align with each other and a closing position where the toner opening port is closed by the cover, which closing position is in a skewed position with respect to the opening position. This arrangement provides a toner container that reduces toner leakage when being removed from a toner hopper.
Owner:MURATA MASCH LTD
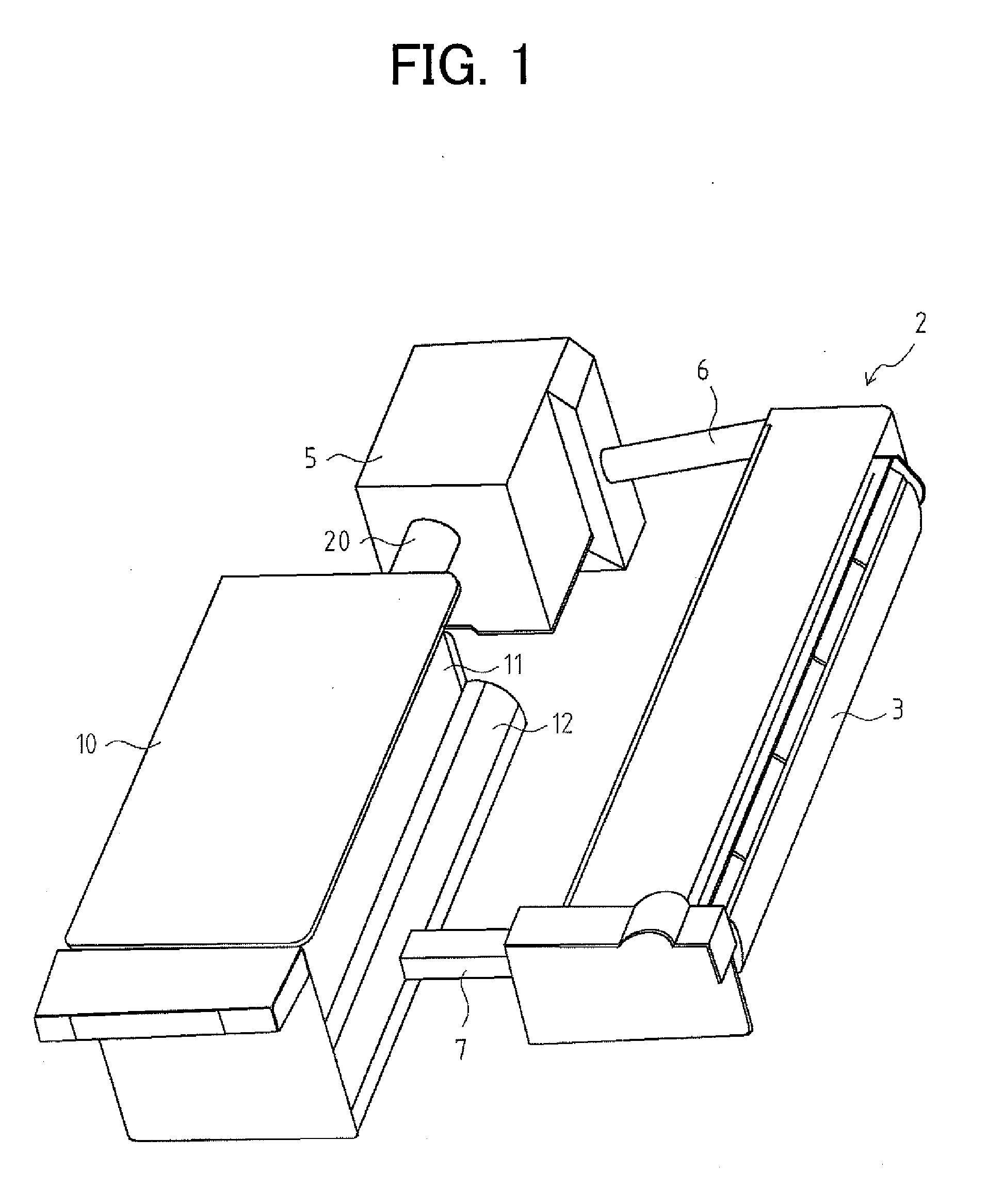
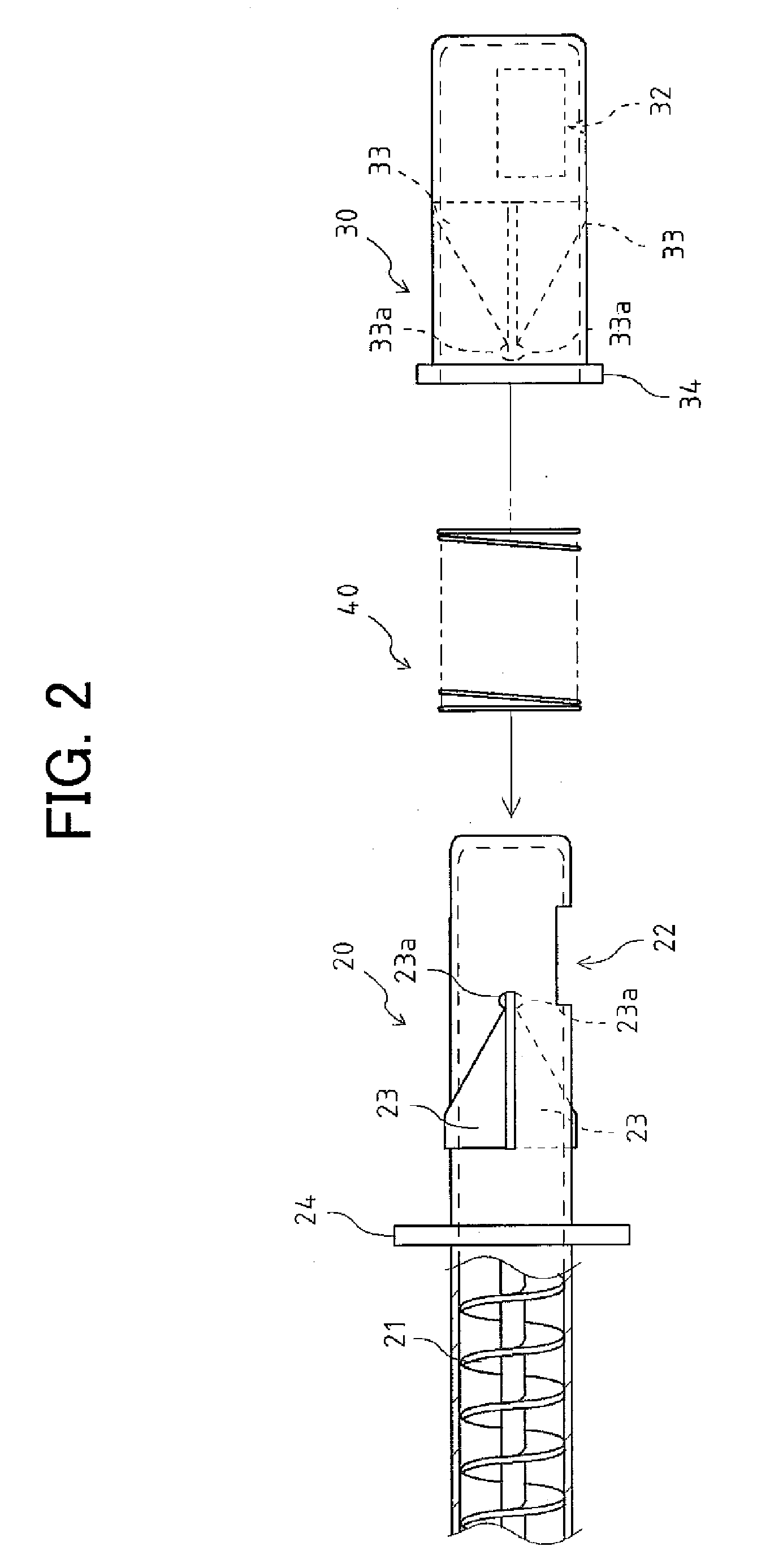
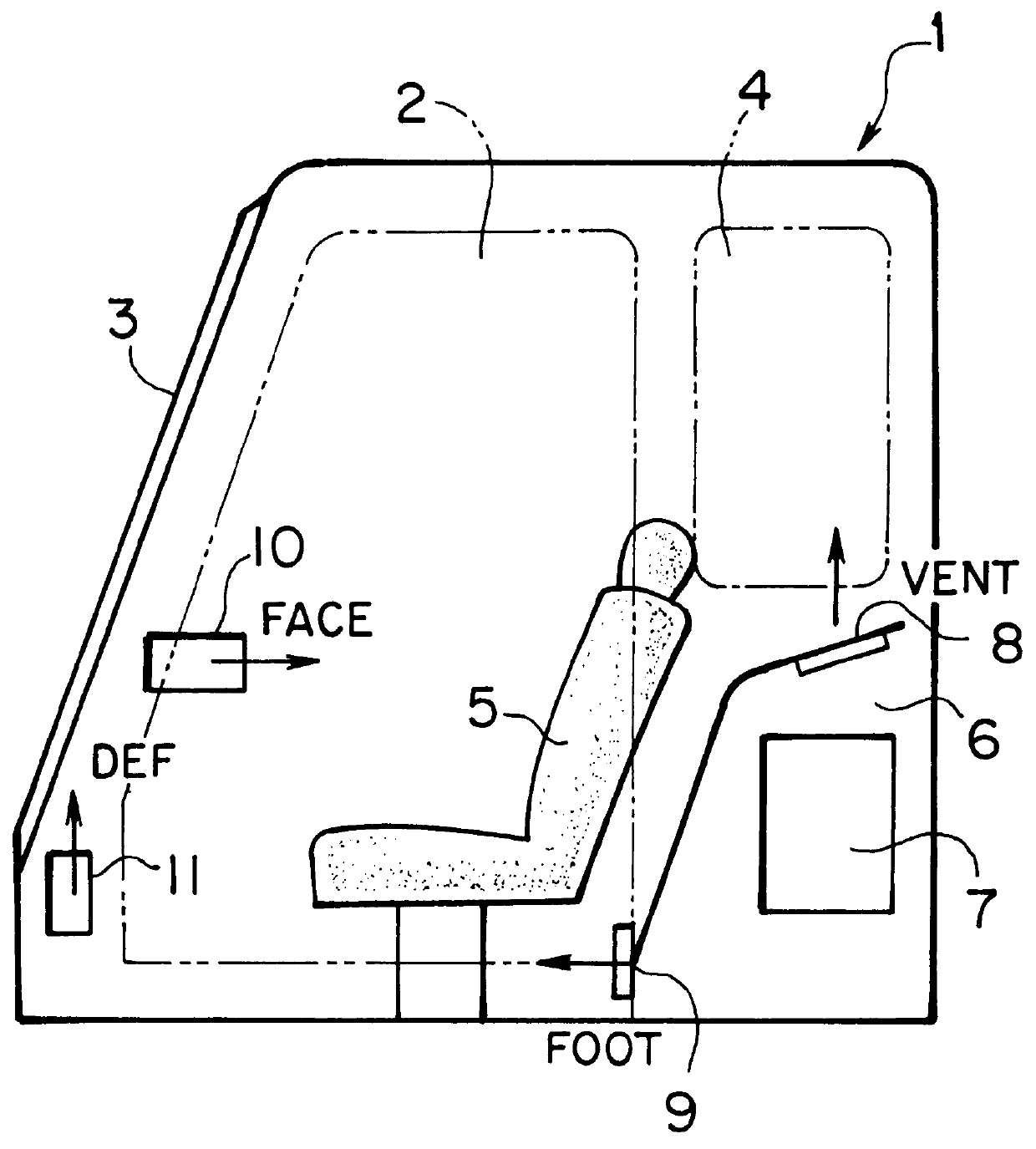
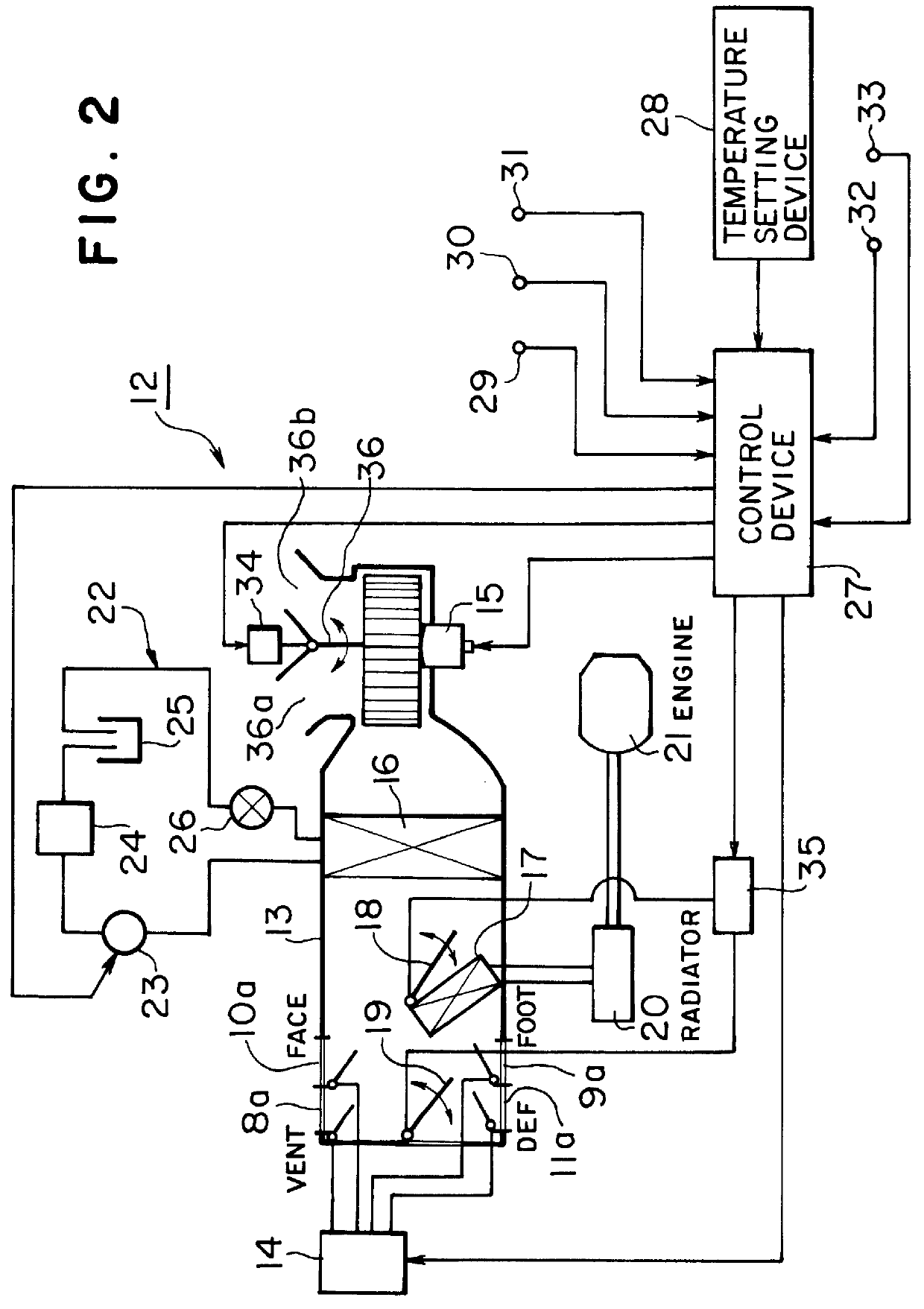
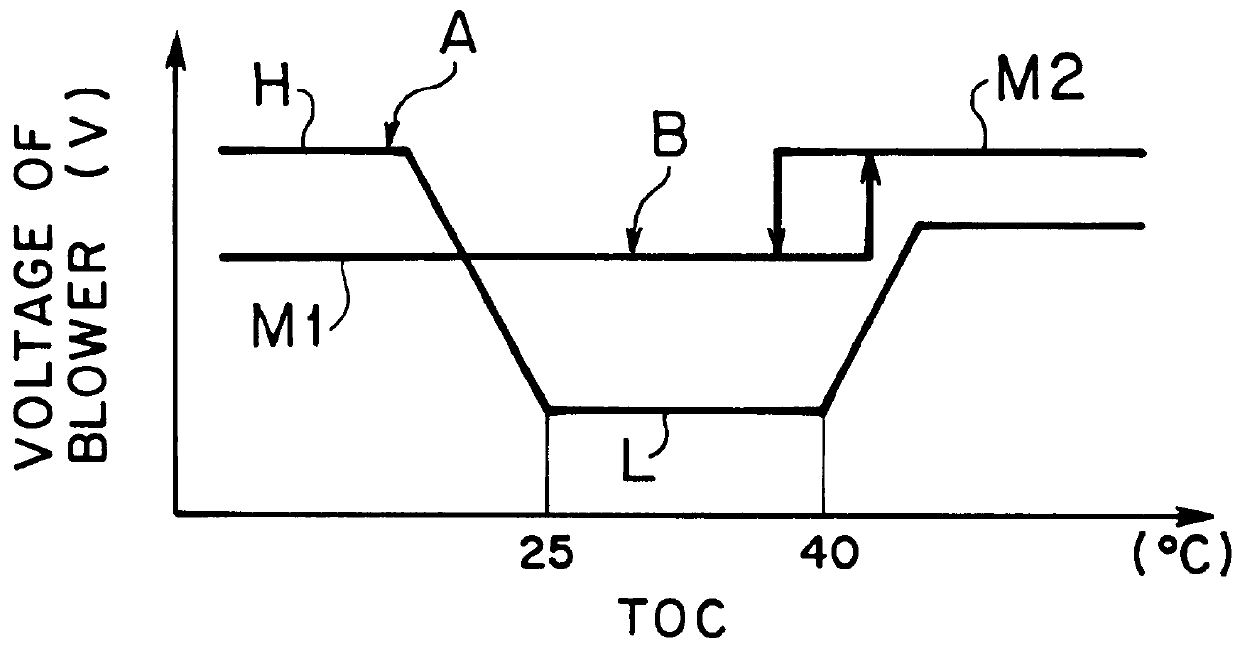
Air conditioning system for vehicles
InactiveUS6012295AReduce wasted powerProlong lifeAir-treating devicesRailway heating/coolingTemperature controlOpen port
An air conditioning system for vehicles includes a sensor for detecting opening and closing of a vehicle portal, such as a door or a window, and a control device for selectively opening ports through which temperature controlled air flows into an interior of a vehicle, in response to a signal generated by the opening and closing detecting sensor and a target air temperature. In the system, even if a door or a window of a cabin is opened, ports are opened according to a most suitable port mode depending on the target air temperature at a present time. Therefore, an improved air conditioning state for an operator, and an improved driving condition with reduced waste power and reduced loads to the respective equipment, may be achieved.
Owner:SANDEN CORP
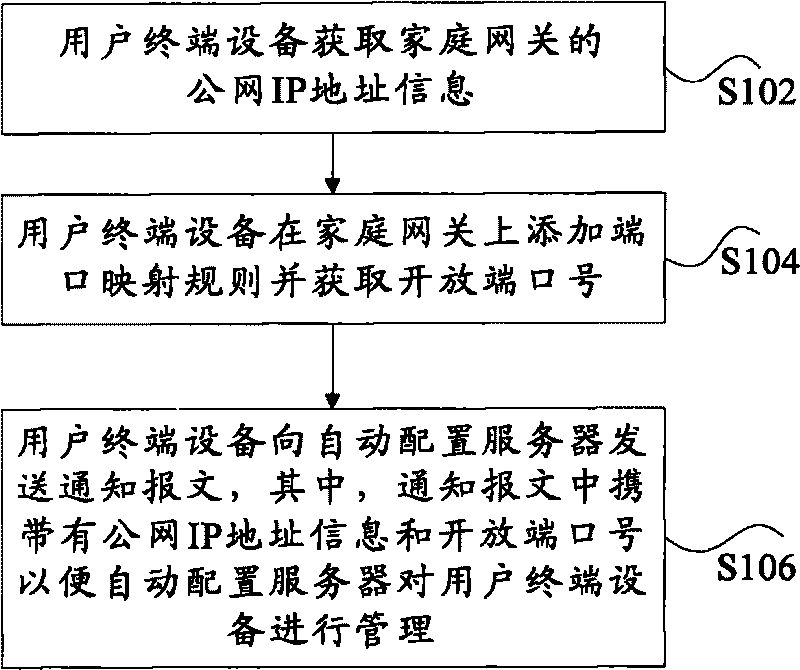
Method and device for managing user terminal equipment
InactiveCN101702718AEasy to manageSolving problems with more complex management methodsNetwork connectionsOpen portIp address
The invention discloses a method and a device for managing user terminal equipment. The method comprises the following steps: the user terminal equipment acquires the IP address information of a public network through a home gateway; the user terminal equipment adds port mapping rules on the home gateway, and acquires an open port number; and the user terminal equipment sends a notification message to an automatic configuration server, wherein the notification message carries the IP address information of the public network and the open port number, so that the automatic configuration server can manage the user terminal equipment. By the invention, the user terminal equipment can be managed simply.
Owner:ZTE CORP
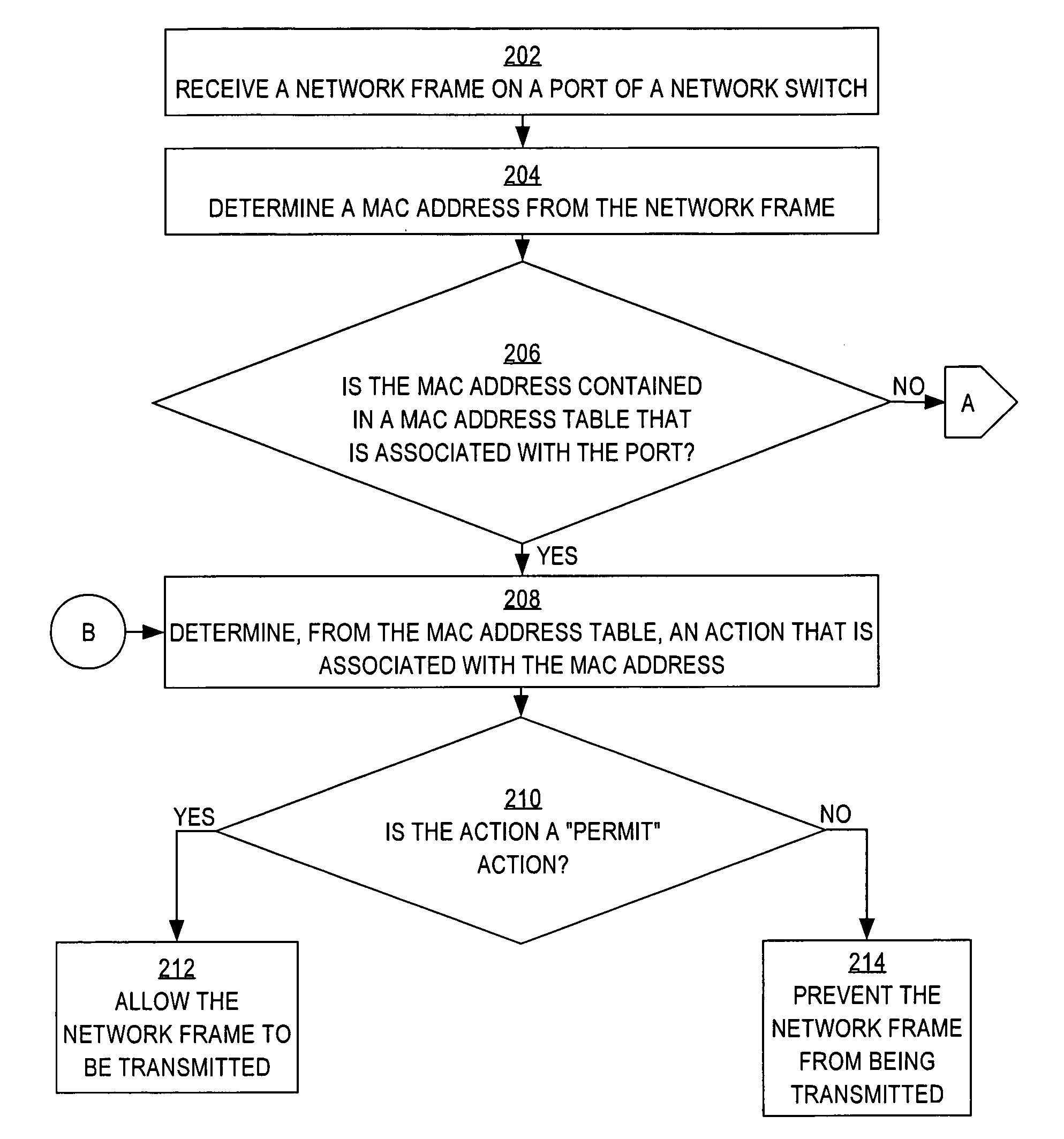
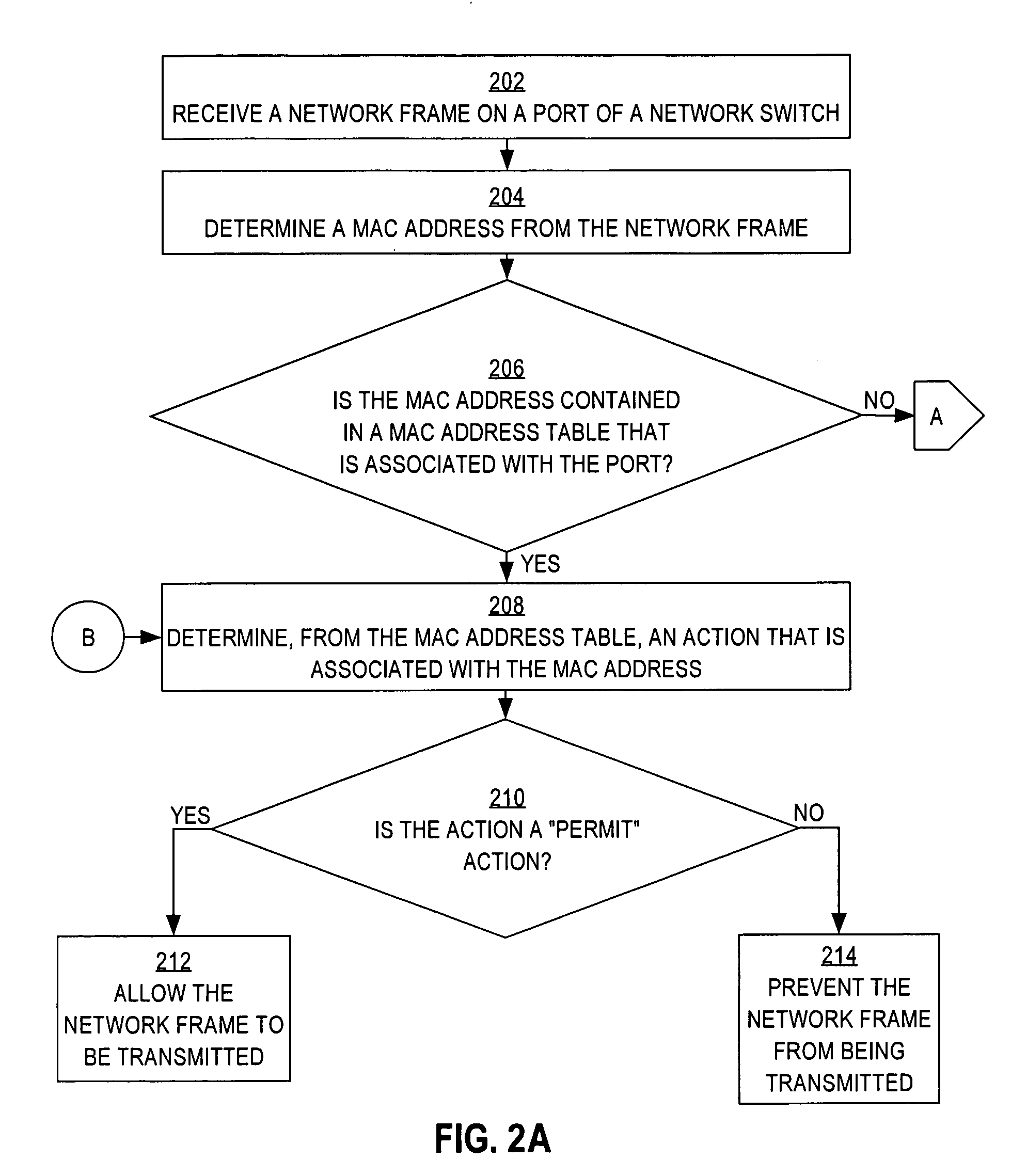
Authenticating multiple network elements that access a network through a single network switch port
InactiveUS20080092214A1Digital data processing detailsUser identity/authority verificationOpen portAuthentication server
A method is disclosed for authenticating multiple network elements that access a network through a single network switch port. Certain authentication protocols, such as EAPoE, leave a port of a network switch indefinitely opened when one particular host is authenticated and authorized to transmit network frames through the port. In one embodiment of the invention, a network frame from a second host that is received by the open port is not automatically transmitted to the network. Instead, techniques are employed locally by the network switch to grant or deny transmission of the network frame received from the second host. An authentication server is contacted only when the network switch cannot locally employ techniques to authorize the transmission of the network frame received from the second host.
Owner:CISCO TECH INC
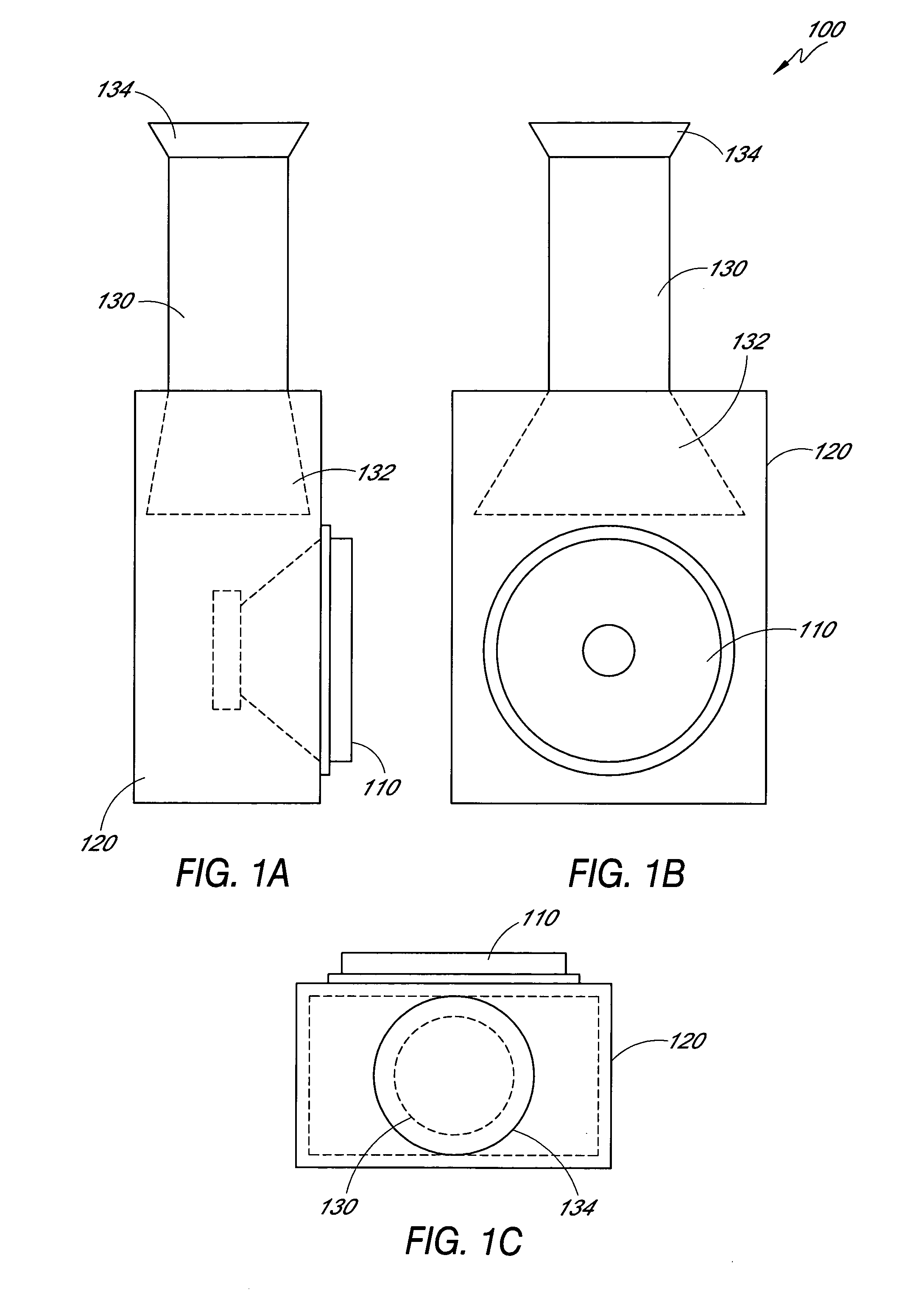
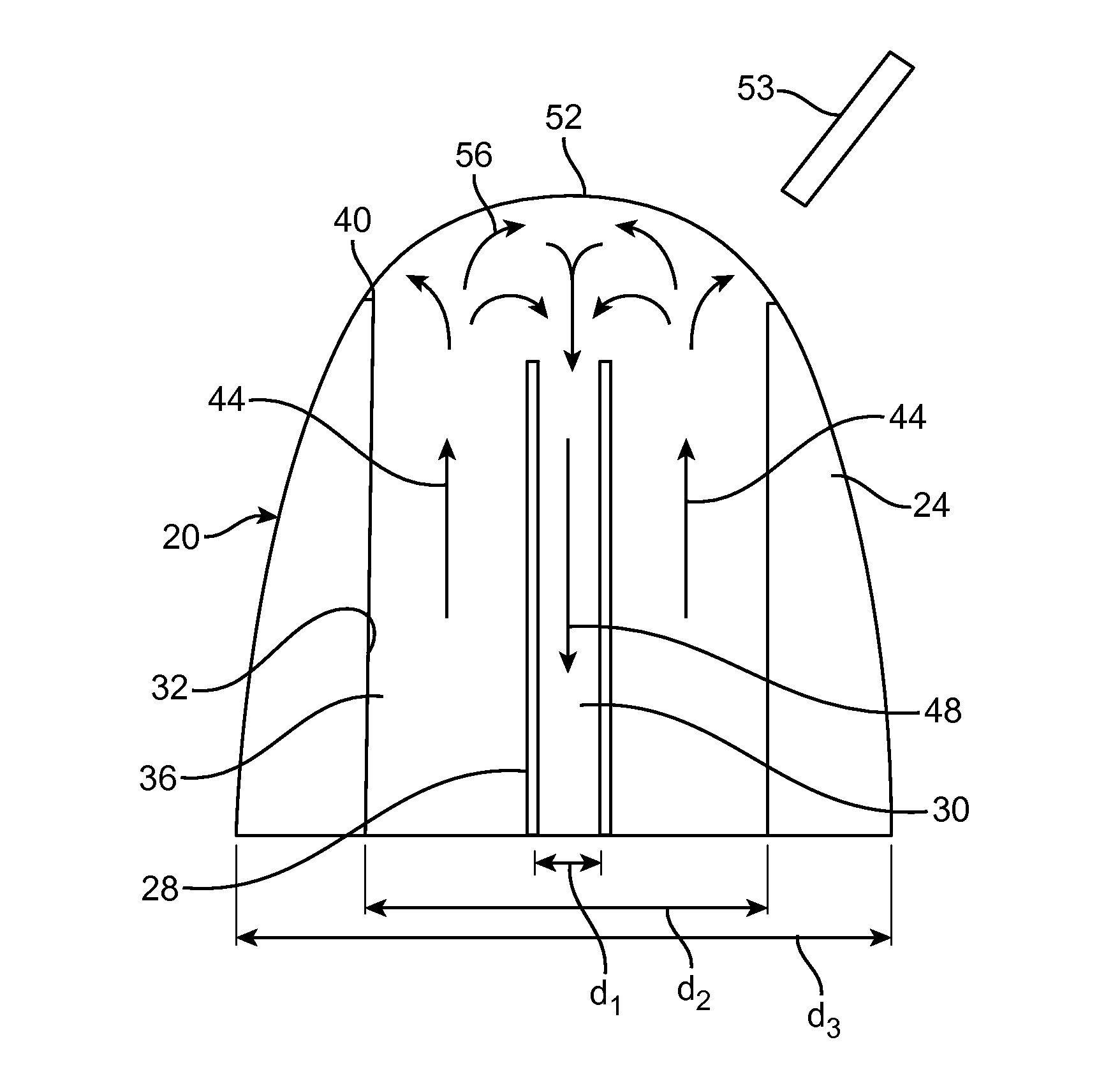
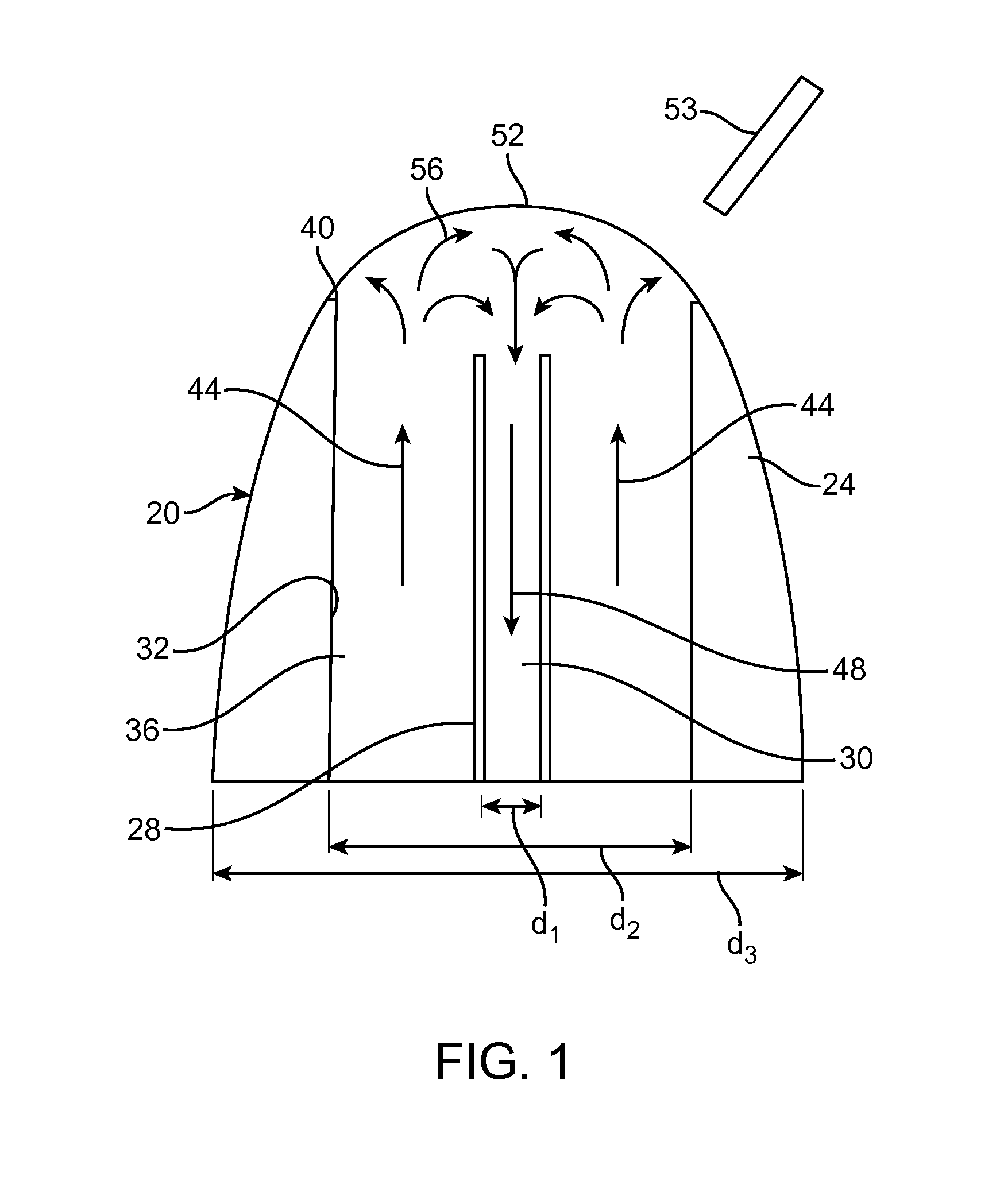
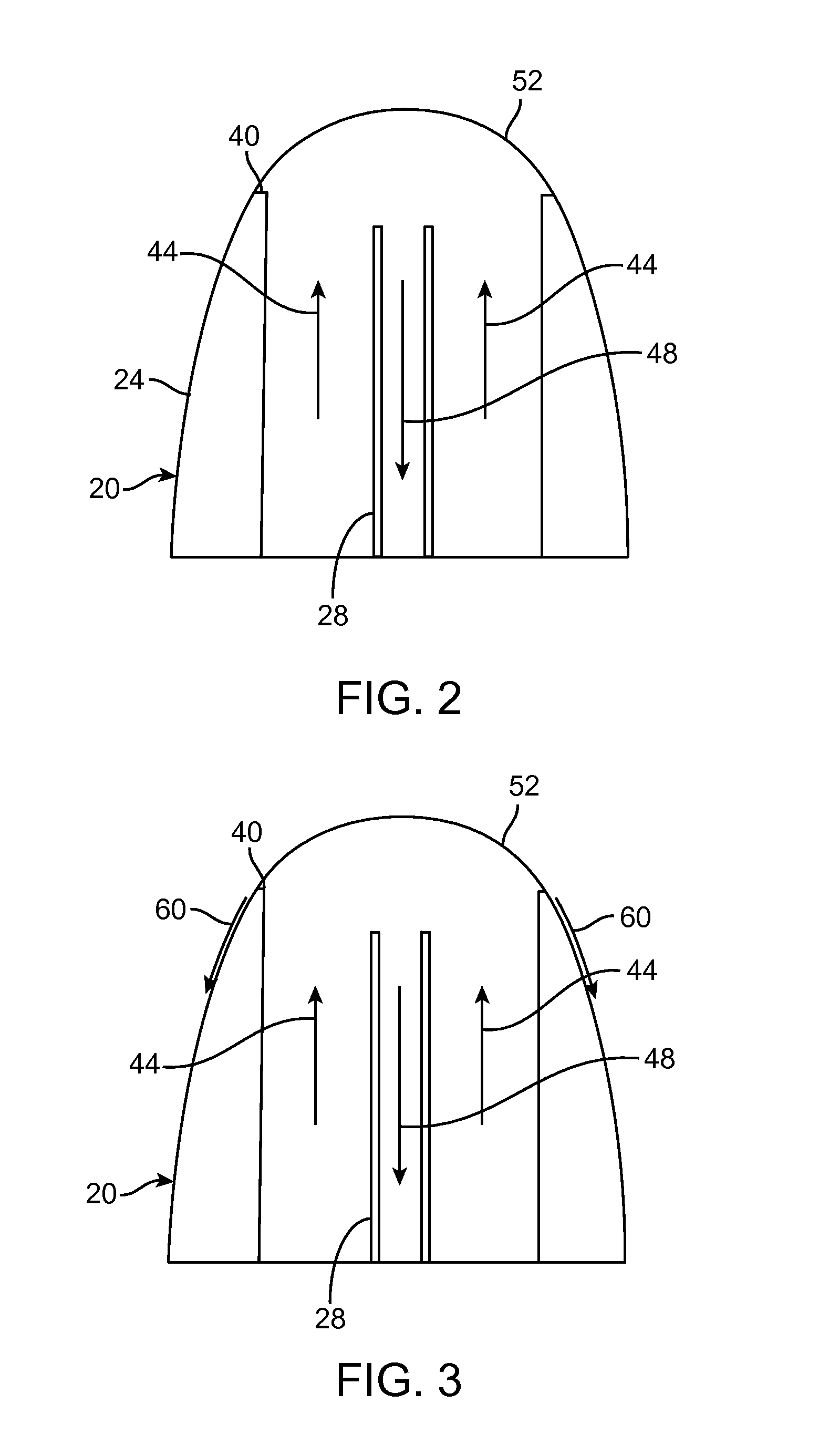
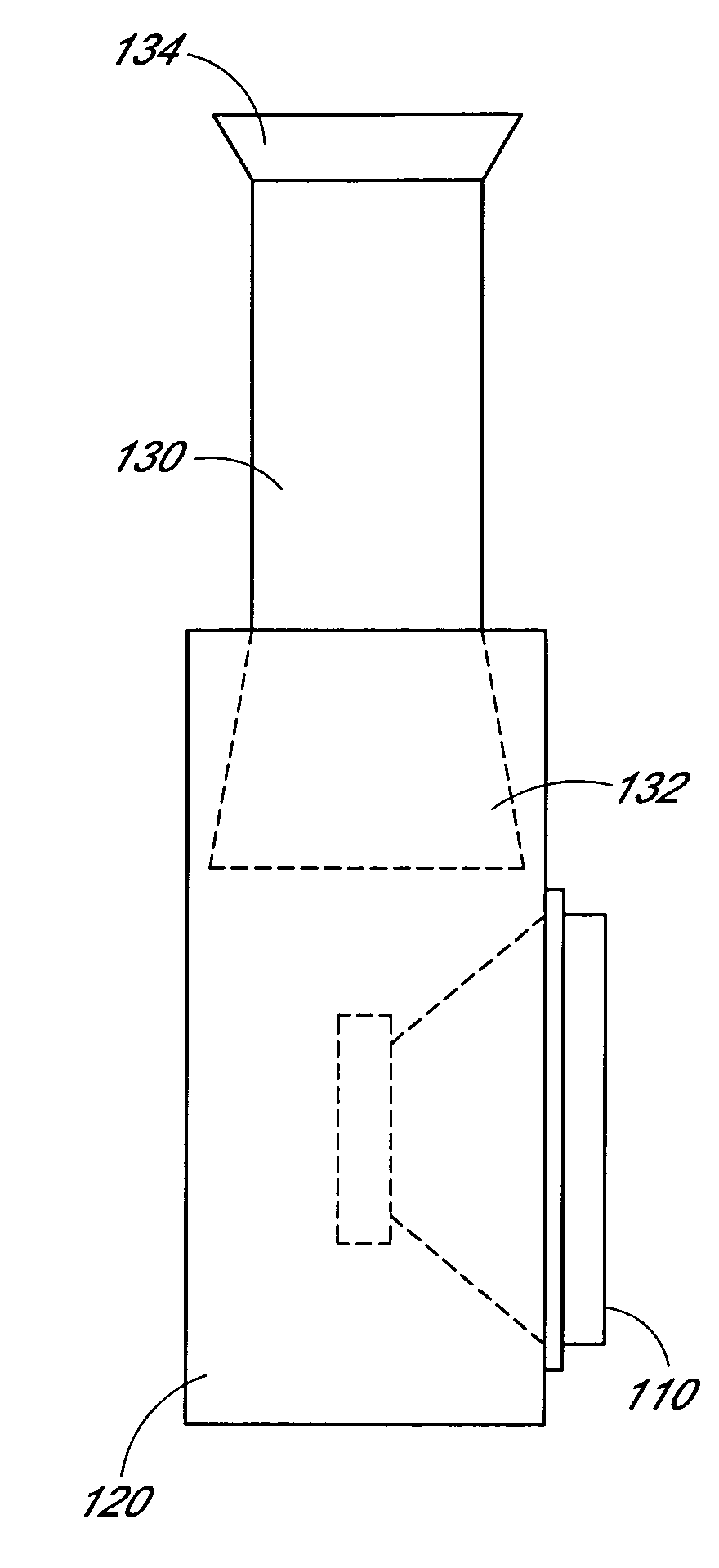
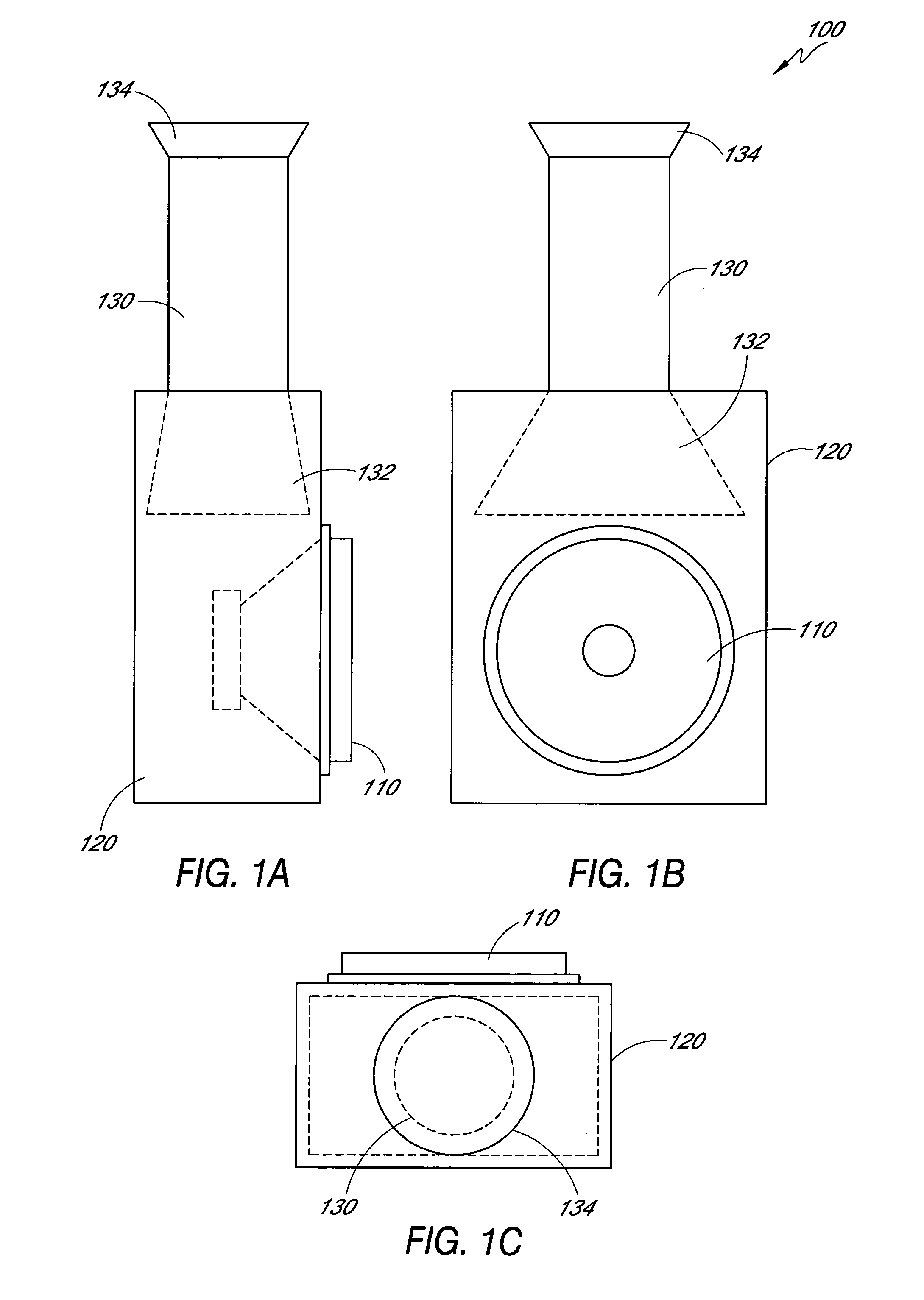
Externally ported loudspeaker enclosure
InactiveUS20050123162A1Improve low frequency responseFrequency/directions obtaining arrangementsTransducer casings/cabinets/supportsOpen portEngineering
An externally ported speaker enclosure includes a primary enclosure having a port or opening. The primary enclosure may continuously vary from a first dimension to a dimension of the port or opening. Alternatively, a duct or tube may extend from, and external to, the primary enclosure. The duct or tube may transition from a first dimension to a dimension of the port or opening. The dimensions of the port, primary enclosure, and transition from primary enclosure to port are configured to reinforce the low frequency response of a speaker mounted to the enclosure. A cylindrical primary enclosure may transition gradually or continuously to a port. The cylindrical primary enclosure can include a closed first end and an open port end. A speaker can be mounted to the cylindrical face of the primary enclosure. Alternatively, the speaker may be mounted parallel to an axis of the cylinder.
Owner:HUFFMAN NICK
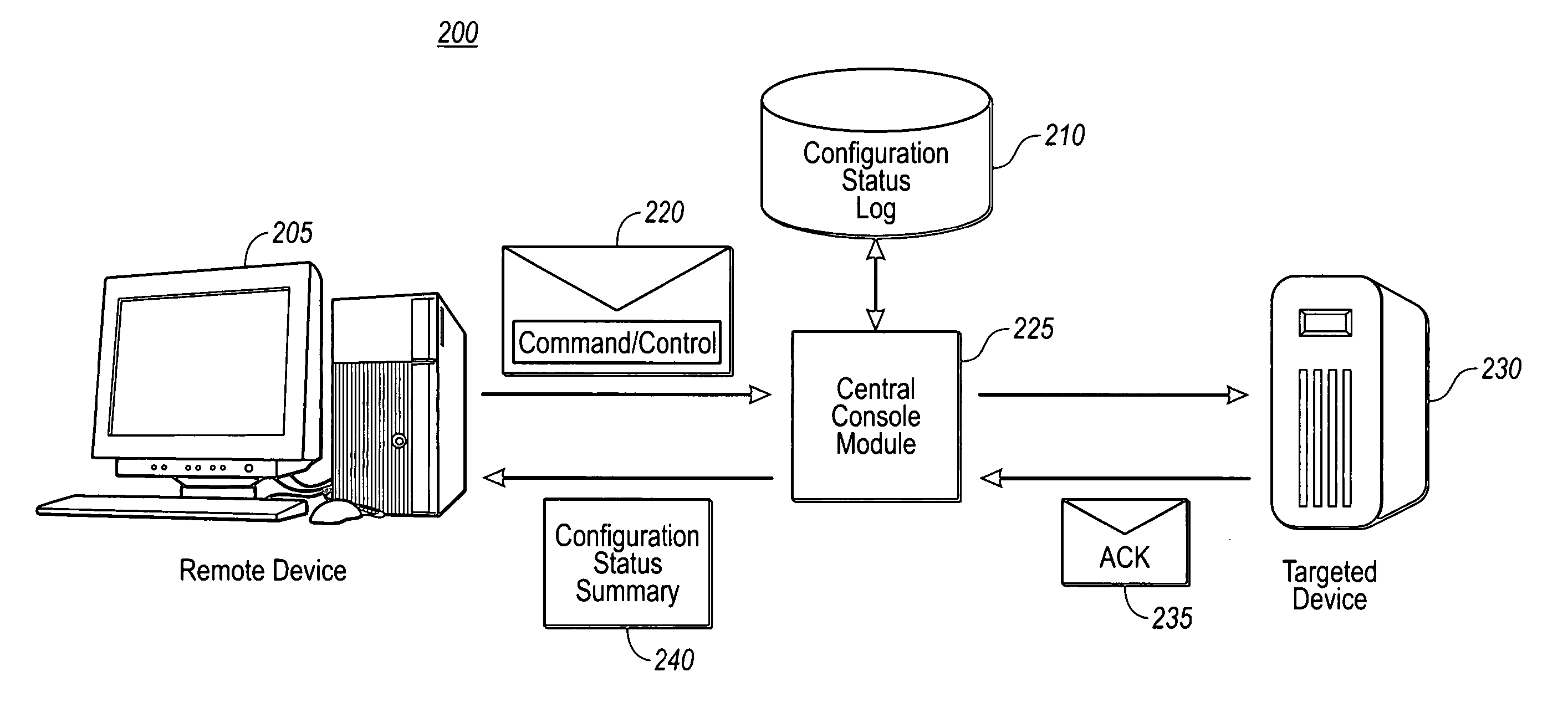
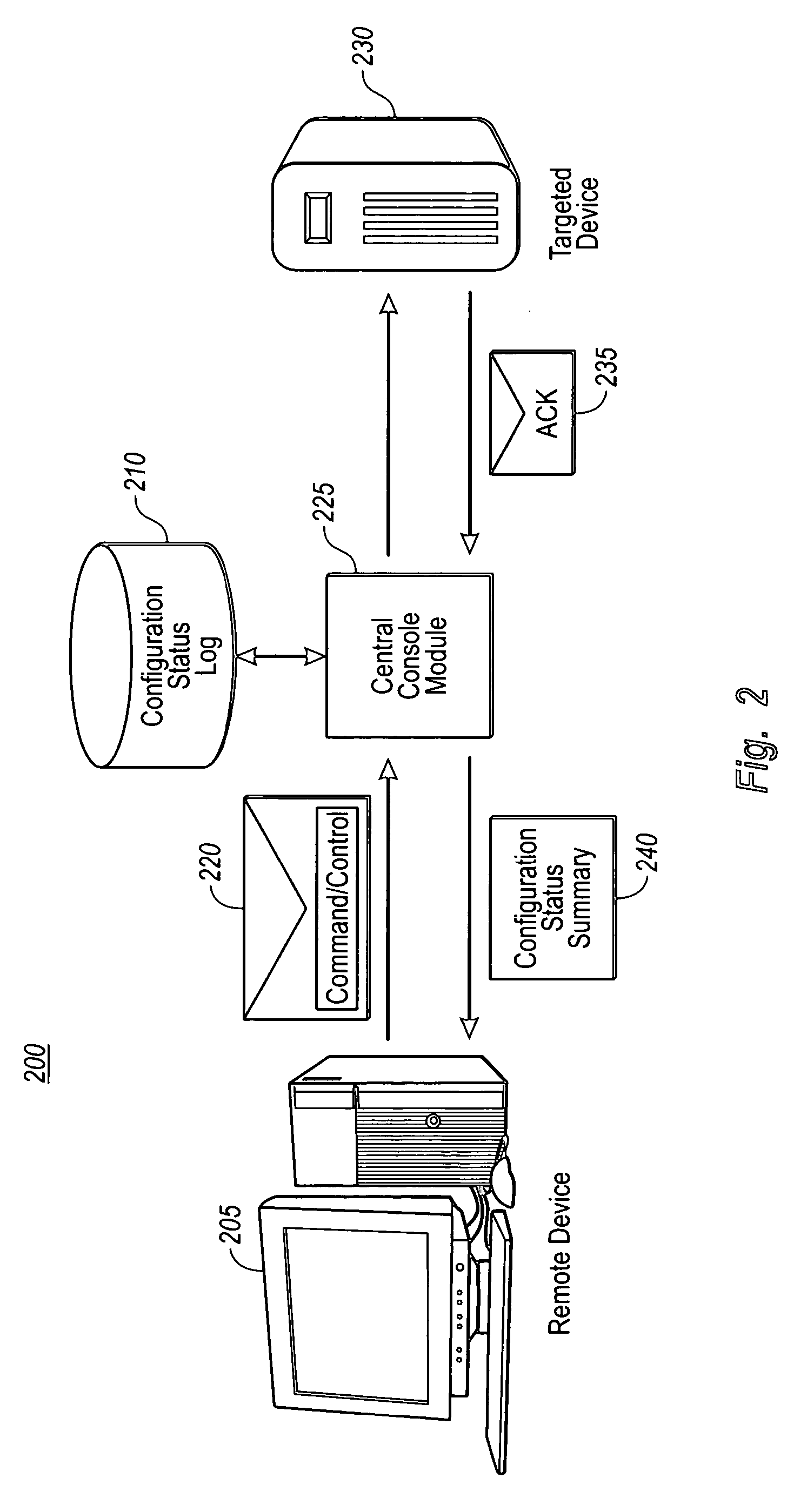
Secure remote configuration of targeted devices using a standard message transport protocol
InactiveUS20060090195A1Minimize the numberDigital data processing detailsUser identity/authority verificationOpen portComputer hardware
The present invention allows for remotely and securely configuring settings for targeted devices within a network with multiple security-trust boundaries. Configuration information is encoded in messages that are digitally signed to ensure the integrity of the configuration information and sent in accordance with a standard messaging transport protocol. By utilizing an already existing port of the standard messaging transport protocol, e.g., SMTP, the number of open ports for configuration purposes is minimized. Further, example embodiments take advantage of hidden fields, i.e., machine readable fields that contain metadata that by default are not presented at a client user interface, for encoding the configuration or command / control information within the messages. The present invention further provides for a central console module that can manage and report on the status of the configuration settings for a plurality of targeted devices that an authorized user or system administrator has attempted to remotely configure.
Owner:MICROSOFT TECH LICENSING LLC
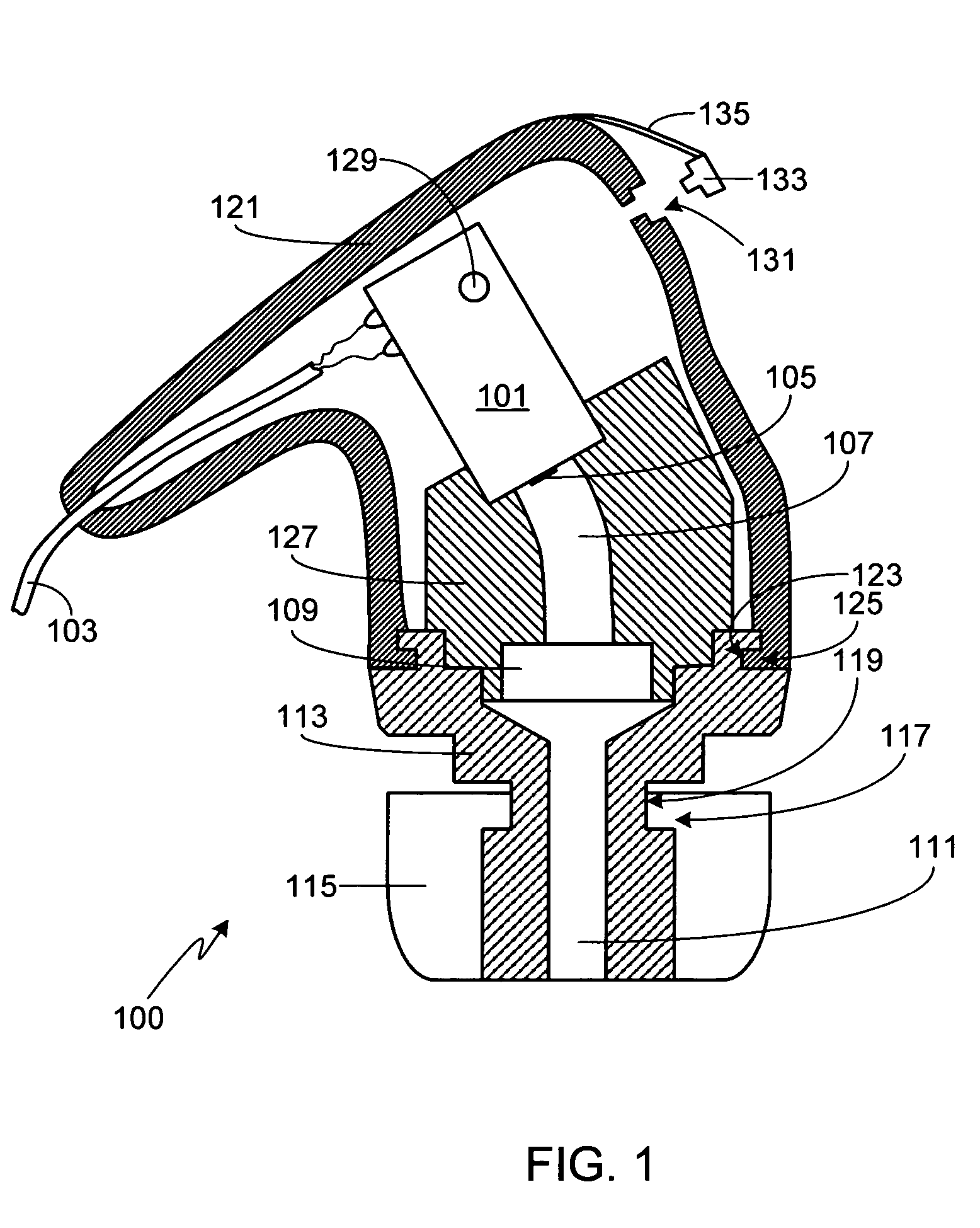
Open port sampling interface
A system for sampling a sample material includes a probe which can have an outer probe housing with an open end. A liquid supply conduit within the housing has an outlet positioned to deliver liquid to the open end of the housing. The liquid supply conduit can be connectable to a liquid supply for delivering liquid at a first volumetric flow rate to the open end of the housing. A liquid exhaust conduit within the housing is provided for removing liquid from the open end of the housing. A liquid exhaust system can be provided for removing liquid from the liquid exhaust conduit at a second volumetric flow rate, the first volumetric flow rate exceeding the second volumetric flow rate, wherein liquid at the open end will receive sample, liquid containing sample material will be drawn into and through the liquid exhaust conduit, and liquid will overflow from the open end.
Owner:UT BATTELLE LLC
Method and system for detecting scanning behaviors of ports
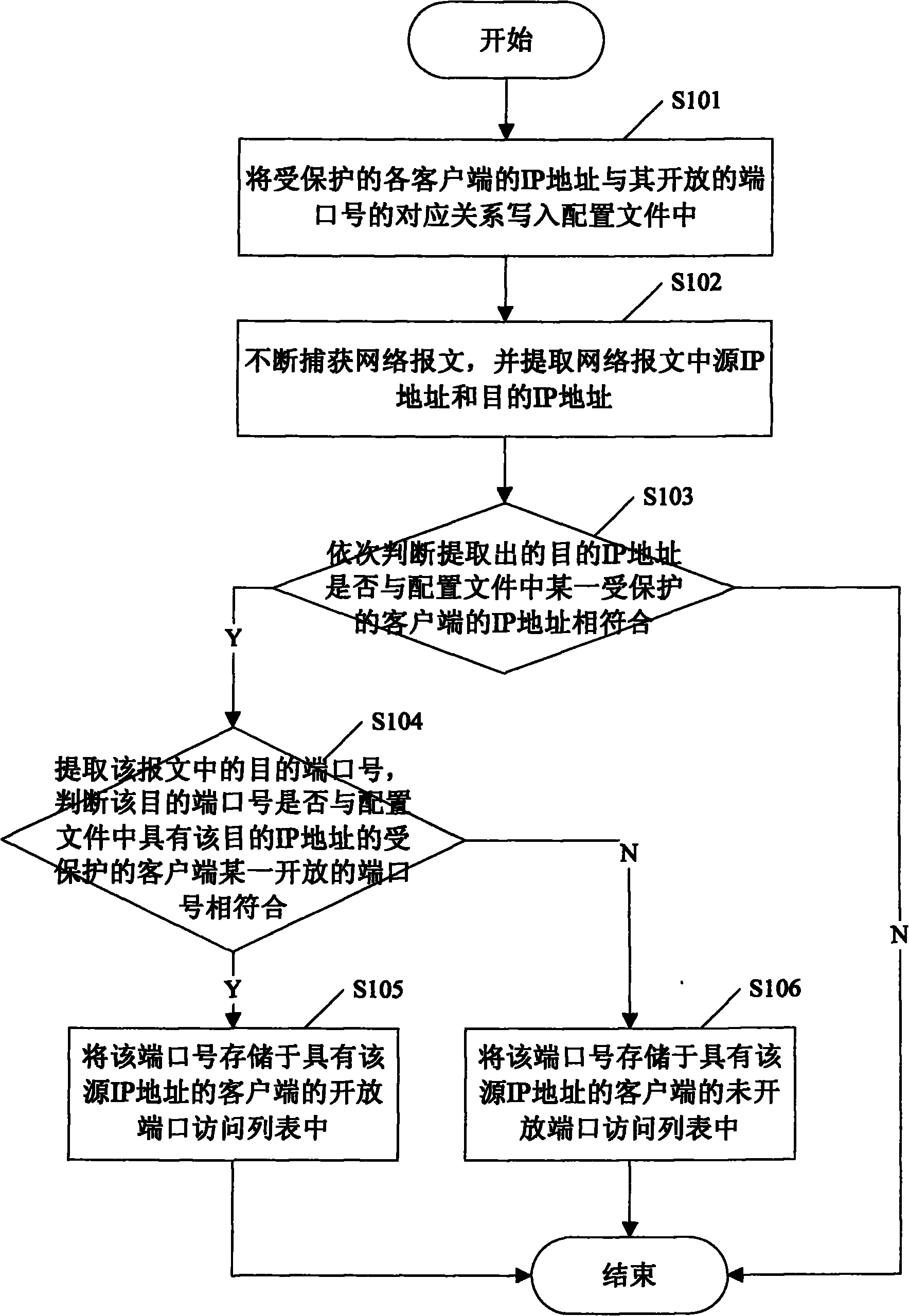
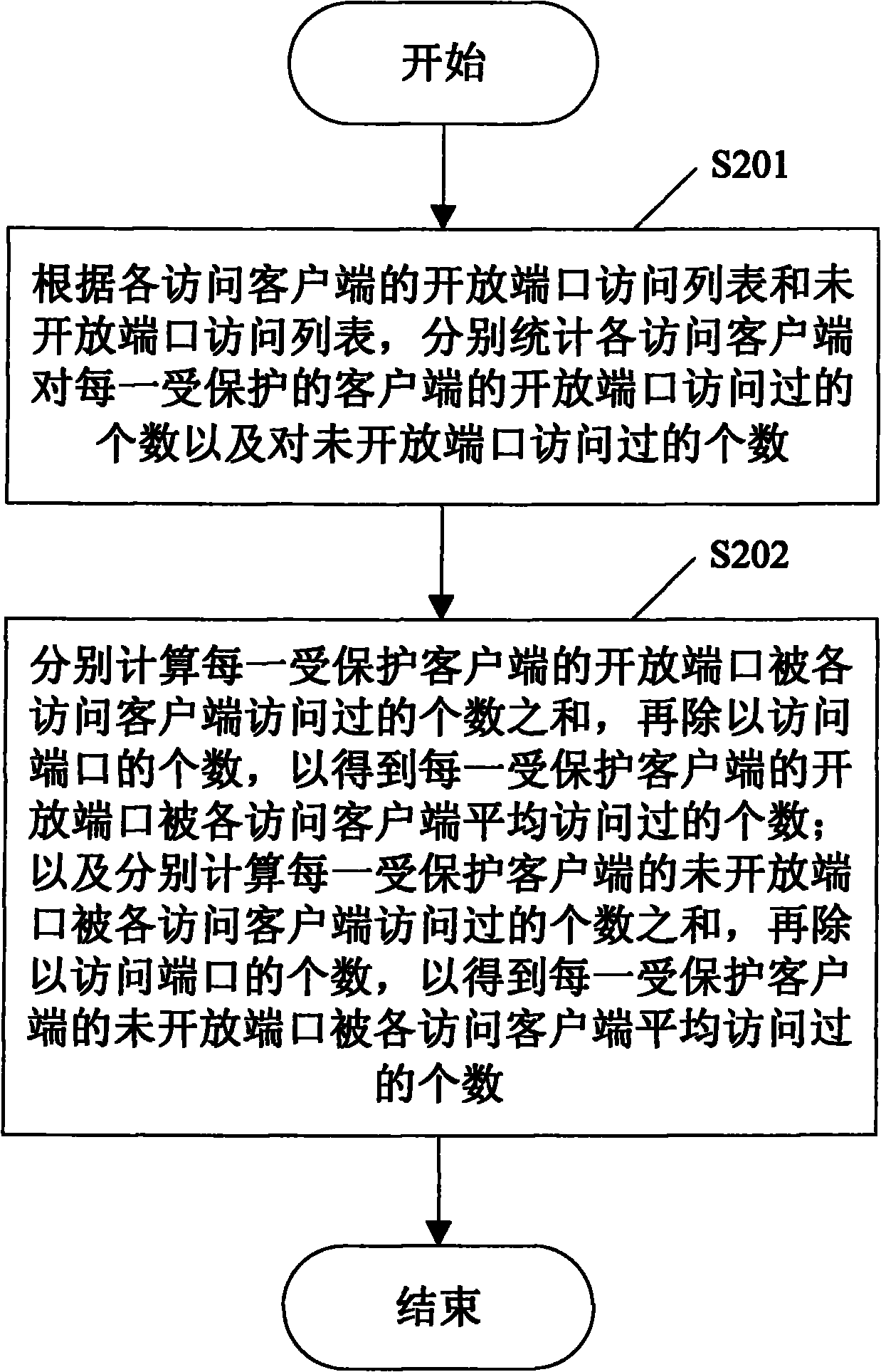
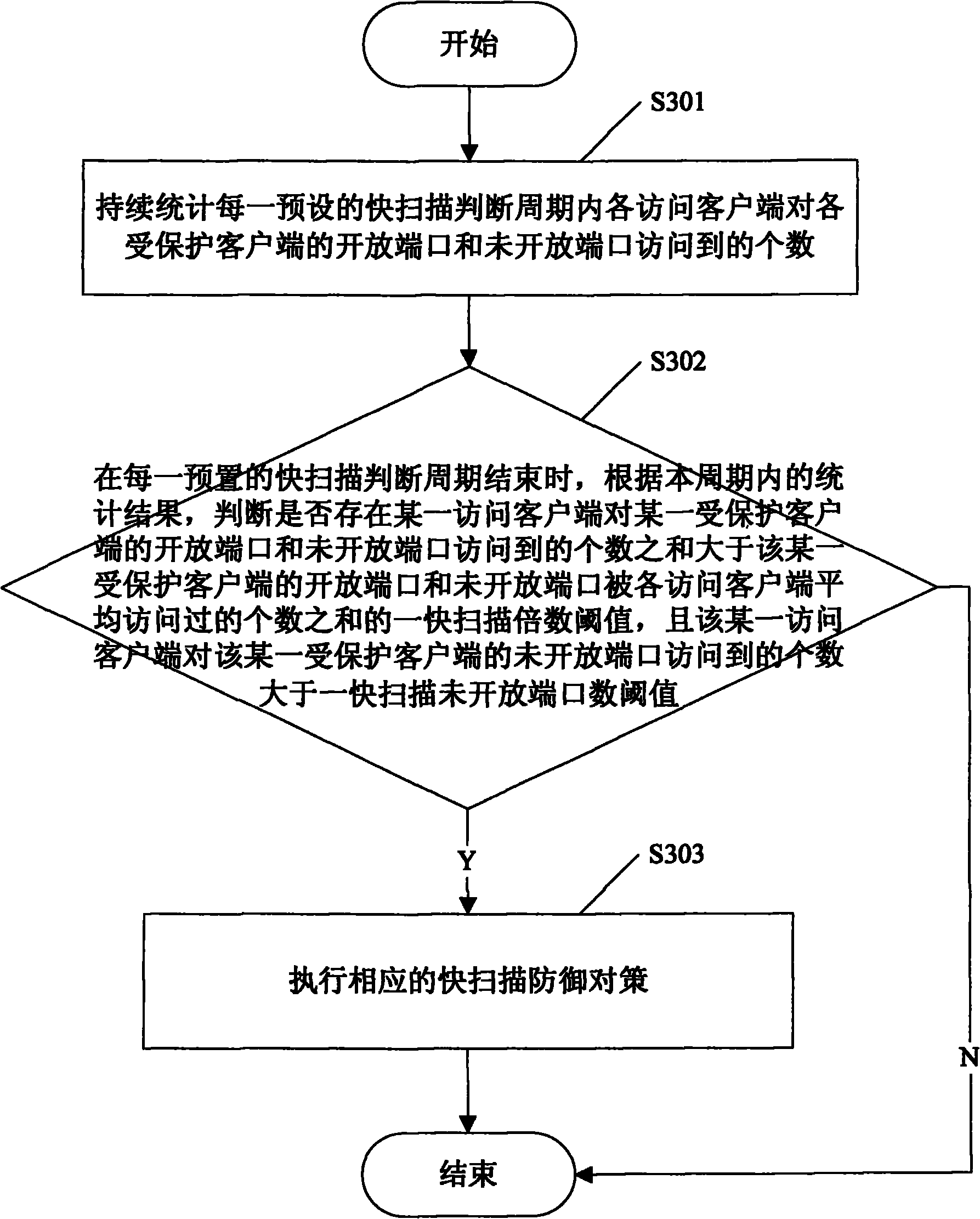
InactiveCN101902349AAvoid false positivesDrawbacks of Avoiding False PositivesData switching networksOpen portIp address
The invention provides a method and a system for detecting scanning behaviors of ports. The method comprises the following steps of: writing a corresponding relationship between the IP address of each protected client and an open port number thereof into a configuration file; monitoring the accessed condition of each protected client, and maintaining an open port access list and an unopened port access list of the access clients for the protected clients; calculating the average numbers of open ports and unopened ports, accessed by the access clients, of the protected clients according to the open port access list and the unopened port access list of the access clients for the protected clients respectively; and simultaneously performing quick scanning judgment and slow scanning judgment according to the preset quick scanning judgment rule and the preset slow scanning judgment rule so as to detect the quick scanning behaviors of the ports and well discover the slow scanning behaviors.
Owner:BEIJING VENUS INFORMATION TECH +1
Externally ported loudspeaker enclosure
InactiveUS7218747B2Frequency/directions obtaining arrangementsTransducer casings/cabinets/supportsOpen portEngineering
An externally ported speaker enclosure includes a primary enclosure having a port or opening. The primary enclosure may continuously vary from a first dimension to a dimension of the port or opening. Alternatively, a duct or tube may extend from, and external to, the primary enclosure. The duct or tube may transition from a first dimension to a dimension of the port or opening. The dimensions of the port, primary enclosure, and transition from primary enclosure to port are configured to reinforce the low frequency response of a speaker mounted to the enclosure. A cylindrical primary enclosure may transition gradually or continuously to a port. The cylindrical primary enclosure can include a closed first end and an open port end. A speaker can be mounted to the cylindrical face of the primary enclosure. Alternatively, the speaker may be mounted parallel to an axis of the cylinder.
Owner:HUFFMAN NICK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com