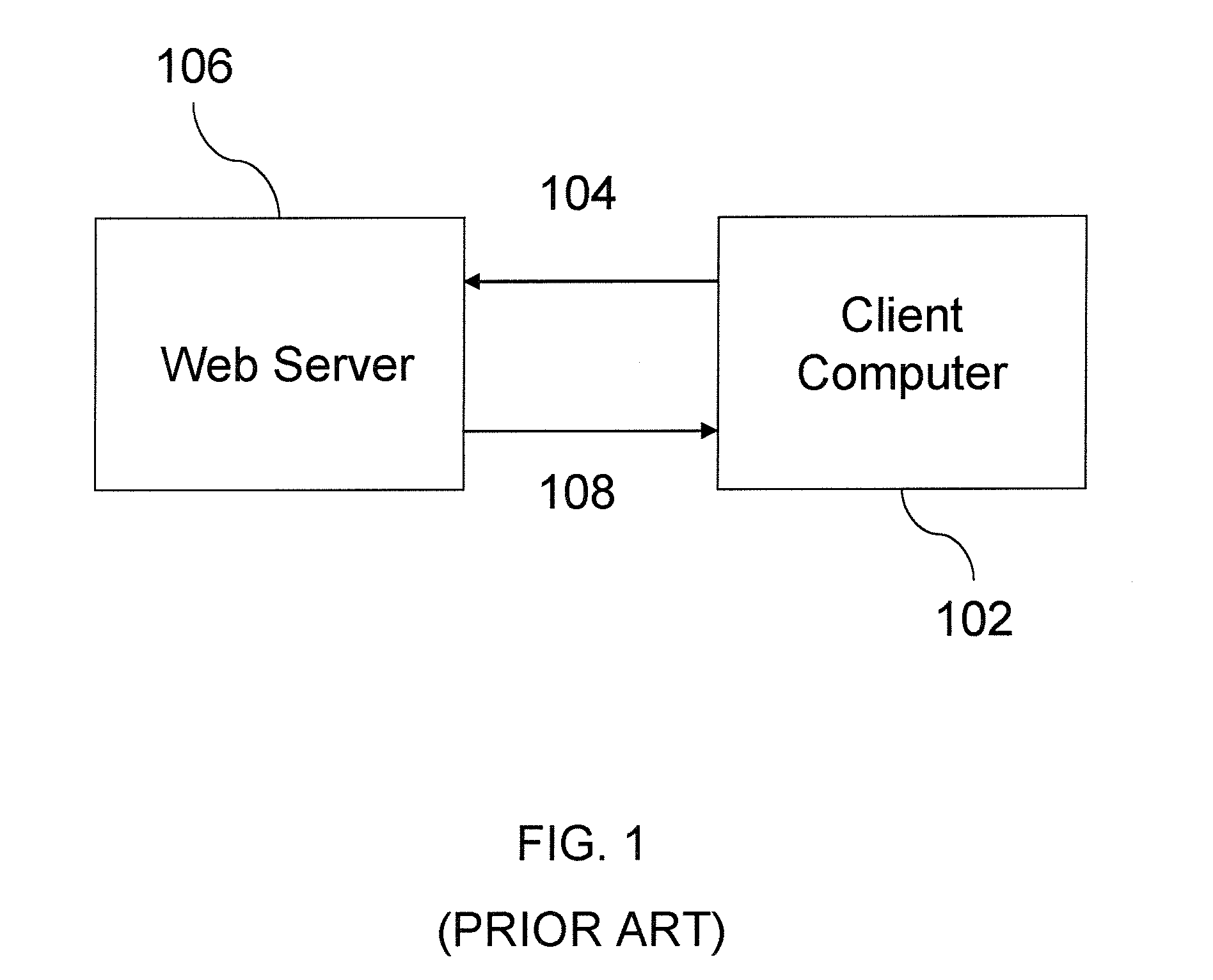
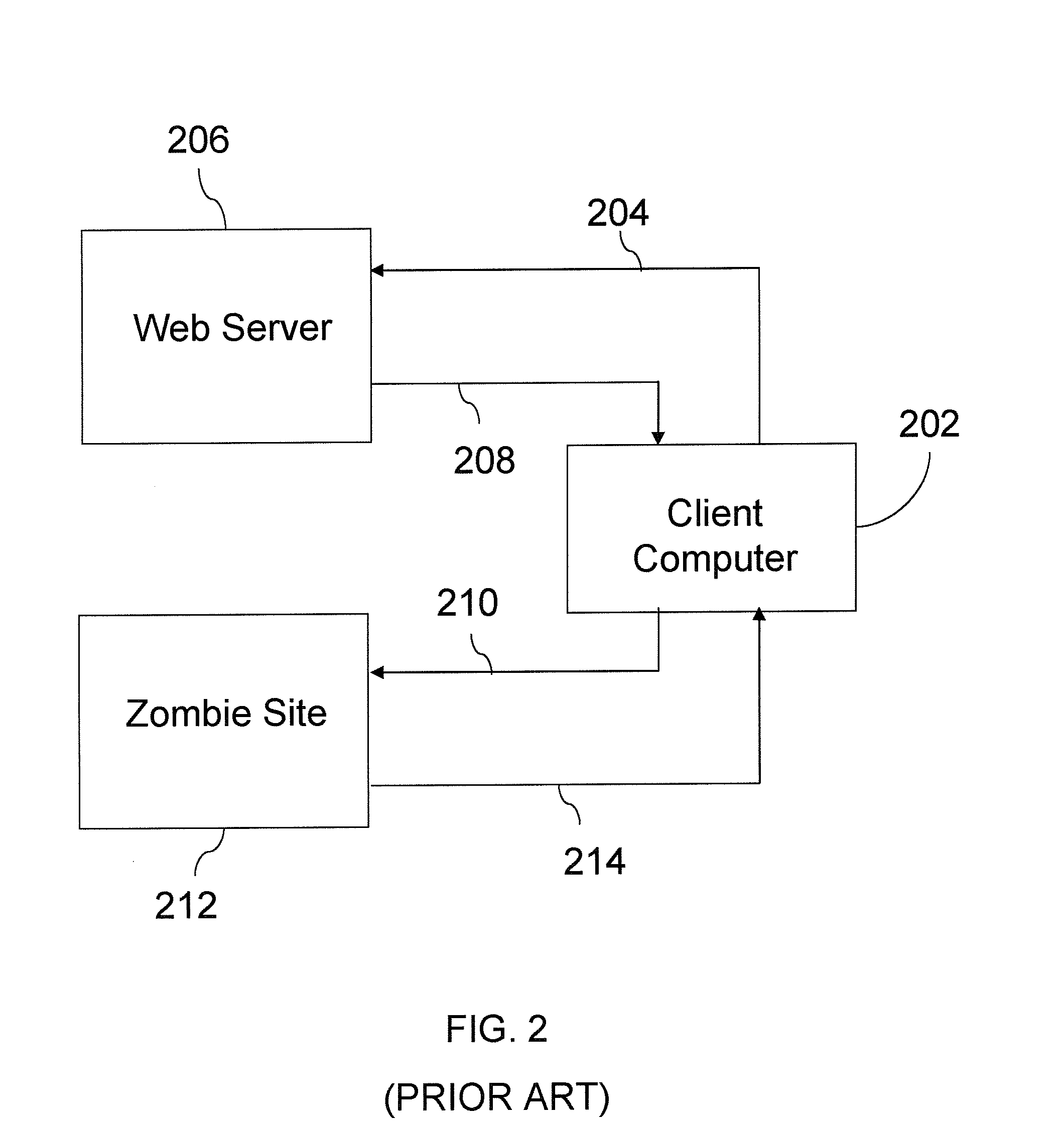
Patents
Literature
2764 results about "Risk level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Risk Level. Definition. Your “Risk Level” is how much risk you are willing to accept to get a certain level of reward; riskier stocks are both the ones that can lose the most or gain the most over time.
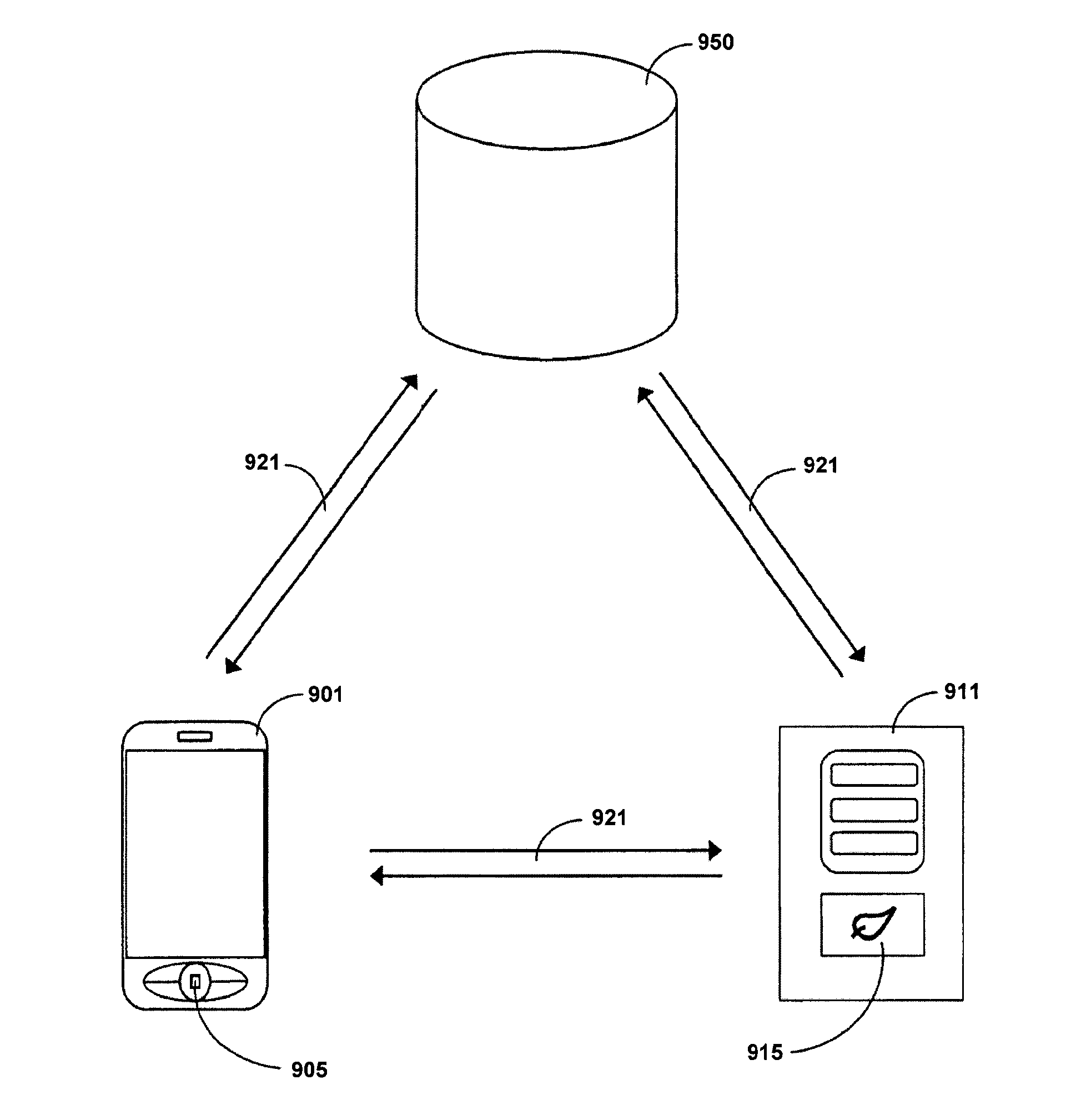
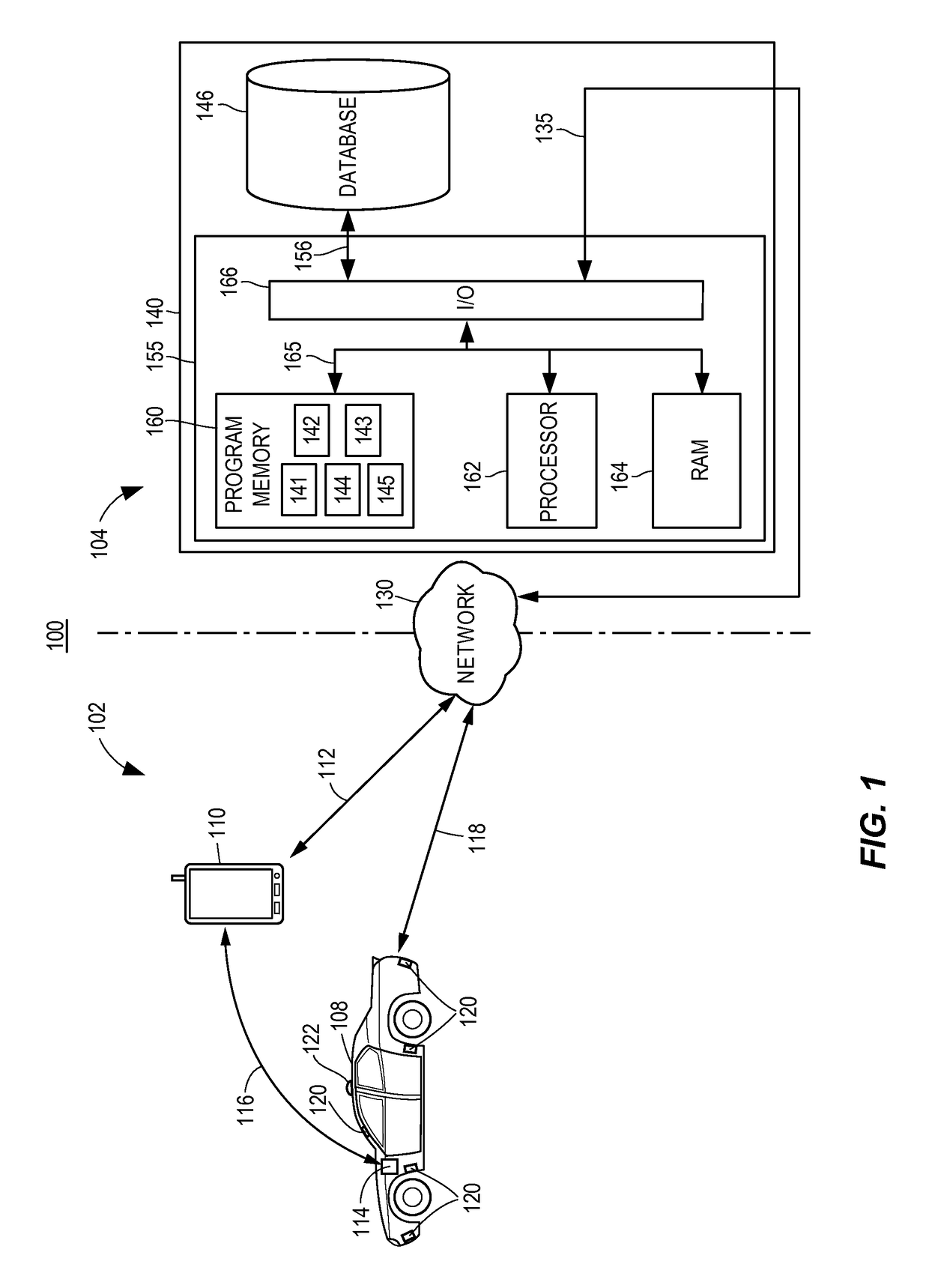
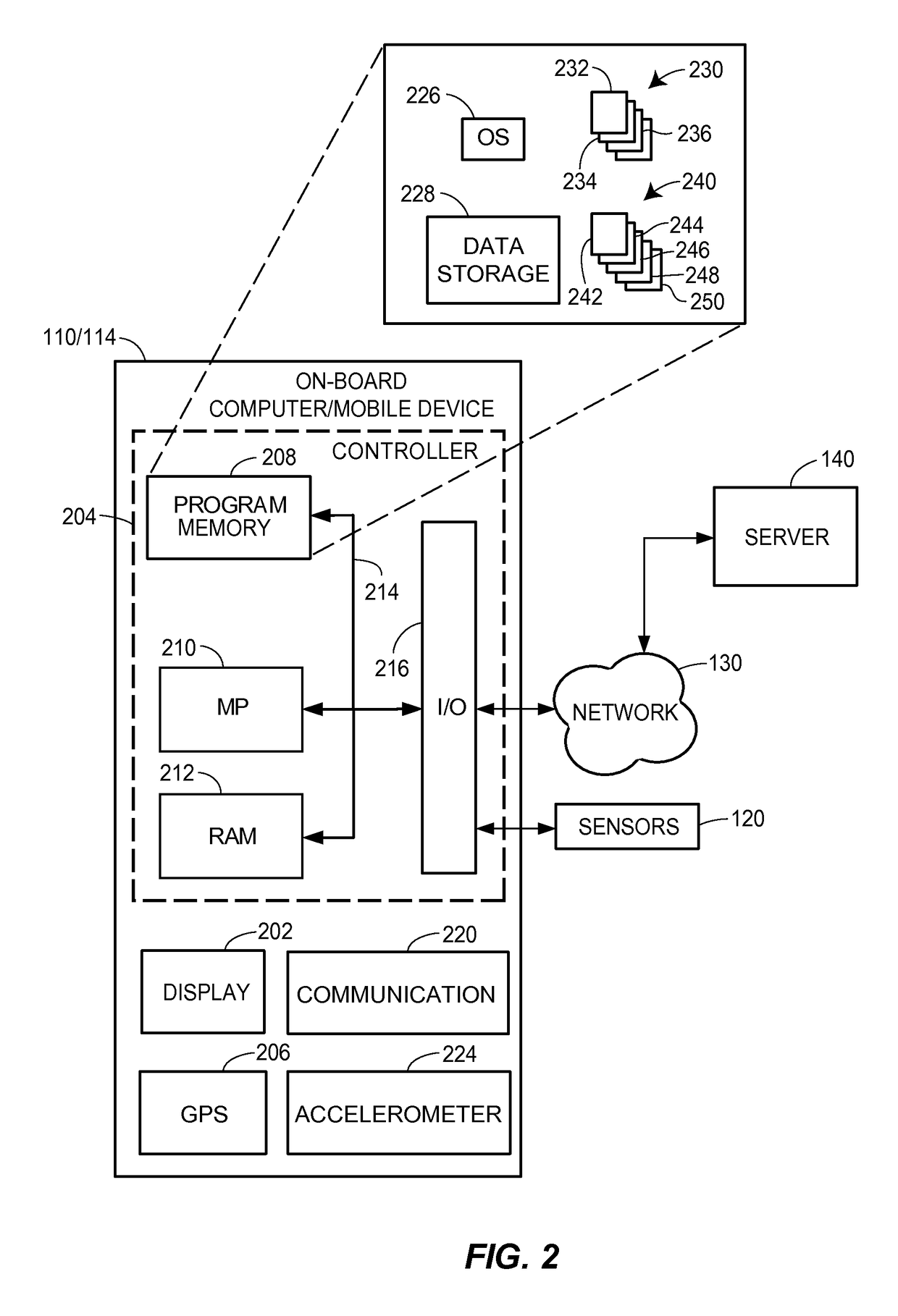
Methods and systems for sharing risk responses between collections of mobile communications devices
Methods are provided for determining an enterprise risk level, for sharing security risk information between enterprises by identifying a security response by a first enterprise and then sharing the security response to a second enterprise when a relationship database profile for the first collection indicates the security response may be shared. Methods are also provided for determining whether to allow a request from an originating device where the request may have been initiated by a remote device.
Owner:LOOKOUT MOBILE SECURITY
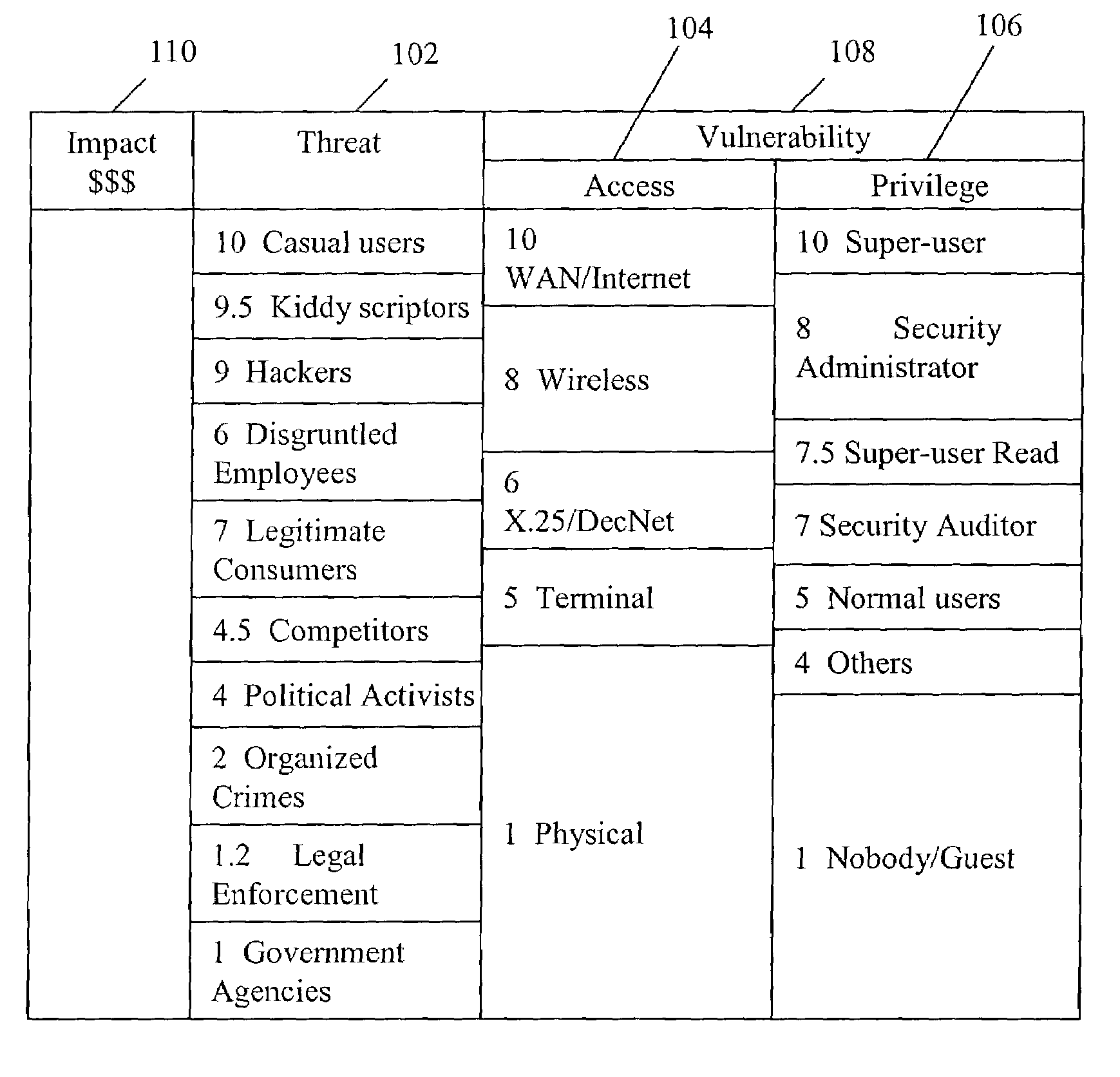
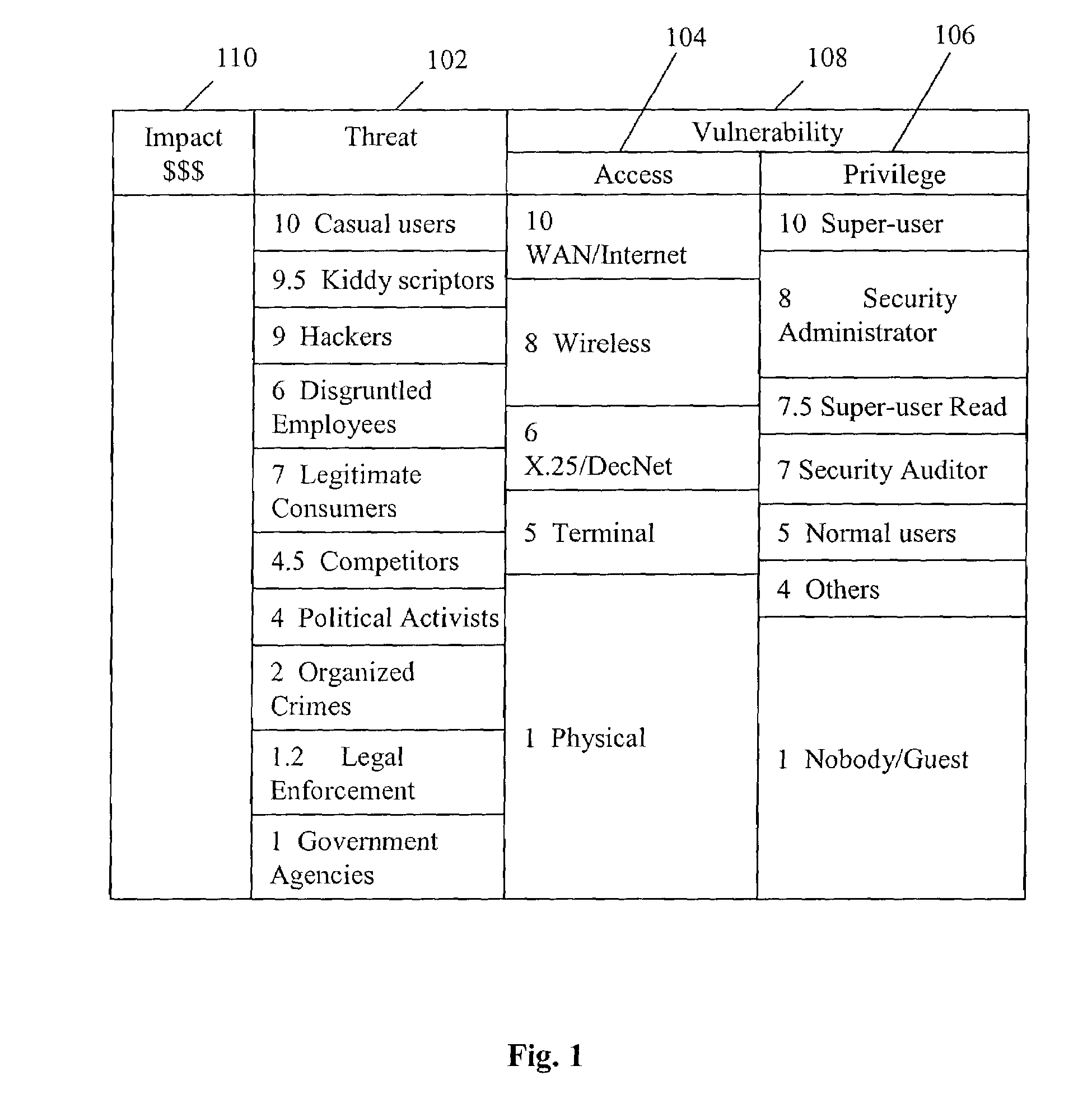
Method and system of assessing risk using a one-dimensional risk assessment model
A quantitative model combines a one-dimensional risk-assessment approach with expert knowledge to enable calculation of a probability or likelihood of exploitation of a threat to an information system asset without referring to actuarial information. A numerical value is established for one or more threats of attack on the information system asset based on expert knowledge without reference to actuarial data, and likewise, based on expert knowledge without reference to actuarial data, a numerical value is established for each of one or more access and privilege components of one or more vulnerabilities to attack on the information system asset. A security risk level for the information system asset is computed based upon the numerical values for threat and the access and privilege components for vulnerability so established.
Owner:CITIBANK
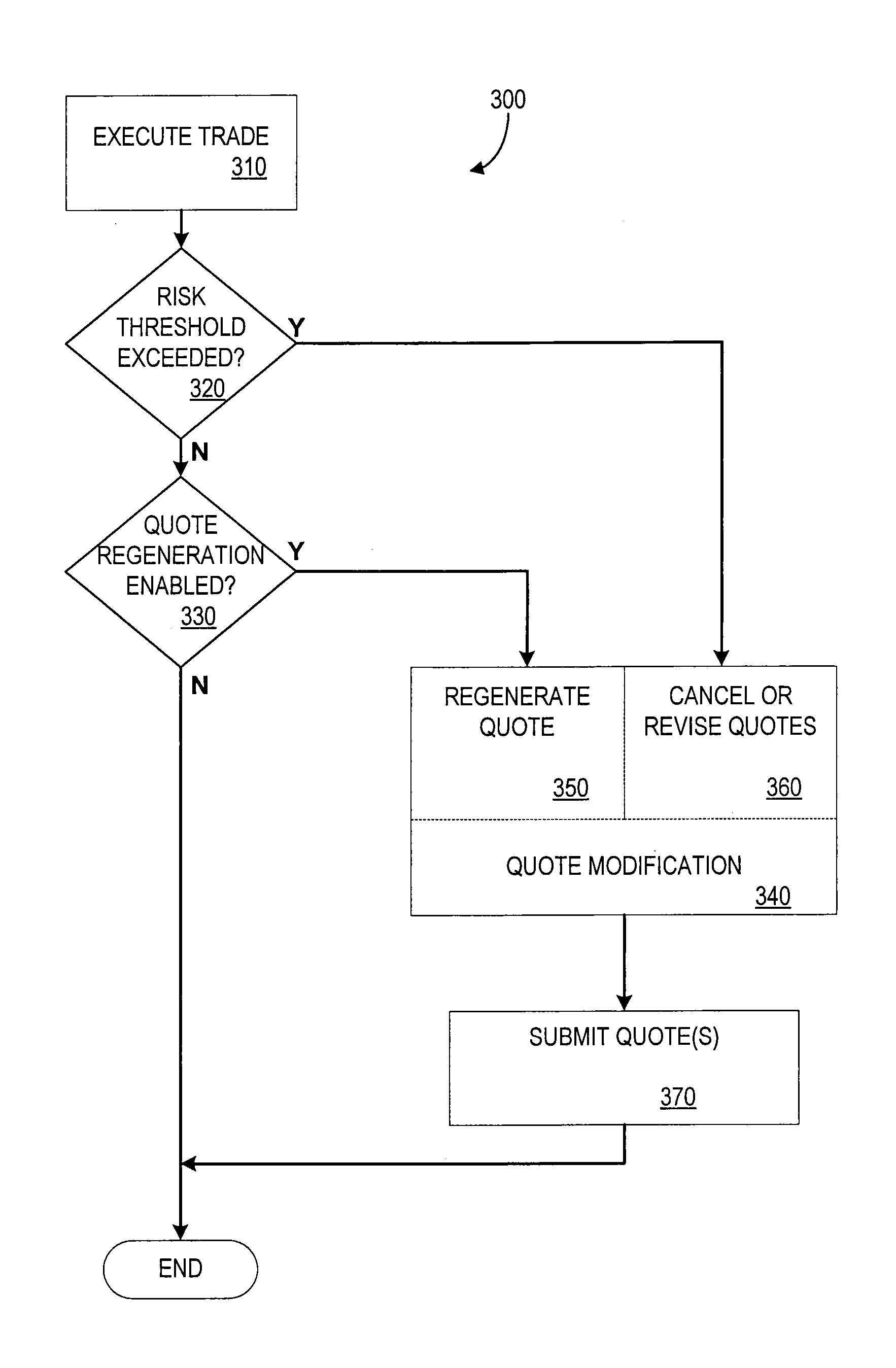
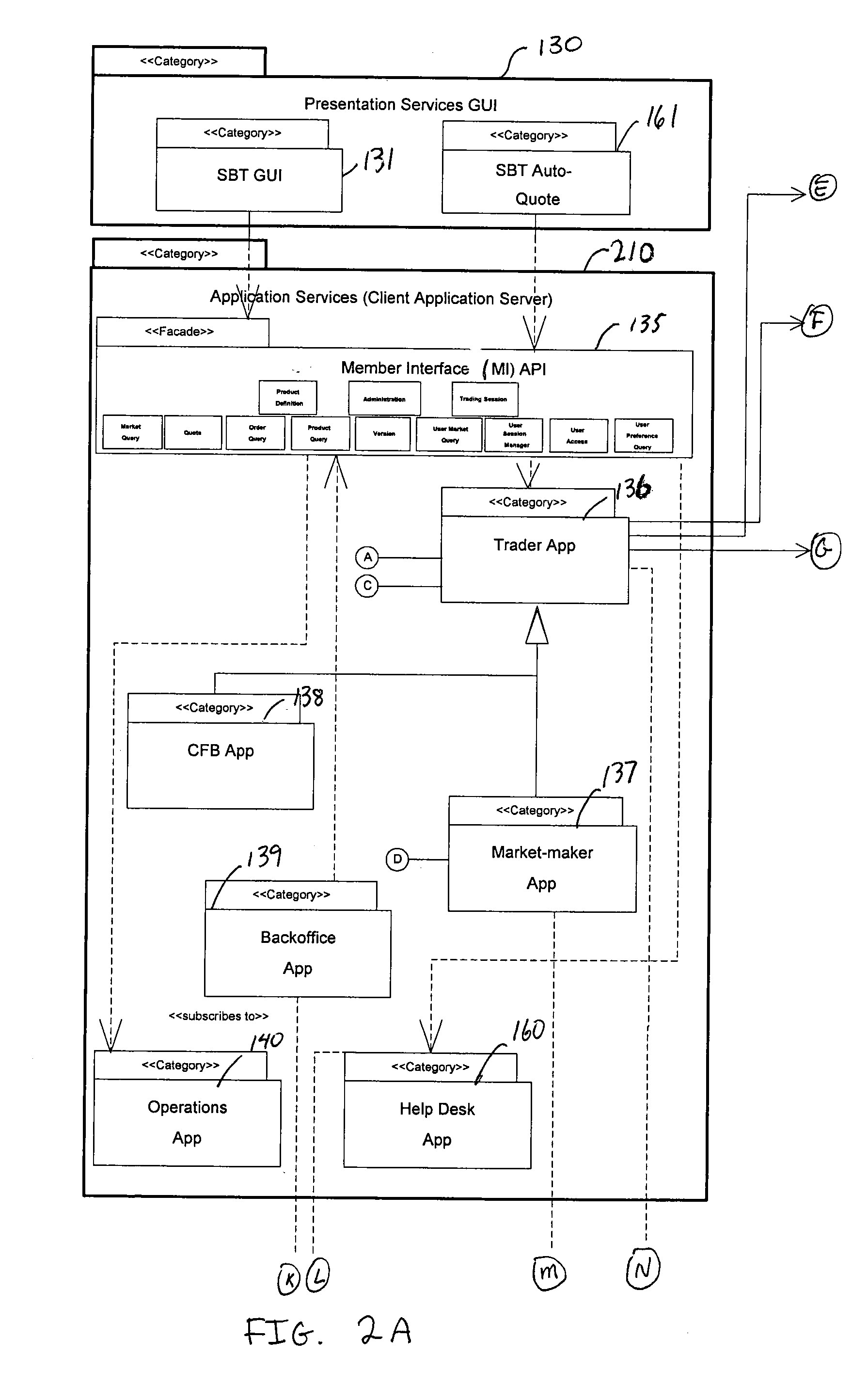
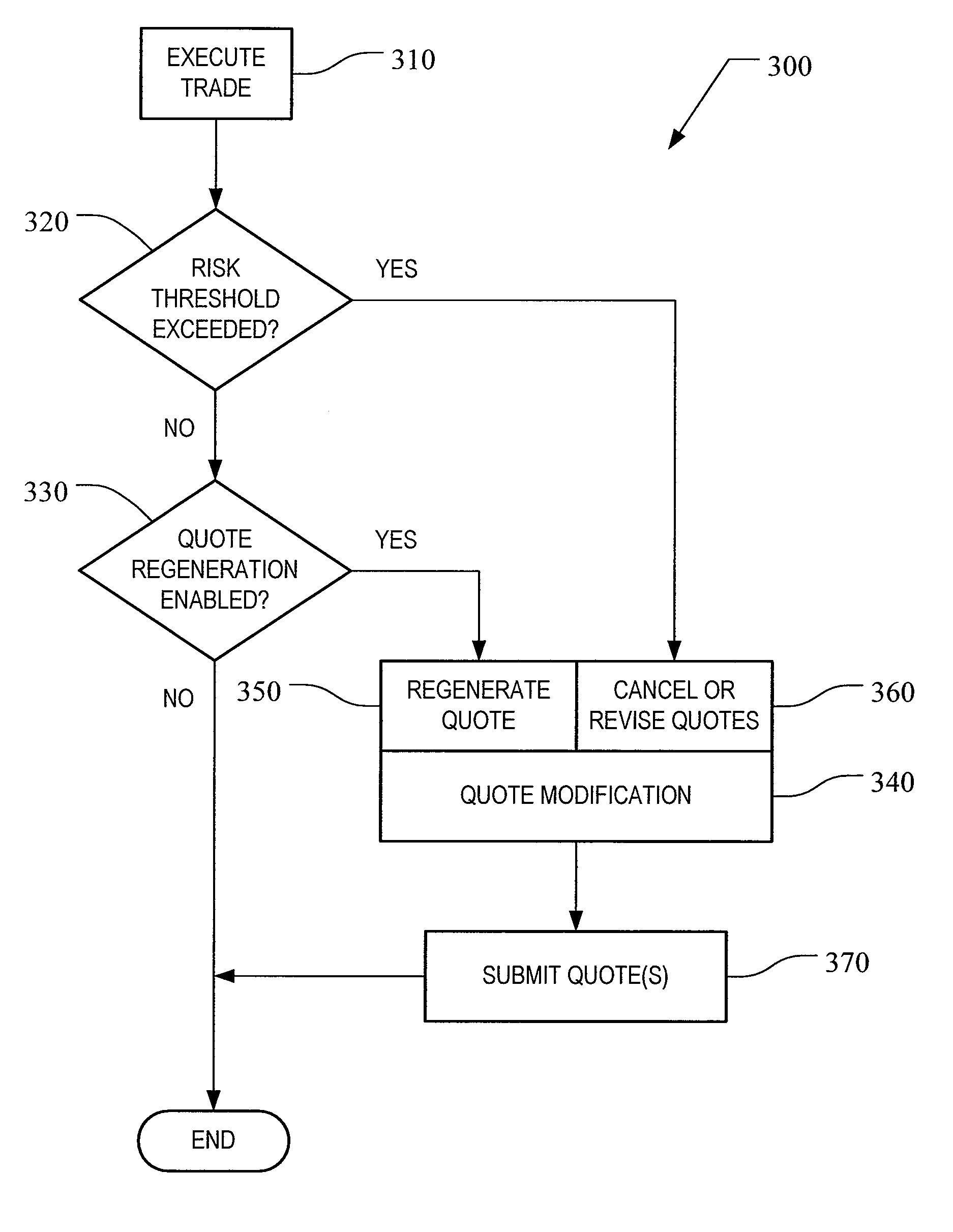
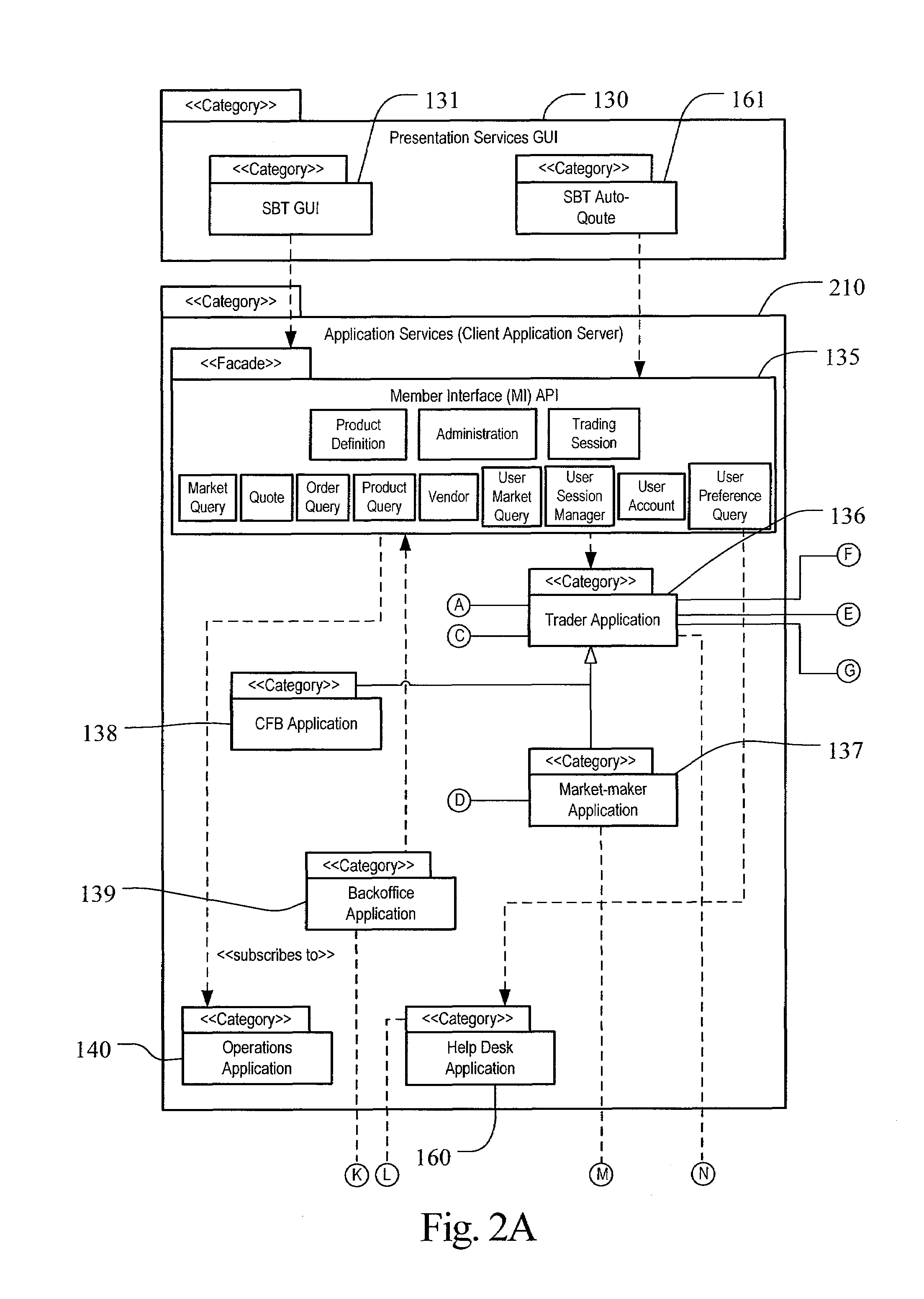
Automated Trading Exchange System Having Integrated Quote Risk Monitoring and Integrated Quote Modification Services
<heading lvl="0">Abstract< / heading> An automated trading exchange having integrated quote risk monitoring and quote modification services. An apparatus is implemented using at least one computer, having memory, and a processor. The computer is configured to receive orders and quotes, wherein specified ones of the quotes are contained in a quote group, and have associated trading parameters such as a risk threshold. Not all received quotes are required to have trading parameters as described herein. Preferably, the quote group contains all the quotes, or a subset of quotes, belonging to an individual market-maker for a given class of options contracts, or possibly the quotes of two or more market-makers that have identified themselves as belonging to a group for the purposes of risk monitoring and quote modification. The computer typically generates a trade by matching the received orders and quotes to previously received orders and quotes, and otherwise stores each of the received orders and quotes if a trade is not generated. The computer then determines whether a quote within the quote group has been filled as a result of the generated trade, and if so, determines a risk level and an aggregate risk level associated with said trade. The computer then compares the aggregate risk level with the market-maker's risk threshold, and if the threshold is exceeded, automatically modifies at least one of the remaining quotes in the quote group. The computer may also automatically regenerate quotes that have been filled.
Owner:CBOE EXCHANGE INC
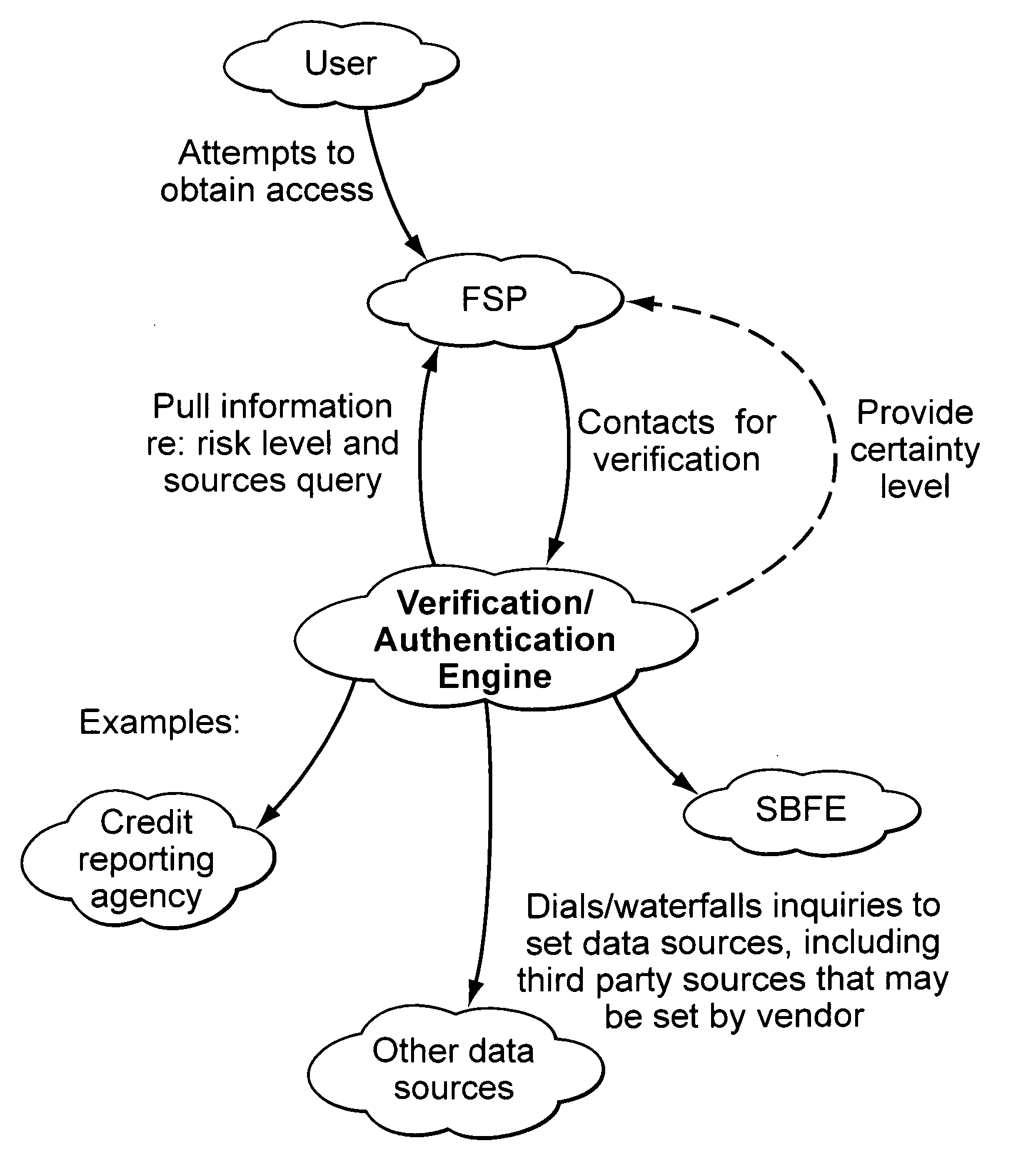
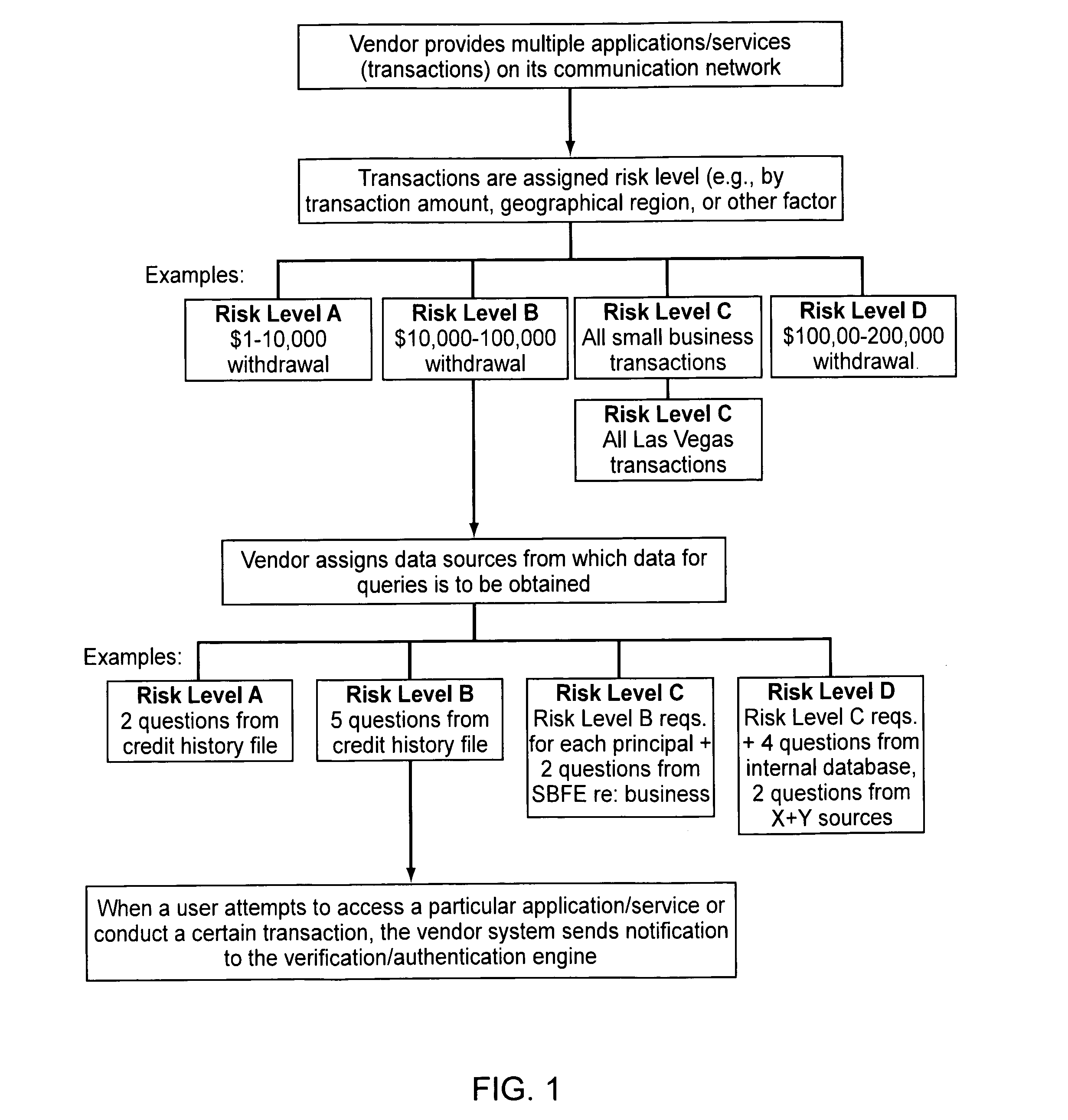
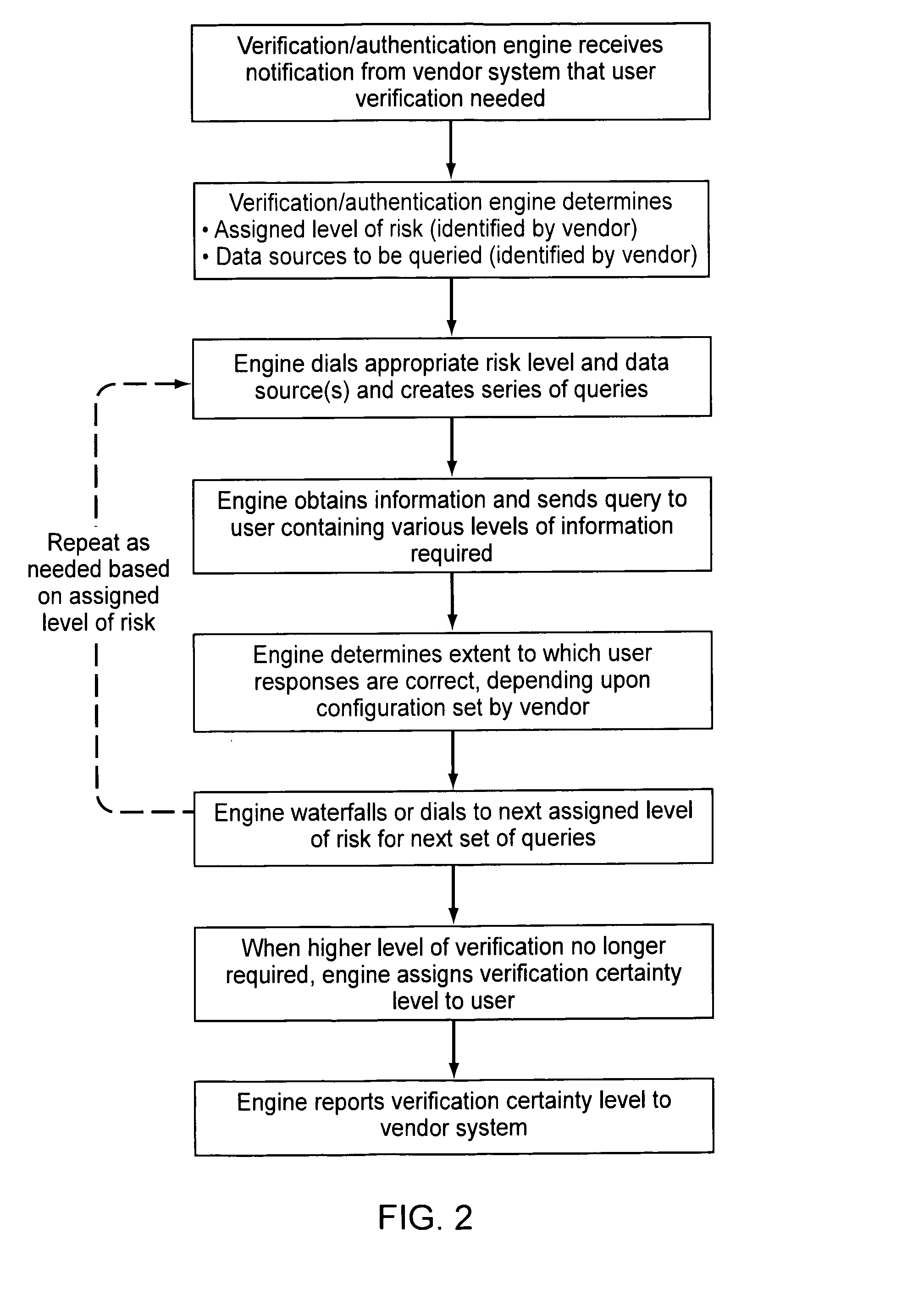
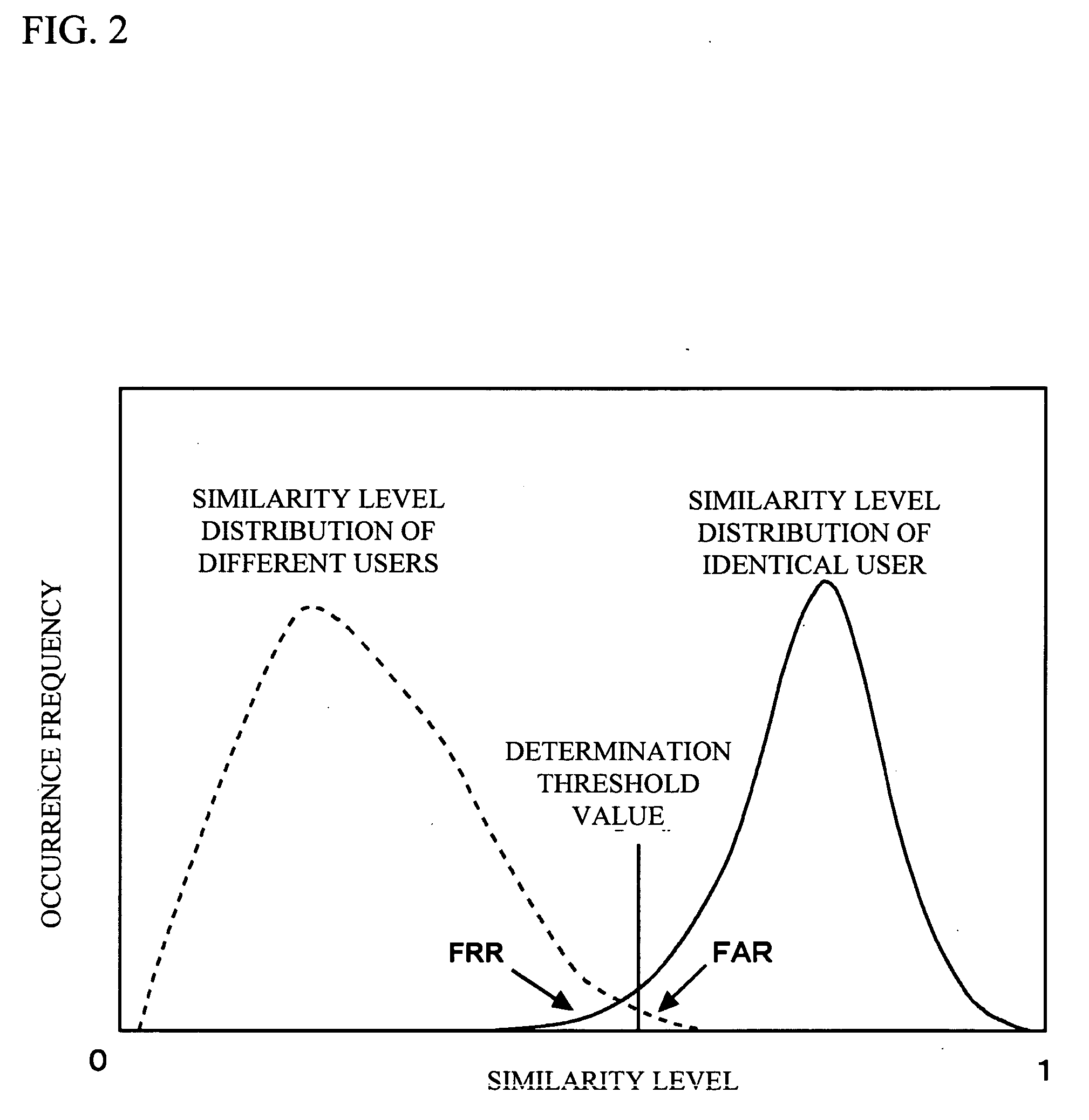
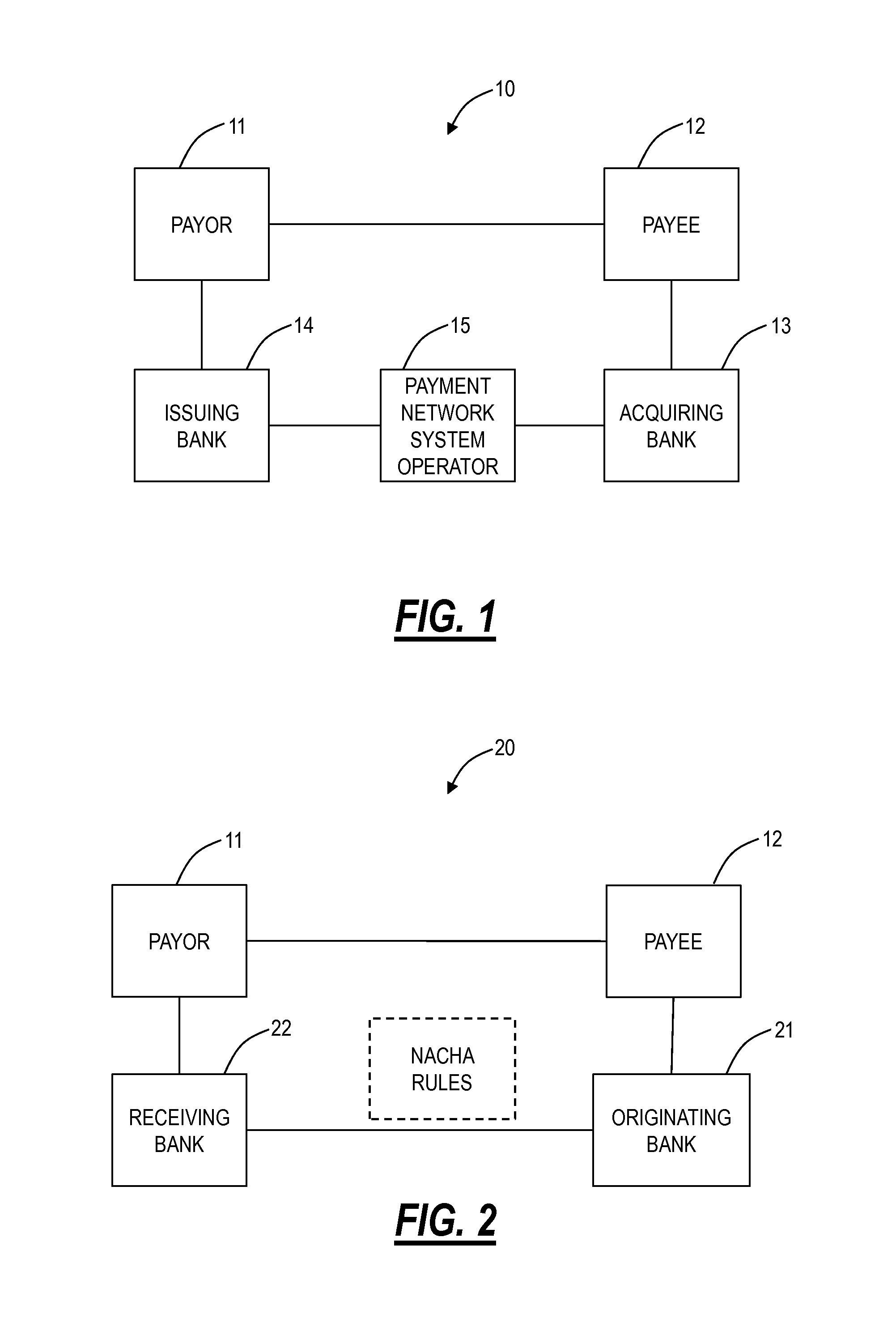
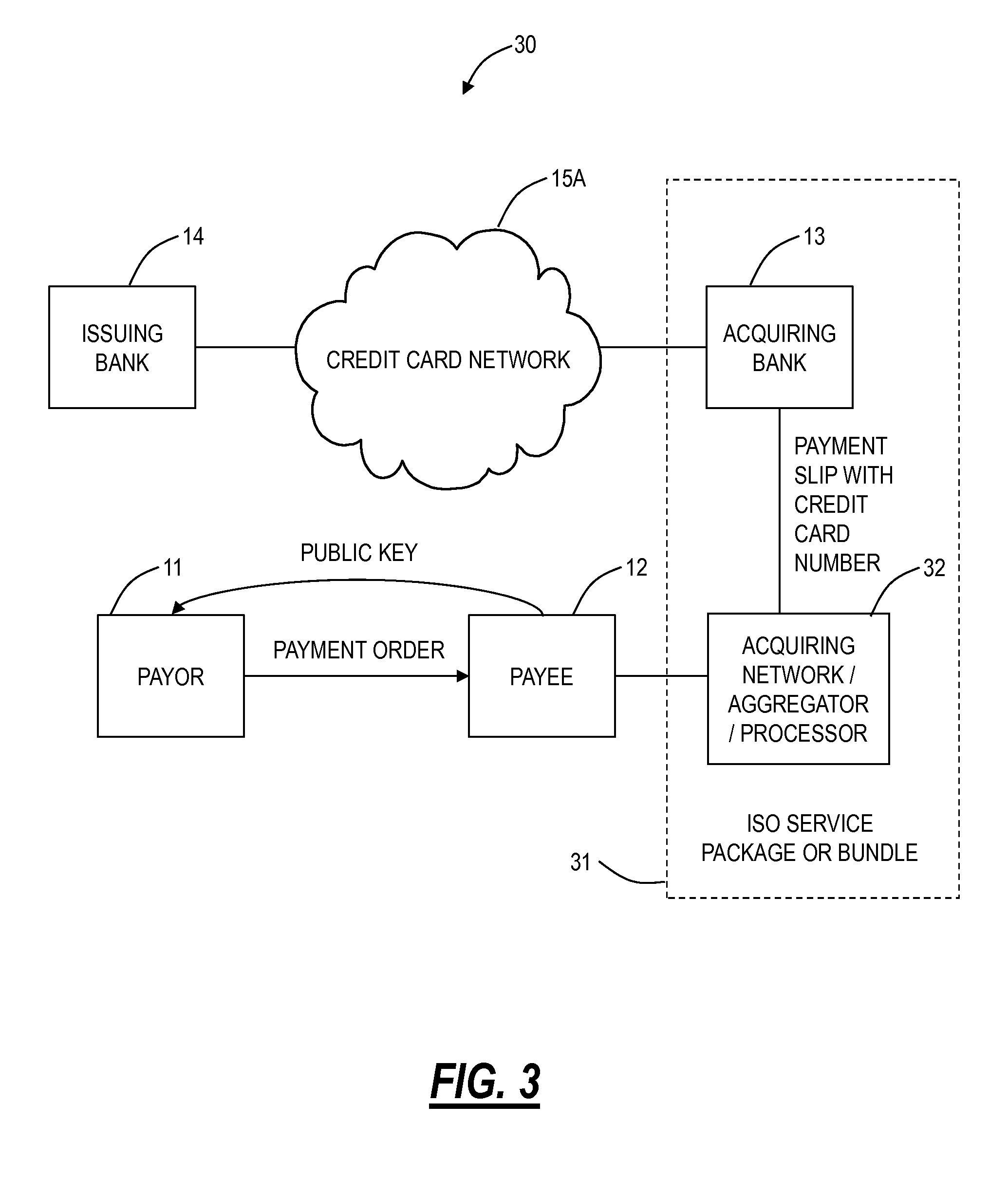
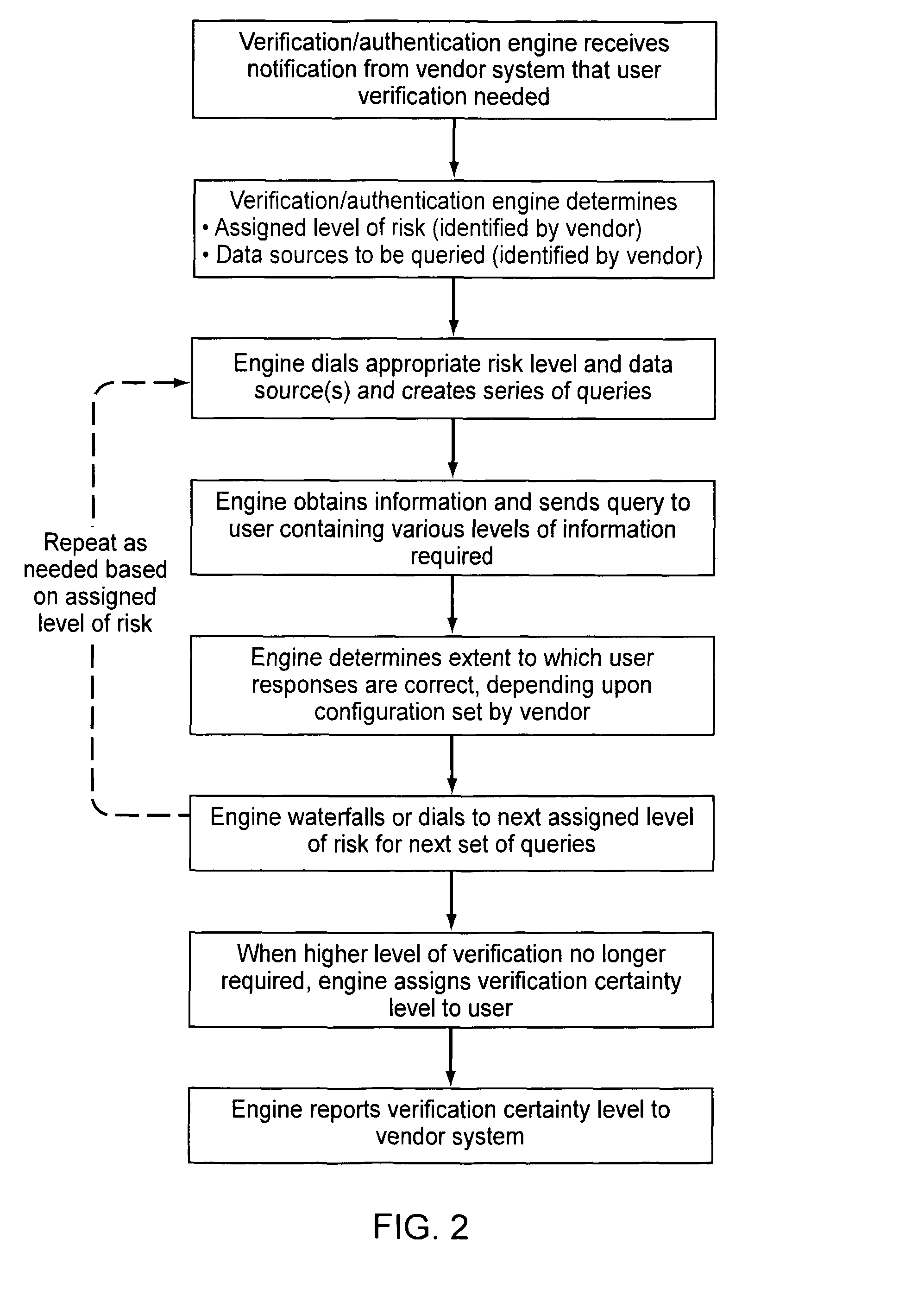
Verification and authentication systems and methods
ActiveUS20080086759A1Improve securityMinimal amountDigital data processing detailsUser identity/authority verificationRisk levelExternal data
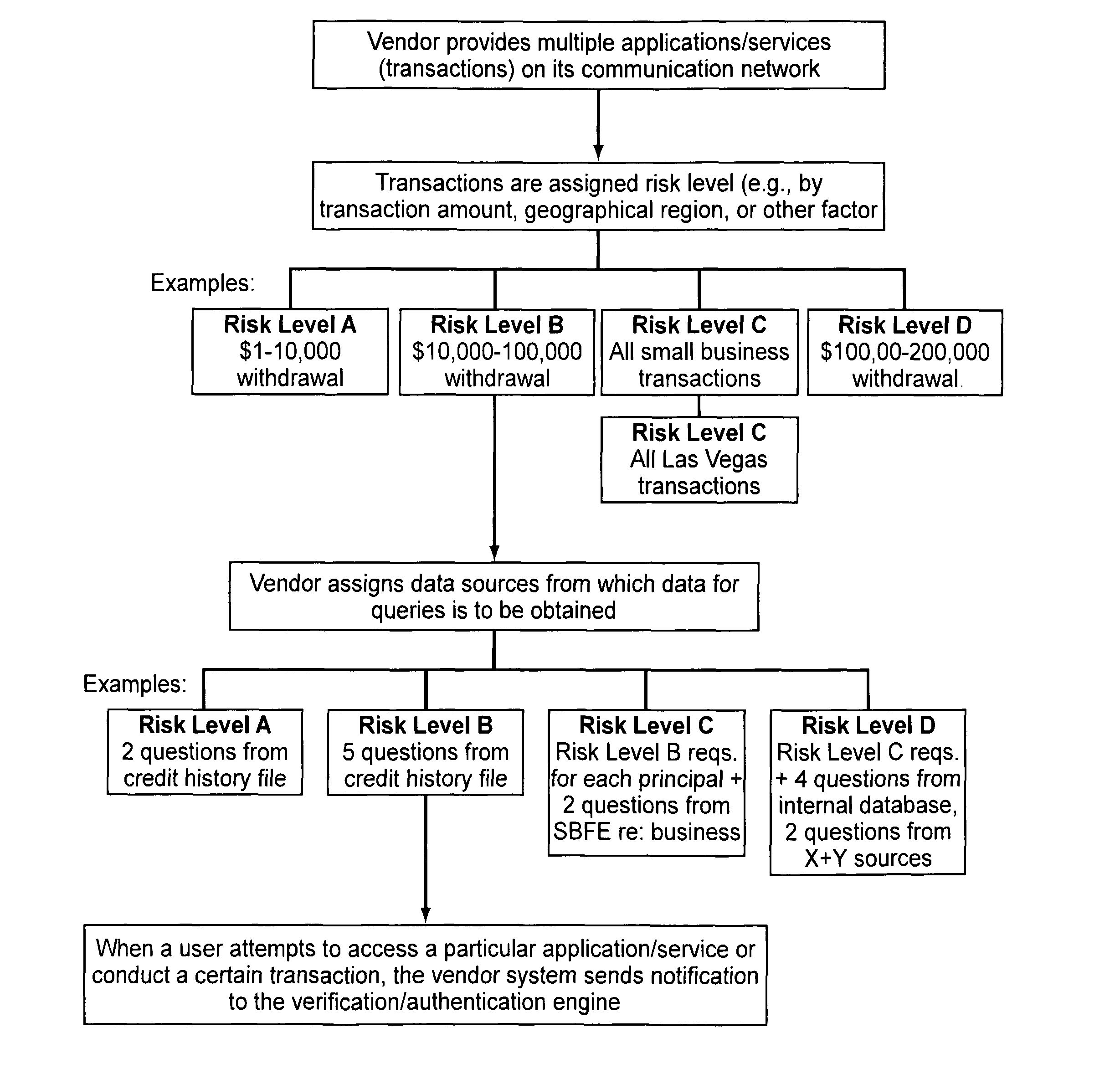
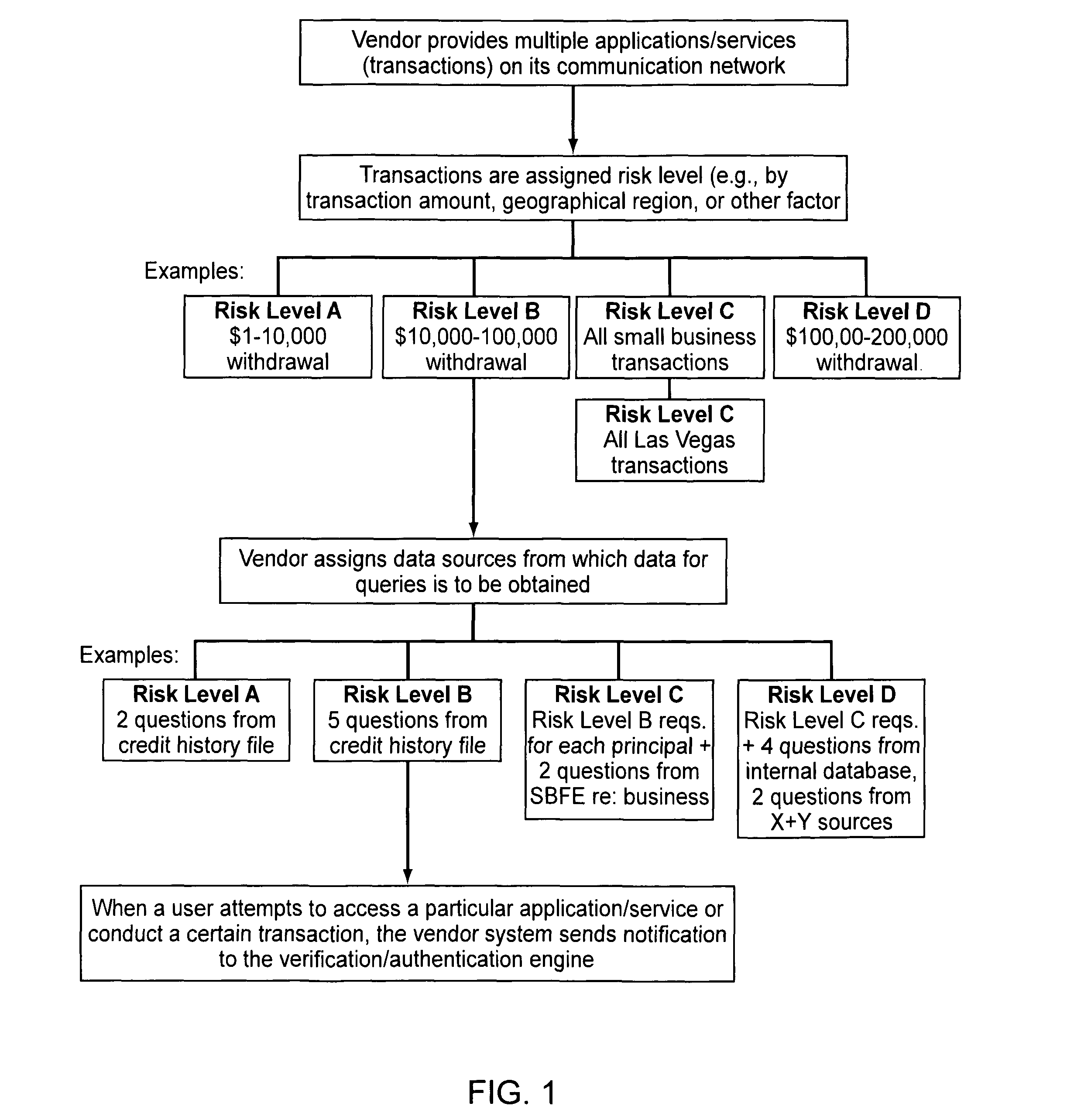
Embodiments of the present invention provide verification and / or authentication service engines that provide a customizable solution that can be “dialed” based on the risk level assigned to individual or grouped applications. The systems can also incorporate internal and external sources of data used to verify information provided by the user. It is dynamic and can pull information from a myriad of sources during the verification process, enabling credit reporting agencies (e.g., Equifax and others), FSPs, and other service providers to facilitate real-time approval and access to products and services.
Owner:EQUIFAX INC
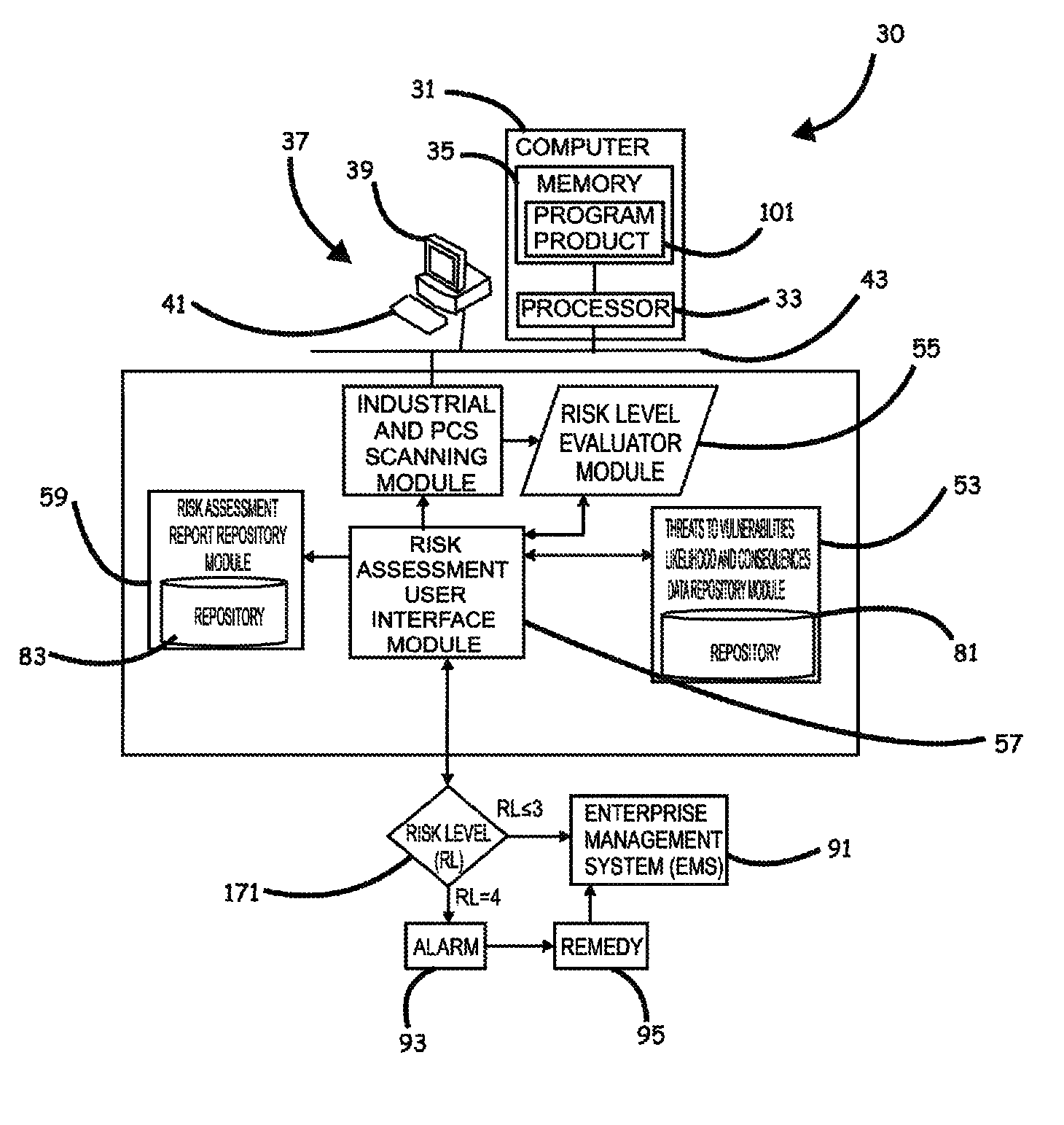
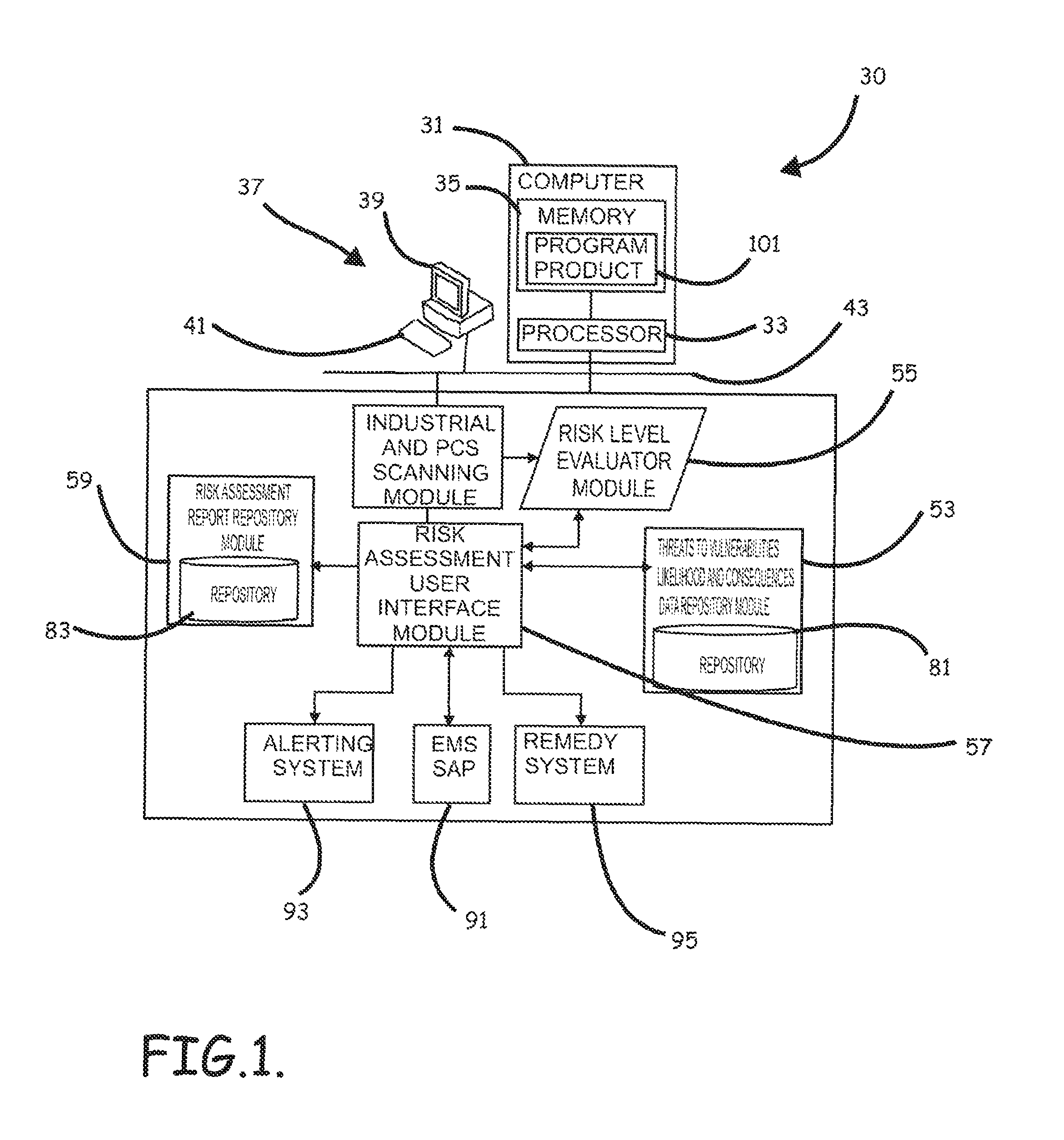
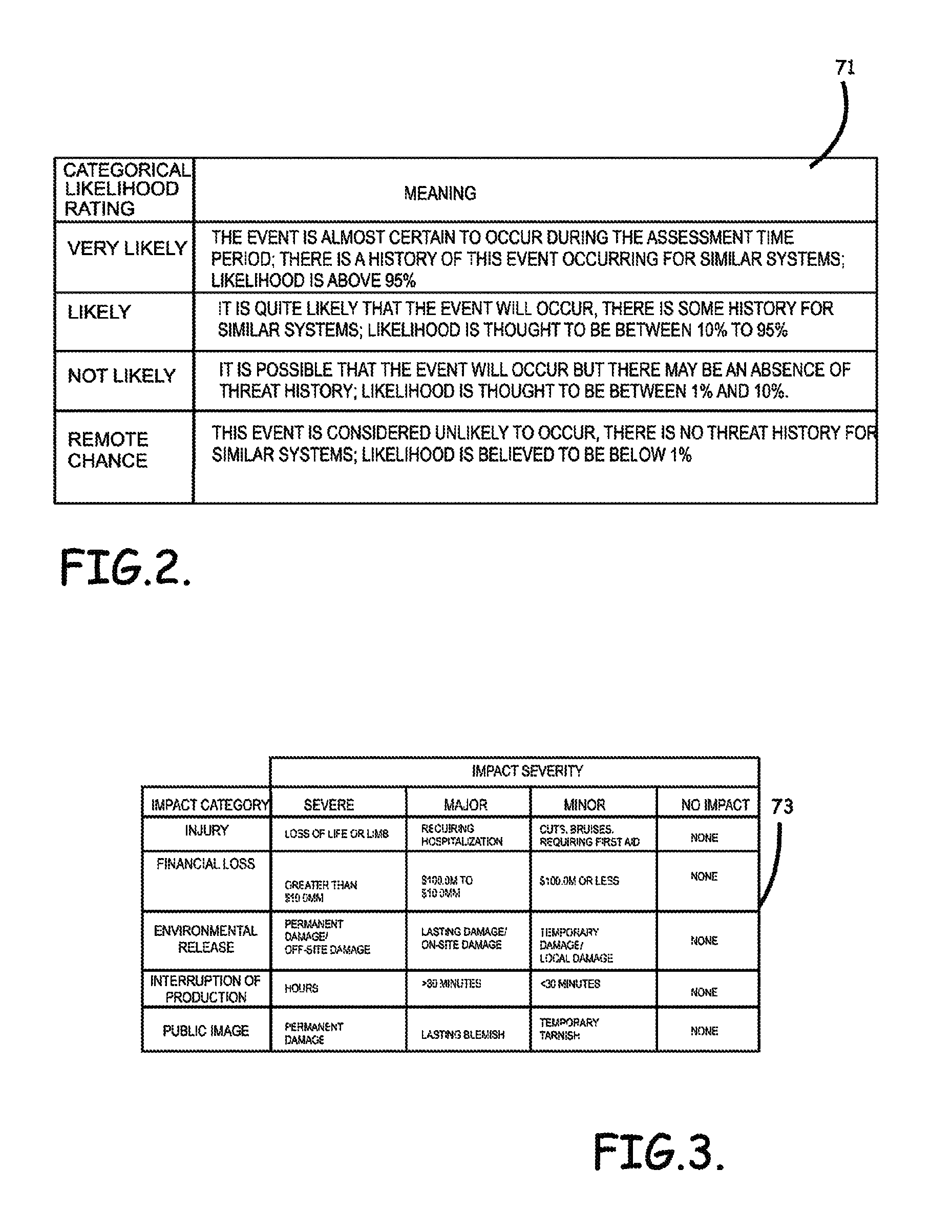
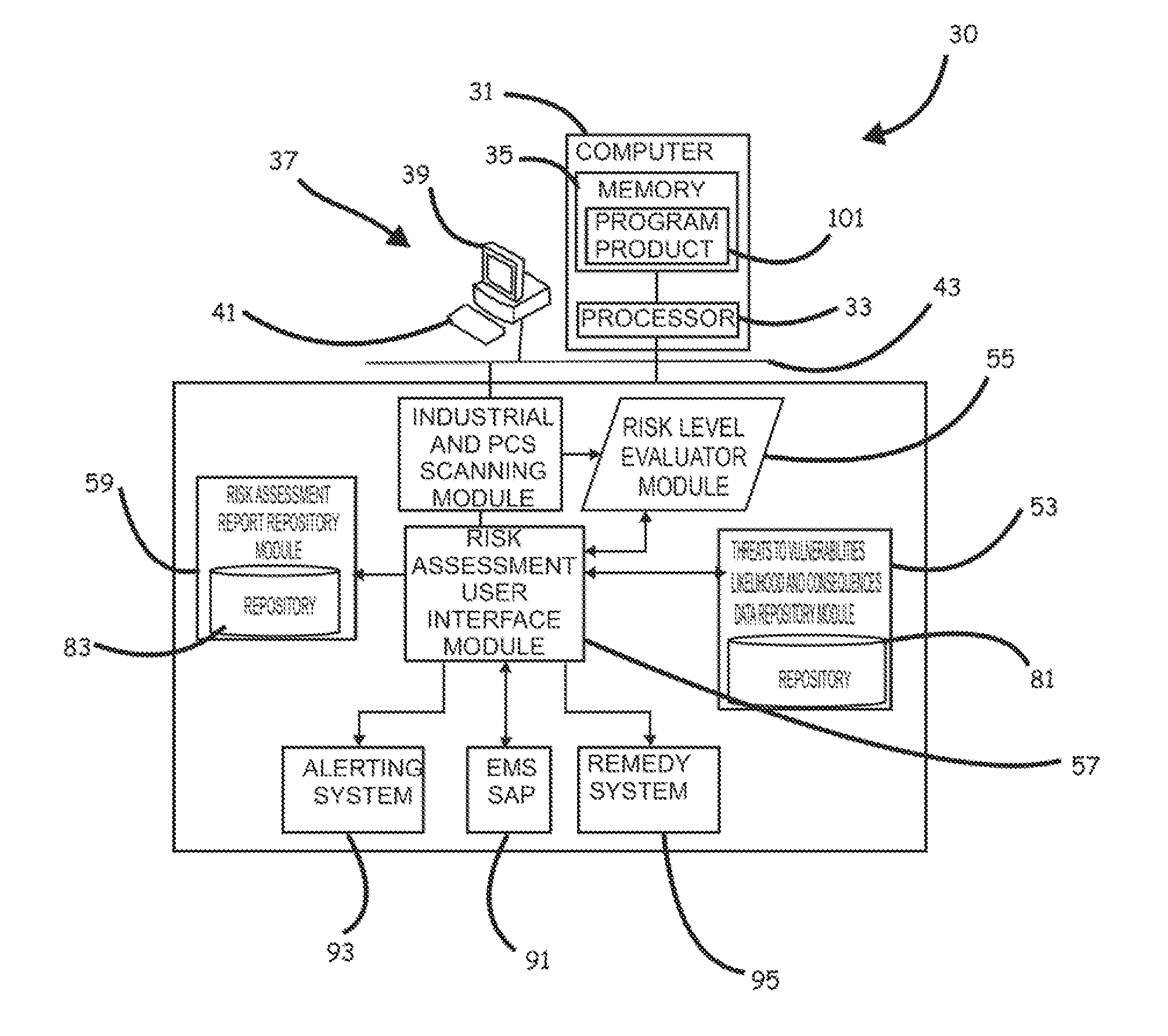
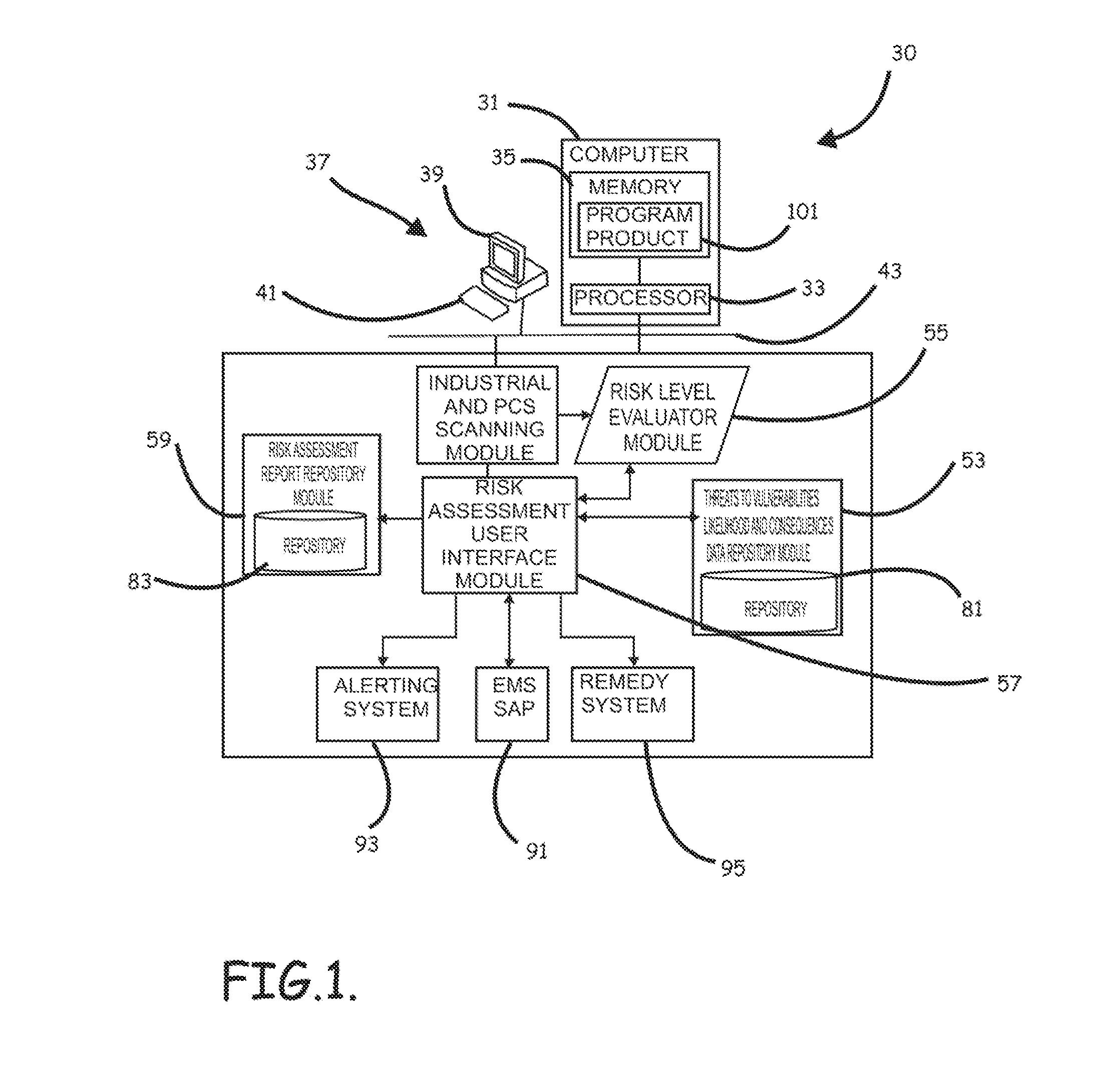
Systems, program product and methods for performing a risk assessment workflow process for plant networks and systems
ActiveUS8621637B2Minimizing human interactionEasy to implementProgramme controlMemory loss protectionRisk levelProcess control network
Systems, methods, and program product to perform a cyber security risk assessment on a plurality of process control networks and systems comprising a plurality of primary network assets at an industrial process facility, are provided. An example of a system and program product can include an industrial and process control systems scanning module configured to identify networks and systems topology and to execute system and network security, vulnerability, virus, link congestion, node congestion analysis to thereby detect susceptibility to know threats to define potential vulnerabilities; a threats to vulnerabilities likelihood and consequences data repository module configured to determine a likelihood of each of a plurality of known threats exploiting identified vulnerabilities and to identify consequences of the exploitation to individual impacted systems and to overall plant operation; and a risk level evaluator module configured to determine a risk level rating for any identified vulnerabilities and provide recommended corrective actions.
Owner:SAUDI ARABIAN OIL CO
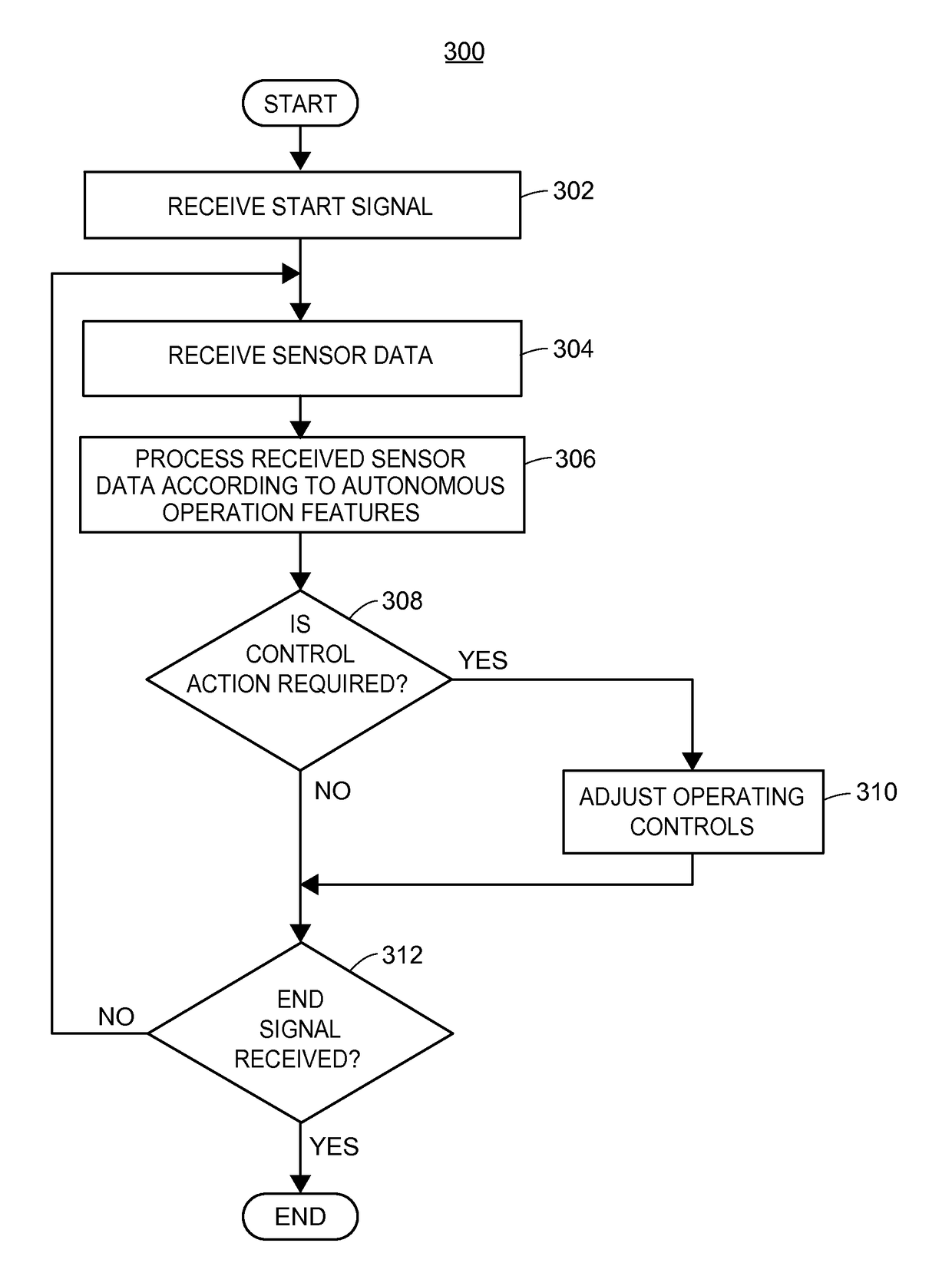
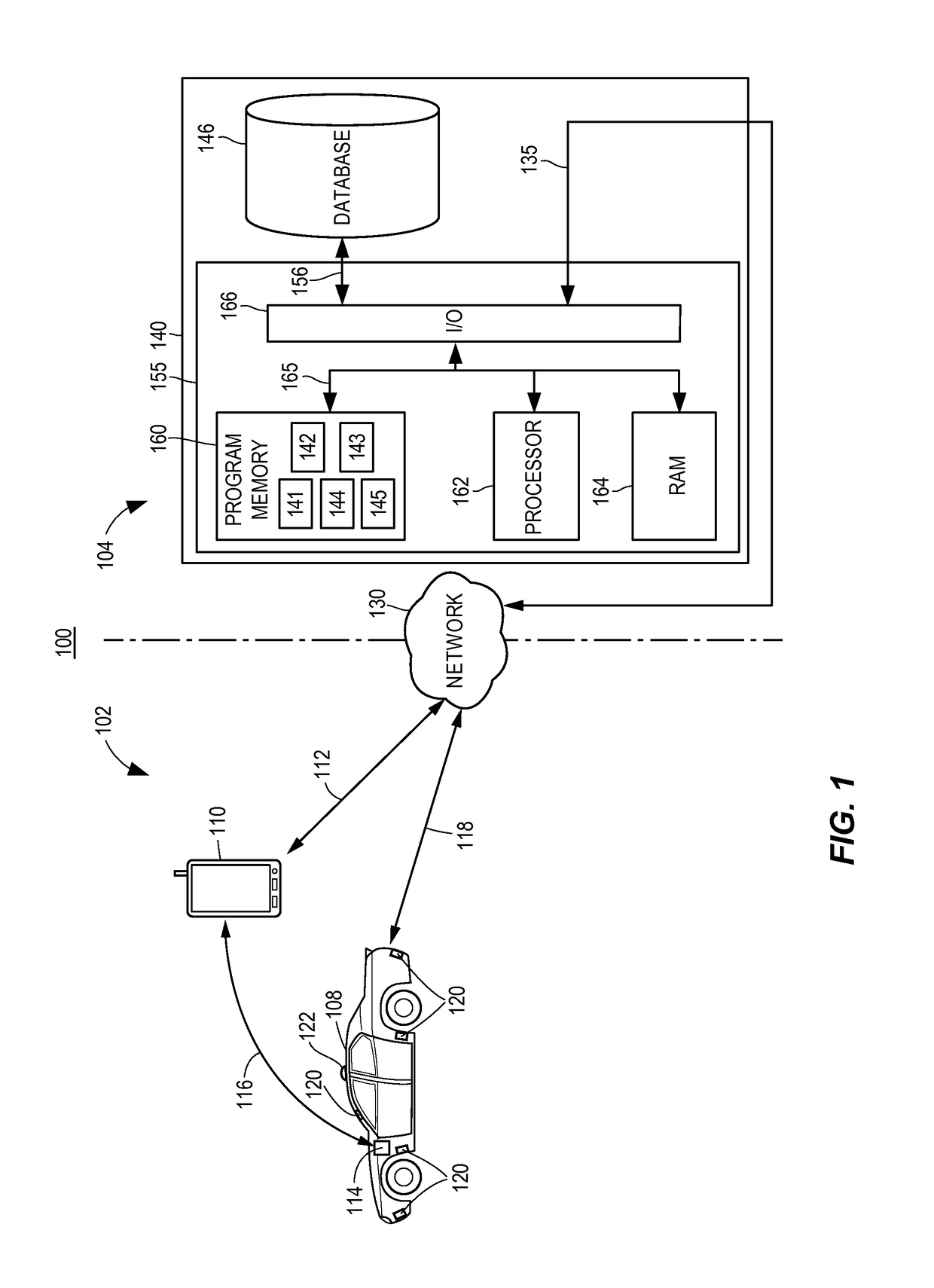
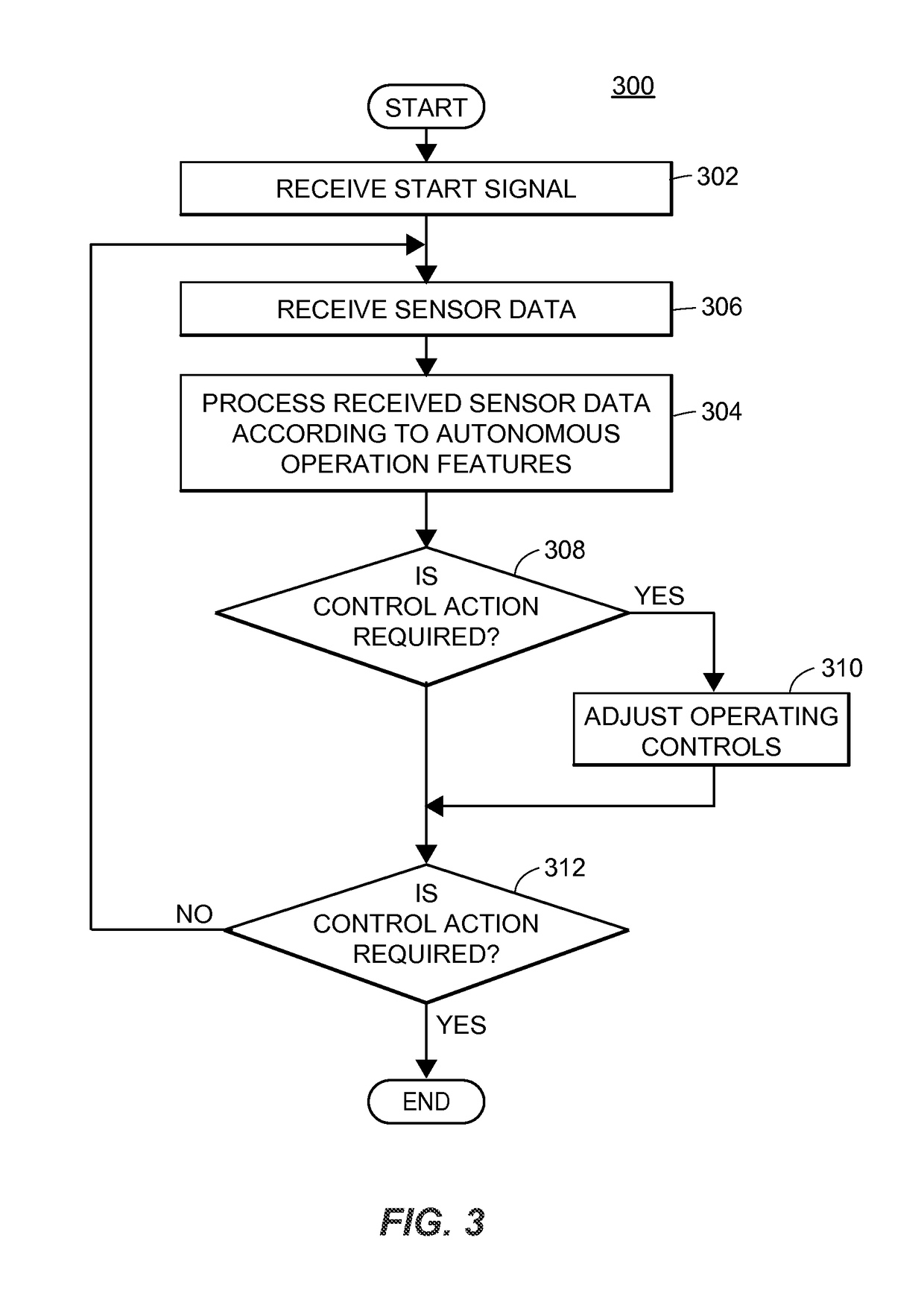
Autonomous vehicle operation feature monitoring and evaluation of effectiveness
ActiveUS9754325B1Operation moreFacilitate risk assessment and premium determinationRegistering/indicating working of vehiclesControl with pedestrian guidance indicatorRisk levelDecision taking
Owner:STATE FARM MUTAL AUTOMOBILE INSURANCE COMPANY
Automated trading exchange system having integrated quote risk monitoring and integrated quote modification services
An automated trading exchange having integrated quote risk monitoring and quote modification services. An apparatus is implemented using at least one computer, having memory, and a processor. The computer is configured to receive orders and quotes, wherein specified ones of the quotes are contained in a quote group, and have associated trading parameters such as a risk threshold. Not all received quotes are required to have trading parameters as described herein. Preferably, the quote group contains all the quotes, or a subset of quotes, belonging to an individual market-maker for a given class of options contracts, or possibly the quotes of two or more market-makers that have identified themselves as belonging to a group for the purposes of risk monitoring and quote modification. The computer typically generates a trade by matching the received orders and quotes to previously received orders and quotes, and otherwise stores each of the received orders and quotes if a trade is not generated. The computer then determines whether a quote within the quote group has been filled as a result of the generated trade, and if so, determines a risk level and an aggregate risk level associated with said trade. The computer then compares the aggregate risk level with the market-maker's risk threshold, and if the threshold is exceeded, automatically modifies at least one of the remaining quotes in the quote group. The computer may also automatically regenerate quotes that have been filled.
Owner:CBOE EXCHANGE INC
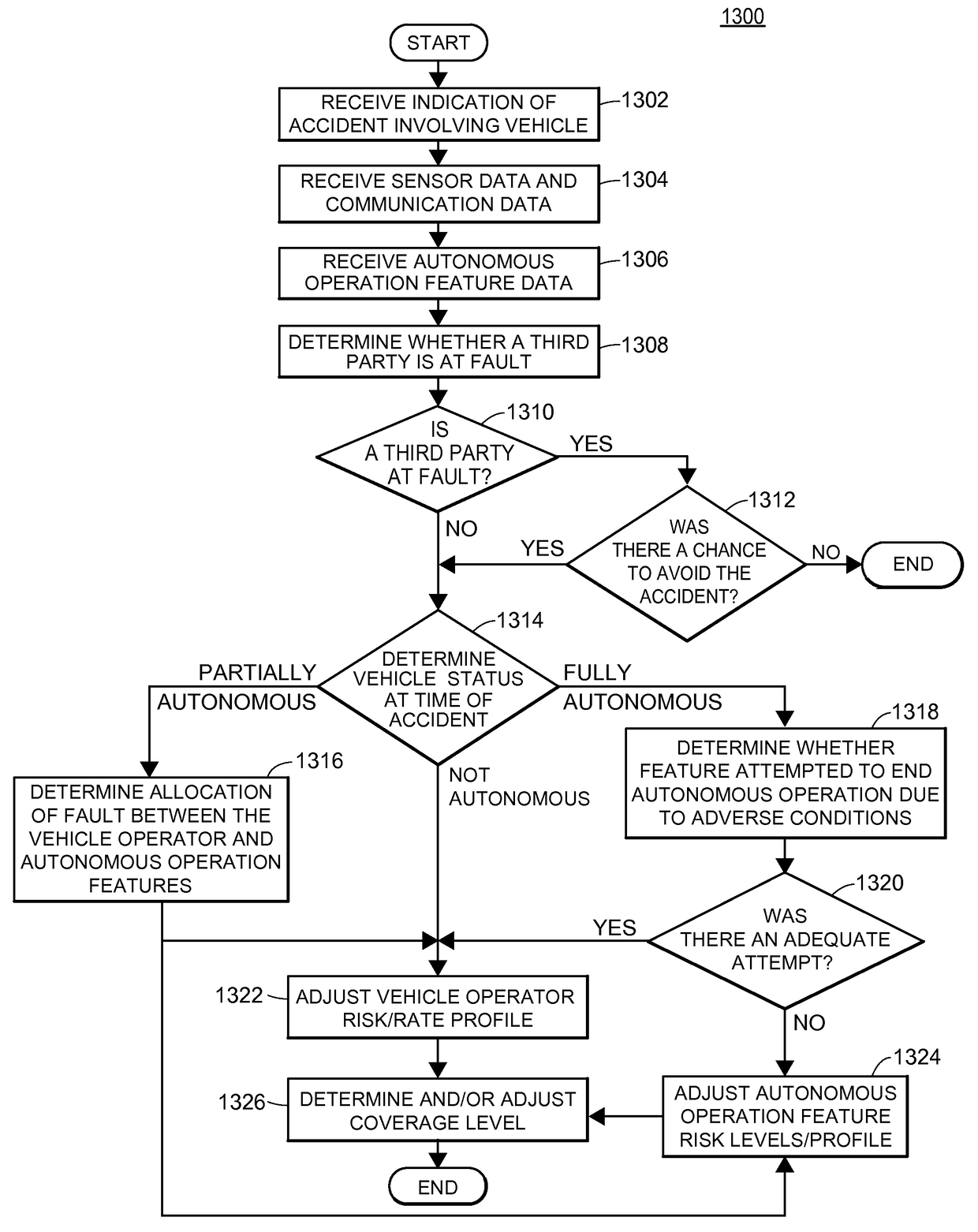
Accident fault determination for autonomous vehicles
ActiveUS9972054B1Operation moreFacilitate risk assessment and premium determinationAutonomous decision making processFinanceRisk levelThird party
Methods and systems for determining fault for an accident involving a vehicle having one or more autonomous and / or semi-autonomous operation features are provided. According to certain aspects, performance data indicative of the performance of the features may be used to determine fault for a vehicle accident, such as a collision, by allocating fault for the accident between a vehicle operator, the autonomous operation features, or a third party. The allocation of fault may be used to determine an adjustment to an insurance policy and / or adjust coverage levels for an insurance policy. The allocation of fault may further be used to adjust risk levels or profiles associated with the autonomous or semi-autonomous operation features, which may be applied to other vehicles having the same or similar features.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
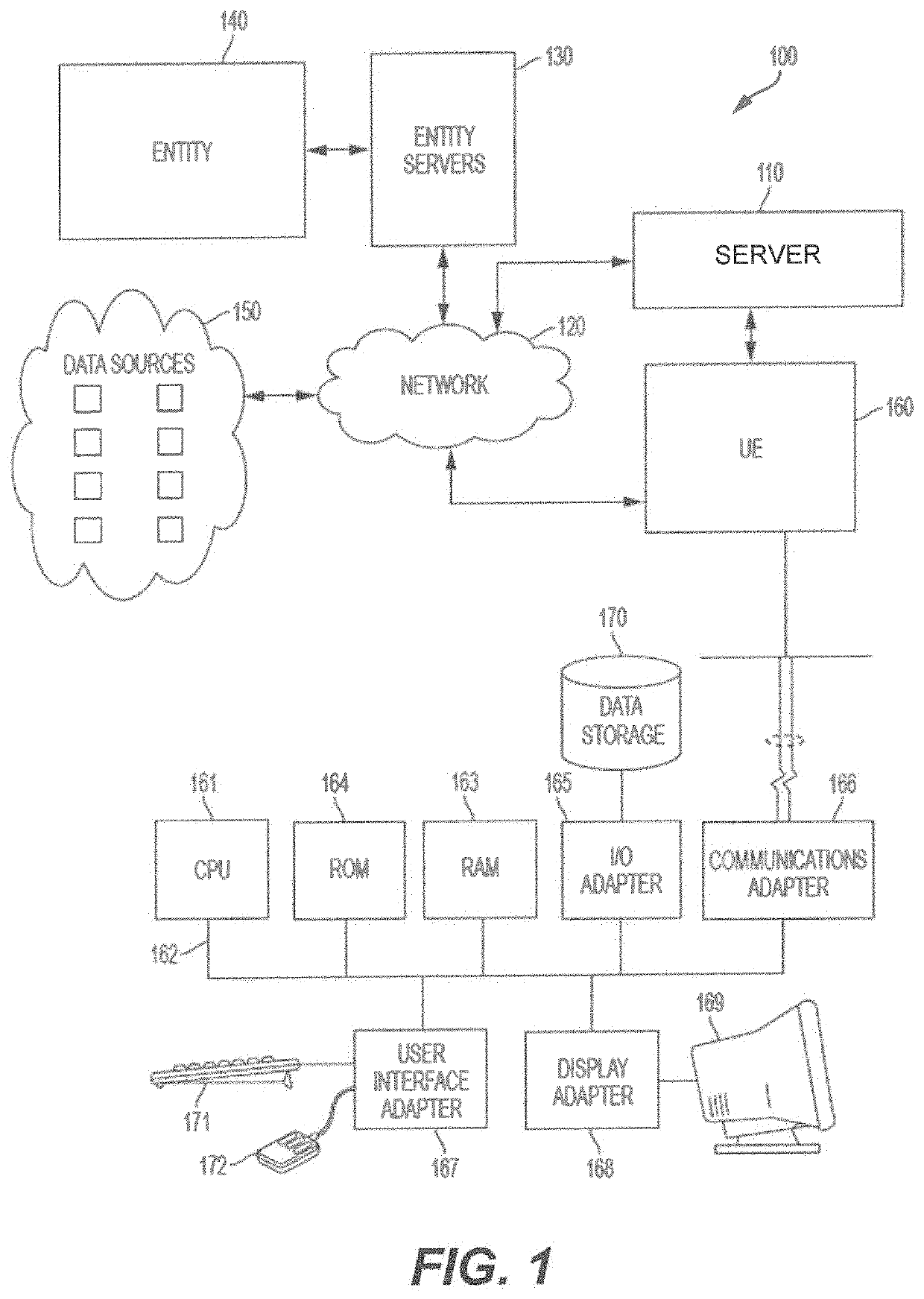
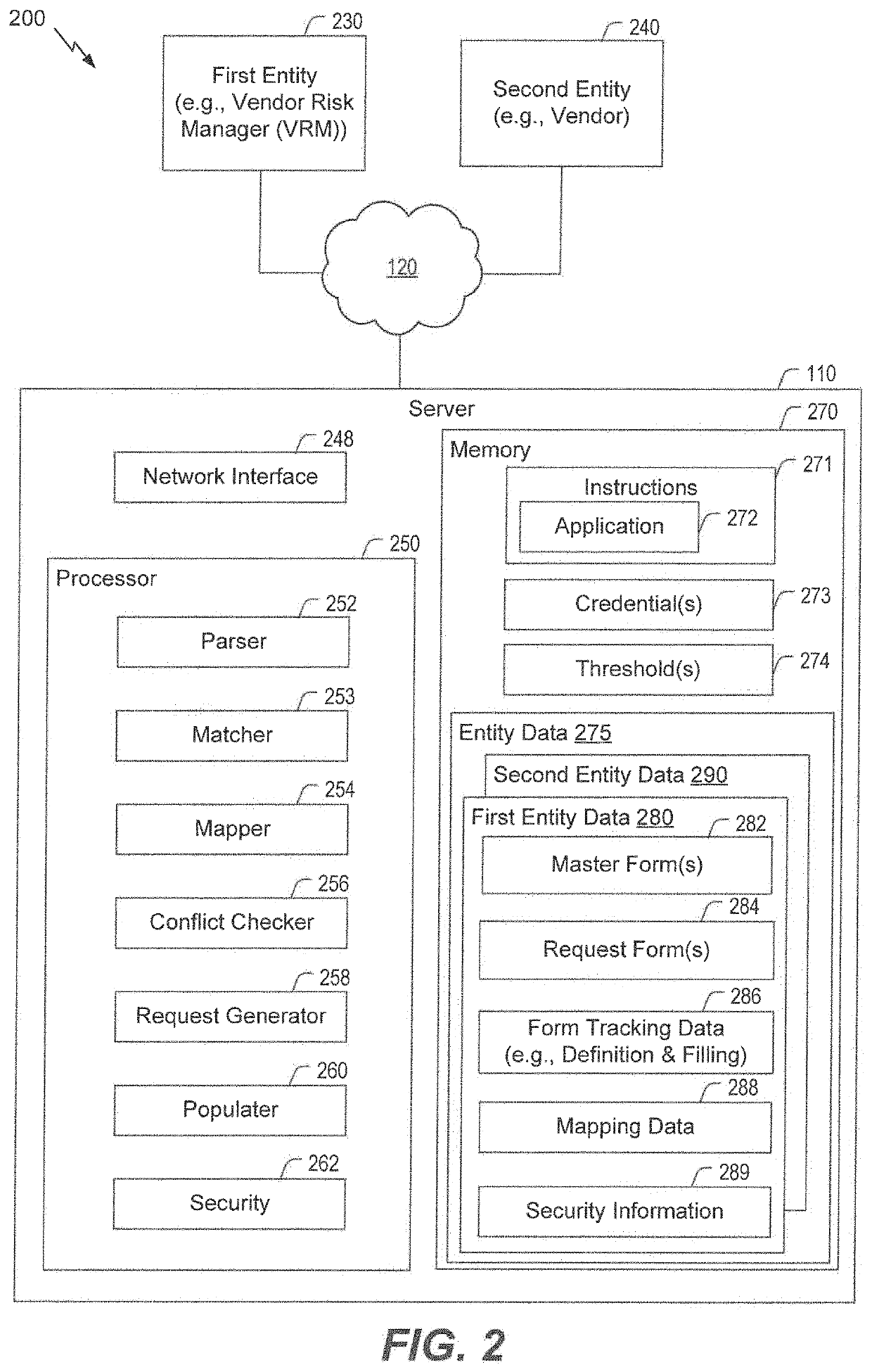
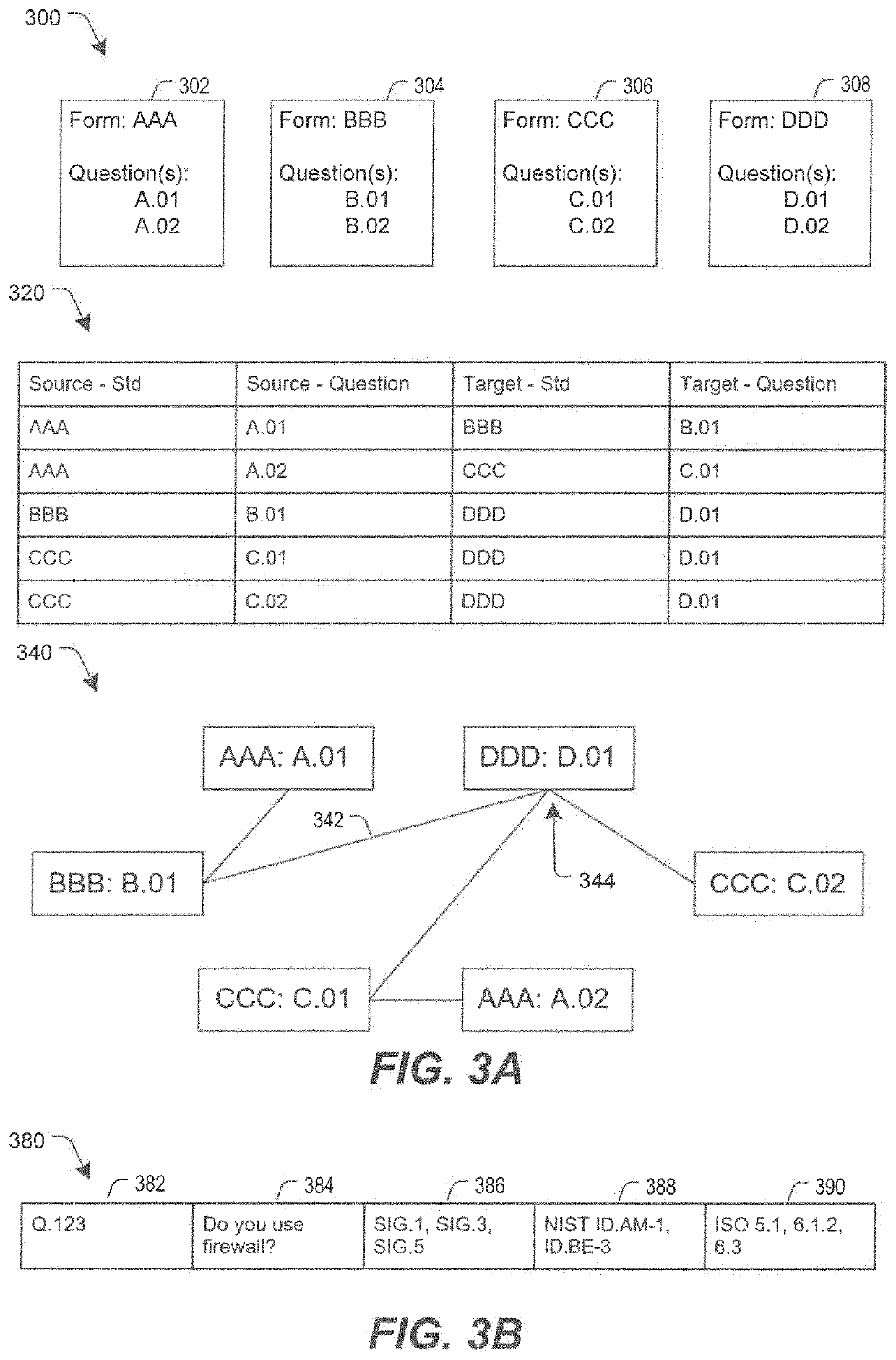
Inquiry response mapping for determining a cybersecurity risk level of an entity
ActiveUS10546135B1Reduce future data conflictImprove response mappingPlatform integrity maintainanceMachine learningRisk levelData set
The present disclosure provides a method, system, and device for inquiry response mapping for determining a cybersecurity risk level of an entity. To manage and / or evaluate a cybersecurity risk level based on a relationship between a first entity and a second entity, questionnaires (e.g., requests or inquires) are often exchanged between two entities. One or more aspects of the present disclosure provide populating data sets (e.g., questionnaires) indicative of risk level for the first entity or the second entity. One or more other aspects of the present disclosure further provide determining a cybersecurity risk level of an entity by mapping responses to a plurality of inquiry sets directed to the first entity or the second entity.
Owner:SECURITYSCORECARD
Systems, Program Product and Methods For Performing a Risk Assessment Workflow Process For Plant Networks and Systems
ActiveUS20120180133A1Easy to editEasy to customizeProgramme controlMemory loss protectionProcess control networkRisk level
Systems, methods, and program product to perform a cyber security risk assessment on a plurality of process control networks and systems comprising a plurality of primary network assets at an industrial process facility, are provided. An example of a system and program product can include an industrial and process control systems scanning module configured to identify networks and systems topology and to execute system and network security, vulnerability, virus, link congestion, node congestion analysis to thereby detect susceptibility to know threats to define potential vulnerabilities; a threats to vulnerabilities likelihood and consequences data repository module configured to determine a likelihood of each of a plurality of known threats exploiting identified vulnerabilities and to identify consequences of the exploitation to individual impacted systems and to overall plant operation; and a risk level evaluator module configured to determine a risk level rating for any identified vulnerabilities and provide recommended corrective actions.
Owner:SAUDI ARABIAN OIL CO
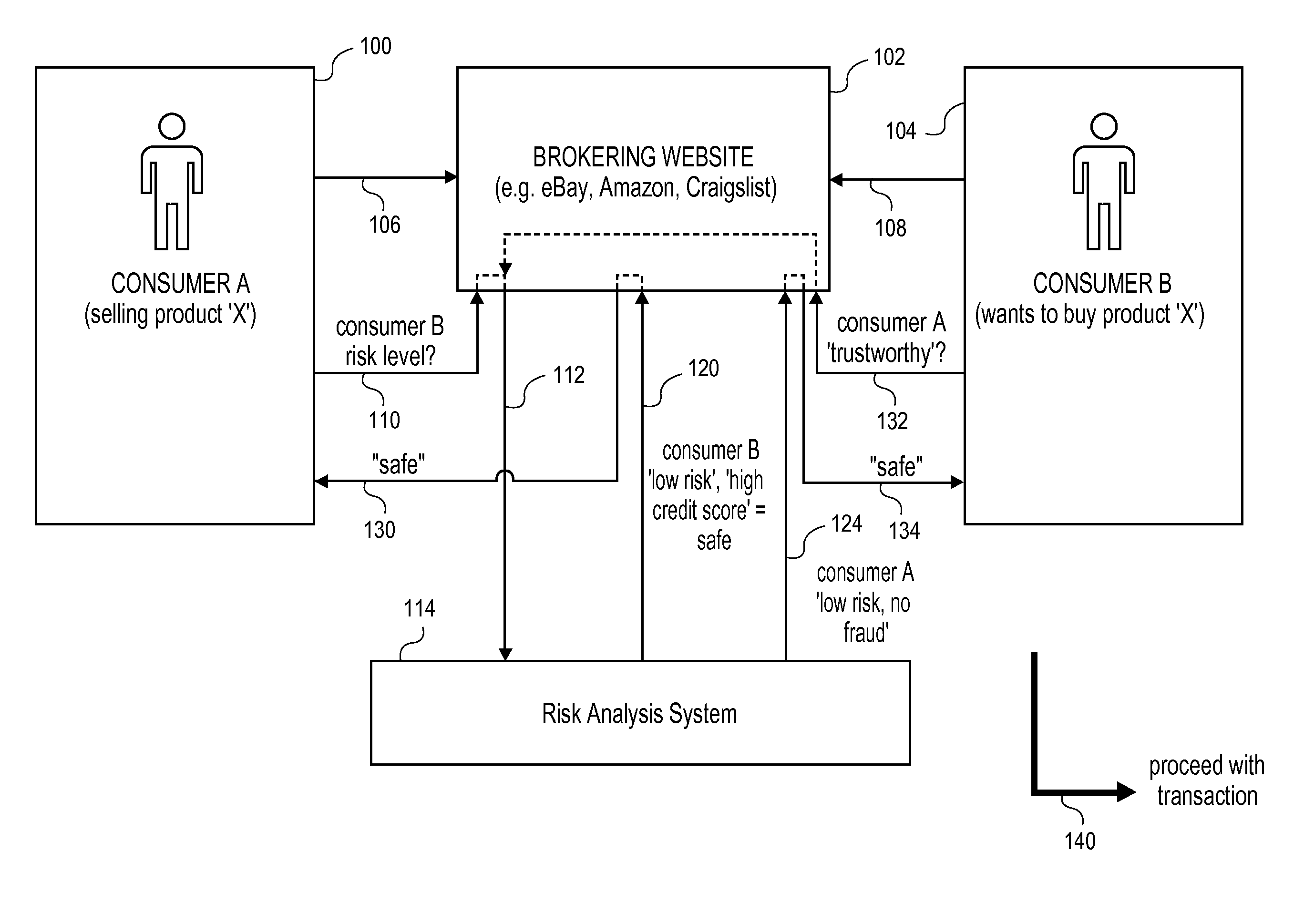
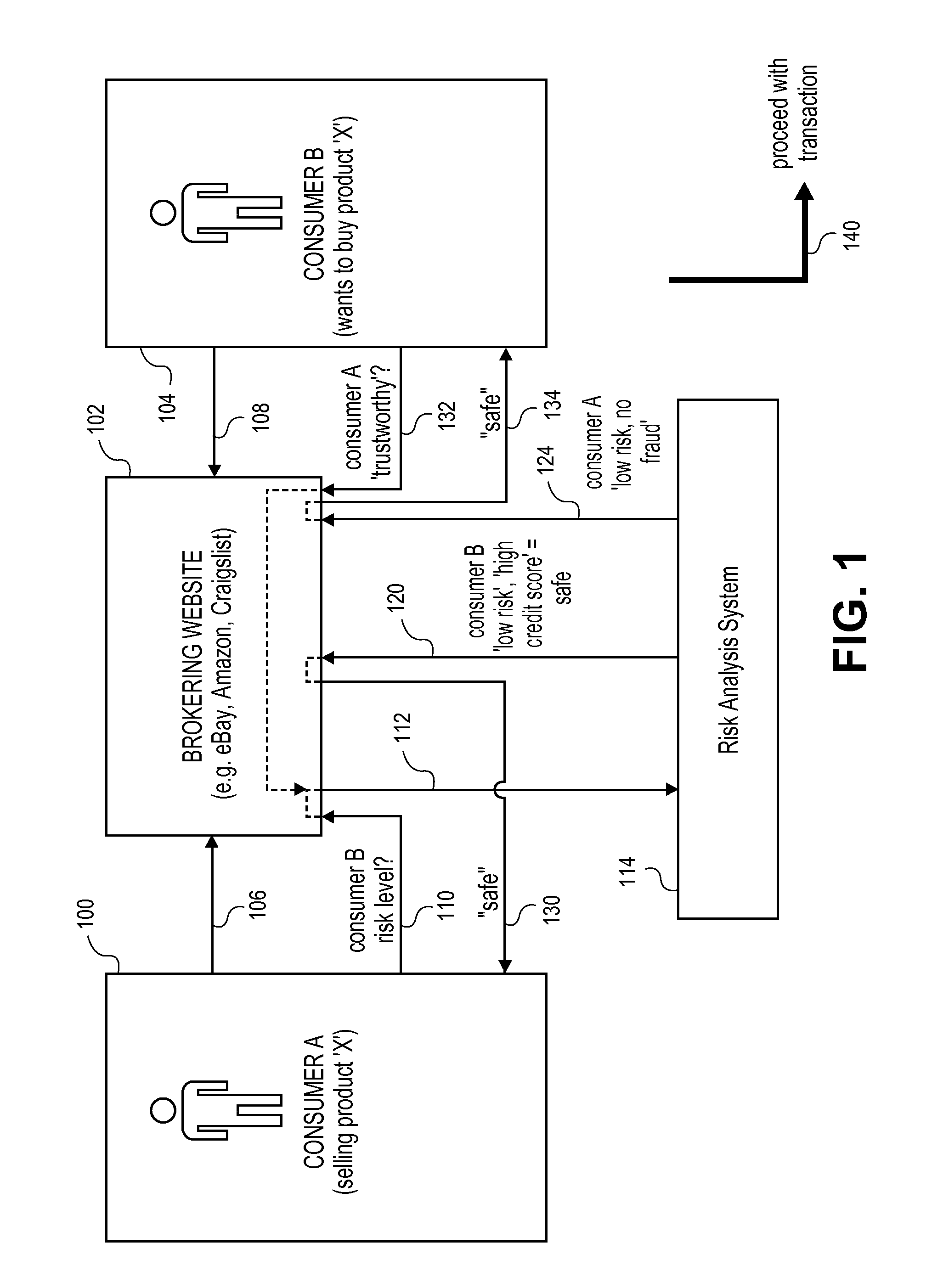
Transaction data repository for risk analysis
ActiveUS20110184838A1Convenient transactionDispel doubtsFinancePayment architectureIp addressGeolocation
Systems and methods are presented for determining risk levels for consumer-to-consumer (C2C) transactions on brokering websites. The risk levels can be based on payment processing network (e.g. Visa) account data as well as external data, such as geo-location using IP addresses, fraud bureau data, and star ratings. The buying and selling consumers can have multiple risk scores for each transaction, such as a fraud, credit, return / chargeback, dissatisfaction, product misuse, nonreturnable, and defect risk scores. The buying and selling consumers can trade their risk levels before proceeding with the transaction.
Owner:VISA INT SERVICE ASSOC
Vehicle security network device and design method therefor
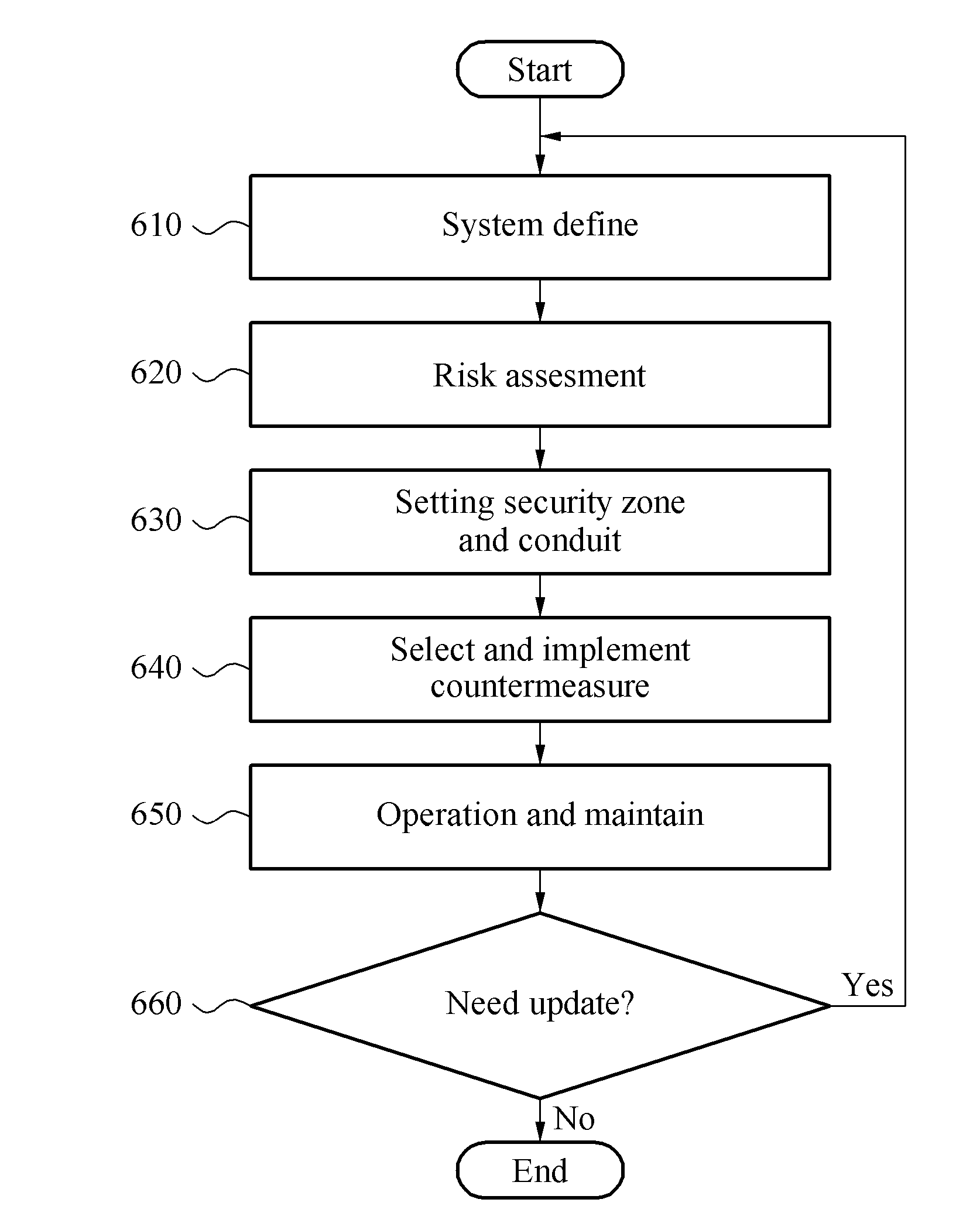
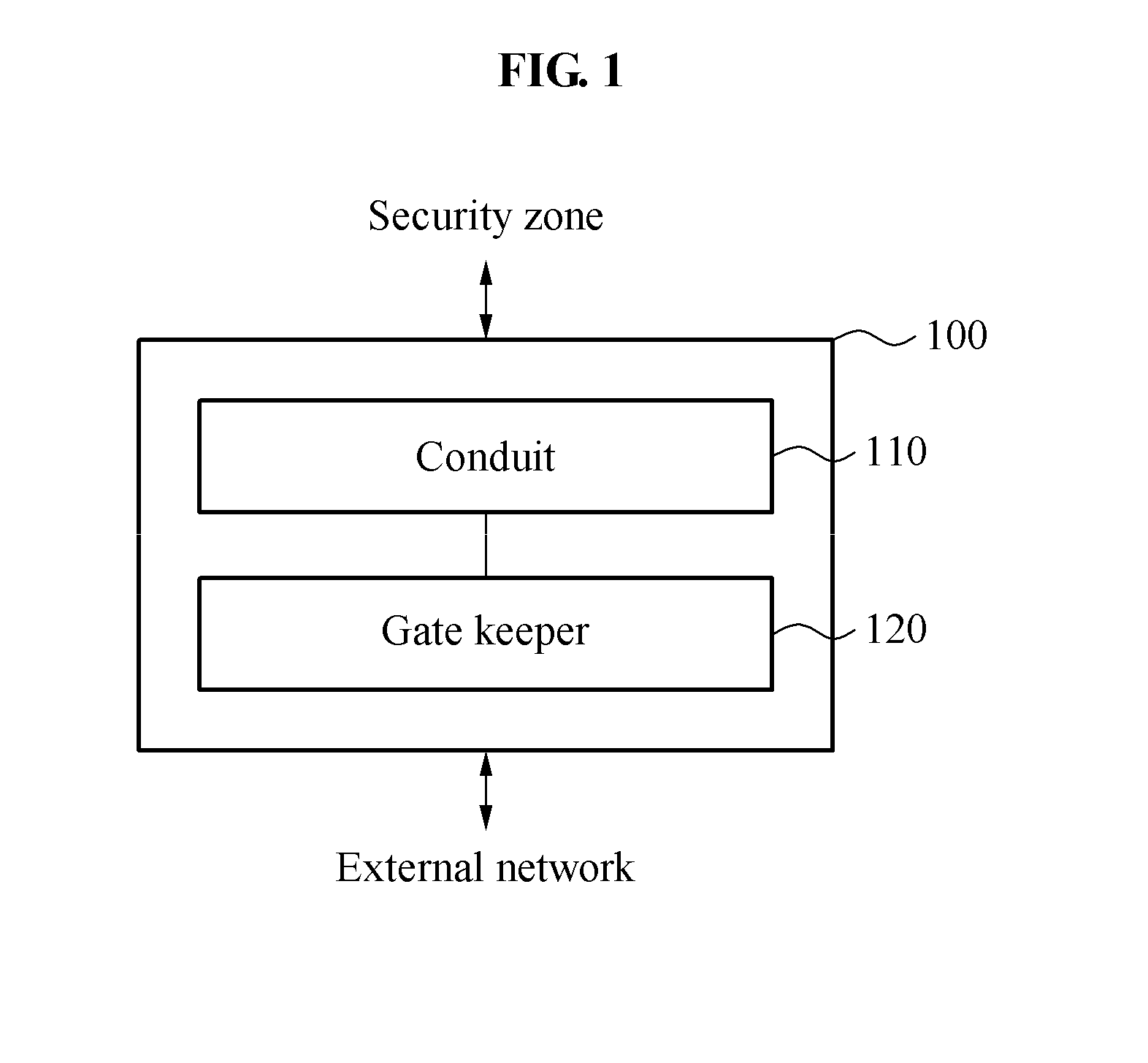
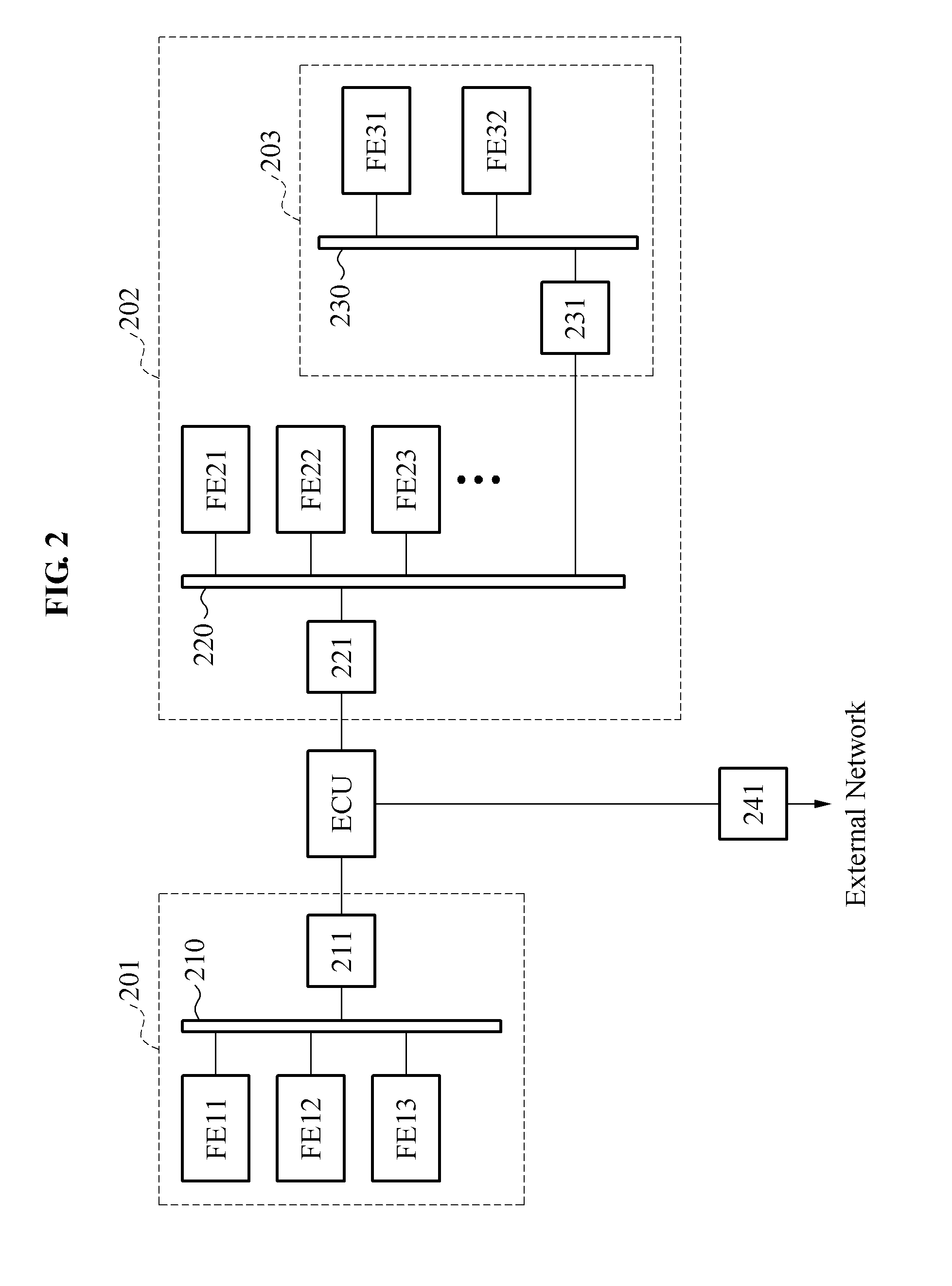
ActiveUS20160255154A1Semiconductor/solid-state device detailsAnti-theft devicesRisk levelCountermeasure
A security system capable of preventing a security attack / threat on a vehicle network is provided. At least one security zone is set by using a risk level which is evaluated for a plurality of vehicle functional elements. In addition, a security countermeasure corresponding to the risk level of the security zone can be provided to a conduit of the security zone so as to perform gate keeping.
Owner:ICTK
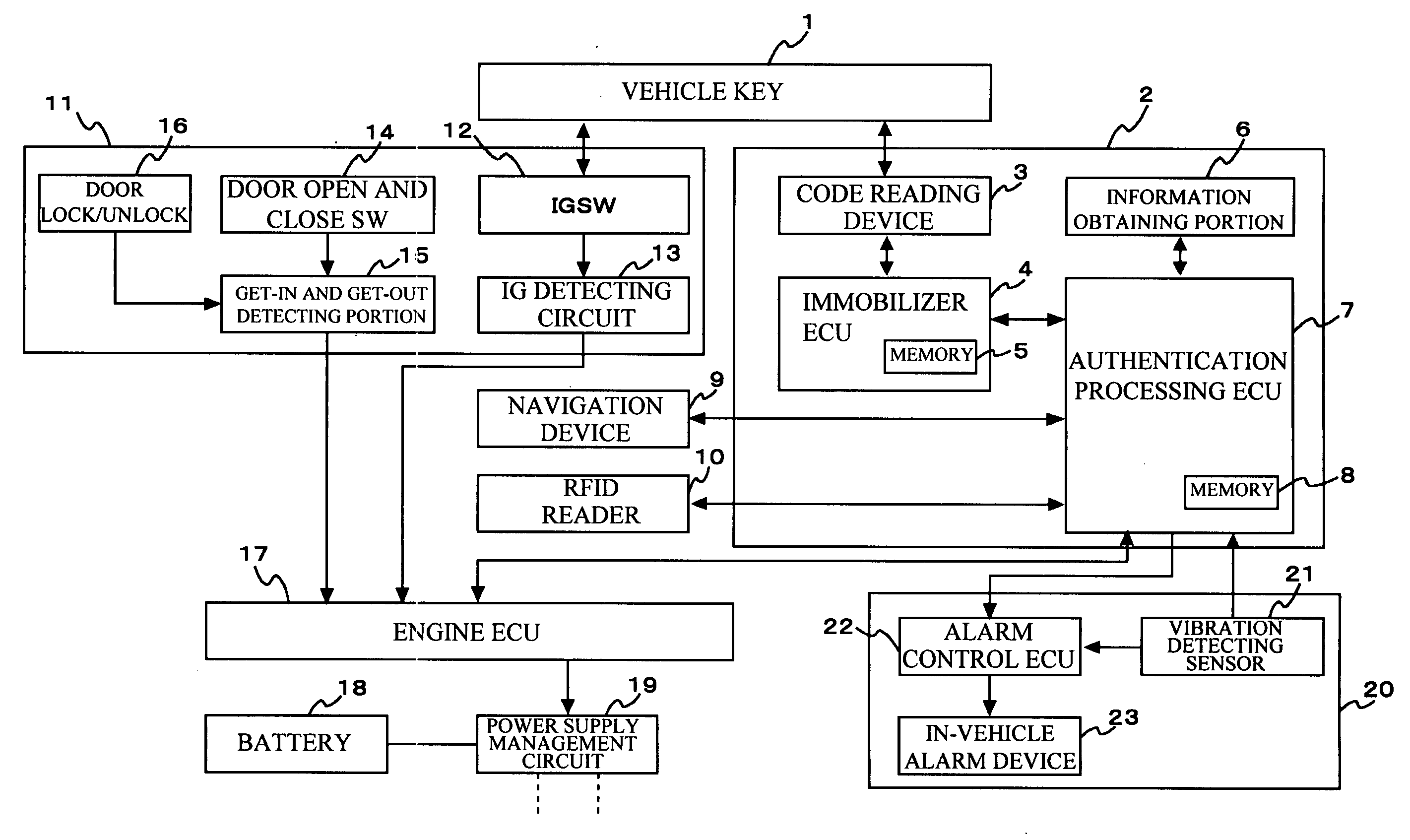
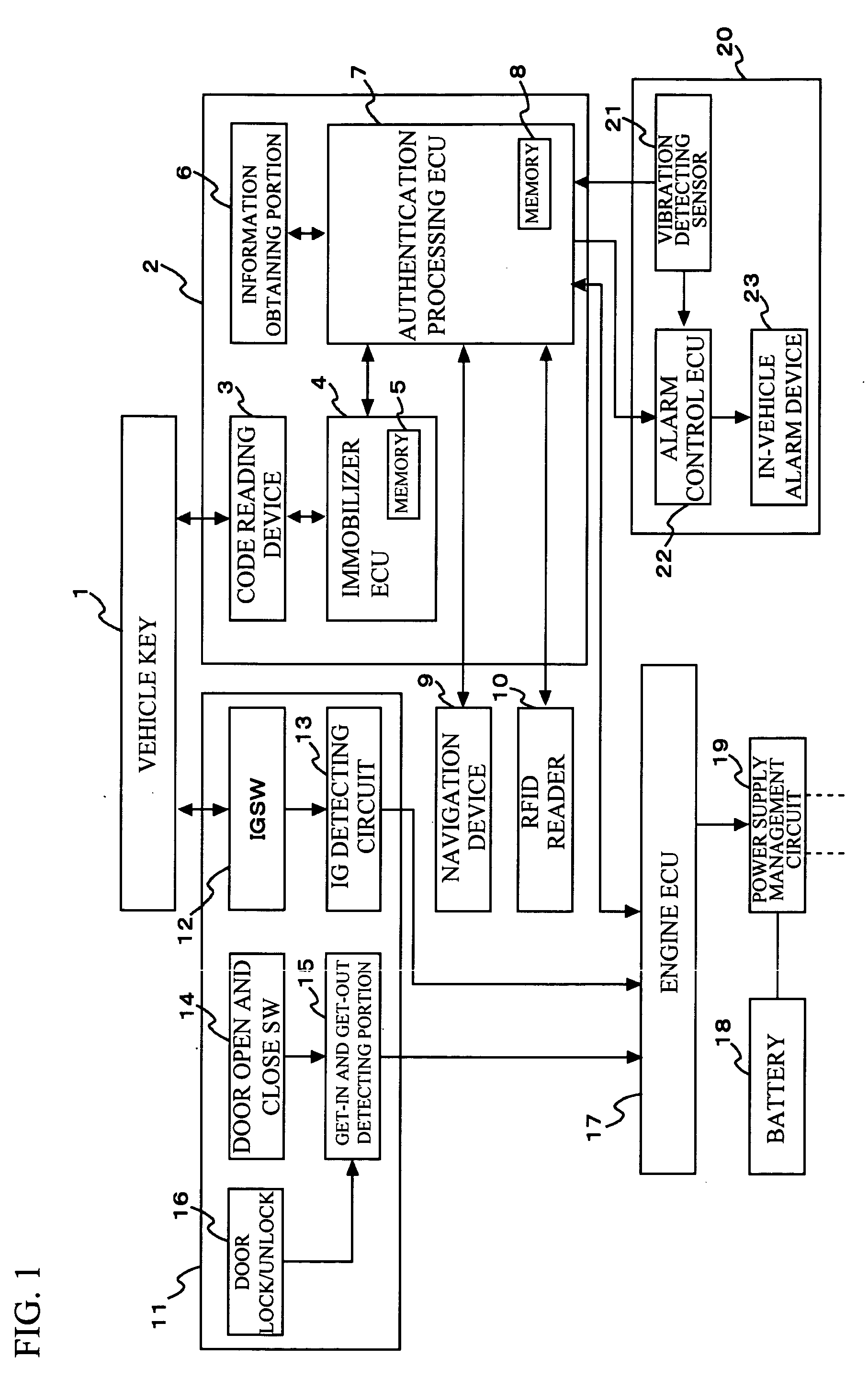
Authentication apparatus and method for use in vehicle
InactiveUS20070124599A1Increasing authentication levelReduce certification timeRandom number generatorsAnti-theft devicesComputer hardwareRisk level
An authentication method for use in a vehicle includes identifying validity by use of identification information stored, detecting an unauthorized use risk level predicted by a state of a vehicle, changing an authentication level according to an identification result and the unauthorized use risk level at the time of processing a biometric authentication, calculating a matching level between first biometric characteristic information of a vehicle passenger and second biometric characteristic information stored, and comparing the matching level calculated and an authentication level to output an authentication result at the time of processing the biometric authentication.
Owner:FUJITSU GENERAL LTD
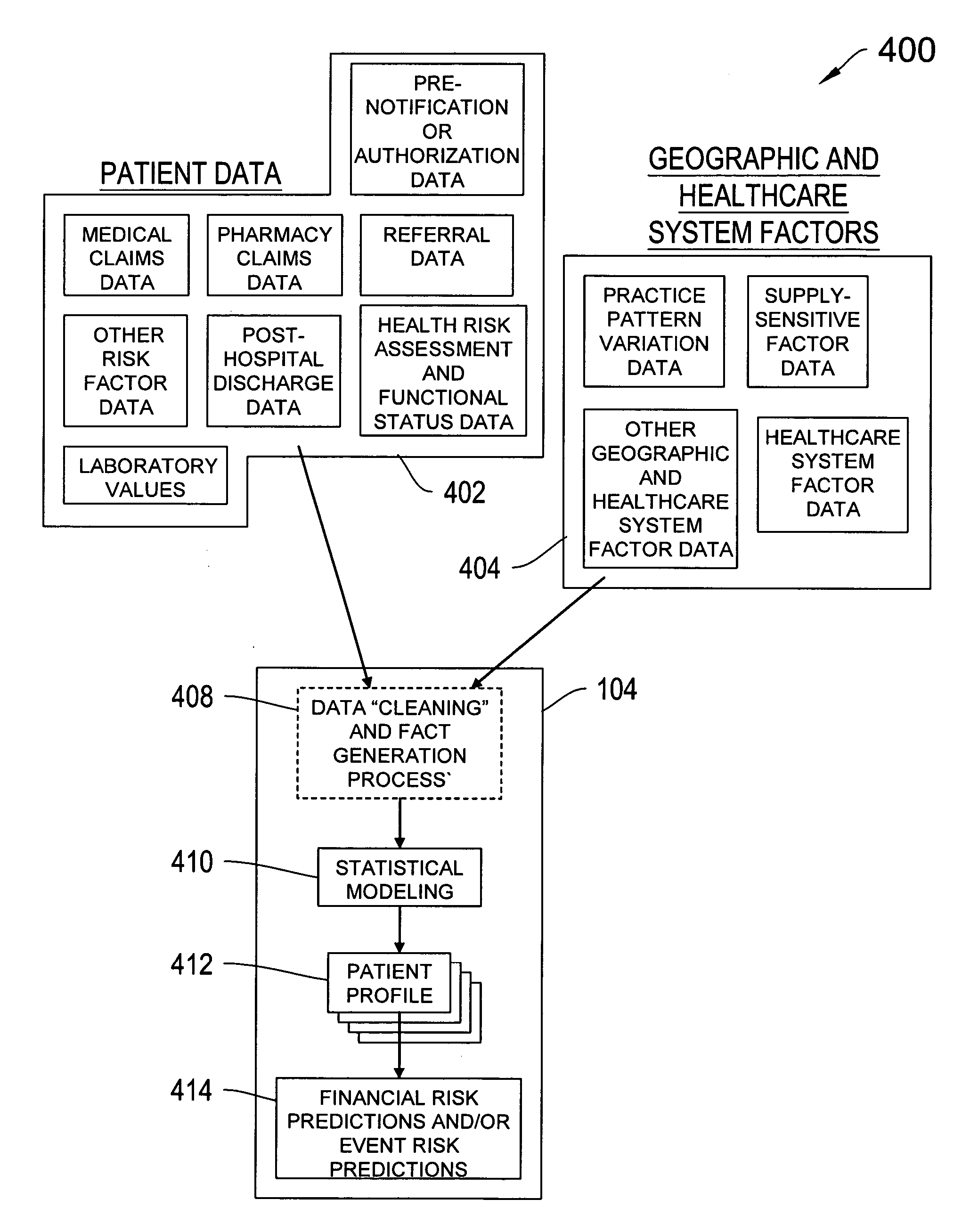
Systems and methods for predicting healthcare related financial risk
ActiveUS20060129428A1Reduce medical costsPrevent and mitigate occurrenceMedical simulationMedical data miningRisk levelRisk model
A system for predicting healthcare financial risk including the process of accessing patient data associated with one or more patents, accessing geographic and healthcare system data, filtering the patient data, geographic data, and healthcare system data into clean data, and applying a predictive risk model to the clean data to generate patient profile data and to identify a portion of the patients associated with a level of predicted financial risk.
Owner:HEALTH DIALOG SERVICES CORP
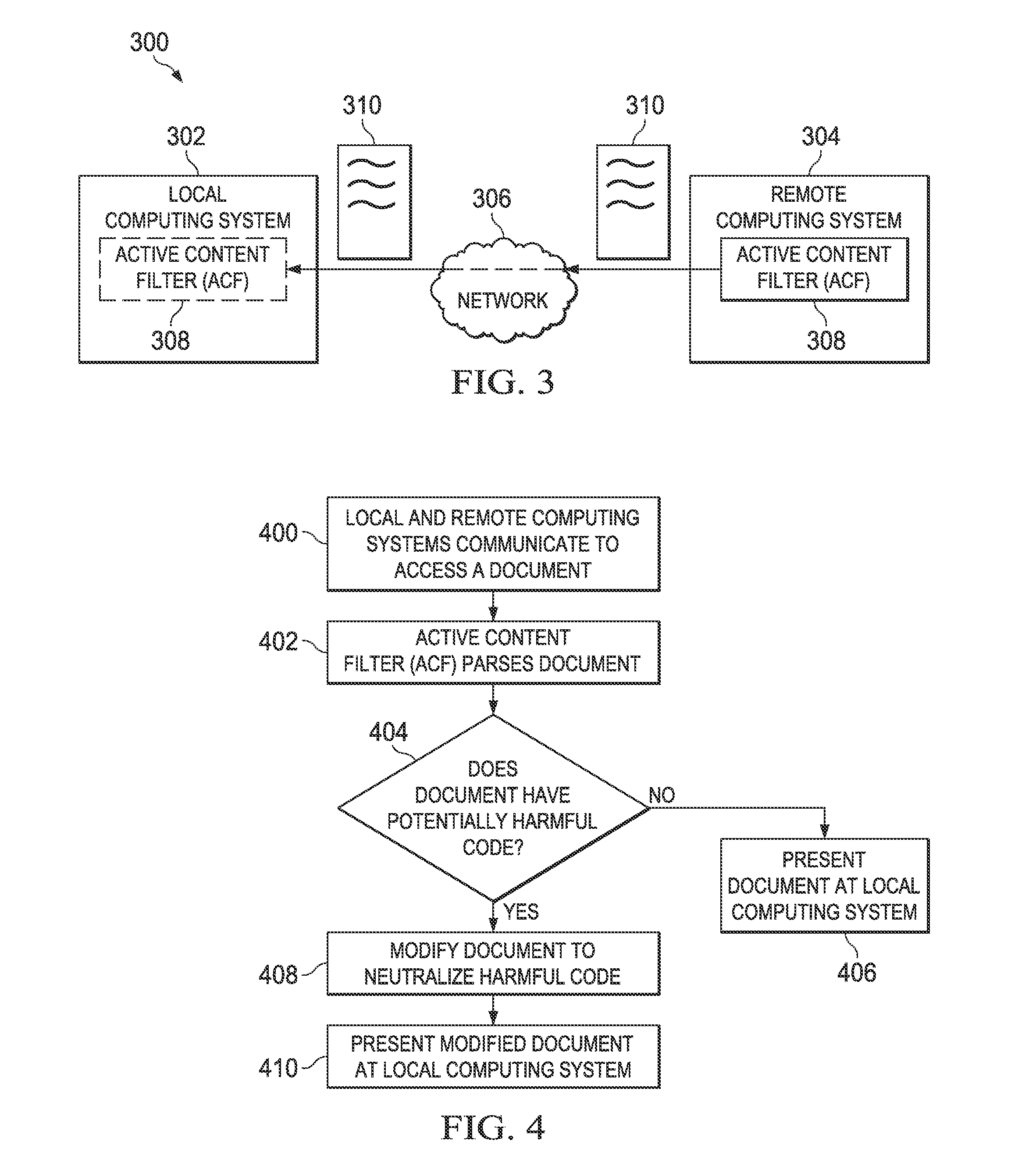
Disambiguating conflicting content filter rules
A content filtering mechanism is enhanced to resolve conflicts in filtering rules (e.g., those created by a whitelist, on the one hand, and a blacklist, on the other hand). Preferably, a conflict between or among content filtering rules is resolved by selecting among conflicting rules based on a notion of “risk” associated with the rules. According to this risk-based approach, when two or more rules conflict with one another, the particular rule whose risk value has a predetermined relationship (e.g., aligns most closely) with a risk level associated with the application (applying the rules) then takes precedence. By selecting among conflicting rules based on risk, the potential or actual conflicts are disambiguated, with the result being that the content is filtered appropriately.
Owner:IBM CORP
Autonomous feature use monitoring and telematics
ActiveUS10185999B1Operation moreFacilitate risk assessmentFinanceRegistering/indicating working of vehiclesRisk levelTotal risk
Methods and systems for monitoring use and determining risk associated with operation of autonomous vehicles are provided. According to certain aspects, autonomous operation features associated with a vehicle may be determined, and operating data regarding vehicle operation may be obtained. The operating data may include information regarding use levels or settings associated with use of the autonomous operation features. Risk levels associated with the features may be determined from test data or actual loss data. The risk levels and operating data may be used to determine a total risk level associated with operation of the vehicle with expected use levels of the autonomous operation features. The total risk level may further be used to determine or adjust aspects of an insurance policy associated with the vehicle.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
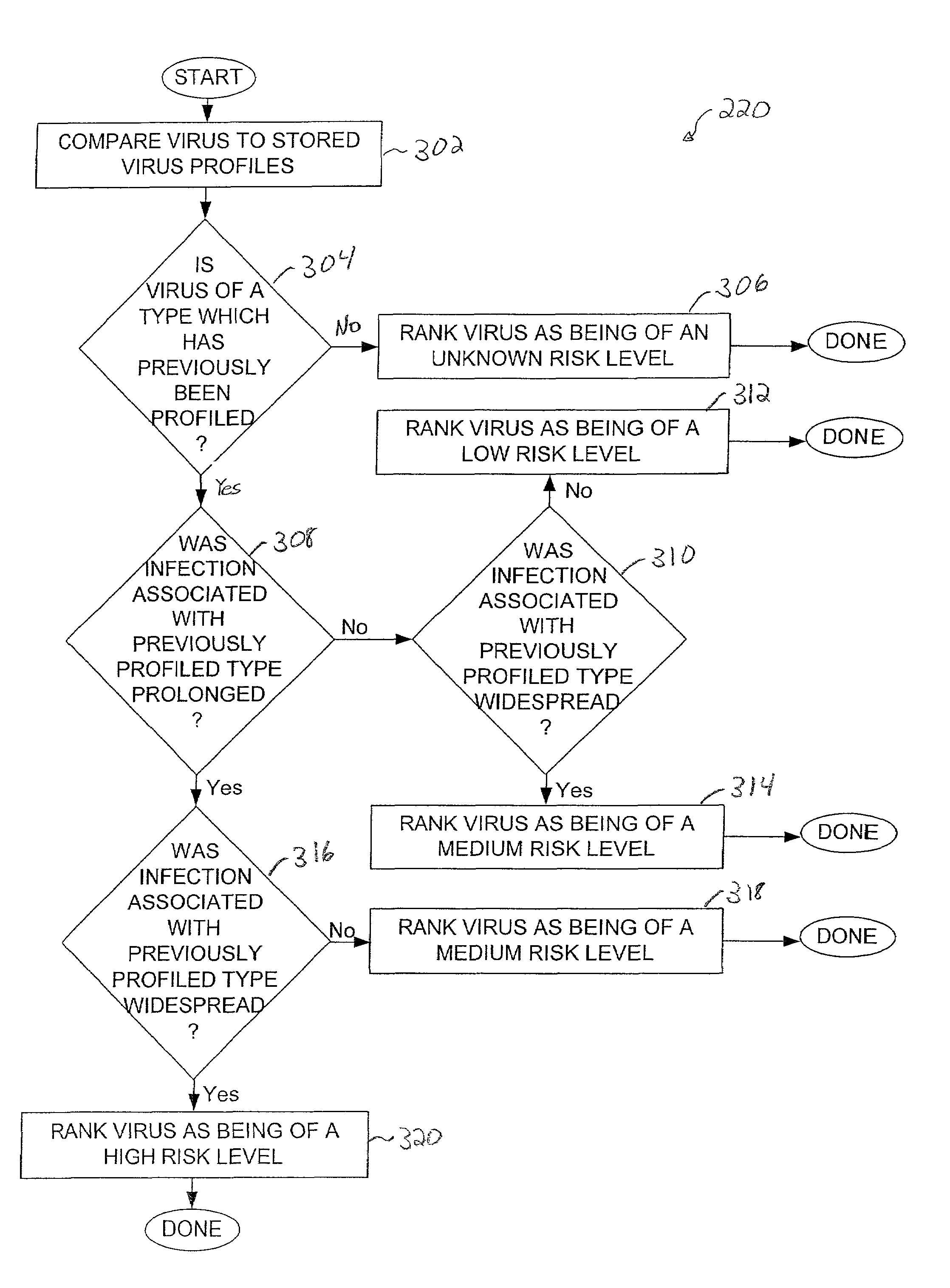
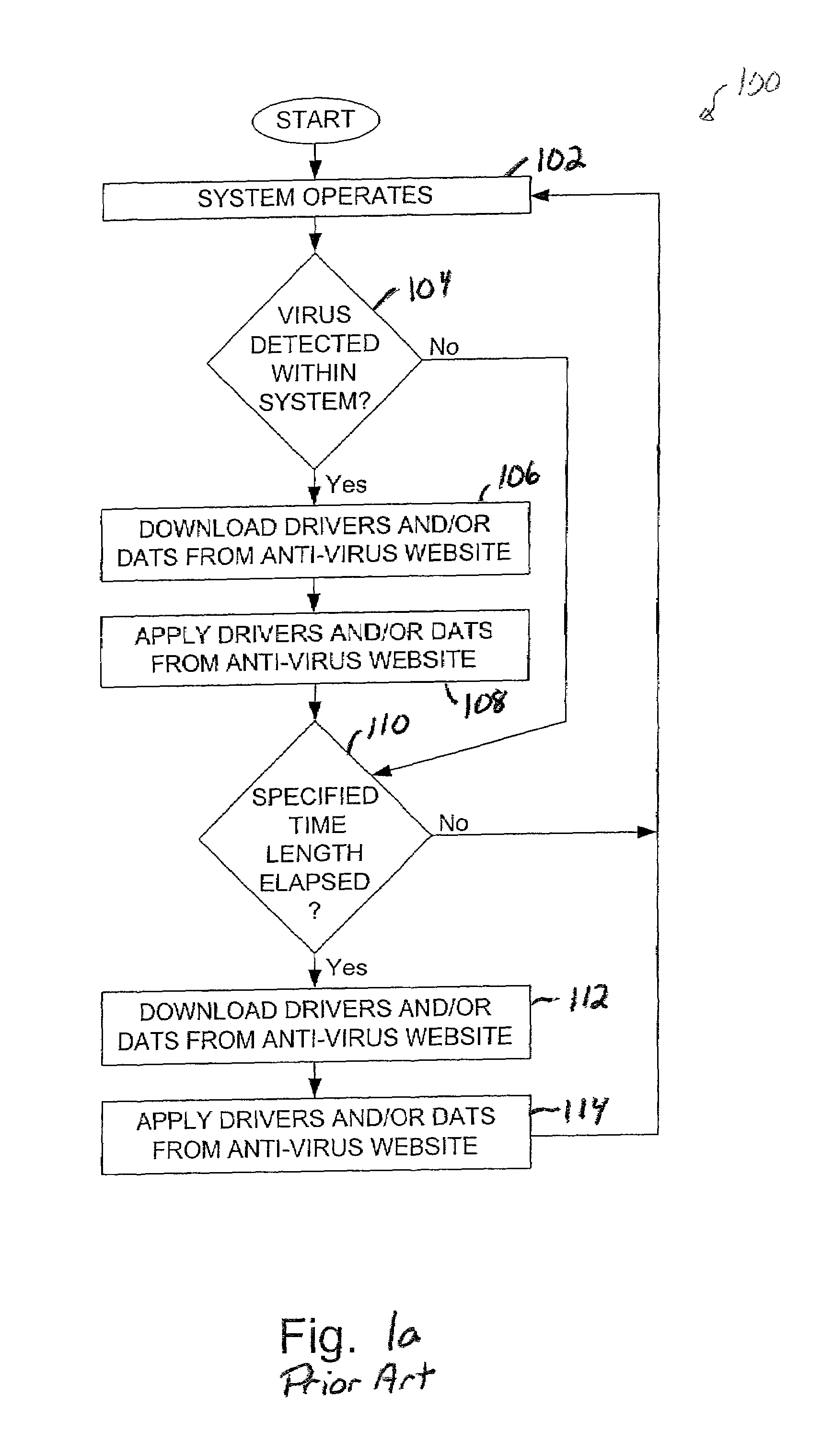
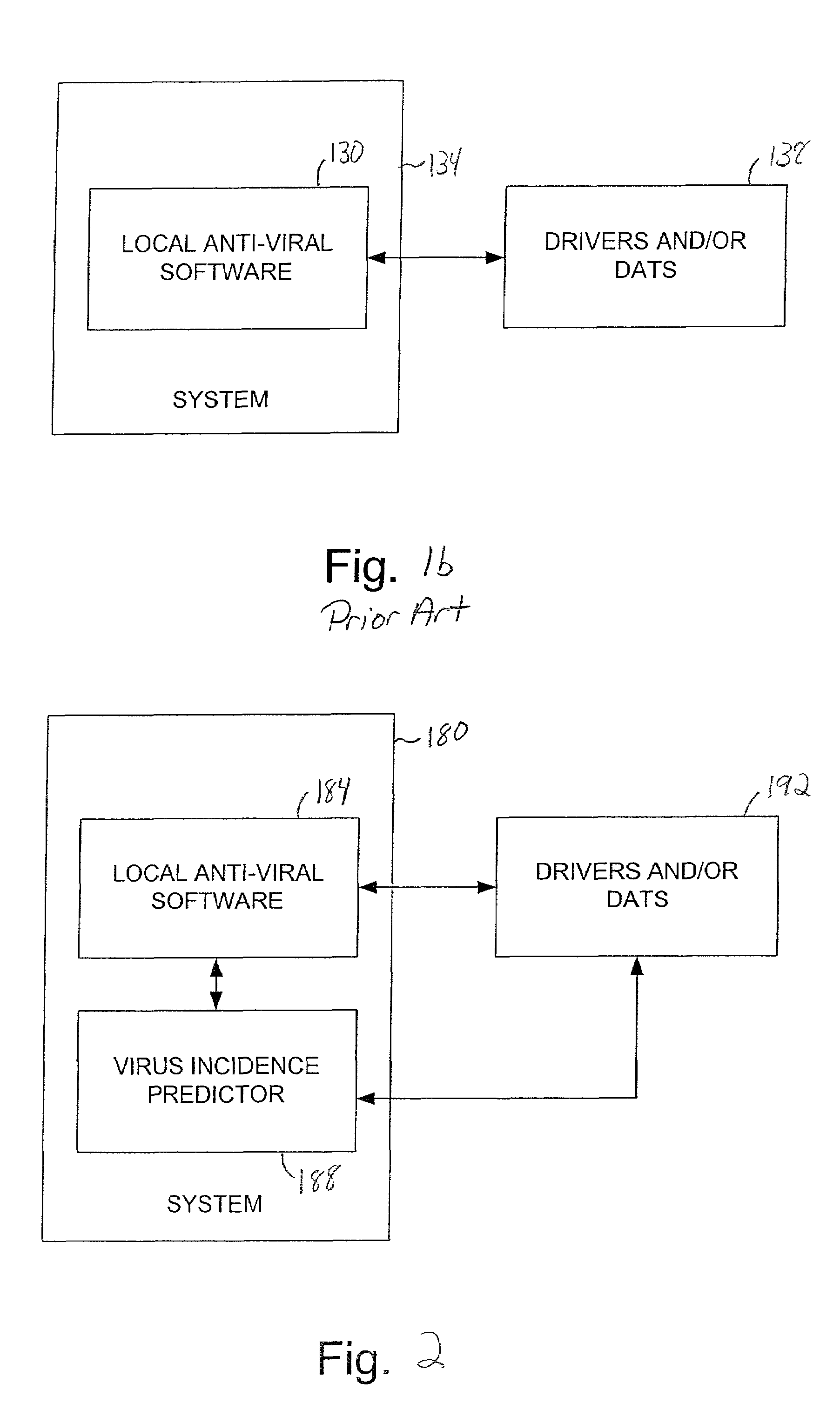
Method and apparatus for predicting the incidence of a virus
ActiveUS7010696B1Intelligent decisionMemory loss protectionUnauthorized memory use protectionRisk levelSignificant risk
Methods and apparatus for predicting the incidence of a new virus a within a system based upon previous infections recorded within the system. According to one aspect of the present invention, a method for responding to a virus alert that provides information pertaining to a new virus includes obtaining the virus alert and assessing a risk level associated with the new virus. The risk level indicates the predicted likelihood that the first virus will cause significant damage in the event that the new virus infects the computer system. Finally, the method includes obtaining computer code such as a driver and / or a dat when the risk level indicates that the new virus may pose a significant risk to the computer system.
Owner:MCAFEE LLC
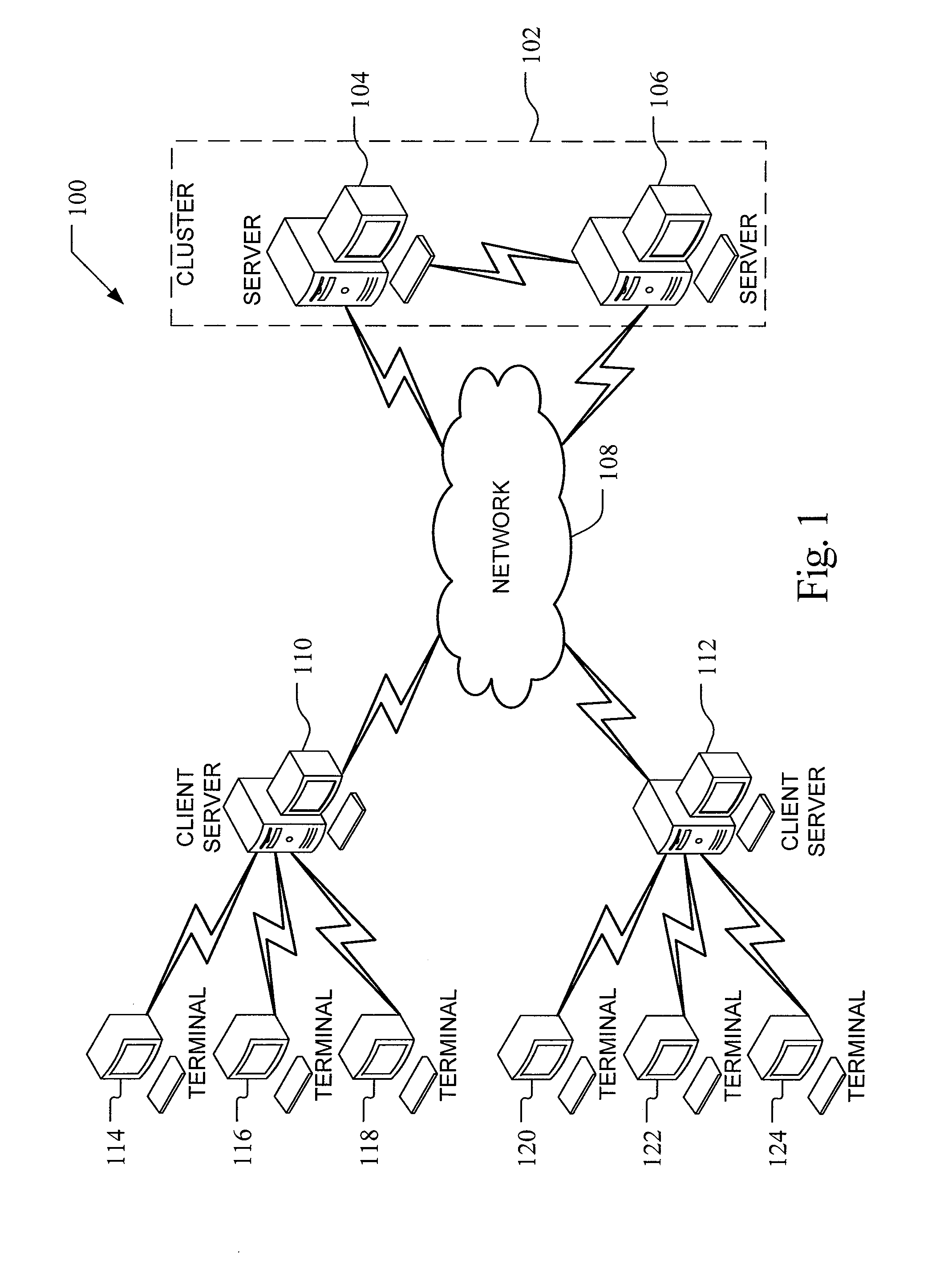
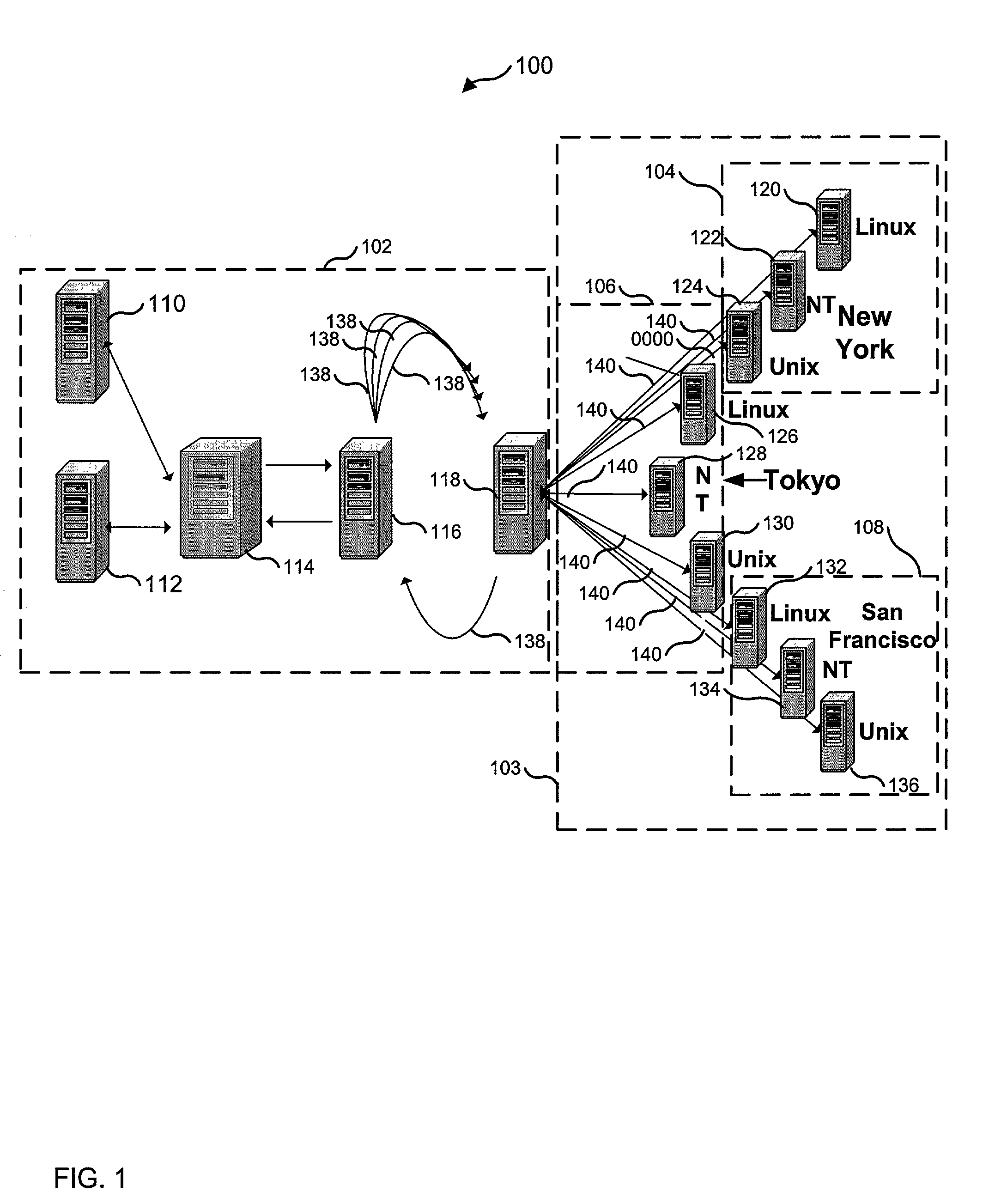
Network security testing
ActiveUS7325252B2Improve viewing effectShort working hoursMemory loss protectionError detection/correctionSecurity solutionWork period
To answer the security needs of the market, a preferred embodiment was developed. A preferred embodiment provides real-time network security vulnerability assessment tests, possibly complete with recommended security solutions. External vulnerability assessment tests can emulate hacker methodology in a safe way and enable study of a network for security openings, thereby gaining a true view of risk level without affecting customer operations. Because this assessment can be performed over the Internet, both domestic and worldwide corporations benefit. A preferred embodiment's physical subsystems combine to form a scalable holistic system that can be able to conduct tests for thousands of customers any place in the world. The security skills of experts can be embedded into a preferred embodiment systems and automated the test process to enable the security vulnerability test to be conducted on a continuous basis for multiple customers at the same time. A preferred embodiment can reduce the work time required for security practices of companies from three weeks to less than a day, as well as significantly increase their capacity. Component subsystems typically include a Database, Command Engine, Gateway, multiple Testers, Report Generator, and an RMCT.
Owner:ALERT LOGIC
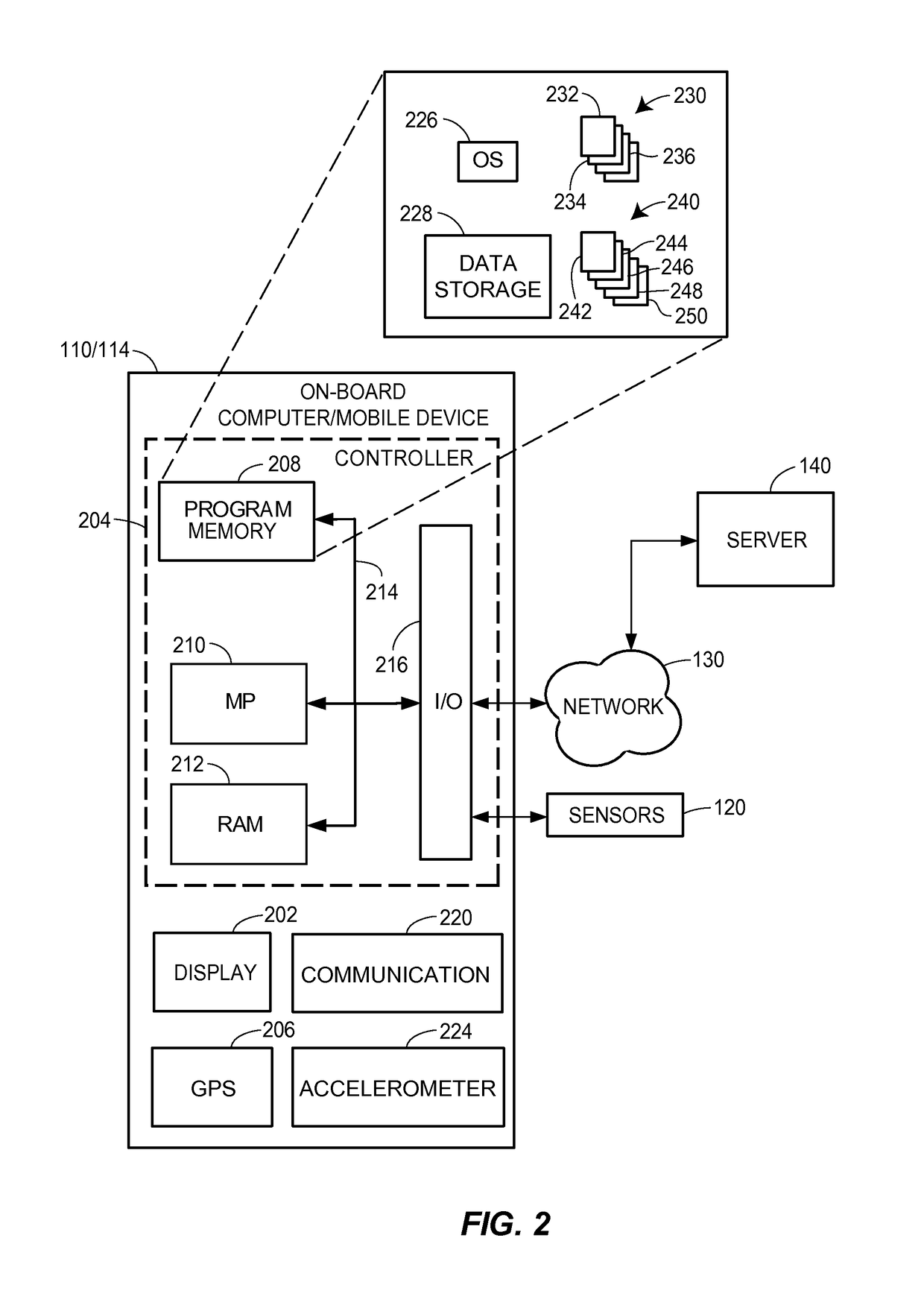
Autonomous vehicle operating style and mode monitoring
ActiveUS10157423B1Operation moreFacilitate risk assessment and premium determinationControl safety arrangementsMarket predictionsRisk levelComputer science
Methods and systems for monitoring use, determining risk, and pricing insurance policies for a vehicle having autonomous or semi-autonomous operation features are provided. According to certain aspects, with the insurance customer's permission, operation of an autonomous (or semi-autonomous vehicle) by a vehicle operator may be monitored. Based upon vehicle and / or other data analysis, an identity of the operator may be determined, and operating data regarding the autonomous or semi-autonomous vehicle while the operator at least partially controls the autonomous vehicle may be monitored. A vehicle operator profile that includes information regarding an operating style of the vehicle operator based upon the operating data may be determined. Risk levels associated with operation of the autonomous vehicle based upon the information regarding the vehicle operator's operating style may be determined. Insurance discounts may be provided to risk averse vehicle owners and / or operators, or those that utilize vehicle risk mitigation or prevention technology.
Owner:STATE FARM MUTAL AUTOMOBILE INSURANCE COMPANY
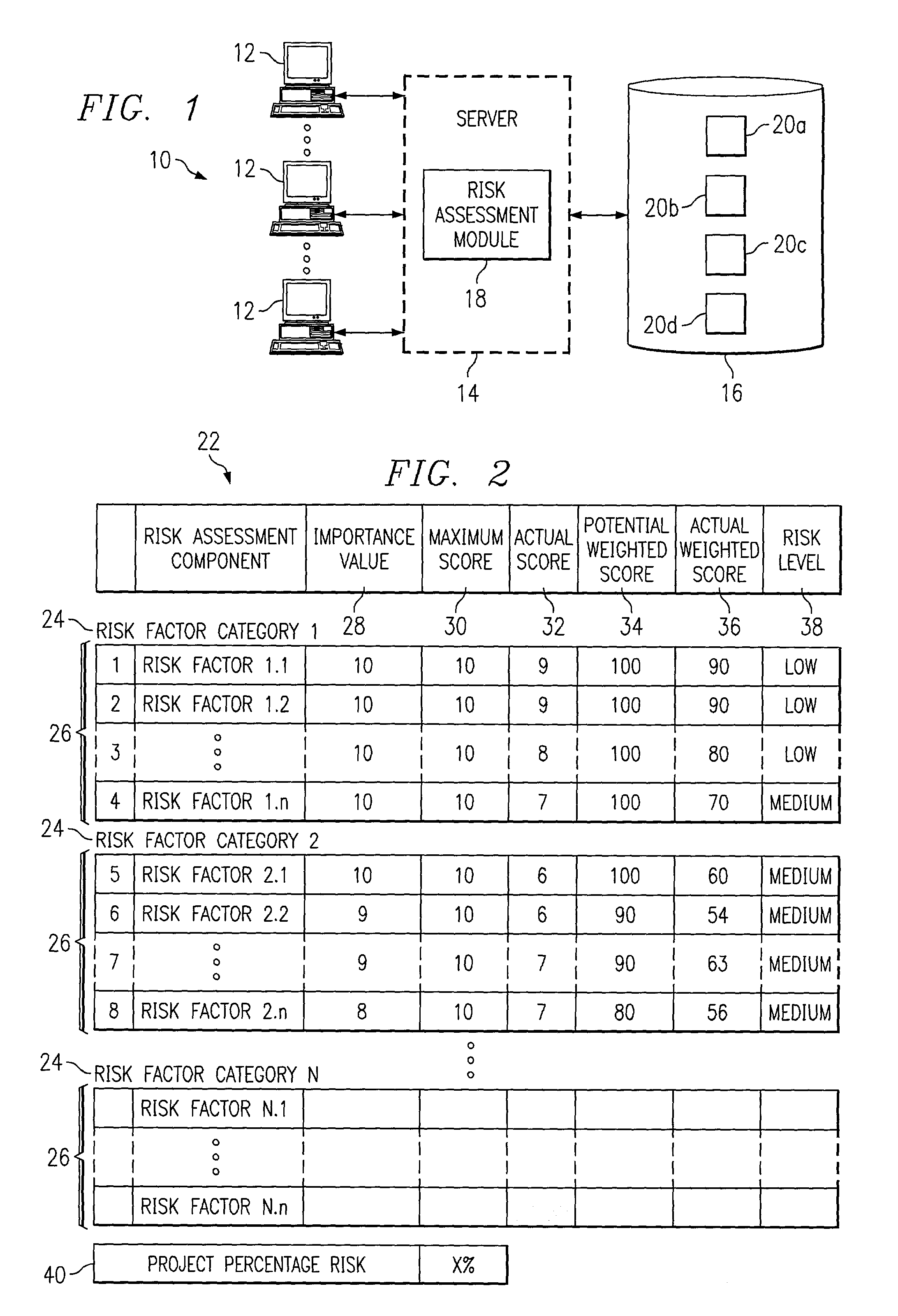
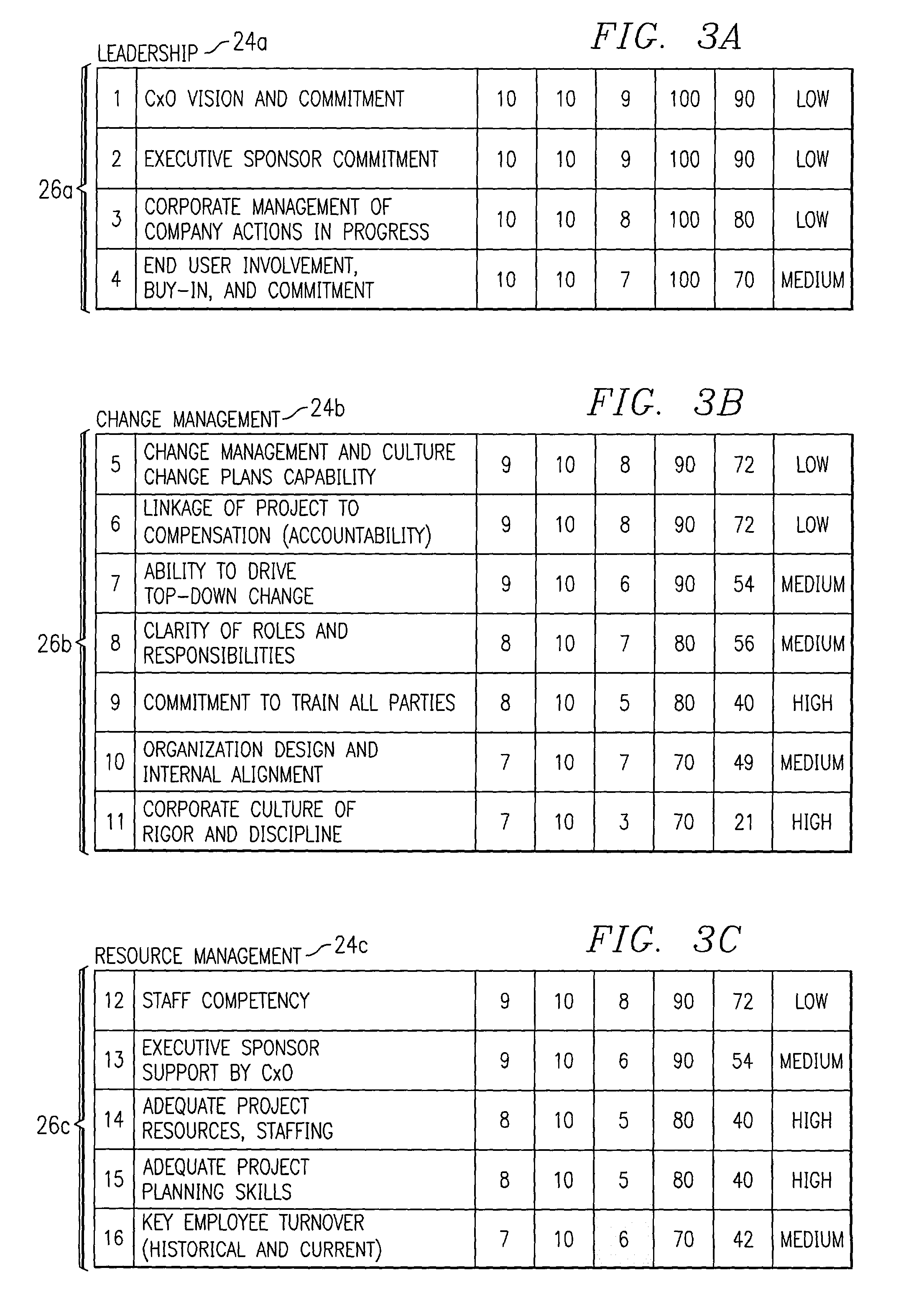
Generating a risk assessment regarding a software implementation project
InactiveUS7359865B1Disadvantages can be reduced eliminatedImplementation be reduced eliminatedFinanceResourcesRisk levelItem generation
A computer-implemented method for generating a risk assessment regarding a software implementation project includes accessing a previously specified importance value and maximum score for each of a multiple of risk factors. The importance value for each risk factor reflects experience of an implementing entity regarding the extent to which the factor may negatively impact a software implementation project if the factor is not adequately addressed, the importance value and maximum score for each factor being multiplied to define a potential weighted score for the factor. An actual score for a particular software implementation project is received for each factor based on an analysis specific to the particular project. An actual weighted score for the particular project is generated for each factor by multiplying the importance value and actual score for the factor, and a relationship between the potential weighted score and actual weighted score for each factor. A risk level for the particular project is assigned to each factor according to the relationship between the potential weighted score and the actual weighted score for the factor. The risk level for each factor represents an assessment regarding the extent to which the factor may negatively impact the particular project if the factor is not adequately addressed. A risk assessment is generated for the particular project including one or more of the assigned risk levels for the particular project for one or more corresponding factors.
Owner:BLUE YONDER GRP INC
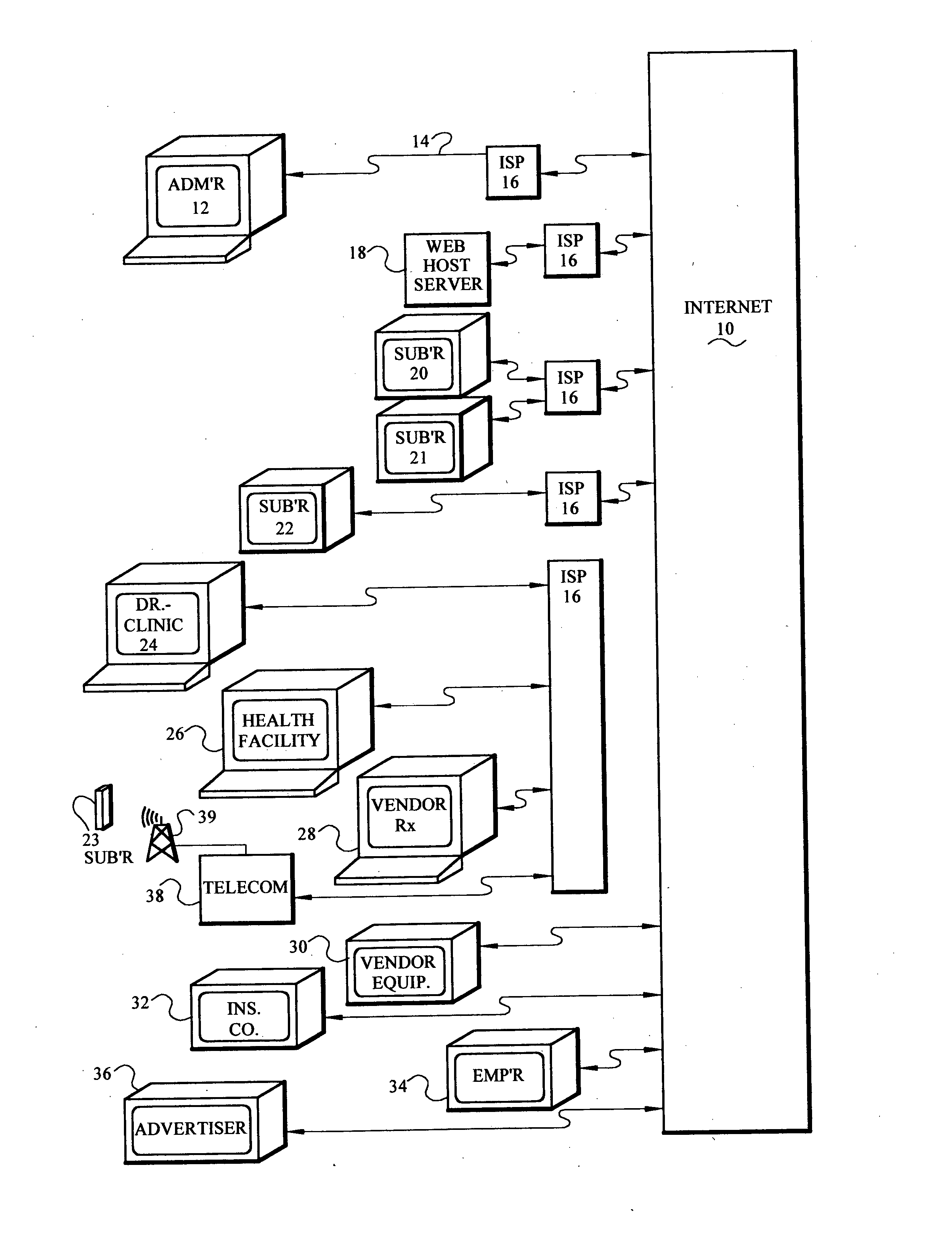
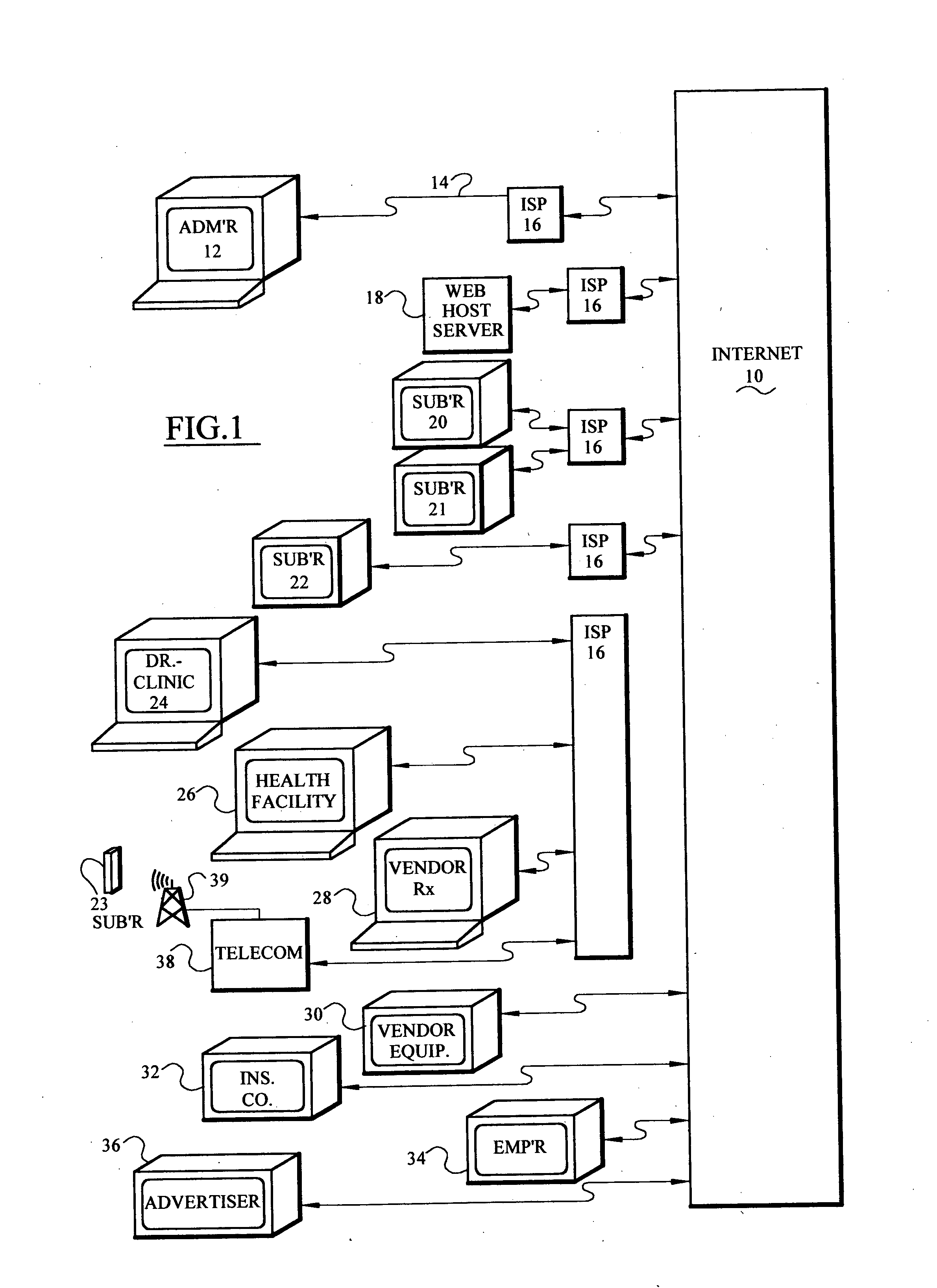
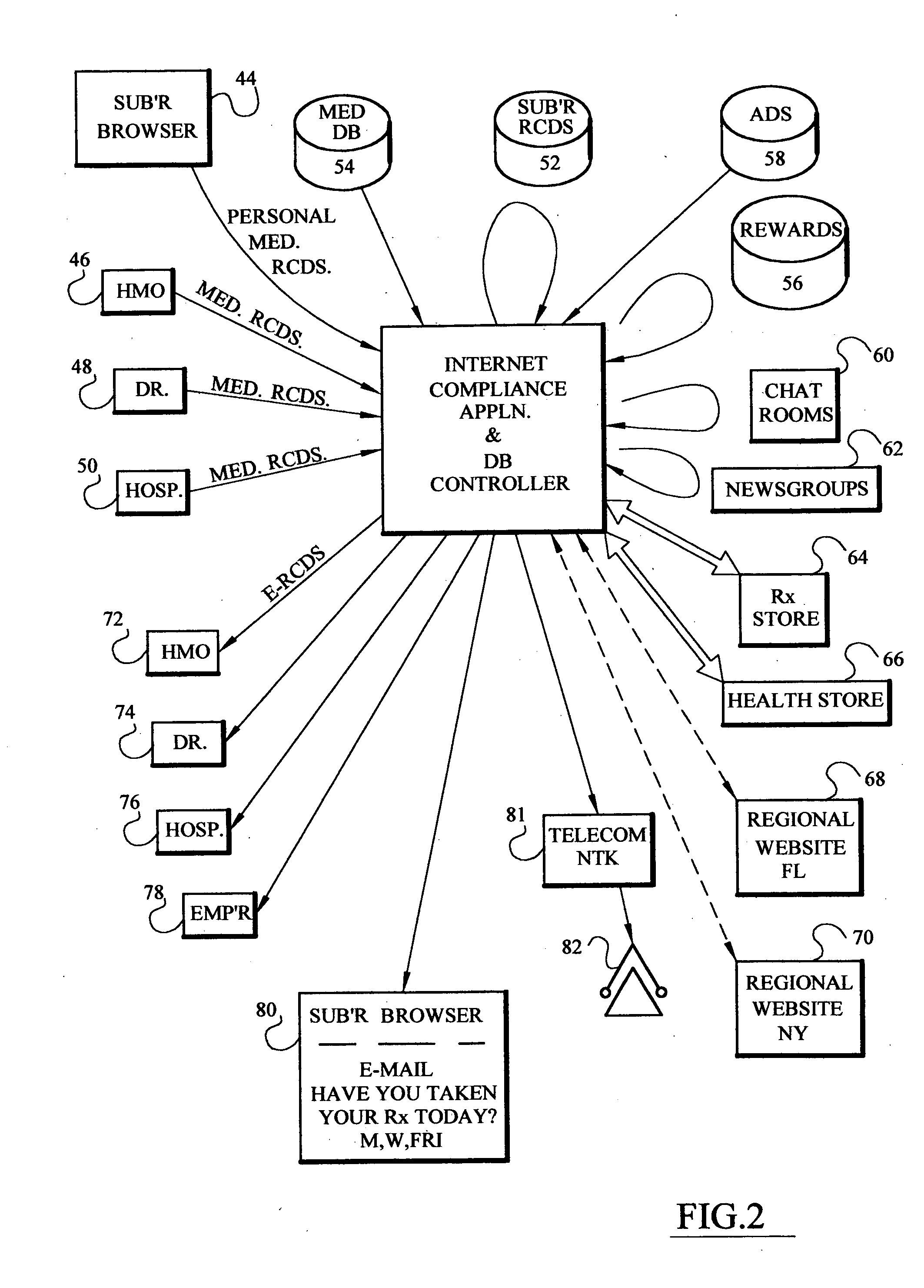
Computer based risk level monitor and patient compliance method and system
InactiveUS20050102159A1Improve compliance rateVAR reductionData processing applicationsHealth-index calculationRisk levelTotal risk
The risk monitor, as a computer-based method, program or system, monitors medical compliance by a plurality of patients having a corresponding plurality of medical compliance plans. The plans for each patient are displayed and the system accepts input from the patient indicative and / or heathcare providers of the patient's compliance with the plan. The system then assesses or analyzes the input and assigns a corresponding risk value based upon a range of risk values for various degrees of compliance. In addition, the patient's lifestyle inputs can be added to determine the risk value. The assessment continues for a plurality of patients thereby providing an indication of the risk value (a total risk value) for a patient, doctor, group of healthcare providers, a clinic or a hospital. By implementing various communication episodes (telephone calls, e-mails, letters), the system seeks to reduce the risk value for a particular patient and for the plurality of patients by altering the communication episodes and monitoring the resulting risk values both individually and as a group.
Owner:MONDSHINE ROBERT B
Estimation of cardiac death risk
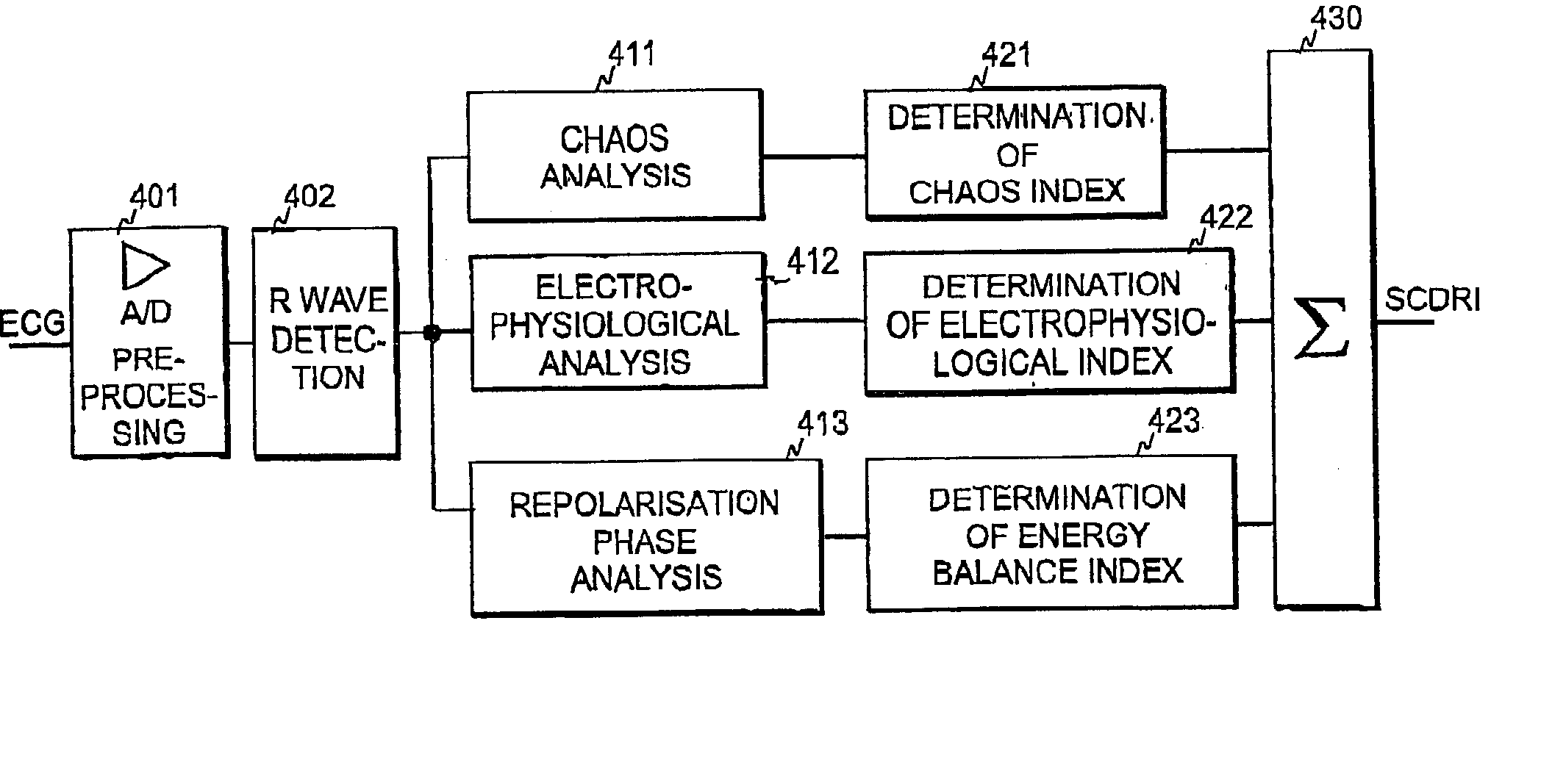
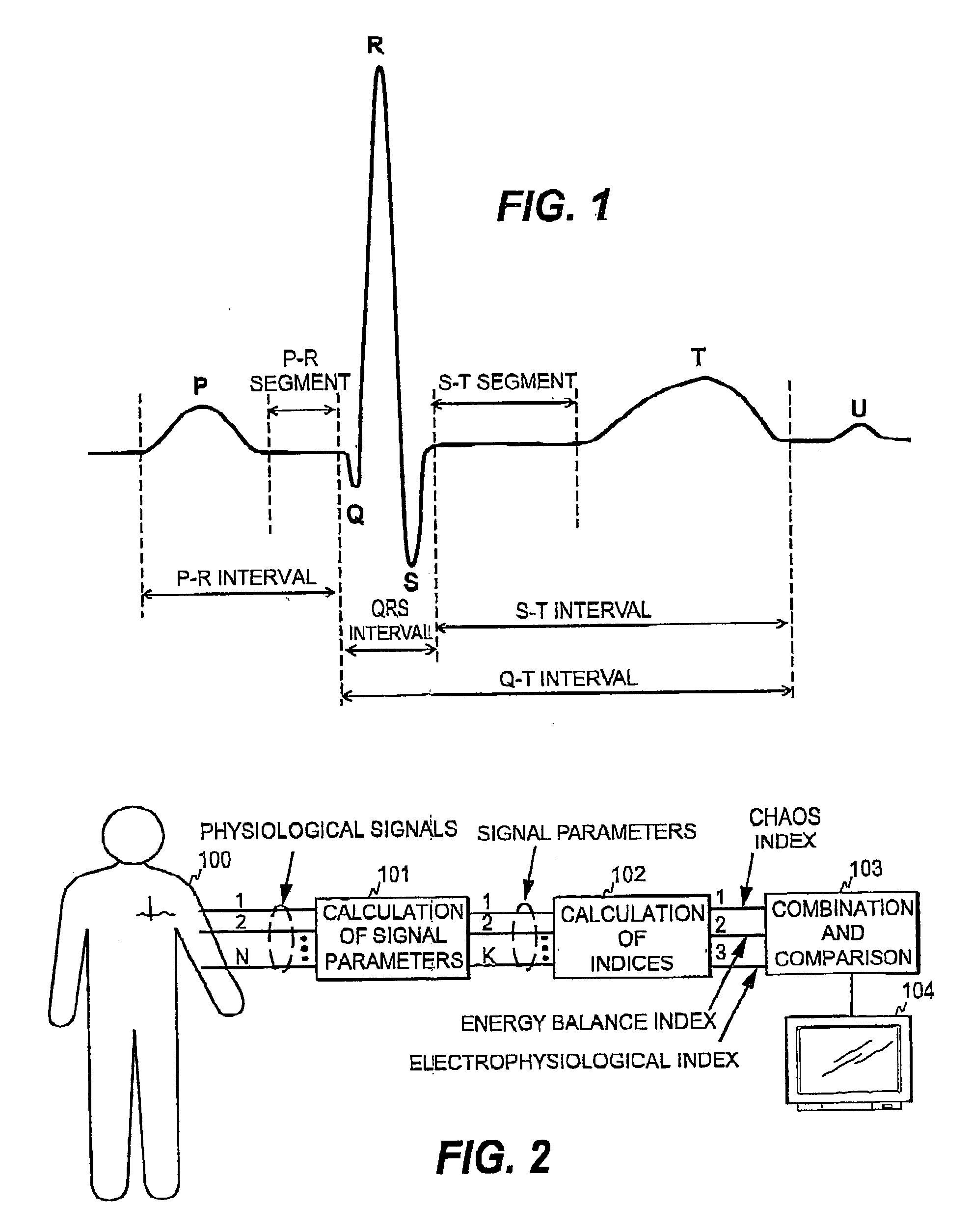
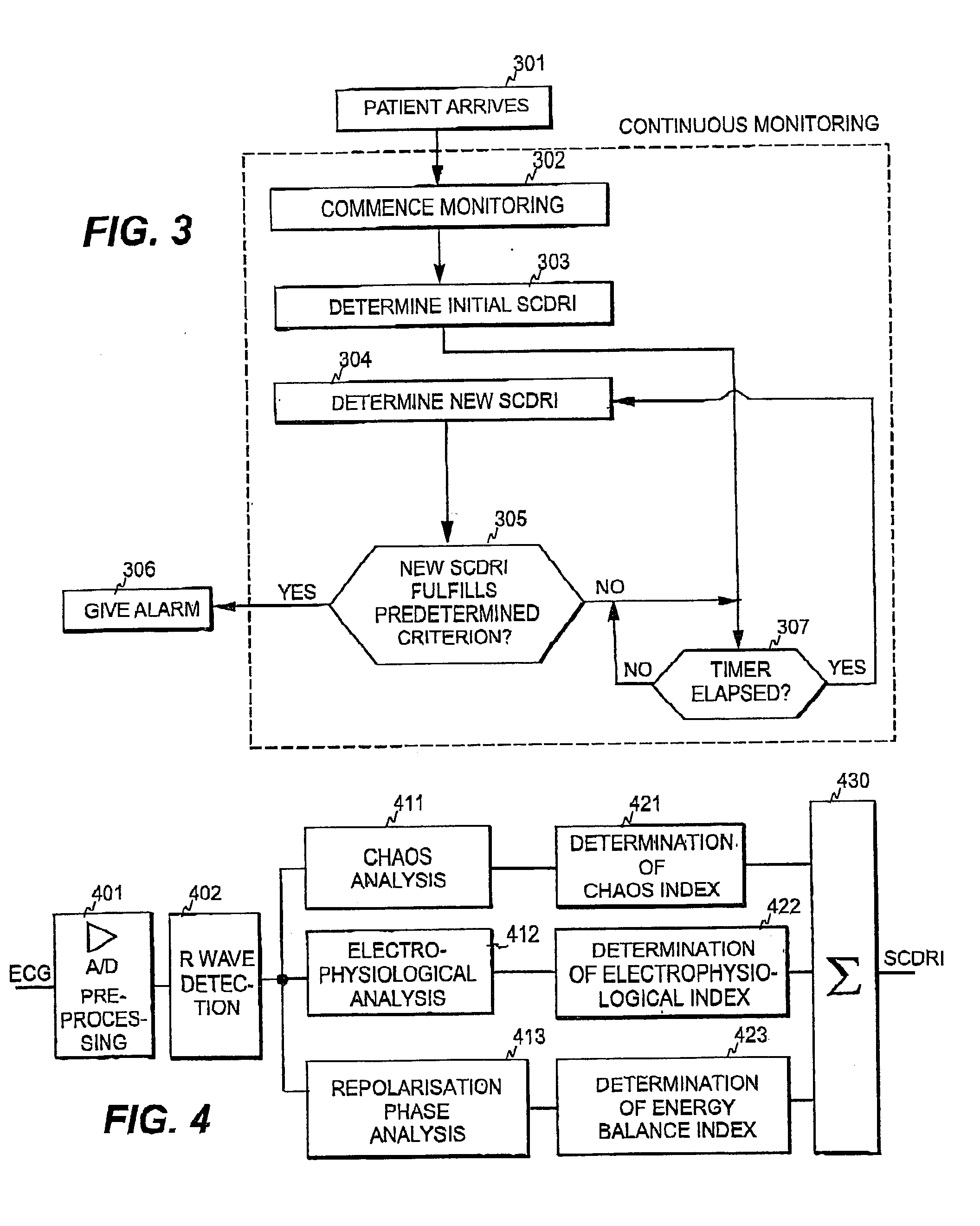
ActiveUS20040215090A1Improve predictive performanceRisk is particularly acuteElectrocardiographyHealth-index calculationVentricular dysrhythmiaRisk level
The invention relates to a method and apparatus for predicting a sudden heart abnormality for an individual patient. In order to provide a prediction mechanism that is suitable for acute care, three sub-indices are determined based on medical data obtained from the patient. The first sub-index indicates the level of deterministic chaos in the heart rate variability of the patient, the second sub-index indicates the energy level in the myocardium of the patient, and the third sub-index indicates the degree of ventricular arrhythmia of the patient. Based on the first, second, and third sub-indices, at least one overall risk index is then determined, the overall risk index indicating the risk level of a sudden heart abnormality for the patient.
Owner:INSTRUMENTARIUM CORP
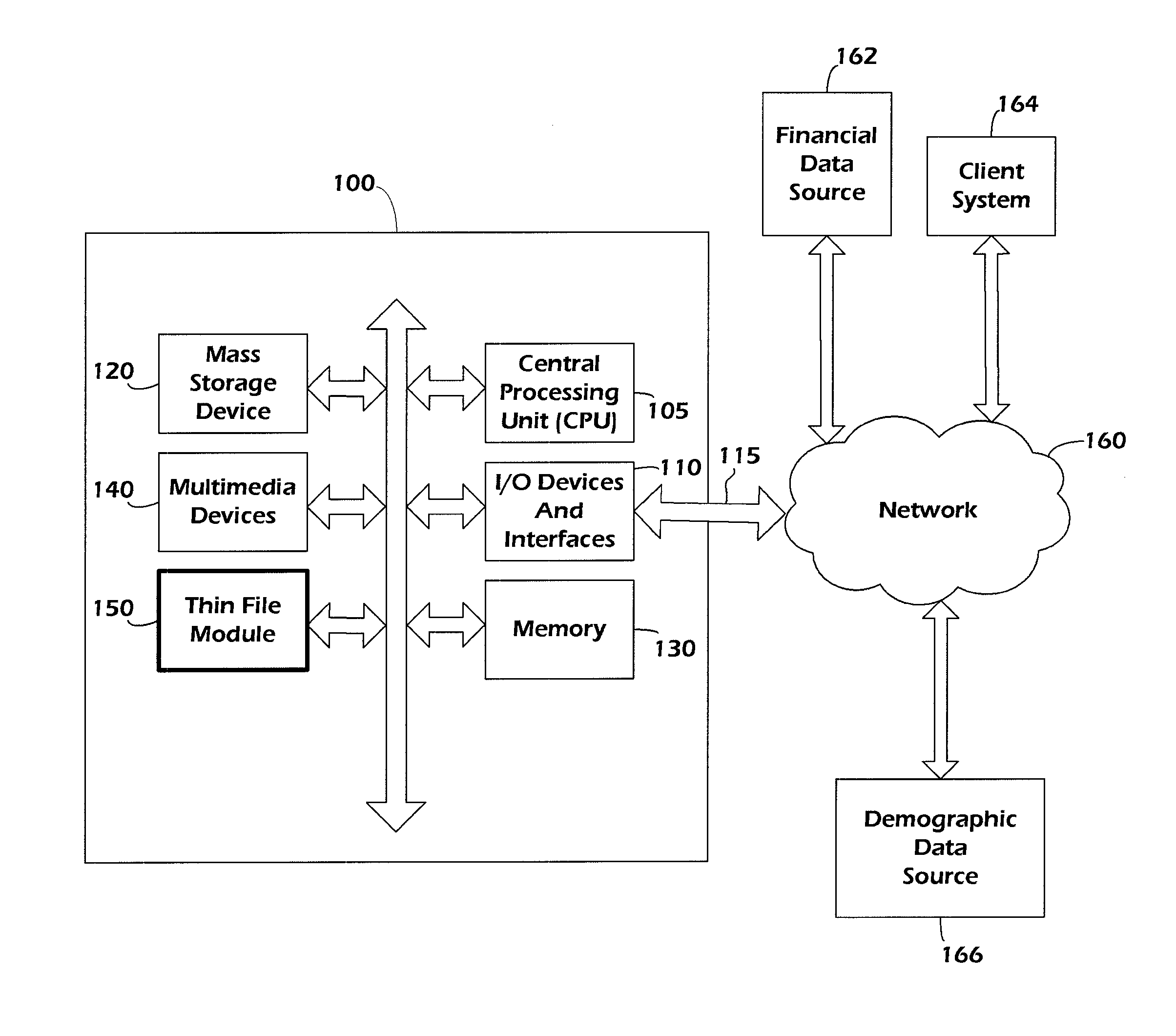
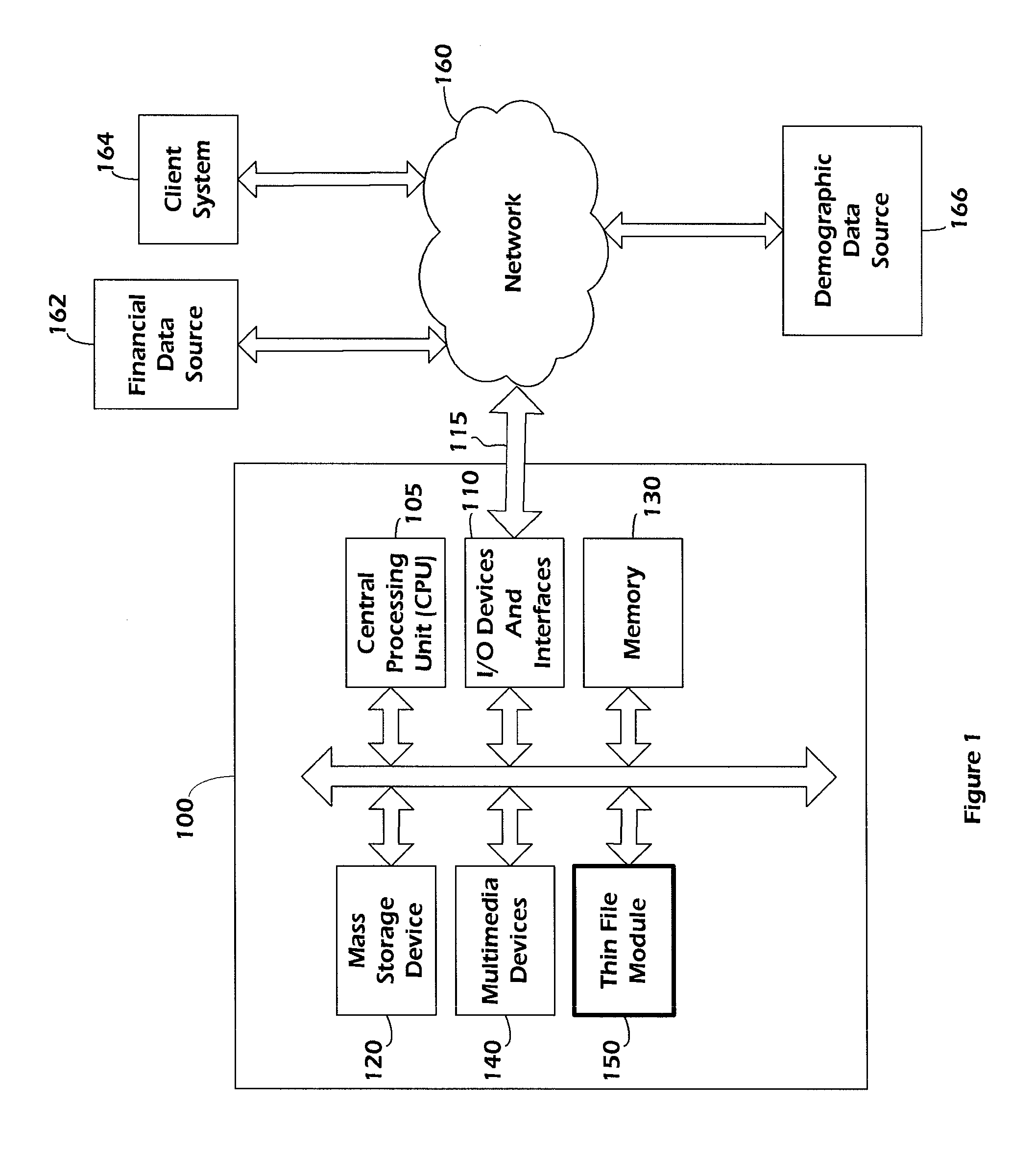
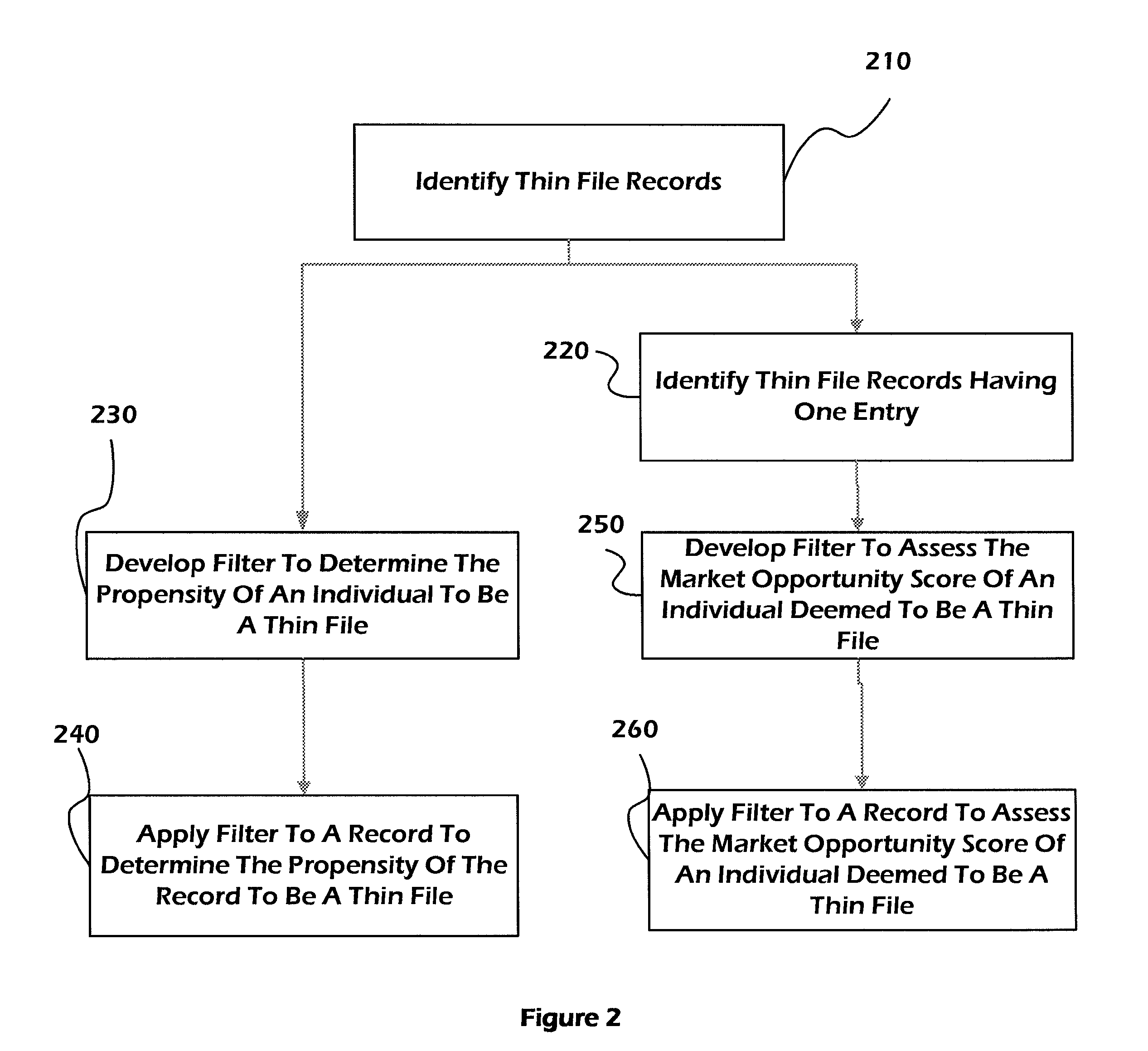
Systems and methods for determining thin-file records and determining thin-file risk levels
In some embodiments, systems and methods are disclosed for generating filters to determine whether a consumer is likely to have a scoreable credit record based on non-credit data, and to determine a potential risk level associated with an unscoreable credit record based on non-credit data. Existing scoreable and unscoreable records are compared to determine factors correlated with having an unscoreable record, and a multi-level filter is developed. Unscoreable records having at least one entry are compared to determine whether they are “good” or “bad” risks, factors correlated with either condition are determined, and a filter is developed. The filters can be applied to records comprising demographic data to determine consumers that are likely to have unscoreable records but represent good risks.
Owner:EXPERIAN MARKETING SOLUTIONS
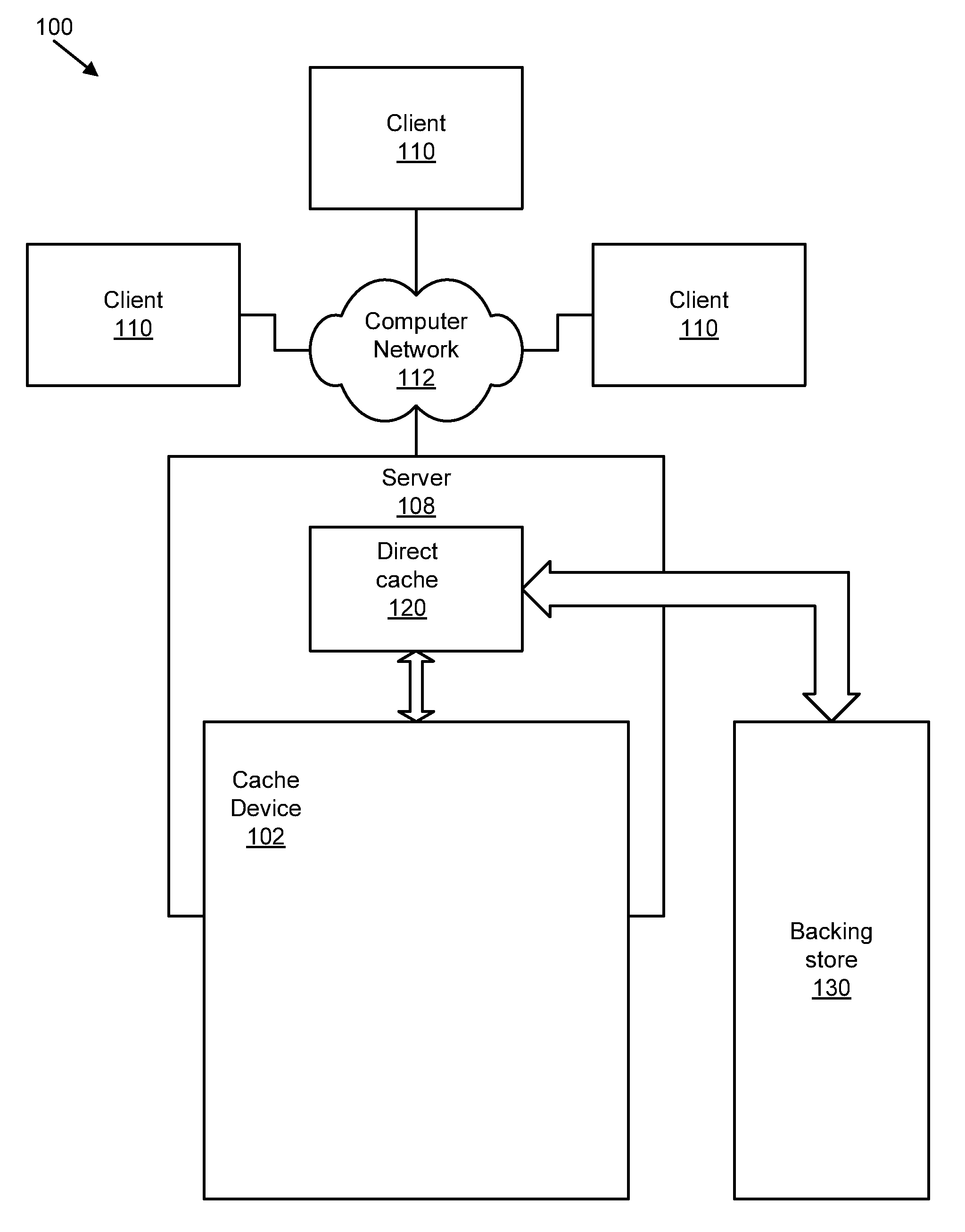
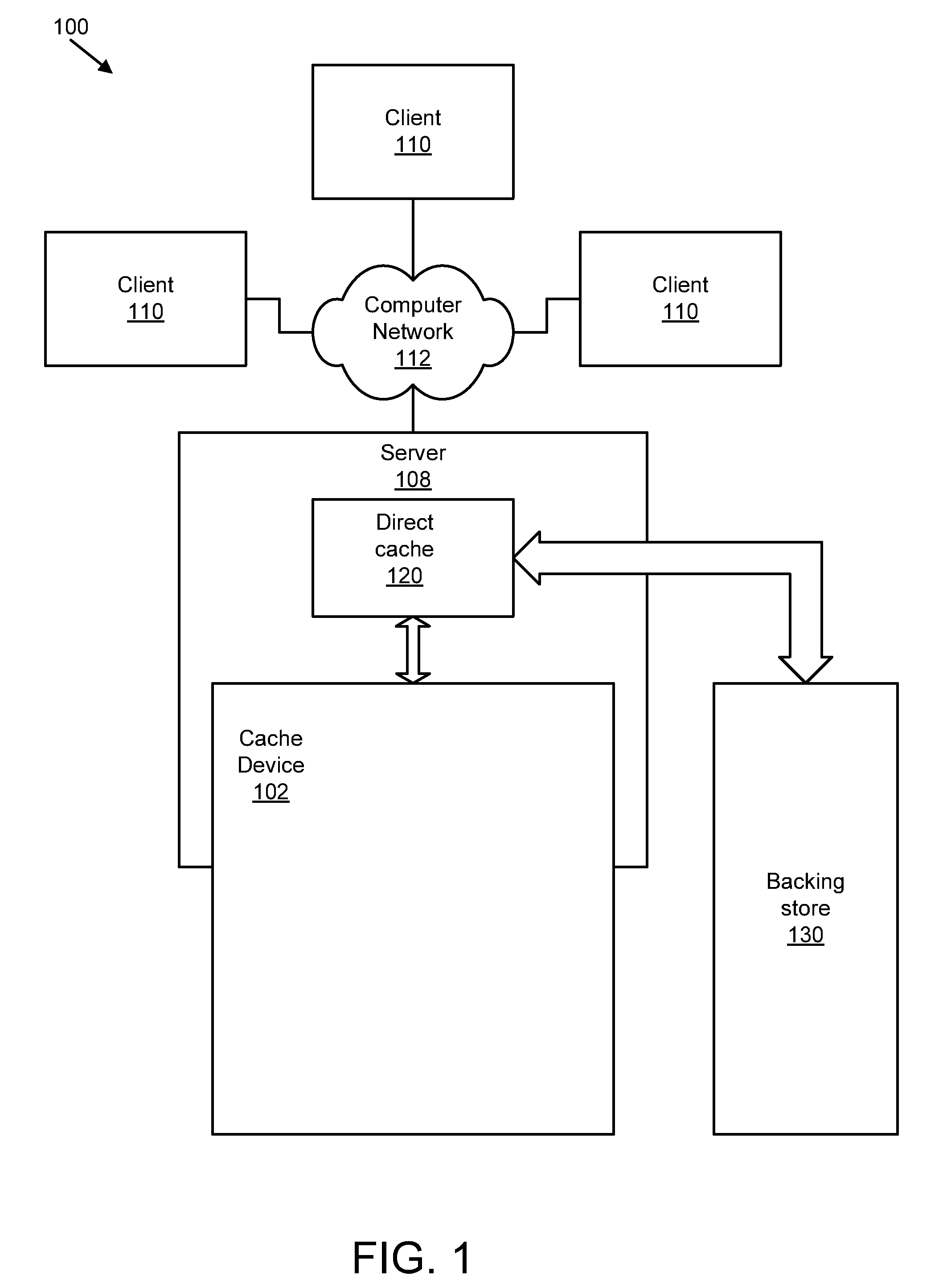
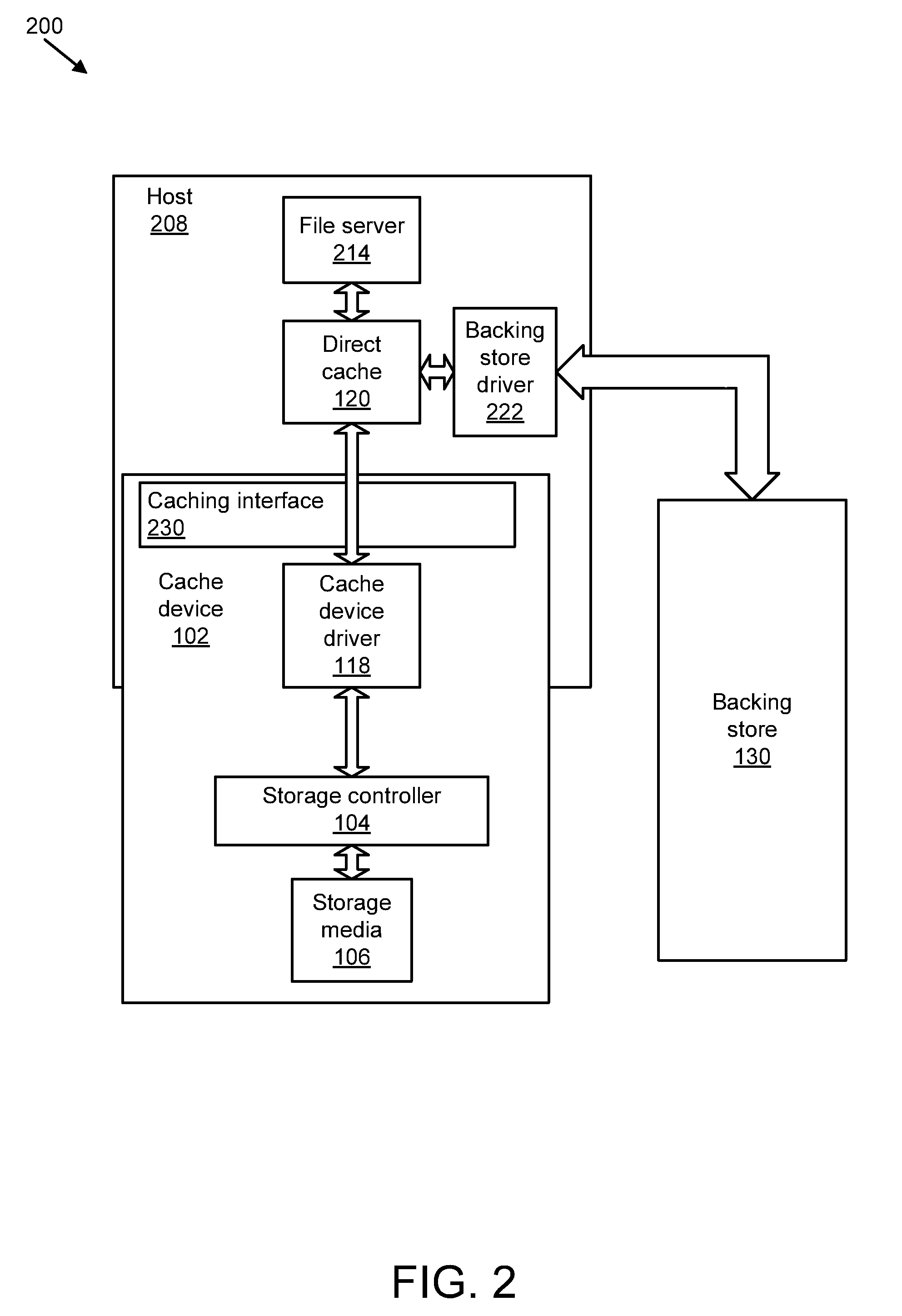
Apparatus, system, and method for graceful cache device degradation
ActiveUS20110047437A1Reduce riskLoss of dataMemory architecture accessing/allocationProgram synchronisationRisk levelClient-side
An apparatus, system, and method are disclosed for graceful cache device degradation. The method may include determining the risk of data loss on the cache device, which may increase (as with Flash memory) with use and age. If the risk of data loss on the cache devices exceeds a threshold risk level, a modified cache policy may be implemented for the cache device to reduce the risk of data loss below the threshold level. This process may iterate until the cache device cannot guarantee performance sufficient to merit continued use of the cache device, and the cache device is logically removed from the system. The changes in cache policy and in the risk of data loss may be hidden from clients that make use of the cache device. The cache policies may transition, for example, in the following order: write back; write through; write around; read only; and bypass.
Owner:SANDISK TECH LLC
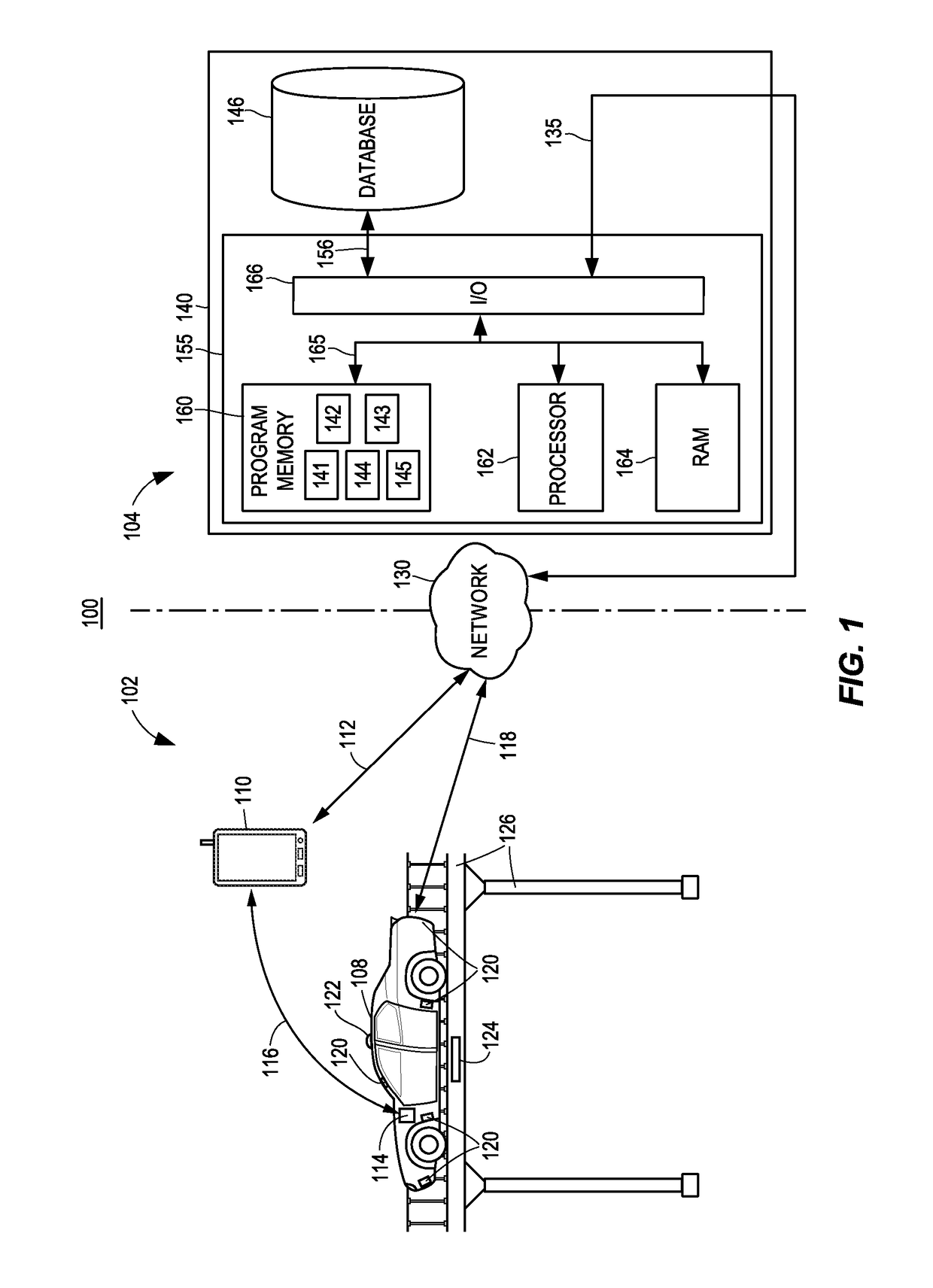
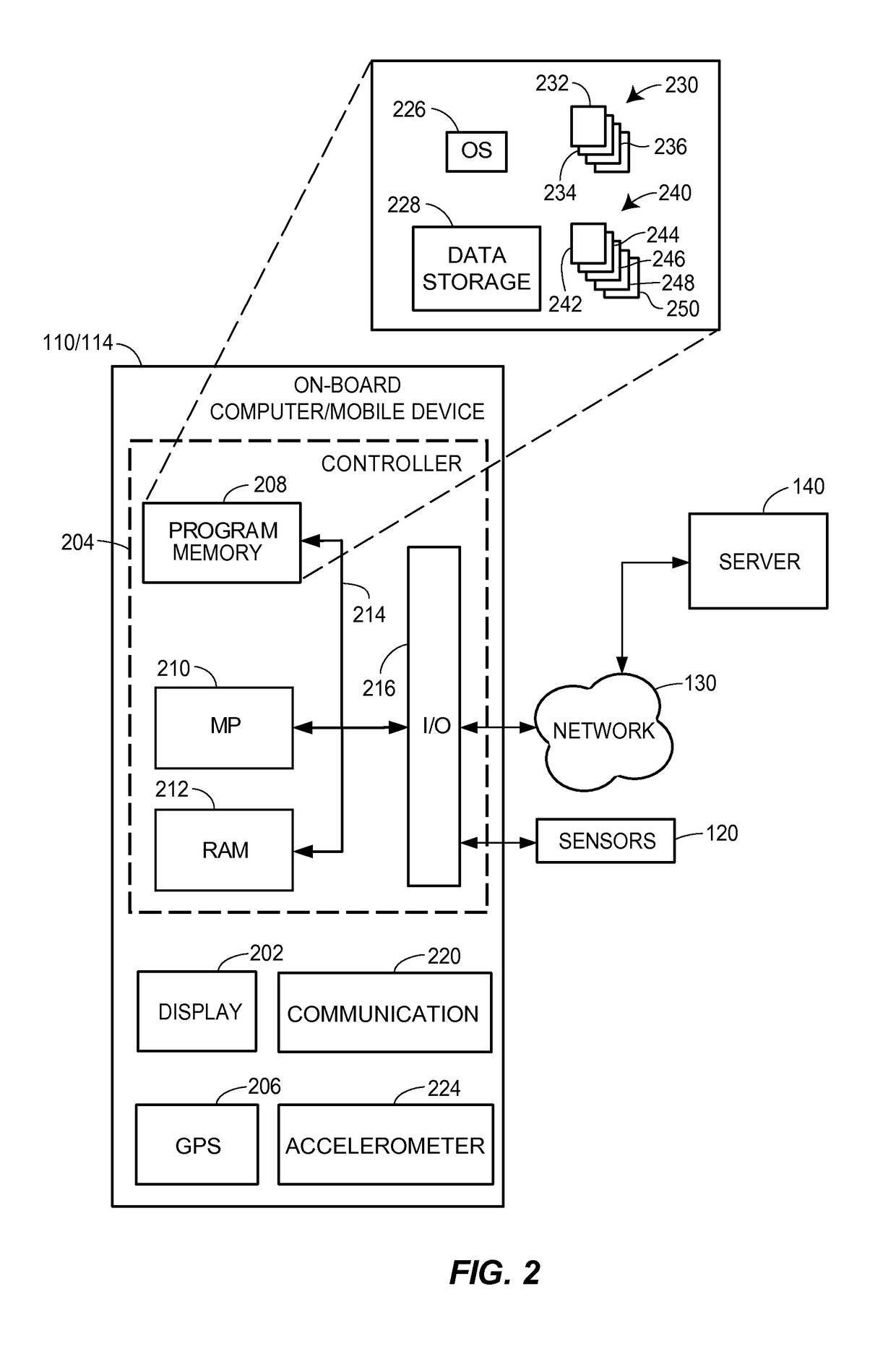
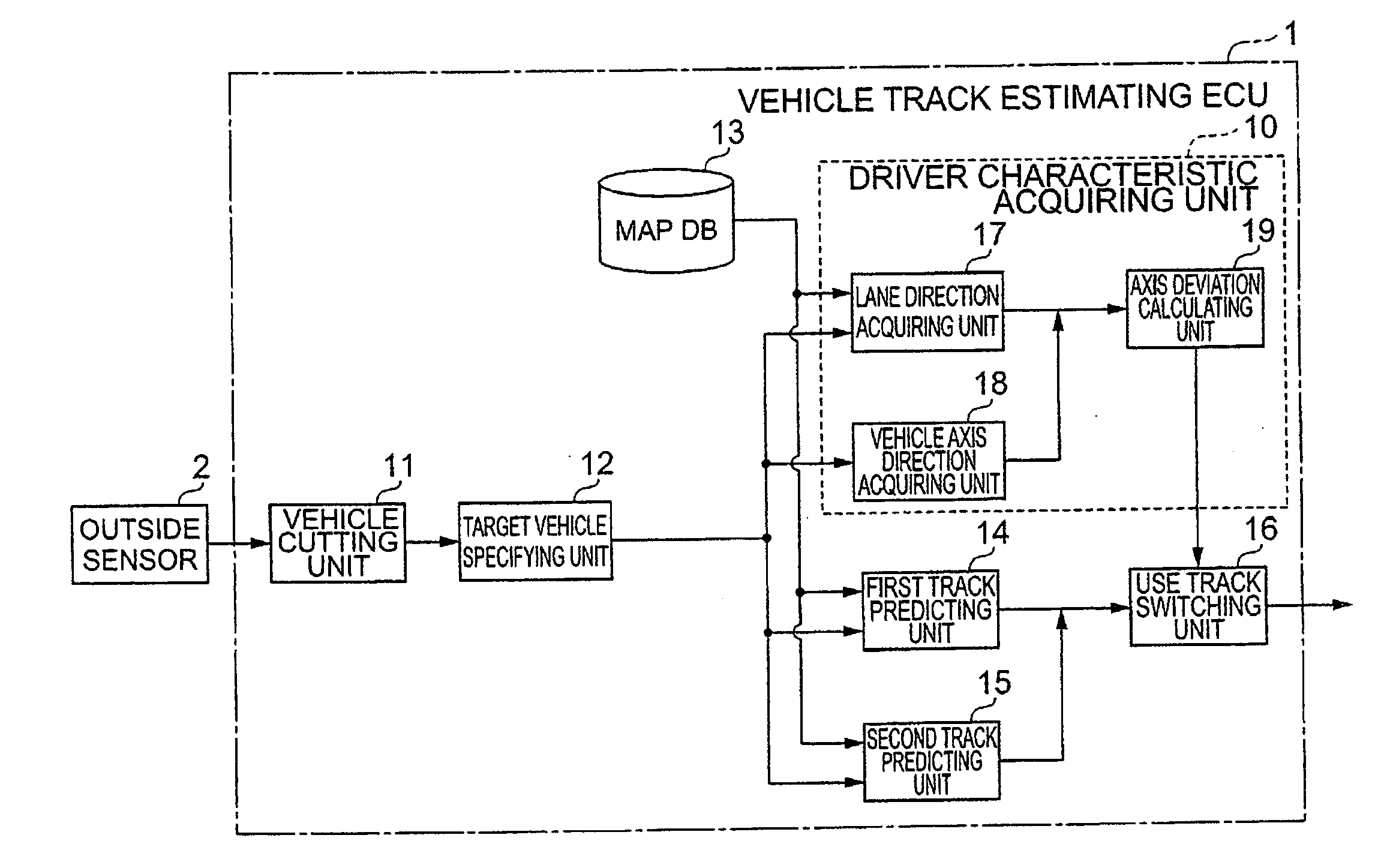
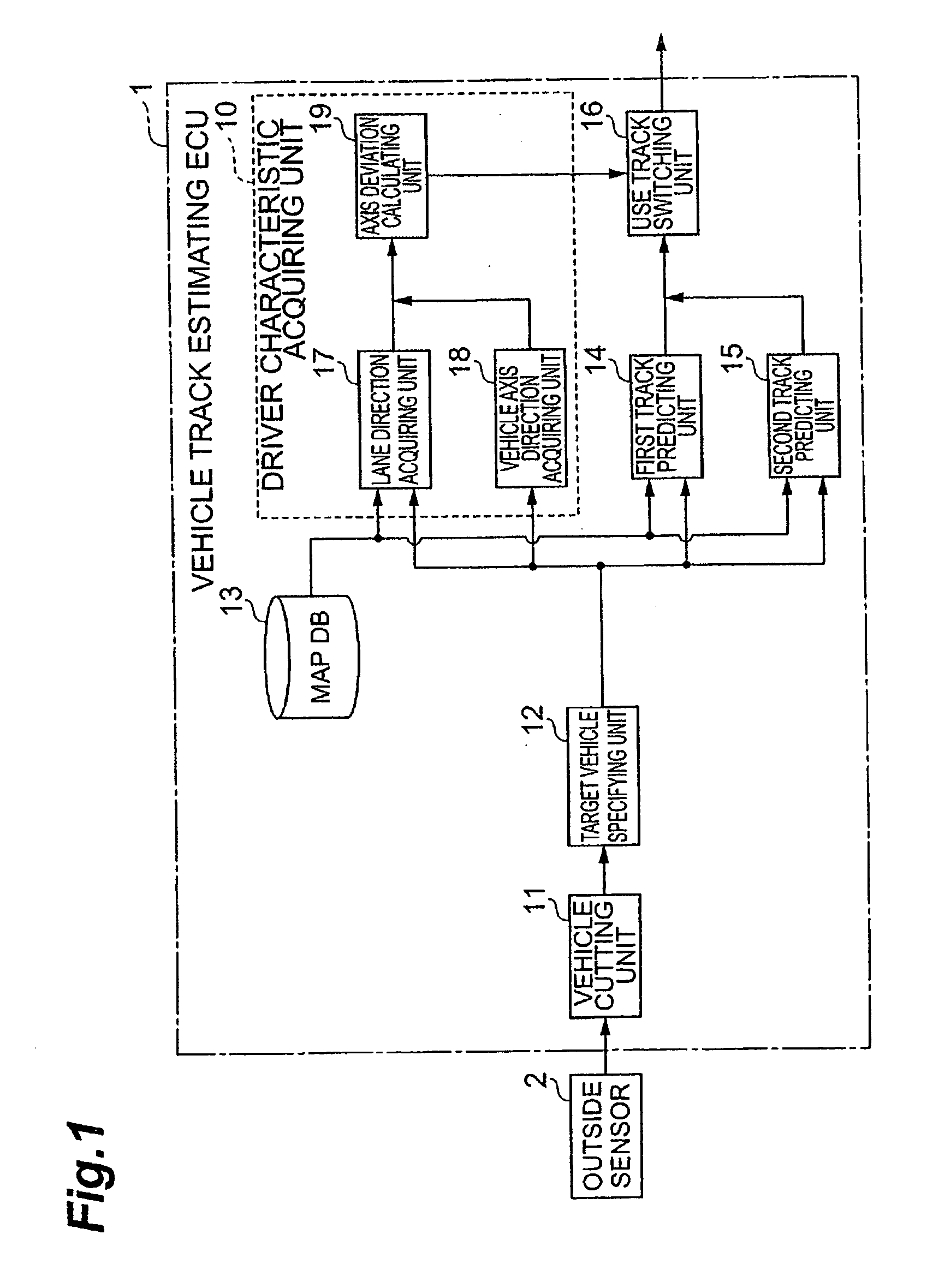
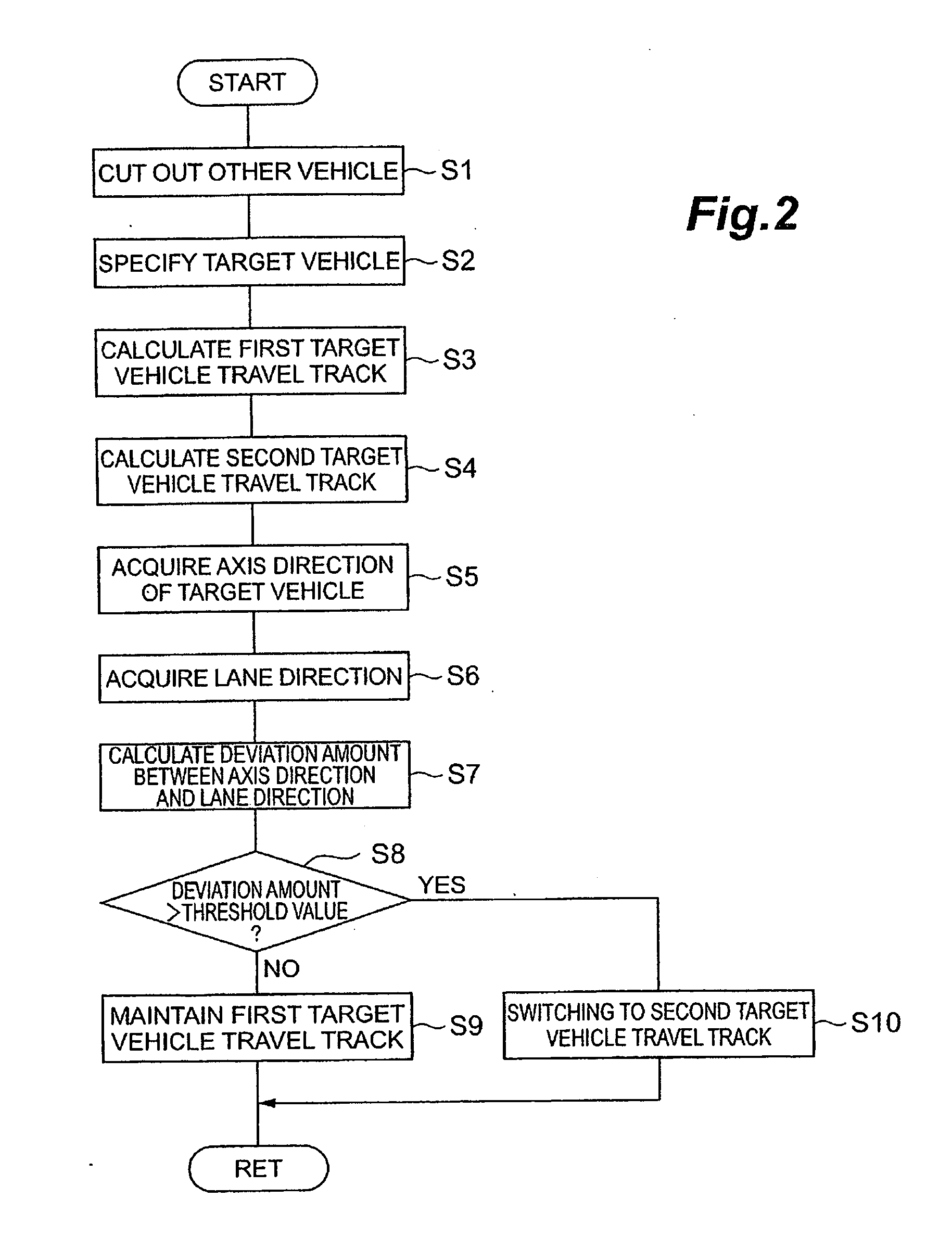
Vehicle travel track estimator
ActiveUS20100106418A1Accurate estimateAnti-collision systemsExternal condition input parametersRisk levelDriver/operator
A vehicle risk level acquiring ECU calculates and acquires a plurality of courses of other vehicles around a driver's own vehicle, and acquires the predicted course of the driver's own vehicle. The vehicle risk level acquiring ECU calculates the collision probability of the driver's own vehicle as collision possibility on the basis of the predicted course of the driver's own vehicle and the plurality of courses of other vehicles.
Owner:TOYOTA JIDOSHA KK
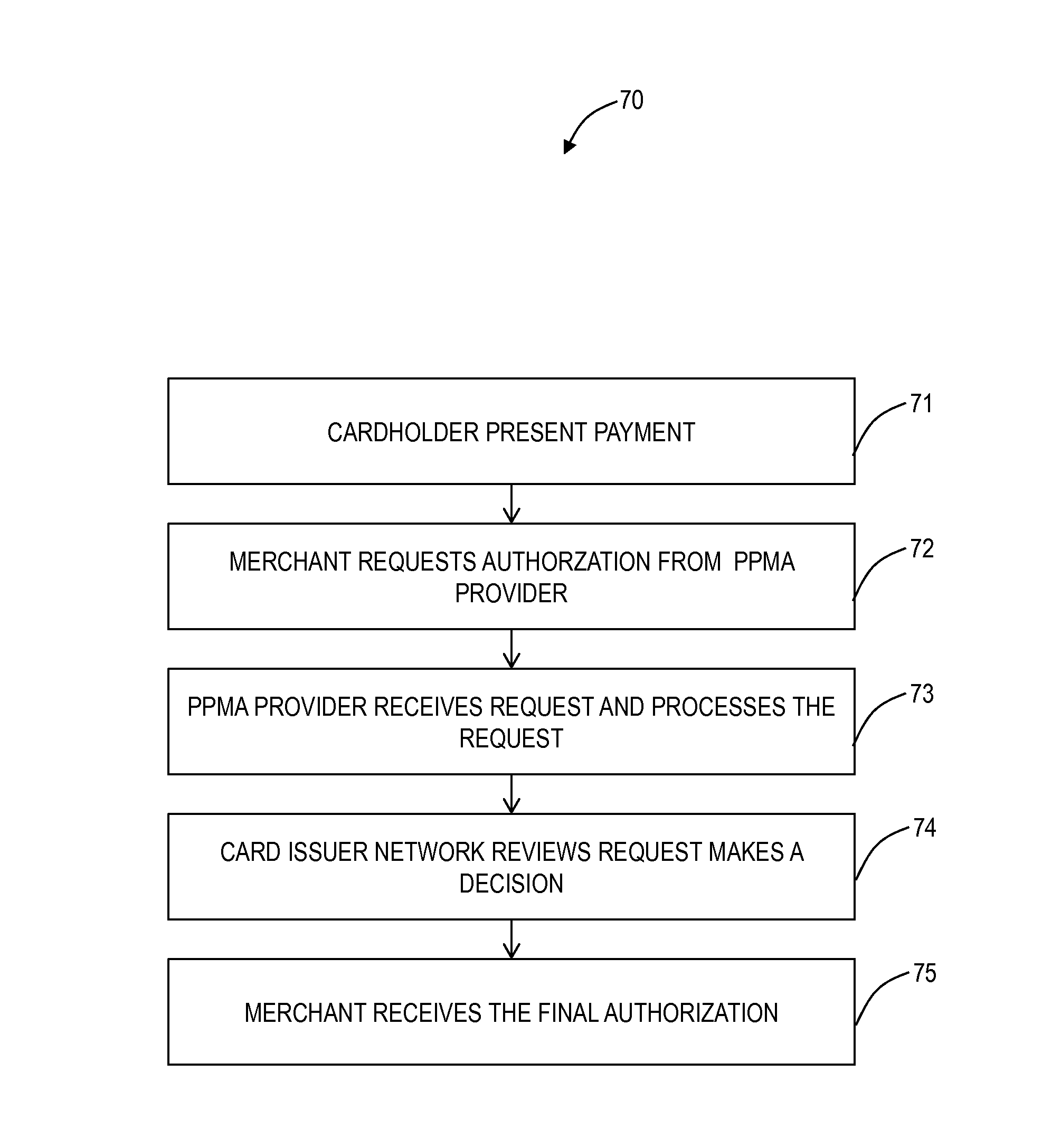
Systems and methods for prepaid merchant payment services
A computer implemented method, a system, and software provides a new processing origination model allowing a new 6th party in payment processing systems and networks, to inspect transactions before they are authorized, enabled or further processed by the payment or settlement network. This new processing delivery system and method may limit or reduce the service operators risk exposure to a defined limit, thereby improving the service providers' ability to manage a known and quantifiable risk level per merchant while limiting the system implementer's total amount of risk and improving both the speed of underwriting and merchant approval process.
Owner:GLOBAL STANDARD FINANCIAL
Verification and authentication systems and methods
ActiveUS8239677B2Improve securityMinimal amountDigital data processing detailsUser identity/authority verificationRisk levelExternal data
Embodiments of the present invention provide verification and / or authentication service engines that provide a customizable solution that can be “dialed” based on the risk level assigned to individual or grouped applications. The systems can also incorporate internal and external sources of data used to verify information provided by the user. It is dynamic and can pull information from a myriad of sources during the verification process, enabling credit reporting agencies (e.g., Equifax and others), FSPs, and other service providers to facilitate real-time approval and access to products and services.
Owner:EQUIFAX INC
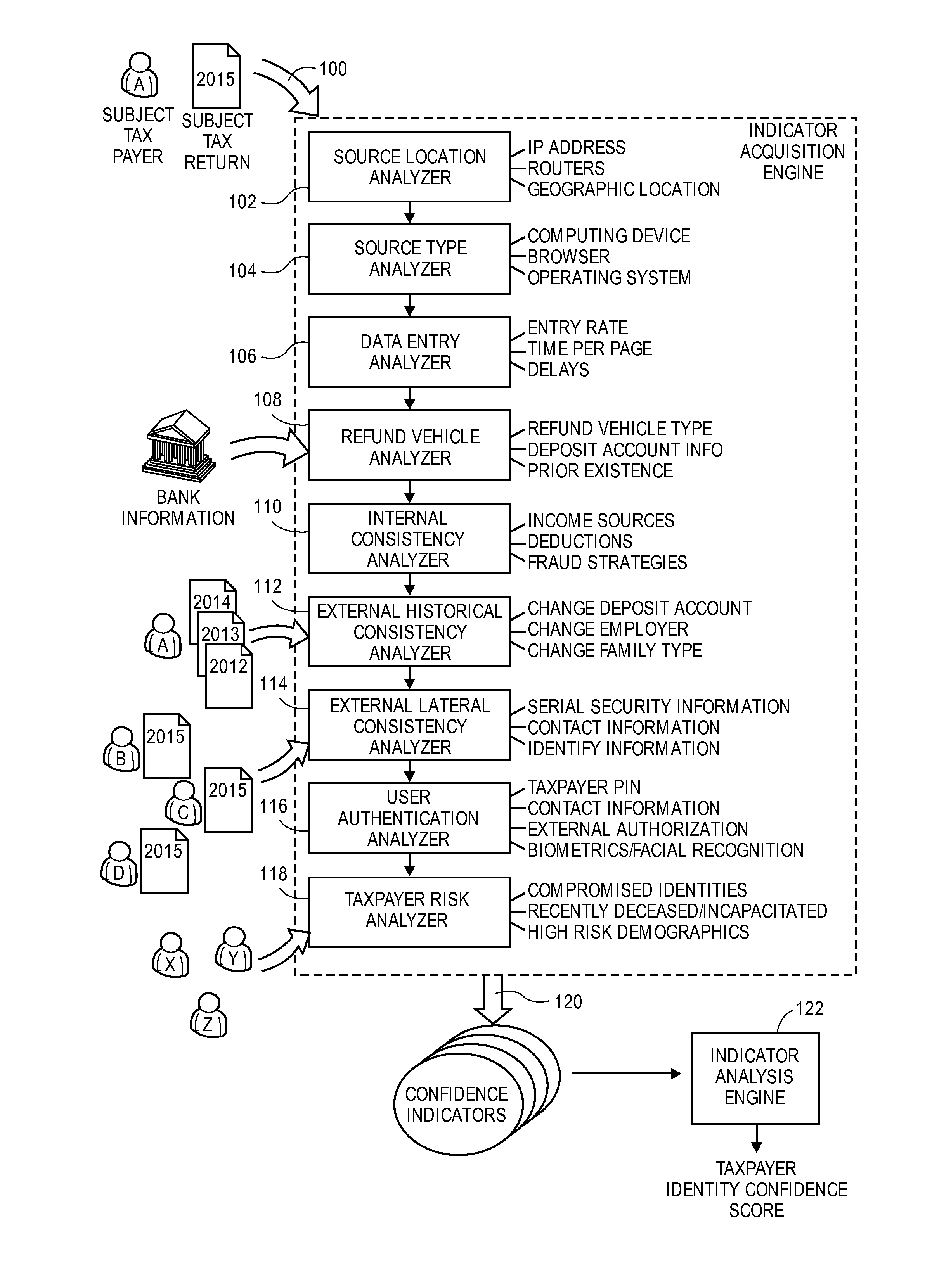
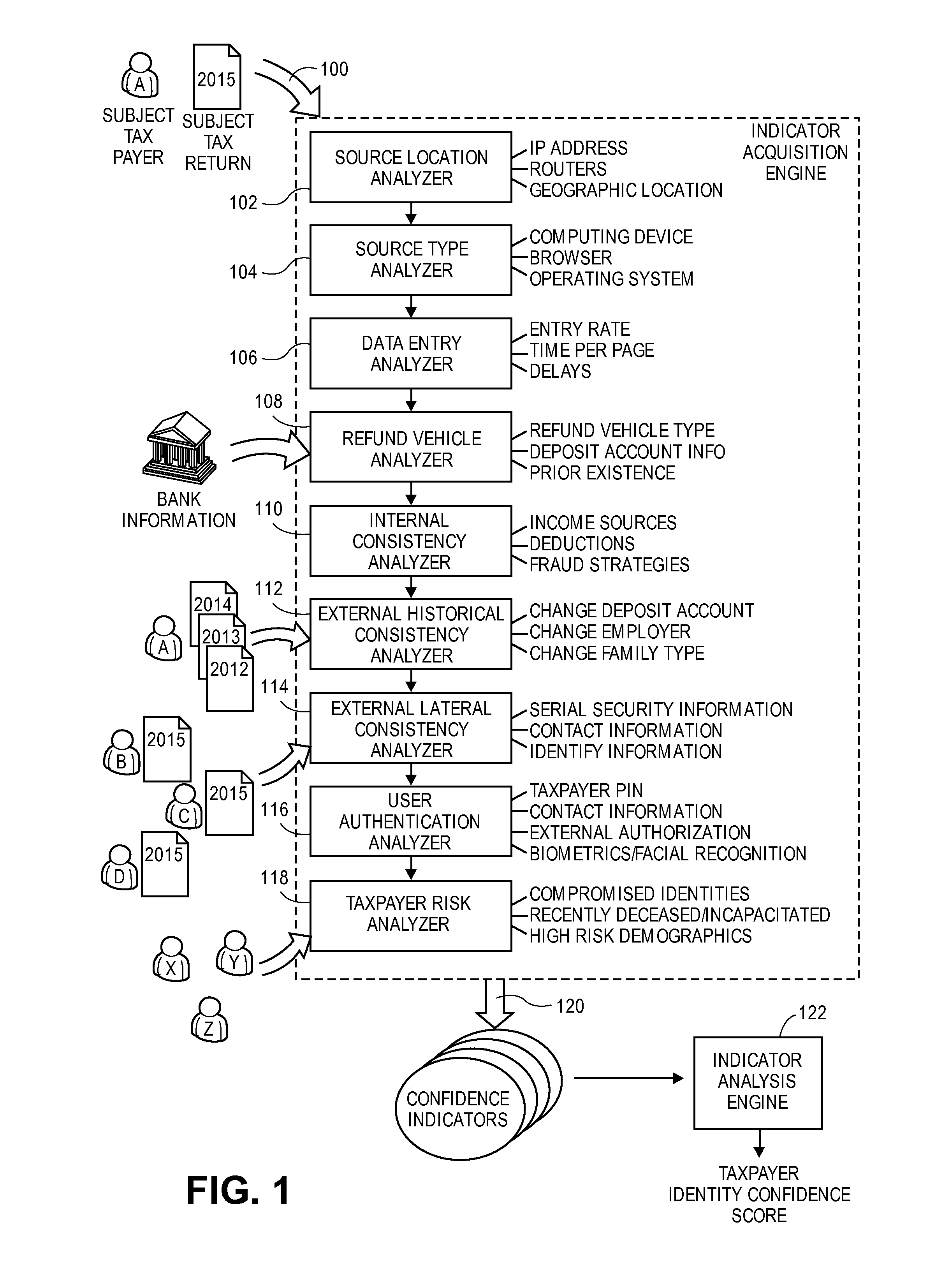
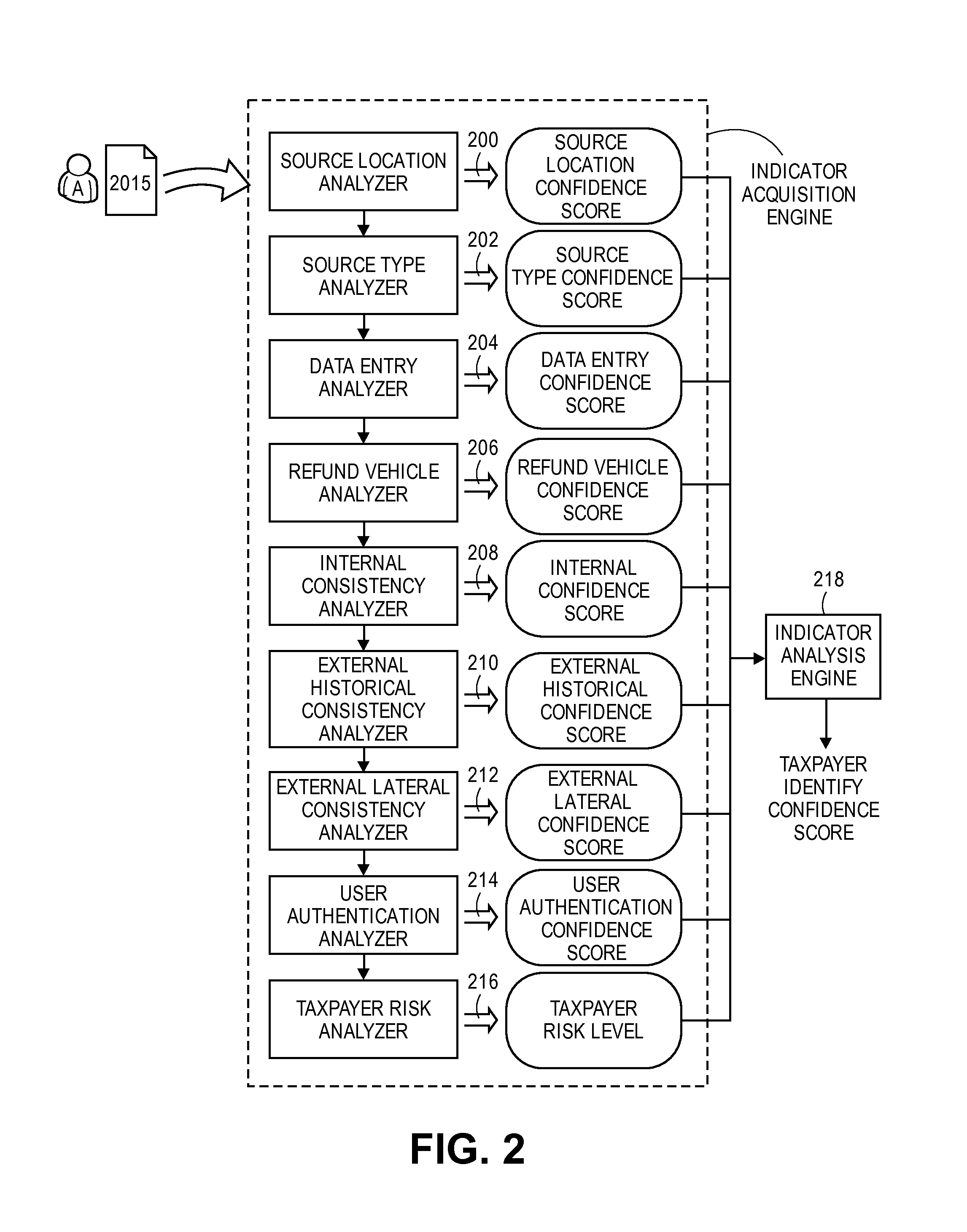
Computer program, method, and system for detecting fraudulently filed tax returns
Embodiments of the invention detect fraudulently filed tax returns when a user prepares or submits a subject tax return that relates to a subject taxpayer for filing with a government taxing authority. Embodiments analyze tax information of various sources to determine whether the subject tax return is genuine (i.e., not fraudulent). The invention determines confidence indicators based upon some or all of a source location, a source type, data entry characteristics, refund vehicle characteristics, internal consistencies, external historical consistencies, external lateral consistencies, user authentication methods, and a taxpayer risk level. Based upon these analyses the invention calculates a taxpayer identity confidence score, which may be utilized to allow or deny the filing of the subject tax return.
Owner:HRB INNOVATIONS
Apparatus and method for detecting characteristics of electronic mail message
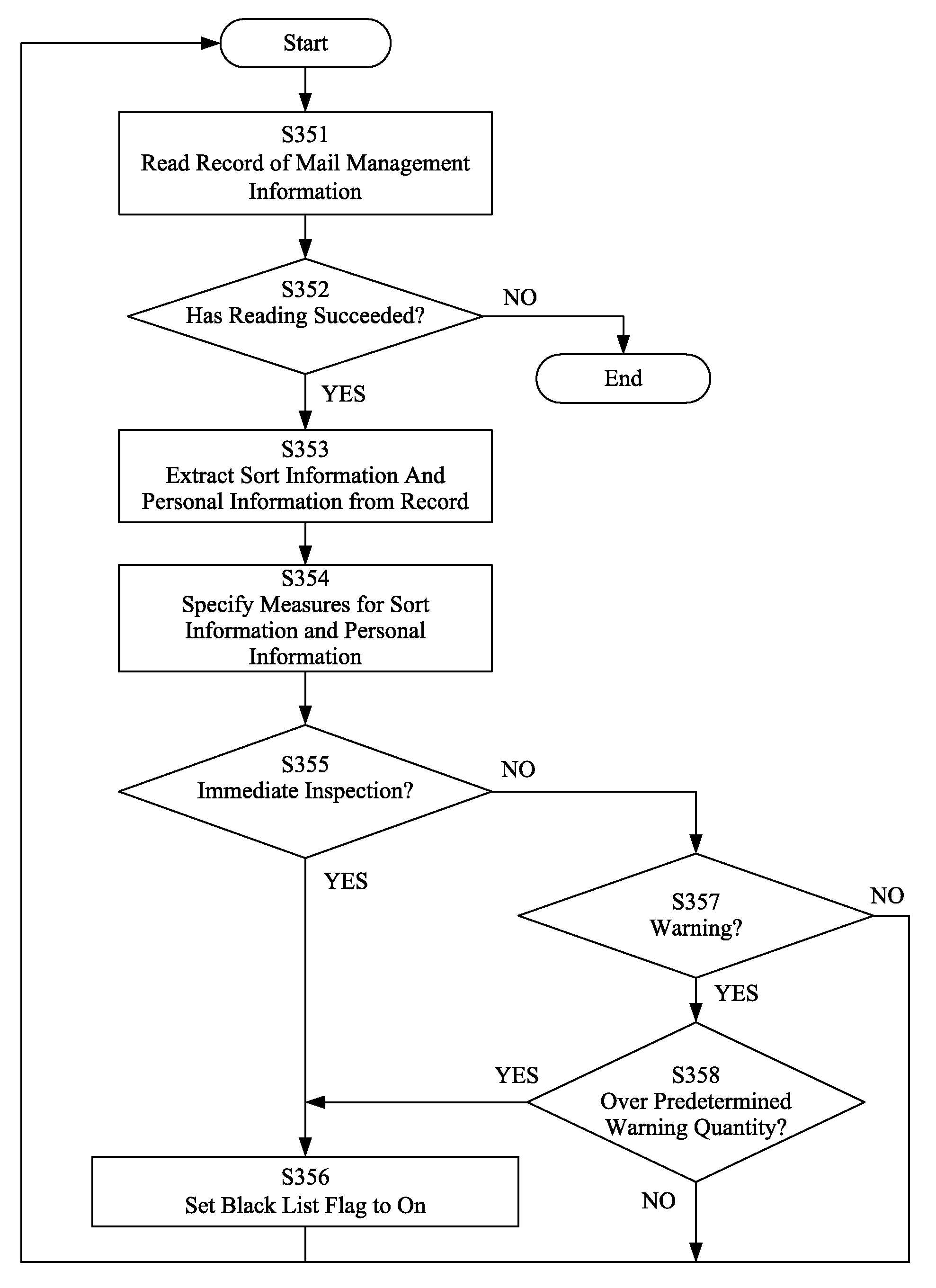
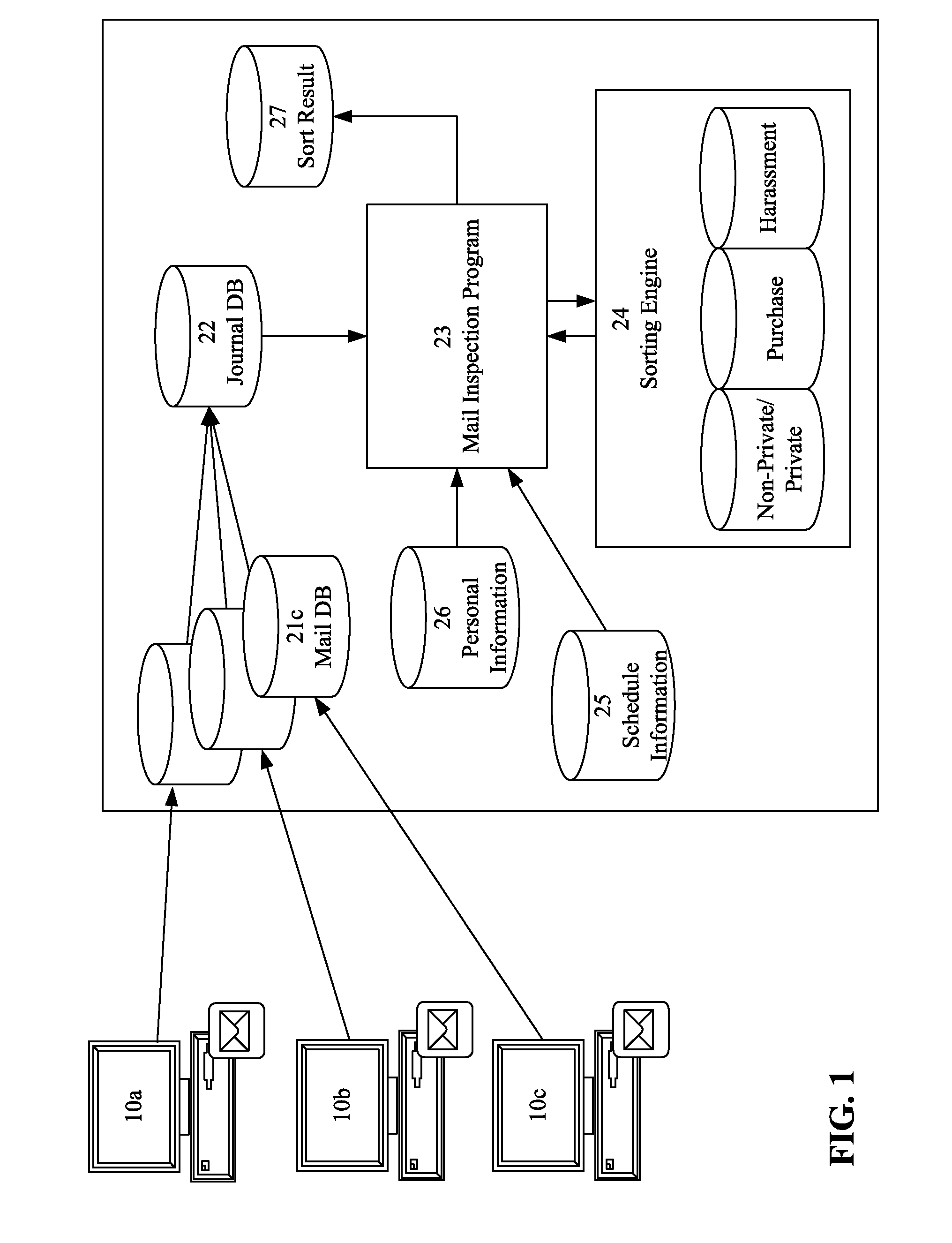
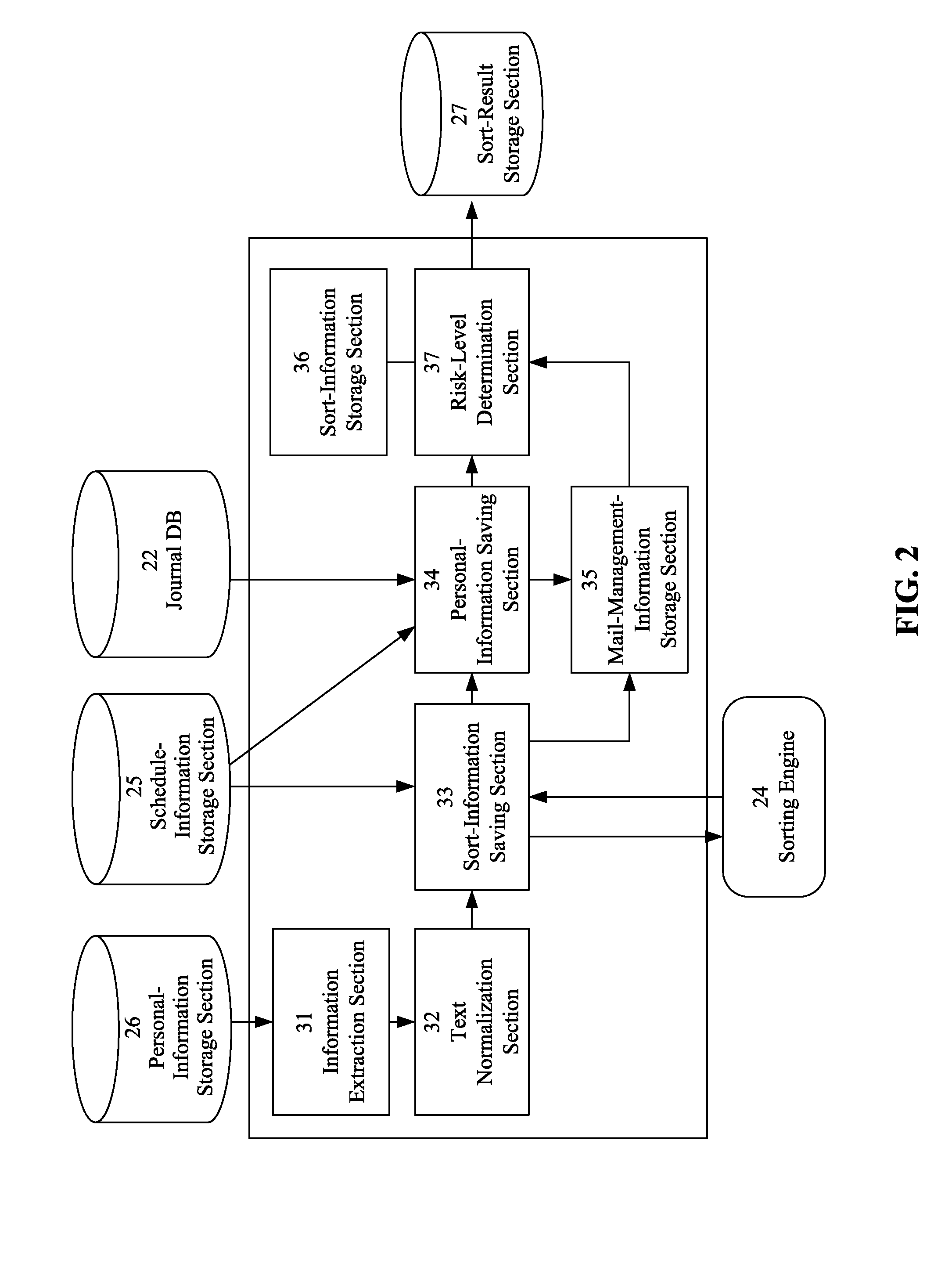
InactiveUS8131808B2Accurate detectionMemory loss protectionError detection/correctionRisk levelDatabase
The present invention enables accurate detection of risks from an electronic mail message. In a mail inspection unit, an information extraction section extracts text and a mail address from electronic mail accumulated in a journal DB, and a text normalization section normalizes the text. A sort-information saving section generates text sort information according to the score obtained from a sorting engine, and stores it in a mail-management-information storage section. A personal-information saving section extracts personal information from a personal-information storage section according to the mail address, and stores it in the mail-management-information storage section. Finally, a risk-level determination section compares the information stored in the mail-management-information storage section with the information stored in a category-information storage section to determine the risk level of the electronic mail.
Owner:INT BUSINESS MASCH CORP
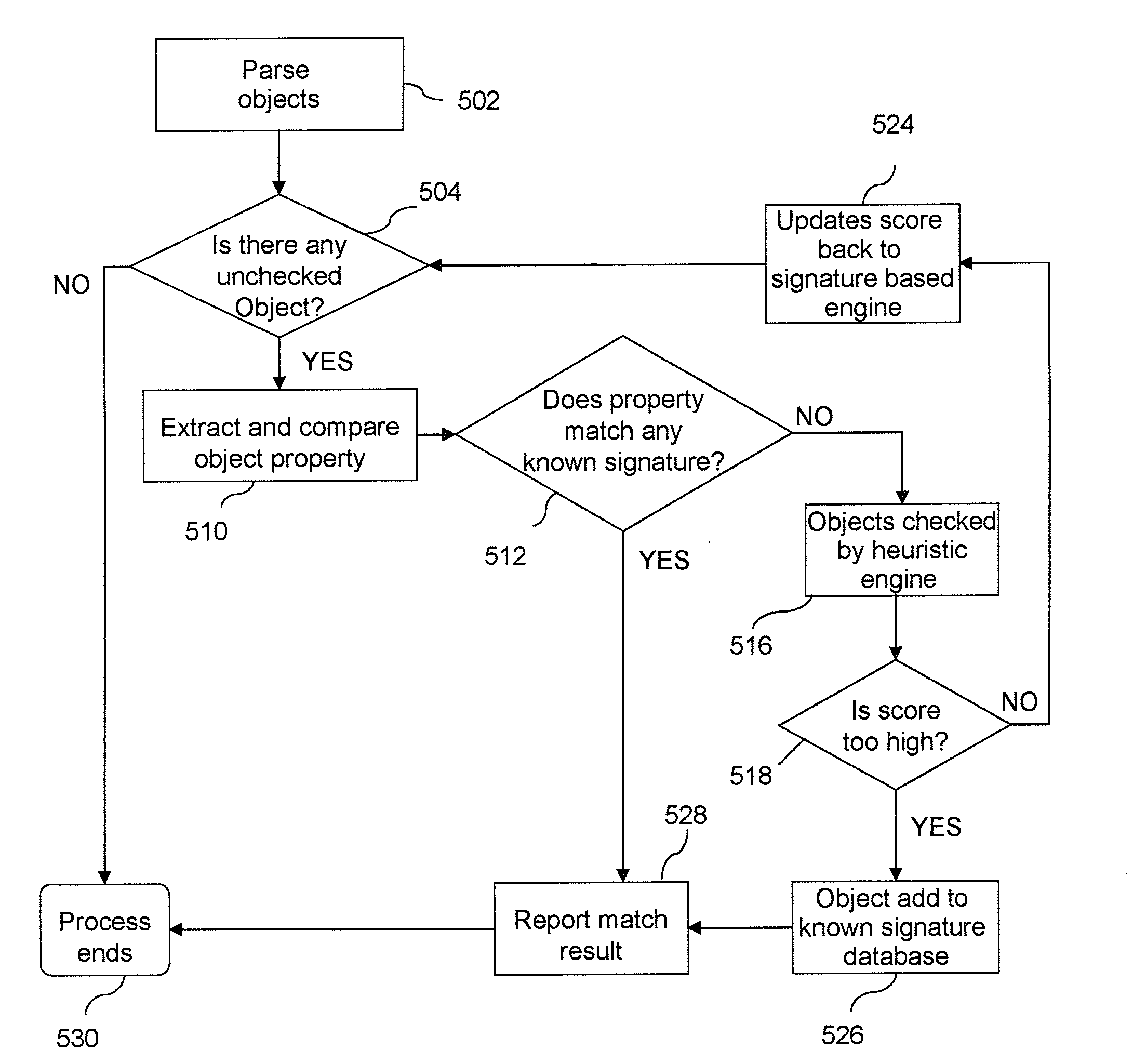
Method and apparatus for preventing web page attacks
A method and apparatus for preventing web page attacks are disclosed. Specifically, one embodiment of the present invention sets forth a method, which includes the steps of examining an object property from a web page requested by a client computer in real-time before the client computer receives the web page, assessing a collective risk level associated with the web page causing harm to the client computer based on the result of examining the object property, and performing an action with regards to the web page according to the collective risk level.
Owner:LIONIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com