Patents
Literature
418 results about "Content filtering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Content Filtering. Definition - What does Content Filtering mean? Content filtering, in the most general sense, involves using a program to prevent access to certain items, which may be harmful if opened or accessed. The most common items to filter are executables, emails or websites.
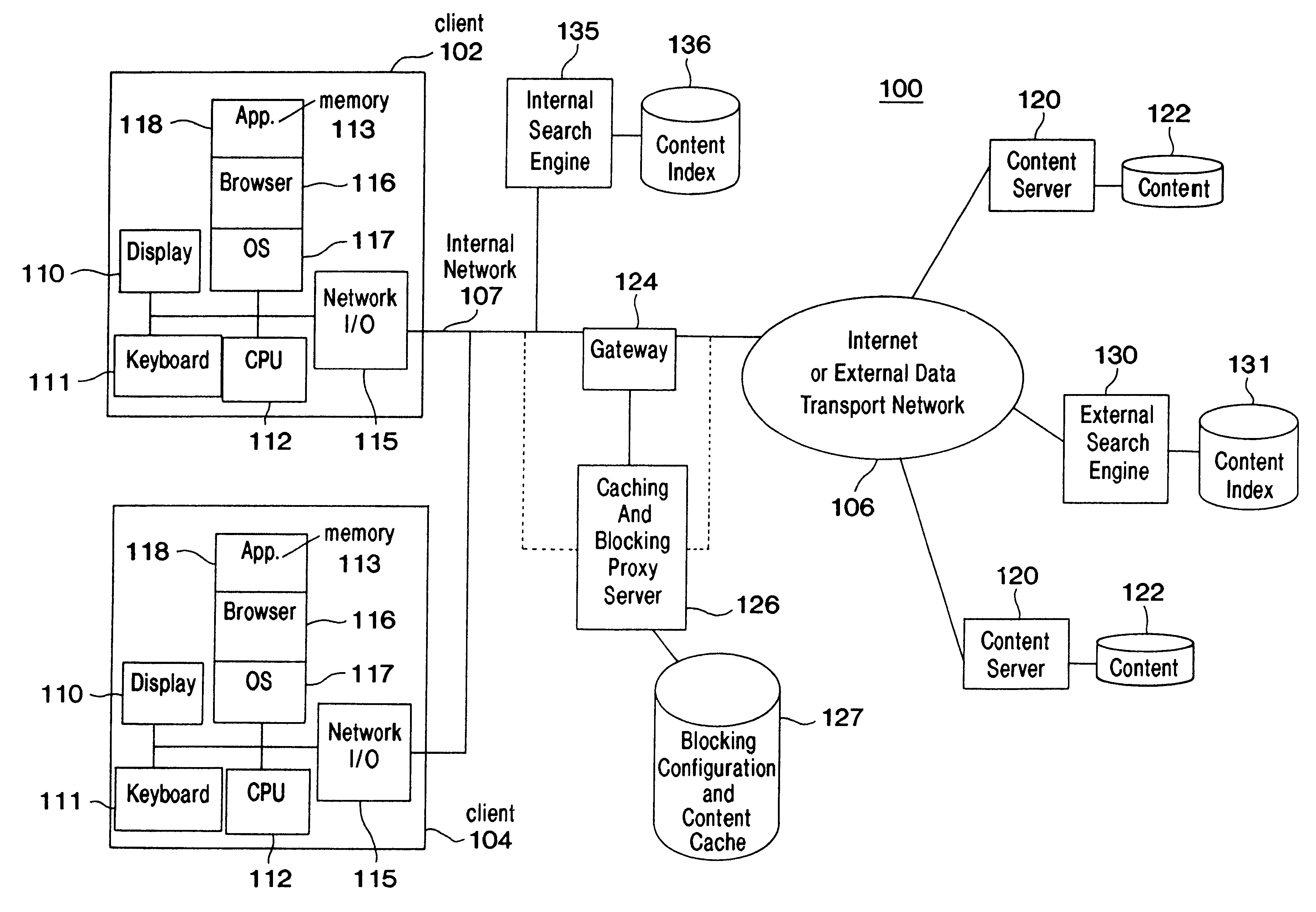
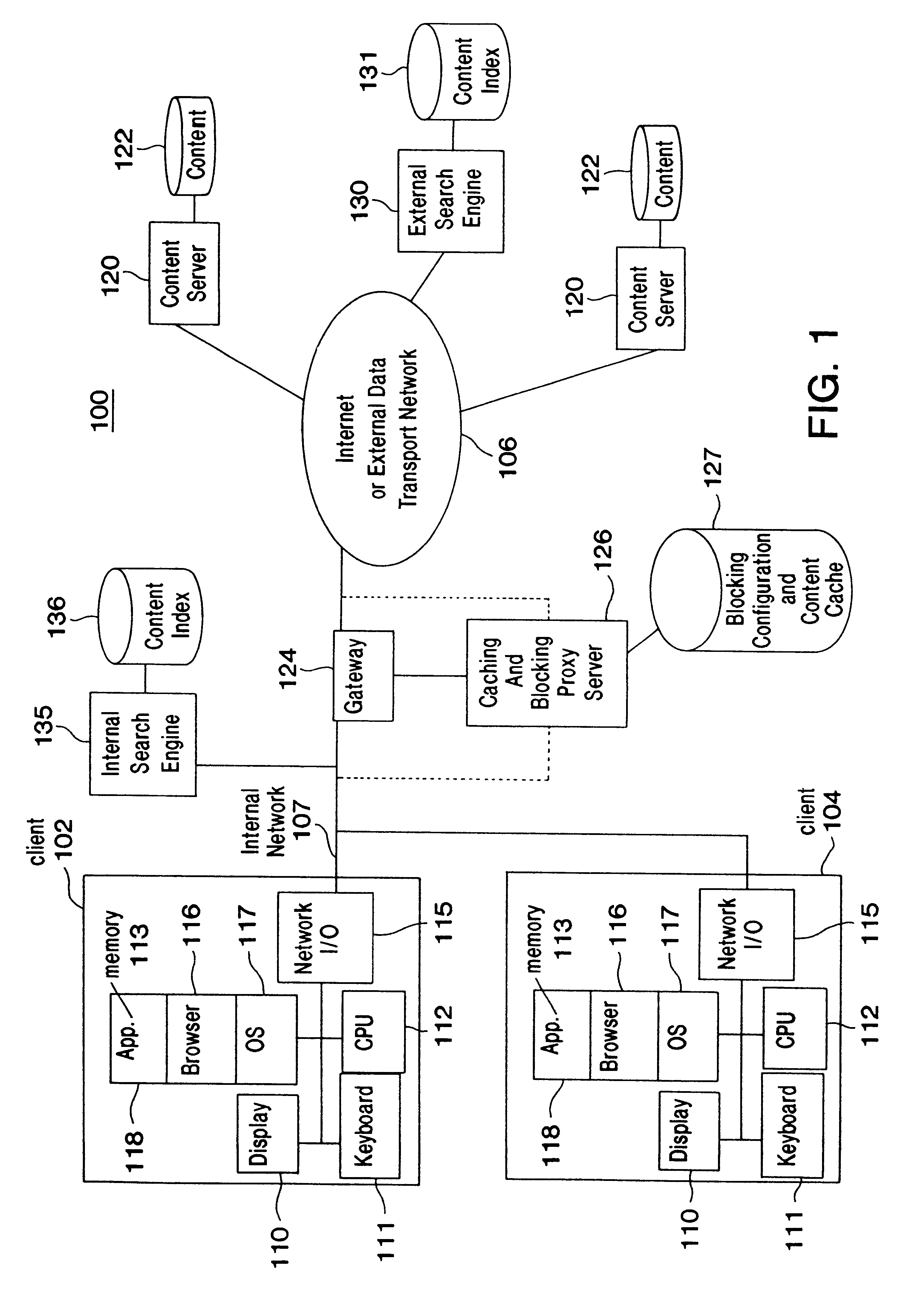
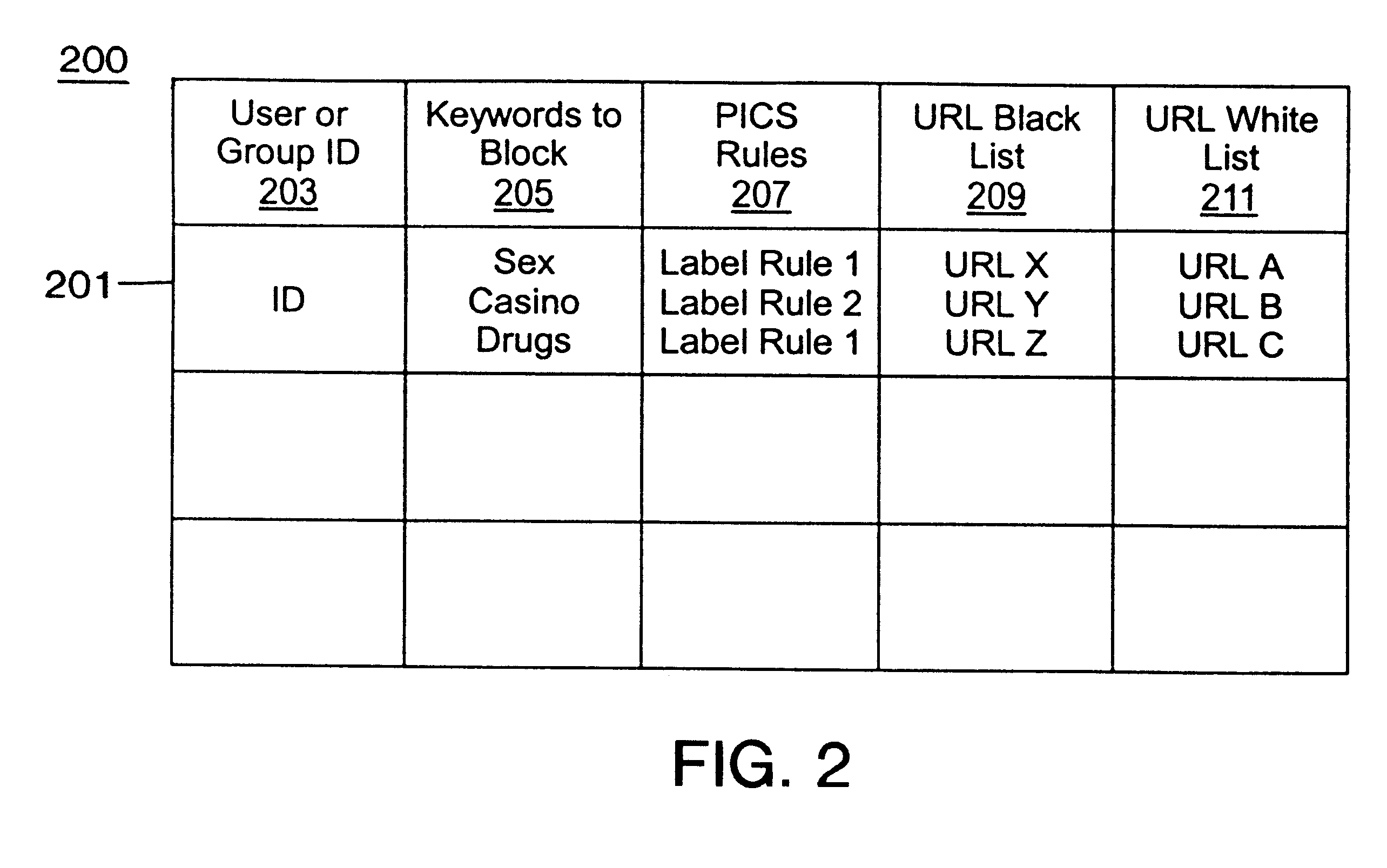
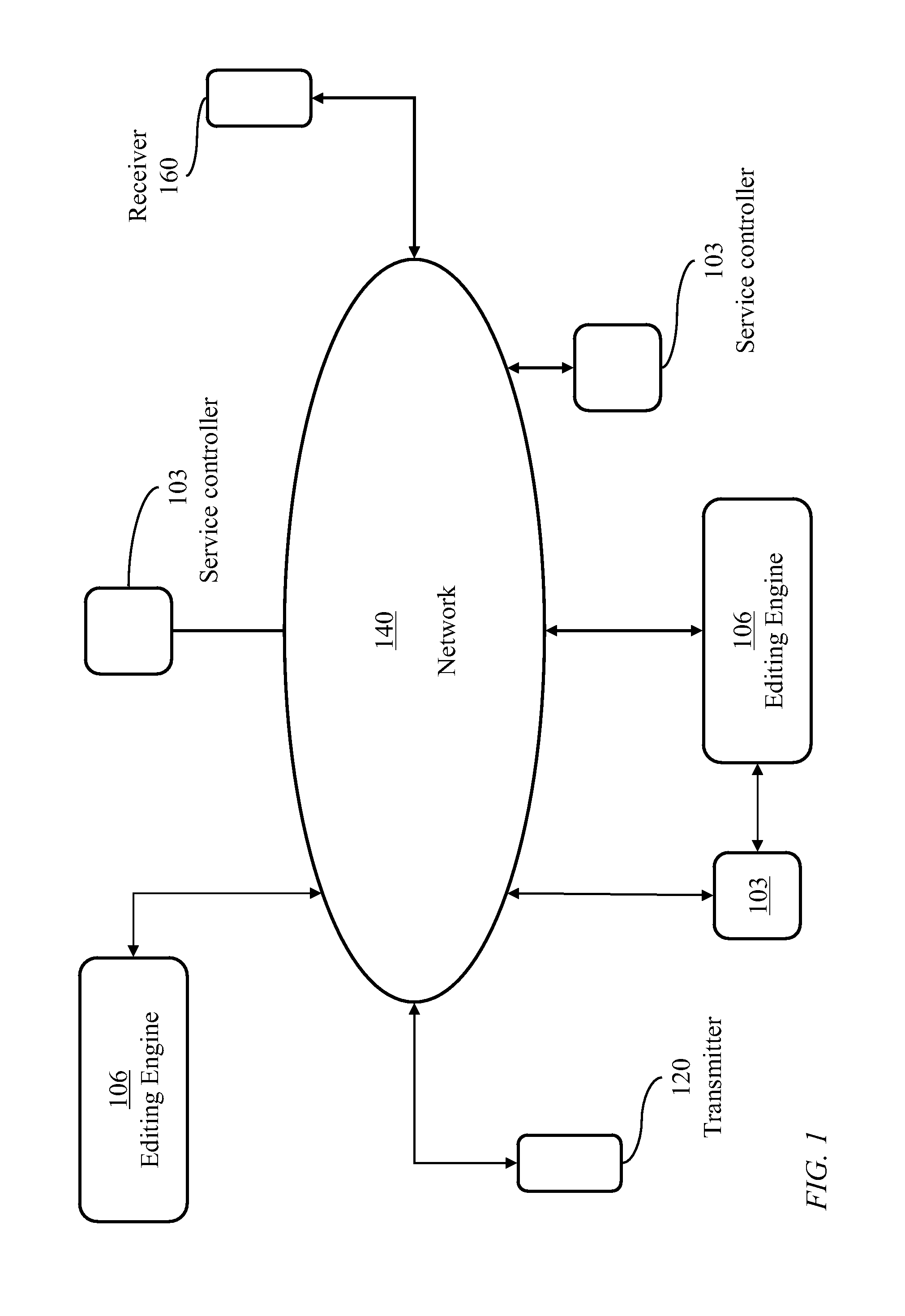
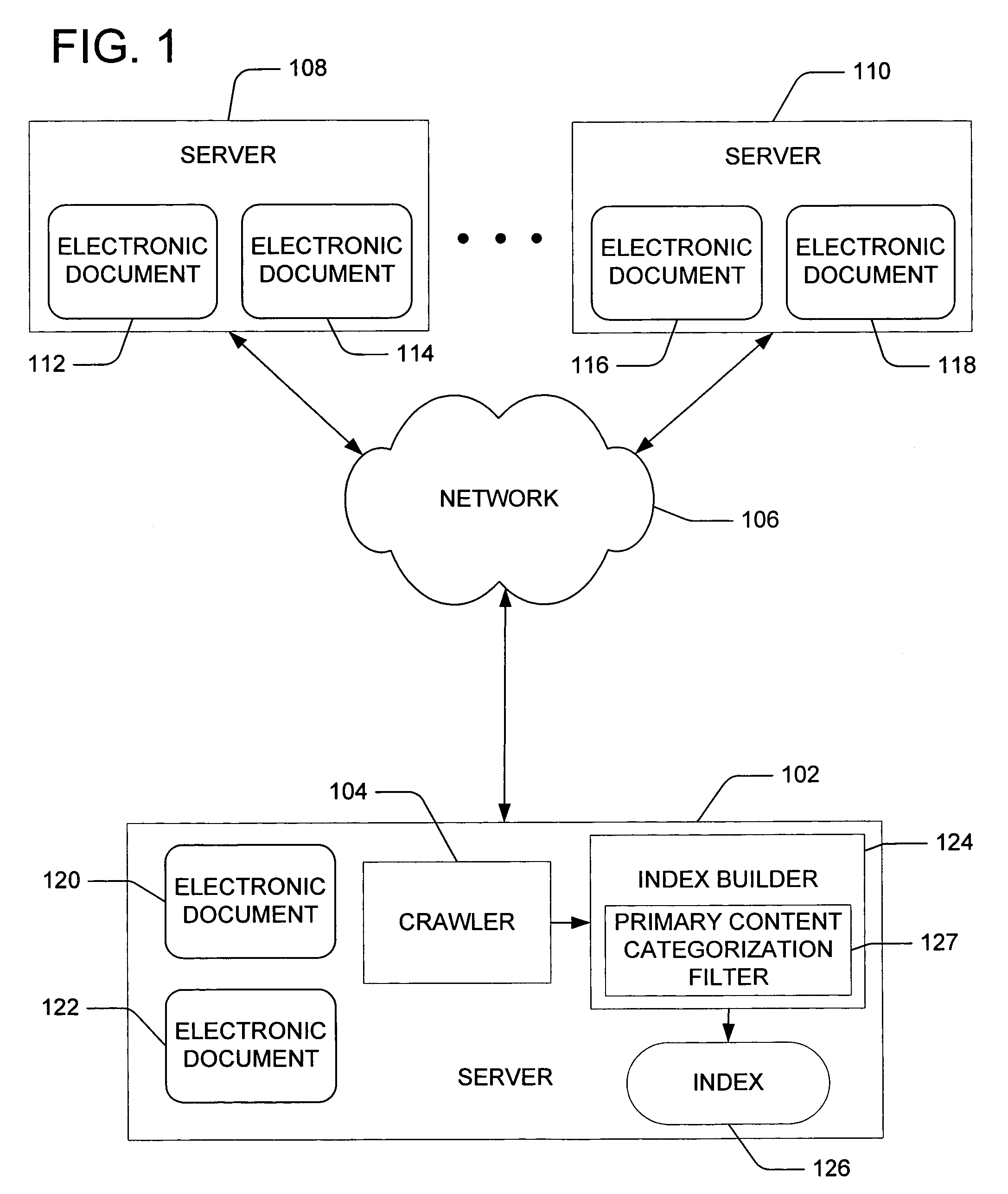
Content-indexing search system and method providing search results consistent with content filtering and blocking policies implemented in a blocking engine
InactiveUS6336117B1Data processing applicationsDigital data information retrievalInformation retrievalContent filtering
A content-indexing search system and method provides search results consistent with content filtering and blocking policies. The search system comprises a content-indexing search engine including a database coupled to an information network. A user provides search queries to the search engine through a gateway serving as a proxy server and cache and blocking engine. The blocking engine implements content filtering and blocking policies with respect to the search results. Alternative embodiments provide consistency between the results of the user content searches and the content filtering / blocking policies. One embodiment modifies the search engine to implement the same content blocking policy as the caching and filtering engine. Another embodiment modifies the search engine to build an indexing database by searching the caching and engine content. A third embodiment modifies the search engine to go through the cache and filter engine as the search engine builds its indexing database. A fourth embodiment modifies a search engine to go through a caching and filtering engine as it builds an indexing database.
Owner:IBM CORP
Apparatus and method for remotely monitoring a computer network
InactiveUS20060031476A1Easy to provideMinimize the possibilityDigital computer detailsTransmissionAnti virusPrivate network
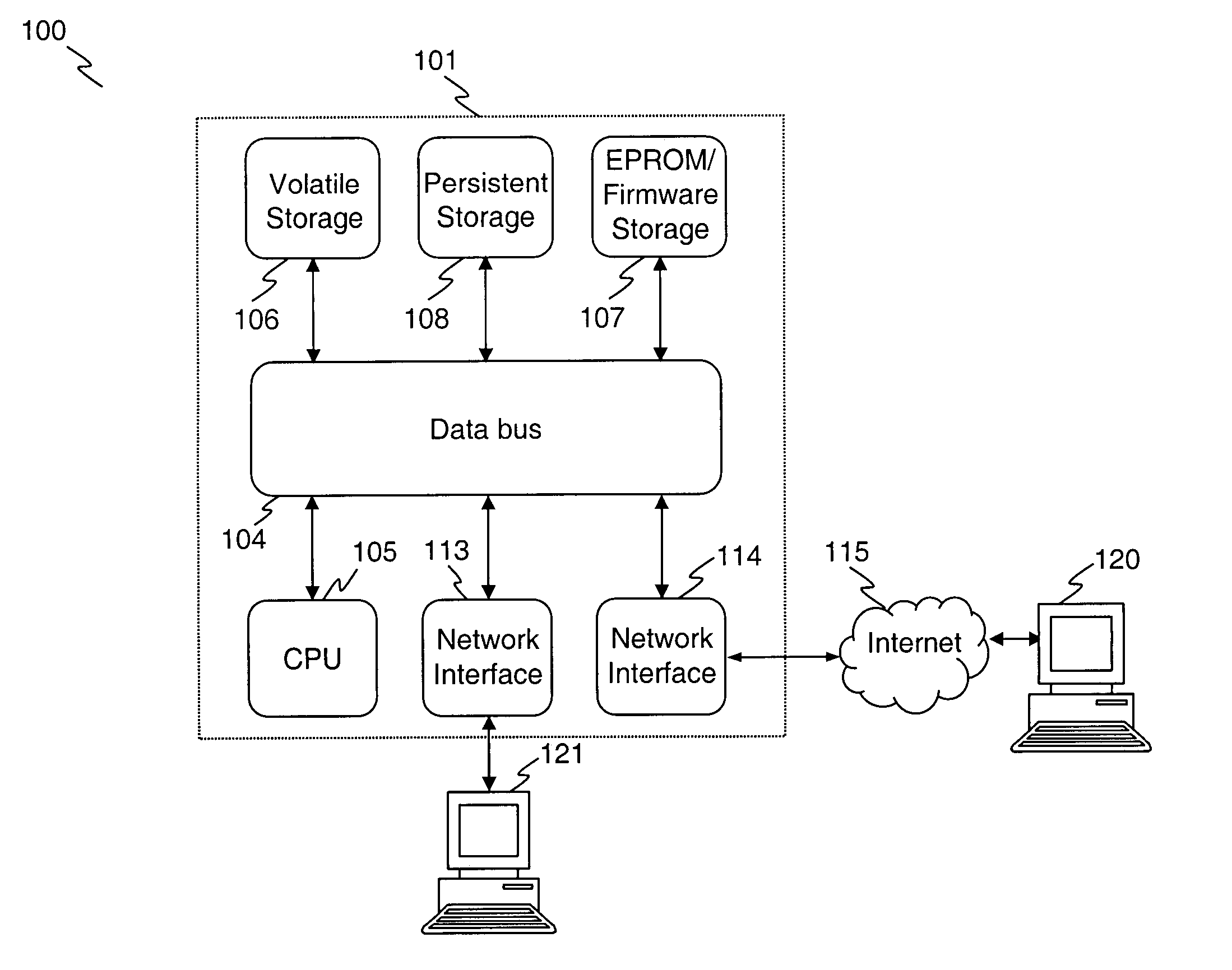
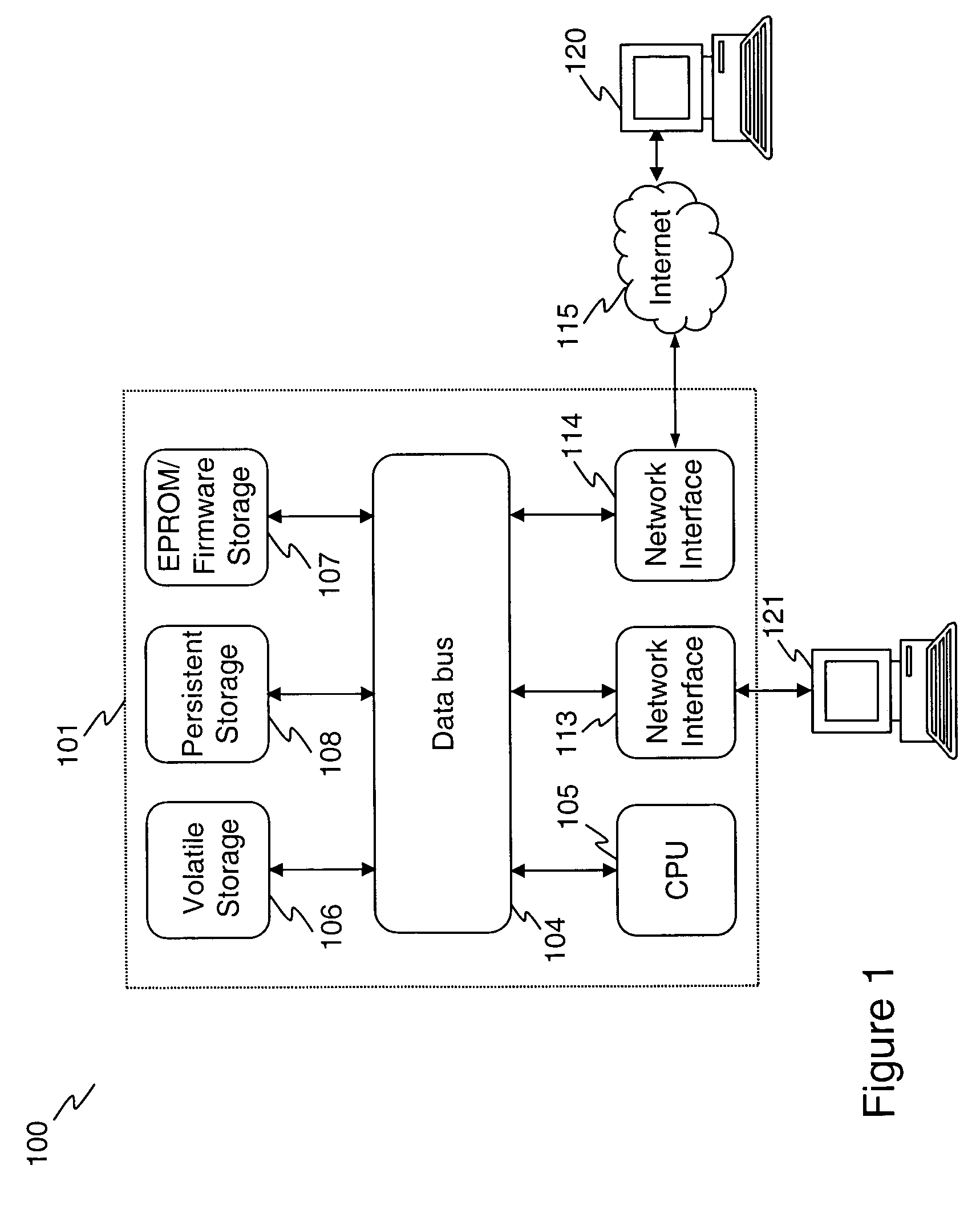
There is provided an apparatus for remotely monitoring a computer network. Monitoring is performed using an inside out approach from behind firewalls and other security devices. The monitoring appliance is shipped to a client site preconfigured and typically requires no technically trained person for installation. Collected network data is periodically transmitted to a remote monitoring facility where it is recorded and analyzed. Both the monitoring appliance and the remote center maintain the configuration data. Typically, no client data is transmitted to the remote monitoring site. If the monitoring appliance fails, a completely configured replacement may be shipped to the site and easily installed. The monitoring appliance is optionally equipped to provide network services. Services such as web hosting, file server, print server, virtual private network (VPN), shared Internet access, web content filtering, anti-virus, spam e-mail elimination, and IP telephony services as well as other such services may be easily provided.
Owner:MATHES MARVIN LEE +1
Statistical metering and filtering of content via pixel-based metadata
Data supplied to a display having a plurality of pixels comprises both content to be displayed and metadata that identifies the content of the respective pixel as being of a particular type by setting the metadata for each pixel to a value that is one of a predefined set of values. The identification of the content as being of a particular type enables the classification of the pixels on a per pixel basis into one or more categories. Pixels containing data for an advertisement can be identified and metered to determine the total display space they occupy and length of time they are displayed, which are both considered measures of the effectiveness of the advertisement. This metering can therefore be used to more equitably charge for advertising on web pages because an advertiser can be charged on the basis of what a user actually sees on the display. If only a percentage of the advertisement is visible, the advertiser pays an amount in proportion to the percentage of the advertisement that is visible. Pixels belonging to an advertisement can also be metered by a video game in a manner that gives an incentive to a game player to view advertisements. Additionally, metadata can be used to identify a pixel as containing objectionable content or some other information or type of content not desired by a user. The pixels containing objectionable or undesired content, which usually are pixels that display an object or portions thereof, can then be filtered out of the picture in a more precise way to either delete or leave a blurred image of the object or objectionable / undesirable portion thereof only, without hiding an entire screen of data.
Owner:NOKIA TECHNOLOGLES OY
Apparatus and method for analyzing and filtering email and for providing web related services
InactiveUS20060184632A1Eliminate the problemSoftware engineeringDigital data processing detailsService provisionSpamming
The inventive methodology provides an integrated plug and play solution designed to protect home networks against spam, phishing emails, viruses, spyware as well as other similar threats. The described content filtering appliance can be used for processing of web and email traffic implemented and can be deployed as a stand-alone appliance. In one implementation, the content processing appliance utilizes backend content filtering provided by a remote scanning service accessed via a network. The system employs network level analysis and translation of content and executes various procedures to handle the network traffic. In an embodiment of the invention, the appliance is provided with an automatic remote updating capability, wherein the software and data used by the appliance can be updated remotely via a network. Finally, the appliance may also implement parental controls.
Owner:MARINO JOSEPH P
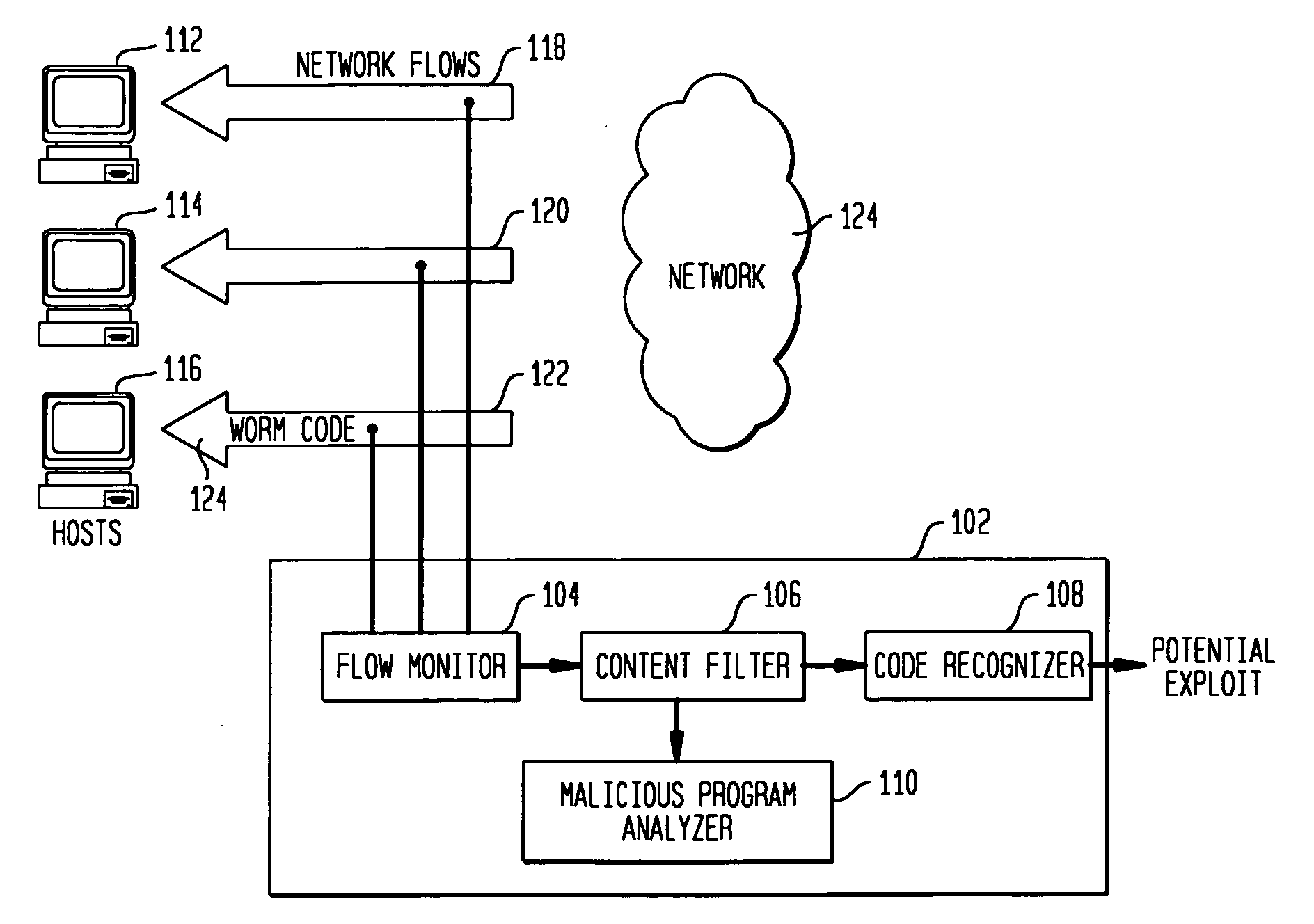
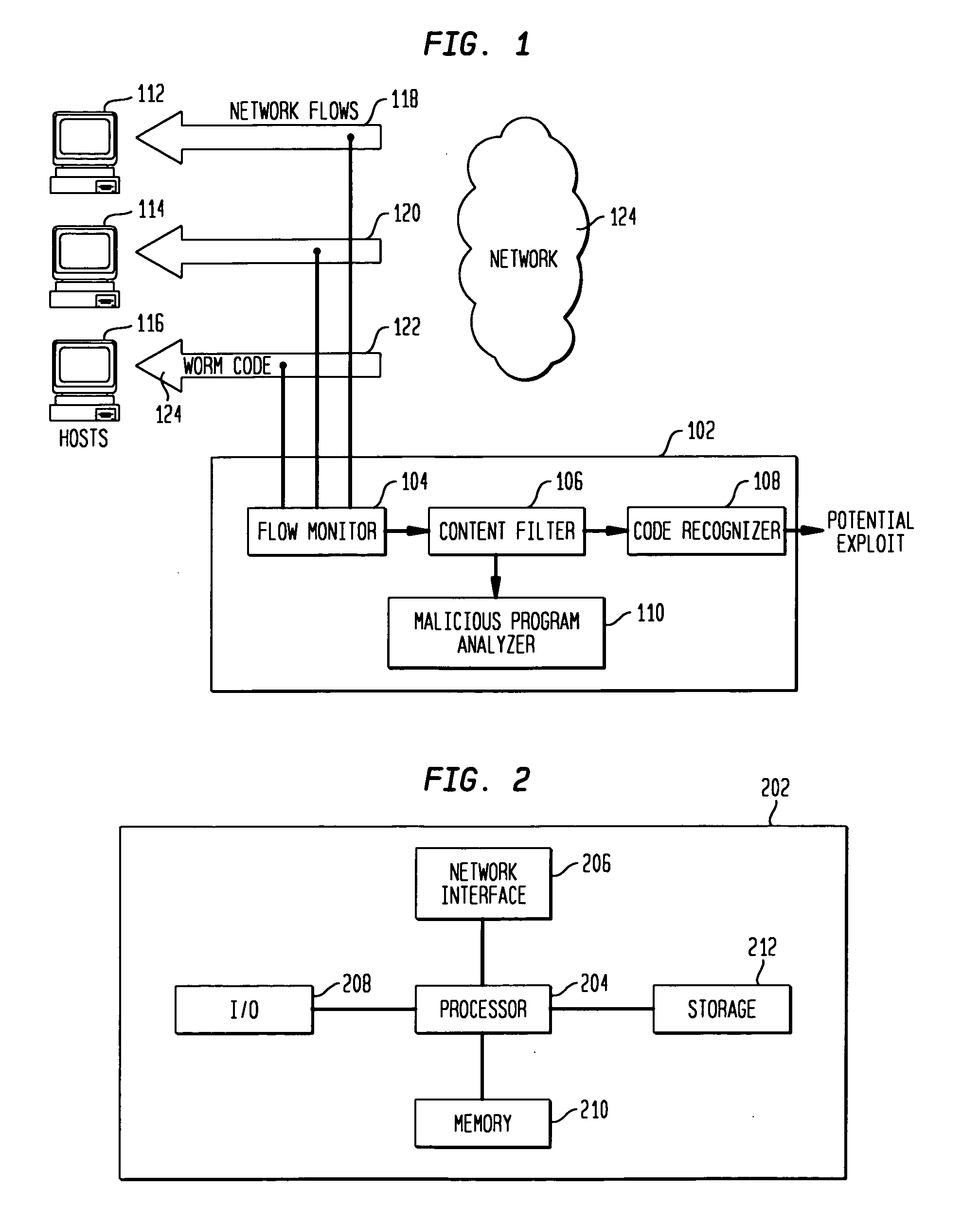
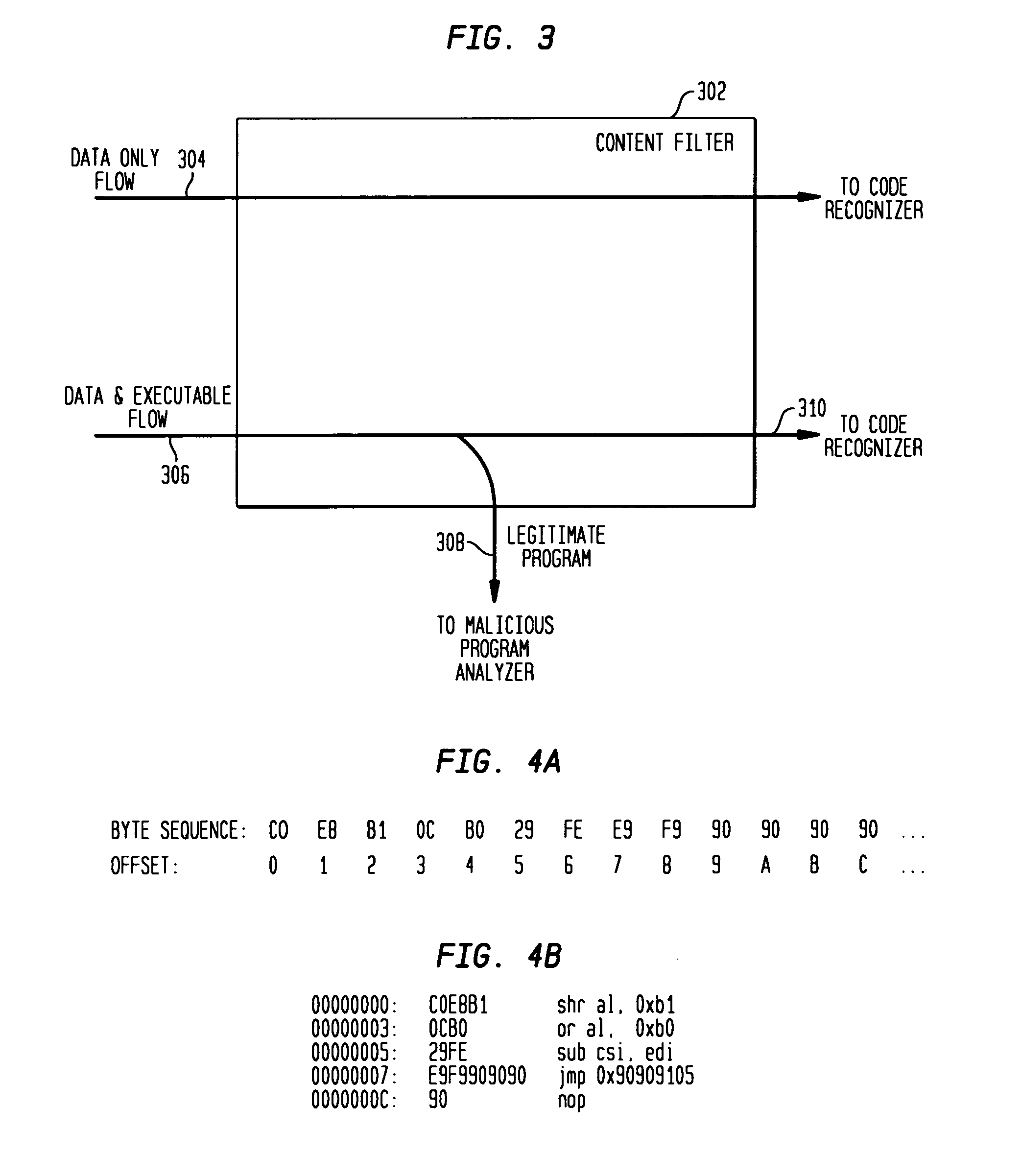
Detecting exploit code in network flows
InactiveUS20090328185A1Memory loss protectionUnauthorized memory use protectionData streamNetwork packet
Disclosed is a method and apparatus for detecting exploit code in network flows. Network data packets are intercepted by a flow monitor which generates data flows from the intercepted data packets. A content filter filters out legitimate programs from the data flows, and the unfiltered portions are provided to a code recognizer which detects executable code. Any embedded executable code in the unfiltered data flow portions is identified as a suspected exploit in the network flow. The executable code recognizer recognizes executable code by performing convergent binary disassembly on the unfiltered portions of the data flows. The executable code recognizer then constructs a control flow graph and performs control flow analysis, data flow analysis, and constraint enforcement in order to detect executable code. In addition to identifying detected executable code as a potential exploit, the detected executable code may then be used in order to generate a signature of the potential exploit, for use by other systems in detecting the exploit.
Owner:TELCORDIA TECHNOLOGIES INC
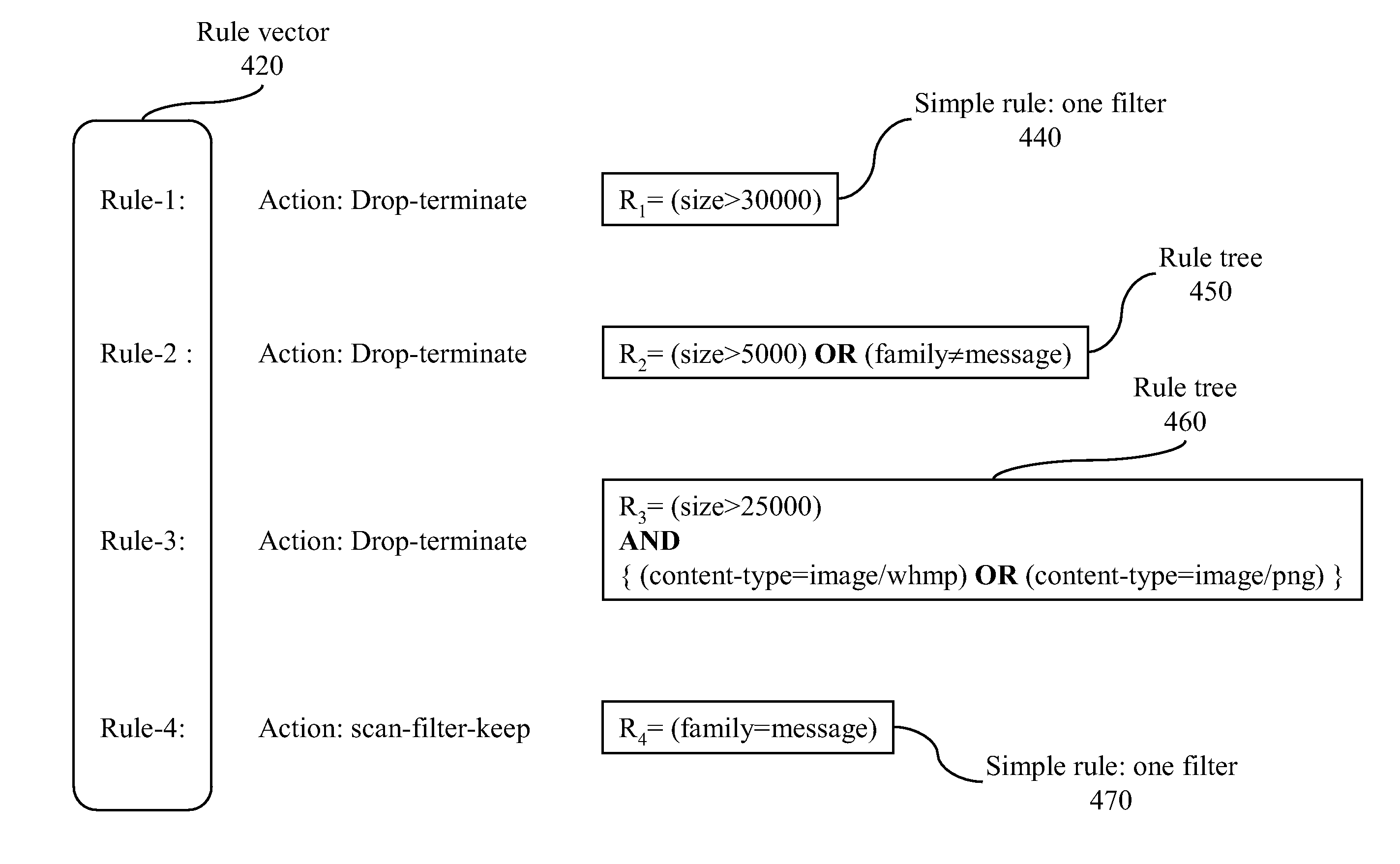
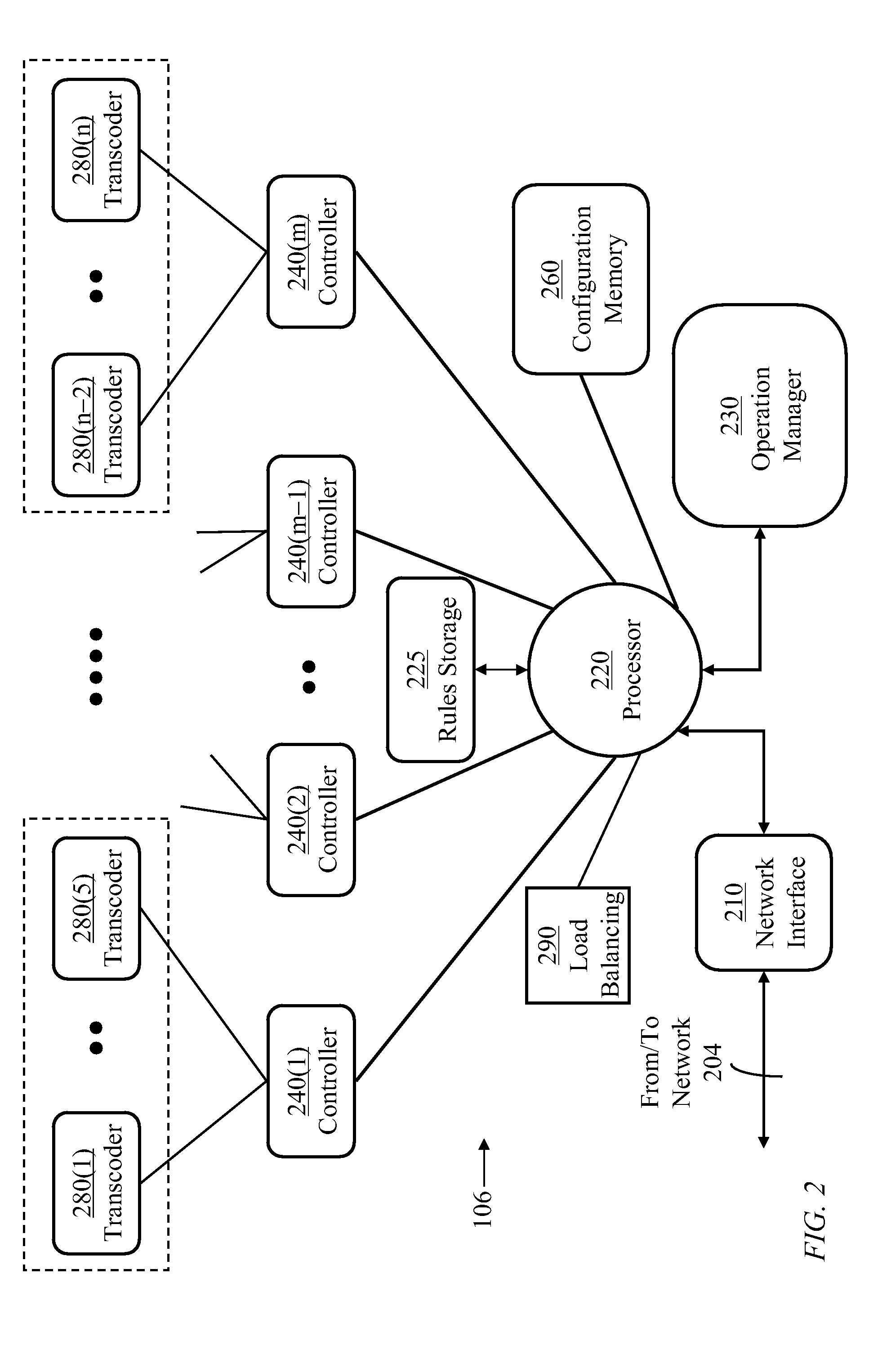
Method and system for rule-based content filtering
ActiveUS20090125459A1Comprehensive and efficient and economical systemGuaranteed economic efficiencyDigital computer detailsDigital dataContent adaptationData mining
A system and method for content-filtering of data containers in a network supporting versatile communications services are disclosed. The content-filtering system is integrated with a content-adaptation system. Several server units handle data containers formulated at source according to different protocols. A content filtering process relies on characterizing each component of a container to produce a set of content descriptors and producing a set of binary conditions for each component according to a preset criterion for each descriptor. A set of rules is devised where each rule applies a respective Boolean expression to a subset of the conditions to prescribe a respective content-editing action. Methods of specifying and evaluating a rule's Boolean expression are disclosed. A formal graph is used to define inter-dependence of rules.
Owner:MASIMO CORP
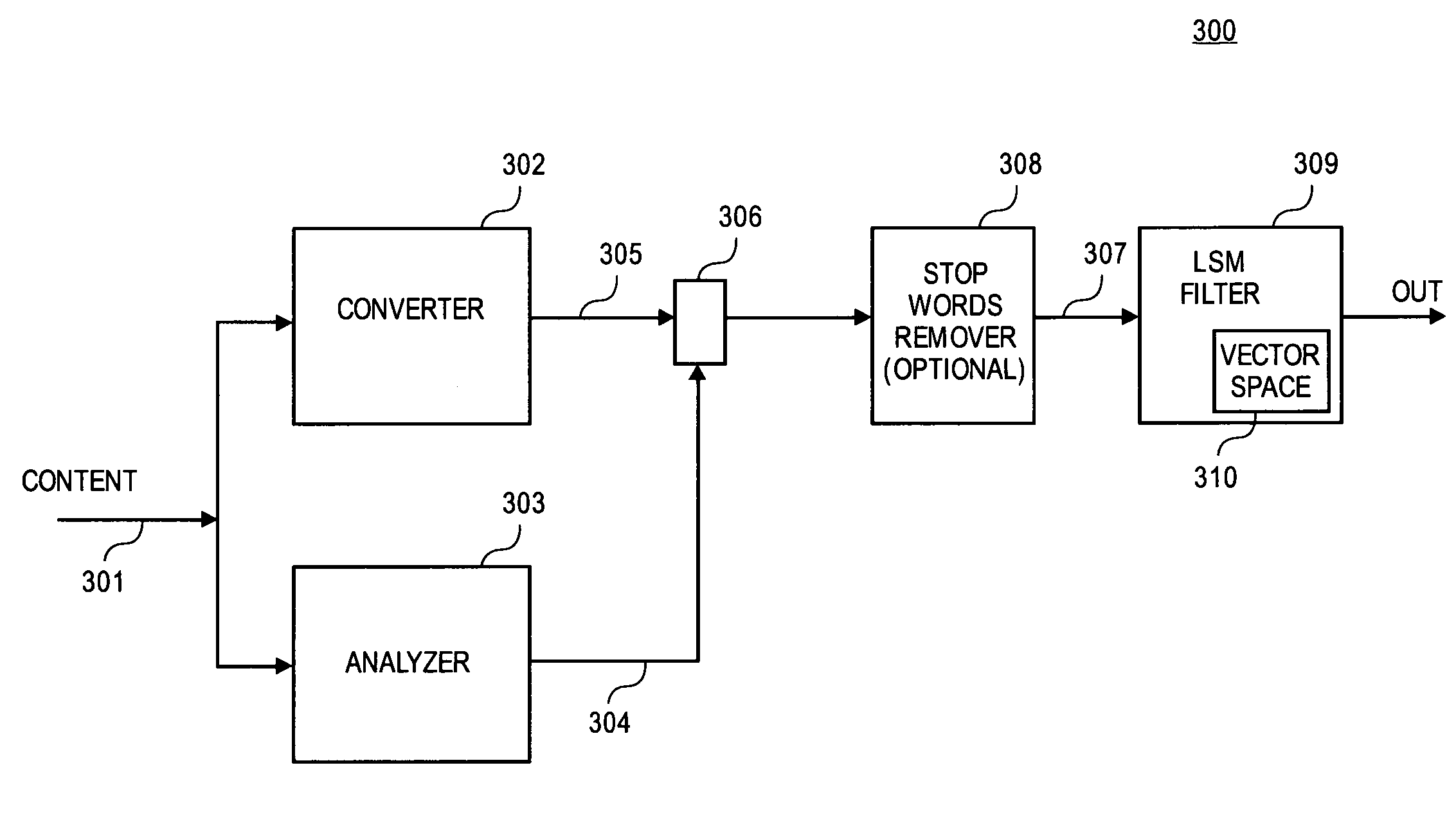
Multimedia content filtering
ActiveUS20080228928A1Digital data information retrievalMultiple digital computer combinationsLatent semantic mappingParameter analysis
Methods and apparatuses to filter multimedia content are described. The multimedia content in one embodiment is analyzed for one or more parameters. The multimedia content in one embodiment is filtered based on the one or more parameters using a latent semantic mapping (“LSM”) filter. In one embodiment, the one or more parameters include information about a structure of the multimedia content. A tag that encapsulates the one or more parameters may be generated. Then, the tag is input into the latent semantic mapping filter. In one embodiment, the LSM filter is trained to recognize the multimedia content based on the one or more parameters. In one embodiment, more than two categories are provided for a multimedia content. The multimedia content is classified in more than two categories using the LSM filter. The multimedia content may be blocked based on the classifying.
Owner:APPLE INC
Automatic Content Filtering
InactiveUS20150070516A1Gauge the effectiveness of the content filtering processTelevision system detailsColor television detailsWorld Wide WebCable television
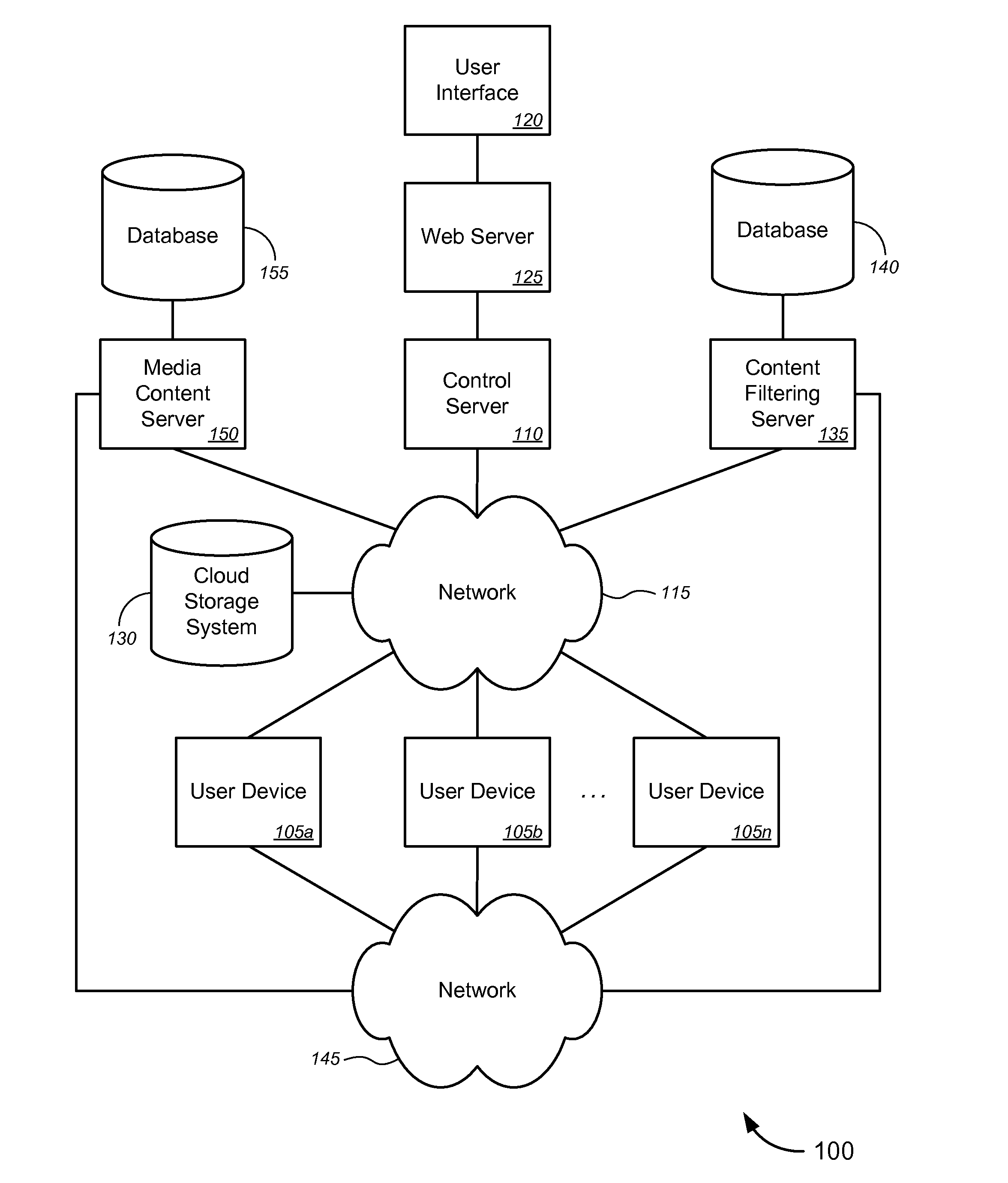
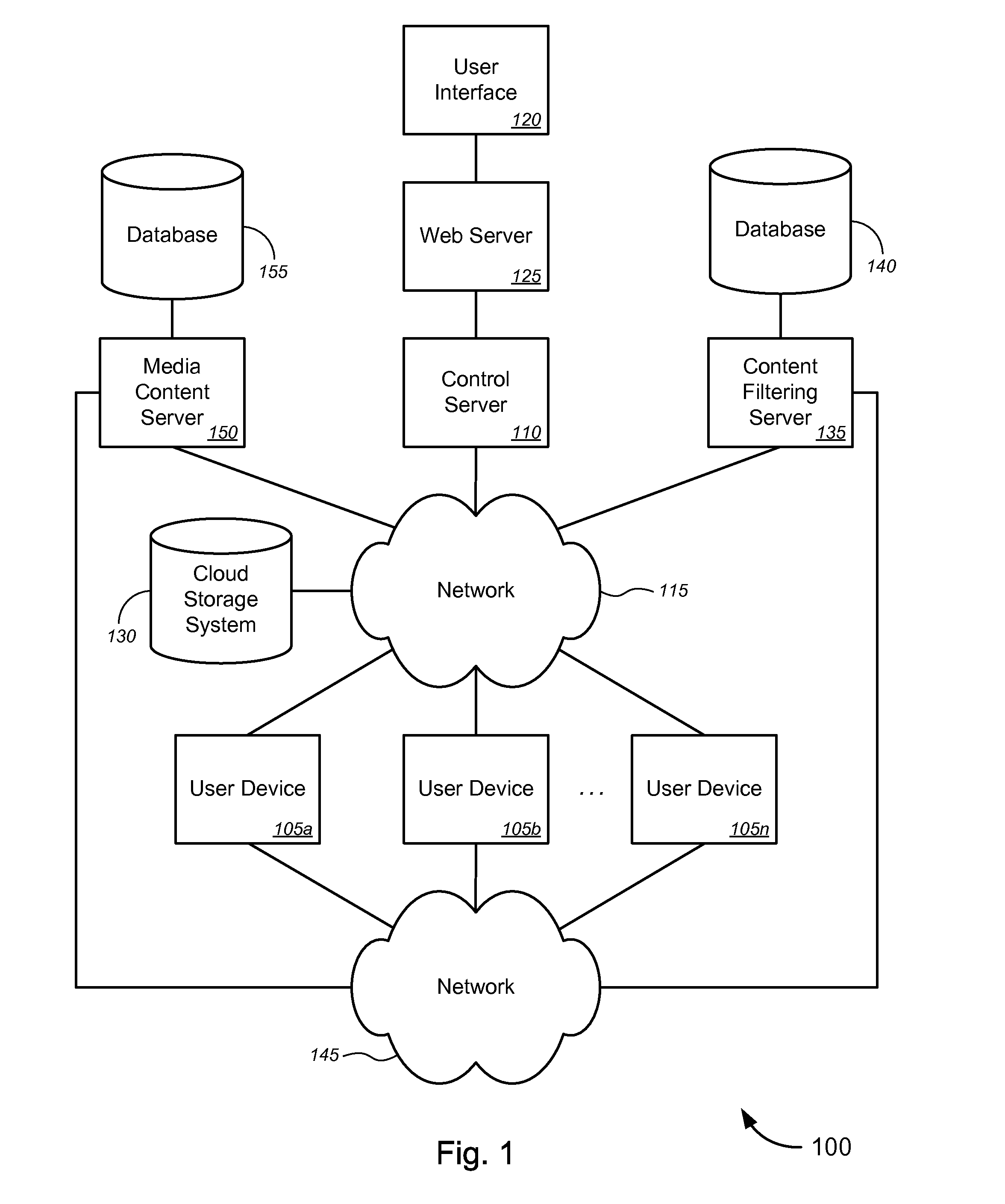
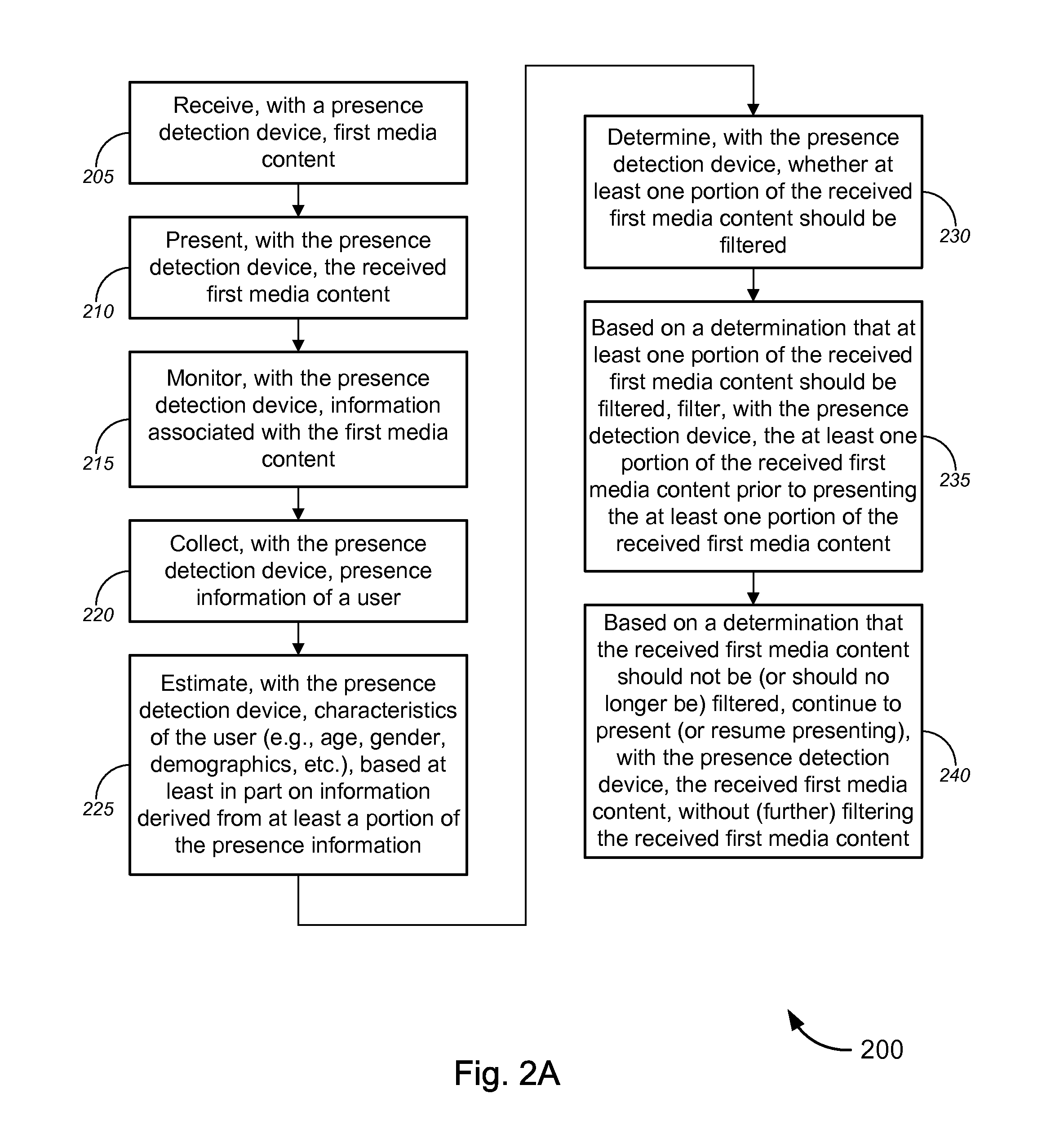
Novel tools and techniques are provided for enabling or implementing presence detection and / or automatic content filtering of media content based on detected presence of users. In some embodiments, media content—including, without limitation, movies, television programs, music, video games, and / or the like—may be presented to a user(s) via a presence detection device (“PDD”). The PDD and / or a server over a network may collect presence information of a user(s), and may determine, based on the presence information of the user(s), whether (and how) at least one portion of the media content should be filtered or censored. Based on a determination that at least one portion of the media content should be filtered or censored, the PDD and / or the server might implement filtering or censoring of the at least one portion of the media content prior to presentation of (the at least one portion of) the media content to the user(s).
Owner:BISCOTTI
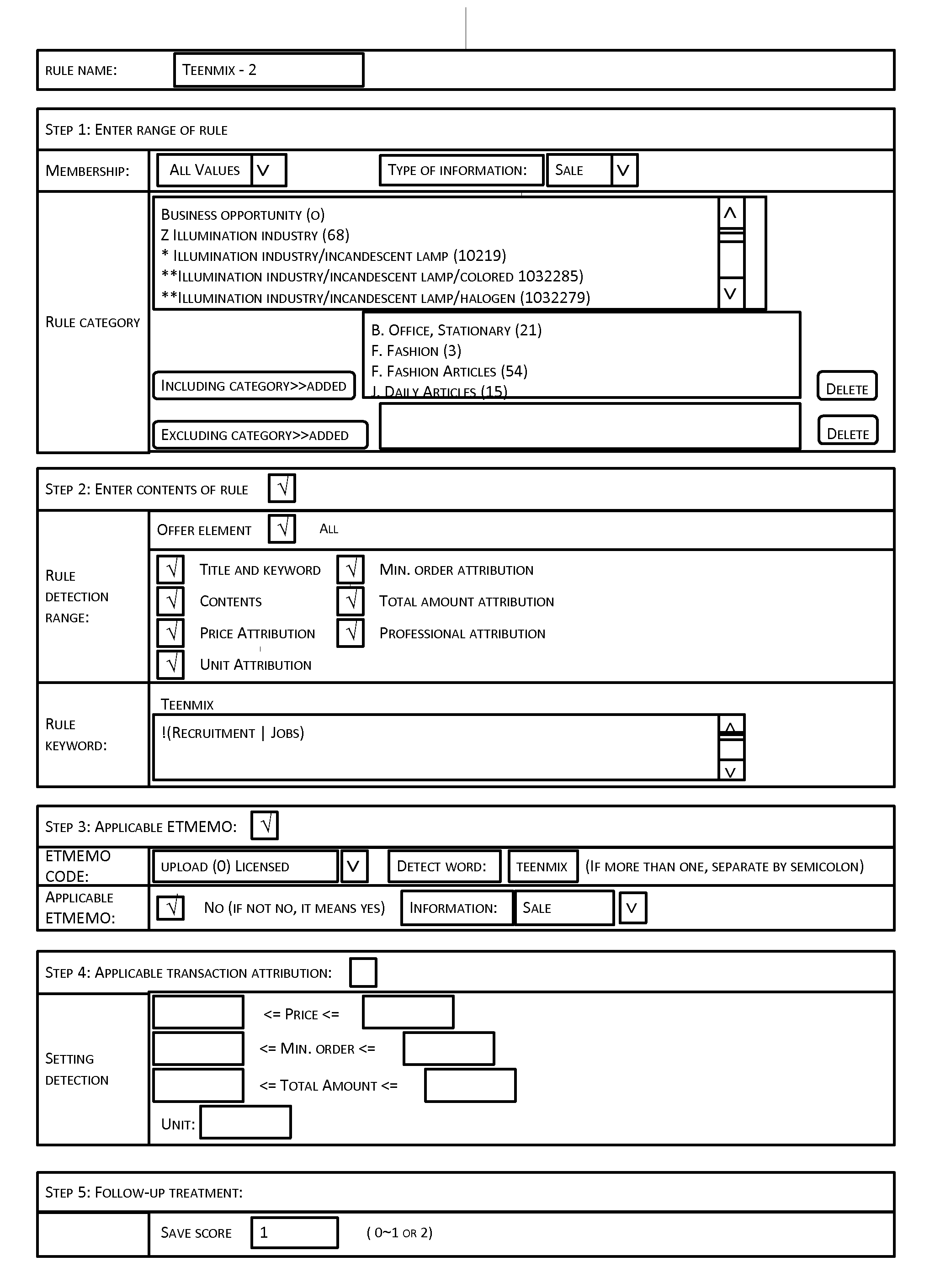
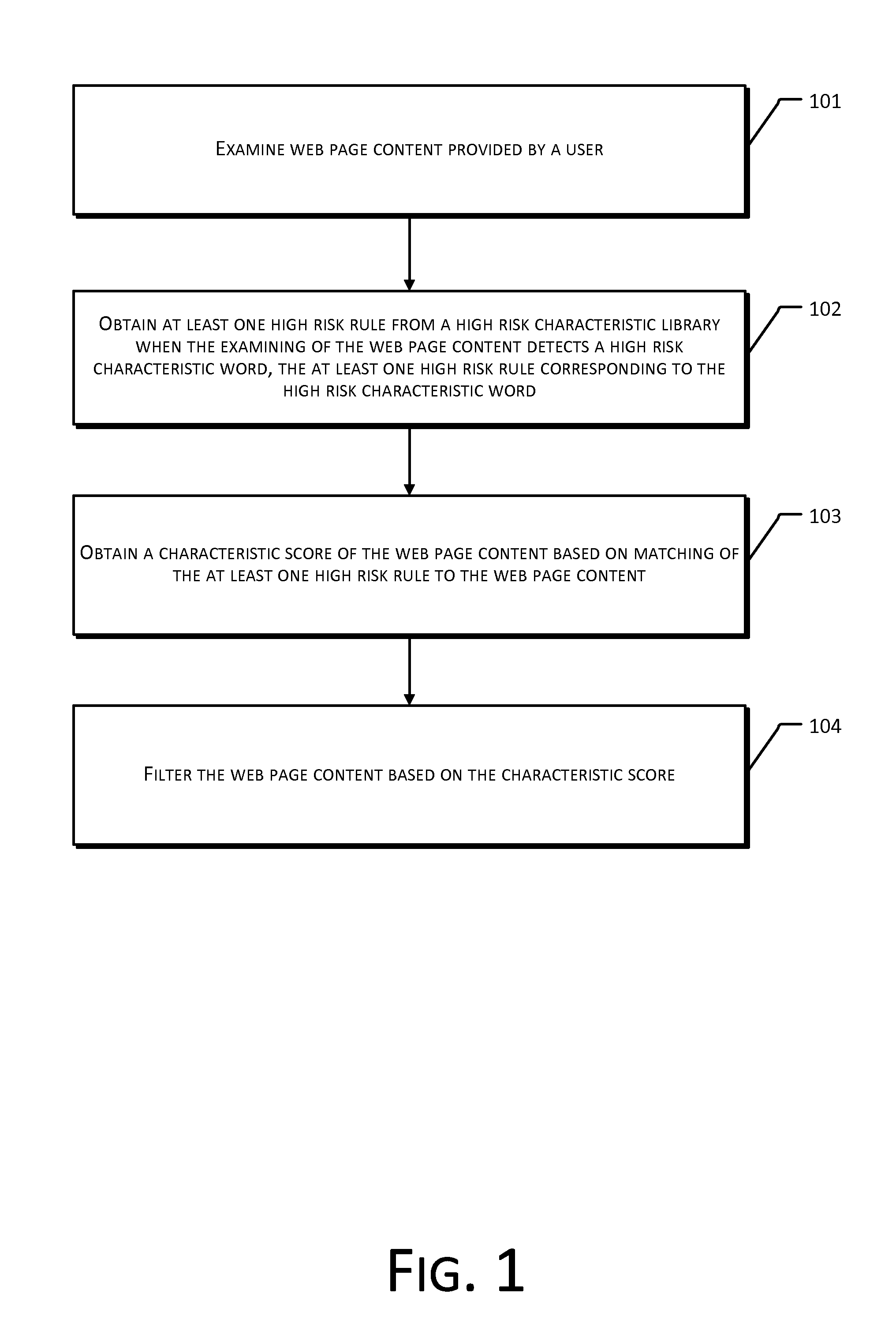
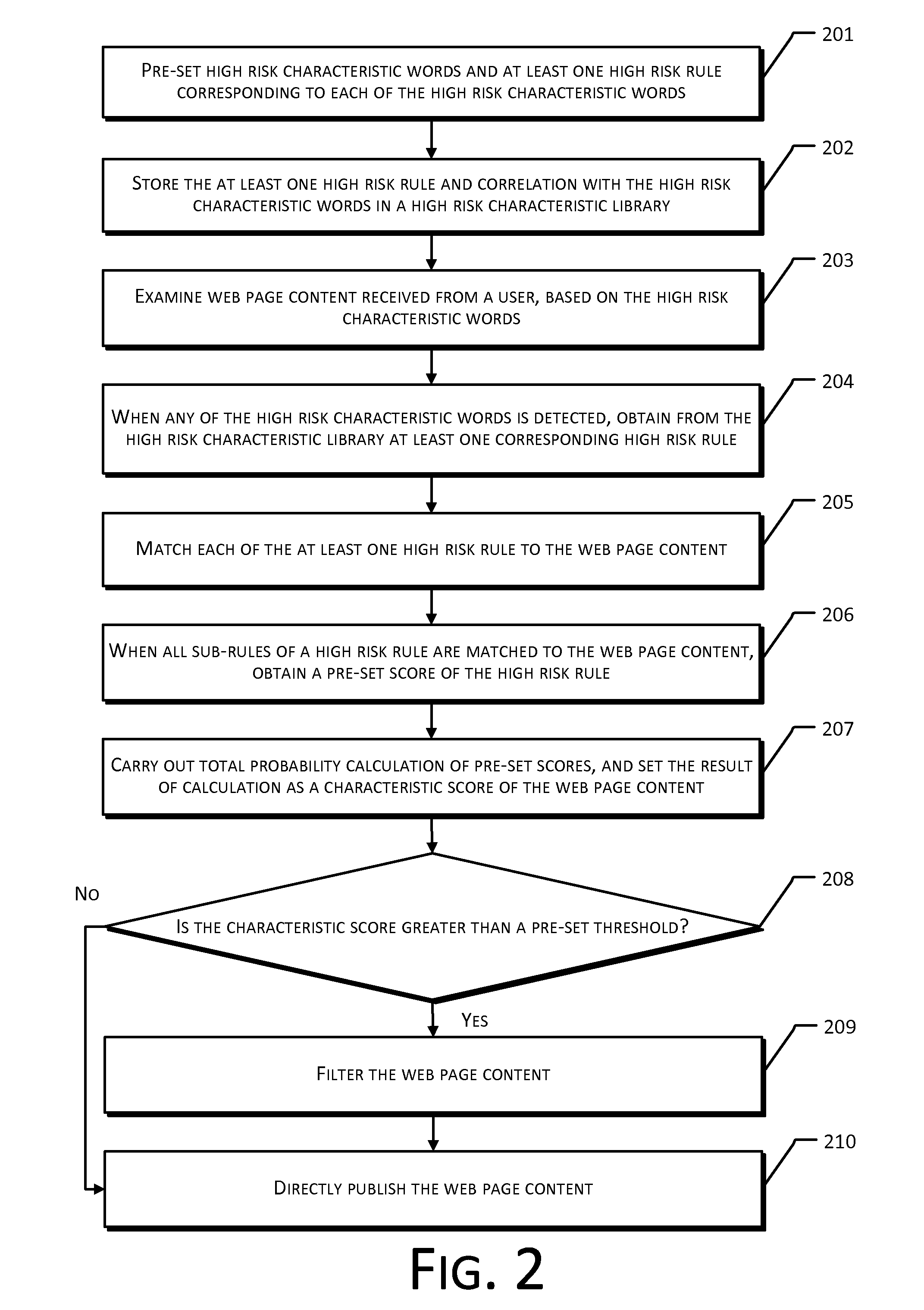
Method and System of Web Page Content Filtering
InactiveUS20120131438A1Low efficiencyAccurate contentComputer security arrangementsTransmissionE-commerceWeb page
The present disclosure provides a method and system for web page content filtering. A method comprises: examining the web page content provided by a user; obtaining at least one high risk rule from a high risk characteristic library when the examining of the web page content detects a high risk characteristic word, the at least one high risk rule corresponding to the high risk characteristic word; obtaining a characteristic score of the web page content based on matching of the at least one high risk rule to the web page content; and filtering the web page content based on the characteristic score. The difference between the present disclosure and prior art techniques is that the disclosed embodiments can more precisely carry out web page content filtering to achieve better real-time safety and reliability of an e-commerce transaction.
Owner:ALIBABA GRP HLDG LTD
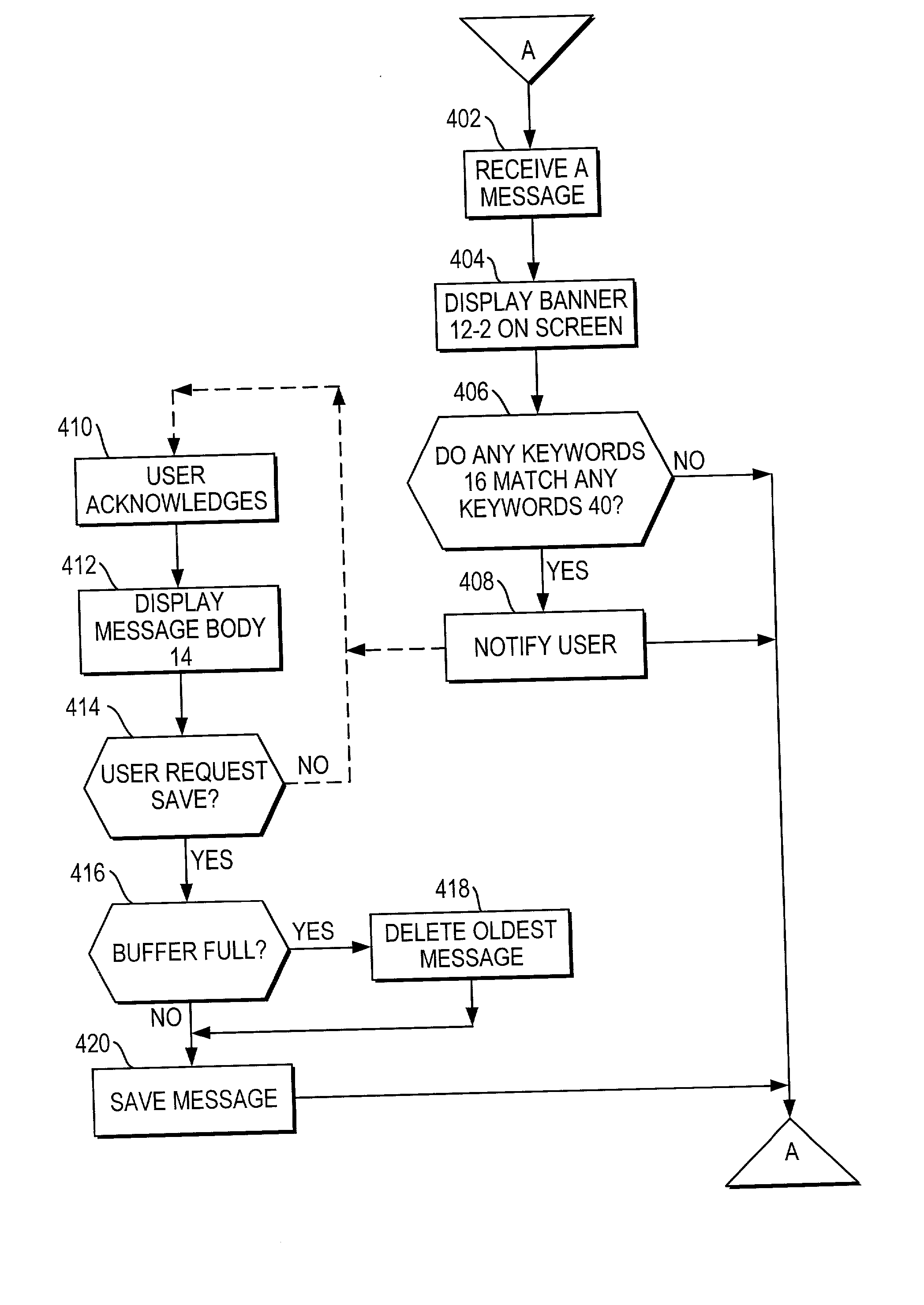
Push content filtering
InactiveUS20020160805A1Data processing applicationsDigital data processing detailsTelecommunicationsUser input
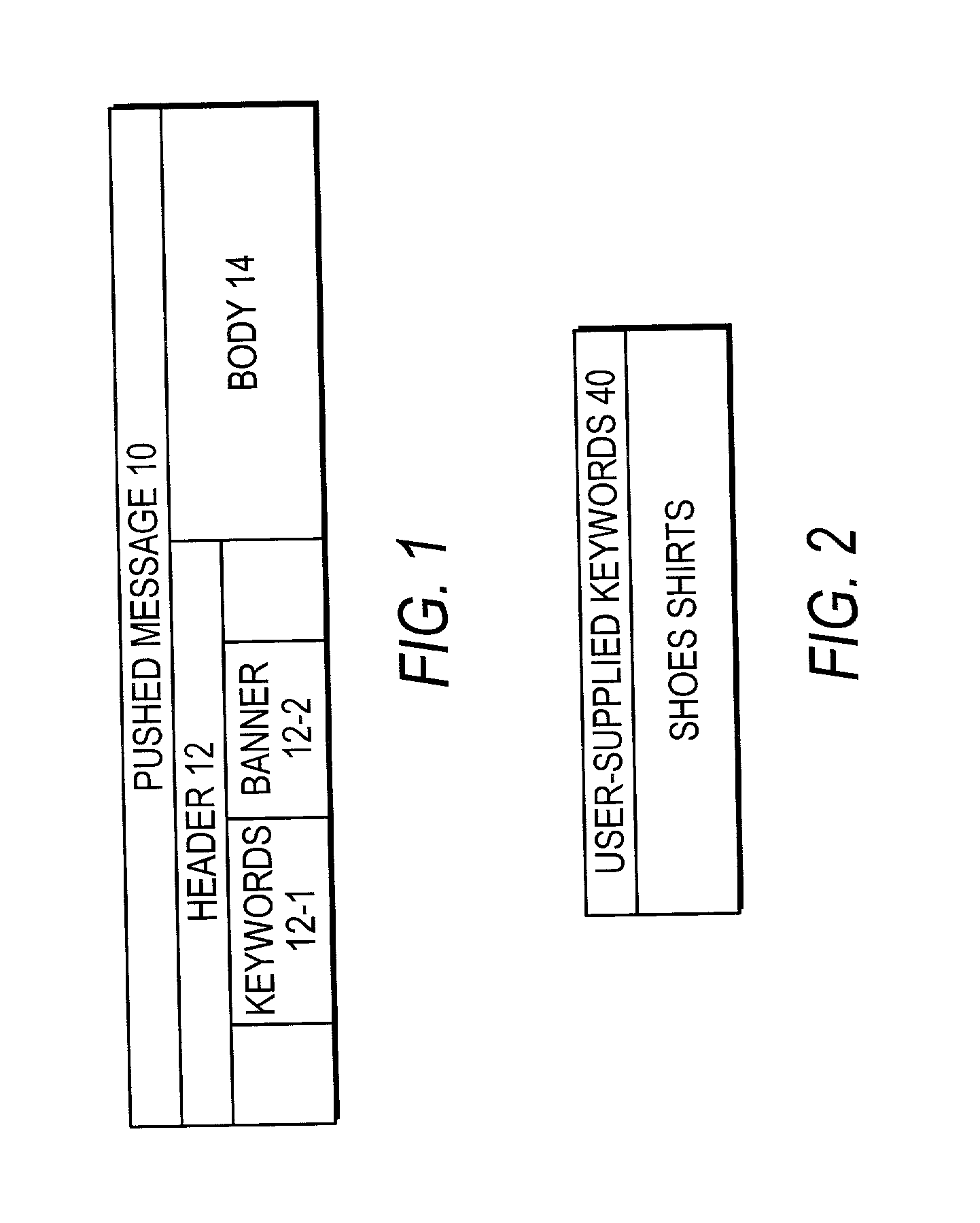
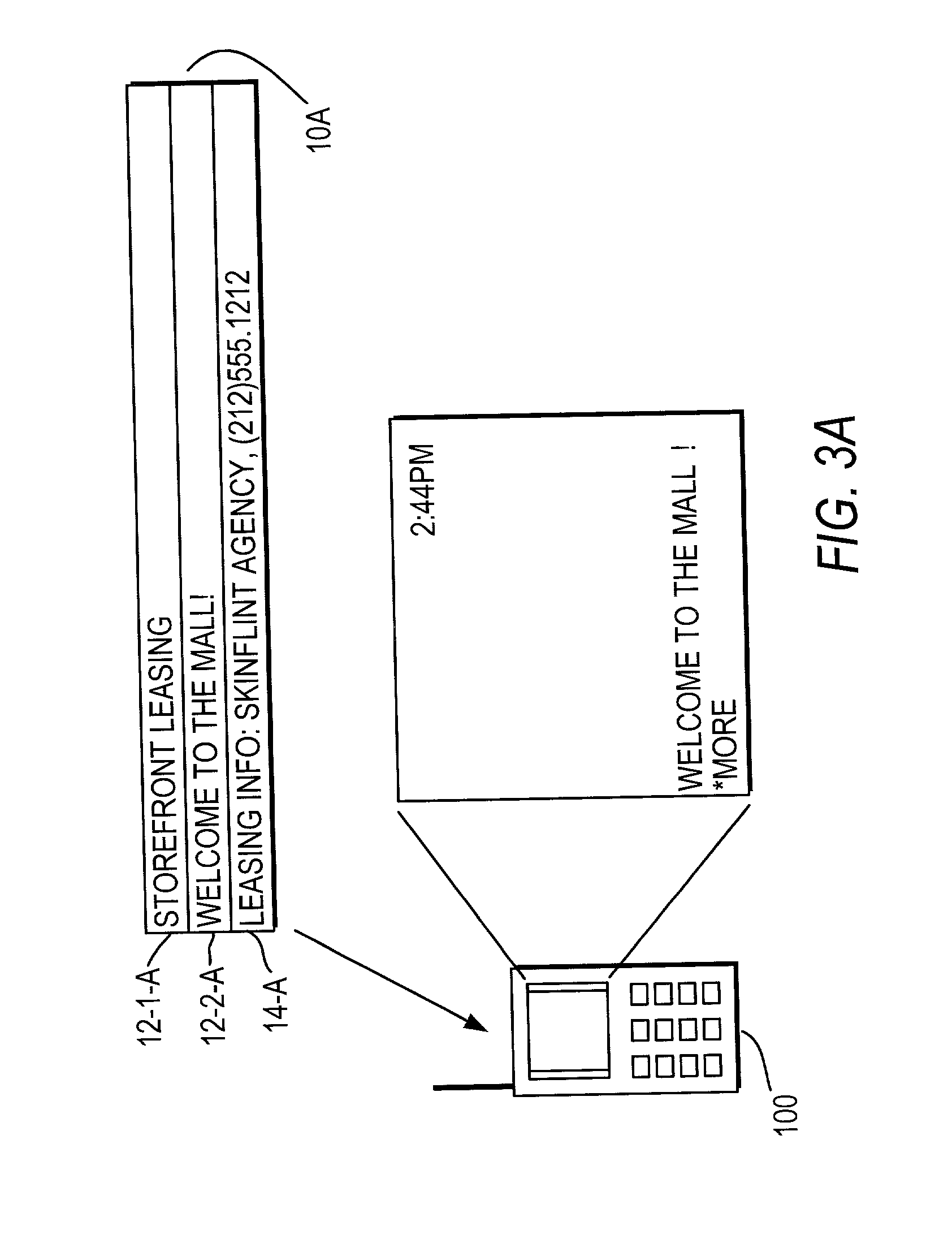
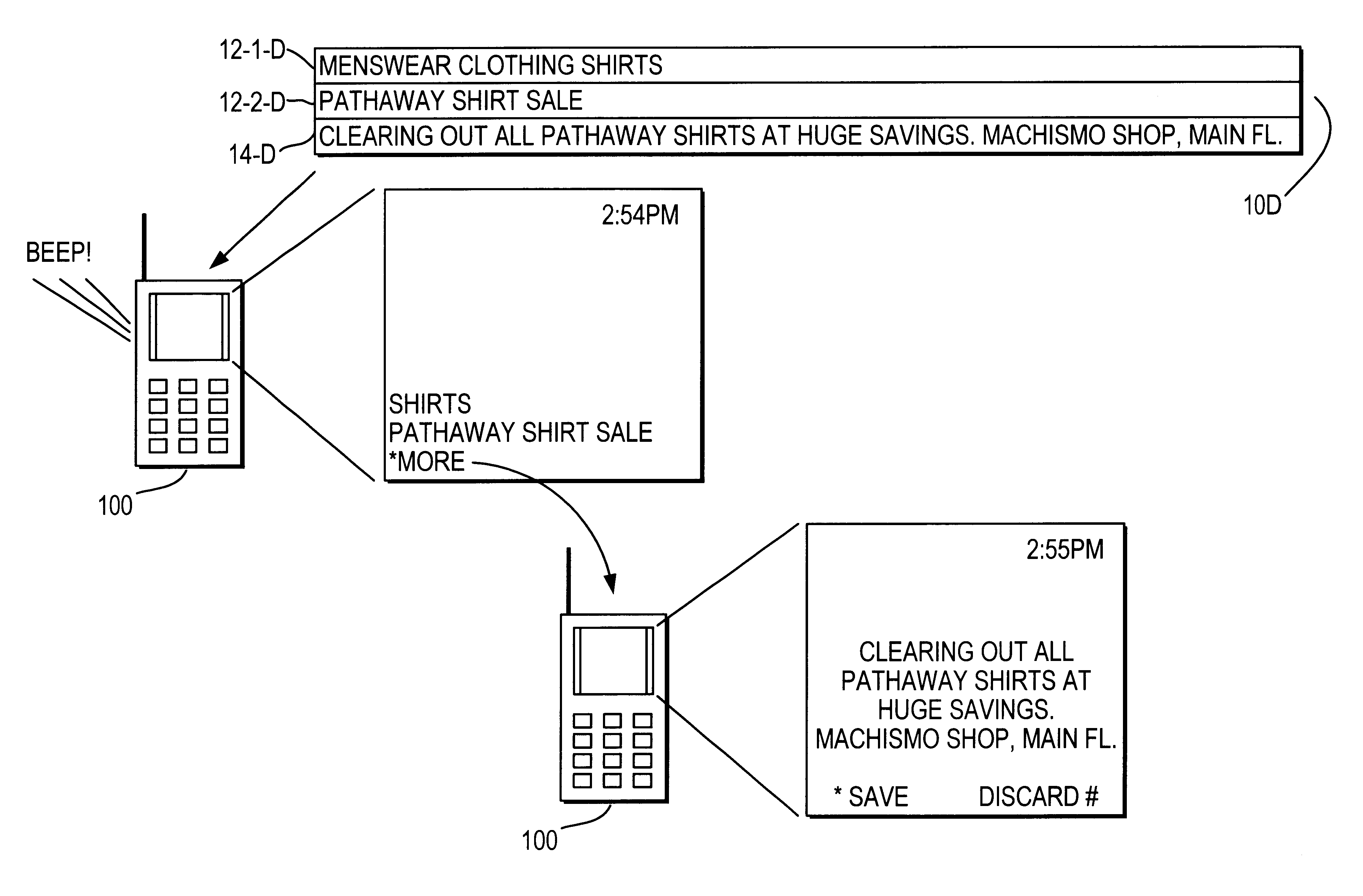
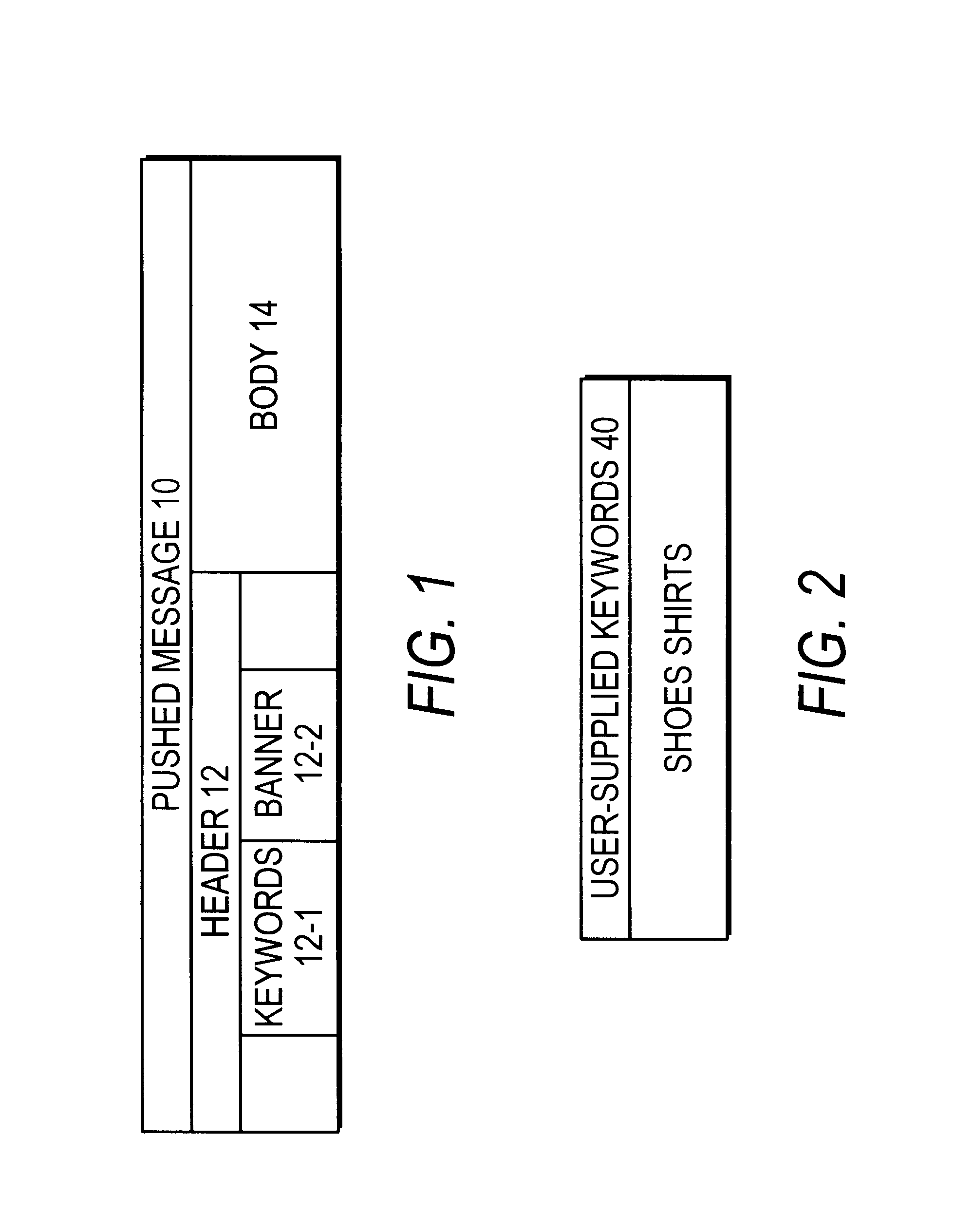
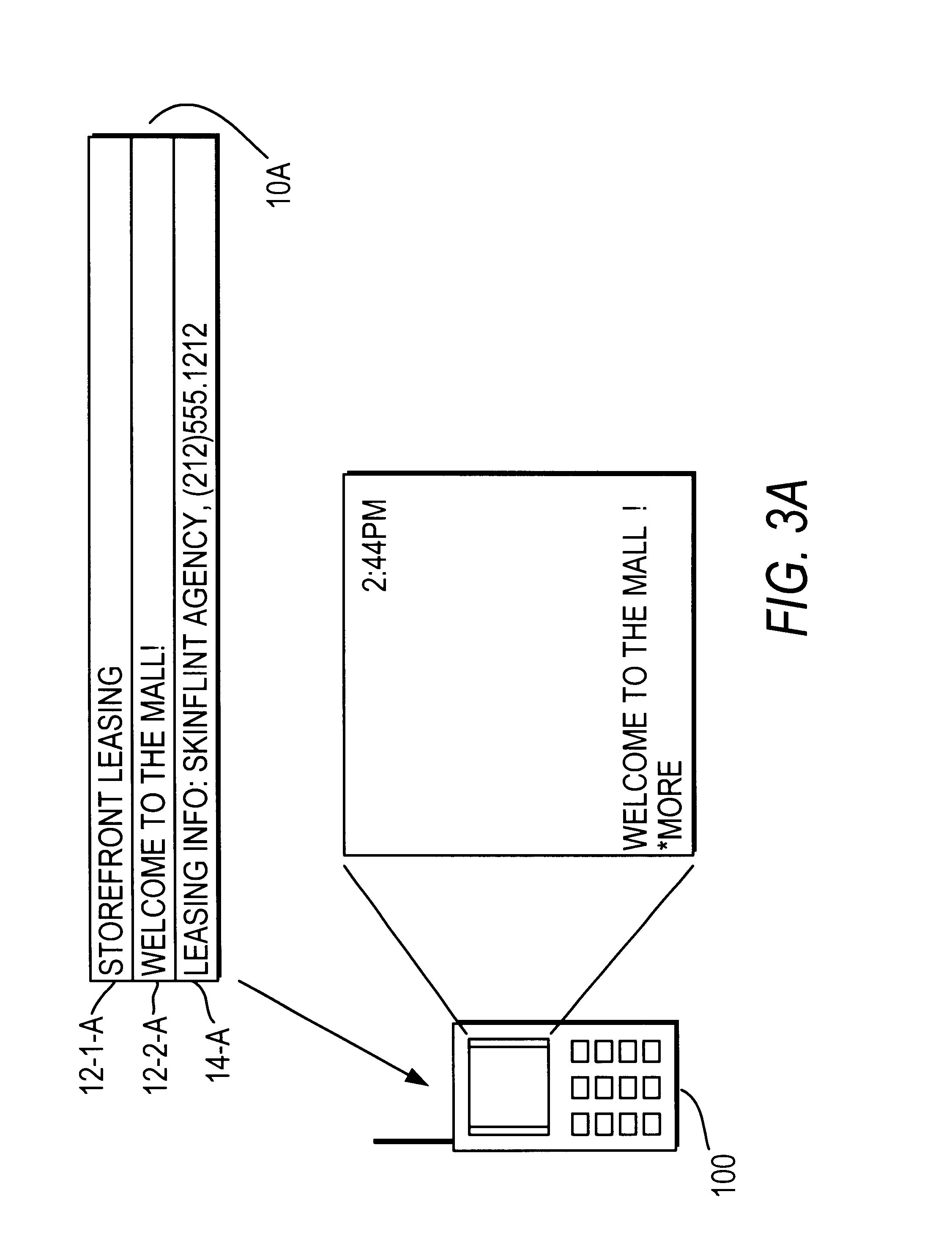
The user of a mobile terminal enters keywords indicative of categories of messages he wishes to peruse. When the mobile terminal receives a message, keywords associated with the message are compared with the user-entered keywords; if any match, a banner portion of the message is displayed on the mobile terminal and the mobile terminal issues a sensible alert. The user may request to view the message body associated with the banner portion. The user may request to take actions regarding the message body, such as storing the message body in the mobile terminal or calling a telephone number contained in the message body.
Owner:NOKIA TECHNOLOGLES OY
Intelligent message processing
ActiveUS20090125595A1Overcome deficienciesIntelligent processingTelephonic communicationMultiple digital computer combinationsComputer hardwareWeb service
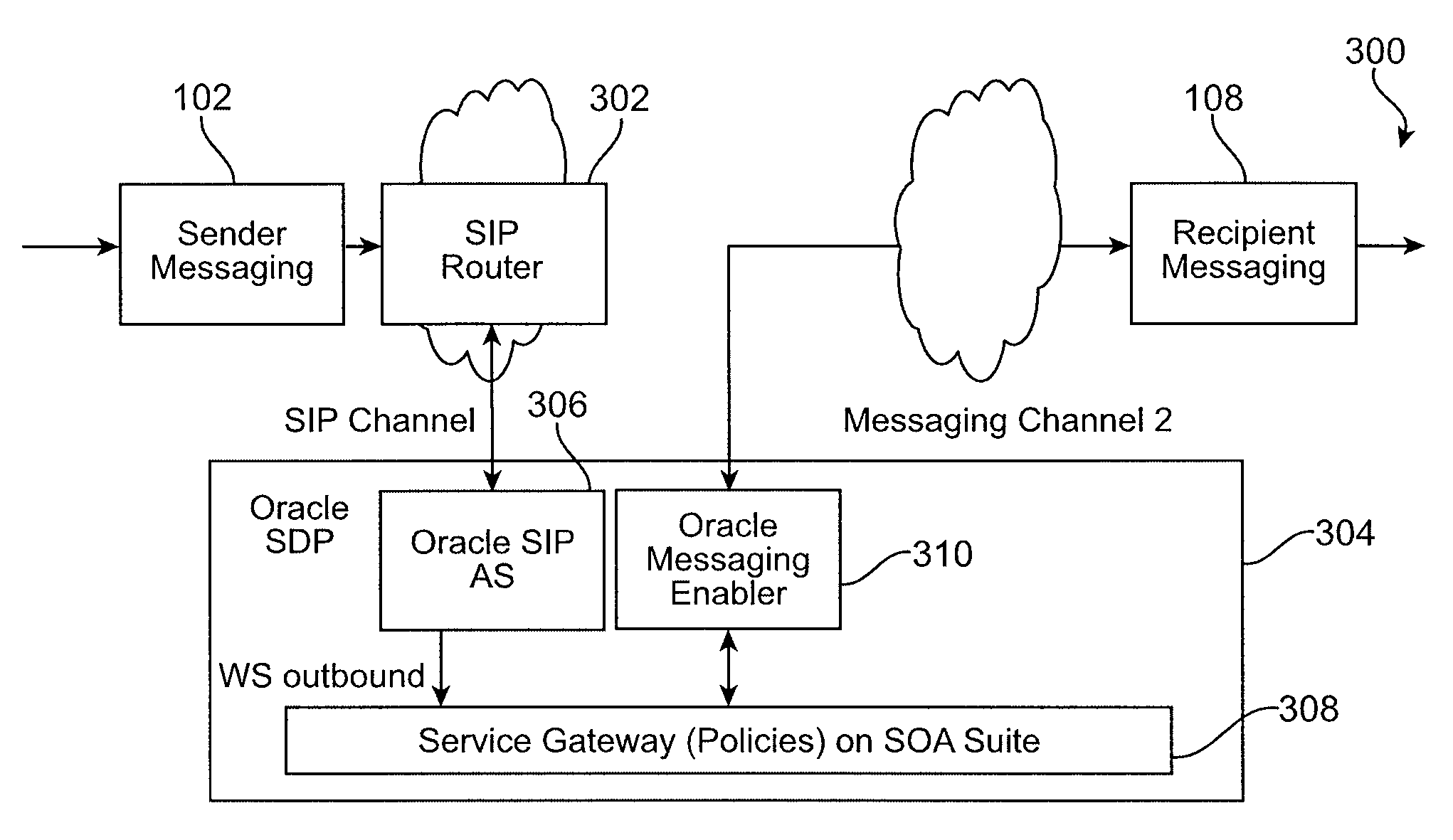
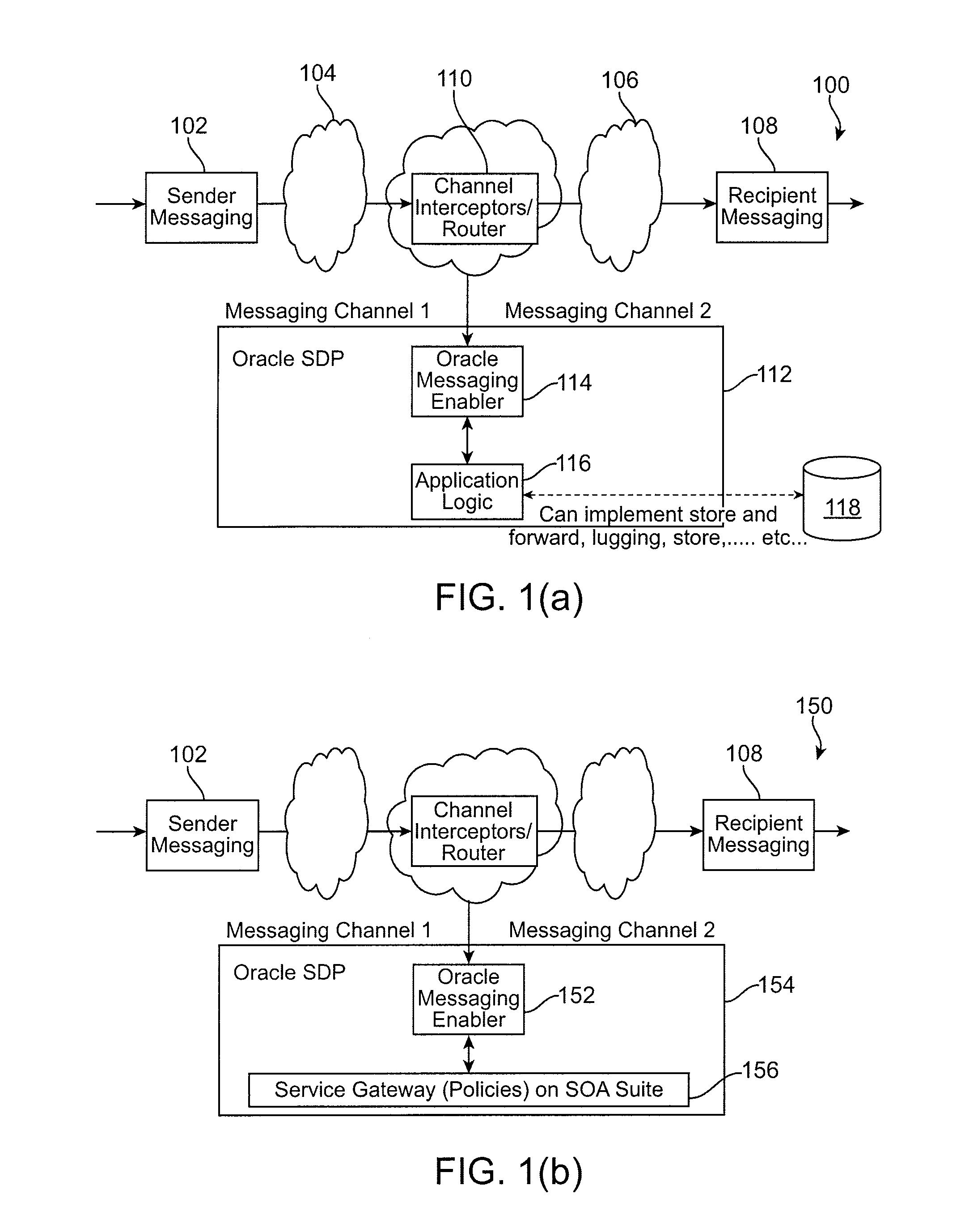
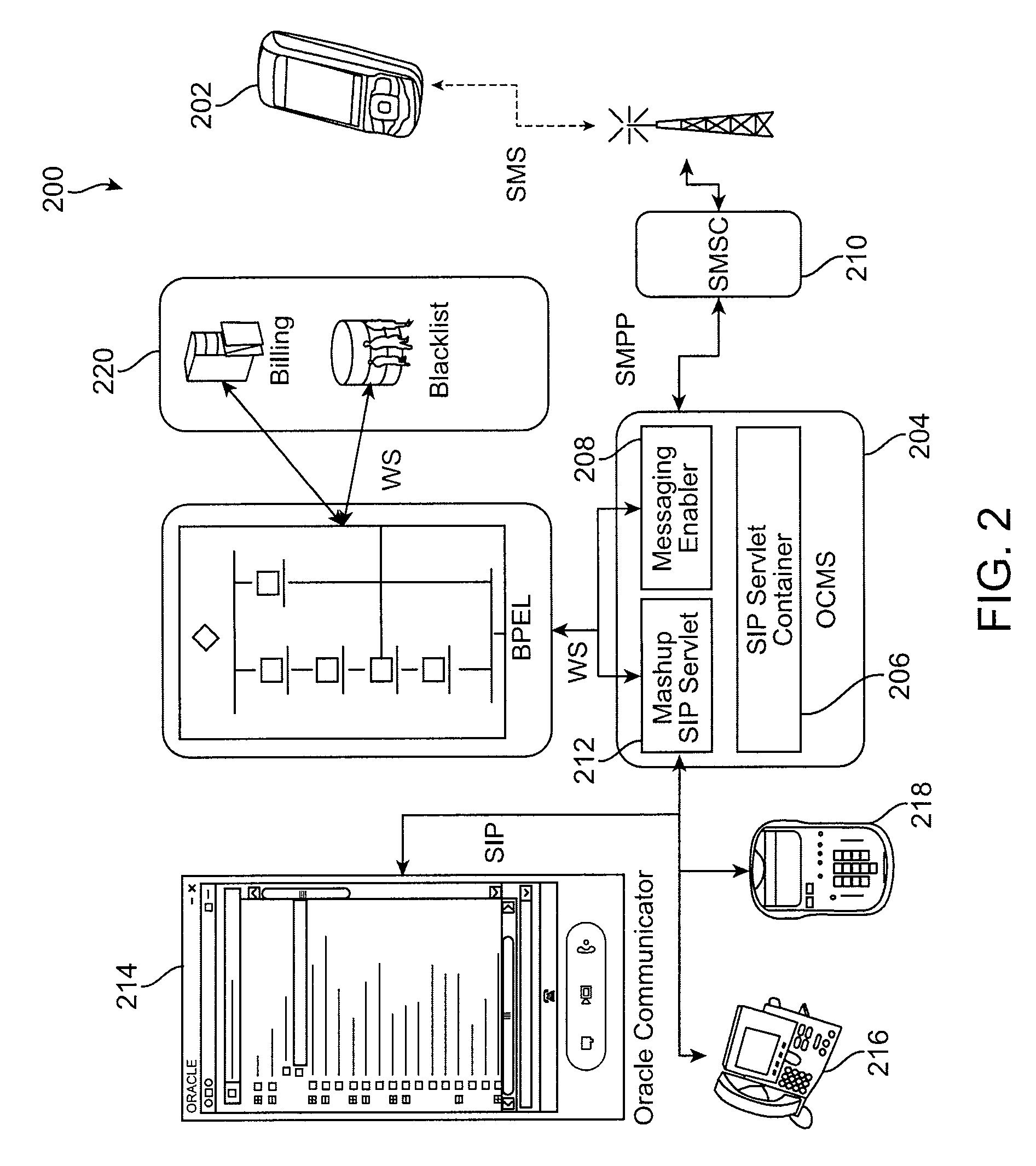
Intelligent message processing is provided for person to person (P2P) messaging by intercepting the message and processing the message before directing the message to the recipient. The messaging system then acts as a person to application (P2A) and application to person (A2P) system, wherein any P2P message can be intercepted and processed as necessary. Such functionality allows any desired processing of the message, such as to allow for transformation, charging, content filtering, screening, parsing, and any other such processing. Further, such an approach allows the message to be received from the sender and directed to the recipient on different channels. A messaging enabler allows the message to be processed using application logic and / or Web services, for example.
Owner:ORACLE INT CORP
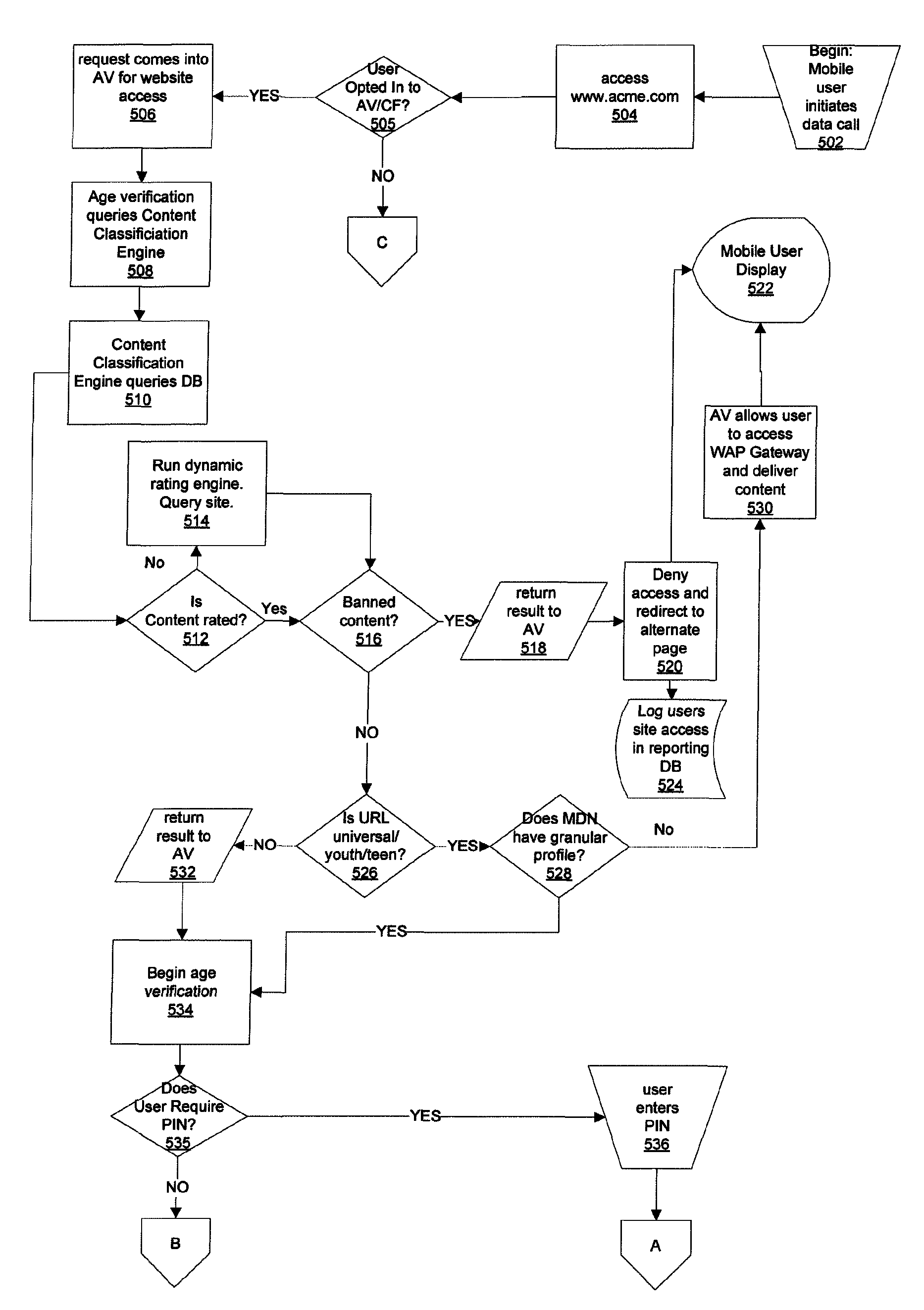
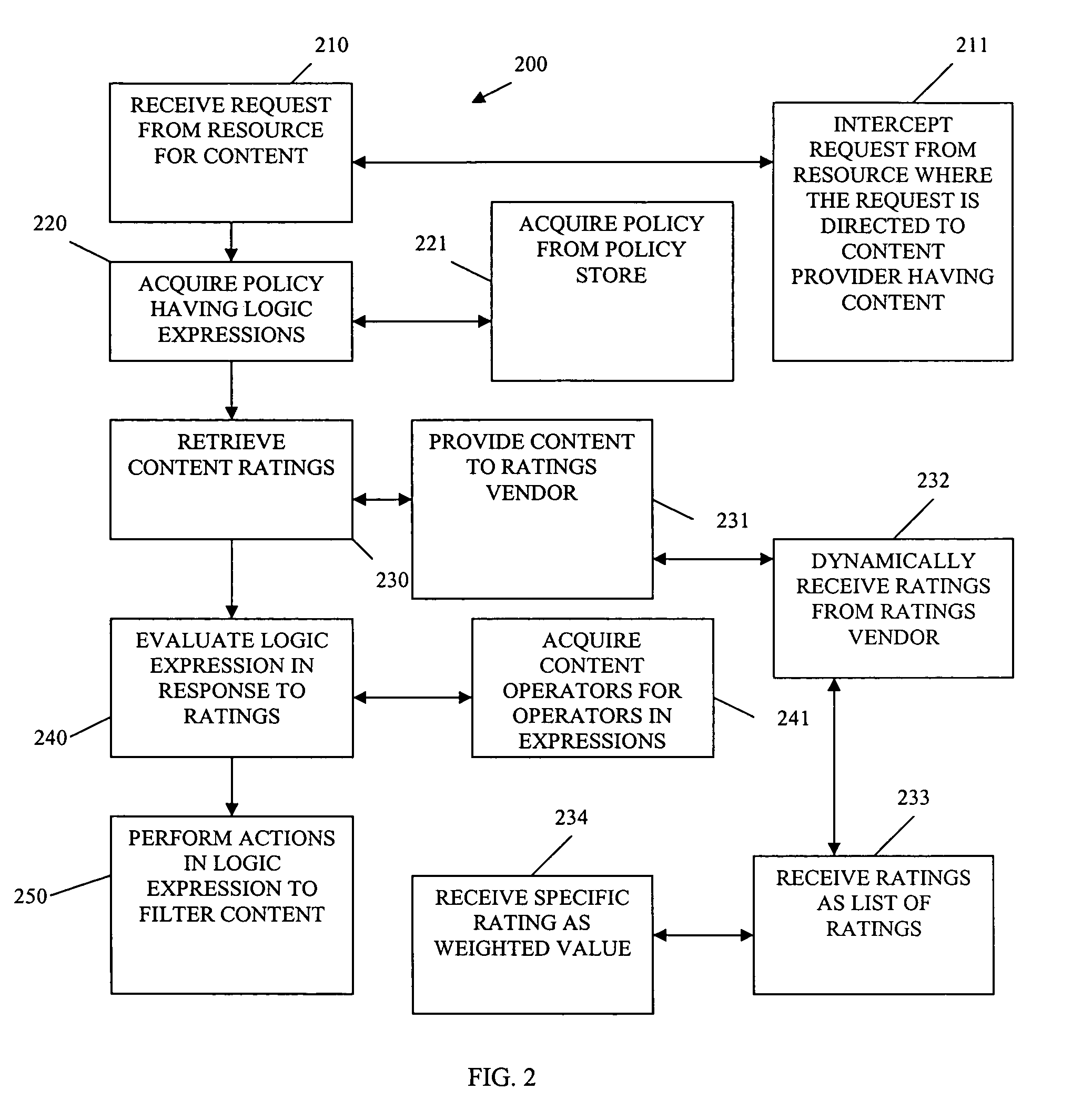
Age verification and content filtering systems and methods
ActiveUS20070260603A1Additional revenue opportunityRiskDigital data processing detailsAnalogue secracy/subscription systemsThe InternetTelenet
A system and method is provided for age verification and content filtering (AV / CF) on a wireless telecommunications system capable of providing enhanced products such as Internet, WAP, messaging, games, video, music, applications, etc. A profile controls content that is accessible by a user depending upon the user's age or restrictions placed on accessible content in accordance with content categories. Rating information is obtained from content providers and mapped to content categories or content is rated dynamically. User's requests for access may be recorded whether access is provided or denied and used to provide reports including reports to account holders responsible for the user's account. In some instances, attempts to access banned information may be reported to law enforcement officials.
Owner:CELLCO PARTNERSHIP INC
Push content filtering
InactiveUS6778834B2Data processing applicationsDigital data processing detailsTelecommunicationsUser input
The user of a mobile terminal enters keywords indicative of categories of messages he wishes to peruse. When the mobile terminal receives a message, keywords associated with the message are compared with the user-entered keywords; if any match, a banner portion of the message is displayed on the mobile terminal and the mobile terminal issues a sensible alert. The user may request to view the message body associated with the banner portion. The user may request to take actions regarding the message body, such as storing the message body in the mobile terminal or calling a telephone number contained in the message body.
Owner:NOKIA TECH OY
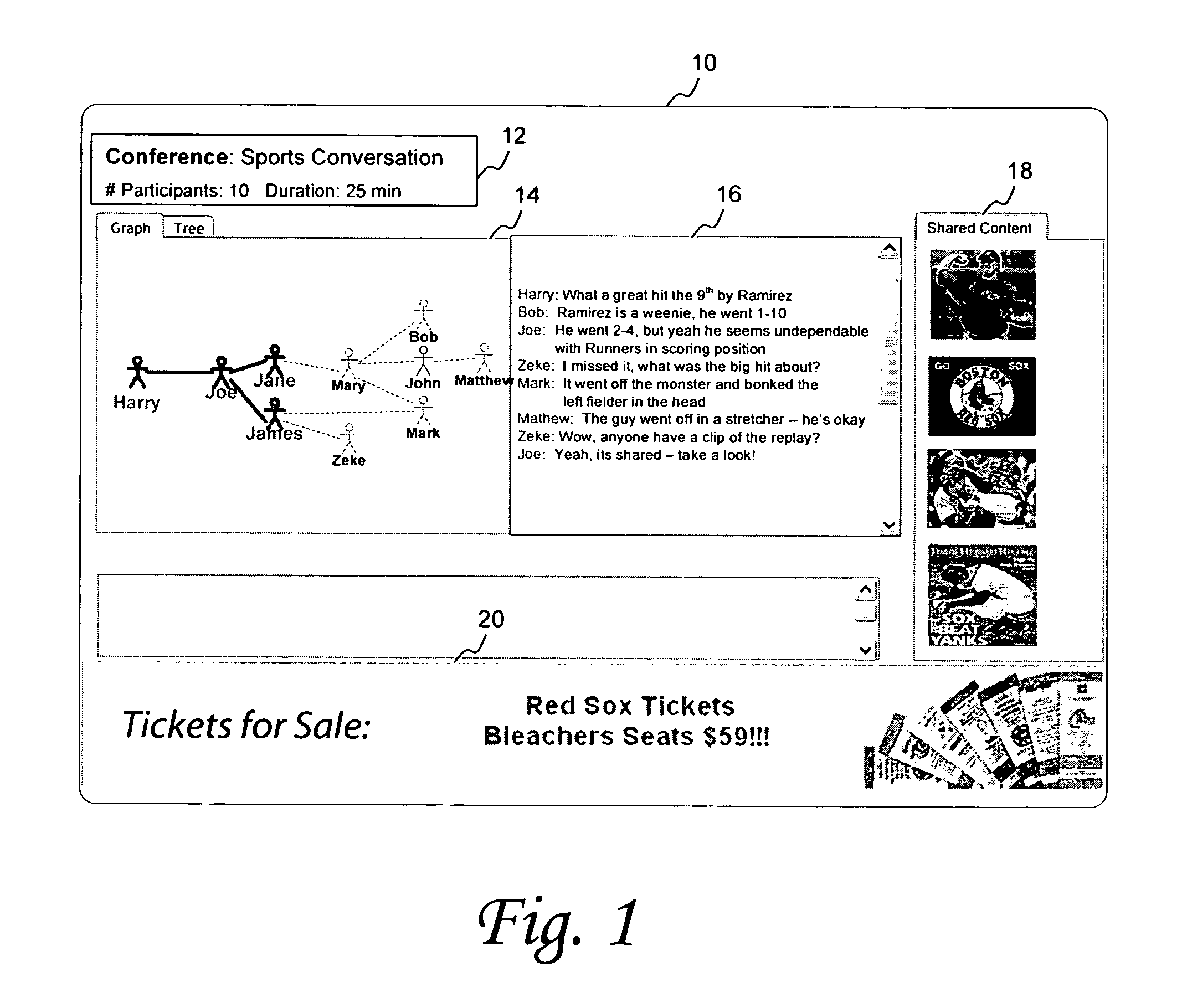
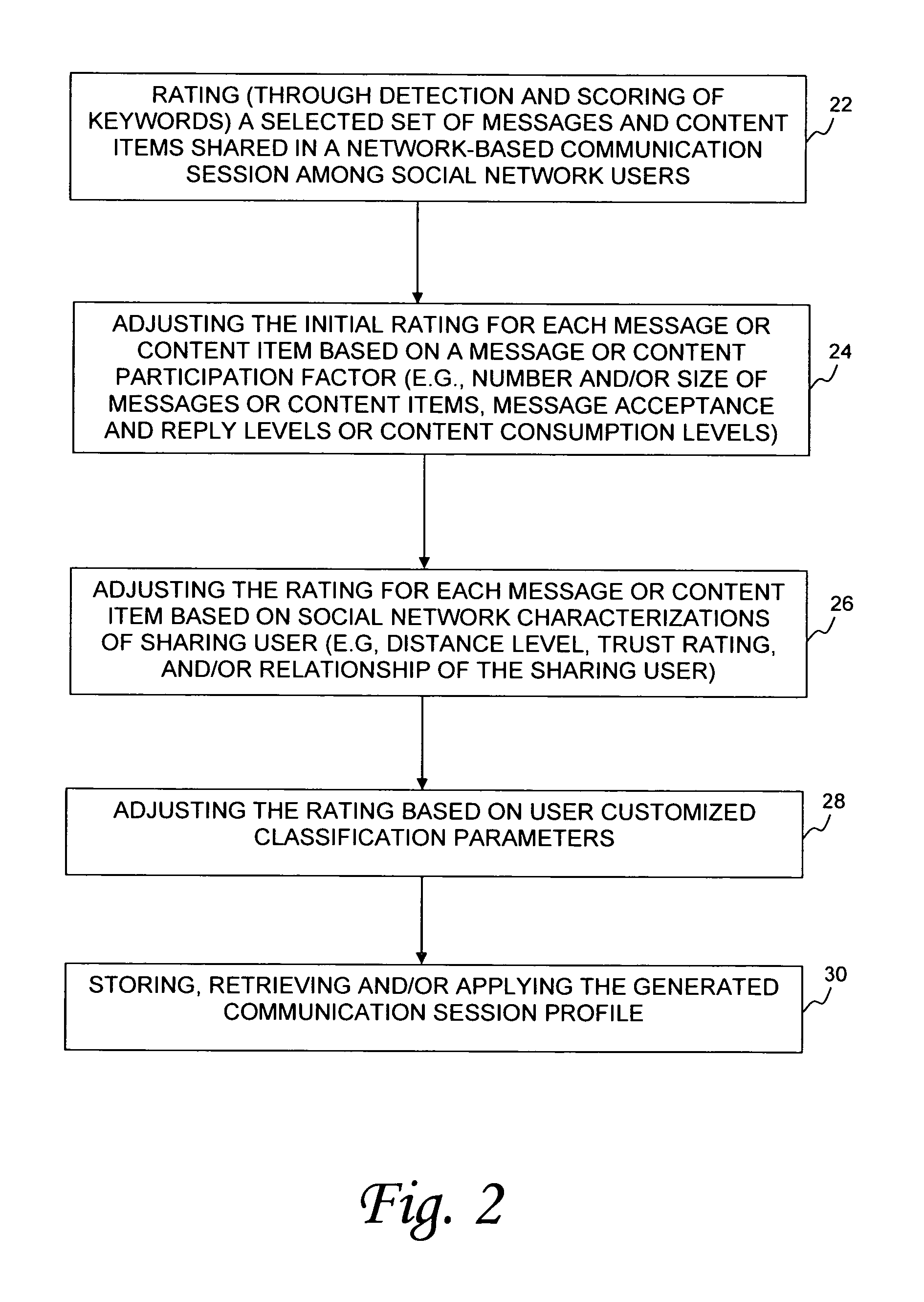
System and method for classification of communication sessions in a social network
ActiveUS9195996B1Simple methodIncreased influence levelDigital data processing detailsMultiple digital computer combinationsUser participationSocial web
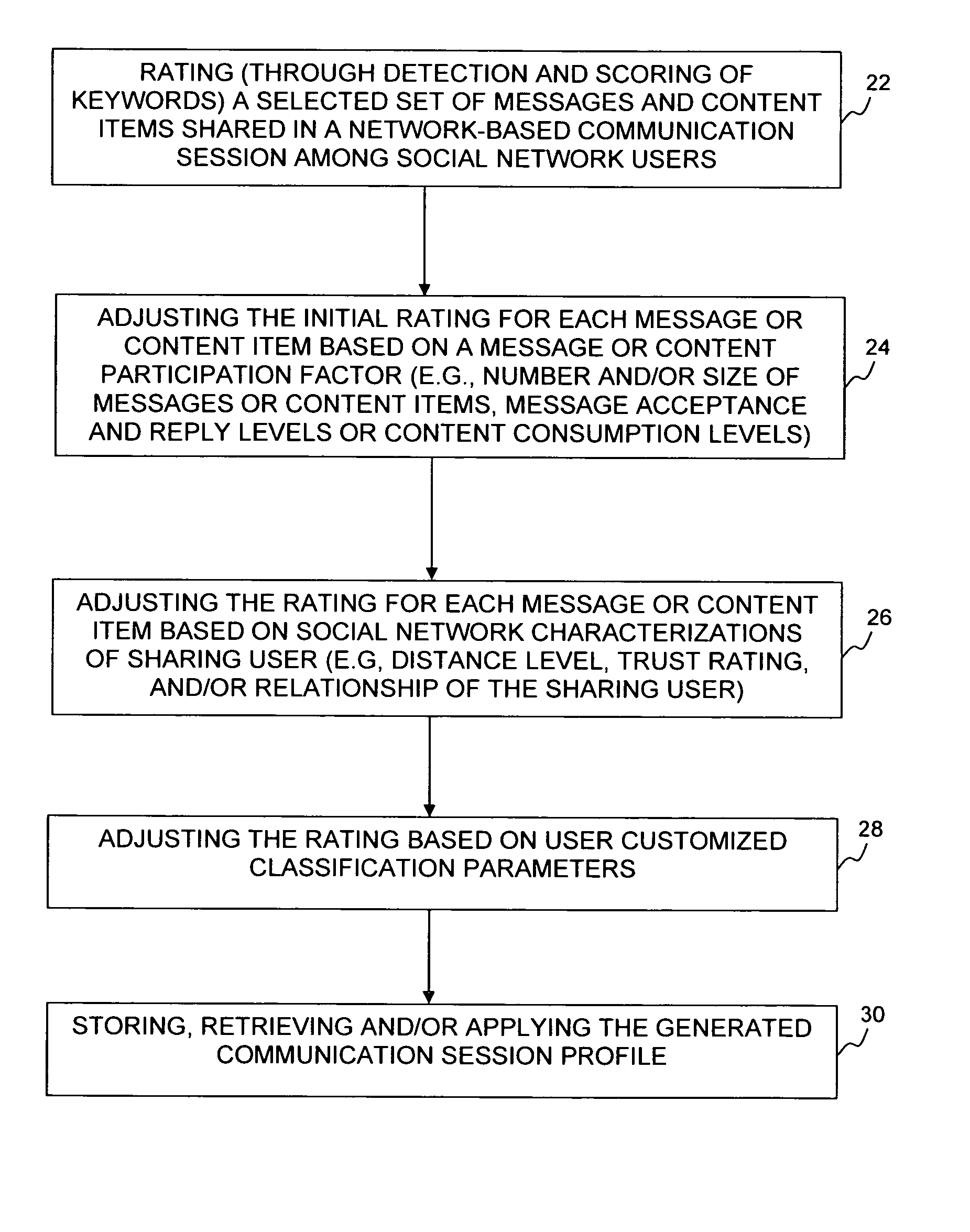
A system and method for generating a profile of communication sessions involves generating ratings for a selected set of messages and metadata associated with content items that are shared by social network users participating in a communication session. Ratings may be based on keyword scores which may then be adjusted based on user participation parameters, social network characterization parameters, and user selected options. Communication session profiles change over time and so recomputation is effected on periodic or scheduled bases. Generated profiles may be stored, frequently retrieved, or used in applications such as but not limited to content filtering, recommending content shared by participating social network members, selecting relevant advertisements, providing topic suggestions or user list invitations.
Owner:QURIO HLDG
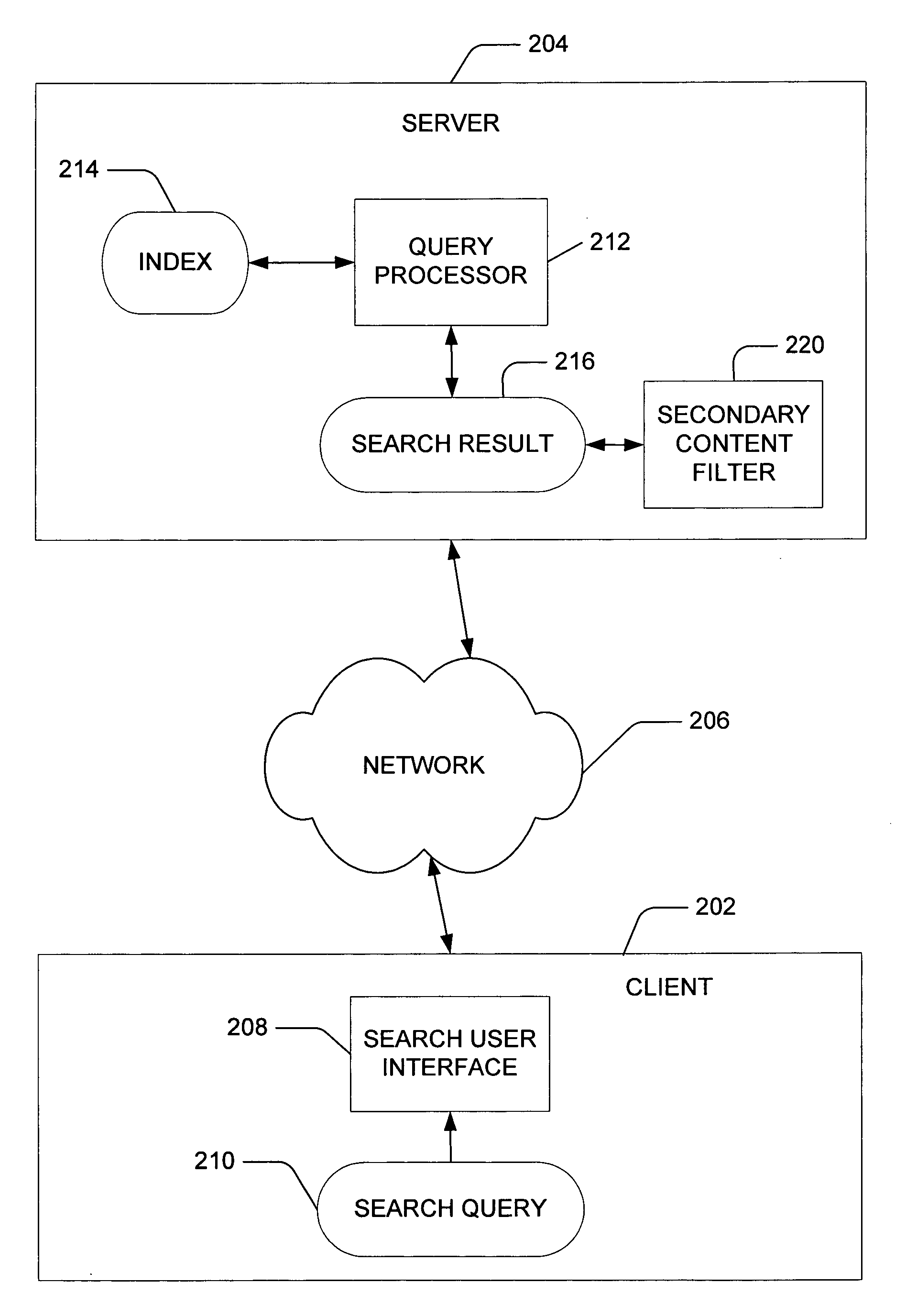
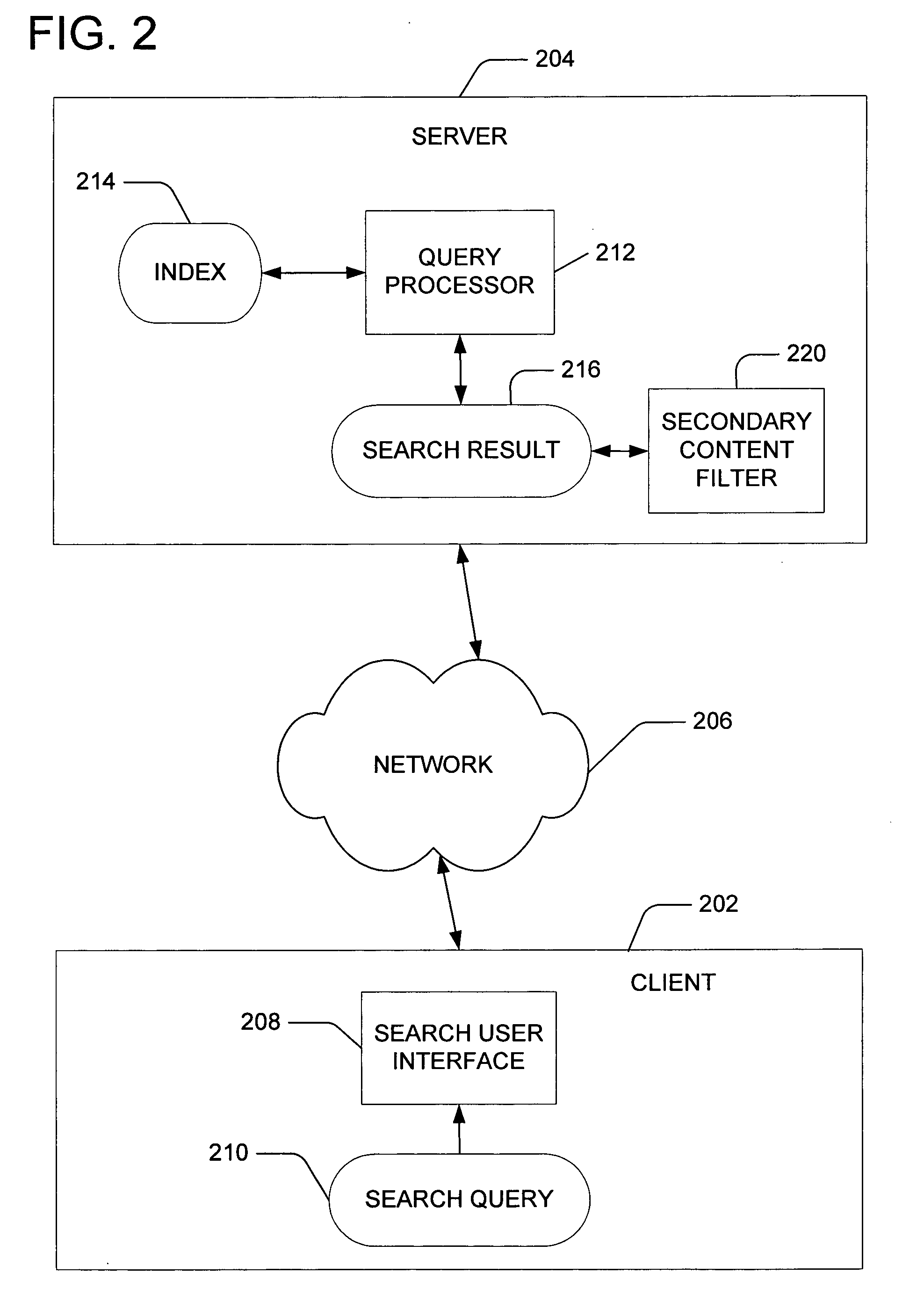
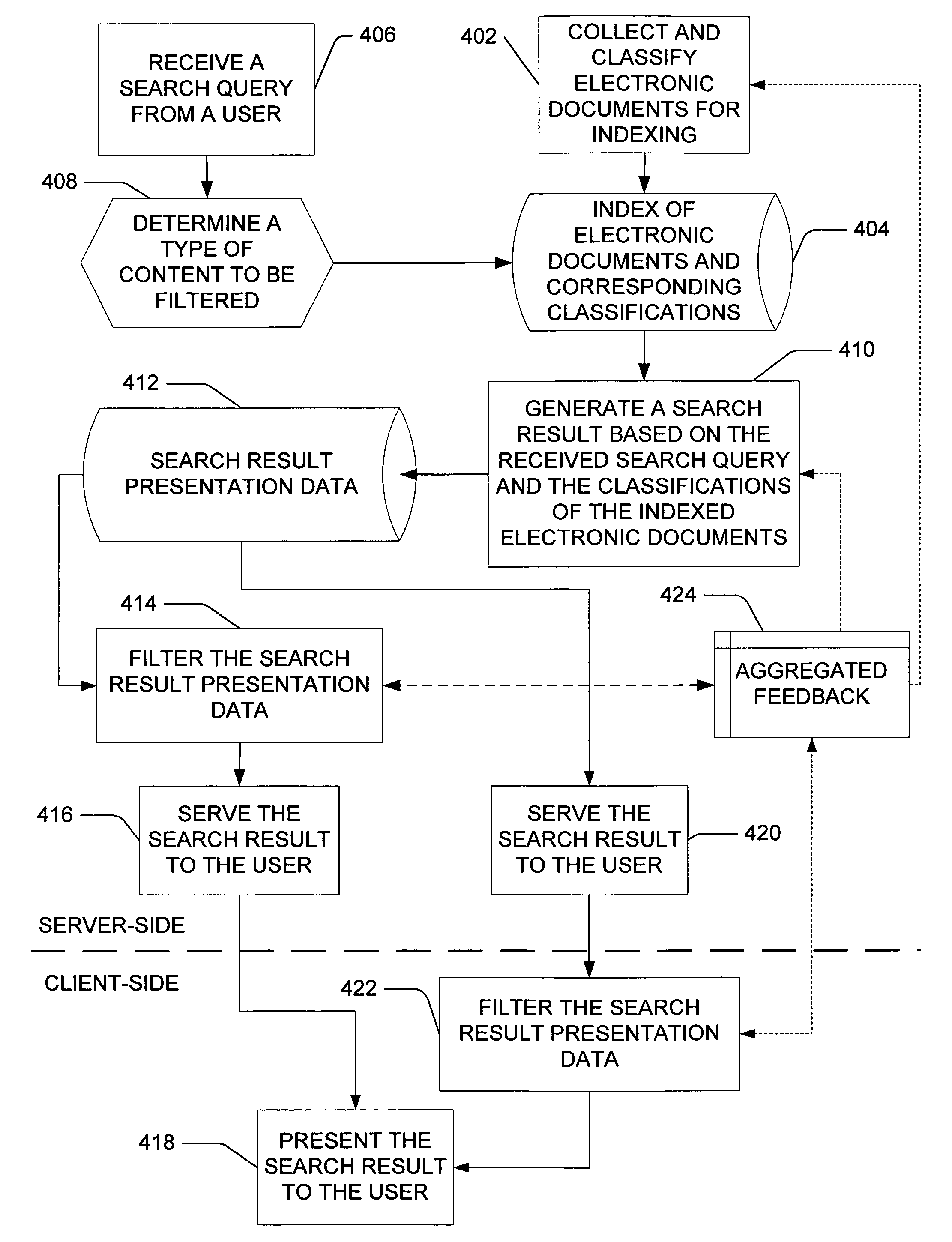
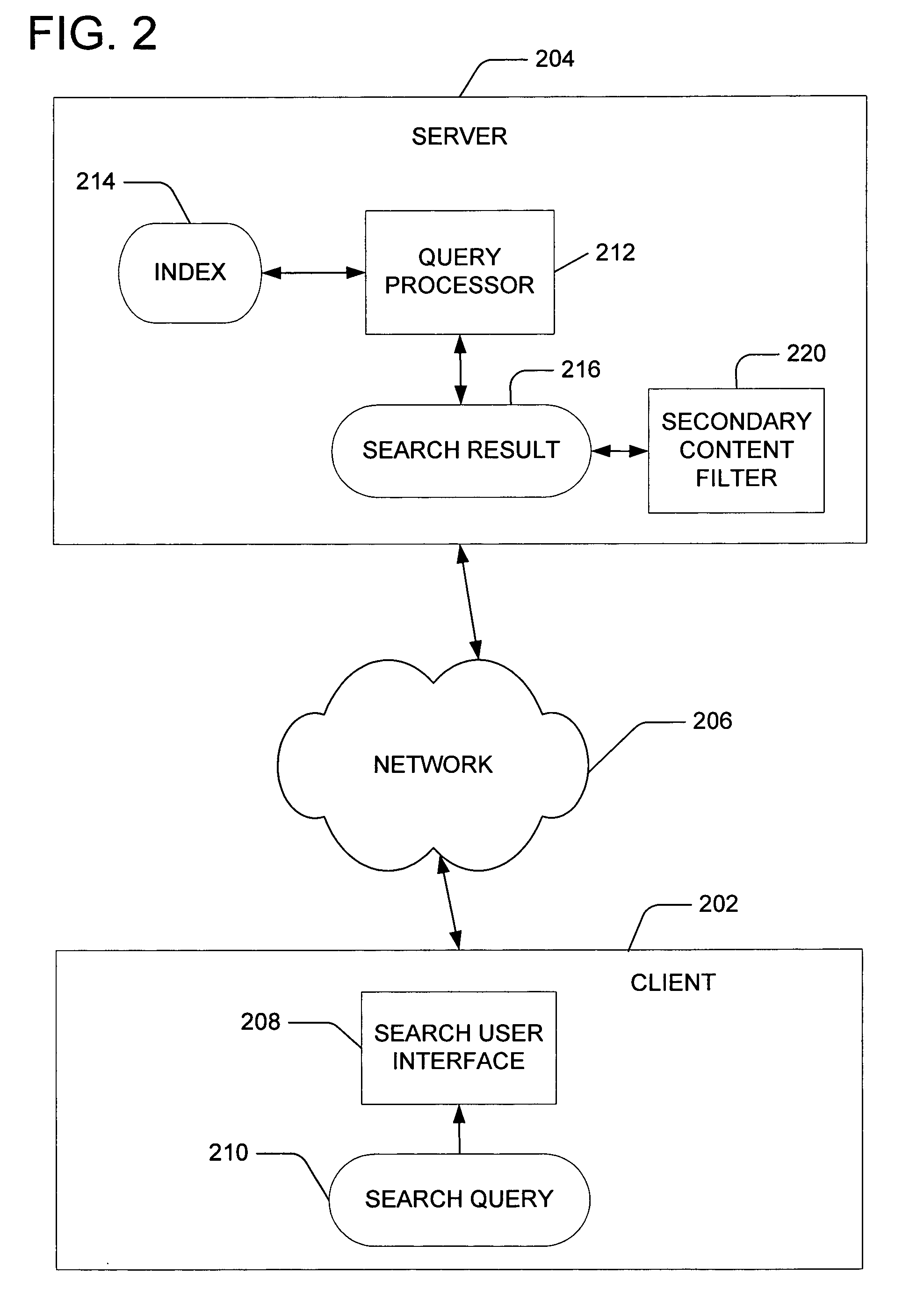
Presentation-level content filtering for a search result
ActiveUS20060004716A1Easy to classifyImprove accuracyData processing applicationsDigital data information retrievalElectronic documentDocumentation
Owner:MICROSOFT TECH LICENSING LLC
Age verification and content filtering systems and methods
ActiveUS8131763B2Additional revenue opportunityRiskDigital data processing detailsAnalogue secracy/subscription systemsThe InternetContent filtering
A system and method is provided for age verification and content filtering (AV / CF) on a wireless telecommunications system capable of providing enhanced products such as Internet, WAP, messaging, games, video, music, applications, etc. A profile controls content that is accessible by a user depending upon the user's age or restrictions placed on accessible content in accordance with content categories. Rating information is obtained from content providers and mapped to content categories or content is rated dynamically. User's requests for access may be recorded whether access is provided or denied and used to provide reports including reports to account holders responsible for the user's account. In some instances, attempts to access banned information may be reported to law enforcement officials.
Owner:CELLCO PARTNERSHIP INC
Disambiguating conflicting content filter rules
A content filtering mechanism is enhanced to resolve conflicts in filtering rules (e.g., those created by a whitelist, on the one hand, and a blacklist, on the other hand). Preferably, a conflict between or among content filtering rules is resolved by selecting among conflicting rules based on a notion of “risk” associated with the rules. According to this risk-based approach, when two or more rules conflict with one another, the particular rule whose risk value has a predetermined relationship (e.g., aligns most closely) with a risk level associated with the application (applying the rules) then takes precedence. By selecting among conflicting rules based on risk, the potential or actual conflicts are disambiguated, with the result being that the content is filtered appropriately.
Owner:IBM CORP
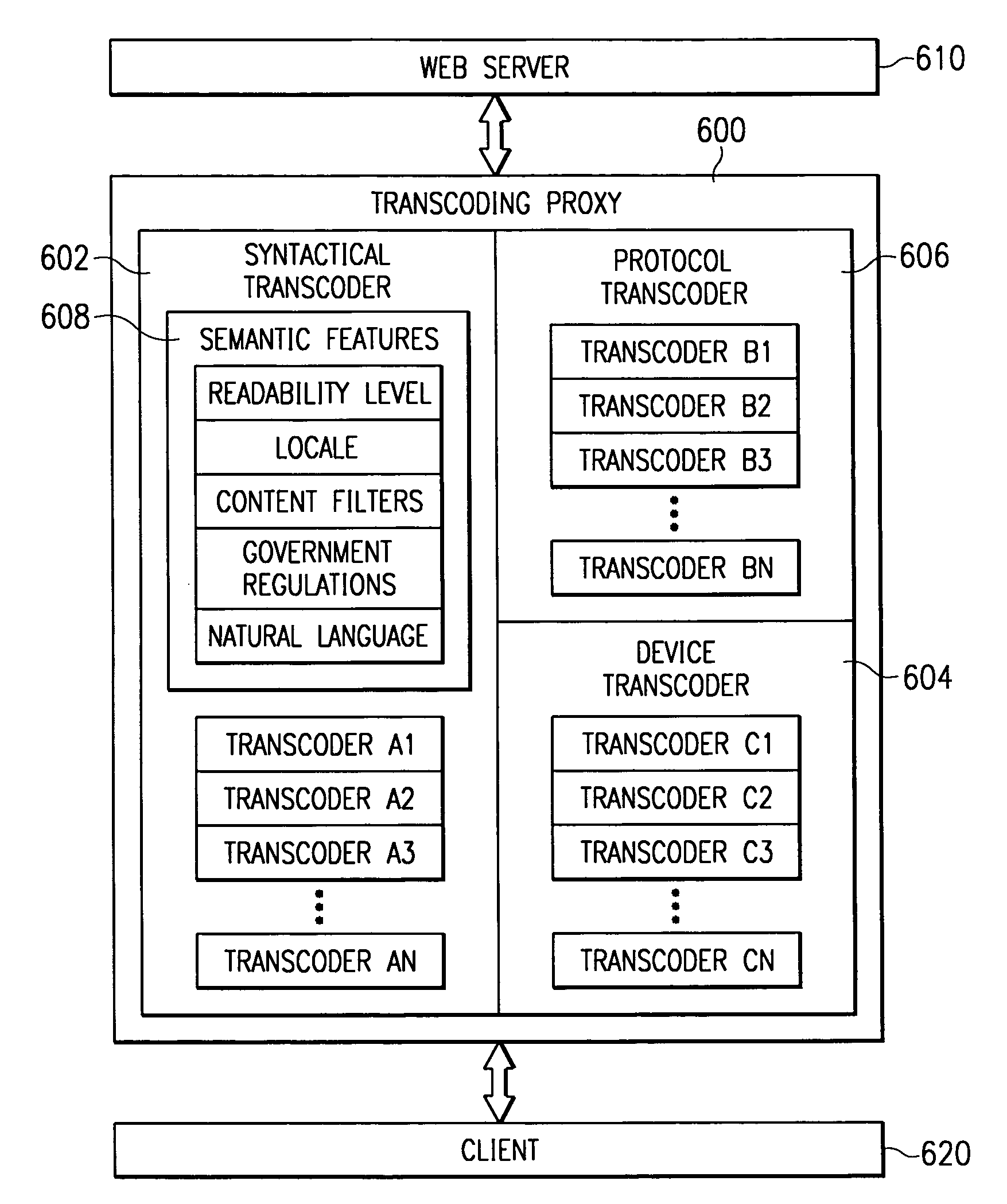
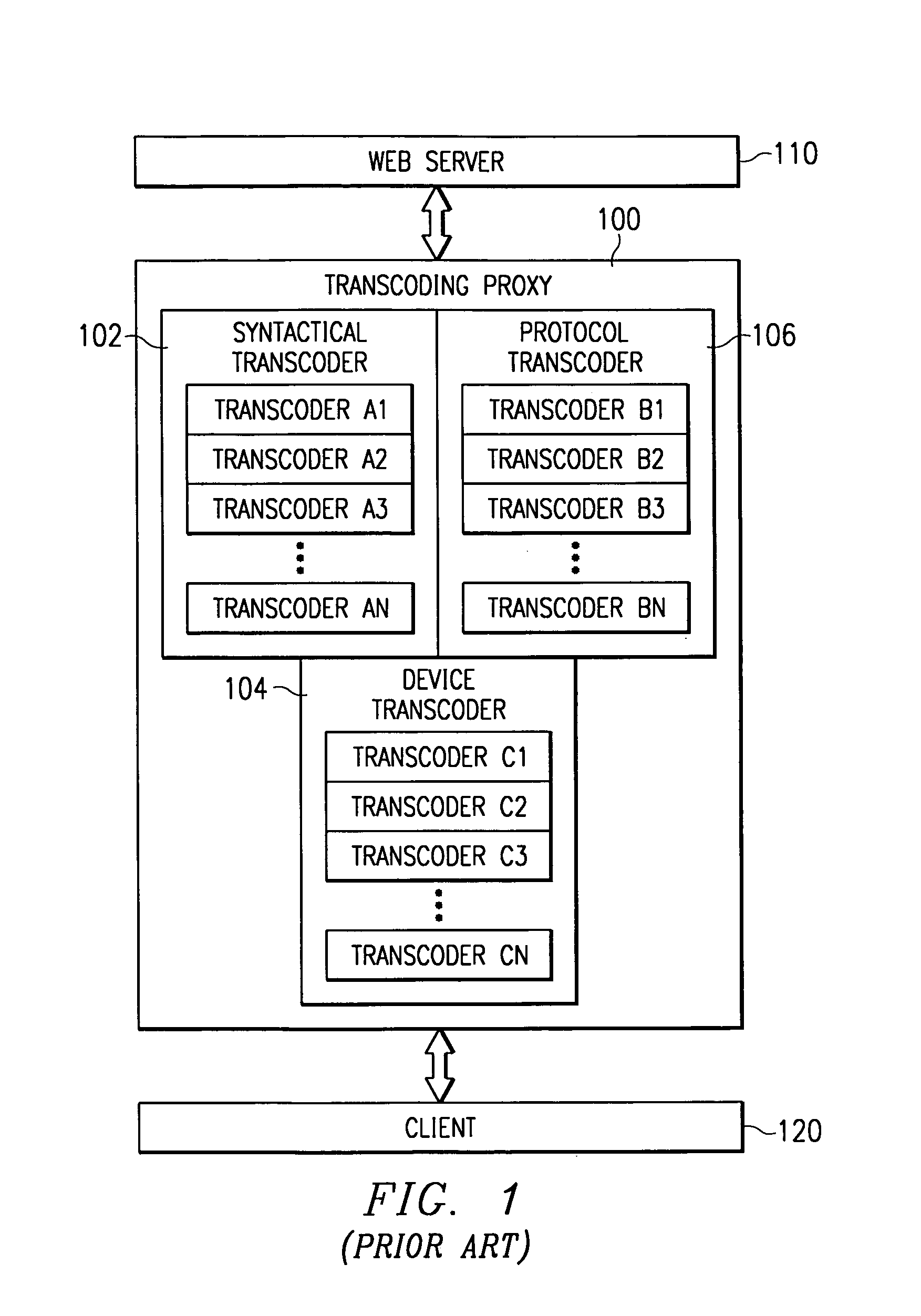
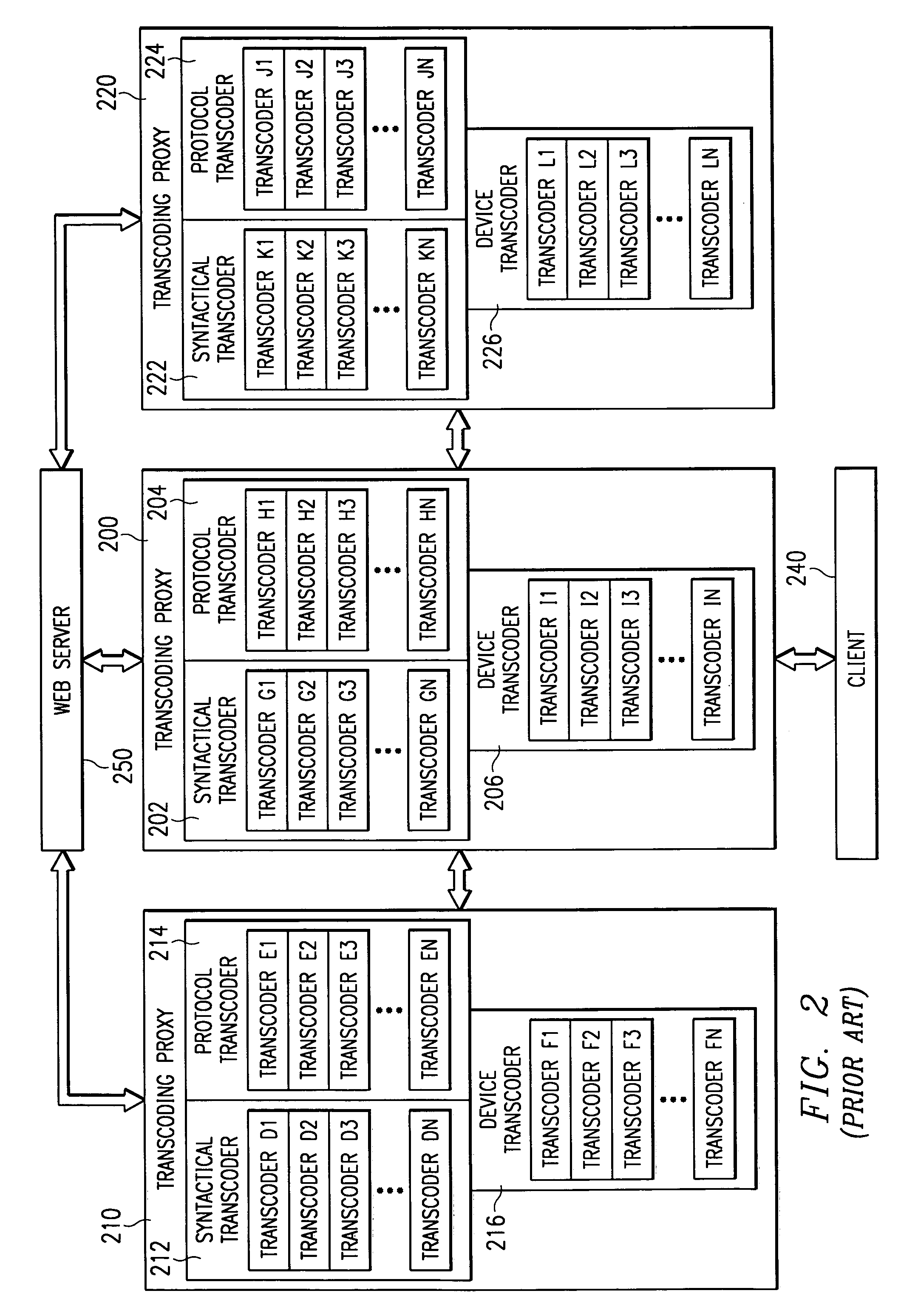
System and method for incorporating semantic characteristics into the format-driven syntactic document transcoding framework
InactiveUS6993476B1Digital data information retrievalMultiple digital computer combinationsSemanticsSemantic feature
Initially, a client requests a specific document and provides the preferences, including readability level preferences of the document, locale preferences, content filtering instructions preferences, governmental regulations preferences, natural language preferences, and document syntactic format preferences. The transcoding proxy requests and receives the document from the origin server, with the document having origin semantic characteristics. The document from the origin server has an origin readability level and origin locale, is conformant with origin content filtering instructions and origin governmental regulations, and is in origin natural language and in origin document syntactic format. Using the client semantics preferences, the transcoding proxy revises the document in a sequential or parallel fashion. The origin semantics characteristics of the document are, thus, revised to the semantic preferences specified by the client.
Owner:NUANCE COMM INC
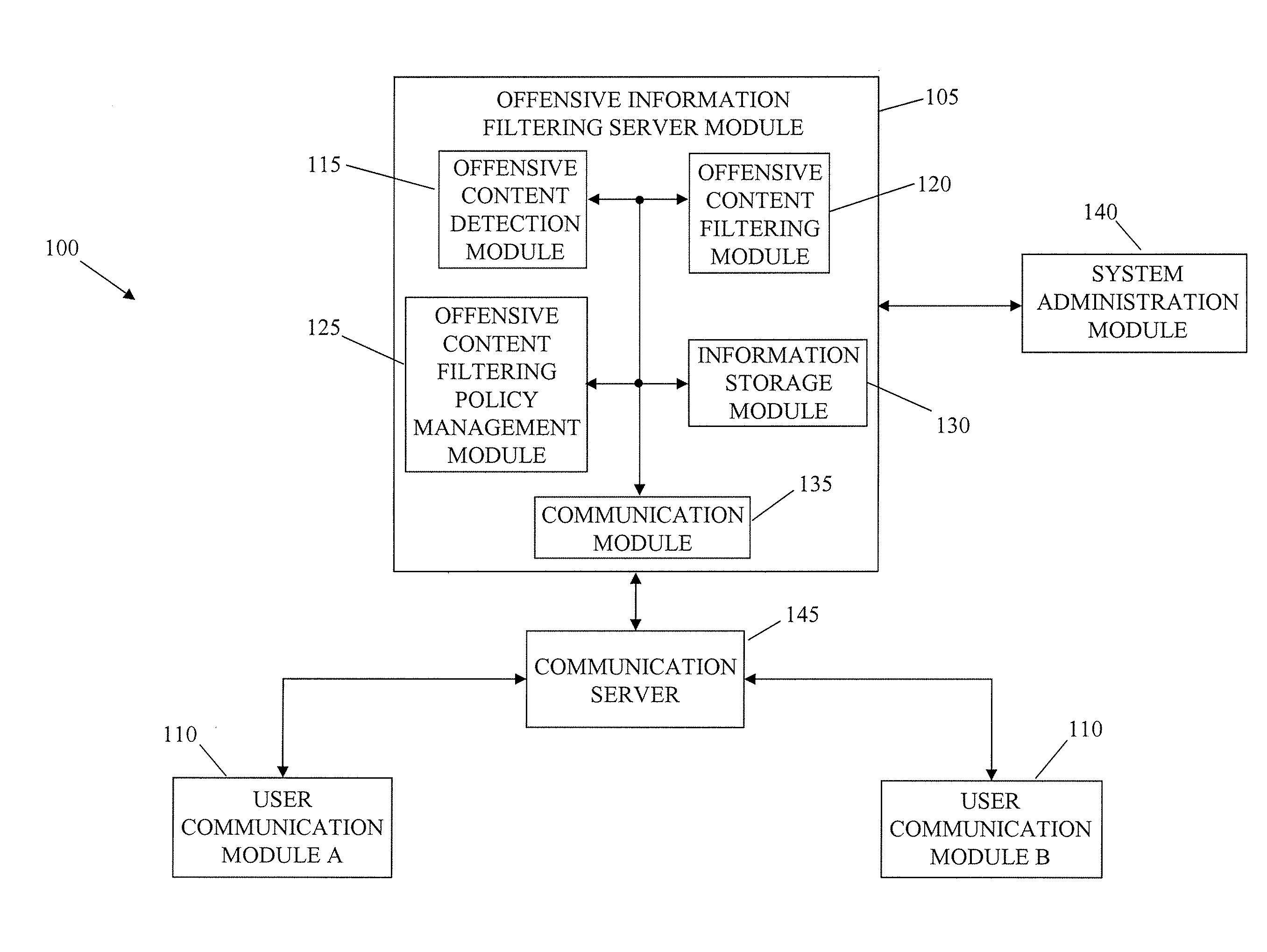
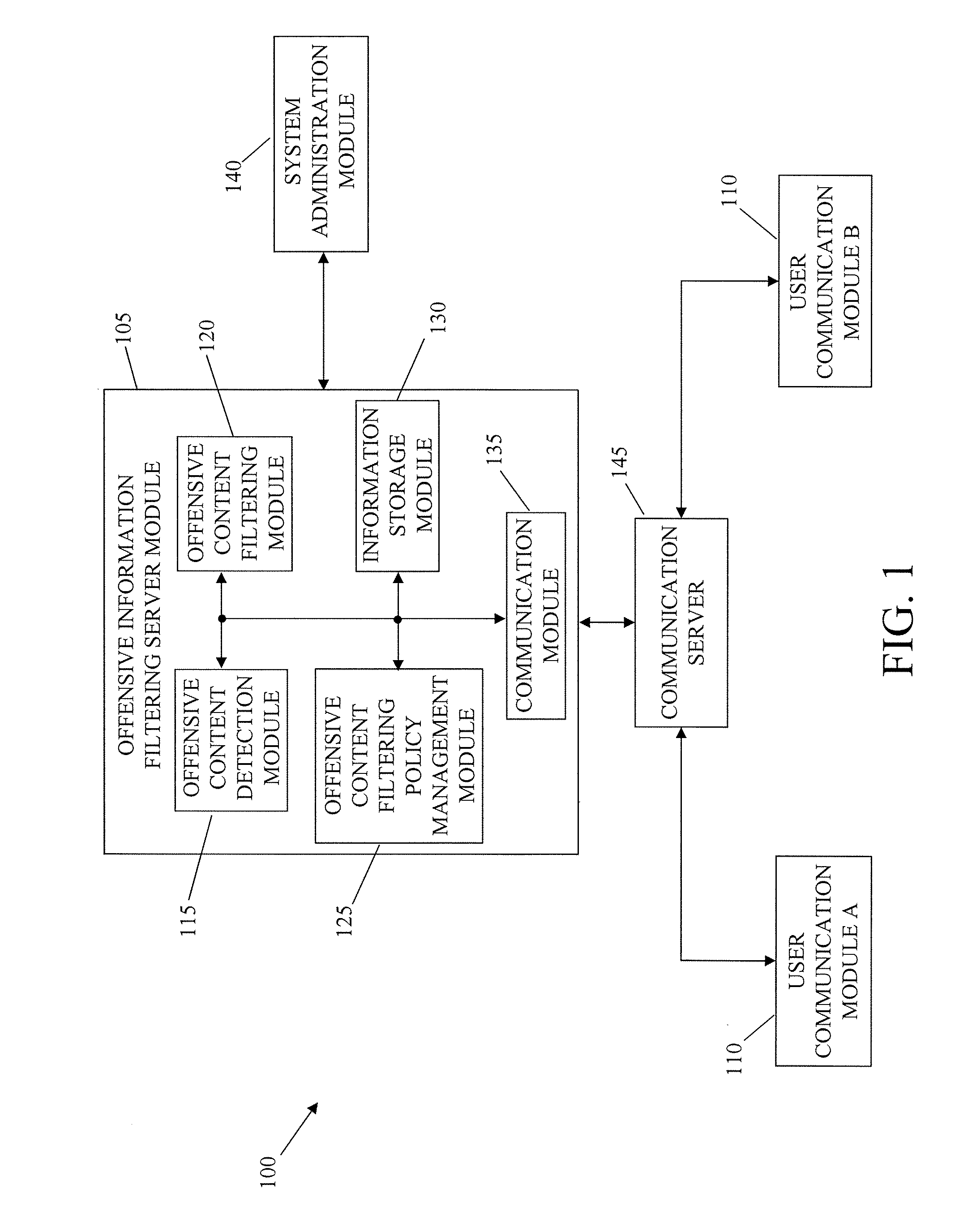
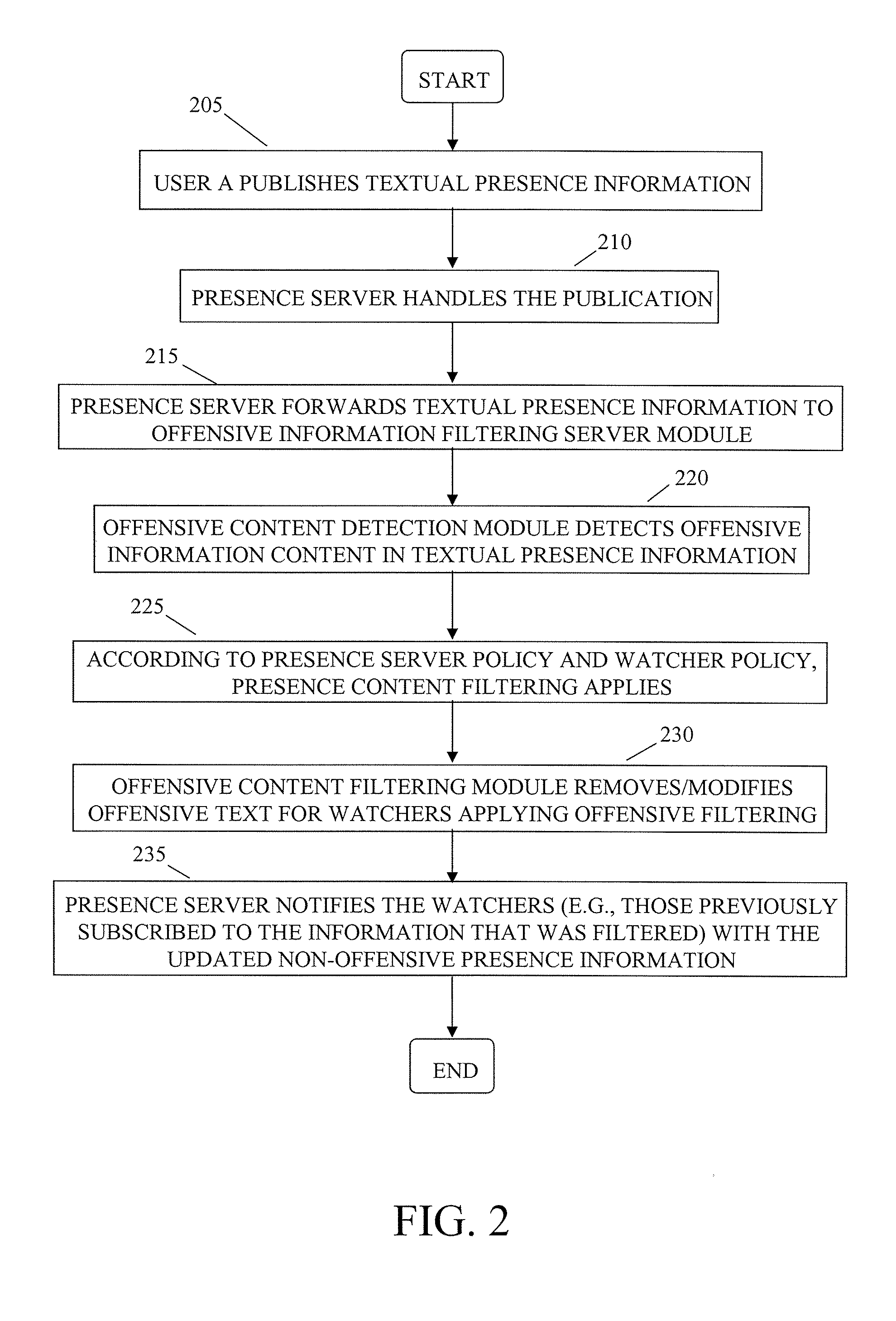
System and method for filtering offensive information content in communication systems
InactiveUS20080134282A1Computer security arrangementsOffice automationCommunications systemCommunication device
The present invention is directed to a system and method for filtering offensive information content in communication environments. The system includes an offensive information filtering server module in communication with a plurality of user communication devices. The offensive information filtering server module includes an offensive content detection module. The offensive content detection module is configured to detect offensive information content in communications between the user communication devices. The offensive information filtering server module includes an offensive content filtering module in communication with the offensive content detection module. The offensive content filtering module is configured to filter the offensive information content detected in the communications by the offensive content detection module.
Owner:NEUSTAR
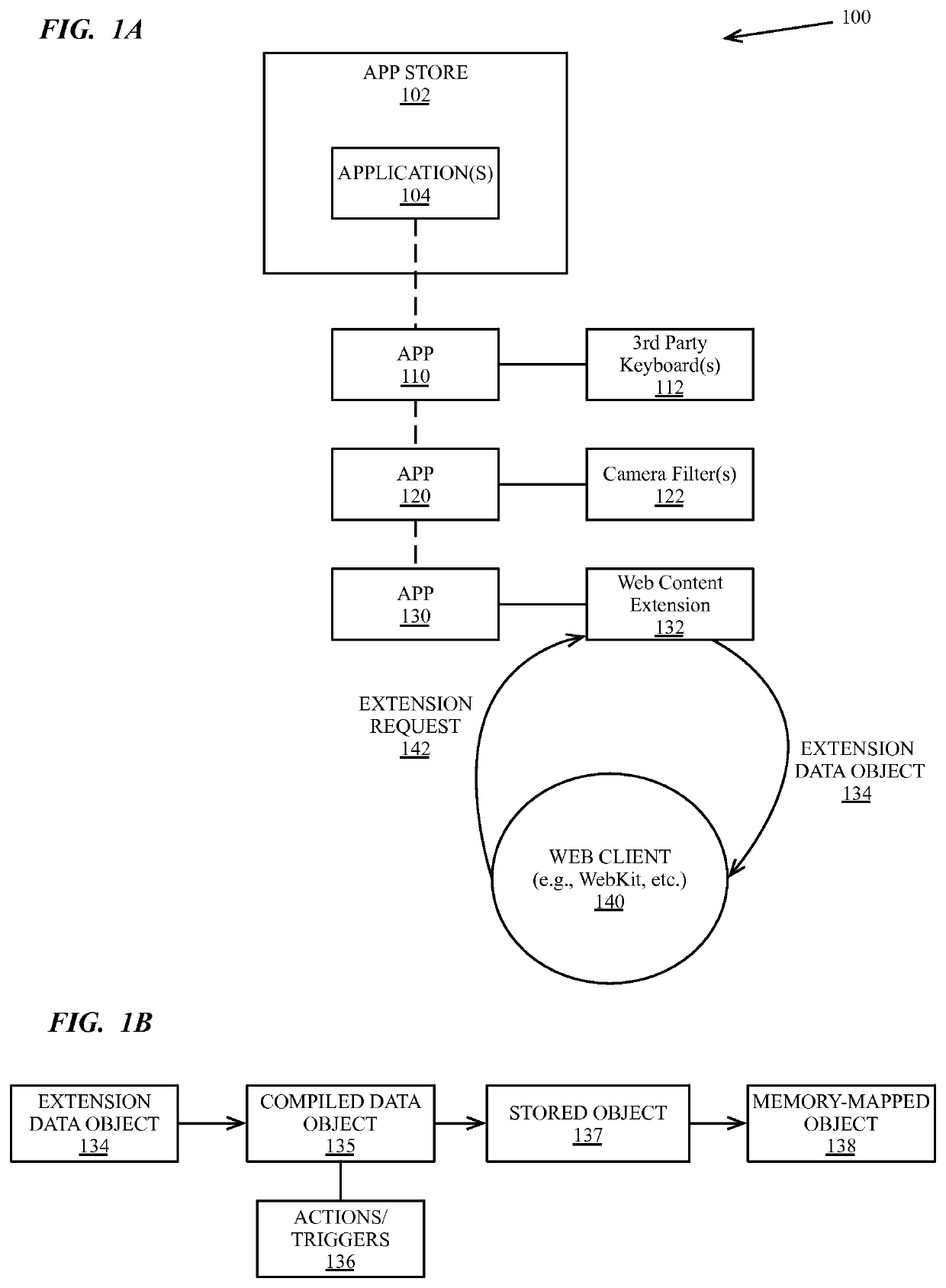
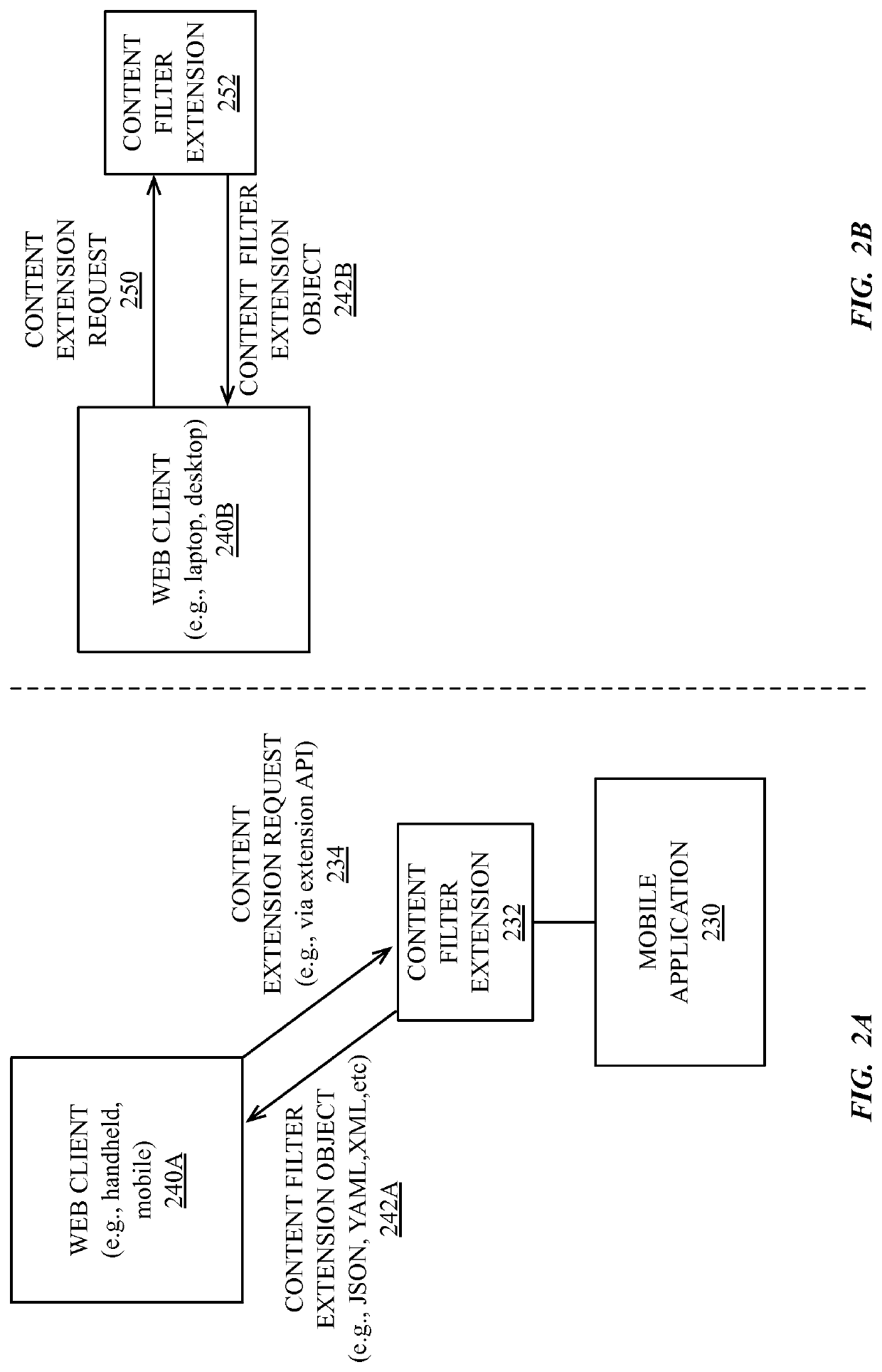
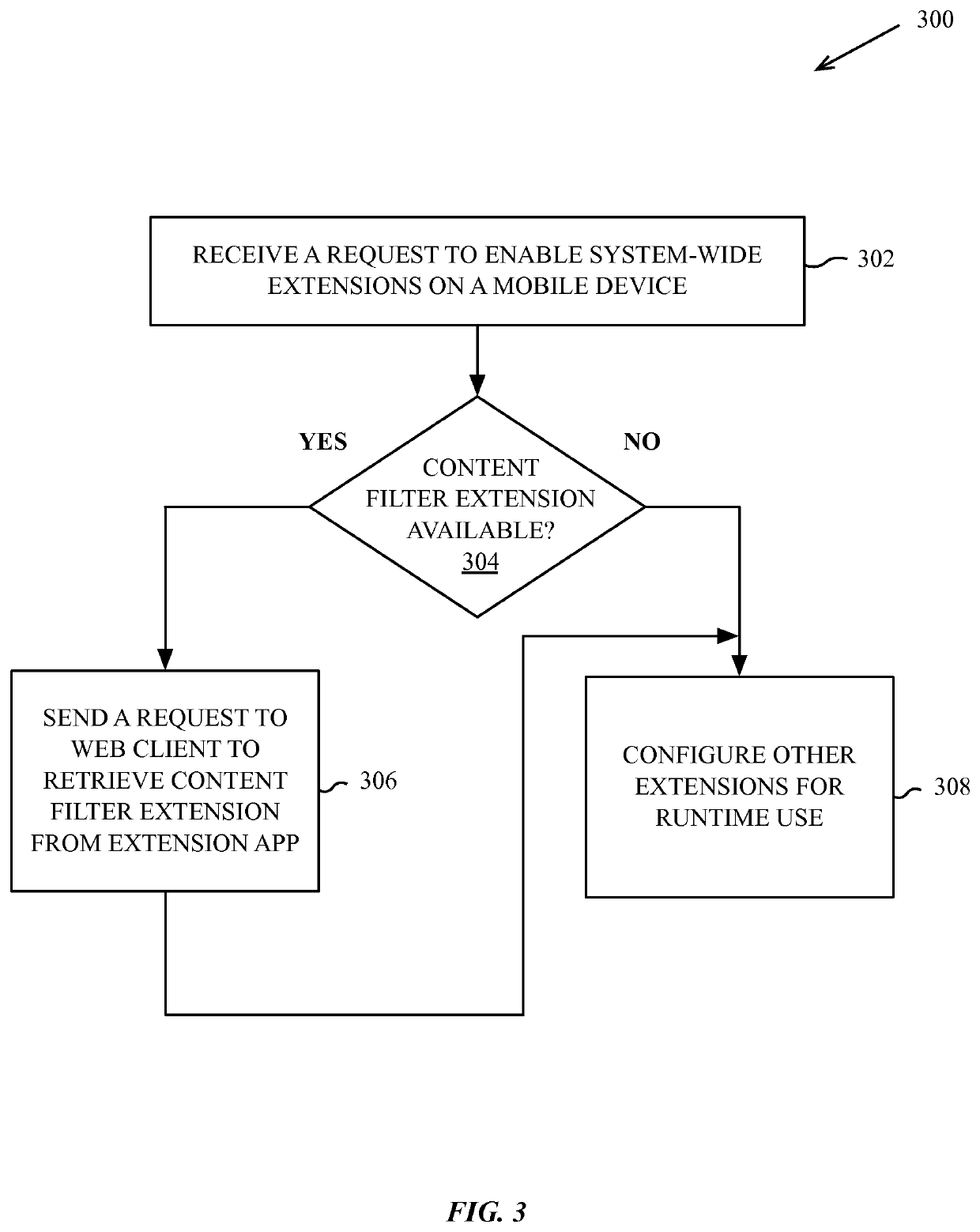
Web resource load blocking API
In various embodiments described herein, a content extension and programming interface enable third-party content extensions to supply transformation and filtering actions and associated criteria to native web clients on a system. In one embodiment, the native web client loads data for a third-party content filtering, blocking, or transformation extension and conducts extension defined actions without requiring additional intermediation by the third-party content. In one embodiment, a third-party application downloaded to a mobile or handheld device can include an extension data object that provides actions and triggers that are loaded by a native web client of the system. The third-party application is not required to execute continuously and can exit or be terminated once the web client retrieves the extension data object.
Owner:APPLE INC
Distributed, multi-tenant virtual private network cloud systems and methods for mobile security and policy enforcement
ActiveUS8464335B1Computer security arrangementsMultiple digital computer combinationsCloud systemsPrivate network
The present disclosure provides distributed, multi-tenant Virtual Private Network (VPN) cloud systems and methods for mobile security and user based policy enforcement. In an exemplary embodiment, plural mobile devices are configured to connect to one or more enforcement or processing nodes over VPN connections. The enforcement or processing nodes are configured to perform content filtering, policy enforcement, and the like on some or all of the traffic from the mobile devices. The present invention is described as multi-tenant as it can connect to plural clients across different companies with different policies in a single distributed system. Advantageously, the present invention allows smartphone and tablet users to protect themselves from mobile malware, without requiring a security applications on the device. It allows administrators to seamless enforce policy for a user regardless of the device or network they are connecting to, as well as get granular visibility into the user's network behavior.
Owner:ZSCALER INC
System and method for content filtering using static source routes
A packet containing a request for content is initially received at a content filtering router. The packet comprises a destination Internet Protocol (IP) address of a content server that stores the content and a bogus IP address. It is ascertained that the destination IP address is on a list of approved destination IP addresses and the packet is routed in accordance with the destination IP address. Alternatively, it is ascertained that the destination IP address is on a list of probably unapproved destination IP addresses and the packet is routed in accordance with an alternative IP address to a content filtering server. In this alternative, at the content filtering server the bogus IP address is used to determine a content filtering category and it is ascertained whether the destination IP address with the content filtering category should be filtered based upon a list of IP addresses and associated content filtering categories.
Owner:DIRECTV LLC
Computerized system and method for policy-based content filtering
ActiveUS20070118893A1Eliminate the problemMultiple digital computer combinationsProgram controlComputerized systemNetsniff-ng
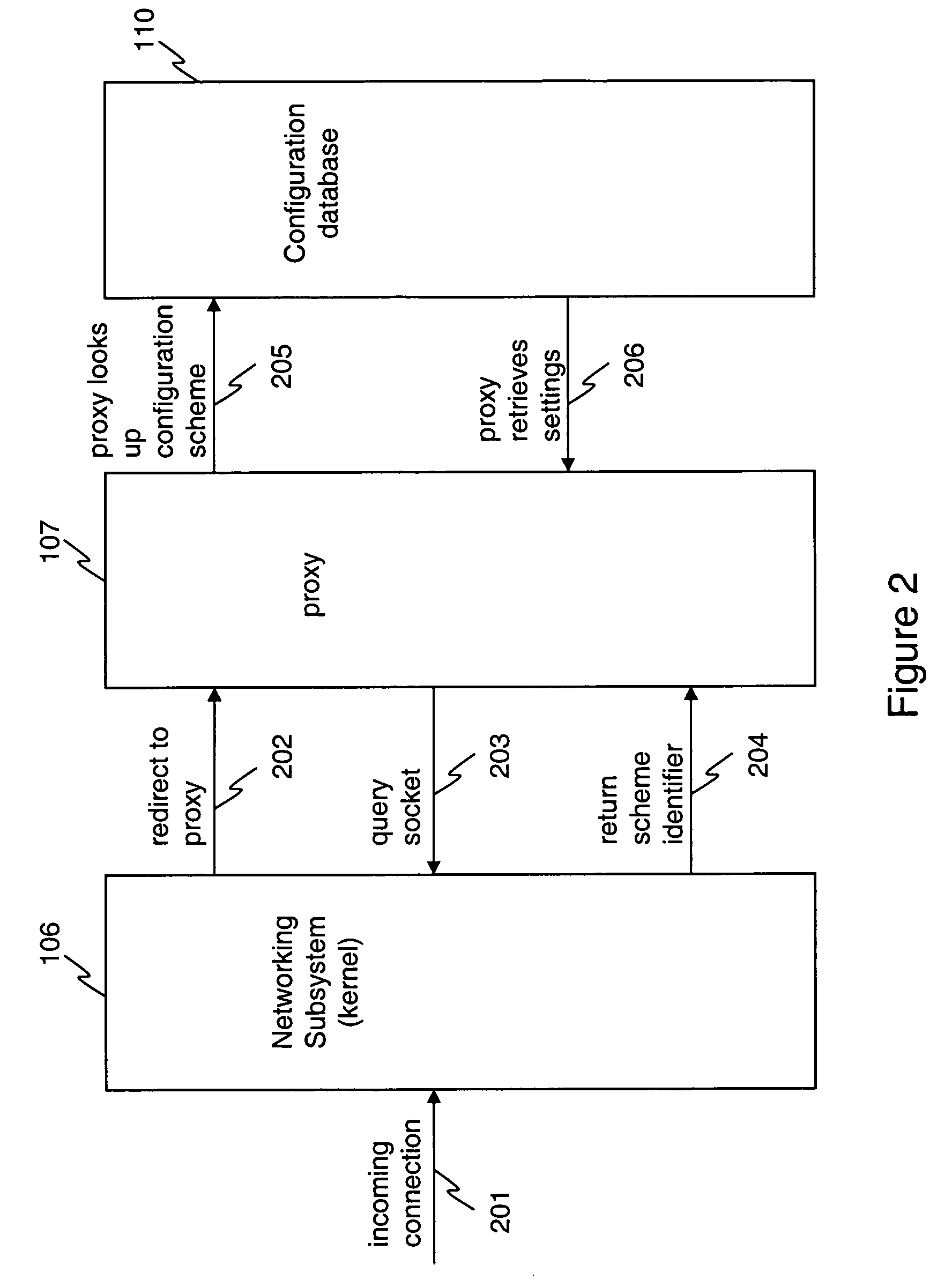
Firewalls and other filtering gateways have become common security devices for improving computer network security. As more features and functionality are added to these devices they become quite complex to configure. By associating configuration schemes with firewall policies, configuration can be simplified without compromising flexibility. Administrators have more options to filter different traffic streams based on their type and sources. They also have increased flexibility to be able to filter traffic on a per user basis, through authentication mechanisms tied to various filtering options.
Owner:FORTINET +1
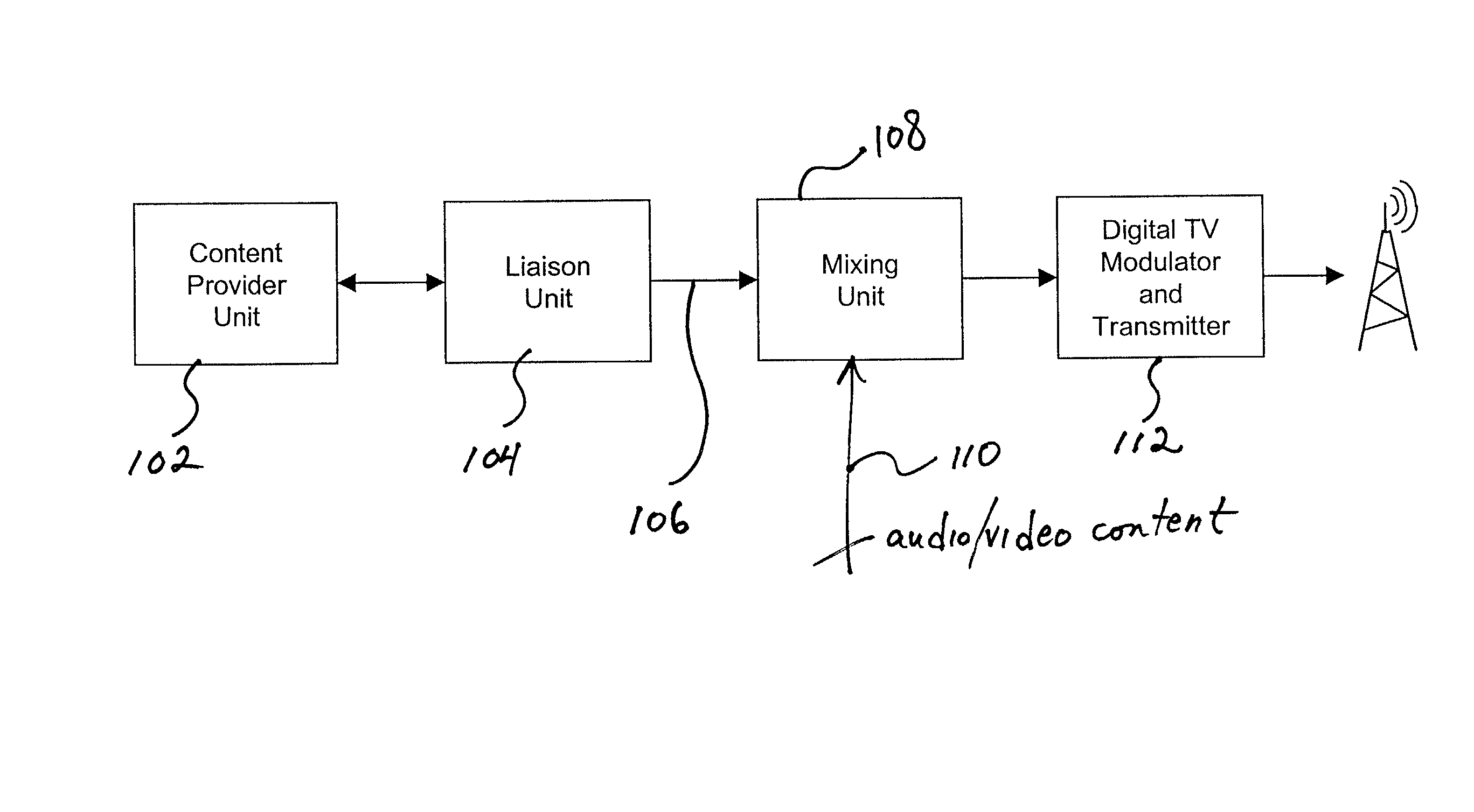
Three part architecture for digital television data broadcasting
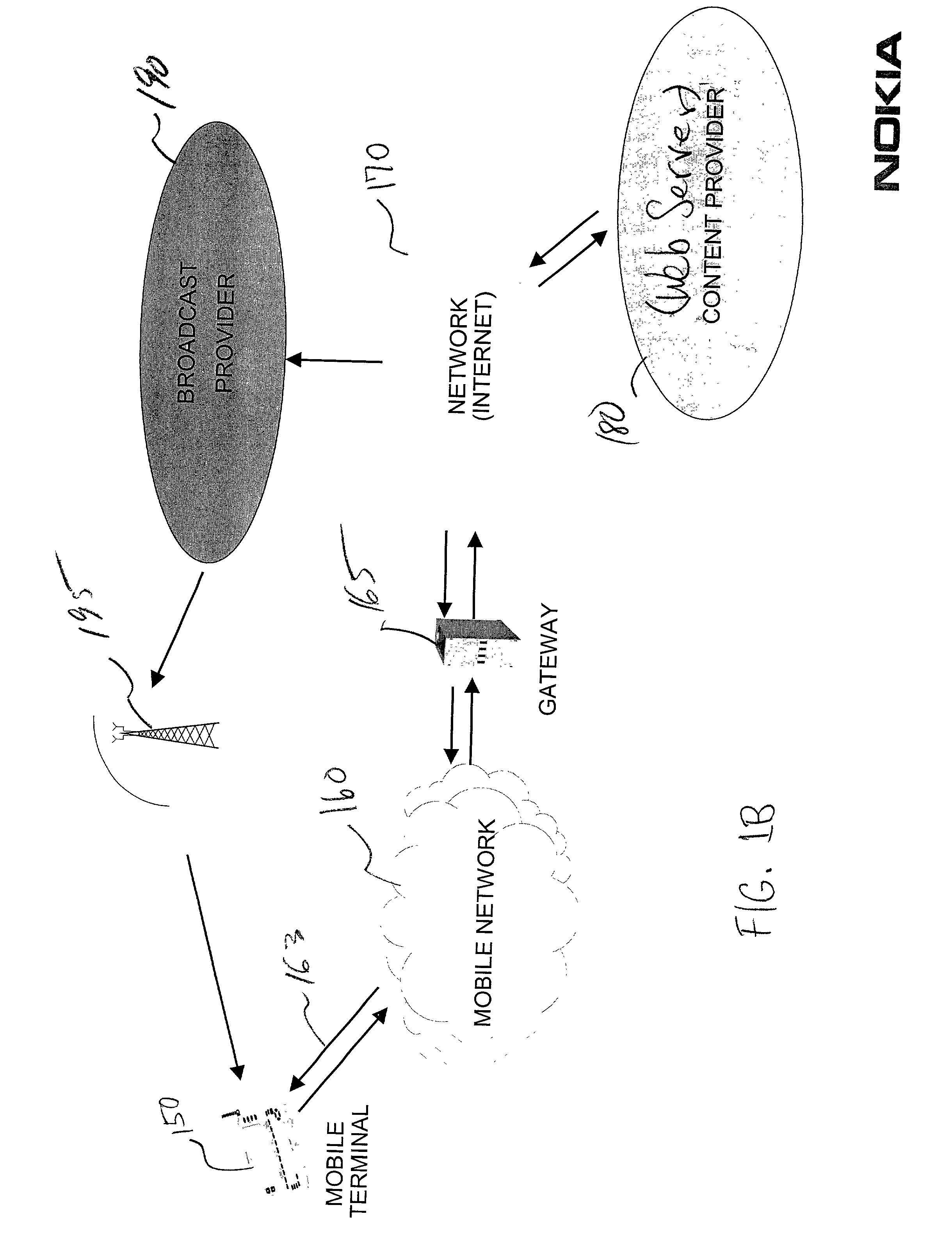
This invention provides technology (including apparatus, method, software, and / or data structures) to broadcast data from one or more content providers via one or more broadcast channels to one or more content recipients. This technology meets the different needs of the three major stakeholders—the content providers, the broadcasters, and the content recipients. The technology provides support for identifying the data to be broadcast, setting the broadcast schedule, getting the data inserted into the broadcast stream, extracting it from the broadcast stream at the receiver, and many ancillary activities such as compression, error correction, bandwidth management, bandwidth usage reporting, and content filtering at the receiver.
Owner:TRIVENI DIGITAL
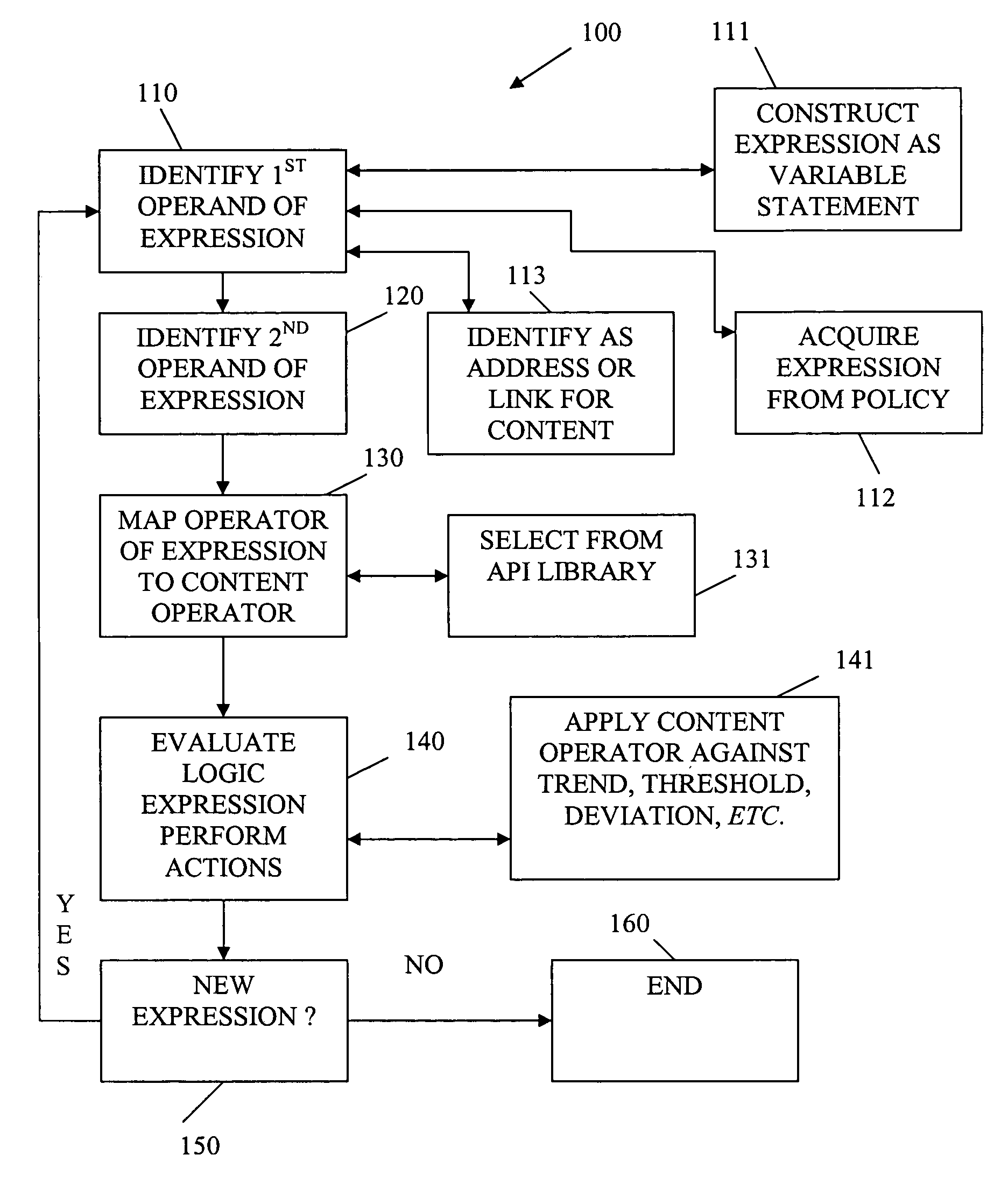
Techniques for content filtering
InactiveUS7043555B1Digital data information retrievalAnalogue secracy/subscription systemsRating systemWorld Wide Web
Techniques are provided for content filtering. Logic expressions are evaluated to filter content in response to content ratings. The logic expressions include operators that are overloaded and associated with content operators for specific content providers or specific rating systems. By evaluating the logic expressions with the content operators, one or more actions can be automatically and dynamically performed.
Owner:APPLE INC
Presentation-level content filtering for a search result
ActiveUS7293017B2Easy to classifyImprove accuracyData processing applicationsDigital data information retrievalElectronic documentDocumentation
Owner:MICROSOFT TECH LICENSING LLC
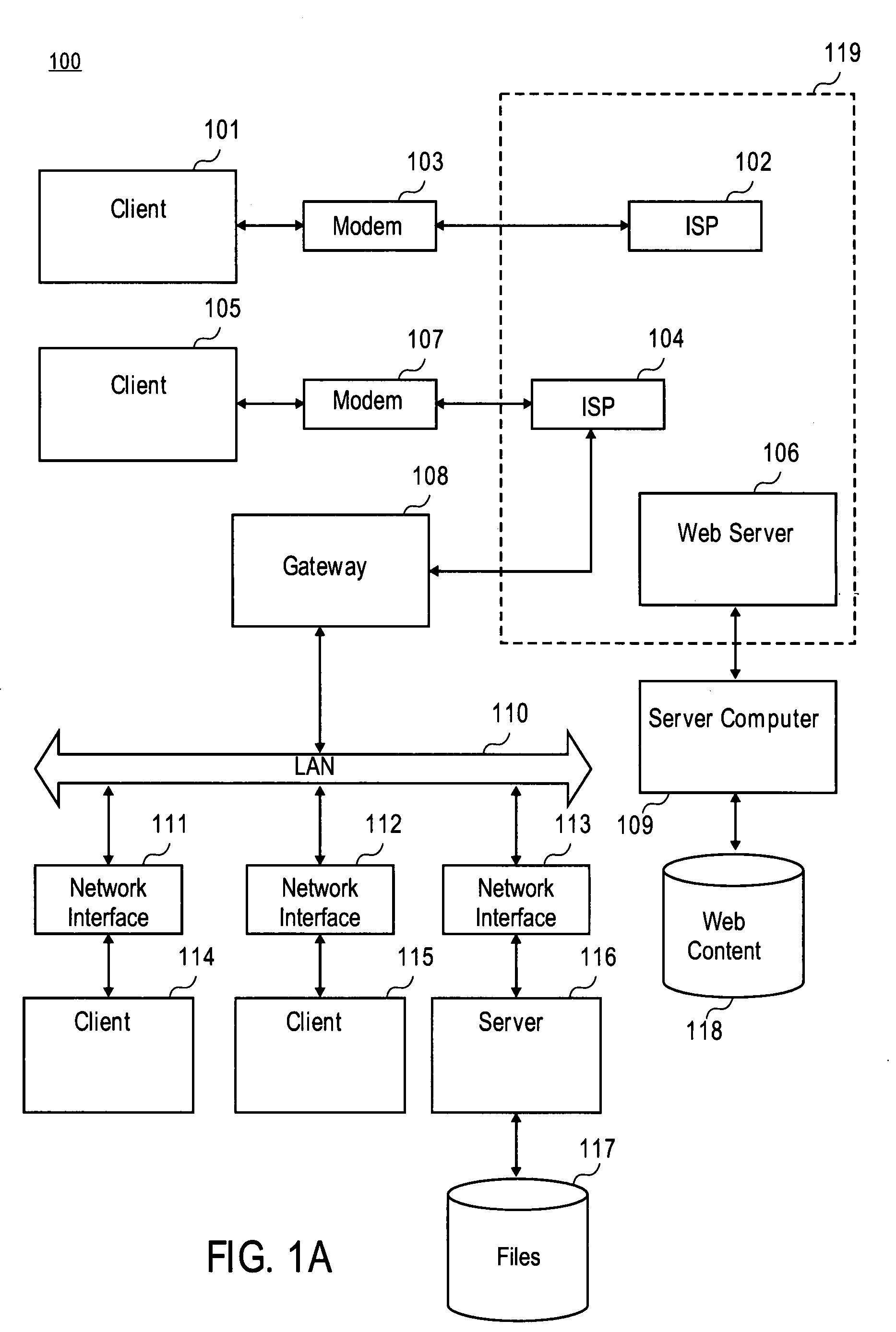
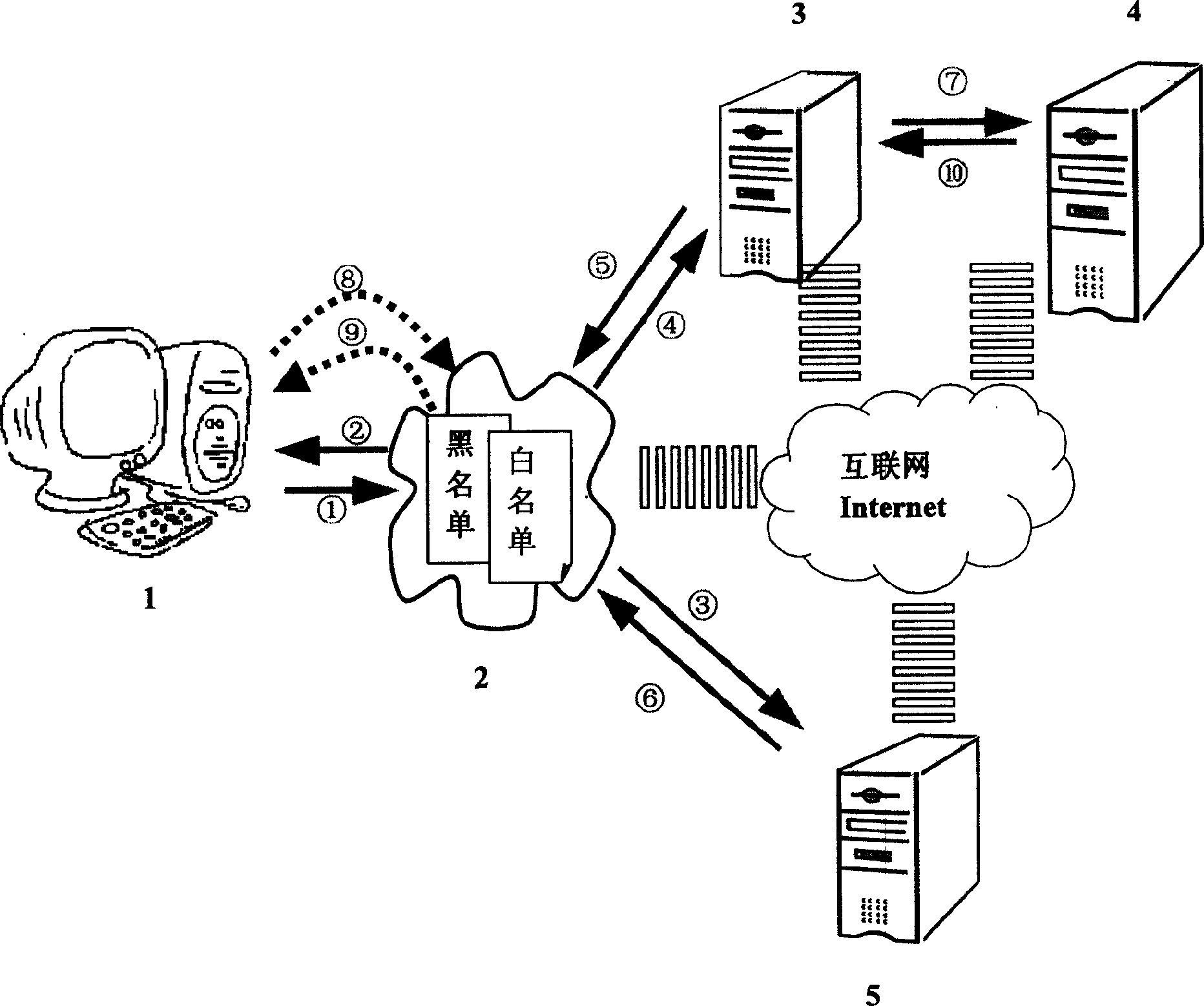
Internet content filtering system and method
This invention relates a filter system and a filter method for Internet content. The system includes: a content filter agent(CFA), a question server (QS) and a content analysis and management server (CAMS). The flow of the content filter system is that when a user sends a request of accessing a URL, CFA permits or for bits the said acc request according to the white and black name list set by the user. If the URL is not in the CFA name list, CFA delivers an inquiry the hierachical information of the URL in its own library and feeds back the result to CFA. CFA responds it and QS will download even new URL hierachical information. The invention can accurately identify poor information in network and prevent users from accessing them actively.
Owner:FUDAN UNIV
Method to block unauthorized network traffic in a cable data network
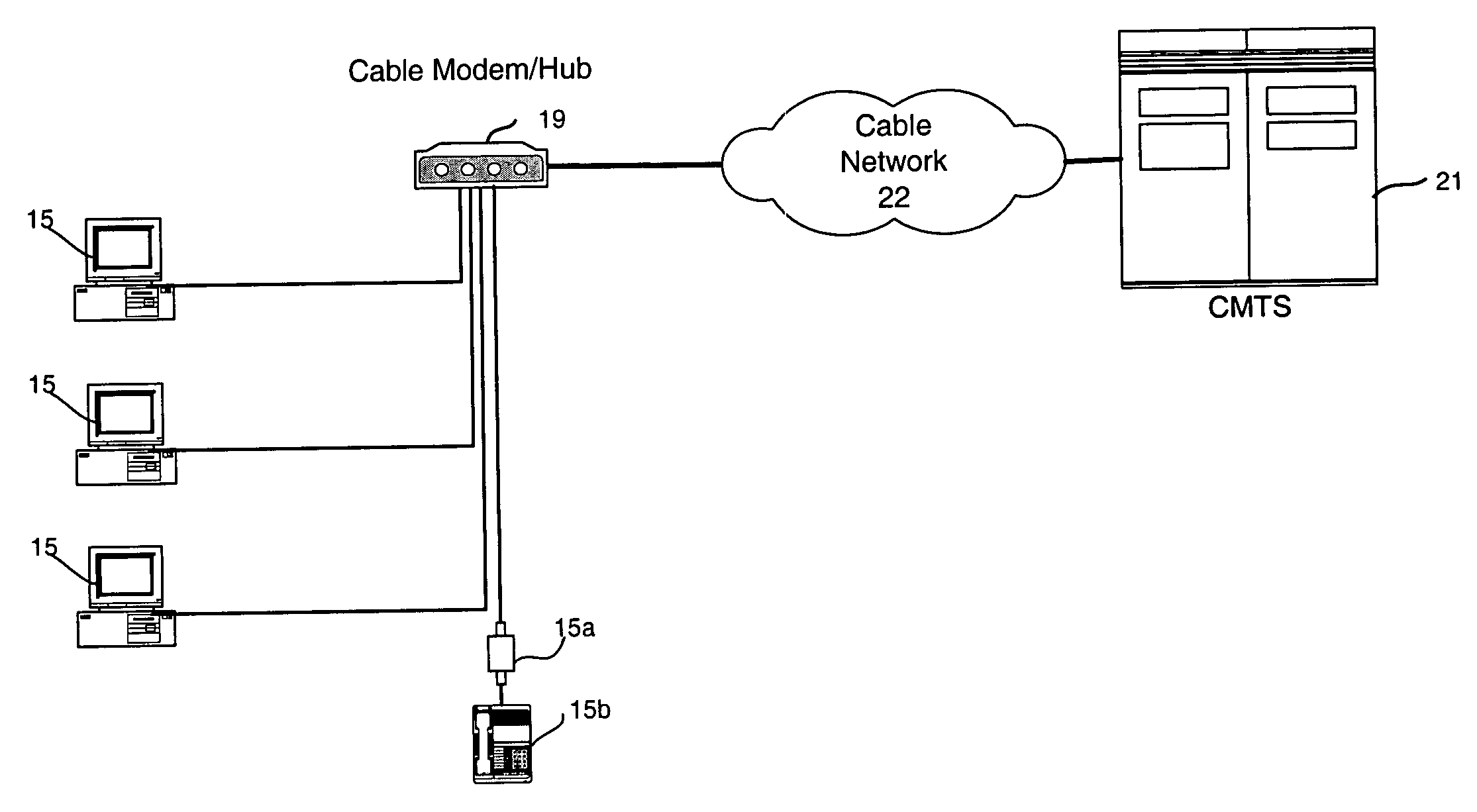
ActiveUS20050055708A1Reduce and eliminate unauthorized network trafficEliminate chargeAnalogue secracy/subscription systemsMultiple digital computer combinationsModem deviceInternet traffic
The present invention teaches methods and systems for subscriber blocking of unauthorized network traffic in a cable data network. The cable modem termination system (CMTS) incorporates a data gateway agent that filters unauthorized traffic thereby eliminating consumption based subscribers from being responsible for related service charges. Embodiments incorporate the use of packet filtering, hybrid stateful packet filtering, content filtering, application layer filtering and time based filtering. Greater acceptance of consumption based billing is achieved by having the filter settings directed by the subscriber.
Owner:TIME WARNER CABLE ENTERPRISES LLC
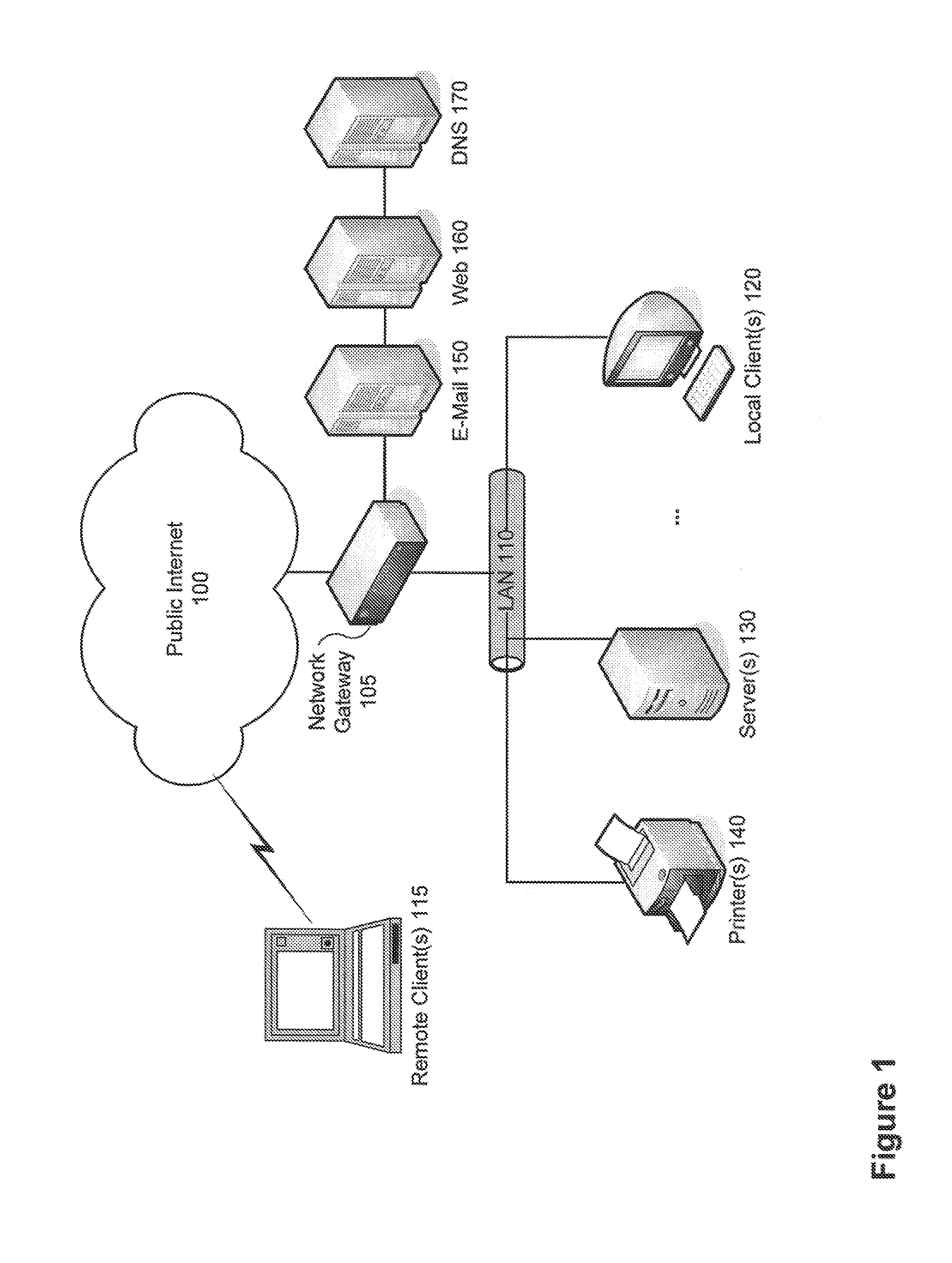
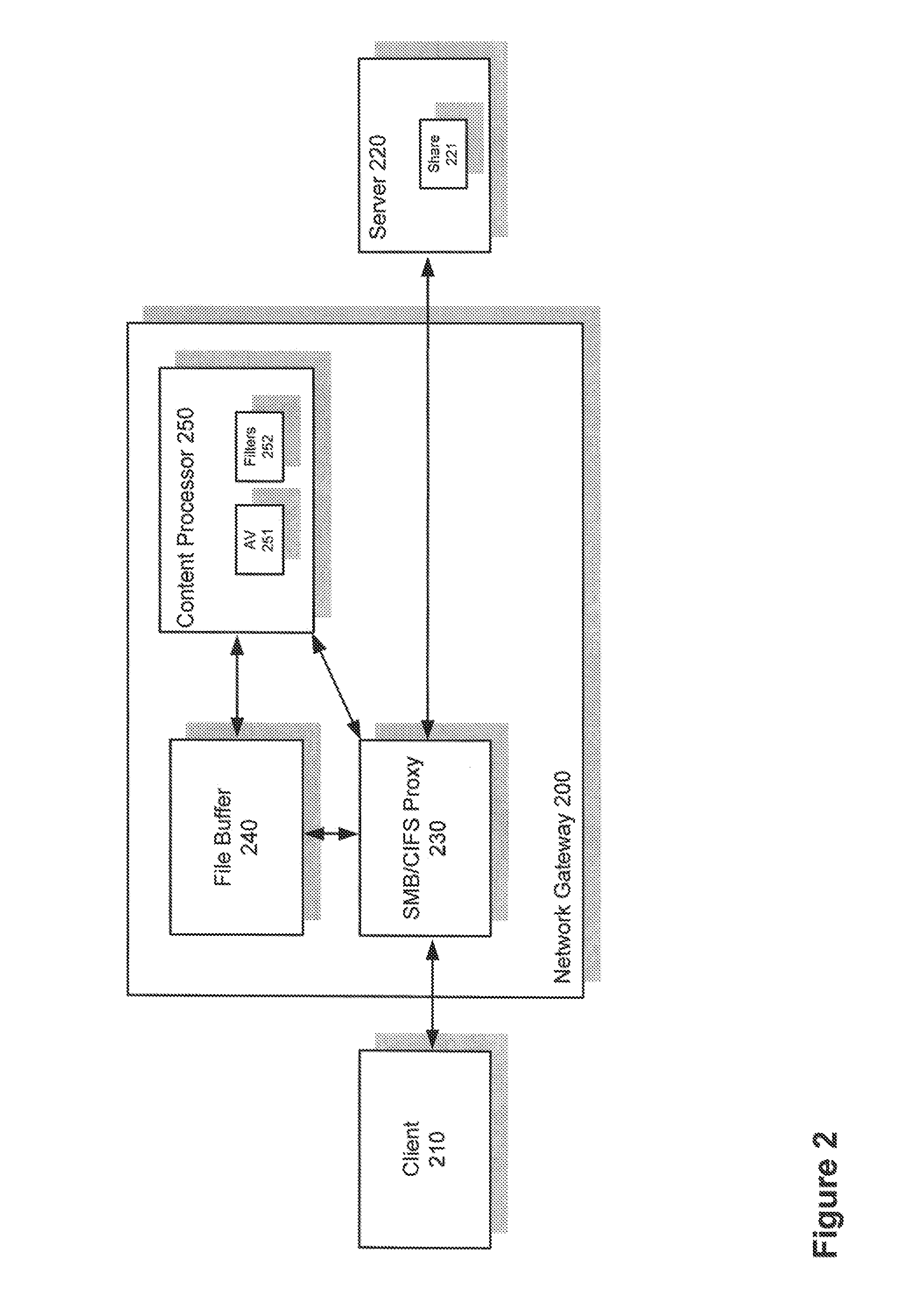
Content filtering of remote file-system access protocols
Methods and systems for content filtering of remote file-system access protocols are provided. According to one embodiment, a transparent proxy running within a network gateway logically interposed between a client and a server intercepts remote file-system access protocol requests / responses. Responsive to receipt of a remote file-system access protocol request from the client, the network gateway issues the remote file-system access protocol request to the server on behalf of the client. The network gateway buffers into a holding buffer associated with the network gateway data being read from or written to a file associated with a share of the server. Then, responsive to a predetermined event in relation to the remote file-system access protocol or the holding buffer, the network gateway determines the existence or non-existence of malicious, dangerous or unauthorized content contained within the holding buffer by performing content filtering on the holding buffer.
Owner:FORTINET
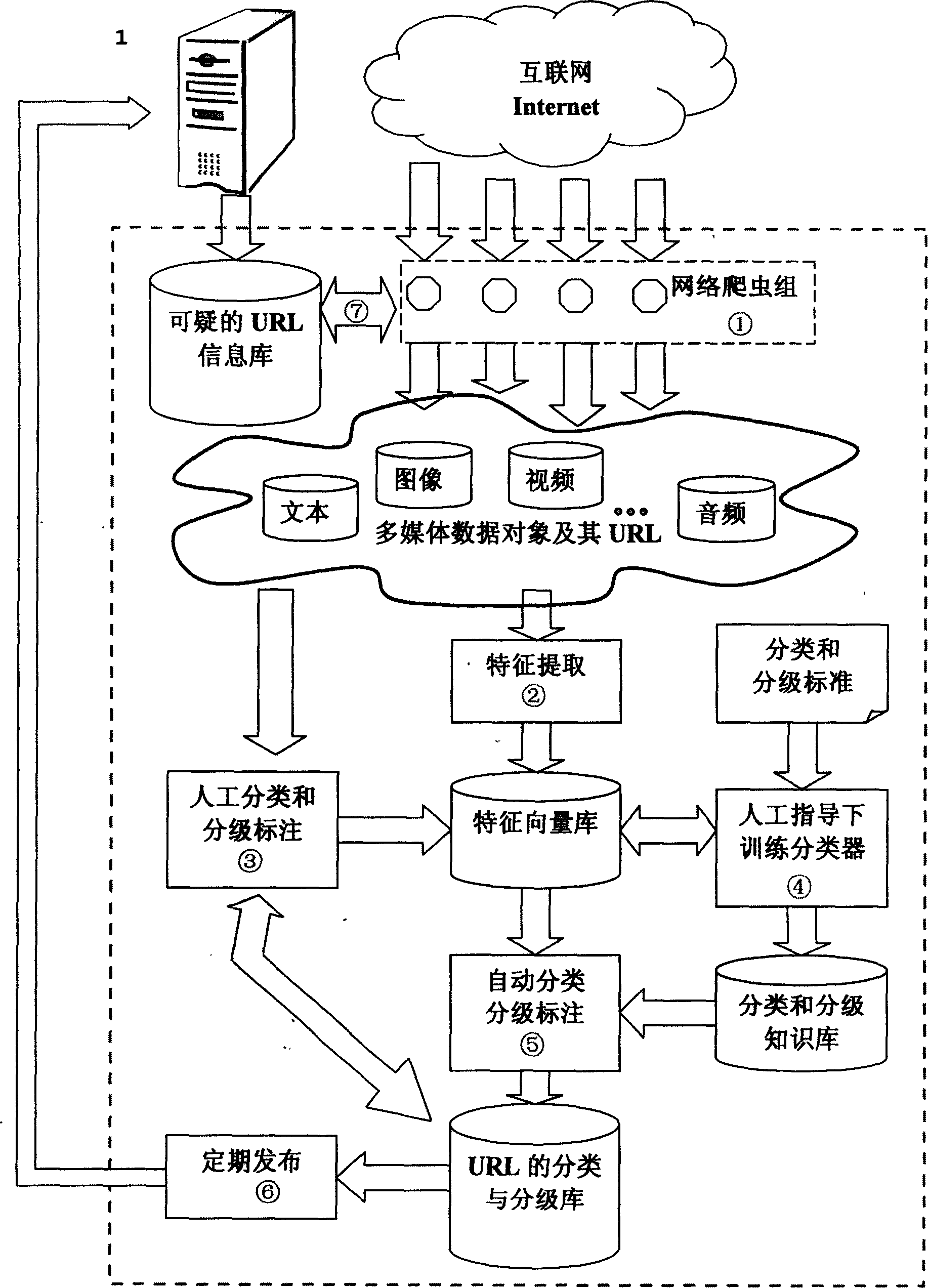
Content filtering gateway realizing method based on network filter
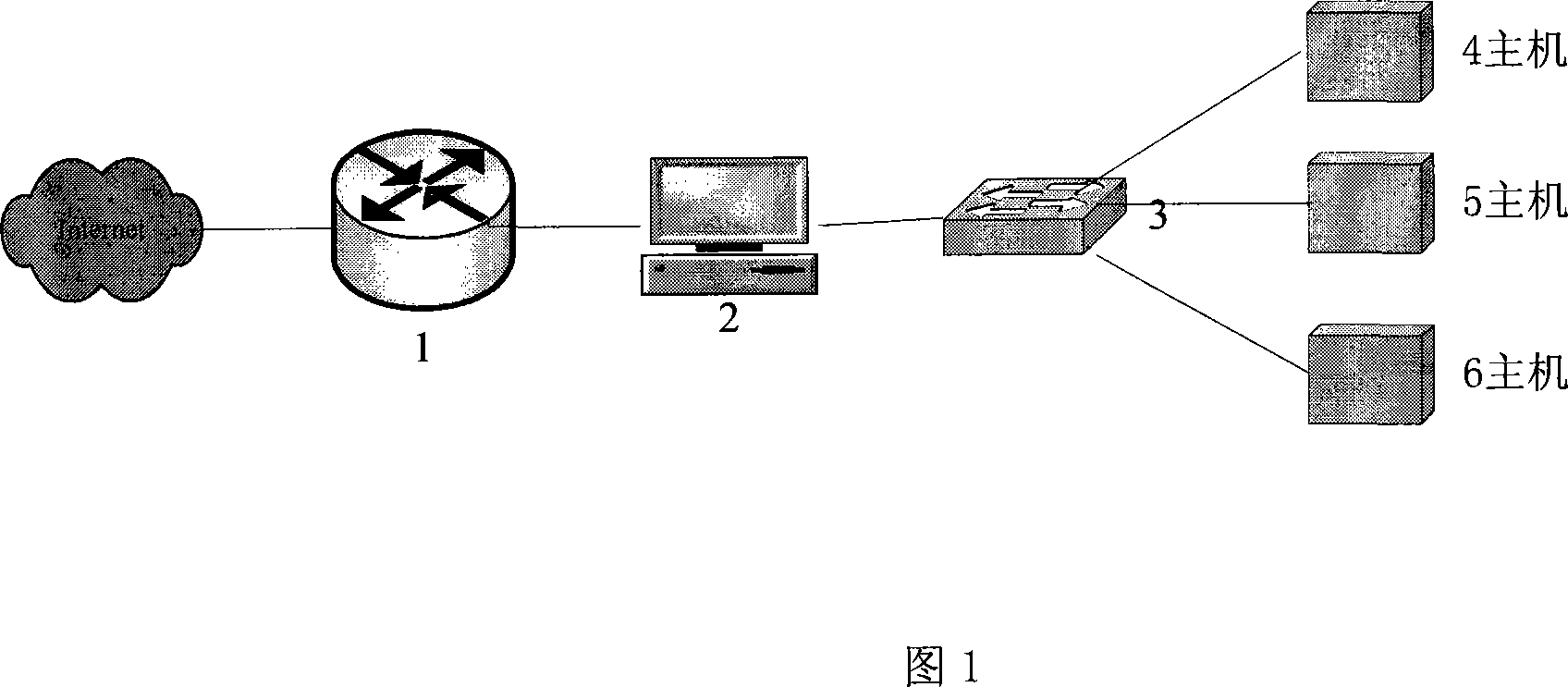
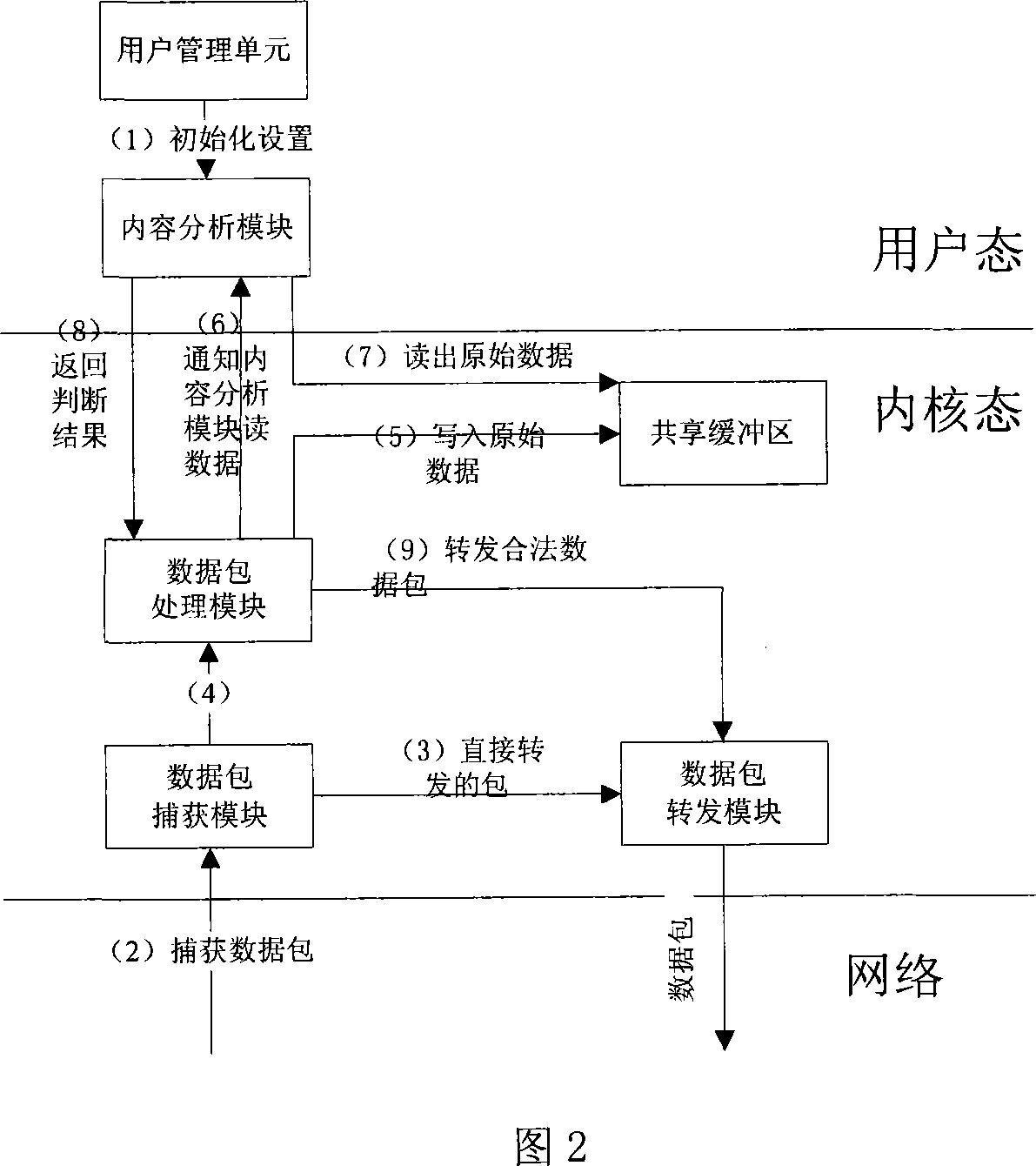
InactiveCN101068229AEasy maintenanceNot easy to attackNetwork connectionsInternal memoryCommunications security
A method for realizing content filtering gateway based on network filter includes realizing network content analysis and real time monitor as well as realizing purpose of filtering application layer information at network layer based on Linux system platform, utilizing network filter Net-filter frame to carry out collection and filtering on data packet under kernel state for optimizing network path of data packet and for raising collection efficiency of data, furthermore using shared internal memory technique of user space and kernel space to submit session content from kernel state to content filtering module of user state.
Owner:BEIJING UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com