Patents
Literature
24353results about "Network connections" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
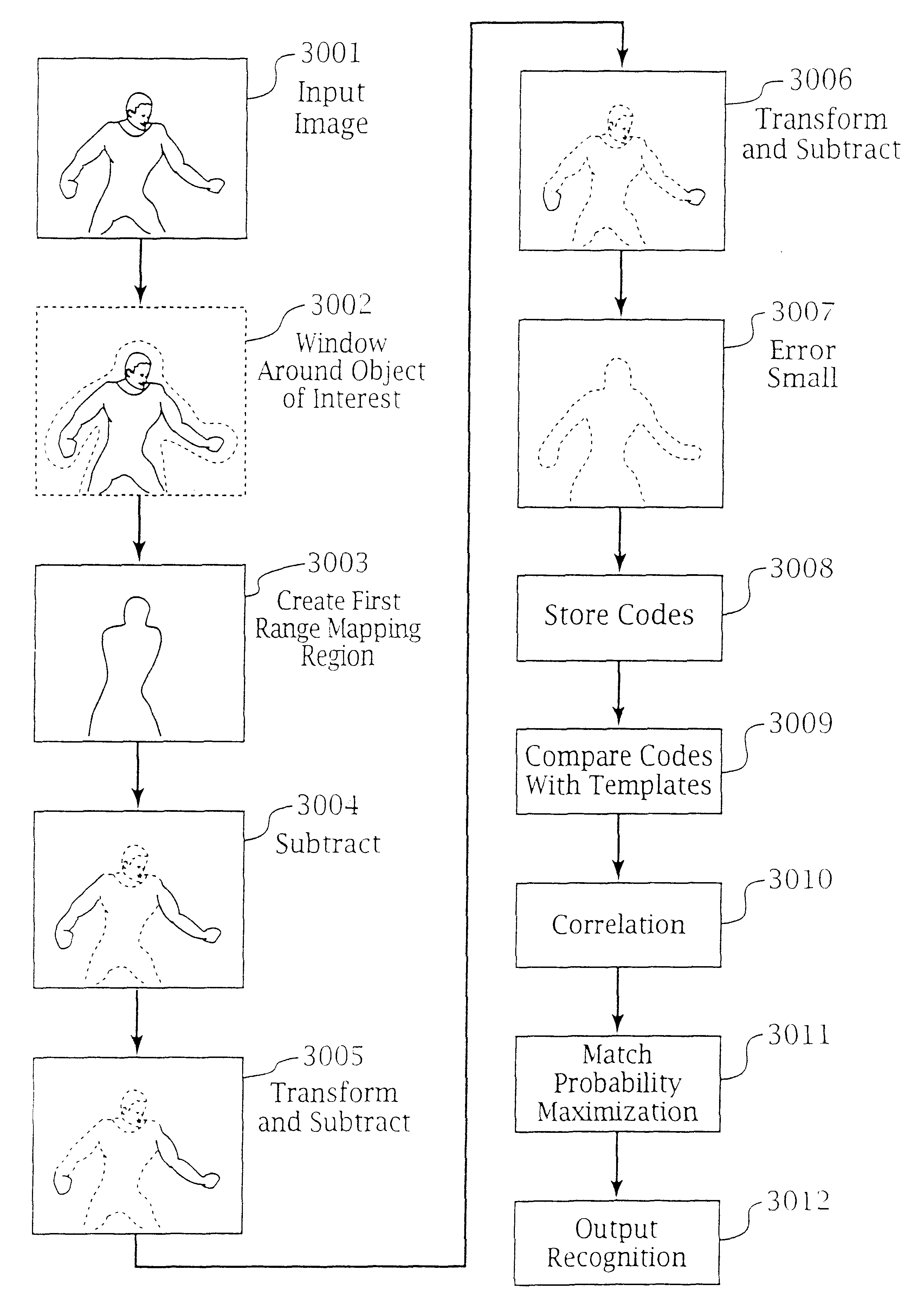
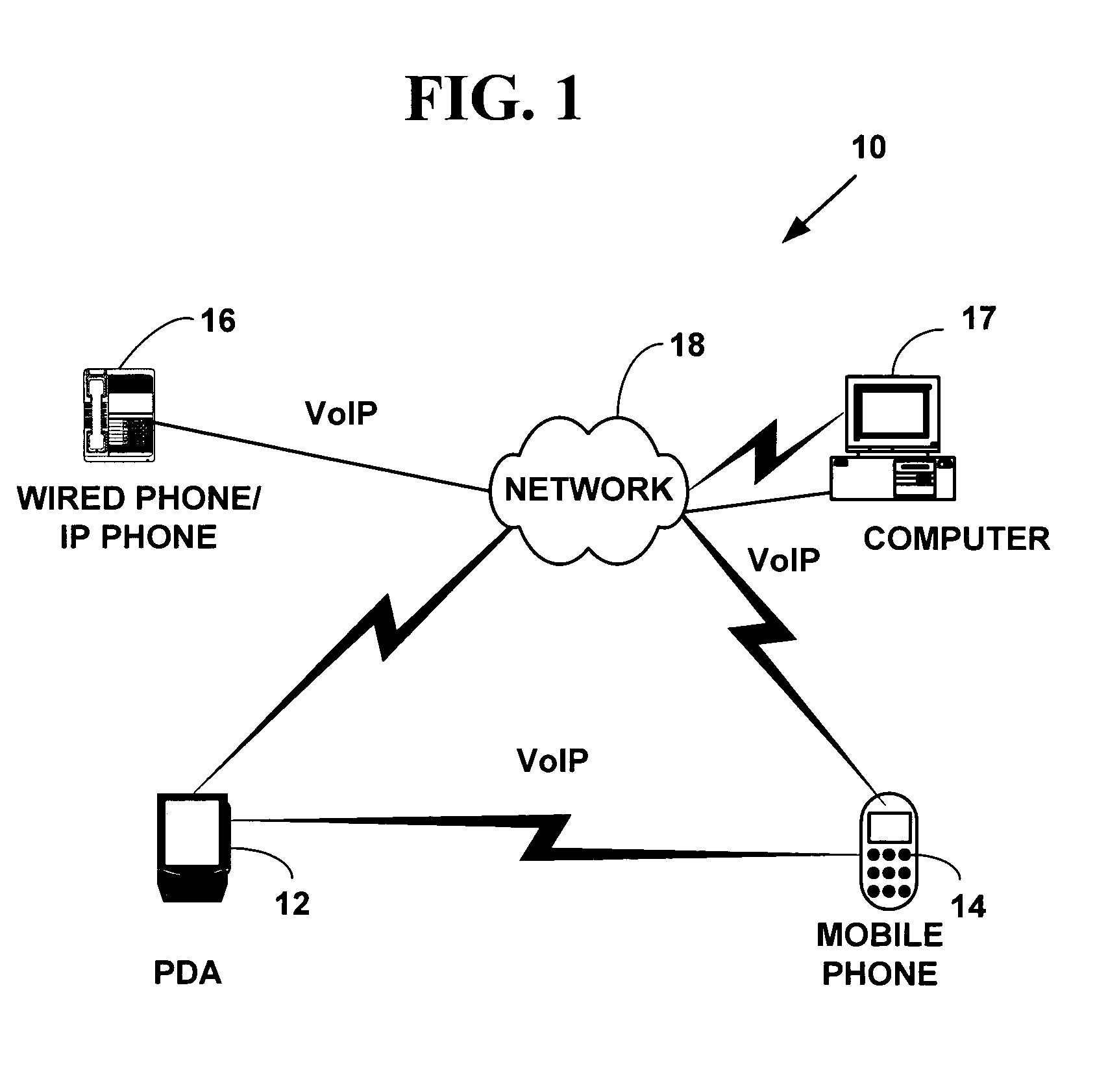
Adaptive pattern recognition based control system and method
InactiveUS6400996B1Minimize timeEasy to implementError preventionFrequency-division multiplex detailsData streamSmart house
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation that may be efficiently processed to determine correspondence. Applications of the interface and system include a video cassette recorder (VCR), medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
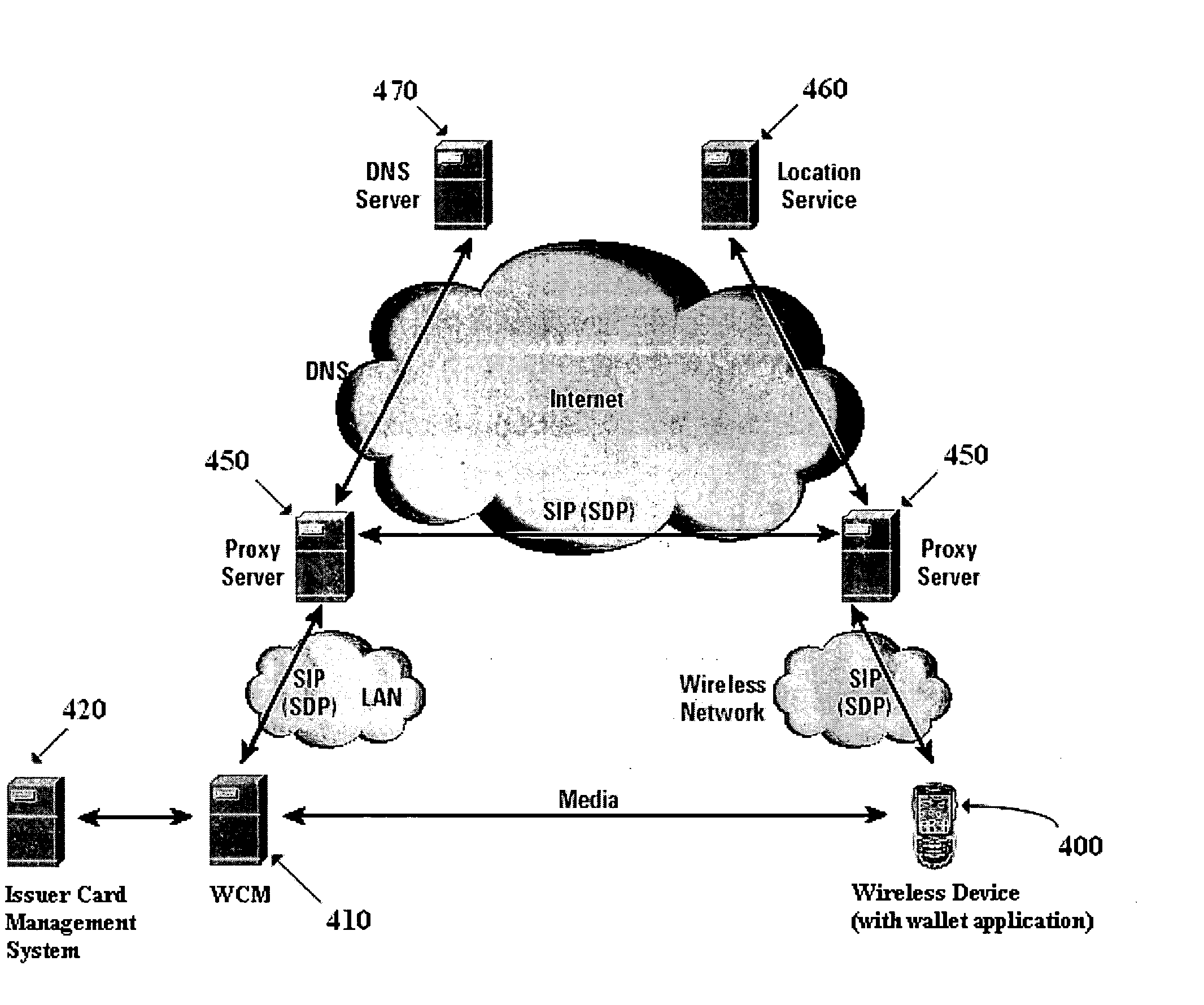
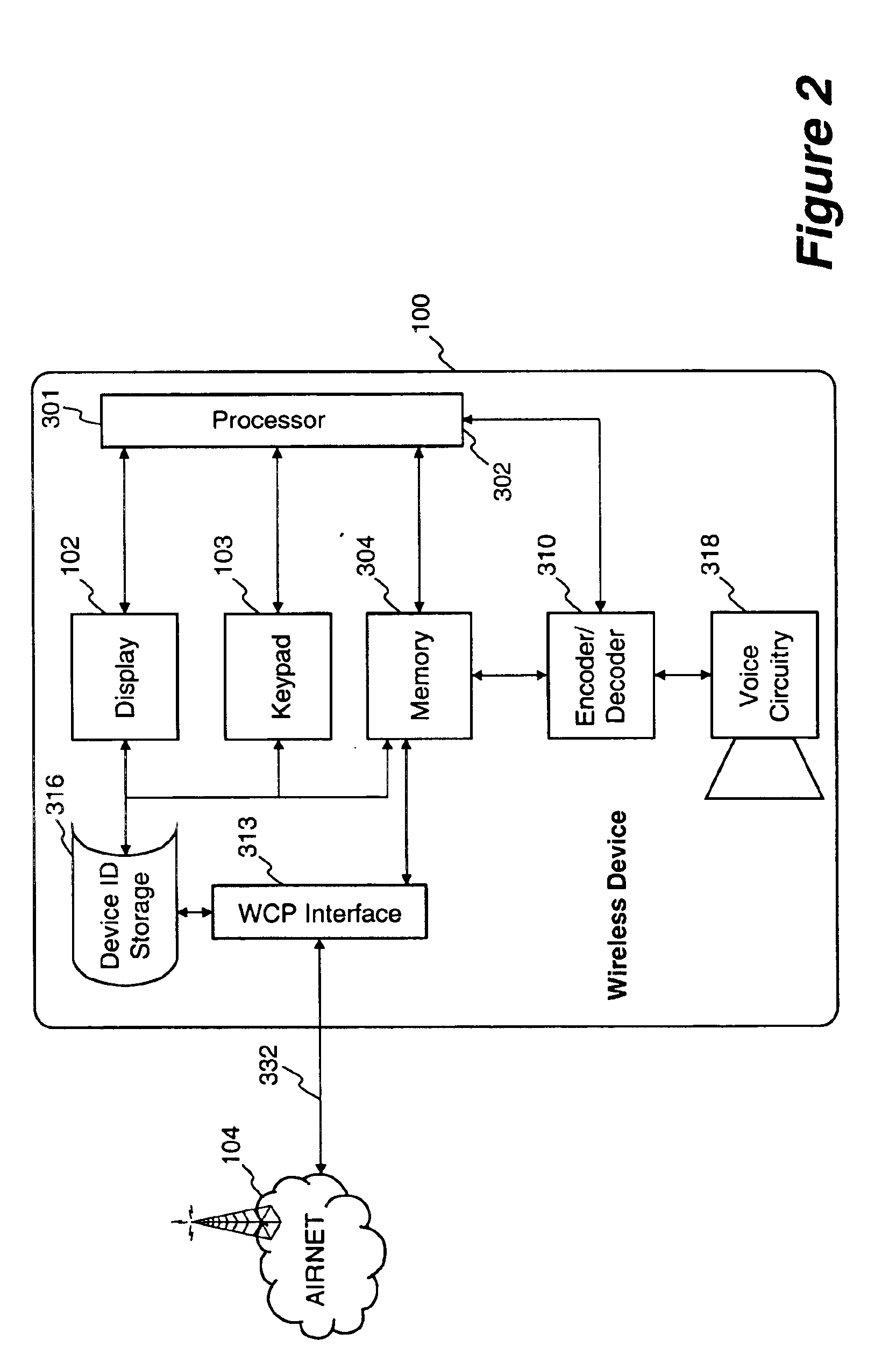
Method and apparatus for managing credentials through a wireless network
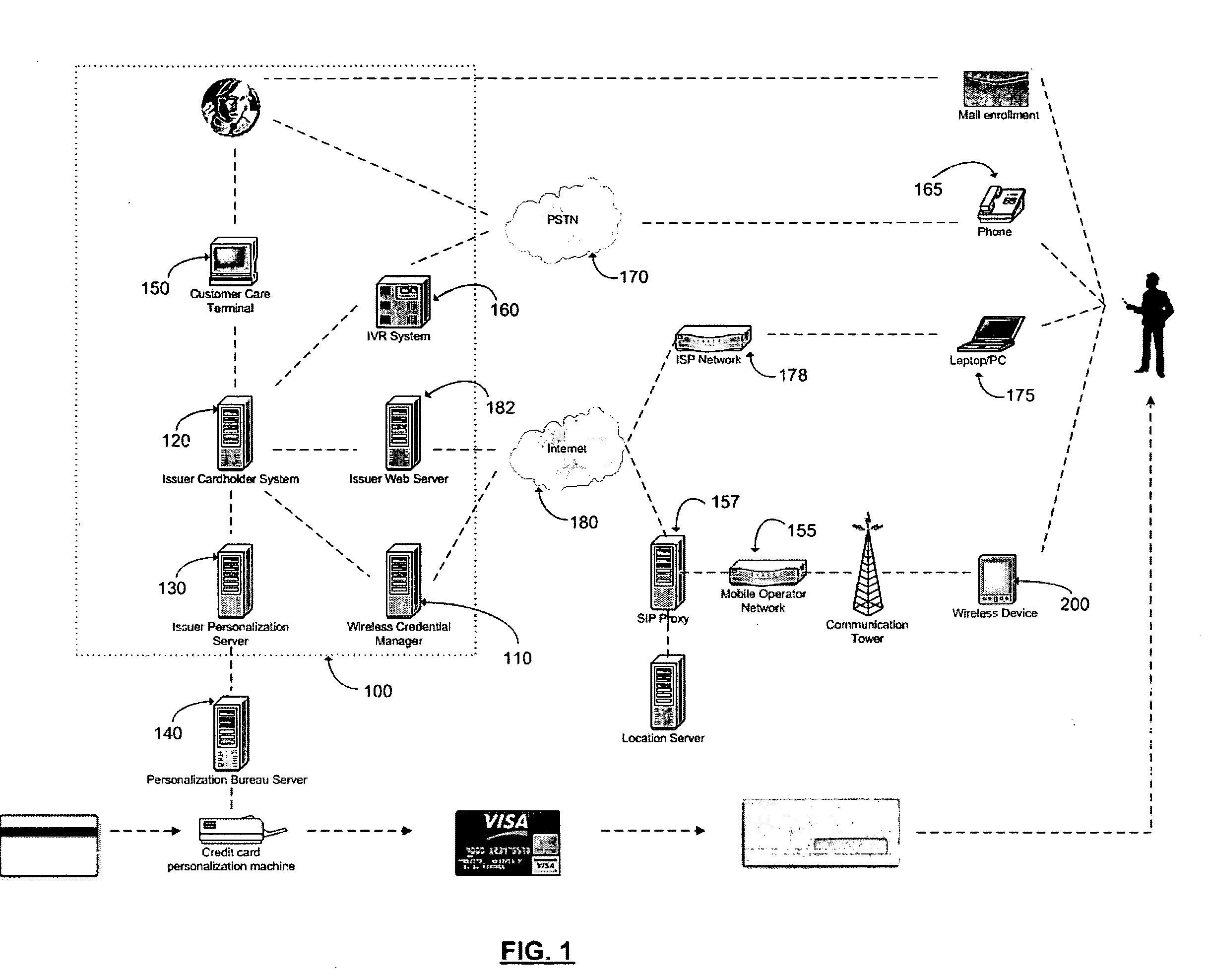
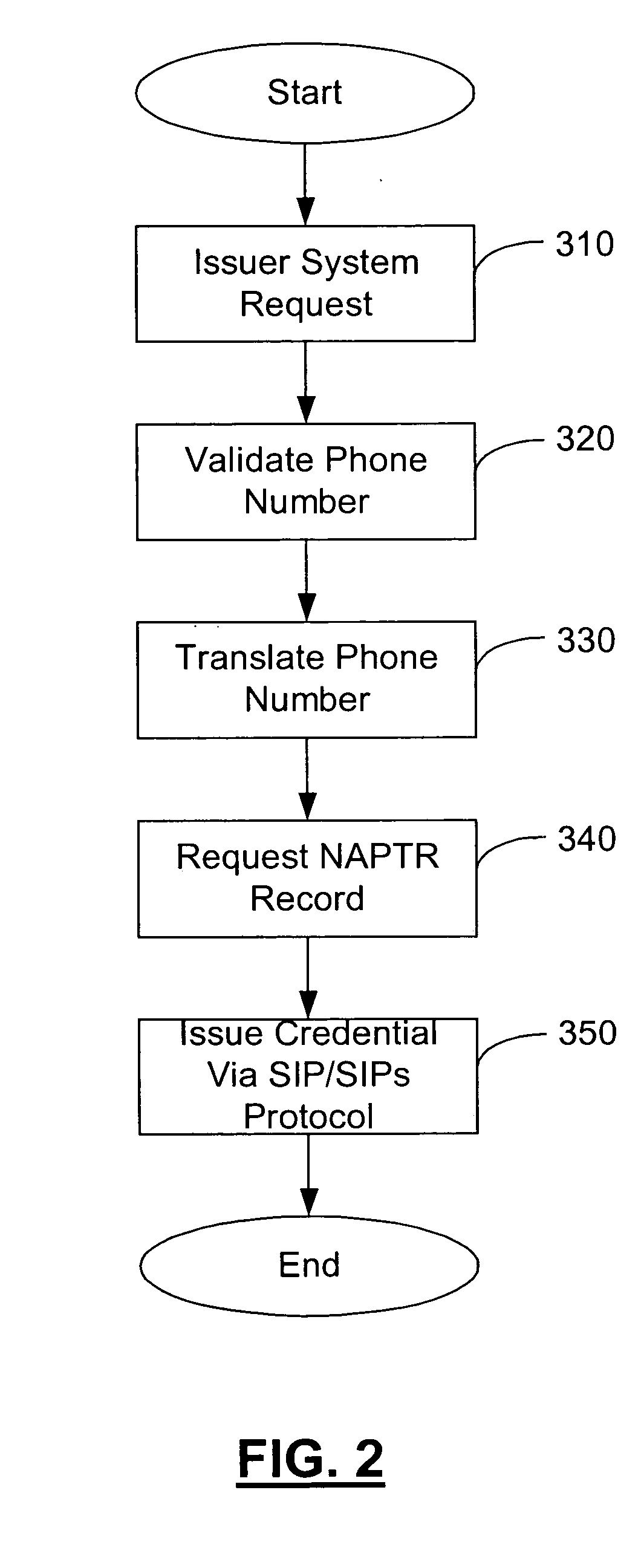
ActiveUS20060165060A1Convenient and efficient and secure distributionNear-field in RFIDData switching by path configurationCredit cardWireless mesh network
A novel system and methodology for conducting financial and other transactions using a wireless device. Credentials may be selectively issued by issuers such as credit card companies, banks, and merchants to consumers permitting the specific consumer to conduct a transaction according to the authorization given as reflected by the credential or set of credentials. The preferred mechanism for controlling and distributing credentials according to the present invention is through one or more publicly accessible networks such as the Internet wherein the system design and operating characteristics are in conformance with the standards and other specific requirements of the chosen network or set of networks. Credentials are ultimately supplied to a handheld device such as a mobile telephone via a wireless network. The user holding the credential may then use the handheld device to conduct the authorized transaction or set of transactions via, for example, a short range wireless link with a point-of-sale terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
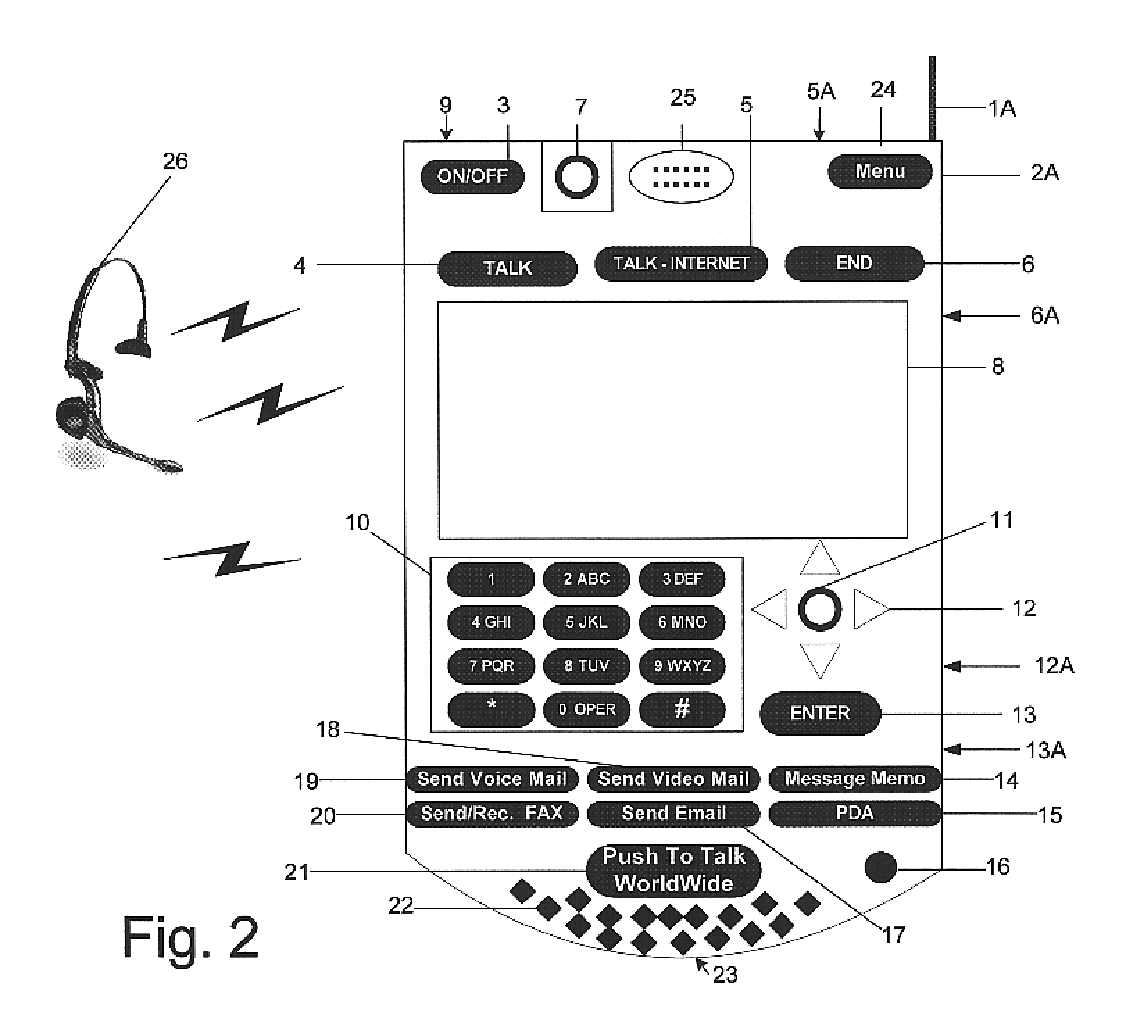
Multifunctional world wide walkie talkie, a tri-frequency cellular-satellite wireless instant messenger computer and network for establishing global wireless volp quality of service (QOS) communications, unified messaging, and video conferencing via the internet
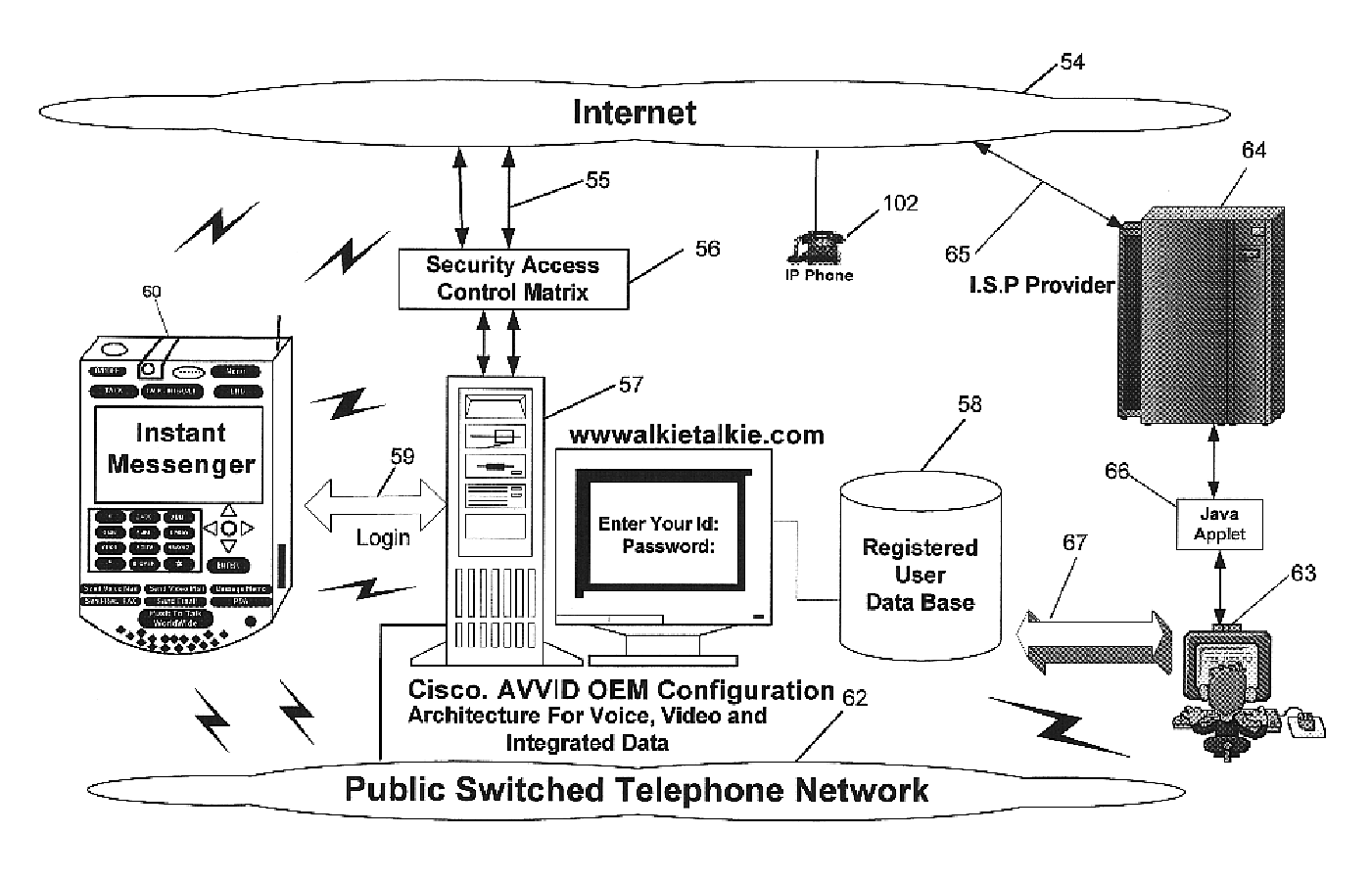
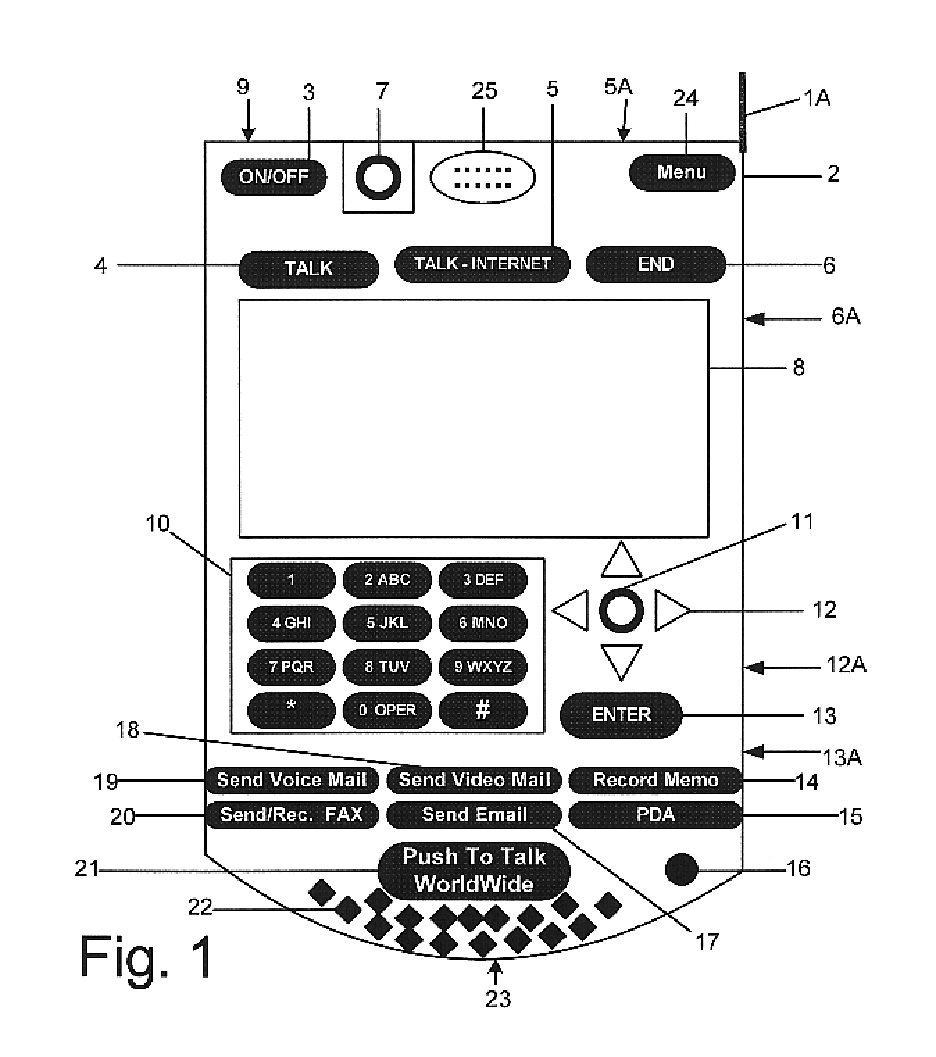
InactiveUS6763226B1High quality voice and data communicationMinimal costCordless telephonesInterconnection arrangementsQuality of serviceMass storage
World-Wide-Walkie-Talkie, a high speed multifunction interstellar wireless computer / instant messenger communicator, Personal Digital Assistant (PDA), coupled with a resilient, robust, VoIP data network and internet server method, deploying multiple wireless networks and protocols such as Voice Over IP, GPRS, WAP, Bluetooth, PCS, I-Mode, comprising a high speed Intel Pentium 4 Mobile(TM) or compatible Processor, to formulate a internet gateway system (99) and network bridge (150) for establishing instant low cost, real time global communications to the Public Switched Telephone Network via the internet (54). A PUSH-TO-TALK-WORLDWIDE button (21) instantly initiates global bisynchronous communications, or videoconferencing sessions. Fax, VideoMail, and unified messaging services are immediately available. GPS and mass memory provides global navigational tracking and data storage. Internet users, telephones, and cellular / satellite phone users can intercommunicate with the invention via VoIP / IM services. The invention provides uniformed global wireless communications, eliminates traditional long distance costs, and operates anywhere on earth.
Owner:COMP SCI CENT
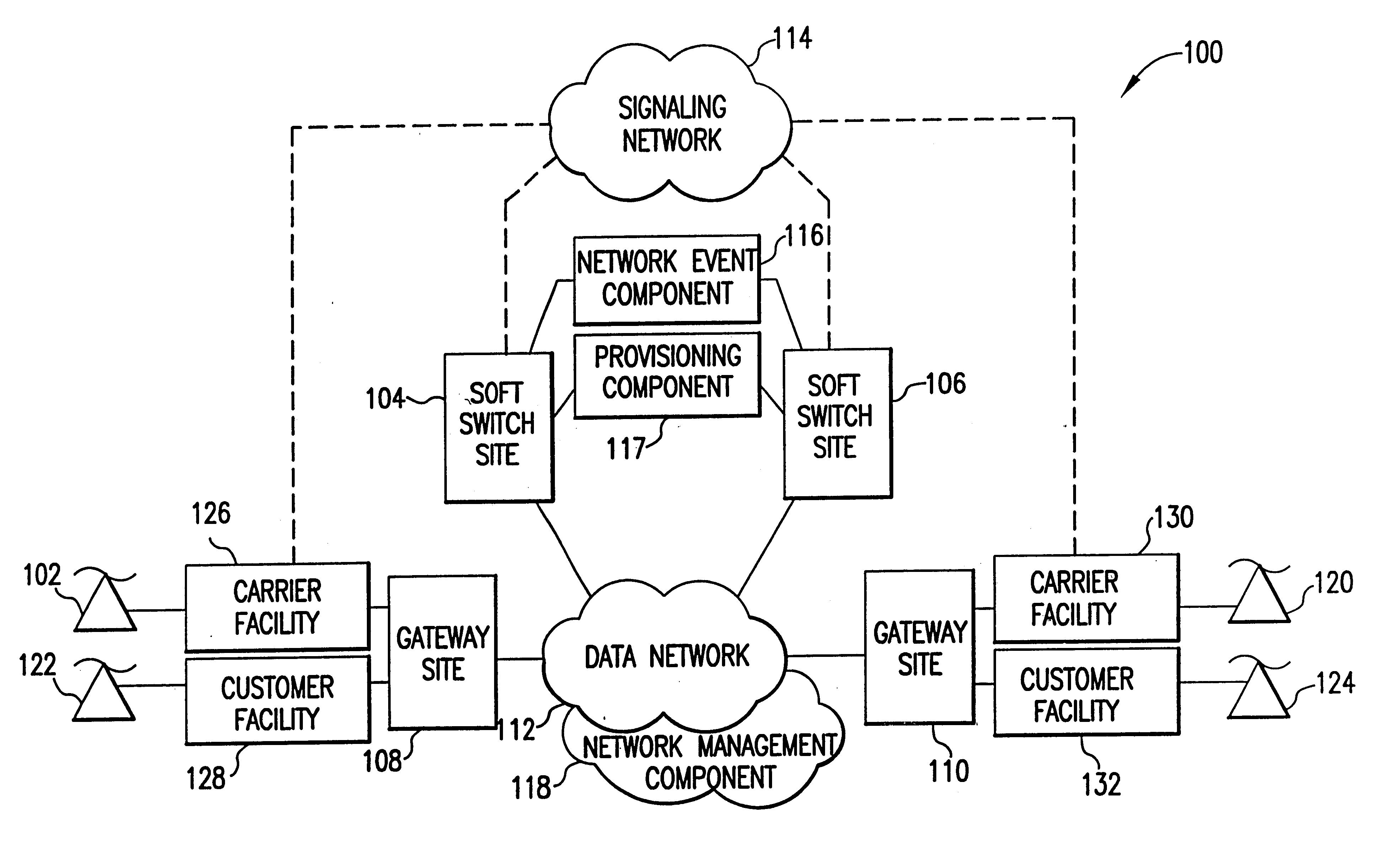
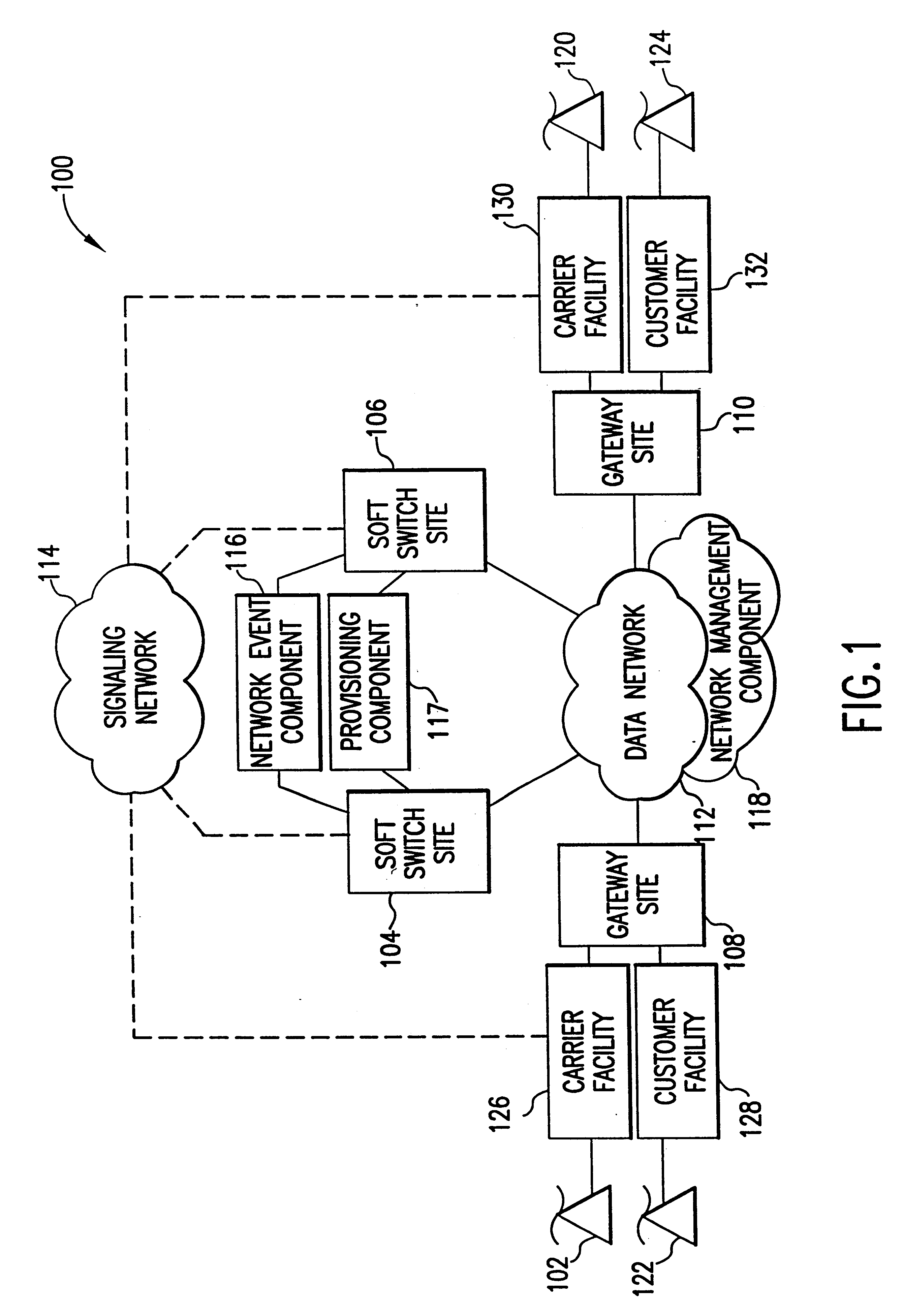
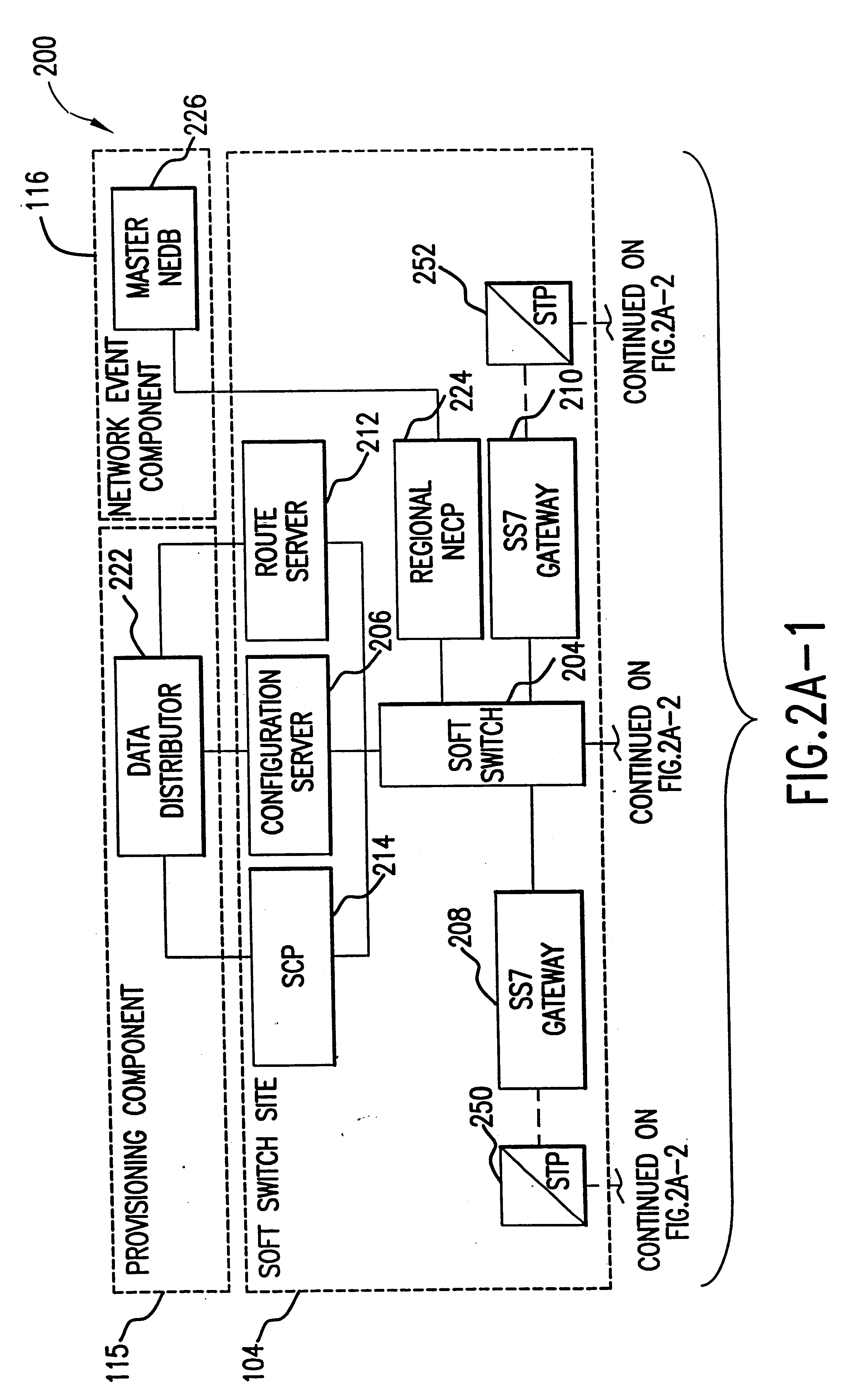
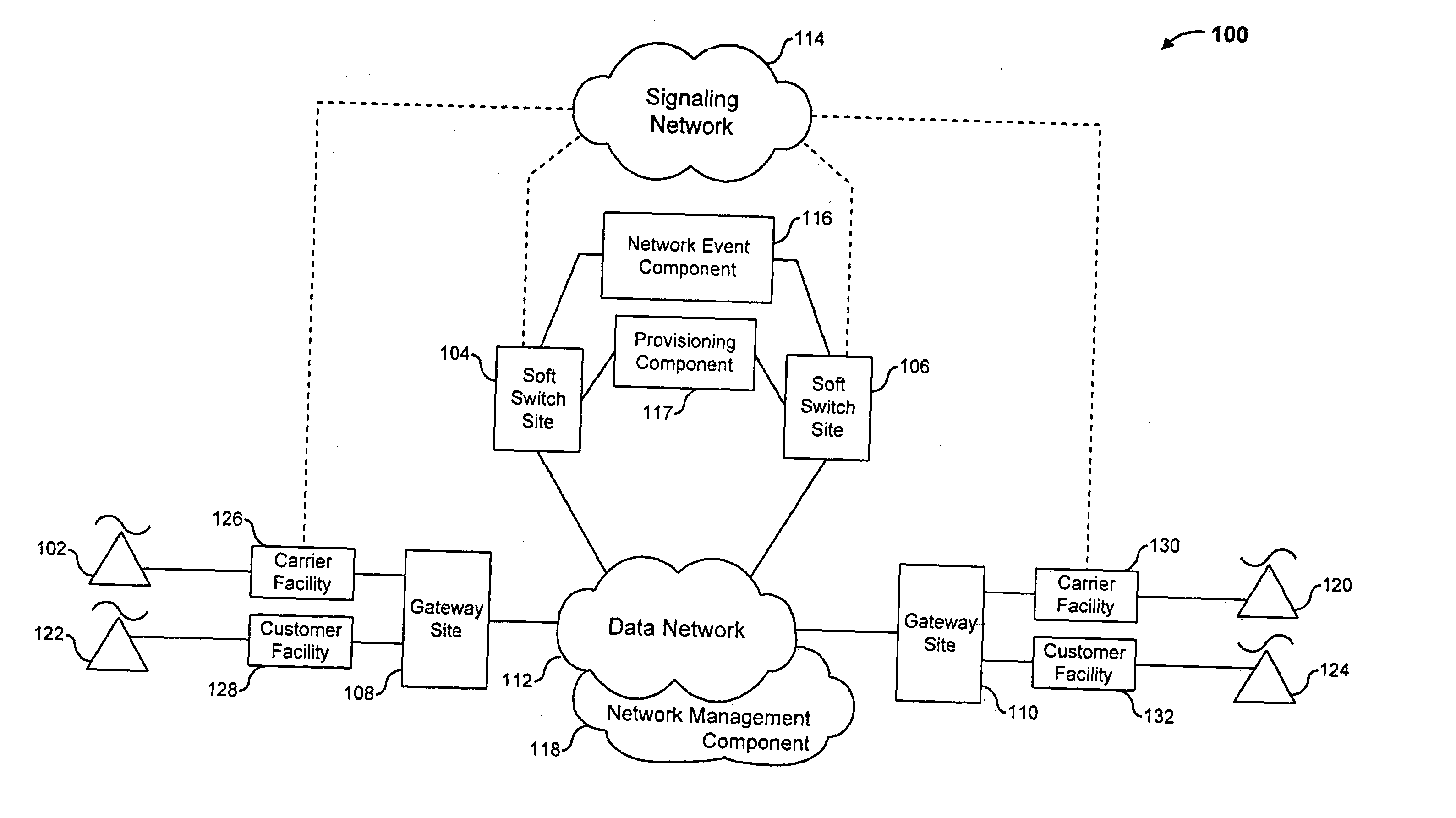
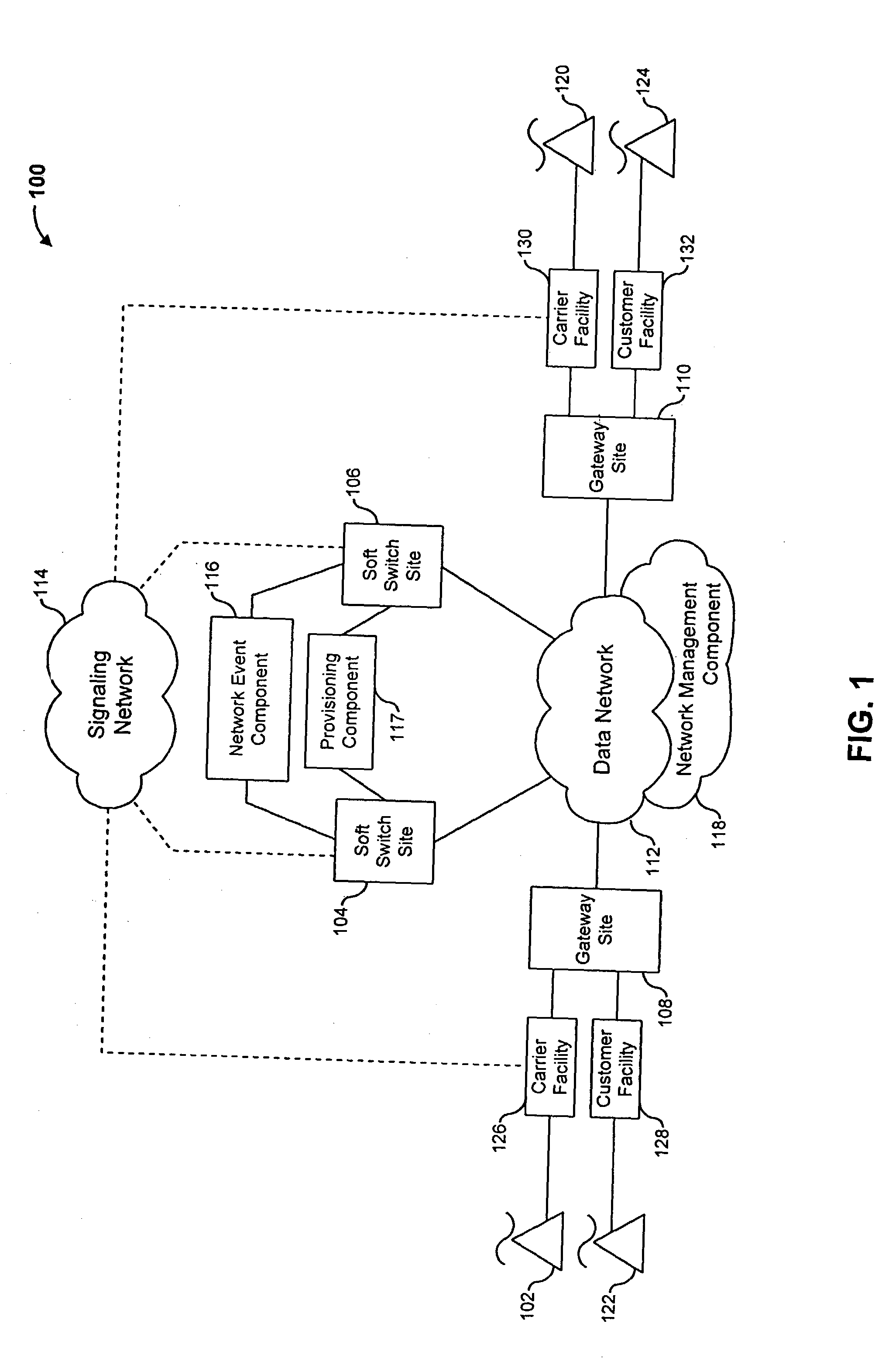
Voice over data telecommunications network architecture
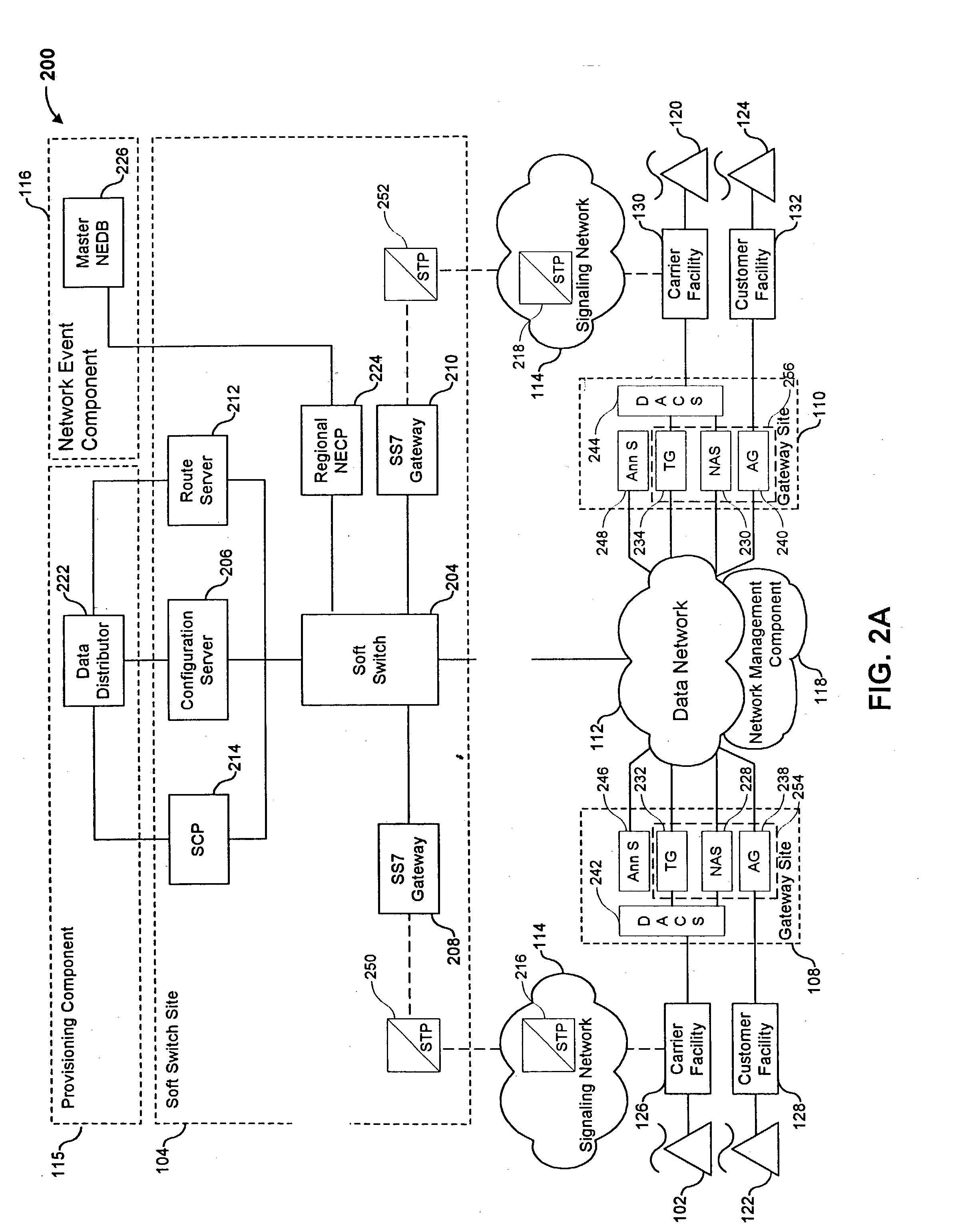
InactiveUS6614781B1Interconnection arrangementsDc level restoring means or bias distort correctionNetwork operations centerNetwork architecture
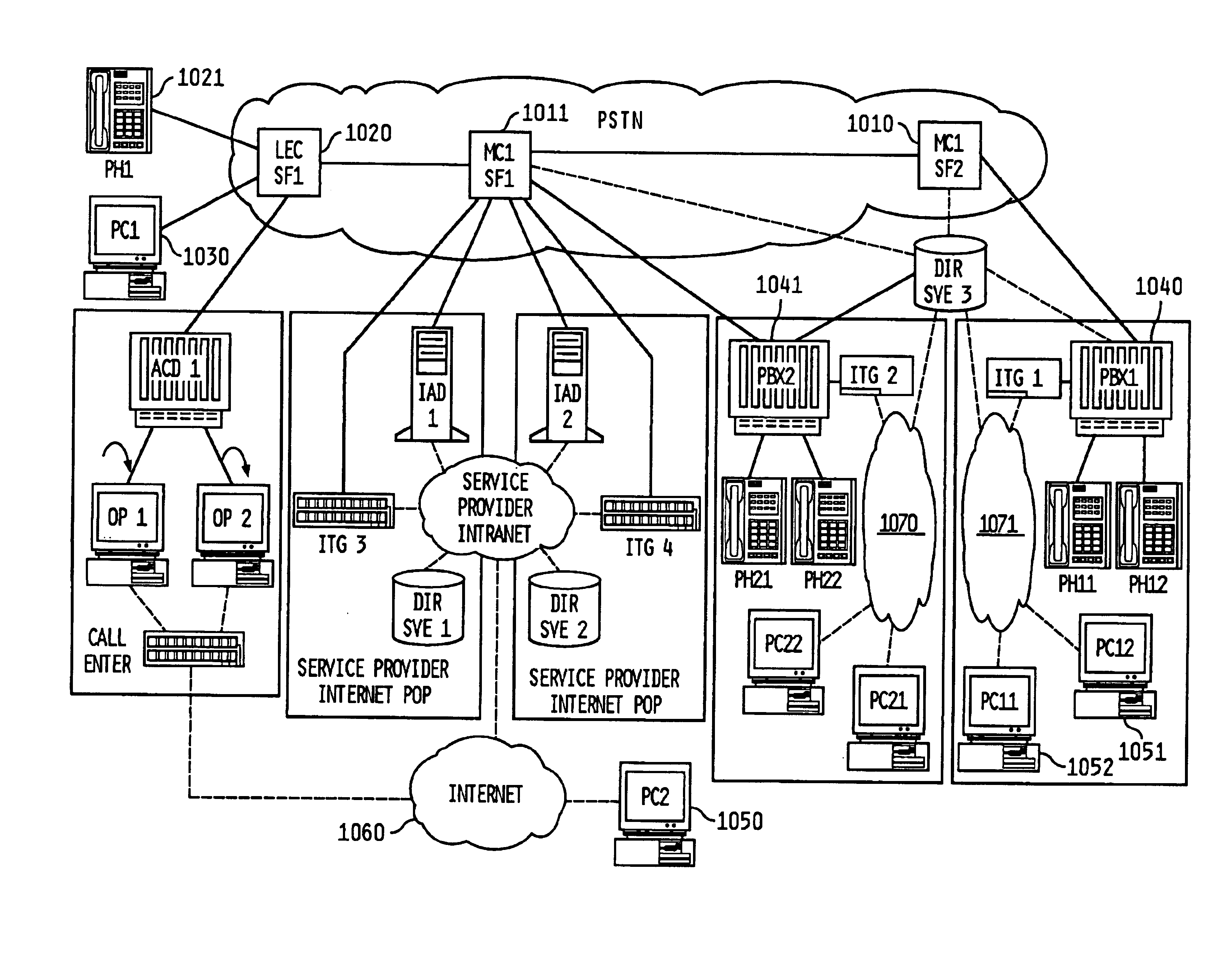
The present invention describes a system and method for communicating voice and data over a packet-switched network that is adapted to coexist and communicate with a legacy PSTN. The system permits packet switching of voice calls and data calls through a data network from and to any of a LEC, a customer facility or a direct IP connection on the data network. The system includes soft switch sites, gateway sites, a data network, a provisioning component, a network event component and a network management component. The system interfaces with customer facilities (e.g., a PBX), carrier facilities (e.g., a LEC) and legacy signaling networks (e.g., SS7) to handle calls between any combination of on-network and off-network callers.The soft switch sites provide the core call processing for the voice network architecture. The soft switch sites manage the gateway sites in a preferred embodiment, using a protocol such as the Internet Protocol Device Control (IPDC) protocol to request the set-up and tear-down of calls. The gateway sites originate and terminate calls between calling parties and called parties through the data network. The gateway sites include network access devices to provide access to network resources. The data network connects one or more of the soft switch sites to one or more of the gateway sites. The provisioning and network event component collects call events recorded at the soft switch sites. The network management component includes a network operations center (NOC) for centralized network management.
Owner:LEVEL 3 COMM LLC
Method and system for disaggregating audio/visual components
ActiveUS7295548B2Improve user experiencePlural information simultaneous broadcastTwo-way working systemsComputer networkBrick
The present invention is directed to a method and system for disaggregating and connecting A / V components, and communicating A / V content stream information. An A / V stream from a source device is packaged for transmission over an IP network to one or more output devices. A brick device enables the integration of legacy A / V systems into the network supported A / V system. The brick device operates to provide analog signal and IP protocol conversion, along with the synchronization of received A / V stream data packets. The rendering and play of the A / V stream content on multiple output devices is synchronized to overcome distortions and other network idiosyncrasy and to facilitate a pleasant user experience.
Owner:MICROSOFT TECH LICENSING LLC
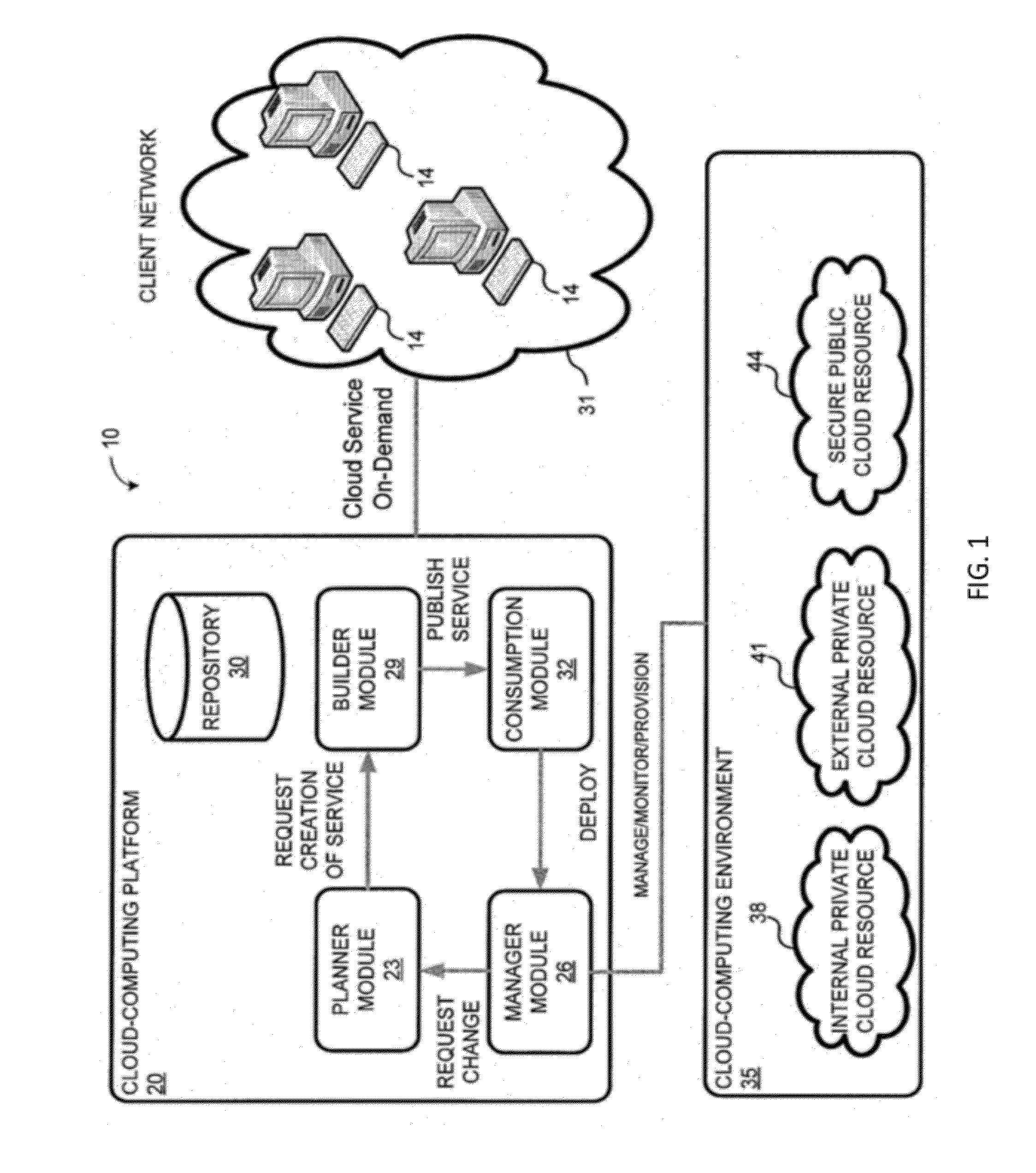
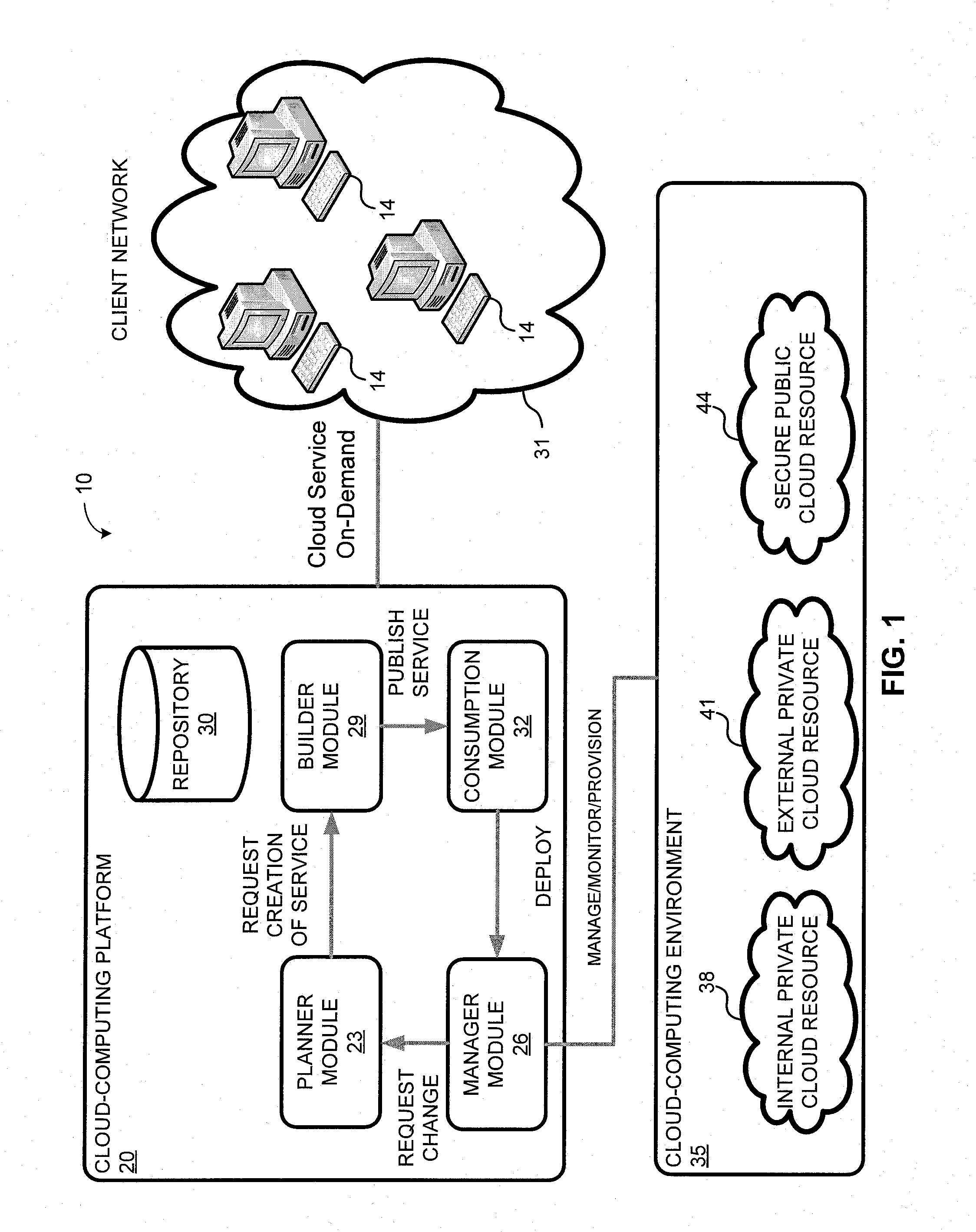
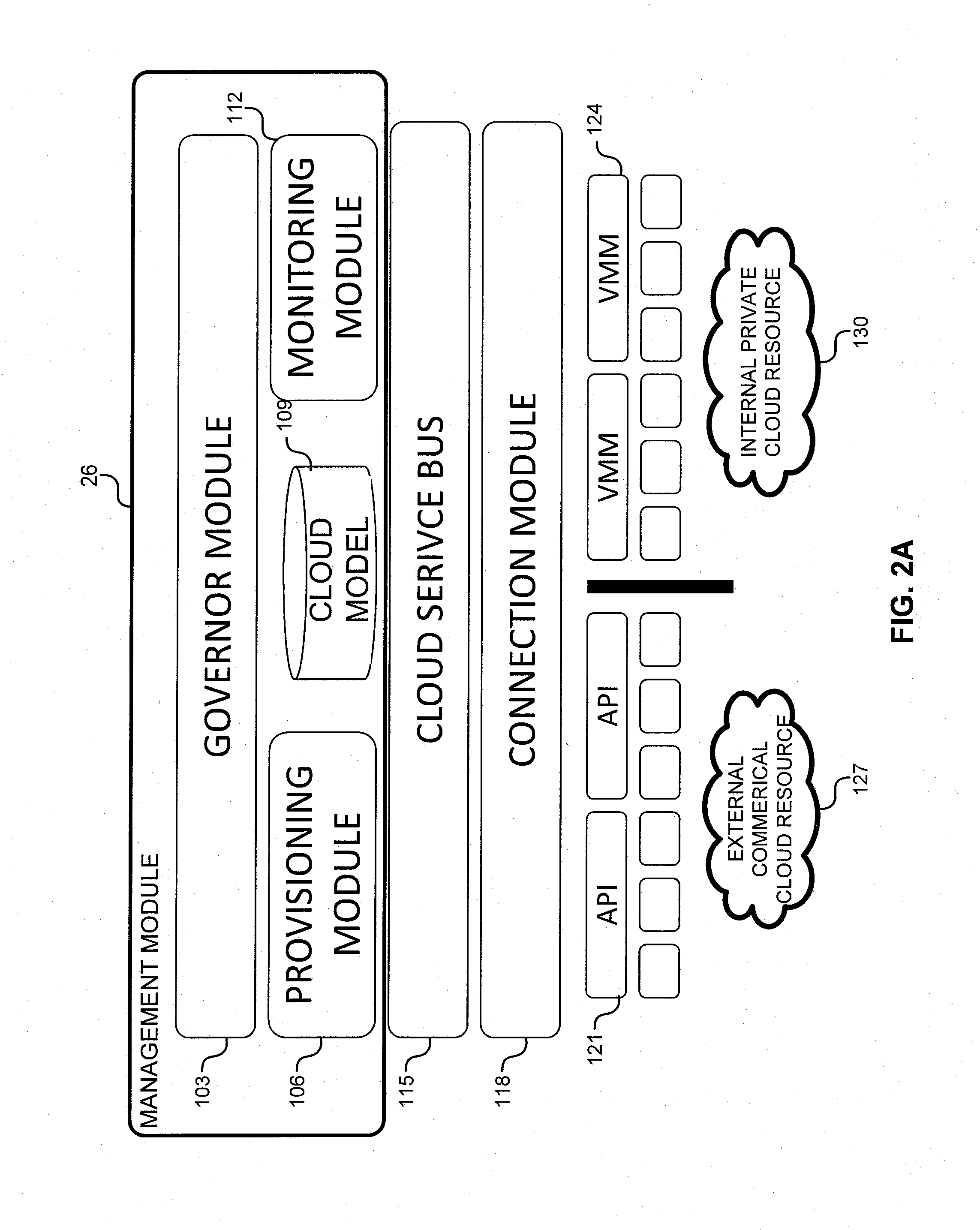
System and method for a cloud computing abstraction layer with security zone facilities
ActiveUS20120185913A1Rapid and dynamic deployment and scalingShorten the timeComputer security arrangementsHybrid transportVirtualizationAbstraction layer
In embodiments of the present invention improved capabilities are described for a virtualization environment adapted for development and deployment of at least one software workload, the virtualization environment having a metamodel framework that allows the association of a policy to the software workload upon development of the workload that is applied upon deployment of the software workload. This allows a developer to define a security zone and to apply at least one type of security policy with respect to the security zone including the type of security zone policy in the metamodel framework such that the type of security zone policy can be associated with the software workload upon development of the software workload, and if the type of security zone policy is associated with the software workload, automatically applying the security policy to the software workload when the software workload is deployed within the security zone.
Owner:DXC US AGILITY PLATFORM INC
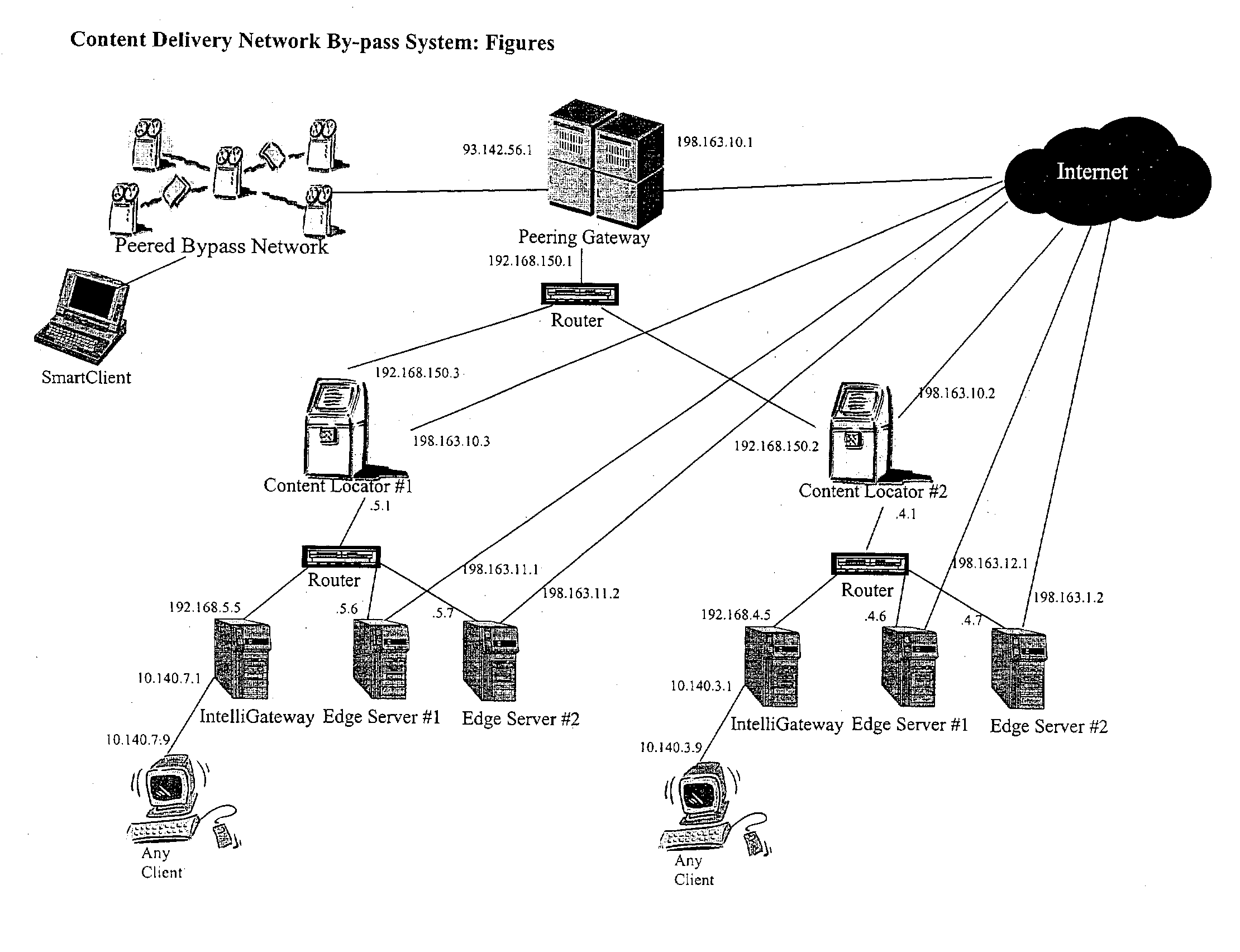
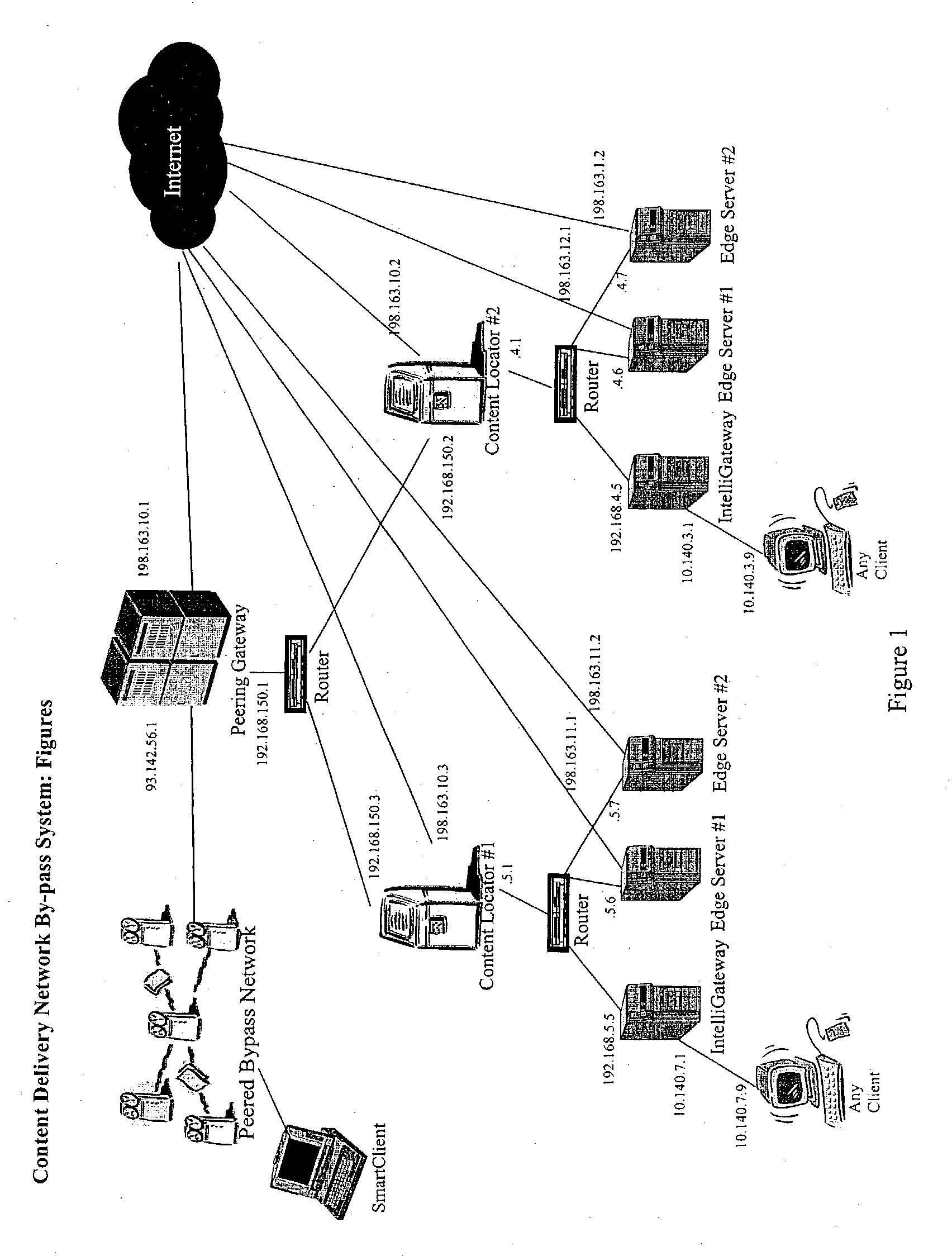
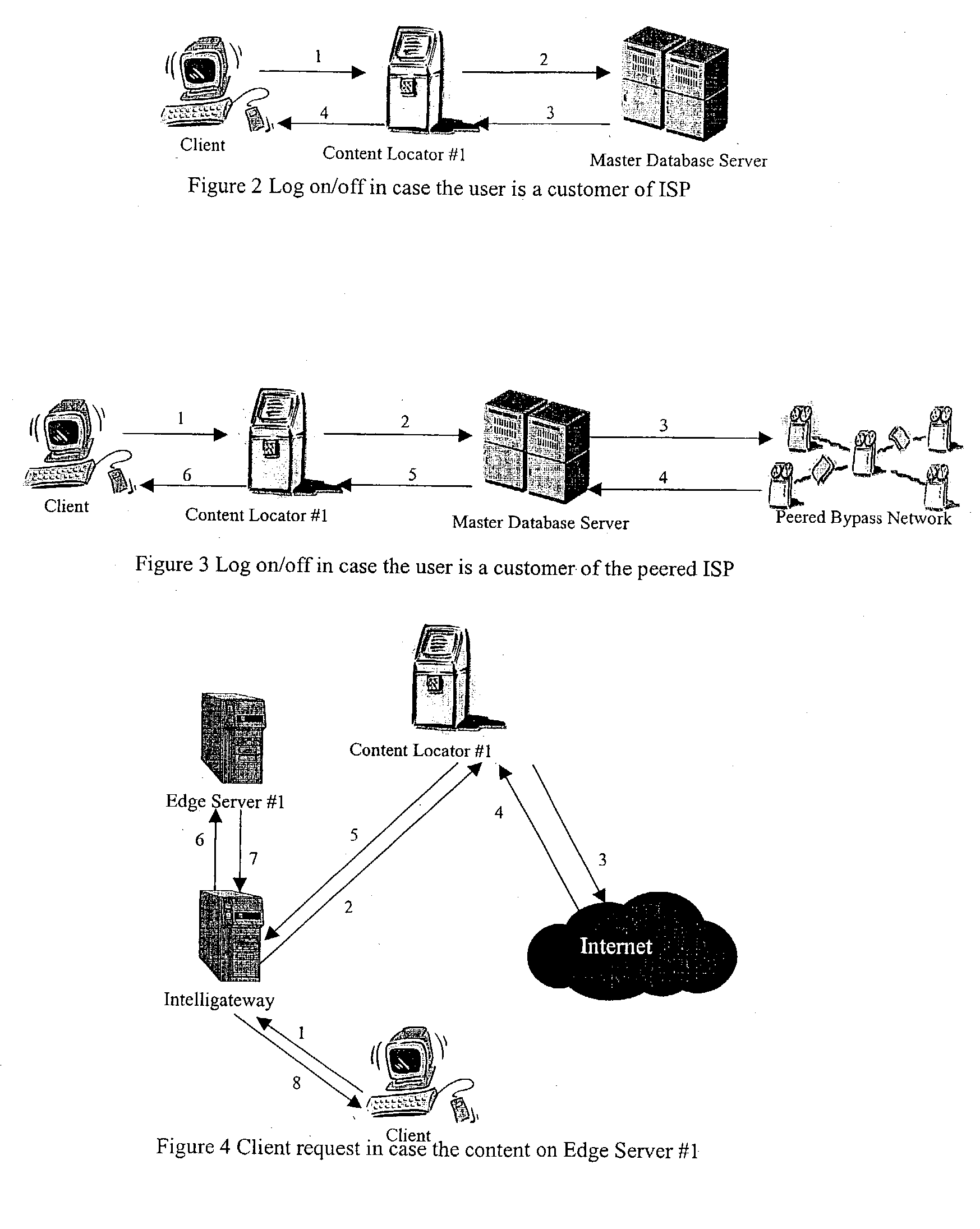
Content delivery network by-pass system
InactiveUS20030174648A1Increase capacityIncrease in sizeError preventionTransmission systemsWeb sitePeering
The bypass network is designed to provide fast access and high quality streaming media services anywhere anytime. There are five major components including Peering Gateway, Content Locator, Edge Server, Gateway and Client. The whole bypass network is divided into number of self-managed sub-networks, which are referred as local networks in this document. Each local network contains Edge Servers, gateways, and a Content Locator. The Edge Servers serve as cache storage and streaming servers for the local network. The gateways provide a connection point for the client computers. Each local network is managed by a Content Locator. The Content Locator handles all client requests by communicating with the Peering Gateway and actual web sites, and makes the content available on local Edge Servers. The Content Locator also balances the load on each Edge Server by monitoring the workload on them. One embodiment is designed for home users whose home machine does not move around frequently. A second embodiment is designed for business users who travel around very often where the laptops would self-configure as a client of the network.
Owner:TELECOMM RES LAB
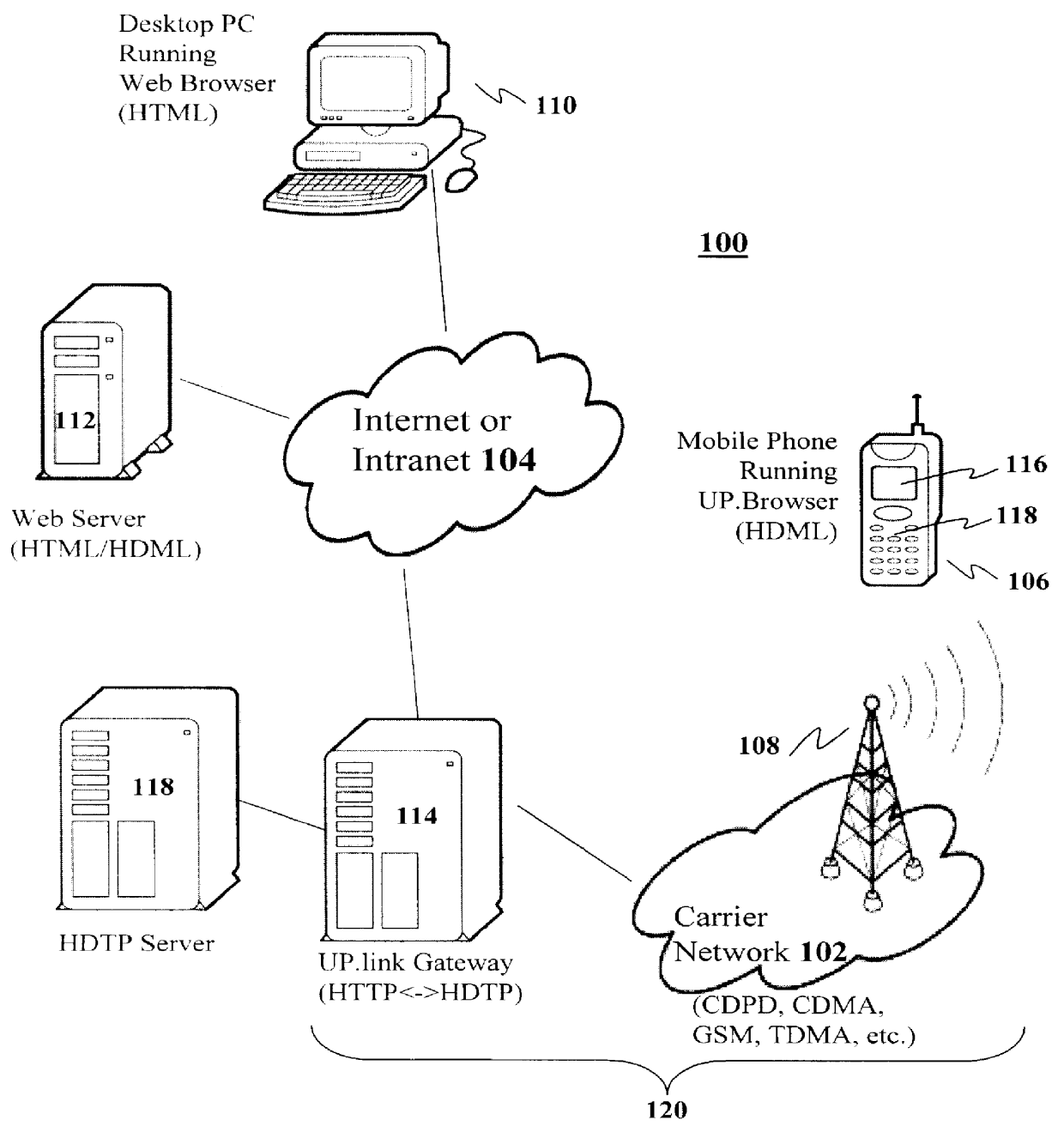
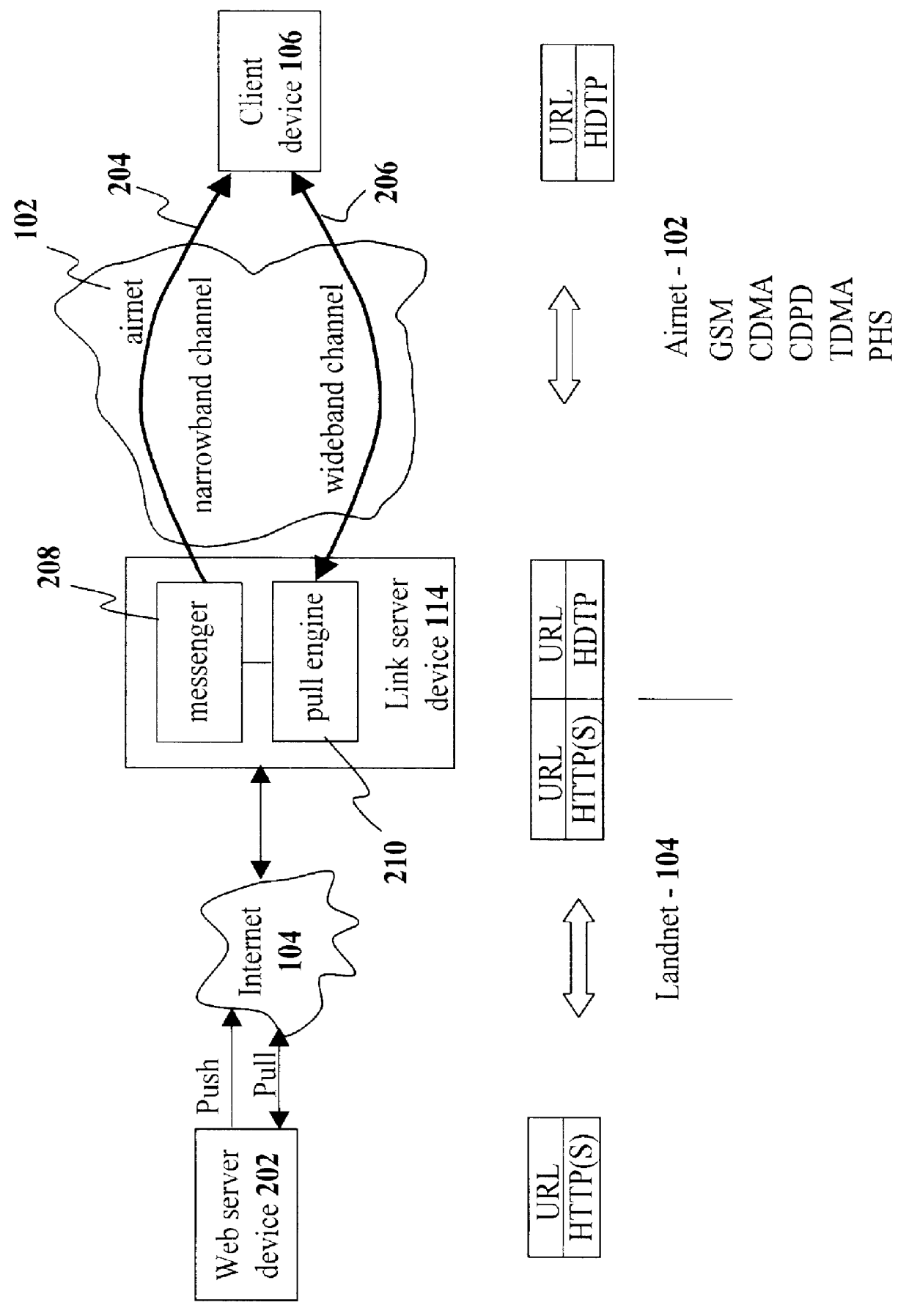
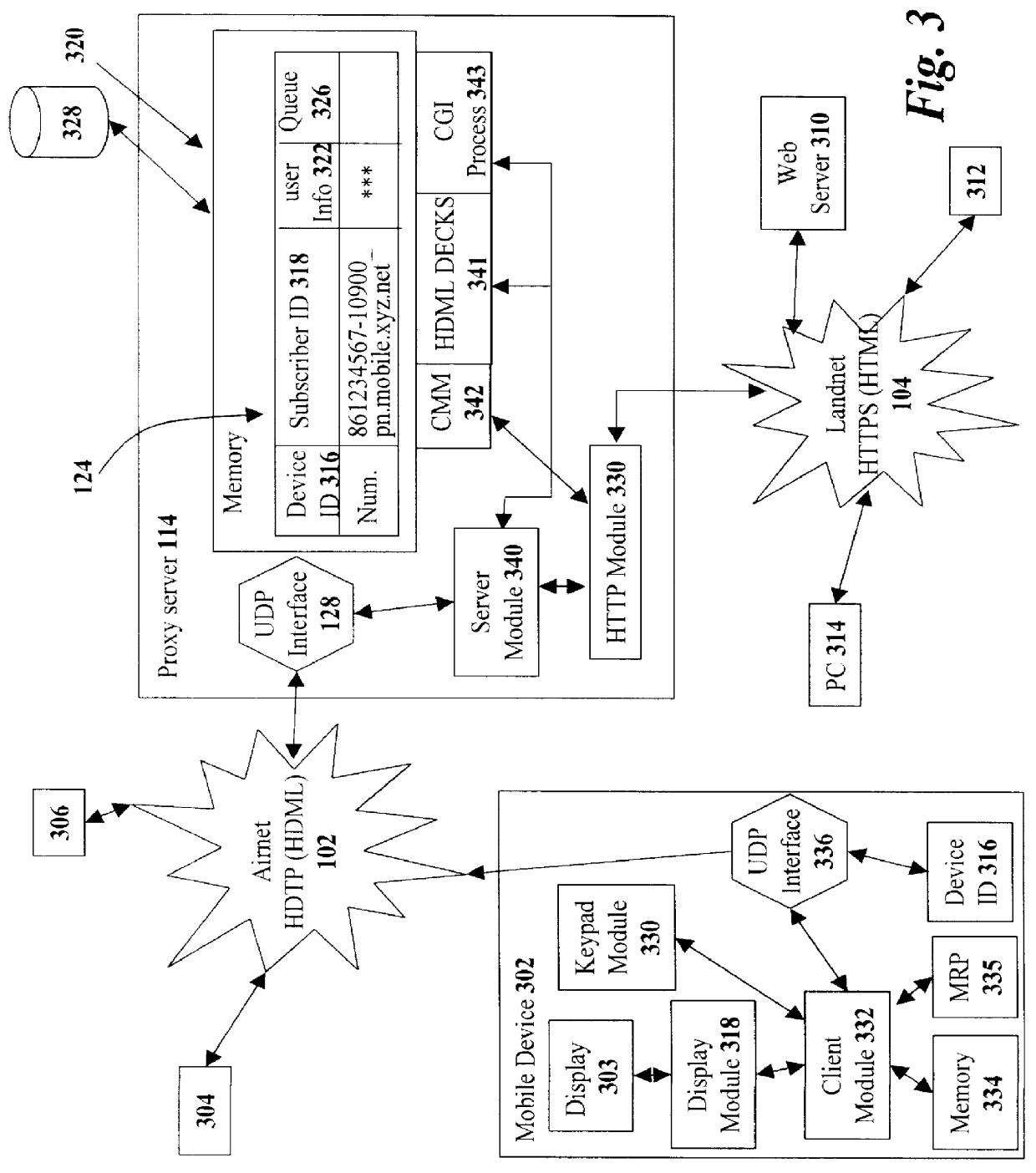
Method and system for pushing and pulling data using wideband and narrowband transport systems
InactiveUS6138158AWithout incurring uncontrollable costHigh trafficNetwork traffic/resource managementNetwork topologiesTransport systemThe Internet
The present invention has particular applications to the navigation of Internet web pages using two-way interactive communication devices, such as a mobile device, a mobile phone, a landline telephone, and an Internet capable remote controller. According to one aspect of the present invention, each of the two-way interactive communication devices is a node in a distributed network, thus the devices can access hypermedia or hierarchic layers of information stored in server devices on the network. When one or more pages of information are updated, rather than sending the entire updated information to users of the devices subscribing to the updated information through the network, the present invention sends a notification to a proxy server that forwards the notification to the users using a messaging system via a low cost narrowband channel. Upon receiving the notification, the users can fetch the updates, when needed, through a wideband channel. Hence systemic solutions are provided in the present invention to integrate wideband and narrowband channels so as to keep the users informed of any updates to their desired information and meanwhile provide efficient means to the users for retrieving the latest updates without incurring uncontrollable costs and increasing unnecessary network traffics.
Owner:UNWIRED PLANET
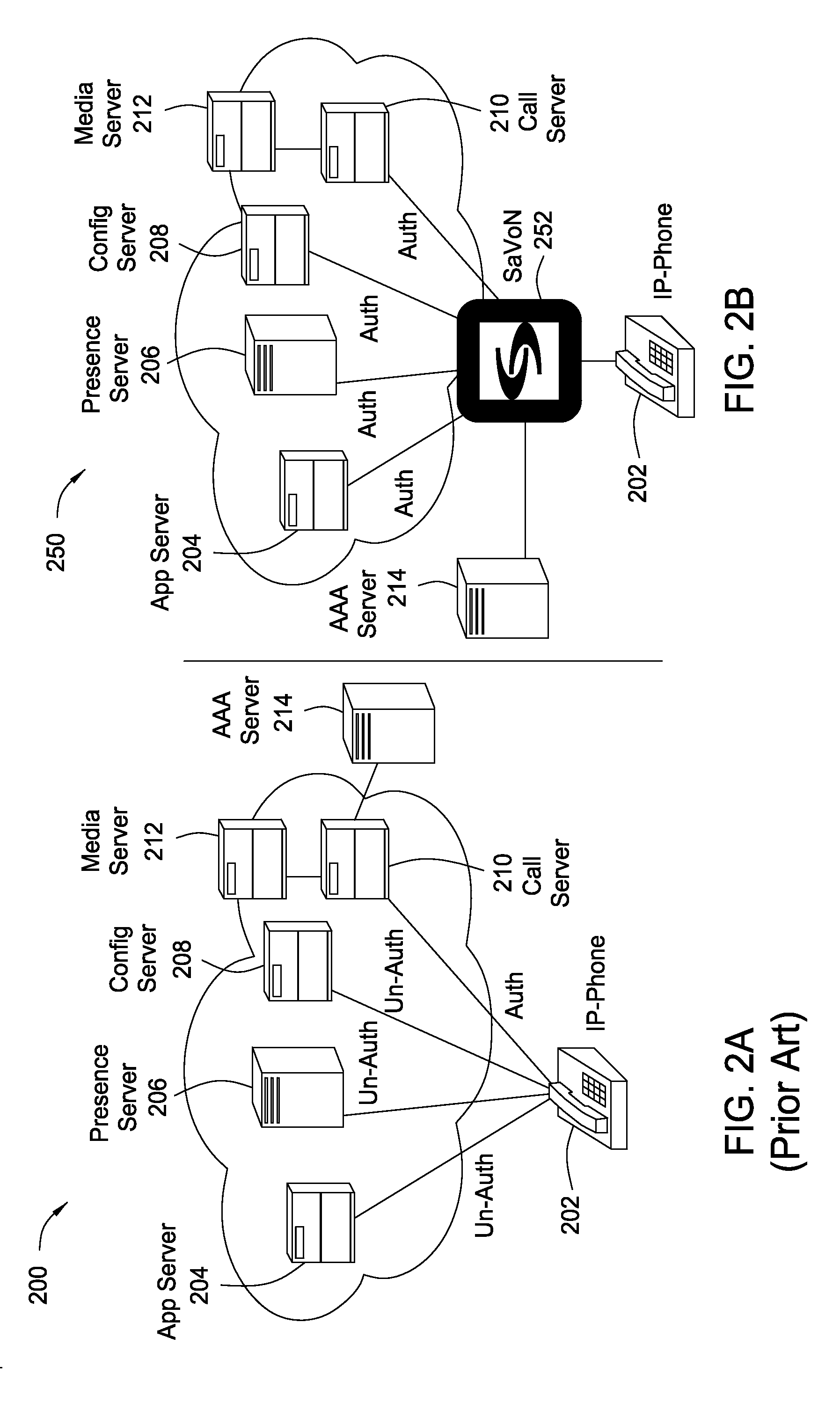
System, method and article of manufacture for selecting a gateway of a hybrid communication system architecture
Telephone calls, data and other multimedia information is routed through a hybrid network which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. A media order entry captures complete user profile information for a user. This profile information is utilized by the system throughout the media experience for routing, billing, monitoring, reporting and other media control functions. Users can manage more aspects of a network than previously possible, and control network activities from a central site. A directory service that supports a hybrid communication system architecture is provided for routing traffic over the hybrid network and the internet and selecting a network proximal to the origination of the call.
Owner:VERIZON PATENT & LICENSING INC
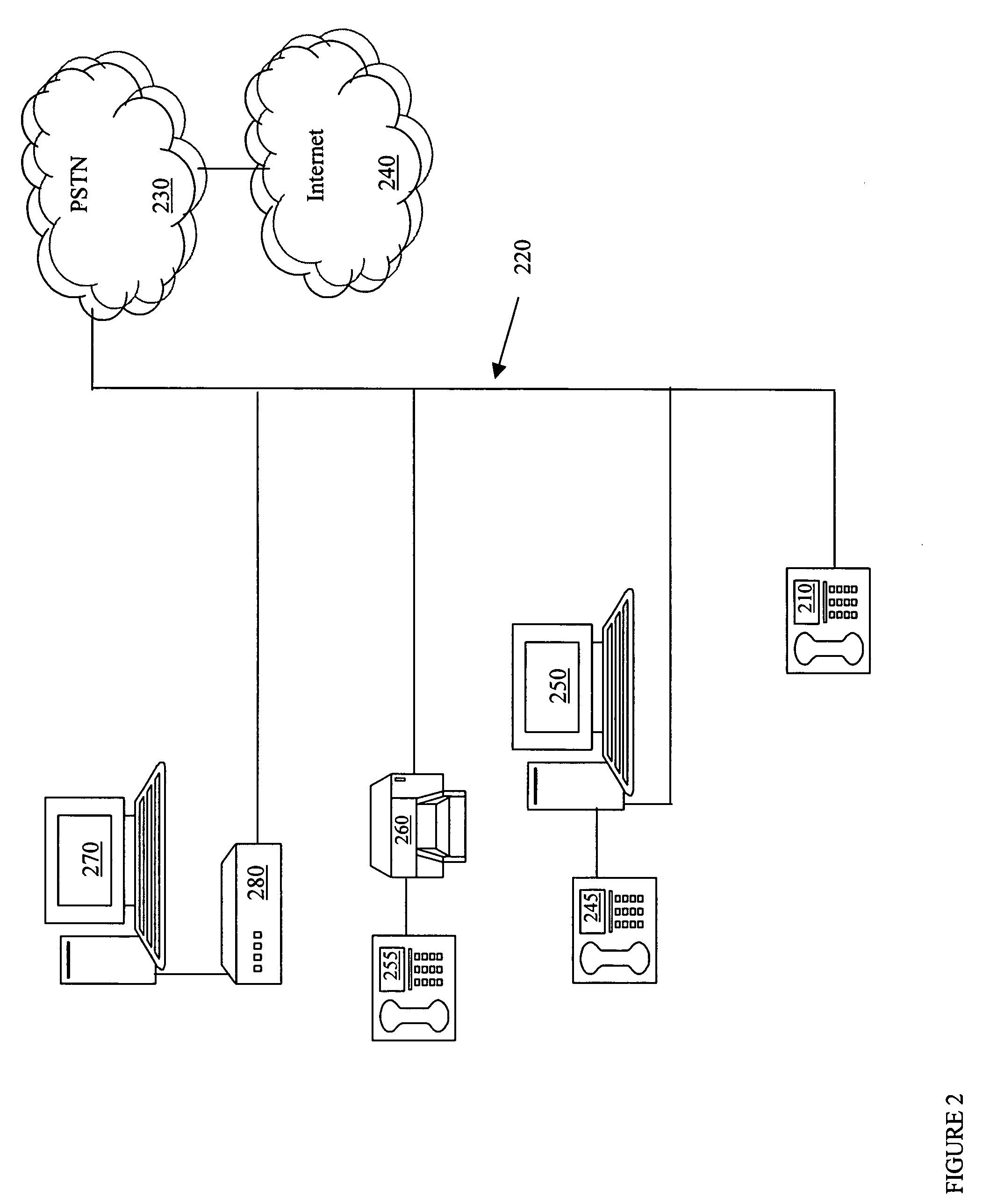
Multi-access terminal with capability for simultaneous connectivity to multiple communication channels
ActiveUS20060193295A1Improve reliabilityImprove behaviorNetwork traffic/resource managementTime-division multiplexTransceiverOperational system
An apparatus is disclosed for permitting a mobile terminal having multiple, heterogeneous network connections (e.g., multiple wired or wireless transceivers of various types) to set up and maintain virtual connections over multiple networks to either the same or to multiple destinations. The mobile terminal can “load-share” traffic, i.e., it can distribute segments of traffic over a full set of heterogeneous networks, significantly improving the reliability and availability of communications. In a first embodiment, a mobile terminal is configured with multiple radio frequency (RF) transceivers. Operating system software is provided for dynamically establishing and maintaining traffic flow for user applications over multiple communications paths, and for automatically adapting to variations in the networking environment, application traffic flow requirements, end user preferences, or mobility. In a second embodiment, a software-defined radio is used to implement the physical layer protocols for each desired network, eliminating the need for multiple transceivers.
Owner:TRUSTEES OF STEVENS INST OF TECH THE
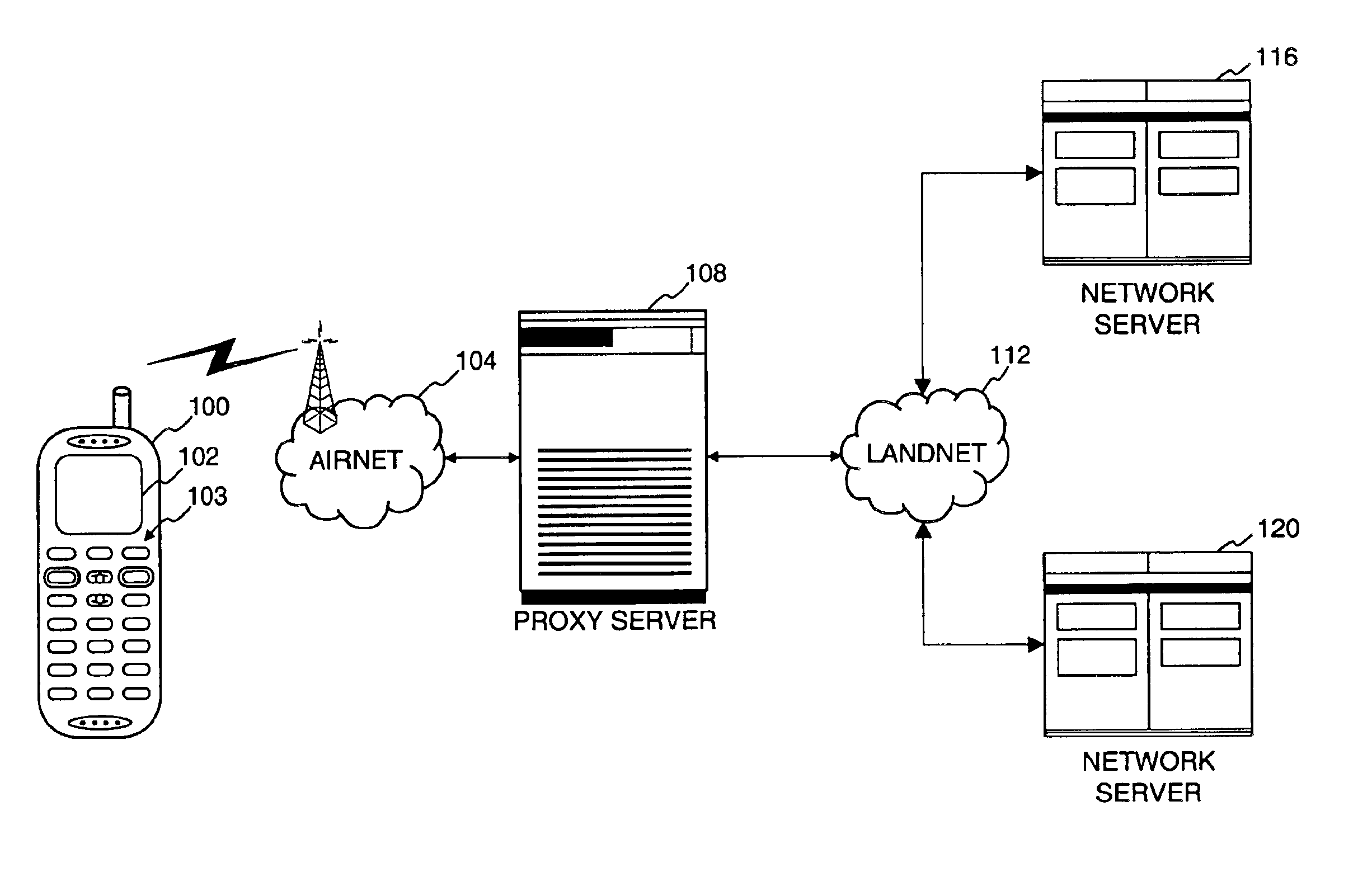
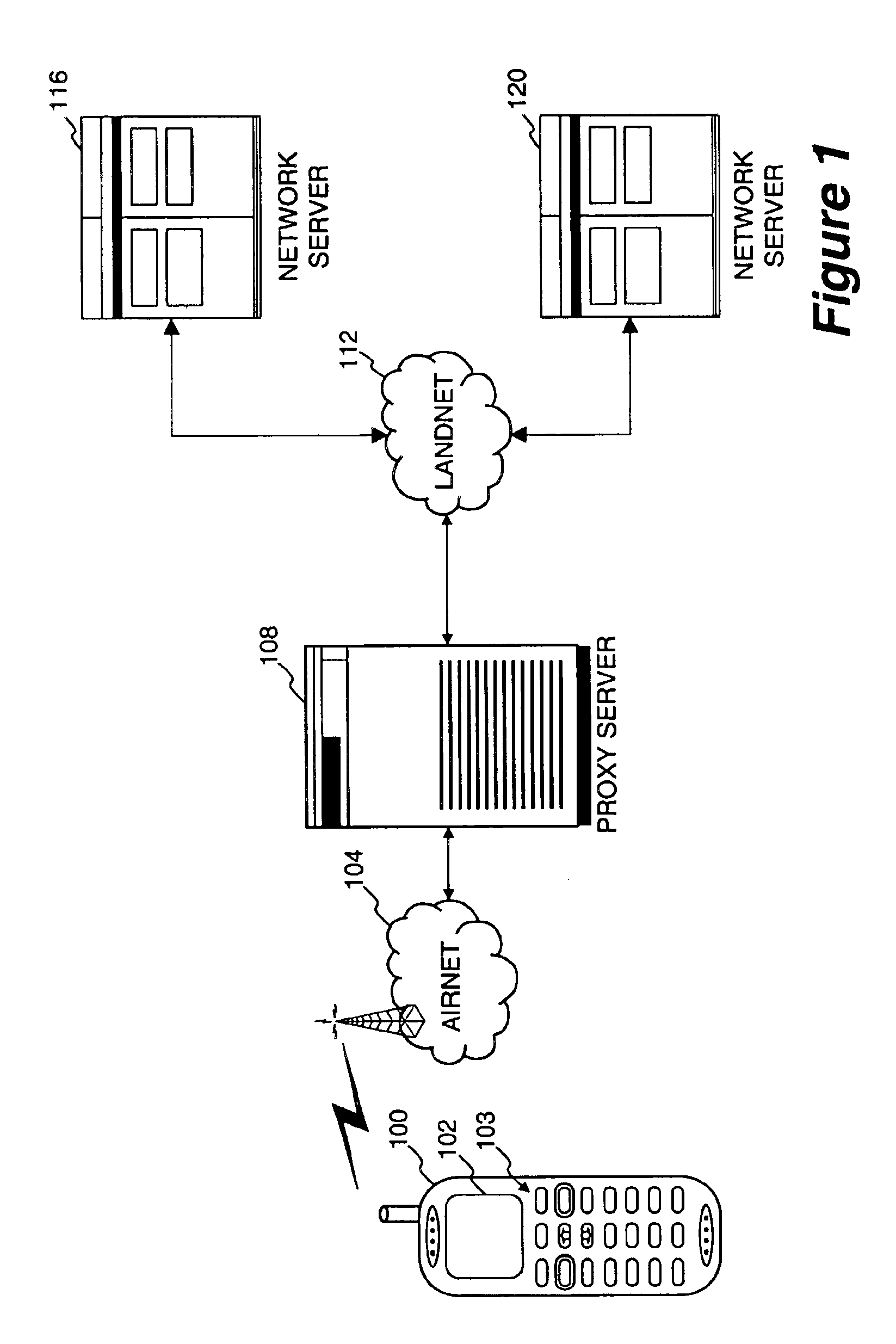
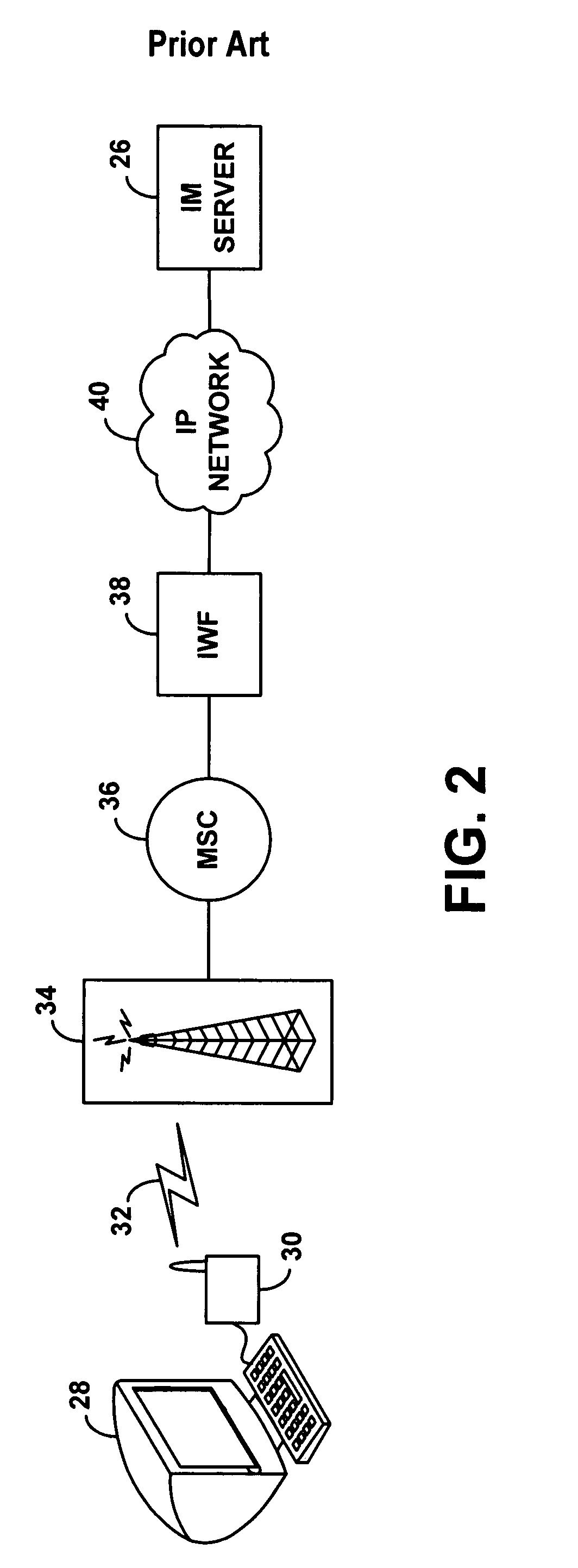
Method and apparatus for providing internet content to SMS-based wireless devices
A method and apparatus for providing hypermedia content maintained remotely on a network to a wireless device without a browser are described. A Short Message Service (SMS) request for Internet-based content is received from the wireless device at a proxy server, via an SMS Center (SMSC). The SMS request is transmitted to the SMSC on a wireless network. The proxy server transcodes the SMS request from a character set of the SMSC to a character set of an application and extracts a keyword from the trancoded request. The proxy server maintains a mapping of keywords to URLs. The proxy server looks up the extracted keyword in the keyword-to-URL mapping to identify the URL of an application associated with the keyword. The proxy server constructs an HTTP POST operation containing the keyword and the URL, and submits the HTTP POST operation to the application over a wireline network such as the Internet. Upon receiving an HTTP response containing the requested content from the application in response to the POST operation, the proxy server extracts the content from the HTTP response. The proxy server then translates the content from the content-type used by the application to the content-type used by the SMSC and transcodes the content from the character set used by the application to the character set used by the SMSC. The proxy server then sends the translated and transcoded content in an SMS response to the SMSC, for subsequent delivery to wireless device as an SMS message.
Owner:UNWIRED PLANET
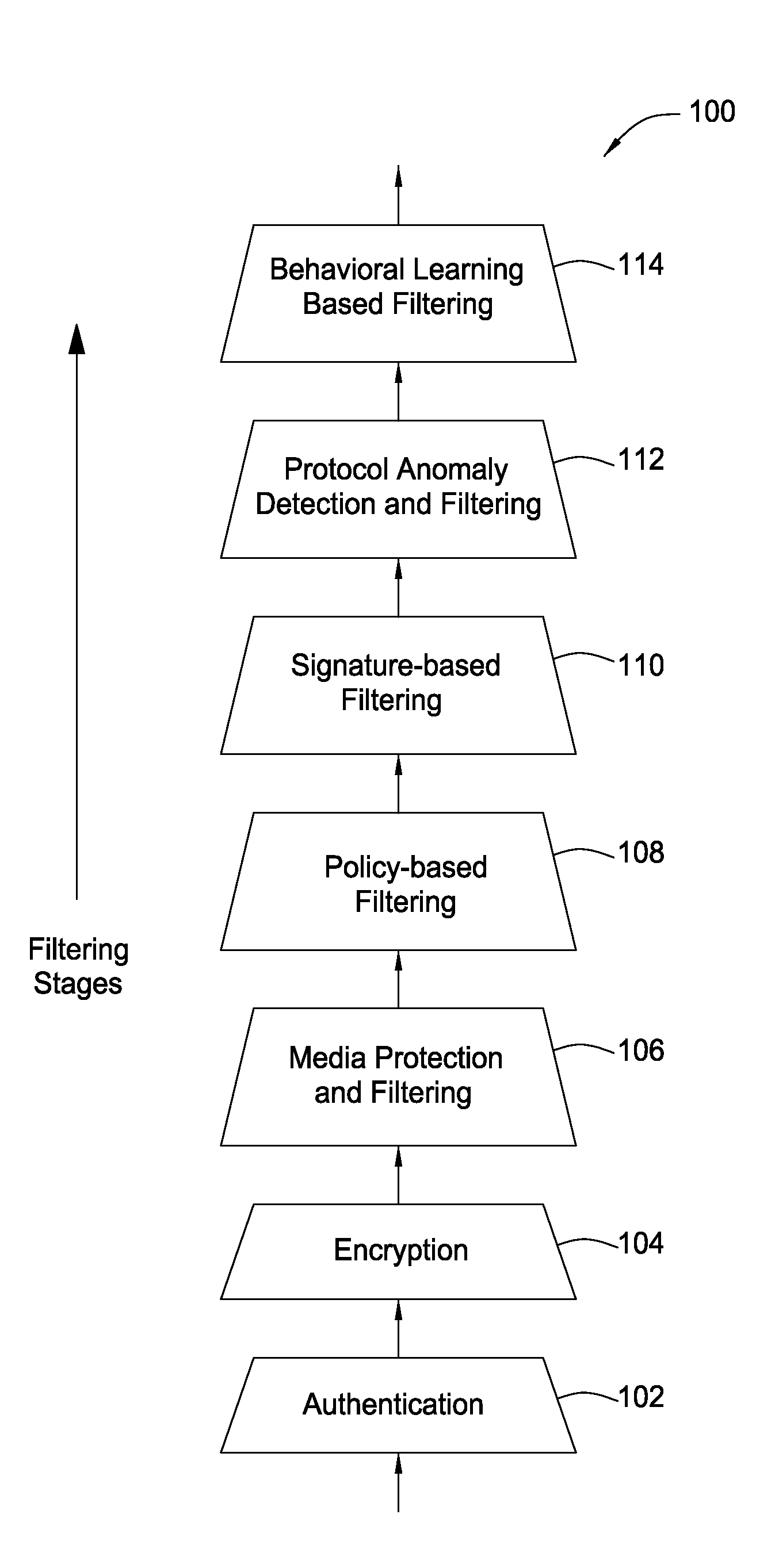
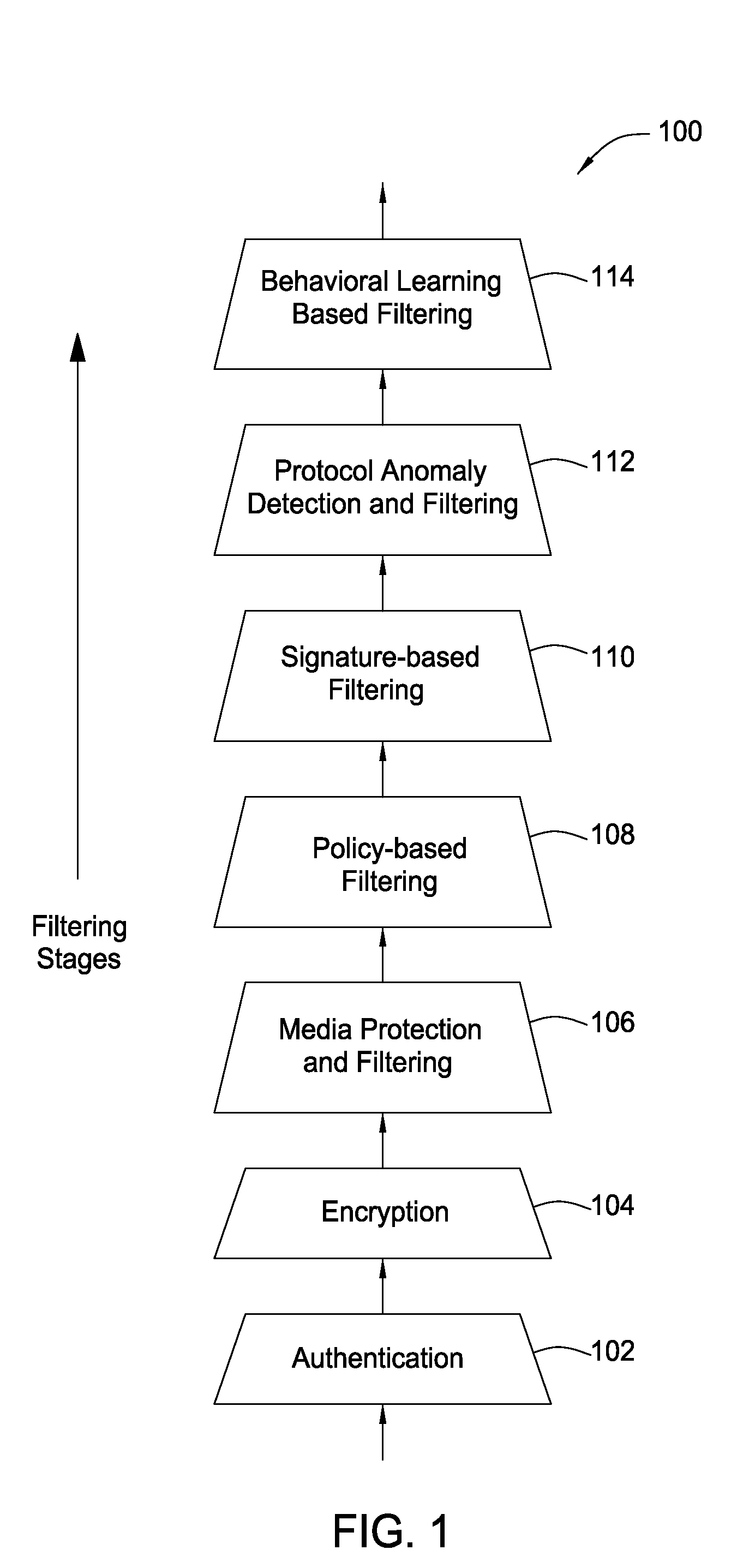
System and method for providing network level and nodal level vulnerability protection in VoIP networks
ActiveUS20070121596A1Unauthorized usePrivacy protectionInterconnection arrangementsAutomatic exchangesComputer networkAnomaly detection
The present invention provides a system, method and apparatus for providing network level and nodal level vulnerability protection in VoIP networks by receiving a communication, filtering the received communication using three or more stages selected from the group comprising a media protection and filtering plane, a policy based filtering plane, a signature based filtering plane, a protocol anomaly detection and filtering plane and a behavioral learning based filtering plane, and either allowing or denying the received communication based the filtering step. The stages are applicable to one or more protocols including SIP, IMS, UMA, H.248, H.323, RTP, CSTA / XML or a combination thereof. In addition, the stages can be implemented within a single device or are distributed across a network (e.g., SIP network, a UMA network, an IMS network or a combination thereof).
Owner:AVAYA INC
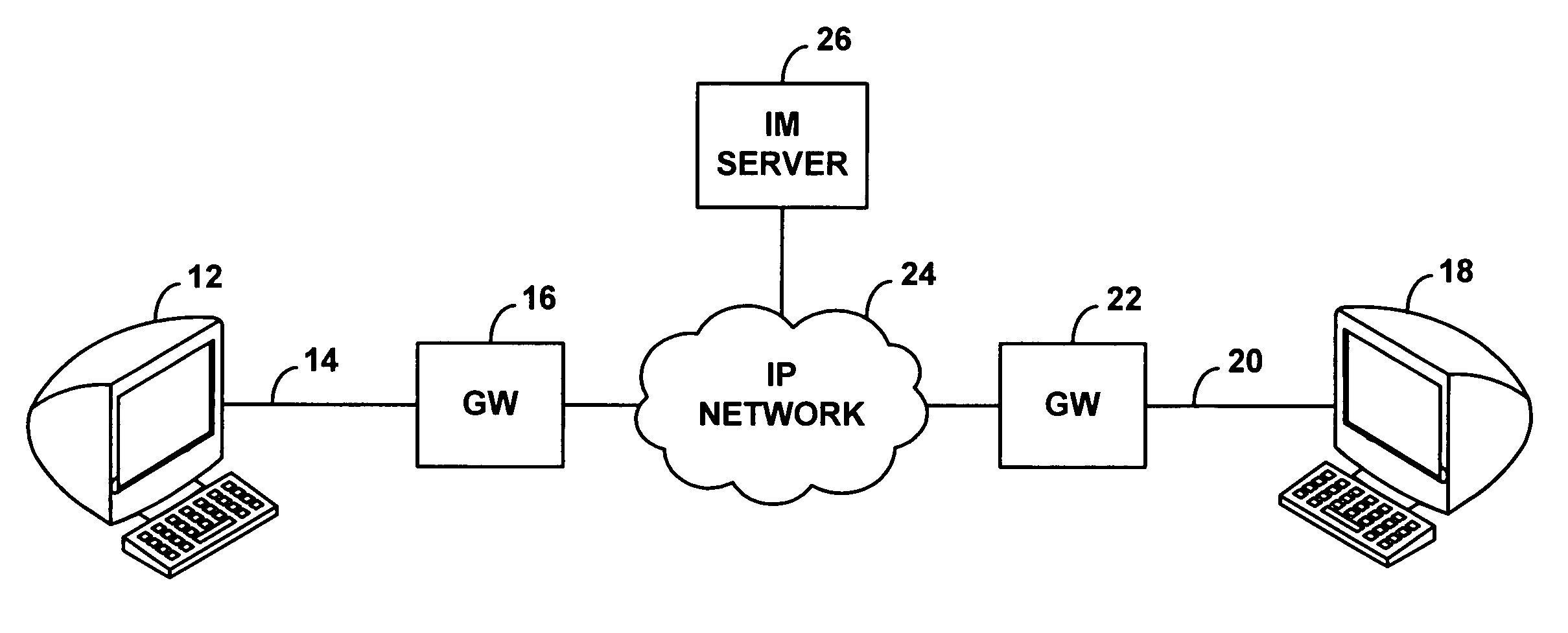
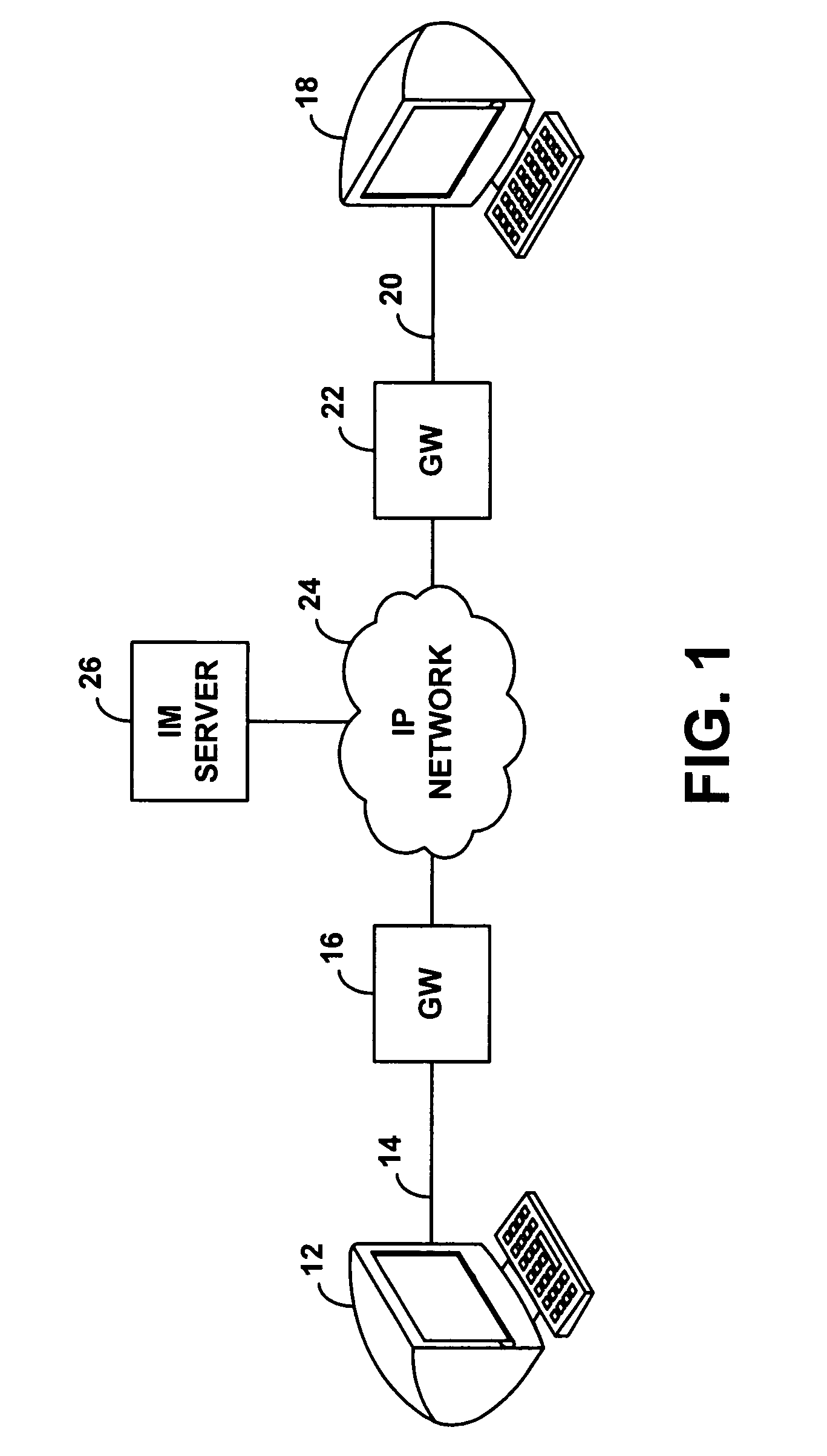
Method and system for wireless instant messaging
InactiveUS7058036B1Increase demandIncreased complexityAutomatic call-answering/message-recording/conversation-recordingData switching by path configurationText entryComputer terminal
A wireless instant messaging system is disclosed. A mobile station (MS), such as a cellular telephone for instance, may be registered with an instant messaging (IM) server as being available to receive instant messages via an IM proxy. A user at an IM client terminal may then send an instant message destined for a user at the MS. The IM server may direct the message to a service node (SN), which may convert the message into an industry standard SMS message and send the SMS message to the MS. At the MS, a user may read the SMS message and engage a callback feature, which will establish a dial-up voice connection between the MS and the SN. The user at the MS may then speak an instant message response, and the SN may record the response as a compressed audio file. The SN may then send the compressed audio file as an attachment to an instant message back to the user at the IM client terminal. The IM client terminal may then play the spoken response message. The invention facilitates robust instant messaging communication, while avoiding the need for a user at the mobile station to engage in cumbersome text entry via a numeric keypad.
Owner:SPRING SPECTRUM LP
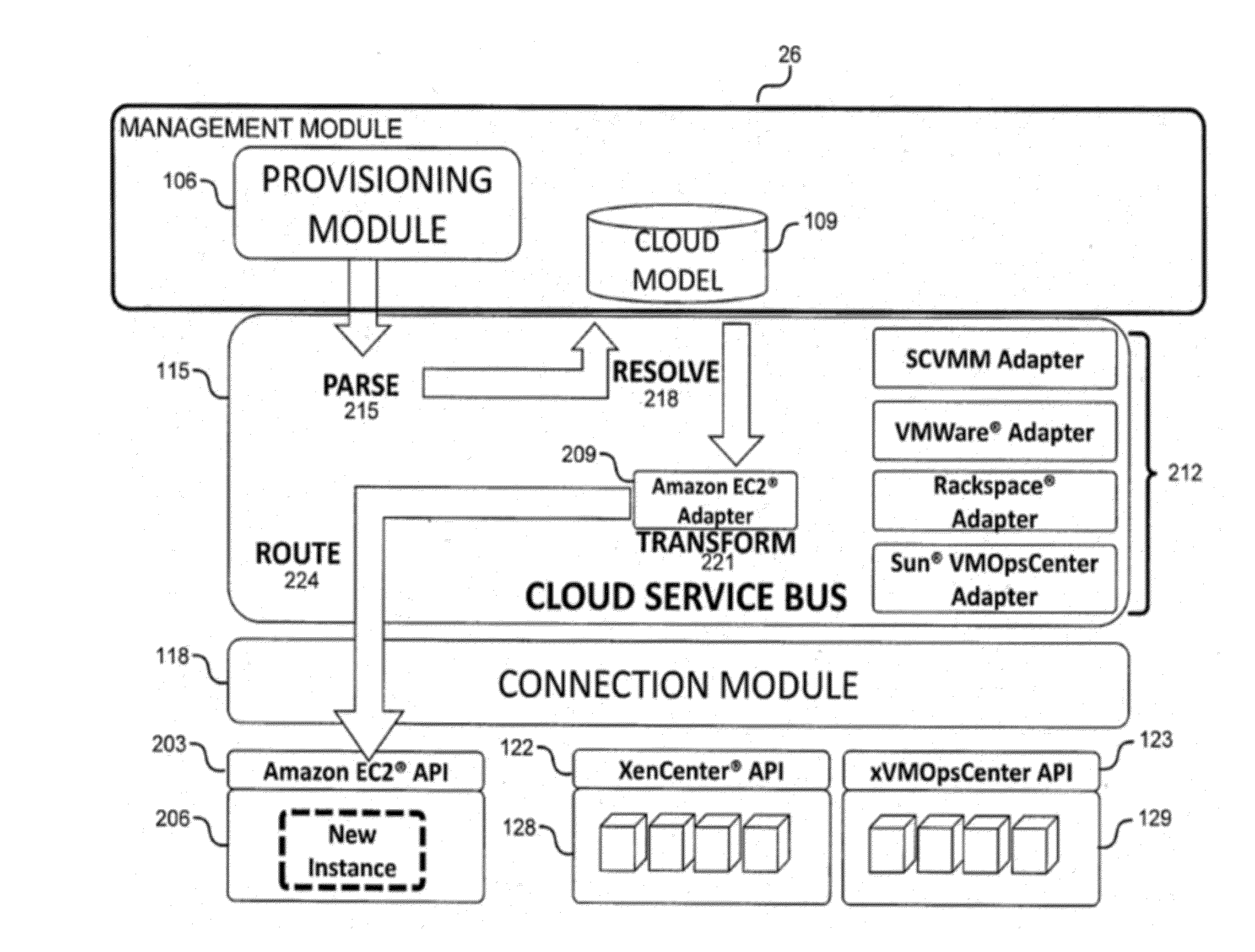
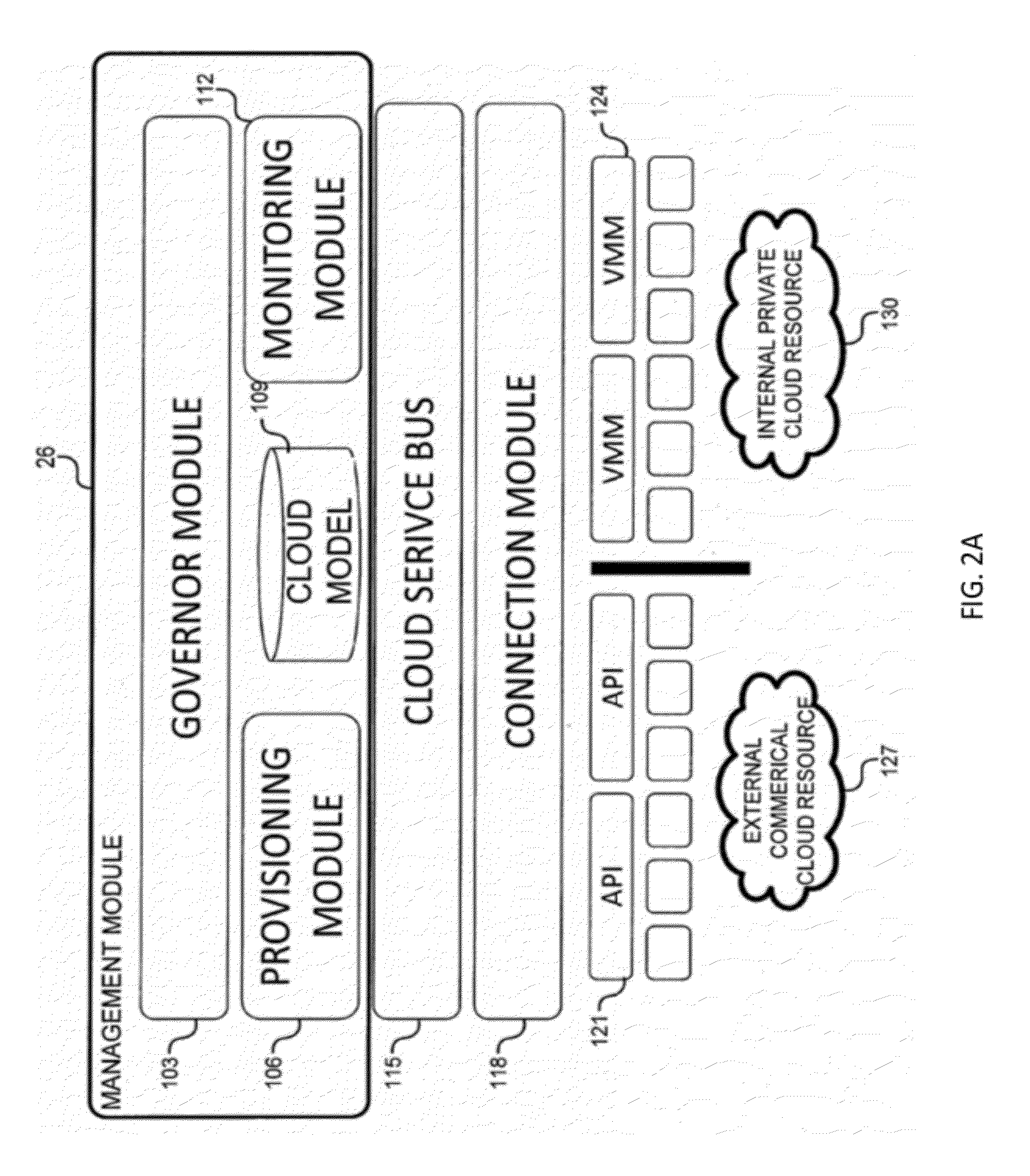
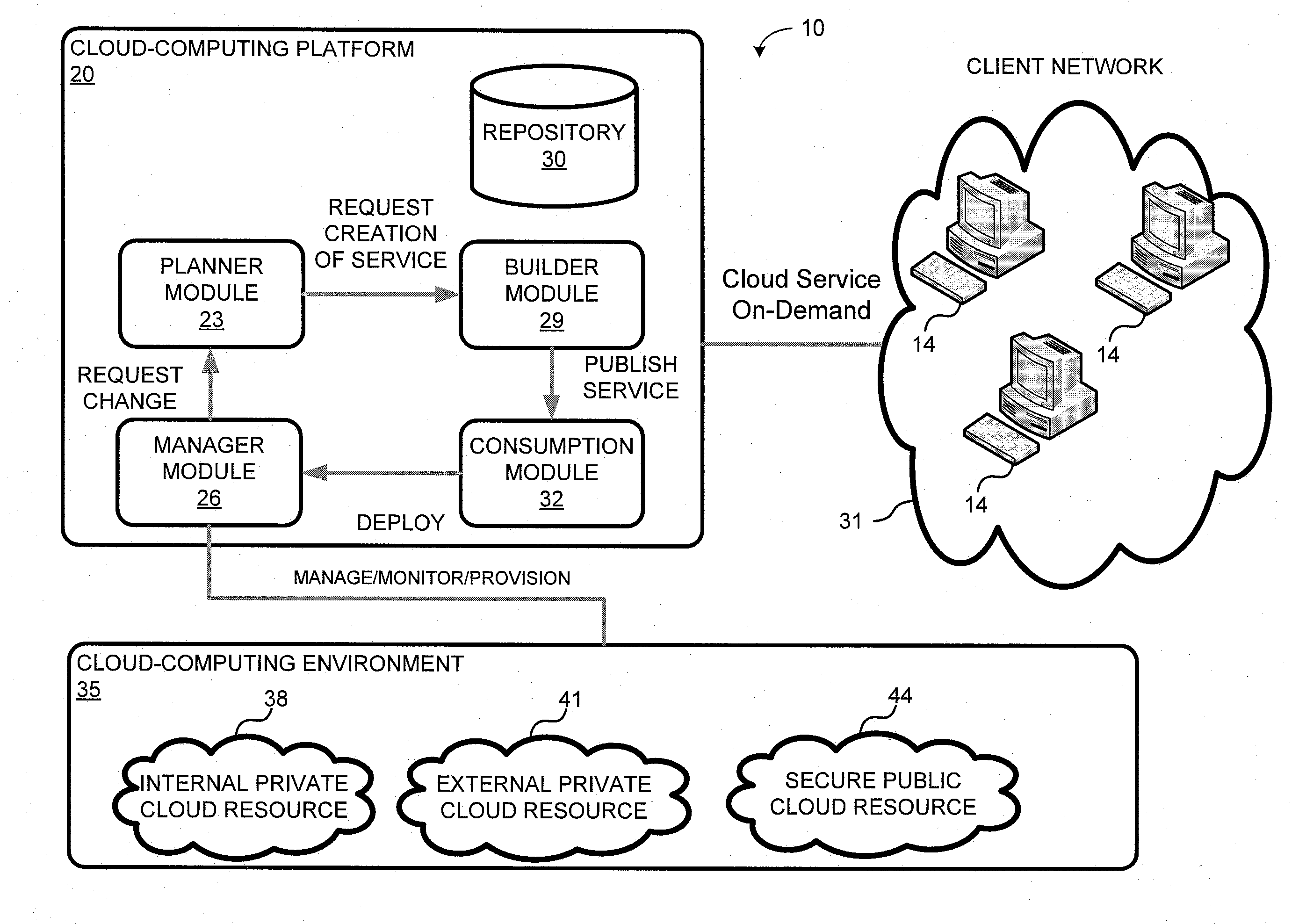
System and method for a cloud computing abstraction layer
ActiveUS20110231899A1Rapid and dynamic deployment and scalingShorten the timeDigital computer detailsComputer security arrangementsAbstraction layerWorkload
According to one system of the invention, the system provides a cloud-computing service from a cloud-computing environment comprising a plurality of cloud-computing resources. The system may comprise: a management module configured to manage a cloud-computing resource of the plurality of cloud-computing resources as a cloud-computing service, wherein the cloud-computing service performs a computer workload; an adapter configured to connect to the cloud-computing resource to the system and translate a management instruction received from the management module into a proprietary cloud application program interface call for the cloud-computing resource; a cloud service bus configured to route the management instruction from the management module to the adapter; a consumption module configured to allow a user to subscribe the cloud-computing service; a planning module configured to plan the cloud-computing service; and a build module configured to build the cloud-computing service from the cloud-computing resource and publish the cloud-computing service to the consumption module.
Owner:DXC US AGILITY PLATFORM INC
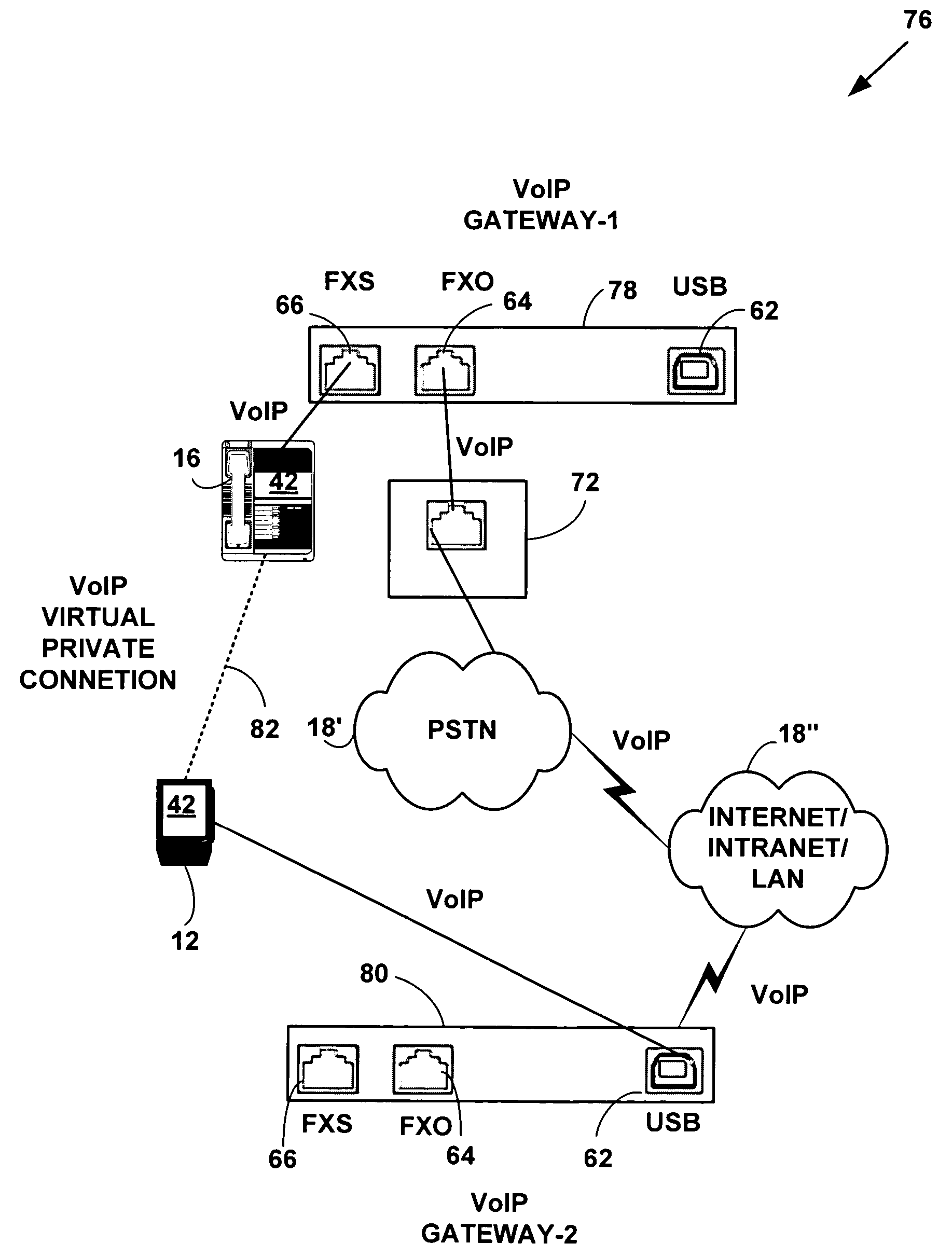
Method and system for providing private virtual secure Voice over Internet Protocol communications
InactiveUS20060187900A1Maintain privacyInterconnection arrangementsFrequency-division multiplex detailsVoice communicationPrivate network
A method and system for secure Voice over Internet Protocol (IP) (VoIP) communications. The method and system provide secure VoIP voice calls, video, Instant Messaging (IM), Short Message Services (SMS), or Peer-to-Peer (P2P) communications while maintaining privacy over the Internet and other communications networks such as the pubic switched telephone network (PSTN) to and from any network device through a virtual private network infrastructure interconnecting private VoIP network devices. The method and system allow a network device to function as an IP private branch exchange (PBX) or a private VoIP gateway and provide and control VoIP voice communications without using other public or private VoIP gateways or VoIP servers or devices on a communications network such as the PSTN or the Internet.
Owner:LESAVICH HIGH TECH LAW GRP SC
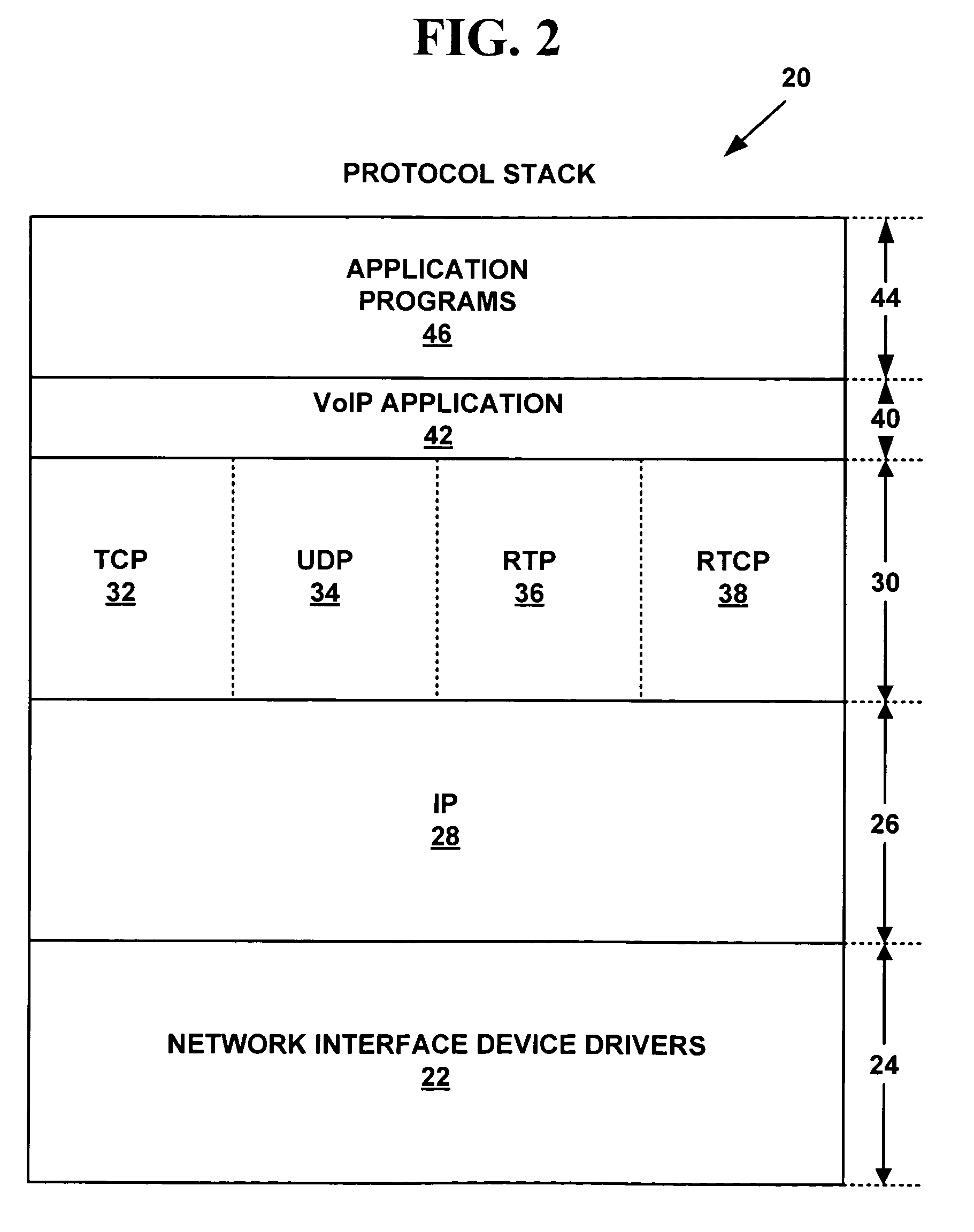
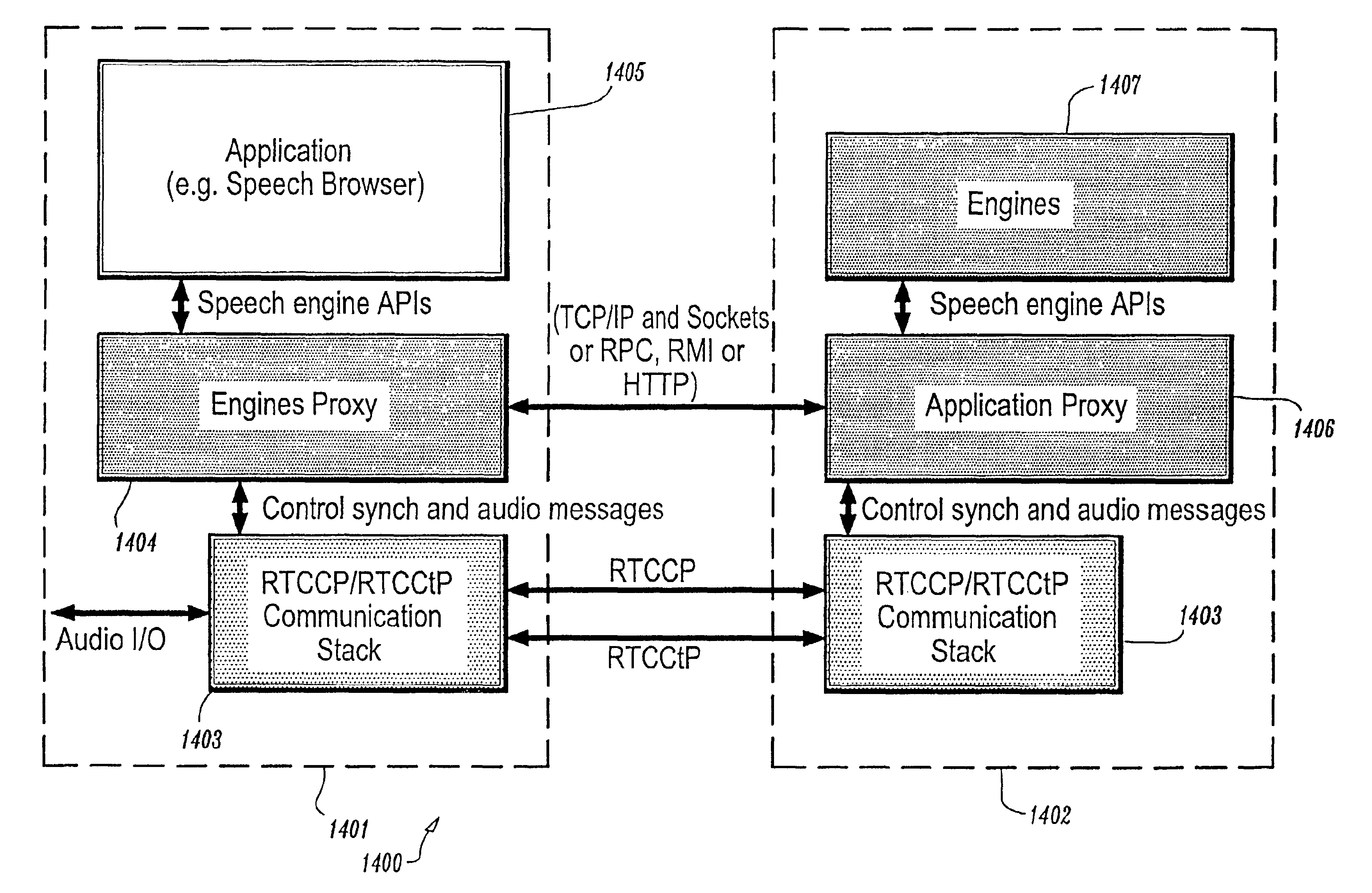
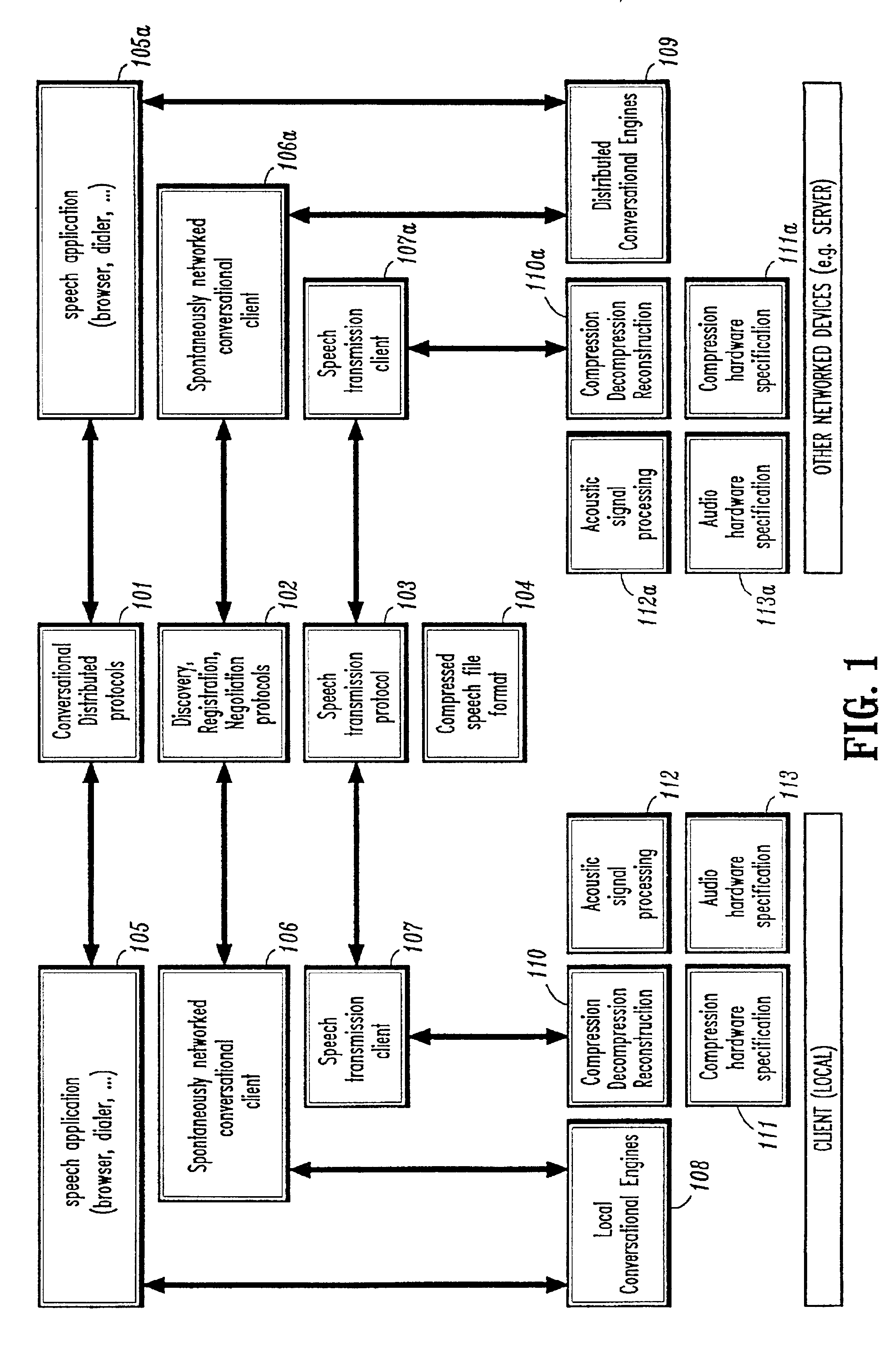
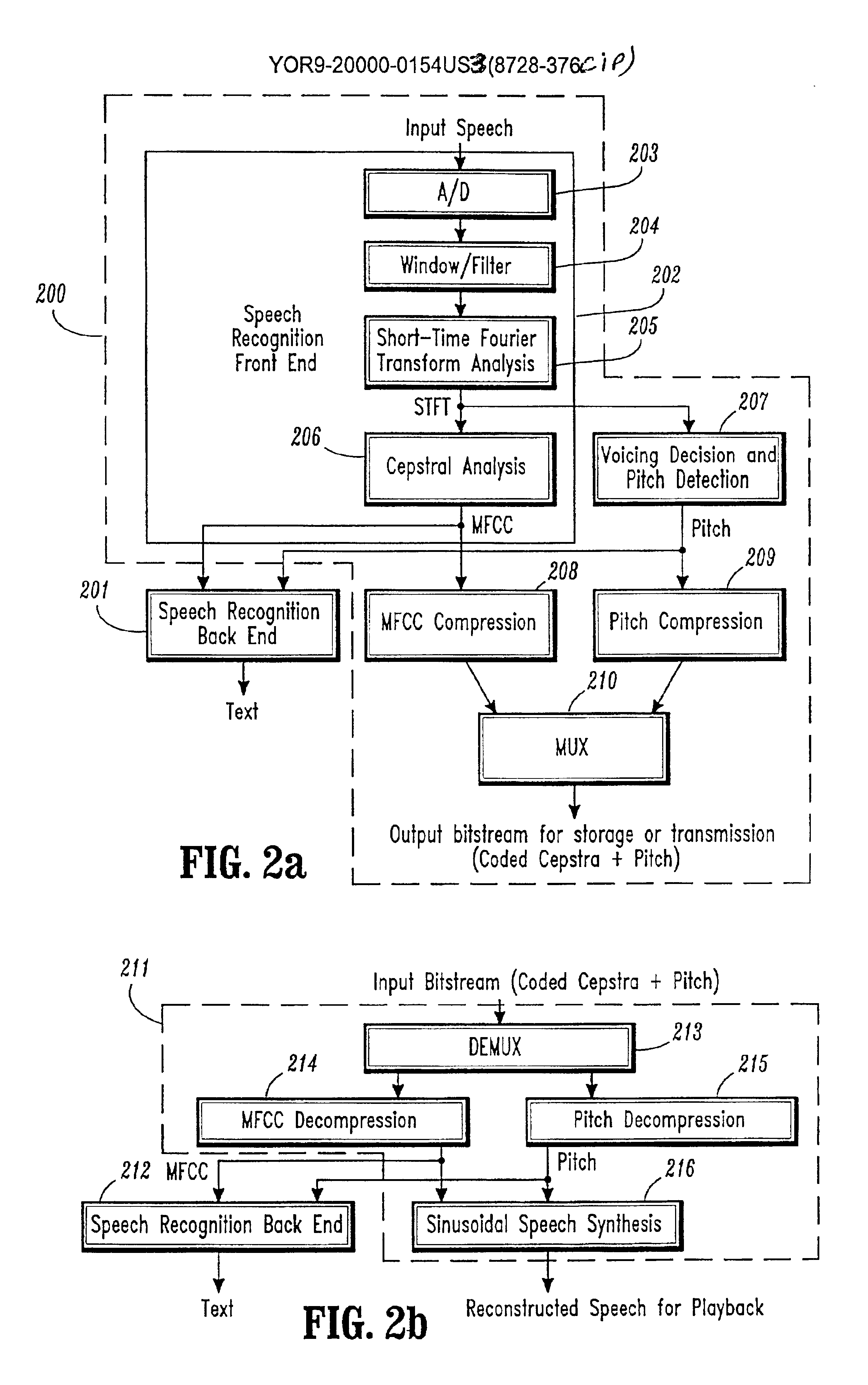
Conversational networking via transport, coding and control conversational protocols
InactiveUS6934756B2Broadcast transmission systemsMultiple digital computer combinationsSession controlRemote control
A system and method for implementing conversational protocols for distributed conversational networking architectures and / or distributed conversational applications, as well as real-time conversational computing between network-connected pervasive computing devices and / or servers over a computer network. The implementation of distributed conversational systems / applications according to the present invention is based, in part, on a suitably defined conversational coding, transport and control protocols. The control protocols include session control protocols, protocols for exchanging of speech meta-information, and speech engine remote control protocols.
Owner:IBM CORP
Multimedia access device and system employing the same
ActiveUS20050249196A1Interconnection arrangementsTime-division multiplexCommunications systemVoice communication
A method of establishing a voice communication session with a multimedia access device employable in a multimedia communication system. In one embodiment, the method includes initiating a session request from a first endpoint communication device employing an instant messaging client and coupled to a packet based communication network. The method also includes processing the session request including emulating the instant messaging client for a second endpoint communication device coupled to said packet based communication network. The second endpoint communication device is a non-instant messaging based communication device. The method still further includes establishing a voice communication session between the first and second endpoint communication devices in response to the session request.
Owner:KIP PROD P1 LP
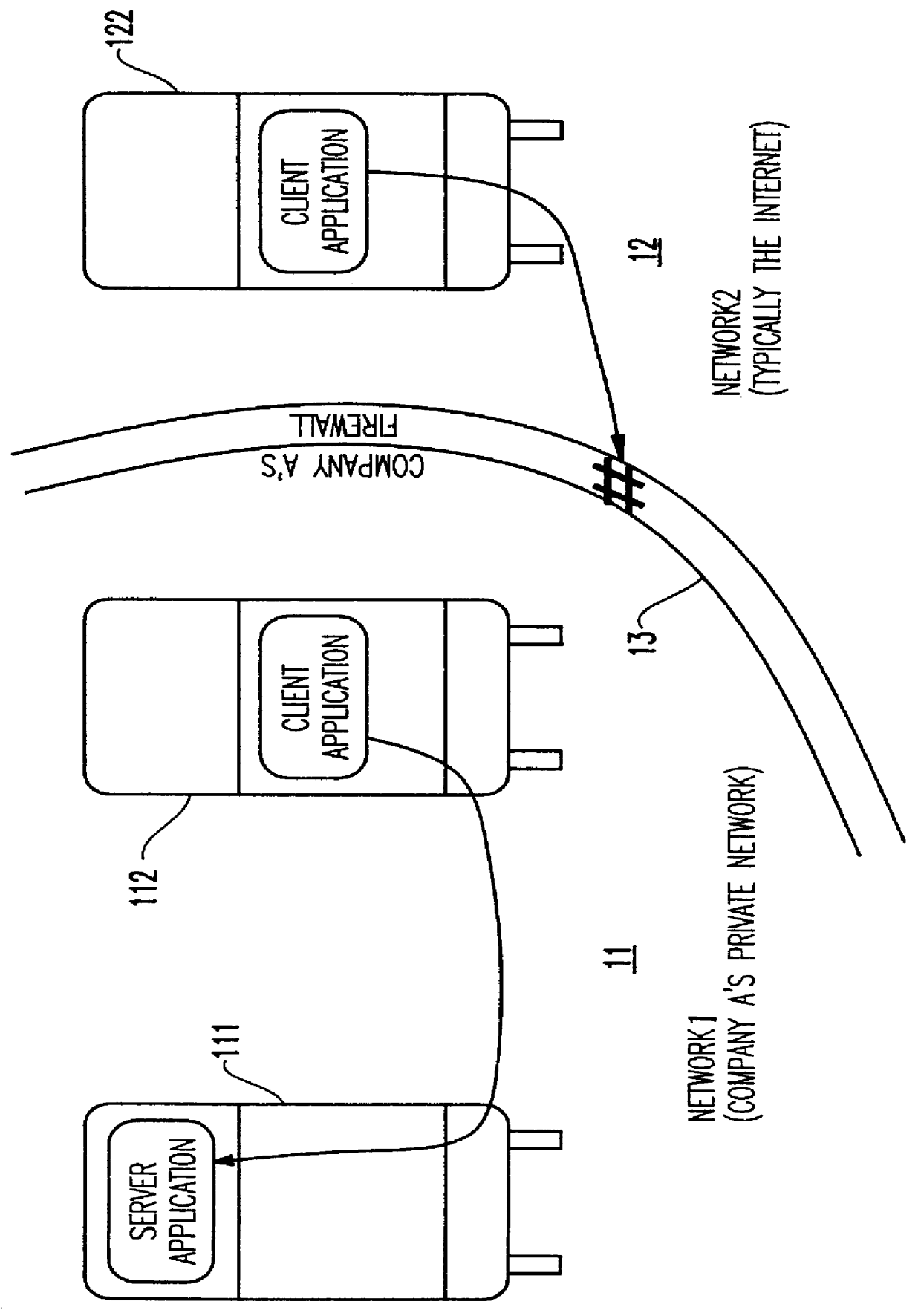
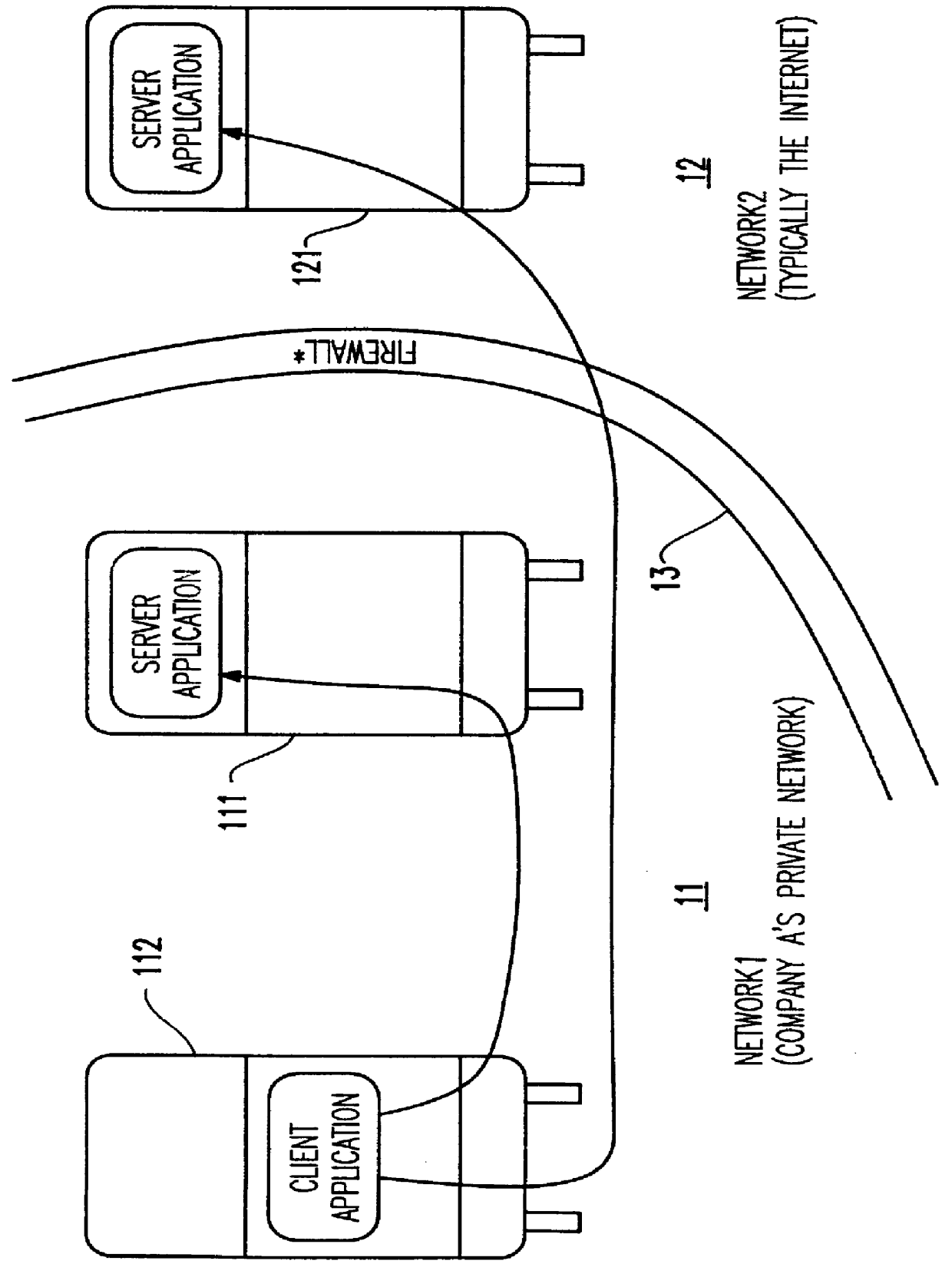
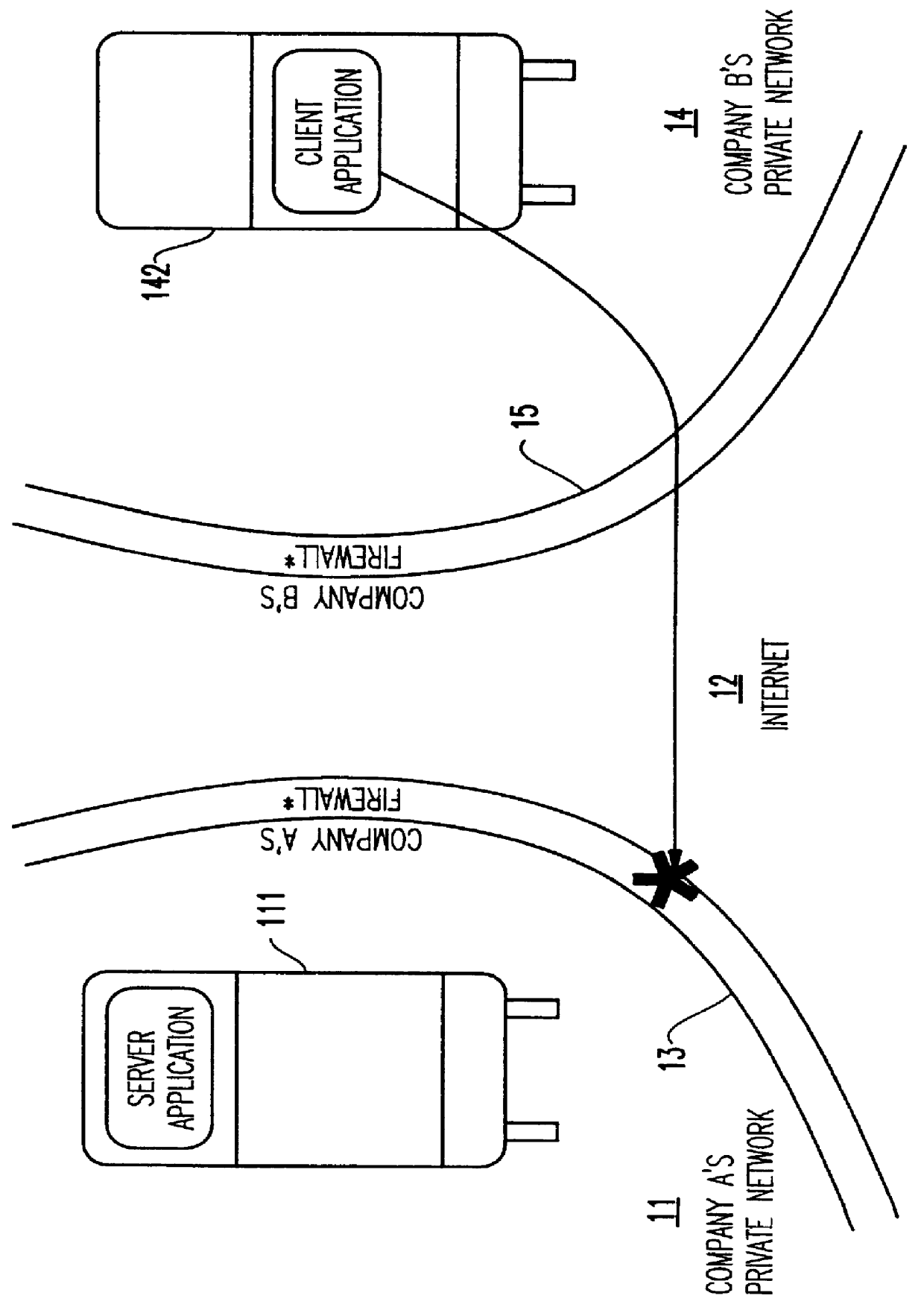
Method and apparatus for lightweight secure communication tunneling over the internet
InactiveUS6104716AData switching by path configurationMultiple digital computer combinationsSOCKSSecure communication
A lightweight secure tunneling protocol or LSTP permits communicating across one or more firewalls by using a middle server or proxy. Three proxies are used to establish an end-to-end connection that navigates through the firewalls. In a typical configuration, a server is behind a first firewall and a client behind a second firewall are interconnected by an untrusted network (e.g., the Internet) between the firewalls. A first inside firewall SOCKS-aware server-side end proxy connects to the server inside the first firewall. A second inside firewall SOCKS-aware client-side end proxy is connected to by the client inside the second firewall. Both server-side and client-side end proxies can address a third proxy (called a middle proxy) outside the two firewalls. The middle proxy is usually started first, as the other two end proxies (server and client) will initiate the connection to the middle proxy some time after they are started. Since the middle proxy is mutually addressable by both inside proxies, a complete end-to-end connection between the server and client is established. It is the use of one or more middle proxies together with the LSTP that establishes the secure communications link or tunnel across multiple firewalls.
Owner:IBM CORP
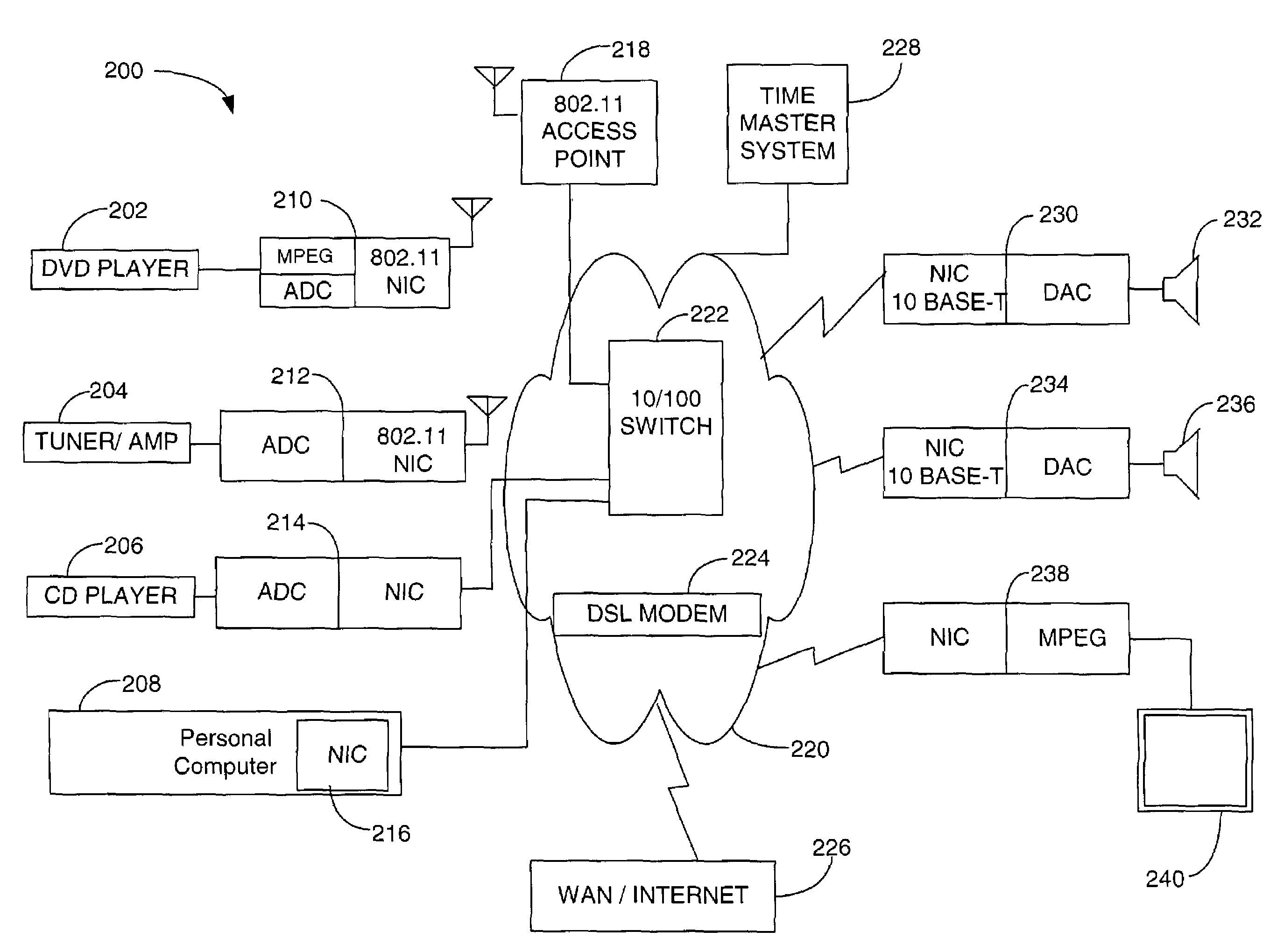
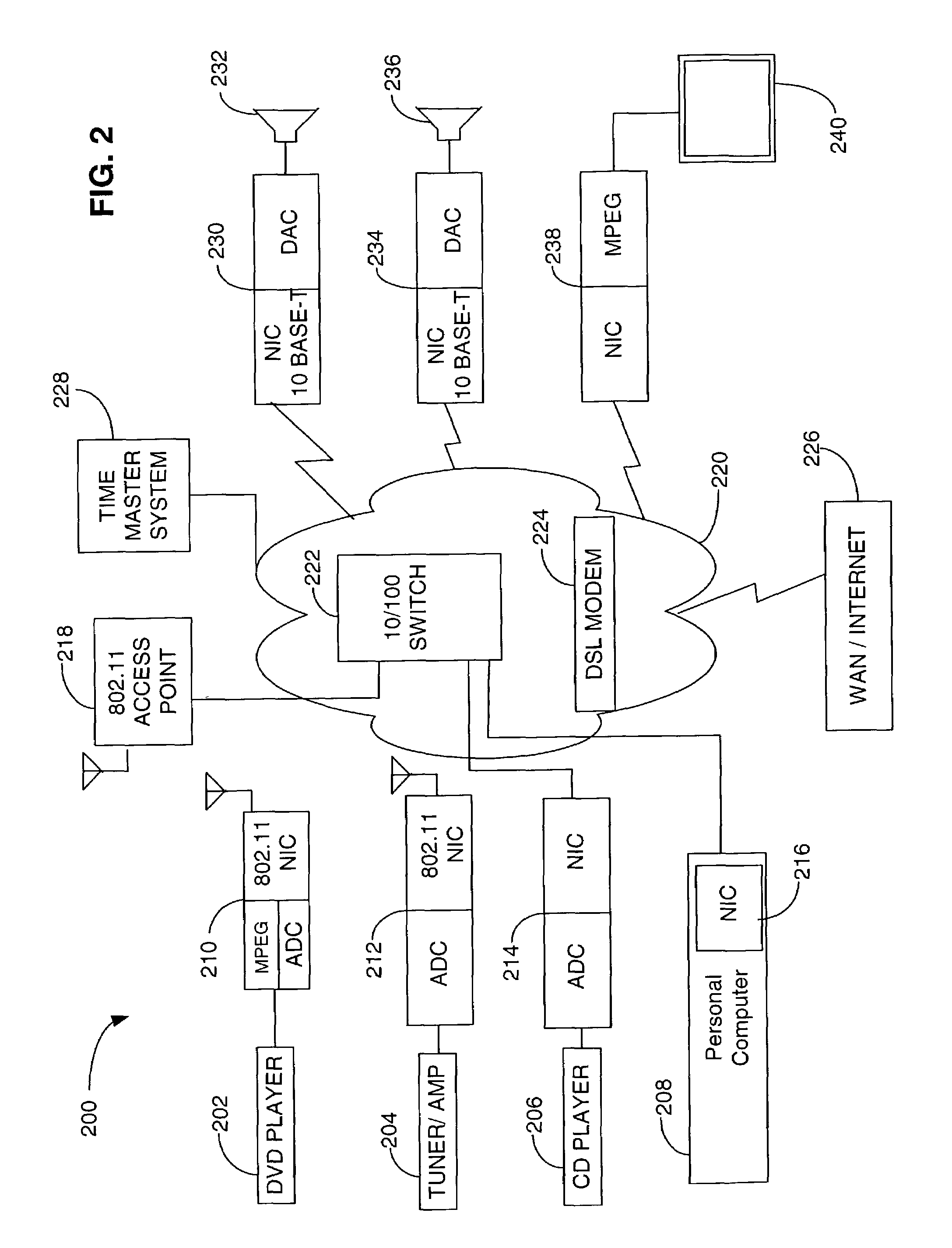
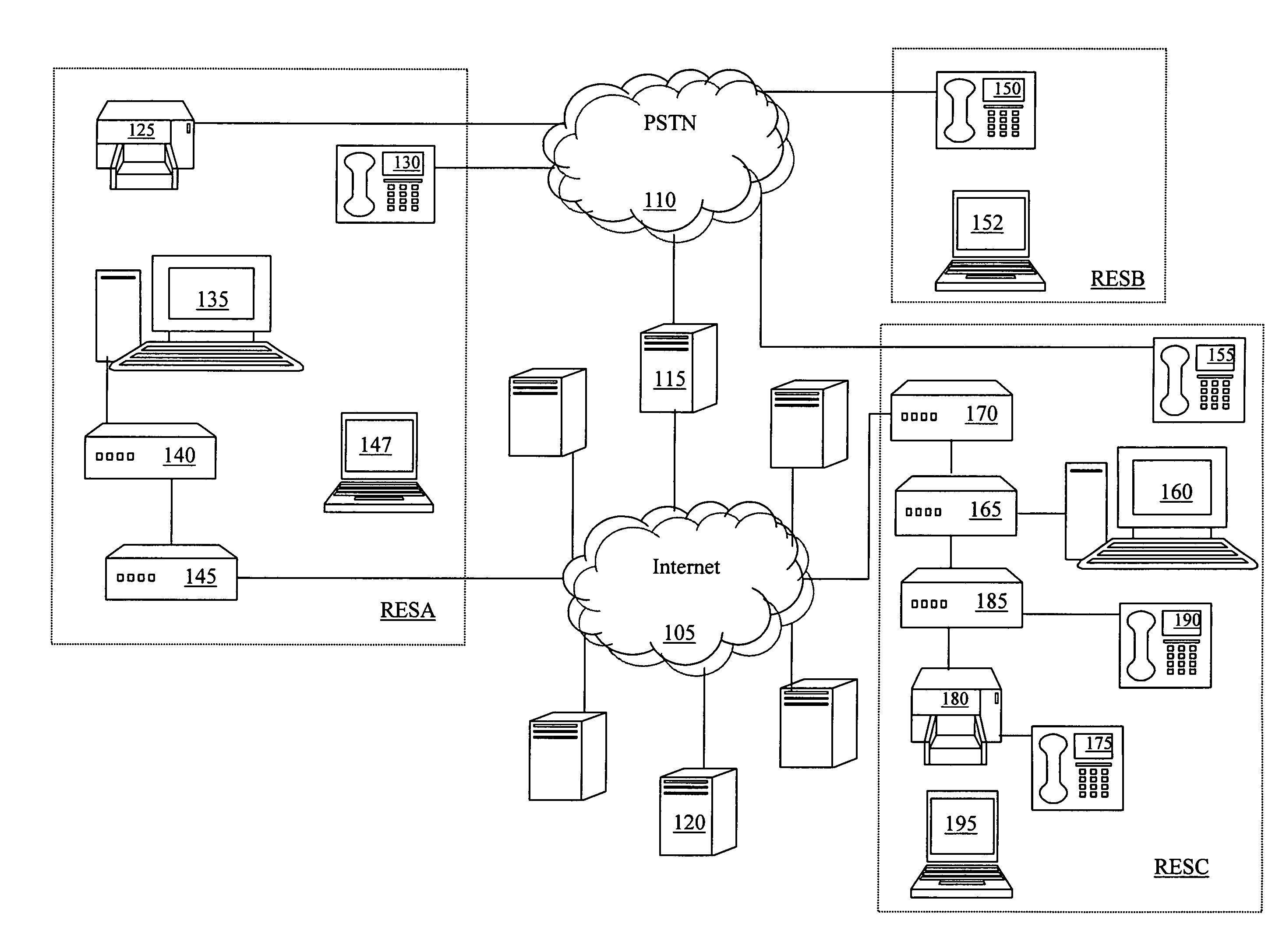
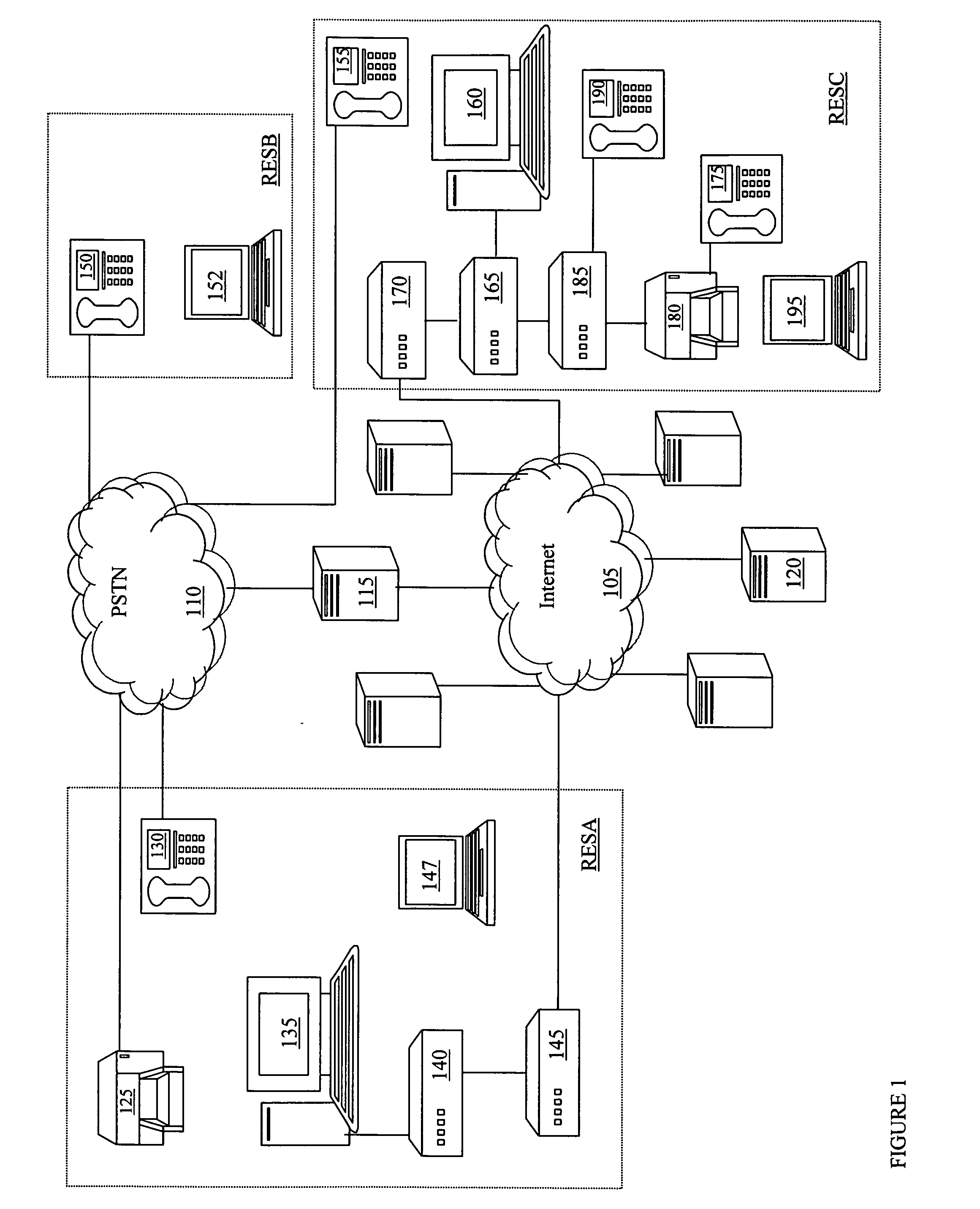
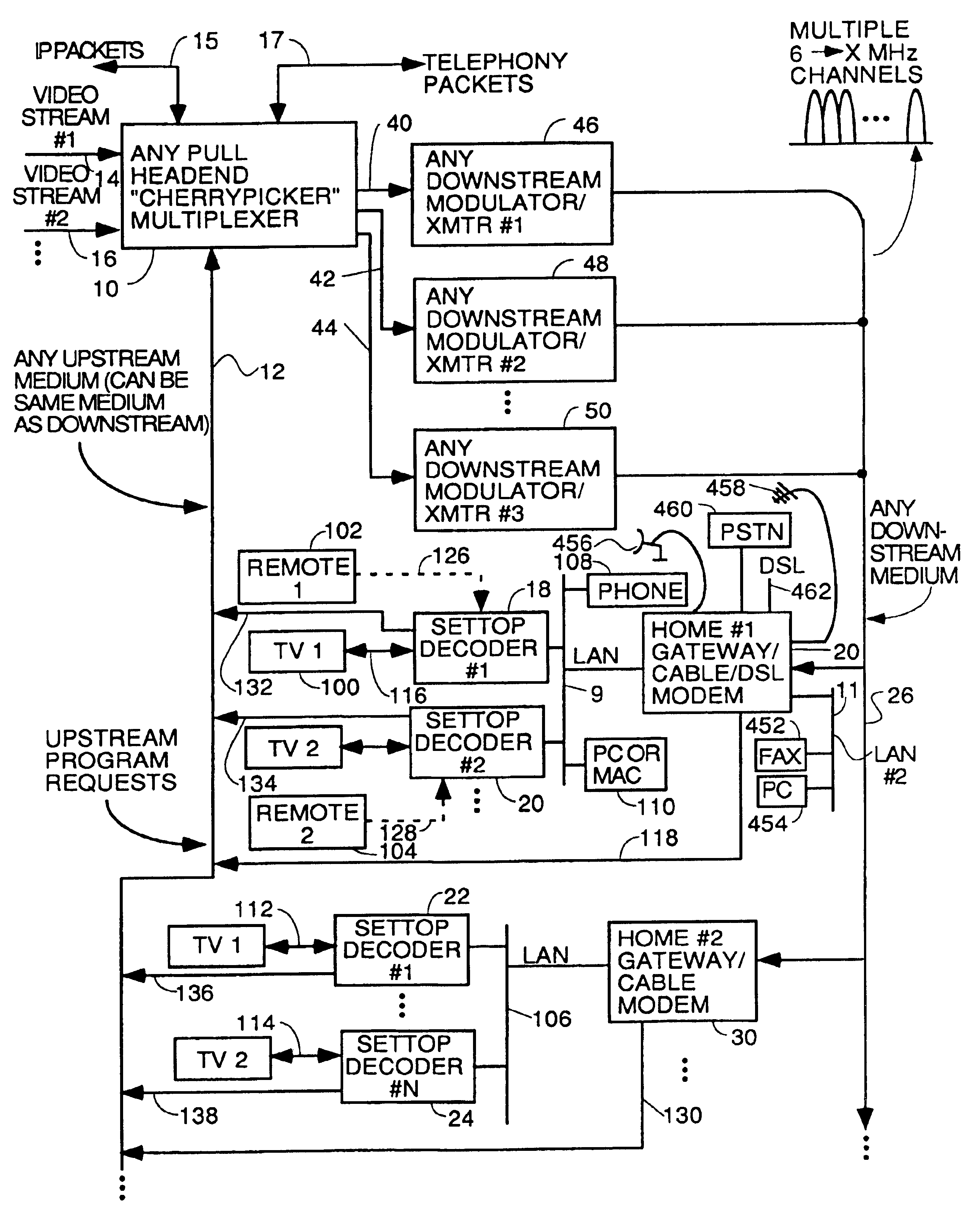
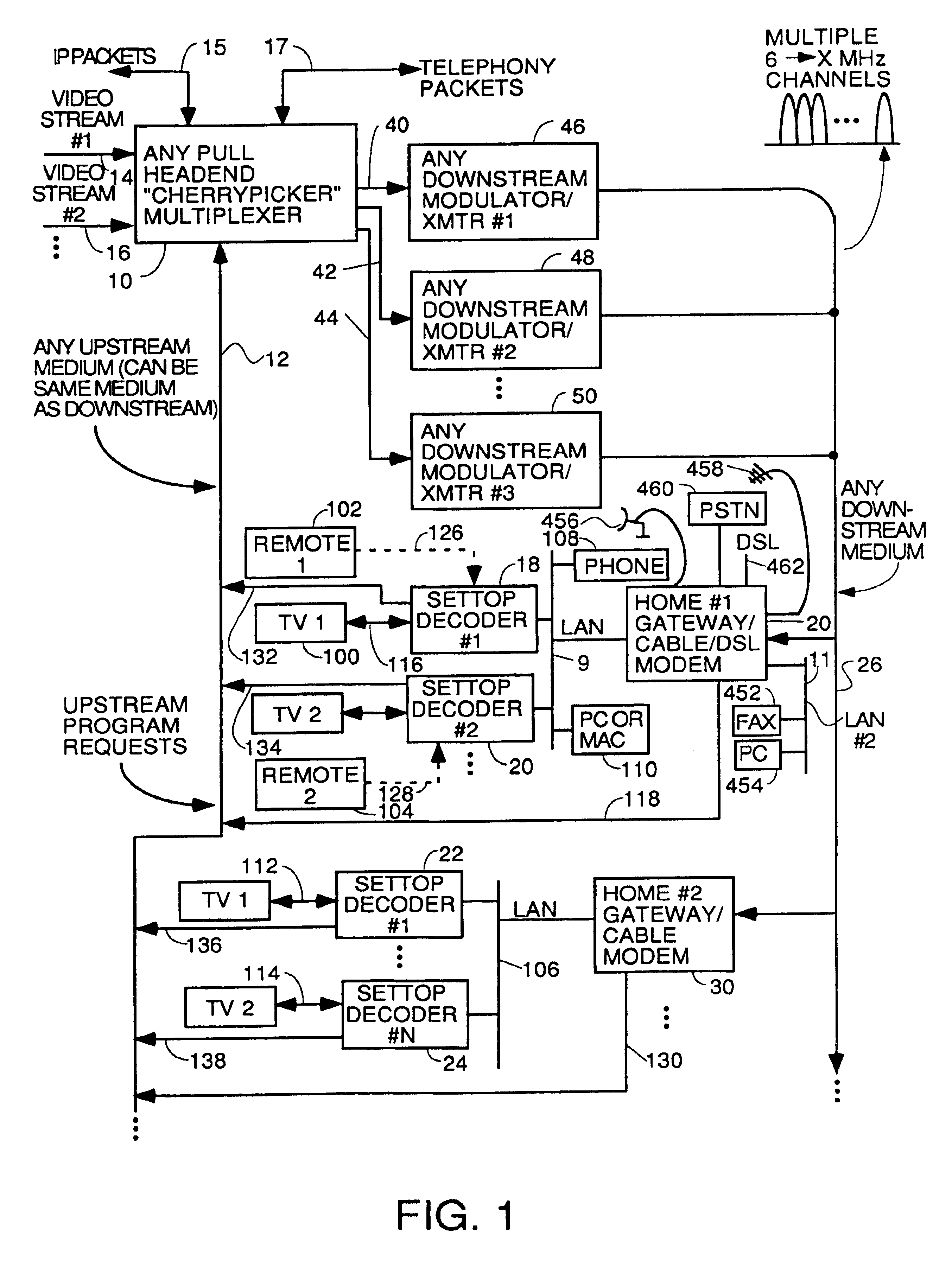
Home network for receiving video-on-demand and other requested programs and services
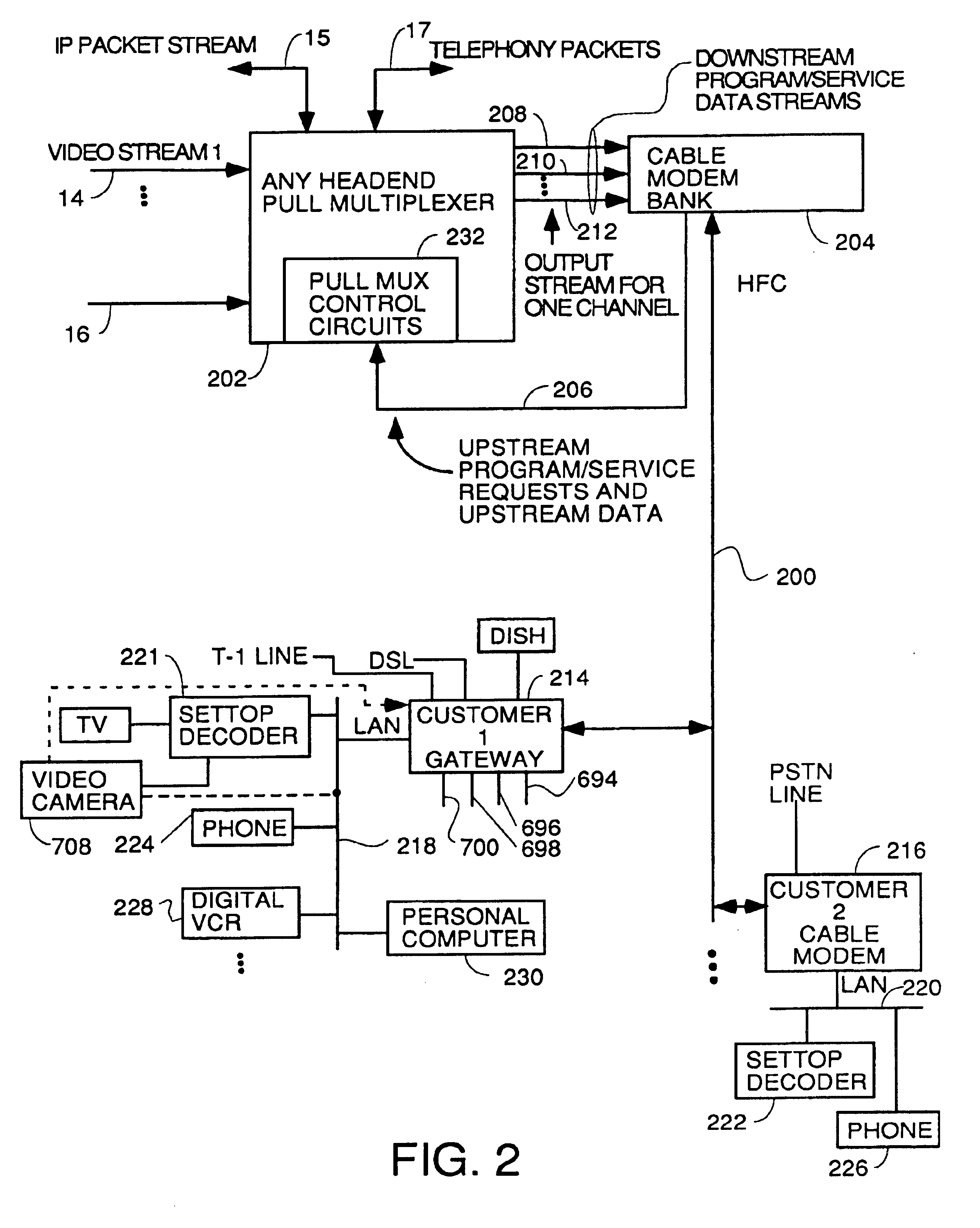
InactiveUS6889385B1Reduce quality problemsReduce bandwidth consumptionBroadband local area networksAnalogue secracy/subscription systemsVideocassette recorderTransceiver
A system for providing video-on-demand service, broadband internet access and other broadband services over T-carrier systems including a pull multiplexer cherrypicker at the head end is disclosed. The pull multiplexer receives upstream requests and cull out MPEG or other compressed video packets, IP packets and other data packet types to satisfy the requests or to send pushed programming downstream. The downstream can be DSL or HFC. Each customer has a cable modem, DSL modem or a gateway which interfaces multiple signal sources to a LAN to which settop decoders, digital phones, personal computers, digital FAX machines, video cameras, digital VCRs etc. can be attached. Each gateway can coupled the LAN to a DSL line or HFC through a cable modem or a satellite dish through a satellite transceiver. A PSTN and conventional TV antenna interface is also provided.
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
System And Method To Acquire, Aggregate, Manage, And Distribute Media
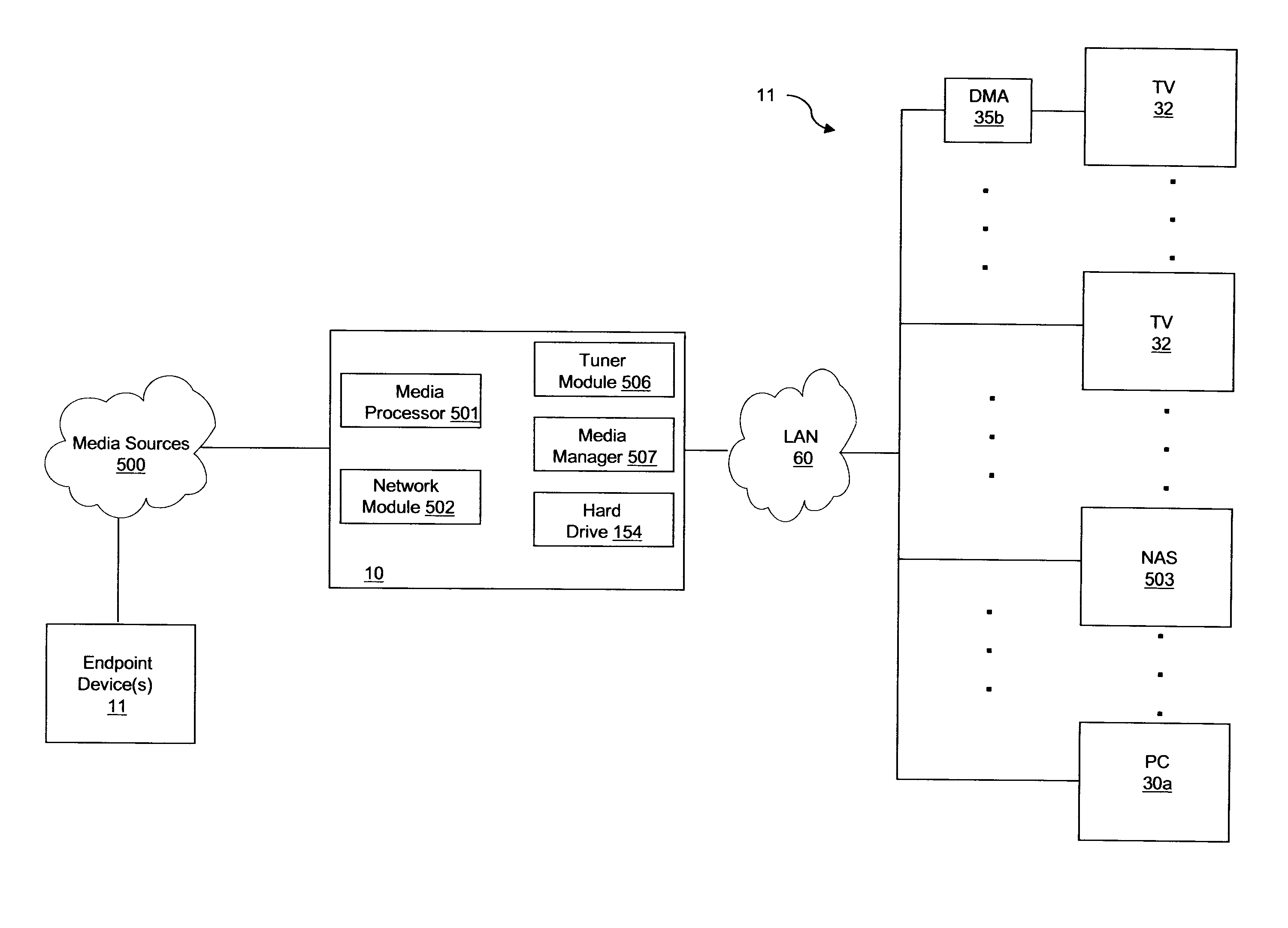
ActiveUS20080168523A1Simplify overall management of serviceReduce complexityMultiplex communicationBilling/invoicingComputer networkData format
A media content manager residing at a user premises having a tuner coupled to at least one media source operable to selectively receive at least one media stream of at least one type of media content. The media content manager also including a media processor coupled to the tuner and operable to receive the at least one media stream and convert the media stream to a predetermined data format, the at least one media stream comprising metadata. Additionally, the media content manages has a media manager coupled to the media processor and operable to receive the at least one media stream in the predetermined data format and direct the media stream to a selected media player device coupled to the media processor. Furthermore, the media content manager includes a storage device coupled to the media manager and operable to receive and store the at least one media stream in the predetermined data format.
Owner:KIP PROD P1 LP
Distributed data center access switch
ActiveUS20100214949A1Data switching by path configurationNetwork connectionsData centerUnique identifier
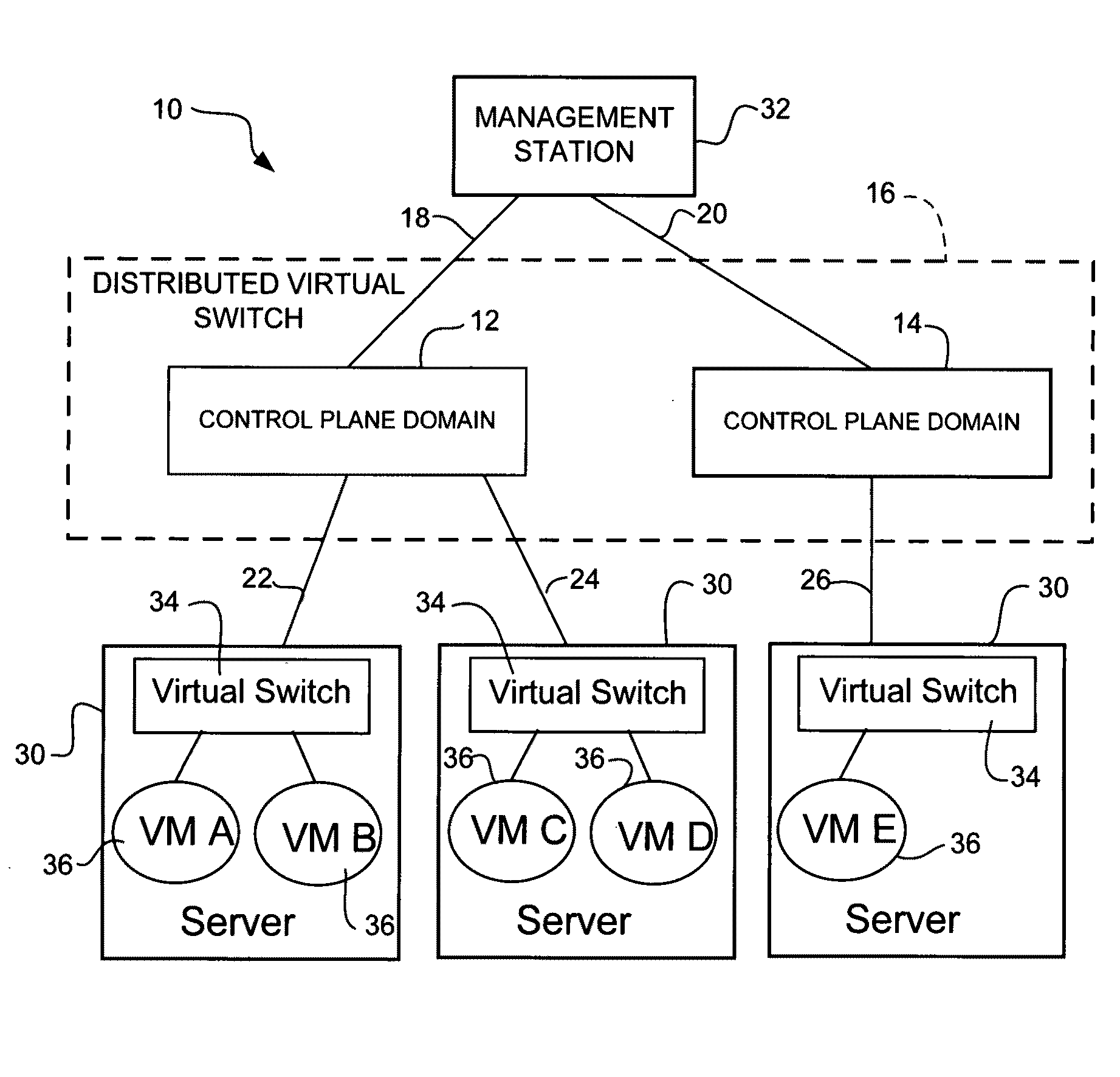
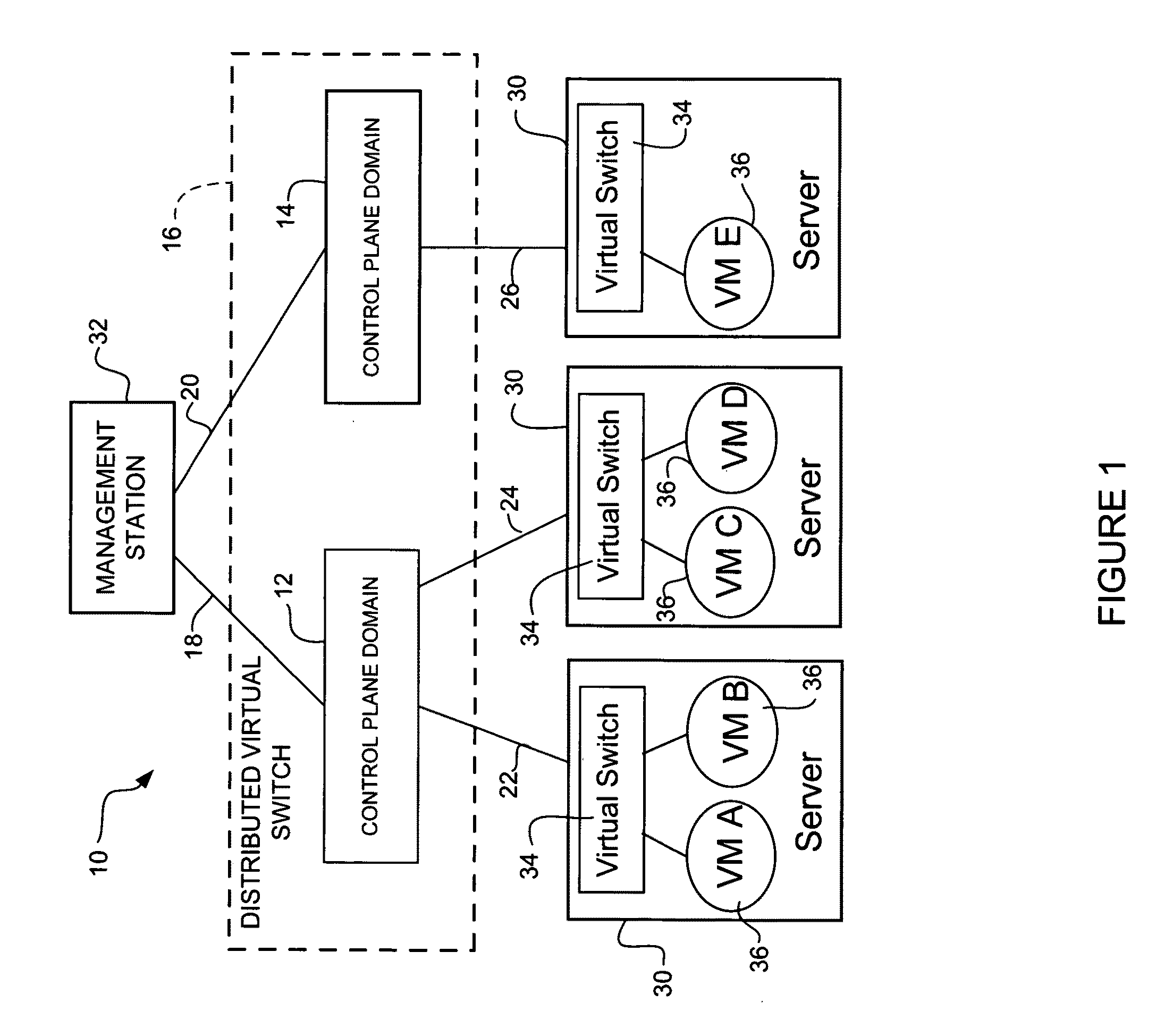
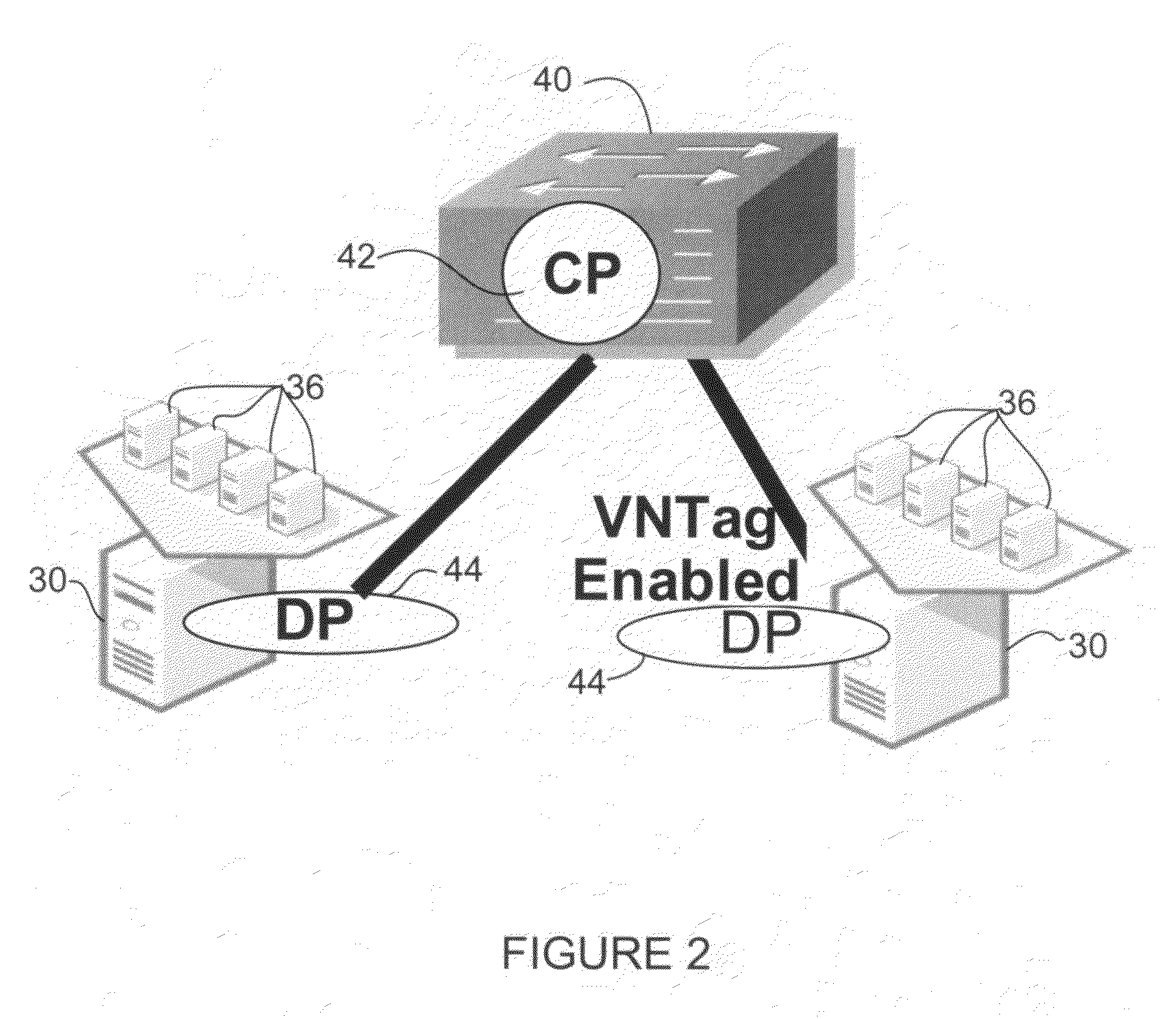
In one embodiment, an apparatus includes a processor configured for operation in a control plane in a distributed virtual switch in communication with a plurality of virtual machines each having a virtual interface. The processor is operable to identify other control planes in the distributed virtual switch, assign a virtual interface identifier to one of the virtual interfaces, receive a configuration for the virtual interface, and share the configuration with the other control planes in the distributed virtual switch. The virtual interface identifier provides a unique identifier for the virtual interface across all of the control planes. The apparatus further includes memory for storing the configuration of the virtual interface. A method for operating a network device associated with a control in the distributed virtual switch is also disclosed.
Owner:CISCO TECH INC
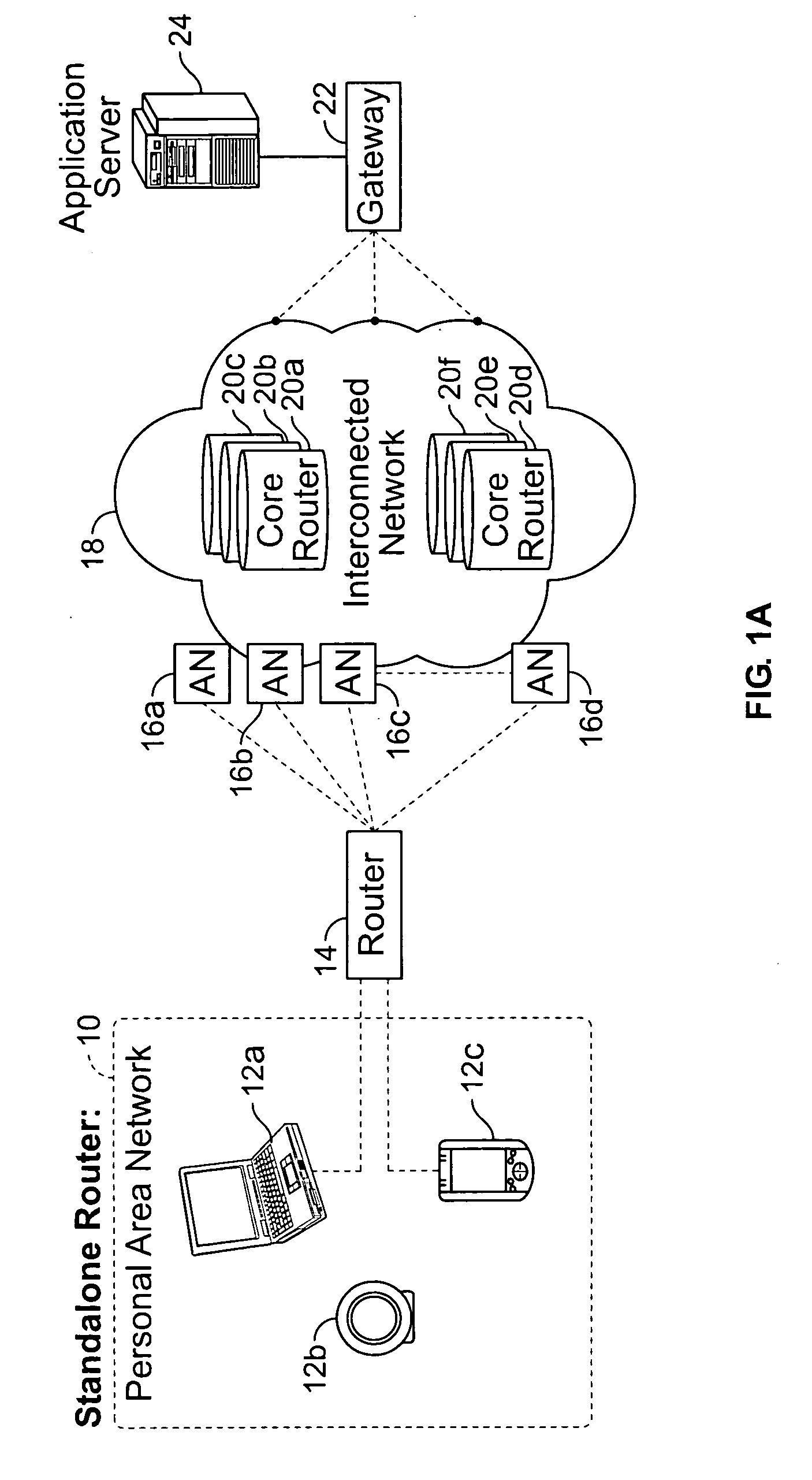
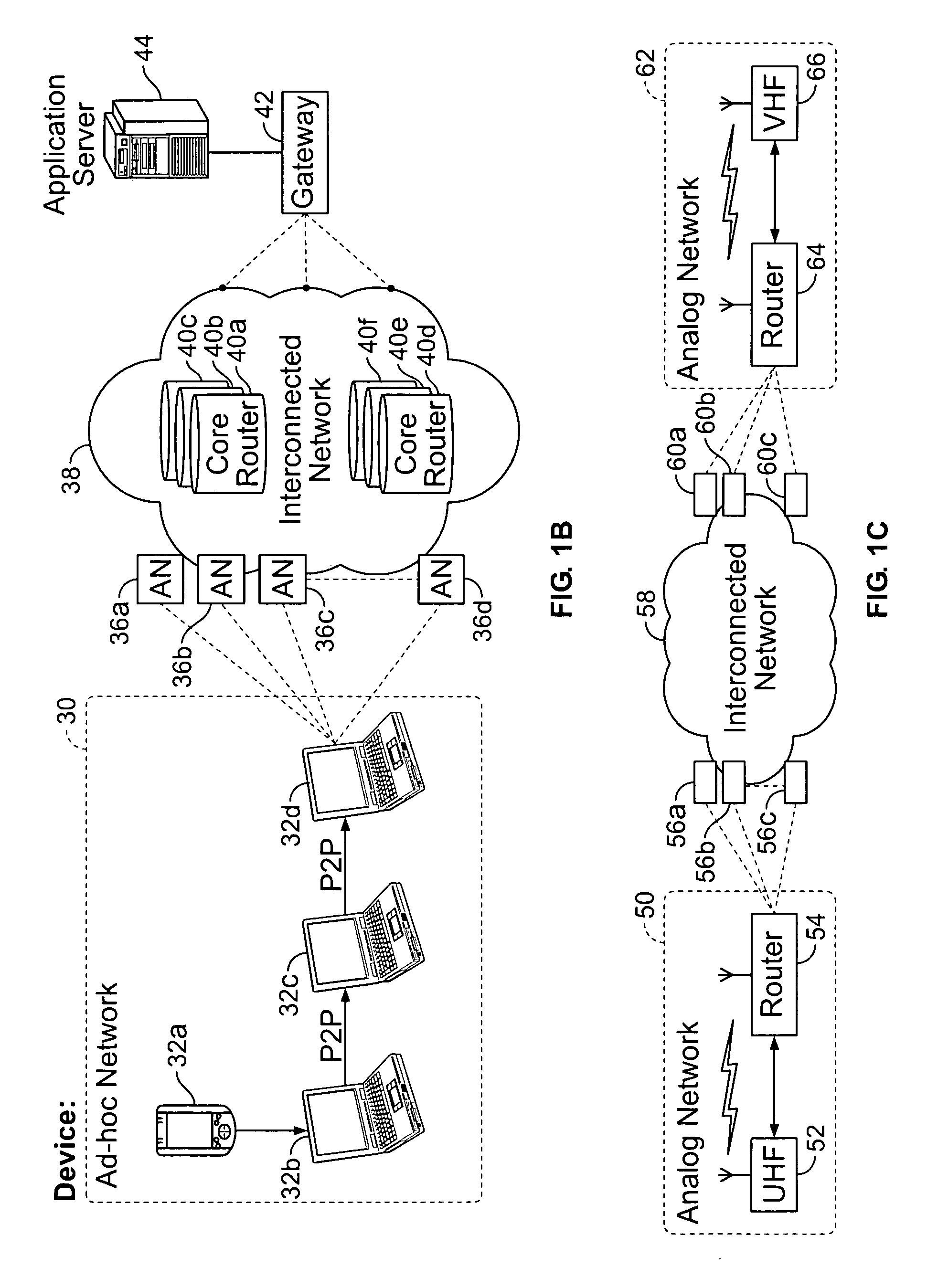
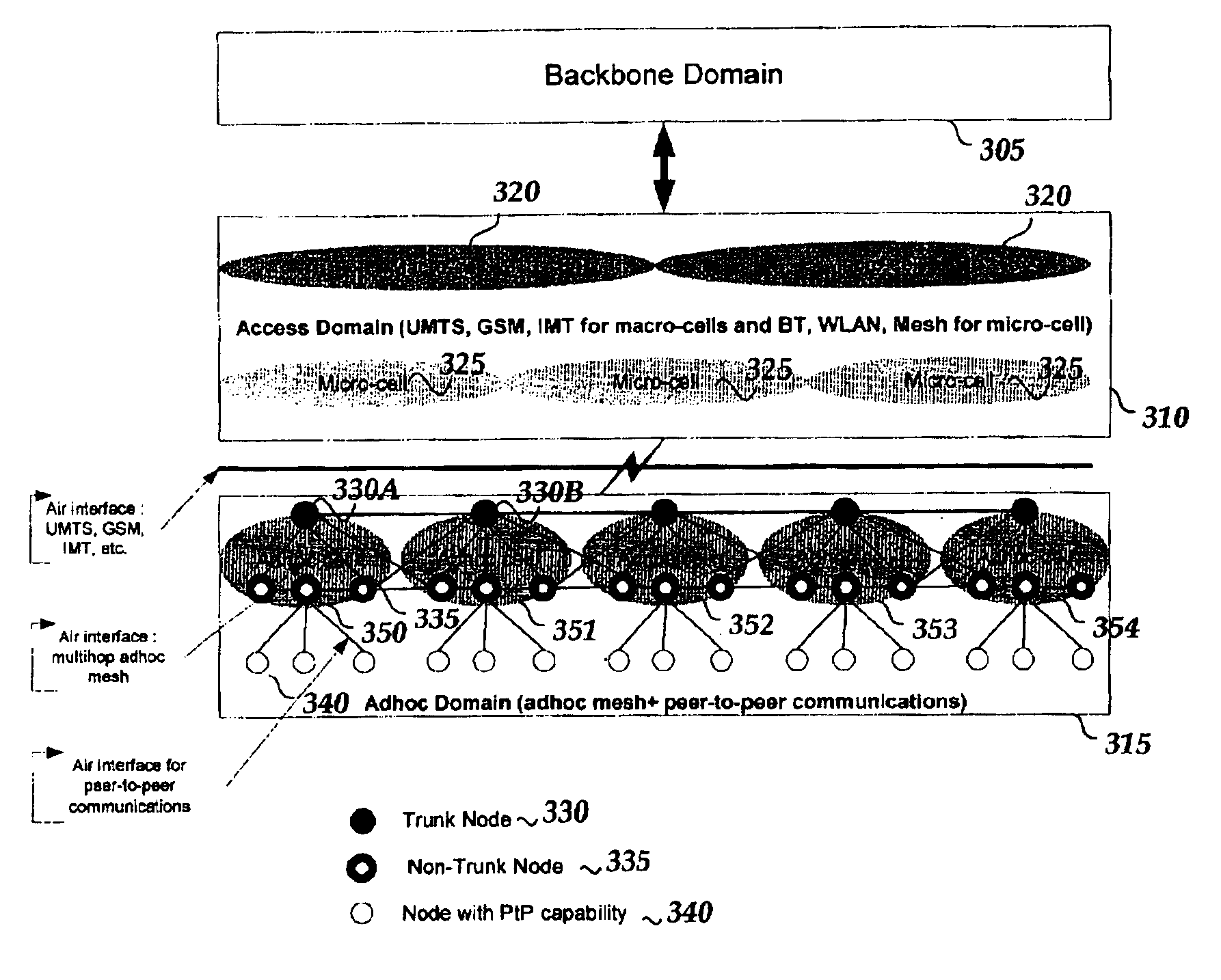
Mobile mesh Ad-Hoc networking
InactiveUS6879574B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCyber operationsAccess network
An architectural solution in which standalone ad-hoc network cells are used as an extension of the backbone infrastructure in terms of network architecture or / and its service capabilities is provided. These Ad-Hoc networks will integrate to the Internet via cellular and other access networks. This integration brings new possibilities to network operators and ISP's. In its extended architecture, it is envisaged that the mobility issues are handled by utilizing the IP mobility capabilities, taking into account the mobile mesh Ad-Hoc specific requirements.
Owner:NOKIA TECHNOLOGLES OY
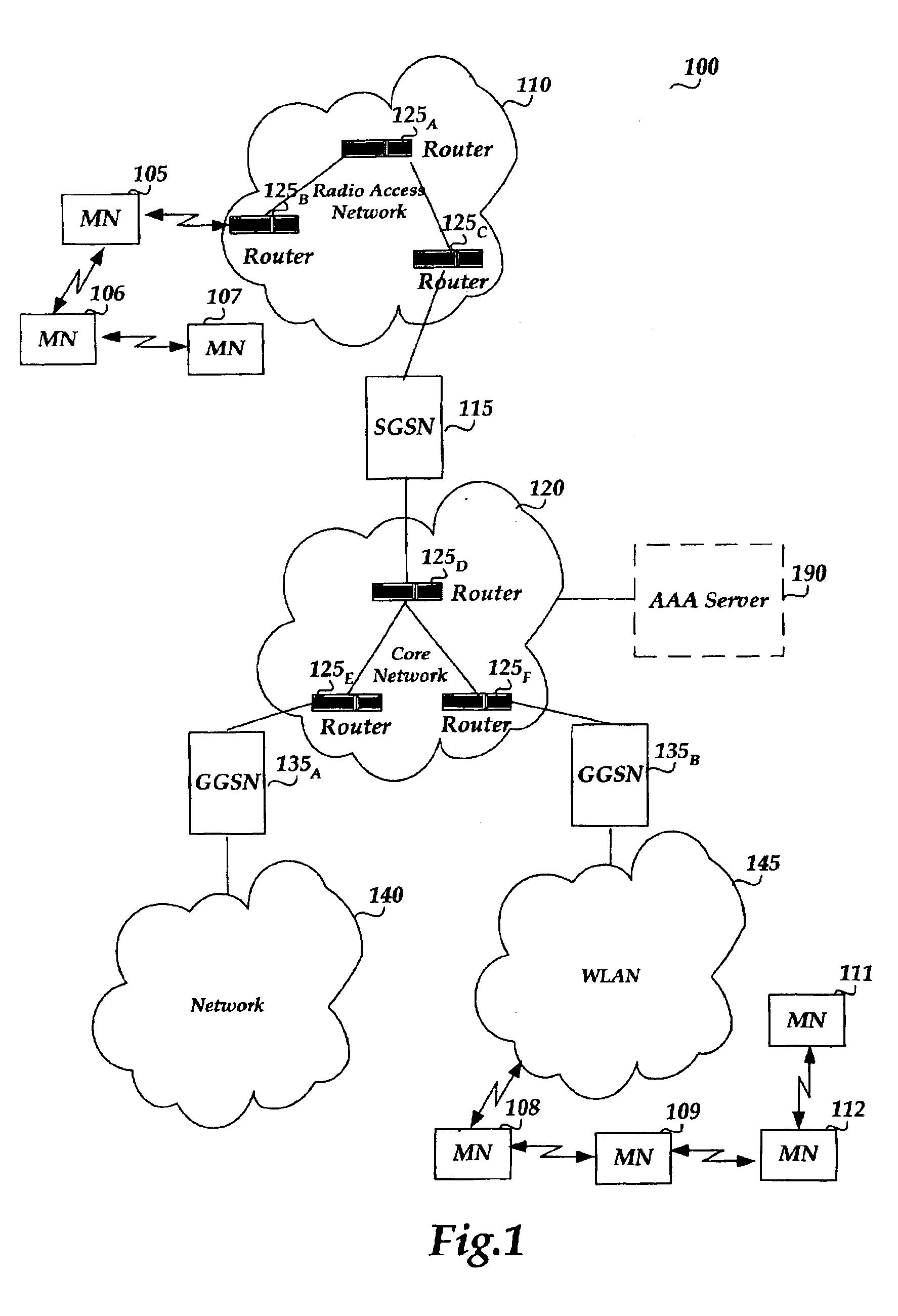
Voice over data telecommunications network architecture
InactiveUS20040022237A1Interconnection arrangementsDc level restoring means or bias distort correctionNetwork operations centerNetwork architecture
Owner:LEVEL 3 COMM LLC
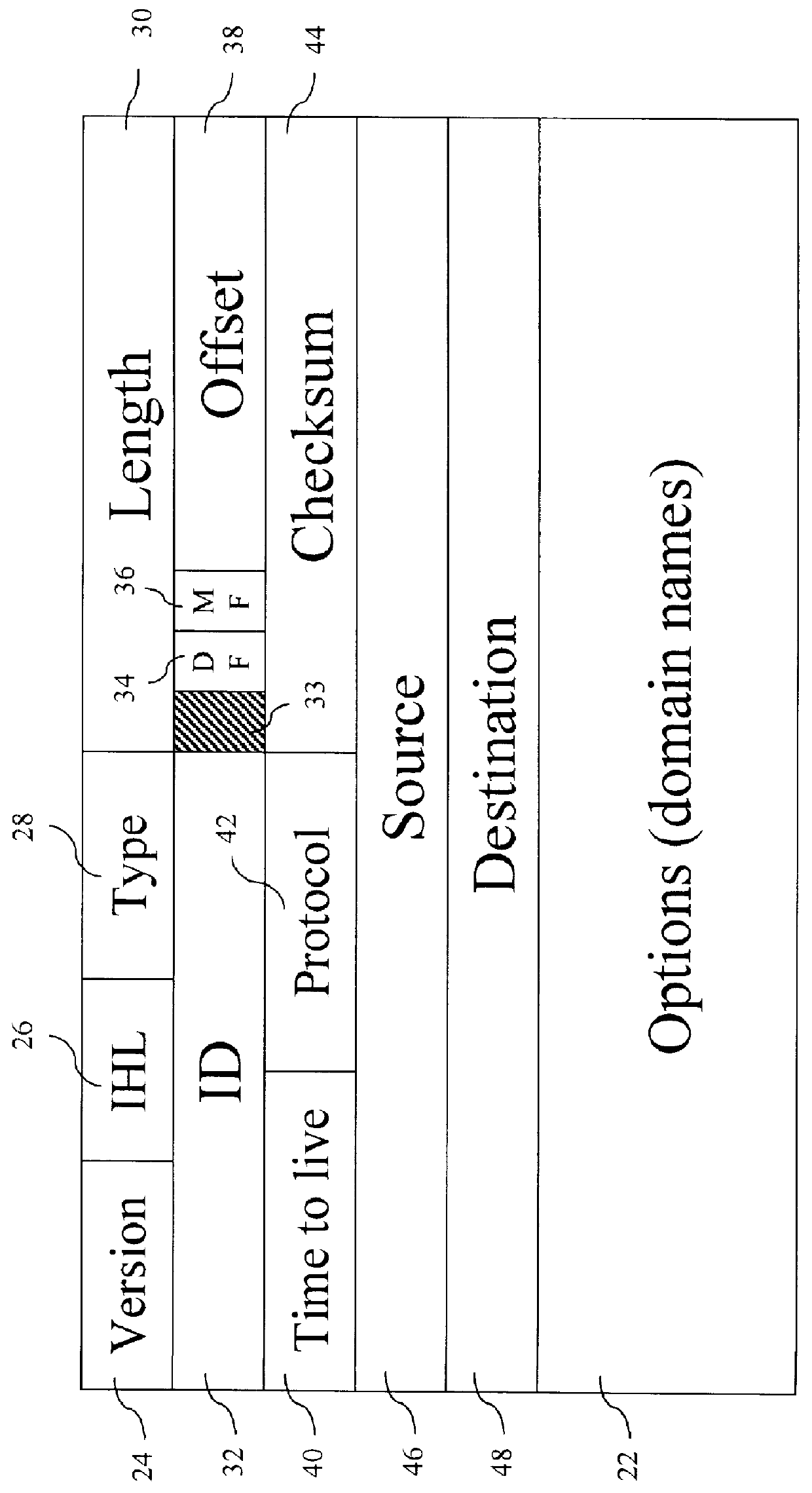
Domain name routing
InactiveUS6119171AImprove service qualityEasy to useTime-division multiplexData switching by path configurationDomain nameComputer network
The present invention provides for a Domain Name Router (DNR) that uses domain names to route data sent to a destination on a network (e.g., a stub network). Each corporate entity or stub network can be assigned one or a small number of global addresses. Each of the hosts on the stub network can be assigned a global address. When a source entity sends data to a destination entity with a local address, the data is sent to the DNR using a global address. The source entity embeds the destination's domain name and its own domain name inside the data. The DNR extracts the destination's domain name from the data, translates that domain name to a local address and sends the data to the destination.
Owner:F POSZAT HU +1
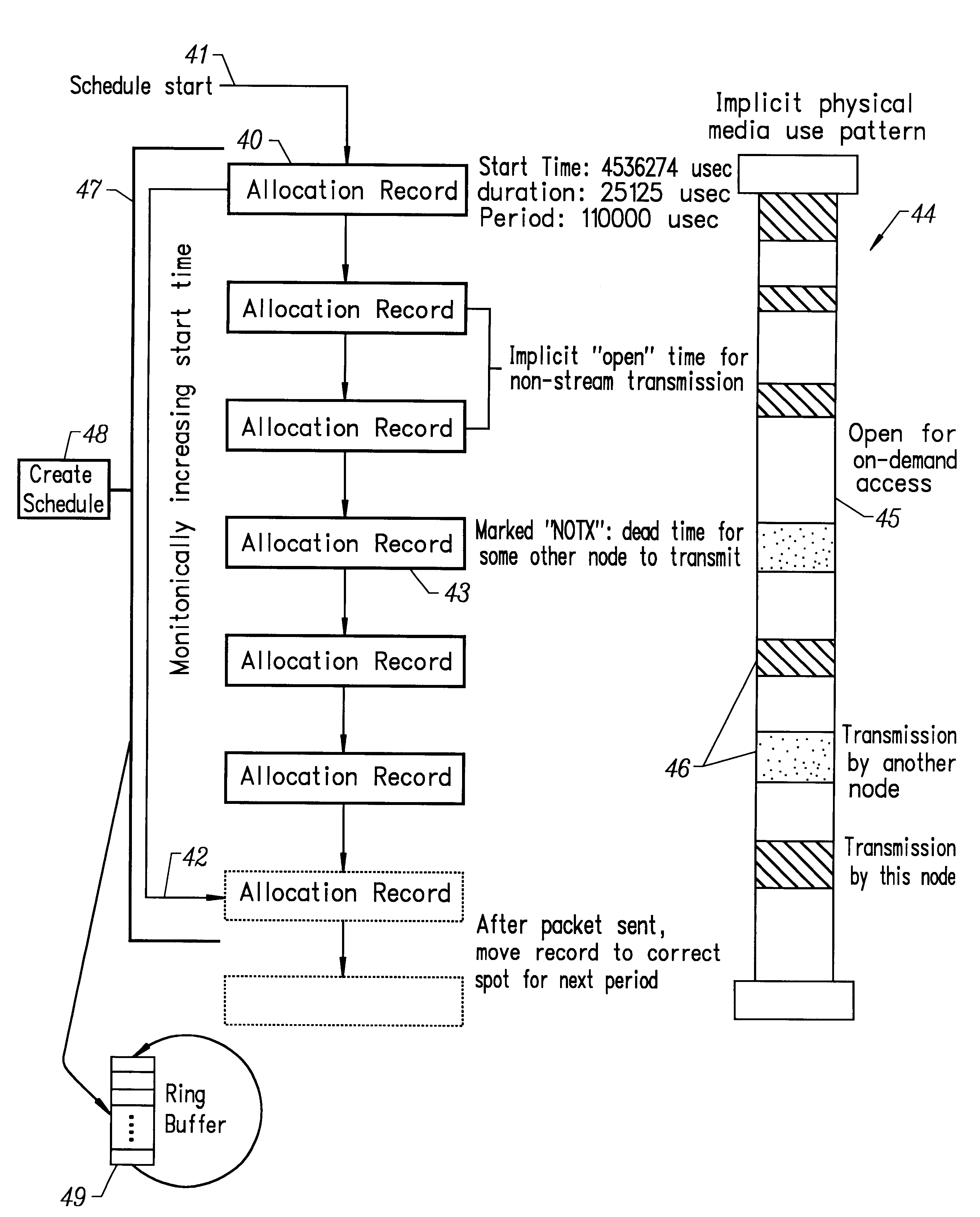
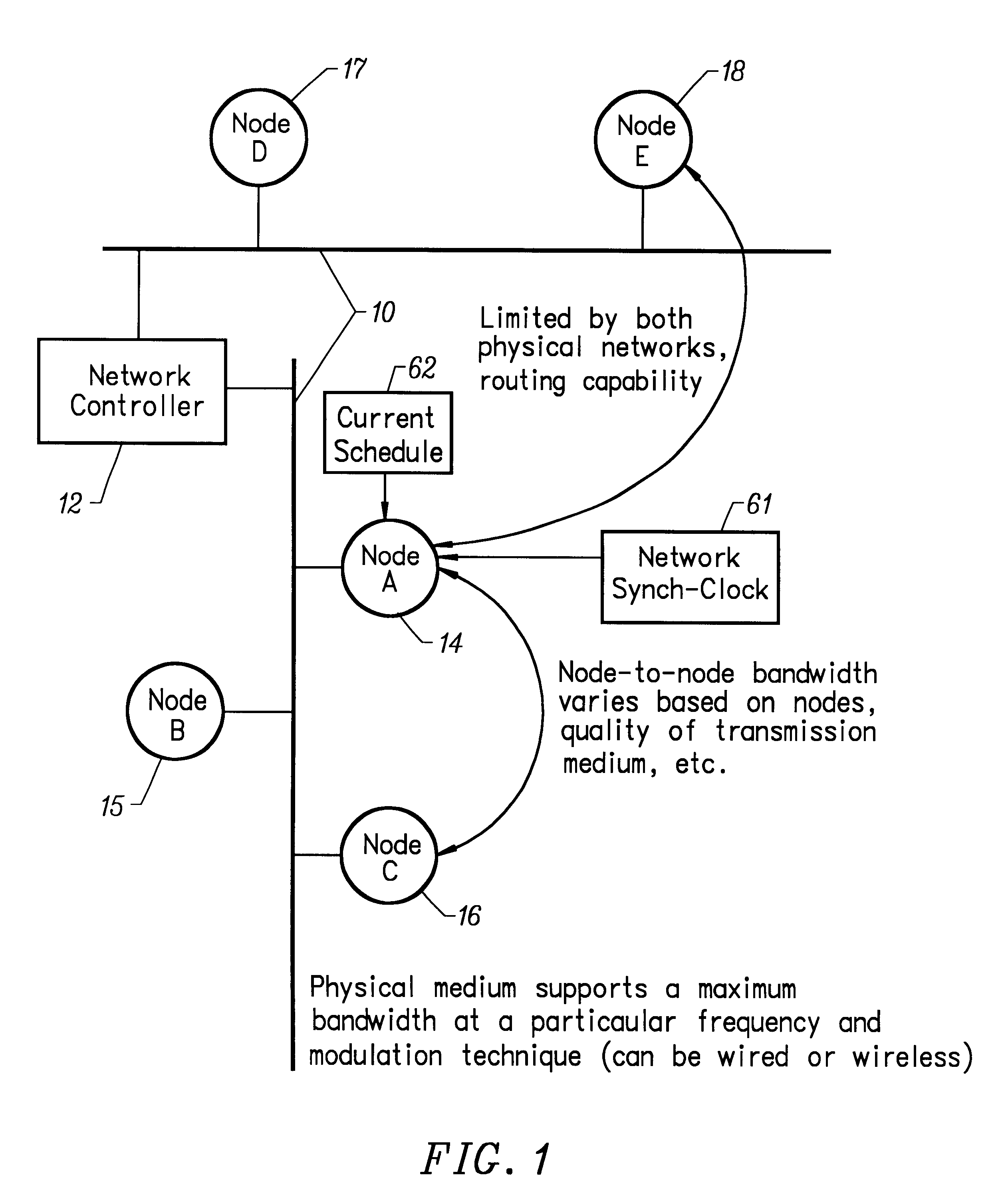
Method and apparatus implementing a multimedia digital network
InactiveUS6310886B1Most efficientHybrid switching systemsTime-division multiplexData capacityLong term data
A method and apparatus for efficiently managing the allocation of available data capacity on a physically shared digital network among devices connected to that network is disclosed. Also disclosed is a method and apparatus for managing the ongoing timely movement of data on the shared network such that precise long-term data rates are achieved between attached devices with minimal additional buffering. The invention further comprises a method and apparatus which allows the use of any remaining network capacity for non time-critical data movement without the need for centralized access management.
Owner:TIVO SOLUTIONS INC
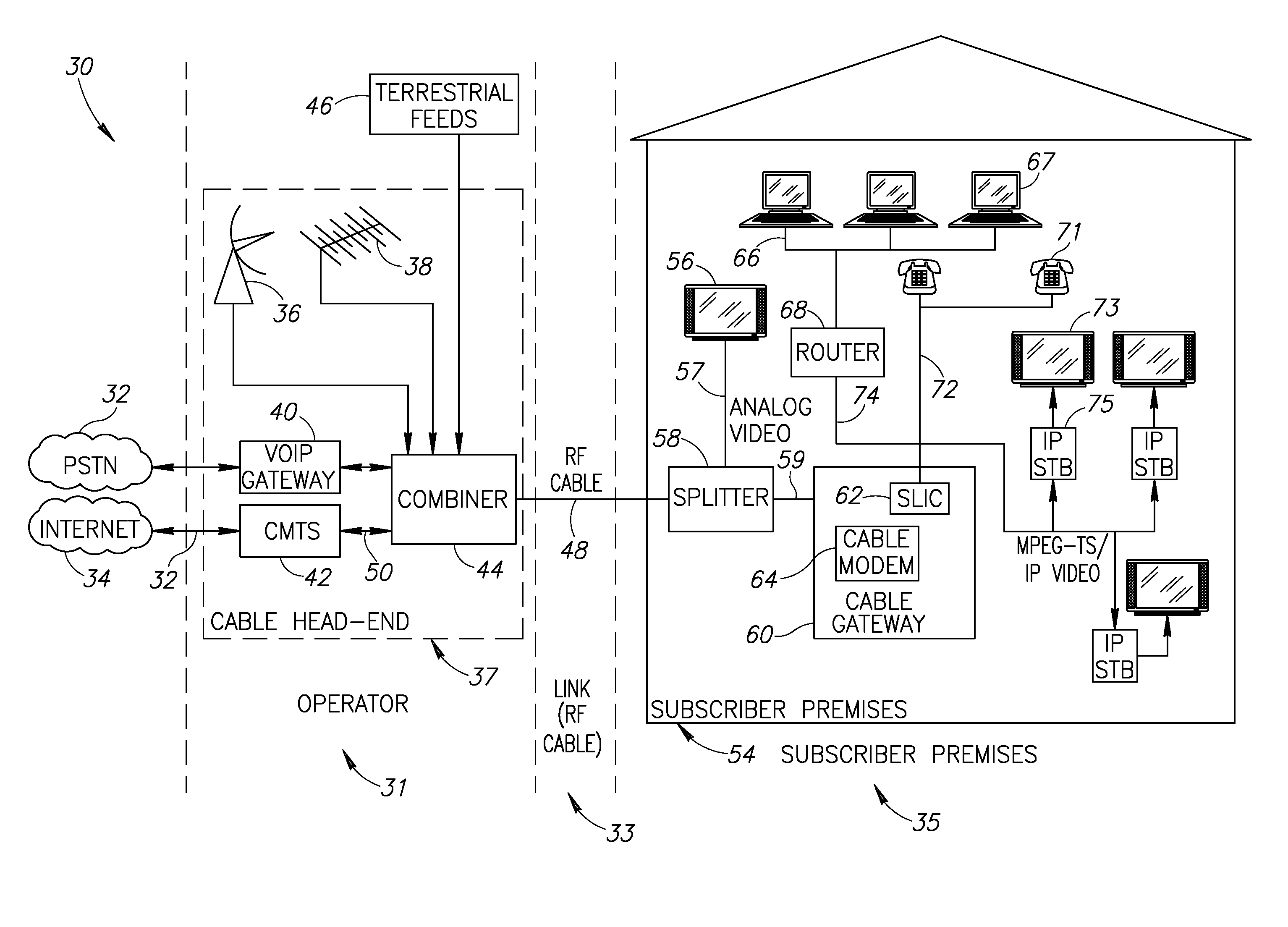
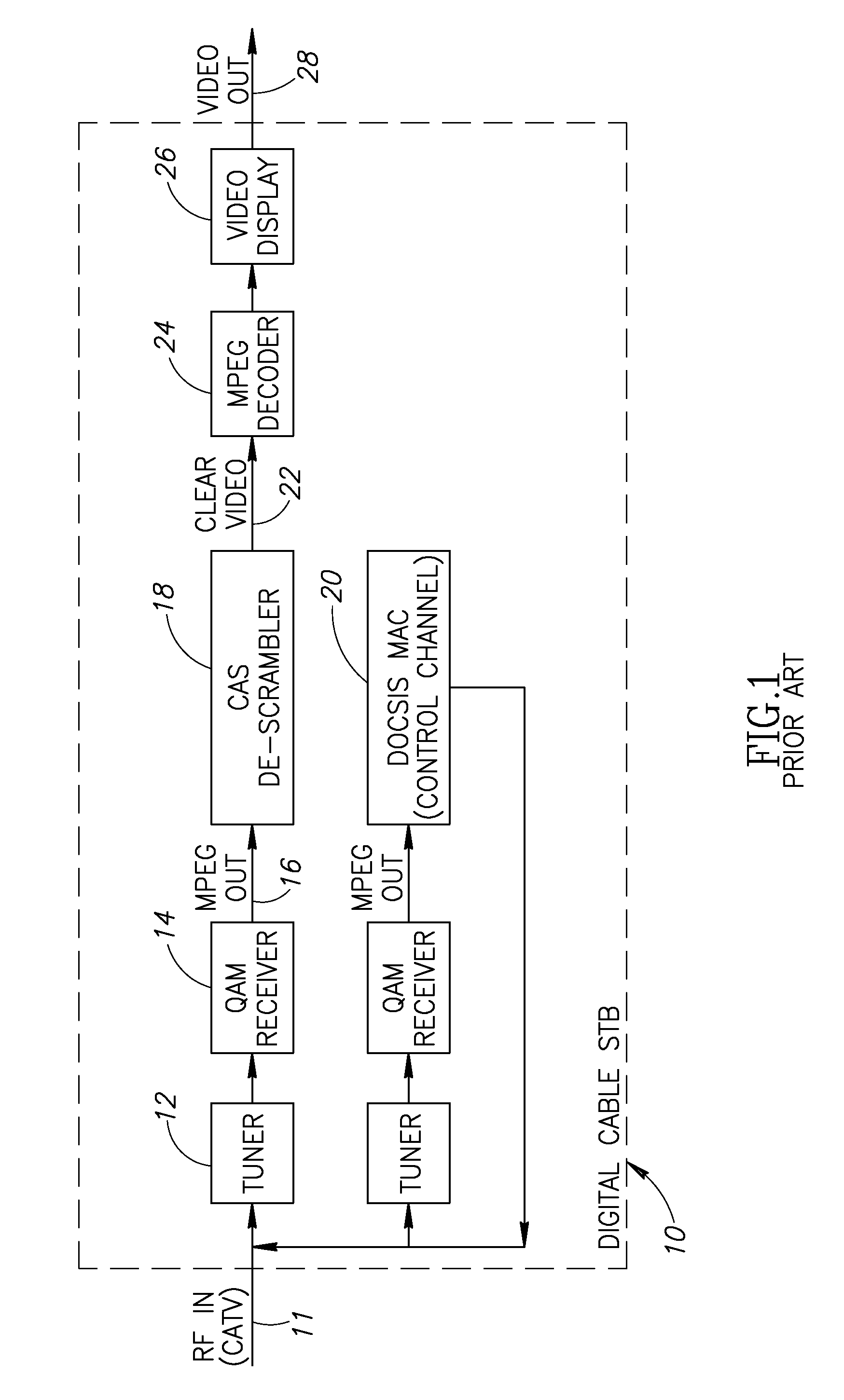
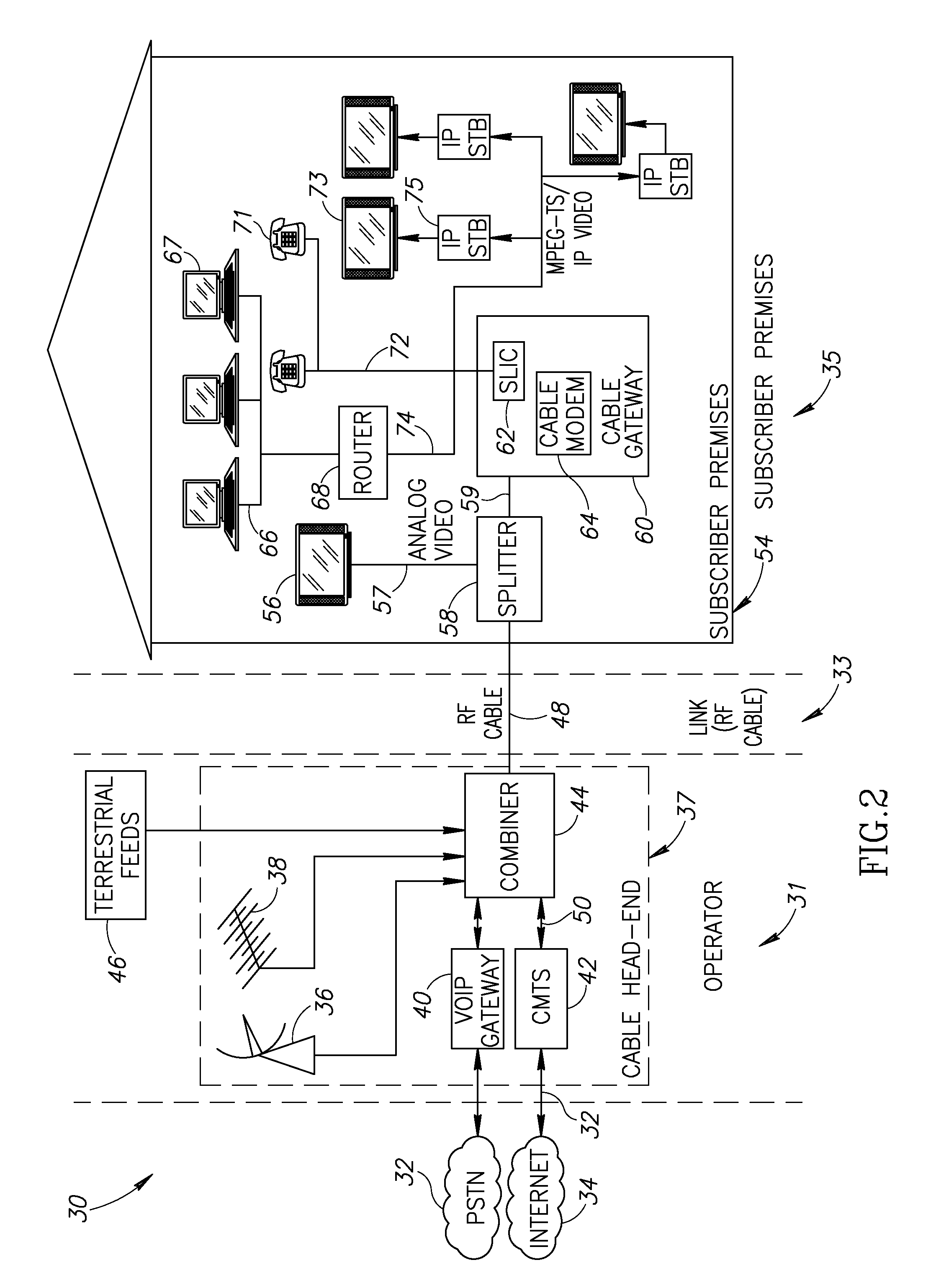
Hybrid mpeg/ip digital cable gateway device and architecture associated therewith
A novel cable gateway system and architecture incorporating a hybrid digital video transceiver. The digital cable system architecture combines reception of legacy video such as MPEG-TS based DVB-C streams with that of original IP video over DOCSIS channels. The system comprises a hybrid DVB / IP cable gateway STB capable of receiving both legacy DVB-C video and original IP video streams. The cable gateway device performs the front-end functionality (including QAM receiver, tuner and broadband connection) while the back-end functionality of video decoding and display is performed by one or more standard IP-STBs connected to the cable gateway device over a network (e.g., home LAN). Legacy MPEG-TS based DVB-C video is captured and encapsulated into packets for distribution over the network to the IP-STBs. The cable gateway distributes the original IP video received over the CATV source and the encapsulated legacy video as video over IP packets over the network.
Owner:INTEL CORP
Communications system for providing broadband communications using a medium voltage cable of a power system
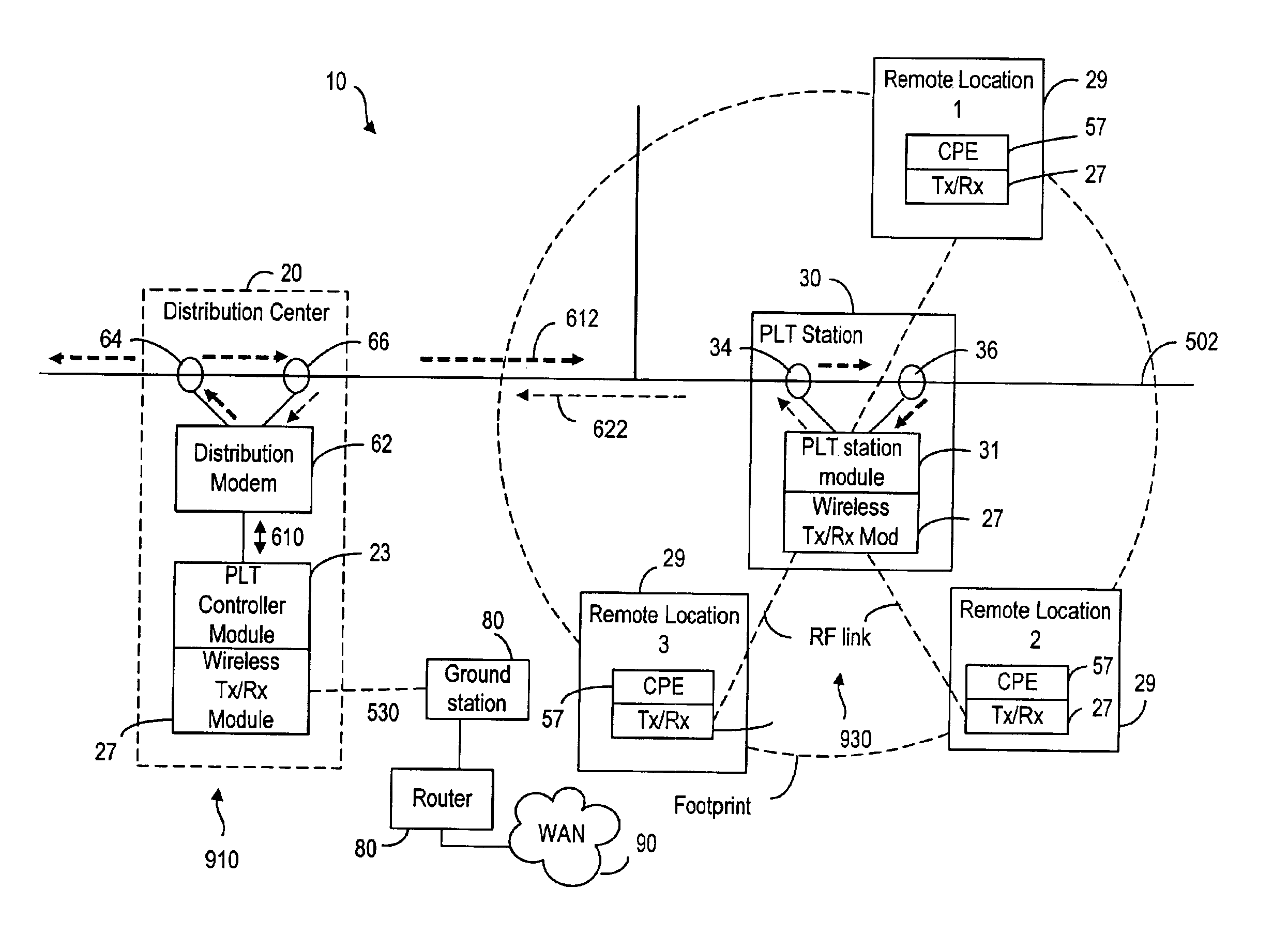
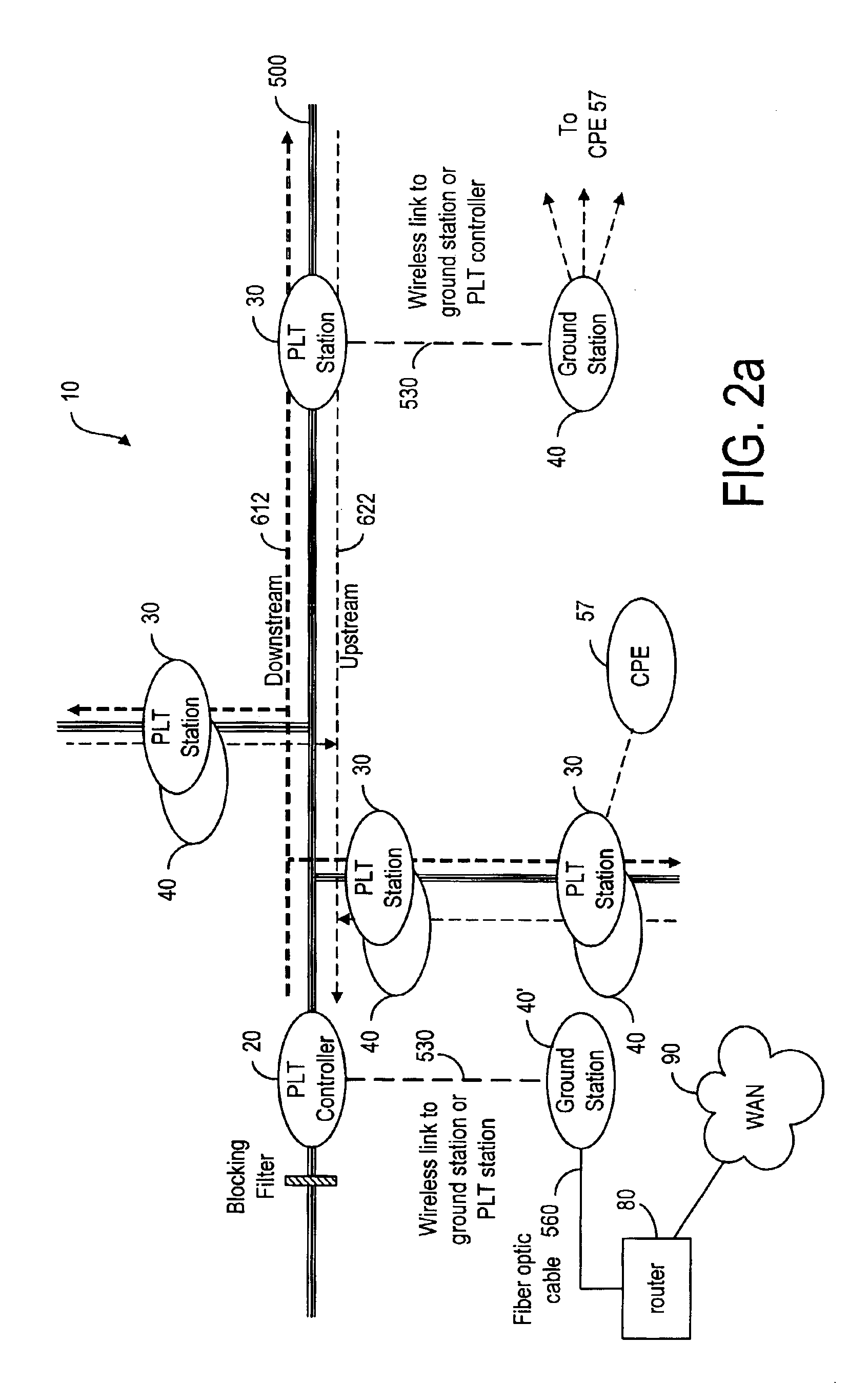
InactiveUS6885674B2High frequencyModulated-carrier systemsTransmission path divisionModem deviceCommunications system
A broadband service communication system using an MV cable for conveying RF signals in a network segment, which includes a distribution center (PLT controller) and a plurality of power line telecommunication (PLT) stations. The PLT controller has a distribution modem for conveying downstream and upstream RF signals to and from the PLT stations through the MV cable via couplers. Each PLT station has a modem for conveying the downstream and upstream RF signals via couplers and for conveying media signals to one or more customer premises equipment (CPE) via, e.g. wireless links. The PLT controller controls each PLT station regarding upstream communications transfer of all downstream communications and also controls. The PLT controller can be connected via a router to a WAN to convey media signals to and from the WAN. Repeaters and interlinks are used to join multiple network segments.
Owner:AMPERION
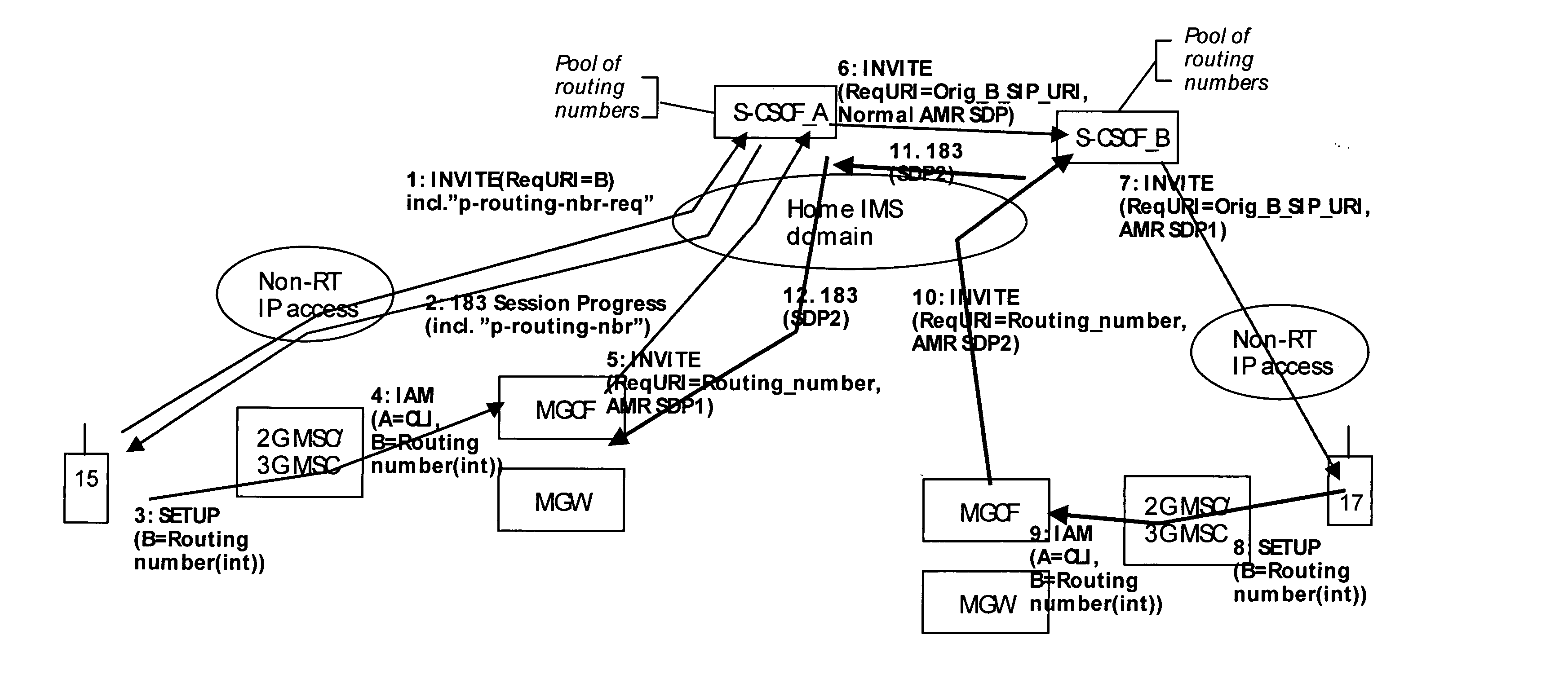
IP-based services for circuit-switched networks
ActiveUS20050058125A1Multiplex system selection arrangementsInterconnection arrangementsRadio access networkVoice over IP
A mechanism for providing a connection from an IP-based network to a circuit-switched network, such as a GSM network is disclosed. A temporary routing number for the circuit-switched network, such as an E.164 number, is delivered to a user terminal, and a circuit-switched call leg is established from the user terminal to the IP-based network using the routing number. Thereby, IMS-services are provided for end users which are located in the radio access network not having sufficient QoS required for voice over IP. In the example of a conference call service, a request for a conference call may forwarded via a data channel or data path to an application server which provides that conference call service. The application server then selects a conference routing number and returns the routing number to the conference host terminal via the data channel. Using the received conference routing number, the conference host terminal can then set up a circuit-switched connection as a call leg of the conference call.
Owner:NOKIA TECHNOLOGLES OY
System and method for connection failover using redirection
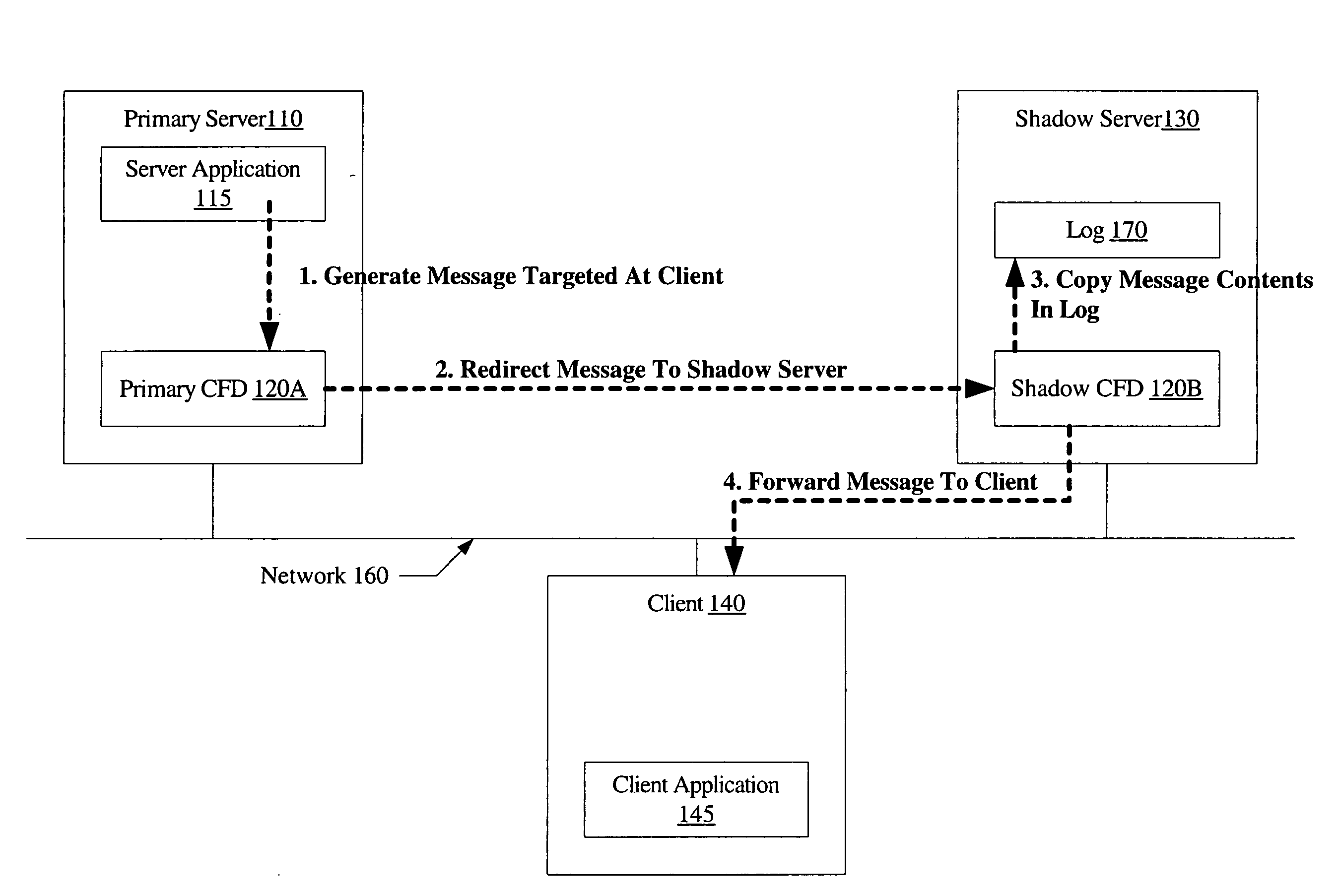
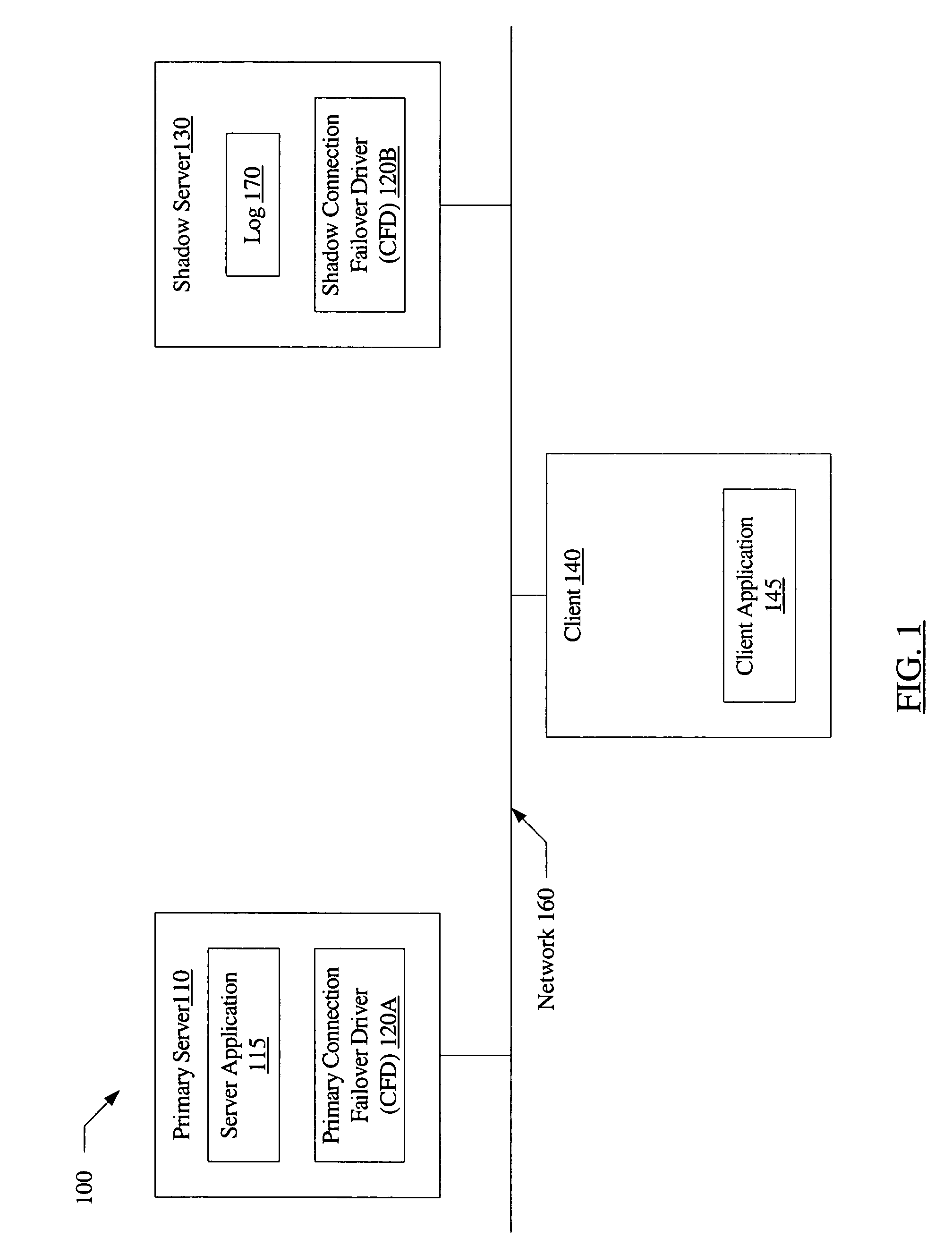
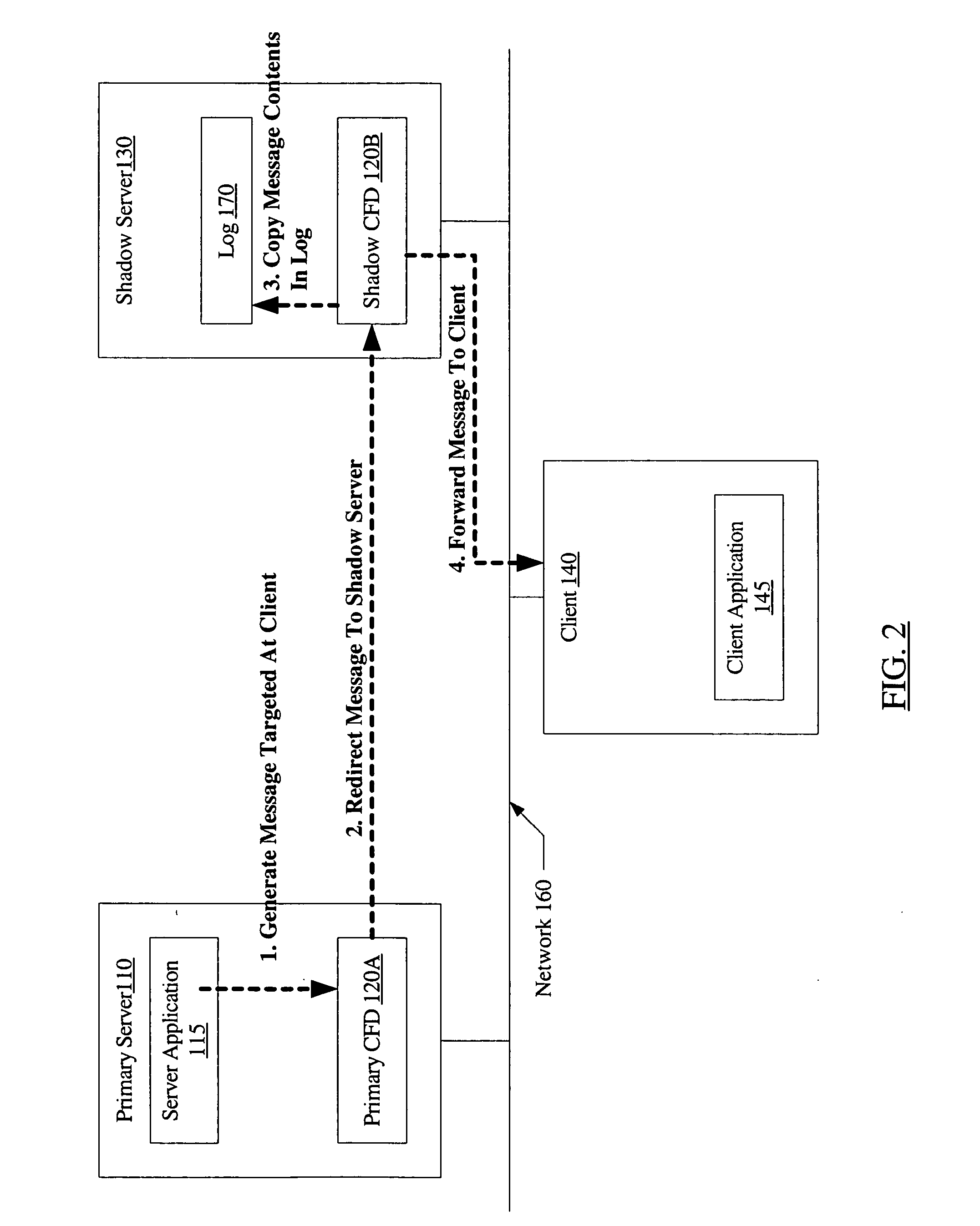
InactiveUS20060179147A1Multiple digital computer combinationsNetwork connectionsFailoverNetwork connection
A system for connection failover using redirection includes a primary server comprising a primary connection failover driver (CFD), a shadow server comprising a shadow CFD, and a client. The primary and shadow servers and the client are coupled via a network. The primary server and the client are configured to cooperate to establish a network connection. The primary CFD is configured to redirect a first message packet, targeted for transmission to the client over the network connection, to the shadow server. The shadow CFD is configured to copy contents of the first message packet into a log, and forward the first message packet to the client after the contents have been copied.
Owner:SYMANTEC OPERATING CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com