Patents
Literature
7222 results about "Wireless mesh network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
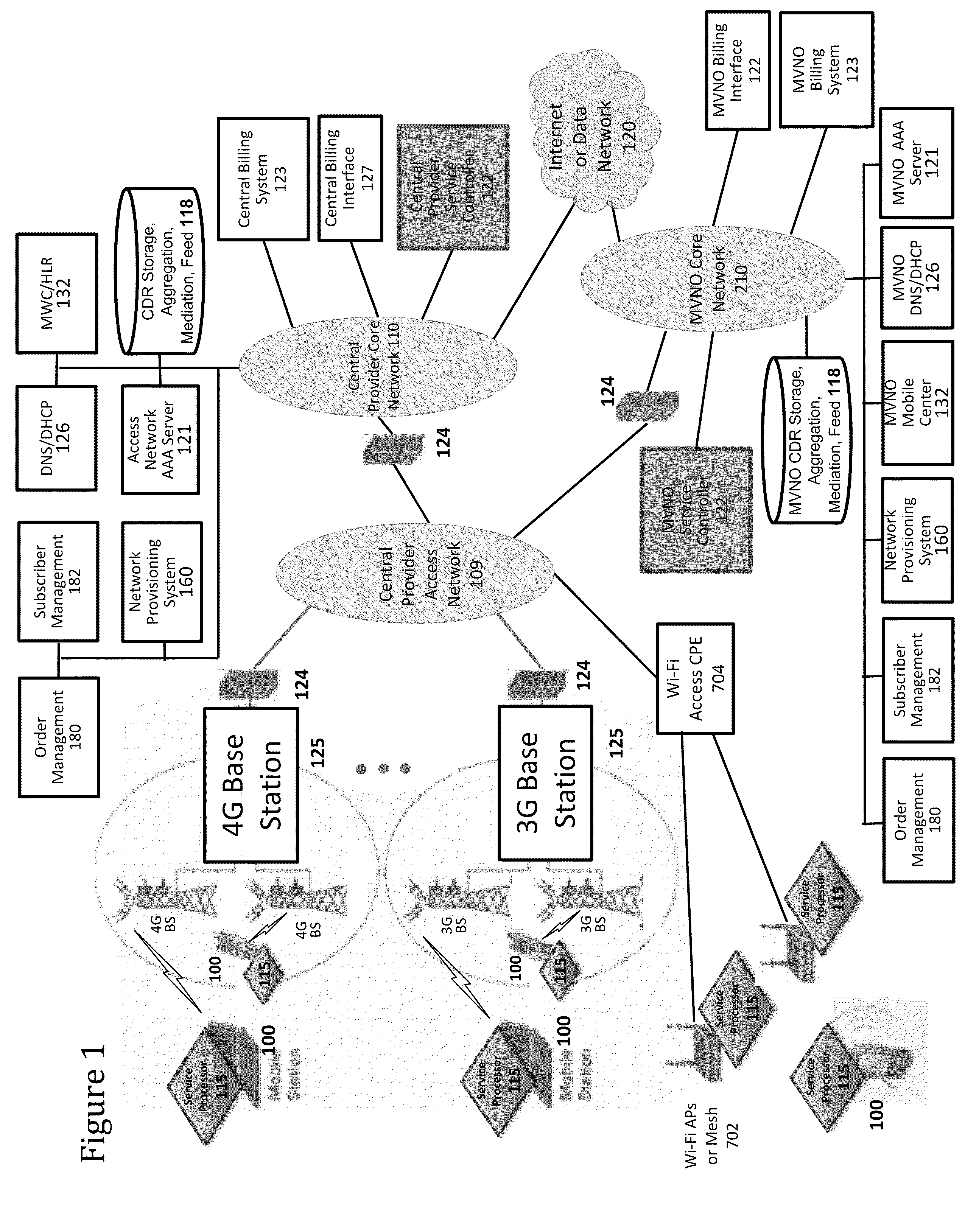
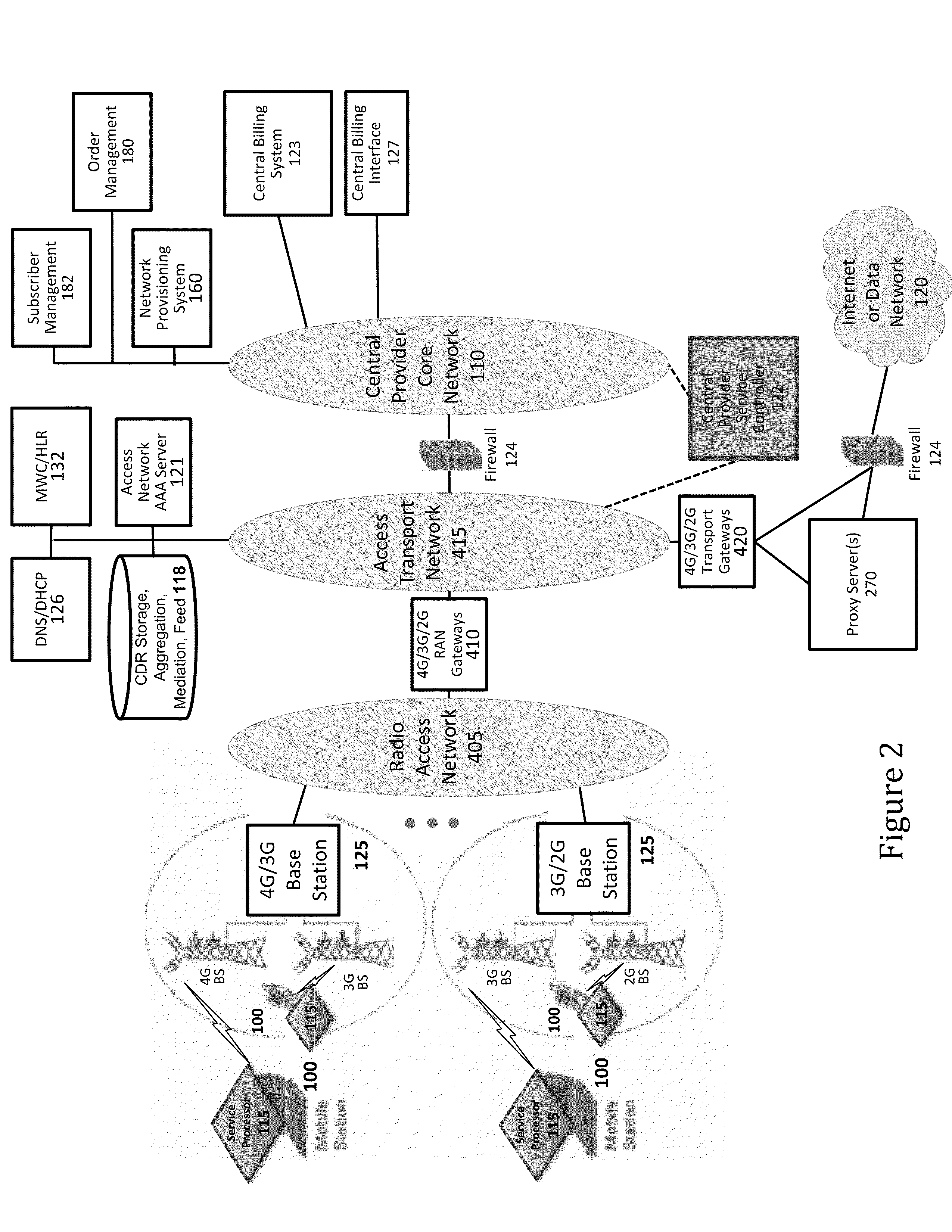
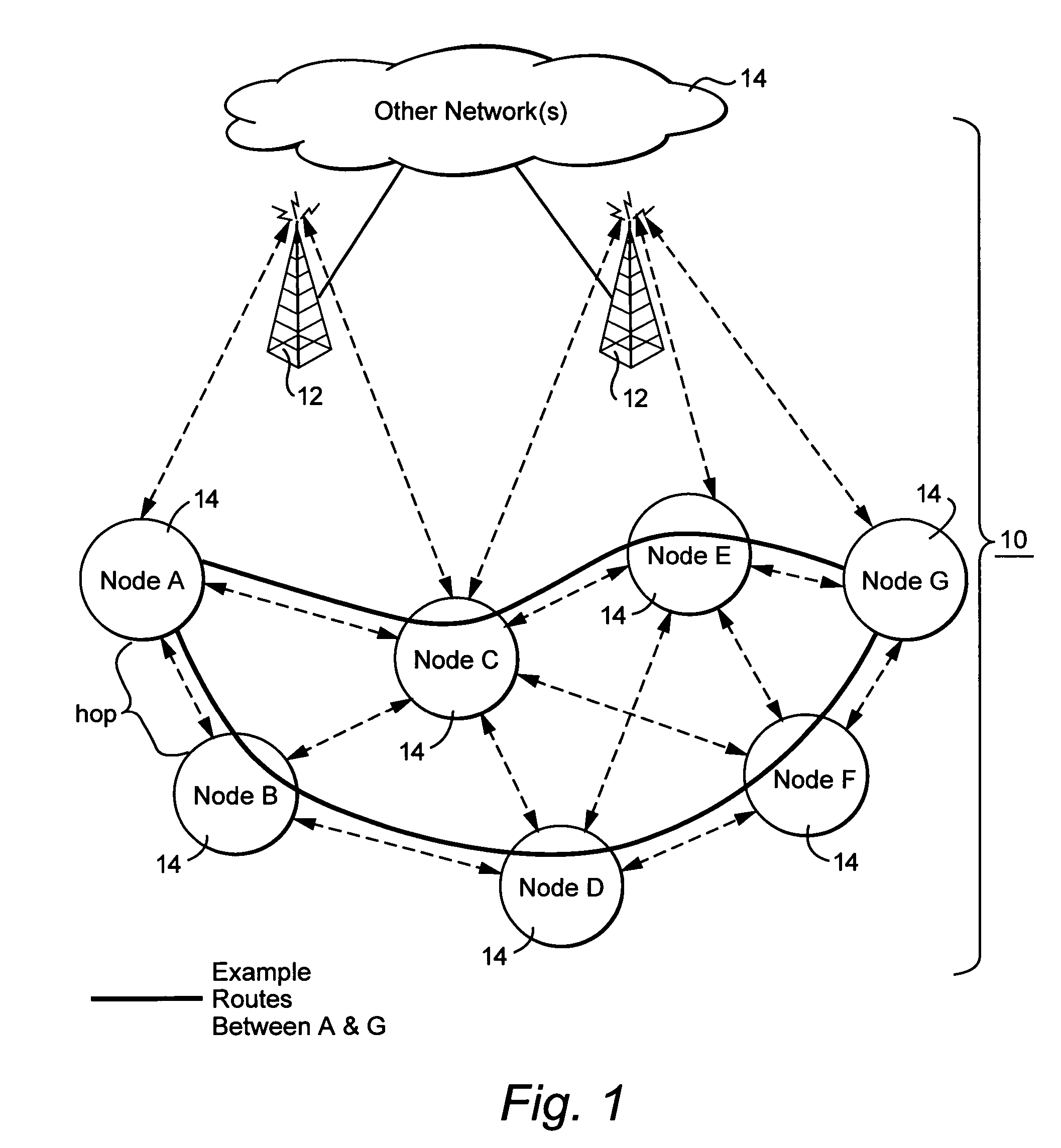
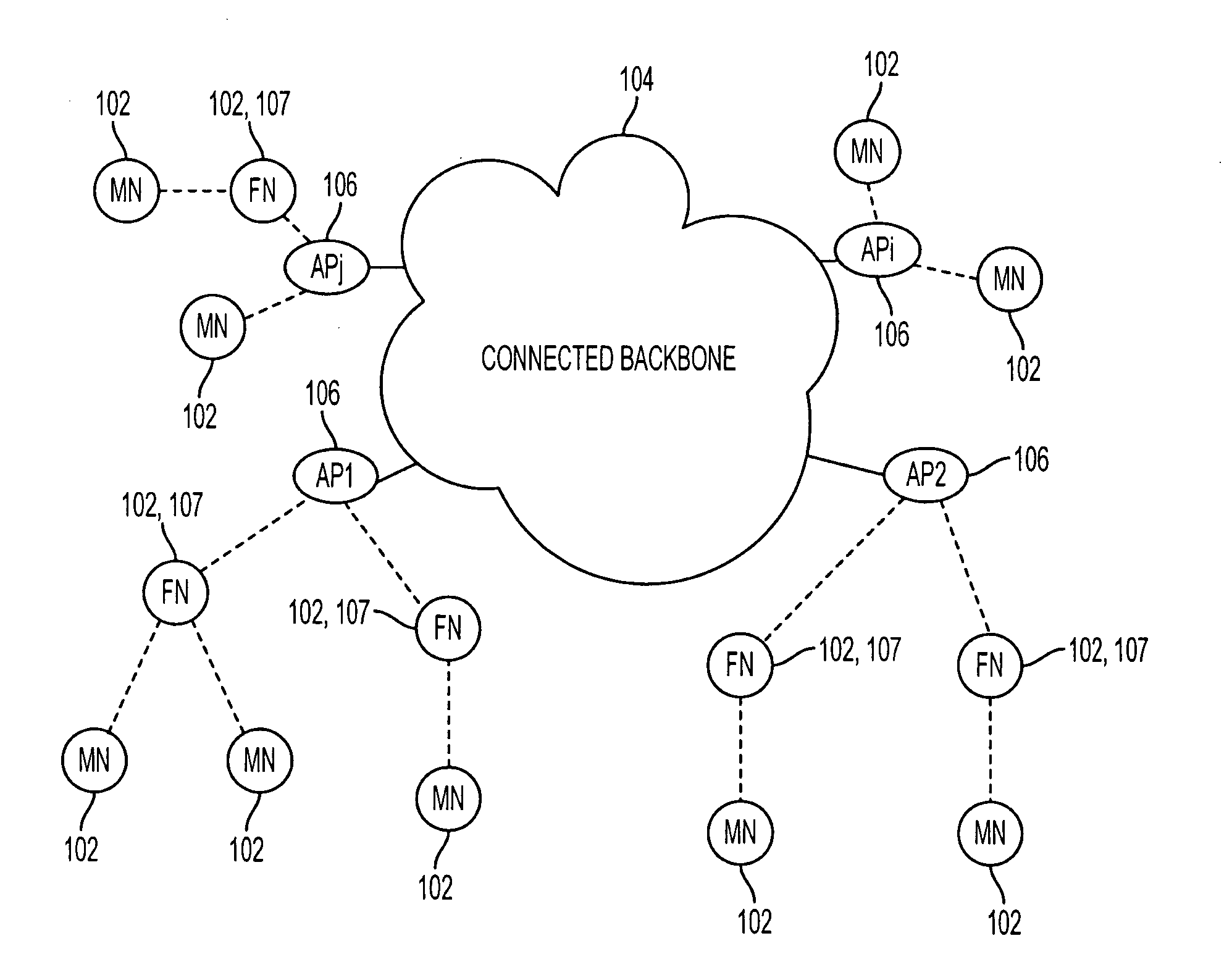
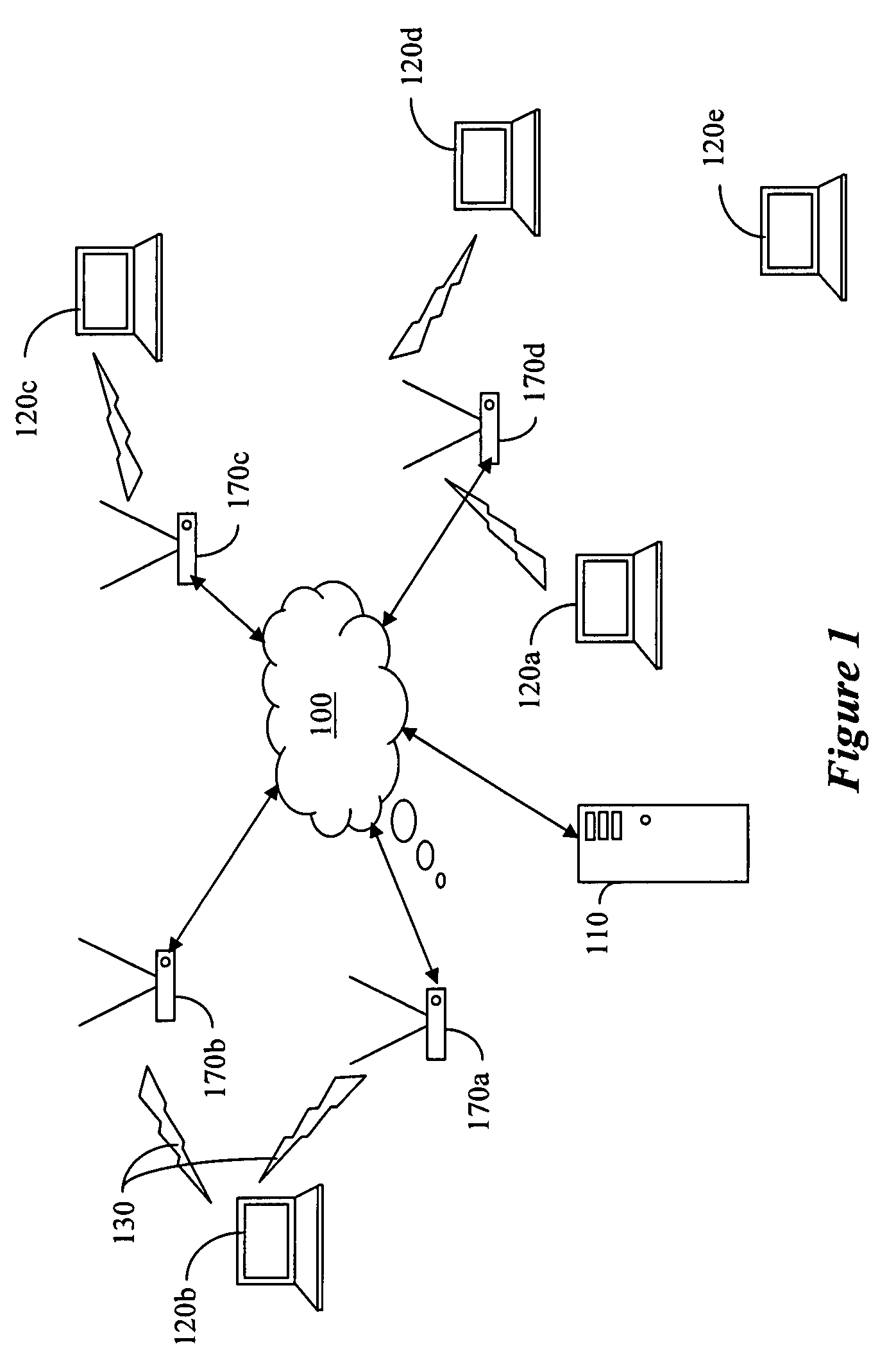
A wireless mesh network (WMN) is a communications network made up of radio nodes organized in a mesh topology. It is also a form of wireless ad hoc network. A mesh refers to rich interconnection among devices or nodes. Wireless mesh networks often consist of mesh clients, mesh routers and gateways. Mobility of nodes is less frequent. If nodes constantly or frequently move, the mesh spends more time updating routes than delivering data. In a wireless mesh network, topology tends to be more static, so that routes computation can converge and delivery of data to their destinations can occur. Hence, this is a low-mobility centralized form of wireless ad hoc network. Also, because it sometimes relies on static nodes to act as gateways, it is not a truly all-wireless ad hoc network.
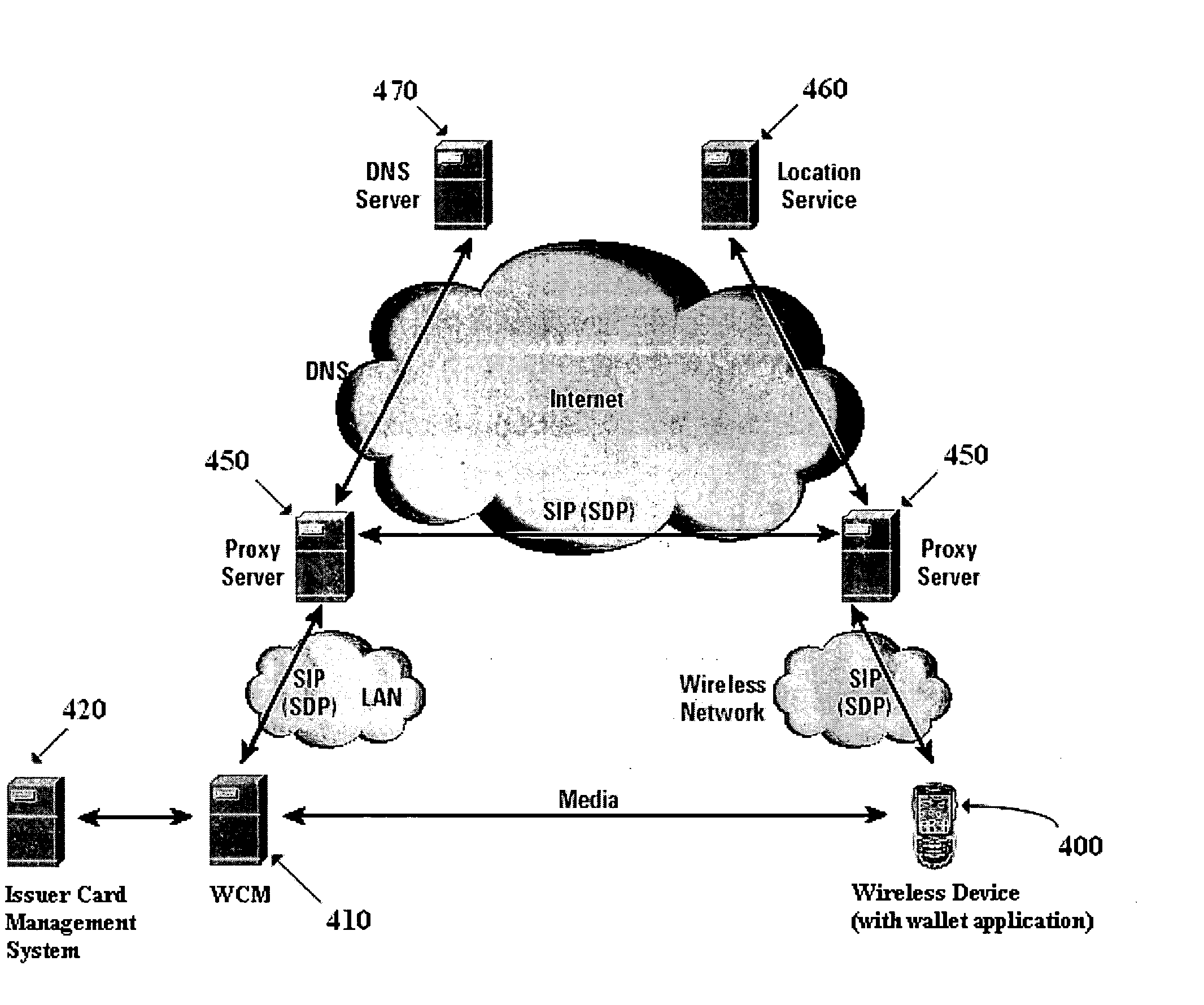
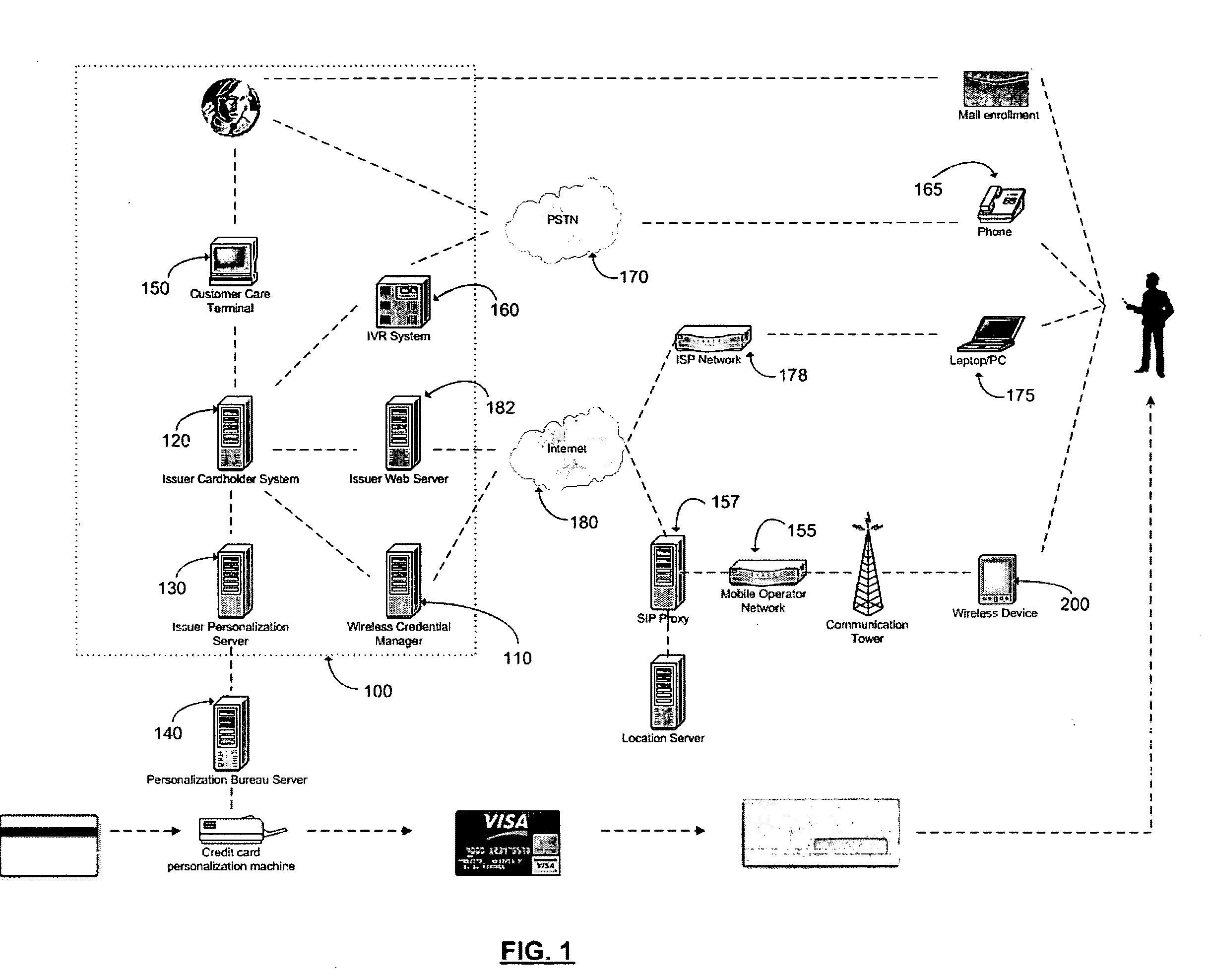
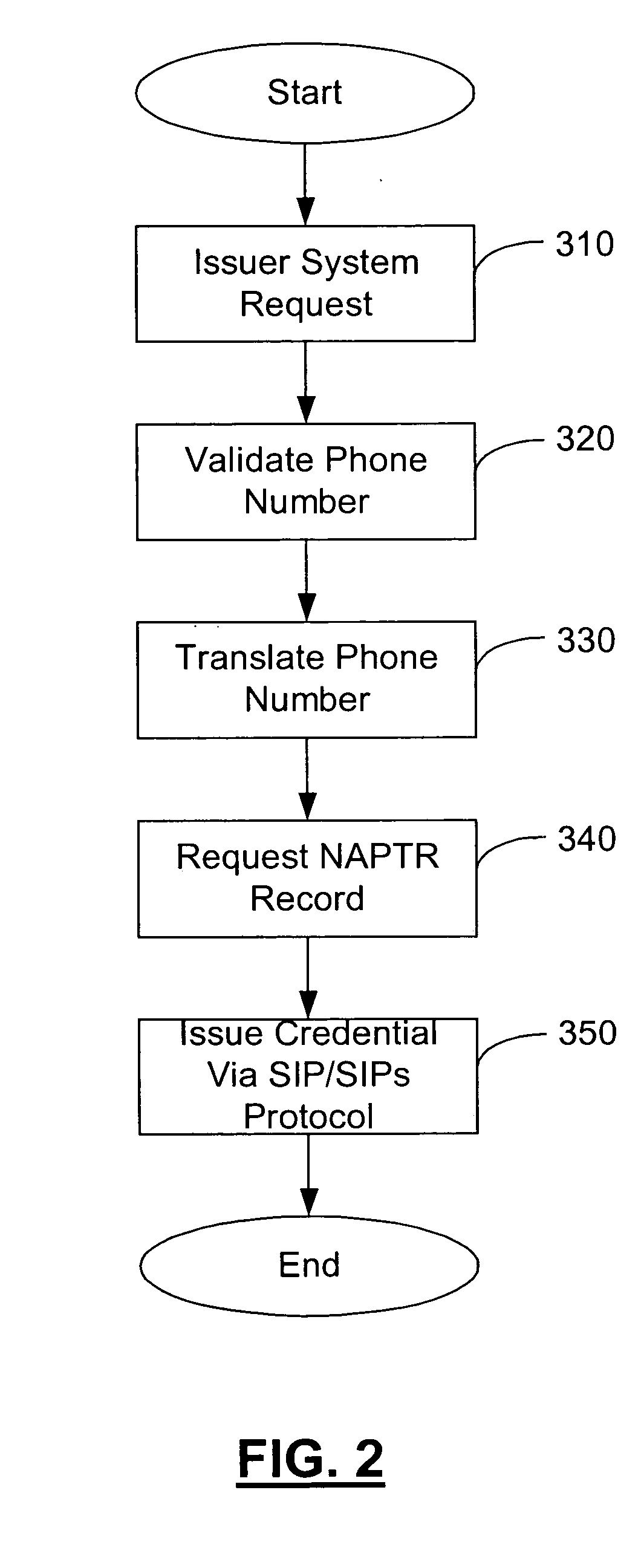
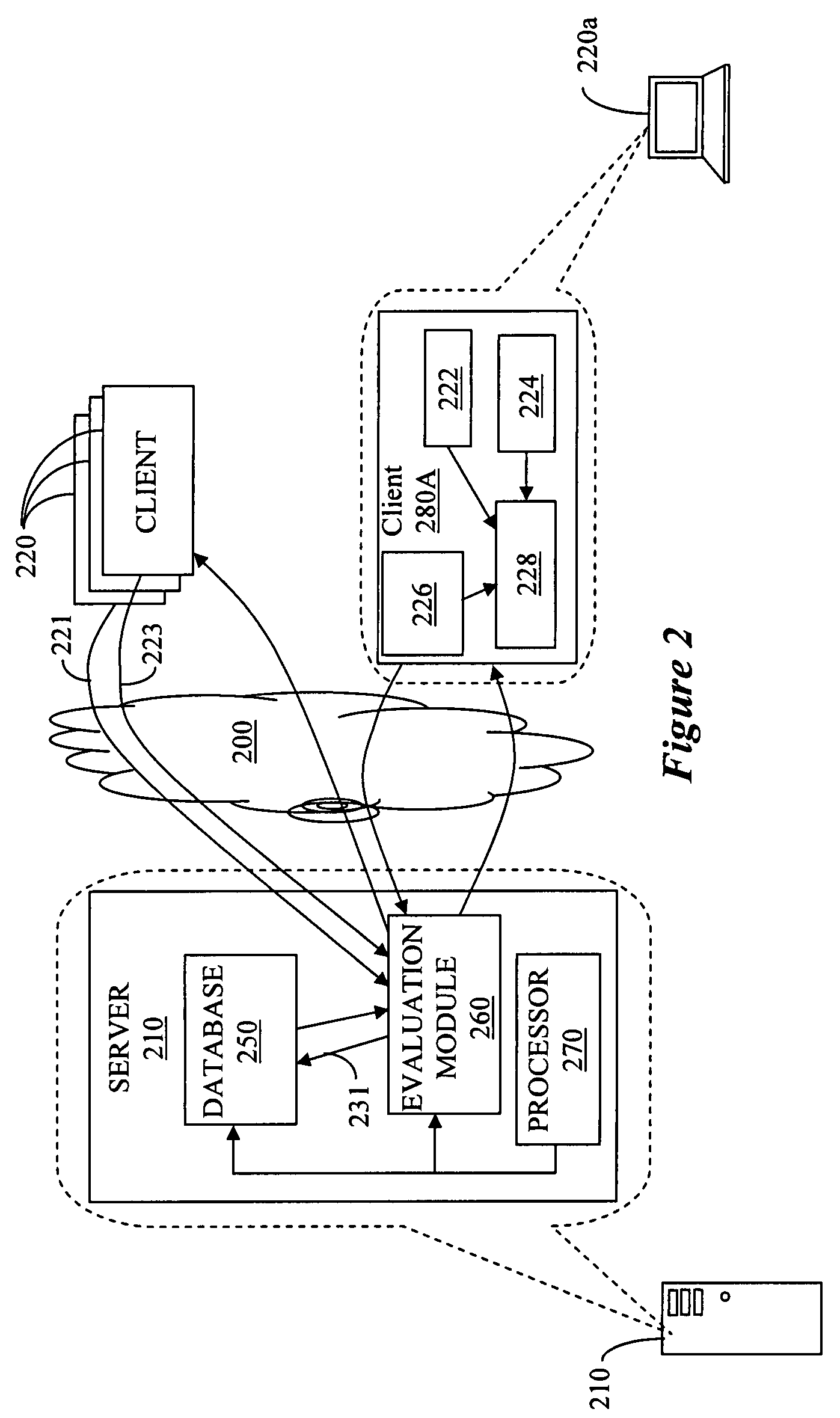
Method and apparatus for managing credentials through a wireless network
ActiveUS20060165060A1Convenient and efficient and secure distributionNear-field in RFIDData switching by path configurationCredit cardWireless mesh network
A novel system and methodology for conducting financial and other transactions using a wireless device. Credentials may be selectively issued by issuers such as credit card companies, banks, and merchants to consumers permitting the specific consumer to conduct a transaction according to the authorization given as reflected by the credential or set of credentials. The preferred mechanism for controlling and distributing credentials according to the present invention is through one or more publicly accessible networks such as the Internet wherein the system design and operating characteristics are in conformance with the standards and other specific requirements of the chosen network or set of networks. Credentials are ultimately supplied to a handheld device such as a mobile telephone via a wireless network. The user holding the credential may then use the handheld device to conduct the authorized transaction or set of transactions via, for example, a short range wireless link with a point-of-sale terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
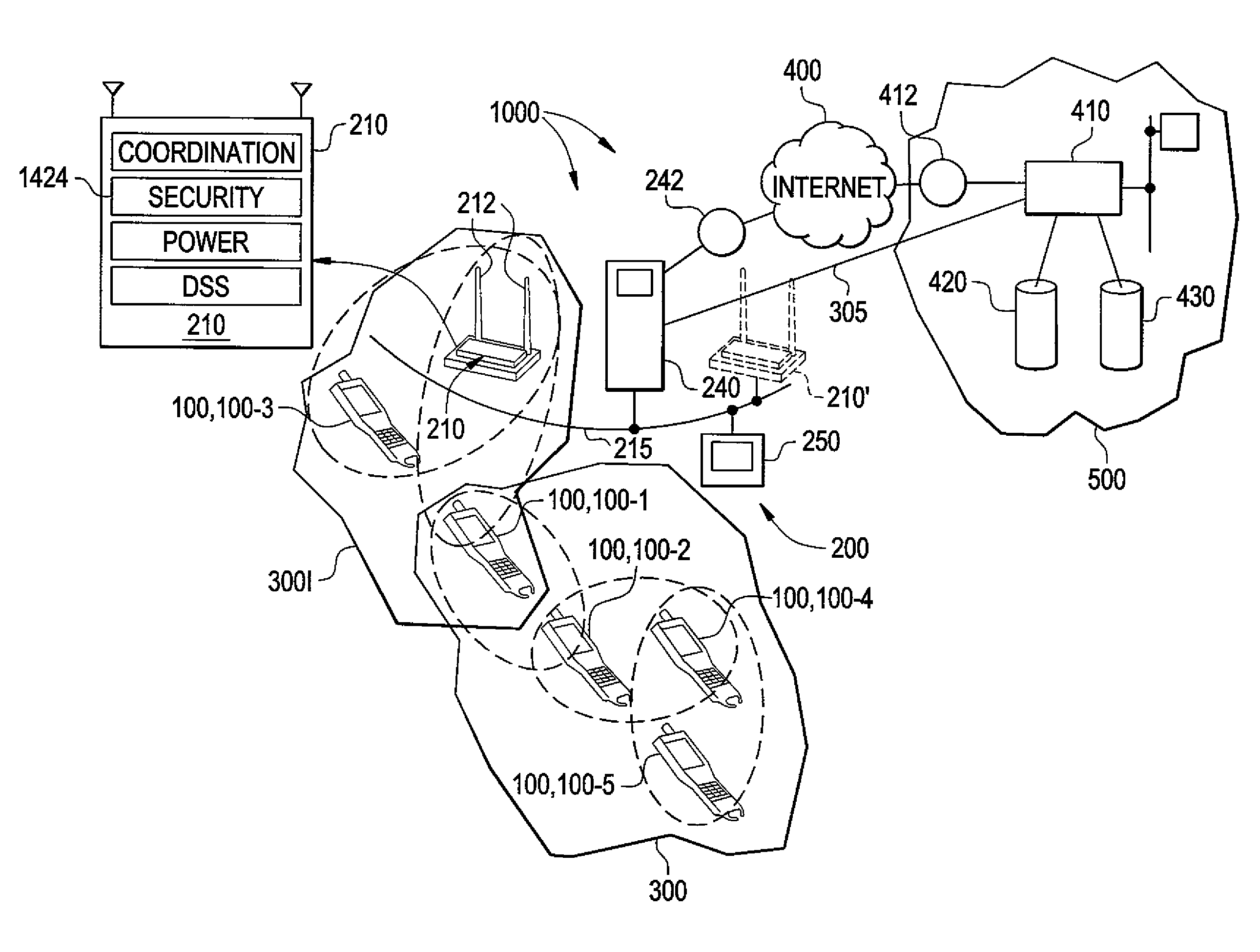
Wireless mesh point portable data terminal
ActiveUS8638806B2Power managementDigital data processing detailsMicrocontrollerWireless mesh network
A portable data terminal (PDT) adapted to participate in a wireless mesh network including a plurality of peer PDTs can comprise: a PDT module including an encoded information reading (EIR) device, and a mesh point (MP) module communicatively coupled to the PDT module. The MP module can include a microcontroller and at least one wireless communication interface and can be configured to perform IEEE 802.11-conformant wireless station services including authentication, de-authentication, privacy, and MAC service data unit delivery, and IEEE 802.11-conformant wireless distribution system services including association, disassociation, distribution, integration, and re-association. The MP module can be further configured, responsive to receiving a MAC frame addressed to a recipient inside the wireless mesh network, to deliver the MAC frame using the distribution service. The MP module can be further configured, responsive to receiving a MAC frame addressed to a recipient outside of the wireless mesh network, to deliver the MAC frame using the integration service. The MP module can be further configured to route an incoming MAC frame according to its destination address and the frame control field. The MP module can be further configured to cause the PDT module to exit said sleeping state responsive to receiving a mobile management software (MMS) wake-up command.
Owner:HAND HELD PRODS
Method and system for managing data traffic in wireless networks
ActiveUS7042988B2Facilitate secure integrationExtensive controlError preventionUnauthorised/fraudulent call preventionWireless mesh networkNetwork architecture
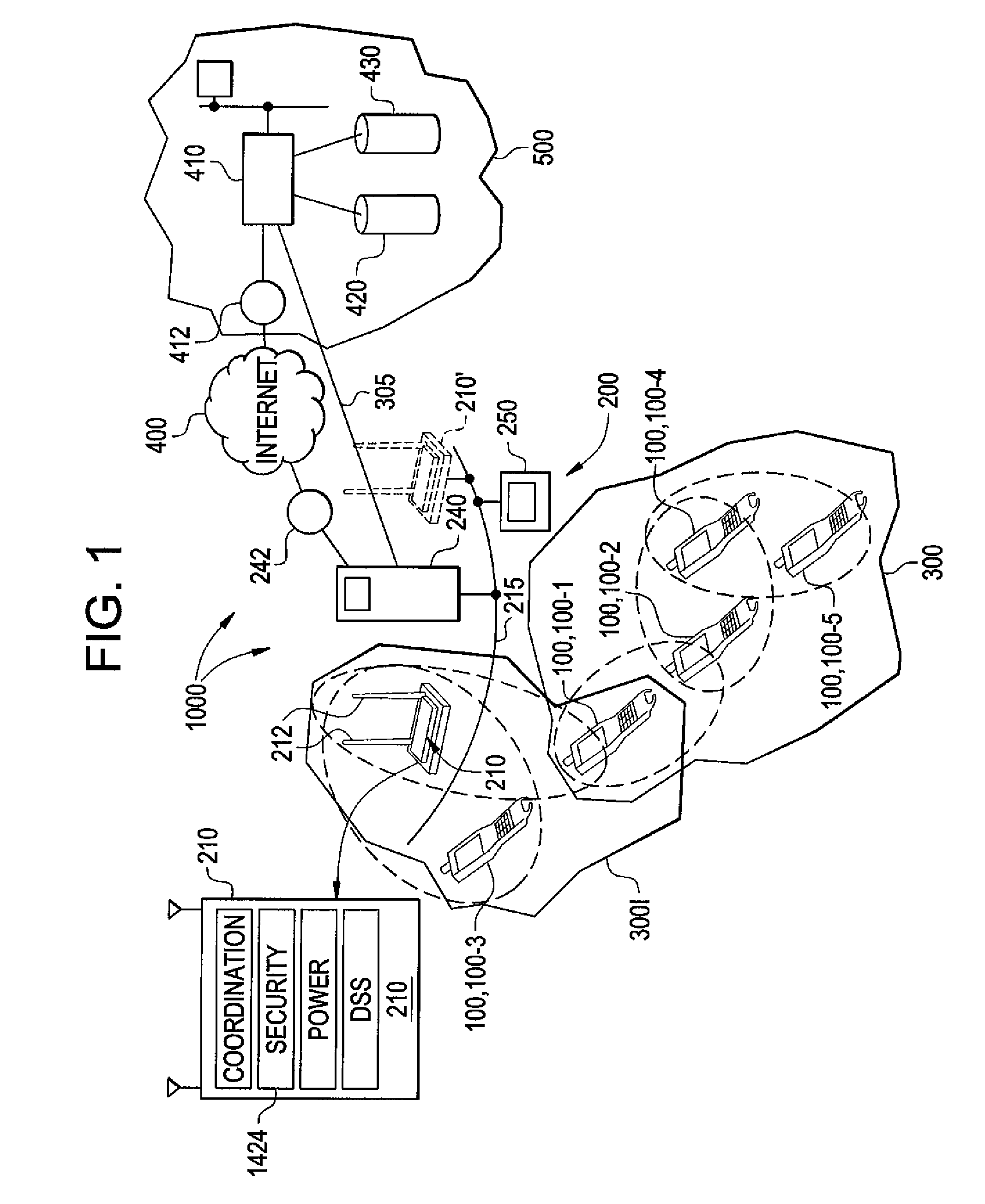
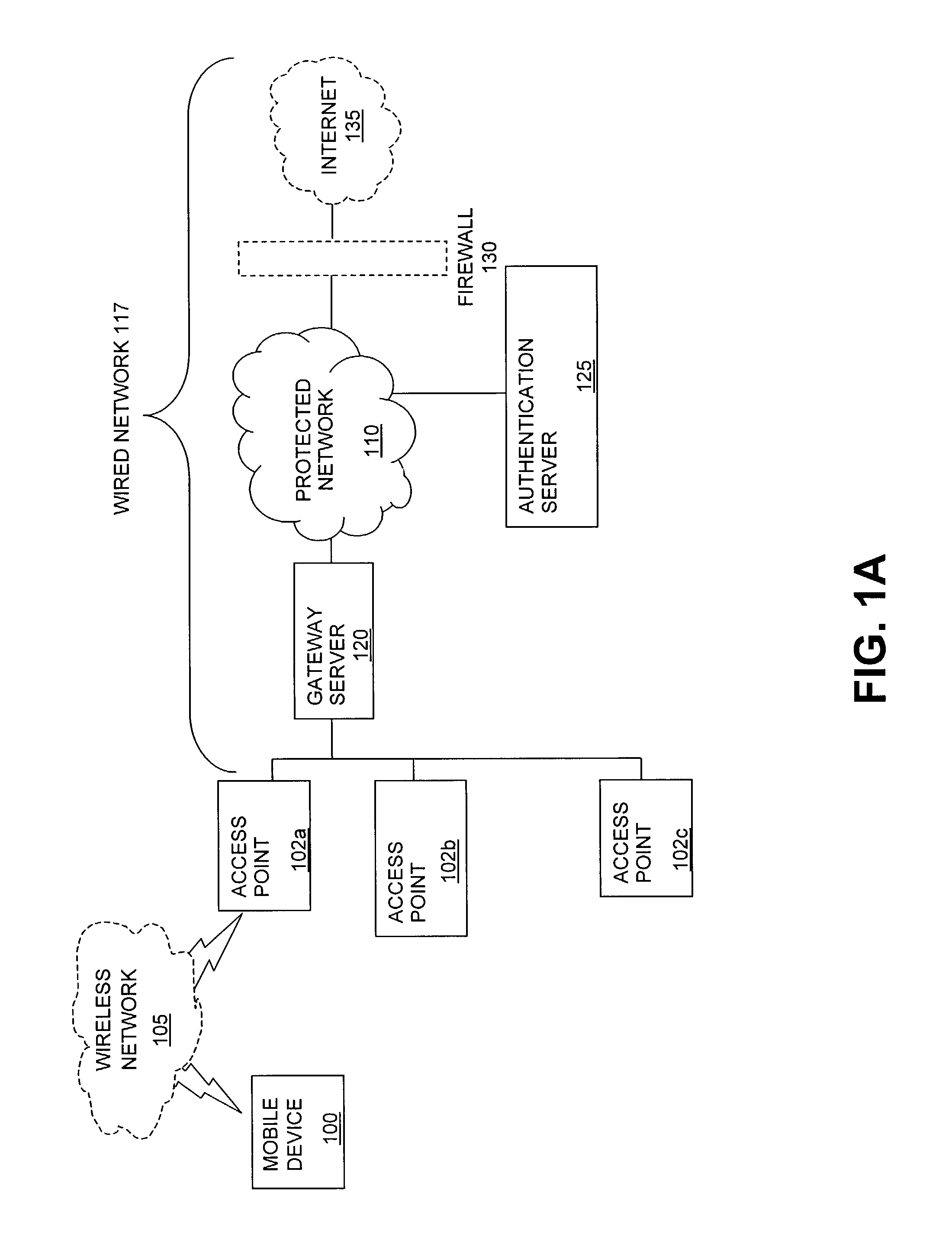
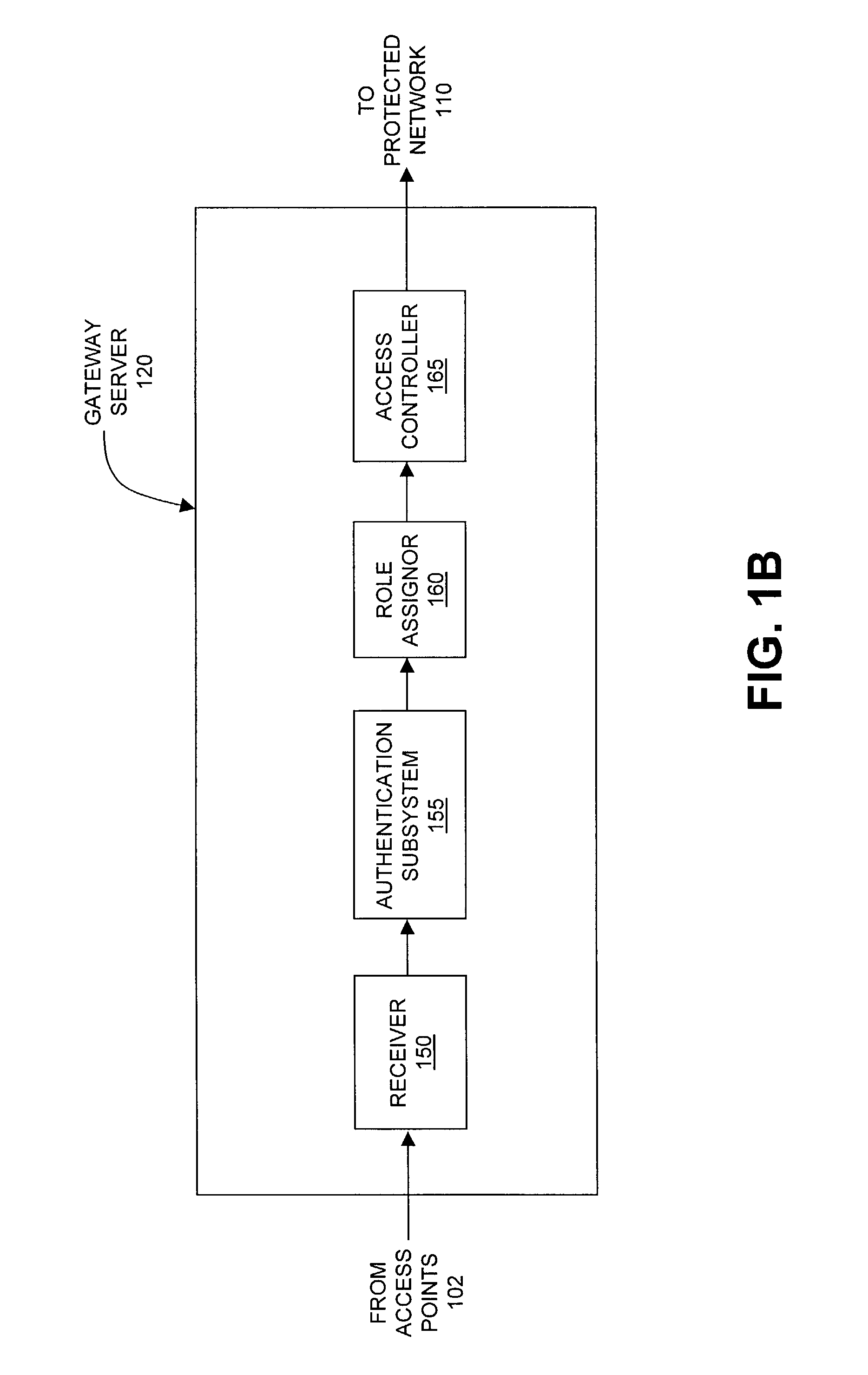
The present invention can be used to facilitate the integration of wireless capability provided by wireless access points into an enterprise computer network. A gateway server is interposed between wireless access points and protected networks to provide security and integration functions, for example, authentication, access control, link privacy, link integrity, and bandwidth metering in various embodiments. Use of such a gateway server allows substantial control to be gained over network access even with the use of relatively simple access points. In general, such a gateway server receives a request to access the protected network. An authentication subsystem of the gateway server authenticates the user, preferably by accessing an external authentication server and returns a role to the authenticated user. An access controller in the gateway server provides differential access to the protected network based on the user's assigned role. A multiple gateway servers can be connected together to form a mesh network architecture.
Owner:BLUESOCKET
Area based position determination for terminals in a wireless network
InactiveUS6865395B2Accurate estimateDirection finders using radio wavesTelephonic communicationWireless mesh networkEngineering
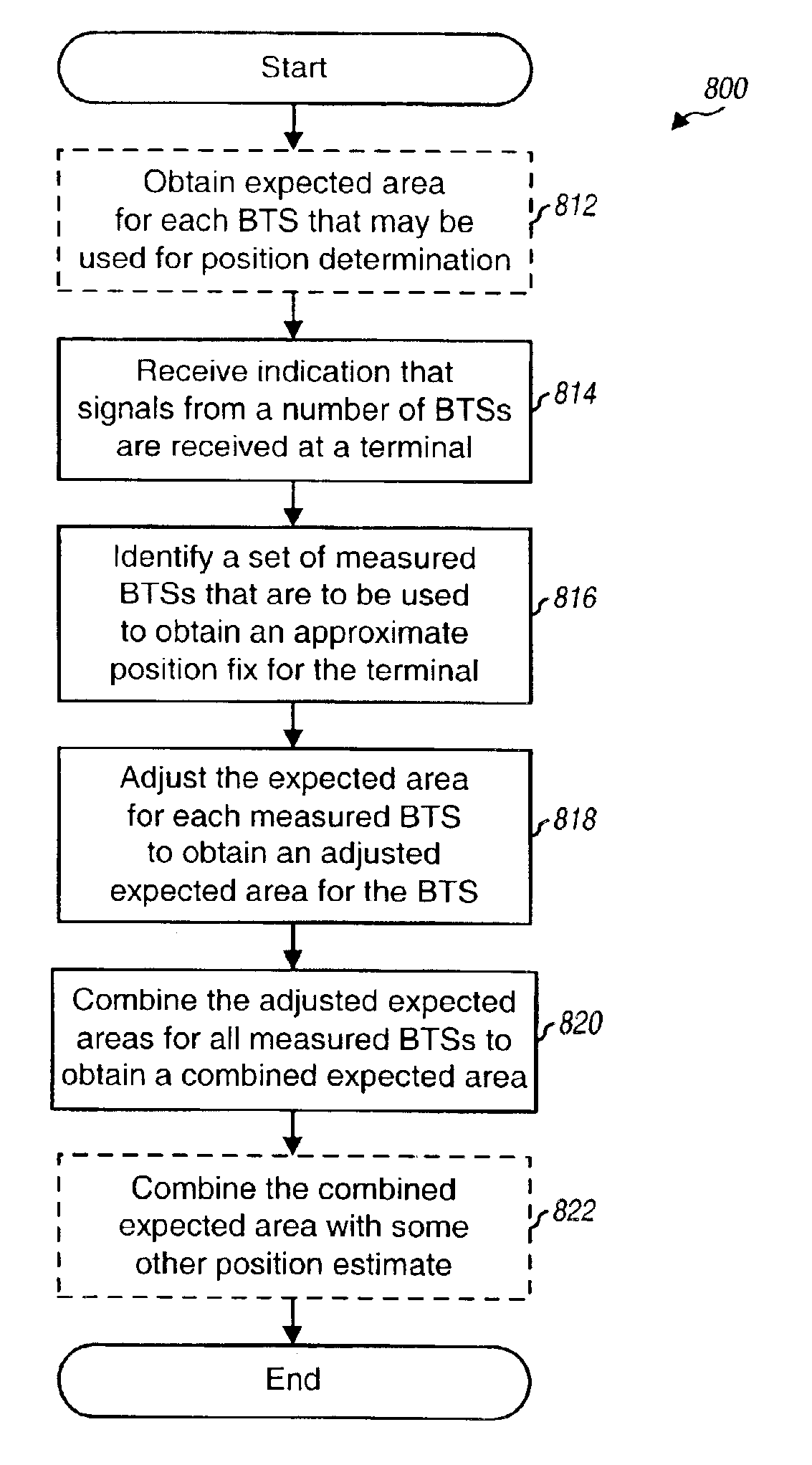
Techniques to estimate the position of a wireless terminal. In a method, the identities of a number of transmitters (e.g., BTSs) to be used to estimate the position are initially received. Expected areas for these transmitters are then determined. The expected area associated with each transmitter is indicative of an area where the terminal is likely to be located given that the signal from the transmitter is received by the terminal. Each expected area may comprise a location (e.g., the expected area center) to be used as an estimated position of the terminal and an uncertainty (or error estimate) associated with that estimated position. The expected areas for the transmitters are then combined (e.g., based on a weighted average) to determine a combined expected area, which is then provided as the estimate of the position of the terminal.
Owner:QUALCOMM INC
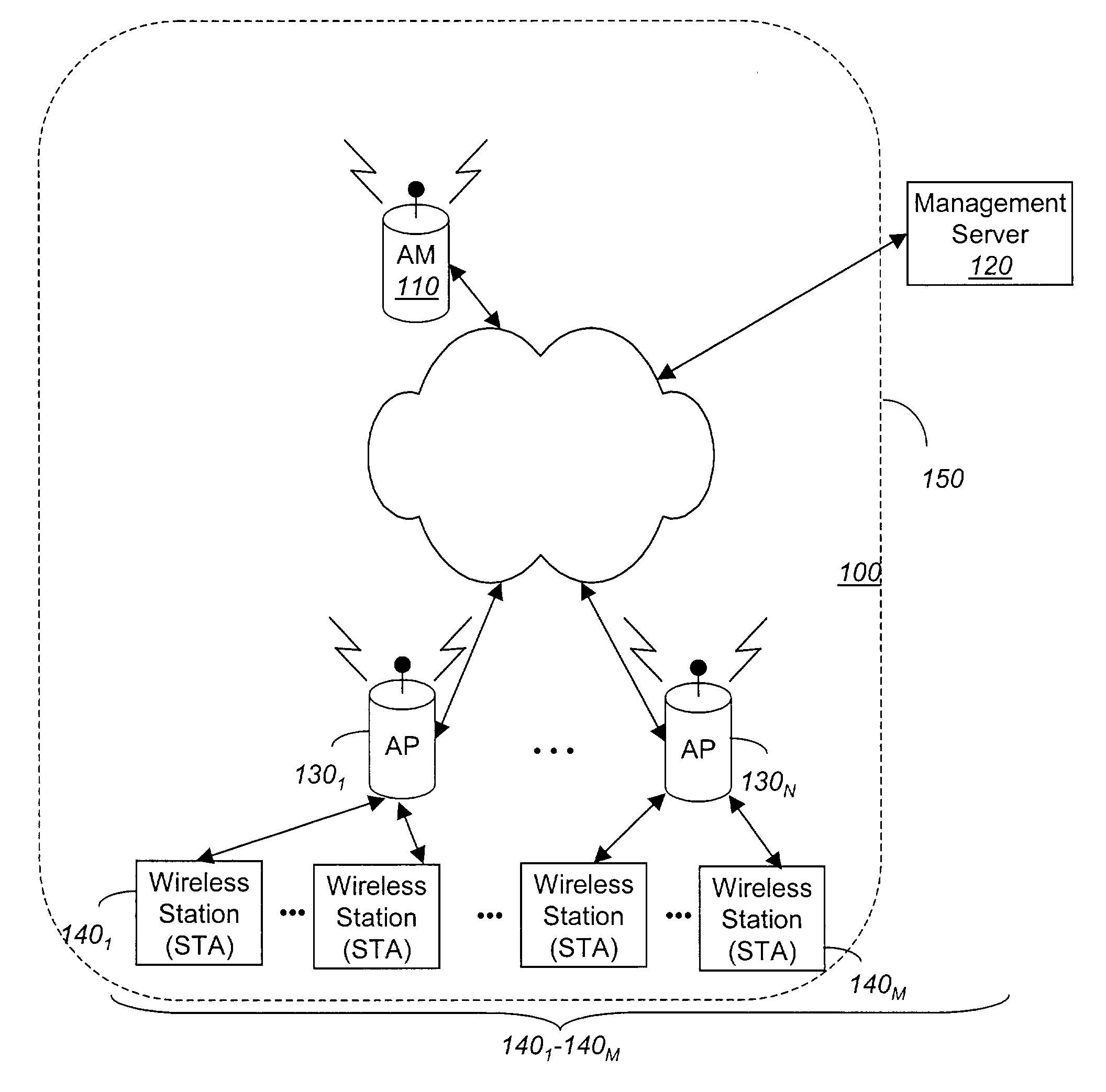
System and method for monitoring and enforcing policy within a wireless network
ActiveUS6957067B1Digital computer detailsRadio/inductive link selection arrangementsWireless mesh networkTelecommunications
In general, one embodiment of the invention is a air monitor adapted to a wireless network. The air monitor enforces policies followed by the wireless network even though it is not involved in the exchange of data between wireless devices of the wireless network such as access points and wireless stations.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Method and system for measuring data quality of service in a wireless network using multiple remote units and a back end processor
InactiveUS6928280B1Cost-effective and easy to useData is very largeMicrobiological testing/measurementRadio/inductive link selection arrangementsPush technologyWireless mesh network
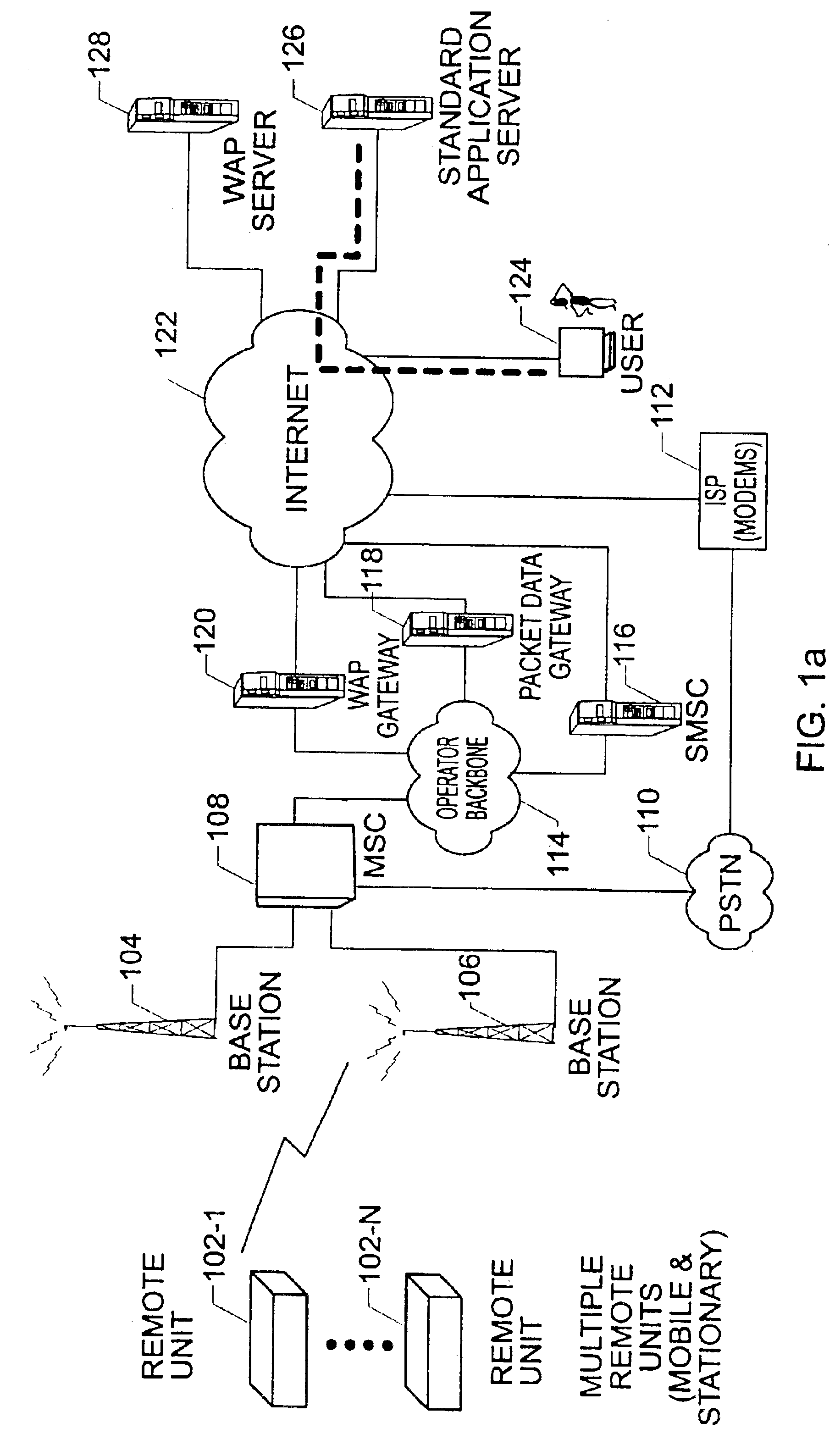
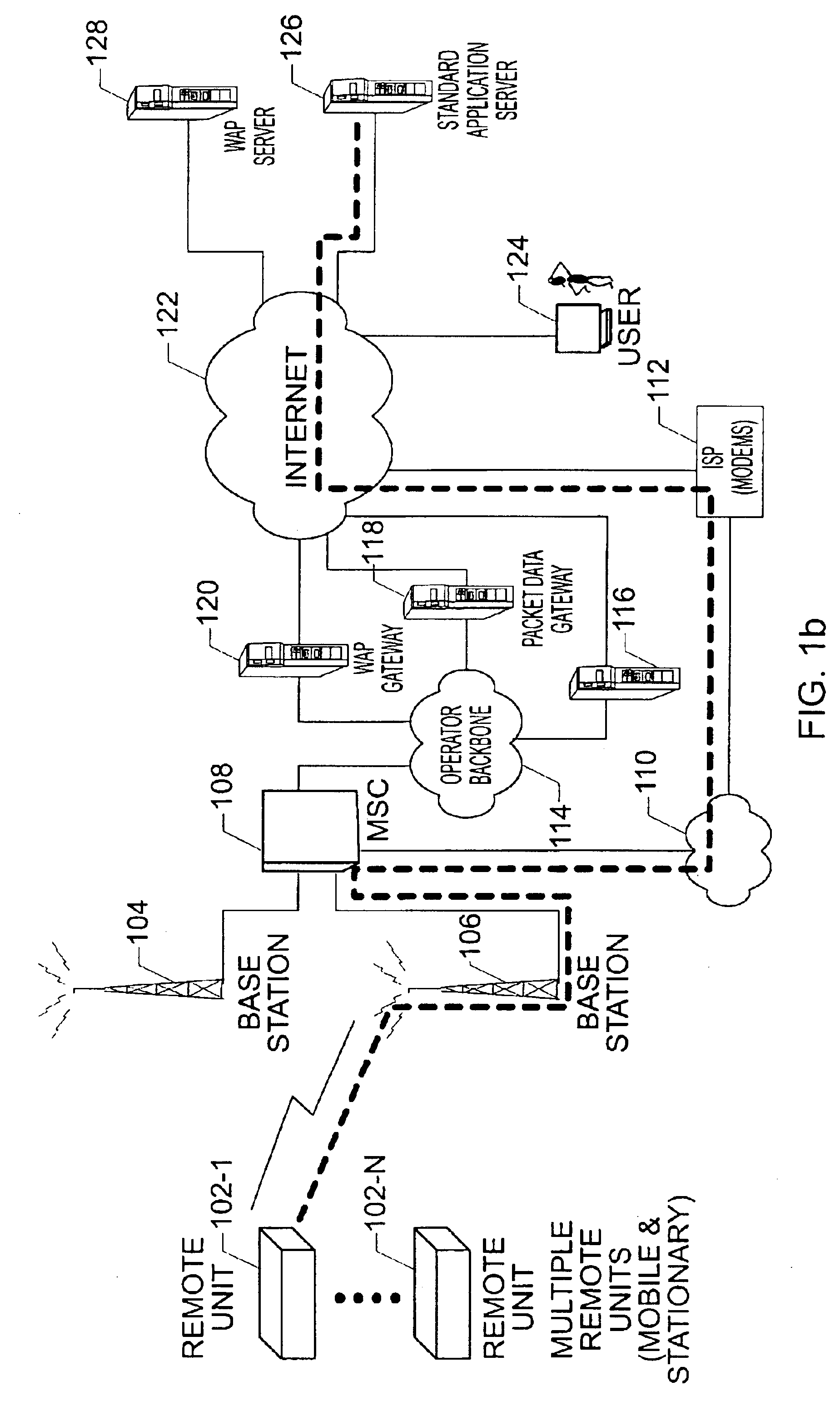
The present invention provides for a method and system for measuring data quality of service in a wireless network using multiple peripatetic (i.e. mobile) and / or stationary, unattended, position, and performance instruments (PUPPIs) that are remotely controlled by a back end processor. In some embodiments of the invention, the data service whose quality is measured relates to wireless Internet access, e-commerce transactions, wireless messaging, or push technologies. In other embodiments of the invention, the system includes an element that is located within the wireless network infrastructure, for example, at the WAP gateway to monitor the wireless data protocol and to perform benchmarking measurements.
Owner:INVERTIX +1
Wireless multimedia player
InactiveUS6845398B1Network traffic/resource managementMultiple digital computer combinationsWireless mesh networkMultimedia servers
A wireless device, system and method for receiving and playing multimedia files streamed from a multimedia server over a wireless telecommunications network. A desired multimedia file is selected from one or more multimedia files stored in the multimedia server, which server is operatively connected to the wireless telecommunications network. Successive blocks of data from the desired multimedia file are streamed over the wireless telecommunications network in a digitized and compressed format and received by the wireless telecommunications device. The received blocks of data from the streamed multimedia file are temporarily stored in a buffer in the wireless device, decoded and decompressed, and successively played through an audio and / or video output in the wireless device. The wireless device monitors the blocks of data stored in the buffer and signals the wireless telecommunications network to increase the rate that the data blocks are transmitted over the wireless network in the event that the data stored in the buffer falls below a minimum threshold level.
Owner:LUCENT TECH INC
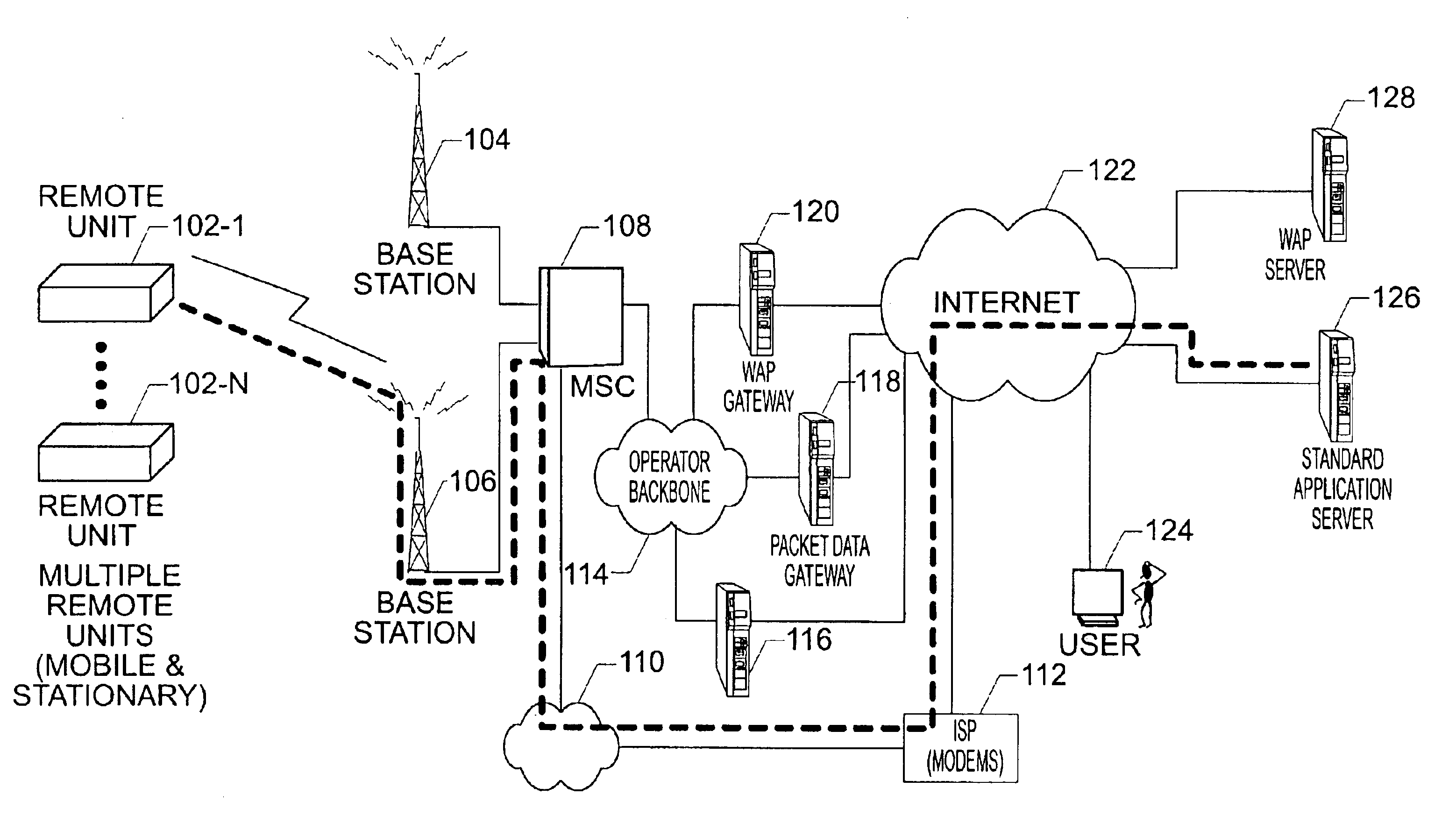
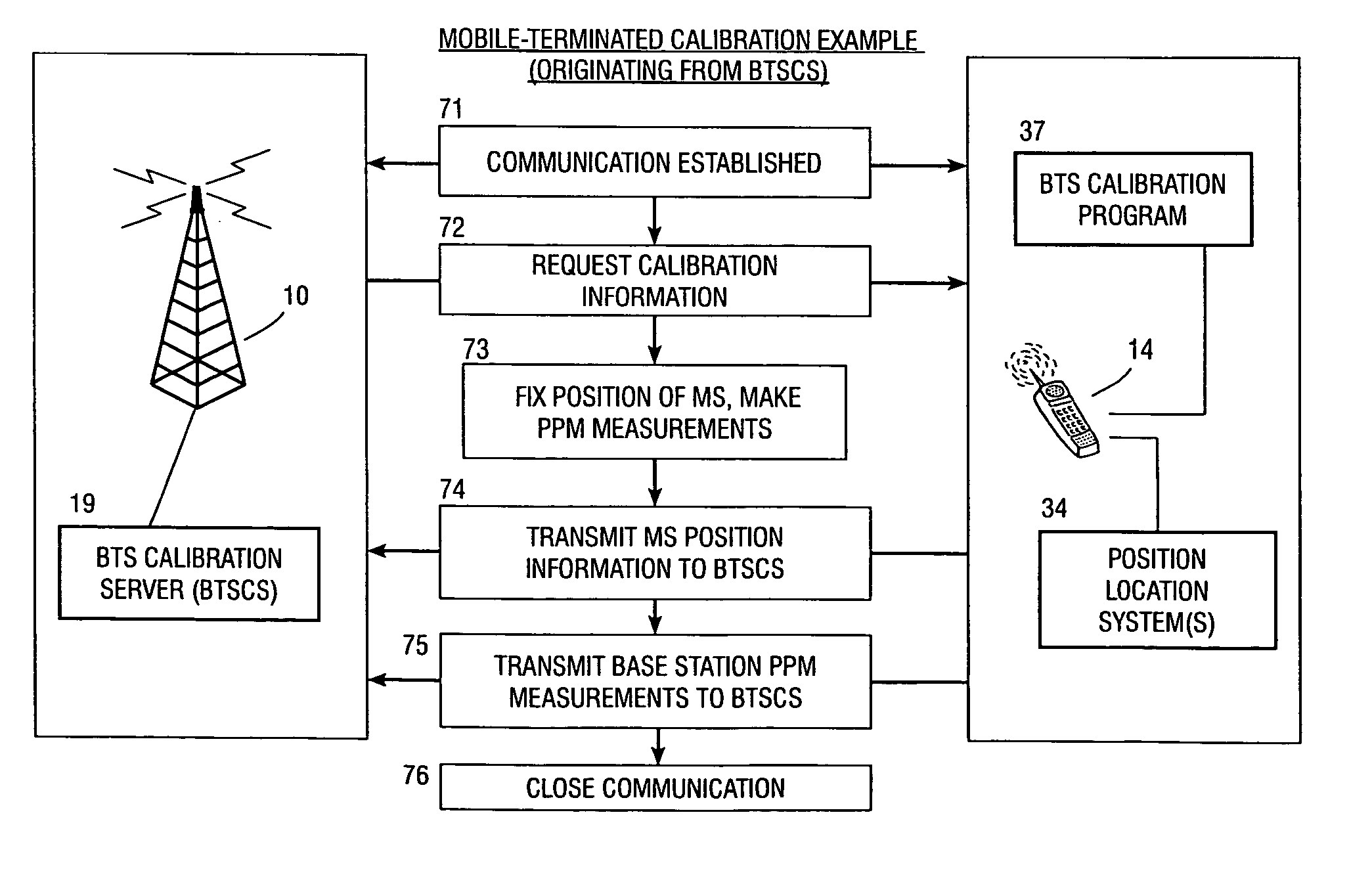
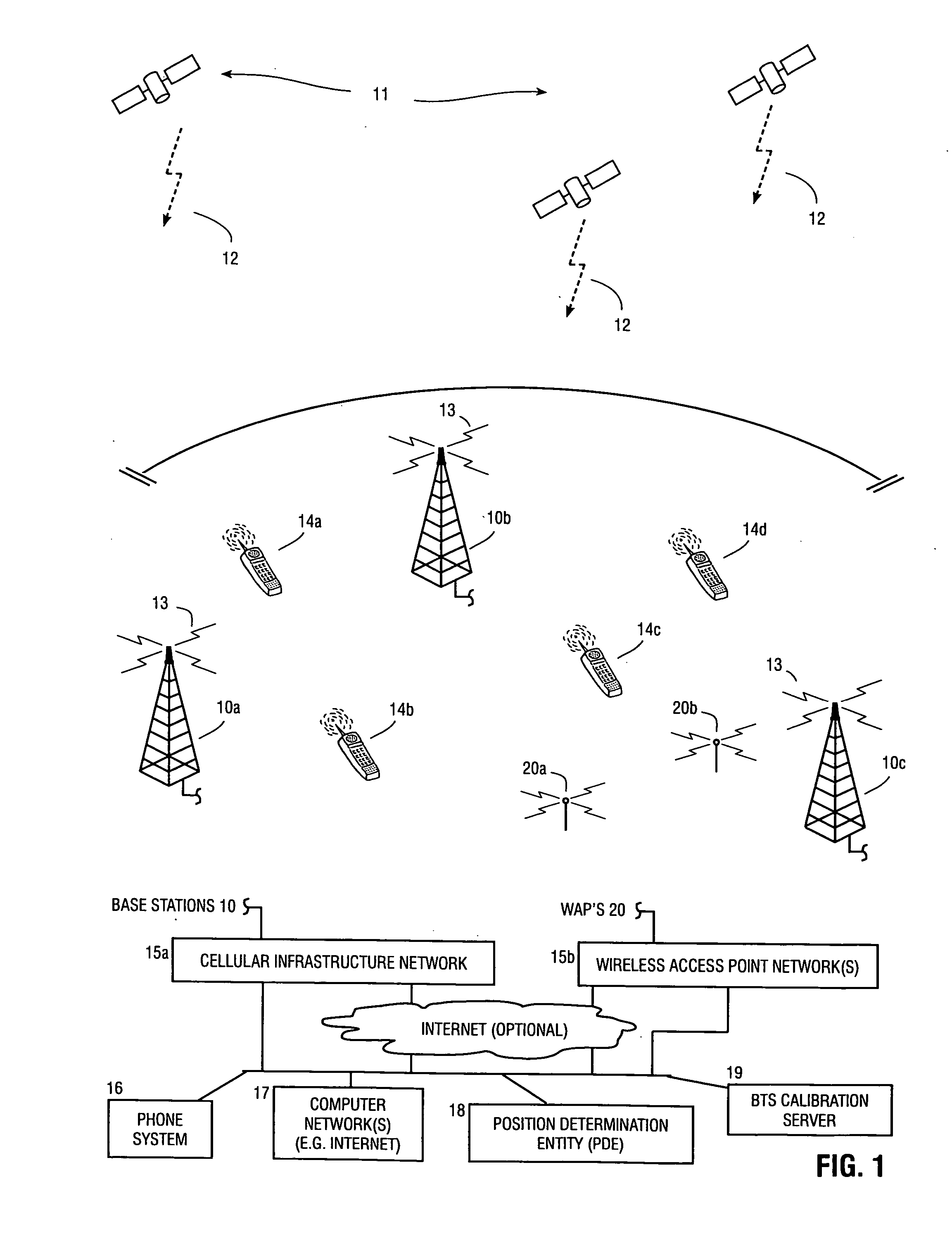
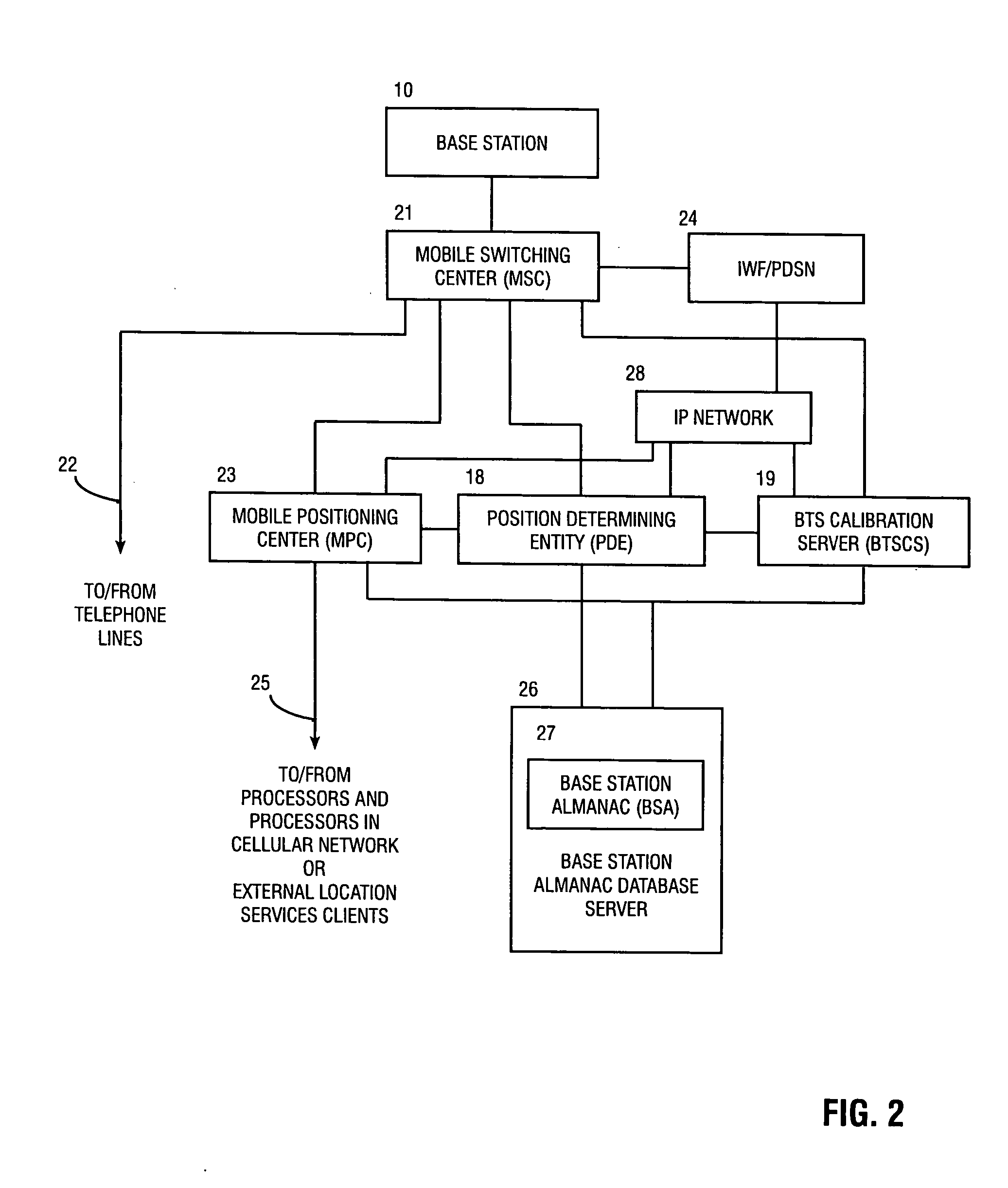
Method and apparatus for determining location of a base station using a plurality of mobile stations in a wireless mobile network
A method and apparatus for determining a position of a base station in a wireless communication network that includes a mobile station in communication with base stations. A BTS calibration server is networked with the base stations. A BTS calibration program is programmed into a group of mobile stations that have position location capabilities. Using the BTS calibration program, calibration information may be requested by the BTS calibration server, or a session may be initiated by the mobile station. The BTS calibration program also provides privacy features that allow user of the mobile station to prevent it from being used for base station location. If authorized, the BTS calibration program determines the position of the mobile station, and provides calibration information, such as position and base station phase measurements, to the server. The calibration information may be used to calibrate the base station almanac.
Owner:QUALCOMM INC
Adaptive ambient services
ActiveUS20100198698A1Error preventionFrequency-division multiplex detailsService profileWireless mesh network
Adaptive ambient services are provided. In some embodiments, an adaptive ambient service includes providing an ambient service profile. In some embodiments, an ambient service includes implementing an ambient service profile for assisting control of the communications device use of an ambient service on a wireless network, in which the ambient service profile includes a plurality of service policy settings, and in which the ambient service profile is associated with an ambient service plan that provides for initial access to the ambient service with limited service capabilities prior to activation of a new service plan; monitoring use of the ambient service based on the ambient service profile; and adapting the ambient service profile based on the monitored use of the ambient service.
Owner:HEADWATER RES LLC
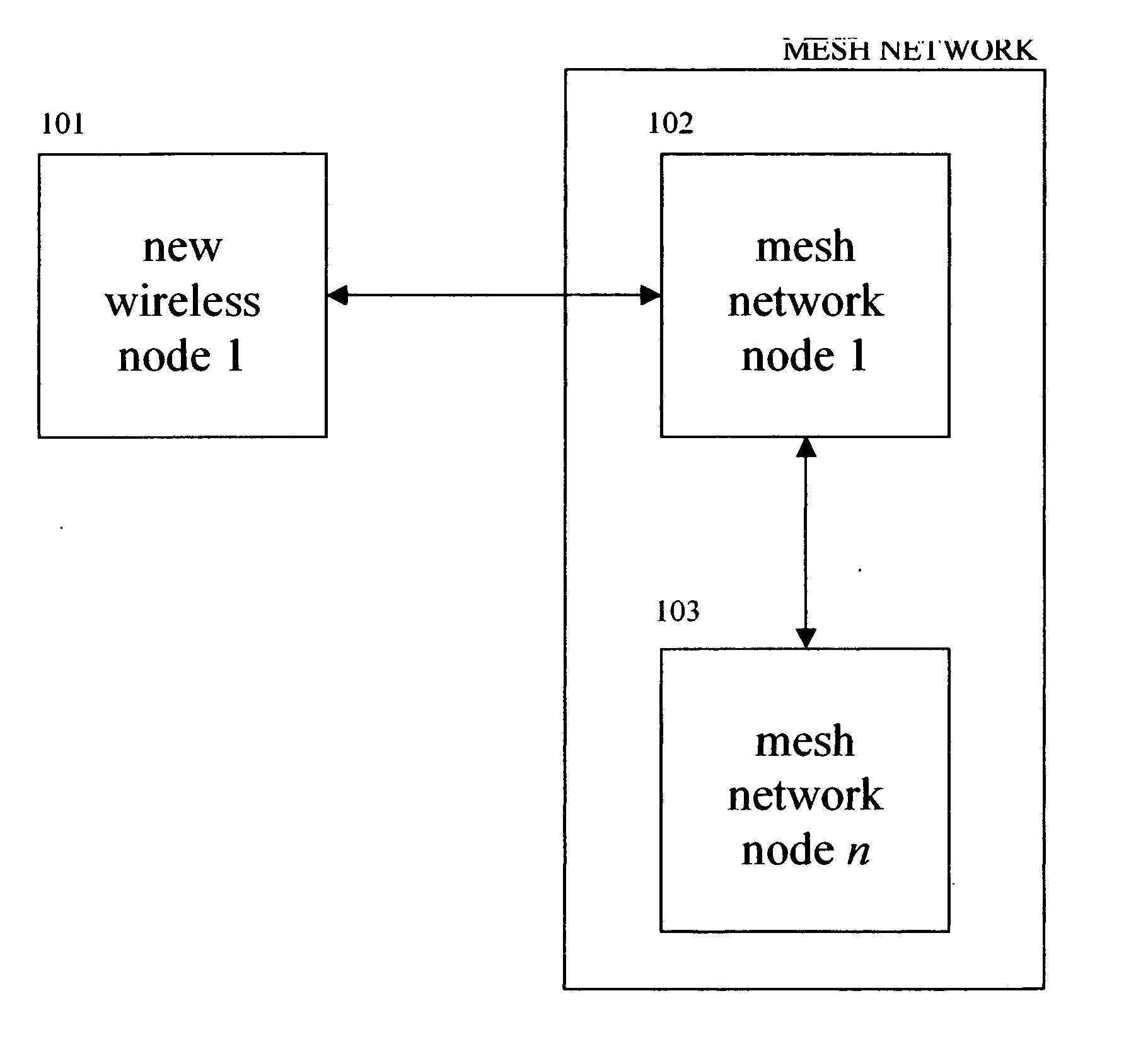
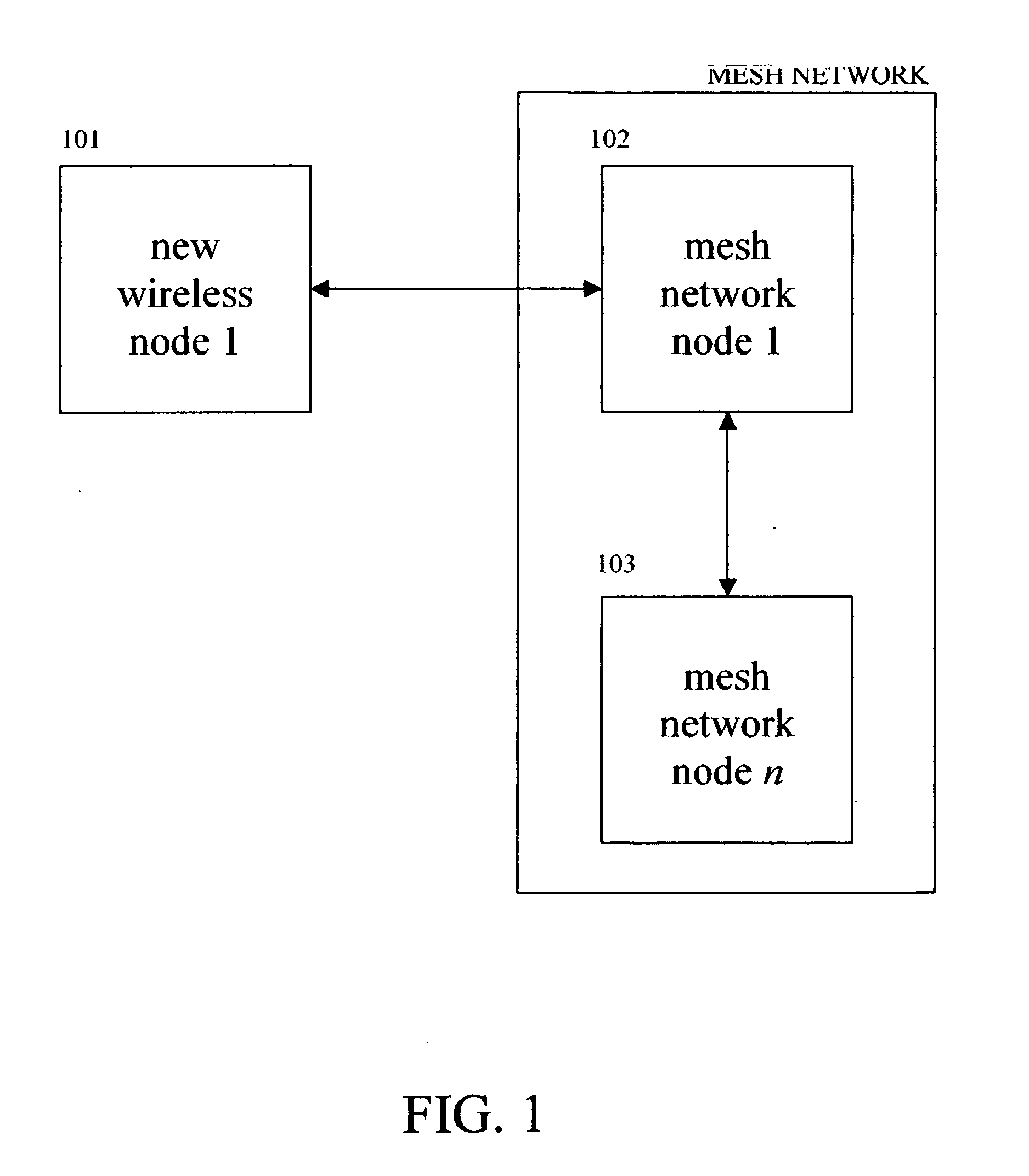
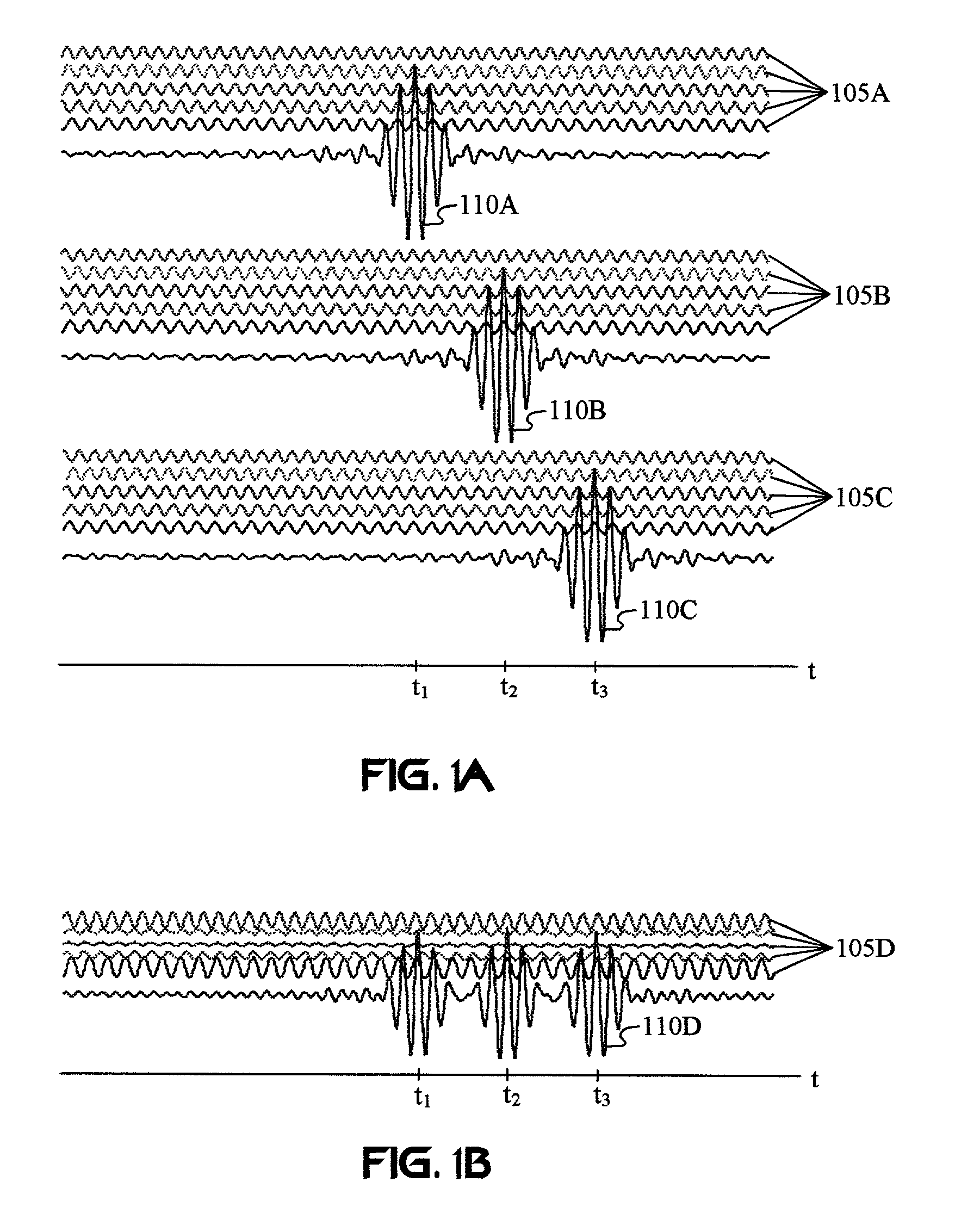
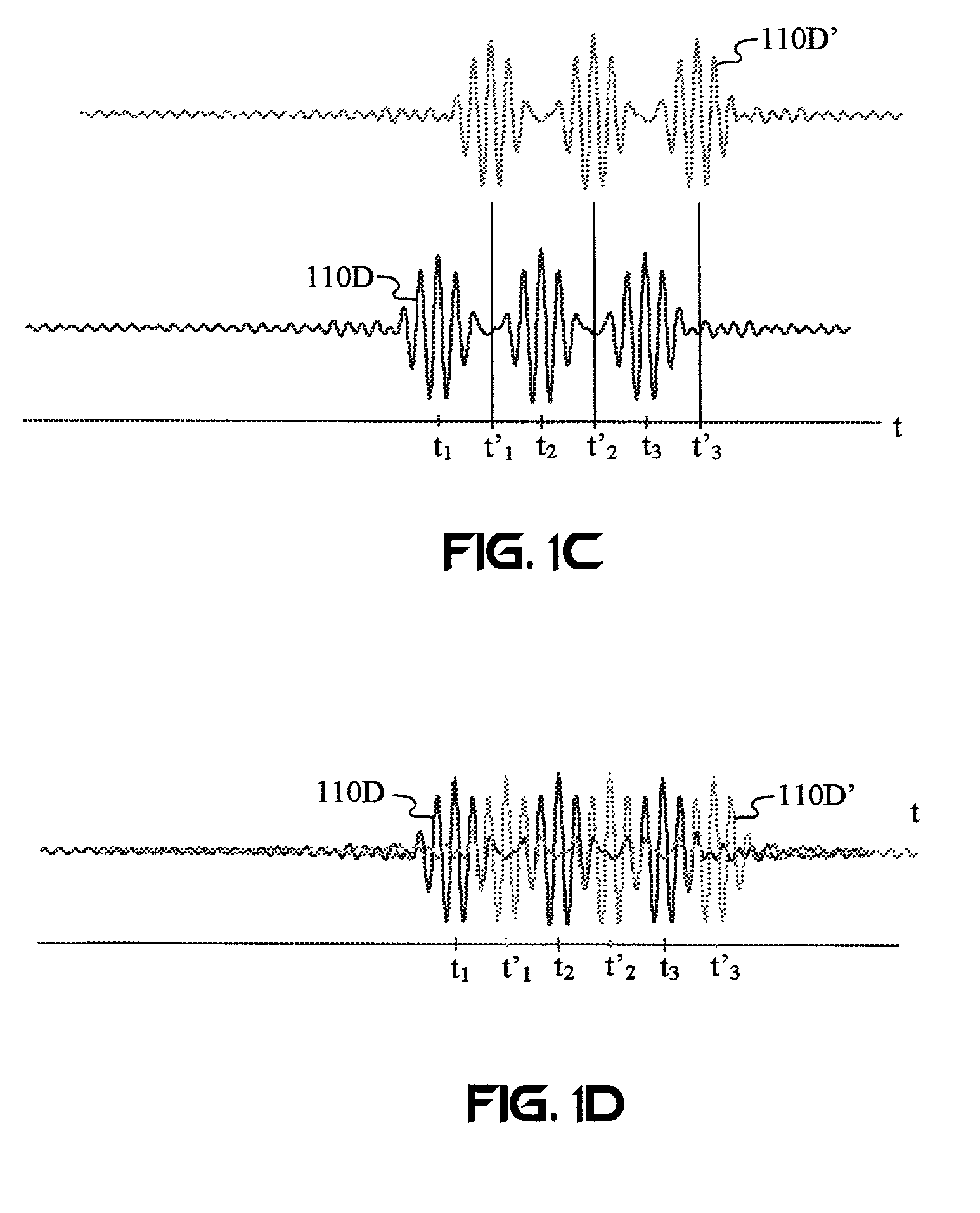
Diagnosis of embedded, wireless mesh networks with real-time, flexible, location-specific signaling
InactiveUS20050201297A1More specificityError preventionFrequency-division multiplex detailsWireless mesh networkNetsniff-ng
A system for optimizing the security of data communication on wireless mesh networks invention uses existing mesh network nodes to control new nodes that attempt to join the network. In a preferred embodiment, this is achieved by (1) testing that a new node is “clean” before allowing it to join the wireless mesh network by scanning the new node for viruses, checking for security patches, etc., (2) quarantining an “infected” node from joining the wireless mesh network until it is cleaned, (3) signaling other nodes in the existing mesh network that a node is either “infected” or “clean”, (4) cleaning a new node by supplying it with antivirus software, vendor patches, etc. from nearby nodes in the existing wireless mesh network, (5) updating the wireless mesh network in real time with a list of clean and infected nodes, and (6) performing the above steps without the need for a central, controlling server.
Owner:PEIKARI CYRUS
Wireless gaming network
InactiveUS20080176619A1Facilitating playerBoard gamesApparatus for meter-controlled dispensingWeb siteWireless mesh network
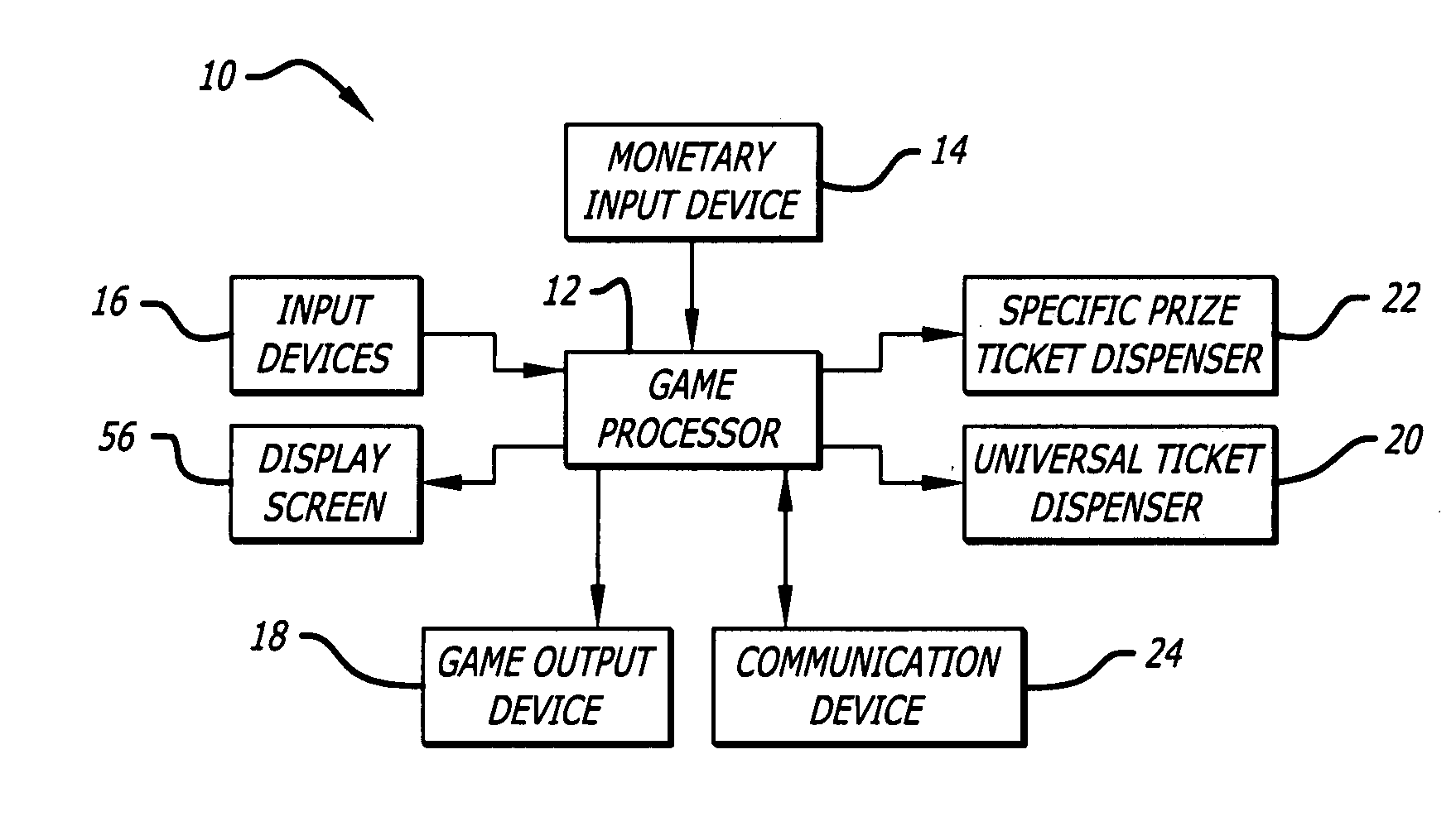
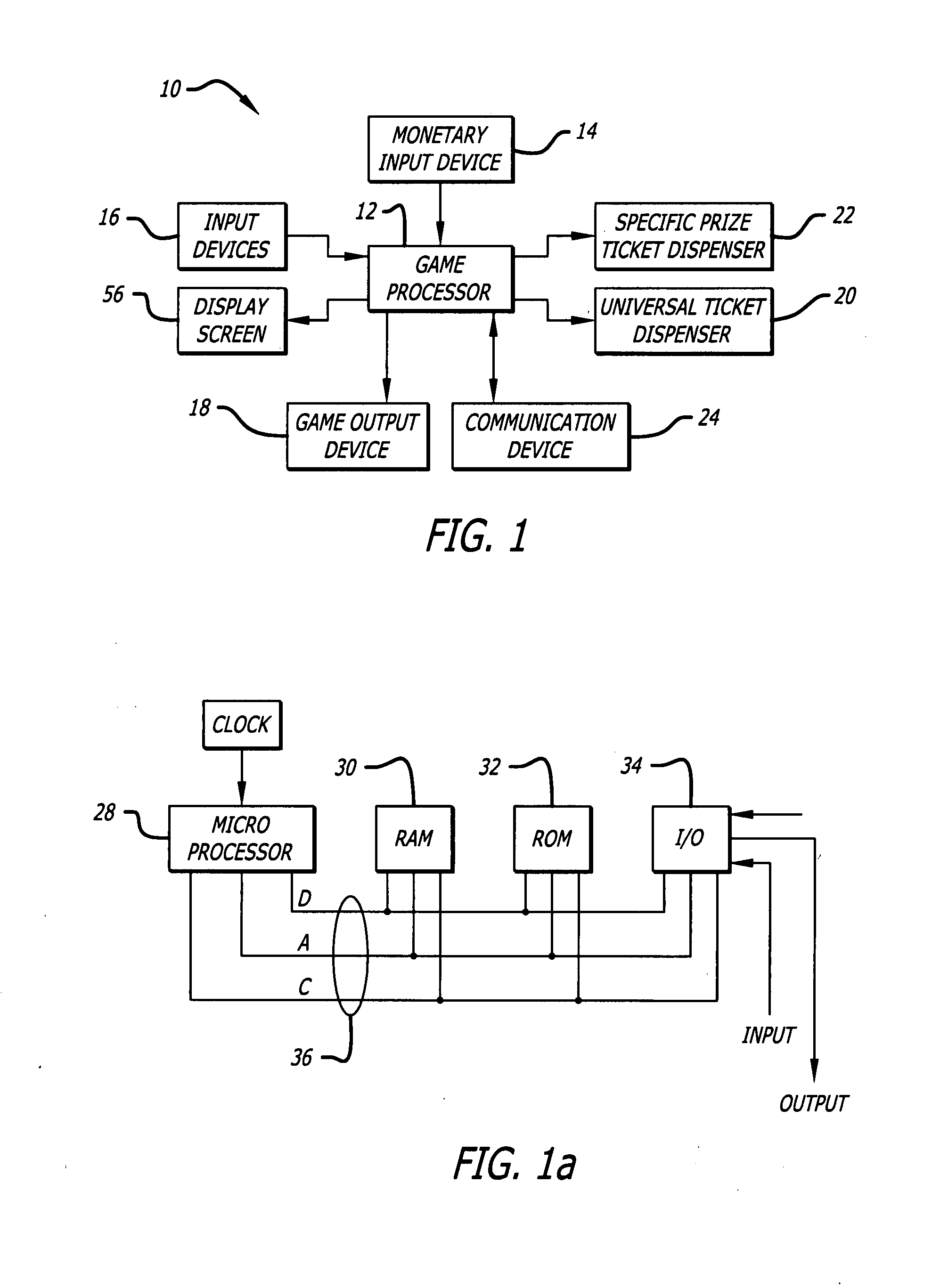
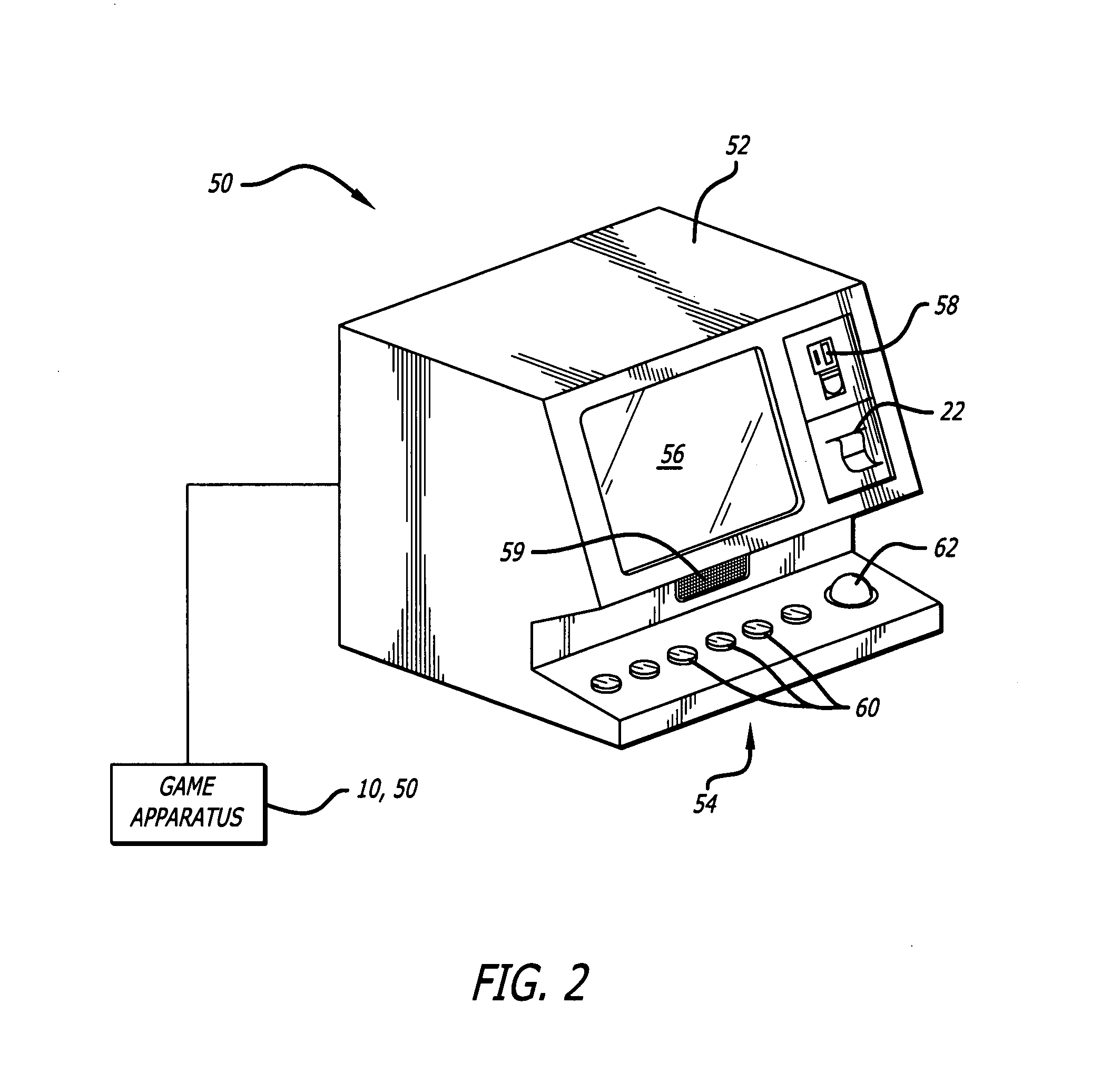
The invention provides a prize redemption system for use with one or more game apparatuses. A game is provided on a game apparatus for a player to play in exchange for monetary input, and prize credits are credited to the player based on the game outcome. A prize selection menu is then displayed by the game apparatus, the menu including one or more prizes, where the player may select a prize that has a prize cost within the player's prize credit amount. The player is dispensed a specific prize ticket that is redeemable for the selected prize. The game apparatus can also provide specific prizes and tournament games played for a tournament prize contributed to by multiple players. An operator can adjust prizes and payout percentages of the system to achieve a desired profitability for game apparatuses. Prize input is entered into a prize table describing multiple available prizes and also describing payout information that indicates a desired amount of payout that the operator wishes to provide back to players of the game apparatus in terms of the value of the prizes. Prize information, such as prize costs and specific prize win ratios, is automatically determined by the system for each of the prizes in view of the desired profitability of the game apparatus.Additionally, the invention provides method and article of manufacture for implementing a user profile-driven gaming and prize redeeming system. The user profile-driven gaming and prize redemption system allows for the tailoring of a user's experience of playing a computer implemented game on a network gaming system by first receiving an identifier selected from a group of identifiers including a user identifier relating to the user (i.e., player) of the network gaming system, a game identifier relating to a particular game played by the user of the network gaming system, and a site identifier relating to the location (i.e. web site) from which the game is being played. The network gaming system then alters the computer-implemented game played by the user in a manner based upon the selected identifier. The foregoing technique may also be applied to a prize redemption system.
Owner:BALLY GAMING INC
Geographical location authentication method
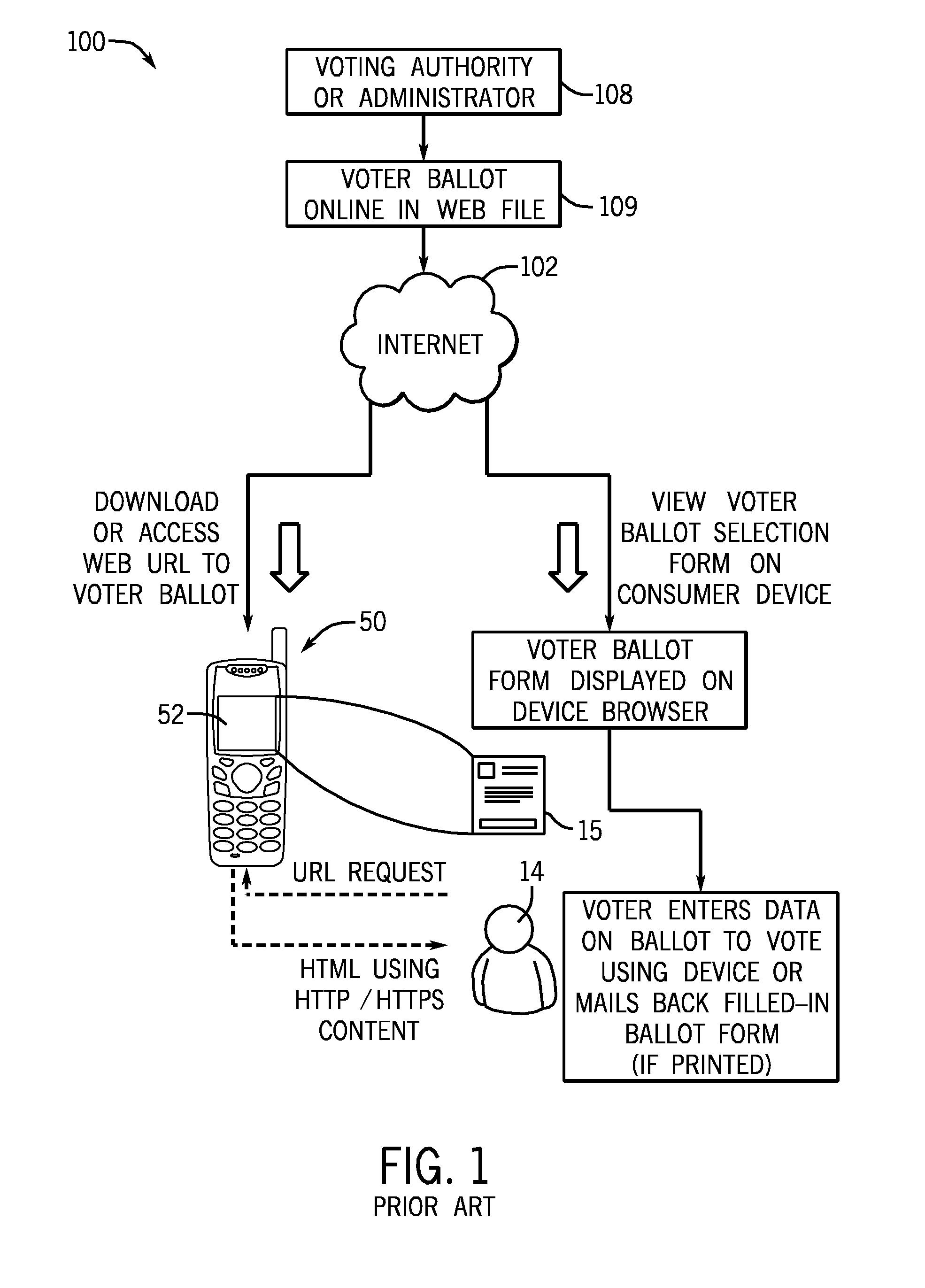
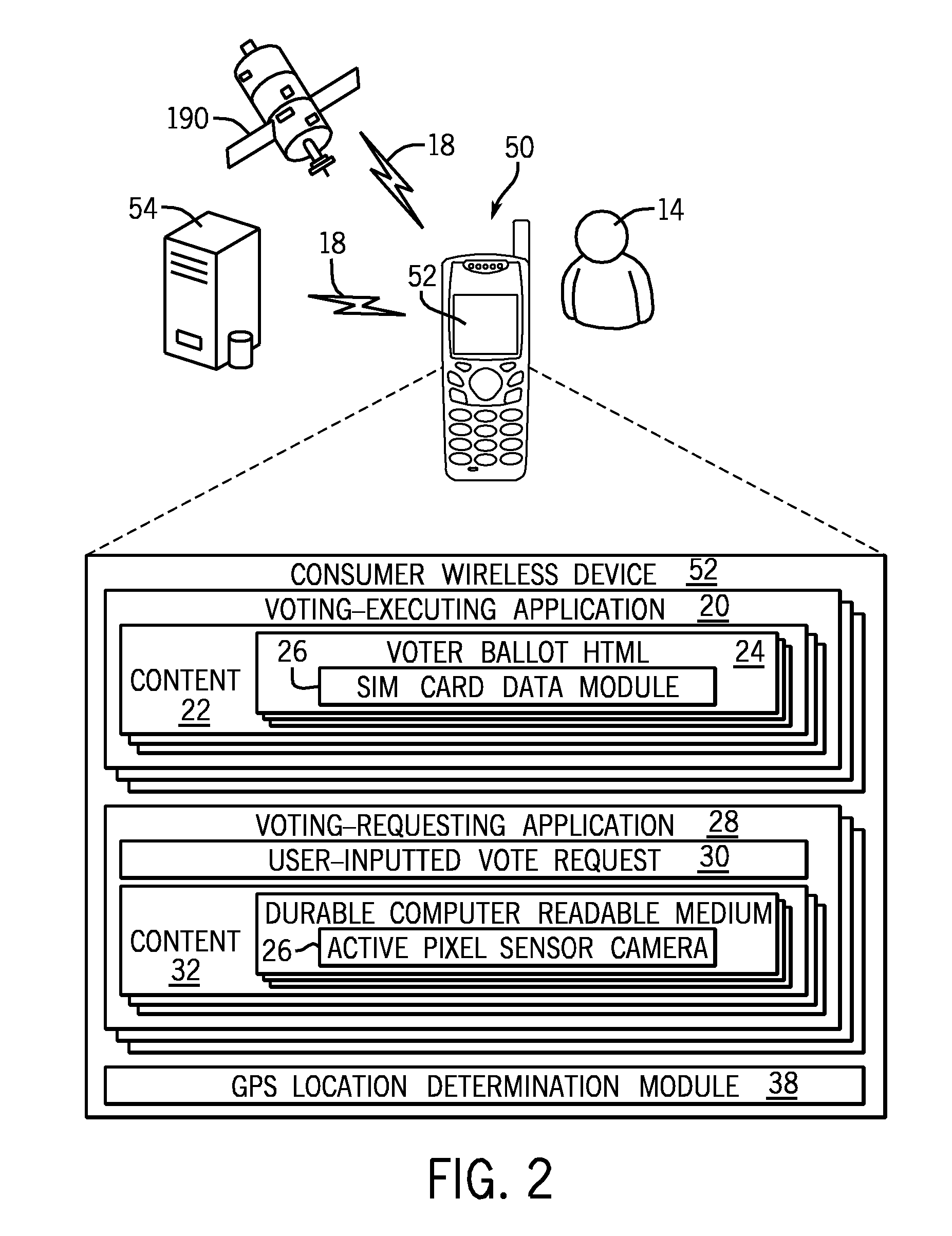
ActiveUS8090351B2Voting apparatusUnauthorised/fraudulent call preventionGeographic siteWireless mesh network
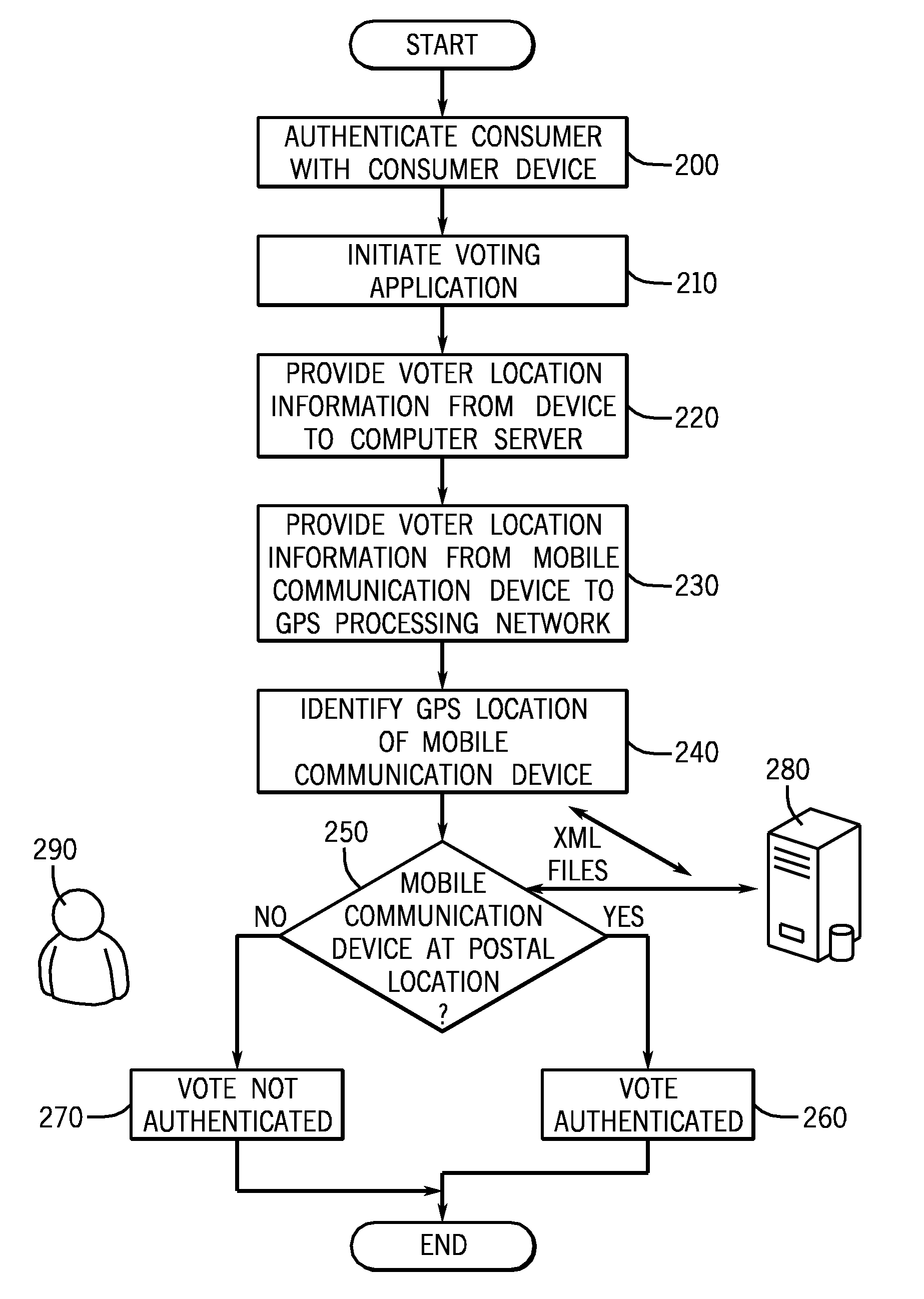
A system and method for authenticating votes received from a voter's mobile device. A computer is programmed with a set of computer-readable instructions and a includes database accessable by mobile device reading a durable computer readable medium stored in a computer hardware server, the database comprising a registered voter and a geographical location for the registered voter's postal mail delivery address. The system and method receive a vote in an election over a wireless carrier network, determine the geographical location of a device which transmitted the vote over the wireless network comprising cell tower triangulation, and reject the vote if the geographical location of the device which transmitted the vote is not within a predetermined distance from the geographical location for the registered voter stored in the database.
Owner:RPX CORP
Mathods & apparatus dynamically managing parking
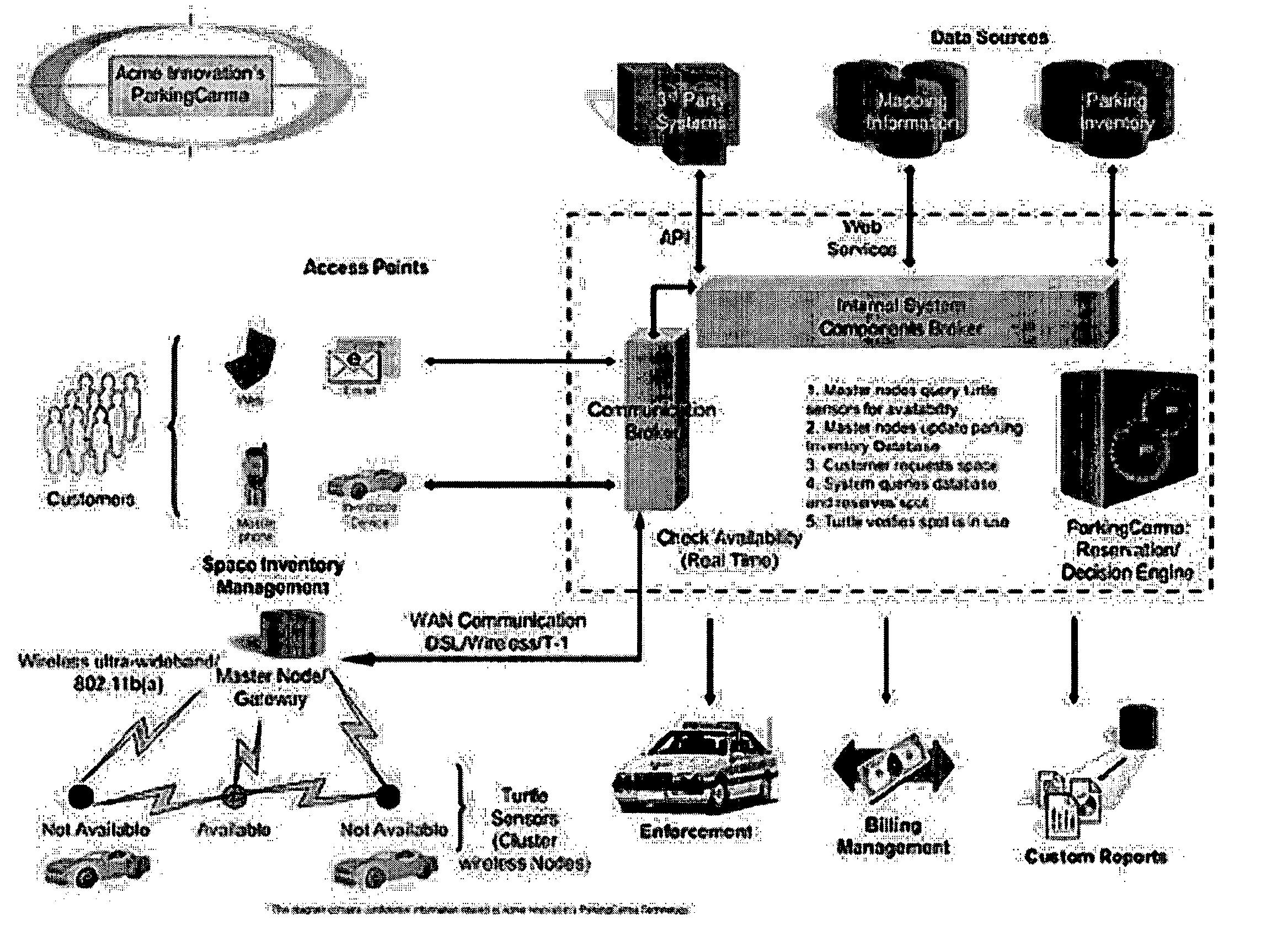
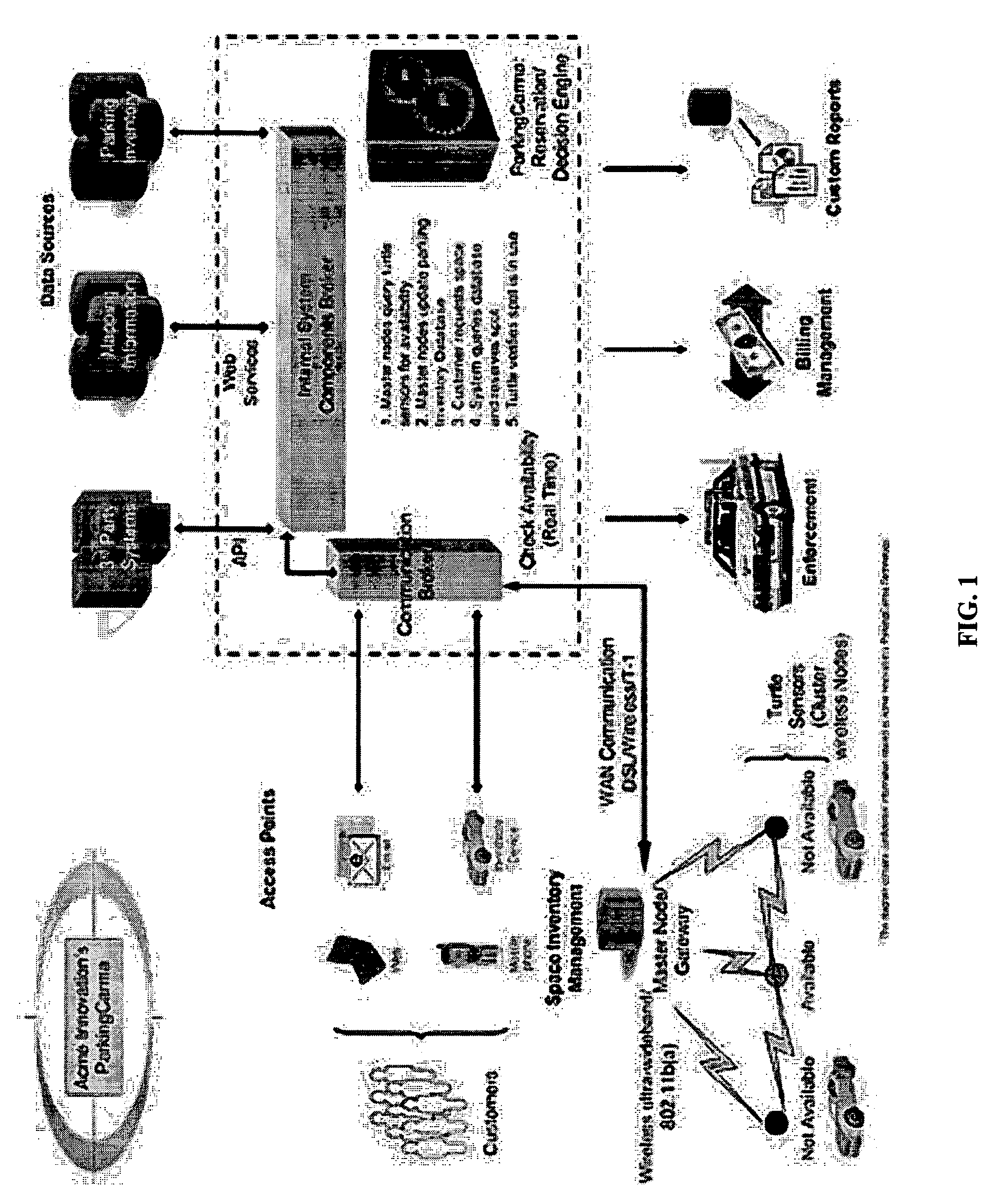
InactiveUS20050280555A1Efficient additionTicket-issuing apparatusIndication of parksing free spacesTransceiverWireless mesh network
A dynamic parking management system and method includes use of an intelligent software engine that, in some embodiments, interfaces with a wireless mesh network and multi-channel communication devices that, as a system, increases customer convenience which maximizes return on parking resources. The present invention uses a parking transceiver mesh network node located proximate to one or more parking spaces to provide accurate and current data to a database of available parking assets. Parking availability algorithms are used to analyze this data to select optimal parking spaces for subscribers / drivers and predict future availability of parking spaces. Additional functionality comes from the parking transceiver's ability to recognize specific vehicles and specific customers with predefined requirements.
Owner:WARNER FREDERICK MALTBY IV
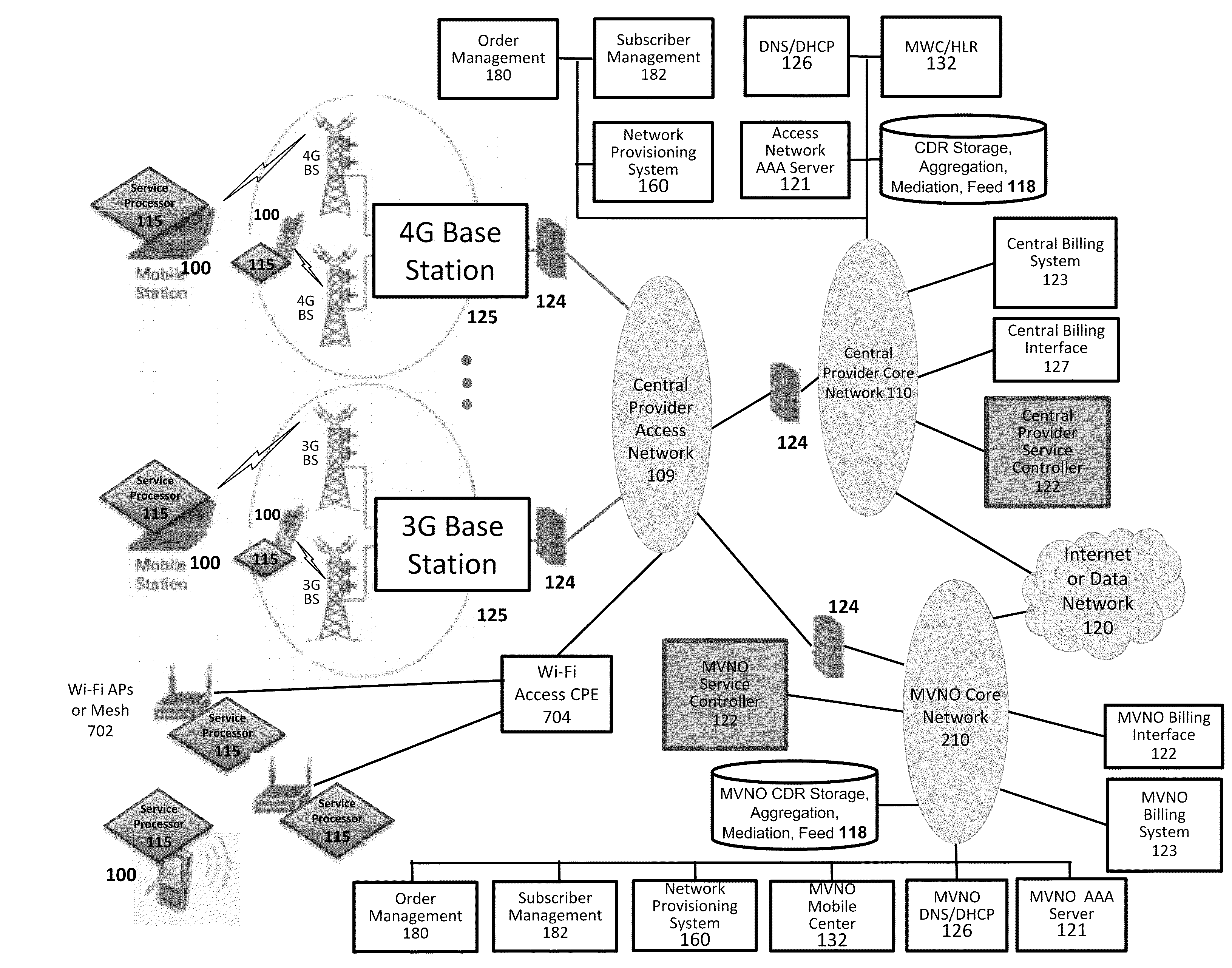
Optimized broadband wireless network performance through base station application server
ActiveUS20140003394A1Reduce time delayHigh bandwidthPower managementSpatial transmit diversityWireless mesh networkApplication server
Owner:ALL PURPOSE NETWORKS INC
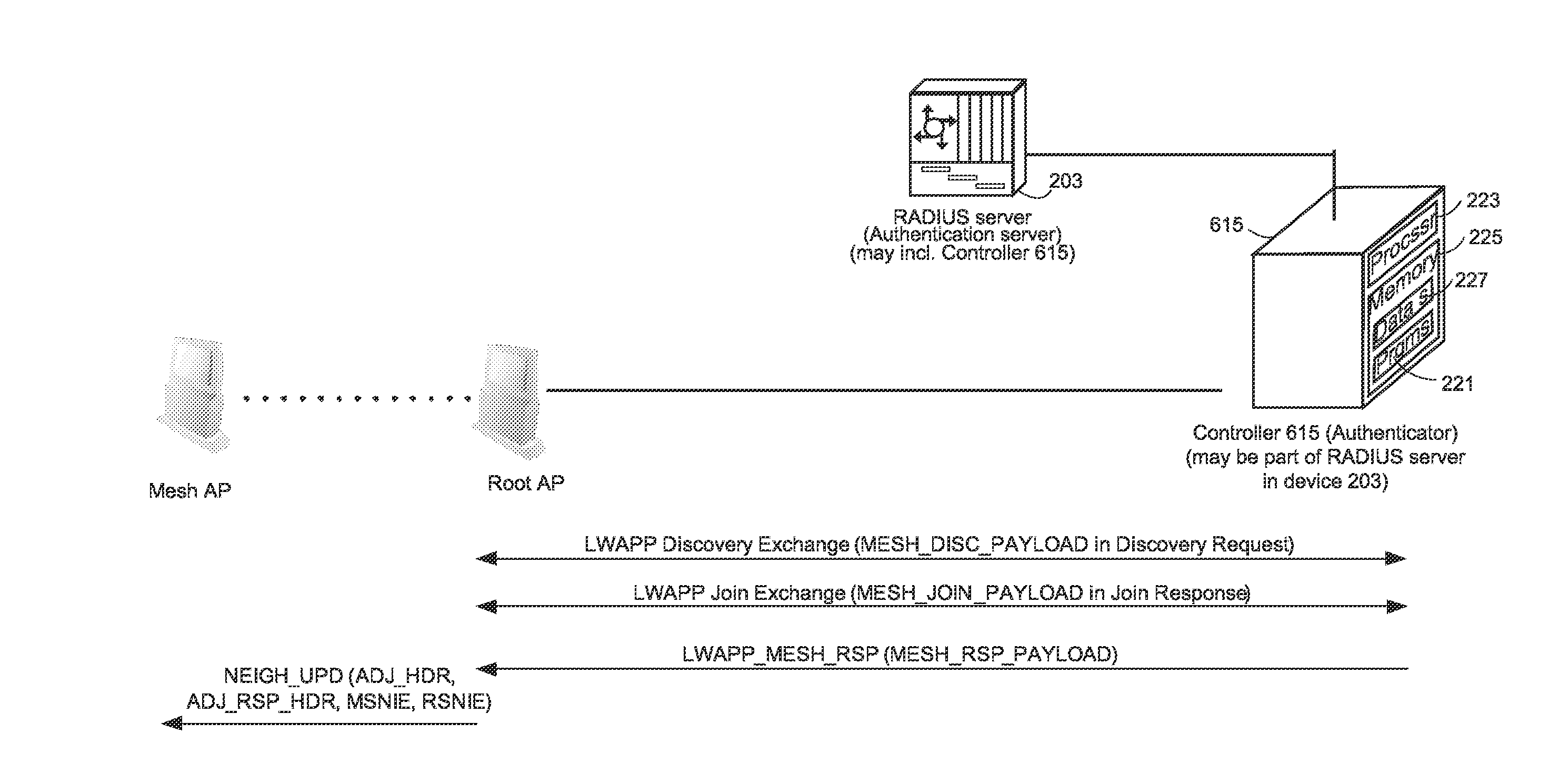
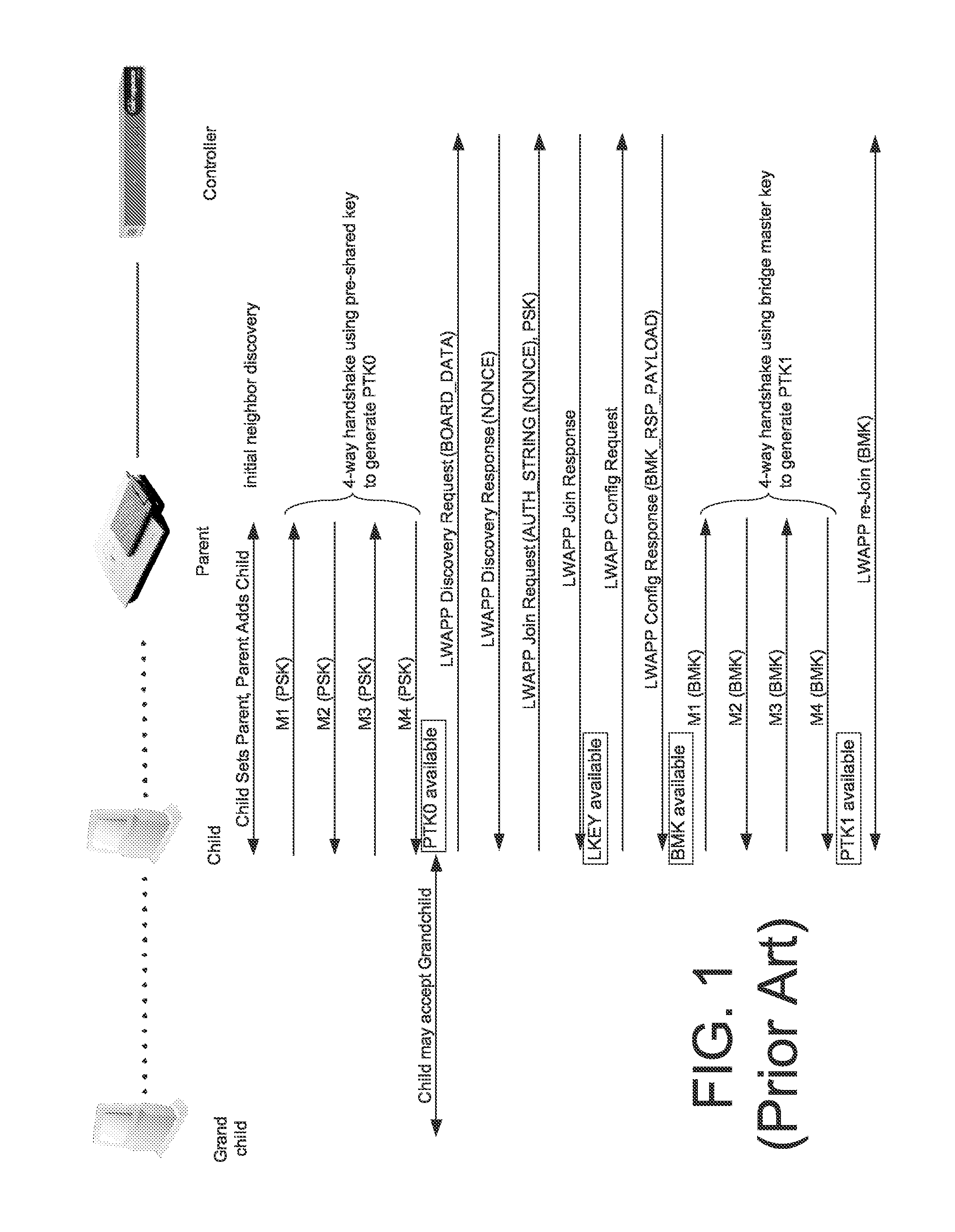
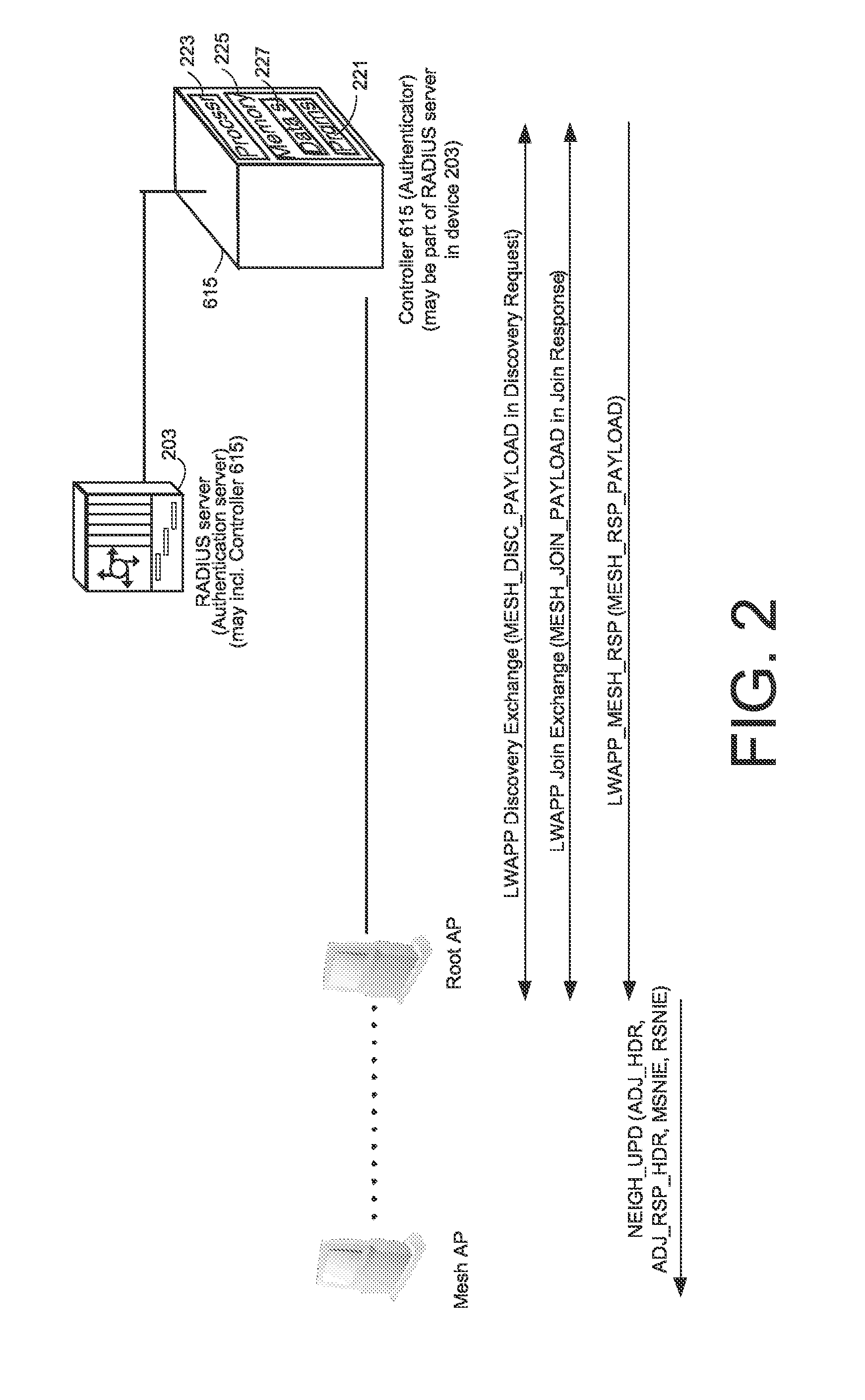
System and method for securing mesh access points in a wireless mesh network, including rapid roaming
ActiveUS20070206537A1Fast rebuildFast roamingUnauthorised/fraudulent call preventionEavesdropping prevention circuitsRoamingWireless mesh network
An authentication method in a mesh AP including using standard IEEE 802.11i mechanisms between the mesh AP and an authenticator for authenticating the mesh AP to become a child mesh AP with a secure layer-2 link to a first parent mesh AP that has a secure tunnel to a Controller, including, after a layer-2 link between the child mesh AP and the first parent mesh AP is secured, undergoing a join exchange for form a secure tunnel between the child mesh AP and the Controller. Further, a fast roaming method for re-establishing a secure layer-2 link with a new parent mesh AP including, while the mesh AP is a child mesh AP to the first parent mesh AP and has a secure layer-2 link to the first parent mesh AP, caching key information and wireless mesh network identity information, and using the cached information to establish a secure layer-2 link with a new parent mesh AP without having to undergo a 4-way authentication. Further, while the mesh AP is a child mesh AP to the first parent mesh AP, has a secure layer-2 link to the first parent mesh AP, and has a secure tunnel to the Controller, caching session information on the secure tunnel, and using the cached information to re-establish the secure tunnel with the Controller, the secure tunnel now via the new mesh AP.
Owner:CISCO TECH INC
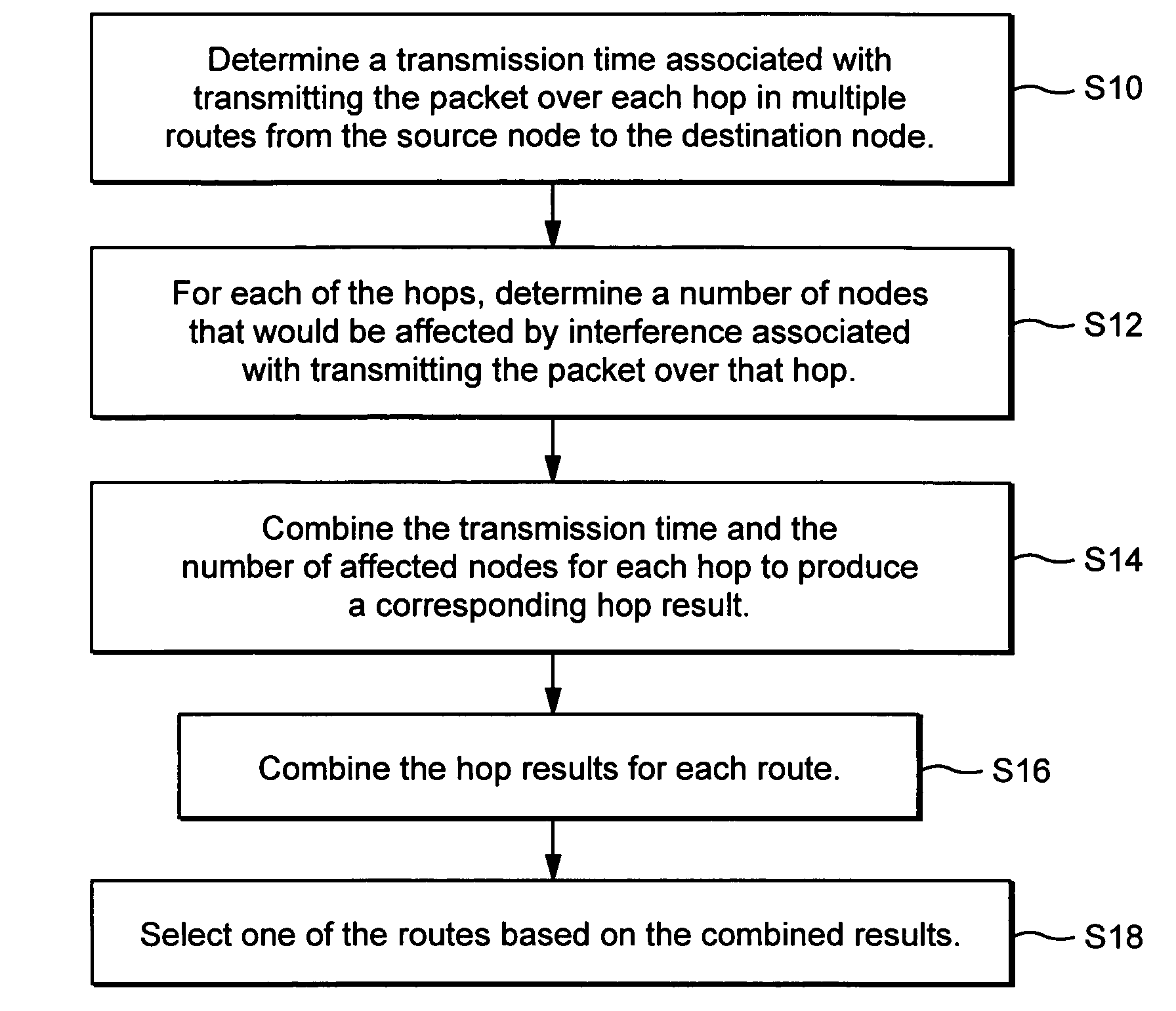
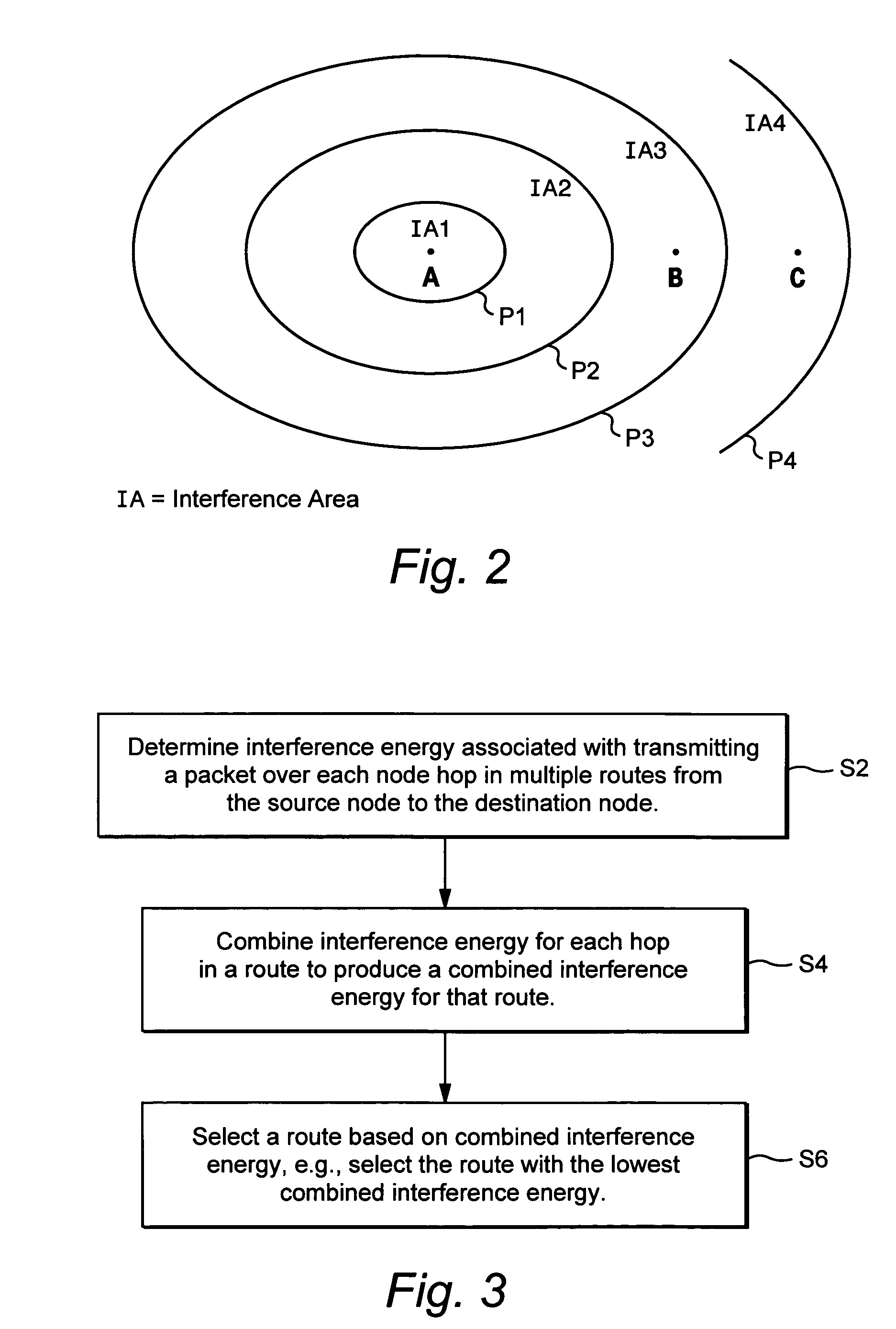
Interference-based routing in a wireless mesh network
ActiveUS7554998B2Low costReduce data rateEnergy efficient ICTError preventionComputer networkWireless mesh network
Route selection through a wireless mesh network between a source node and a destination node is based on minimizing generated interference in order to increase the capacity of the network. An interference energy associated with transmitting a packet over each hop in multiple routes from the source node to the destination node is determined. The interference energy for each hop is combined to generate a combined interference energy for each route. One of the routes is selected based on the combined interference energy determined for each route.
Owner:TELEFON AB LM ERICSSON (PUBL)
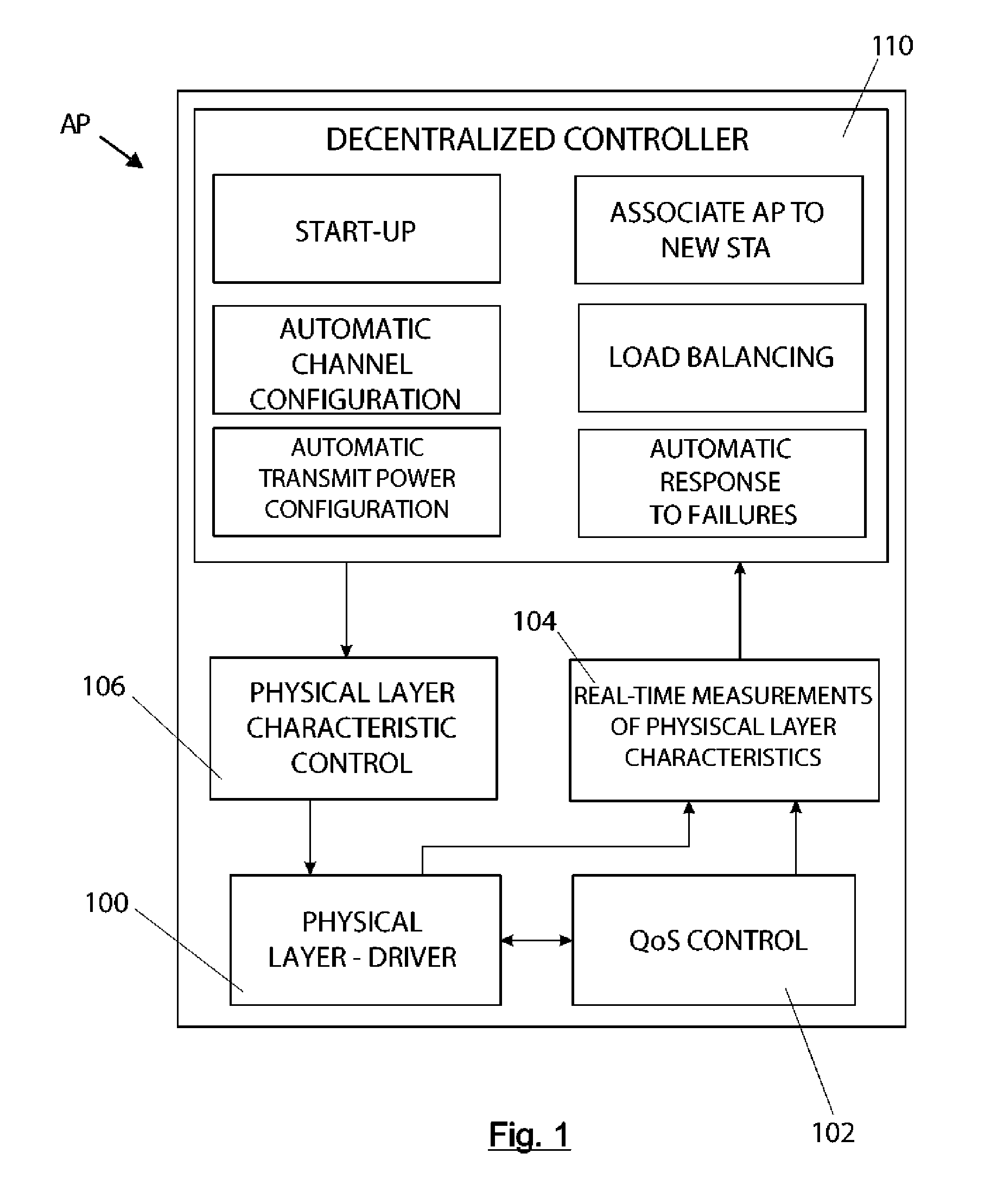
System and method for decentralized control of wireless networks
ActiveUS20160262163A1Easy to operateReduce or eliminate impactPower managementNetwork topologiesWireless mesh networkTransmitted power
System and method for decentralized control of wireless networks, made up by a set of access points (AP) that provide connection service to a set of stations (STA). The method comprises carrying out, during the start-up process, an automatic selection of the transmission channel (S7) of each access point (AP) to minimize interference, and which is based on the following information transmitted between the access points (AP) in the network:a list of the access points (AP) that are within the range of reach of each access point (AP) in the network;the powers with which each access point (AP) receives signals from the access points within its reach;a list of preferred channels, with the lowest level of interference, for each access point (AP) in the network.The method also enables, among other features, carrying out an automatic transmit power selection (S8).
Owner:AOIFE SOLUTIONS
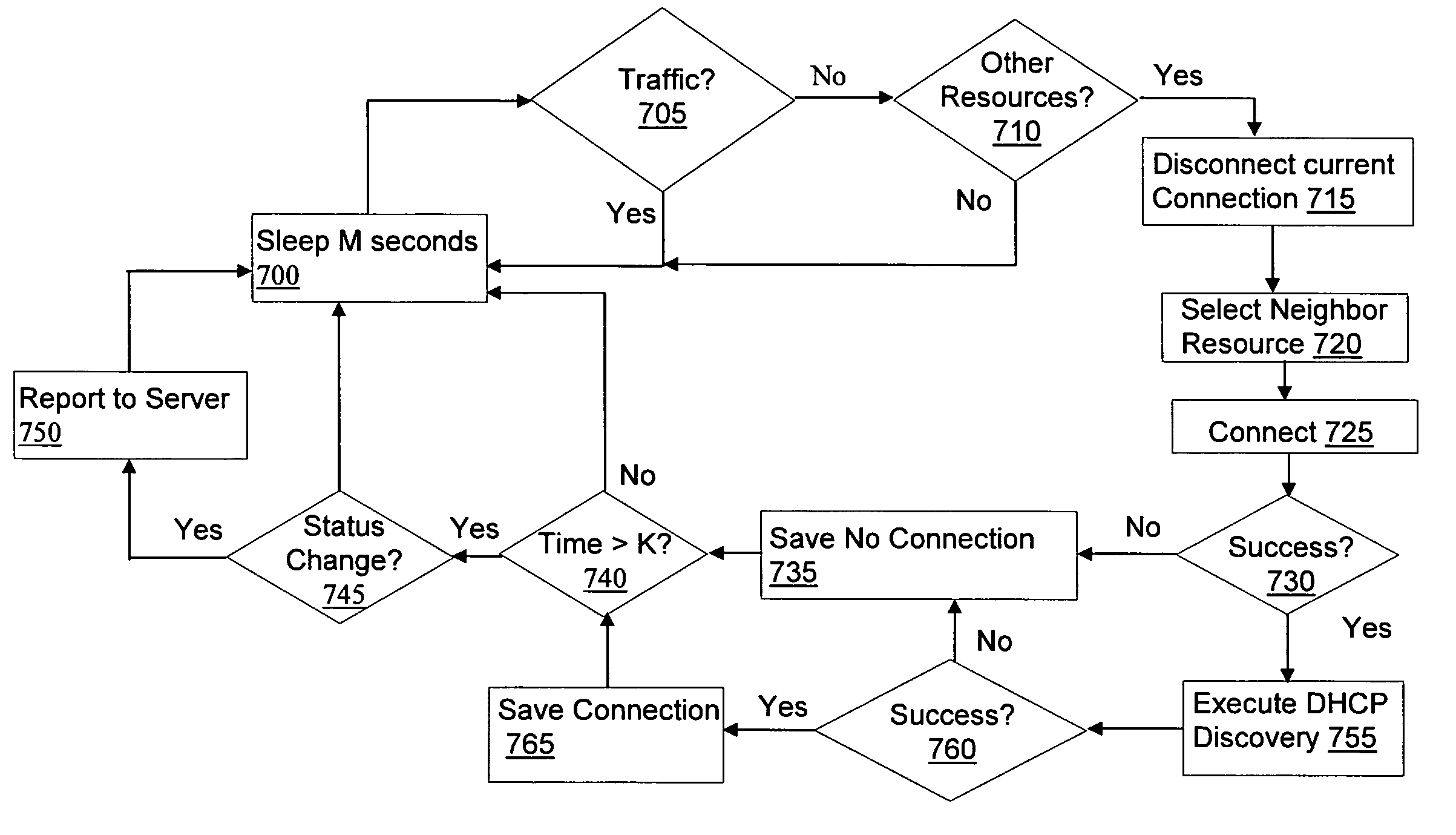
Method and system for data transmission in a wireless network
A method and system for data transmission by computational devices in a wireless network (100) are disclosed. A computational device (102) organizes the wireless network in a hierarchical topology having at least one root node and updates a list of interferers and a list of descendents. Then, the computational device allocates a Contention Free Period (CFP) slot to each computational device in the wireless network based on at least one of the list of interferers and the list of descendents and transmits data during the allocated CFP slot.
Owner:ARRIS ENTERPRISES LLC
System and method to support multicast routing in large scale wireless mesh networks
ActiveUS20060098607A1Quick changeReduce overheadMultiplex system selection arrangementsNetwork topologiesTree rootWireless mesh network
Provided is a system and method for a multicast routing algorithm to work in infrastructure based mesh networks. It chooses access points, fixed infrastructure gateway nodes connected to each other and / or the global internet via a wired / wireless backbone, as a group of local multicast group leaders to form a multicast group leader cloud. Each local multicast group leader is elected on-demand according to the local multicast group member's request. Each local multicast group leader forms a local multicast tree rooted at this leader connecting all multicast group members associated with the AP. The processes of electing and maintaining local multicast trees rooted at APs enable efficient coordination with underlying unicast routing to exploit the advantages of fixed infrastructure nodes. Therefore, routing overhead and multicast tree convergence time are reduced. The method can support large networks with fast topology change due to fast convergence and reduced routing overhead.
Owner:ARRIS ENTERPRISES LLC
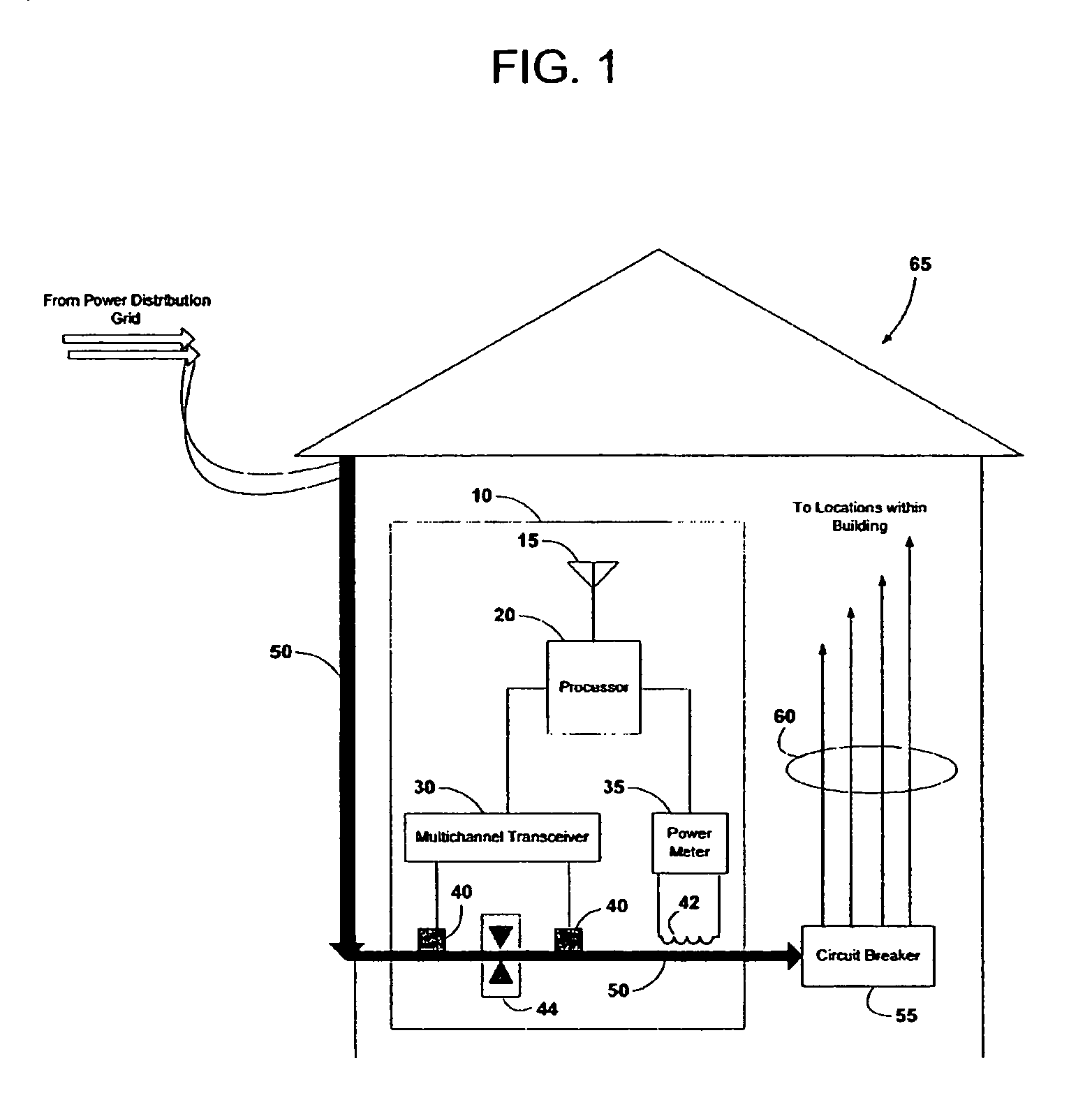
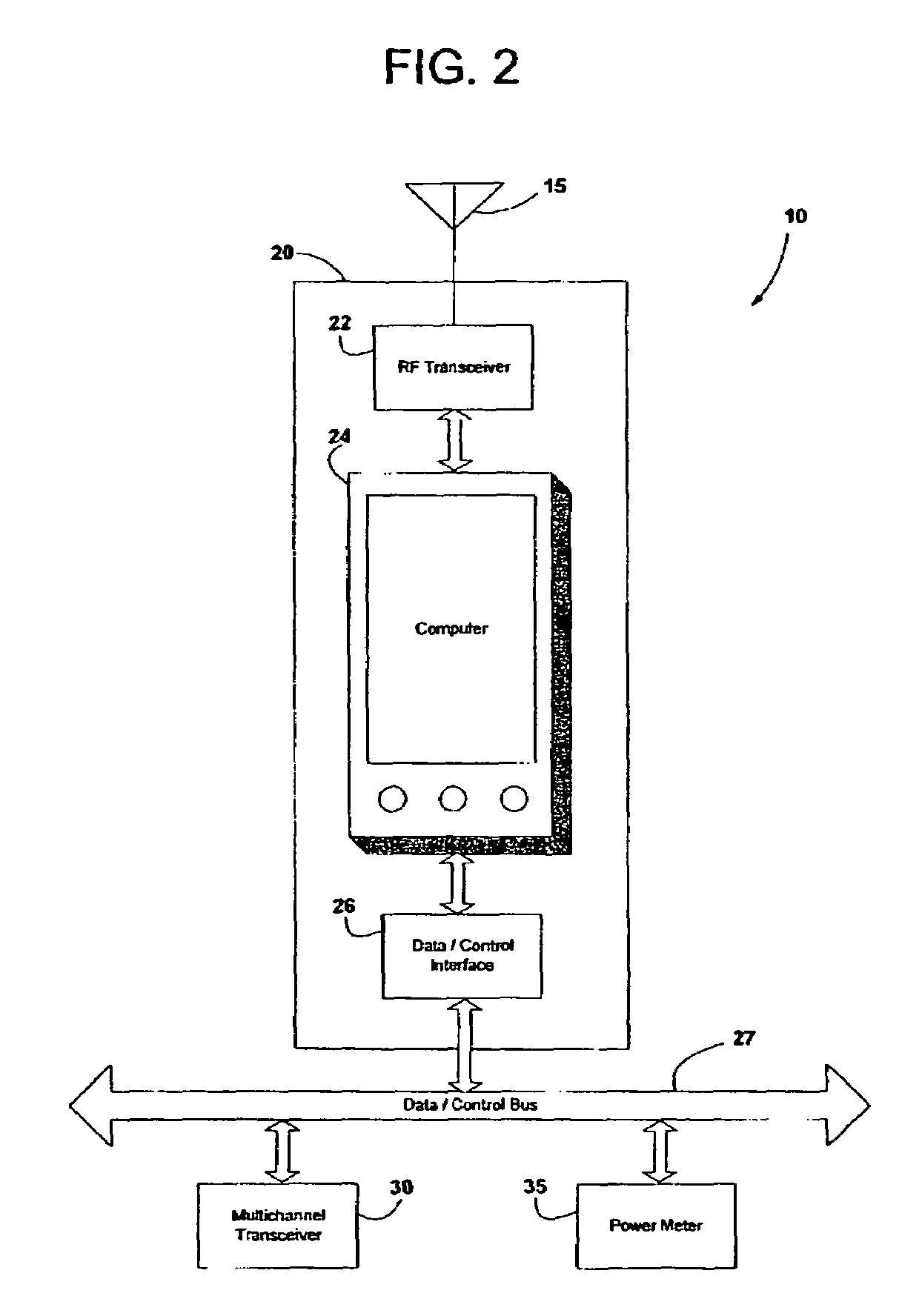
Electrical power metering system
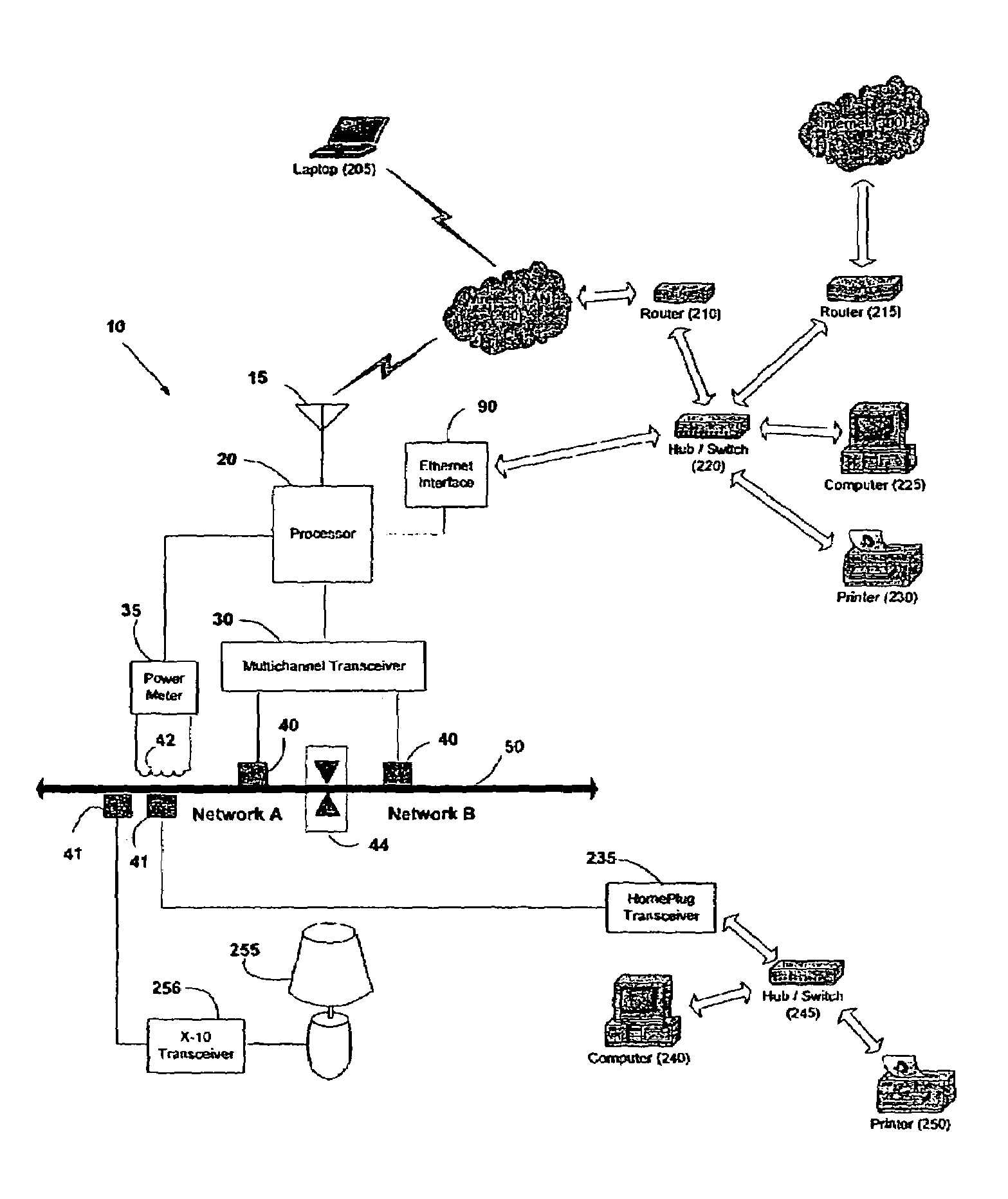
InactiveUS7058524B2Maximize energy savingElectric signal transmission systemsCircuit arrangementsWireless mesh networkPower line network
A wireless electrical power metering system is provided. A processor having a multichannel power line transceiver, a wireless transceiver, and a power meter attached thereto measures power consumption information on a power line inductively coupled with the power meter. The processor converts the power consumption information into IP-based data, and transmits same over the wireless transceiver. The information can be wirelessly received by a remote monitoring station or transmitted across the Internet for storage, analysis, and billing. The processor generates appliance control signals and generates same across the multichannel power line transceiver to remotely control appliances in response to power consumption trends. The processor provides firewall capabilities, and relays information between a wired or wireless network and a power line network, thereby expanding the size of existing household networks. Further, the processor allows multiple dwellings to be networked using power lines, and households to be connected to the Internet via a power line network.
Owner:HUDSON BAY WIRELESS
Methods and apparatus for selecting a wireless network based on quality of service (QoS) criteria associated with an application
In one illustrative example, a mobile communication device has a plurality of software applications including an Internet browser application, an electronic mail (e-mail) communication application, and an audio or video player application. The mobile device is adapted to receive, from wireless communication networks or through use thereof, available quality of service data for the wireless networks and store the corresponding data in association with each network identification. The available quality of service data includes at least a bandwidth criterion and a delay criterion associated with each wireless network. For each one of the software applications, the mobile device is adapted to execute the software application; identify, based on the stored quality of service data, one or more wireless networks having a bandwidth criterion and a delay criterion that best match a bandwidth requirement and a delay requirement, respectively, of the executed software application; and select, based on the identifying, an available wireless network for communication using the executed software application.
Owner:MALIKIE INNOVATIONS LTD
Anonymous location service for wireless networks
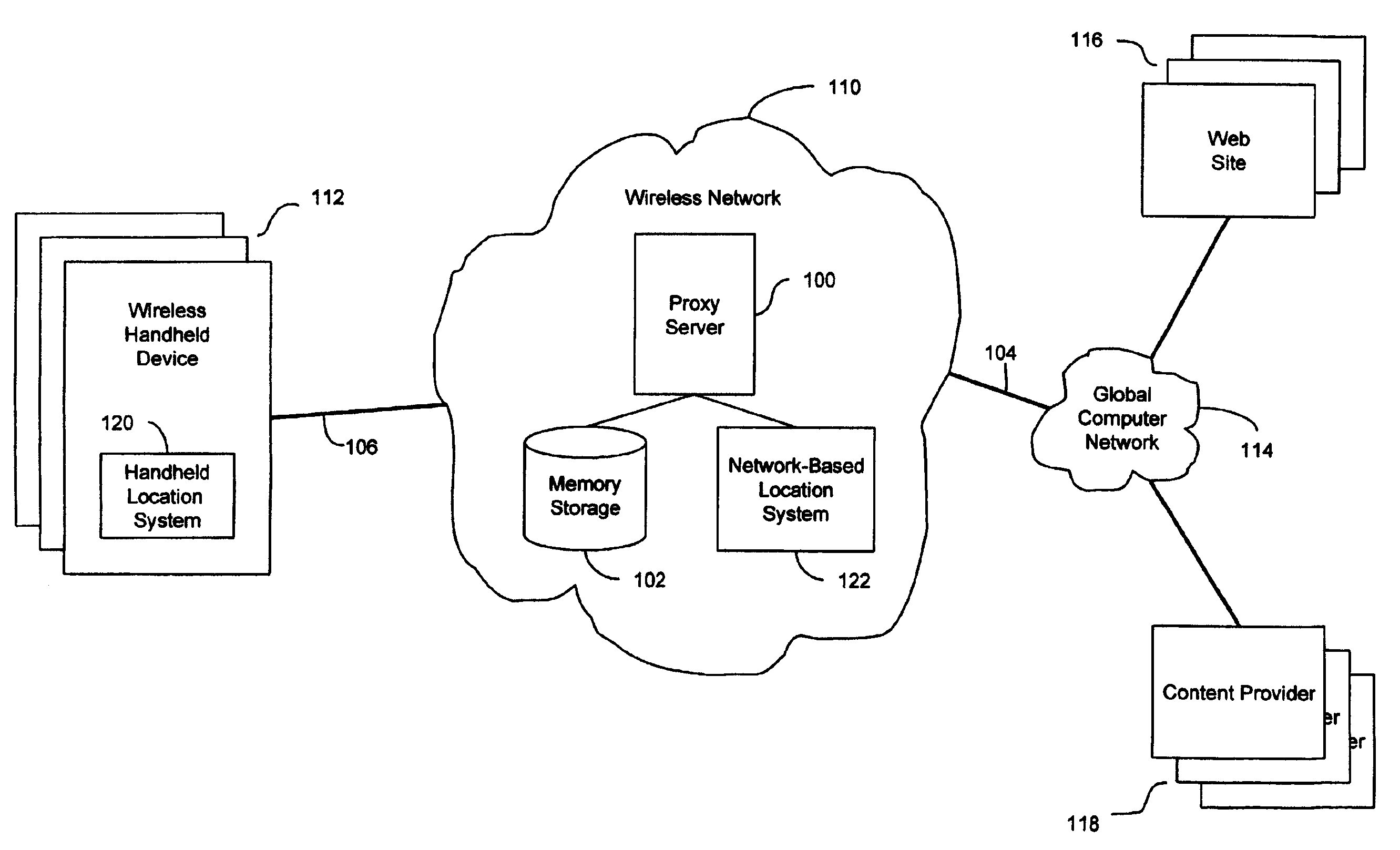
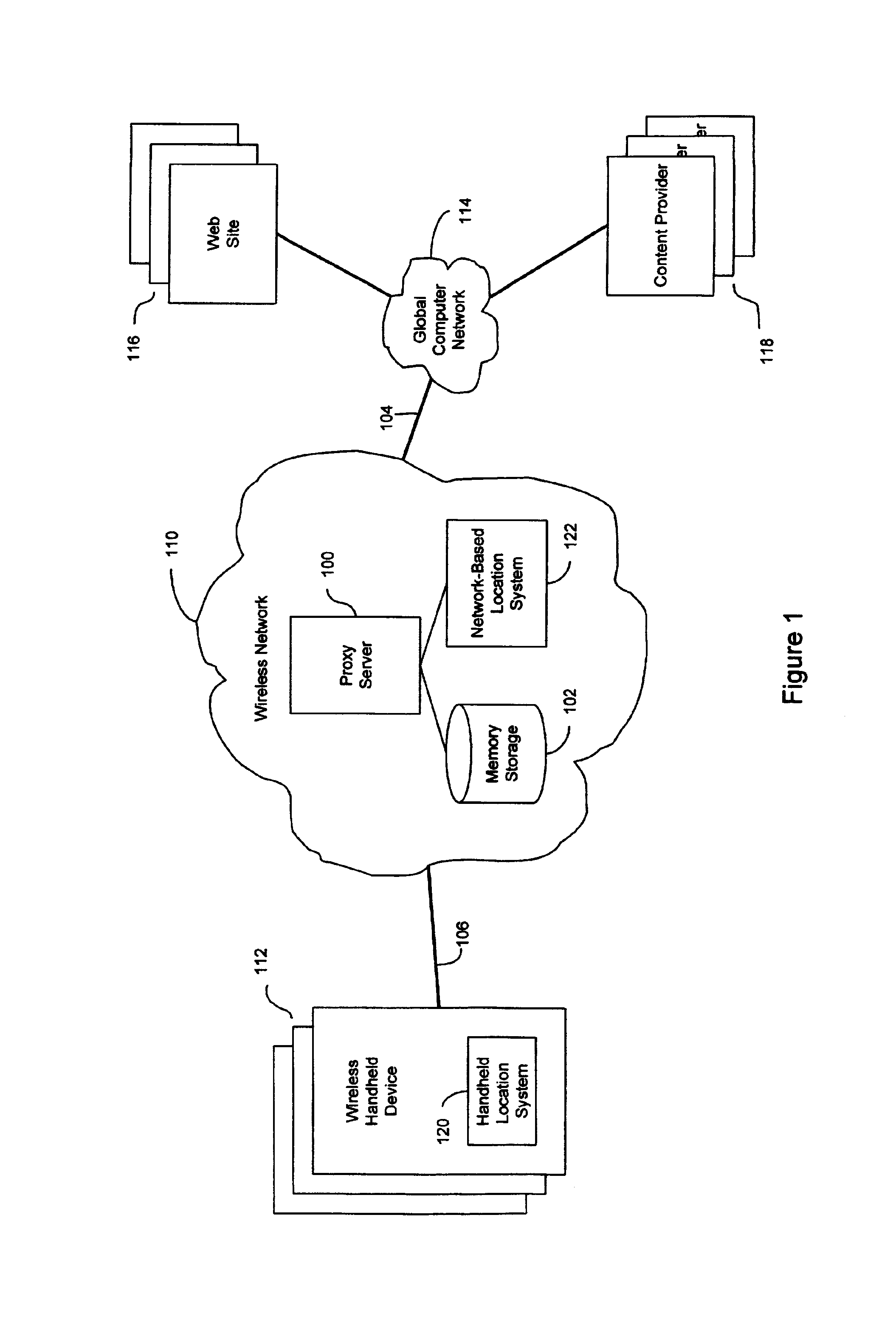
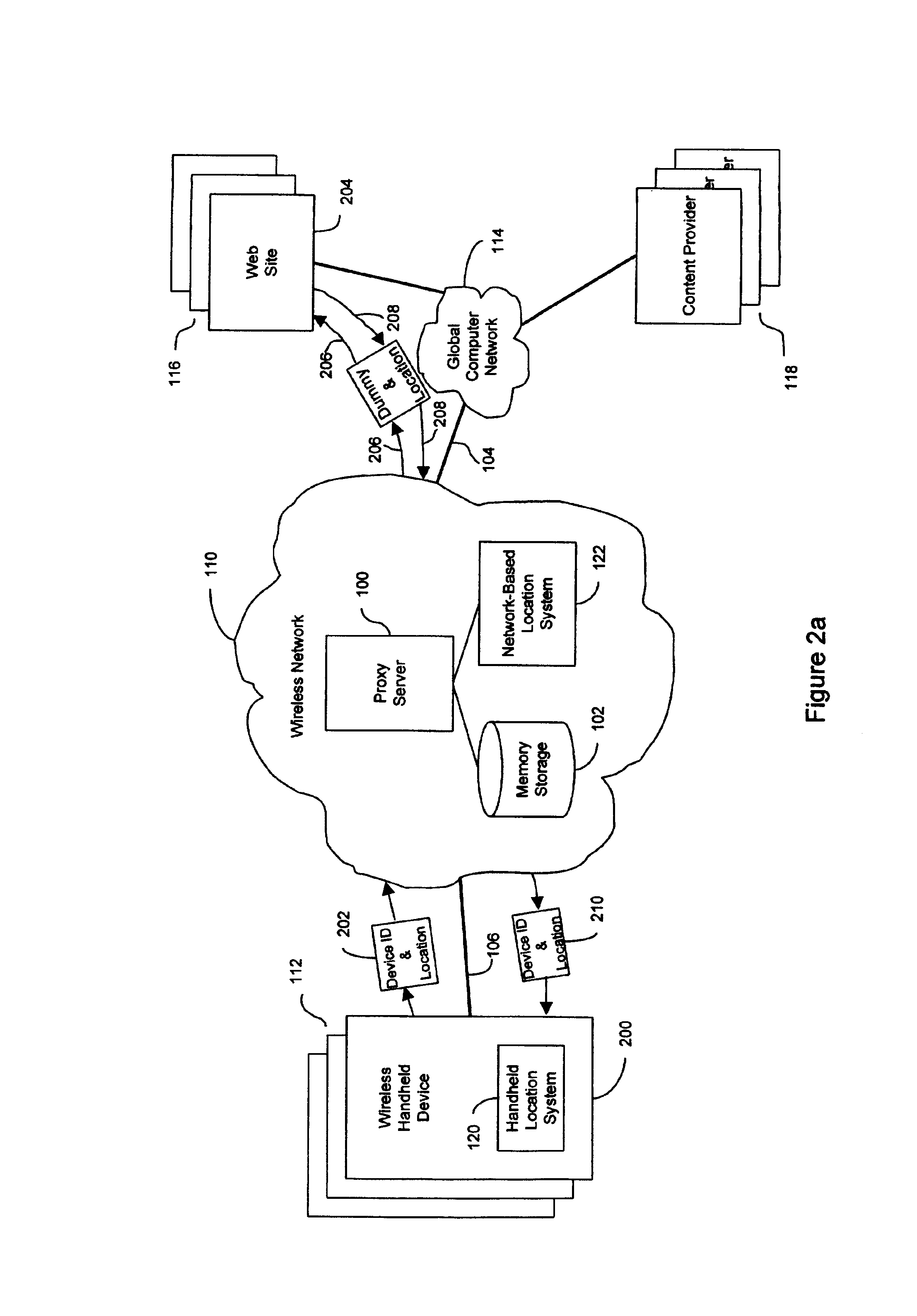
InactiveUS7069319B2Efficient content deliveryImprove identityDevices with GPS signal receiverMultiple digital computer combinationsWeb siteTelecommunications link
An anonymous location wireless network service for use in a wireless network that tracks the location and identity of network users, such as networks complying with enhanced 911 standards. The service provides content providers with the location of network users without revealing their identities. The service includes a wireless network having a proxy server, a network communication link to a plurality of web sites, and a wireless communication link to a plurality of handheld devices. The proxy server blocks identity by reading the location and identity information of network devices, generating dummy identifications, relating the dummy identifications to the identity information, storing the relationships in a memory storage, and forwarding the location information and dummy identifications to the global computer network. Upon receiving return messages from the global computer network, the proxy server reads the dummy identifications, looks up the related identity information in the memory storage, and forwards the data to the appropriate network devices.
Owner:GOOGLE LLC
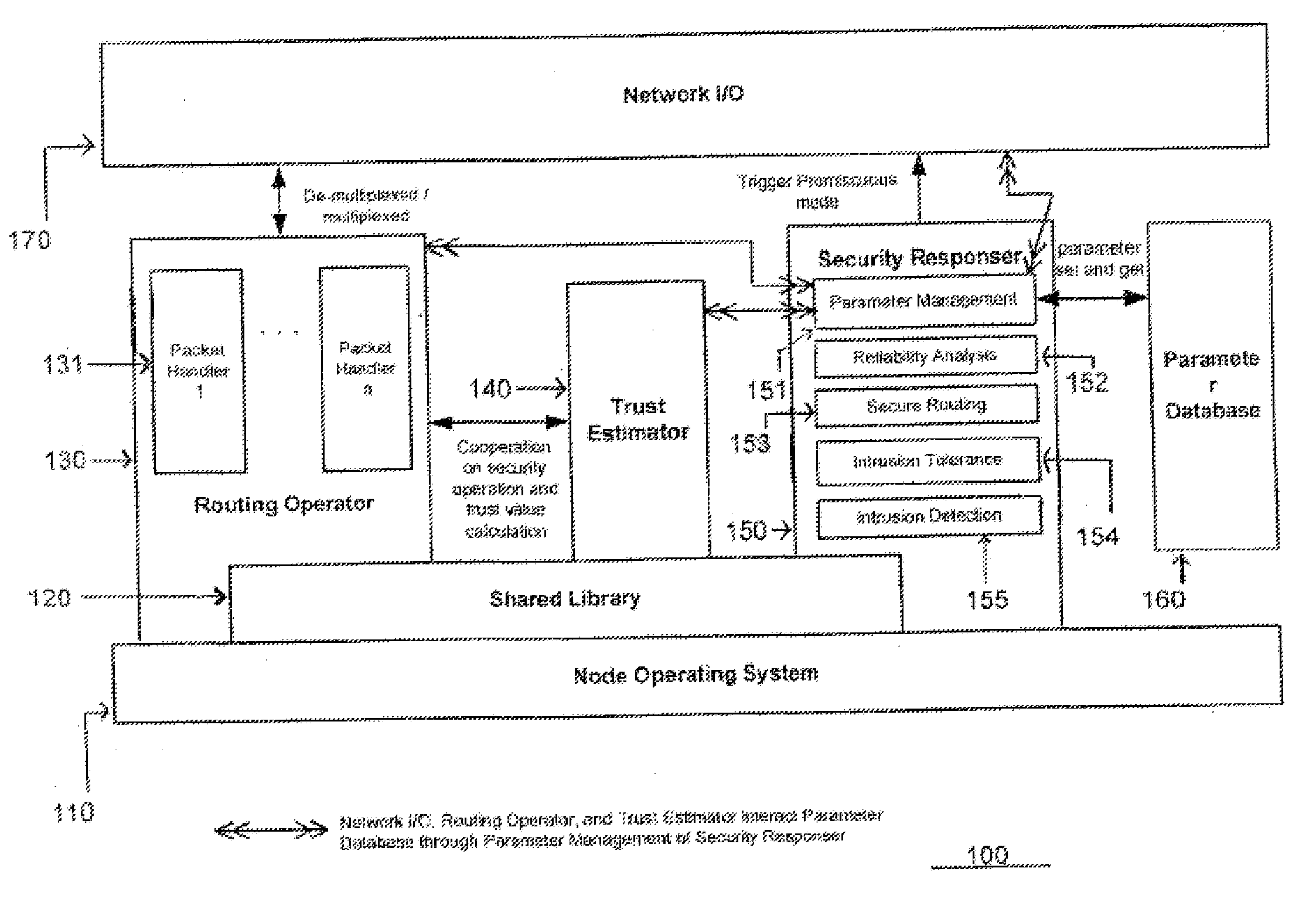
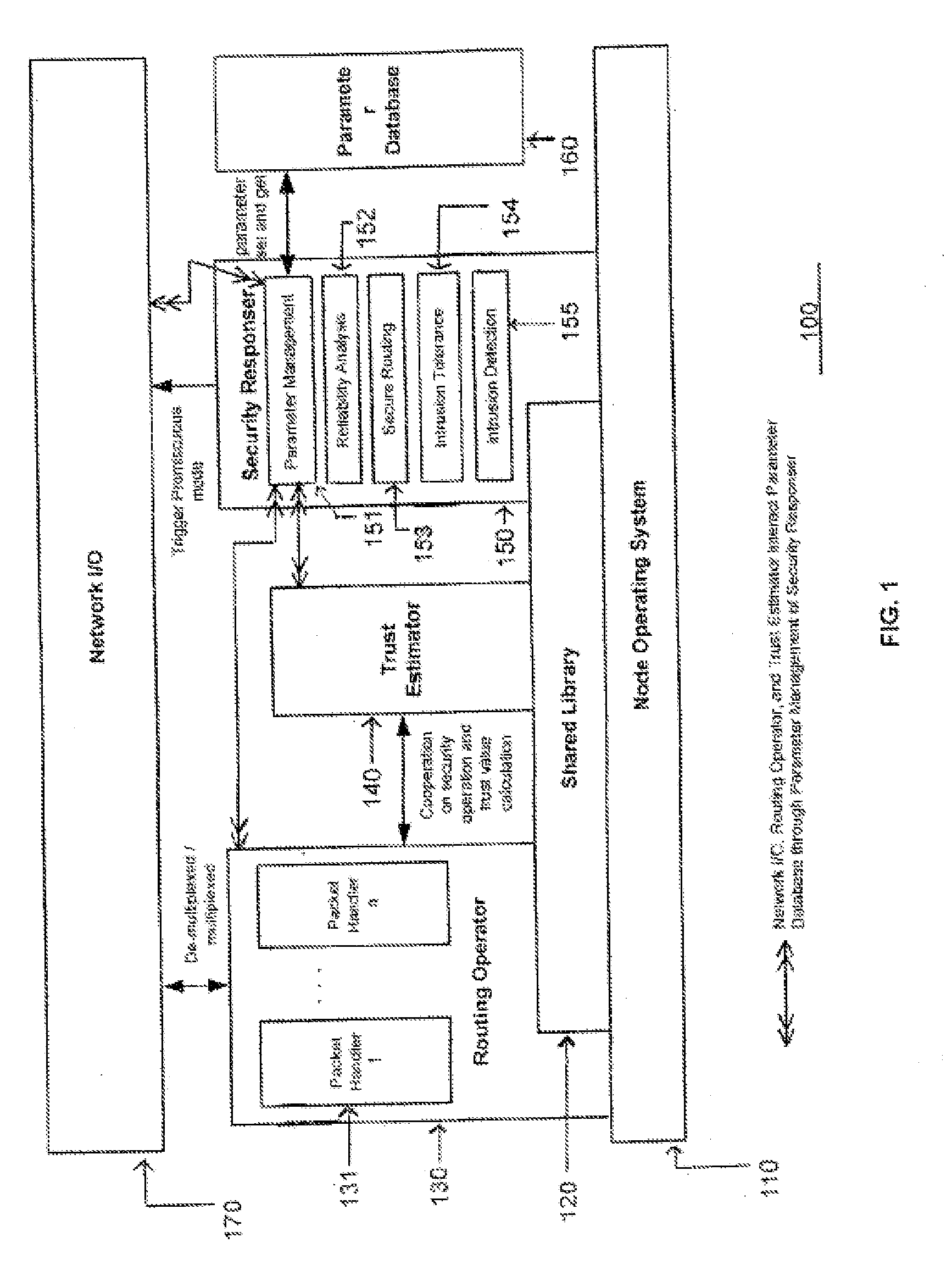
Wireless sensor network and adaptive method for monitoring the security thereof
InactiveUS20080084294A1Data taking preventionNetwork topologiesWireless mesh networkWireless sensor networking
The present invention relates to a sensor network having node architecture for performing trust management of neighboring sensor nodes, and to an adaptive method for performing trust management of neighboring sensor nodes for monitoring security in the sensor network. The sensor network includes a base station and a plurality of sensor nodes for reporting sensed information packets to the base station through radiofrequency signals relayed by other sensor nodes. A judge sensor node may have a trust estimator in its node architecture to evaluate trustworthiness of a neighboring suspect sensor node by determining a personal reference and receiving personal references from jury sensor nodes. Based on the trustworthiness of the suspect, the judge may modify a route for transmitting packets to the base station.
Owner:ELECTRONICS & TELECOMM RES INST
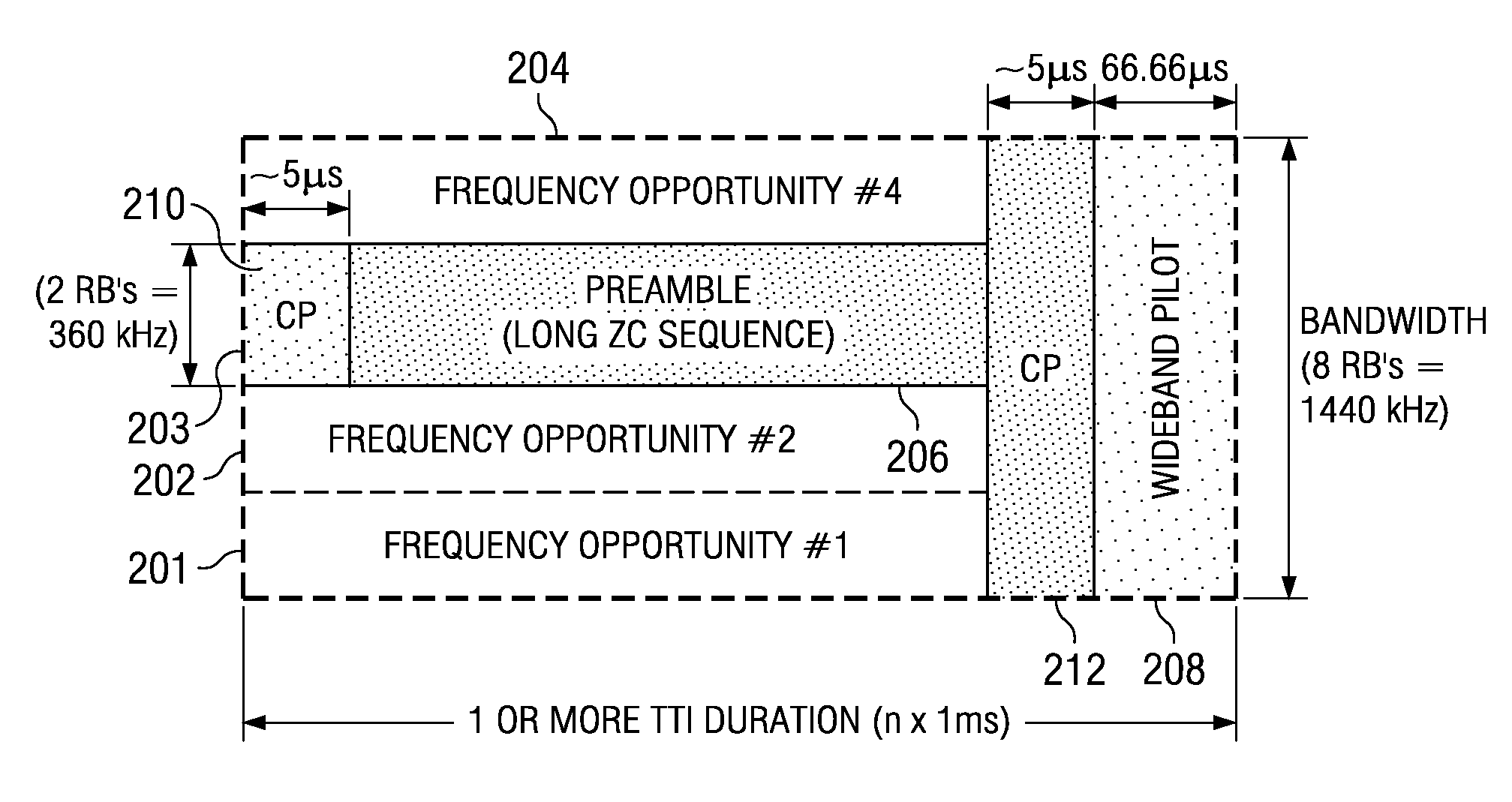
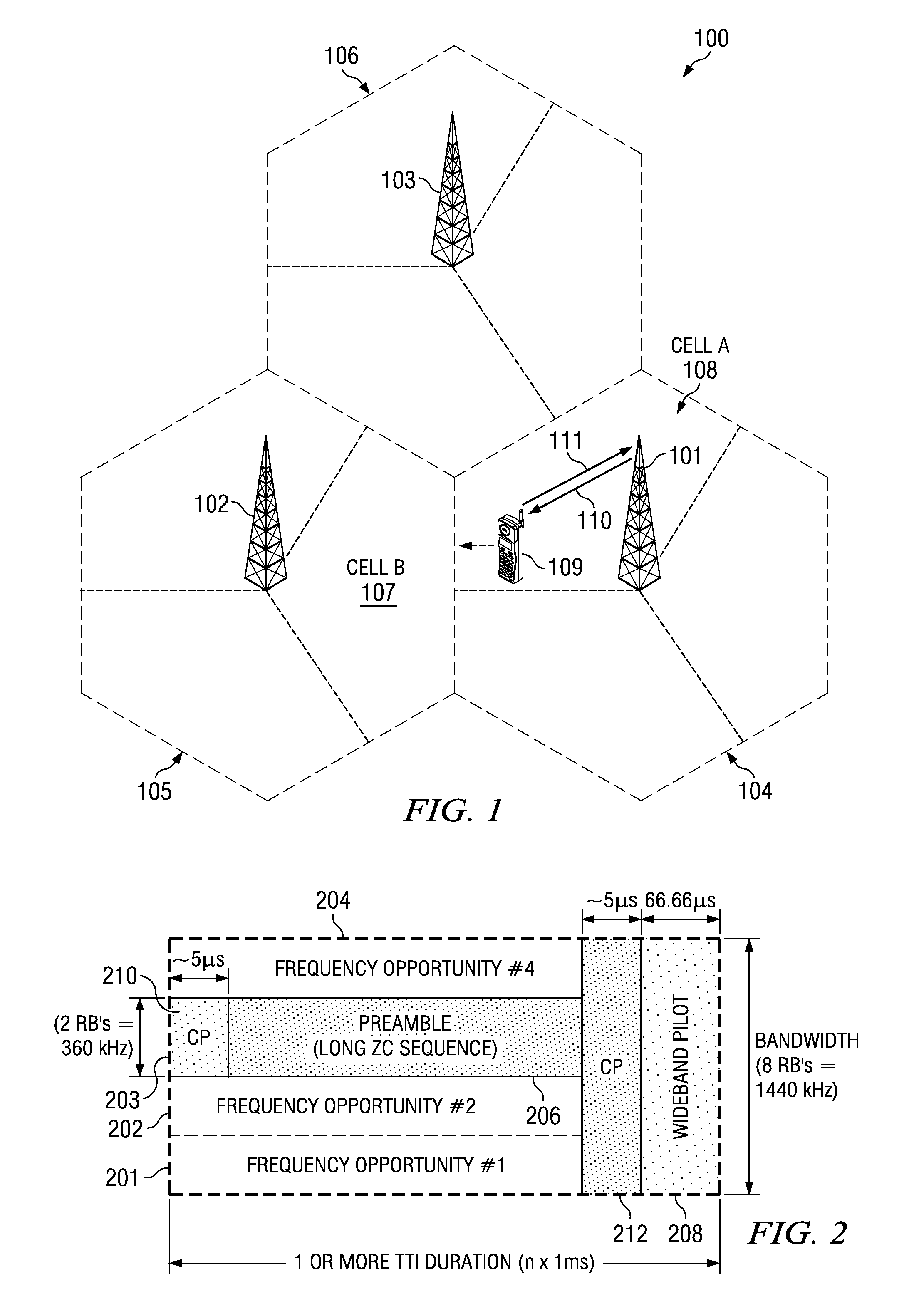
Efficient Scheduling Request Channel for Wireless Networks
ActiveUS20080080472A1Reduce overhead costsFast and robustModulated-carrier systemsTransmission path divisionWireless mesh networkUser equipment
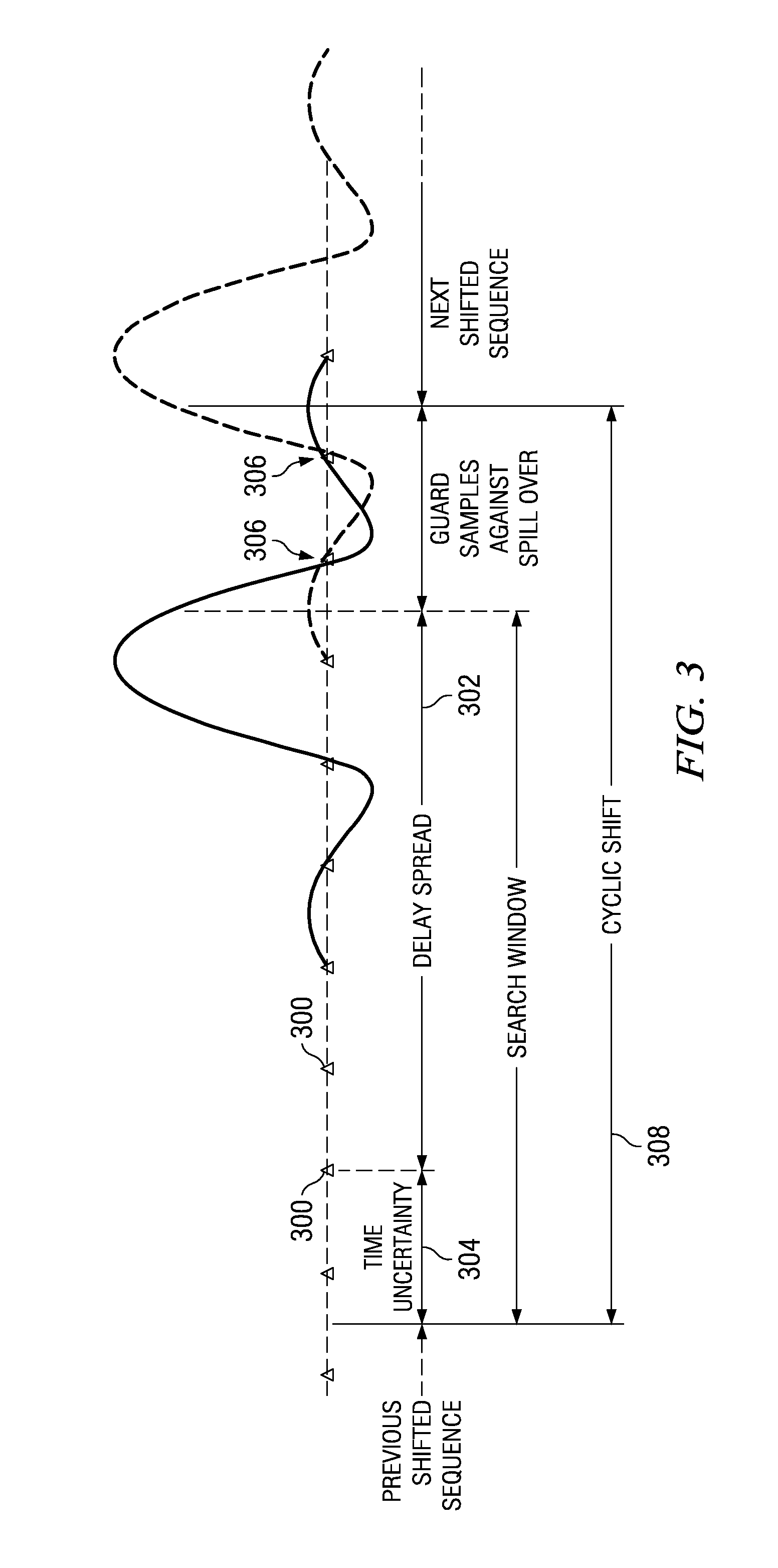
In a method for transmitting a contention free scheduling request in a cellular network, a set of N frequency opportunities is defined within a scheduling request slot. A set of R CAZAC root sequences is then defined per frequency opportunity. A set of C cyclic shifts is then defined per CAZAC root sequence. Within a given cell, a unique identification number is assigned to each user equipment (UE) that is in an uplink (UL) synchronized state. Each UL synchronized UE is mapped to a unique combination of one of the N frequency opportunities, one of the R CAZAC root sequences and one of the C cyclic shifts. A cyclic shifted preamble sequence for a given UE is transmitted as a scheduling request on the mapped frequency, CAZAC root sequence and cyclic shift opportunity, wherein the unique identification number of the given UE is encoded by the combination of the frequency opportunity, CAZAC root sequence opportunity, and amount of cyclic shift, such that up to all of the plurality of UE can transmit a schedule request (SR) in a non-contentious manner in one schedule request slot.
Owner:TEXAS INSTR INC
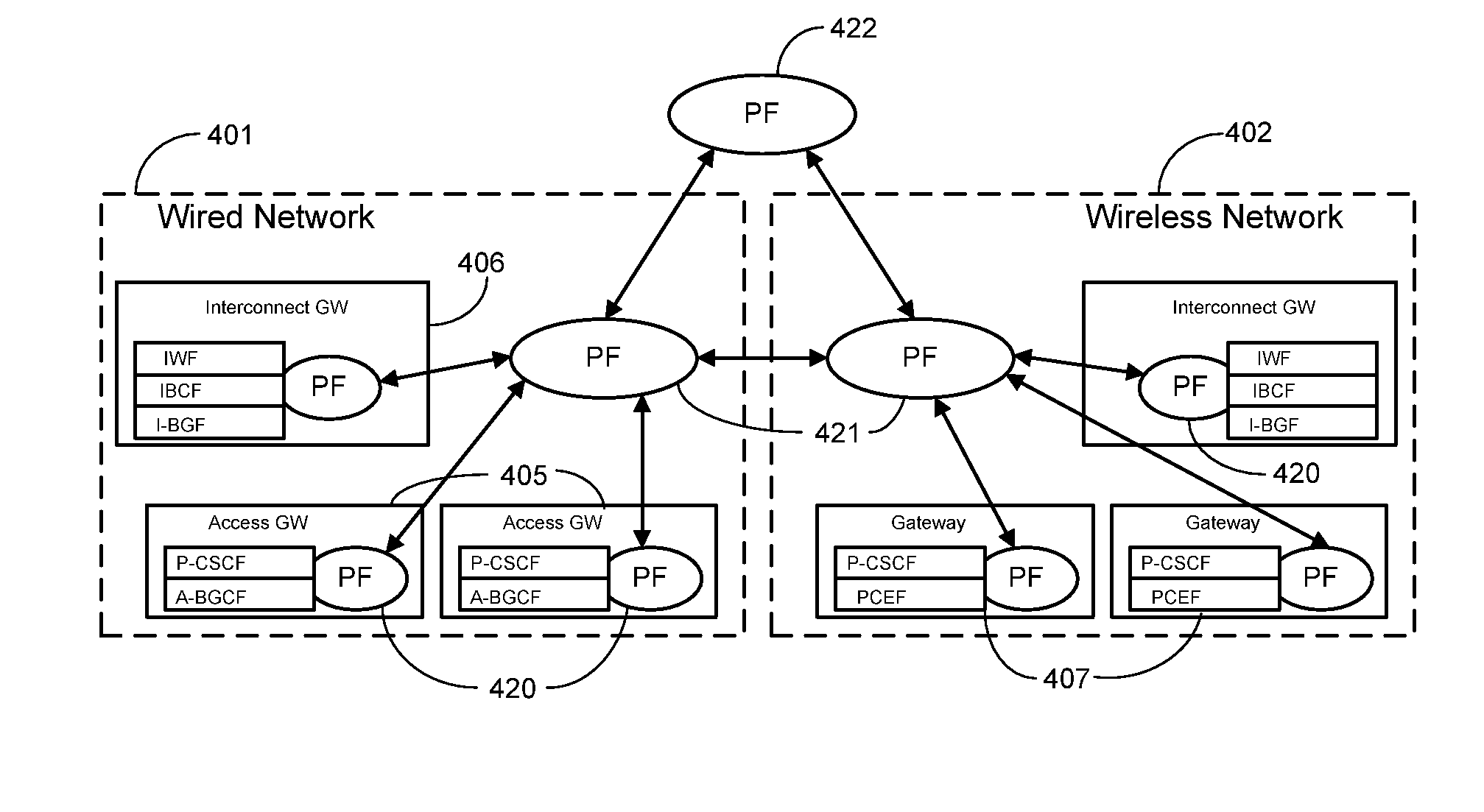
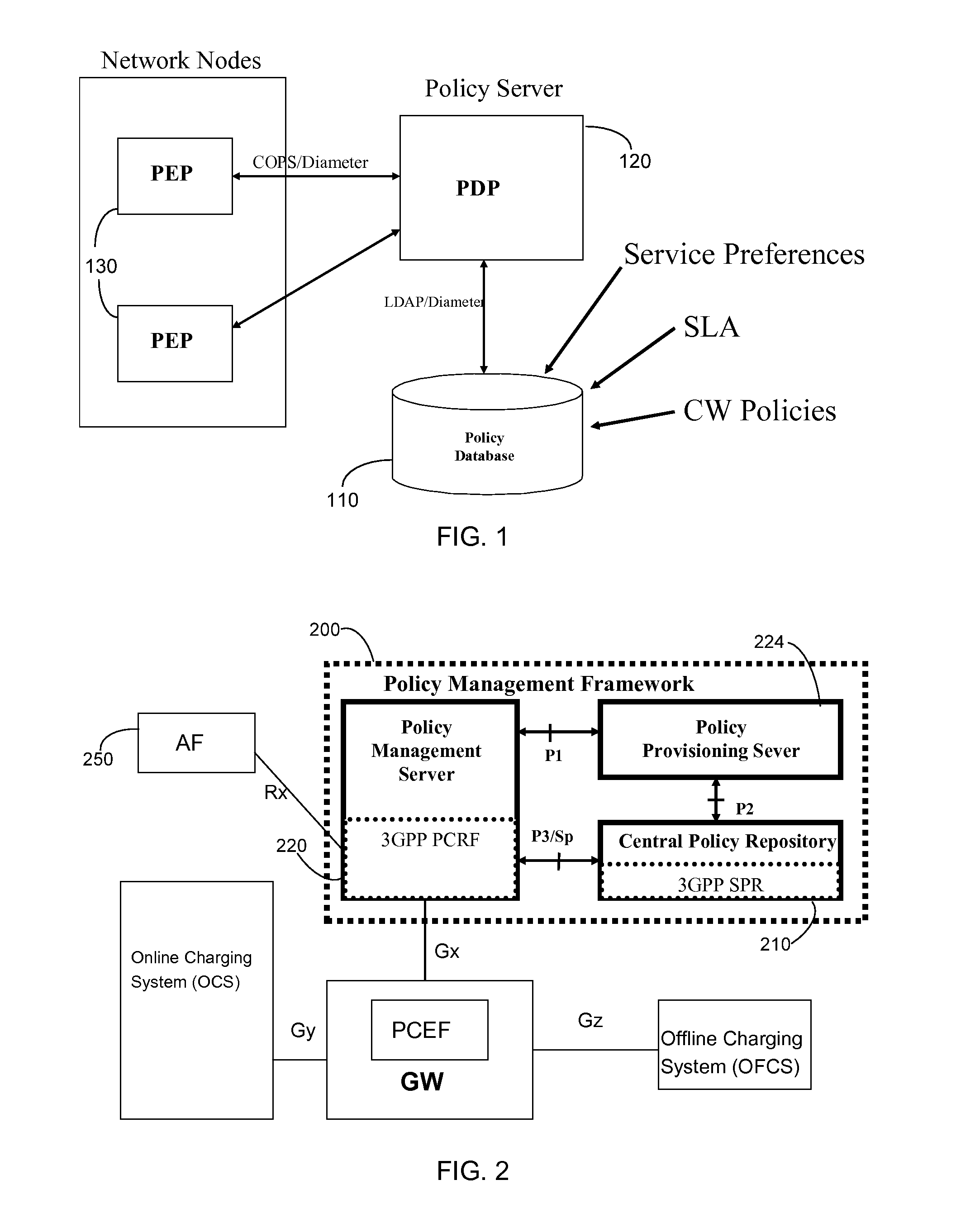
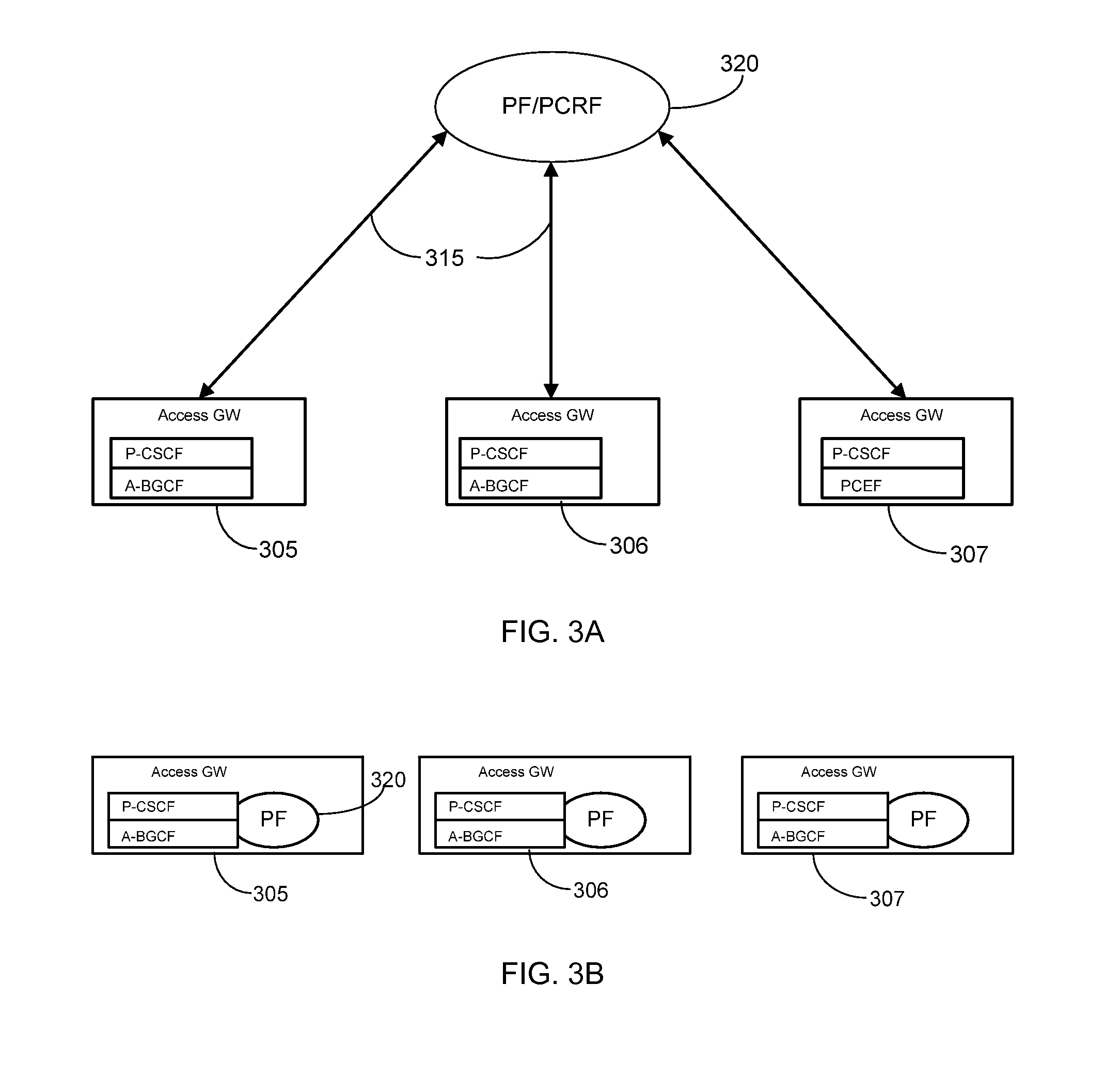
Cascading Policy Management Deployment Architecture
InactiveUS20090113514A1Improve performanceLimitation is enforcedError preventionTransmission systemsPolicy decisionWireless mesh network
Systems and methods are provided to implement a dynamic and efficient cascading policy management framework architecture for both wired and wireless networks. A plurality of Policy Functions (PFs) are assigned to a plurality of Policy Enforcement Points (PEP). The PFs make decisions regarding local policy control at the specific PEP. The PFs then delegate the policy requests or IP flows to a separate PEP that is more conducive to enforcing that policy request. Thus, policy decisions are made at the point where the most information is available, leading to fewer policy requests traversing back and forth across a network. Additionally, this cascading Policy Management Framework Architecture allows for unified policy management across multiple types of networks, including wired (Internet) and wireless (UMTS).
Owner:AT&T MOBILITY II LLC
Handling broadcast and multicast traffic as unicast traffic in a wireless network
An access point is to handle received broadcast or multicast traffic as multiple instances of unicast traffic, where each instance is destined for a corresponding wireless client device associated with the access point. A client device may adjust its listen interval parameter according to predefined considerations, for example a charge level of a battery to power the client device and an expected usage model for the device. A client device may initiate a reassociation request to inform the access point of its adjusted listen interval parameter.
Owner:MALIKIE INNOVATIONS LTD
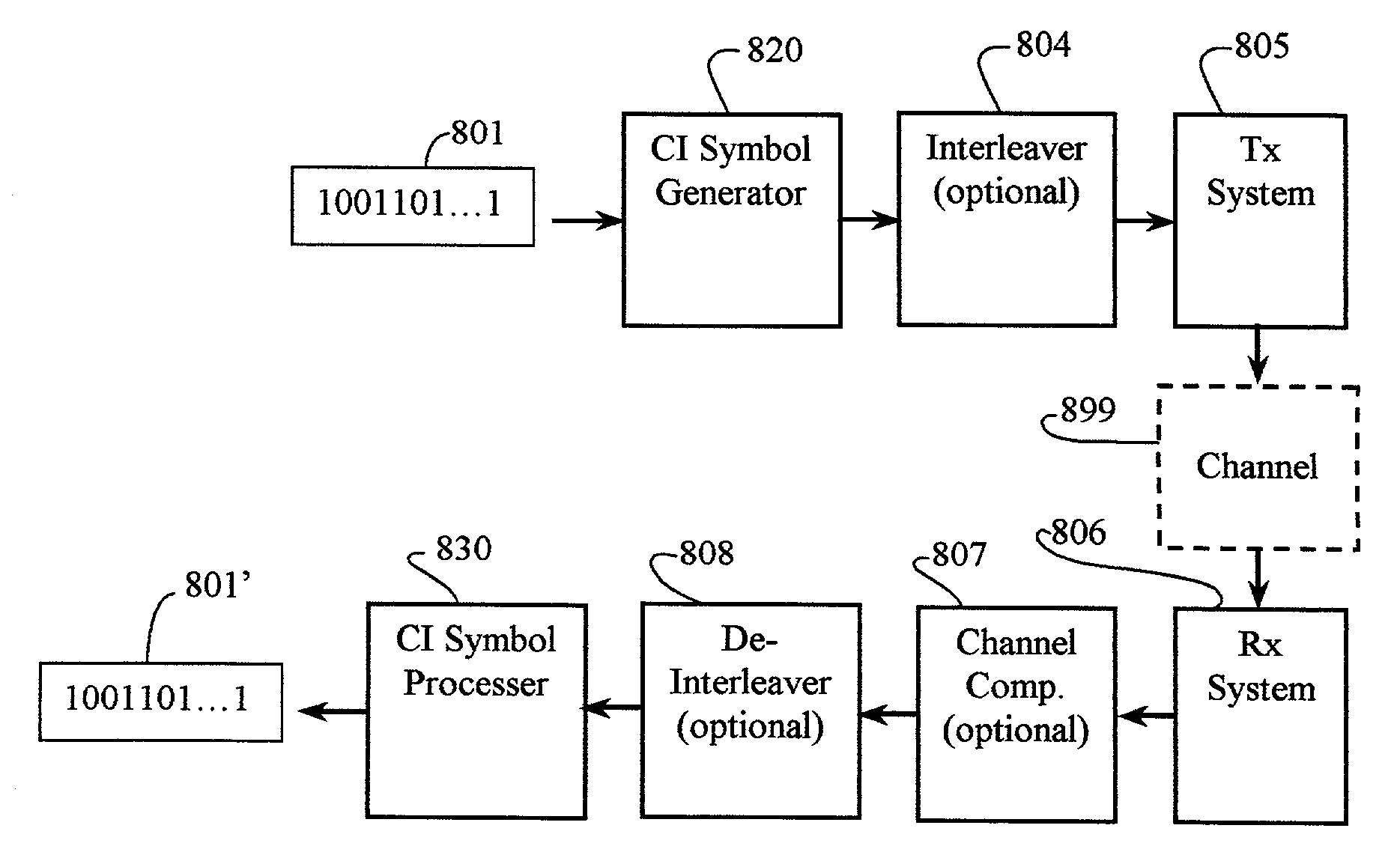
Carrier interferometry networks
ActiveUS20080095121A1Improve throughputImprove bit error rateEnergy efficient ICTModulated-carrier systemsWireless mesh networkTelecommunications link
Applications of CI processing to ad-hoc and peer-to-peer networking significantly improve throughput, network capacity, range, power efficiency, and spectral efficiency. CI-based subscriber units perform network-control functions to optimize network performance relative to channel conditions, network loads, and subscriber services. CI codes are used to identify and address network transmissions. Channel characteristics of communication links are employed to encode, address, and authenticate network transmissions. CI transceivers used as relays and routers employ unique characteristics of transmission paths to code and decode network transmissions. A central processor is adapted to perform array processing with signals received from, and transmitted by, a plurality of subscriber units in a wireless network.
Owner:GENGHISCOMM HLDG
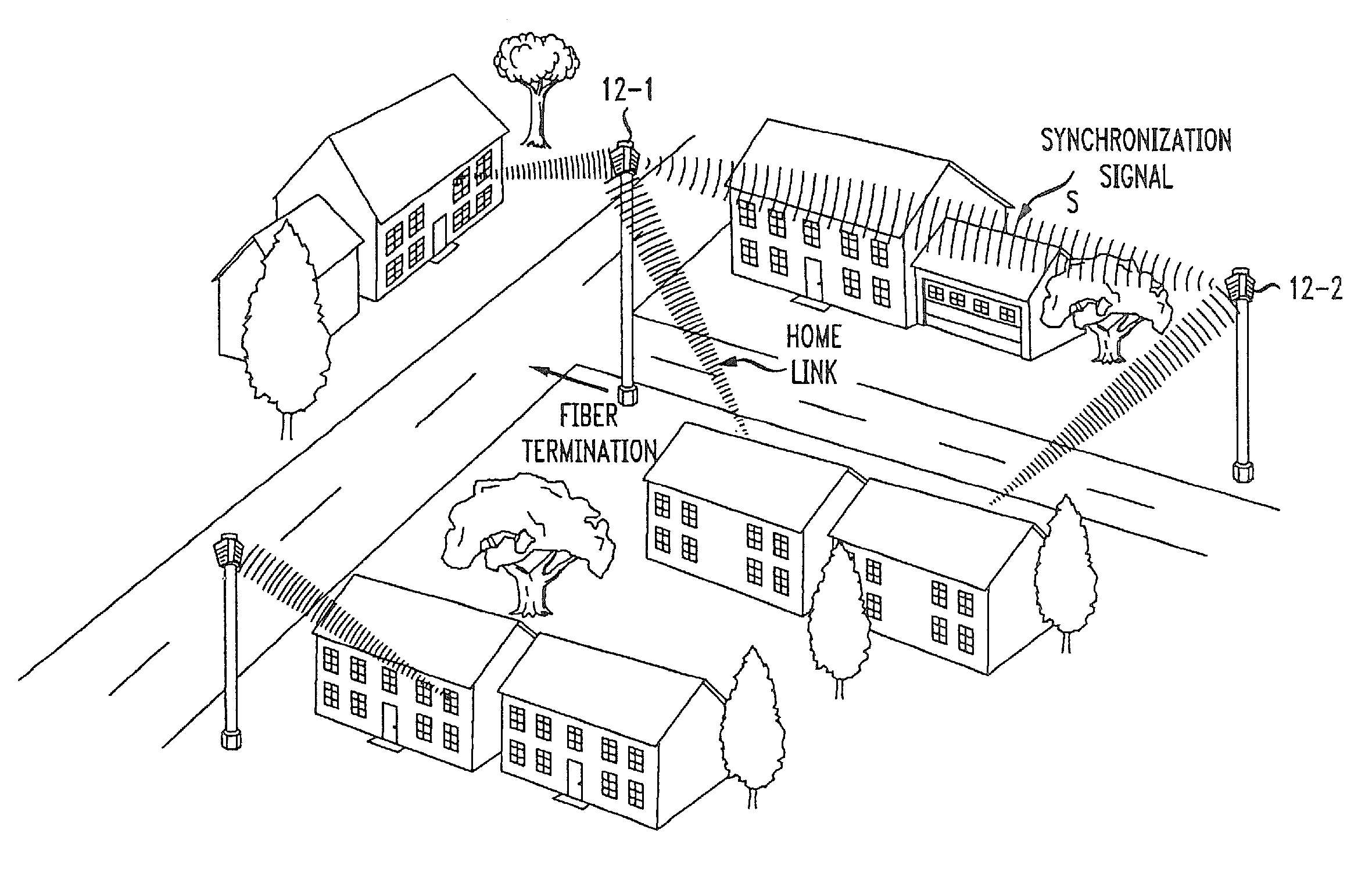
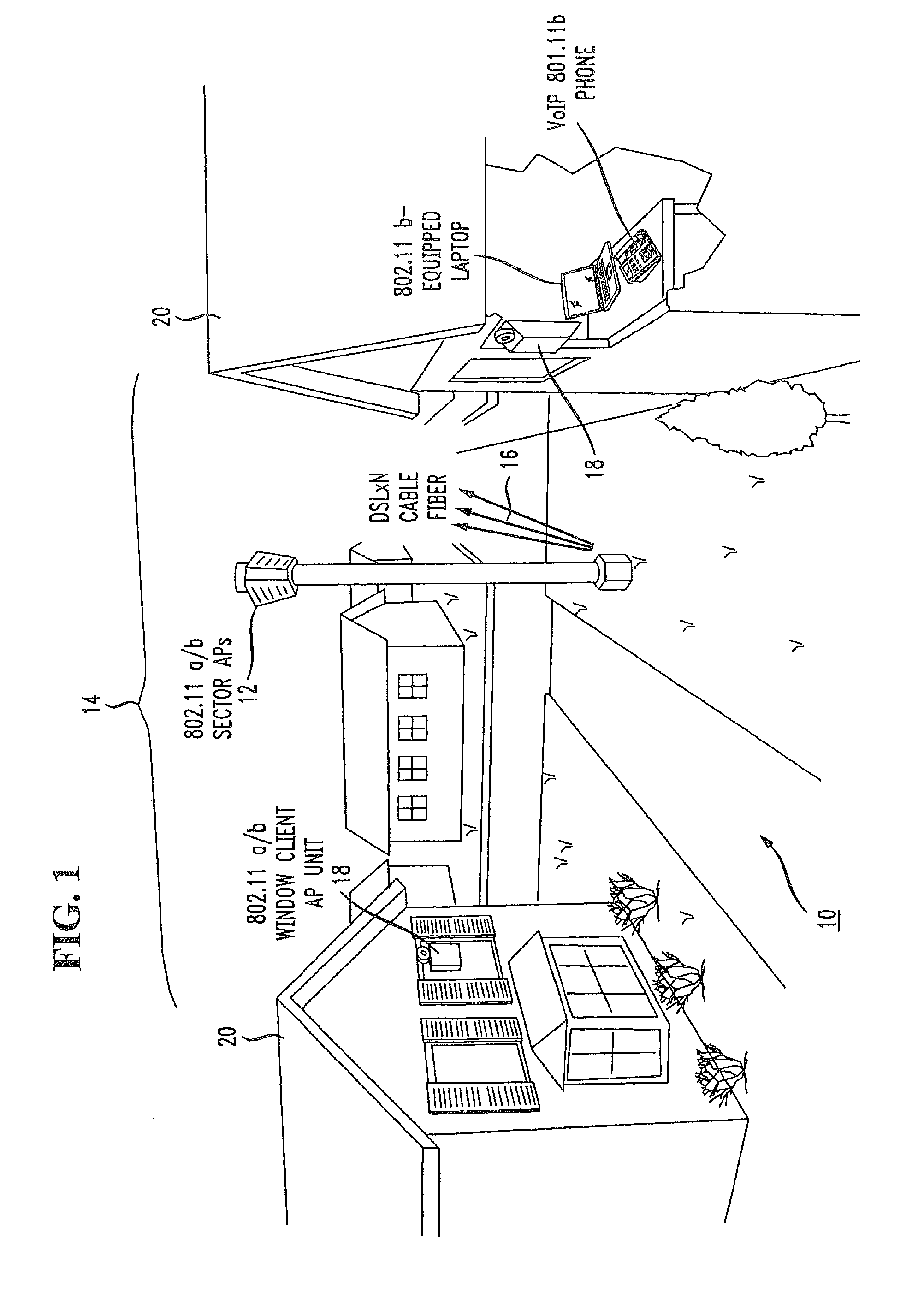
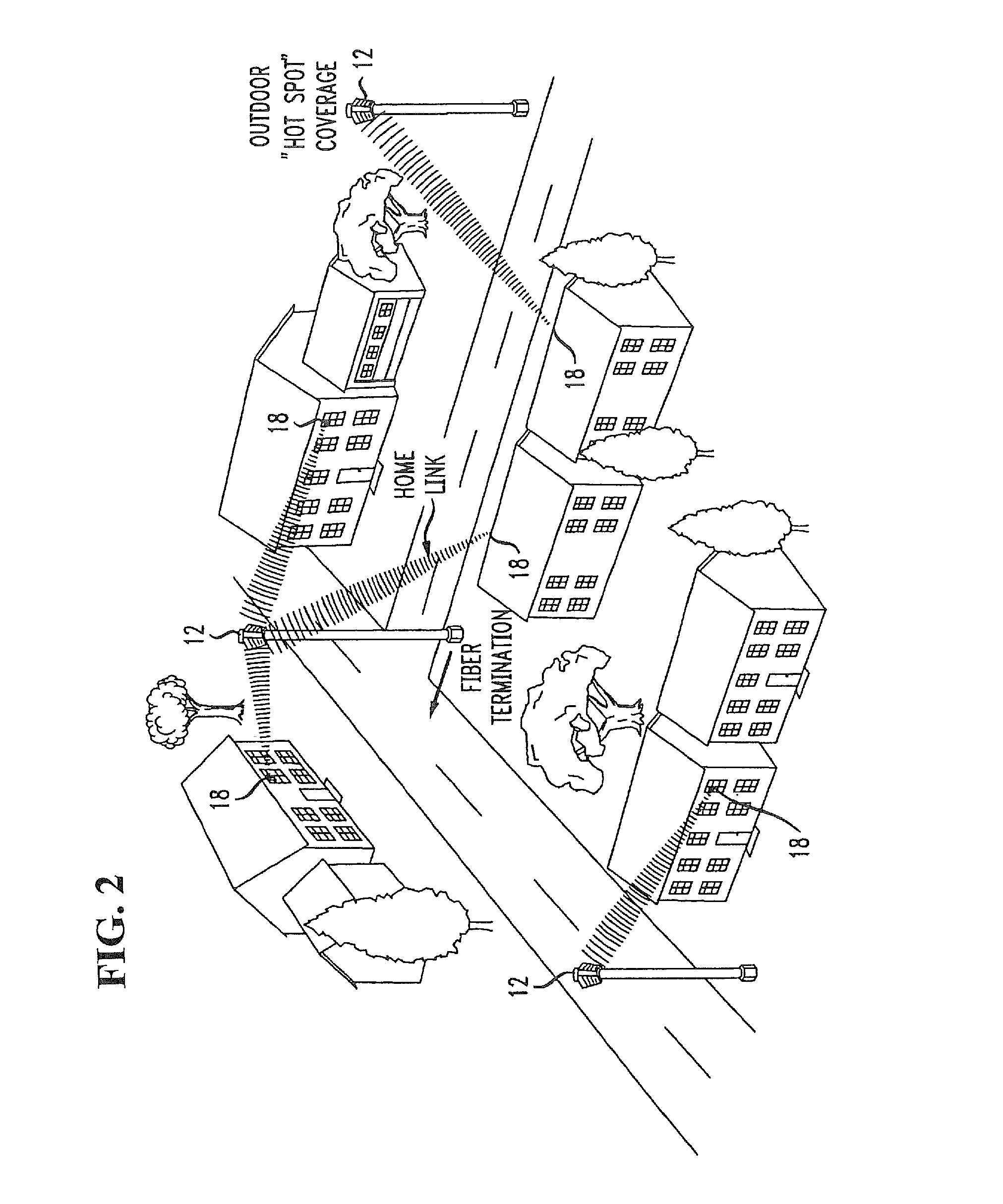
Two-tier wireless broadband access network
ActiveUS8625547B1Quality improvementEasy to installSite diversityNetwork topologiesAccess networkWireless mesh network
A wireless access network is based on a two-tier access point (AP) structure to provide effective and efficient wireless communication into an individual home / office building. A first tier of the network utilizes “neighborhood” APs, relatively low power, and utilized to provide wireless communication with a “nanocell” boundary (e.g., 300-1000 feet). A second tier of the network utilizes a set of “network concatenation devices” (window bridge), with a separate network concatenation device at each permanent facility in the nanocell that houses wireless devices. The network concatenation device is attached to a window, for example, of a home in communication with the neighborhood AP. The network concatenation device functions as a bridge to couple to each of the wireless devices within the home. This communication is then relayed in an efficient manner between the network concatenation device and the neighborhood AP. By using a number of neighborhood APs, rather extensive wireless coverage can be obtained.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
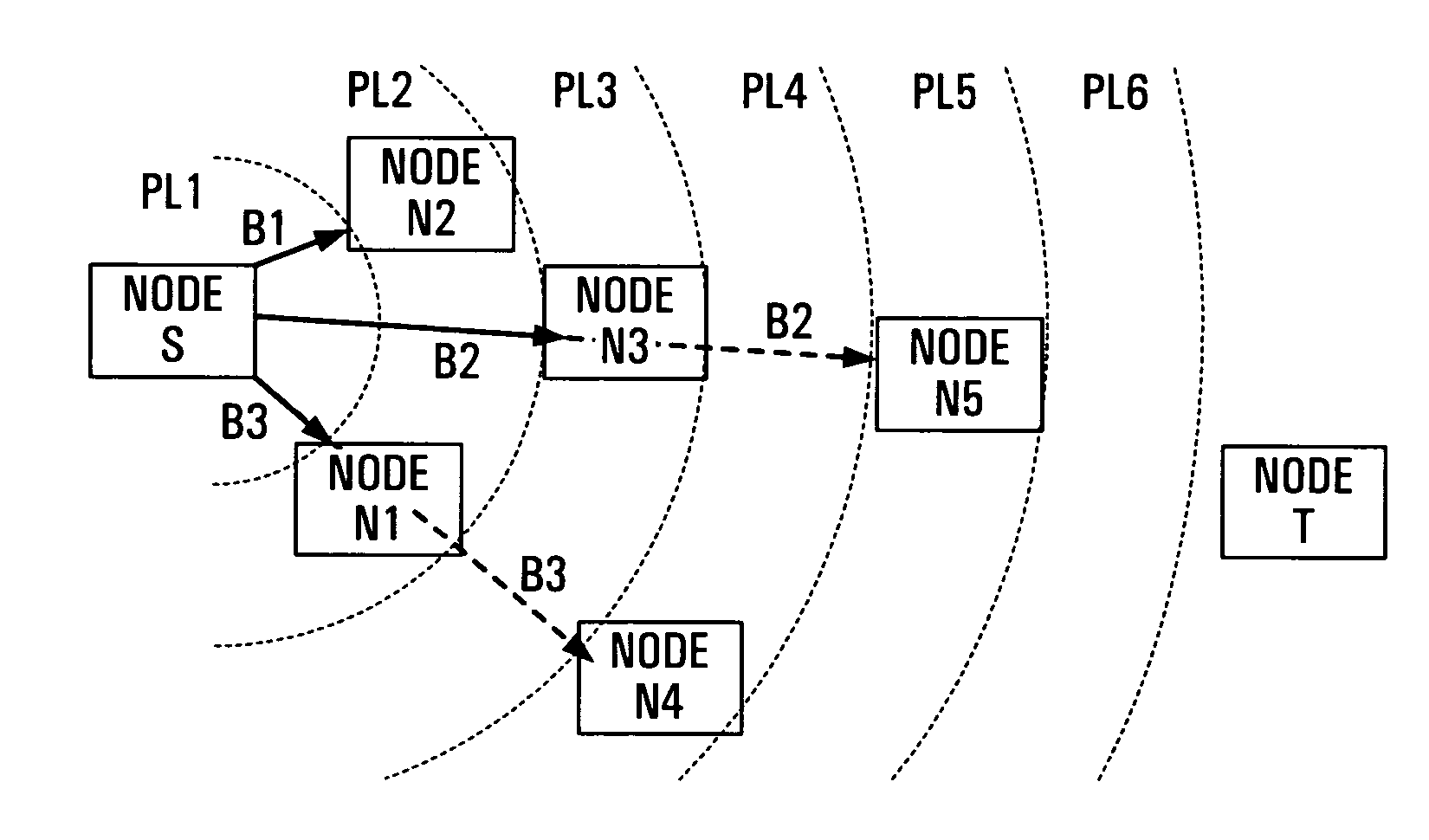
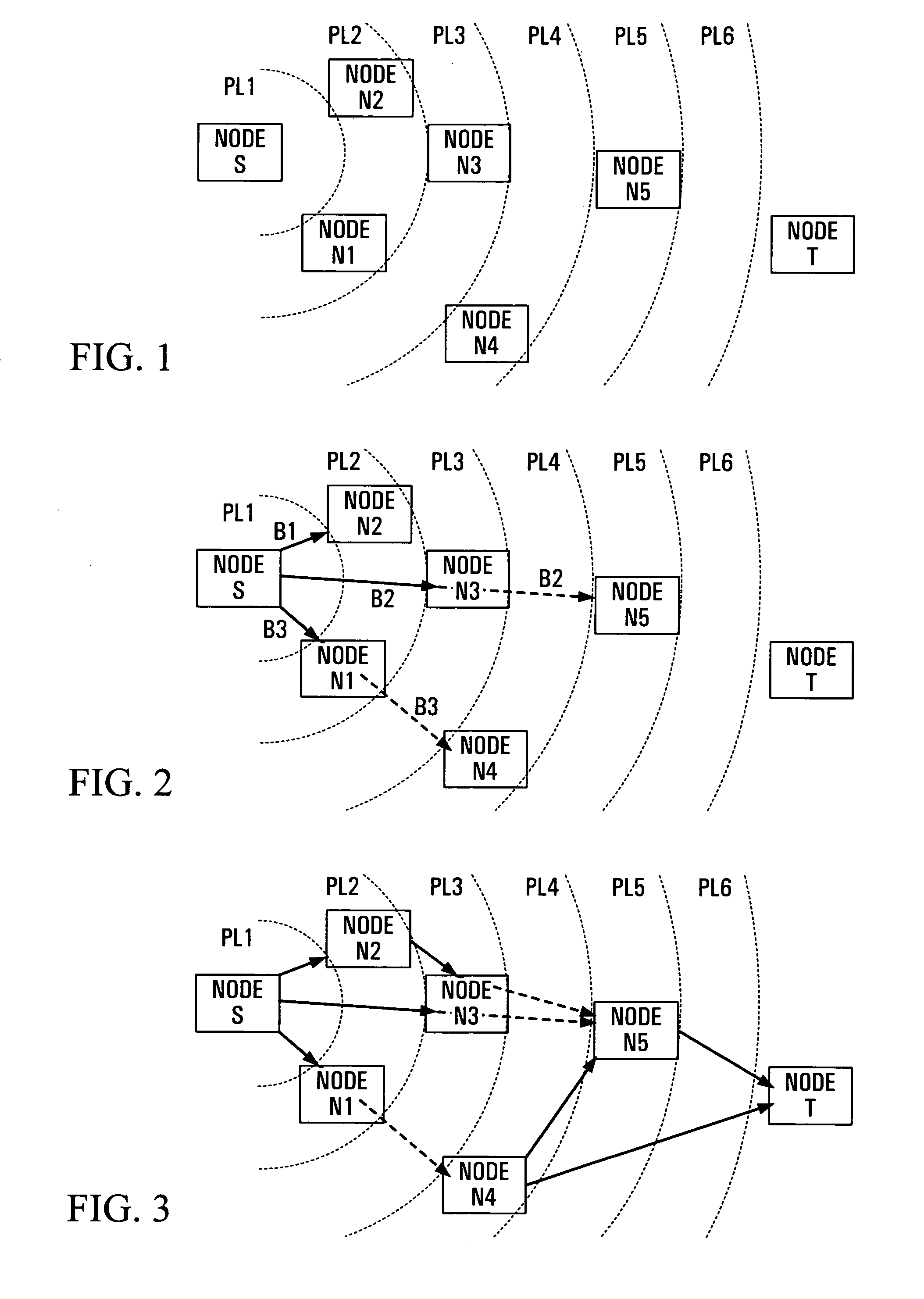
Path selection in wireless networks
ActiveUS7215928B2Low costError prevention/detection by using return channelInterconnection arrangementsWireless mesh networkData rate
In a wireless network, a lowest cost path from a source node to a target node is selected from a plurality of potential paths. The source node sums costs for the links of each potential path. For each link, these costs include a cost of interference, dependent on a number of nodes affected by a signal sent via the respective link. The link costs can also include a cost of transmission, dependent upon a data rate for the respective link, and a cost of coordination for transmissions with other nodes of the network.
Owner:APPLE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com