Patents
Literature
2796 results about "Netsniff-ng" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
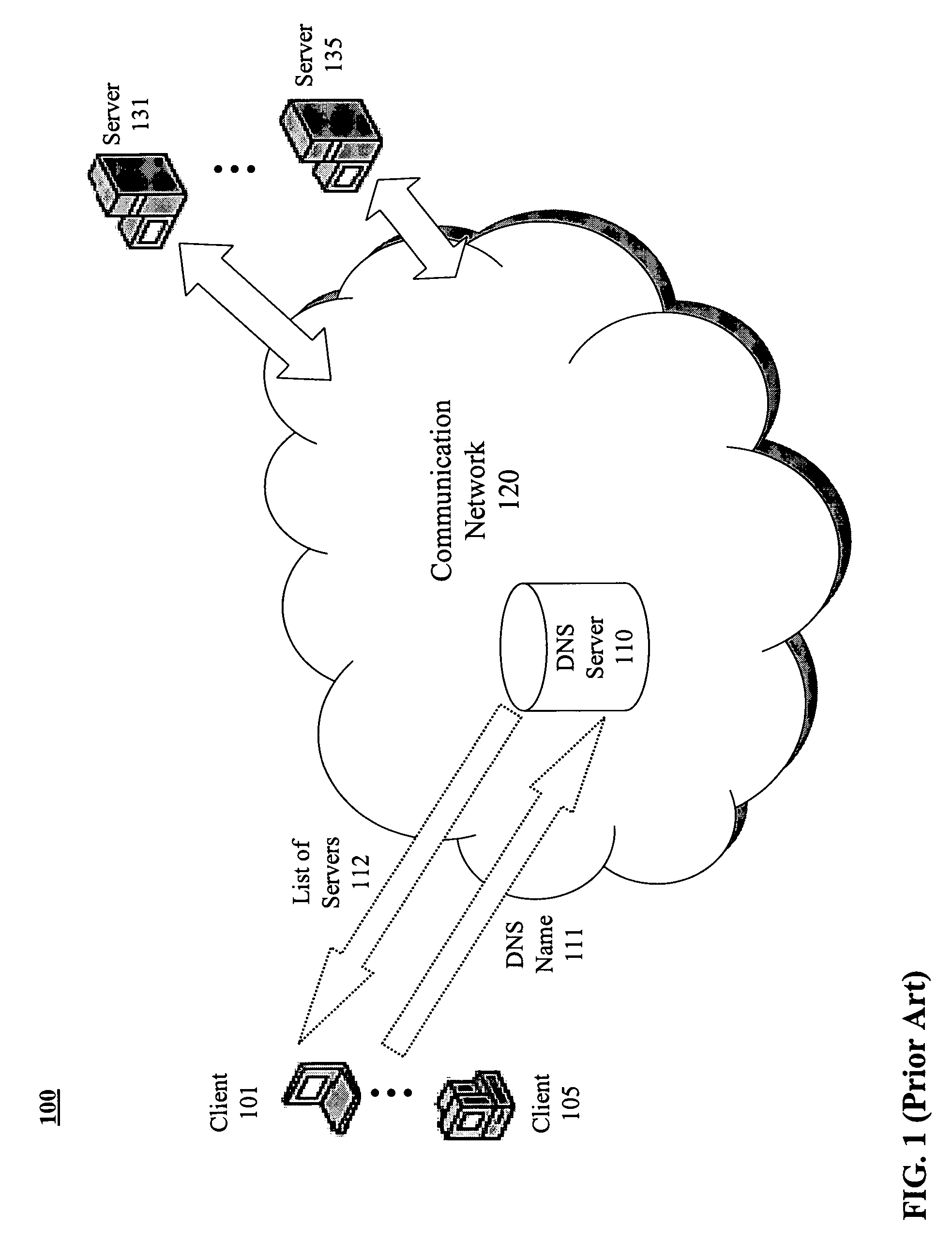
Netsniff-ng is a free Linux network analyzer and networking toolkit originally written by Daniel Borkmann. Its gain of performance is reached by zero-copy mechanisms for network packets (RX_RING, TX_RING), so that the Linux kernel does not need to copy packets from kernel space to user space via system calls such as recvmsg(). libpcap, starting with release 1.0.0, also supports the zero-copy mechanism on Linux for capturing (RX_RING), so programs using libpcap also use that mechanism on Linux.
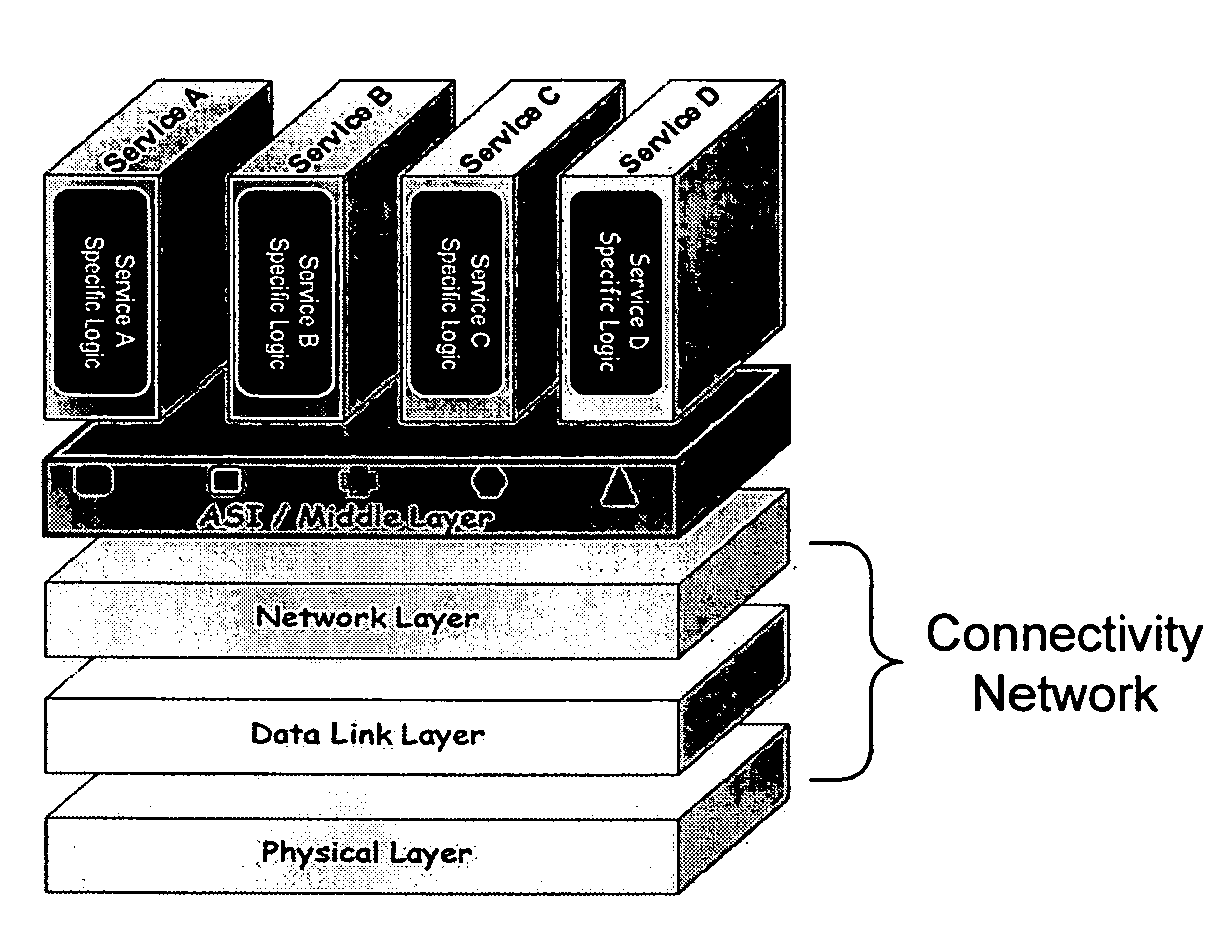
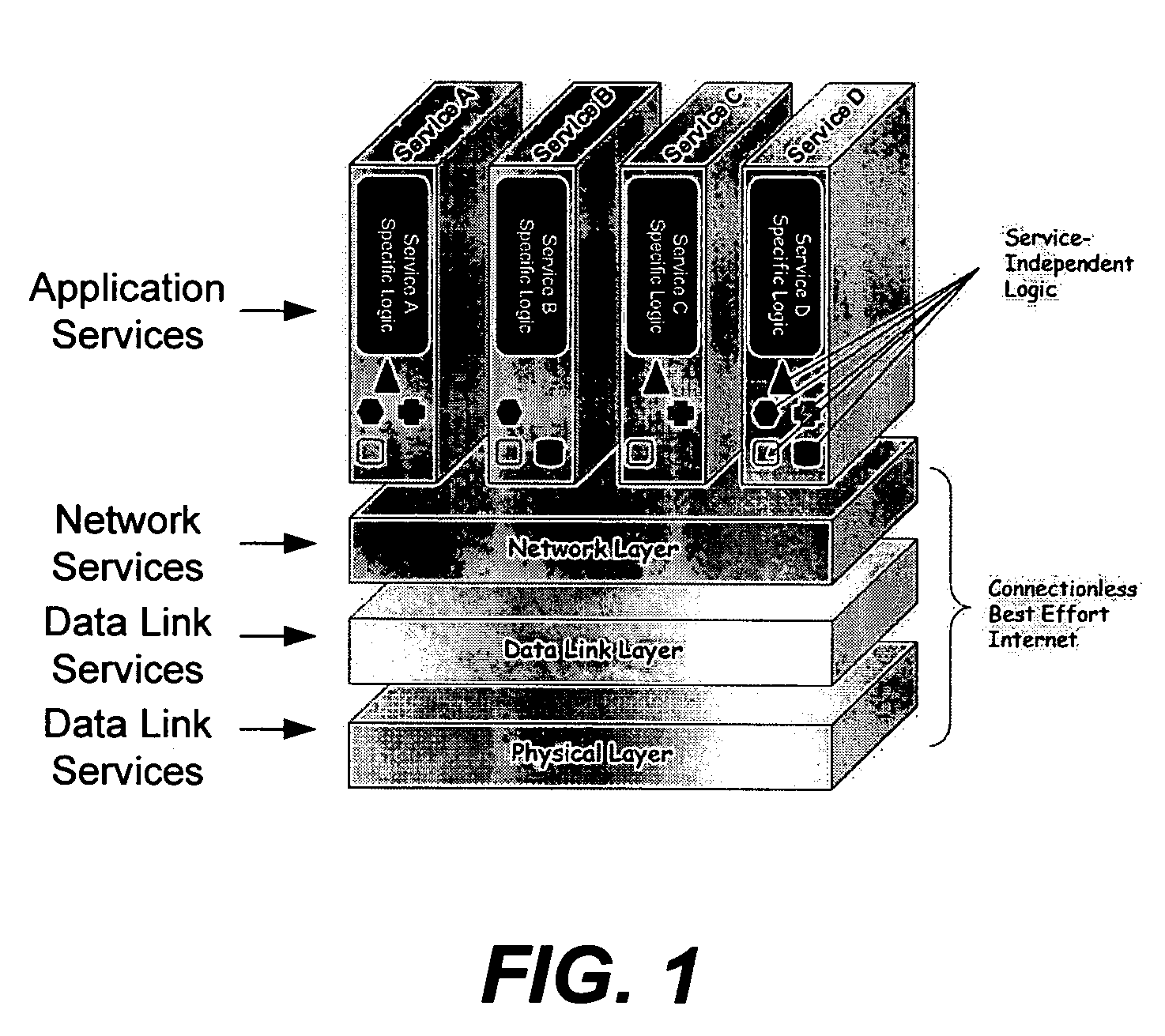
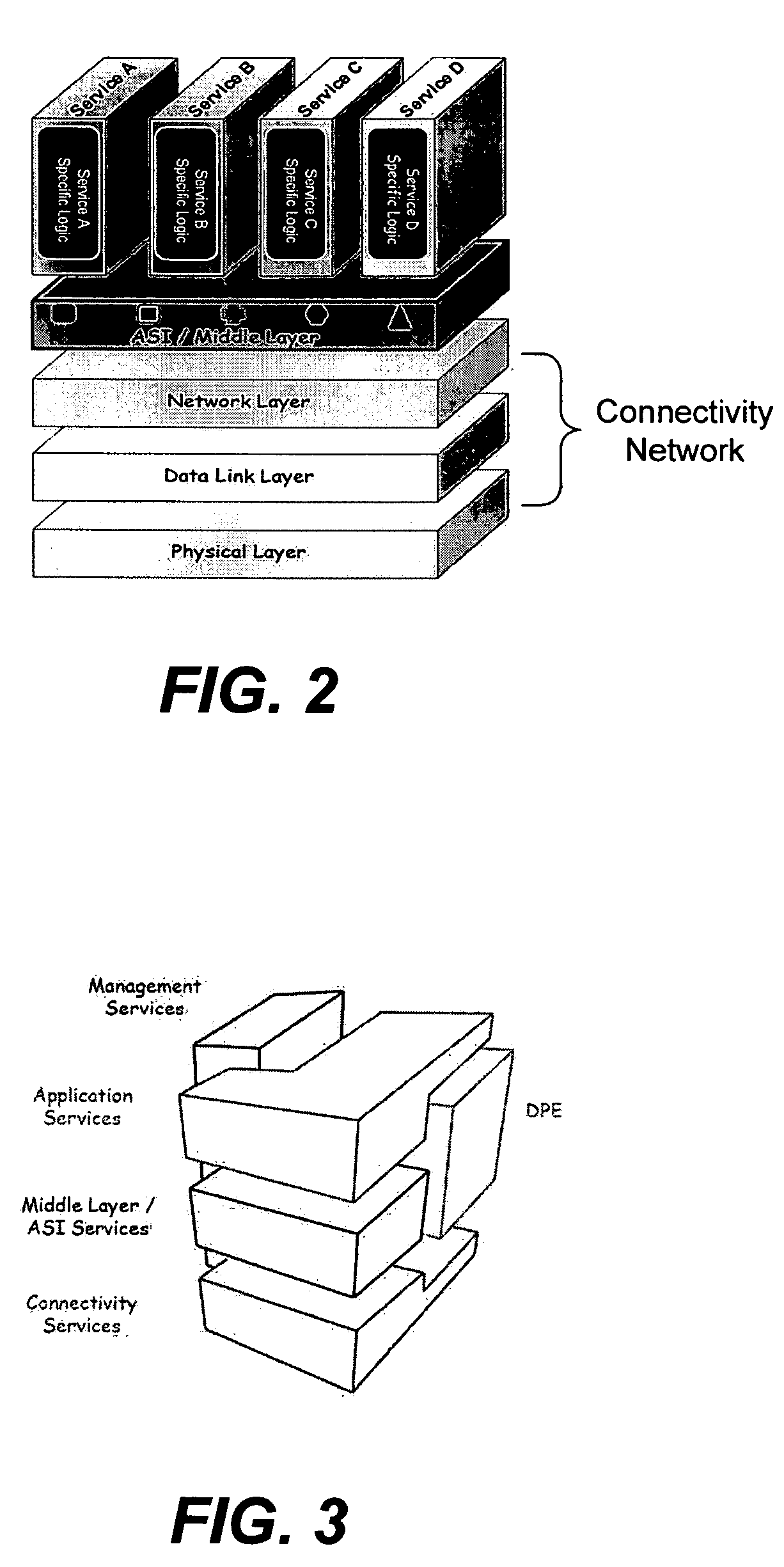
Application services infrastructure for next generation networks including one or more IP multimedia subsystem elements and methods of providing the same
A system for supporting a plurality of different applications utilizing a next generation network having a network layer includes an application services middleware between the applications and the network layer that includes a plurality of common infrastructure elements usable by the different applications. The common infrastructure elements provide both services associated with use of the network and services that are not associated with use of the network. At least one of the common infrastructure elements is an Internet Protocol (IP) Multimedia Subsystem (IMS) element.
Owner:BELLSOUTH INTPROP COR
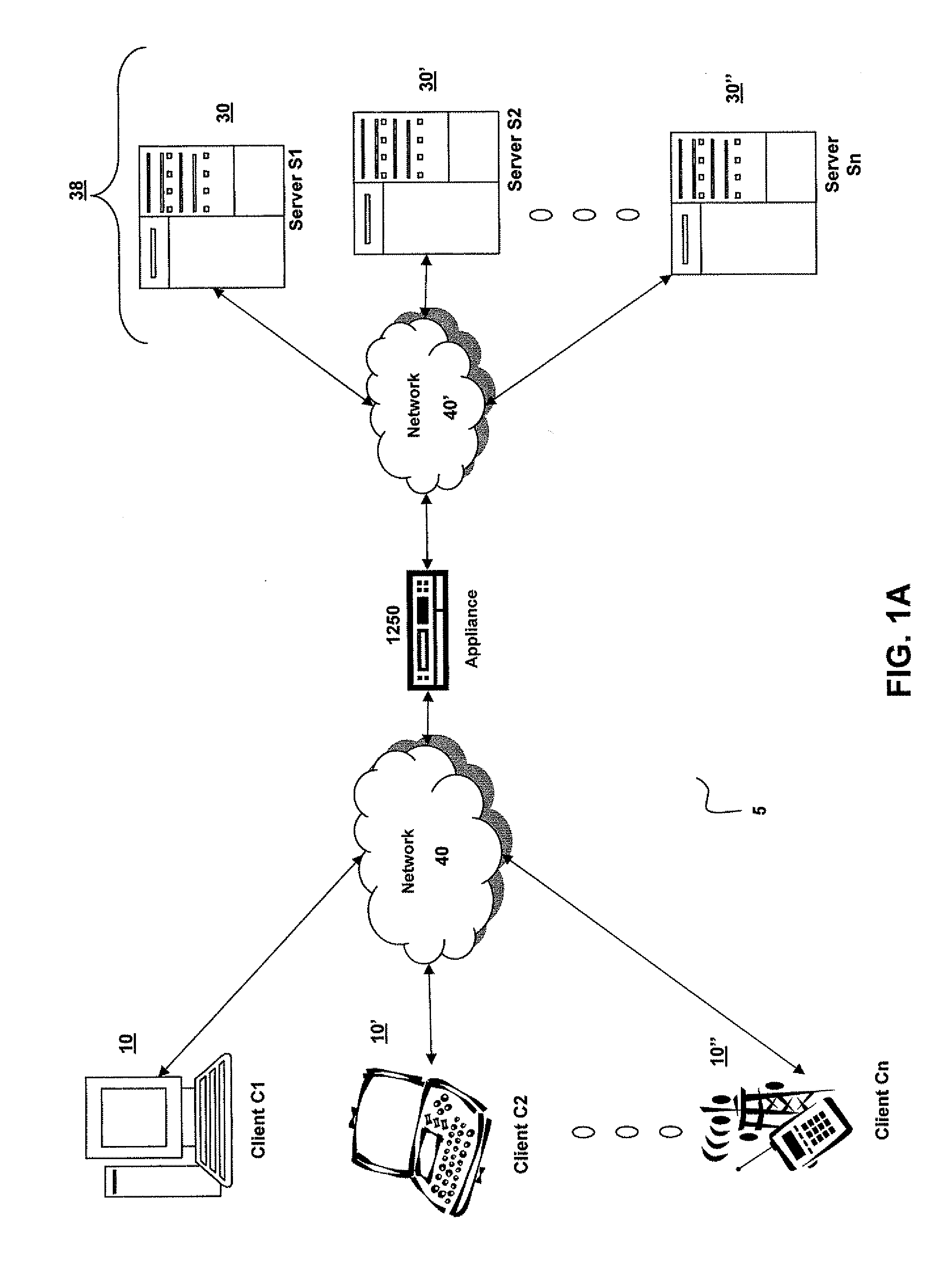
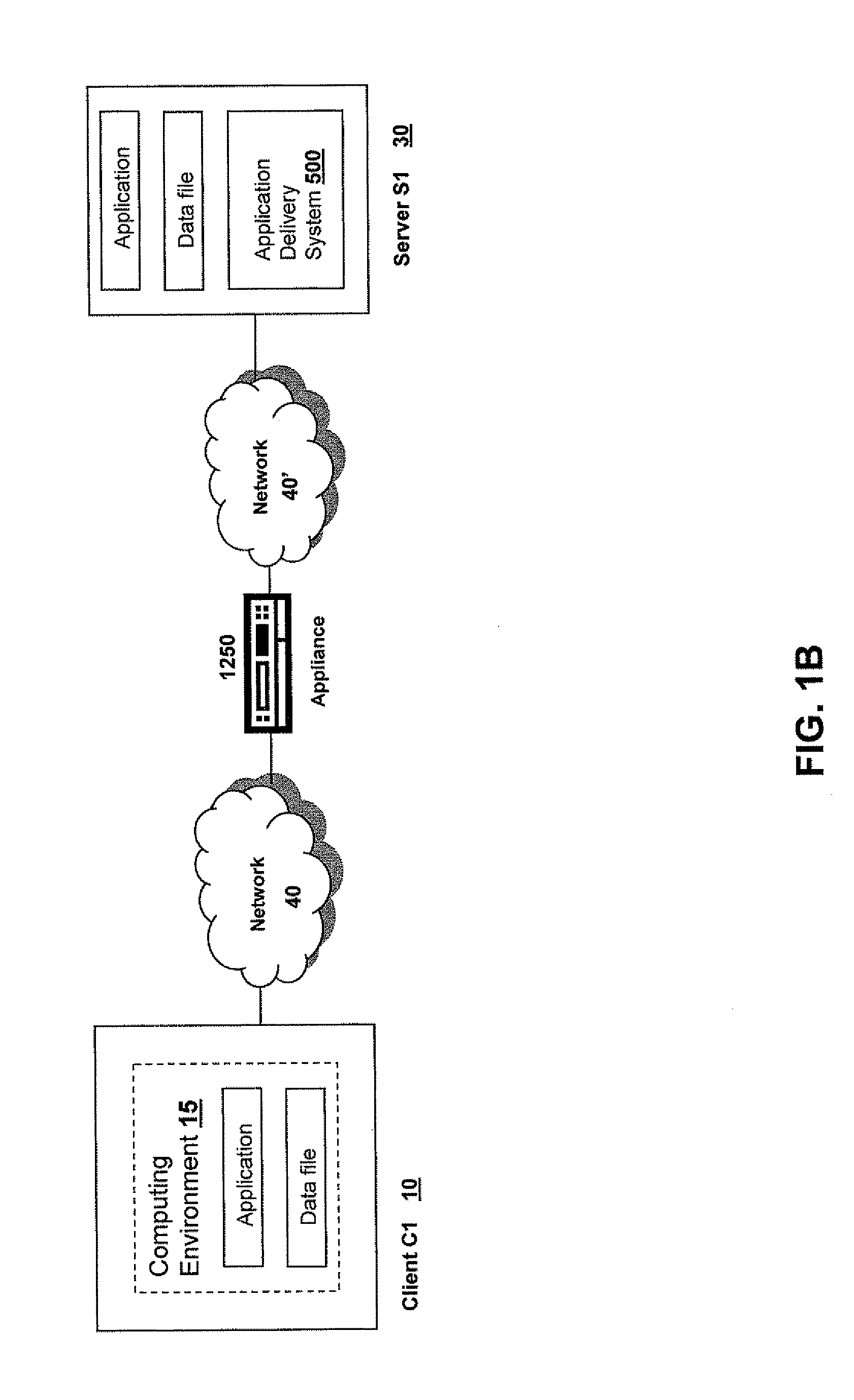
Systems and Methods for Accelerating Delivery of a Computing Environment to a Remote User
ActiveUS20070244987A1Reduce deliveryFacilitate communicationMultiple digital computer combinationsData switching networksNetwork connectionData file
The present invention is directed towards the acceleration of delivery of a computing environment to a remote user of a client at a remote location. The computing environment may include an application and a data file used or processed by the application. The application and data file may be stored or provided via a server remote to the client. The user can request a computing environment from the server that provides for execution of the application by the user via the remote computer. For example, the server may stream the application to the remote client. The client and server may communicate via an appliance that accelerates communications between the client and server. For example, the appliance may accelerate the streaming of the application to the remote user. In some cases, the application or remote user may also request a data file from the server, and the appliance accelerates the delivery of the data file to the remote user. As such, users at remote locations obtain accelerated access via any network connected device to applications and data files located remotely to the user.
Owner:CITRIX SYST INC
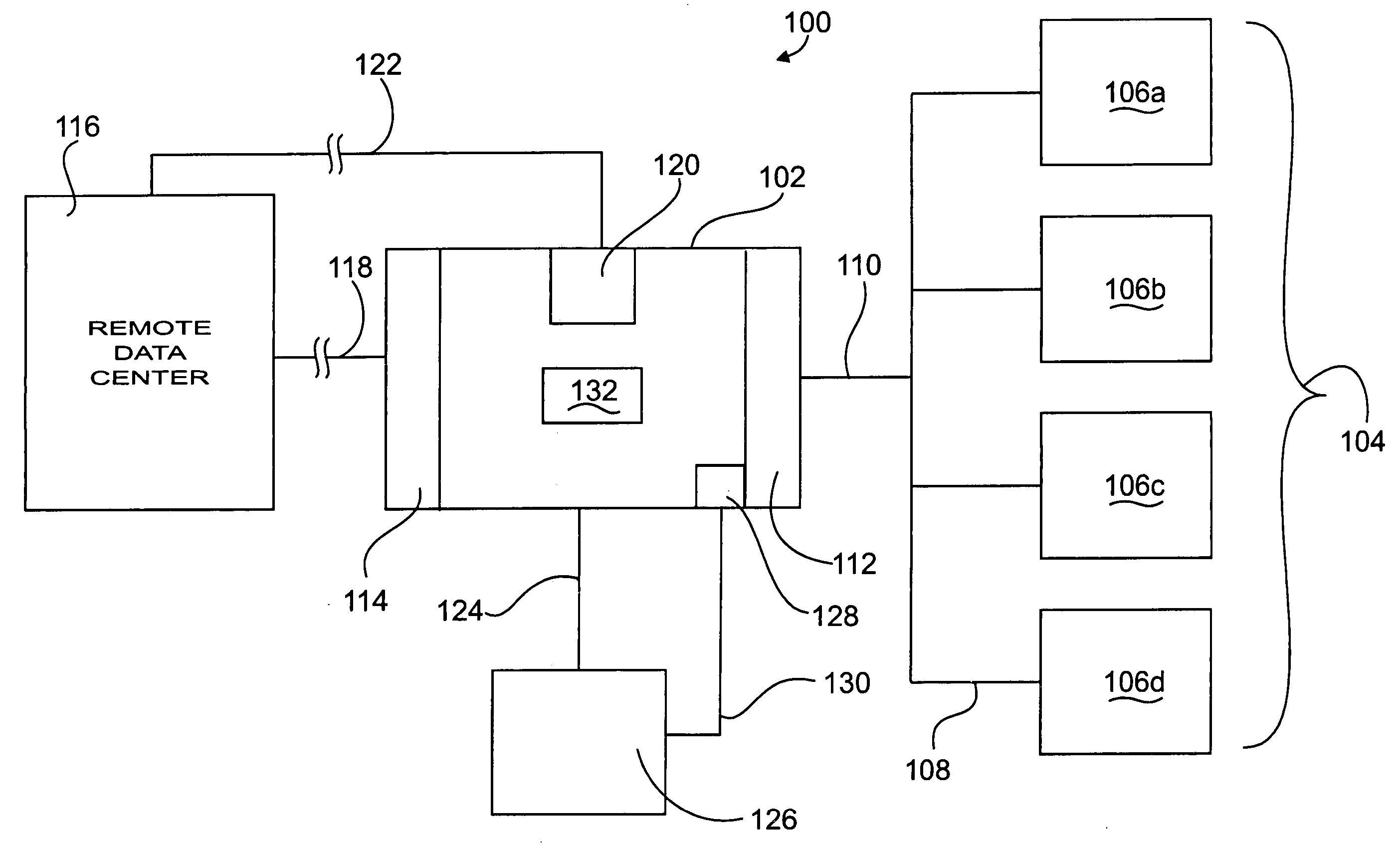
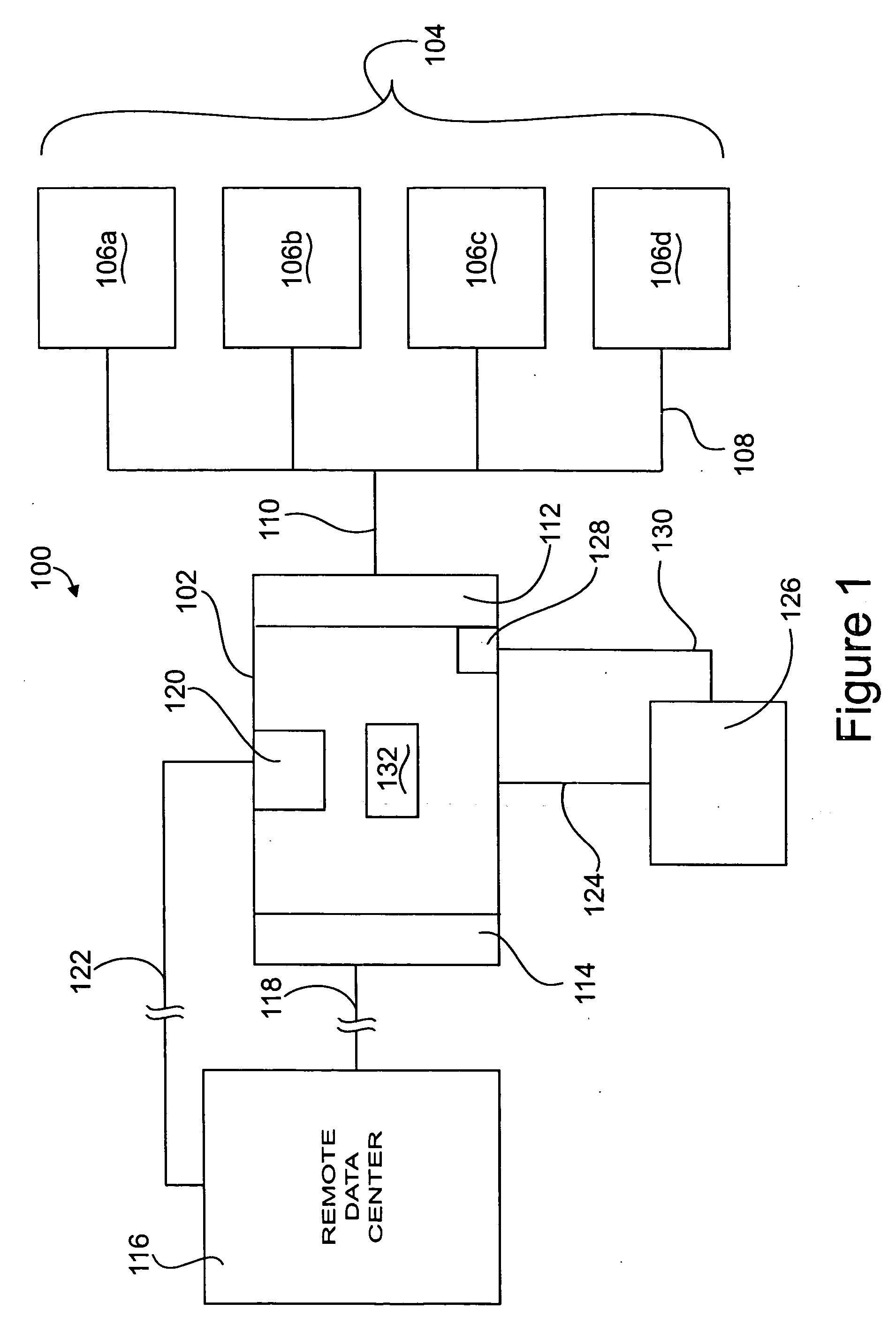
Apparatus and method for remotely monitoring a computer network
InactiveUS20060031476A1Easy to provideMinimize the possibilityDigital computer detailsTransmissionAnti virusPrivate network
There is provided an apparatus for remotely monitoring a computer network. Monitoring is performed using an inside out approach from behind firewalls and other security devices. The monitoring appliance is shipped to a client site preconfigured and typically requires no technically trained person for installation. Collected network data is periodically transmitted to a remote monitoring facility where it is recorded and analyzed. Both the monitoring appliance and the remote center maintain the configuration data. Typically, no client data is transmitted to the remote monitoring site. If the monitoring appliance fails, a completely configured replacement may be shipped to the site and easily installed. The monitoring appliance is optionally equipped to provide network services. Services such as web hosting, file server, print server, virtual private network (VPN), shared Internet access, web content filtering, anti-virus, spam e-mail elimination, and IP telephony services as well as other such services may be easily provided.
Owner:MATHES MARVIN LEE +1
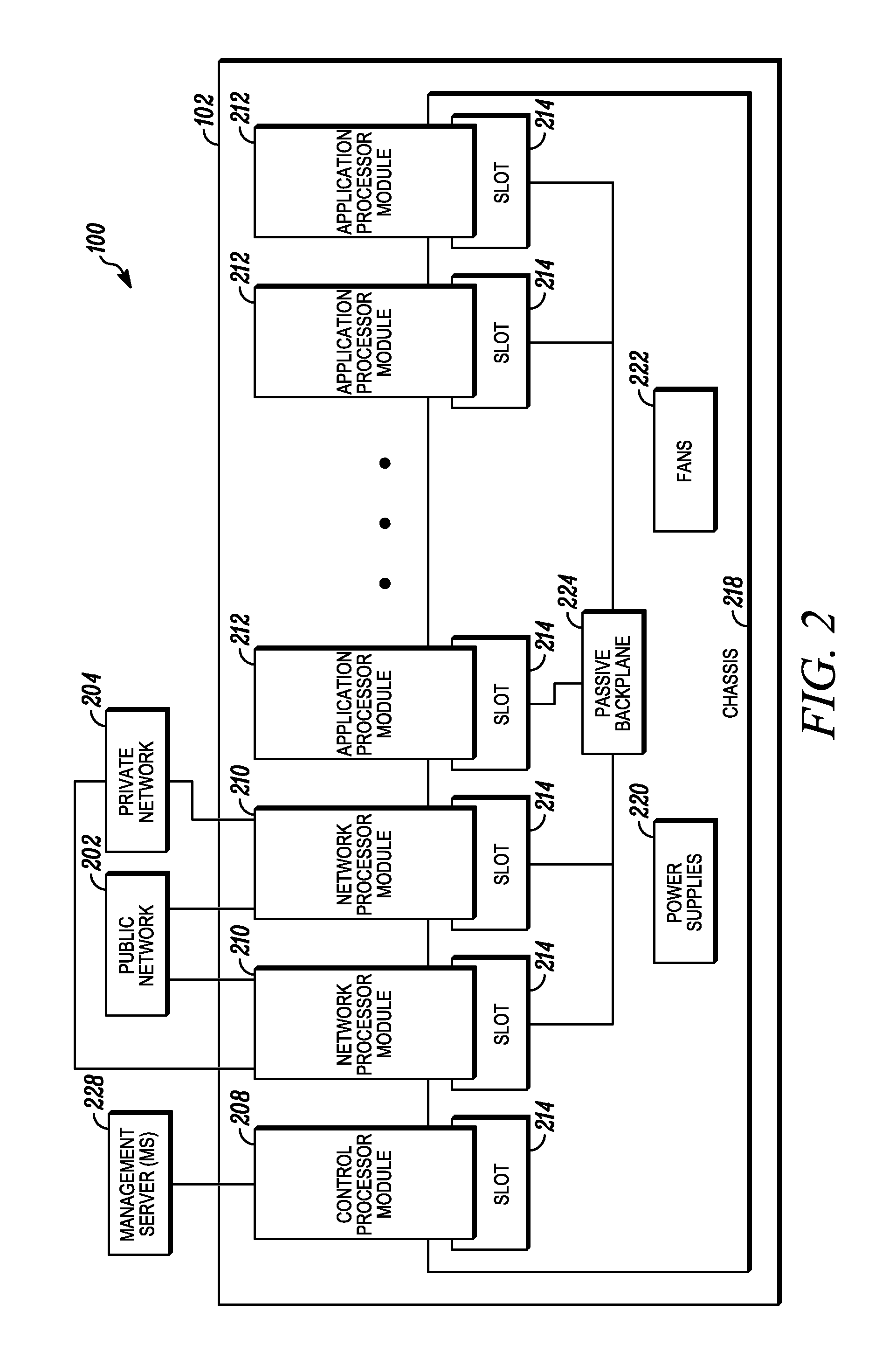
Processing data flows with a data flow processor
InactiveUS20110238855A1Increased complexityAvoid problemsMultiple digital computer combinationsPlatform integrity maintainanceData controlConfigfs
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
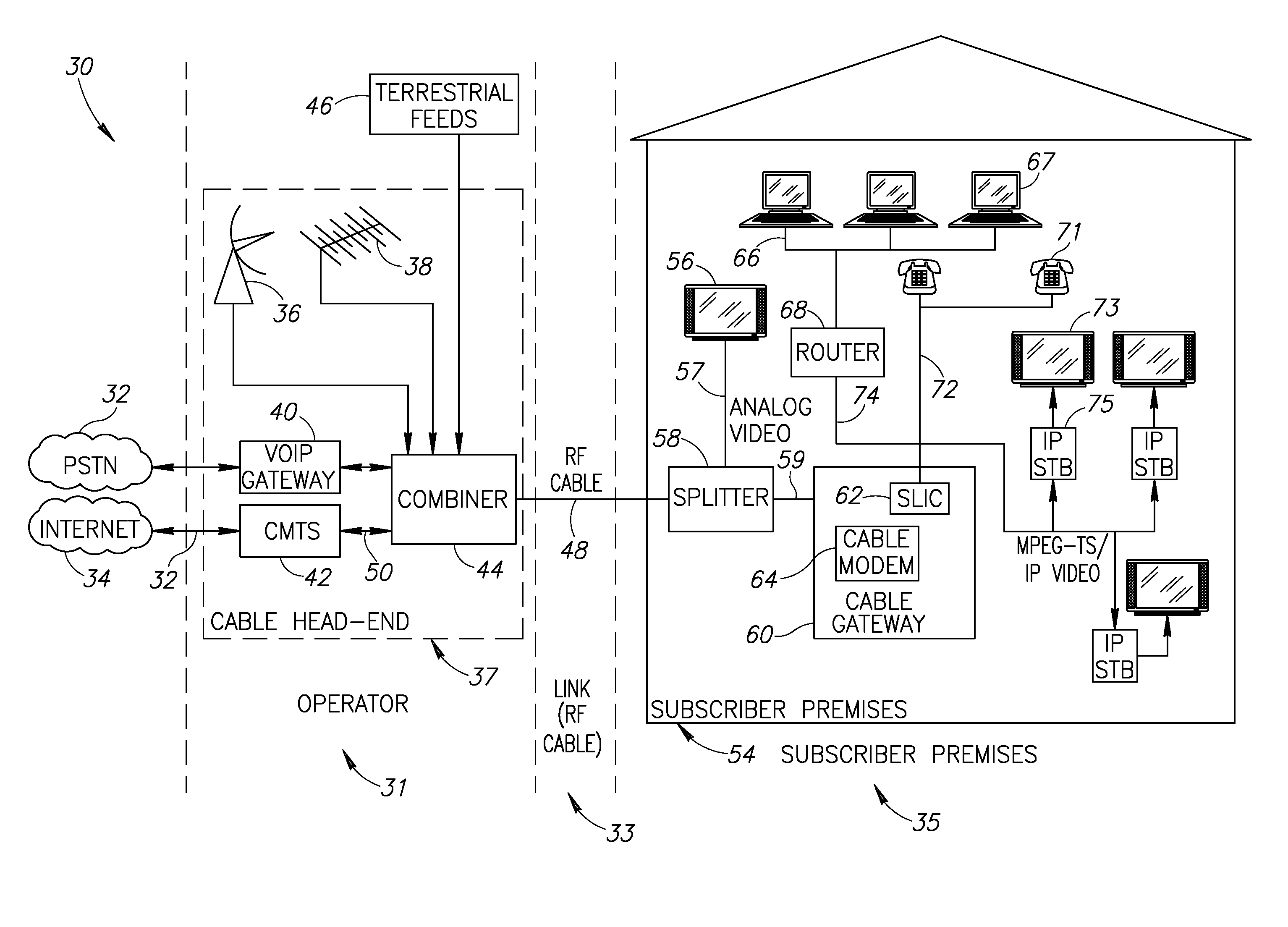
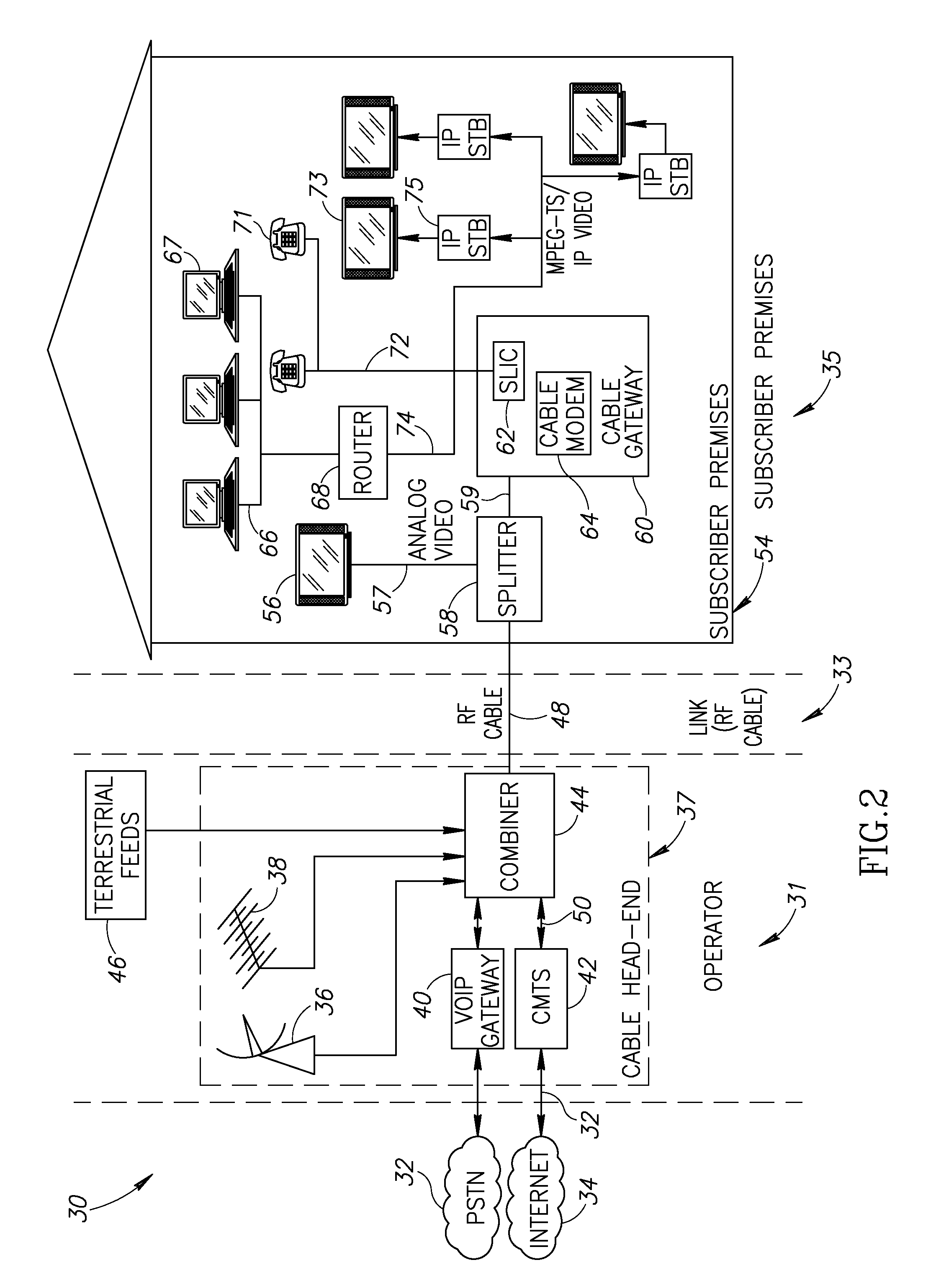
Hybrid mpeg/ip digital cable gateway device and architecture associated therewith
A novel cable gateway system and architecture incorporating a hybrid digital video transceiver. The digital cable system architecture combines reception of legacy video such as MPEG-TS based DVB-C streams with that of original IP video over DOCSIS channels. The system comprises a hybrid DVB / IP cable gateway STB capable of receiving both legacy DVB-C video and original IP video streams. The cable gateway device performs the front-end functionality (including QAM receiver, tuner and broadband connection) while the back-end functionality of video decoding and display is performed by one or more standard IP-STBs connected to the cable gateway device over a network (e.g., home LAN). Legacy MPEG-TS based DVB-C video is captured and encapsulated into packets for distribution over the network to the IP-STBs. The cable gateway distributes the original IP video received over the CATV source and the encapsulated legacy video as video over IP packets over the network.
Owner:INTEL CORP
Push-Pull Based Content Delivery System
InactiveUS20080059631A1Maximize QoSImprove scalabilityDigital computer detailsTelevision systemsClosed loop feedbackPush pull
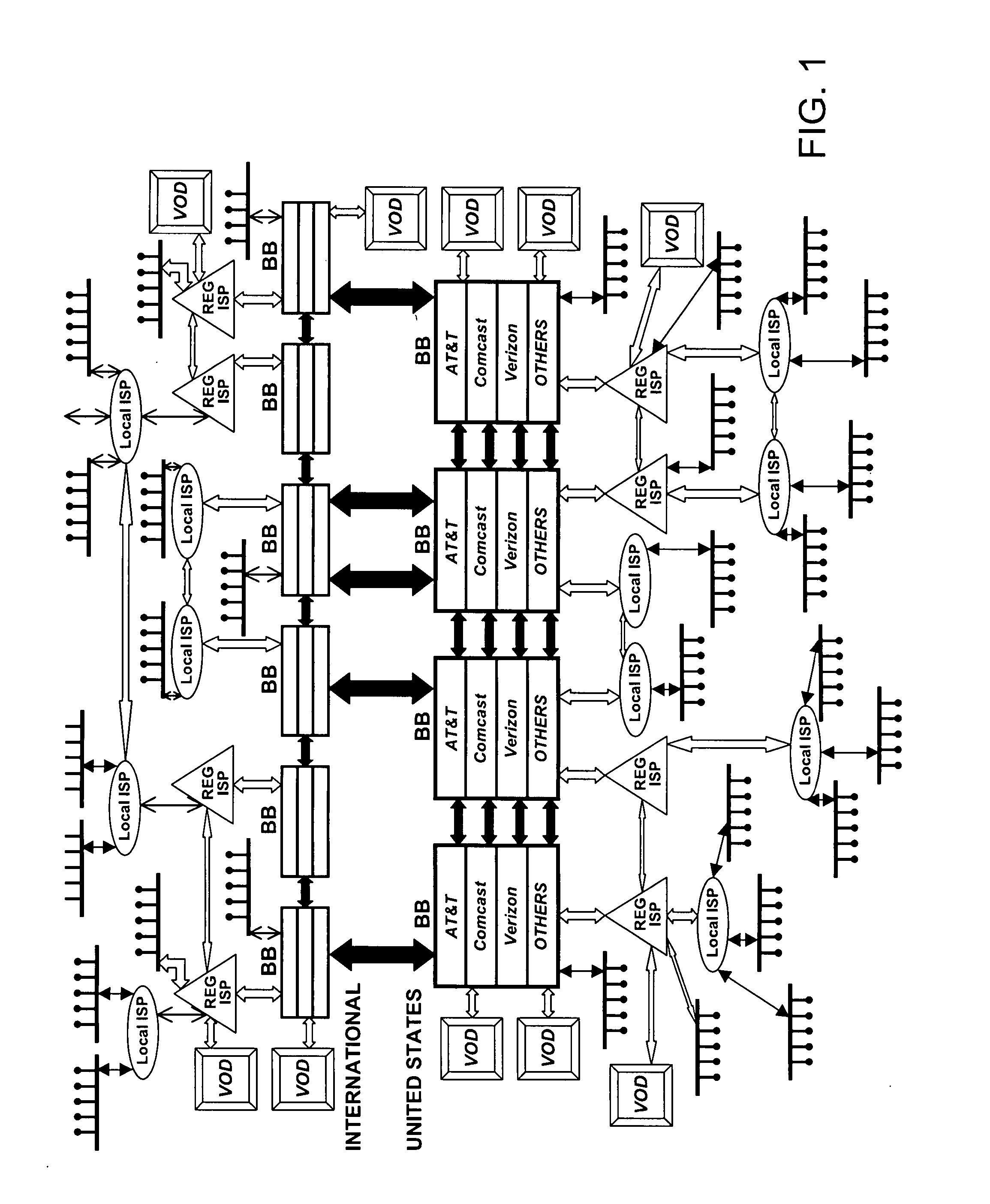
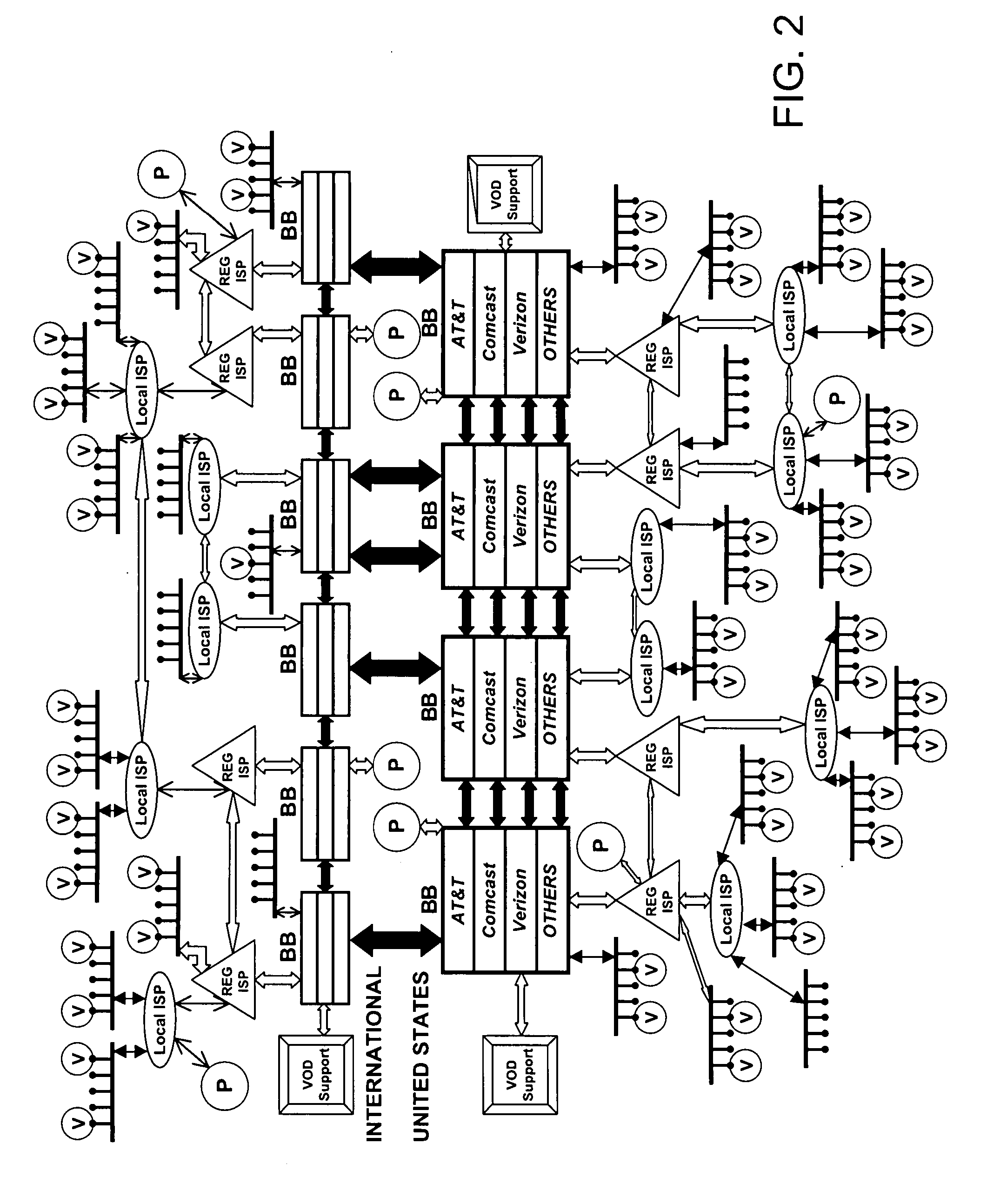
QoS is built into a peer network within existing Internet infrastructure itself lacking QoS, by enabling a network peer to continuously discern the network's ability to deliver to that peer a particular Content Object (distributed in groups of component Packages among neighboring VOD peers) within predetermined times. Content Objects are divided into groups of component Packages and distributed to Clusters of neighboring network peers, enhancing QoS upon subsequent retrieval. Tracking Files (lists of network peers storing Package groups) and Tracking Indexes (lists of network peers storing Tracking Files) are generated to facilitate “on demand” Content Objects retrieval. Dynamically monitoring network traffic (including VOD functionality, bandwidth and reliability) creates “distributed closed-loop feedback,” and in response, attributes of individual network peers (e.g., Trust Level and membership within a particular Cluster) are modified, and “content balancing” functions performed (e.g., redistribution of Package groups among network peers) enables maintaining high QoS.
Owner:VODDLER GRP
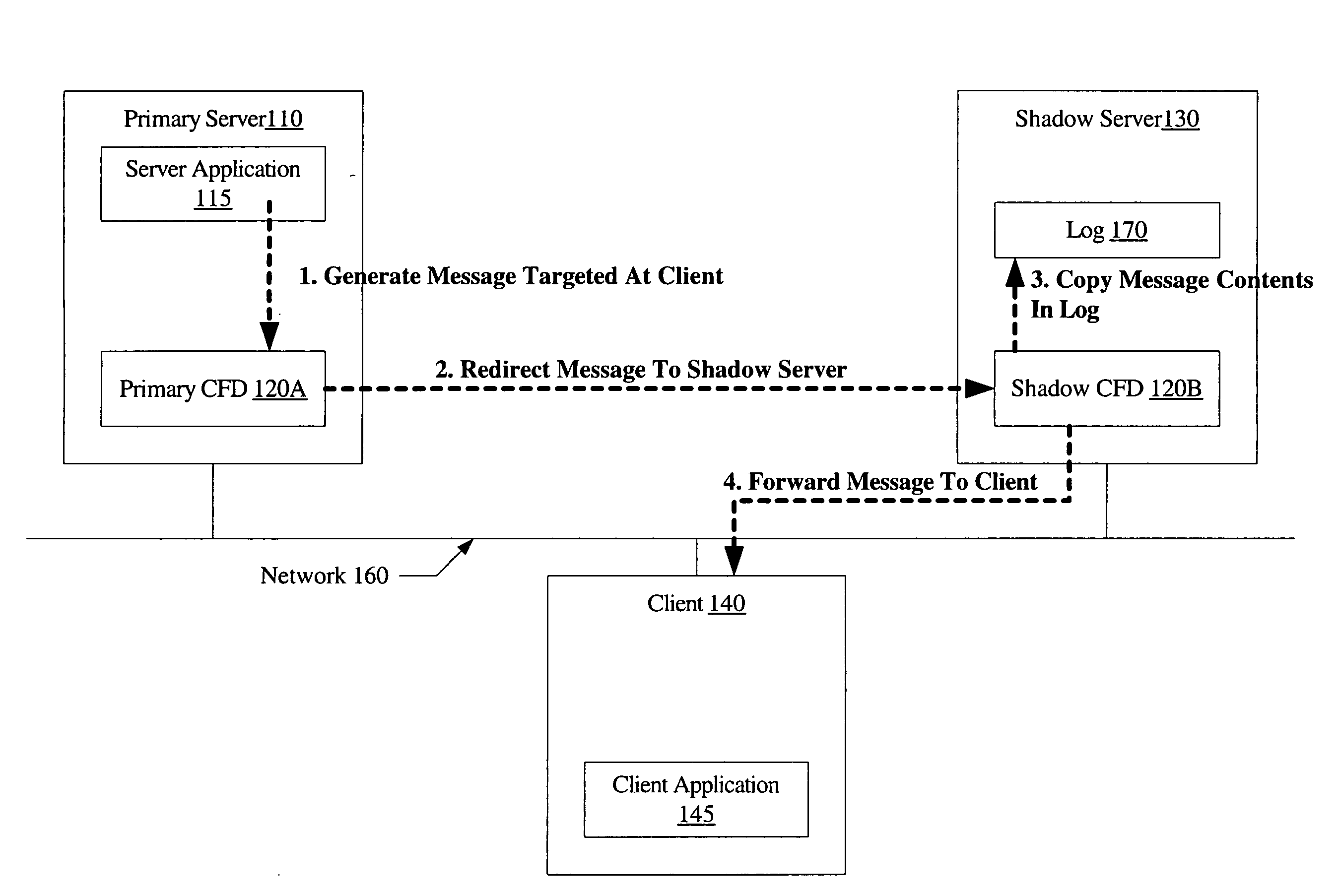
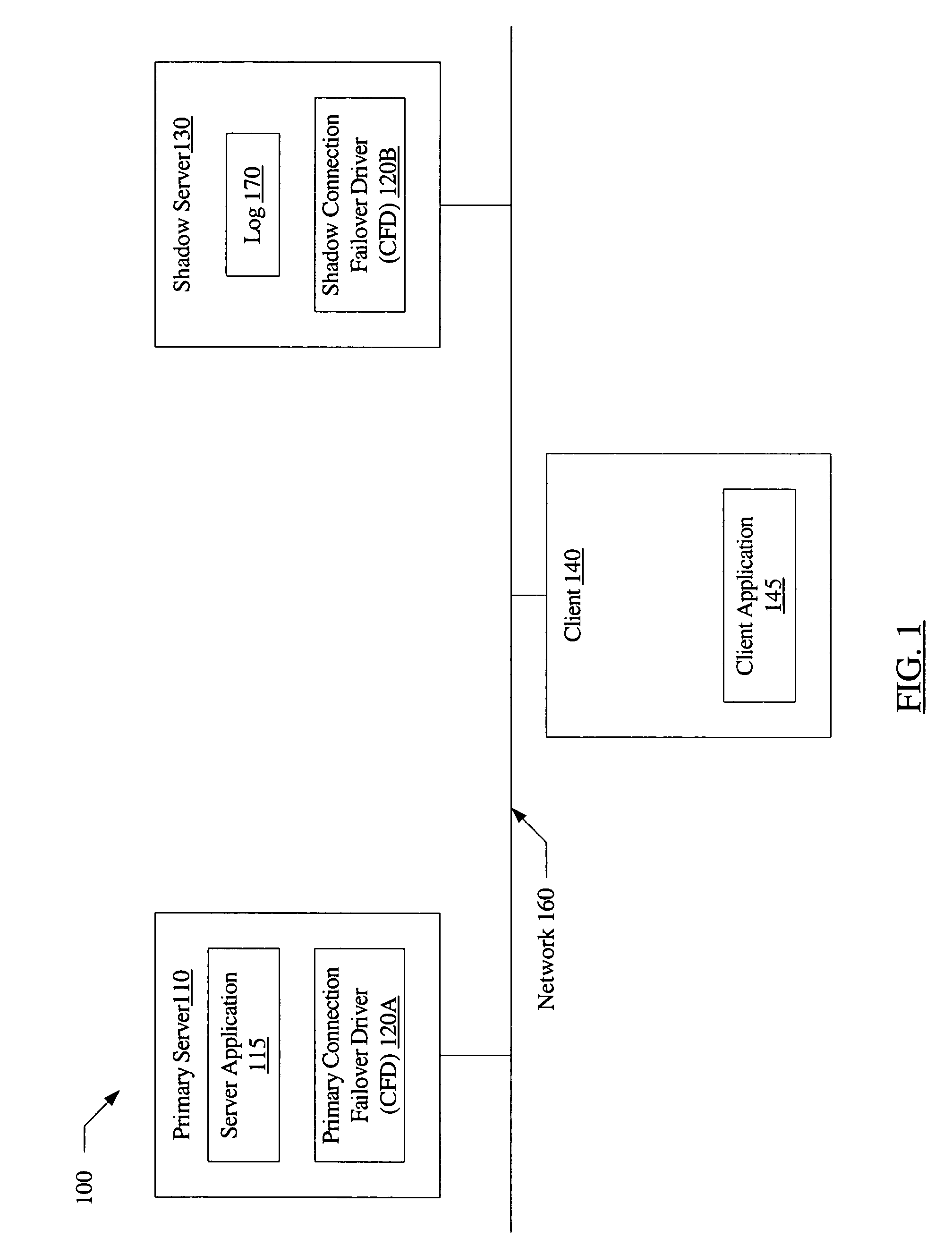
System and method for connection failover using redirection
InactiveUS20060179147A1Multiple digital computer combinationsNetwork connectionsFailoverNetwork connection
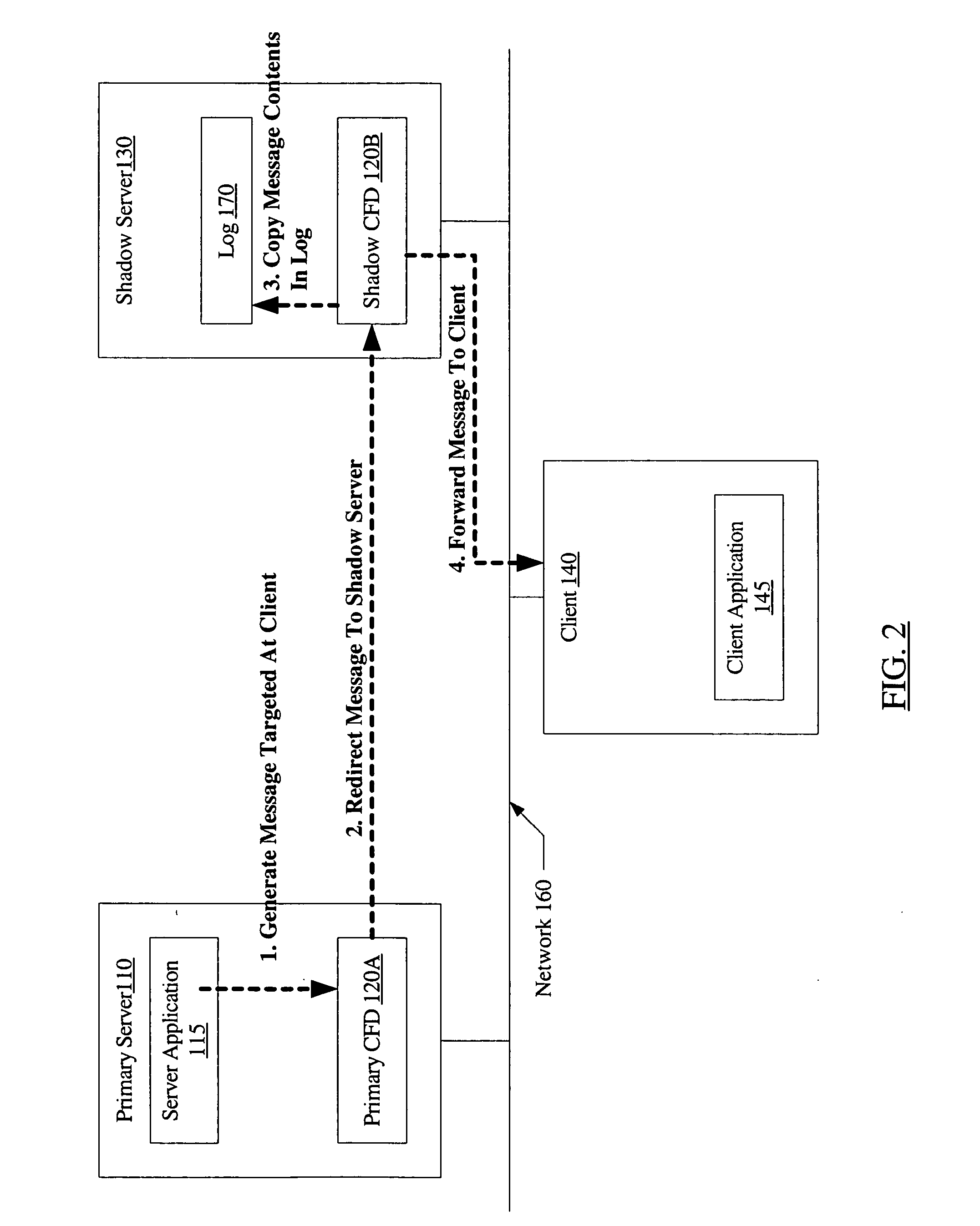
A system for connection failover using redirection includes a primary server comprising a primary connection failover driver (CFD), a shadow server comprising a shadow CFD, and a client. The primary and shadow servers and the client are coupled via a network. The primary server and the client are configured to cooperate to establish a network connection. The primary CFD is configured to redirect a first message packet, targeted for transmission to the client over the network connection, to the shadow server. The shadow CFD is configured to copy contents of the first message packet into a log, and forward the first message packet to the client after the contents have been copied.
Owner:SYMANTEC OPERATING CORP
Mobile provisioning tool system
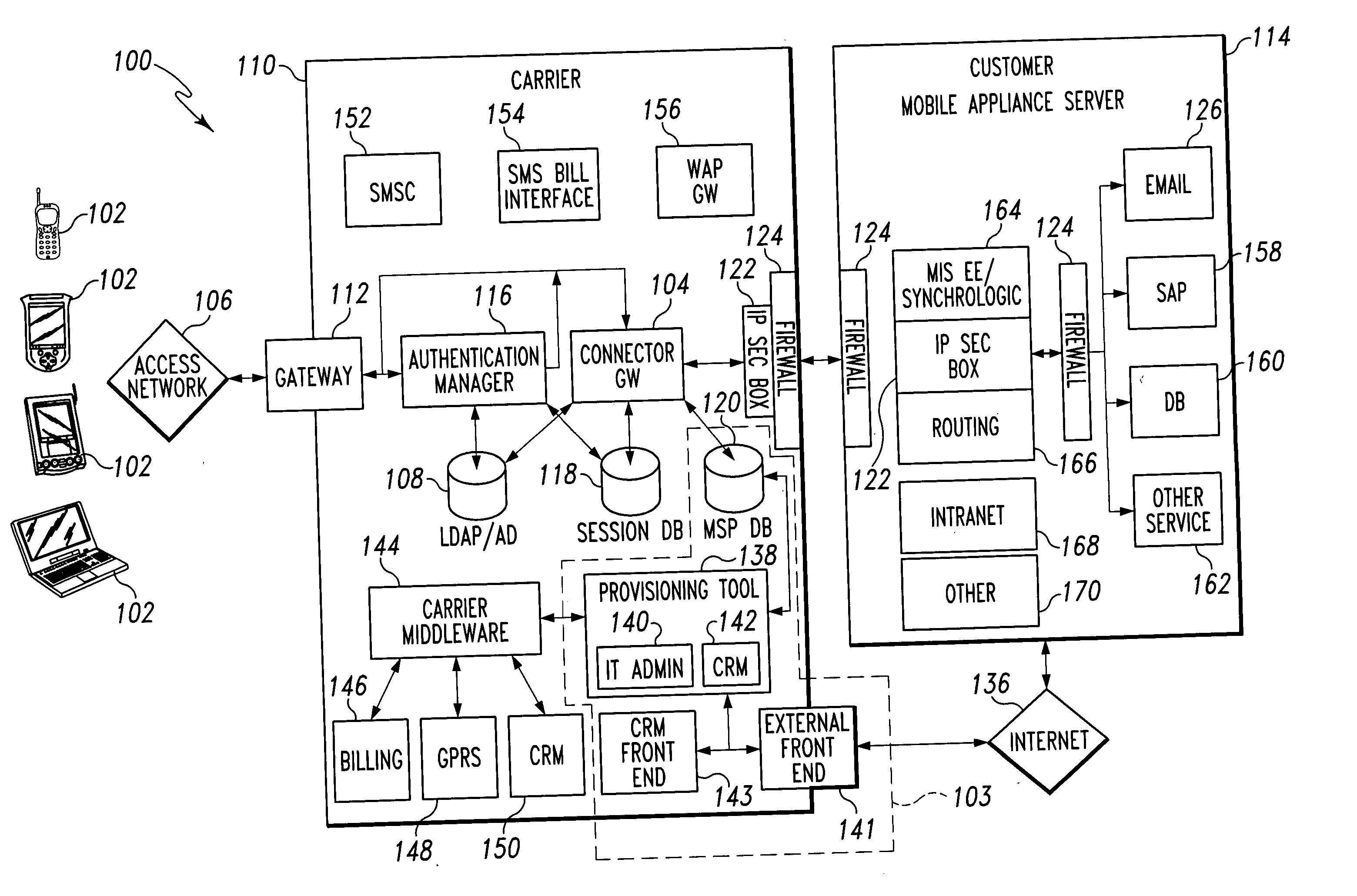
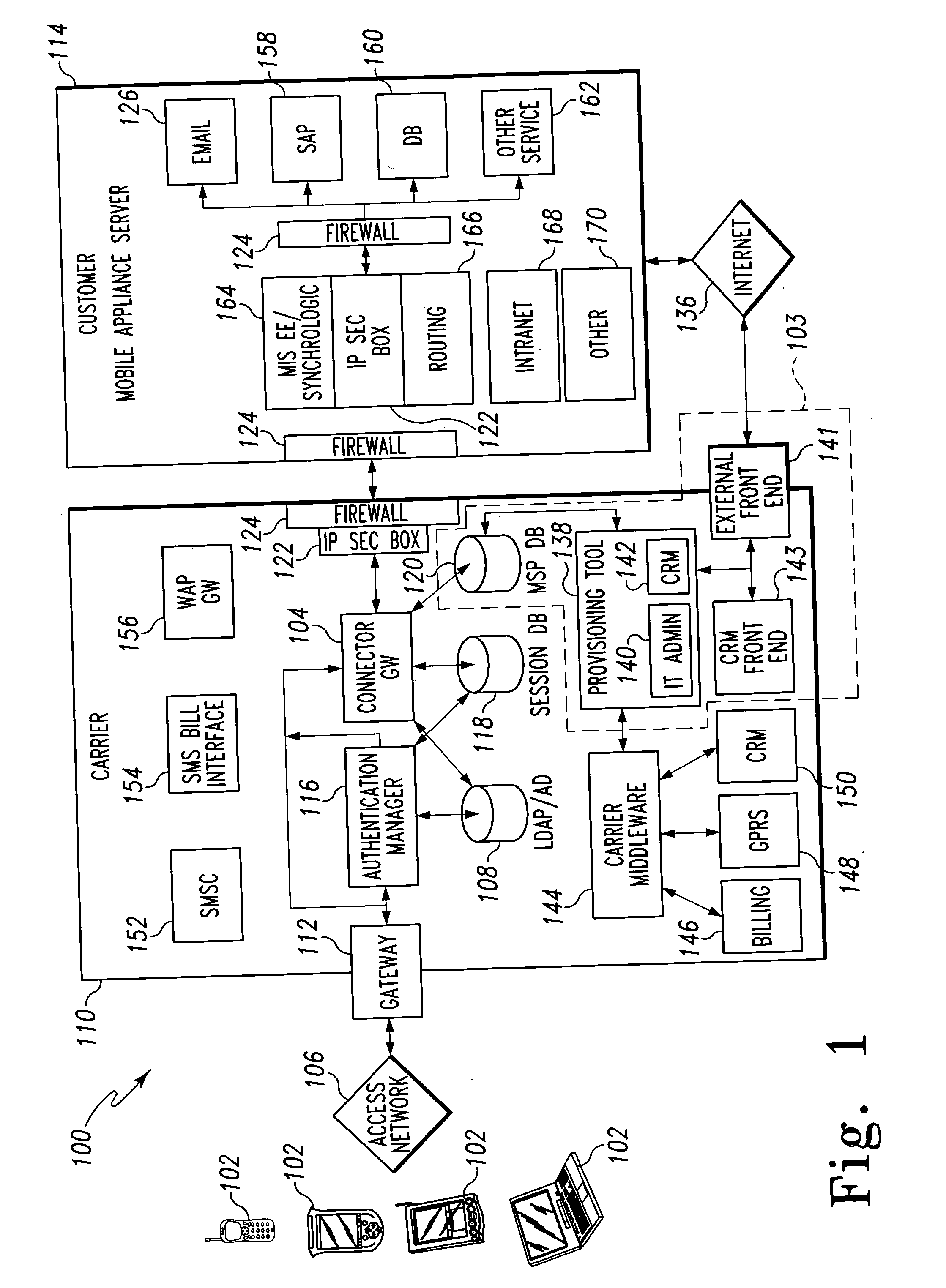
ActiveUS20050075115A1Simple processLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile businessWorkstation
A mobile provisioning tool system including a software provisioning tool application. The mobile provisioning tool system includes mobile devices capable of conducting wireless communication with wireless access points. A carrier network is connected with the wireless access points and a customer network that includes at least one business application. A provisioning tool application is located on a provisioning server. The provisioning tool application includes a CRM Rep component and an IT Admin component. A software provisioning tool application allows the provisioning workstation to automatically install mobile business services and configure network configuration settings on the mobile device.
Owner:ACCENTURE GLOBAL SERVICES LTD
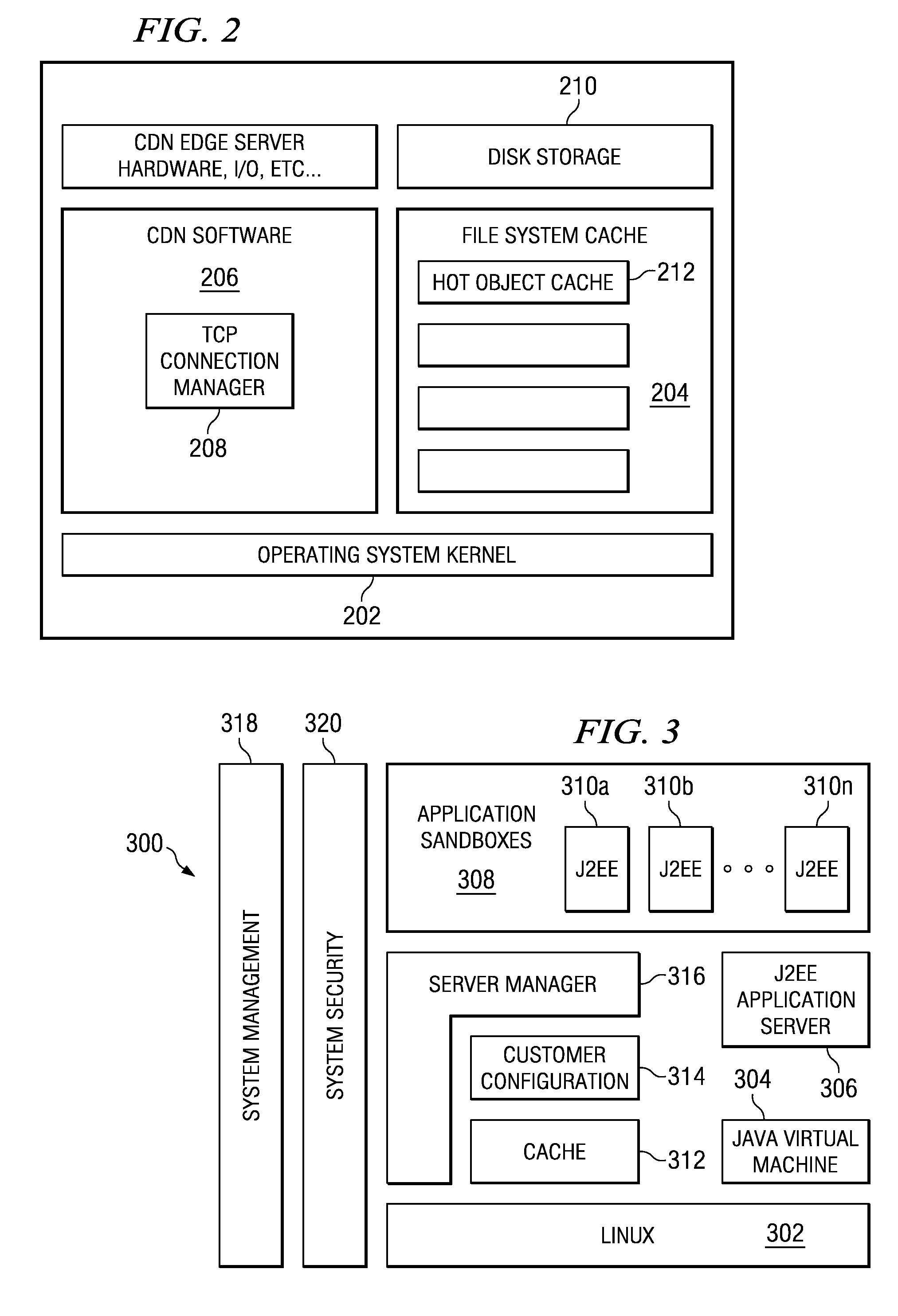
Managing web tier session state objects in a content delivery network (CDN)
InactiveUS20070271385A1Error detection/correctionMultiple digital computer combinationsEdge serverClient-side
Business applications running on a content delivery network (CDN) having a distributed application framework can create, access and modify state for each client. Over time, a single client may desire to access a given application on different CDN edge servers within the same region and even across different regions. Each time, the application may need to access the latest “state” of the client even if the state was last modified by an application on a different server. A difficulty arises when a process or a machine that last modified the state dies or is temporarily or permanently unavailable. The present invention provides techniques for migrating session state data across CDN servers in a manner transparent to the user. A distributed application thus can access a latest “state” of a client even if the state was last modified by an application instance executing on a different CDN server, including a nearby (in-region) or a remote (out-of-region) server.
Owner:AKAMAI TECH INC
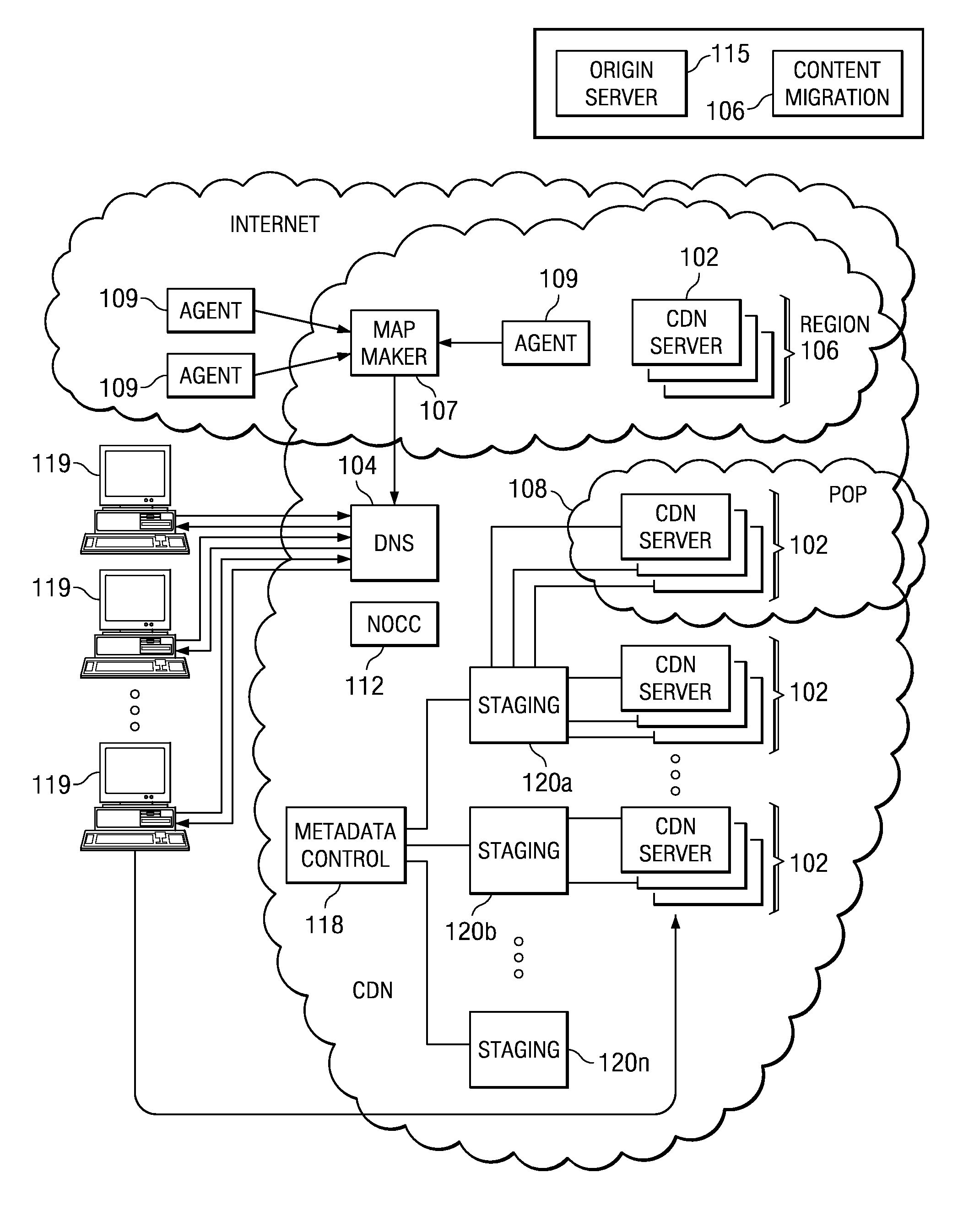
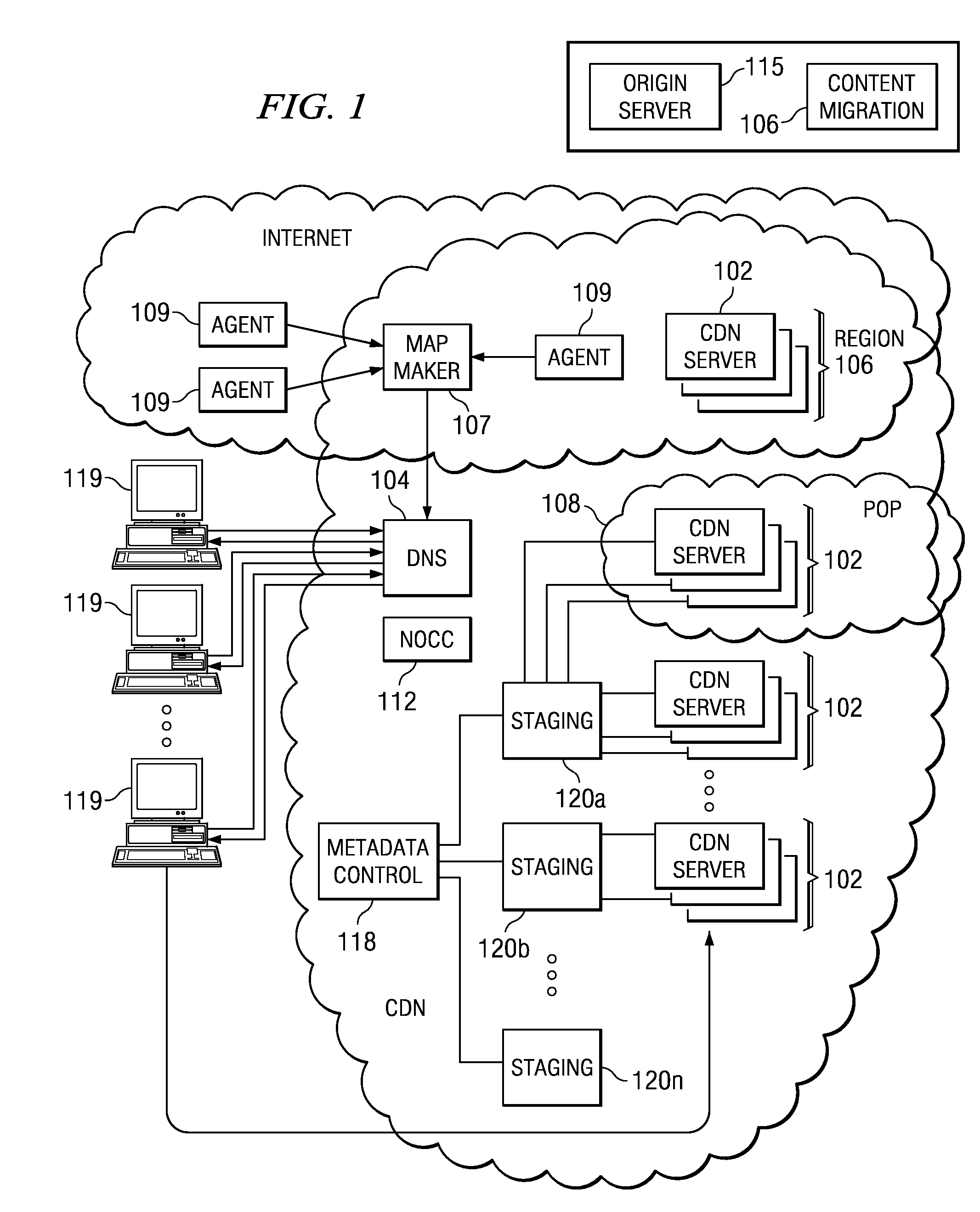
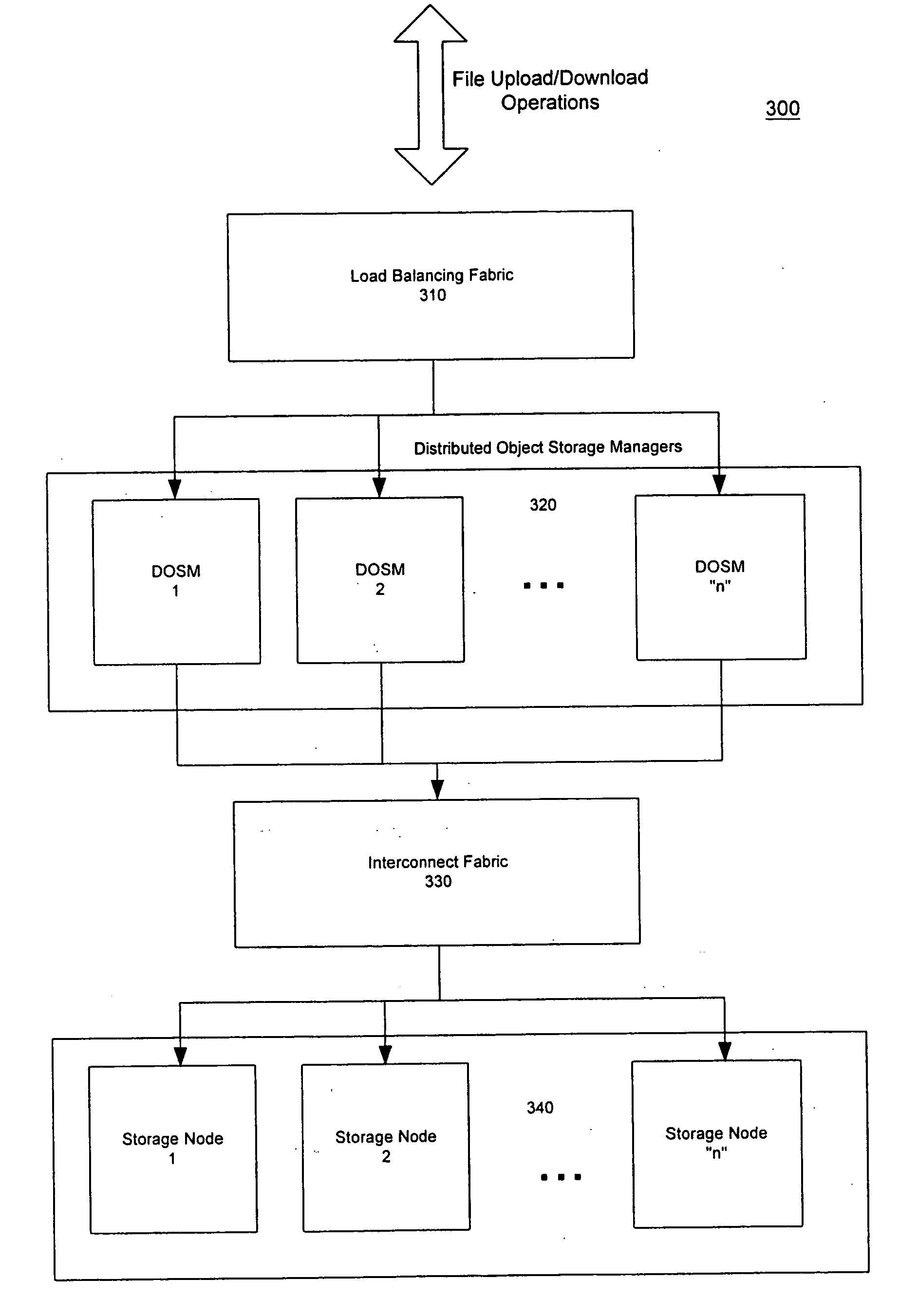
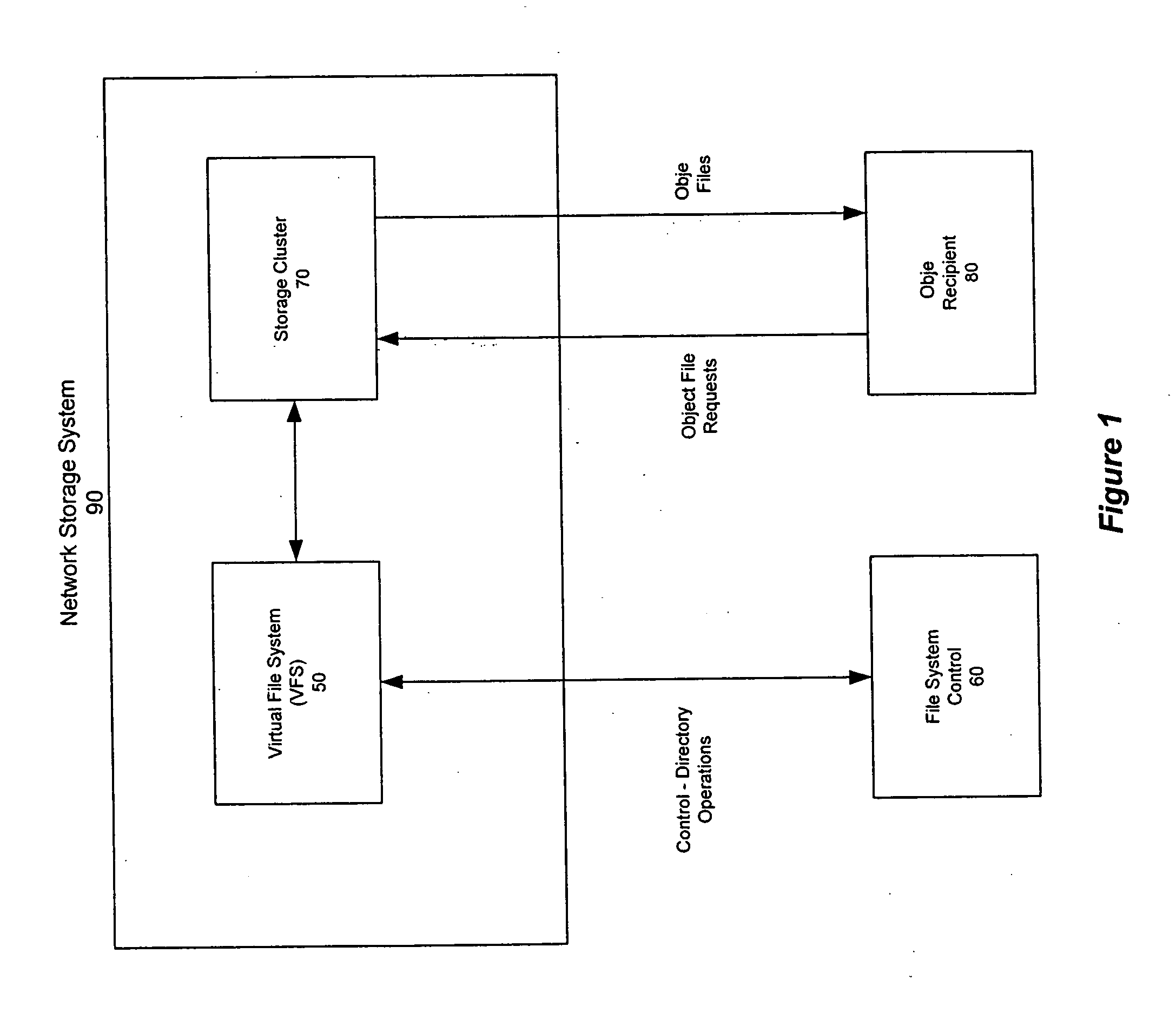
Distributed storage cluster architecture
InactiveUS20050246393A1Input/output to record carriersDigital data information retrievalVirtual file systemDistributed object
A network storage system includes a virtual file system (“VFS”) that manages the files of the network storage system, and a storage center that stores the files. The VFS and the storage center are separated, such that a client accesses the VFS to conduct file system operations and the client accesses the storage center to upload / download files. The client accesses the network storage system through one or more storage ports. The storage center includes a plurality of distributed object storage managers (DOSMs) and a storage cluster that includes a plurality of intelligent storage nodes. The network storage system includes additional storage centers at geographically disparate locations. The network storage system uses a multi-cast protocol to maintain file information at the DOSMs regarding files stored in the intelligent storage nodes, including files stored in disparate storage centers.
Owner:INTEL CORP
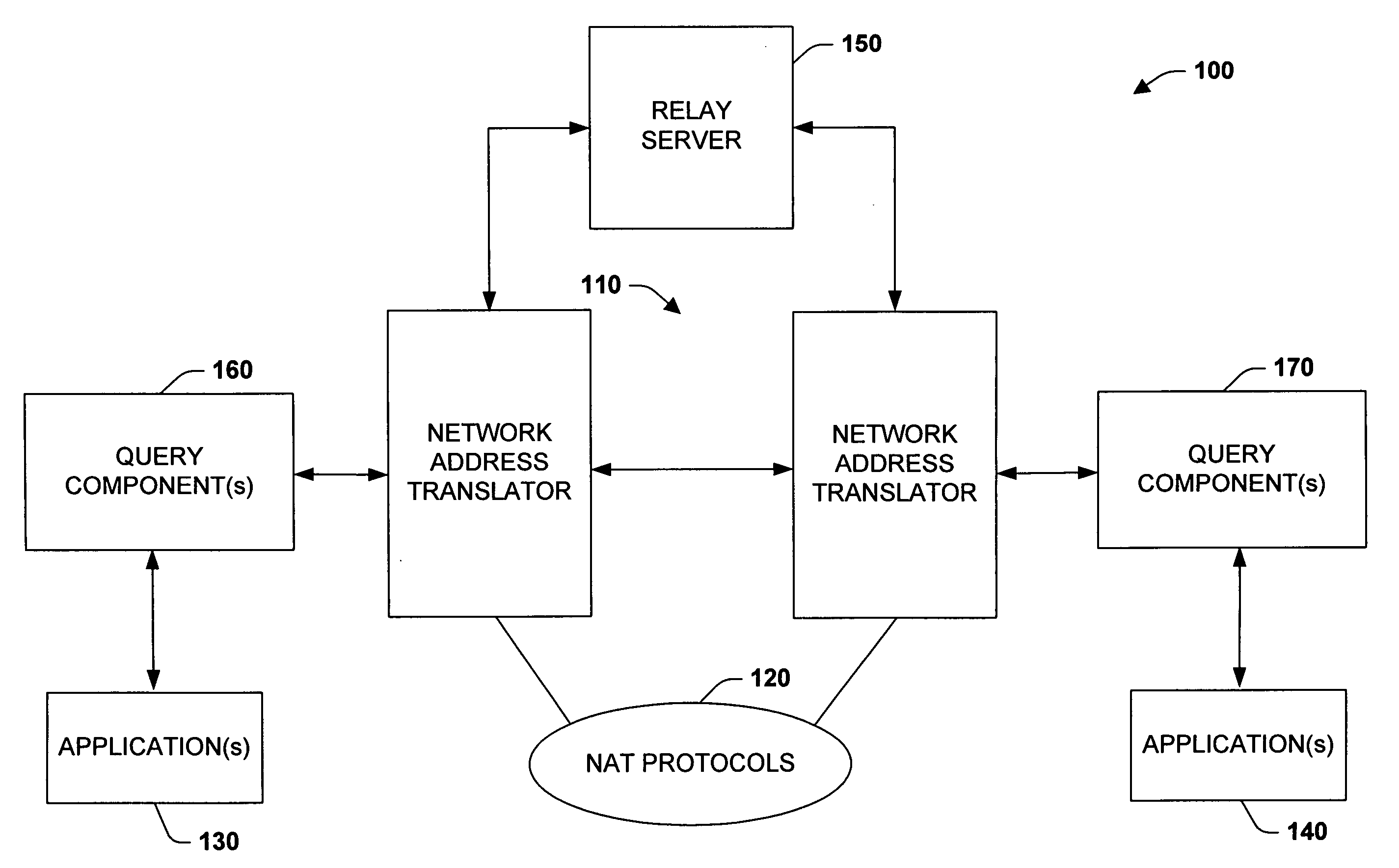
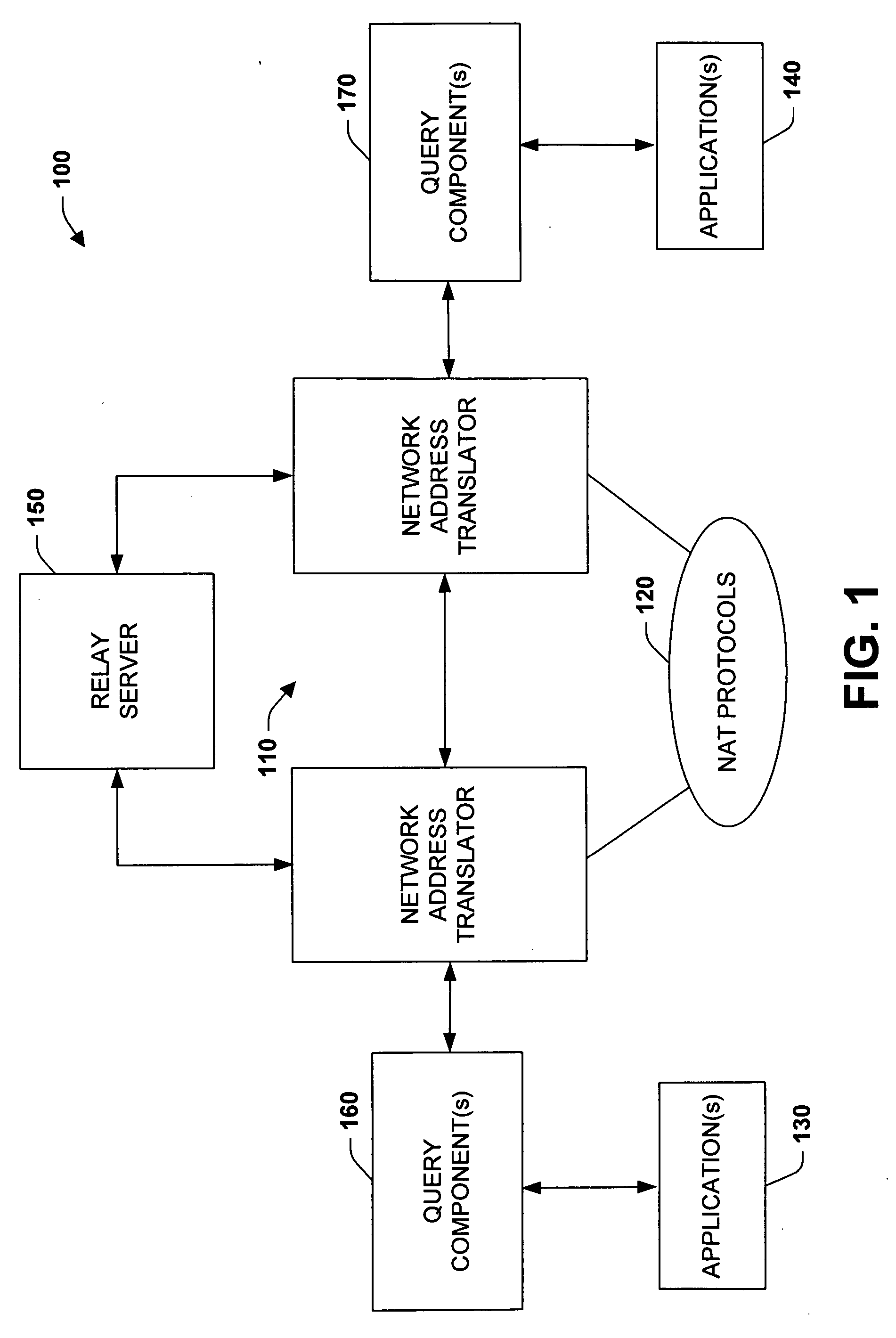
Automated NAT traversal for peer-to-peer networks
InactiveUS20060182100A1Facilitate communicationReduce administrative burdenData switching by path configurationMultiple digital computer combinationsCommunications systemNAT traversal
The subject invention relates to systems and methods that facilitate direct network communications between peers that operate behind Network Address Translators. In one aspect, a network communications system is provided. The system includes one or more Network Address Translators (NAT) to communicate data across a network between peers. A protocol selection component that automatically selects among a plurality of protocols according to one or more NAT types in order to determine a subset of the protocols that facilitate communications between the peers.
Owner:MICROSOFT TECH LICENSING LLC
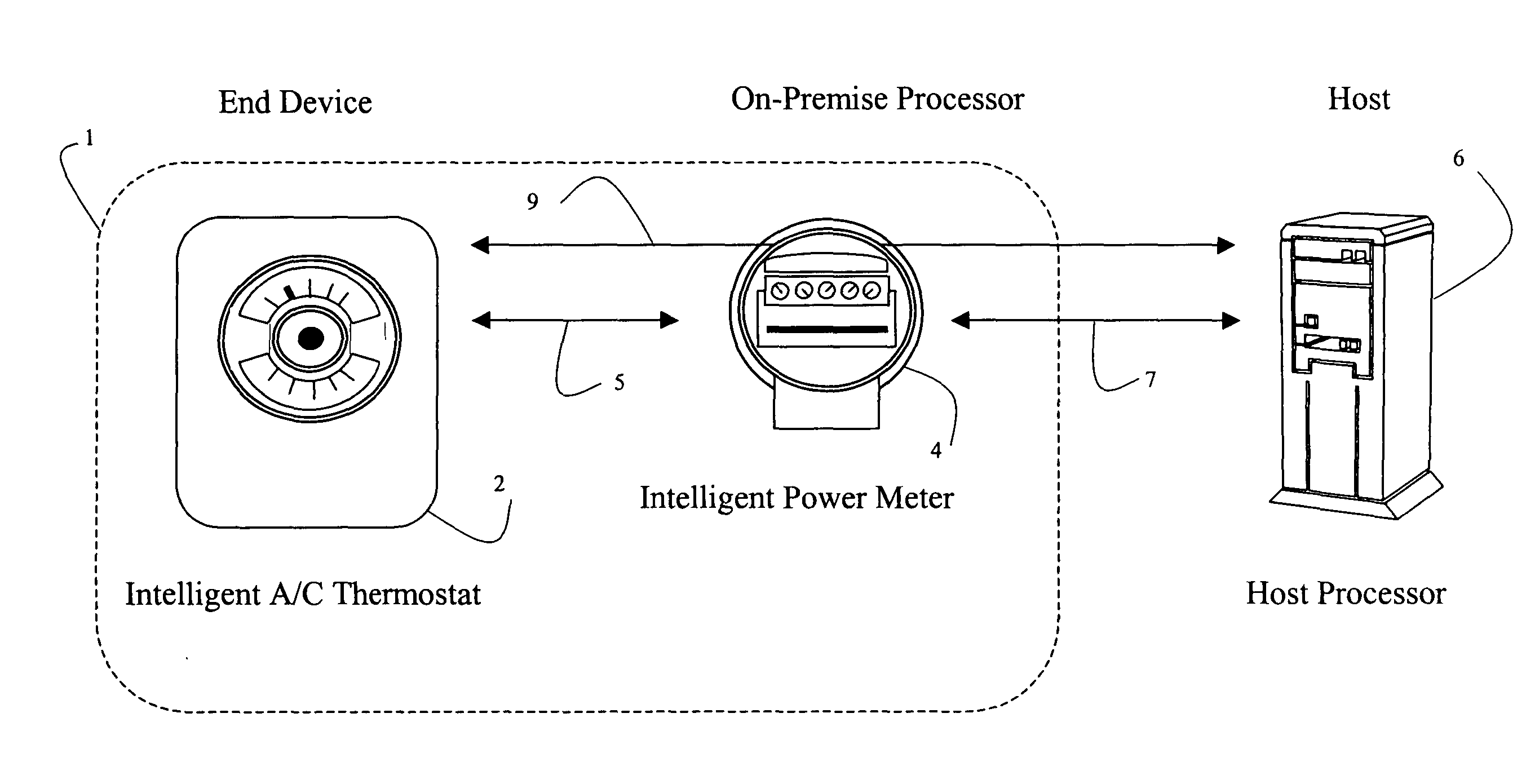
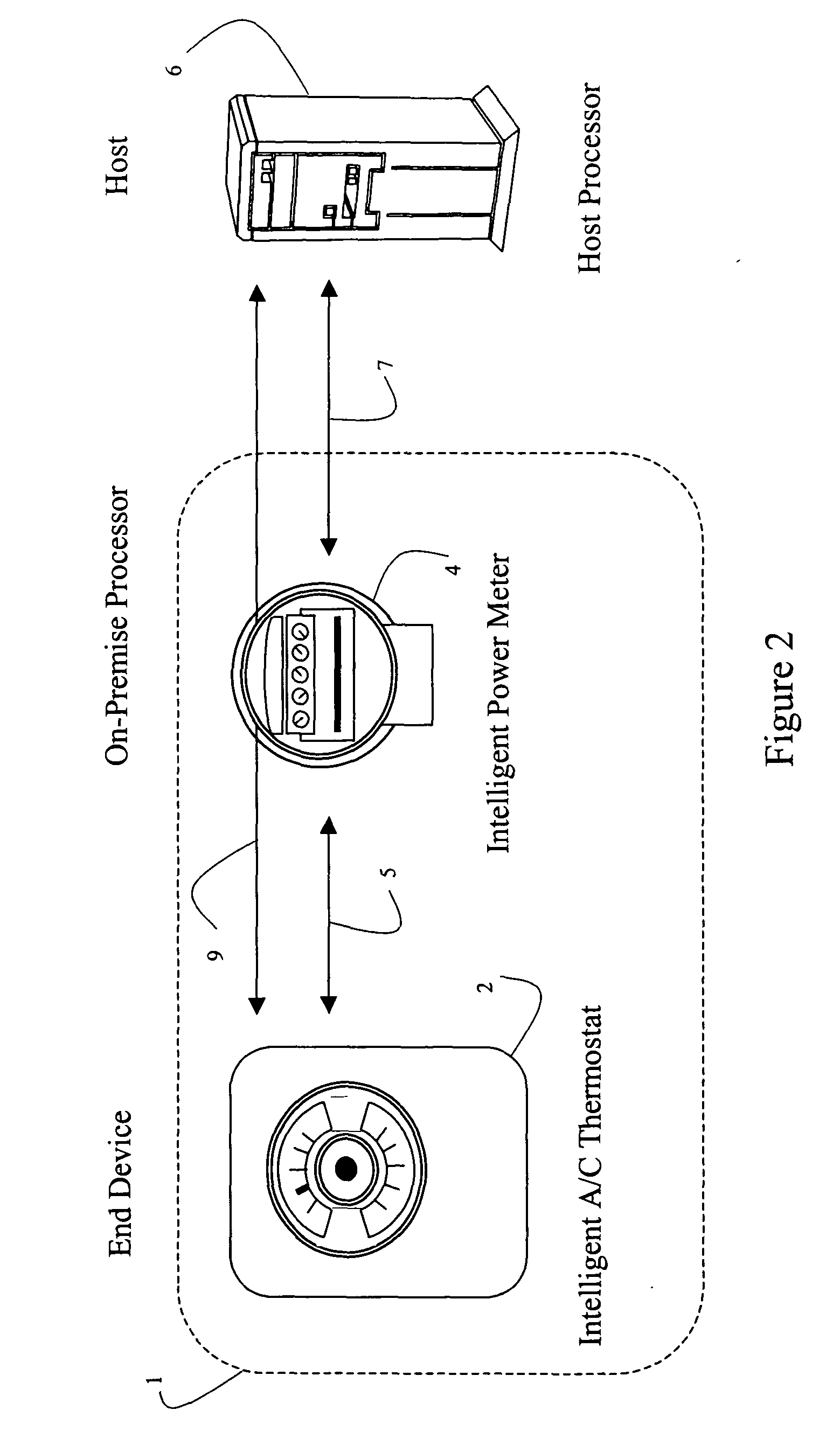
Systems and methods for remote power management using 802.11 wireless protocols
InactiveUS20050055432A1Reduce power consumptionLow costTariff metering apparatusNetwork topologiesTerminal equipmentUsage data
Systems and methods are disclosed for using 802.11 based wireless protocols in various energy management applications wherein a host controller uses various types of communication networks to distribute information to an on-premise processor that in turn uses 802.11 based wireless protocols to communicate with various types of end devices, such as utility meters. Various forms of communication are defined between the end device, the on-premise processor, and the energy management host for accomplishing power load control, including determining when to activate or deactivate a load, requesting permission to activate a load, reading usage data, activating or deactivating a meter, and determining rate schedules. A flexible scheme allows control to be shifted to be resident in various entities. The architecture is applicable not only for power load control, but other control type and metering devices.
Owner:SMARTSYNCH
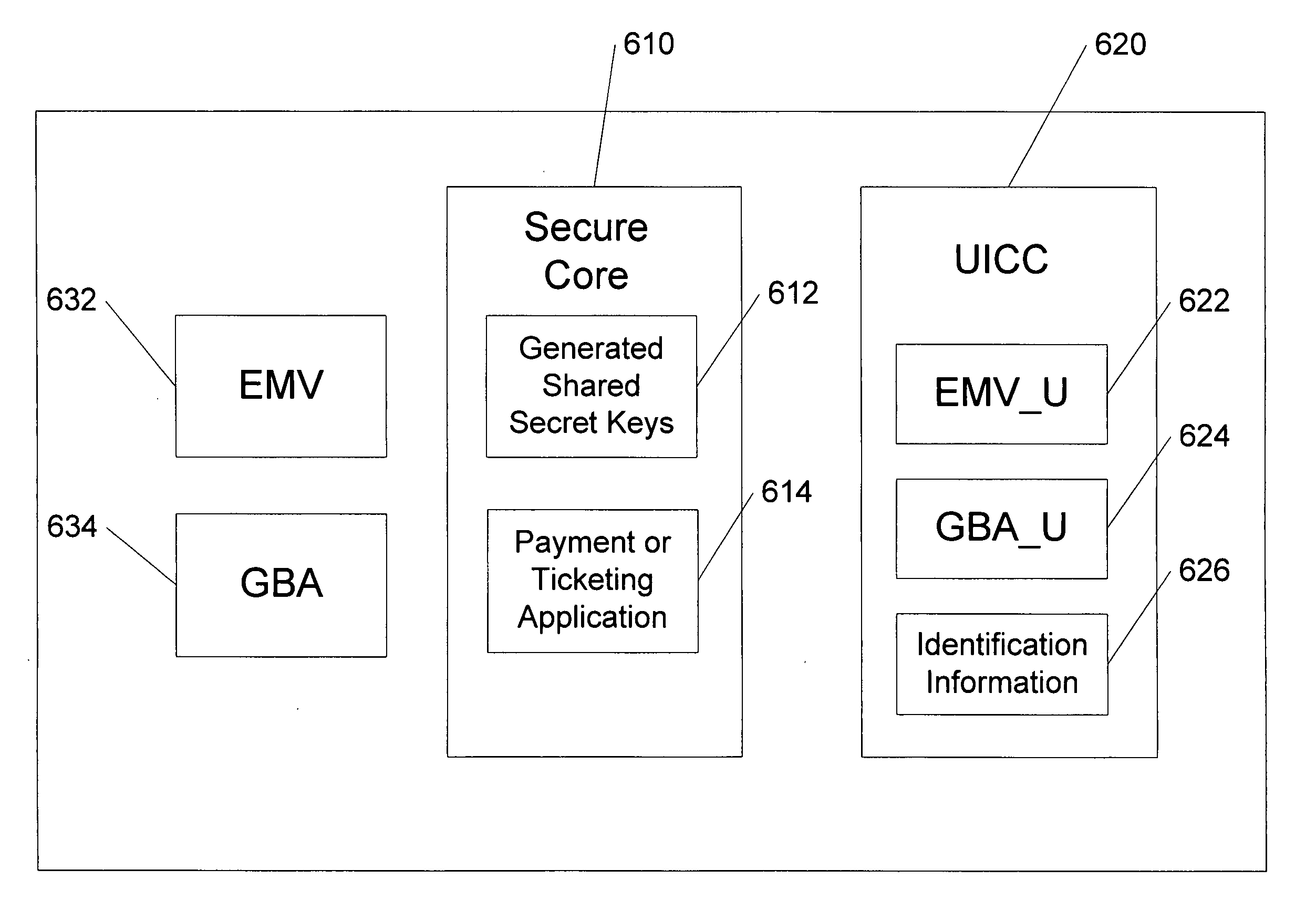
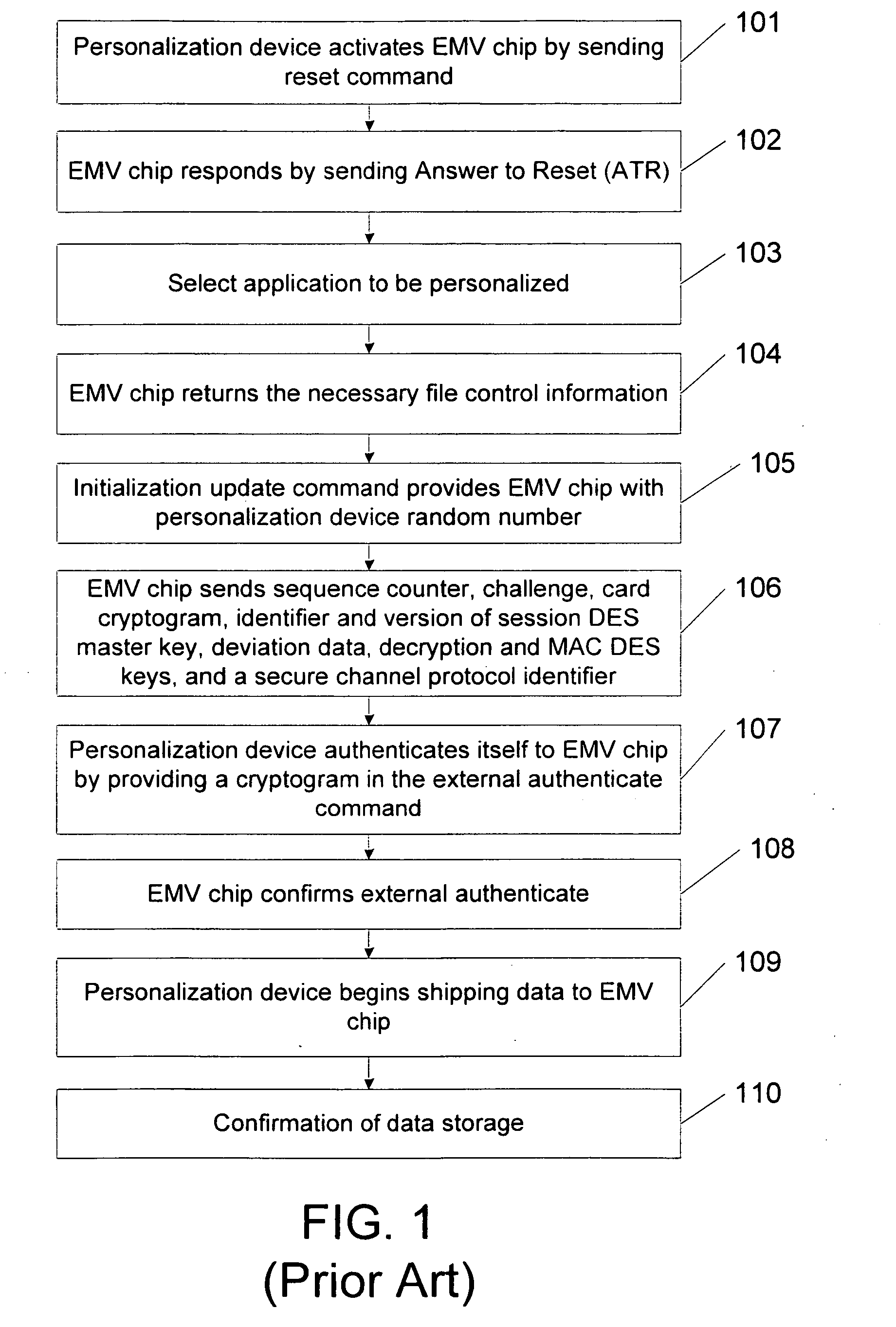
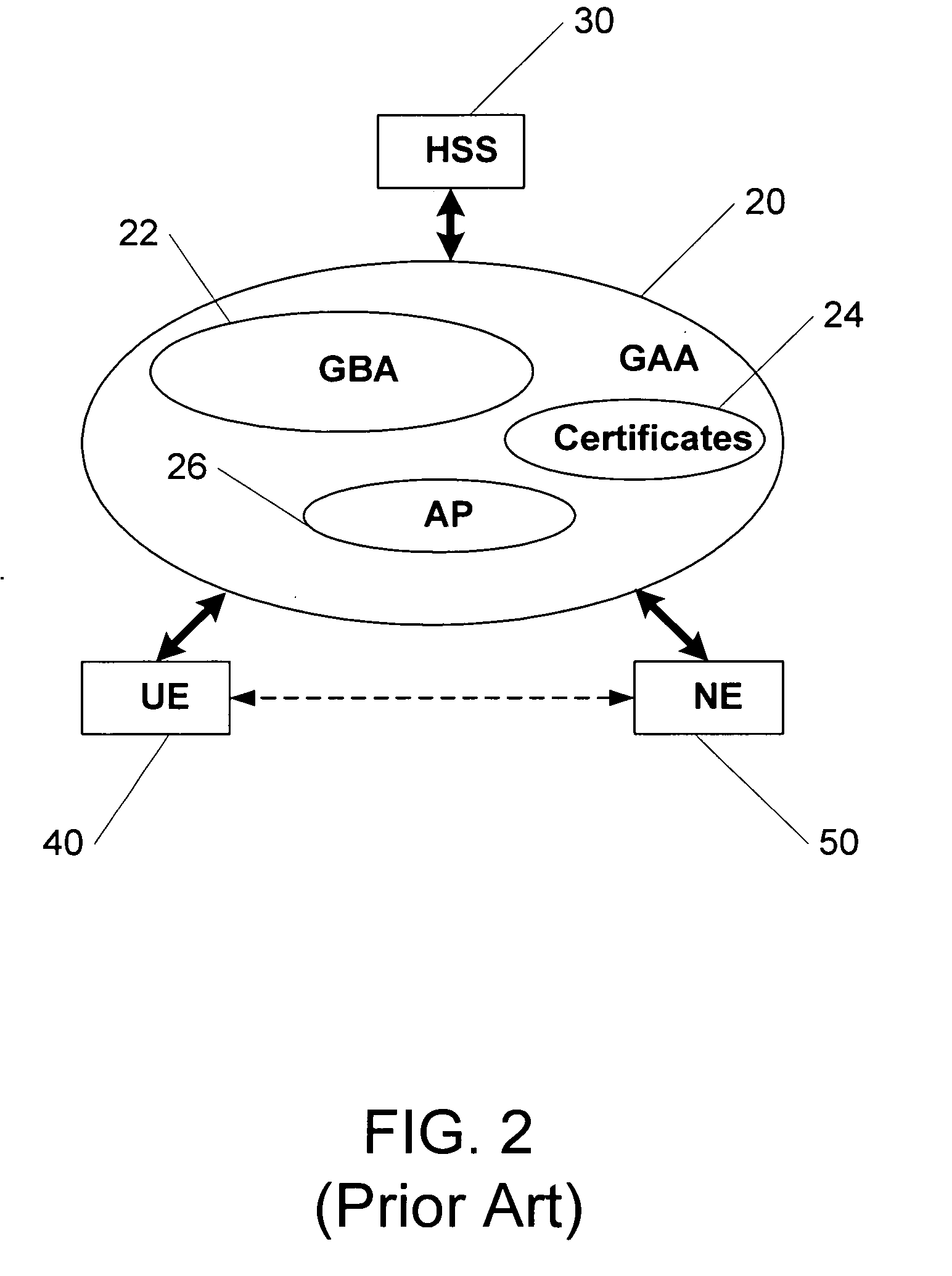
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECHNOLOGLES OY
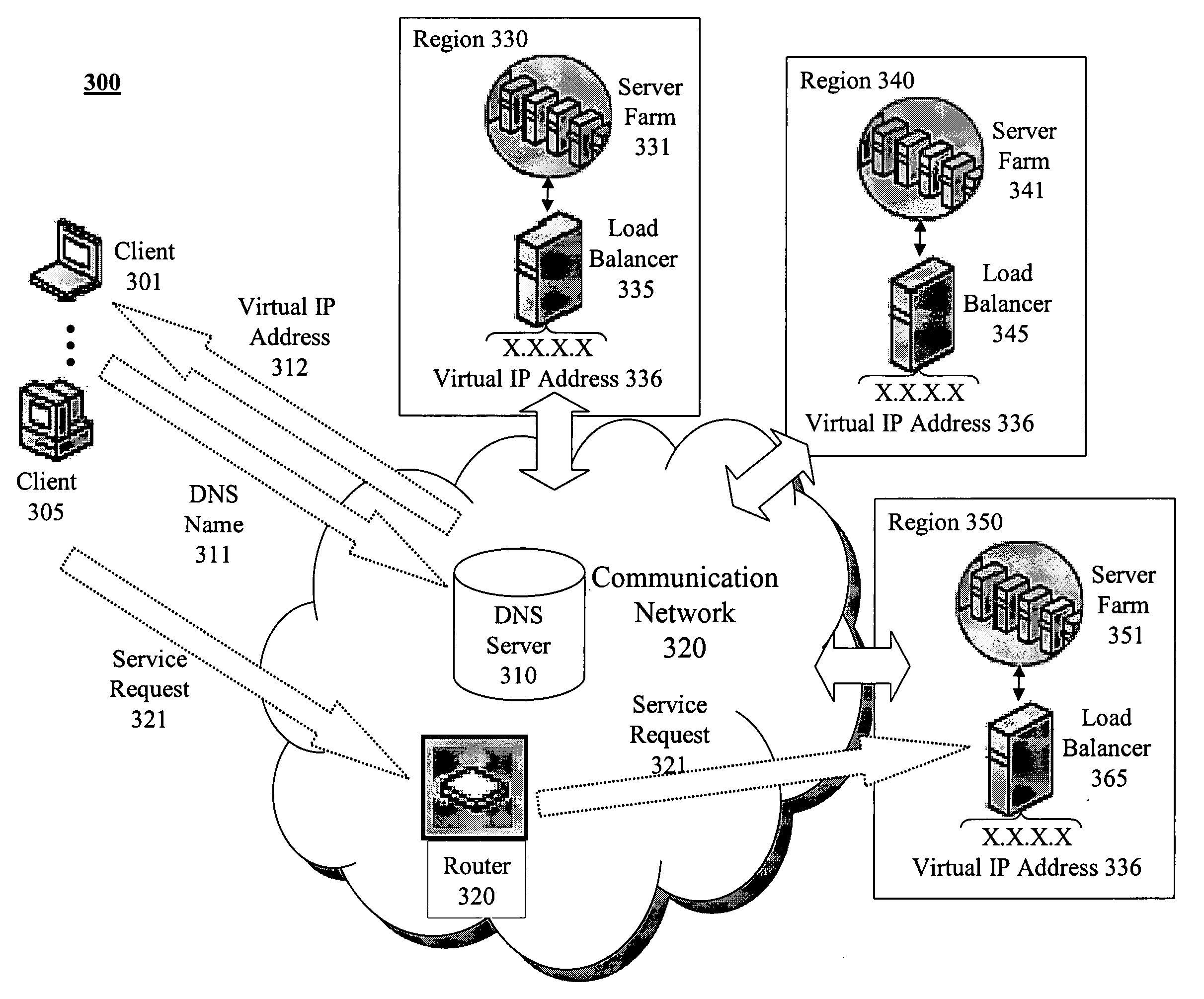
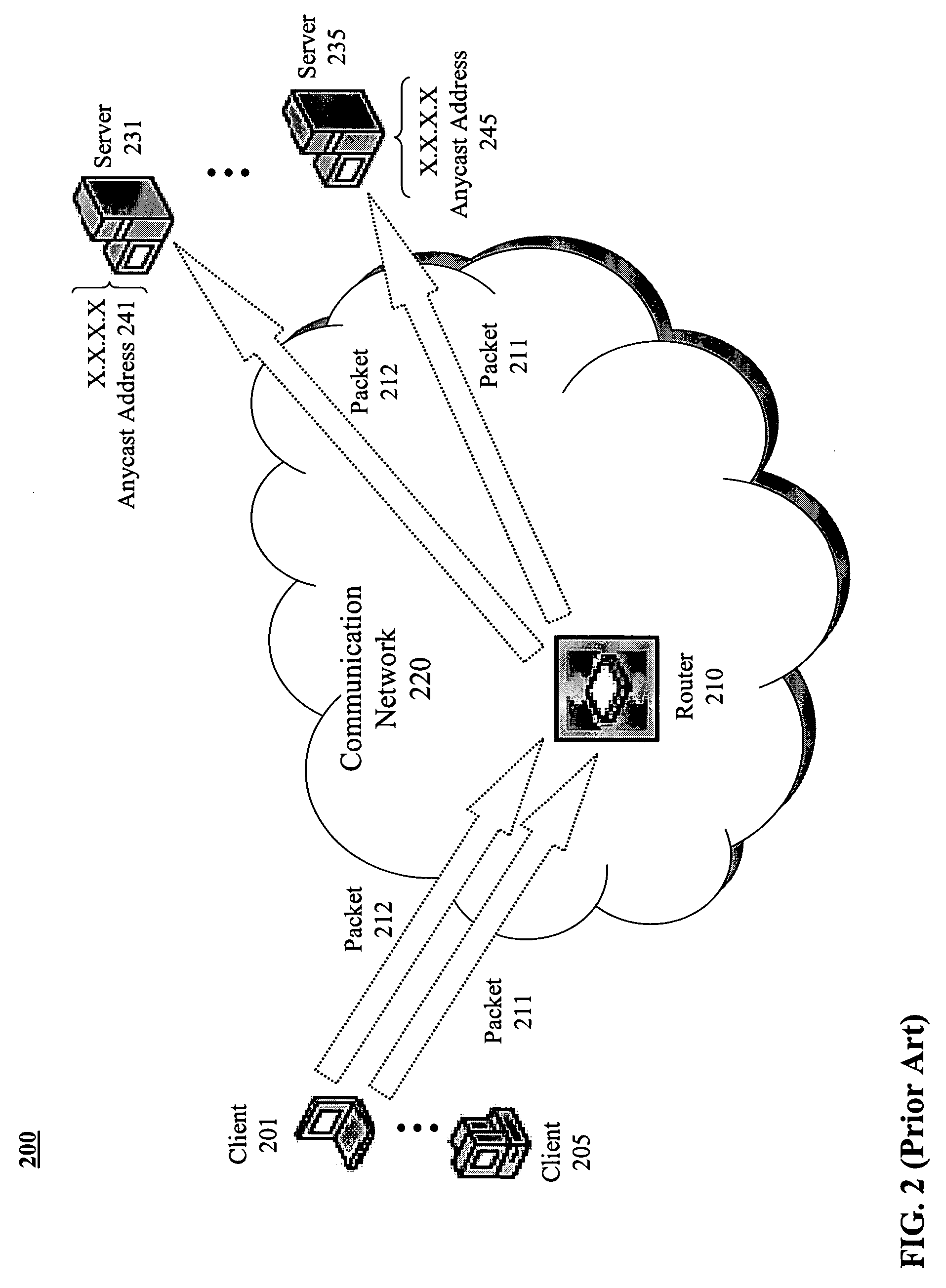
Geo-locating load balancing
Methods and apparatus are provided for geo-locating load balancing. According to one embodiment, a communication network architecture includes multiple servers, multiple load balancers, and multiple geographically dispersed communication devices. The servers provide services to the communication devices within the communication network. The load balancers each service a shared virtual Internet Protocol (IP) address common to all of the load balancers and perform load balancing of service requests on behalf of two or more of the servers that are located geographically proximate to the load balancer. The communication devices are communicatively coupled with the load balancers and are configured to issue service requests intended for any of the servers to the shared virtual IP address, whereby, upon issuing a service request, a communication device is directed to a particular server selected by a load balancing routine that is associated with a load balancer that is closest to the communication device.
Owner:LEVEL 3 COMM LLC
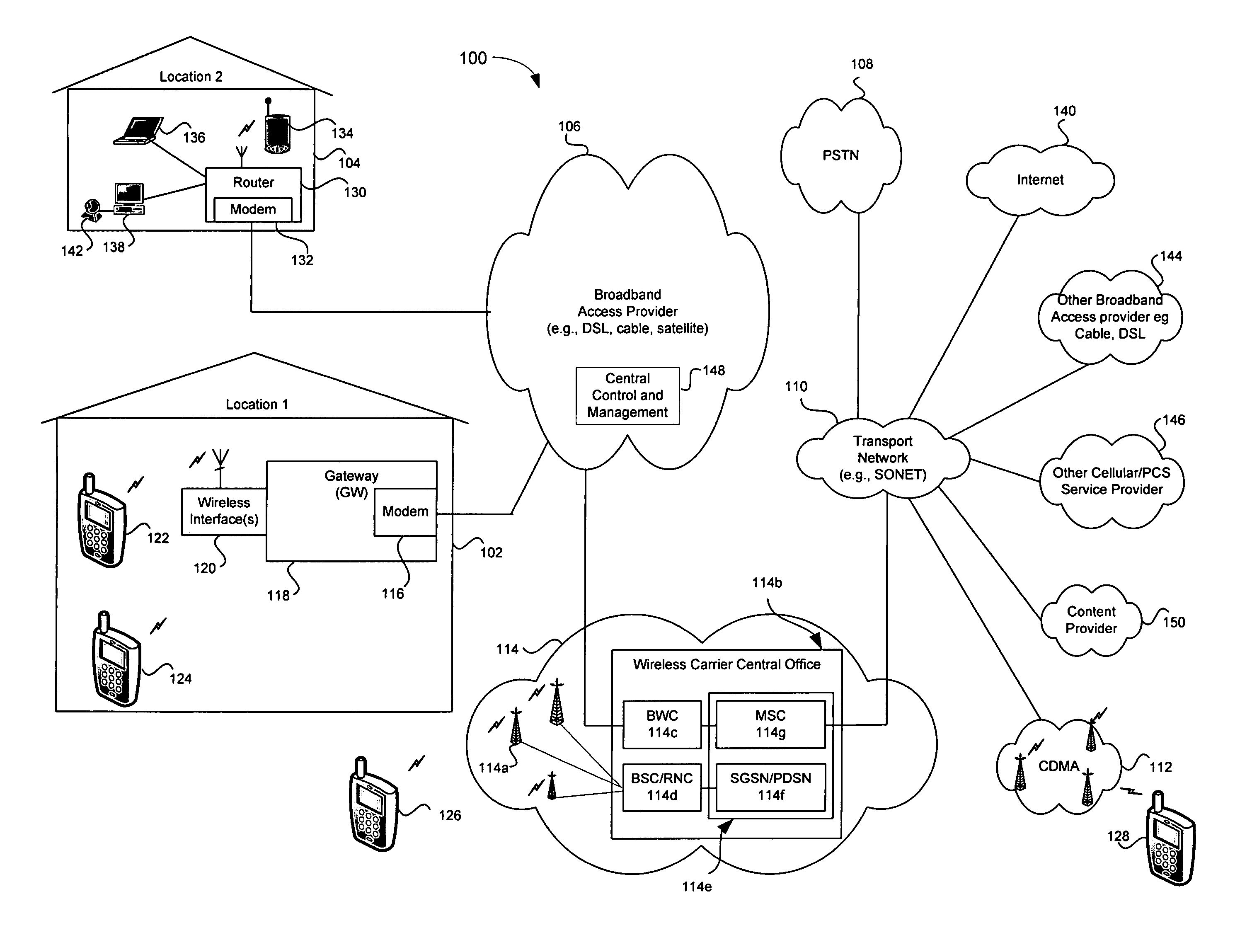
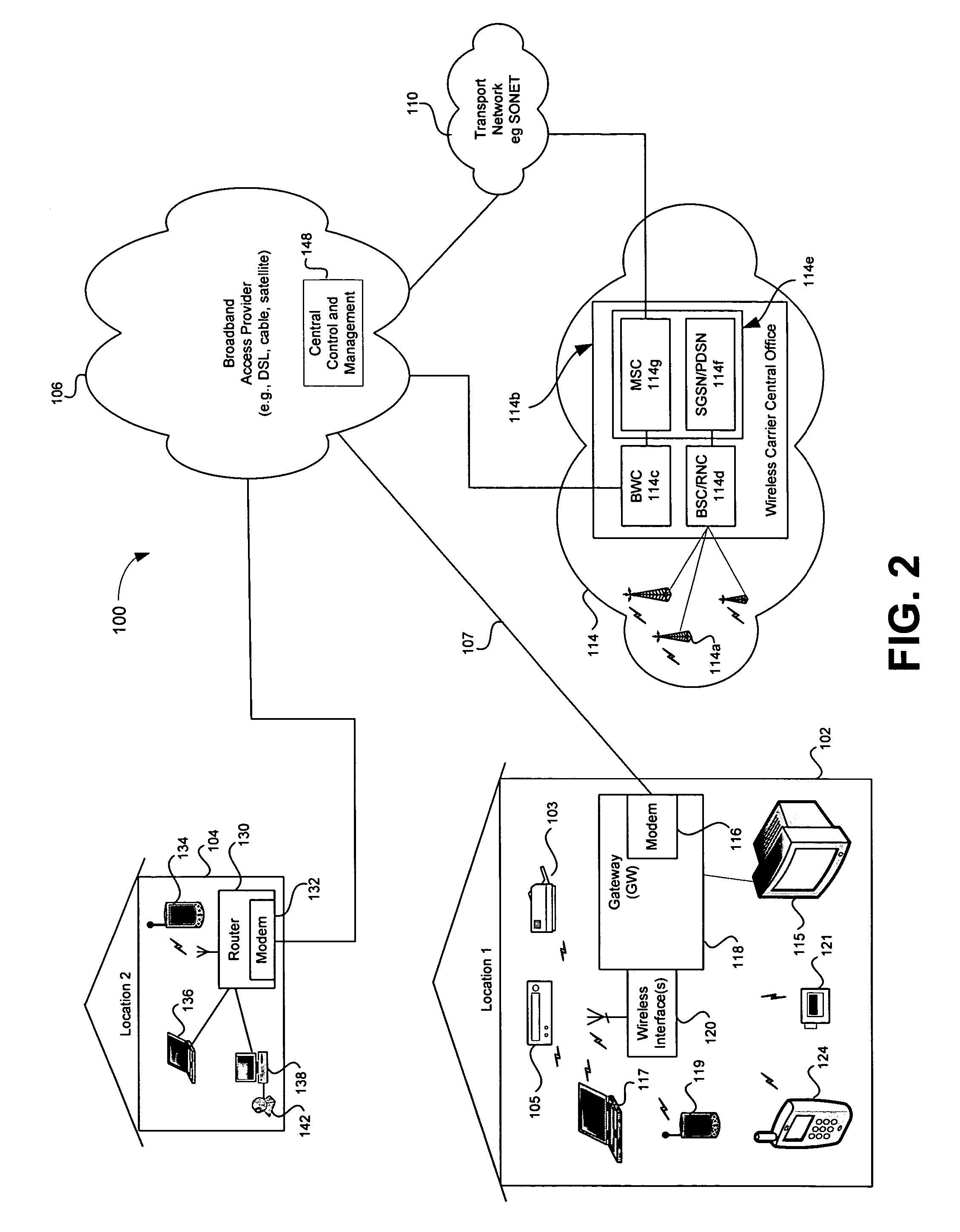
Remote configuration and control of local devices via a broadband access gateway
A system and method for the remote configuration and control of a access devices via a broadband access gateway is disclosed. The broadband access gateway may comprise a wireless interface and a broadband network connection for exchanging information via, for example, a digital subscriber loop, a cable connection, a T1 connection, and T3 network connection. A user using any of a plurality of access devices may communicate with the broadband access gateway via the wireless interface or the broadband network connection to make remote requests of another of the access devices. Such requests may comprise, for example, accessing, recording, playing, exchanging, transmitting, receiving, converting, translating of multimedia information. The remote requests may include enabling, disabling, configuring, monitoring, administering, and scheduling of smart appliances and premise systems such as, for example, security, heating, and cooling systems.
Owner:AVAGO TECH INT SALES PTE LTD
Channel, coding and power management for wireless local area networks
InactiveUS20050003827A1Improve mutual interferenceDecrease network throughputNetwork topologiesRadio/inductive link selection arrangementsInternet trafficTrade offs
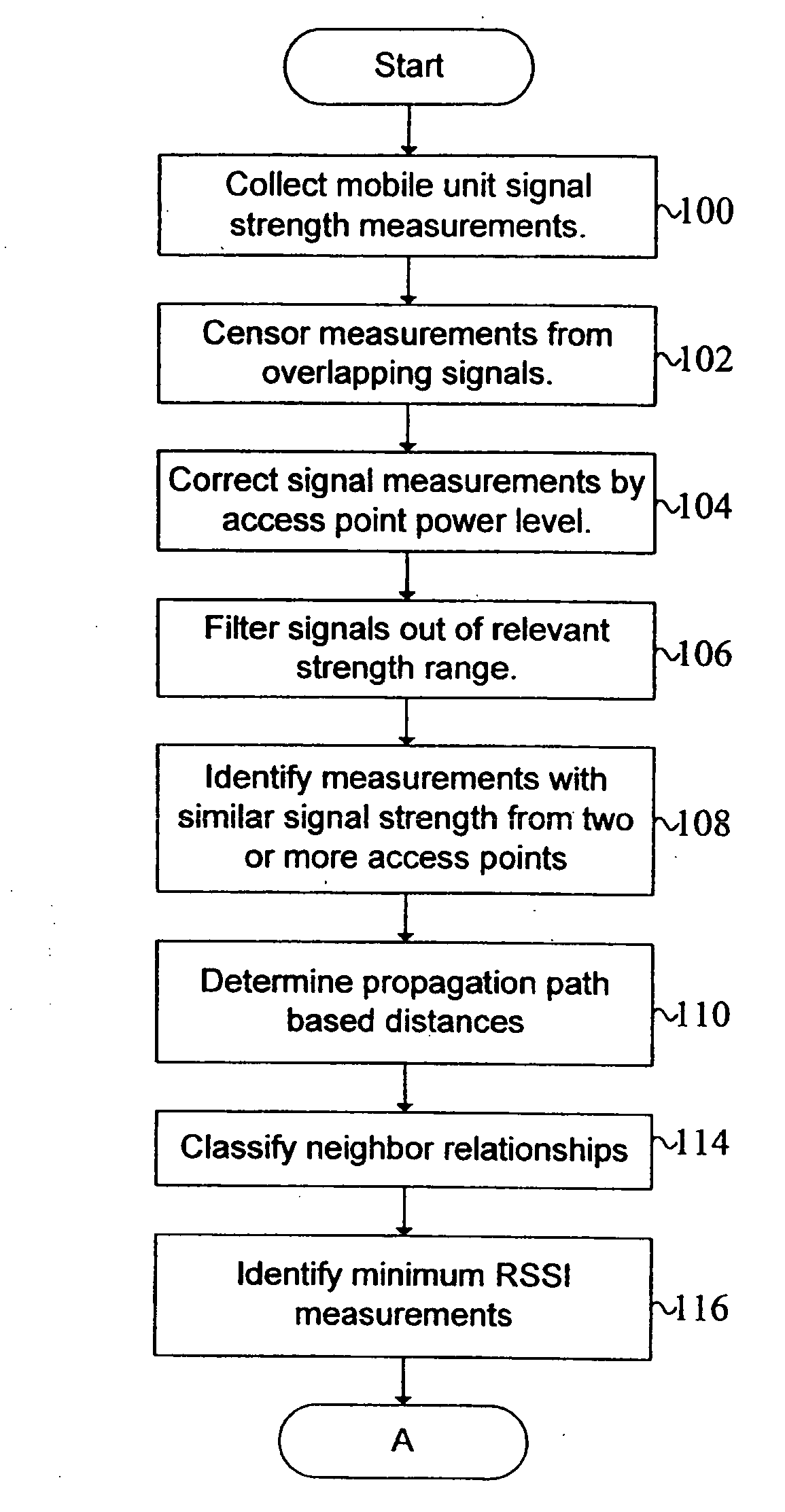
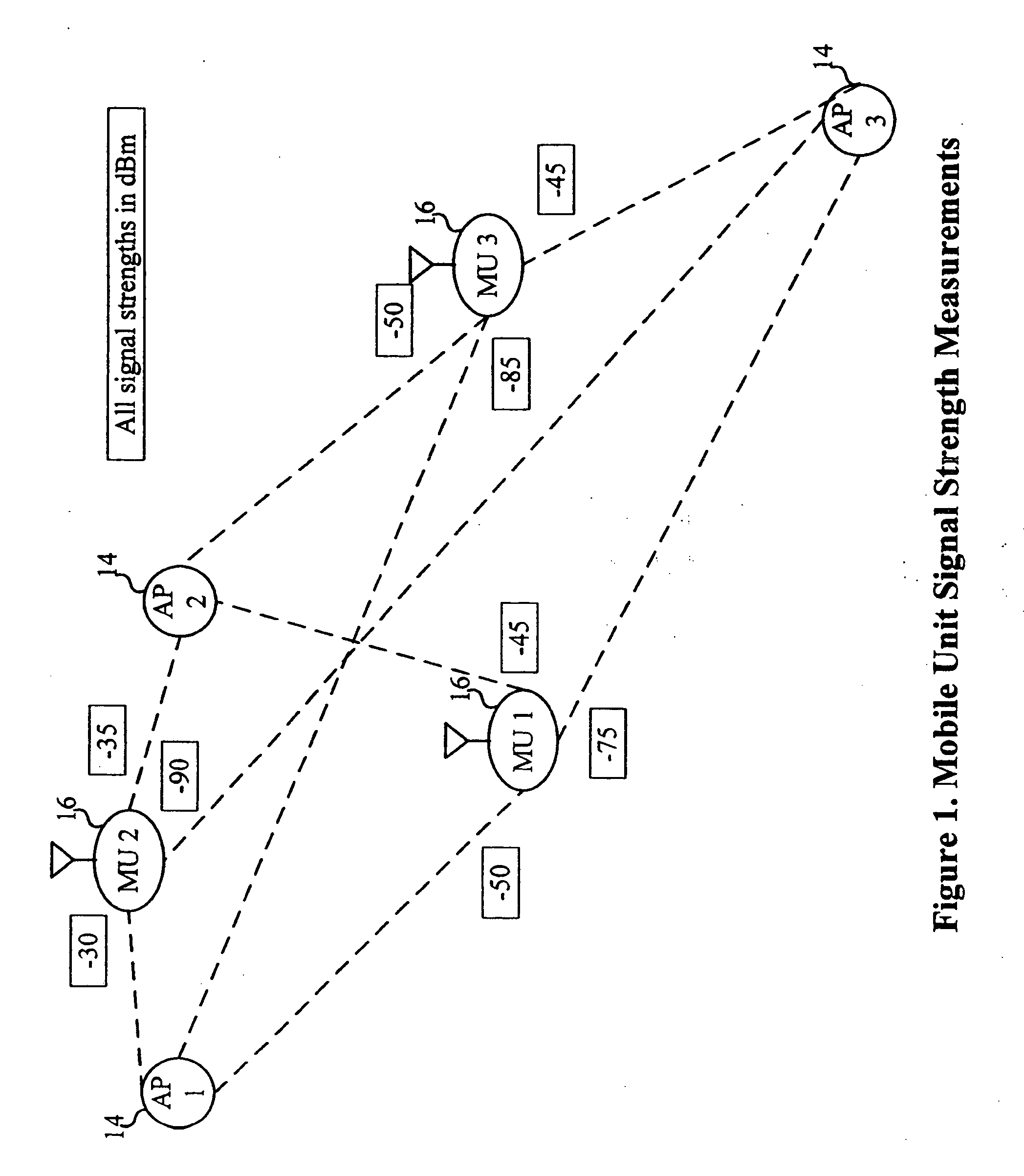
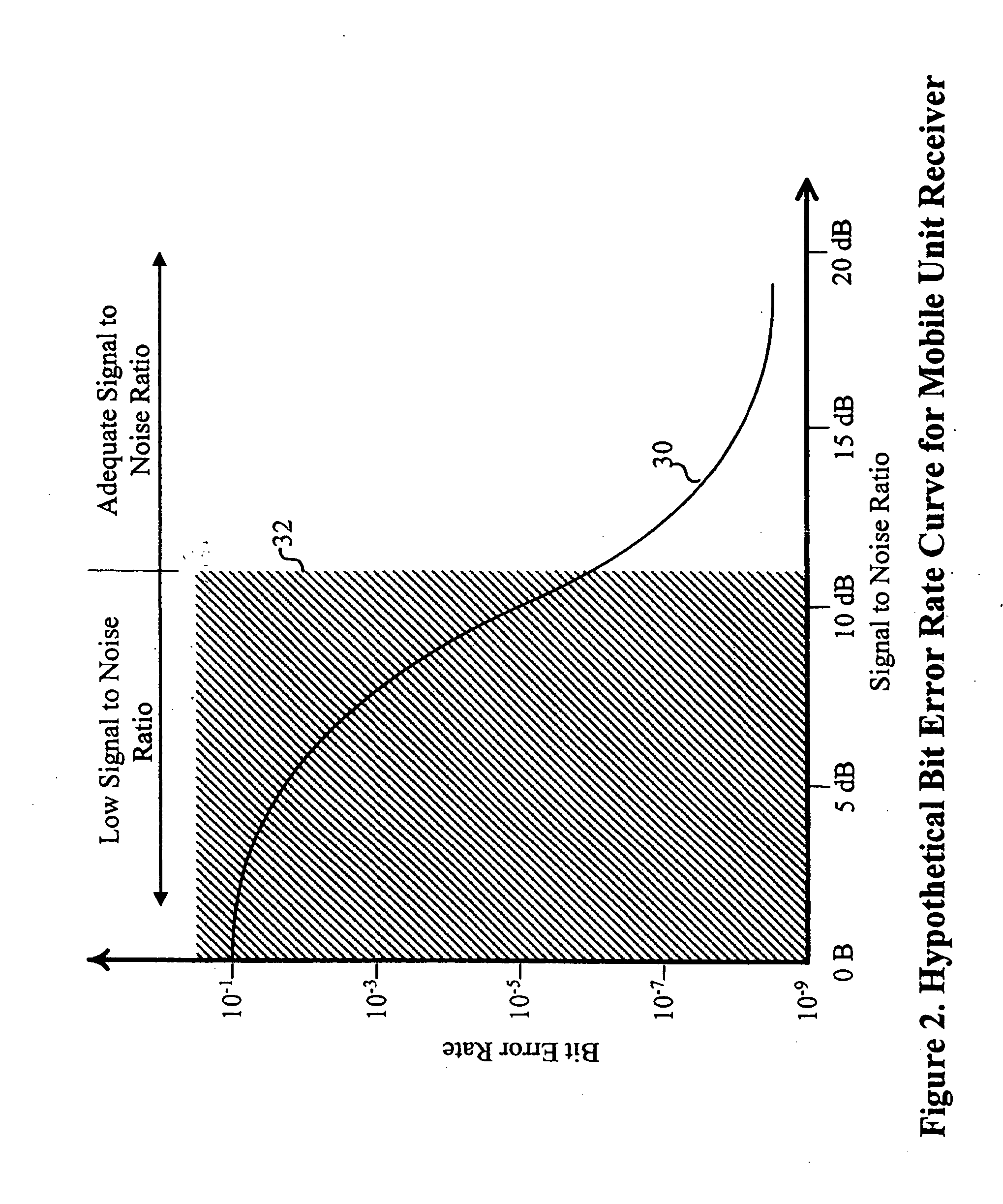
A system and method are disclosed for the management of WLANs in cases where unmanaged access points are present as well as with the addition or removal of access points. The disclosed system and method use signal data and network traffic statistics collected by mobile units to determine optimal configuration settings for the access points. The access point settings so managed can include the operating channel or center frequency, orthogonal signal coding used (optionally including the data rate), if any, and the transmission power. The solutions computed can account for the inherent trade-offs between wireless network coverage area and mutual interference that may arises when two or more access points use the same or overlapping frequency bands or channels and the same or similar signal coding.
Owner:WAVELINK
Diagnosis of embedded, wireless mesh networks with real-time, flexible, location-specific signaling
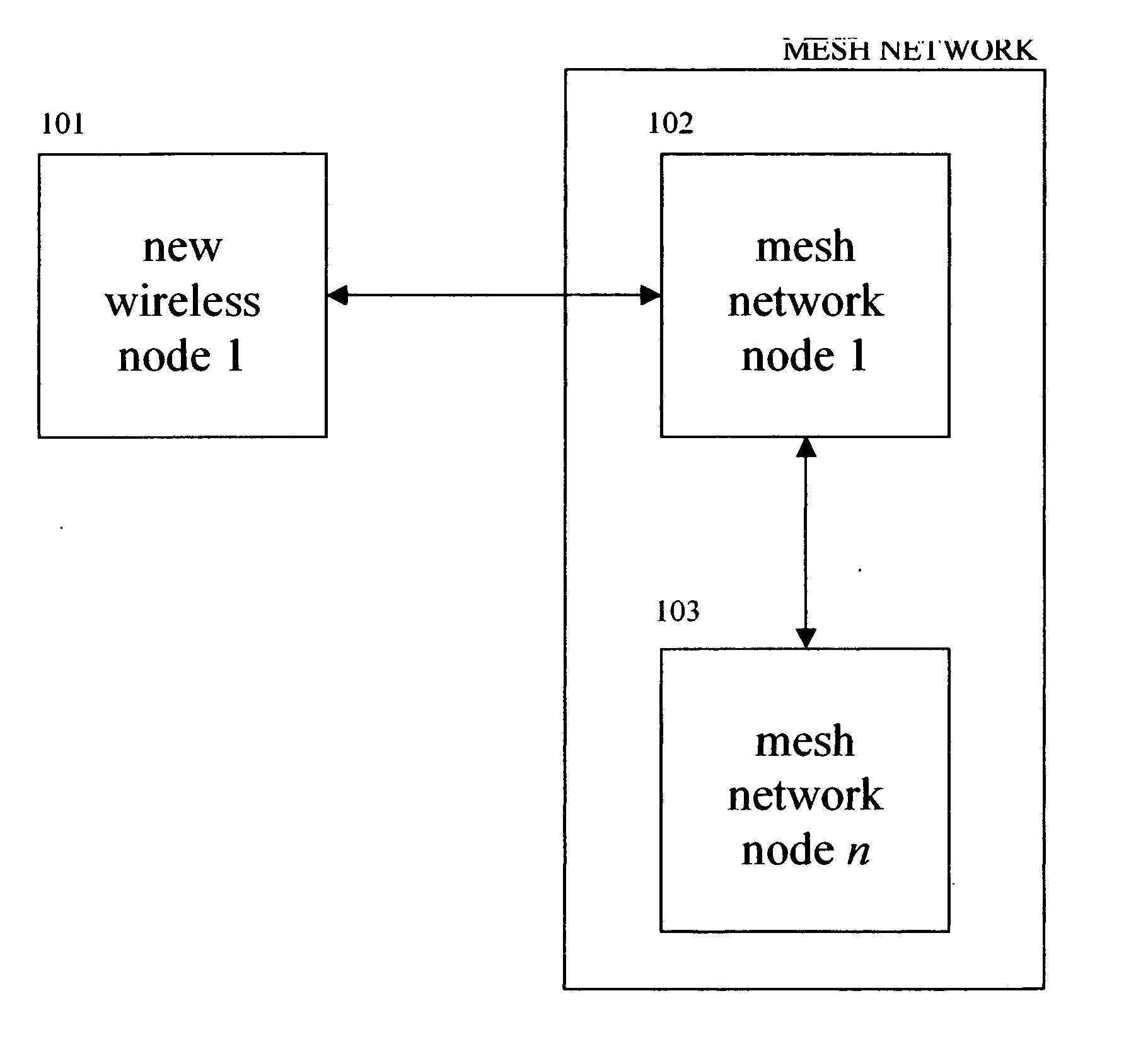
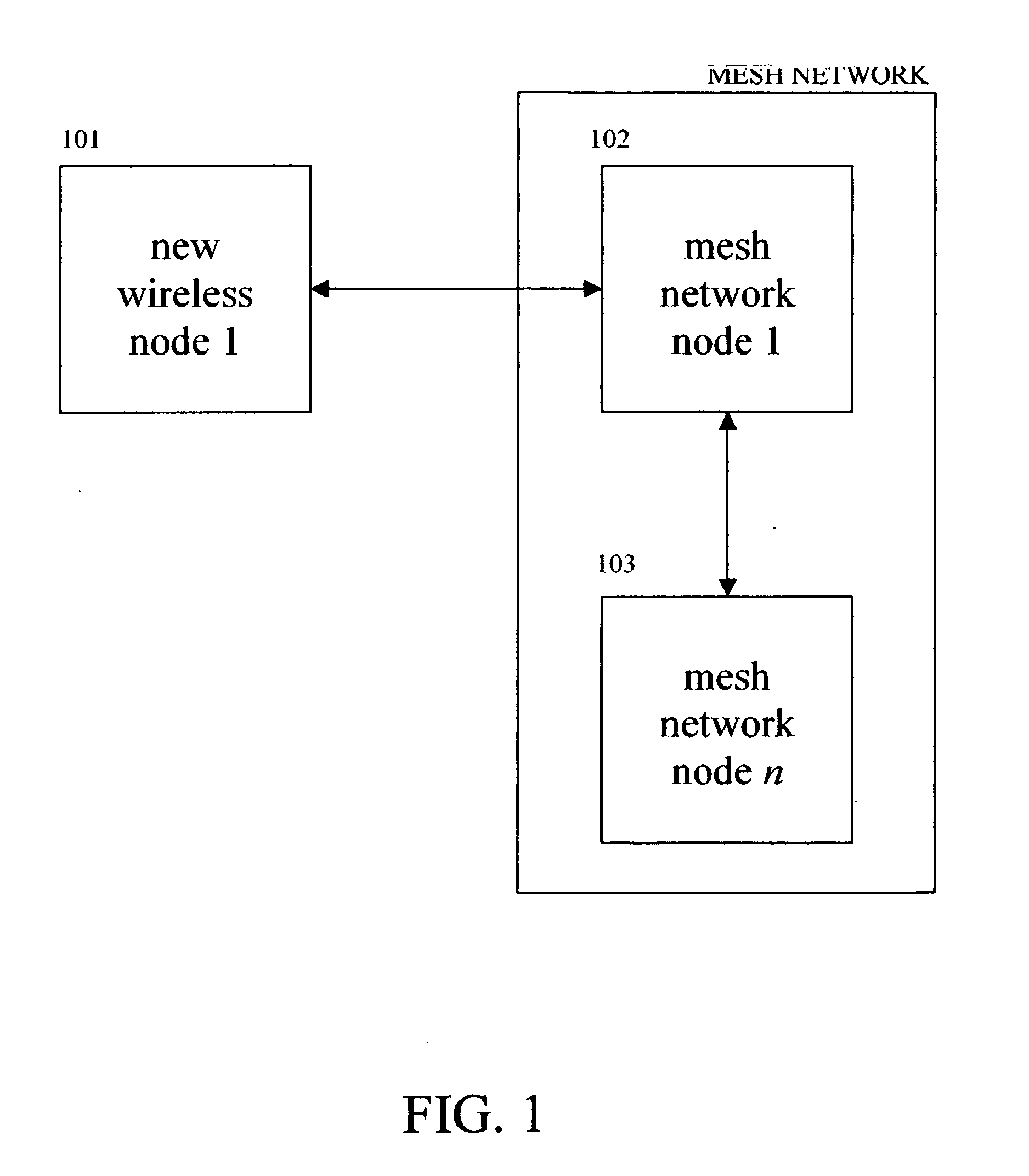
InactiveUS20050201297A1More specificityError preventionFrequency-division multiplex detailsWireless mesh networkNetsniff-ng
A system for optimizing the security of data communication on wireless mesh networks invention uses existing mesh network nodes to control new nodes that attempt to join the network. In a preferred embodiment, this is achieved by (1) testing that a new node is “clean” before allowing it to join the wireless mesh network by scanning the new node for viruses, checking for security patches, etc., (2) quarantining an “infected” node from joining the wireless mesh network until it is cleaned, (3) signaling other nodes in the existing mesh network that a node is either “infected” or “clean”, (4) cleaning a new node by supplying it with antivirus software, vendor patches, etc. from nearby nodes in the existing wireless mesh network, (5) updating the wireless mesh network in real time with a list of clean and infected nodes, and (6) performing the above steps without the need for a central, controlling server.
Owner:PEIKARI CYRUS
Method for resource optimized network virtualization overlay transport in virtualized data center environments
ActiveUS20150195178A1Error preventionFrequency-division multiplex detailsTransport systemData center
A method for resource optimized network virtualization overlay transport in a virtualized data center environment includes an optimized virtualized transport mechanism based on MPLS-TP tunneling technology. The transport mechanism may include a usage monitoring and resource usage advertisement mechanism based on IGP-TE protocol extension. Also, the transport mechanism may include a path computation engine (PCE) based optimal path computation for a virtualized transport tunnel used to carry VM-to-VM traffic across the virtualized data center. Additionally, the transport mechanism may include a SDN controller for provisioning and control of virtualized machines and a virtualized transport system.
Owner:CIENA
Method and System for Mobile Network Security, Related Network and Computer Program Product
ActiveUS20090144823A1Easy to scanReduce overheadMemory loss protectionUnauthorized memory use protectionUser deviceDevice status
A honeypot system for protecting a mobile communication network against malware includes one or more user-less mobile devices including a monitoring module for monitoring the events conveying software applications in the associated mobile device as well as a controller client module that emulates human-like interaction with the user-less devices as a function of the events monitored. The system controllably performs, for the applications conveyed by the events monitored, one or more of the following steps: i) installing the application on the device; ii) executing the application installed on the device; and iii) de-installing the application from the- device. After any of these steps, the state of the device is checked in order to detect if any anomalous variation has occurred in the state of the device indicative of the device being exposed to the risk of malware. If any anomalous variation is detected, the system issues a malware alert message.
Owner:TELECOM ITALIA SPA
Matching network system for mobile devices
InactiveUS20080133716A1Rich web experienceMore granular and targeted accessServices signallingMultiple digital computer combinationsNetworked systemNetwork service
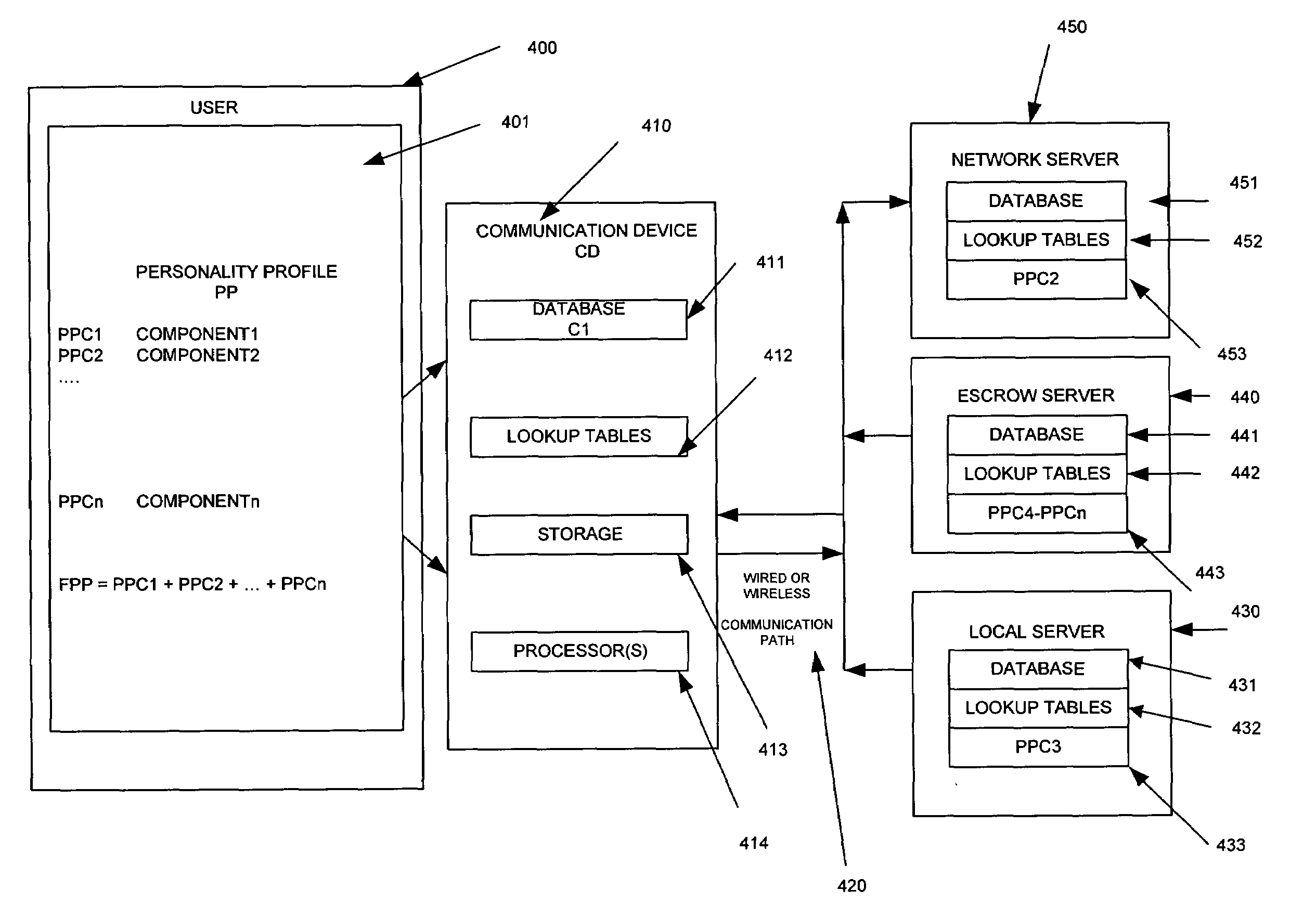
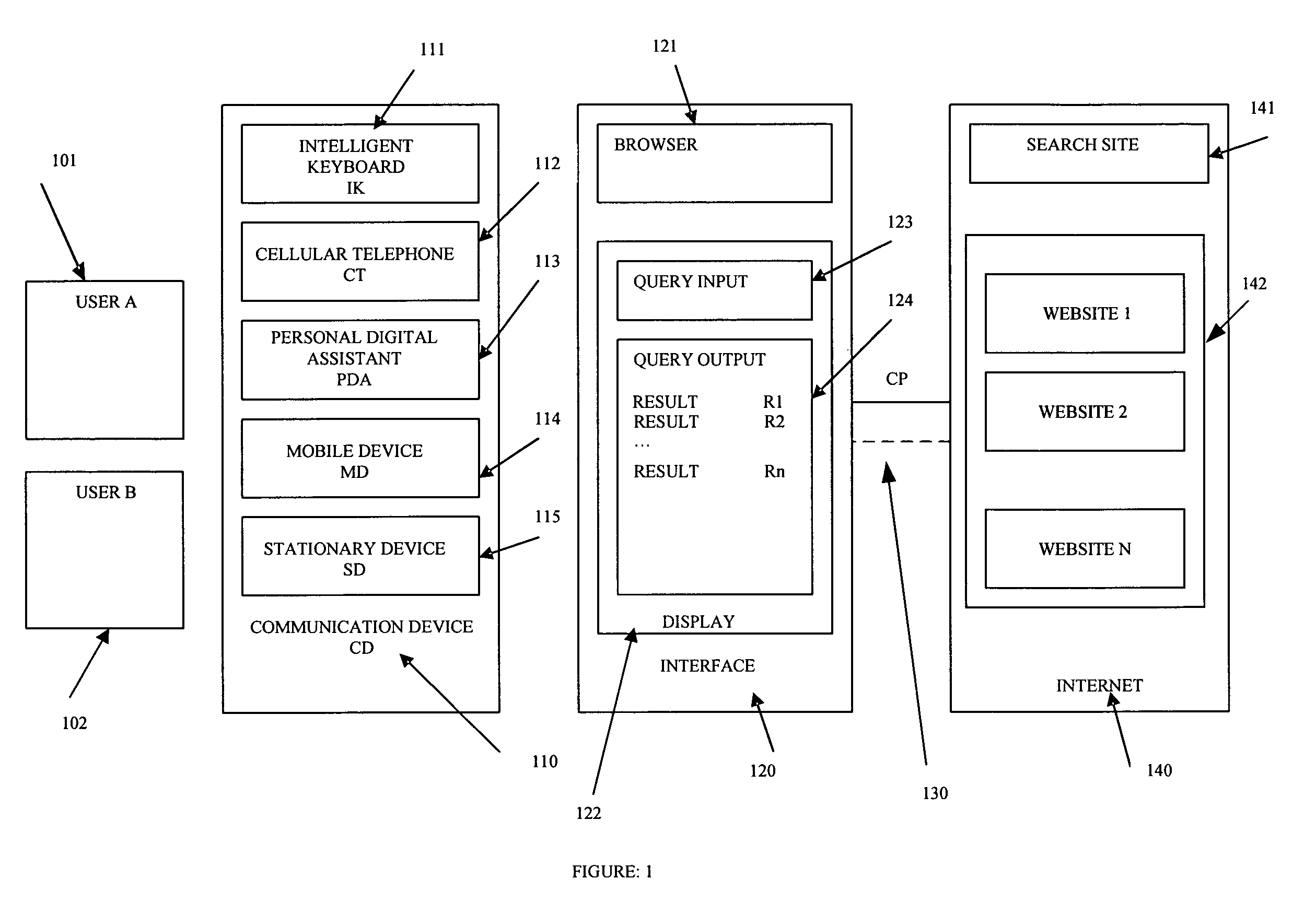
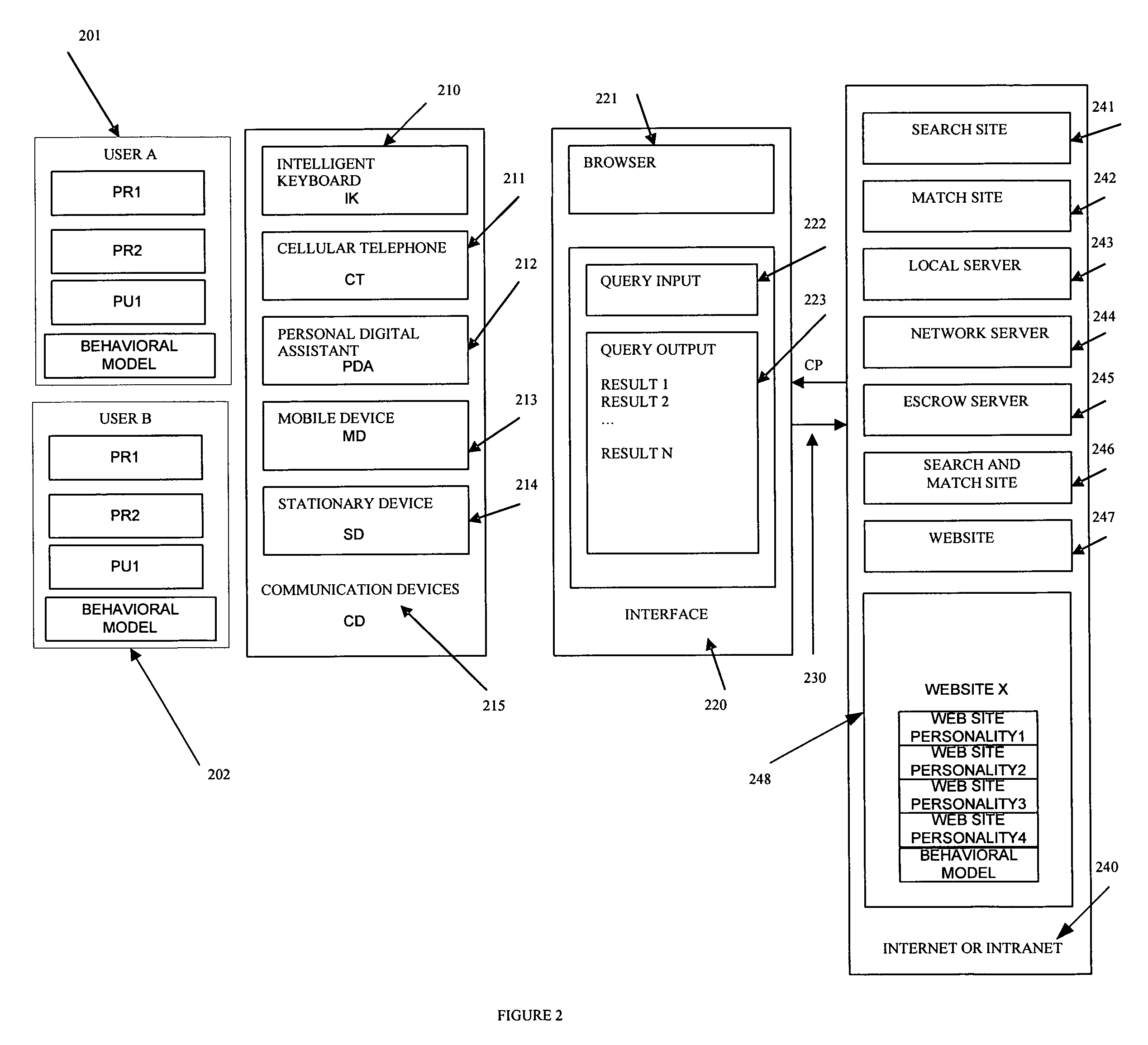
A matching network system including communication devices, servers and software which enables the provisioning of services and execution of transactions based on a plurality of private and public personality profiles and behavior models of the users, of the communication devices, of the products / services and of the servers; in combination with the software resident at the communication device level and or the local / network server level. Matching and searching processes based on a plurality of personality profiles wherein the information, communication and transactions are enabled to be matched with the user, the communication device and or the servers. The communication device is a stationary device or a mobile device, such as a portable computing device, wireless telephone, cellular telephone, personal digital assistant, or a multifunction communication, computing and control device.
Owner:IP HLDG LLC
Router, frame forwarding method, and lower layer frame virtual forwarding system
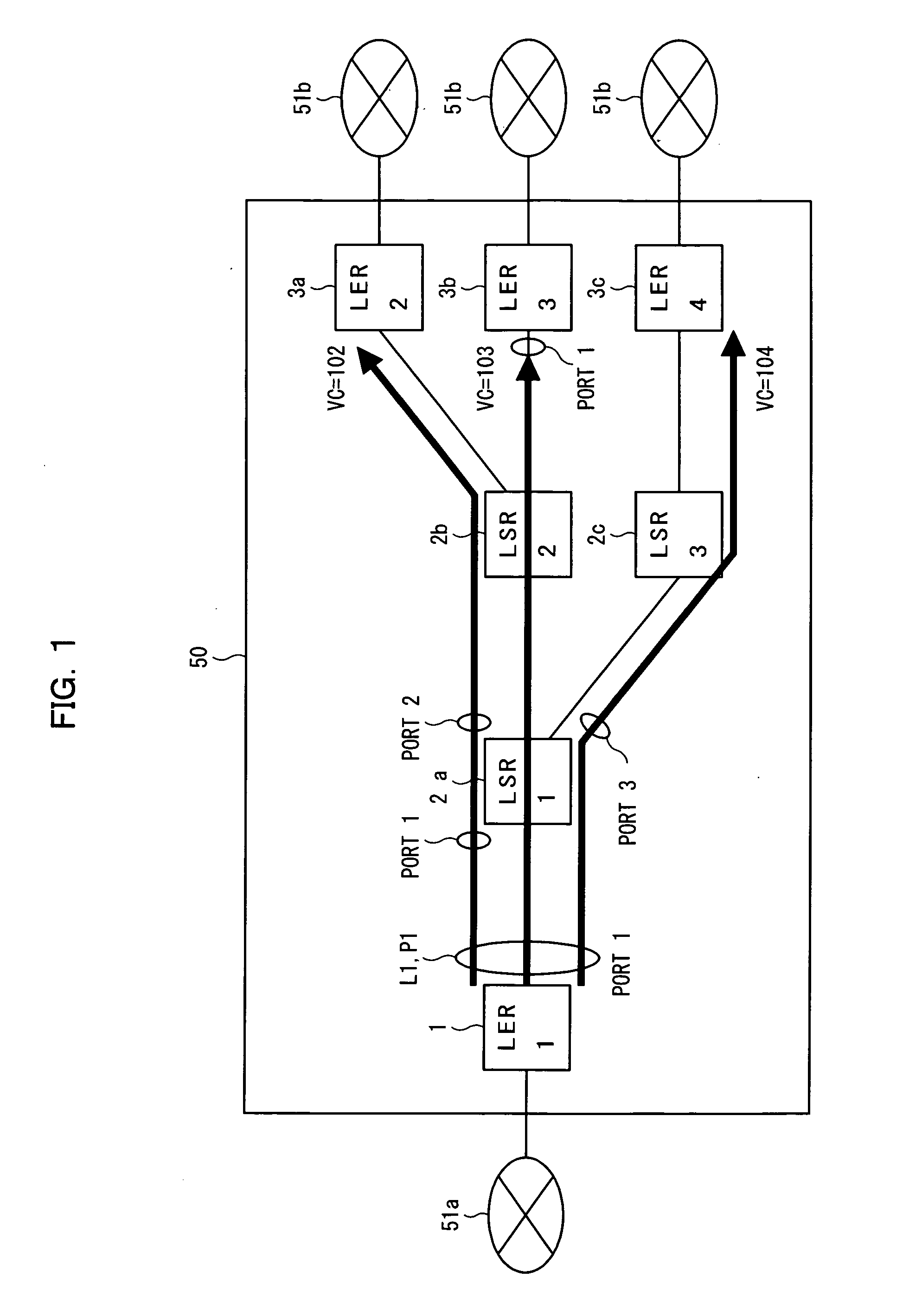
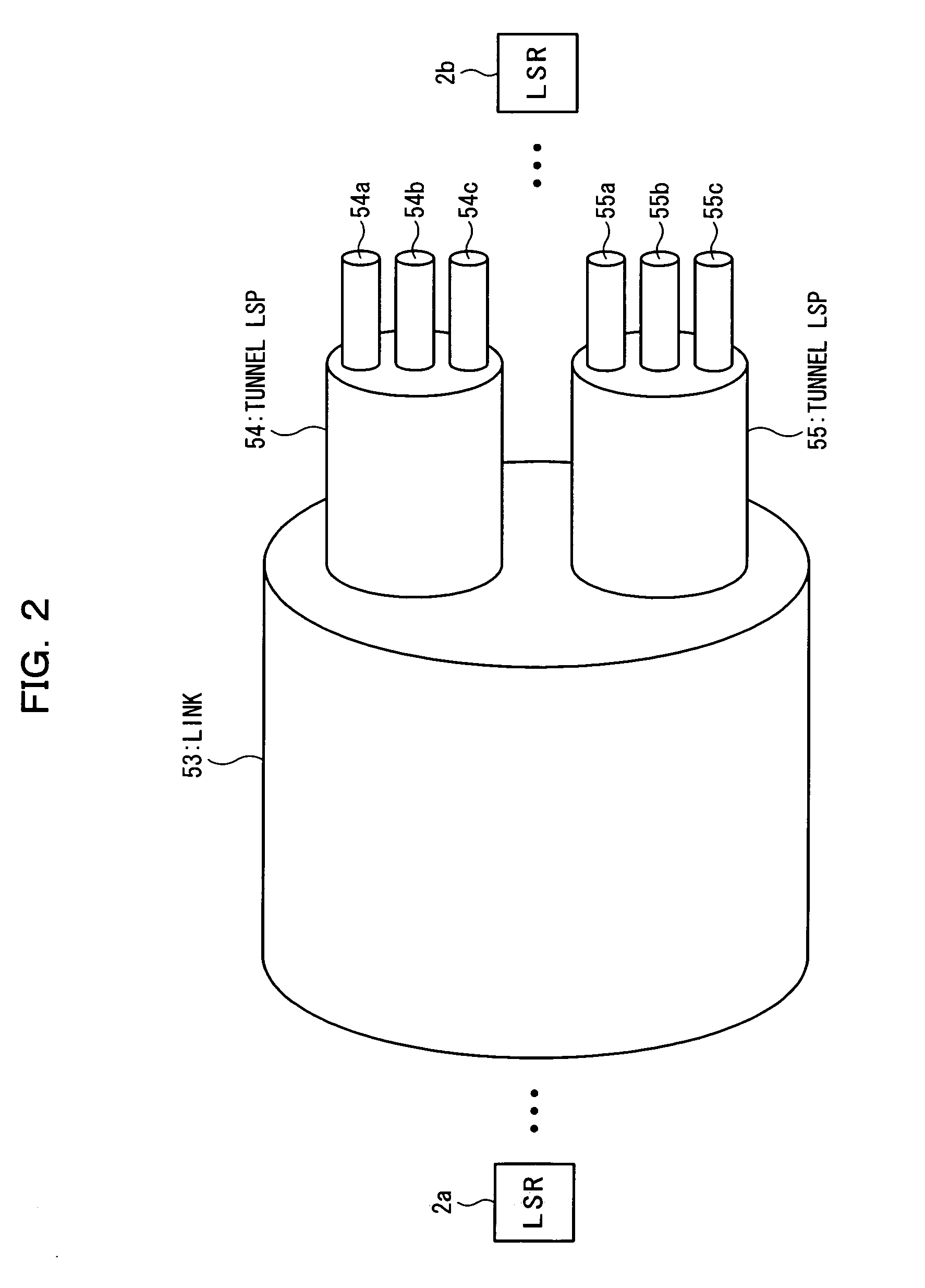
InactiveUS20050169270A1Avoid loadEasy to useTime-division multiplexNetworks interconnectionPhysical addressLabel switching
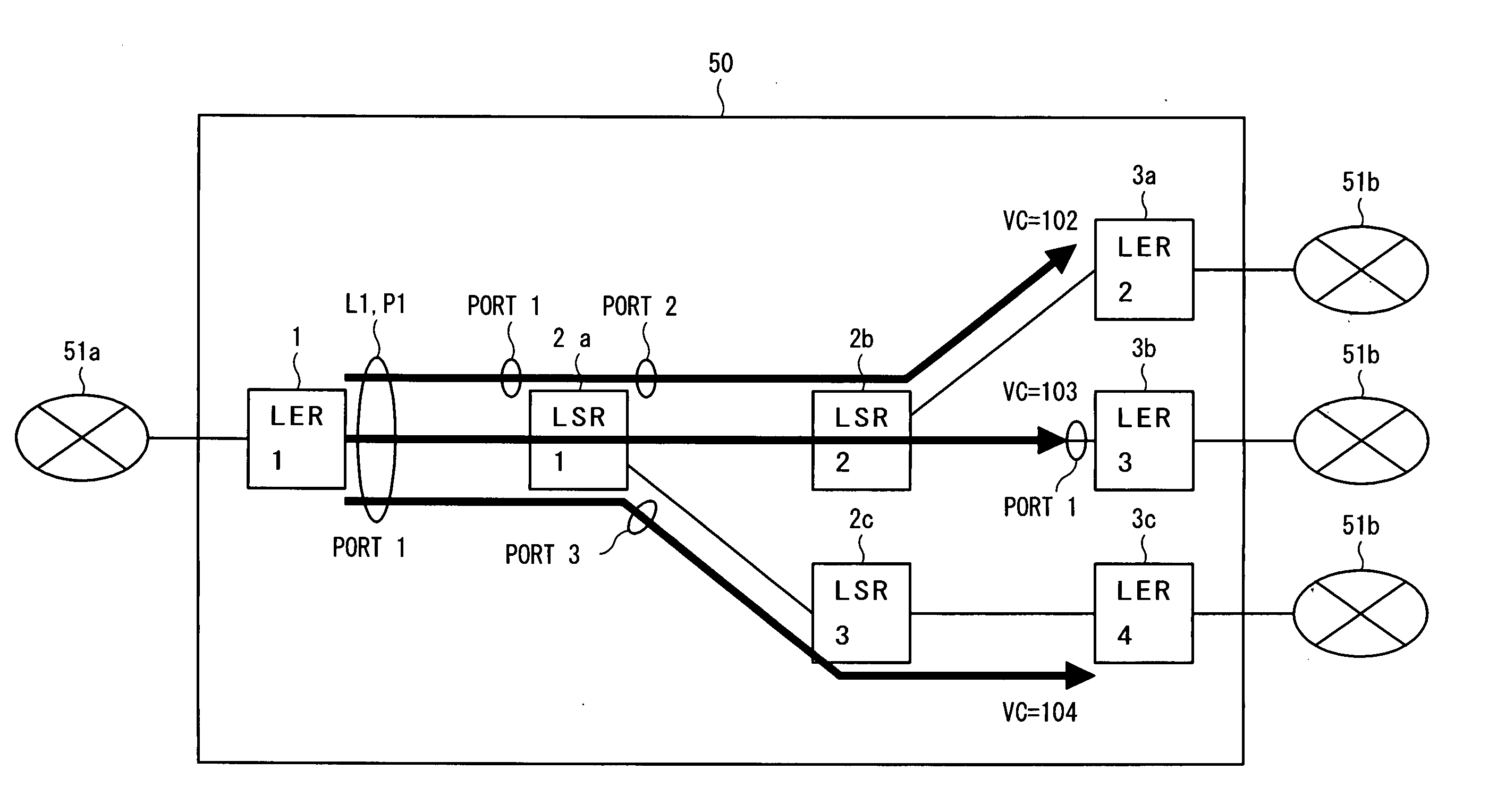
In an MPLS network, multicast, broadcast and address learning belonging to the layer 2 functions are realized. An ingress router comprises a frame receiving unit, a determining unit, a first frame transmitting unit, a physical address table for multicast, a label switching unit, a tunnel label table, a VCID giving unit, a L2 header creating unit and a second frame transmitting unit. The load on the network is suppressed, the band is efficiently used, and wasteful frame duplication and frame forwarding between edge routers are avoided.
Owner:FUJITSU LTD
Centralized Dynamic Security Control for a Mobile Device Network
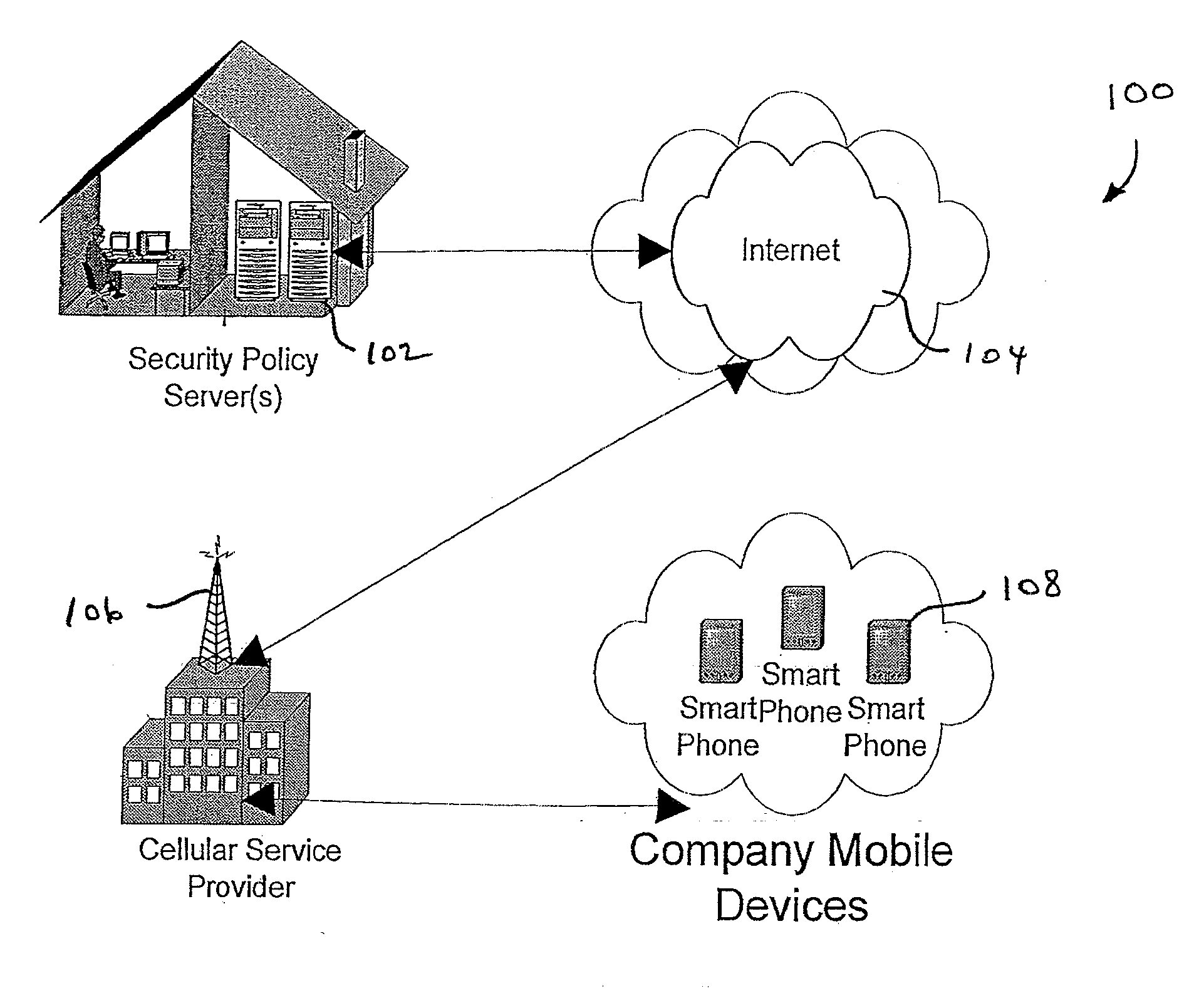
InactiveUS20070266422A1Well formedSecurity arrangementSpecial data processing applicationsTimerSecurity system
An security system for an enterprise network and data automates the revision, deployment, enforcement, auditing and control of security policies on mobile devices connected to said enterprise network, through automated communication between a security policy server and the mobile device. Control of the security system is centralized through administrative control of security policies stored on the security policy server. Automation of deployment of security policies to mobile devices occurs through transparent background communication and transfer of updated policies either triggered by a change in a security policy within the central repository of security policies or upon the expiration of a certain time period during which no policies were downloaded to the mobile device. When the mobile device is not in compliance with a security policy, a software security agent operating thereon limits access to said enterprise network and enterprise data. To aid in preventing the overwhelming of the enterprise network and the security policy server as a result of to many synchronization communications coming from too many mobile devices, a randomized timer is set by the software security agent upon receipt by the mobile device of a synchronization command from the security policy server.
Owner:SQUARE 1 BANK
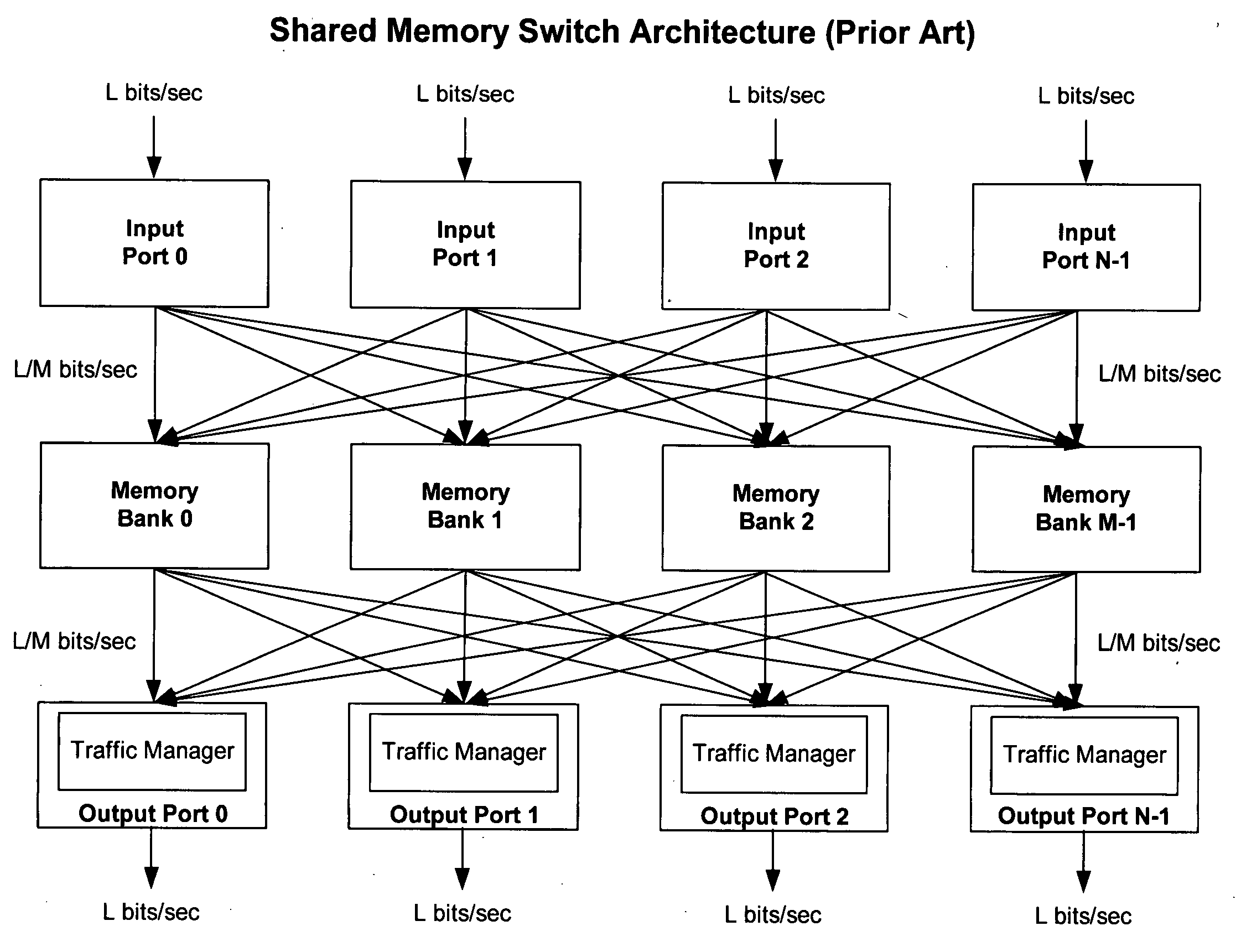
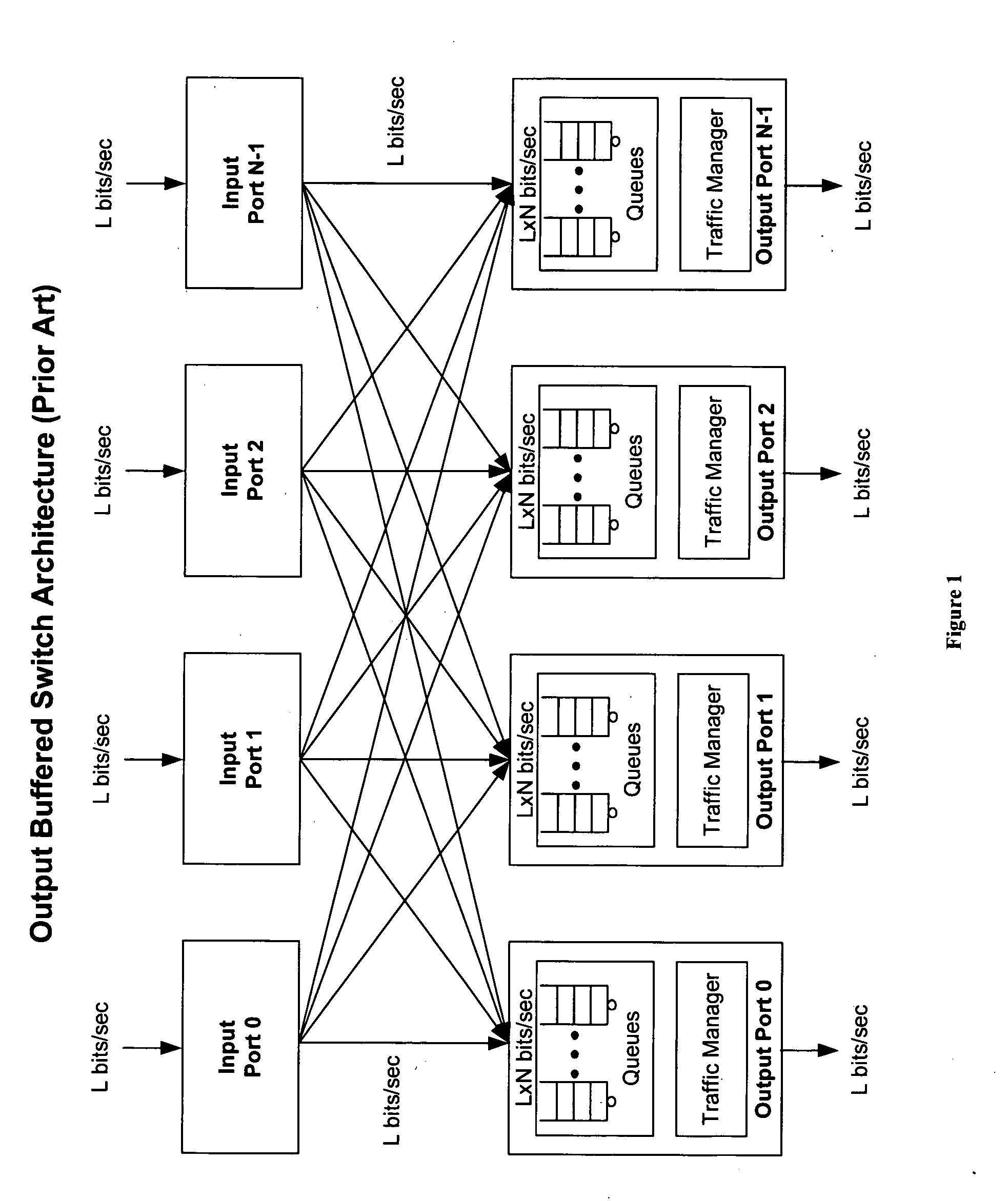
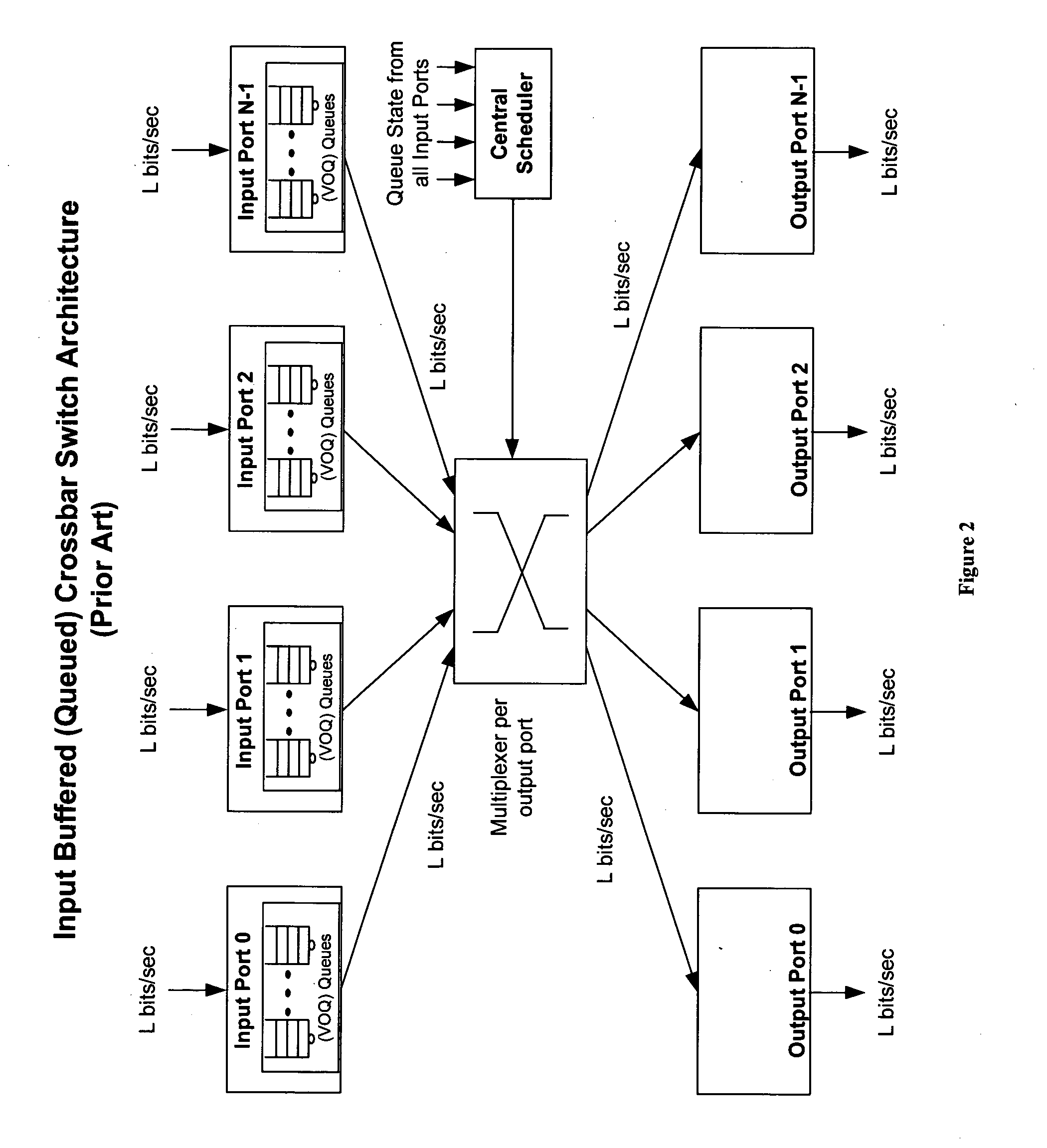
Method of and system for physically distributed, logically shared, and data slice-synchronized shared memory switching
An improved data networking technique and apparatus using a novel physically distributed but logically shared and data-sliced synchronized shared memory switching datapath architecture integrated with a novel distributed data control path architecture to provide ideal output-buffered switching of data in networking systems, such as routers and switches, to support the increasing port densities and line rates with maximized network utilization and with per flow bit-rate latency and jitter guarantees, all while maintaining optimal throughput and quality of services under all data traffic scenarios, and with features of scalability in terms of number of data queues, ports and line rates, particularly for requirements ranging from network edge routers to the core of the network, thereby to eliminate both the need for the complication of centralized control for gathering system-wide information and for processing the same for egress traffic management functions and the need for a centralized scheduler, and eliminating also the need for buffering other than in the actual shared memory itself,—all with complete non-blocking data switching between ingress and egress ports, under all circumstances and scenarios.
Owner:QOS LOGIX
Optimizing Distributed Computer Networks
ActiveUS20120089664A1Uniform applicationIncrease flexibility and efficiency and accelerationMultiple digital computer combinationsProgram controlClient-sideNetwork service
In one general embodiment, a computer-implemented method for managing a distributed computer network performed by one or more processors includes the steps of: receiving a request from a client in the distributed computer network for a network service; optimizing a delivery of the requested network service to the client from a server in the distributed computer network; and monitoring an execution of the delivery of the network service.
Owner:SAP PORTALS ISRAEL
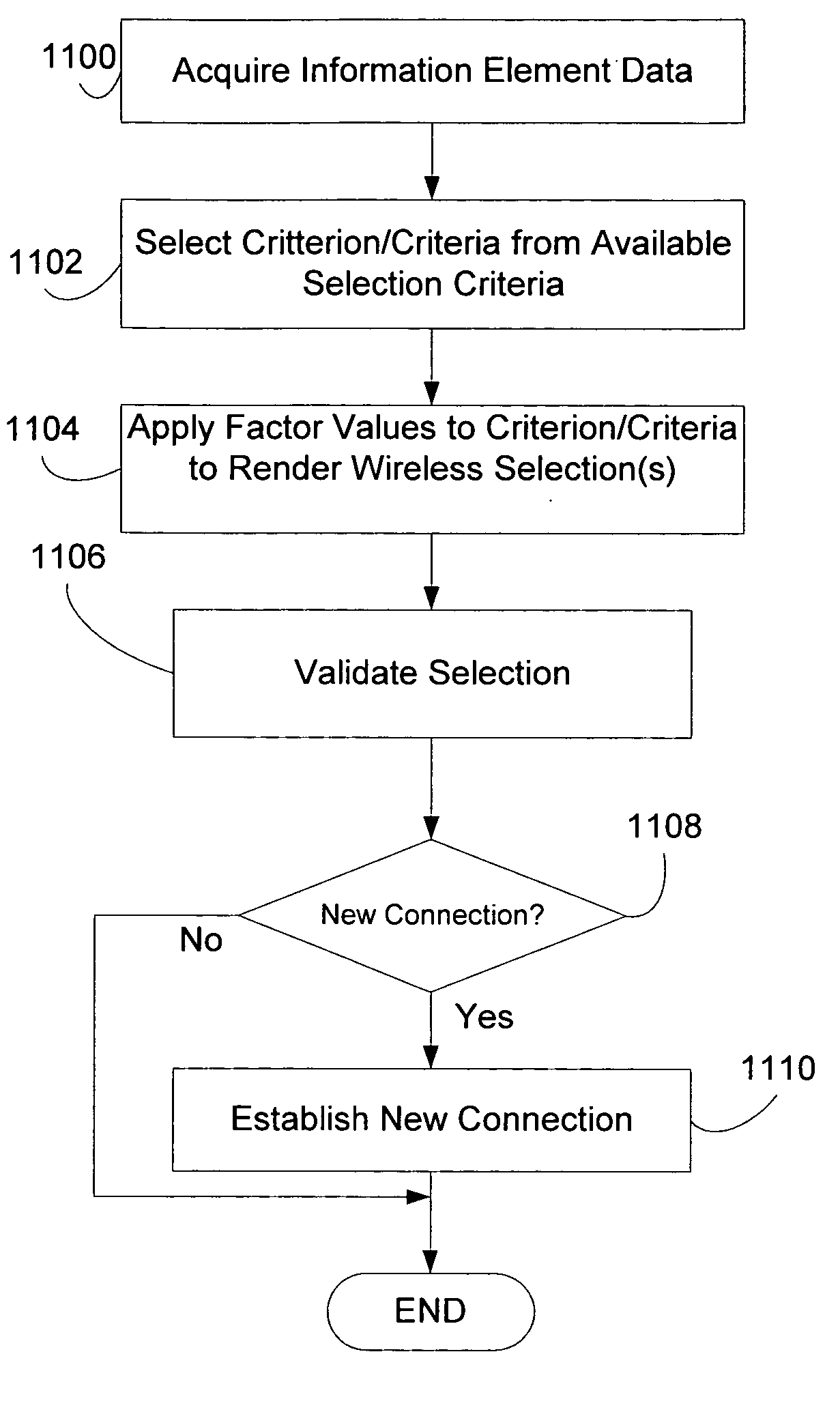
Selecting a wireless networking technology on a device capable of carrying out wireless network communications via multiple wireless technologies
InactiveUS20050239497A1Easy to implementFlushing devicesData switching by path configurationWeb access patternInterface selection
Criteria-driven methods and a framework are disclosed that facilitate configuration / selection of one or more wireless network interfaces / networks for carrying out wireless communications on a computing device. The wireless network interface selection and coexistence driver architecture described herein facilitates automated selection of a particular mode of network access based upon status information provided by a set of network interface drivers associated with particular network interfaces and wireless technologies. Furthermore, a criteria-driven interface / network selection framework is described that is potentially invoked in a variety of situations including, but not limited to, when an application is invoked or to select another interface / network to avoid detected interference.
Owner:MICROSOFT TECH LICENSING LLC
Multi-channel support for virtual private networks in a packet to ATM cell cable system
InactiveUS6917614B1Avoid compromiseExtension of timeBroadband local area networksFrequency-division multiplexQuality of serviceScheduling function
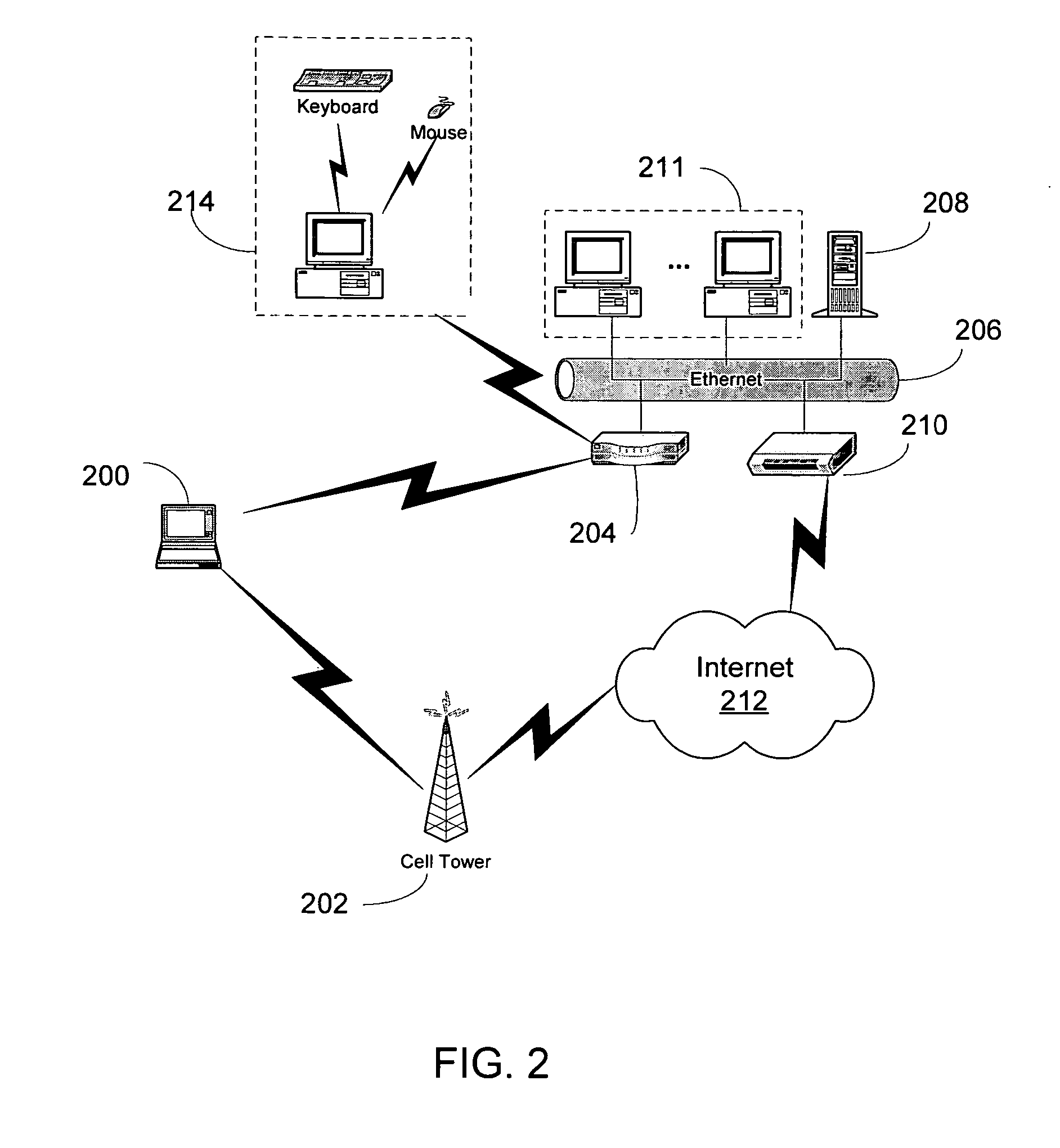
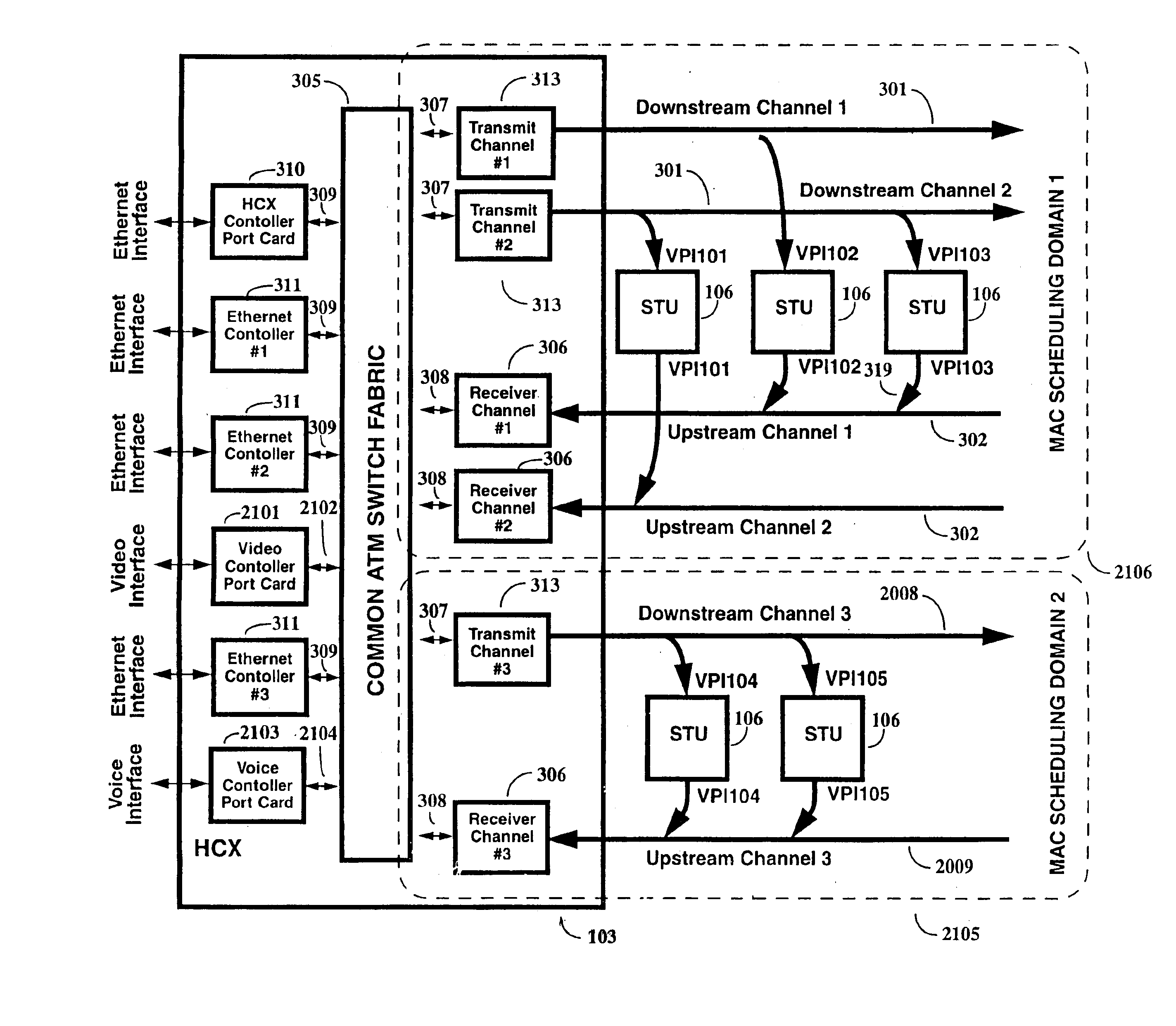
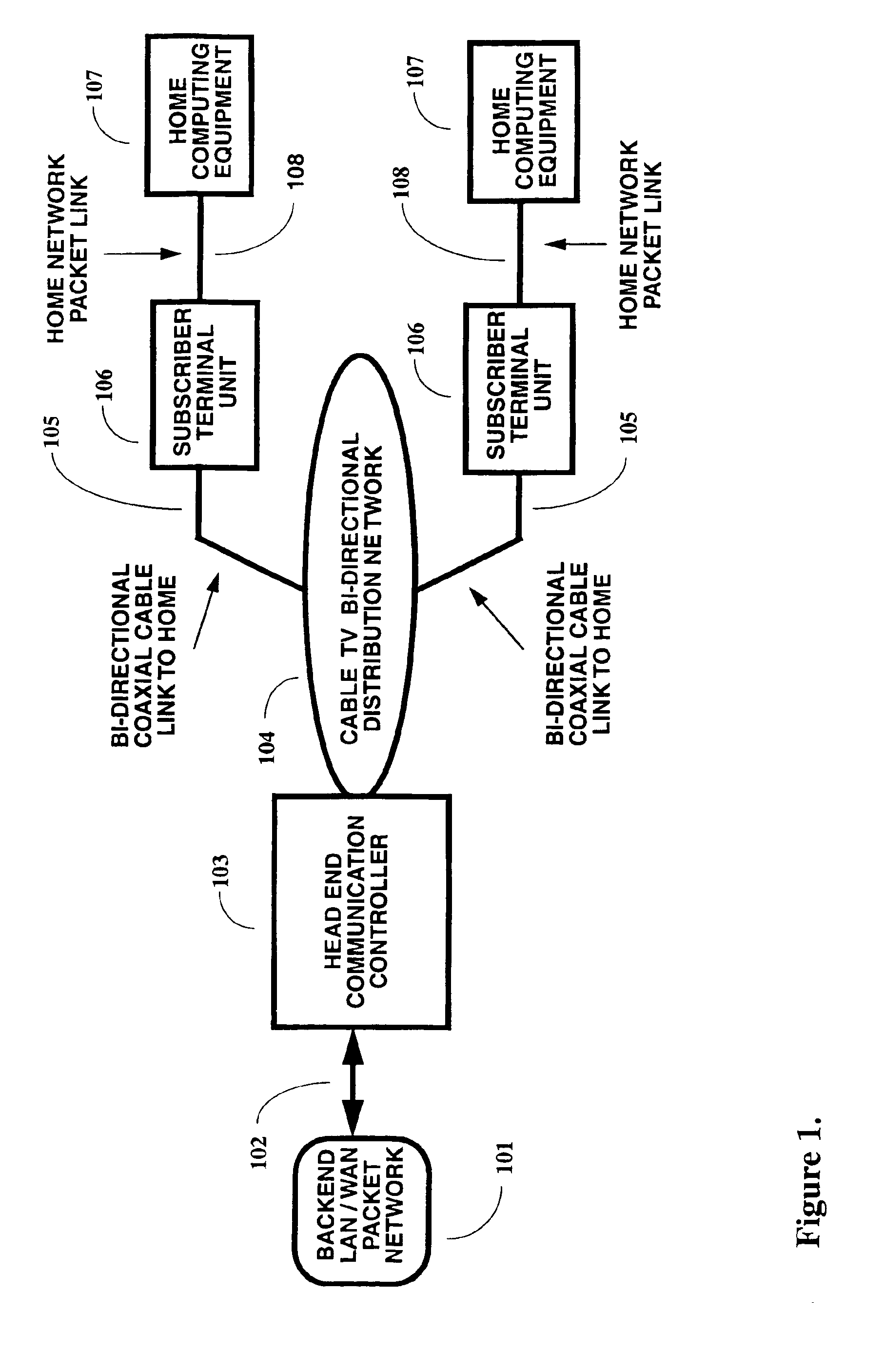
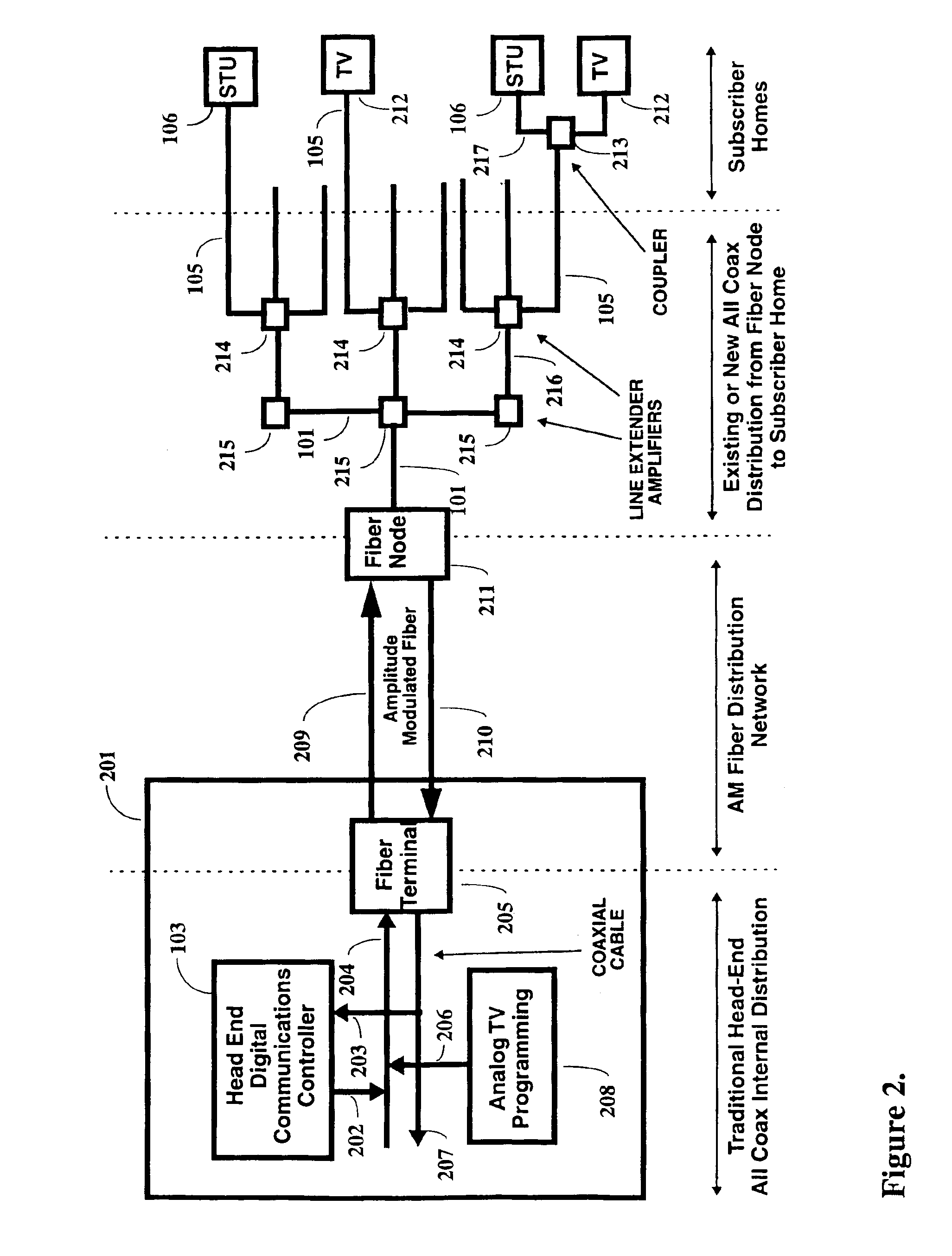
A two-way cable network offering high-speed broadband communications delivered via virtual private networks over a multi-channel shared media system. Bi-directional transmission of packet to ATM cell based communications is established between a head end communication controller and a number of subscriber terminal units, whereby individual cells are prioritized and routed according to a virtual connection. Virtual connections are organized to support multiple virtual private networks in a shared media CATV system. The virtual private network to which a particular STU belongs is user selectable and has the flexibility of handling multi up / downstream channels with different MAC domains. The present invention can also handle non-ATM MAC domains via the same common ATM switch. To overcome the limited number of addresses inherent to common ATM switches, a mapping / remapping function is implemented in the port cards. Furthermore, downstream as well as upstream traffic are filtered at each STU. In one embodiment, information pertaining to downstream traffic is used to implement predictive scheduling in order to improve the timing associated with the request / grant cycle. In another embodiment, a user has the ability to select a quality of service that best suits the needs of the current application. In a further embodiment, the scheduling function is associated with each of the receivers in order to provide improved scalability.
Owner:ARRIS ENTERPRISES LLC
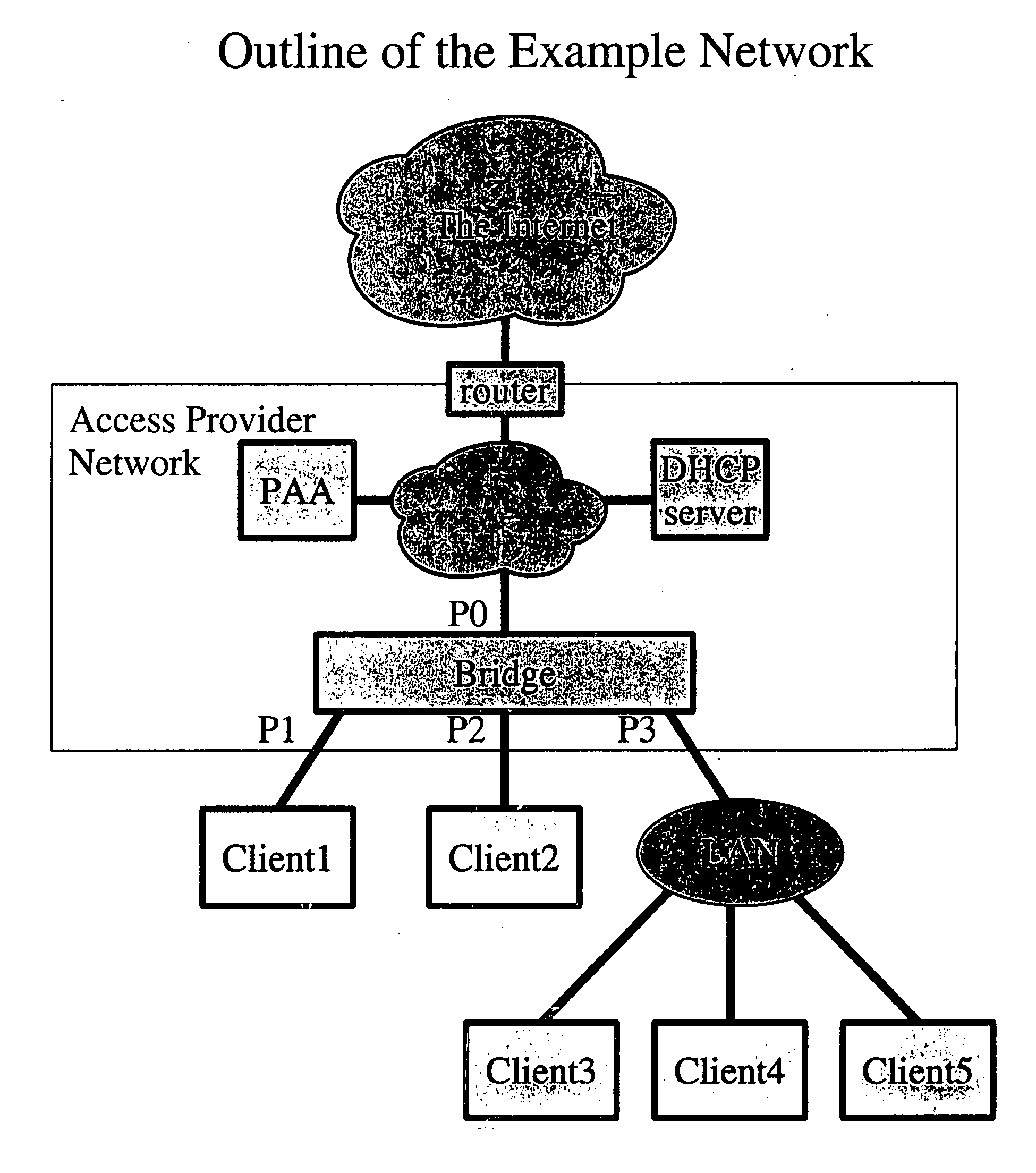
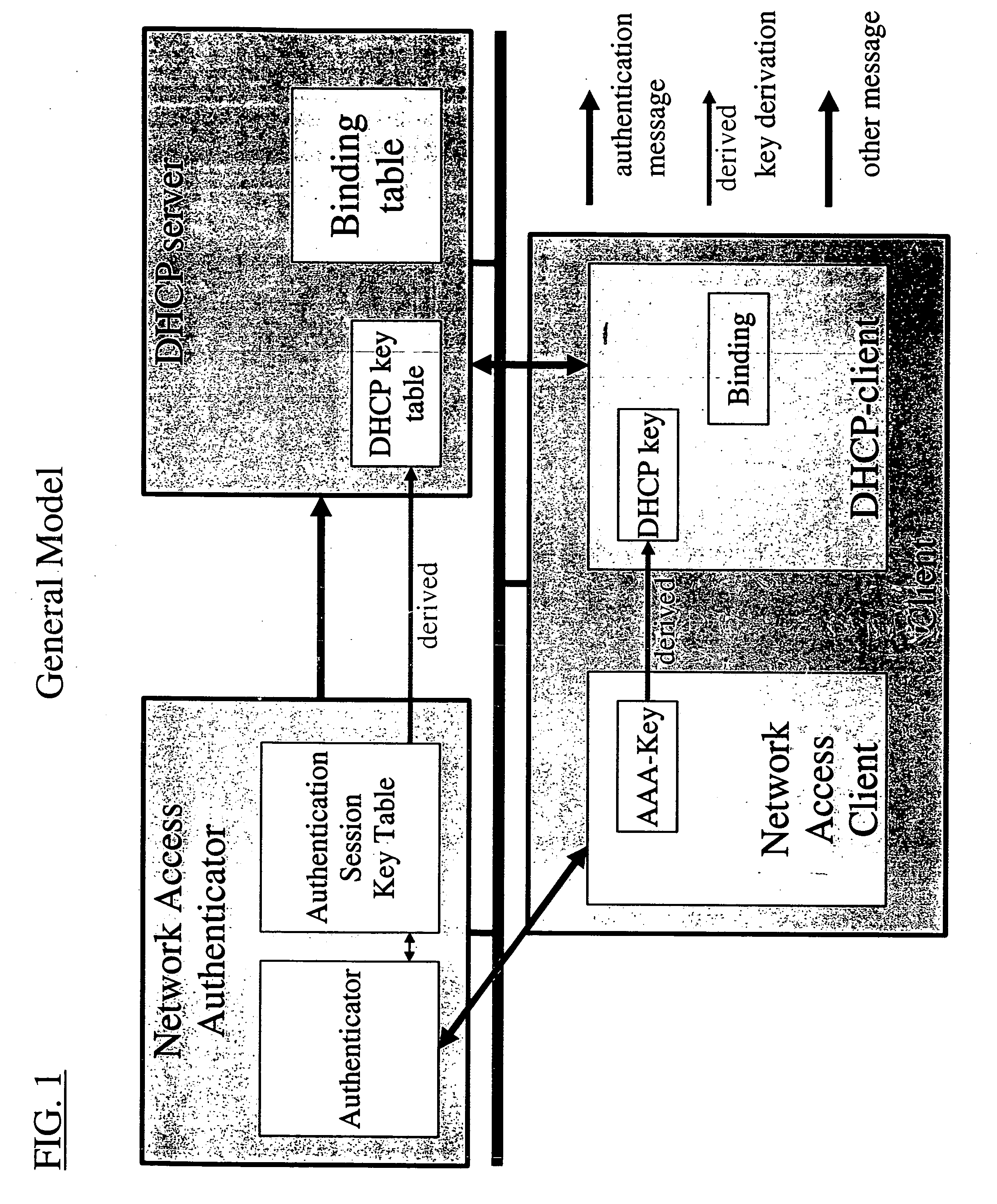
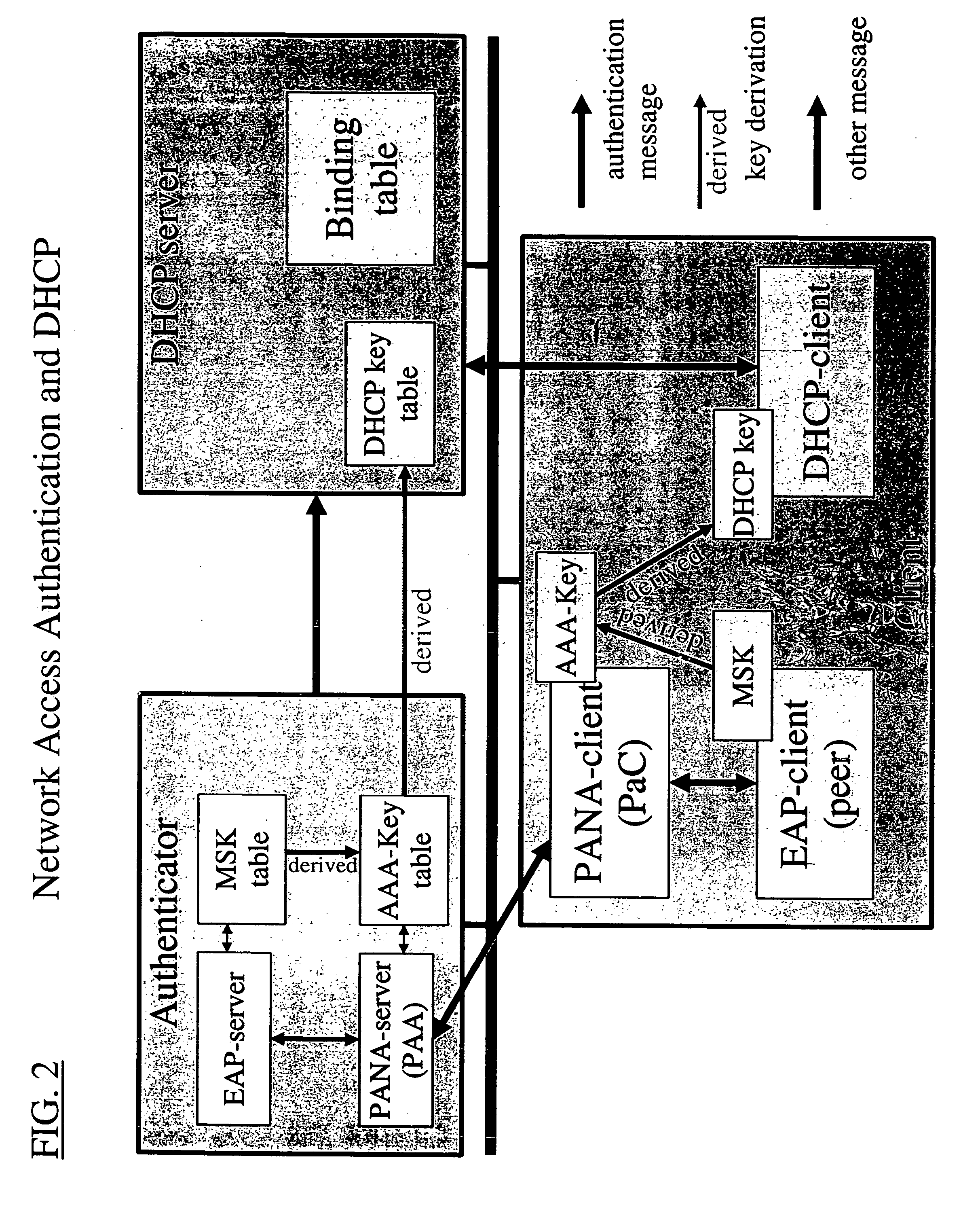
Dynamic host configuration and network access authentication
InactiveUS20060036733A1Digital computer detailsTransmissionIP multicastProtocol for Carrying Authentication for Network Access
Owner:FOUR BATONS WIRELESS LLC
Method and device for authenticated access of a station to local data networks in particular radio data networks
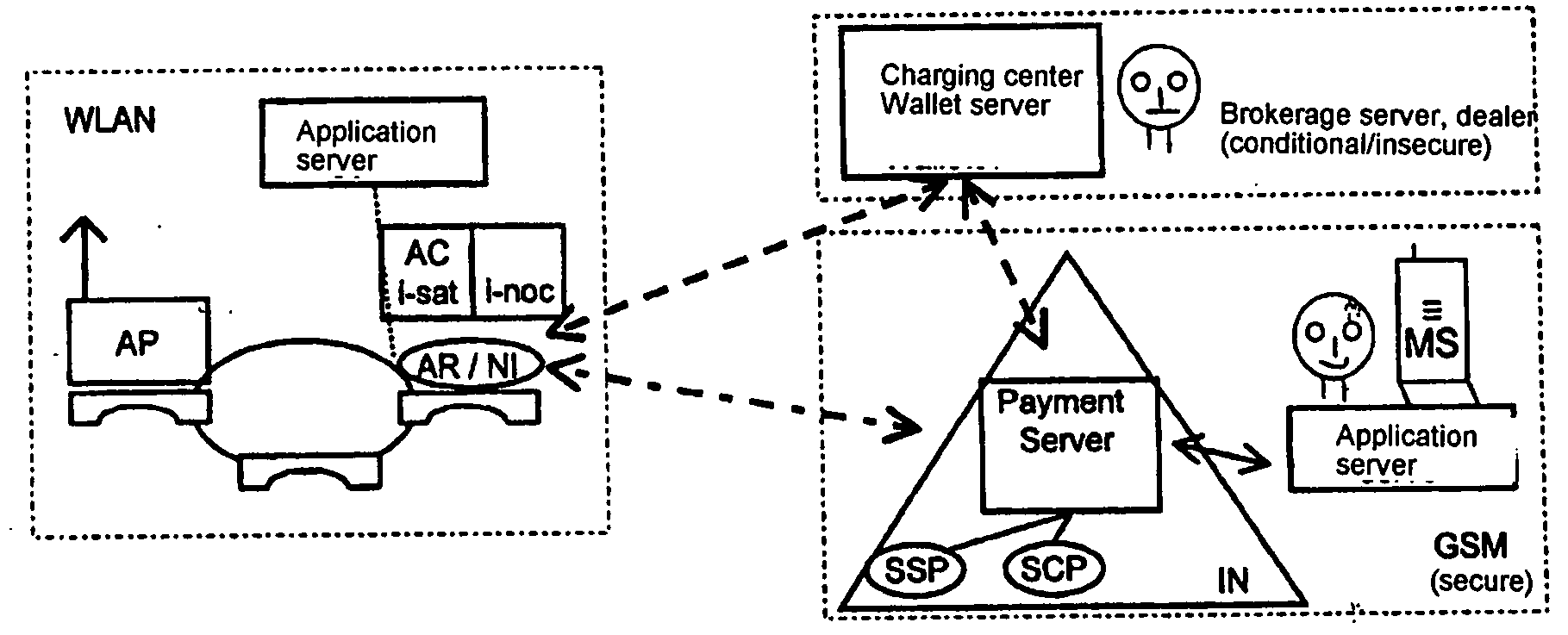
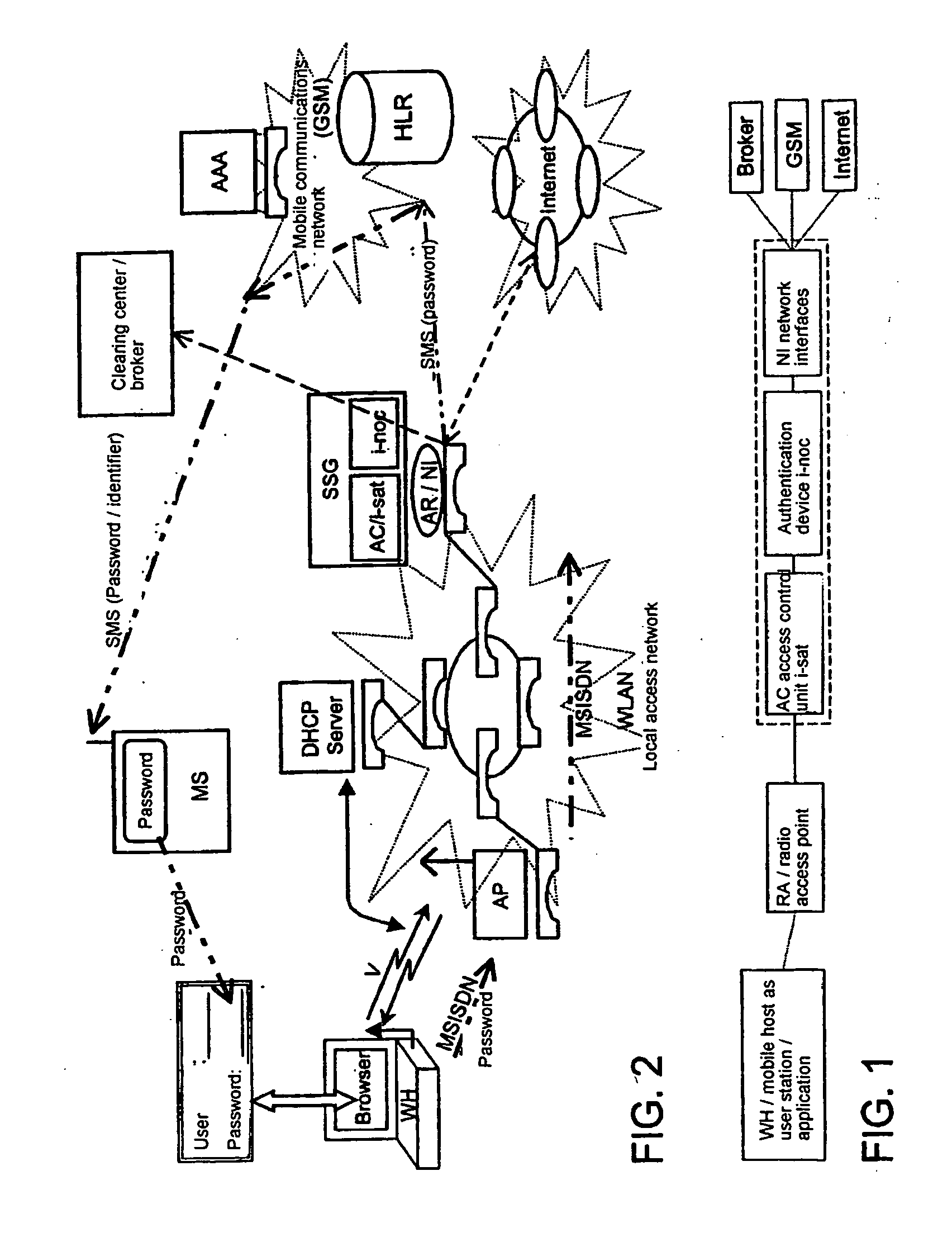
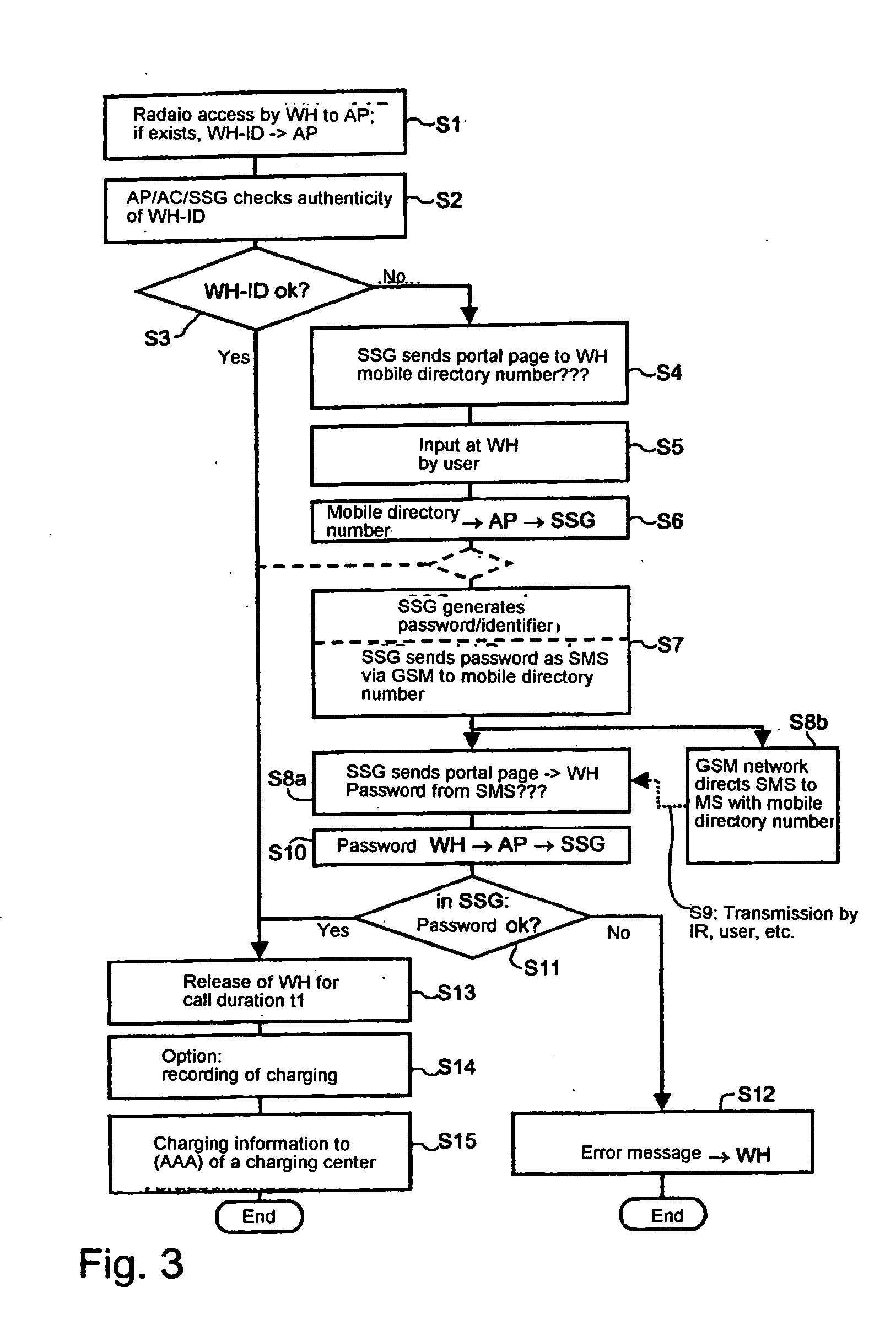
ActiveUS20050048950A1Authentication is simpleEasy to chargeMetering/charging/biilling arrangementsUnauthorised/fraudulent call preventionRadio equipmentCommunications system
The invention relates to methods, devices and systems for the authenticated access to a data network by means of a station (WH) compatible with a data network (WLAN), which permit an authentication of the station and user. A device, for example a mobile radio device, is used for the above, which is authenticated in another system. In addition to the authentication, in particular a charging of services in a data network or another communication system (GSM) which is accessible by means of the data network is thus possible.
Owner:MONARCH NETWORKING SOLUTIONS LLC
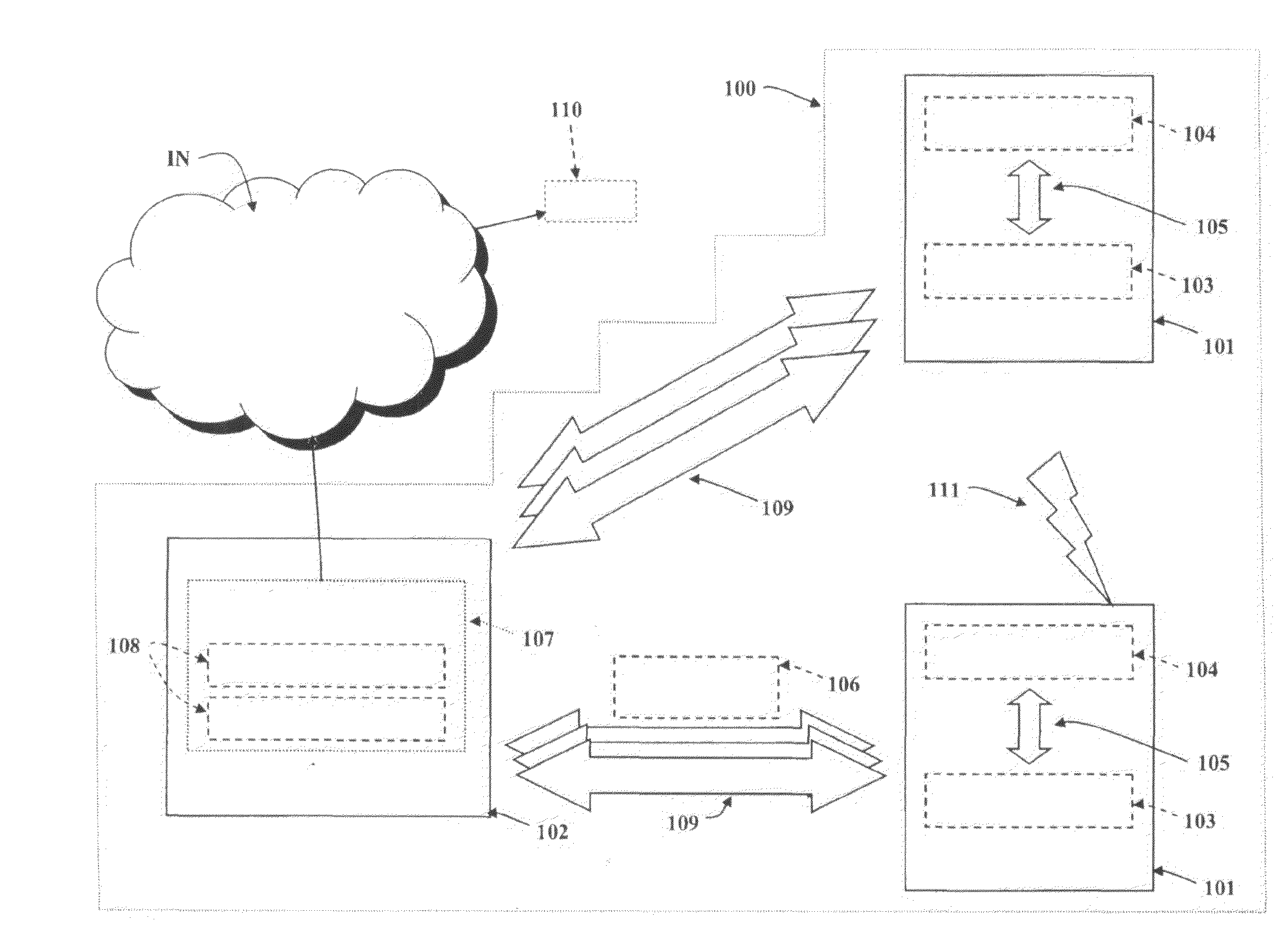
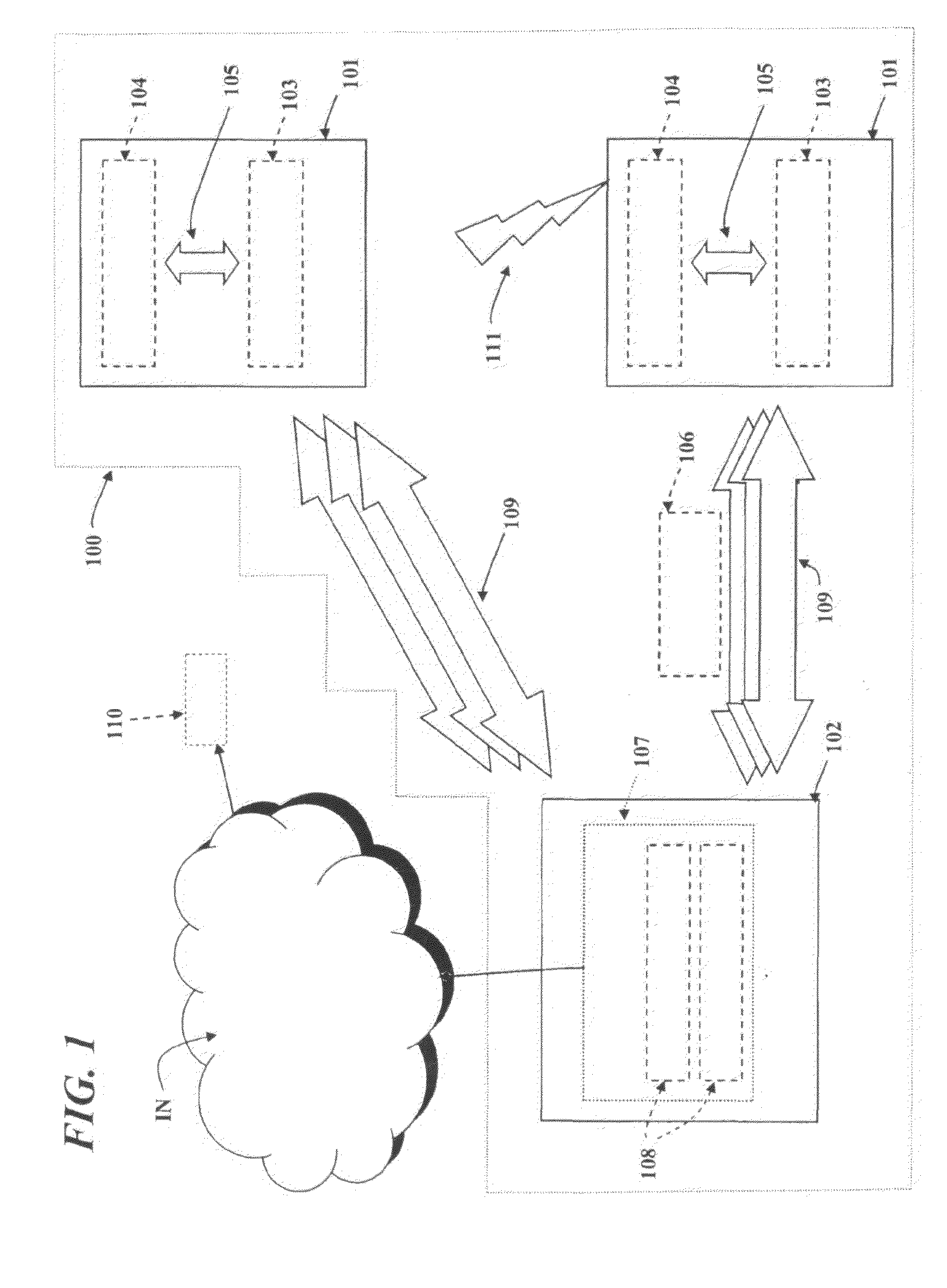
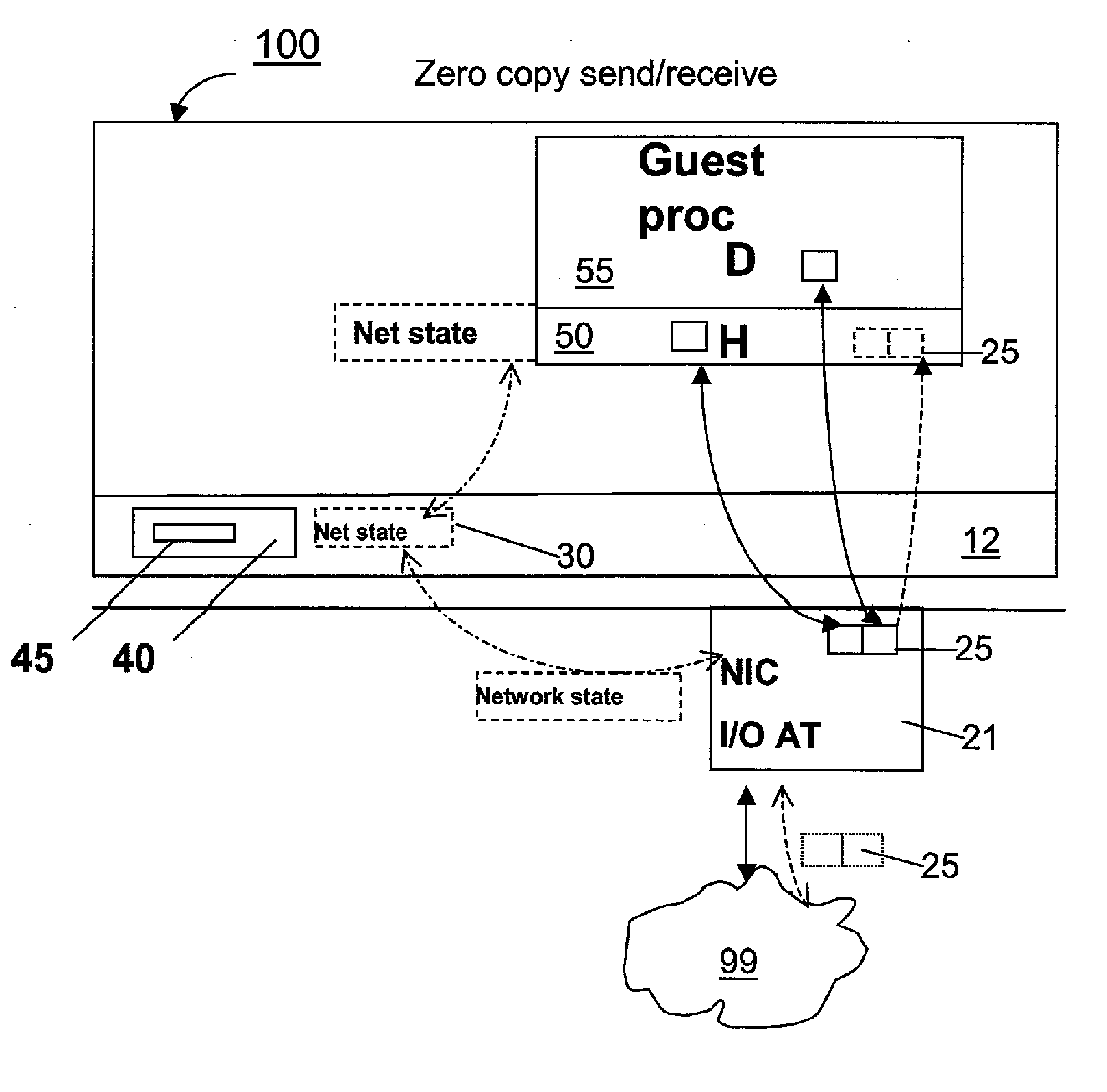
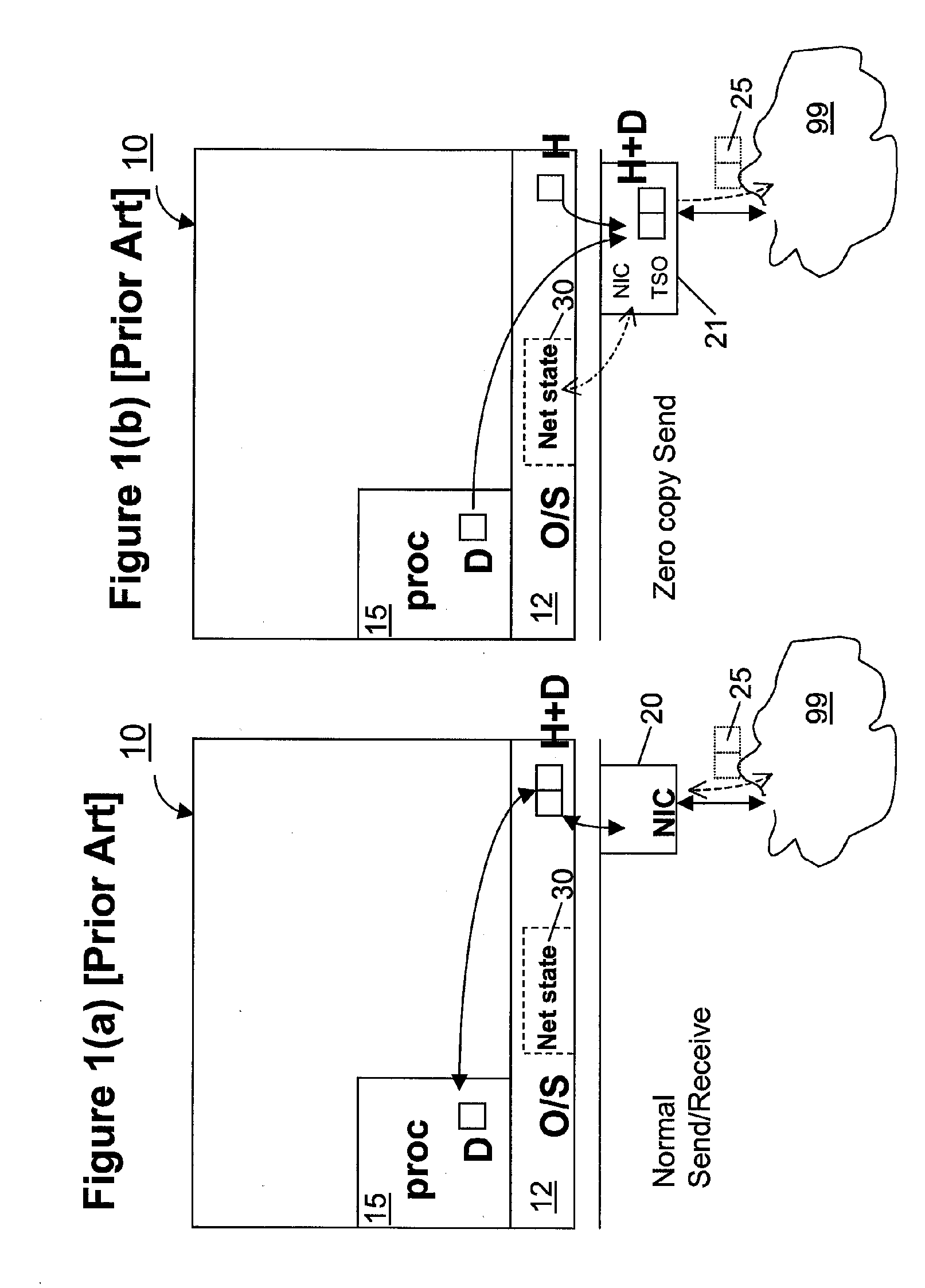
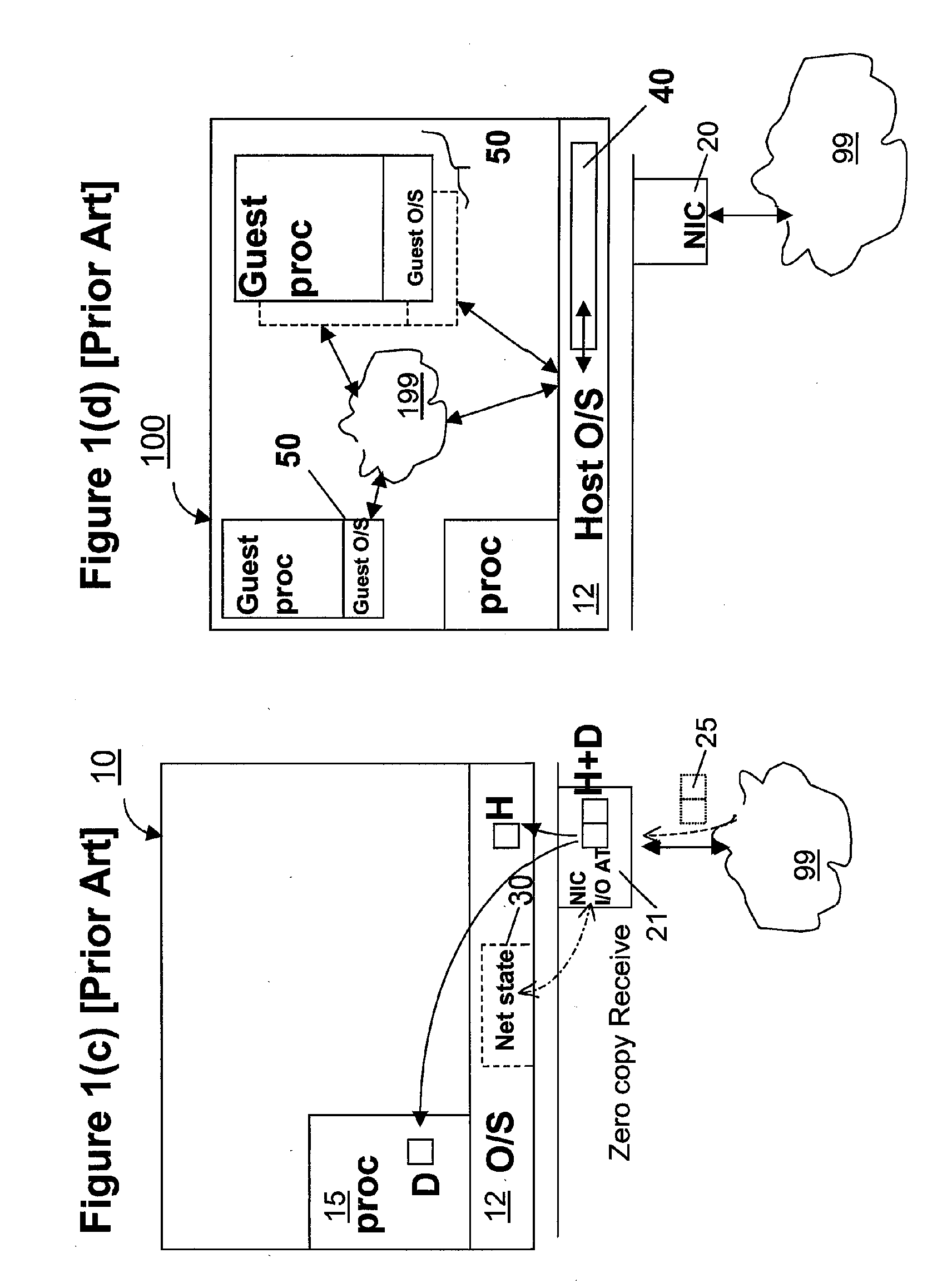
Zero-copy network I/O for virtual hosts
ActiveUS20070061492A1Eliminate the problemSolve excessive overheadDigital computer detailsTransmissionData packVirtualization
Techniques for virtualized computer system environments running one or more virtual machines that obviate the extra host operating system (O / S) copying steps required for sending and receiving packets of data over a network connection, thus eliminating major performance problems in virtualized environment. Such techniques include methods for emulating network I / O hardware device acceleration-assist technology providing zero-copy I / O sending and receiving optimizations. Implementation of these techniques require a host O / S to perform actions including, but not limited to: checking of the address translations (ensuring availability and data residency in physical memory), checking whether the destination of a network packet is local (to another virtual machine within the computing system), or across an external network; and, if local, checking whether either the sending destination VM, receiving VM process, or both, supports emulated hardware accelerated-assist on the same physical system. This optimization, in particular, provides a further optimization in that the packet data checksumming operations may be omitted when sending packets between virtual machines in the same physical system.
Owner:RED HAT
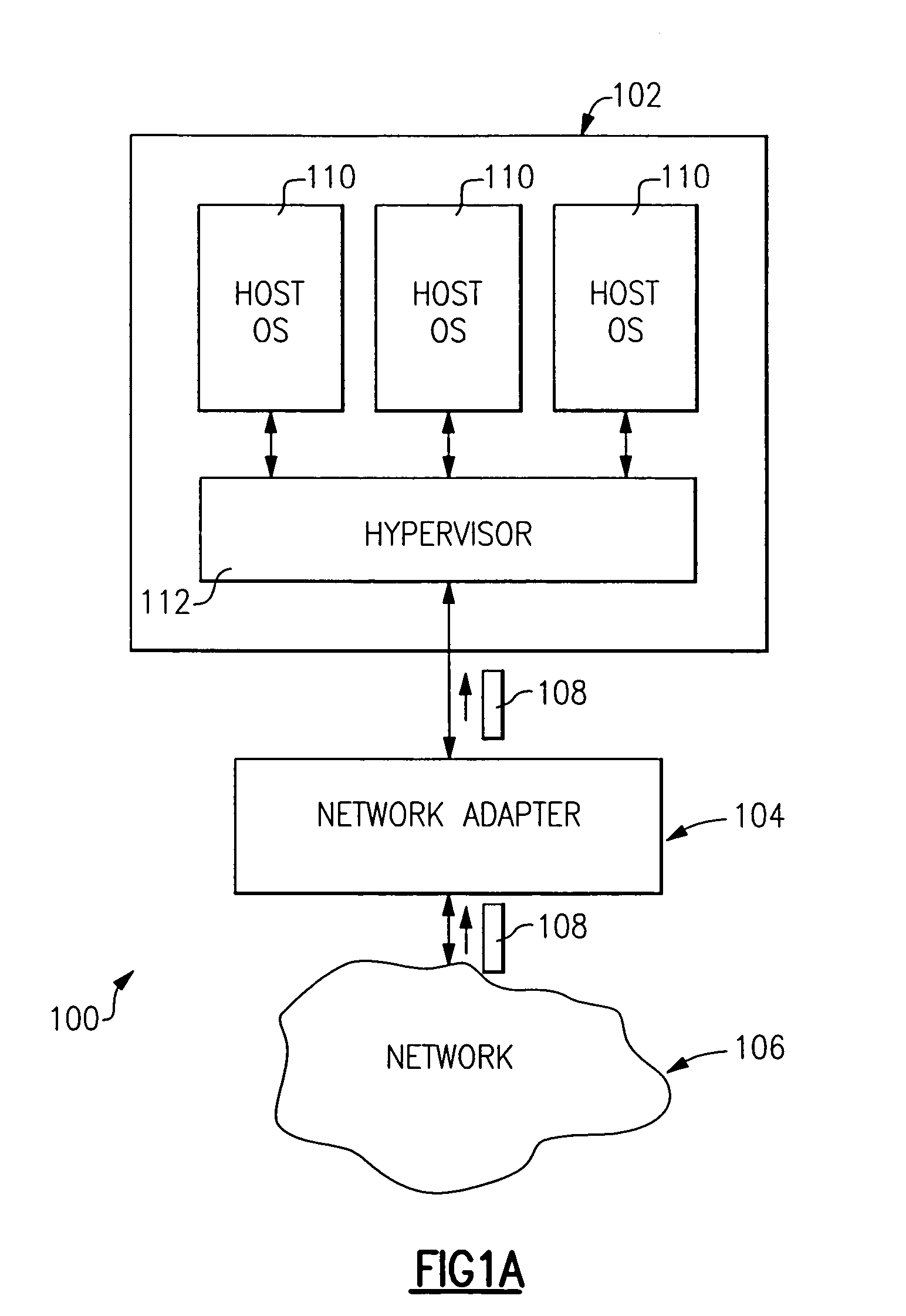
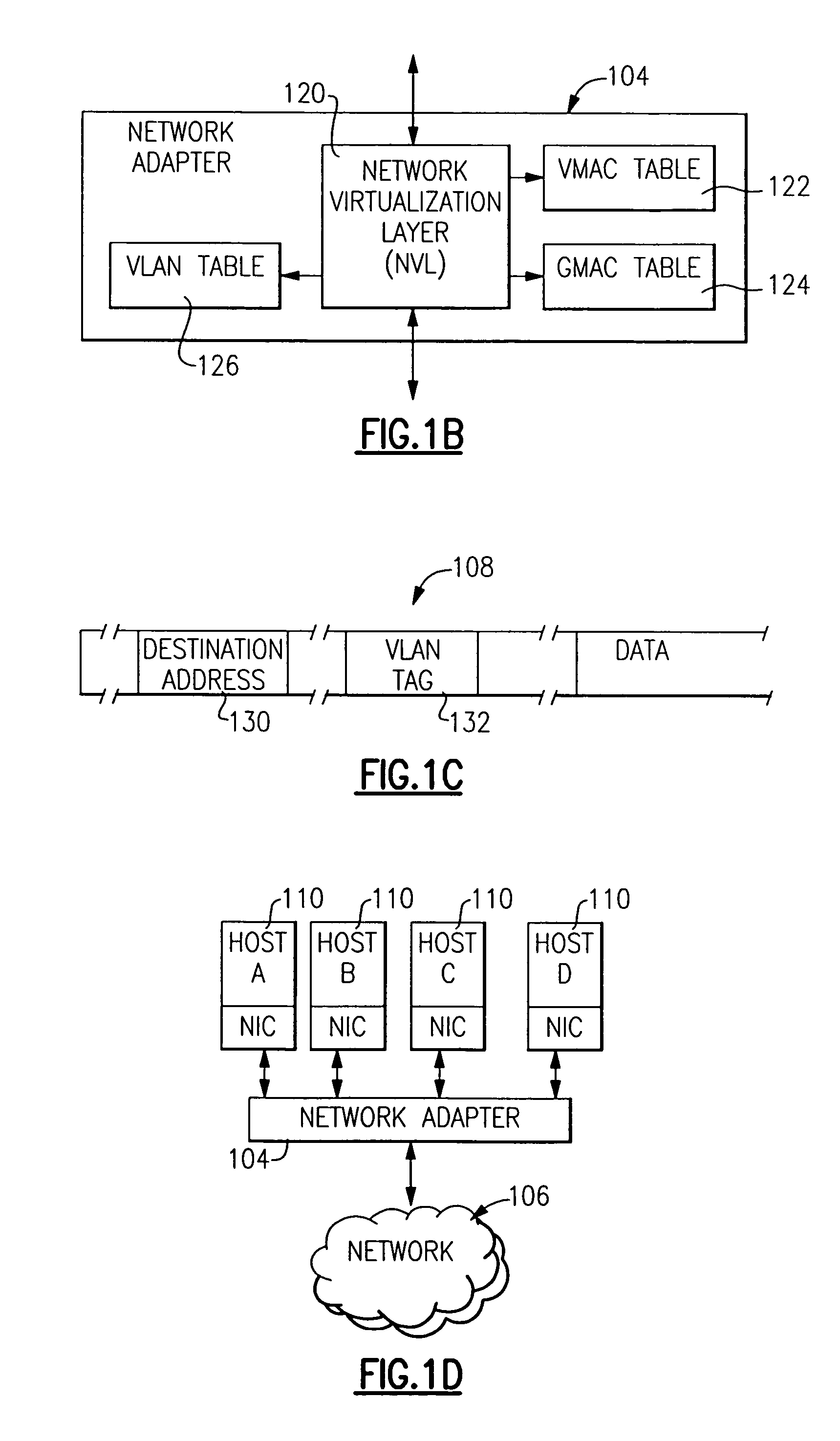
Method and apparatus for providing network virtualization
A network virtualization layer for an information handling system in which a physical machine coupled to a network is divided into a plurality of logical partitions, each of which has a host system residing thereon. In response to receiving a set command from one of the host systems specifying a data link layer (layer 2) address, the virtualization layer associates the data link layer address with the host system and forwards to the host system data packets specifying the data link layer address as a destination address. Unicast packets are forwarded to the single host system specifying the destination address as an individual MAC address, while multicast packets are forwarded to each host system specifying the destination address as a group MAC address. A host system may also specify a virtual LAN (VLAN) ID, which is used to scope the forwarding of packets to host systems sharing that VLAN ID.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com