Patents
Literature
1336 results about "Client data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
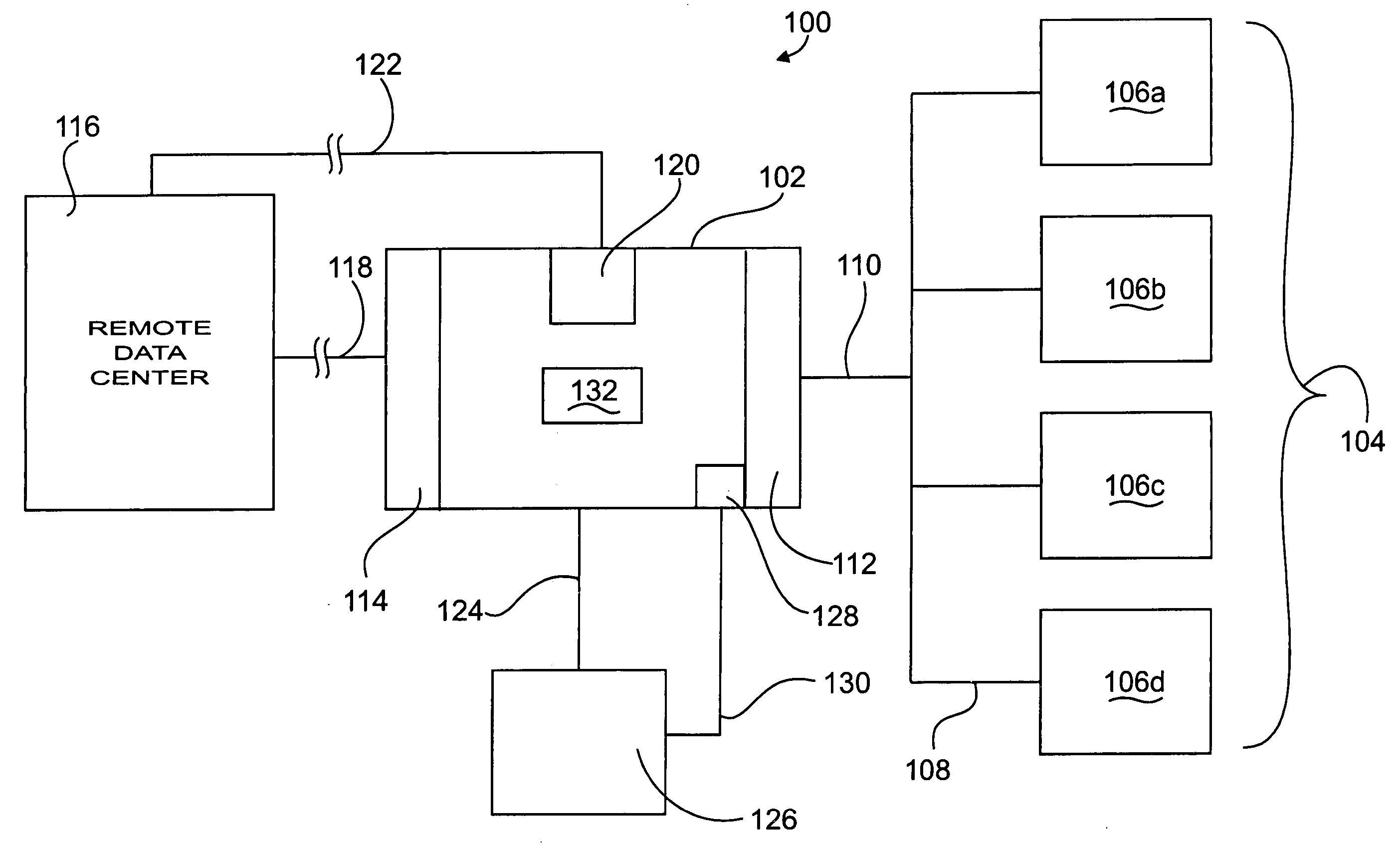
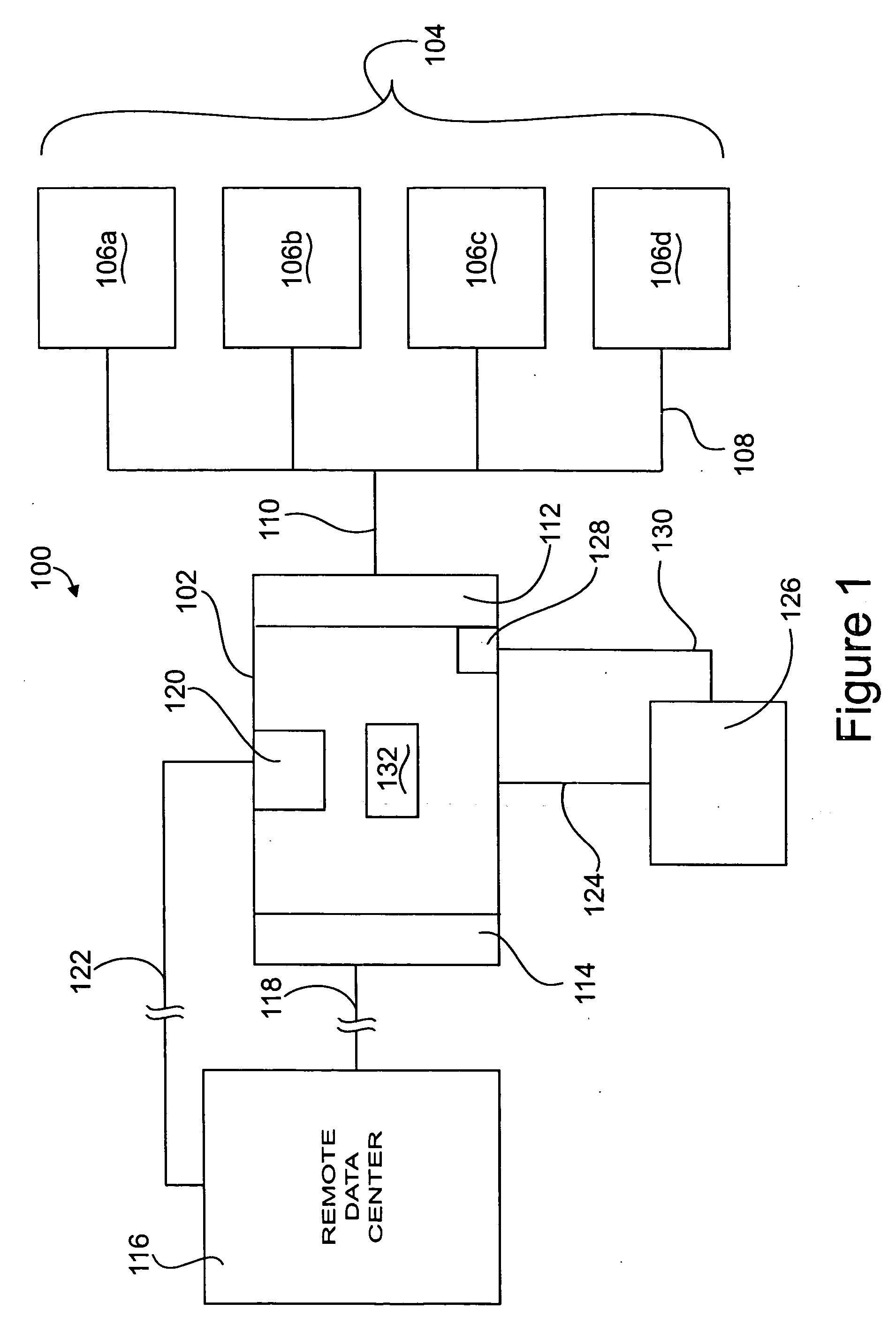
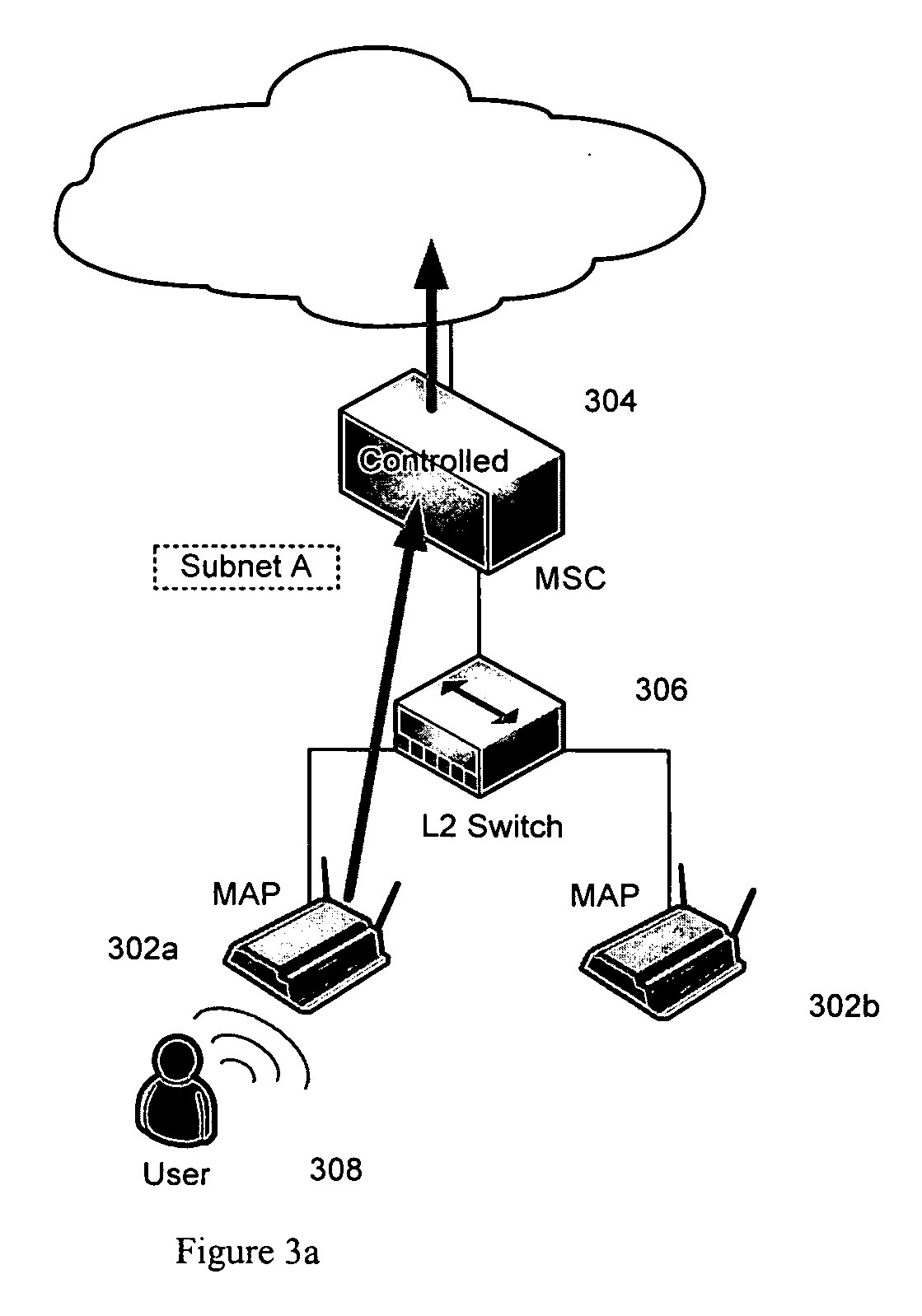
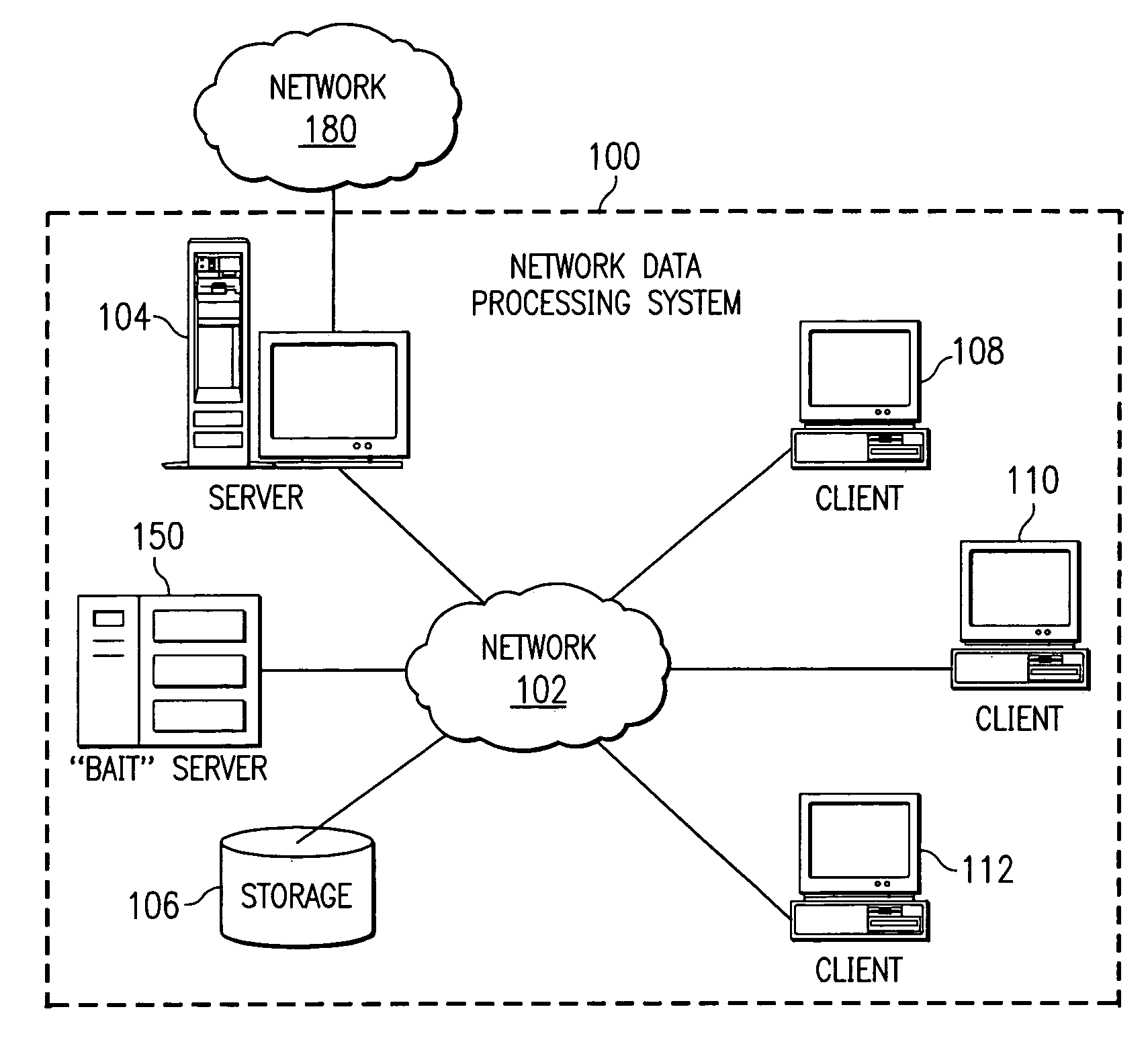
Apparatus and method for remotely monitoring a computer network
InactiveUS20060031476A1Easy to provideMinimize the possibilityDigital computer detailsTransmissionAnti virusPrivate network
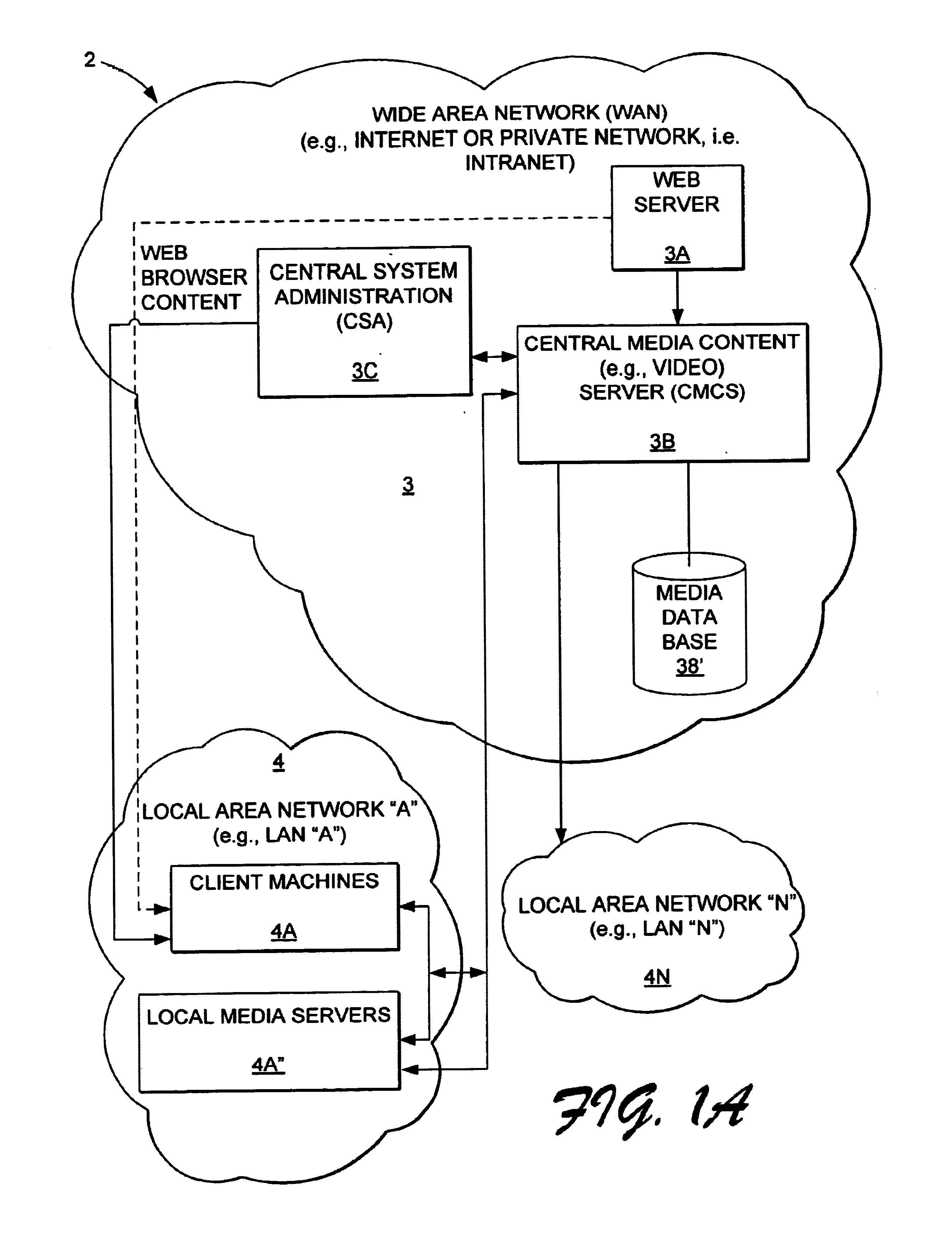
There is provided an apparatus for remotely monitoring a computer network. Monitoring is performed using an inside out approach from behind firewalls and other security devices. The monitoring appliance is shipped to a client site preconfigured and typically requires no technically trained person for installation. Collected network data is periodically transmitted to a remote monitoring facility where it is recorded and analyzed. Both the monitoring appliance and the remote center maintain the configuration data. Typically, no client data is transmitted to the remote monitoring site. If the monitoring appliance fails, a completely configured replacement may be shipped to the site and easily installed. The monitoring appliance is optionally equipped to provide network services. Services such as web hosting, file server, print server, virtual private network (VPN), shared Internet access, web content filtering, anti-virus, spam e-mail elimination, and IP telephony services as well as other such services may be easily provided.
Owner:MATHES MARVIN LEE +1
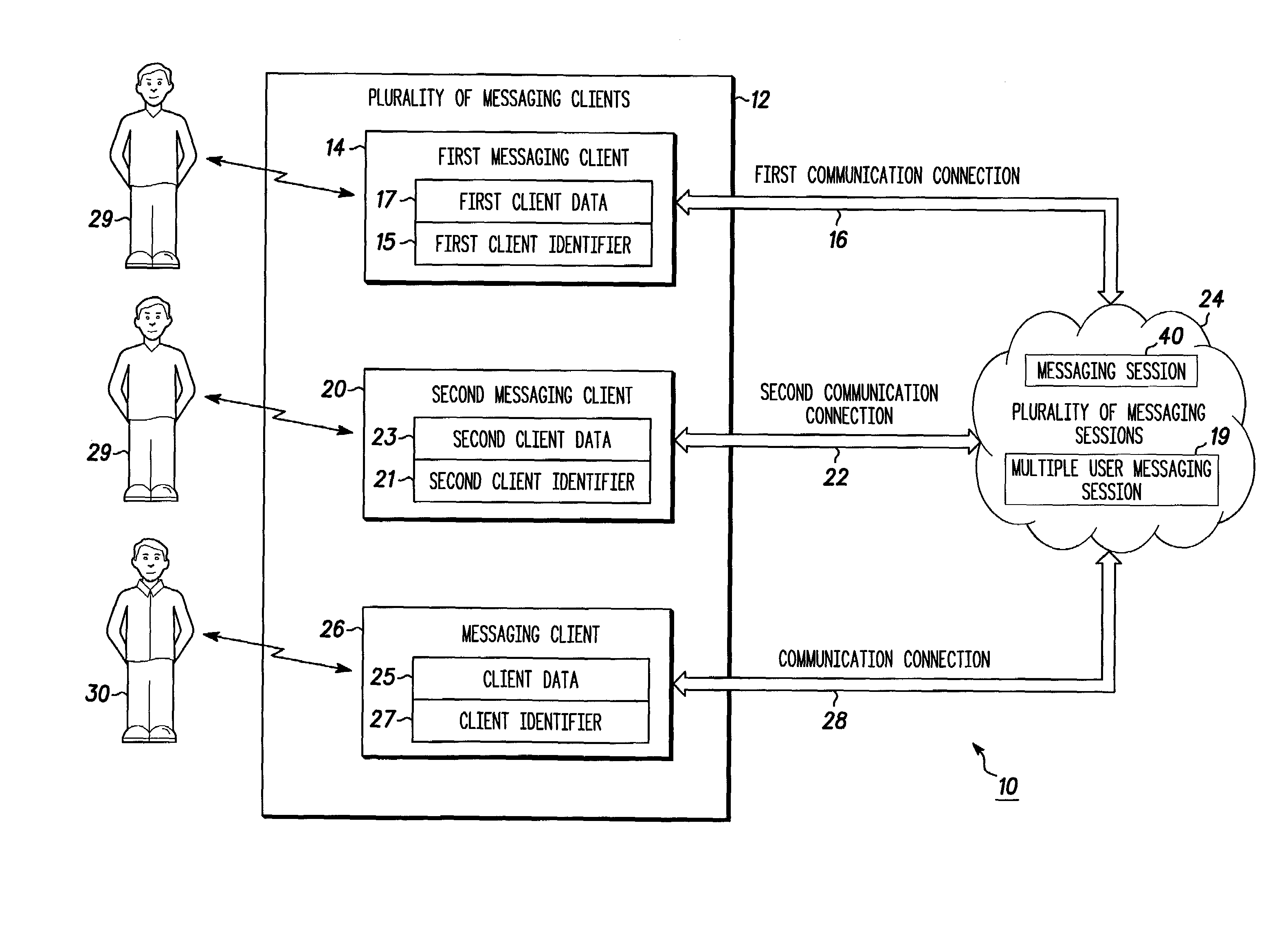
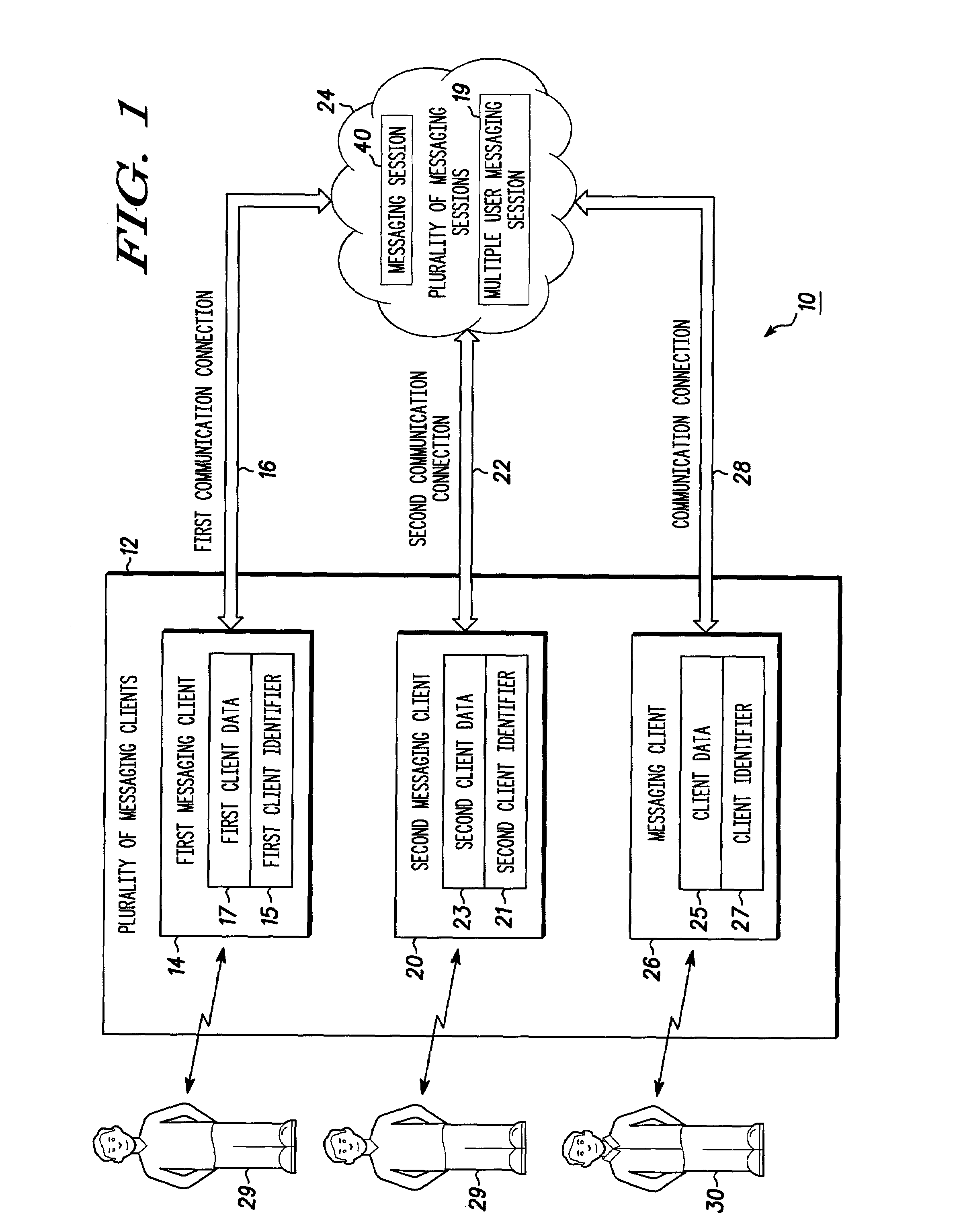
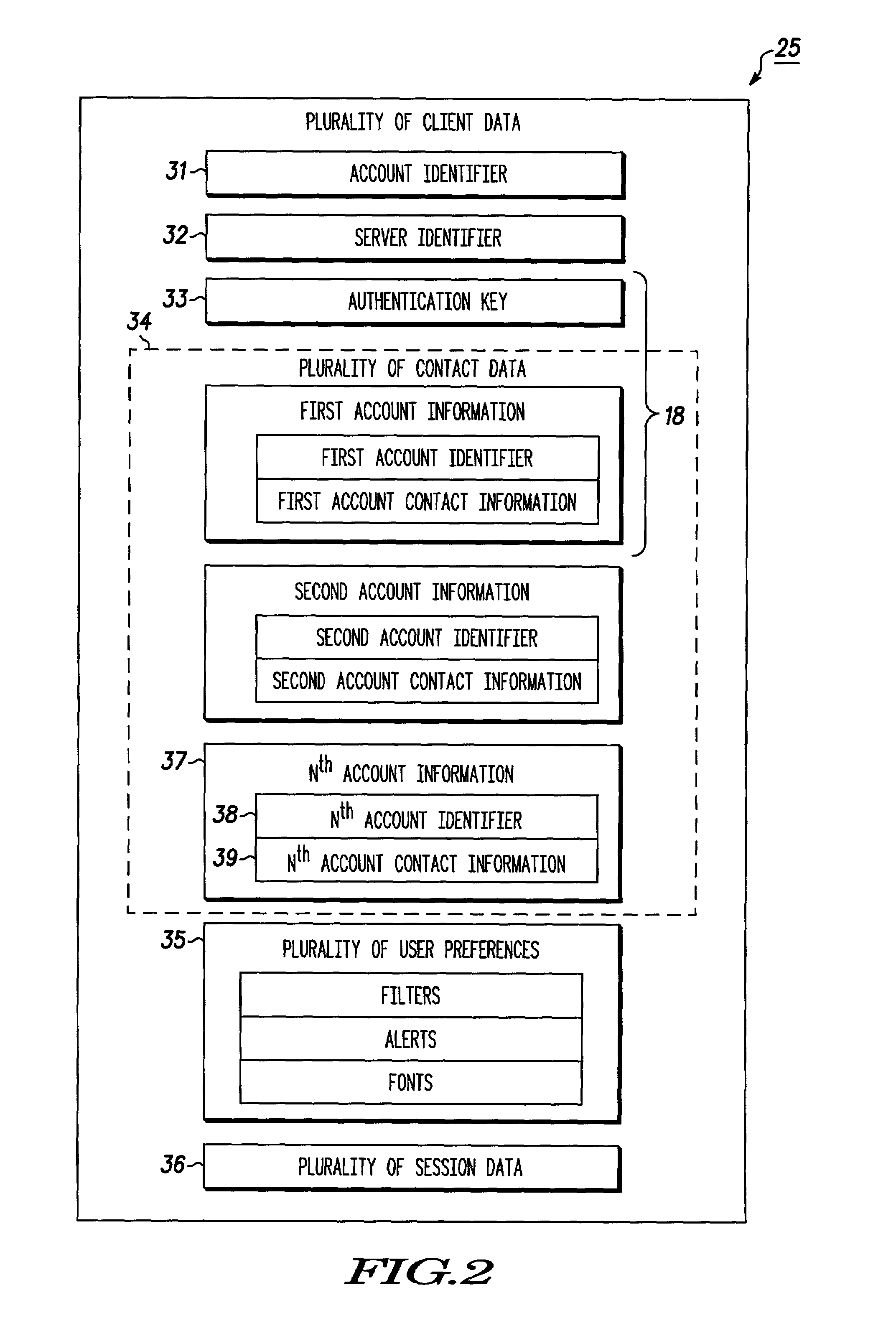
System for providing continuity between messaging clients and method therefor
ActiveUS6983370B2Volume/mass flow measurementUser identity/authority verificationCommunications systemClient data
A messaging communication system (10) includes a plurality of messaging clients (12). A first messaging client (14) establishes a first communication connection (16) operating using a plurality of client data (25). The first messaging client (14) transfers the plurality of client data (25) to a second messaging client (20). The second messaging client (20) establishes a second communication connection (22) operating using the plurality of client data (25).
Owner:GOOGLE TECH HLDG LLC
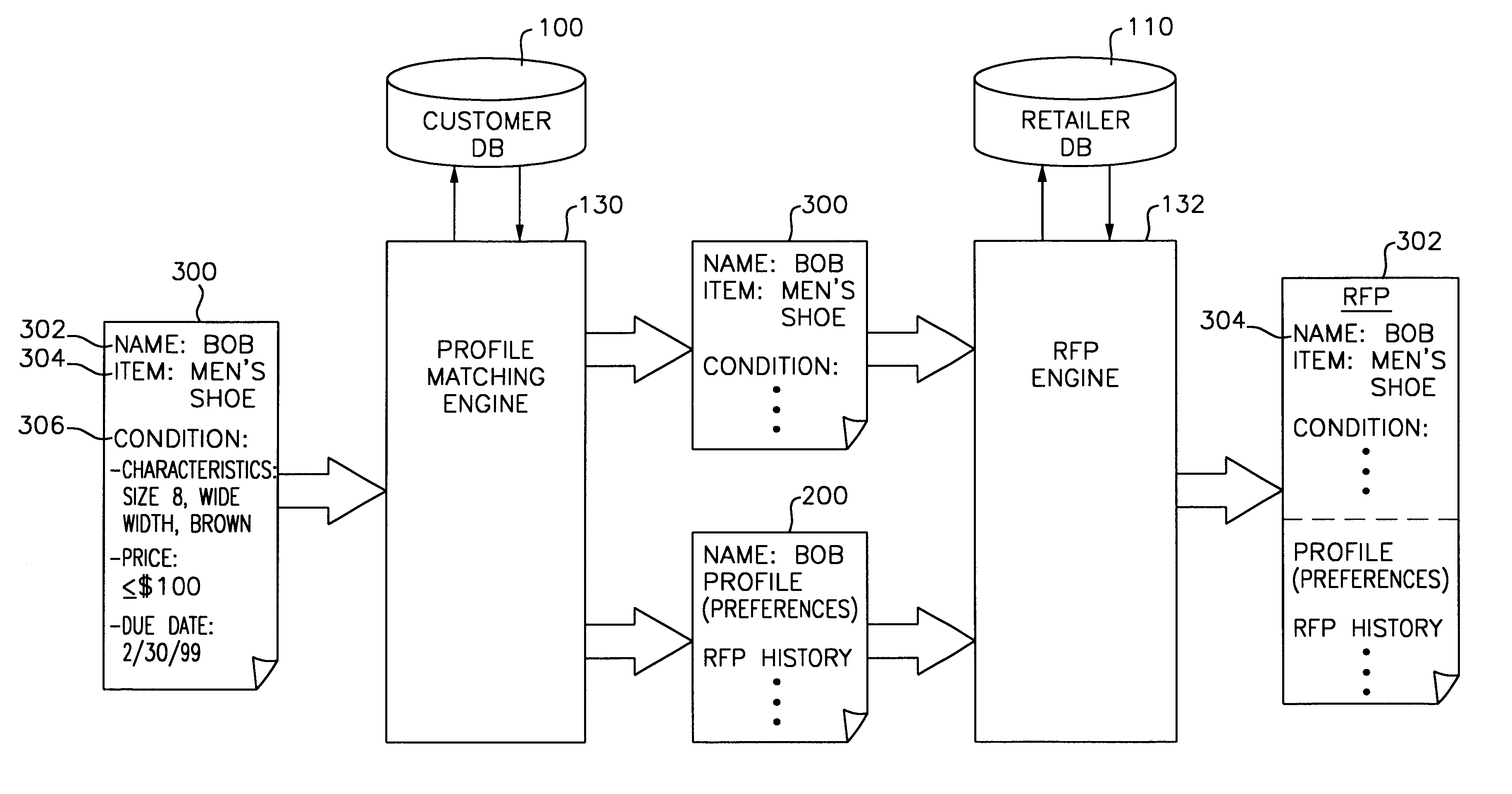
System and method for electronic shopping using an interactive shopping agent
InactiveUS6868392B1More efficient and productive electronic shoppingBuying/selling/leasing transactionsResourcesInternet shoppingDatabase
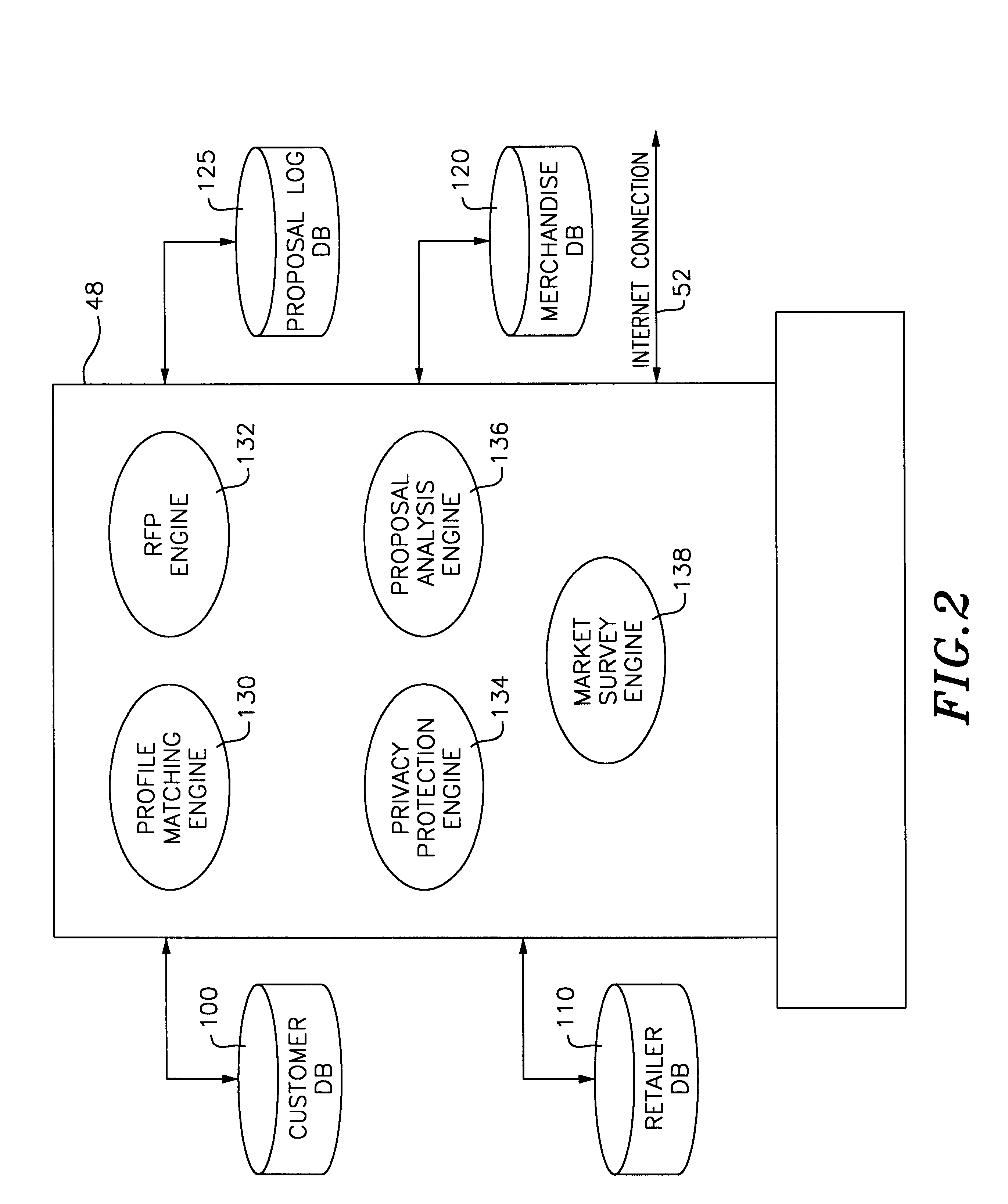
An electronic shopping system which utilizes an electronic shopping agent (ESA) for allowing communication between customers and retailers during Internet shopping. The ESA has access to a customer database and a retailer database. When a request for an item / service is received by the ESA from a customer, the customer profile information is retrieved from the customer database. Appropriate retailers are also selected from the retailer database. The customer profile information and customer request is bundled as a request for proposal (RFP) and forwarded to the selected retailers for servicing. The retailers, upon receipt of the RFP submit proposals to the ESA for forwarding to the requesting customer. The proposals are catered to the requesting customer's needs and preferences. The ESA may analyze the proposals and select the best proposal(s) prior to their forwarding to the requesting customer. The ESA may further provide market survey reports to the retailers based on information accumulated on the customers using the system.
Owner:FUJITSU LTD
Method and system for an online reservation system for services selectable from multiple categories
InactiveUS20080275741A1Improve business satisfactionReservationsCommerceOnline bookingService provision
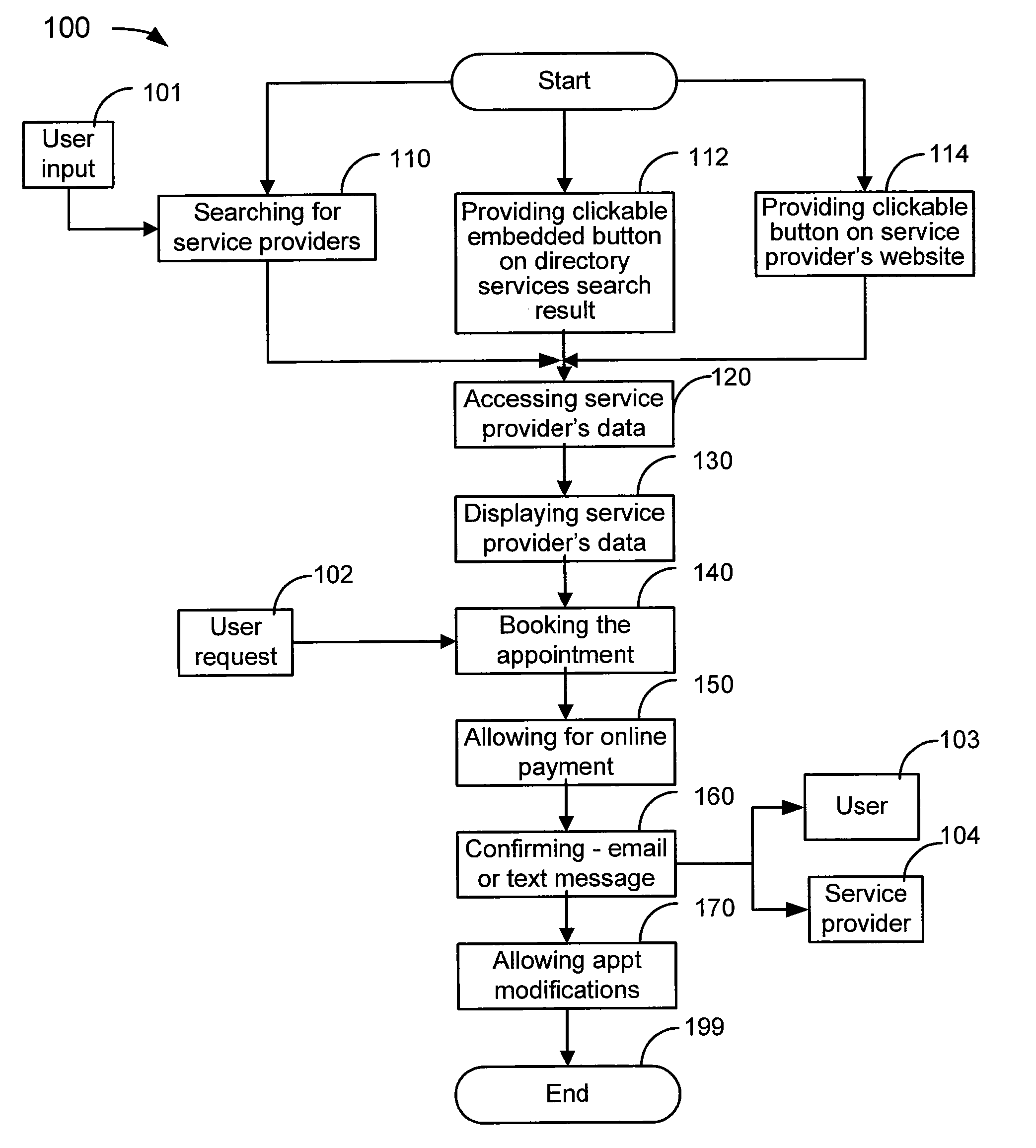
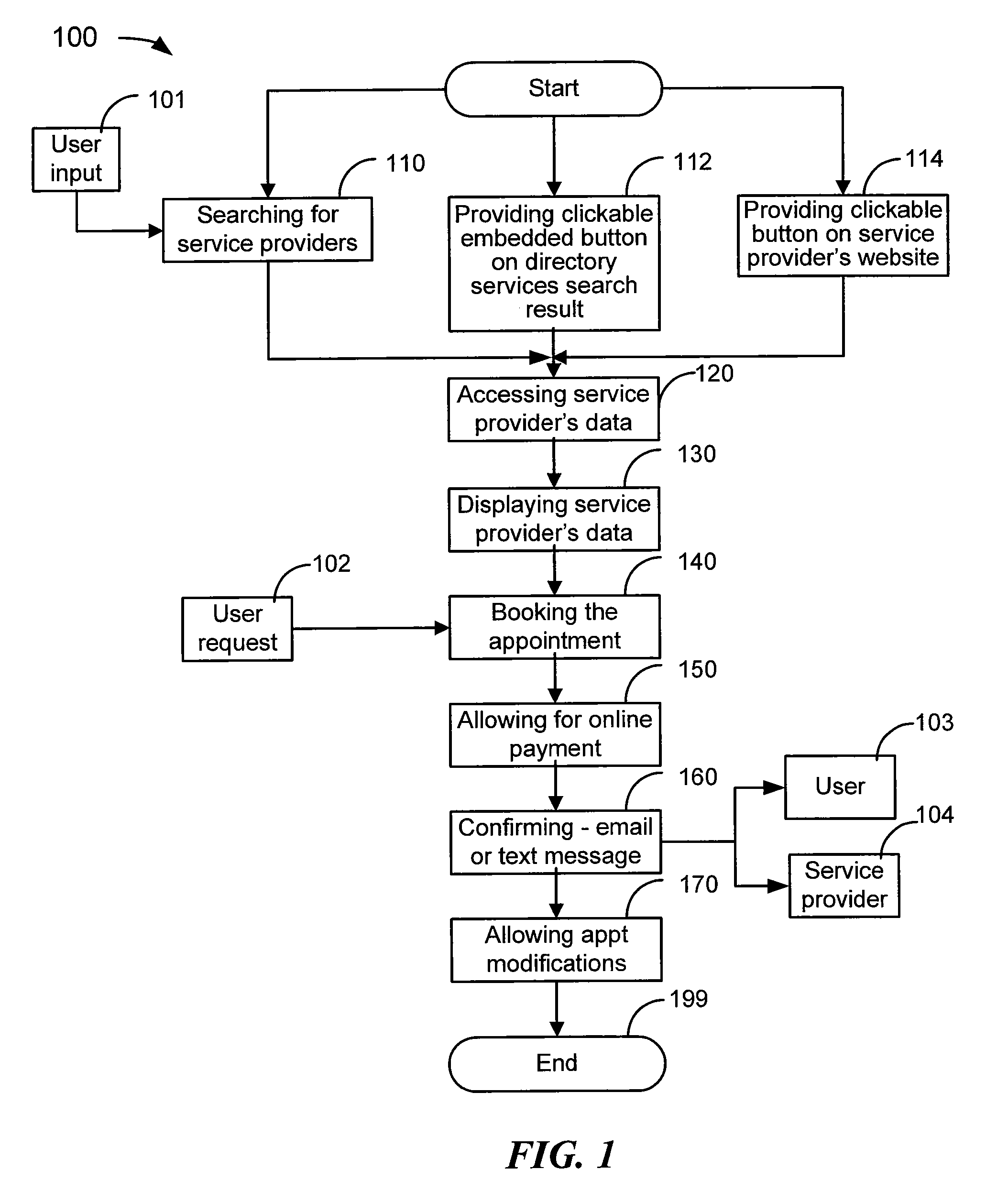
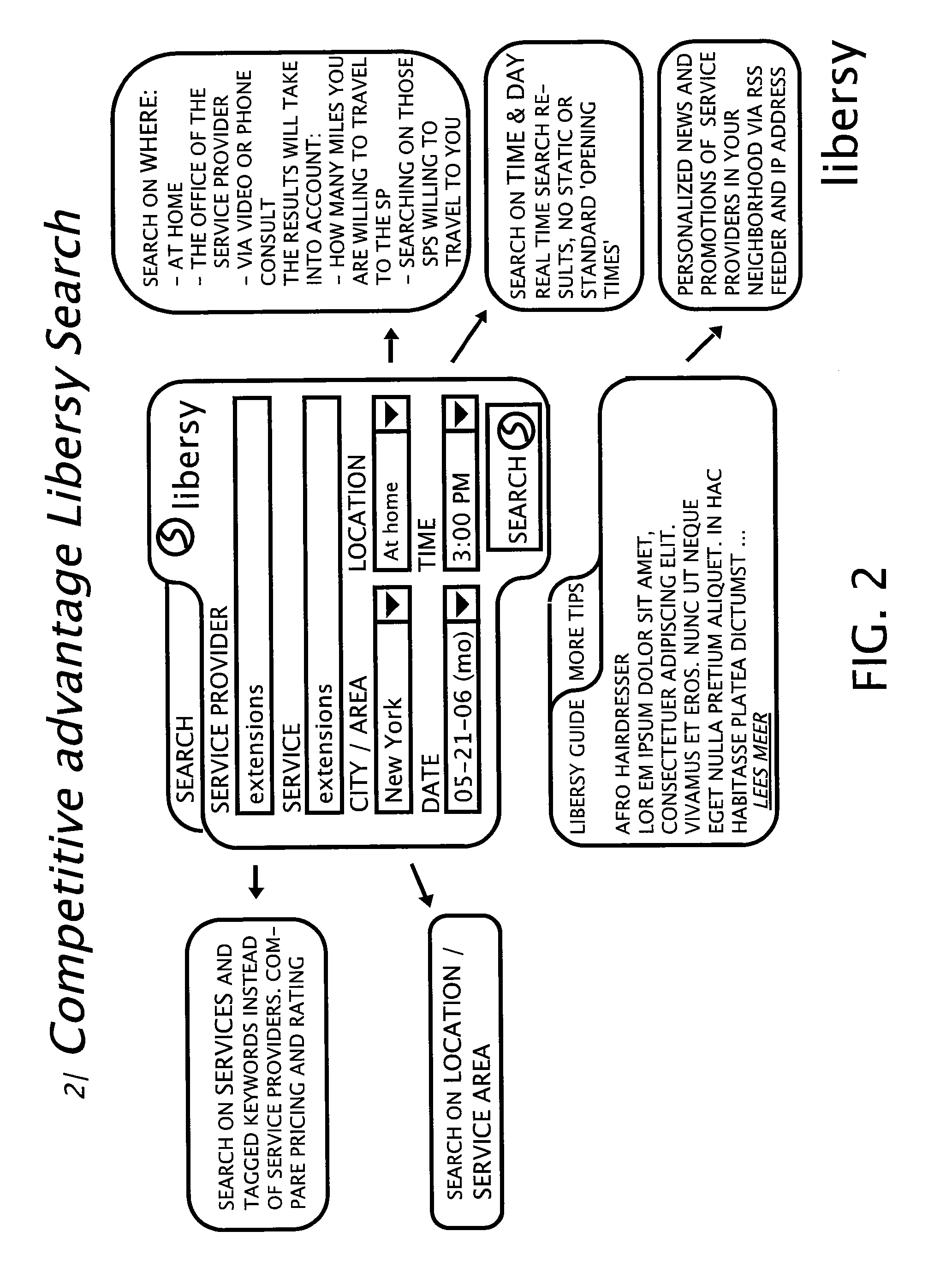
The present invention is a method and system for an online reservation system providing services of multiple categories of service providers. A user may enter the online reservation system by clicking on a button either embedded in a directory services search result for a particular service provider or located on a particular service provider's website. Alternatively, a user may search for service providers through the online reservation system by entering criteria such as category of service, pricing, rating, location, or time and day of availability of the service. Both users and service providers receive electronic confirmation and reminders for the booked appointments.Service providers may integrate all of their appointments with a calendar maintained by the online reservation system. The system automatically collects client data and may provide accounting services.
Owner:LIBERSY BV
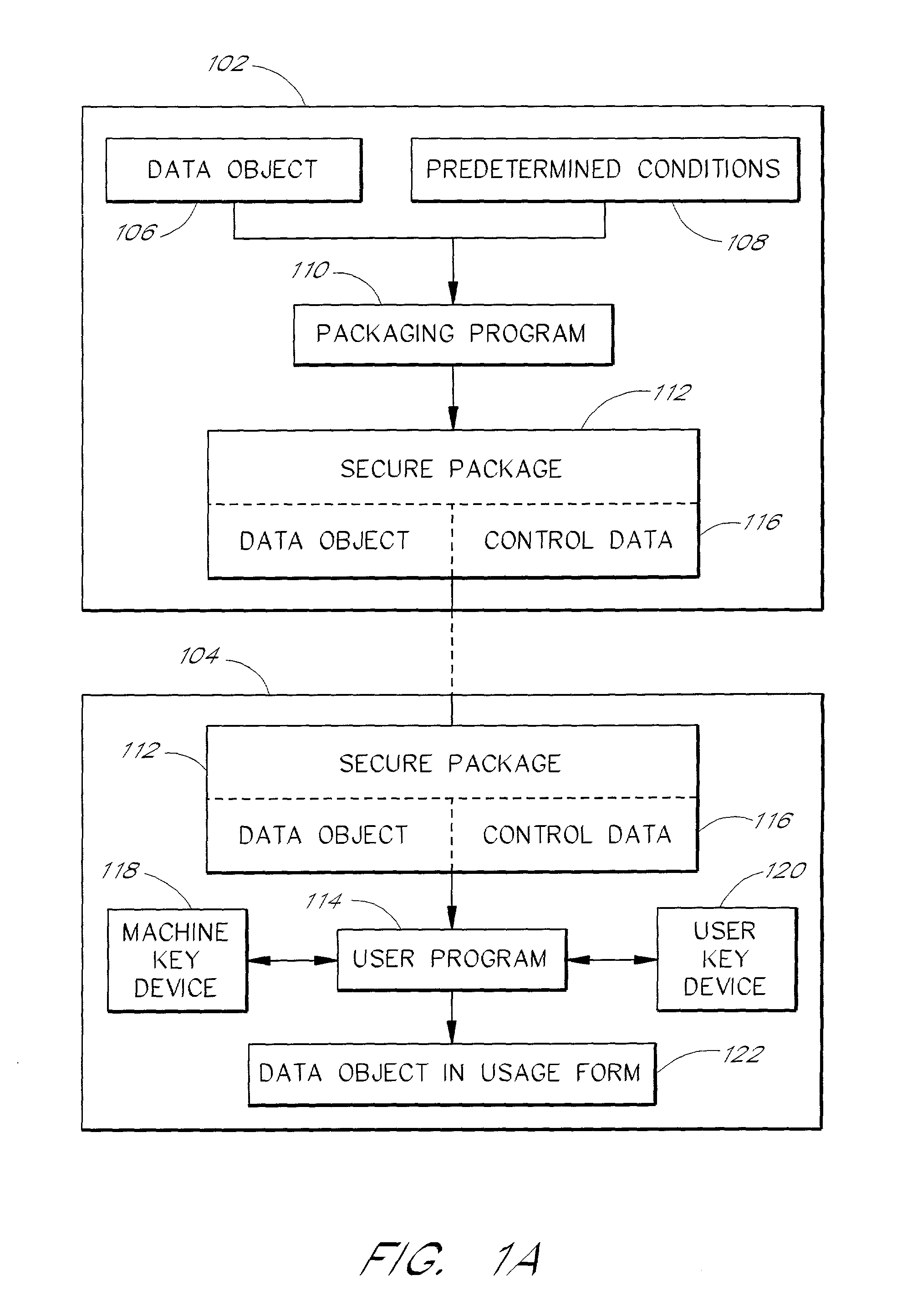
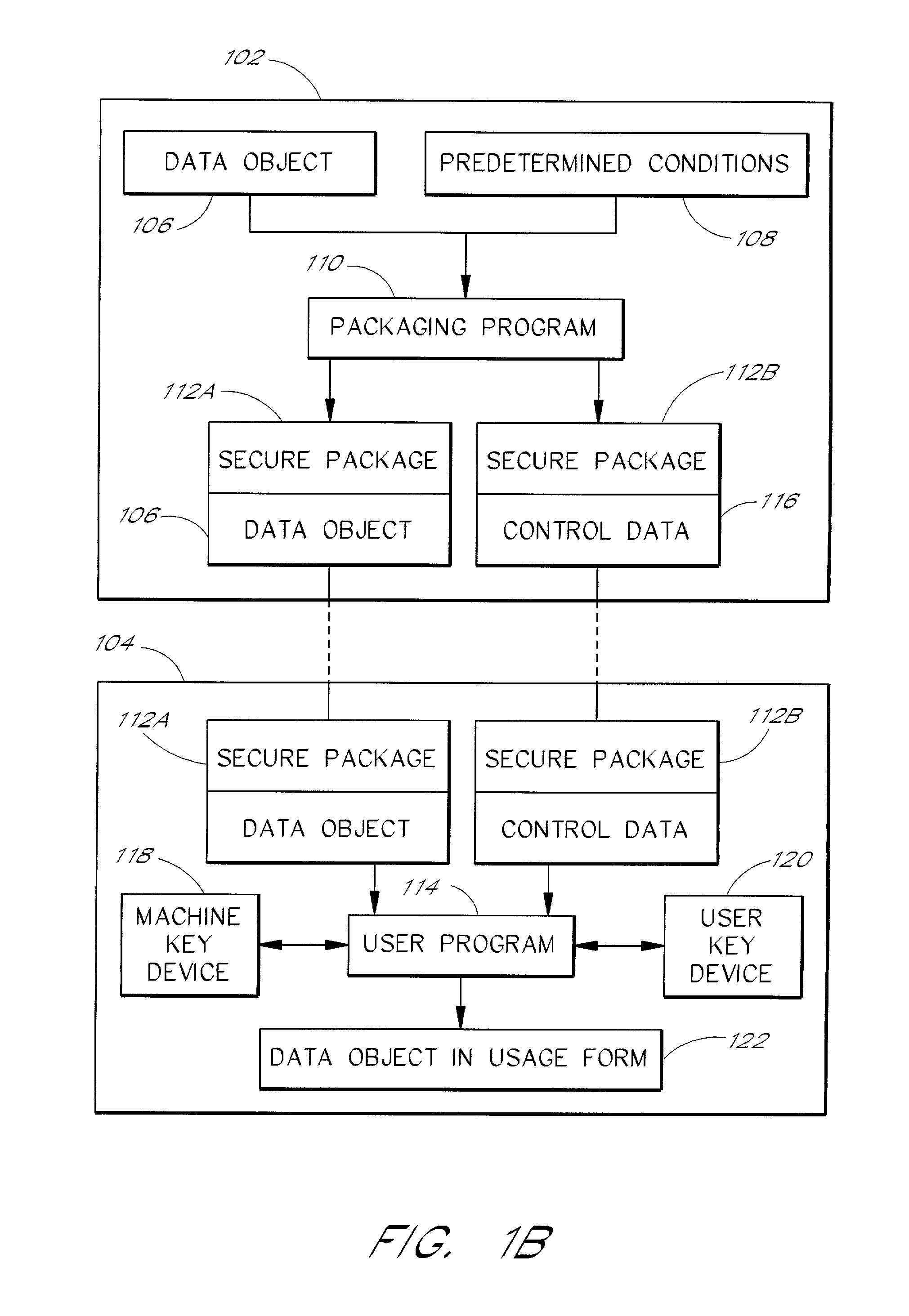
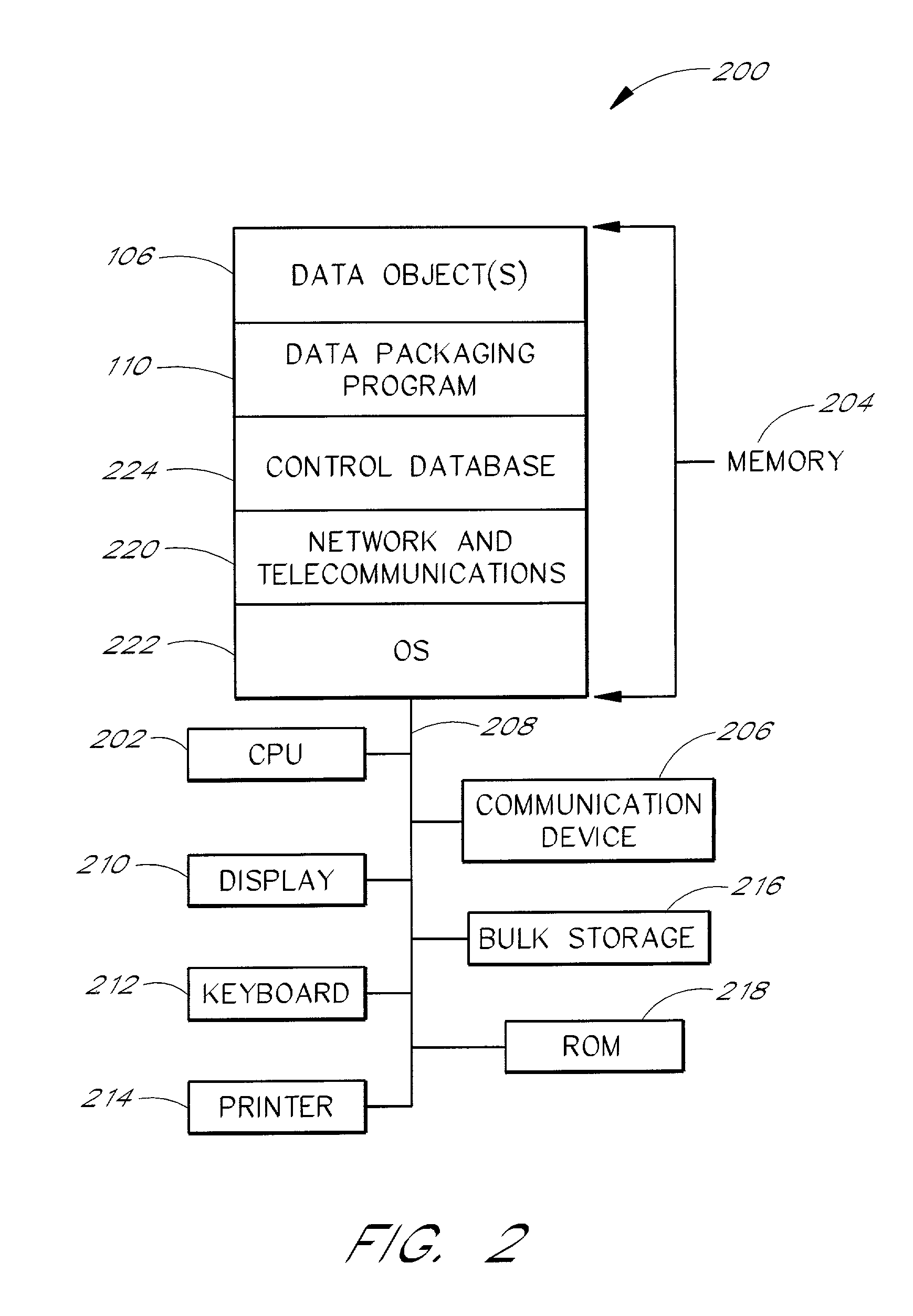
System and method for controlling and enforcing access rights to encrypted media
InactiveUS20010029581A1Digital data processing detailsUser identity/authority verificationComputer hardwareNetwork connection
A system for providing rights controlled access to digital media comprises a server data processor and a client data processor connected by a communications network. The user data processor provides access to a data object in accordance with rules associated with the data object by the server data processor. The client data processor comprises a machine key device and a user key device. The machine key device is preferably an installed component of the client data processor that provides encryption, decryption, and authentication functionality for the client data processor. The user key device is preferably a removable, portable device that connects to the client data processor and provides encryption, decryption, and authentication functionality for the user. A method restricts the use of a data object to a particular user and a particular data processor through the use of additional layers of encryption. The method preferably comprises encrypting a data object such that the it can be decrypted by the machine key device, and further encrypting the data object such that it can be decrypted by the user key device. A method restricts the use of a data object to a particular user and a particular data processor through the use of rules that require authentication of the machine key device and the user key device.
Owner:MARKING OBJECT VIRTUALIZATION INTELLIGENCE LLC
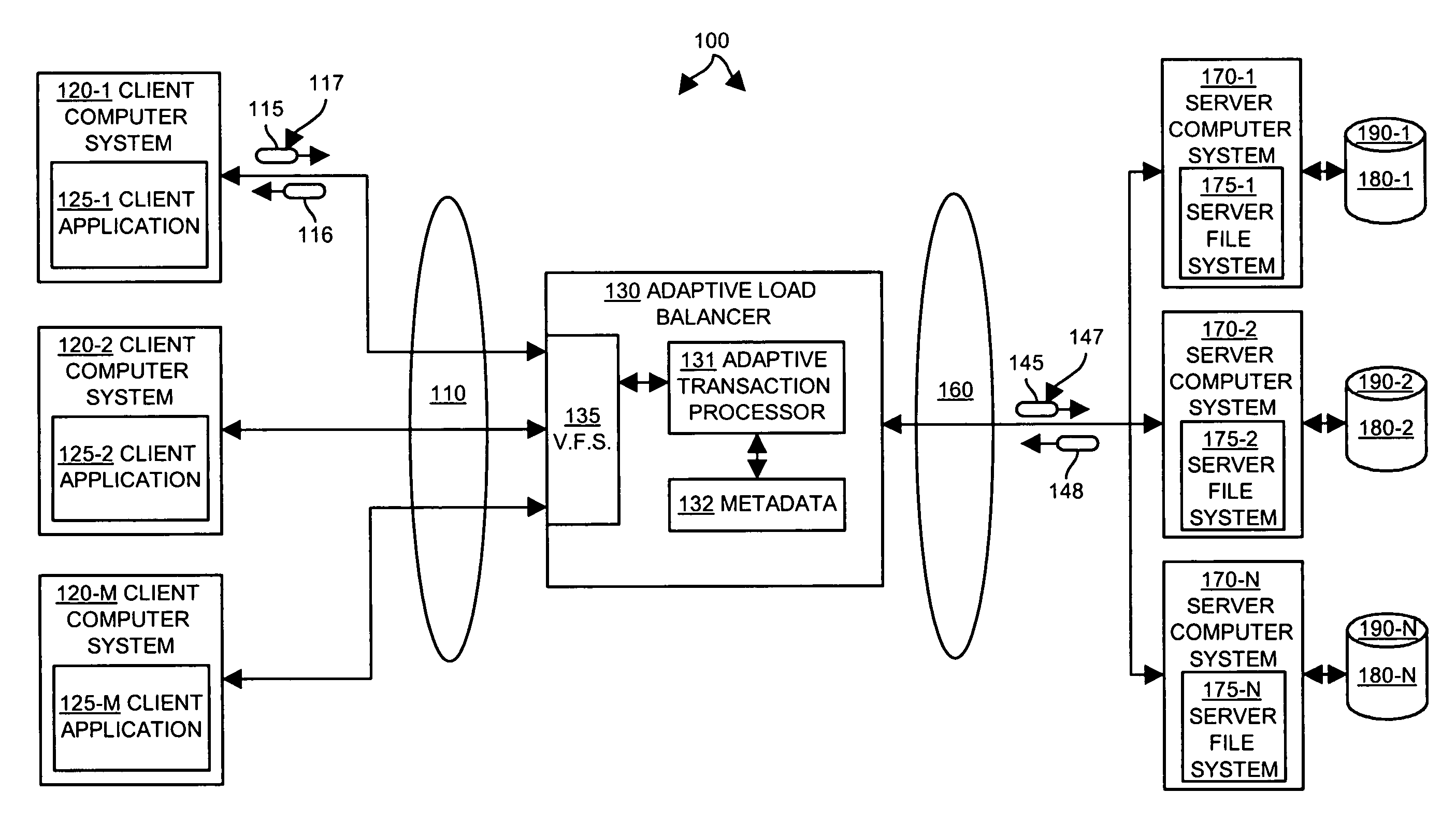
Method and apparatus for adaptive services networking
InactiveUS7877511B1Effective serviceExpand accessMultiple digital computer combinationsTransmissionAdaptive servicesData set
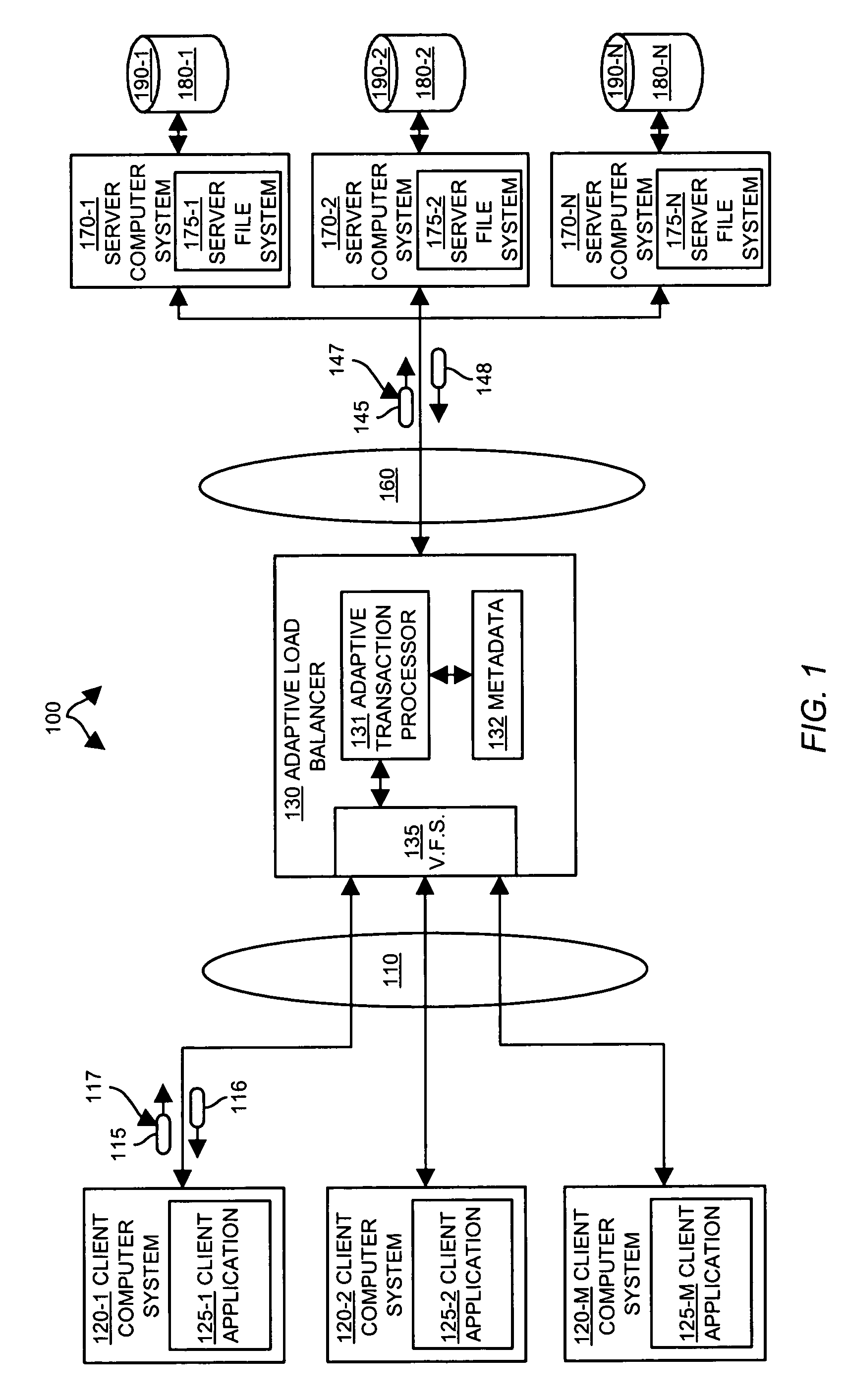
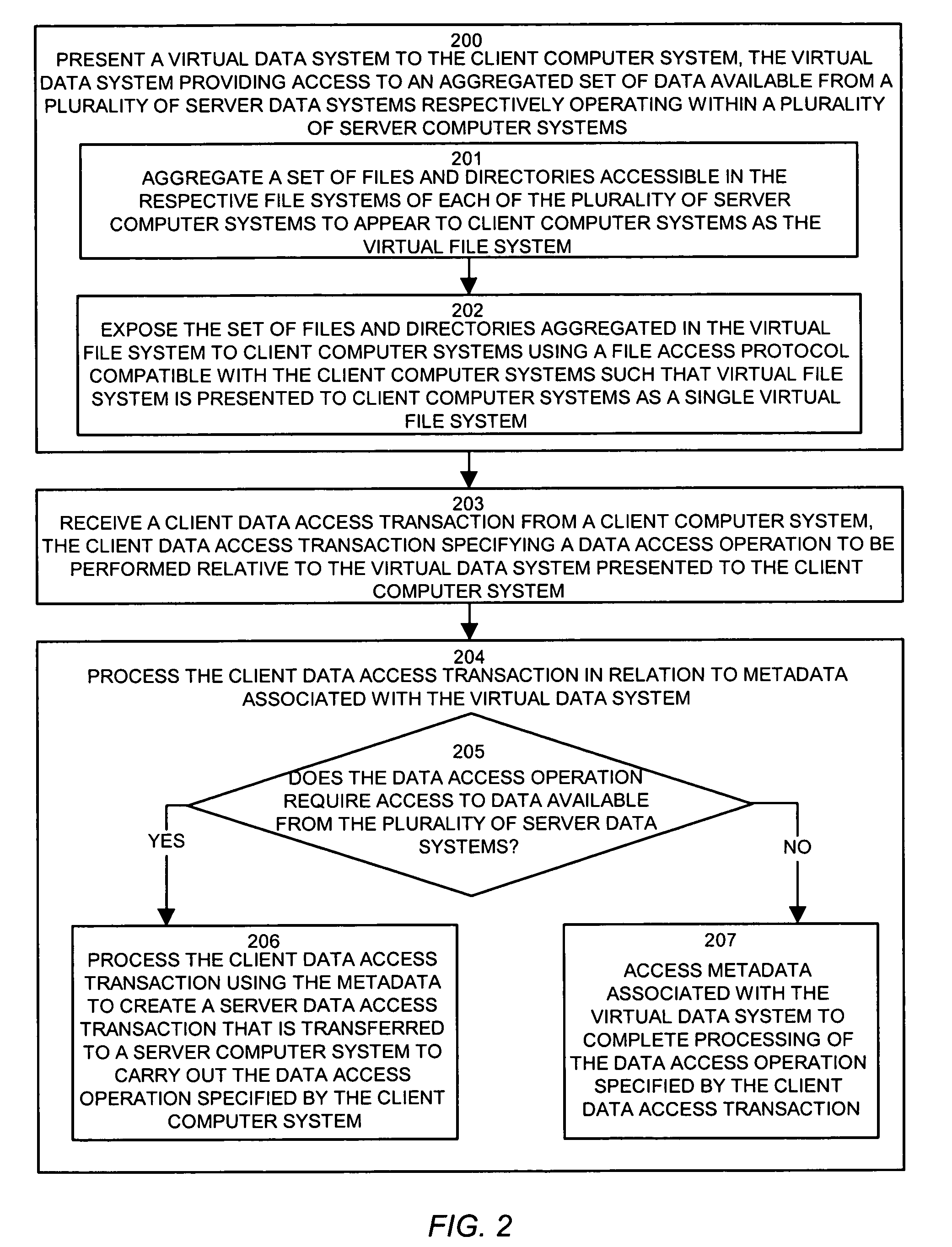
Methods and apparatus provide an adaptive load balancer that presents a virtual data system to client computer systems. The virtual data system provides access to an aggregated set of data, such as files or web service objects, available from a plurality of server data systems respectively operating within a plurality of server computer systems. The adaptive load balancer receives a client data access transaction from a client computer system that specifies a data access operation to be performed relative to the virtual data system presented to the client computer system. The adaptive load balancer processes the client data access transaction in relation to metadata associated with the virtual data system to provide access to the file or service object within a server computer system, or to access the metadata. The adaptive load balancer can work in conjunction with other adaptive load balancers to dynamically adjust to demands for access to data by replicating and migrating data such as files or service objects as needed between the server computer systems to accommodate data access demands.
Owner:F5 NETWORKS INC
Fraud detection based on social data
InactiveUS20120226579A1Easy to getSimple processBuying/selling/leasing transactionsMarketingEmail addressClient data
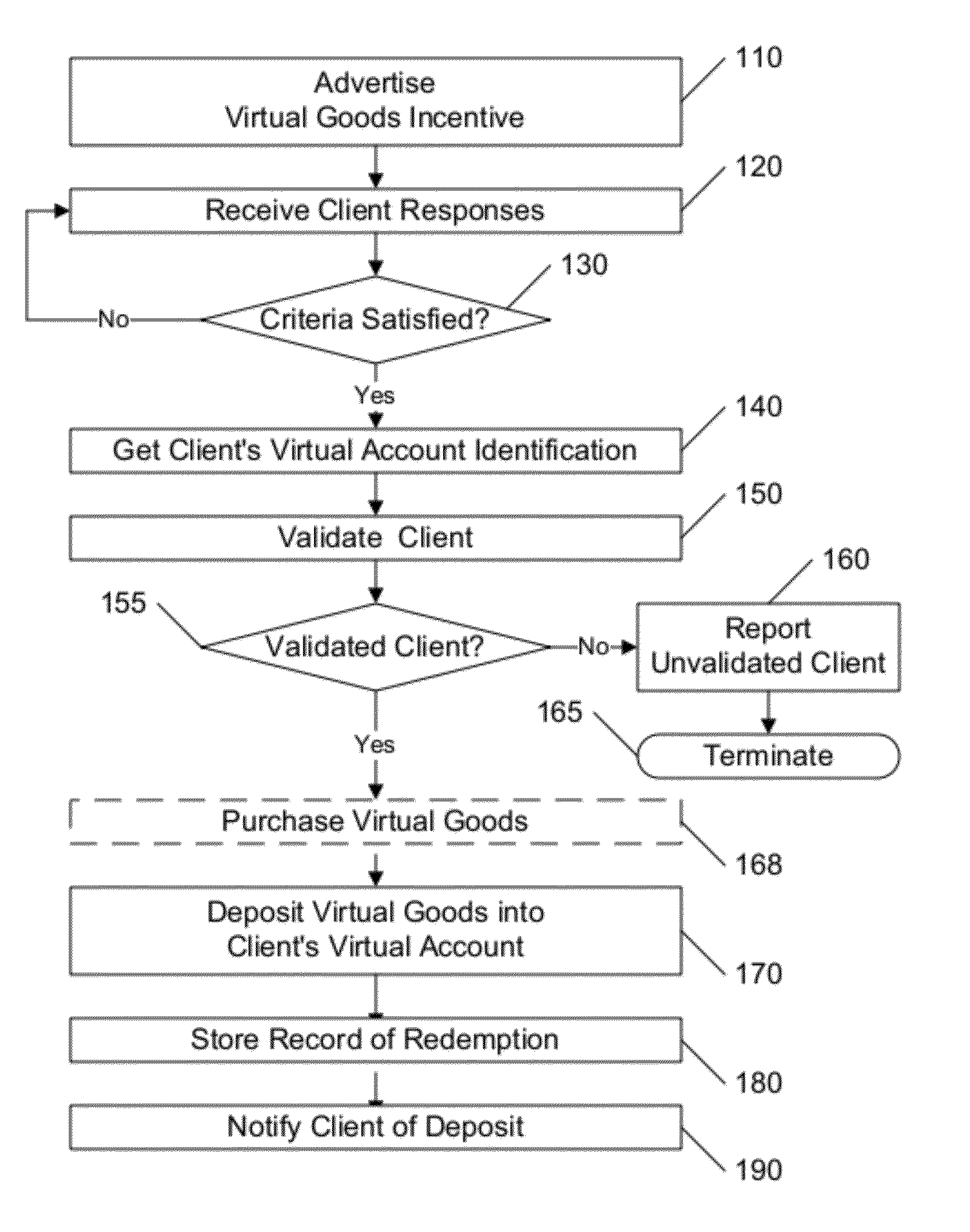
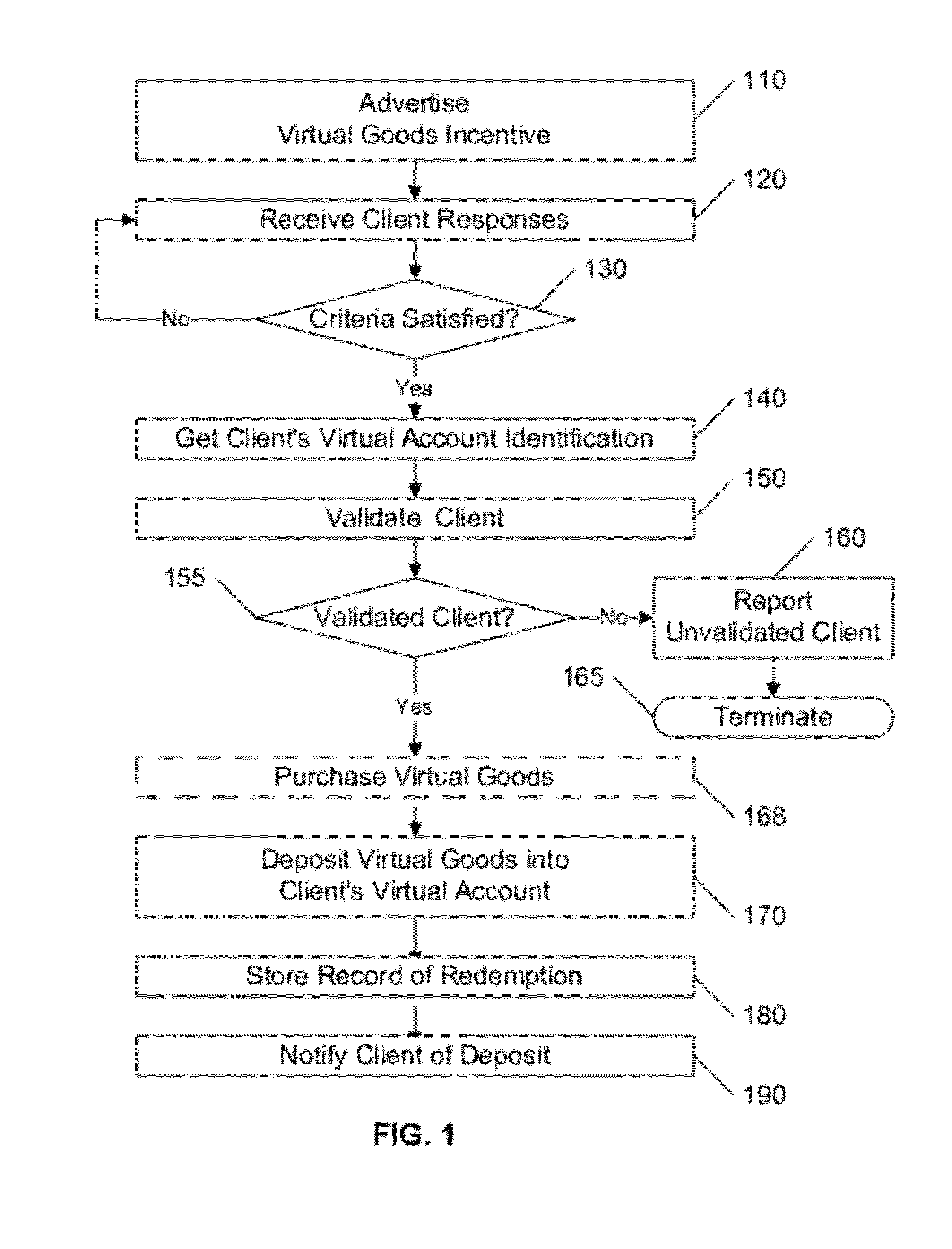
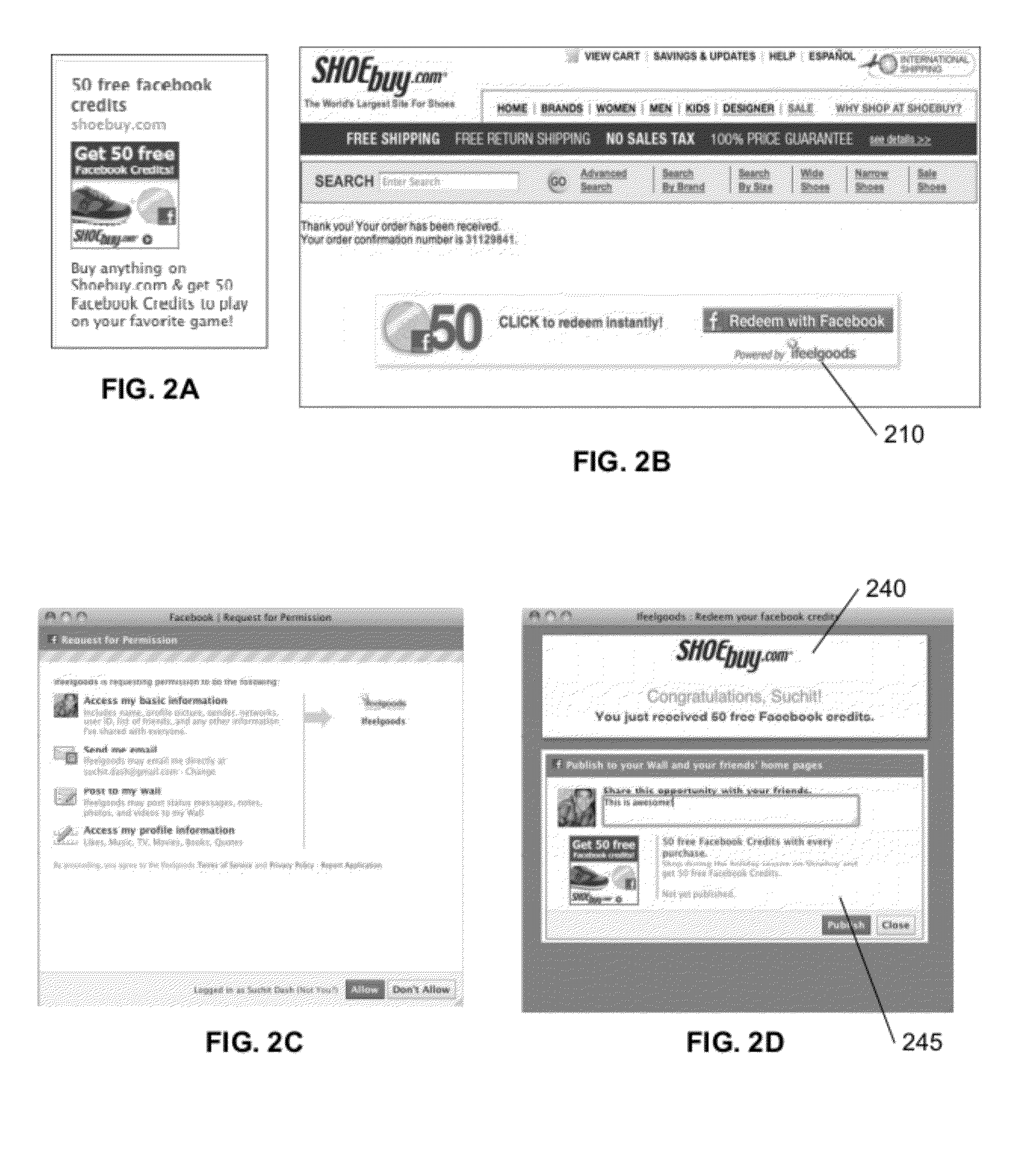
A system or method that assesses a transaction request from a client to identify characteristics that are likely to indicate fraudulent behavior, based on data associated with the request and the client, including client data that is obtained from a social network, such as Facebook. The assessed characteristics may include the client's social profile, including number and status of friends, likes, and virtual account status, as well as parameters associated with the connection used for the transaction, such as IP and email addresses, country of origin, and language. A database is maintained that includes records associated with IP and e-mail addresses, users' characteristics and past redemptions, and the like. Specific criteria, limits, and responses may be defined for each particular class of transaction.
Owner:IFEELGOODS
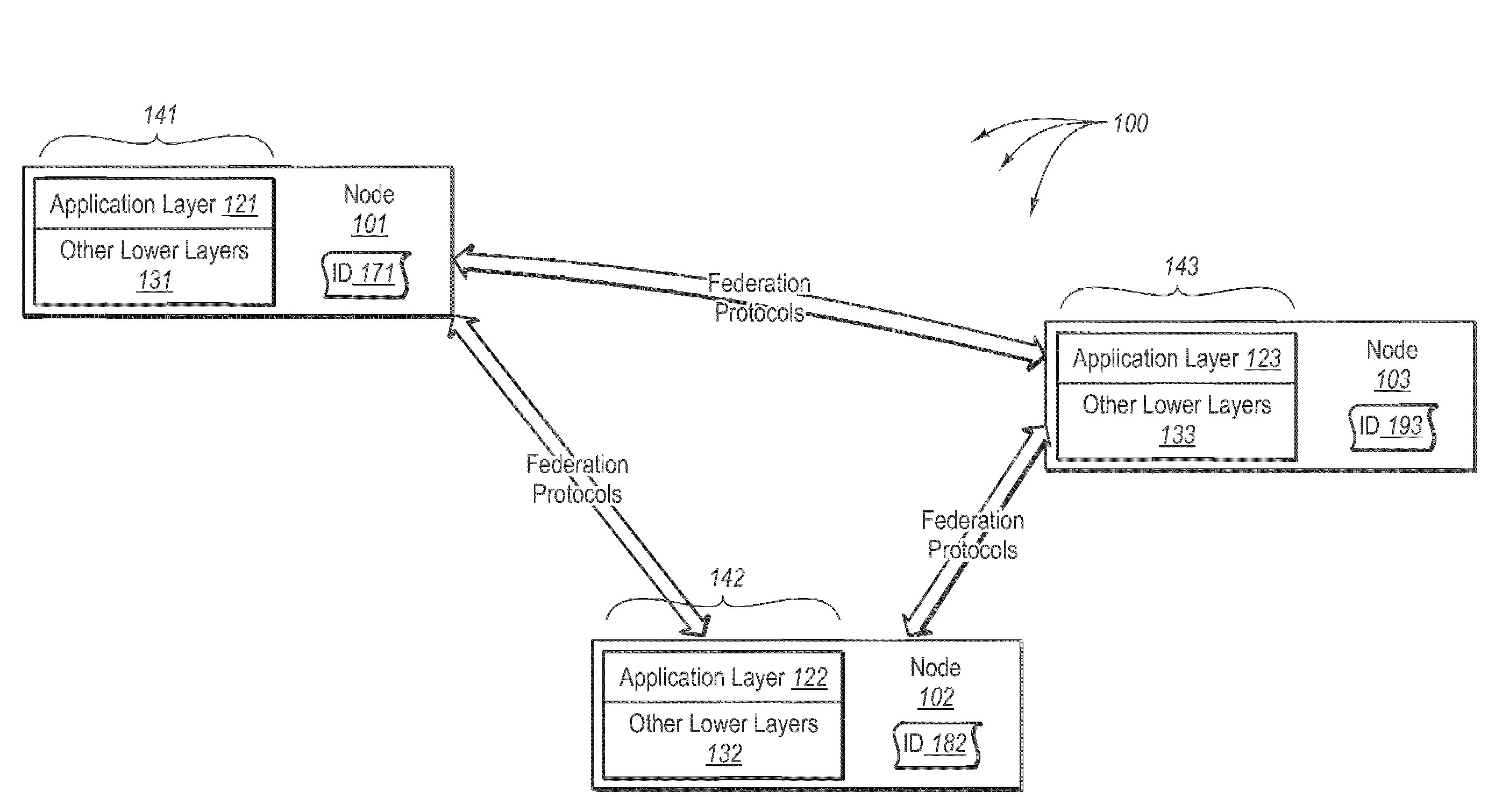
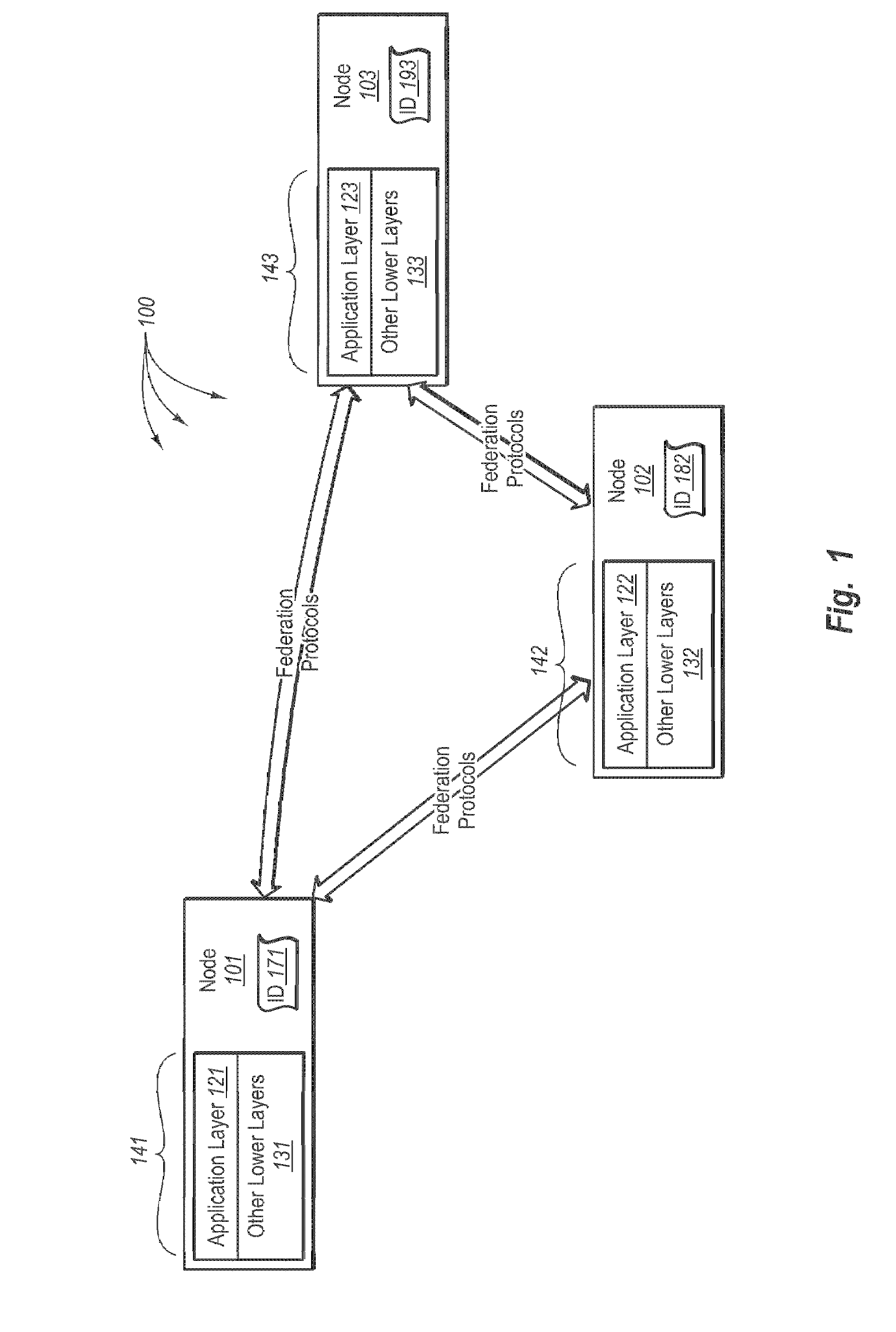
Data consistency within a federation infrastructure
InactiveUS20080288646A1Well formedDigital data information retrievalInput/output to record carriersClient dataClient-side
In some embodiments, it is determined that a primary node has been elected from among a plurality of nodes in a replica set of nodes. The primary node accepts and processes client data access requests. The replica set includes the primary node and other secondary nodes. The primary node receives client data access requests. The primary node assigns a data sequence number to each client data access request that mutates state in the order the client data access requests are received. The data sequence numbers include a linearized processing order that is to be followed by each of the nodes in the replica set. The primary node sends the mutating client data access requests including any corresponding data sequence numbers to the secondary nodes. The primary node receives, from a threshold number of secondary nodes, an acknowledgement indicating reception of the client data access request. The primary node commits the data mutating access request.
Owner:MICROSOFT TECH LICENSING LLC
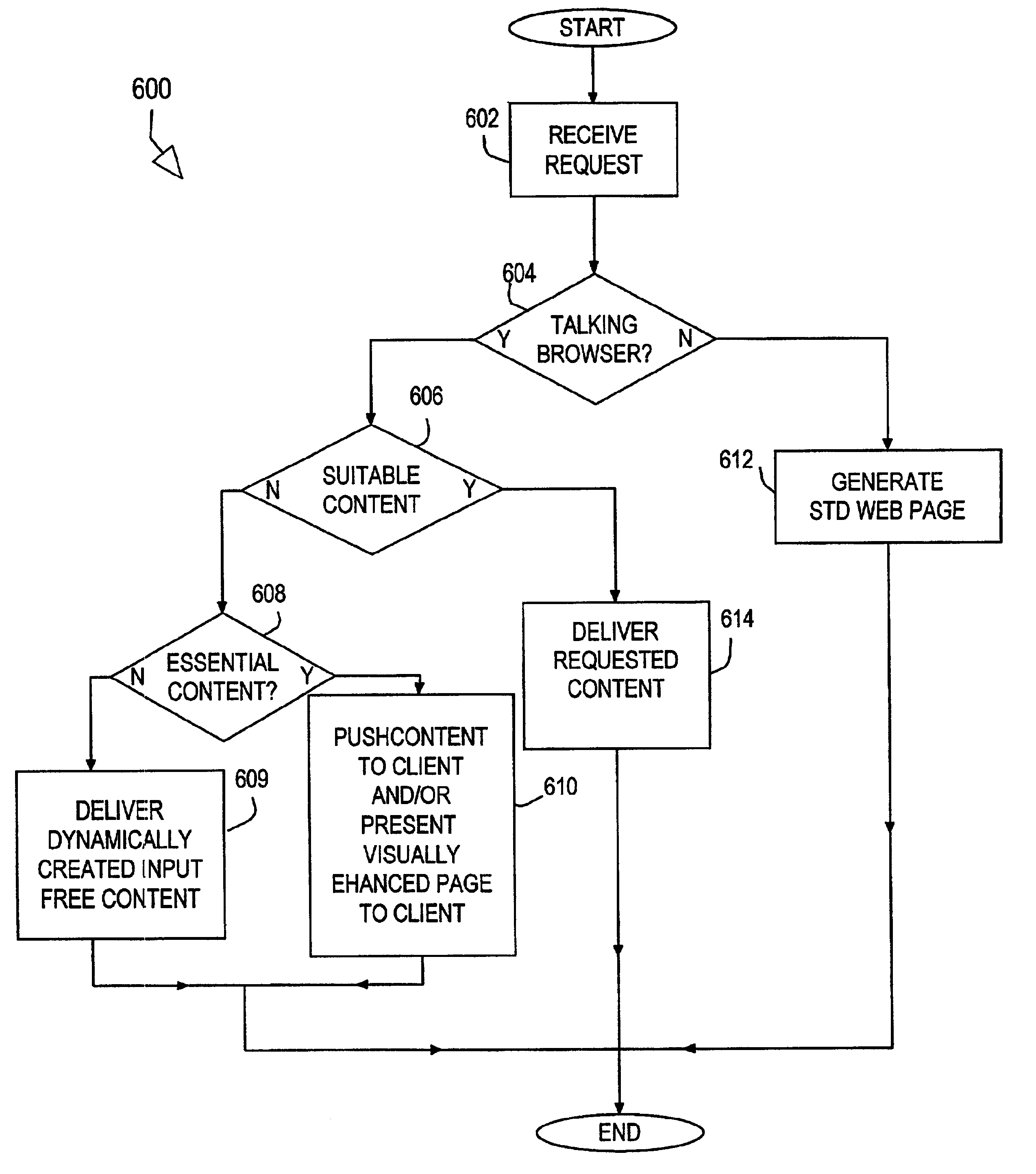
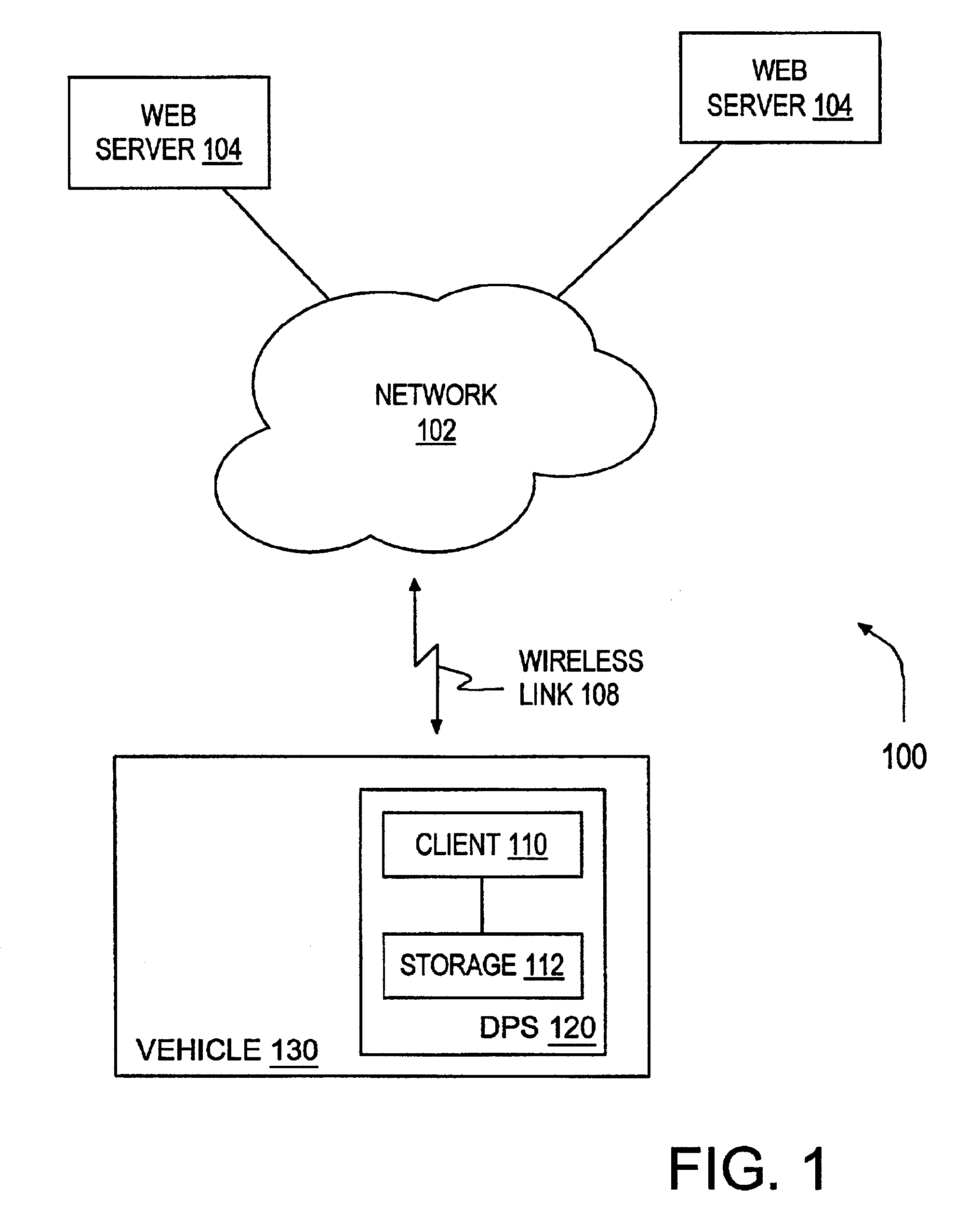
Dynamic data generation suitable for talking browser
InactiveUS7000189B2Easy to watchProvide goodWeb data retrievalMultiple digital computer combinationsClient dataClient-side
A system and method for transferring information a data processing network. A client device suitable for connecting to the network includes a client application configured to receive information from the network and to present the received information to a user as audio information. The server is configured to provide information to the client data processing device responsive to the client request. The system is configured to determine when at least a portion of the information provided by the server is unsuitable for presentation by the client and to respond to the determination by storing the information for later access by the user, presenting a visually enhanced version of the information to the user, or providing portions of the information suitable for audio presentation to the user.
Owner:IBM CORP
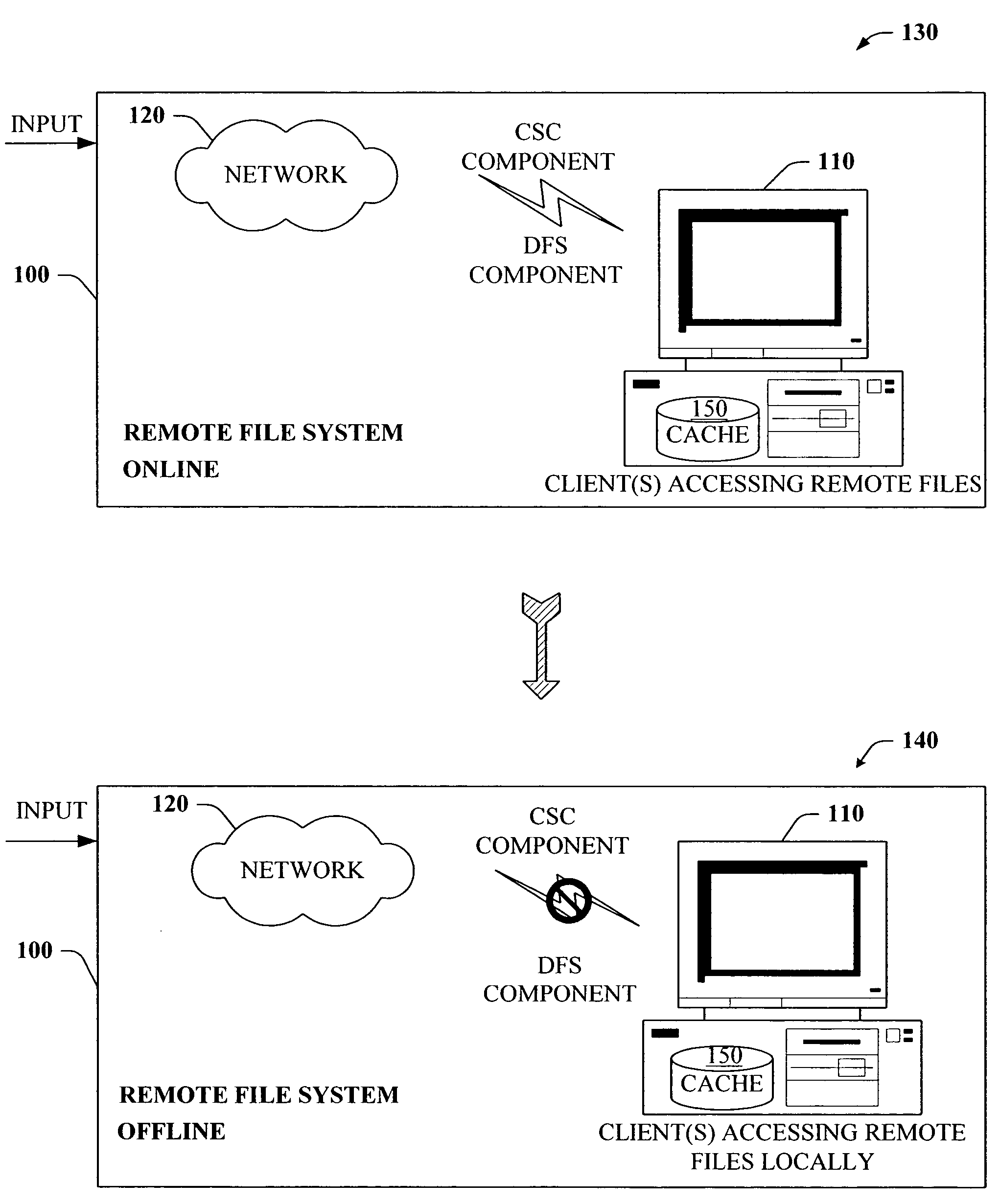
Truth on client persistent caching
ActiveUS20050102370A1Easy to operateMemory architecture accessing/allocationDigital data information retrievalClient dataClient-side
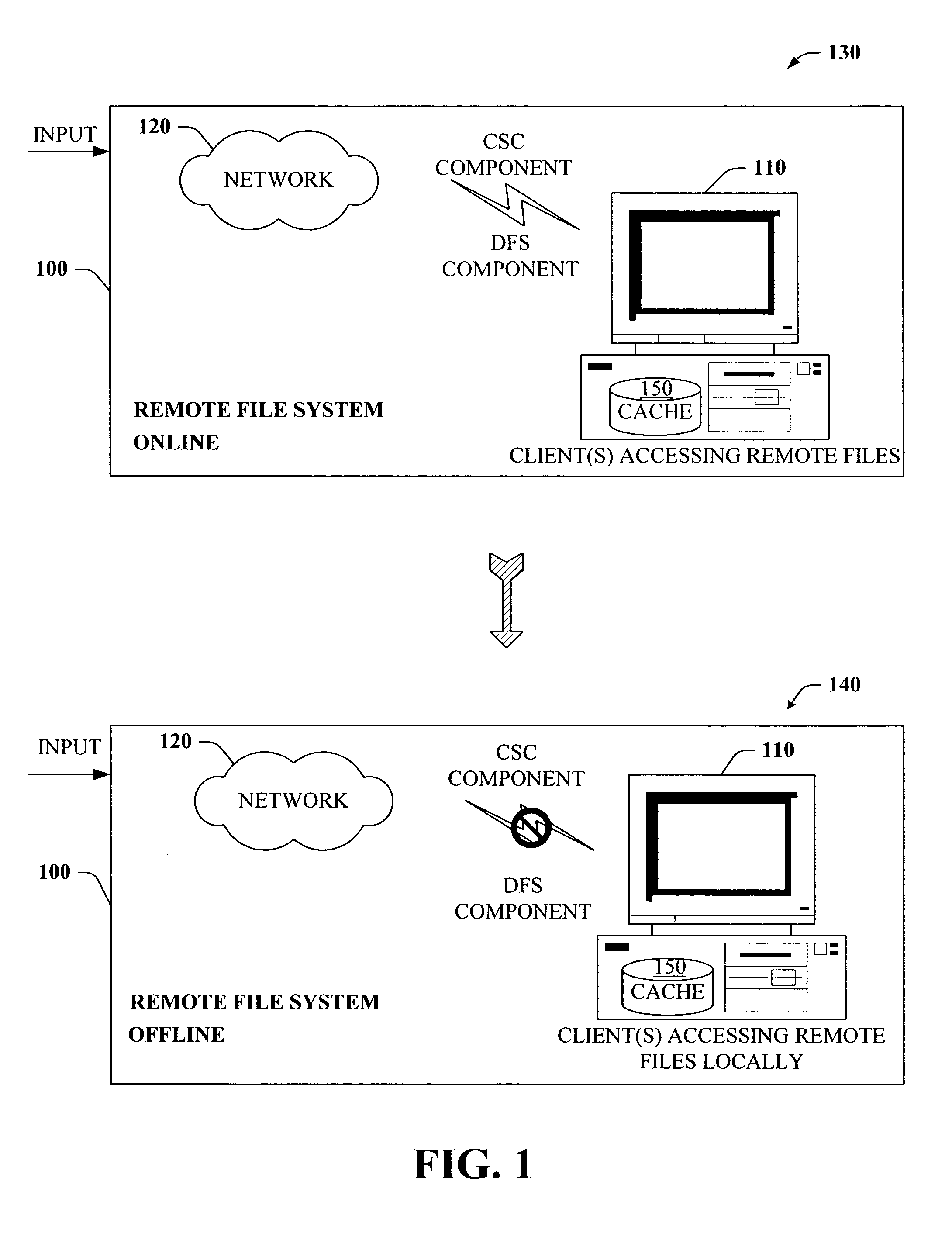
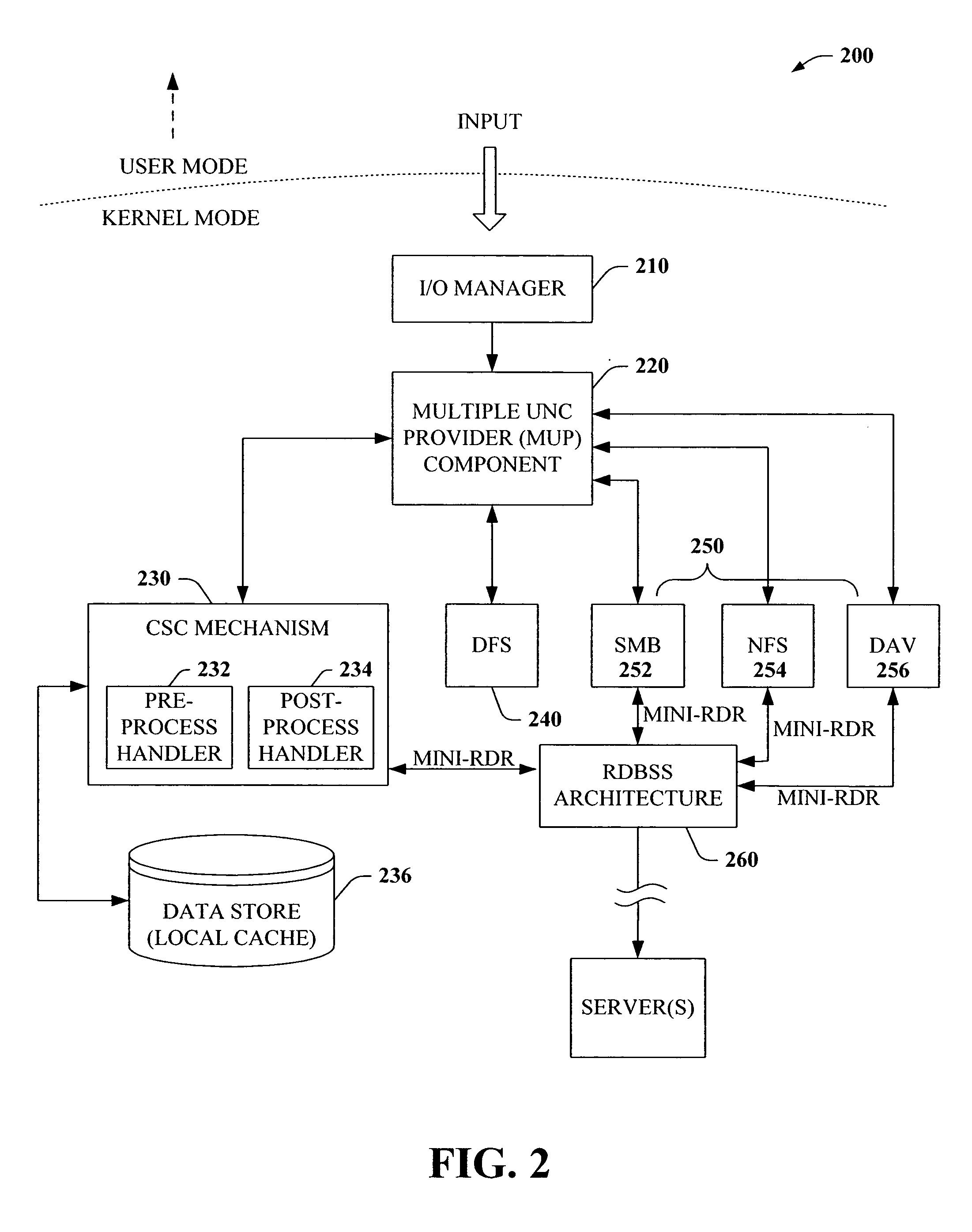
The present invention provides a novel client side caching (CSC) infrastructure that supports transition states at the directory level to facilitate a seamless operation across connectivity states between client and remote server. More specifically, persistent caching is performed to safeguard the user (e.g., client) and / or the client applications across connectivity interruptions and / or bandwidth changes. This is accomplished in part by caching to a client data store the desirable file(s) together with the appropriate file access parameters. Moreover, the client maintains access to cached files during periods of disconnect. Furthermore, portions of a path can be offline while other portions upstream can remain online. CSC operates on the logical path which cooperates with DFS which operates on the physical path to keep track of files cached, accessed and changes in the directories. In addition, truth on the client is facilitated whether or not a conflict of file copies exists.
Owner:MICROSOFT TECH LICENSING LLC
Decision management system providing qualitative account/customer assessment via point in time simulation
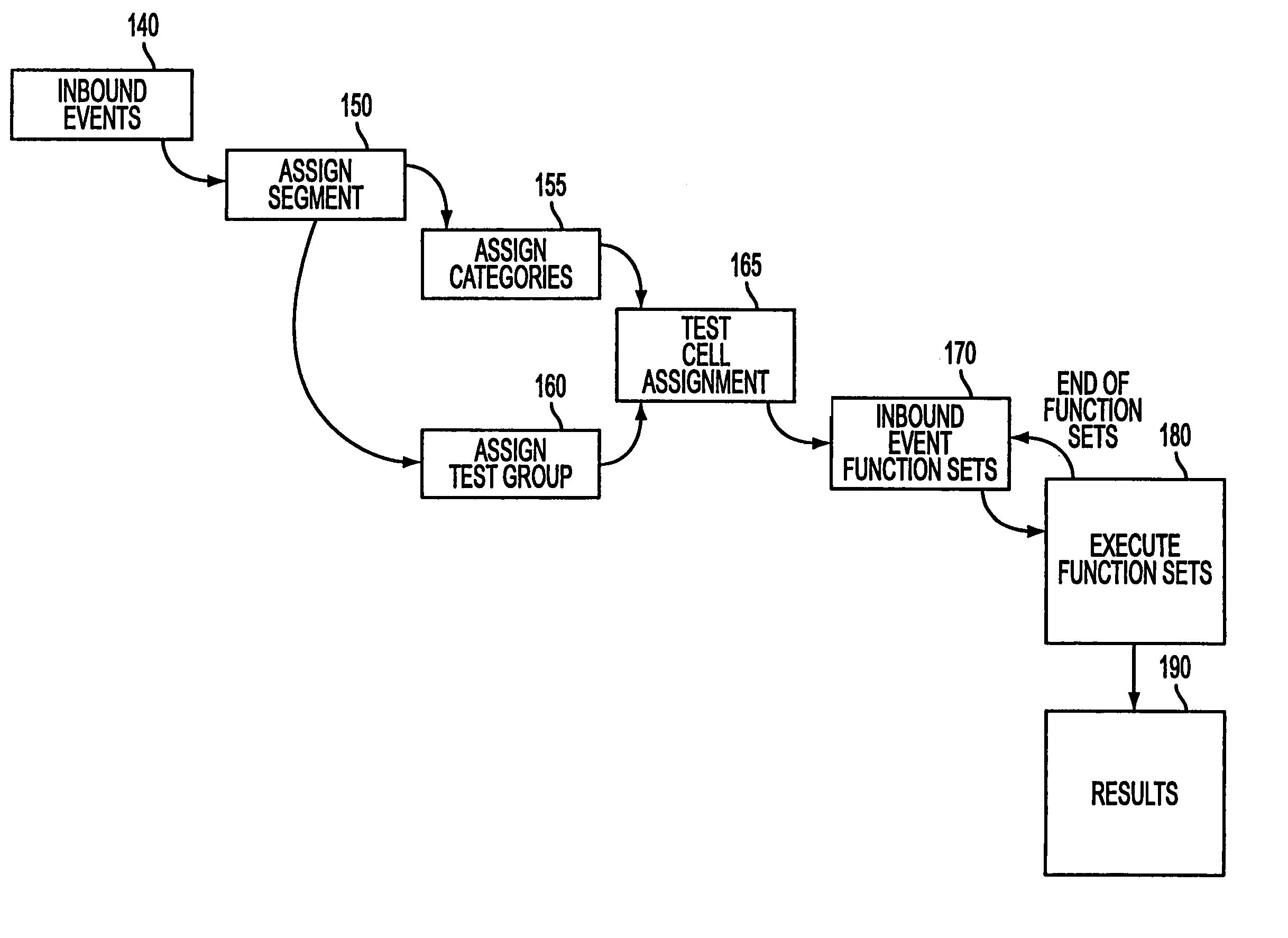
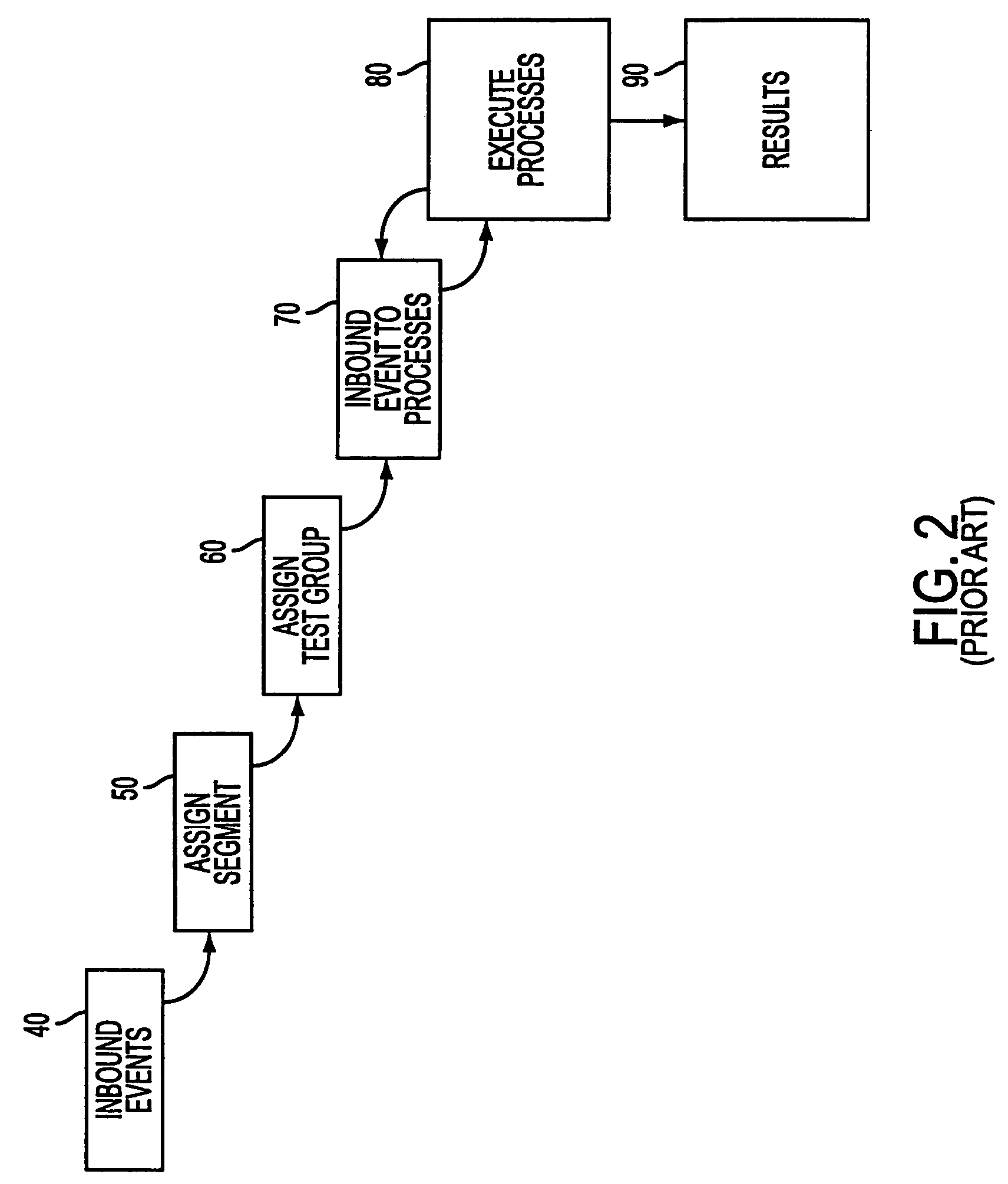
A computer-implemented decision management system which provides qualitative client assessment via point in time simulation. More specifically, the decision management system (a) simulates the effect of a strategy by applying the strategy to client data, and (b) tracks what type of client traveled through a respective decision point in the strategy during the simulation. Simulation parameters can be selected without technical intervention via, for example, a GUI and a relational data model. Such parameters can include which customers and which client data sample will be used for the simulation, and which inbound events will trigger the strategy. Moreover, detailed and aggregate results can be consolidated to determine expected results from the simulated strategies, and traditional and OLAP reporting facilities can be applied to analyze / view the consolidated results.
Owner:CGI TECH & SOLUTIONS
Devices for providing distributable middleware data proxy between application servers and database servers
InactiveUS20100174939A1Shorten the timeSave resourcesDigital data information retrievalResource allocationClient dataTerm memory
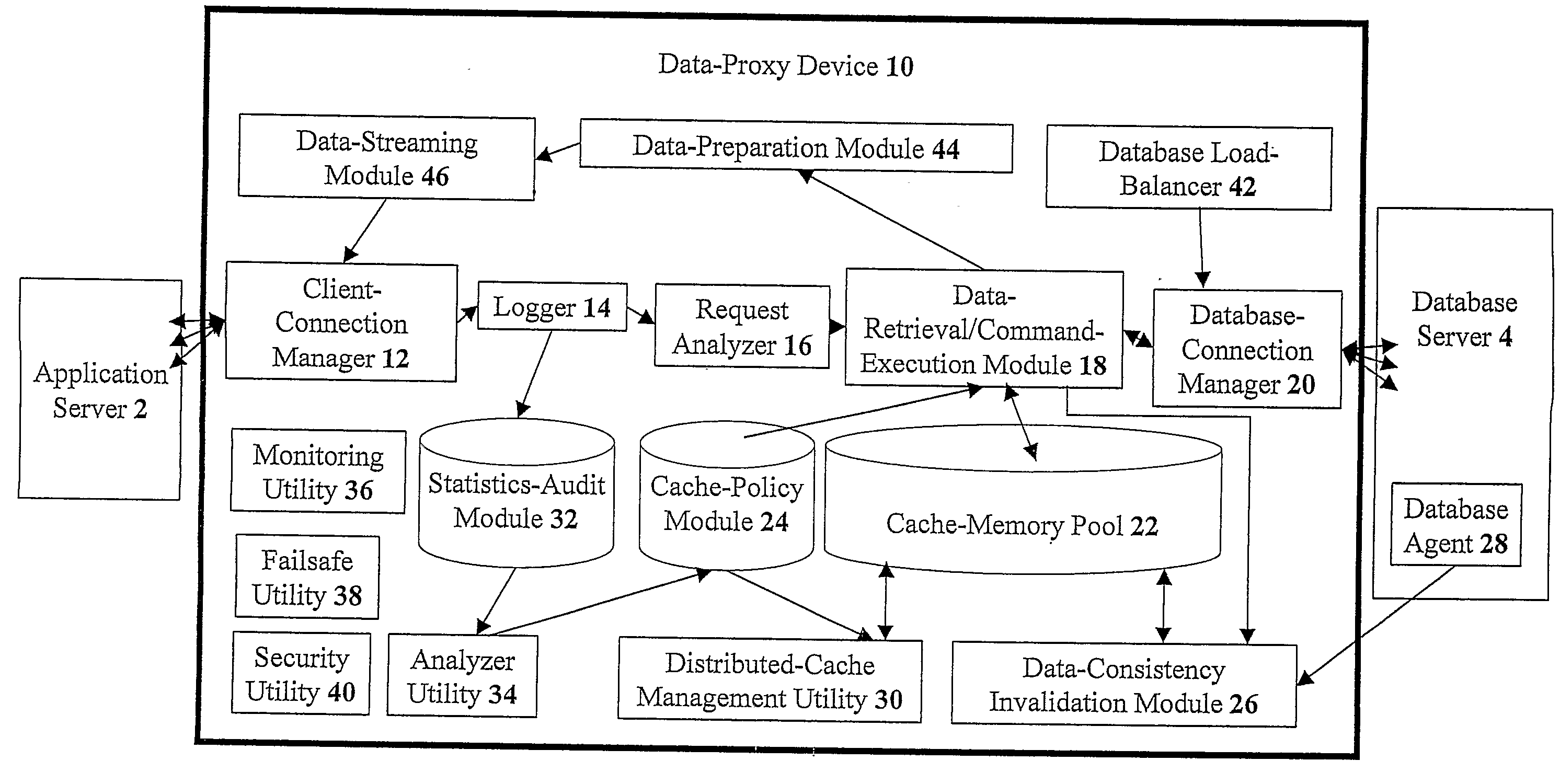
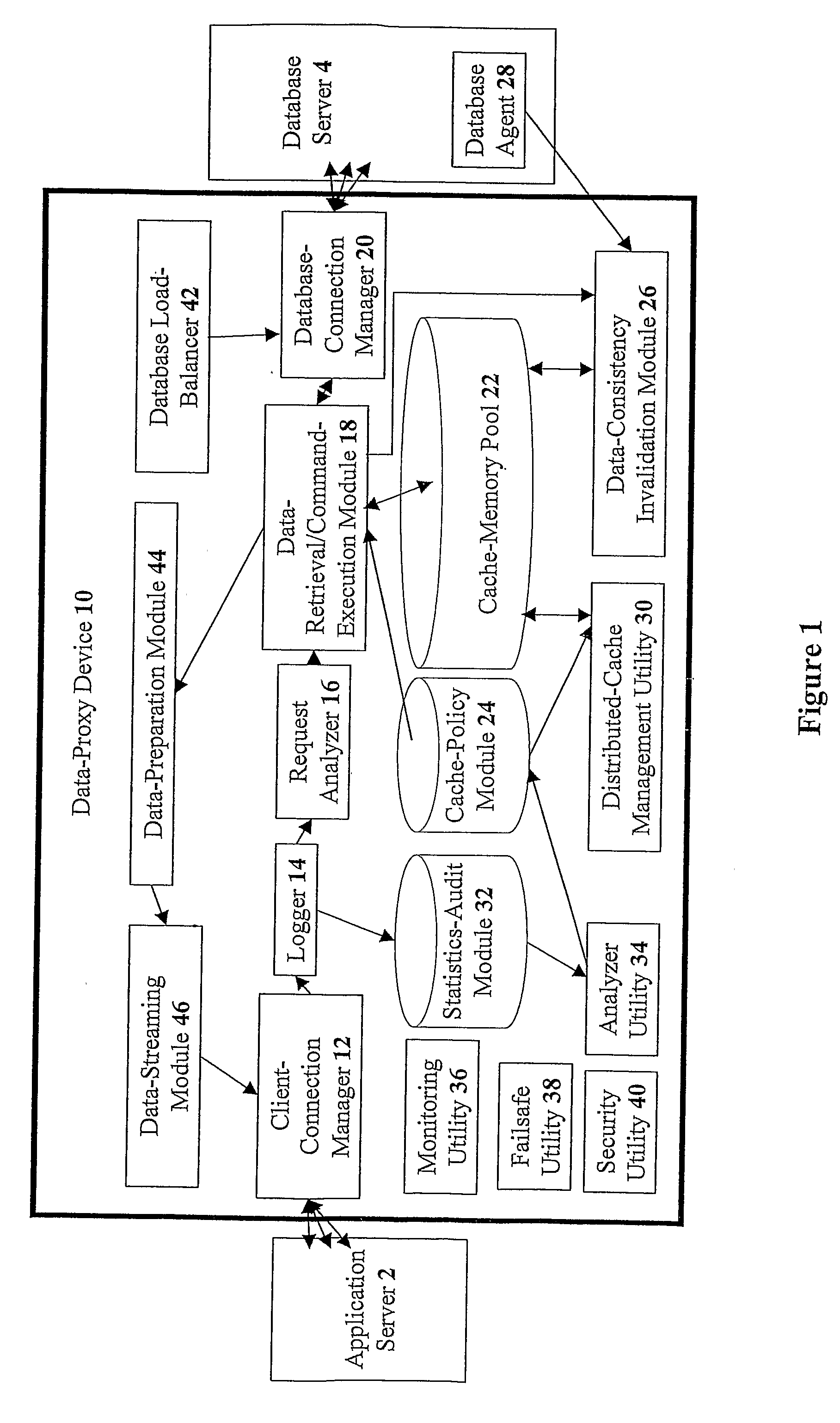
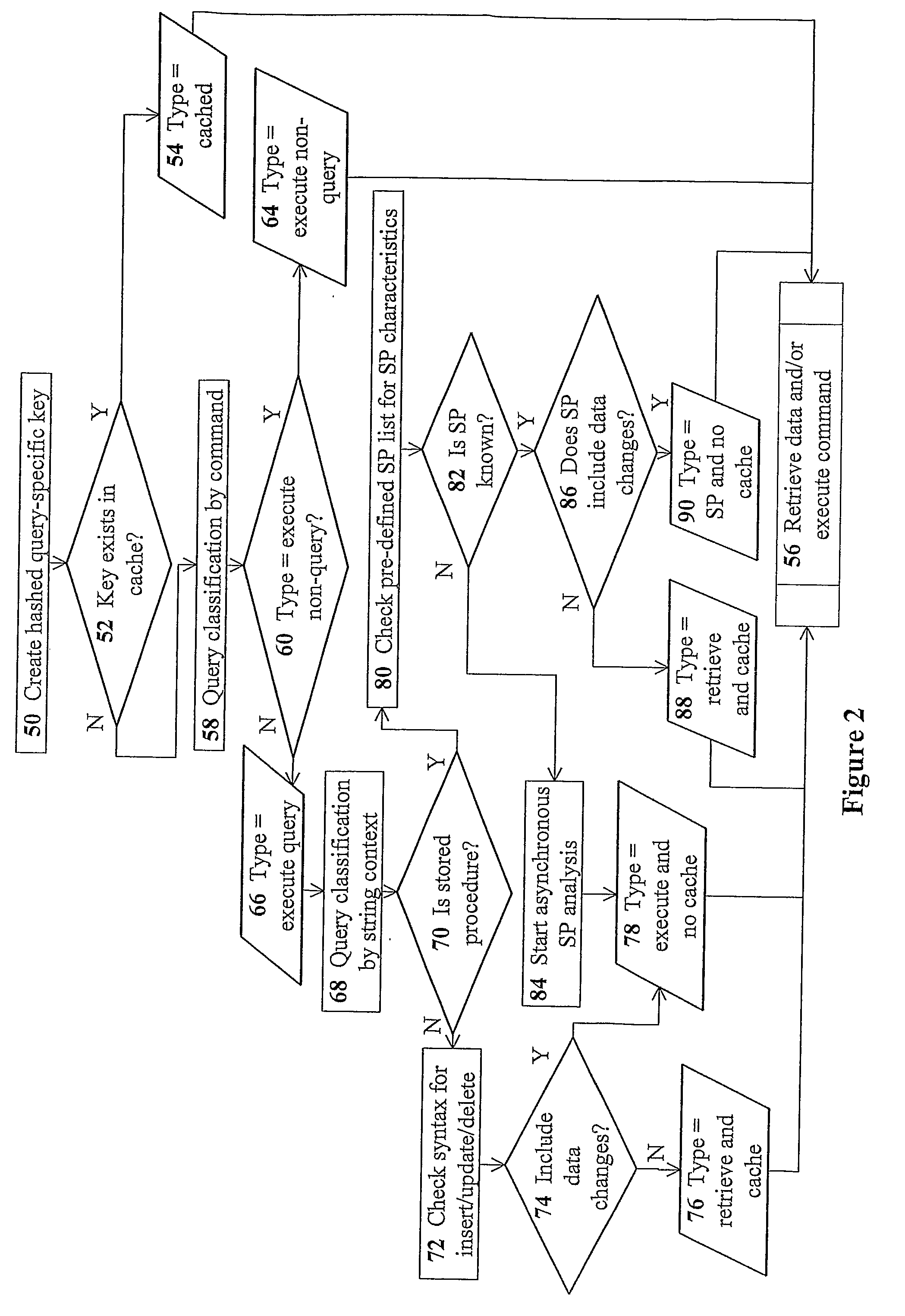
The present invention discloses devices Including a transparent client-connection manager for exchanging client data between an application server and the device: a request analyzer for analyzing query requests from at least one application server; a data-retrieval / command-execution module for executing query requests; a database connection manager for exchanging database data between at least one database server and the device: a cache-memory pool for storing data items from at least one database server: a cache-policy module for determining cache criteria for storing the data Items In the cache-memory pool; and a data-consistency invalidation module for determining invalidated data Items based on invalidation criteria for removing from the cache-memory pool. The cache-memory pool Is configured to utilize memory modules residing in data proxy devices and distributed cache management utility, enabling the memory capacity to be used as a cluster to balance workloads.
Owner:DCF TECH
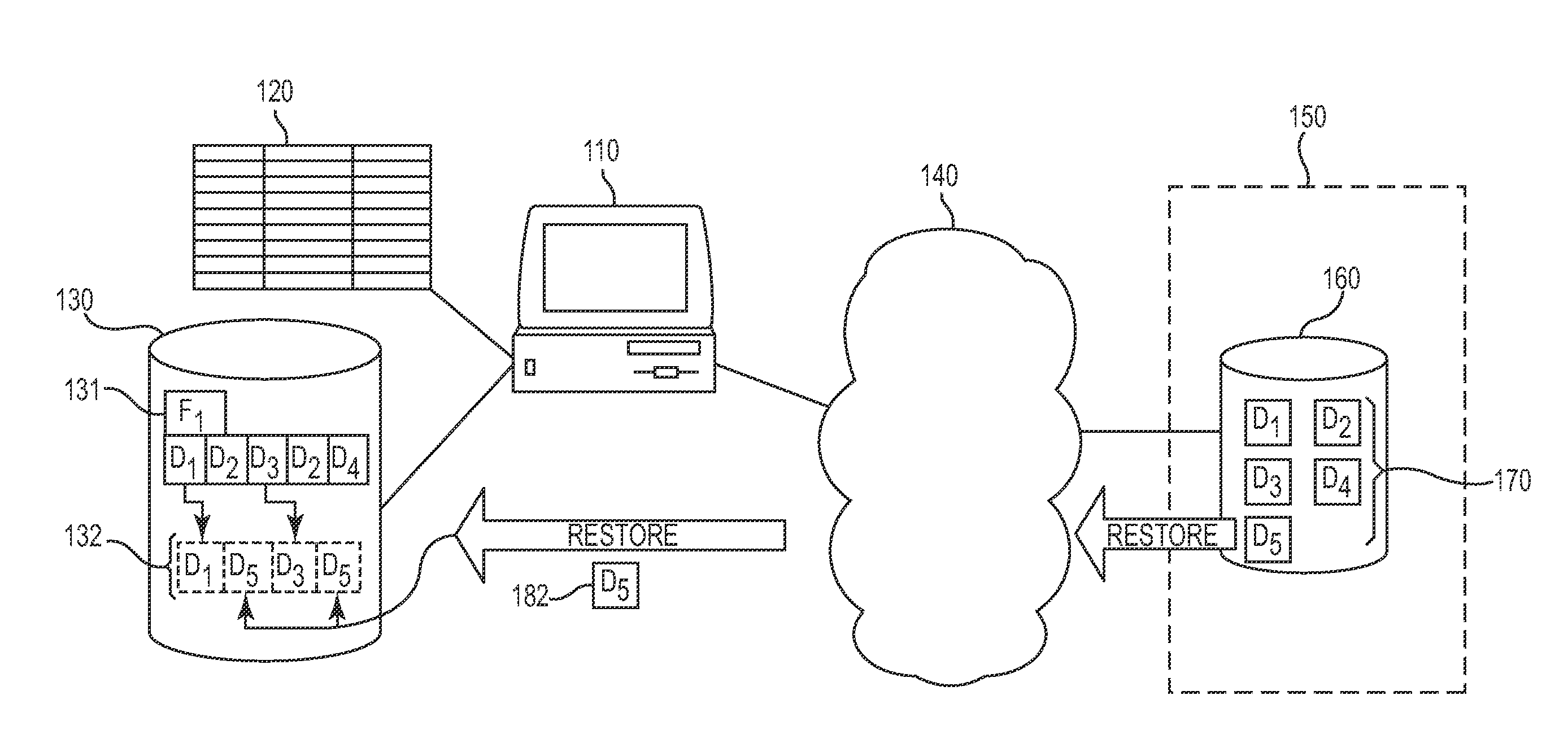
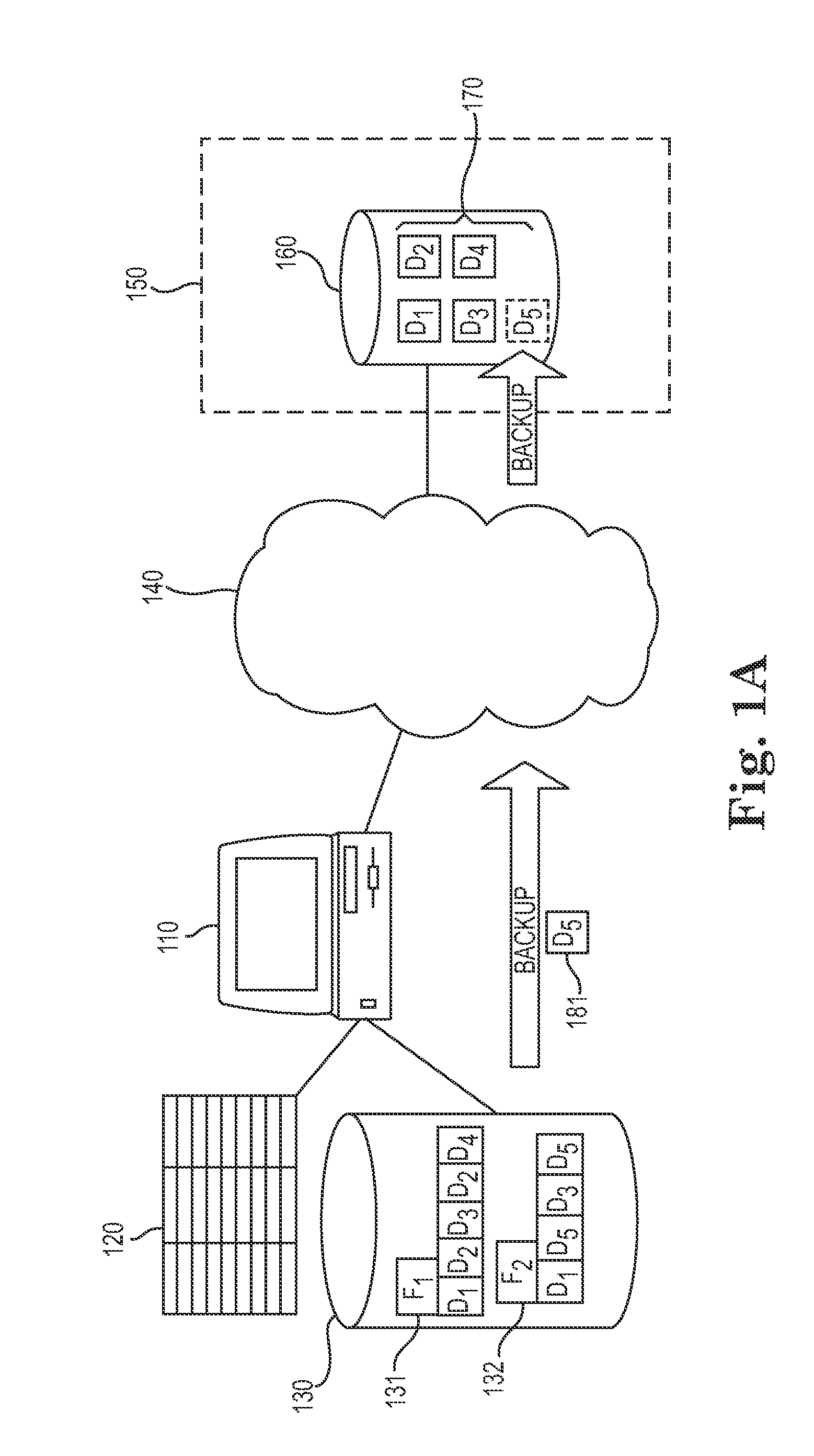
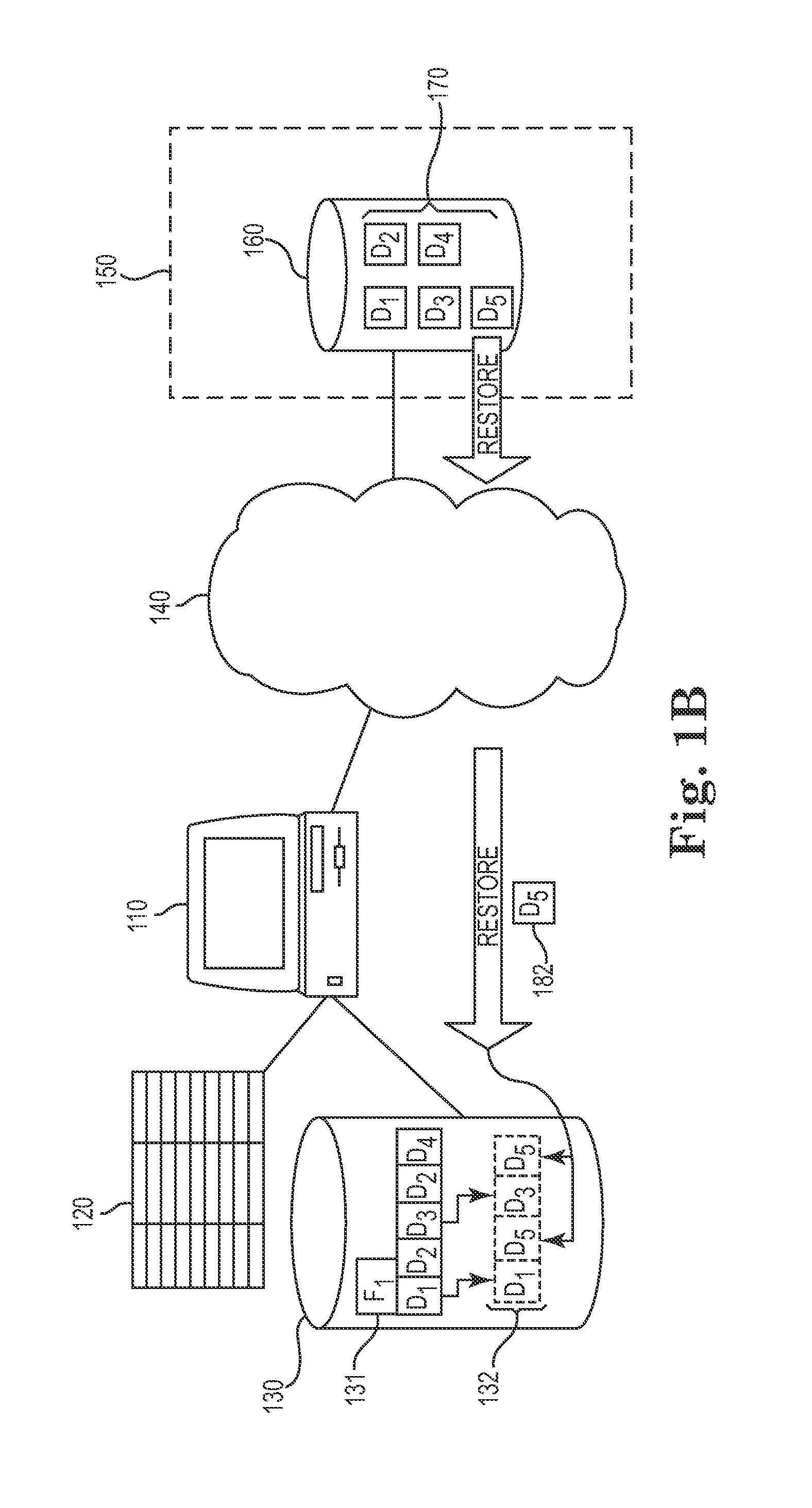
Approach for optimizing restores of deduplicated data
InactiveUS20110218969A1Reduce the amount of processingImprove efficiencyError detection/correctionDigital data processing detailsData fileClient data
Various techniques for improving the performance of restoring deduplicated data files from a server to a client within a storage management system are disclosed. In one embodiment, a chunk index is maintained on the client that tracks the chunks remaining on the client for each data file that is stored to and restored from the storage server. When a specific file is selected for restore from the storage server to the client, the client determines if any local copies of this specific file's chunks are stored in files already existing on the client data store. The file is then reconstructed from a combination of these local copies of the file chunks and chunks retrieved from the storage server. Therefore, only chunks that are not stored or are inaccessible to the client are retrieved from the server, reducing server-side processing requirements and the bandwidth required for data restore operations.
Owner:IBM CORP
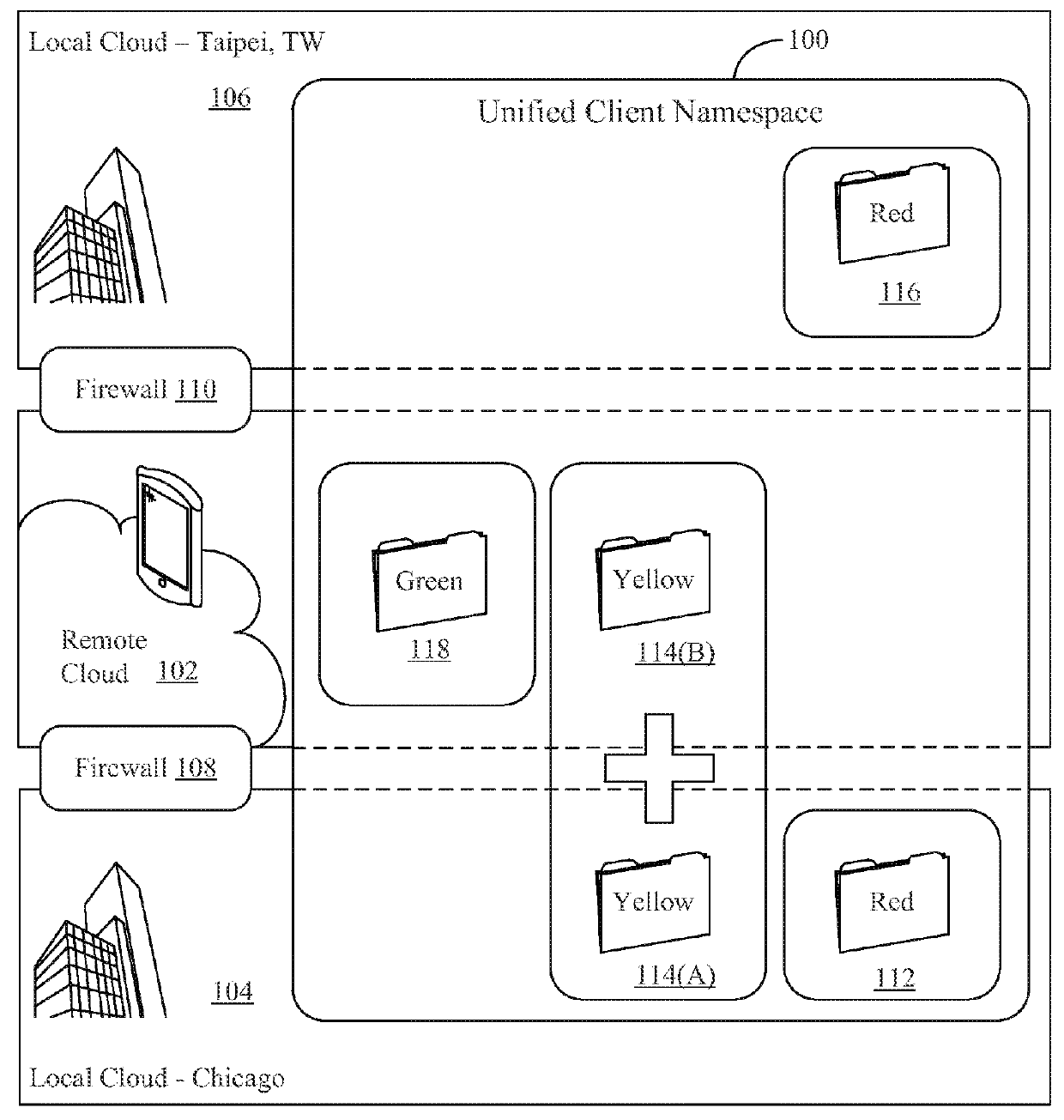
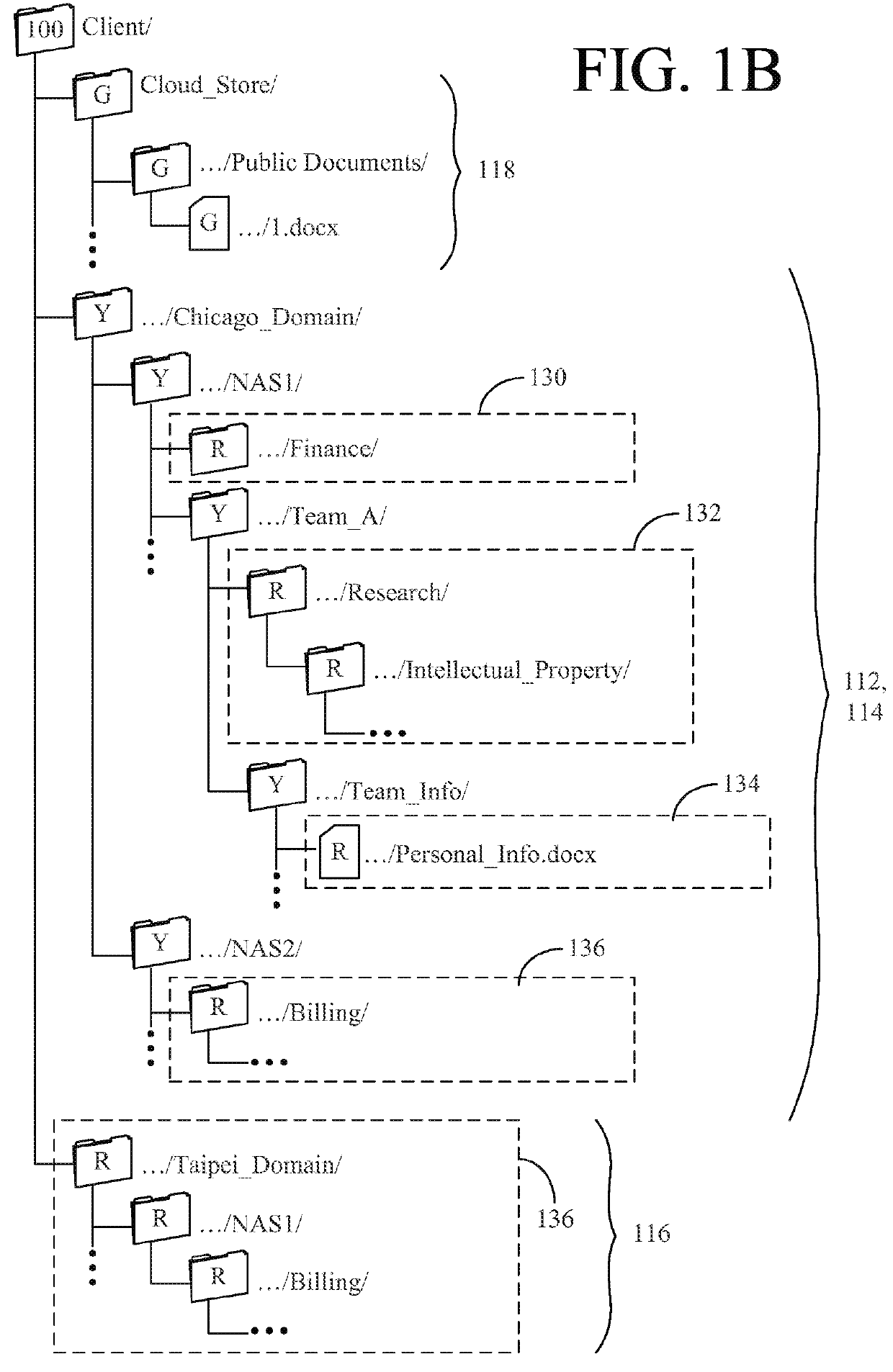
Systems and methods for facilitating access to private files using a cloud storage system
ActiveUS9251114B1Facilitates accessing fileOvercome problemsDatabase distribution/replicationDigital data protectionFile systemObject store
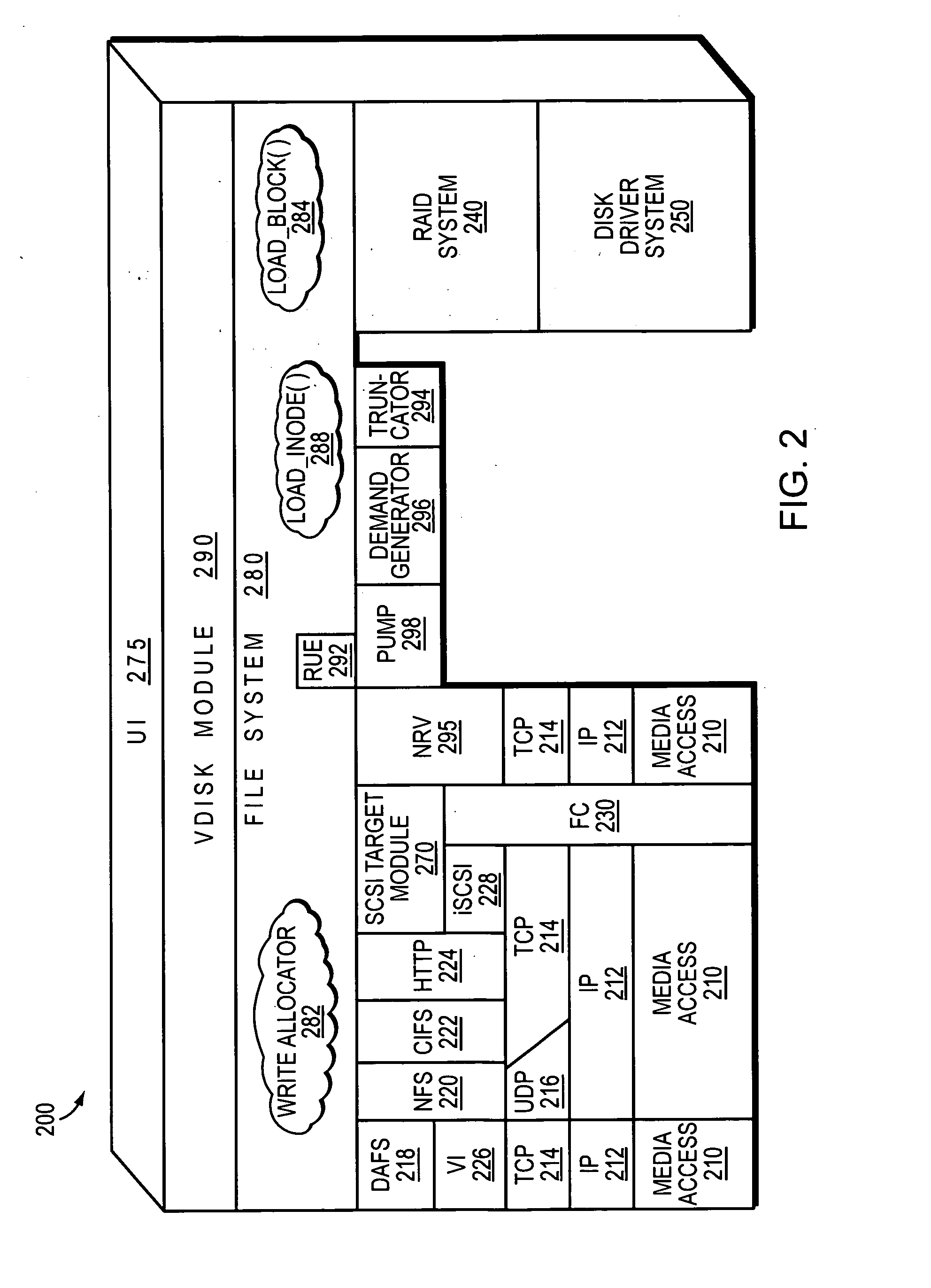
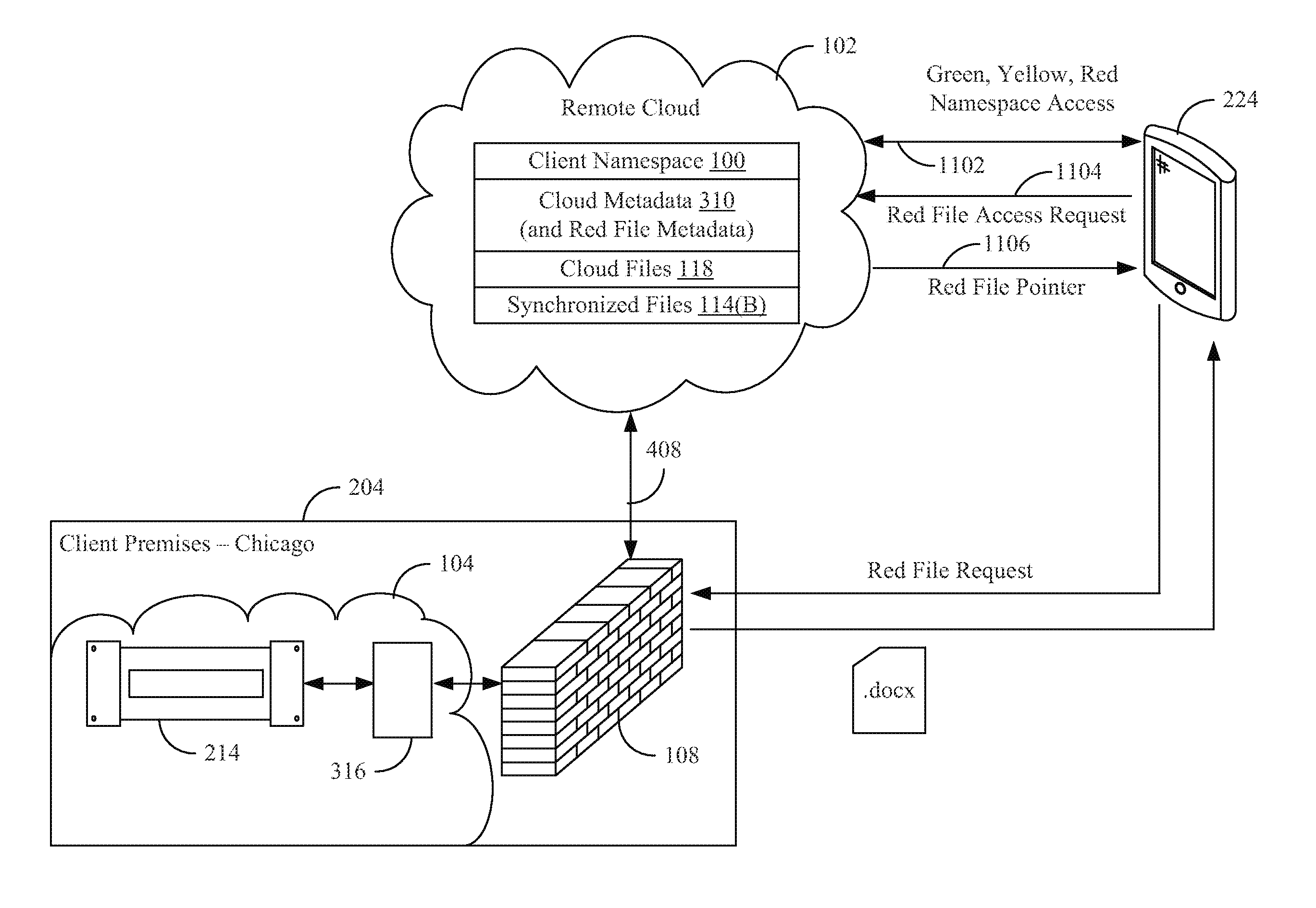
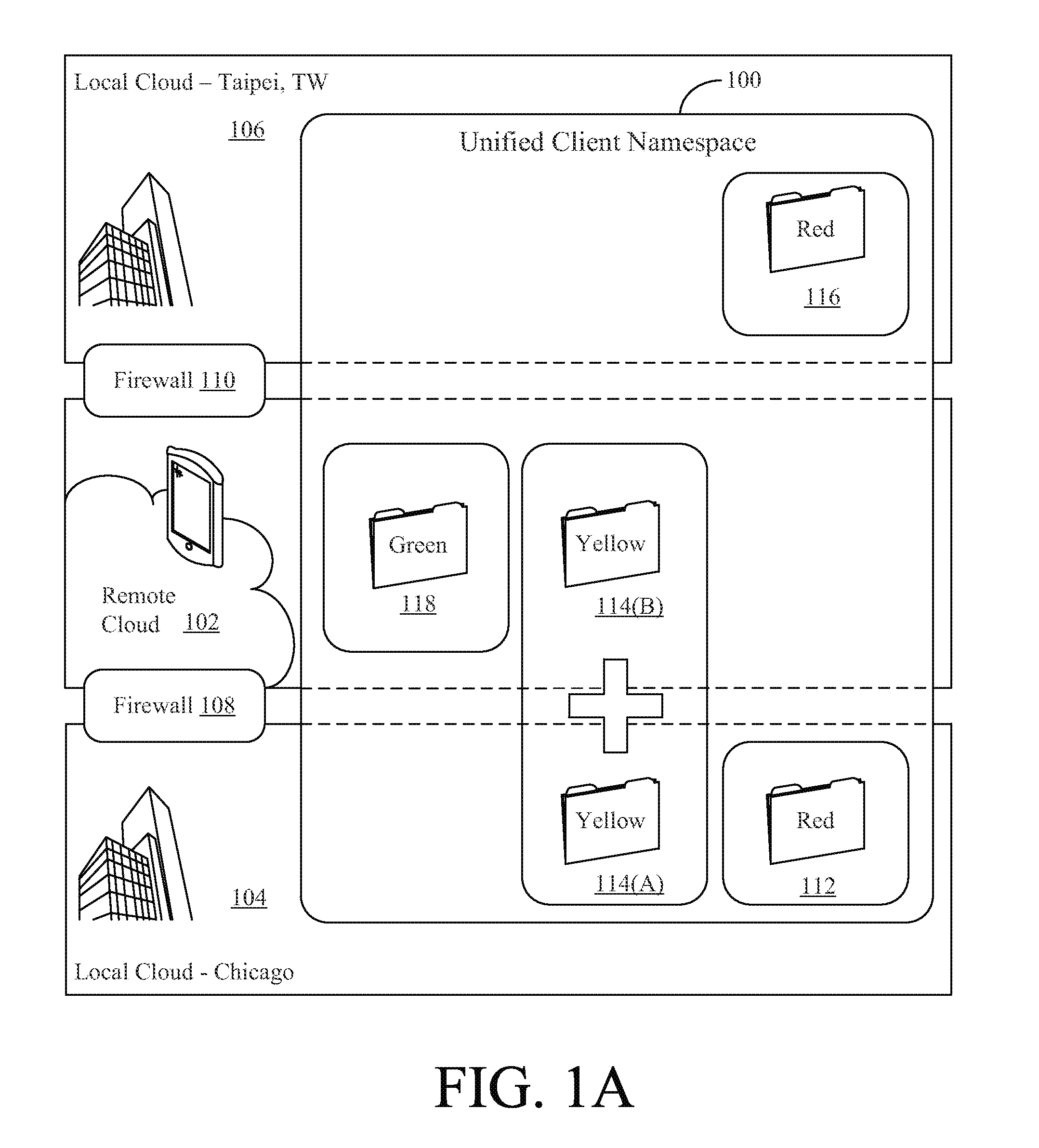
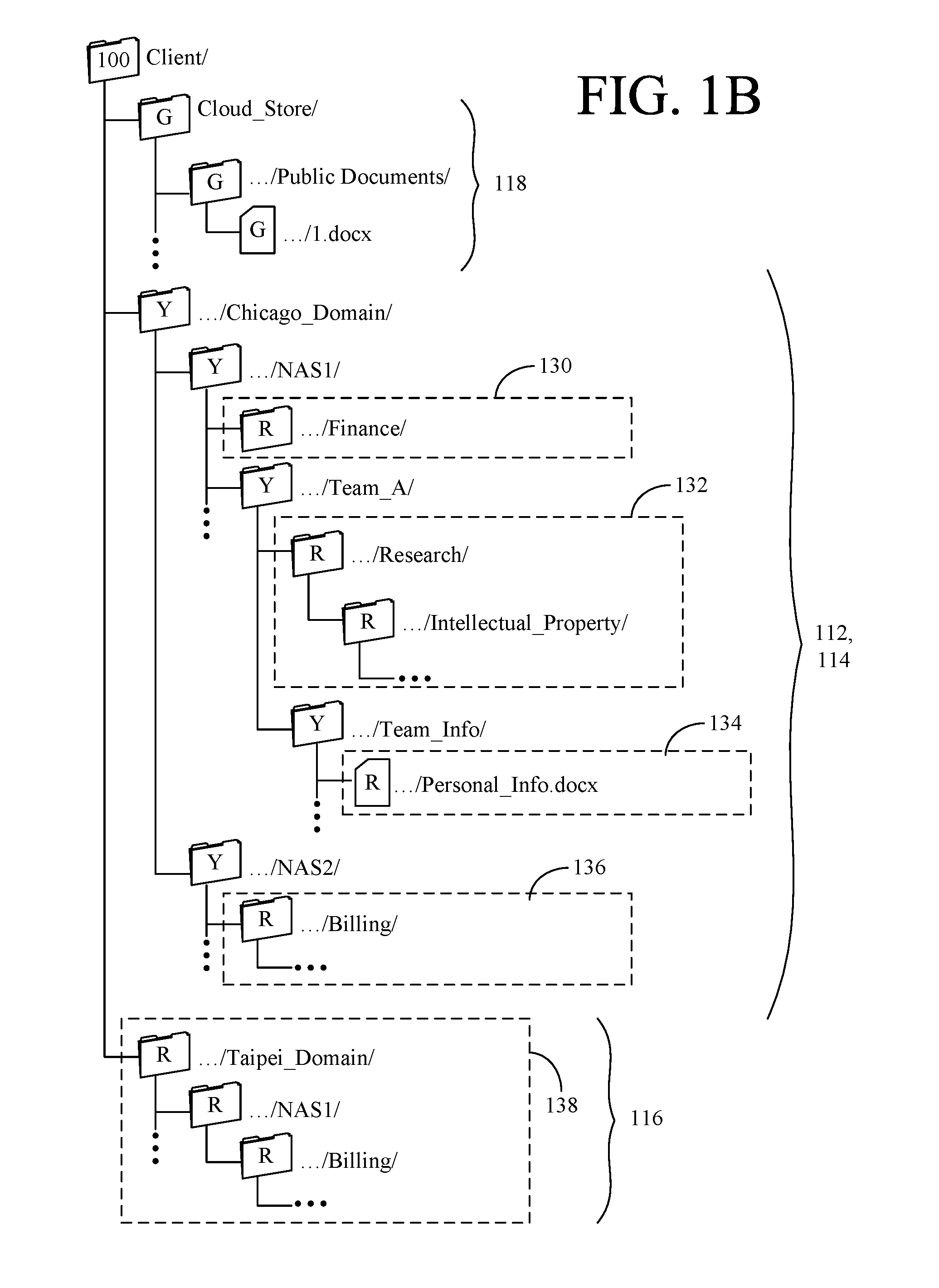
A method for providing access to objects associated with a particular client in a cloud storage system is disclosed. The method includes the steps of establishing a connection with a user, providing a client namespace associated with the client to the user, where the client namespace represents objects stored on the cloud storage system and objects stored on a private storage system apart from the cloud storage system, receiving a request from the user to access an object stored on the private storage system, and providing information to the user to facilitate access to the object stored on the private storage system by said user. Other systems and methods are also disclosed. Important advantages of the present invention are facilitated by separating the logic for user access (control plane) from the actual storage (Storage plane). Private file system access can still be managed from the cloud, while keeping the client data private.
Owner:EGNYTE
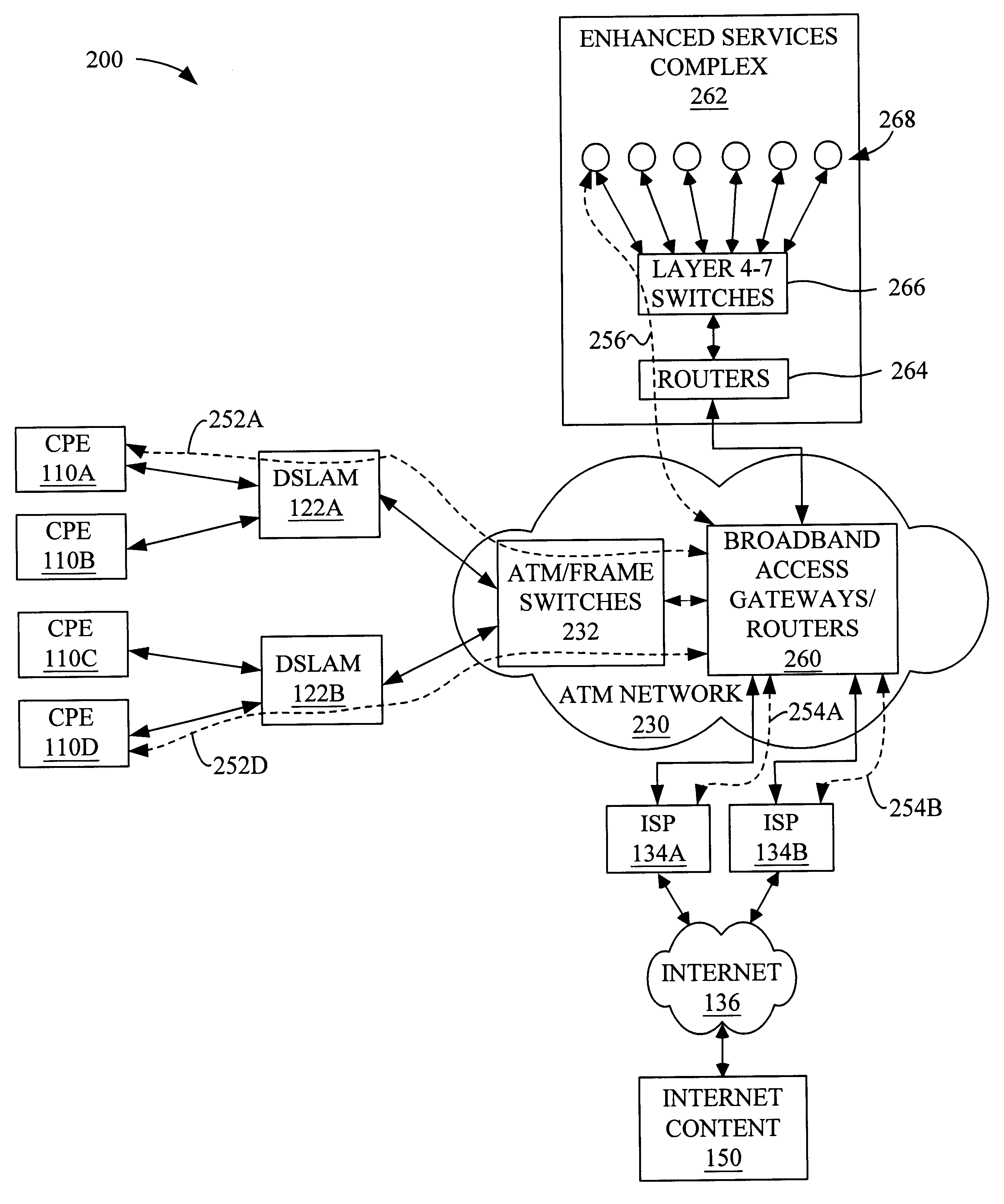
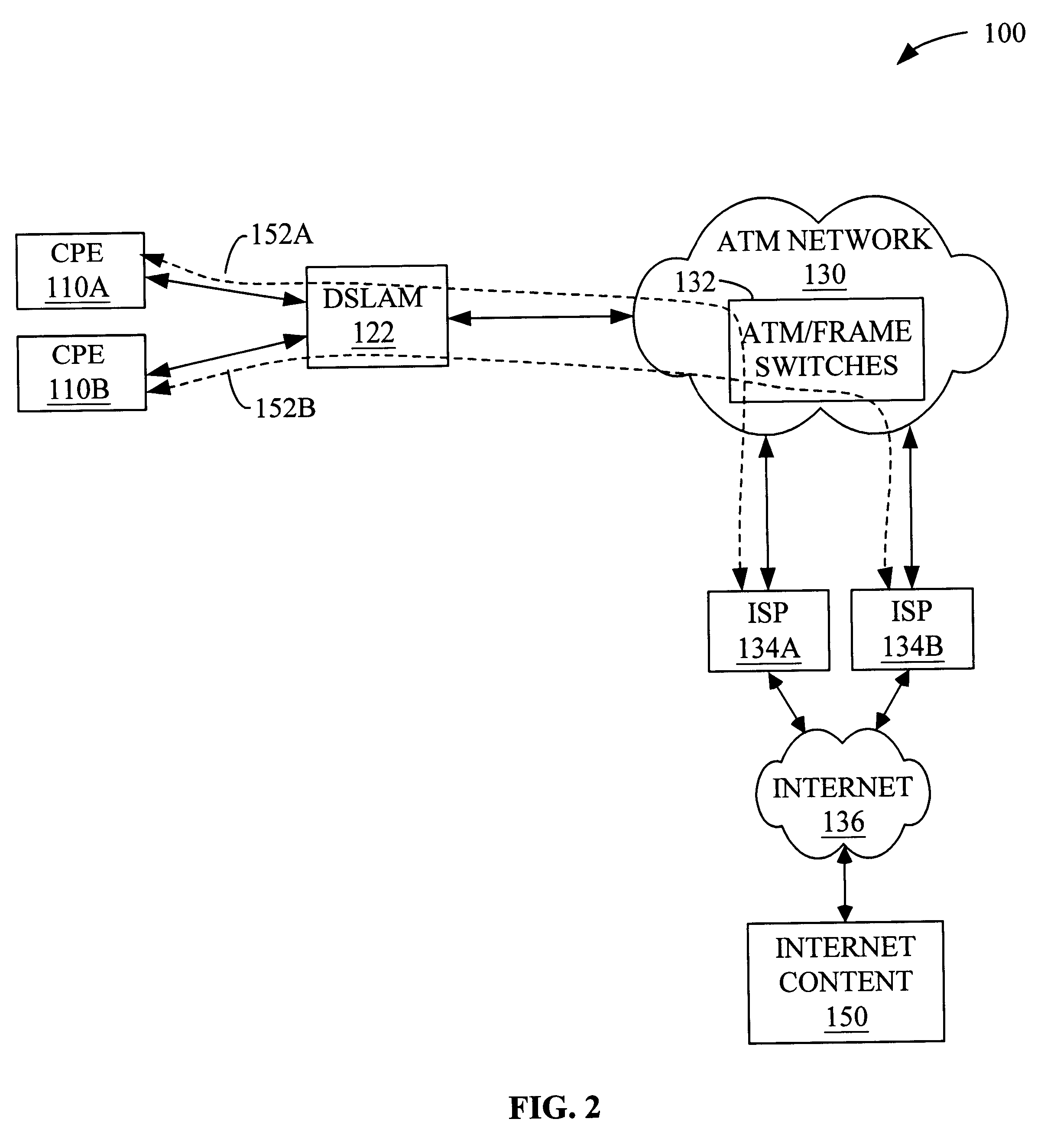
System and method for providing broadband content to high-speed access subscribers
InactiveUS6286049B1Multiple digital computer combinationsData switching networksClient dataData traffic
Systems and methods for providing broadband content to high-speed access subscribers with layer 4-7 switching are disclosed. The system generally comprises an enhanced services complex (ESC) having at least one content server having Internet content stored or cached therein and a broadband access gateway (BAG) in communication with the ESC and to at least one Internet service provider (ISP), where the BAG is configured to transmit and receive data traffic to and from a client premise equipment (CPE) at a client premise, respectively. The BAG is configured to selectively route data traffic received from the CPE to an ESC content server or the ISP based on multiple instances of the content destination address. The method generally comprises routing client data packets from a CPE to a BAG in communication with at least one ISP and an ESC having at least one content server, selectively routing each client data packet from the BAG to the ESC or the Internet, and routing content data packets from the Internet content or the content server to the CPE.
Owner:GC PIVOTAL LLC
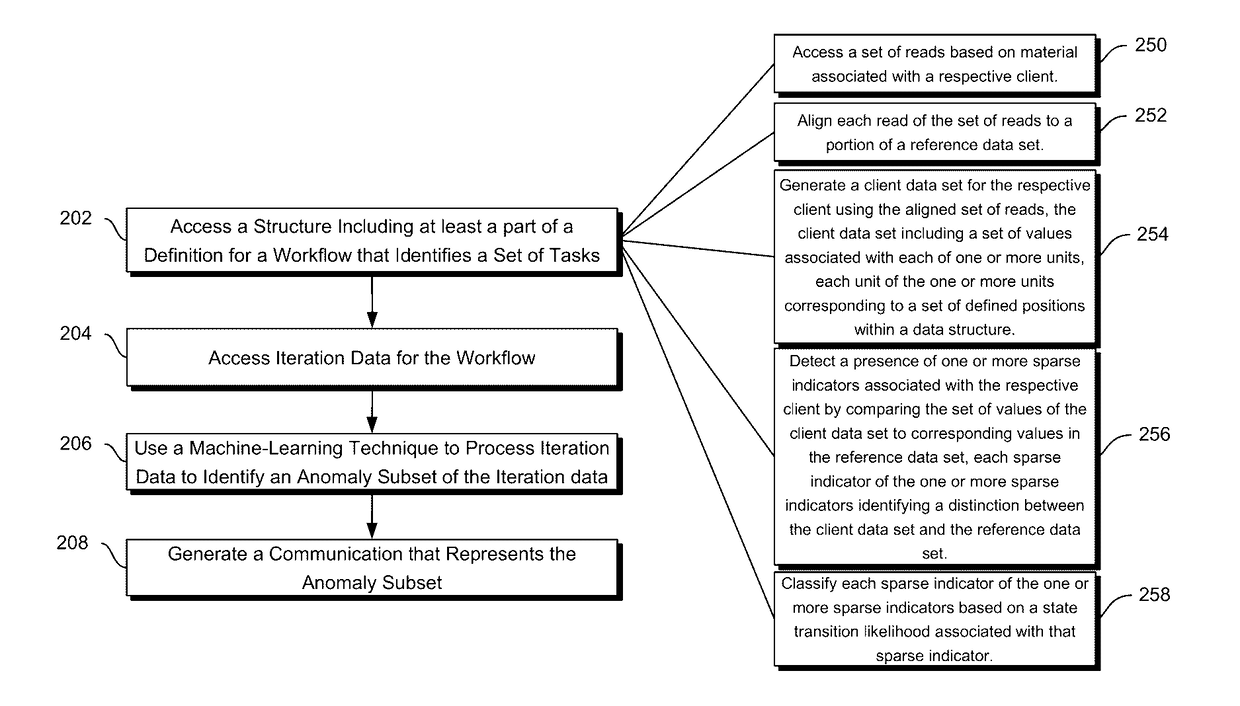
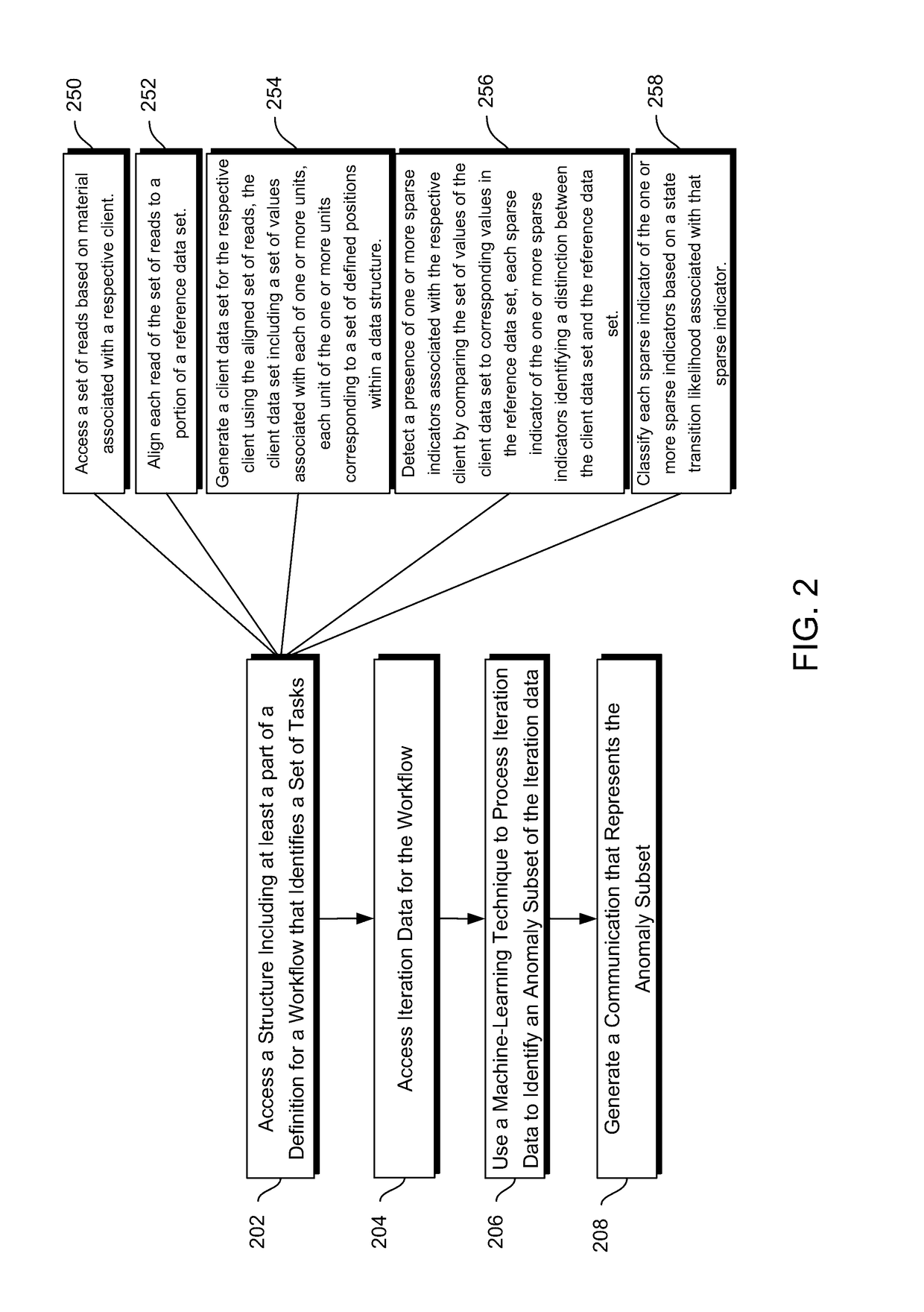
Techniques for processing queries relating to task-completion times or cross-data-structure interactions
Methods and systems disclosed herein relate generally to data processing by applying machine learning techniques to iteration data to identify anomaly subsets of iteration data. More specifically, iteration data for individual iterations of a workflow involving a set of tasks may contain a client data set, client-associated sparse indicators and their classifications, and a set of processing times for the set of tasks performed in that iteration of the workflow. These individual iterations of the workflow may also be associated with particular data sources. Using the iteration data, anomaly subsets within the iteration data can be identified, such as data items resulting from systematic error associated with particular data sources, sets of sparse indicators to be validated or double-checked, or tasks that are associated with long processing times. The anomaly subsets can be provided in a generated communication or report in order to optimize future iterations of the workflow.
Owner:COLOR HEALTH INC
User-personalized media sampling, recommendation and purchasing system using real-time inventory database
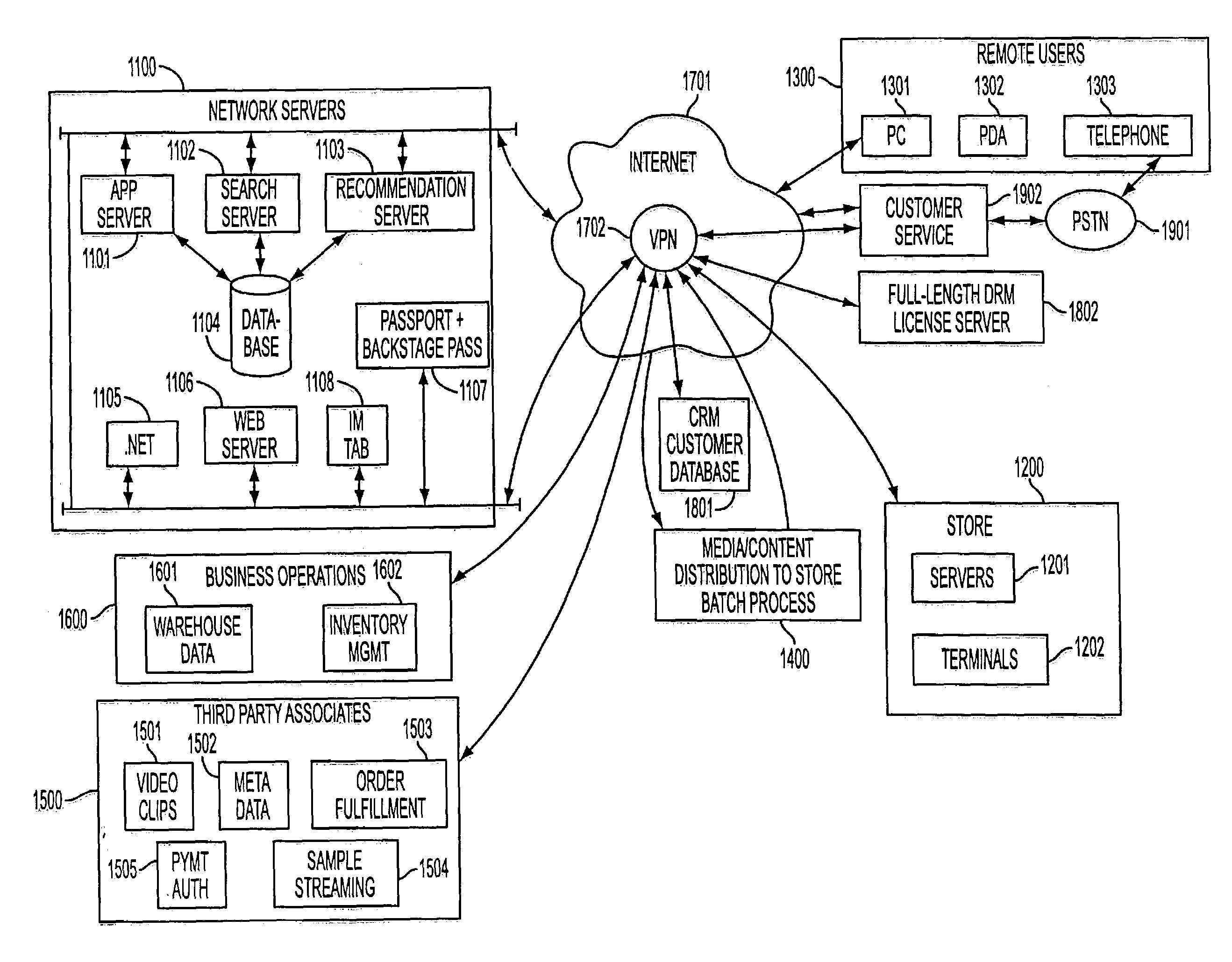
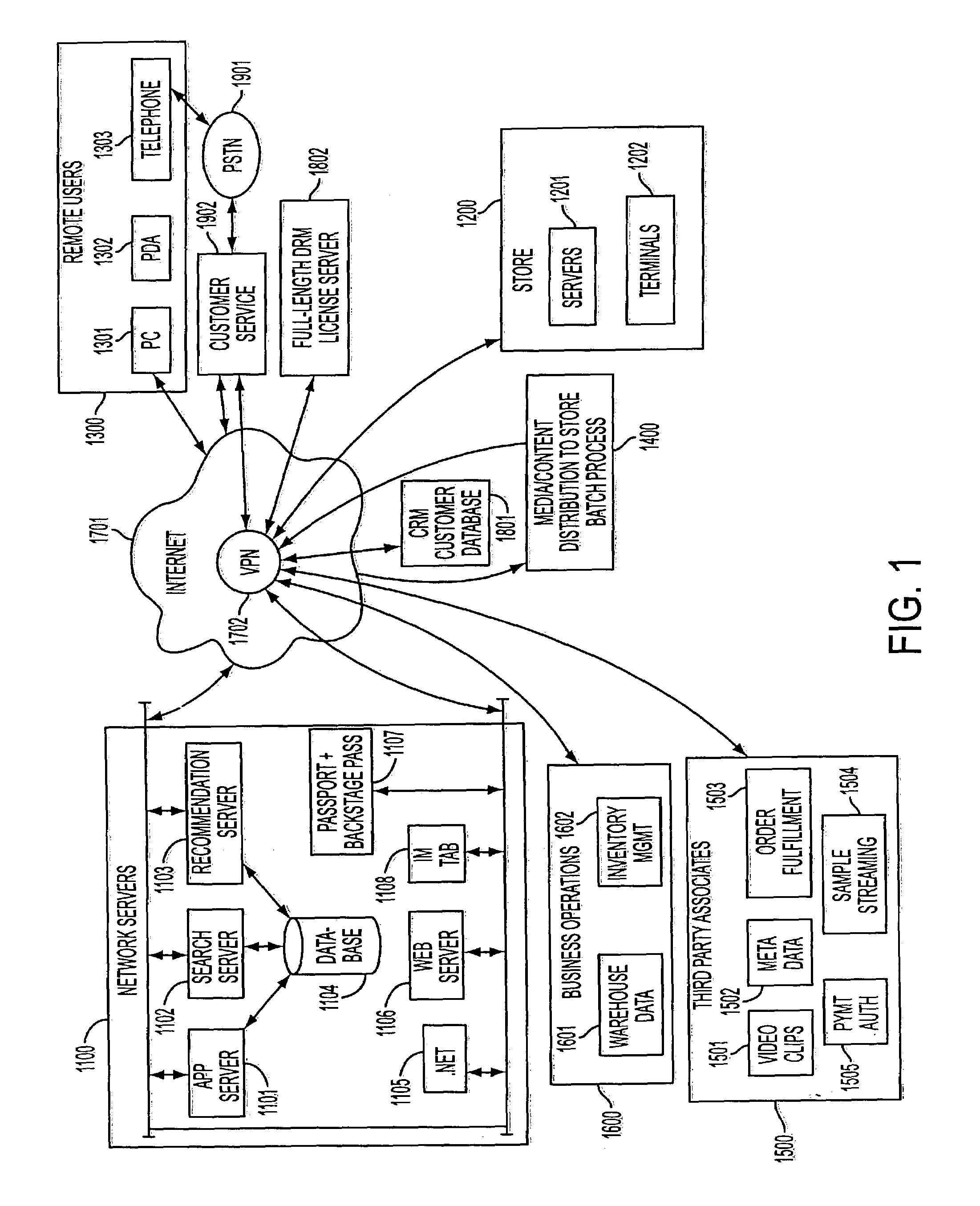
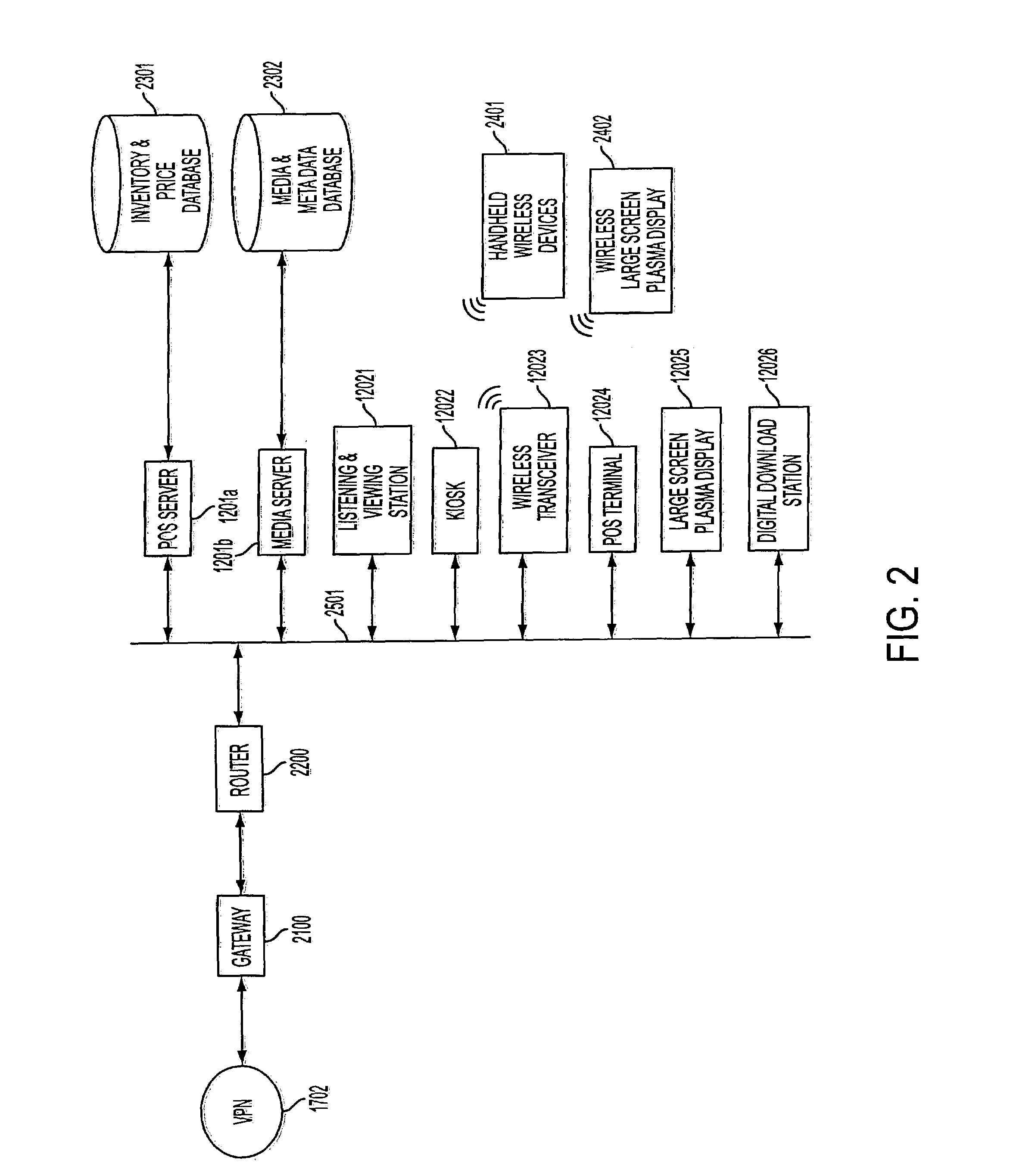
A user-personalized product sampling, recommendation and purchasing system uses customer identification numbers and associated customer profile data to tailor specific product recommendations to a customer at a content sampling station of a retail location. The customer also can use her customer profile to receive the same information from an Internet website of the merchant. In-store sampling stations also may have the capability of checking store inventory and central warehouse inventory and providing recommendations to the customer in accordance with product availability, and optionally may provide the customer with the ability to place product orders directly through the sampling station. The recommendation system also can be used to tailor product recommendations in accordance with a rule-based model and real-time inventory data from a POS database.
Owner:TRANS WORLD NEW YORK
System for broadcasting software applications and portable data communications device for use in such a system
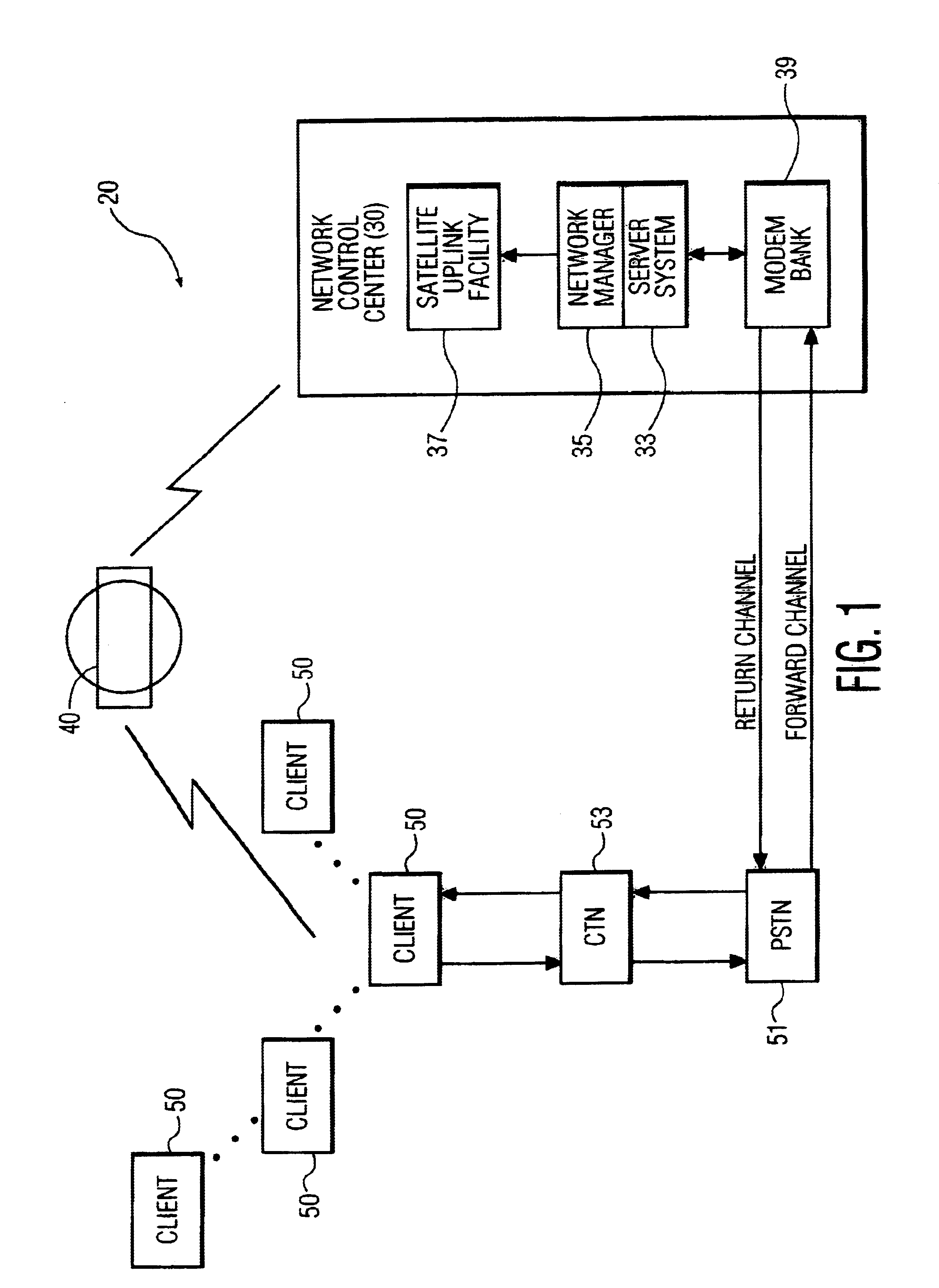
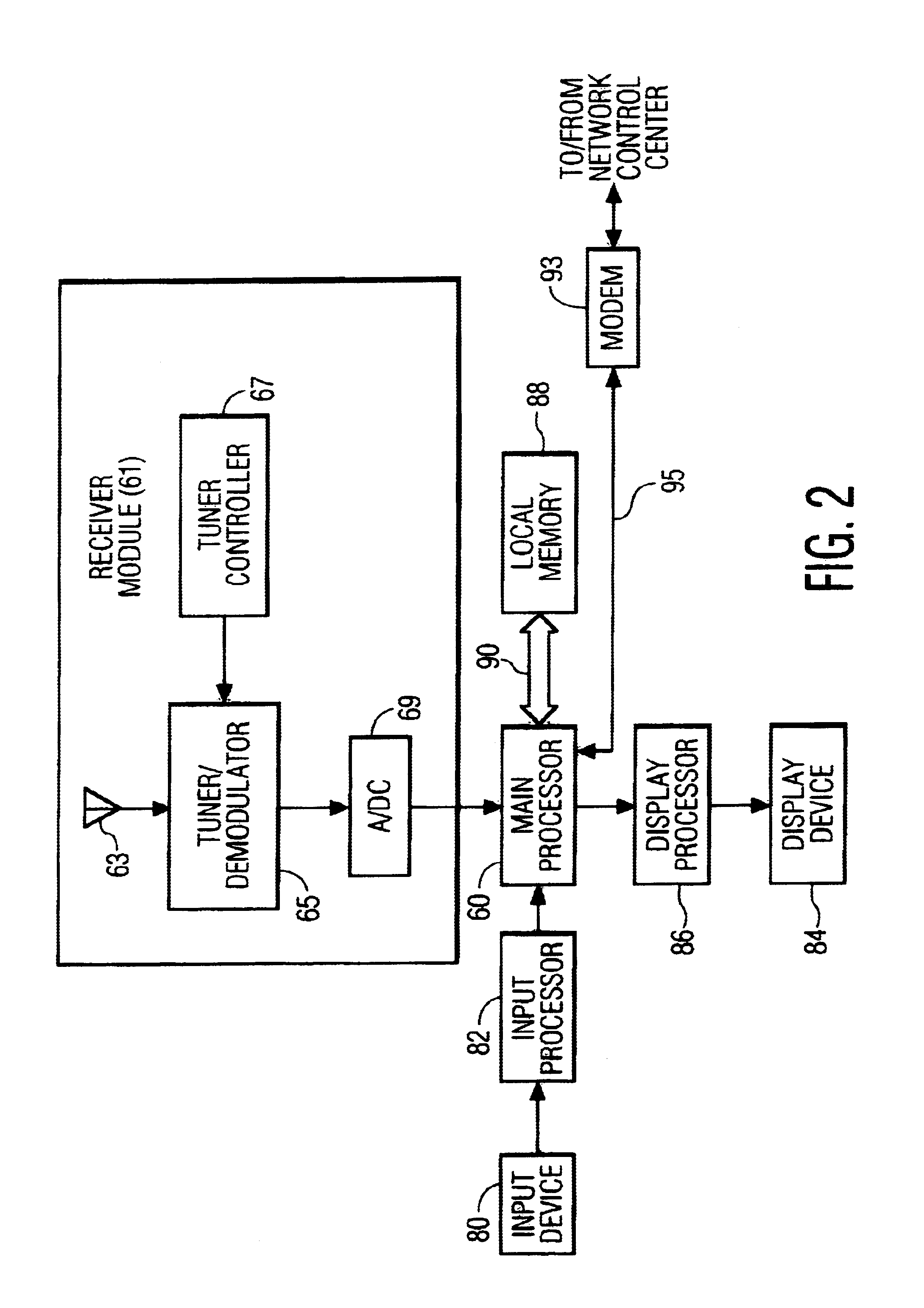
InactiveUS6928468B2Error prevention/detection by using return channelFrequency-division multiplex detailsModem deviceApplication software
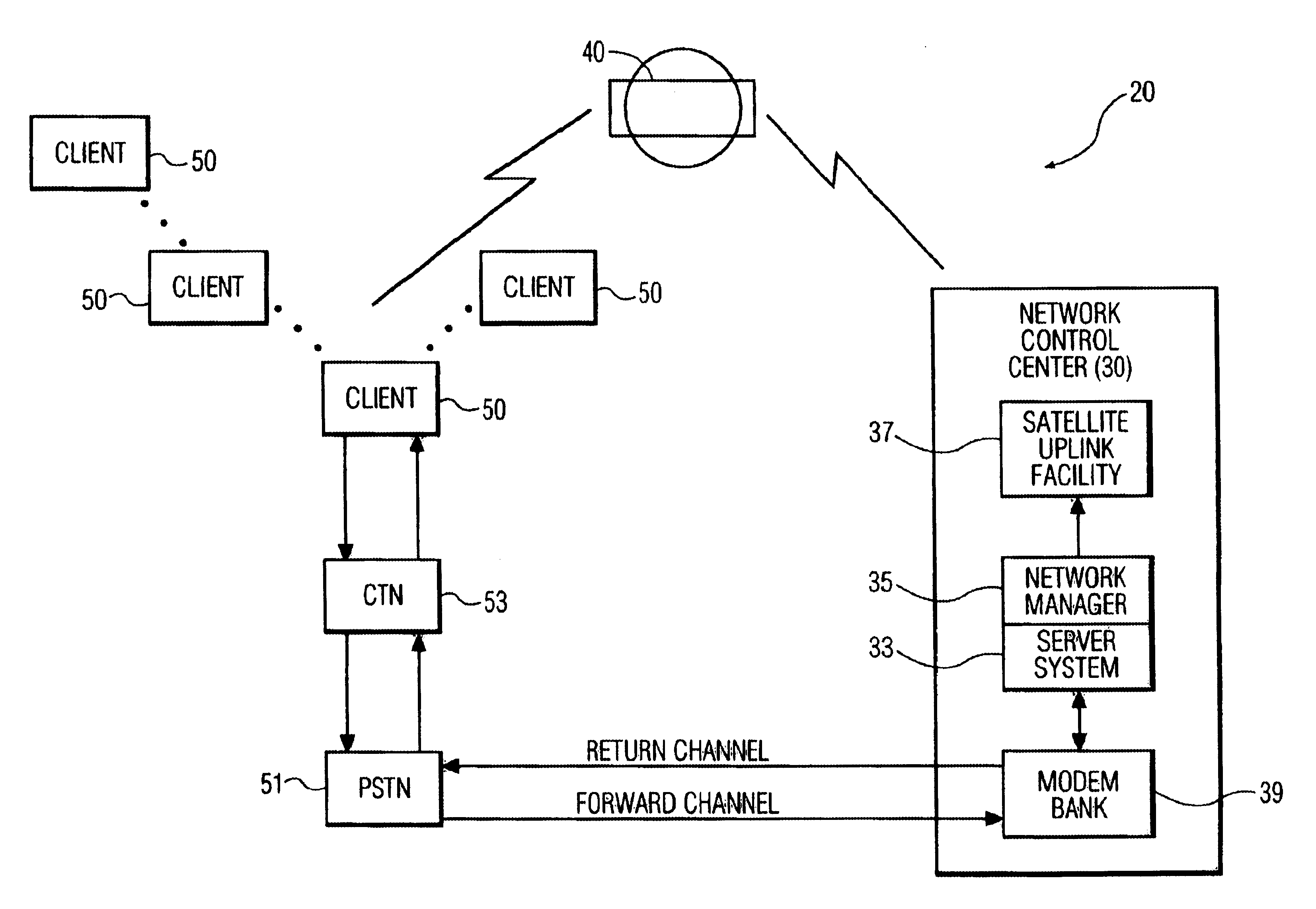
A communications system consisting of a server system that stores software applications, a broadcast system that broadcasts the software applications, and a multiplicity of portable clients that each include a receiver having a tuner that is selectively tunable to receive a selected one of the software applications broadcasted by the broadcast system. The portable clients can be any type of portable data communications device, such as a hand-held, palm-top, or notebook computing device, a PDA, an intelligent cellular phone, or any other personal multimedia appliance or Network Computer (NC). The broadcast system can be any suitable satellite or terrestrial air or cable broadcast system. The software applications can consist of a broad spectrum of different software applications, such as word processing, video games, spreadsheets, address books, calendars, and the like. Each of the portable data communications devices includes a receiver that has a tuner that is selectively tunable to receive a selected one of a plurality of software applications broadcasted by a broadcast system, a user-interface that enables a user to select one of the broadcasted software applications for downloading, a processor for executing the downloaded software applications, and a modem for establishing a two-way communications link with a network control system. The two-way communications link includes a forward channel over which the portable data communication device can transmit client data to the network control system, and a return channel over which the network control system can transmit system data to the portable data communication device. The client data can include requests for unrecoverable software application data and client software download request data.
Owner:KONINK PHILIPS ELECTRONICS NV
Seamless roaming across wireless subnets using source address forwarding
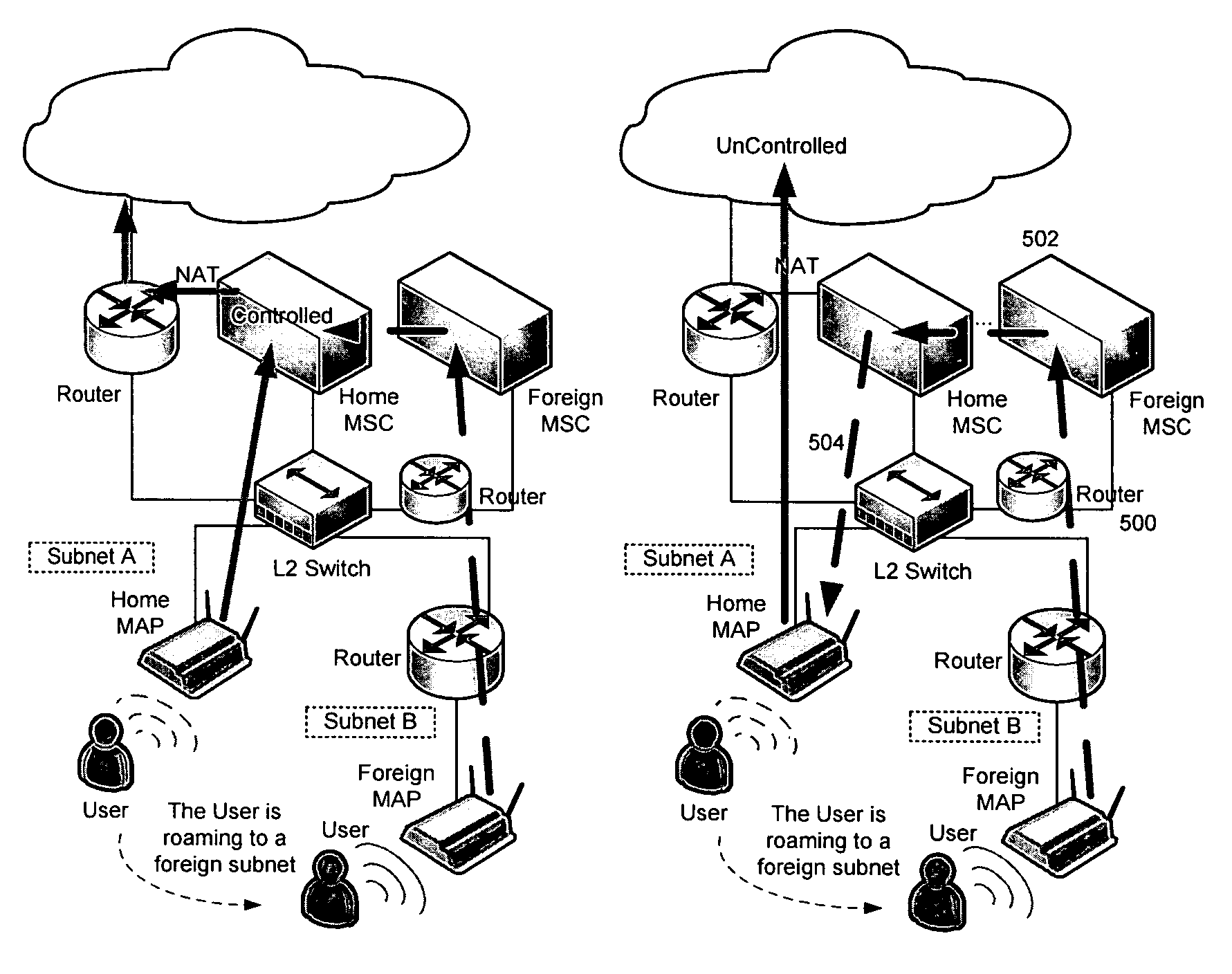
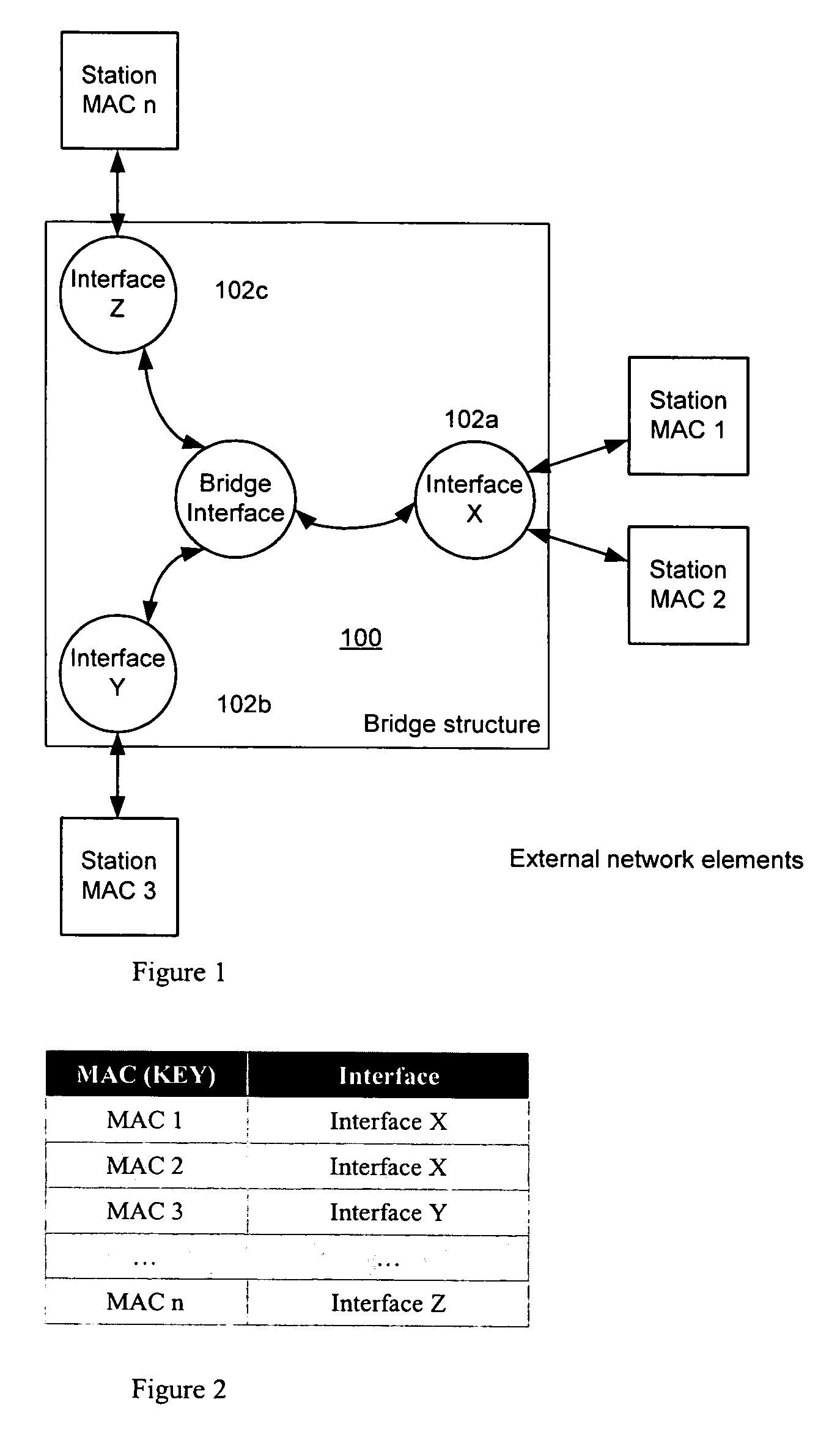
ActiveUS20070153741A1Add supportData switching by path configurationWireless network protocolsTraffic capacityIp address
To enable devices to detect L3 roaming users and to take appropriate forwarding actions, L3 knowledge is introduced inside a bridge in a non-intrusive way. In particular, as a client moves from a subnet associated with a first network element to a subnet associated with a second network element, a determination is made regarding whether the client is roaming. This is done by evaluating a source IP address within a L3 packet header within a first frame received at the second network element. If, as a result of the evaluating step, it is determined that the client is roaming, an L2 bridge forwarding table in the second network element is configured to include a source MAC address of the client together with information identifying at least a destination interface for use in directing client data traffic back towards the subnet associated with the first network element. The first frame is then forwarded. In one embodiment, the traffic is directed back towards the subnet associated with the first network element via a GRE encapsulation tunnel, although any convenient tunneling mechanism can be used. According to another feature, given information cached at the foreign access point is used to enable the roaming client to continue to seamlessly receive inbound traffic prior to or during the configuration of the L2 bridge forwarding table (i.e., before any outbound traffic is actually sent from the client).
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
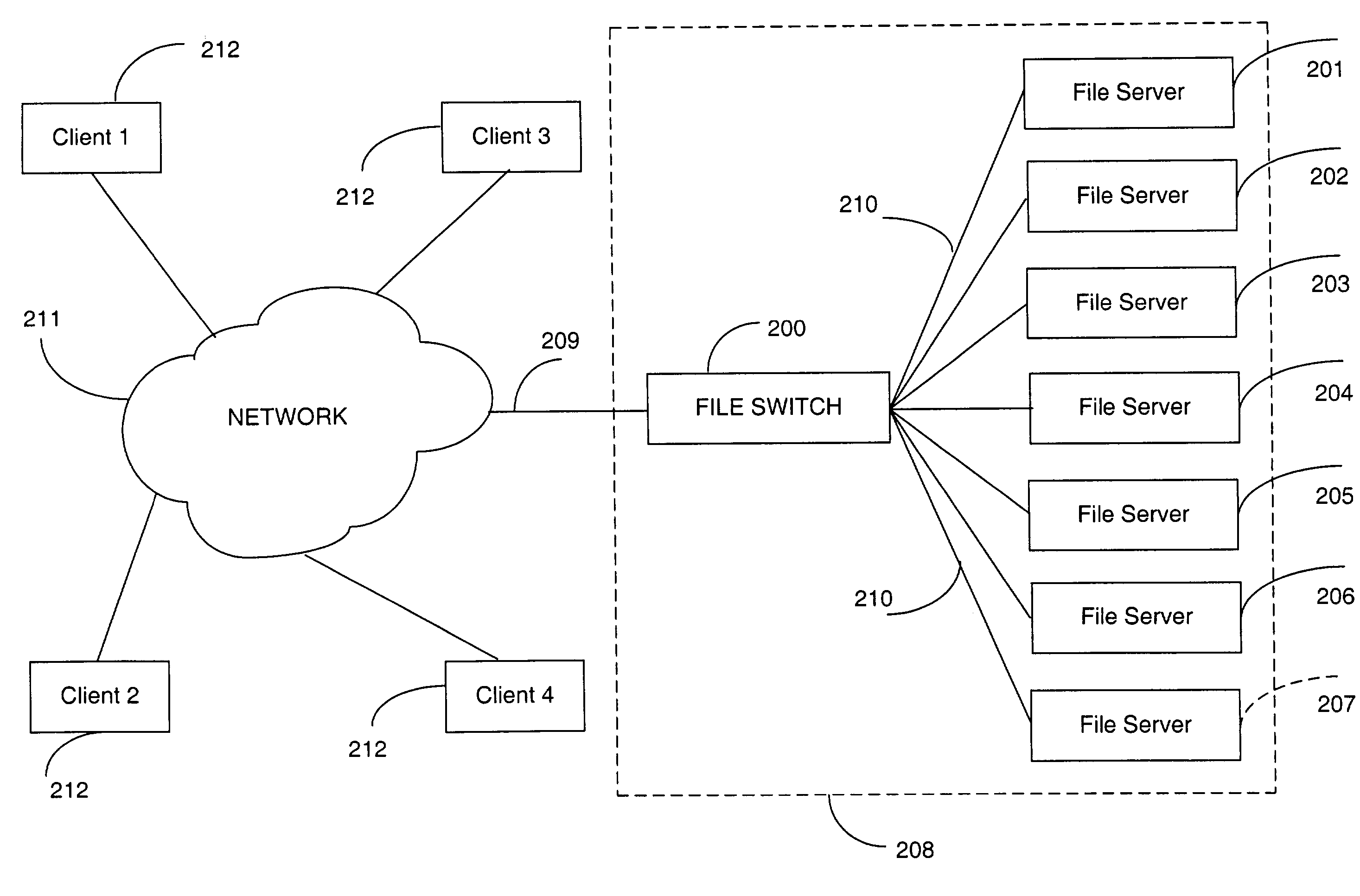
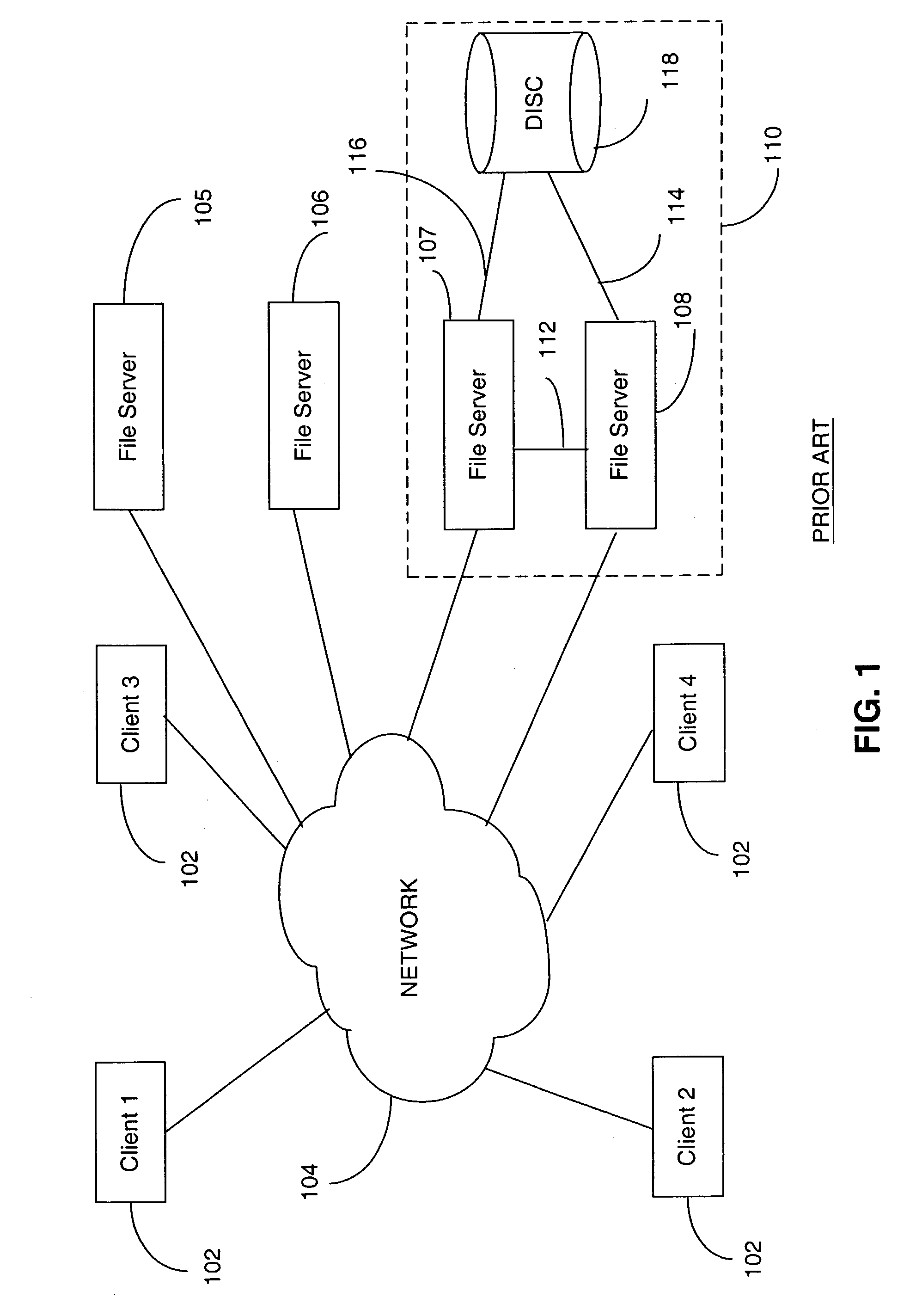
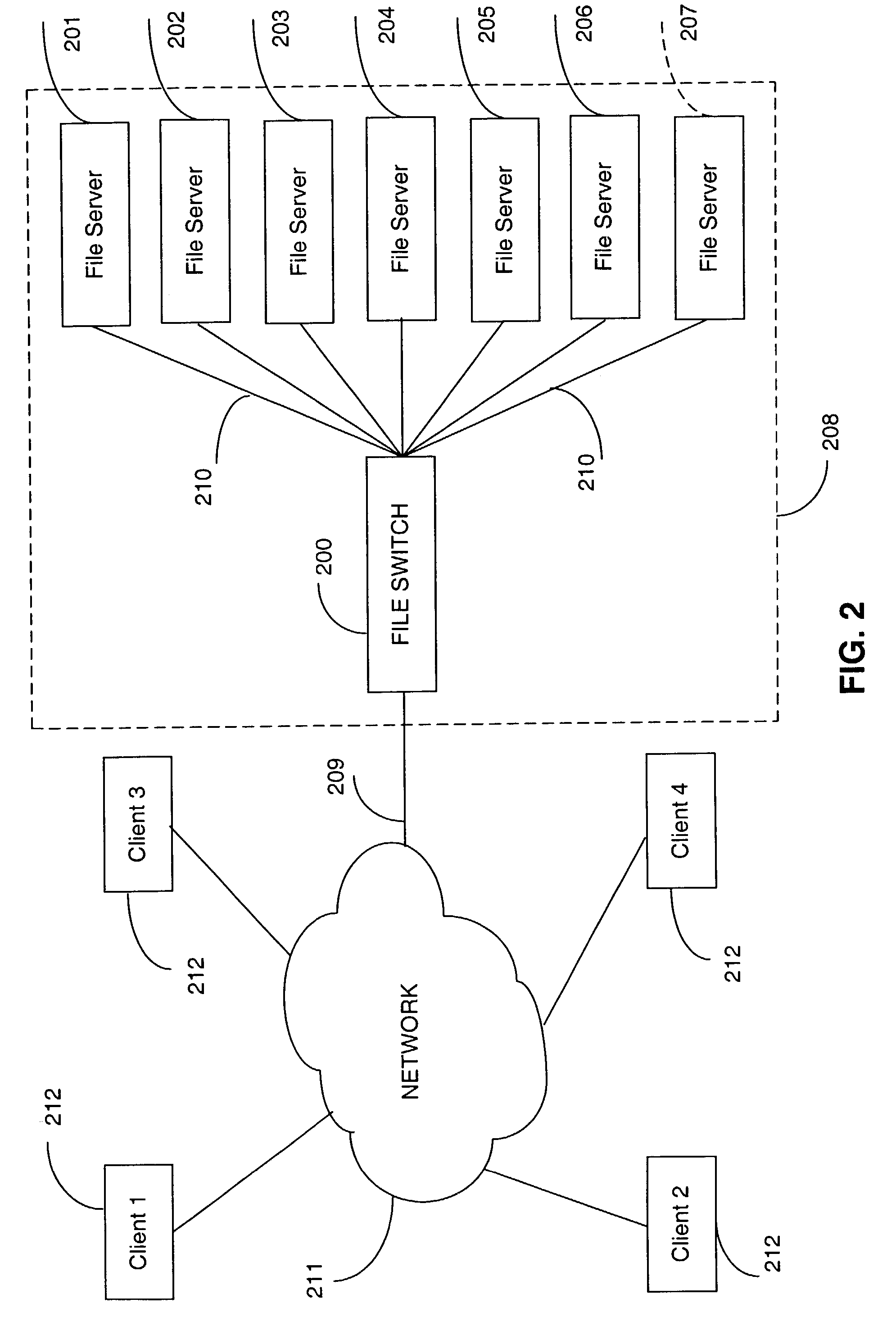
Rule based aggregation of files and transactions in a switched file system
InactiveUS7512673B2Improve performanceLoad balancingMultiple digital computer combinationsLocation information based serviceFile systemData file
A switched file system, also termed a file switch, is logically positioned between client computers and file servers in a computer network. The file switch distributes user files among multiple file servers using aggregated file, transaction and directory mechanisms. The file switch distributes and aggregates the client data files in accordance with a predetermined set of aggregation rules. Each rule can be modified independently of the other rules. Different aggregation rules can be used for different types of files, thereby adapting the characteristics of the switched file system to the intended use and to the expected or historical access patterns for different data files.
Owner:RPX CORP
Trusted card system using secure exchange
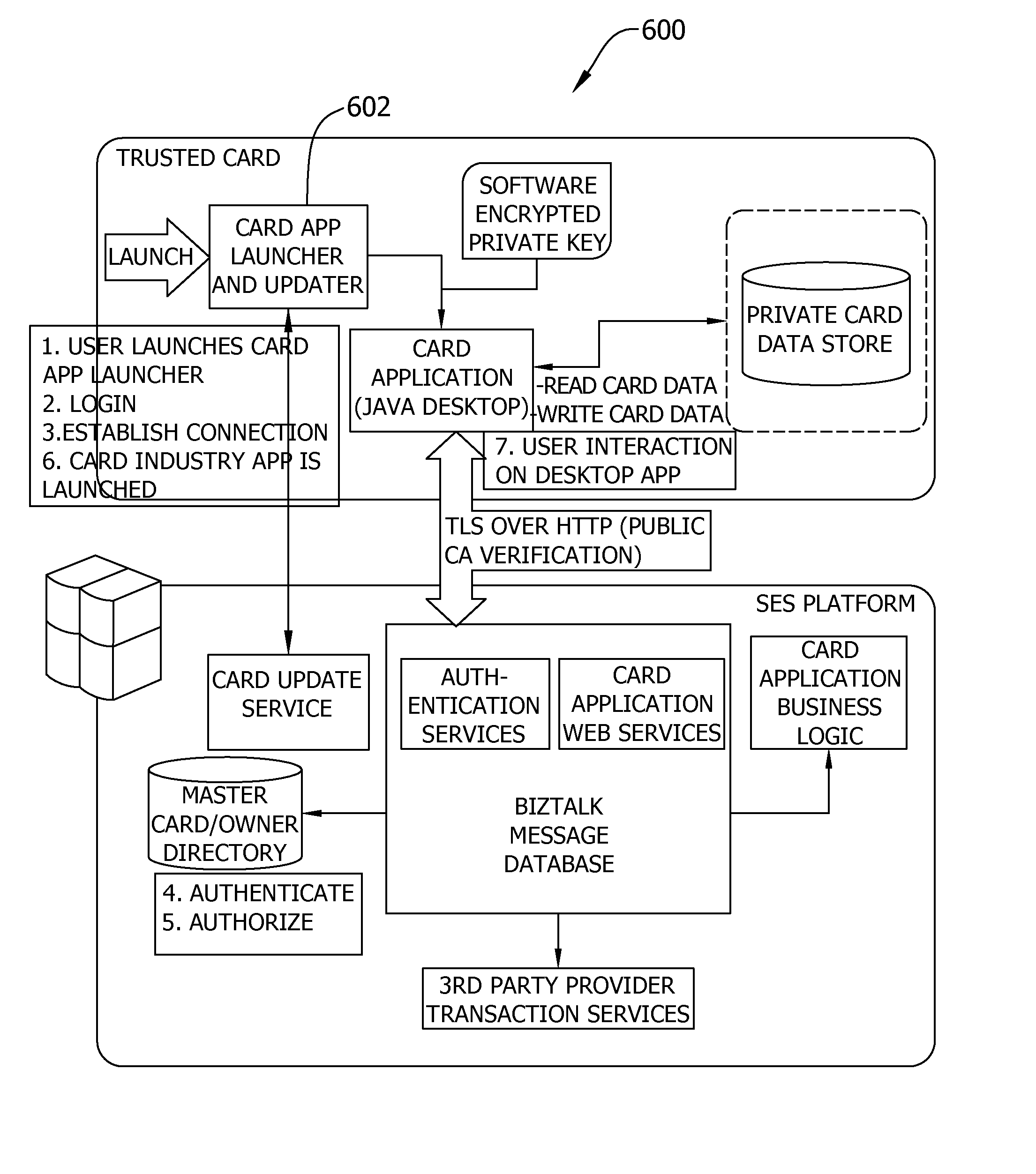
InactiveUS20100042846A1Safe storageLimited accessDigital data processing detailsUser identity/authority verificationAccess methodCoupling
A system for secure, role-based exchange of information between a client and providers of services is described. The system includes a client device having a memory that includes a portion of the data relating to the client, a user access component, and an enforcement agent. The system also includes a central server running an authentication methodology and a roles server. The central server includes the data relating to the client. The system further includes an interface device capable of communications with the central server and capable of communicative coupling with the client device. The system is operable to, upon a communicative coupling between the interface device and the client device, activate the user access method, in conjunction with the authentication method, to ensure that the client is the proper holder of the client device. The enforcement agent is operable with the roles server and user interface input from the client to define access rights to the client data for the providers of services, who also have access to the central server.
Owner:SECURE EXCHANGE SOLUTIONS
Leaderboard system and method
An entertainment device comprises means to obtain a set of GPS co-ordinates describing the location of the device, means to initiate reverse geocoding responsive to the co-ordinates to obtain a hierarchy of geographical names, means to request, from a leaderboard server, leaderboard data corresponding to one of the hierarchy of geographical names, and means to display some or all of the leaderboard. A leaderboard server comprises means to host multiple leaderboards either linked together according to a geographical hierarchy or each associated with a geographical name, means to obtain a hierarchy of geographical names generated by reverse geocoding, means to identify one or more leaderboards either in a hierarchical sequence corresponding to one or more of the geographical names or whose associated geographical name matches one or more of the geographical names in the hierarchy of geographical names, and means to provide to the client data of selected identified leaderboards.
Owner:SONY COMP ENTERTAINMENT EURO
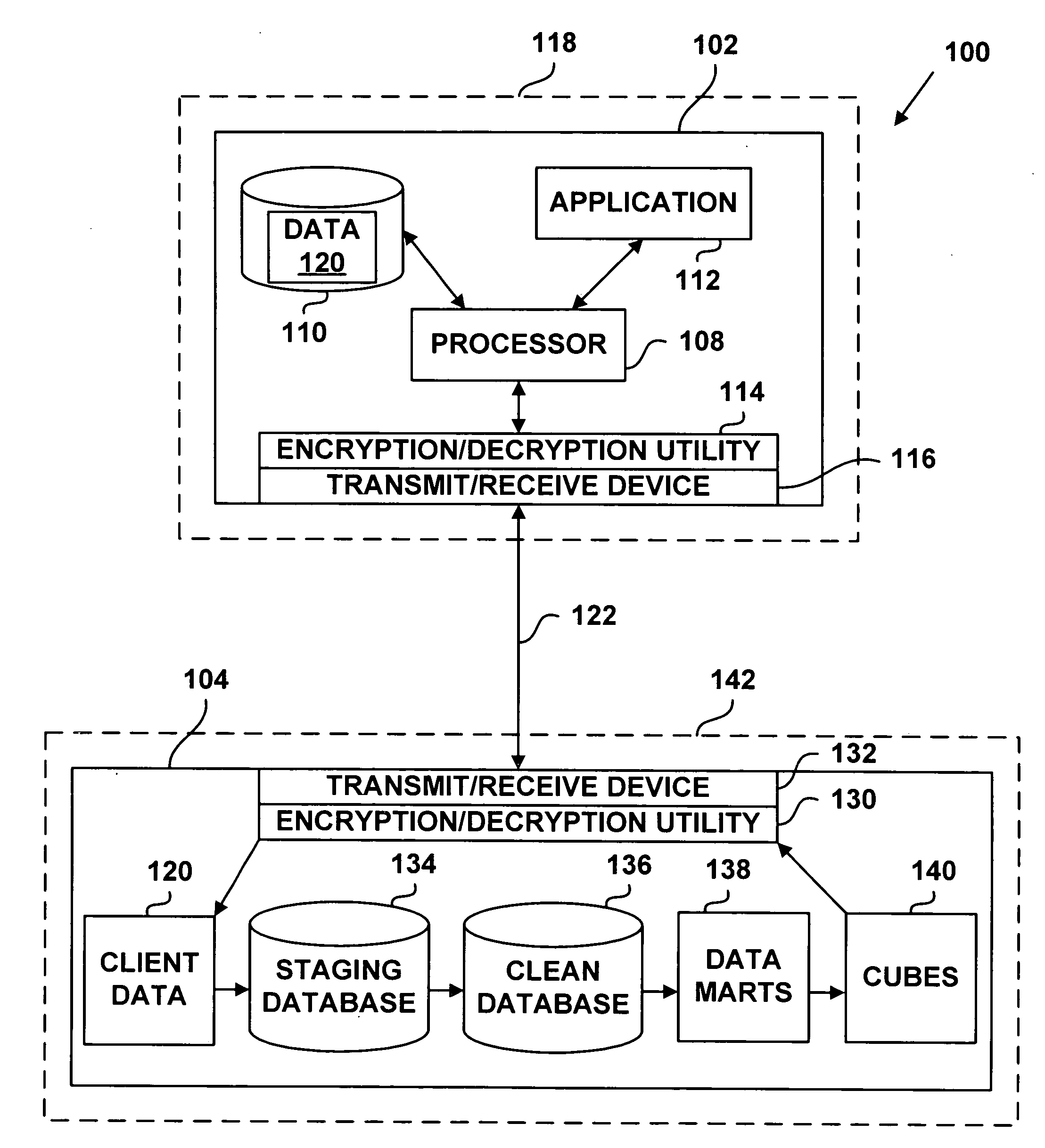
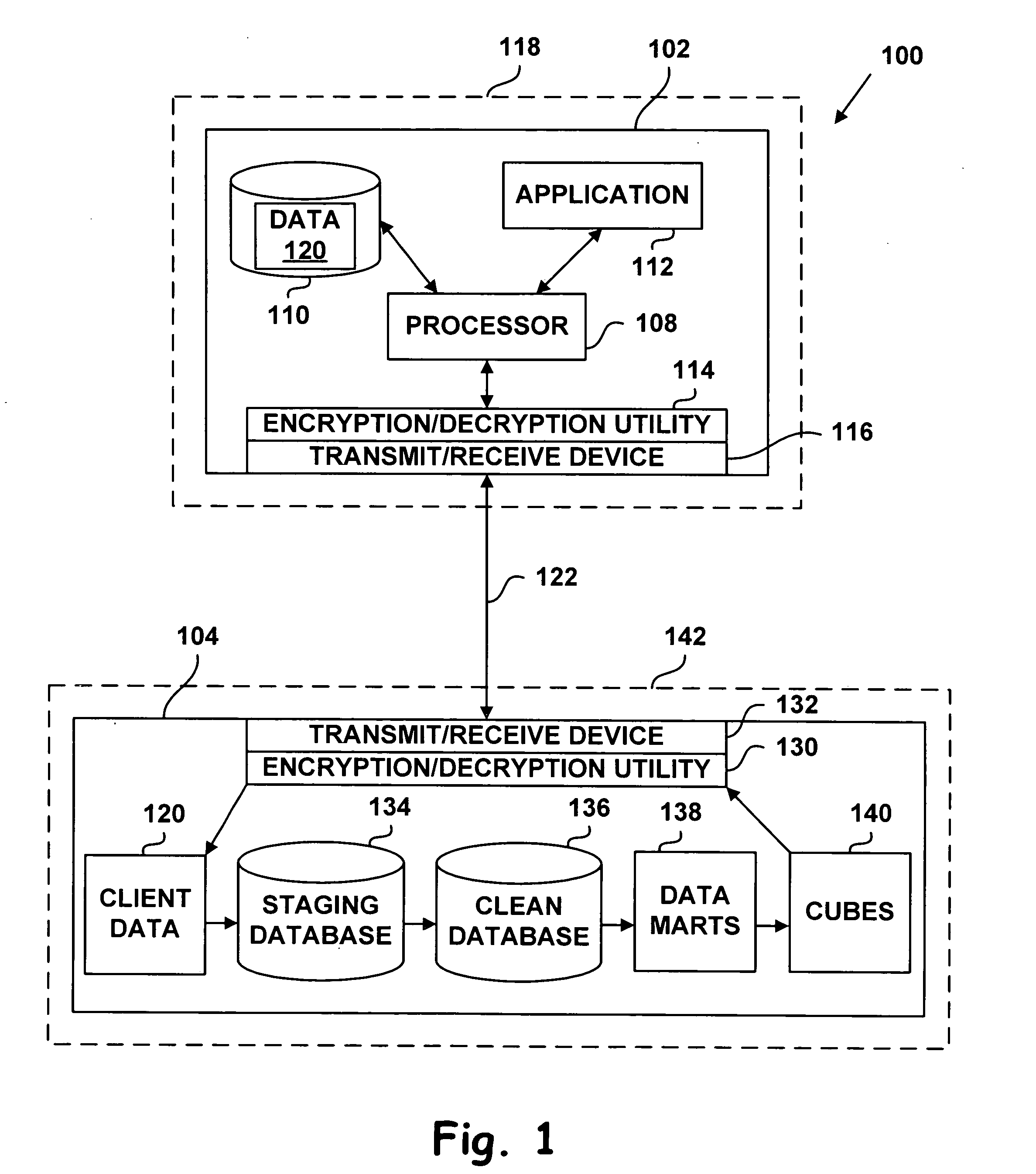
System and method for providing remote users with reports and analyses based on user data and adaptable reporting with the ability to alter, modify or augment such reports and analyses through web-based technology
InactiveUS20080196108A1Improve business performanceImprove patient careDigital data processing detailsAnalogue secracy/subscription systemsData setClient data
A system and method for providing remote users with reports and analyses based on user data is disclosed. The reports are adaptable and the remote user can alter, modify, and argument the reports and analyses. Client data is extracted from a client device and other sources. The client data is quantified by analytic definitions. The analytic definitions are an identification of performance measures. The quantified data is queried and grouped according to the analytic definitions. Datamarts are created by separating the grouped data. The datamarts are then converted into on-line analytical processing (OLAP) cubes. The OLAP cubes are then used by the remote user to create adaptable reports. The adaptable reports may be used by practice professionals to understand their business and clinical operations, and to improve business performance and patient care.
Owner:ICLOPS
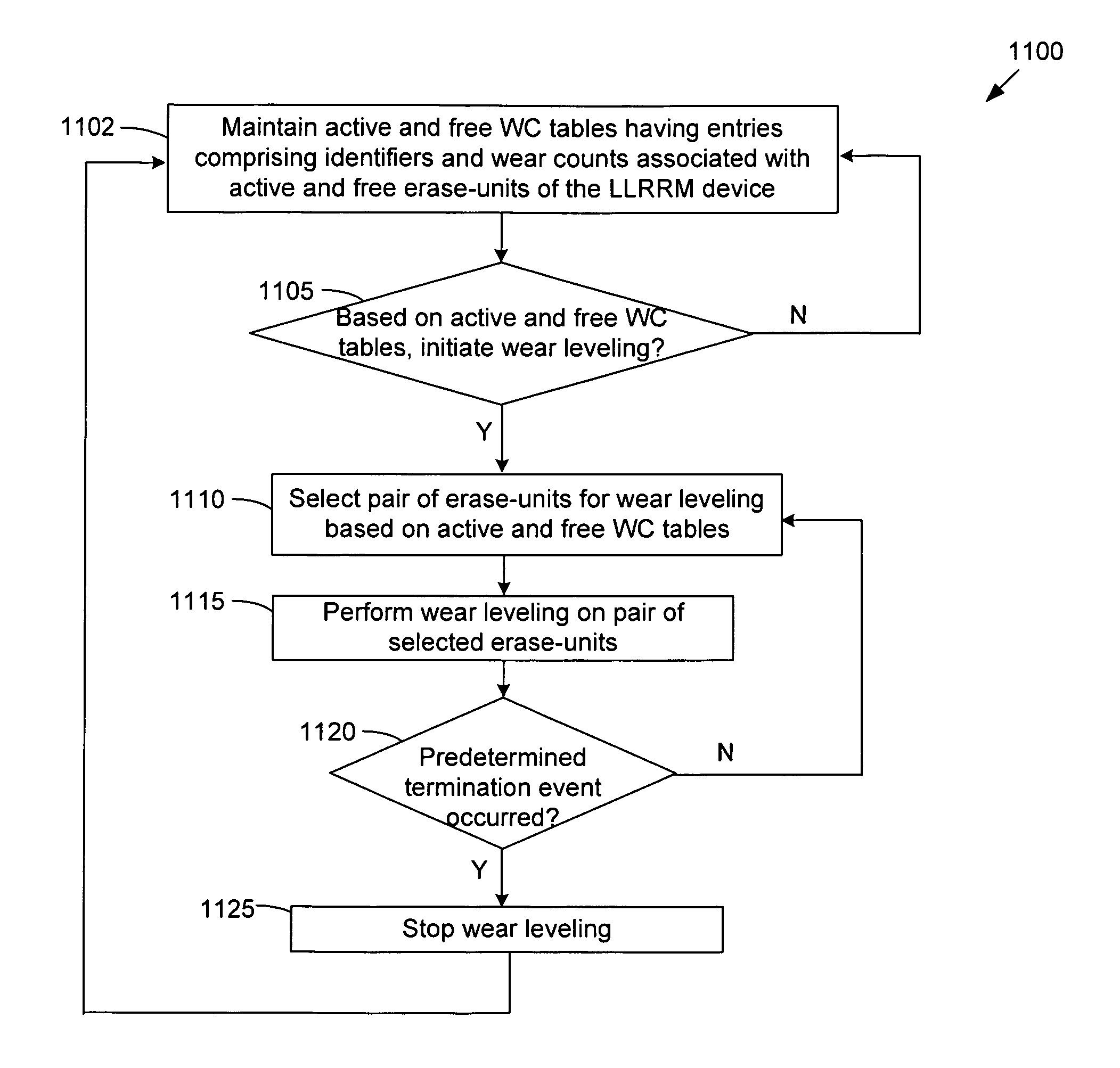
Wear leveling for low-wear areas of low-latency random read memory
ActiveUS8001318B1Increase current rate of wearReduce current rate of wearMemory architecture accessing/allocationMemory loss protectionLatency (engineering)Data content
Described herein are method and apparatus for performing wear leveling of erase-units of an LLRRM device that considers all active erase-units. Wear counts of all active erase-units (containing client data) and free erase-units (not containing client data) are tracked. Wear counts are used to determine low-wear active erase-units having relatively low wear counts and high-wear free erase-units having relatively high wear counts. In some embodiments, data contents of low-wear active erase-units are transferred to high-wear free erase-units, whereby the low-wear active erase-units are converted to free erase-units and may later store different client data which may increase the current rate of wear for the erase-unit. The high-wear free erase-units are converted to active erase-units that store client data that is infrequently erased / written, which may reduce the current rate of wear for the erase-unit. As such, wear is spread more evenly among erase-units of the LLRRM device.
Owner:NETWORK APPLIANCE INC
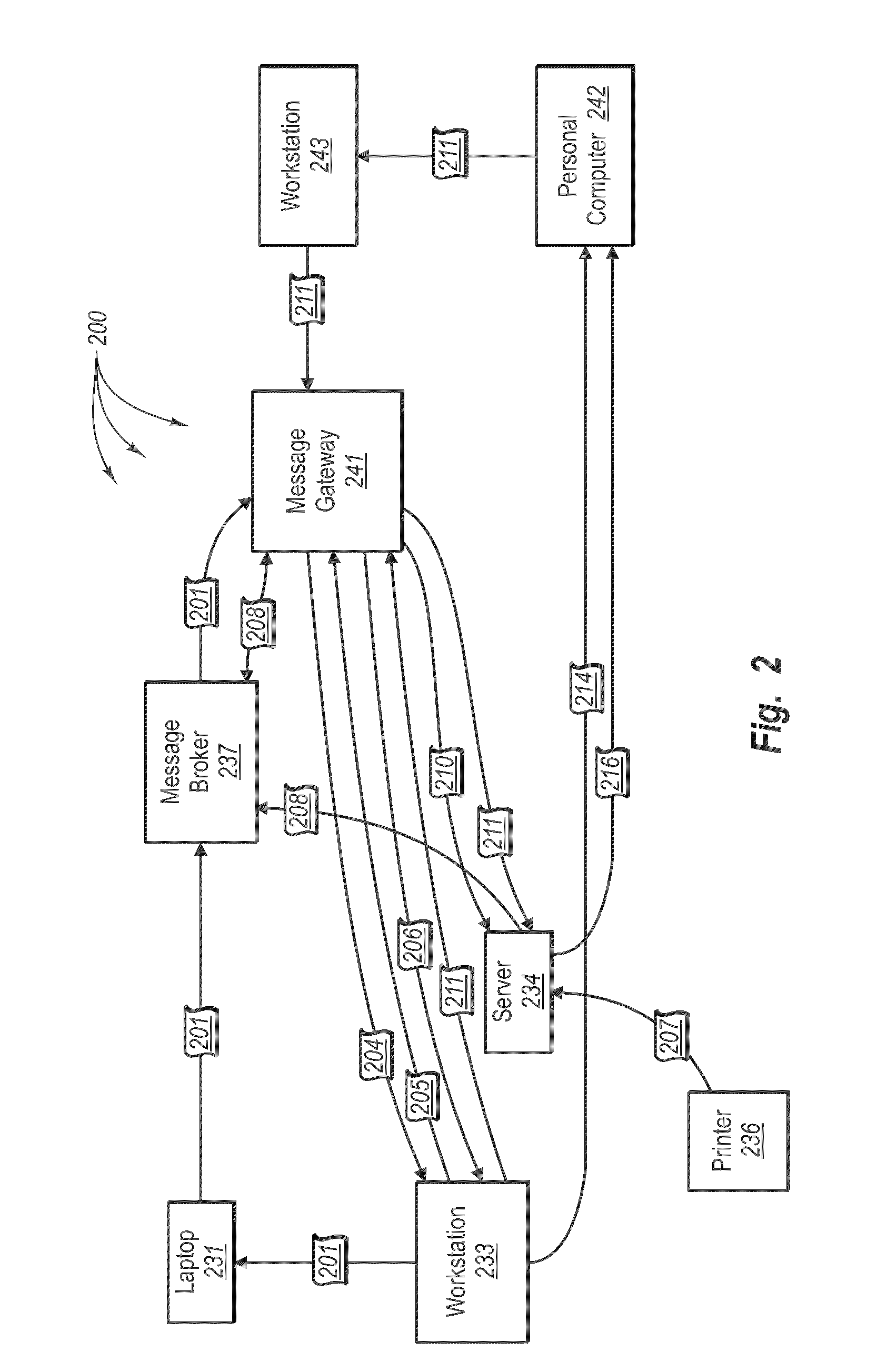
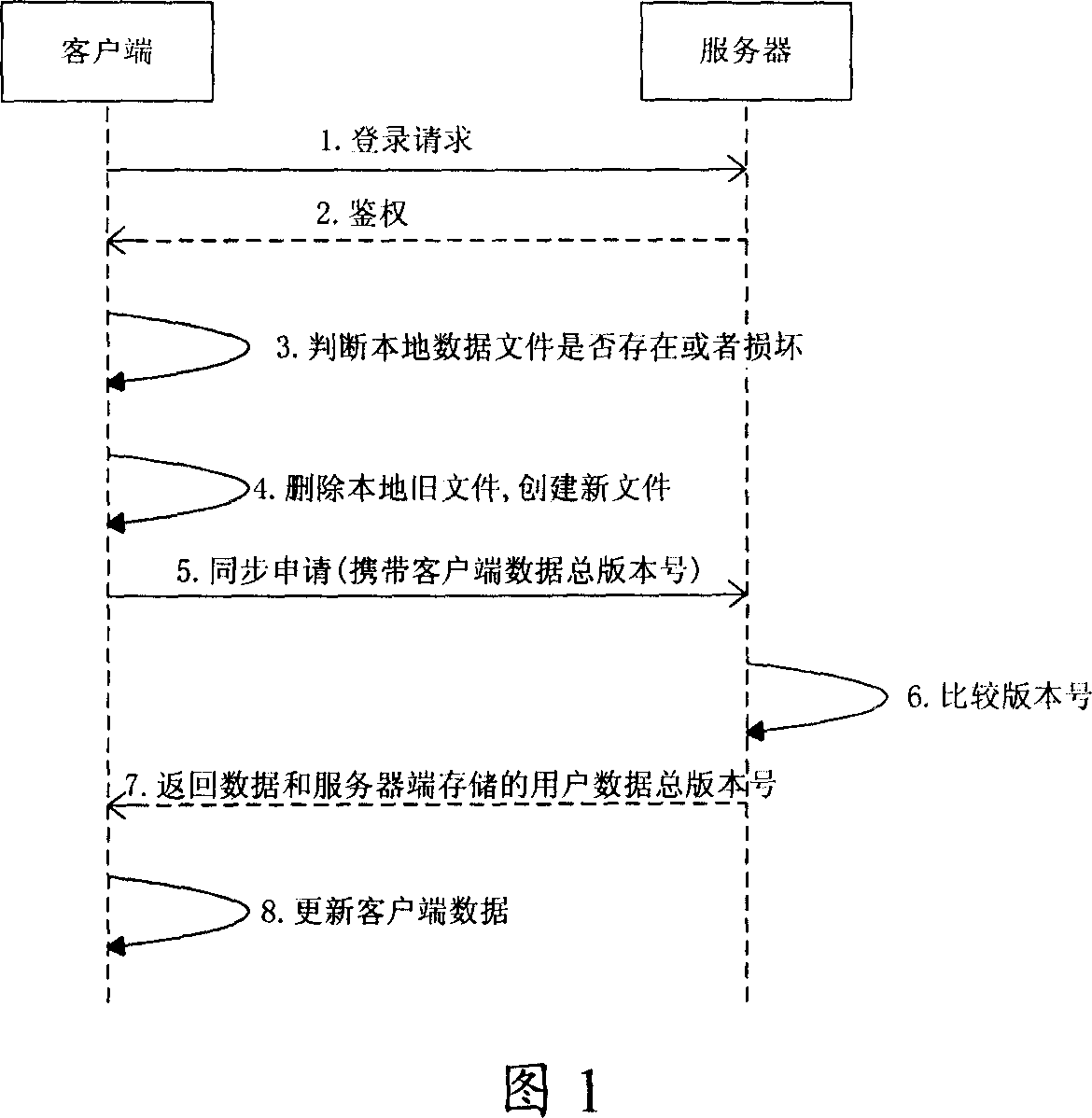
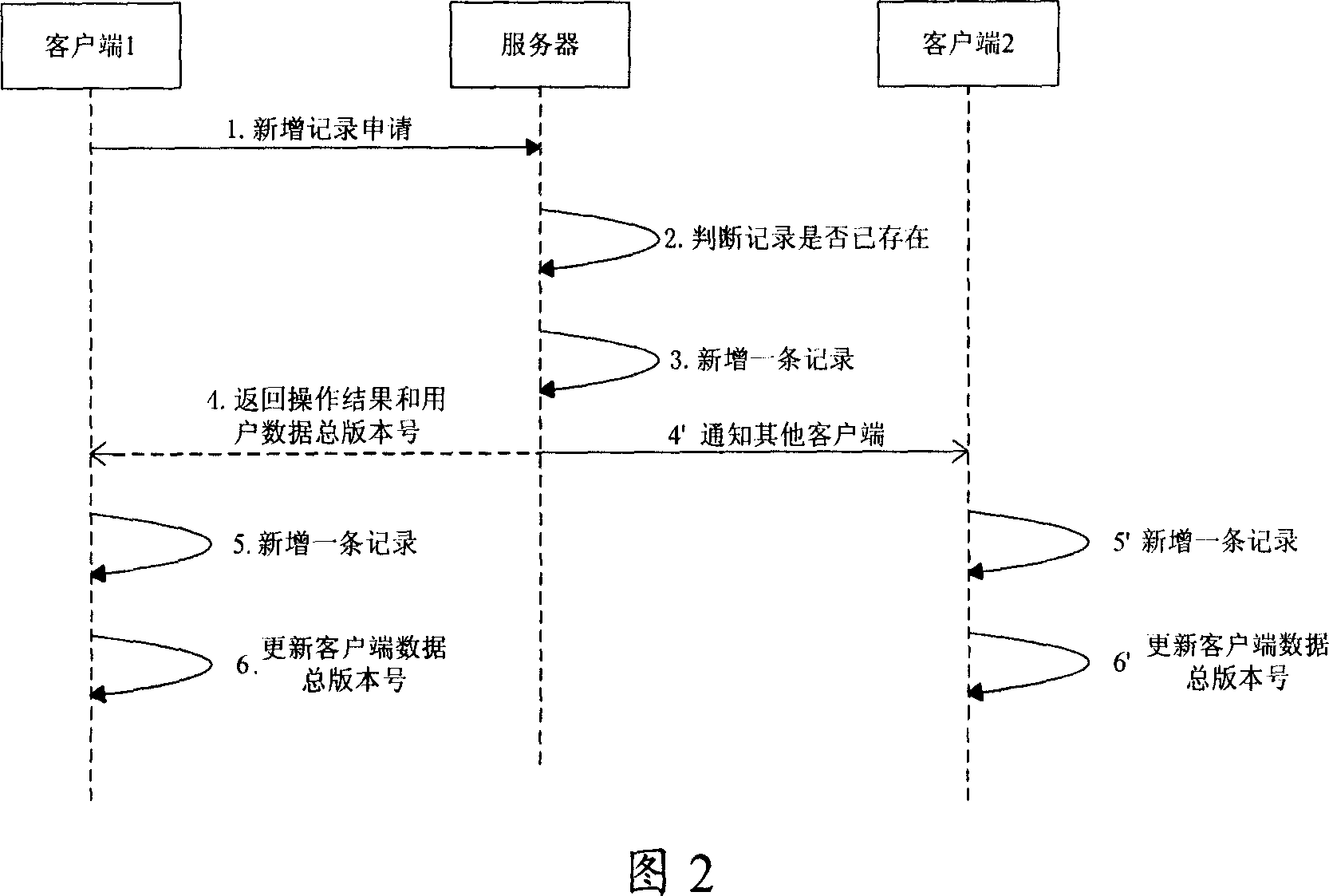
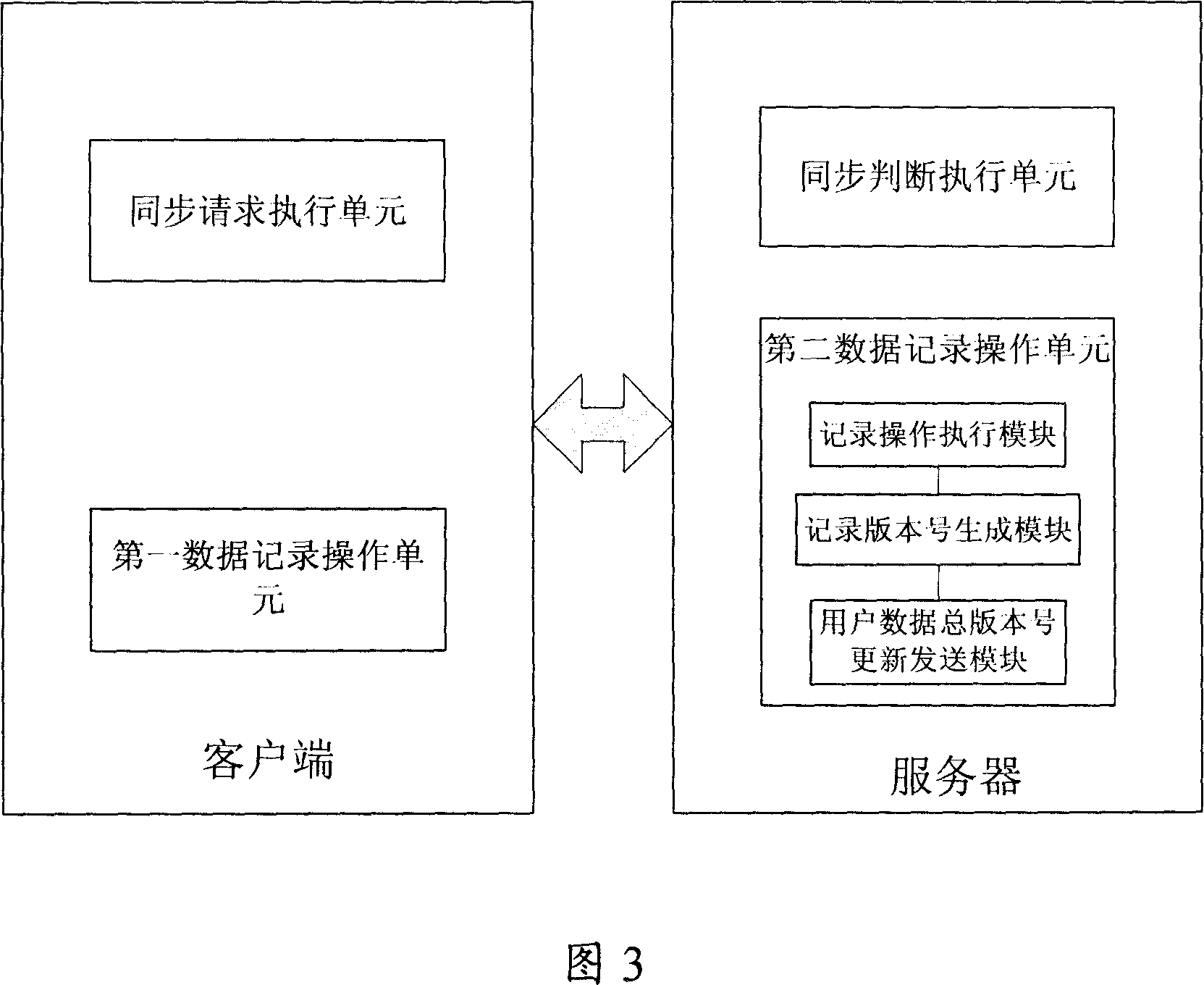
Data synchronization method and system
ActiveCN101064630AImprove synchronization efficiencyReduce the amount of data interactionData switching networksData synchronizationReal-time data
The invention discloses a data synchronization method which is used in data synchronization between client and server. It includes: the user data recording is set with recording version number which is increased by degrees as operation sequence; the client takes the maximum recording version number of local-storage user data recording as the overall recording version number of client data; when client logs on server, the client sends data synchronization request to server, with said overall recording version number of client data; server judges whether said overall recording version number of client data is the same with overall recording version number of user data, when they are different, server sends data recording whose recording version number is bigger than overall recording version number of client data to client for data synchronization. The invention also discloses a corresponding data synchronization system. The invention can realize real time data synchronization between client and server efficiently.
Owner:HUAWEI TECH CO LTD
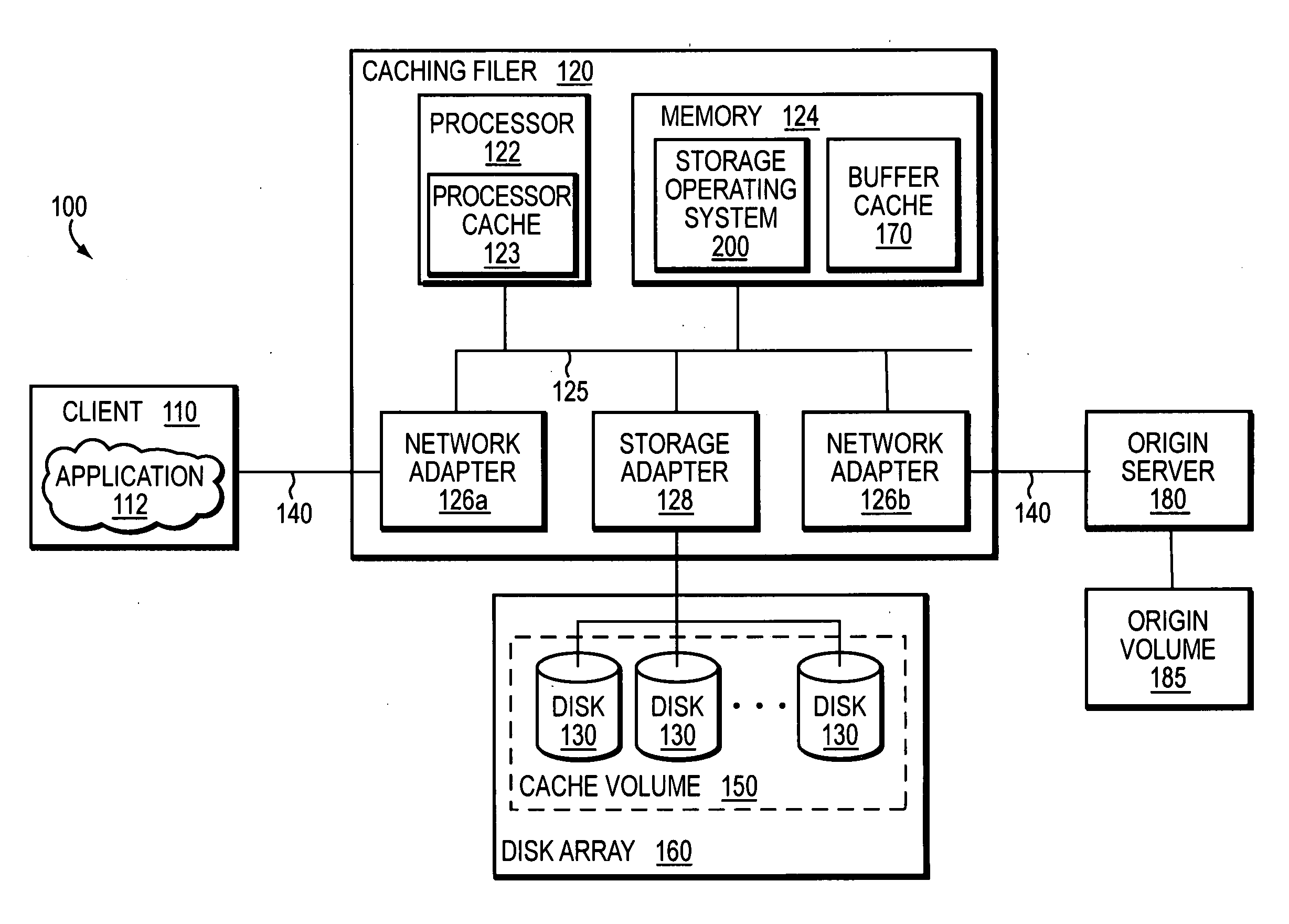
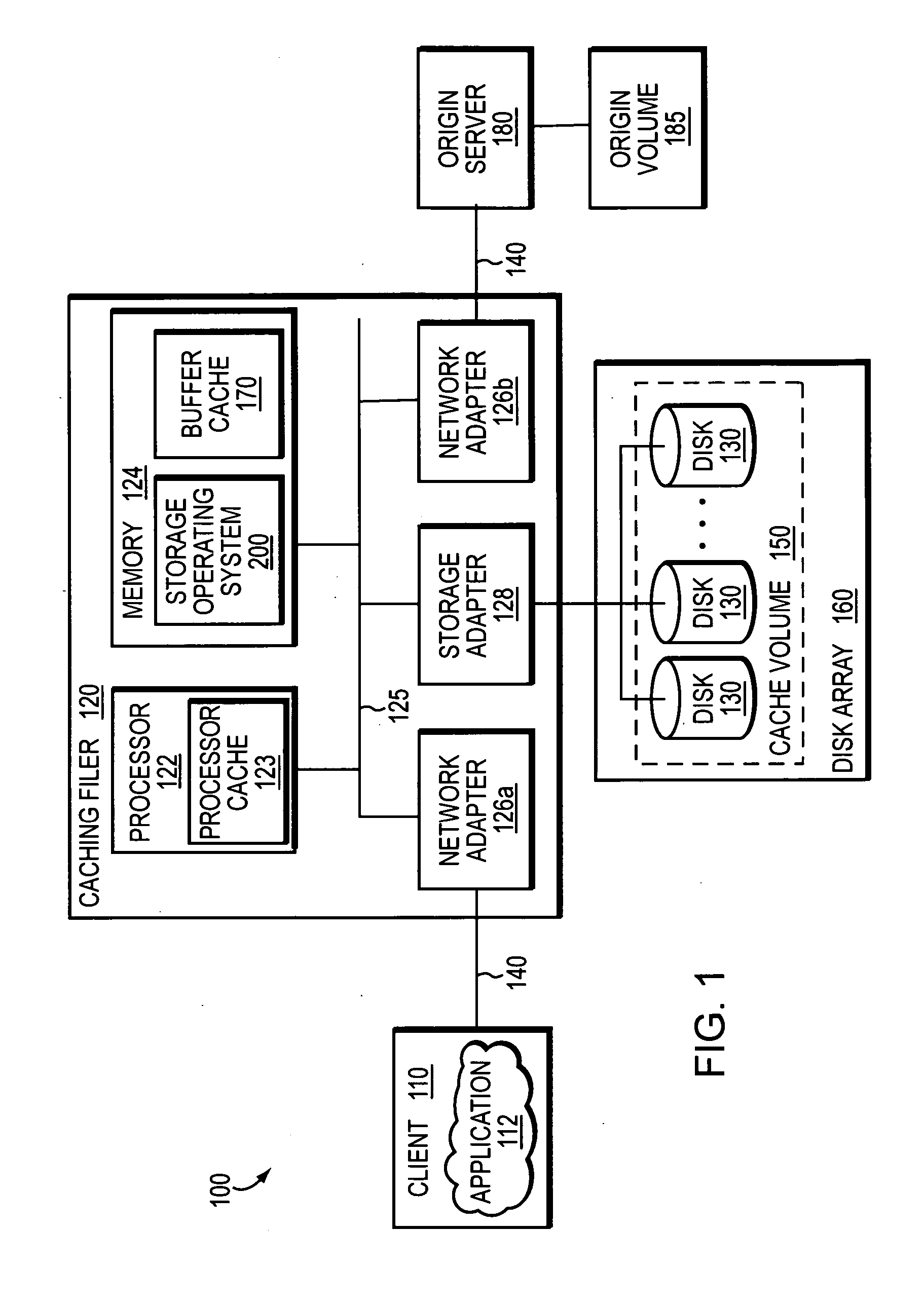
System and method for caching network file systems
ActiveUS20070250552A1Fast and efficient client accessDigital computer detailsTransmissionPrimitive operationFile system
A network caching system has a multi-protocol caching filer coupled to an origin server to provide storage virtualization of data served by the filer in response to data access requests issued by multi-protocol clients over a computer network. The multi-protocol caching filer includes a file system configured to manage a sparse volume that “virtualizes” a storage space of the data to thereby provide a cache function that enables access to data by the multi-protocol clients. To that end, the caching filer further includes a multi-protocol engine configured to translate the multi-protocol client data access requests into generic file system primitive operations executable by both the caching filer and the origin server.
Owner:NETWORK APPLIANCE INC
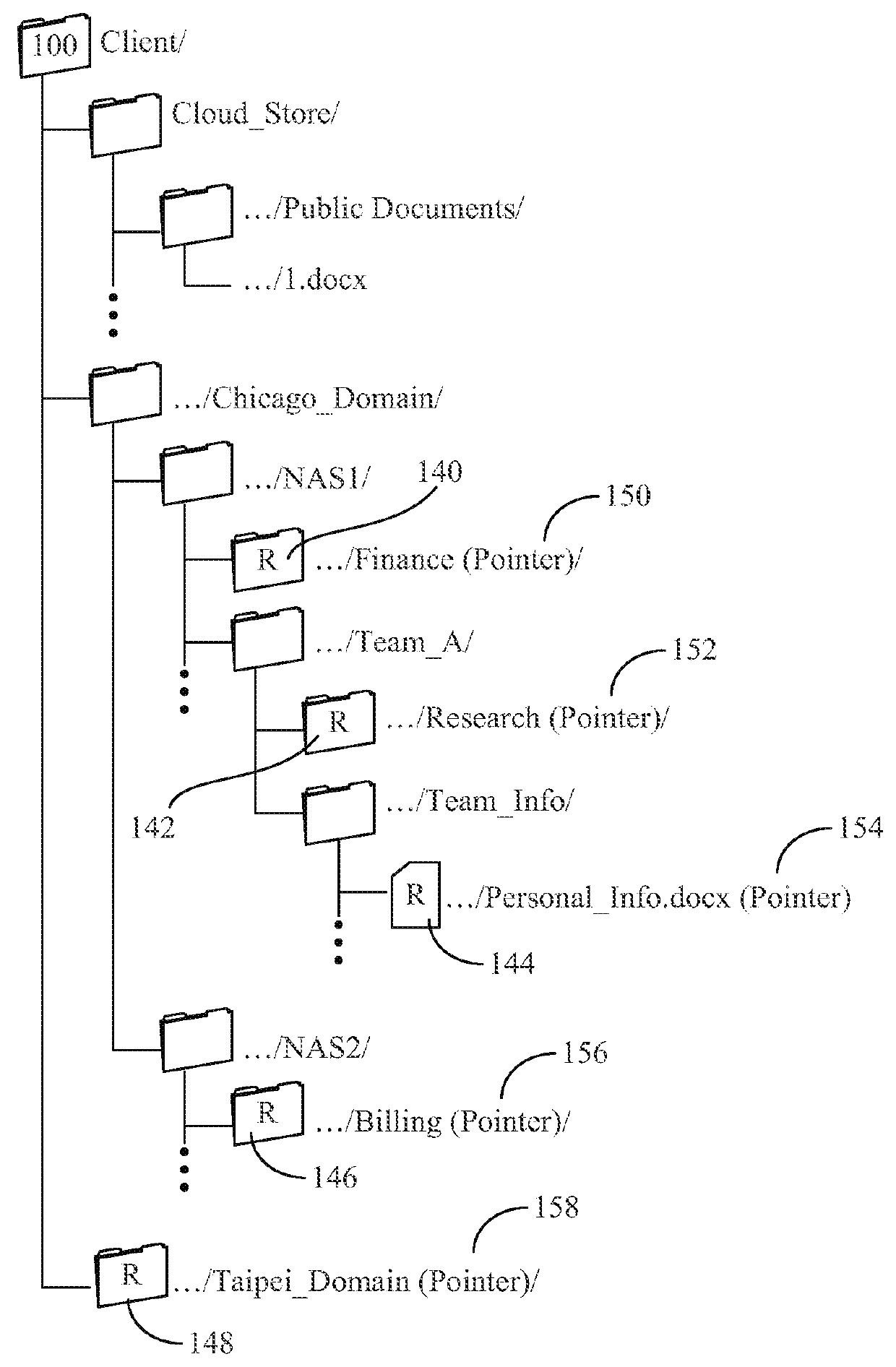
Systems and methods for providing file access in a hybrid cloud storage system
ActiveUS9424437B1Facilitates accessing fileEasy accessDigital computer detailsDatabase distribution/replicationFile systemObject store
A method for providing access to objects associated with a particular client in a cloud storage system is disclosed. The method includes the steps of establishing a connection with a user, providing a client namespace associated with the client to the user, where the client namespace represents objects stored on the cloud storage system and objects stored on a private storage system apart from the cloud storage system, receiving a request from the user to access an object stored on the private storage system, and providing information to the user to facilitate access to the object stored on the private storage system by said user. Other systems and methods are also disclosed. Important advantages of the present invention are facilitated by separating the logic for user access (control plane) from the actual storage (Storage plane). Private file system access can still be managed from the cloud, while keeping the client data private.
Owner:EGNYTE
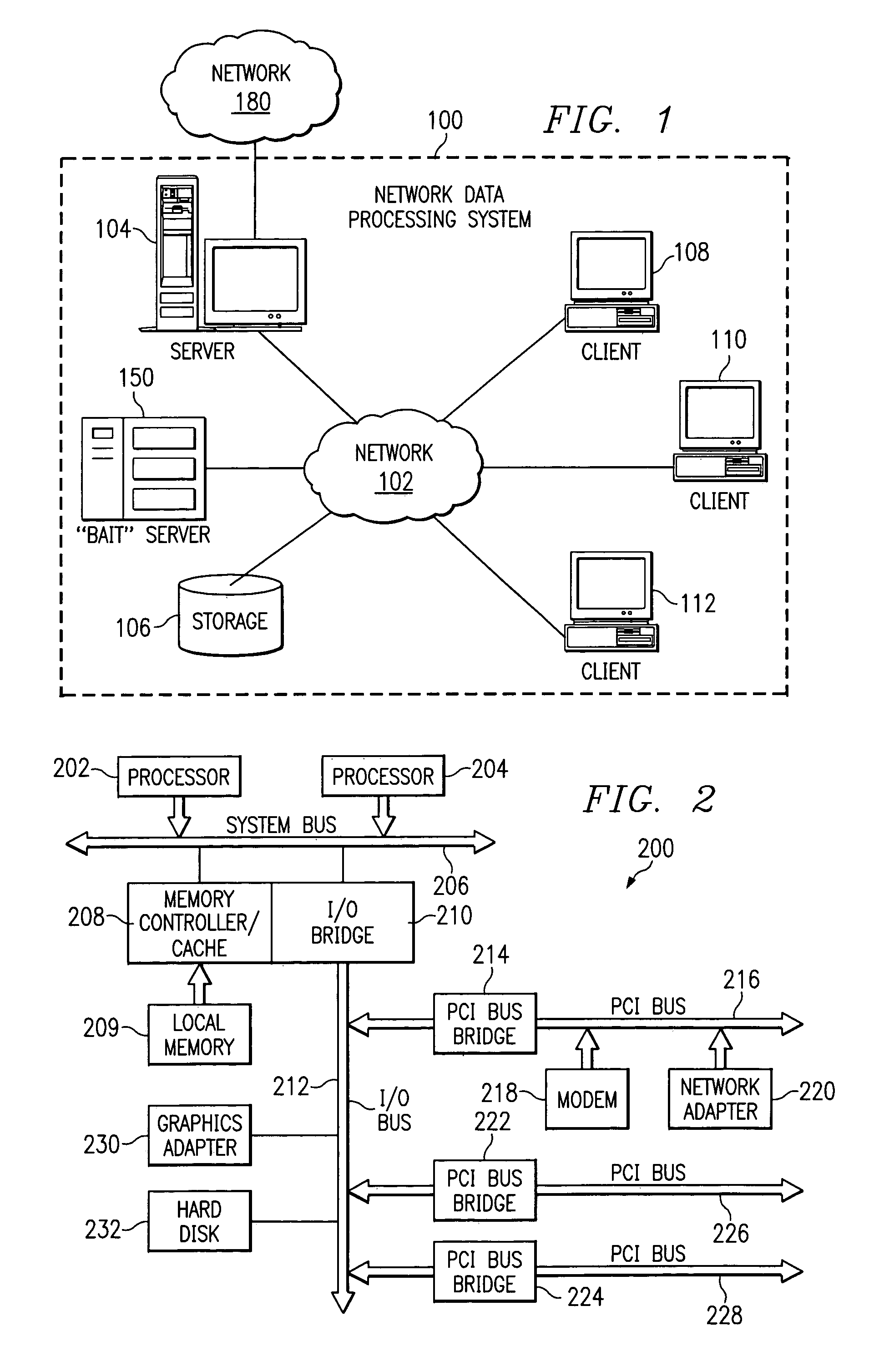
Method and apparatus for the detection, notification, and elimination of certain computer viruses on a network using a promiscuous system as bait
A method, computer program product, and network data processing system for identifying, locating, and deleting viruses is provided. In one embodiment, the network data processing system includes a local server, several client data processing systems, and a bait server. The address of the bait server is not published to the clients. Thus, any attempt to access the bait server would indicate the presence of a virus on the client attempting access. The bait server monitors itself and, responsive to an attempt from a client to access the bait server, broadcasts an indication that a virus attack is underway to all devices within the network. The bait server then ignores all further access requests by the offending client until it receives an indication that the offending client has been disinfected and directs the local server to disconnect the offending client(s) from the network. The bait server also notifies the local server and / or a network administrator of the problem and the identity of the offending client allowing appropriate action to be initiated to disinfect the offending client.
Owner:LENOVO PC INT
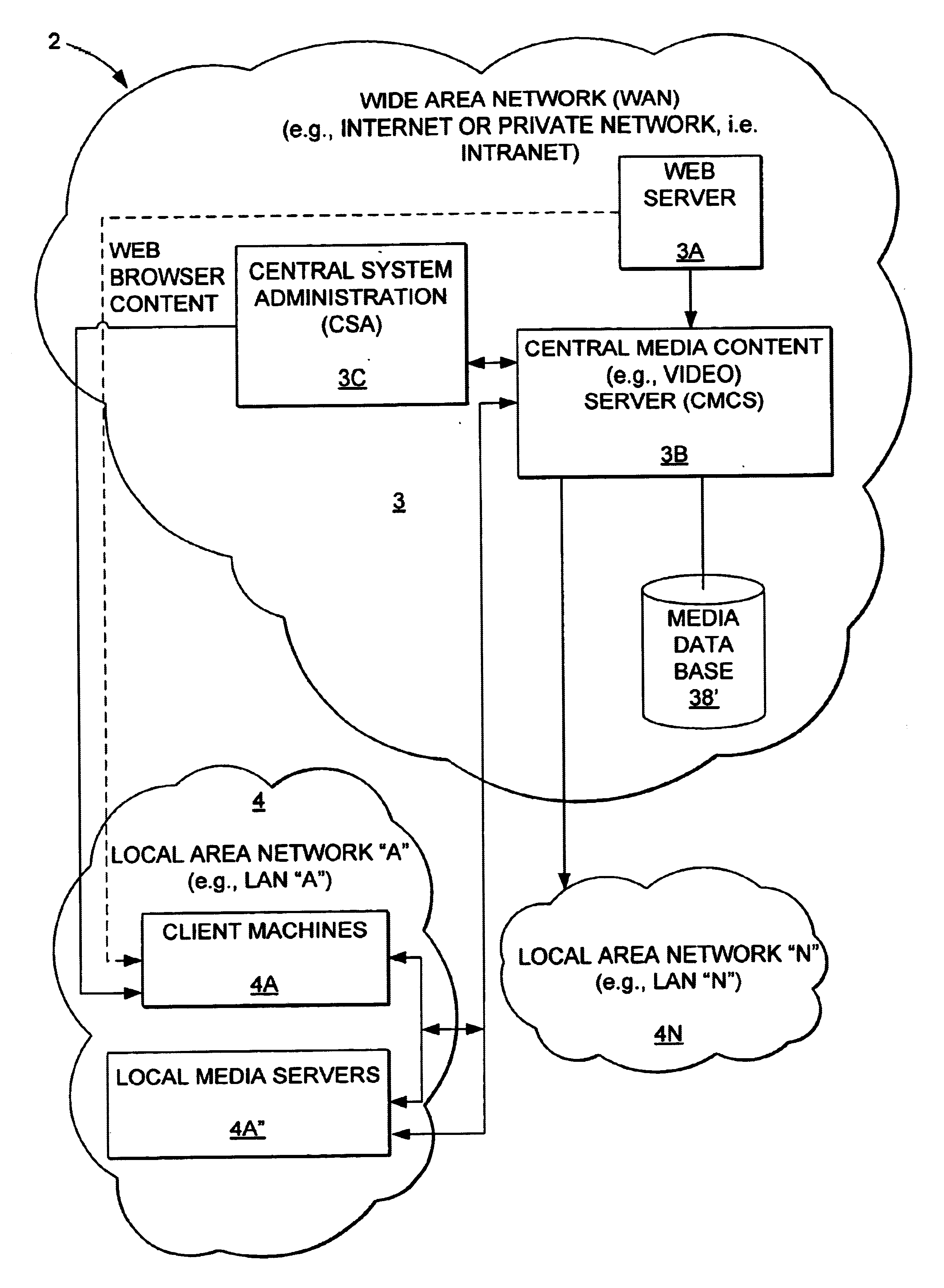
Geographical client distribution methods, systems and computer program products
InactiveUS7058720B1Increase chanceMultiple digital computer combinationsTransmissionDistribution methodClient data
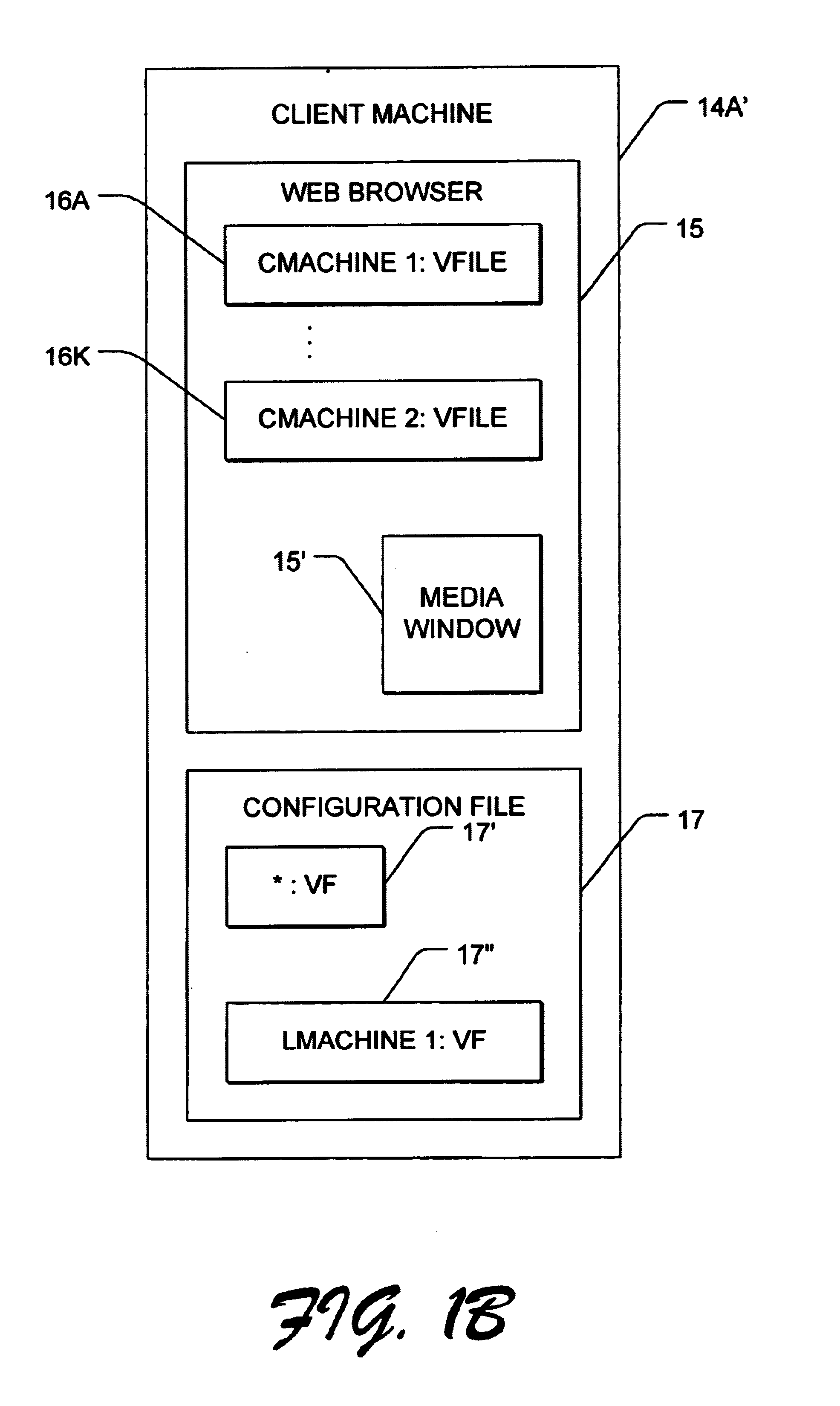
Video or media content is transferred to a local video or media server by a system administrator or central content programmer. Client data processing modules, i.e., client machines, are configured to query for local content associated with a particular file and stream names. The local search replaces the original stream name with a stream name associated with a local area network. The modified configuration file of the client machines provisionally substitutes a local stream name for the original stream name linked to the central media server. If a local query script searching for selected content locally, results in an error response indicating the requested content is unavailable locally, then the provisional stream name is deleted and replaced with the original stream name. The original stream request for selected content, which was made to the central media or video server is accordingly implemented as a fallback.
Owner:MICROSOFT TECH LICENSING LLC
System and method for collaborative data resource representation
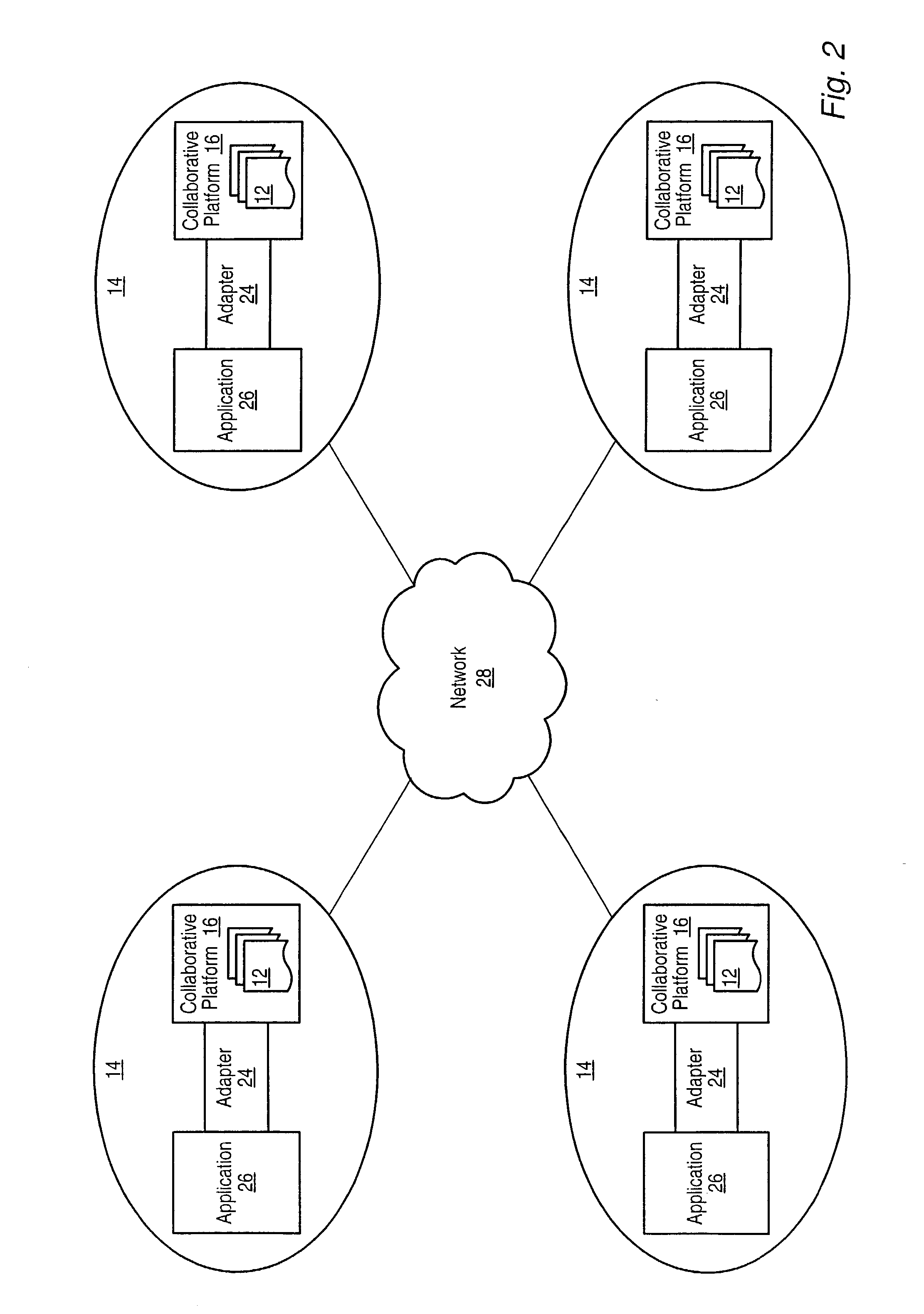
InactiveUS20030014513A1Multiple digital computer combinationsDistributed object oriented systemsClient dataClient-side
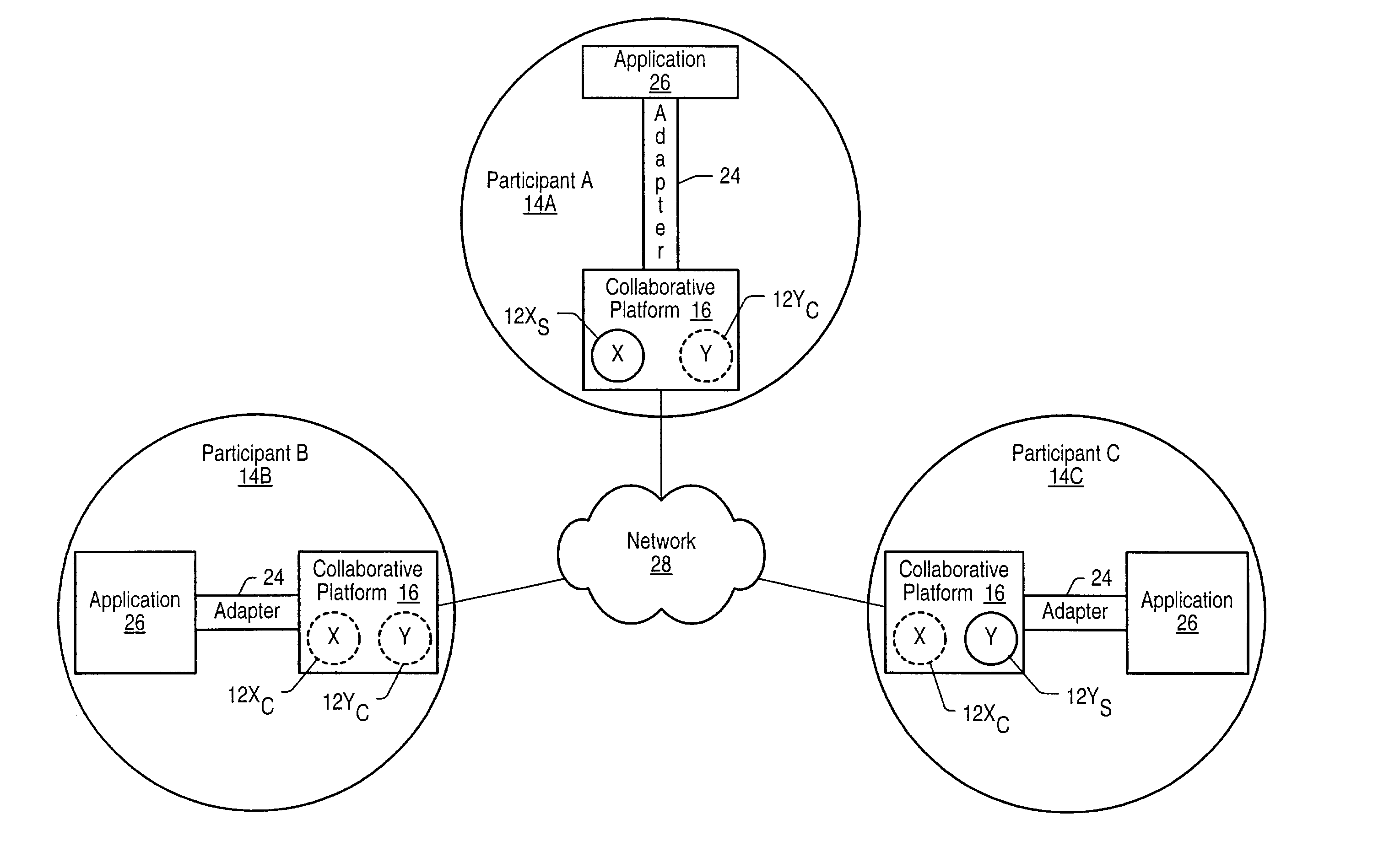
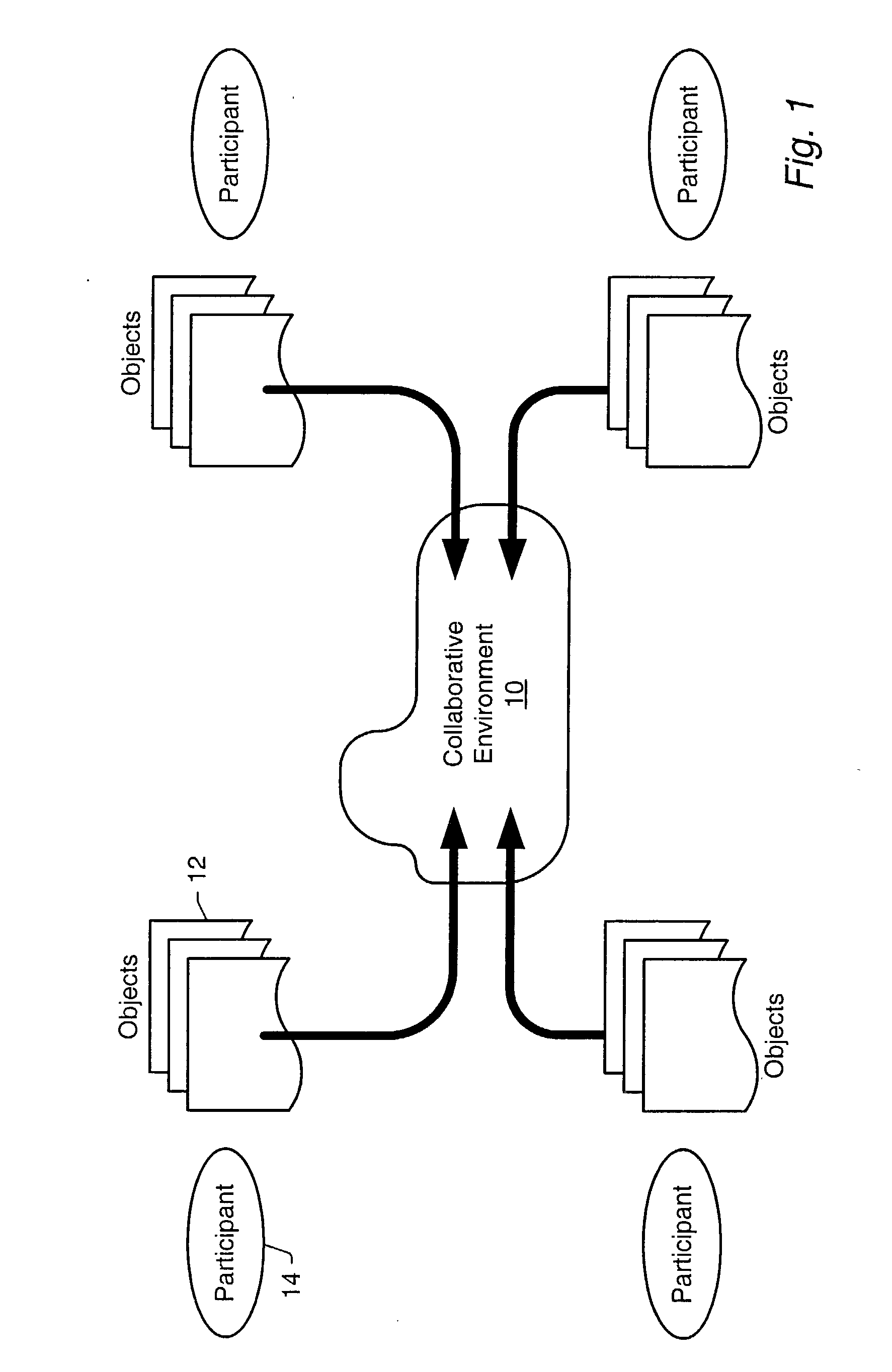
In a collaborative environment a collaborative platform for each participant may include a collaborative data resource representation for each collaborative data resource used in that collaborative environment. For each collaborative data resource, one of the participants' collaborative platform may be the host or server for that collaborative data resource. The collaborative data resource representation managed by the host collaborative platform is referred to as the server data representation. Every other participants' collaborative platform may manage a client data representation of that collaborative data resource. When an application makes a change to a collaborative data resource, the change is made for the server data representation and then the collaborative platform managing the server data representation sends state information to each client data representation of that collaborative data resource to reflect the change made to the server data representation.
Owner:ADVANCED REALITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com