Patents
Literature
3125results about How to "Safe storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
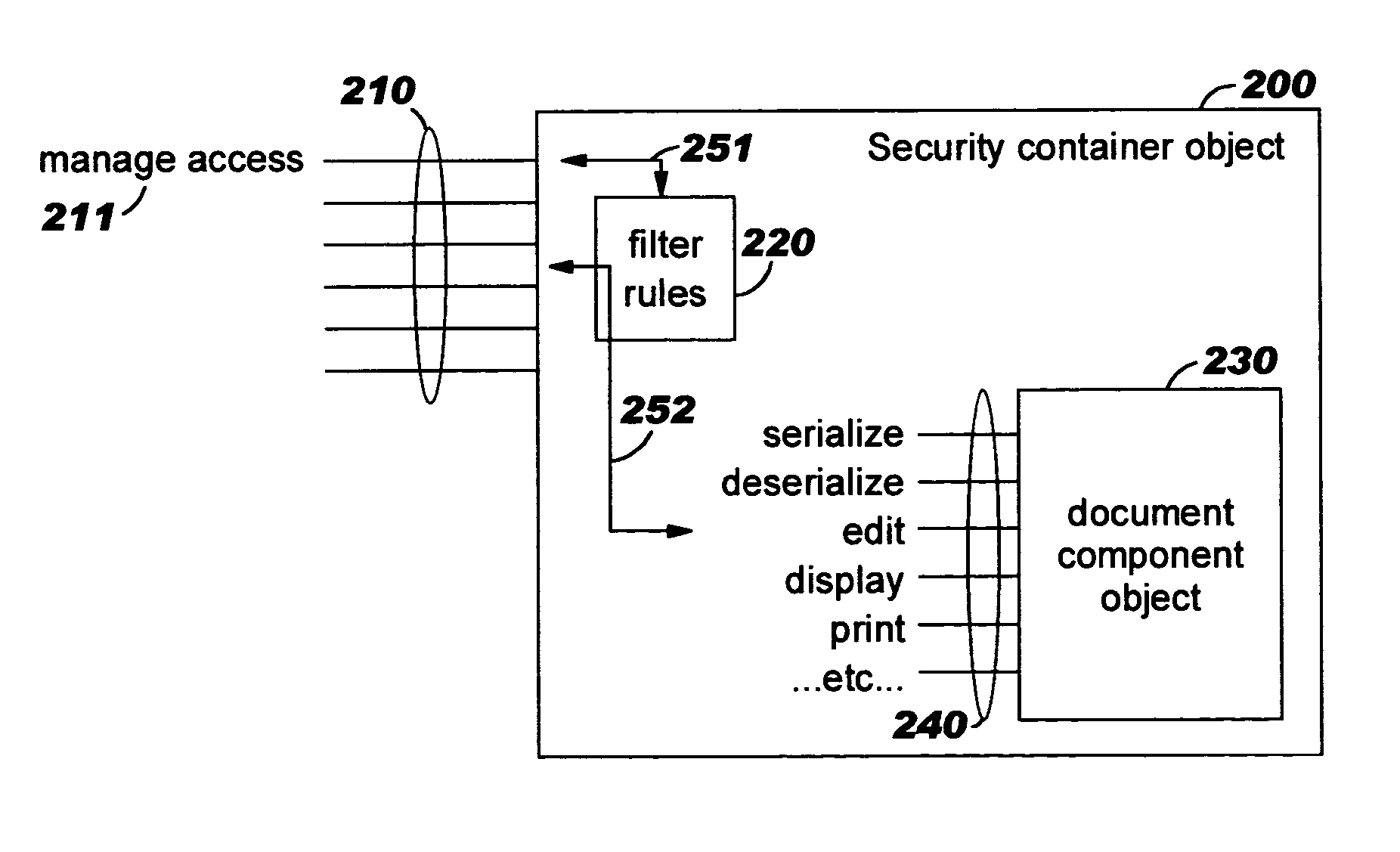
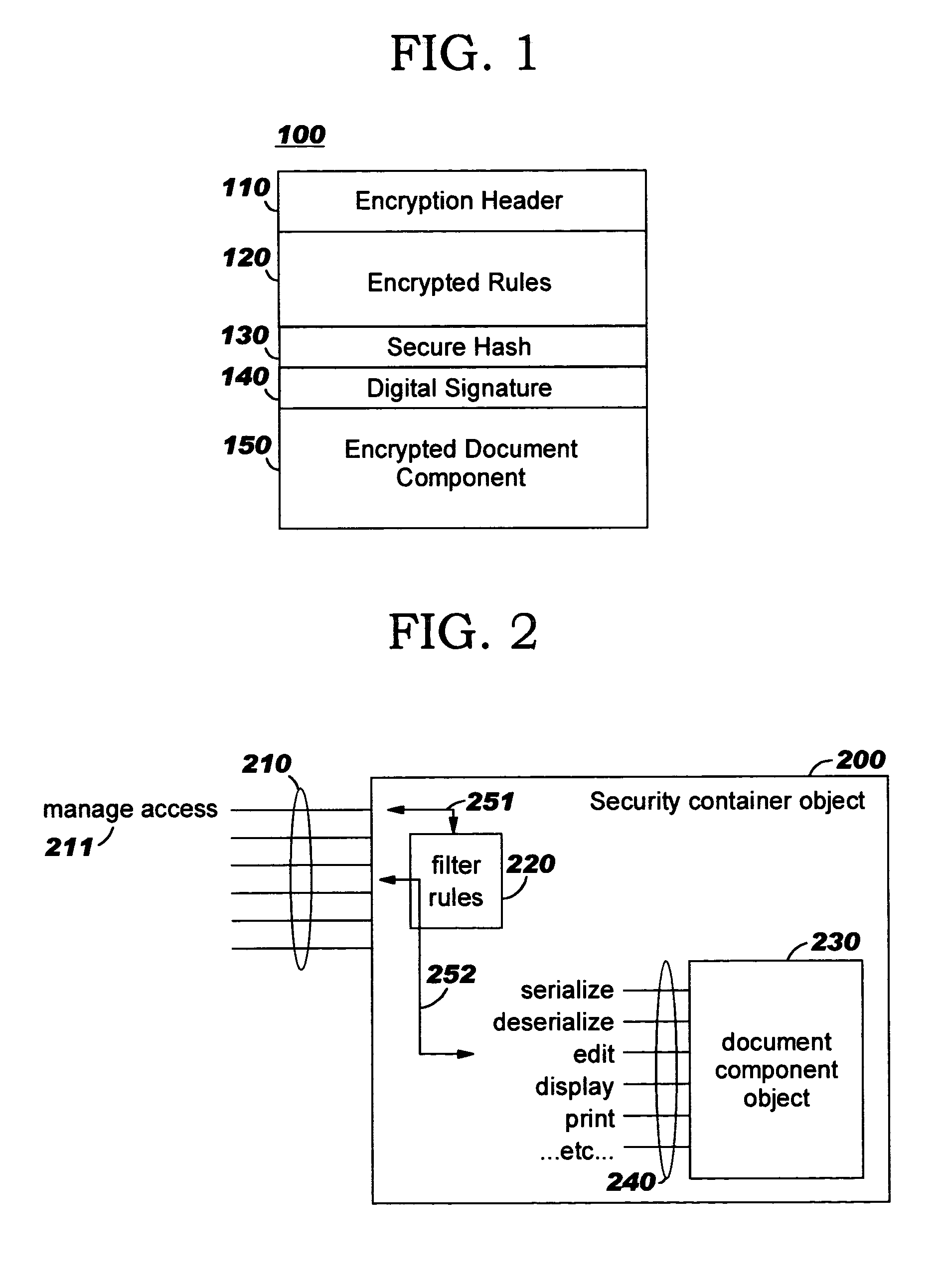
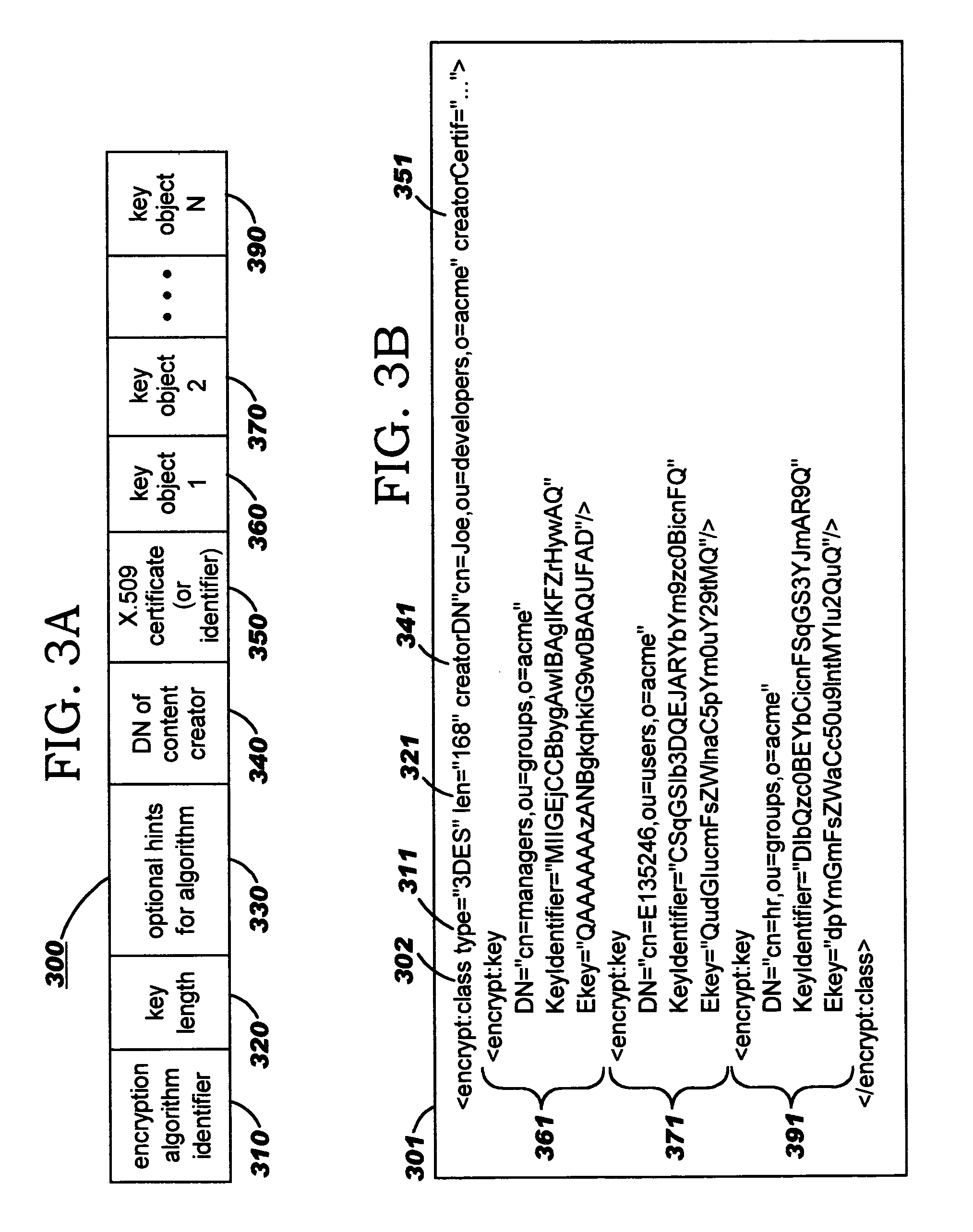
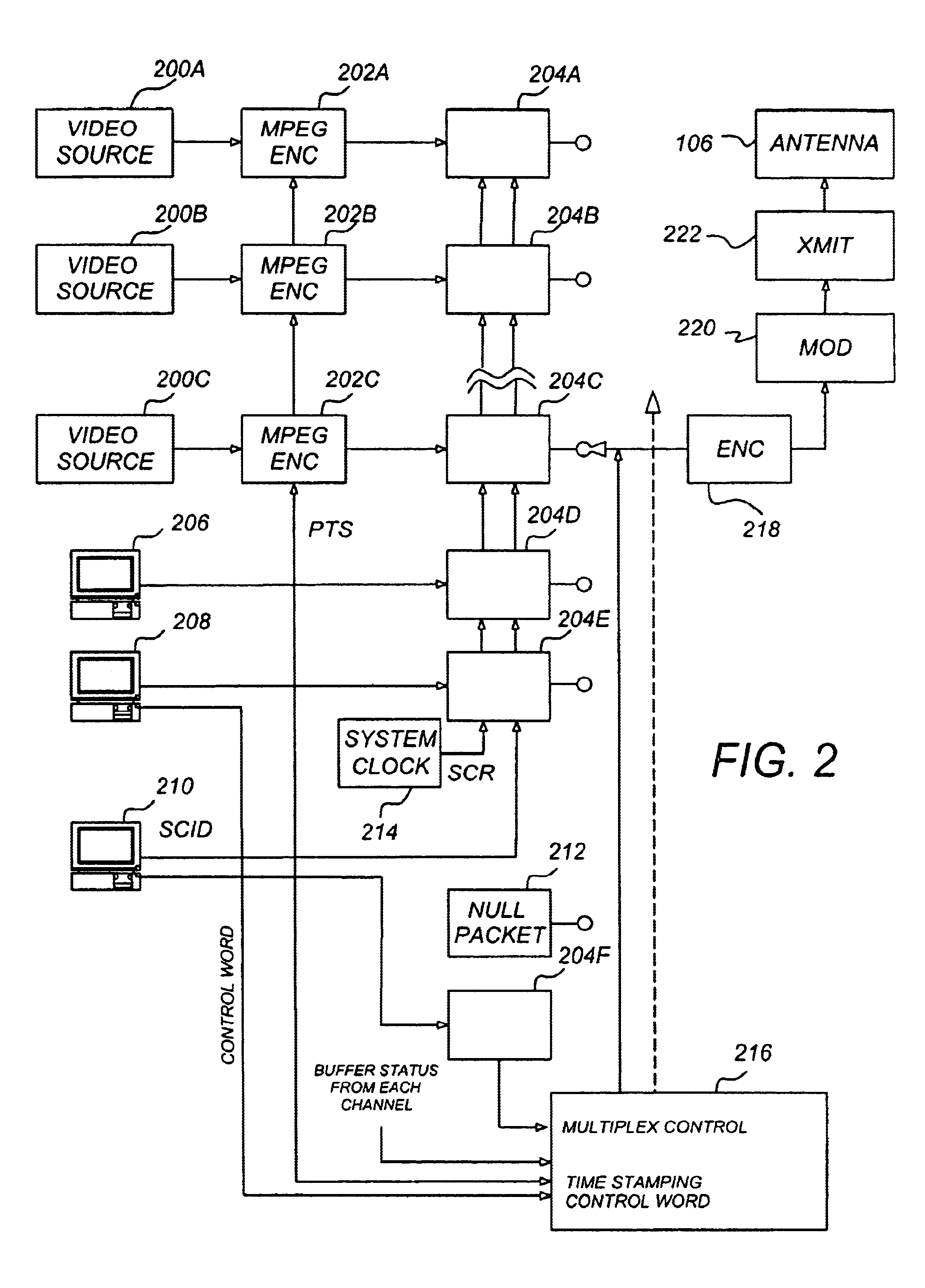
Security containers for document components
ActiveUS20050039034A1Easy to useSafe storageKey distribution for secure communicationUser identity/authority verificationSoftware engineeringPaper document
Methods, systems, computer program products, and methods of doing business whereby document components are secured or controlled using “security containers” which encapsulate the components (and other component metadata). A “security container” encapsulates the component (i.e., content) that is to be controlled within a higher-level construct such as a compound document. The security container also contains rules for interacting with the encapsulated component, and one or more encryption keys usable for decrypting the component and rules for authorized requesters.
Owner:IBM CORP
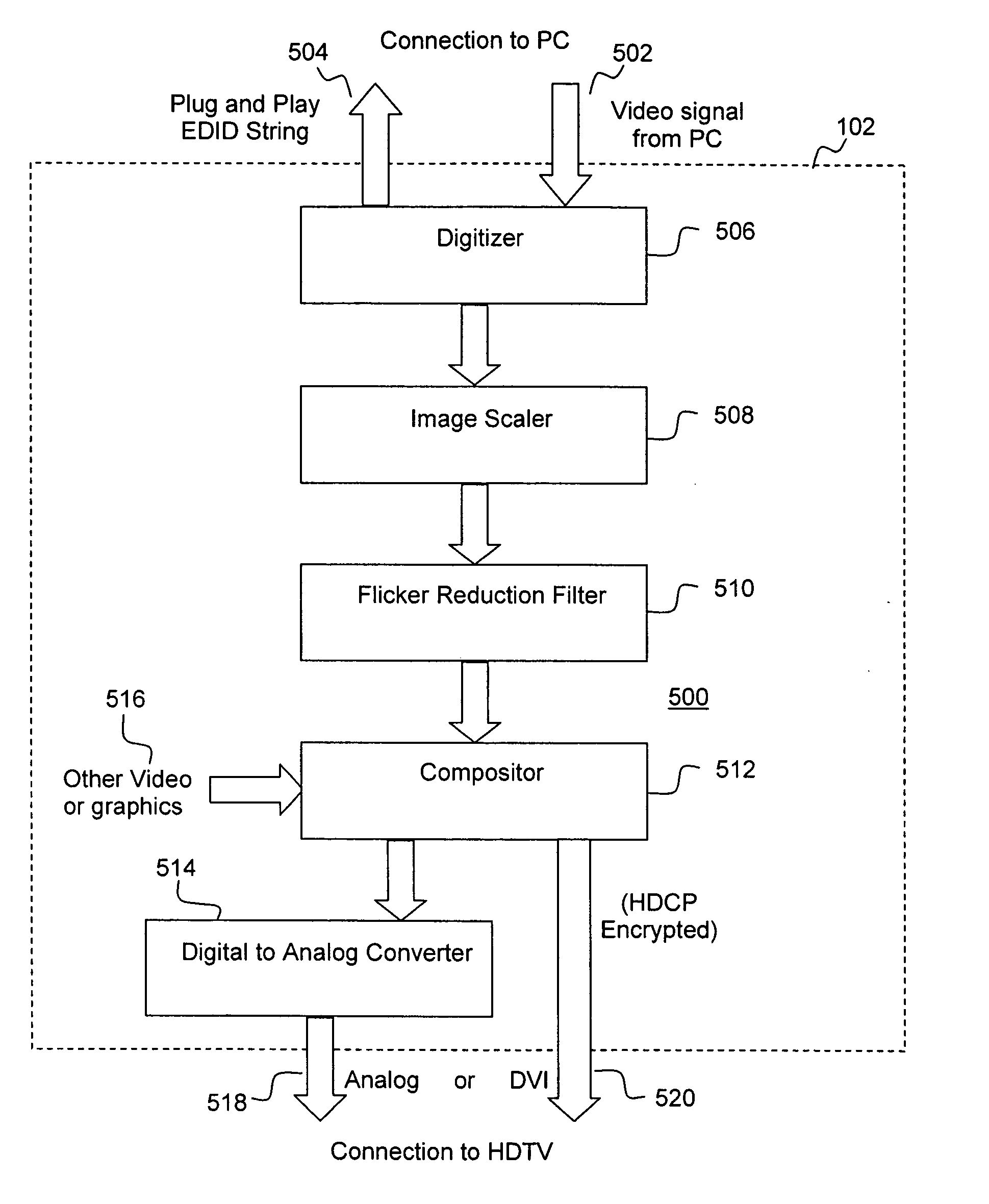
Secure integrated media center
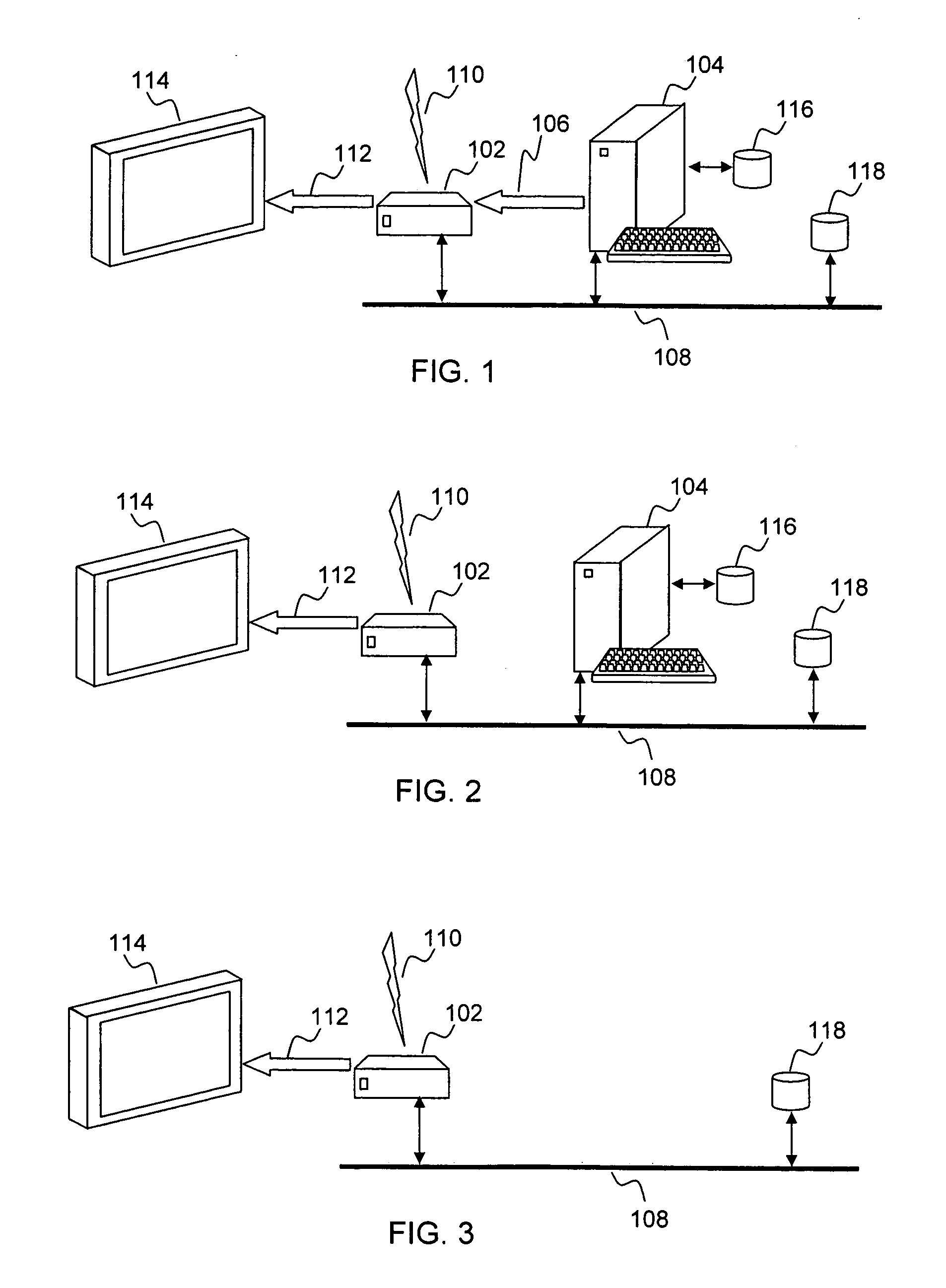
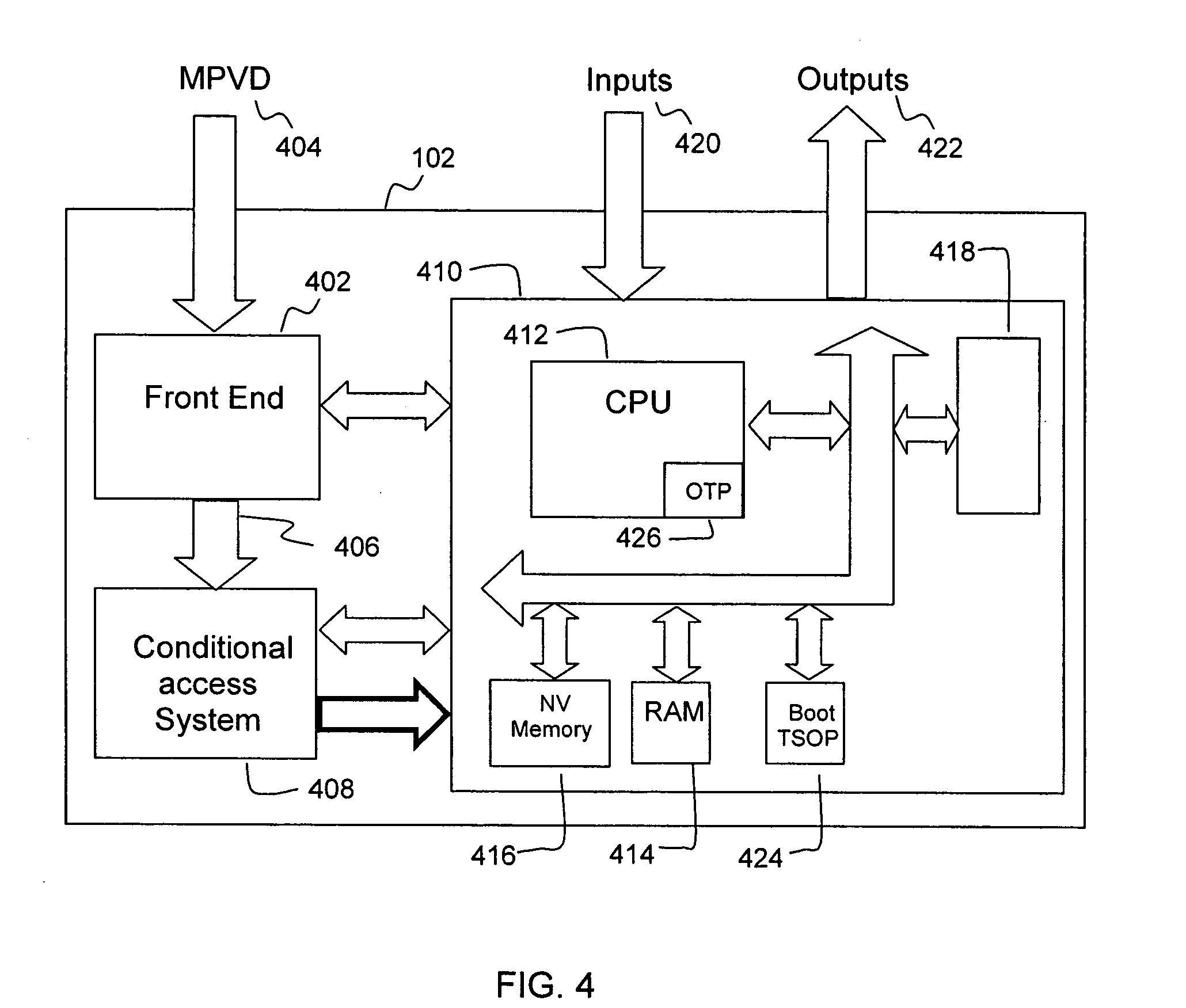
InactiveUS20050125357A1Safe storageTelevision system detailsUnauthorized memory use protectionHard disc driveHigh definition tv
A set-top media system is disclosed which can be combined with an open architecture personal computer (PC) to provide a feature-rich secure integrated media center while meeting security rules of most major conditional access and content protection industry rules such as Cable Labs DFAST and PHILA agreements; and DTLA agreements for 5C-DTCP for IEEE1394, USB, and IP. The set-top media center and PC share common resources such as high definition display, remote control, hard disk drive, and other external unsecure storage devices. All media content is available seamlessly using a PC user interface, including controlled-content media such as high definition TV, within a PC desktop window. All controlled-content media is manipulated and managed within the set-top media system in a seamless manner. A novel mechanism is disclosed to allow controlled-content media to be stored on unsecure devices in encrypted form while overcoming the disk cloning attack problem for move operations.
Owner:SAADAT ABBAS SASAN +1
Video on demand pay per view services with unmodified conditional access functionality
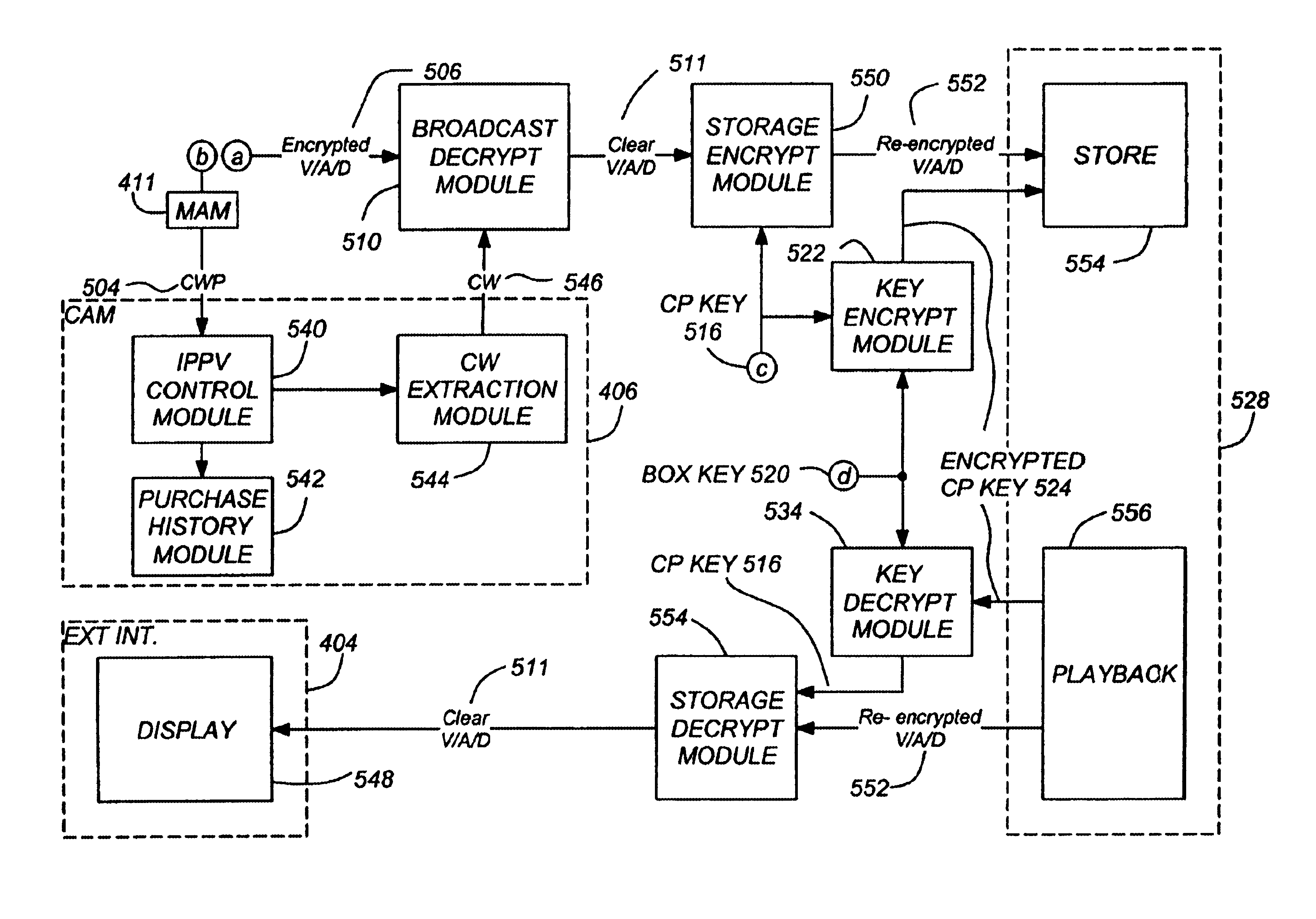
InactiveUS6853728B1Eliminate concernsSafe storageBroadcast with distributionTelevision system detailsConditional accessVideo on demand
A system and method for storing and retrieving program material for subsequent replay is disclosed. The method comprises the steps of receiving access control information and the program material encrypted according to a first encryption key, the access control information including the first encryption key and control data; further encrypting the access control information and the encrypted program material according to a second encryption key; encrypting the second encryption key according to a third encryption key to produce a fourth encryption key; and storing the encrypted access control information and encrypted program material and the fourth encryption key.
Owner:DIRECTV LLC
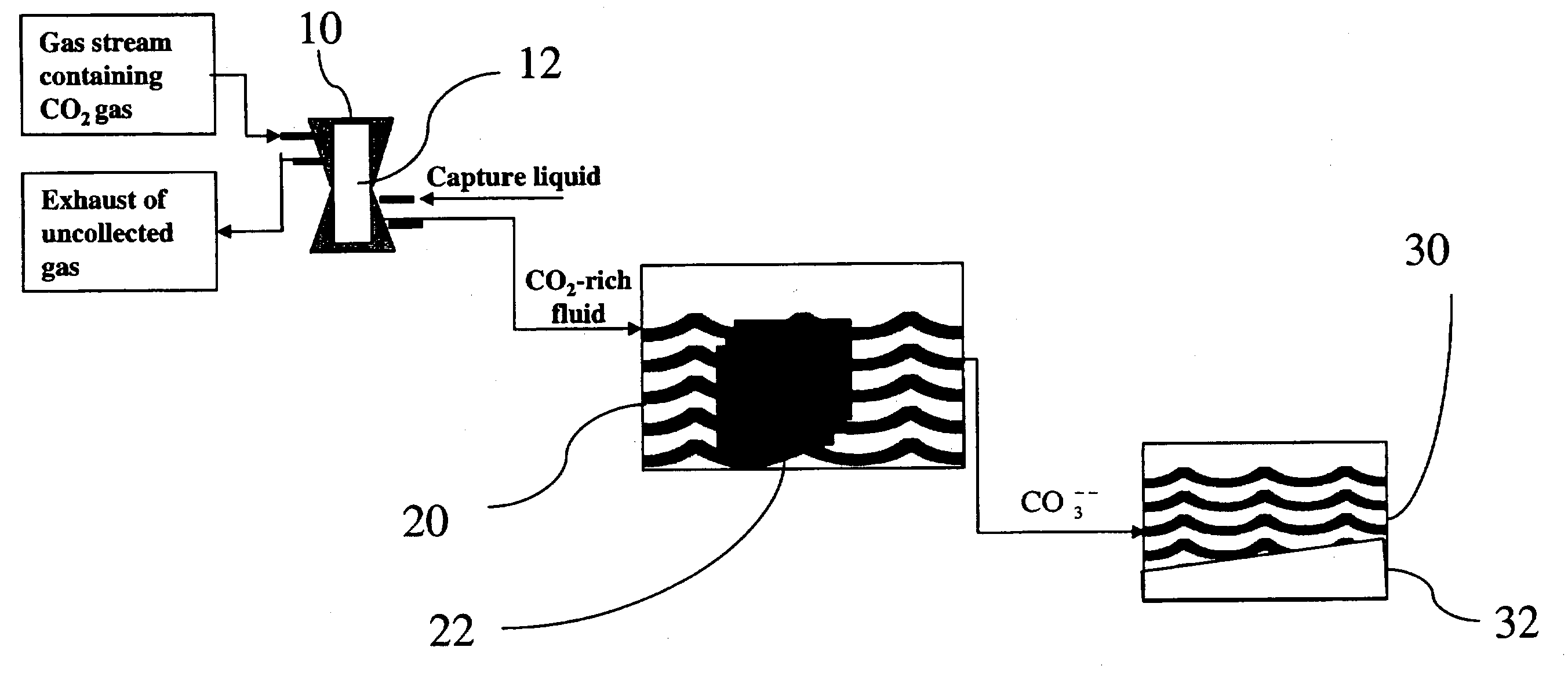
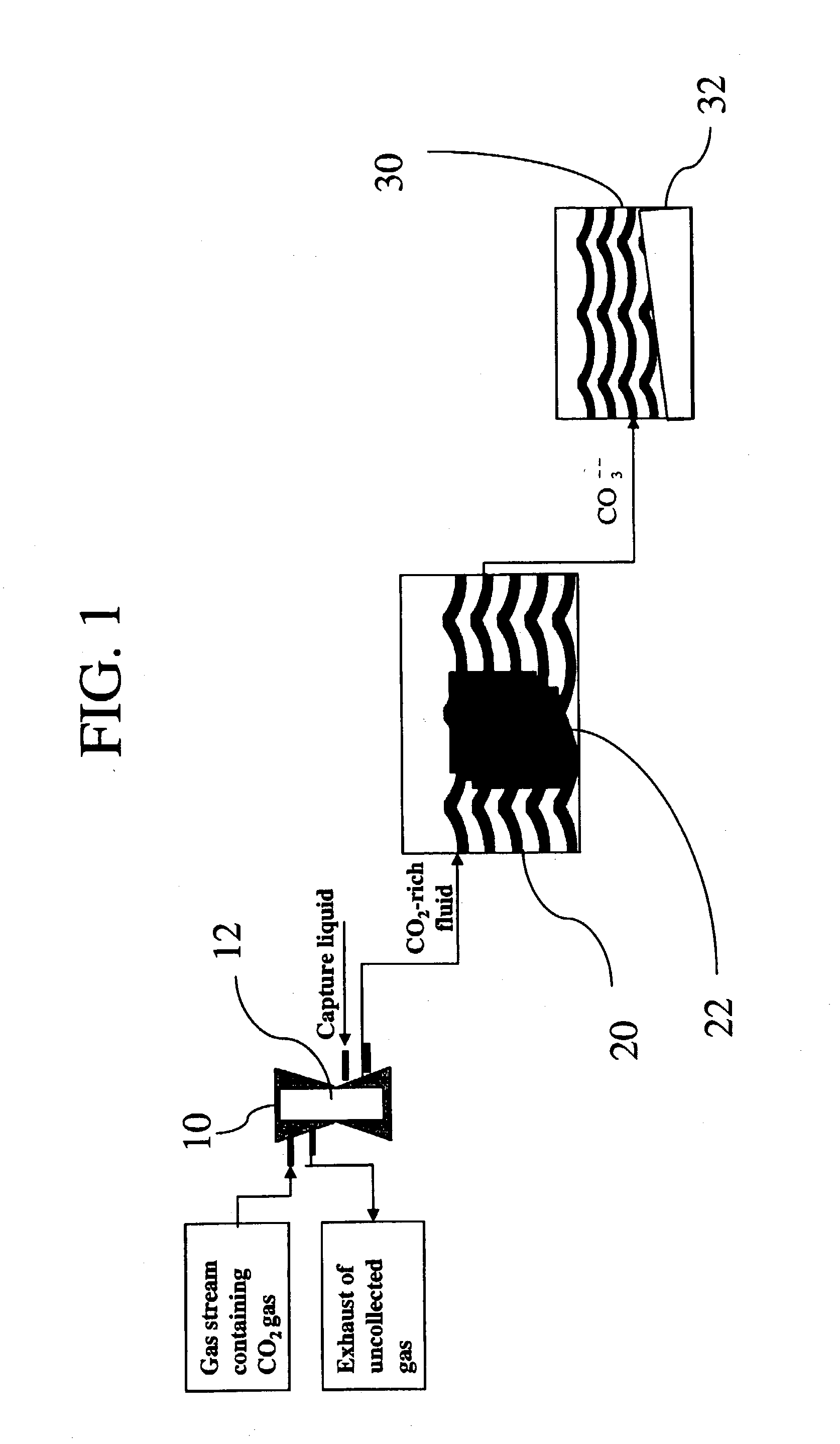
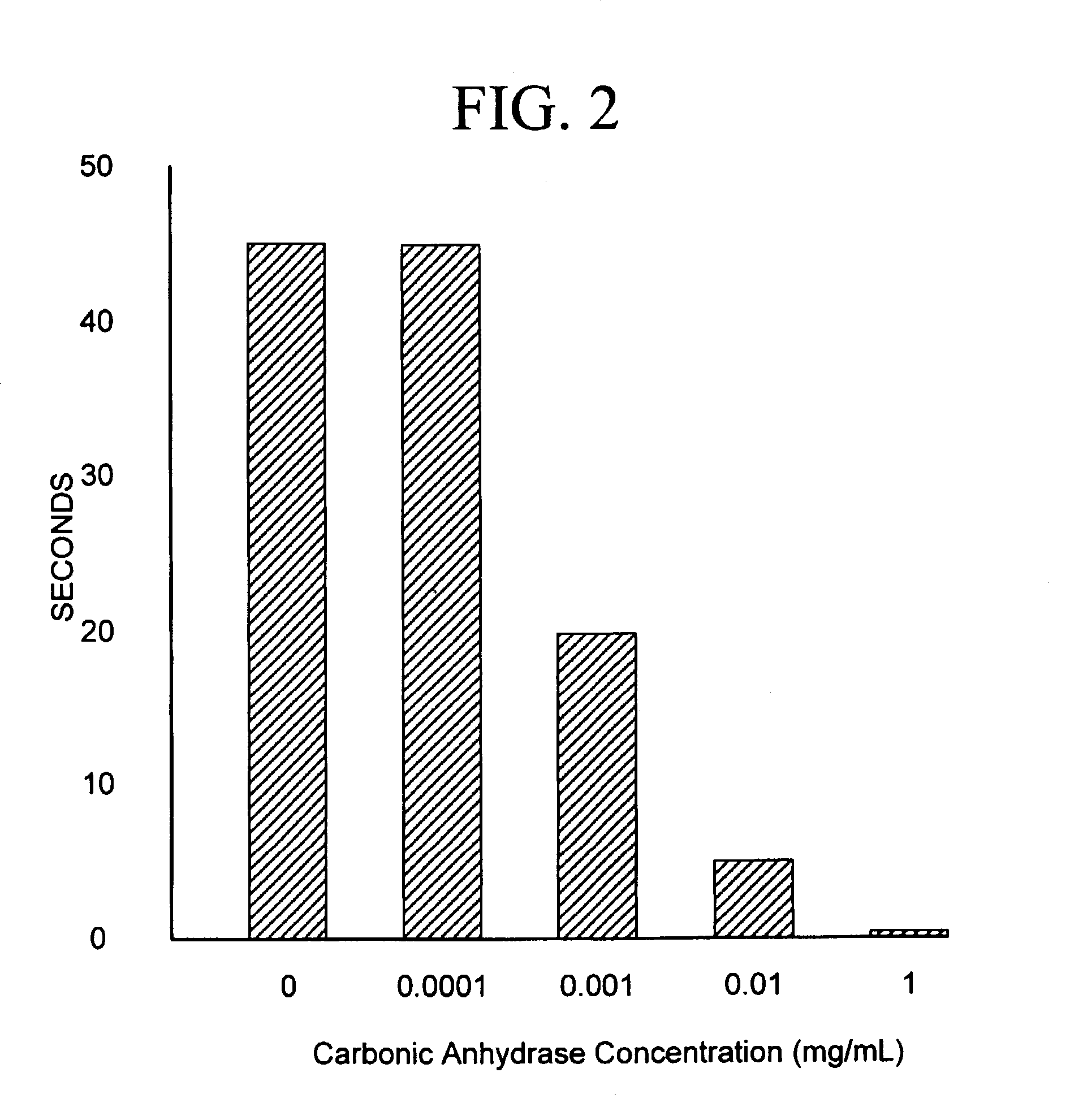
Sequestration of carbon dioxide
ActiveUS7132090B2Safe storageLarge specific surface areaCalcium/strontium/barium carbonatesProductsProduct gasMineral ions
A process for selectively removing carbon dioxide from a gaseous stream by converting the carbon dioxide to a solid, stable form is provided. In a sequestration process, carbon dioxide enriched air is passed through a gas diffusion membrane to transfer the carbon dioxide to a fluid medium. The carbon dioxide rich fluid is then passed through a matrix containing a catalyst specific for carbon dioxide, which accelerates the conversion of the carbon dioxide to carbonic acid. In the final step, a mineral ion is added to the reaction so that a precipitate of carbonate salt is formed. This solid mineral precipitate can be safely stored for extended periods of time, such as by burying the precipitate in the ground or depositing the precipitate into storage sites either on land or into a body of water. An apparatus for removing carbon dioxide from a gaseous stream is also provided.
Owner:GM GLOBAL TECH OPERATIONS LLC
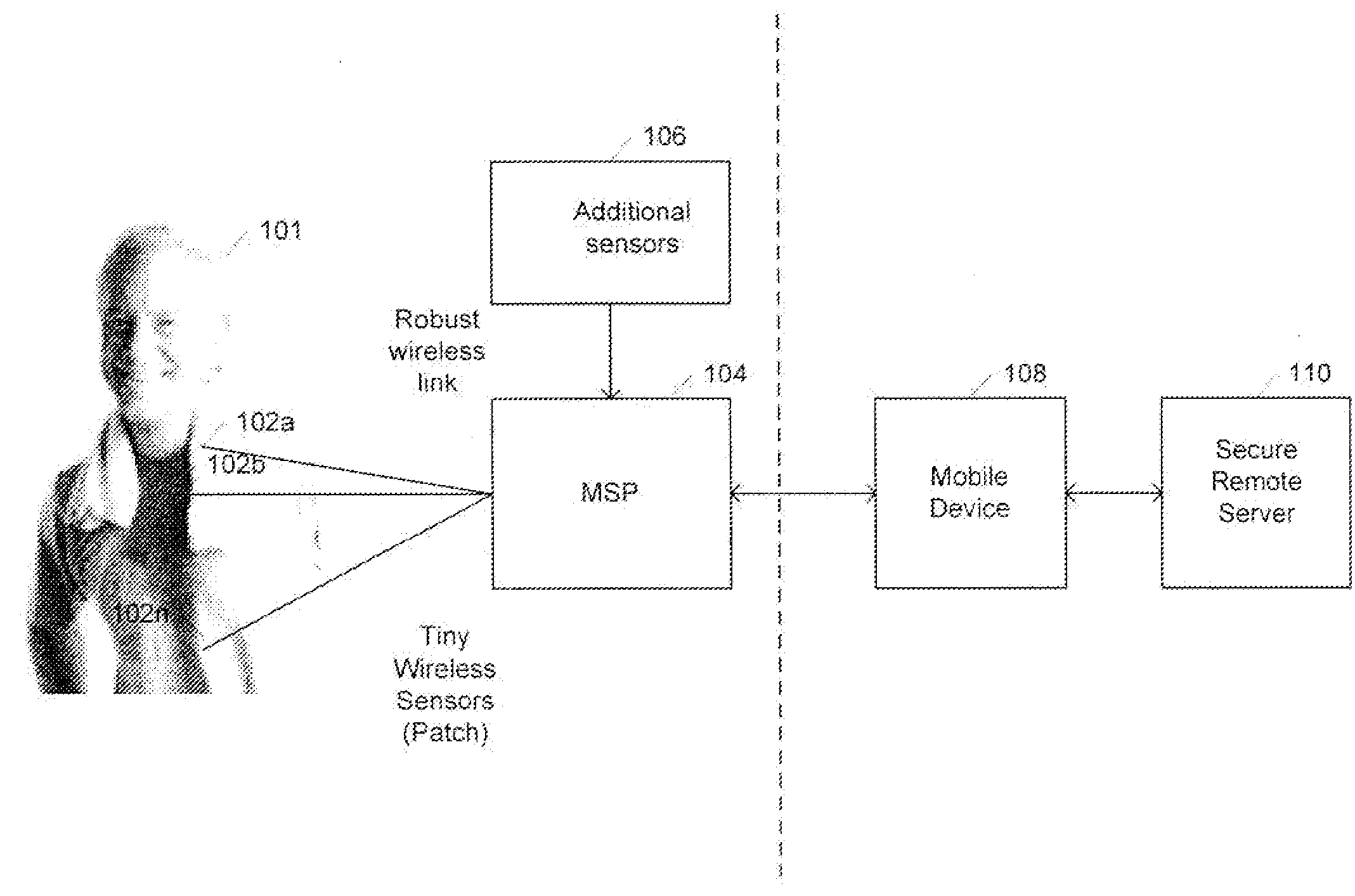
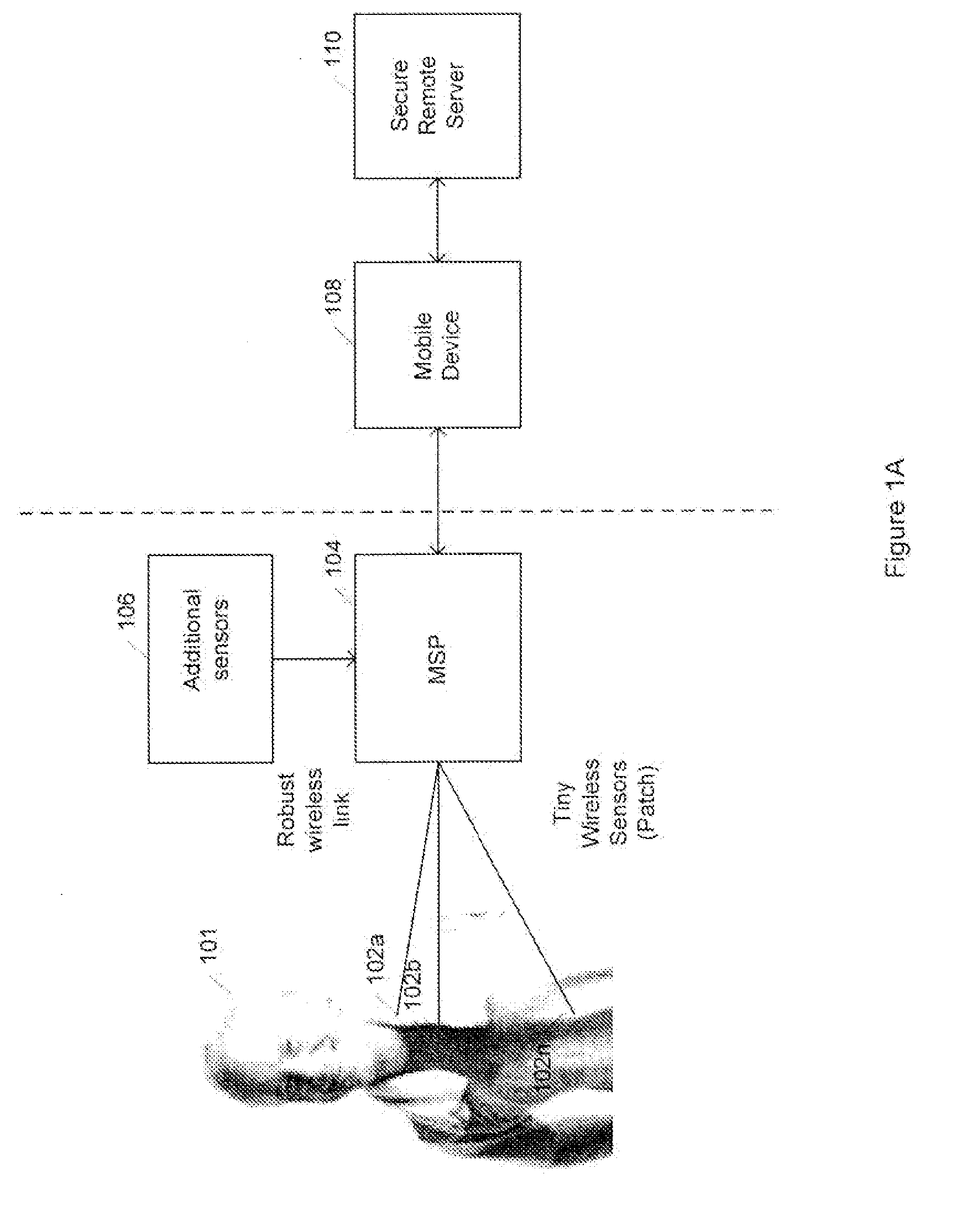
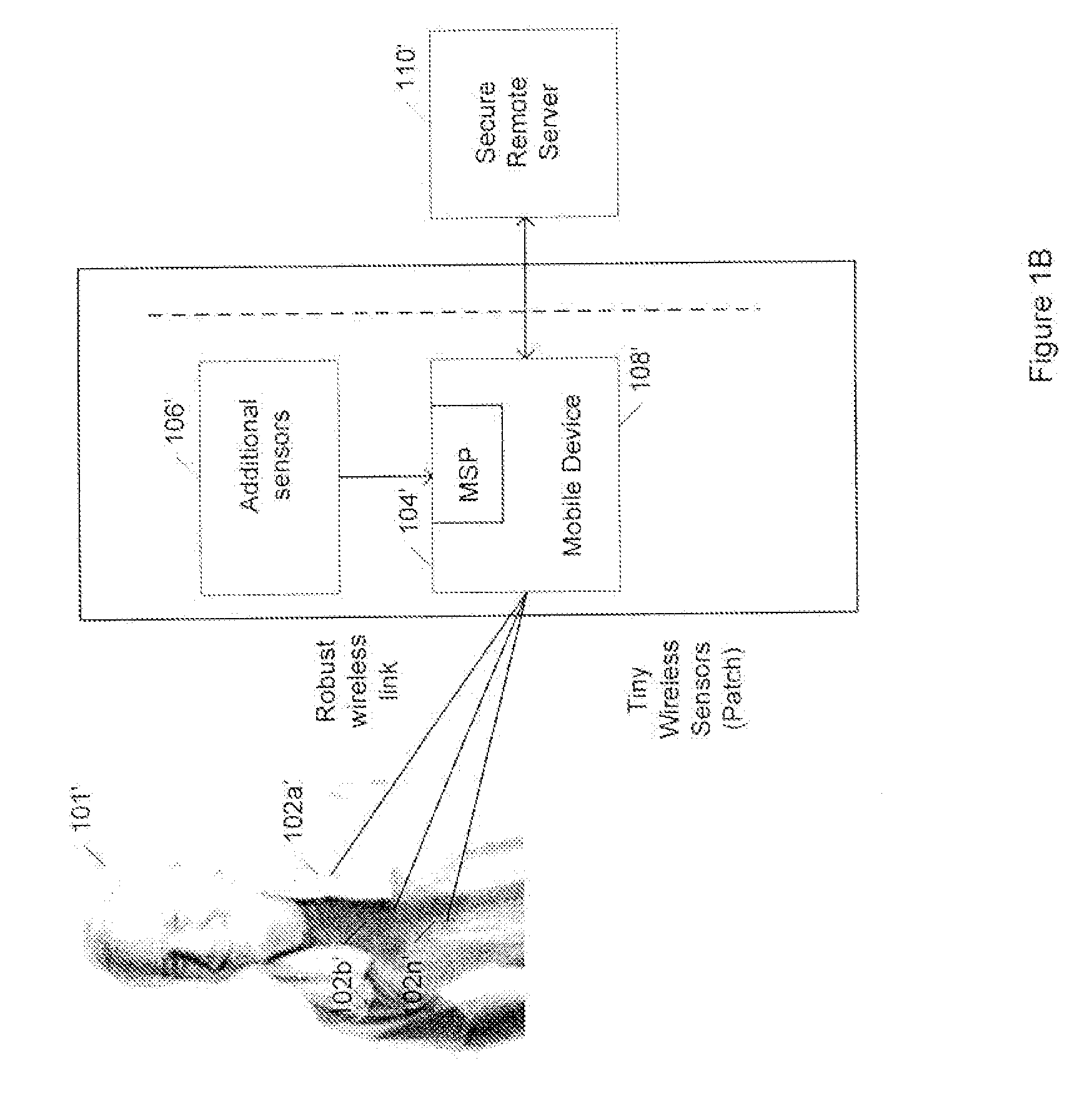
Medical signal processing system with distributed wireless sensors
InactiveUS20100049006A1High wireless link reliability/securityReduce power consumptionElectrocardiographyInertial sensorsDiseaseLine sensor
A wireless medical signal processing system for health monitoring is disclosed which achieves high wireless link reliability / security, low power dissipation, compactness, low cost and supports a variety of sensors for various physiological parameters. The system includes a medical signal processor which communicates with a wireless distributed sensor system as its peripheral for detecting physiological parameters of the person and for providing signals indicative thereof. The medical signal processor wirelessly receives the signals from the distributed wireless sensor system in a multiplexed fashion and processes the signals to provide an indication of the health of the person. The indication of health could relate to a disease state, general health or fitness level of a person. The system also includes a mobile device for receiving the indication of the health of the person to allow for a diagnosis or treatment of the person.
Owner:HMICRO
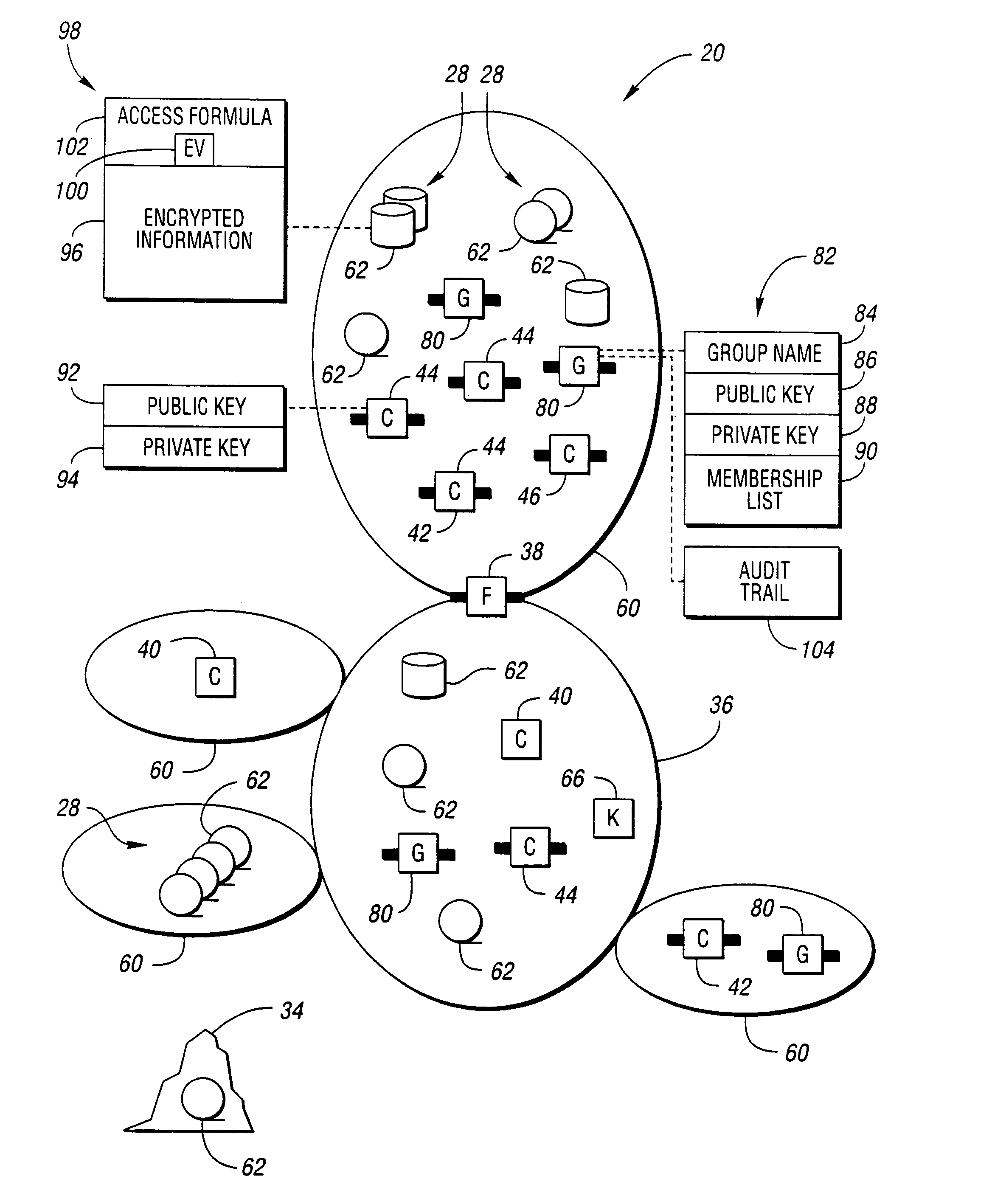
Method and system for secure information handling
InactiveUS6957330B1Safe handlingSafe storageKey distribution for secure communicationUser identity/authority verificationClient-sideSecurity information
Information that must remain secure is often stored on untrusted storage devices. To increase security, this information is encrypted by an encryption value prior to storing on the untrusted storage device. The encryption value itself is then encrypted. The encryption value is decrypted by correctly solving an access formula describing a function of groups. Each group includes a list of at least one consumer client. A requesting consumer client is granted access to the information if the requesting consumer client is a member of at least one group which correctly solves the access formula.
Owner:ORACLE INT CORP
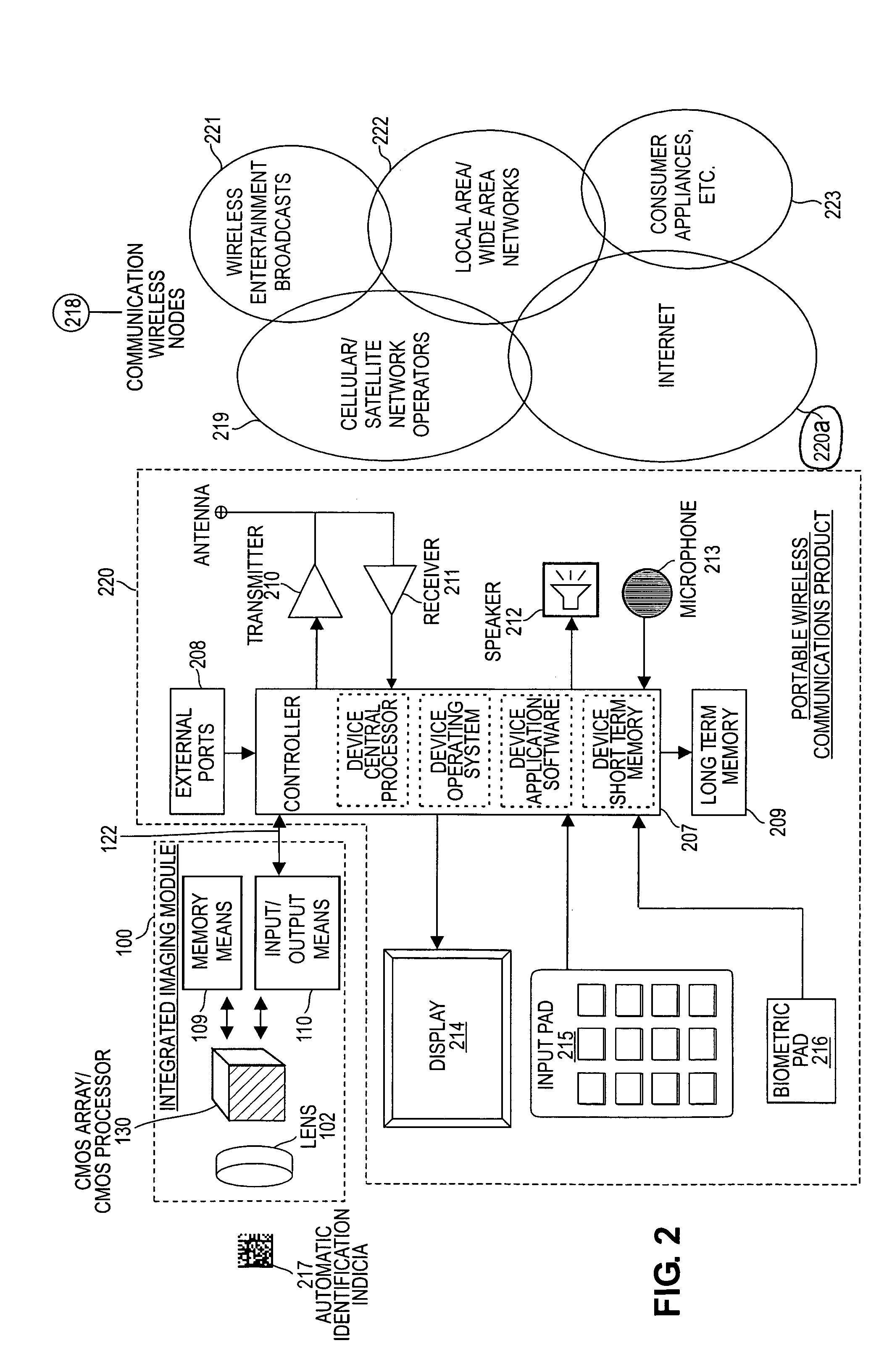
System and architecture that supports a multi-function semiconductor device between networks and portable wireless communications products
InactiveUS7239346B1Enhanced utility and functionalityImprove rendering capabilitiesTelevision system detailsColor television detailsWireless communication protocolDigital imaging
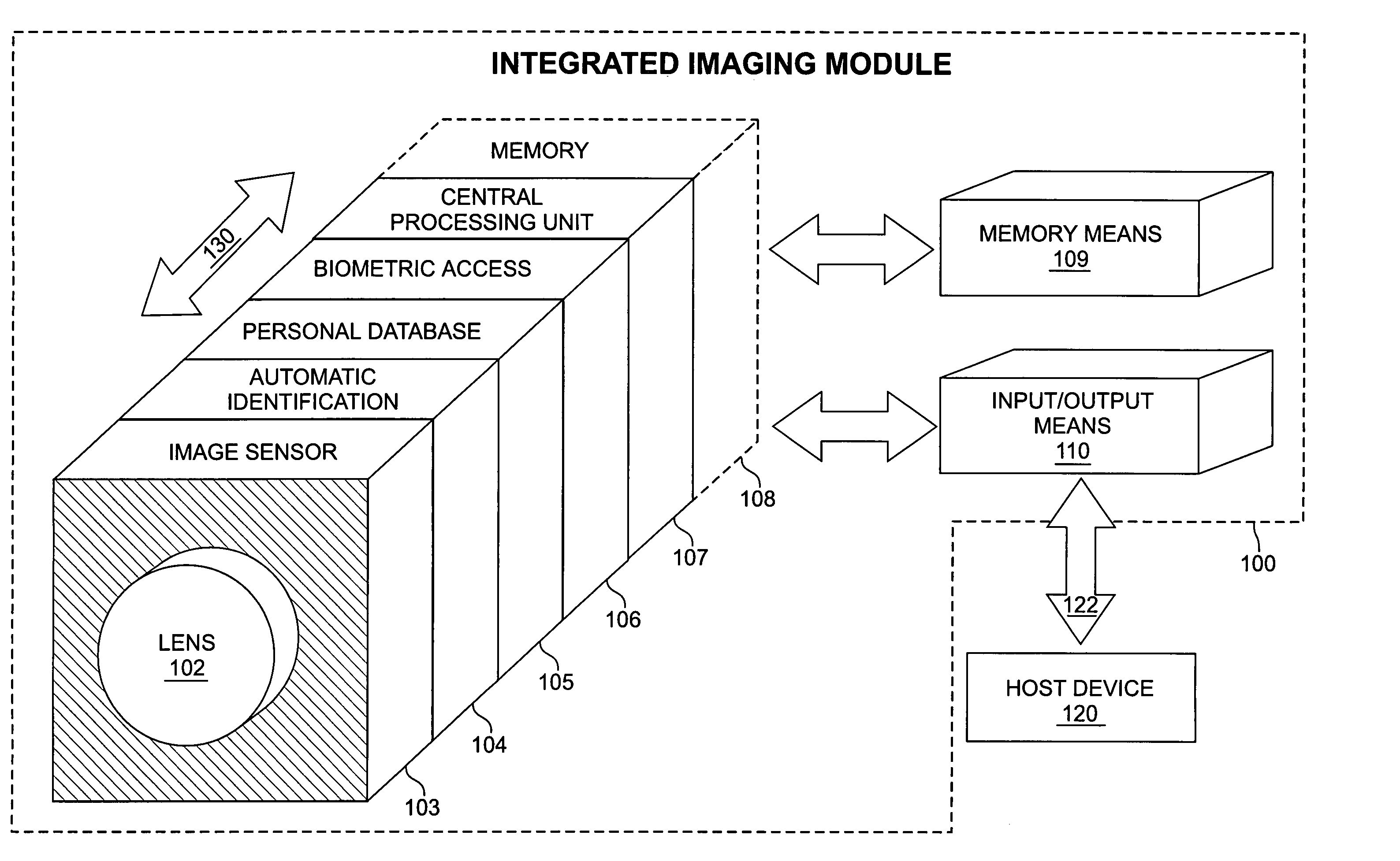
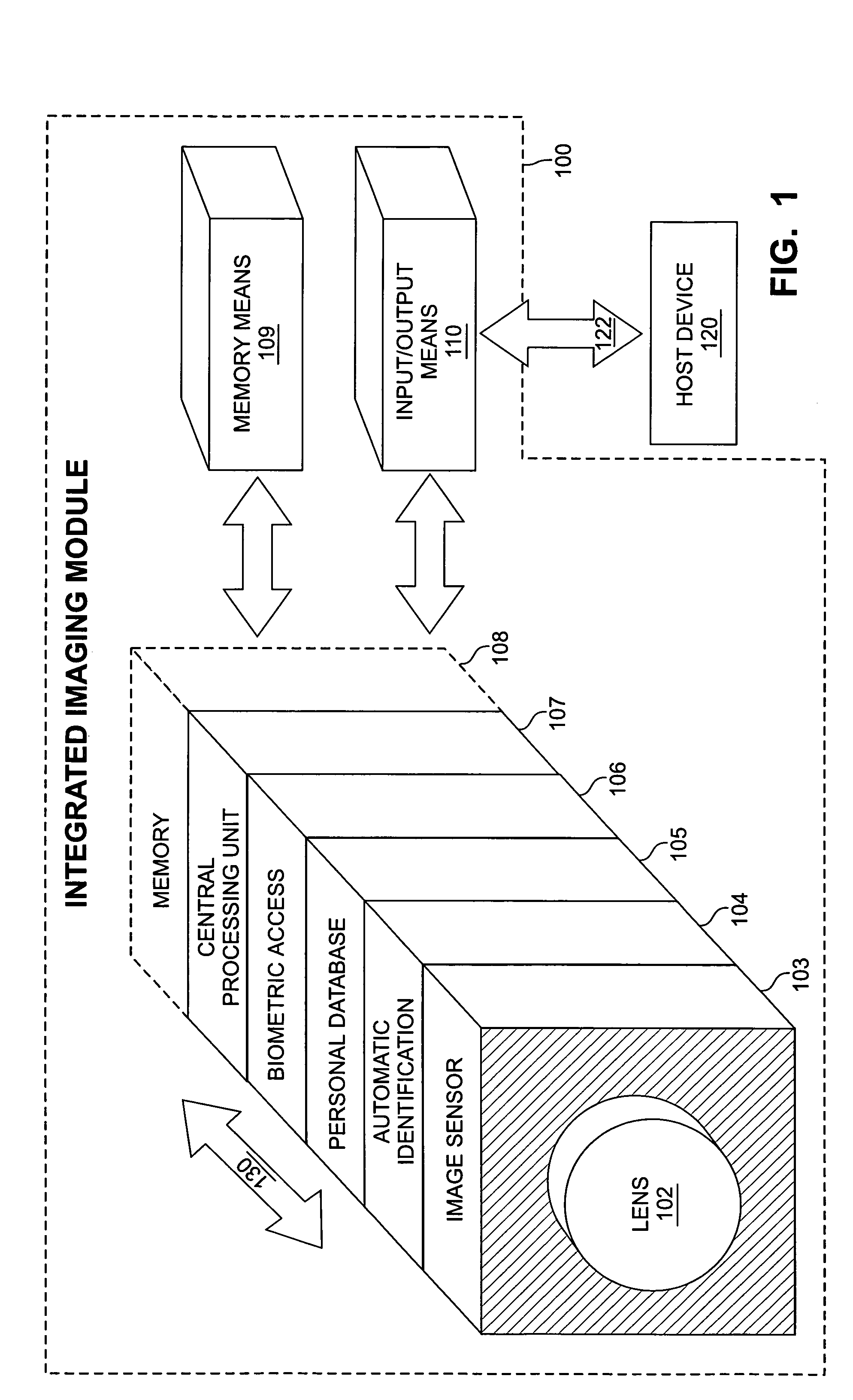
A system and architecture that supports an integrated imaging module for use between networks and portable communications products. The integrated imaging module contains a lens, memory, an input / output device, and a multi-function semiconductor device, such as a Complementary Metal-Oxide Semiconductor (CMOS). Within the design of the multi-function semiconductor device are the functions of still and full-motion digital imaging, image processing, automatic identification, a secure personal database, biometric attribute identification for access control, personal finance information, wireless communication protocols, general purpose processing, and memory. The module may be incorporated into any portable wireless communication product and used to capture text and image data for incorporation into a wireless transmission to a remote device.
Owner:PRIDDY DENNIS G
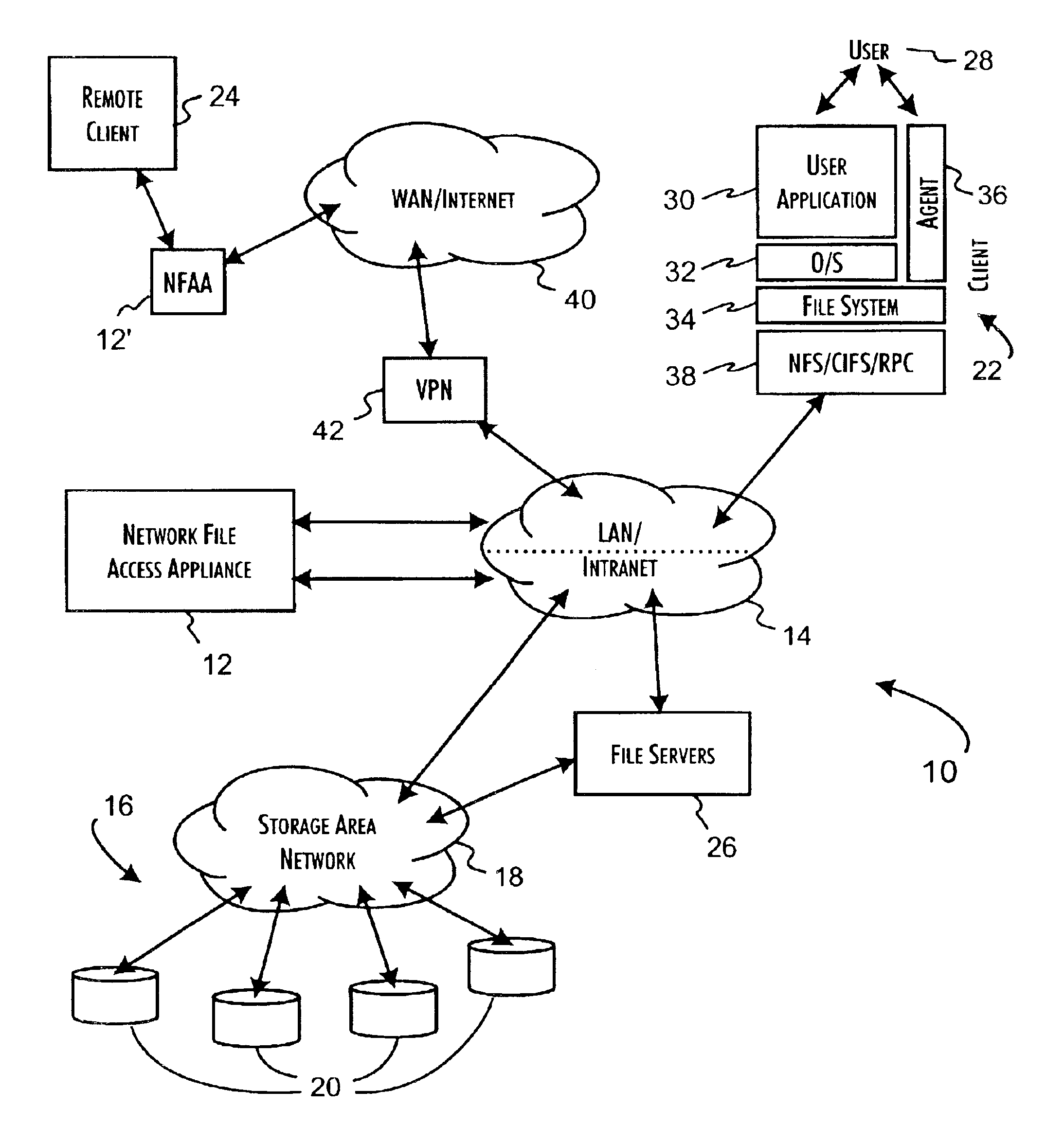
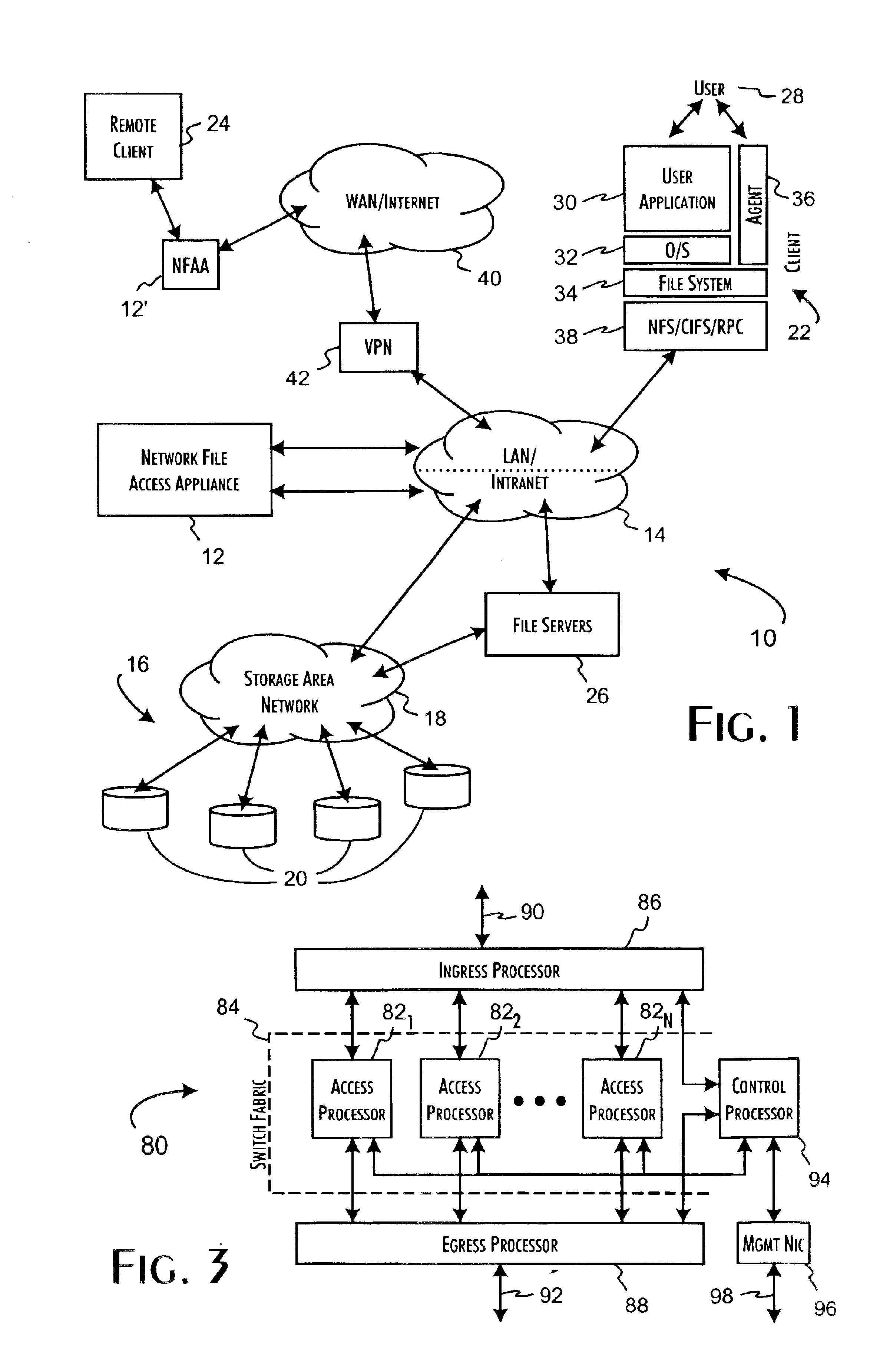
Secure network file access controller implementing access control and auditing
InactiveUS6931530B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationReference mapSecure transmission
A network file access appliance operates as a secure portal for network file access operations between client computer systems and network storage resources. The file access appliance terminates network file access transactions, identified by packet information including client system, mount point, and file request identifiers, between client systems and mount points supported by the access controller. A policy parser determines, based on the packet information, to selectively initiate network file access transactions between the access controller and network storage resources to enable completion of selected network file access transactions directed from the clients to the network file access appliance. The network file access transactions directed to the network storage resources are modified counterparts of policy selected client network file access transactions modified to reference mapped network storage resource mount points and support the secure transfer and storage of network file data.
Owner:THALES DIS CPL USA INC
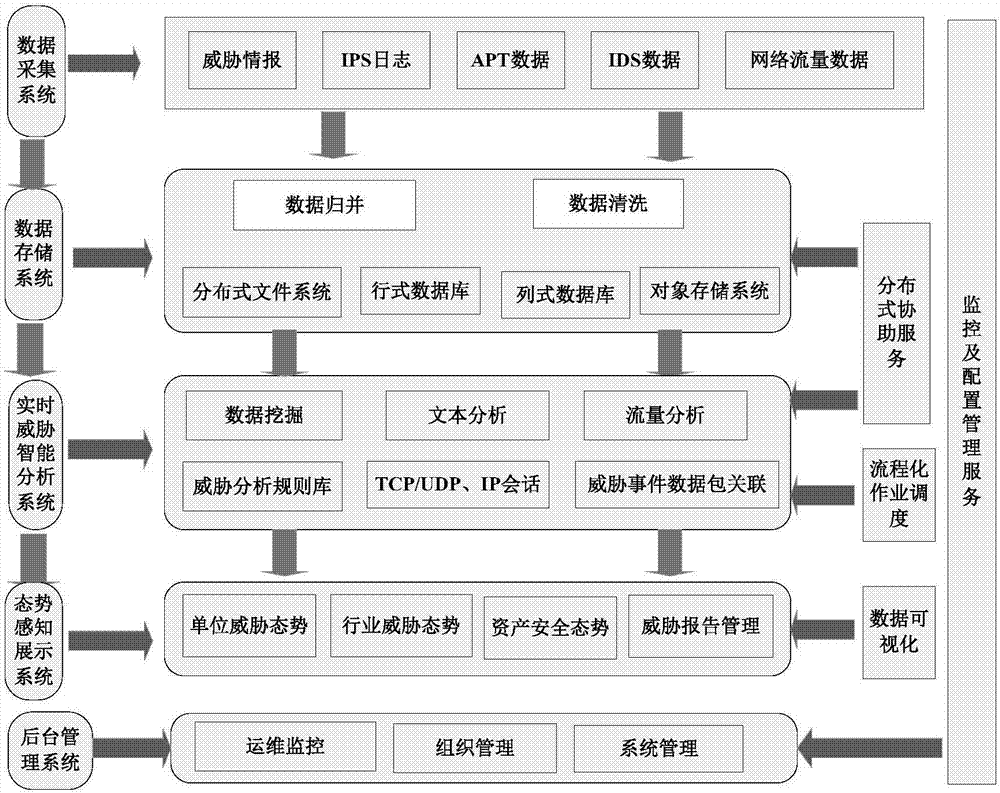
Threat early warning and monitoring system and method based on big data analysis and deployment architecture
ActiveCN107196910ARealize acquisitionRealize multi-dimensional graphical and intuitive displayData switching networksFull text searchTime processing
The invention discloses a threat early warning and monitoring system and method based on big data analysis and a deployment architecture. The system comprises a data acquisition system module, which is used for carrying out real-time data acquisition on original network traffic; a data storage system module, which is used for carrying out data merging and data cleaning on the data collected by the data acquisition system module, and then, carrying out storage management; a real-time threat intelligent analysis system module, which is used for carrying out deep analysis and mining on security data through data mining, text analysis, traffic analysis, full-text search engine and real-time processing, and identifying unknown security threats in real time by combining an intrusion detection module, a network abnormal behavior module and a device abnormal behavior module; and a situation awareness display system module, which is used for carrying out comprehensive display on security threat situations stereoscopically in real time through a data visualization tool library. The threat early warning and monitoring system and method based on big data analysis and the deployment architecture are used for network security threat situation awareness and deep analysis under a plurality of service scenarios, and realize comprehensive abilities from attack early warning, attack identification to analysis and evidence obtaining.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +2
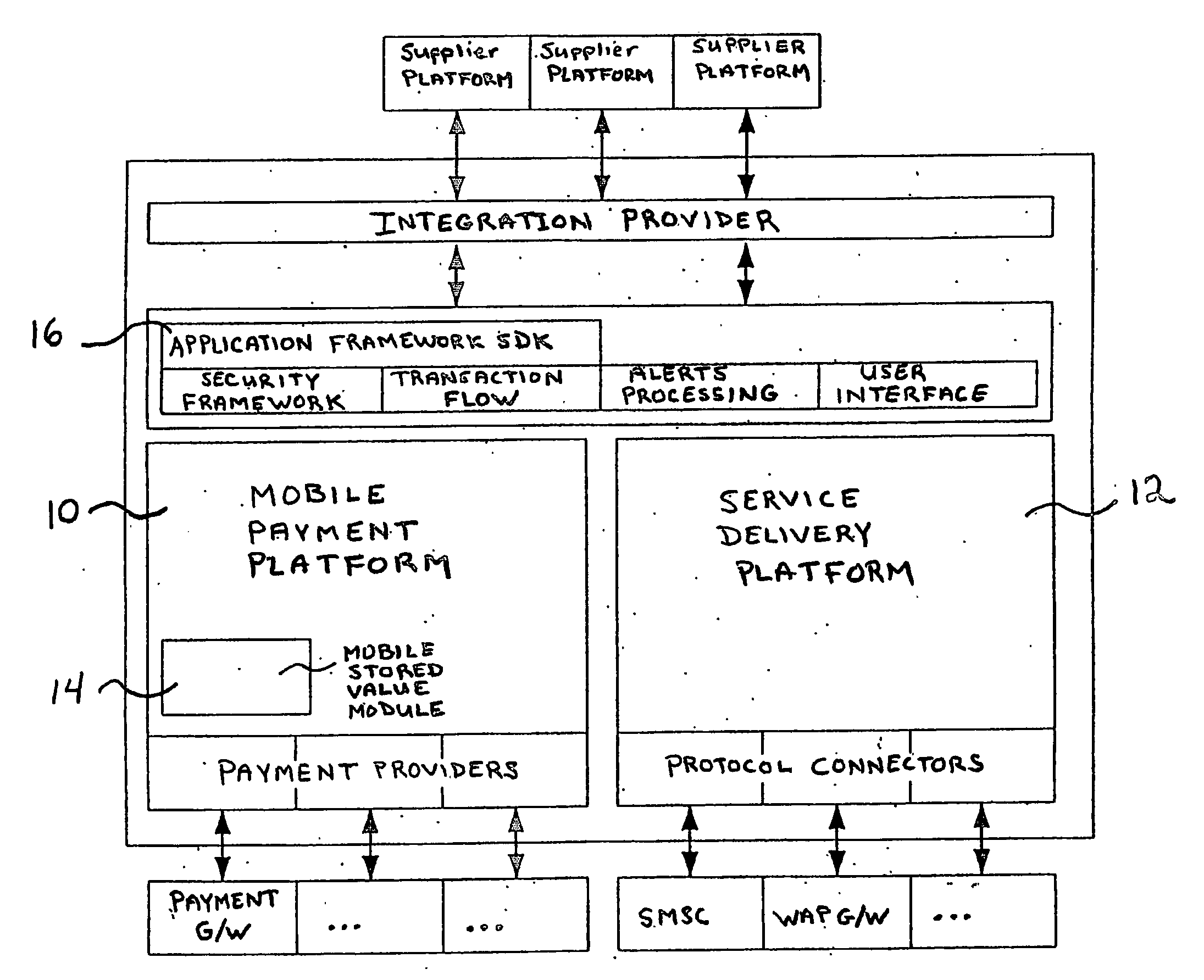
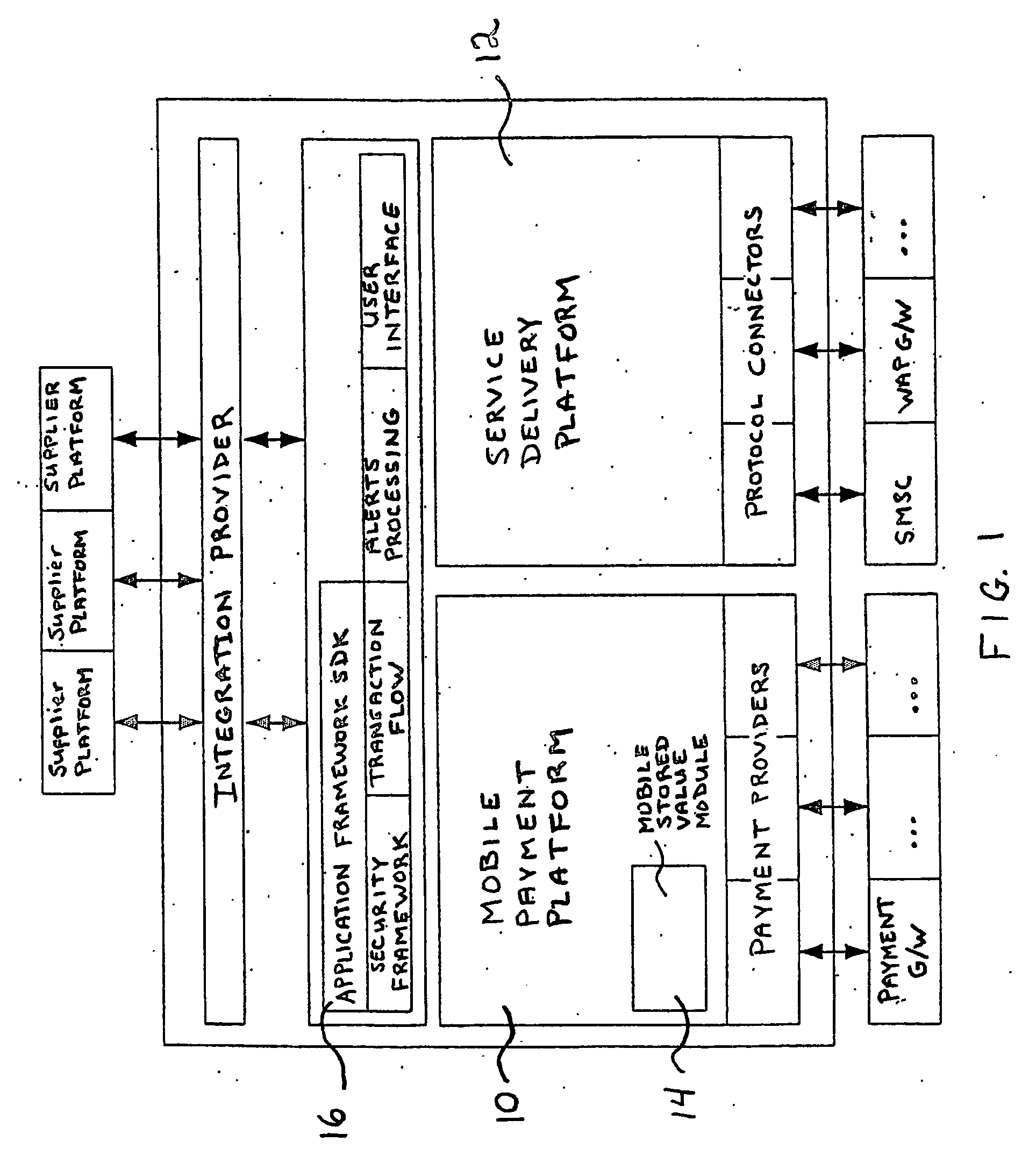
Cash based purchasing using mobile communication
InactiveUS20060253335A1Easy to deployEasily establishingFinanceBuying/selling/leasing transactionsPaymentService provision
A system and method for cash based purchasing using electronic commerce channels such as mobile telephone networks. Customers use cash to purchase goods and services by using a vendor's point of sale device such as a mobile telephone. A server side mobile wallet provides secure storage of user identity and profiles and a payment mechanism for users to obtain goods and services from a point of sale device. Service providers or suppliers pay a commission to point of sale vendors for use of the vendor's account and point of sale device to perform transactions for customers. A platform is provided for establishment and use of hierarchal vendor network over a number of different mobile channels.
Owner:KEENA GERARD +1
Method and system for fully encrypted repository
ActiveUS20120324242A1Safe storageFinanceUnauthorized memory use protectionComputer hardwareEncryption
According to an embodiment of the present invention, a method for using information in conjunction with a data repository includes encrypting data associated with the information with an encryption key, sending at least the encrypted data to the data repository, and possibly deleting the information. The method also includes receiving a request for the information from a remote device, and sending a request for the encrypted data to the data repository. The method further includes receiving the encrypted data from the data repository, decrypting the encrypted data using the encryption key, and sending the information to the remote device.
Owner:NEUSTAR
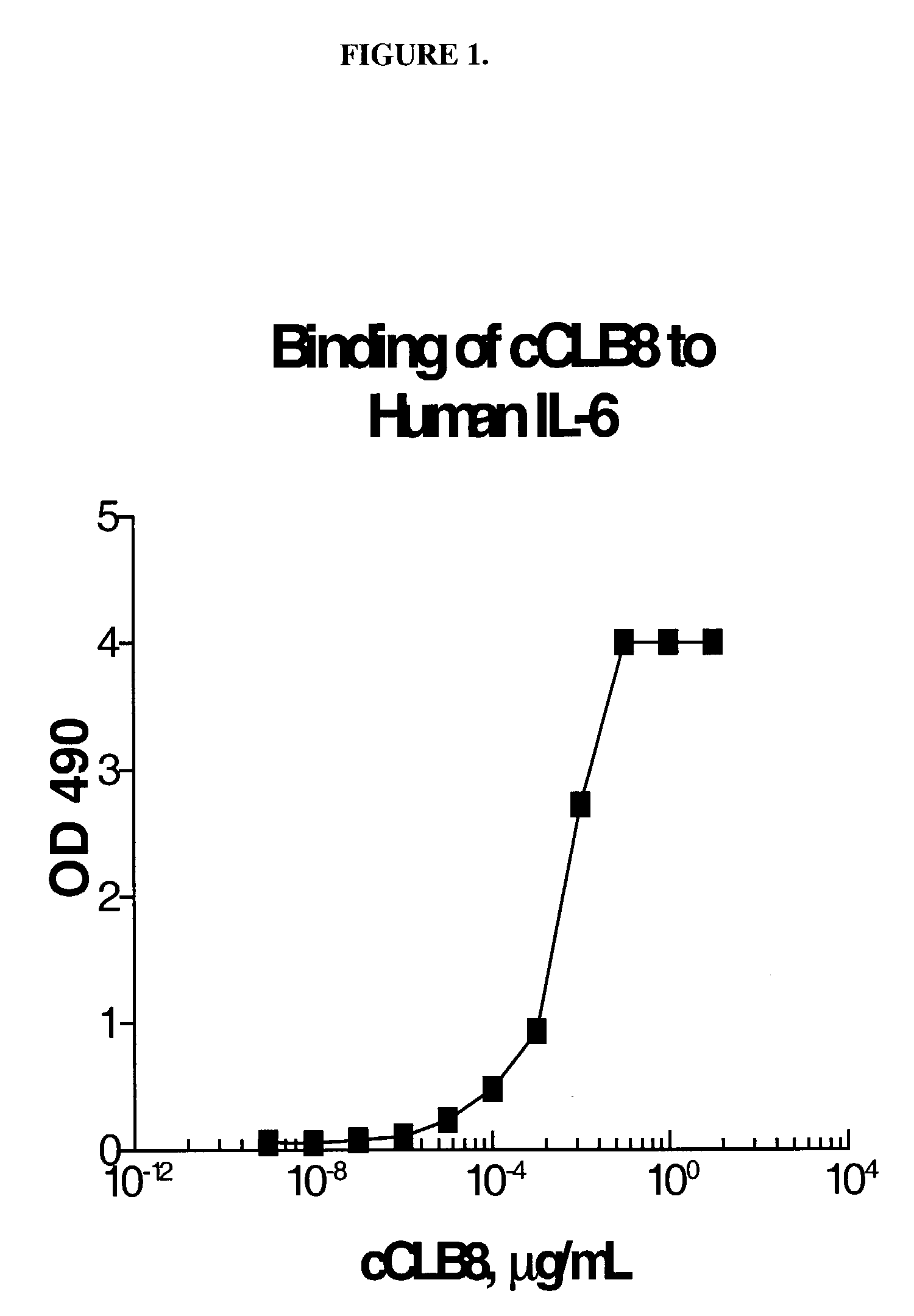
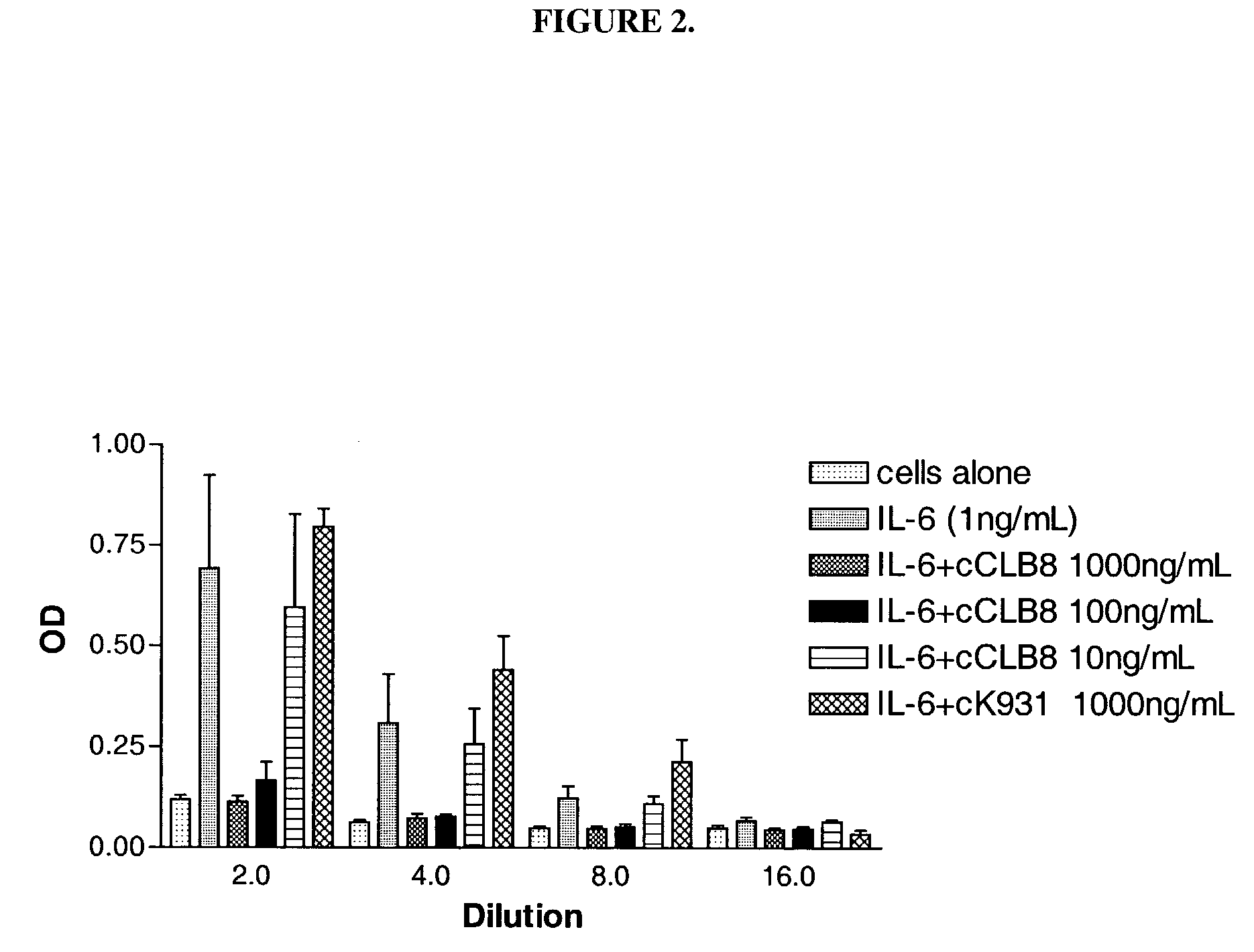
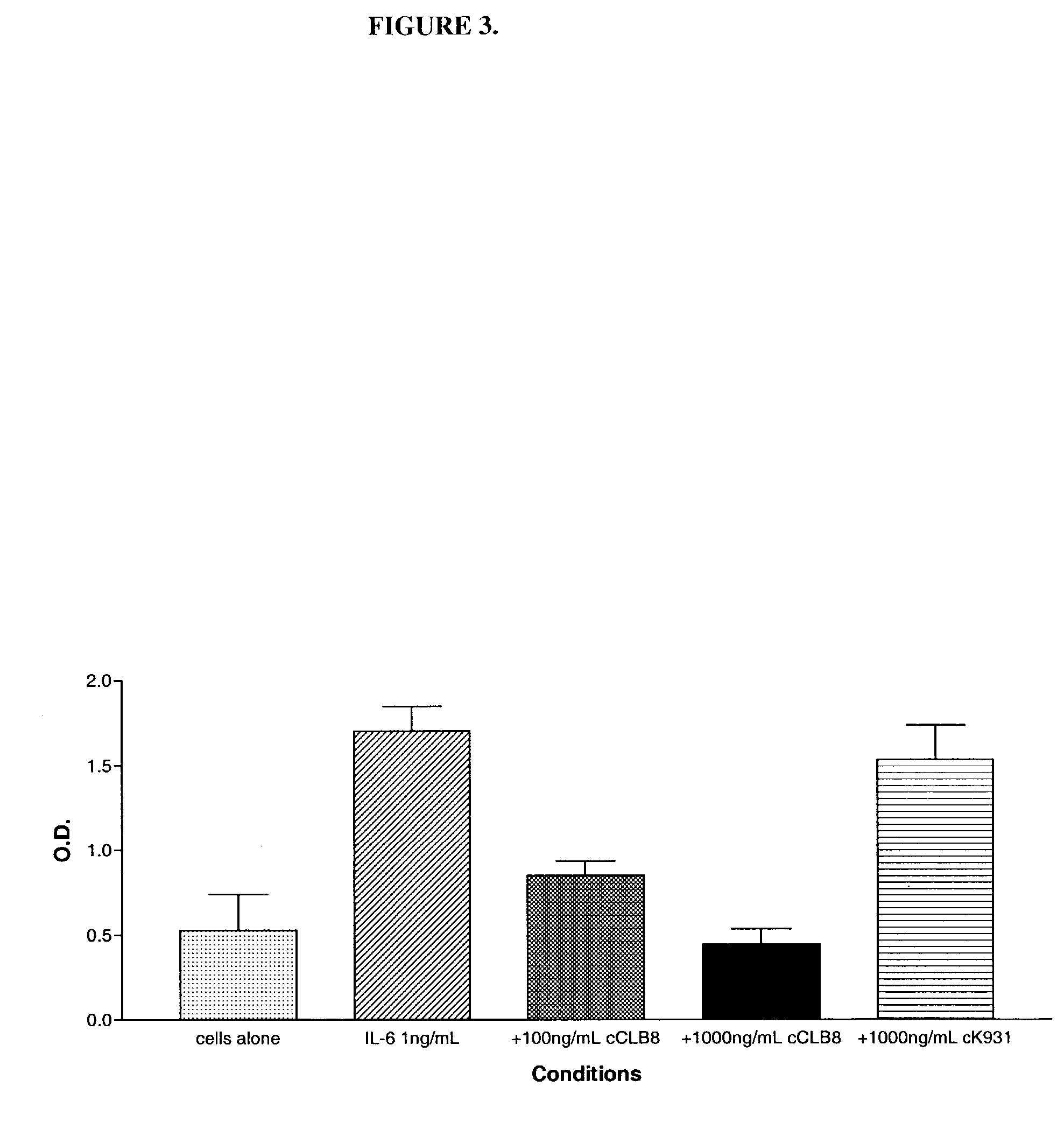
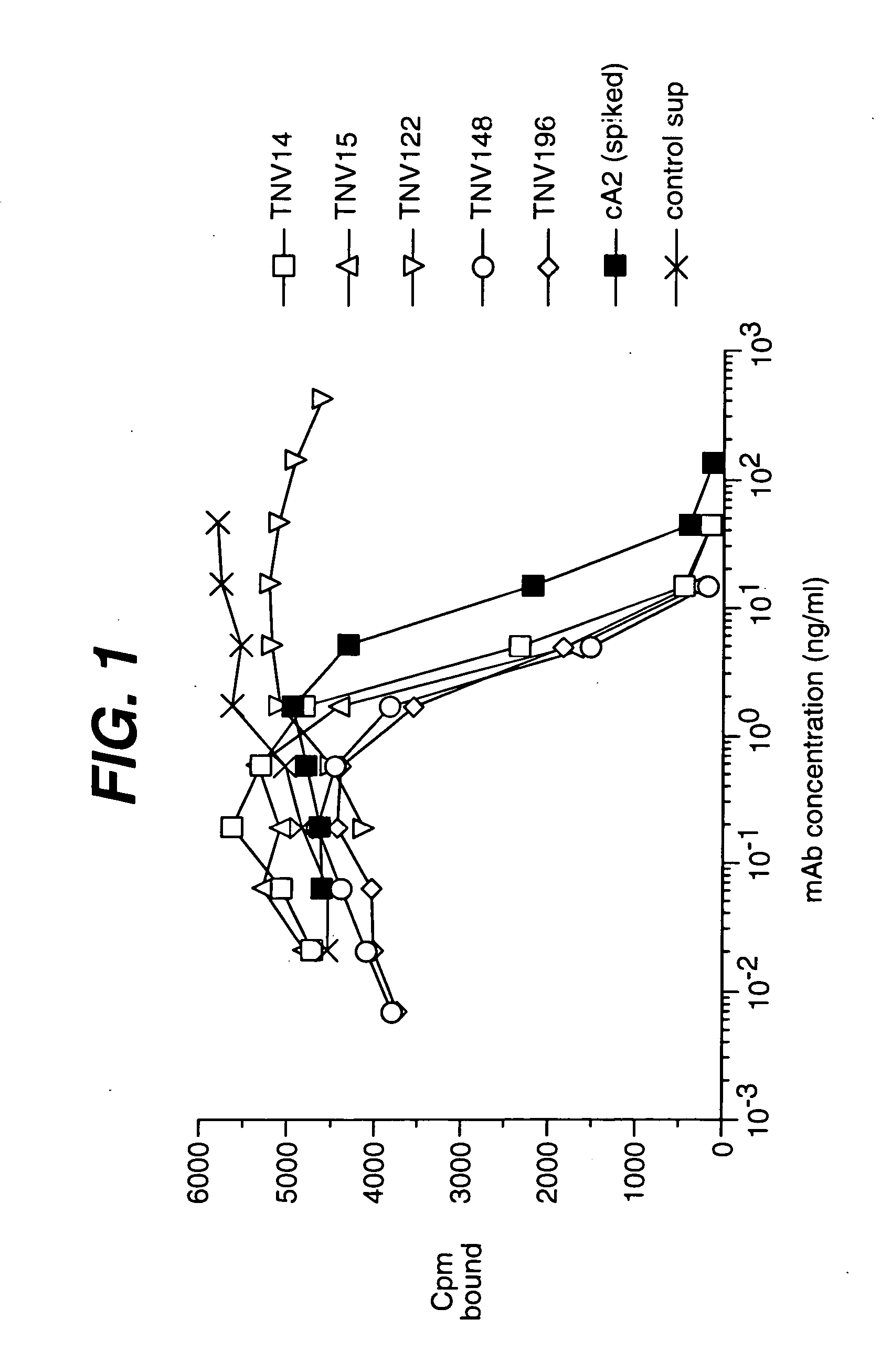
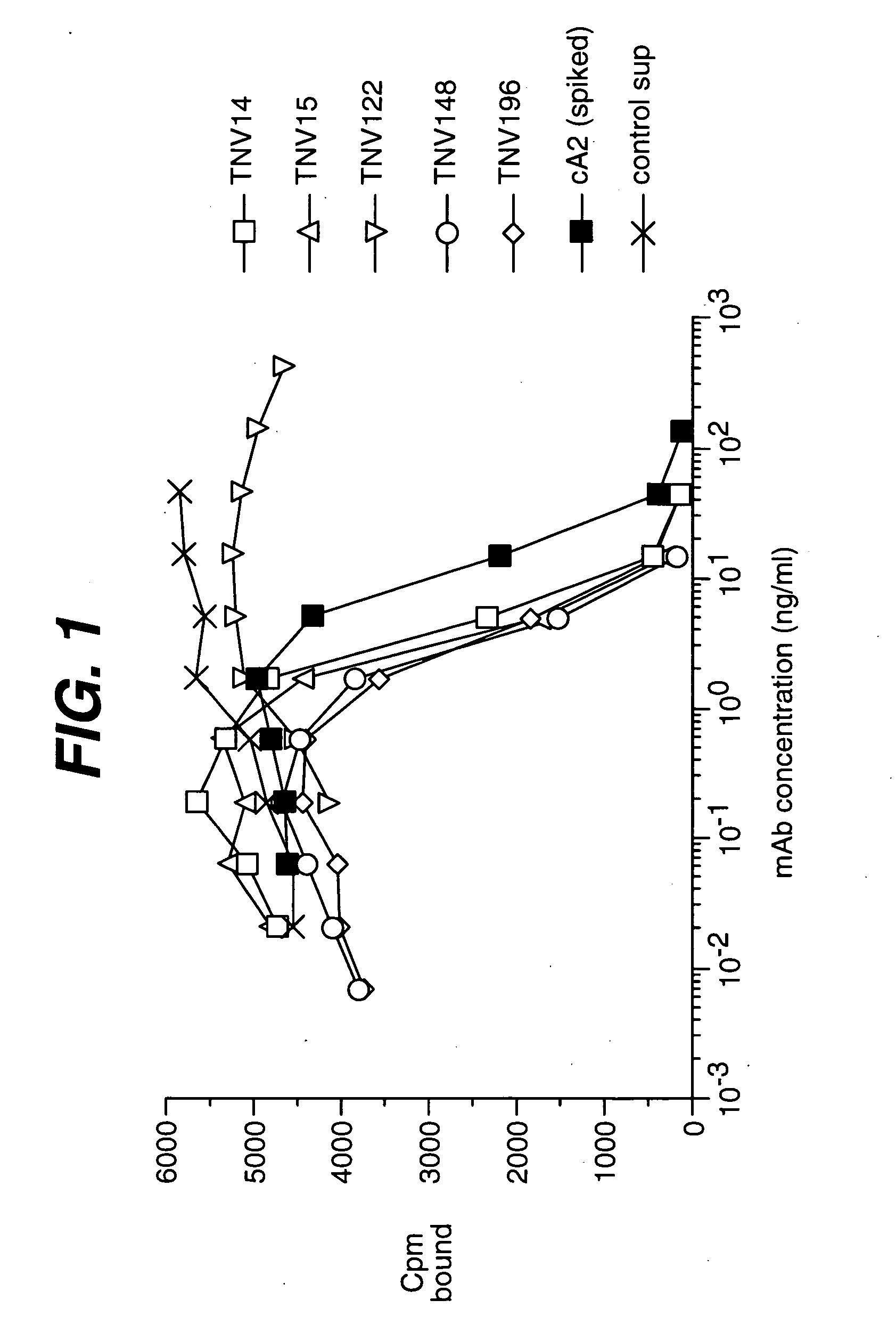
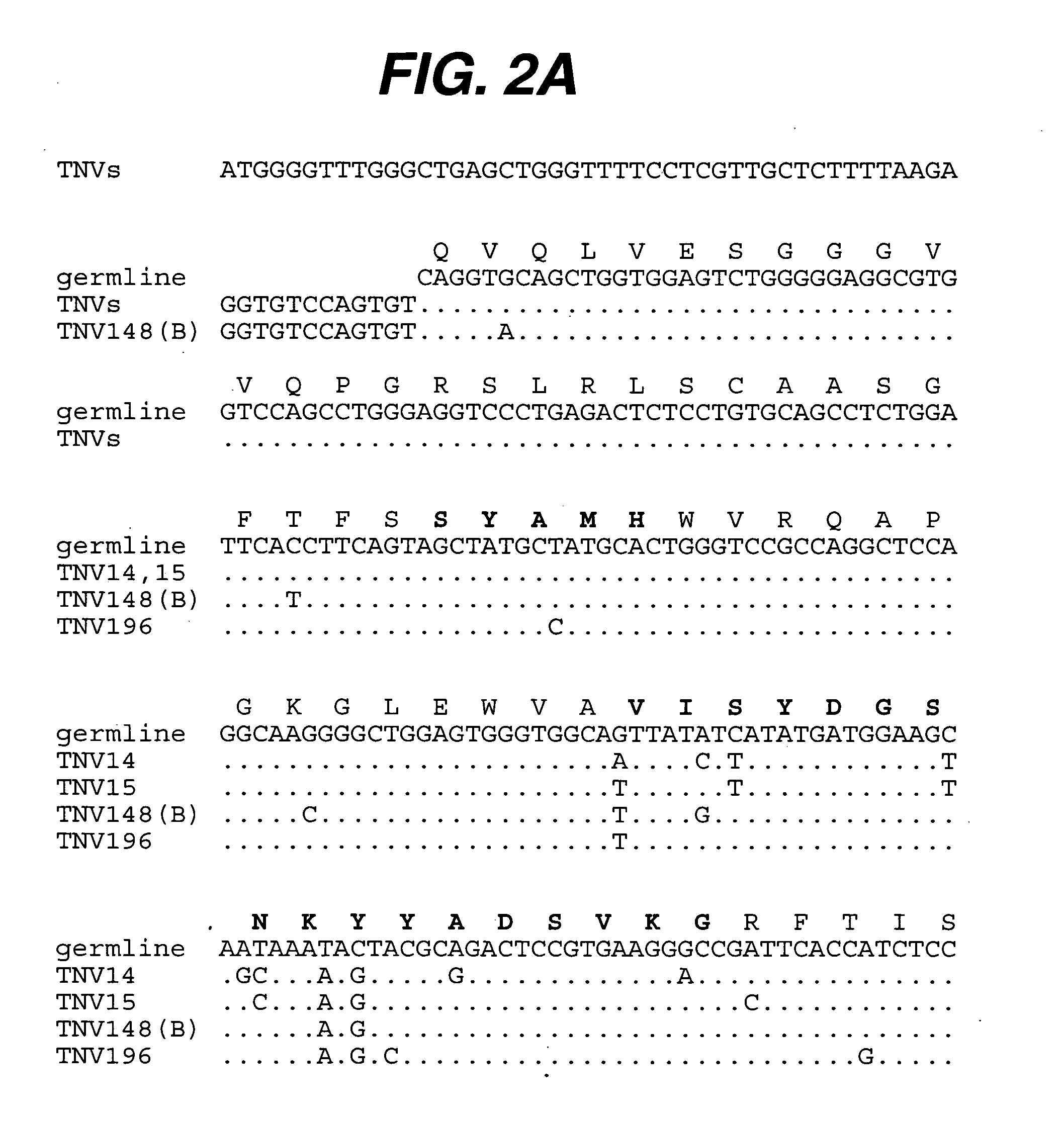
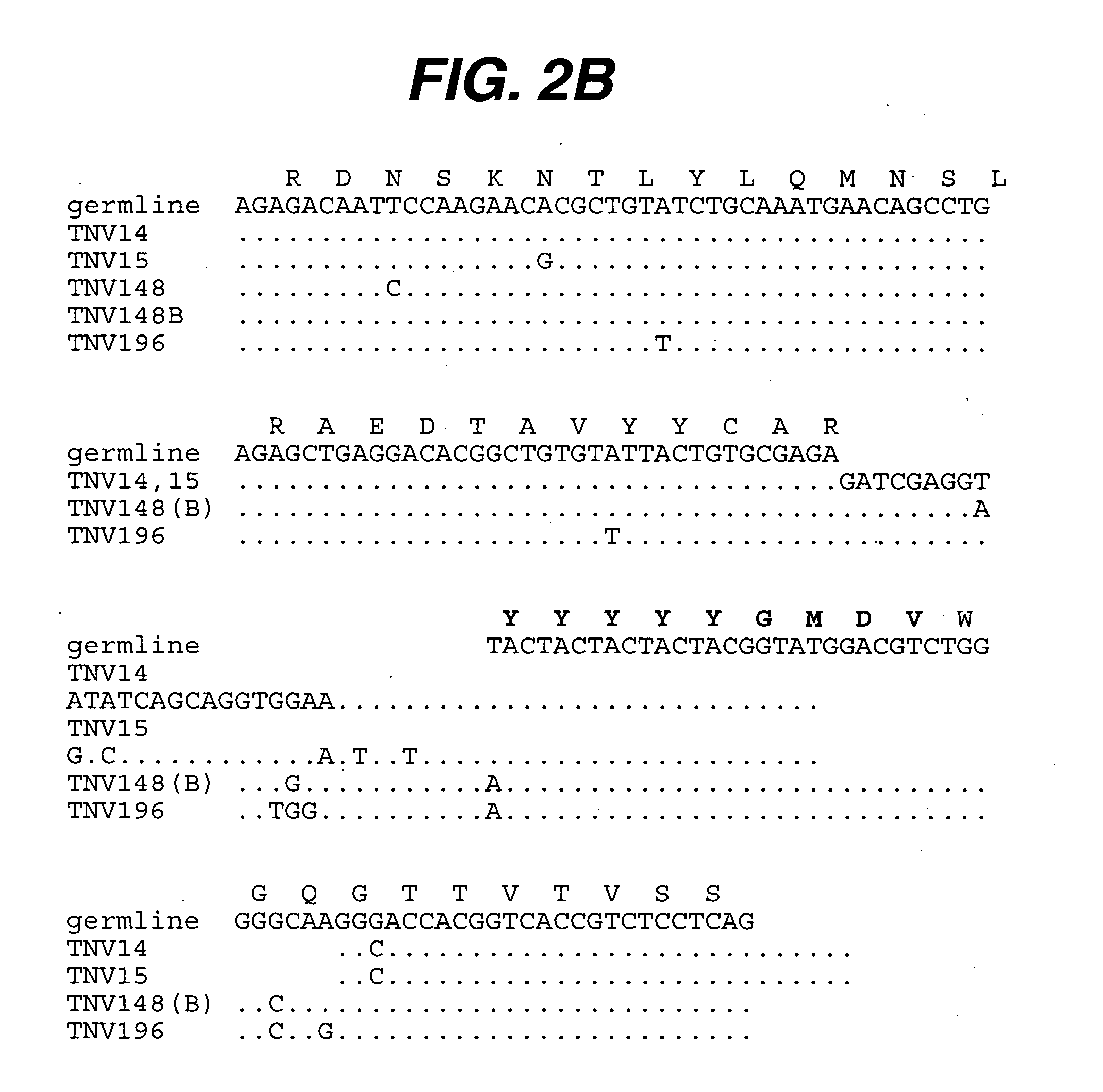
Anti-IL-6 antibodies, compositions, methods and uses
The present invention relates to at least one novel chimeric, humanized or CDR-grafted anti-IL-6 antibodies derived from the murine CLB-8 antibody, including isolated nucleic acids that encode at least one such anti-IL-6 antibody, vectors, host cells, transgenic animals or plants, and methods of making and using thereof, including therapeutic compositions, methods and devices.
Owner:CENTOCOR
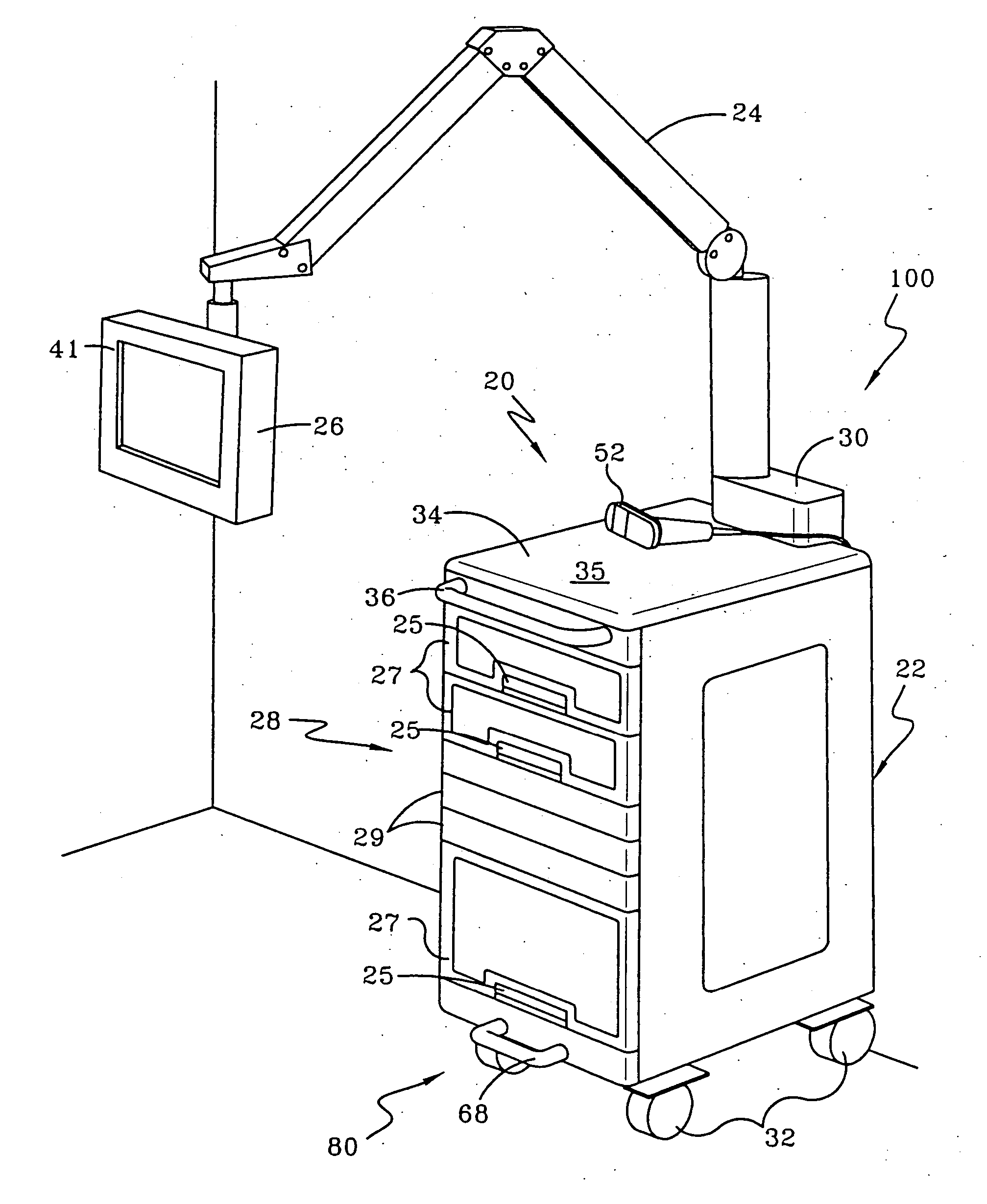
Point of care station
InactiveUS20050062238A1Improve efficiencyImprove securitySurgical furnitureSledgesPatient roomPoint of care
This invention is directed to a point-of-care (POC) station that comprises a mobile cabinet with securable compartments and a pylon release mechanism. The POC station also comprises an immovable pylon, an articulated arm, and a terminal having a monitor. The POC station extends the medication and supply infrastructure into the patient room.
Owner:BROADFIELD LAIRD +10
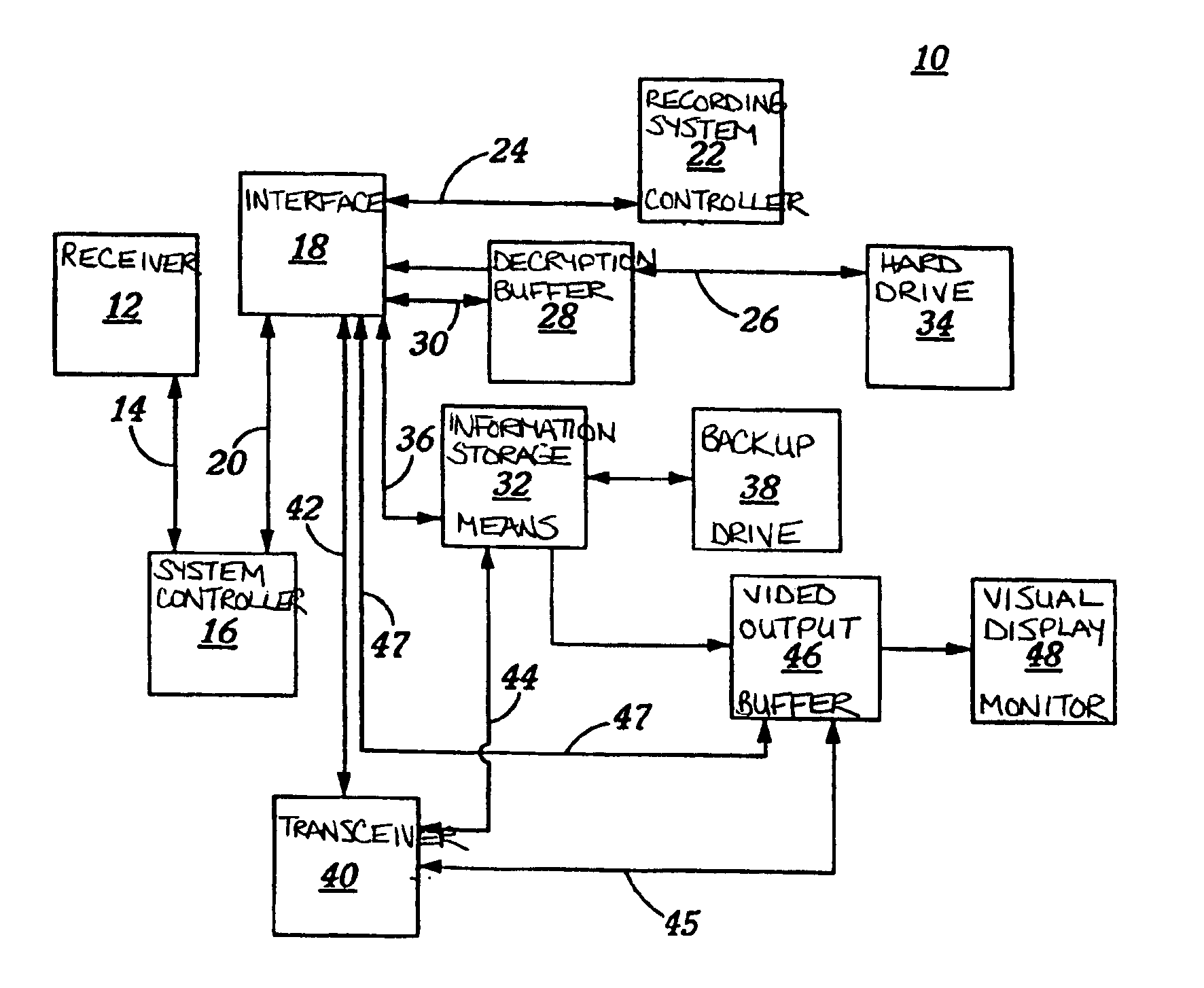
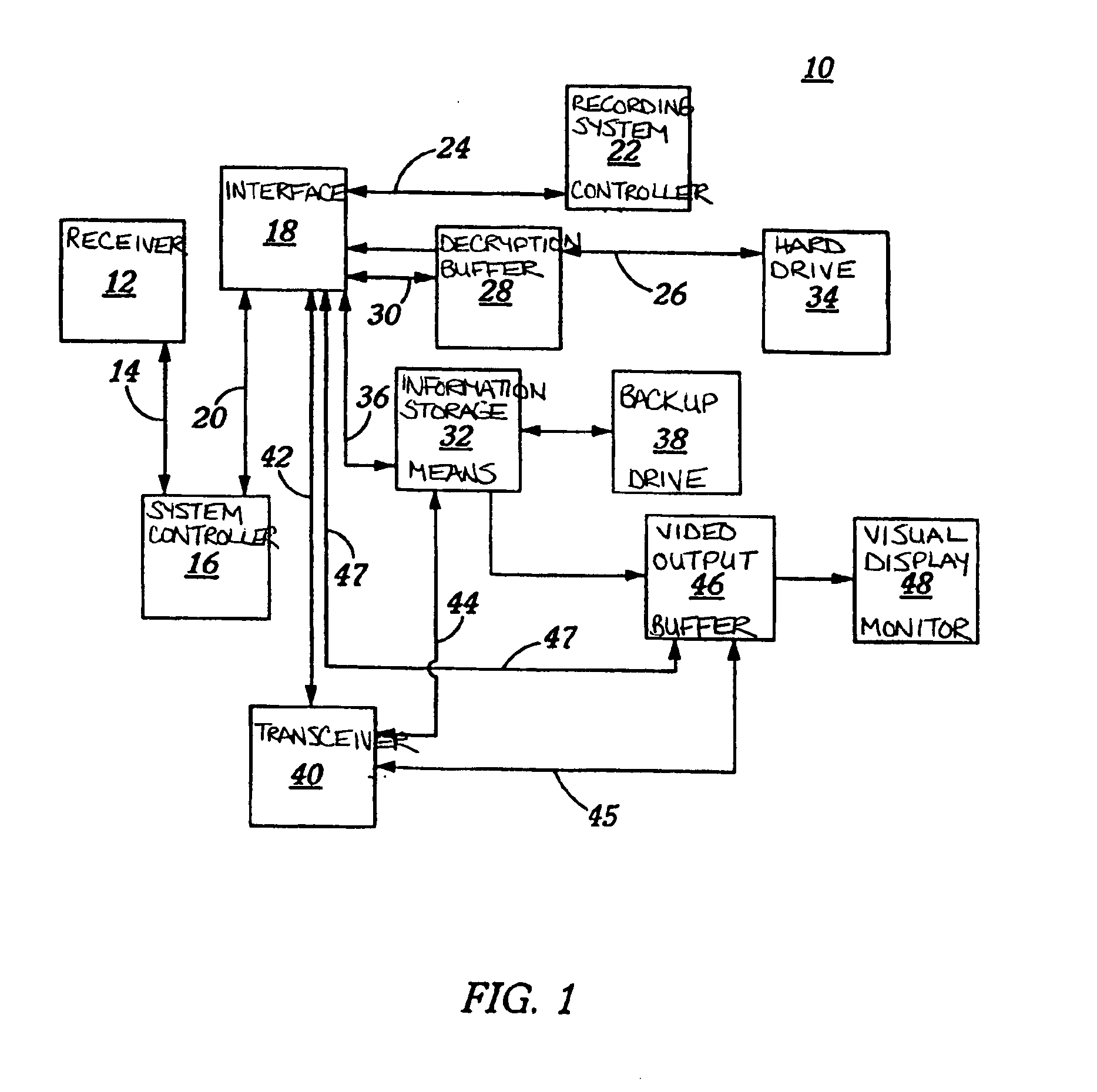
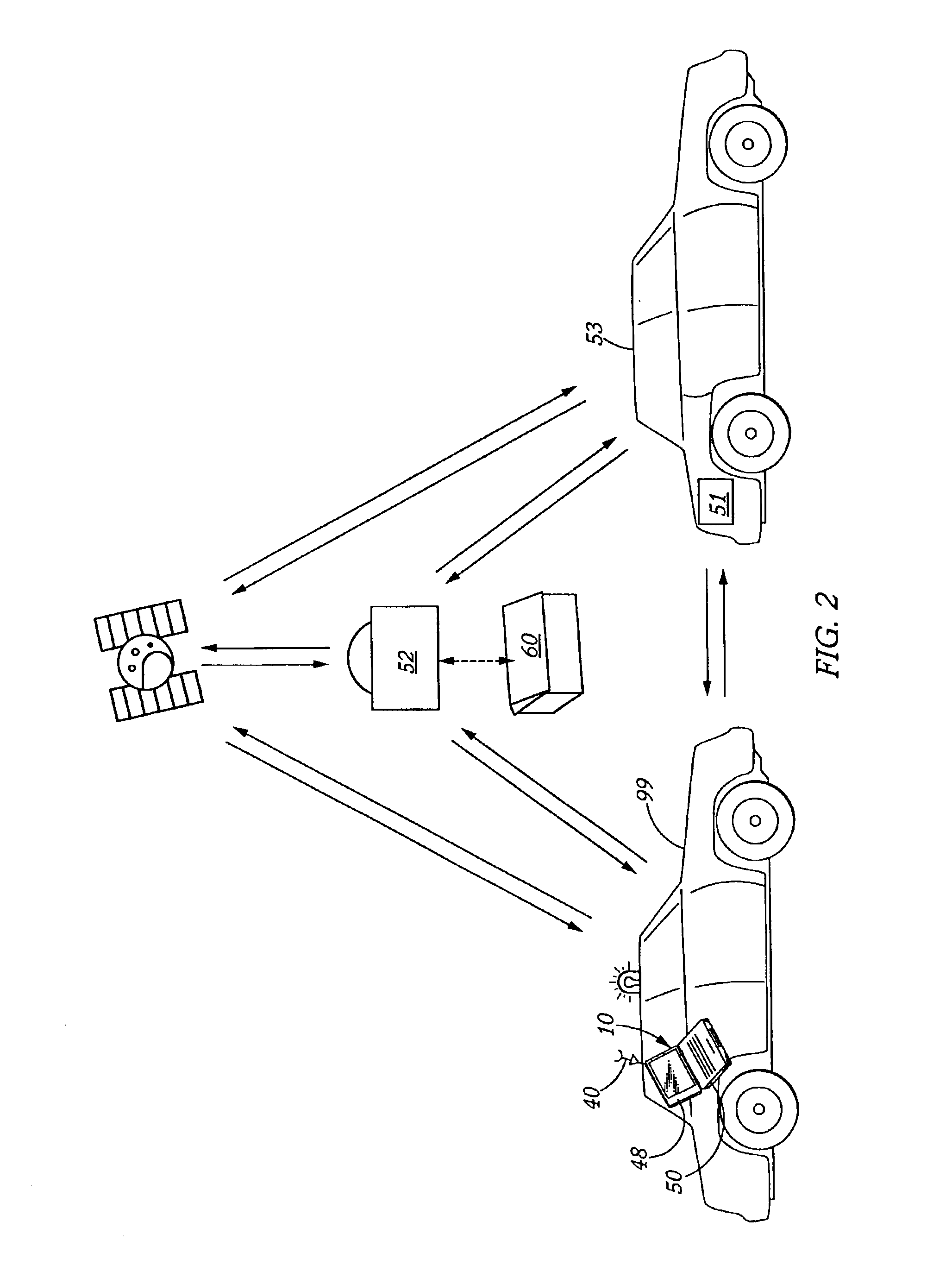
Incident recording secure database
InactiveUS6950013B2Convenient investigationEasy retrievalRegistering/indicating working of vehiclesAnti-theft devicesTransceiverDisplay device
A device and method for permanently and securely storing incident information, relating to a vehicle, from remote download to create a secure non-tamperable, permanent database of criminal activity and / or accident evidence for evidentiary purposes. The information may be directly transferred to an information center and / or the authorities through a transmission link, which is preferably a satellite up / link-down / link or saved directly onto the downloading device for transfer to the secure device. The remote downloading device may be activated automatically or upon a trigger signal and comprises an interface, an information capturing storage device, a video monitor display and preferably a transceiver. The interface communicates with an information storage device, downloads the information saved therein and transmits it to the capture storage device, transceiver or both. The received information is reproduced, integrated into an indexed database and transferred to the secure device as part of a secure, indexed database for non-tamperable permanent storage as evidence.
Owner:EVICAM INT
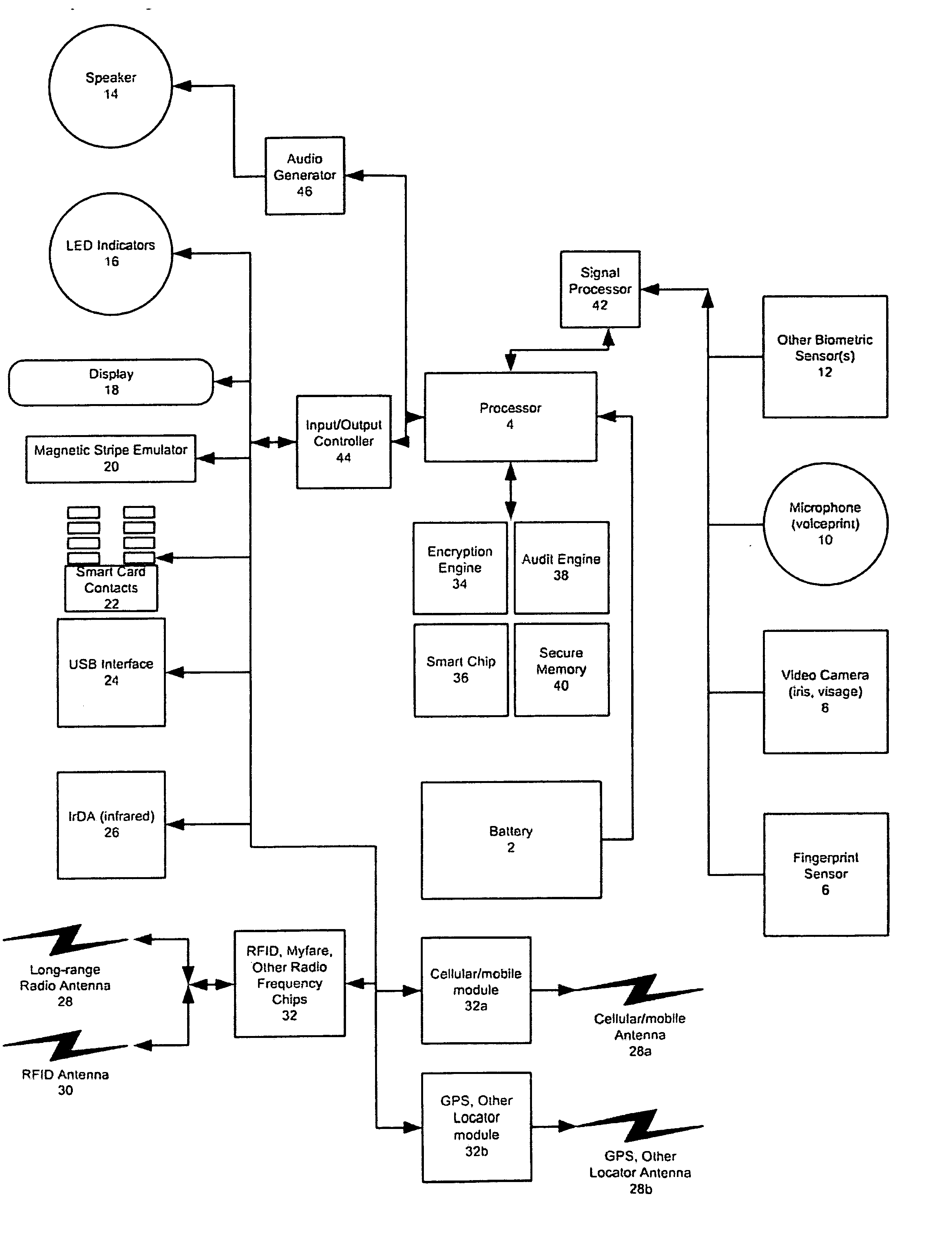
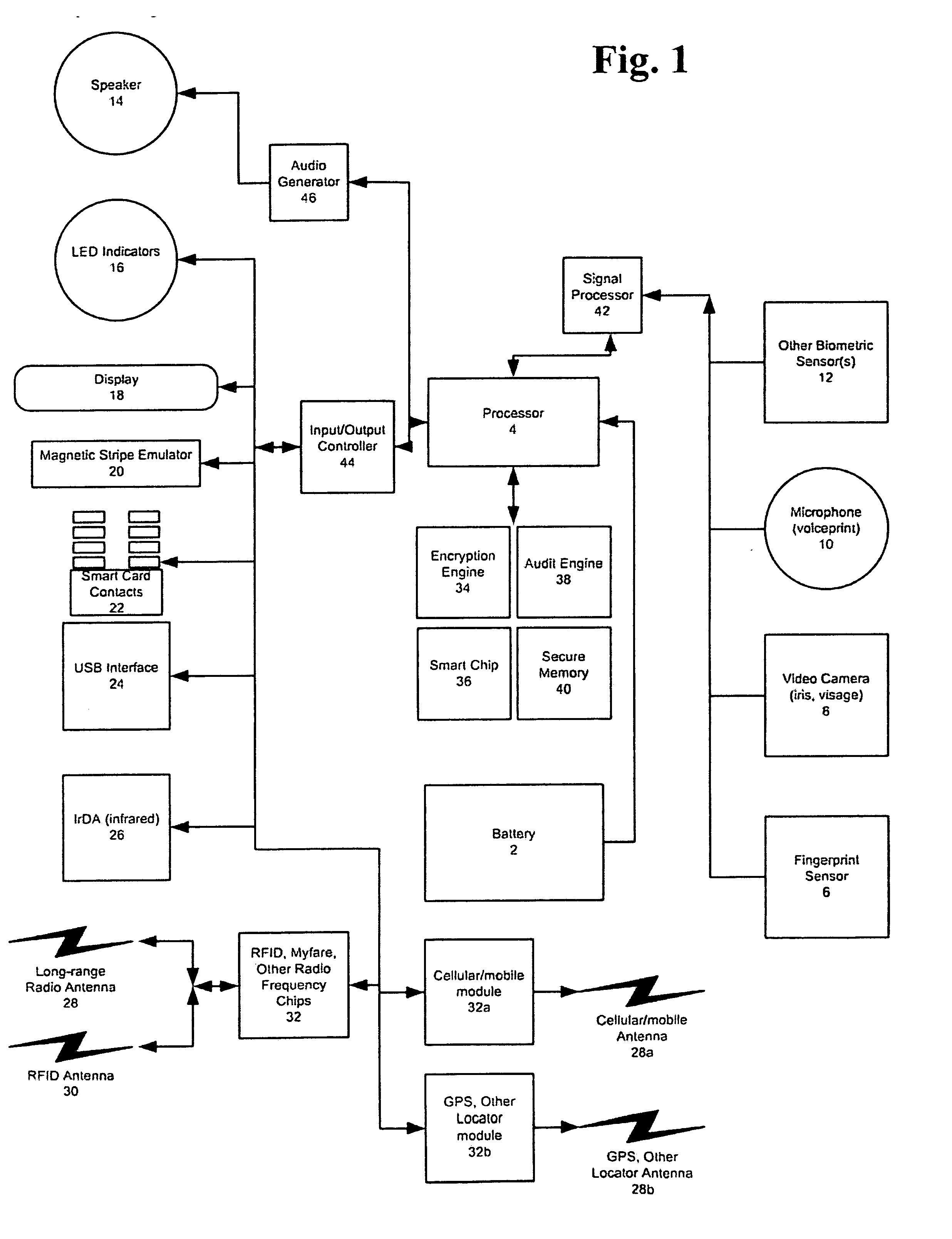
Universal, Biometric, Self-Authenticating Identity Computer Having Multiple Communication Ports
InactiveUS20080148059A1Maintain securityLimited accessUser identity/authority verificationPayment architectureSmart cardCard reader
An improved device for use in authorizing transactions, supplying information and performing applications is provided by the present invention, effectively implementing a secured individual and portable Public Key Infrastructure (PKI) terminal. The device uses a local processor and secure data storage in conjunction with a variety of sensors to perform authentication processes that establish an individuals identity and provide authority to perform a desired transaction. The sensors allow the device to directly scan biometric identifying information from an individual. A card swipe interface and a proximity antenna are provided to facilitate communication between the device and remote interface devices such as magnetic swipe card readers, smart card readers, infrared communications ports and proximity and long range radio scanners. In addition, the local processor, memory, display and user inputs allow the device to run applications such as those performed by a traditional computer, gaming device, personal data assistant and smart phone.
Owner:SHAPIRO MICHAEL F
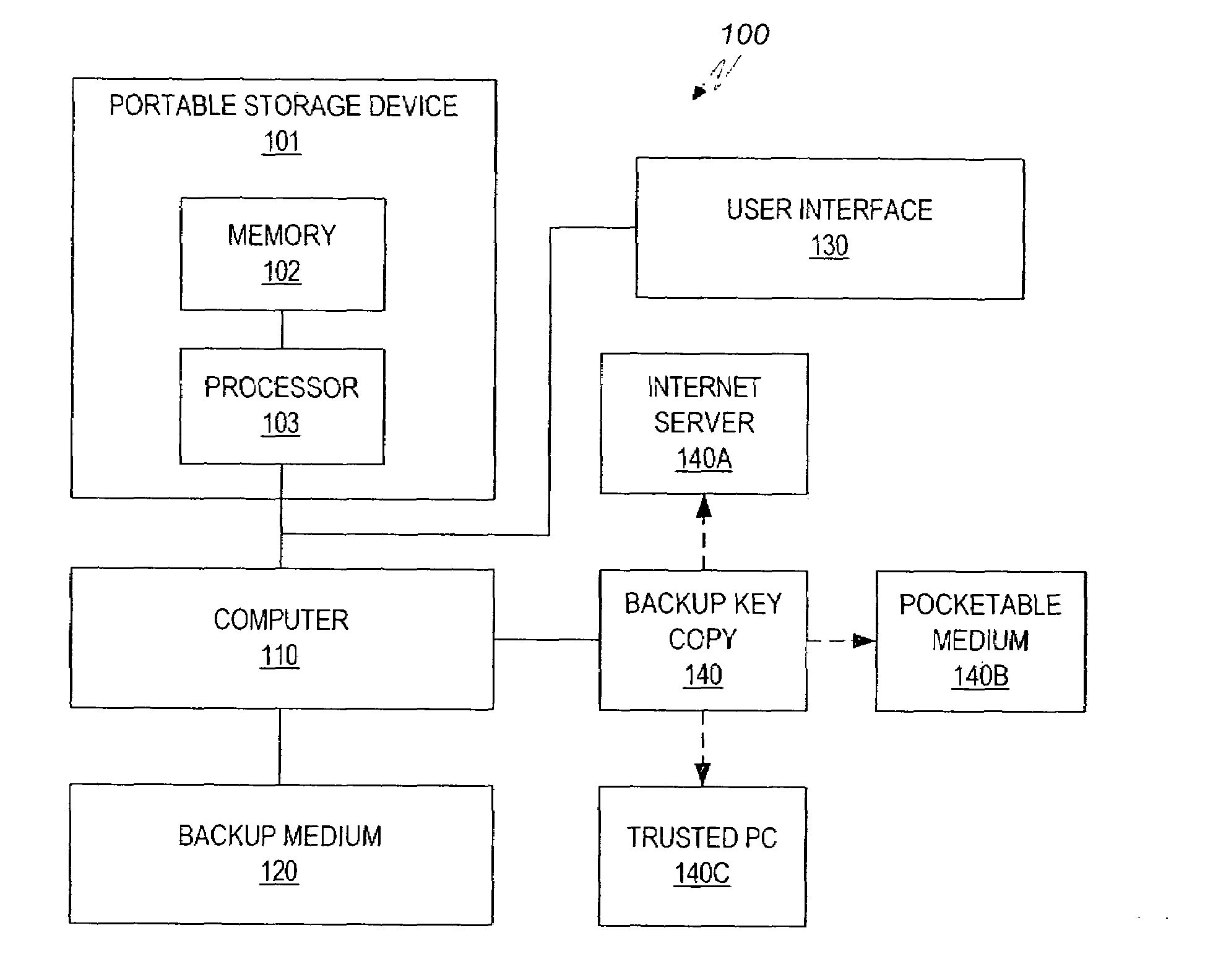
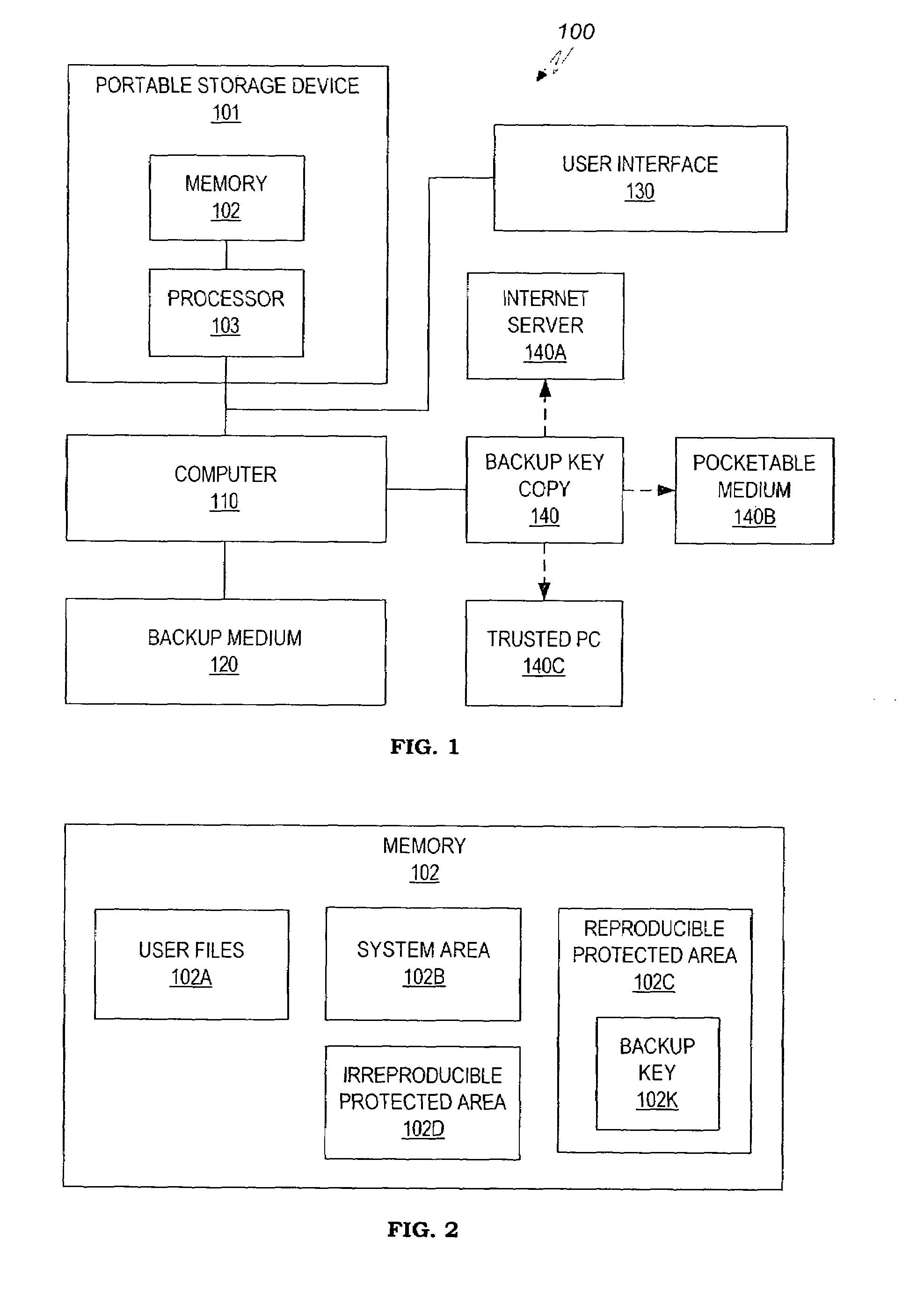
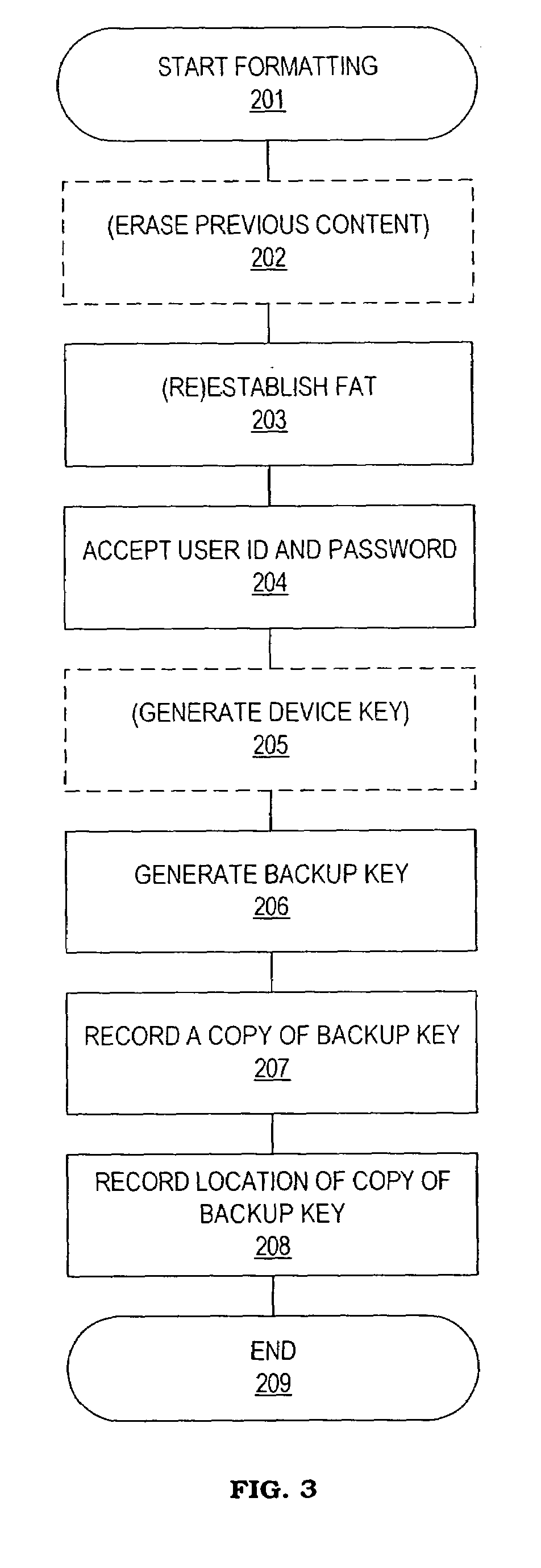
Method and system for maintaining backup of portable storage devices
ActiveUS7240219B2Safe storageEasy to carryUser identity/authority verificationUnauthorized memory use protectionPasswordTrusted Computing
Data stored in a portable storage device are encrypted, for example by a processor of the portable storage device itself, using a backup key and stored in a backup medium. The backup key is protected by being stored in a backup key storage medium, such as an internet server, a pocketable medium or a trusted computer, preferably after being encrypted using a password. As needed, the backup key is retrieved and used to decrypt the data from the backup medium. The decrypted data are restored to the original portable storage device or to a different portable storage device.
Owner:WESTERN DIGITAL ISRAEL LTD
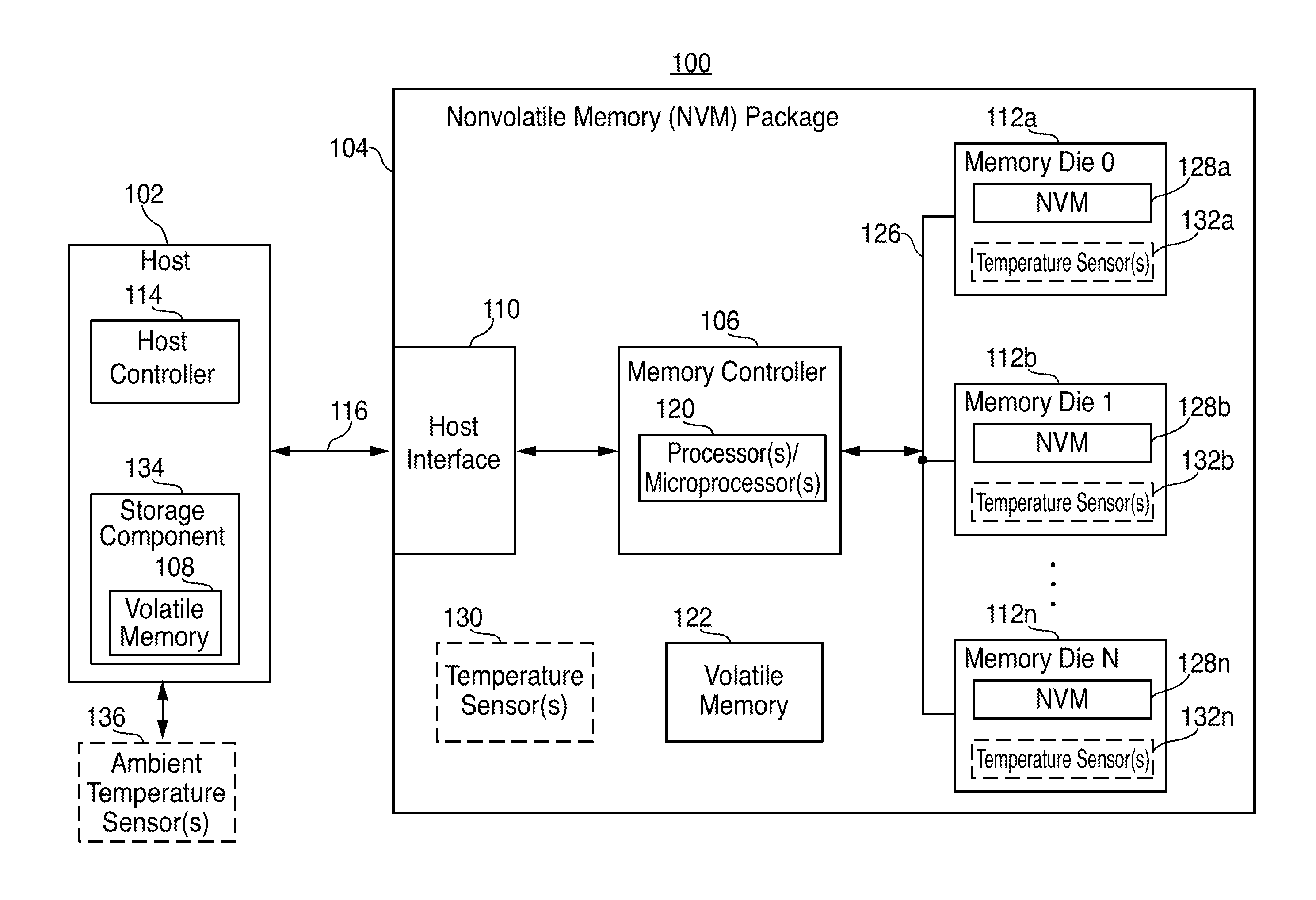
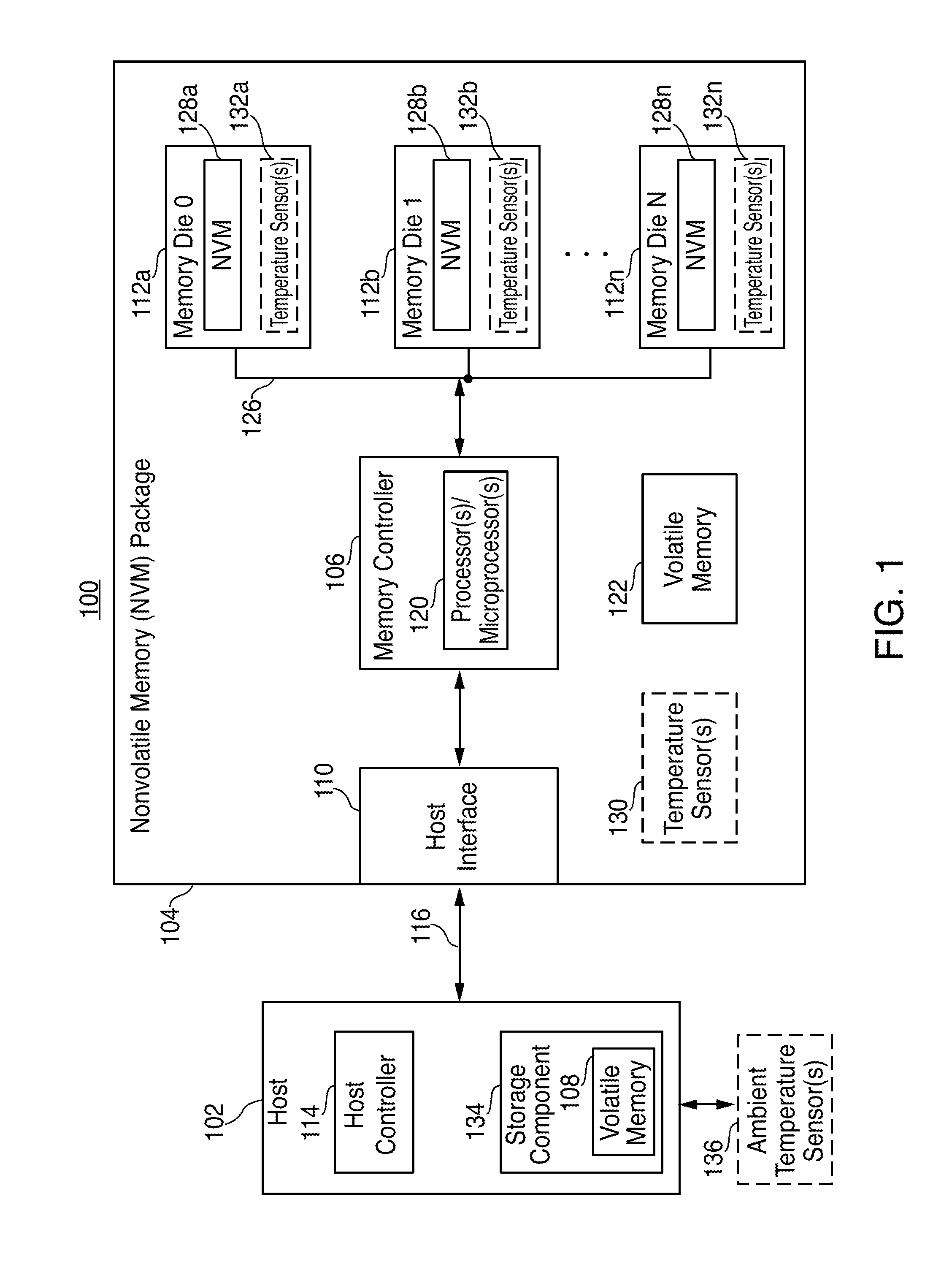
Systems and methods for nonvolatile memory performance throttling
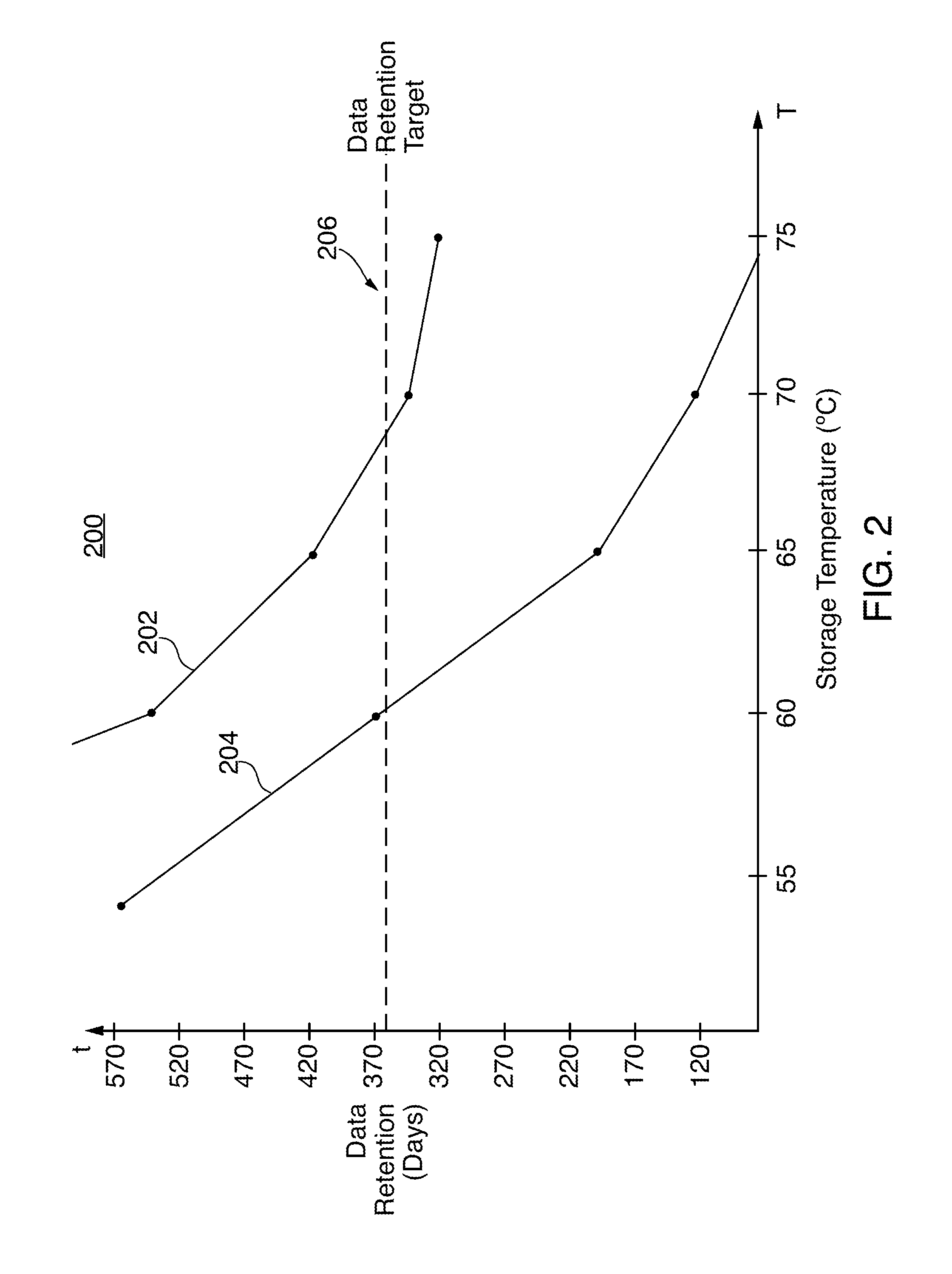
ActiveUS20140101371A1Safe storageMemory architecture accessing/allocationError detection/correctionComputer scienceMemory performance
Systems and methods for nonvolatile memory (“NVM”) performance throttling are disclosed. Performance of an NVM system may be throttled to achieve particular data retention requirements. In particular, because higher storage temperatures tend to reduce the amount of time that data may be reliably stored in an NVM system, performance of the NVM system may be throttled to reduce system temperatures and increase data retention time.
Owner:APPLE INC
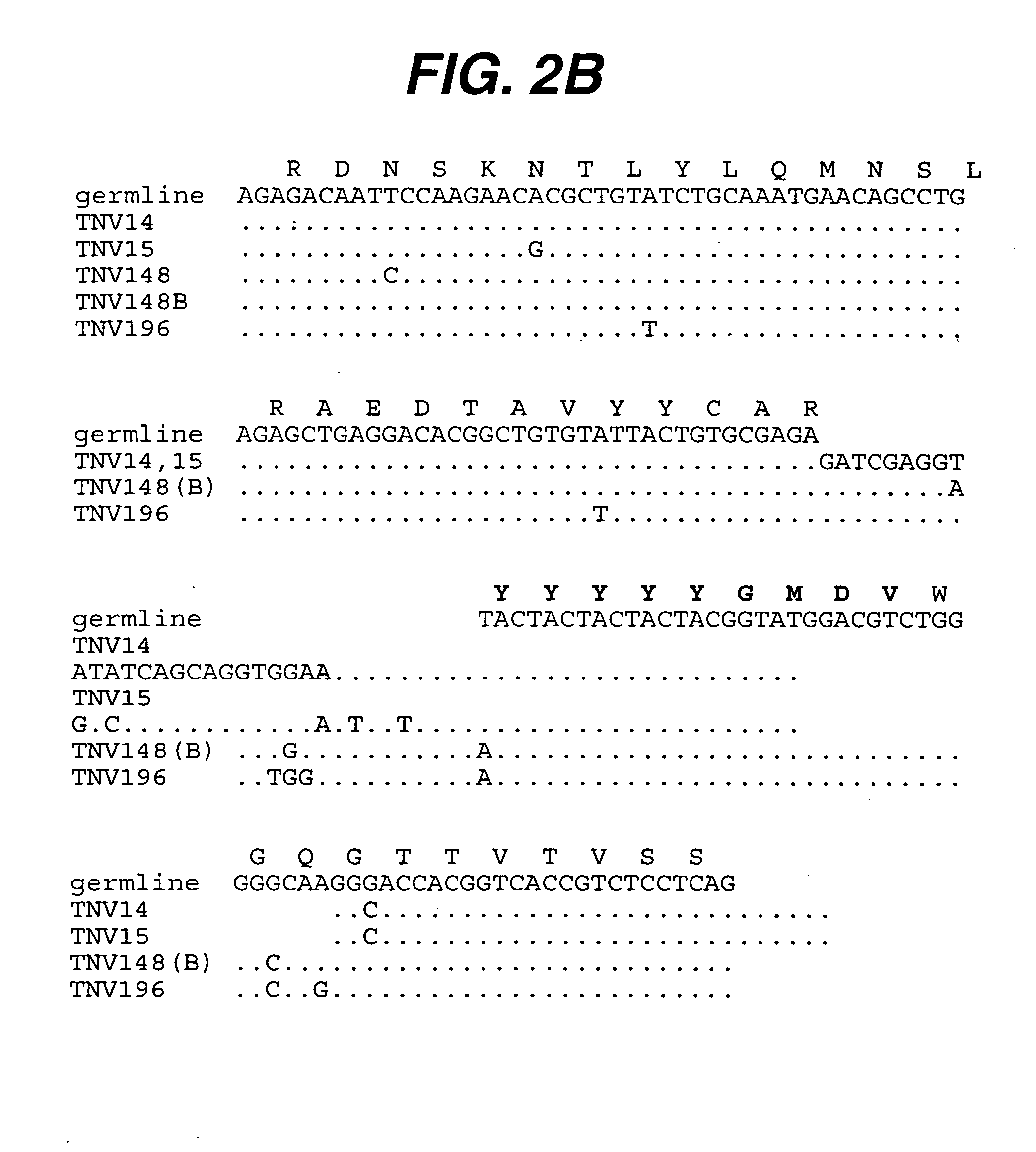
Anti-TNF antibodies, compositions, methods and uses
ActiveUS20050123541A1Big advantageSafe storageAntibacterial agentsOrganic active ingredientsAdenocarcinomaAntibody
The present invention relates to methods for treating carcinomas or adenocarcinomas using at least one anti-TNF antibody.
Owner:JANSSEN BIOTECH INC
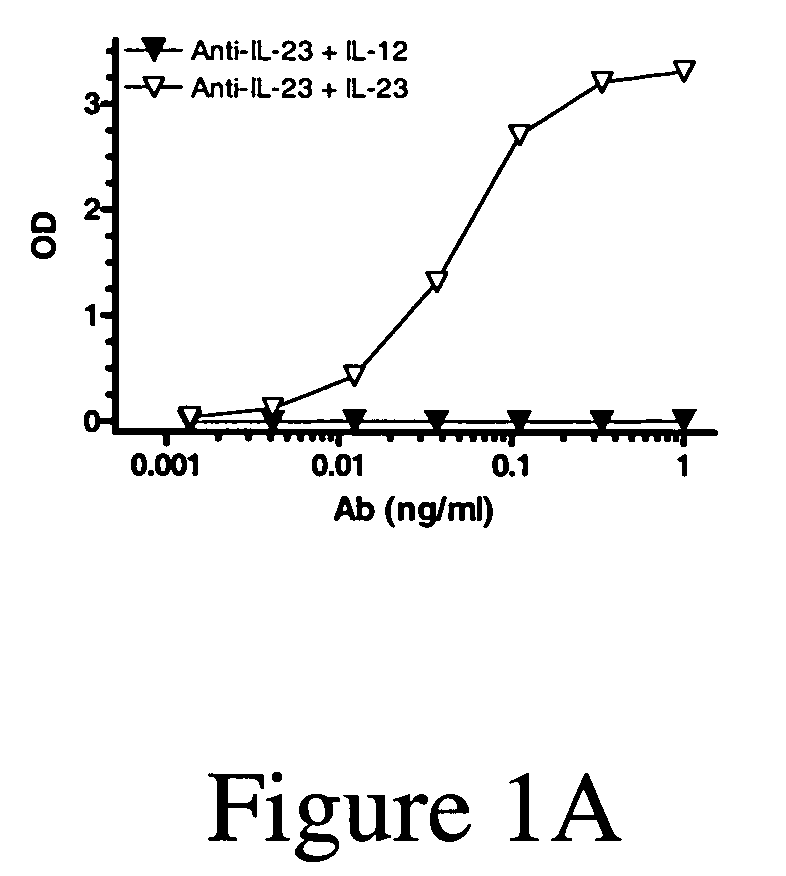
IL-23p40 specific antibody
Novel anti-IL-23p40 specific human Ig derived proteins, including, without limitation, antibodies, fusion proteins, and mimetibodies, isolated nucleic acids that encode the anti-IL-23p40 Ig derived proteins, vectors, host cells, transgenic animals or plants, and methods of making and using thereof, are useful for therapeutic compositions, methods and devices. Preferably, the anti-IL-23p40 specific human Ig derived proteins do not bind the p40 subunit of IL-12 and, thus, do not neutralize IL-12-related activity.
Owner:CENTOCOR
System and method for a secure cardholder load and storage device
ActiveUS20130140360A1Point of failureEnabling ubiquityFinancePayment architectureFinancial transactionUSB
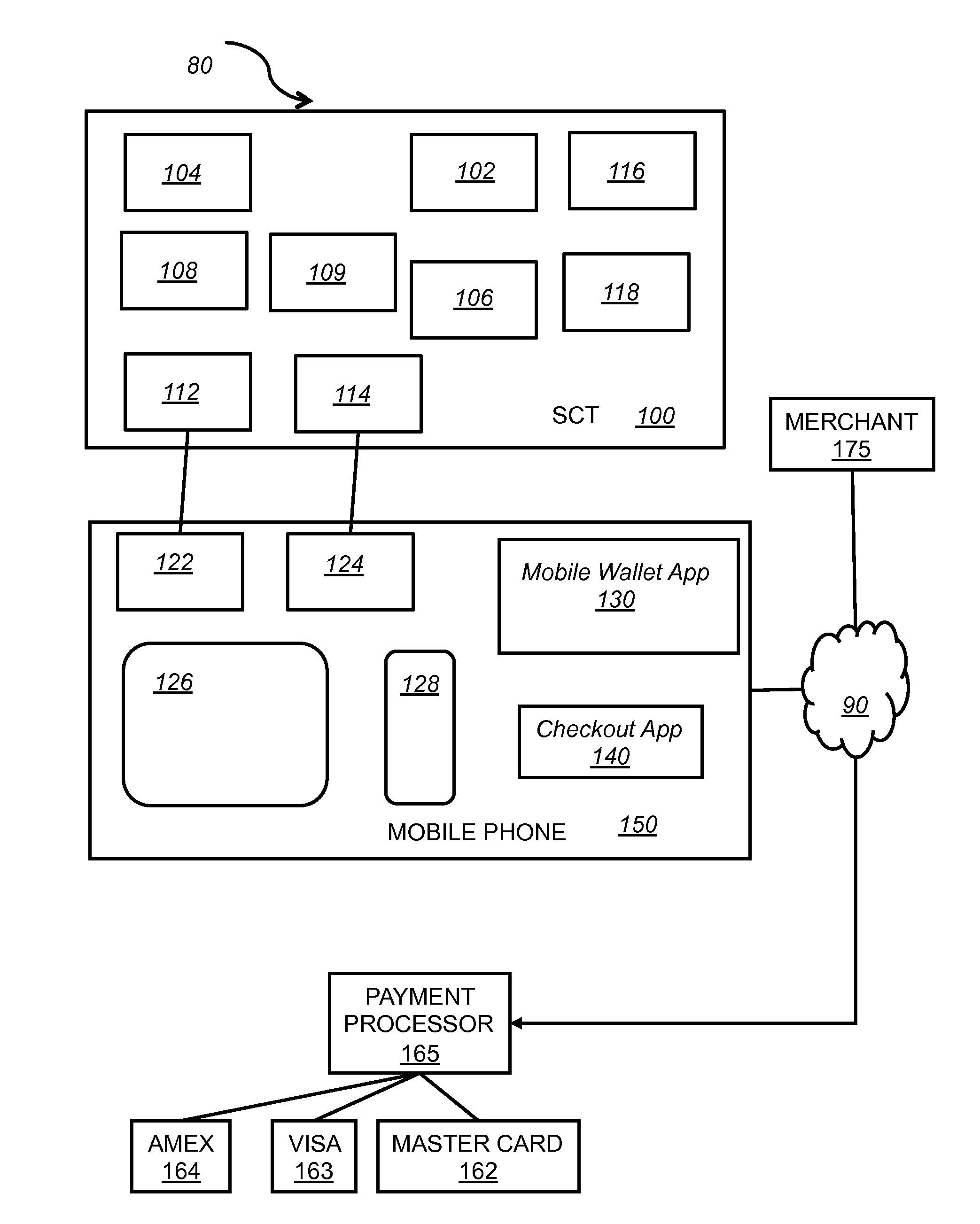
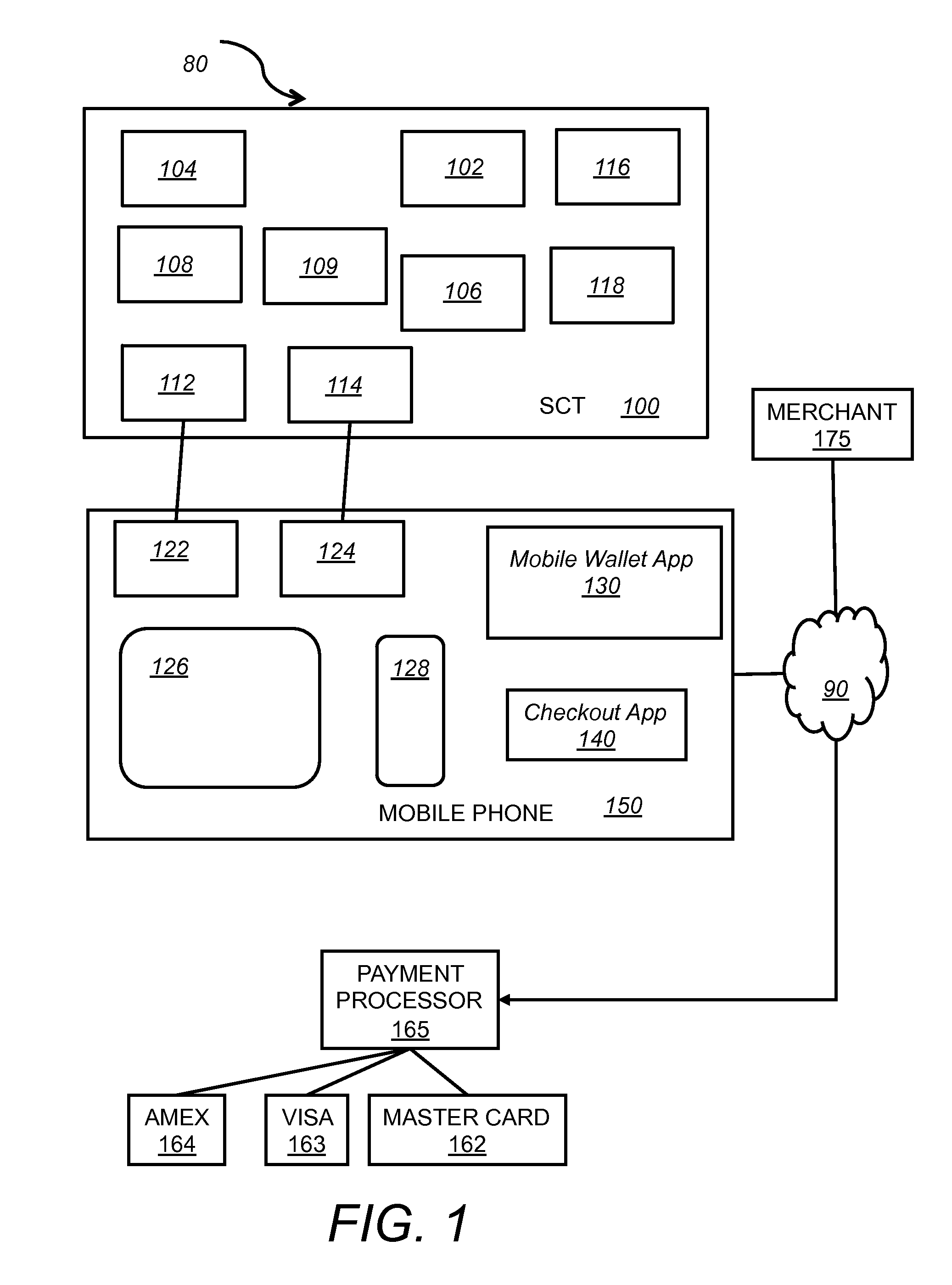
A system for a secure cardholder and storage device includes a mobile communication device and a secure card transporter (SCT). The SCT includes a Near Field Communication (NFC) chip, a microprocessor, a magnetic stripe card reader, a contact chip card reader, a contactless card reader, an audio jack interface and a micro-USB interface. The SCT interfaces with the mobile communication device via the audio jack interface or the micro-USB interface, and the SCT captures payment card data and transmits the captured payment card data to a merchant point of sale (POS) checkout system both in the physical and virtual environments. The system provides convenient buying experience for buyers, and secure and informative transaction for sellers.
Owner:INGENICO INC
Distributive storage controller and method
ActiveUS20040049700A1Safe storageReduce risk of leakageInput/output to record carriersDigital data processing detailsHard disc driveControl store
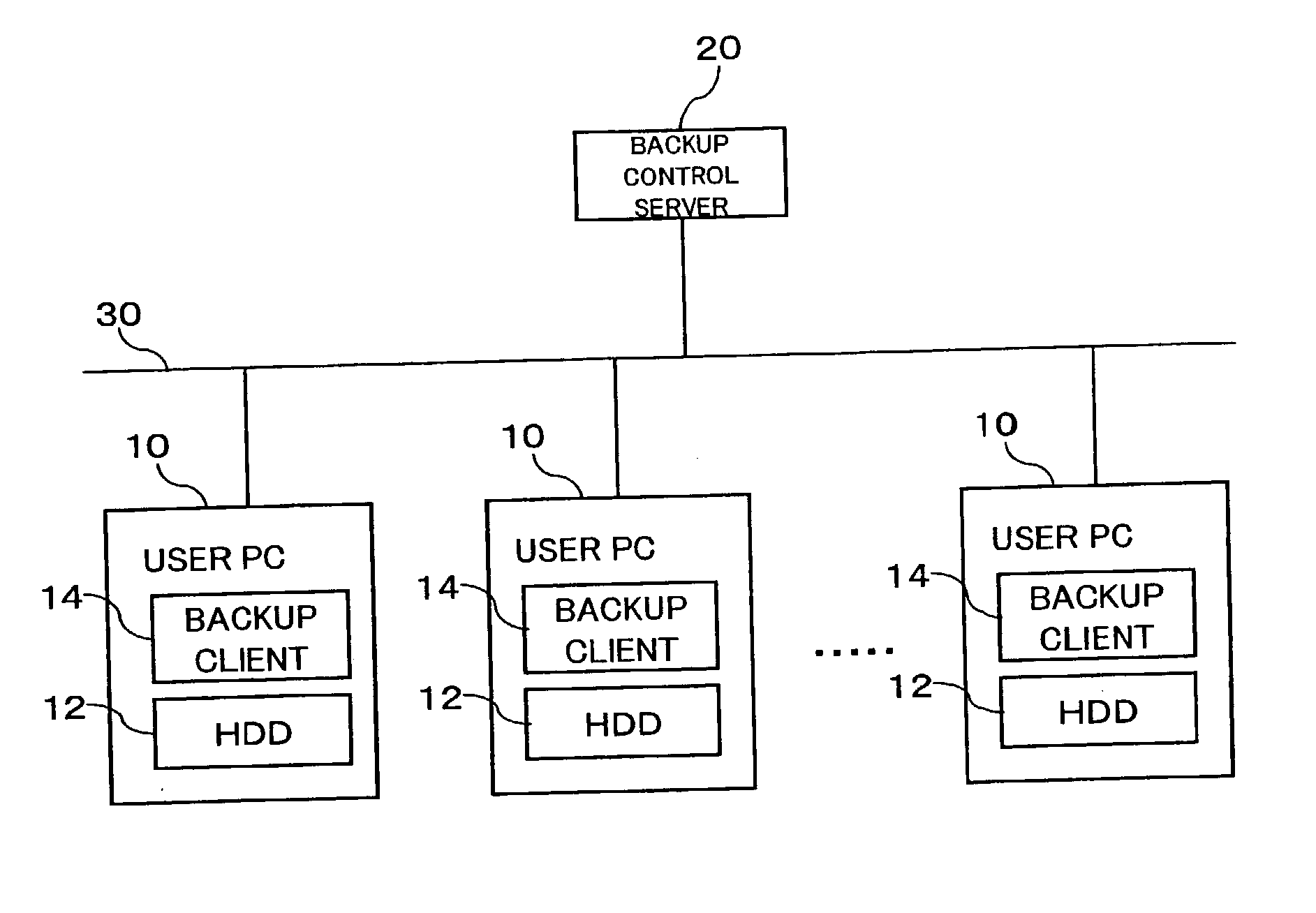
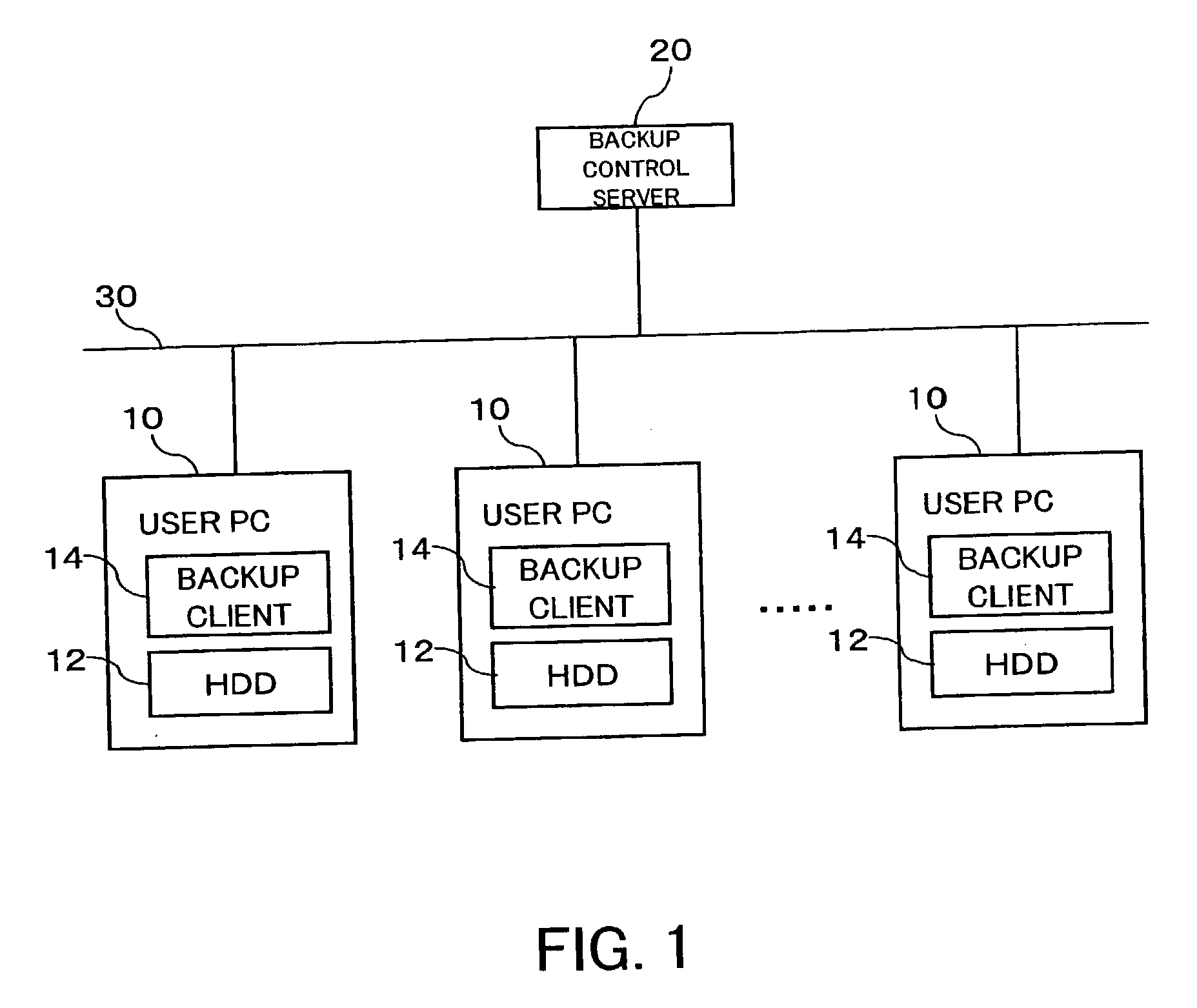
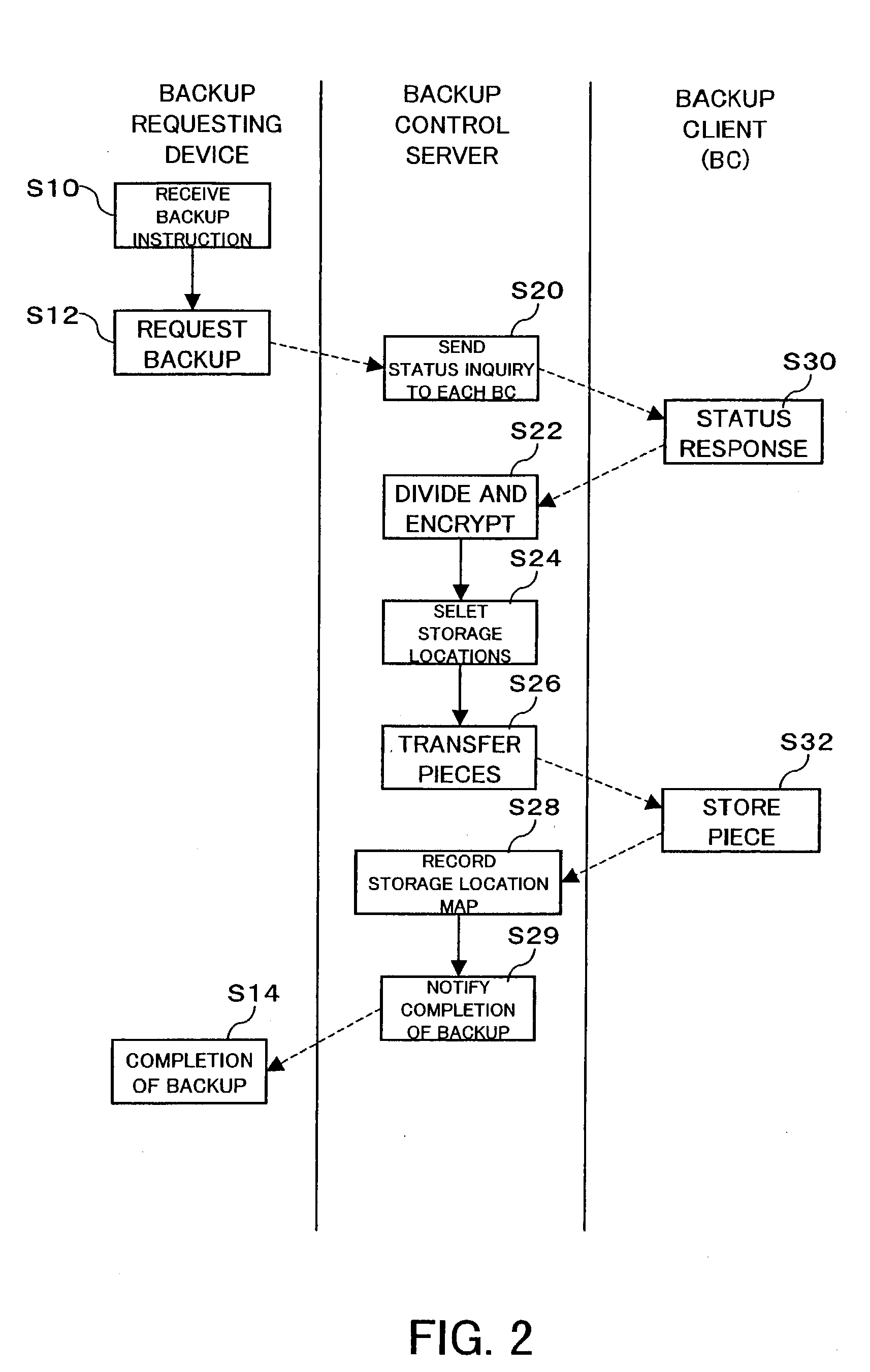
An inexpensive data storage technique utilizing available capacity in individual computer devices connected to a network is provided. When a backup client (BC) (14) of a user PC receives a backup instruction for a file from a user, the backup client (14) requests backup to a backup control server (20). The backup control server (20) divides and encrypts the file to be backed up into a plurality of encrypted pieces, transfers the encrypted pieces to user PCs (10), and stores the encrypted piece in the HDDs (12) of the user PCs (10). When the destributively backed up file is to be extracted, the user PC 10 obtains each encrypted piece from the user PCs 10 on which they are stored, and combines and decrypts the encrypted pieces to restore the original file.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Secure and searchable storage system and method
ActiveUS7512814B2Safe storageUnauthorized memory use protectionHardware monitoringElectronic documentTrusted client
A system and method for securely storing electronic documents is provided. The system includes a client portion and a server portion and the client portion is located at a trusted location. The client portion encrypts each electronic document and produces a list of terms of interest relating to the document, which terms are also encrypted. The encrypted document and the encrypted terms are transferred to a server portion which need not be located at a trusted location. The document is stored at the server portion in a manner which allows for locating the document again via the encrypted terms and returning the encrypted document to the trusted client portion, where it can be decrypted. Attachments to documents can also be encrypted and stored at the server, as can copies of dynamic documents, such as web pages. The server portion can also have a retention manager and encryptor which is used to implement document retention and destruction policies defined by the user of the system.
Owner:PROOFPOINT INC
Electronic document safe sharing system and method thereof
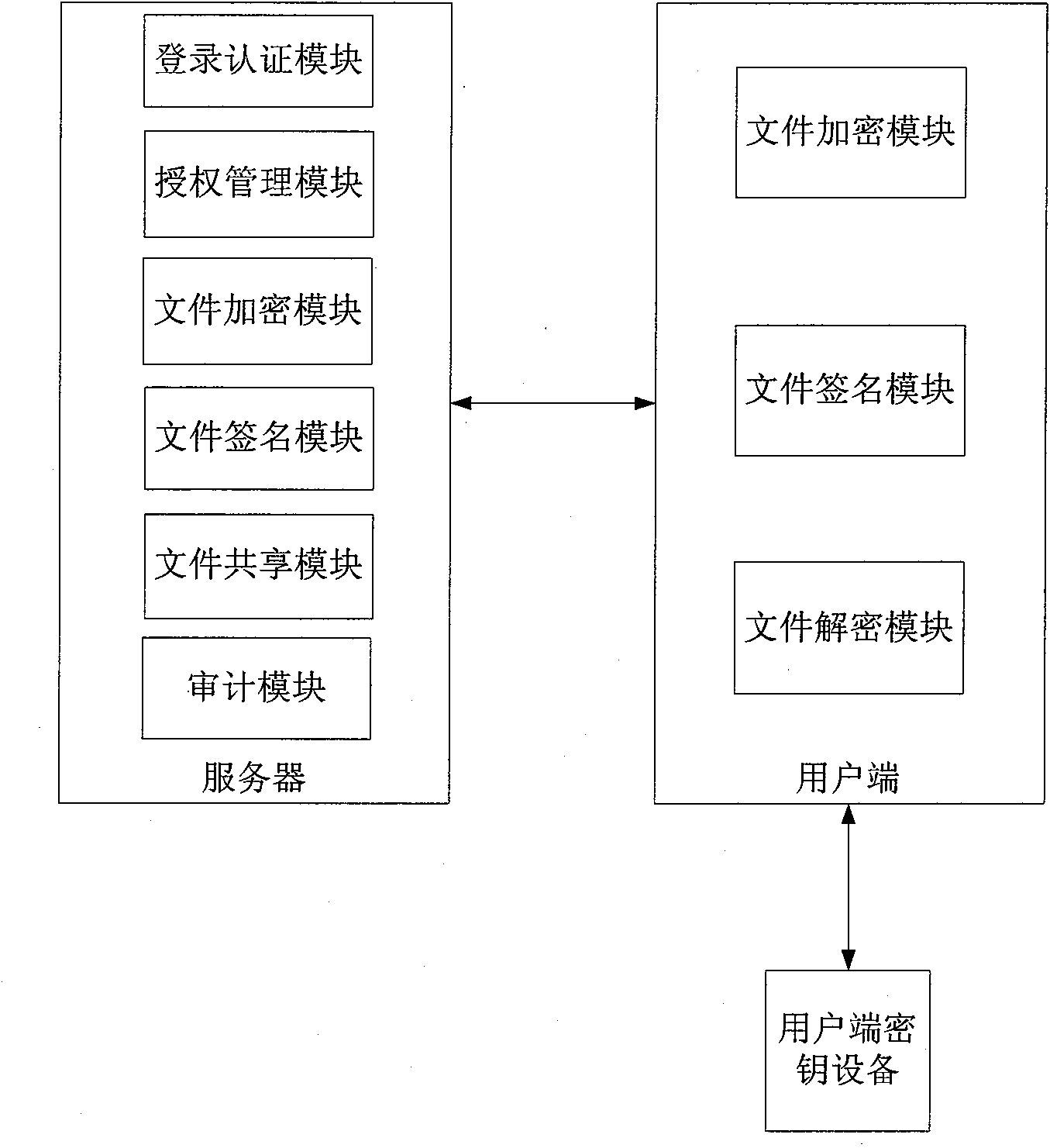
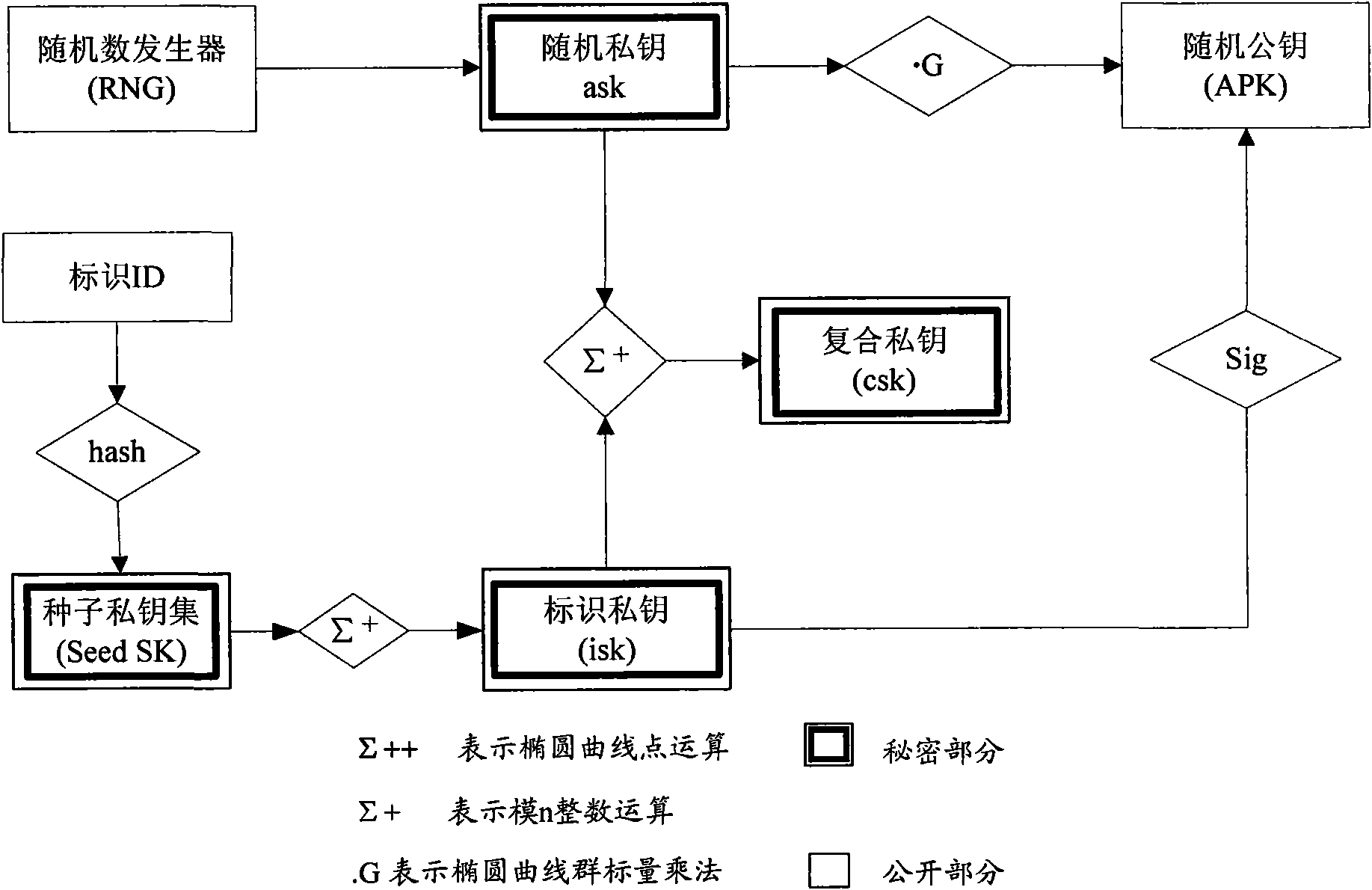
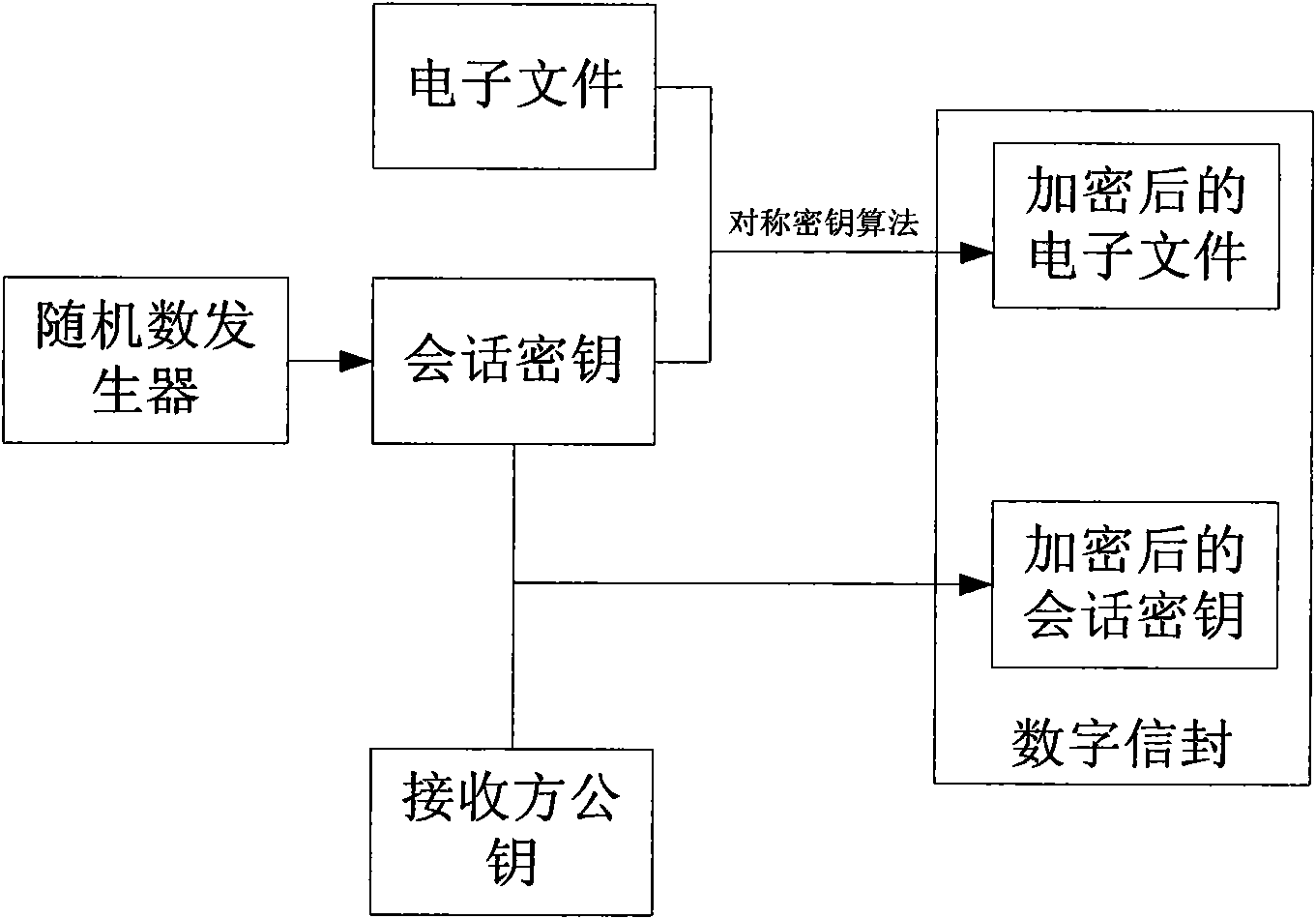
InactiveCN101989984AGuarantee authenticitySafe storagePublic key for secure communicationUser identity/authority verificationClient-sideSafe storage
The invention discloses an electronic document safe sharing system which can realize safe storage and fully sharing of secret document. The electronic document safe sharing system comprises a document encrypting module and a document decrypting module; wherein the document encrypting module utilizes a session key to symmetrically encrypt electronic document data, receiver identification (public key) is utilized to asymmetrically encrypt the session key, and finally the encrypted symmetric key and encrypted electronic document data are packed into a digital envelop; and the document decrypting module utilizes an own private key to decrypt the digital envelop. The electronic document safe sharing method of the invention takes CPK combined public key or CPK compound public key technology as the basis, flexible digital signature and secret key exchange capacity thereof are utilized, and a confidential document management system which is from a server to a client, contains information storage and transmission to each use link and is integrated with document data encryption, access control, authorization management, dynamic key exchange and process audit trail into a whole is constructed.
Owner:BEIJING E HENXEN AUTHENTICATION TECH +1
Anti-TNF antibodies, compositions, methods and uses
InactiveUS20070003548A1Big advantageSafe storageAntibacterial agentsOrganic active ingredientsAntibodyNucleic acid
The present invention relates to at least one novel anti-TNF antibodies, including isolated nucleic acids that encode at least one anti-TNF antibody, TNF, vectors, host cells, transgenic animals or plants, and methods of making and using thereof, including therapeutic compositions, methods and devices.
Owner:CENTOCOR
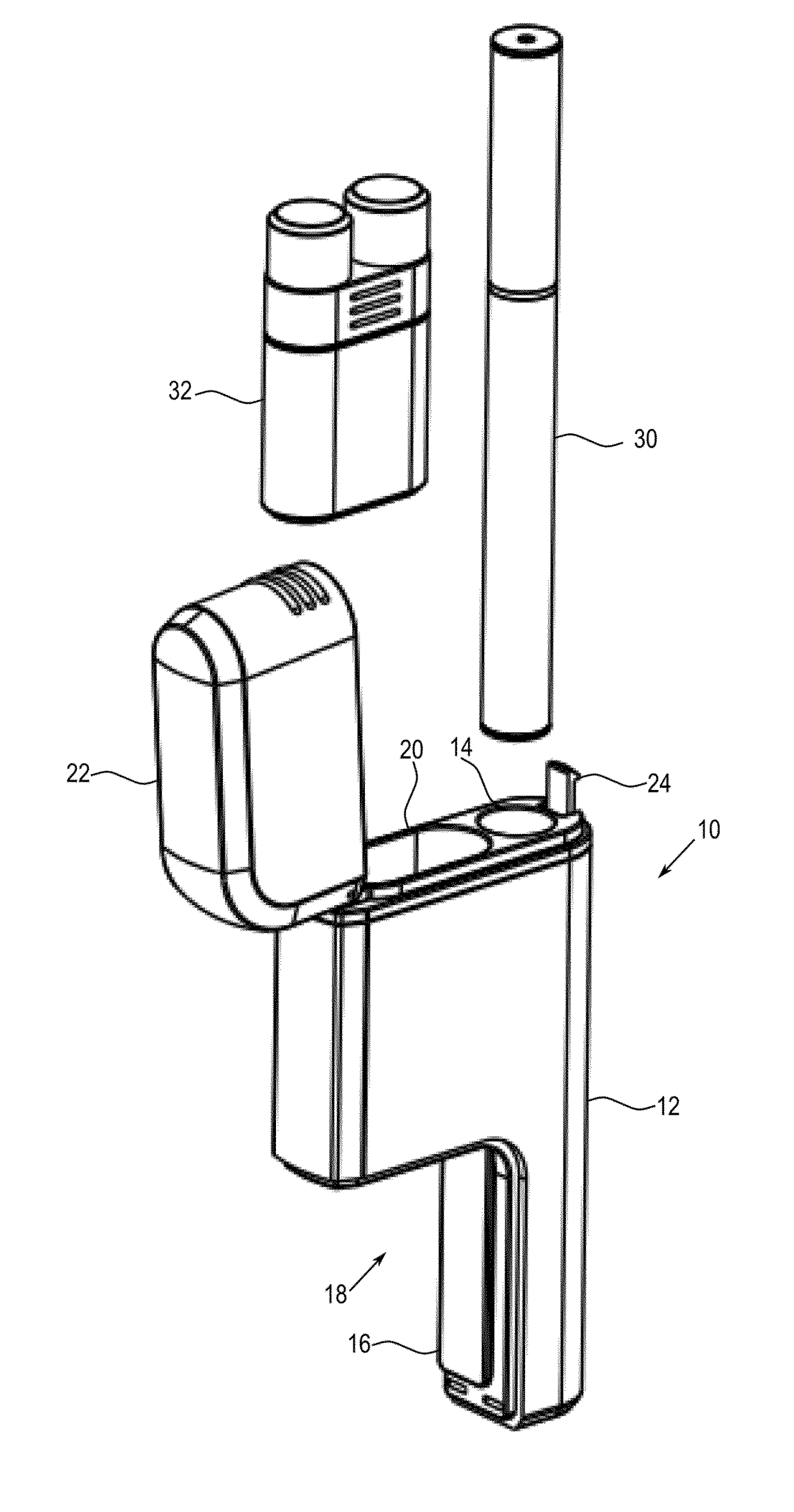
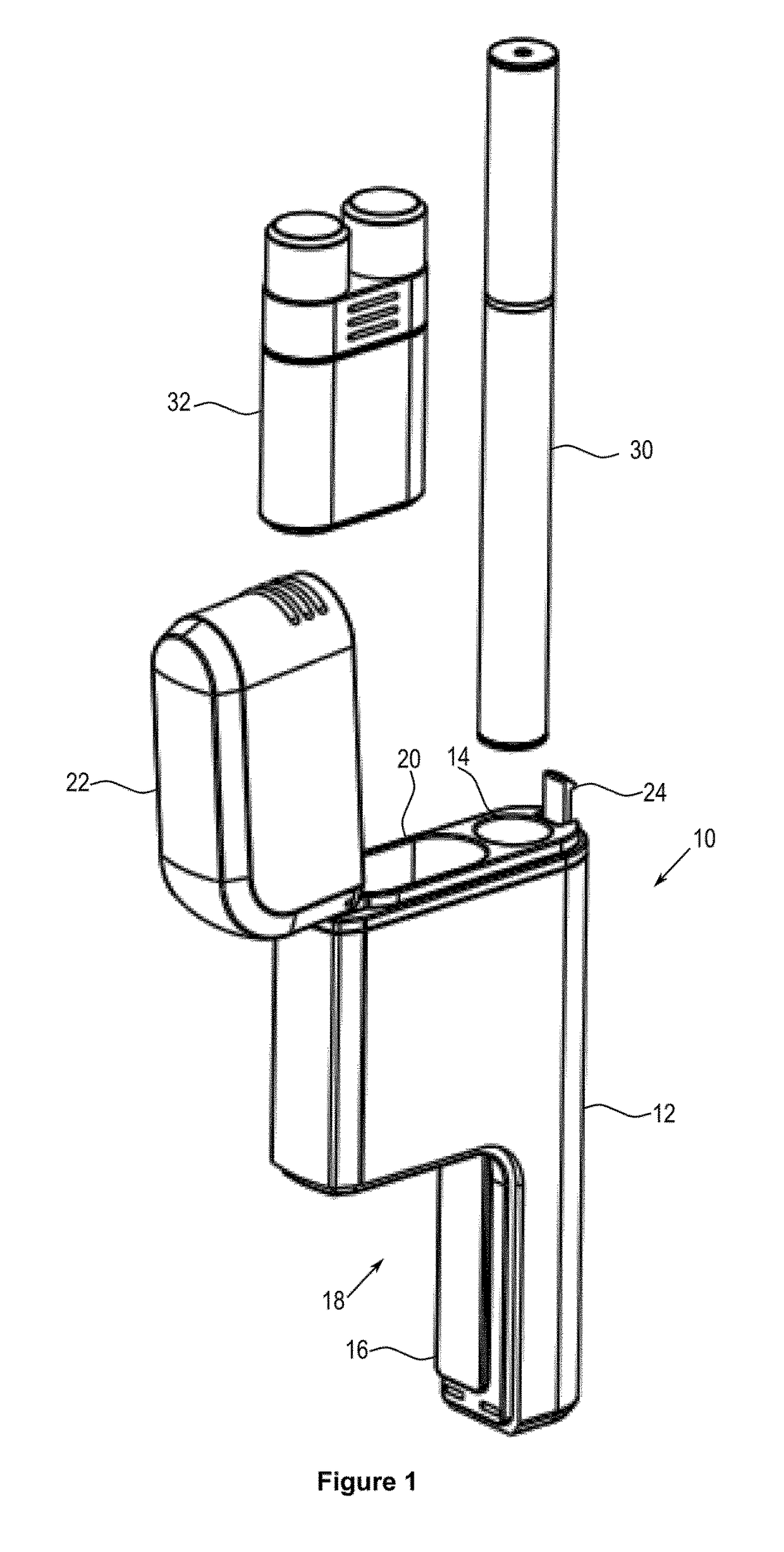
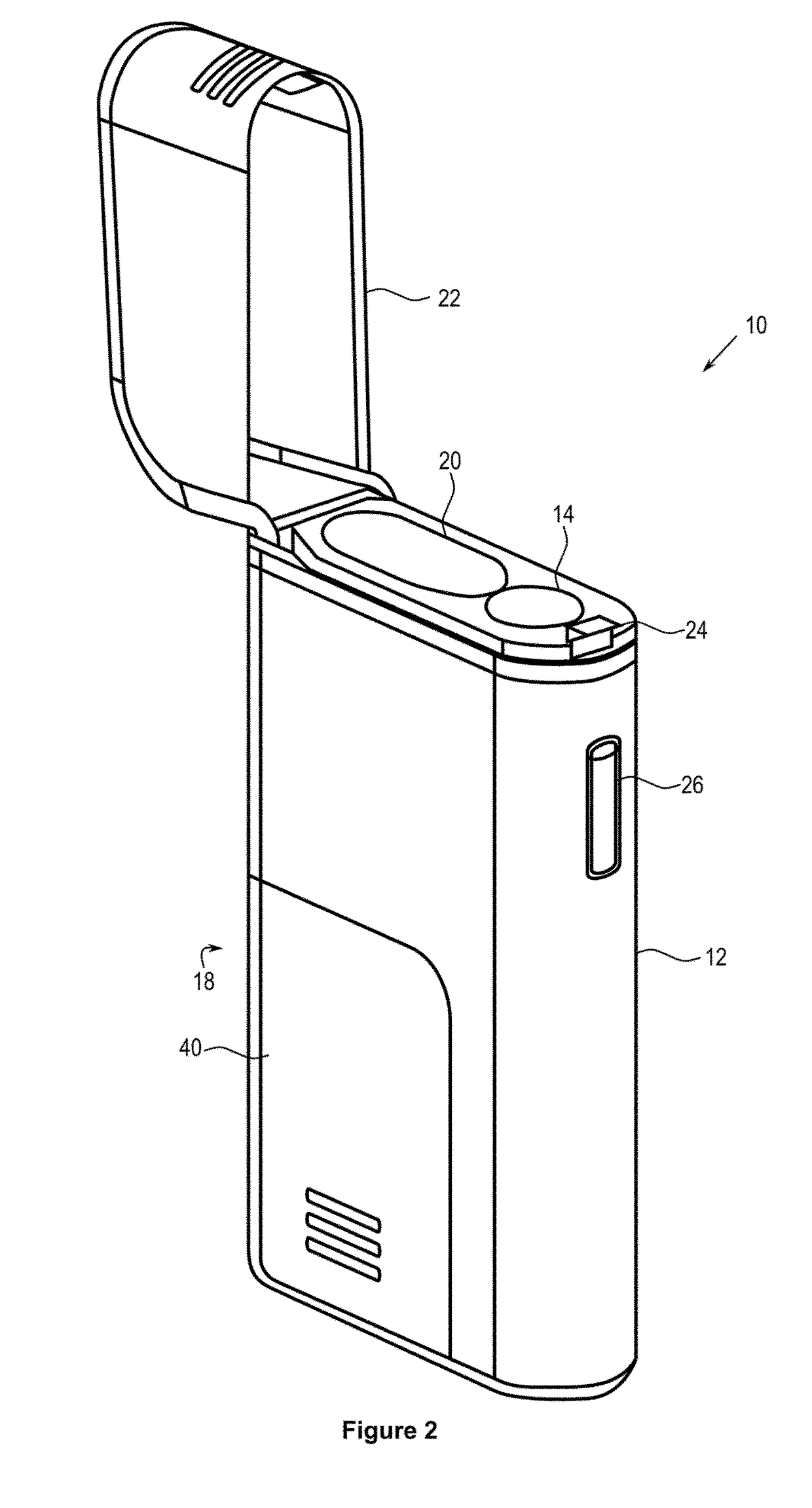
Container for an aerosol generating device
ActiveUS20170334605A1Firmly connectedRobustBatteries circuit arrangementsExhaust apparatusMechanical engineeringAerosol
Owner:JT INT SA
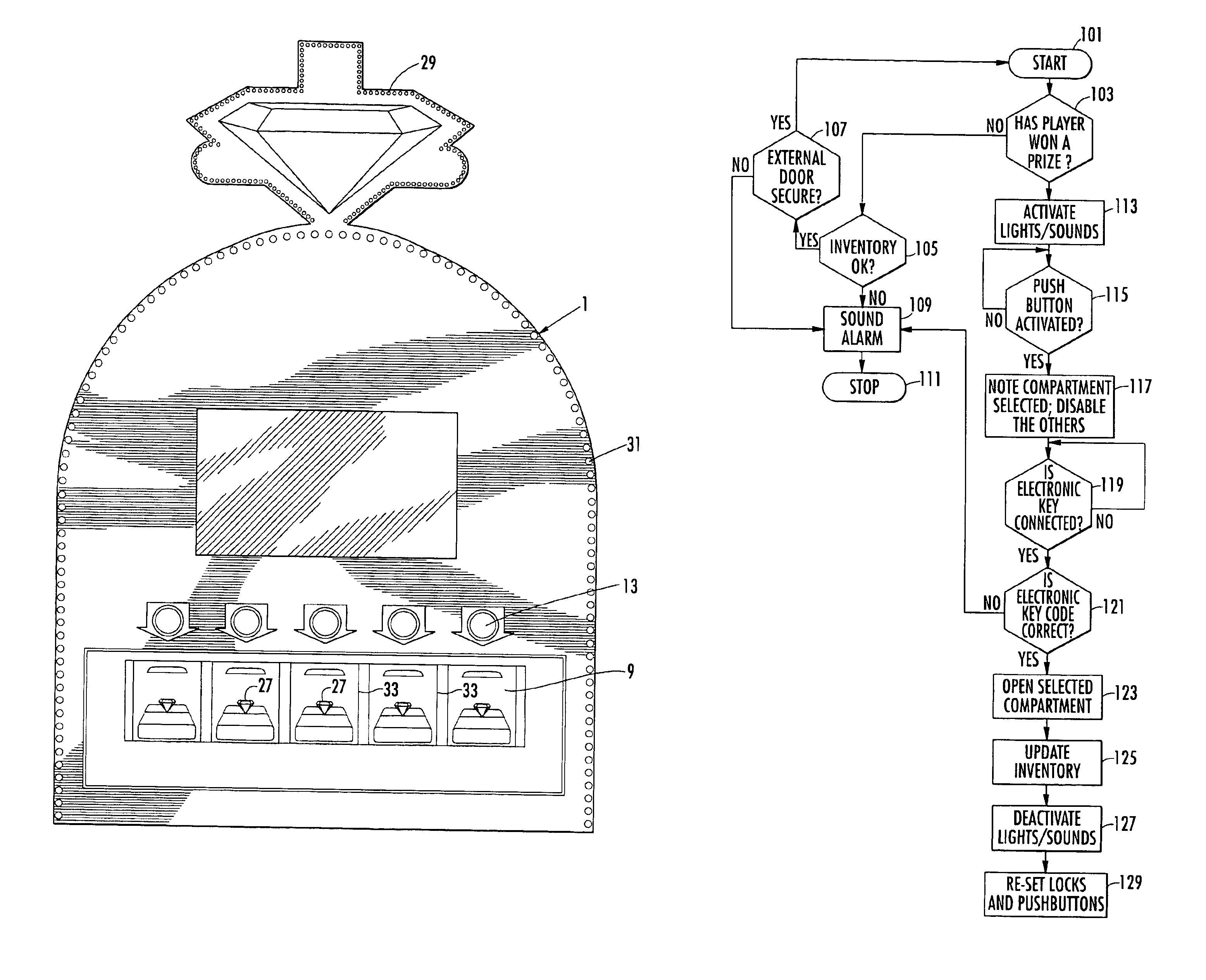
Apparatus and method for dispensing prizes
InactiveUS6899626B1Safe storageIncrease valueRacksCoin-freed apparatus detailsWaiters/waitressesControl system
Owner:BALLY GAMING INC
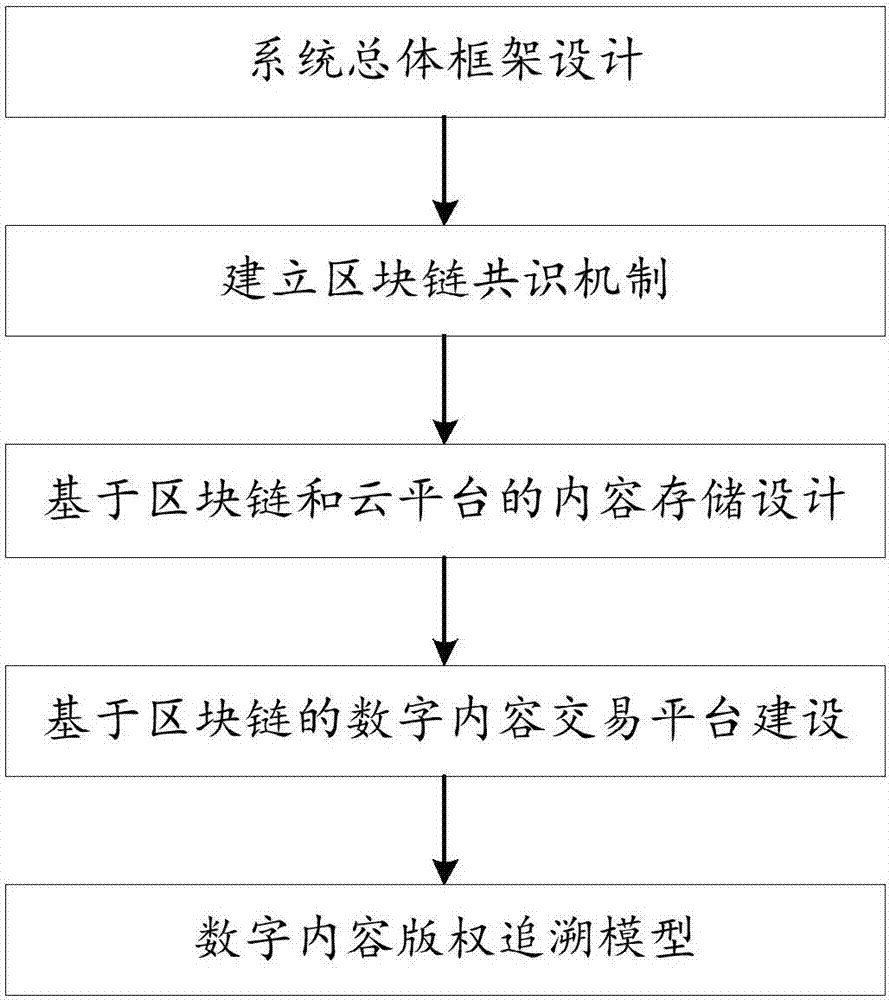
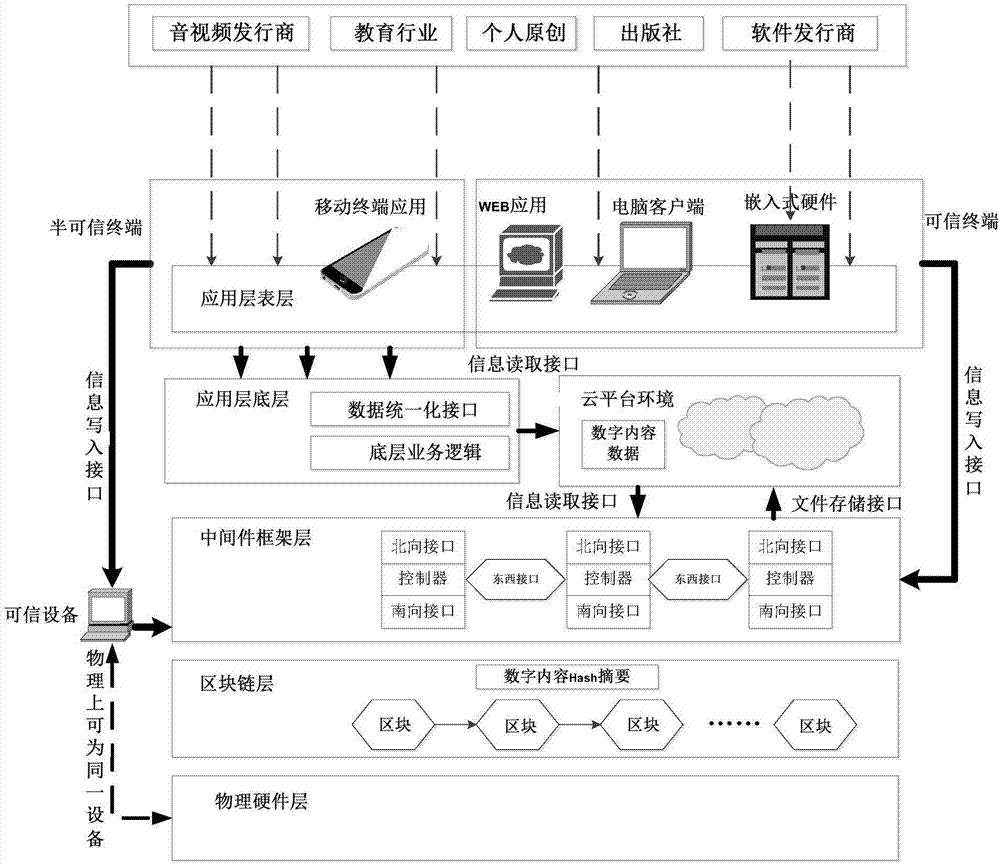
Building method of digital copyright tracing system based on block chain and cloud platform
InactiveCN107222303AReduce economic costsReduce management costsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesBlockchainHash chain
The invention discloses a building method of a digital copyright tracing system based on a block chain and a cloud platform. The method comprises the following steps: designing a general framework of the digital copyright tracing system based on the block chain and the cloud platform; building a block chain consensus mechanism, wherein nodes in the block chain reach a consistent consensus on the aspects of node reliability and data real-time performance; designing a digital content storage way based on the block chain and the cloud platform, wherein the block chain stores a Hash function value formed after dimension reducing processing of digital content, and the cloud platform saves digital content on which a digital content producer performs a digital signature with a private key; building a digital content transaction platform based on the block chain to perform a registration transaction and an authentication transaction of the digital content; and building a digital content copyright tracing model, and performing tracing by using a chain-style relation of a Hash chain in the block chain. Through adoption of the method, safe and effective propagation of digital products can be realized, and the problem that digital content copyrights cannot be traced is solved.
Owner:JINAN UNIVERSITY
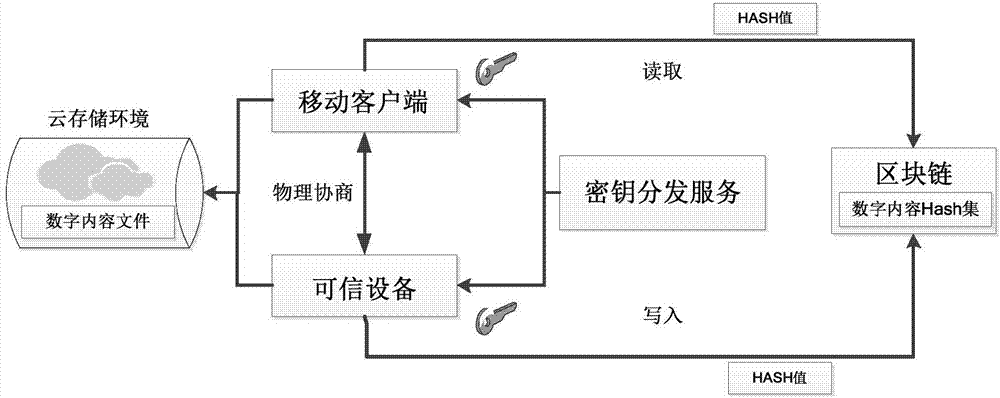
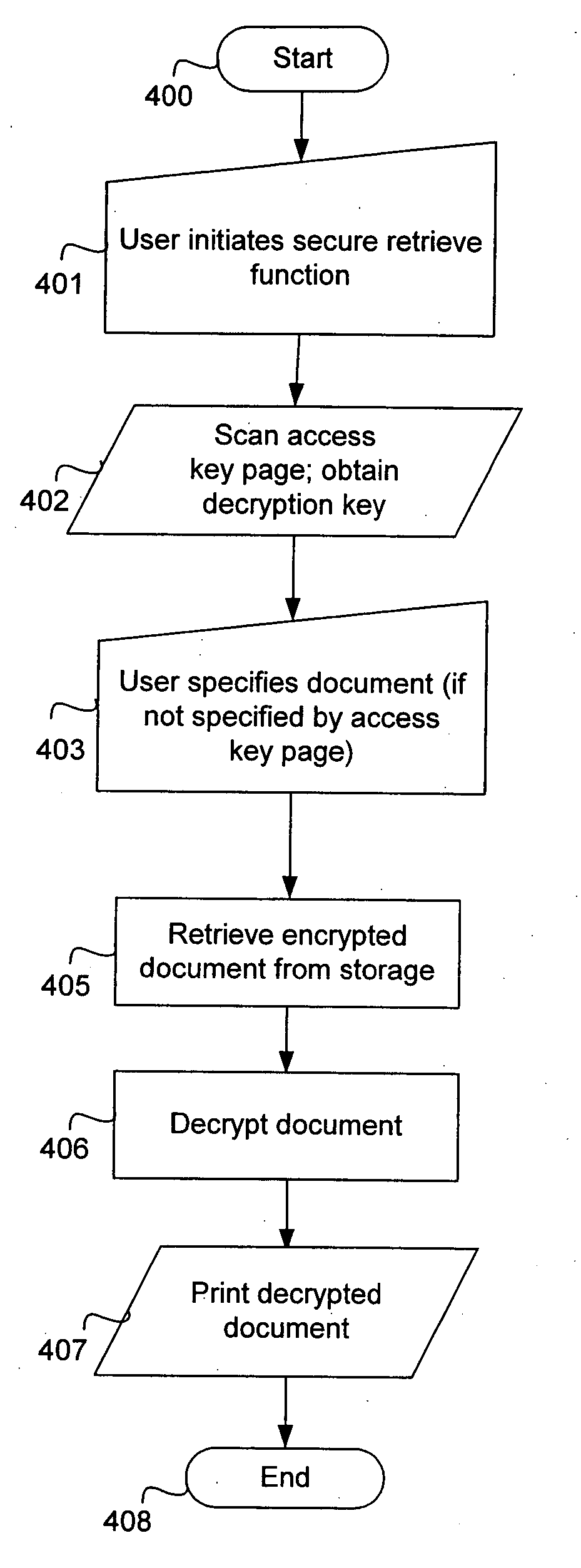
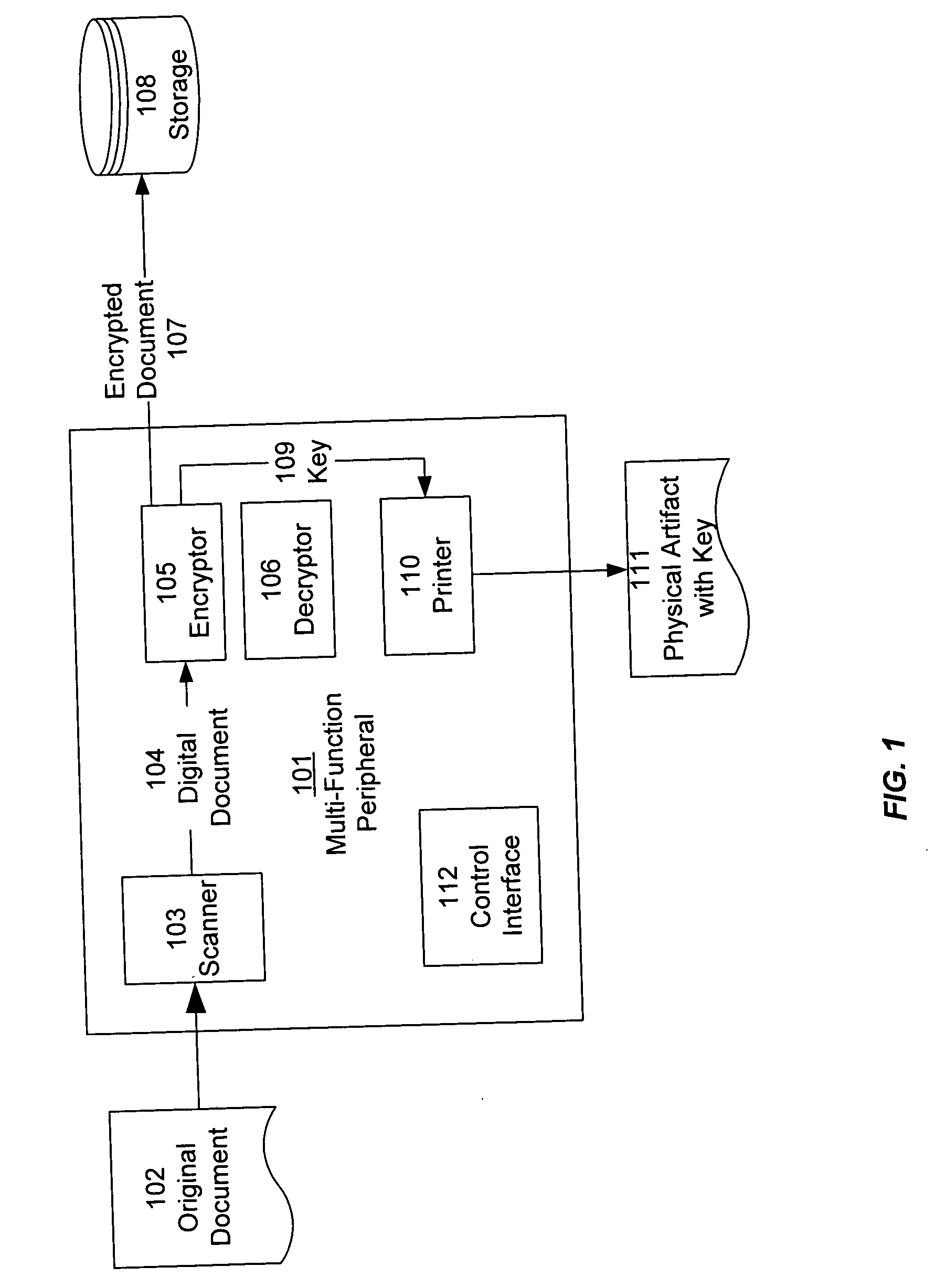
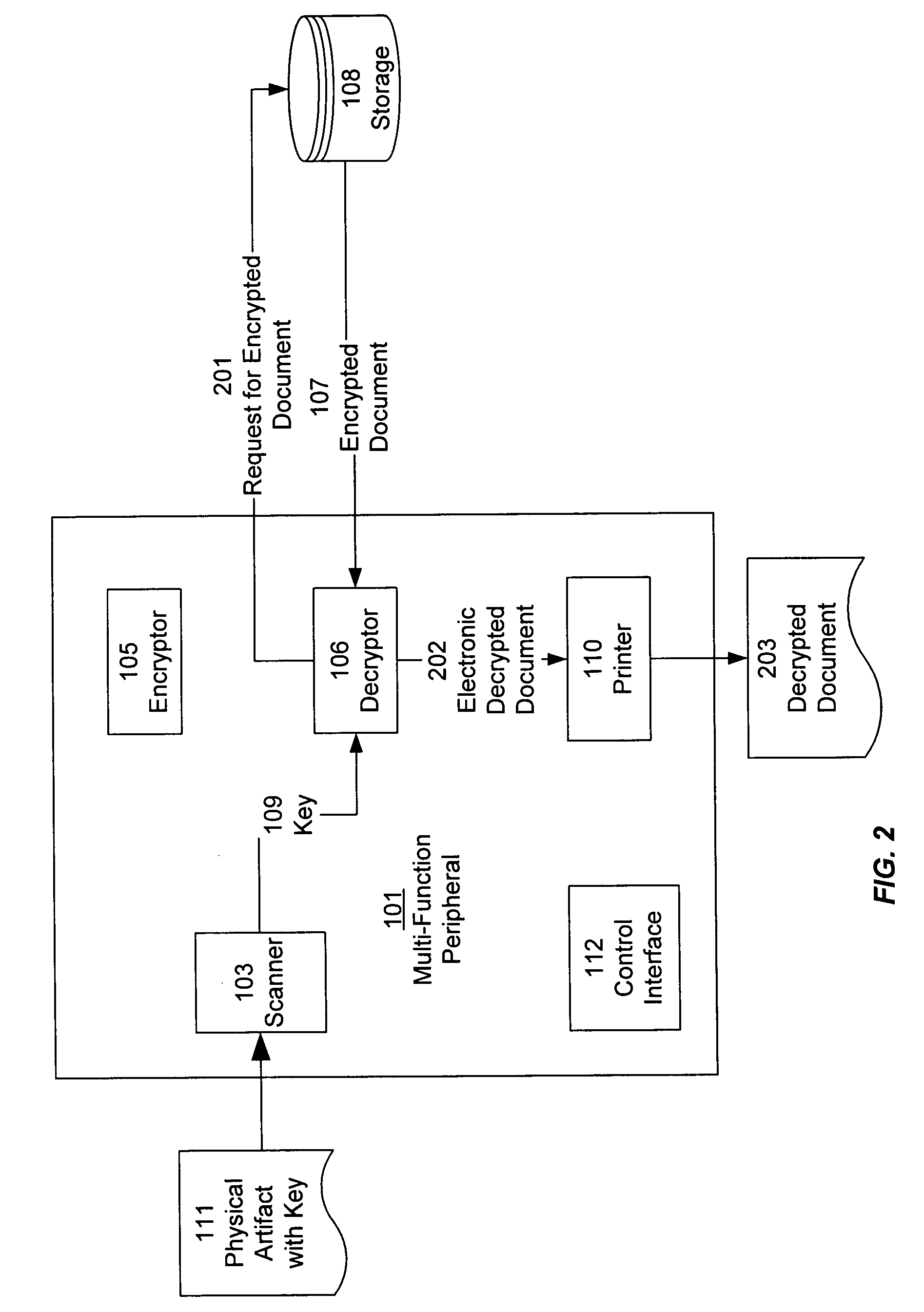
Physical key for accessing a securely stored digital document
InactiveUS20070050696A1Improve securityPromote generationComputer security arrangementsSpecial data processing applicationsComputer hardwareUser authentication
An incoming document is scanned, encrypted, and stored. A decryption key is generated and output on a physical artifact, such as a printed sheet of paper. The decryption key is not stored in any other location. The physical artifact can later be presented to access, decrypt, and output the stored document. Additional features of some embodiments of the invention include user authentication, key expiry, and watermarking.
Owner:RICOH KK
Hand held video game case with universal power pack
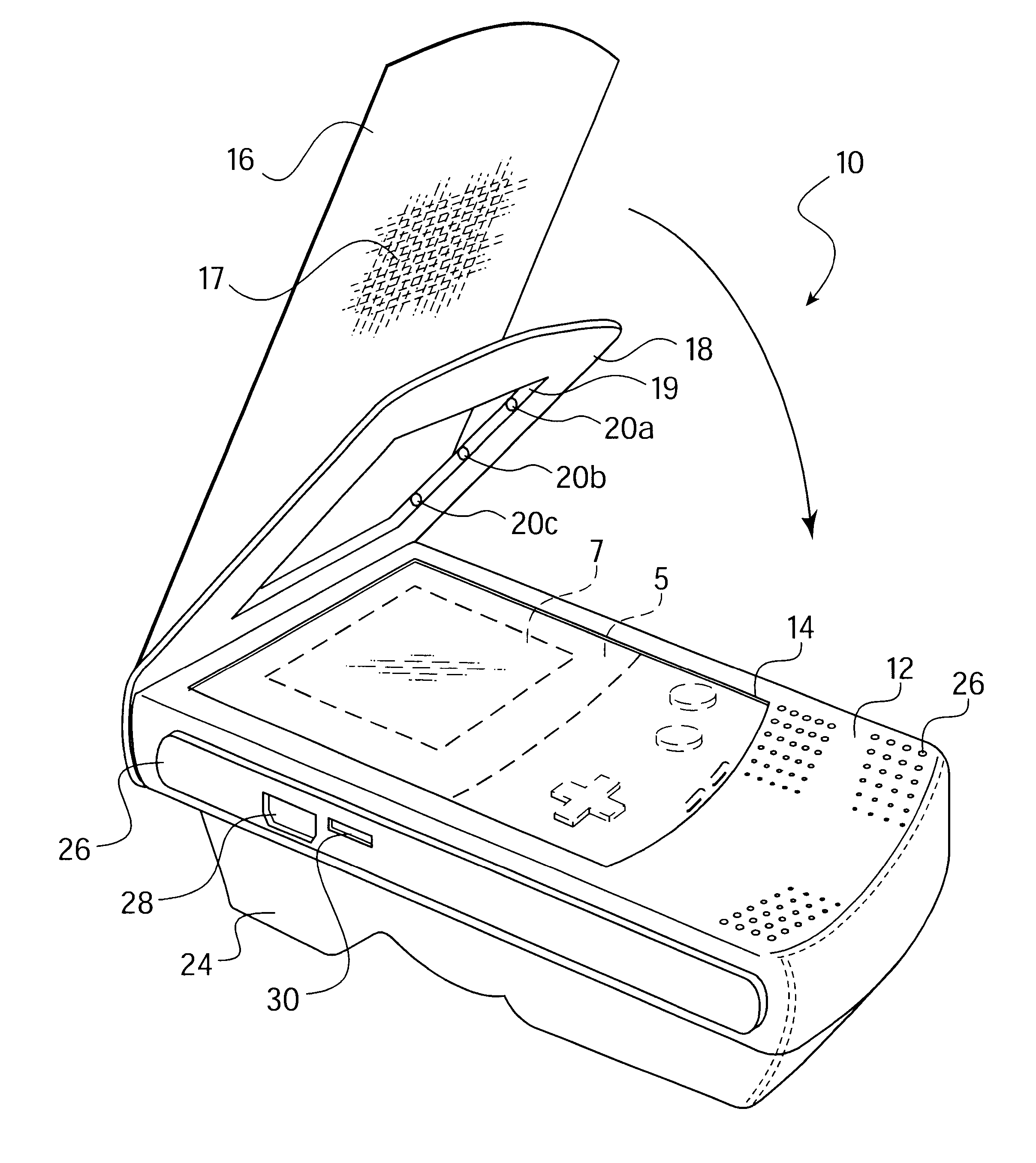
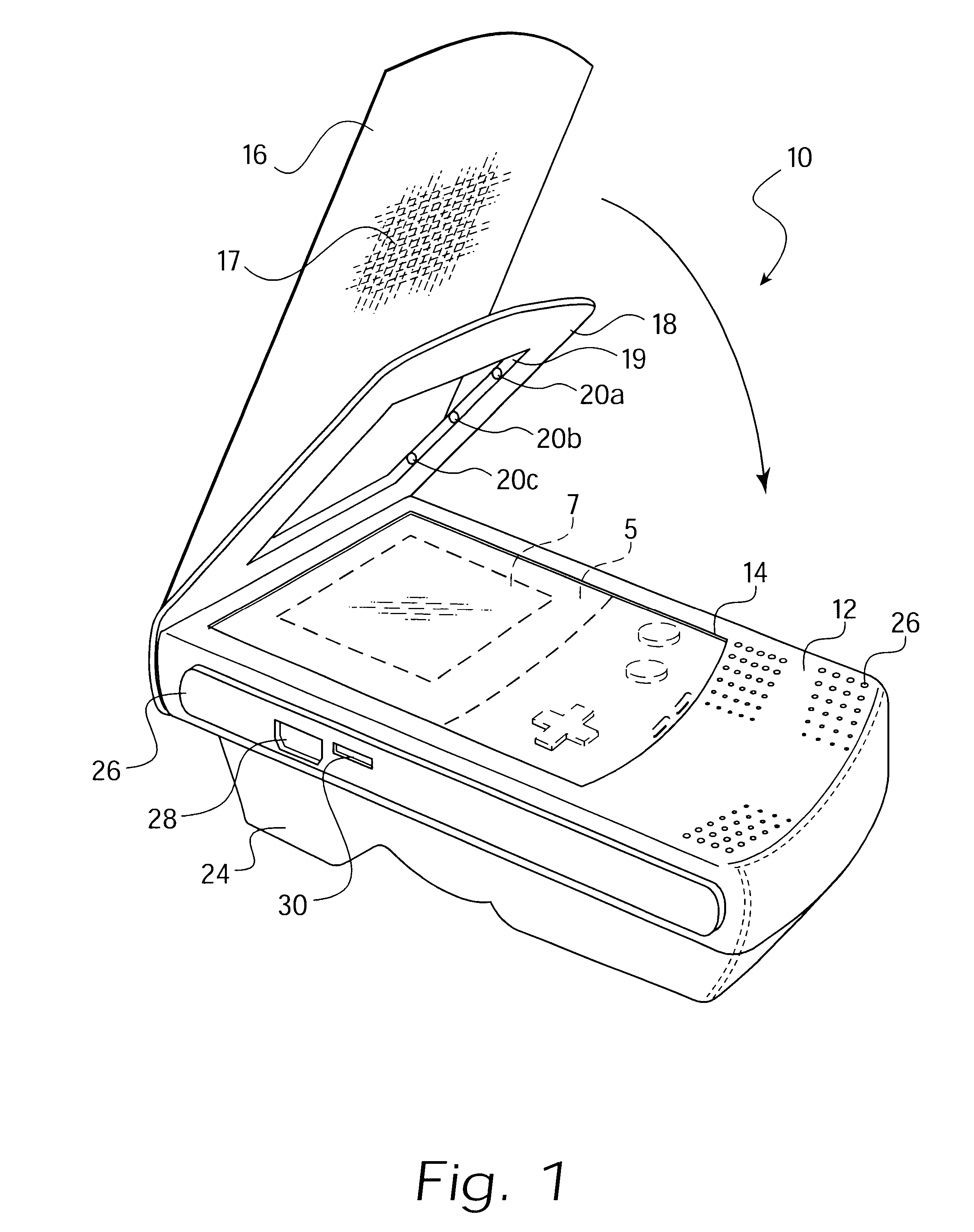
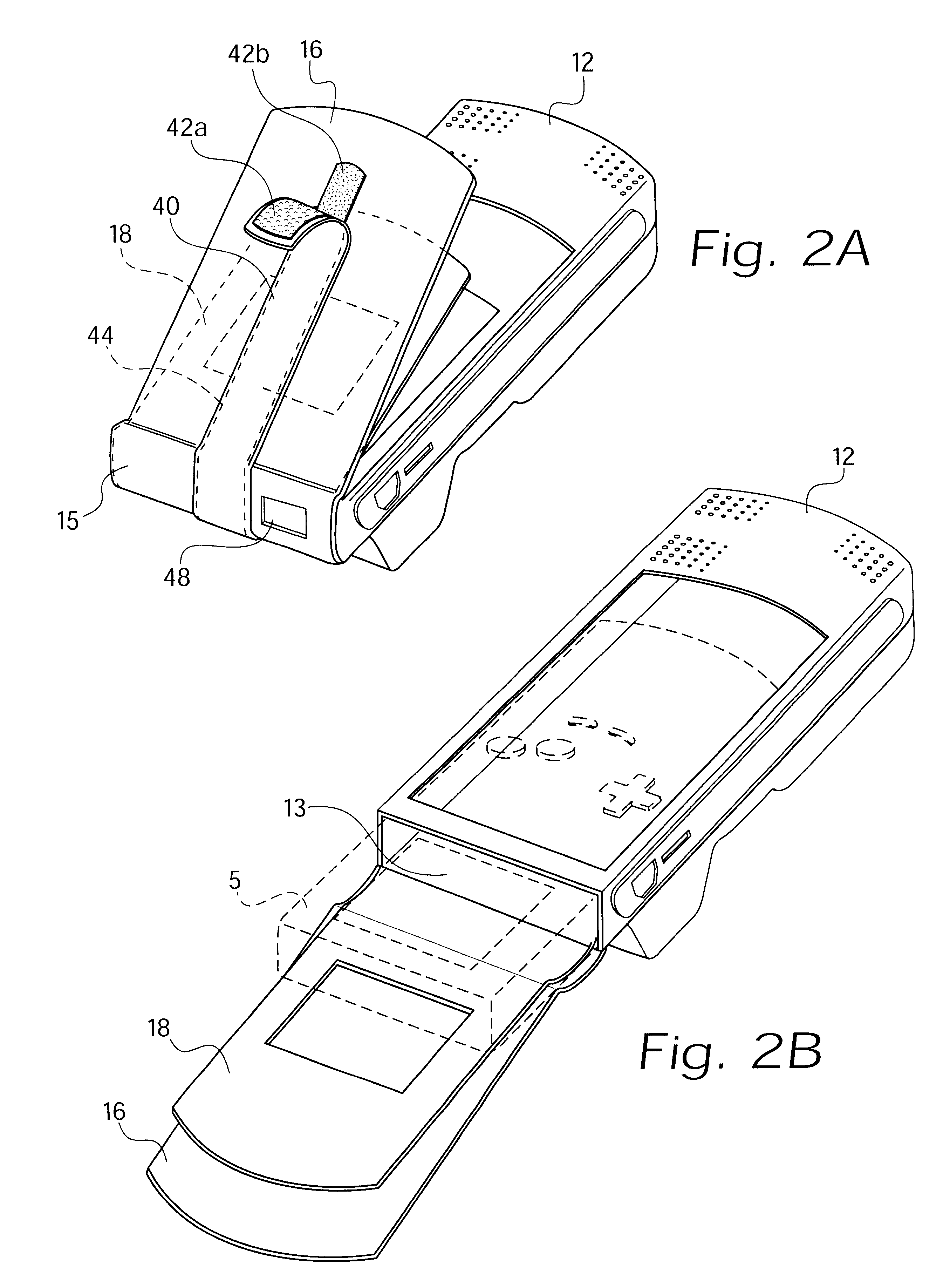
InactiveUS6347796B1Safe storageReduce glareOther accessoriesContainer/bottle contructionHand heldEngineering
A case and universal power pack for a hand held video game device includes a power pack with integrated plug engaging the external power supply jack on the hand held game device, and thereby provides power to the game device. A cover flap may be selectively adjusted by the user to provide optimum playing conditions and includes a glare reducing surface to further aid in providing the optimum playing environment. The case includes grip strips on opposing sides thereof, and includes access points for accessing the various external controls and jacks of the game device. The power pack is accessible from inside the case when the game device is removed therefrom.
Owner:ARISTA ENTERPRISES
Medical apparatus and method for setting up a medical apparatus
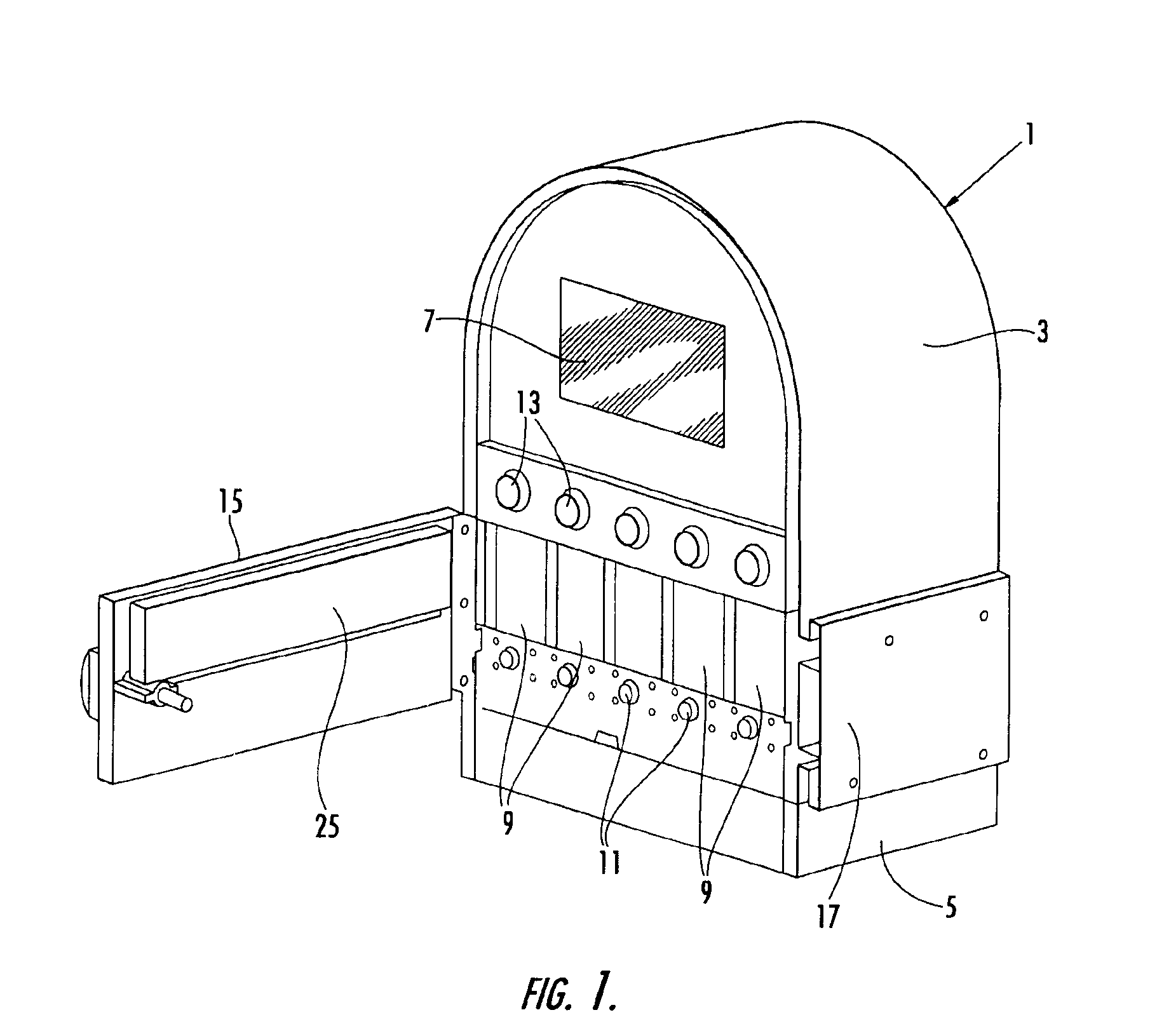
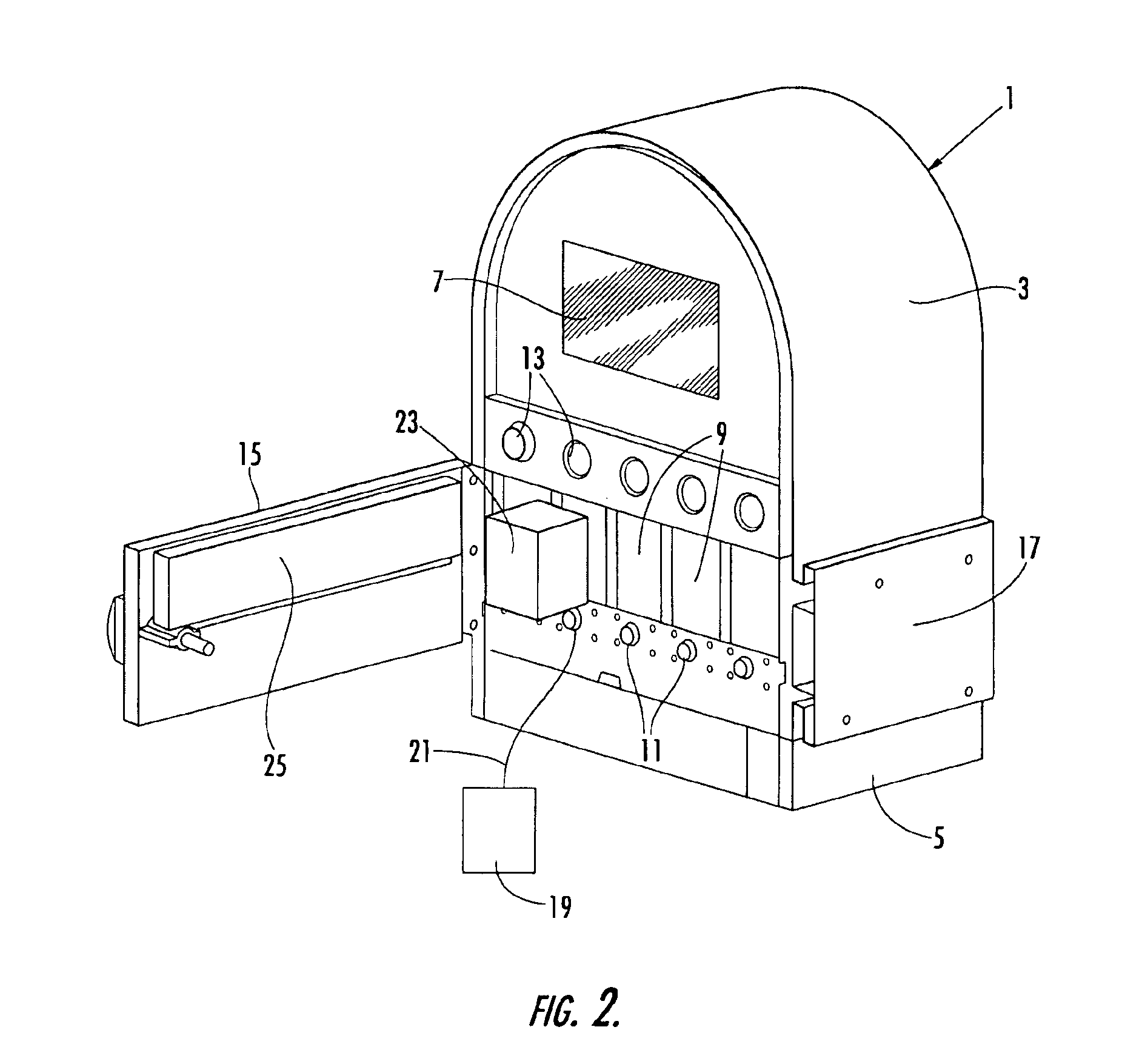
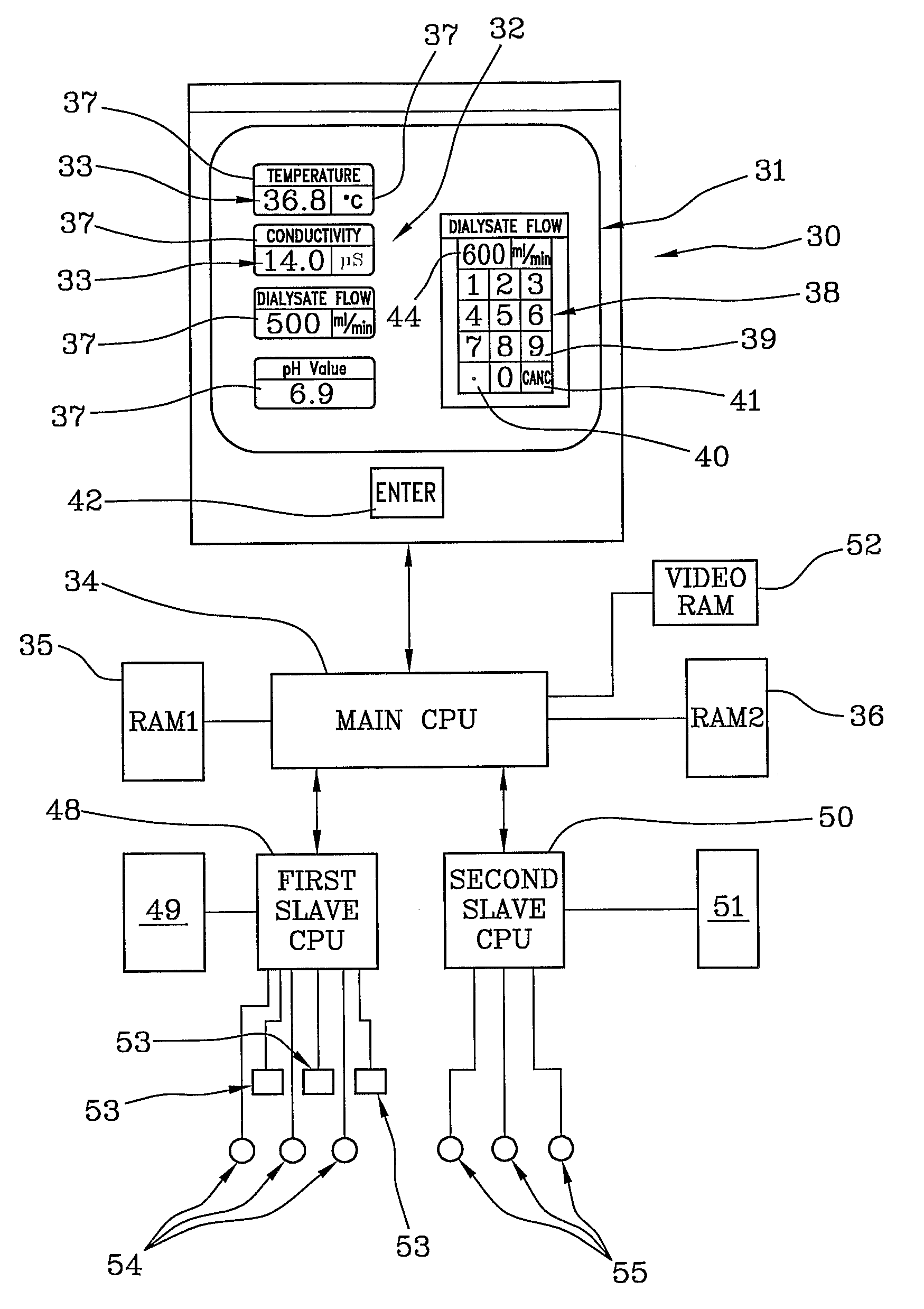
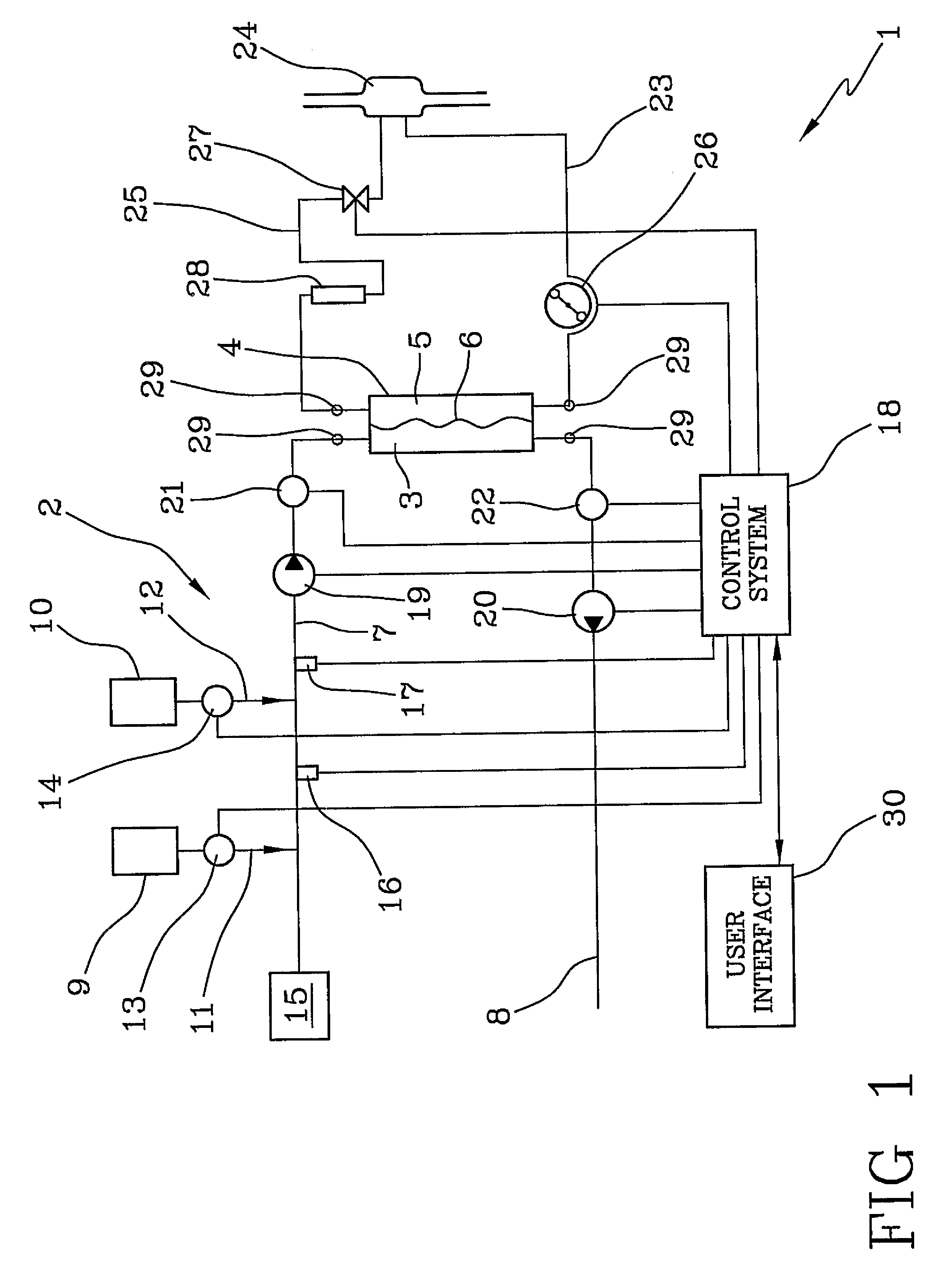
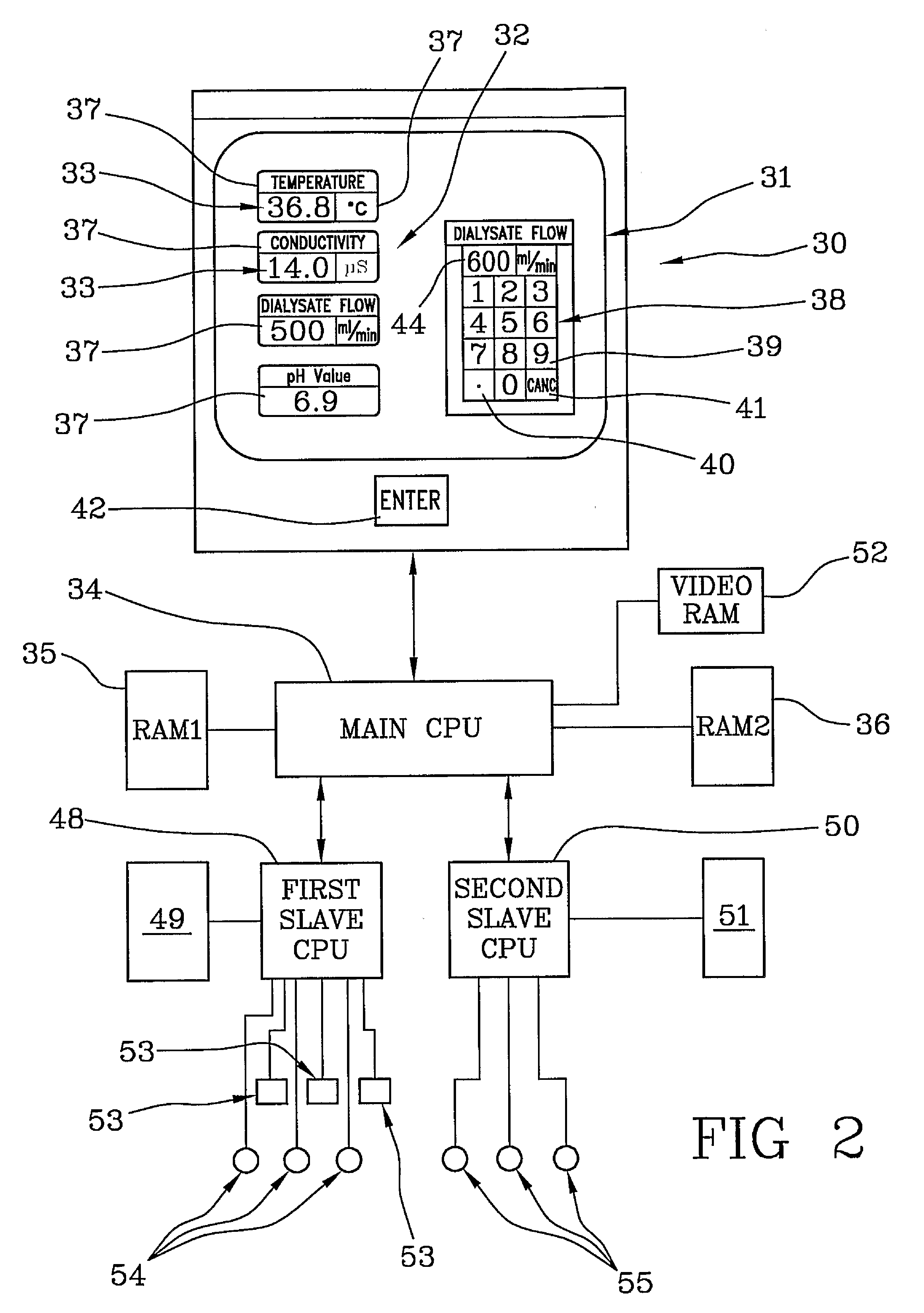
ActiveUS7922899B2Improve ease and reliabilityReduce data entryLiquid separation auxillary apparatusSolvent extractionData validationVideo memory
A medical apparatus comprises a user interface for setting parameters and includes: a screen for visualizing values of said parameters, a main control unit connected to the interface, a first memory and a video memory both connected to the main control unit for storing data corresponding to images on screen; the main control unit allows setting of a new value for a parameter, displays the new value on a screen region, stores the new value in the first memory, captures from the video memory data representative of said screen region, verifies from said representative data if the displayed value corresponds to the value in the first memory. A method for setting up a medical apparatus is also disclosed.
Owner:GAMBRO LUNDIA AB
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com