Patents
Literature
7553 results about "Smart card" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A smart card, chip card, or integrated circuit card (ICC) is a physical electronic authorization device, used to control access to a resource. It is typically a plastic credit card sized card with an embedded integrated circuit. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. Others are contactless, and some are both. Smart cards can provide personal identification, authentication, data storage, and application processing. Applications include identification, financial, mobile phones (SIM), public transit, computer security, schools, and healthcare. Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Several nations have deployed smart cards throughout their populations.
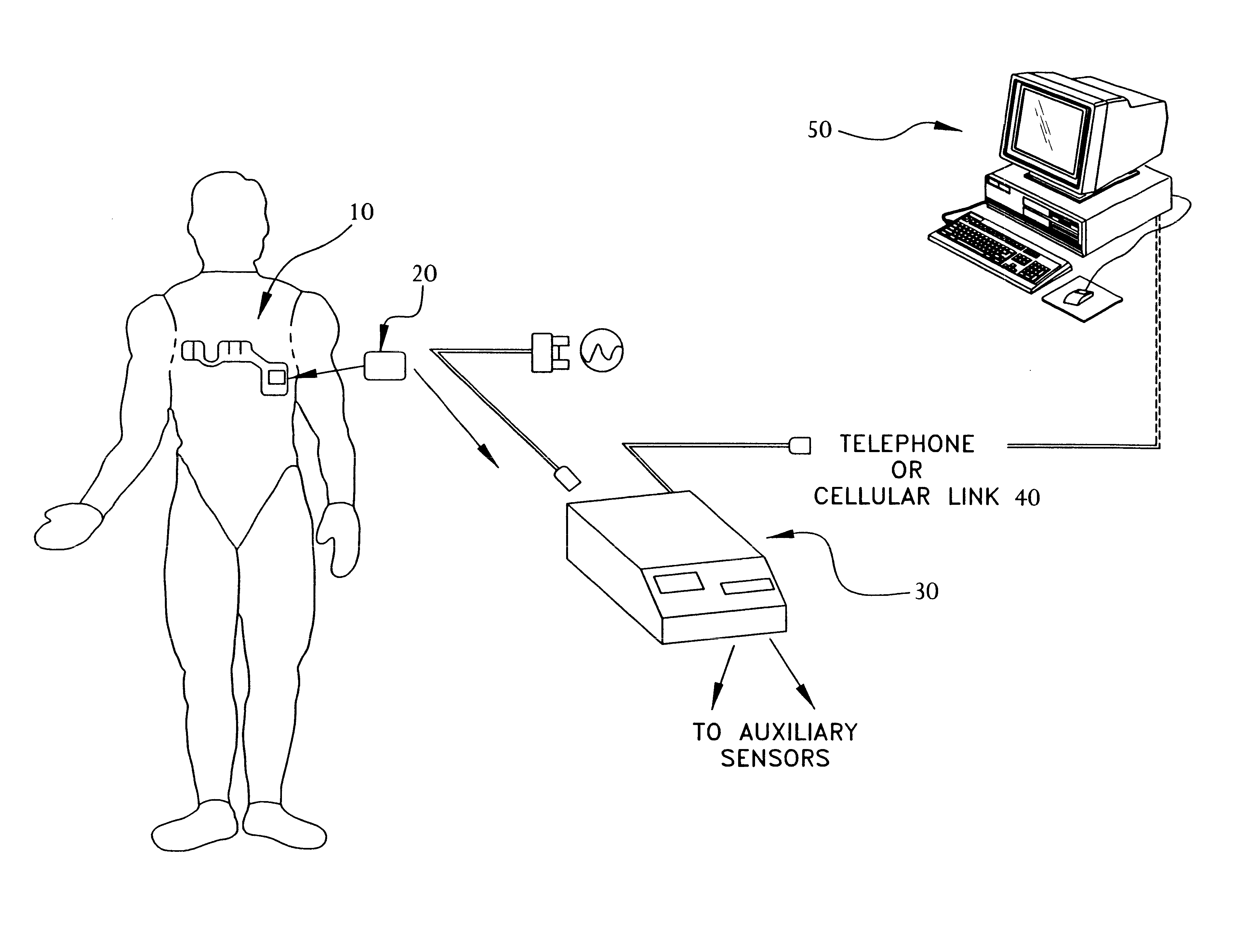
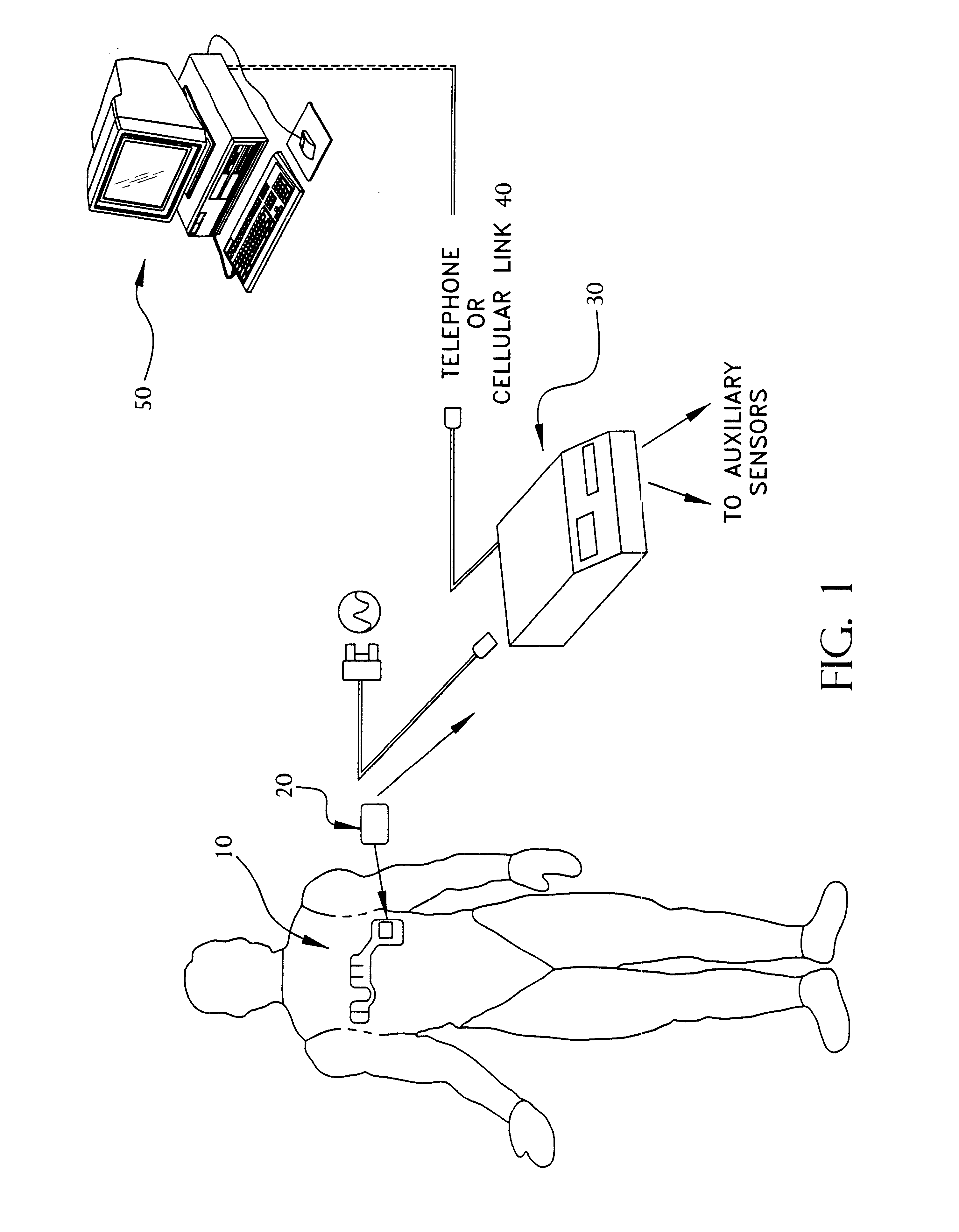
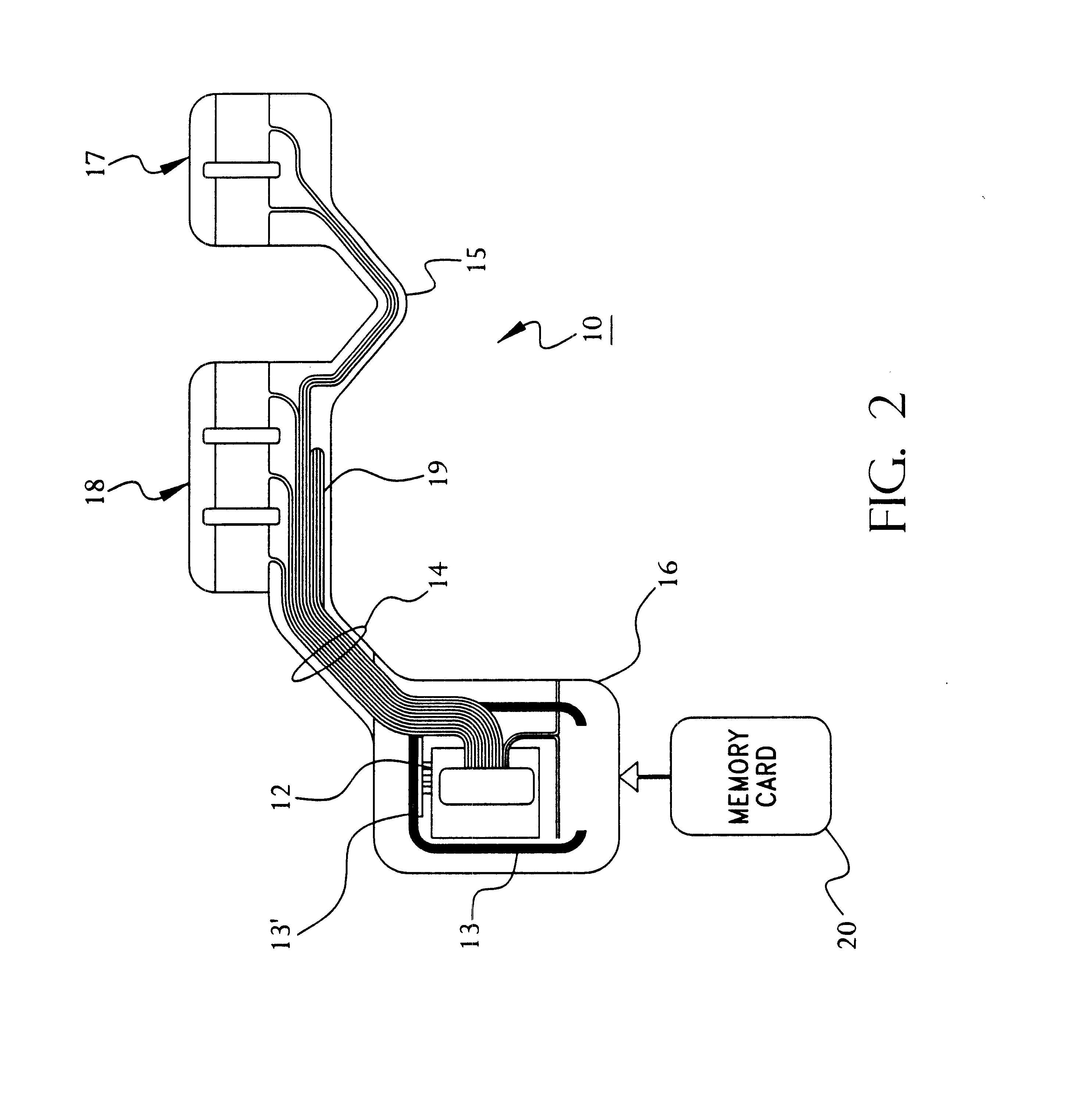
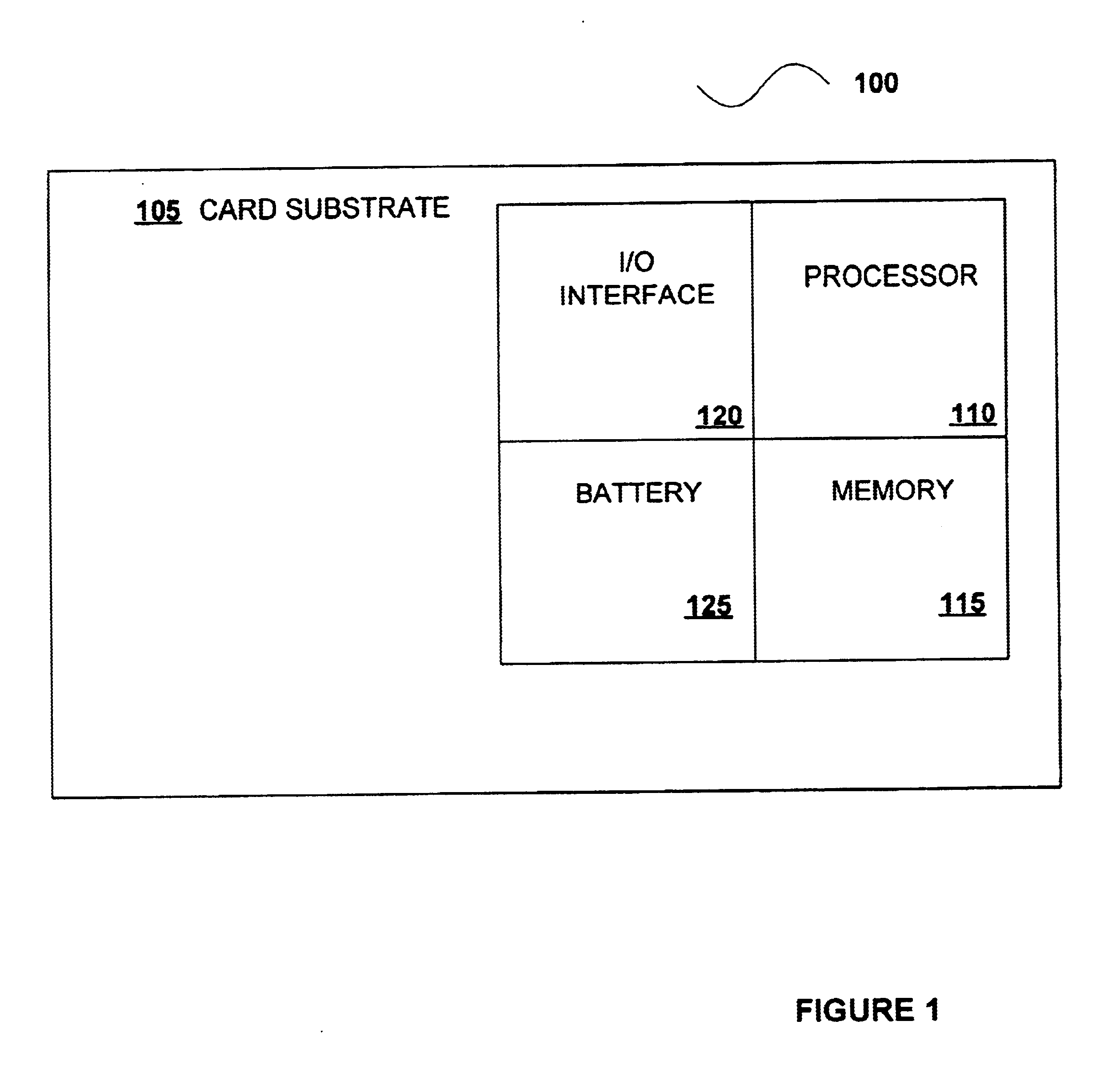
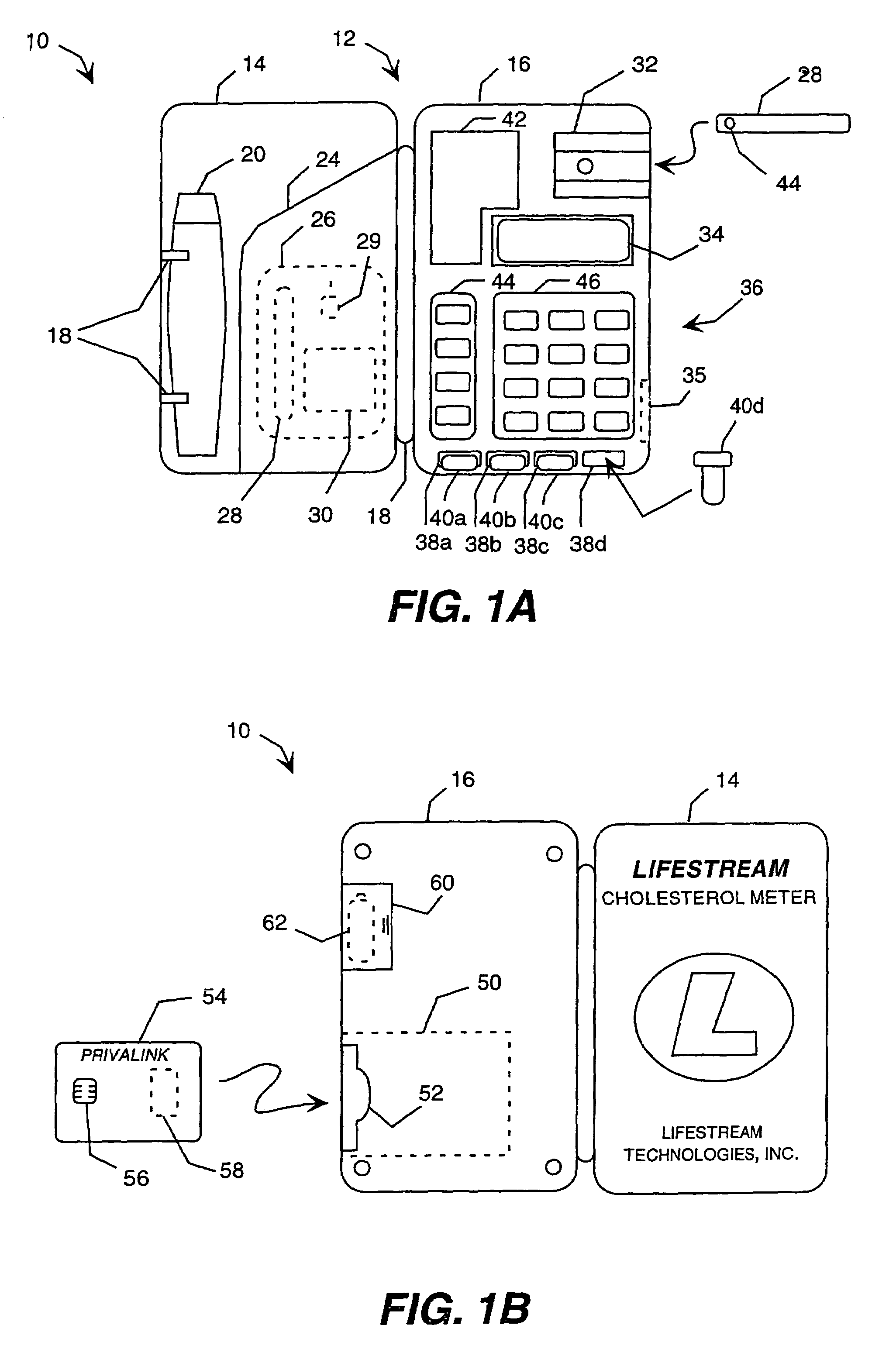
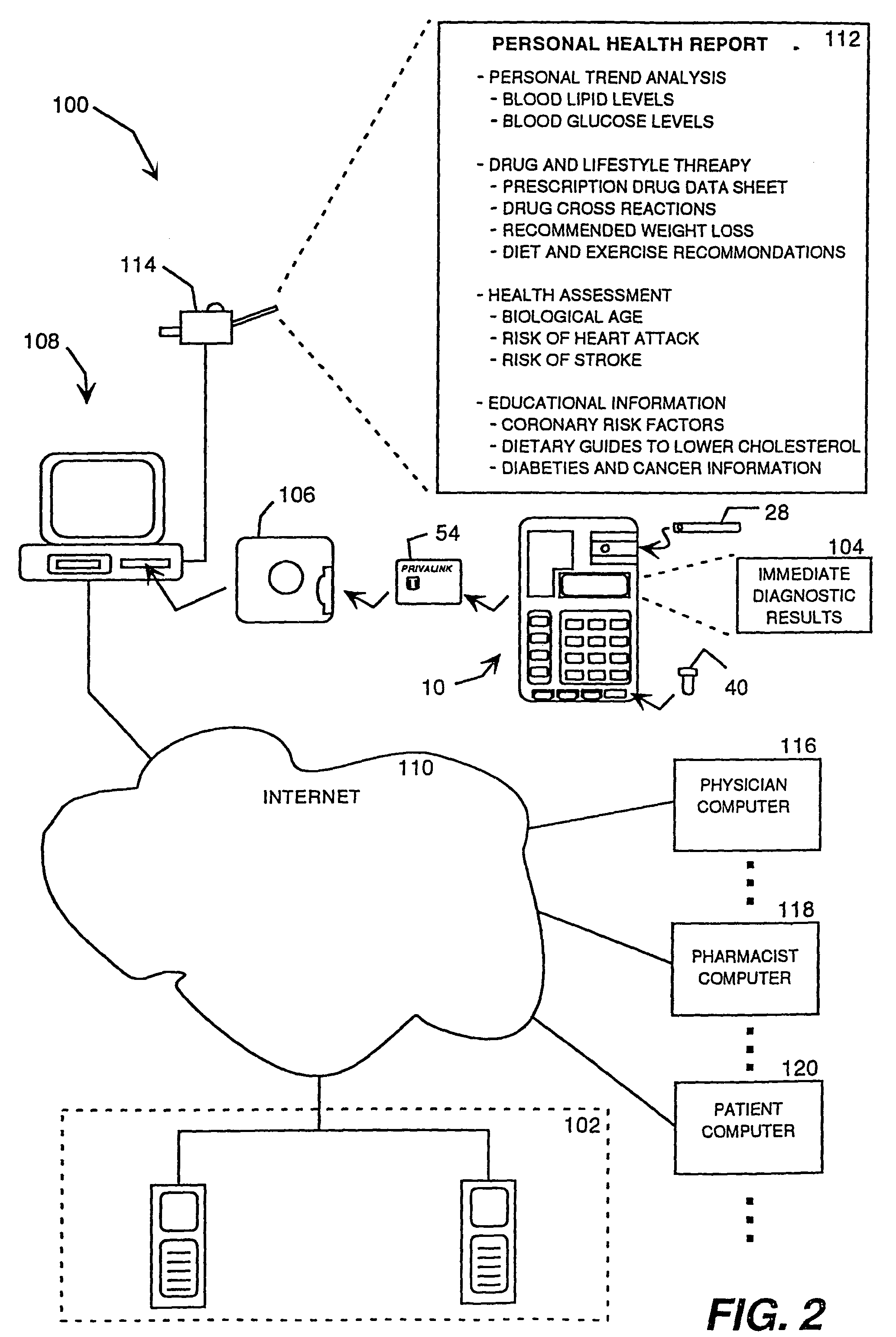
Portable remote patient telemonitoring system using a memory card or smart card
InactiveUS6454708B1Low costIncrease the number ofSurgeryRespiratory organ evaluationSmart cardFull waveform
A system and method for monitoring health parameters and capturing data from a subject. The system is characterized by a cordless, disposable sensor band with sensors for measuring full waveform ECG, full waveform respiration, skin temperature, and motion, and a connector which accepts a memory card or a smart card for storage of the measured data. After a predetermined period of time, such as when the sensor band is removed, the memory card or smart card is removed and inserted into a monitoring device which reads the stored health parameter data of the subject. The monitoring device includes a base station that includes a memory / smart card reader and is connected to conventional phone lines for transferring the collected data to a remote monitoring station. The base station may also capture additional clinical data, such as blood pressure data, and to perform data checks. Subject safety is enhanced by the ability of the base station to compare clinical data, e.g. ECG, against given profiles and to mark events when appropriate or when the base station is programmed to do so. The remote monitoring station allows the presentation and review of data (including events) forwarded by the sensor band. ECG analysis software and a user-friendly graphical user interface are provided to remotely analyze the transmitted data and to permit system maintenance and upkeep. In alternative embodiments, a smart card includes the sensor band's electronics and / or signal transmission circuitry in conjunction with a portable data logger so that the electronics may be reused from one disposable sensor band to the next without limiting the patient's range of movement. The system of the invention has useful application to the collection of subject clinical data during drug trials and medical testing for regulatory approvals as well as management of subjects with chronic diseases.
Owner:CLEARPATH PARTNERS
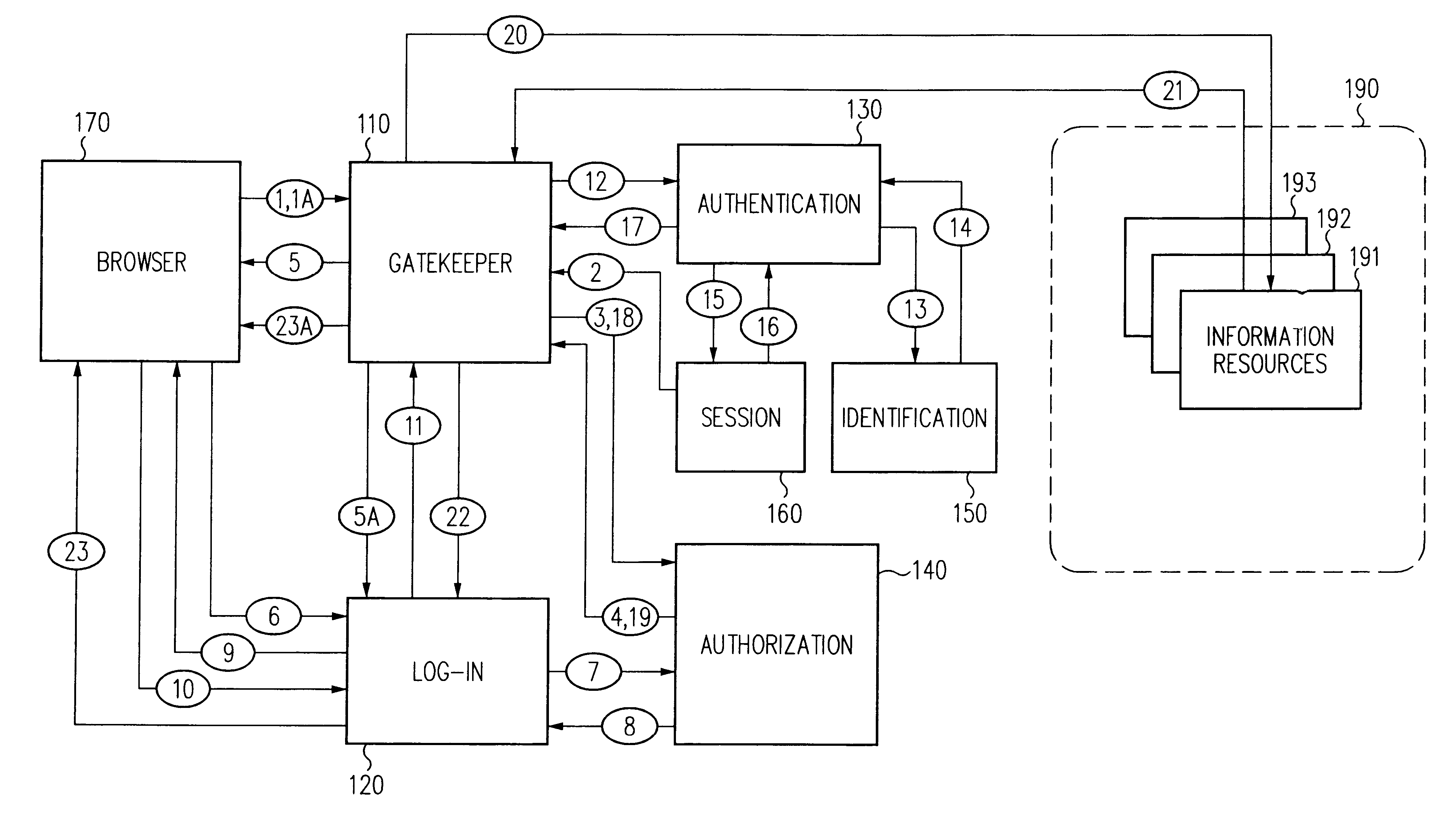
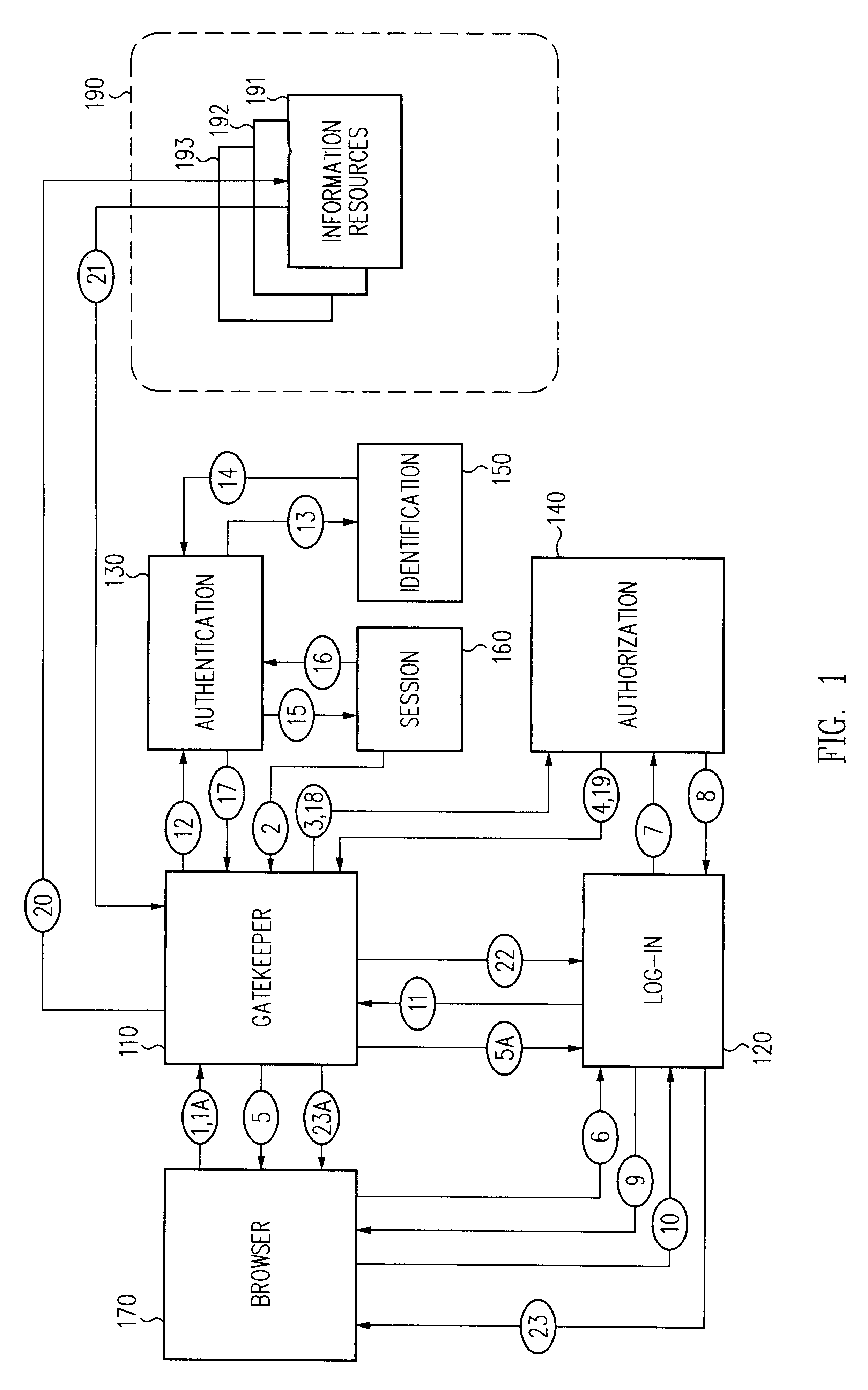
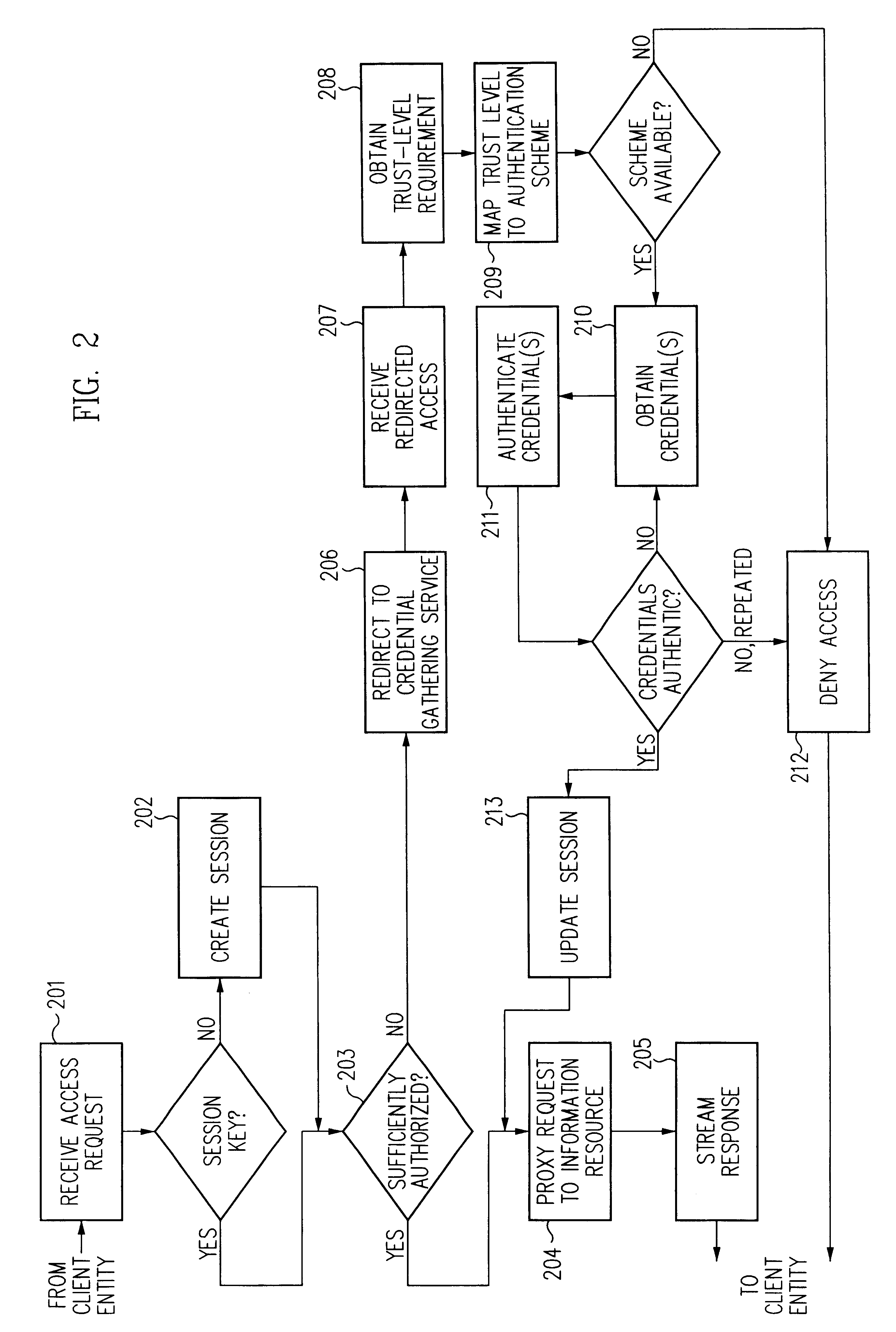
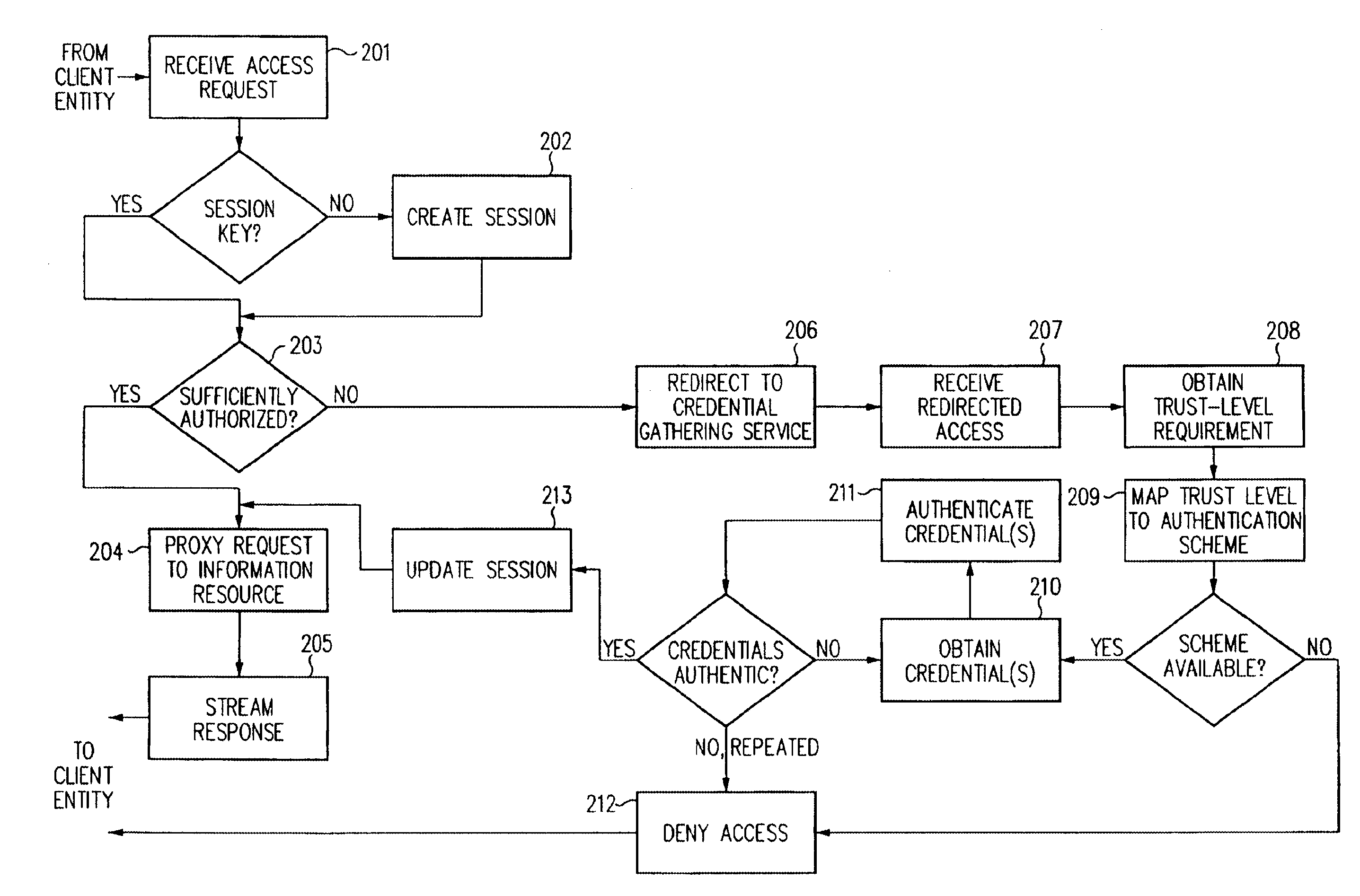
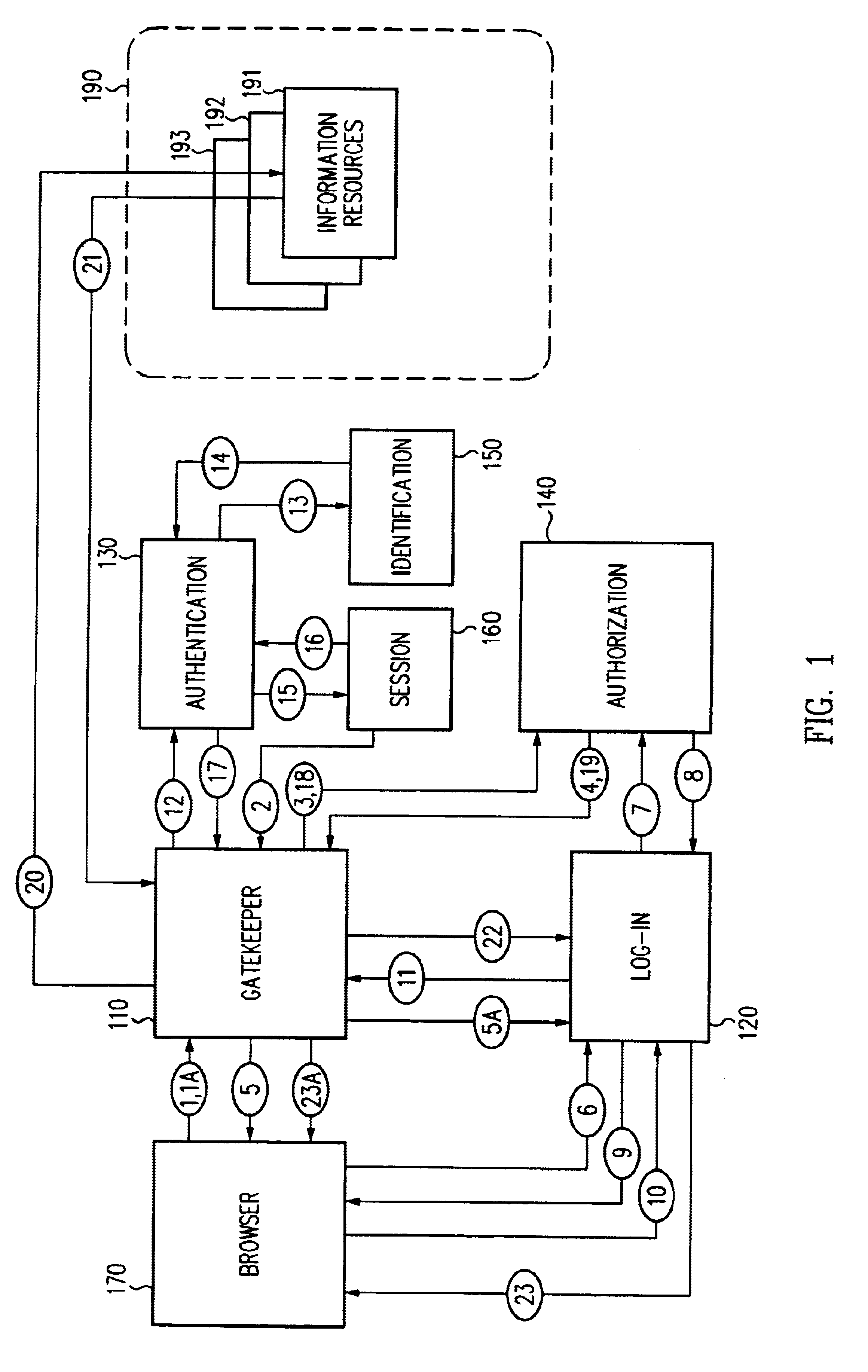
Log-on service providing credential level change without loss of session continuity
InactiveUS6609198B1Volume/mass flow measurementMultiple digital computer combinationsInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient. The security architecture allows upgrade of credentials for a given session. This capability is particularly advantageous in the context of a single, enterprise-wide log-on. An entity (e.g., a user or an application) may initially log-on with a credential suitable for one or more resources in an initial resource set, but then require access to resource requiring authentication at higher trust level. In such case, the log-on service allows additional credentials to be provided to authenticate at the higher trust level. The log-on service allows upgrading and / or downgrading without loss of session continuity (i.e., without loss of identity mappings, authorizations, permissions, and environmental variables, etc.).
Owner:ORACLE INT CORP
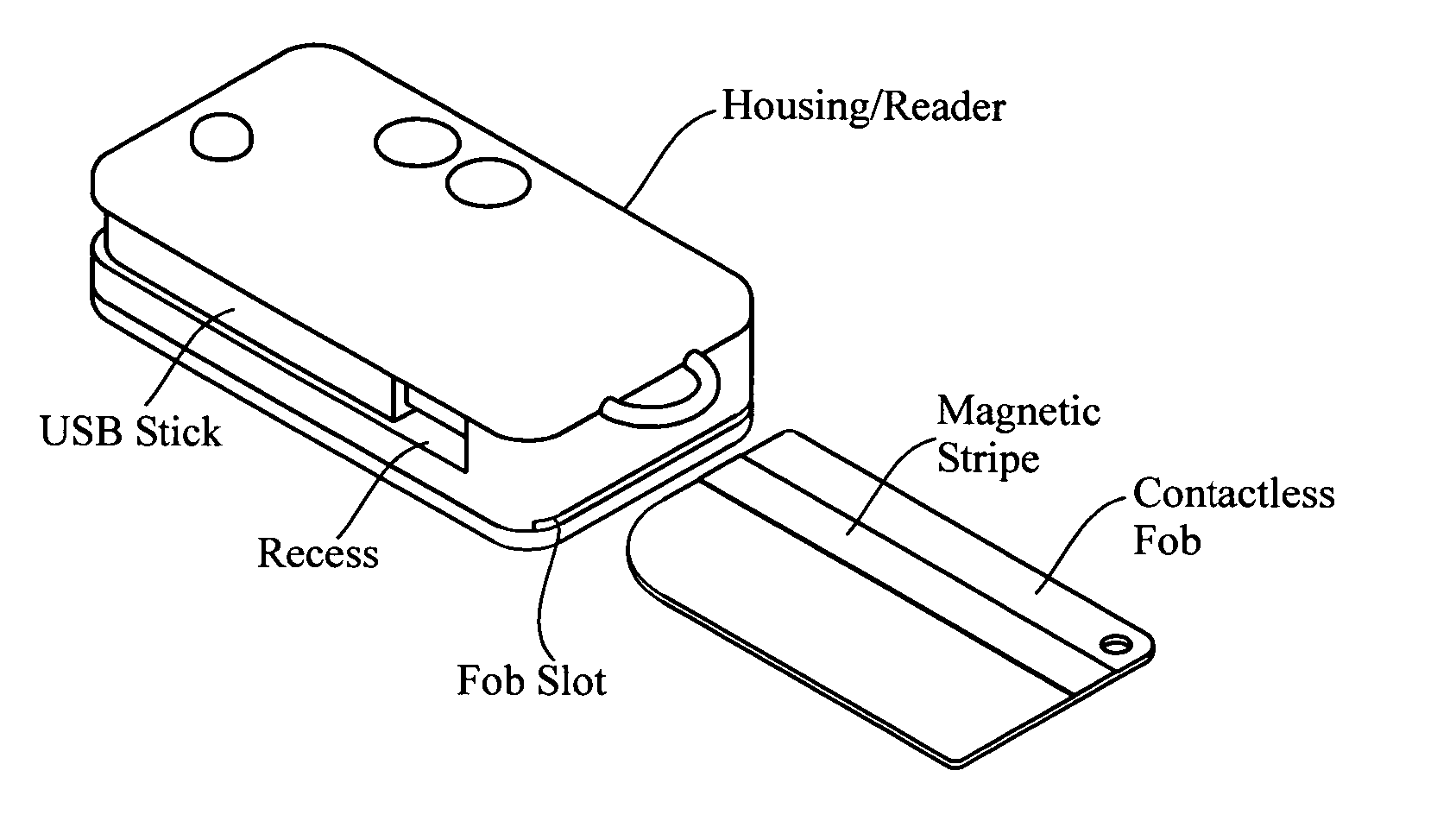
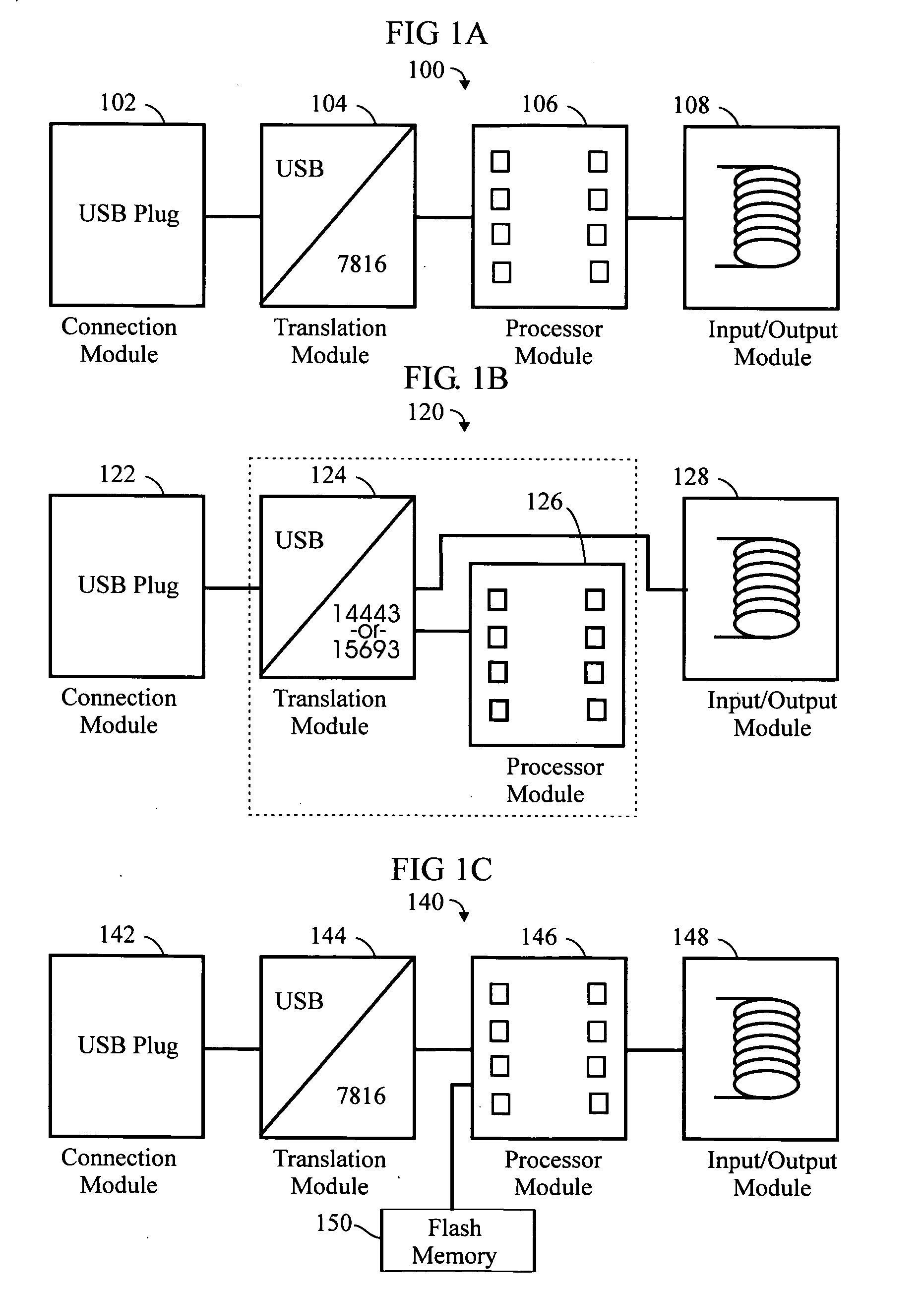
RFID token with multiple interface controller
InactiveUS20060208066A1Acutation objectsBroadcast information characterisationComputer moduleSmart card
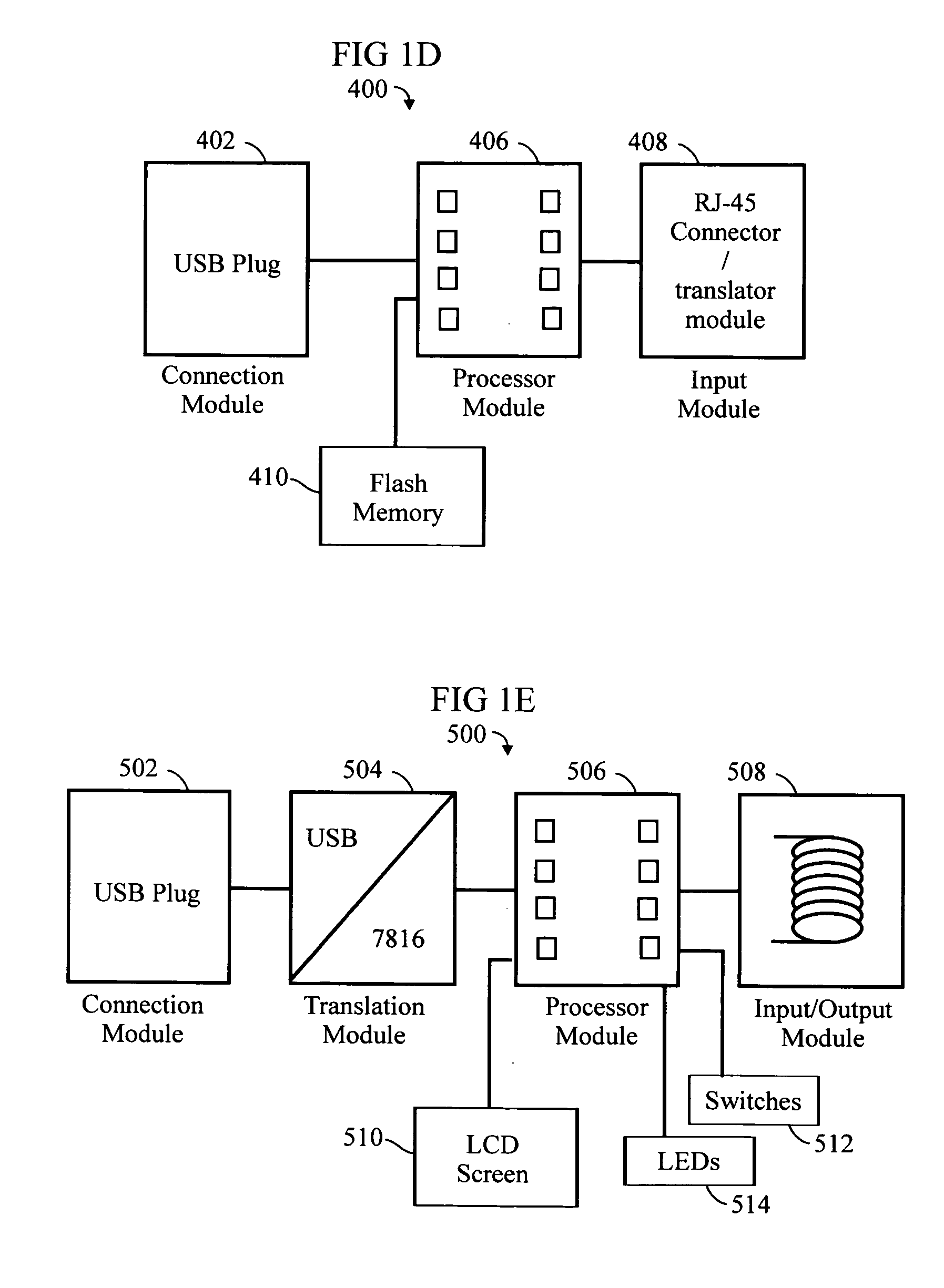
An RFID token apparatus has a connection module for interfacing with an appliance capable of communicating and interacting with remote servers and networks, a translation module for moving signals between a USB interface and a smart card interface, a processor module which may be capable of operating as a dual-interface (DI) chip; and an input / output module having at least one RF antenna and a modulator. An RFID-contactless interface according to ISO 14443 & ISO 15693 and / or NFC. A wireless interface according to Zigbee, Bluetooth, WLAN 802.11, UWB, USB wireless and / or any similar interface. An RFID reader apparatus has a housing; a slot for a contact or contactless fob; and a USB stick alternately protruding from the housing and retracted within the housing.
Owner:DPD PATENT TRUST
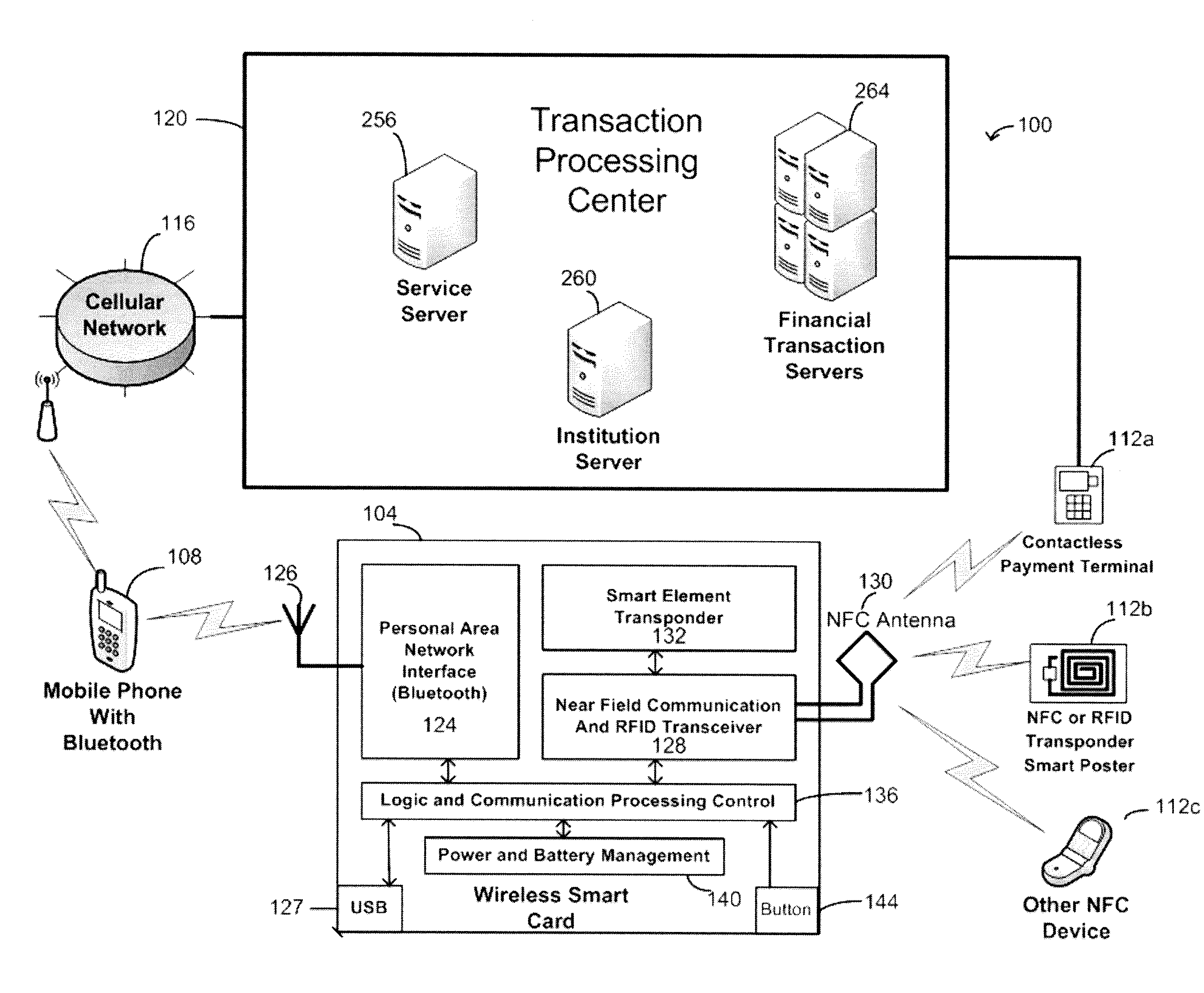
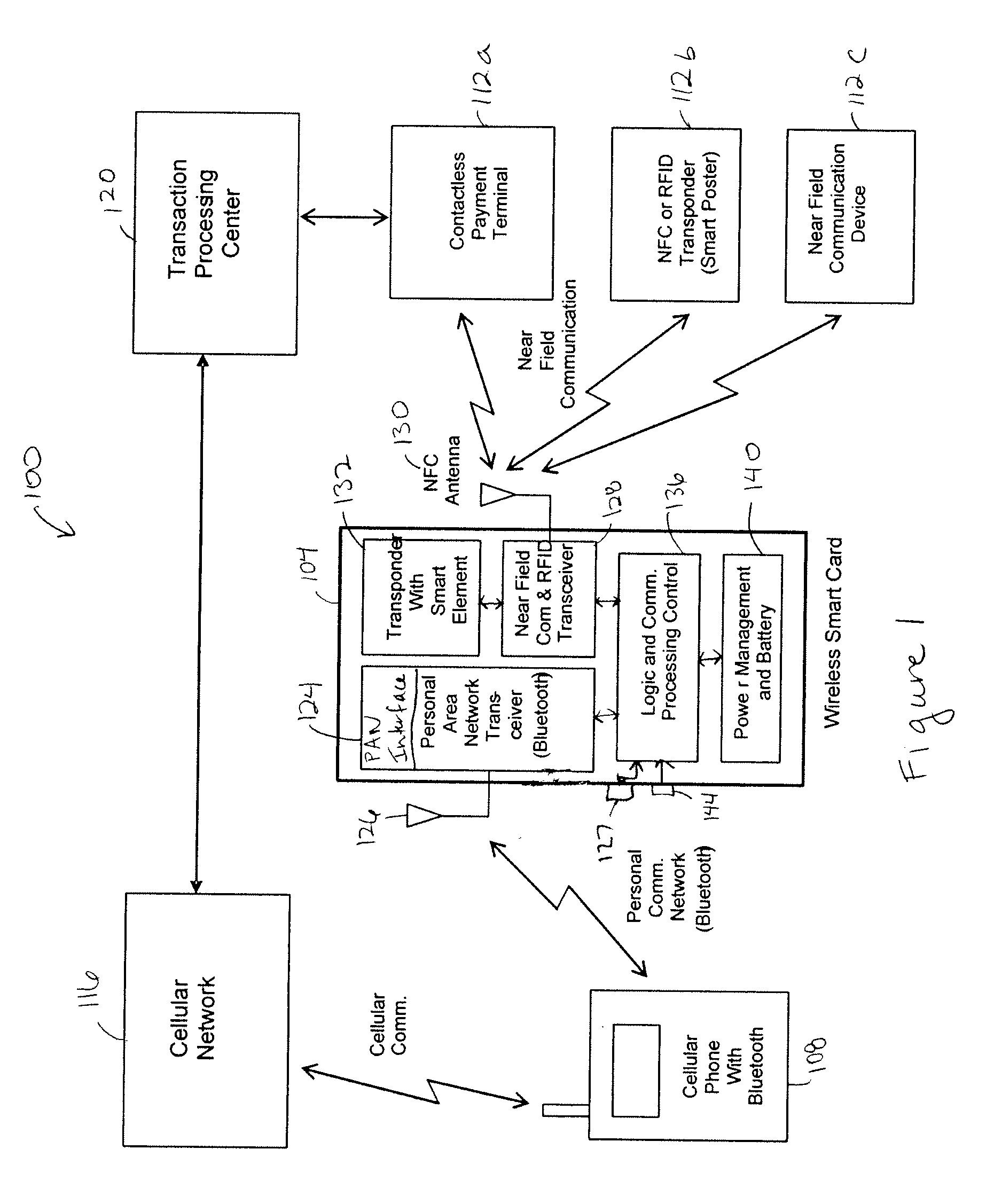
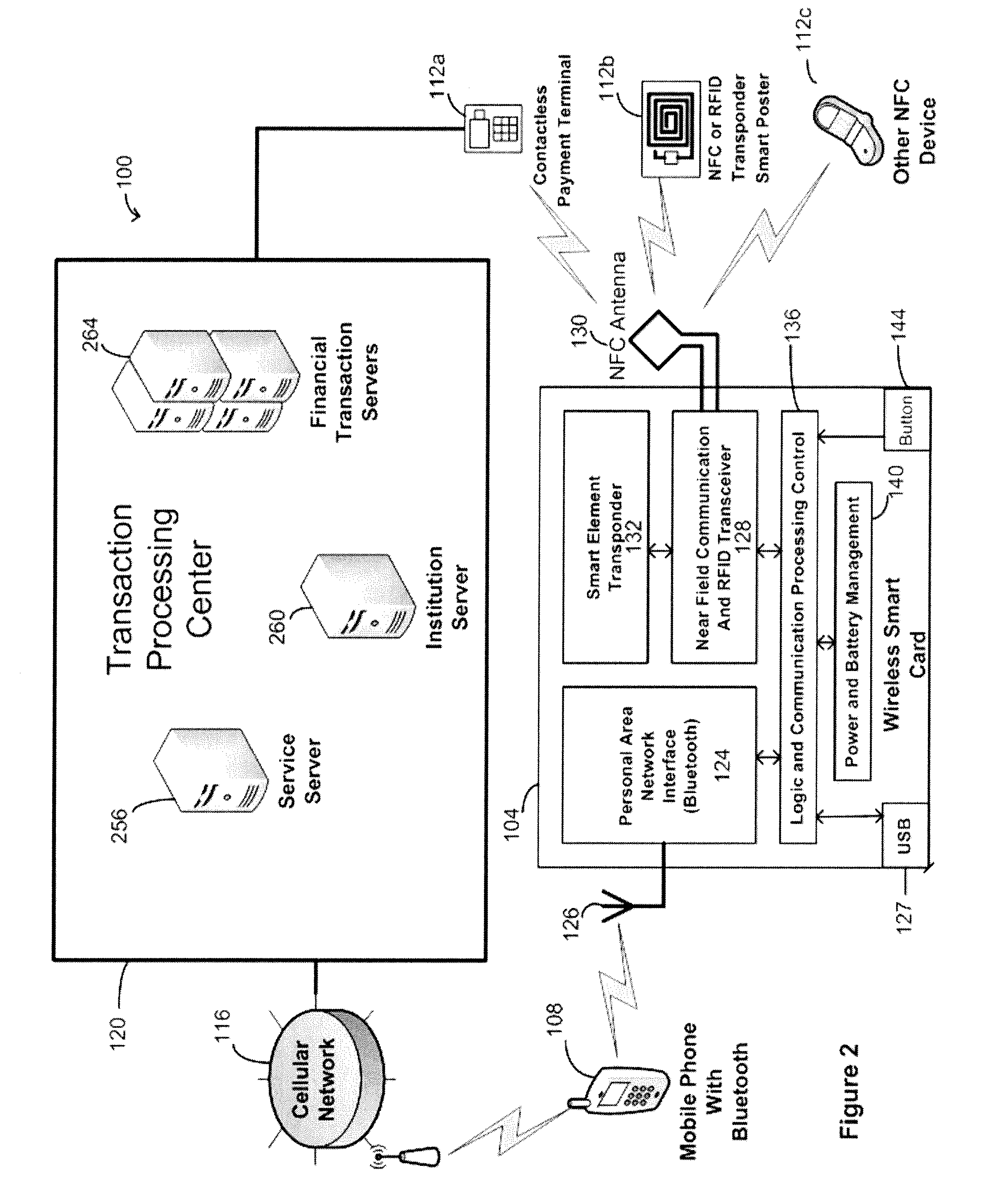
Wireless smart card and integrated personal area network, near field communication and contactless payment system
A wireless smart card having a personal area network transceiver, such as a Bluetooth transceiver, to couple the wireless smart card with a mobile communication device, and a near field communication (NFC) and radio-frequency identification (RFID) transceiver to couple the wireless smart card to a wireless transaction device, and a transponder with a secure element to allow secure communications between the mobile communication device with the wireless smart card and the wireless smart card and the wireless transaction device is described. The wireless smart card allows, for example, contactless payment through a Bluetooth-enabled mobile communication device without modification to the mobile communication device.
Owner:WIRELESS DYNAMICS
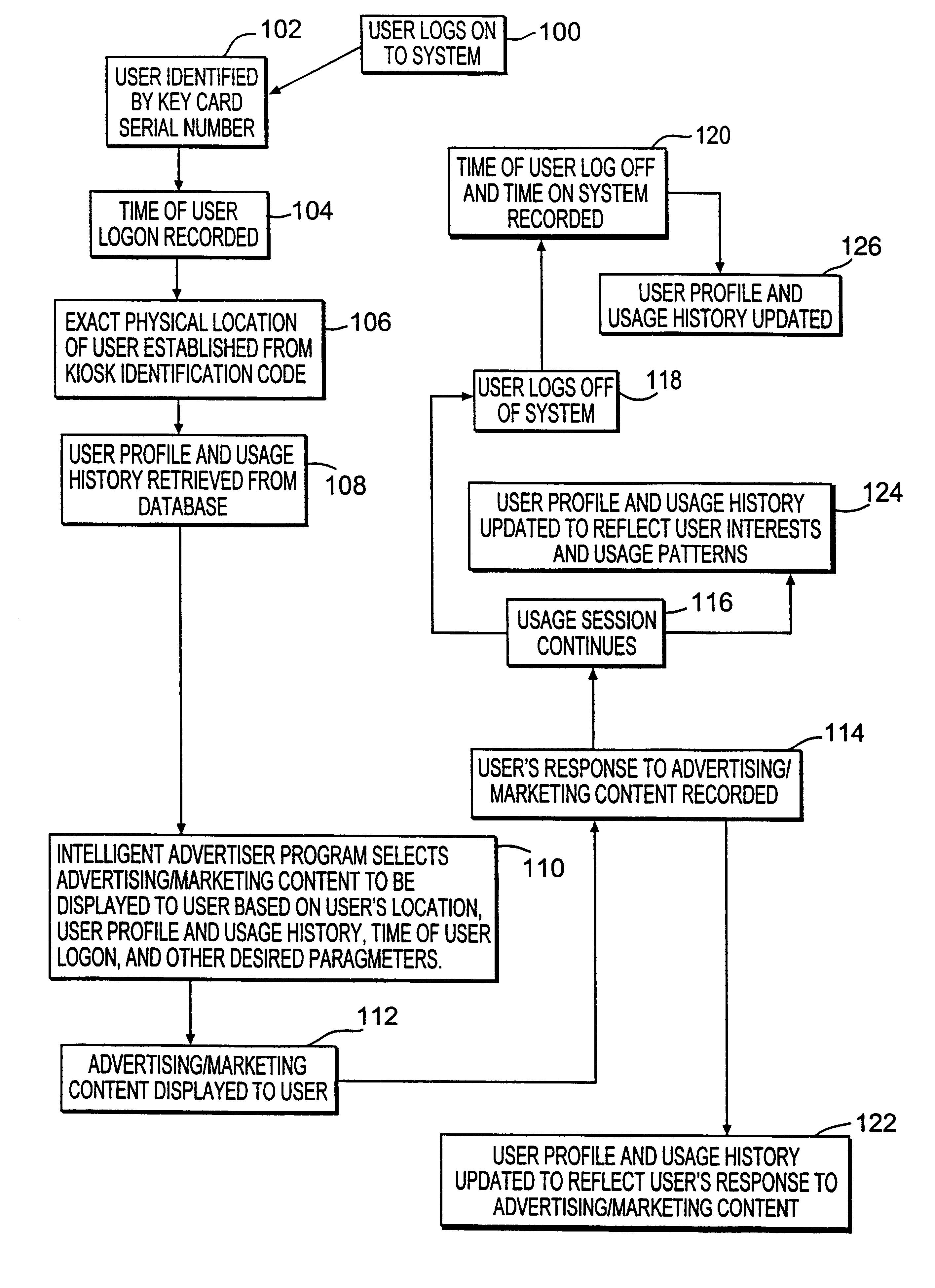
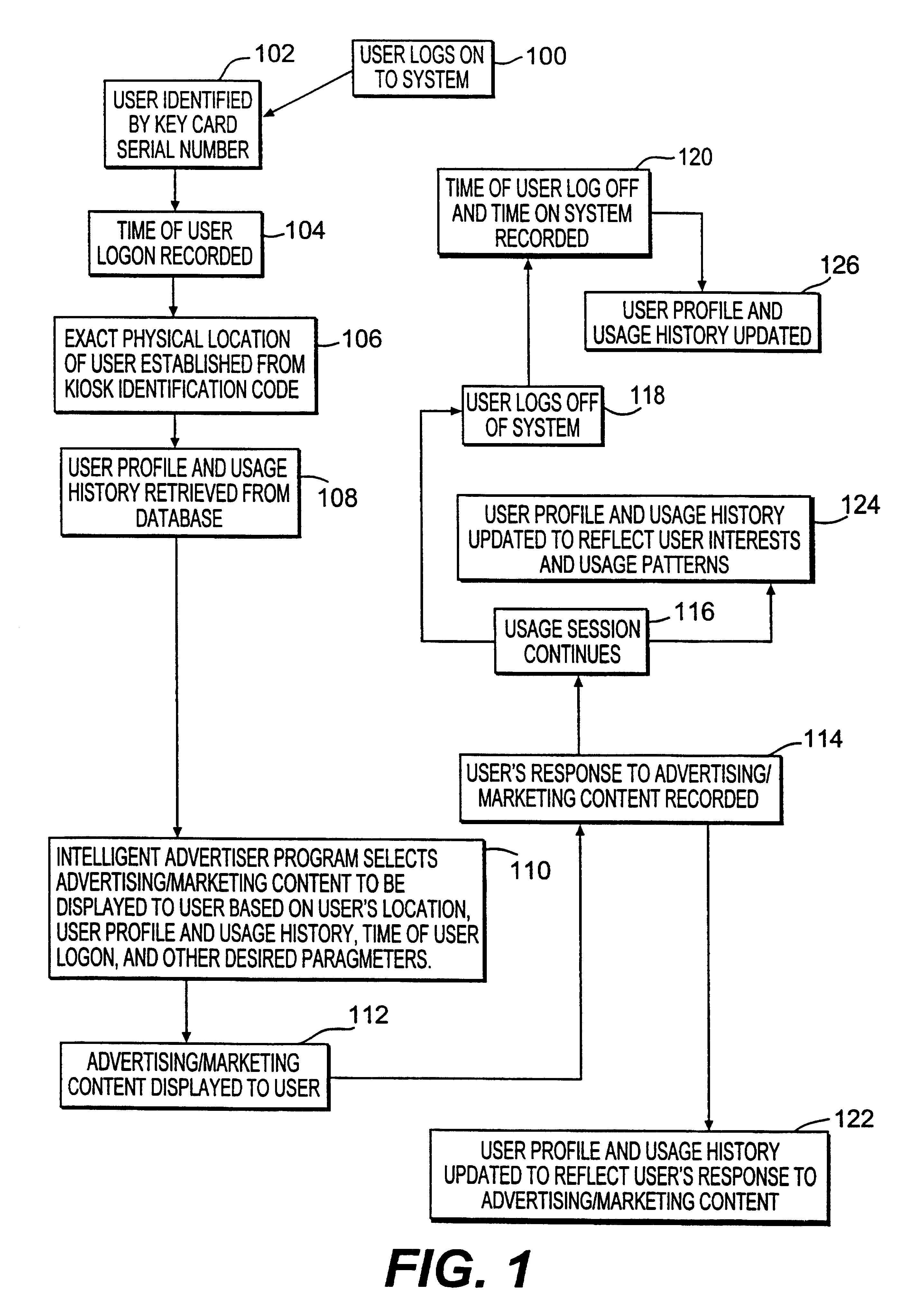
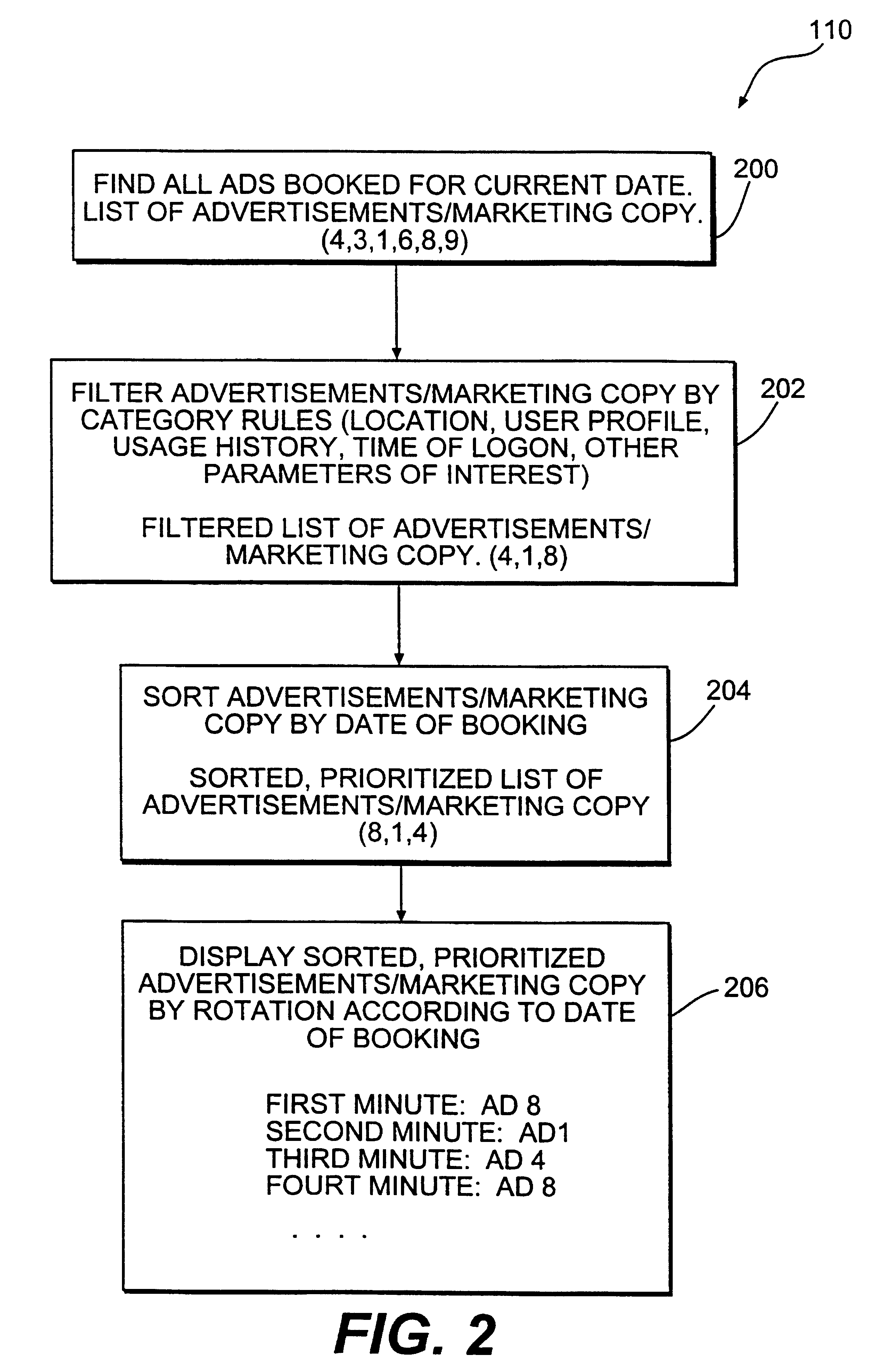
Method and system for providing personalized online services and advertisements in public spaces
InactiveUS6847969B1Without time-consuming searchingComplete banking machinesAcutation objectsPersonalizationPersonal details
A method and system for providing, personalized and integrated online services for communications and commercial transactions both in private and public venues. The invention provides personalized information that is conveniently accessible through a network of public access stations (or terminals) which are enabled by a personal system access card (e.g., smart card). The invention also provides advertisers the opportunity to directly engage action; and potential user-consumers with selected advertising or marketing content based on each user's profile and usage history.
Owner:STREETABPACE
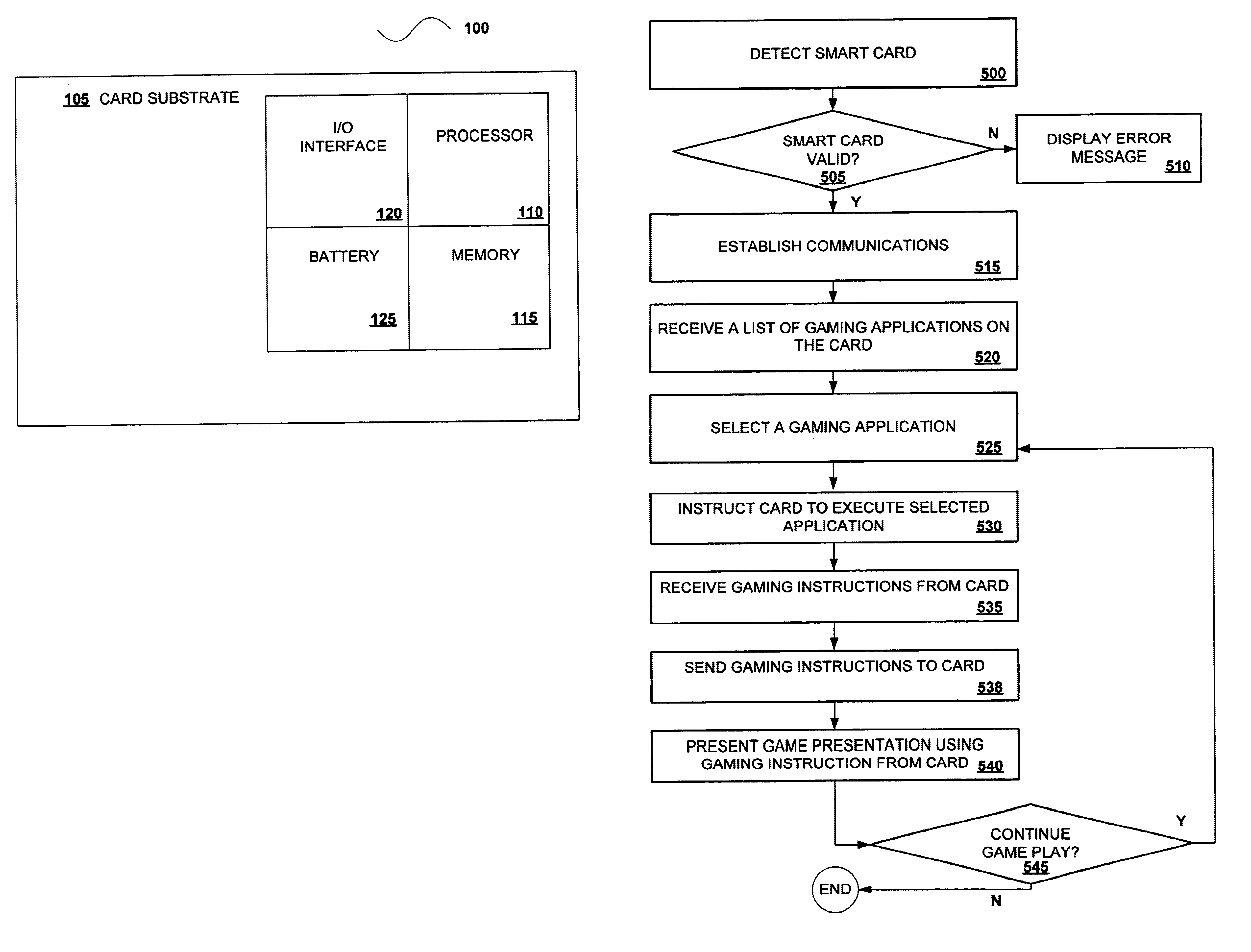
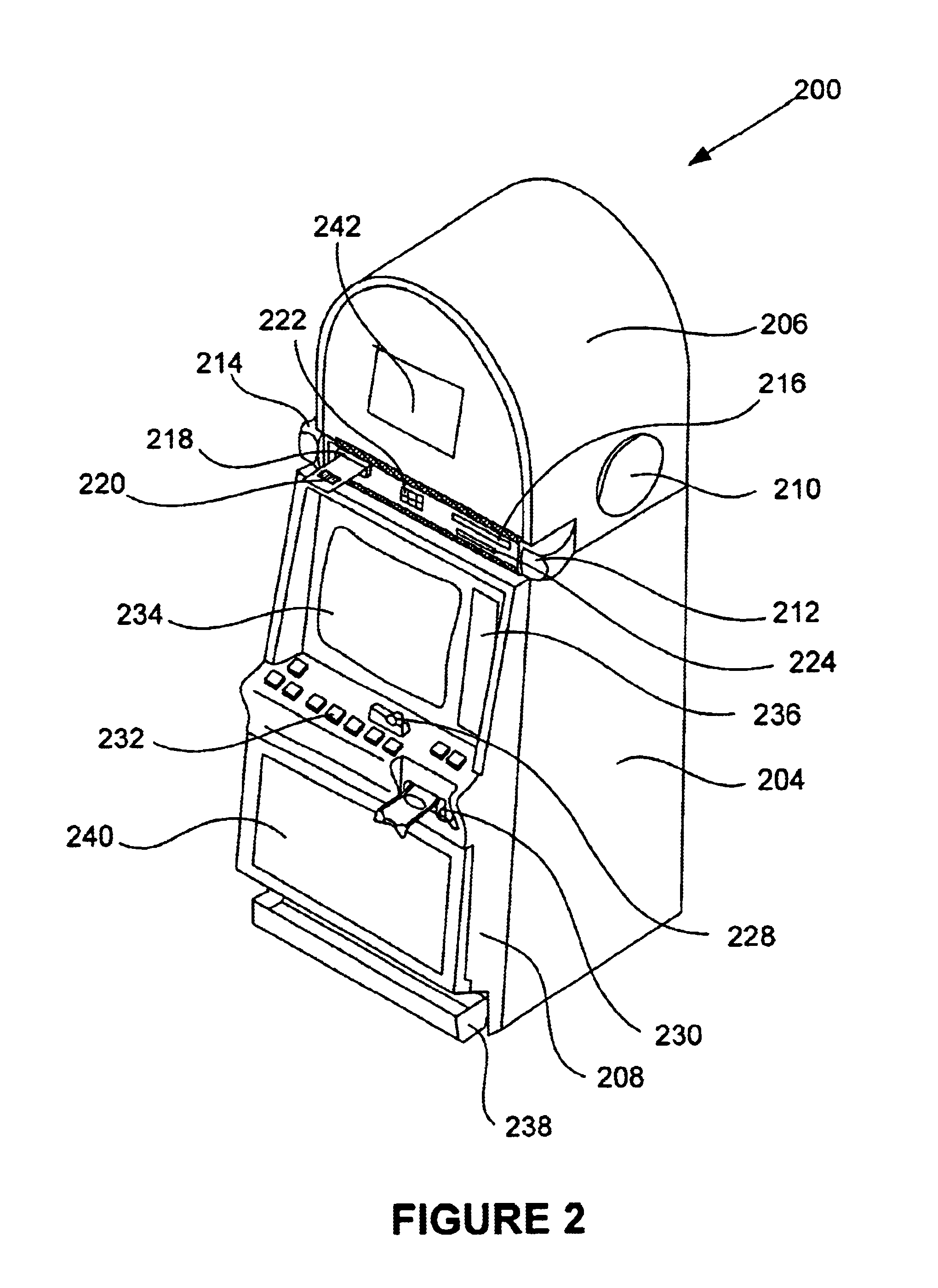
EZ pay smart card and ticket system
A disclosed smart card includes a processor and memory configured to execute a number of gaming applications, such as a bonus game application, a progressive game application, a voucher application and a paytable application, and communicate with a master gaming controller on the gaming machine. Gaming instructions, generated during the execution of one or more of the gaming application on the smart card, may be used to affect game play on the gaming machine. The gaming instructions for various gaming services may be supplied to gaming machines operating in a “stand alone” mode or gaming machine connected to some type of dedicated network. In addition, the smart card may store game components including audio game components and video game components that may be downloaded into a gaming machine and incorporated into a game presentation on the gaming machine. The smart card may be utilized at many different venues including casinos, hotels, bars, restaurants and retail stores.
Owner:IGT
Single sign-on framework with trust-level mapping to authentication requirements
InactiveUS6892307B1Digital data processing detailsUser identity/authority verificationPasswordInformation resource
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels and a log-on service obtains credentials for an entity commensurate with the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:ORACLE INT CORP
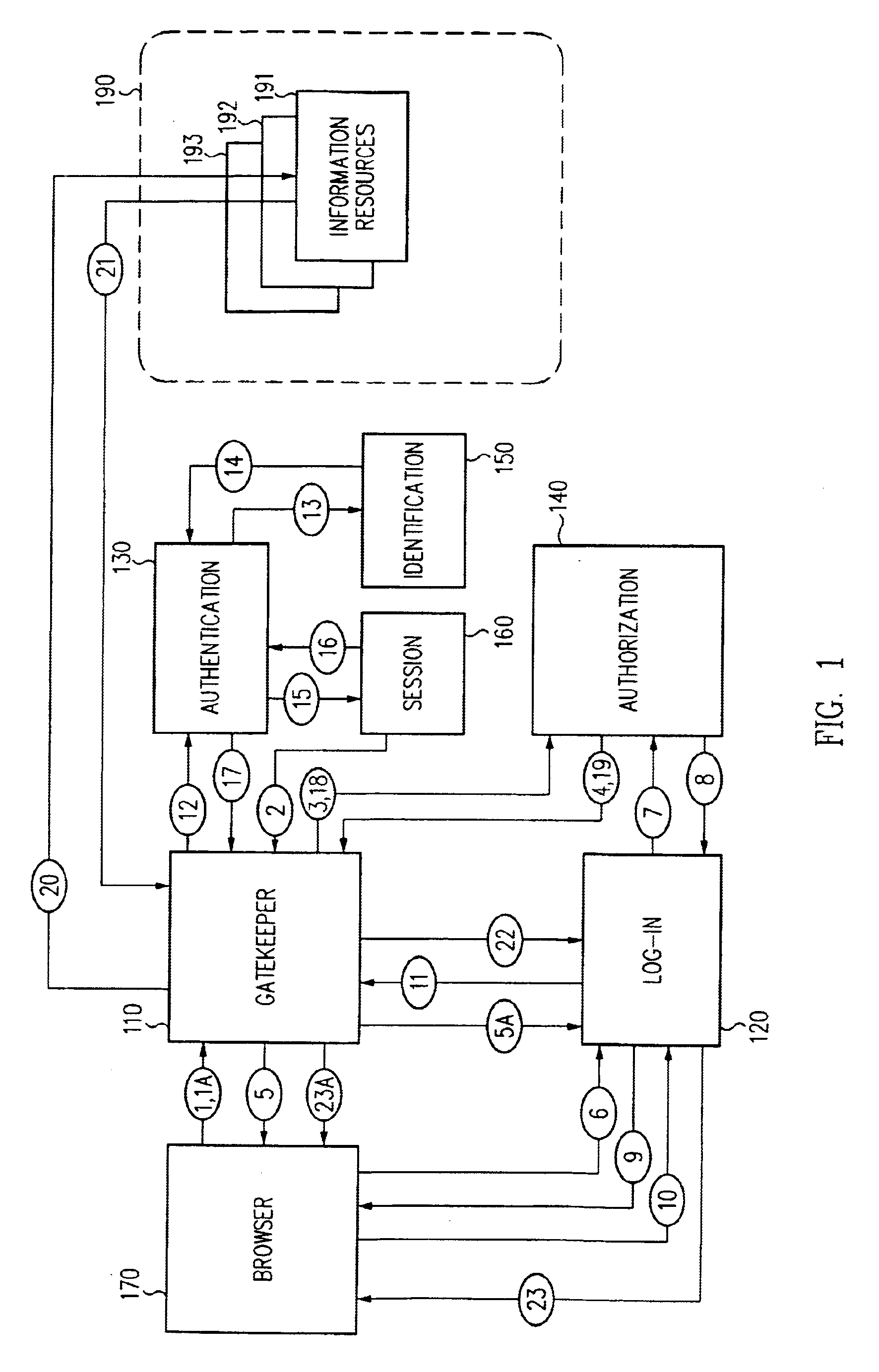
Access management system and method employing secure credentials
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
Method and apparatus for a web-based application service model for security management
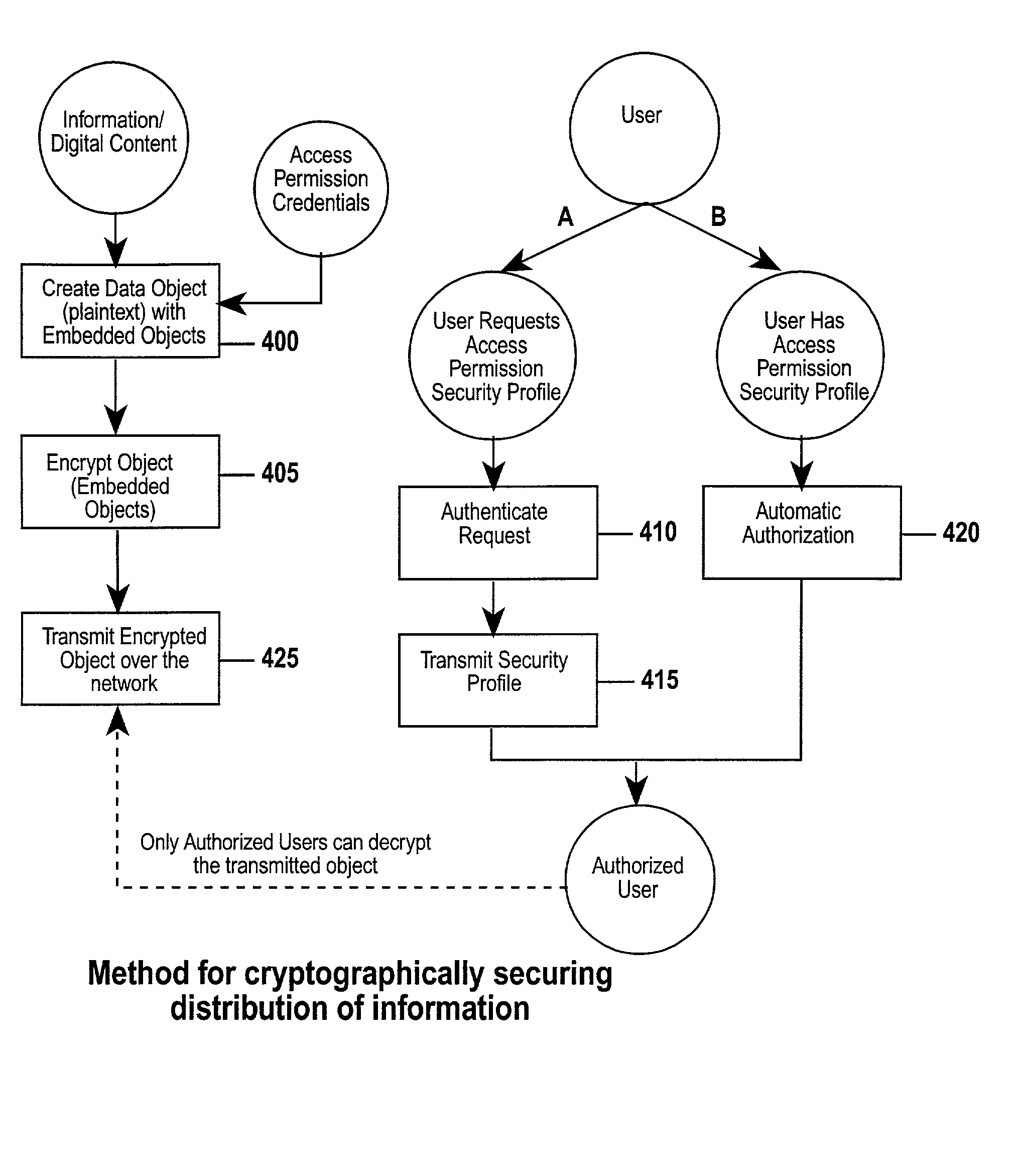
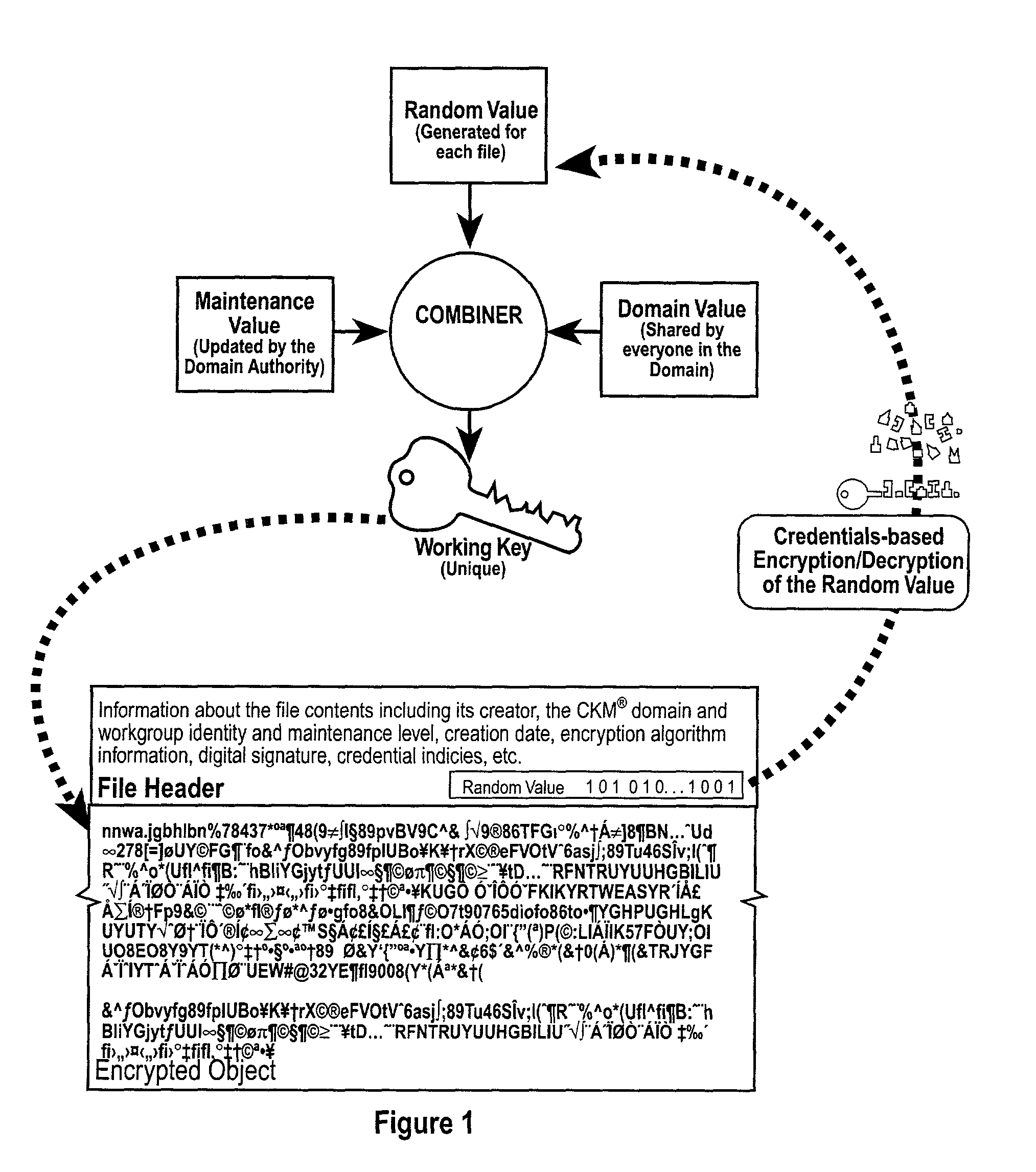
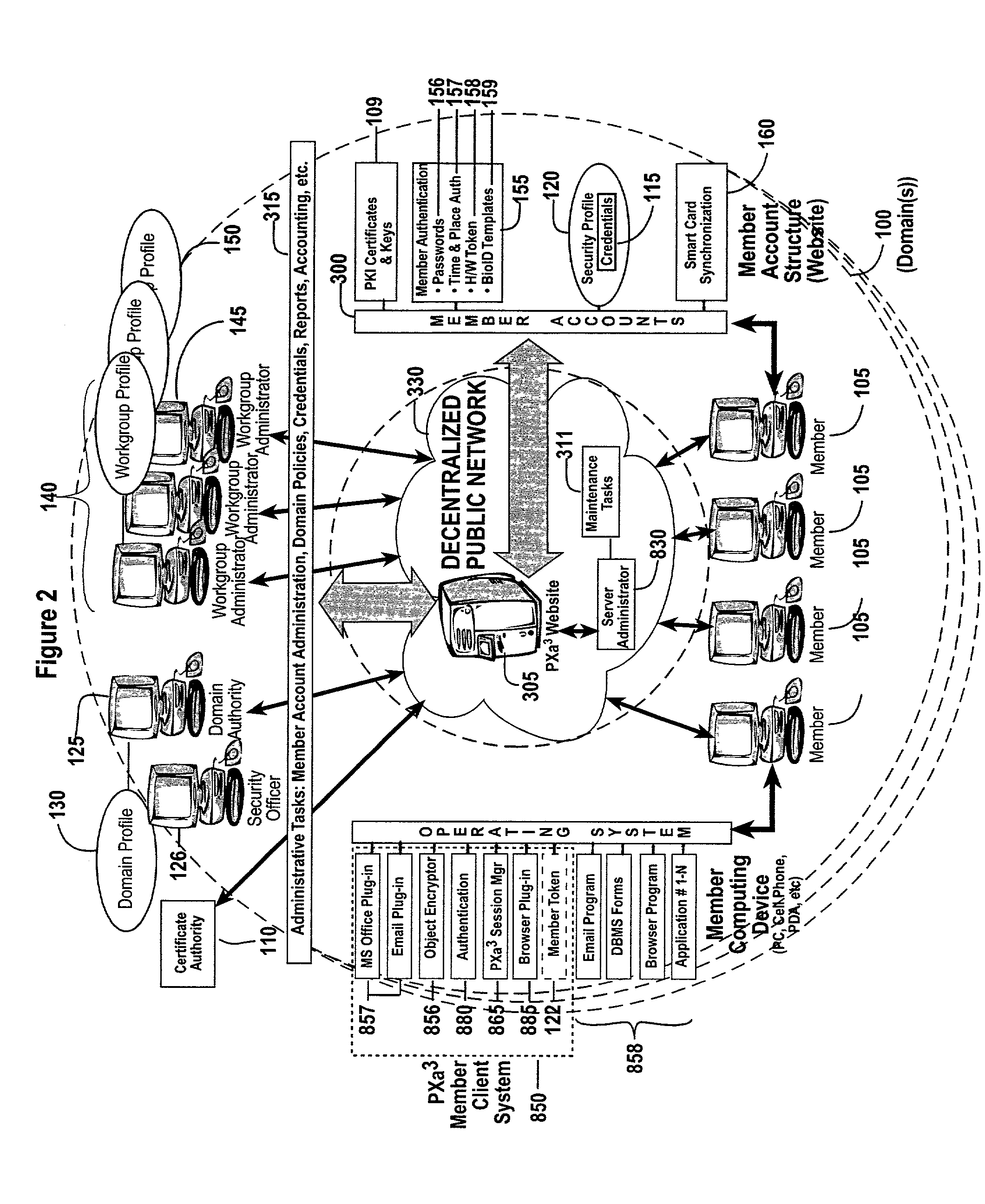
The invention combines cryptographic key management technology with various authentication options and the use of a companion PKI system in a web-centric cryptographic key management security method and apparatus called PXa3(TM) (Precise eXtensible Authentication, Authorization and Administration). The PXa3 model uses a security profile unique to a network user and the member domain(s) he / she belongs to. A PXa3 server holds all private keys and certificates, the user's security profile, including credentials and the optional authentication enrollment data. The server maintains a security profile for each user, and administrators simply transmitted credential updates and other periodic maintenance updates to users via their PXa3 server-based member accounts. Domain and workgroup administrators also perform administrative chores via a connection to the PXa3 web site, rather than on a local workstation. A member's security profile, containing algorithm access permissions, credentials, domain and maintenance values, a file header encrypting key, optional biometric templates, and domain-specific policies is contained in one of two places: either on a removable cryptographic token (e.g., a smart card), or on a central server-based profile maintained for each member and available as a downloadable "soft token" over any Internet connection.
Owner:SIVAULT INC
Programmable and expandable building automation and control system
InactiveUS20050090915A1Readily modified and expanded and repairedReduces warranty and support costProgramme controlSampled-variable control systemsModem deviceSmart card
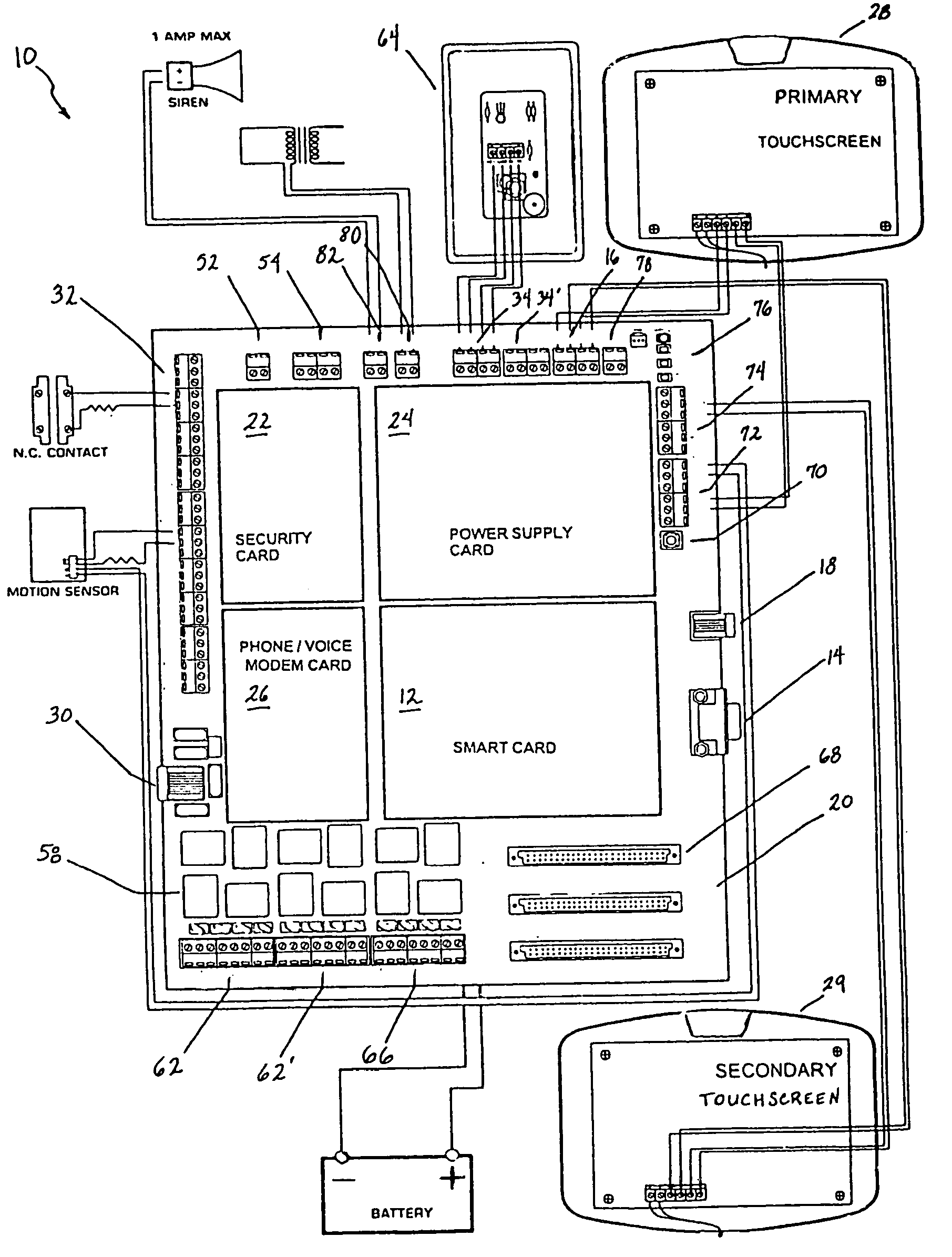
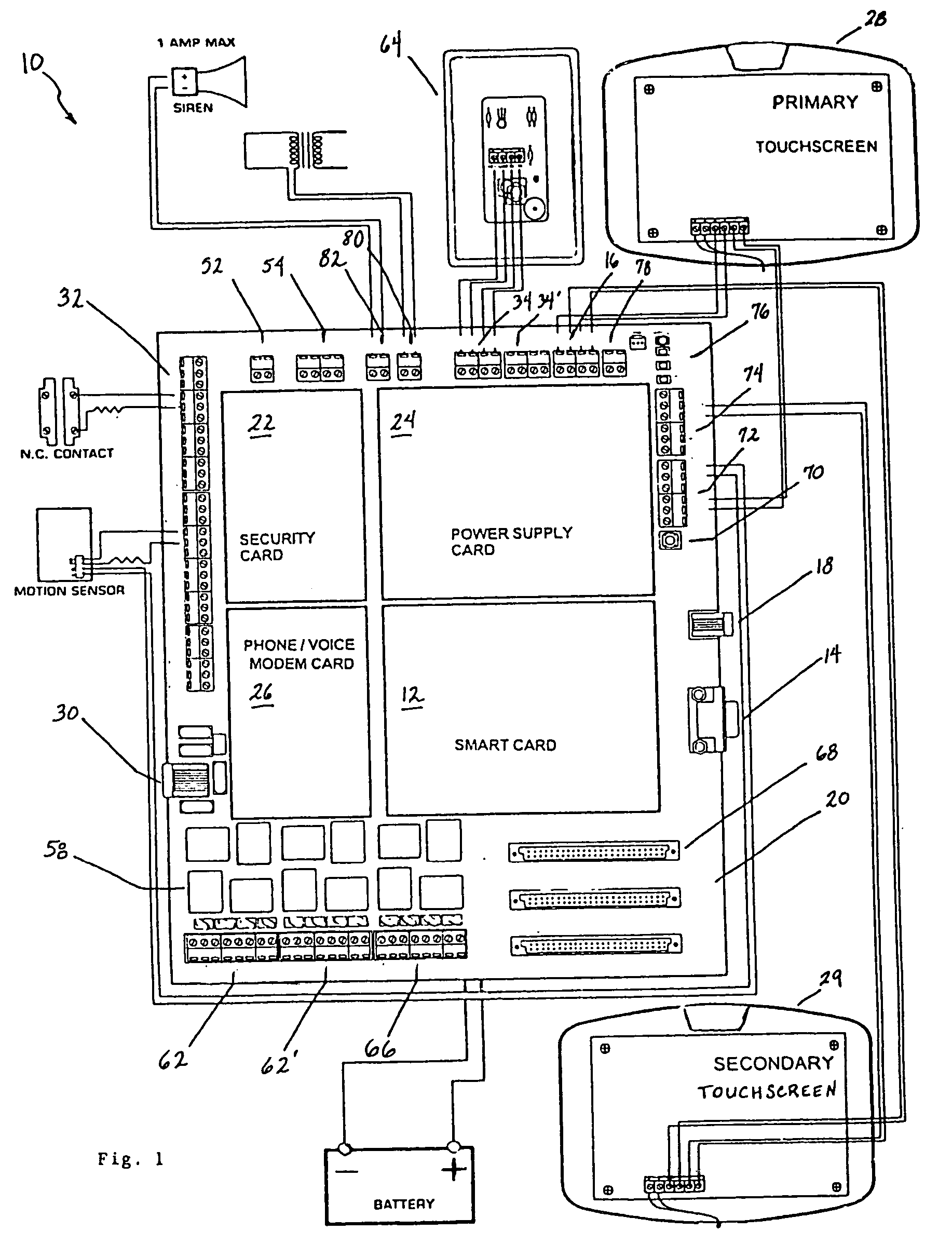
A programmable and expandable building automation and control system 10. A system platform supports interchangeable smart card 12, security card 22, power supply card 24, telephone / voice / modem card 26, HVAC relay control 62, auxiliary relay control 66, power 80, telephone interface 30, sensor analog inputs 32, smoke detector interface 54, siren / strobe output 82, tamper loop 52, protected peripheral power supply 72, switched peripheral power supply 74, PLC communication protocol interface 18, RS 232 communication interface 14, RS 485 communication interface 16, touchscreen user interface 28, and “smart” key interface 34 via “smart” key 104. In addition to touchscreen and smart key interface, user-interface with system 10 is accommodated via telephone, personal computer or personal digital assistant, or through infrared or radio frequency transmission.
Owner:SMART SYST TECH
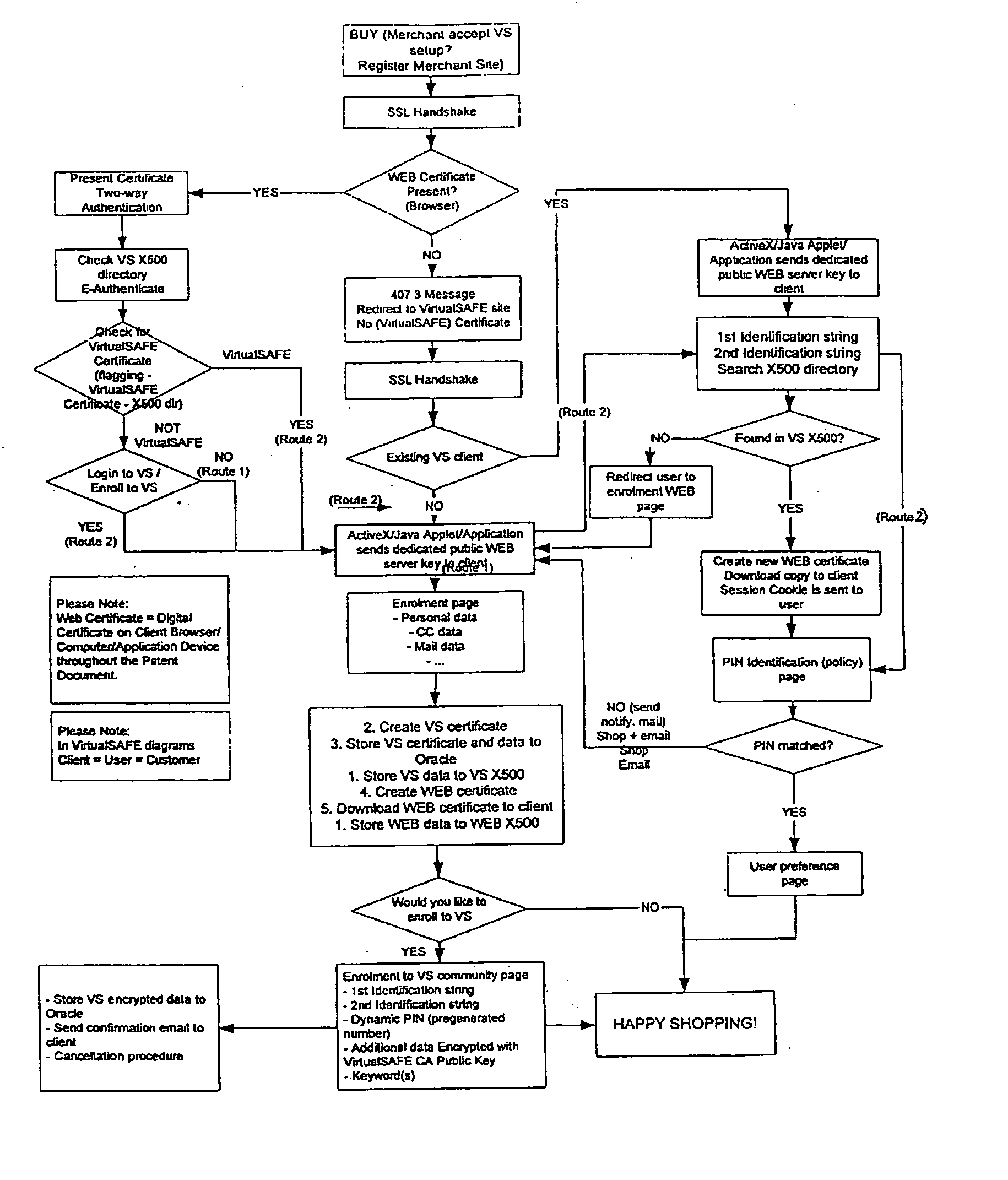
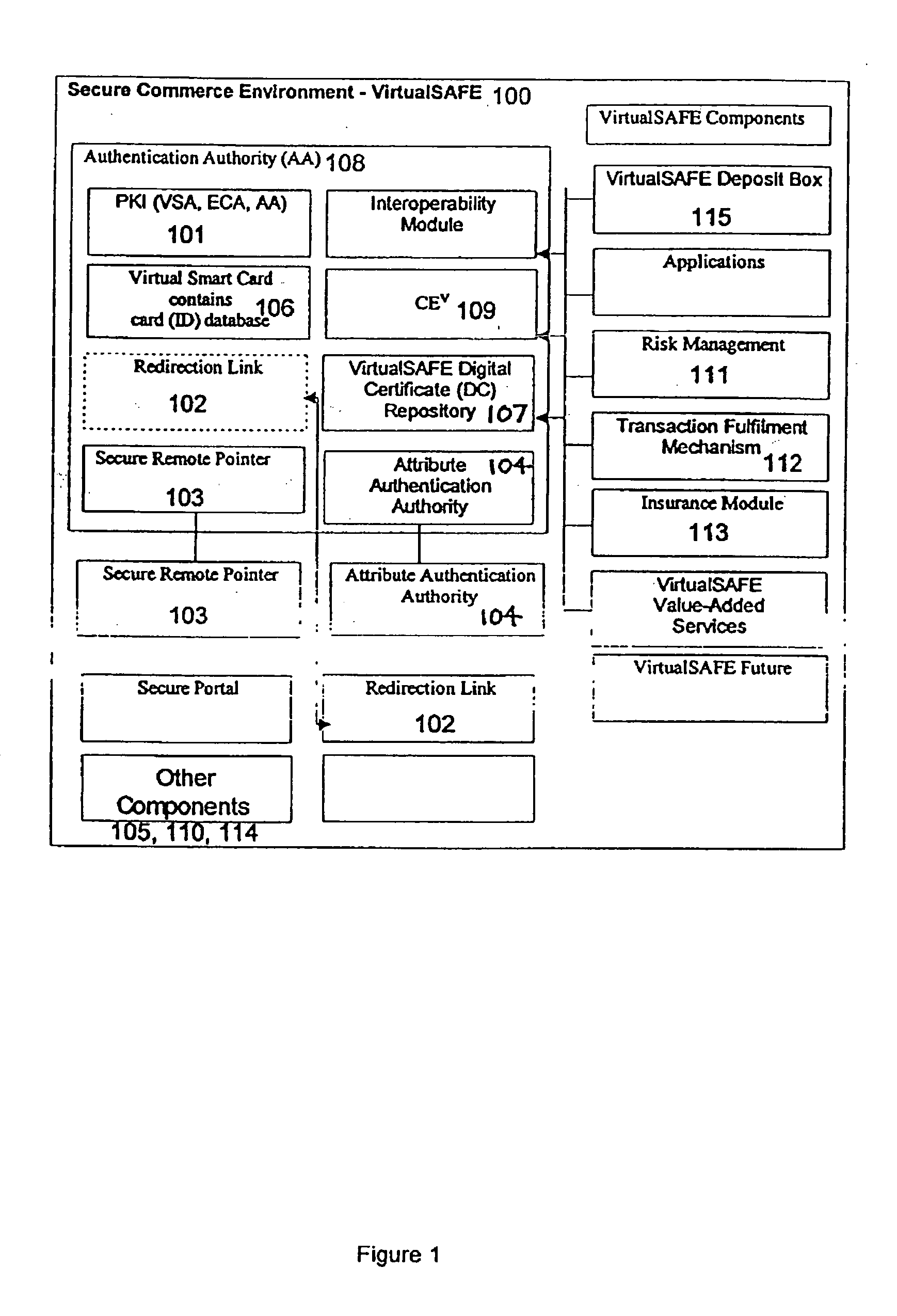
Method and system for a virtual safe
Owner:SARCANIN BRANKO
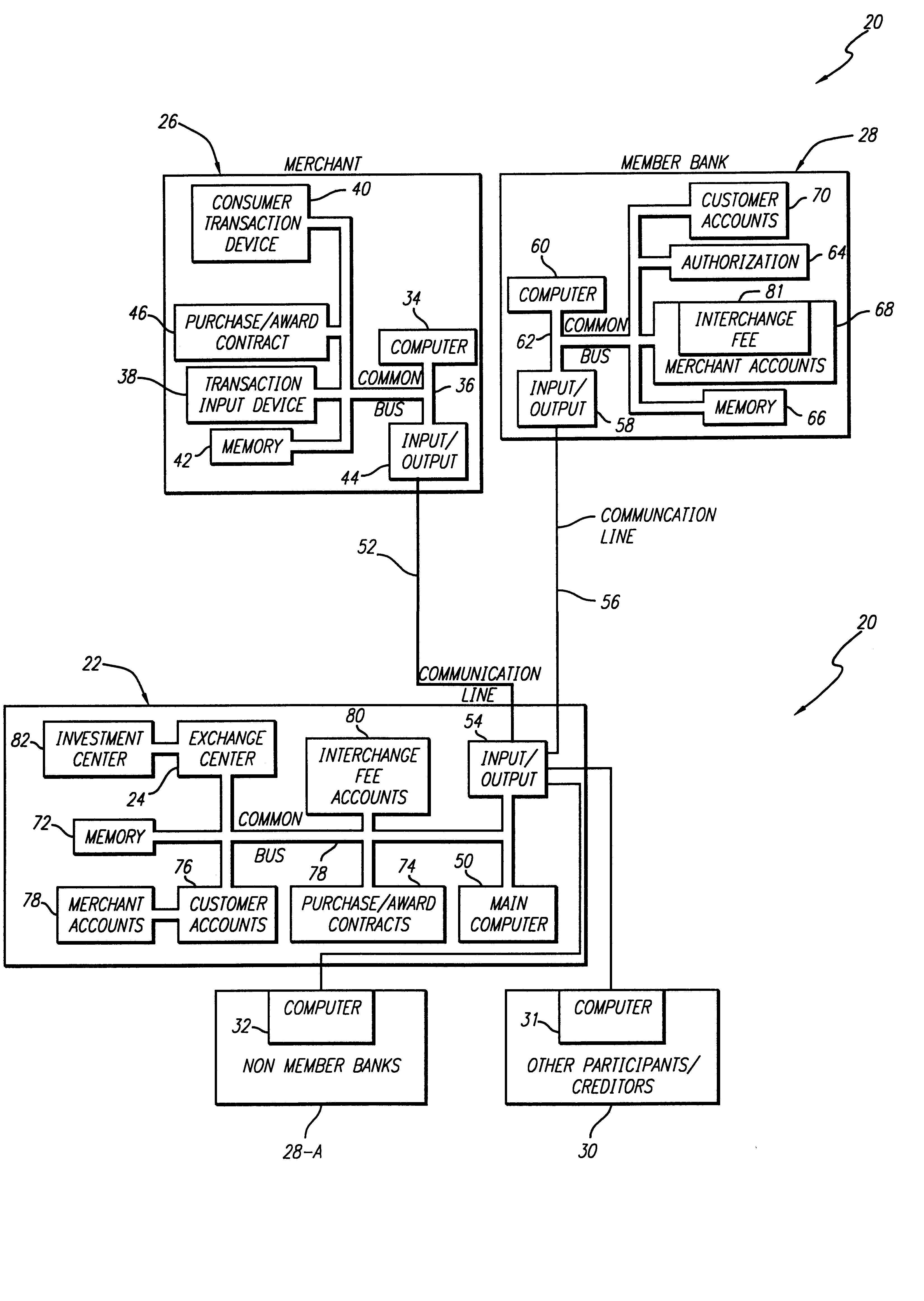
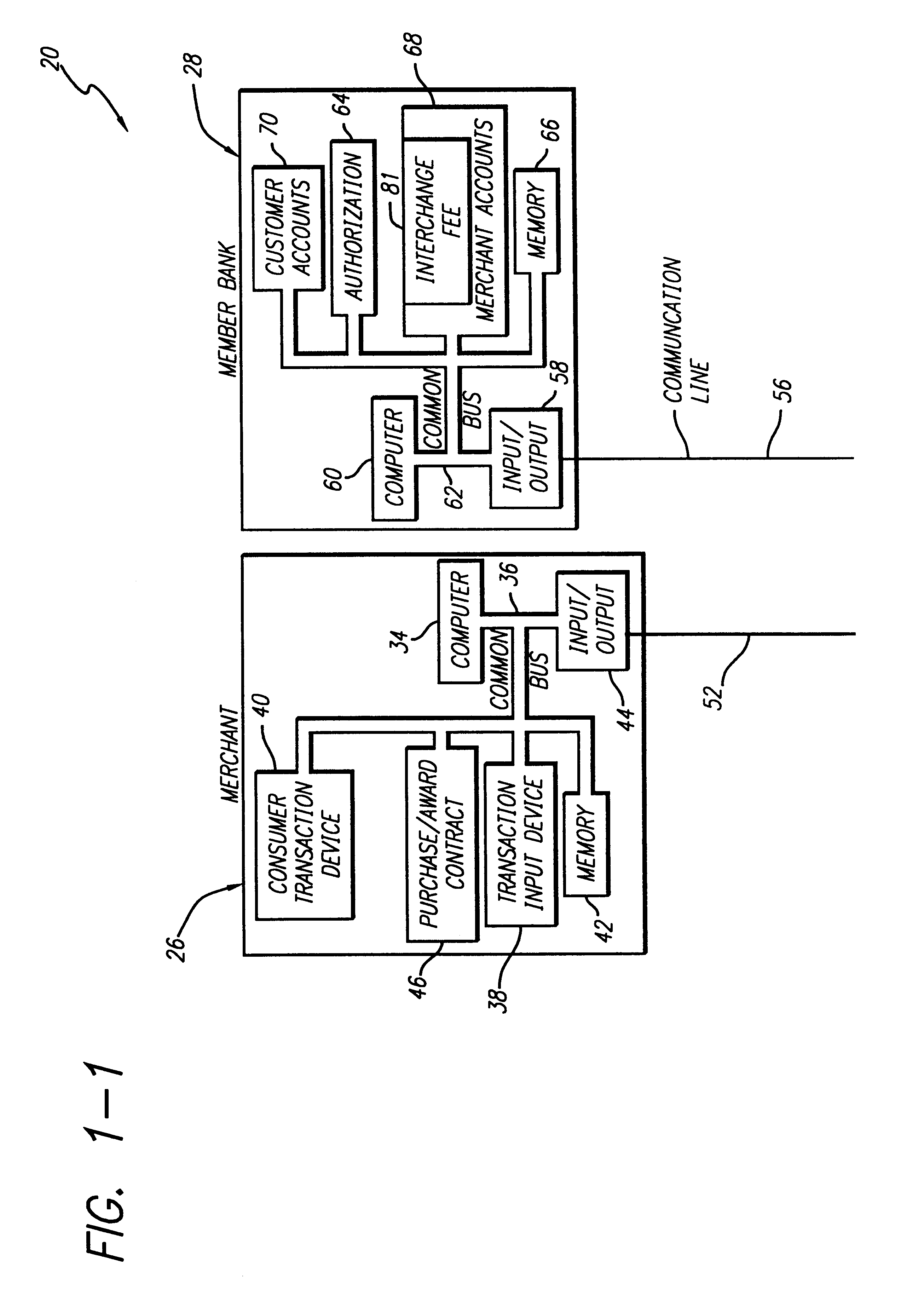
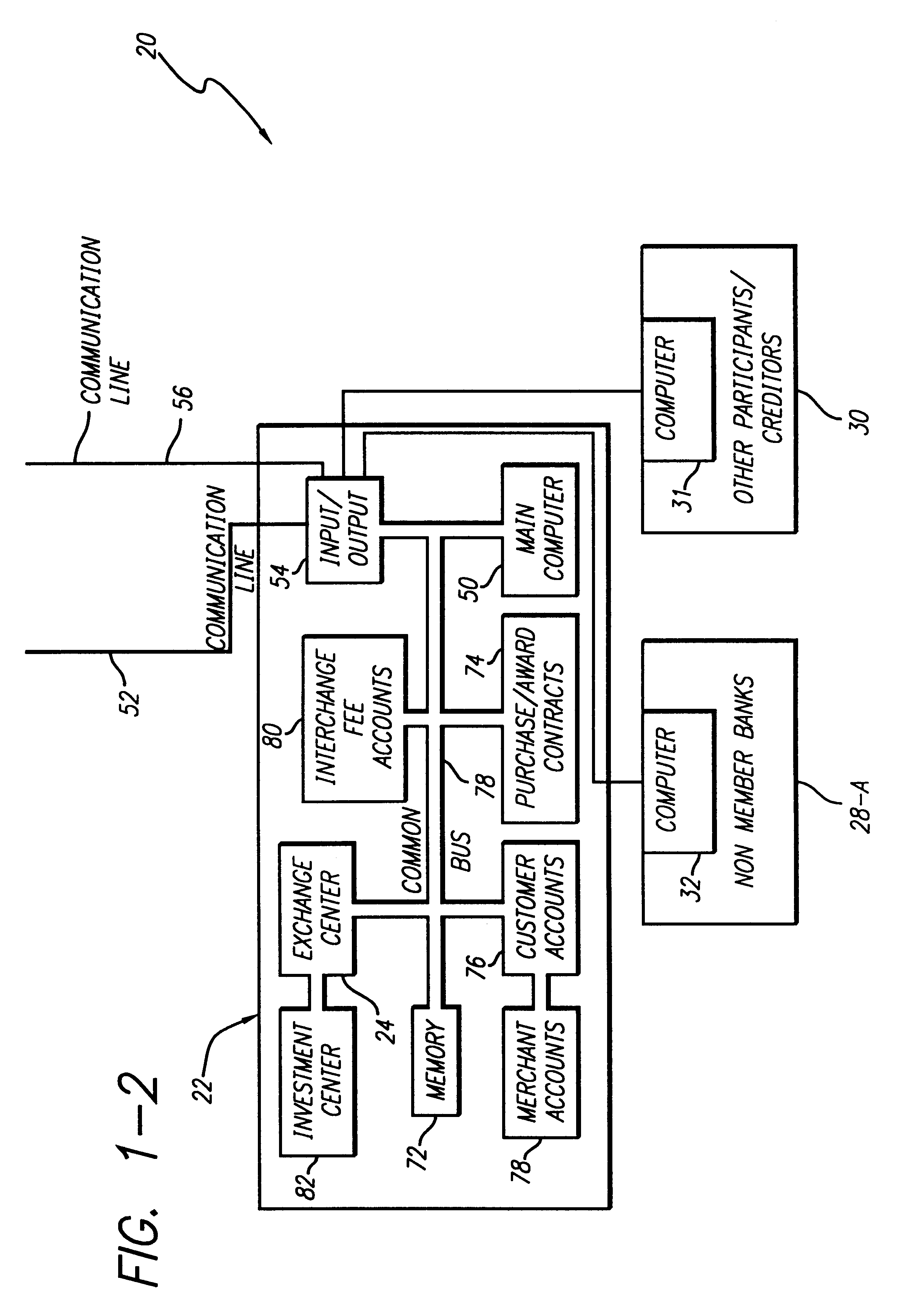
Internet-based credit interchange system of converting purchase credit awards through credit exchange system for purchase of investment vehicle
An Internet-based purchase credit award interchange center is described which interfaces with a credit award exchange center for conversion of any form of merchant or purchase credit award resulting from customer purchase of goods or services to investment in a mutual fund and / or investment vehicle utilizing computer data processing methods. Preassigned purchase credit accumulations earned by a consumer are exchanged from a merchant or creditor through or combination of credit cards, co-branded credit cards, PIN cards, debit and smart cards, coupons, stamps, proof of purchase, rebates, or any form of purchase award of merchant or creditors choice for an investment in a mutual fund or other investment vehicle. A specific implementation is described wherein a credit card account having investment credit awards is issued through the Internet to a customer. While inputting information through the Internet necessary for establishing the credit card account, the customer also provides any information needed to authorize the purchase of investment vehicles on his or her behalf. Any forms that need to be signed by the customer to authorize purchase of the investment vehicles may be printed out by the customer. The customer may also select, via the Internet, particular investment vehicles out of a group of possible investment vehicles. Subsequent use of the credit card by the customer automatically results in accrual of credit award accumulations in the selected investment vehicle.
Owner:KALINA DYAN T
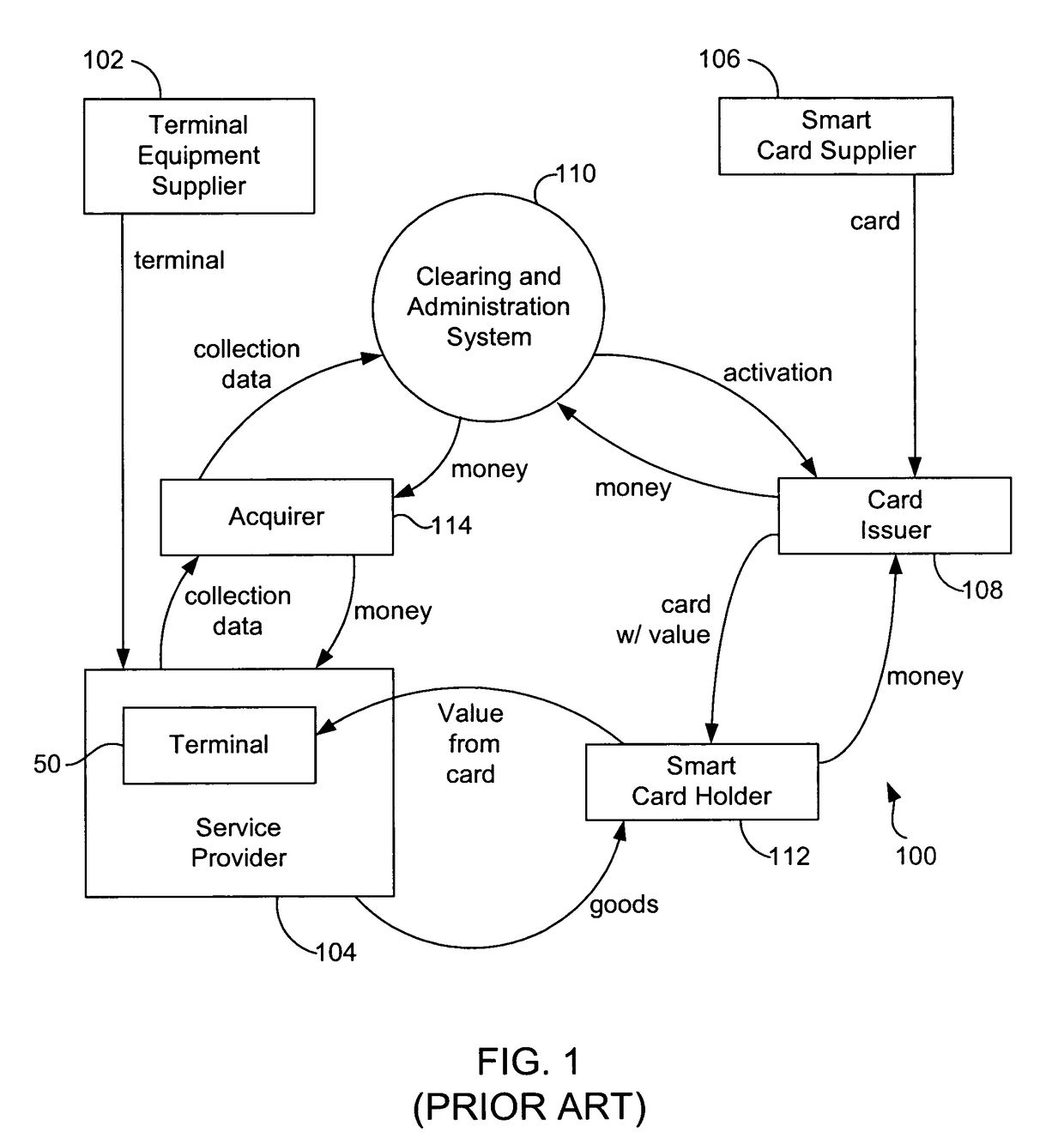
Secure credit card
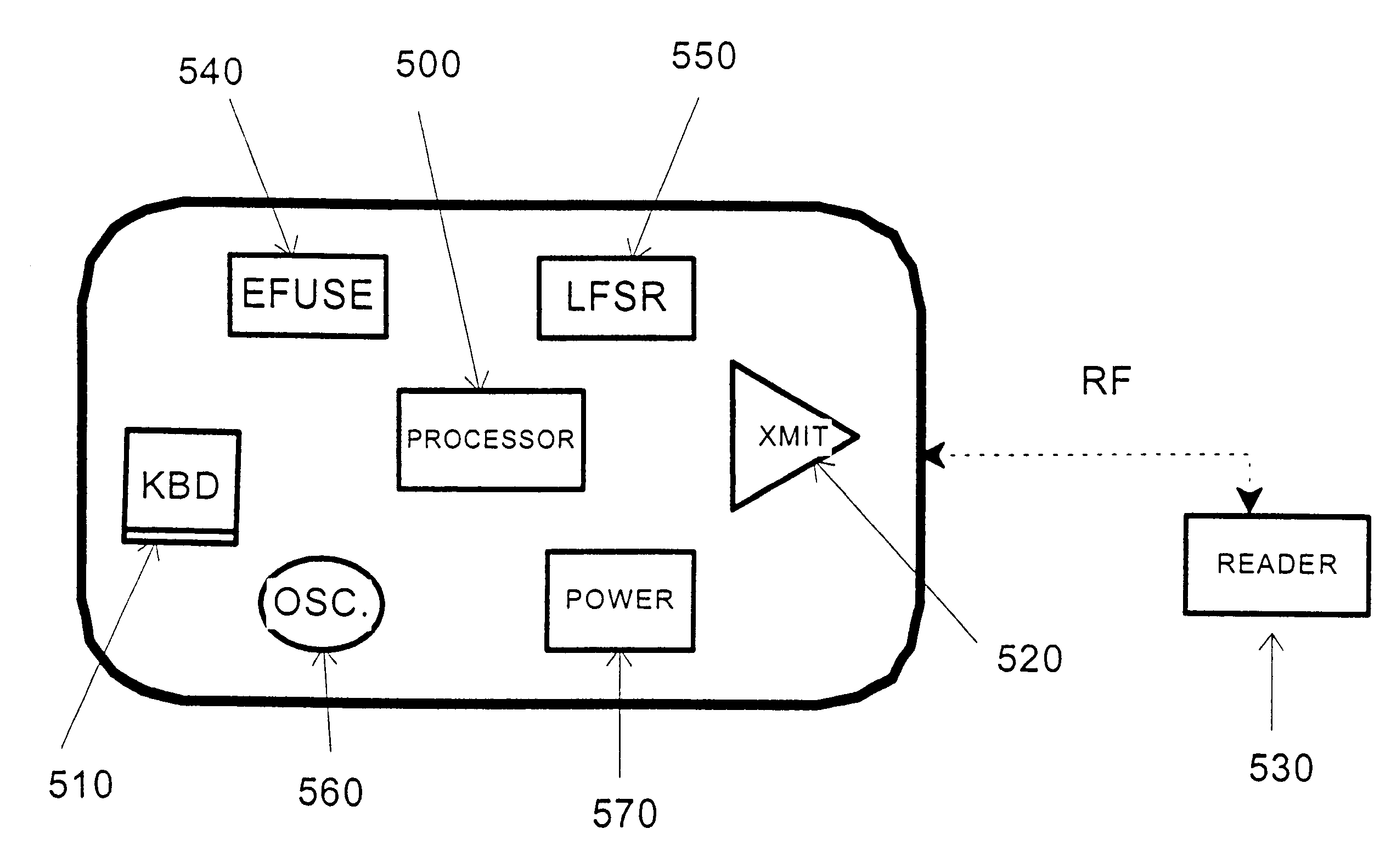
Credit card or portable identification cards containing smart card technology and electronic fuse (e-fuse) technology are combined with an LFSR pseudo random number generator to provide a secured method to prevent fraud and unauthorized use. Secure personalization via e-fuses, a pseudo-random number generator linear feedback shift register, free running clock oscillator, and power source embedded in the card provide a highly secured method to render a lost or stolen card useless. A unique card ID is permanently encoded within the card which requires a specific activation code to activate the card. A PIN number permits the card owner to activate the card for a predetermined length of time while processing a transaction. The card dynamically generates random code sequences and synchronization keys to secure a transaction.
Owner:KYNDRYL INC
Smart card for passport, electronic passport, and method, system, and apparatus for authenticating person holding smart card or electronic passport
InactiveUS20050240778A1Co-operative working arrangementsDigital data authenticationWireless transceiverTransmitted power
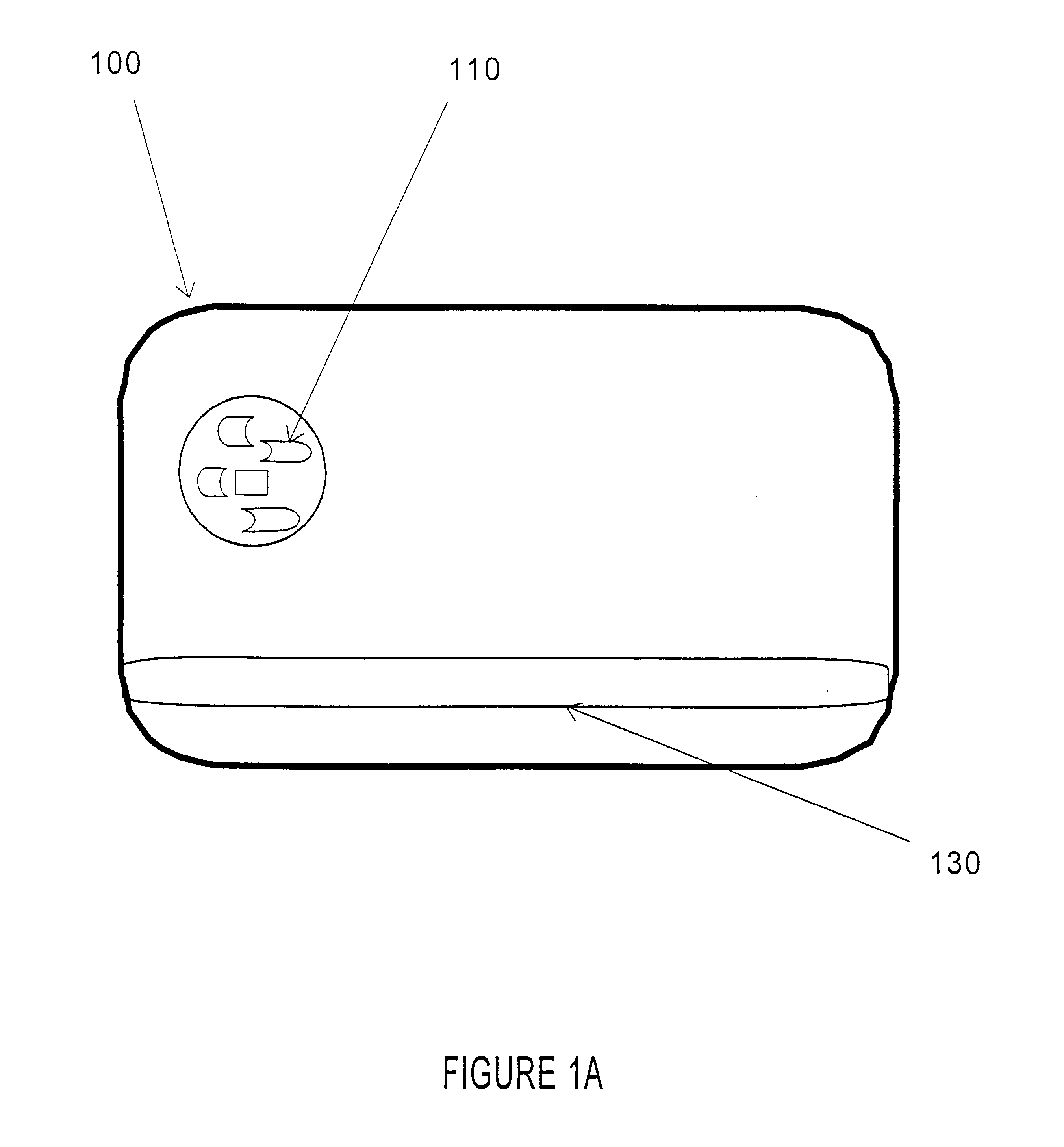
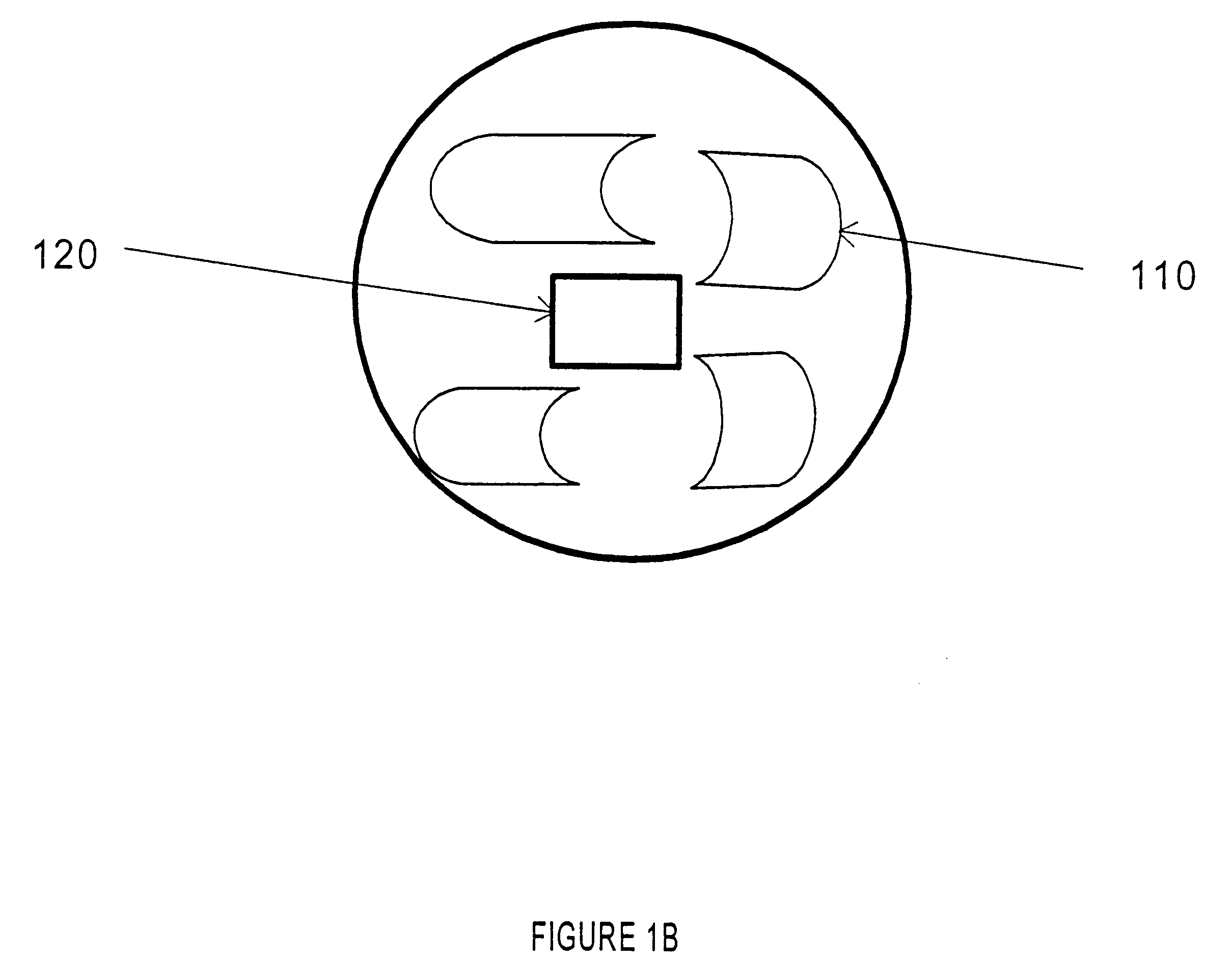
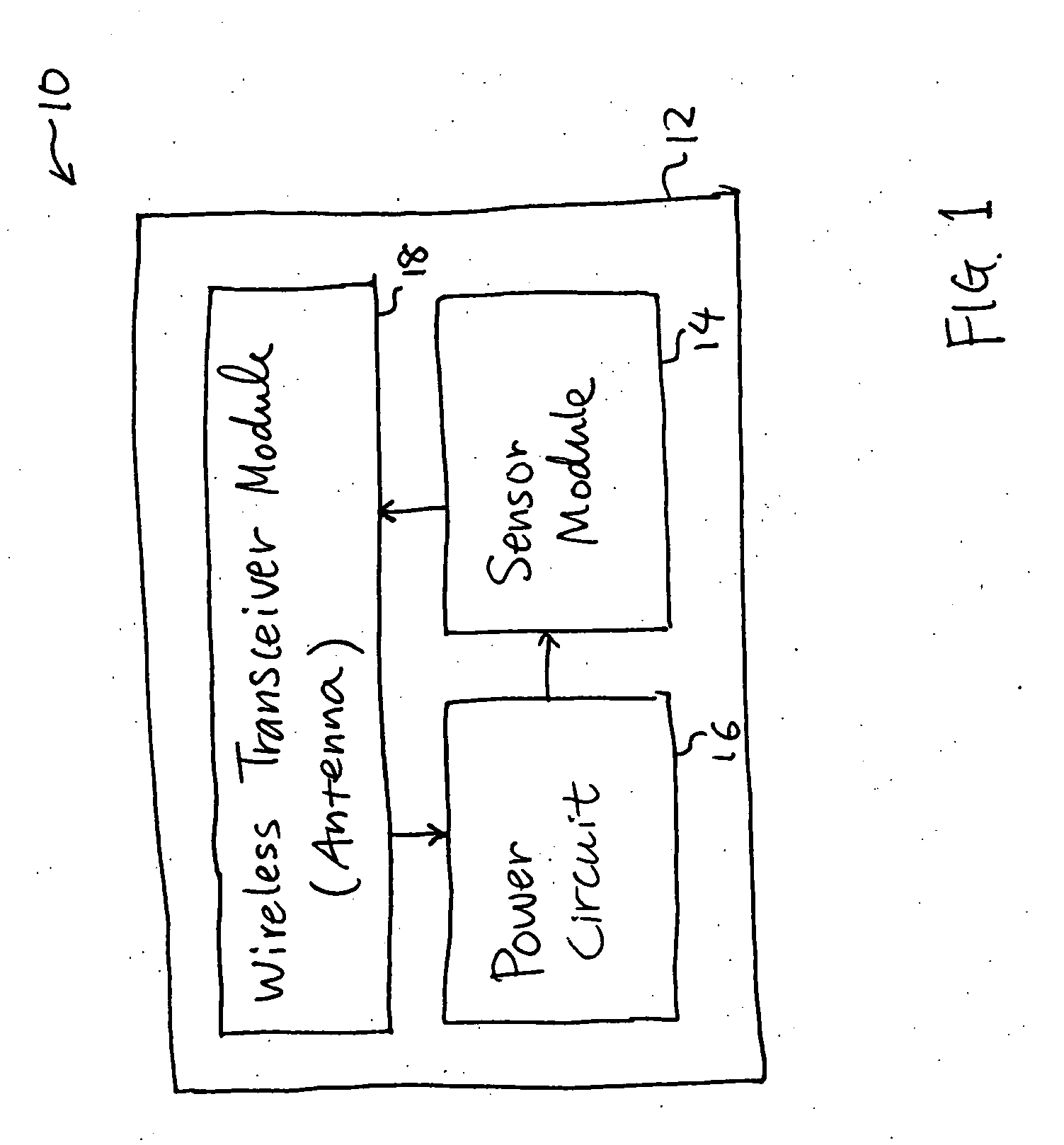
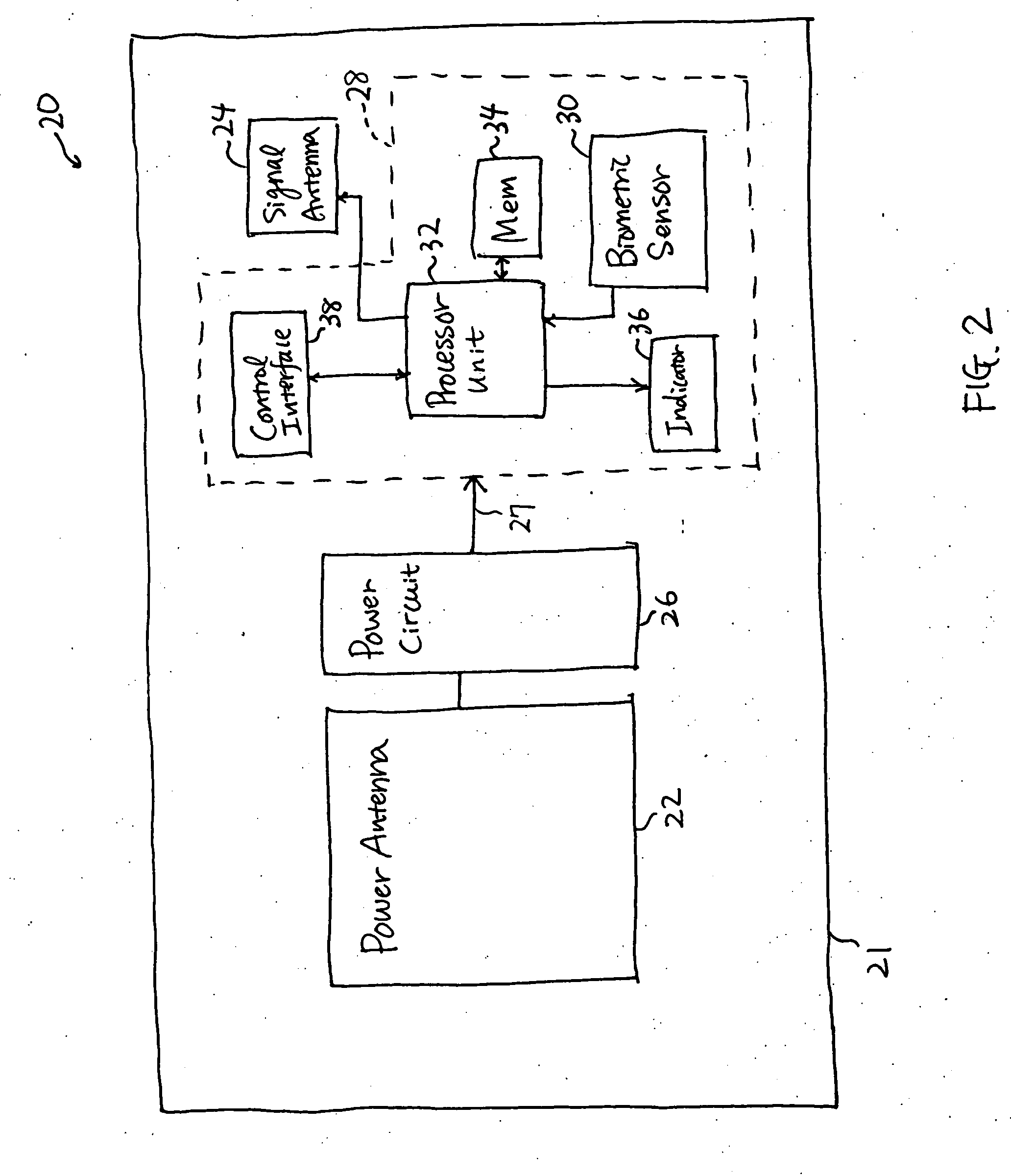
A smart card authenticates a cardholder. The smart card includes a substrate, a sensor module, a wireless transceiver module, and a power circuit. The sensor module includes (a) a biometric sensor adapted to detect biometric information from a person's body, (b) a processor unit adapted to authenticate the person in response to the detected biometric information and generate an authentication signal representing an authentication result, and (c) a memory adapted to store biometric information of a specific individual associated with the smart card. The wireless transceiver module transmits signals received from the processor unit and receives a wirelessly-transmitted power signal. The power circuit generates at least one supply voltage from the received power signal and provides the supply voltage to the sensor module. An electronic passport is embedded with the smart card, and a terminal module is used for wirelessly transmitting power to and receiving signals from the electronic passport.
Owner:IVI HLDG
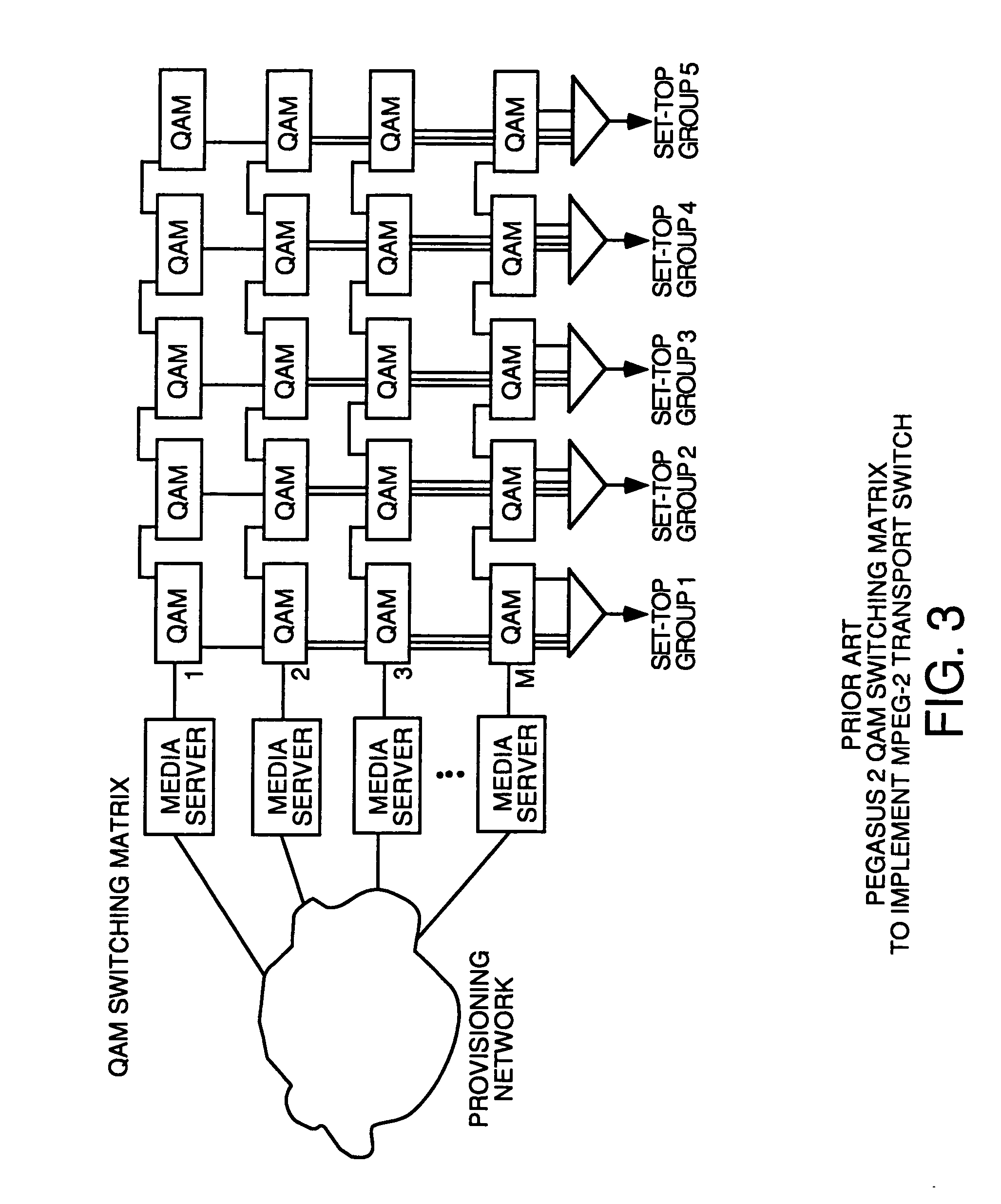
Thin DOCSIS in-band management for interactive HFC service delivery
InactiveUS20040181800A1Simple processLess-expensive to buildAnalogue secracy/subscription systemsTwo-way working systemsModem deviceConditional access
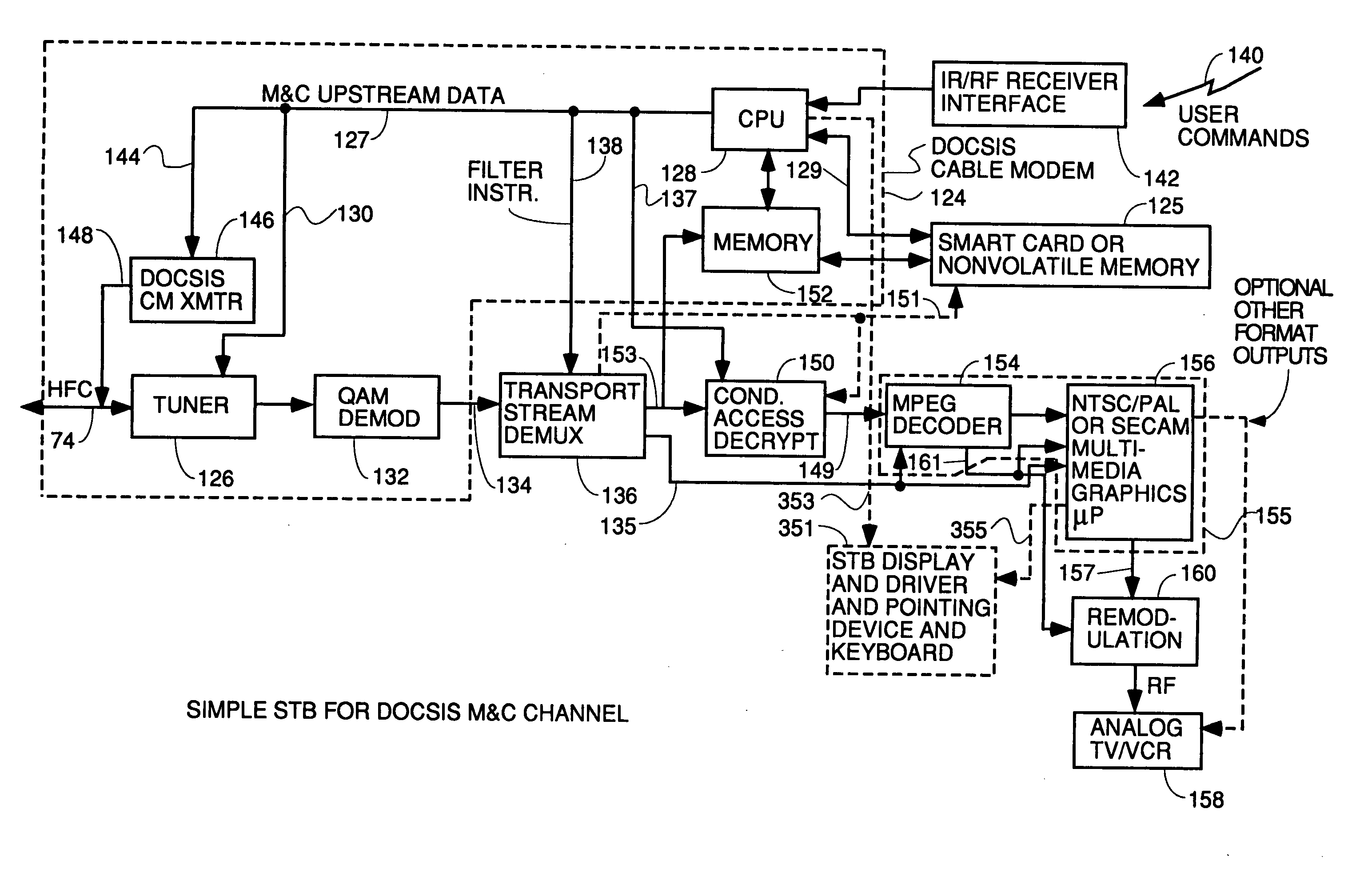
Circuitry and processes carried out thereby are disclosed for implementing simple single tuner set top box decoders which do not require a separate tuner for an out of band management and control channel. Removable smart card conditional access circuitry and replaceable modules having decoding circuitry for different compression schemes and encoding circuitry for different format television circuits is disclosed. An embodiment with a single tuner and a full DOCSIS compatible modem which can interface to personal computers, etc. is also disclosed to make the set top box a simple, inexpensive home gateway is also disclosed.
Owner:TERAYON COMM SYST
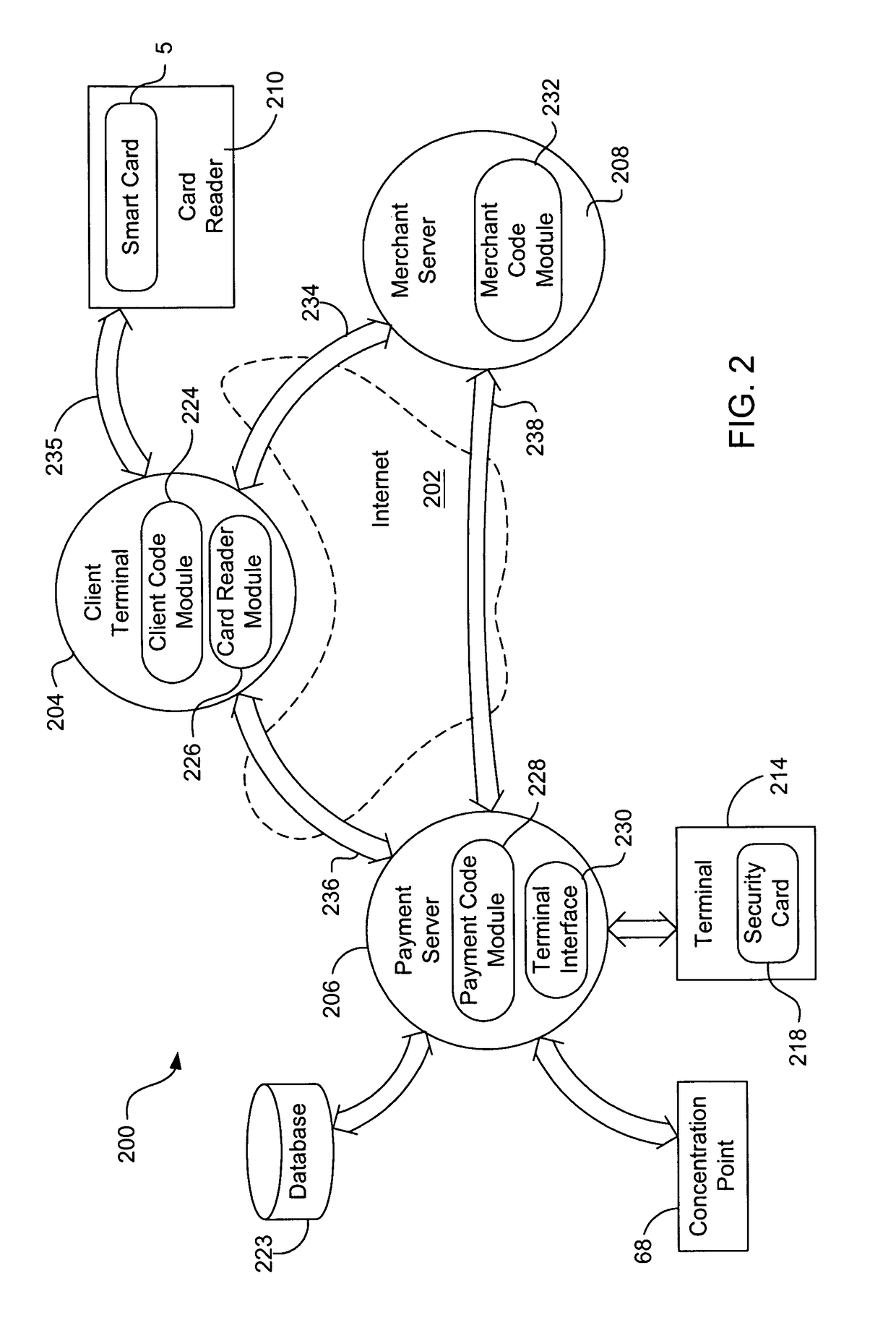
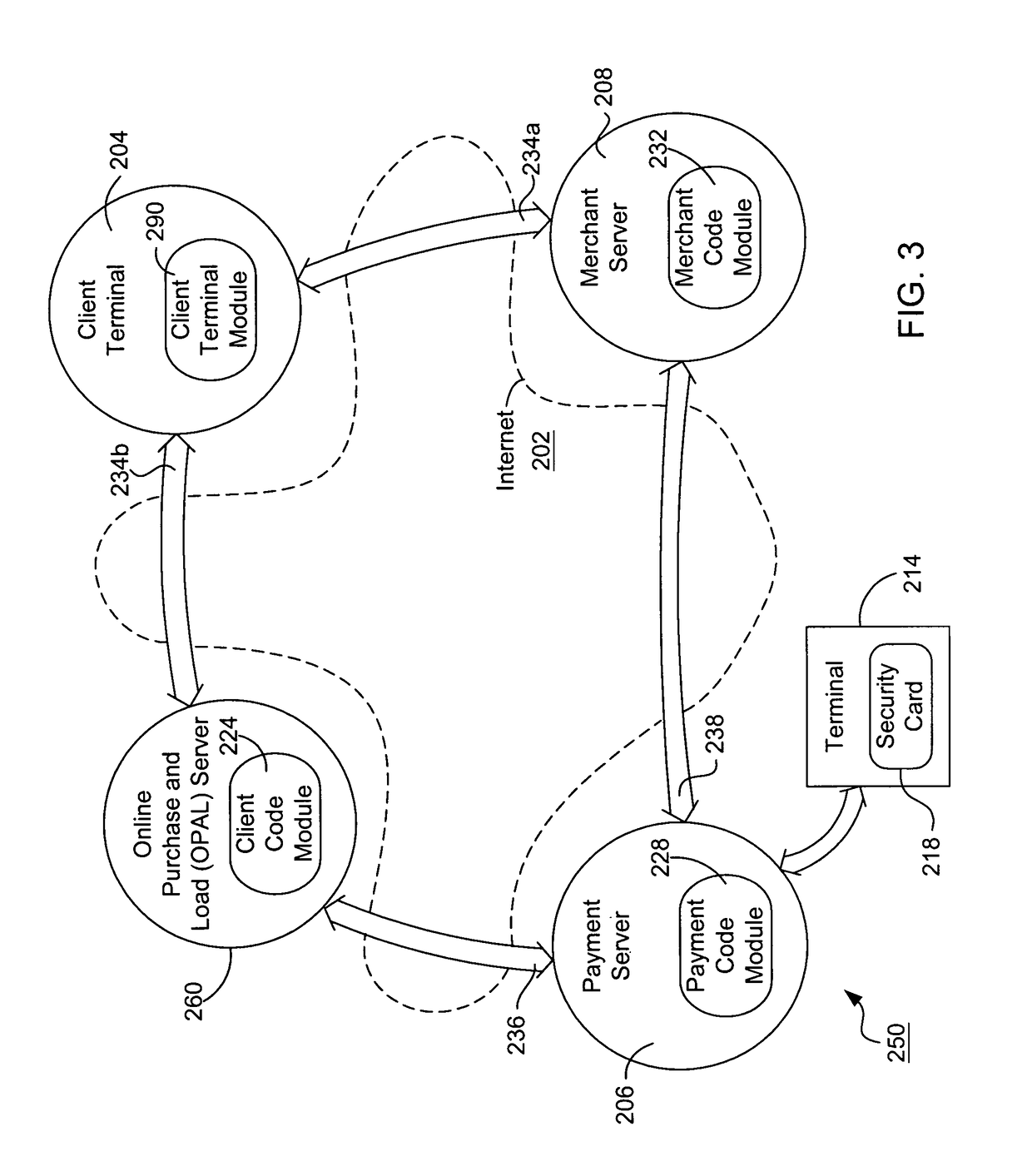
Internet payment, authentication and loading system using virtual smart card
InactiveUS7908216B1Advantageous for small dollar amount transactionMinimal timeFinancePayment circuitsMerchant servicesPayment
A system loads, authenticates and uses a virtual smart card for payment of goods and / or services purchased on-line over the Internet. An online purchase and load (OPAL) server includes a virtual smart card data base that has a record of information for each smart card that it represents for a user at the behest of an issuer. The server includes a smart card emulator that emulates a smart card by using the card data base and a hardware security module. The emulator interacts with a pseudo card reader module in the server that imitates a physical card reader. The server also includes a client code module that interacts with the pseudo card reader and a remote payment or load server. A pass-through client terminal presents a user interface and passes information between the OPAL server and a merchant server, and between the OPAL server and a bank server. The Internet provides the routing functionality between the client terminal and the various servers. A merchant advertises goods on a web site. A user uses the client terminal to purchase goods and / or services from the remote merchant server. The payment server processes, confirms and replies to the merchant server. The payment server is also used to authenticate the holder of a virtual card who wishes to redeem loyalty points from a merchant. To load value, the client terminal requests a load from a user account at the bank server. The load server processes, confirms and replies to the bank server.
Owner:VISA INT SERVICE ASSOC
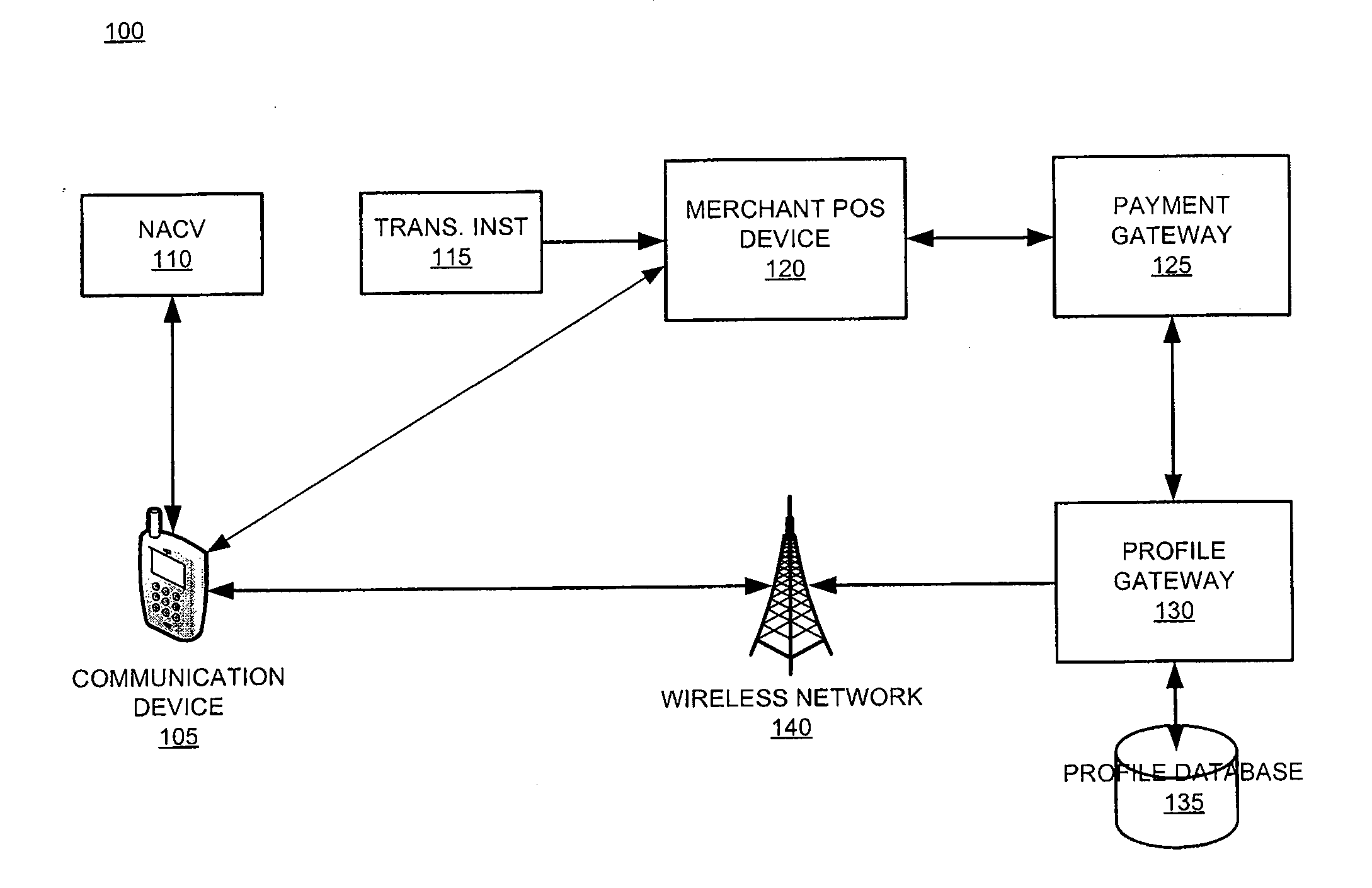
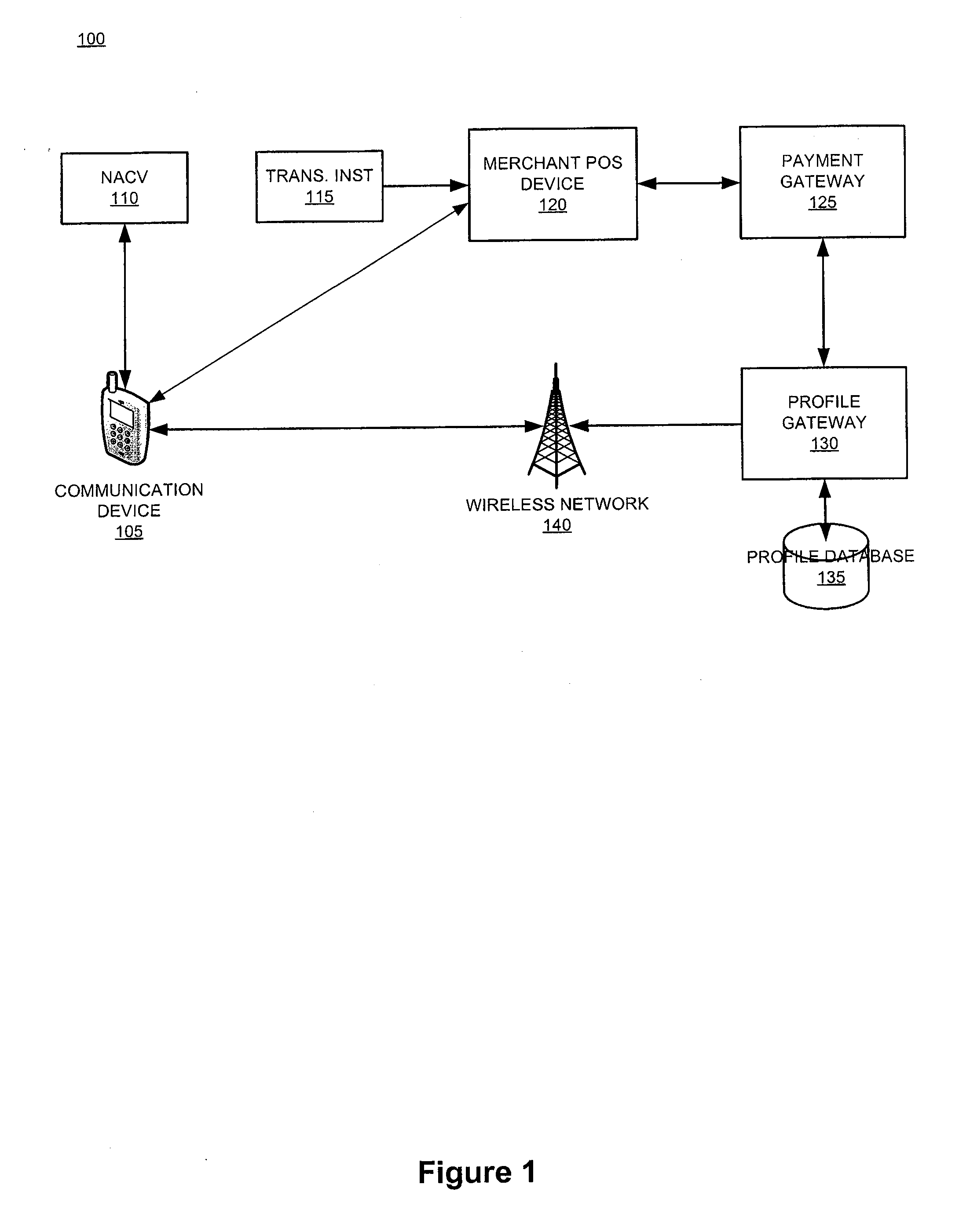
System and device for facilitating a transaction by consolidating sim, personal token, and associated applications for electronic wallet transactions
InactiveUS20120231844A1Increase dependenceFacilitating secure and convenient electronic transactionsPayment architectureSubstation equipmentPayment transactionSmart card
The invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
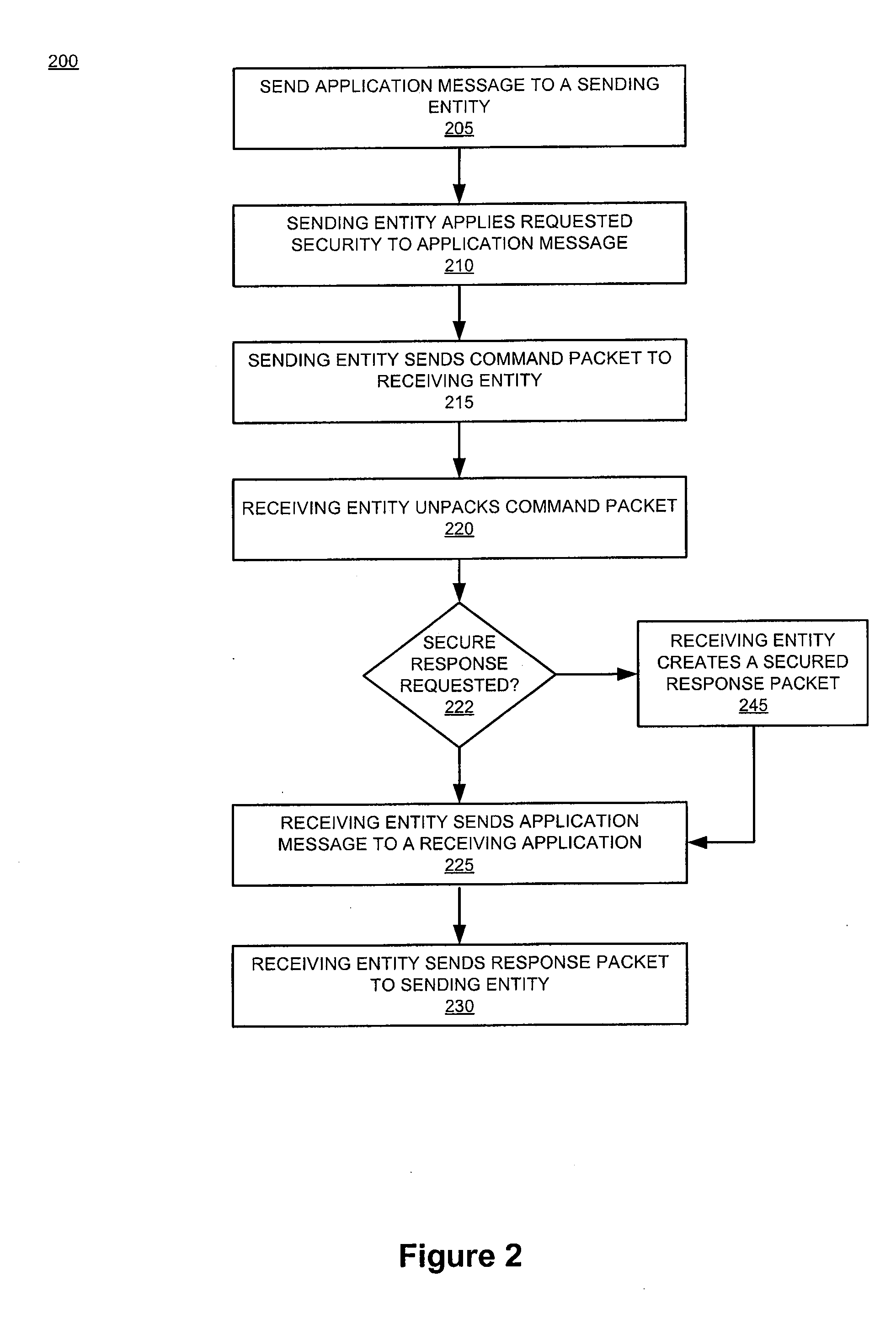
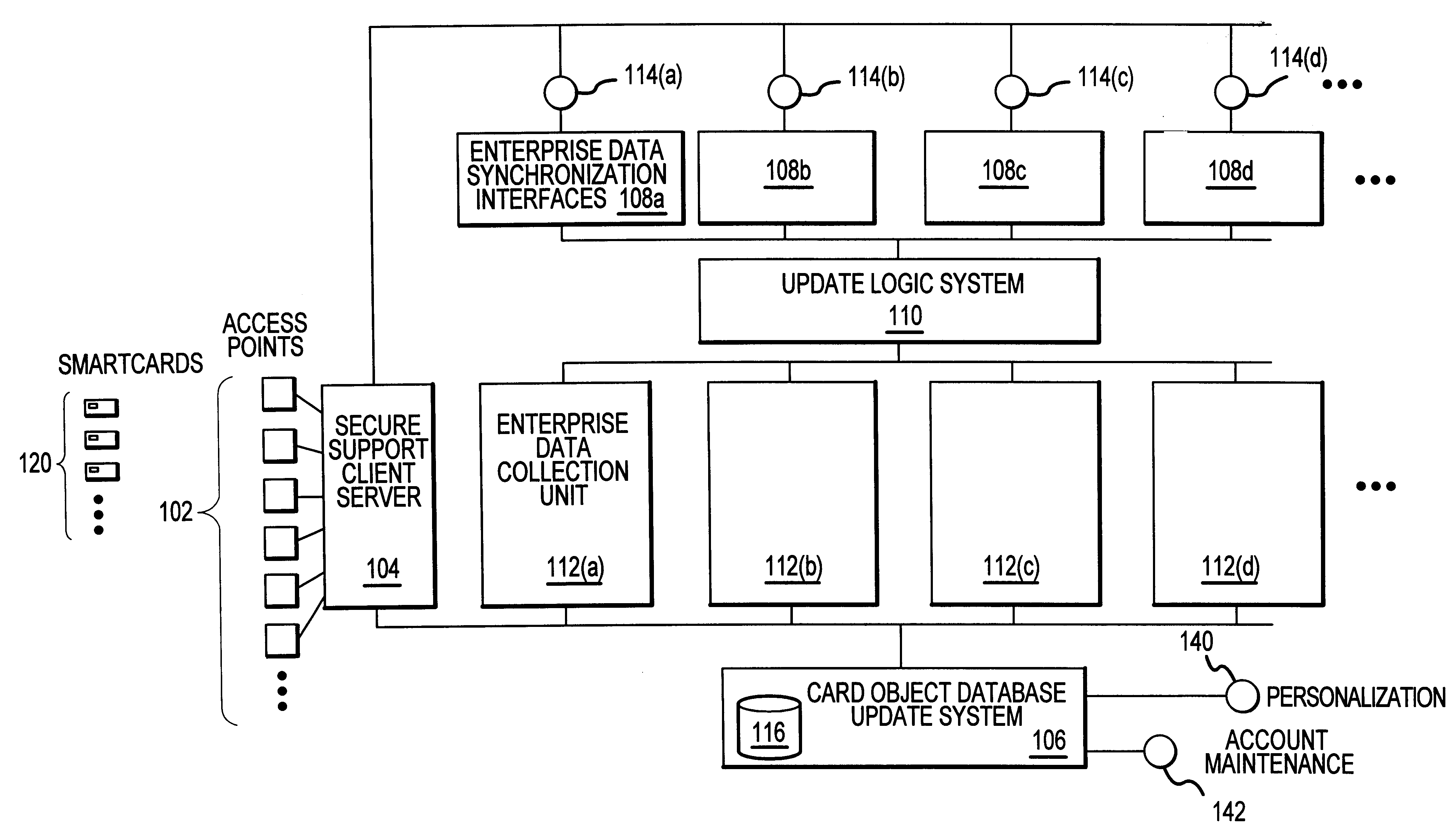
Methods and apparatus for dynamic smartcard synchronization and personalization
InactiveUS6199762B1Sensing by mechanical meansCo-operative working arrangementsPersonalizationData synchronization
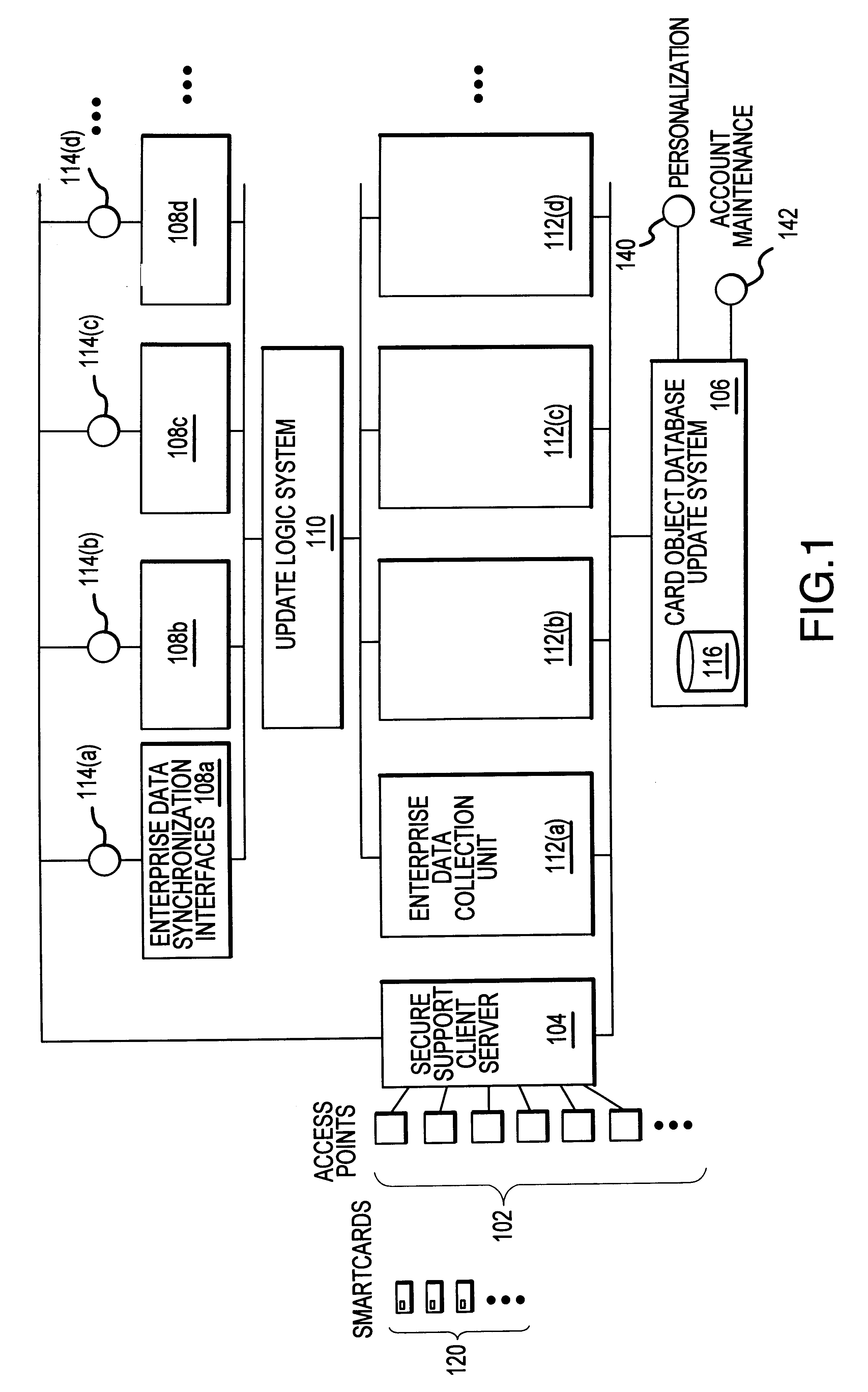
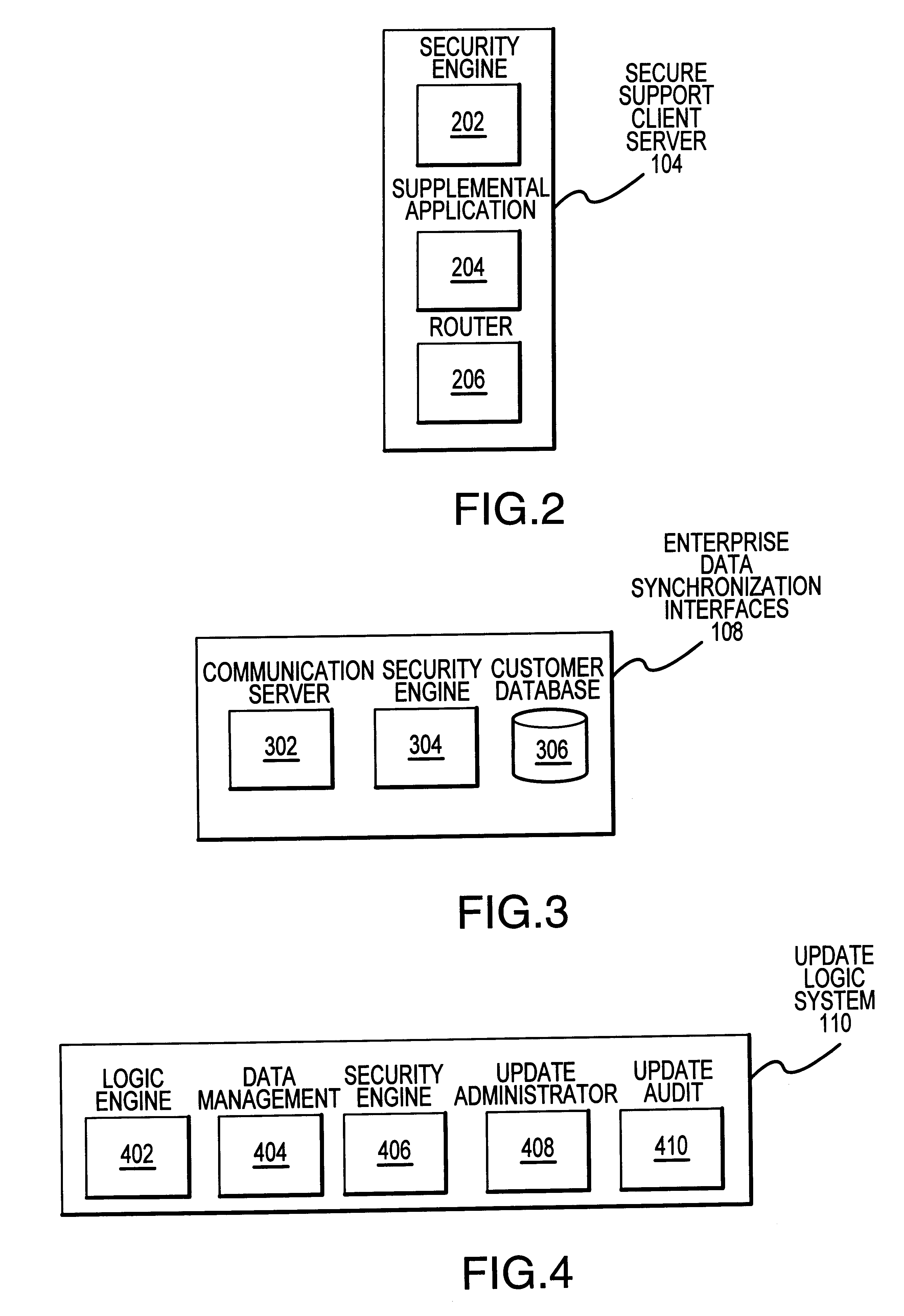
A system generally for personalizing and synchronizing smartcard data in the context of a distributed transaction system is disclosed. A dynamic smartcard synchronization system comprises access points configured to initiate a transaction in conjunction with a smartcard, an enterprise data collection unit, and a card object database update system. An exemplary dynamic synchronization system (DSS) preferably comprises various smartcard access points, a secure support client server, a card object database update system (CODUS), one or more enterprise data synchronization interfaces (EDSI), an update logic system, one or more enterprise data collection units (EDCUs), and one or more smartcard access points configured to interoperably accept and interface with smartcards. In an exemplary embodiment, DSS comprises a personalization system and an account maintenance system configured to communicate with CODUS. Personalization of multi-function smartcards is accomplished using a security server configured to generate and / or retrieve cryptographic key information from multiple enterprise key systems during the final phase of the smartcard issuance process.
Owner:LIBERTY PEAK VENTURES LLC
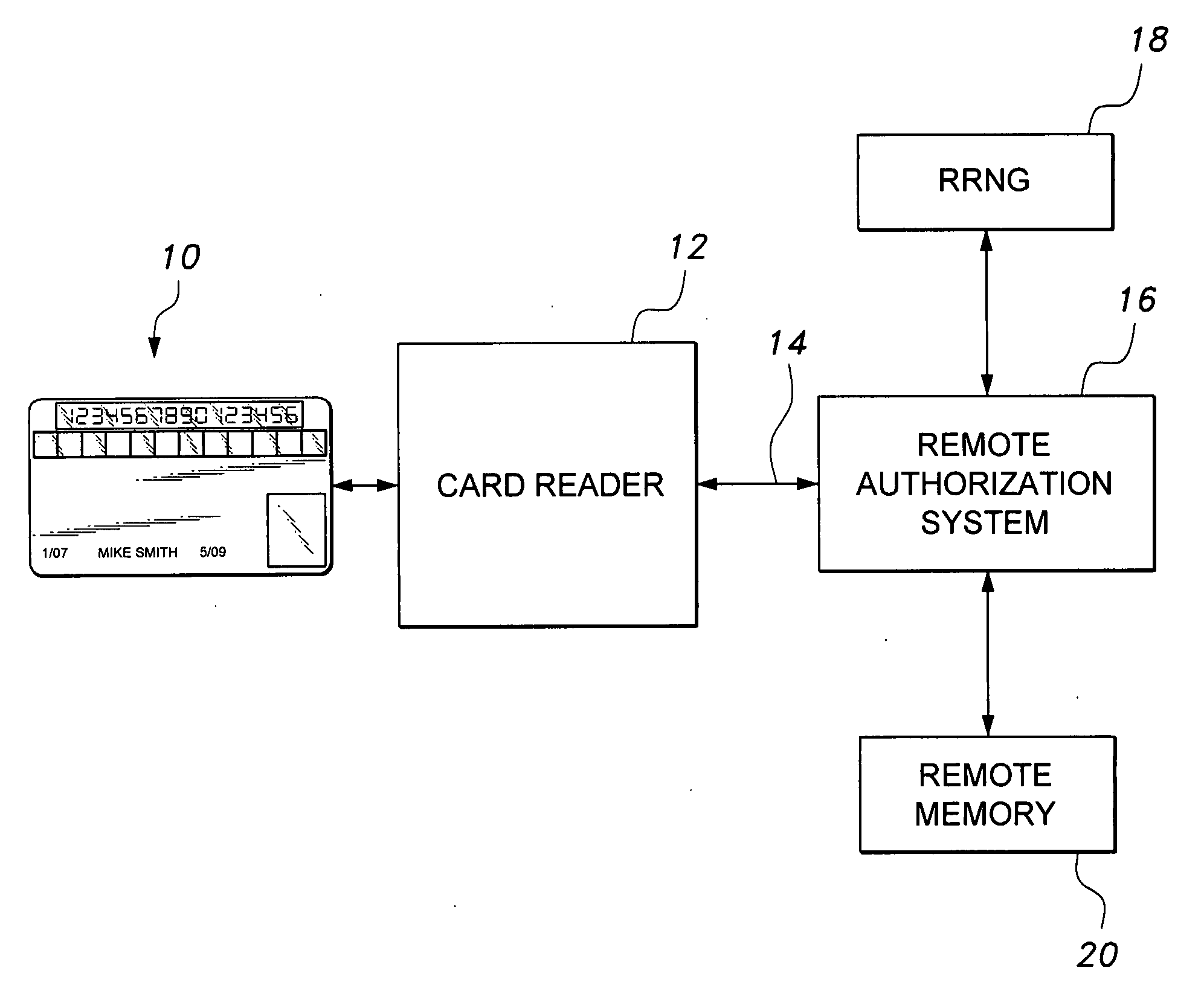
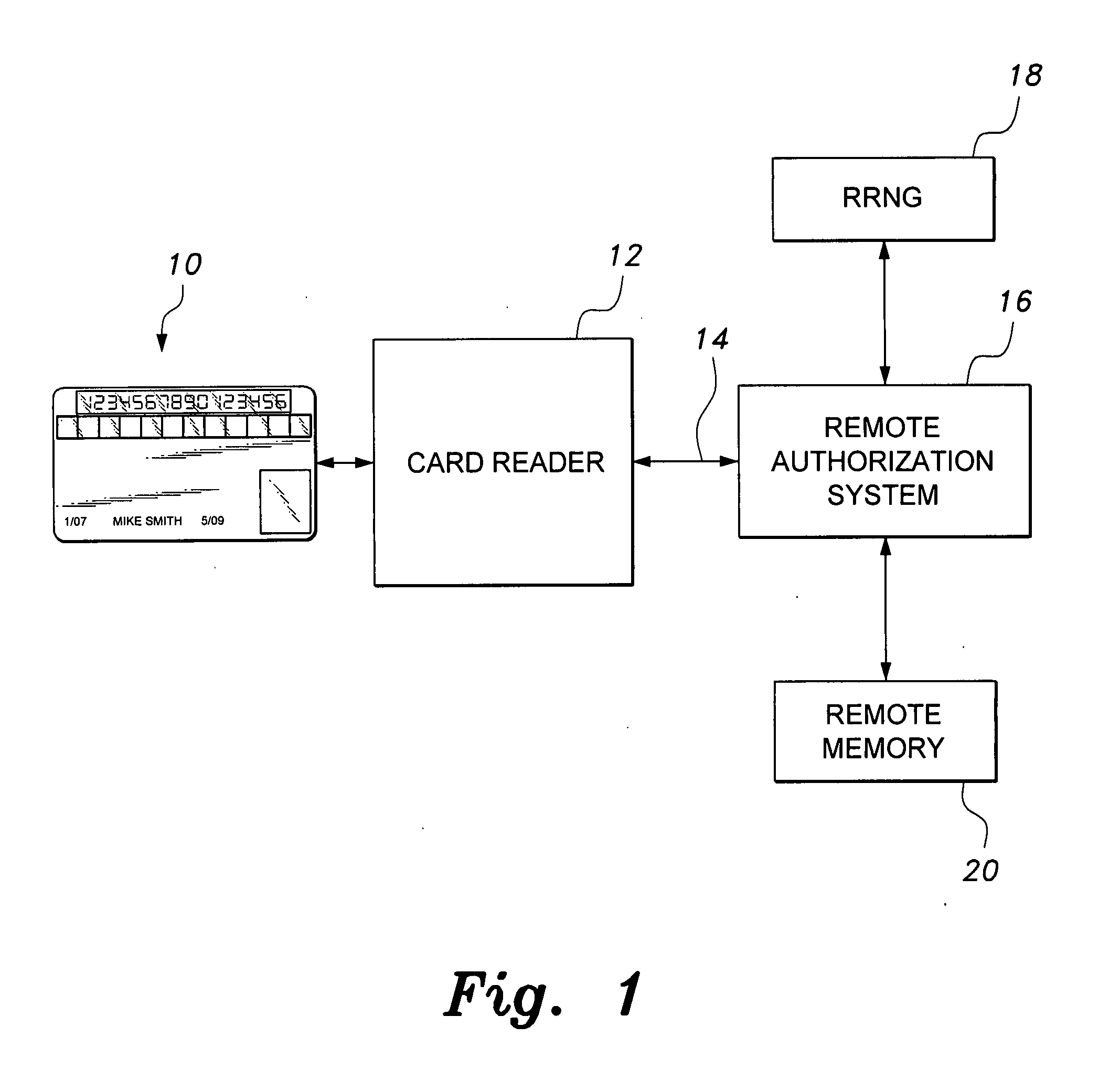
Smart card with random temporary account number generation
The smart card with random temporary account number generation provides an authenticating system coupled with an access or transaction card, such as a credit card. The card includes first and second memory storage media, with the first memory medium containing a plurality of temporary account or authentication numbers. The card also has a biometric sensor, such as a fingerprint scanner, and the second memory stores the biometric parameters of the authorized user. A processor compares the biometric parameters with the measured biometric readings to enable the card. The processor has a random number generator, allowing for the randomized selection of one of the account numbers stored in the first memory, thus providing a temporary account number for the transaction. A remote site includes an identical random number generator and set of account numbers, allowing the temporary account number to be verified and then discarded, following the transaction.
Owner:HEWTON ALFRED
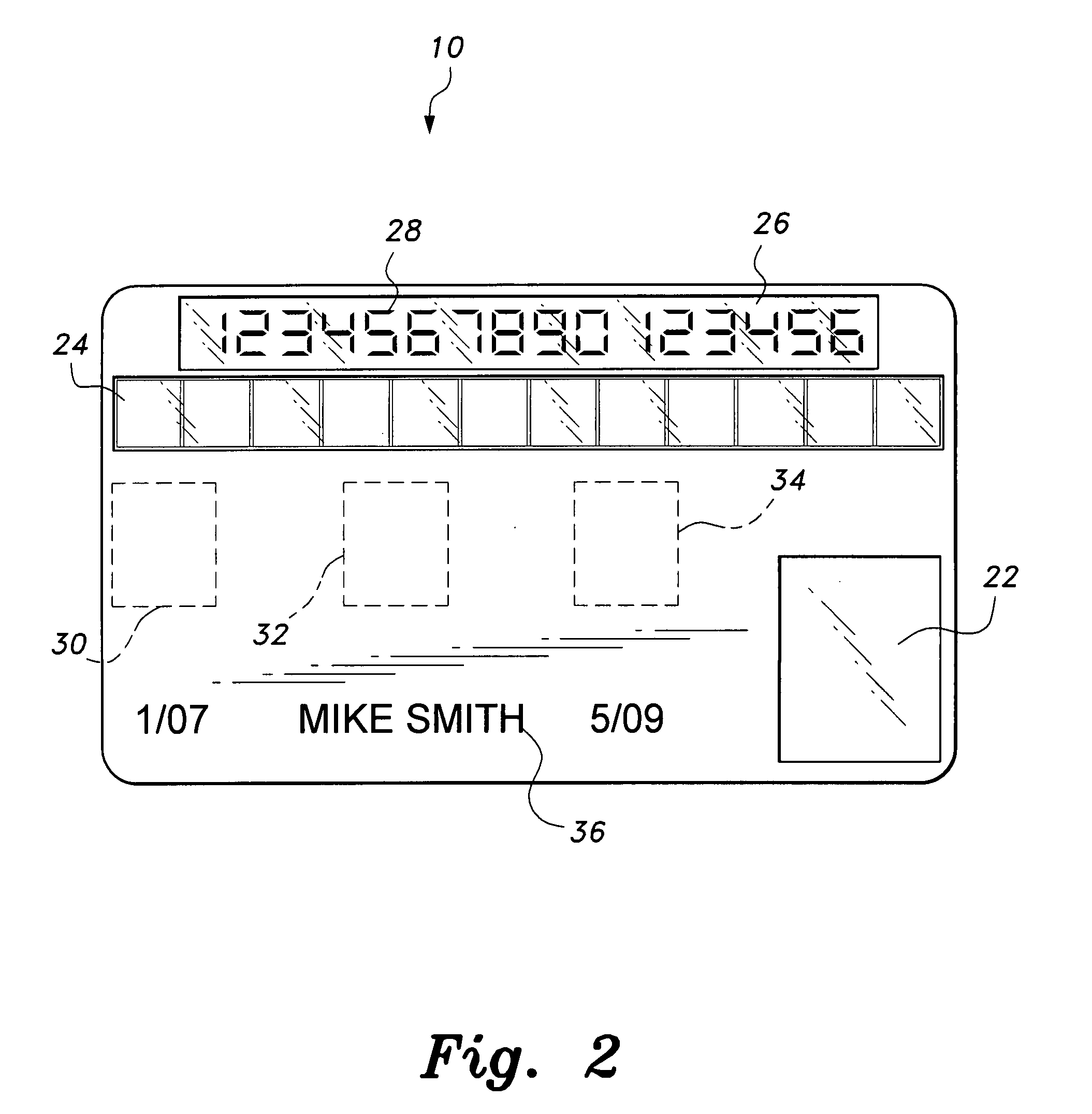
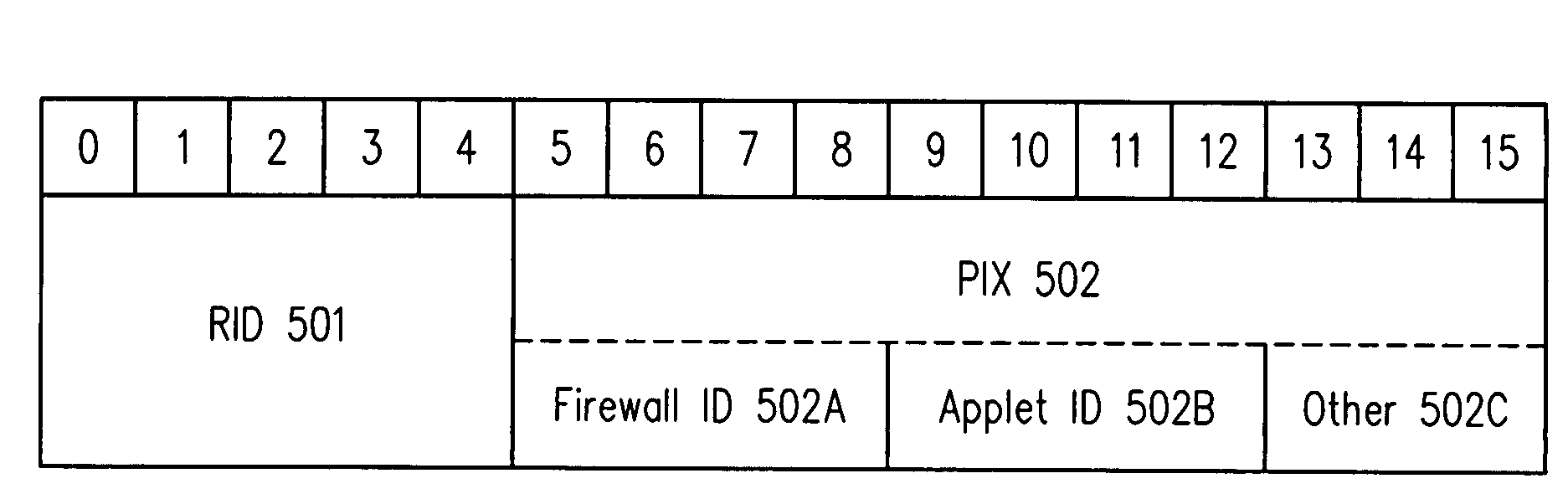
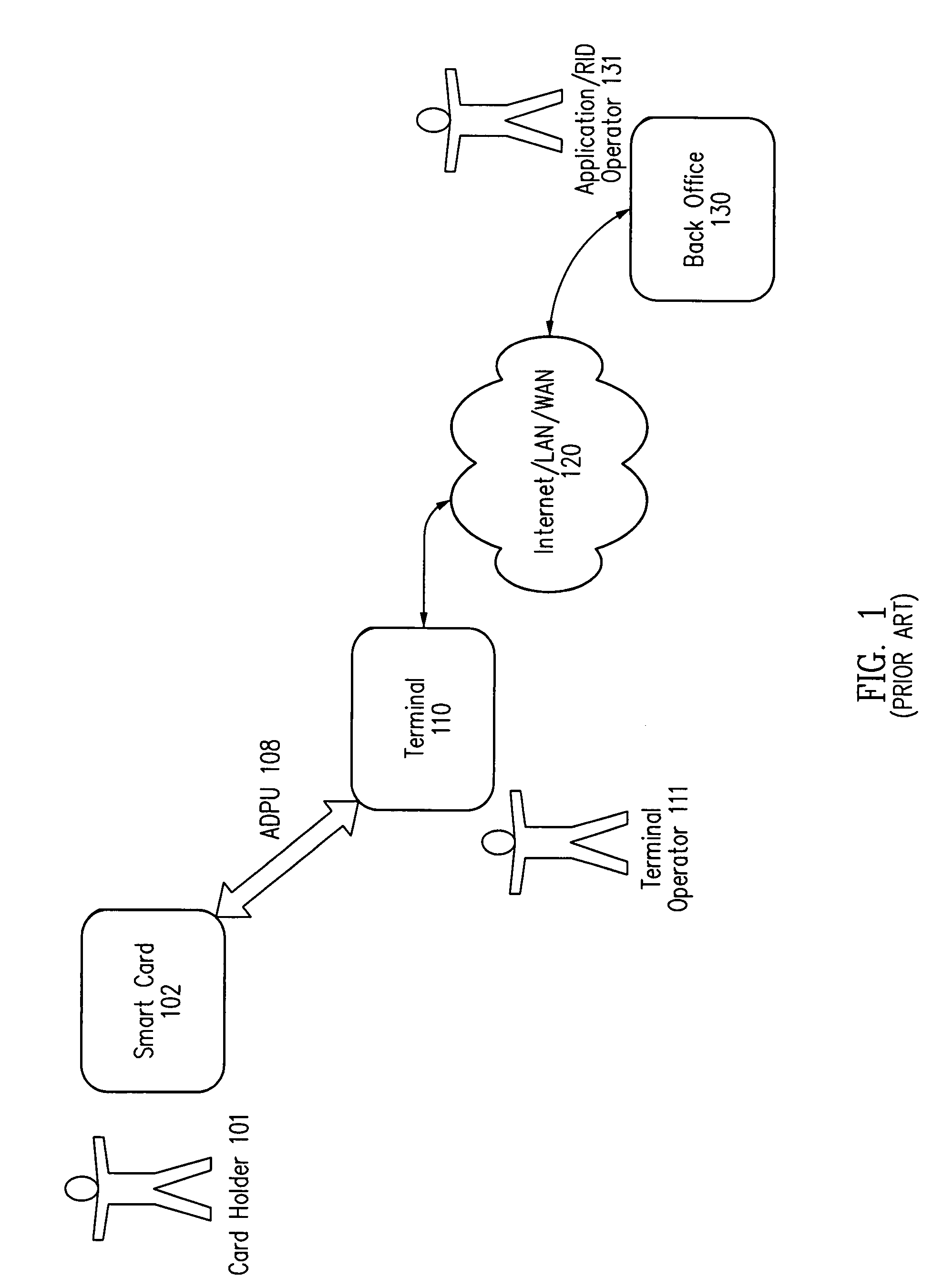
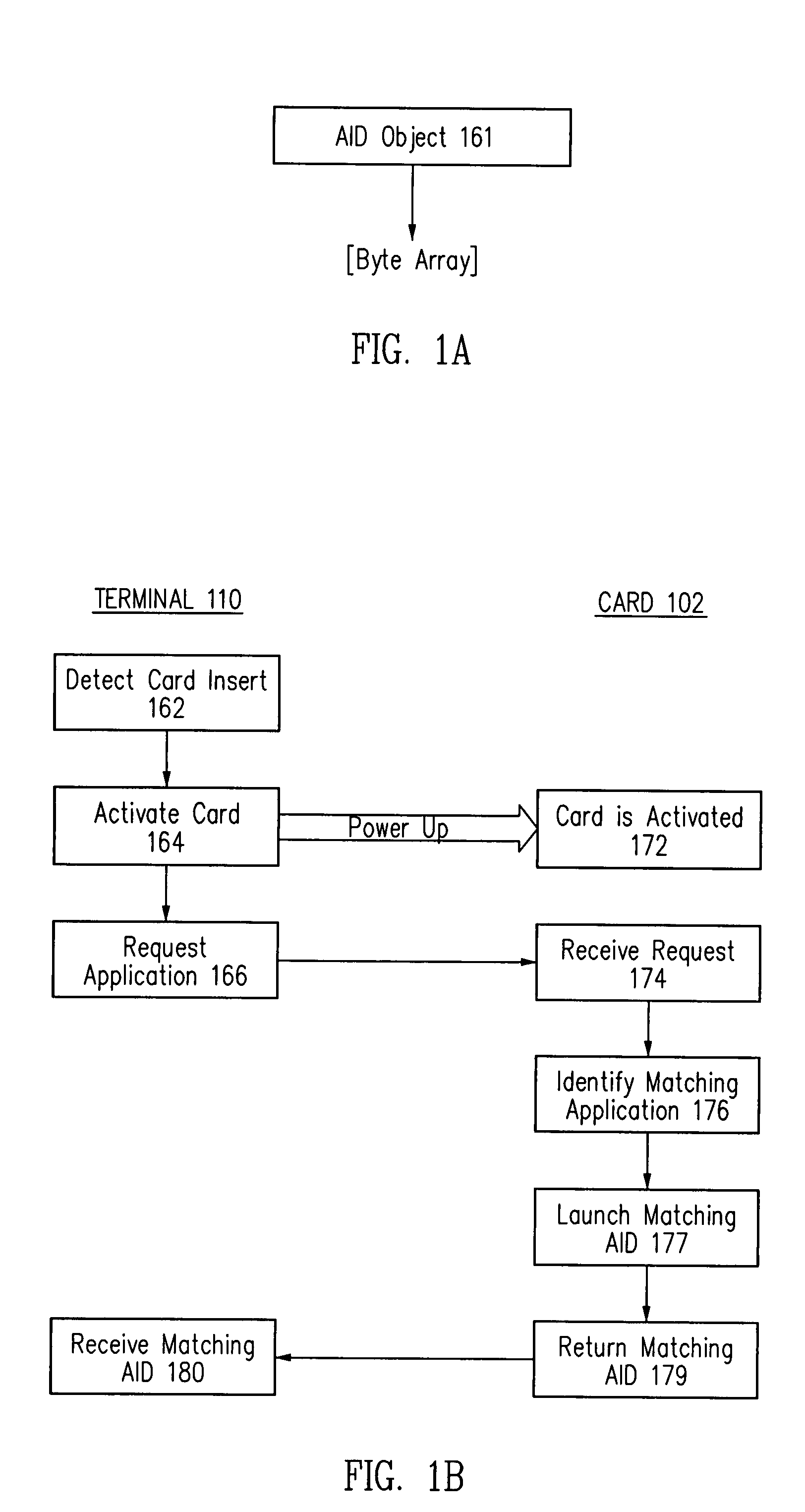
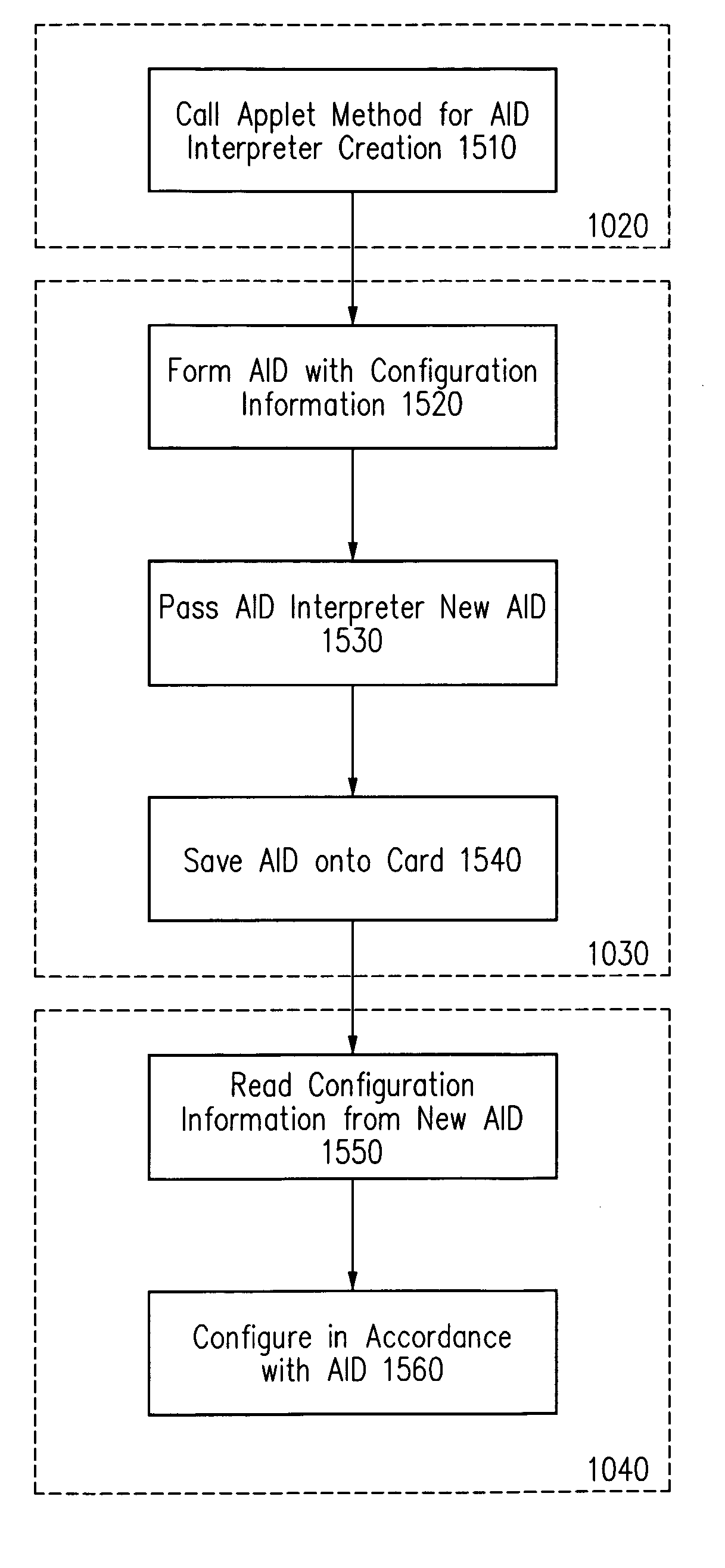
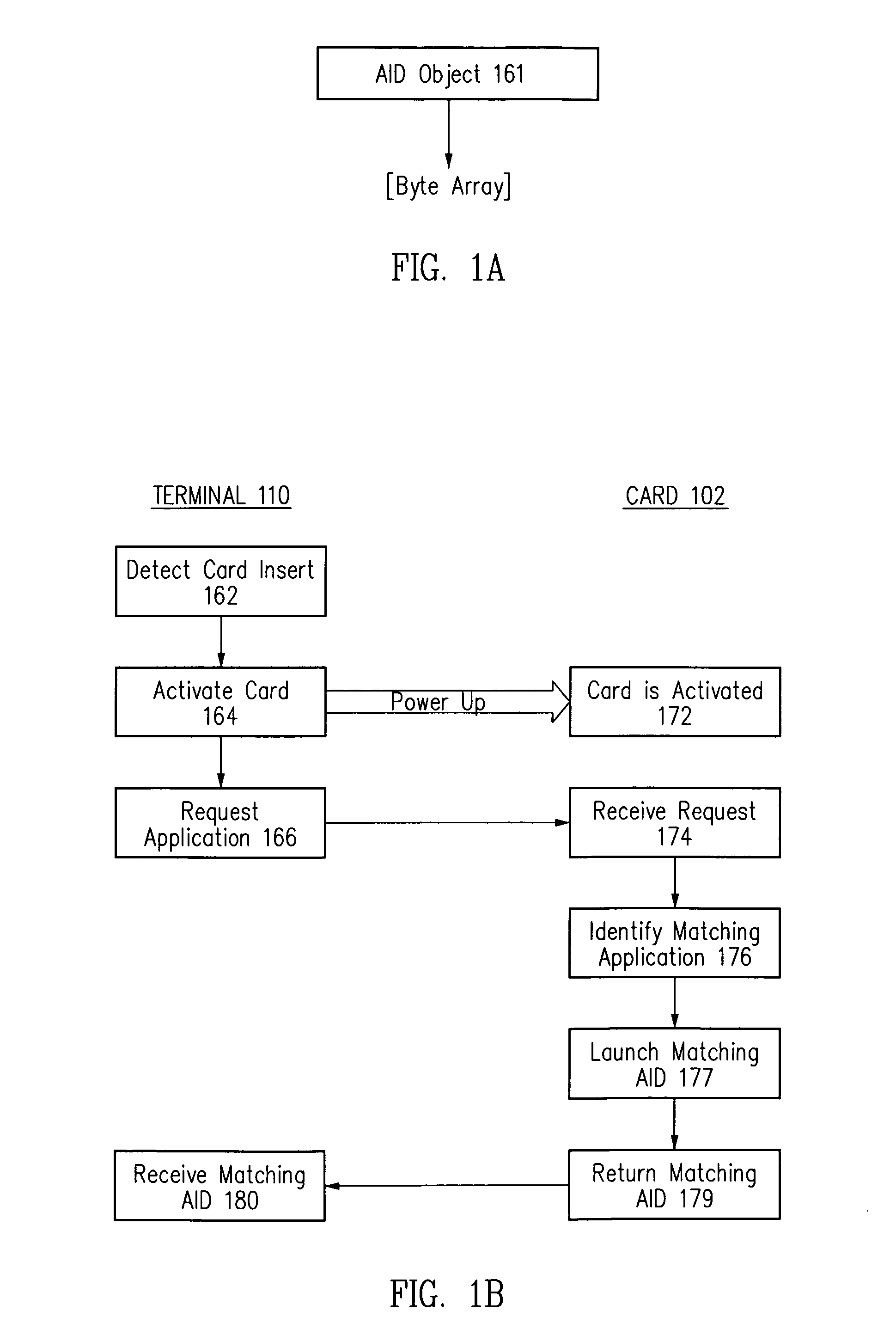
Method and apparatus for processing an application identifier from a smart card
An application identifier (AID) for an application installed on a smart card comprises a registered application provider identifier (RID). The AID may be processed by determining the RID for an application from the AID of the application, generating an identifier for a network resource from the RID, transmitting a request to the network resource using the identifier, and receiving a response to the request. The response comprises material for use in handling the application on the smart card.
Owner:ORACLE INT CORP
Method and apparatus for summaries of prepaid instrument transaction activity
InactiveUS6115458AConveniently and efficiently generatingConveniently and efficiently and transmittingPayment circuitsVerifying markings correctnessCredit cardSummary data
A system for generating and transmitting summary transaction data includes a computer database from which information is compiled and forwarded to a requesting party automatically, i.e., without the need to interface with a human operator. A party having access to a prepaid transaction account number may access the host computer from a remote location and interactively request transaction information pertaining to the account using virtually any communication modality. The computer is suitably configured to communicate with one or more of the foregoing communication modalities and to automatically compile and transmit the summary data to a requested destination, for example, to a PC. The computer may further be configured to allow the requesting party to select among various formats to configure the form of the summary data. Summary transaction data may be generated and transmitted for virtually any type of prepaid transaction card, including phone cards, travel, credit cards, stored value (e.g., smart cards) cards, and the like.
Owner:LIBERTY PEAK VENTURES LLC +1
System for personalized mobile navigation information
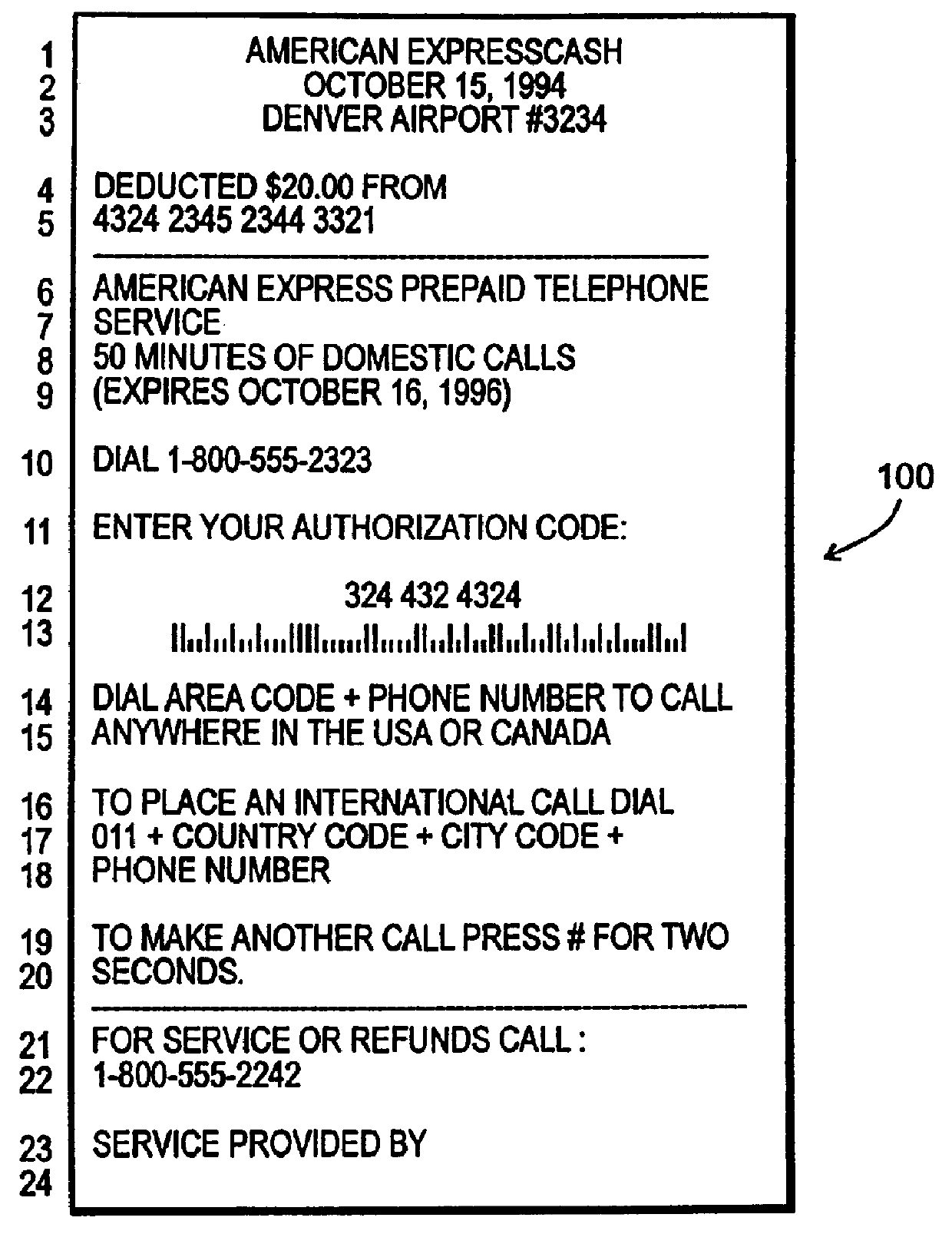
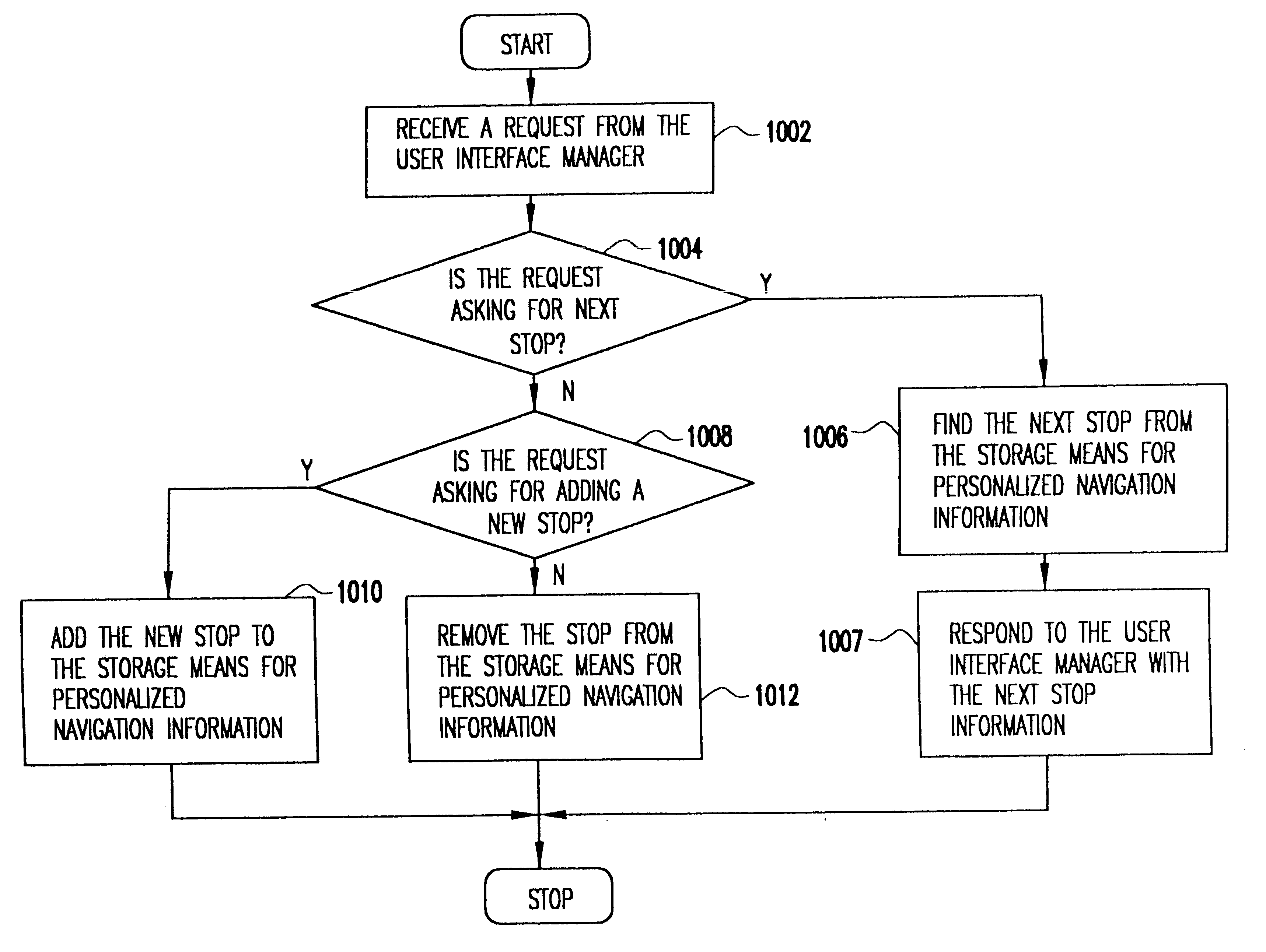
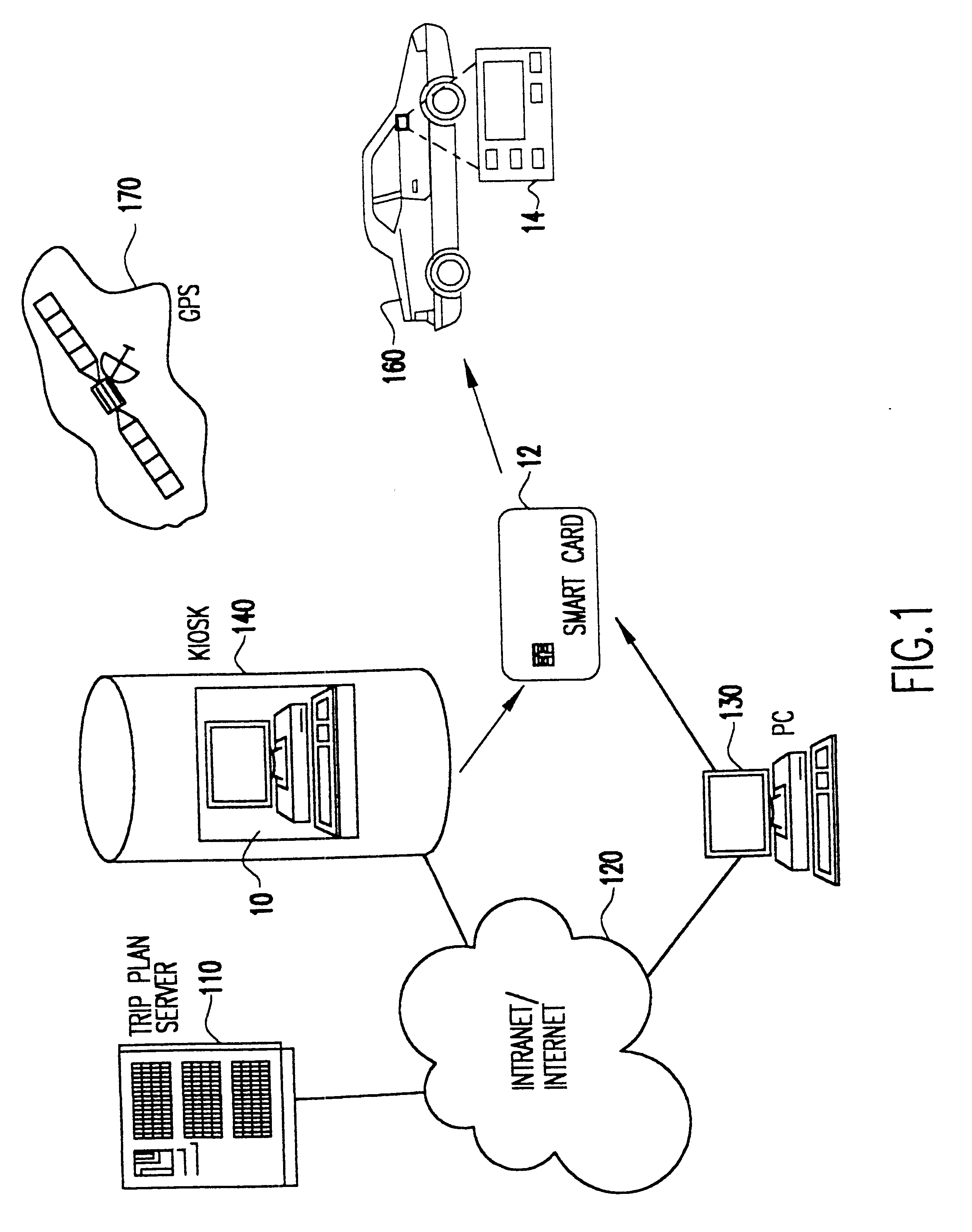
InactiveUS6349257B1Analogue computers for vehiclesElectric signal transmission systemsPersonalizationMobile navigation
A mobile navigation system implemented as an embedded system in a vehicle is easy to use, does not detract the driver's attention from the road, and limits the number of choices presented to the user of the navigation system according to a predetermined set of preferences or personalized information. Choices are filtered according to a set of driver preferences, according to the vehicle's geographic position, direction of motion, and the driver's intended itinerary. The itinerary, including intermediate stops, is calculated on an external computing system. The information is downloaded from the computing system to a memory device such as, for example, a smart card. The information is then transferred from the smart card to the embedded vehicle navigation system. In one application of the invention, a kiosk located at a car rental agency may be used to create and store personalized navigation information onto a smart card which the customer then inserts into the vehicle navigation system that is installed in the rental car.
Owner:IBM CORP
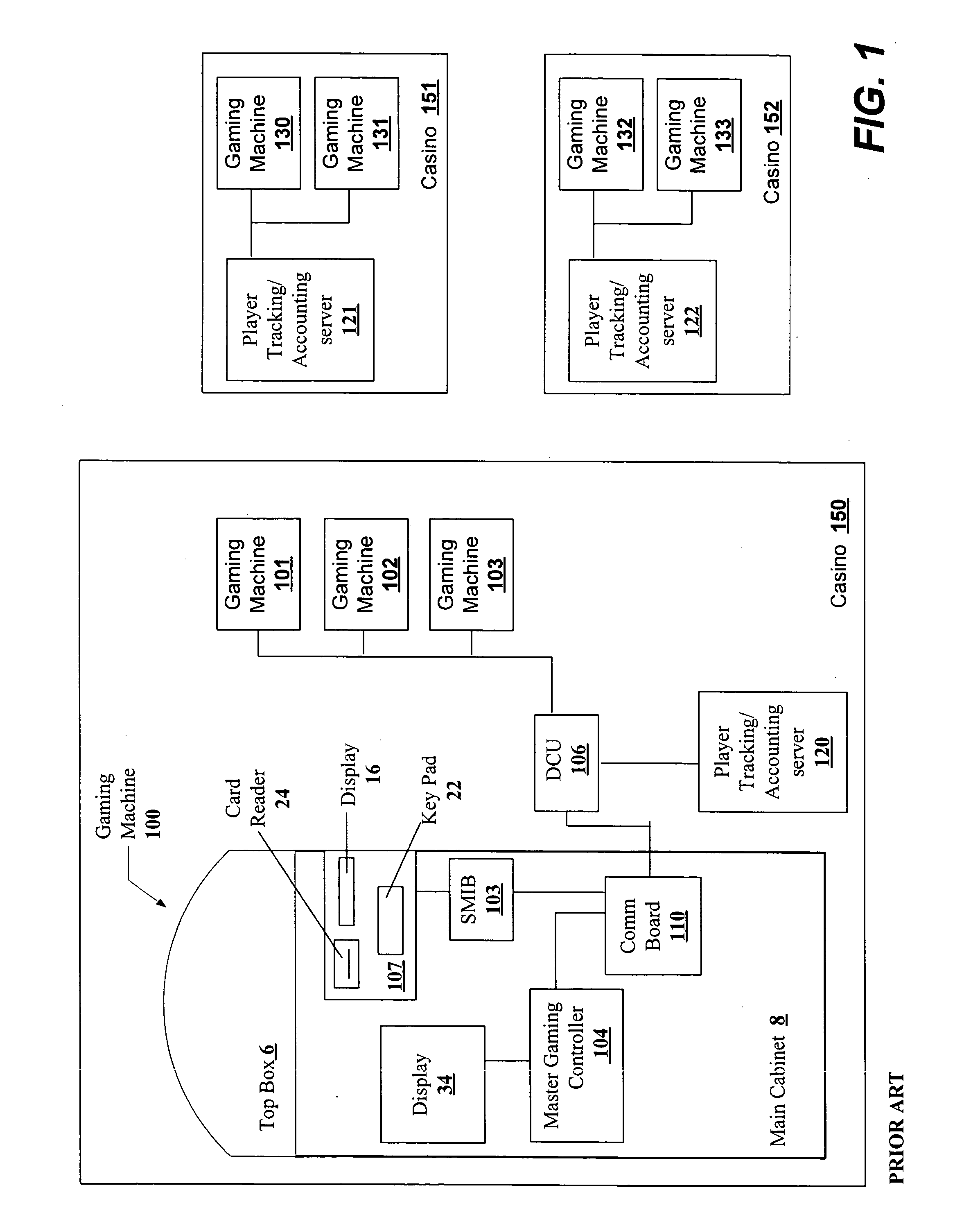
Wide area gaming and retail player tracking
InactiveUS20050054439A1Easy to trackFacilitate awardingCredit registering devices actuationPayment architectureWide areaEngineering
Systems and methods for tracking, differentiating and awarding loyalty credits to patrons of a gaming establishment are disclosed. Tracking can be facilitated by and loyalty credits can be stored on patron issued loyalty credit instruments such as printed tickets, magnetic-striped cards, room keys, portable wireless devices and smart cards. Loyalty credits can be awarded for and combined with other loyalty credits awarded for gaming activities involving wagers, game play, and possible monetary awards, as well as purchasing activities involving the procurement of food, lodging, entertainment, transportation, merchandise or services. Theoretical all expenditures profiles can be established for patrons based upon the gaming activities and purchasing activities of the patrons. Customized comps can be awarded on the initiative of the gaming establishment and without any specific request from a patron. Such comps can be based on tracked information on gaming activities and purchasing activities of the patrons.
Owner:IGT
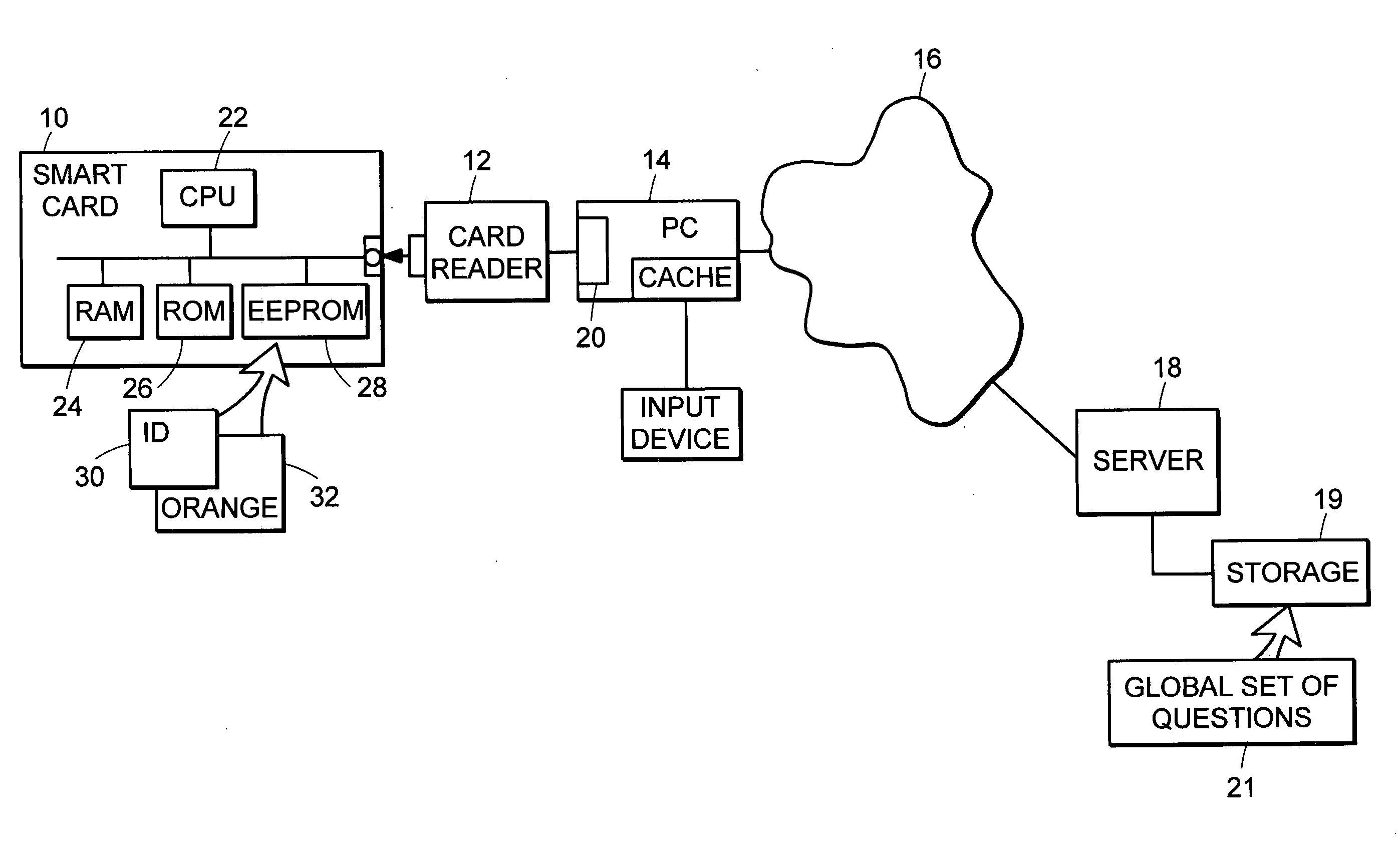
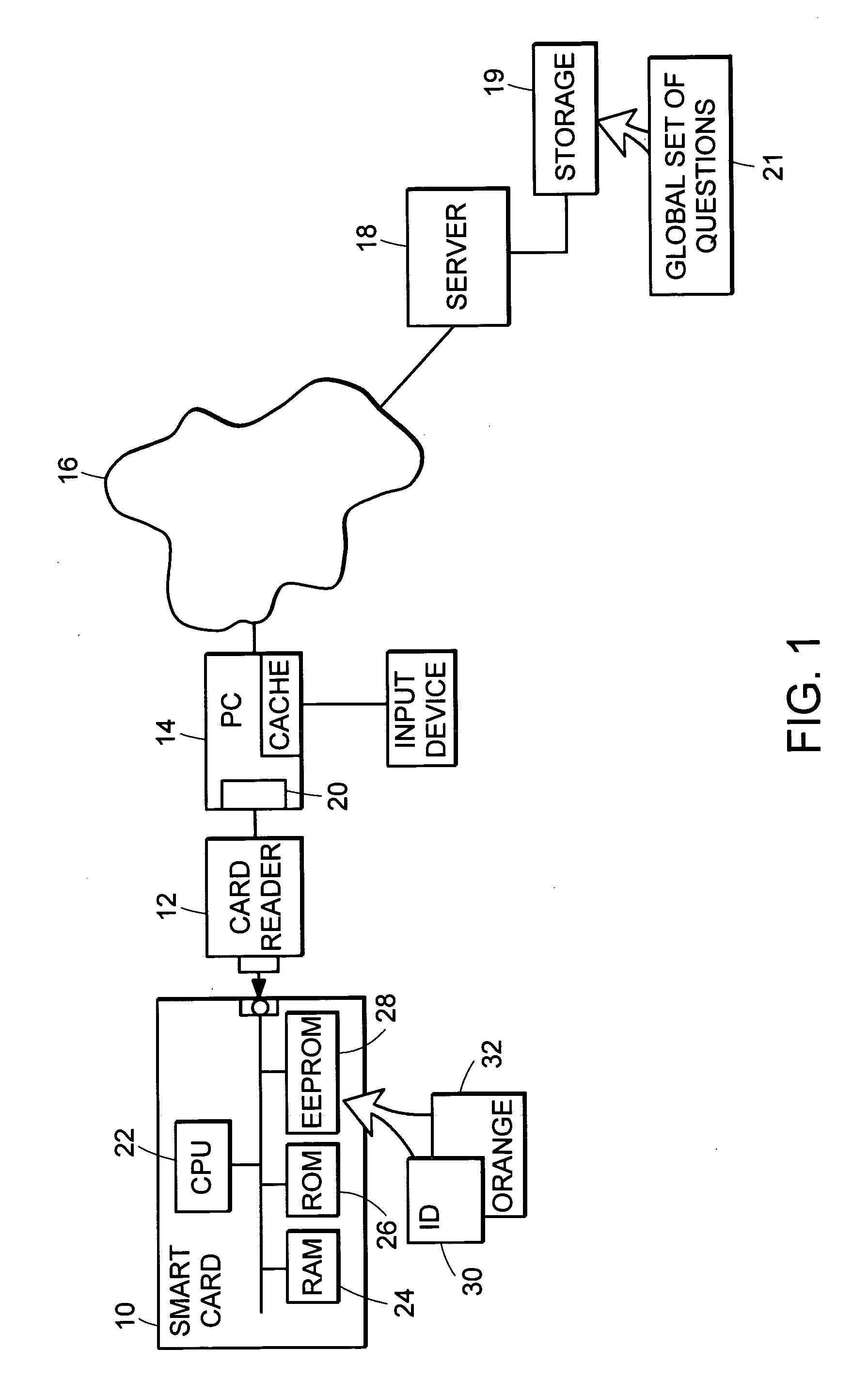
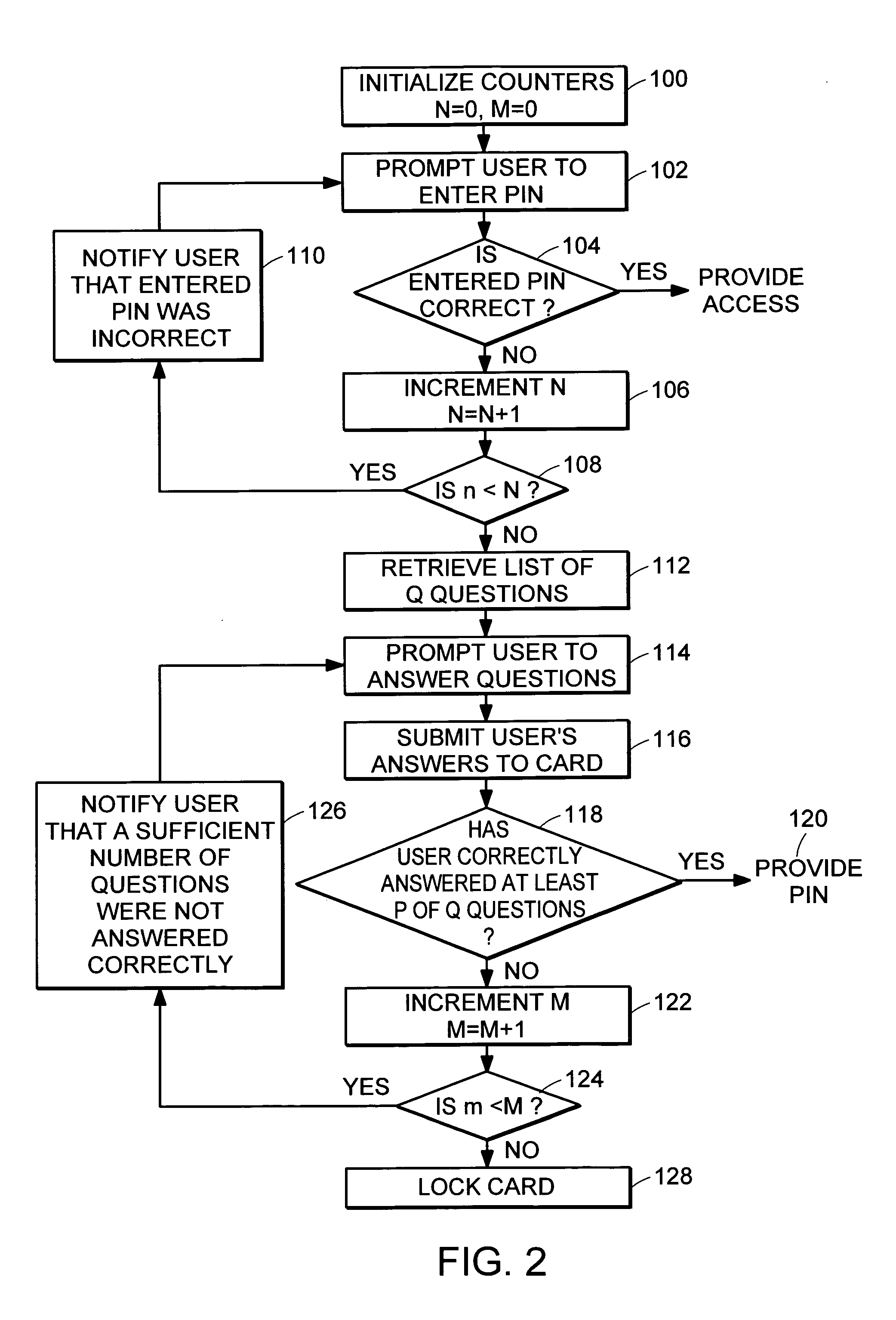
PIN recovery in a smart card
A method of controlling access to resources on a smart card, the method involving: providing a list of n questions for presentation to the user, where n is an integer; receiving from the user answers to questions among the list of n questions; determining how many of the received answers are correct; and if a sufficient number of the n questions was answered correctly, granting access to the resources on the smart card.
Owner:EMC IP HLDG CO LLC
Method and apparatus for installing an application onto a smart card
Owner:ORACLE INT CORP
Secure medical records maintenance system
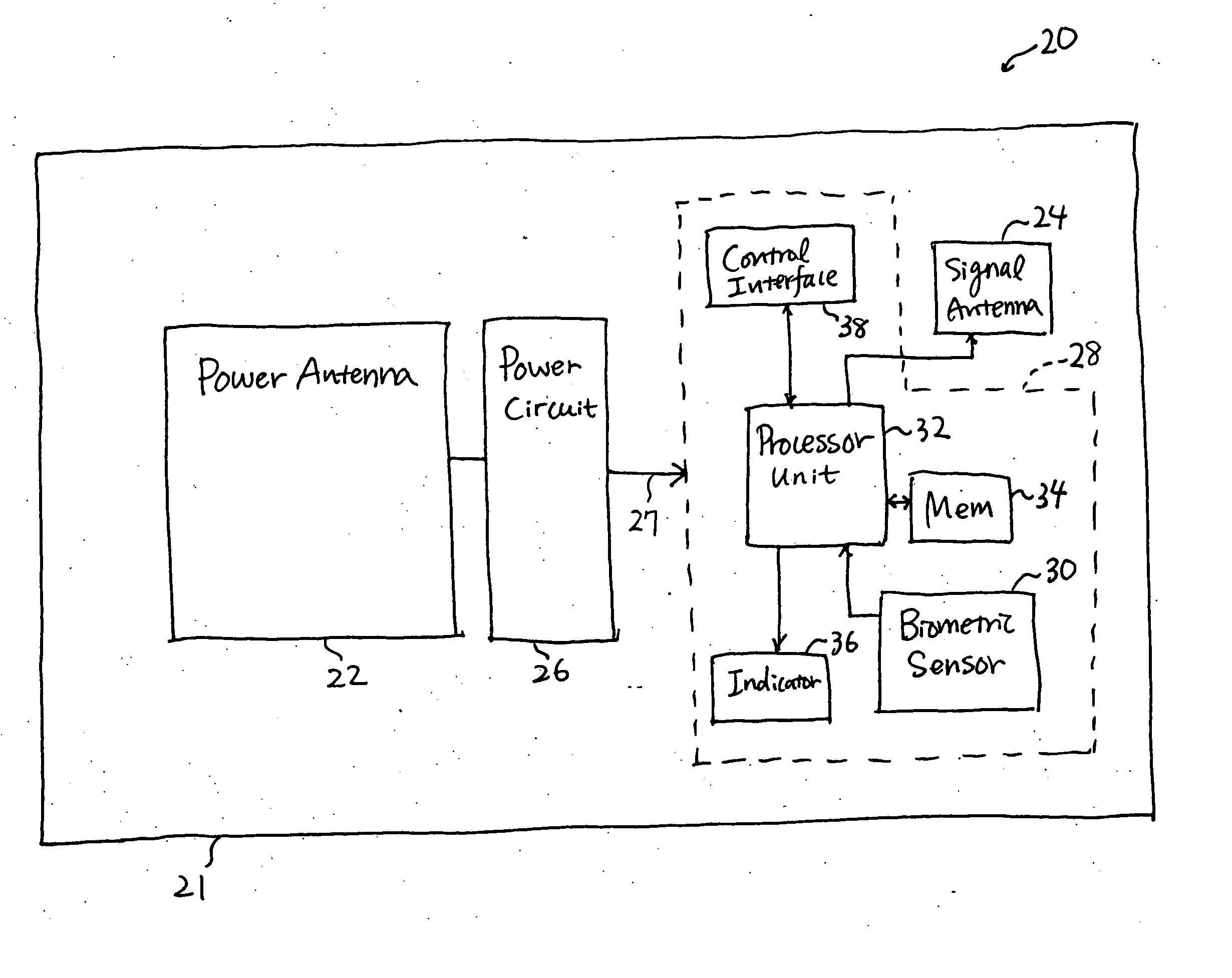
InactiveUS7092891B2Low costReduce inconvenienceBiomass after-treatmentAngiographyMedical recordRemovable media
A secure medical records maintenance system including a first server that stores patient identification information indexed by patient identification numbers (PINs) and a second server that stores patient medical data indexed by medical record identification numbers. For security purposes, the medical data maintained in the second remote server cannot be correlated to the associated patient identification information maintained in the first server based on the information contained in the servers. A correlation table uniquely associating each medical record identification number with a particular one of the patient identification numbers is used to allow correlation of the databases. The correlation table for a particular patient typically resides on a patient's removable memory storage device (smartcard). The correlation table for a practaioner's patients may also reside on the practitioner's computer, which is associated with the licensed medical practitioner having an assigned professional registration number
Owner:ORANGEHOOK INC
Methods and apparatus for conducting electronic transactions
InactiveUS7343351B1Improve reliabilityConfidenceDigital data processing detailsAnalogue secracy/subscription systemsSmart cardE-commerce
A system and method for conducting electronic commerce are disclosed. In various embodiments, the electronic transaction is a purchase transaction. A user is provided with an intelligent token, such as a smartcard containing a digital certificate. The intelligent token suitably authenticates with a server on a network that conducts all or portions of the transaction on behalf of the user. In various embodiments a wallet server interacts with a security server to provide enhanced reliability and confidence in the transaction. In various embodiments, the wallet server includes a toolbar. In various embodiments, the digital wallet pre-fills forms. Forms may be pre-filled using an auto-remember component.
Owner:LIBERTY PEAK VENTURES LLC
System for card to card transfer of monetary values
InactiveUS6394343B1Less incentiveIncrease valueComplete banking machinesFinanceSmart cardData transmission
A smart card stores monetary values and selectively transfers monetary values to and receives monetary values from a compatible smart card. The smart card includes a data storage device that stores data representing monetary values. Control circuitry controls the transfer of the monetary values into the data storage device and controls the transfer of the monetary values out of the data storage device. A data transfer interface couples directly to a like interface on the compatible card to enable data to be transferred between the smart card and the compatible card. A system for electronic transfer of monetary values includes first and second smart cards. Each of the first and second smart cards includes a data storage device that stores data representing monetary values.
Owner:BERG JON N +1
Satellite TV security system
InactiveUS20050198673A1Transmission becomes disabledGHz frequency transmissionAnalogue secracy/subscription systemsIntegrated receiver/decoderOperability
A satellite TV security system including a TV satellite operated by a satellite TV provider directed to a television set of a satellite TV subscriber that defends the satellite TV provider from illegal reception of TV signals from a TV satellite. An addressable integrated receiver / decoder (IRD) positioned in the TV set top box has an assigned identification number and a smart card positioned in the IRD has an assigned identification number. A security module is provided that is integrated with the IRD. Upon command of the satellite TV provider or automatically, the security module makes a periodic verification of a match of the two identification numbers. Lack of verification of a match triggers a signal from the security module to the IRD to stop transmitting TV signals to the subscriber television. As an alternative verification, the security module initiates periodic verifications of the operability of the telephone line connection between the satellite TV provider and the IRD of the subscriber. Lack of verification of the operability of the telephone line triggers a signal from the security module to the IRD to stop transmitting TV signals to the subscriber TV. The two systems of verification can be operated independently or simultaneously. The subscriber telephone number can be added as an assigned identification number, so that a three-way verification of identification numbers by the security module is required for continued transmission of TV signals to the subscriber television.
Owner:KIT JOHN +2
Event-recorder for transmitting and storing electronic signature data
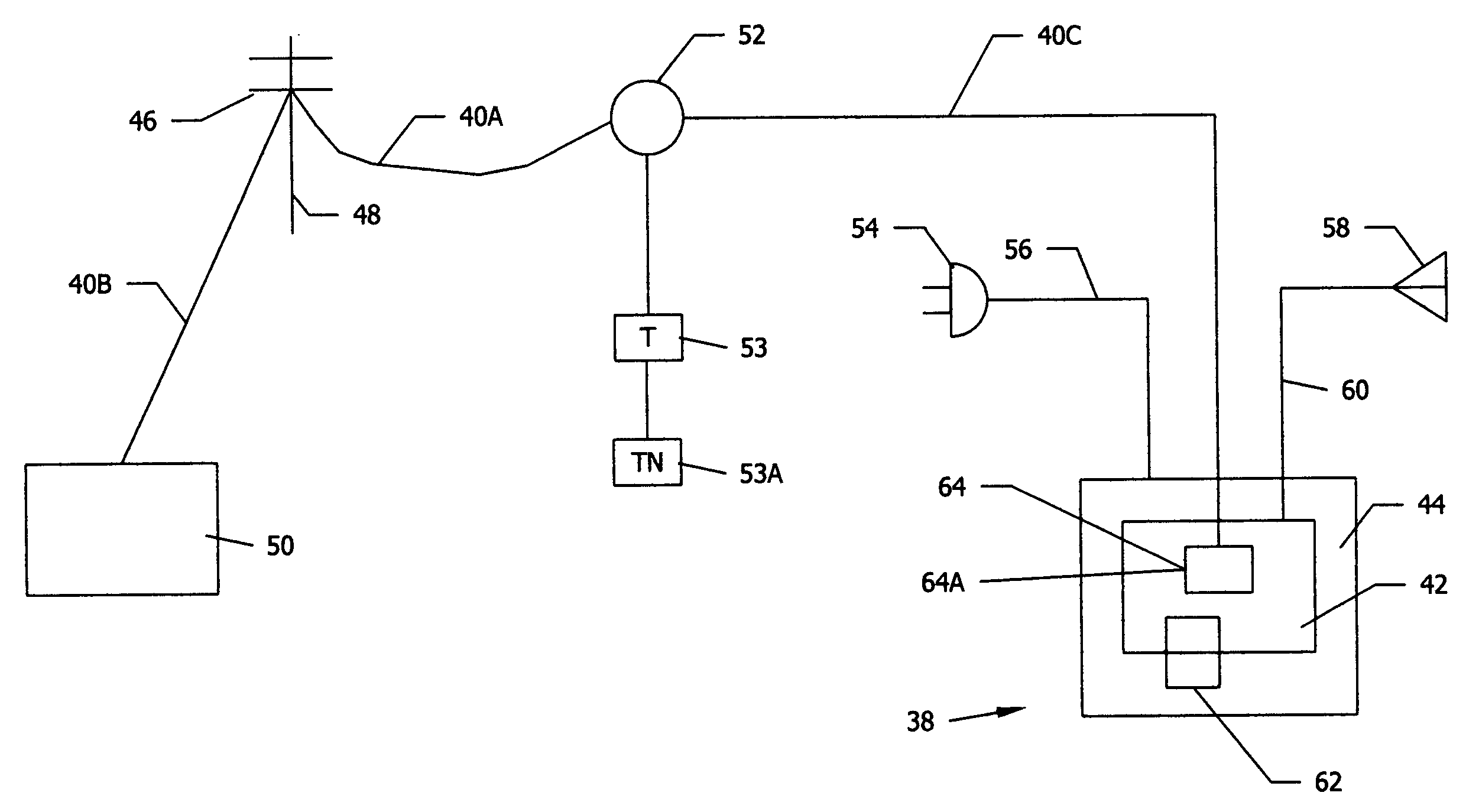
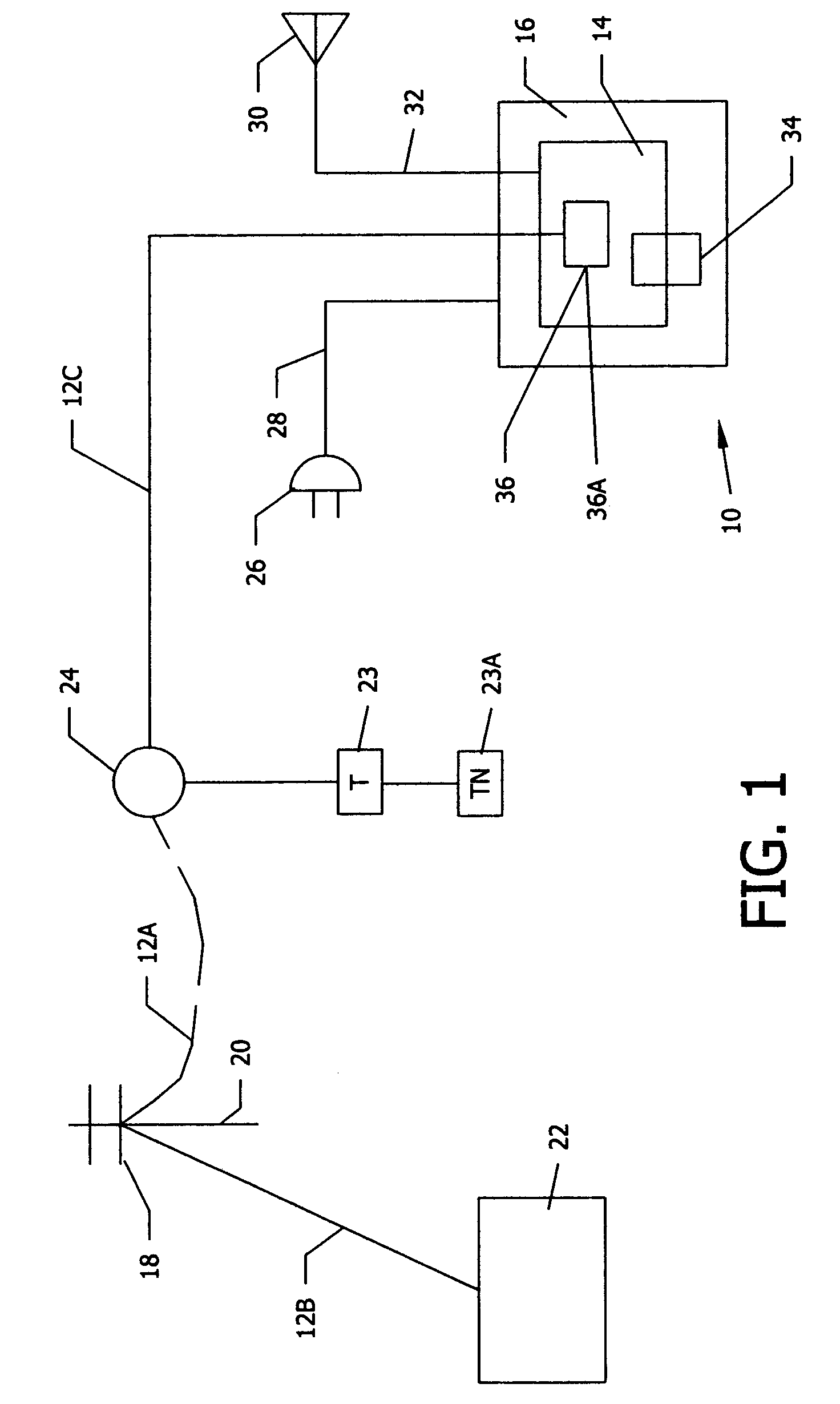
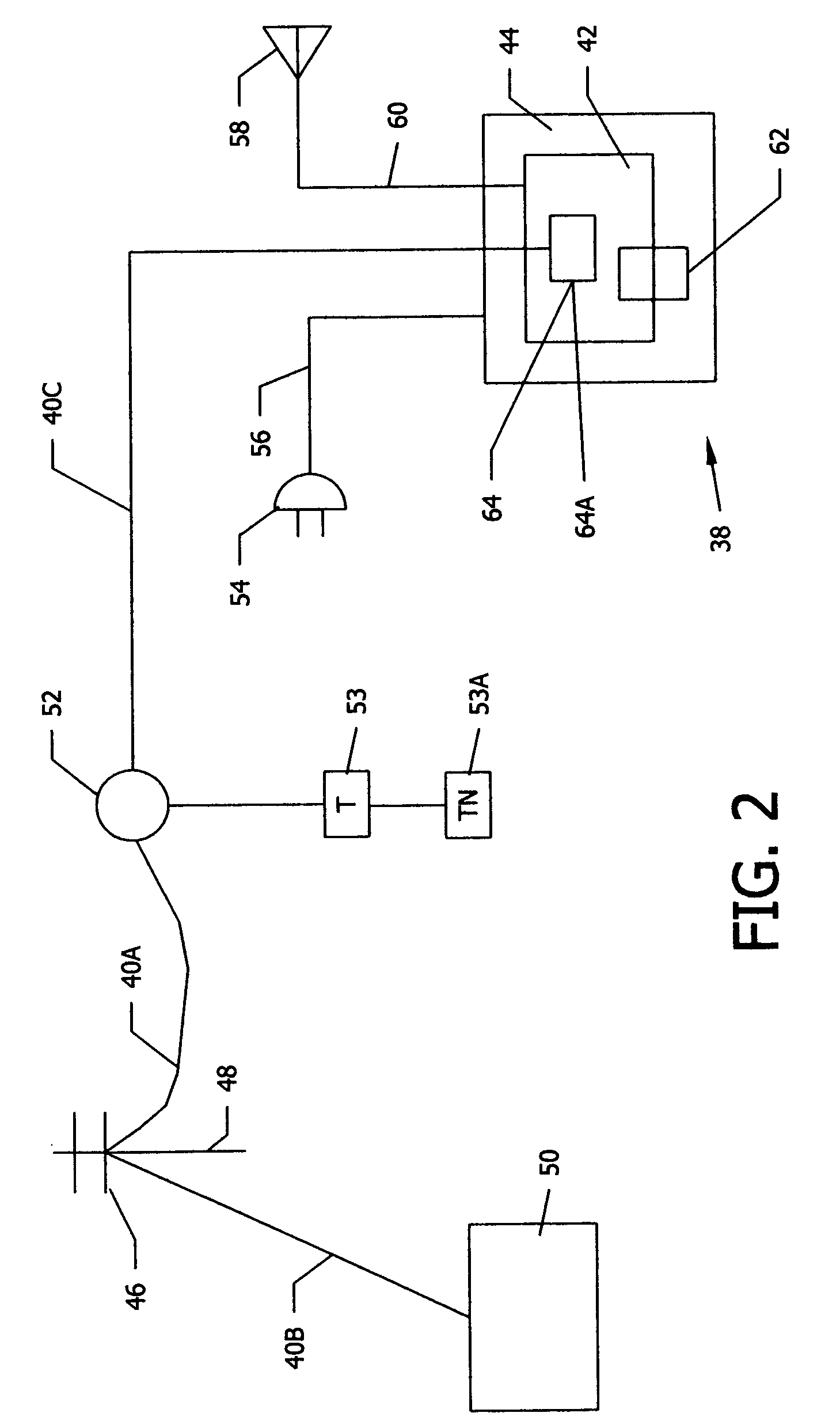
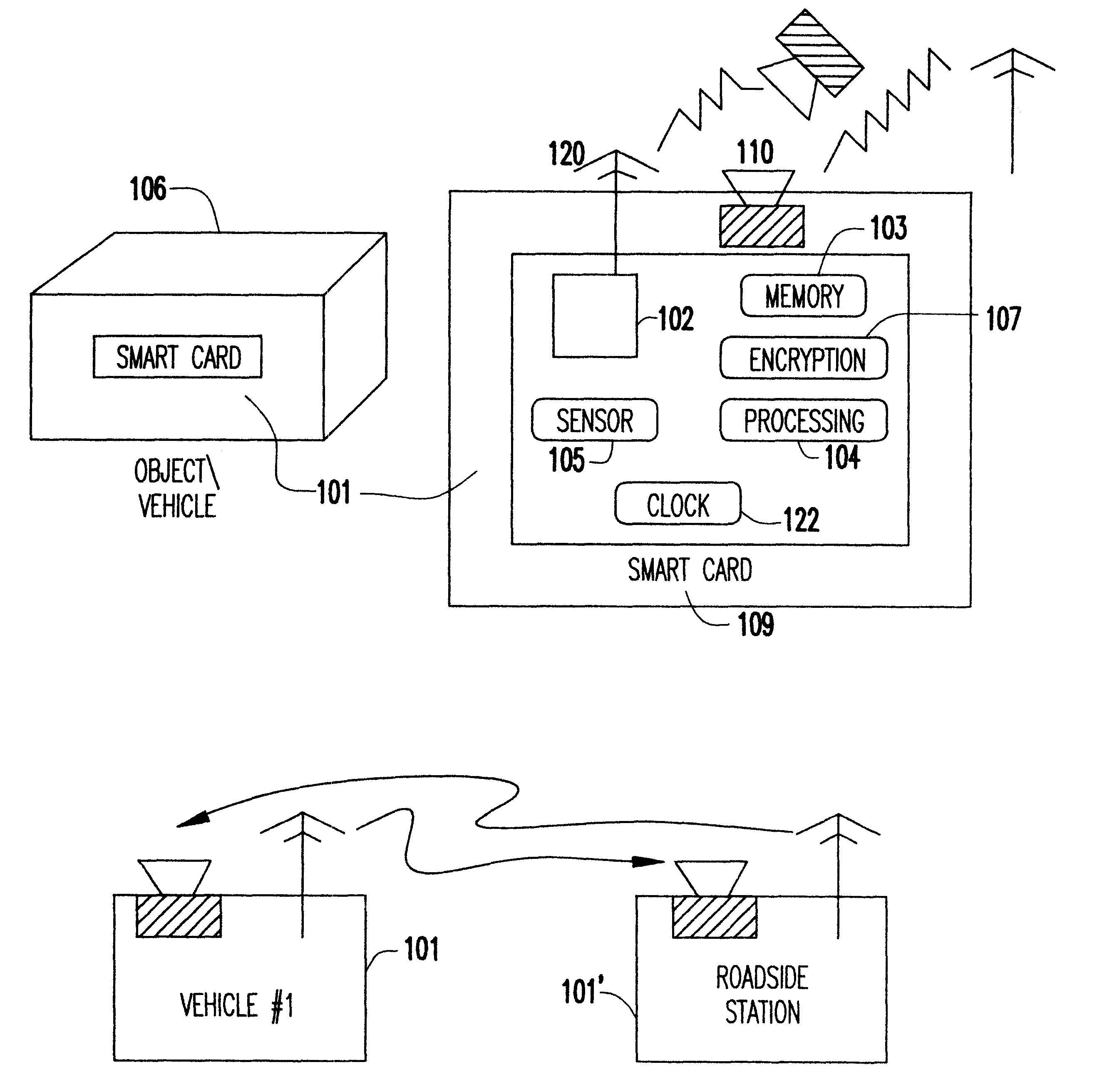
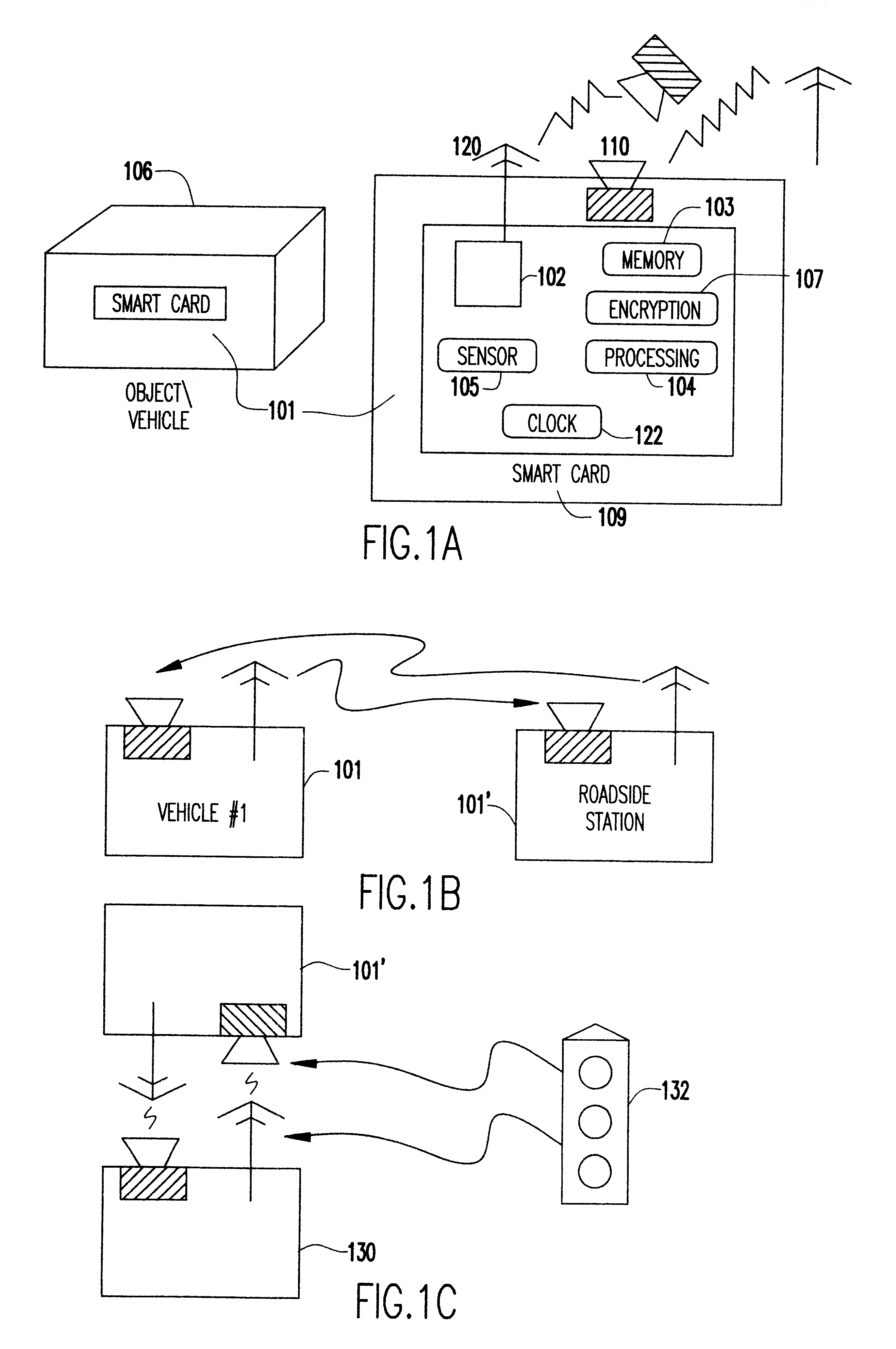
An electronic event recorder for attachment to a vehicle is provided which can broadcast encrypted signature and data, thereby leaving behind an electronic version of a "fingerprint" in the event of an accident or traffic violation. The fingerprint, captured by an external data acquisition system or another vehicle so equipped, provides a history of events related to the vehicle. The event recorder is preferably integrated on a smart card and housed in a tamper proof casing. In a first mode of operation, monitoring stations along the roadways periodically send an interrogation signal, such as when radar detects that the vehicle is speeding. Upon receiving the interrogation signal the smart card transmits the vehicle's signature information to the monitoring station where it is time and date stamped along with the speed of the vehicle. In a second mode of operation, when a sensor detects a sudden or violent acceleration or deceleration, such as occurs during a collision, a smart card mounted in each car will exchange signature information automatically. This is particularly useful when the collision occurs in a parking lot when one of the hit vehicles is typically unattended.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com