Patents
Literature
1816 results about "Tamper resistance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Tamper resistance is resistance to tampering by either the normal users of a product, package, or system or others with physical access to it. There are many reasons for employing tamper resistance. Tamper resistance ranges from simple features like screws with special drives, more complex devices that render themselves inoperable or encrypt all data transmissions between individual chips, or use of materials needing special tools and knowledge. Tamper-resistant devices or features are common on packages to deter package or product tampering. Anti-tamper devices have one or more components: tamper resistance, tamper detection, tamper response, and tamper evidence. In some applications, devices are only tamper-evident rather than tamper-resistant.
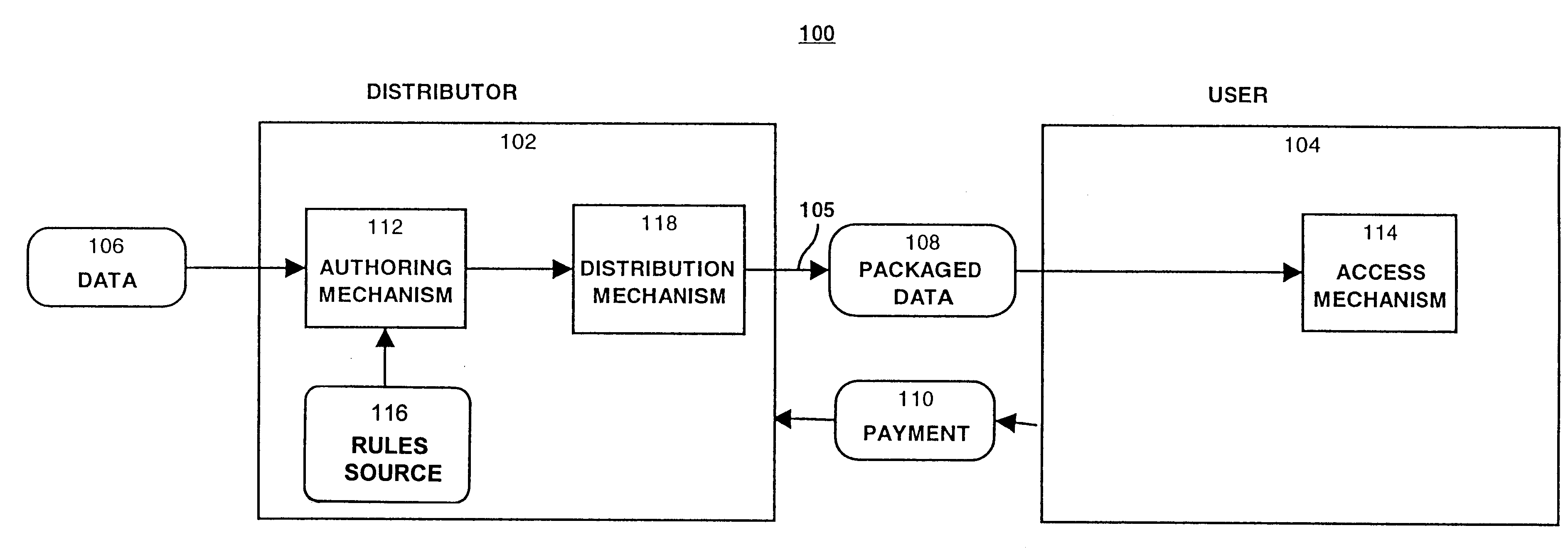
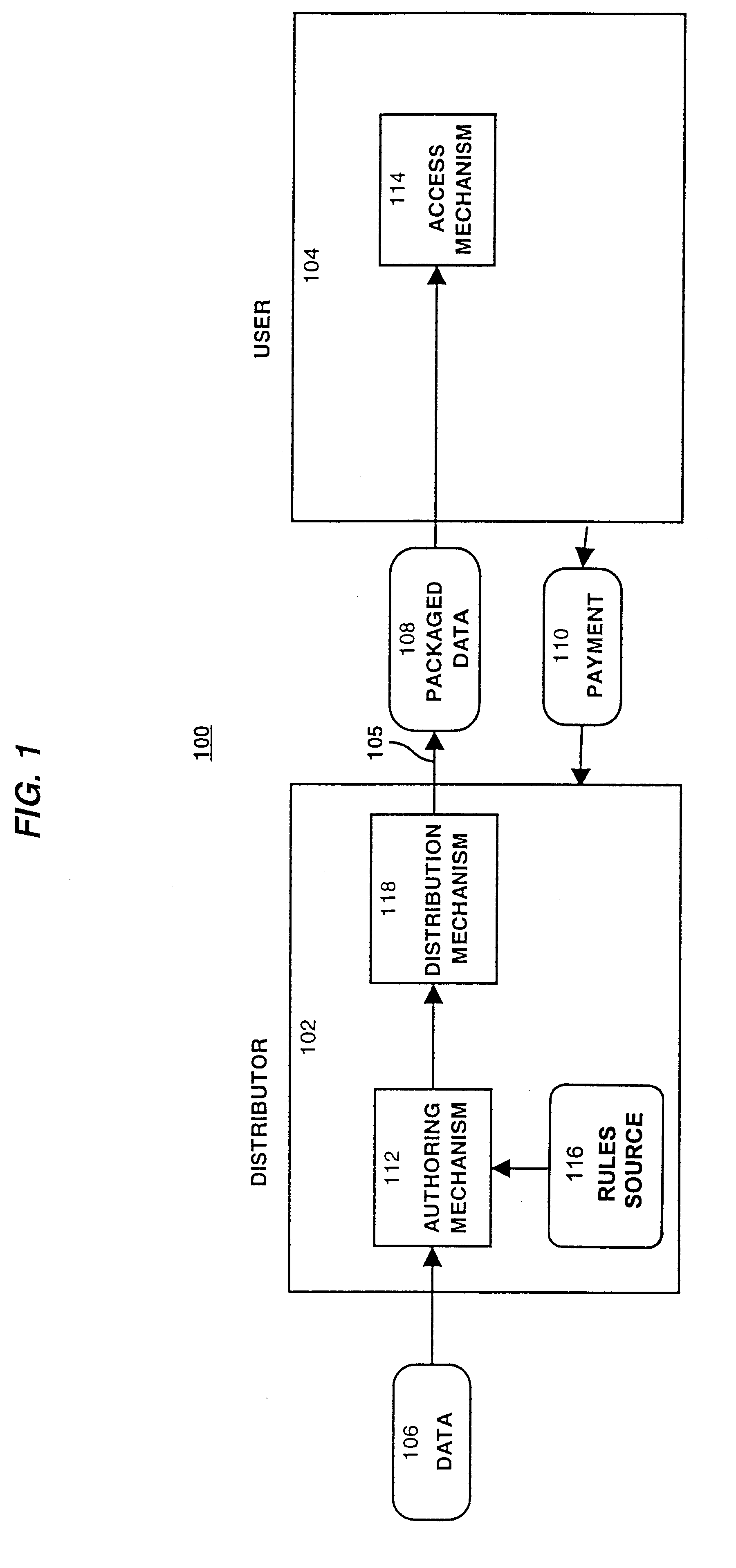
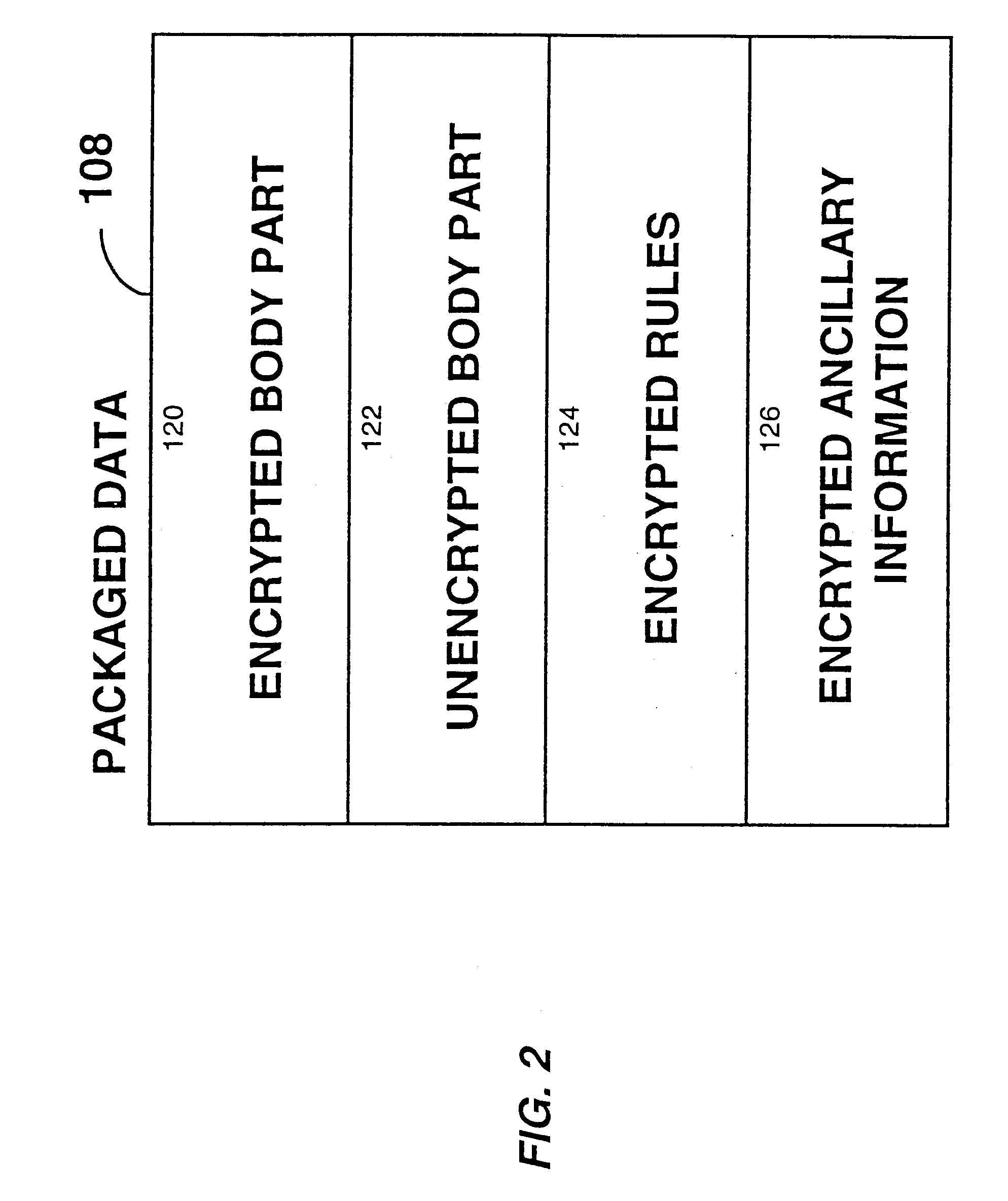
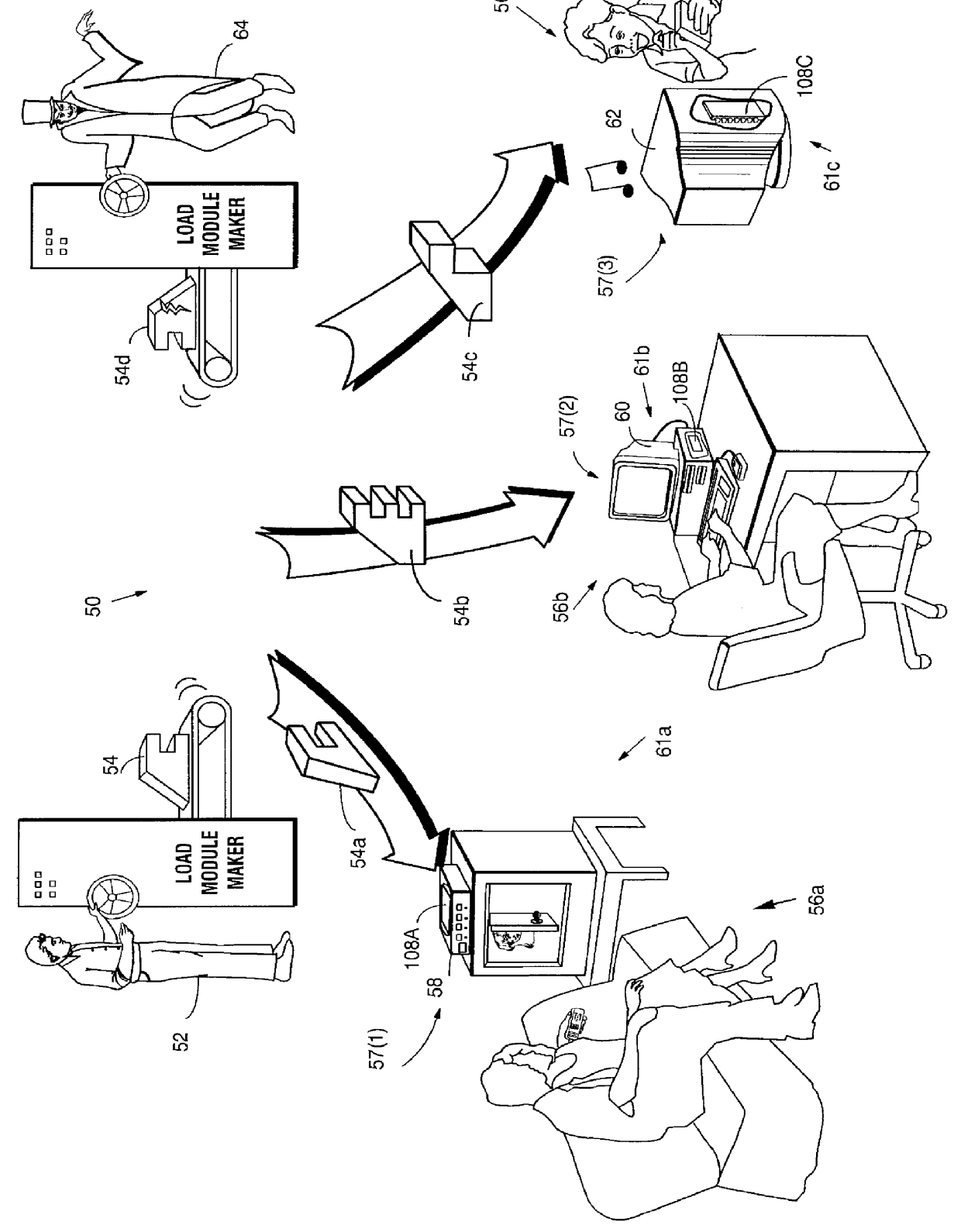
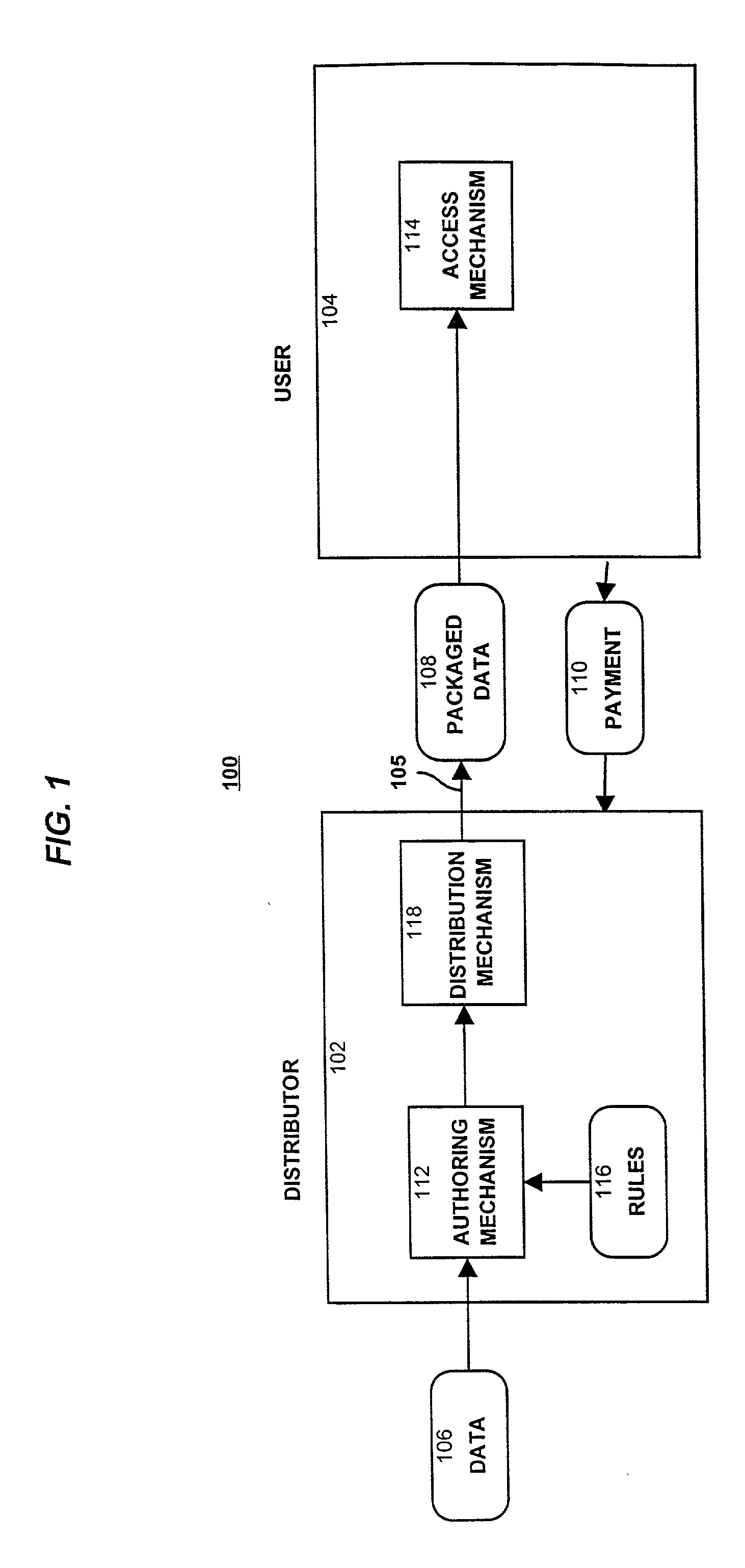
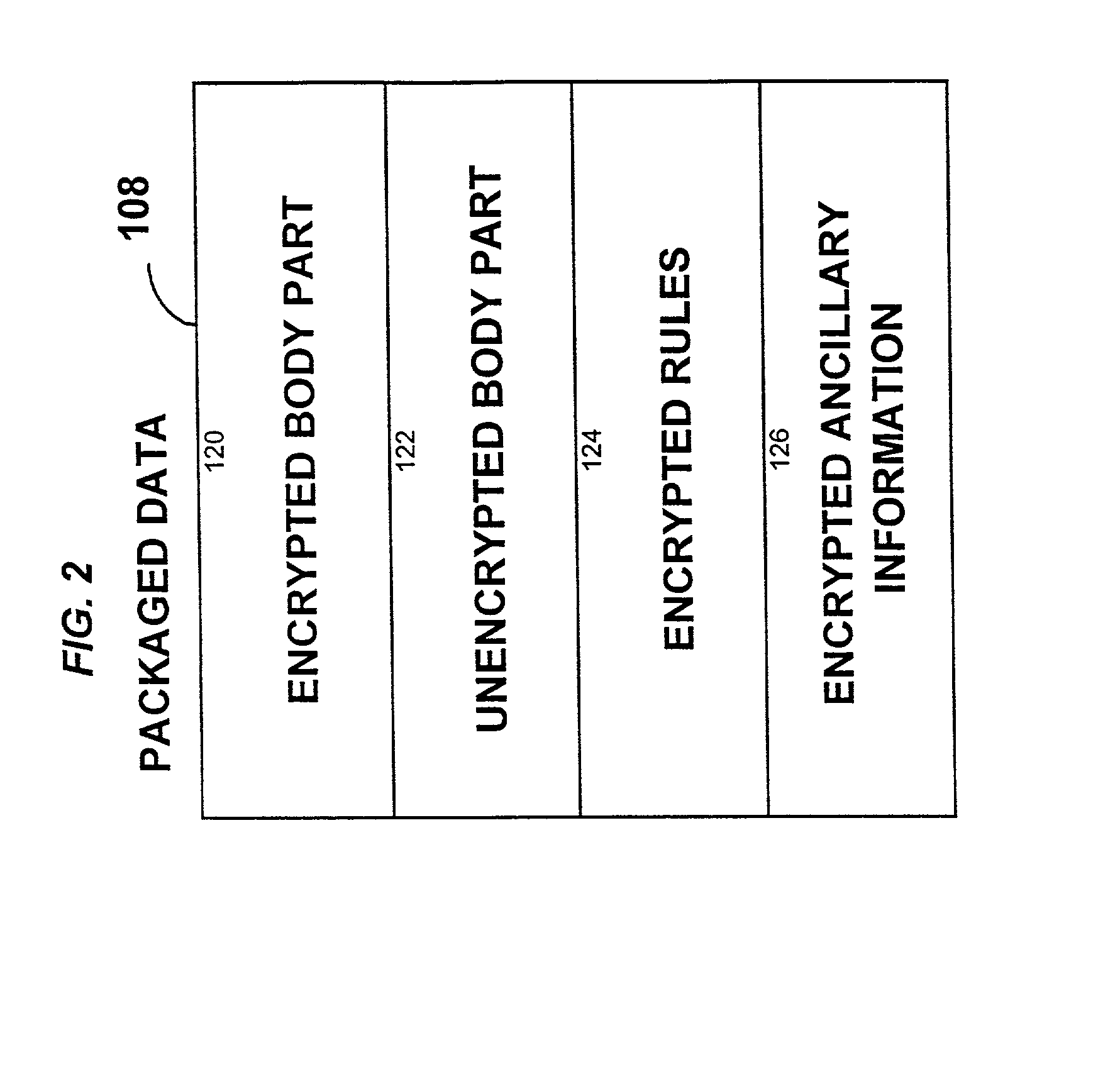
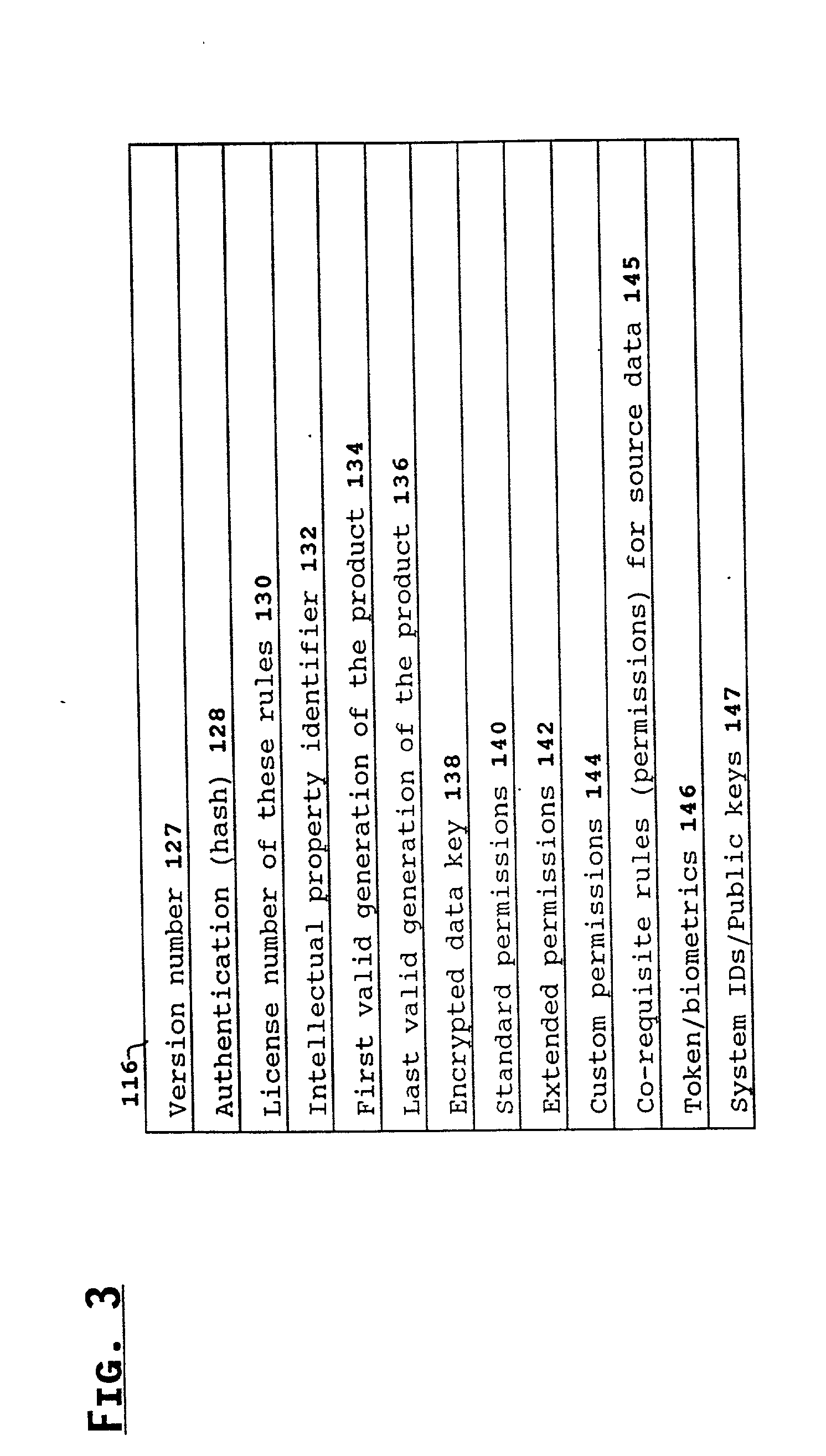
System for controlling access and distribution of digital property
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
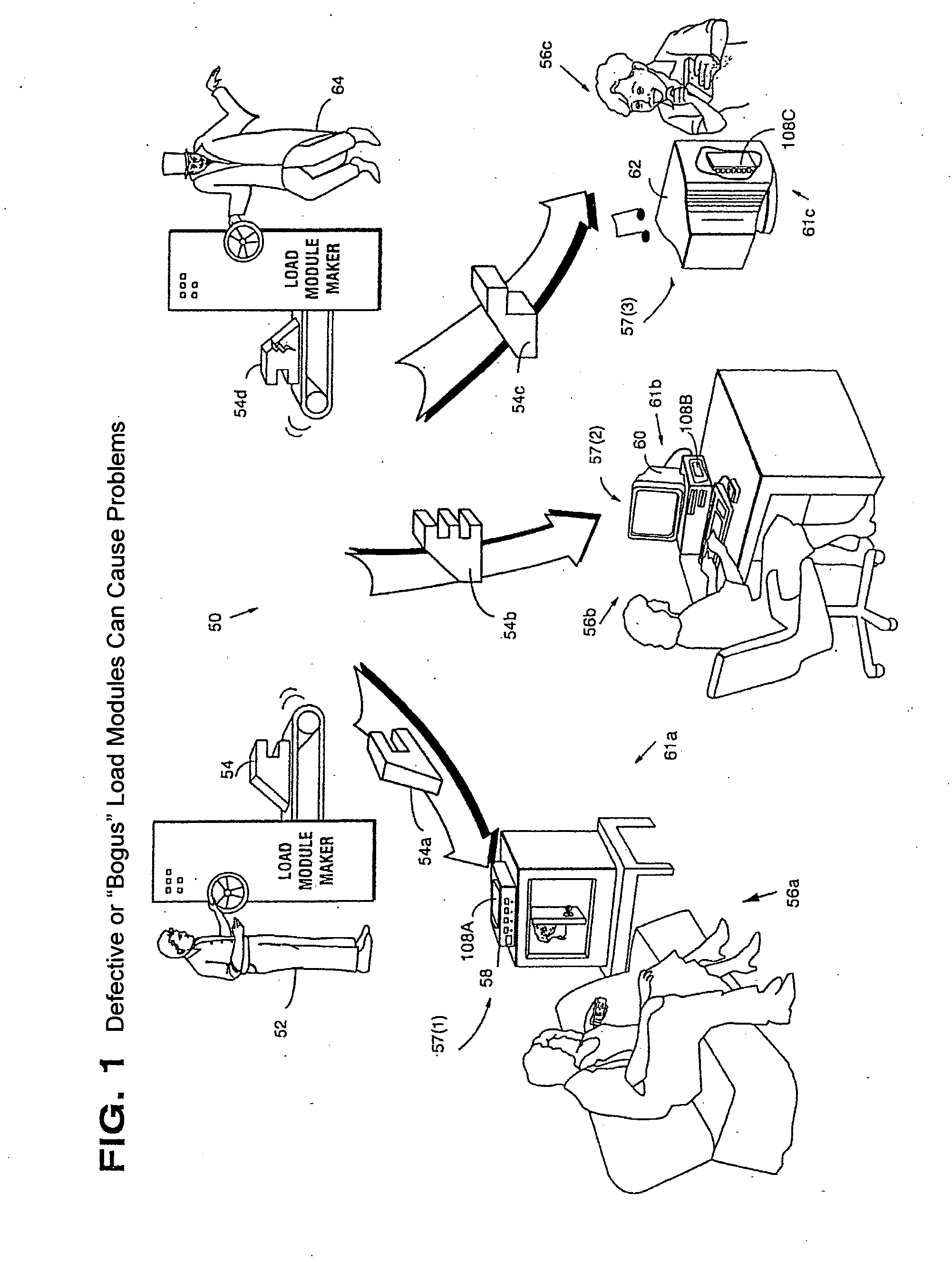
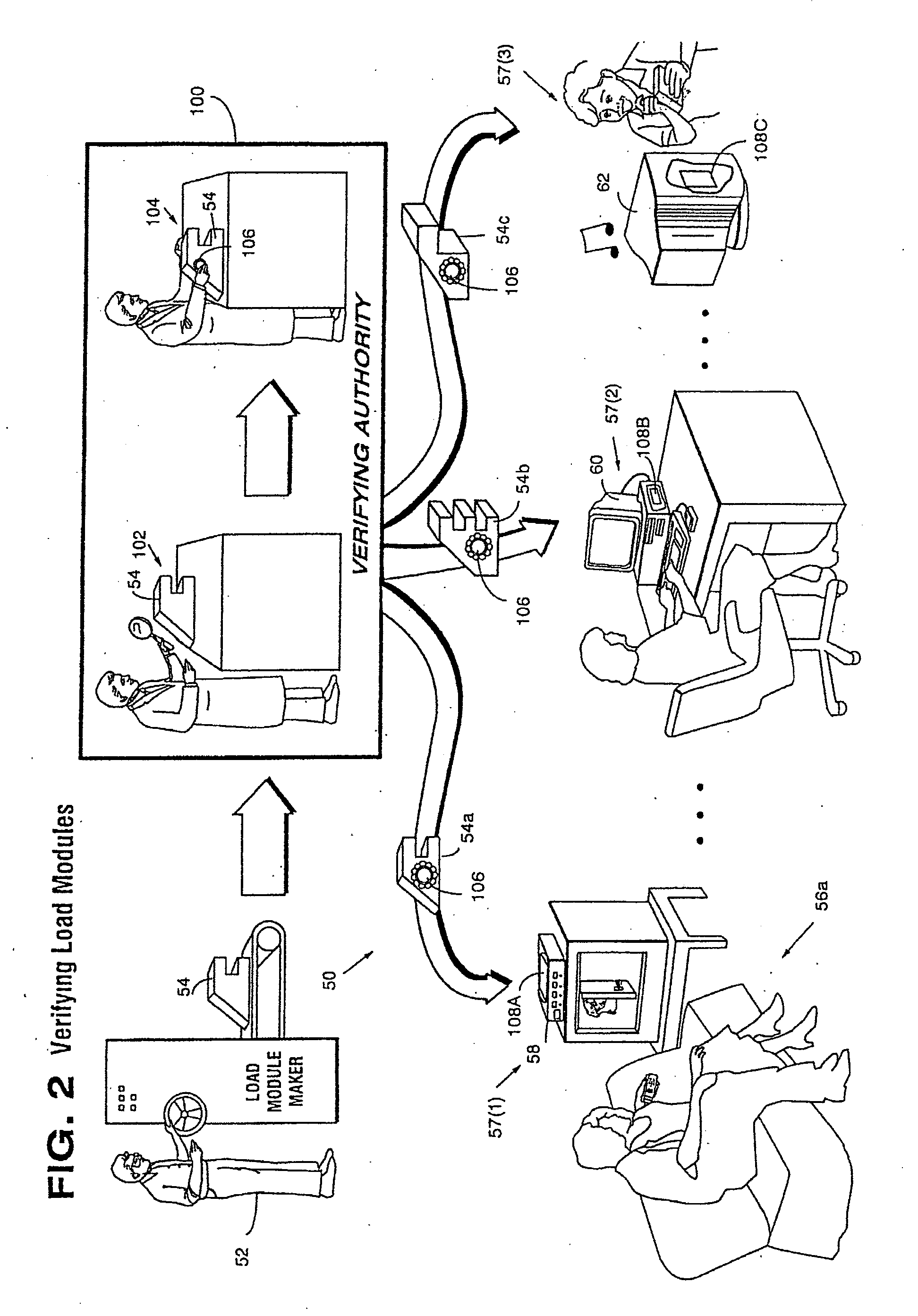
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
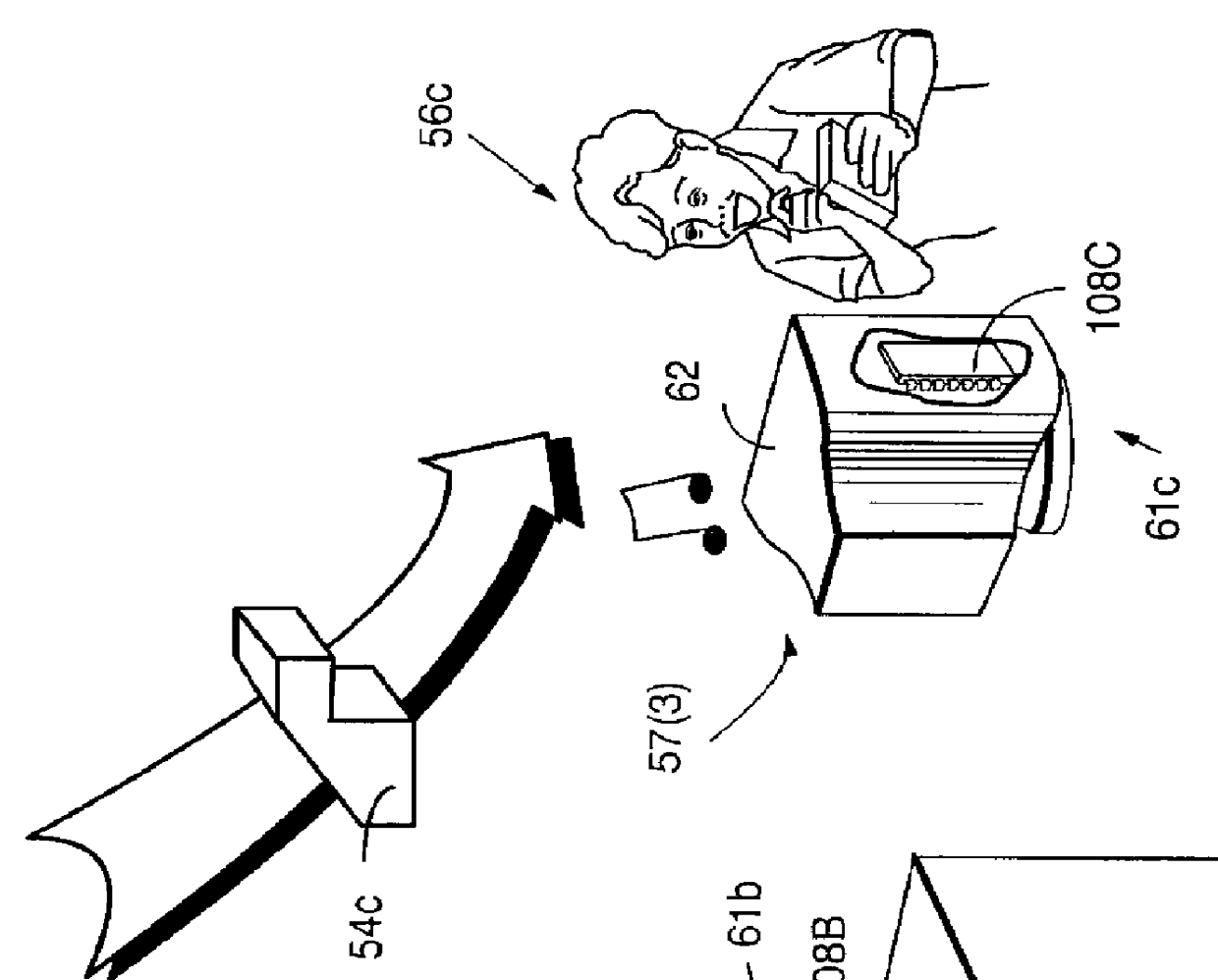
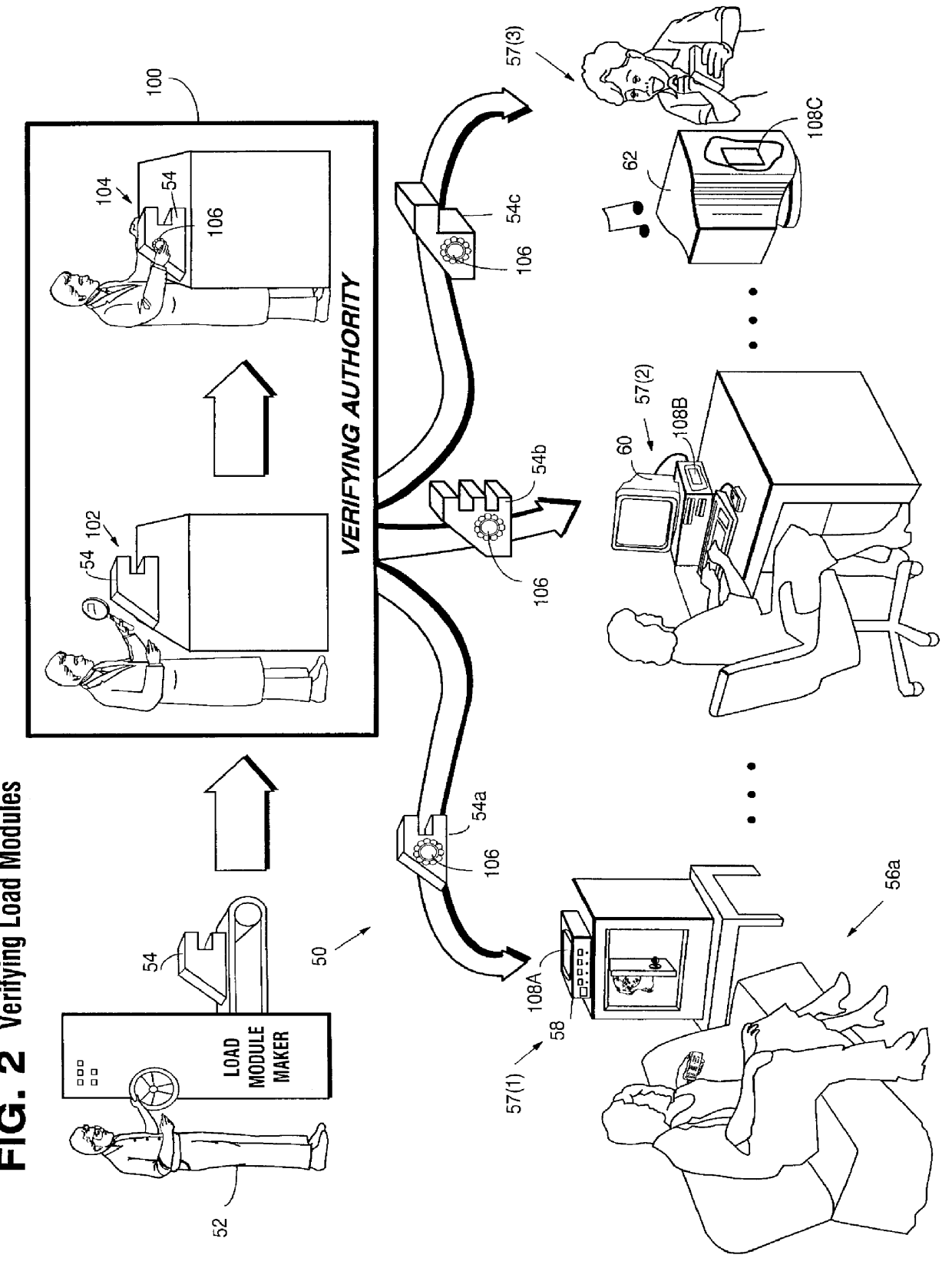
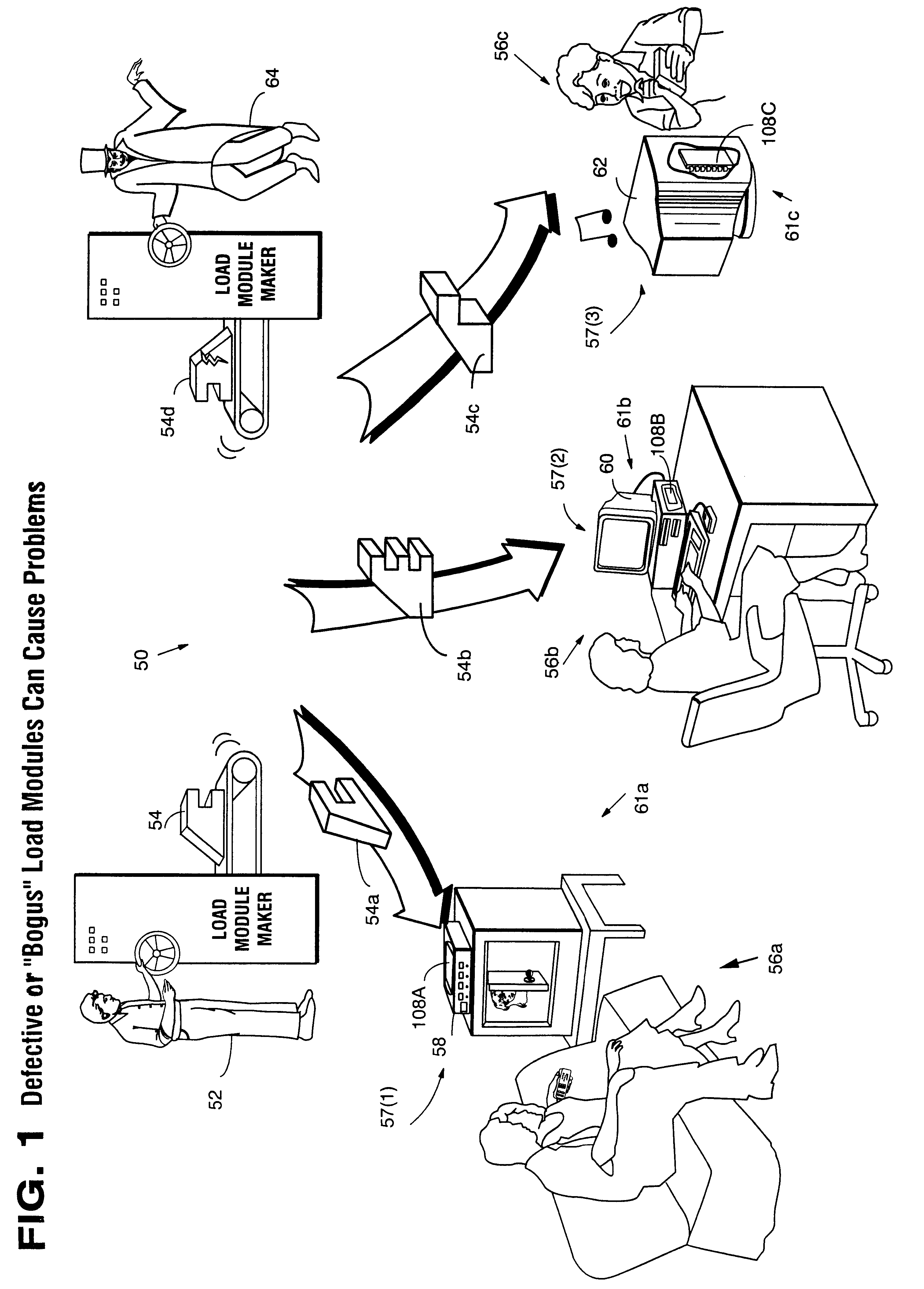
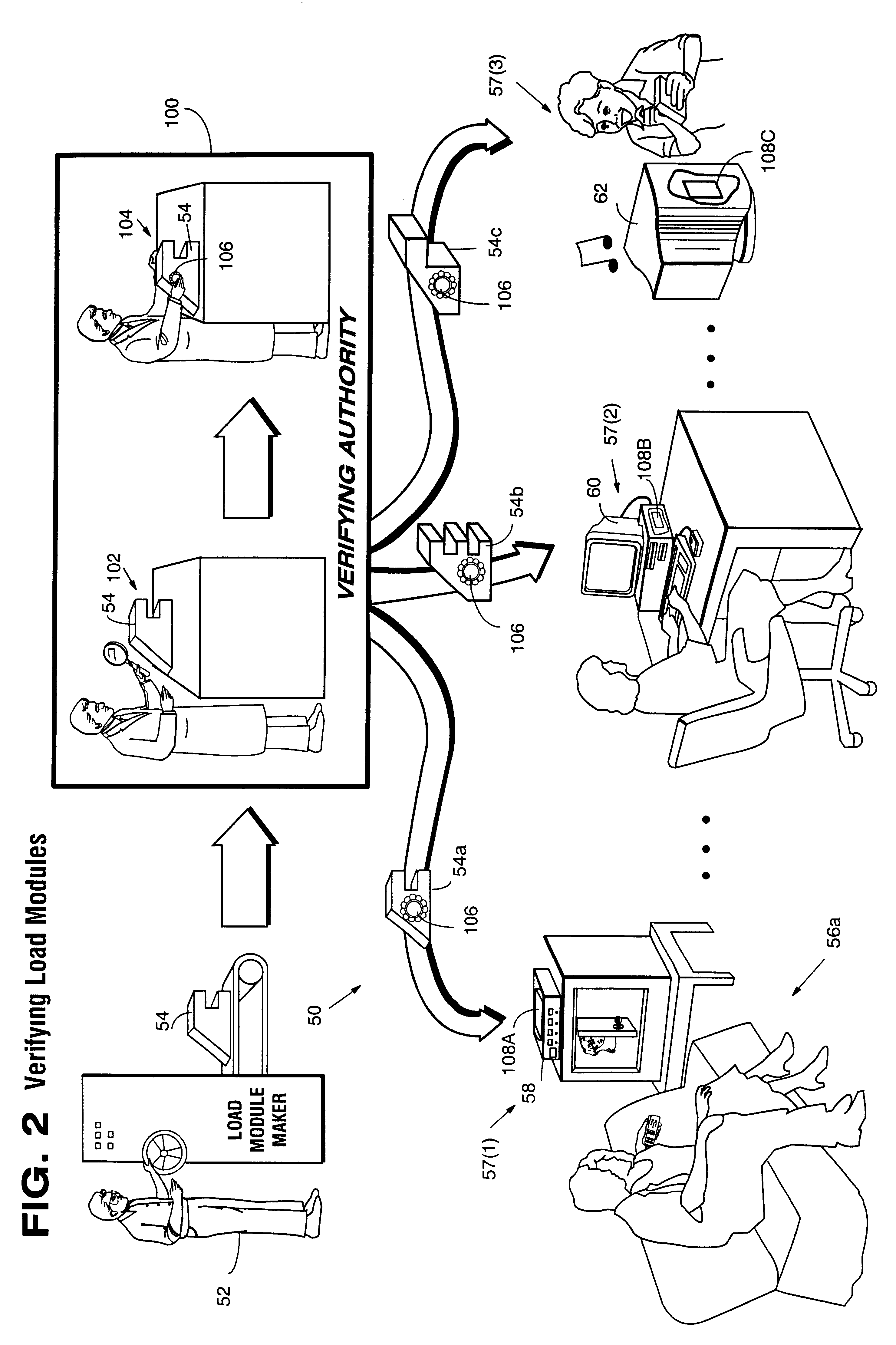
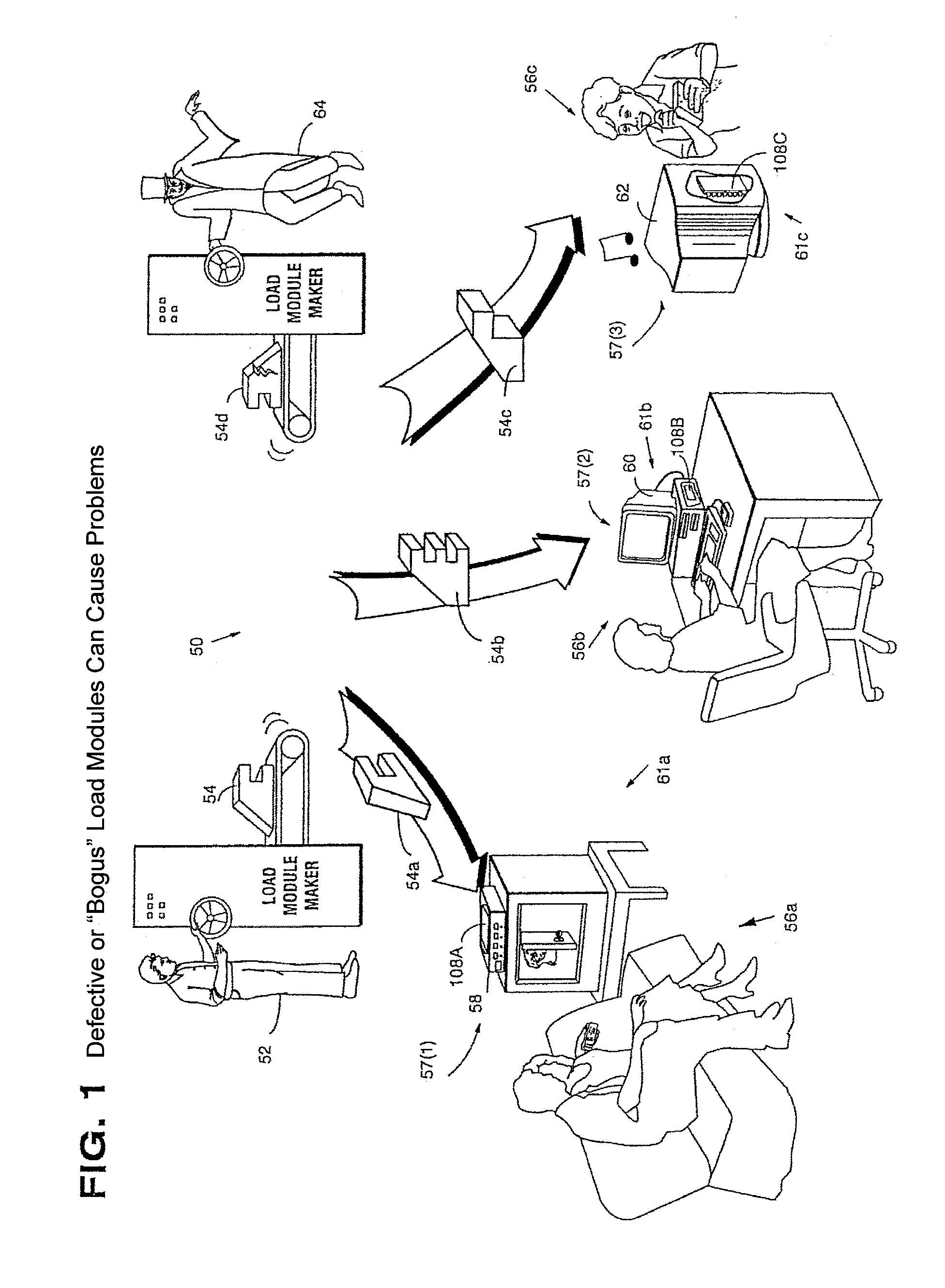
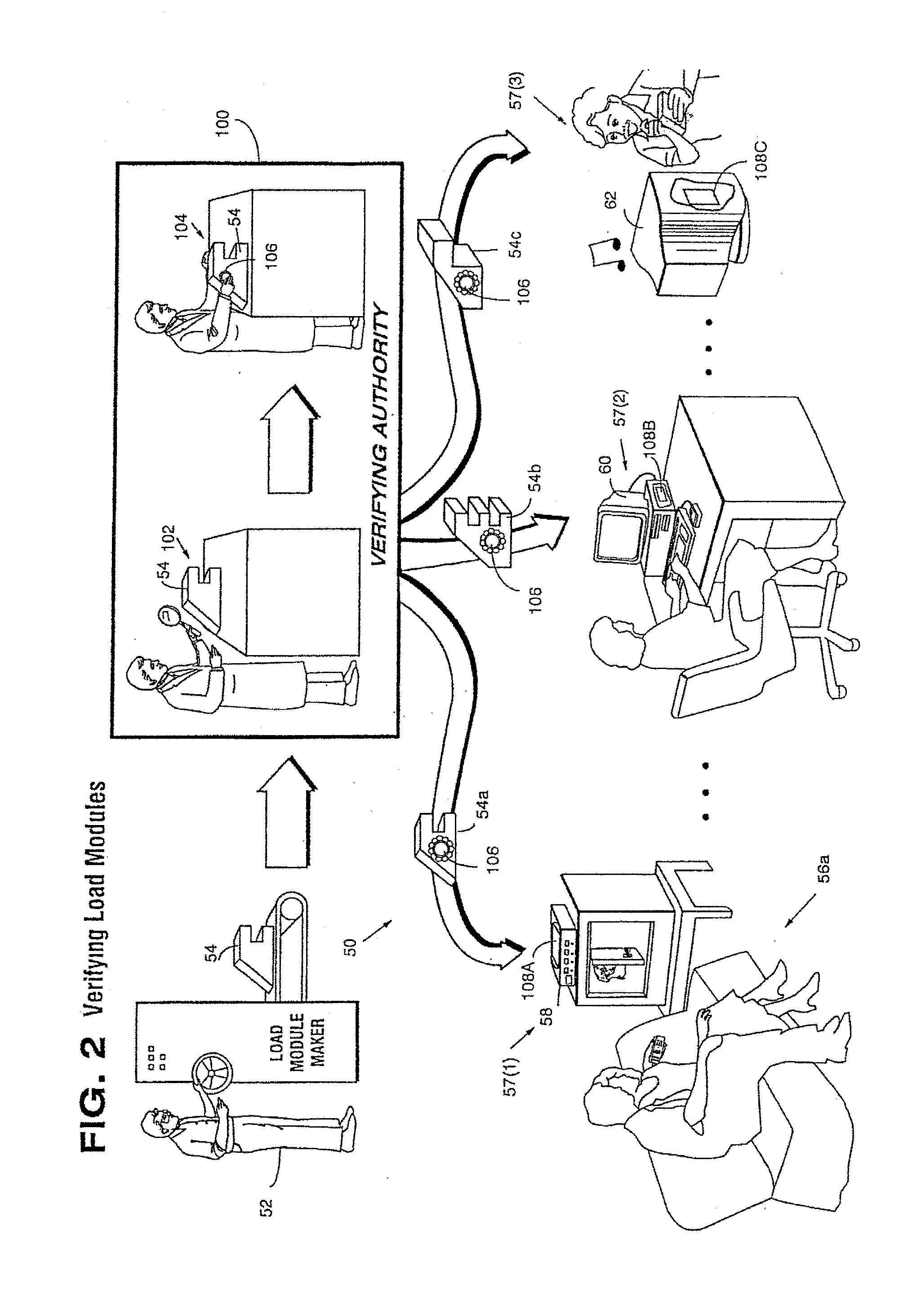
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
Electronic security seal and system
InactiveUS8031069B2Easy constructionSimple in useStampsAnti-theft devicesTamper resistanceElectronic security
A tamper-proof electronic security seal which includes a bolt and a locking element and an electronic seal element. The bolt has a head and a hollow shank extending therefrom having a longitudinal bore formed therein. The shank is dimensioned to pass through a lock hasp and has a free end formed for locking engagement with the locking element. The electronic seal element is formed for mechanical connection to the bolt head, and includes an electrical power source, a control unit, communications means responsive to the control unit and a sensor adapted for insertion into the longitudinal bore of the shank, and connected to the control unit. In response to a severing of the shank and the sensor inserted therein, the control unit is operative to activate the communications means to emit an alarm signal.
Owner:COHN ODED YAIR +1
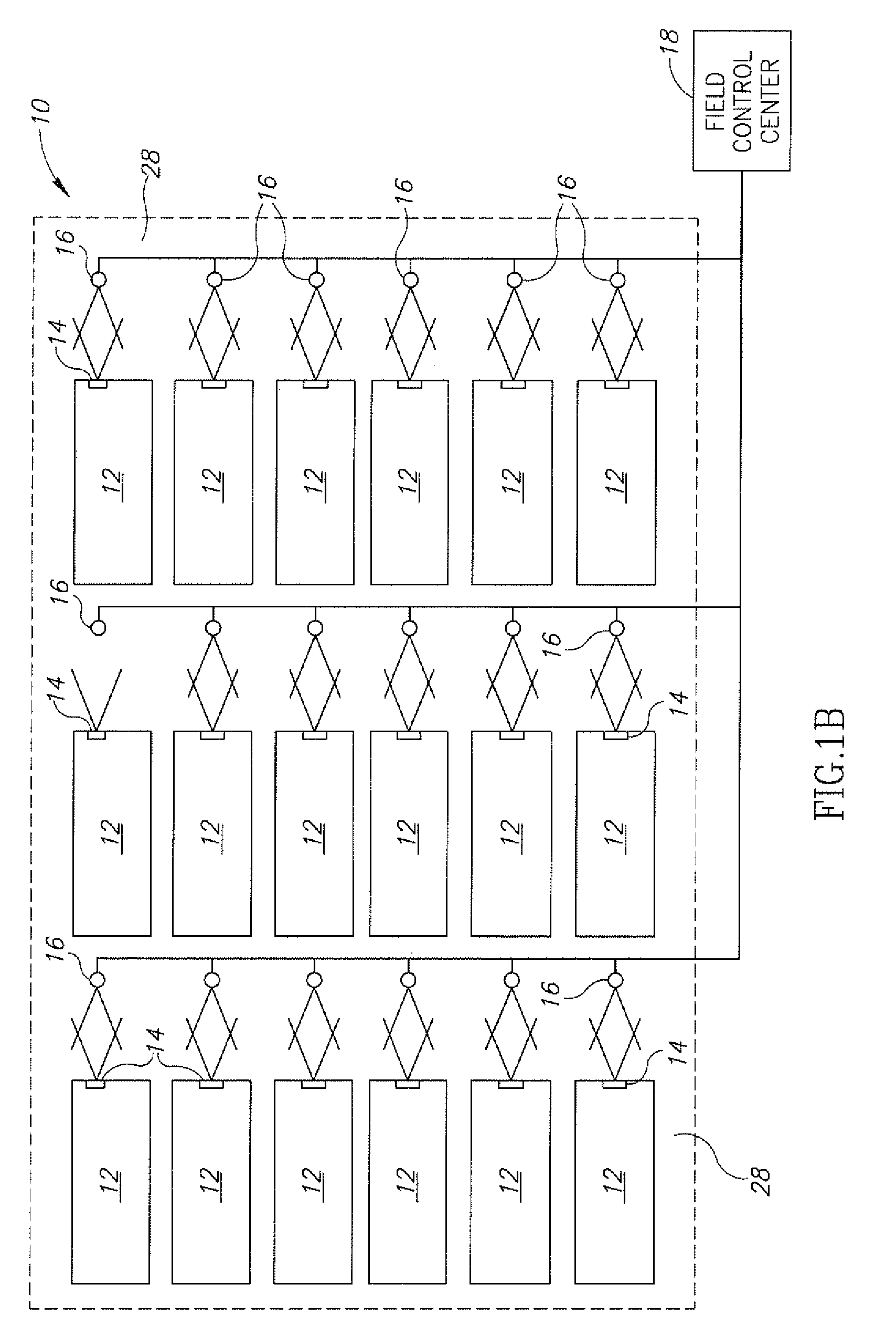
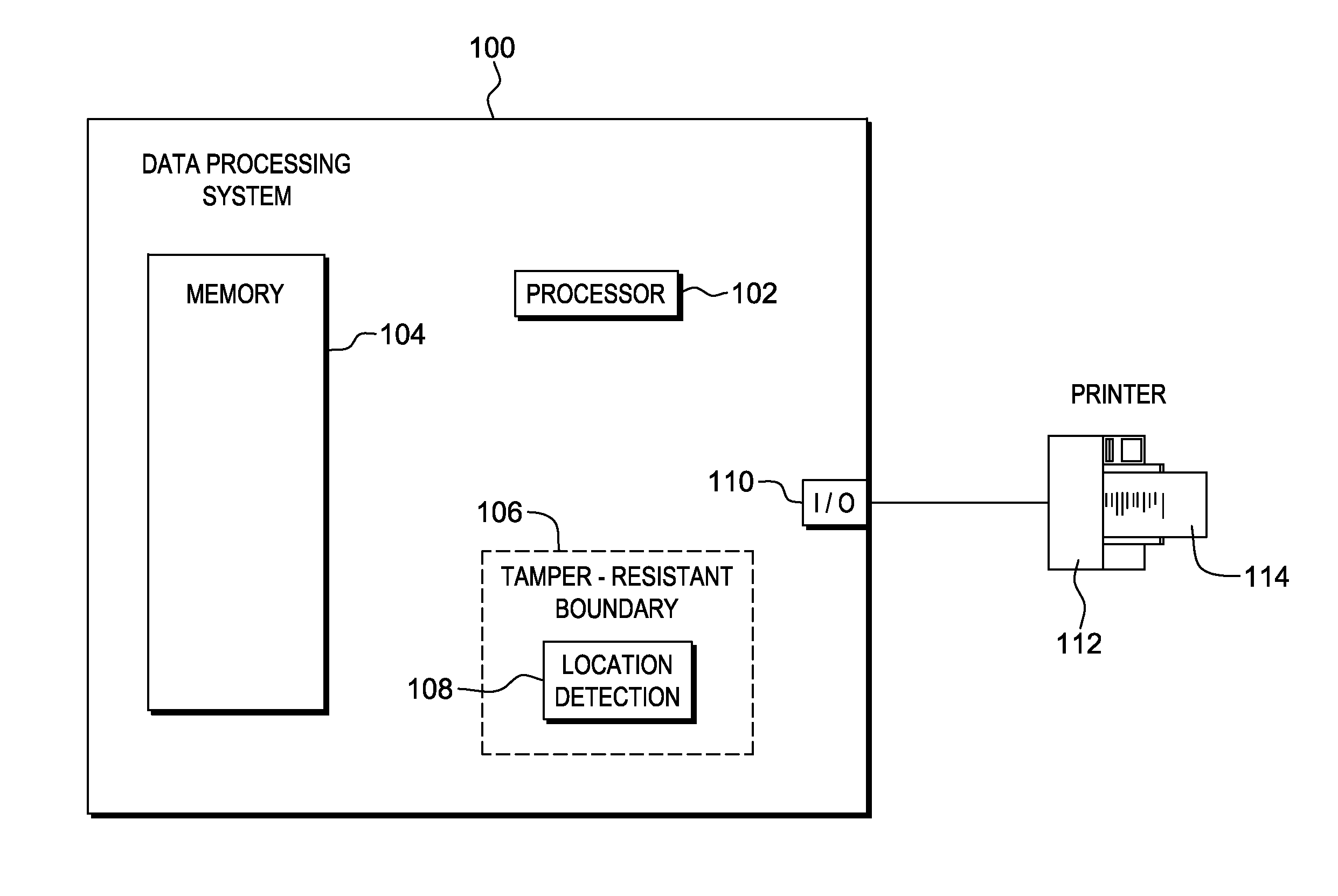
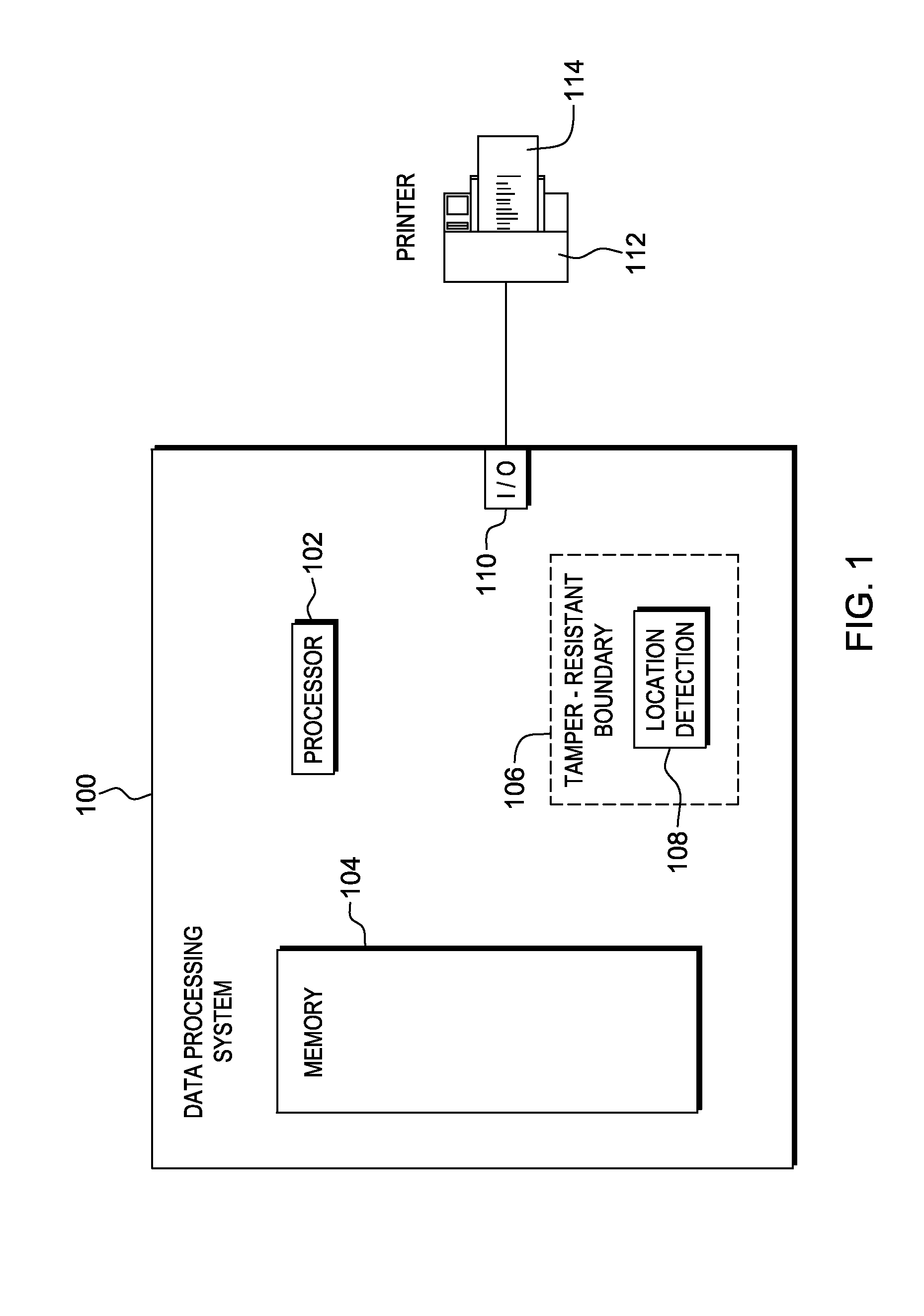
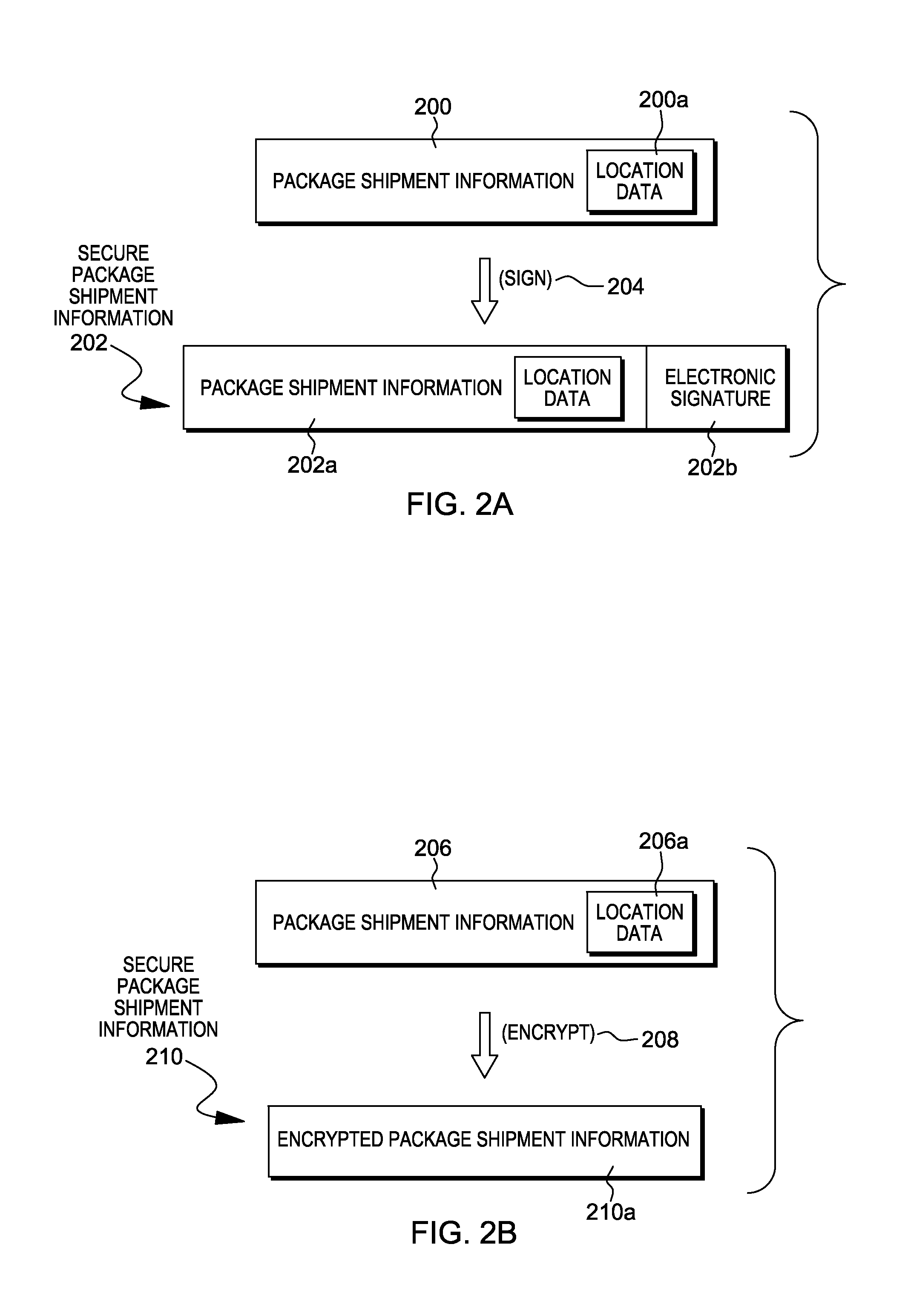
Package source verification
InactiveUS20140074746A1Convenient verificationOvercomes shortcomingCommerceLogisticsData terminalTamper resistance
Verification of a source of a package is facilitated. A data terminal certified by an authority obtains location data from a location detection component. The location data indicates a source location from which the package is to be shipped, and is detected by the location detection component at the source location. Secure package shipment information, including the location data, is provided with the package to securely convey the detected source location to facilitate verifying the source of the package. The data terminal can be a portable data terminal certified by the authority and have a tamper-proof boundary behind which resides the location detection component and one or more keys for securing the package shipment information. Upon tampering with the tamper-resistant boundary, the certification of the portable data terminal can be nullified.
Owner:HAND HELD PRODS
Tamper proof circuit for surgical instrument battery pack
ActiveUS20180064443A1Mechanical/radiation/invasive therapiesSurgical manipulatorsTamper resistanceData storing
A surgical instrument includes a shaft, an end effector extending distally from the shaft, and a housing extending proximally from the shaft. The housing includes a motor configured to generate at least one motion to effectuate the end effector, and a power source configured to supply power to the surgical instrument, wherein the power source includes a casing, a data storage unit, and a deactivation mechanism configured to interrupt access to data stored in the data storage unit. In addition, the power source includes a battery pack and a deactivation mechanism configured to deactivate the battery pack if the casing is breached.
Owner:CILAG GMBH INT
Systems and methods using cryptography to protect secure computing environments
InactiveUS6292569B1Improve connectivityComputationally orRecording carrier detailsError detection/correctionThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm.
Owner:INTERTRUST TECH CORP
Tamper proof circuit for surgical instrument battery pack
ActiveUS20180064441A1Mechanical/radiation/invasive therapiesSurgical manipulatorsTamper resistanceEngineering
A surgical instrument includes a shaft, an end effector extending distally from the shaft, and a housing extending proximally from the shaft. The housing includes a motor configured to generate at least one motion to effectuate the end effector, and a power source configured to supply power to the surgical instrument, wherein the power source includes a casing, a data storage unit, and a deactivation mechanism configured to interrupt access to data stored in the data storage unit. In addition, the power source includes a battery pack and a deactivation mechanism configured to deactivate the battery pack if the casing is breached.
Owner:CILAG GMBH INT
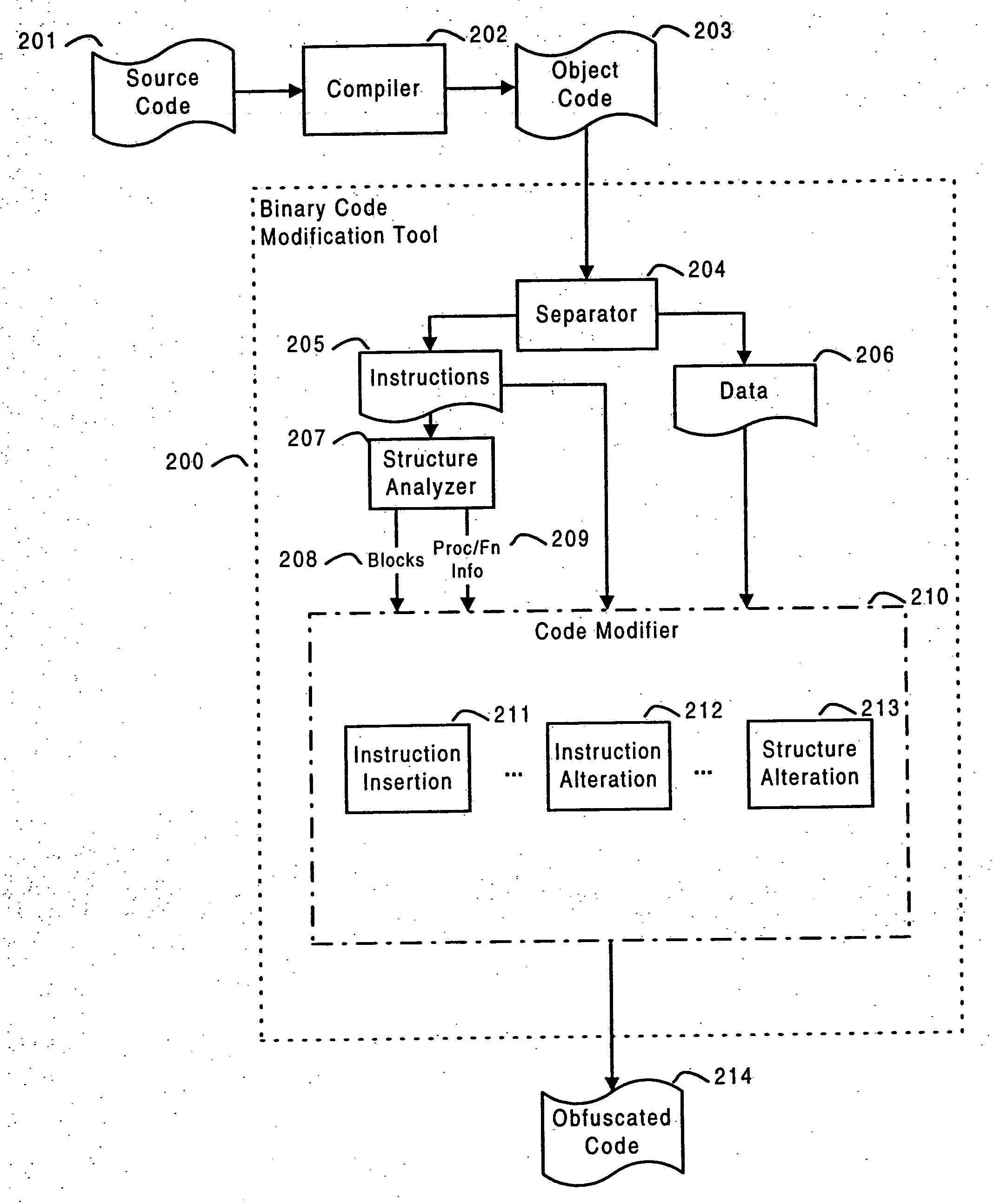
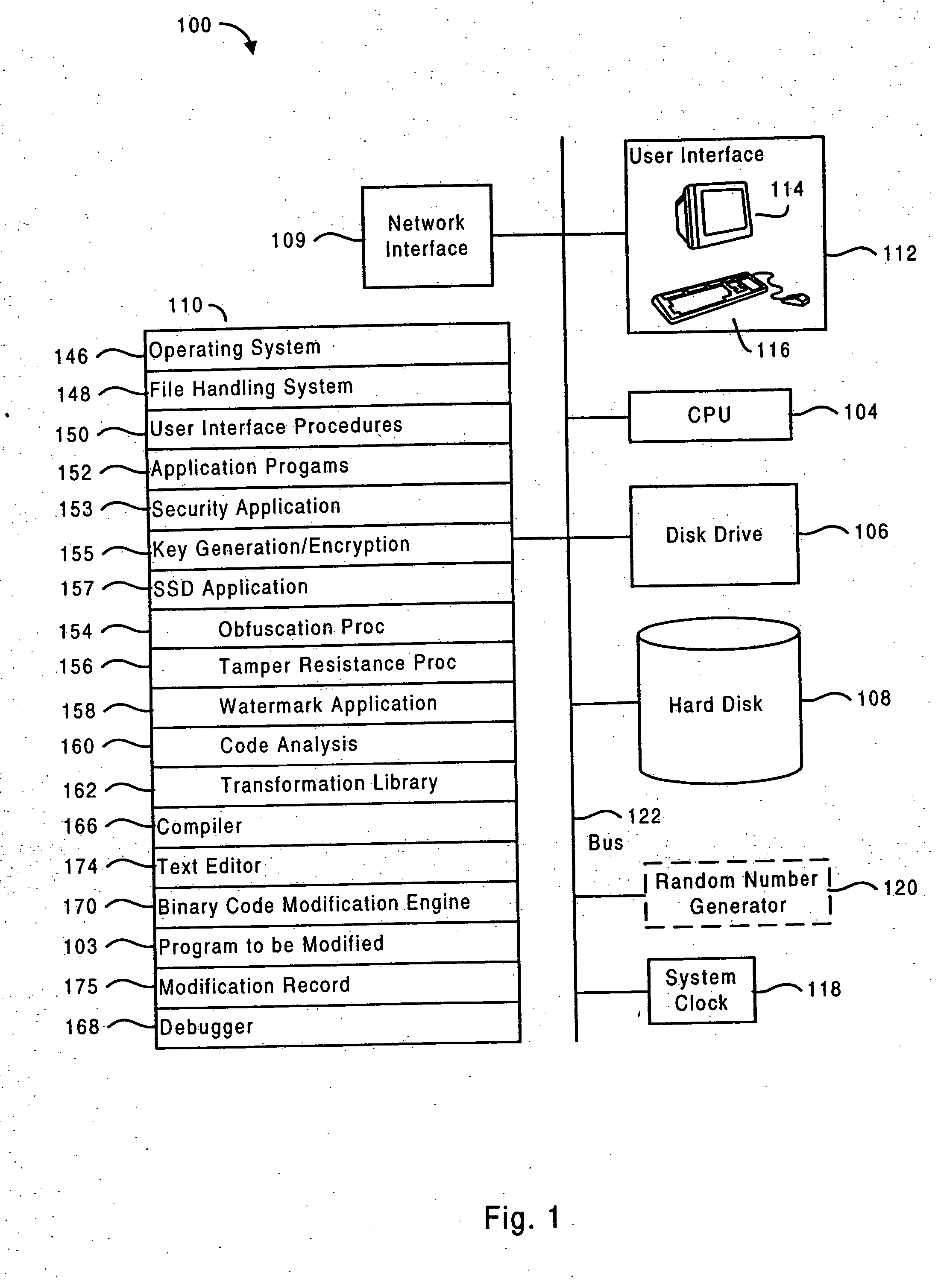
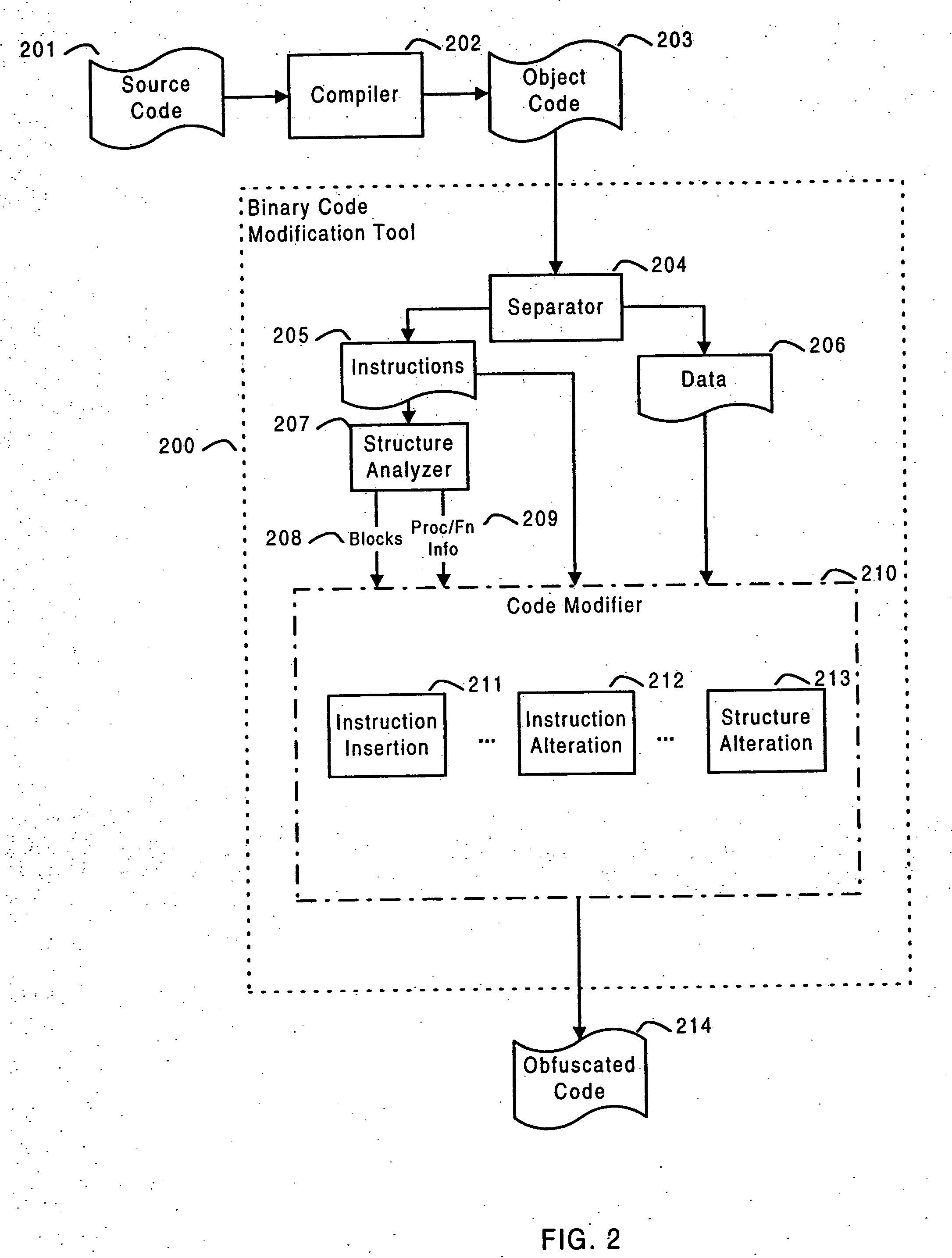
Software self-defense systems and methods
ActiveUS20050183072A1Error detection/correctionProgram/content distribution protectionTamper resistanceObfuscation
Systems and methods are disclosed for protecting a computer program from unauthorized analysis and modification. Obfuscation transformations can be applied to the computer program's local structure, control graph, and / or data structure to render the program more difficult to understand and / or modify. Tamper-resistance mechanisms can be incorporated into the computer program to detect attempts to tamper with the program's operation. Once an attempt to tamper with the computer program is detected, the computer program reports it to an external agent, ceases normal operation, and / or reverses any modifications made by the attempted tampering. The computer program can also be watermarked to facilitate identification of its owner. The obfuscation, tamper-resistance, and watermarking transformations can be applied to the computer program's source code, object code, or executable image.
Owner:INTERTRUST TECH CORP
System for controlling access and distribution of digital property
InactiveUS20010021926A1Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
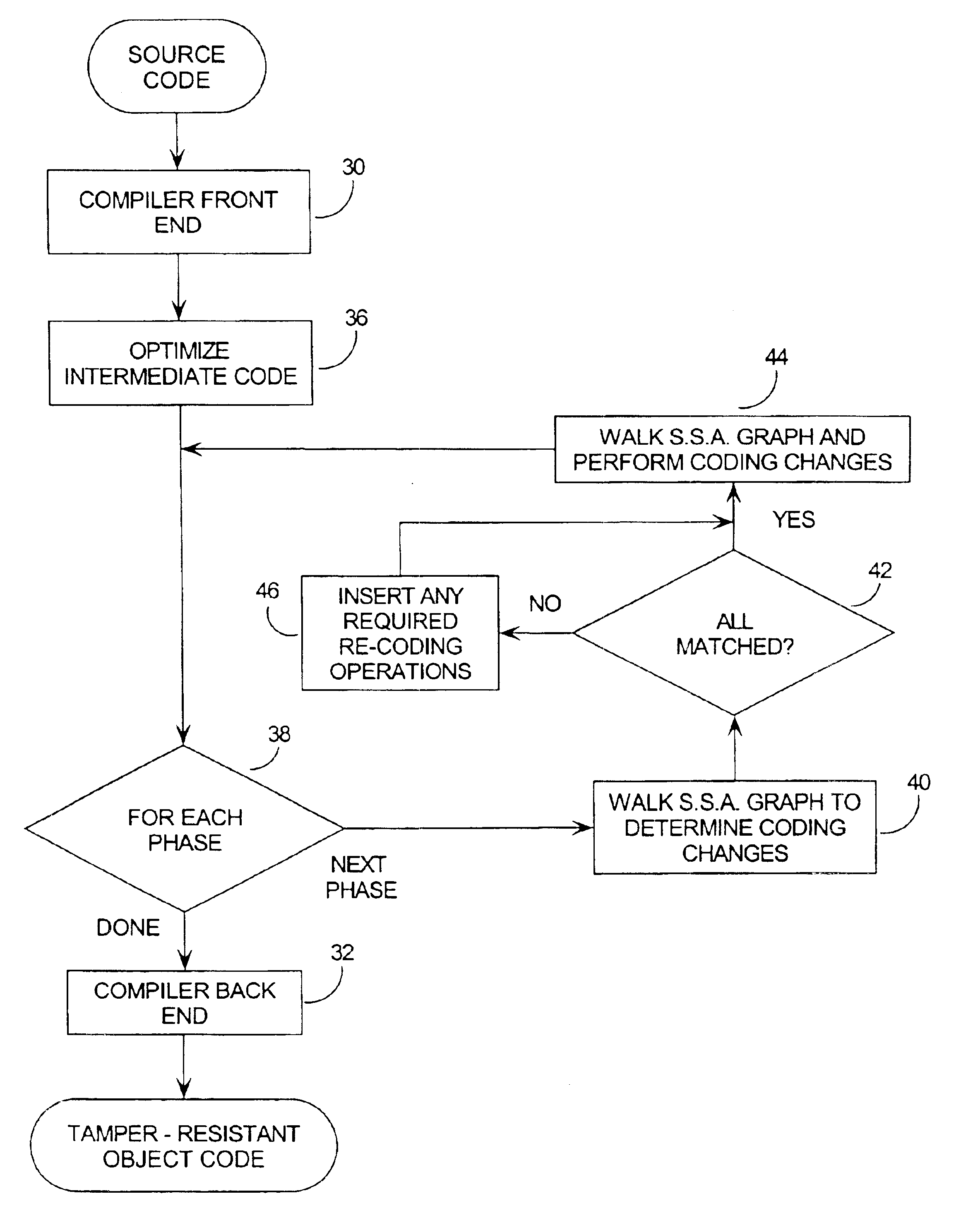
Tamper resistant software encoding
InactiveUS6842862B2Improvement in tamper-resistanceIncreased complexityMemory loss protectionUnauthorized memory use protectionTamper resistancePassword
The present invention relates generally to computer software, and more specifically, to a method and system of making computer software resistant to tampering and reverse-engineering. “Tampering” occurs when an attacker makes unauthorized changes to a computer software program such as overcoming password access, copy protection or timeout algorithms. Broadly speaking, the method of the invention is to increase the tamper-resistance and obscurity of computer software code by transforming the data flow of the computer software so that the observable operation is dissociated from the intent of the original software code. This way, the attacker can not understand and decode the data flow by observing the execution of the code. A number of techniques for performing the invention are given, including encoding software arguments using polynomials, prime number residues, converting variables to new sets of boolean variables, and defining variables on a new n-dimensional vector space.
Owner:IRDETO ACCESS
Event-recorder for transmitting and storing electronic signature data
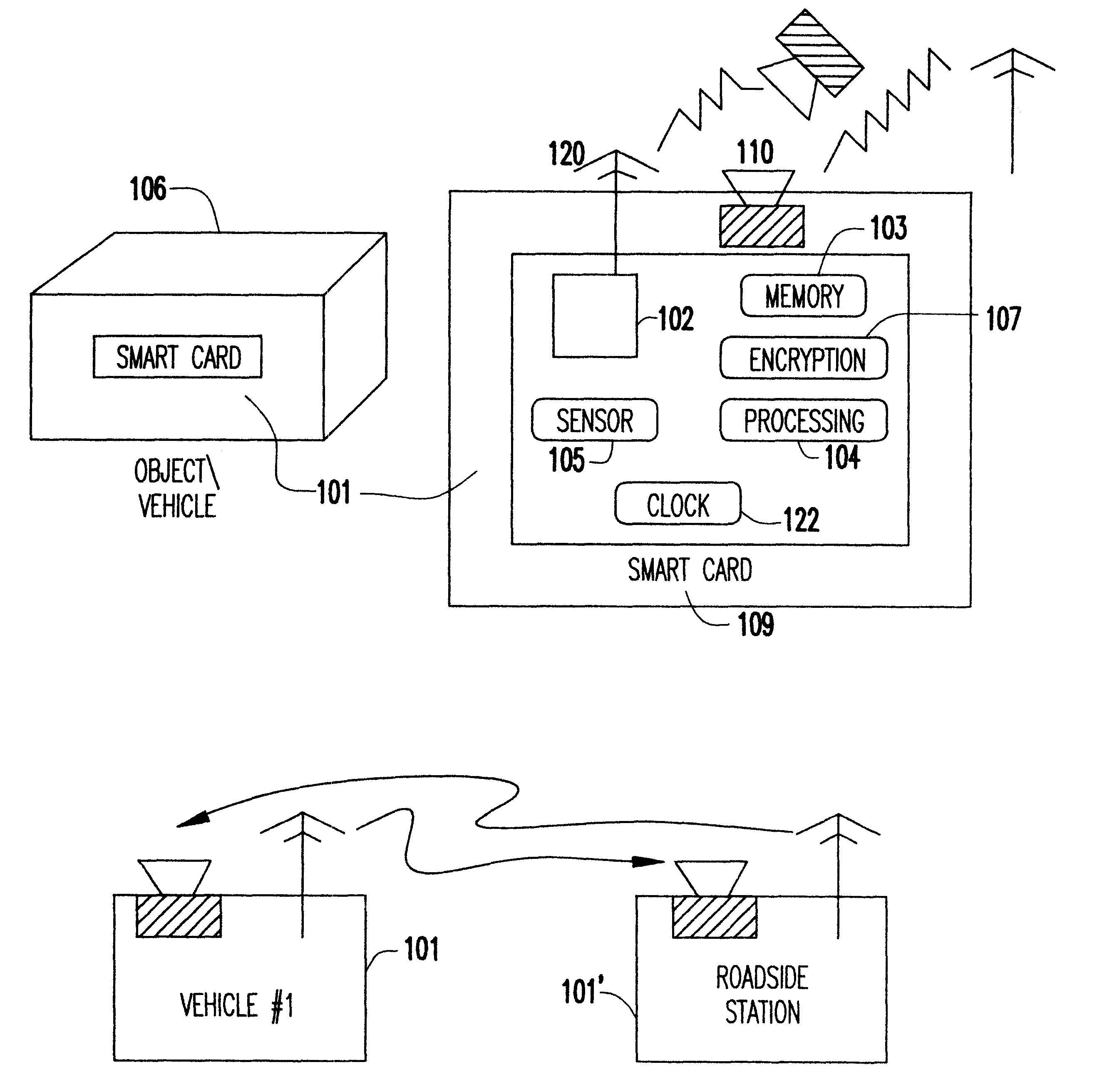
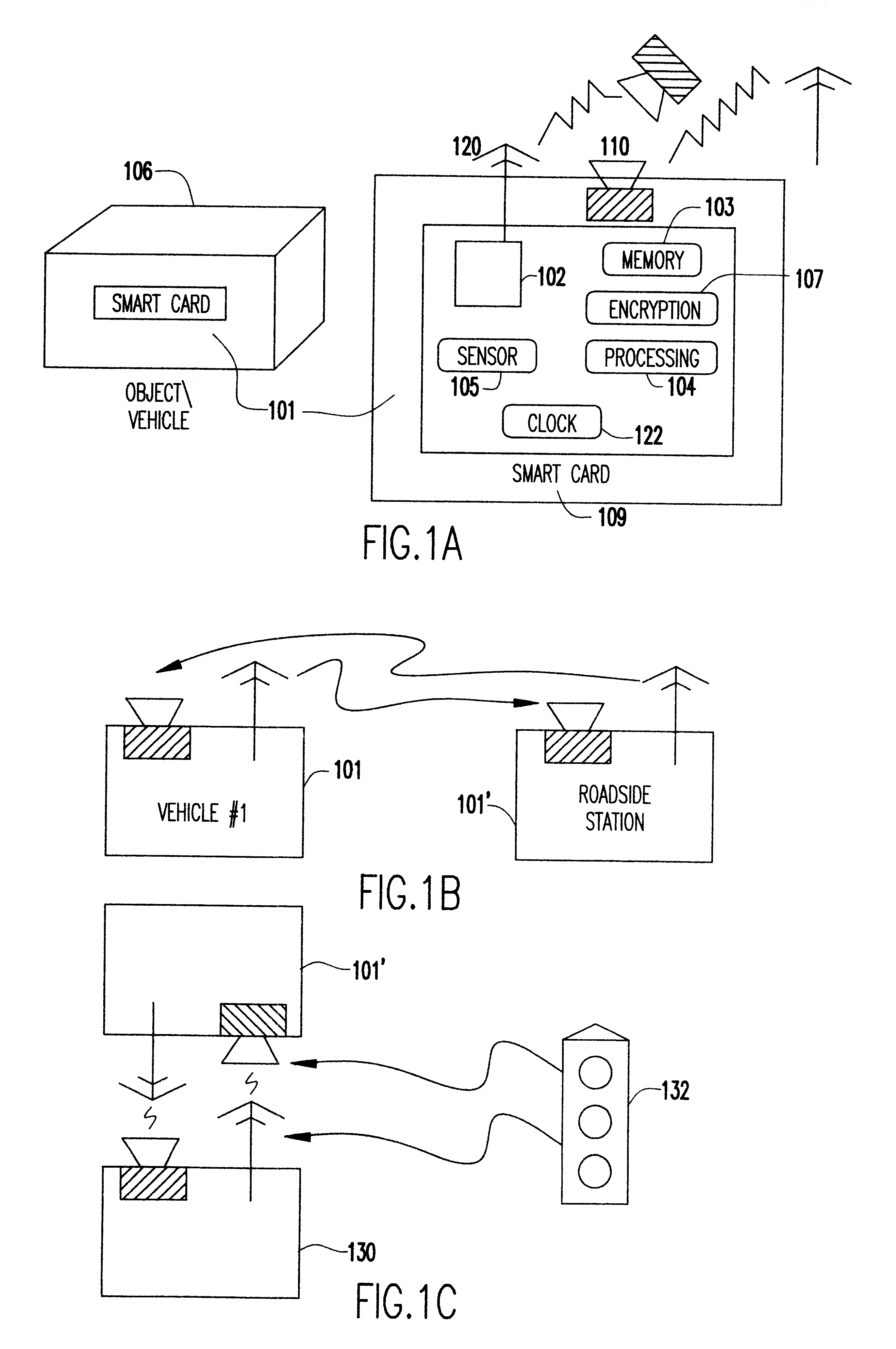
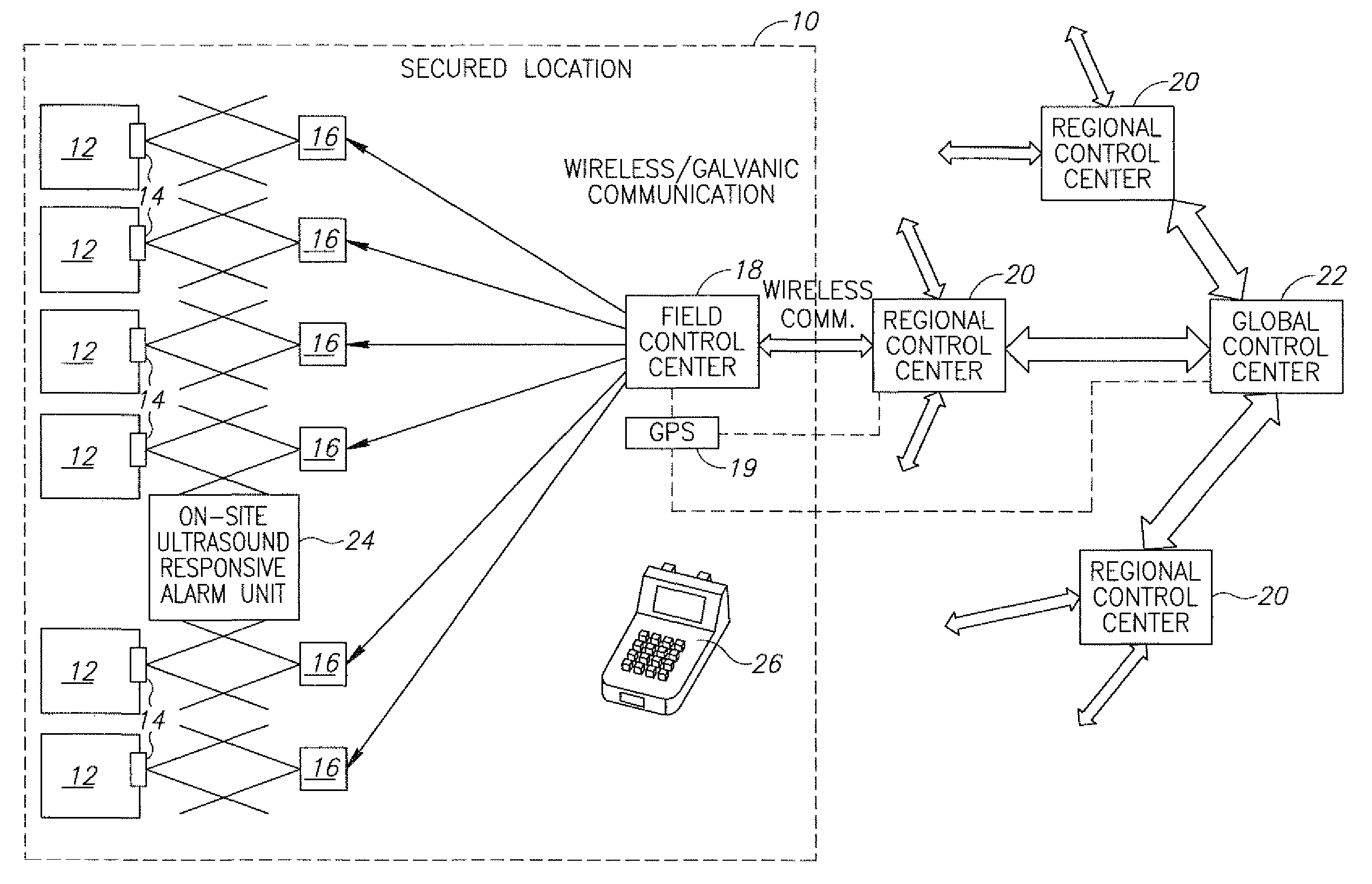
An electronic event recorder for attachment to a vehicle is provided which can broadcast encrypted signature and data, thereby leaving behind an electronic version of a "fingerprint" in the event of an accident or traffic violation. The fingerprint, captured by an external data acquisition system or another vehicle so equipped, provides a history of events related to the vehicle. The event recorder is preferably integrated on a smart card and housed in a tamper proof casing. In a first mode of operation, monitoring stations along the roadways periodically send an interrogation signal, such as when radar detects that the vehicle is speeding. Upon receiving the interrogation signal the smart card transmits the vehicle's signature information to the monitoring station where it is time and date stamped along with the speed of the vehicle. In a second mode of operation, when a sensor detects a sudden or violent acceleration or deceleration, such as occurs during a collision, a smart card mounted in each car will exchange signature information automatically. This is particularly useful when the collision occurs in a parking lot when one of the hit vehicles is typically unattended.
Owner:INT BUSINESS MASCH CORP
Method and system for providing tamper-resistant software
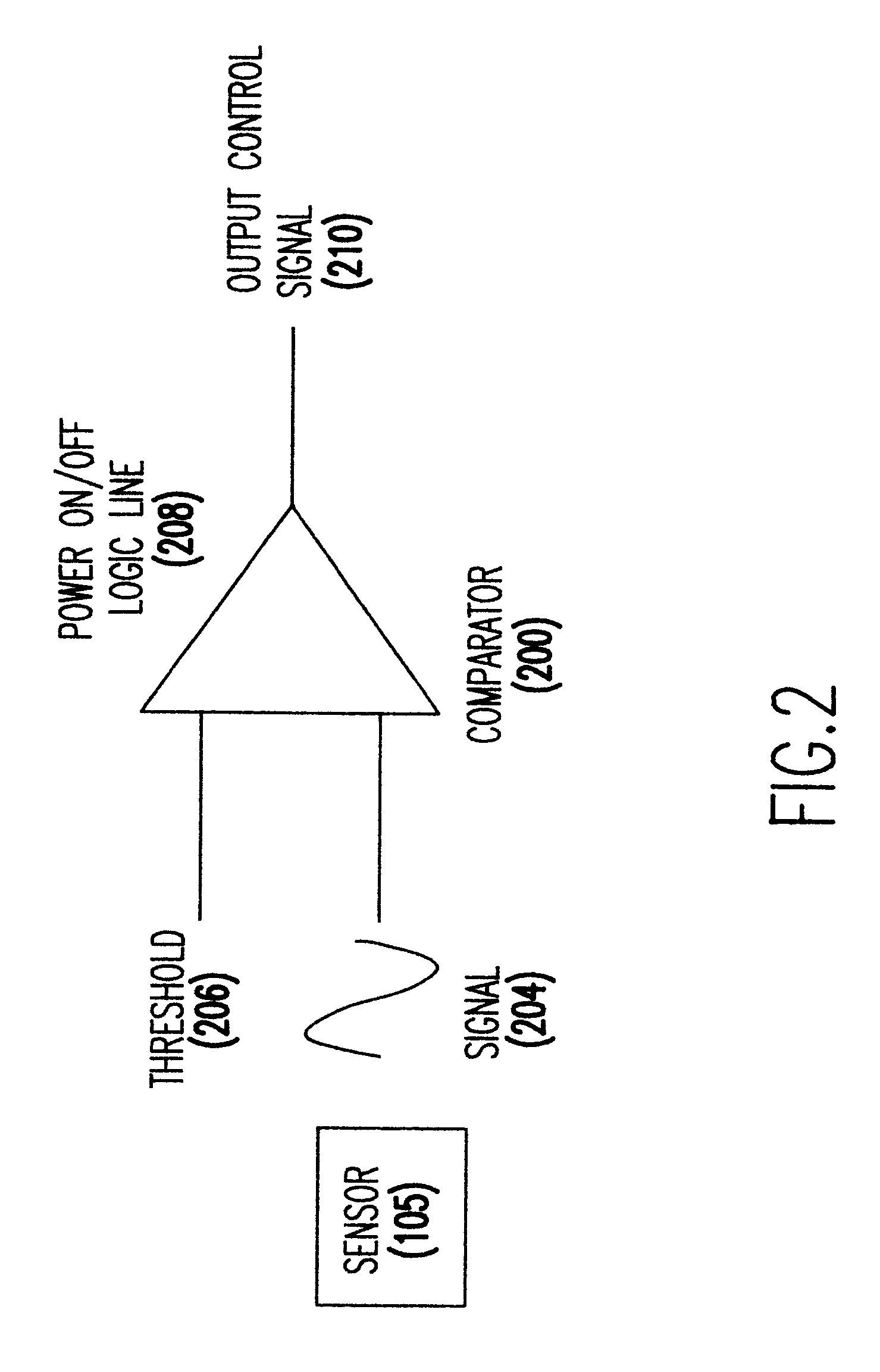
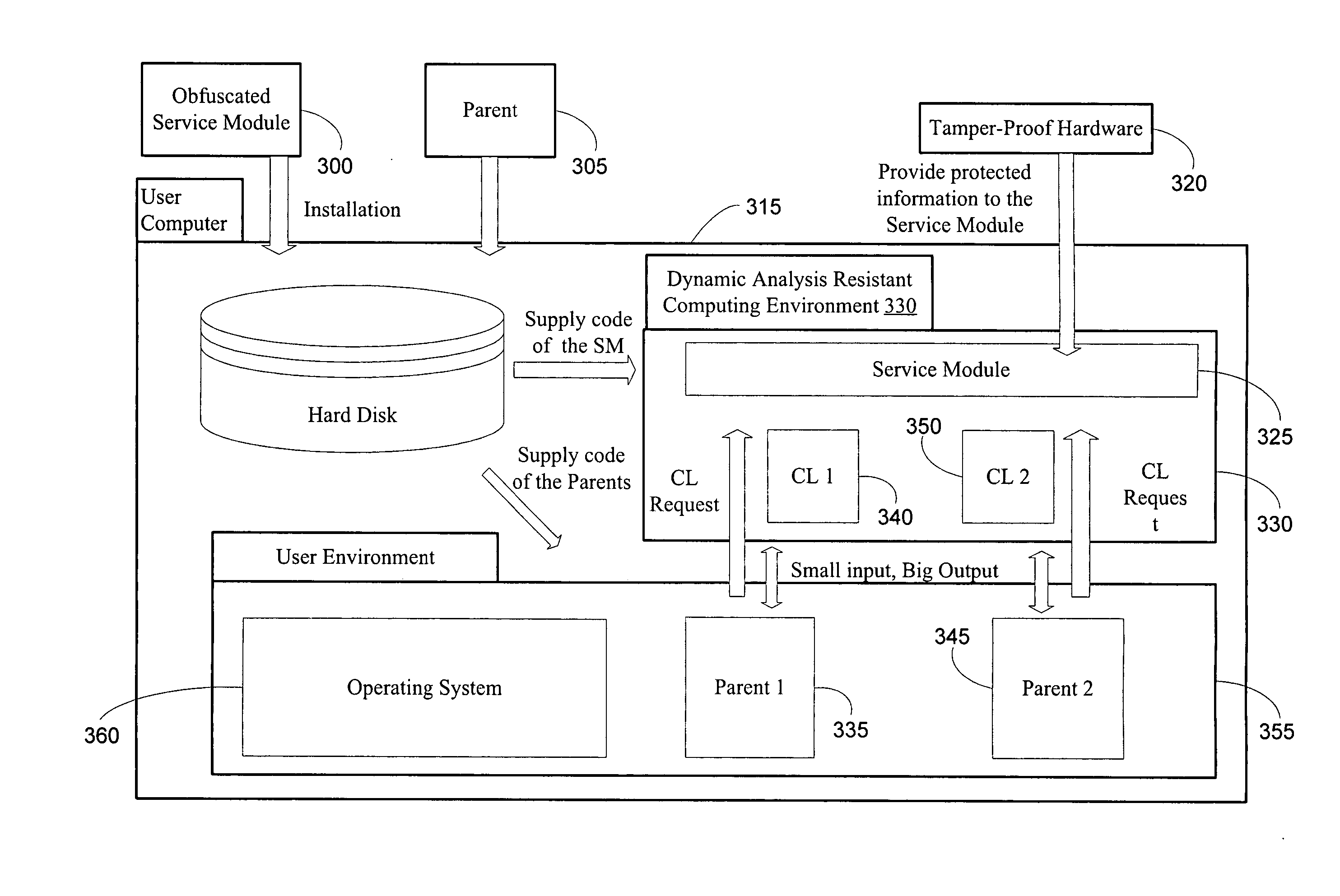
InactiveUS20060048223A1Performance penaltyImprove tamper resistanceMemory loss protectionDetecting faulty computer hardwareTamper resistanceObfuscation
A method and system for protecting only a portion of the software to be protected against tampering is described. Such a portion may be stored in a tamper-resistant physical device, with optional encryption, for downloading when needed for execution. Several layers of tamper resistance are provided without excessively impacting performance of the protected software. For instance, obfuscation is applied to the code for the service module to minimize the large expense associated with obfuscation. The invention includes embodiments that deliver critical logic, policy information and other similar information with the help of mobile agents, which may be hosted by a server in a smart card.
Owner:THE UNIVERSITY OF HONG KONG
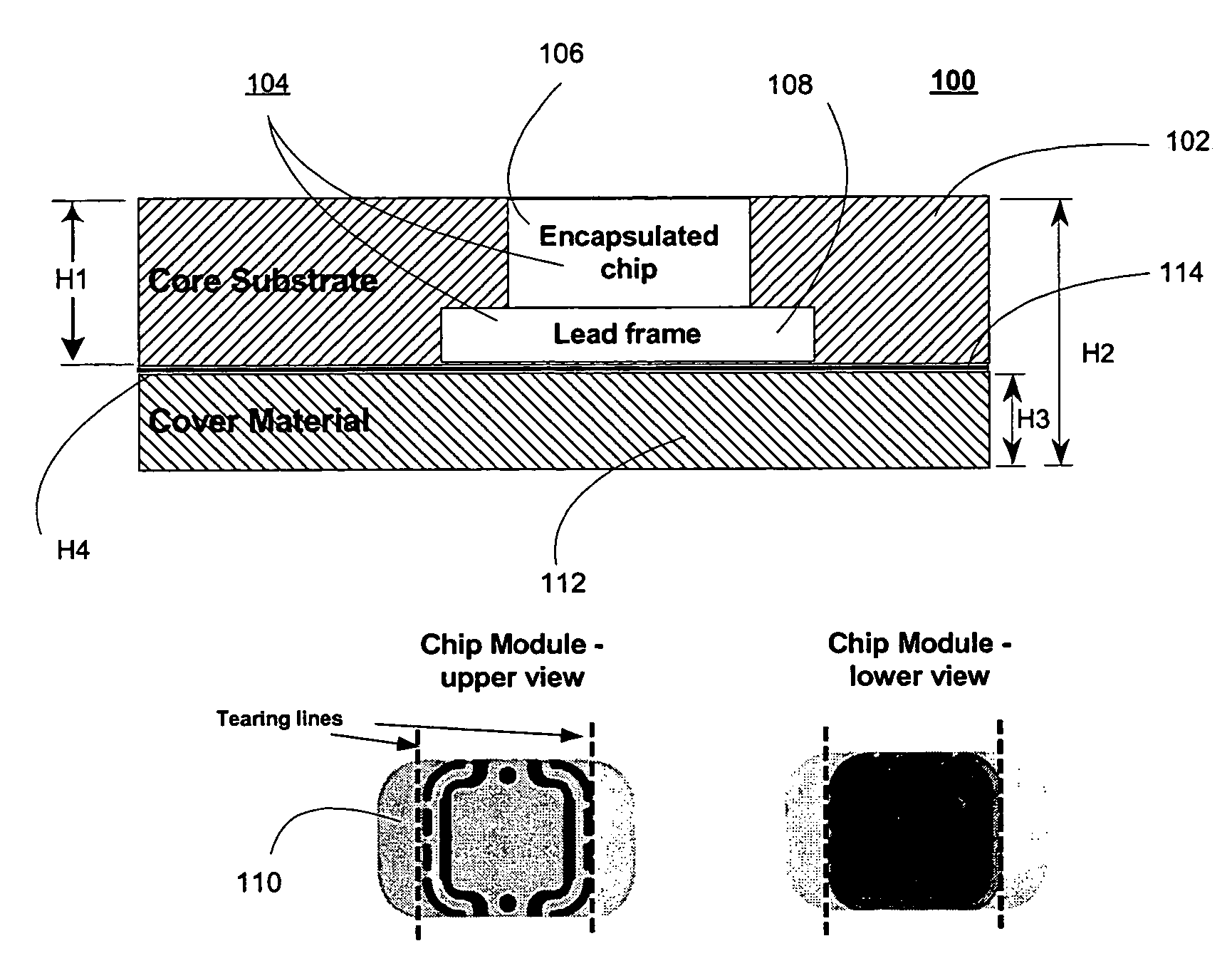
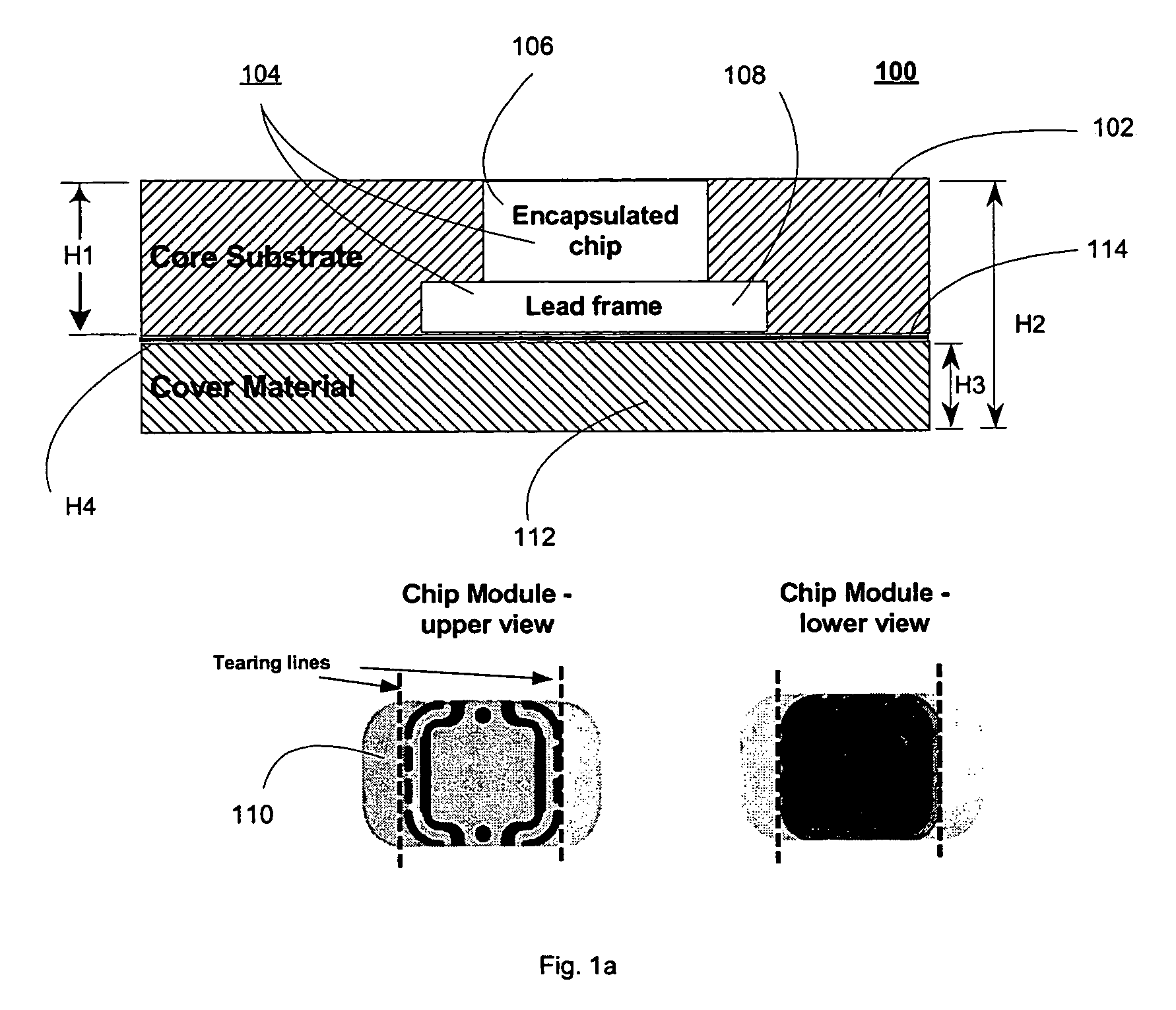
Method for making memory cards and similar devices using isotropic thermoset materials with high quality exterior surfaces
InactiveUS7225537B2Shorten the timeQuality improvementPrinted circuit assemblingLine/current collector detailsEngineeringInjection moulding
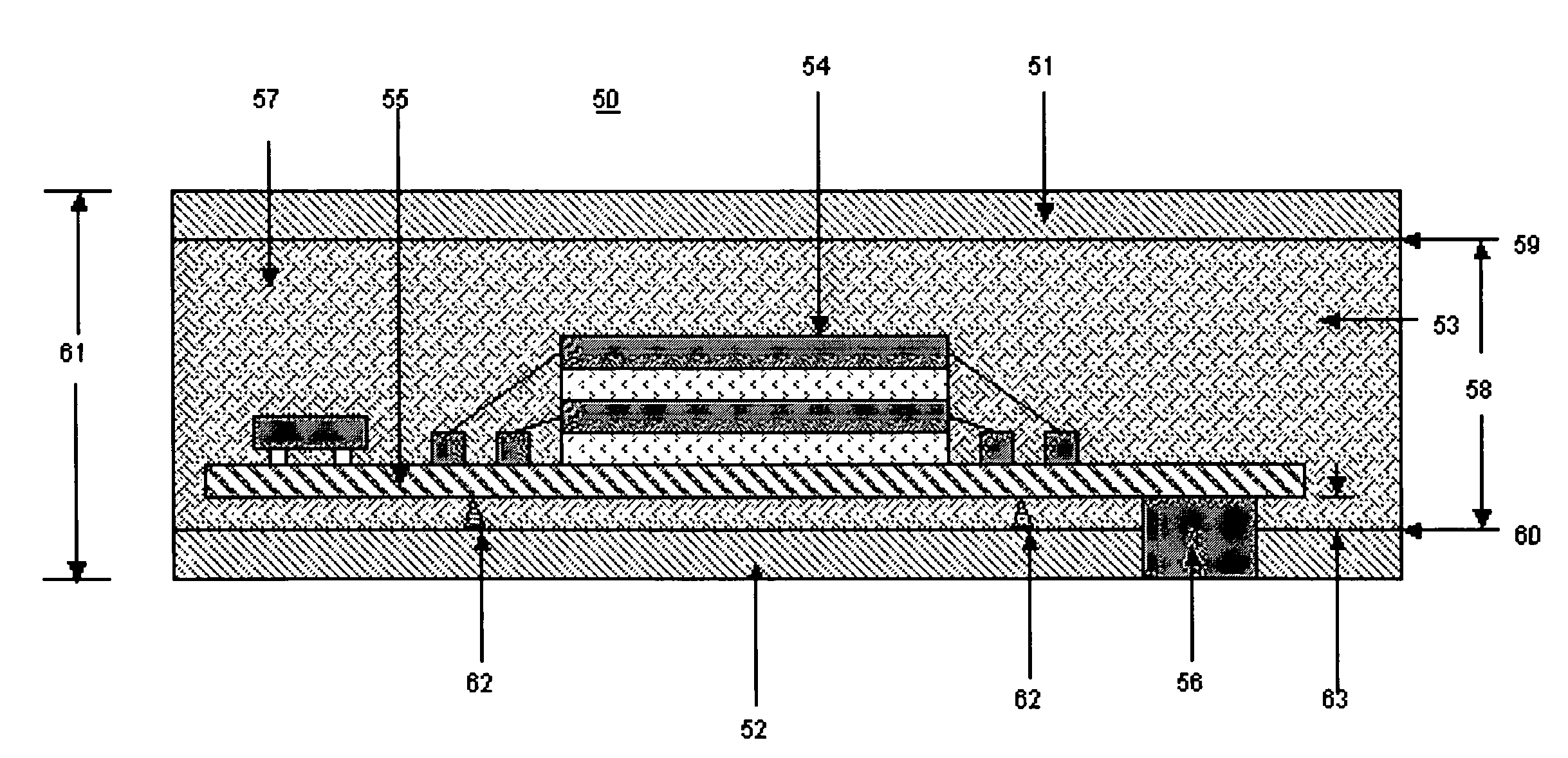
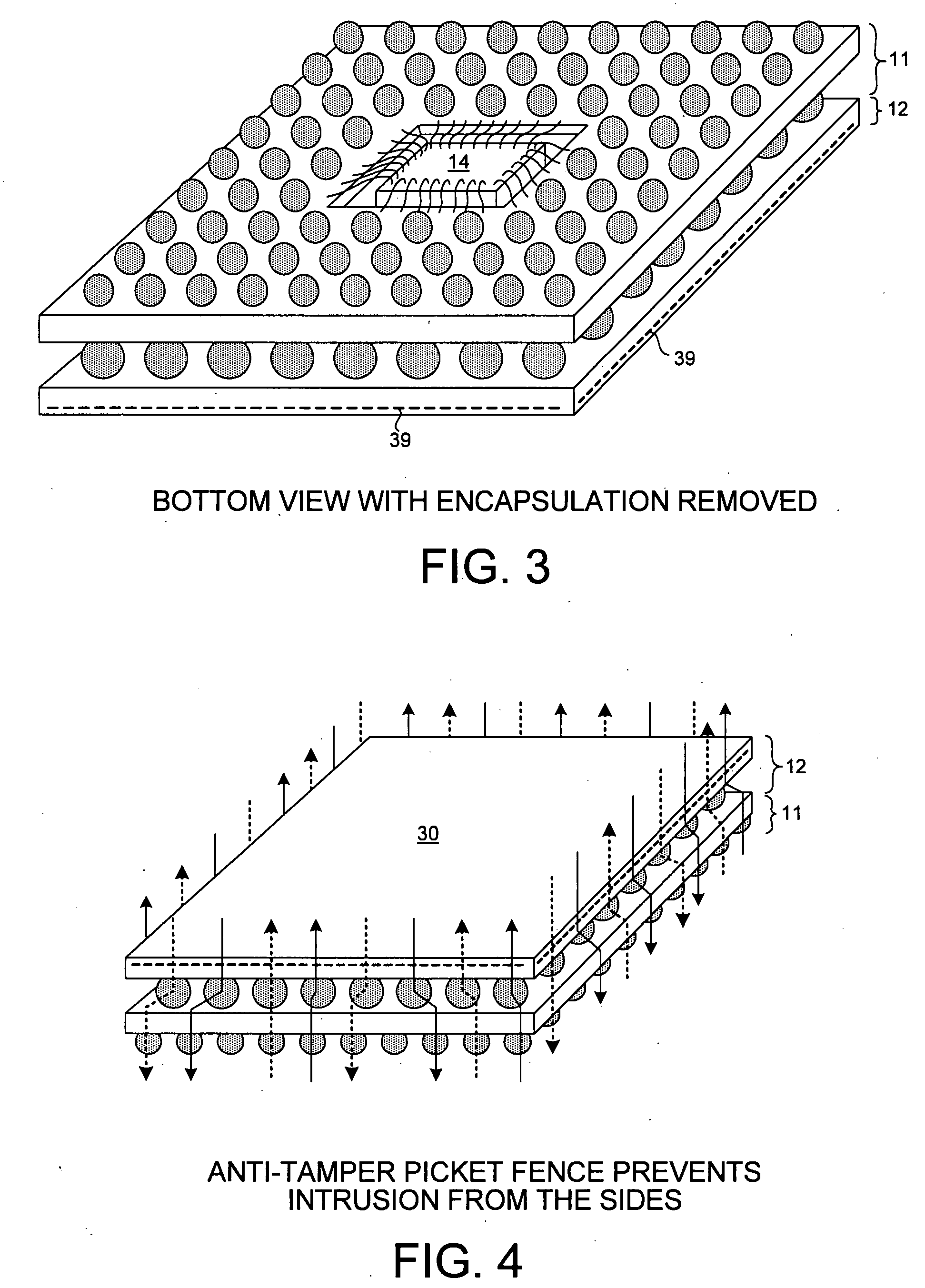
Memory Cards containing Integrated Circuits and other electronic components (e.g. resistors) in a variety of form factors having high quality external surfaces of polycarbonate, synthetic paper (e.g. Teslin), or other suitable material (e.g. PVC) can be made through use of injection molded thermoplastic material or thermosetting material that becomes the core layer of said Memory Cards and similar devices. The object of the invention is to provide the following properties to Memory Cards: rapid production cycle, high volume manufacturing throughput, security, electronics protection, better tamper resistance, durability, and highly reliable complex electronics encapsulation, achieved through a process utilizing low temperature and low pressure.
Owner:CARDXX
Electronic security seal and system
InactiveUS20090179757A1Easy constructionSimple in useStampsAnti-theft devicesTamper resistanceEngineering
A tamper-proof electronic security seal which includes a bolt and a locking element and an electronic seal element. The bolt has a head and a hollow shank extending therefrom having a longitudinal bore formed therein. The shank is dimensioned to pass through a lock hasp and has a free end formed for locking engagement with the locking element. The electronic seal element is formed for mechanical connection to the bolt head, and includes an electrical power source, a control unit, communications means responsive to the control unit and a sensor adapted for insertion into the longitudinal bore of the shank, and connected to the control unit. In response to a severing of the shank and the sensor inserted therein, the control unit is operative to activate the communications means to emit an alarm signal.
Owner:COHN ODED YAIR +1
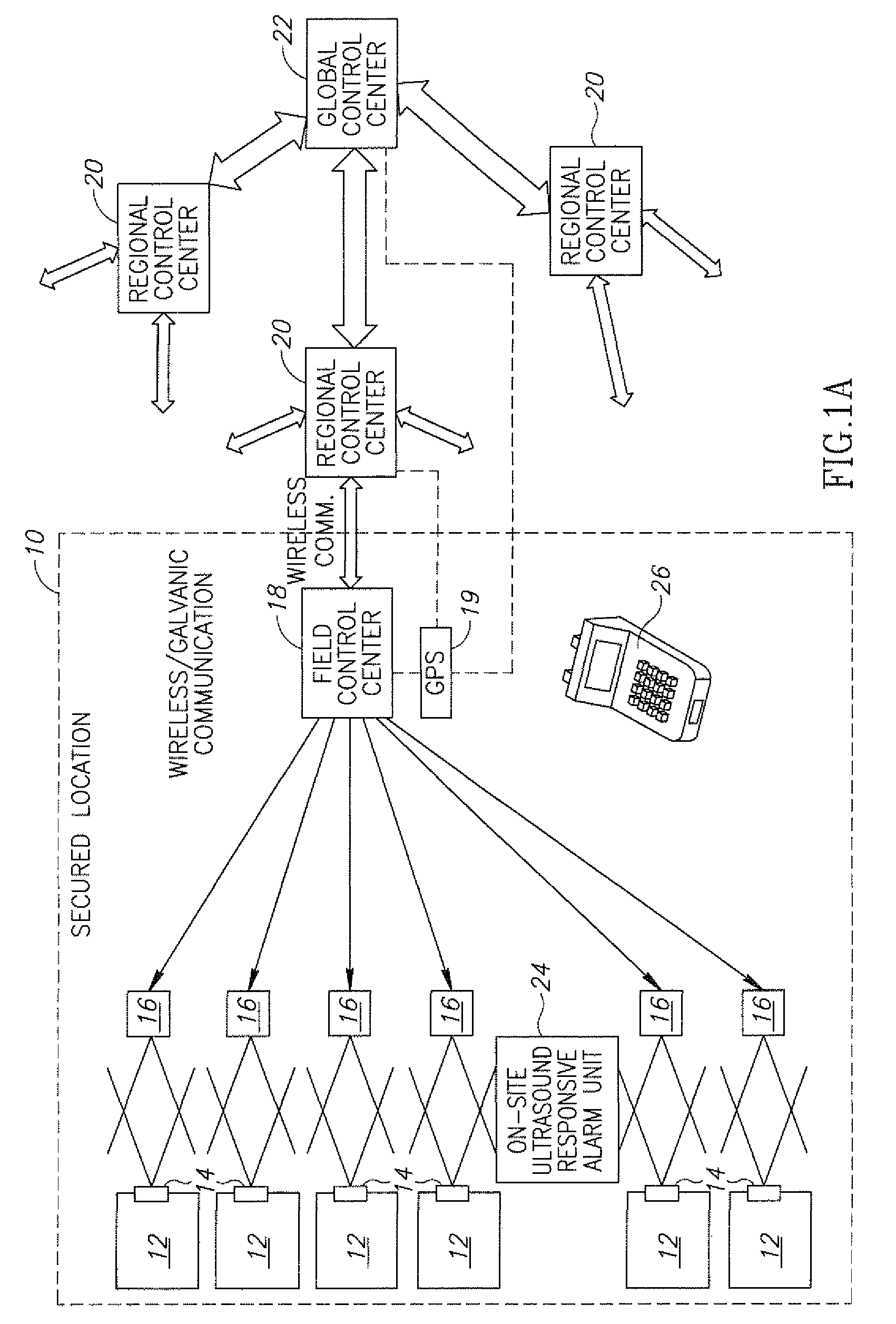
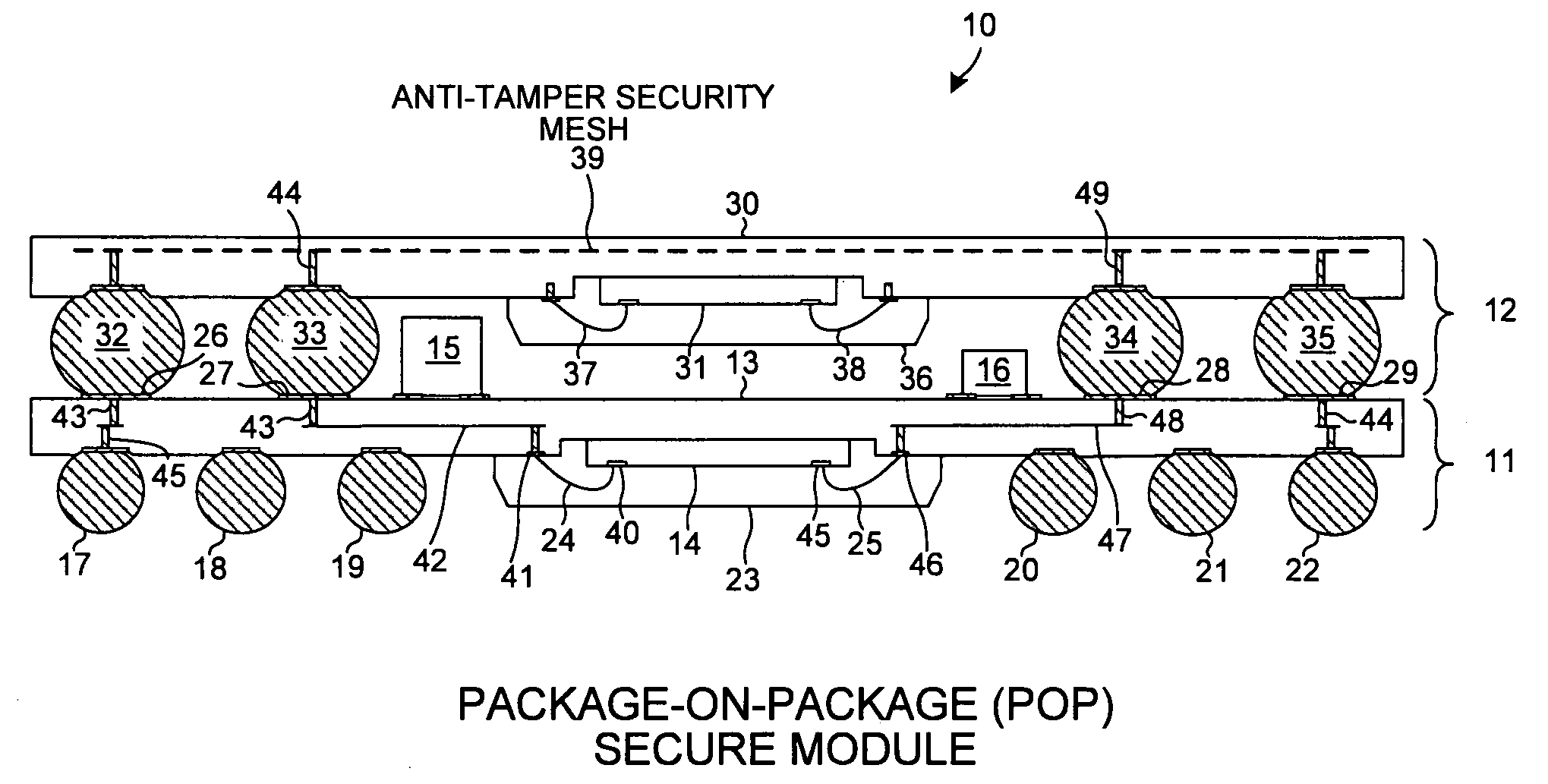
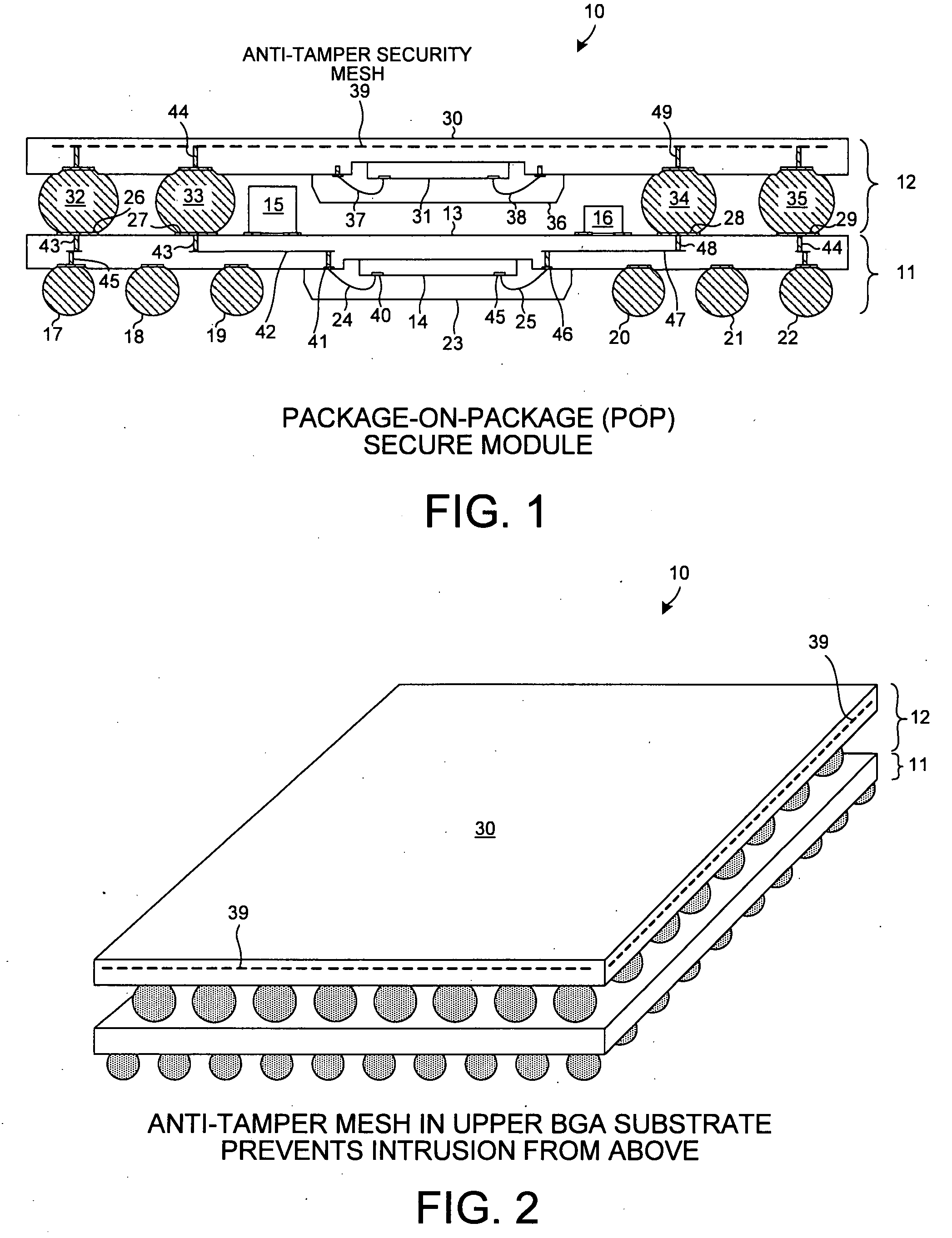
Package-on-package secure module having BGA mesh cap
InactiveUS20080251906A1Low costLarge massSemiconductor/solid-state device detailsSolid-state devicesMicrocontrollerTamper resistance
A package-on-package (POP) secure module includes a BGA mesh cap, a first BGA package, and a second BGA package. The first BGA package includes a first integrated circuit (for example, a microcontroller that includes tamper detect logic). The second BGA package includes a second integrated circuit (for example, a memory). The second BGA package is piggy-back mounted to the first BGA package and the BGA mesh cap is piggy-back mounted to the second BGA package. A printed circuit board substrate member of the BGA mesh cap includes an embedded anti-tamper mesh. This mesh is connected in a protected manner within the module to the first integrated circuit. When the module is in use, a mesh embedded in an underlying printed circuit board is coupled to the BGA cap mesh so that both anti-tamper meshes are controlled by the tamper detect logic.
Owner:MAXIM INTEGRATED PROD INC
Block chain-based distributed storage
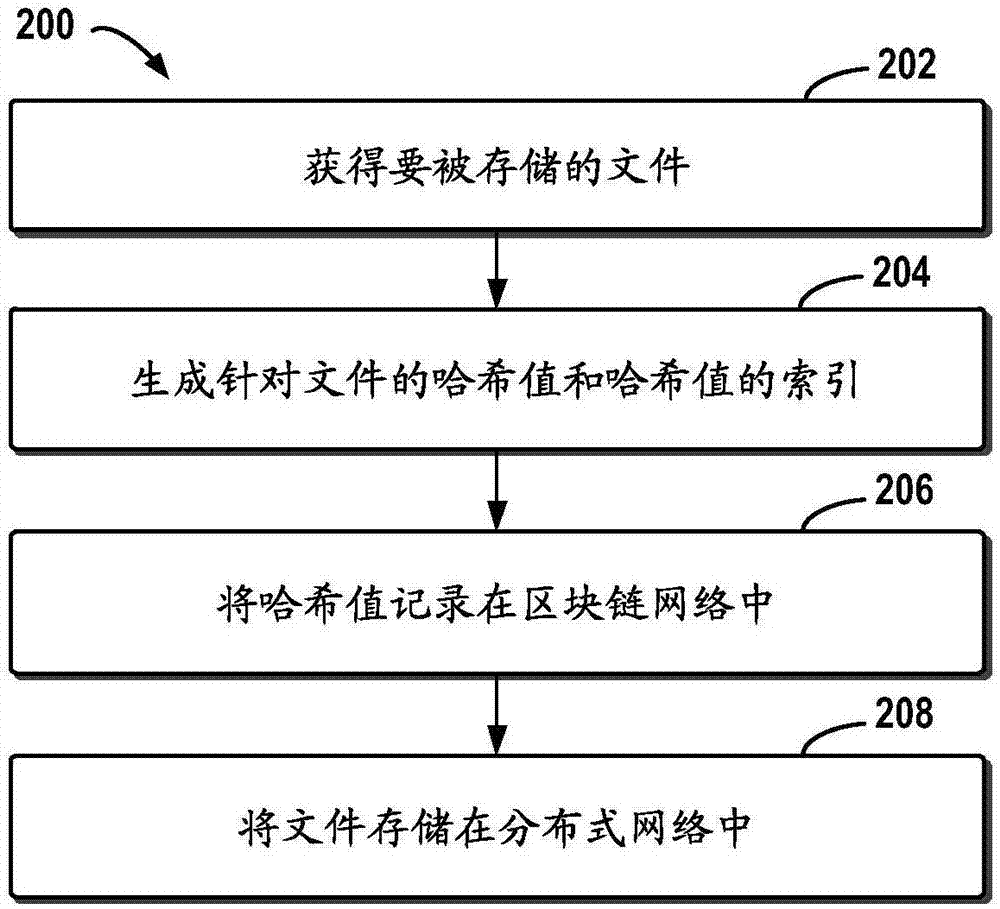
InactiveCN107273410ASolve the problem of limited node capacityAchieve tamper resistanceFile access structuresSpecial data processing applicationsTamper resistanceDistributed File System
The embodiment of the disclosure relates to block chain-based distributed storage, and discloses a block chain-based distributed storage method. The method includes: obtaining a file which needs to be stored, and generating a hash value and an index of the hash value for the file. The method also includes: recording the hash value in a block chain network, and storing the file in a distributed network, wherein the file is located on the basis of the hash value in the distributed network. Therefore, according to the embodiment of the disclosure, tampering proofing and the distributed storage of the file can be realized through combining a block chain and a distributed file system, thus the problem of the limited capacity of block chain nodes is solved, and the authenticity and the availability of the stored file are effectively guaranteed.
Owner:SHANGHAI DIANRONG INFORMATION TECH CO LTD
Tamper-proof display
A security display system typically used to display, and permit the handling of, costly items such as cameras, video cameras and recorders, while preventing the theft of those items. The system permits persons to handle the item and prevents theft of the item through a cable which acts to tether the item, provide power to the item and trigger an alarm if it is cut or disconnected. The cable is largely hidden until the item is picked up, as the cable runs through the item support and under the counter.
Owner:CDA INDS
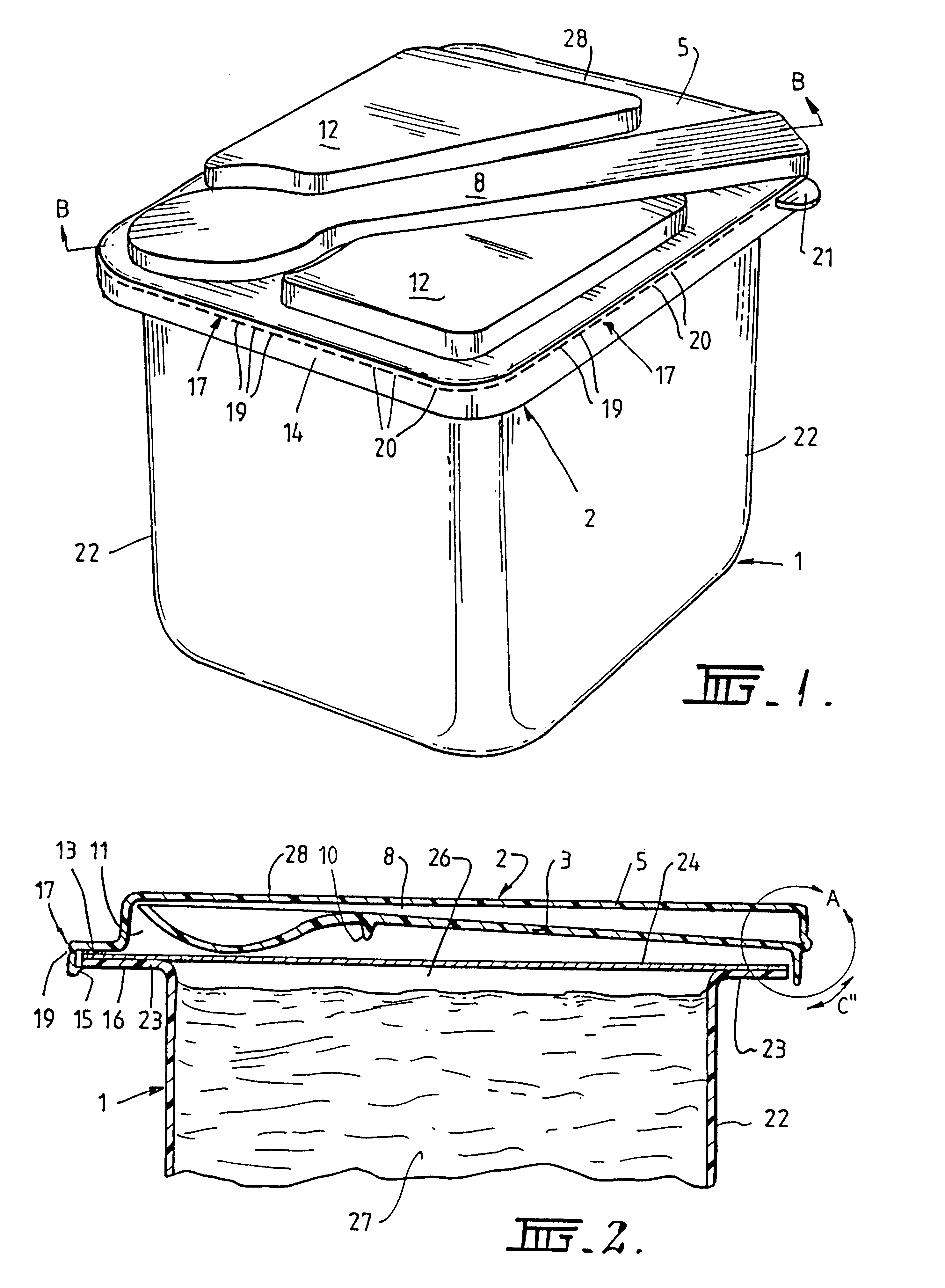
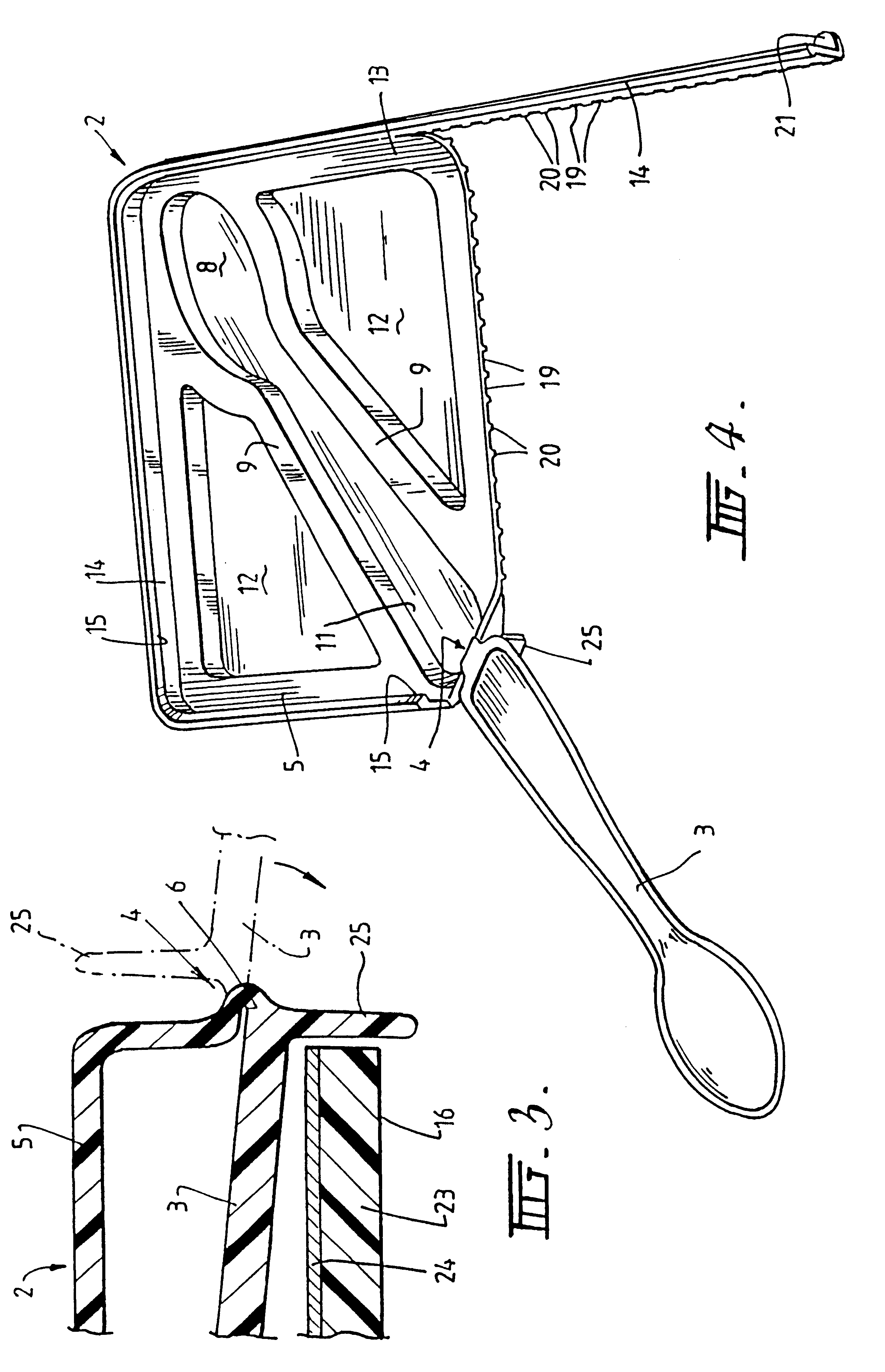
Container lid and implement
Owner:AUS LID ENTERPRISES
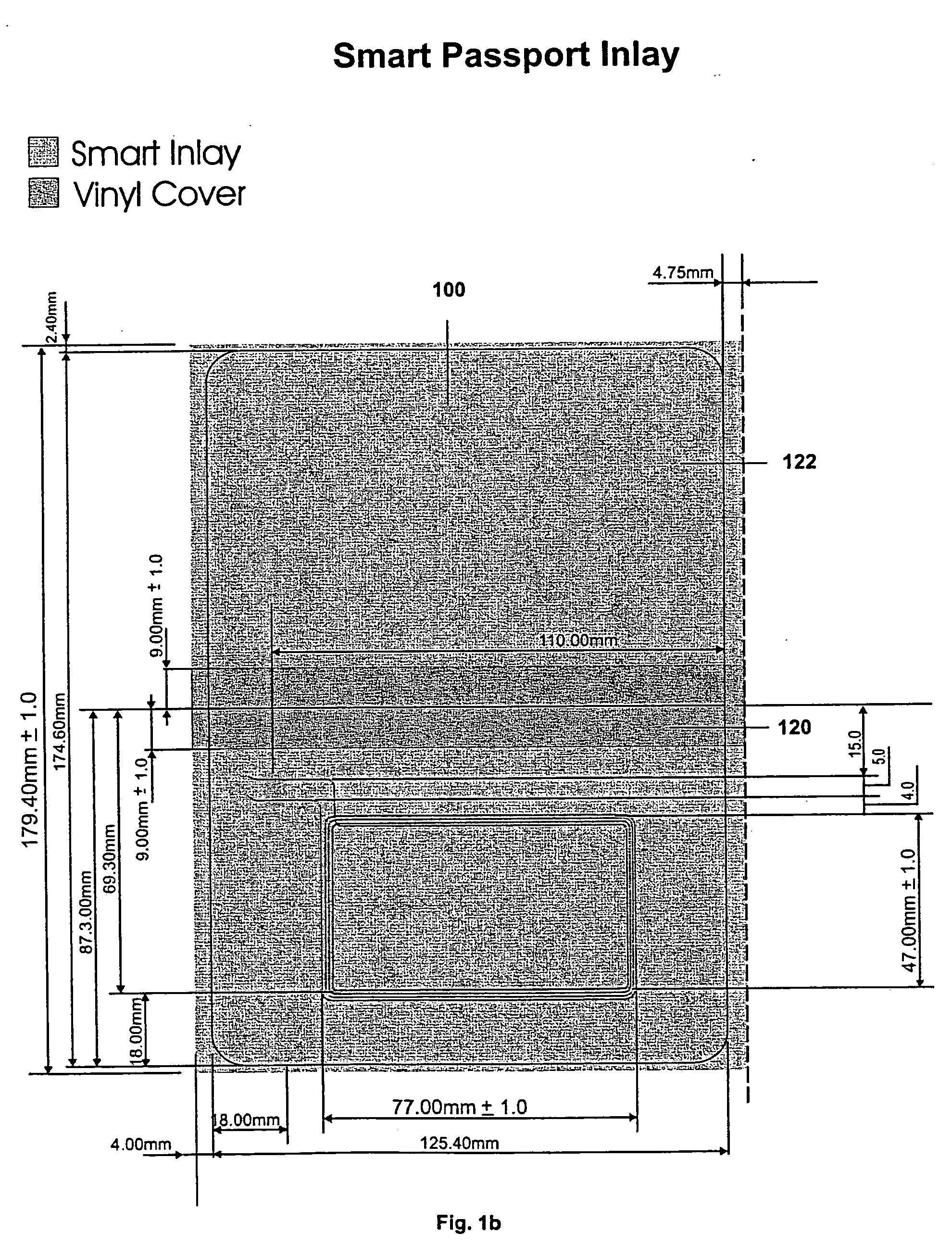
Tamper-free and forgery-proof passport and methods for providing same
InactiveUS20060005050A1Prevent tamperingUnauthorized memory use protectionHardware monitoringTamper resistancePhysical security
A smart passport comprising a smart inlay that includes a core substrate operative to store and exchange information contactlessly with an external reader, at least one physical security component coupled to the core substrate and operative to render the smart inlay and thereby the passport tamper-proof, and a logical security component incorporated in the core substrate and operative to render the smart inlay and thereby the passport forgery-proof. The physical security component is preferably selected from the group at least one tear line and at least one patterned adhesive, both operative to cause irreversible damage to the information storage and communication capabilities of the passport in case of tampering.
Owner:SUPERCOM IP LLC +1
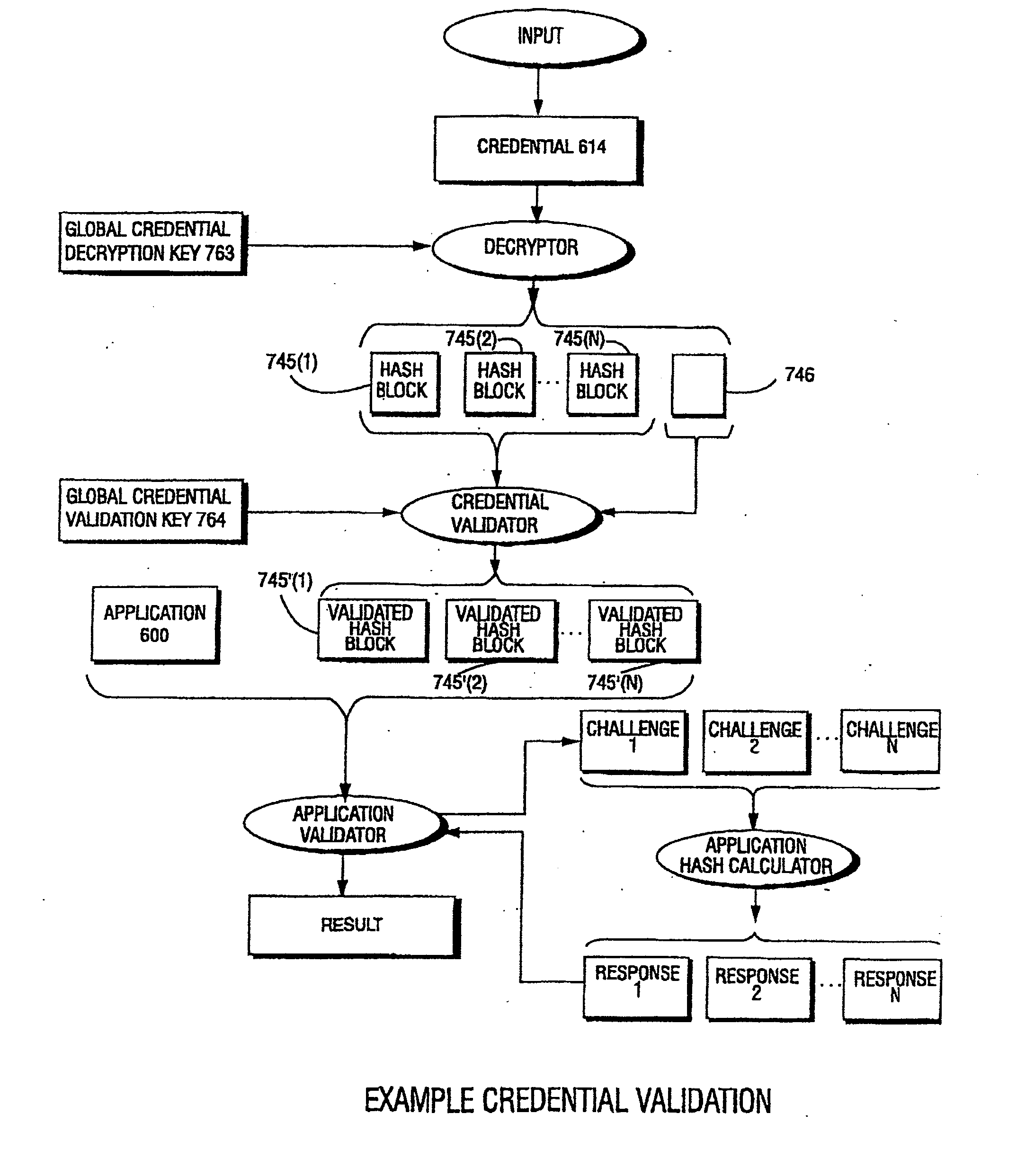
Systems and methods for using cryptography to protect secure and insecure computing environments
InactiveUS20070226798A1Memory loss protectionDigital data processing detailsThird partyTamper resistance
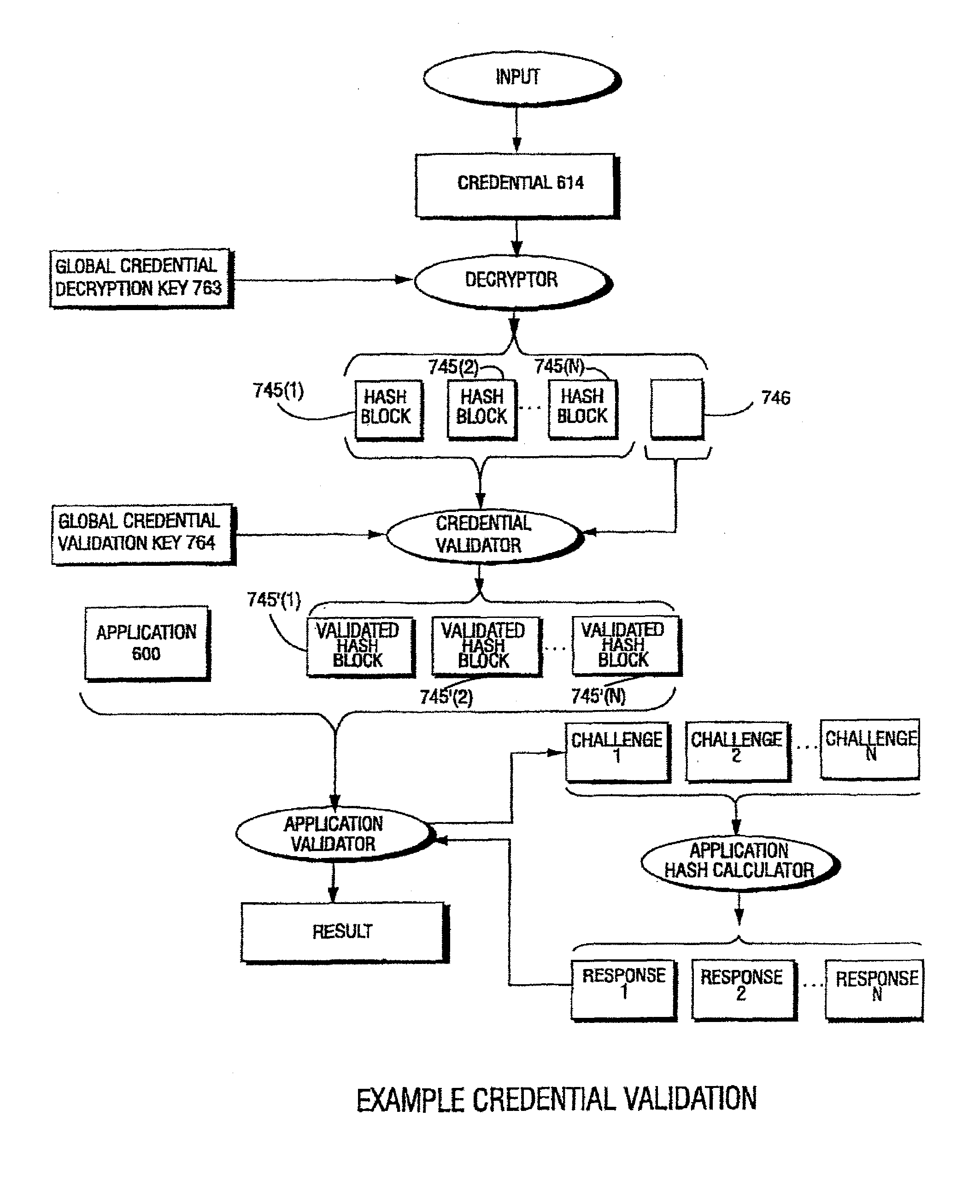
Computation environments are protected from bogus or rogue load modules, executables, and other data elements through use of digital signatures, seals, and certificates issued by a verifying authority. A verifying authority—which may be a trusted independent third party—tests the load modules and / or other items to verify that their corresponding specifications are accurate and complete, and then digitally signs them based on a tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys), allowing one tamper resistance work factor environment to protect itself against load modules from another tamper resistance work factor environment. The verifying authority can provide an application intended for insecure environments with a credential having multiple elements covering different parts of the application. To verify the application, a trusted element can issue challenges based on different parts of the authenticated credential that the trusted element selects in an unpredictable (e.g., random) way, and deny service (or take other appropriate action) if the responses do not match the authenticated credential.
Owner:INTERTRUST TECH CORP
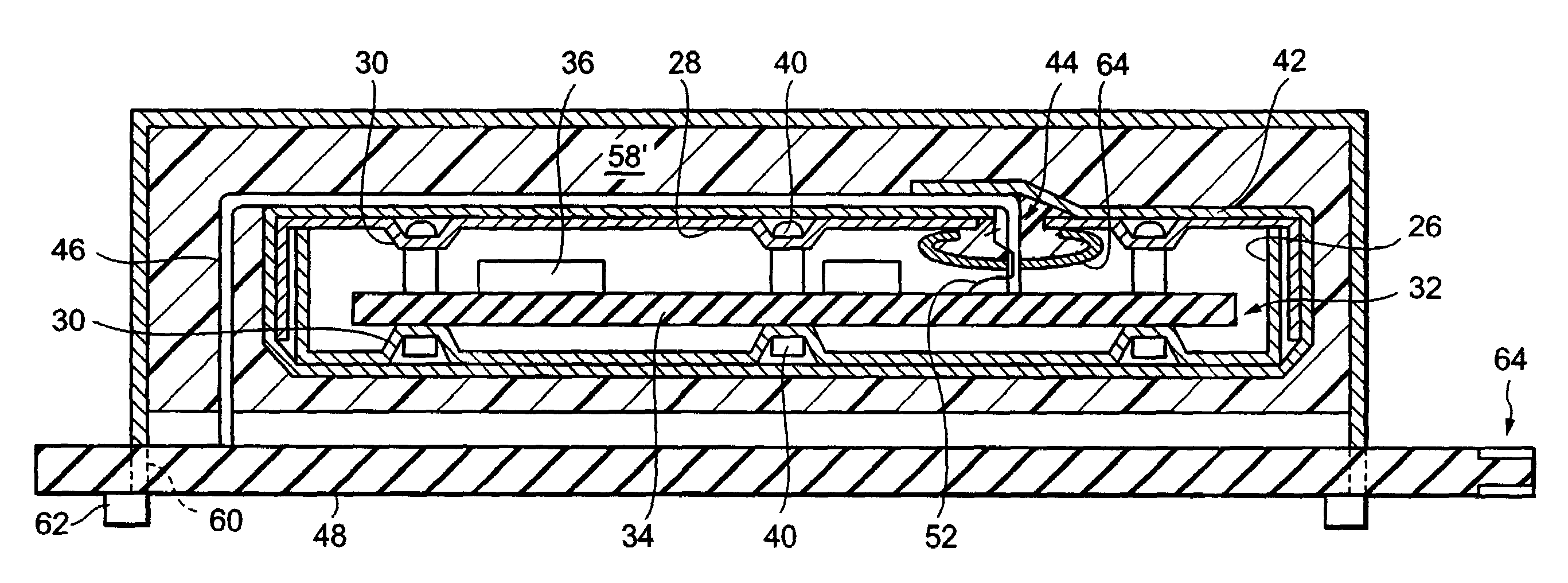
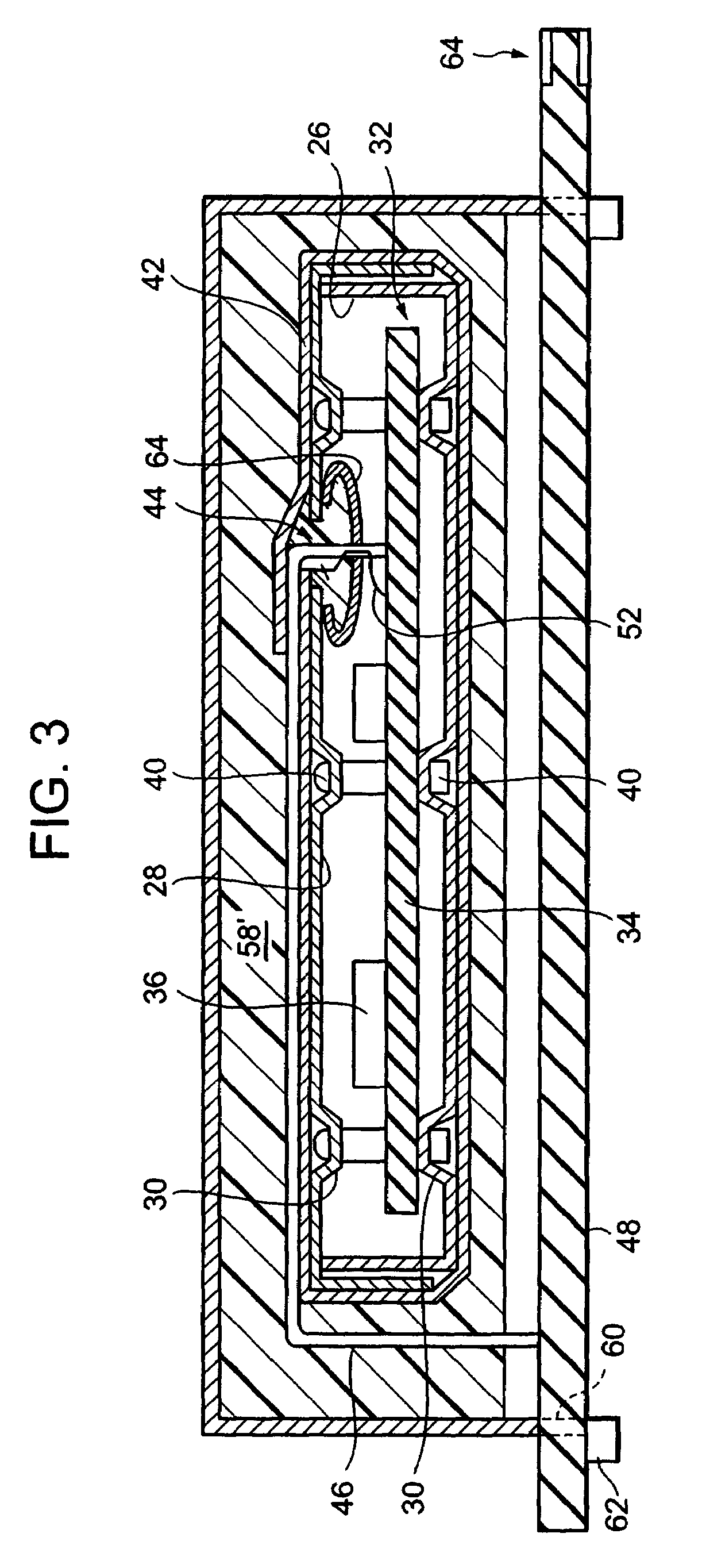
Tamper-proof enclosure for a circuit card
InactiveUS6970360B2Improve reliabilityImprove securitySemiconductor/solid-state device detailsSolid-state devicesInternal pressureTamper resistance
A tamper-proof enclosure for an electrical card, such as a high speed communications card, includes an enclosure in which the card is mounted. The enclosure has a wall with an opening, and a cup member is attached to the wall at the opening. A bus that is connected to the card extends through a passage in the cup member and through the opening in the wall. A security mesh is wrapped around the enclosure. The cup member is filled with liquid resin, which is also coated onto the security mesh. After the resin is cured, the resin in the cup member forms a plug that seals the security mesh from inner pressure when the enclosure is heated to an elevated temperature. The resin is preferably polyamide.
Owner:INT BUSINESS MASCH CORP
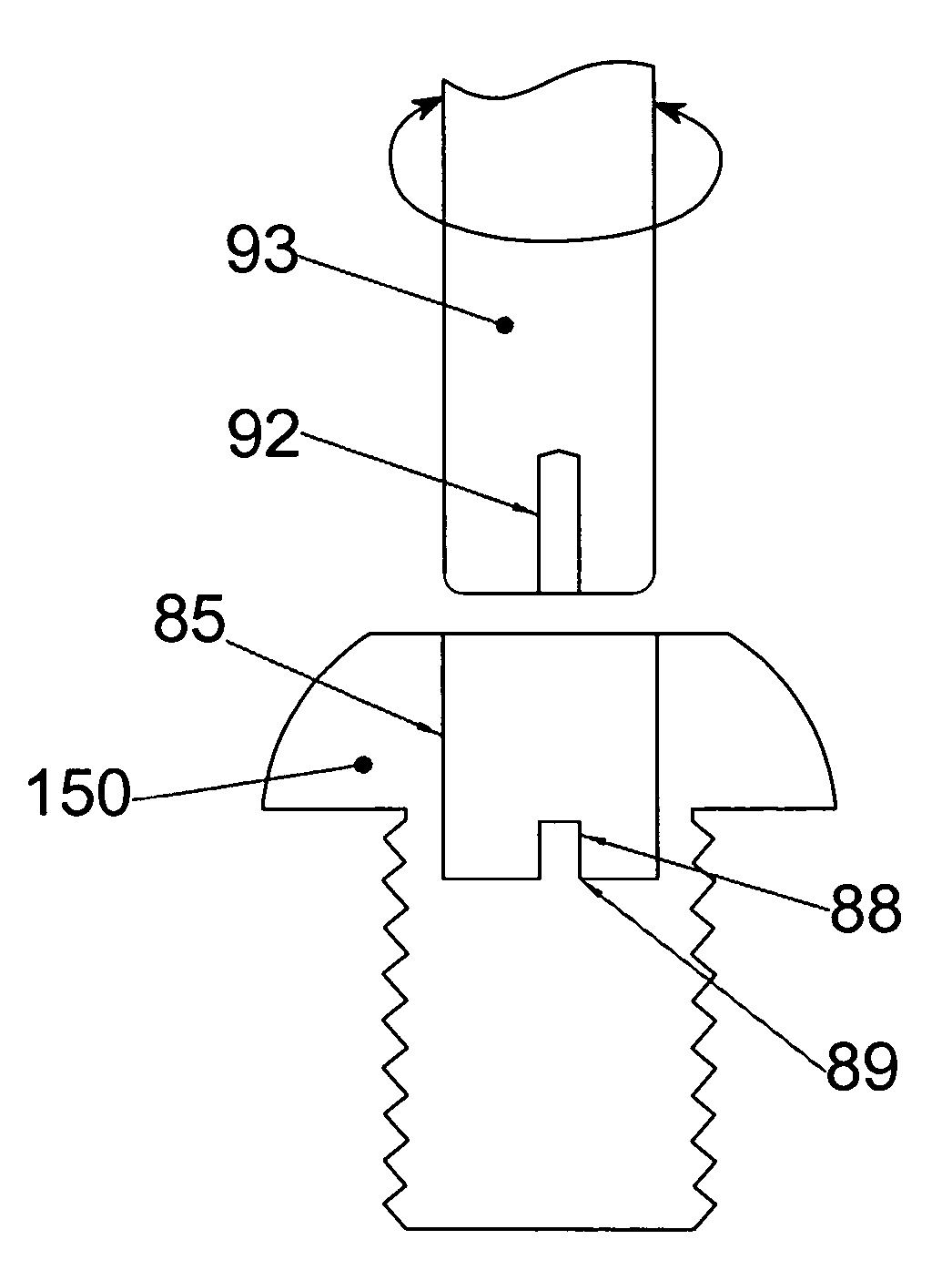
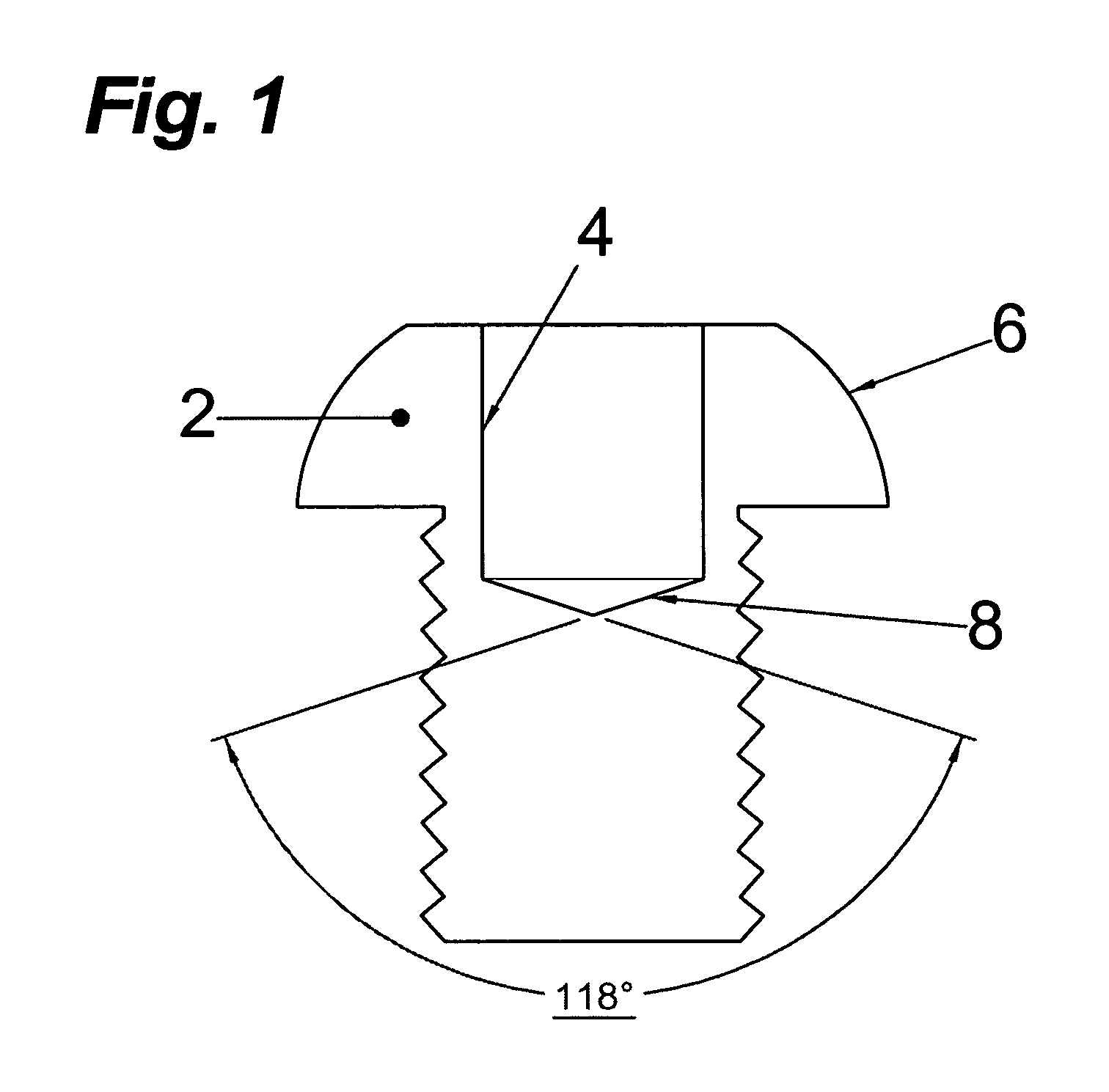
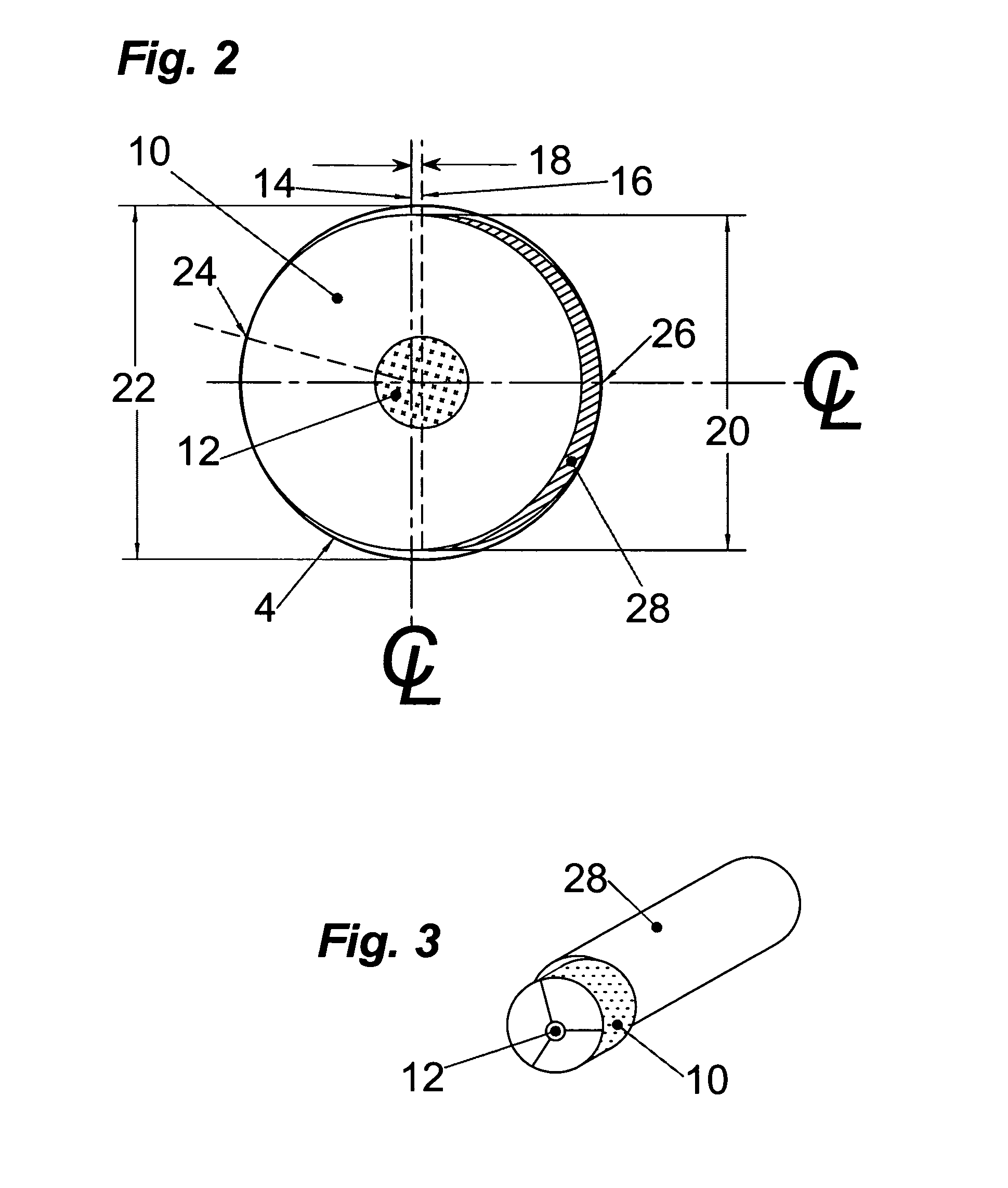
Torque-setting, tamper-resistant fastener and method and tool for use with same
A fastener includes a round, blind hole or pocket in its head. Installation and removal of the fastener is accomplished with a tool containing an eccentric segment on the end of a shaft. When rotated within the pocket, the eccentric segment displaces laterally relative to the shaft to provide a friction grip to the lateral wall of the pocket. The strength of the grip is proportional to the applied torque. Eccentric displacement allows rotation but prevents the tool from spinning out of the fastener thereby eliminating cam-out and surface damage resulting from contact with a spinning tool tip. The eccentric head of the tool can be made disposable and to shear off when a predetermined torque is reached. The smooth-sided round hole offers no purchase for commonly available tools; making the fastener tamper-resistance. In another embodiment, the fastener includes a raised portion in the pocket. A tool having a complementary opening shears off the raised portion at a predetermined torque.
Owner:FLESHER ROBERT W
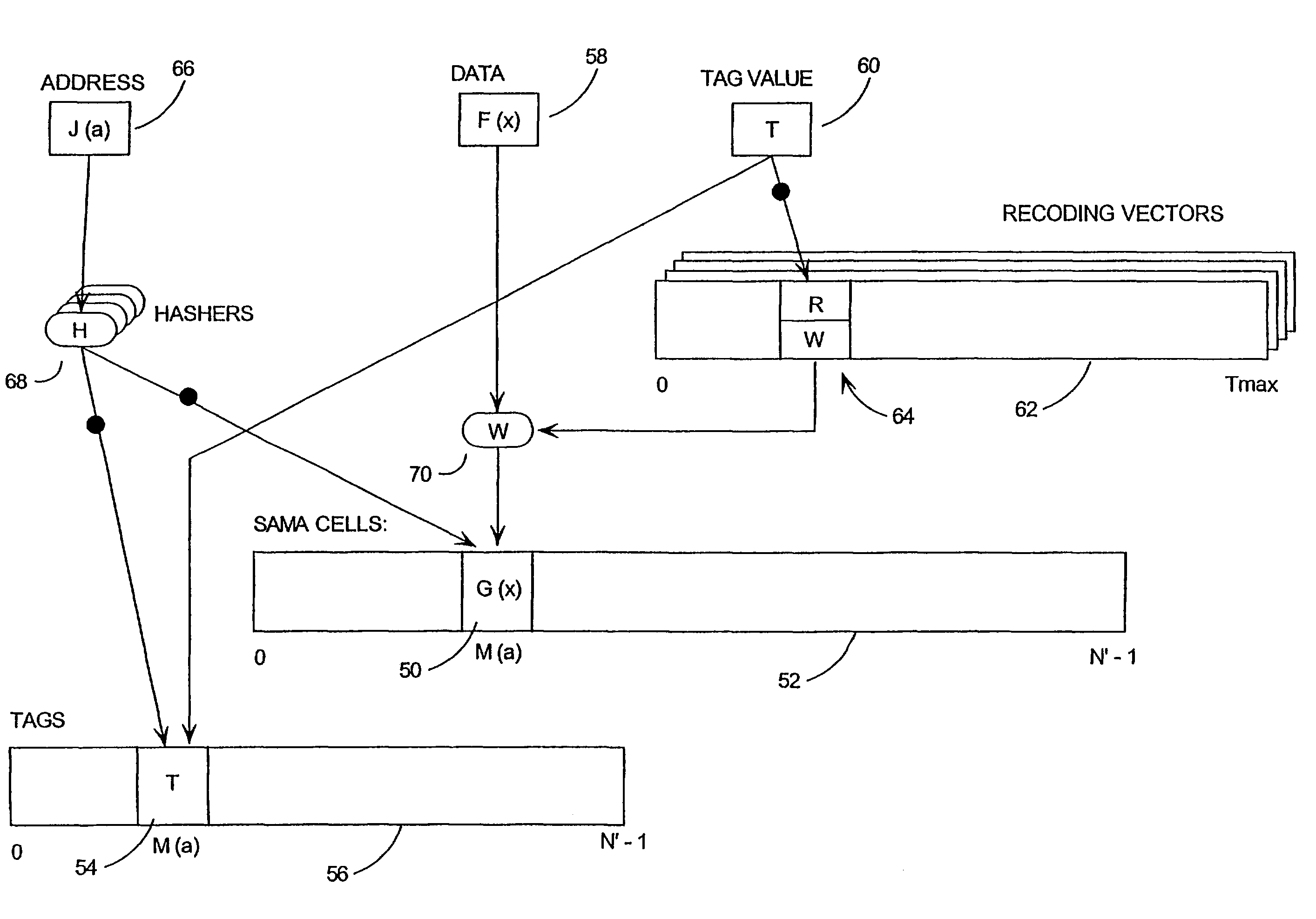
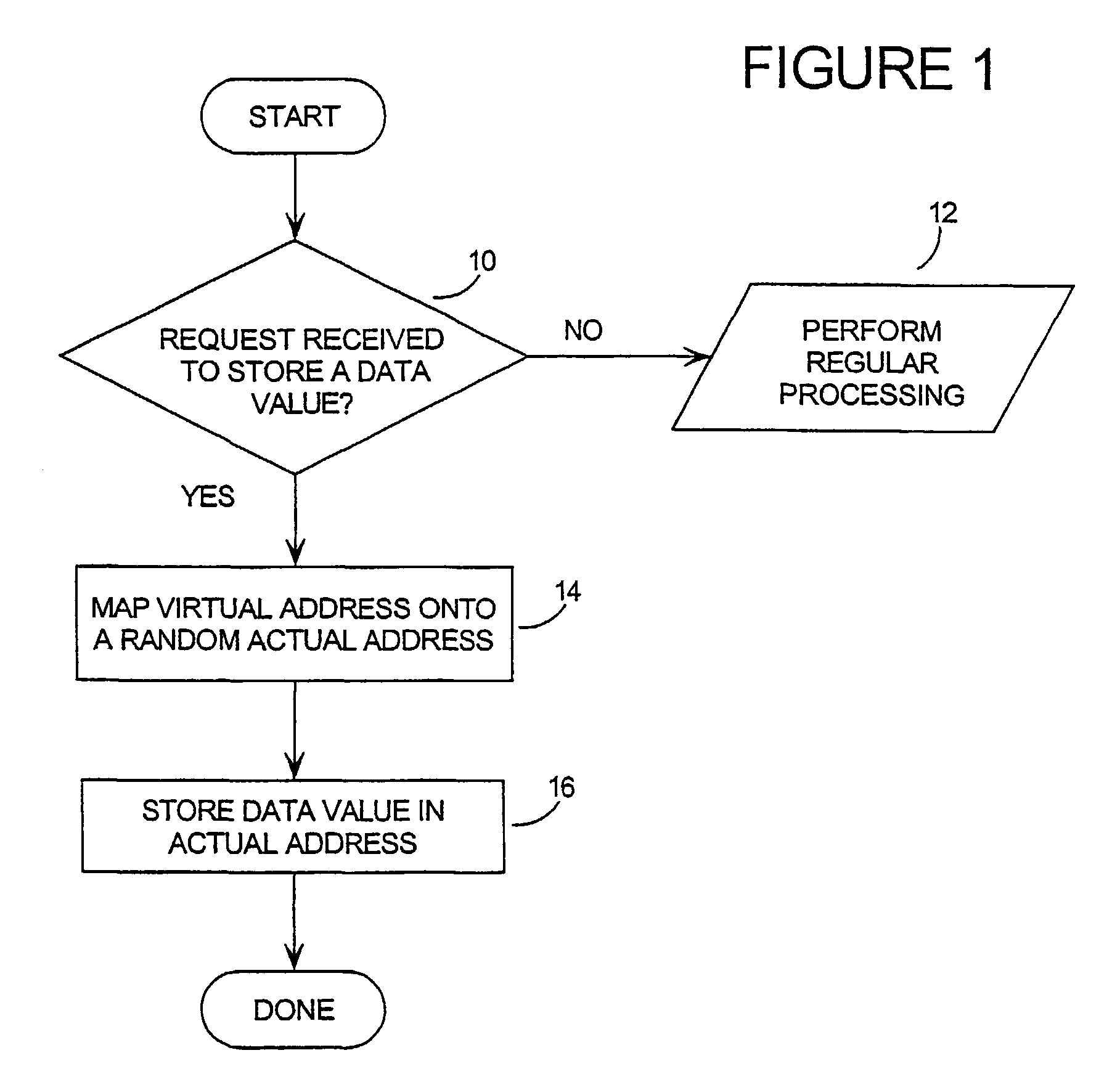
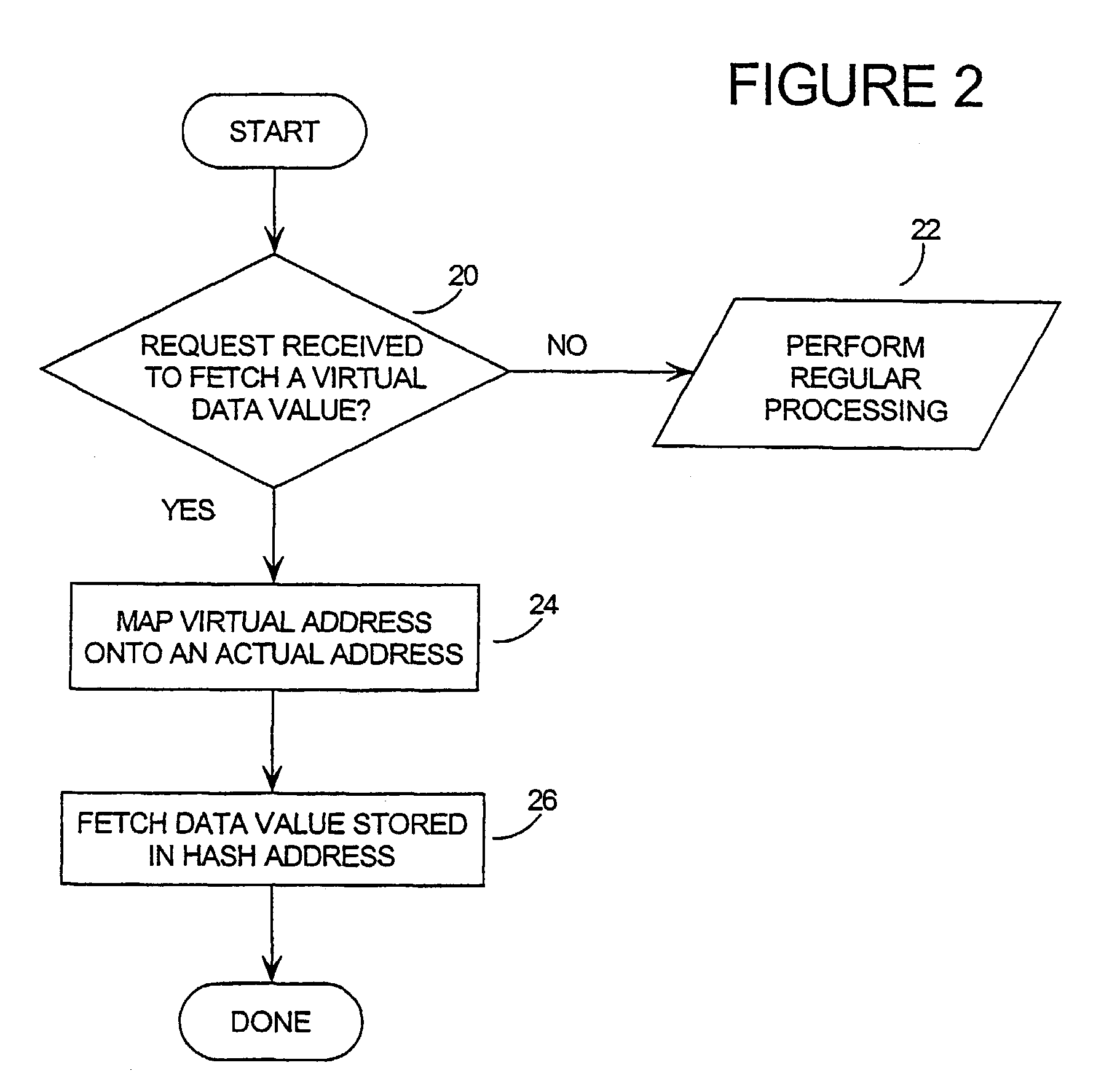
Tamper resistant software-mass data encoding
InactiveUS7350085B2Unauthorized memory use protectionHardware monitoringArray data structureBiometric data
Mass data (the contents of arrays, large data structures, linked data structures and similar data structures stored in memory) are common targets for attack. The invention presents a method and system of protecting mass data by mapping virtual addresses onto randomly or pseudo-randomly selected actual addresses. This mapping distributes data values throughout the memory so an attacker cannot locate the data he is seeking, or identify patterns which might allow him to obtain information about his target (such as how the software operates, encryption keys, biometric data or passwords stored therein, or algorithms it uses). Additional layers of protection are described, as well as efficient techniques for generating the necessary transforms to perform the invention.
Owner:IRDETO ACCESS
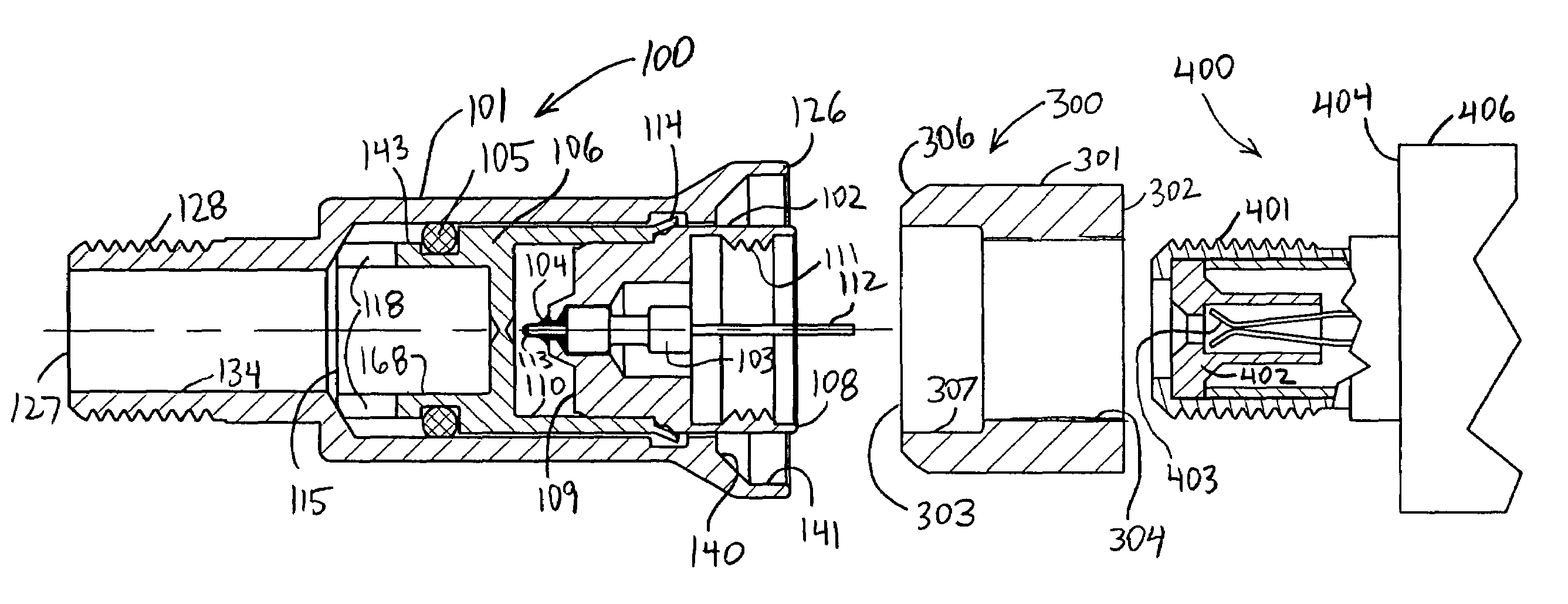
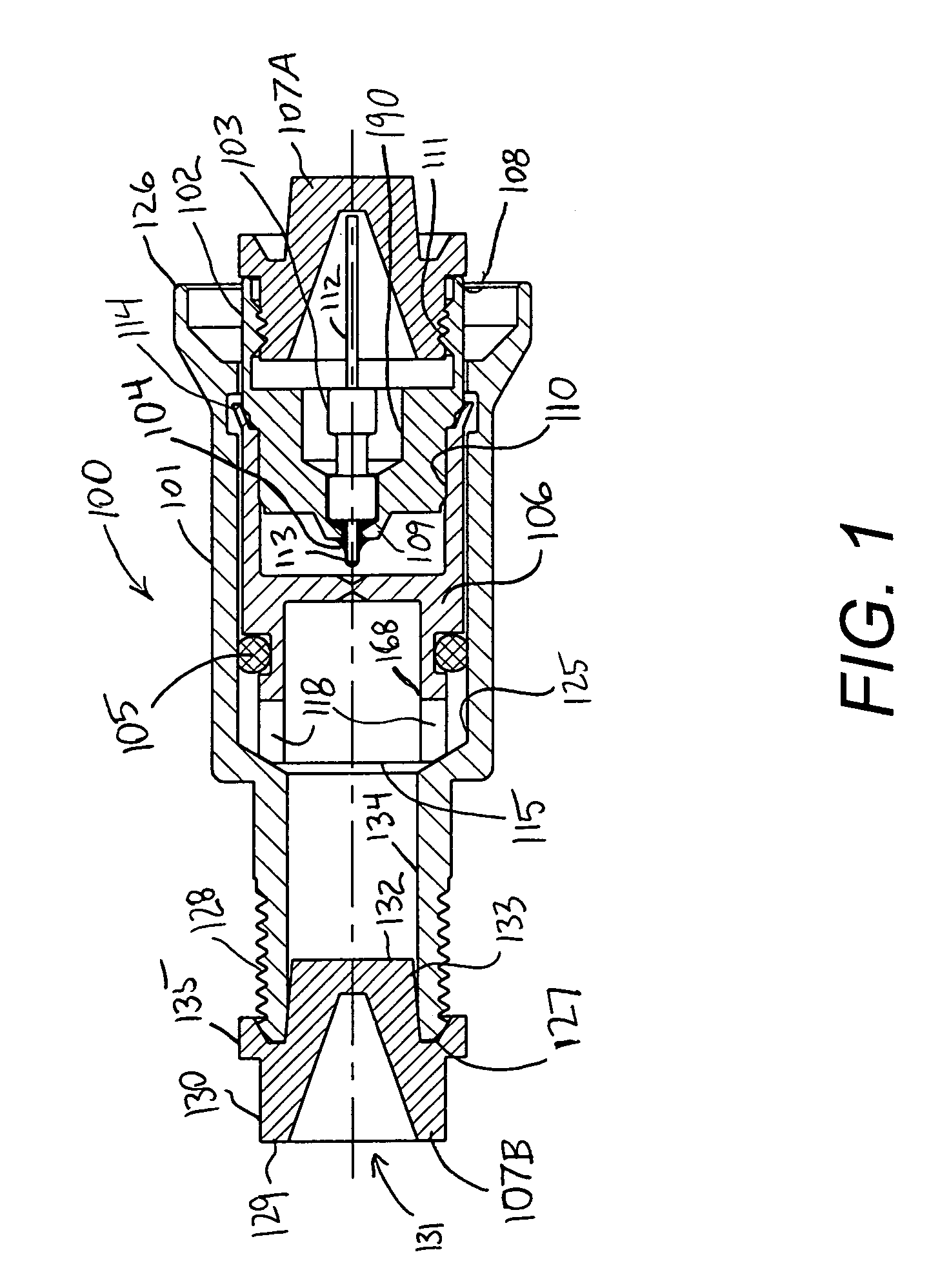
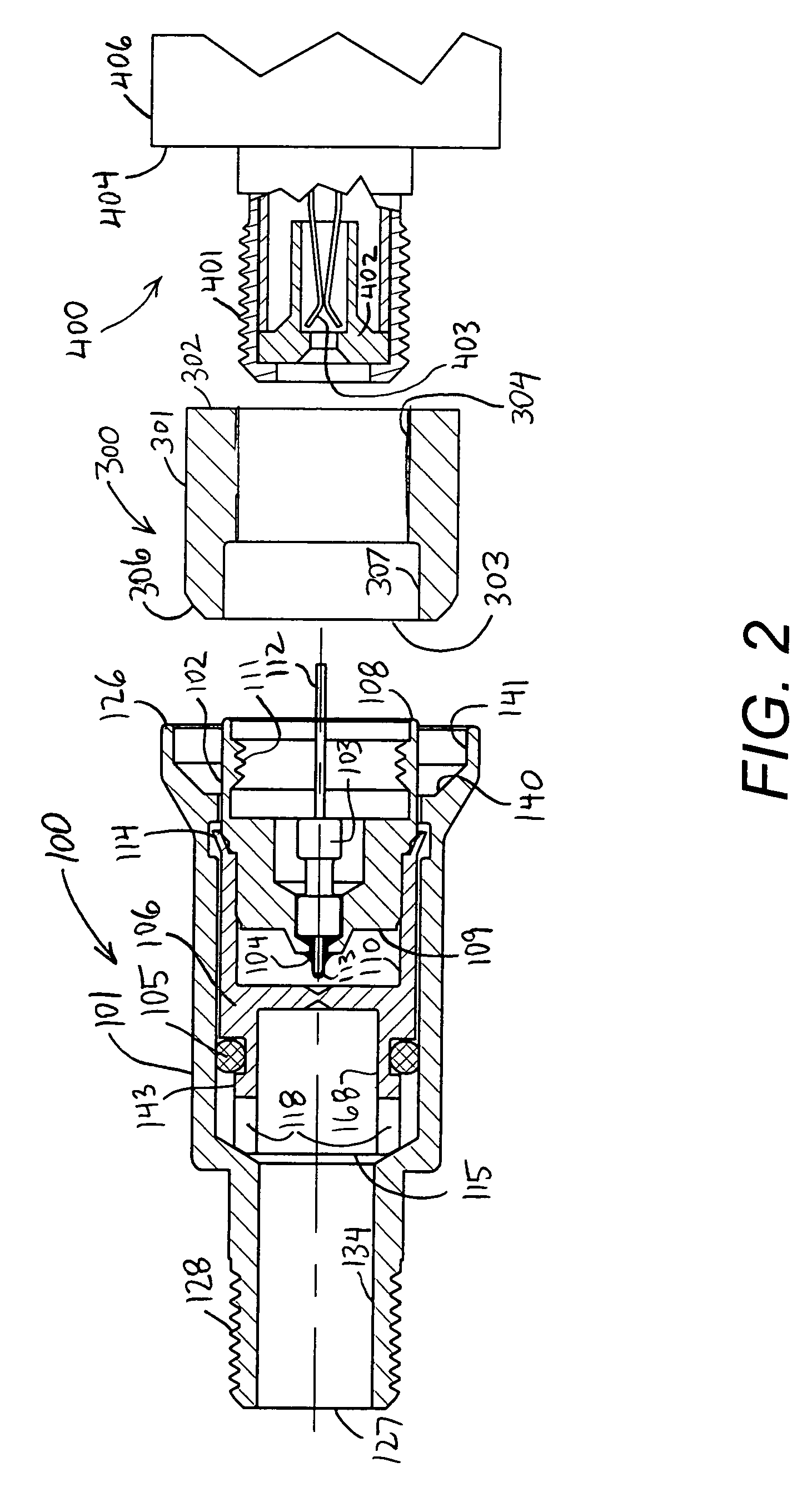
Sealed tamper resistant terminator
ActiveUS7144271B1Without excessive wobbleReduce the likelihood of failureElectrically conductive connectionsTwo pole connectionsElectrical conductorEngineering
A tamper-resistant coaxial terminator includes an inner body rotatably captivated within an outer shield. A deformable portion of the inner body extends within an annular recess formed in the outer shield. An optional RF port, containing a resistor, is press-fit within the inner body. The RF port, or alternatively, the inner body, is internally-threaded for engaging the outer conductor of an equipment port. A seal ring extends over the outer conductor of the equipment port and is urged by the outer shield to directly engage the internally-threaded portion of the terminator. A seal is also optionally disposed between the outer shield and the inner body to minimize moisture induced corrosion. A shipping cap, usable at either end of the terminator, helps protect the terminator during shipment and prevents entry of debris.
Owner:PPC BROADBAND INC
Electronic invoice management system and method based on distributed accounting
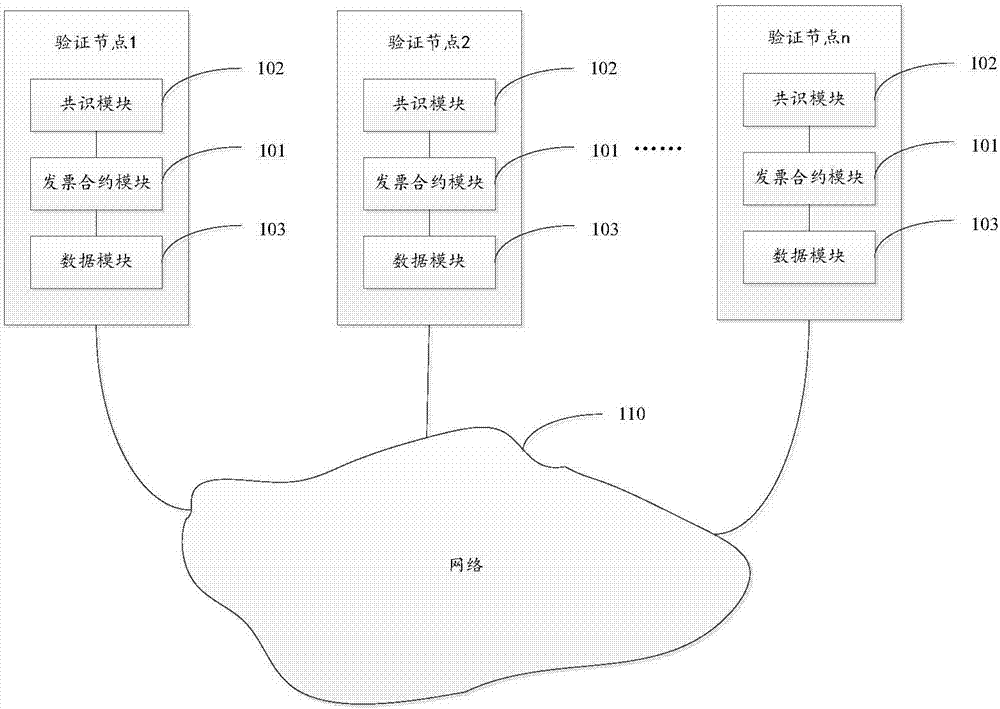
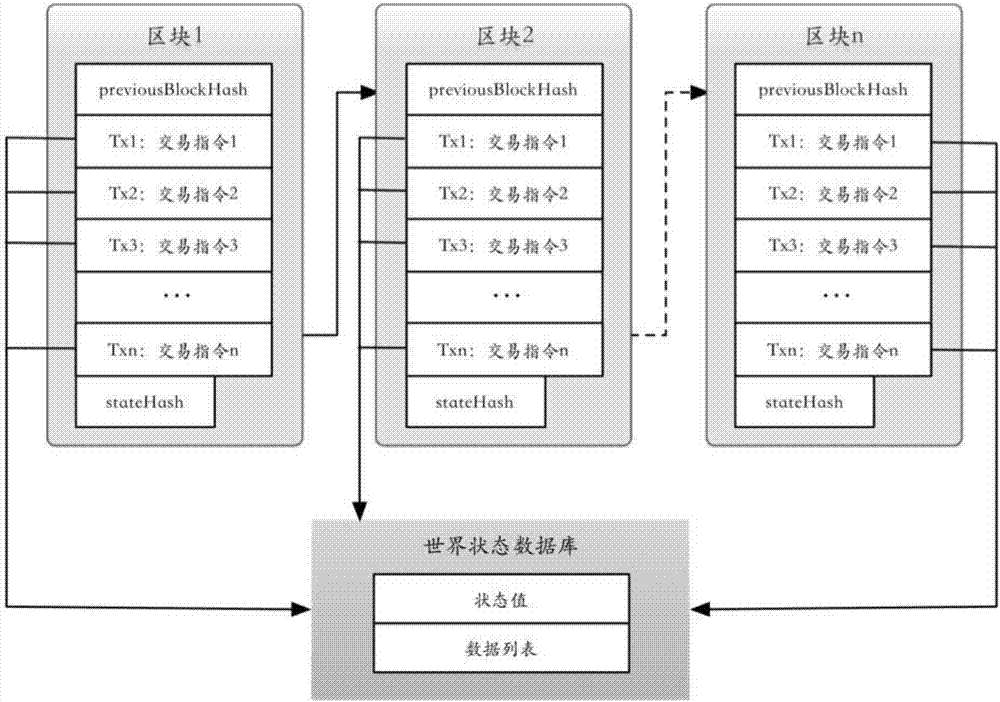
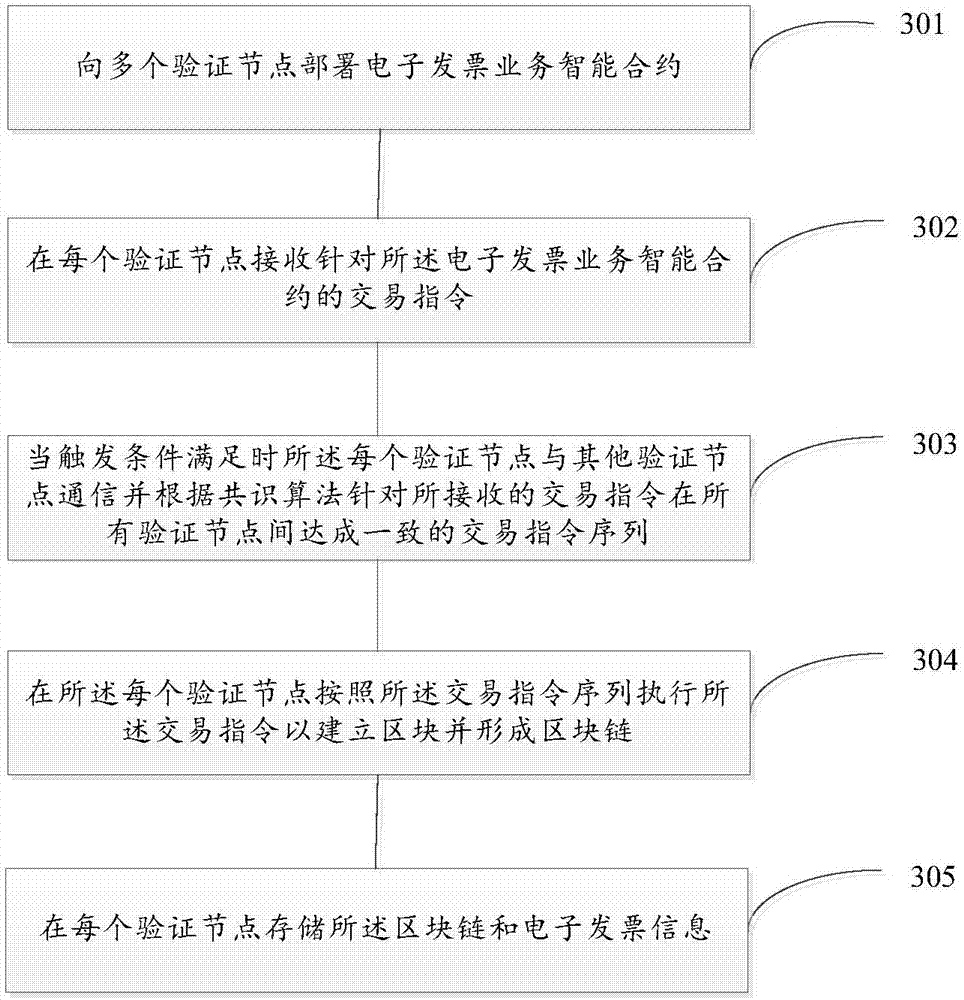
InactiveCN106952124APrevent tamperingAvoid attackUser identity/authority verificationBilling/invoicingTamper resistanceInvoice
The invention discloses an electronic invoice management system and a method based on distributed accounting. The system comprises multiple verification nodes. Each verification node comprises an electronic invoice contract module and an agreement module, wherein the electronic invoice contract module comprises an electronic invoice service intelligent contract and is configured to be used for receiving a transaction command of the electronic invoice service intelligent contract and executing the transaction command according to a result of the agreement module so as to establish a block and form a block link, and the electronic invoice service intelligent contract is operation performed on an electronic invoice. The agreement module is configured to be used for communicating with other verification nodes when being triggered and making an agreement on a transaction command sequence between all verification nodes for the received transaction command according to an agreement algorithm. According to the invention, tamper-proofing is realized and the system and the method are cost-effective.
Facilitating secure communication between utility devices
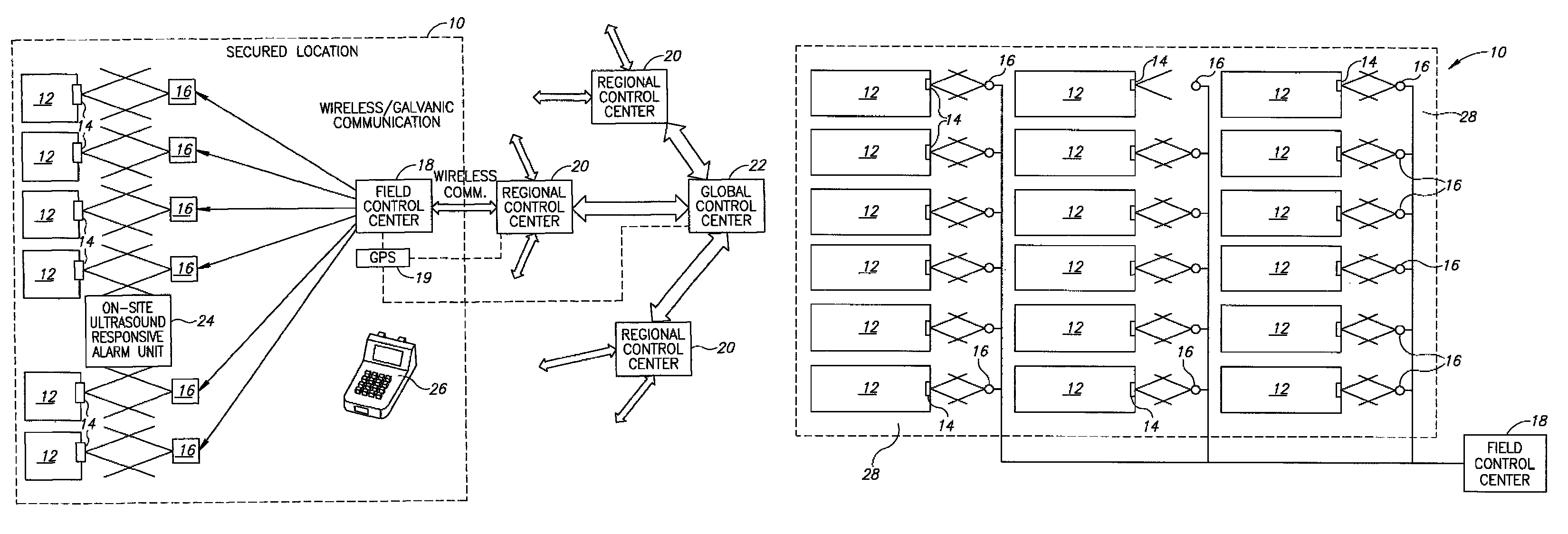
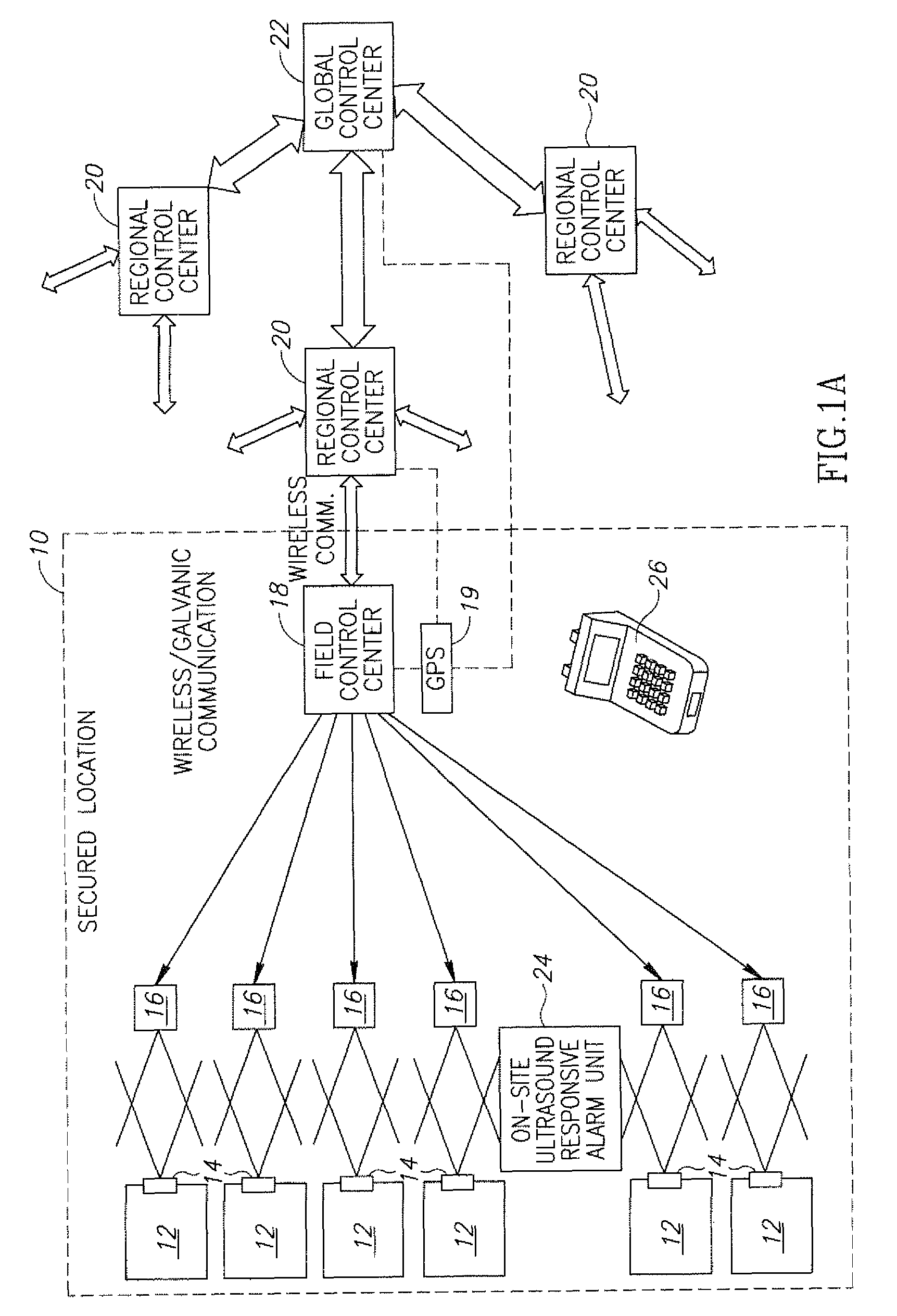
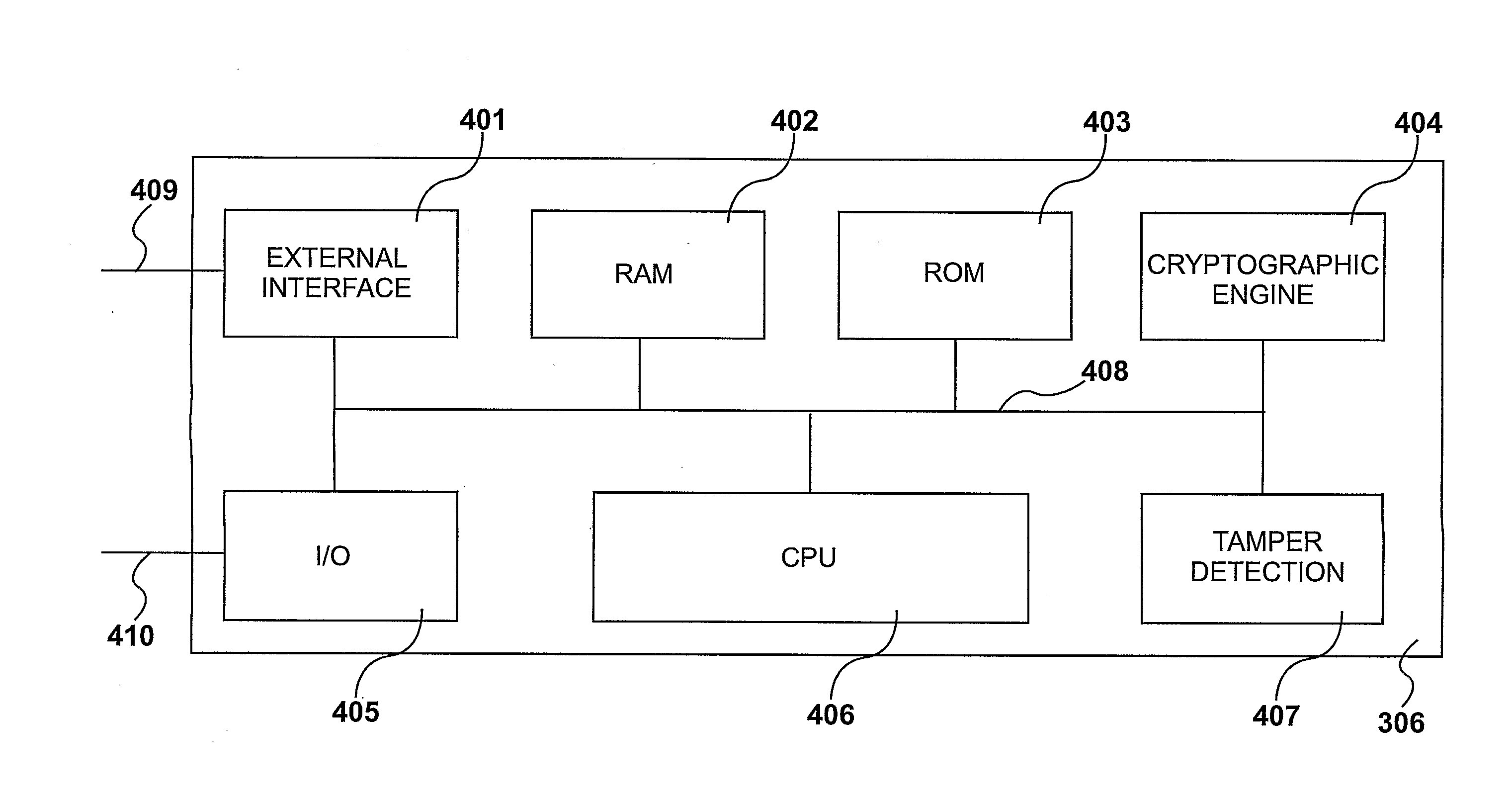
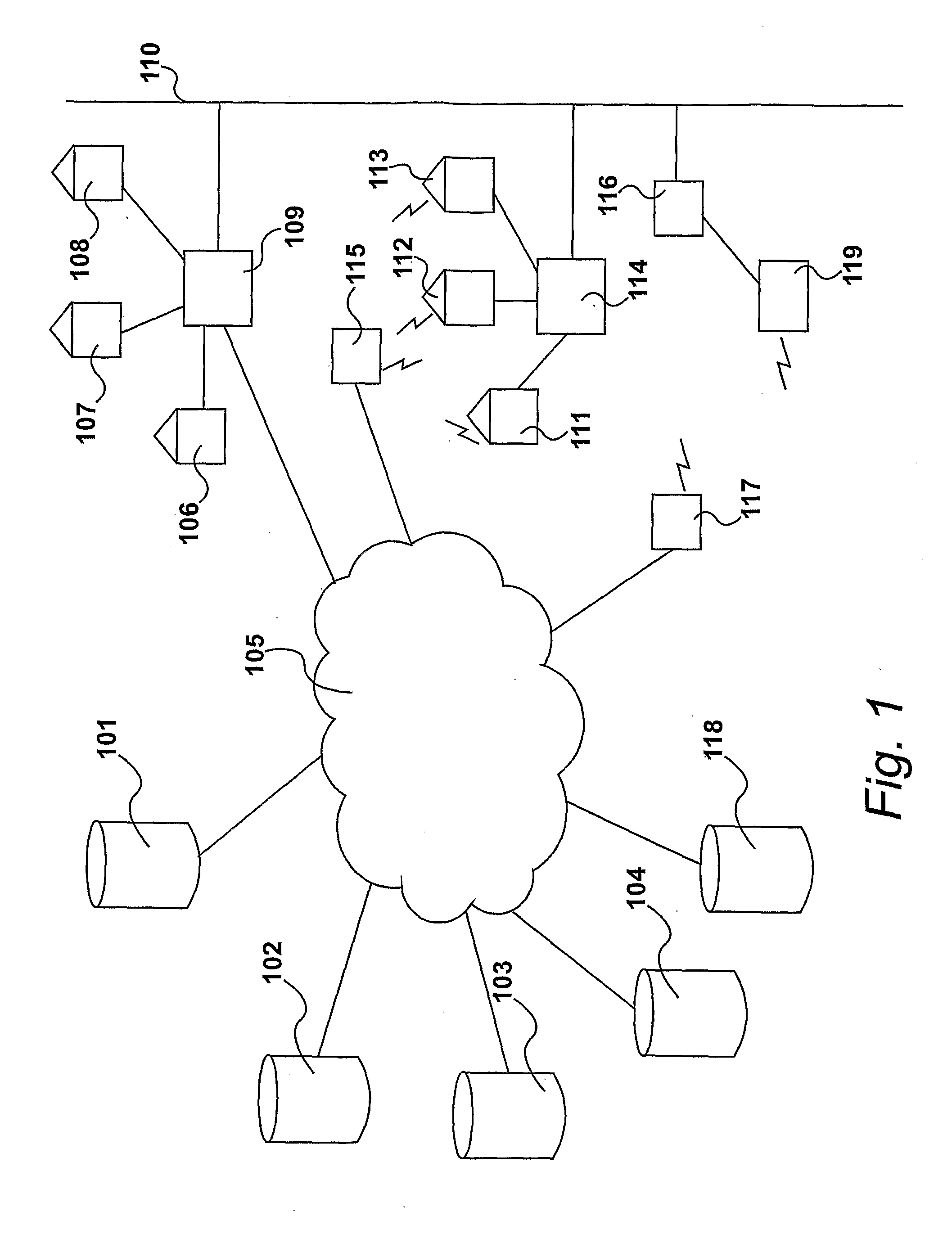
InactiveUS20110296169A1Facilitate communicationSecuring communicationHome automation networksMicrocontrollerTamper resistance
Communication is facilitated between a plurality of servers (101,102,103) and a plurality of local devices (204,206,207,208,210). An apparatus comprises a first network interface for communicating with the servers, a second network interface for communicating with the local devices, and a microcontroller having a processor, memory, a cryptographic engine for carrying out cryptographic calculations, and a tamper-resistance element configured to resist tampering with the apparatus. A plurality of programs, each comprising instructions and data, are stored in the memory. The processor is configured to, for a first local device, identify a first program which is associated with the first local device, and using the first program, provide a secure communications channel between the first local device and a first server. The processor is unable to accept commands from any other of the programs to access or change the first program, and the processor is unable to route messages over the secure communications channel that are not from or to the first local device and the first server.
Owner:PALMER CHARLES GRAHAM
Memory device and electronic device using the same
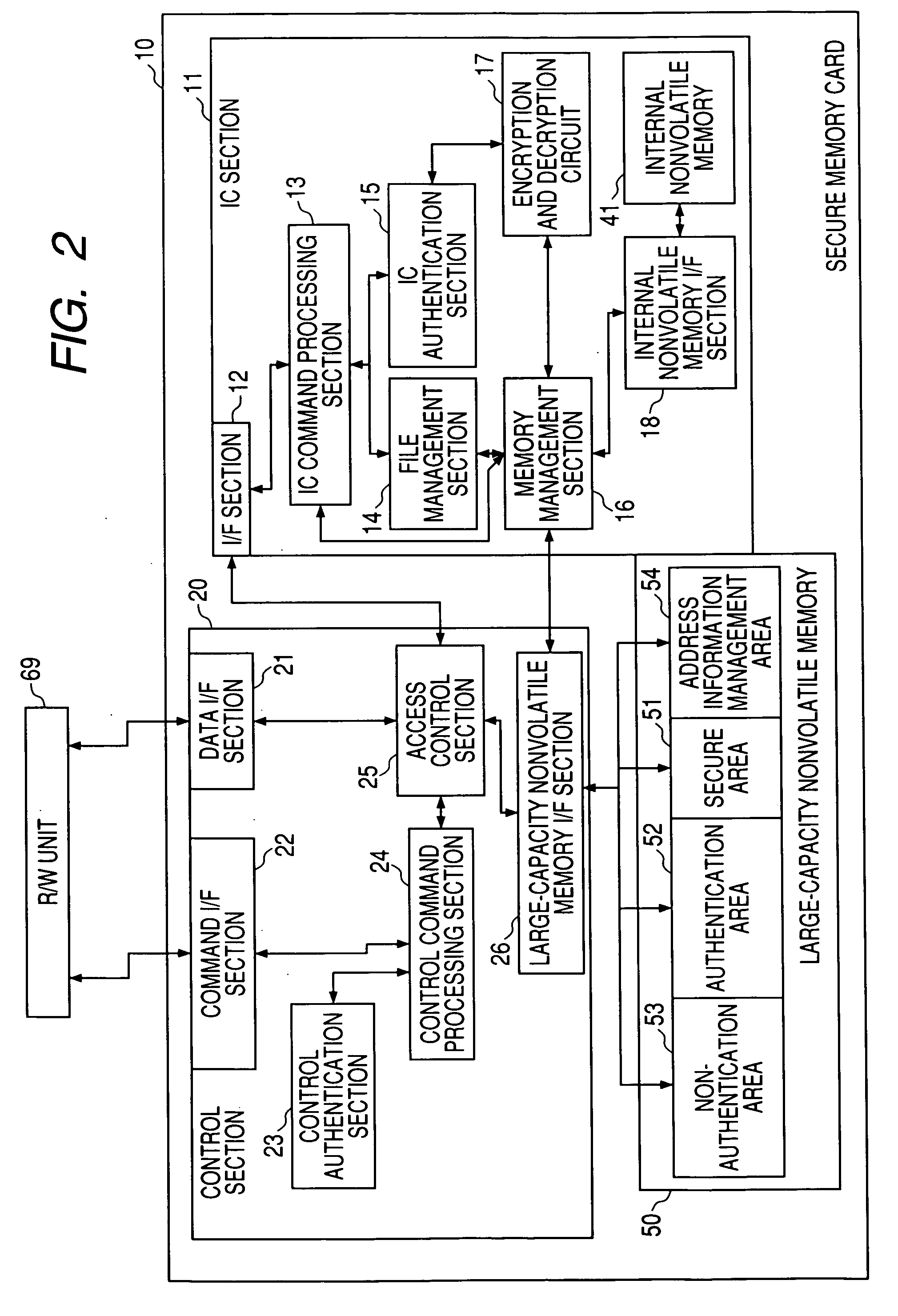
InactiveUS20060126422A1Improve security levelLarge storage capacityKey distribution for secure communicationUnauthorized memory use protectionTamper resistanceSmart card
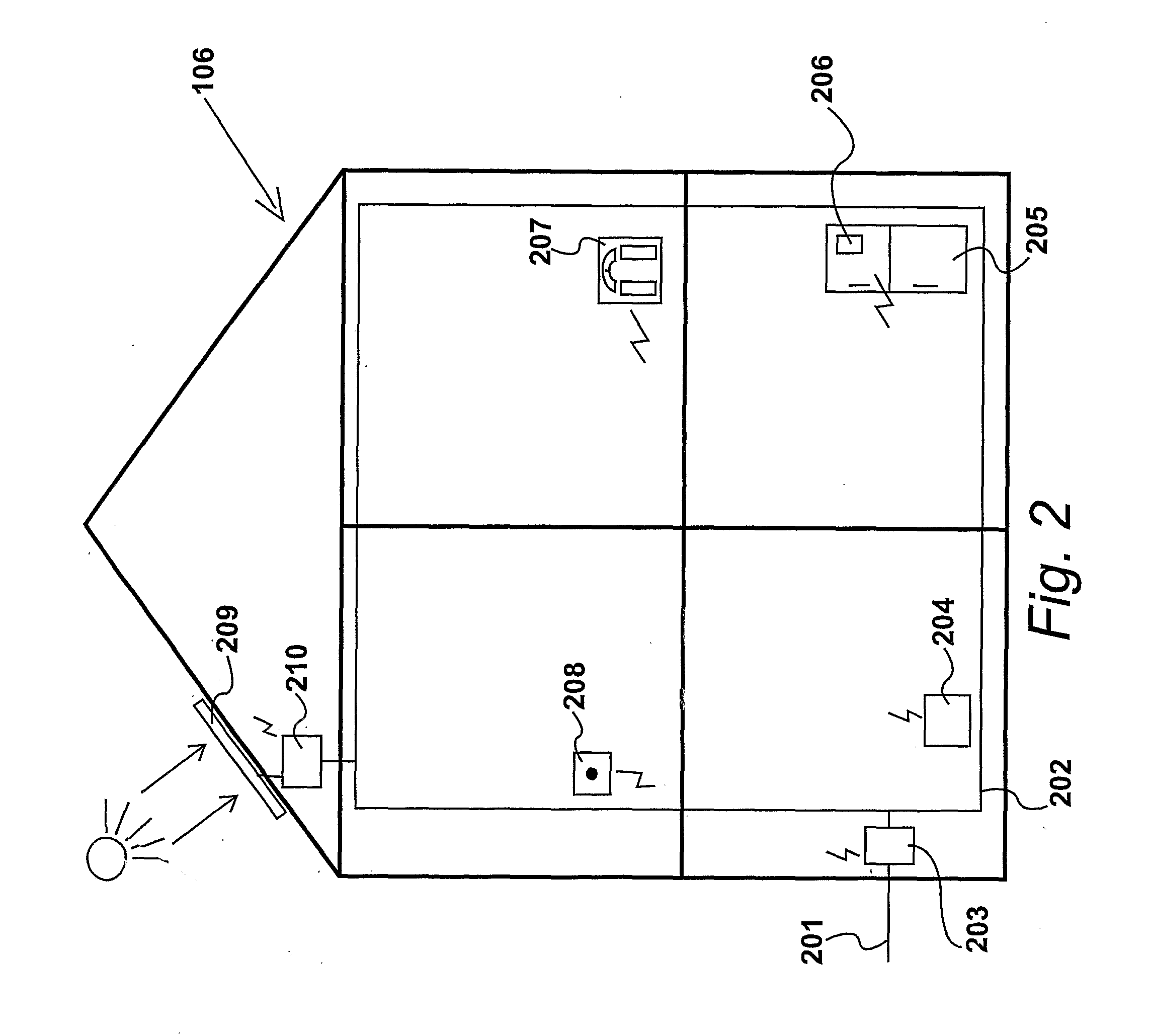
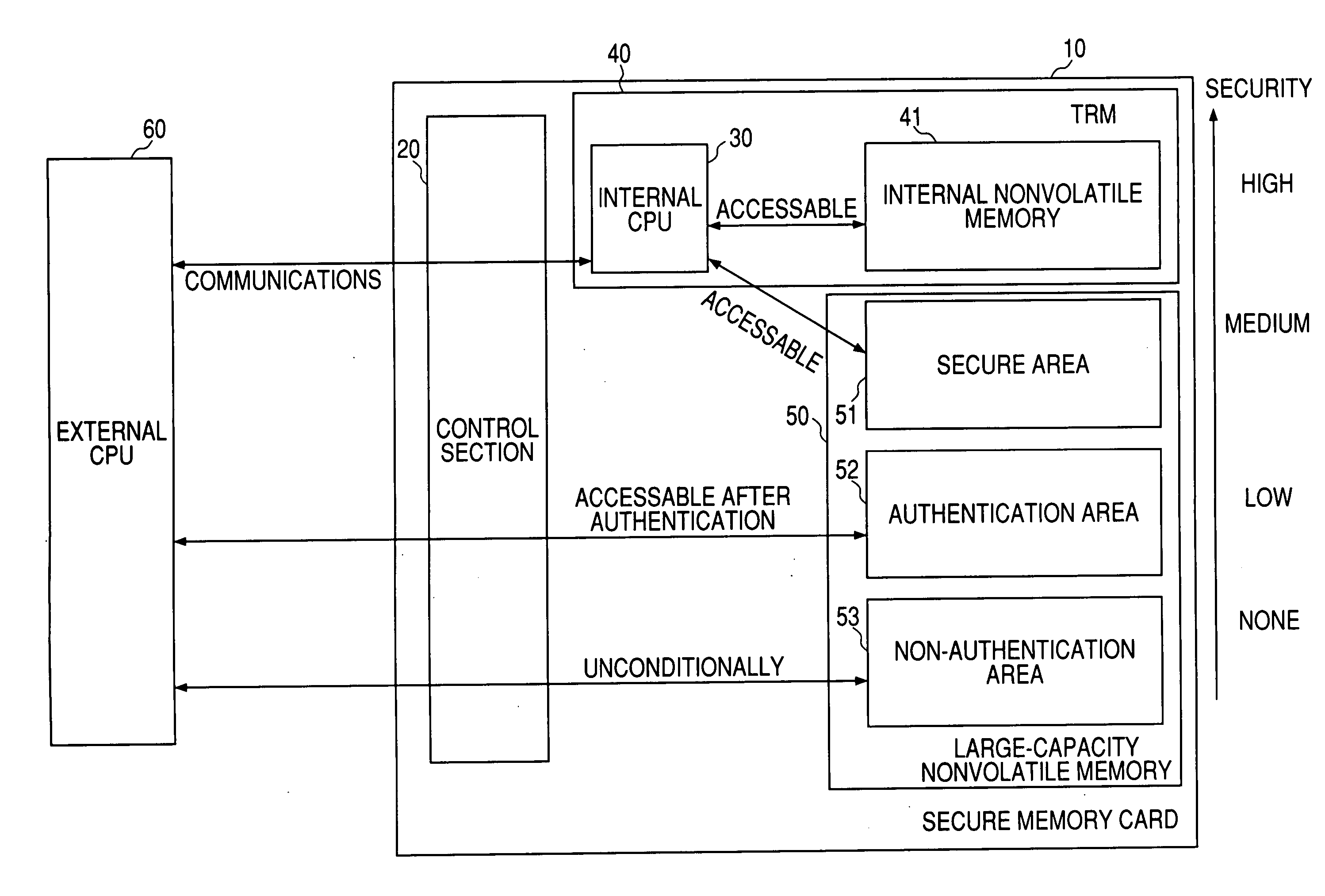
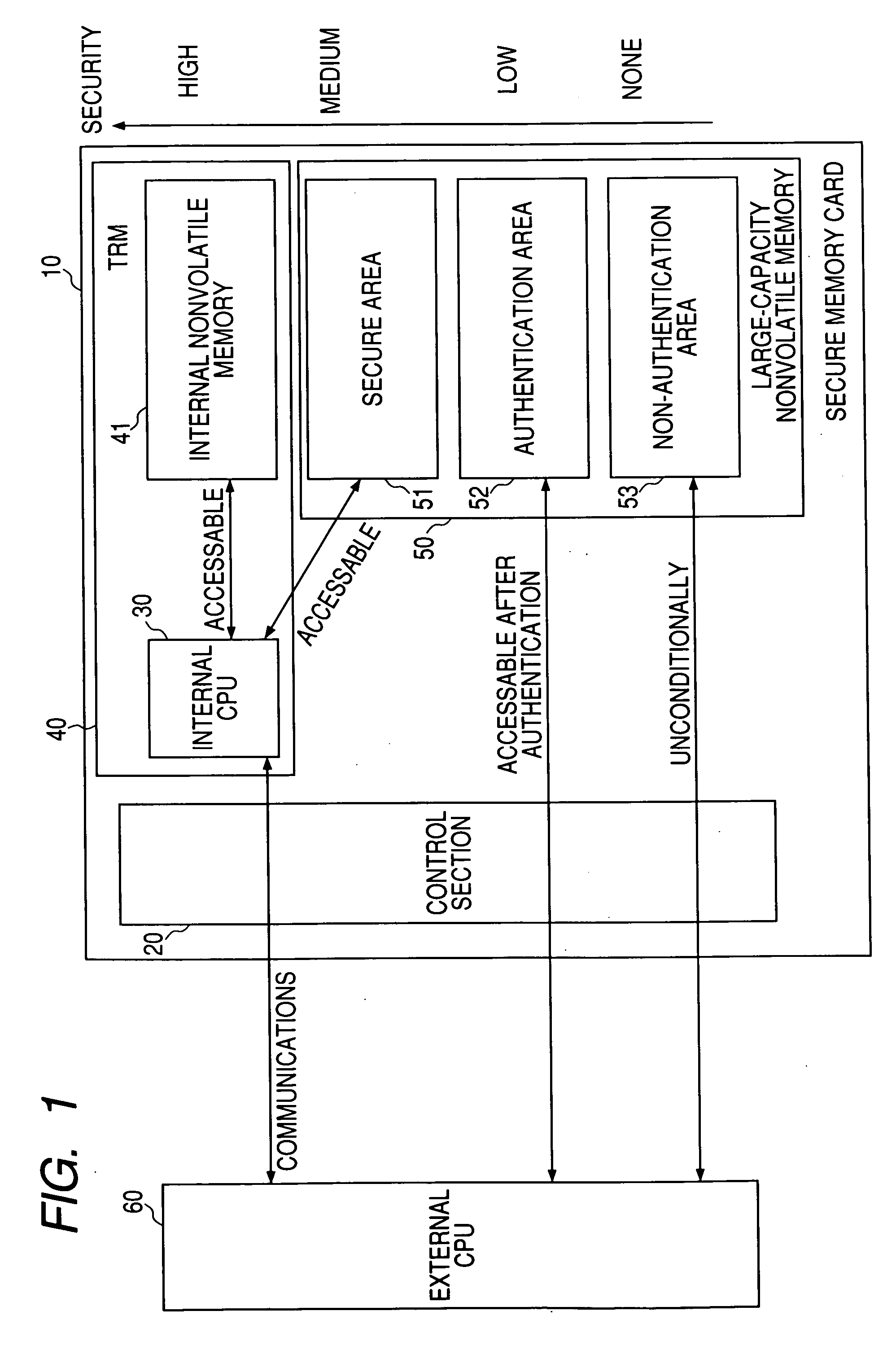
It is an object of the invention to provide a memory device including a memory area having a large storage capacity and an equal security level to that of a Smart card. A semiconductor memory card 10 that can be attached to and detached from an electronic device is provided with first memory 50 of non-tamper-resistance having usual areas 52 and 53 that can be accessed from the electronic device and a secure area 51 that cannot directly be accessed from the electronic device, and second memory 41 of tamper resistance that cannot directly be accessed from the electronic device, wherein access to the secure area 51 of the first memory 50 can be made only through a secure control section 30 for managing access to the second memory 41. The secure area 51 cannot directly be accessed by an external device and therefore has the higher security level than the authentication area 52. Since the secure area 51 is placed in the non-tamper-resistant memory 50, a large storage capacity can be reserved.
Owner:PANASONIC CORP
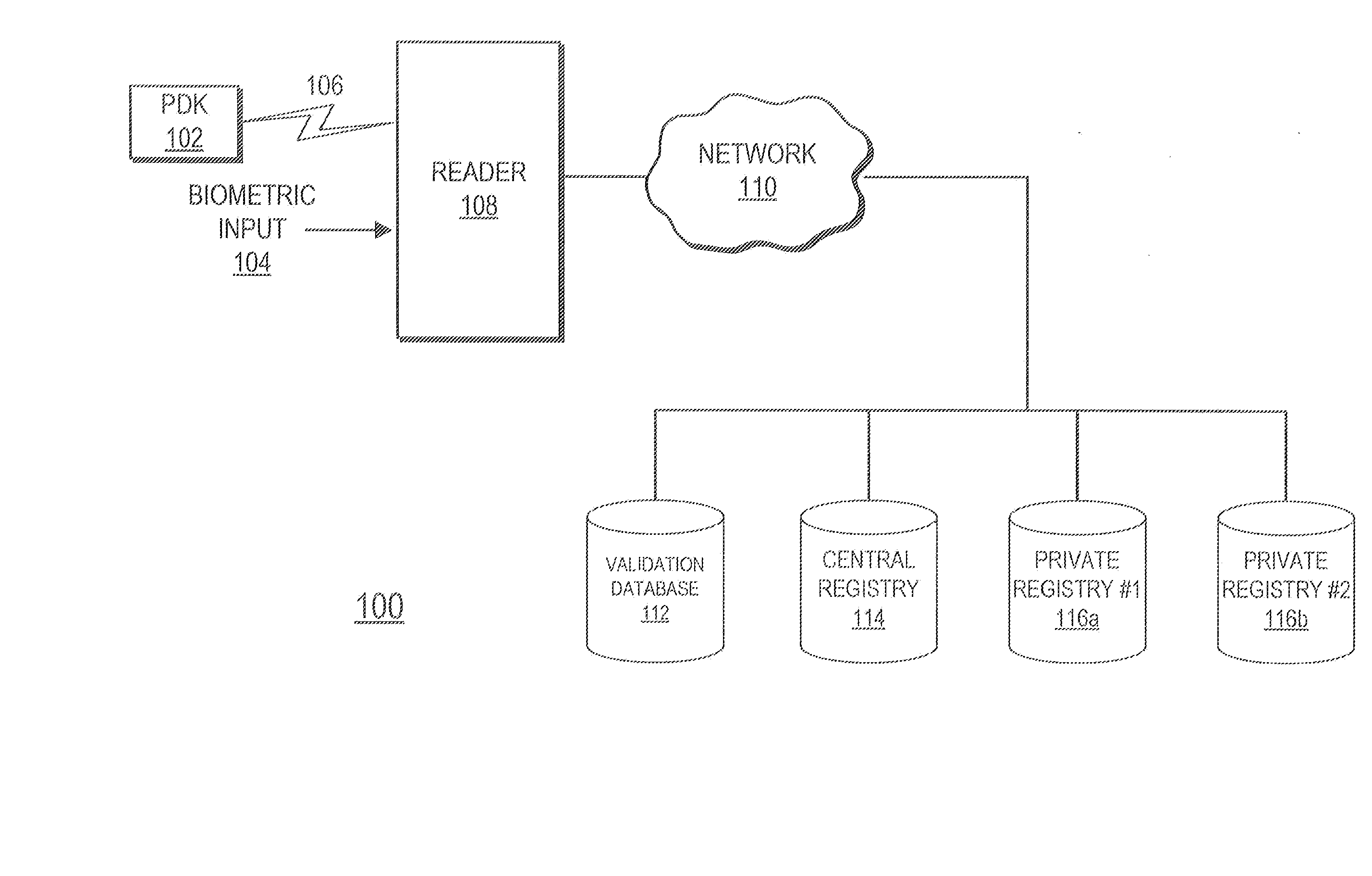
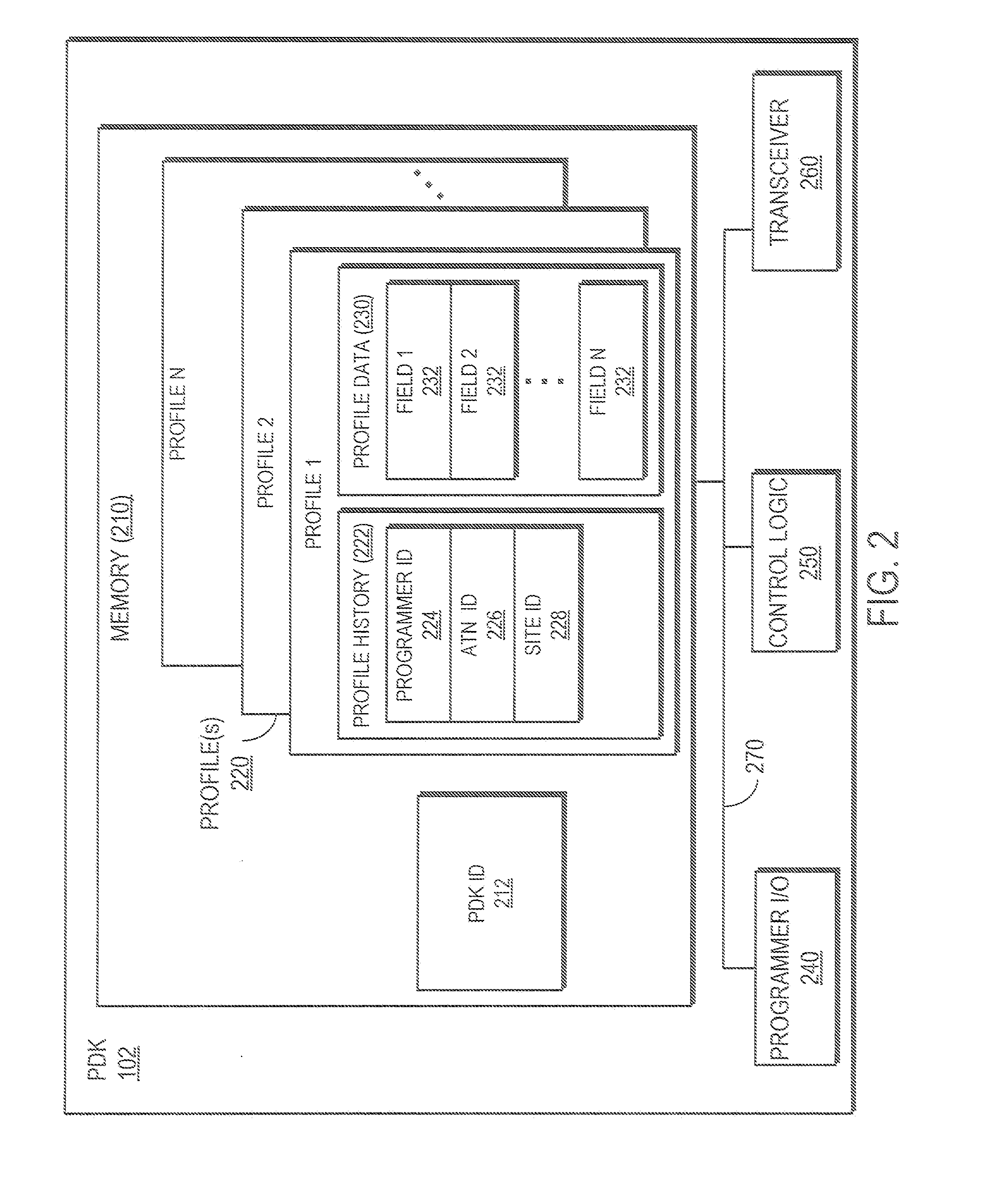
Personal digital key differentiation for secure transactions
ActiveUS20070260883A1Efficient and secure and highly reliable authenticationCompared quicklyAcutation objectsUser identity/authority verificationTamper resistanceTemporal information
Owner:PROXENSE
Software self-defense systems and methods
ActiveUS20050204348A1Error detection/correctionProgram/content distribution protectionTamper resistanceObfuscation
Systems and methods are disclosed for protecting a computer program from unauthorized analysis and modification. Obfuscation transformations can be applied to the computer program's local structure, control graph, and / or data structure to render the program more difficult to understand and / or modify. Tamper-resistance mechanisms can be incorporated into the computer program to detect attempts to tamper with the program's operation. Once an attempt to tamper with the computer program is detected, the computer program reports it to an external agent, ceases normal operation, and / or reverses any modifications made by the attempted tampering. The computer program can also be watermarked to facilitate identification of its owner. The obfuscation, tamper-resistance, and watermarking transformations can be applied to the computer program's source code, object code, or executable image.
Owner:INTERTRUST TECH CORP
Systems and methods for using cryptography to protect secure and insecure computing environments
InactiveUS7243236B1Digital data processing detailsUser identity/authority verificationTamper resistanceThird party
Computation environments are protected from bogus or rogue load modules, executables, and other data elements through use of digital signatures, seals, and certificates issued by a verifying authority. A verifying authority—which may be a trusted independent third party—tests the load modules and / or other items to verify that their corresponding specifications are accurate and complete, and then digitally signs them based on a tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys), allowing one tamper resistance work factor environment to protect itself against load modules from another tamper resistance work factor environment. The verifying authority can provide an application intended for insecure environments with a credential having multiple elements covering different parts of the application. To verify the application, a trusted element can issue challenges based on different parts of the authenticated credential that the trusted element selects in an unpredictable (e.g., random) way, and deny service (or take other appropriate action) if the responses do not match the authenticated credential.
Owner:INTERTRUST TECH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com