Patents
Literature
403 results about "Electronic security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic security relates to leveraging innovation in defensive holding by anticipating unapproved access to individuals and property. The government is a universal and major customer of such security administrations and business sections also utilizes the security systems for their workers for giving security.
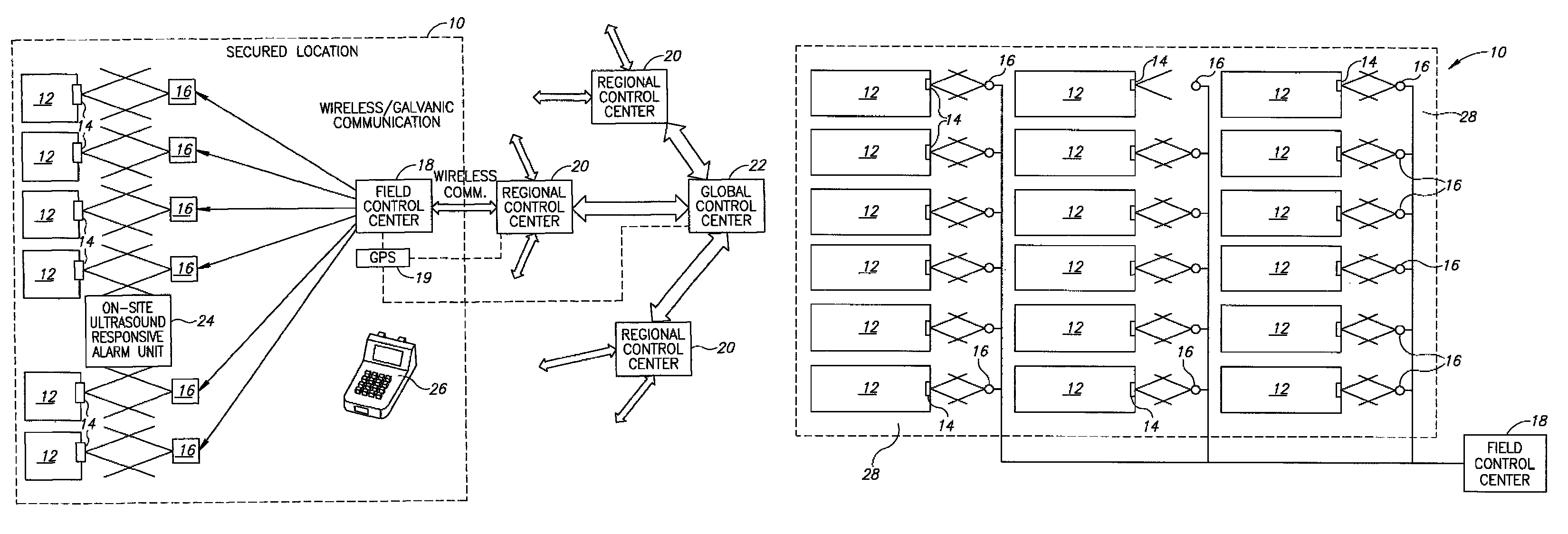
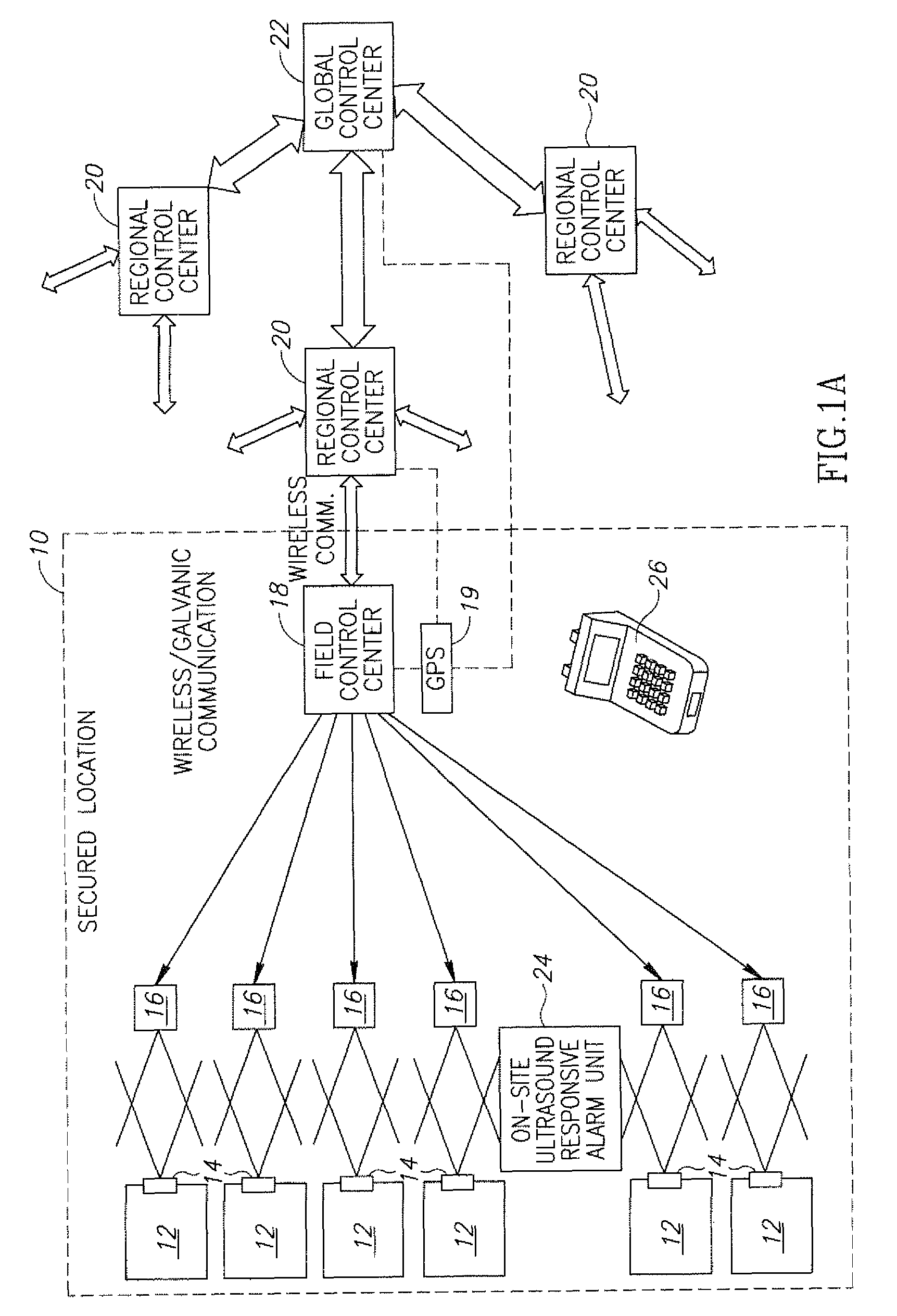
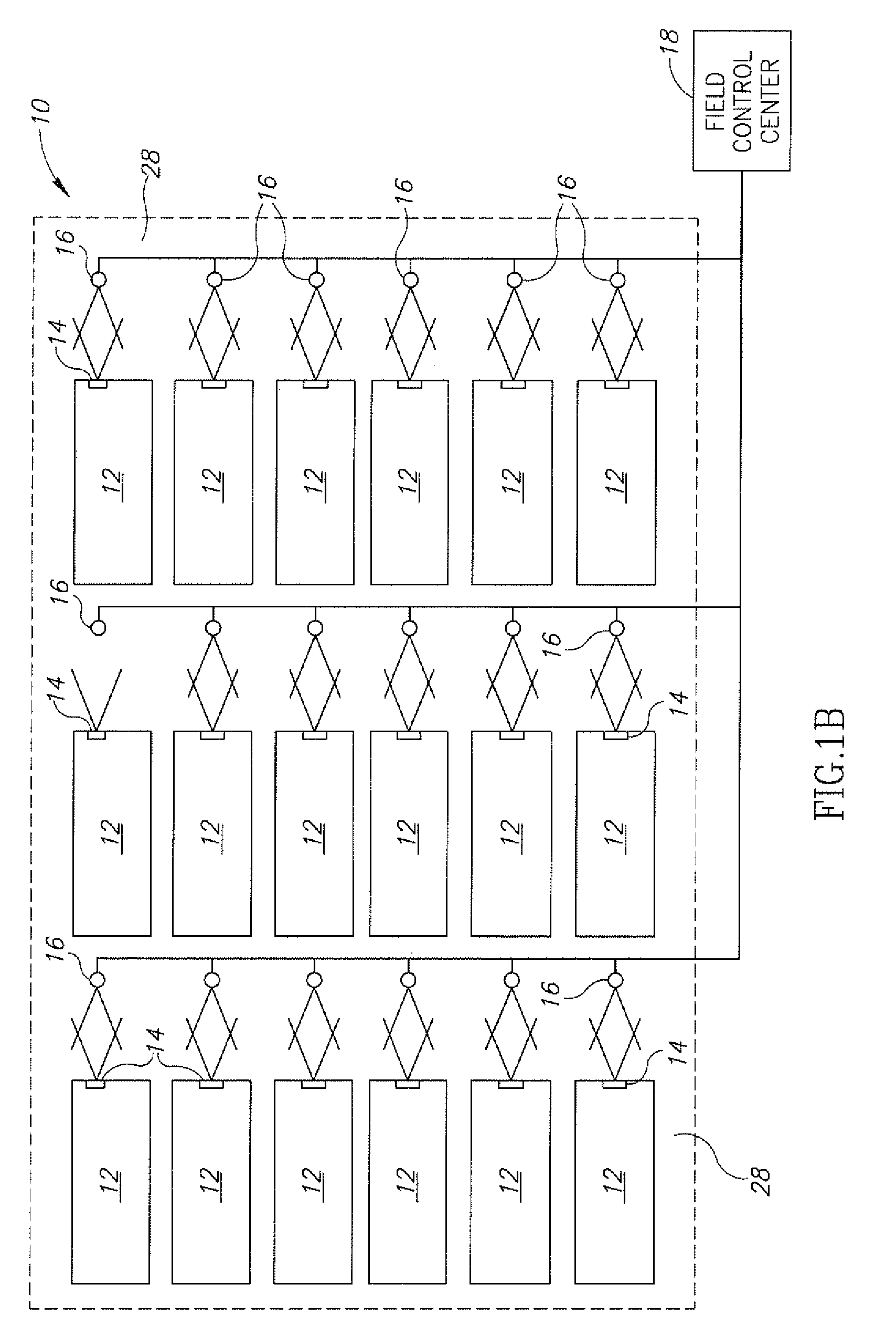
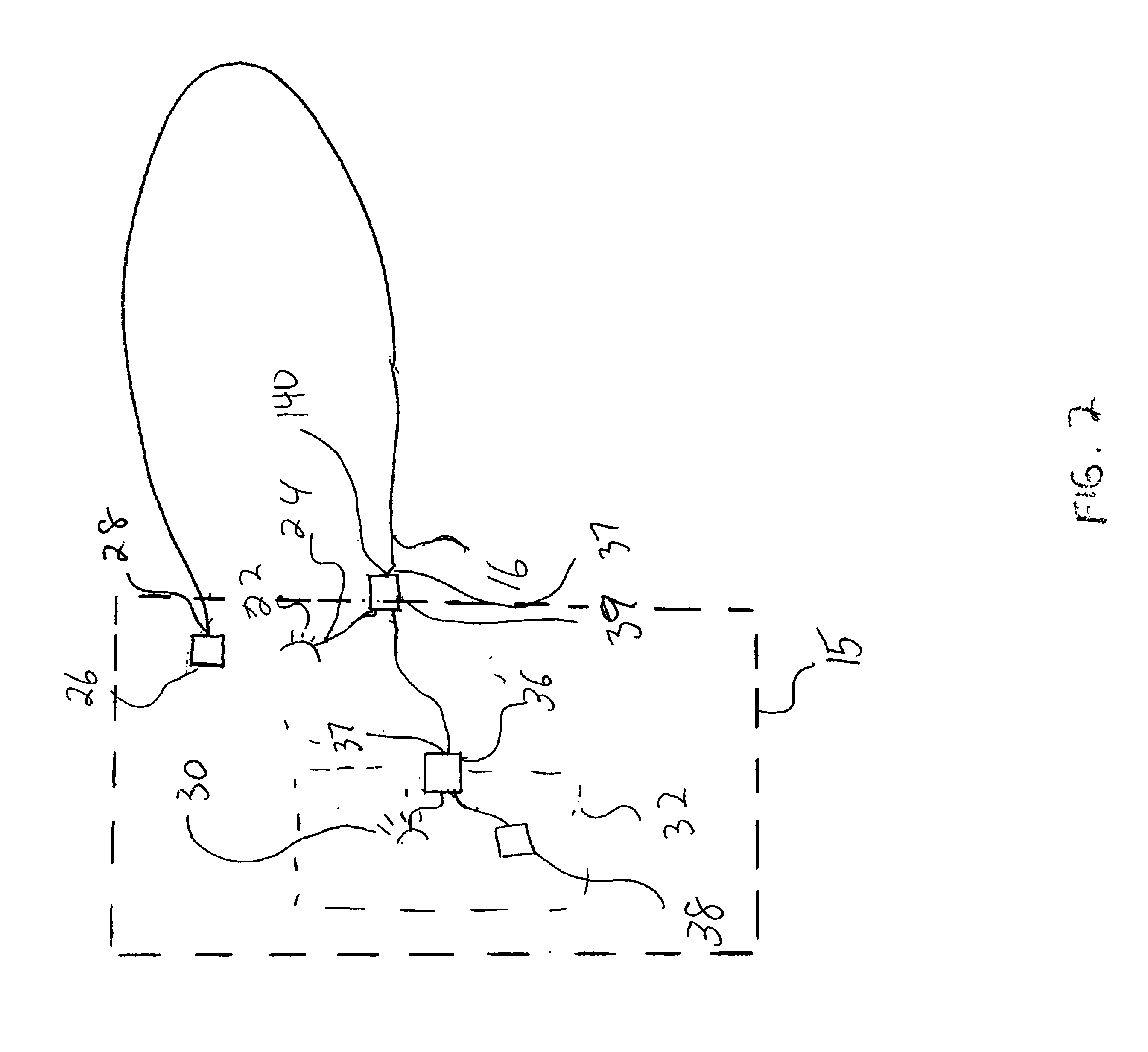
Electronic security seal and system
InactiveUS8031069B2Easy constructionSimple in useStampsAnti-theft devicesTamper resistanceElectronic security
A tamper-proof electronic security seal which includes a bolt and a locking element and an electronic seal element. The bolt has a head and a hollow shank extending therefrom having a longitudinal bore formed therein. The shank is dimensioned to pass through a lock hasp and has a free end formed for locking engagement with the locking element. The electronic seal element is formed for mechanical connection to the bolt head, and includes an electrical power source, a control unit, communications means responsive to the control unit and a sensor adapted for insertion into the longitudinal bore of the shank, and connected to the control unit. In response to a severing of the shank and the sensor inserted therein, the control unit is operative to activate the communications means to emit an alarm signal.
Owner:COHN ODED YAIR +1
Non-invasive monitoring of the effectiveness of electronic security services
InactiveUS7509675B2Non-invasive monitoringMemory loss protectionDigital data processing detailsEngineeringNon invasive
Systems for the non-invasive monitoring of the effectiveness of a customer's electronic security services include a test generation engine for generating and launching a denatured attack towards a customer's network. A monitoring and evaluation agent is operatively coupled to the test generation engine and is adapted to monitor and evaluate the denatured attack. A recording and analysis engine is adapted to record and analyze the results of the denatured attack. Other systems and methods are also provided.
Owner:RPX CORP
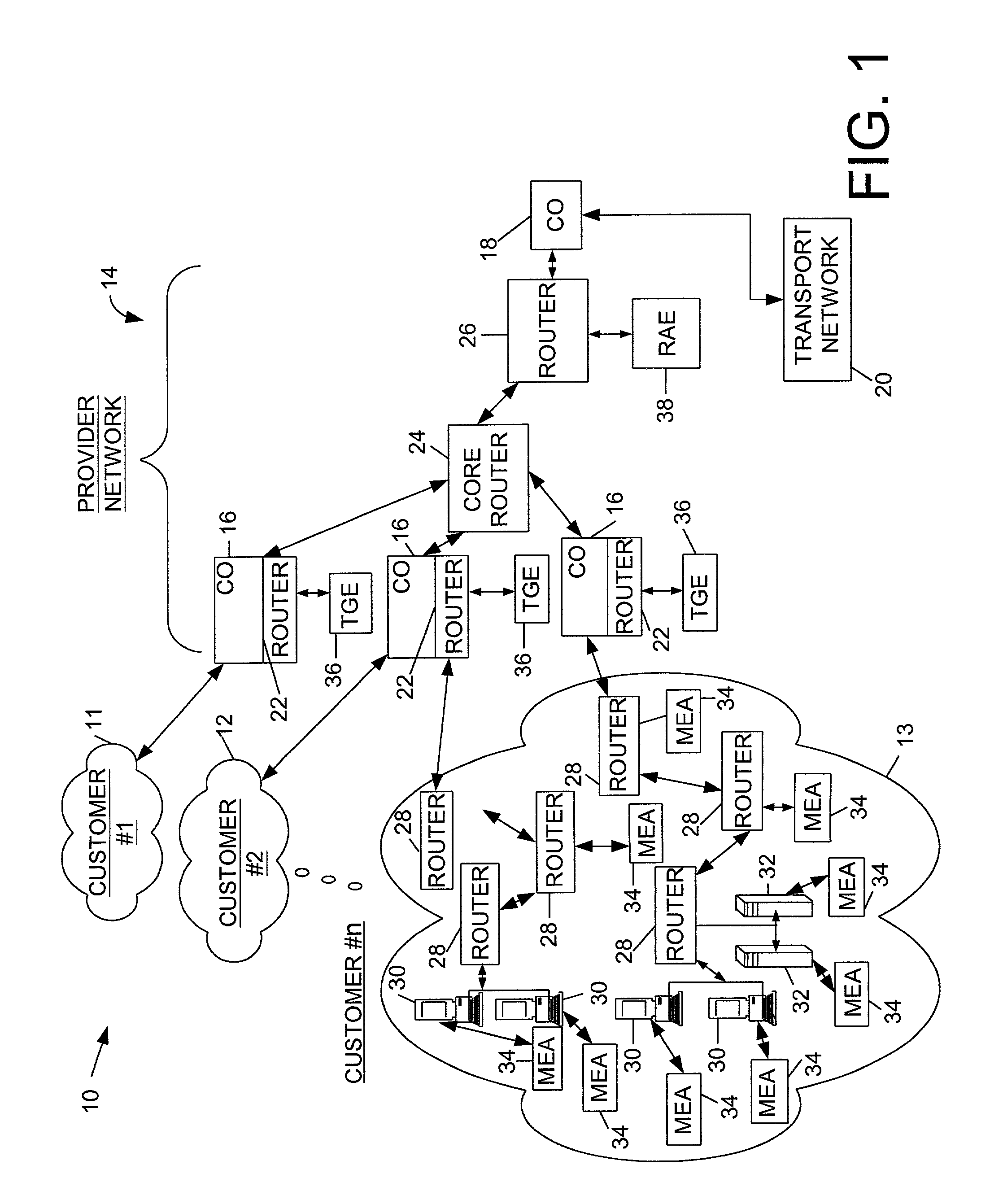
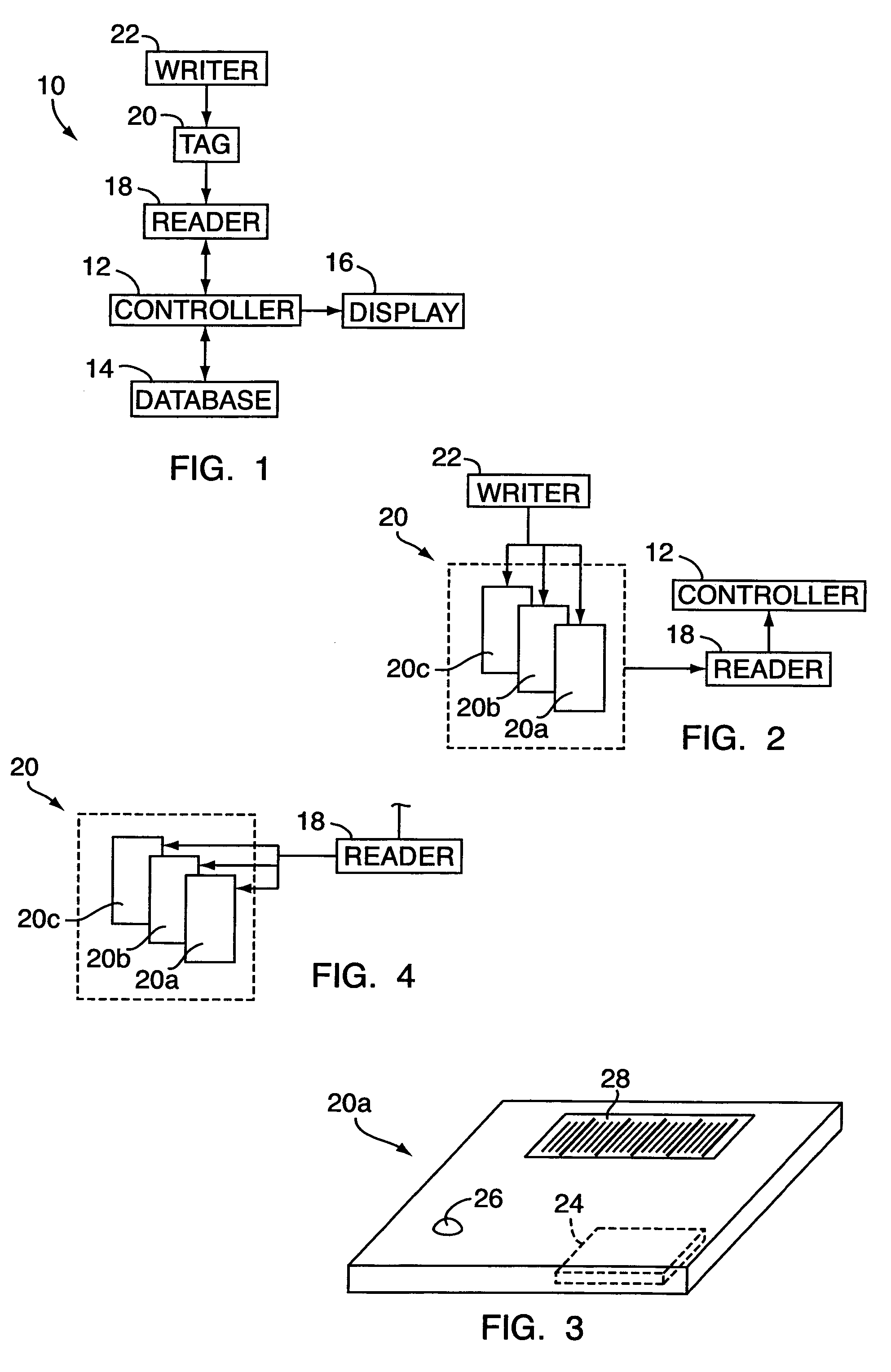
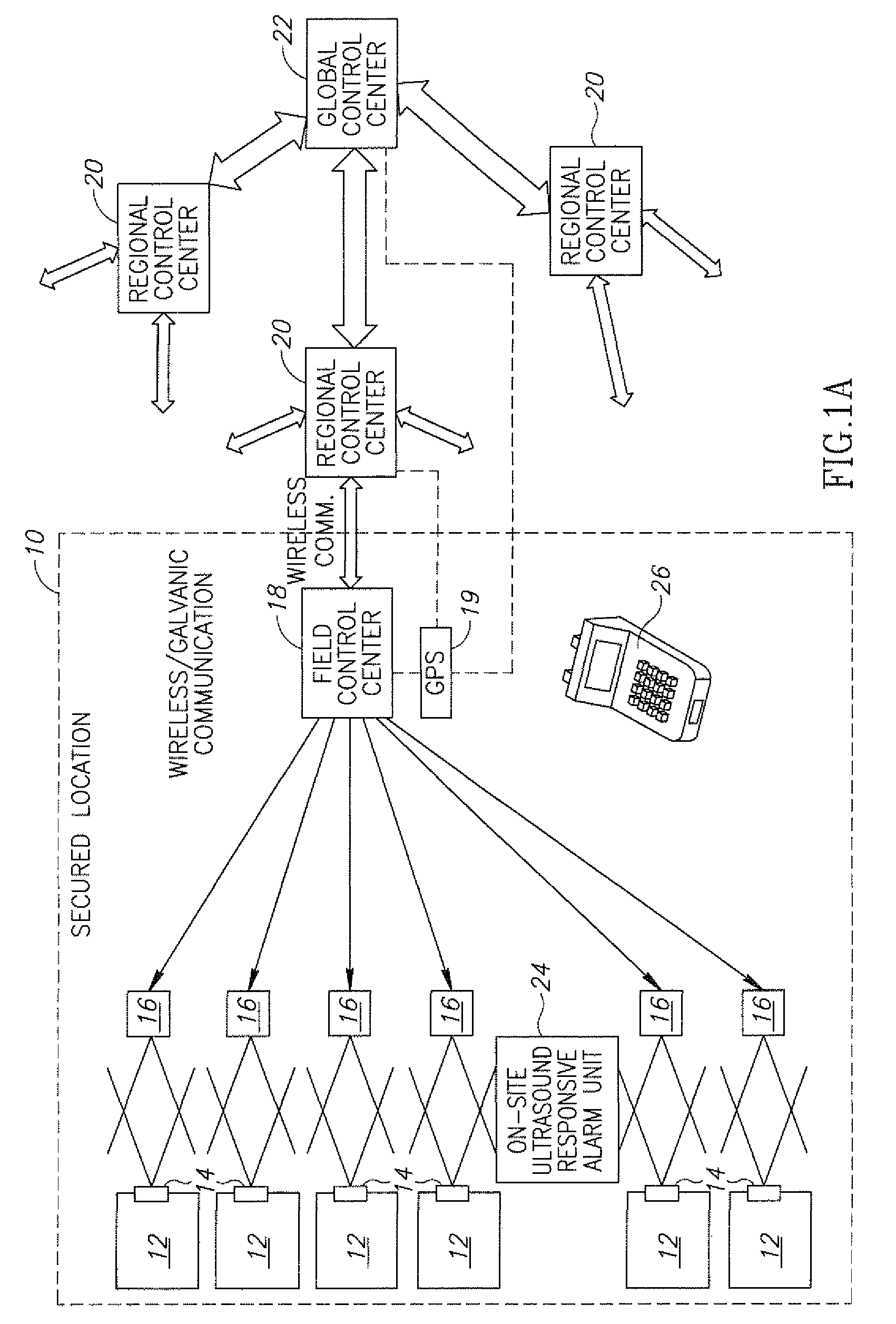
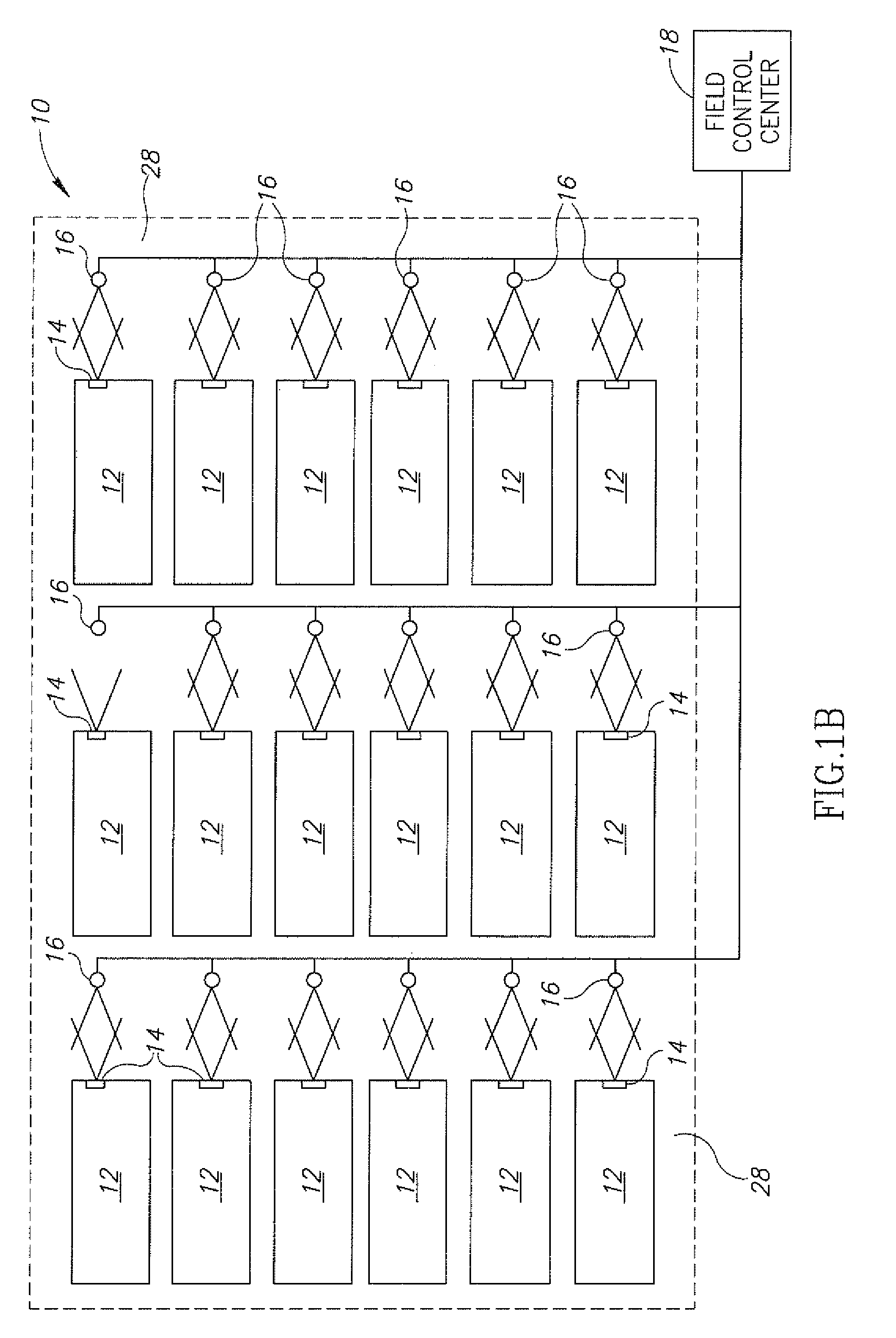
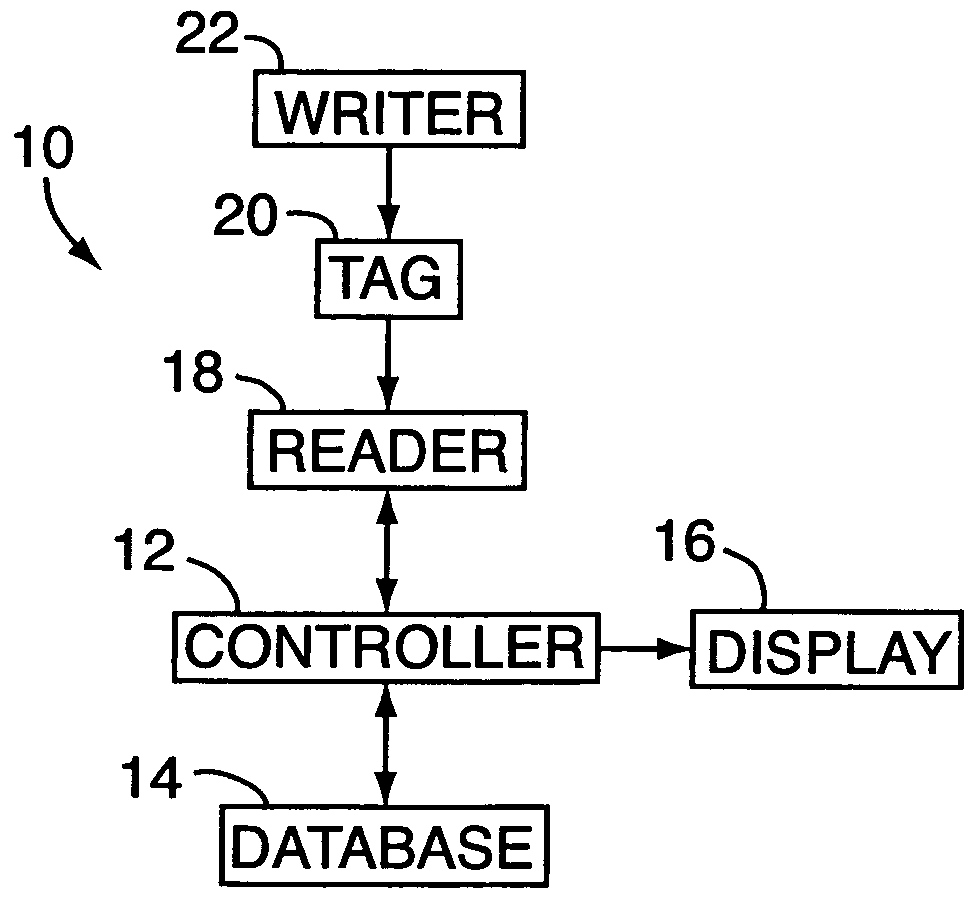
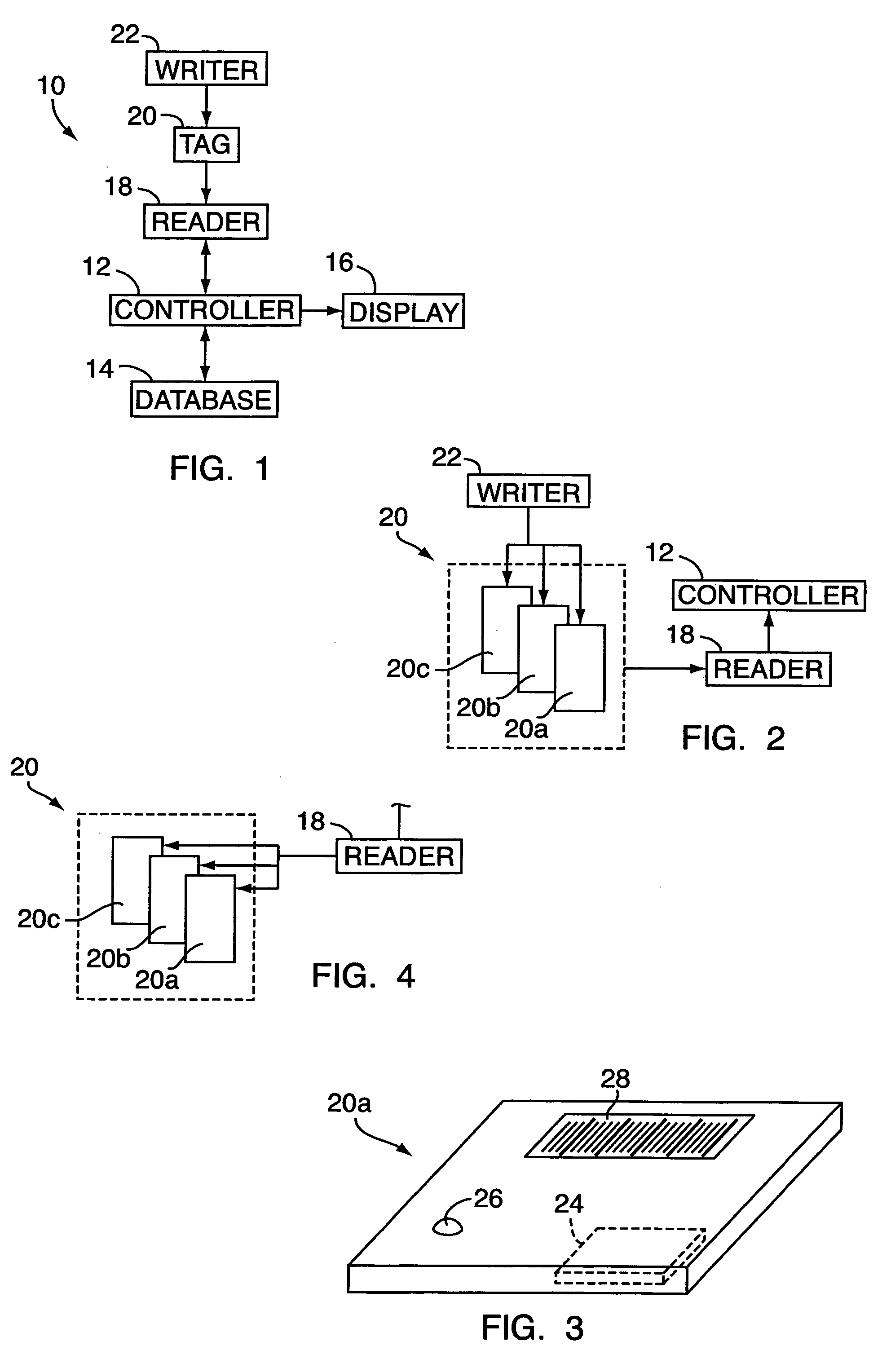
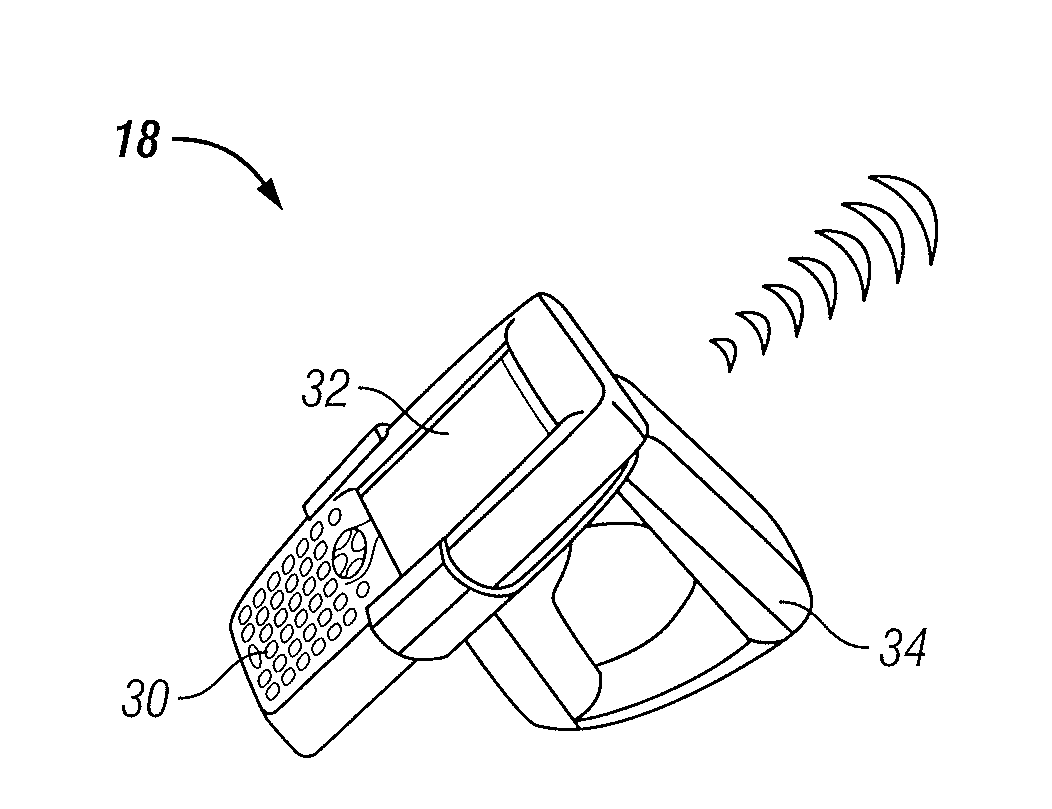
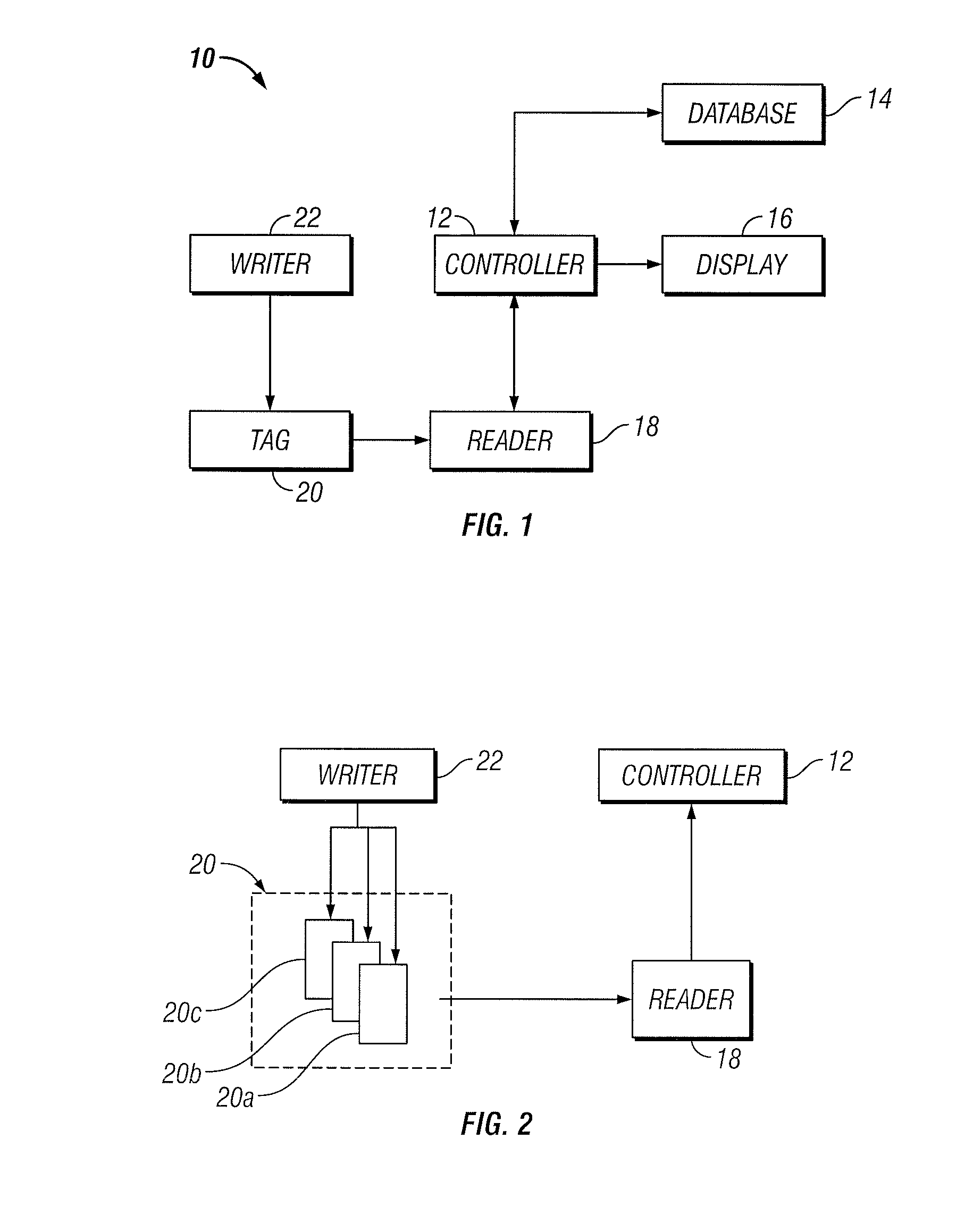
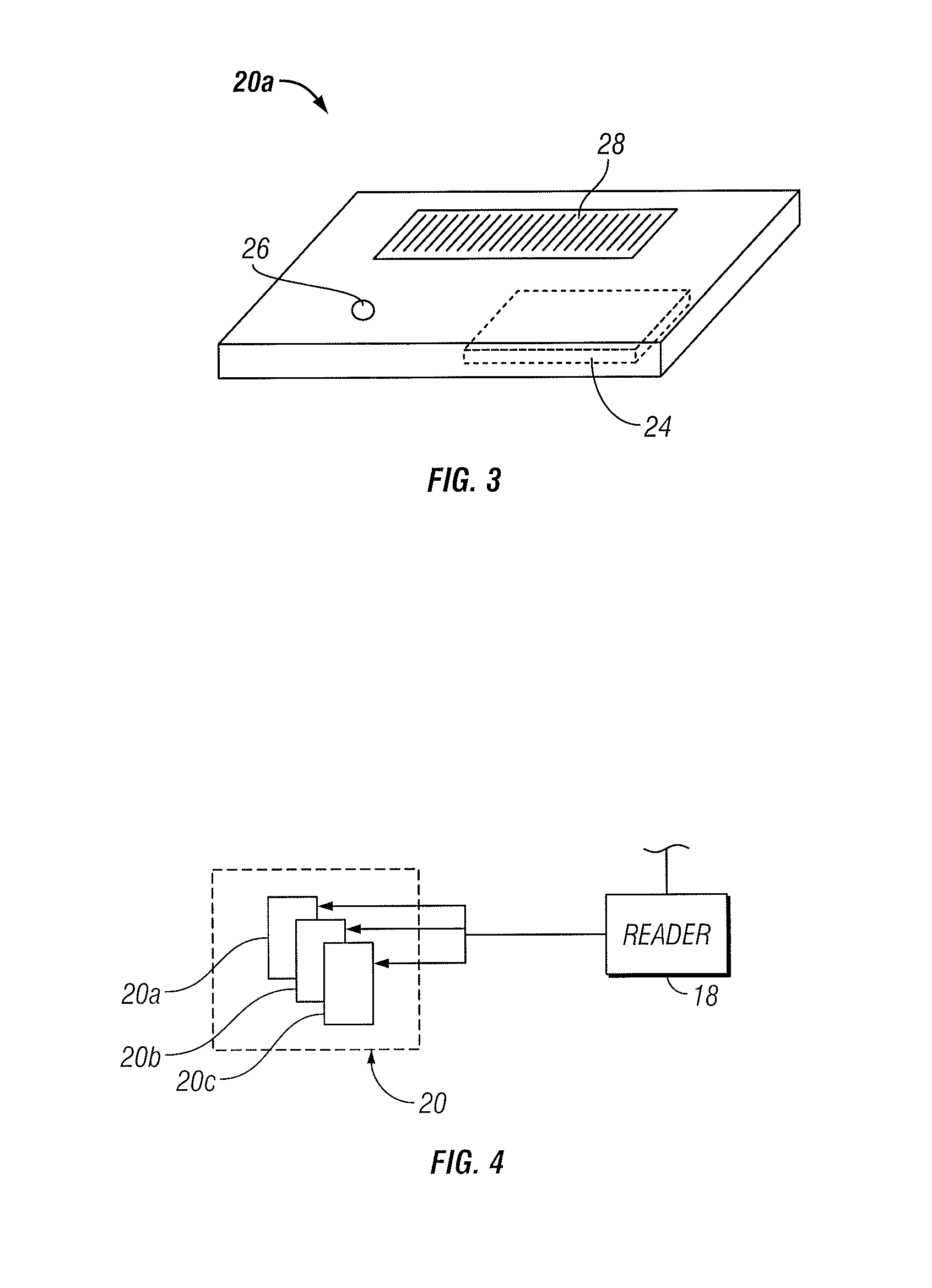
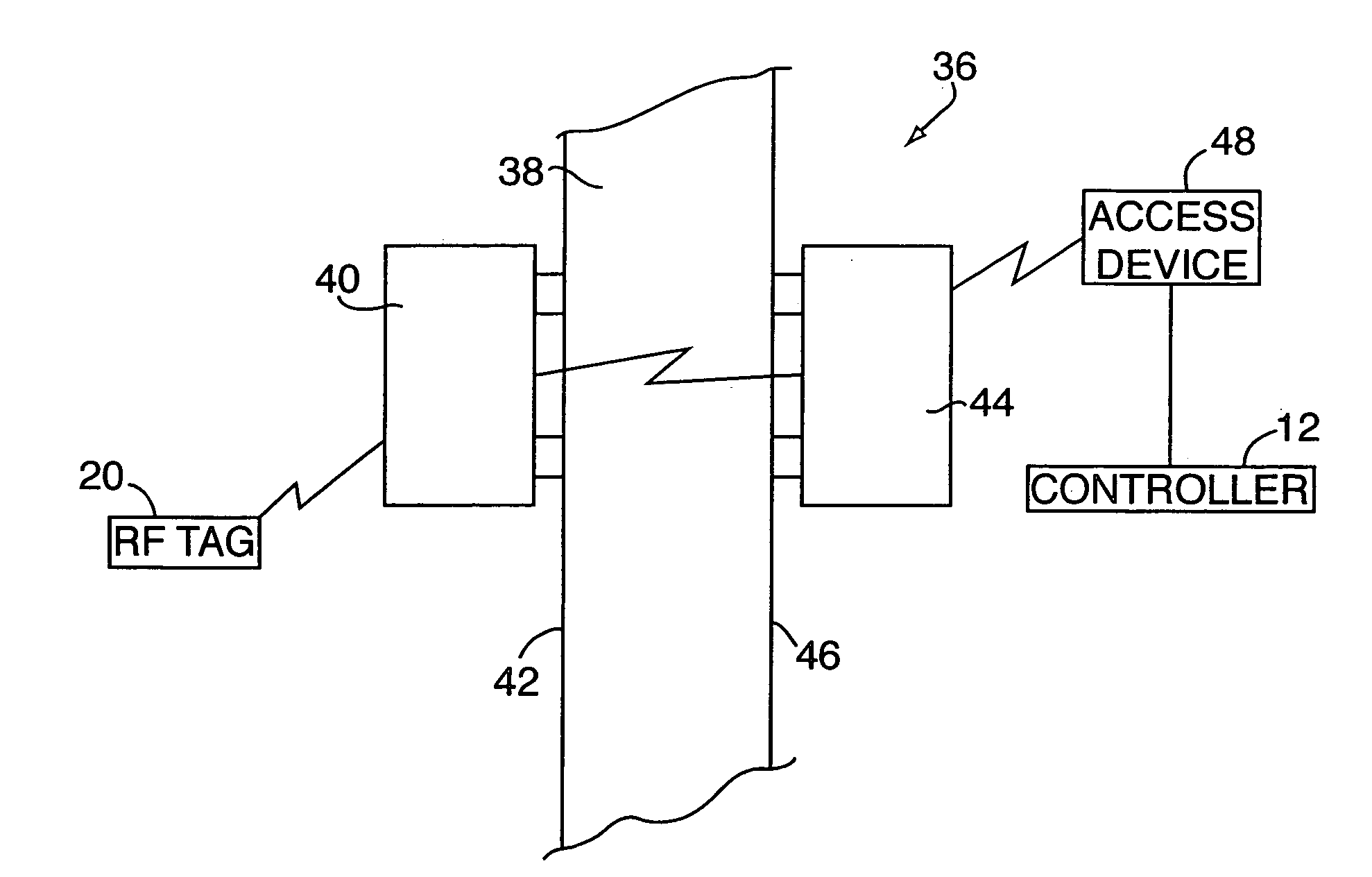
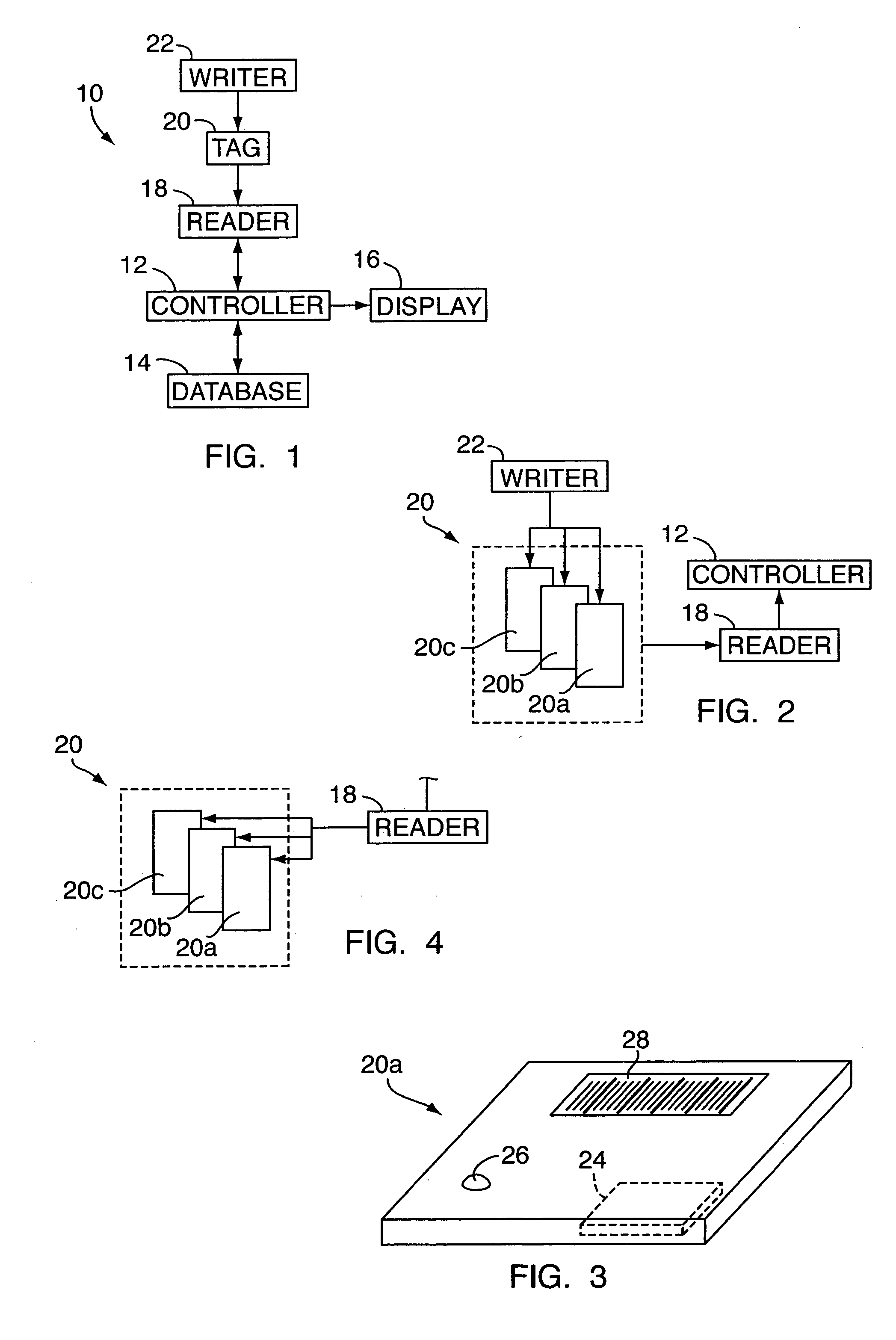
Electronic security system for monitoring and recording activity and data relating to cargo
ActiveUS7012529B2Co-operative working arrangementsIndividual entry/exit registersData setData signal
A tracking system for identifying contents of a container includes an electromagnetic identification apparatus that provides an electromagnetic signal indicative of a container content data set; a writer for use in encoding the container signal onto the apparatus; a controller for receiving the encoded signal and for storing the signal in a master database storage apparatus; and a reader configured outside the container for communicating with the electromagnetic identification apparatus and for receiving the encoded signal therefrom and corresponding to the container content data signal set. A system for tracking items in an assembly includes an apparatus for receiving electromagnetic identification tag signals; an apparatus for creating a first tier aggregate signature; an apparatus for storing the signature in a master database; and an apparatus for receiving modifying command signals for creating a second tier aggregate signature corresponding to a modified set of electromagnetic identification tags in an augmented assembly.
Owner:UNITED SECURITY APPL ID
Electronic security system for monitoring and recording activity and data relating to persons
InactiveCN1833397ACo-operative working arrangementsSecuring communicationData fieldIdentification device
Owner:UNITED SECURITY APPL ID
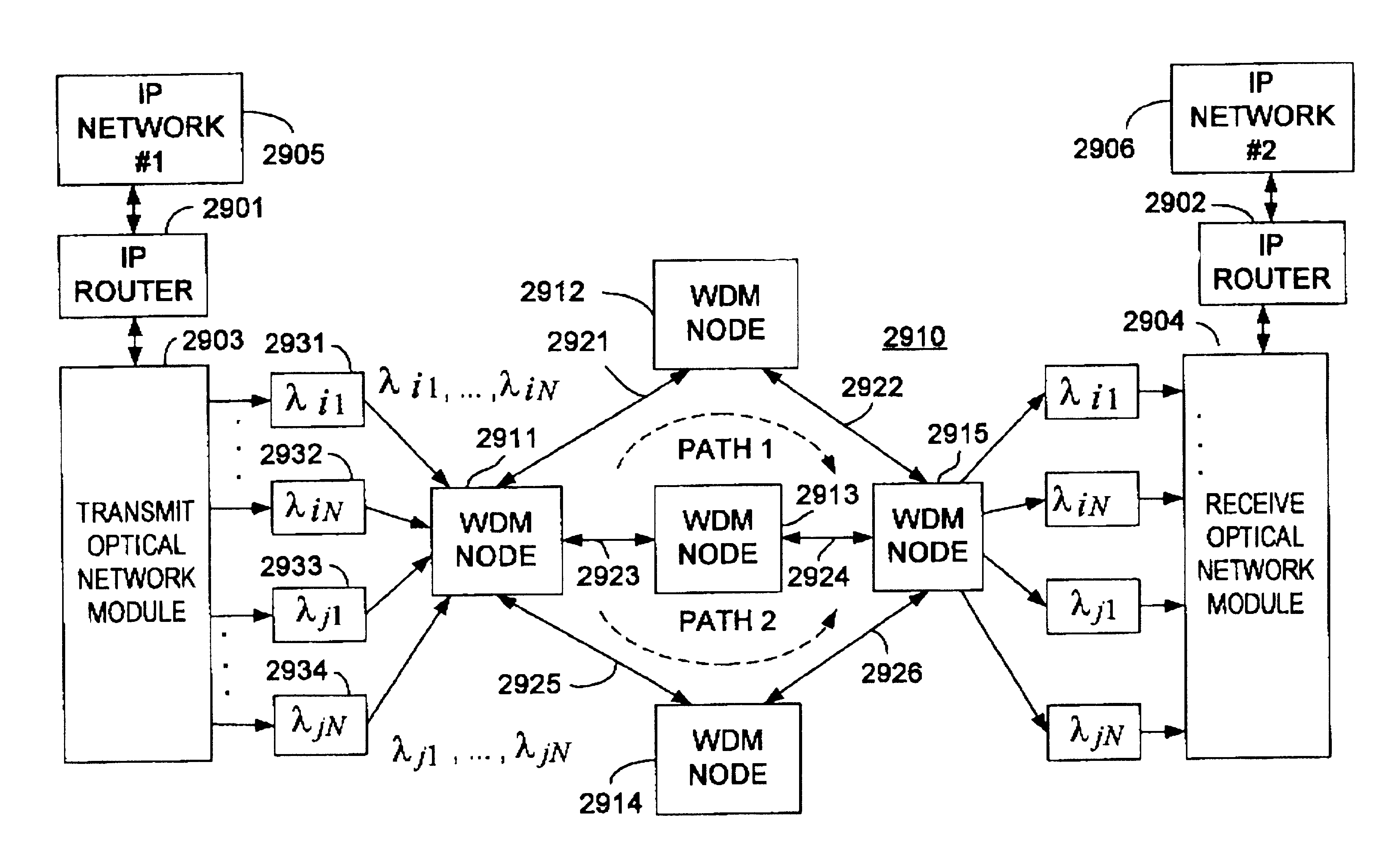
Optical layer survivability and security system using optical label switching and high-speed optical header generation and detection
InactiveUS6271946B1Increase probabilityIncrease optical powerMultiplex system selection arrangementsWavelength-division multiplex systemsSurvivabilityOptical burst switching
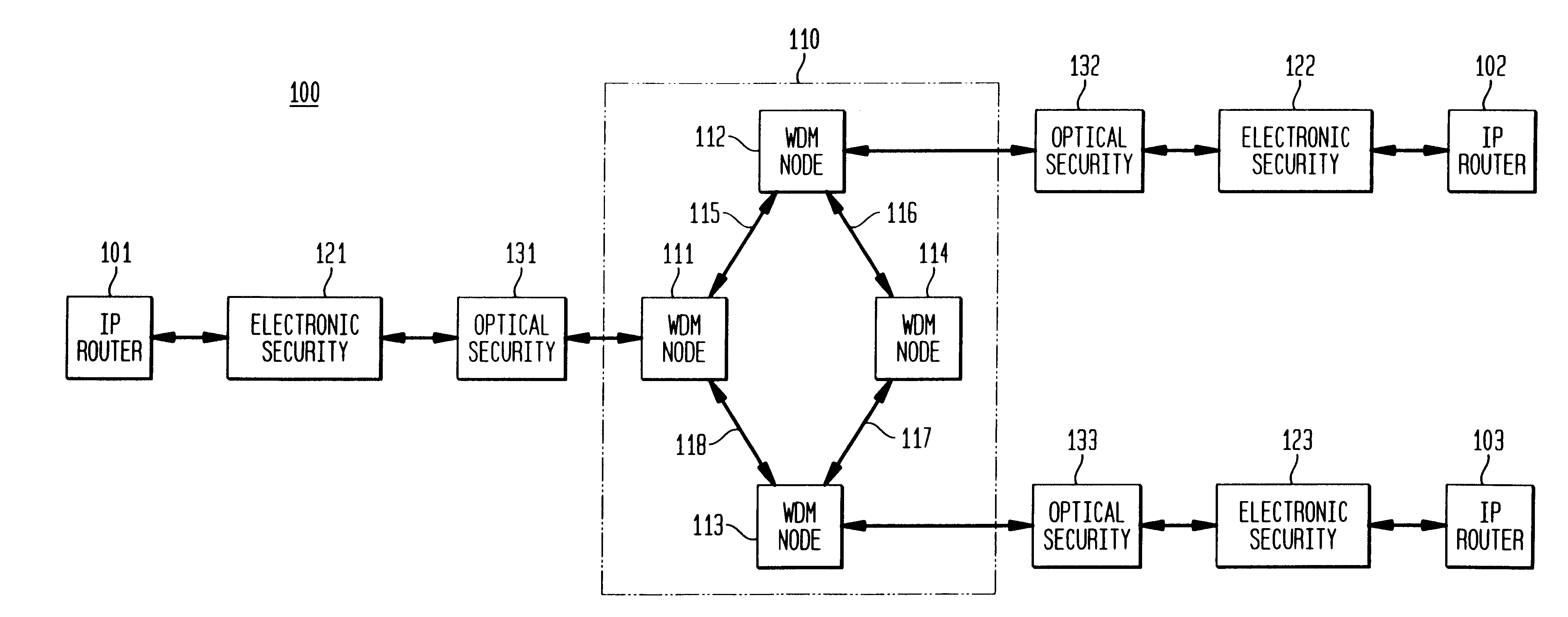
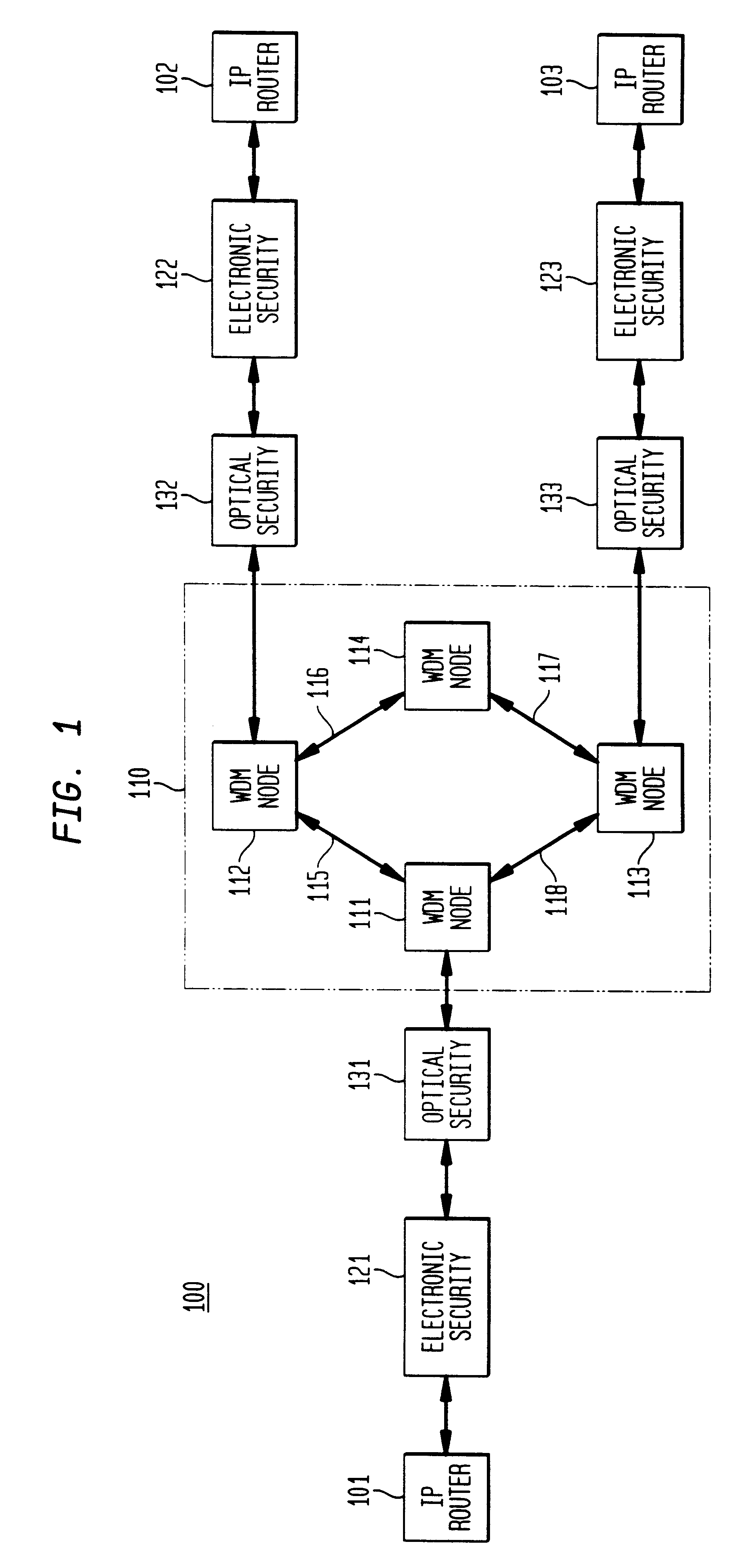
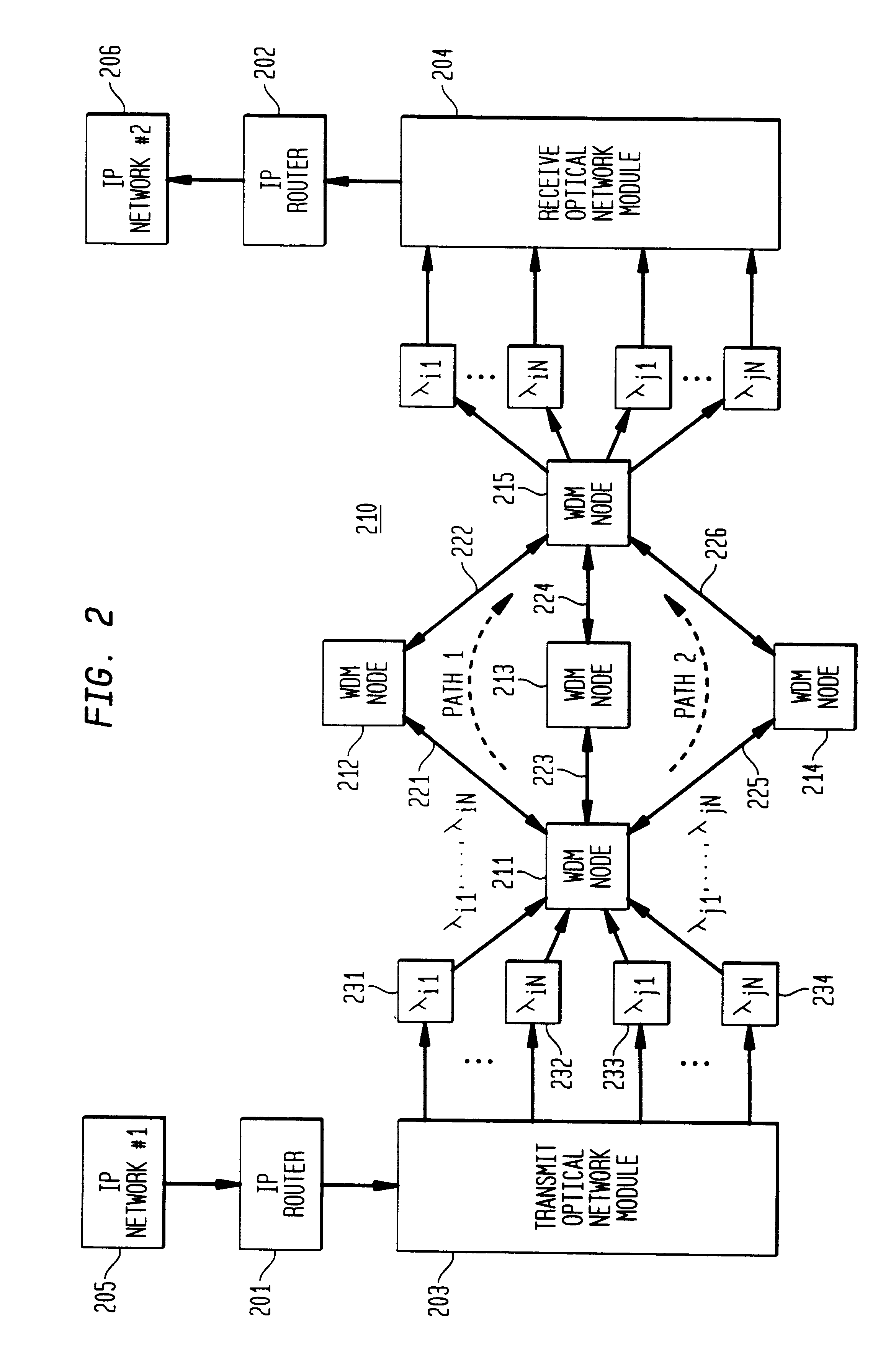
An optical signaling header technique applicable to optical networks wherein packet routing information is embedded in the same channel or wavelength as the data payload so that both the header and data payload propagate through network elements with the same path and the associated delays. The technique effects survivability and security of the optical networks by encompassing conventional electronic security with an optical security layer by generating replicated versions of the input data payload at the input node, and the transmission of each of the replicated versions over a corresponding one of the plurality of links. Moreover, each of the links is composed of multiple wavelengths to propagate optical signals or optical packets, and each of the replicated versions of the data payload may be propagated over a selected one of the wavelengths in each corresponding one of the plurality of links.
Owner:RGT UNIV OF CALIFORNIA
Electronic security seal and system
InactiveUS20090179757A1Easy constructionSimple in useStampsAnti-theft devicesTamper resistanceEngineering
A tamper-proof electronic security seal which includes a bolt and a locking element and an electronic seal element. The bolt has a head and a hollow shank extending therefrom having a longitudinal bore formed therein. The shank is dimensioned to pass through a lock hasp and has a free end formed for locking engagement with the locking element. The electronic seal element is formed for mechanical connection to the bolt head, and includes an electrical power source, a control unit, communications means responsive to the control unit and a sensor adapted for insertion into the longitudinal bore of the shank, and connected to the control unit. In response to a severing of the shank and the sensor inserted therein, the control unit is operative to activate the communications means to emit an alarm signal.
Owner:COHN ODED YAIR +1
Electronic security system for monitoring and recording activity and data relating to cargo
ActiveUS20050099292A1Co-operative working arrangementsIndividual entry/exit registersData setData signal
A tracking system for identifying contents of a container includes an electromagnetic identification apparatus that provides an electromagnetic signal indicative of a container content data set; a writer for use in encoding the container signal onto the apparatus; a controller for receiving the encoded signal and for storing the signal in a master database storage apparatus; and a reader configured outside the container for communicating with the electromagnetic identification apparatus and for receiving the encoded signal therefrom and corresponding to the container content data signal set. A system for tracking items in an assembly includes an apparatus for receiving electromagnetic identification tag signals; an apparatus for creating a first tier aggregate signature; an apparatus for storing the signature in a master database; and an apparatus for receiving modifying command signals for creating a second tier aggregate signature corresponding to a modified set of electromagnetic identification tags in an augmented assembly.
Owner:UNITED SECURITY APPL ID
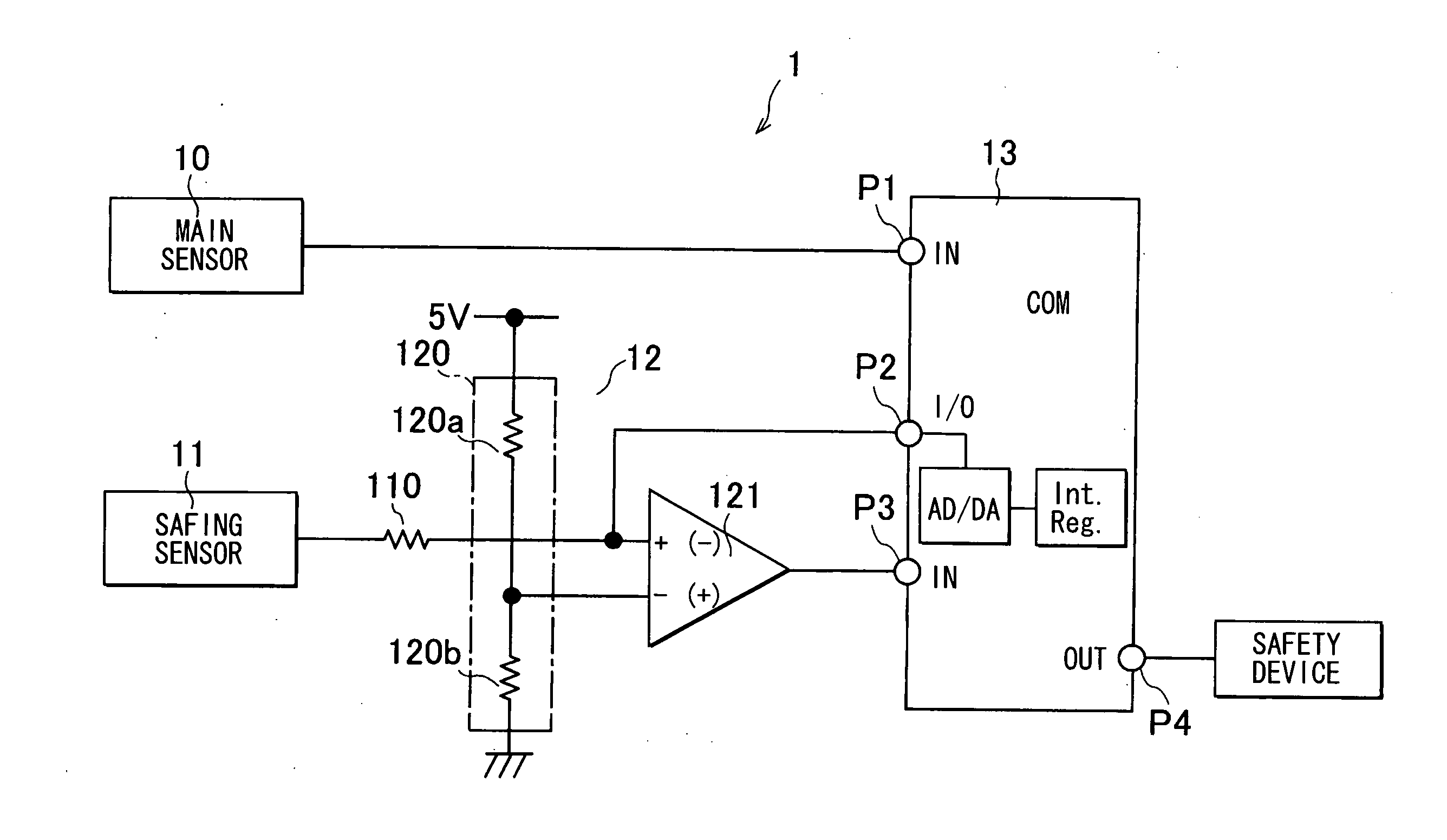
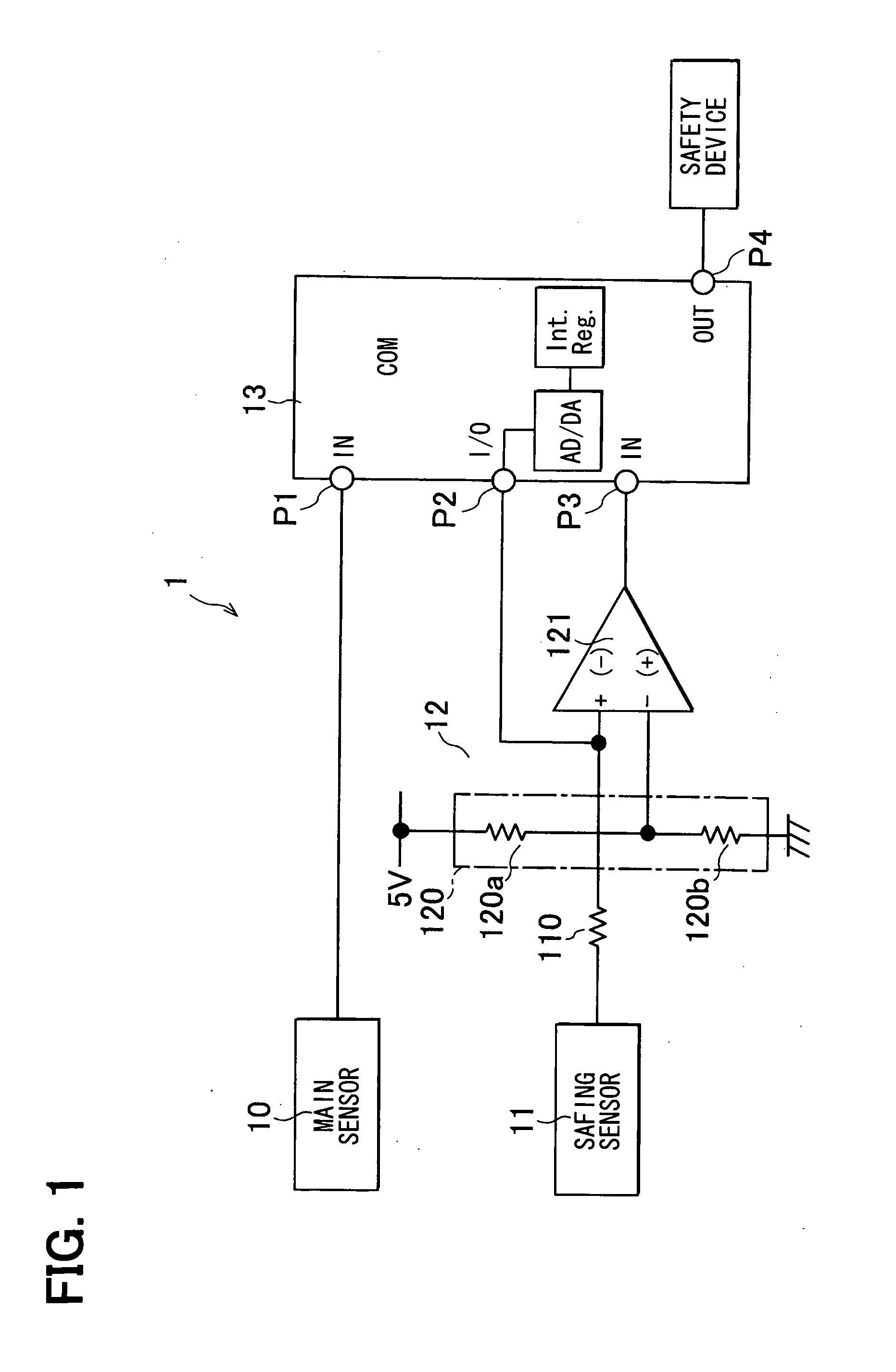
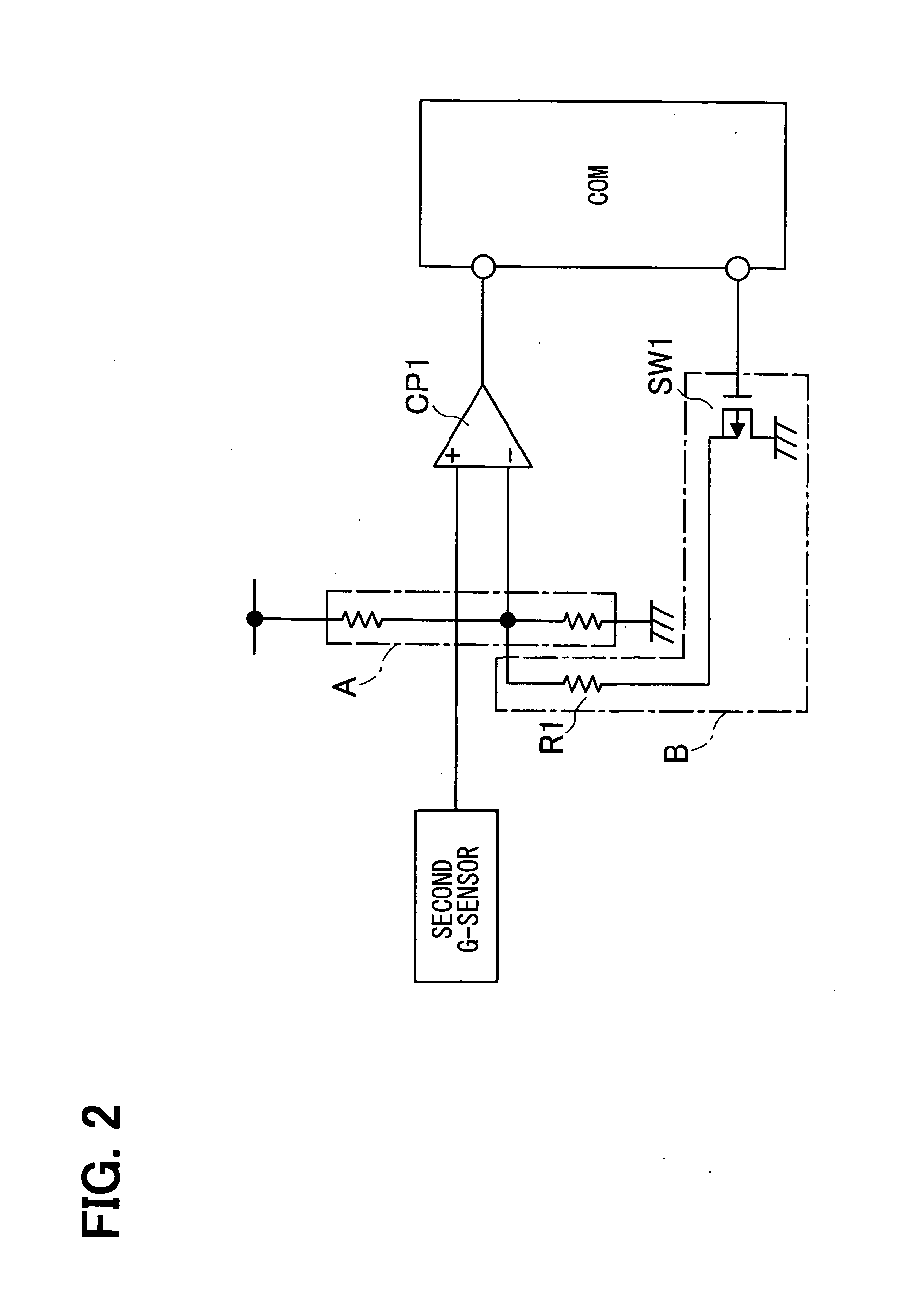
Electronic safing system
InactiveUS20100121521A1Improve reliabilityLow costVehicle testingIncandescent ignitionMicrocomputerProcessor register
The electronic safing system is provided with a safing sensor, a comparator, and a microcomputer. The microcomputer has a programmable analog I / O port which is connected to a built-in AD-DA converter. The programmable analog I / O port can be switched to an analog input port and an analog output port according to an internal register. The programmable analog I / O port is connected to an input terminal of the comparator. When diagnosing the comparing circuit, the microcomputer switches the programmable analog I / O port to the analog output port and outputs a predetermined voltage for diagnosis. Then, the microcomputer diagnoses the comparing circuit by monitoring the output of the comparing circuit.
Owner:DENSO CORP
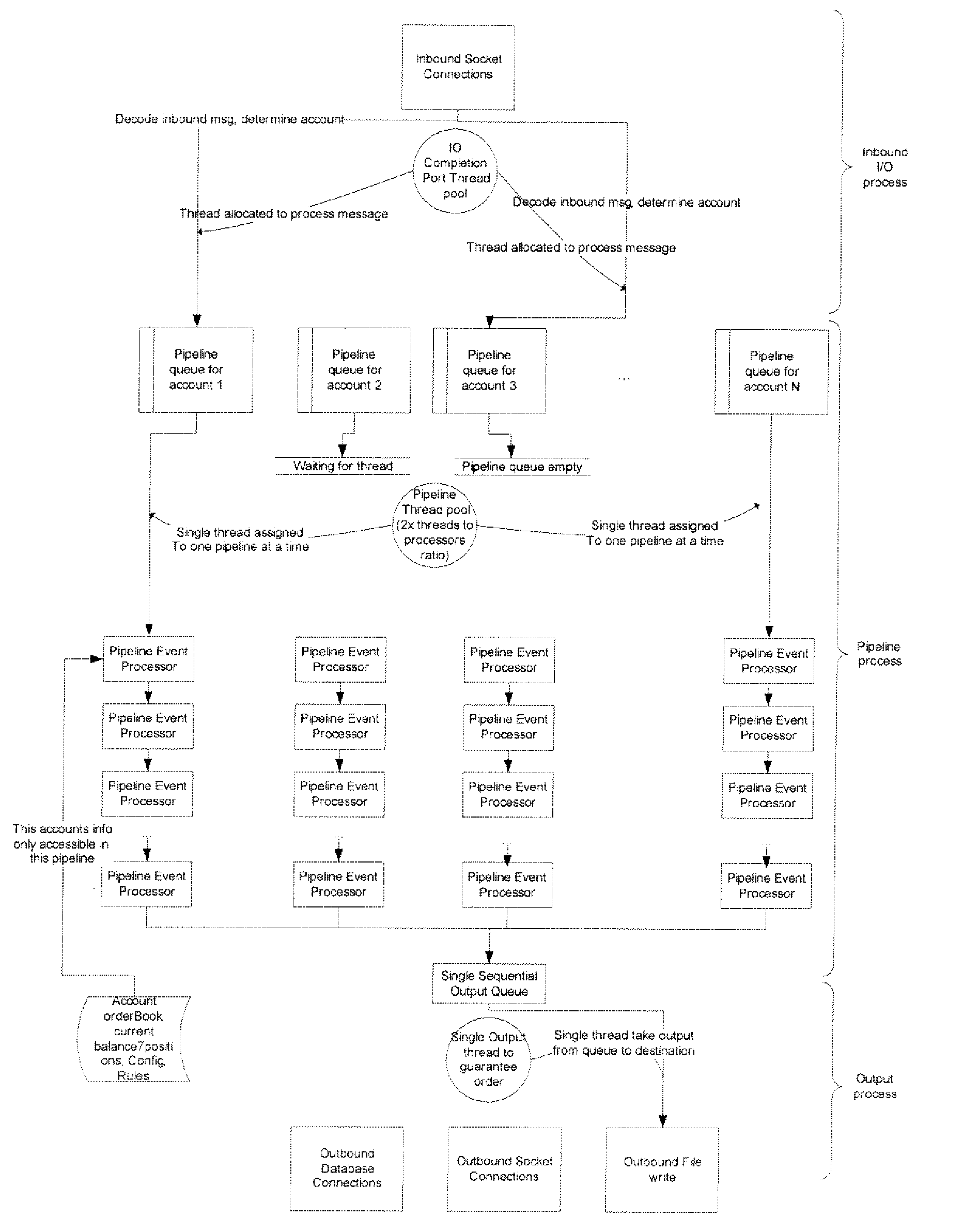
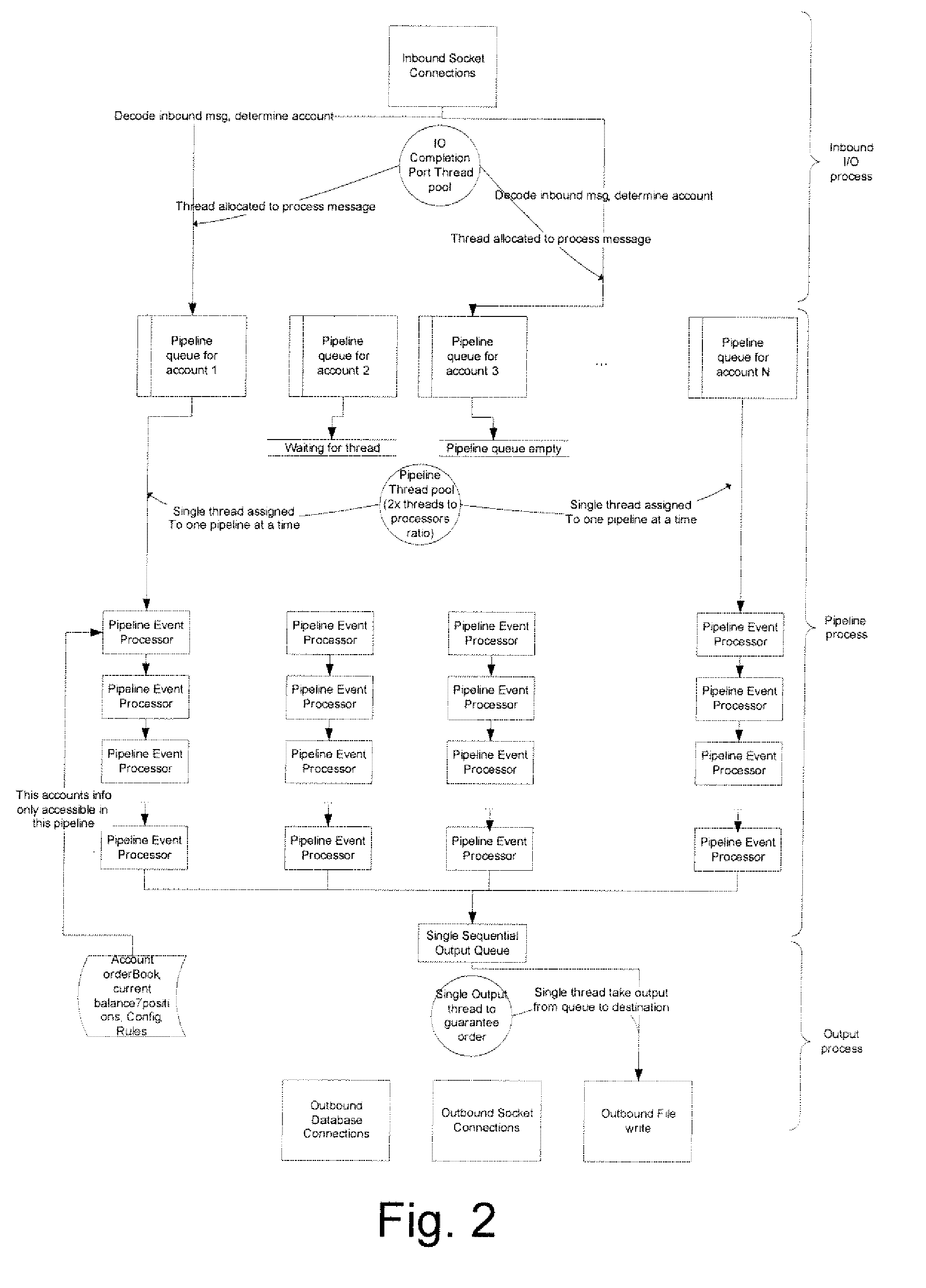
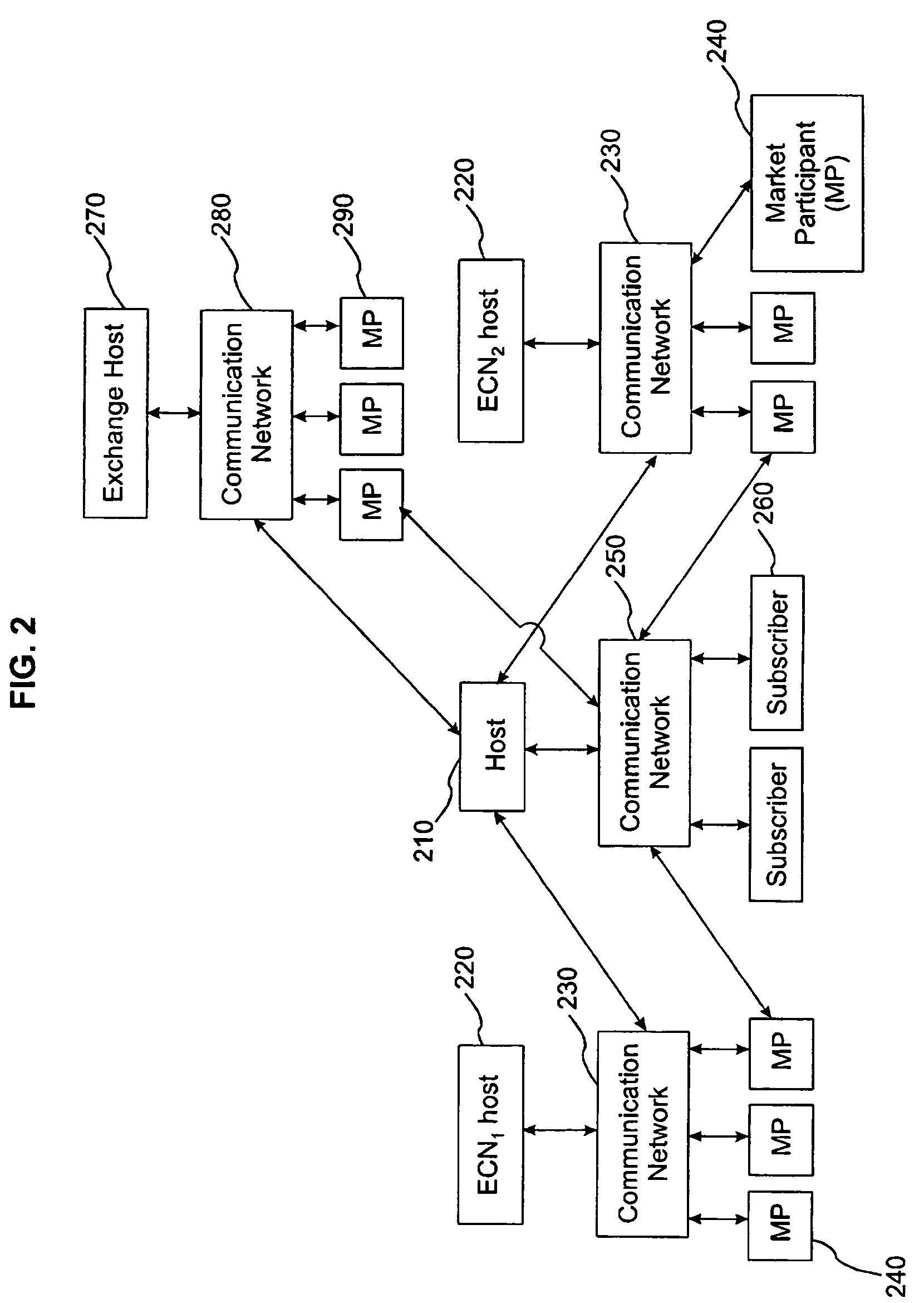
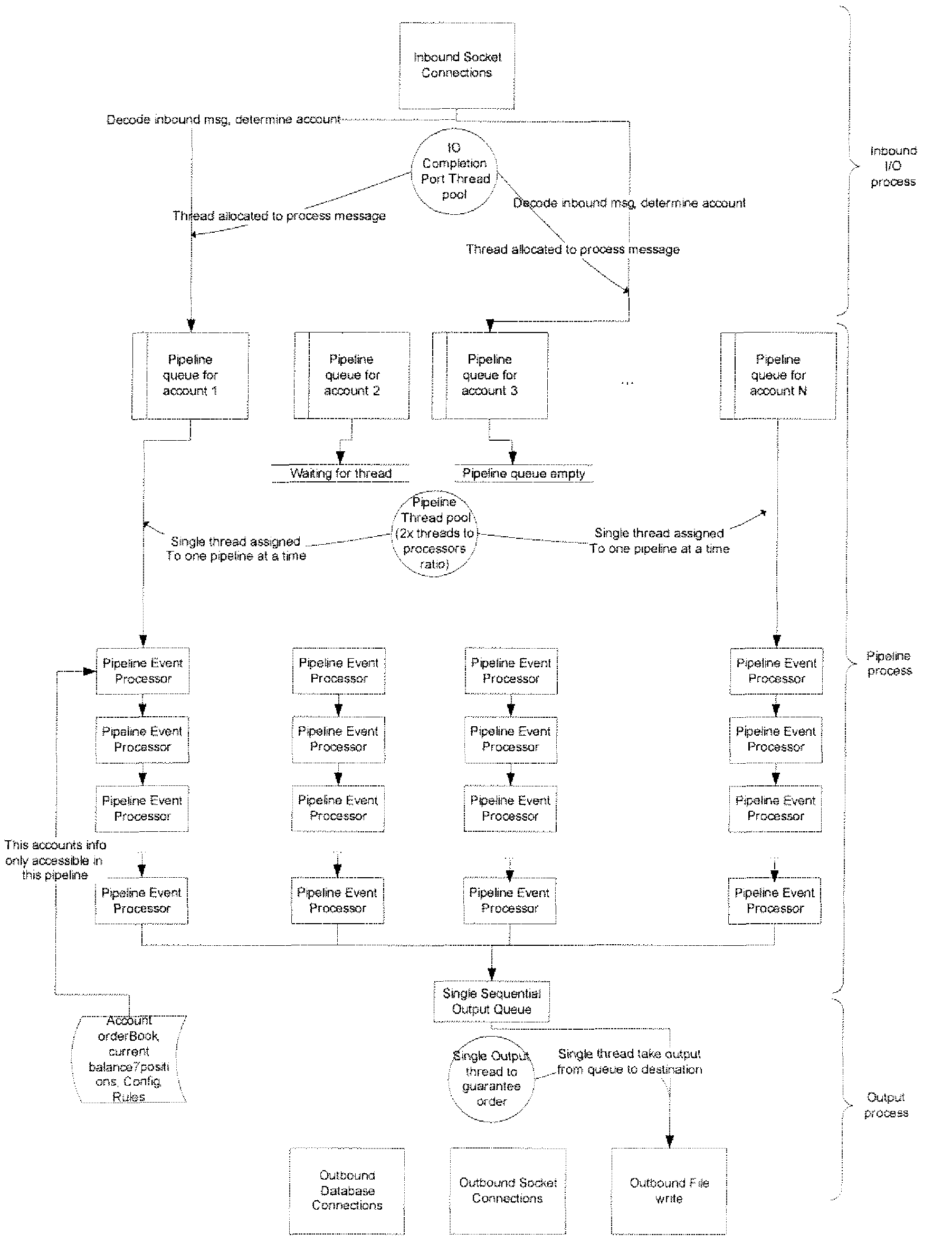
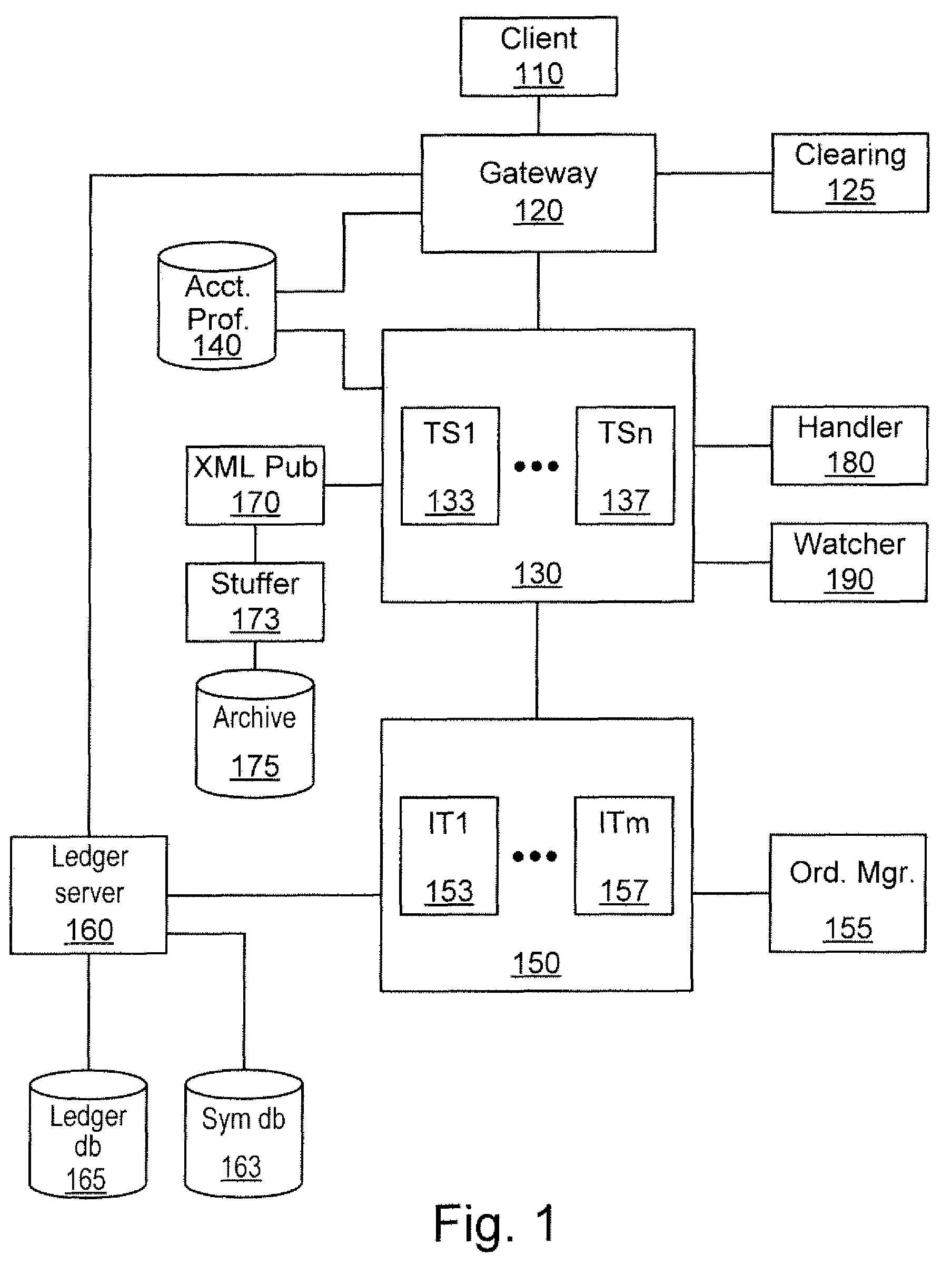
Order Management System and Method for Electronic Securities Trading
ActiveUS20080015970A1Eliminate needEnhance profit or mitigate lossFinanceProgram synchronisationOrder management systemClient-side
A system includes a communication module to communicate with at least one client; and a server to process a task identified by the client, the task associated with an account, the server including a plurality of account-centric pipelines, one or more account-centric pipelines each configured to process the task.
Owner:EZE CASTLE SOFTWARE
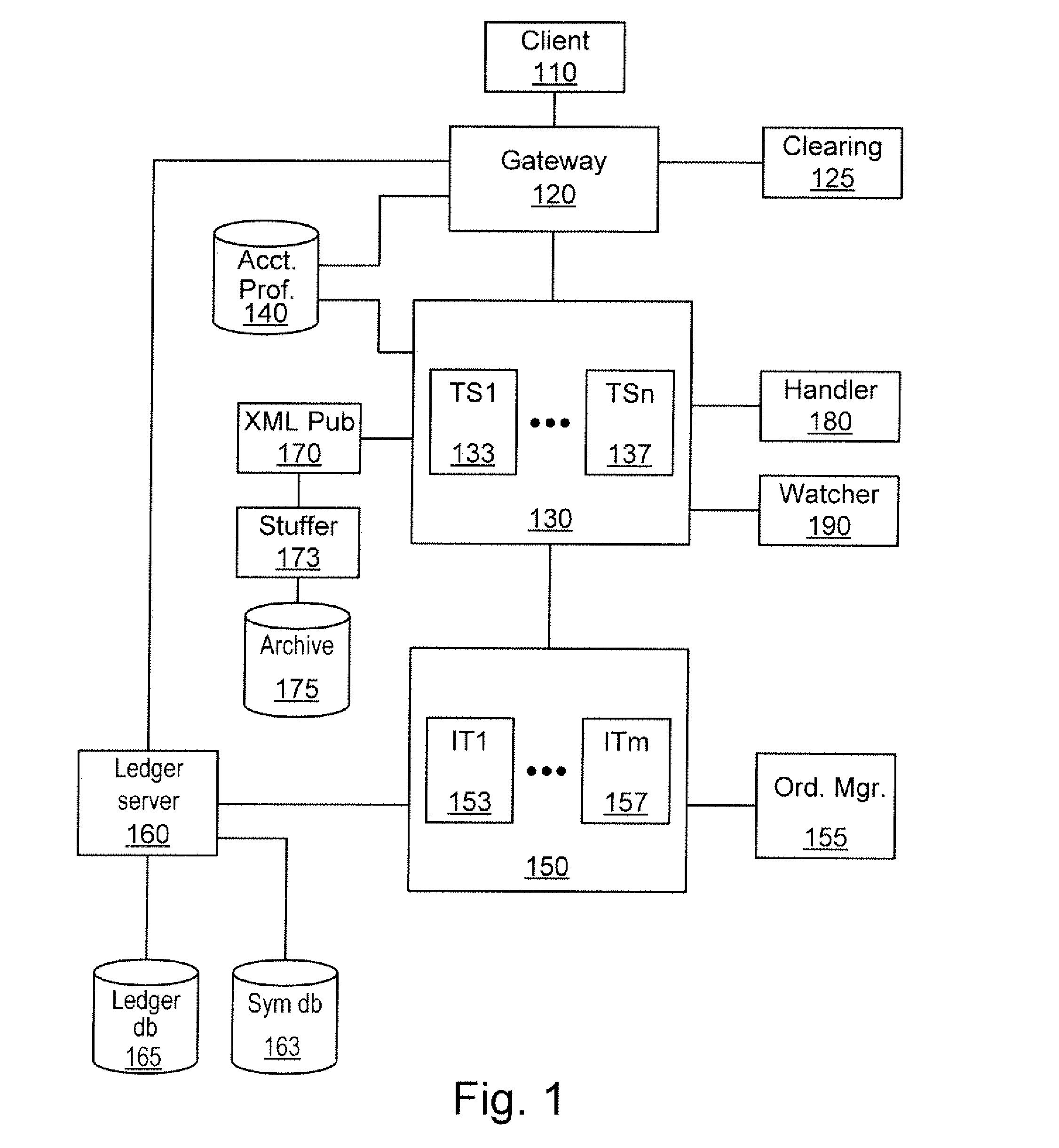
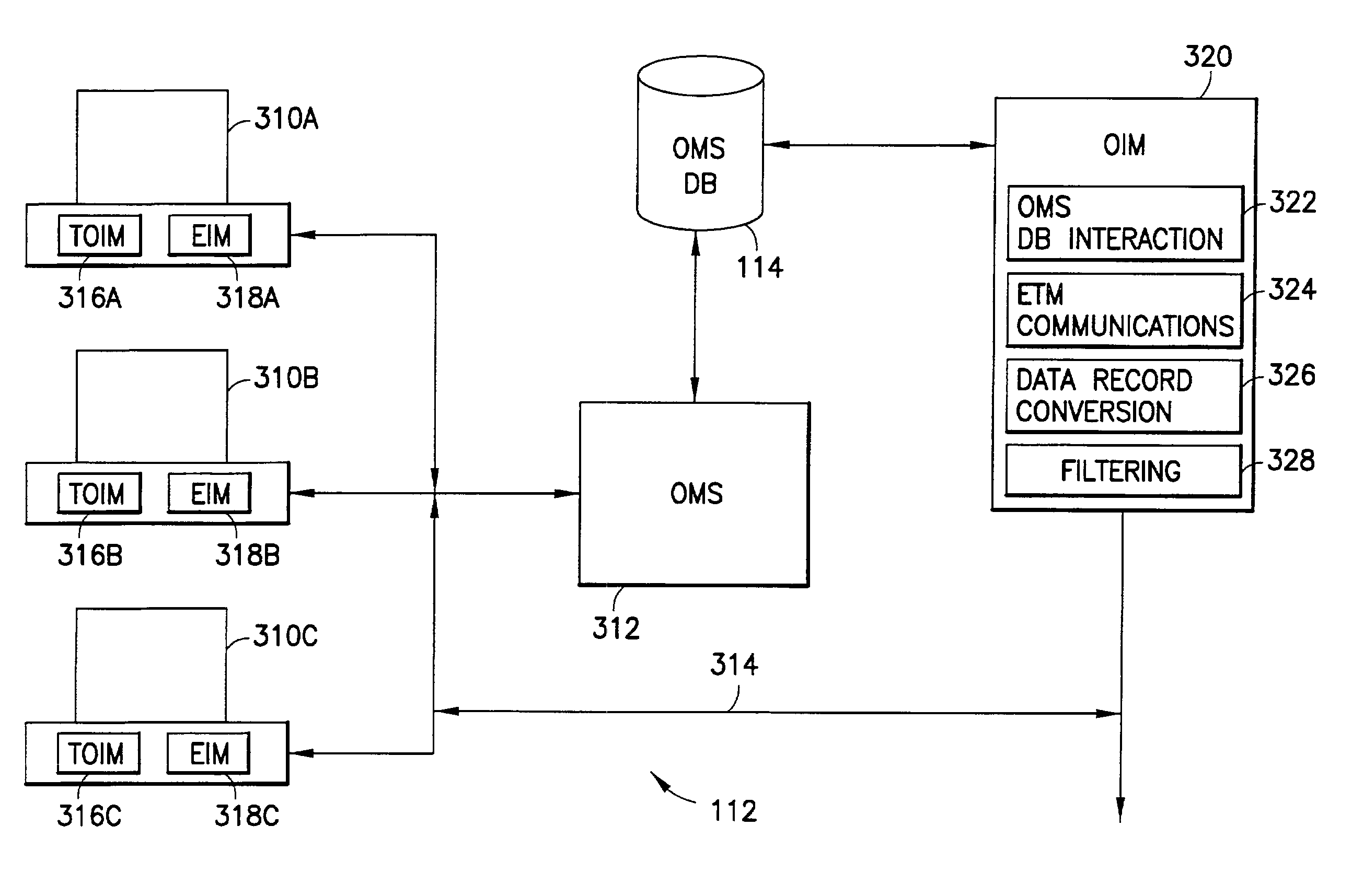
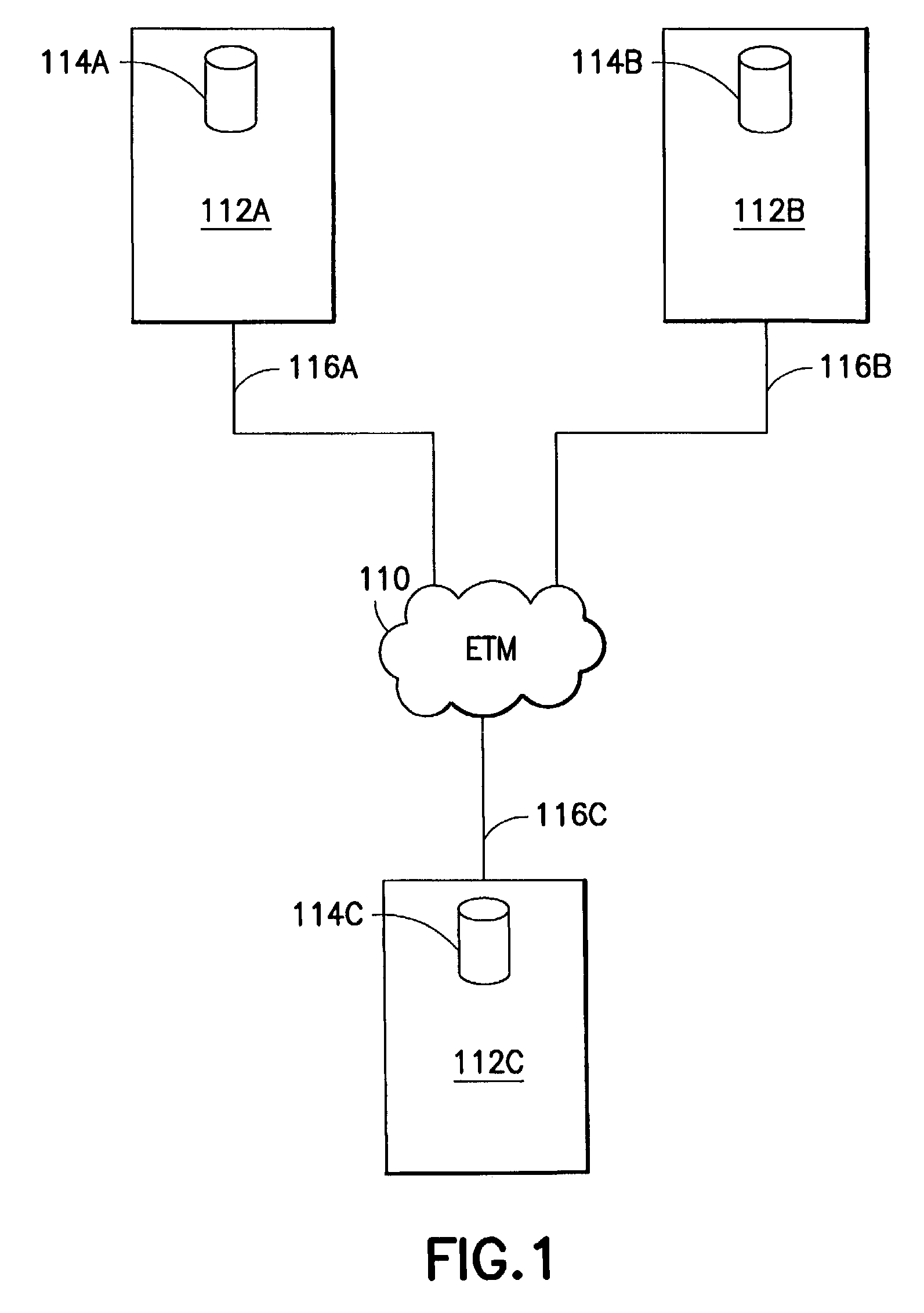
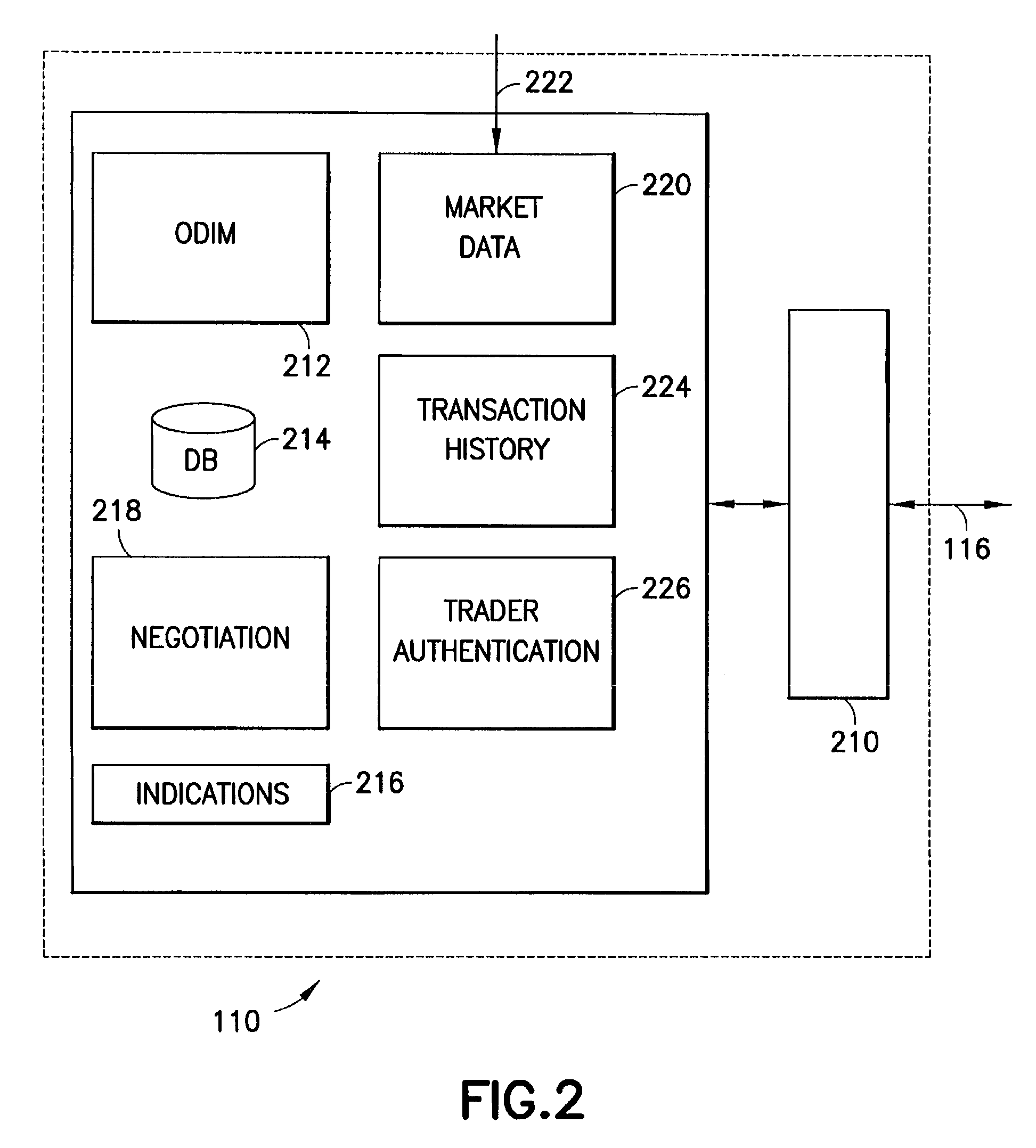
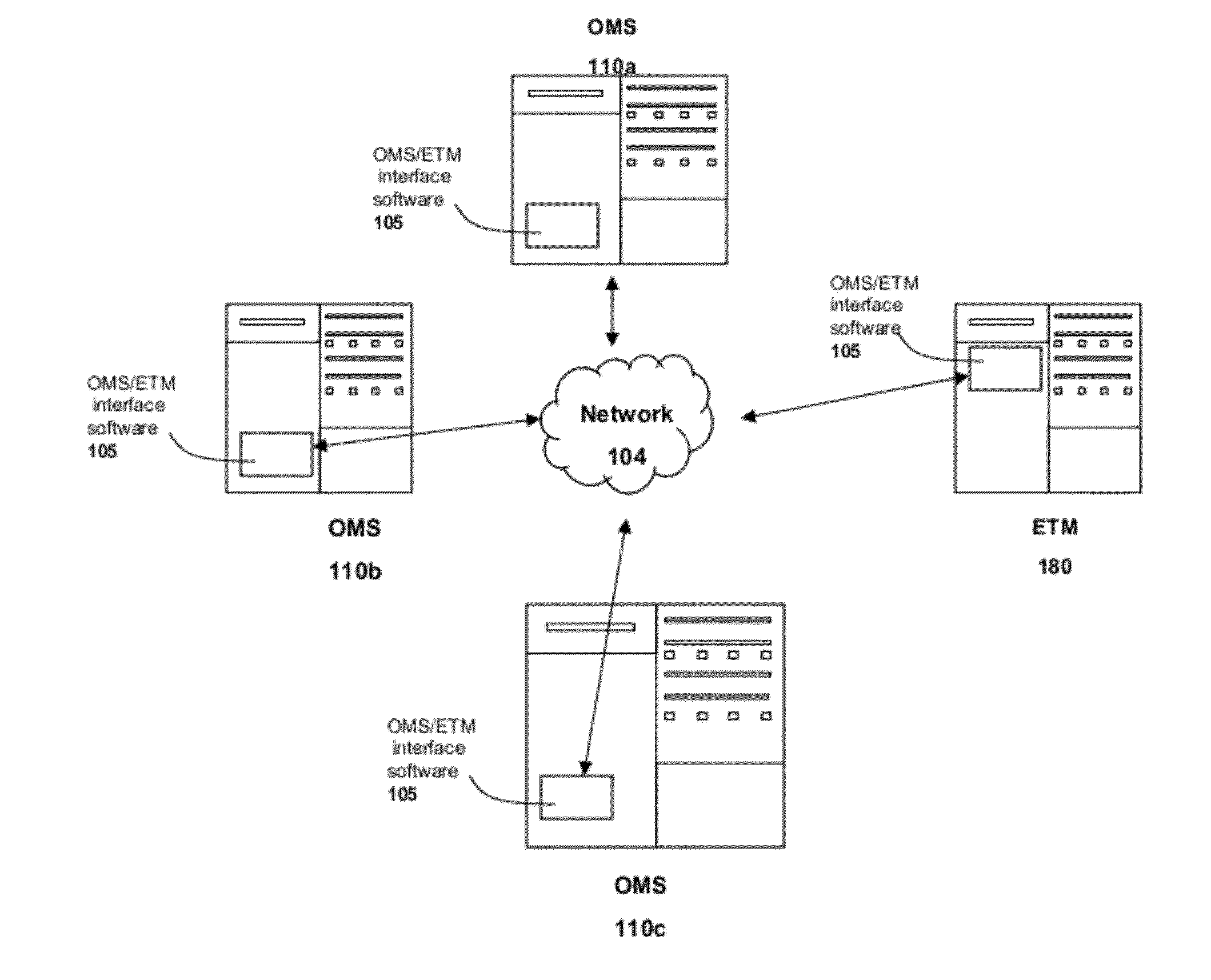
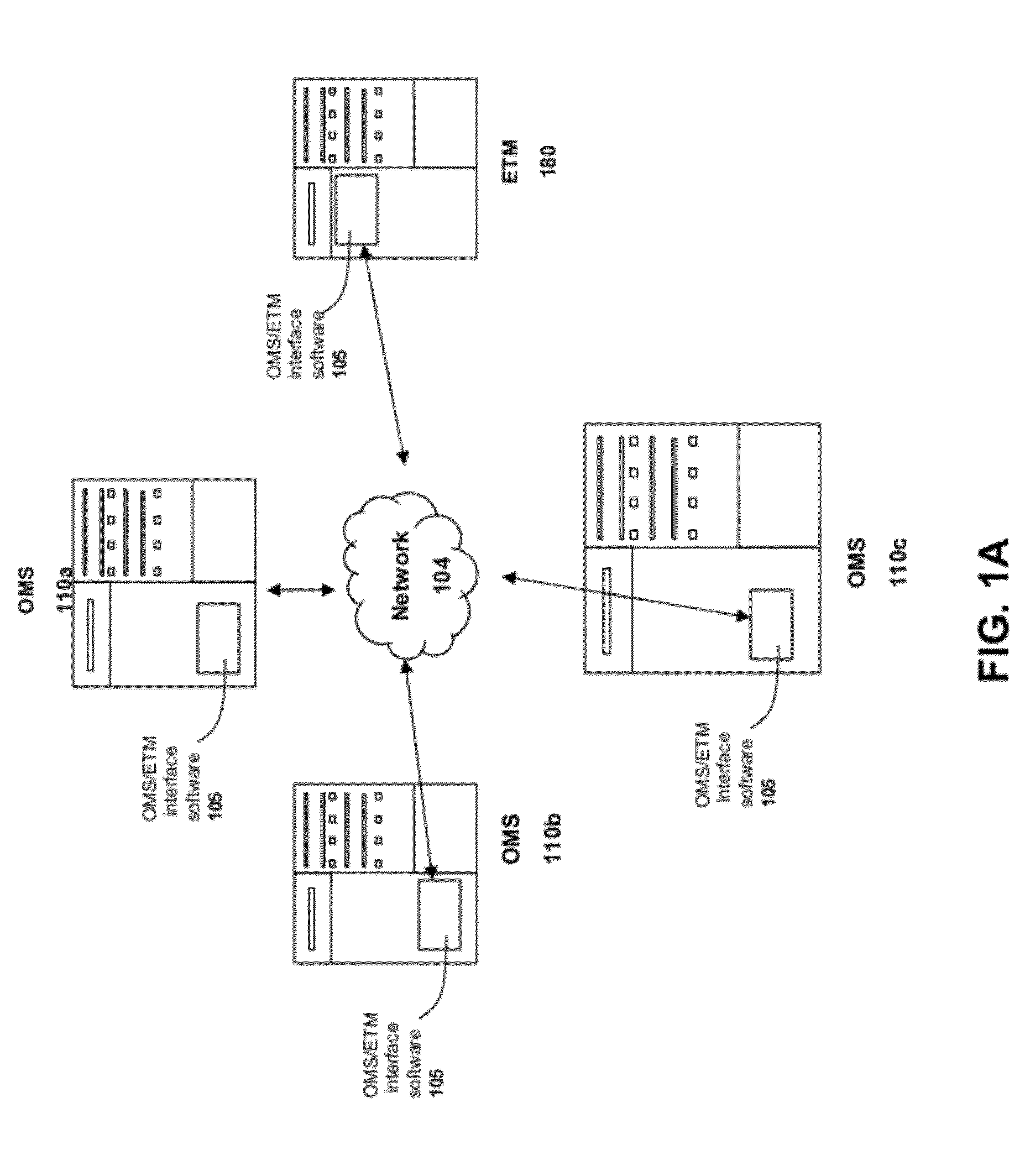
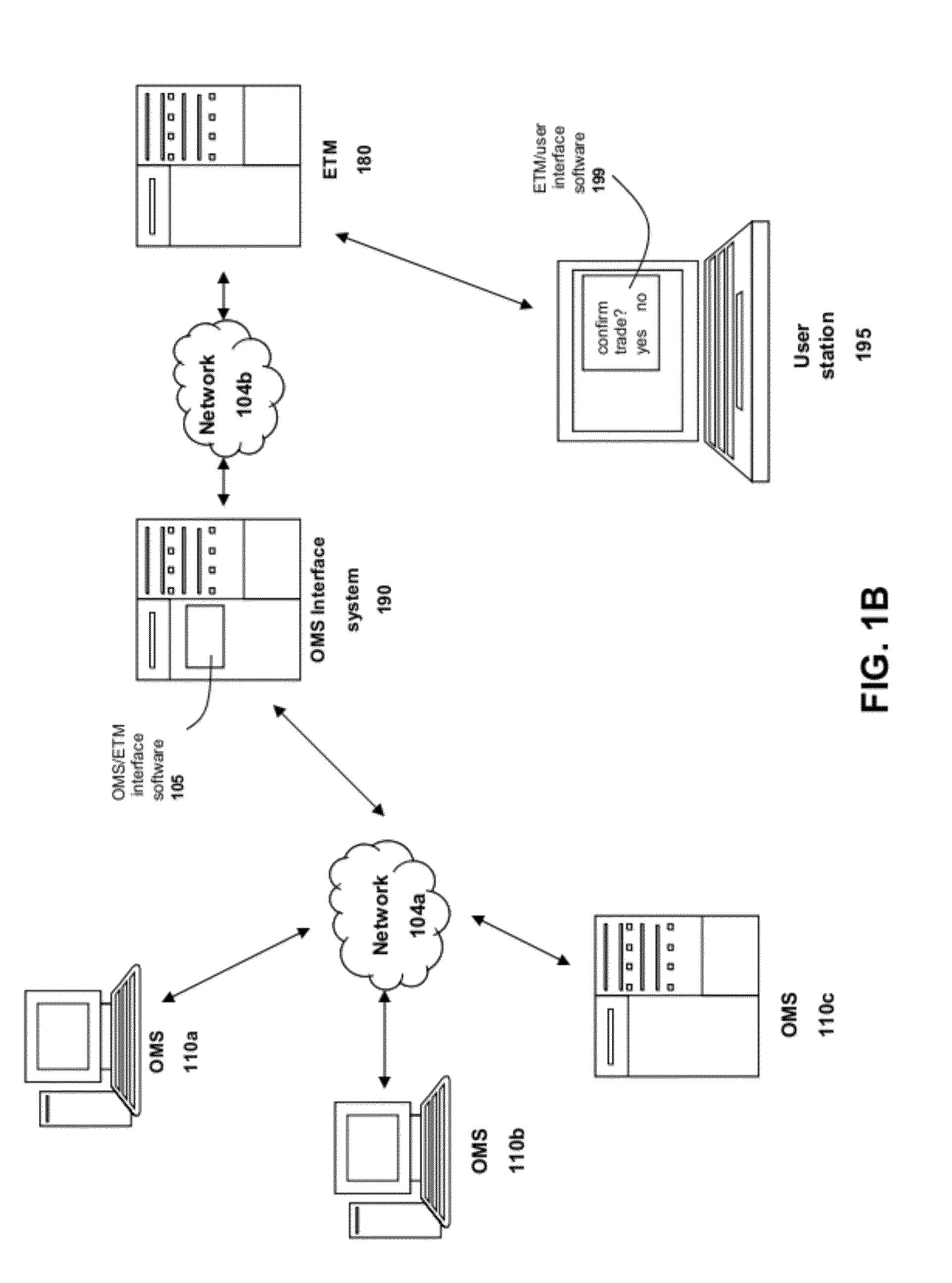
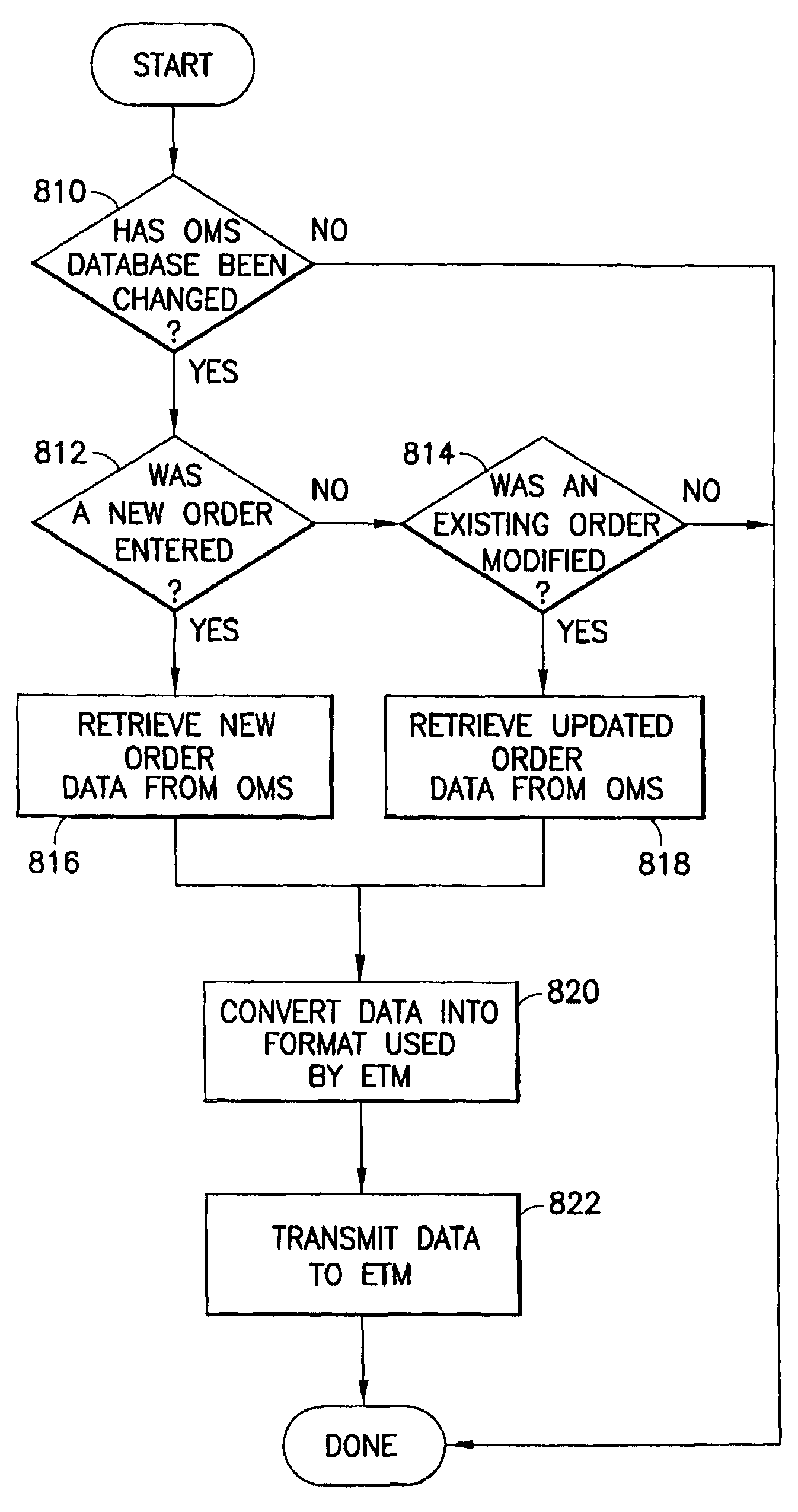
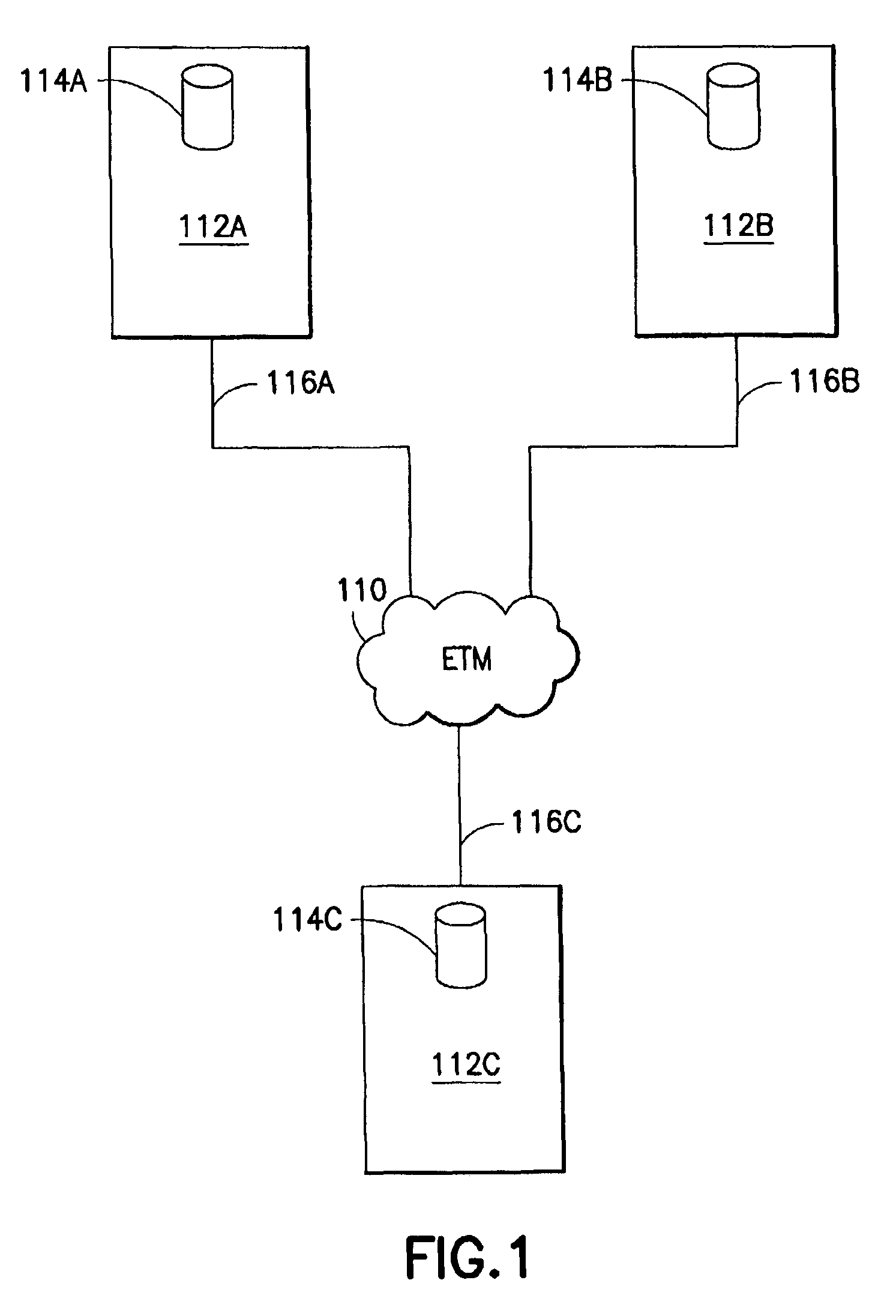
Electronic securities marketplace having integration with order management systems
An electronic trading marketplace (ETM) communicates with interfacing modules interfacing directly with order management systems (OMS's) at trading institutions. The interfacing modules automatically transmit orders from the OMS databases to the ETM and update the OMS databases in response to orders executed at the ETM. Traders can communicate with the ETM to anonymously negotiate trades of securities.
Owner:LIQUIDNET HLDG
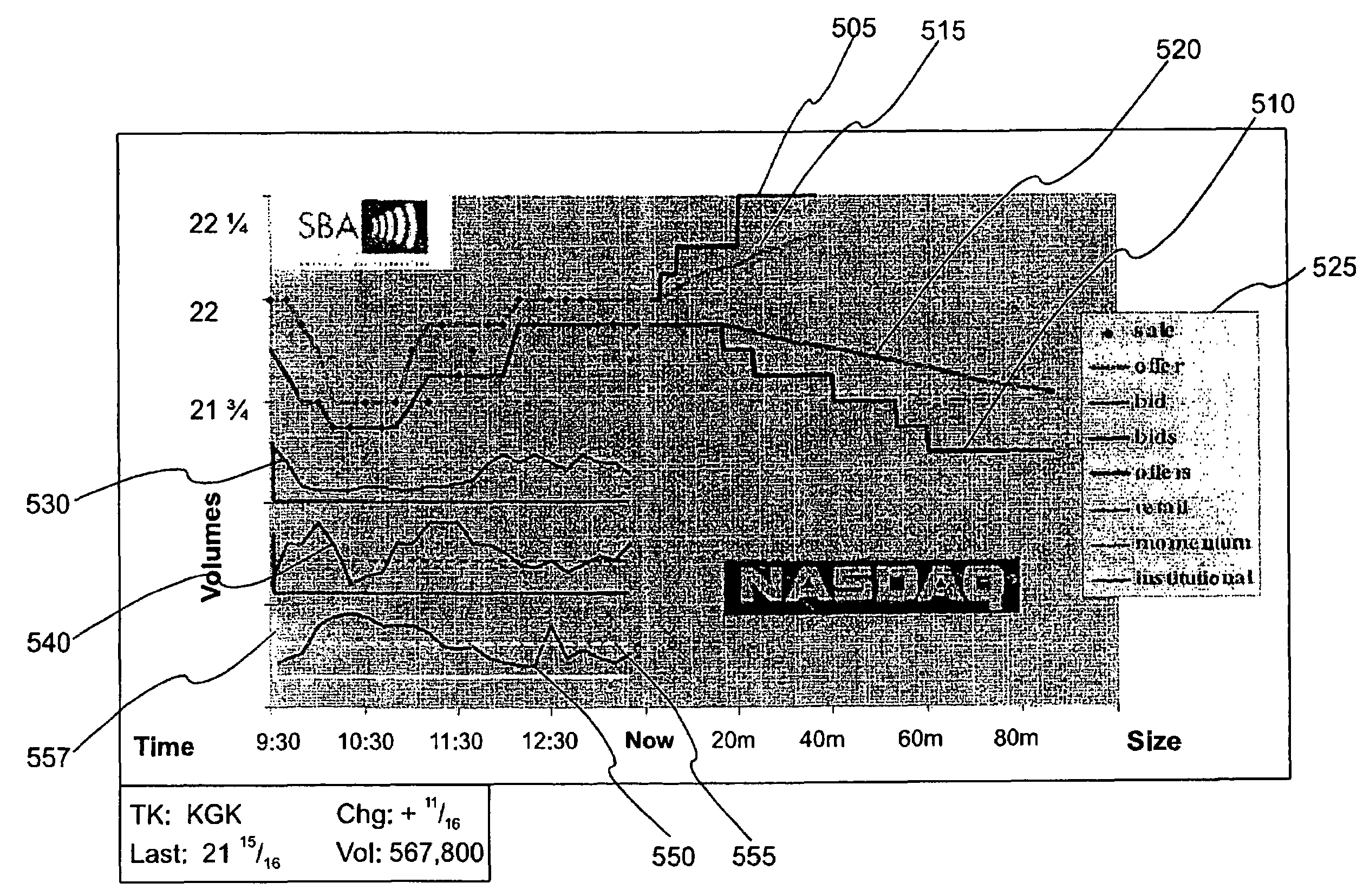
System and method for displaying market information
The subject invention overcomes the limitations of known market data displays by producing a graphical market display that integrates analysis of both 1) intra-day trading activity by classes of market participant, and 2) projected market impact as a function of trade size give the present set of executable orders in an electronic securities trade execution network. In a preferred embodiment, the display is used as the graphic user interface (GUI) of an ECN. In alternate preferred embodiments, the display is offered by a market data analysis service that accesses information form one or more ECNs, exchanges, or stock market. In another alternate embodiment, the display is created by software on a user computer form liquidity information already on that user computer.
Owner:ITG SOFTWARE SOLUTIONS INC
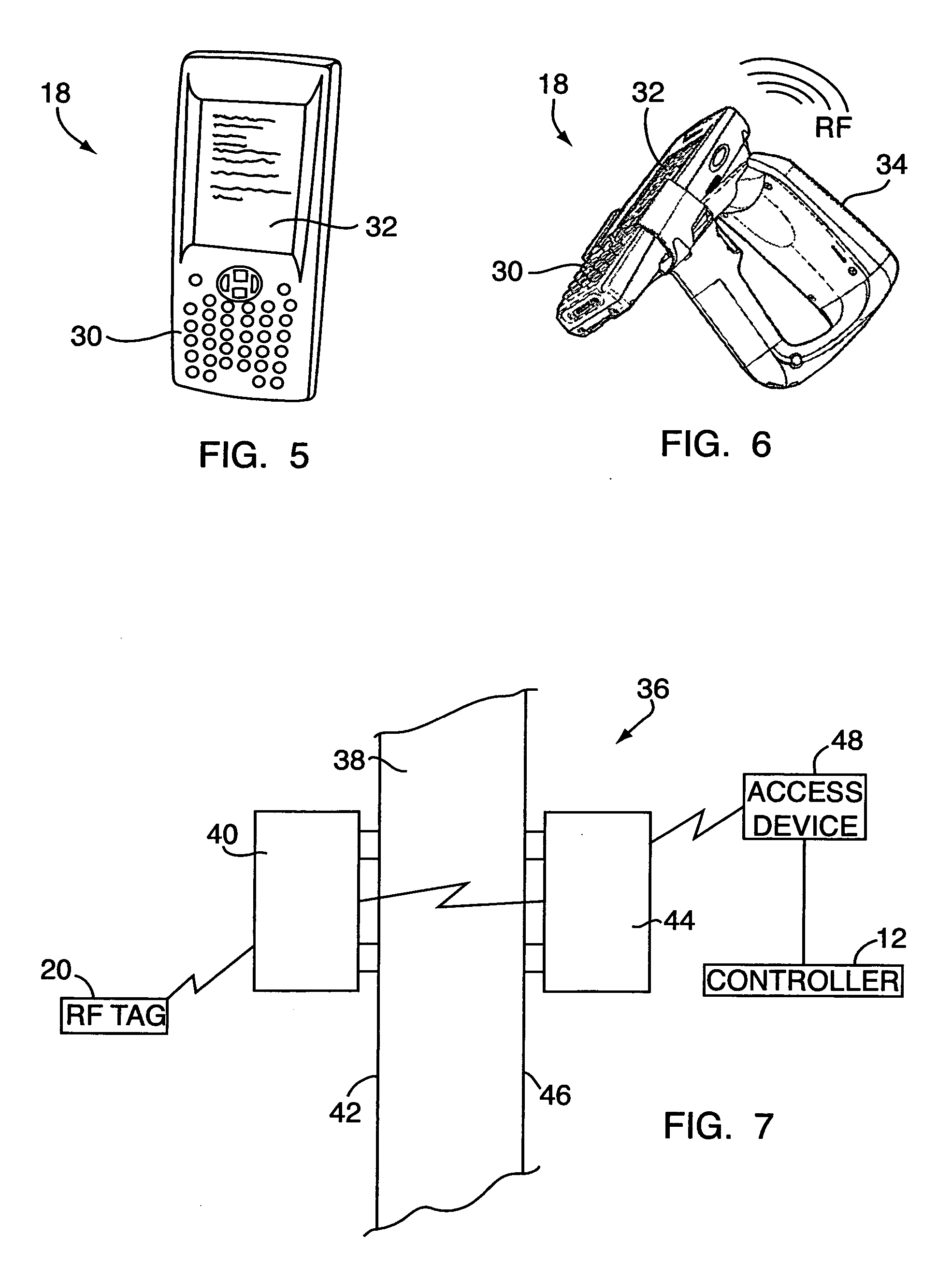
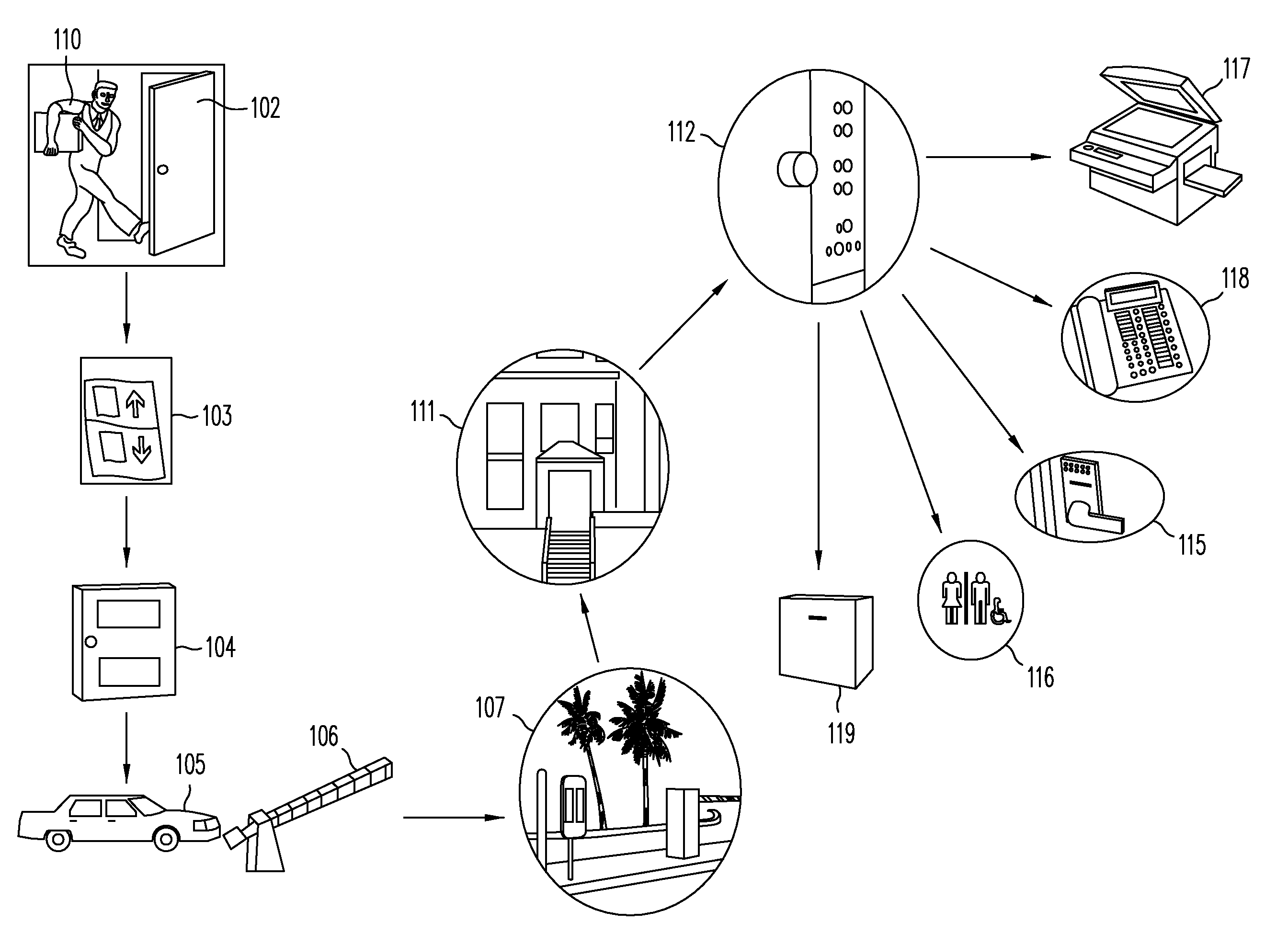
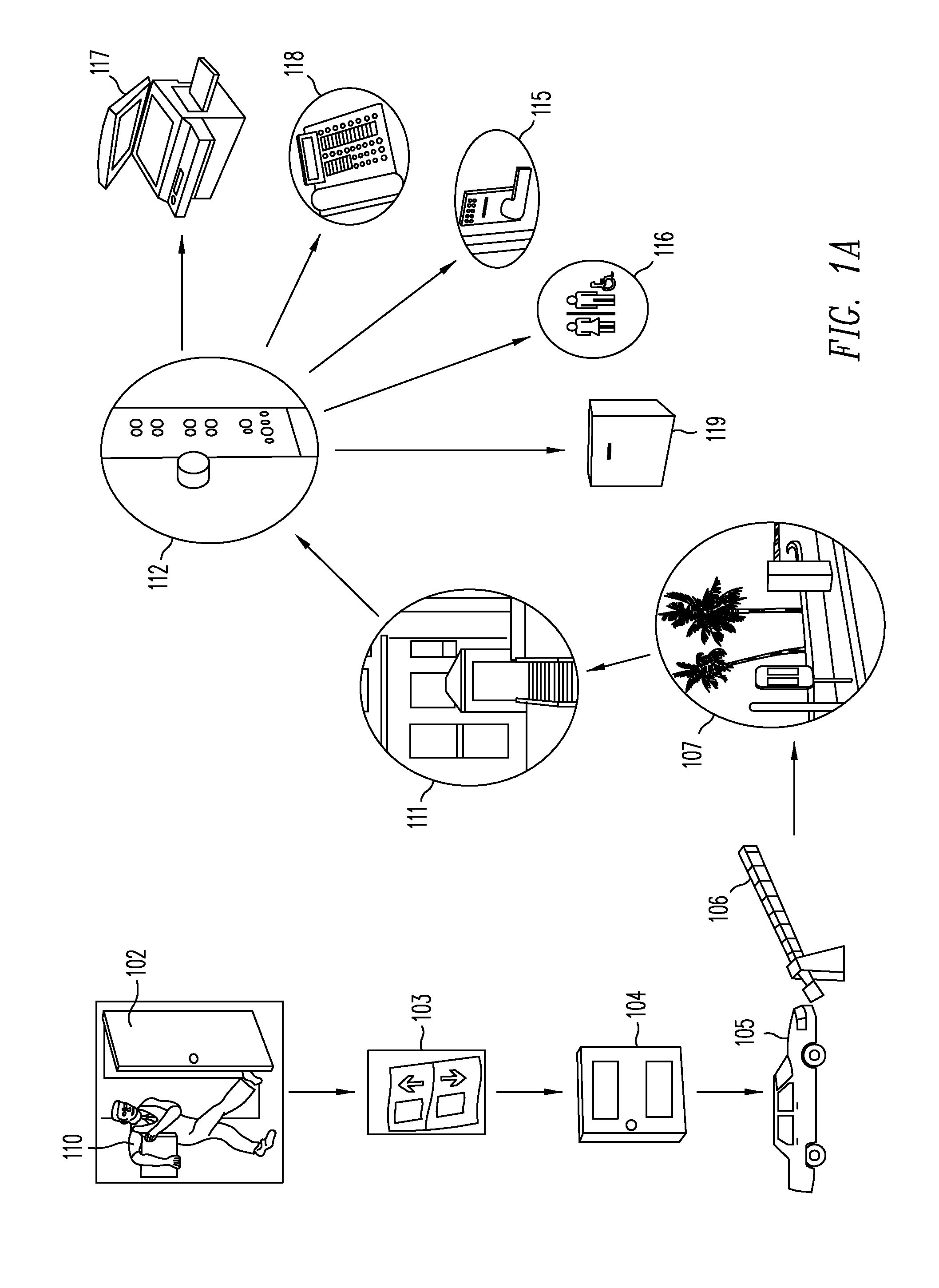
Universal hands free key and lock system
InactiveUS7446644B2Quickly and easily pass through otherwise locked doorEliminate needElectric signal transmission systemsDigital data processing detailsUser needsEngineering
Methods and systems are provided for a universal key that enables a user to have access to any type of secured portal, both physical and electronic, in a wireless, hands-free, distance-independent manner without requiring contact or line of sight access between the key and the secured portal. The universal key is not distance-dependent, and each secured portal can be provided with its own prescribed activation range, if desired. Some portals may be provided with long range activation, such as 50 feet, while other portals may be provided with short range activation of a few feet or less. The type of portal being secured and the range of activation may be selected by the user and is not limited by the universal key. In addition, the universal key will provide access to the secured portals in a hands-free fashion so that the user need not push any buttons or take any other action in order to obtain access to the portal. The user need only carry the universal key somewhere on their person in order to access the portal.
Owner:SECUREALL CORP
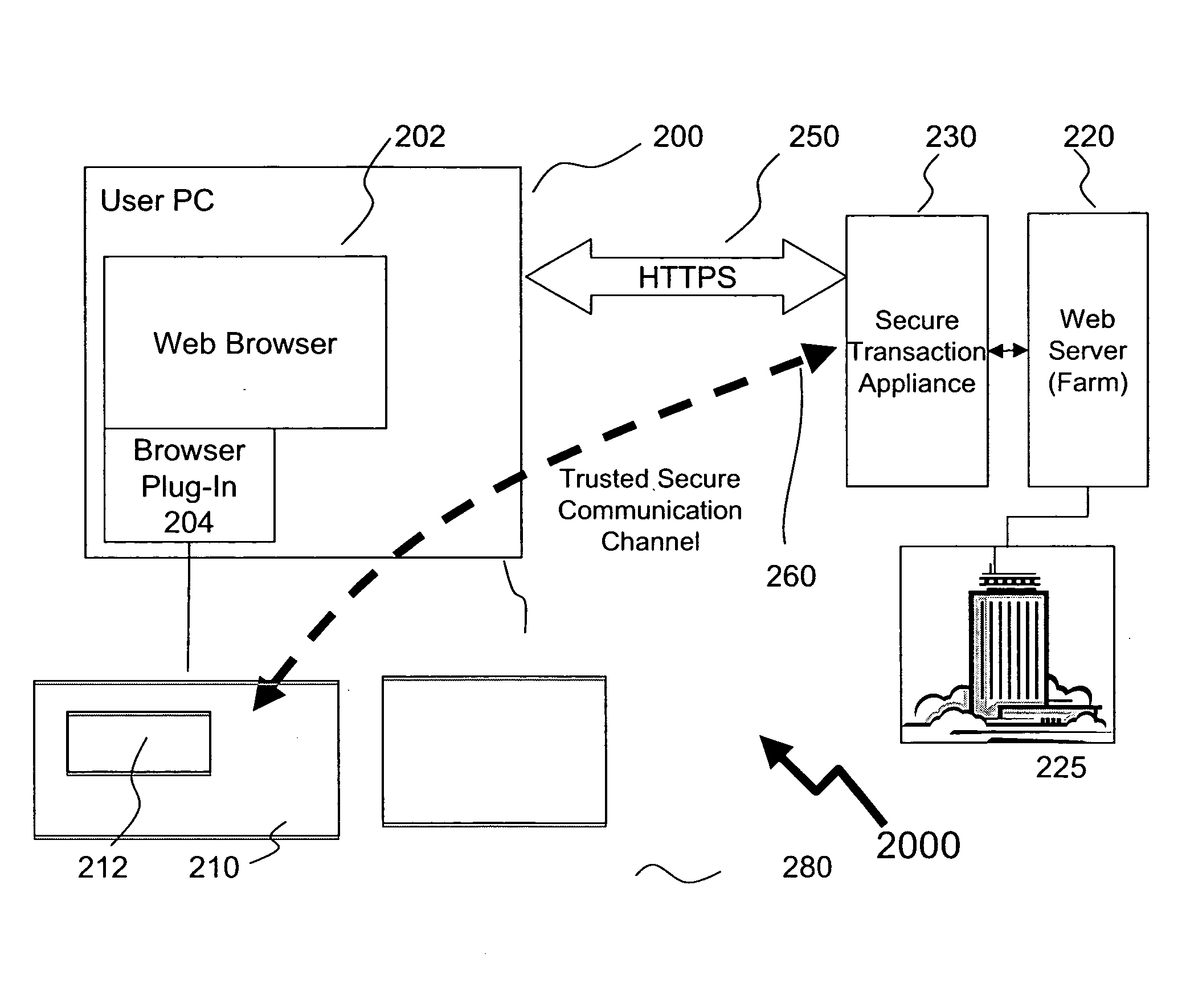
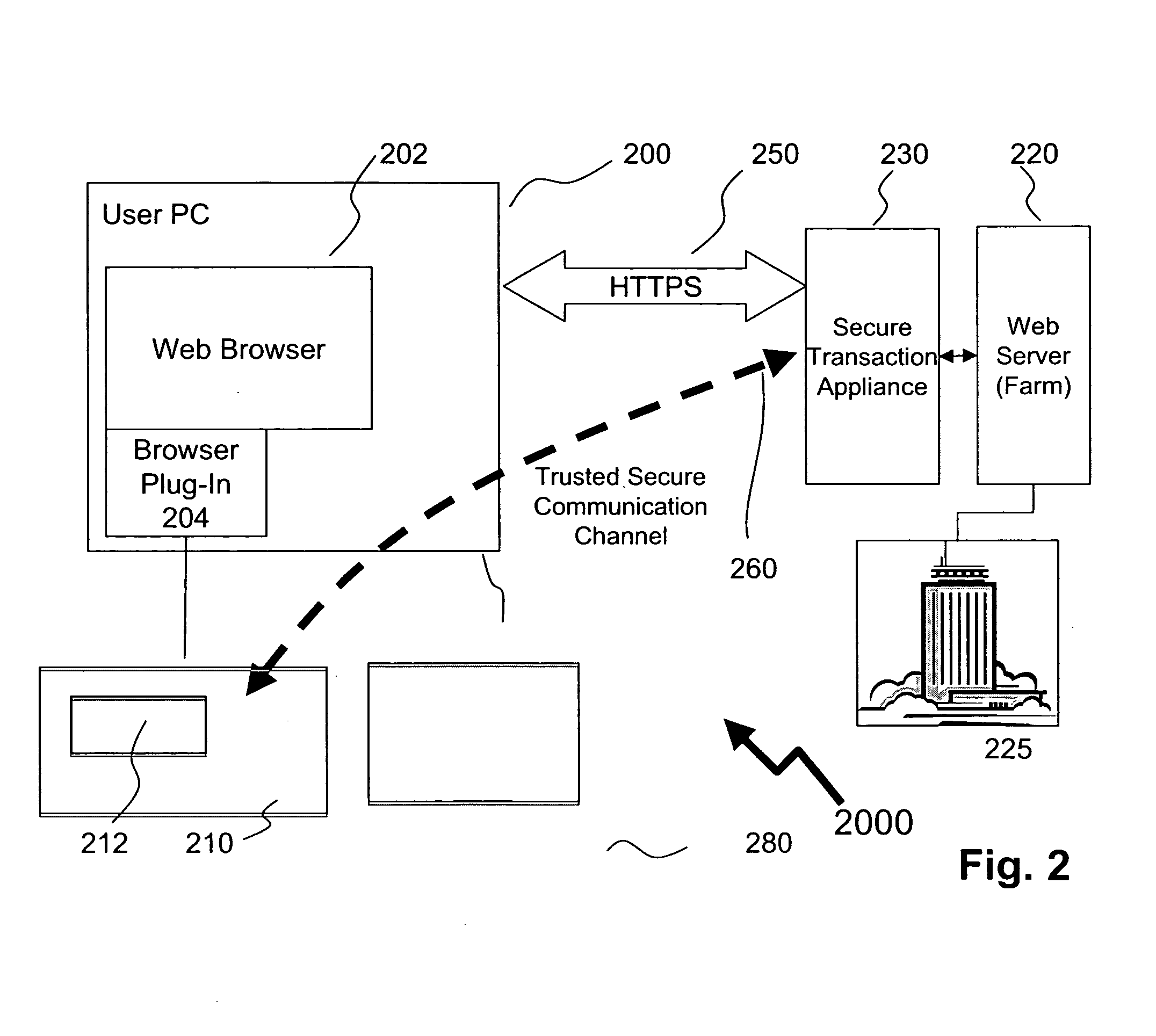
Method of providing assured transactions using secure transaction appliance and watermark verification
ActiveUS20090106556A1User identity/authority verificationComputer security arrangementsPersonalizationElectronic security
Disclosed is a method of improving electronic security by establishing a path between a user and a secure transaction appliance. The secure transaction appliance receiving information destined for the user which includes a tagged portion, said tagged portion triggering the secure transaction appliance to forward the information to the computer from which the request was issued, and to seeking an electronic signature to verify the content or transaction by transmitting a watermark, tagged portion of the content, or similar electronic content. The secure trusted path providing the user with the tagged portion incorporating additional elements such as a watermark, or in some embodiments only the additional elements, upon a personalized security device associated with the user making interception or manipulation more complex and difficult.
Owner:DATA LOCKER INC
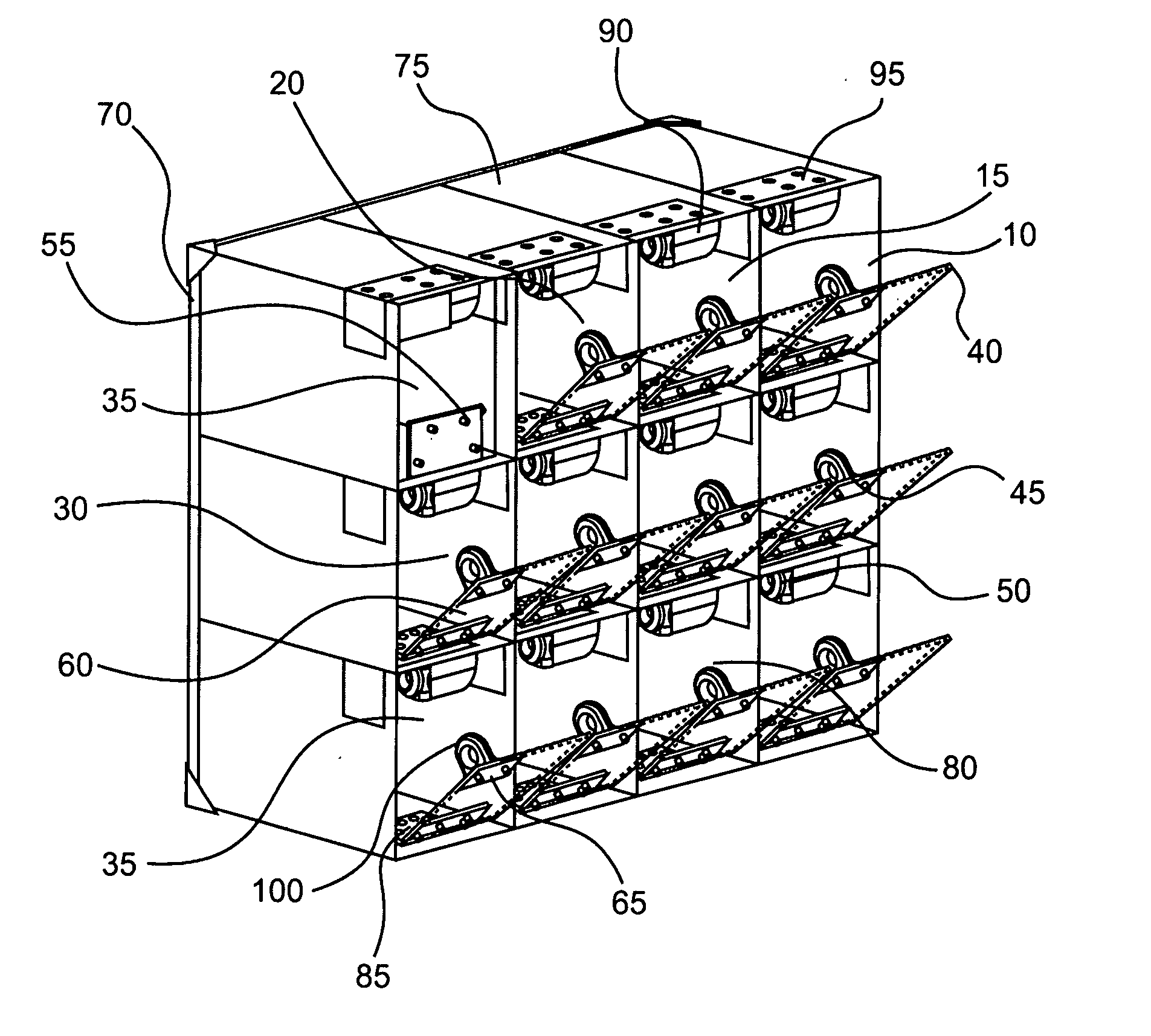
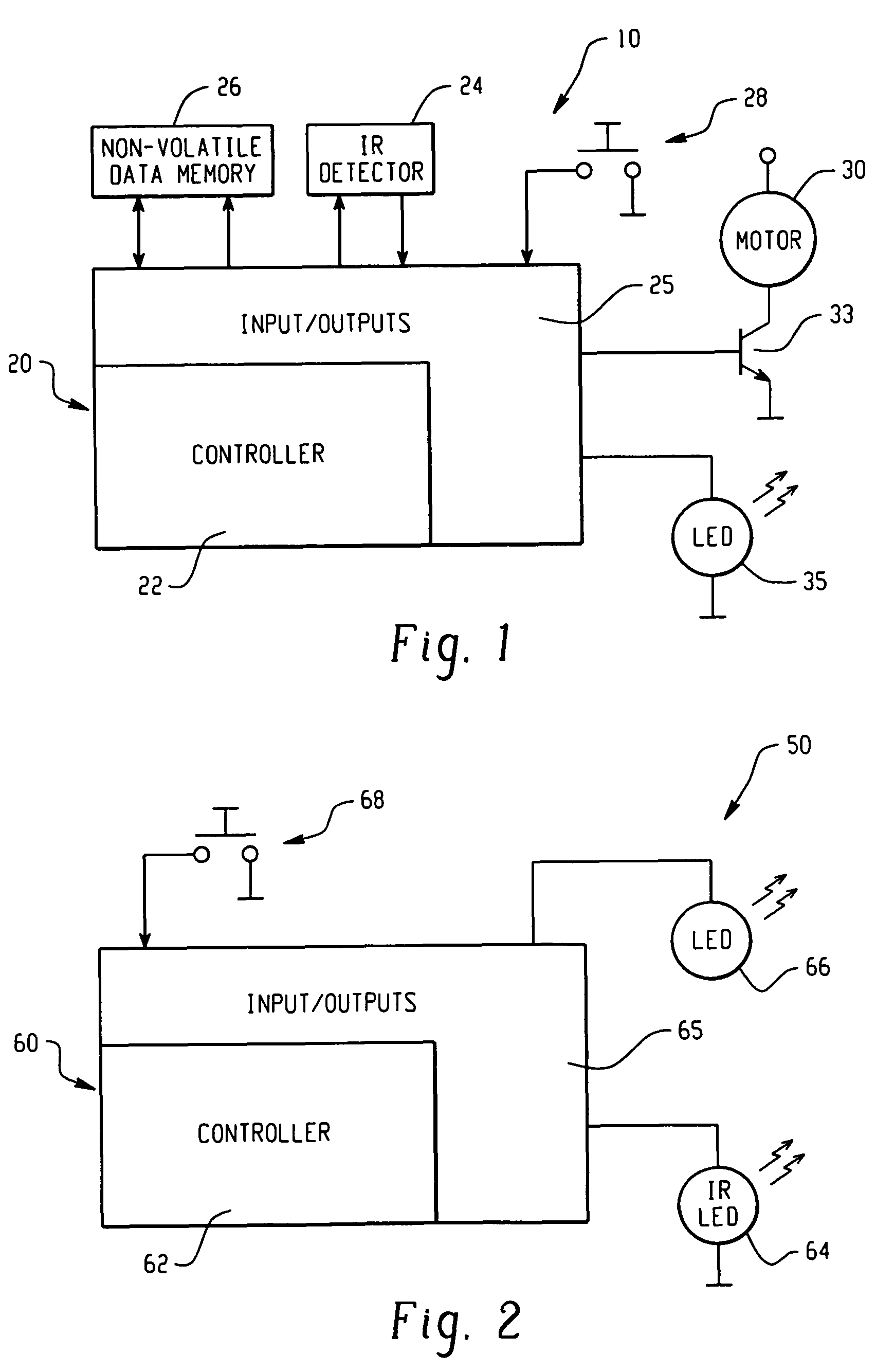
Compact electronic security locker system
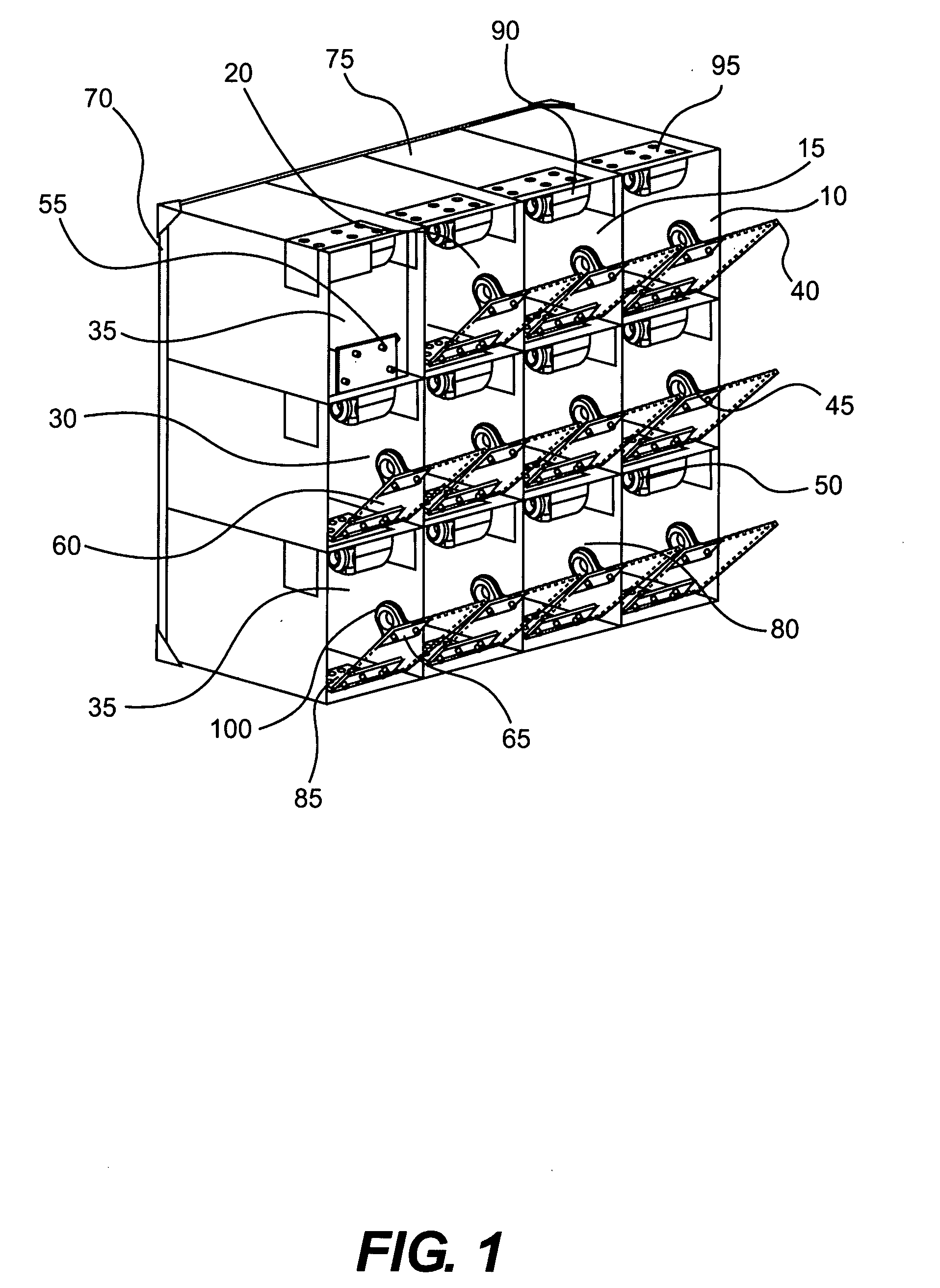
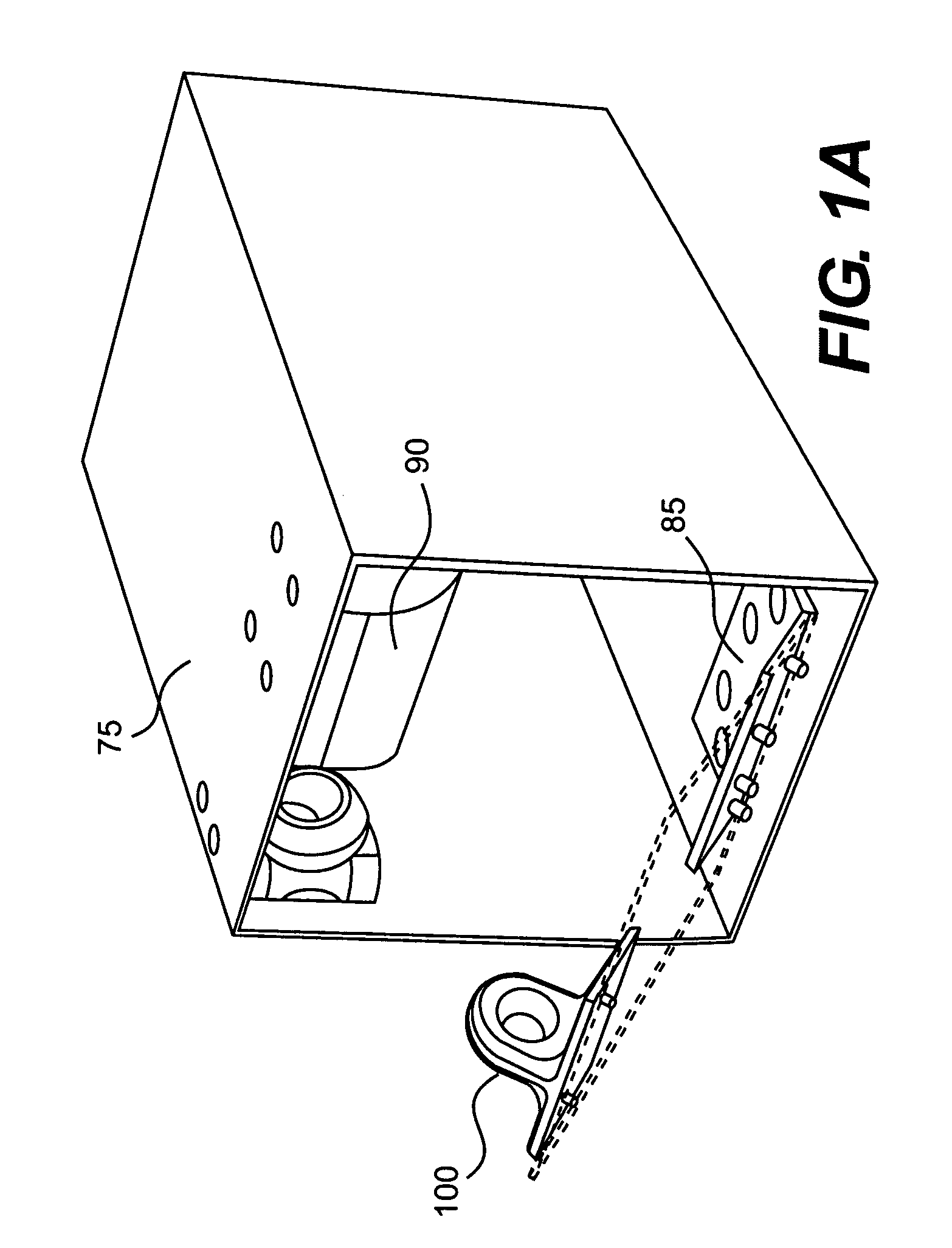
InactiveUS20090033456A1Electric signal transmission systemsMultiple keys/algorithms usageElectronic accessEngineering
An embodiment of the present invention provides a compact electronic security locker system that includes an array of lockers, each of which is electronic locked and electronically accessed. One aspect of an embodiment of the present invention allows authorized personnel access to the identification of the person storing an article in a particular locker. In another aspect of an embodiment of the present invention, the storage lockers are arranged in a matrix of rows and columns and are constructed to have a size to accommodate items having a size of common cell phones.
Owner:CASTILLO GILBERT +4
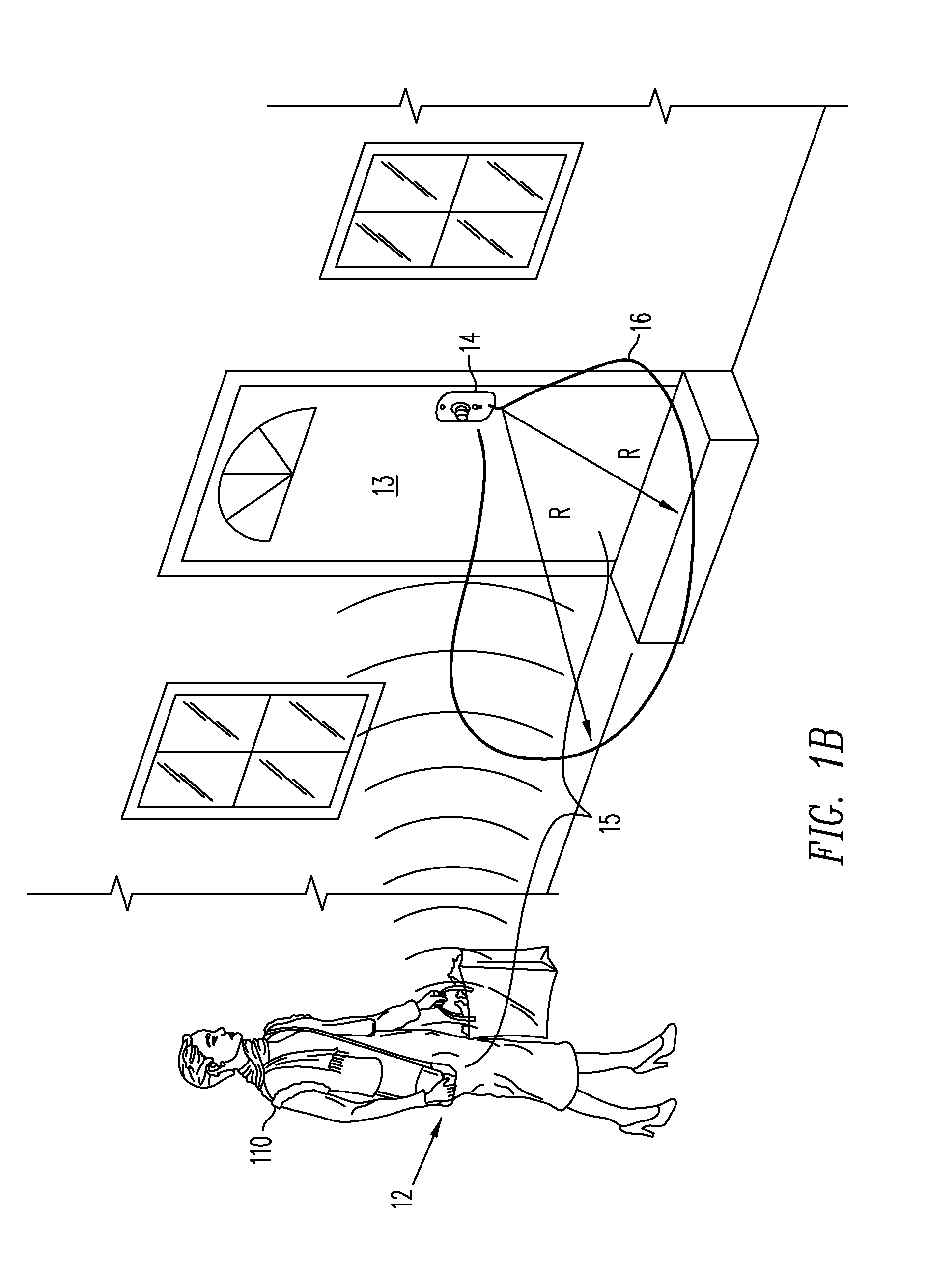
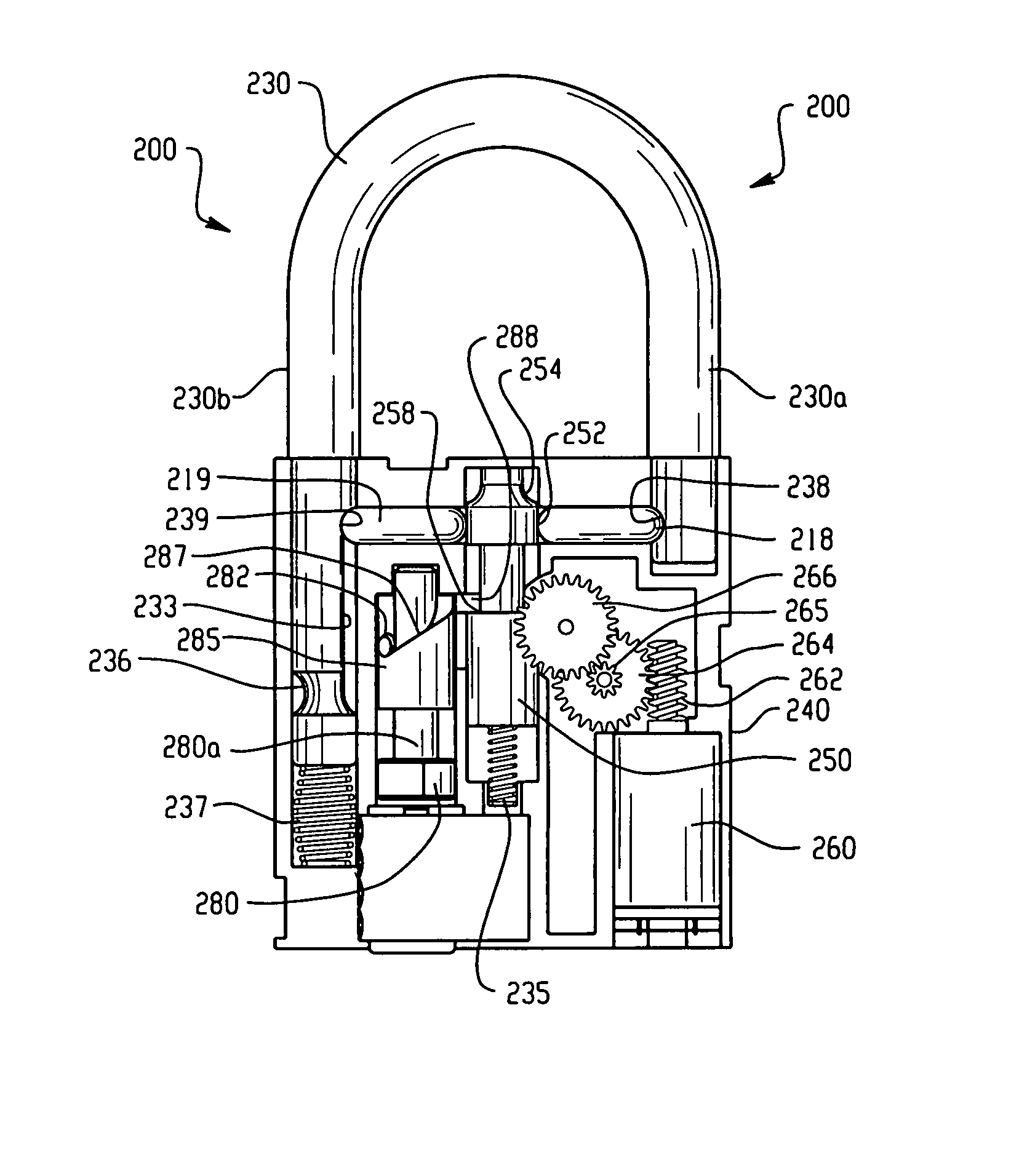
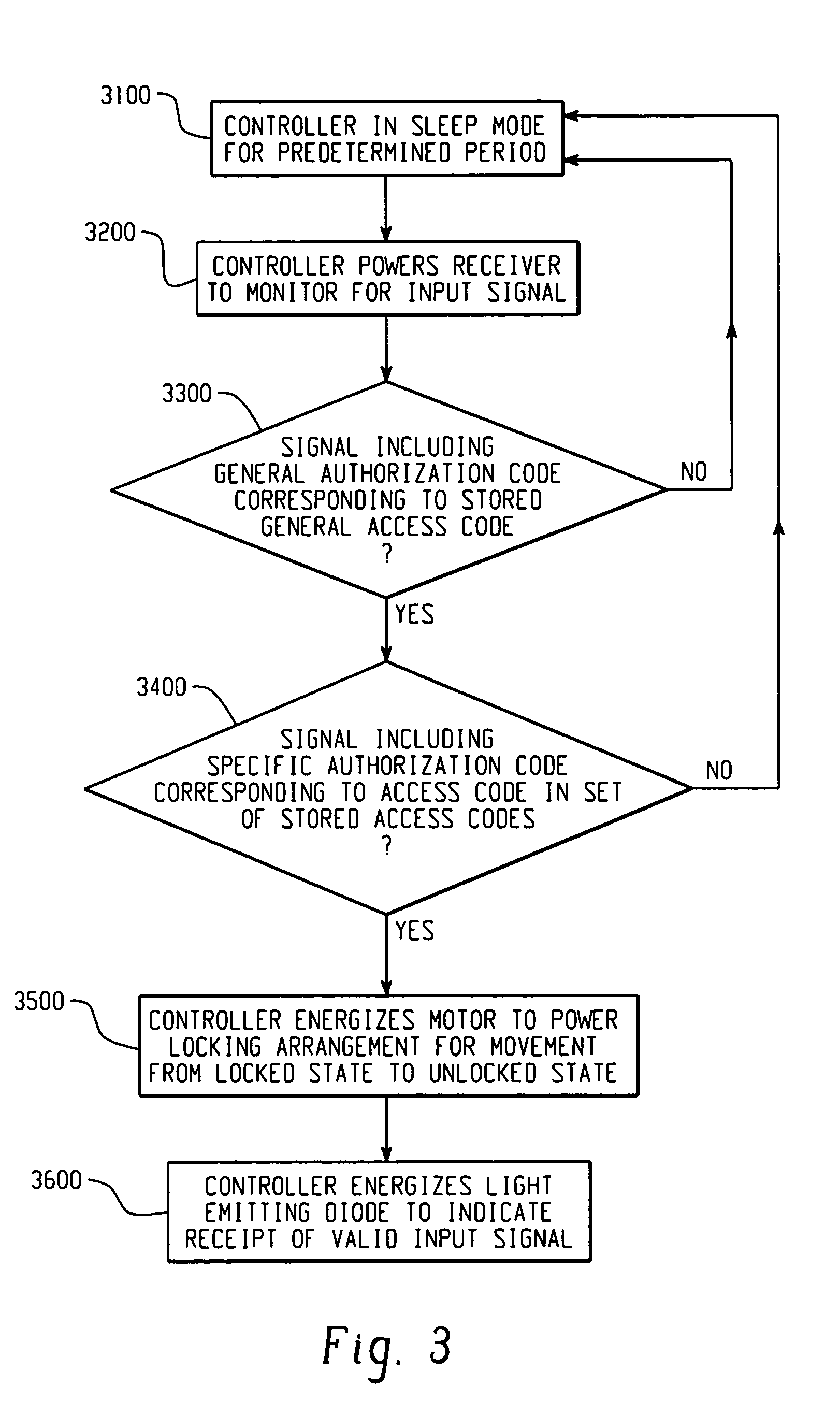
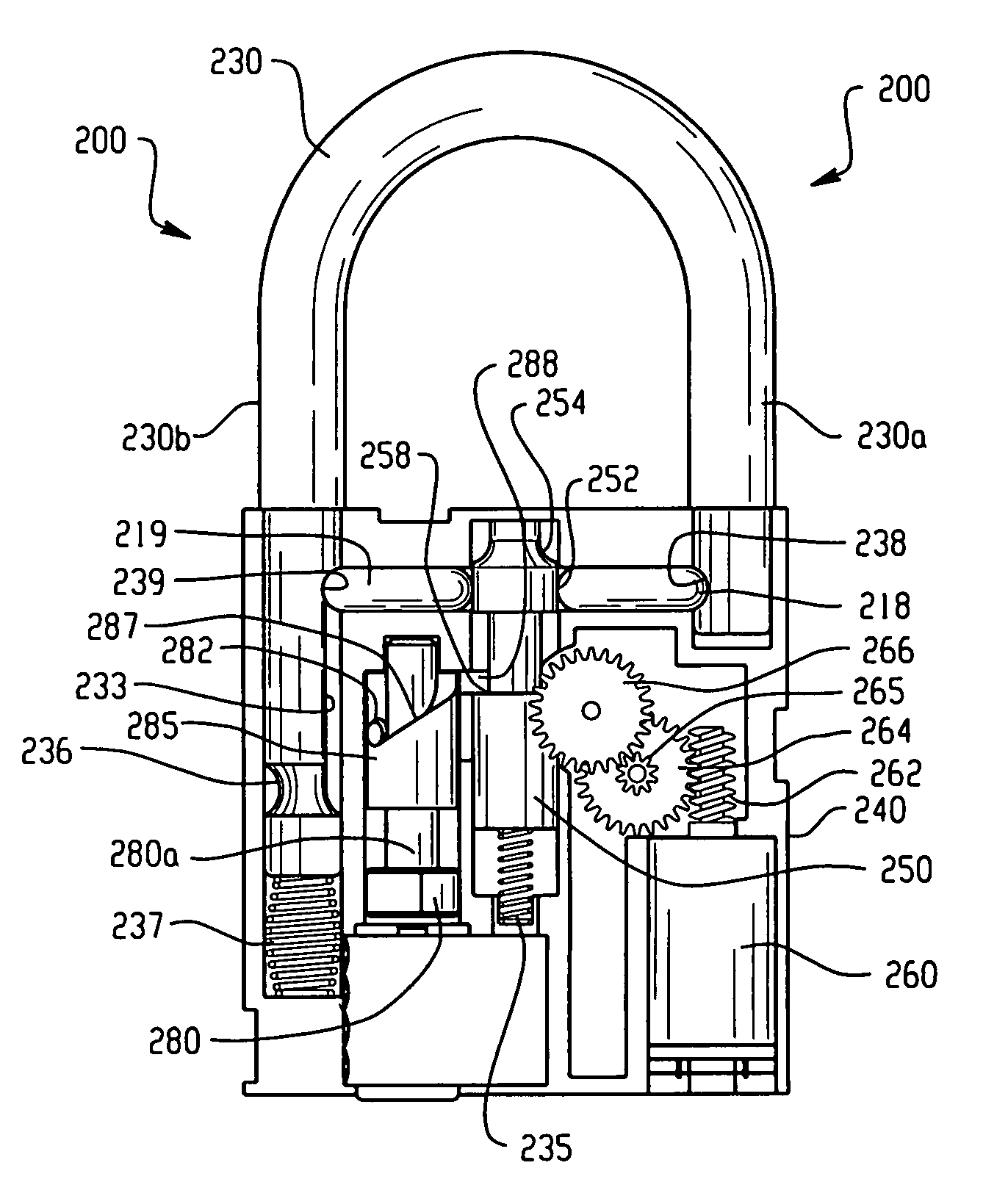
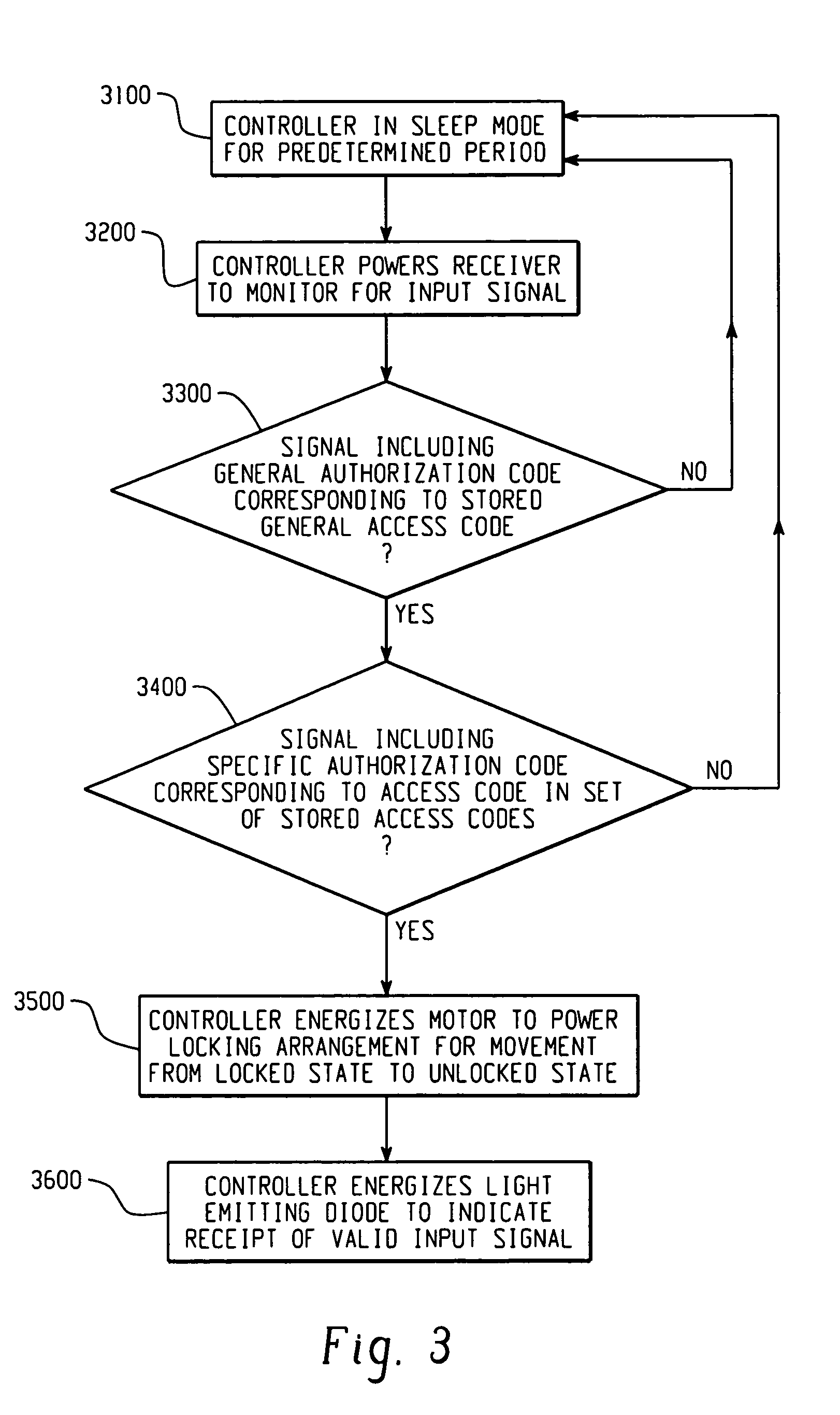
Electronic security device
InactiveUS20060283216A1Electric signal transmission systemsDigital data processing detailsEngineeringElectronic security
A lock is provided with a housing, a shackle movably coupled to the housing, and a locking arrangement movable between a locked state and an unlocked state. The lock includes a receiver arranged to receive a remote input signal including at least one authorization code. The lock includes a logic applying arrangement programmed to selectively store at least one access code responsive to a corresponding authorization code received by the receiver and to energize the locking arrangement to move from the locked state to the unlocked state when an authorization code received by the receiver corresponds with one of a set of stored access codes. The locking arrangement is configured to secure the shackle within the housing when the locking arrangement is in the locked state, and the locking arrangement is configured to allow the shackle to move relative to the housing when the locking arrangement is in the unlocked state.
Owner:MASTER LOCK CO INC
Optical layer multicasting
InactiveUS6873797B2Special service provision for substationMultiplex system selection arrangementsOptical packetEngineering
An optical signaling header technique applicable to optical networks wherein packet routing information is embedded in the same channel or wavelength as the data payload so that both the header and data payload propagate through network elements with the same path and the associated delays. The technique effects survivability and security of the optical networks by encompassing conventional electronic security with an optical security layer by generating replicated versions of the input data payload at the input node, and the transmission of each of the replicated versions over a corresponding one of the plurality of links. Moreover, each of the links is composed of multiple wavelengths to propagate optical signals or optical packets, and each of the replicated versions of the data payload may be propagated over a selected one of the wavelengths in each corresponding one of the plurality of links.
Owner:TELCORDIA TECHNOLOGIES INC +1
Human guard enhancing multiple site integrated security system
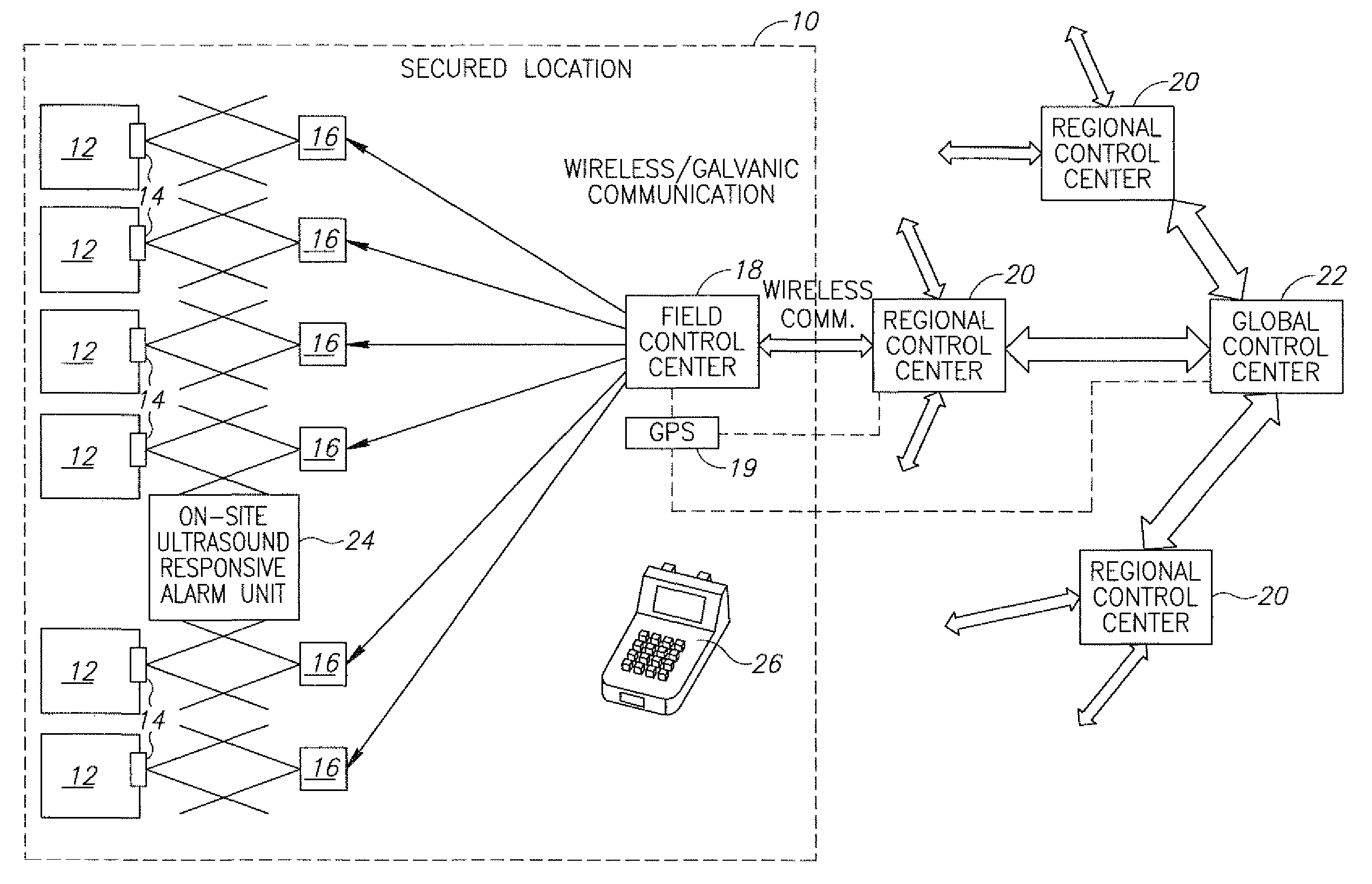
InactiveUS6894617B2Improve human performanceCathode-ray tube indicatorsBurglar alarmHand heldSystem configuration
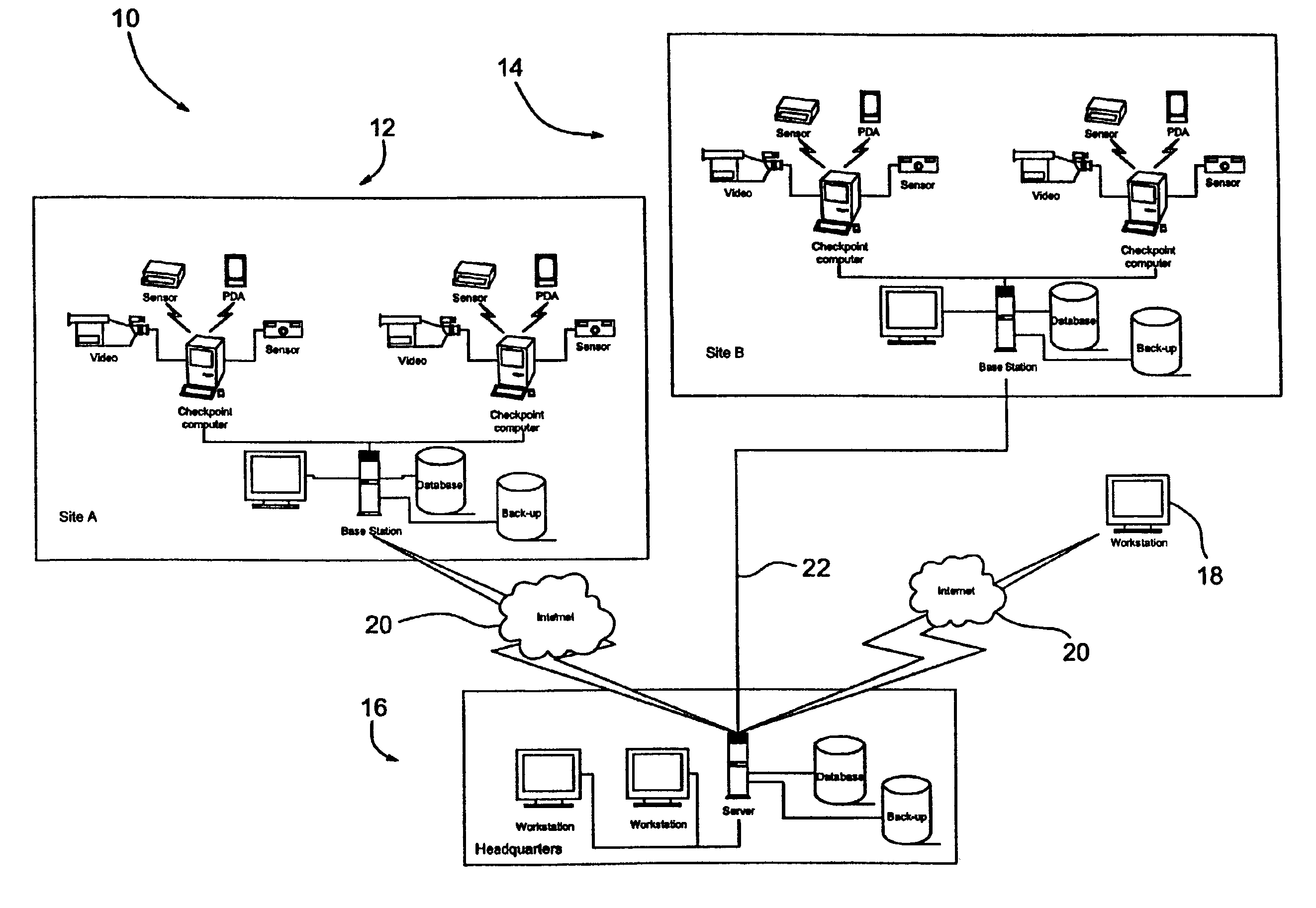
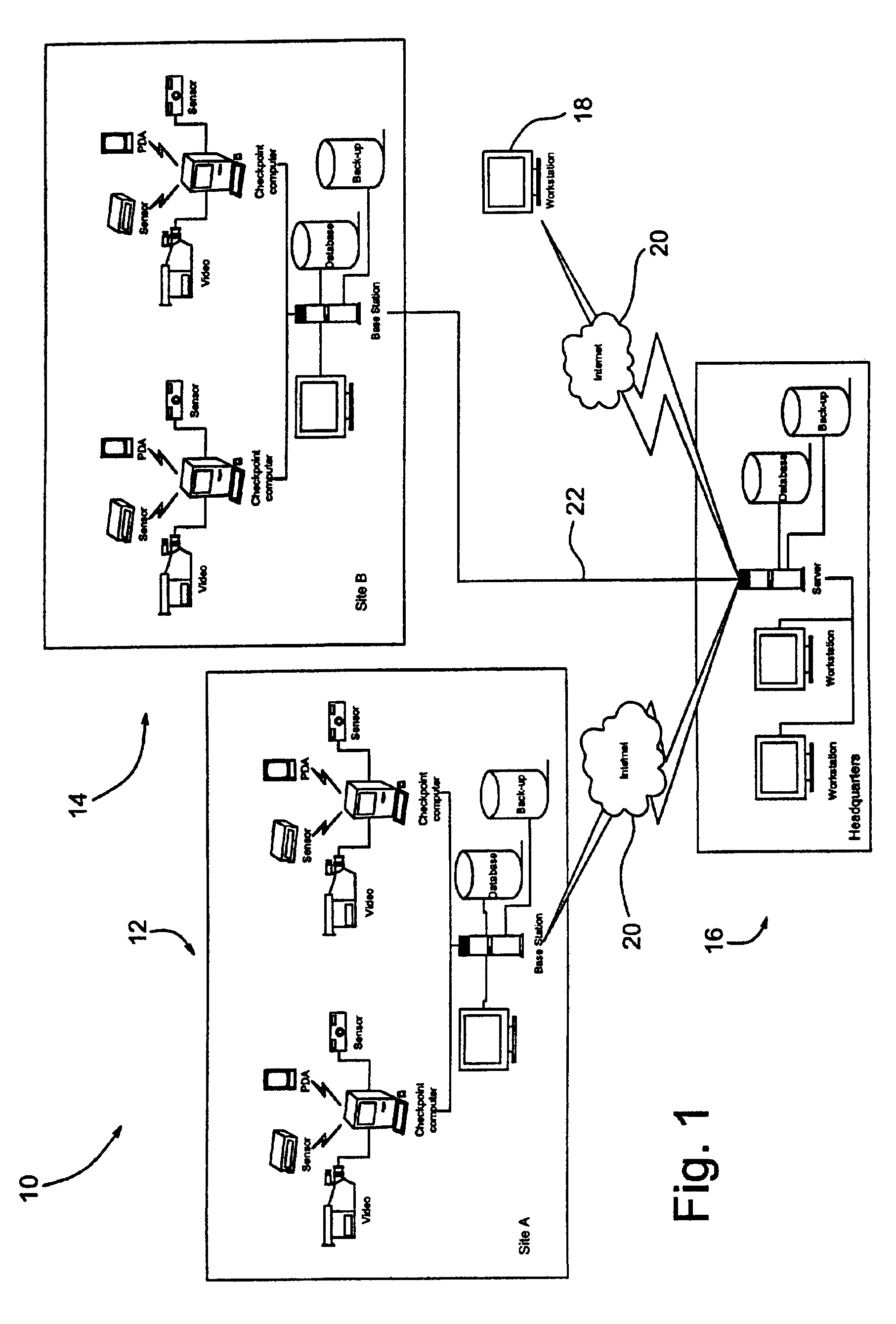
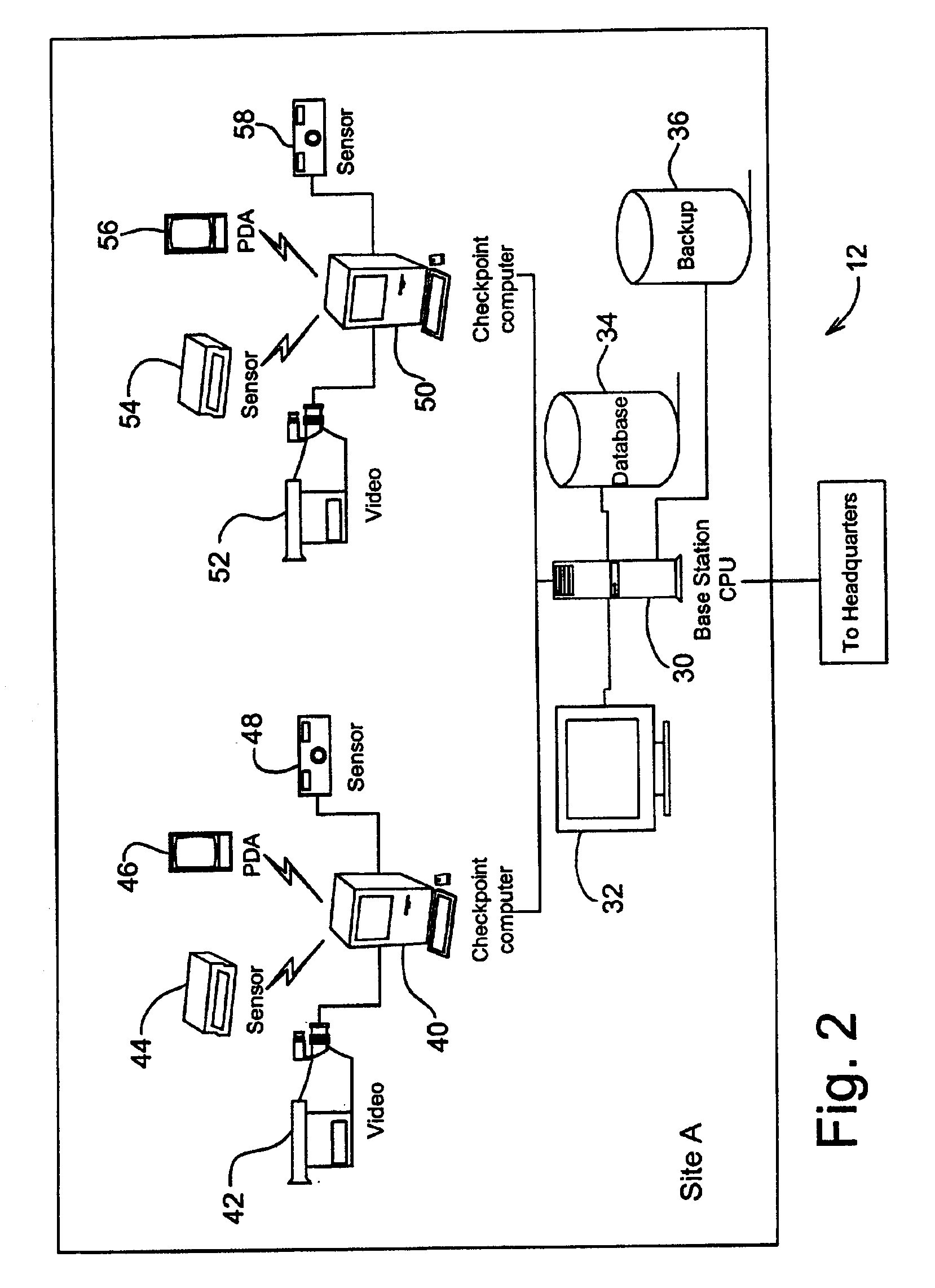
A guard enhancing multiple site, readily scalable security system combines human-based security personnel with a diverse array of fixed and movable electronic security enhancing components, and numerous modes of communications between said components, including hard wired and wireless applications. The security related components include event sensors, identification tracking for people and things, access control devices, security guard wearable computers and hand held computers as well as embedded data processing control and communications systems, with all sensors and sites capable of being monitored by a designated headquarters through checkpoint data processing components and base station components. The security system provides better trained security guards, who are more alert and responsive, and more closely supervised and easily scheduled, enhanced financial monitoring, more accurately paid and expensed security services, better archived and reported security related events, as well as being better coordinated with public agencies, enhanced safety, and readily upgraded and integrated with existing and future technologies. The primary goal of the system configuration is to make human security guard tour tasks planned, controlled, monitored, recorded and paid in a highly efficient and effective manner.
Owner:RICHMAN TECH CORP
Electronic safe/arm system and methods of use thereof
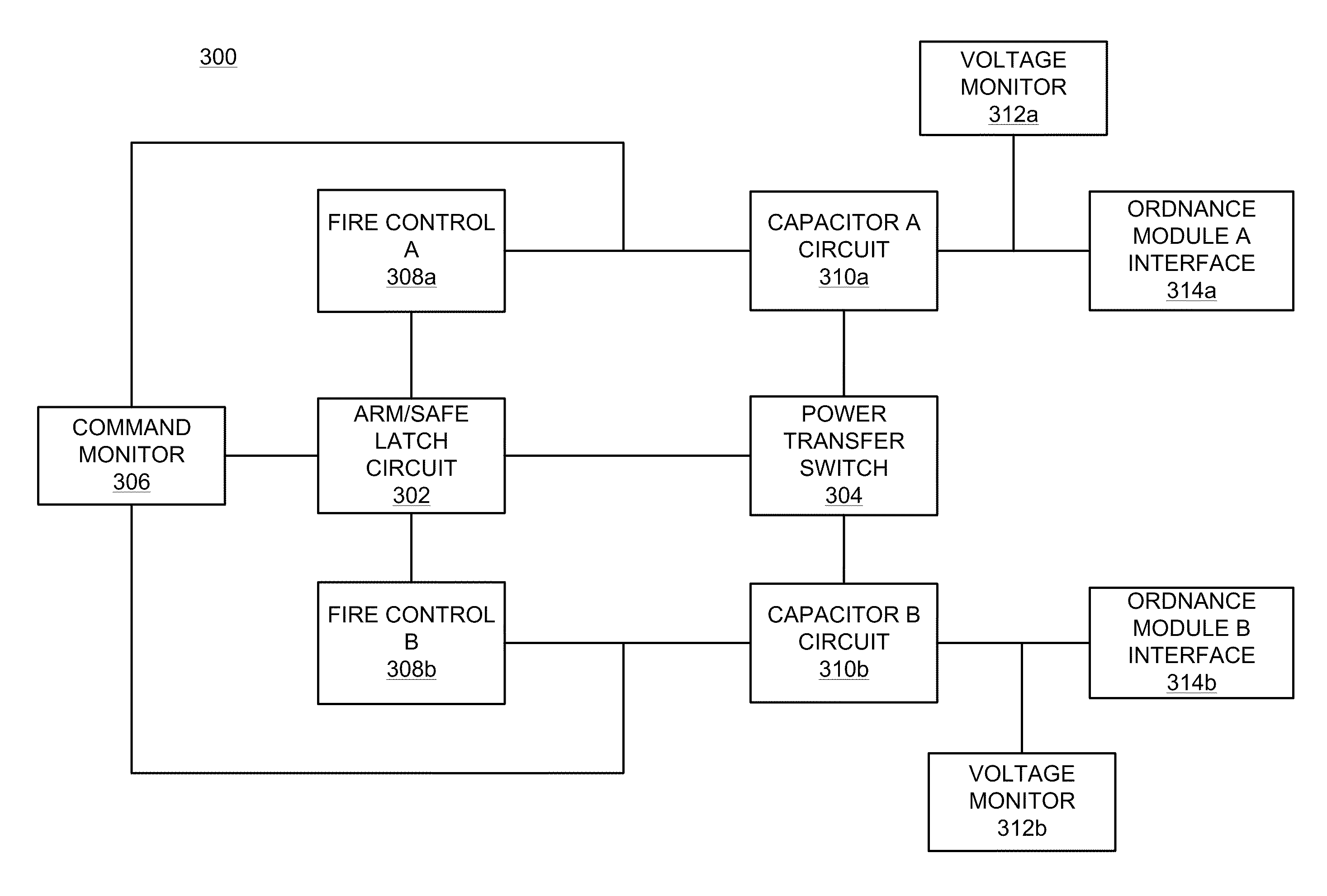
ActiveUS20110277620A1Low impedance connectionGood adhesionCosmonautic vehiclesIncandescent ignitionDetonatorElectricity
An ordnance firing system is disclosed that includes a reusable electronics module and an ordnance module, each enclosed in a separate, sealed housing. The electronics module housing encloses firing electronics for electrically triggering initiation of a detonator in the ordnance module. The electronics module detachably connects to the ordnance modules via a connector which extends away from the electronics module housing. The housing of the ordnance module is constructed to be blast-resistant to prevent detonation of the detonator from rendering the electronics module inoperable.
Owner:NORTHROP GRUMMAN SYST CORP
Optical fiber cable based intrusion detection system
InactiveUS6980108B1Improve integrityMinimize false alarmsMaterial analysis by optical meansUsing optical meansFiberUltrasound attenuation
There is provided an electronic security system for a perimeter structure that incorporates a fiber optic cable secured to the perimeter structure. Typically the perimeter structure is a fence. A light pulse is transmitted down the fiber optic cable. Mechanical attenuation devices disposed at various locations along the fiber optic cable are responsive to intrusion attempts. The mechanical attenuation devices produce measurable attenuations to the light pulse. Using backscattering light detection technology an intrusion attempt and the location of an intrusion is detected.
Owner:FIBER INSTR SALES
Systems and methods for facilitating electronic securities transactions
ActiveUS20120158568A1Efficient executionConvenient transactionFinanceFinancial transactionElectronic security
A method for facilitating securities transactions is shown. In one embodiment, the method provides for pricing shares of stock traded between anonymous parties without requiring pricing negotiations between parties. The method can include matching, via an electronic trading system, a first party and a second party in response to receiving contra binding orders for a security from the parties, transmitting, to each of the parties, an indication of the matching, receiving, via an electronic trading system, a first trade confirmation from the first party, determining, for the security, a midpoint of a price spread at the time the first trade confirmation was entered, receiving, via the electronic trading system, a second trade confirmation for the security from the second party, and executing, via the electronic trading system, a transaction for the security between the first and second parties, wherein the security price is determined in response to the determined midpoint.
Owner:INSTINET HLDG INC
Non-invasive monitoring of the effectiveness of electronic security services
InactiveUS20090044277A1Non-invasive monitoringMemory loss protectionDigital data processing detailsEngineeringNon invasive
Systems for the non-invasive monitoring of the effectiveness of a customer's electronic security services include a test generation engine for generating and launching a denatured attack towards a customer's network. A monitoring and evaluation agent is operatively coupled to the test generation engine and is adapted to monitor and evaluate the denatured attack. A recording and analysis engine is adapted to record and analyze the results of the denatured attack. Other systems and methods are also provided.
Owner:RPX CORP
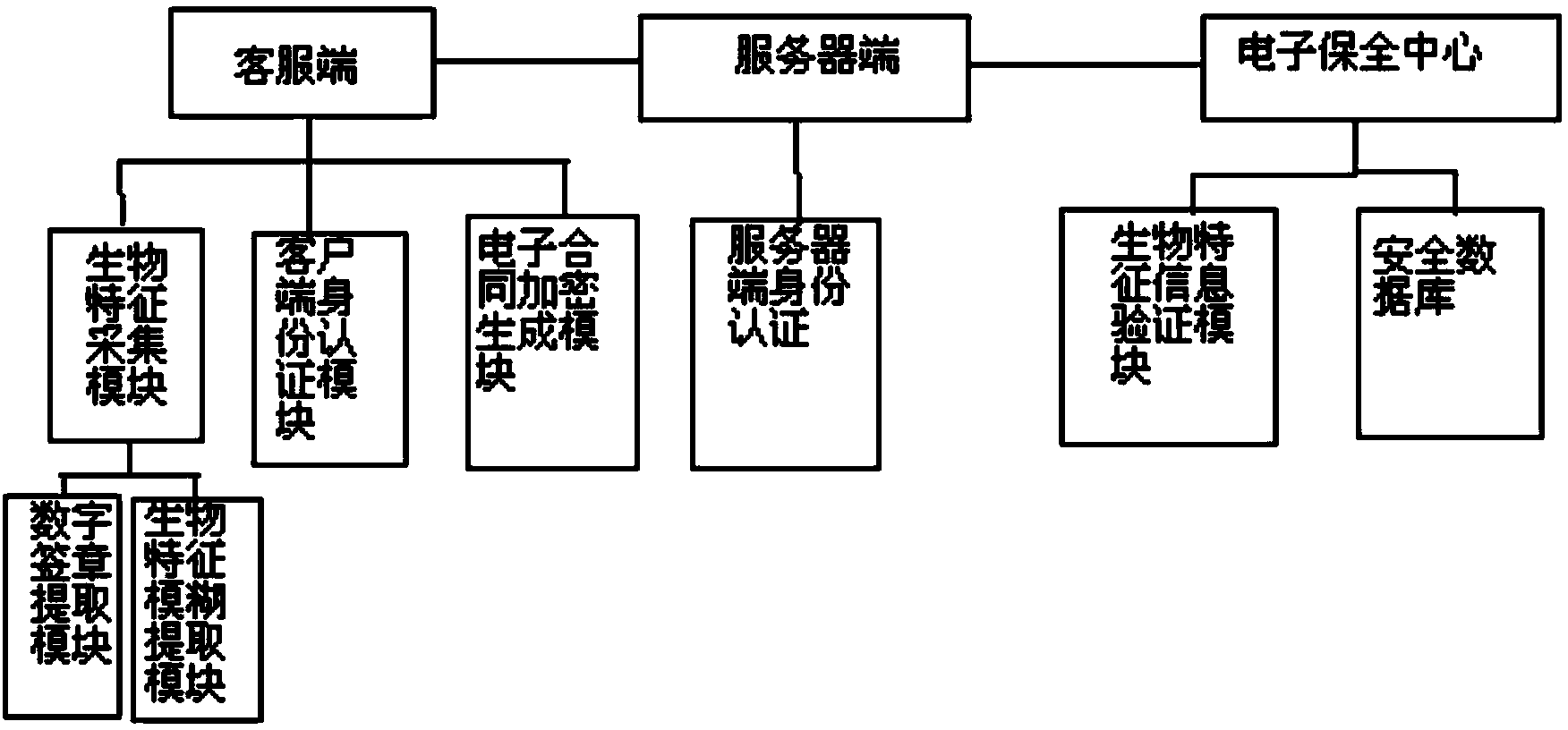
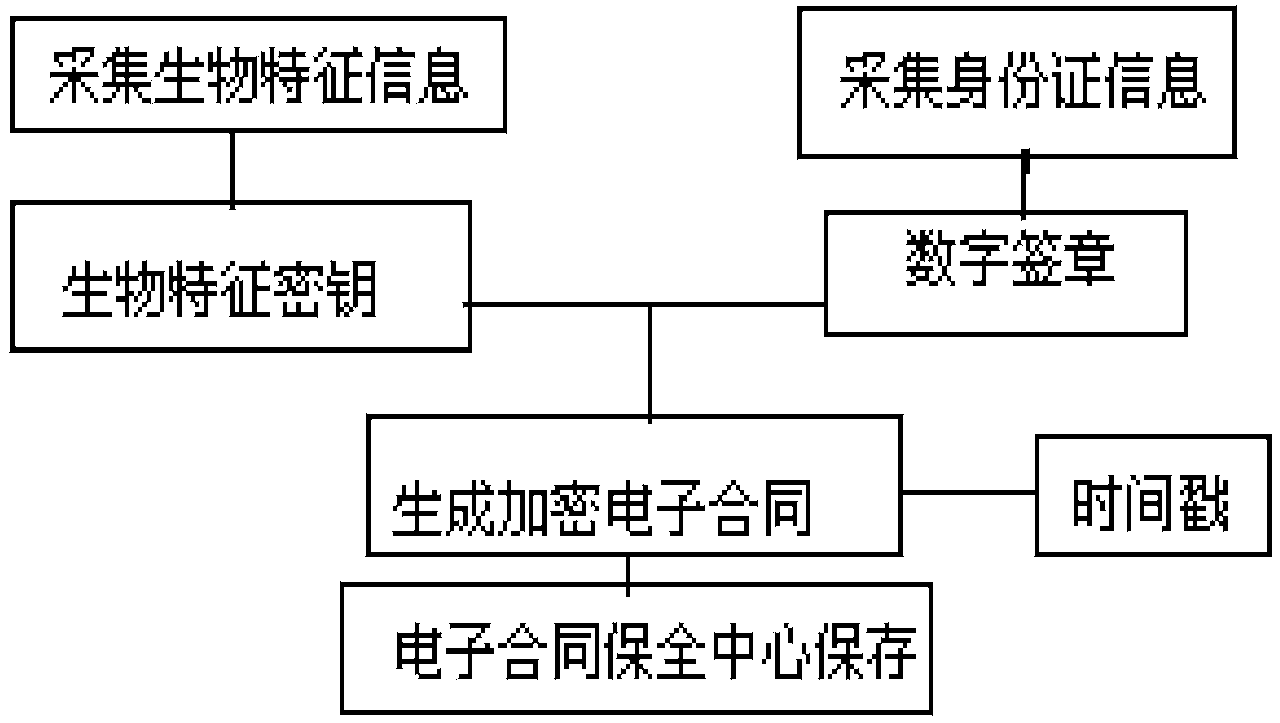
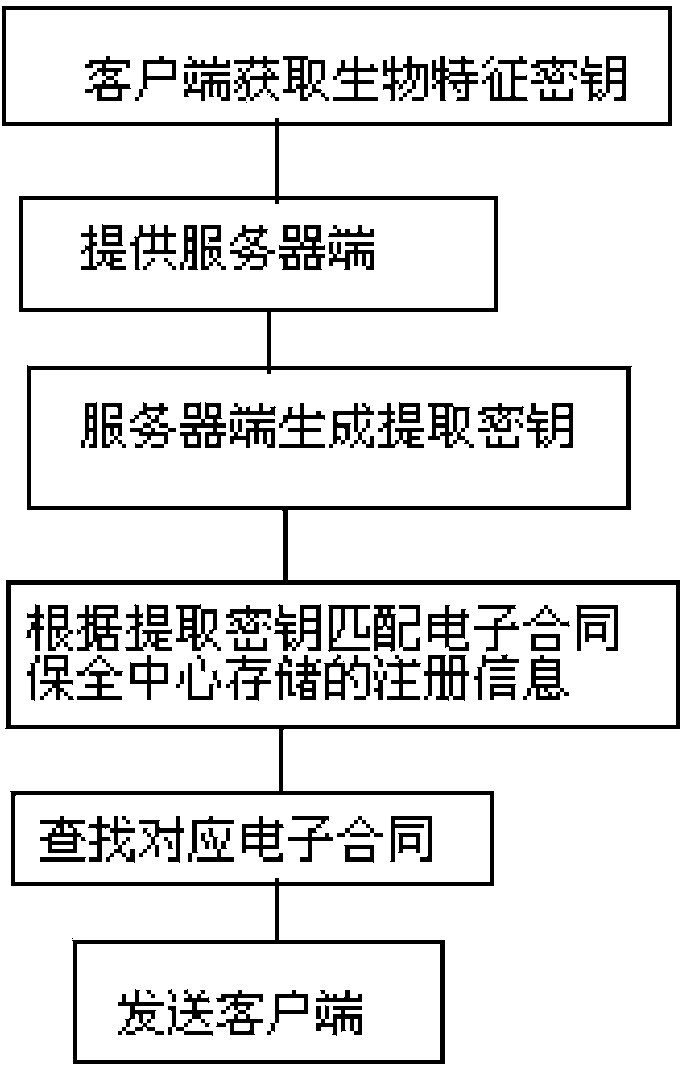
Electronic contract security system and method based on biological information identification
ActiveCN103679436AAuthentication is convenientImprove securityUser identity/authority verificationPayment protocolsInformation processingThird party
The invention discloses an electronic contract security system and method based on biological information identification, and relates to the technical field of computer information processing. In the prior art, electronic contracts can be tampered when the electronic contracts are handed to a third party to be saved, secrete keys generated by individual biological characteristics cannot be exactly the same, and exposure of characteristic information can be caused easily due to information matching and information extraction of different ways and methods. According to the electronic contract security system based on the biological information identification, encryption is carried out in the generated electronic contracts by using the biological information of applicants, identification card information of users are further overlaid to serve as the only authentication marks of the electronic contracts, time stamps are added to the electronic contracts, the electronic contracts are sent to a third party electronic security center for being saved and when clients need to have related services again or contract disputes appear, the secured electronic contracts are extracted from the electronic security center only by checking the biological characteristic information of the users and logging in an identification authentication server.
Owner:重庆信科通信建设监理咨询有限公司
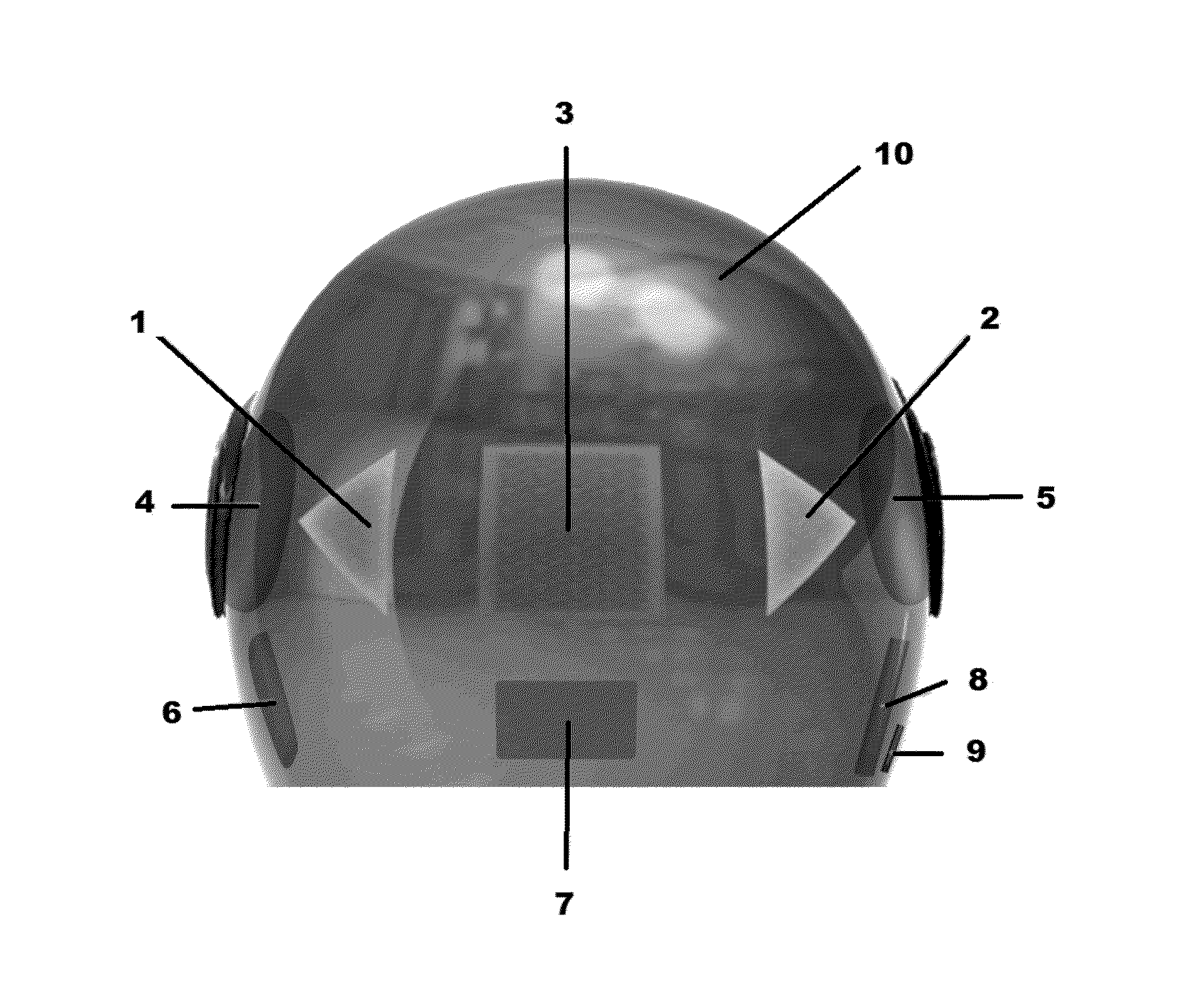
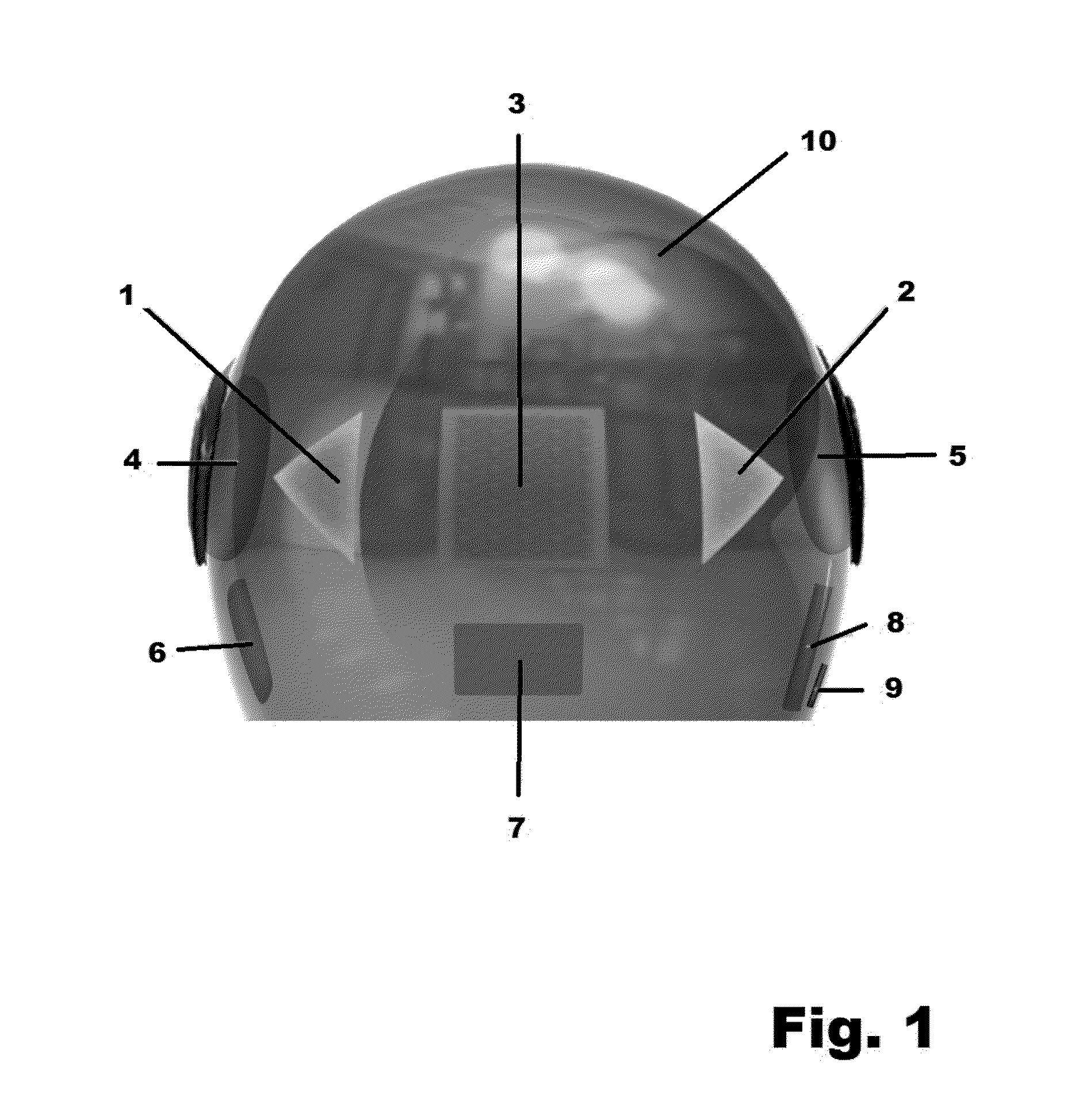
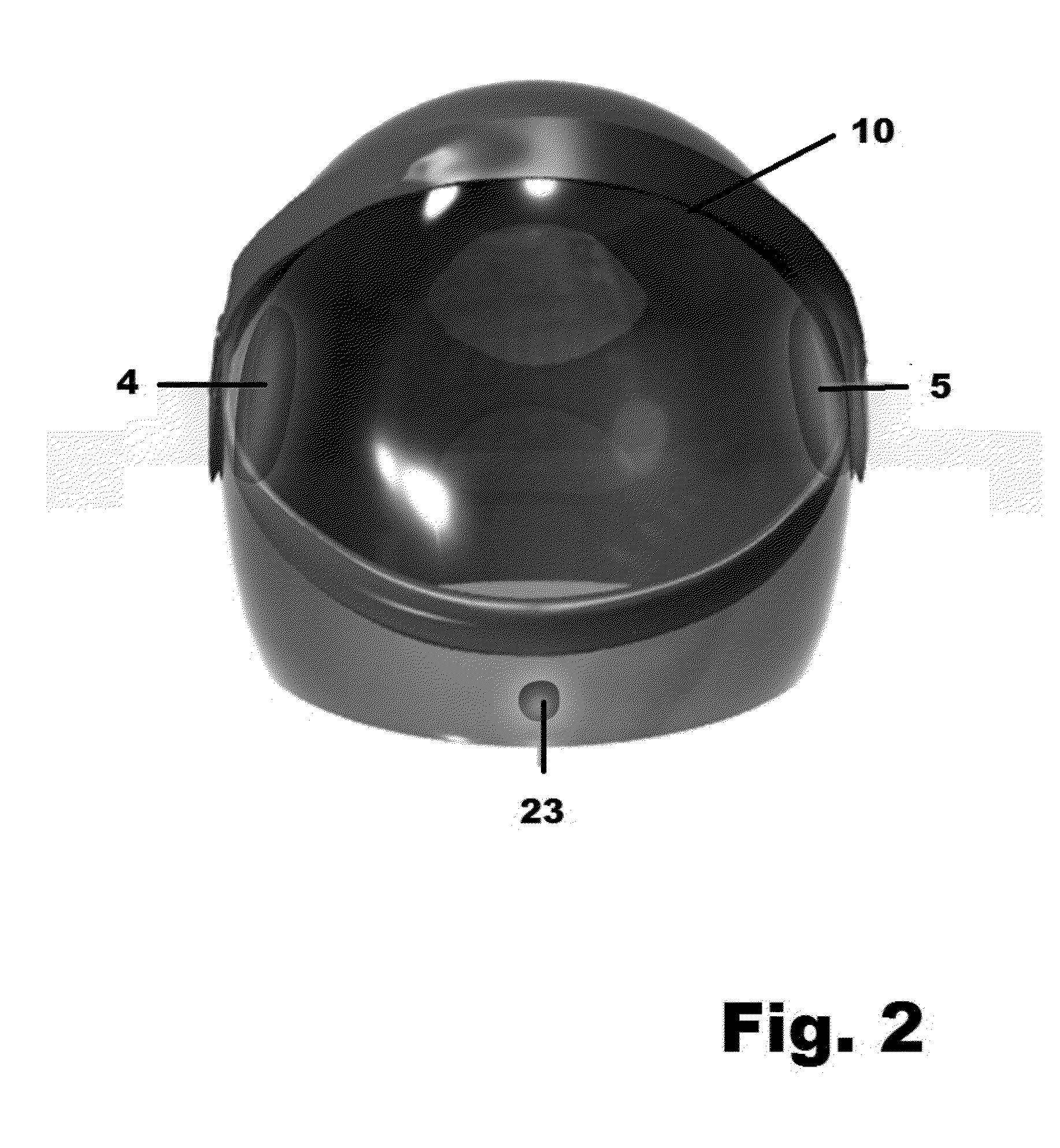
Motorcycle helmet with electronic safety features
InactiveUS20130093585A1Improve securityImprove security featuresOptical signalCycle safety equipmentsTransceiverEngineering
A system for enhancing the safety and functionality of a motorcycle or bicycle type helmet includes built-in turn and brake indicators, a transceiver for wireless communications with a corresponding transceiver mounted on a motorcycle, bicycle, or other vehicle, and a speaker and a microphone. The speaker and microphone permits two-way audio communications between the wearer of the helmet and others, either through a cellular network or through a wireless connection to the helmet of a passenger of the vehicle, and further permits such enhanced features as transmission of voice instructions to a navigation system and reception / playback of responsive navigation information, playback from a music system, and audio feedback that the turn signals are being operated, as well as anti-theft protection.
Owner:AMBANI AMAR VIMAL
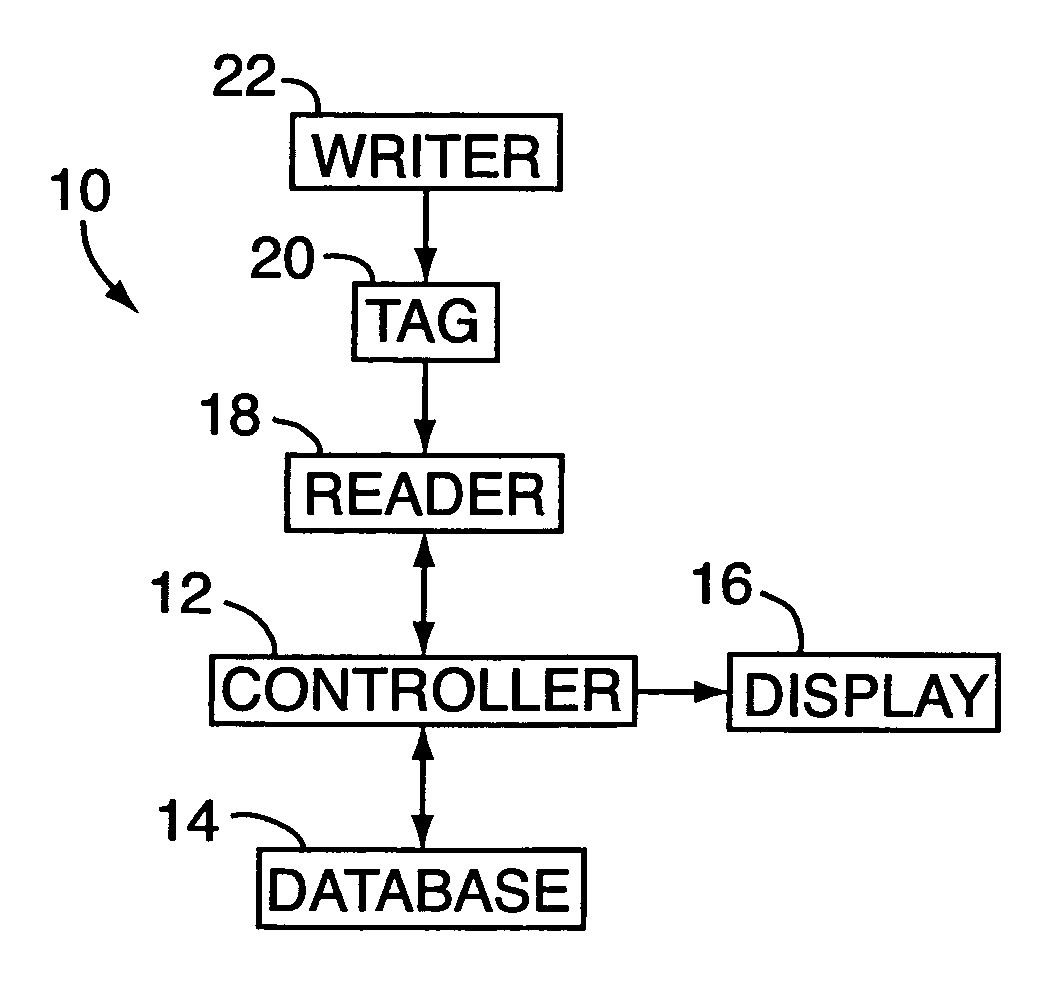
Electronic security system for monitoring and recording activity and data relating to institutions and clients thereof
A tracking system for use in identifying individuals of a group, each of the individuals having an associated data set indicative of the identity of those individuals, includes an electromagnetic identification apparatus configured with each of the individuals for providing an electromagnetic identification signal indicative of the content data set of that apparatus; a writer for use in encoding the electromagnetic identification signals with signals indicative of the individual onto the electromagnetic identification apparatus; a controller for receiving the encoded signals and for storing the encoded signals in a master database storage apparatus; and a reader remotely positioned from the controller and configured for communicating with the electromagnetic identification apparatus and receiving the encoded signals therefrom corresponding to the content data signal set, the reader also for providing the controller with signals indicative of the same.
Owner:UNITED SECURITY APPL ID
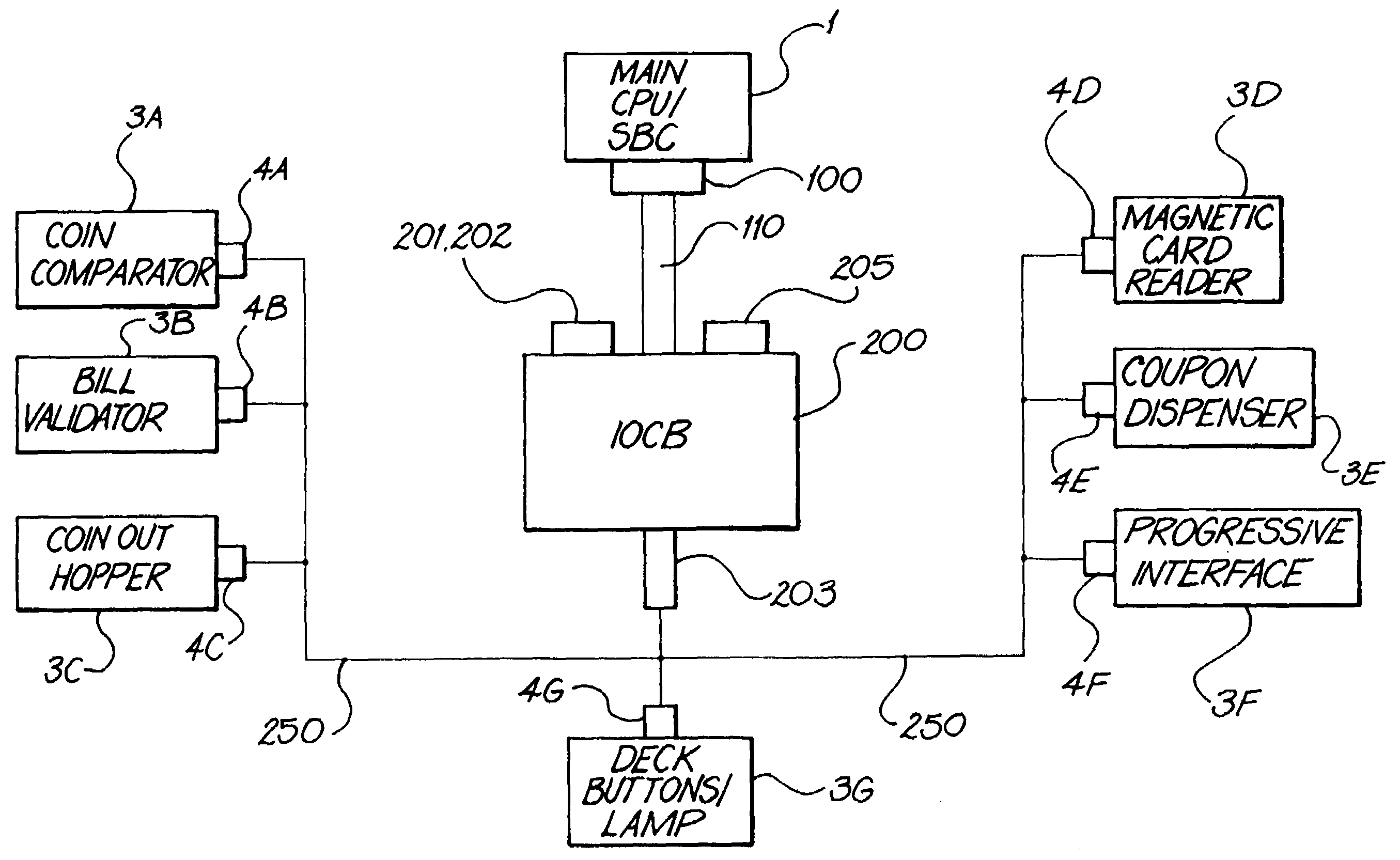
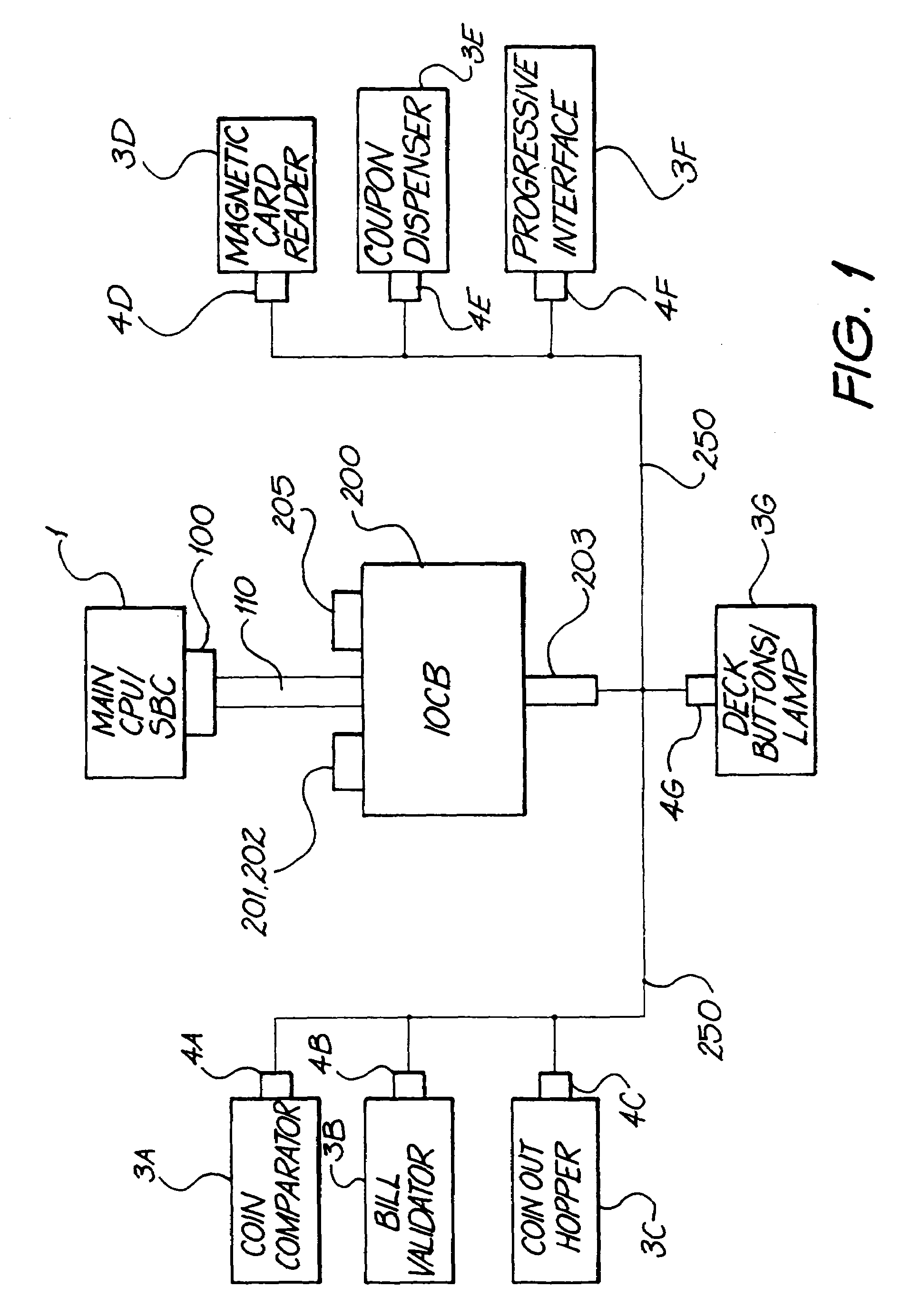
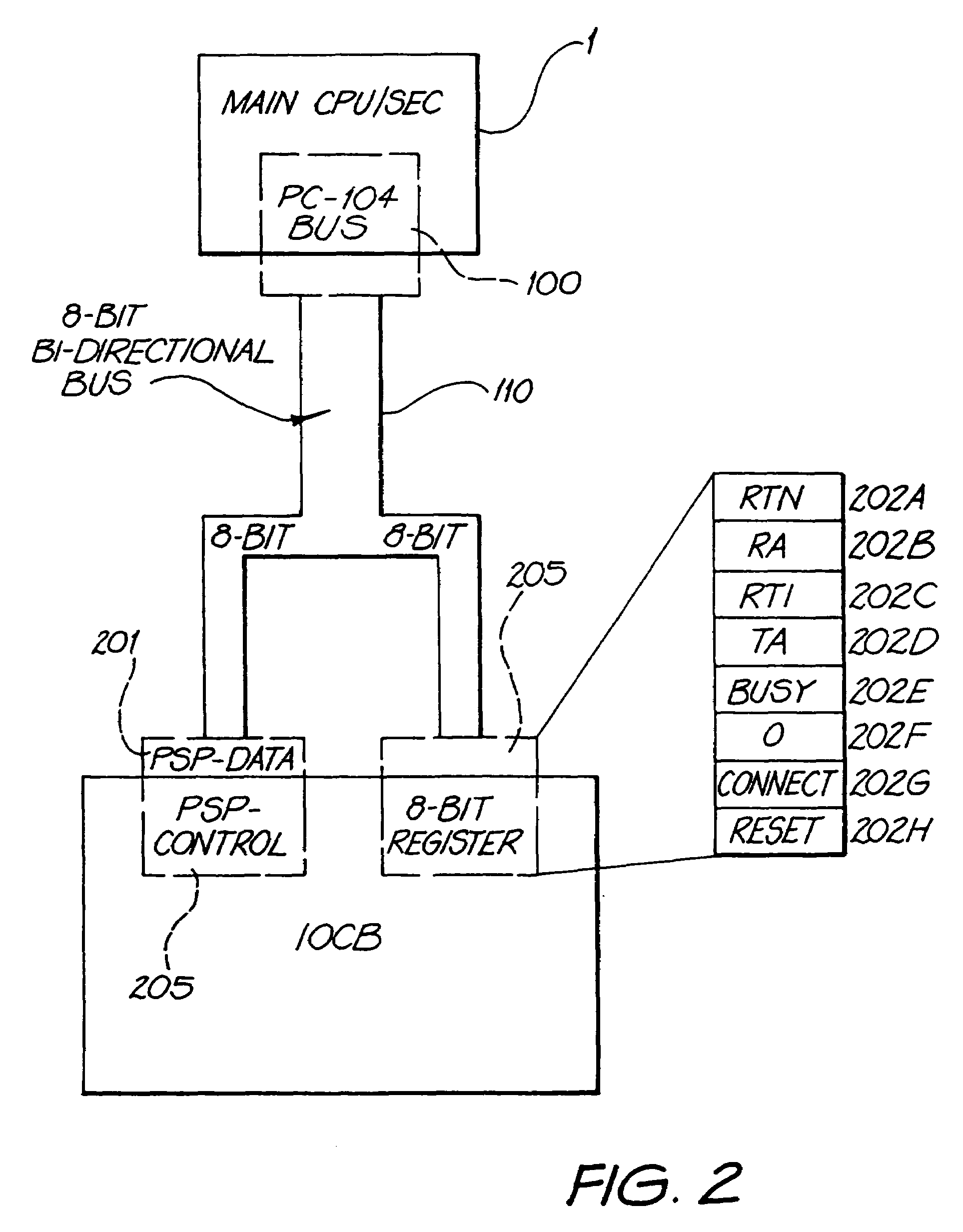
Secured inter-processor and virtual device communications system for use in a gaming system
InactiveUS7093040B1Reliable dataFacilitate communicationDigital computer detailsInternal/peripheral component protectionCommunications systemMultidrop bus
The invention comprises an electronically secured inter-processor and virtual device communications system, with an input / output controller board, a multi-drop bus interface to multiple devices, and a parallel interface to an industry standard single board computer. The invention assigns a bus address and virtual identification number to each device and controls communications between the main central processing unit and the devices through a Plug-n-Play protocol.
Owner:ARISTOCRAT TECH AUSTRALIA PTY LTD
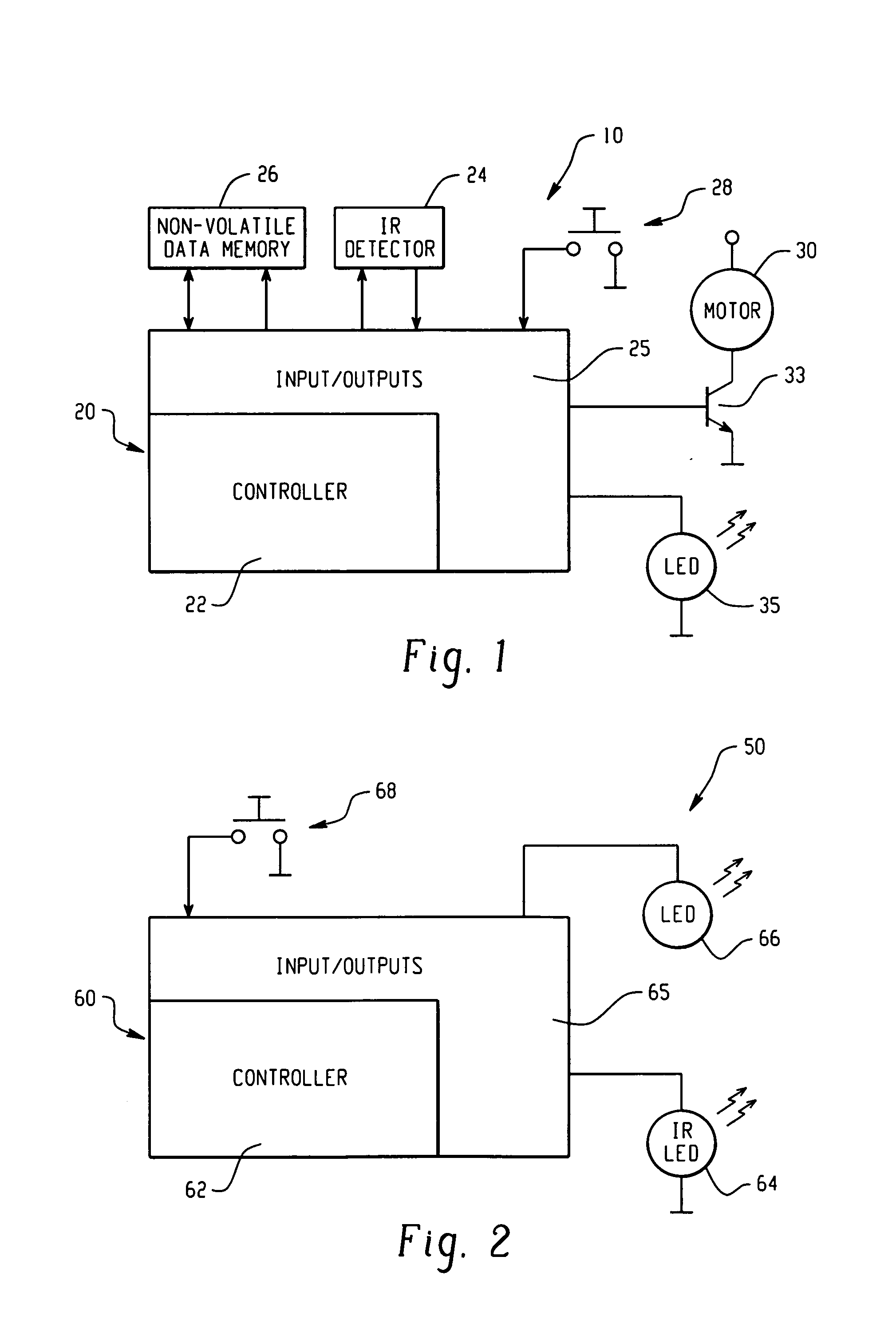
Electronic security device
InactiveUS7948359B2Electric signal transmission systemsDigital data processing detailsElectronic securityAuthorization
Owner:MASTER LOCK CO INC
Electronic securities marketplace having integration with order management systems
An electronic trading marketplace (ETM) communicates with interfacing modules interfacing directly with order management systems (OMS's) at trading institutions. The interfacing modules automatically transmit orders from the OMS databases to the ETM and update the OMS databases in response to orders executed at the ETM. Traders can communicate with the ETM to anonymously negotiate trades of securities.
Owner:LIQUIDNET HLDG
Methods and apparatus for an electronic drop safe
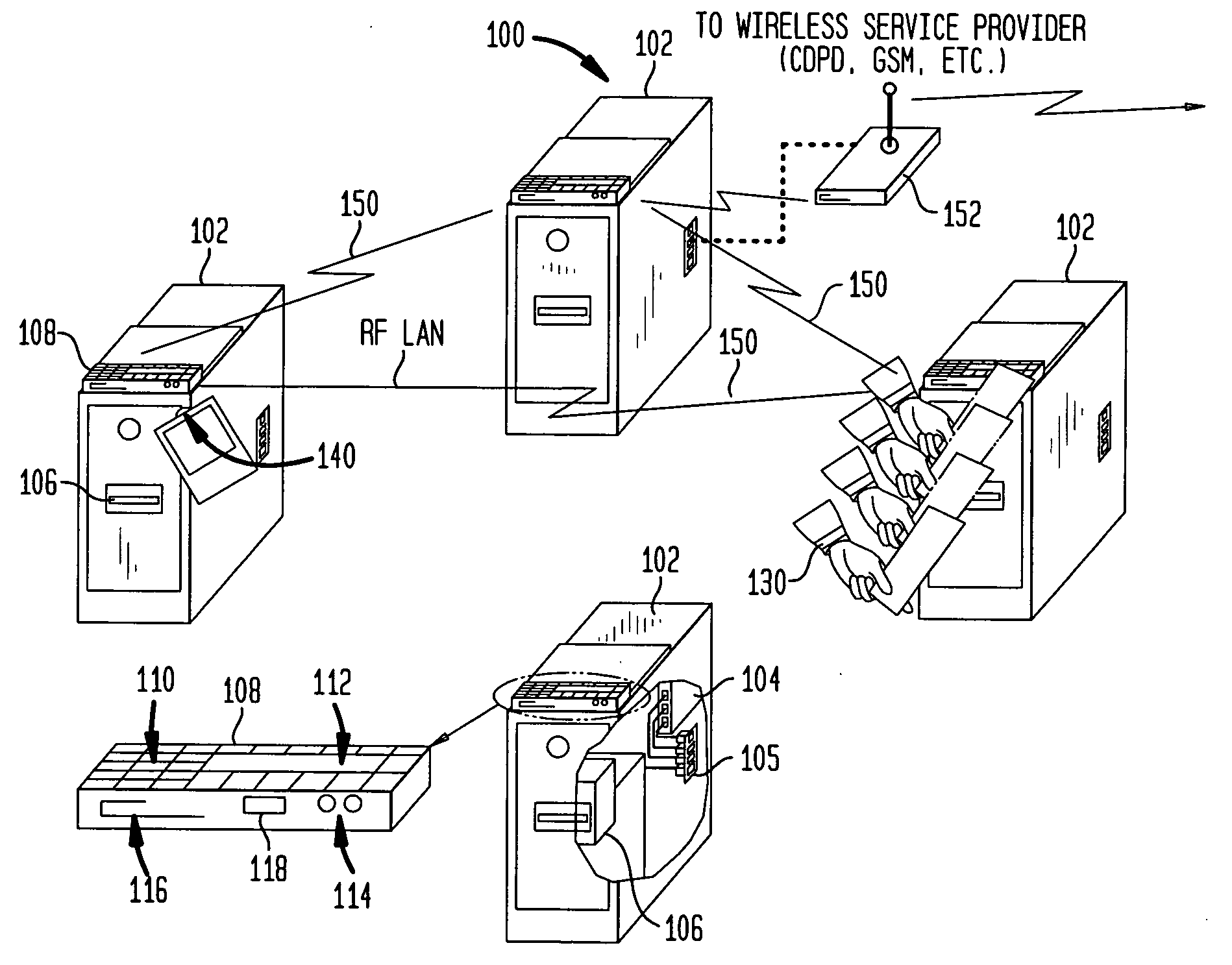
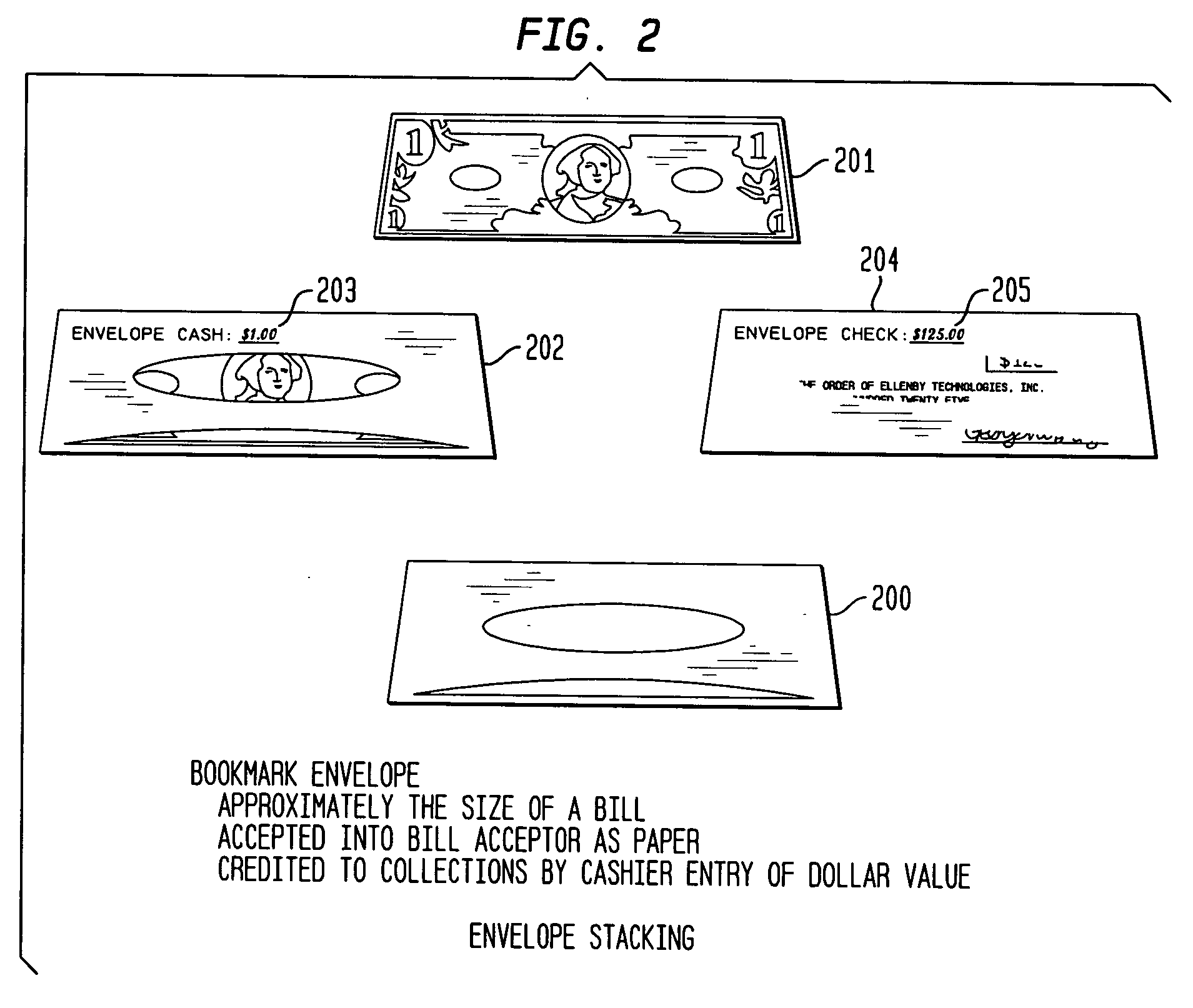
InactiveUS20060253332A1Improve business satisfactionHand manipulated computer devicesCoin/currency accepting devicesTelecommunications linkMagnetic tape
Systems and techniques for providing an improved electronic safe are described. In one aspect, an electronic safe is provided with enhanced security, increased functionality and ease of use. The electronic safe may accept both cash and non-cash deposits, identifying tags and envelopes or folders. A wireless tag may be used to identify the person making deposits. A plurality of electronic safes may be networked together in a wireless local area network. The wireless local area network of electronic safes may be wirelessly networked with an off site host system. In another aspect, an electronic safe is provided with a wireless communications link for communicating with a handheld terminal which may be used to update the electronic safe and initiate the generation of automatic reports. In another aspect, an electronic safe automatically generates reports detailing the operation of the safe. The electronic safe may predict the time when a cassette for storing deposits will be full.
Owner:ELLENBY TECH
Order management system and method for electronic securities trading
ActiveUS7752123B2Eliminate needEnhance profit or mitigate lossFinanceProgram synchronisationOrder management systemClient-side
A system includes a communication module to communicate with at least one client; and a server to process a task identified by the client, the task associated with an account, the server including a plurality of account-centric pipelines, one or more account-centric pipelines each configured to process the task.
Owner:EZE CASTLE SOFTWARE
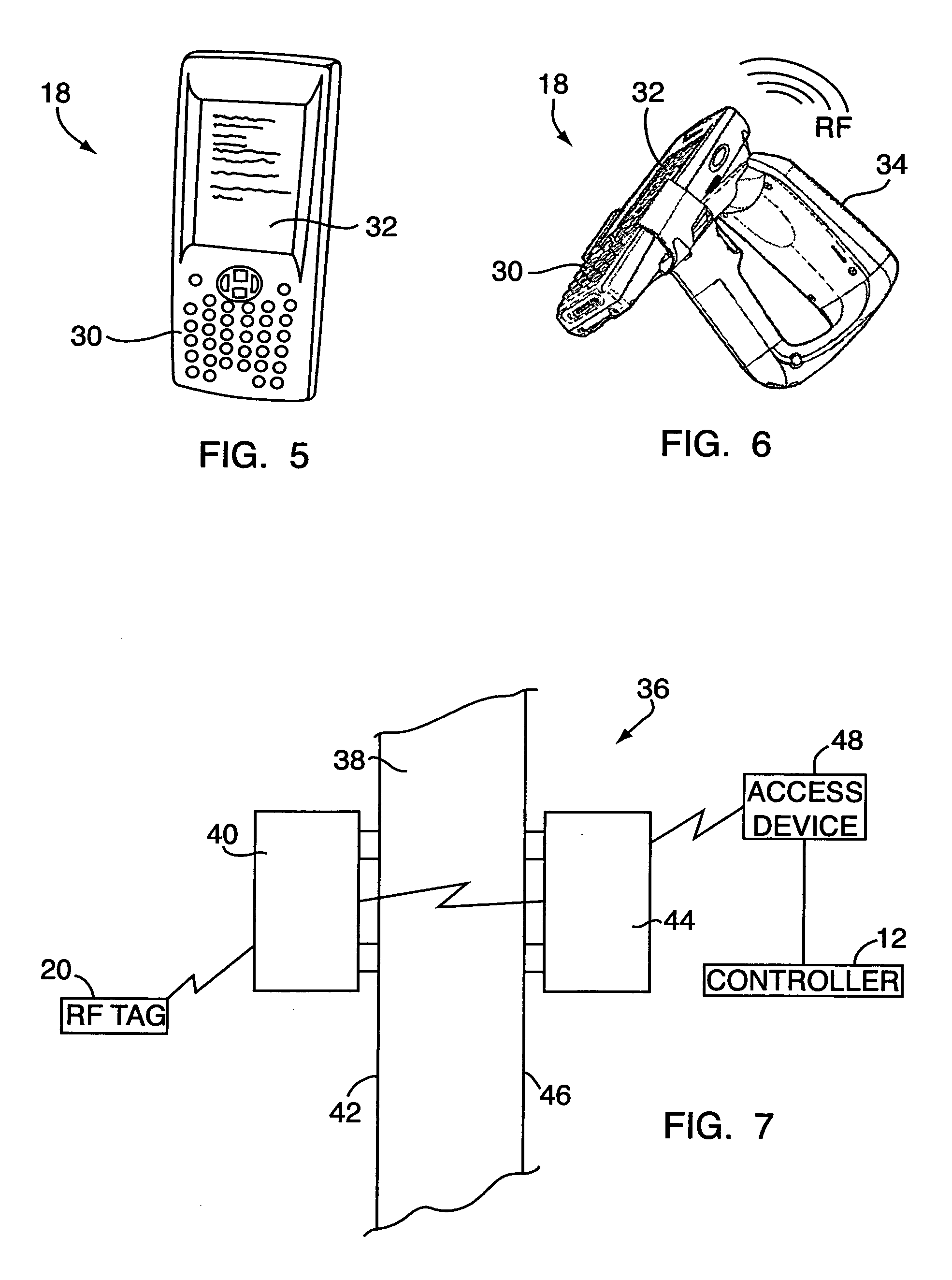
Electronic security system for monitoring and recording activity and data relating to persons or cargo
ActiveUS20070008135A1Registering/indicating time of eventsCo-operative working arrangementsElectronic securityComputer science
A security system and method for the limited monitoring of visitors to a country or territory has an input component such as a keyboard or electronic reader configured for receiving information pertaining to a visitor's stay in a country or territory. The information includes the scheduled departure of the visitor. A controller communicates with the input component, and a database communicates with the controller for storing the information pertaining to the visitor's stay. The controller is configured for polling the database to determine if the visitor has departed as scheduled, and for sending an alert if the visitor has not left as scheduled.
Owner:UNITED SECURITY APPL ID
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com