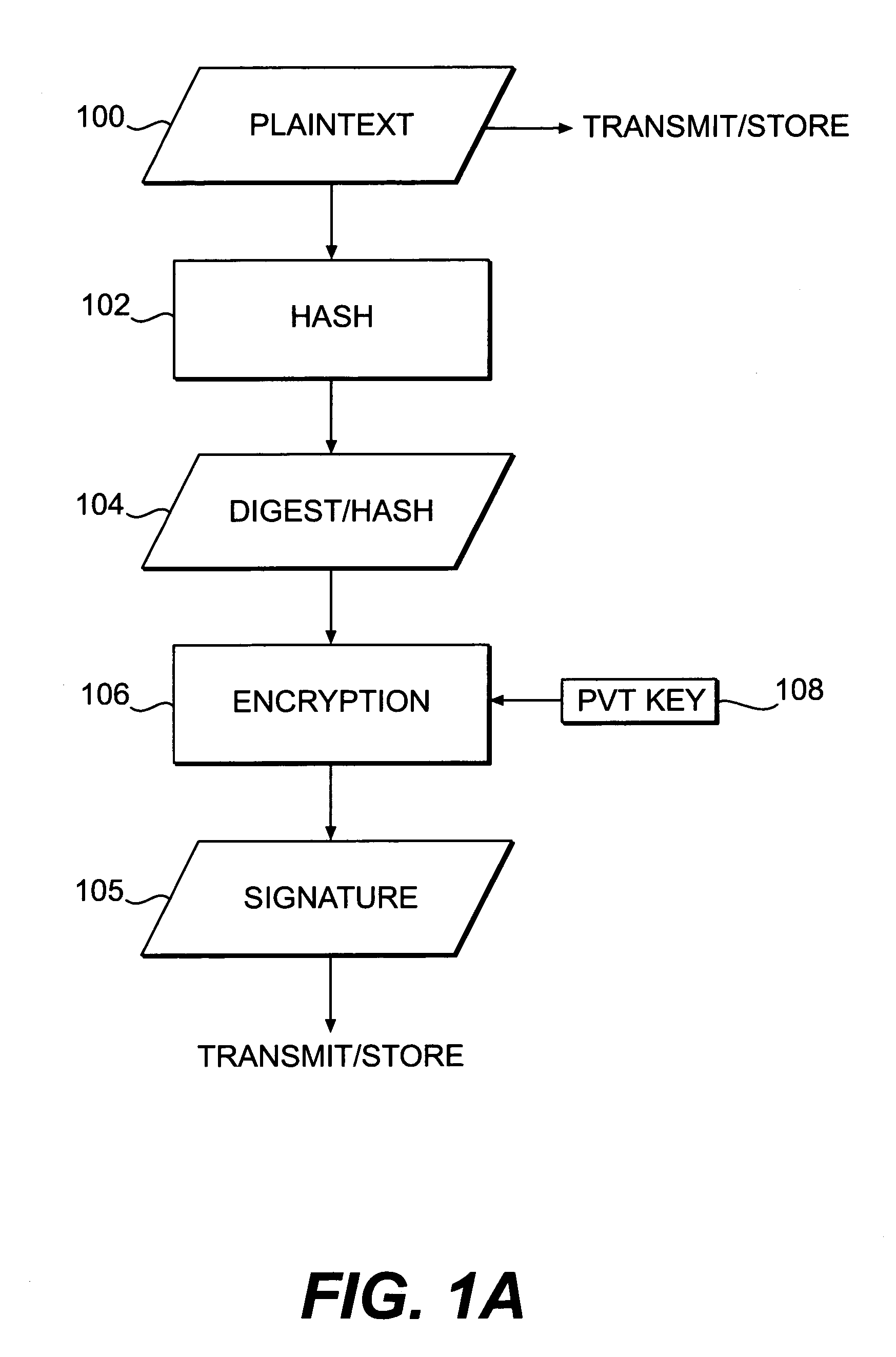
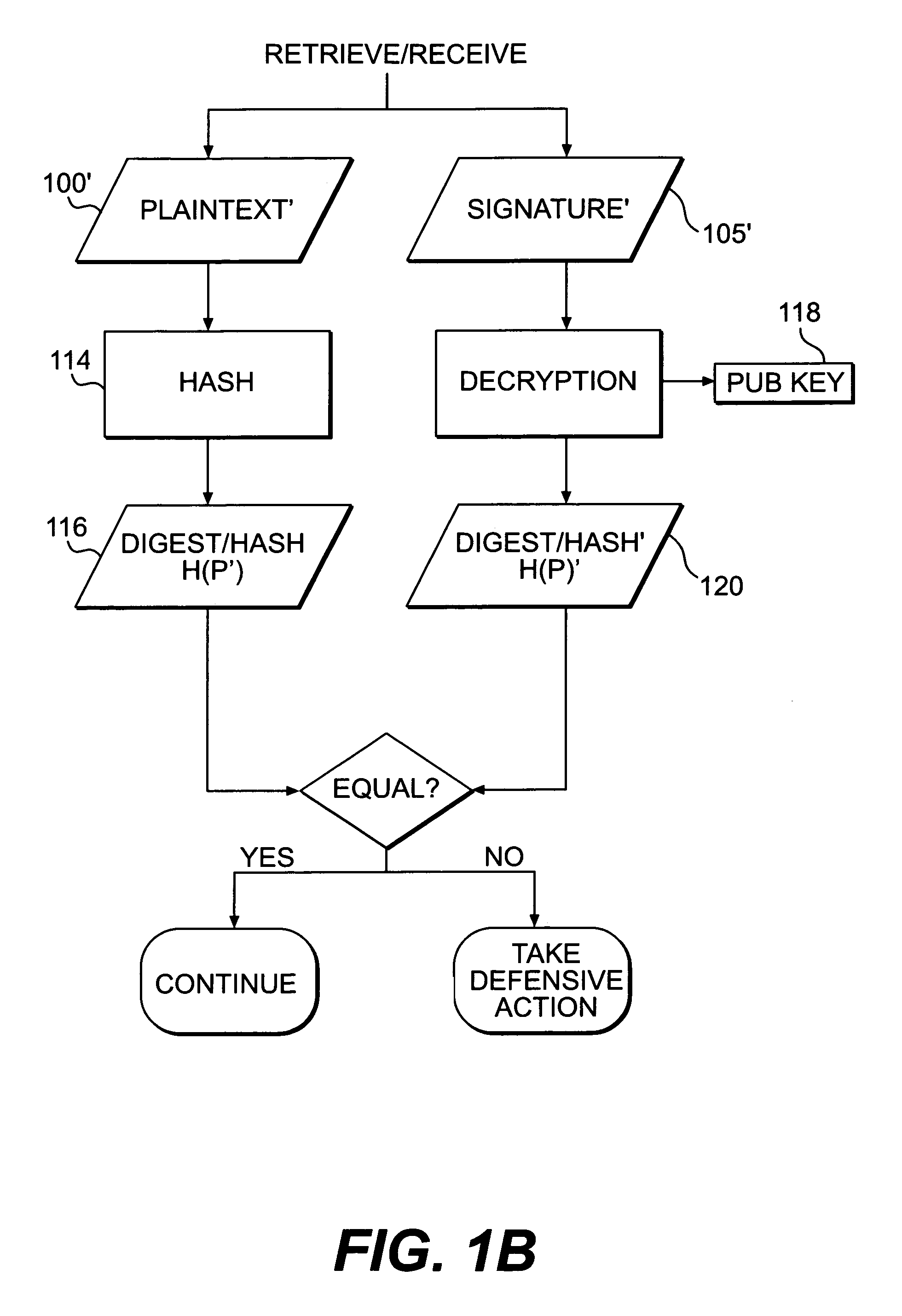
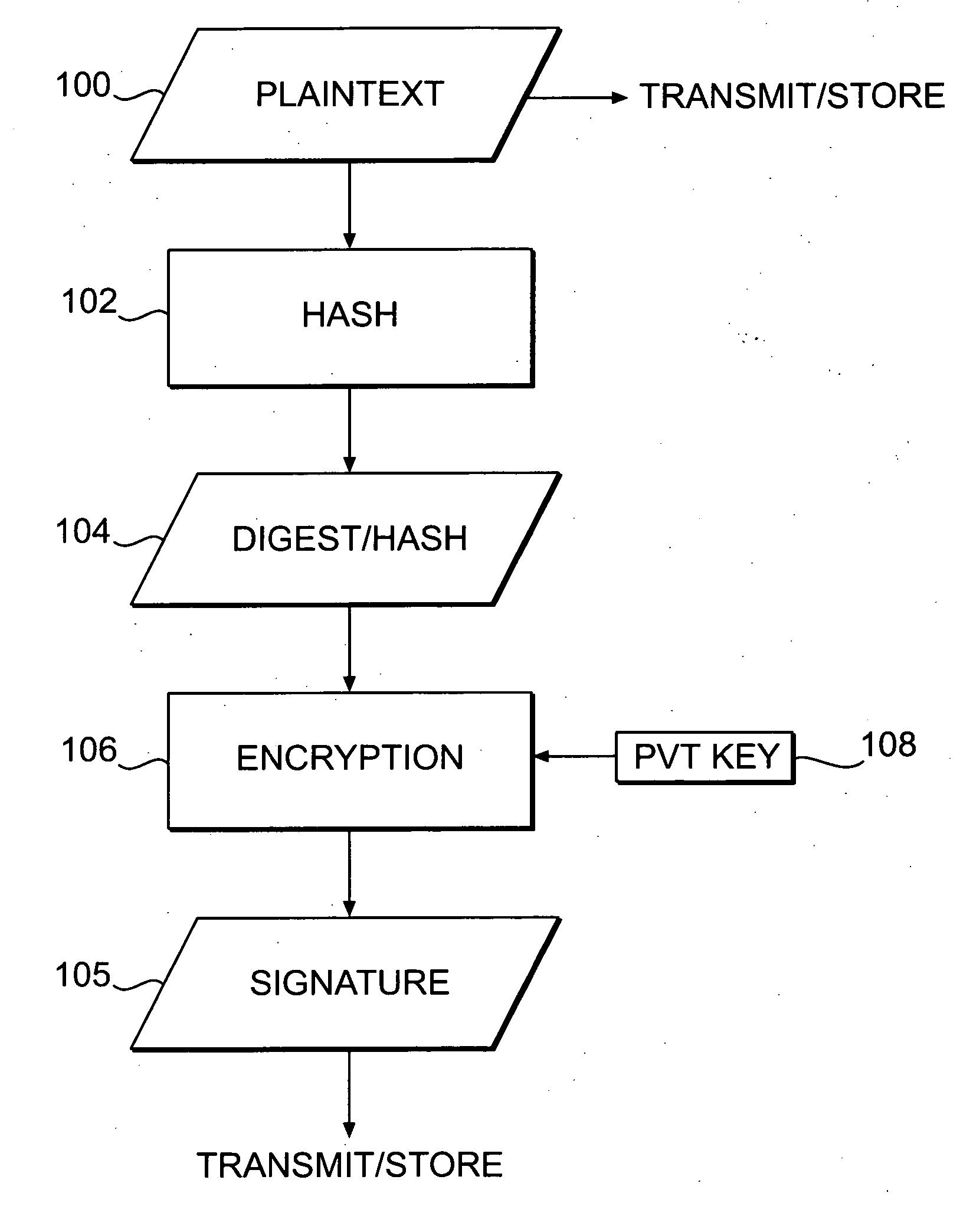
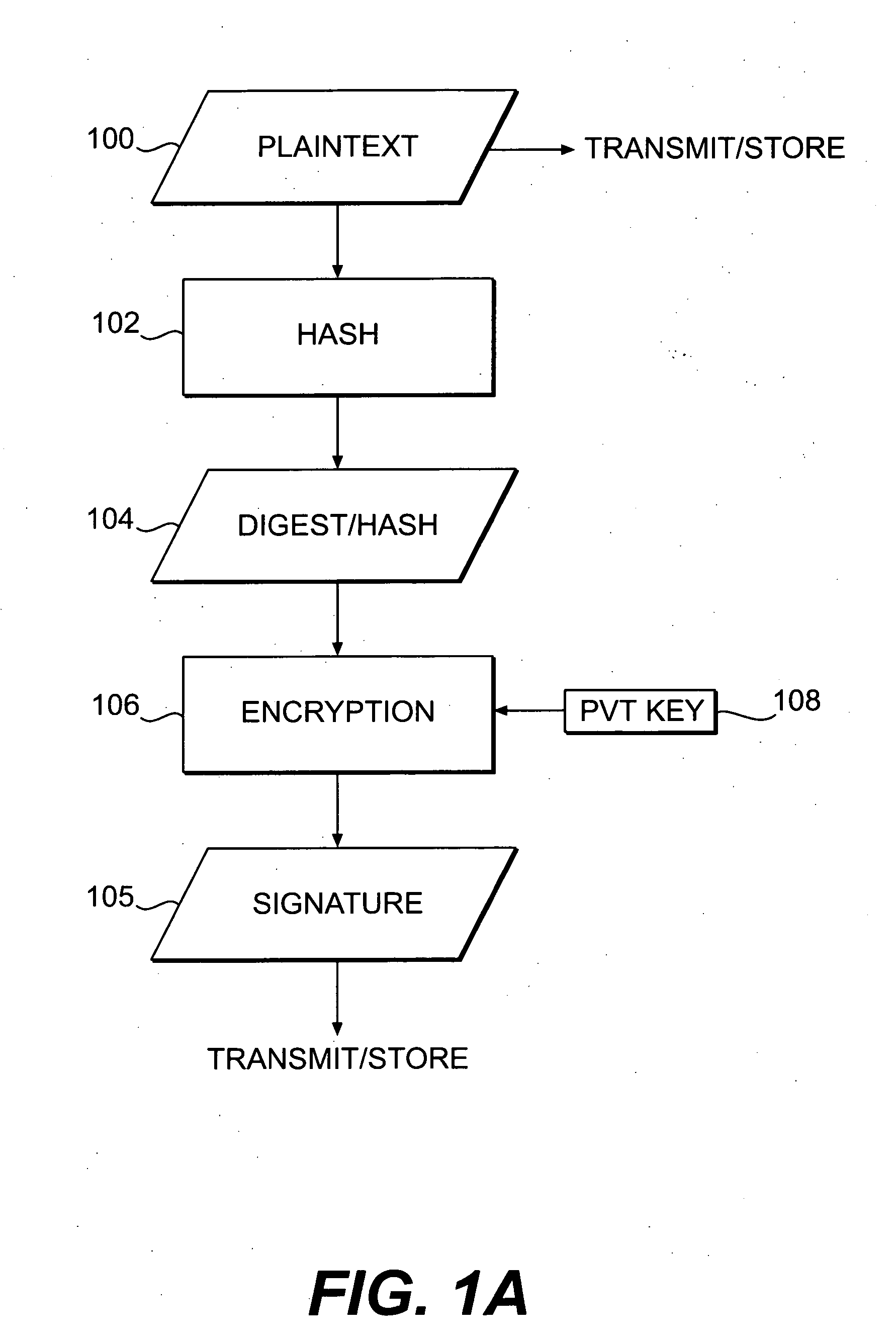
Patents
Literature
221results about How to "Authentication is convenient" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
User-convenient authentication method and apparatus using a mobile authentication application
ActiveUS20140040628A1Authentication process can be made convenientCost-effectiveDigital data authenticationCoding/ciphering apparatusUser authenticationApplication software
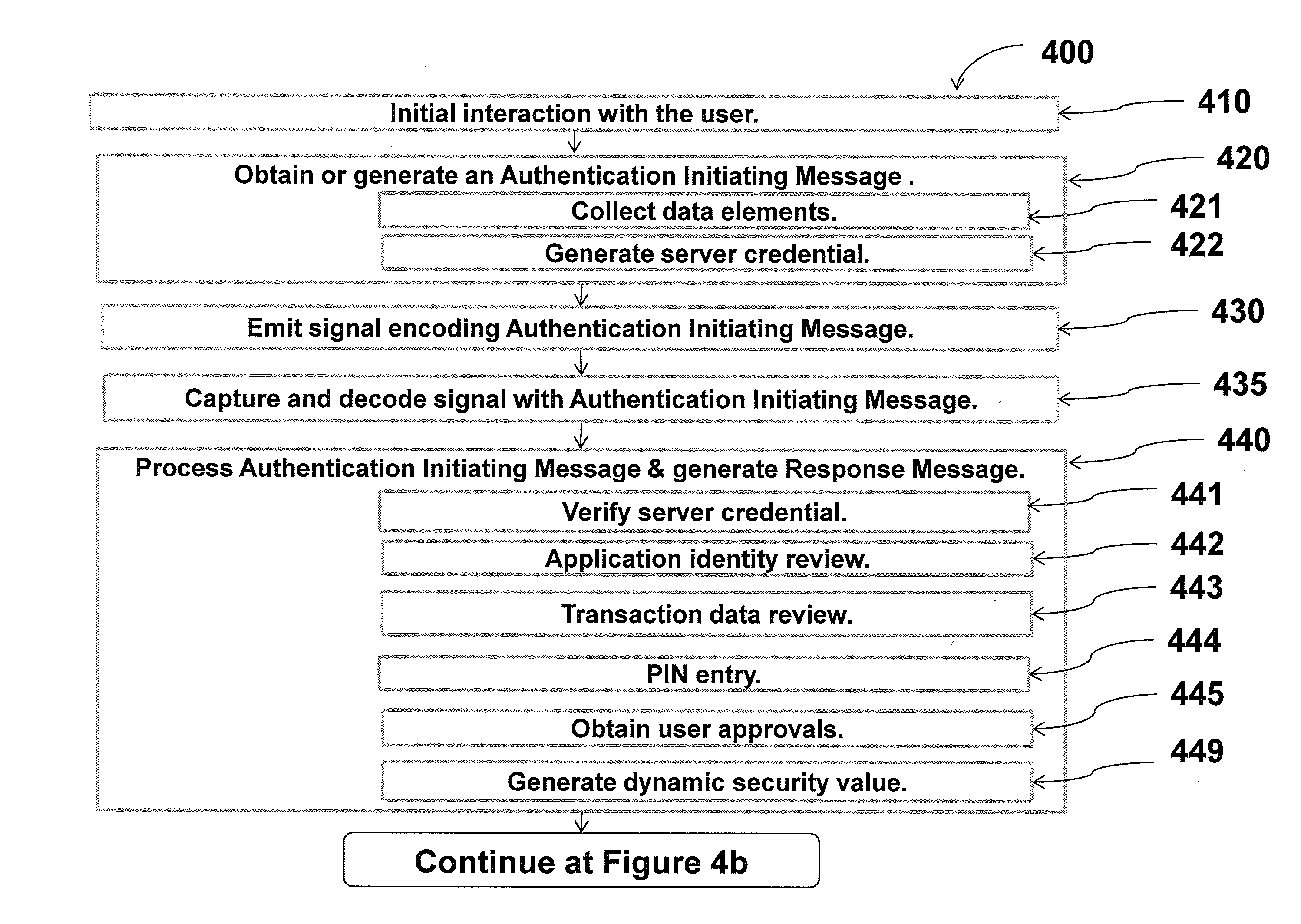
Methods, apparatus, and systems for securing application interactions are disclosed. Application interactions may be secured by, at a user authentication device, capturing a signal emitted by an access device encoded with an authentication initiating message including an application identifier, decoding the signal and obtaining the authentication initiating message, retrieving the application identifier, presenting a human interpretable representation of the application identity to the user, obtaining user approval to generate a response message available to a verification server, generating a dynamic security value using a cryptographic algorithm that is cryptographically linked to the application identity, and generating a response message including the generated dynamic security value; making the response message available to a verification server; and, at the verification server, receiving the response message, verifying the response message including verifying the validity of the dynamic security value, and communicating the result of the verification of the response message to the application.
Owner:ONESPAN NORTH AMERICA INC
Mouse performance identification
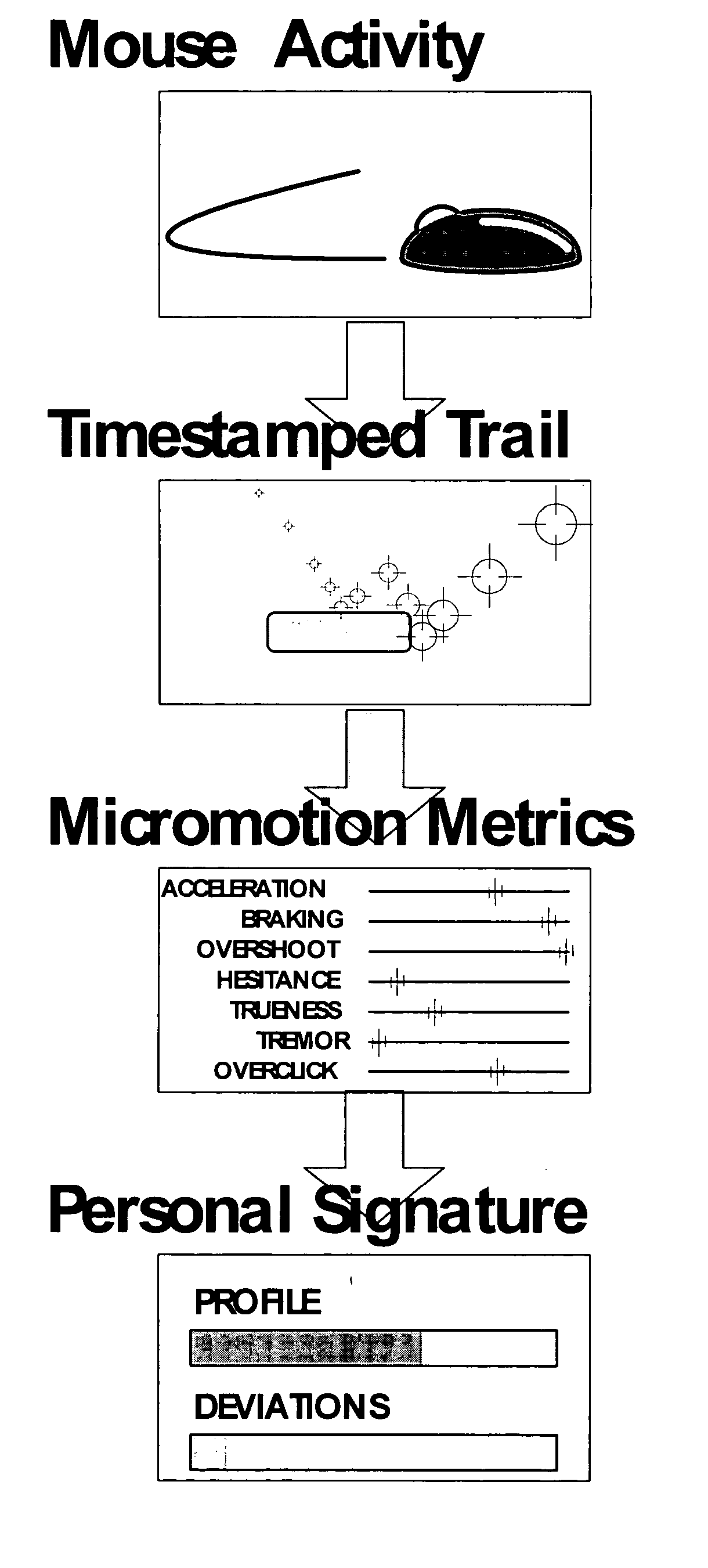
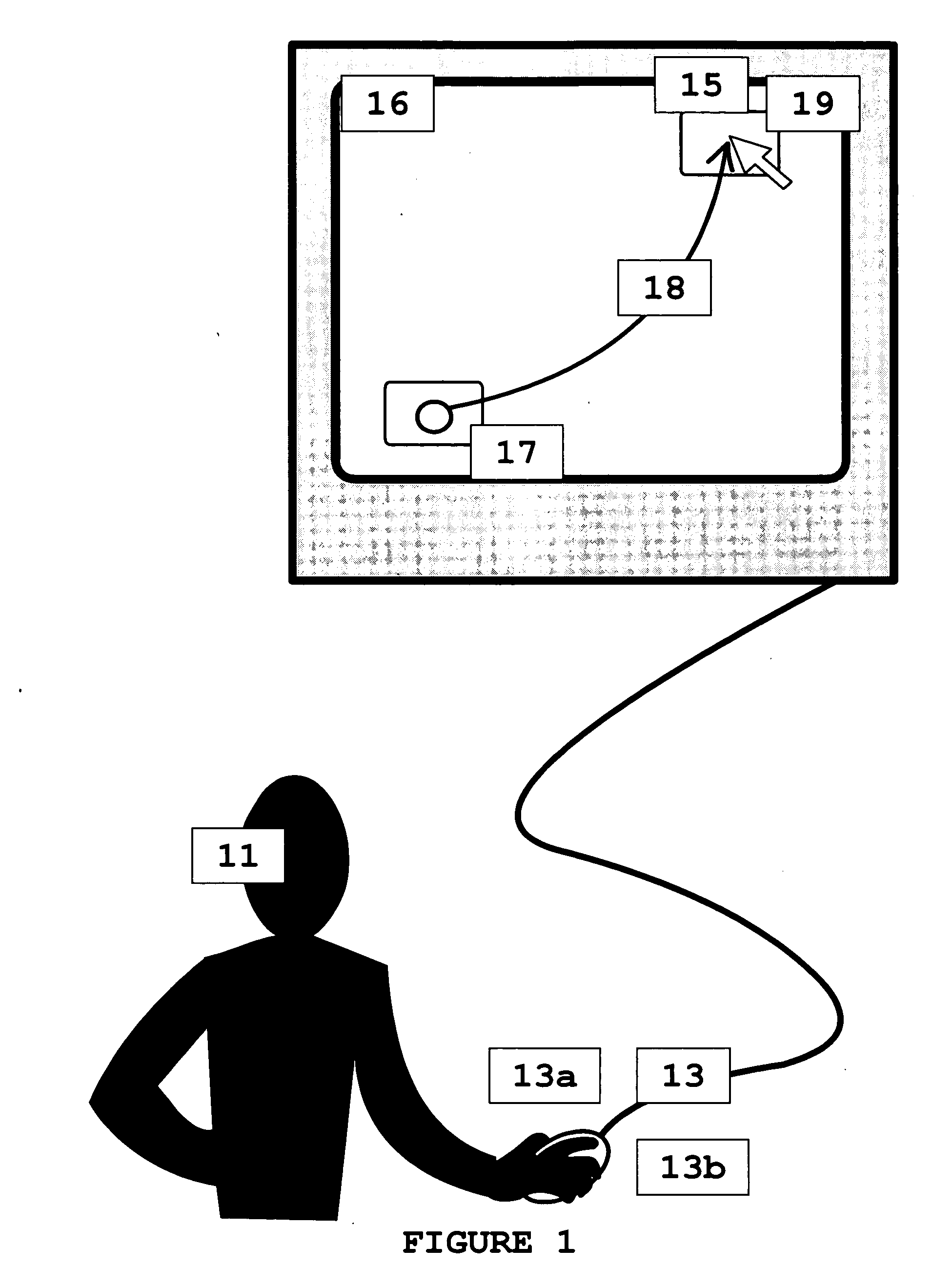
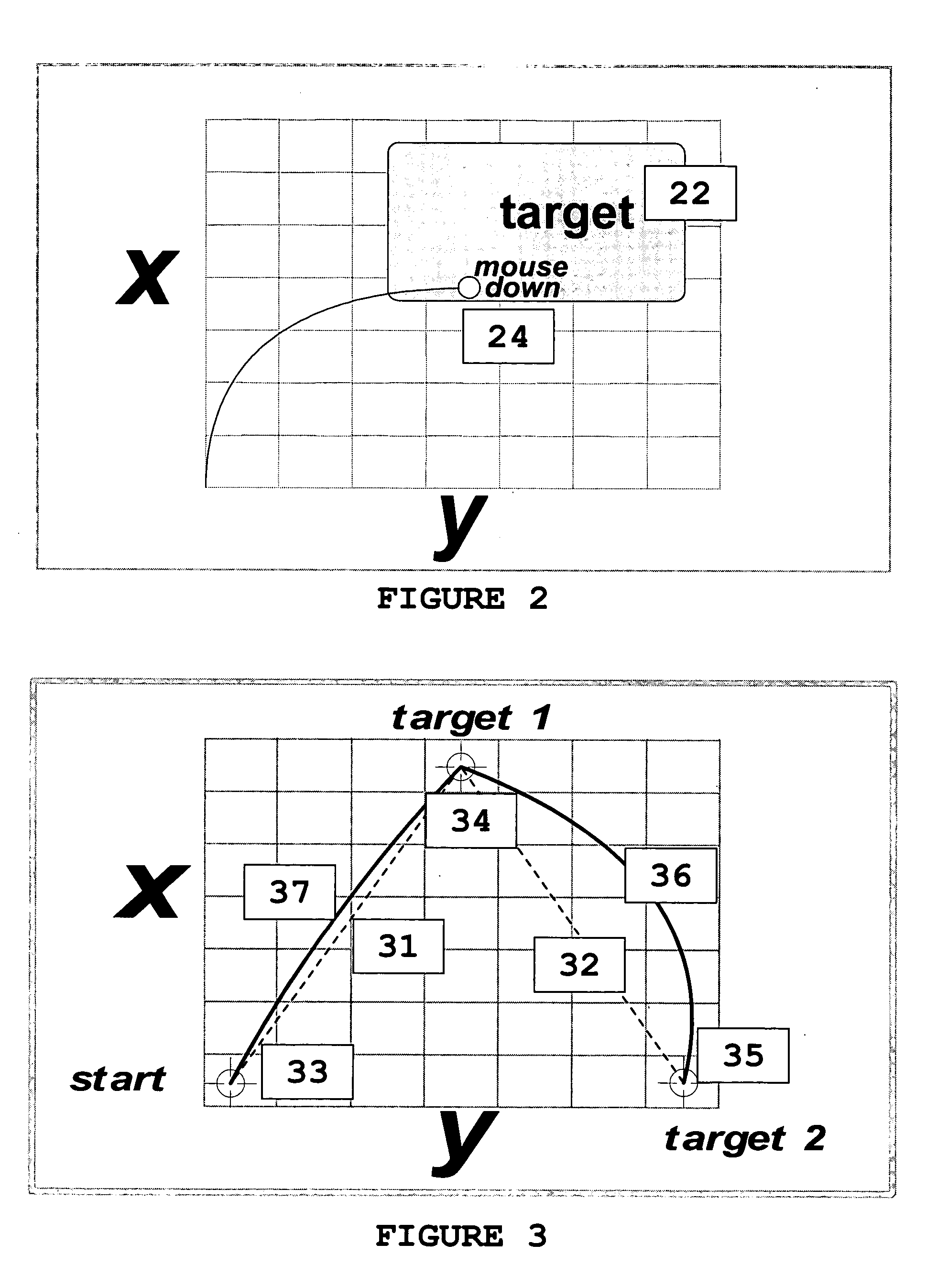
InactiveUS20050008148A1Authentication is convenientDigital data processing detailsUser identity/authority verificationSoftwareComputer science
Methods and system for facilitating authentication of users of a mouse device. Different individuals have different ways of manipulating a mouse to enter mouse-clicks requested via an on-screen image or other software programs. An individual's characteristic way of manipulating the mouse is determined and stored and later retrieved to facilitate verification of a user's identification.
Owner:JACOBSON DOV
Method and apparatus for efficient package delivery and storage
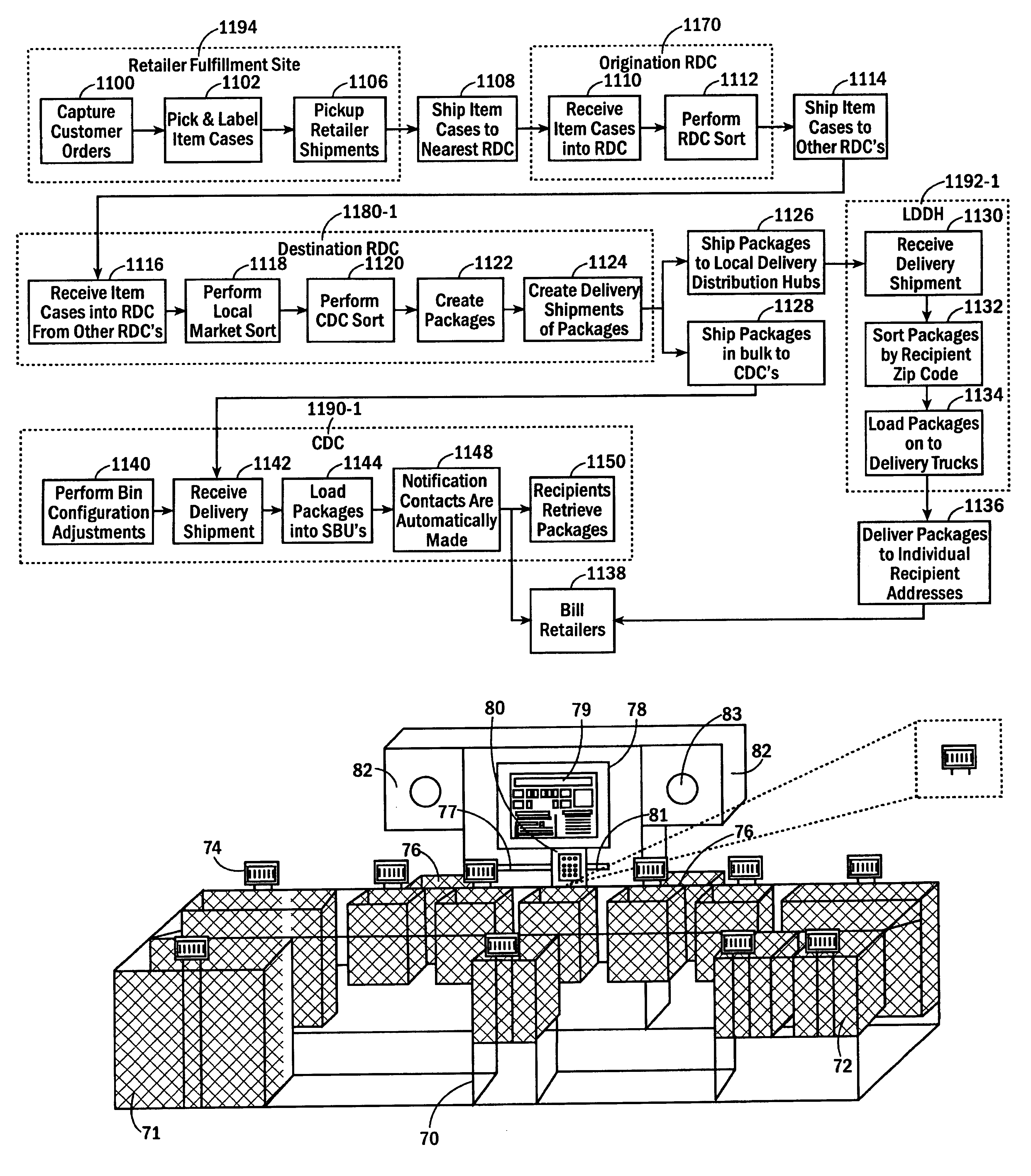
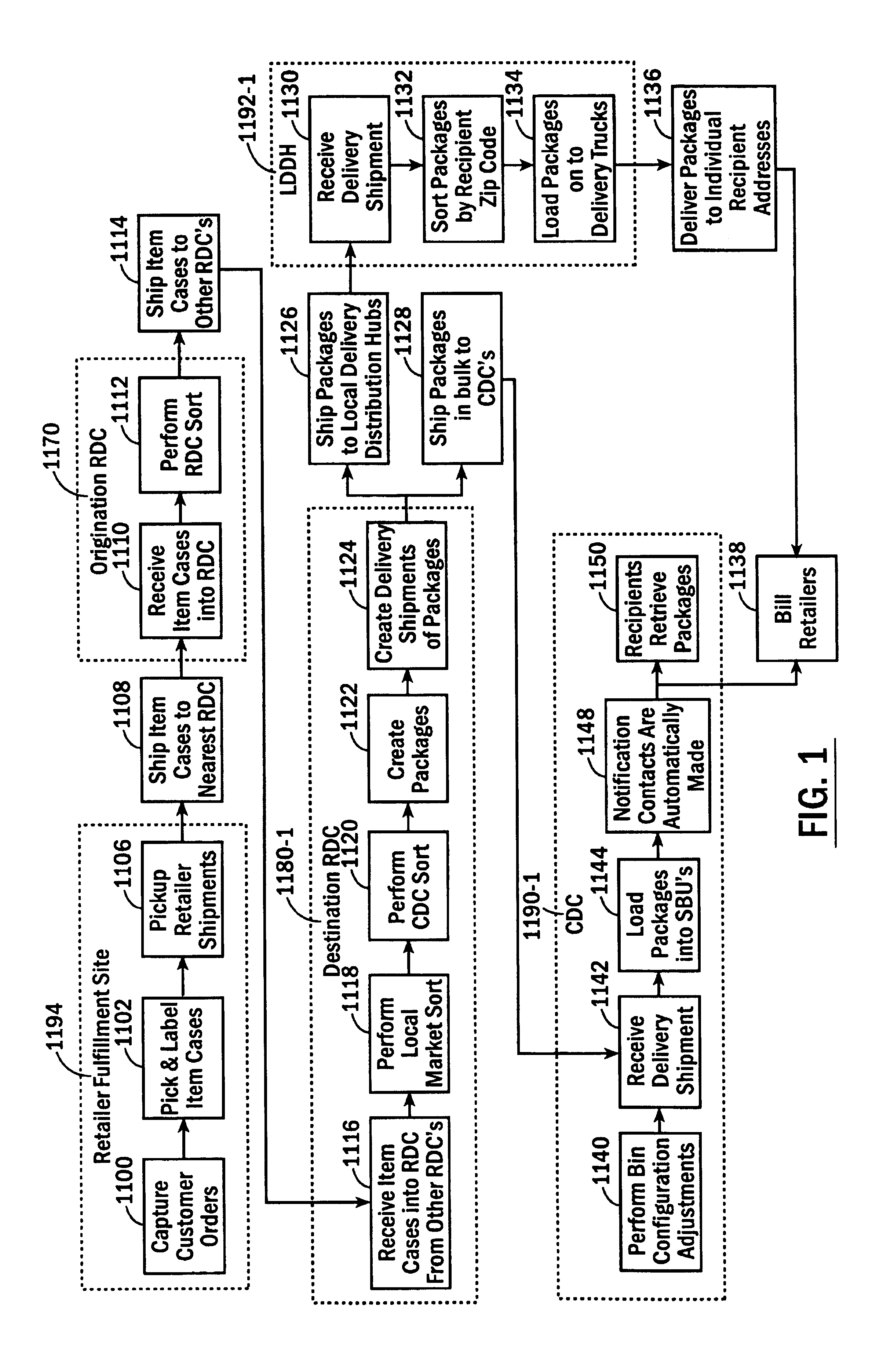
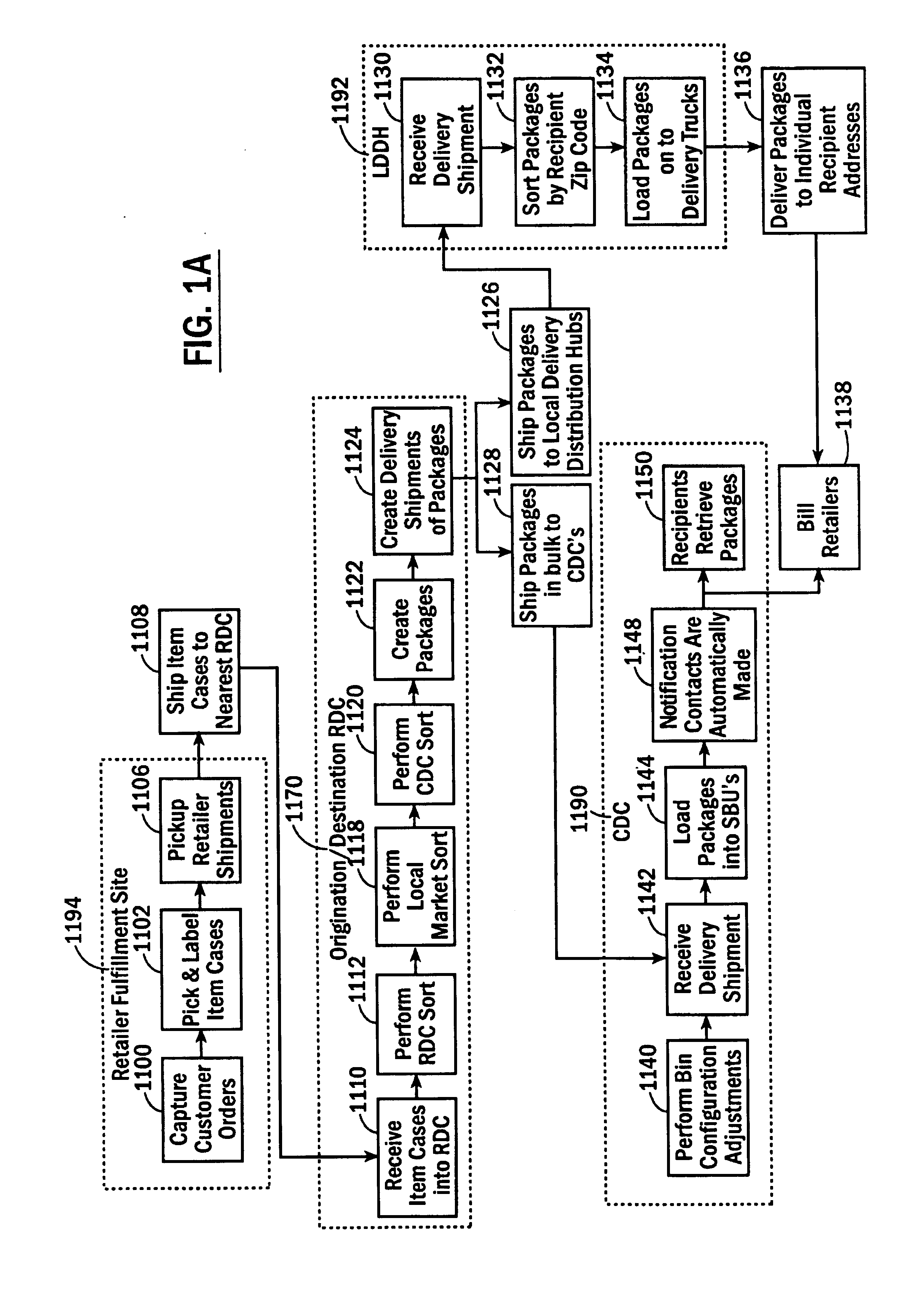
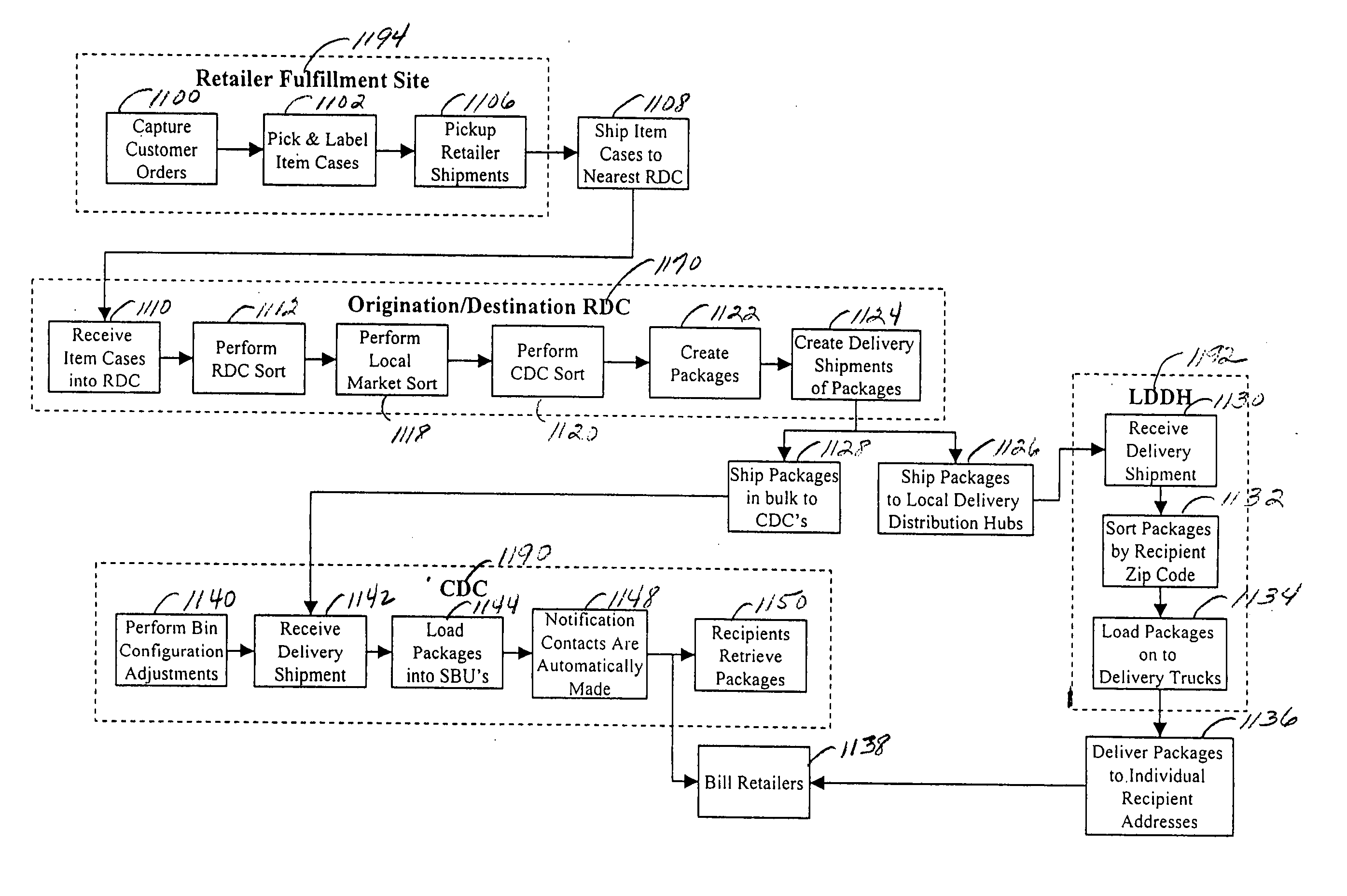
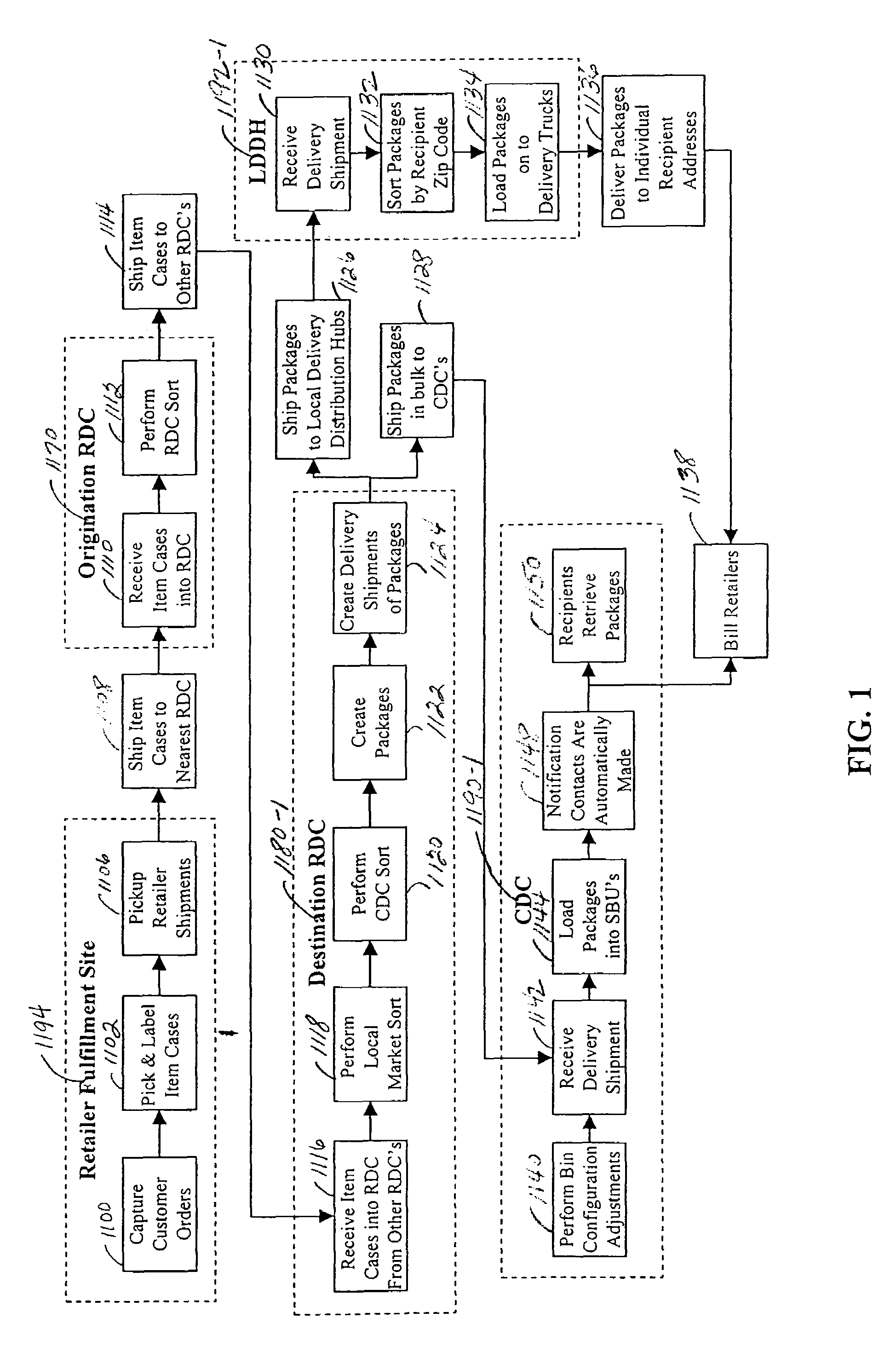
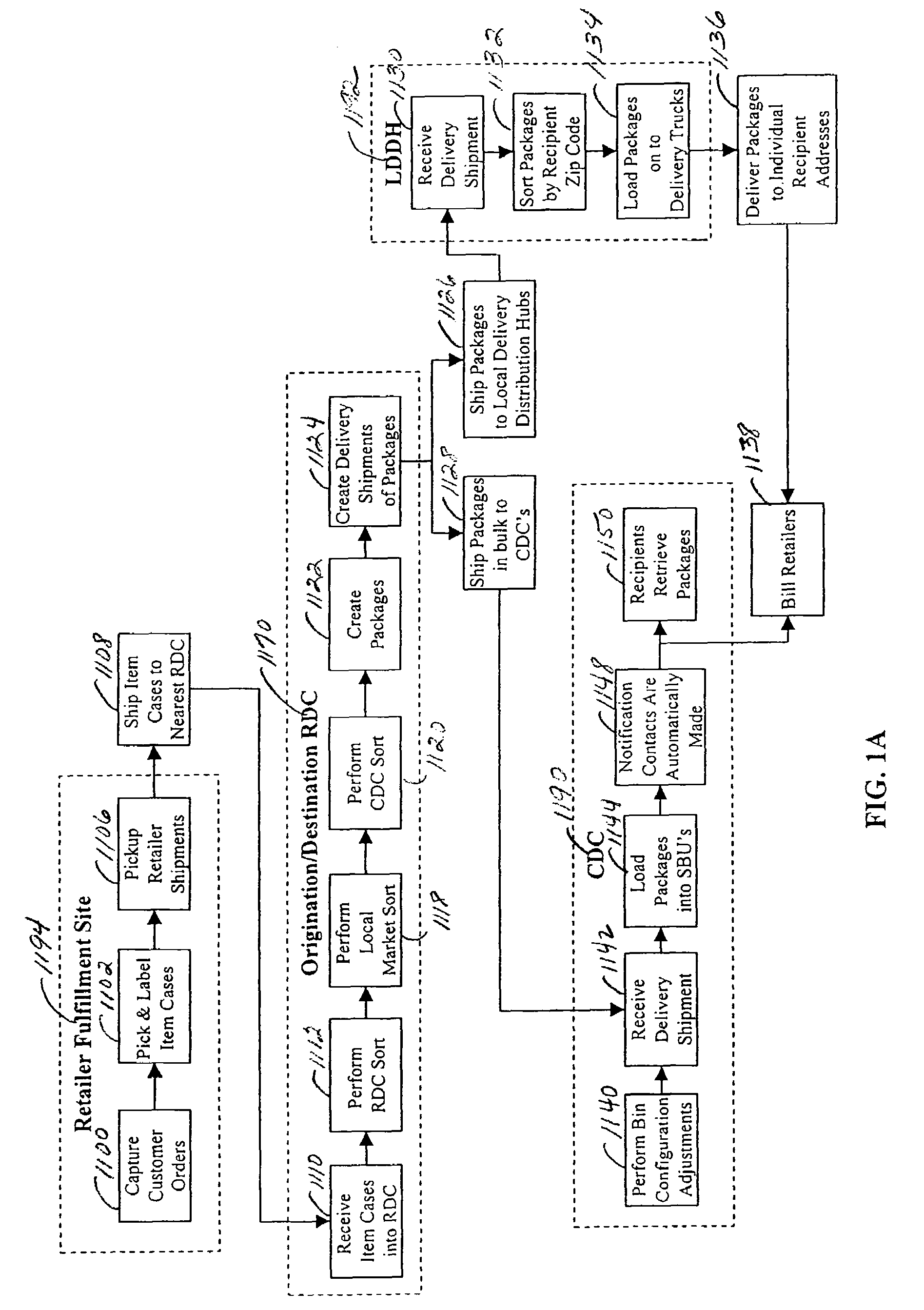
InactiveUS6974928B2Efficient package creationAuthentication is convenientAcutation objectsDigital data processing detailsComputer scienceSelf-service
A method and system for the efficient bulk package delivery for recipients. Items ordered by different customers from different retailers, suppliers or manufacturers can be organized by common item identifiers and shipped in bulk from retailers or manufacturers, to an origination regional distribution center. The items can be sorted at the origination regional distribution center in bulk based on the location of destination regional distribution centers that can serve destination centralized pickup locations chosen by the customers placing the orders for those items. Ordered items can be sorted by recipient and the destination centralized pickup location specified in the customer's order and packed into recipient-specific packages at the destination regional distribution center. The packages can be transported in bulk to the destination centralized pickup locations where they can be randomly loaded into any available locker bins in an automated system of stationary and moveable, configurable storage locker bins. During loading, an association can be made between an identifier of the locker bin and an identifier of the bulk delivered package for subsequent self service identification and retrieval. An electronic notification of the delivery can be automatically dispatched to the recipient by the automated system of storage locker bins to alert the recipient of the delivery.
Owner:BREAKTHROUGH LOGISTICS CORP
Method and system for efficient package delivery and storage
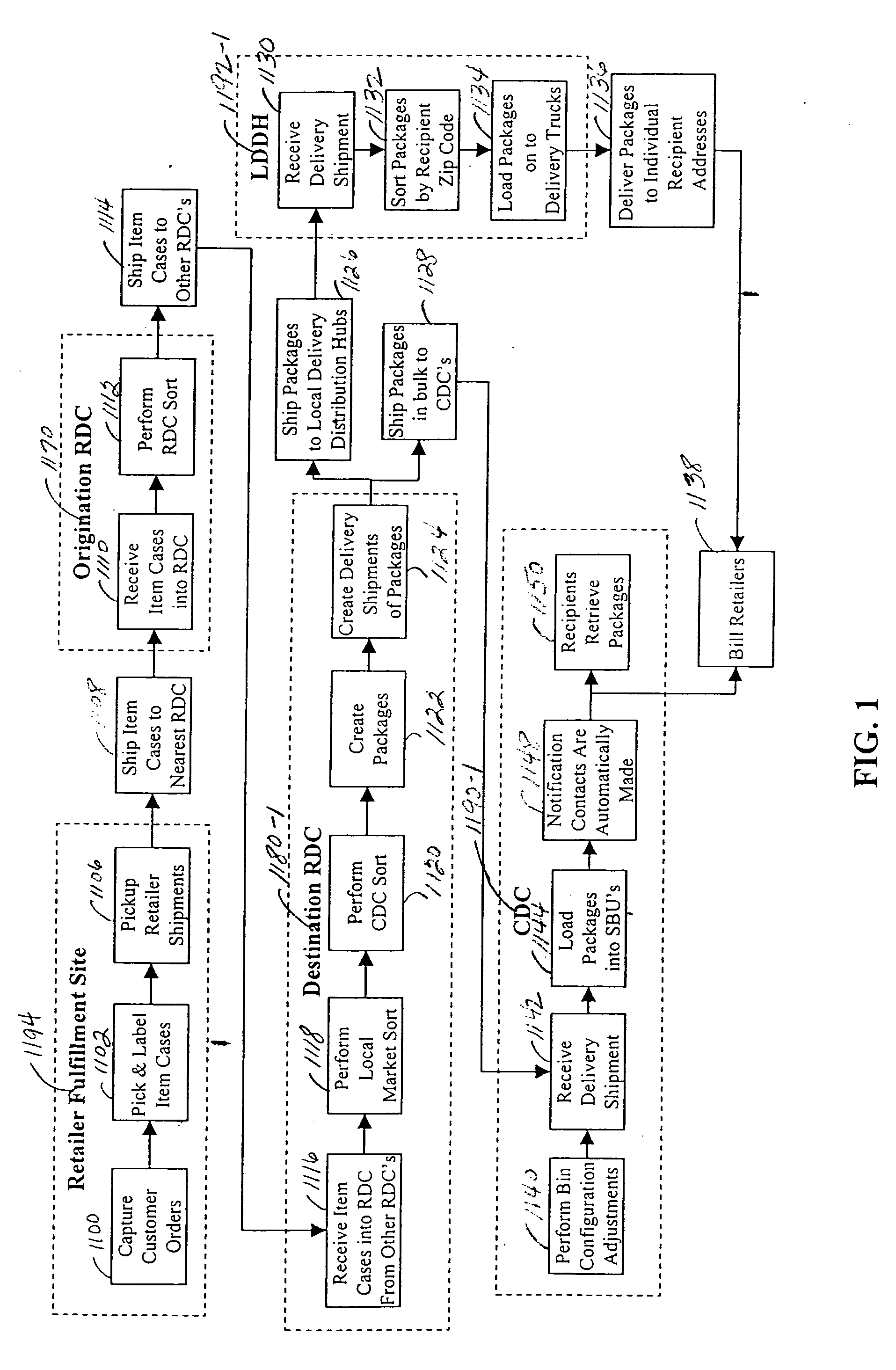
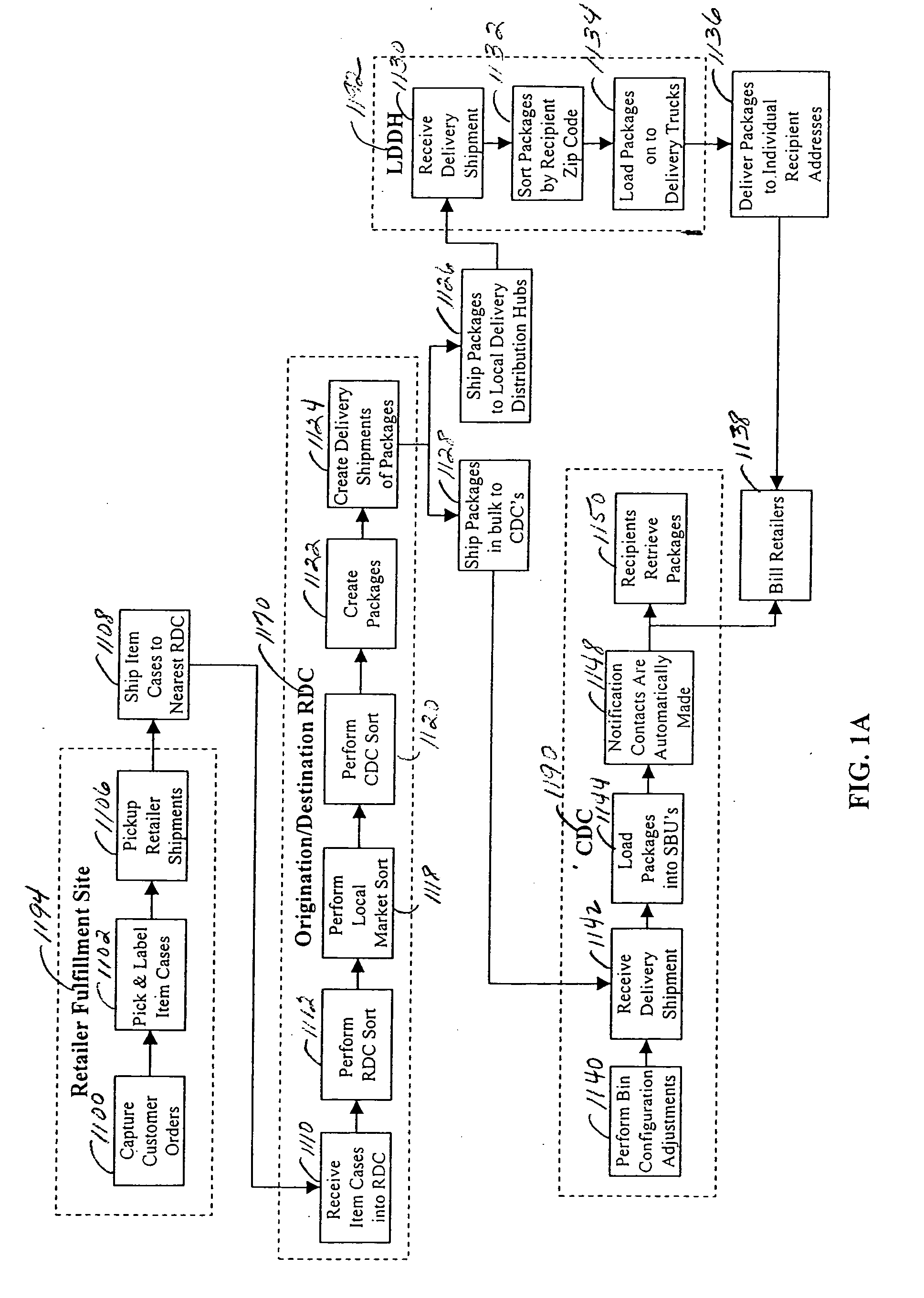
InactiveUS20060020366A1Authentication is convenientEfficient deliveryAcutation objectsDigital data processing detailsInventory levelComputer science
A method and system for efficient package delivery in bulk to pickup locations for recipients in which items ordered by different customers from one or more different retailers, suppliers, manufacturers, and the like can be sorted within and picked from an on-hand inventory at a distribution center and packed into a package for delivery to a specific pickup location for a specific recipient. A replenishment order for items to replace the on-hand inventory at the distribution center can be made to a fulfillment location to maintain inventory levels defined for an item at a distribution center. The items to replenish the on-hand inventory at the distribution center can be shipped in bulk from a fulfillment location in containers organized by item identifier. The items can be sorted at a different distribution center, still organized within containers of all the same item identifier, to reach the distribution center placing the replenishment order for the items.
Owner:BREAKTHROUGH LOGISTICS CORP
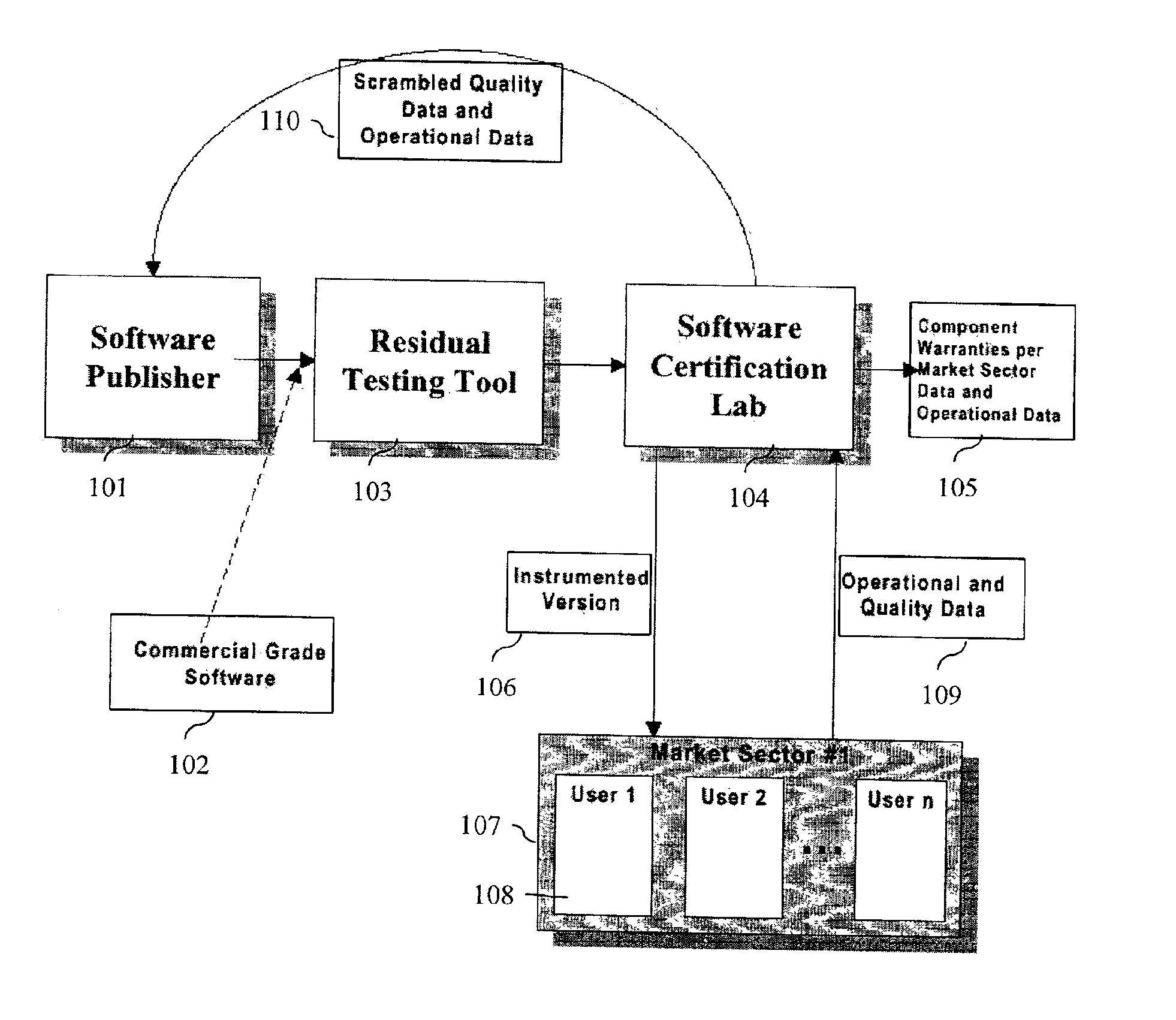
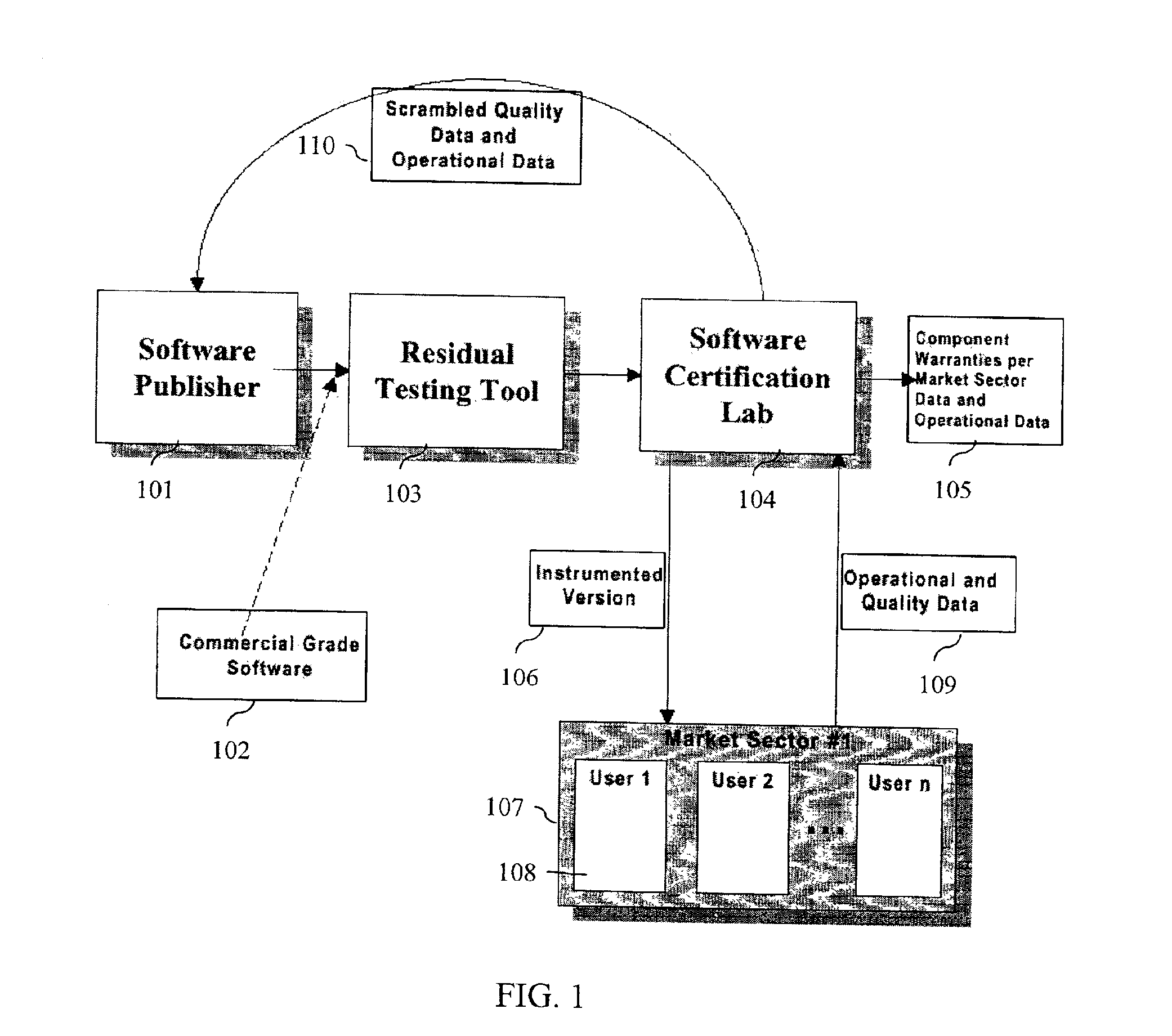
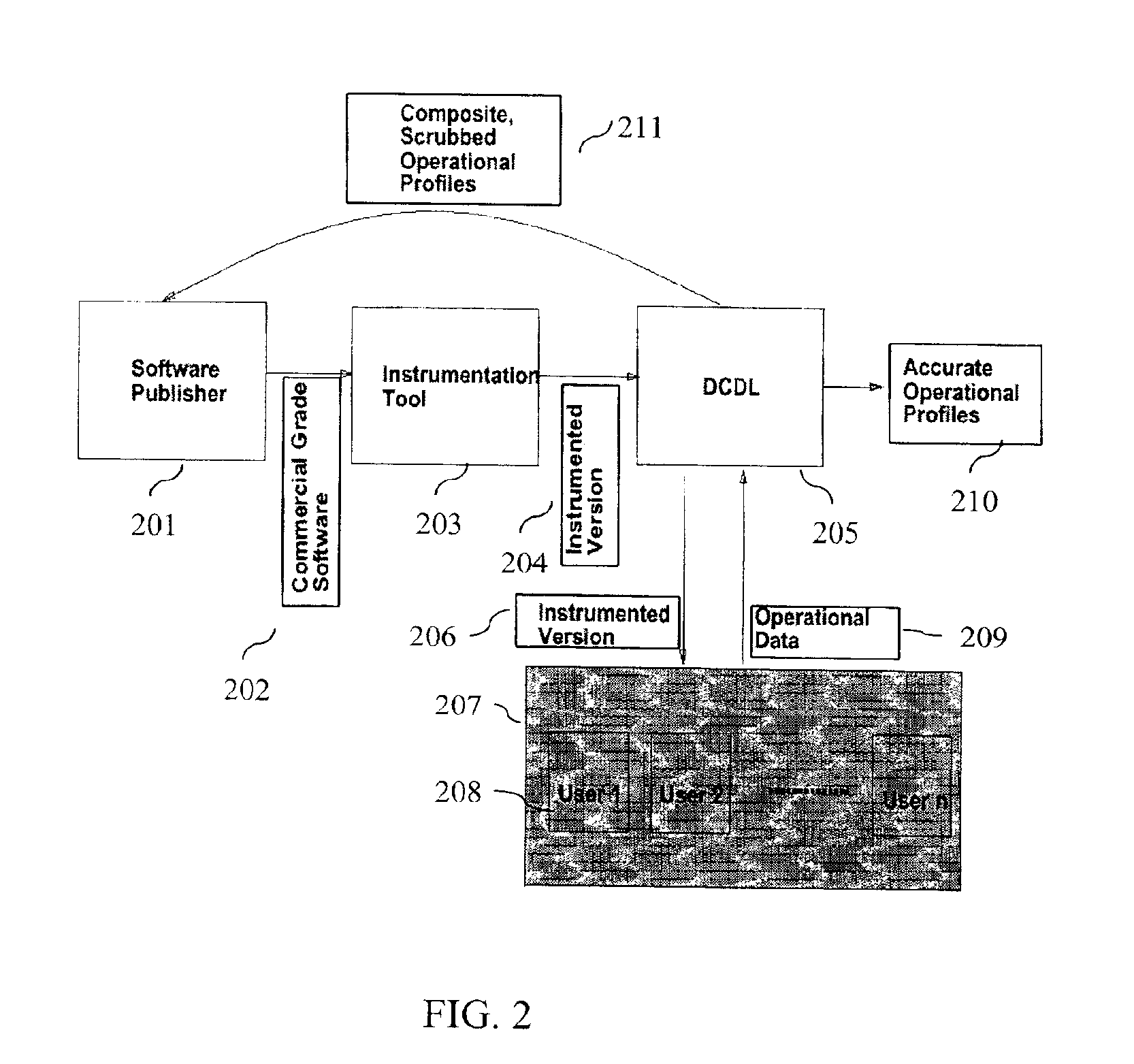
System and method for software certification
InactiveUS6862696B1Improve product reliabilityImprove reliabilityHardware monitoringSpecific program execution arrangementsSoftware engineeringHabit
A method and method that builds accurate operational profiles for COTS software. The systems and methods disclosed allow software vendors to detect misused and unused features; identify common machine configurations for a given piece of software or software component; monitor changing user habits as new software version are released; derive more accurate testing methods for in-house testing purposes; and create user manuals which focus on those features most frequently used, or misused, by users. The disclosed system and method provides the tools enabling a software certification laboratory (SCL) to gather detailed usage data and failure data for a software application as it is used in the field. With this data the SCL can confidently issue certificates of reliability for software products.
Owner:SYNOPSYS INC
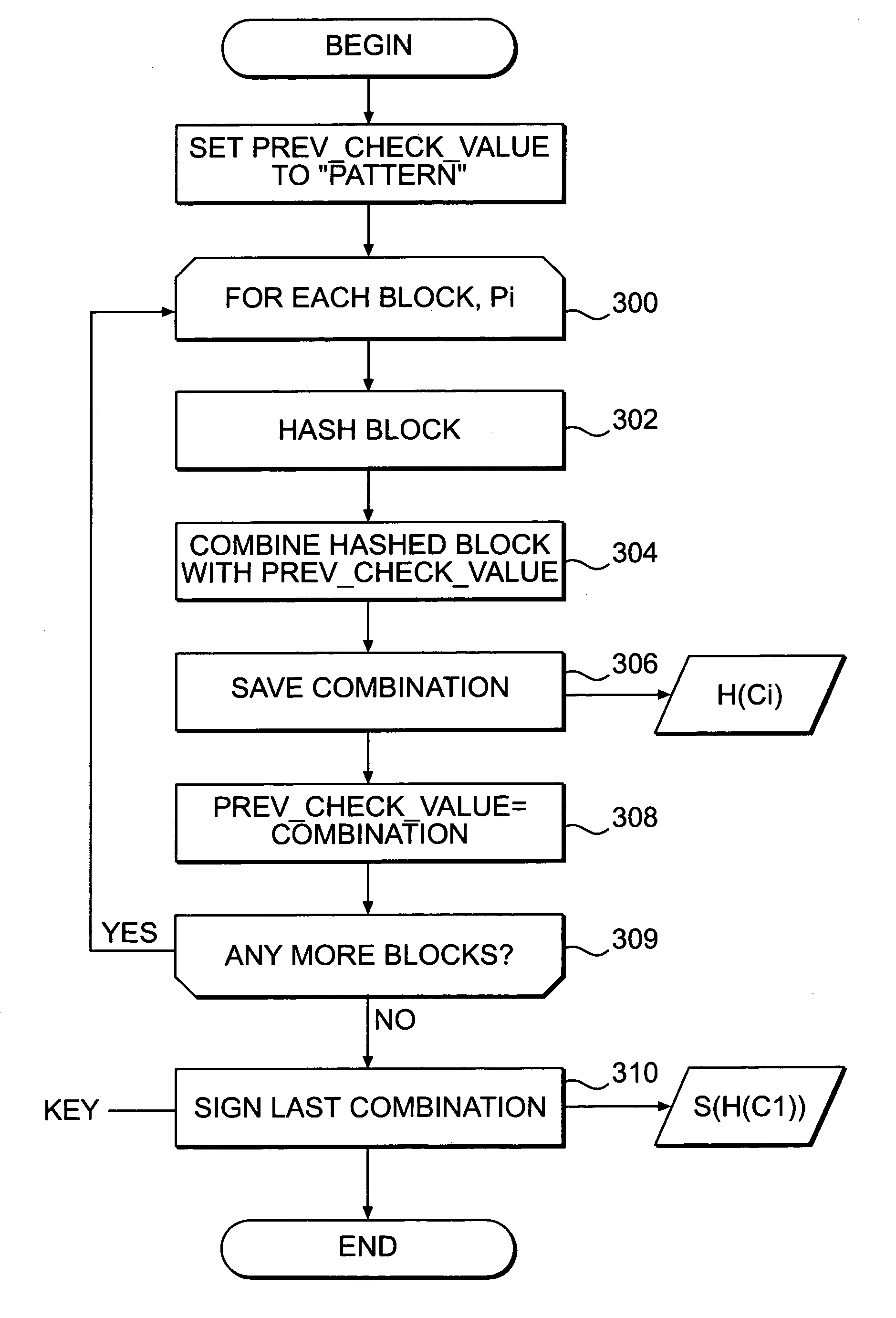
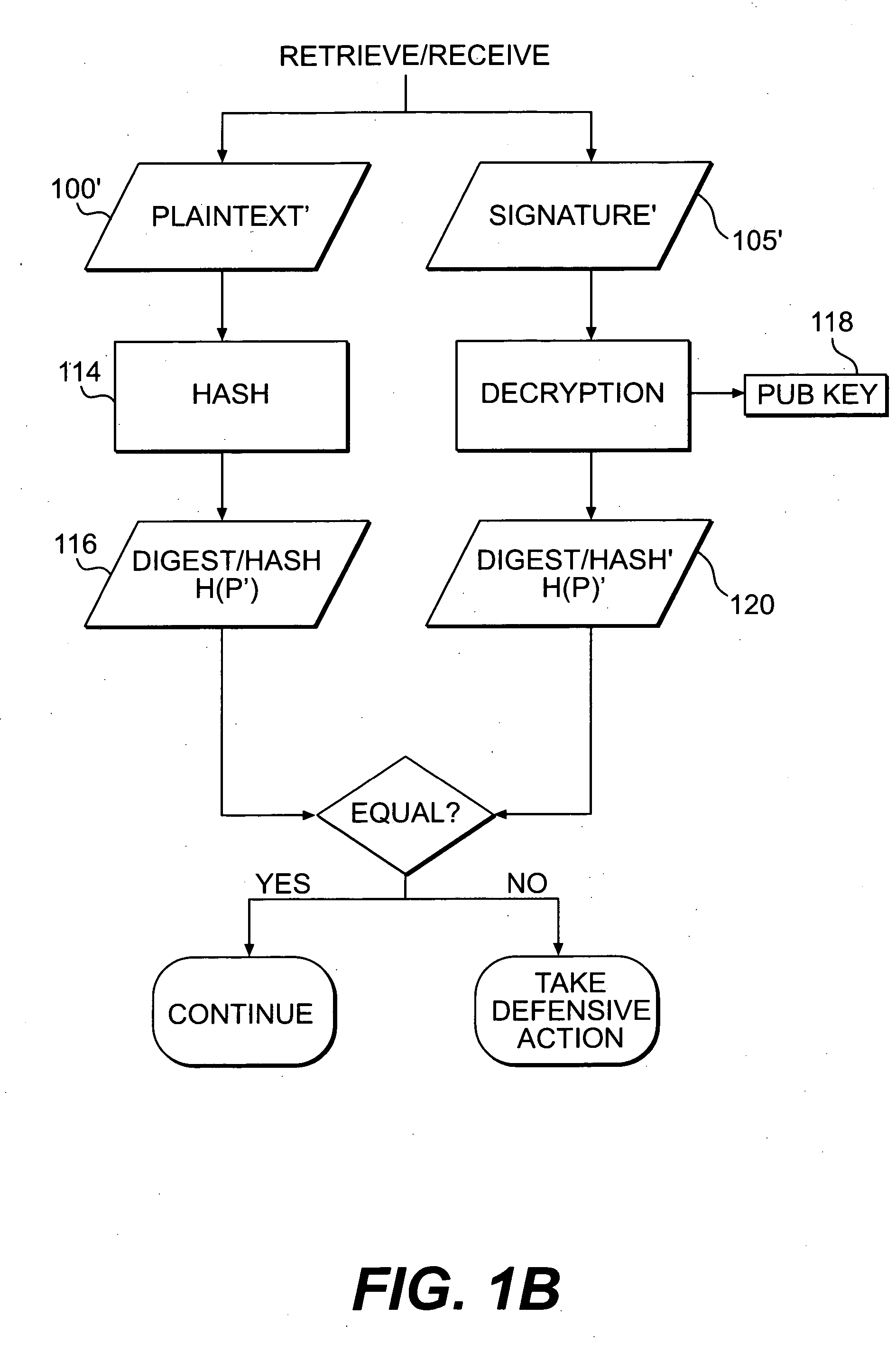
Systems and methods for authenticating and protecting the integrity of data streams and other data
InactiveUS6959384B1Authentication is convenientDetecting errorUser identity/authority verificationDigital data protectionError checkFault tolerance
Systems and methods are disclosed for enabling a recipient of a cryptographically-signed electronic communication to verify the authenticity of the communication on-the-fly using a signed chain of check values, the chain being constructed from the original content of the communication, and each check value in the chain being at least partially dependent on the signed root of the chain and a portion of the communication. Fault tolerance can be provided by including error-check values in the communication that enable a decoding device to maintain the chain's security in the face of communication errors. In one embodiment, systems and methods are provided for enabling secure quasi-random access to a content file by constructing a hierarchy of hash values from the file, the hierarchy deriving its security in a manner similar to that used by the above-described chain. The hierarchy culminates with a signed hash that can be used to verify the integrity of other hash values in the hierarchy, and these other hash values can, in turn, be used to efficiently verify the authenticity of arbitrary portions of the content file.
Owner:INTERTRUST TECH CORP
Systems and methods for authenticating and protecting the integrity of data streams and other data
InactiveUS20050235154A1Authentication is convenientDetecting errorUser identity/authority verificationDigital data protectionError checkFault tolerance
Systems and methods are disclosed for enabling a recipient of a cryptographically-signed electronic communication to verify the authenticity of the communication on-the-fly using a signed chain of check values, the chain being constructed from the original content of the communication, and each check value in the chain being at least partially dependent on the signed root of the chain and a portion of the communication. Fault tolerance can be provided by including error-check values in the communication that enable a decoding device to maintain the chain's security in the face of communication errors. In one embodiment, systems and methods are provided for enabling secure quasi-random access to a content file by constructing a hierarchy of hash values from the file, the hierarchy deriving its security in a manner similar to that used by the above-described chain. The hierarchy culminates with a signed hash that can be used to verify the integrity of other hash values in the hierarchy, and these other hash values can, in turn, be used to efficiently verify the authenticity of arbitrary portions of the content file.
Owner:INTERTRUST TECH CORP
System and method for authenticating users using two or more factors
ActiveUS8751801B2Less increased securityAuthentication—increases the strength of an authenticationDigital data processing detailsUser identity/authority verificationPasswordInternet privacy
A method for authenticating a user based on a plurality of authentication factors includes a step of receiving a first authentication factor from a first communication device of the user. The first authentication factor includes a password. The method includes a step of receiving a second authentication factor. The second authentication factor comprises at least one of at least one device identifier of the first communication device of the user and data transmitted to or received from a second communication device of the user. The method also includes a step of authenticating the user based on at least the received plurality of authentication factors.
Owner:EMC IP HLDG CO LLC
Usable security of online password management with sensor-based authentication
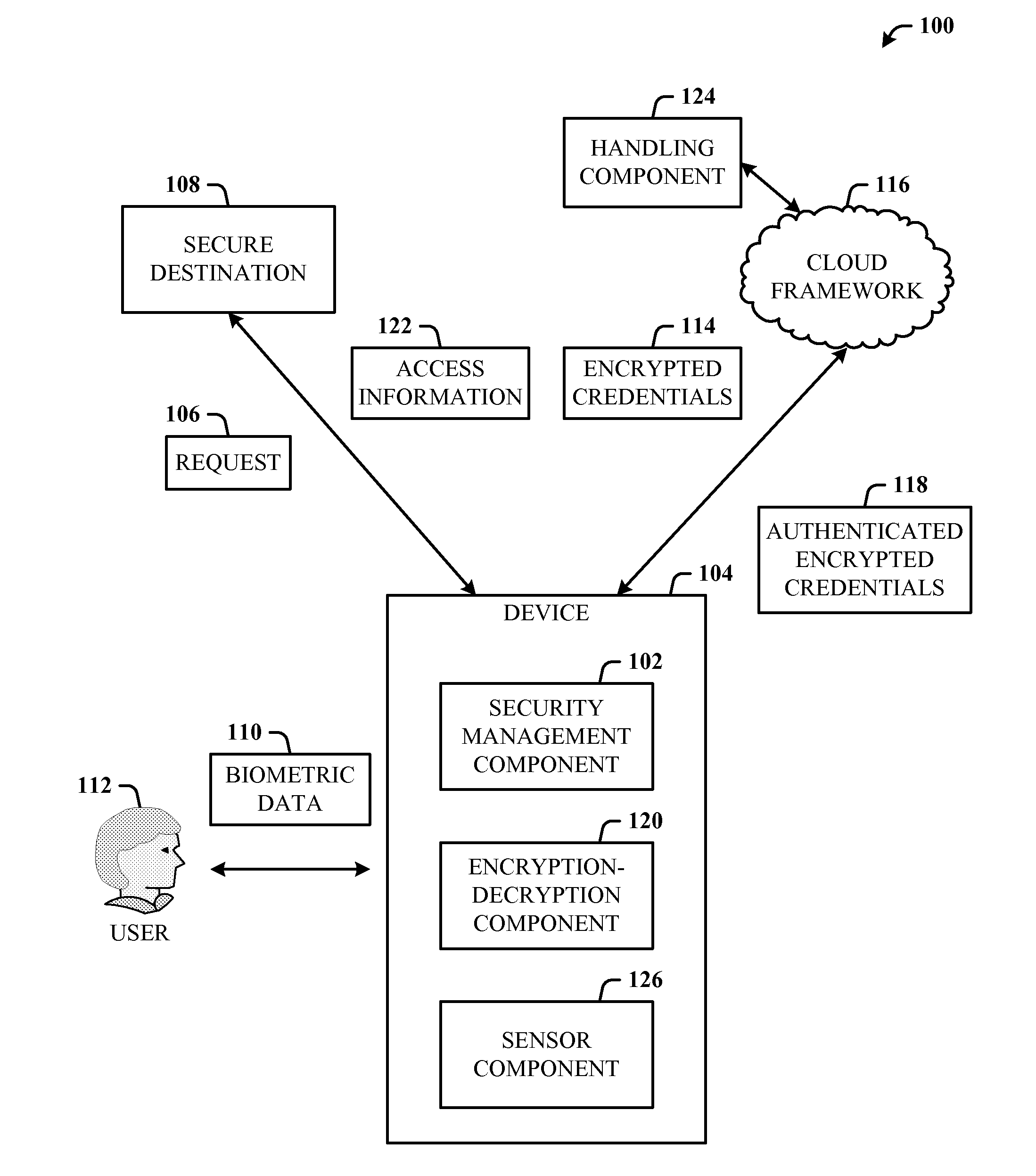
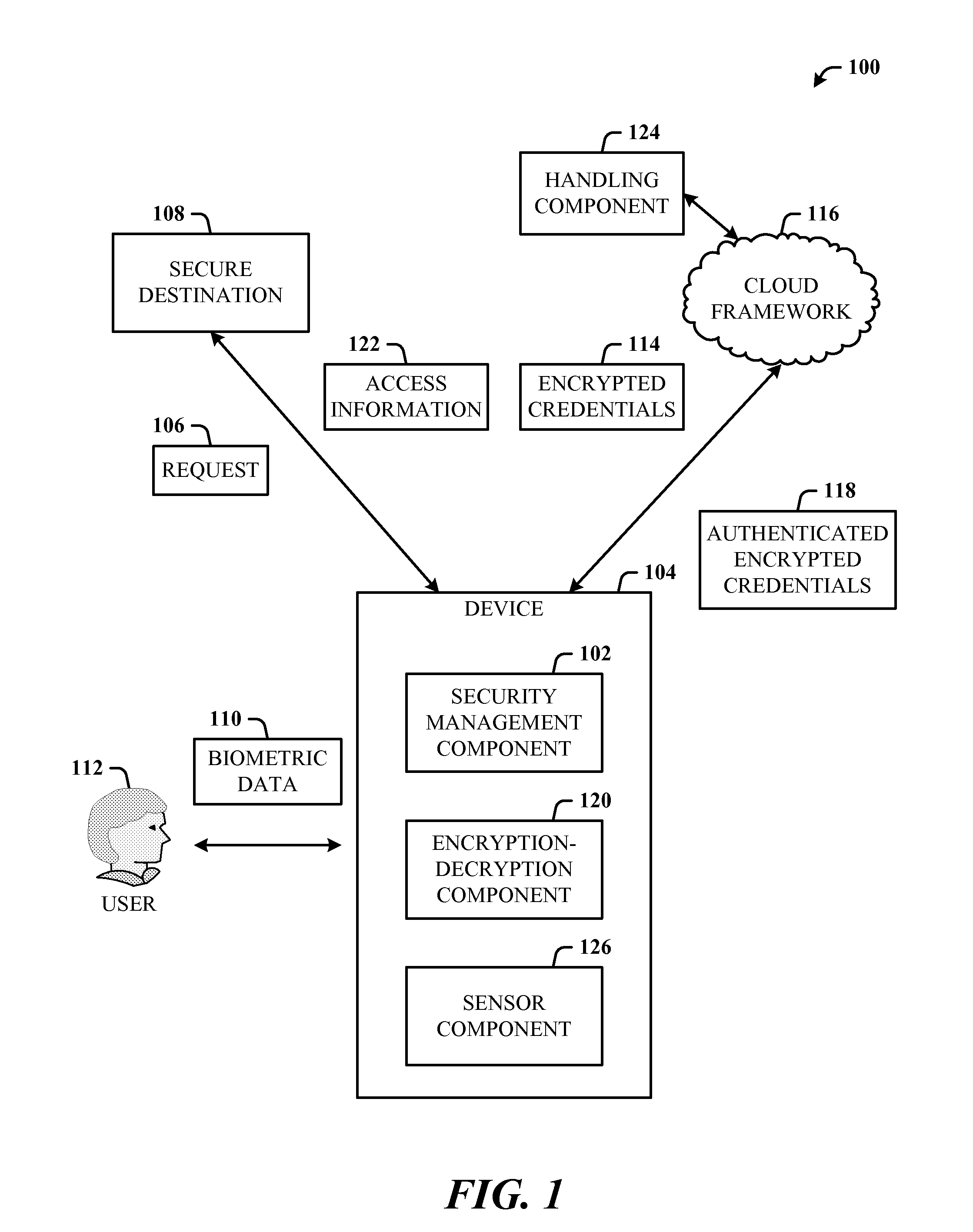
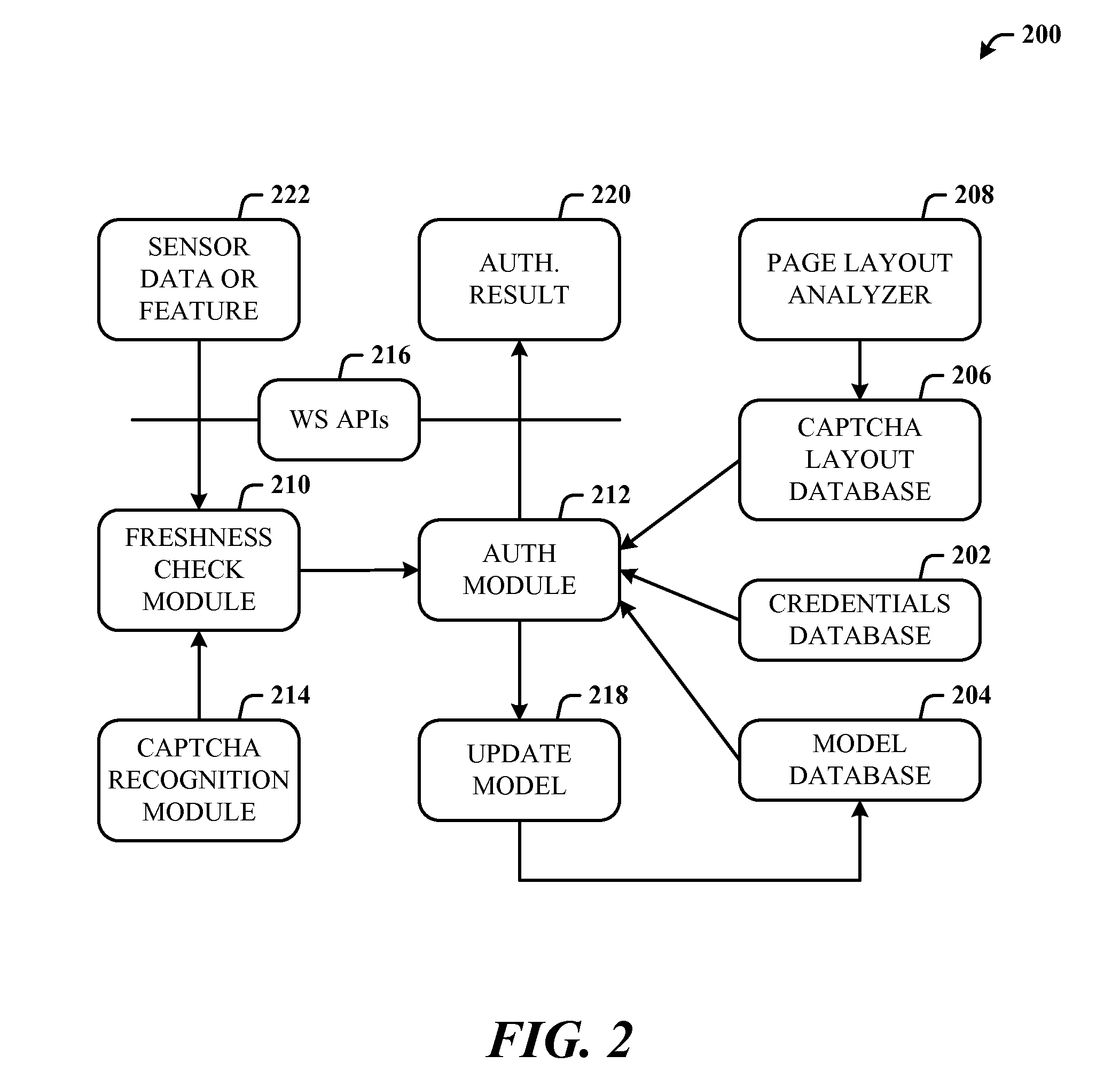
ActiveUS20120297190A1Improve usabilityAuthentication is convenientUser identity/authority verificationDigital data authenticationCryptographic protocolUsability
A multi-party security protocol that incorporates biometric-based authentication and withstands attacks against any single party (e.g., mobile phone, cloud, or the user). The protocol involves the function split between mobile and cloud and the mechanisms to chain-hold the secrets. A key generation mechanisms binds secrets to a specific device or URL (uniform resource locator) by adding salt to a master credential. An inline CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) handling mechanism uses the same sensor modality as the authentication process, which not only improves the usability, but also facilitates the authentication process. This architecture further enhances existing overall system security (e.g., handling untrusted or compromised cloud service, phone being lost, impersonation, etc.) and also improves the usability by automatically handling the CAPTCHA.
Owner:MICROSOFT TECH LICENSING LLC
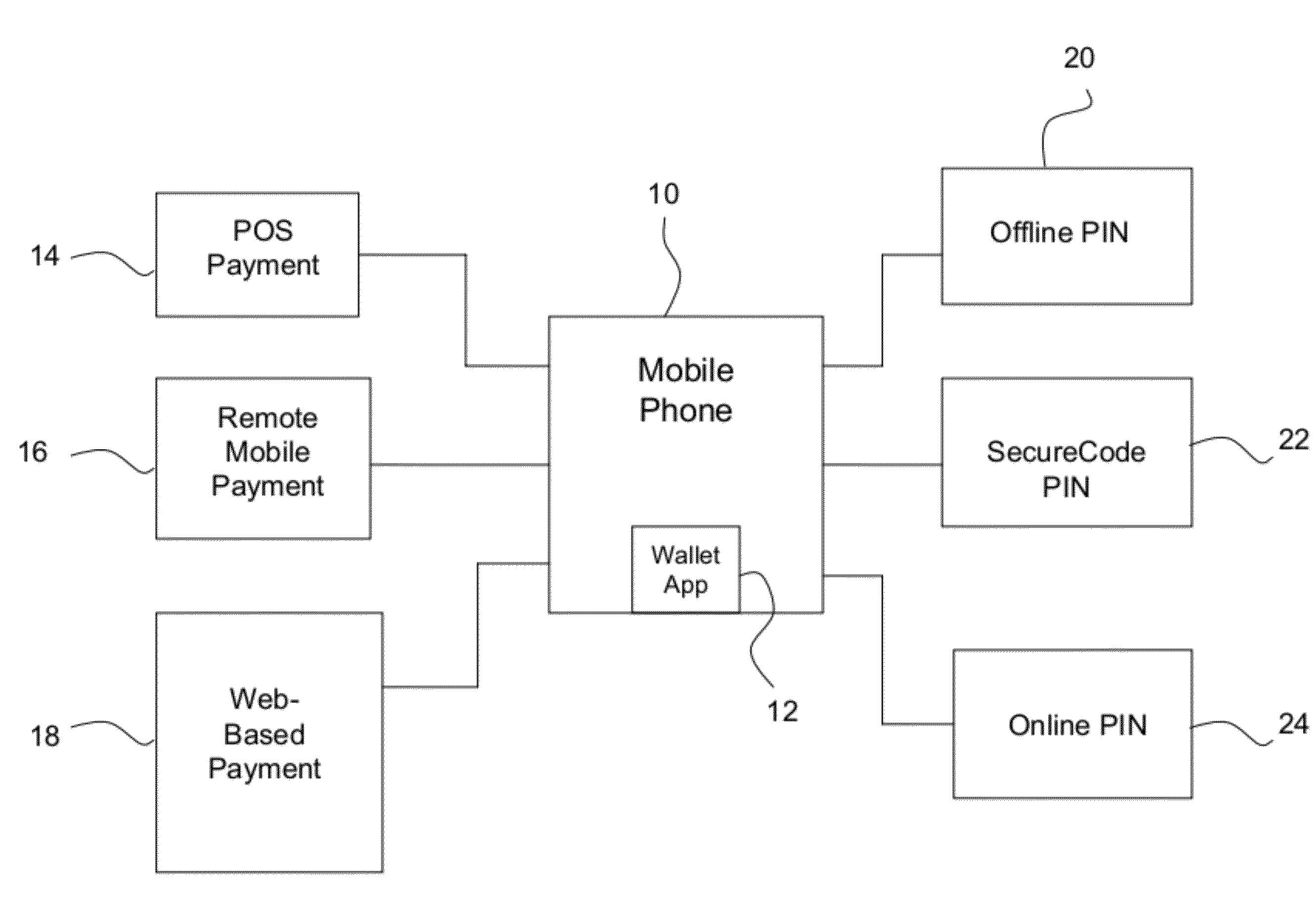
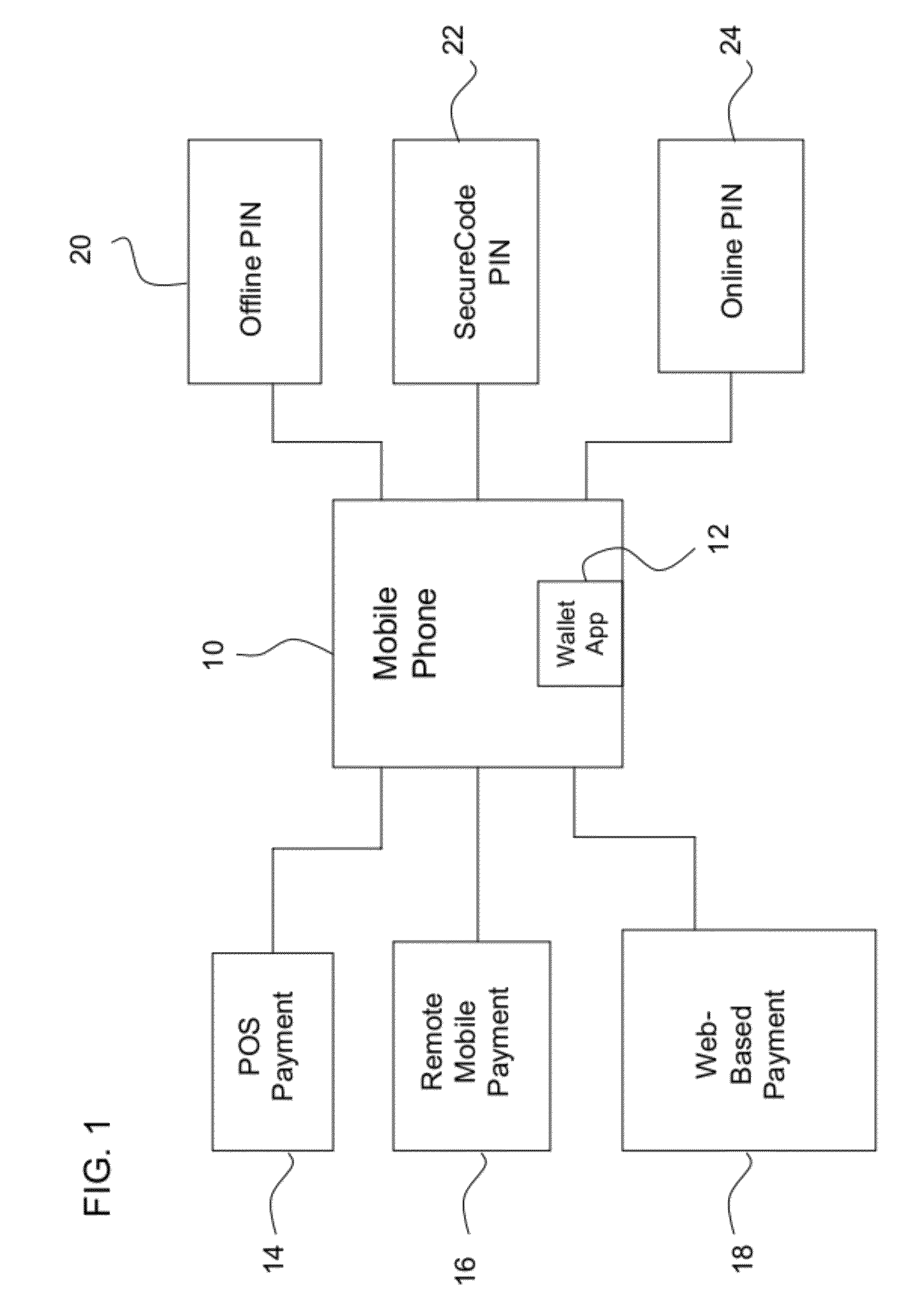
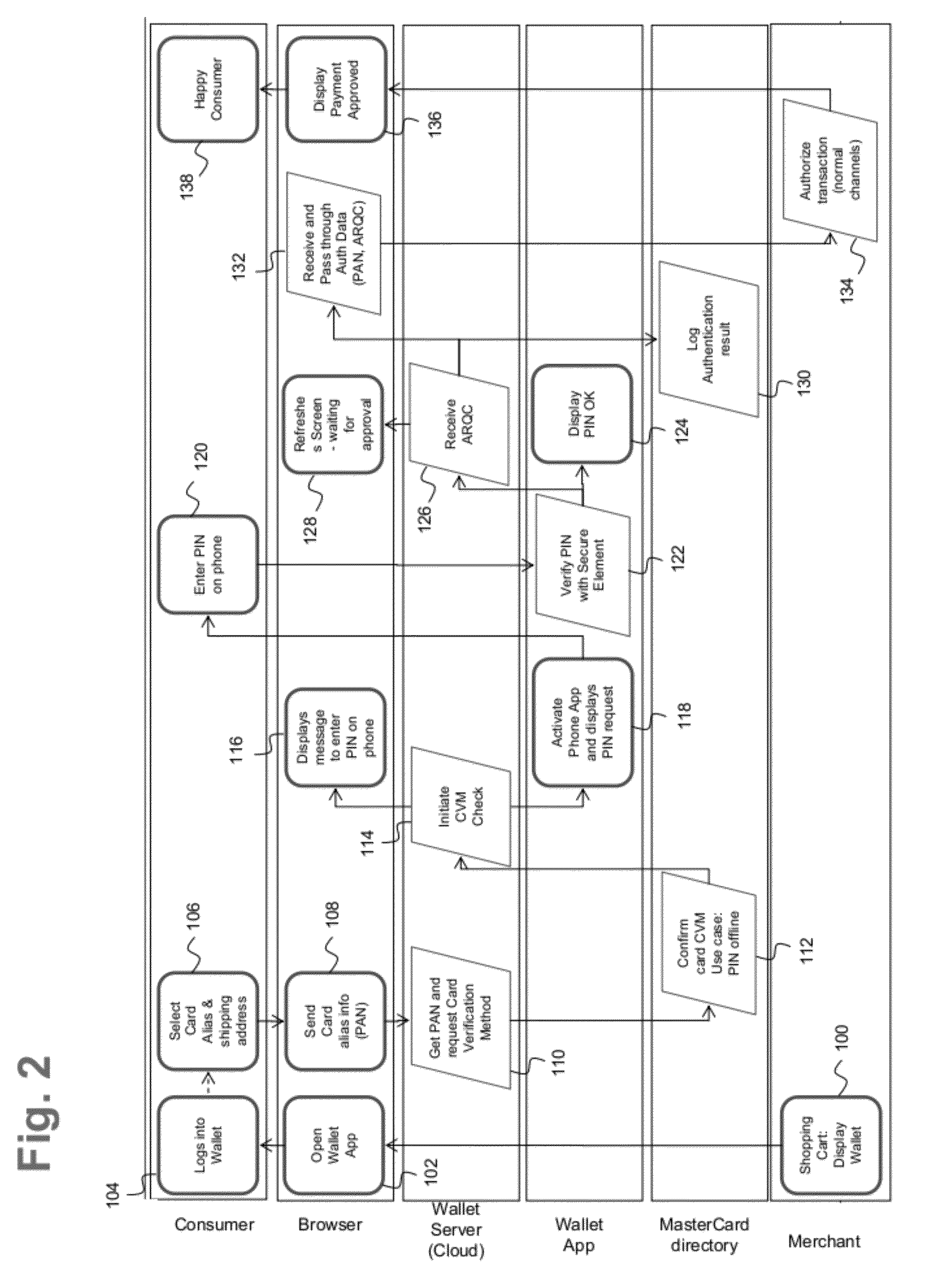
Multi-commerce channel wallet for authenticated transactions
InactiveUS20120143752A1Low implementation requirementsCommunication securityFinanceTransmissionFinancial transactionMobile payment
A phone-based electronic wallet providing authenticated transactions across multiple channels of commerce. The electronic wallet may be used for point-of-sale payments, remote mobile payments and / or web-based payments, and may use authentication tools such as offline PINs, SecureCode PINs and / or online PINs.
Owner:MASTERCARD INT INC
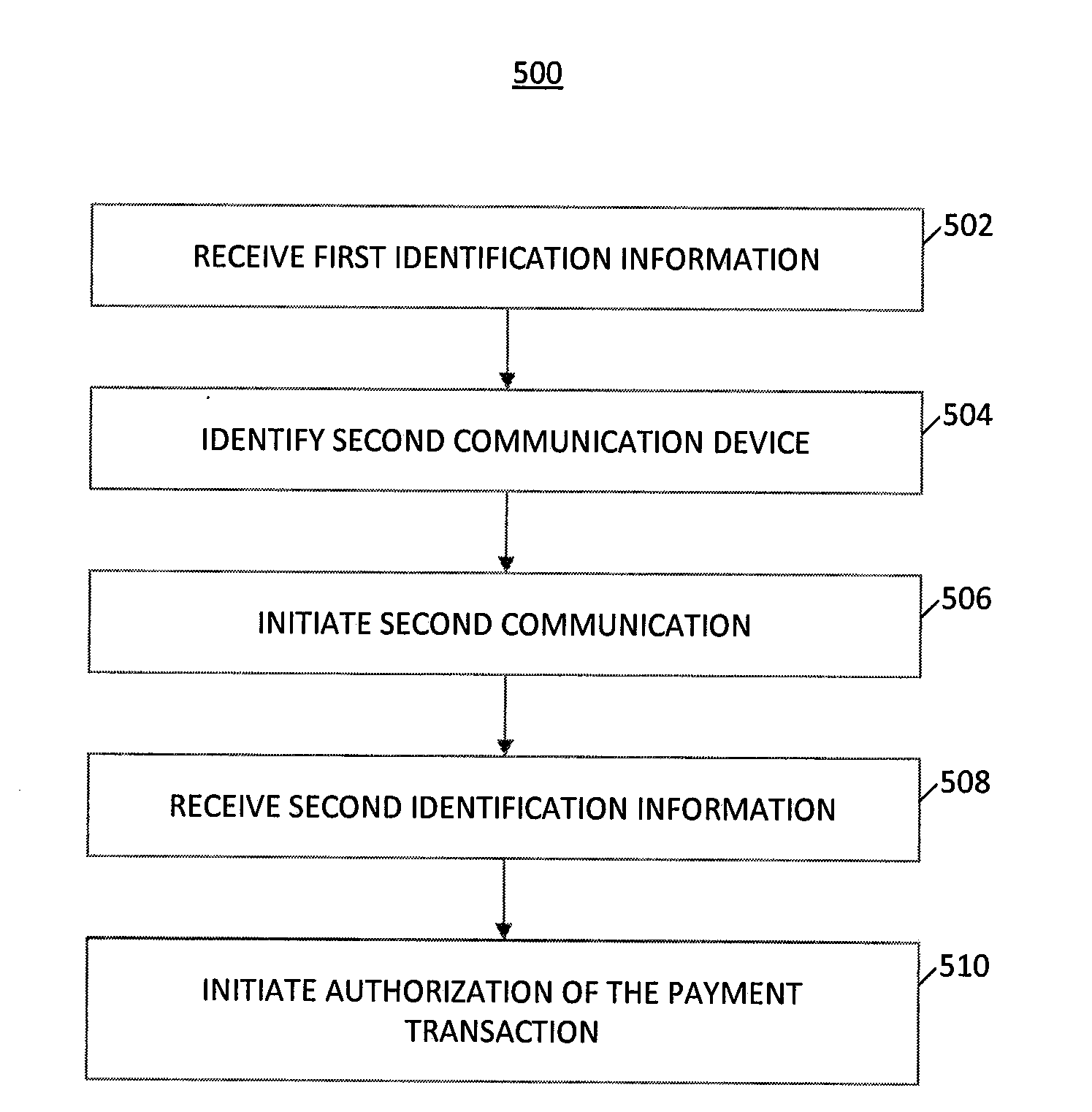
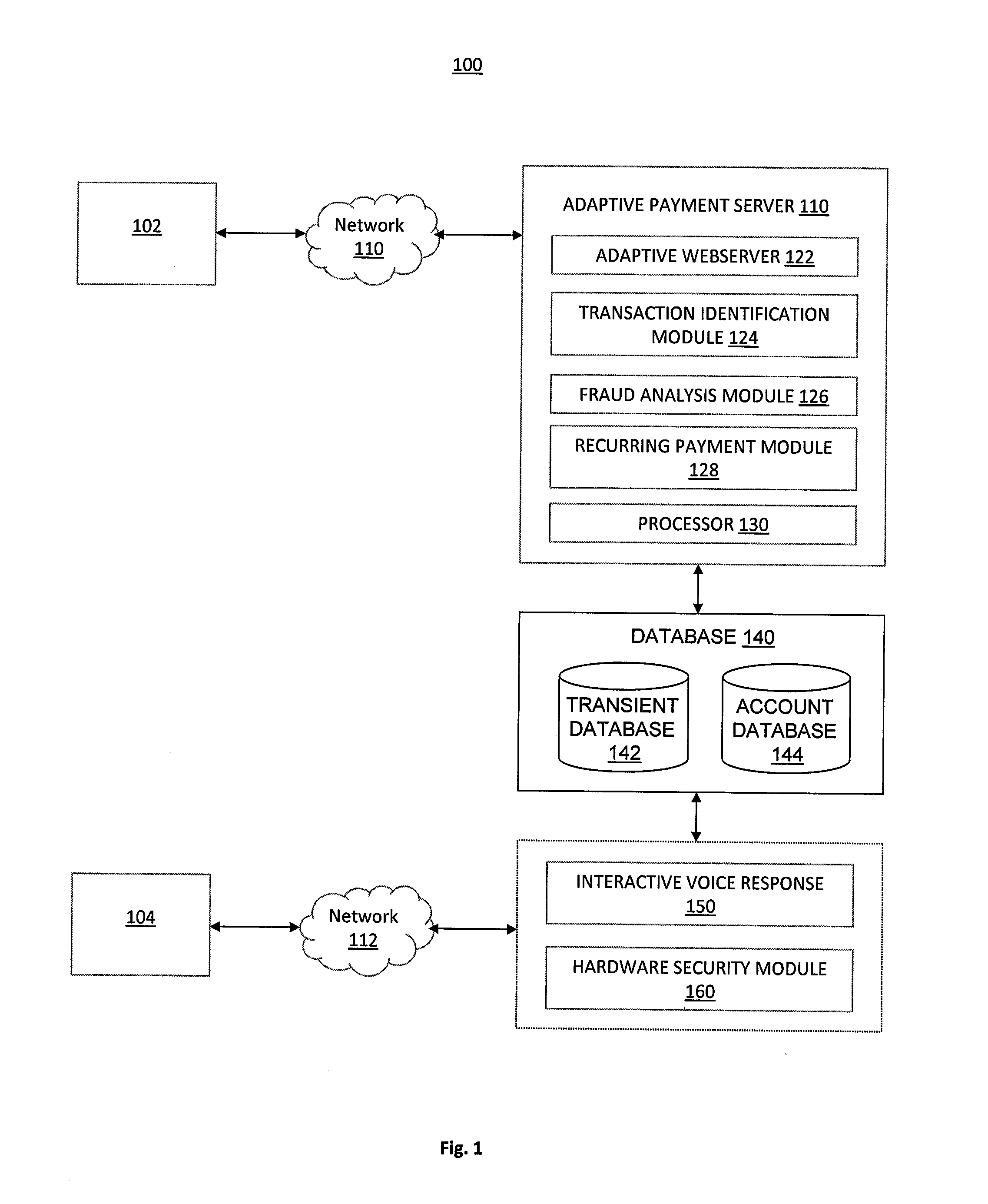
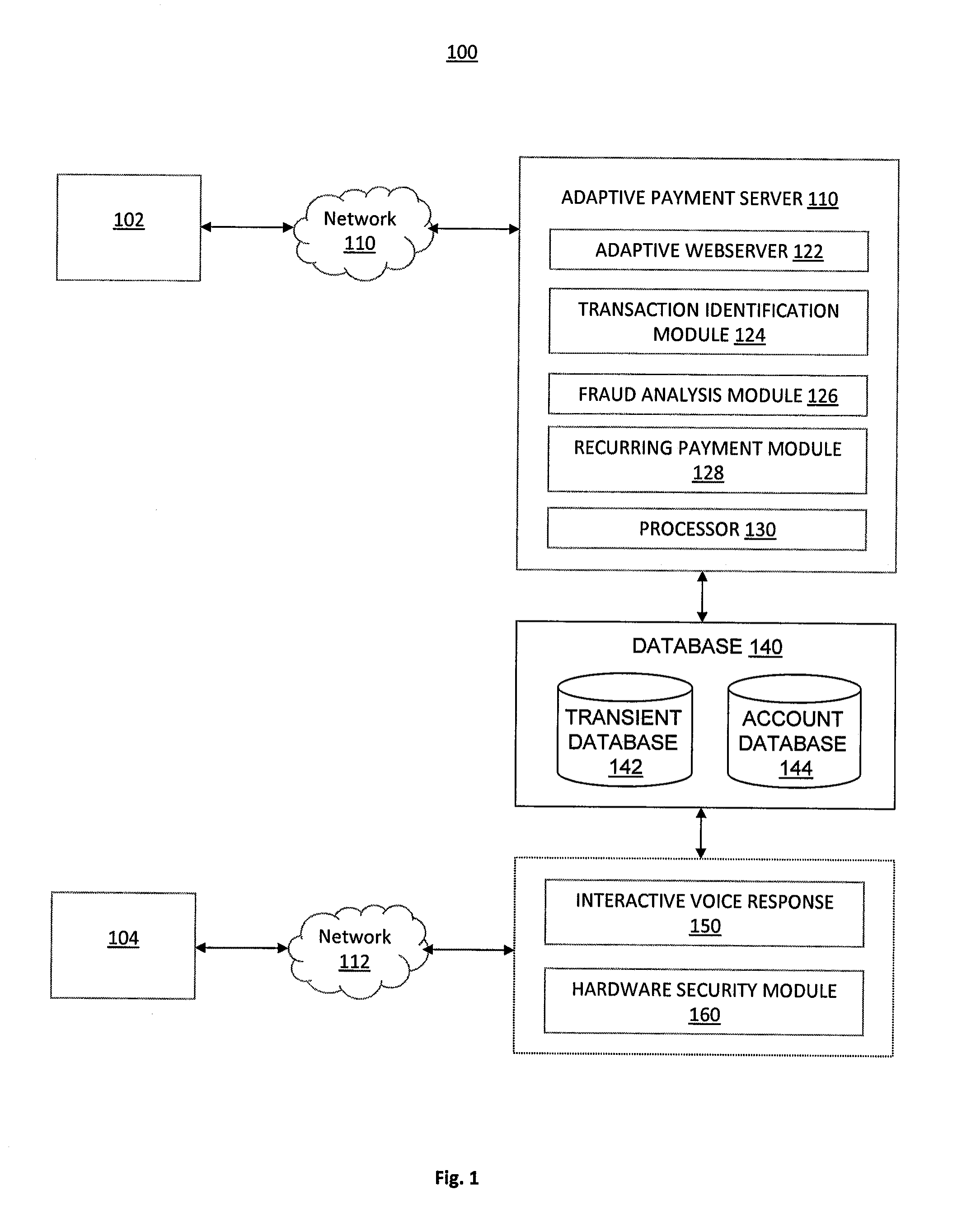
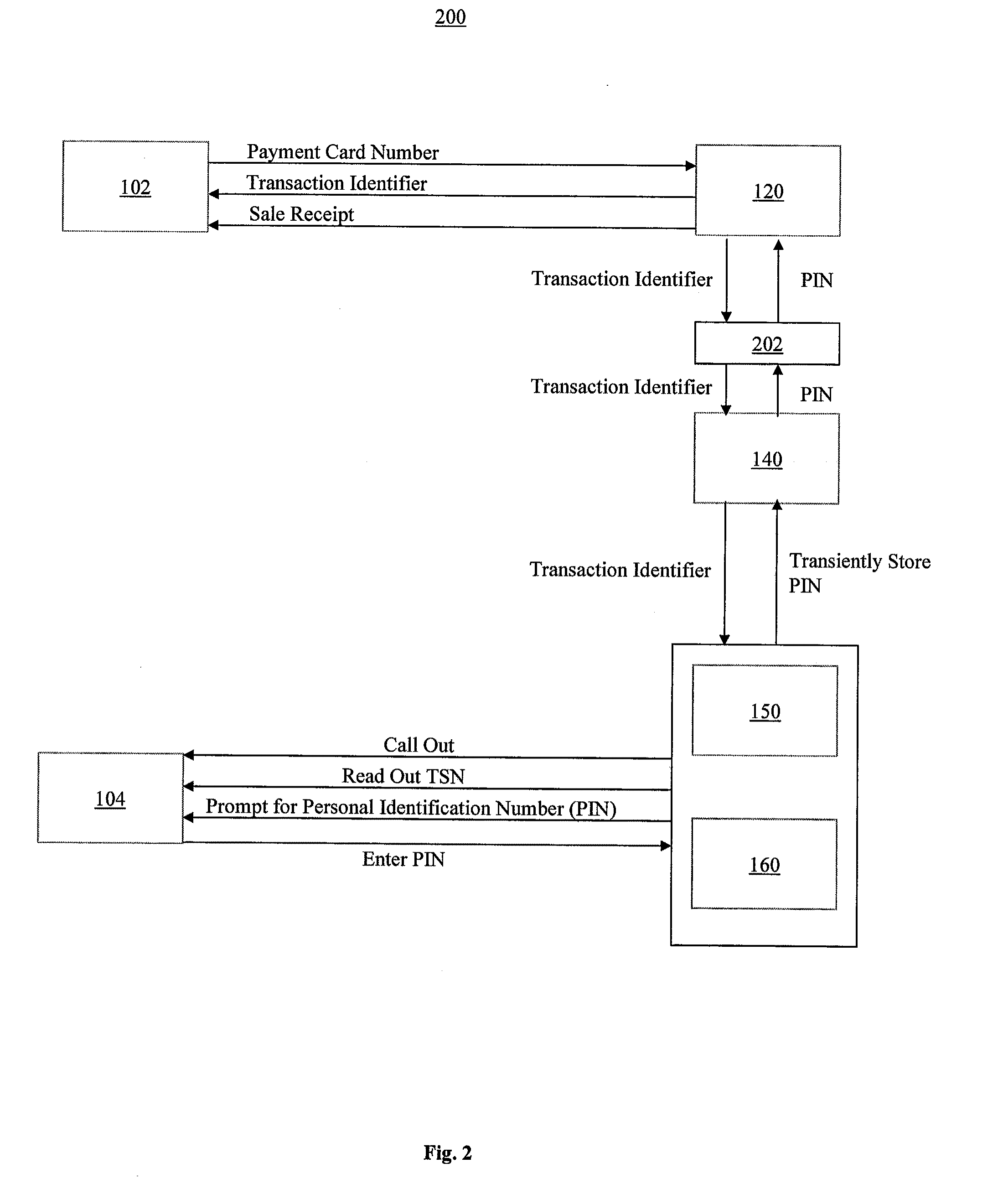
System and Method of Secure Payment Transactions
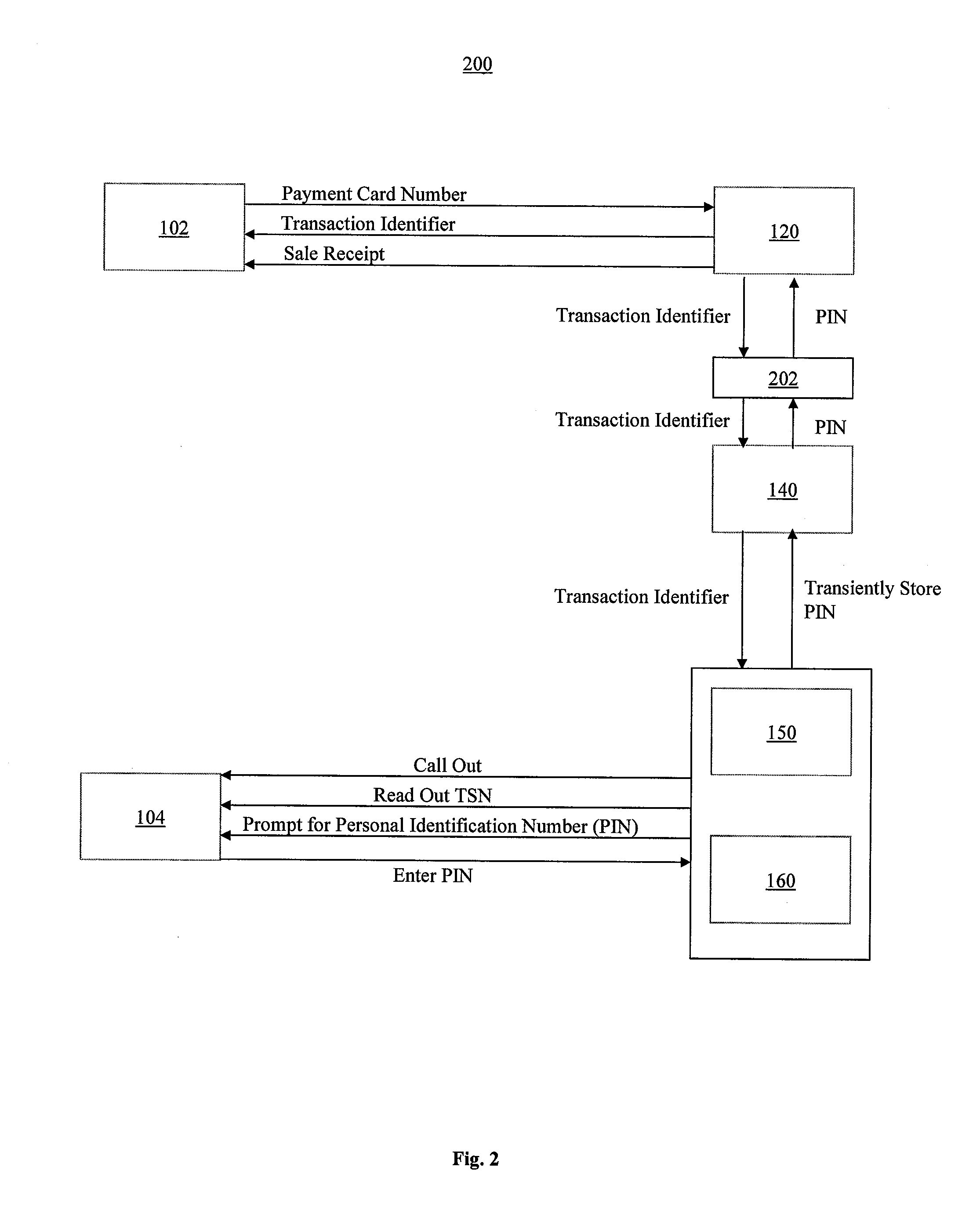
ActiveUS20100057623A1Facilitate secure payment transactionAuthentication is convenientAcutation objectsFinancePayment transactionCommunication device
A system and method for secure payment transactions is provided. The system may include an adaptive payment server including one or more processors configured to receive a first communication including first identification information from a first communication device on a first communication channel. The adaptive payment server may identify a second communication device based on the first identification information and initiate a second communication to the second communication device on a second communication channel, which may be discrete from the first communication channel. The adaptive payment server may receive second identification information from the second communication device on the second communication channel and authenticate the payment transaction using the first identification information and the second identification information.
Owner:MTS HLDG
Method and system for efficient package delivery and storage
InactiveUS7653457B2Authentication is convenientEfficient deliveryAcutation objectsDigital data processing detailsComputer scienceInventory level
A method and system for efficient package delivery in bulk to pickup locations for recipients in which items ordered by different customers from one or more different retailers, suppliers, manufacturers, and the like can be sorted within and picked from an on-hand inventory at a distribution center and packed into a package for delivery to a specific pickup location for a specific recipient. A replenishment order for items to replace the on-hand inventory at the distribution center can be made to a fulfillment location to maintain inventory levels defined for an item at a distribution center. The items to replenish the on-hand inventory at the distribution center can be shipped in bulk from a fulfillment location in containers organized by item identifier. The items can be sorted at a different distribution center, still organized within containers of all the same item identifier, to reach the distribution center placing the replenishment order for the items.
Owner:BREAKTHROUGH LOGISTICS CORP
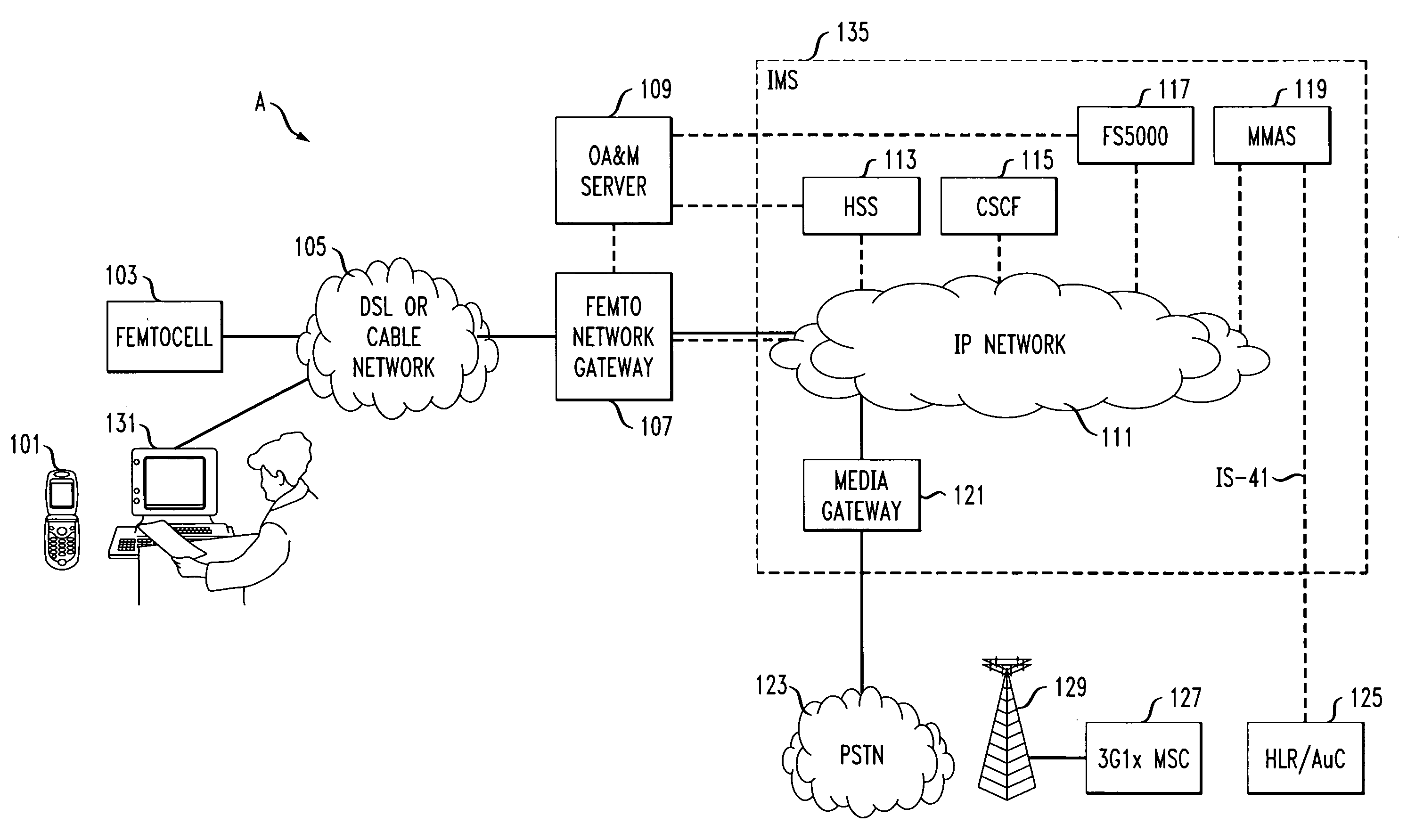
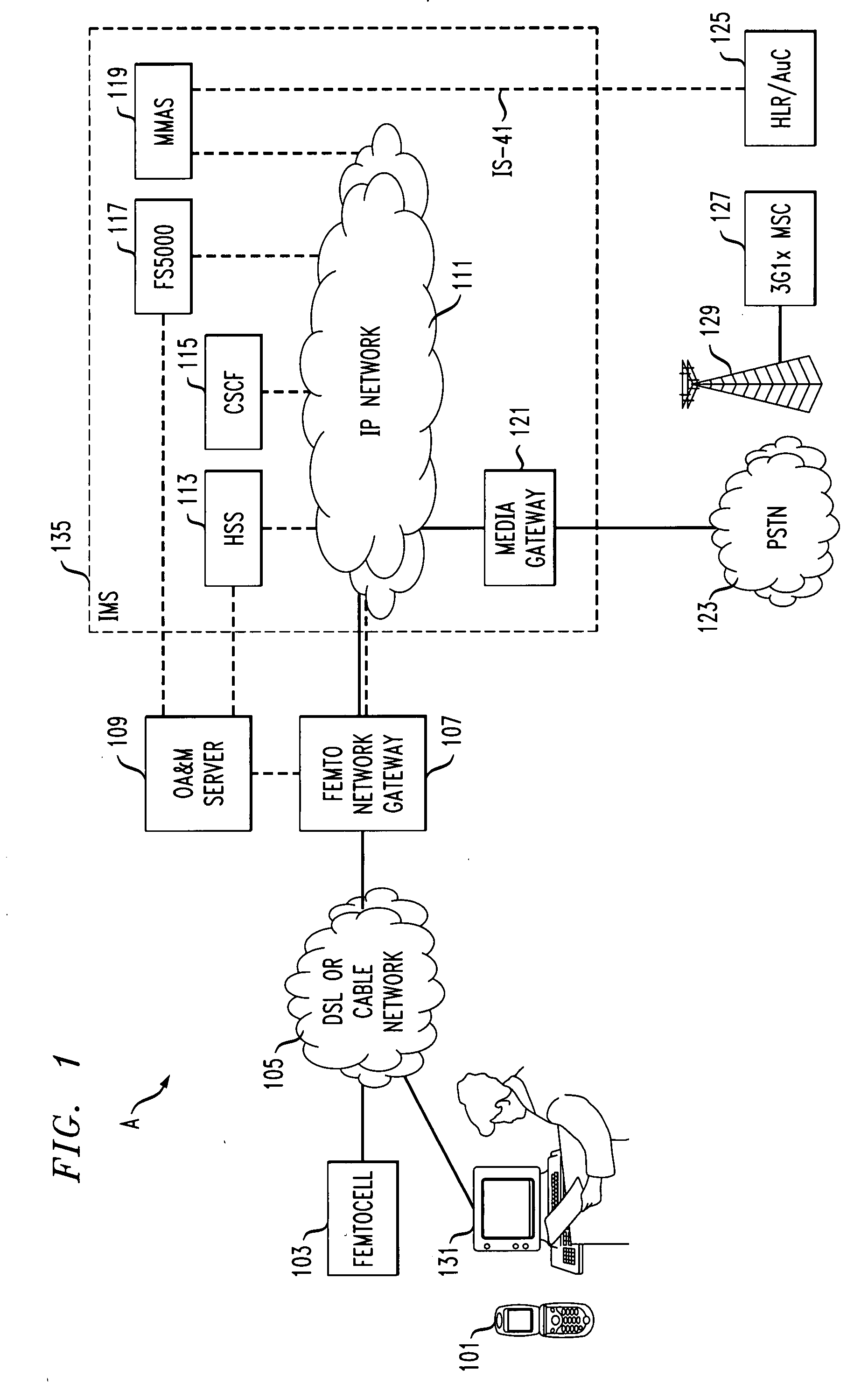
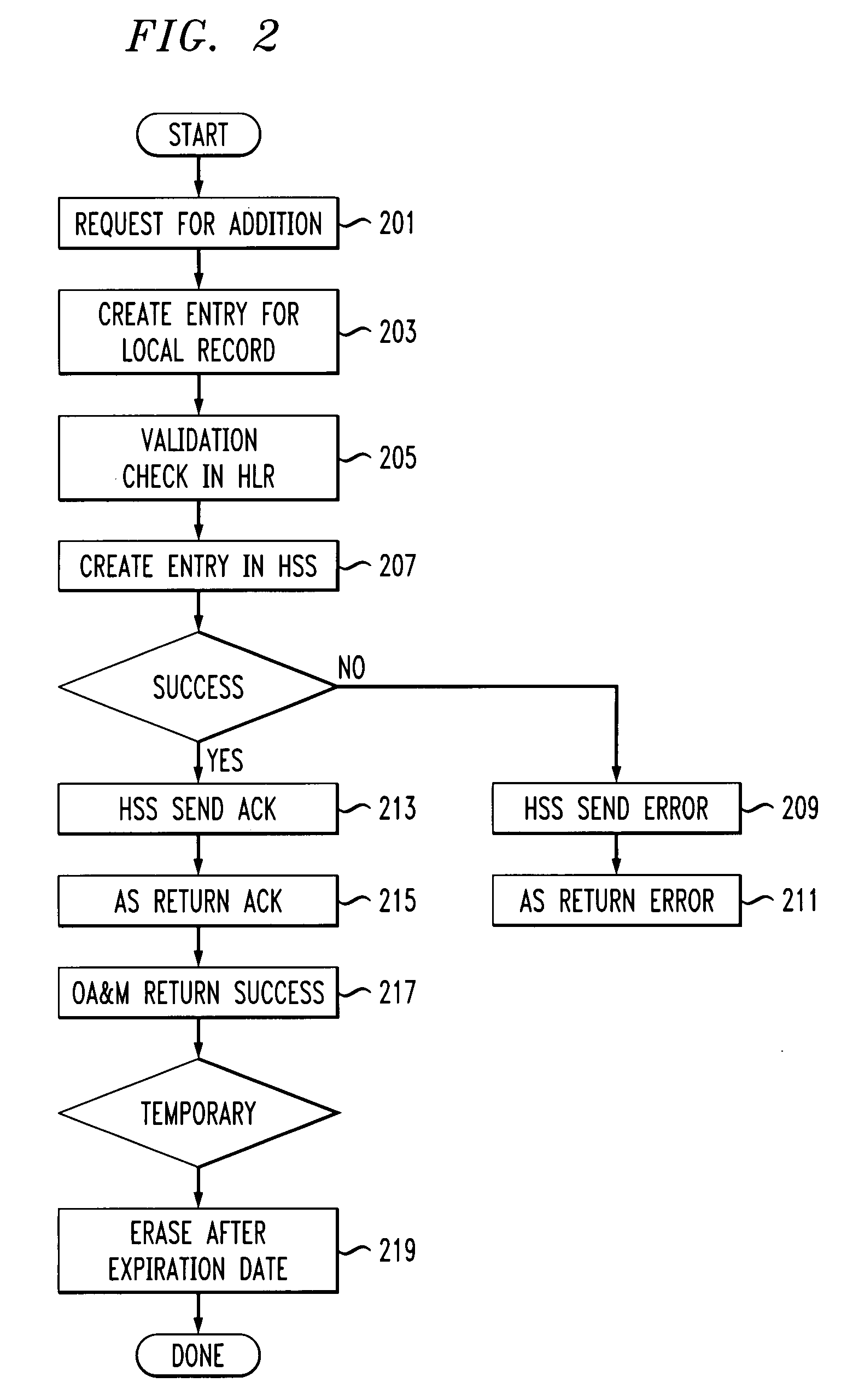
Method and apparatus for provisioning and authentication/registration for femtocell user on IMS core network
InactiveUS20080318551A1Authentication is convenientUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile stationFemtocell
A method for provisioning, registering and authenticating a mobile phone on a basestation is provided. The method includes receiving an addition request for the addition of a mobile station to a basestation authorization record via an interface. The method continues with creating an entry for the mobile station, where the entry includes mobile station information, and receiving a registration request including request information from the mobile station to register to receive basestation based services via the associated internet multimedia subsystem network. The method also includes authorizing registration on the IMS network based at least in part on the request information.
Owner:ALCATEL-LUCENT USA INC
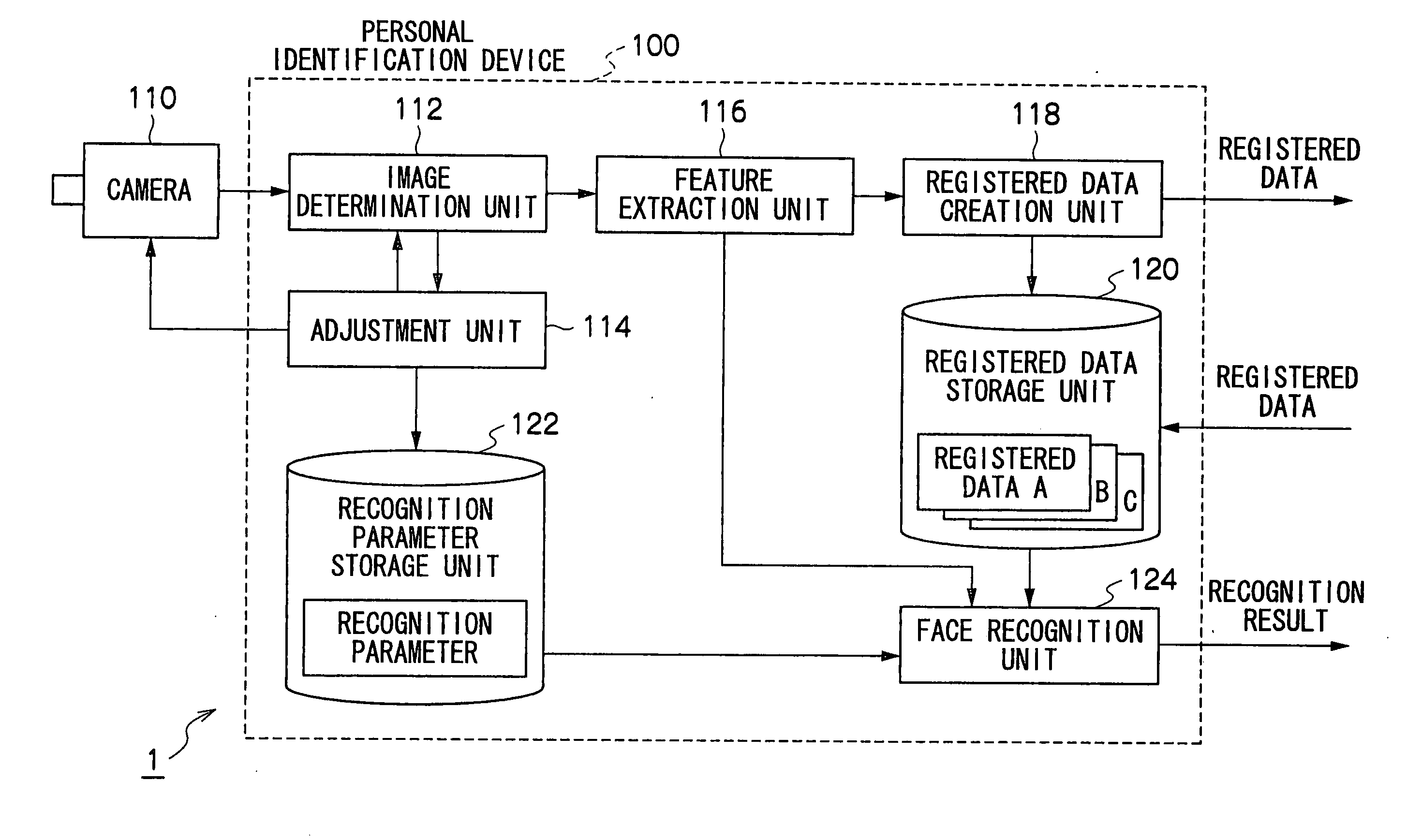
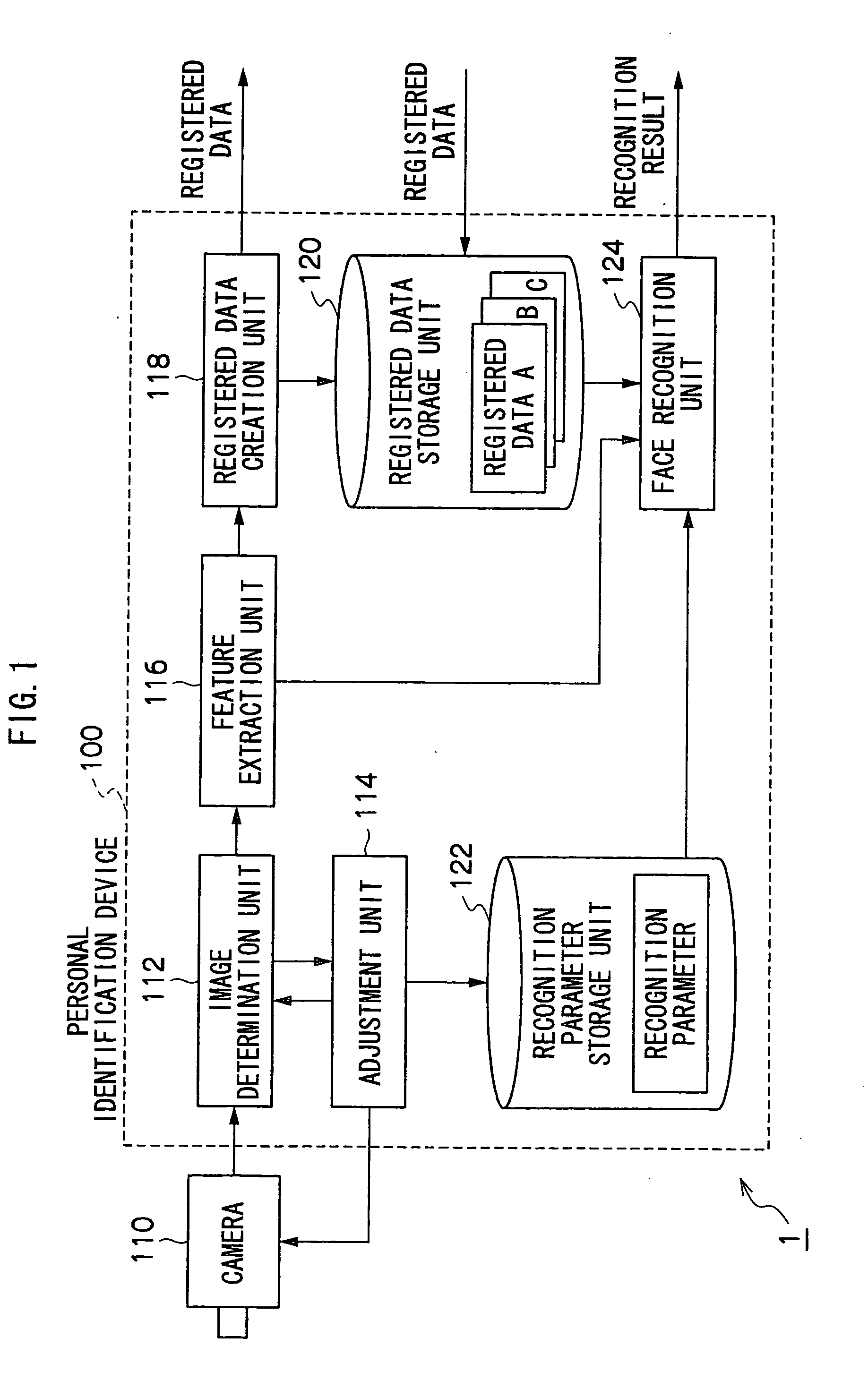
Personal Identification Device and Personal Identification Method
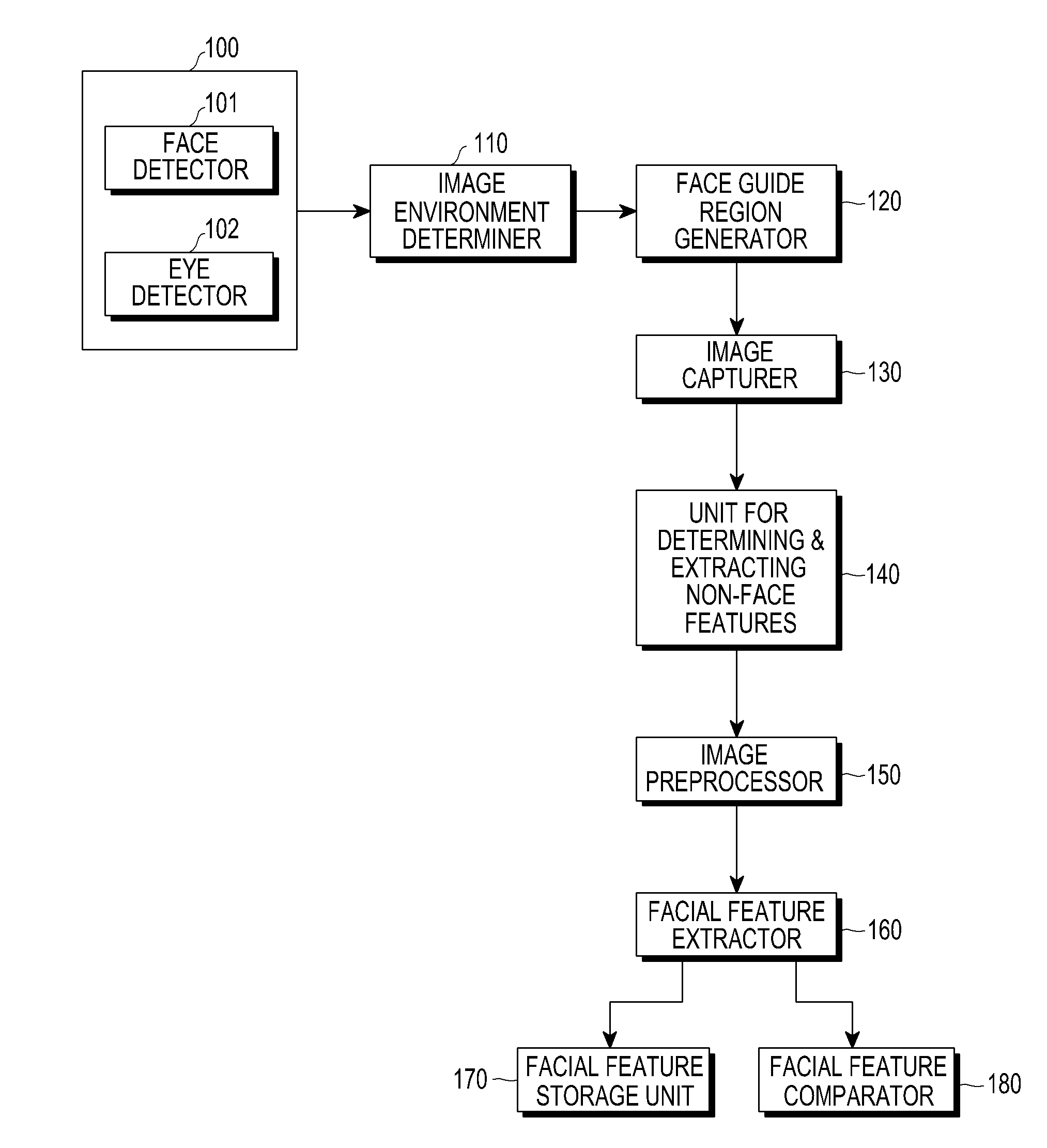
InactiveUS20090060293A1Improve performanceImprove image qualityTelevision system detailsCharacter and pattern recognitionImage extractionFeature extraction
A personal identification device of the present invention is provided with a registered data storage unit for storing registered data containing facial feature data for a registered user, a recognition parameter storage unit for storing recognition parameters, a image determination unit for determining whether or not the image quality of a user facial image input from an imaging device is appropriate, an adjustment unit for adjusting the settings of the imaging device or modifying the recognition parameters, in accordance with the result of determination carried out in the image determination unit, a feature extraction unit for extracting user facial feature data from a facial image, and a face recognition unit for comparing the extracted feature data with the registered data to determine whether or not the user is a registered user based on the result of comparison and the recognition parameters.
Owner:OKI ELECTRIC IND CO LTD
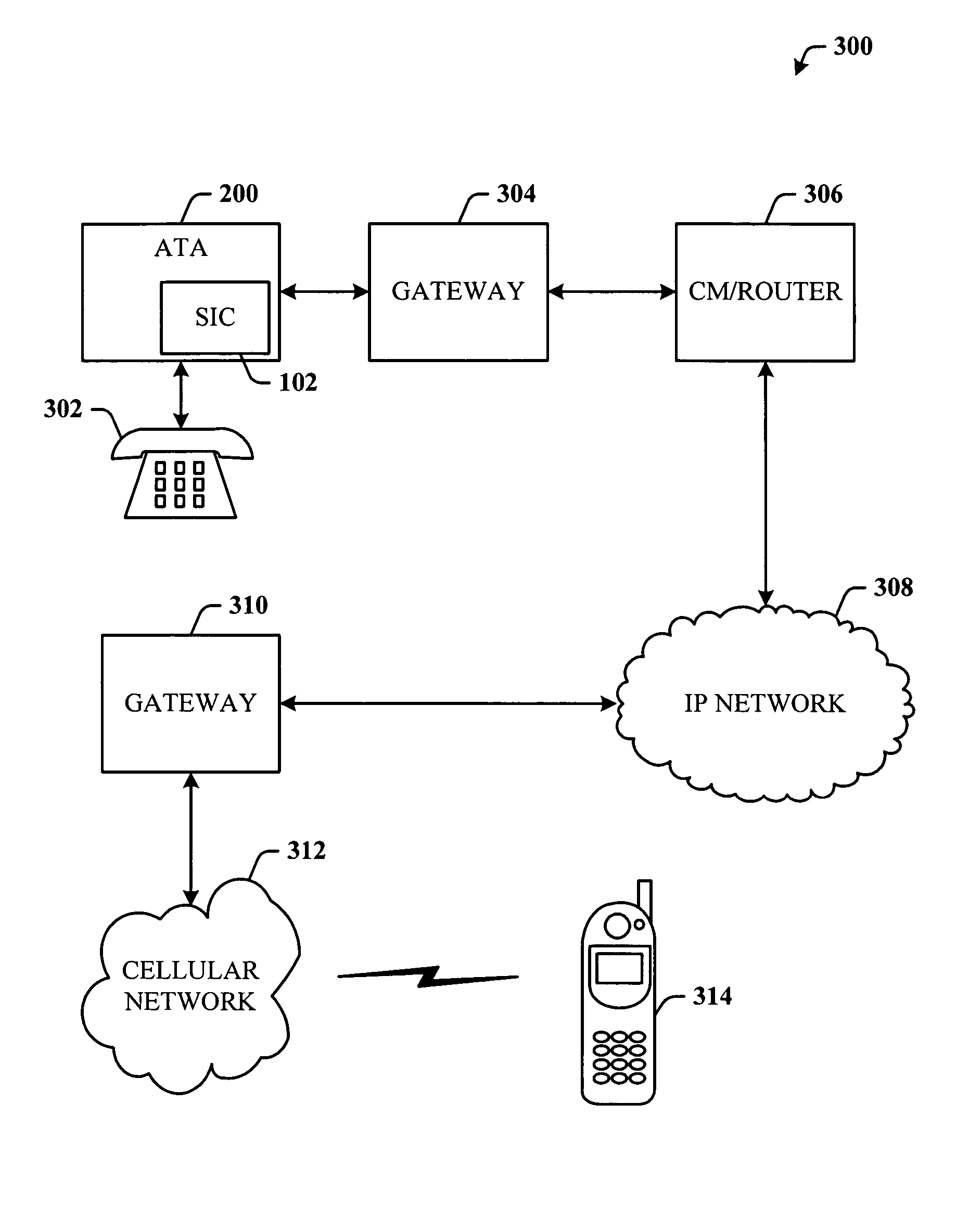
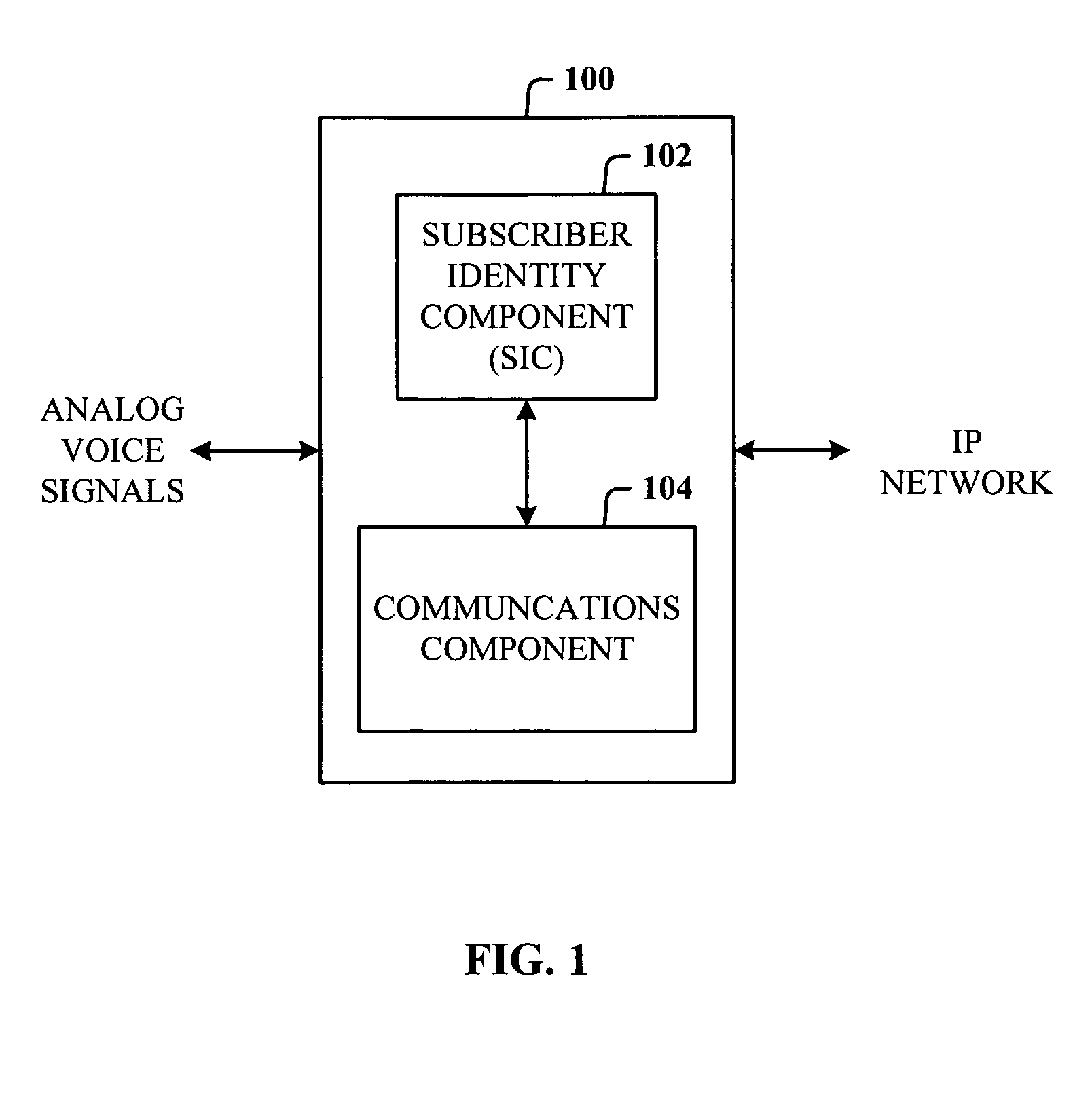
Method, system, and apparatus for providing wireless identification to standard telephone
ActiveUS20050105512A1Reduce and eliminate needAuthentication is convenientSubstations coupling interface circuitsUnauthorised/fraudulent call preventionService userDigital signal
An analog telephone adapter (ATA) having a subscriber identity component in the format of a Subscriber Identity Module (SIM) that couples a telephone to a cellular network via Voice over Internet Protocol (VoIP), thereby allowing a cellular service provider to provide an alternative communication service for the home or business. Instead of using the plain old telephone service, a subscriber can plug their analog telephone into the SIM-enabled ATA (SIM-ATA) and receive telephone service from a cellular service provider, eliminating or reducing the need for a traditional Local Exchange Carrier. The SIM-ATA converts signals from analog to digital, and vice-versa. Once the analog telephone signal has been converted to digital, an IP-based protocol (e.g., VoIP) can be used to transmit the telephone call over a digital network. The cellular service provider can then track usage and bill the subscriber accordingly.
Owner:CHANYU HLDG
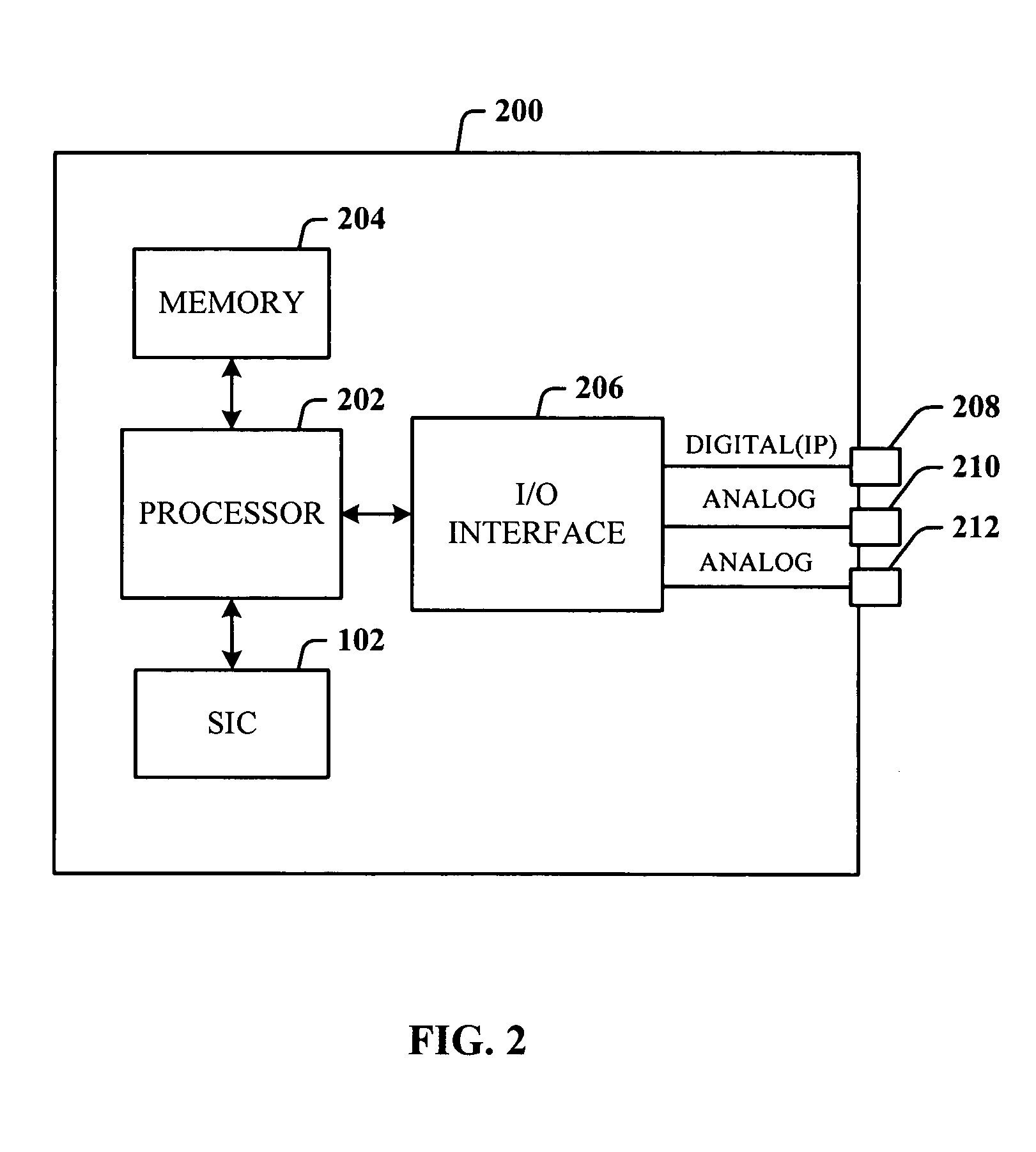
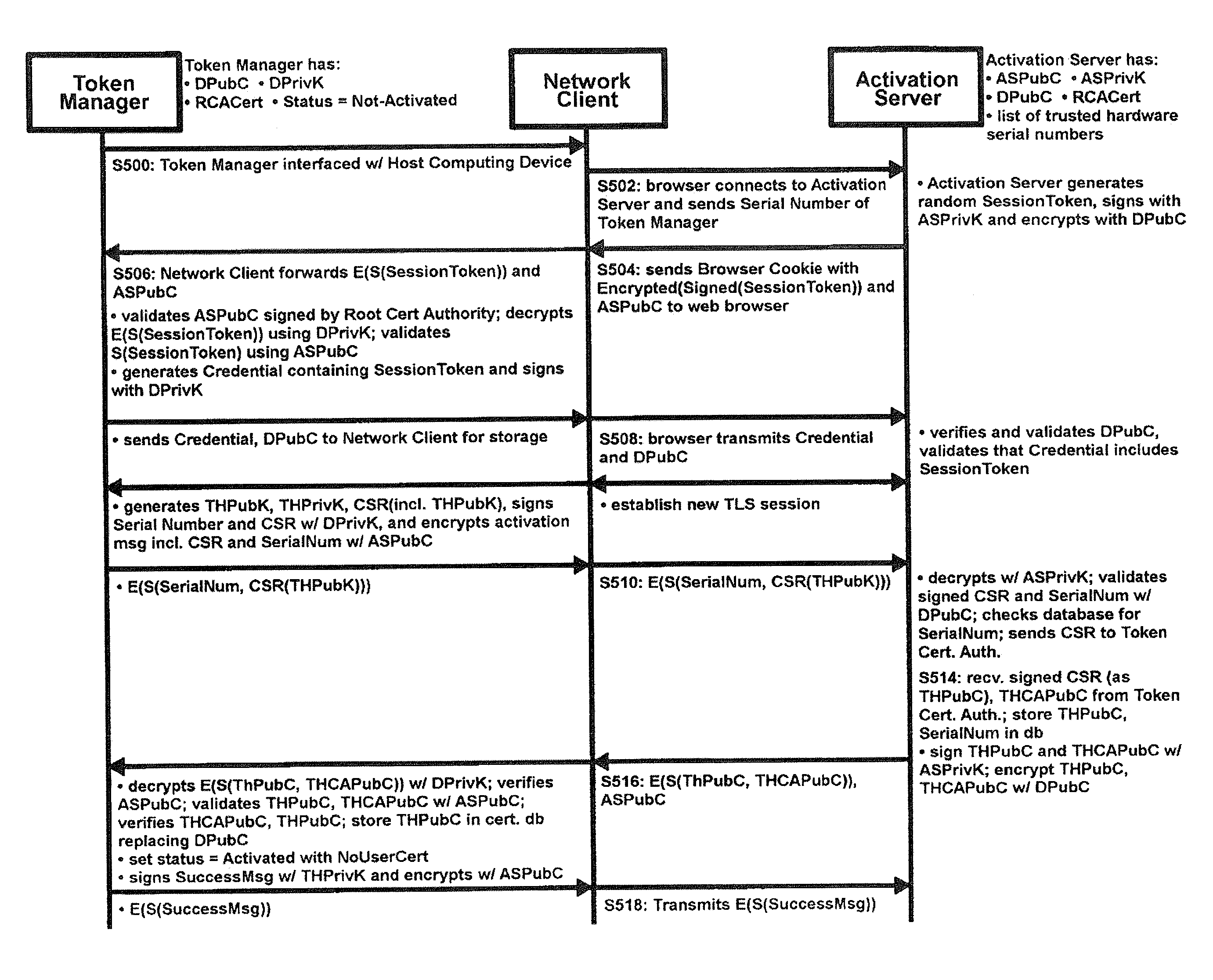
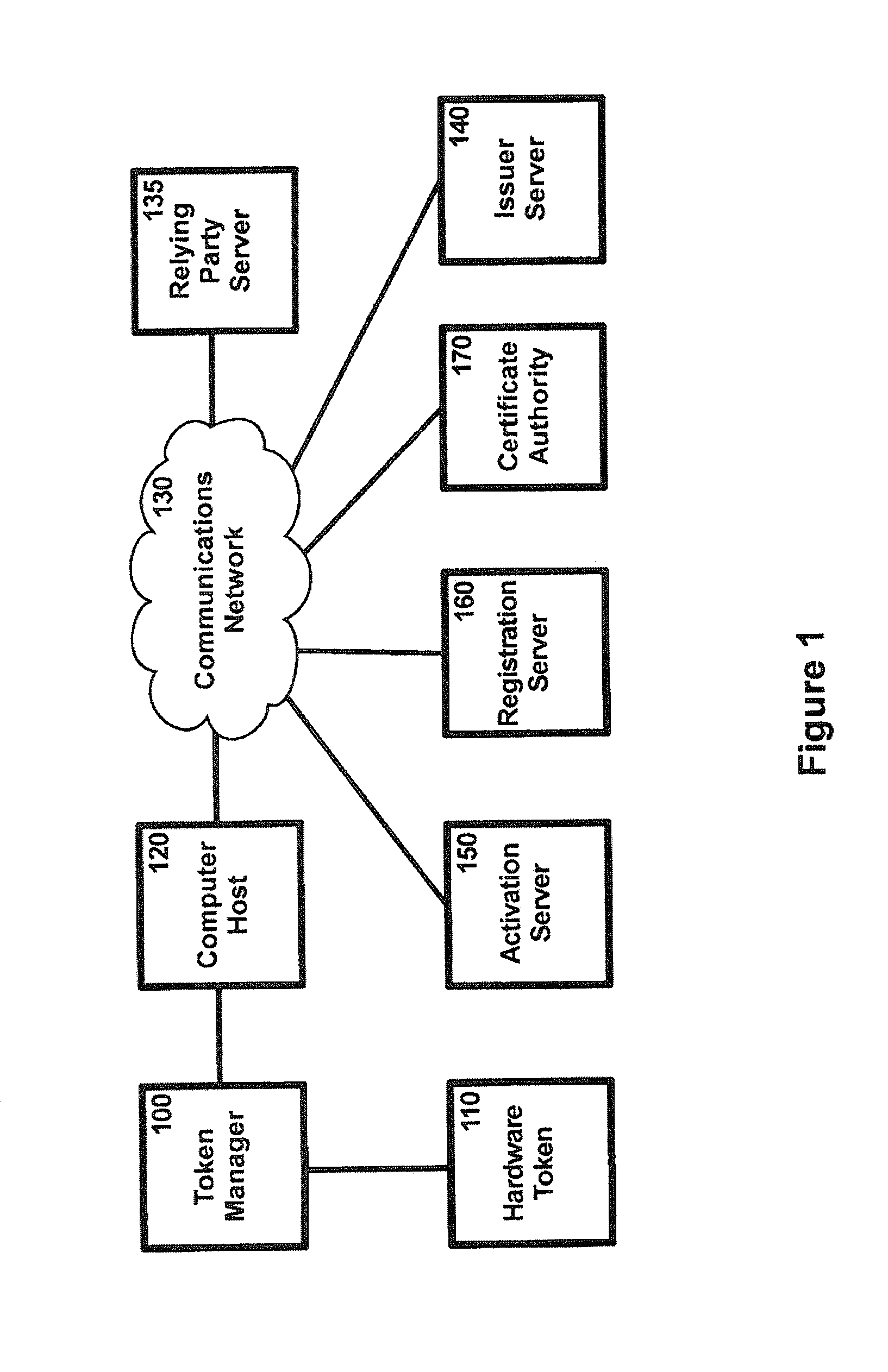
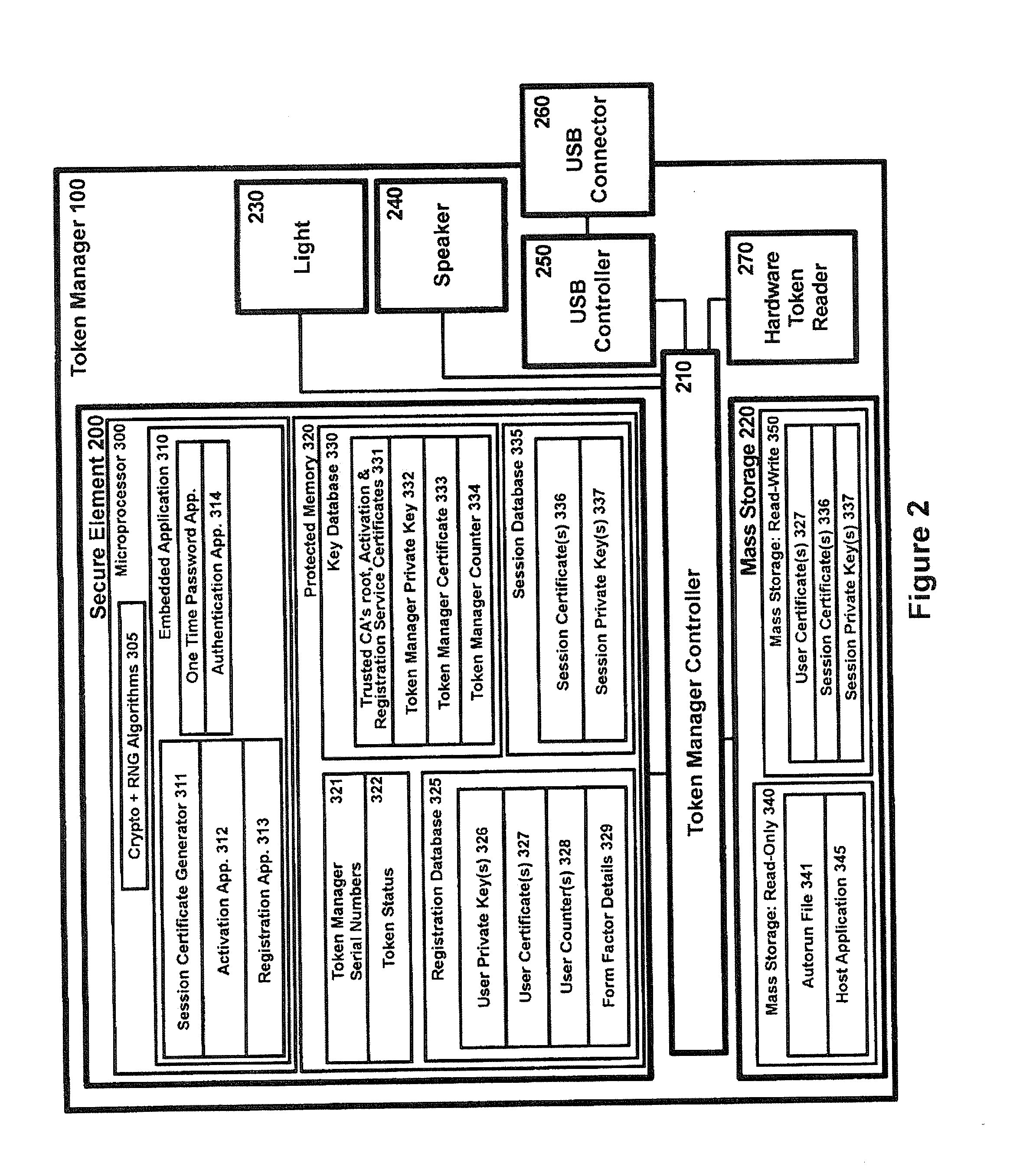
System and methods for online authentication
ActiveUS20110307949A1Authentication is convenientDigital data processing detailsUser identity/authority verificationClient-sideAuthorization
A method of authenticating a network client to a relying party computer via a computer server comprises the computer server receiving a transaction code from a token manager via a first communications channel. The network client is configured to communicate with a token manager which is configured to communicate with a hardware token interfaced therewith. The network client is also configured to communicate with the relying party computer and the computer server. The computer server also receives a transaction pointer from the relying party computer via a second communications channel that is distinct from the first communications channel. Preferably, the transaction pointer is unpredictable by the computer server. The computer server transmits an authorization signal to the relying party computer in accordance with a correlation between the transaction code and the transaction pointer. The authorization signal facilitates authentication of the network client to the relying party computer.
Owner:SECUREKEY TECH
Computer Session Management Device and System
InactiveUS20090183254A1Authentication is convenientDigital data processing detailsUser identity/authority verificationSession managementComputer Session
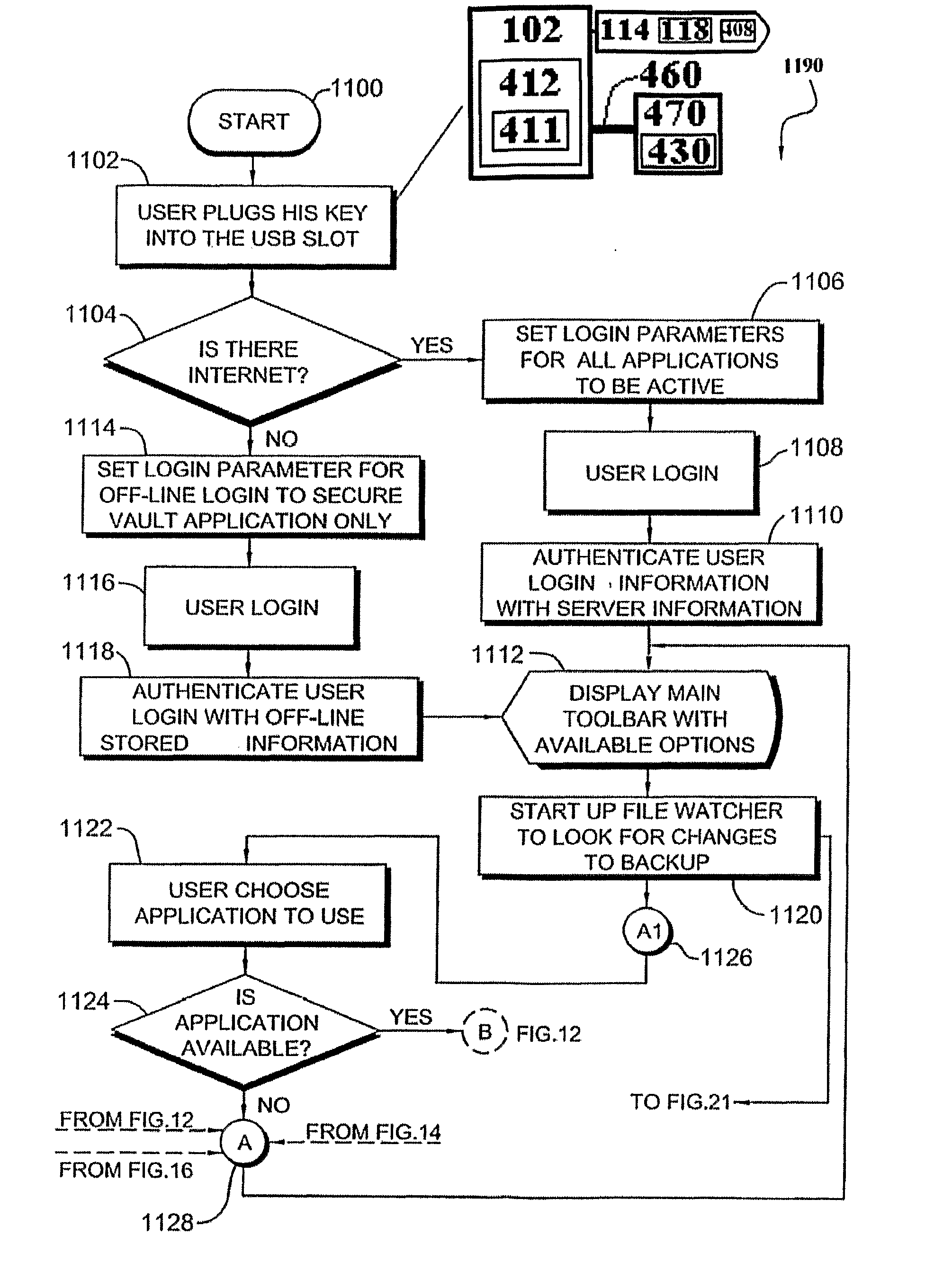
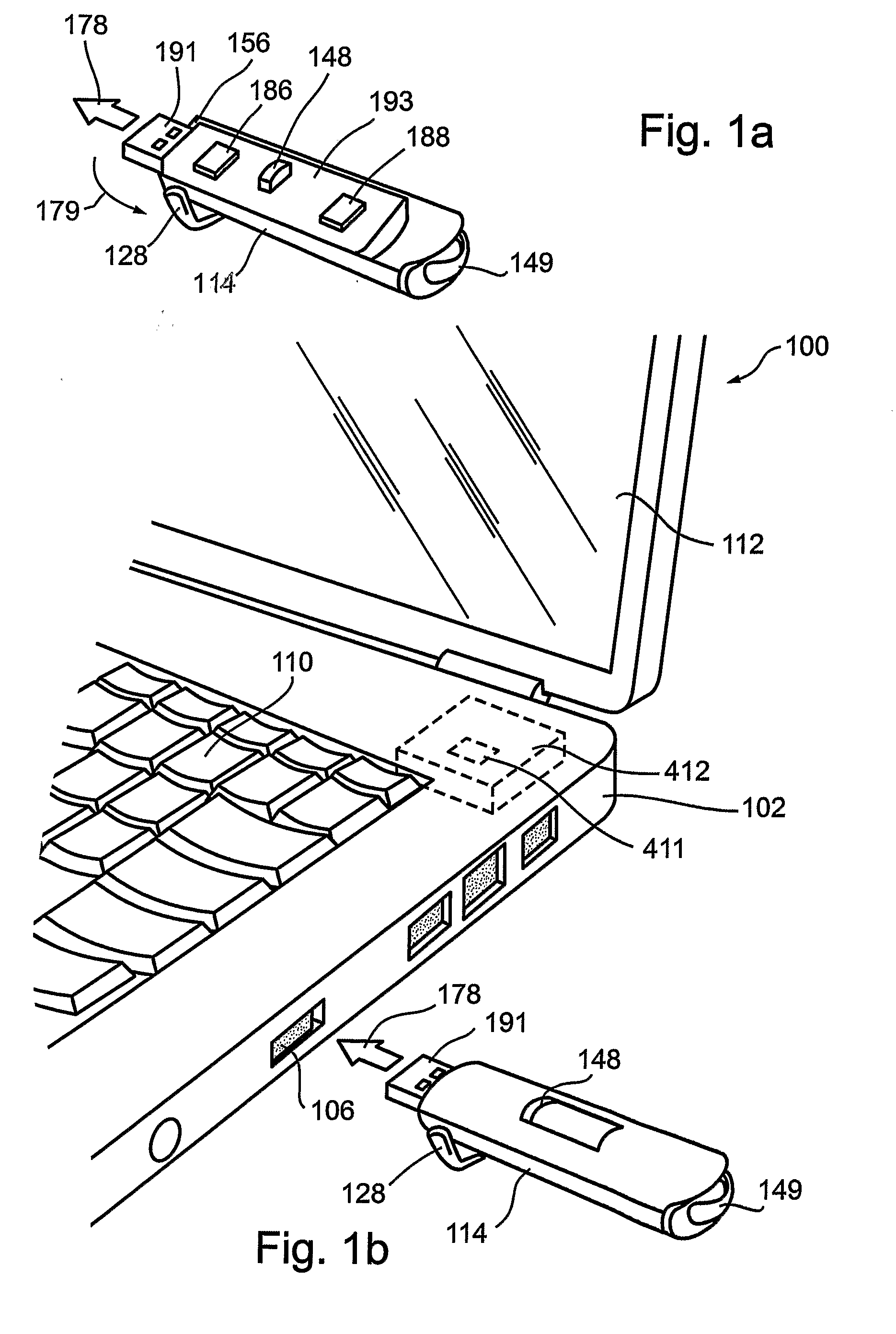
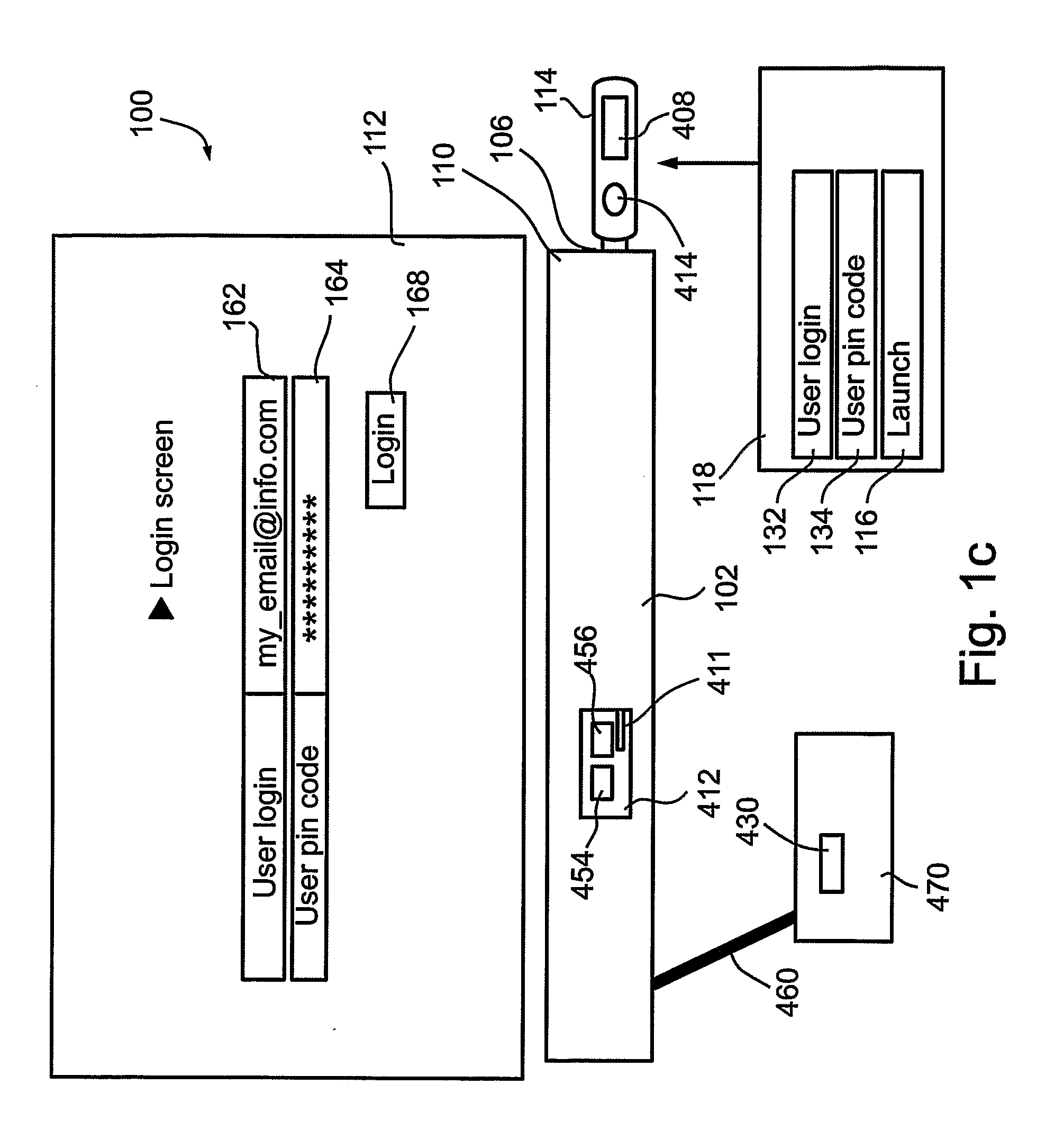
A portable session management device configured for insertion into an input on a host computer, the portable session management device comprising: an authentication unit configured to obtain authentication of the user portable session management device with respect to the host computer; and a safe access unit operatively associated with the authentication unit and configured to facilitate safe access to at least one computer-based application in conjunction with the host computer.
Owner:ATOMYNET
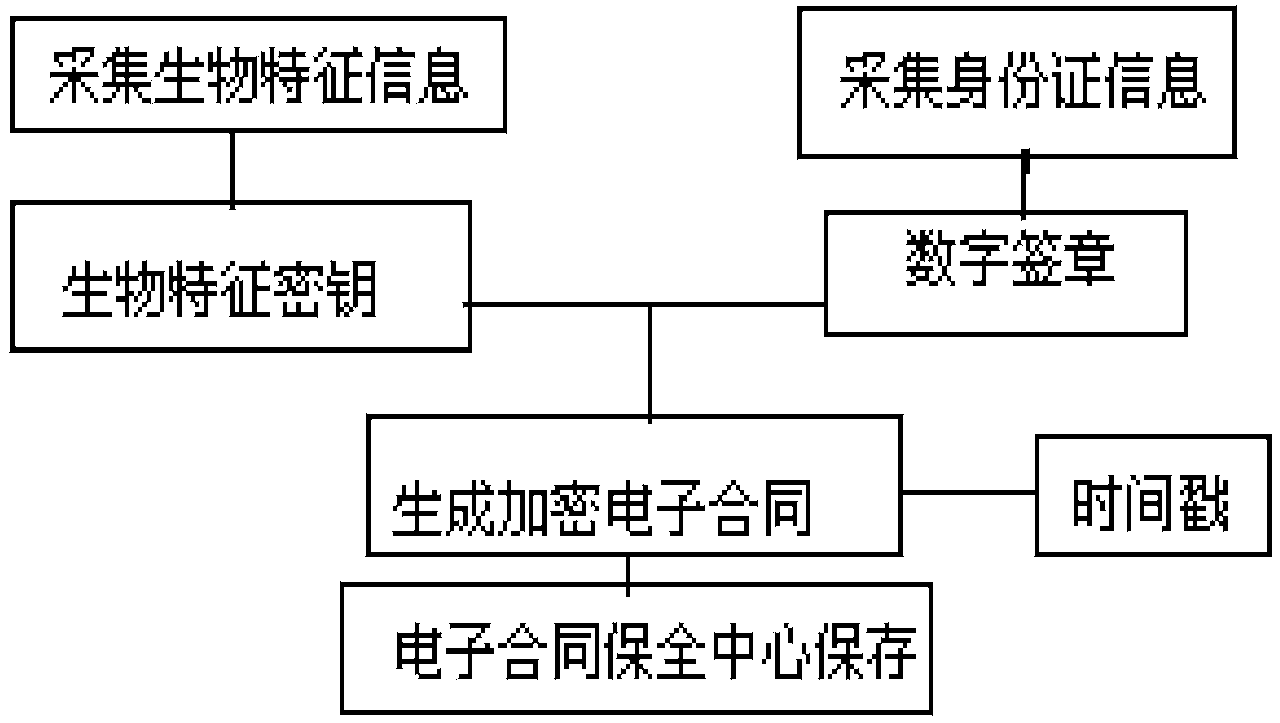
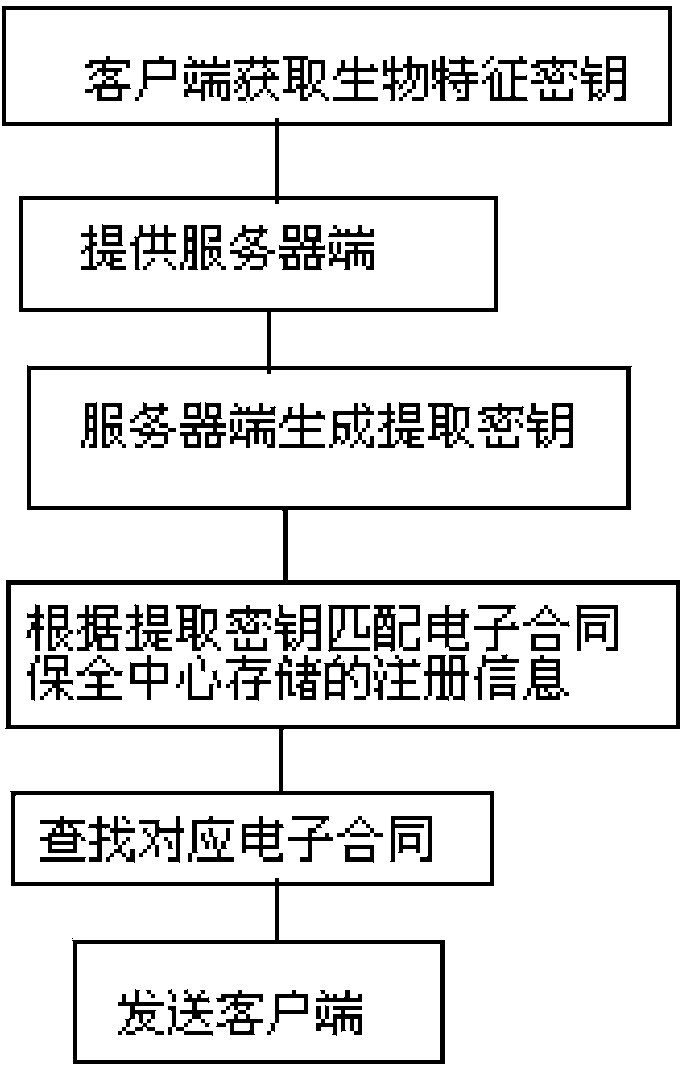
Electronic contract security system and method based on biological information identification
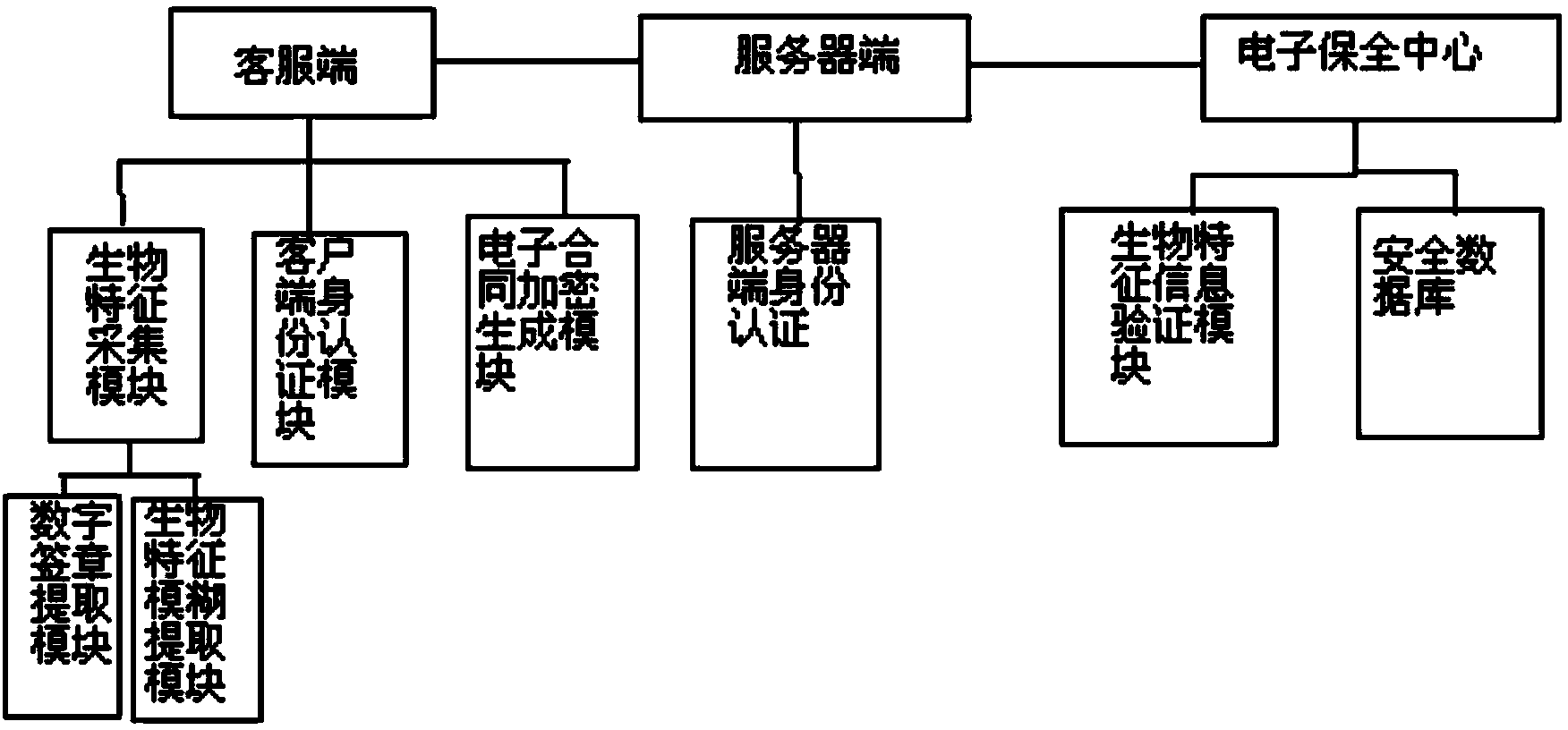
ActiveCN103679436AAuthentication is convenientImprove securityUser identity/authority verificationPayment protocolsInformation processingThird party
The invention discloses an electronic contract security system and method based on biological information identification, and relates to the technical field of computer information processing. In the prior art, electronic contracts can be tampered when the electronic contracts are handed to a third party to be saved, secrete keys generated by individual biological characteristics cannot be exactly the same, and exposure of characteristic information can be caused easily due to information matching and information extraction of different ways and methods. According to the electronic contract security system based on the biological information identification, encryption is carried out in the generated electronic contracts by using the biological information of applicants, identification card information of users are further overlaid to serve as the only authentication marks of the electronic contracts, time stamps are added to the electronic contracts, the electronic contracts are sent to a third party electronic security center for being saved and when clients need to have related services again or contract disputes appear, the secured electronic contracts are extracted from the electronic security center only by checking the biological characteristic information of the users and logging in an identification authentication server.
Owner:重庆信科通信建设监理咨询有限公司
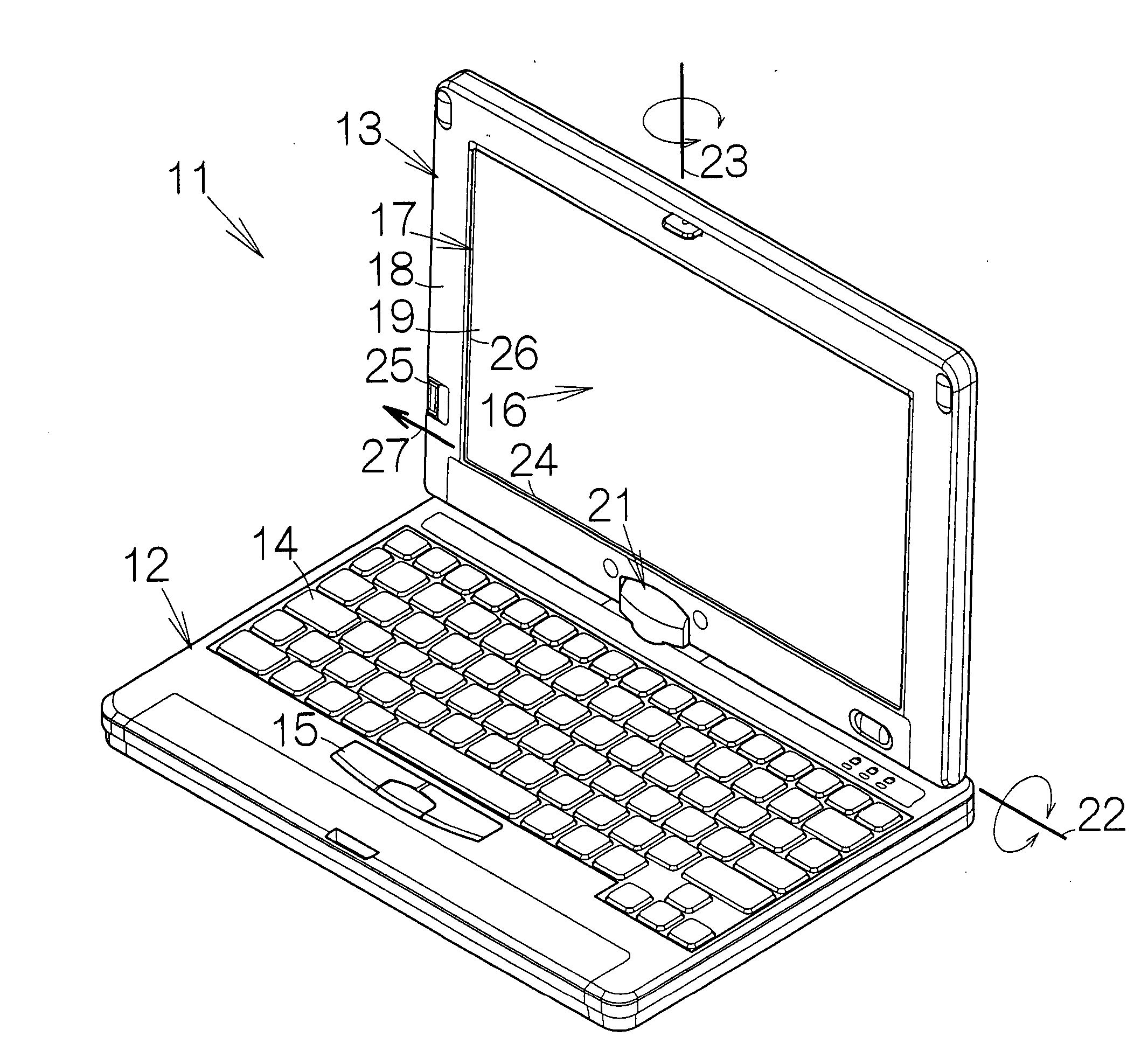
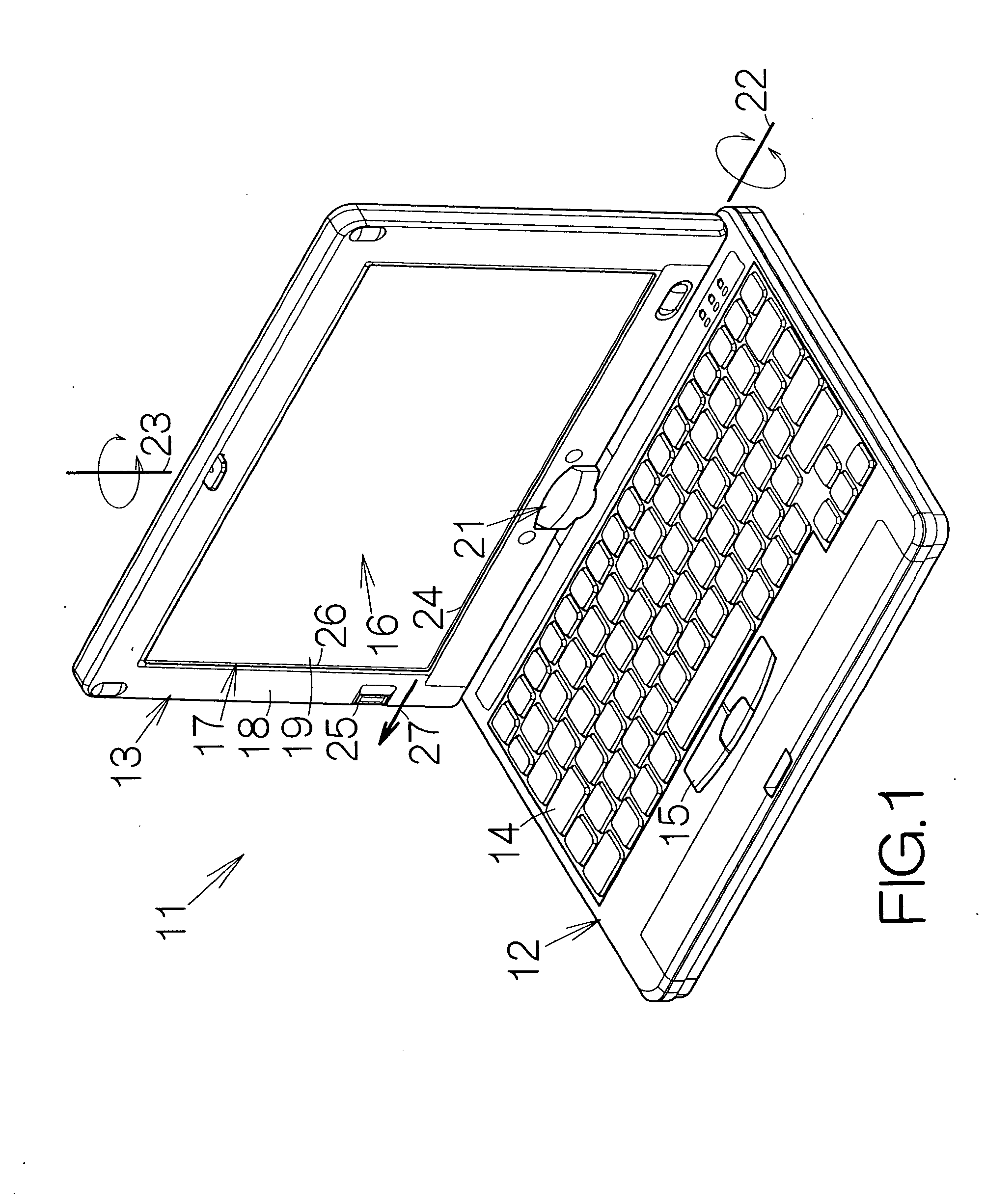
Electronic apparatus including fingerprint sensor
InactiveUS20060214910A1Authentication is convenientSimple wayCathode-ray tube indicatorsDigital data authenticationClassical mechanicsFingerprint
A rectangular screen is defined on the front surface of a second enclosure coupled to a first enclosure. The second enclosure rotates relative to the first enclosure around a first rotation axis established along a first side of the rectangular screen and around a second rotation axis defined within a plane perpendicular to the first rotation axis. A fingerprint sensor is located on the front surface of the second enclosure outside a second side of the rectangular screen intersecting with the first side. When the second enclosure takes an upright attitude relative to the first enclosure, or when the back surface of the second enclosure is received on the front surface of the first enclosure based on the rotation around the first and second axes, the authentication of fingerprints can reliably can be achieved in a facilitated manner irrespective of the relative position between the first and second enclosures.
Owner:FUJITSU LTD
Face image recording system
ActiveUS7158657B2Reduce system installation costsHighly “ convenient ”Image analysisCharacter and pattern recognitionComputer graphics (images)Image recording
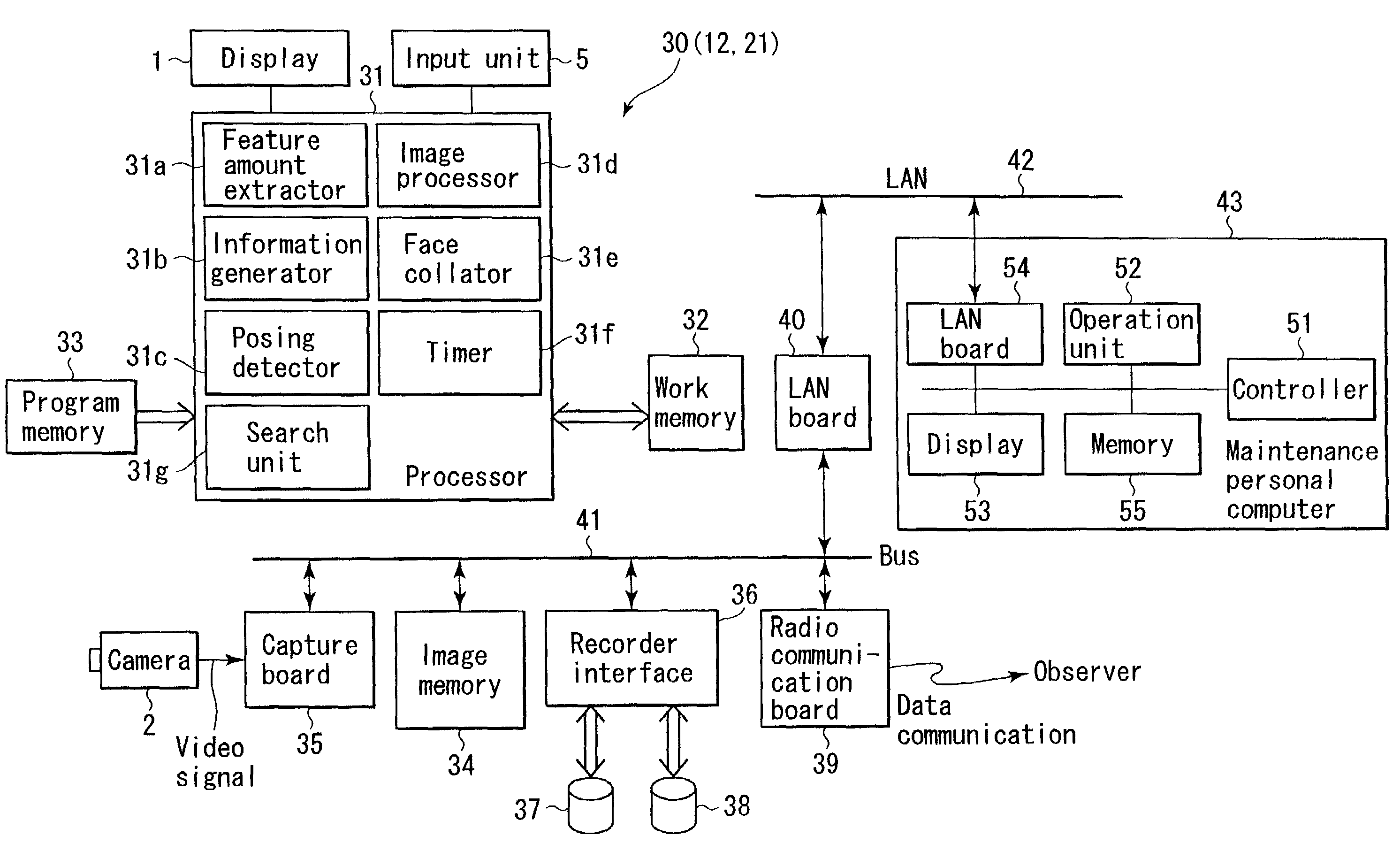
In a face image recording apparatus, a camera photographs the face of a person a plurality of number of times, a processor extracts at least one high-quality image from the plurality of images photographed by the camera, and this high-quality image extracted by the processor is recorded in a memory.
Owner:KK TOSHIBA
Method, system, service device and certification server for realizing device access control
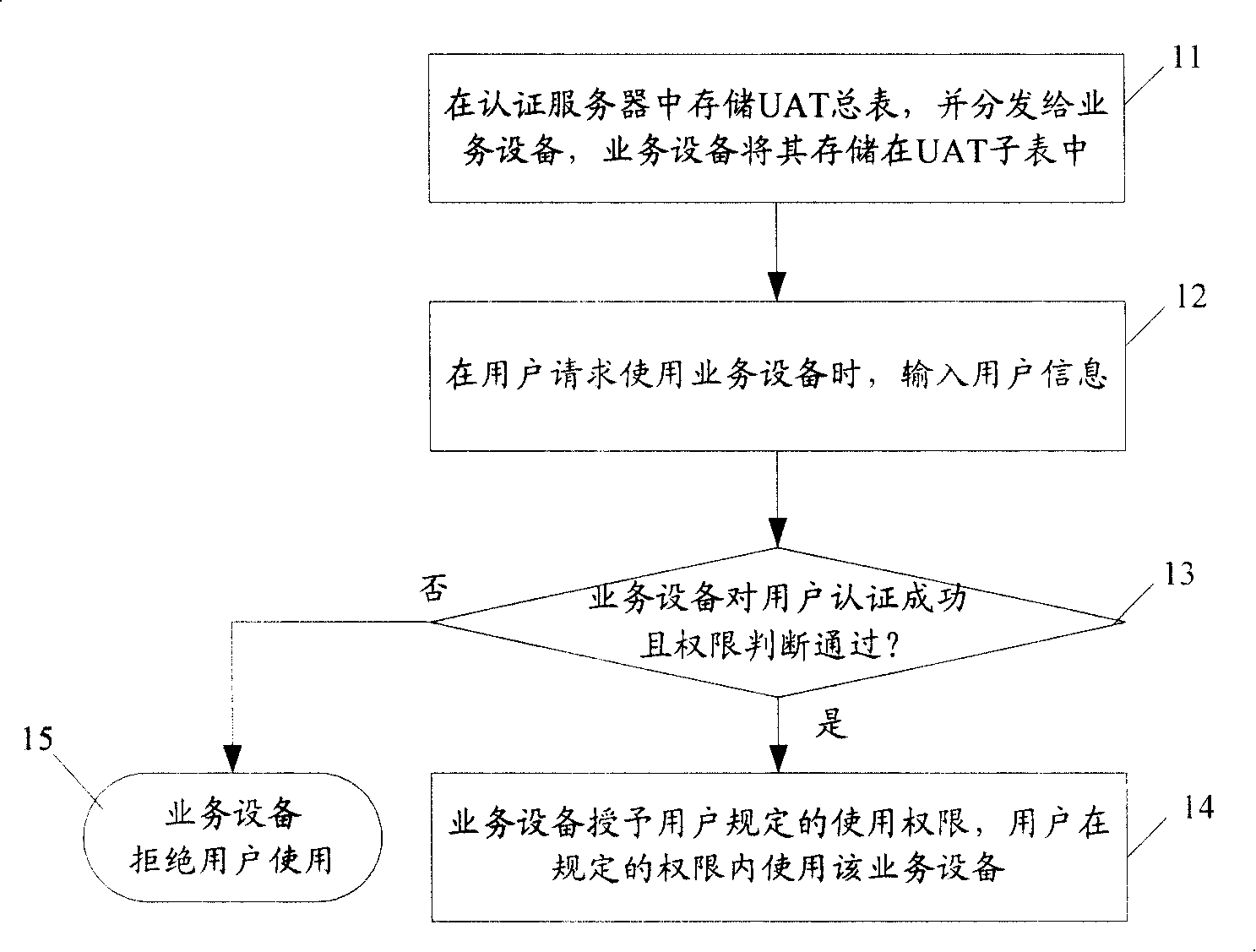
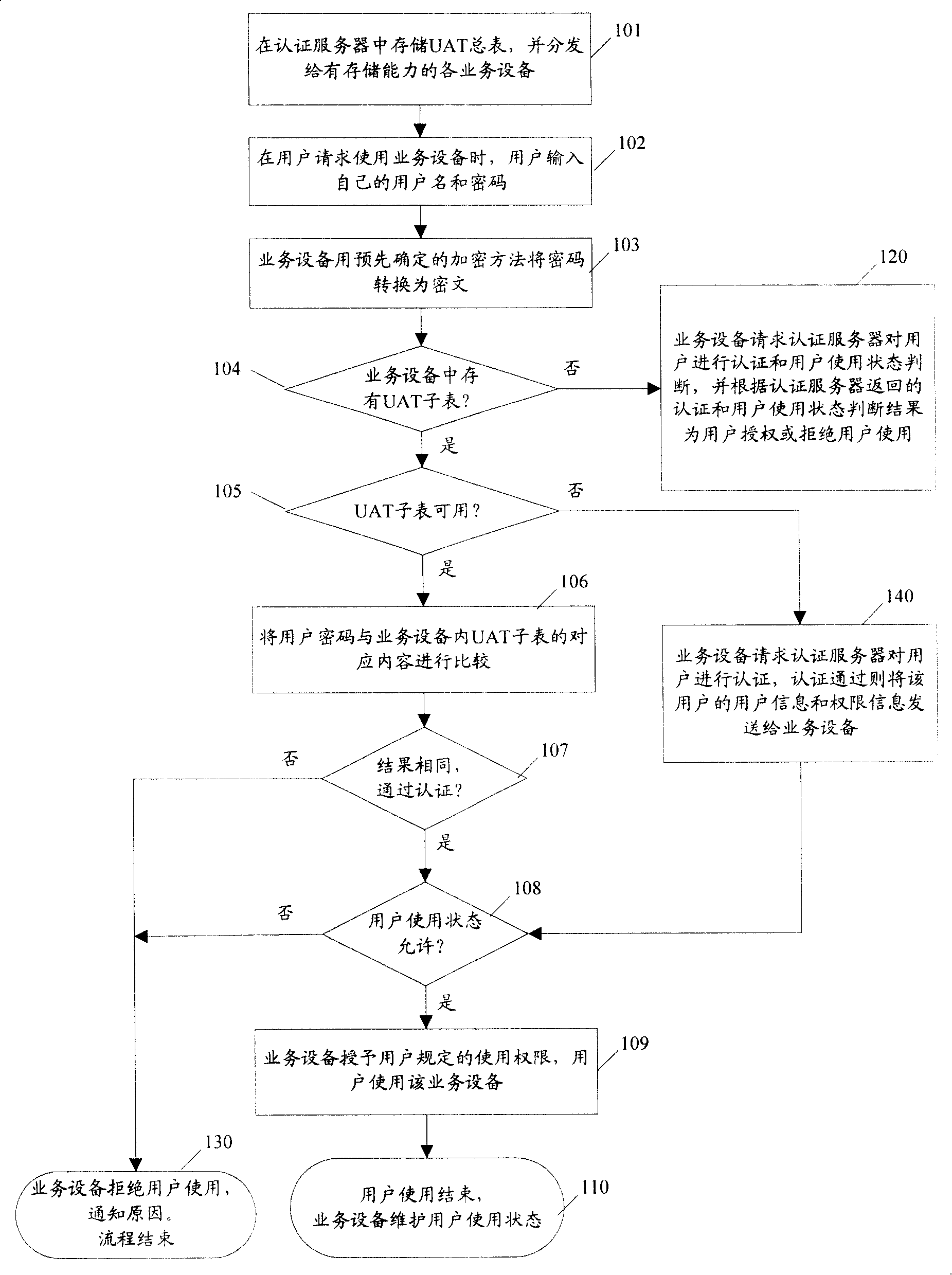
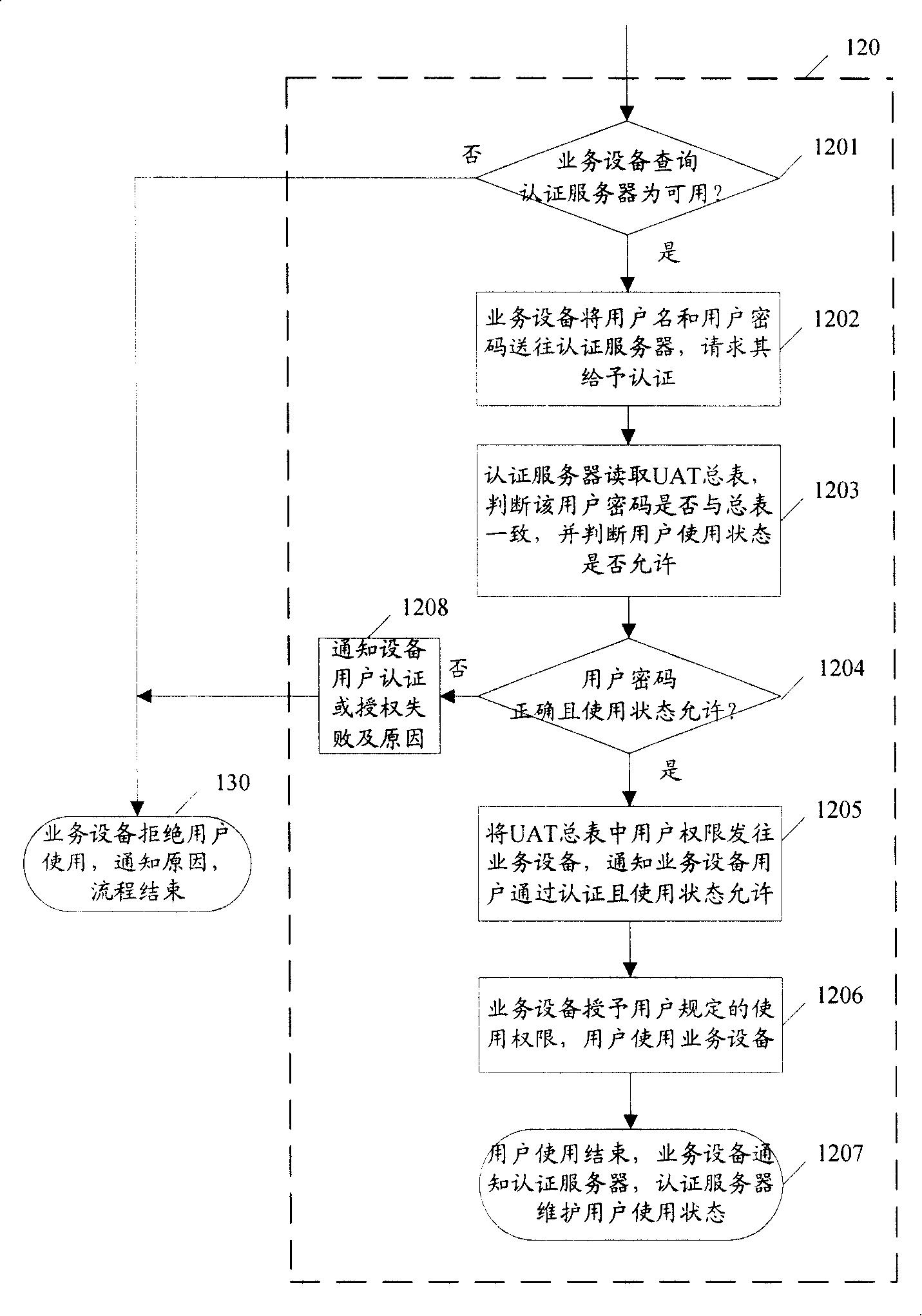
ActiveCN101170409AAuthentication does not affectAuthentication is convenientUser identity/authority verificationData switching networksManagement processControl system
The embodiment of the invention discloses an equipment access control method, which comprises the following steps: a user sends a service request to authentication equipment, which authenticates and authorizes according to the service request and pre-set authentication information in a user authorization list; service equipment provides a service for the user according to the authentication and authorization result. The method reduces the complexity of the service equipment access control. The invention also discloses an equipment access control system, and the service equipment and an authentication server to realize the control of the equipment access. The equipments simply realizes the authentication, authorization and management processes of the service equipment access control, and reduces the complexity of the equipment access control as well with safety and effectiveness and convenient use.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
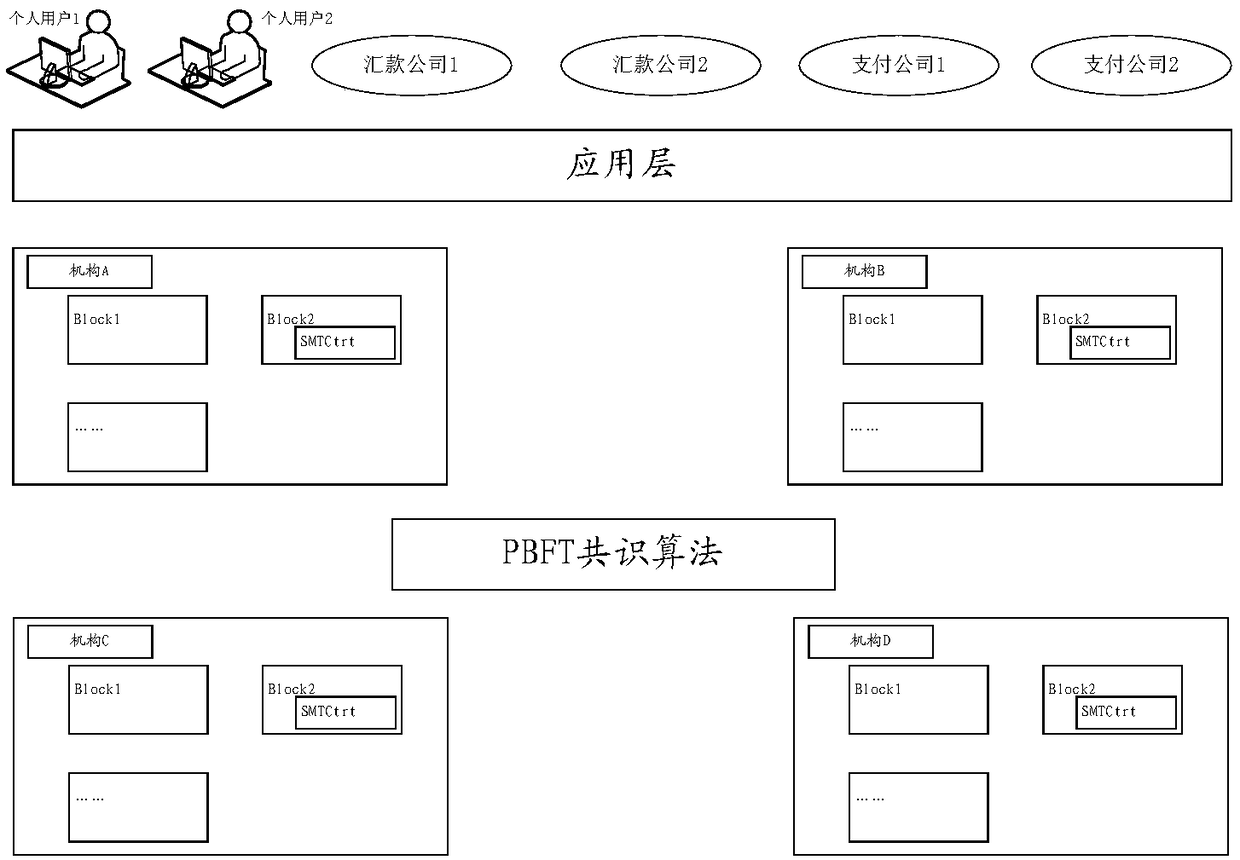
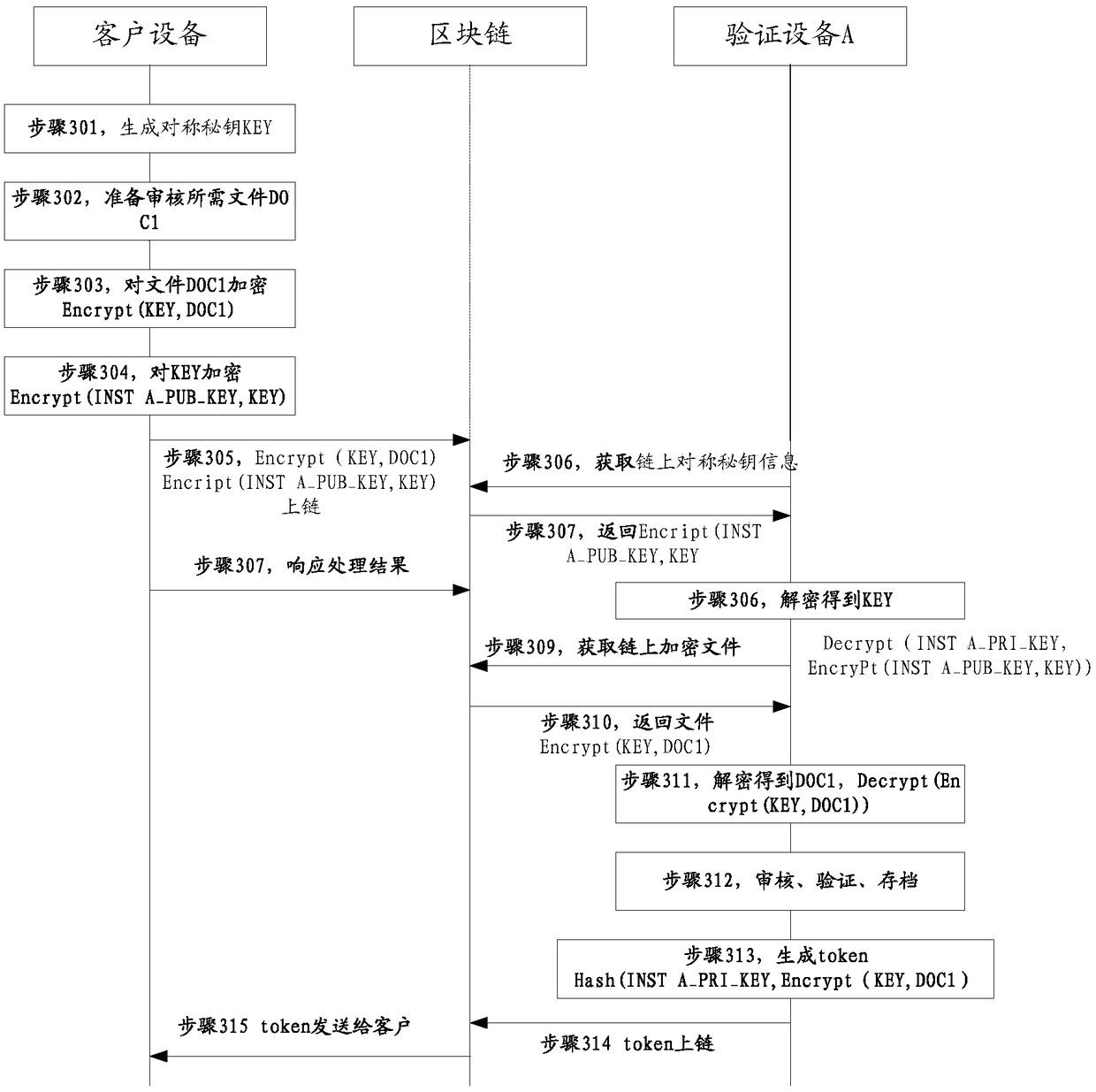
Inter-agency client verification method based on block chain, transaction supervision method and device
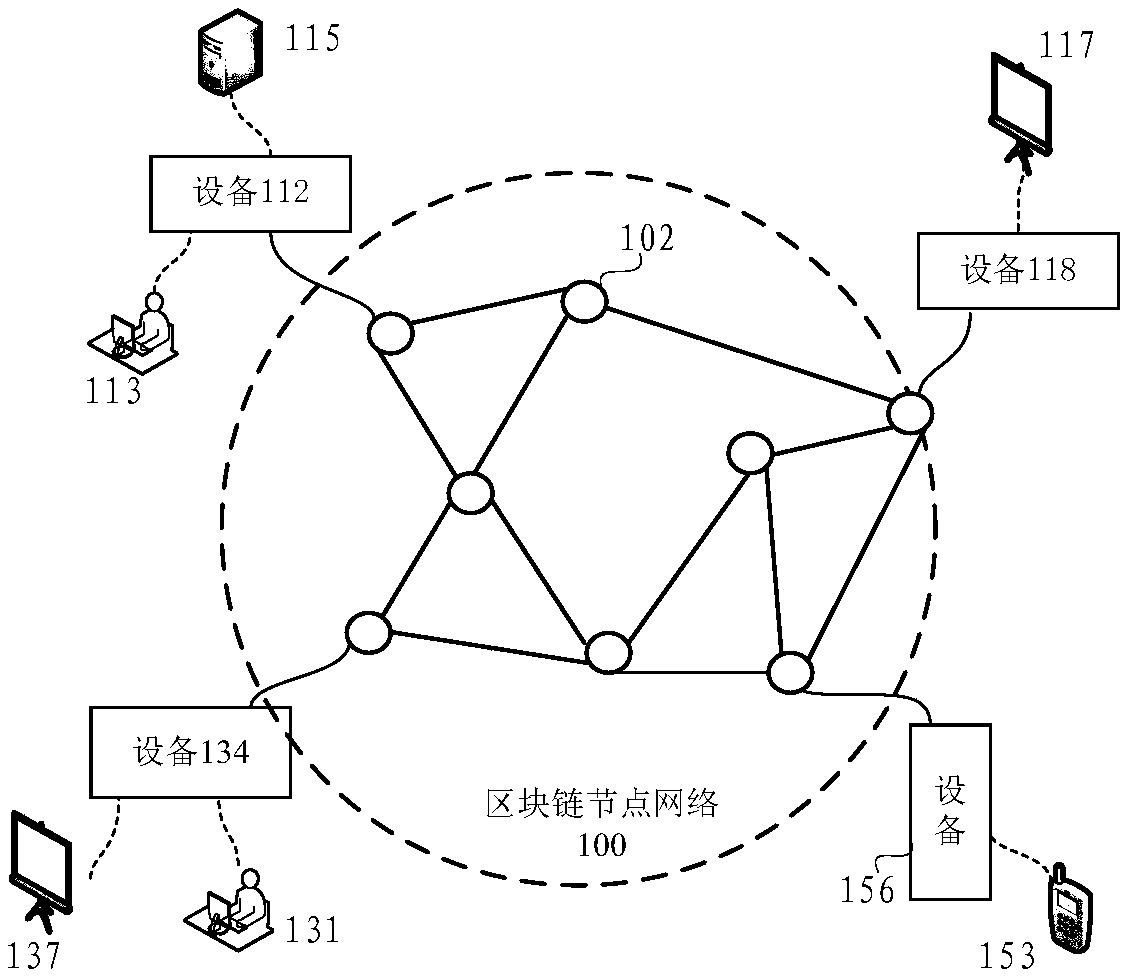
ActiveCN108765240AAuthentication is convenientSimplify the calling processData processing applicationsUser identity/authority verificationInter agencyEngineering
The embodiment of the invention provides an inter-agency client verification method based on a block chain, a transaction supervision method and device. In one embodiment of the invention, the equipment located by the client encrypts a file by utilizing a symmetric key, and the encrypted file and the symmetric key encrypted by utilizing the mechanism A public key are uploaded to the block chain; the equipment of the client acquires a token issued by the mechanism A based on a checking result on the file; the equipment located by the client sends the token and the address of the encrypted fileon the block chain to the equipment of the mechanism B, thereby accelerating the checking process on the file by the mechanism B. Through the method provided by the embodiment of the invention, the file calling process between agencies at present is simplified, and the hit rate of the anti-money laundering rule is increased.
Owner:ADVANCED NEW TECH CO LTD
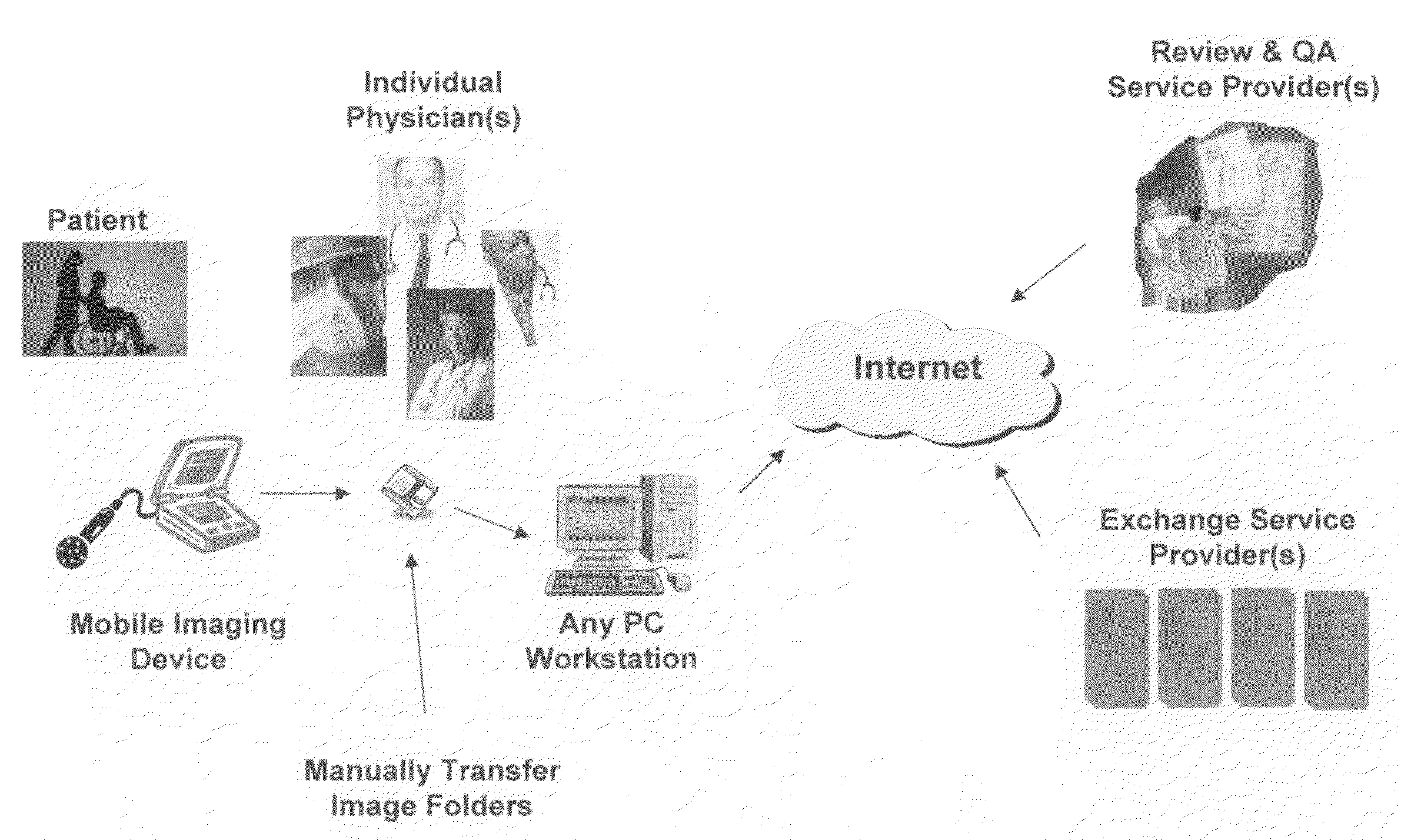
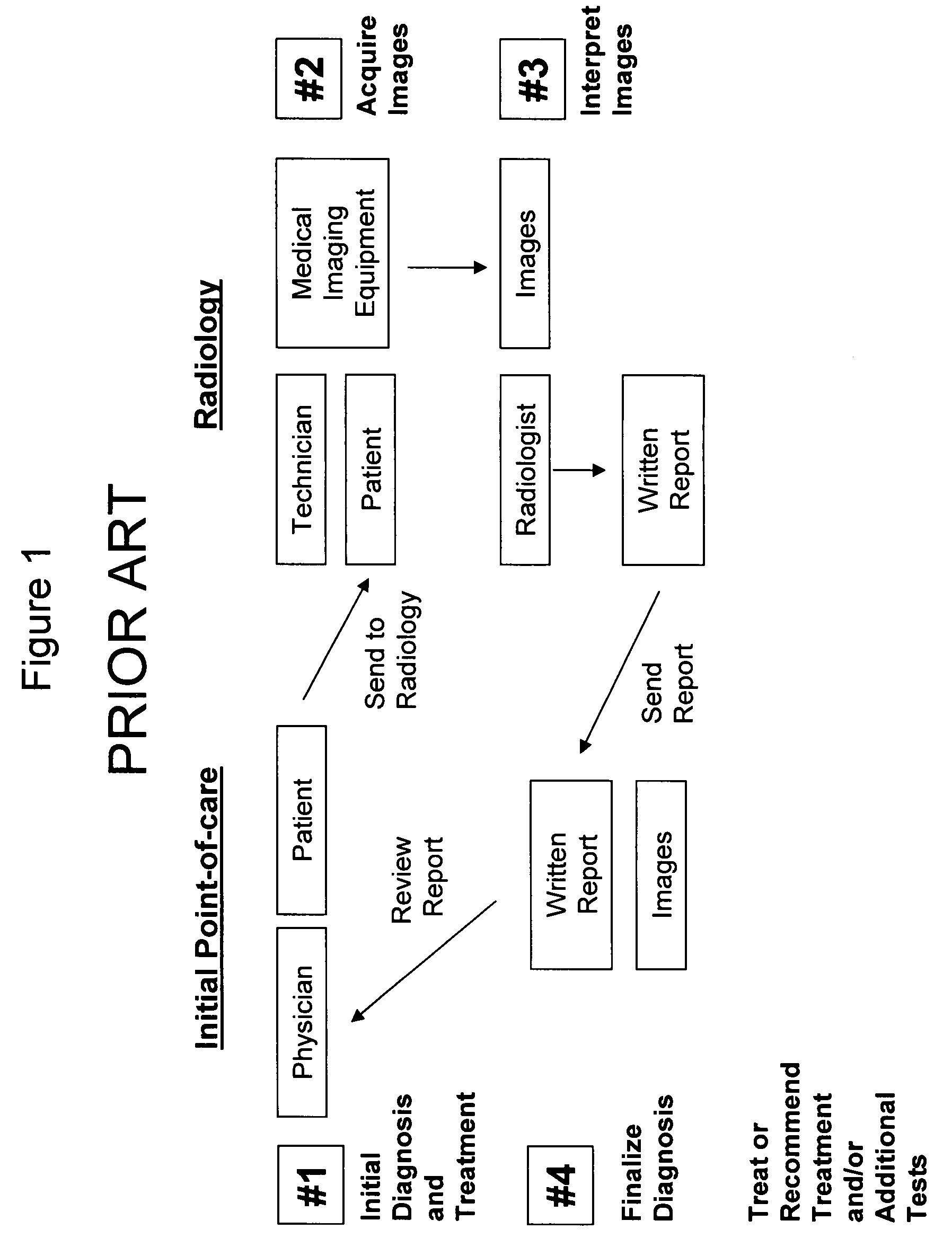
Medical imaging examination review and quality assurance system and method
InactiveUS20070232885A1Authentication is convenientEffectively use and diagnoseMedical communicationDiagnostic recording/measuringPoint of careCredentialing
The present invention is a computer-based review and quality assurance system and method for physicians who use portable imaging technology to diagnose and treat patients at a point of care. The system and method facilitates the credentialing of physicians, provides on-going quality assurance (QA), and integrates medical imaging equipment with software that runs over a network. Such credentialing assists medical institutions by identifying physicians who effectively use and diagnose patients with the imaging equipment.
Owner:COOK THOMAS +2
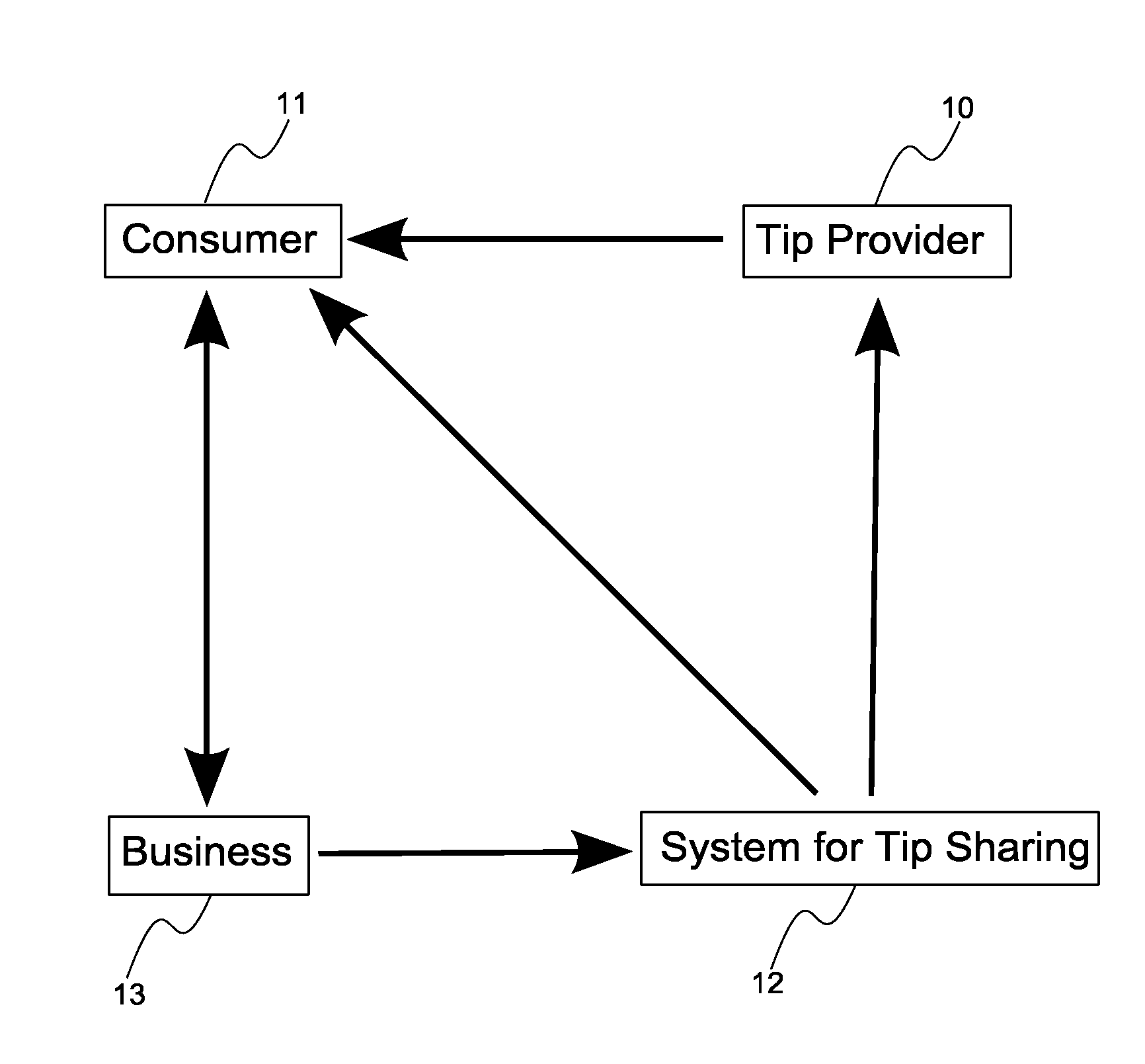
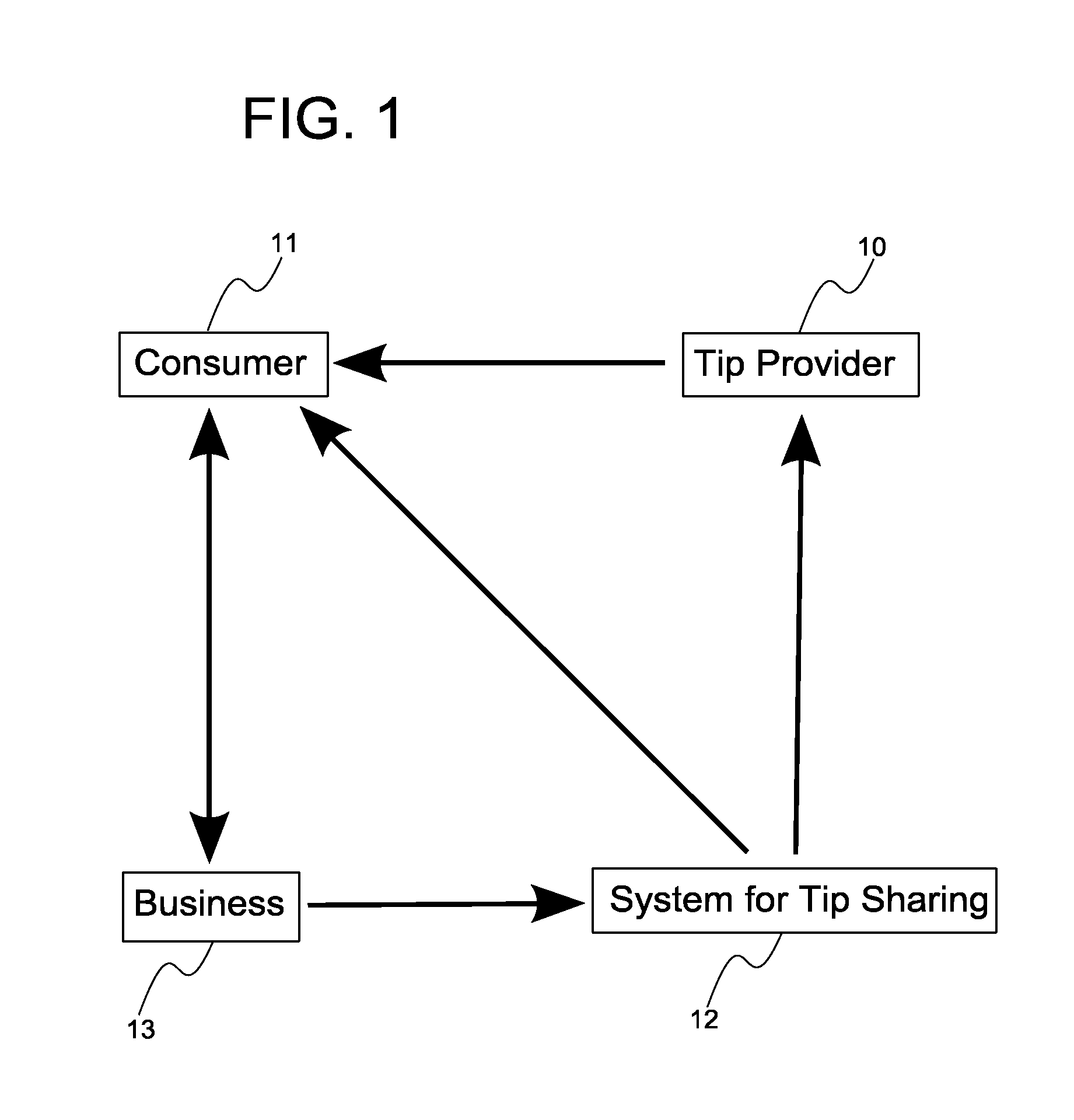
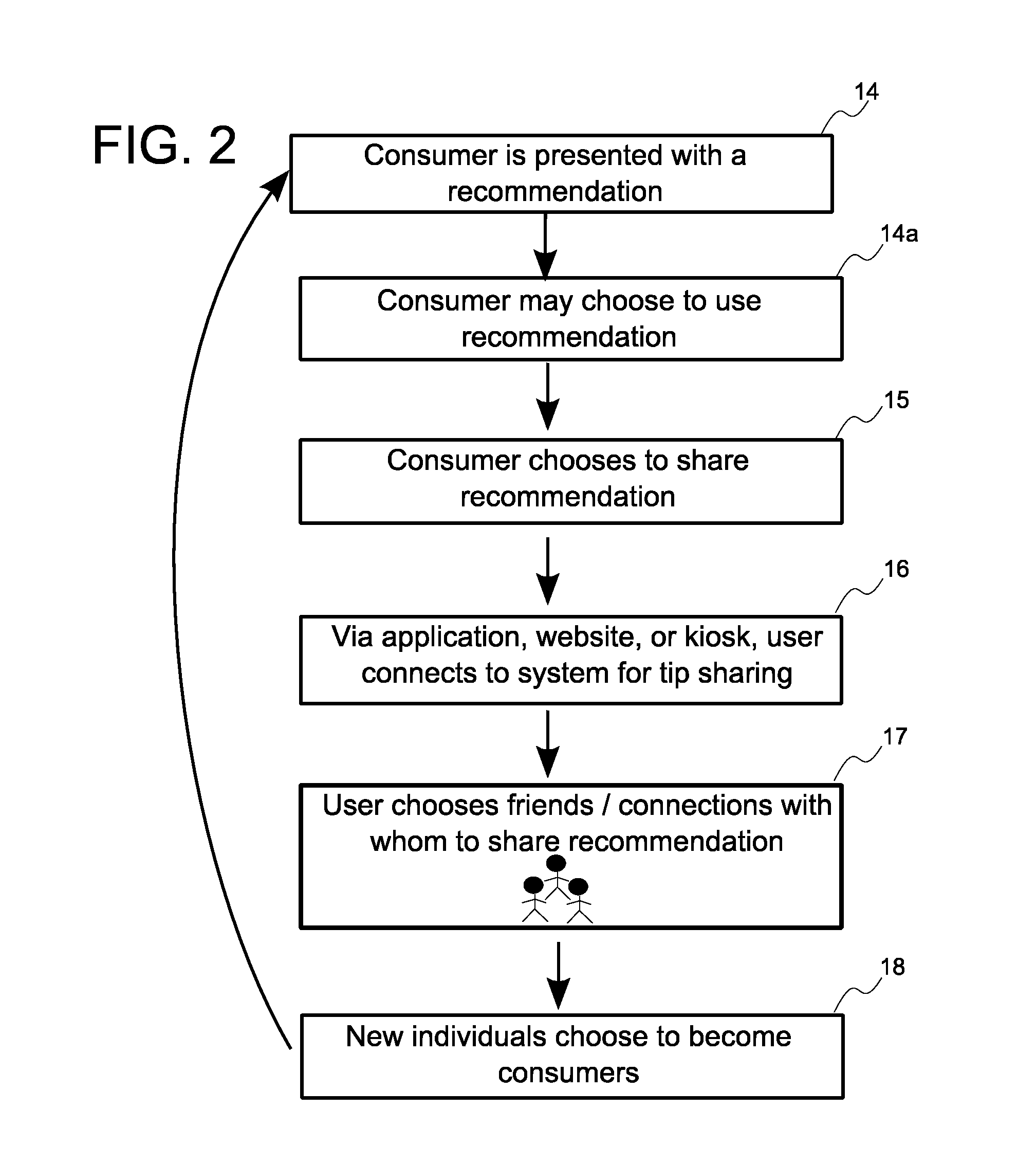
System, method, and computer program product for tip sharing using social networking
A system, method, and computer program product for making a product recommendation that pays cash or non-cash awards to a network of tip sharers / providers. The system may be used to increase traffic to a business by sharing recommendations, which may include discounts or other exclusive offerings, to network connections that may be interested in buying a product or service, or engaging in any activity, of the business. A user of the system shares a tip or recommendation with their friend, this friend becomes a customer after making use of the tip, and a fee paid by the business is used to pay cash incentives to the individual who provided the tip and / or the customer who purchased the product based upon the tip. Additional embodiments are also described for sharing cash incentives with a greater network of individuals including those that invite others to join the tip sharing system.
Owner:OFFICER REISE +2
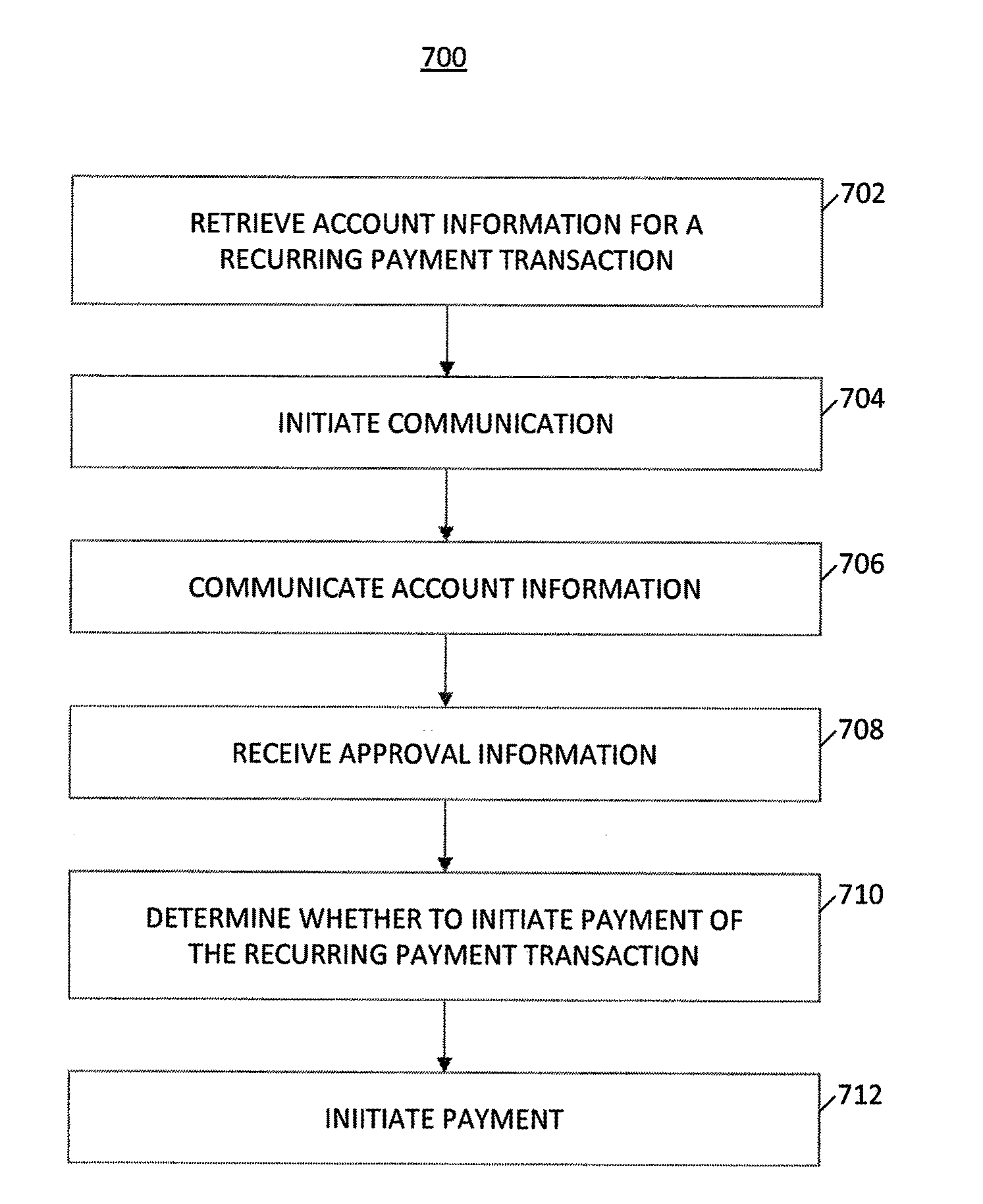
System and Method of Recurring Payment Transactions
InactiveUS20100057616A1Facilitate secure payment transactionAuthentication is convenientAcutation objectsFinanceInternet privacyPayment transaction
A system and method for a recurring payment transaction is provided. A system of authenticating a recurring payment transaction may include an adaptive payment server that includes one or more processors configured to retrieve account information, which may include a payment date and an identification of a communication device of a payor. The adaptive payment server may initiate a communication to the communication device on or before the payment date and communicate at least a portion of the account information to the communication device. The adaptive payment server may receive, from the communication device, approval information and determine whether to initiate payment of the recurring payment transaction using the approval information. The adaptive payment server may initiate payment of the recurring payment transaction based on the determination.
Owner:MTS HLDG
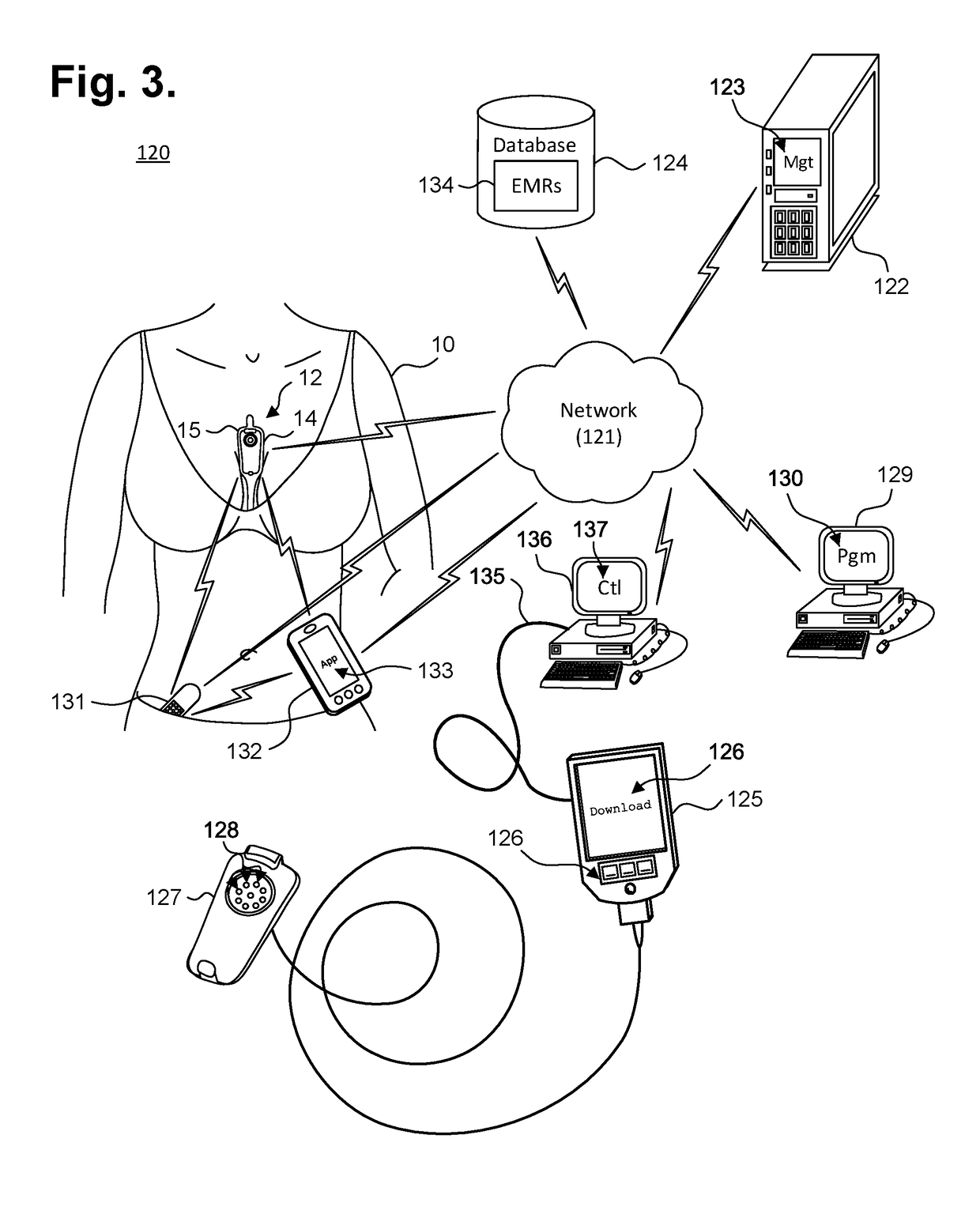
Computer-implemented system and method for providing a personal mobile device-triggered medical intervention
Physiological monitoring can be provided through a wearable monitor that includes two components, a flexible extended wear electrode patch and a removable reusable monitor recorder. The wearable monitor sits centrally on the patient's chest along the sternum oriented top-to-bottom. The placement of the wearable monitor in a location at the sternal midline (or immediately to either side of the sternum) benefits extended wear by removing the requirement that ECG electrodes be continually placed in the same spots on the skin throughout the monitoring period. The wearable monitor can interoperate wirelessly with other physiology and activity sensors and mobile devices. An application executed by the sensor or device can trigger the dispatch of a wearable monitor to the patient upon detecting potentially medically-significant events. The dispatched wearable monitor would then be capable of providing precise medically-actionable data, not merely an alert that some abnormality may be present. The patient can then use the sensor or device to physically record the placement and use of the medically-actionable wearable monitor, thereby facilitating the authentication of the data recorded.
Owner:BARDY DIAGNOSTICS
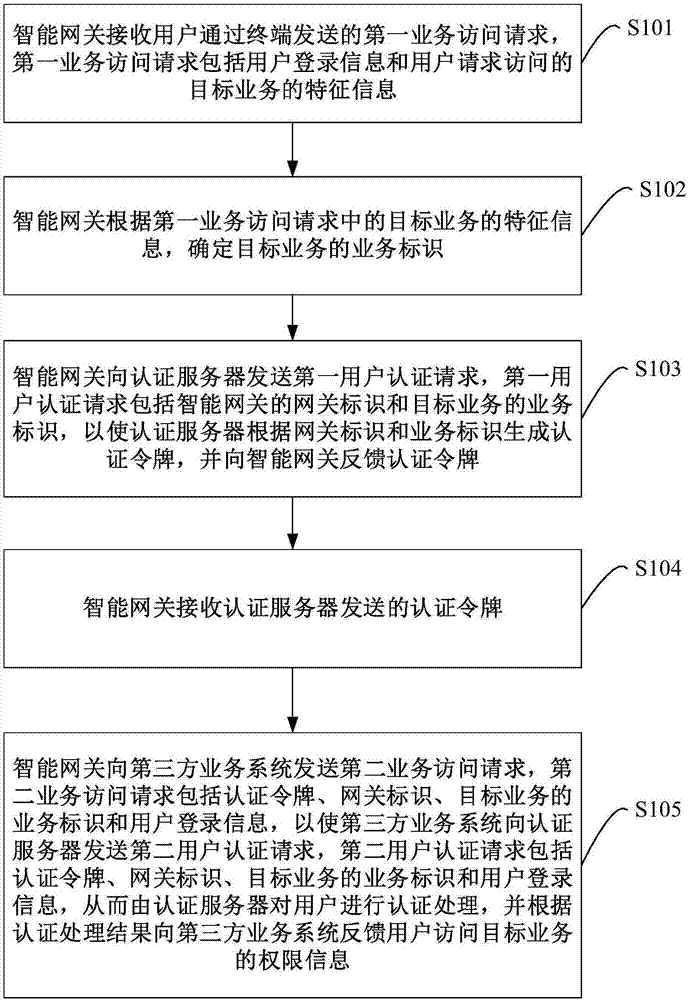
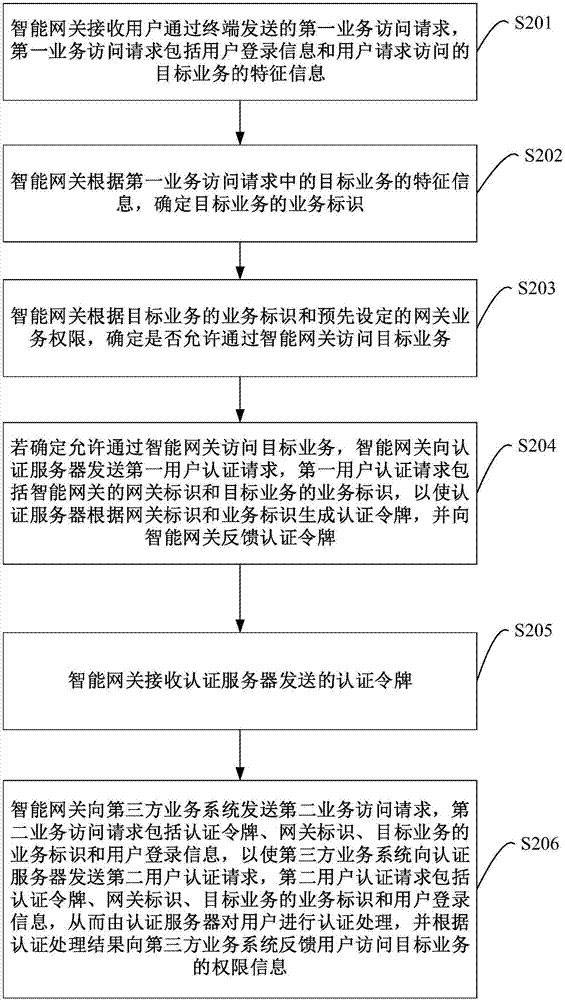
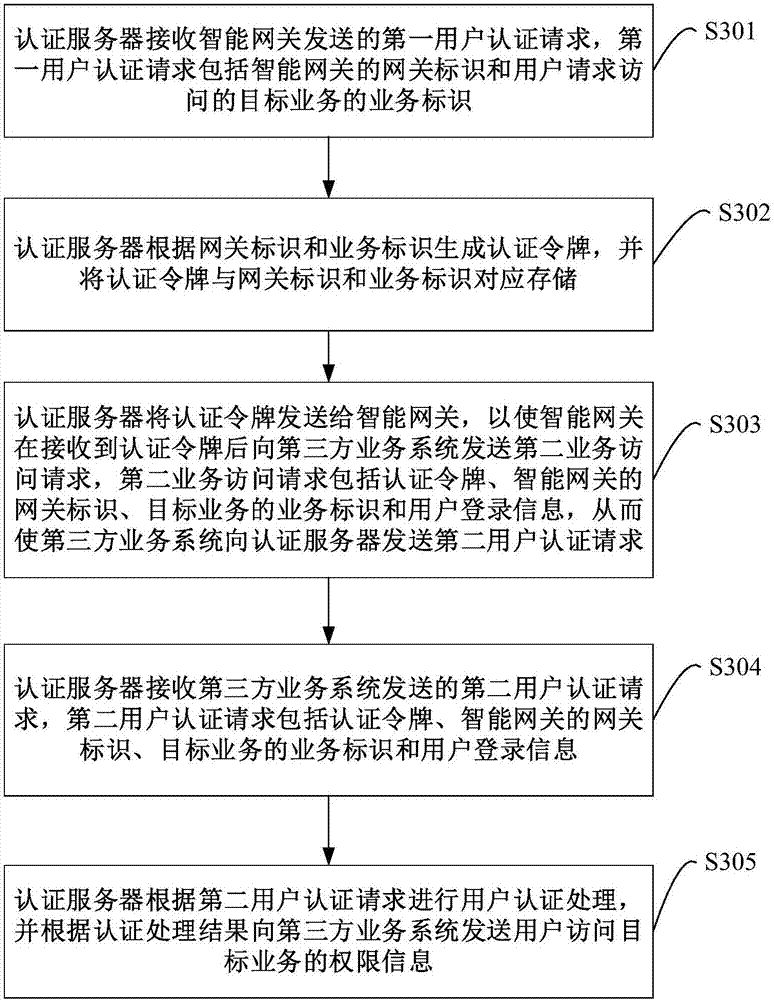
User authentication method, intelligent gateway and authentication server
ActiveCN107493280AAuthentication is convenientUser identity/authority verificationData switching networksThird partyUser authentication
The embodiment of the invention provides a user authentication method, an intelligent gateway and an authentication server. In the embodiment of the invention, after receiving a first service access request sent by a user through a terminal, the intelligent gateway sends a first user authentication request including a gateway identifier and the service identifier of a target service to the authentication server; the authentication server generates an authentication token according to the gateway identifier and the service identifier, and feeds back the authentication token to the intelligent gateway; the intelligent gateway sends a second service access request carrying the authentication token, the gateway identifier, the service identifier and user login information to a third-party service system, so that the third-party service system sends a second user authentication request to the authentication server; the authentication server performs authentication processing of the user, and feeds back the authority information that the user accesses the target service to the third-party service system; thereby, the authentication server uniformly authenticates users initiating third-party service access requests; and thus, the process that the users access the third-party service system is relatively convenient and rapid.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
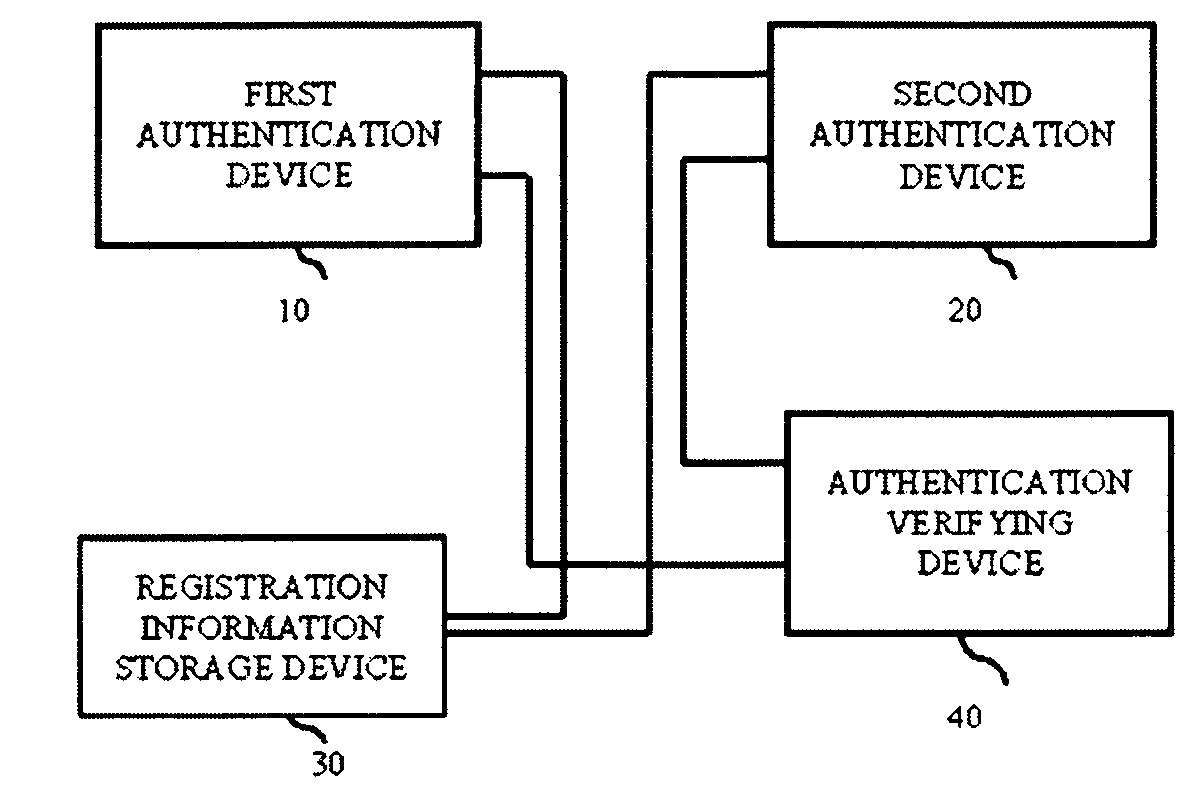
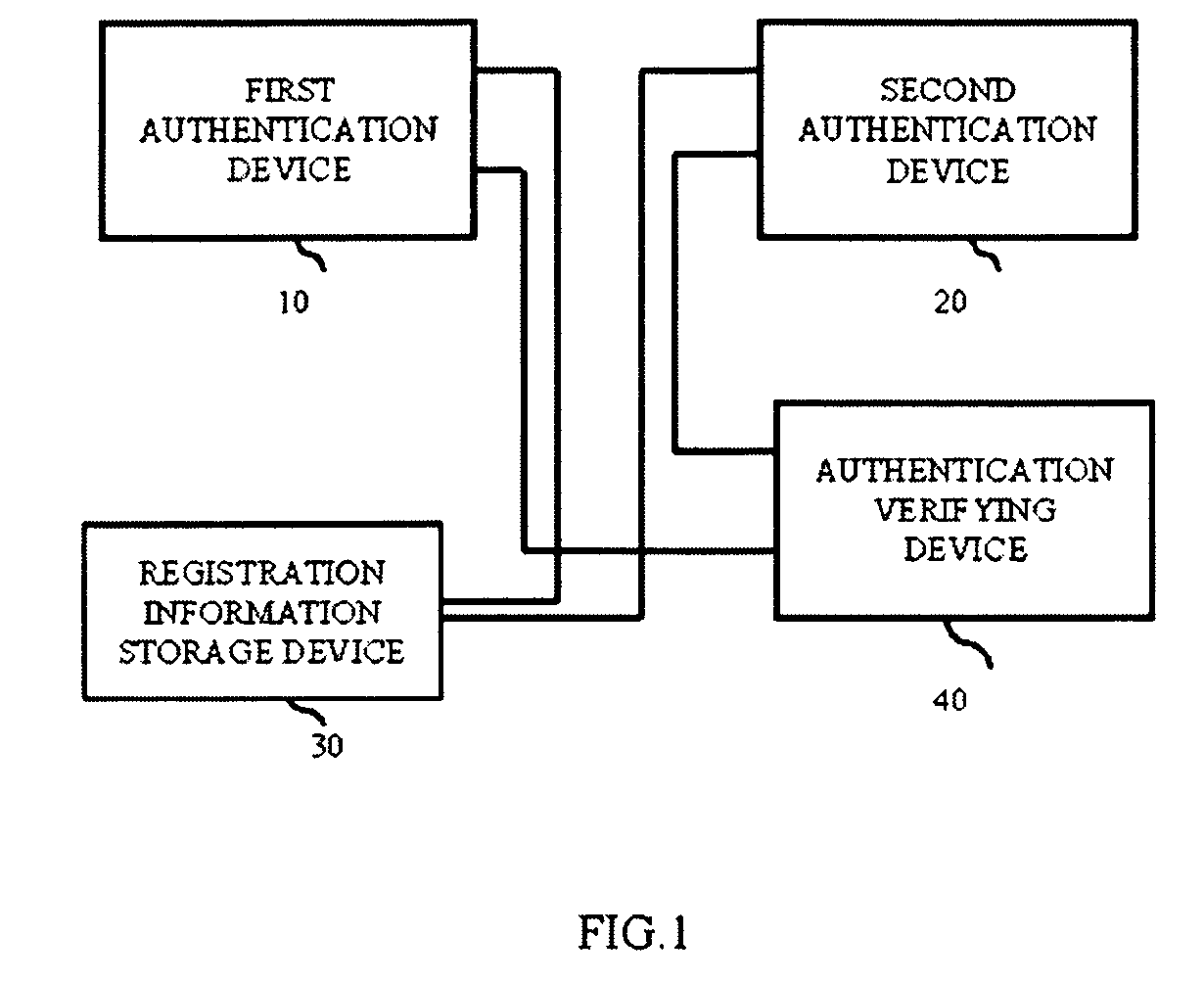
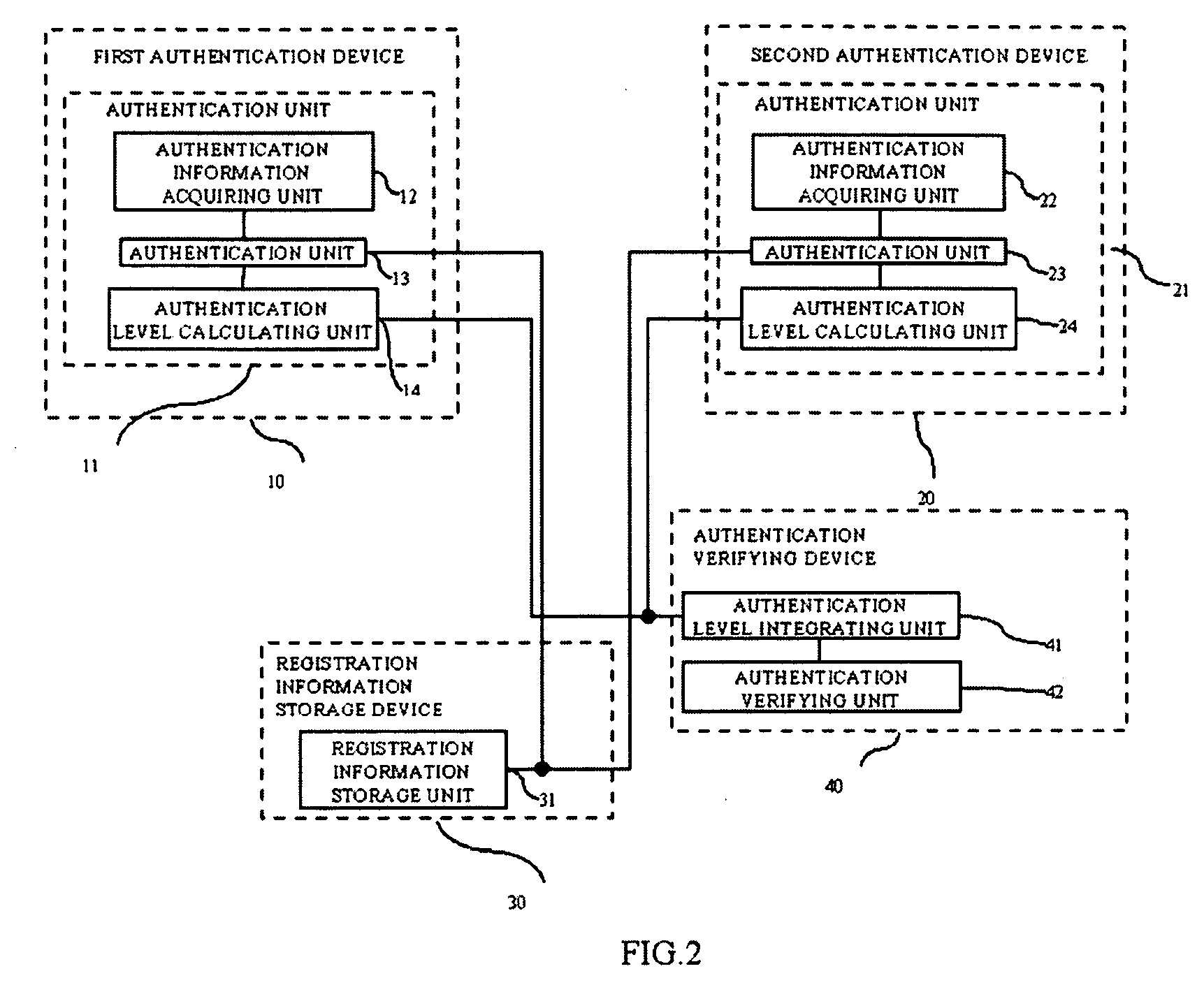
Authentication system, authentication method, and authentication program
InactiveUS20100079243A1Required authentication accuracyAuthentication is convenientElectric signal transmission systemsImage analysisAuthentication systemAuthentication protocol
An object of an exemplary embodiment of the present invention is to provide an authentication system which can perform highly convenient authentication while ensuring minimum required authentication accuracy. An authentication system of an exemplary embodiment of the present invention includes a first authentication device which acquires a first authentication level, a second authentication device which acquires a second authentication level, and an authentication verifying device which authenticates based on a comparison between a predetermined value and a sum of the first authentication level and the second authentication level.
Owner:NEC CORP
Security token and authentication
ActiveUS20140015242A1Authentication is convenientProvide wear resistanceOther printing matterPaper-money testing devicesOptical detectorAuthentication
Owner:KEYTHROUGH LTD
Apparatus and method for security using authentication of face
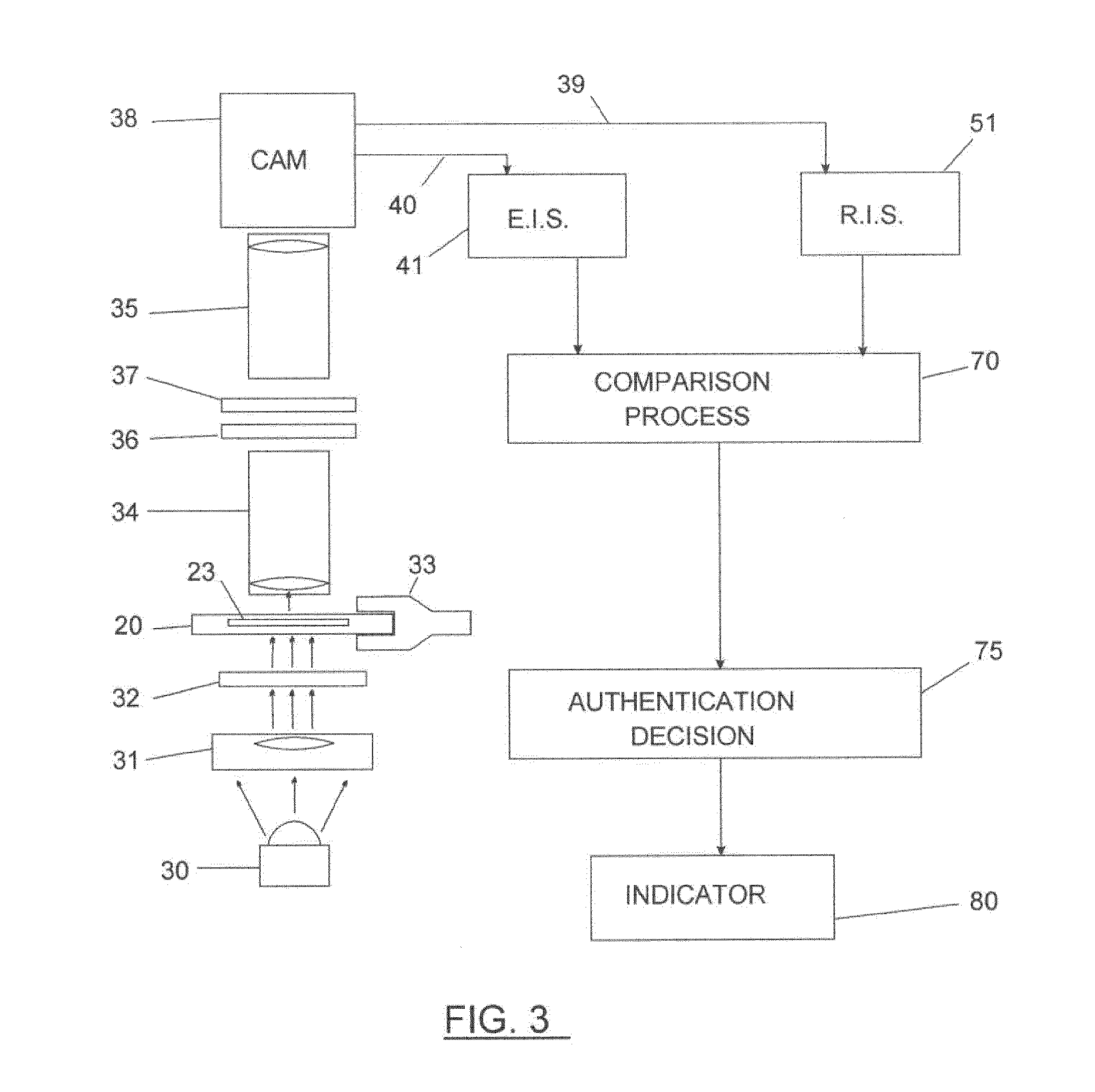
InactiveUS20120320181A1Authentication is convenientCharacter and pattern recognitionColor television detailsPattern recognitionFacial region
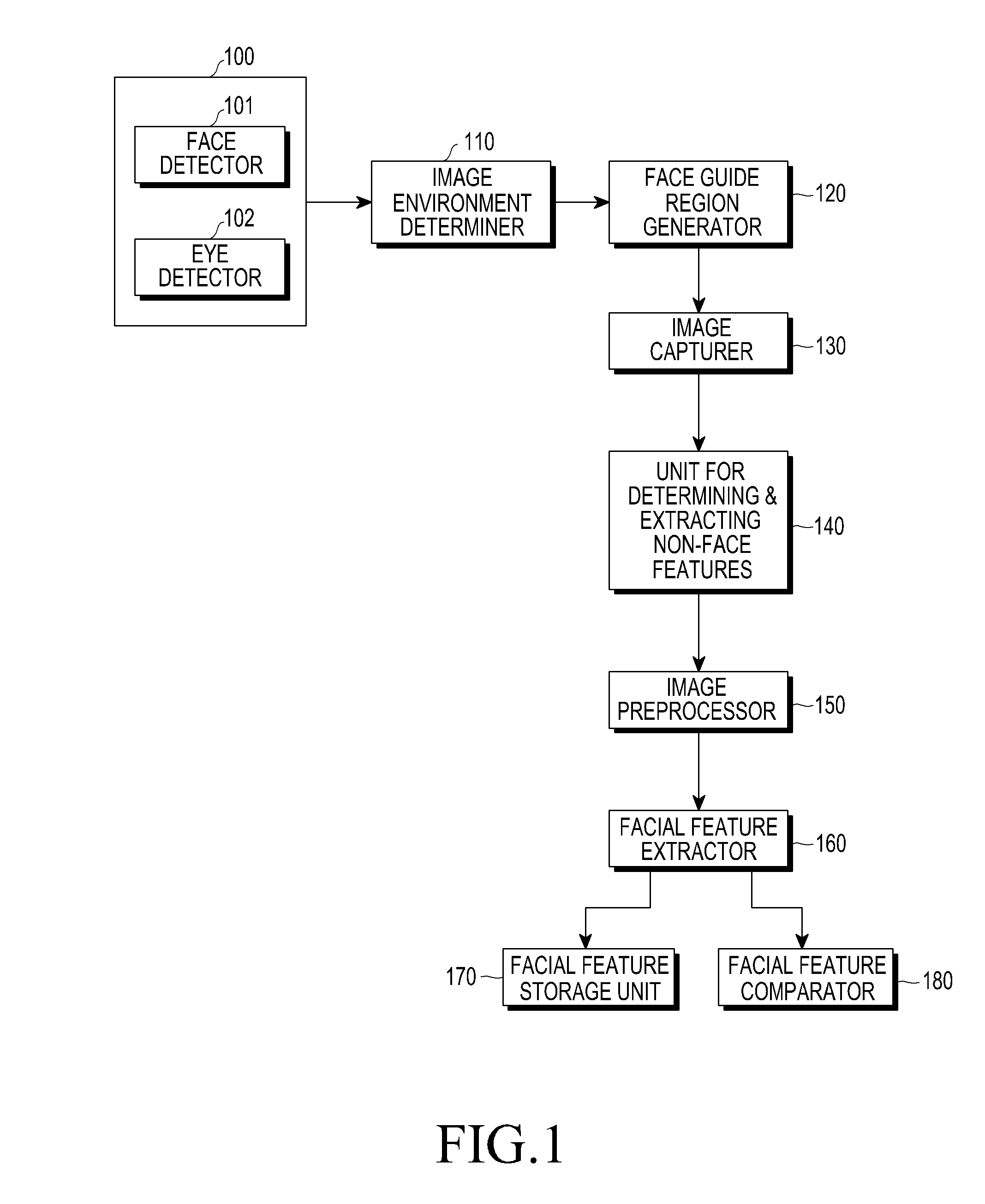
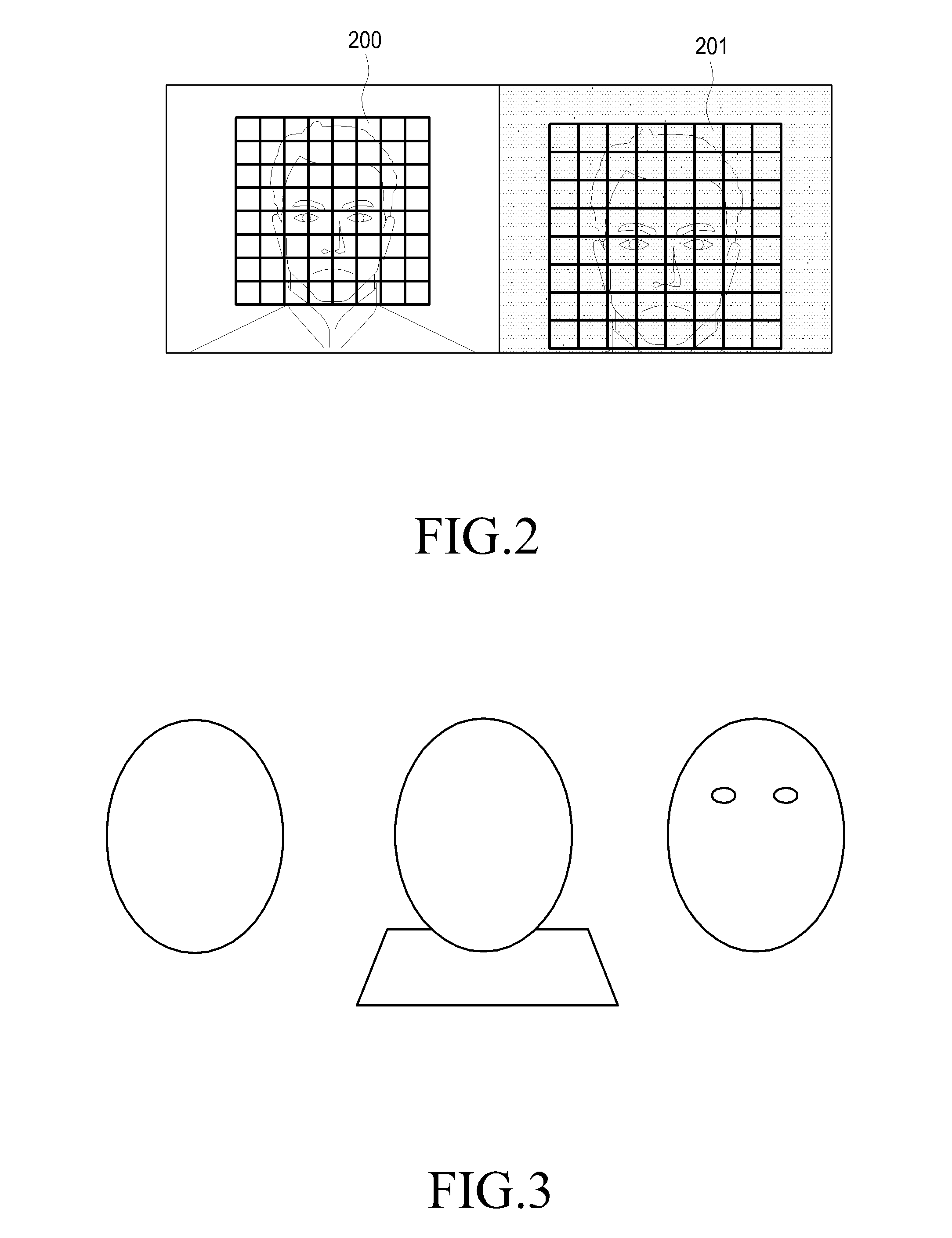
An apparatus and a method for security using the face authentication is provided. The apparatus includes a face detector for detecting a facial region in an input image; a face guide region generator for generating a face guide region for authenticating a face in the input image, and displaying the generated face guide region on a screen; an image capturer for capturing the input image when the detected facial region is matched with the face guide region; a facial feature extractor for extracting information regarding features of the face from the captured input image; and a facial feature storage unit for storing the extracted information regarding the features of the face.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com