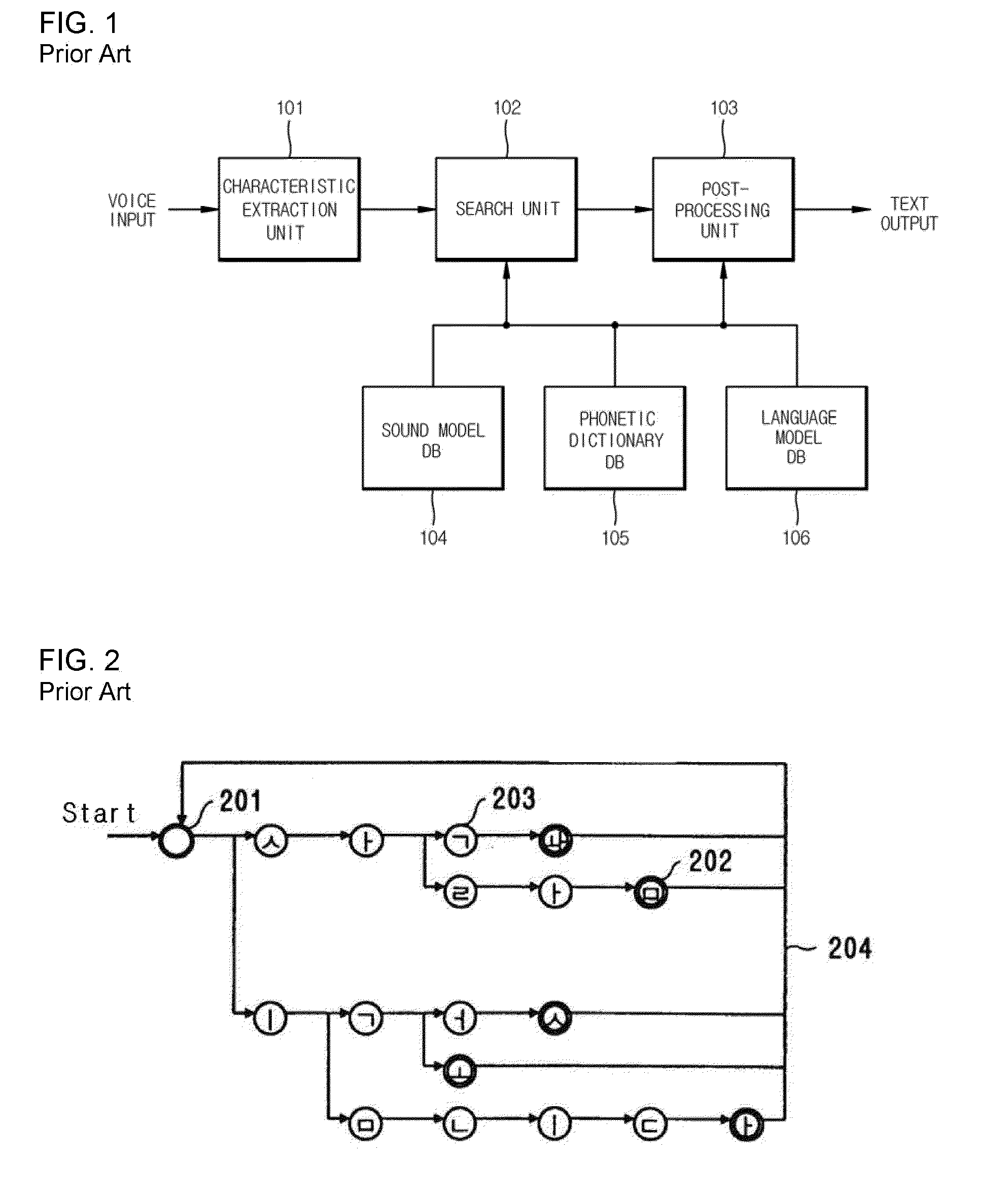
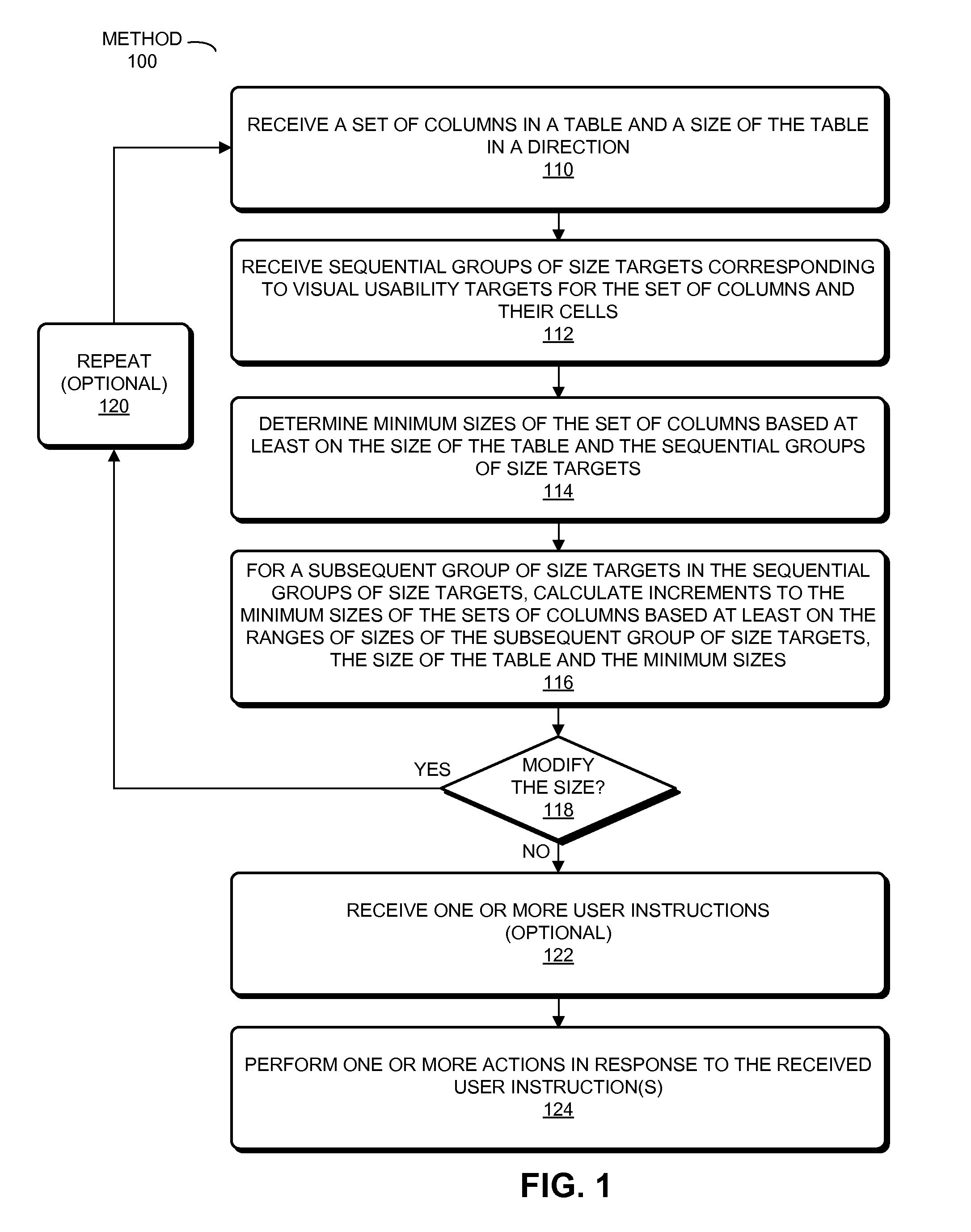
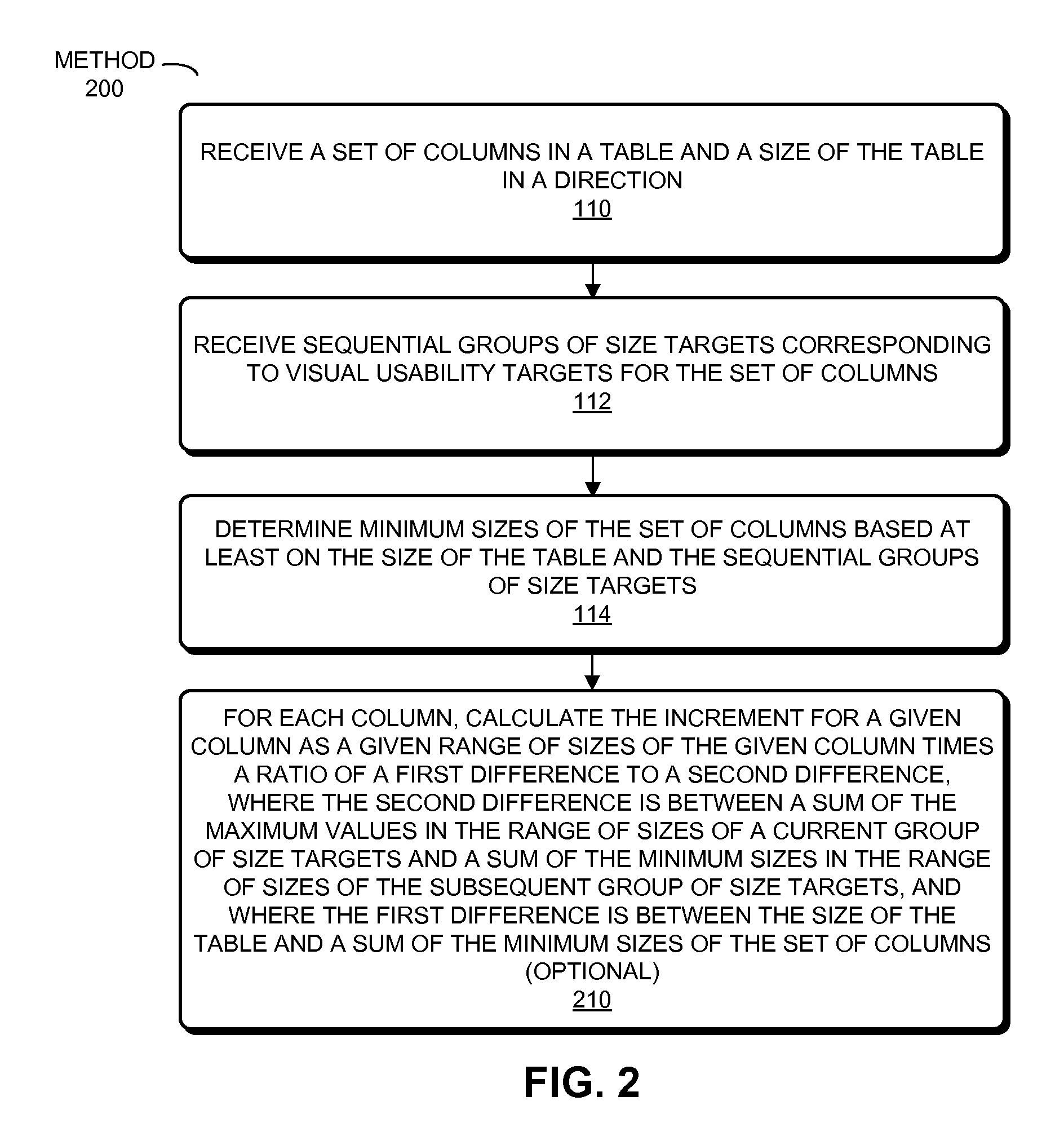
Patents
Literature
6285 results about "Usability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Usability is the ease of use and learnability of a human-made object such as a tool or device. In software engineering, usability is the degree to which a software can be used by specified consumers to achieve quantified objectives with effectiveness, efficiency, and satisfaction in a quantified context of use.
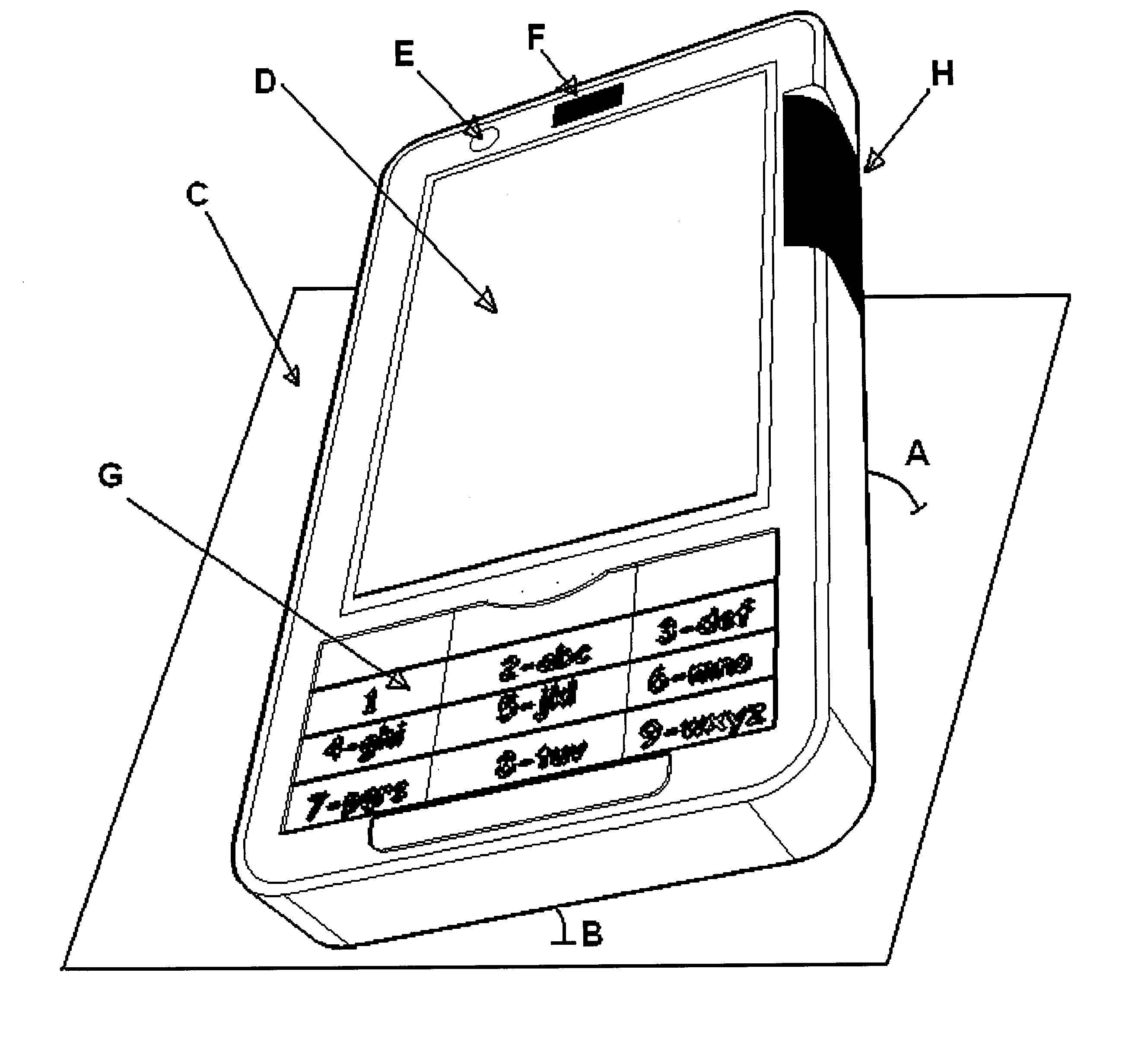
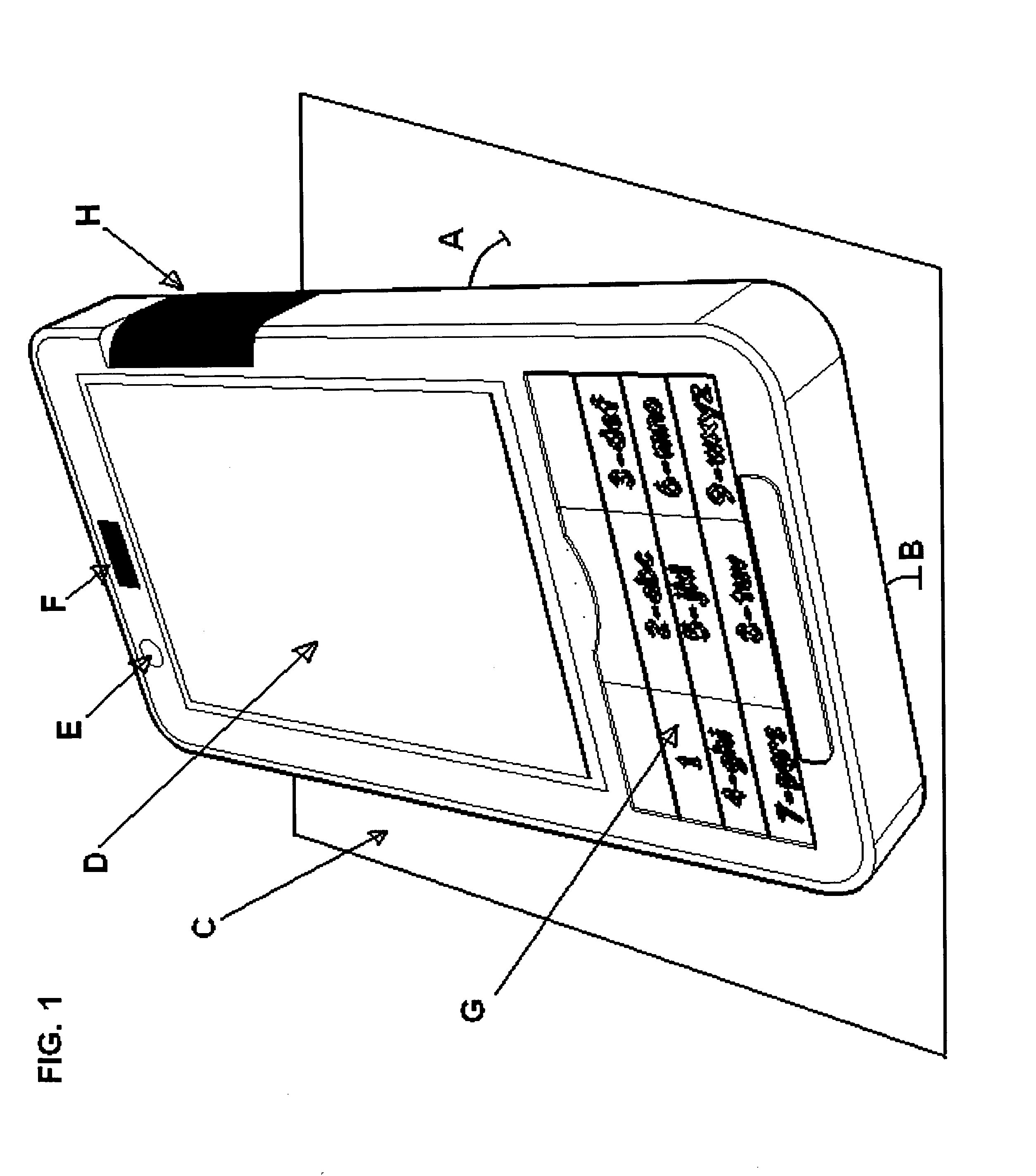
Cellular phone with special sensor functions
InactiveUS20090262078A1Input/output for user-computer interactionUnauthorised/fraudulent call preventionProximity sensorDisplay device
Specific ambient and user behaviour sensing systems and methods are presented to improve friendliness and usability of electronic handheld devices, in particular cellular phones, PDAs, multimedia players and similar.The improvements and special functions include following components:a. The keypad is locked / unlocked (disabled / enabled) and / or the display activated based on the device inclination relative to its longitudinal and / or lateral axes.b. The keypad is locked if objects are detected above the display (for example the boundary of a bag or pursue).c. The keypad is locked / unlocked (disabled / enabled) and / or the display activated based on electric field displacement or bio-field sensing systems recognizing the user hand in any position behind the handheld device.d. The electric response signal generated by an electric field through the user hand in contact with a receiver plate is used to identify the user and in negative case lock the device.e. Connection with incoming calls is automatically opened as soon as a hand is detected behind the device and the device is put close to the ear (proximity sensor).f. The profile (ring-tone mode, volume and silent mode) can be changed just putting the device in a specific verse (upside up or upside down).g. Has a lateral curved touchpad with tactile markings over more surfaces to control a mouse pointer / cursor or selection with the thumb finger.
Owner:PIZZI DAVID
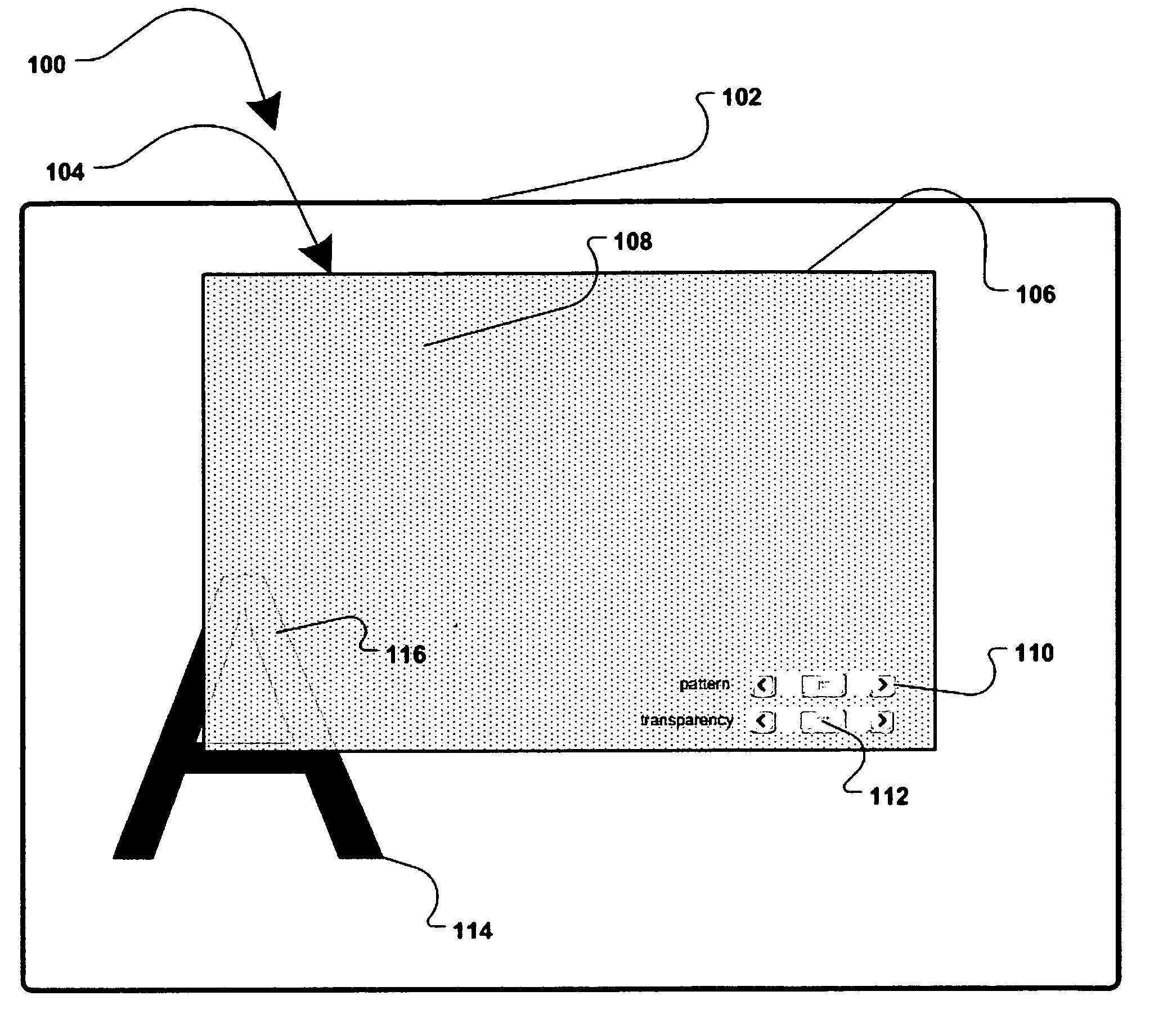
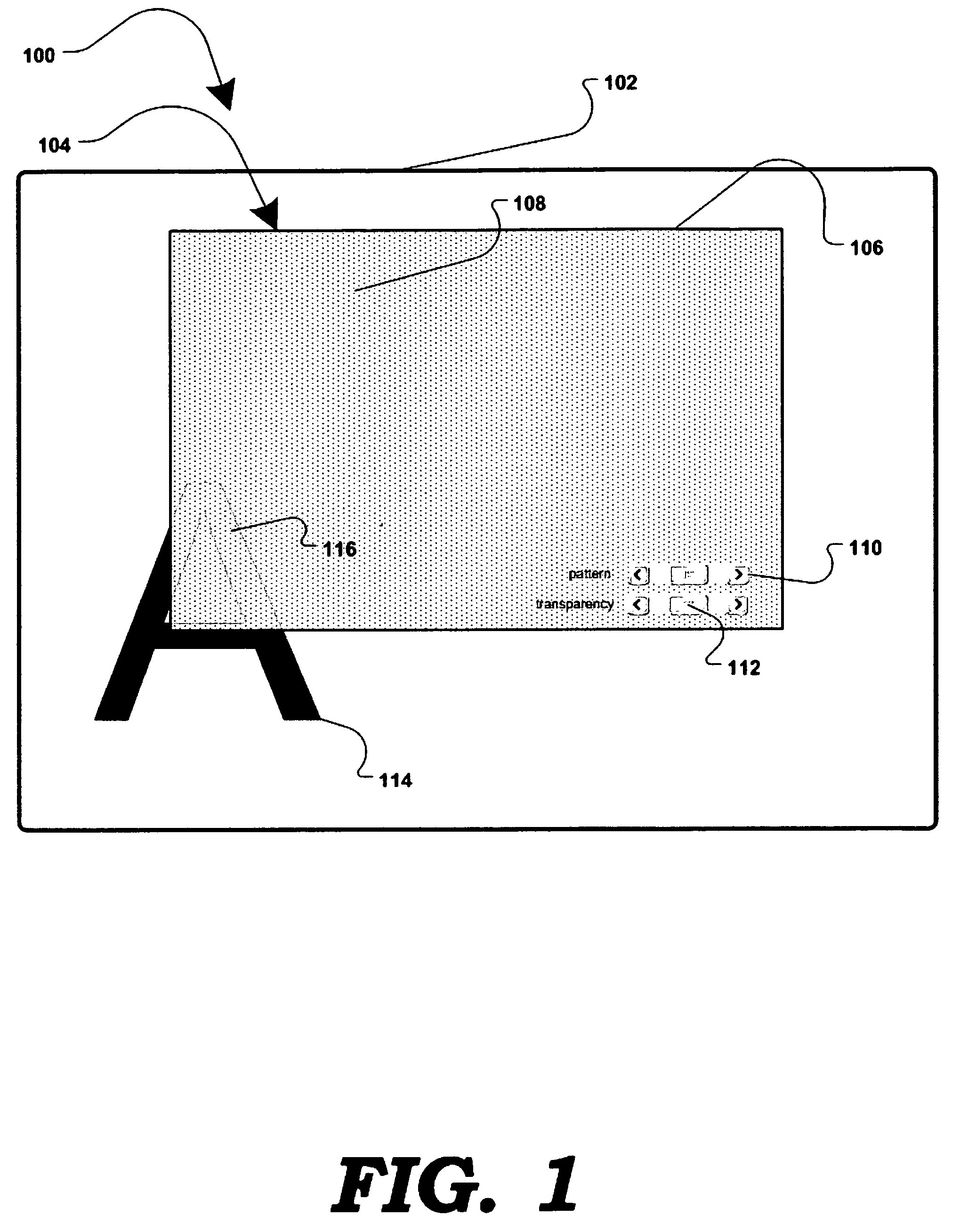
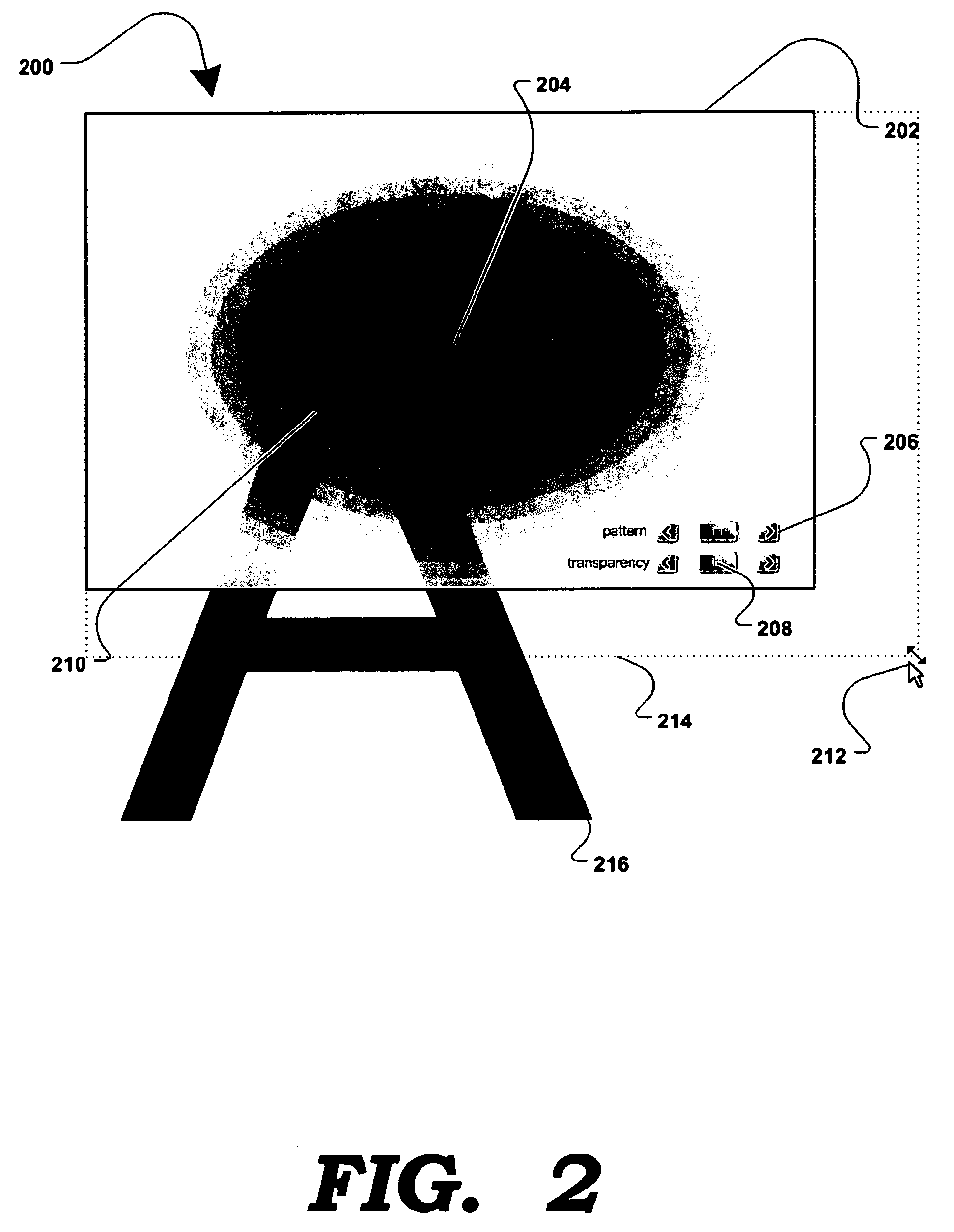
Software-based method for gaining privacy by affecting the screen of a computing device
InactiveUS7779475B2Improve privacyMinimal impactDigital data processing detailsUnauthorized memory use protectionGraphicsInternet privacy
A method and apparatus for allowing the user of an electronic device to enhance privacy over a display with the use of software, are disclosed. A security window including a translucent graphical effects region may be displayed on the electronic device such that it overlays content the user may choose to protect. The security window allows the protected content to remain discernable for the user of the device yet substantially indiscernible to a person at a further distance and / or greater viewing angle from the screen of the device. One or more security windows, each of which may be of any size, shape, texture, translucency level and any other graphical or behavioral properties may be displayed on the display associated with the electronic device. The user may control the size, shape, texture, translucency level and any other graphical or behavioral properties of the security window and graphical effects region. The user may invoke or terminate a security window with the single click of a button. Security windows may automatically attach to applications in focus, or be attached in response to a user command, and allow uninterrupted usability of those applications.
Owner:PETNOTE
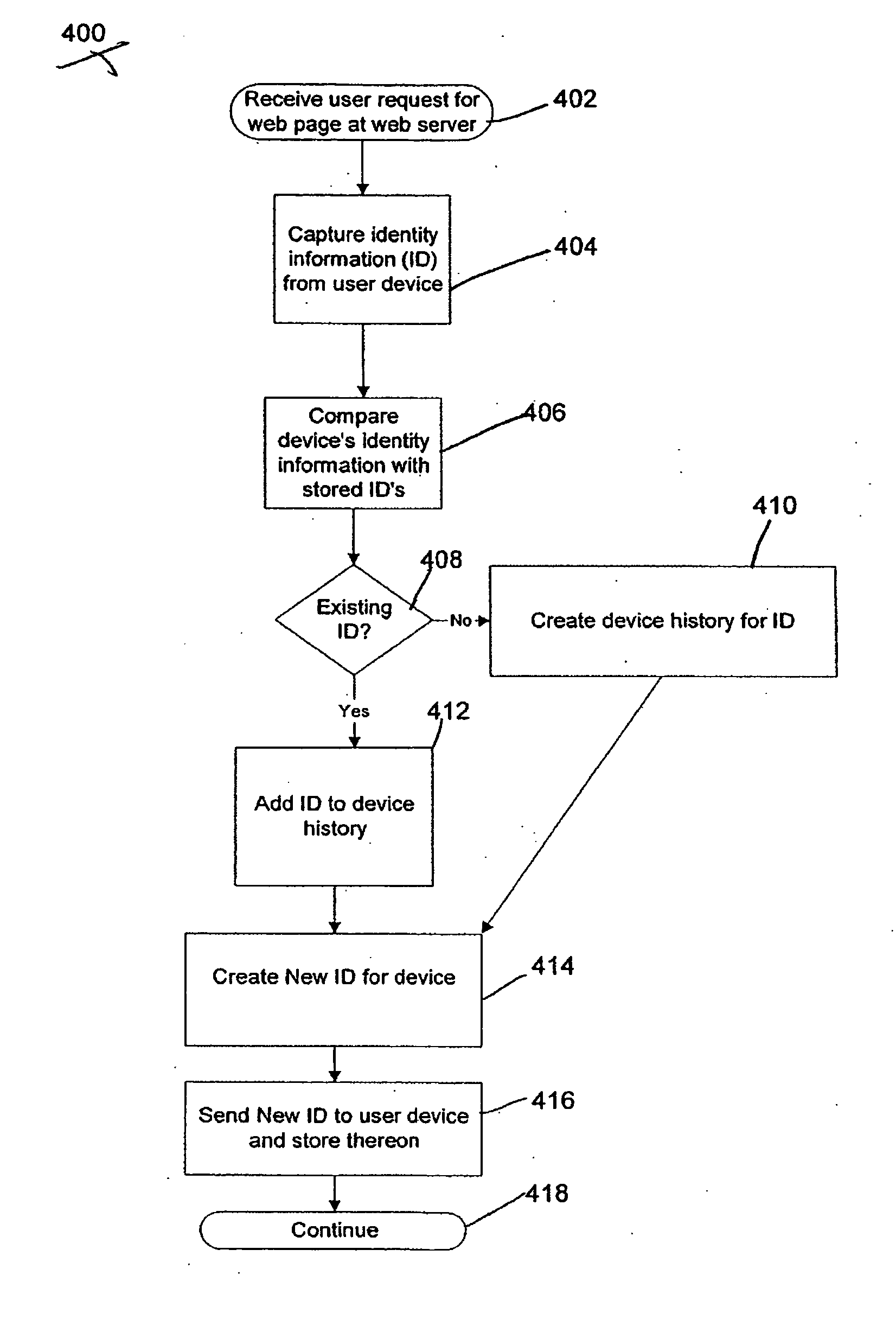
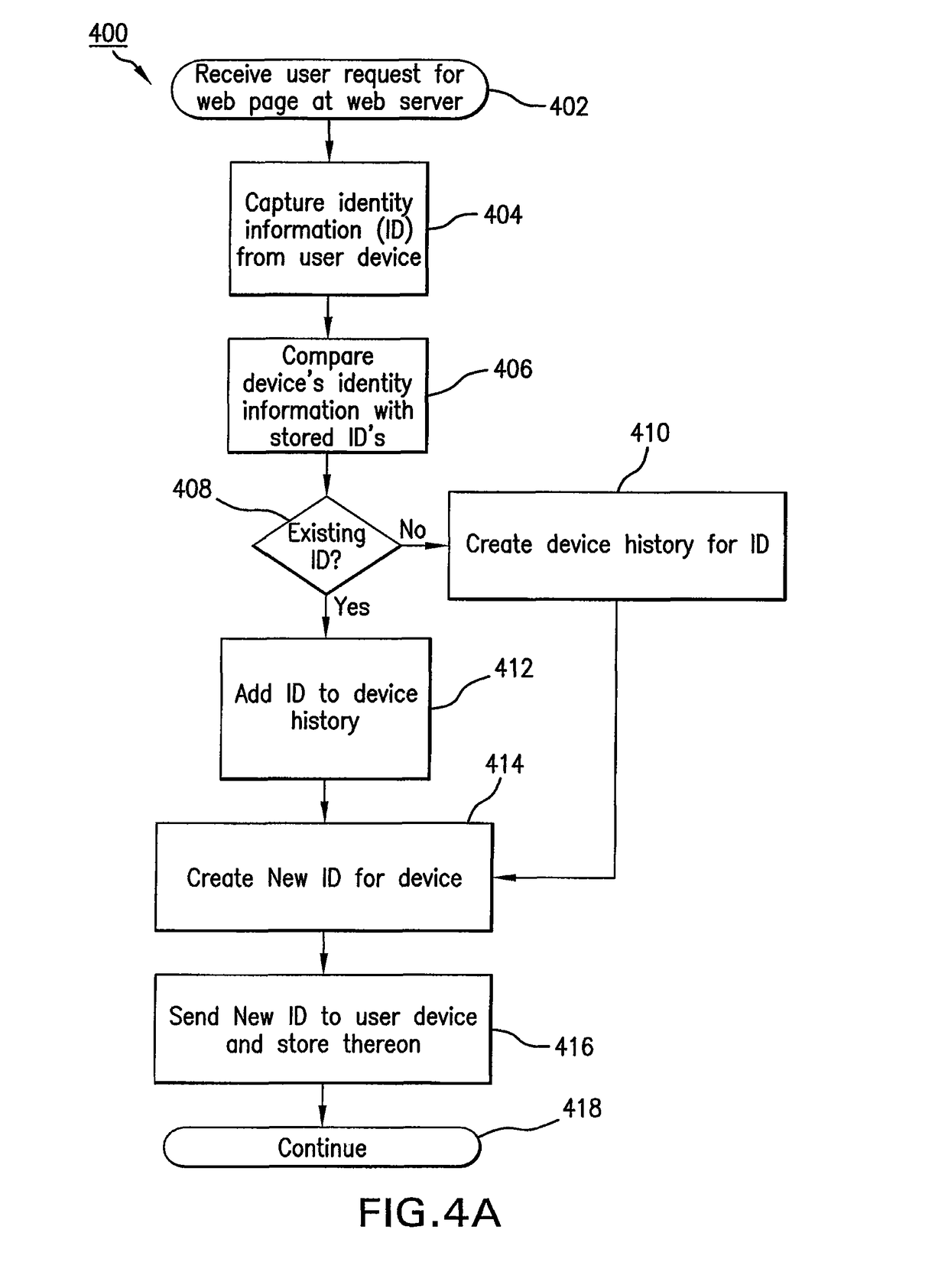
System and method for fraud monitoring, detection, and tiered user authentication
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
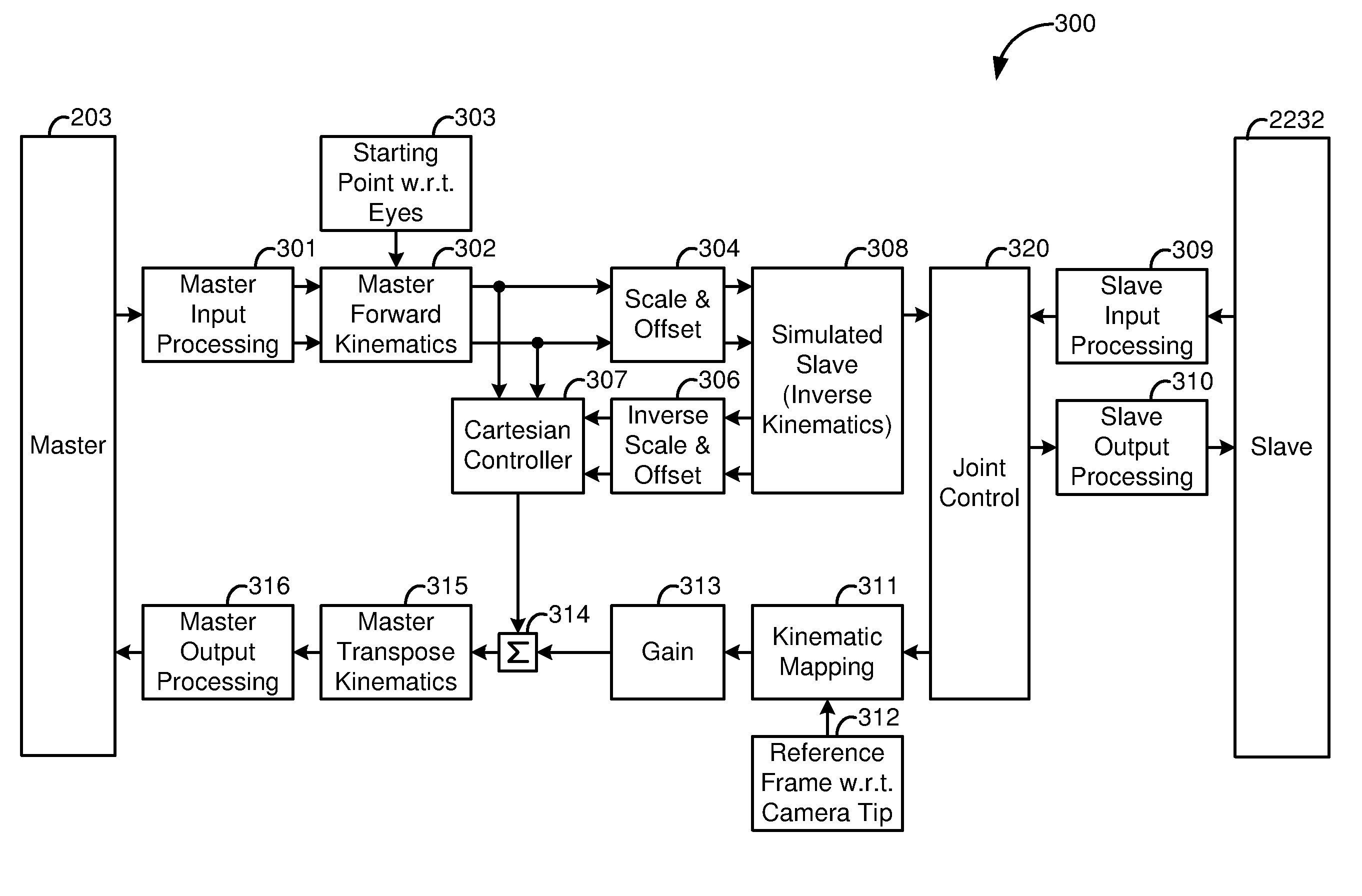
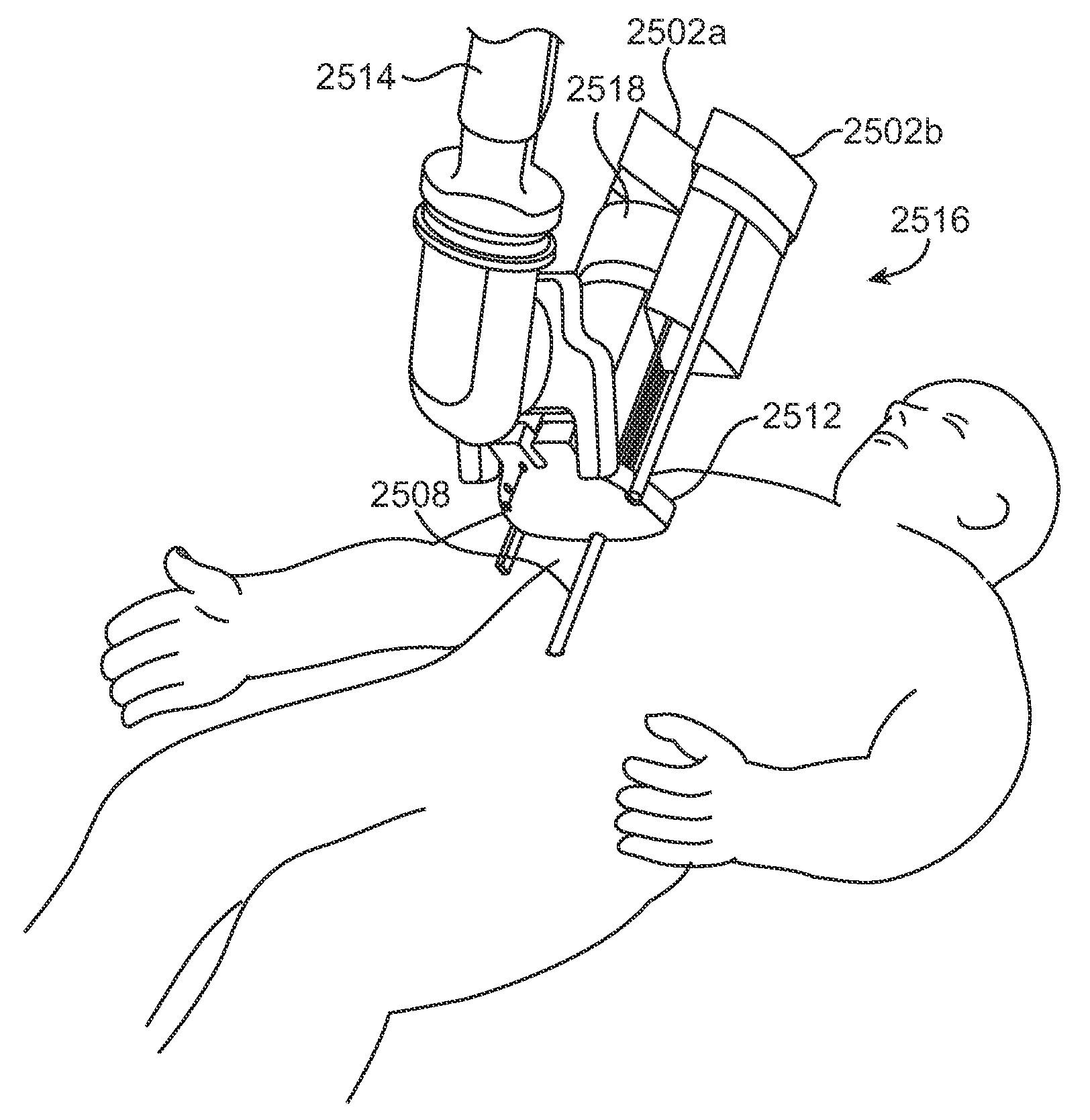
Medical robotic system with coupled control modes
In a coupled control mode, the surgeon directly controls movement of an associated slave manipulator with an input device while indirectly controlling movement of one or more non-associated slave manipulators, in response to commanded motion of the directly controlled slave manipulator, to achieve a secondary objective. By automatically performing secondary tasks through coupled control modes, the system's usability is enhanced by reducing the surgeon's need to switch to another direct mode to manually achieve the desired secondary objective. Thus, coupled control modes allow the surgeon to better focus on performing medical procedures and to pay less attention to managing the system.
Owner:INTUITIVE SURGICAL OPERATIONS INC
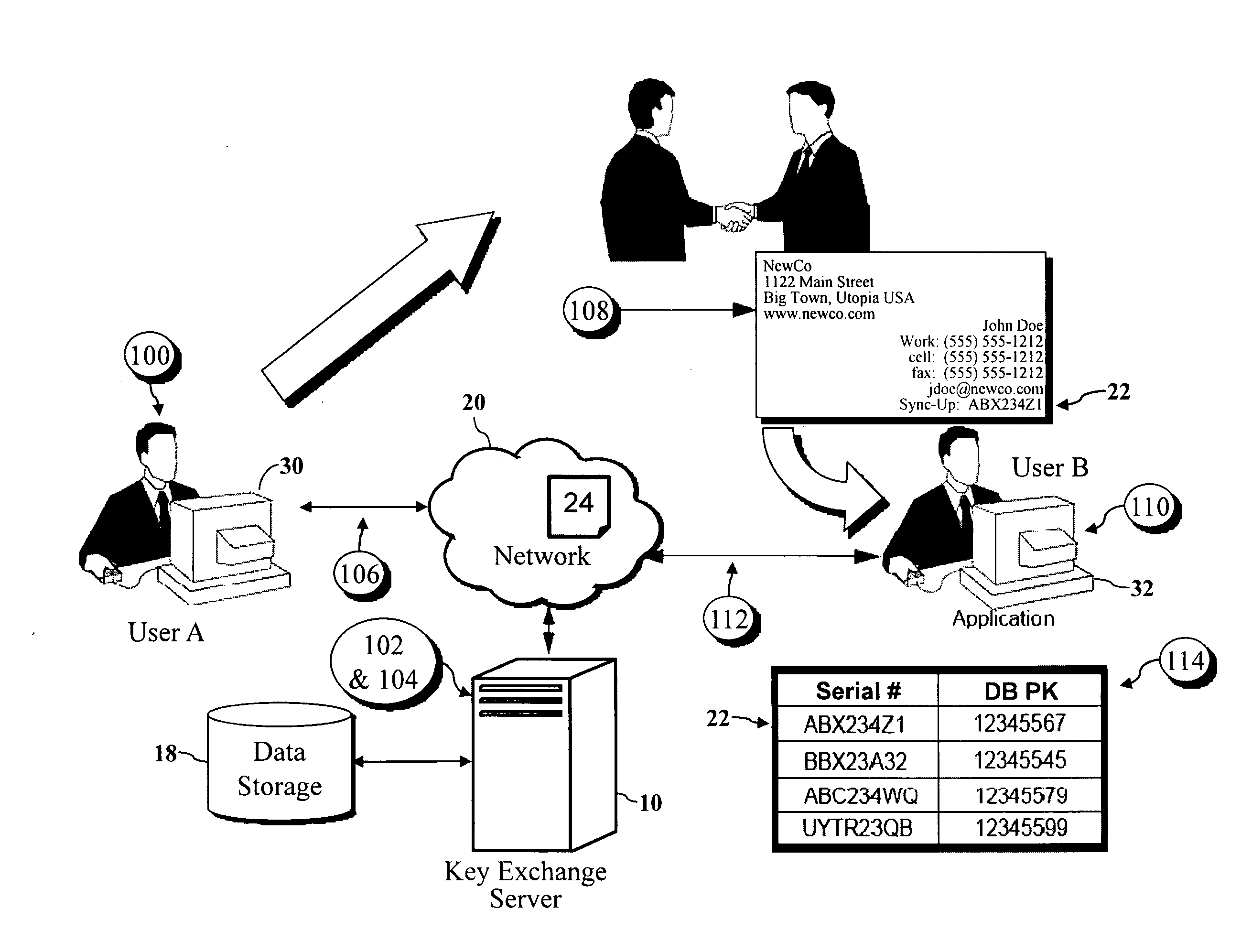
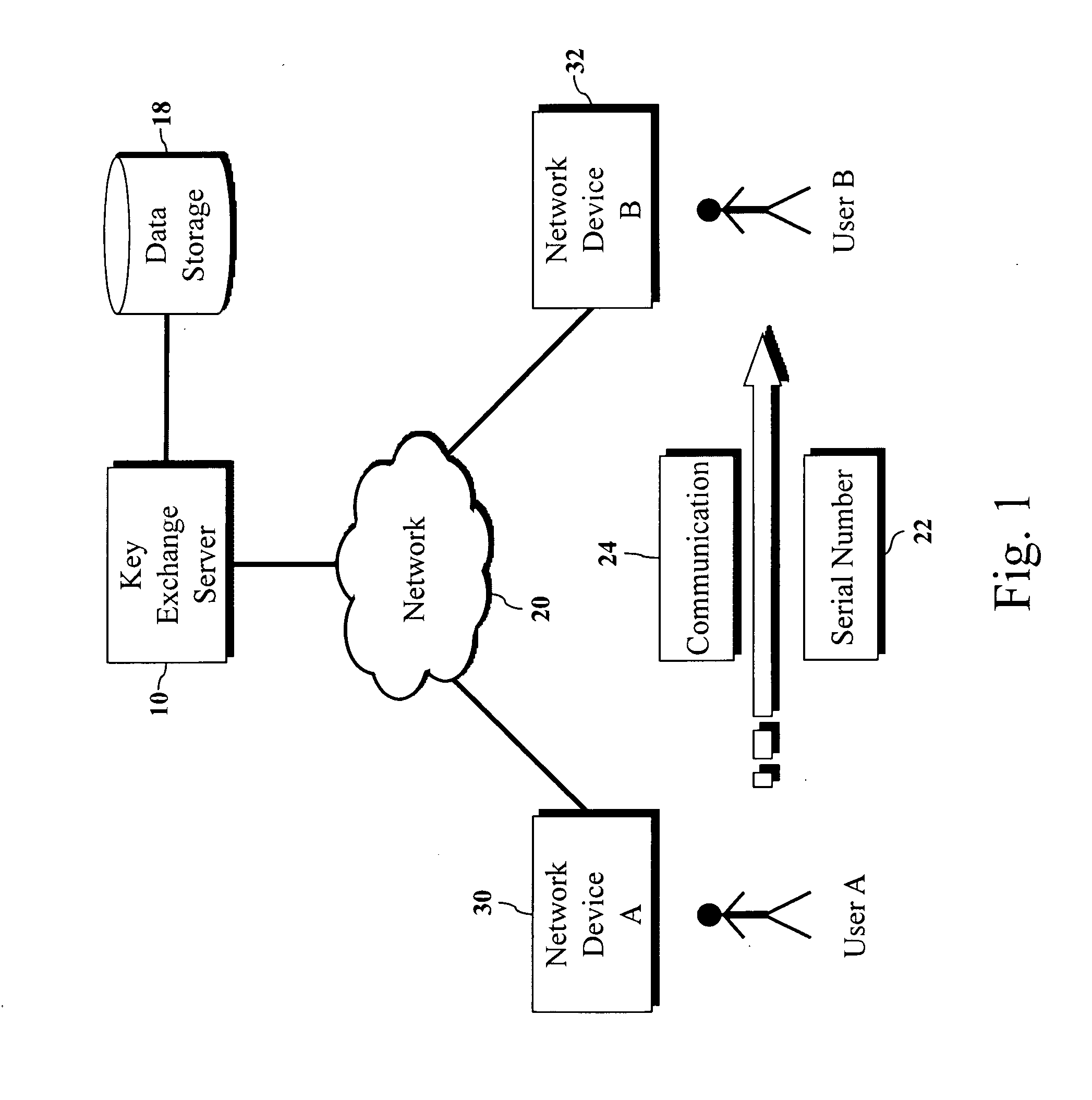
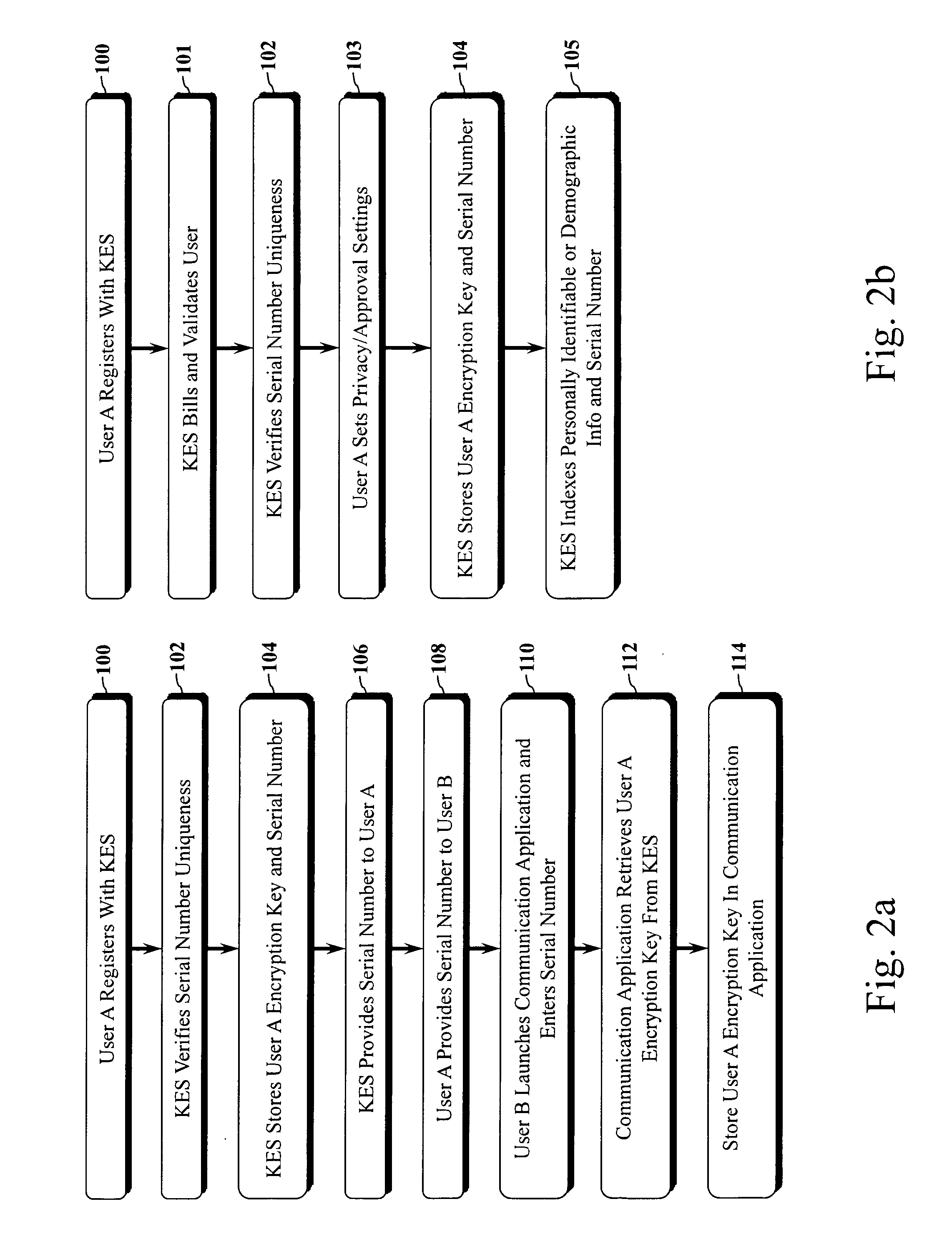
Encryption key exchange system and method
InactiveUS20120204032A1Improve usabilityUser identity/authority verificationPublic key infrastructure trust modelsUsabilityEncryption
The present invention is a computer-implemented key exchange system and methods for improving the usability of encryption technologies such as Public Key Infrastructure (PKI). One aspect of the present invention includes registering users, verifying user identity, and classifying users such that the users may send a communications such that communication recipients can verify the user identity and classification of the communication sender. Another aspect of the present invention includes users initiating relationships with other users, approving the establishment of relationships, and exchanging encryption keys between users after the establishment of a relationship.
Owner:SYNC UP TECH
Practical platform for high risk applications
InactiveUS20070180509A1Safe and reliable and easy to use practicalIncrease system complexityDigital data processing detailsUser identity/authority verificationSystem integrationComputer hardware
The present invention is a portable device that a computer can boot from, containing a prefabricated independent operating system environment which is engineered from the ground up to prioritize security while maximizing usability, in order to provide a safe, reliable and easy to use practical platform for high risk applications. An embodiment of the present invention may temporarily transform an ordinary computer into a naturally inexpensive logical appliance which encapsulates a turn-key functional solution within the digital equivalent of a military grade security fortress. This allows existing hardware to be conveniently leveraged to provide a self contained system which does not depend on the on-site labor of rare and expensive system integration and security experts.
Owner:SWARTZ ALON R +1
Touch screen and graphical user interface
InactiveUS20090213134A1Improve accuracyImprove usabilityCathode-ray tube indicatorsInput/output processes for data processingGraphicsGraphical user interface
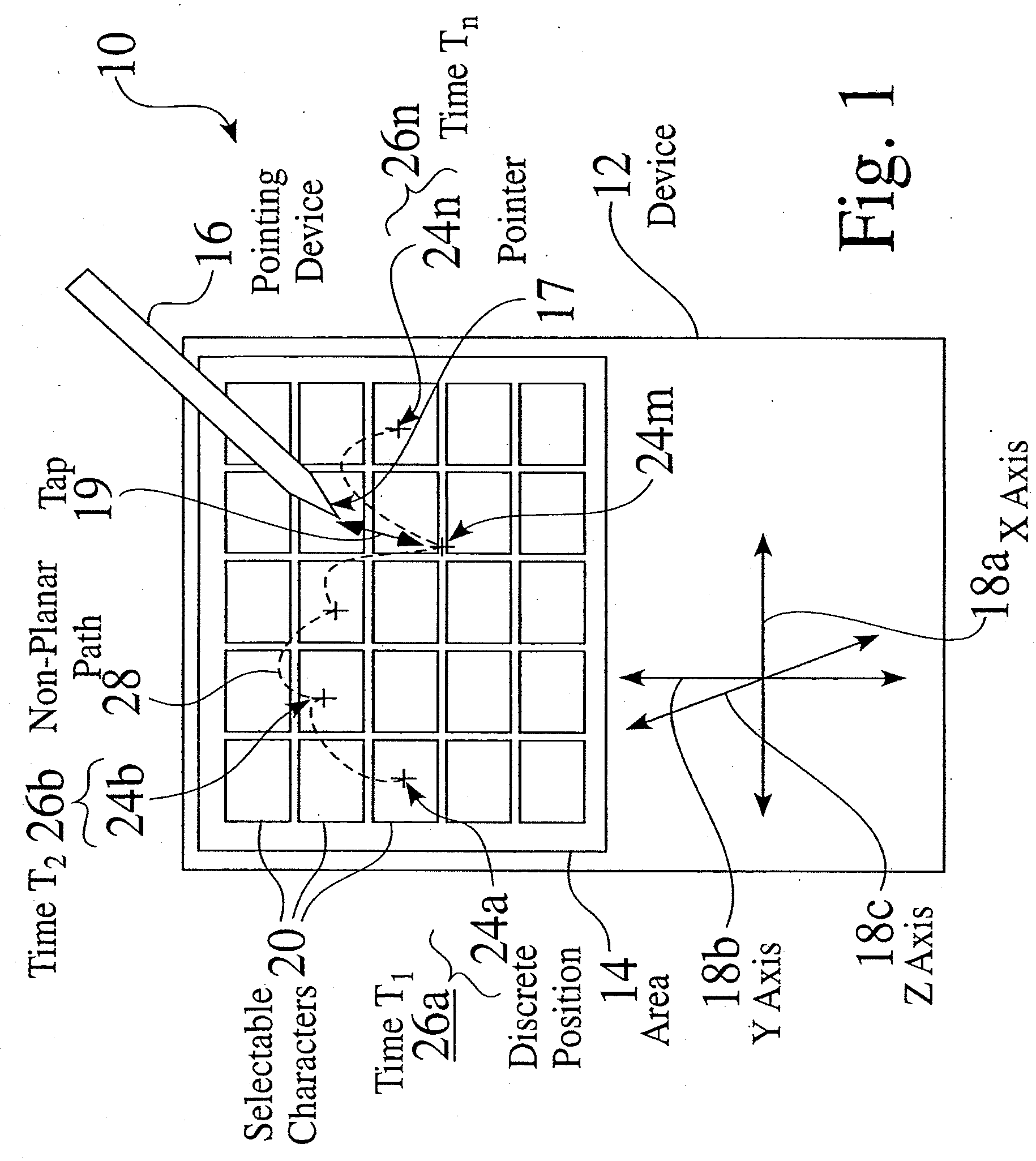
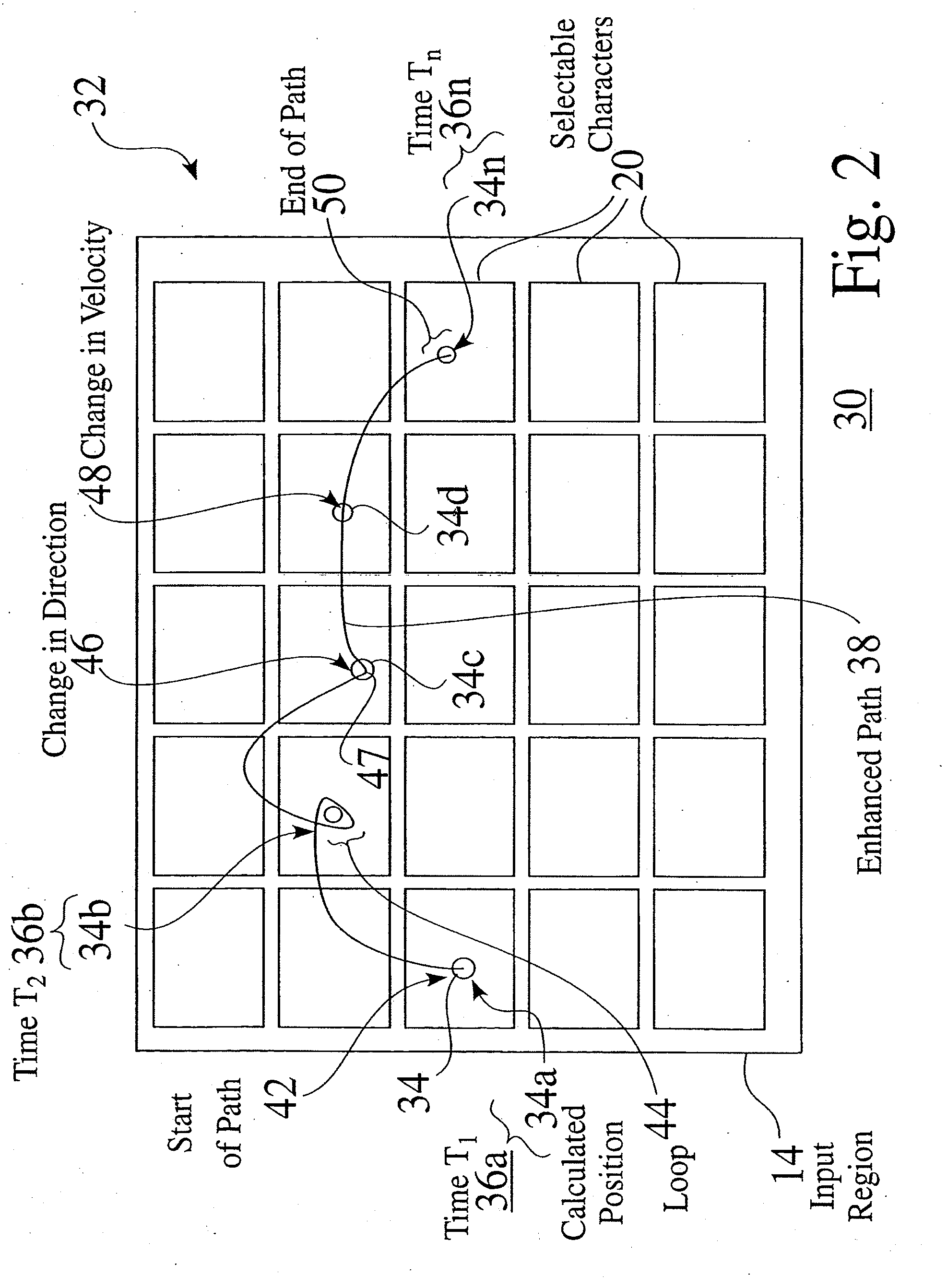
A selective input system and associated method is provided which tracks the motion of a pointing device over a region or area. The pointing device can be a touchpad, a mouse, a pen, or any device capable of providing two or three-dimensional location. The region or area is preferably augmented with a printed or actual keyboard / pad. Alternatively, a representation of the location of the pointing device over a virtual keyboard / pad can be dynamically shown on an associated display. The system identifies selections of items or characters by detecting parameters of motion of the pointing device, such as length of motion, a change in direction, a change in velocity, and or a lack of motion at locations that correspond to features on the keyboard / pad. The input system is preferably coupled to a text disambiguation system such as a T9® or Sloppytype™ system, to improve the accuracy and usability of the input system.
Owner:CERENCE OPERATING CO
Data aggregation server for managing a multi-dimensional database and database management system having data aggregation server integrated therein
InactiveUS20020029207A1Reduce the burden onImprove system performanceData processing applicationsDigital data processing detailsData aggregatorThe Internet
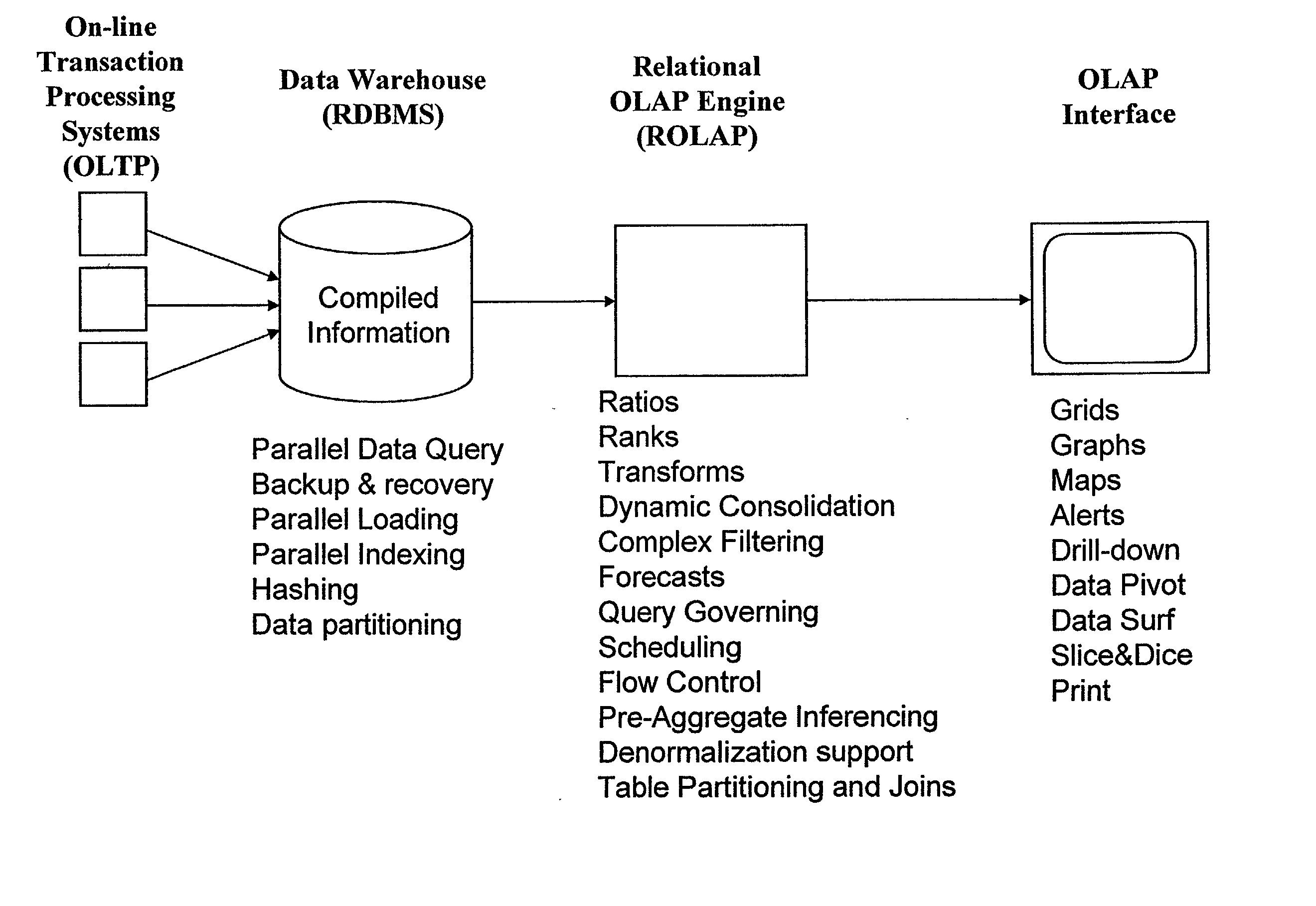
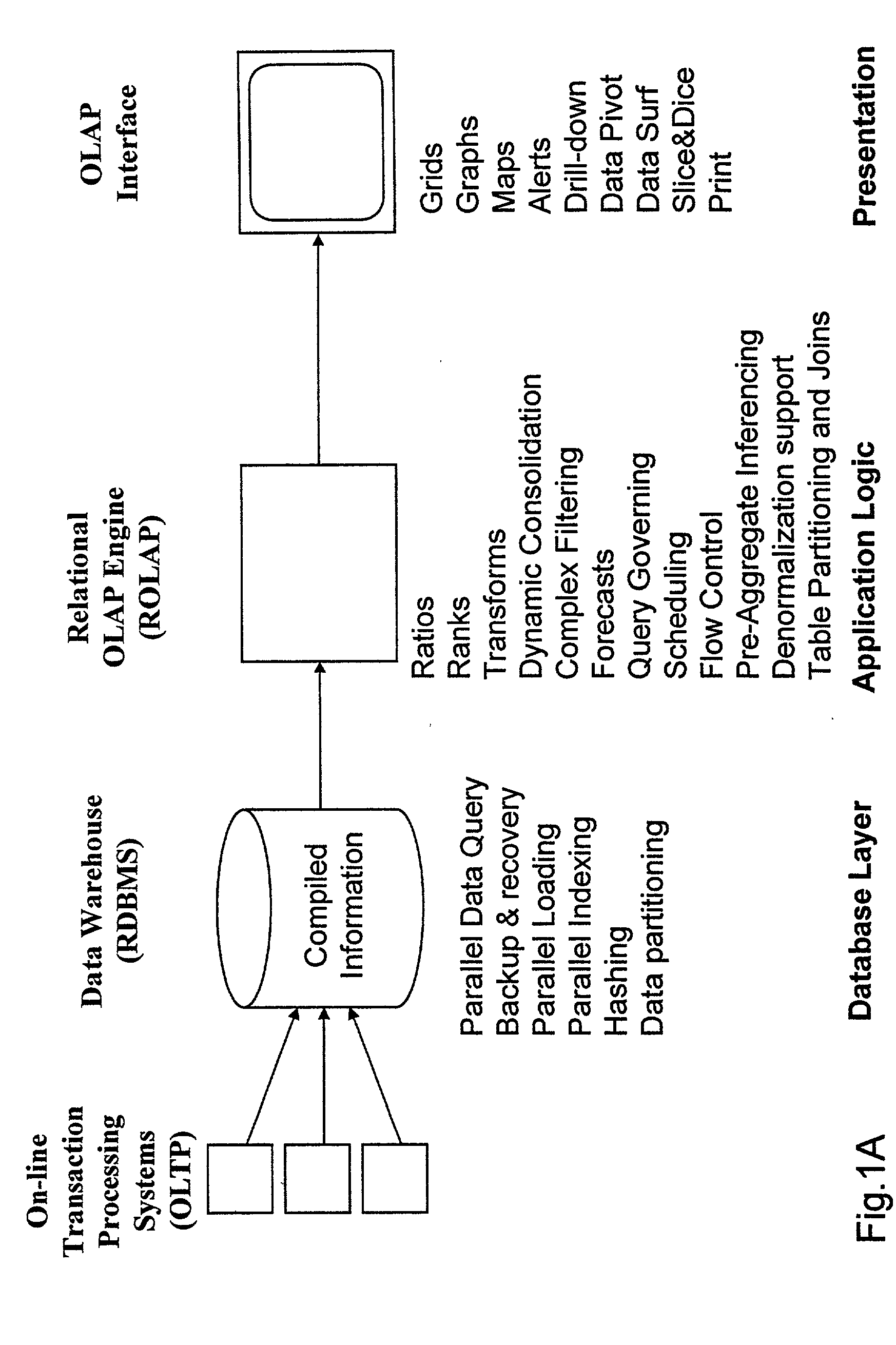
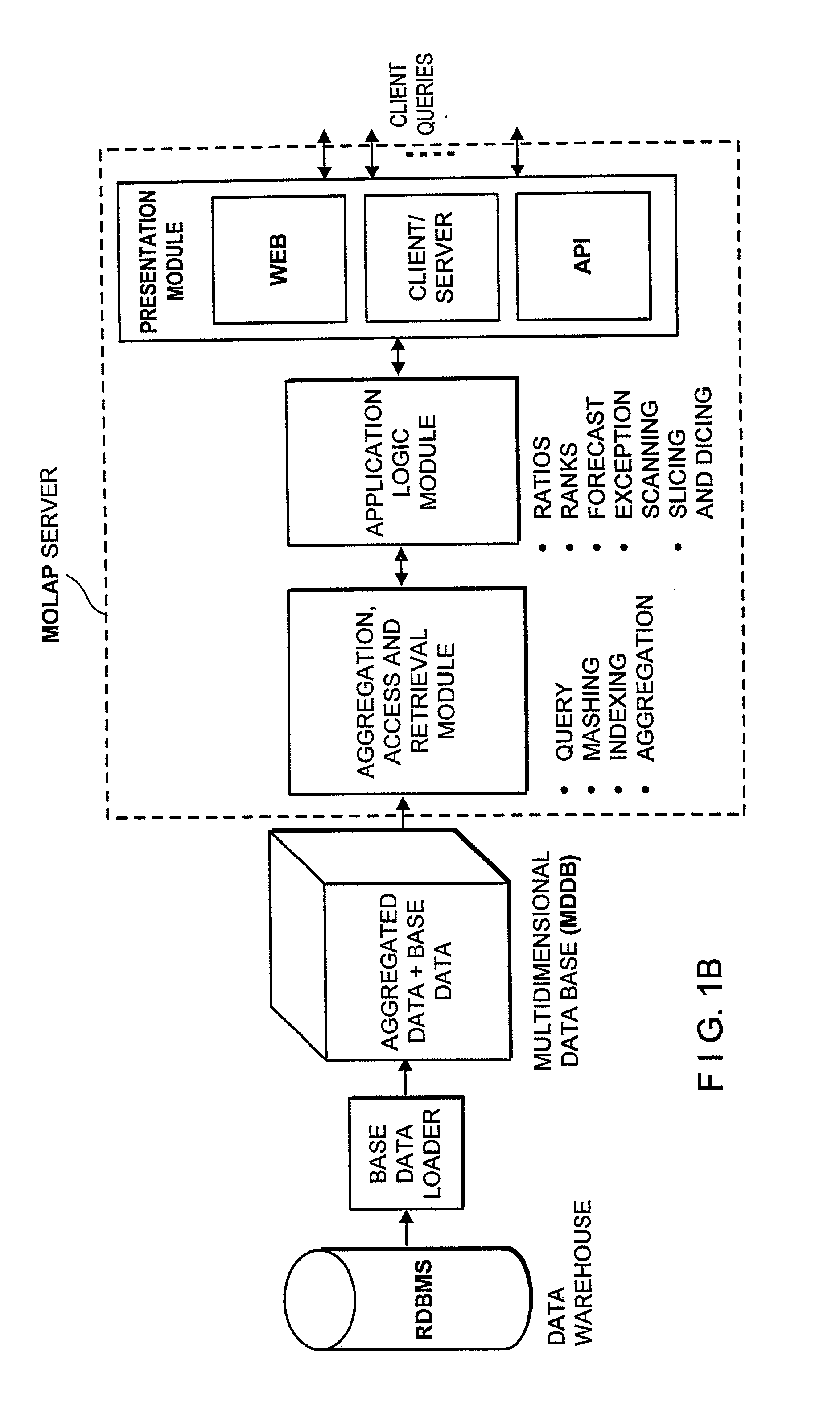
Improved method of and apparatus for aggregating data elements in multidimensional databases (MDDB). In one aspect of the present invention, the apparatus is realized in the form of a high-performance stand-alone (i.e. external) aggregation server which can be plugged-into conventional OLAP systems to achieve significant improments in system performance. In accordance with the principles of the present invention, the stand-alone aggregation server contains a scalable MDDB and a high-performance aggregation engine that are integrated into the modular architecture of the aggregation server. The stand-alone aggregation server of the present invention can uniformly distribute data elements among a plurality of processors, for balanced loading and processing, and therefore is highly scalable. The stand-alone aggregation server of the present invention can be used to realize (i) an improved MDDB for supporting on-line analytical processing (OLAP) operations, (ii) an improved Internet URL Directory for supporting on-line information searching operations by Web-enabled client machines, as well as (iii) diverse types of MDDB-based systems for supporting real-time control of processes in response to complex states of information reflected in the MDDB. In another aspect of the present invention, the apparatus is integrated within a database management system (DBMS). The improved DBMS can be used to realize achieving a significant increase in system performance (e.g. deceased access / search time), user flexibility and ease of use. The improved DBMS system of the present invention can be used to realize an improved Data Warehouse for supporting on-line analytical processing (OLAP) operations or to realize an improved informational database system, operational database system, or the like.
Owner:YANICKLO TECH LIABILITY +1
Medical robotic system with coupled control modes
In a coupled control mode, the surgeon directly controls movement of an associated slave manipulator with an input device while indirectly controlling movement of one or more non-associated slave manipulators, in response to commanded motion of the directly controlled slave manipulator, to achieve a secondary objective. By automatically performing secondary tasks through coupled control modes, the system's usability is enhanced by reducing the surgeon's need to switch to another direct mode to manually achieve the desired secondary objective. Thus, coupled control modes allow the surgeon to better focus on performing medical procedures and to pay less attention to managing the system.
Owner:INTUITIVE SURGICAL OPERATIONS INC
System and method for fraud monitoring, detection, and tiered user authentication
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
Subject matter context search engine
ActiveUS20050289168A1Raise the possibilityEasy retrievalWeb data indexingRelational databasesRelevant informationSubject matter
A search system associates contextual metadata with search terms and / or stored terms to facilitate identification of relevant information. In one implementation, a search term is identified (4304) from a received search request. The search term is then rewritten (4306) in standard form and the standard form term is then set (4308) as the current search parameter. A source database is then searched (4310) using the current search parameter. If any results are obtained (4312) these results may be output (4320) to the user. If no results are obtained, a parent classification of the search term is set (4316) as the current search parameter and the process is repeated. The invention thereby provides the ease of use of term searching with the comprehensiveness of category searching.
Owner:ORACLE INT CORP
Systems And Methods For Wireless Power System With Improved Performance and/or Ease of Use
ActiveUS20140142876A1Easy to deployFacilitate communicationNear-field transmissionTransformersElectric power systemPower grid
A device for testing a wireless power network is disclosed. The network includes at least one power source, at least one load, and multiple resonators configured to couple wireless power from the at least one power source to the at least one load. The device includes: a user interface for receiving input from a user and providing information to the user; a measurement module for measuring, whether directly or indirectly, at least one operational characteristic of the wireless power network and information about the geometric arrangement of the multiple resonators in the wireless power network; a memory for storing design specifications about the wireless power network; and an electronic processor configured to calculate information about a performance of the wireless power network based on the measured operational characteristic, the information about the geometric arrangement of the multiple resonators, and the stored design specifications, and further configured to provide the performance information to the user through the user interface.
Owner:WITRICITY CORP
Administration of wireless local area networks
ActiveUS20060251256A1Improve securityImprove usabilityKey distribution for secure communicationAssess restrictionProbable CaseNetwork addressing
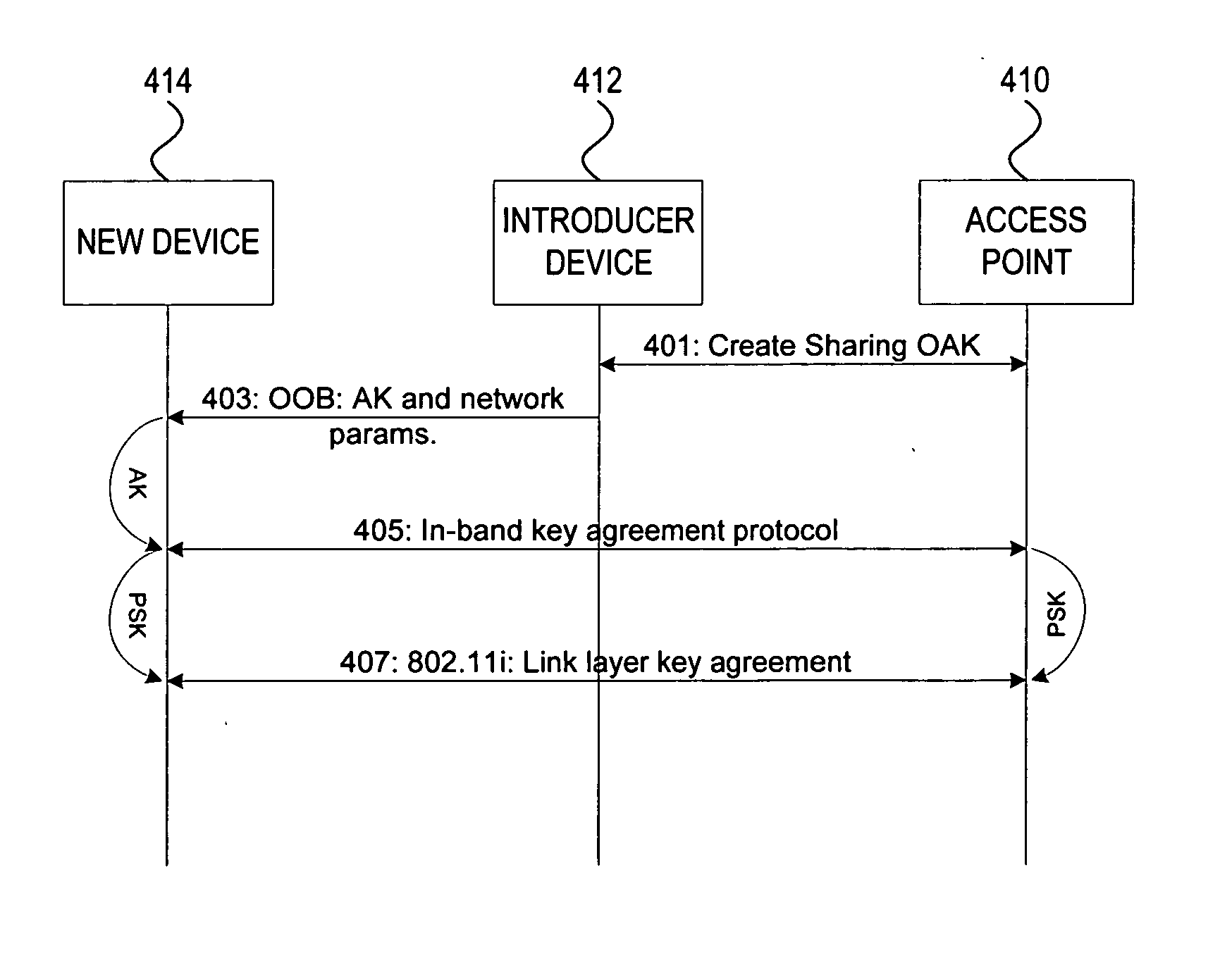
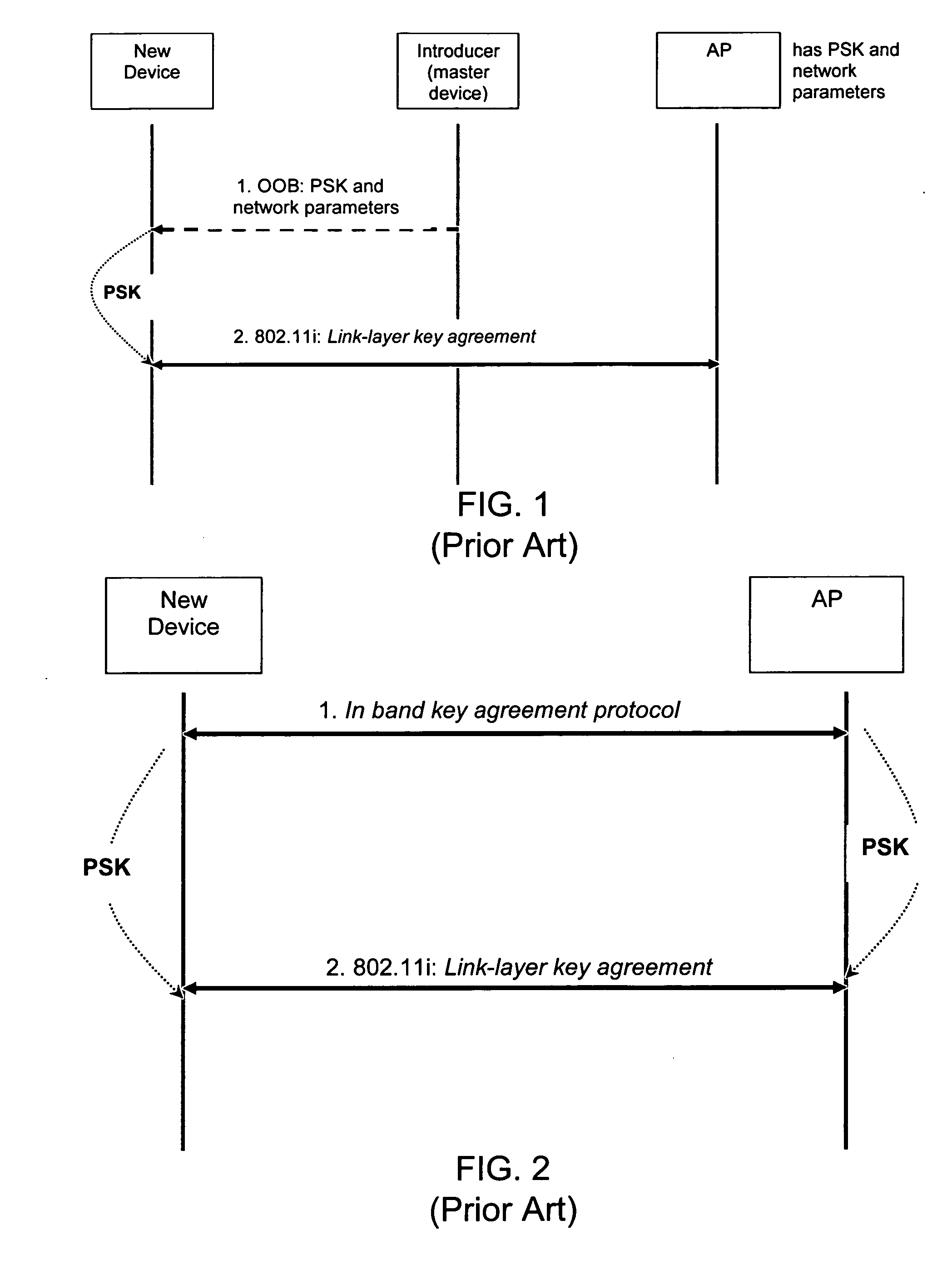
Methods and systems for managing access to a wireless local area network are provided. A wireless access point (AP) may use a unified approach that utilizes an out-of-band channel to communicate authentication key and network address information to a guest device, and utilizes an in-band channel to establish communications with the guest device, and also provides support for in-band setup on all devices. The ability to use out-of-band where possible provides for an increase to security and usability, and the possibility of delegating access from one device to another. The unified approach thereby also provides easy management of guest access to the WLAN.
Owner:NOKIA TECHNOLOGLES OY
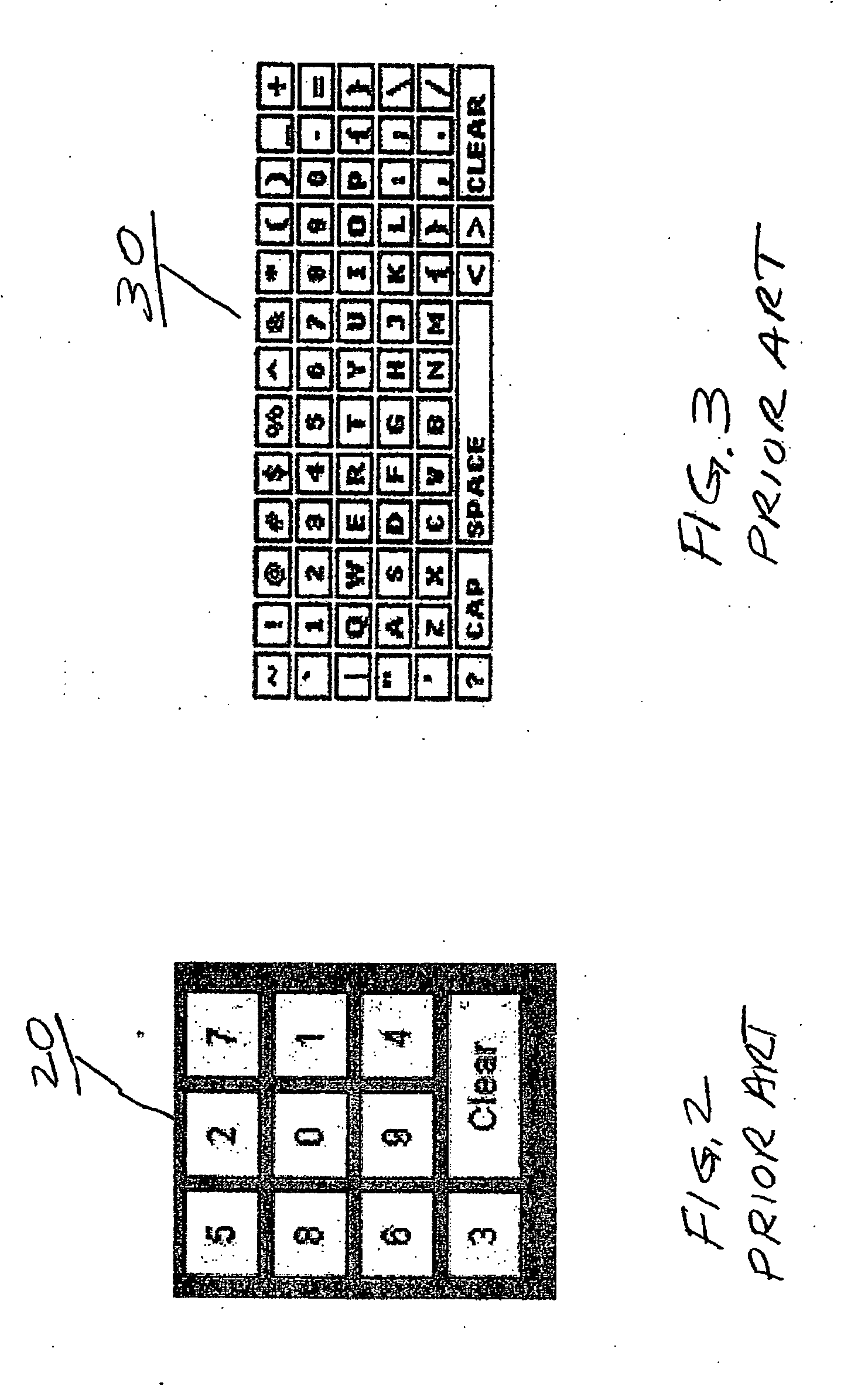
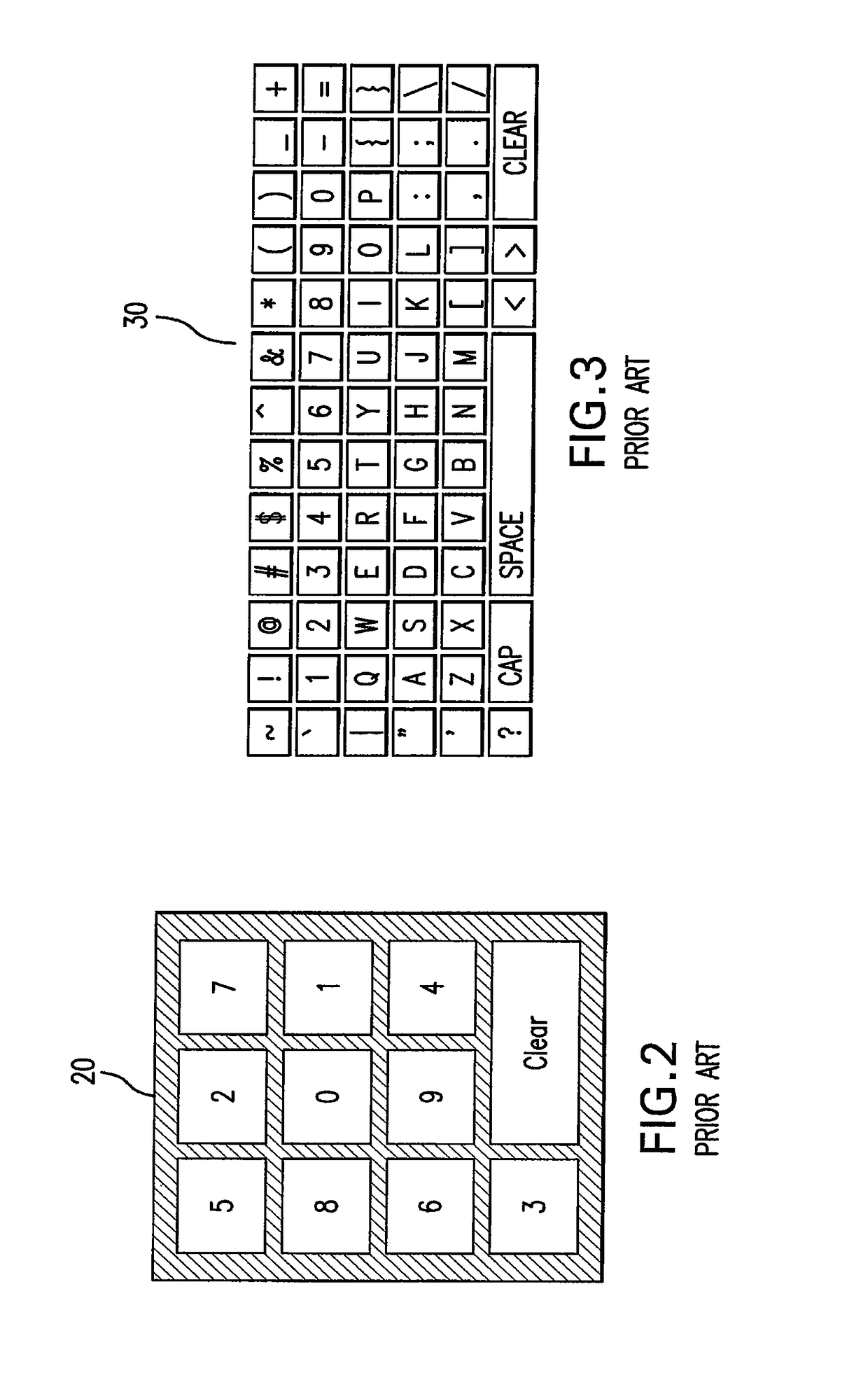
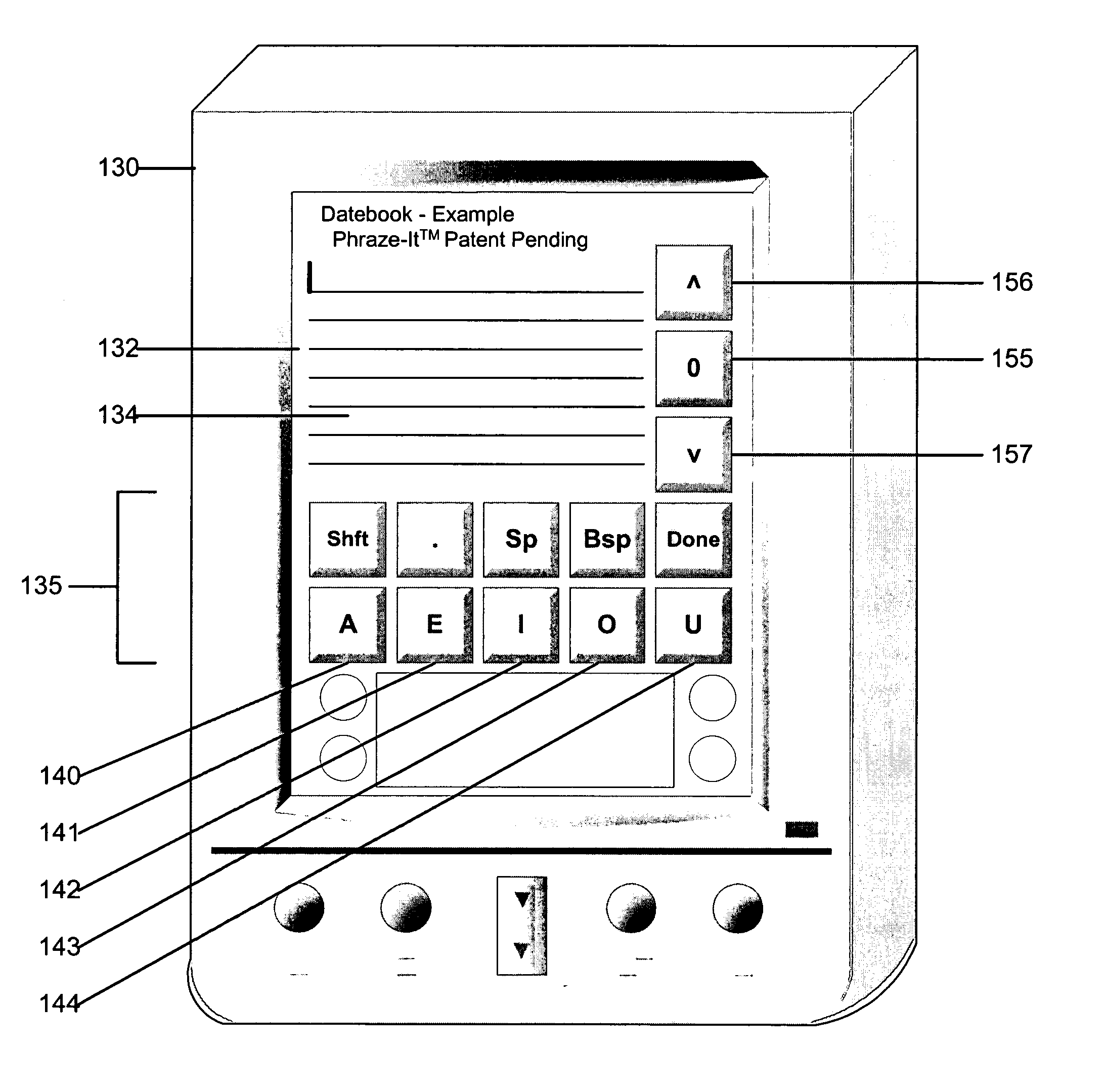
System and method for data input
ActiveUS7190351B1Easy to learnEasy to integrateDigital data processing detailsCathode-ray tube indicatorsUsabilityComputer science
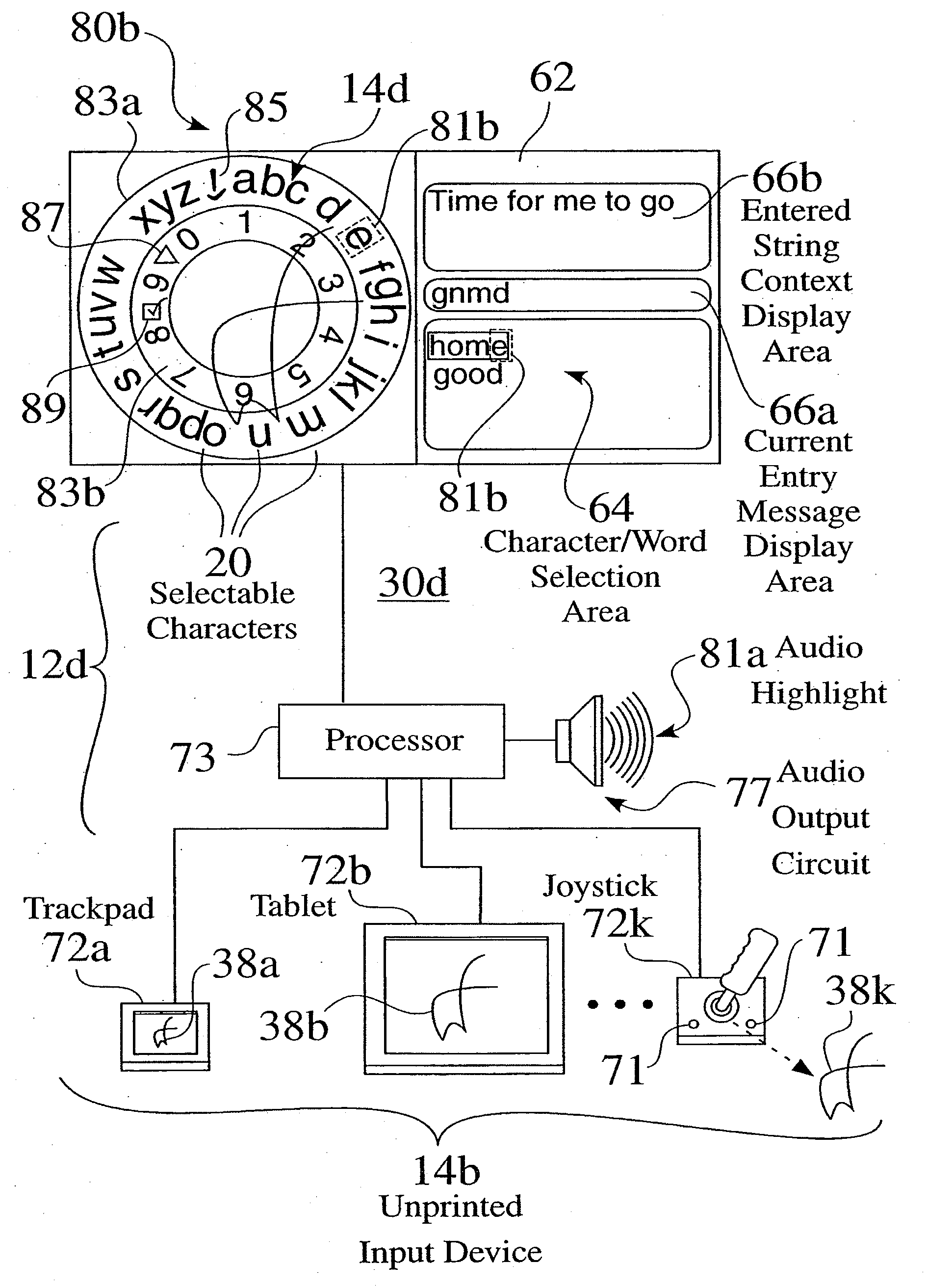
The invention provides a system and a method for data input that can be used with or incorporated into electronic, computer, and portable devices. The interface includes a small set of control buttons or keys that are used to provide access to an associated set of secondary keys, from which the user can select a character for input into the device. Intelligent ordering and grouping of the control and secondary keys allows the user to input information in a manner conducive to speed, accuracy, and ease of use, while the interface can be minimized to require less real estate than traditional keyboards. In accordance with one embodiment, a set of characters or symbols is divided into subsets, each subset being represented by a control button. Selecting a control button displays a secondary set of buttons representing actual characters or symbols that can be selected, stored, or displayed.
Owner:NUANCE COMM INC
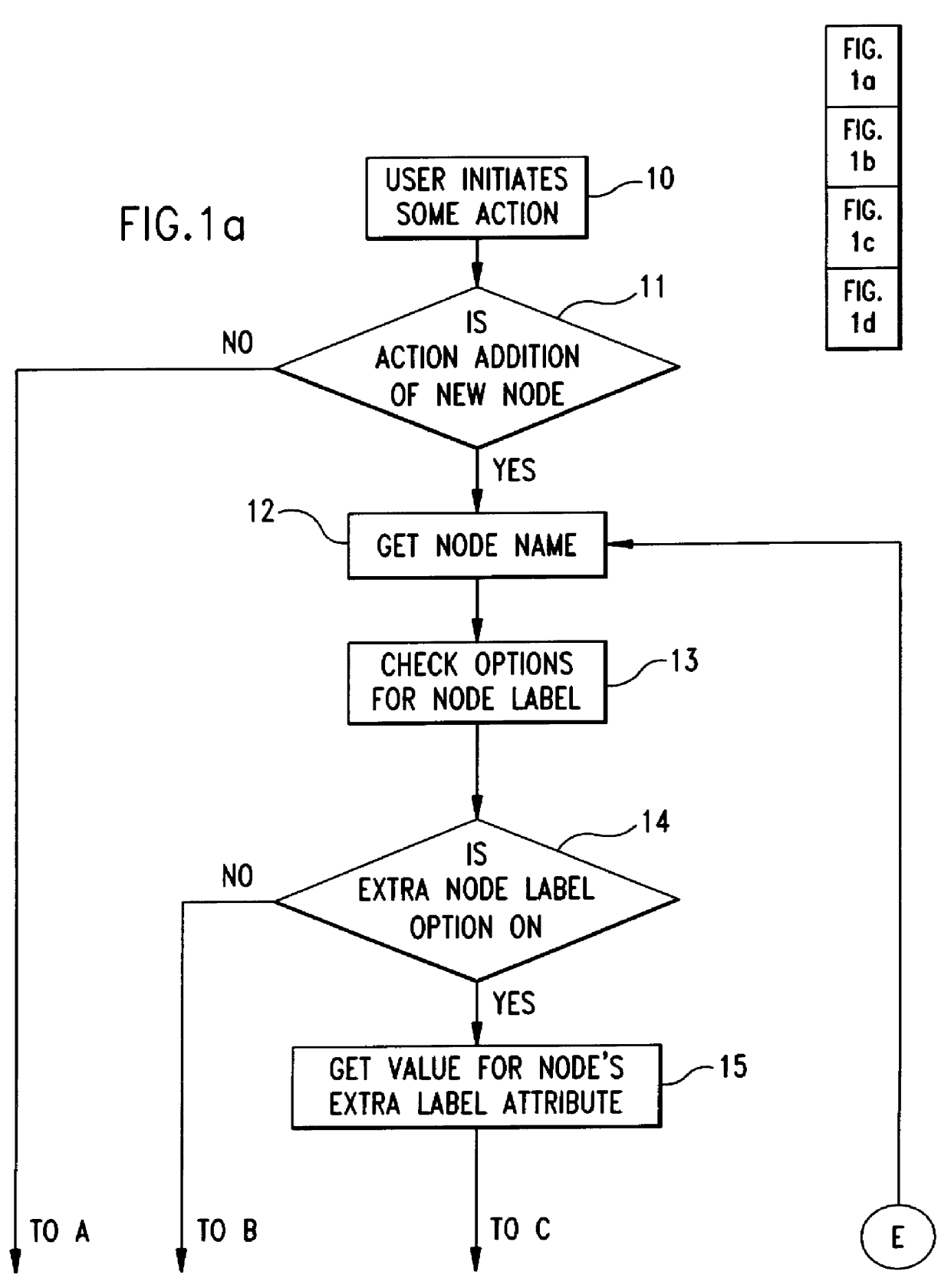
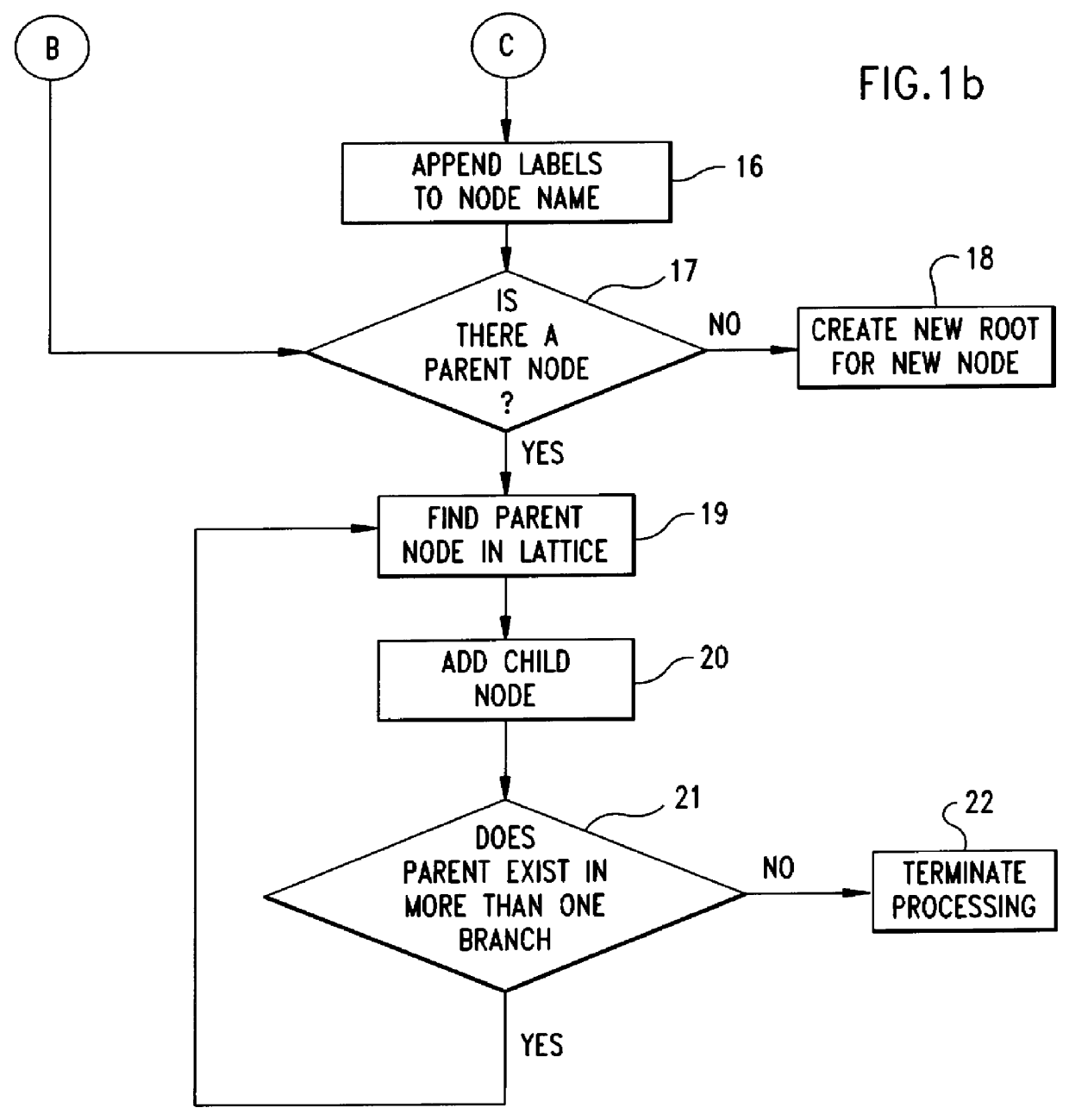
Enhanced tree control system for navigating lattices data structures and displaying configurable lattice-node labels
InactiveUS6055515AEasy to buildEasy maintenanceCommerceSpecial data processing applicationsControl systemMultiple inheritance
The objective of the instant invention is to define a computer user interface display system that presents hierarchical data in an enhanced tree presentation control that blends the ease-of-use character of the familiar "tree presentation control" with a technique for navigating more complex lattice data structures, while at the same time providing more node information by displaying configured lattice-node labels along with the node's name. Thus a primary objective of this invention is to facilitate building, maintaining and using a multiple inheritance taxonomy such as a product catalog data base by means of a multi-navigation path browsing system, which is made possible through the capability of this system's multiple inheritance capability; with indicators in the tree view to indicate ancestors such as immediate parents and further removed ancestors.
Owner:IBM CORP
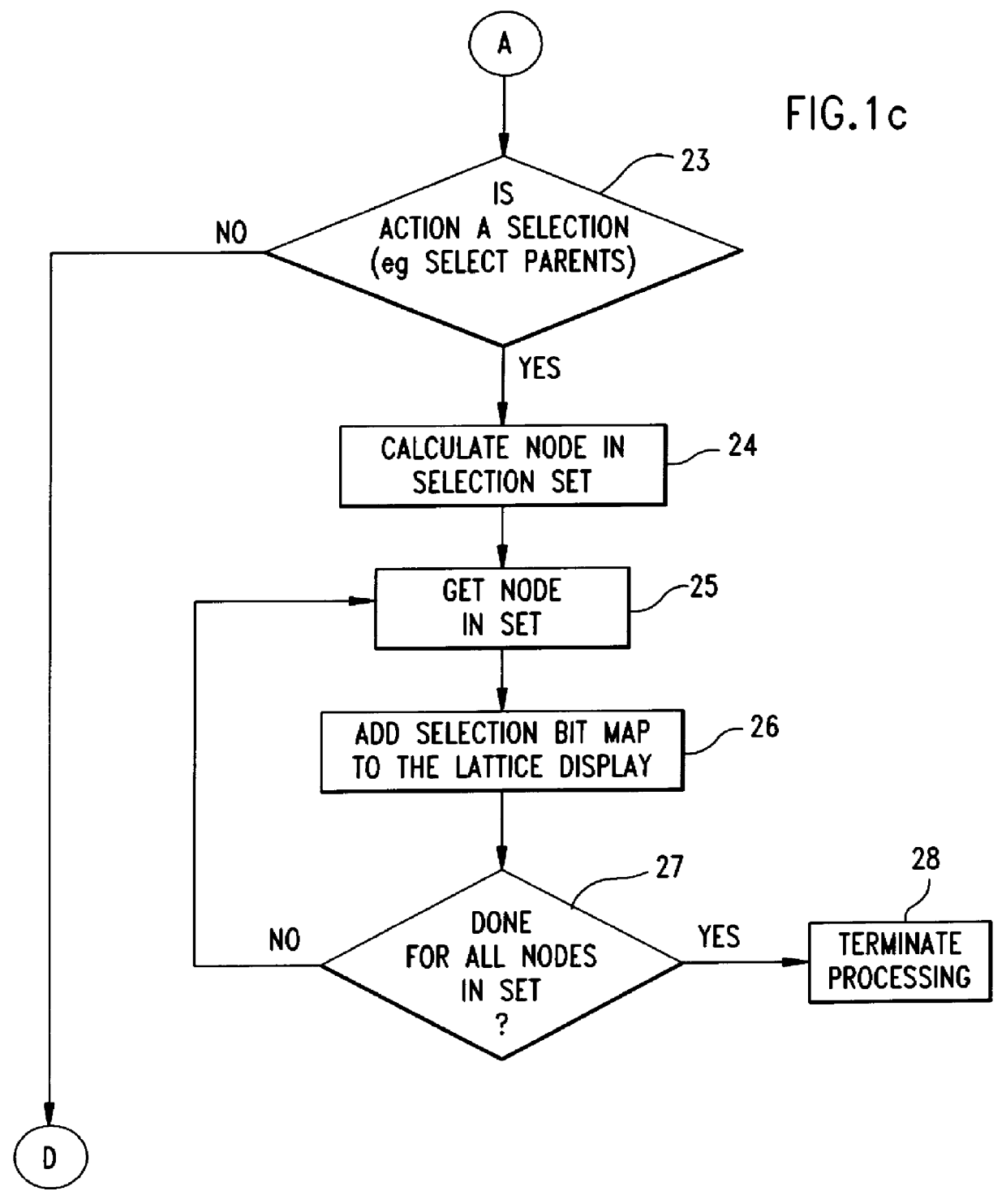
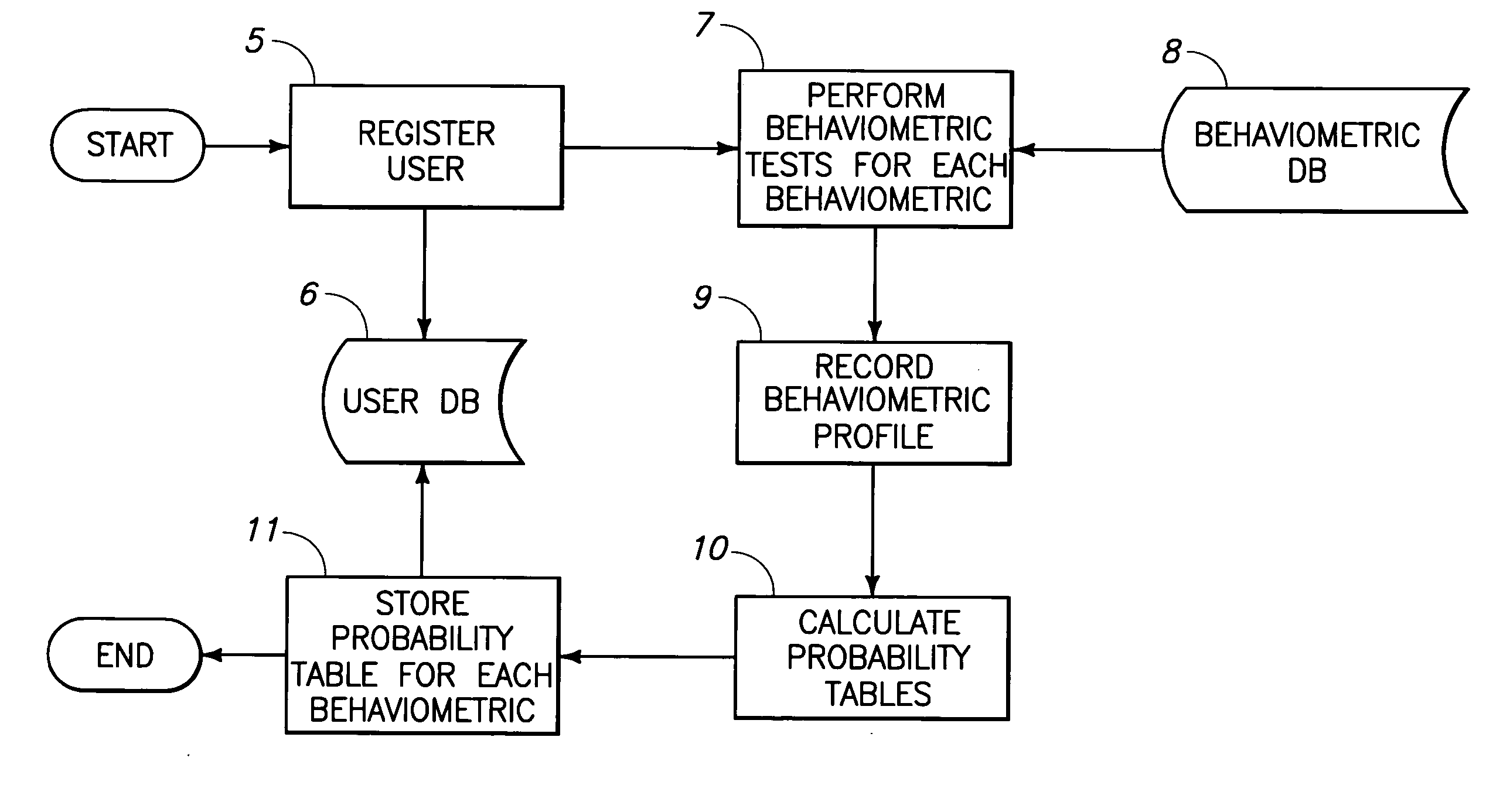
Multi-touch device behaviormetric user authentication and dynamic usability system
InactiveUS20080092245A1Fast and adaptable and scalable mechanismBetter securingDigital data processing detailsUnauthorized memory use protectionUsabilityUser authentication
This invention discloses a system for determining whether a purported or alleged authorized user is in fact the authorized user, by comparing new data on a real-time basis against probability distribution representations including an authorized user probability distribution representation and a global or wide population probability distribution representation, to provide a probability as to whether the purported authorized user is the authorized user. This invention may utilize touch dynamics or data, or other data from similar measurable characteristics, to determine the probability that the new data from the purported authorized user indicates or identifies that user as the authorized user. This invention uses the same data to determine the probability for the most optimal position and sizes for user interface components.
Owner:IDENTITY METRICS
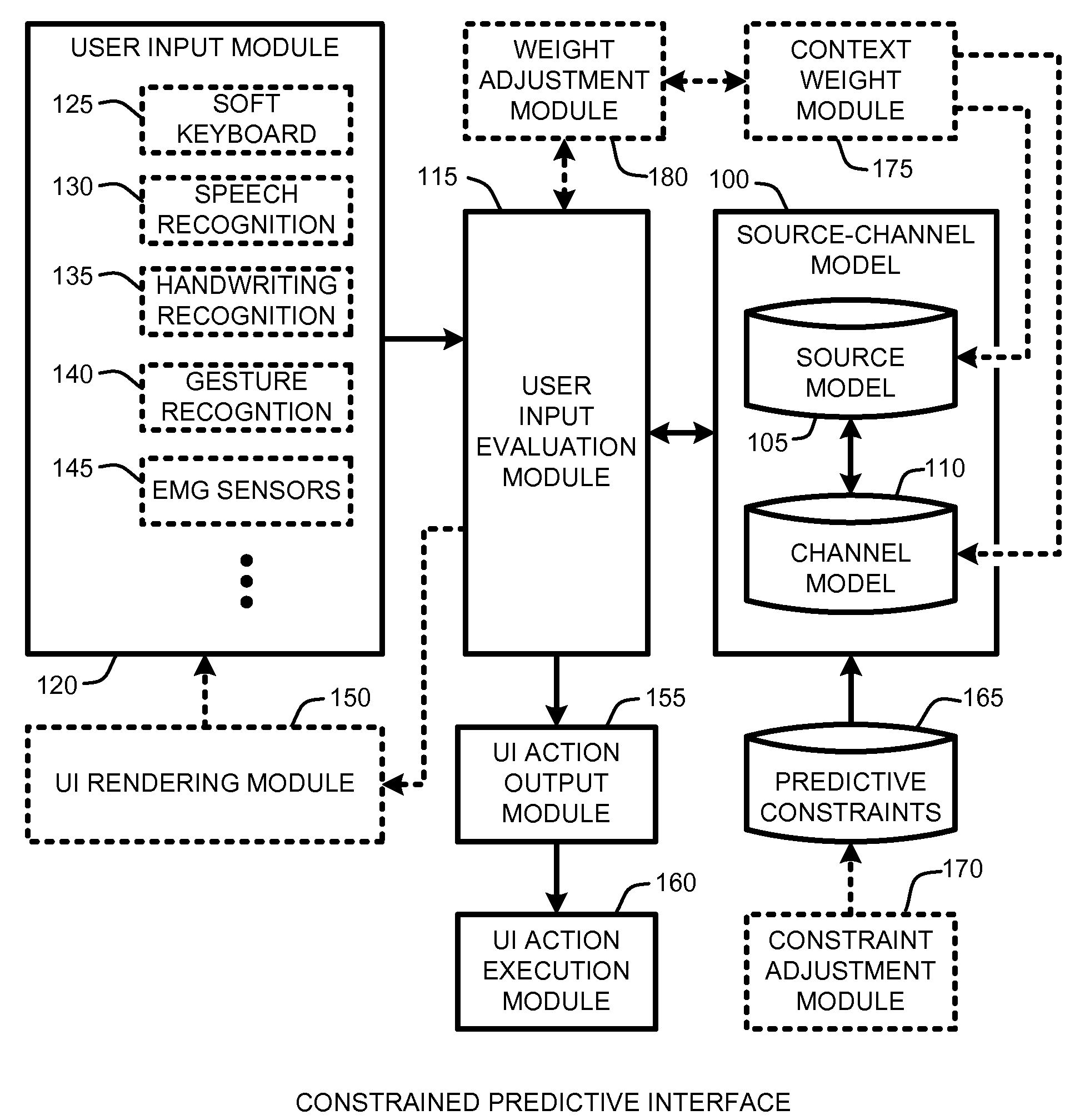
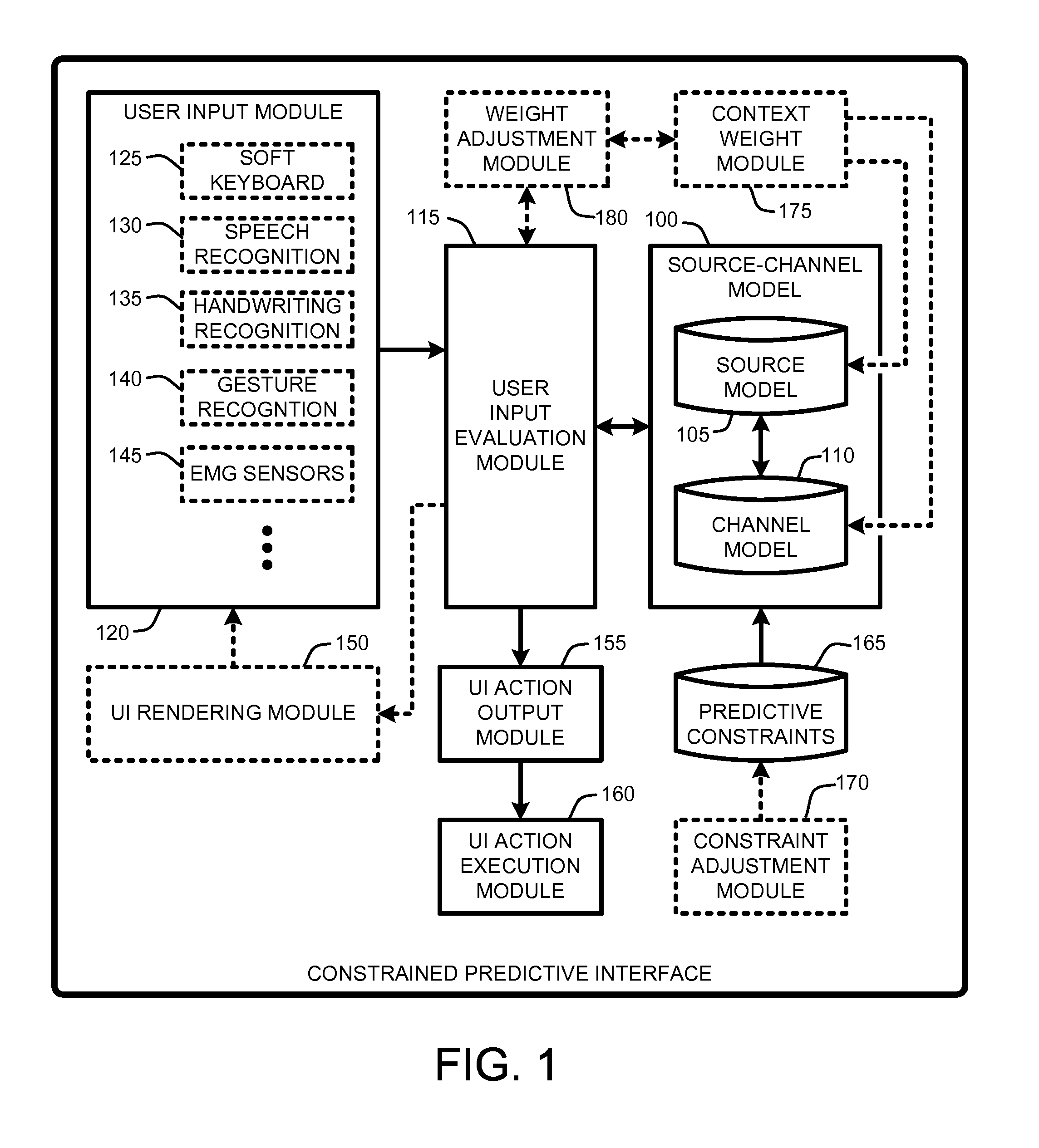
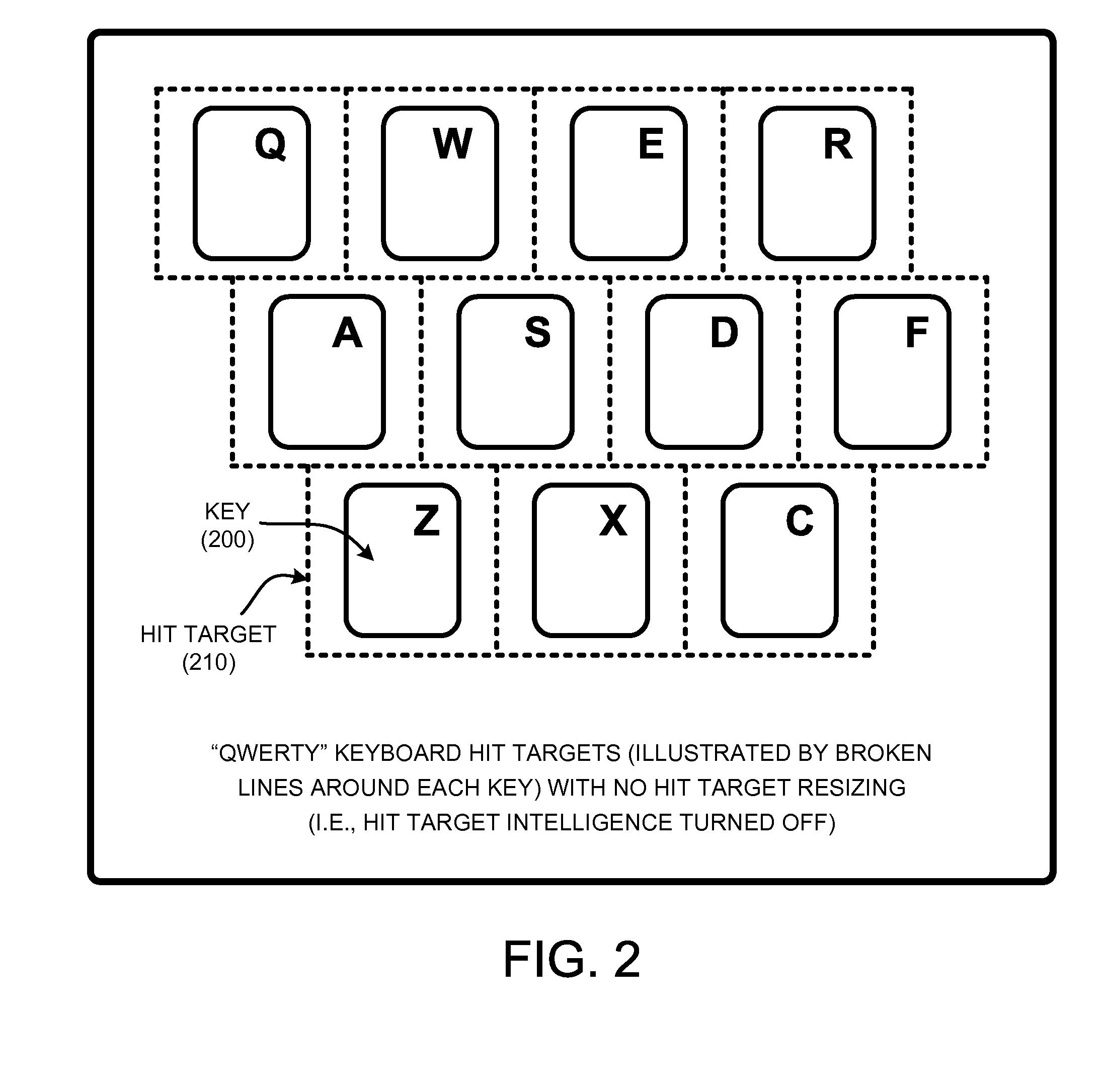
Predictive interfaces with usability constraints
InactiveUS20100315266A1Improve featuresGood user interfaceElectronic switchingInput/output processes for data processingMulti touch interfaceUsability
A “Constrained Predictive Interface” uses predictive constraints to improve accuracy in user interfaces such as soft keyboards, pen interfaces, multi-touch interfaces, 3D gesture interfaces, EMG based interfaces, etc. In various embodiments, the Constrained Predictive Interface allows users to take any desired action at any time by taking into account a likelihood of possible user actions in different contexts to determine intended user actions. For example, to enable a virtual keyboard interface, various embodiments of the Constrained Predictive Interface provide key “sweet spots” as predictive constraints that allow the user to select particular keys regardless of any probability associated with the selected or neighboring keys. In further embodiments, the Constrained Predictive Interface provides hit target resizing via various piecewise constant touch models in combination with various predictive constraints. In general, hit target resizing provides dynamic real-time virtual resizing of one or more particular keys based on various probabilistic criteria.
Owner:MICROSOFT TECH LICENSING LLC
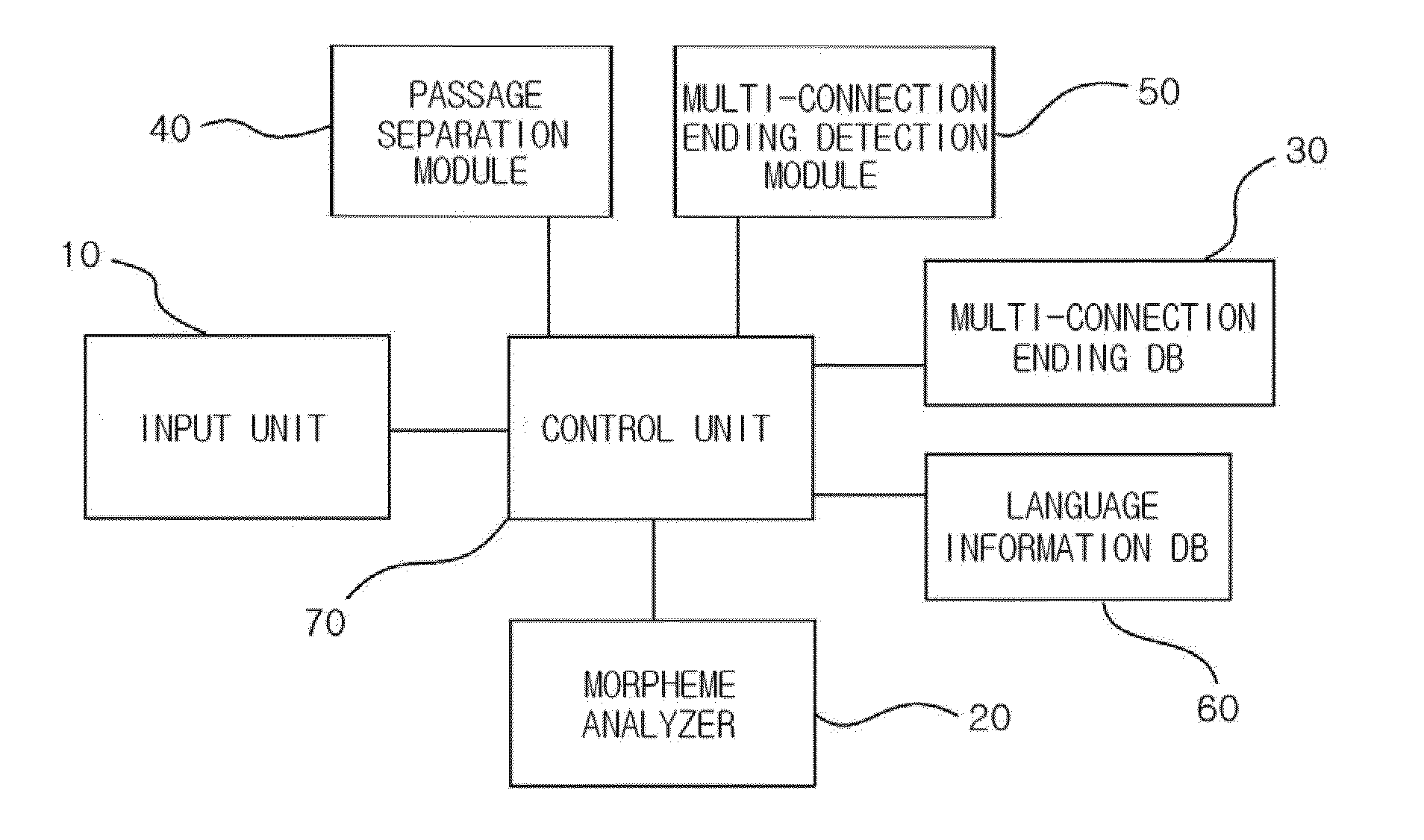
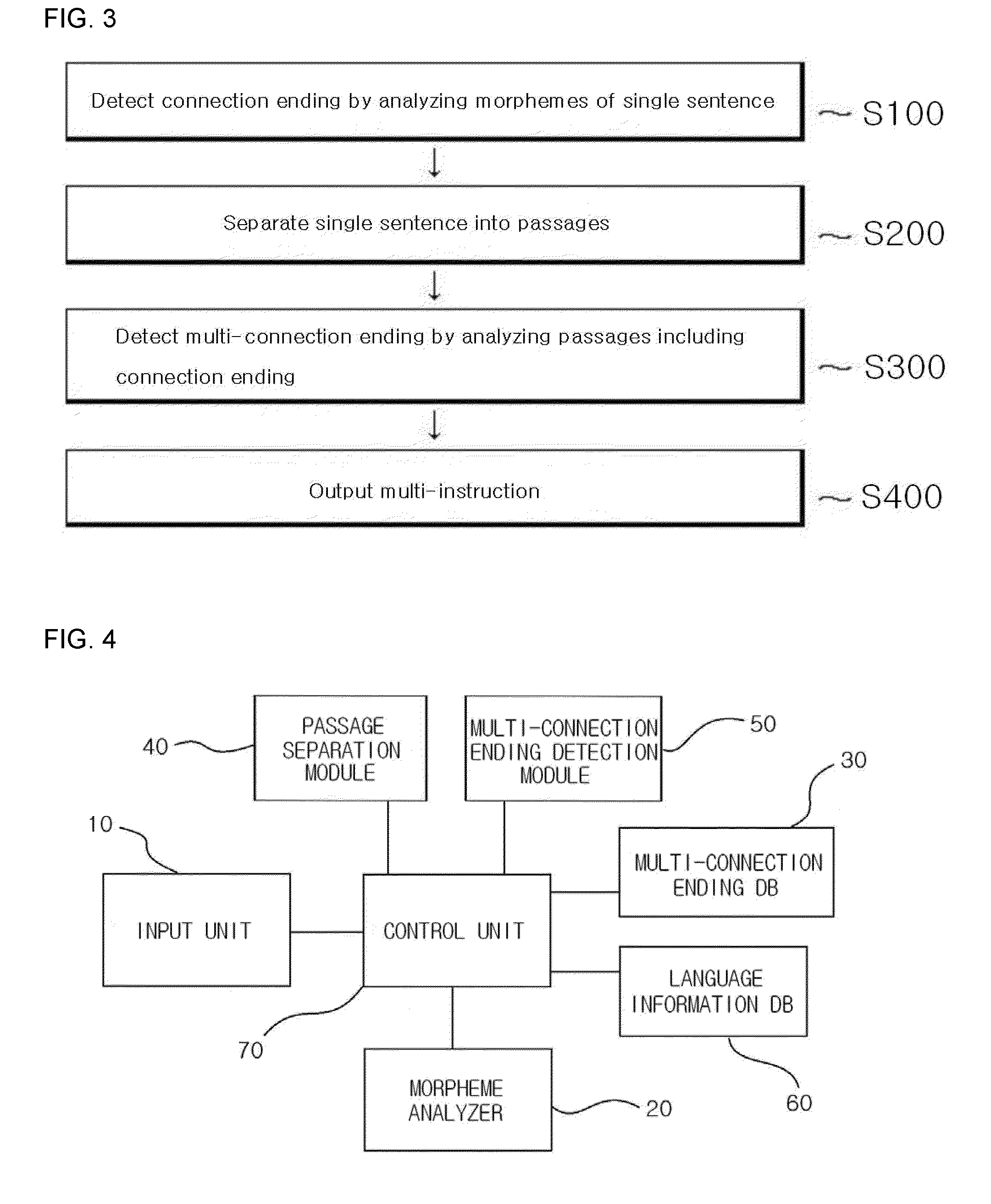
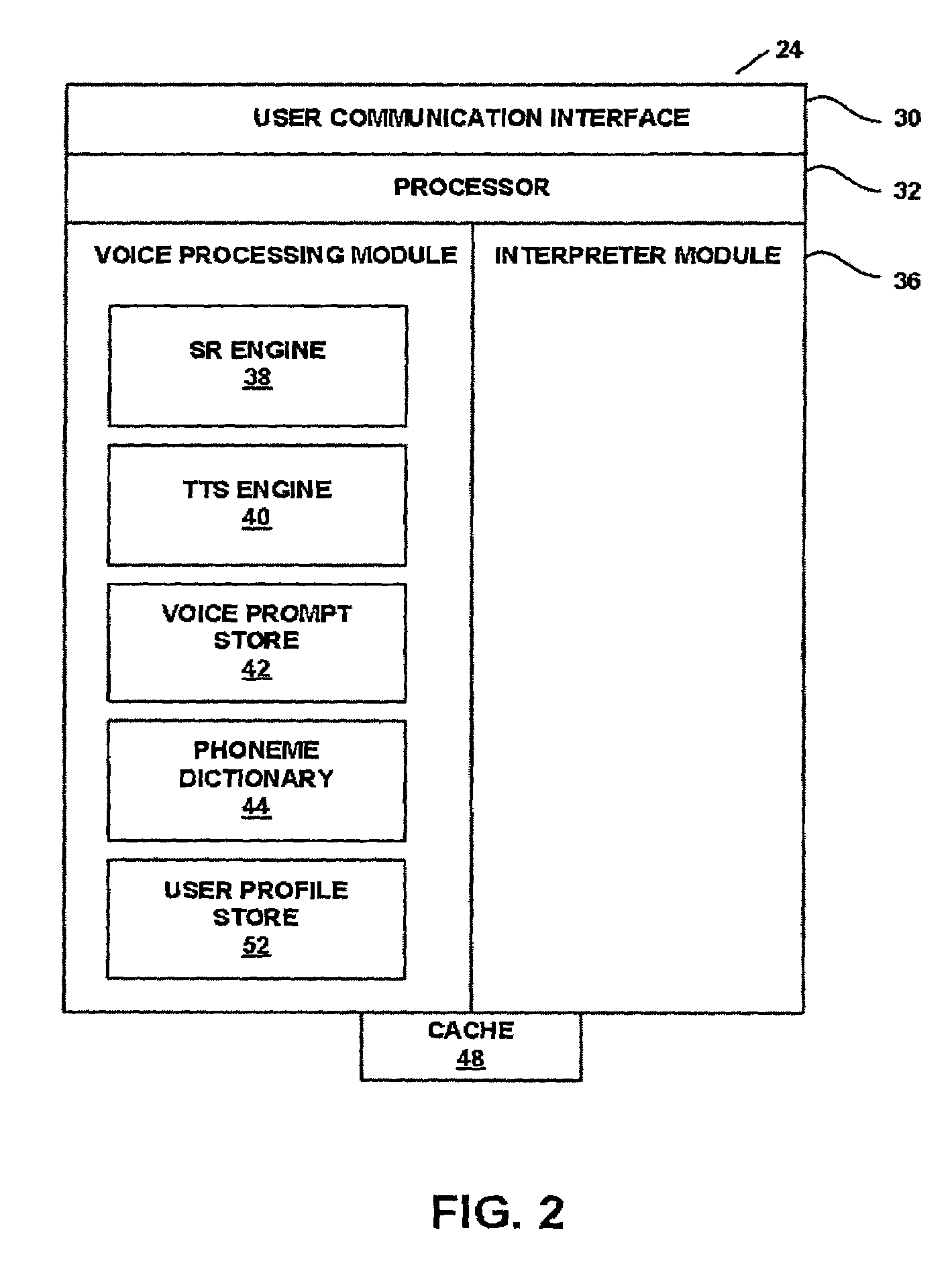
Speech recognition method of sentence having multiple instructions
InactiveUS20140244258A1Increase success rateLow success ratioSpeech recognitionSingle sentenceMorpheme
A voice recognition method for a single sentence including a multi-instruction in an interactive voice user interface, method includes steps of detecting a connection ending by analyzing the morphemes of a single sentence on which voice recognition has been performed, separating the single sentence into a plurality of passages based on the connection ending, detecting a multi-connection ending by analyzing the connection ending and extracting instructions by specifically analyzing passages including the multi-connection ending and outputting a multi-instruction included in the single sentence by combining the instructions extracted in the step of extracting instructions. In accordance with the present invention, consumer usability can be significantly increased because a multi-operation intention can be checked in one sentence.
Owner:MEDIAZEN
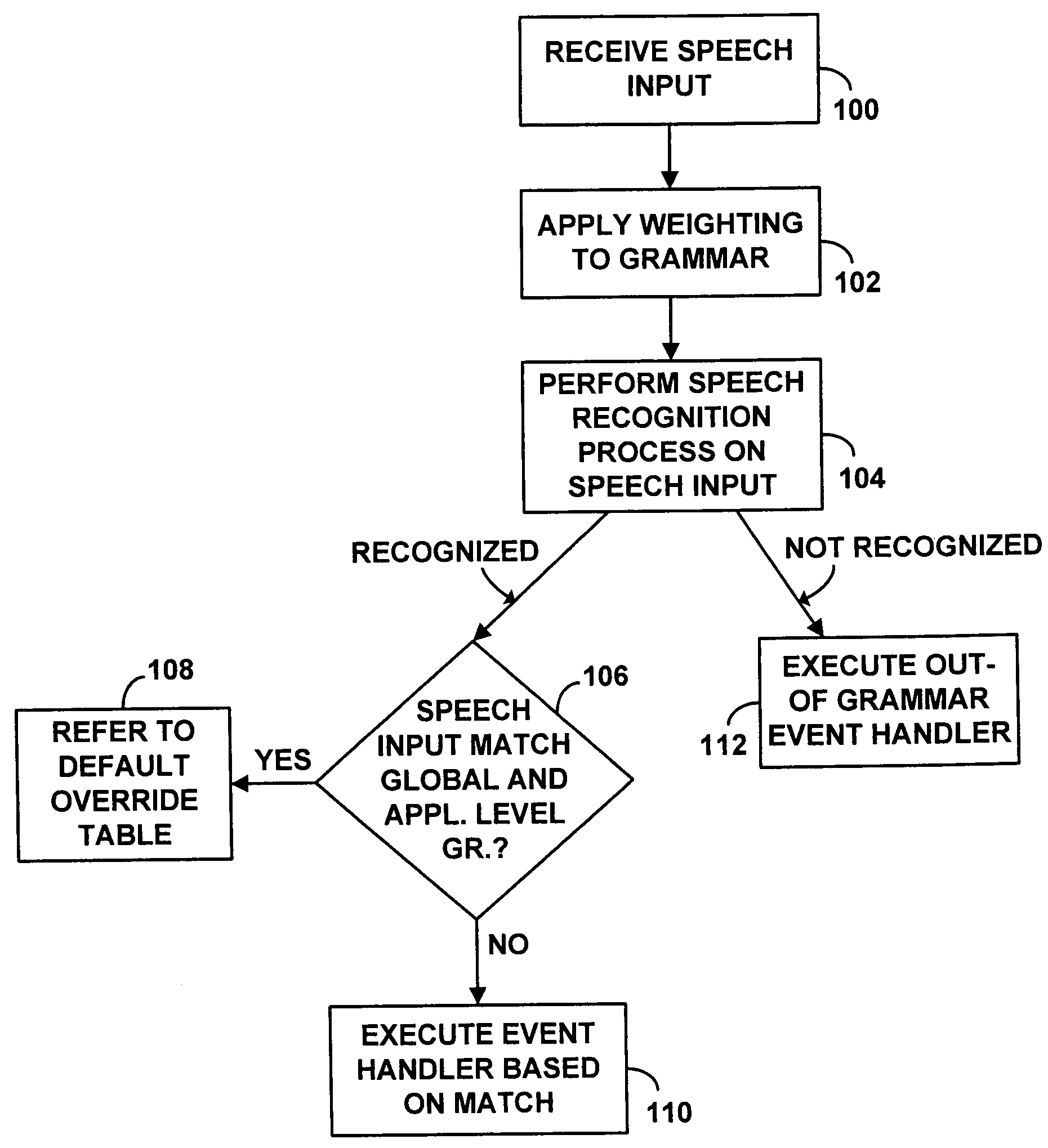
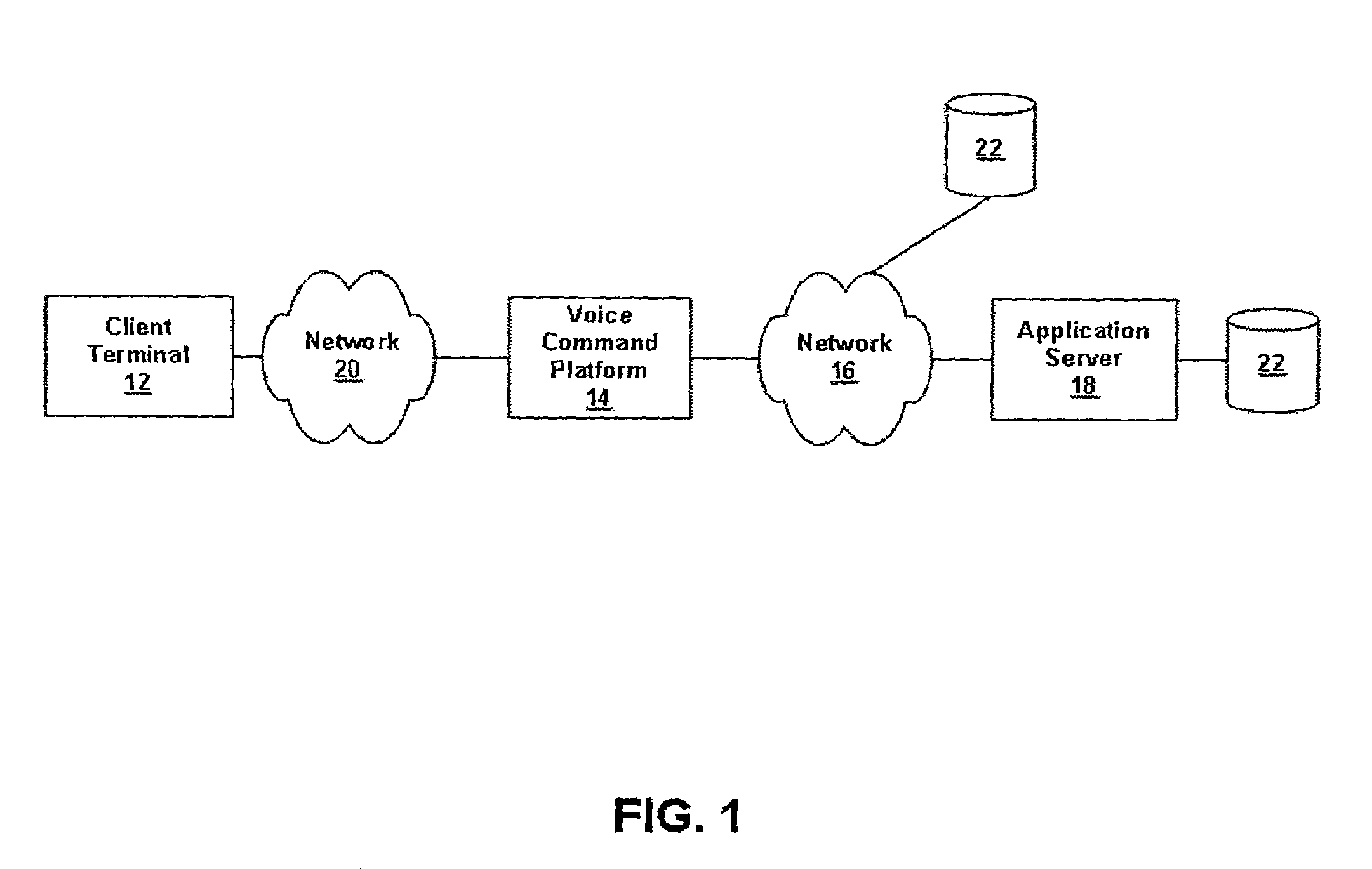
Voice browser with weighting of browser-level grammar to enhance usability
A computer system in the form of a voice command platform includes a voice browser and voice-based applications. The voice browser has global-level grammar elements and the voice applications have application-level grammar and grammar elements. A programming feature is provided by which developers of the voice applications can programmably weigh or weight global-level grammar elements relative to the application-level grammar or grammar elements. As a consequence of the weighting, a speech recognition engine for the voice browser is more likely to accurately recognize voice input from a user. The weighting can be applied on the application as a whole, or at any given state in the application. Also, the weighting can be made to the global level grammar elements as a group, or on an individual basis.
Owner:SPRINT SPECTRUM LLC
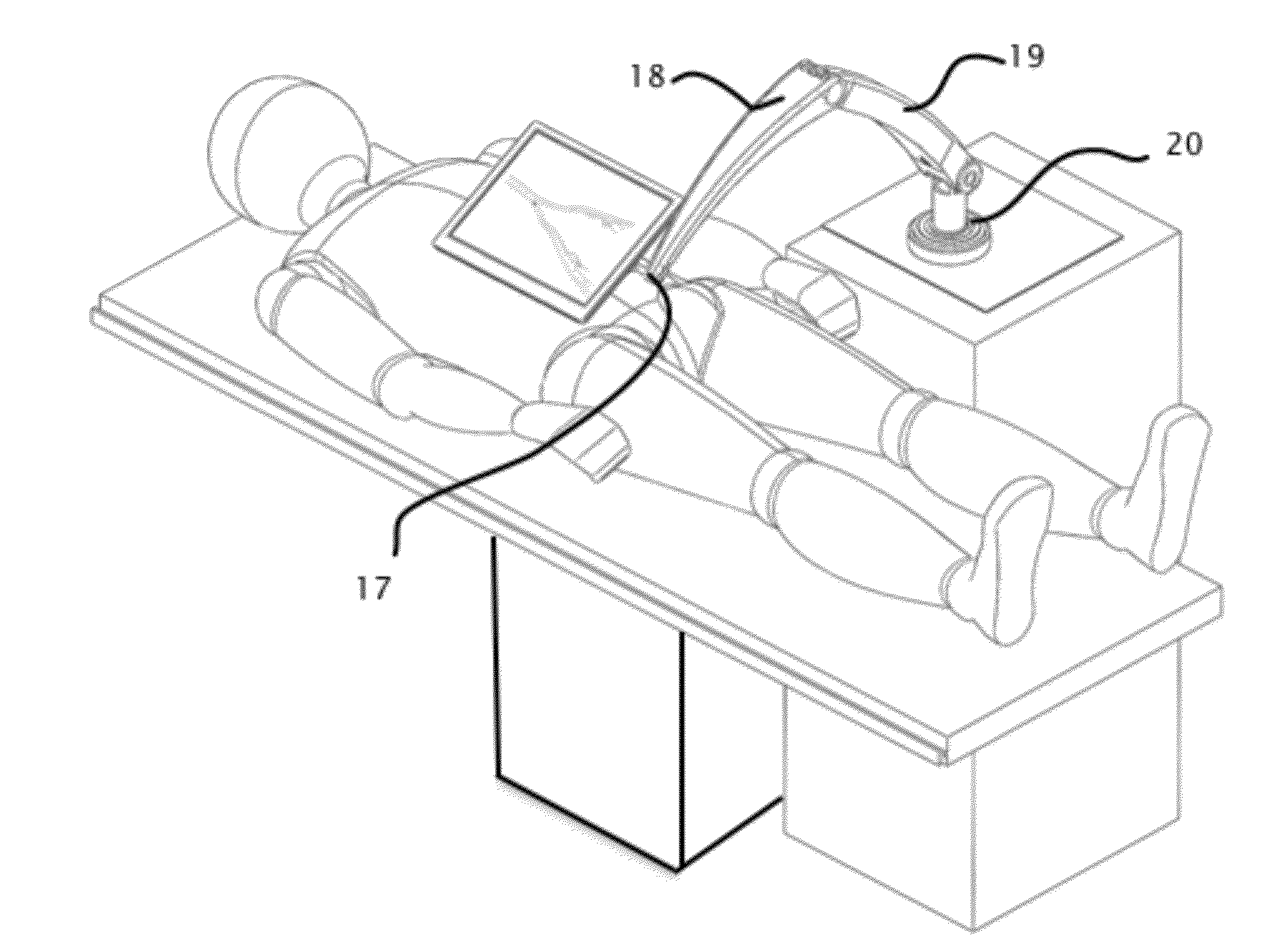
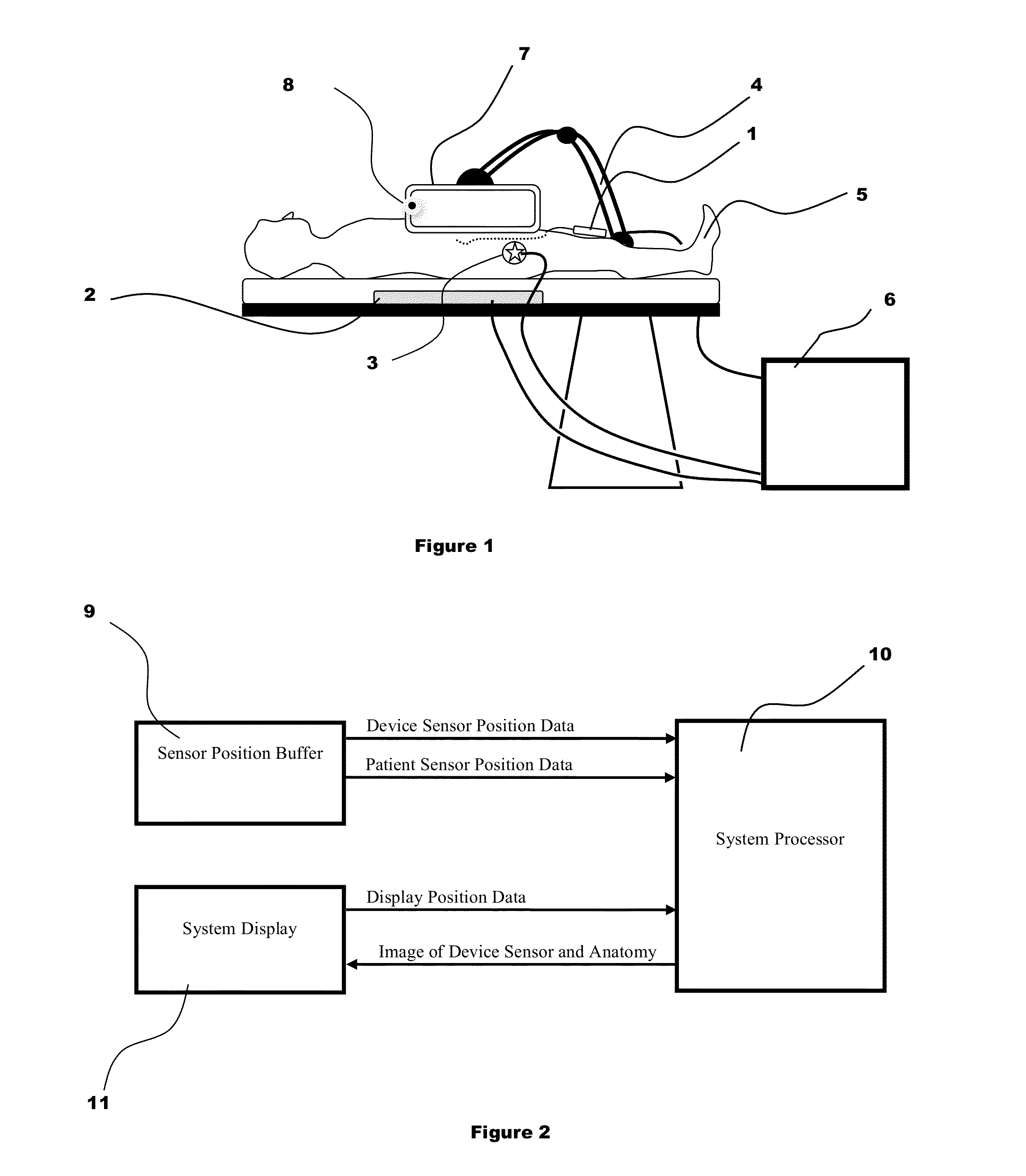
System and method for displaying anatomy and devices on a movable display
ActiveUS20140357984A1Easy to browseQuick selectionMechanical/radiation/invasive therapiesOrgan movement/changes detectionComputer graphics (images)Display device
An image display system is provided comprised of a virtual window system that creates a visual coherency between the patient's anatomical images and the actual patient by aligning the image on the display to the patient and then presenting the image to the user in a way that feels as if the user is looking directly into the patient through the display. The image shown within the image display system is dependent upon the position of the image display apparatus and the position of the user so that the display orientation of the image may be biased slightly toward the user to improve ergonomics and usability.
Owner:AURIS HEALTH INC
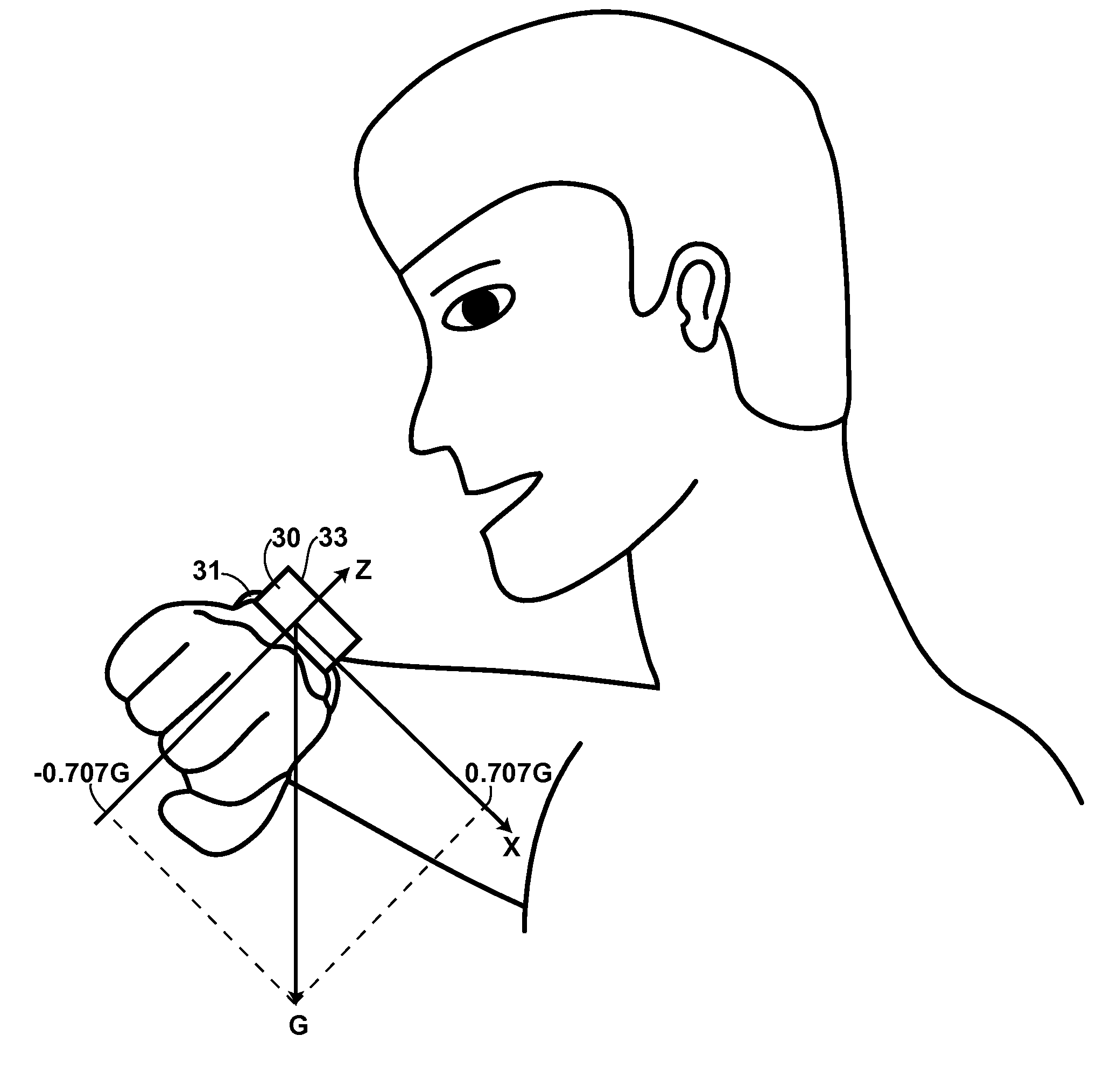
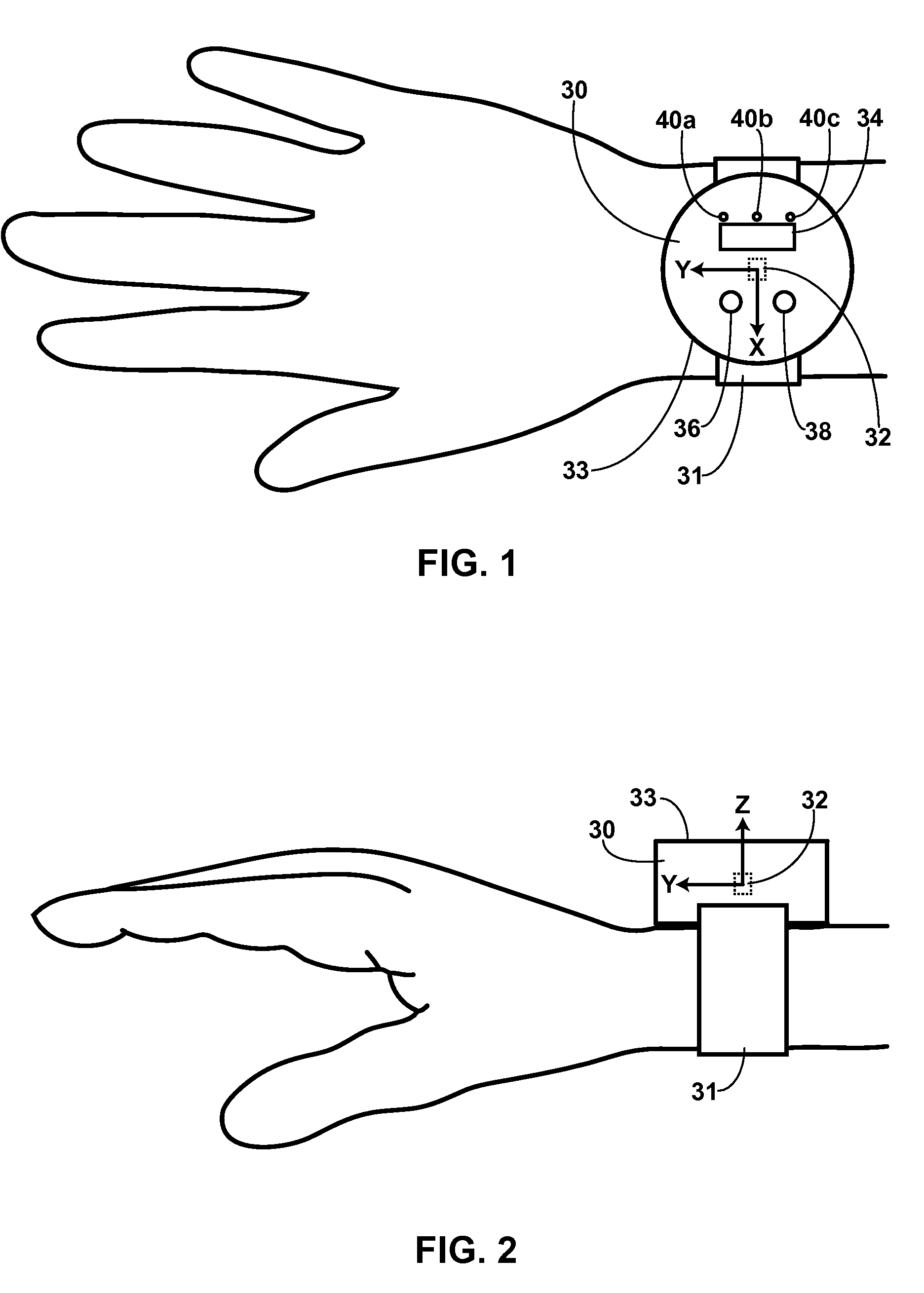
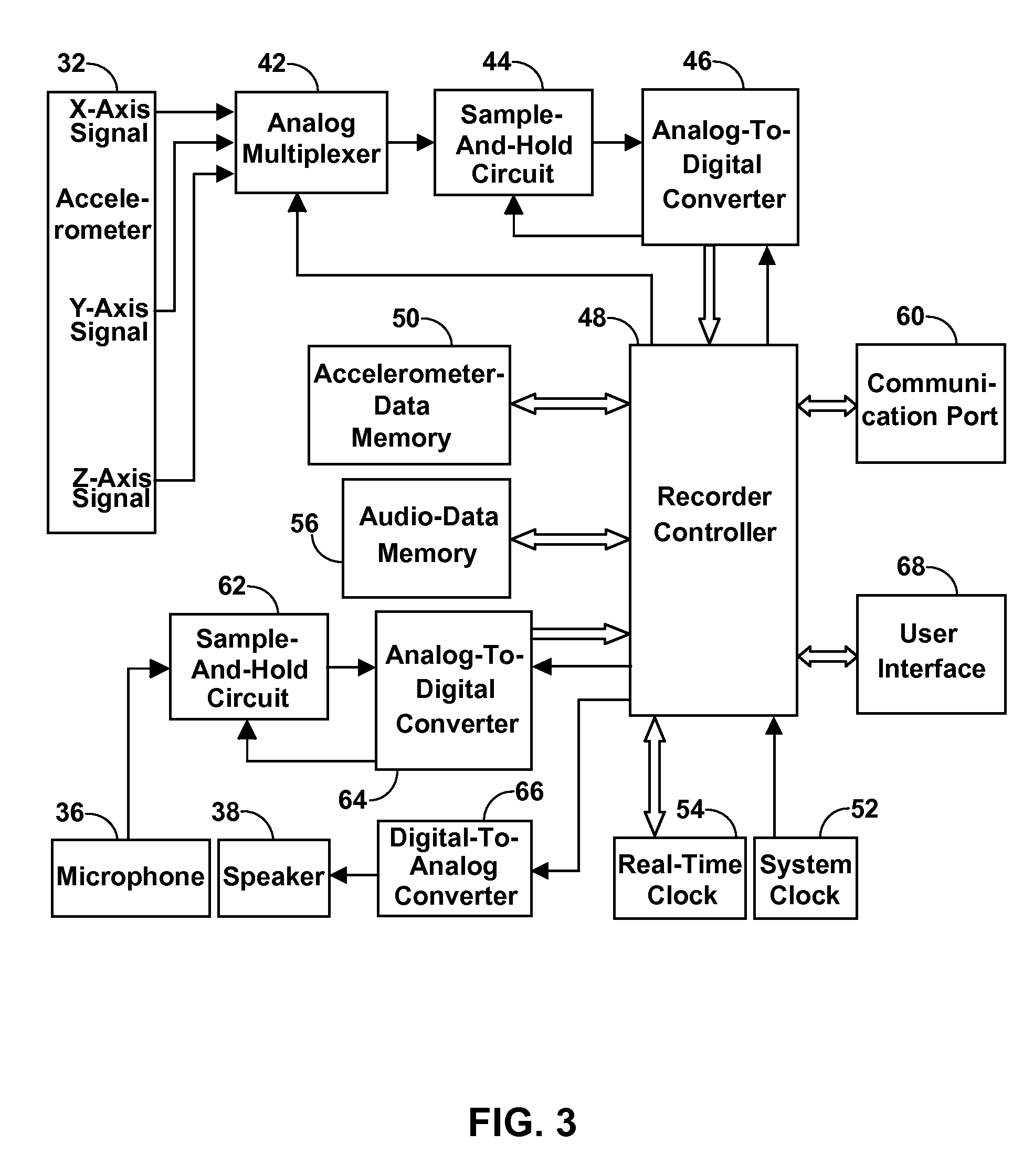
Accelerometer-Based Control of Wearable Devices
ActiveUS20090164219A1Input/output for user-computer interactionElectric windingAccelerometerUsability
Accelerometer-based orientation and / or movement detection for controlling wearable devices, such as wrist-worn audio recorders and wristwatches. A wrist-worn audio recorder can use an accelerometer to detect the orientation and / or movement of a user's wrist and subsequently activate a corresponding audio-recorder function, for instance recording or playback. A wearable device with a vibration mechanism can use this method to remind a user of an undesirable movement such as restless leg movement. Likewise, a talking wristwatch can use this method to activate audio reporting of time when a user moves or orients his or her wrist in close proximity to his or her ear. In such applications, and many others, accelerometer-based control of the wearable device offers significant advantages over conventional means of control, particularly in terms of ease of use and durability.
Owner:ENBIOMEDIC
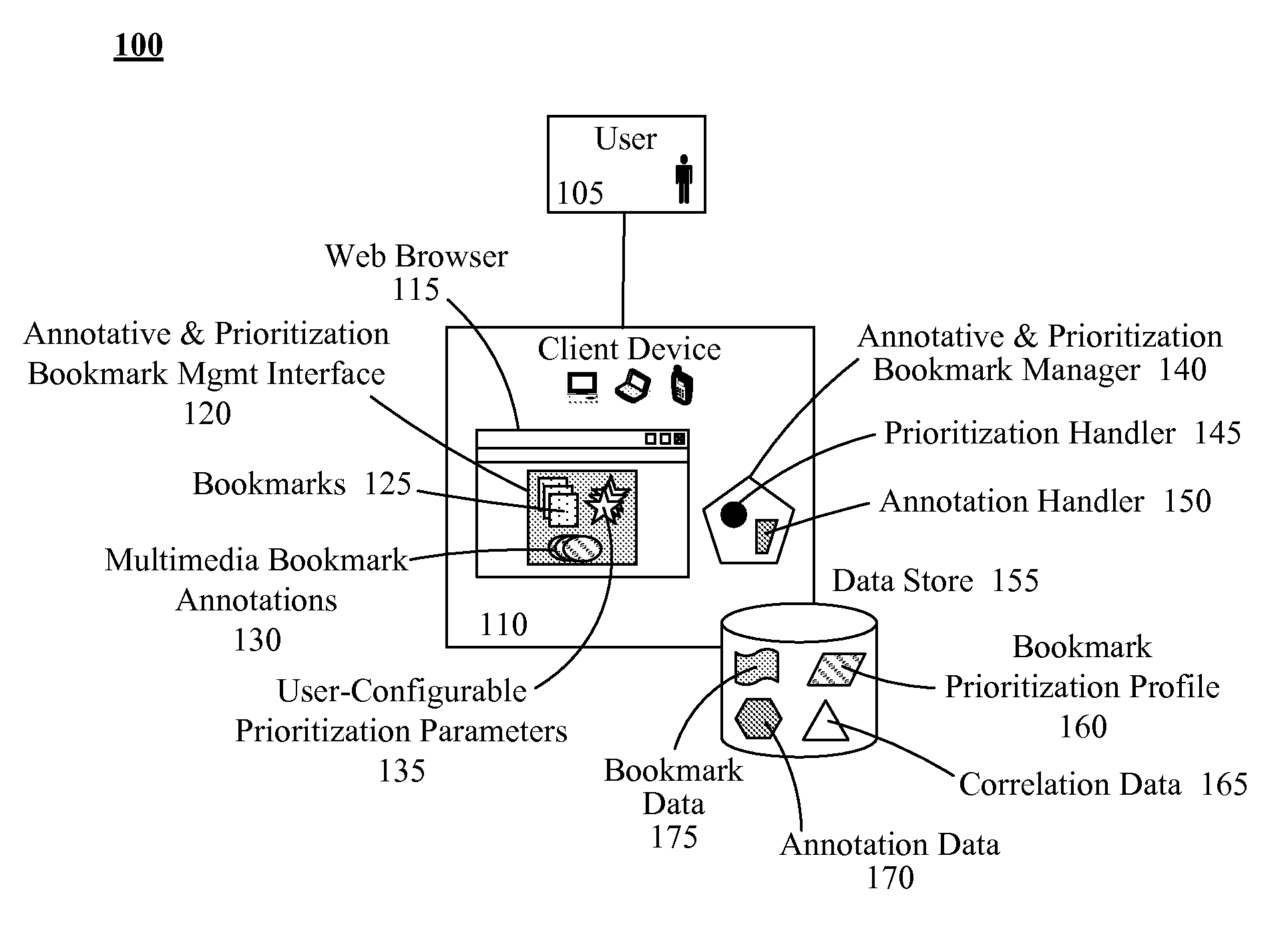
Usability enhancements for bookmarks of browsers
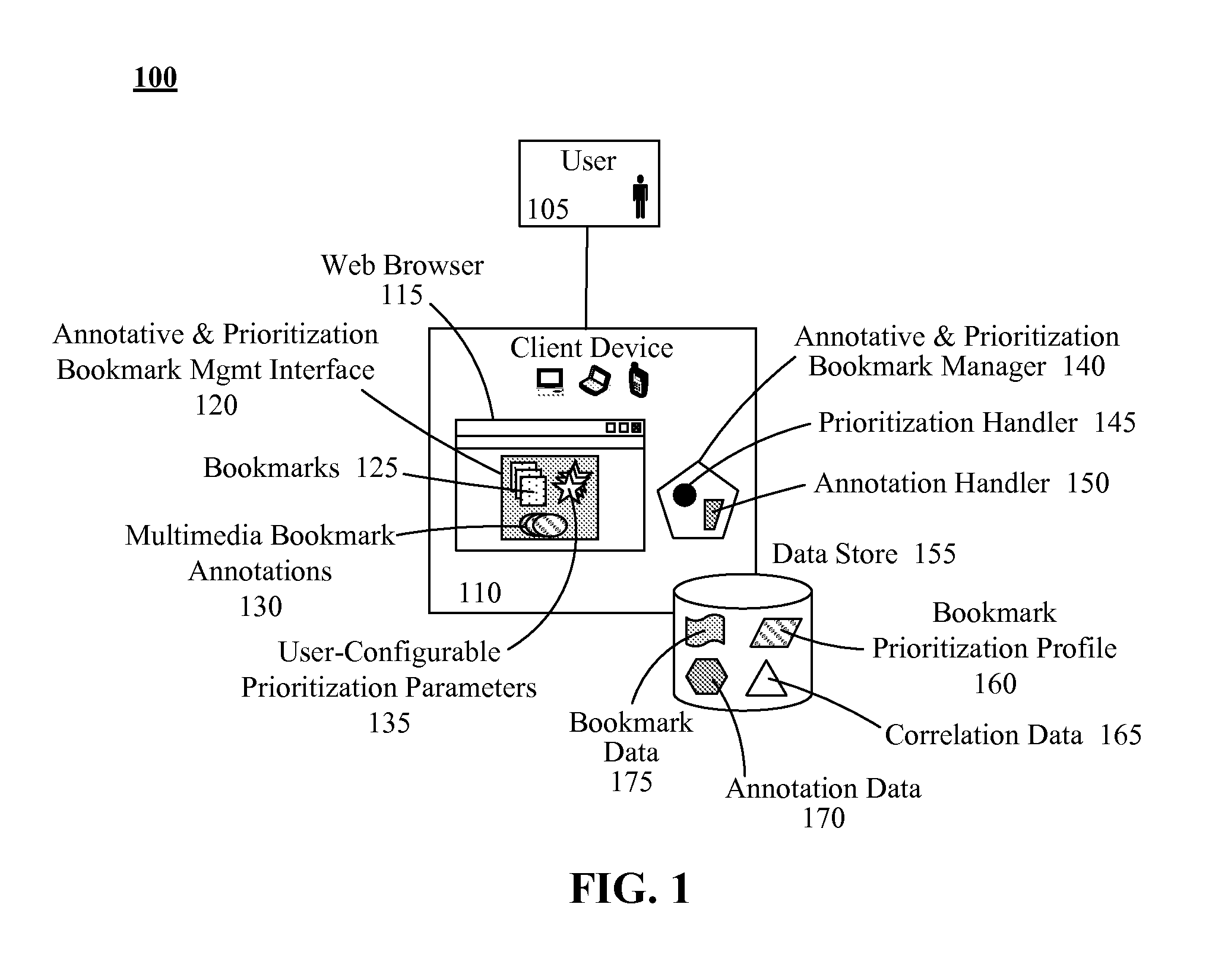
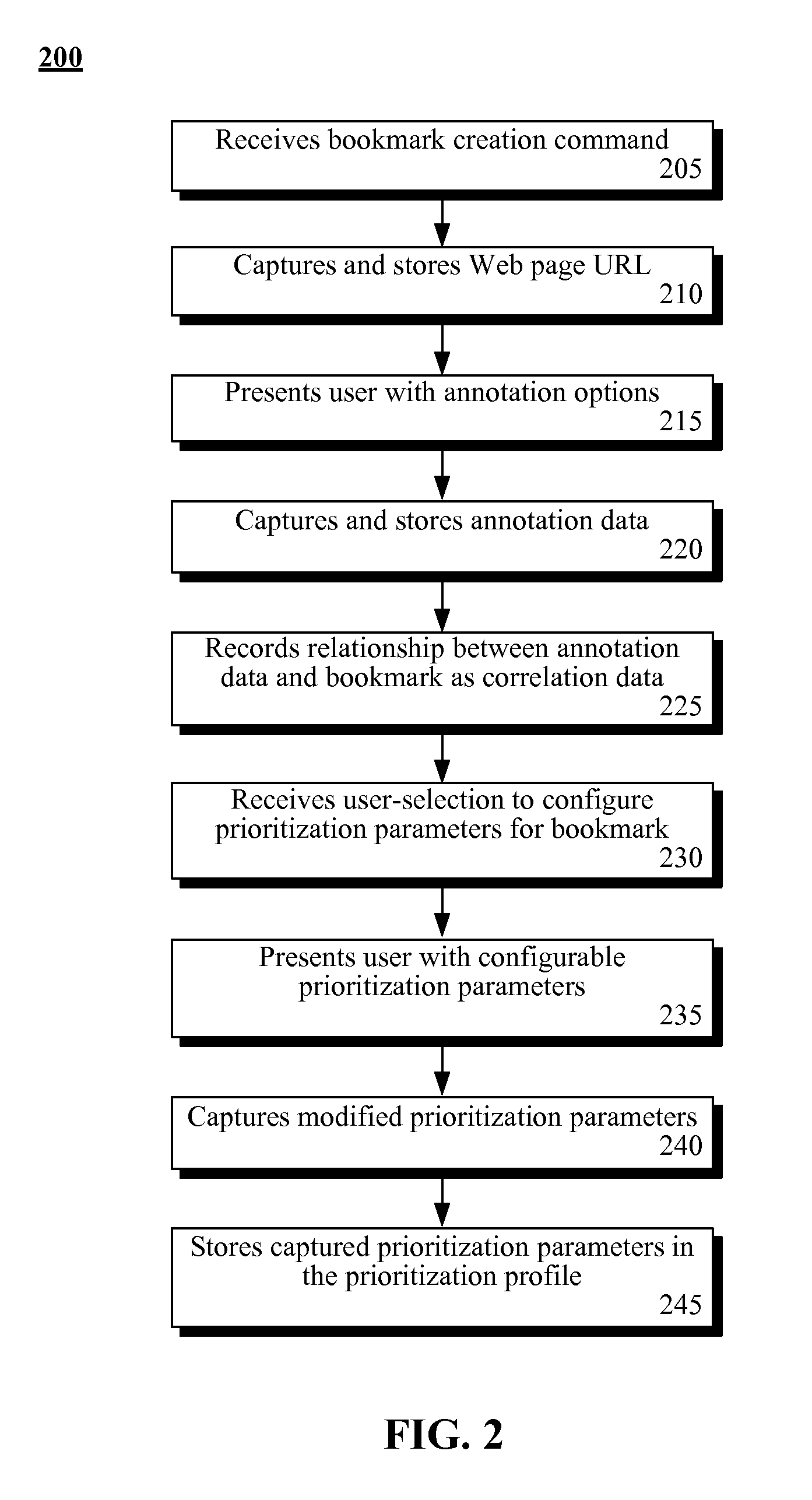
InactiveUS20110258216A1Improve usabilityDigital data information retrievalDigital data processing detailsWeb browserDigital content
Bookmarks can reference uniquely addressed Web resources. Bookmark annotations can include user specified, digital content related to uniquely addressed Web resources. An user interface of an annotative bookmark manager can permit users to create, edit, and delete bookmark annotations. A browser interface of a Web browser can include a bookmark section that displays a listing of textual descriptors for bookmarks. An annotation handler can present one of the bookmark annotations within the browser user interface responsive to a detection of a mouseover event for a corresponding textual descriptor. The bookmark annotation can be automatically hidden when the mouseover event ends. Bookmark prioritization enables listing of highly weighted parameterized bookmarks in a user friendly manner.
Owner:IBM CORP
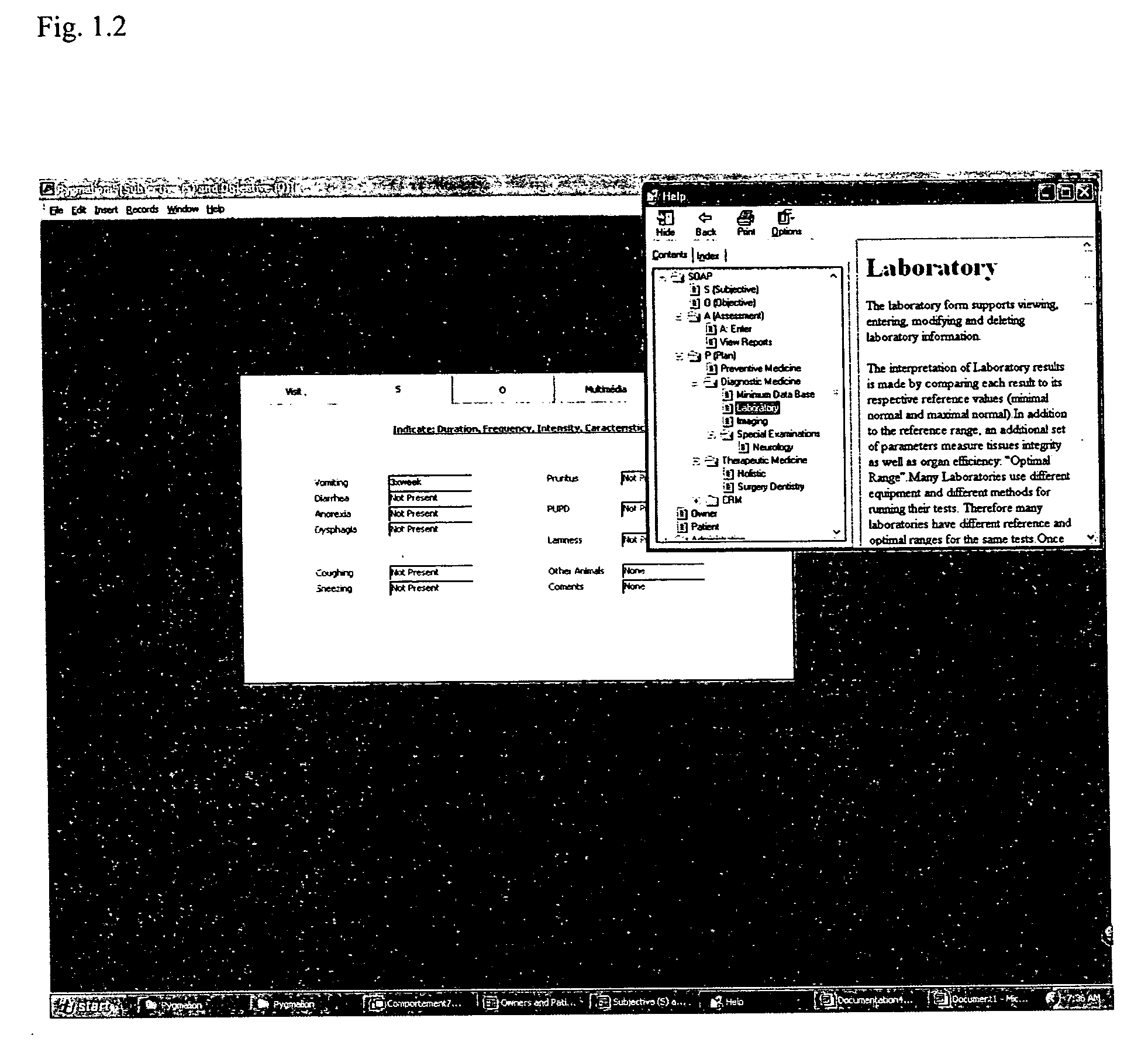
Proces for diagnosic system and method applying artificial intelligence techniques to a patient medical record and that combines customer relationship management (CRM) and enterprise resource planning (ERP) software in a revolutionary way to provide a unique-and uniquely powerful and easy-to-use-tool to manage veterinary or human medical clinics and hospitals
InactiveUS20050108052A1Precise and time-saving and stress-free communicationAvoid misplacementData processing applicationsMedical automated diagnosisMedical recordDiagnostic program
This medical (human and veterinary) CRM and ERP software affects every step of patient interaction: marketing, sales or service-related. It allows management of the workload by distributing the chores among staff members and automates medical and business processes through workflow rules. It enables users to view and update tasks, medical cases, appointments, sales, phone calls, faxes, emails, letters and automatic input of lab results into the patient's medical record. It also serves the needs of people in human resources; finance and inventory control, and integrates with Microsoft Word, Outlook, Excel, Great Plains and other business systems. It delivers detailed diagnostic differentials associated with a likelihood of their applicability to the given patients' record and physician's experience in his contextual situation; selects the most appropriate diagnostic procedures; offers the possibility for the user to implement context-sensitive tutorials; presents a context-sensitive source of information on diseases and medical procedures.
Owner:OMABOE NORTEY JEAN
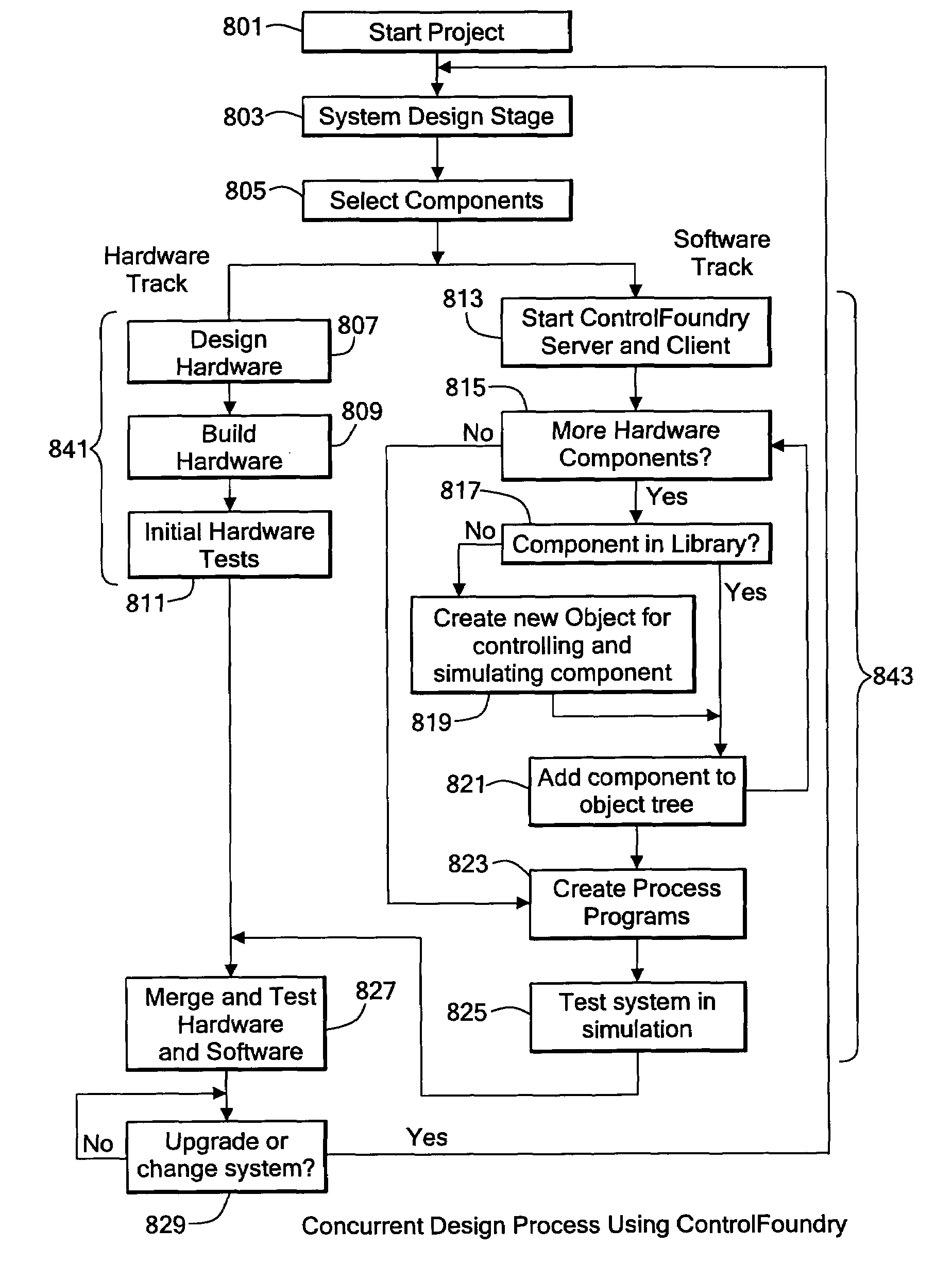
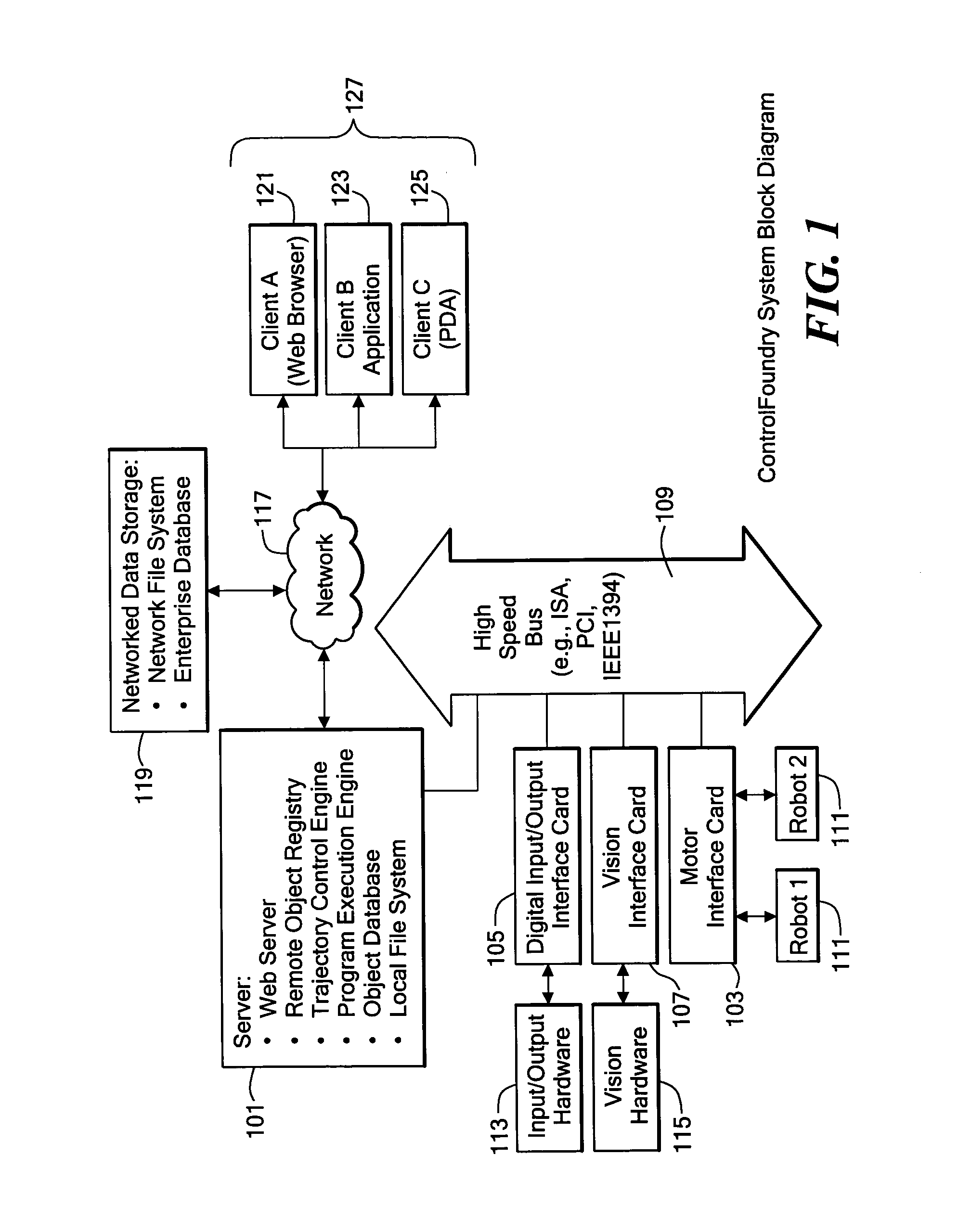
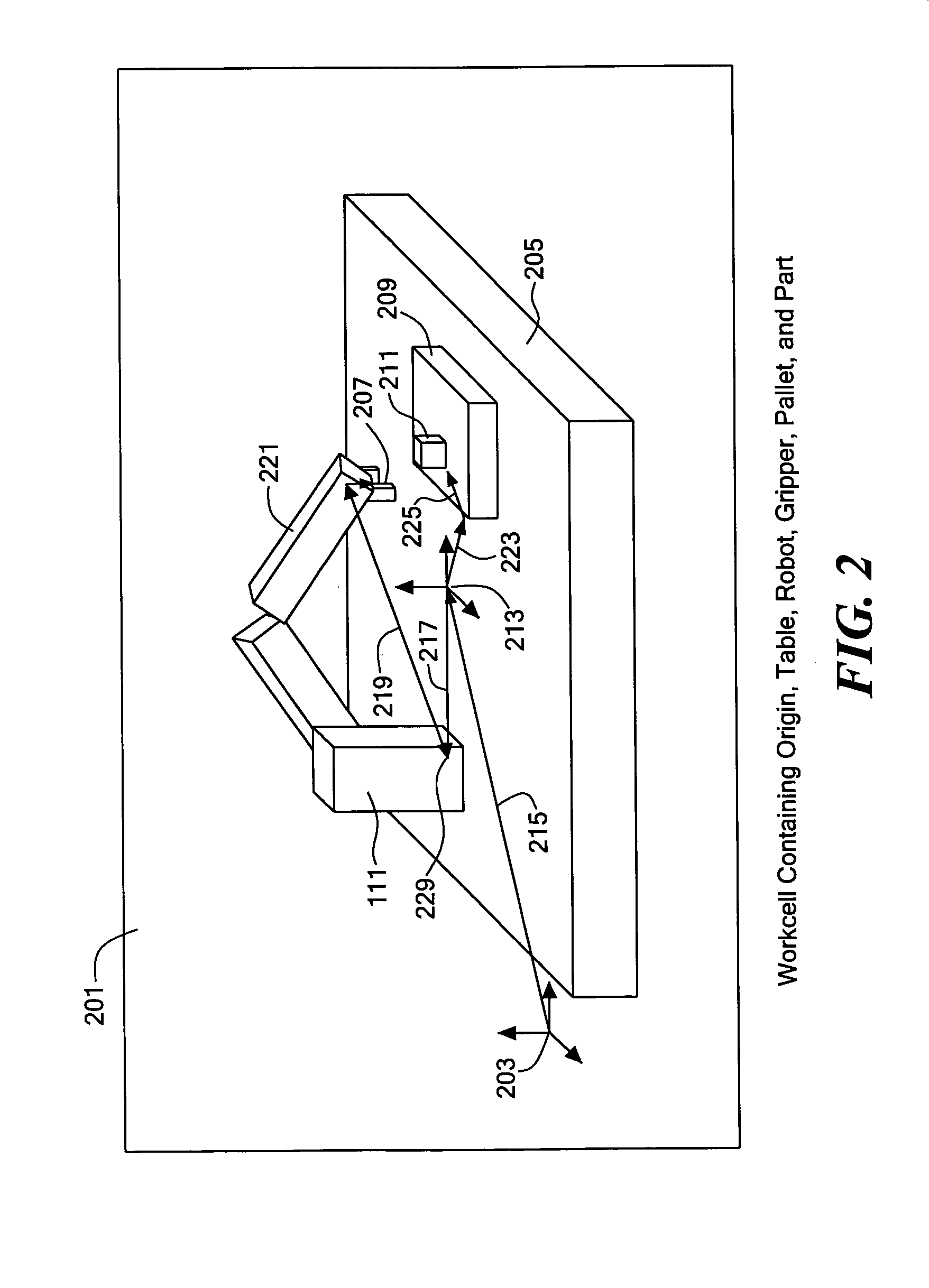
System and method for control and simulation
InactiveUS6944584B1Simplify the development processEasy to controlProgramme-controlled manipulatorComputer controlThree dimensional simulationUsability
A system that controls devices and integrally simulates the controlled motion of devices. The control and simulation system allows simultaneous development hardware and software in controlled device installations and increase operational ease-of-use and diagnostic capabilities. The control and three dimensional simulation system also allows client computers to remotely control the system and other devices connected to a network.
Owner:BOOKS AUTOMATION US LLC
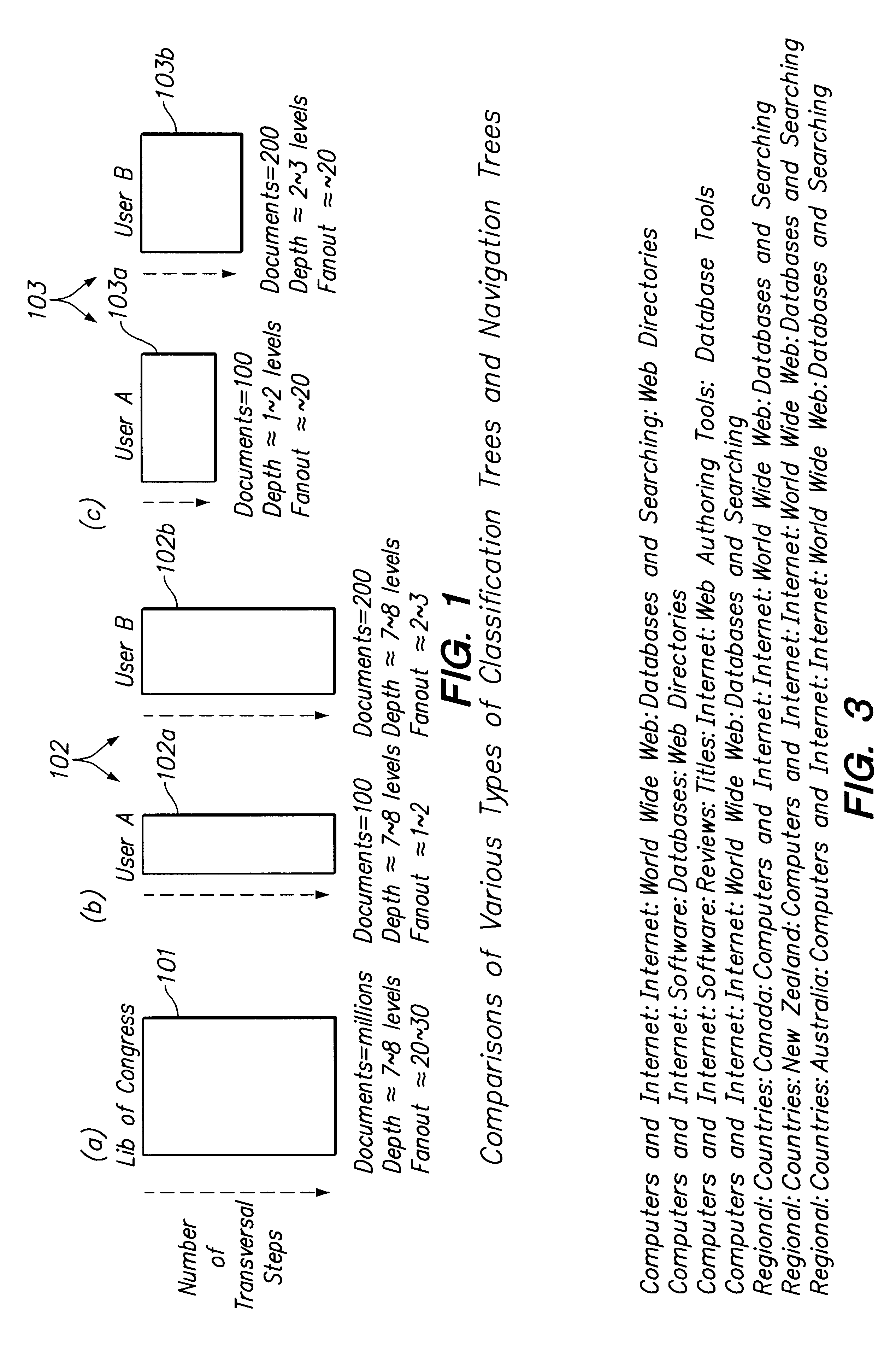
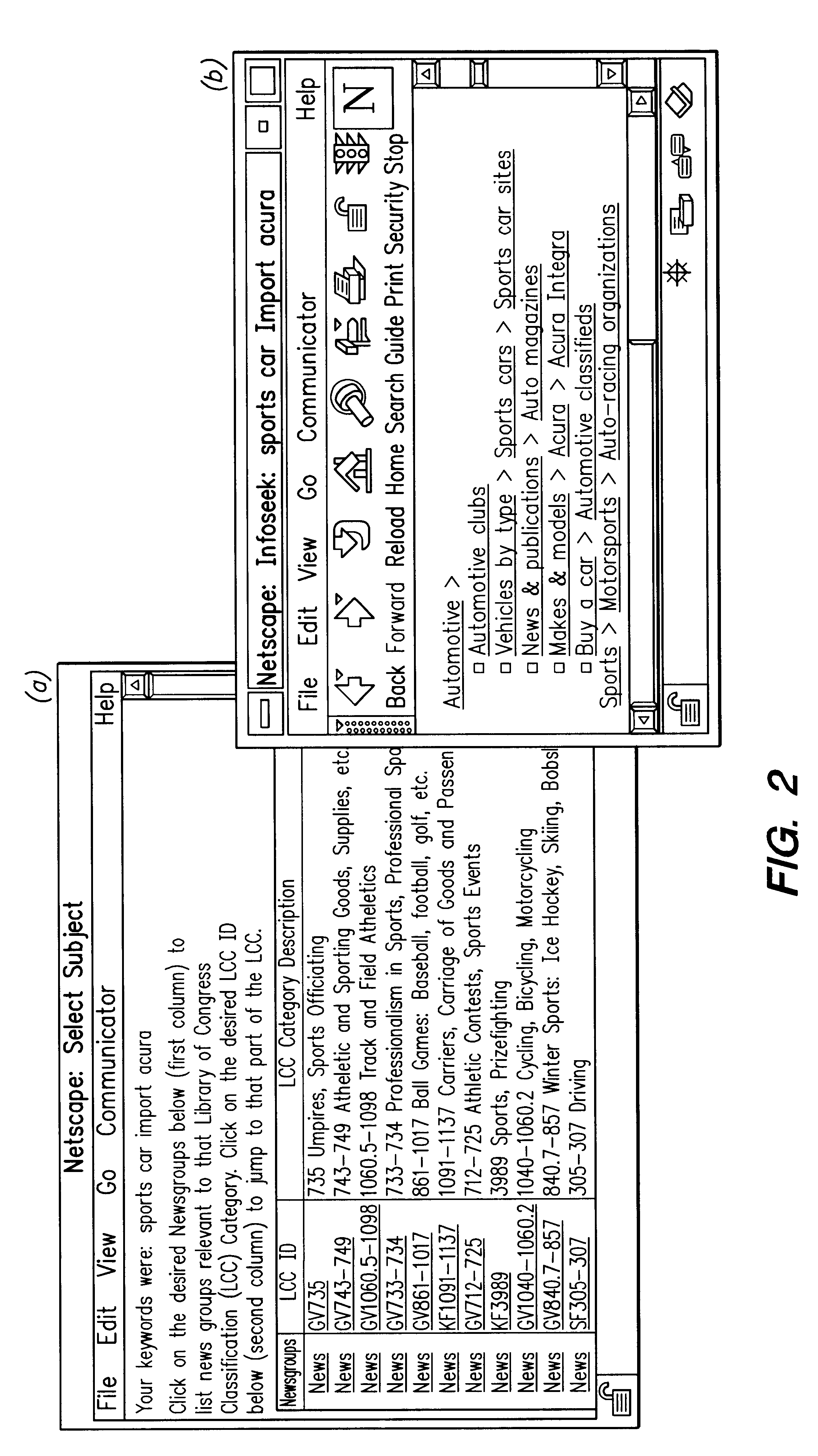
Personalized navigation trees
InactiveUS6393427B1Minimize the numberData processing applicationsDigital data processing detailsPersonalizationUsability
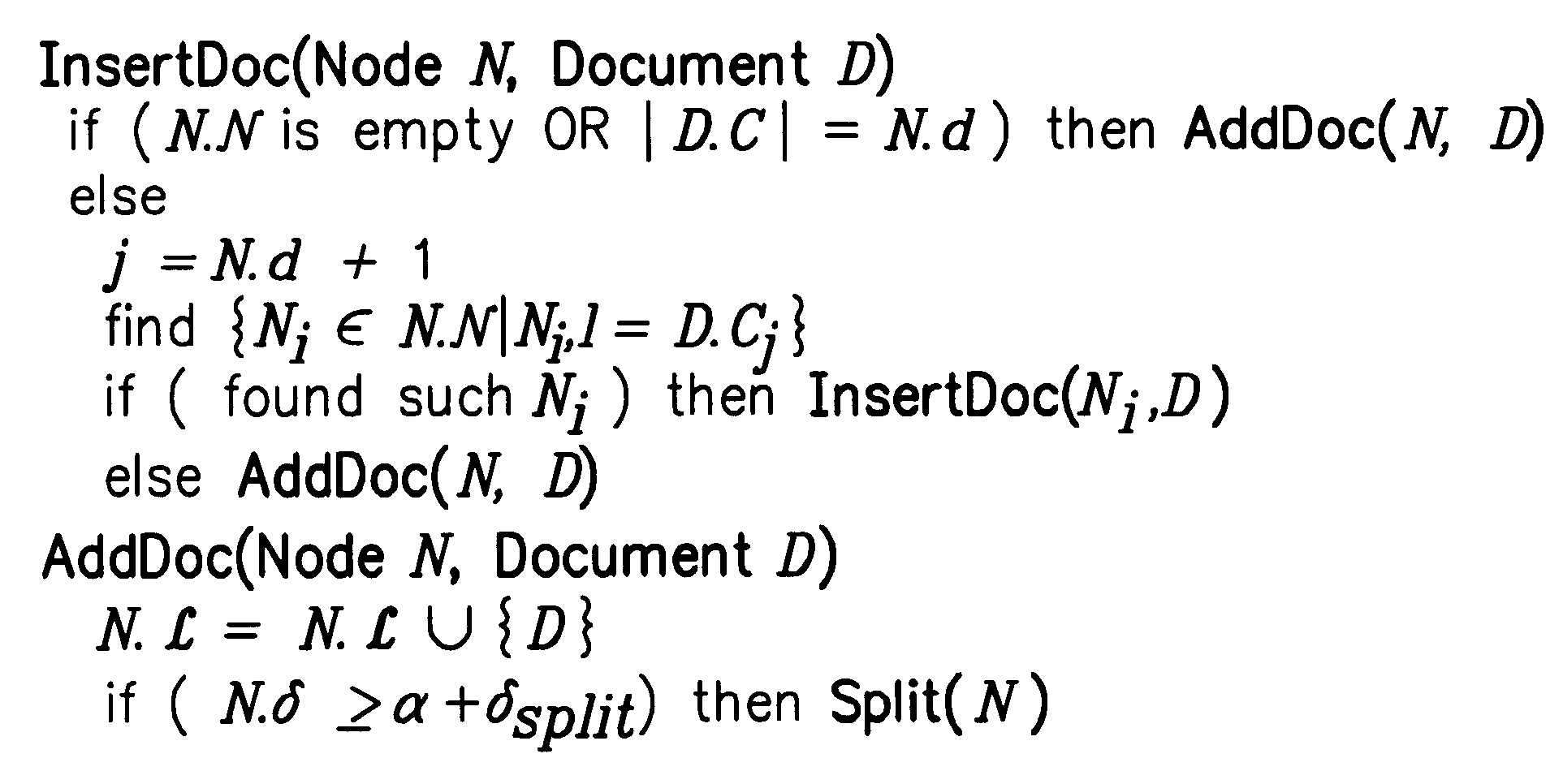
A method for constructing and maintaining a navigation tree based on external document classifiers is provided. In one embodiment, based on the returned category labels from the classifiers, a navigation tree is constructed by taking usability and user preferences into consideration. Control parameters and algorithms are provided for inserting into and deleting documents from the navigation tree, and for splitting and merging nodes of the navigation tree, are provided.
Owner:NEC CORP
Ergonomic lift-clicking method and apparatus for actuating home switches on computer input devices
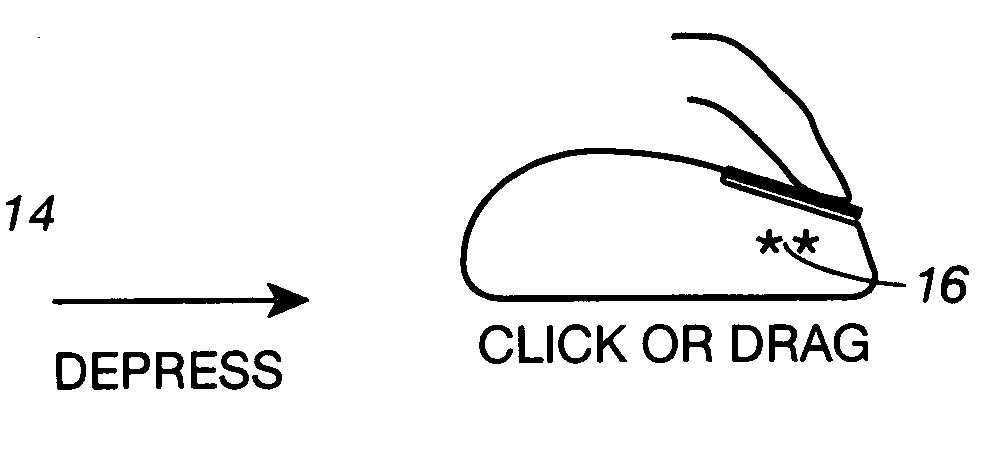
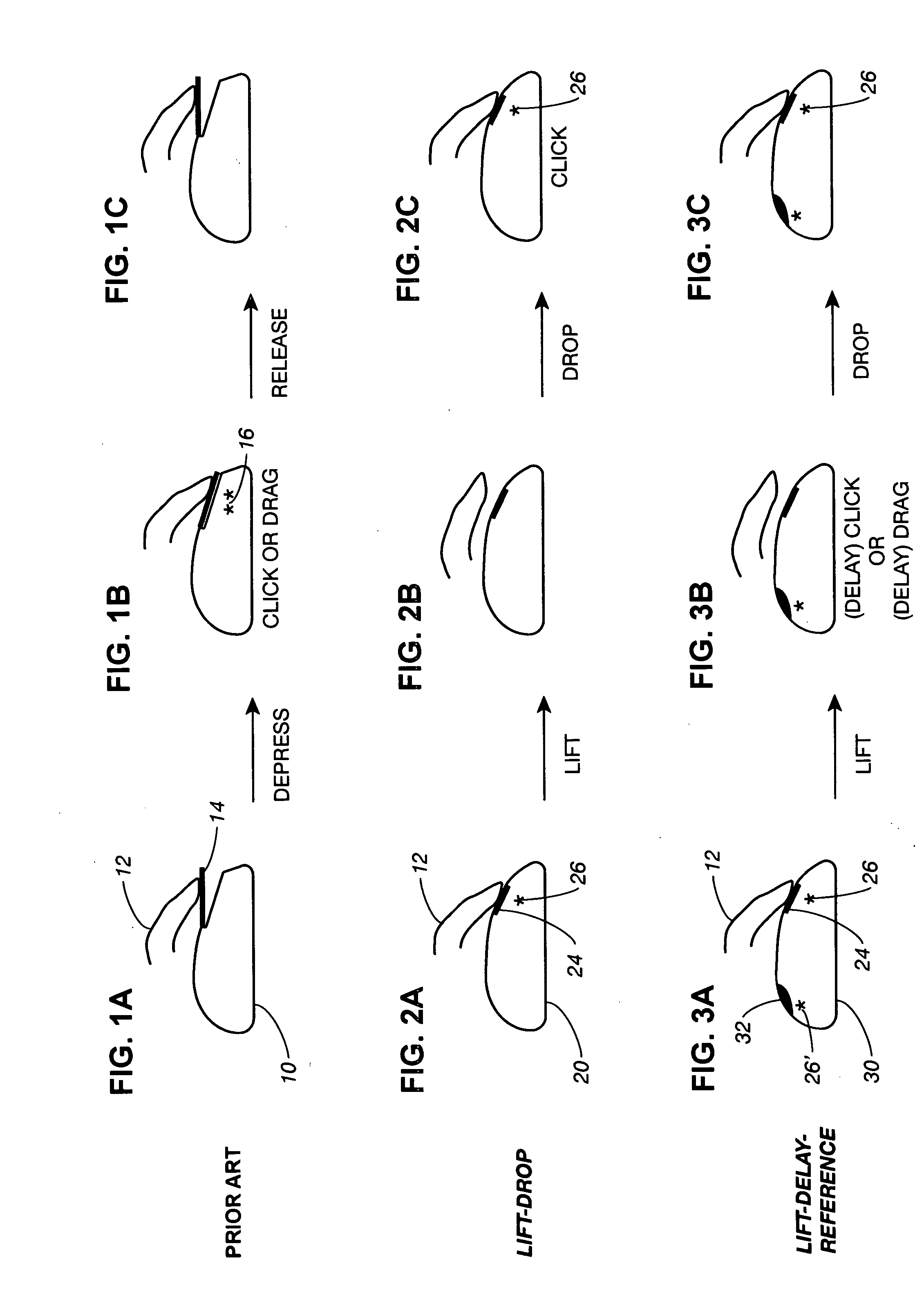
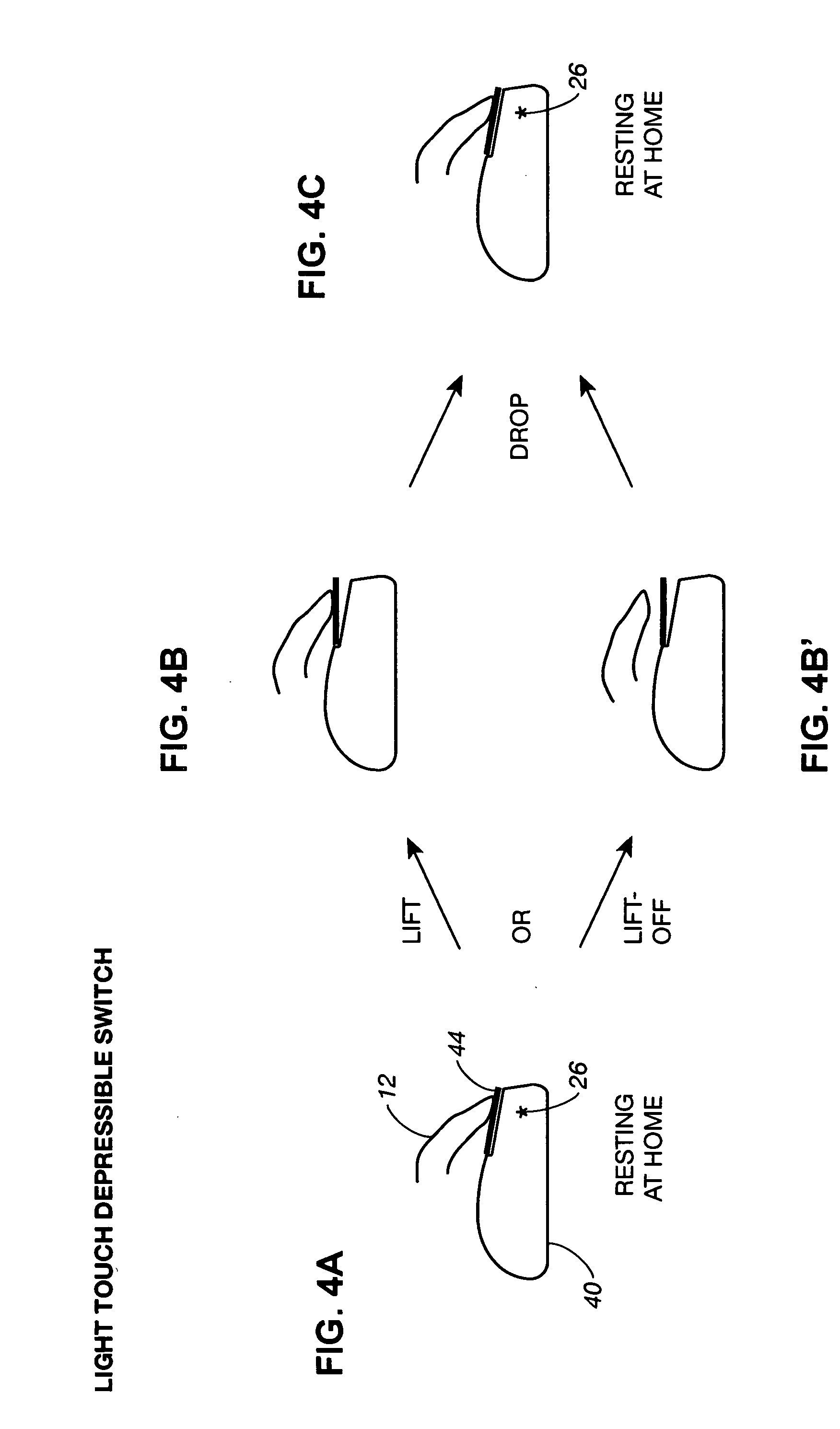
This invention introduces lift-clicking, a gentle method of clicking that utilizes light touch home sensors on the mouse and other computer input devices. It can be used either to replace the prior art depression-type mouse button with a home touch surface and a light touch or proximity sensor, or to add a touch / proximity sensor to an existing mouse button, providing three or more additional functions for each finger. It is a very ergonomic method that uses less force than the weight of the relaxed resting finger. It employs a finger lift, or a finger lift followed by a gentle drop, and utilizes unique combinations of windows, timing, hand presence reference, and logic sequences carefully designed to automatically prevent the production of unwanted clicks when the finger first arrives on or leaves the home sensor as the hand arrives or departs the input device. The initial condition is a finger resting on a touch switch / proximity sensor surface at a home resting position. A function is triggered either by lifting (or sliding) the finger away from its home touch surface (lift-delay-reference mode) or by dropping the finger back to the surface soon after the lift (lift-drop mode). Unwanted clicks do not occur because the function is triggered either by a lift after a very short delay with a requirement for hand presence reference, or by a drop within a time window opened by the previous lift. The gentle lift of the finger followed by a passive drop eliminates the push-down muscle twitch of prior art depression clicking, without any sacrifice of speed. Optionally included are click-inhibiting means so that unwanted clicks are not produced when a finger leaves a home sensor to actuate a non-home switch or scroll device. Momentary lifted modes can be used to enable scrolling with mouse motion, a fine cursor control feature, or to ignore all XY data so that the mouse can be repositioned without lifting it off the desktop and without moving the cursor (disengage clutch feature). Dragging can be accomplished with either the finger held lifted or with the finger resting at home. A single lift-click sensor can be used to trigger two different functions, the function chosen depending on the amount of time between the lift and the drop. The lift-click sensor can be piggybacked together with a prior art mouse button to provide lift-clicking while still allowing depression clicking, greatly increasing the number of triggerable functions. A lift-click sensor can be of a fixed type with no moving parts, (a zero button mouse) allowing the manufacture of pointing devices that are completely solid state, low in cost and sealed from the environment. The lift-click method makes it possible to replace the click buttons on a horizontal mouse with a programmable multi-point XY(Z) multi-functional touchpad which can be used to provide not only lift-clicks, but by toggling to new function sets, can also offer arrow / nudge key functions, page navigation, fine cursor control, and gesturing. Lift-clicking can greatly improve versatility and ease of use in most types of pointing devices.
Owner:CONRAD RICHARD H
Obfuscating sensitive data while preserving data usability
InactiveUS20090132419A1Computer security arrangementsSecuring communicationConfidentialityData field
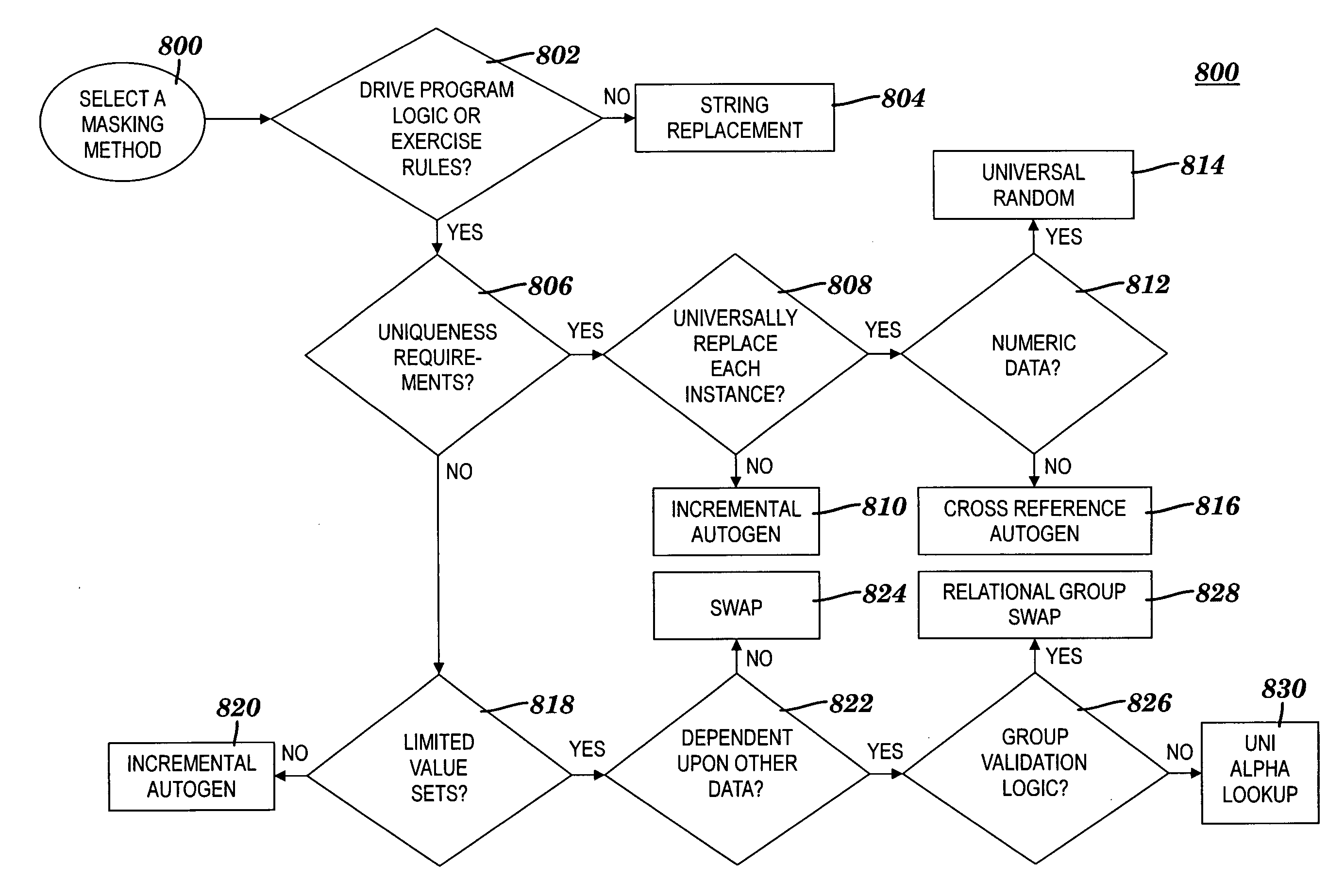
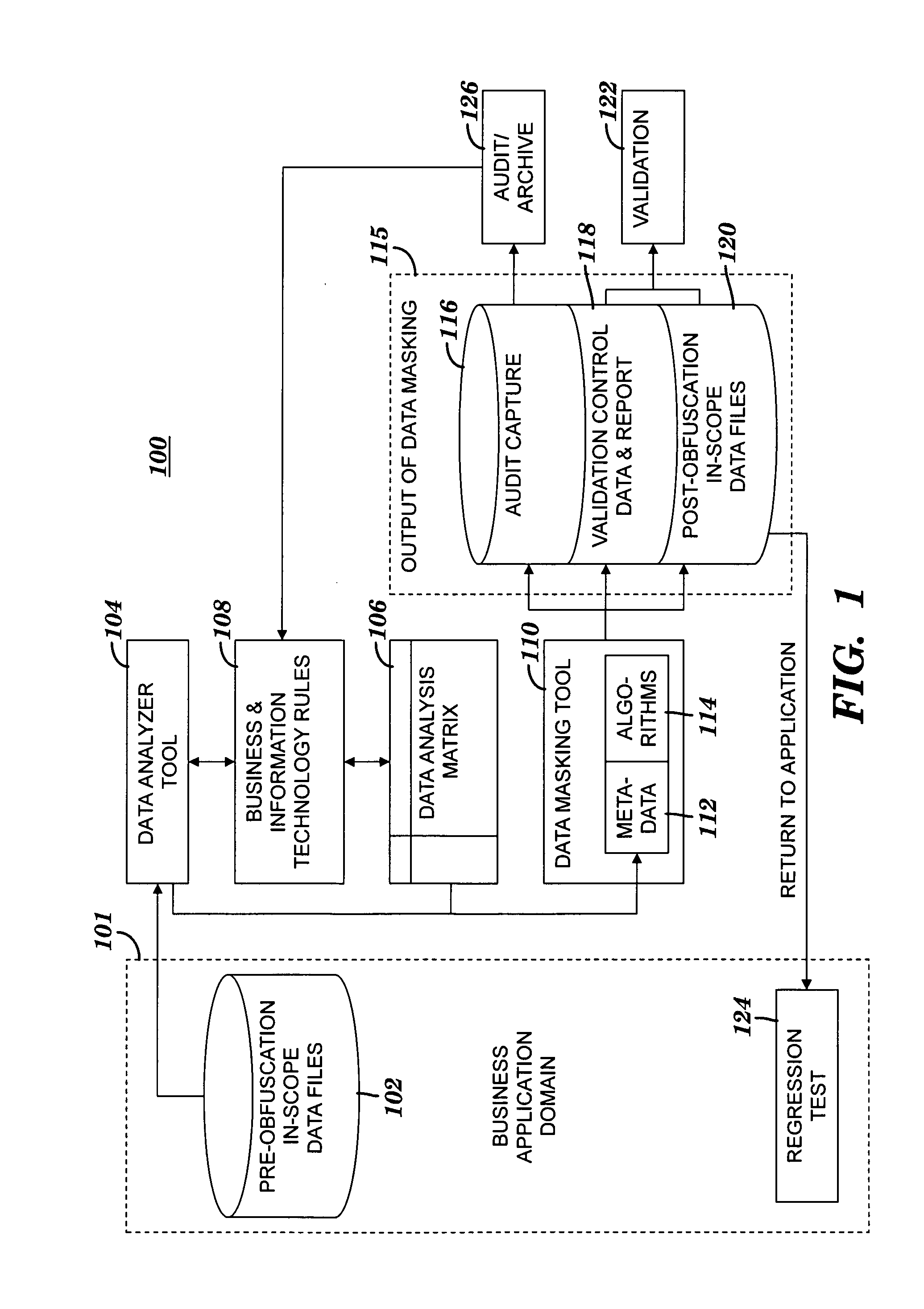
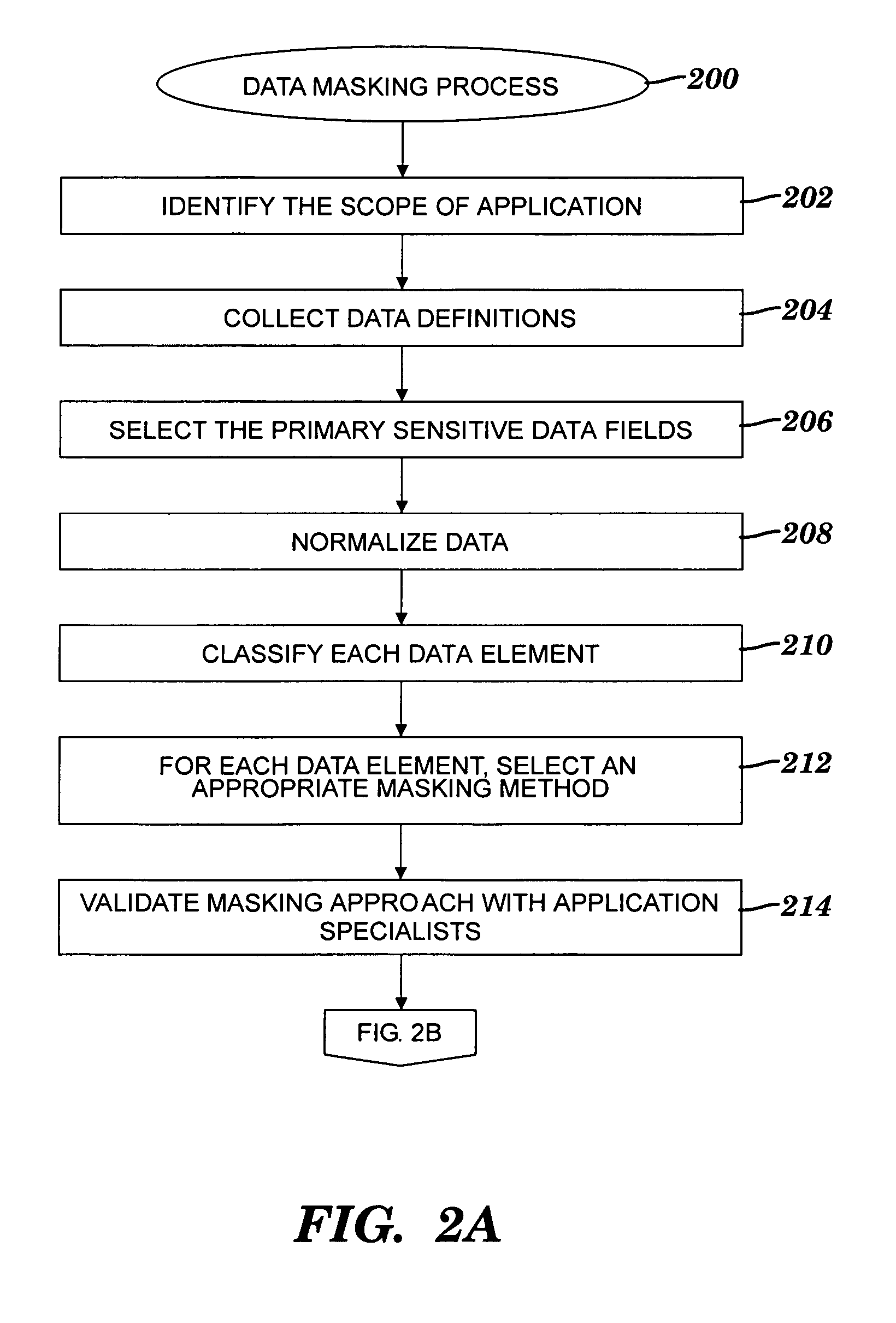
A method and system for obfuscating sensitive data while preserving data usability. The in-scope data files of an application are identified. The in-scope data files include sensitive data that must be masked to preserve its confidentiality. Data definitions are collected. Primary sensitive data fields are identified. Data names for the primary sensitive data fields are normalized. The primary sensitive data fields are classified according to sensitivity. Appropriate masking methods are selected from a pre-defined set to be applied to each data element based on rules exercised on the data. The data being masked is profiled to detect invalid data. Masking software is developed and input considerations are applied. The selected masking method is executed and operational and functional validation is performed.
Owner:IBM CORP
Method and apparatus for managing policies for time-based licenses on mobile devices
ActiveUS8544105B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsInternet privacyUsability
Owner:QUALCOMM INC
Methods, software programs, and systems for electronic information security
InactiveUS7395436B1Digital data processing detailsUser identity/authority verificationConfidentialityDigital signature
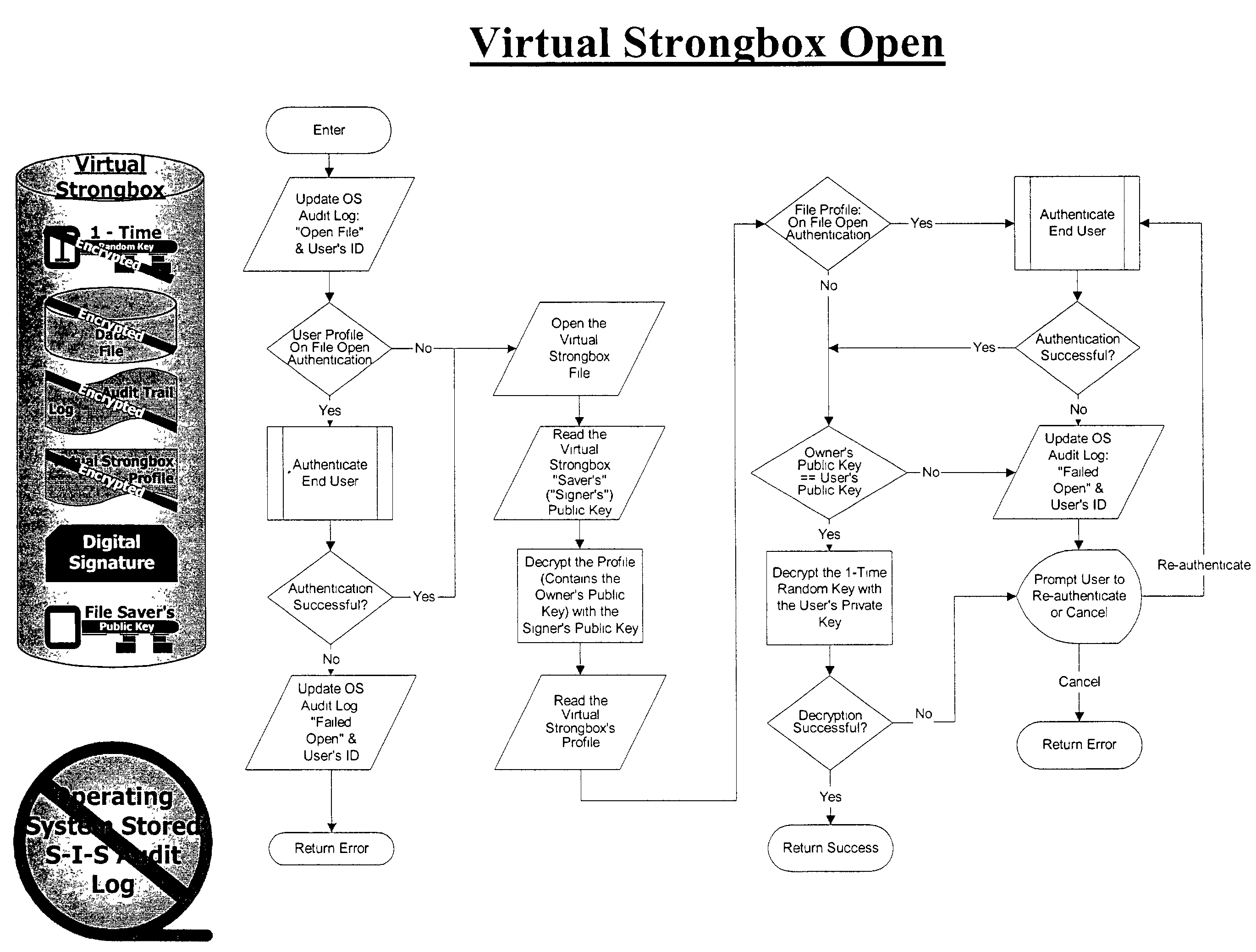
The present invention relates to various methods, software programs, and systems for electronic information security. More particularly, these various methods, software programs, and systems may serve to protect information security by providing an integrated system that helps ensure confidentiality, integrity, accountability, and ease of use. Certain embodiments of the present invention relate to methods, software programs, and systems for electronic information security utilizing a file container for storing: (a) a data file, which data file is encrypted with a one-time random encryption key; (b) the one-time random encryption key, which one-time random encryption key is encrypted with a public key portion of a public key / private key pair associated with an owner of the file container; (c) an audit trail log of the history of the file container, which audit trail log is encrypted with the one-time random encryption key with which the data file is encrypted; (d) a digital signature based upon a hash of the combined data file and the audit trail log, which hash is encrypted with a private key portion of a public key / private key associated with a writer / creator of the file container; and (e) a profile associated with the file container. Additional embodiments of the present invention relate to methods, software programs, and systems for electronic information security utilizing a fully integrated system for user authentication, virus scanning, time / date certification, encryption / decryption, digital signatures, stored document protection, transmitted document protection, and delivery verification.
Owner:KENEISYS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com