Patents
Literature
5809 results about "Network addressing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
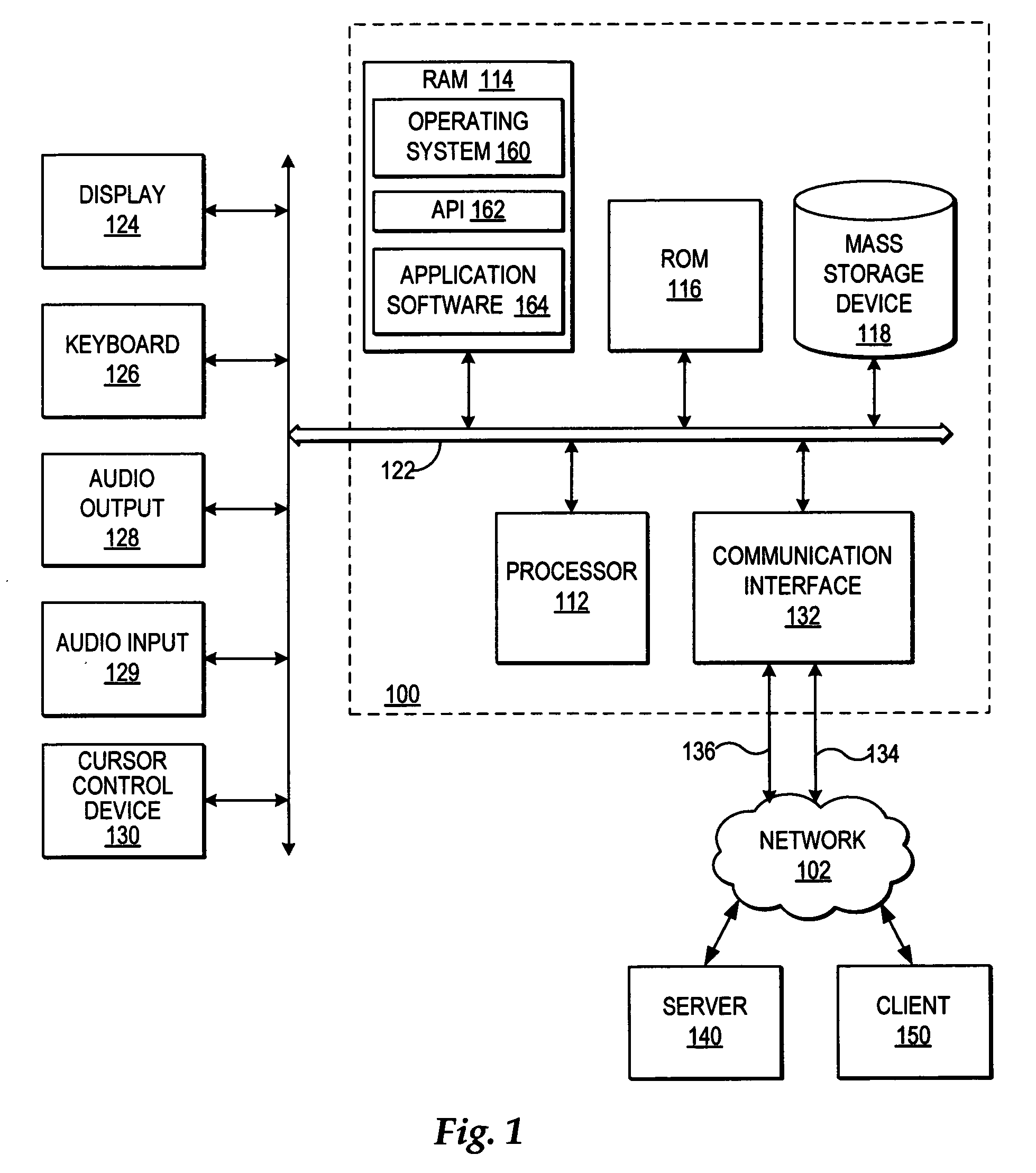
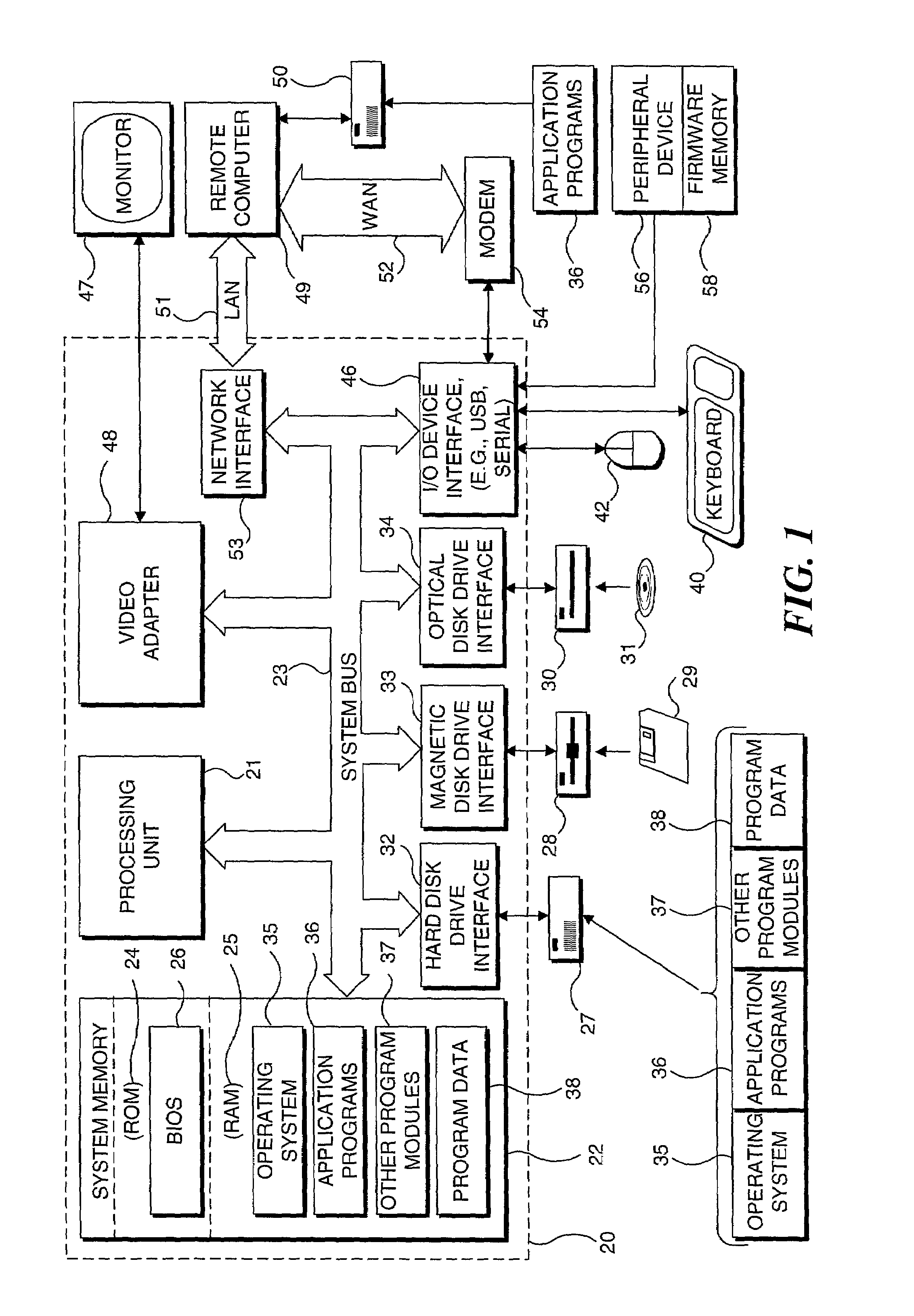
A network address serves as a unique identifier for a computer or other device on a network. When setting up correctly, computers can determine the addresses of other computers and devices on the network and use these addresses to communicate with one another..
Method and apparatus for installation abstraction in a secure content delivery system
InactiveUS6374402B1Expand accessAvoid leverageTelevision system detailsBroadband local area networksOperational systemNetwork addressing
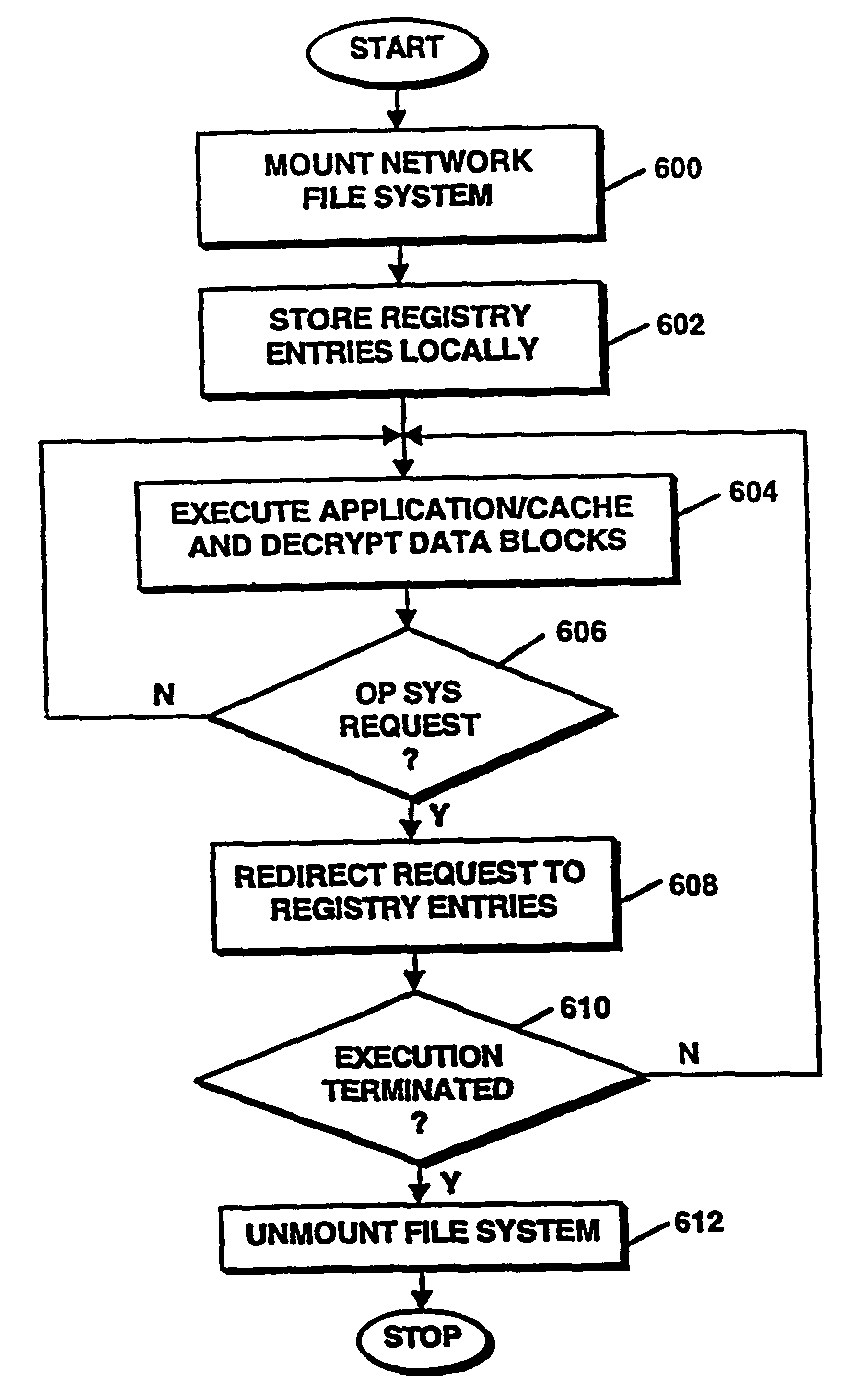
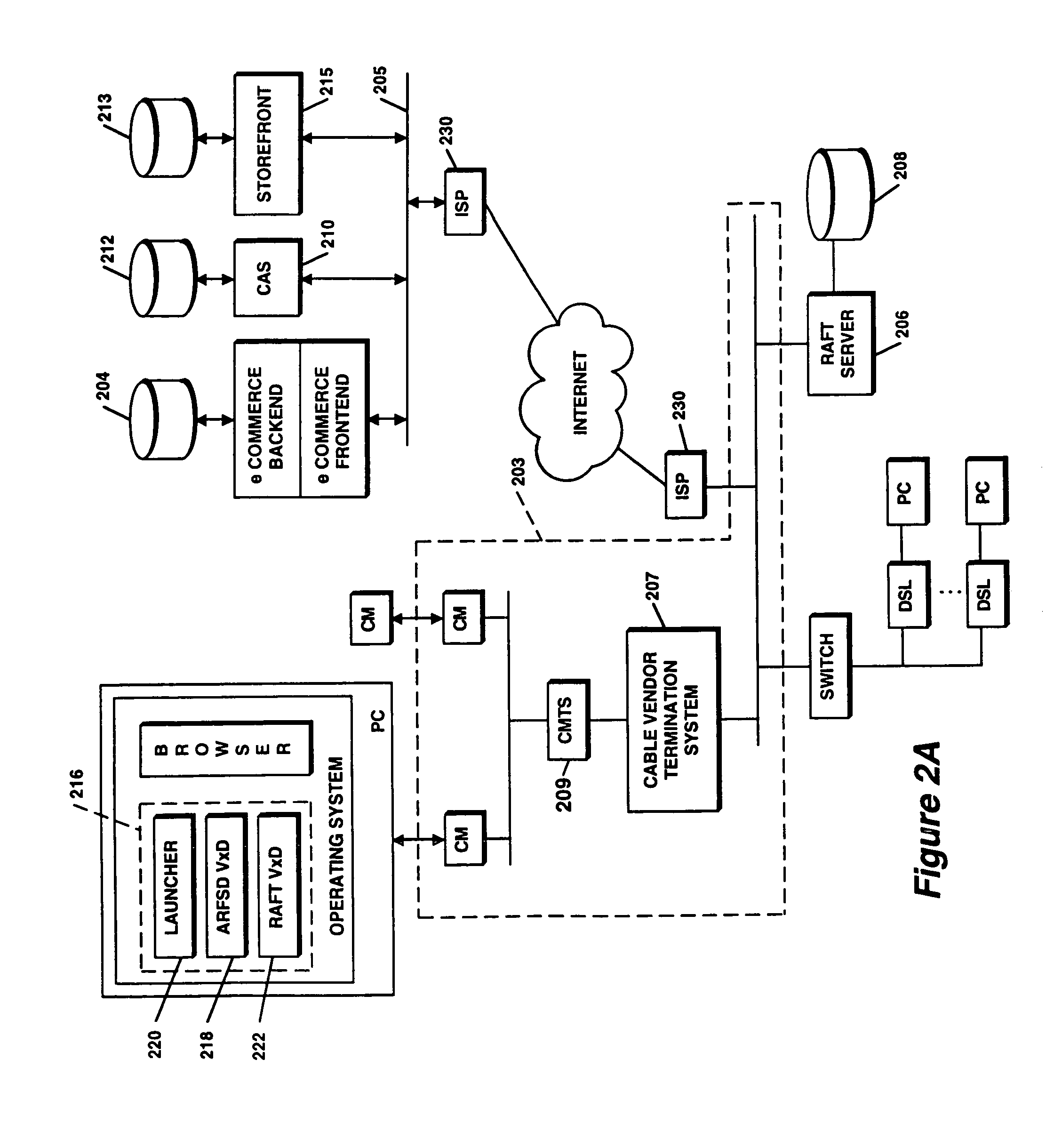
A system for secure delivery of on-demand content over broadband access networks includes a client application executing on a user's local computer system. The client application interacts with a content server on which a plurality of selectable titles are stored and further interacts with an access server which provides the network address of a title and keying data necessary for to the client process access and execute the title. The client process utilizes an installation abstraction which enables a title to be executed on the local computer system without ever being installed. The abstraction is achieved by mounting a network file system and storing a set of registry entries related to the title on the local computer system. Portions of the title are retrieved from the content server and executed by the local operating system. During title execution, requests from the local operating system are intercepted and redirected to the set of registry entries, as applicable. The times at which the client process may retrieve the title data from the content server are defined by the access server through use of an activator and token.
Owner:MICROSOFT TECH LICENSING LLC
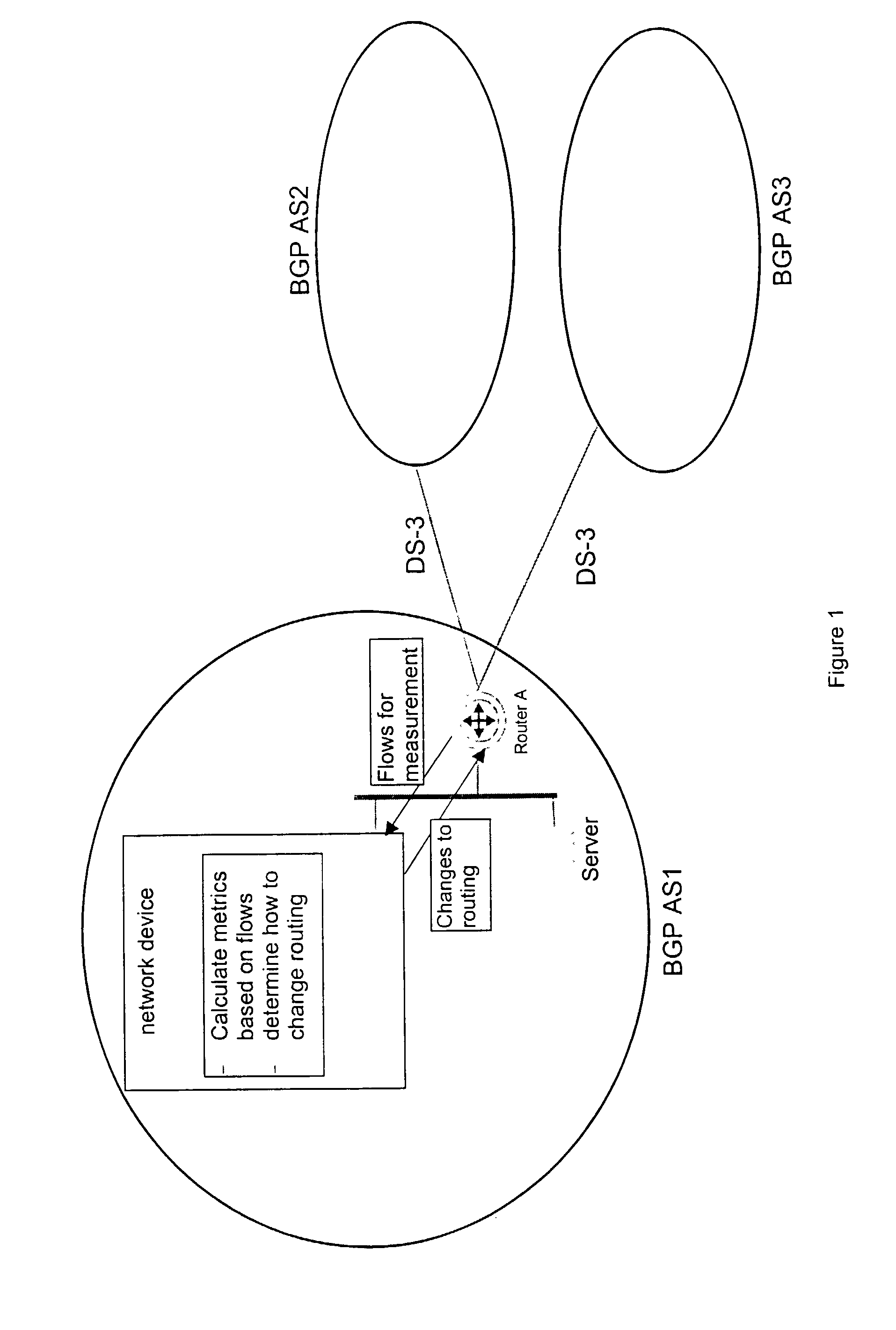
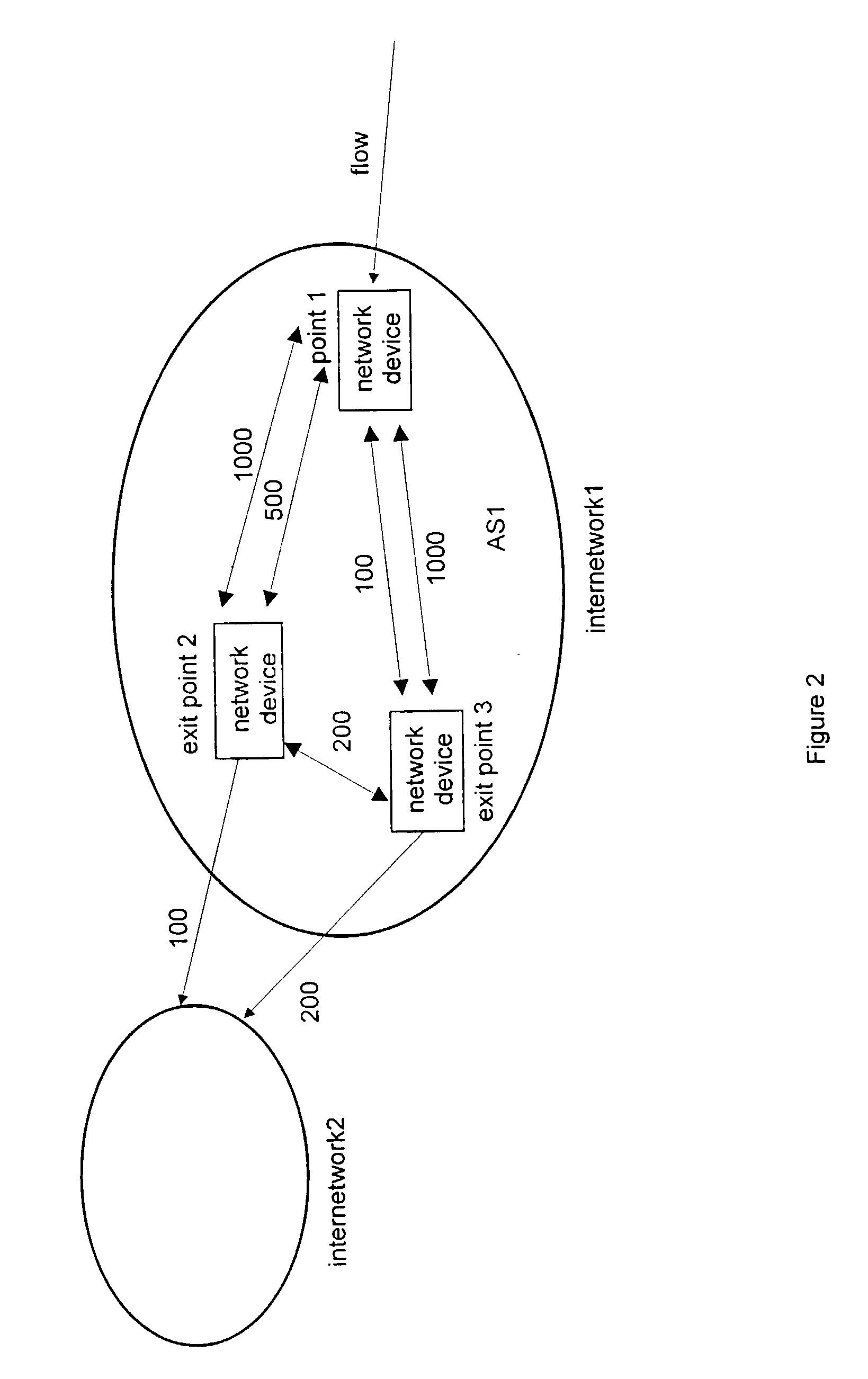
Method and apparatus for the assessment and optimization of network traffic
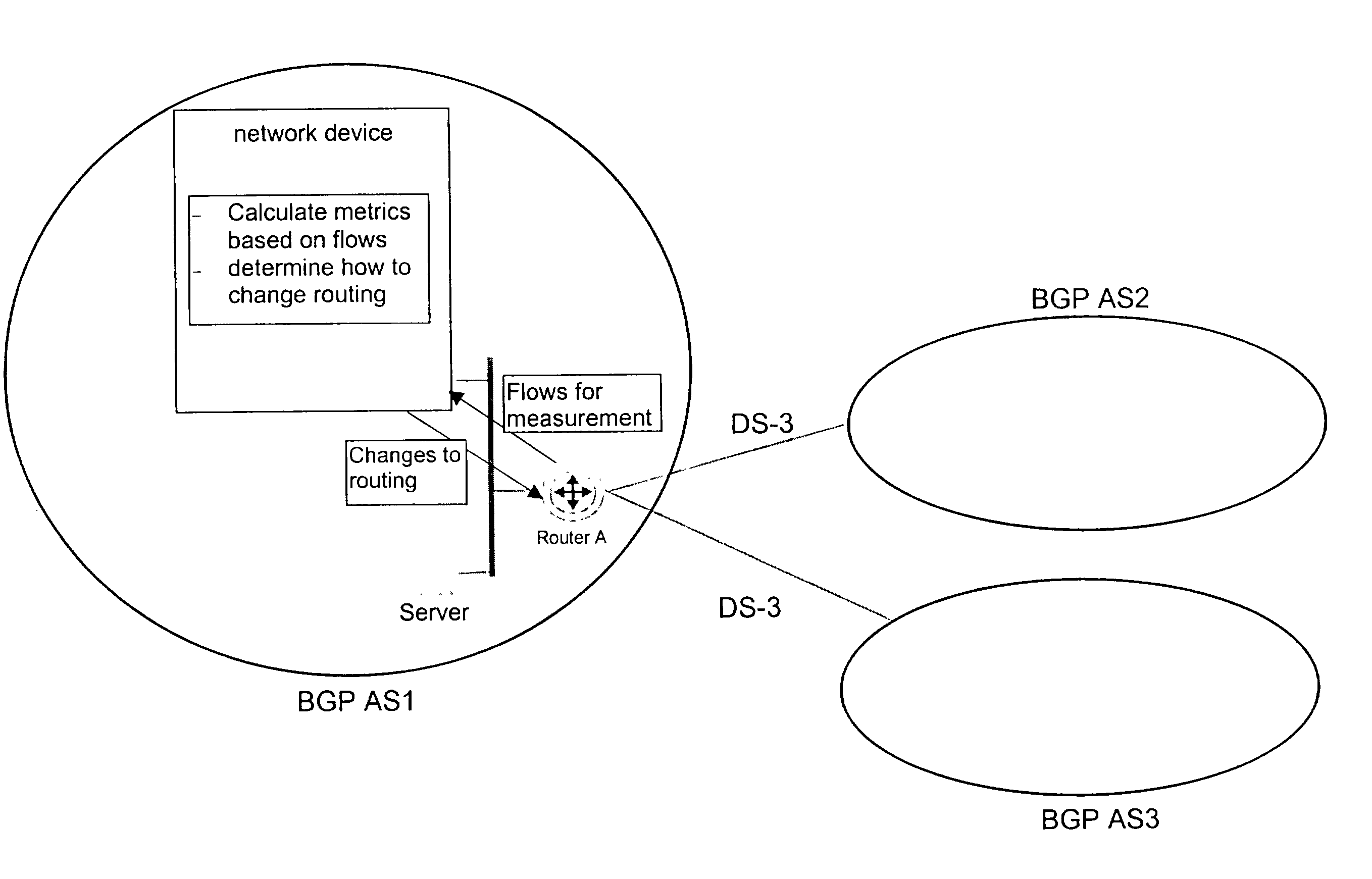
A system for the assessment of network performance criteria, and applying this criteria to the classification of network addresses into appropriate ranges, using these ranges to consolidate performance measurements for the associated addresses, and applying these metrics toward the optimization of the network towards performance or policy objectives.
Owner:AVAYA INC
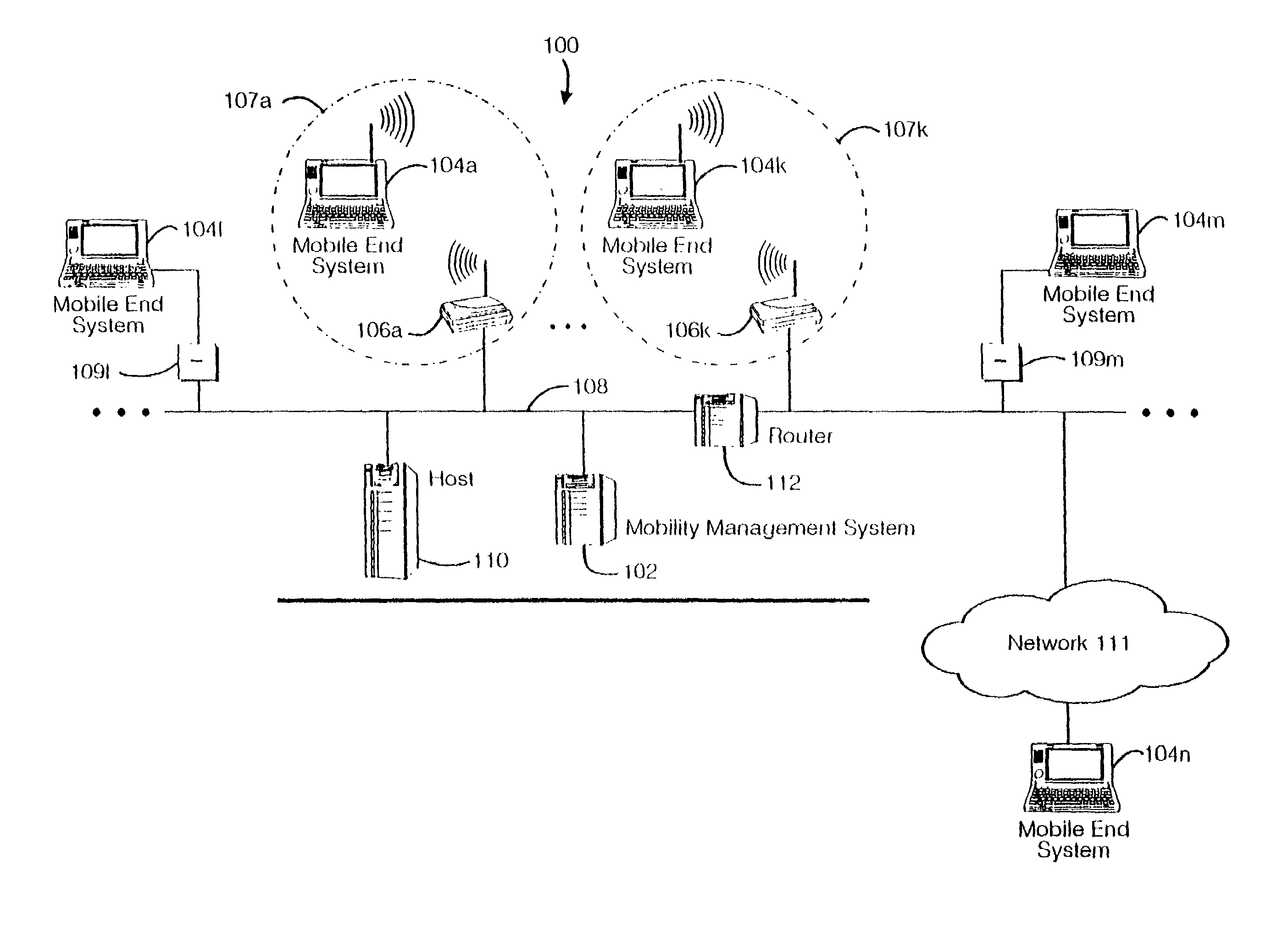
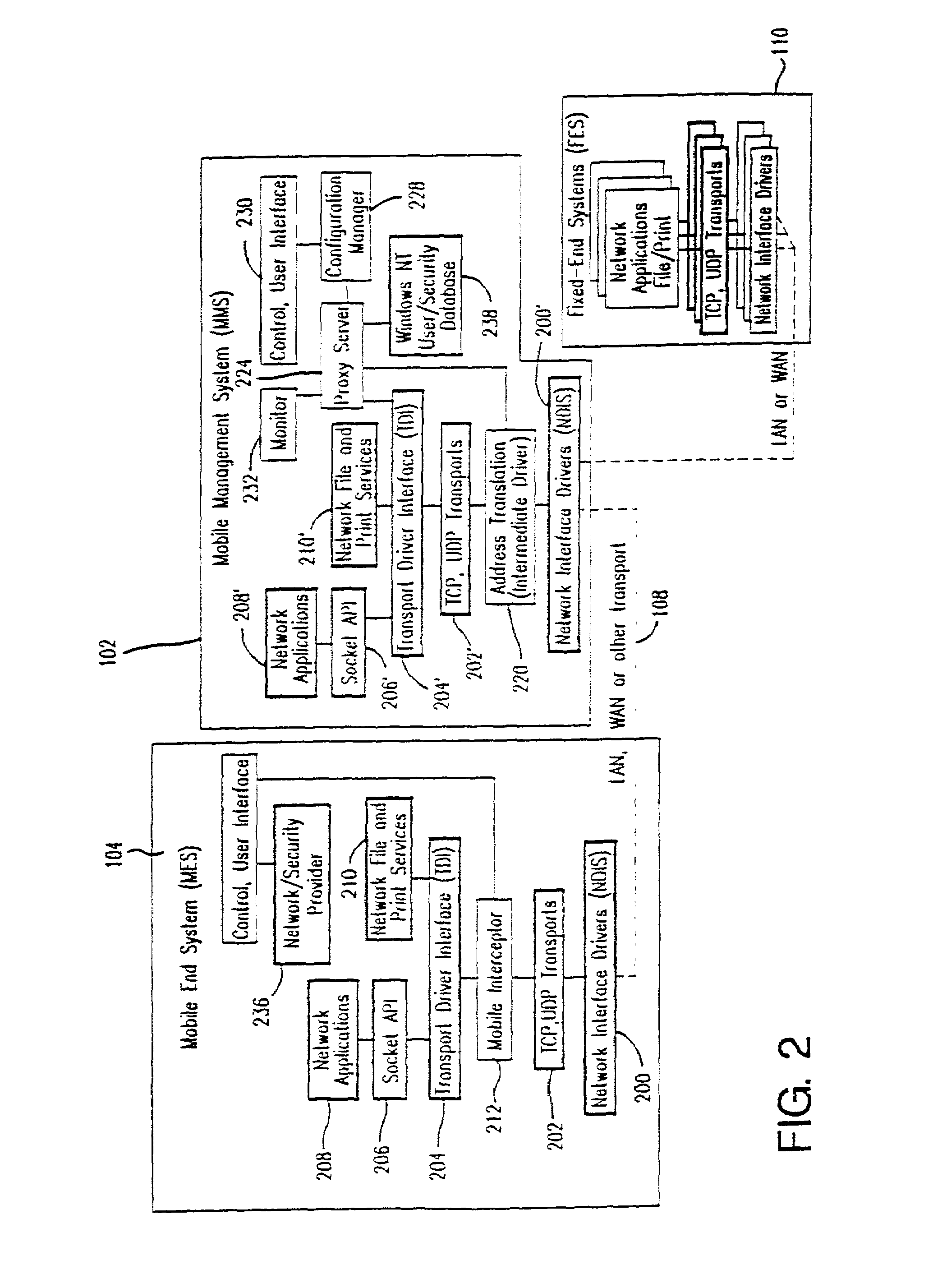
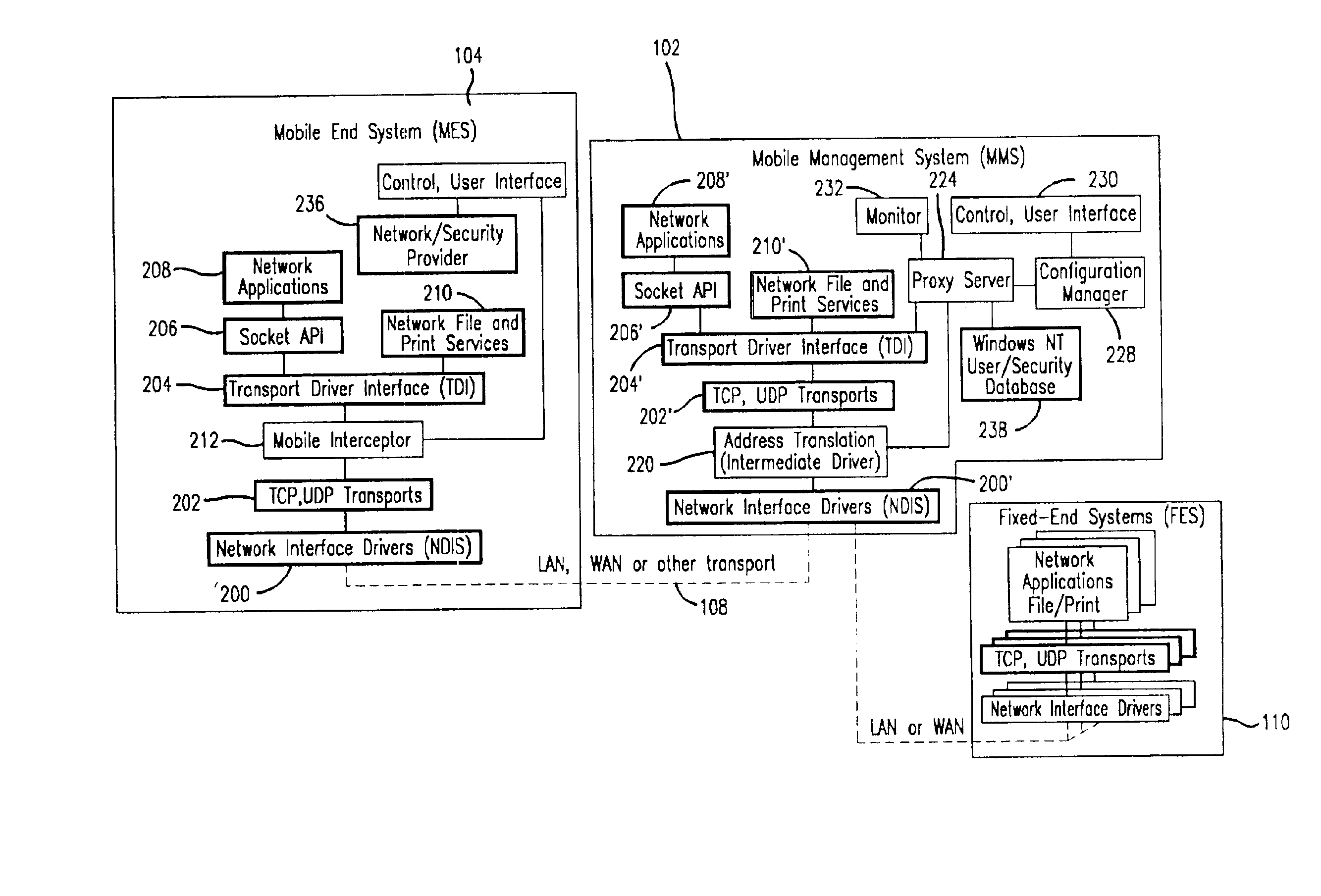
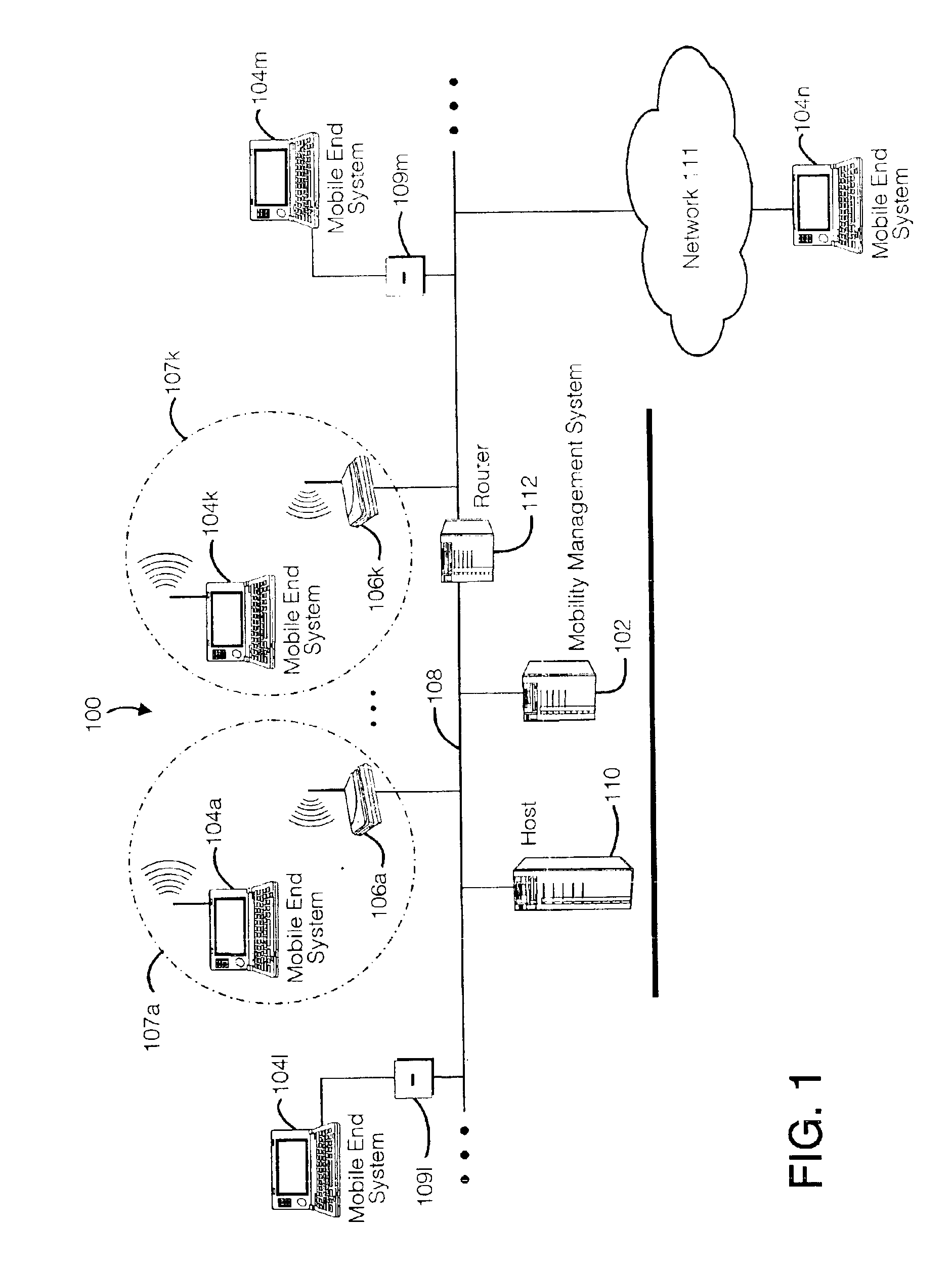
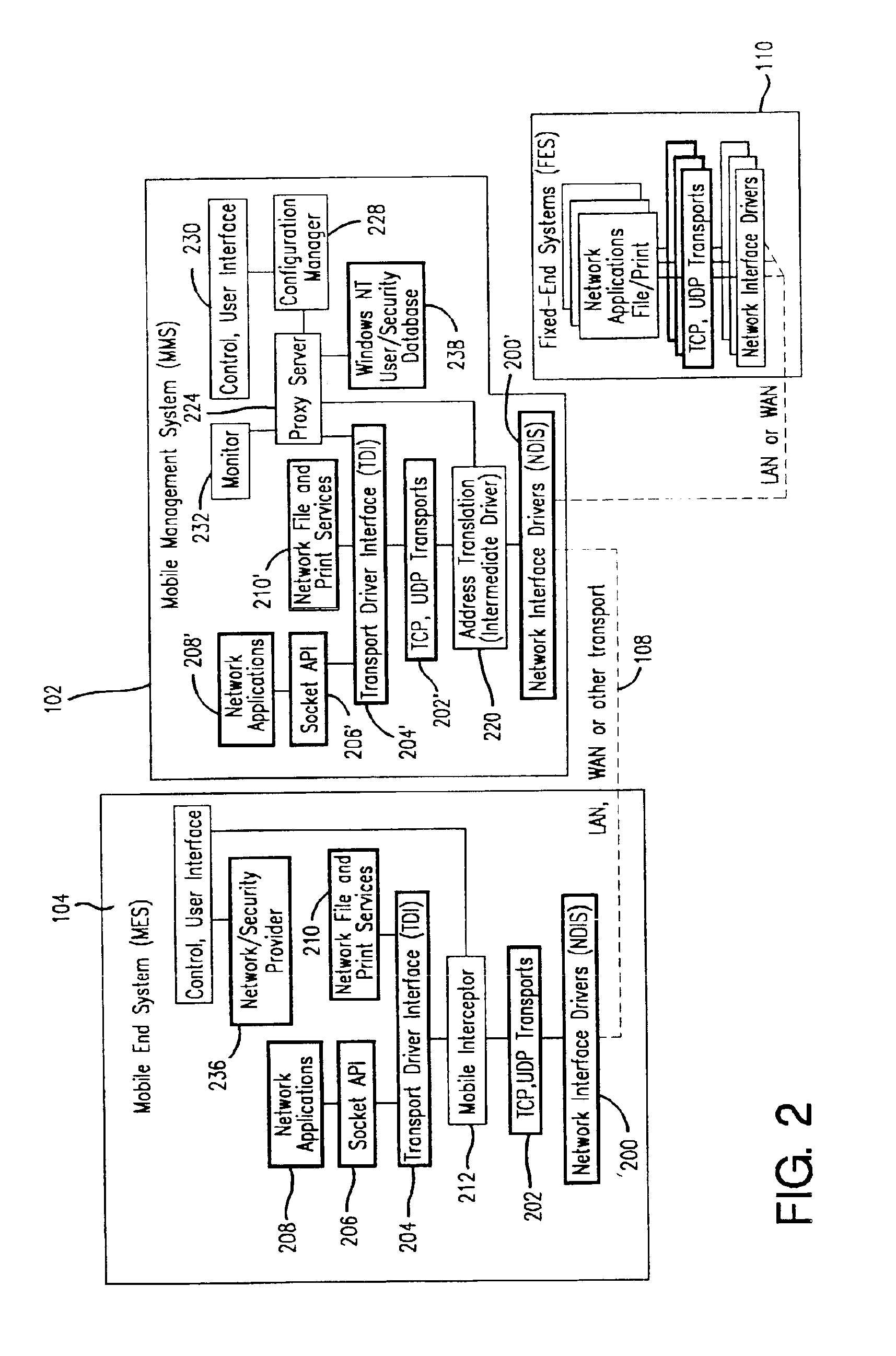
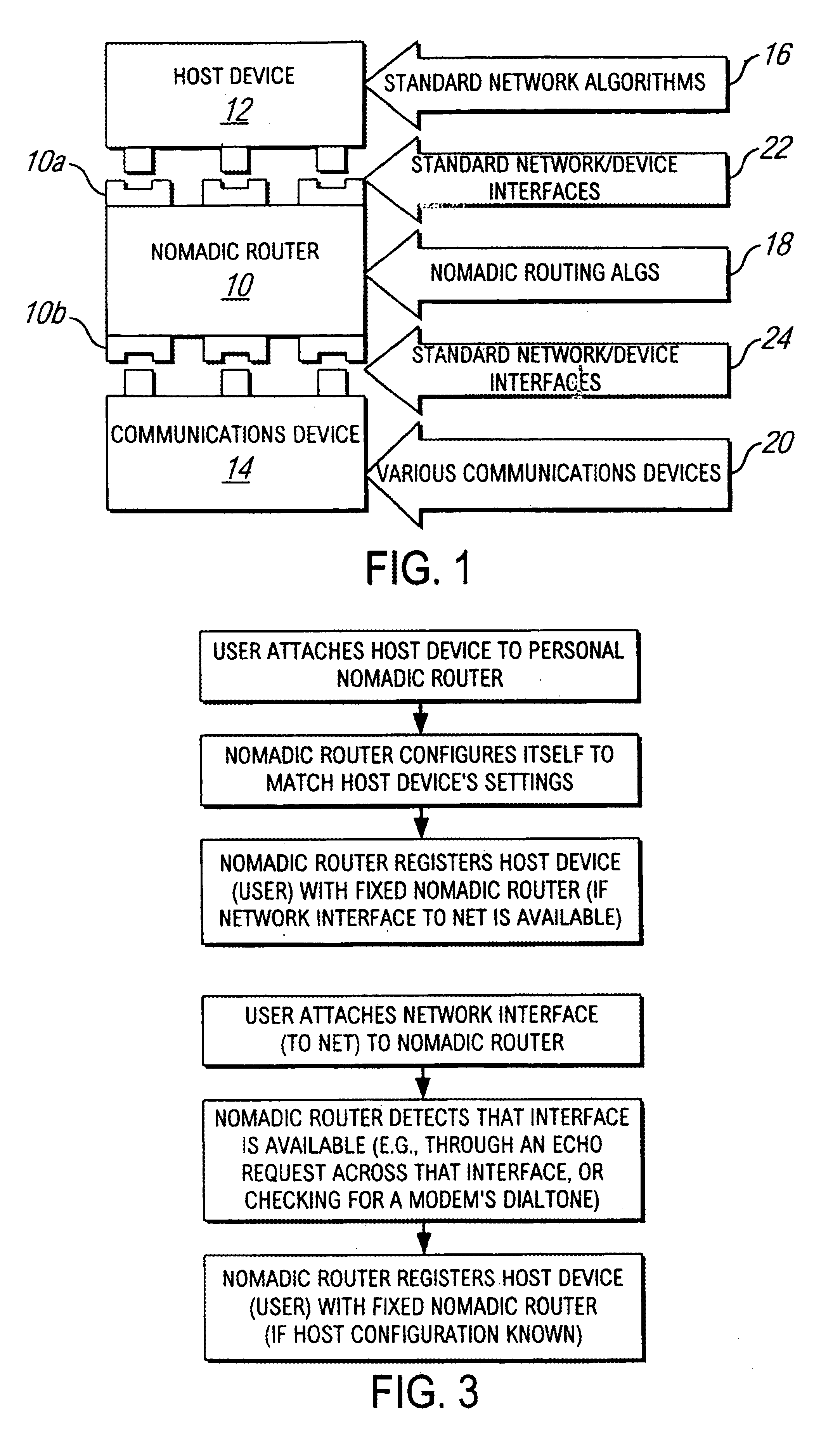
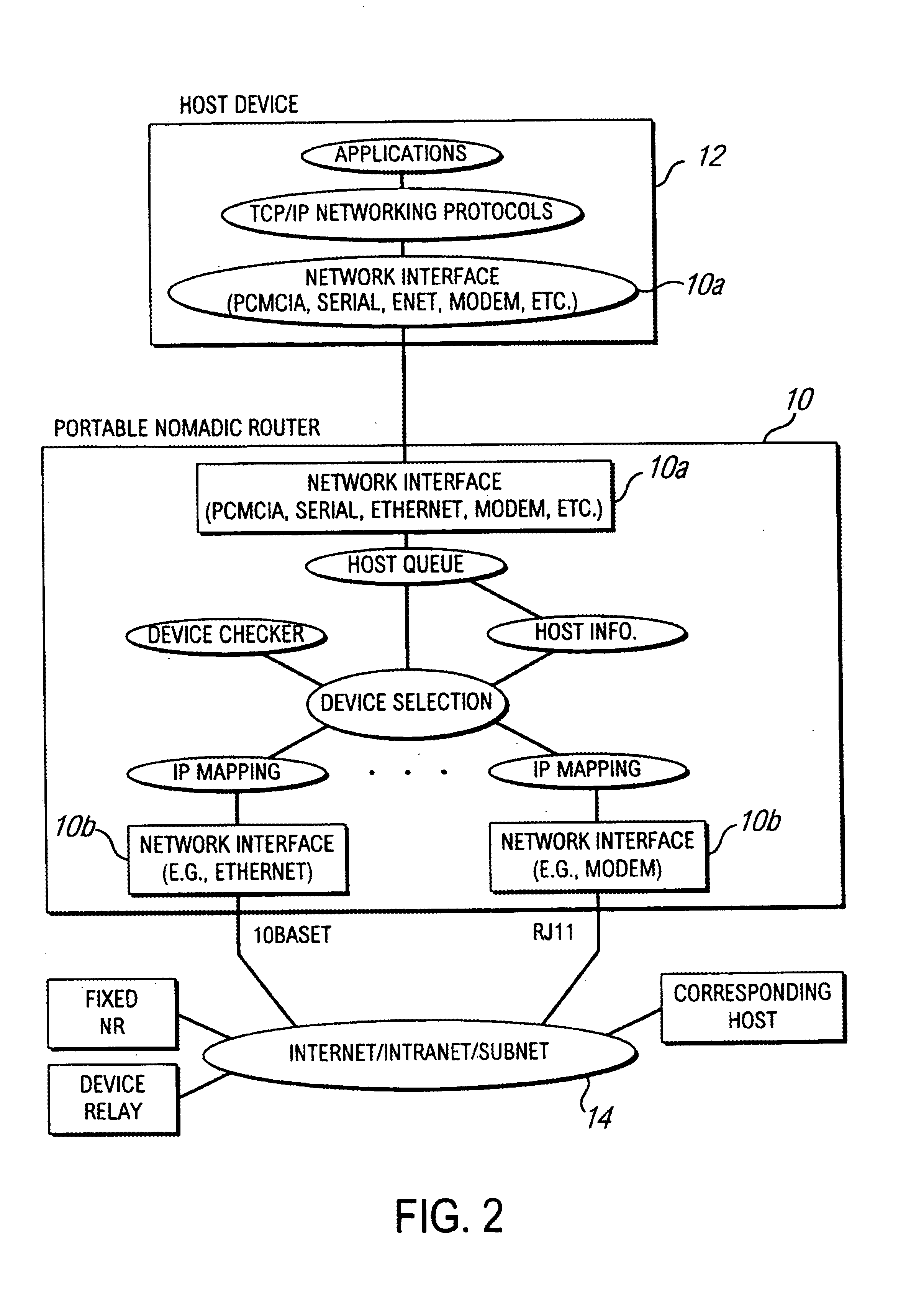
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
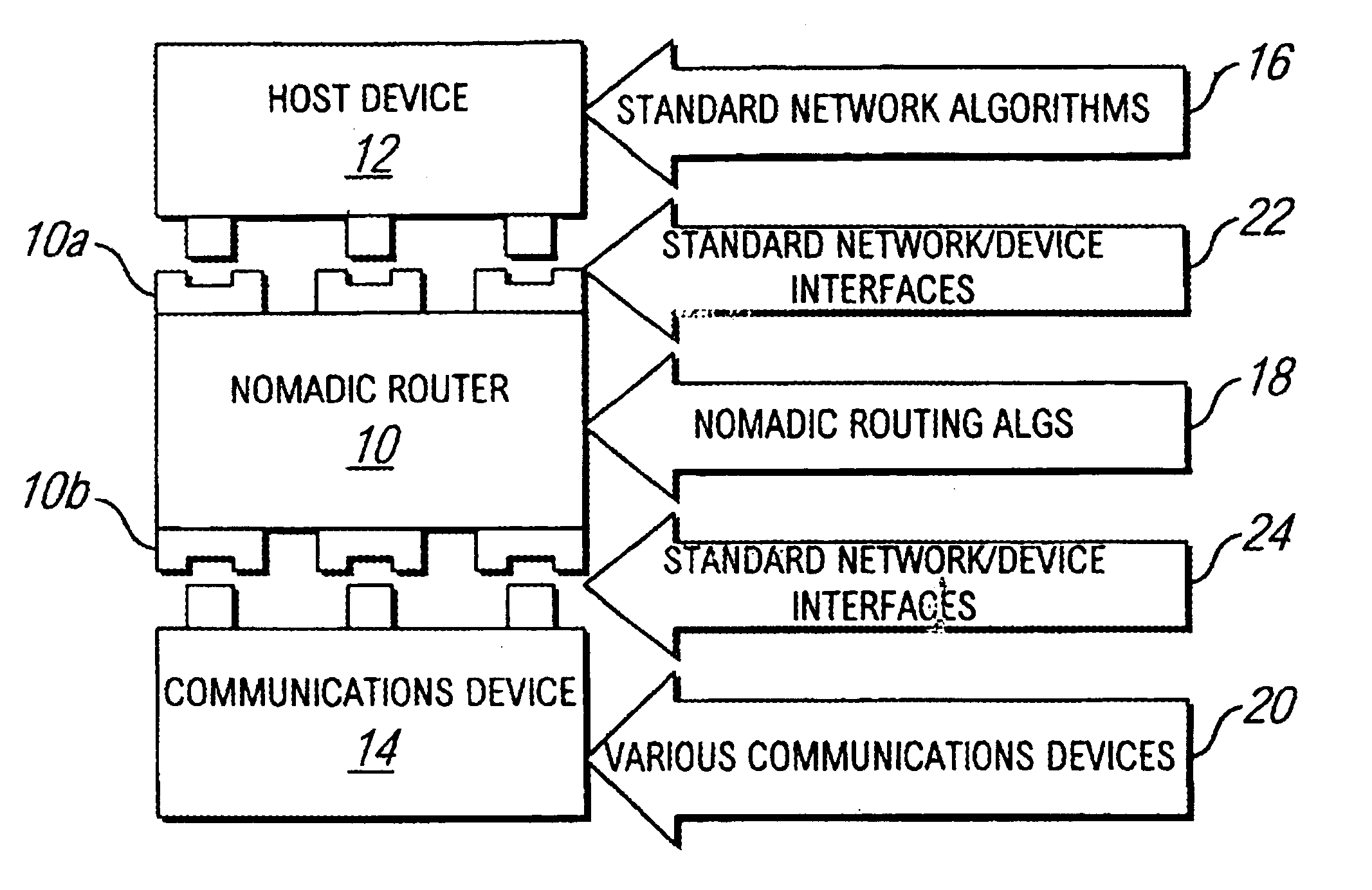
InactiveUS7136645B2Low costEasy accessError prevention/detection by using return channelNetwork traffic/resource managementNetwork connectionMobile end
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. An interface-based listener uses network point of attachment information supplied by a network interface to determine roaming conditions and to efficiently reestablish connection upon roaming. The Mobility Management Server can distribute lists to Mobile End Systems specifying how to contact it over disjoint networks.
Owner:MOBILE SONIC INC
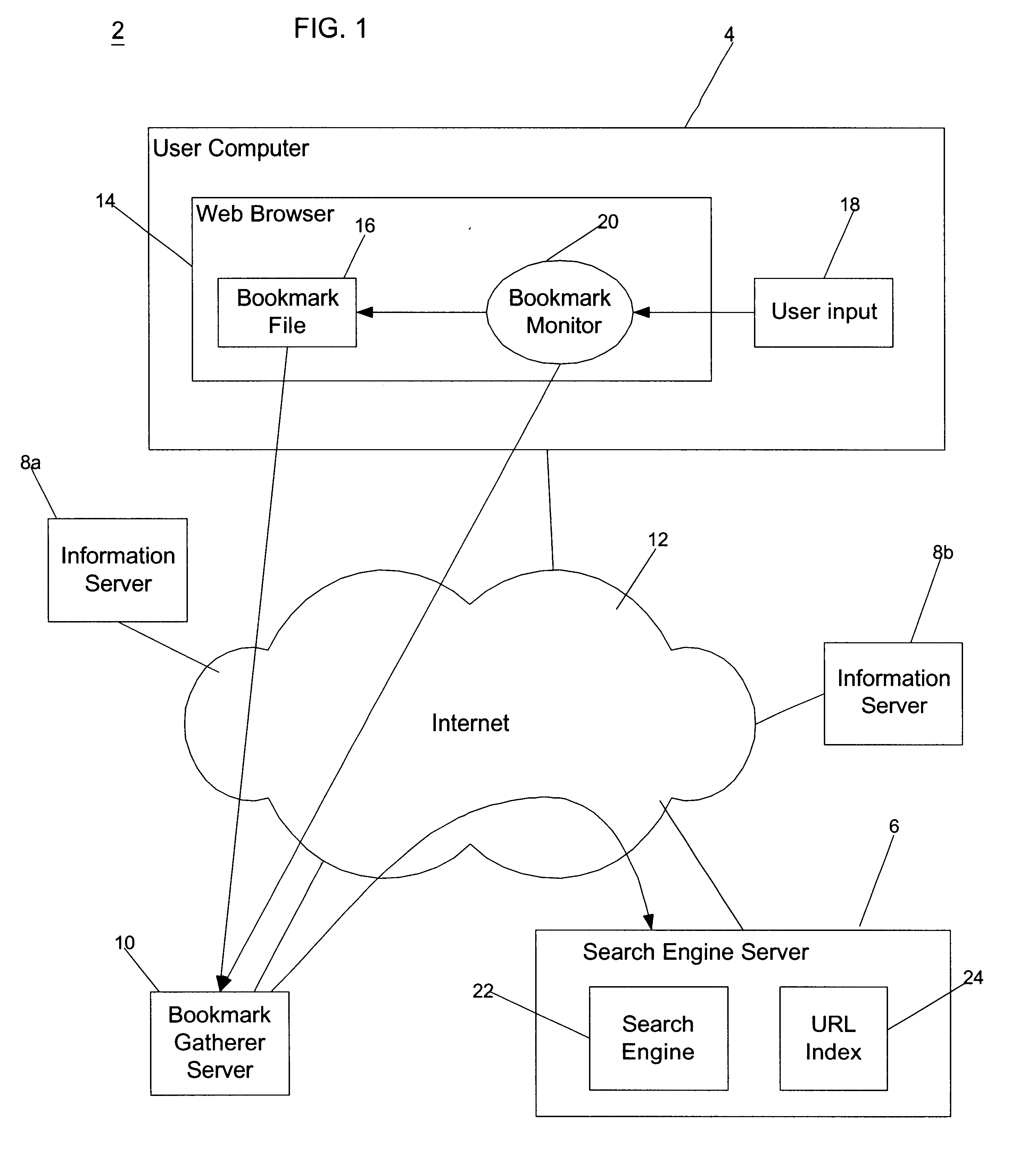
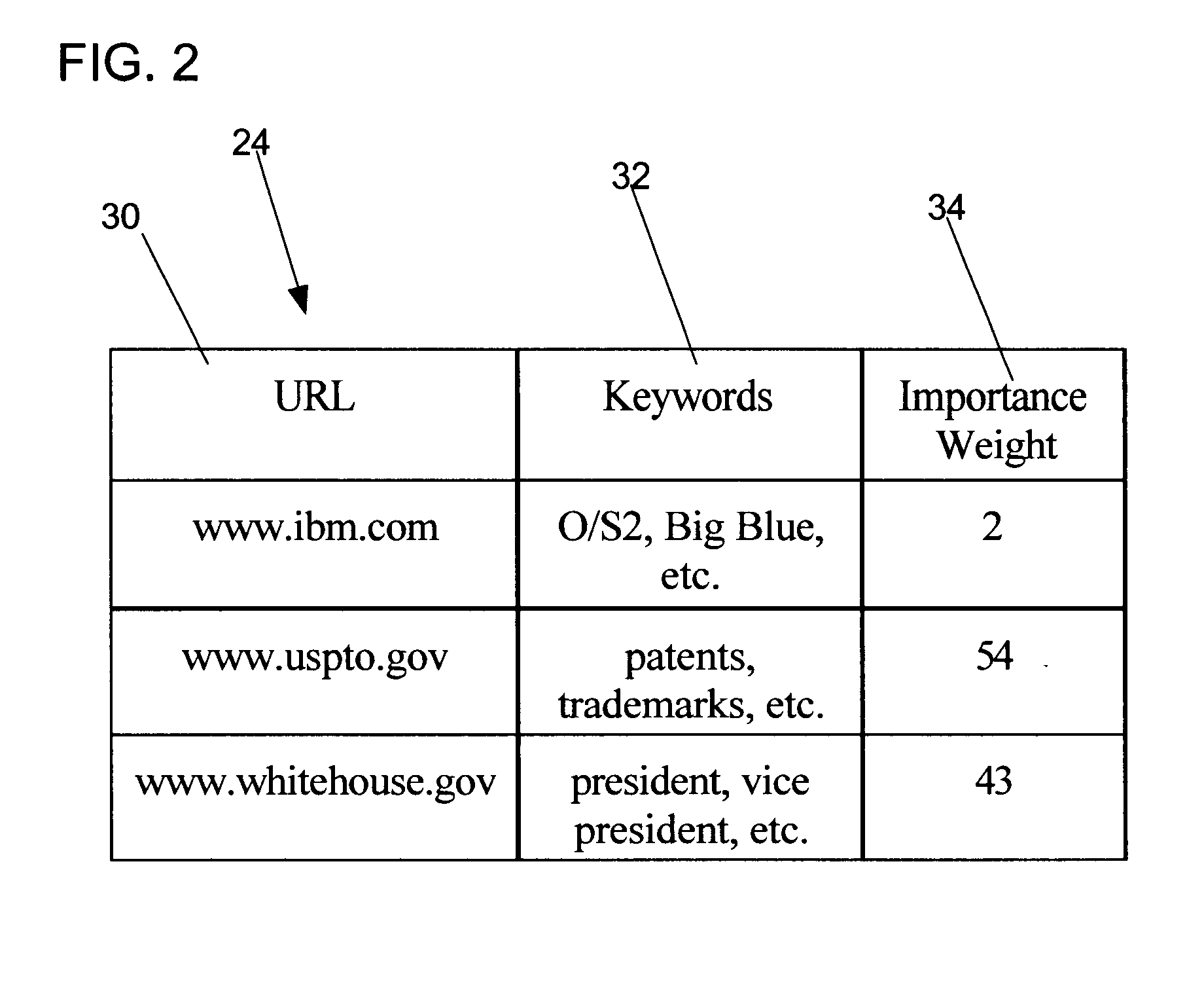
Method, system, and program for ordering search results using an importance weighting
InactiveUS6718365B1Simple processData processing applicationsWeb data indexingObservation dataInternet users
Disclosed is a technique for providing, accessing, and using bookmark data to supplement information in a search engine database. The bookmark data indicates saved user selected network addresses, e.g., URLs, that are capable of being selected to access observable data, e.g., a page of text, images, sound file, movie file, etc., at the selected network address. A user computer receives user modifications to bookmark data and transmits the modifications to the bookmark data to a server over a network. A server gathers bookmark data indicating saved user selected network addresses that the user is capable of selecting to access observable data at the selected network address. A search engine server receives bookmark data gathered from multiple Internet users and determines an importance rating for at least one network address from the received bookmark data. The determined importance rating is included in the search engine index. Further, when executing a search query against the index to determine at least one search result, the search engine server presents the search results ordered according to their importance rating.
Owner:GOOGLE LLC
Monitoring the flow of messages received at a server
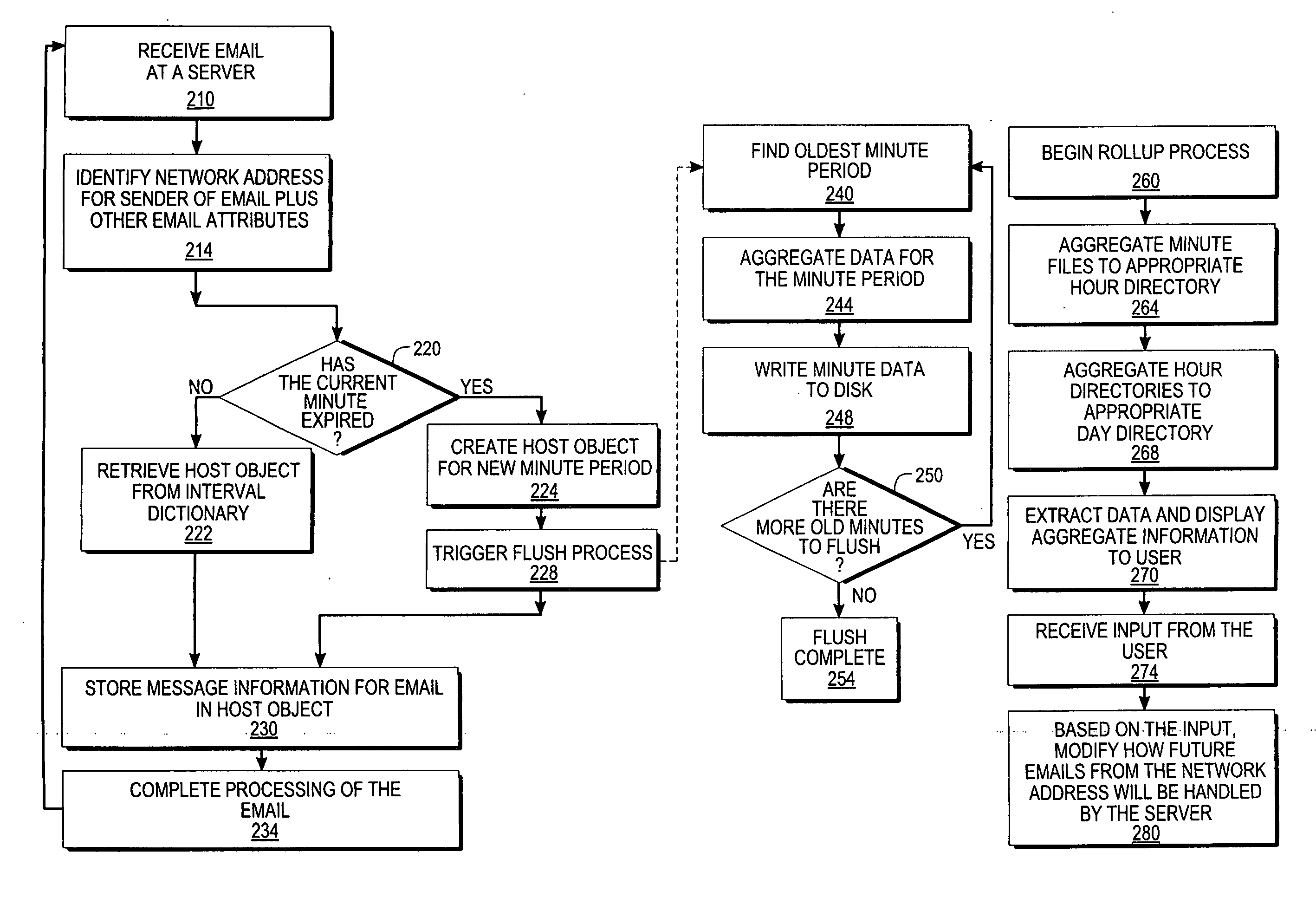
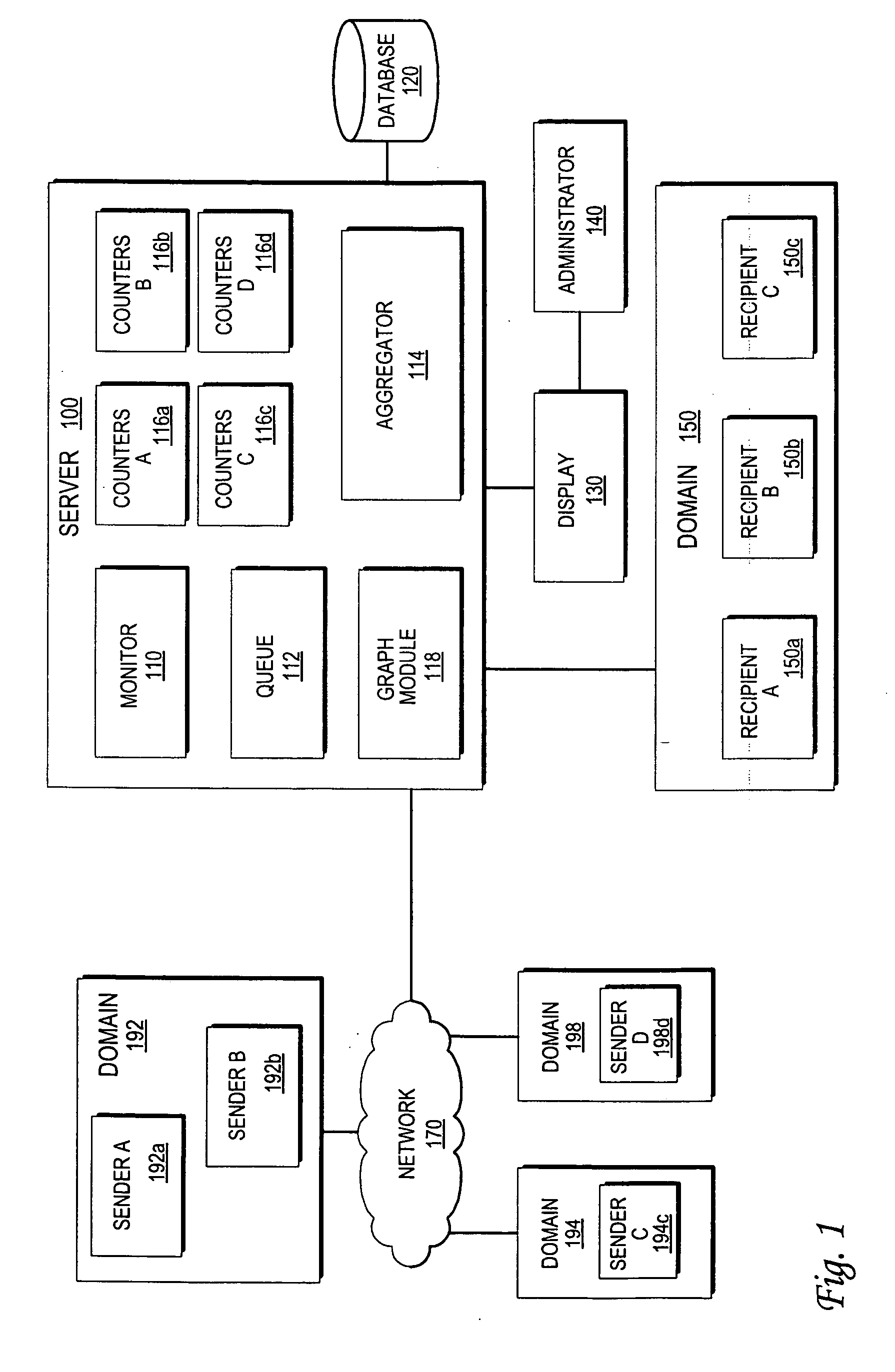
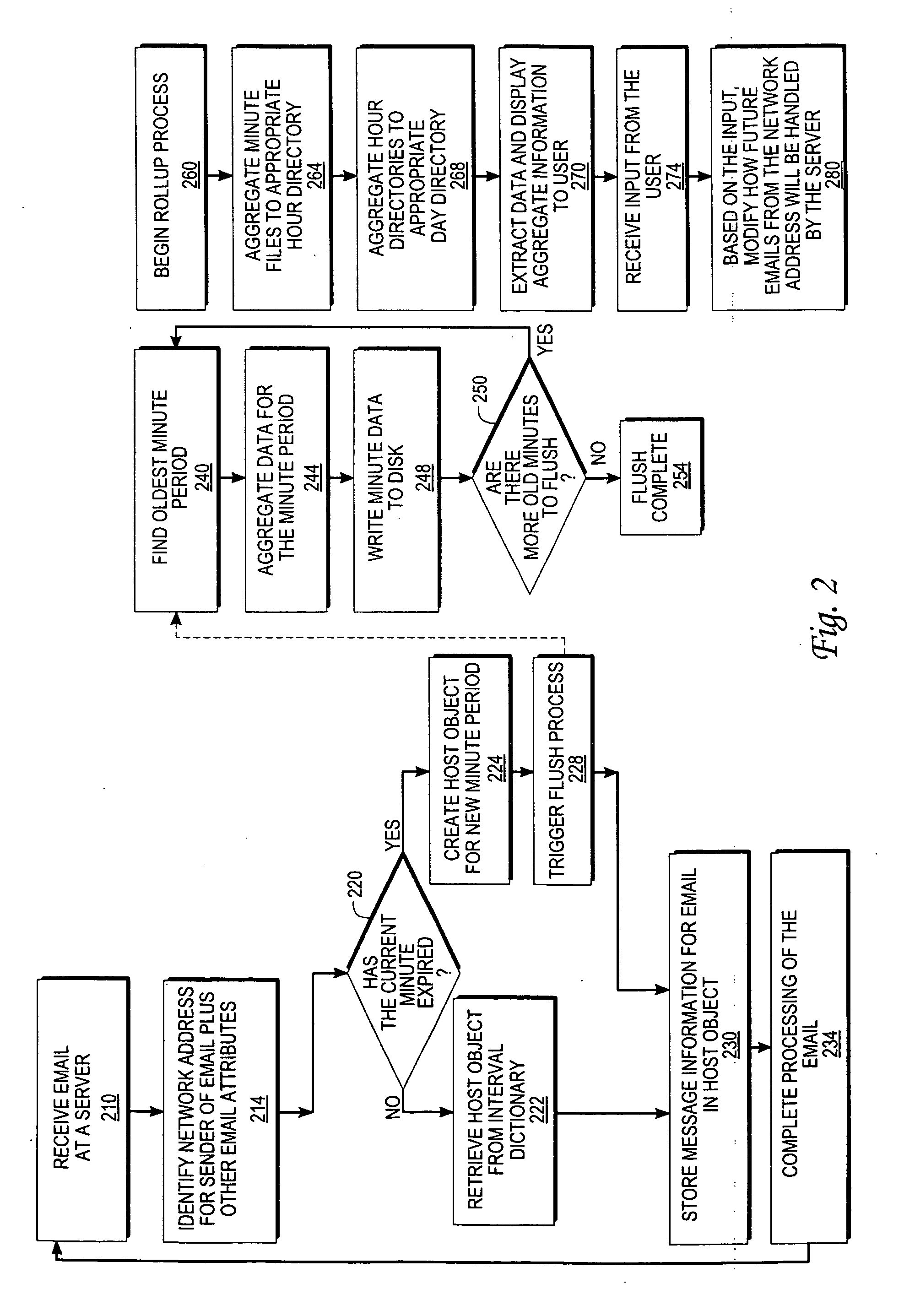
InactiveUS20060059238A1Multiple digital computer combinationsData acquisition and loggingMessage flowNetwork addressing
An approach for monitoring electronic messages received at a server is disclosed. Message information for a plurality of electronic messages received at the server: is determined and stored in a queue. Based on the queue, aggregate information is generated for a particular network address of a plurality of network addresses. The aggregate information is generated for each time interval of a plurality of time intervals and displayed for the plurality of time intervals. In some implementations, input from a user is received, and based on the input, a modification is made regarding how future electronic messages from the particular network address are handled by the server. In some implementations, combined aggregate information is generated for two or more network addresses and then displayed. In some implementations, aggregate policy information indicating which policies have been applied to the electronic messages is generated and displayed for the time intervals.
Owner:IRONPORT SYST
Router and methods using network addresses for virtualization
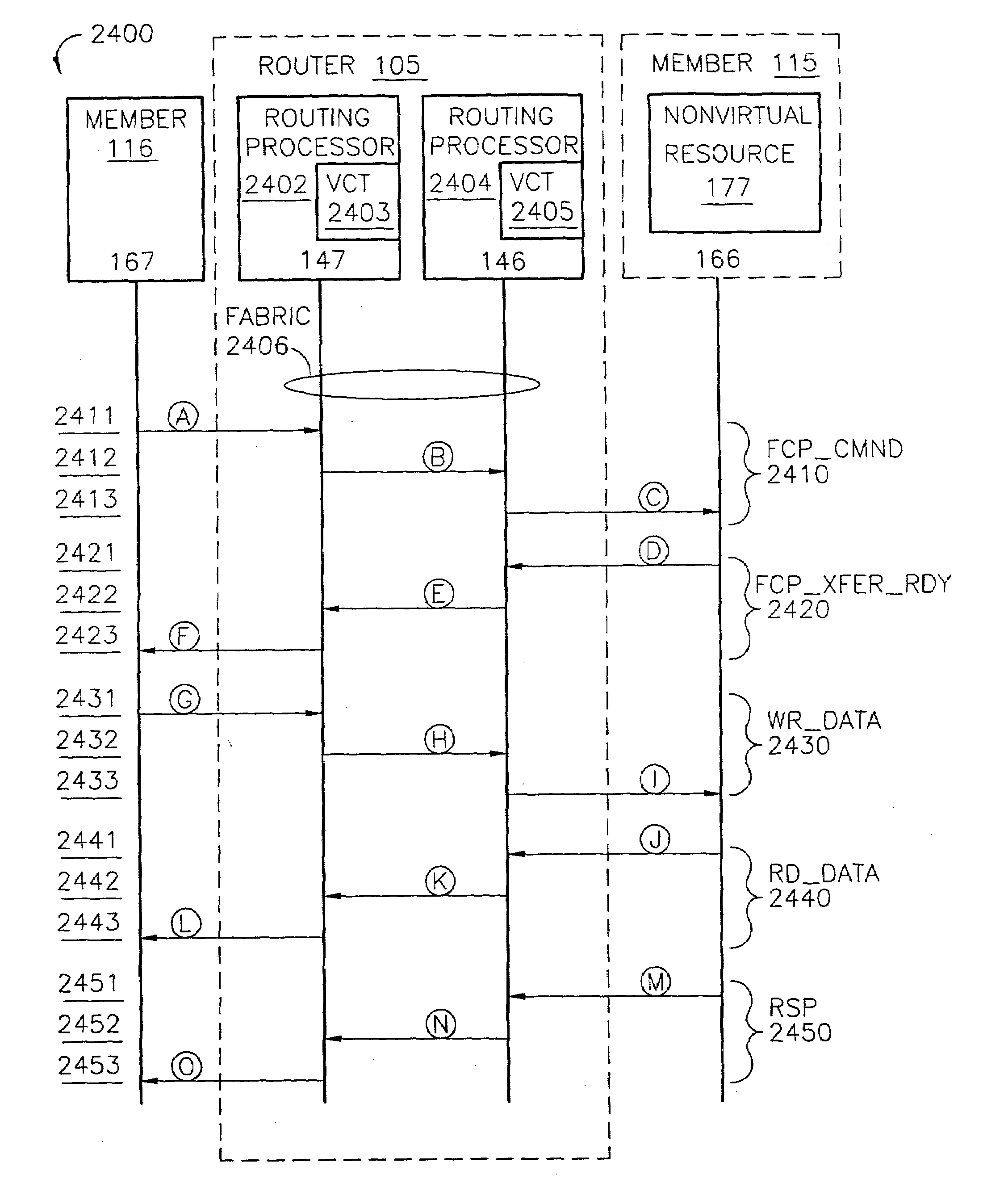
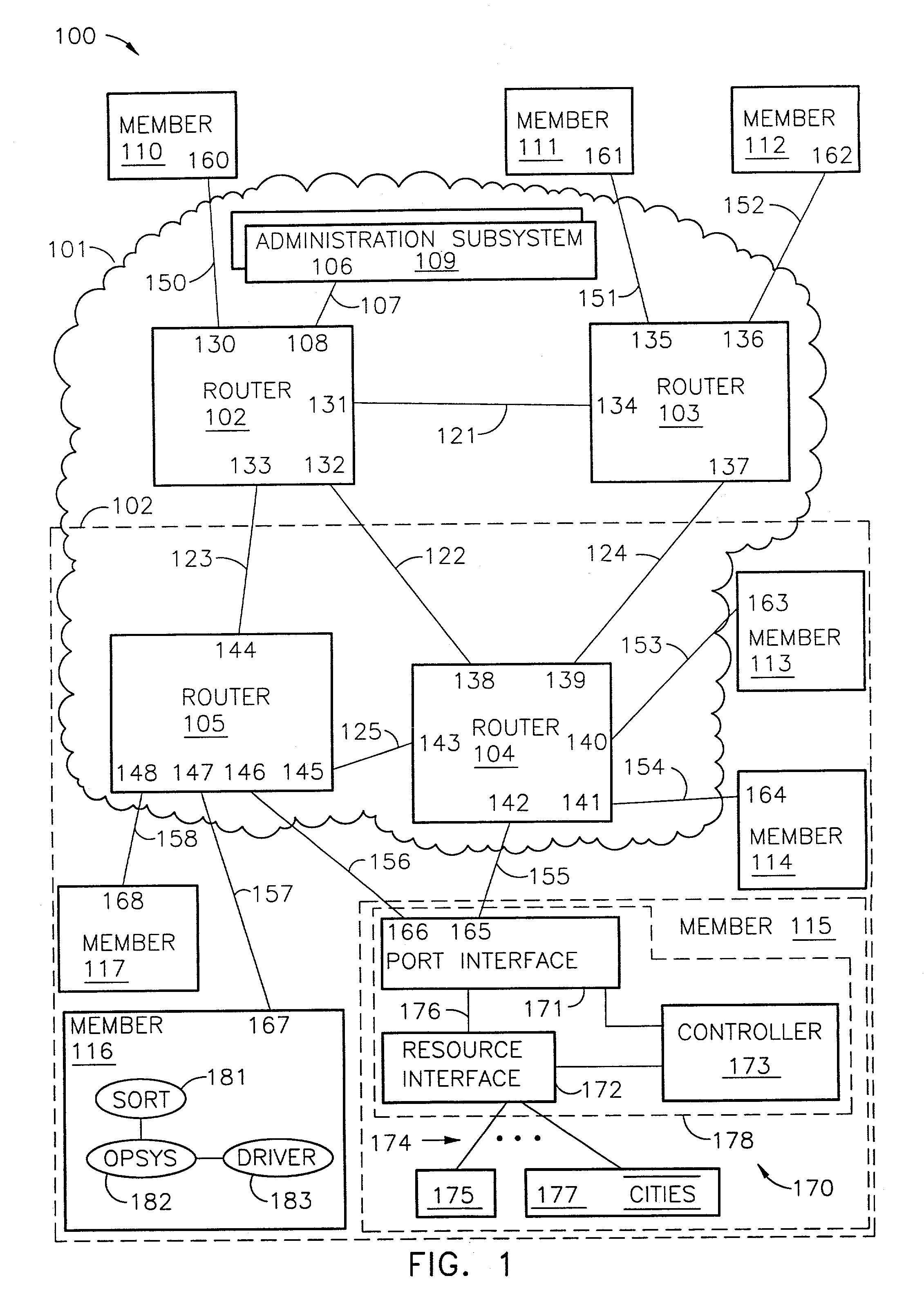
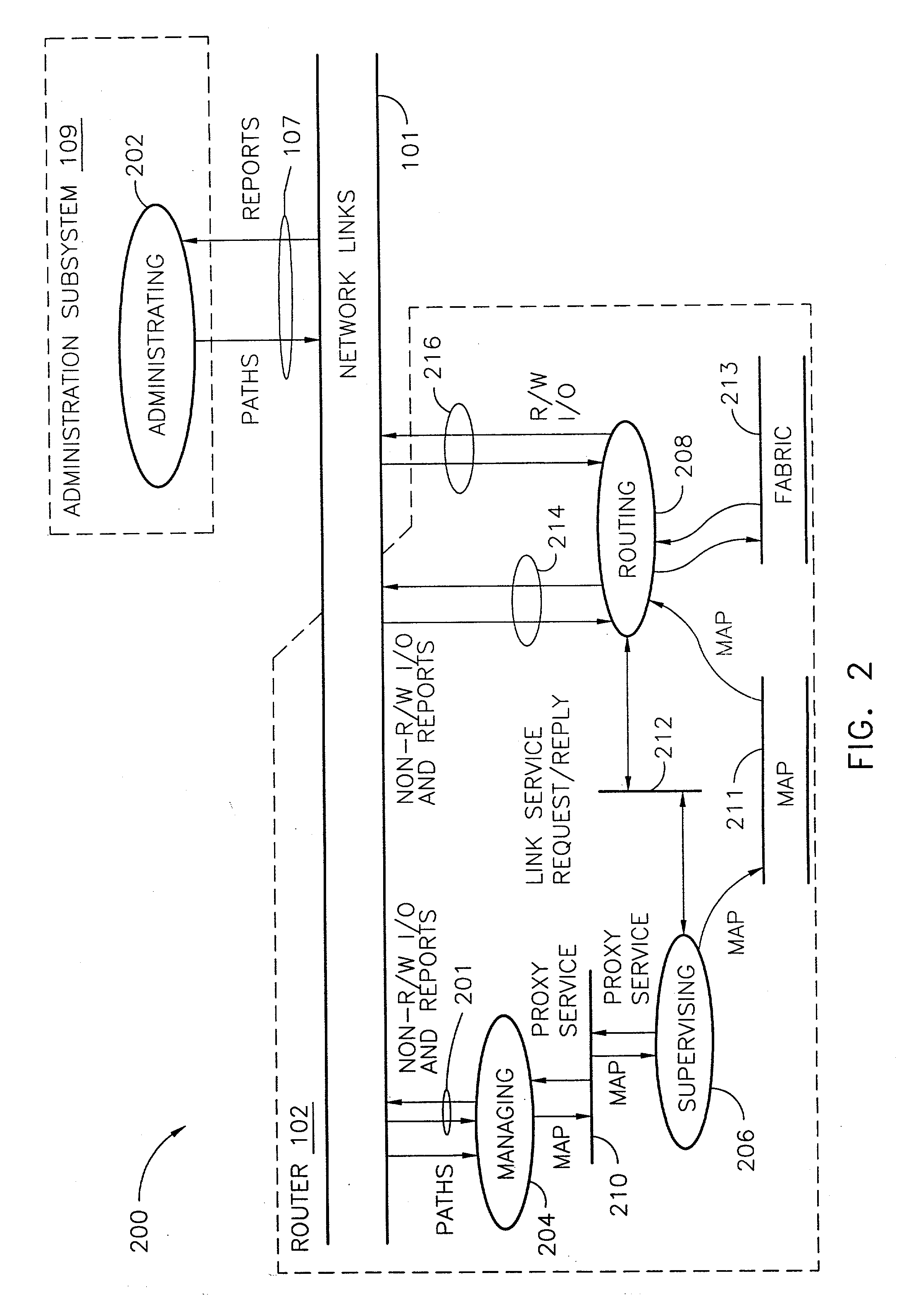
ActiveUS7200144B2Easy to operateImprove efficiency and reliabilityData switching by path configurationQuality of serviceDeficit round robin
A router for use in a network includes a scalable architecture and performs methods for implementing quality of service on a logical unit behind a network port; and for implementing storage virtualization. The architecture includes a managing processor, a supervising processor; and a plurality of routing processors coupled to a fabric. The managing processor has an in-band link to a routing processor. A routing processor receives a frame from the network, determines by parsing the frame, the protocol and logical unit number, and routes the frame to a queue according to a traffic class associated with the logical unit number in routing information prepared for the processors. An arbitration scheme empties the queue in accordance with a deficit round robin technique. If a routing processor detects the frame's destination is a virtual entity, and so is part of a virtual transaction, the router conducts a nonvirtual transaction in concert with the virtual transaction. The nonvirtual transaction accomplishes the intent of the virtual transaction but operates on an actual network port, for example, a storage device.
Owner:MARVELL ASIA PTE LTD
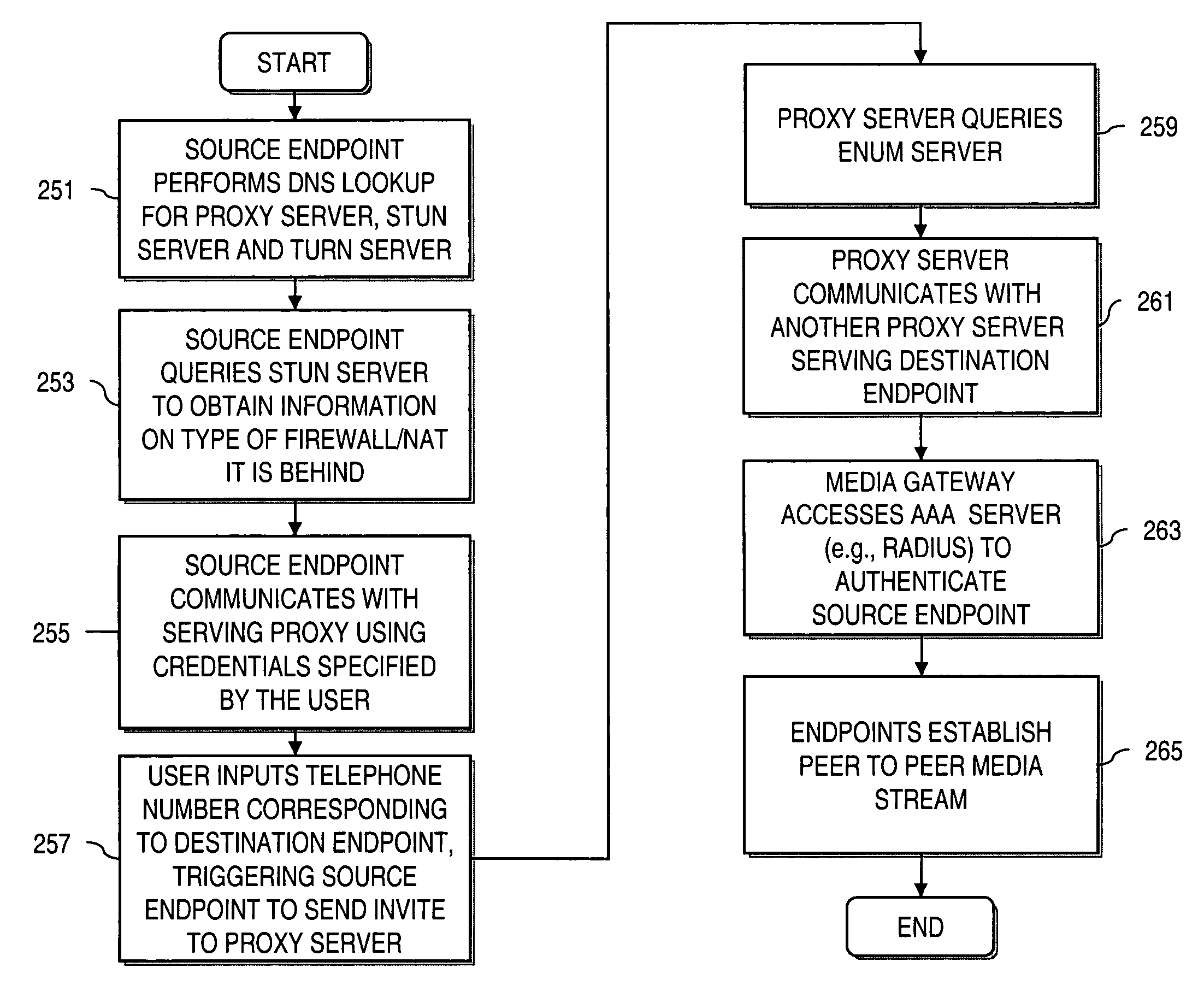
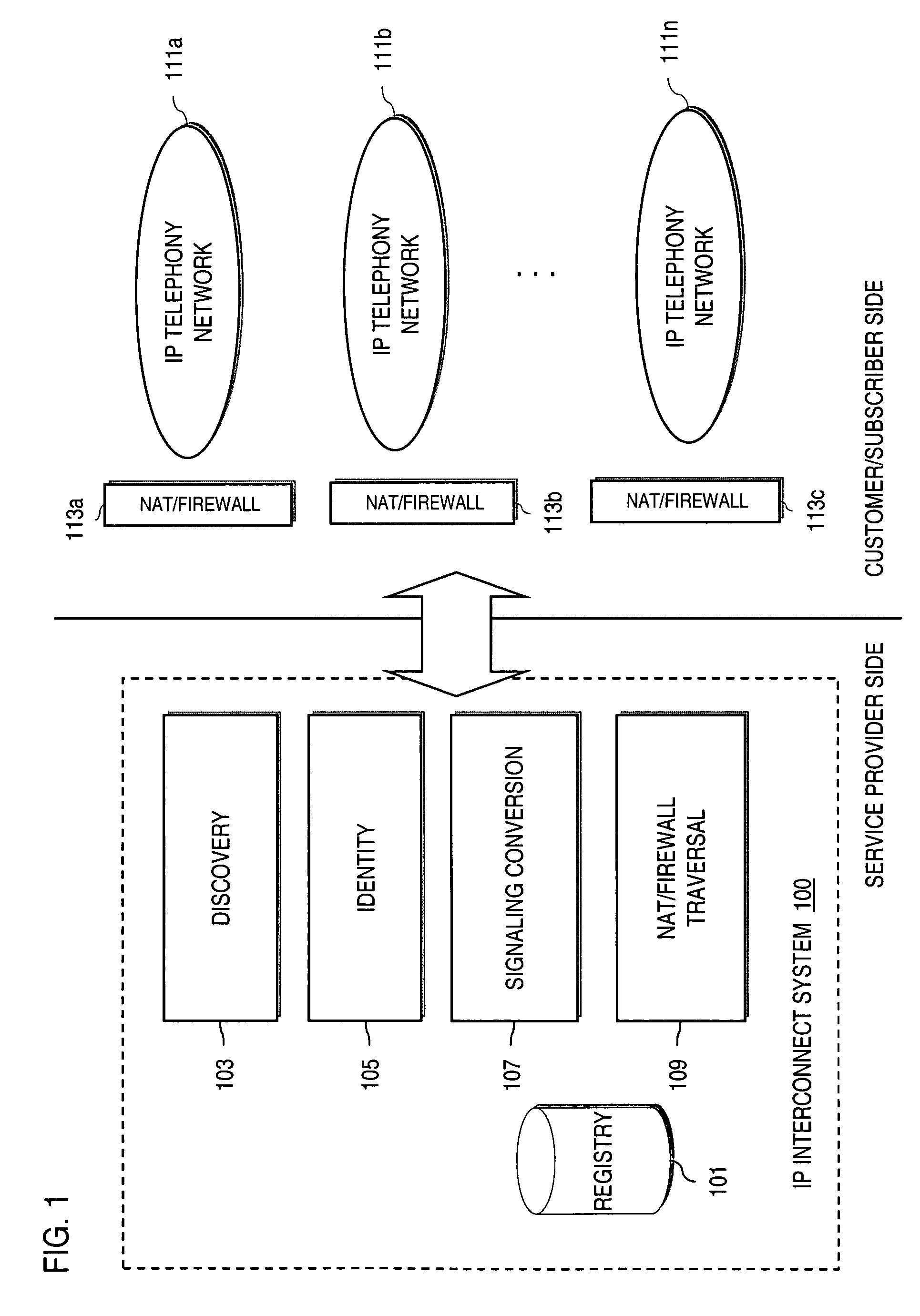
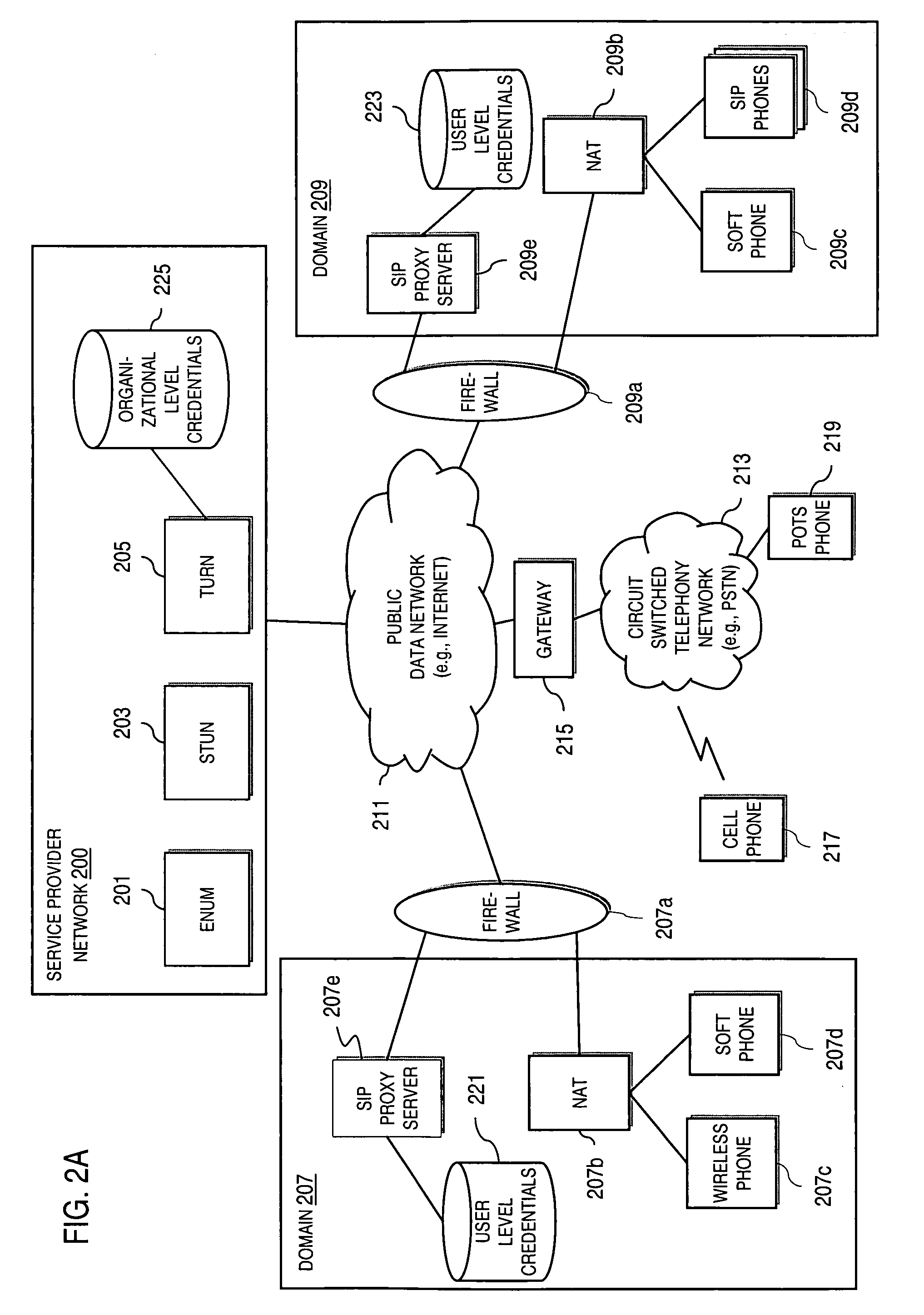
Method and system for providing secure credential storage to support interdomain traversal
An approach provides interdomain traversal to support packetized voice transmissions. A request is received from a first endpoint of a first domain for establishing a communication session with a second endpoint of a second domain. Encrypted user credential information is retrieved from a credentials database resident within the first domain, wherein the encrypted user credential includes a password associated with a user associated with the first endpoint. Further, the encrypted user credential information is transmitted to a tunneling server in response to the request, wherein the tunneling server is configured to selectively setup a tunnel to support the communication session based on the encrypted user credential information. The tunnel traverses a first firewall and a first network address translator of the first domain and a second firewall and a second network address translator of the second domain to reach the second endpoint.
Owner:VERIZON PATENT & LICENSING INC
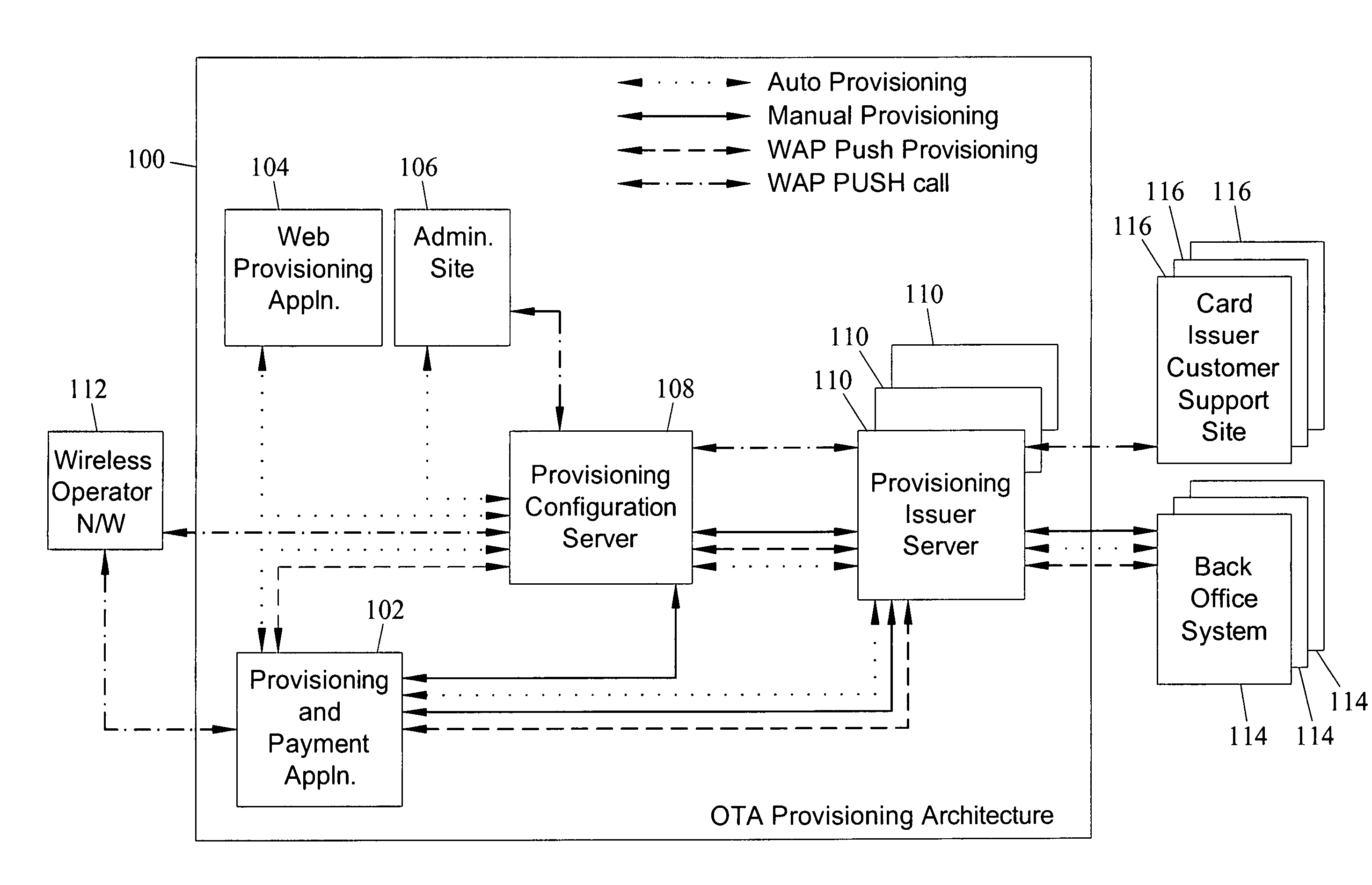
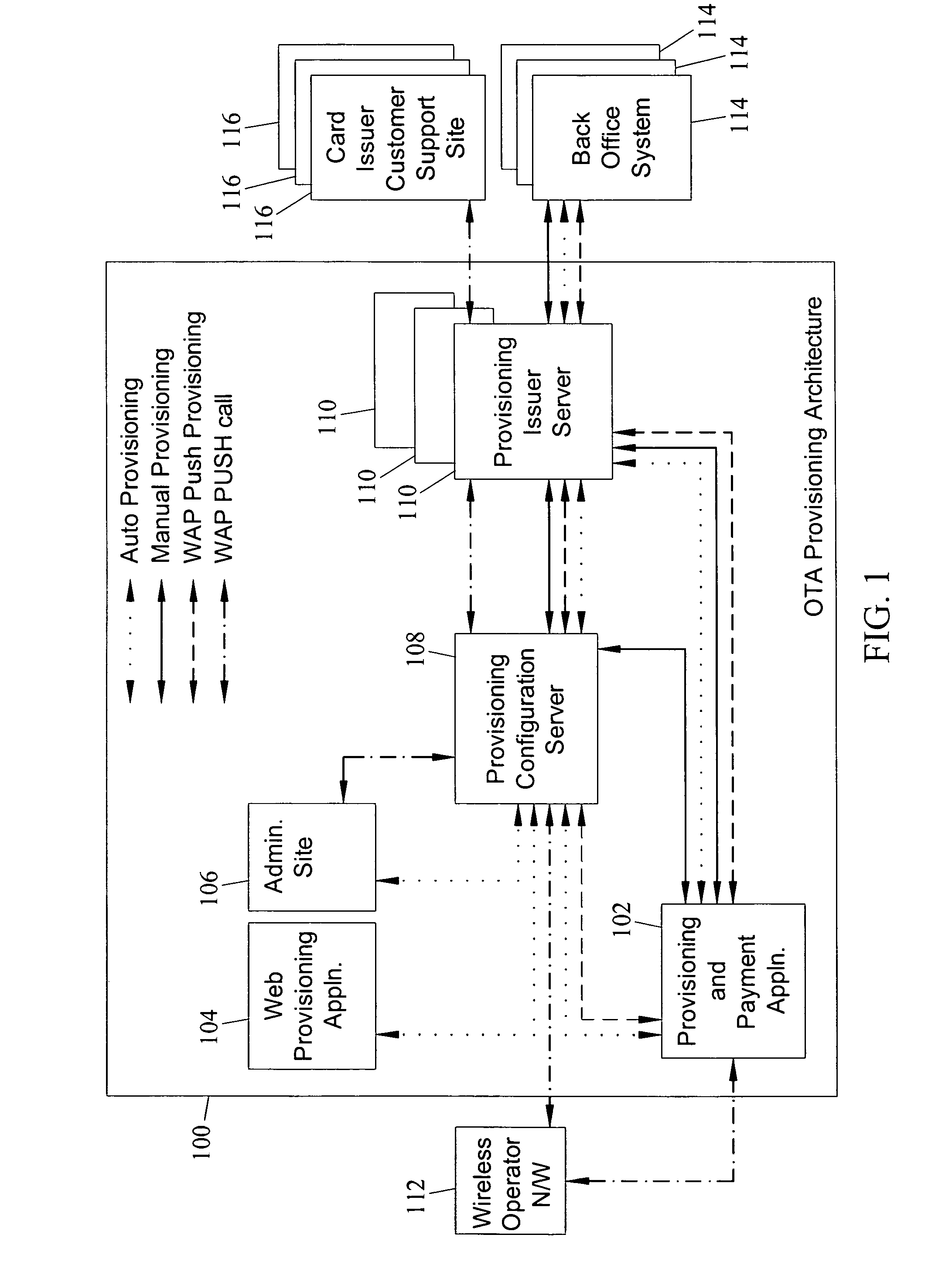
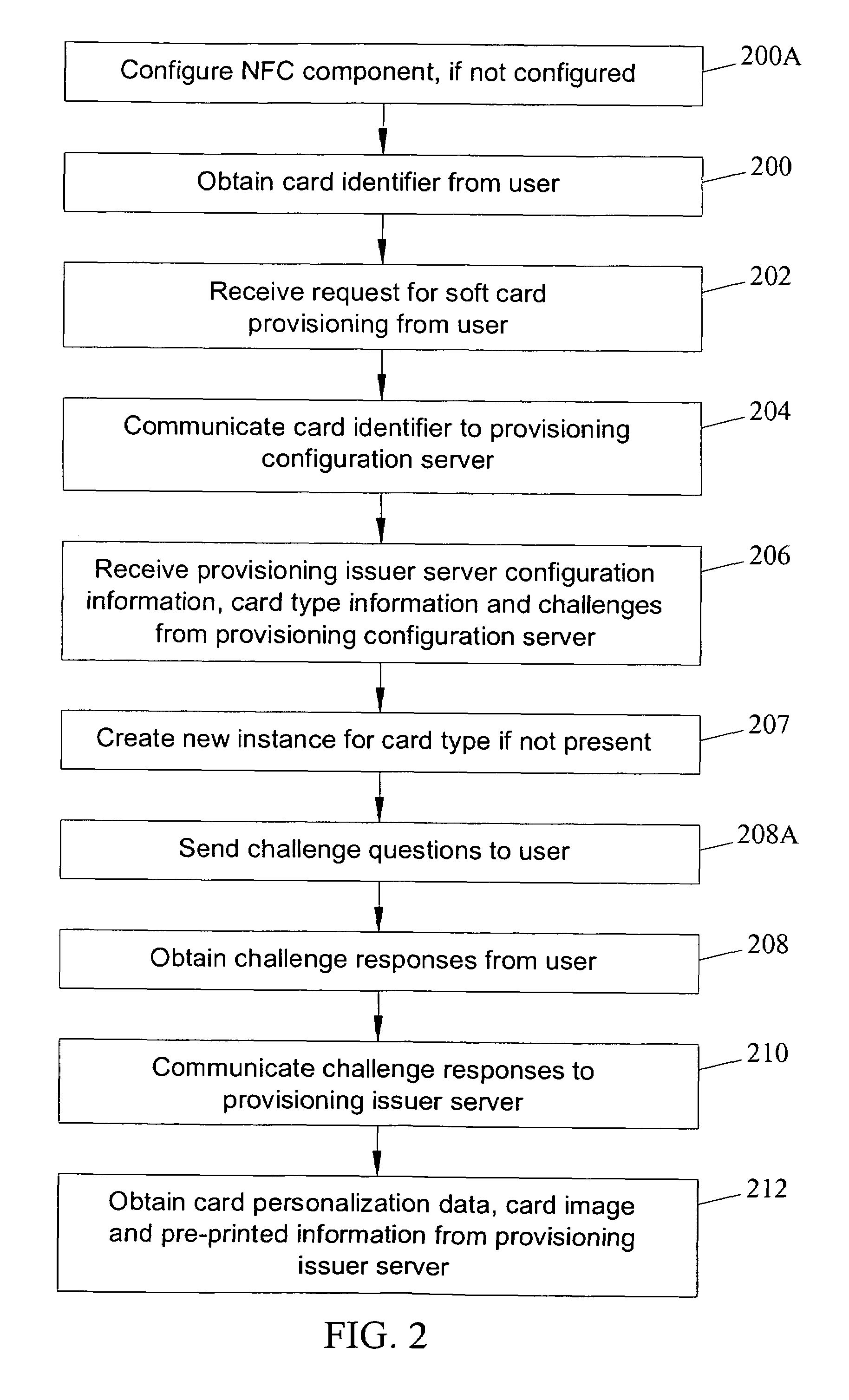
Methods, systems and computer program products for over the air (OTA) provisioning of soft cards on devices with wireless communications capabilities
ActiveUS7469151B2Shorten the timeEliminate needAcutation objectsSpecial service for subscribersComputer hardwarePersonalization
Methods, systems, and computer program products for over the air provisioning of soft cards on devices with wireless communications capabilities are disclosed. According to one method, a soft card provisioning application is instantiated on a device with wireless communications capabilities. A card number for a soft card desired to be provisioned on the device is obtained from a user of the device. The card number is communicated to a provisioning configuration server over an air interface. Card-issuer-specific challenges corresponding to the card number and a provisioning issuer server network address are obtained from the provisioning configuration server. The challenges are presented to the user, and the user's responses to the challenges are received. A connection is made to the provisioning issuer server corresponding to the network address. The challenge responses are communicated to the provisioning issuer server. Soft card personalization data for activating the soft card is received from the provisioning issuer server. The soft card is provisioned for use on the device based on the personalization data.
Owner:MASTERCARD INT INC
Statistical tracking of global server load balancing for selecting the best network address from ordered list of network addresses based on a set of performance metrics
ActiveUS7086061B1Multiprogramming arrangementsMultiple digital computer combinationsPolicy decisionIp address
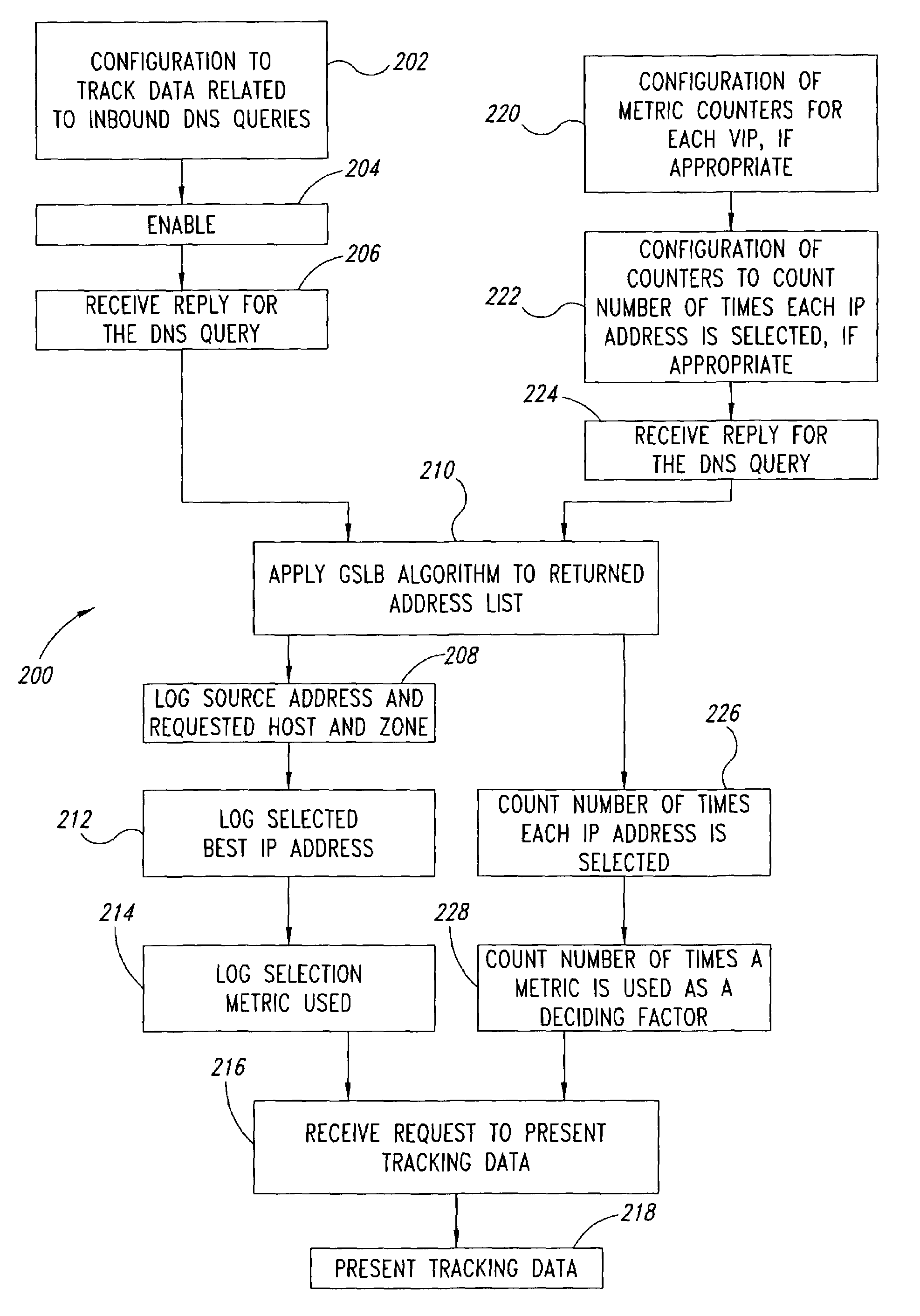
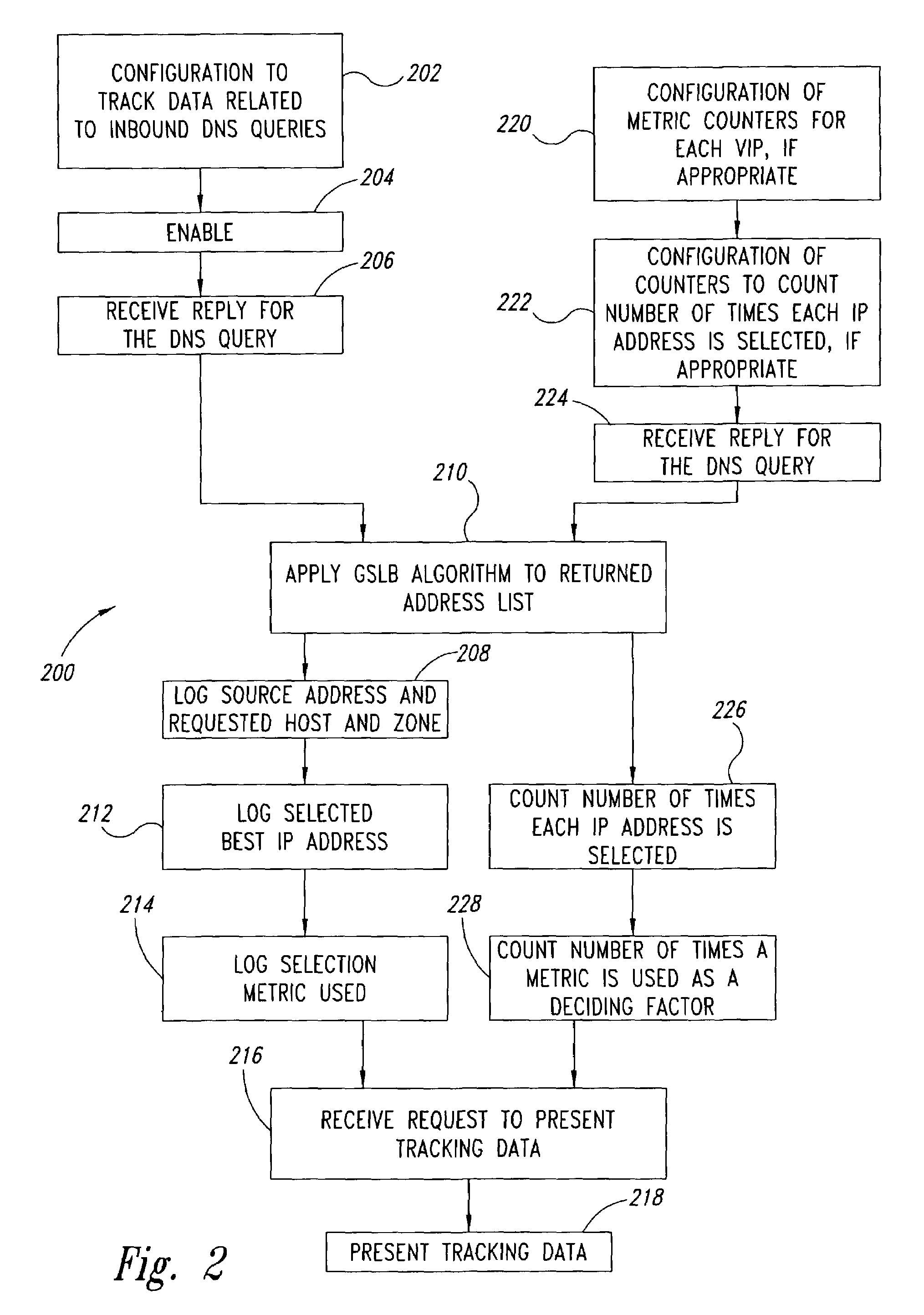
Server load-balancing operation-related data, such as data associated with a system configured for global server load balancing (GSLB) that orders IP addresses into a list based on a set of performance metrics, is tracked. Such operation-related data includes inbound source IP addresses (e.g., the address of the originator of a DNS request), the requested host and zone, identification of the selected “best” IP addresses resulting from application of a GSLB algorithm and the selection metric used to decide on an IP address as the “best” one. Furthermore, the data includes a count of the selected “best” IP addresses selected via application of the GSLB algorithm, and for each of these IP addresses, the list of deciding performance metrics, along with a count of the number of times each of these metrics in the list was used as a deciding factor in selection of this IP address as the best one. This tracking feature allows better understanding of GSLB policy decisions (such as those associated with performance, maintenance, and troubleshooting) and intelligent deployment of large-scale resilient GSLB networks.
Owner:AVAGO TECH INT SALES PTE LTD
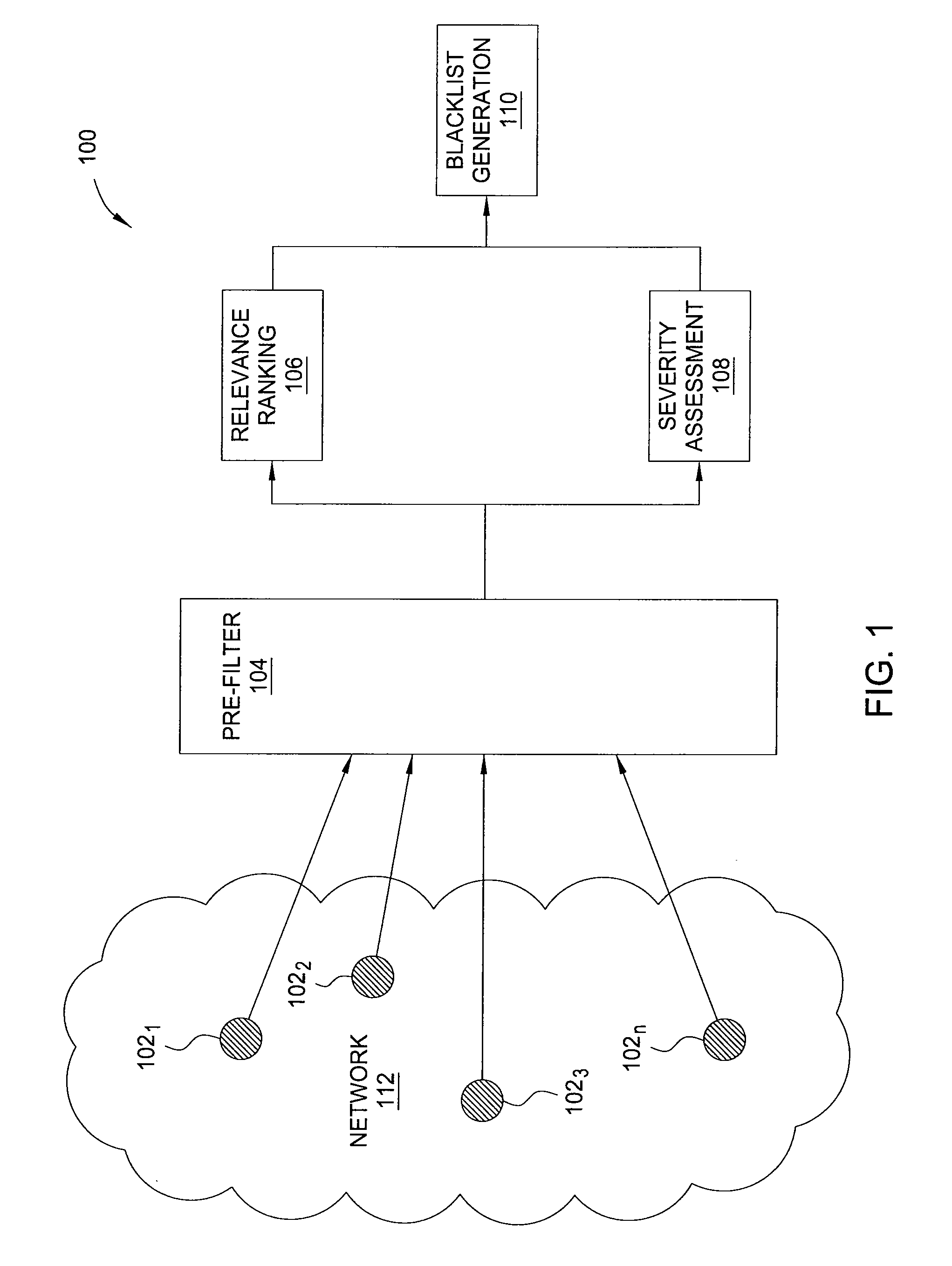
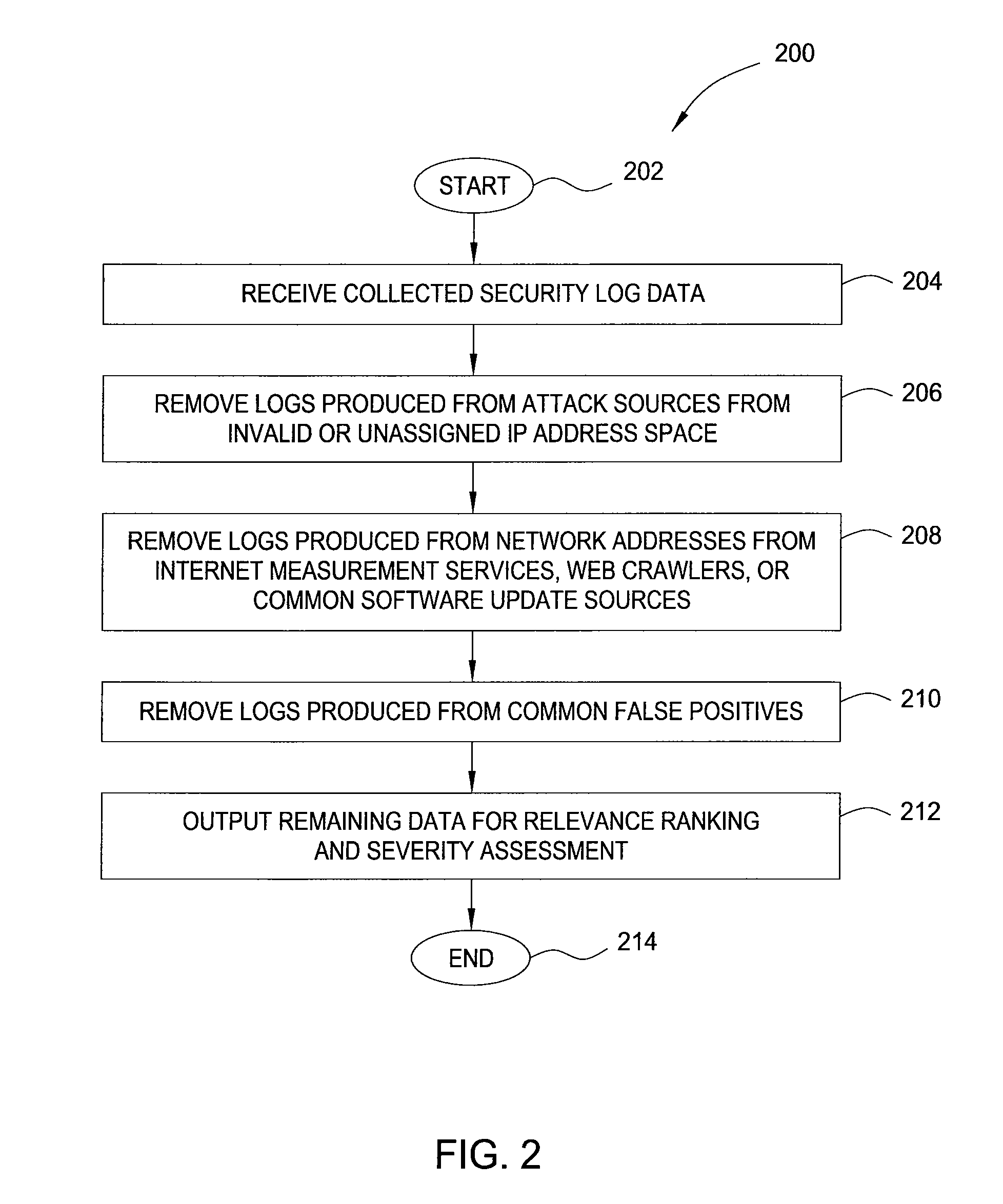
Method and apparatus for generating highly predictive blacklists
ActiveUS20090064332A1Memory loss protectionError detection/correctionNetwork addressingNetwork address
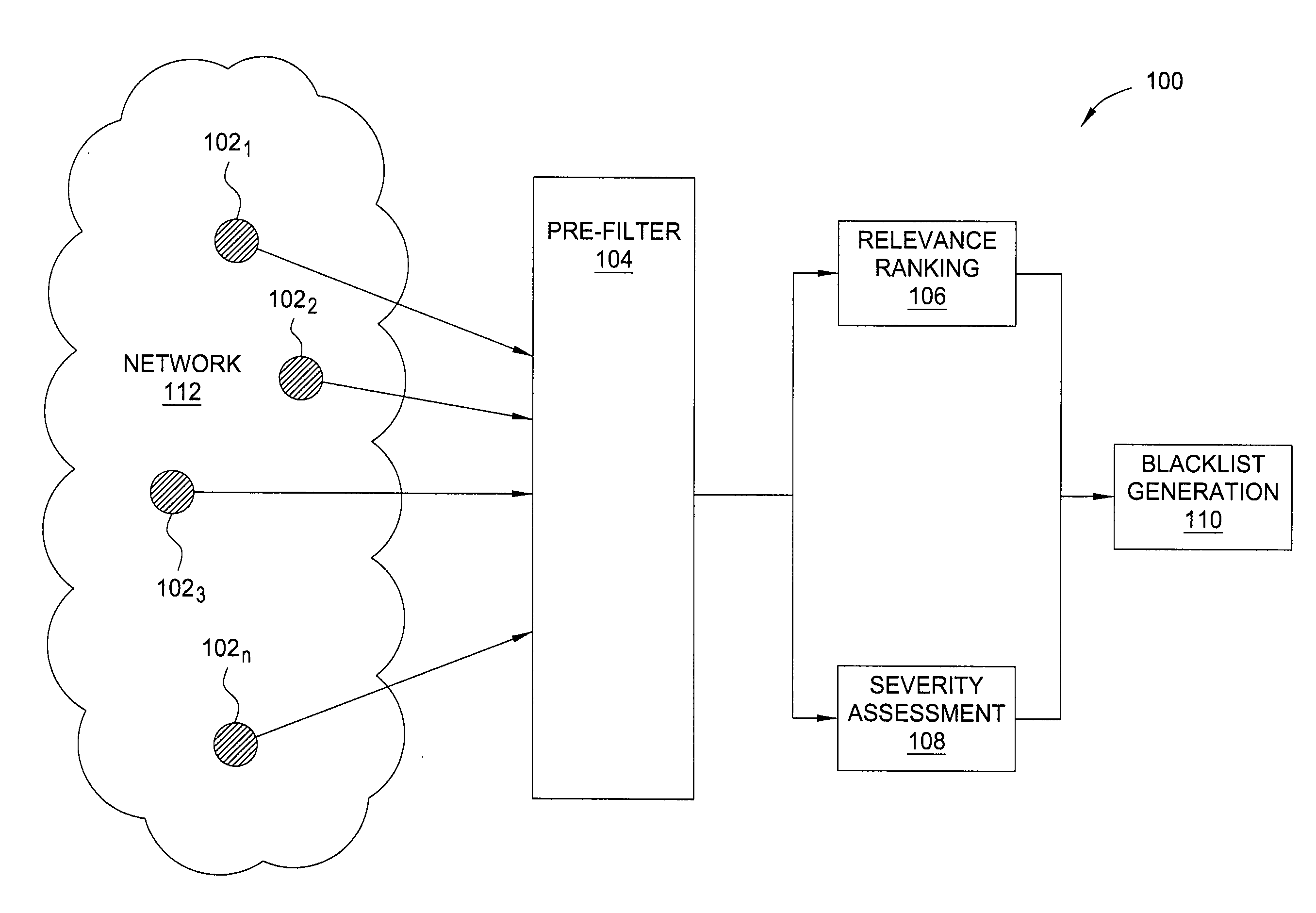
In one embodiment, the present invention is a method and apparatus for generating highly predictive blacklists. One embodiment of a method for generating a blacklist of network addresses for a user of a network includes collecting security log data from users of the network, the security log data identifying observed attacks by attack sources, assigning the attack sources to the blacklist based on a combination of the relevance each attack source to the user and the maliciousness of the attack source, and outputting the blacklist.
Owner:SRI INTERNATIONAL
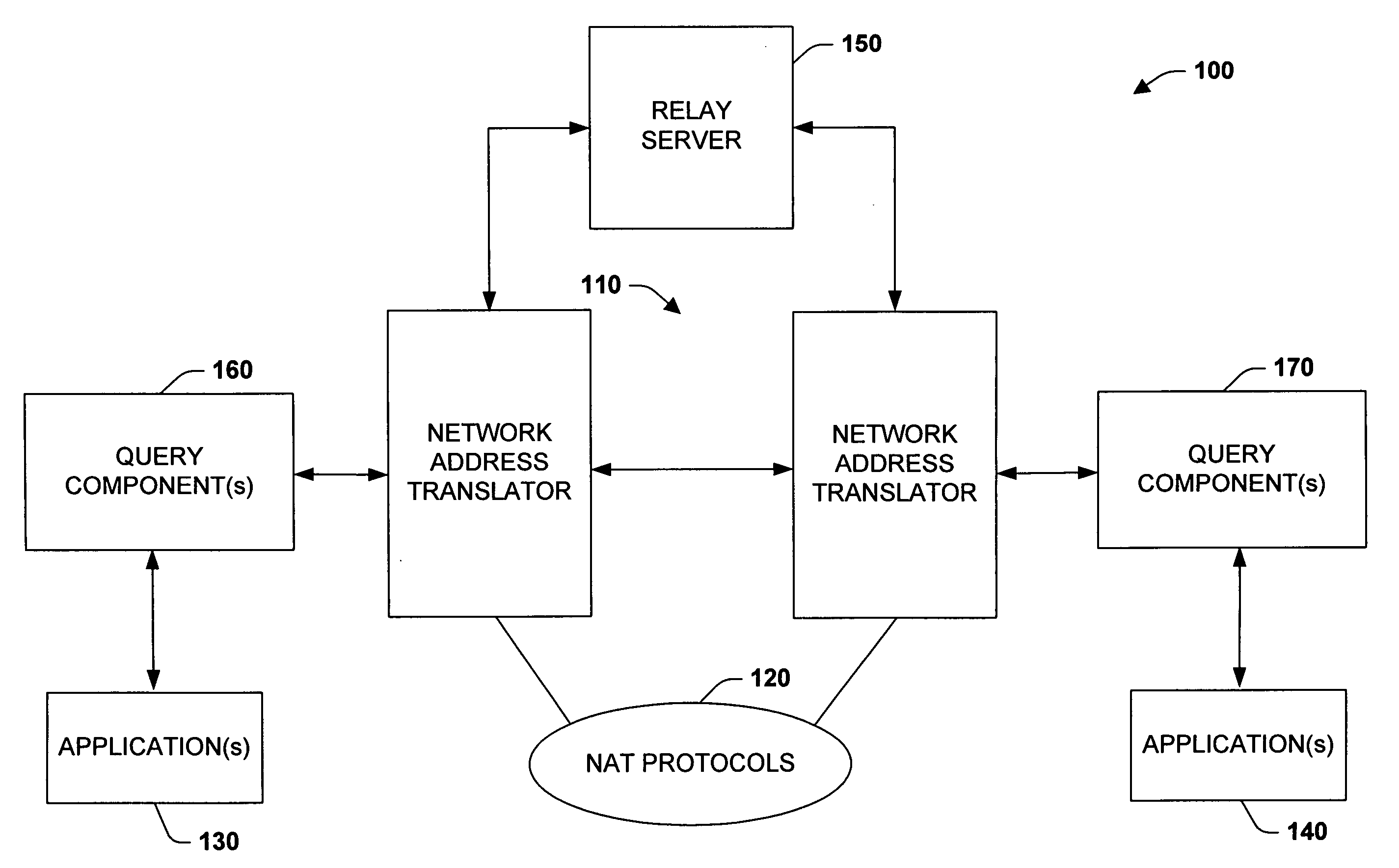
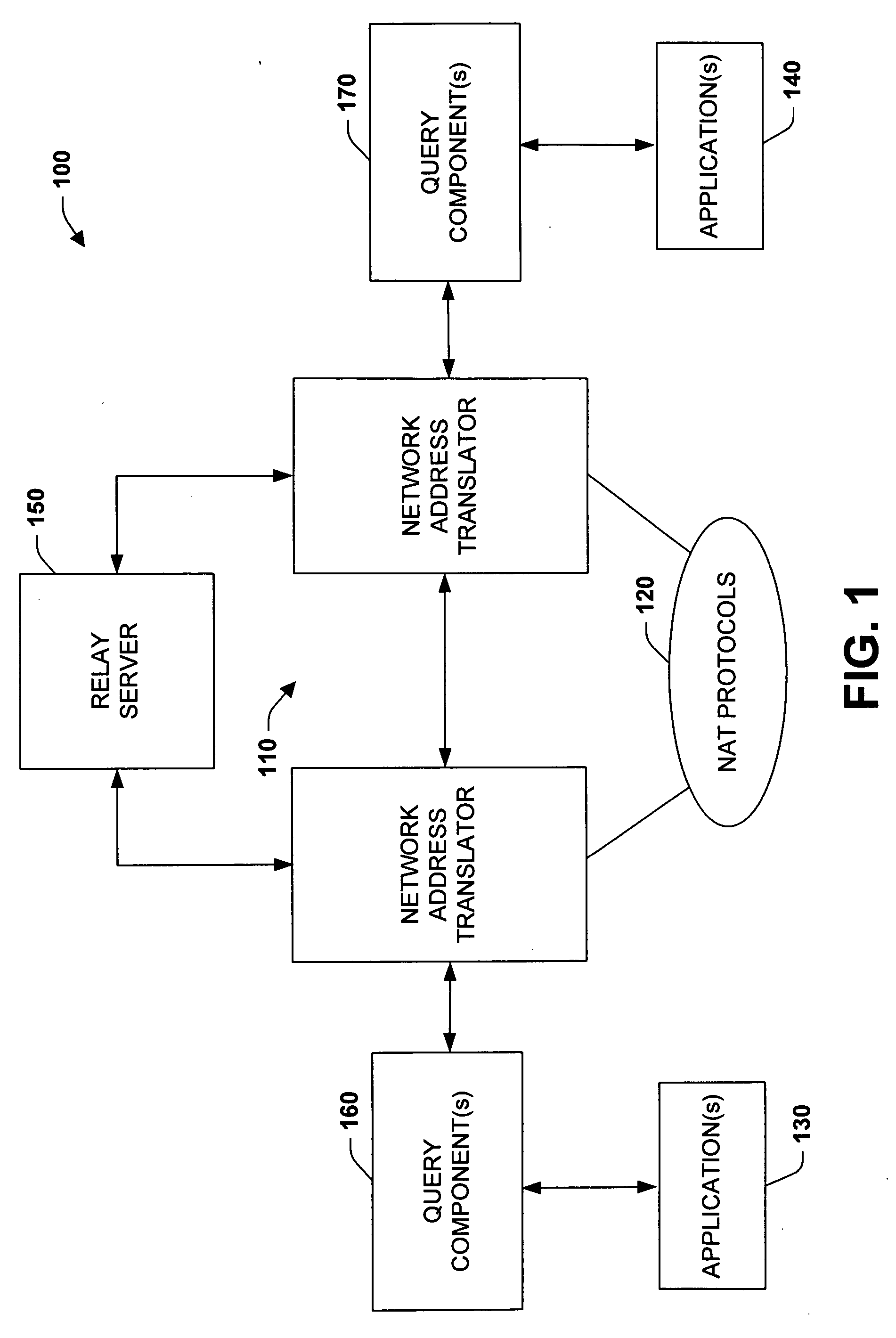
Automated NAT traversal for peer-to-peer networks
InactiveUS20060182100A1Facilitate communicationReduce administrative burdenData switching by path configurationMultiple digital computer combinationsCommunications systemNAT traversal
The subject invention relates to systems and methods that facilitate direct network communications between peers that operate behind Network Address Translators. In one aspect, a network communications system is provided. The system includes one or more Network Address Translators (NAT) to communicate data across a network between peers. A protocol selection component that automatically selects among a plurality of protocols according to one or more NAT types in order to determine a subset of the protocols that facilitate communications between the peers.
Owner:MICROSOFT TECH LICENSING LLC
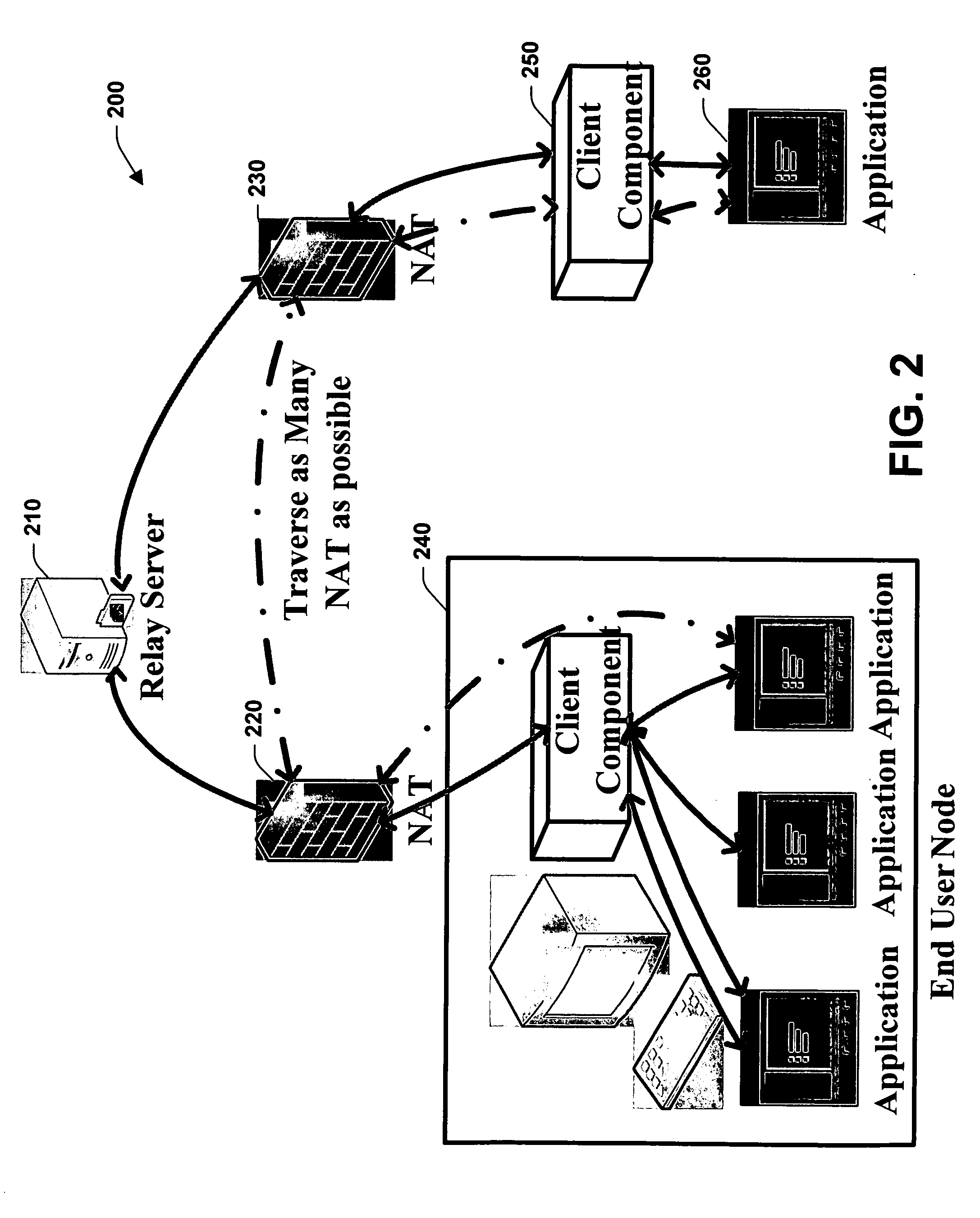
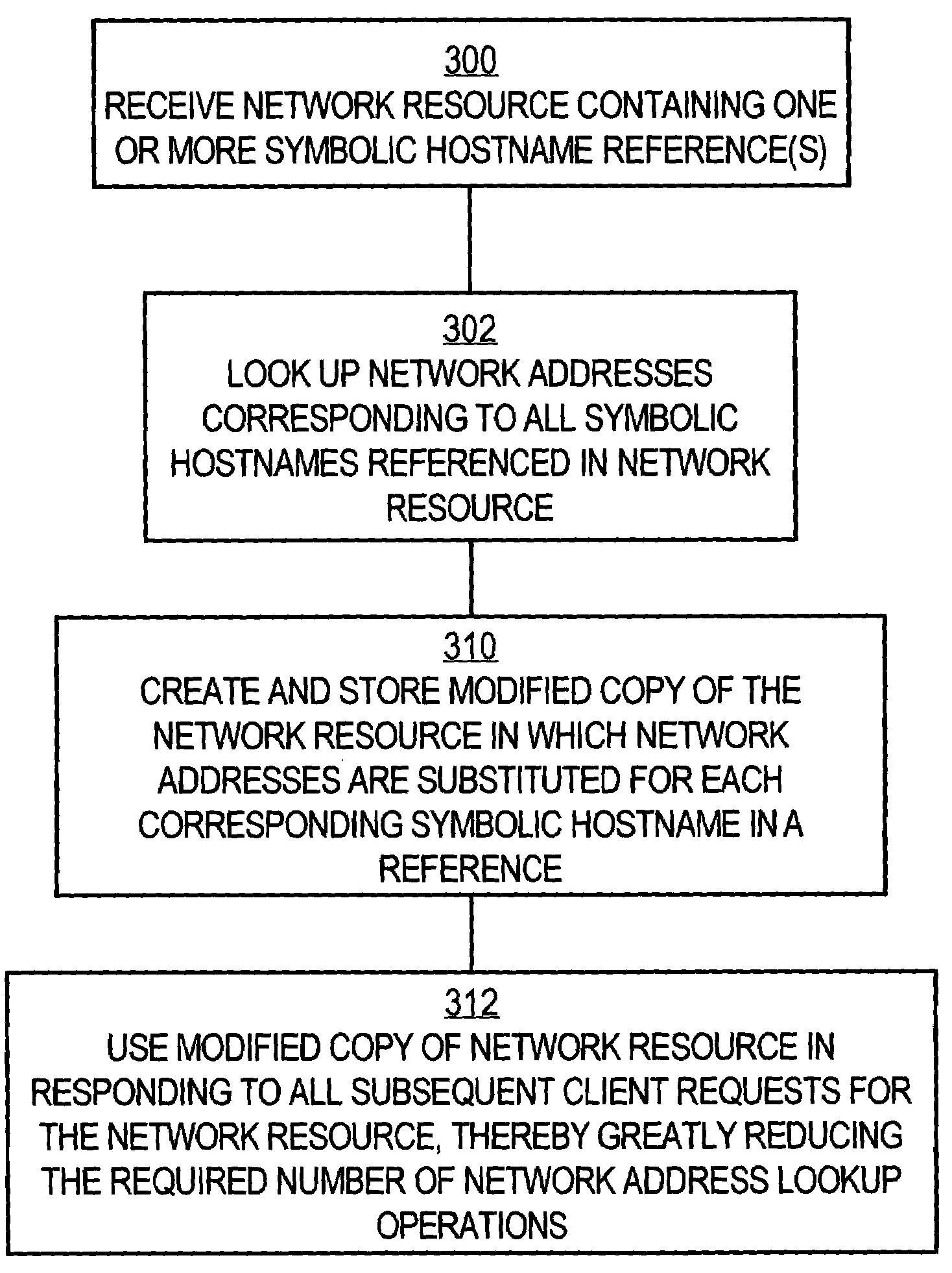
System and method of optimizing retrieval of network resources by identifying and substituting embedded symbolic host name references with network addresses in accordance with substitution policies
InactiveUS7082476B1Reduce in quantityEasy accessMultiple digital computer combinationsTransmissionCache serverNetwork addressing
A method and apparatus are provided for optimizing retrieval of network resources. In one embodiment, a method of optimizing access to a network resource is implemented in a computer program executed by a router, cache server, or proxy server. A network resource that contains one or more embedded symbolic host name references is received. A network address corresponding to each of the embedded symbolic host name references is determined. A modified copy of the network resource is created and stored; in the modified copy, a network address is substituted for each corresponding embedded symbolic host name reference. Thereafter, the modified copy of the network resource in responding to all subsequent client requests for the network resource, thereby greatly reducing the required number of network address lookup operations. In one specific embodiment, IP addresses are determined using DNS queries for the hostname portion of all URLs that are embedded in a Web page using image, applet, object, or embed tags. The IP addresses are stored in place of the hostname portions in a modified copy of the Web page, typically in a cache. As a result, when the modified page is subsequently served to clients, the clients need not carry out DNS resolution of all the embedded URLs, resulting in reduced network message traffic and more rapid page display.
Owner:CISCO TECH INC
Detecting Public Network Attacks Using Signatures and Fast Content Analysis
ActiveUS20080307524A1Memory loss protectionUser identity/authority verificationComputer hardwarePrivate network
Network worms or viruses are a growing threat to the security of public and private networks and the individual computers that make up those networks. A content sifting method if provided that automatically generates a precise signature for a worm or virus that can then be used to significantly reduce the propagation of the worm elsewhere in the network or eradicate the worm altogether. The content sifting method is complemented by a value sampling method that increases the throughput of network traffic that can be monitored. Together, the methods track the number of times invariant strings appear in packets and the network address dispersion of those packets including variant strings. When an invariant string reaches a particular threshold of appearances and address dispersion, the string is reported as a signature for suspected worm.
Owner:RGT UNIV OF CALIFORNIA
Method for optimal path selection in traversal of packets through network address translators
InactiveUS20050259637A1Reduce administrative overheadFast convergenceMultiplex system selection arrangementsError preventionNetwork addressNetwork address translation
Reduction of administrative overhead in maintaining network information, rapid convergence on an optimal routing path through the data network, and utilization of only required network resources are realized by a novel method for establishing a call path between network users. The method is based upon deployment of a network information server that stores network topology information and that is addressable by each end user. In this method, the network information server receives a request to establish a call path. The request identifies at least the calling party. In response to the request, the network information server determines a network traversal between the calling party and a root network wherein the network traversal includes call path information about the sub-networks between the calling party and the root network. The request for establishing a call path can also identify the called party. Based on the calling and called party identification, the network information server also determines a second network traversal between the called party and the root network. The second network traversal is sent to either the calling party or the called party or to both the calling and called parties. The server can determine an intersection of the traversals and send the intersection information to the parties. The intersection information is known as a merge point and represents an optimal call path between the parties.
Owner:ALCATEL-LUCENT USA INC
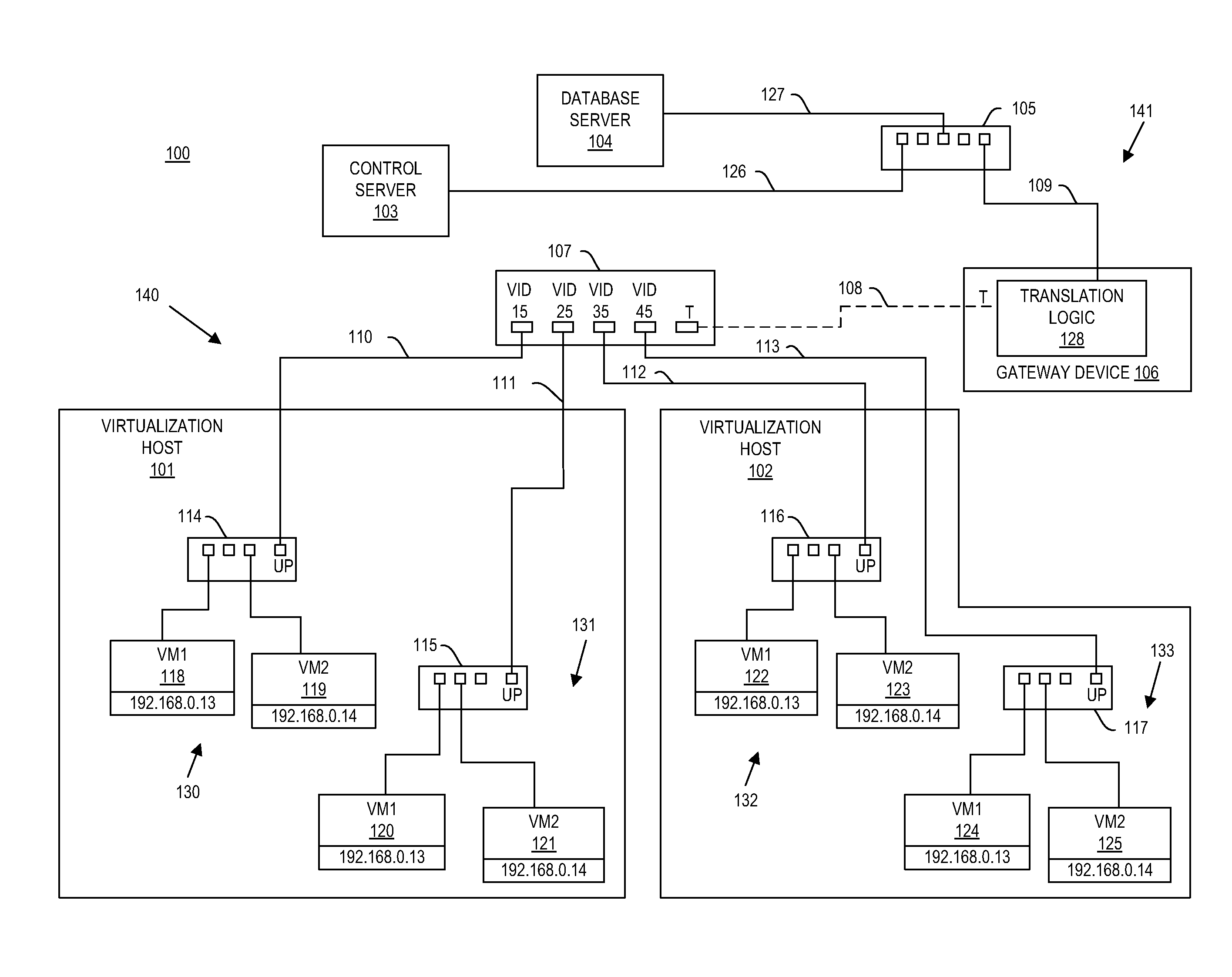
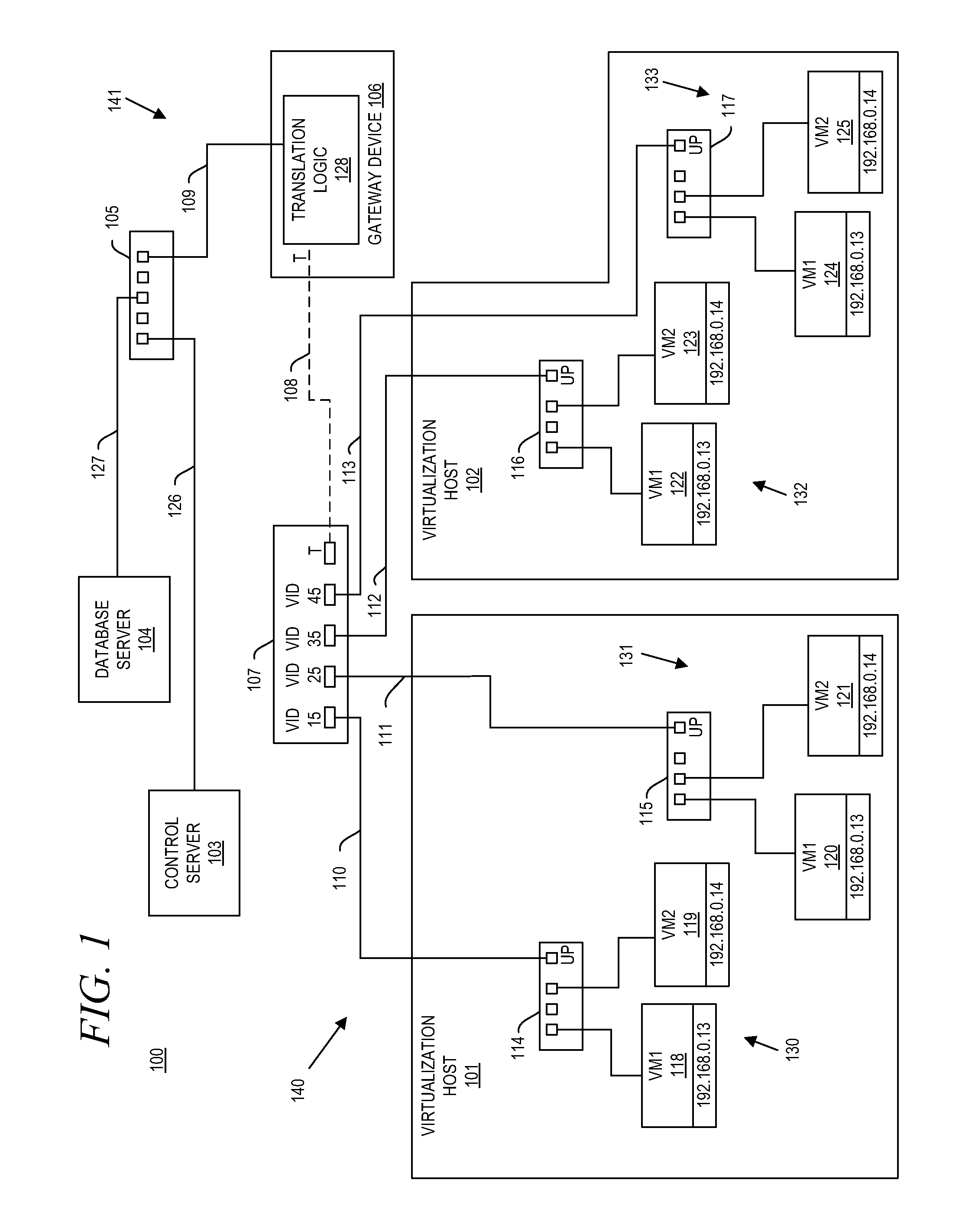
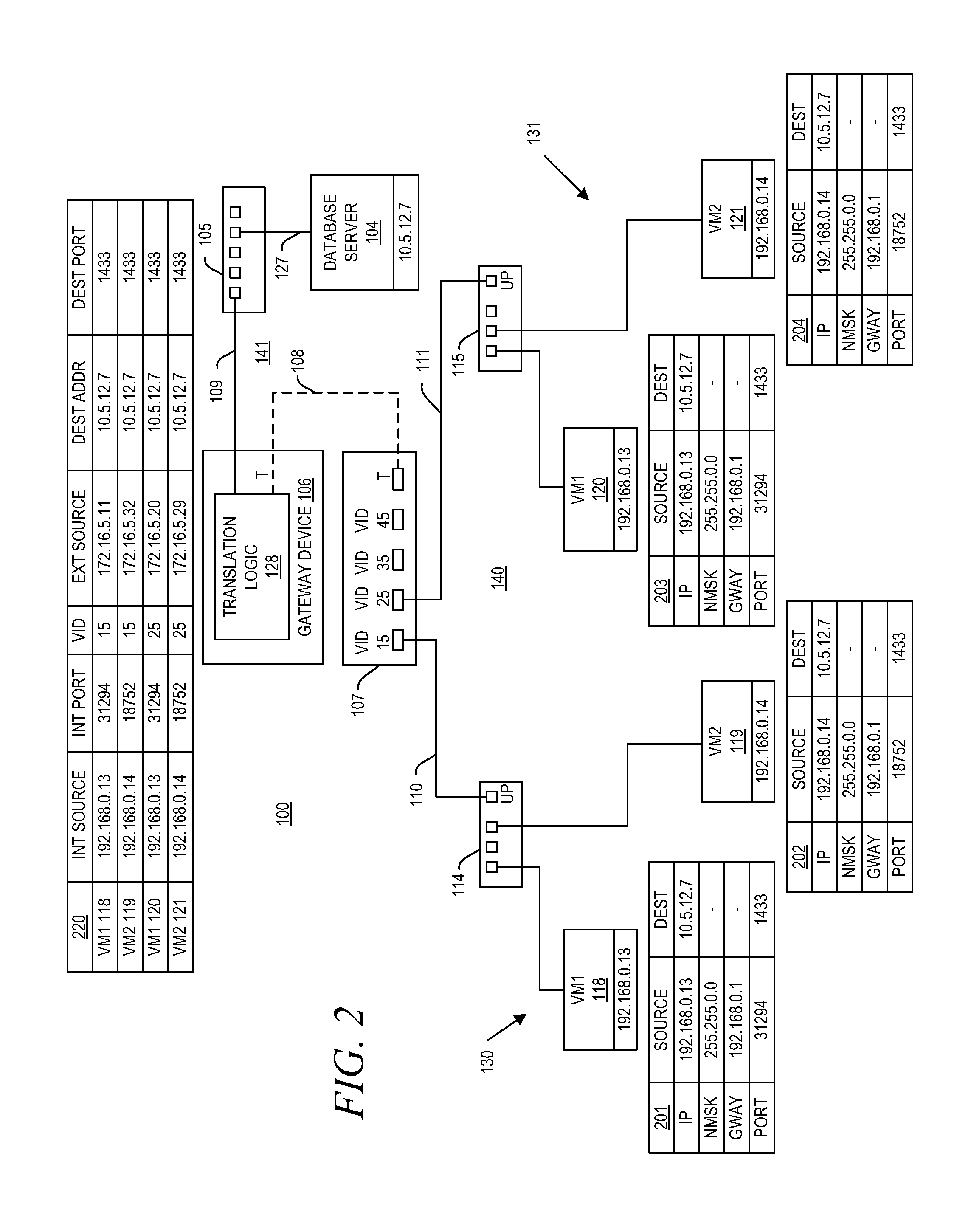
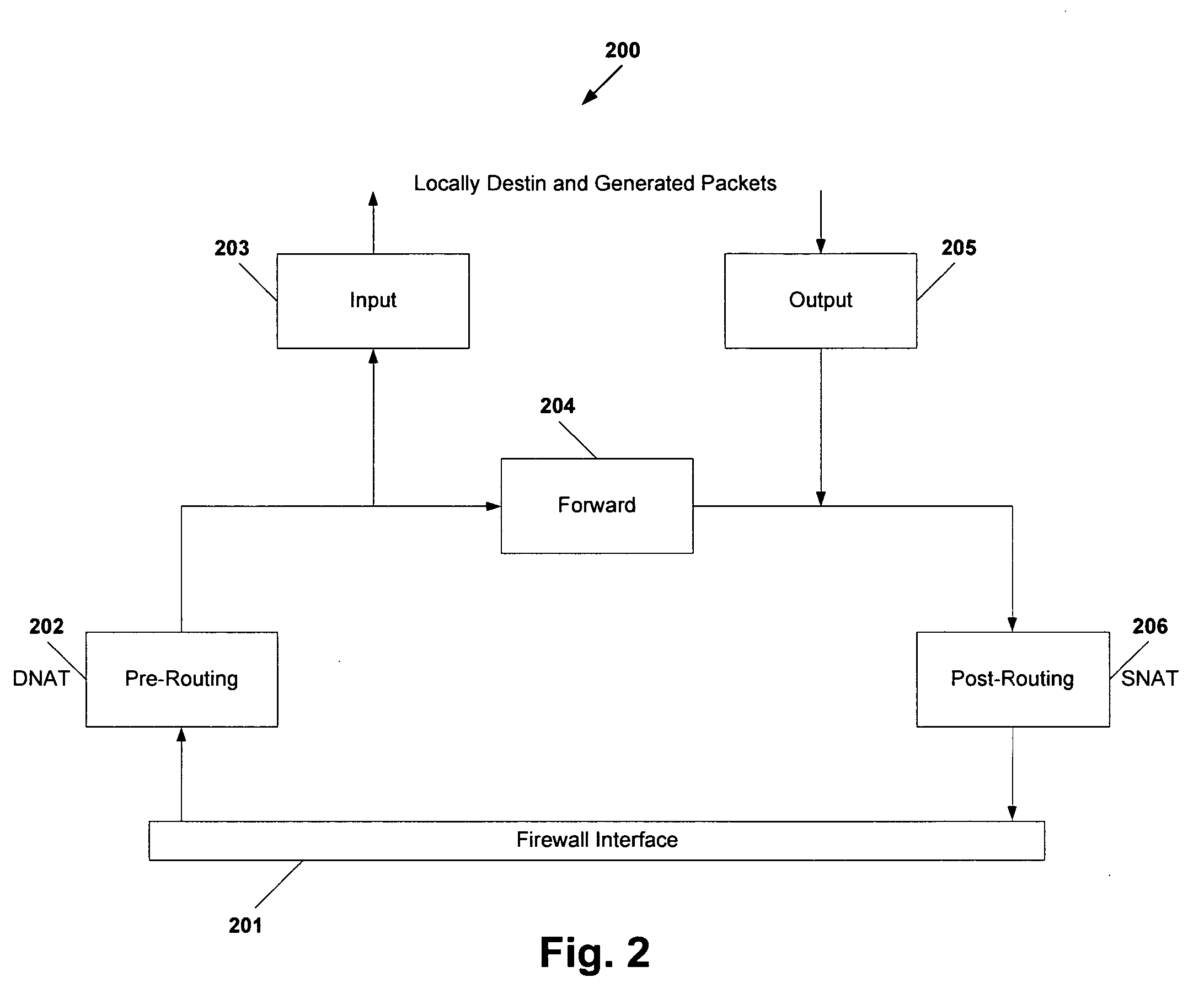
System and method for aggregating communications and for translating between overlapping internal network addresses and unique external network addresses
A gateway device including an access interface to an external network, a trunked interface, and translation logic. The access interface is associated with multiple external source addresses. The trunked interface is interfaced with multiple different virtual local area networks (VLANs), where each VLAN is associated with a corresponding VLAN tag and at least one of potentially overlapping internal source addresses. The translation logic translates between each external source address and each unique combination of internal source address and VLAN tag. A method of network address translation including assigning one of first network addresses to each first device of a first network, dividing the first network into a plurality of VLANs, separating the first devices with the same first network address into different VLANs, and assigning first devices with the same first address to different second network addresses.
Owner:QUEST SOFTWARE INC
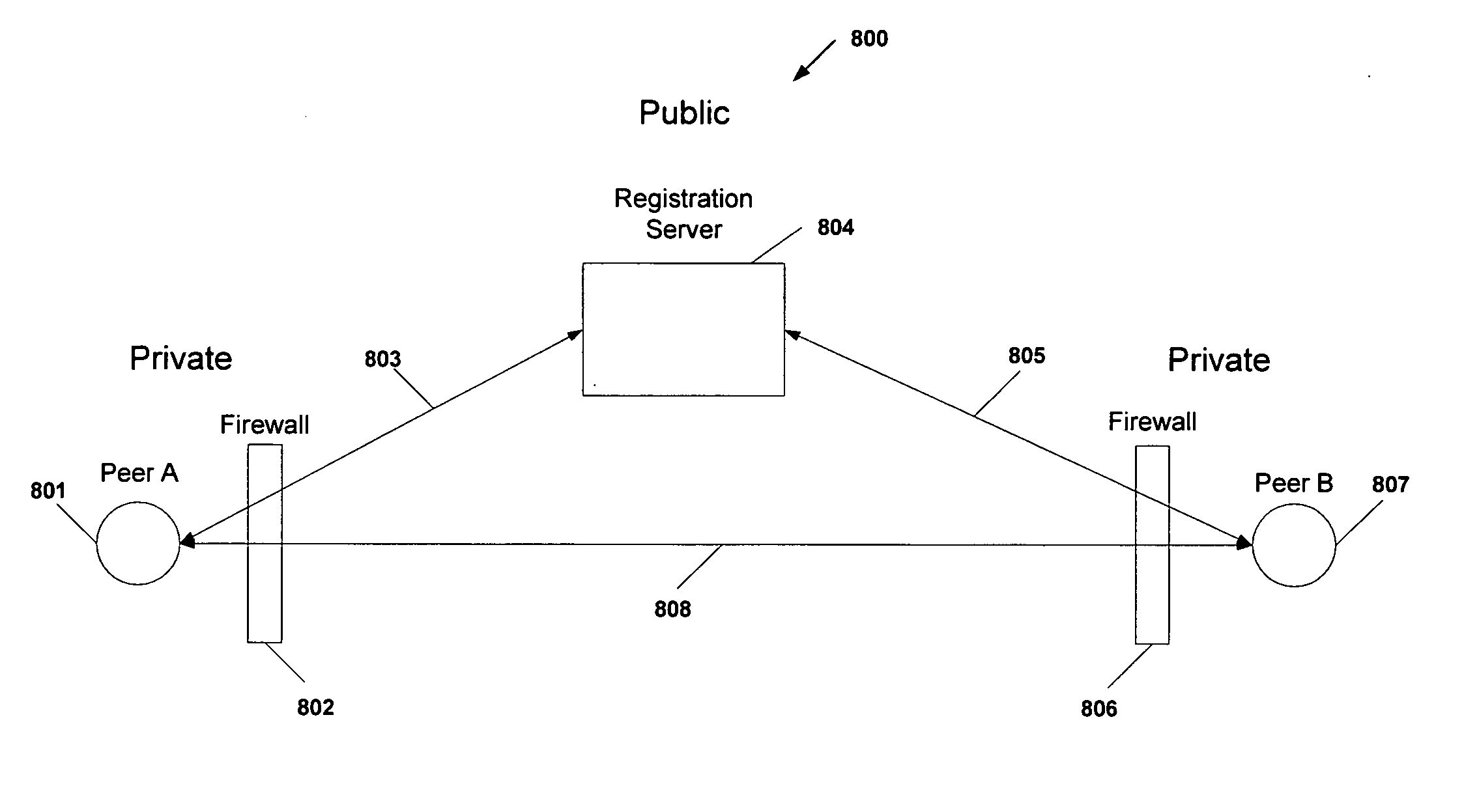
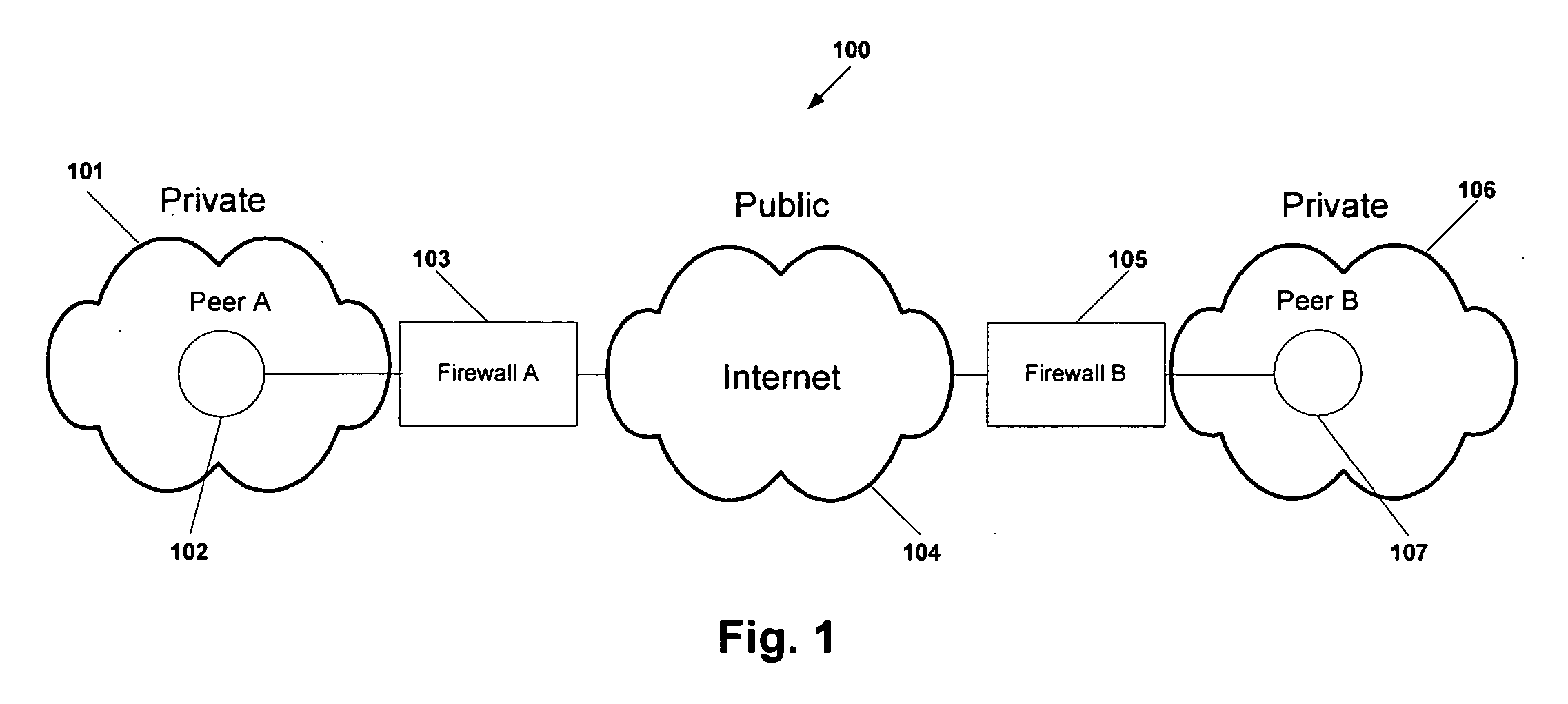
Protocol and system for firewall and NAT traversal for TCP connections
ActiveUS20060215684A1Time-division multiplexData switching by path configurationServer agentNAT traversal
Firewalls and network address translators (NAT) provide many advantages for client and the Internet itself, however, these devices break many existing transmission control protocol (TCP) / Internet Protocol (IP) applications, since they conceal the identity of IP clients (i.e., peers) and block transmission control protocol (TCP) call setup requests. Firewalls and NATs make it impossible for one TCP peer to discover another and establish a connection. Embodiments of this invention provides a system and a protocol to enable two TCP peers that exist behind one or more firewalls and NATs to automatically setup a true peer-to-peer TCP connection and exchange data without making changes to the firewall or NAT devices or existing TCP-based applications. In embodiments of this invention, the synchronization between the blind TCP peers is achieved using a system that consists of a registration server, an agent application, and a virtual network interface that together relay and replicate the control signals between the two TCP peers. In addition, embodiments of this invention are also used to traverse the NAT and establish a bi-directional peer-to-peer TCP connection in the firewall.
Owner:NETGEAR INC
System and method for a specialized dynamic host configuration protocol proxy in a data-over-cable network
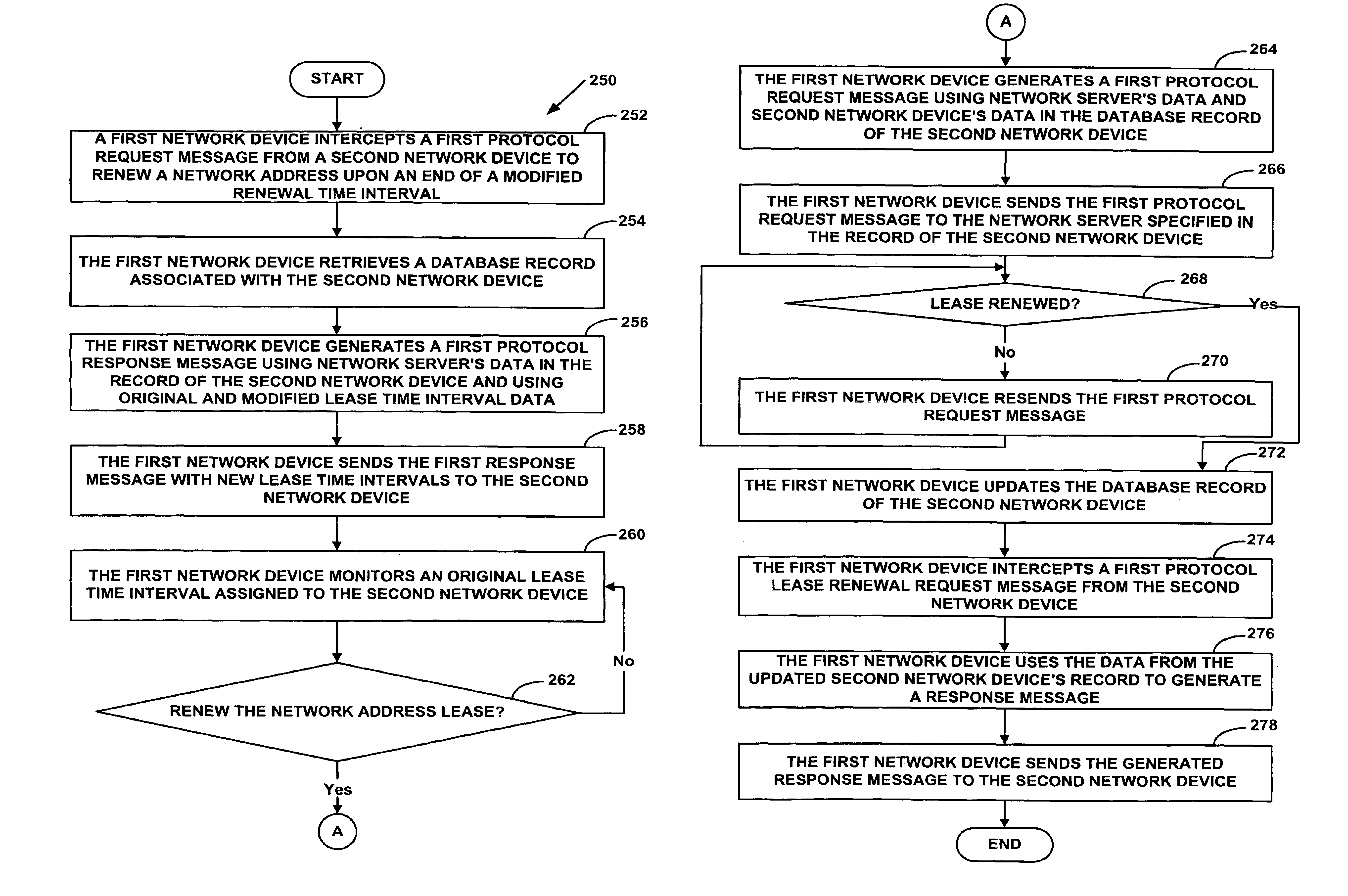
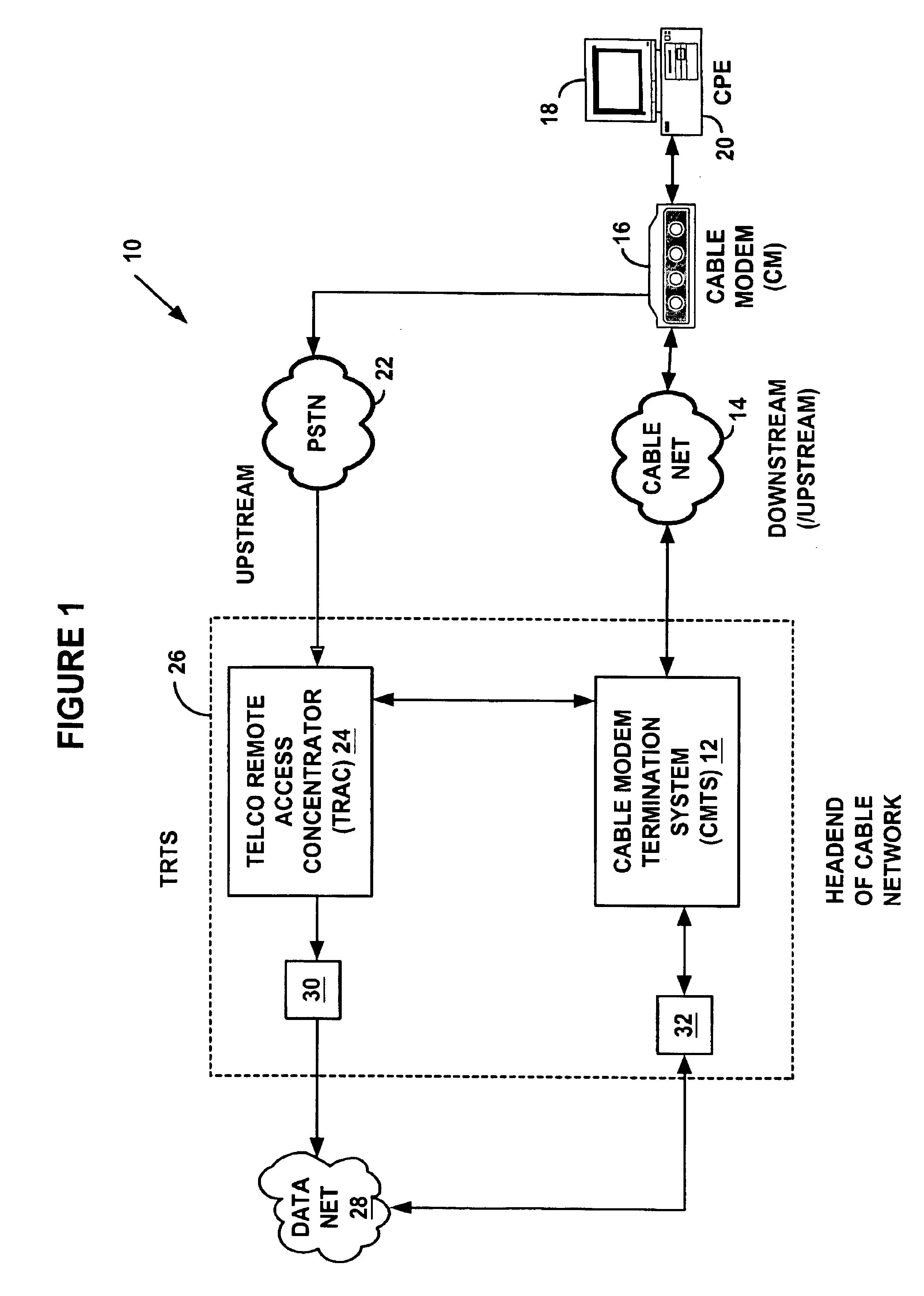
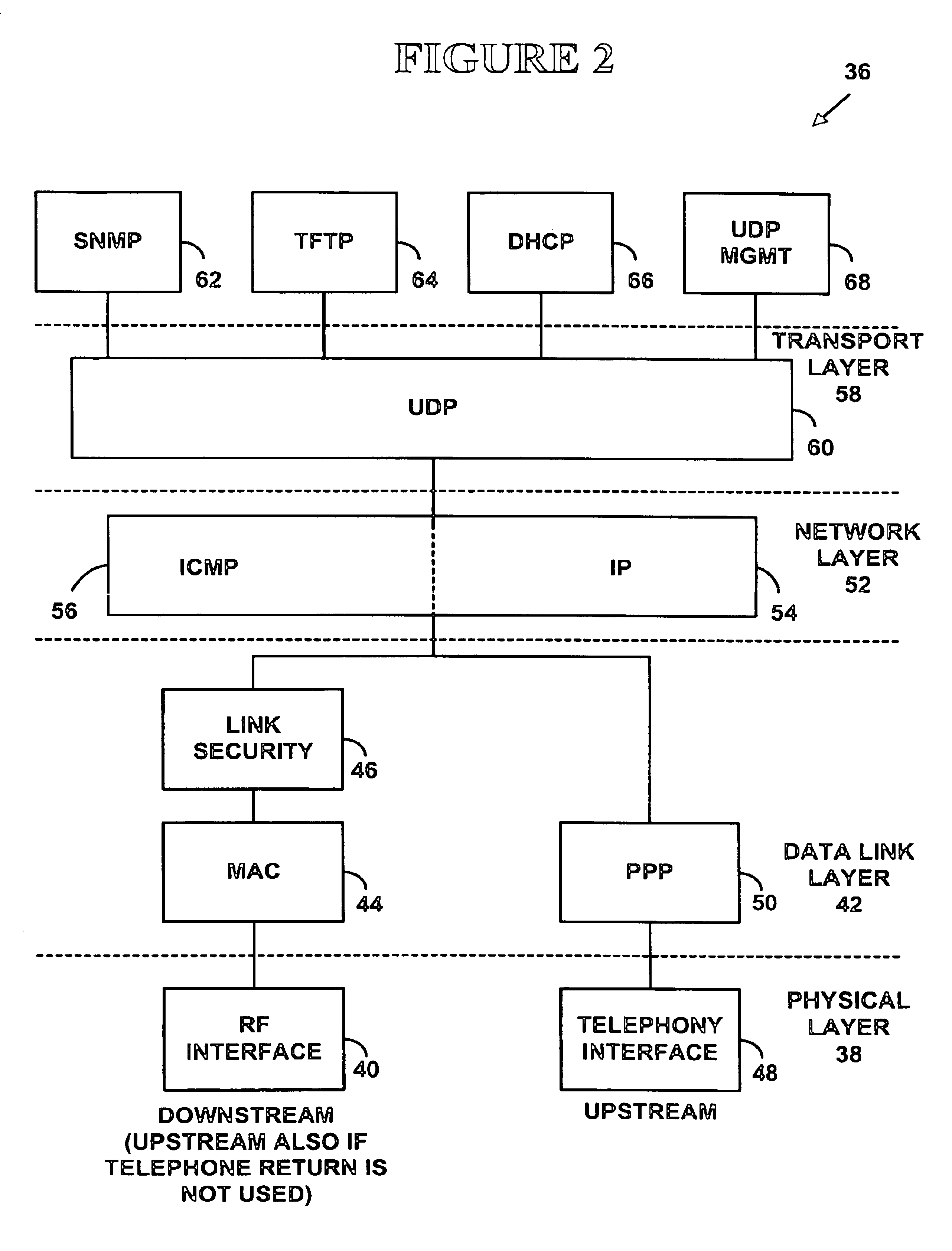
A system and method for proxying Dynamic Host Configuration Protocol (“DHCP”) network services for a network device, such as, a customer premise equipment entity, on a network device, such as, a cable modem, include creating a specialized proxy task for the customer premise equipment entity on the cable modem. One method of the present invention includes intercepting DHCP message flow between a customer premise equipment having a specialized proxy task created on the cable modem and a DHCP server selected by the customer premise equipment entity. The methods further include modifying lease time intervals prior to providing a routable network address lease to a customer premise equipment entity and renewing an initial lease for the customer premise equipment entity by a cable modem prior to expiration of the lease time interval provided by a DHCP server. The methods include using known protocols, such as, for example, the Dynamic Host Configuration Protocol.
Owner:VALTRUS INNOVATIONS LTD
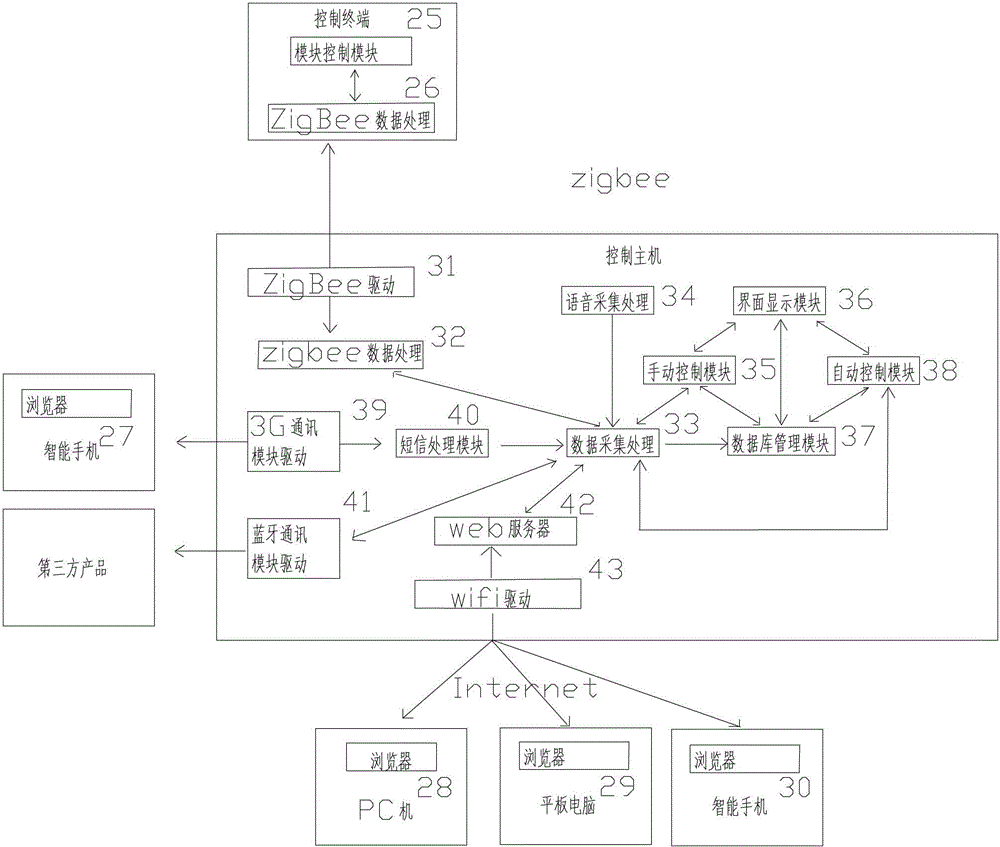
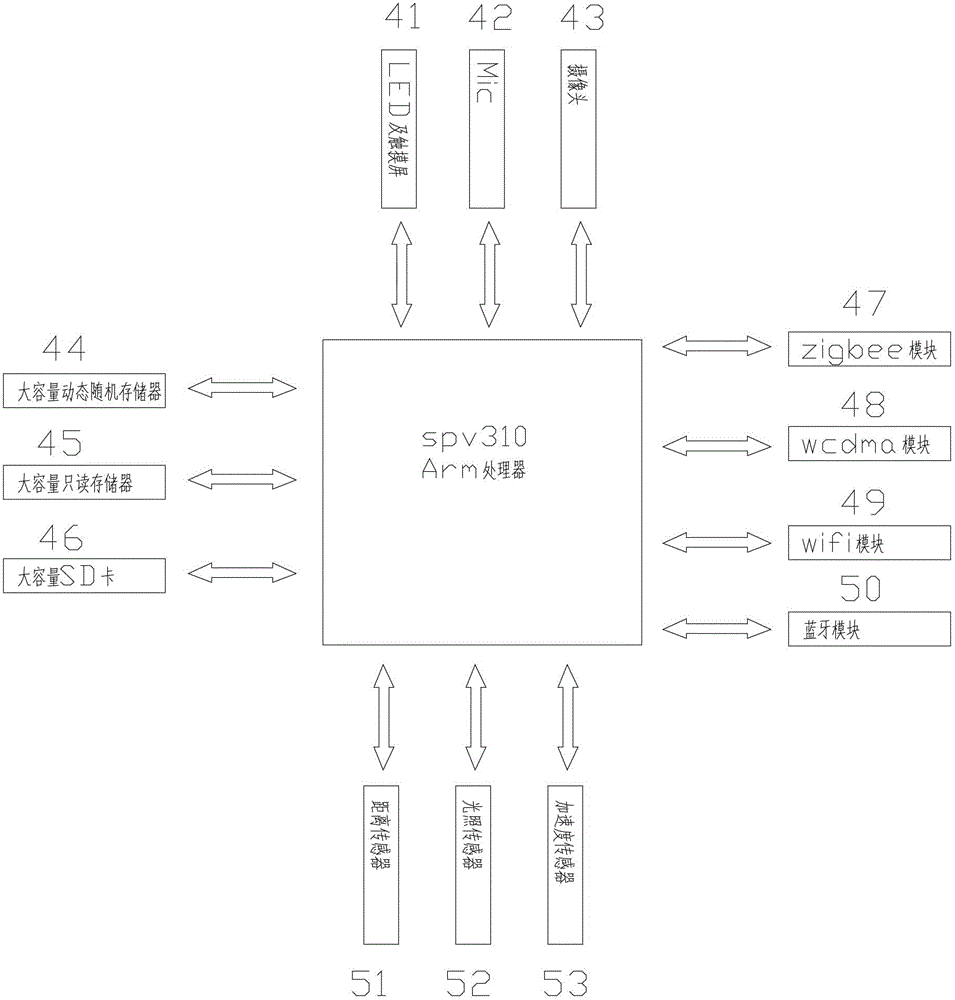
Internet-of-things and android system based intelligent home system and control method
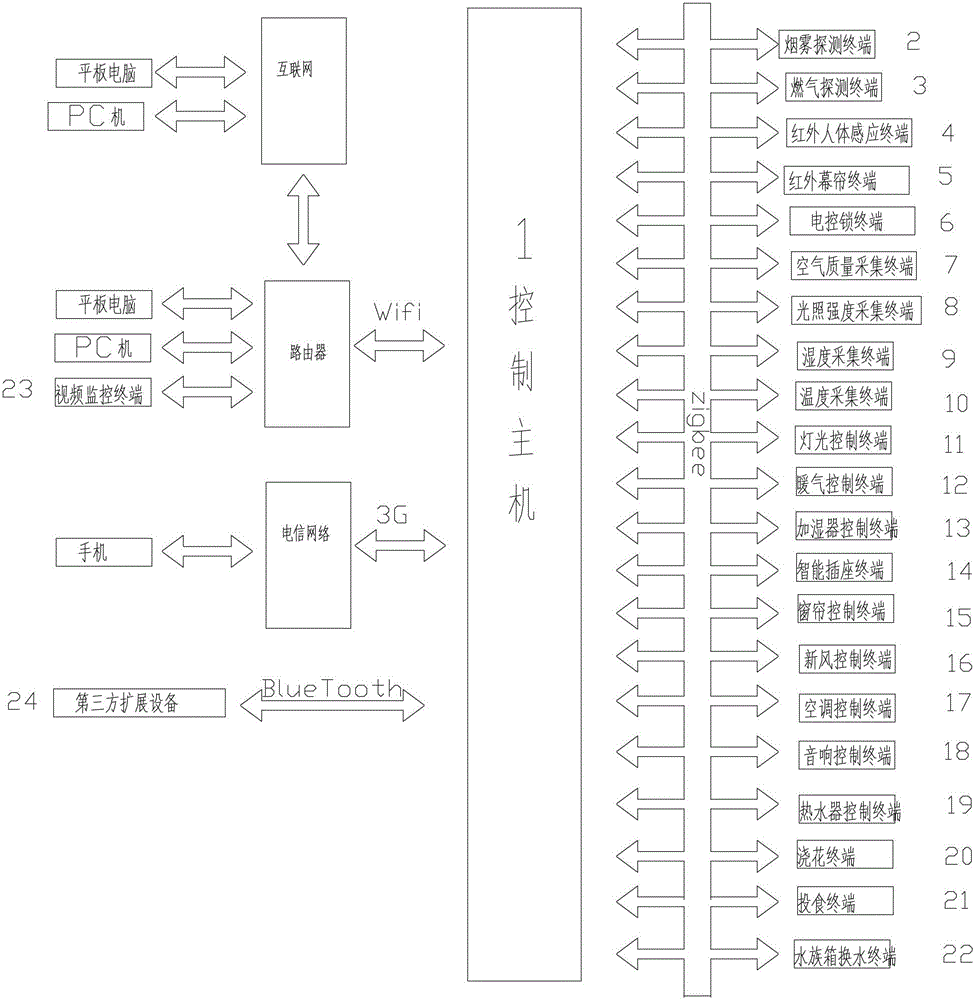
InactiveCN102882752ARealize automatic arming and disarmingReduce complexityData switching by path configurationAutomatic controlWeb service
The invention discloses an internet-of-things and android system based intelligent home system which comprises a control host and a plurality of terminal devices. The control host is provided with a high-performance arm processor, a touch screen and an android operation system, supports zigbee, blueTooth, wifi (wireless fidelity), 3G (the third generation) communication, is provided with a built-in web server and a built-in database, has functions of display, operation, control data storage, server, energy management, and particularly has functions of automatic control, hand-operated control, voice control and remote control. The terminal devices include a sensor terminal, a security terminal and a control terminal, are provided with independent processors and network addresses, have functions of data acquisition, data transmission, instruction receiving, transmitting and processing and IO (input / output) control, and support one or multiple wireless communication manners of zigbee, blueTooth, wifi and 3G.
Owner:TIANJIN GUANGHONG TECH
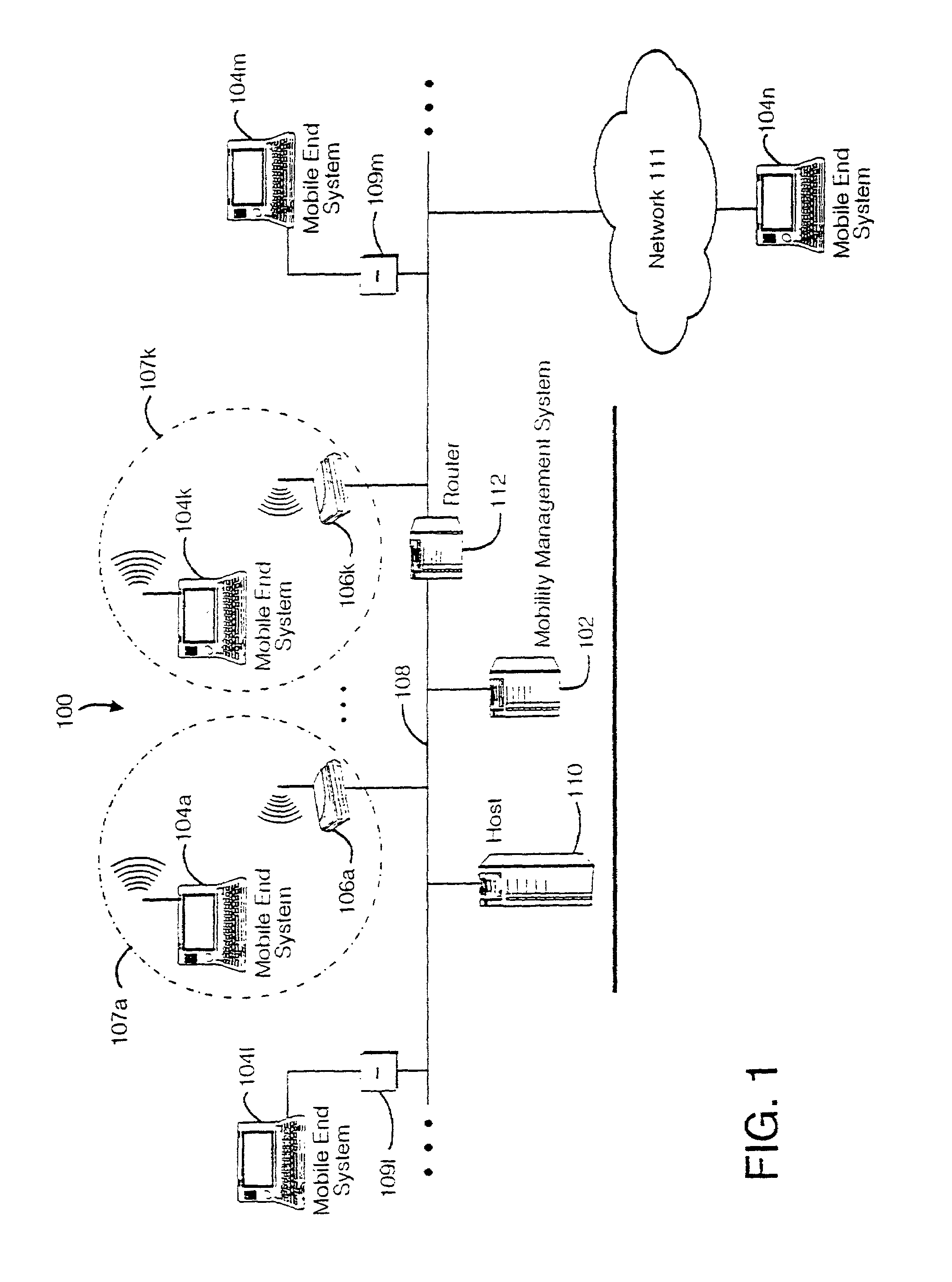
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
InactiveUS6981047B2Error prevention/detection by using return channelData switching by path configurationMobile endNetwork address
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. The solution extends the enterprise network, letting network managers provide mobile users with easy access to the same applications as stationary users without sacrificing reliability or centralized management. The solution combines advantages of existing wire-line network standards with emerging mobile standards to create a solution that works with existing network applications. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. In one example, Mobility Management Server communicates with Mobile End Systems using Remote Procedure Call and Internet Mobility Protocols.
Owner:MOBILE SONIC INC
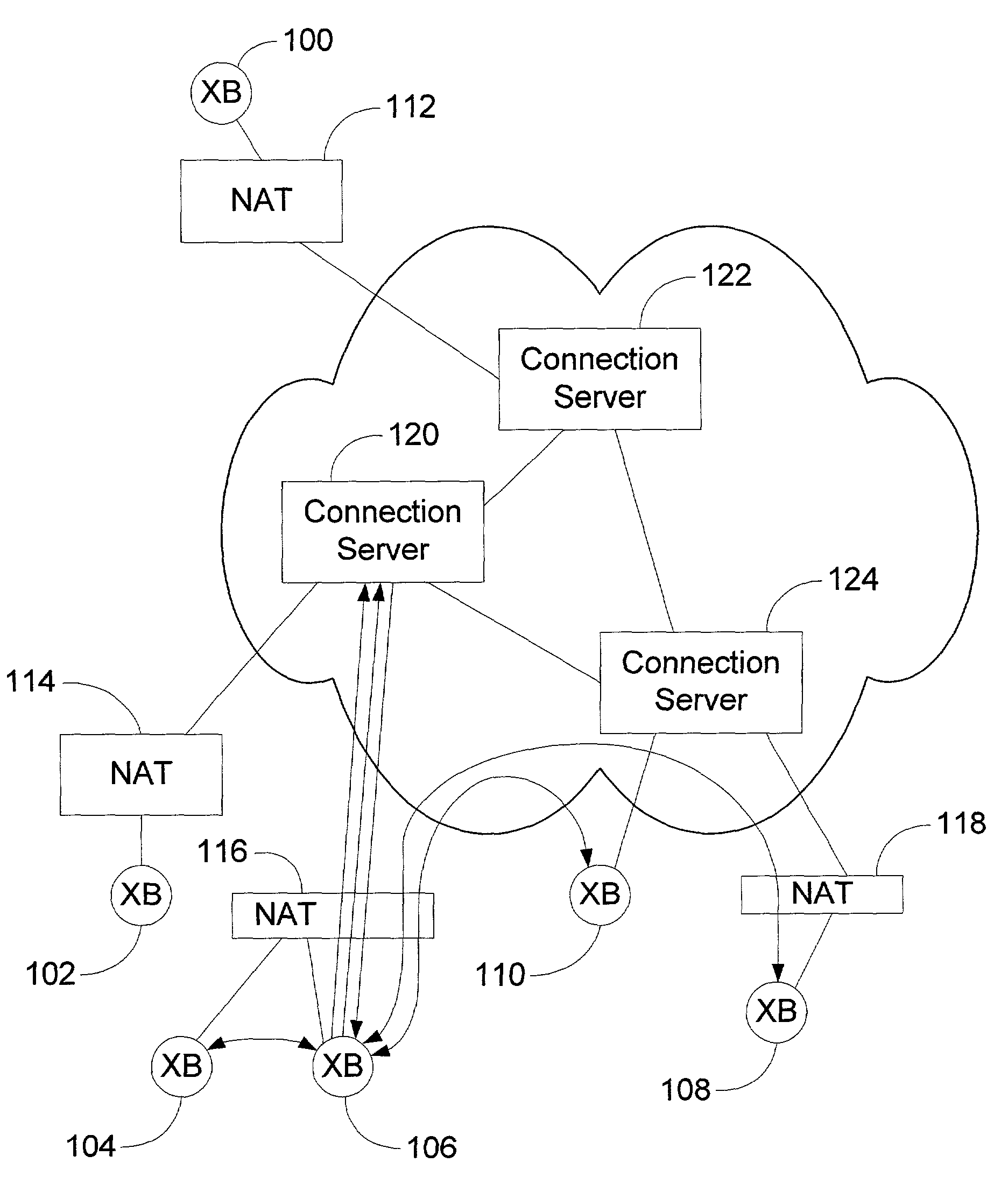
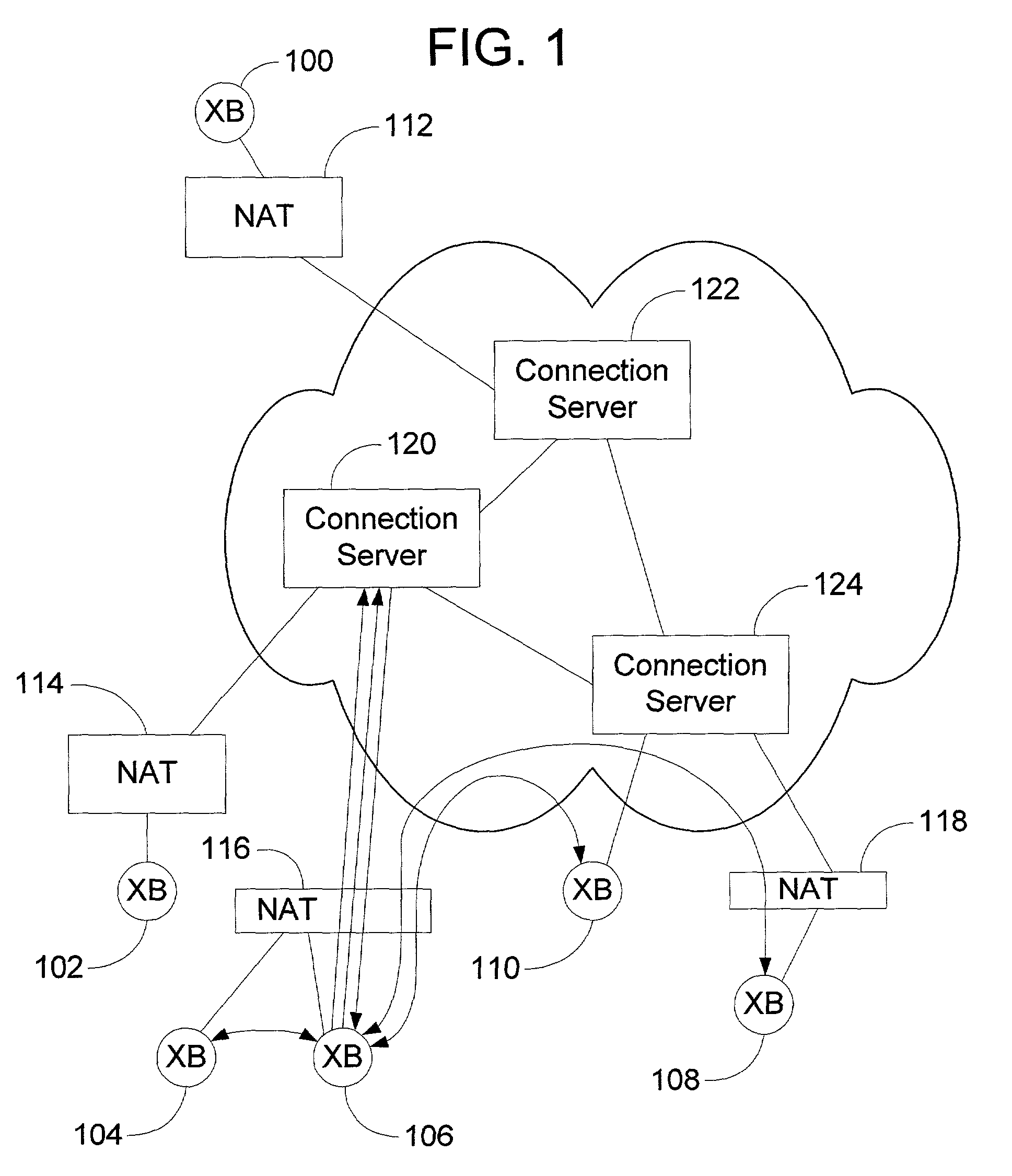
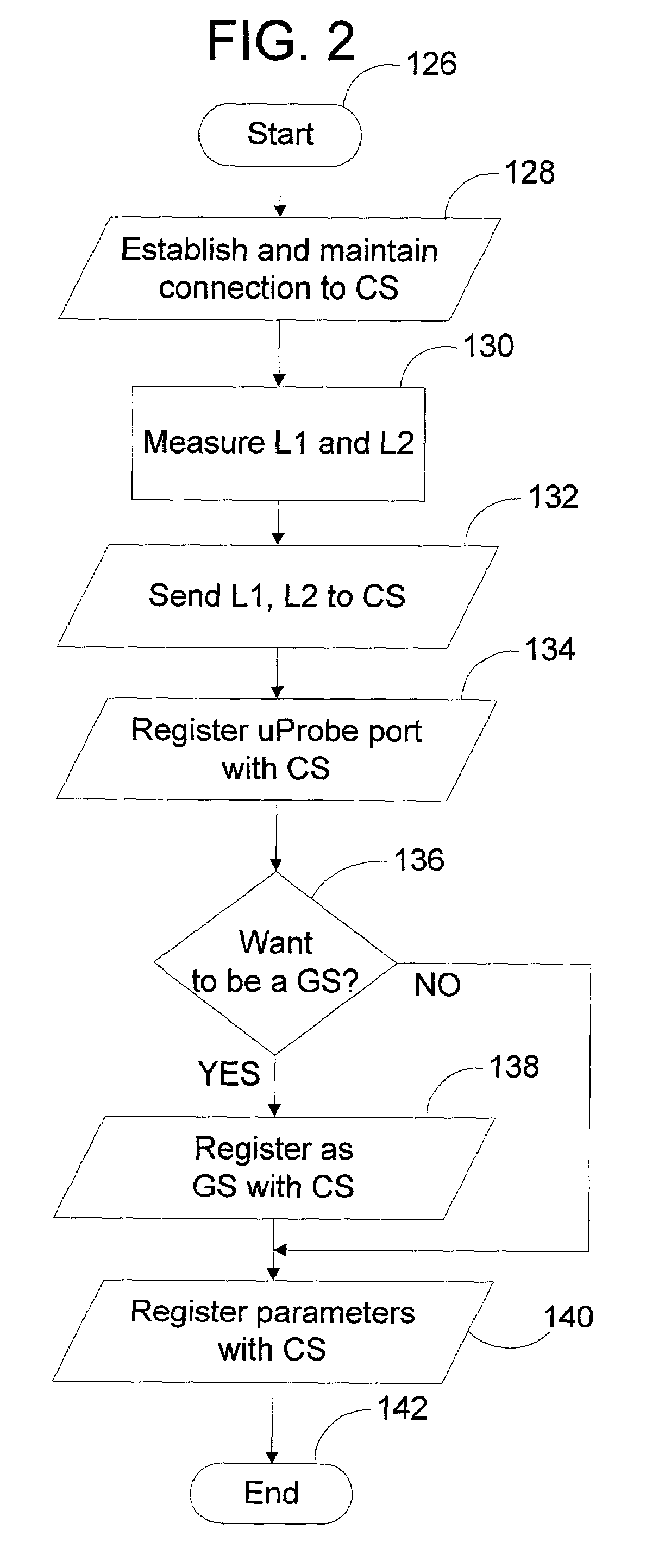
Peer-to-peer method of quality of service (QoS) probing and analysis and infrastructure employing same
InactiveUS7133368B2Improve gaming experienceImprove performanceError preventionTransmission systemsQuality of servicePacket loss
A peer-to-peer (P2P) probing / network quality of service (QoS) analysis system utilizes a UDP-based probing tool for determining latency, bandwidth, and packet loss ratio between peers in a network. The probing tool enables network QoS probing between peers that connect through a network address translator. The list of peers to probe is provided by a connection server based on prior probe results and an estimate of the network condition. The list includes those peers which are predicted to have the best QoS with the requesting peer. Once the list is obtained, the requesting peer probes the actual QoS to each peer on the list, and returns these results to the connection server. P2P probing in parallel using a modified packet-pair scheme is utilized. If anomalous results are obtained, a hop-by-hop probing scheme is utilized to determine the QoS of each link. In such a scheme, differential destination measurement is utilized.
Owner:MICROSOFT TECH LICENSING LLC
Secure wireless local area network
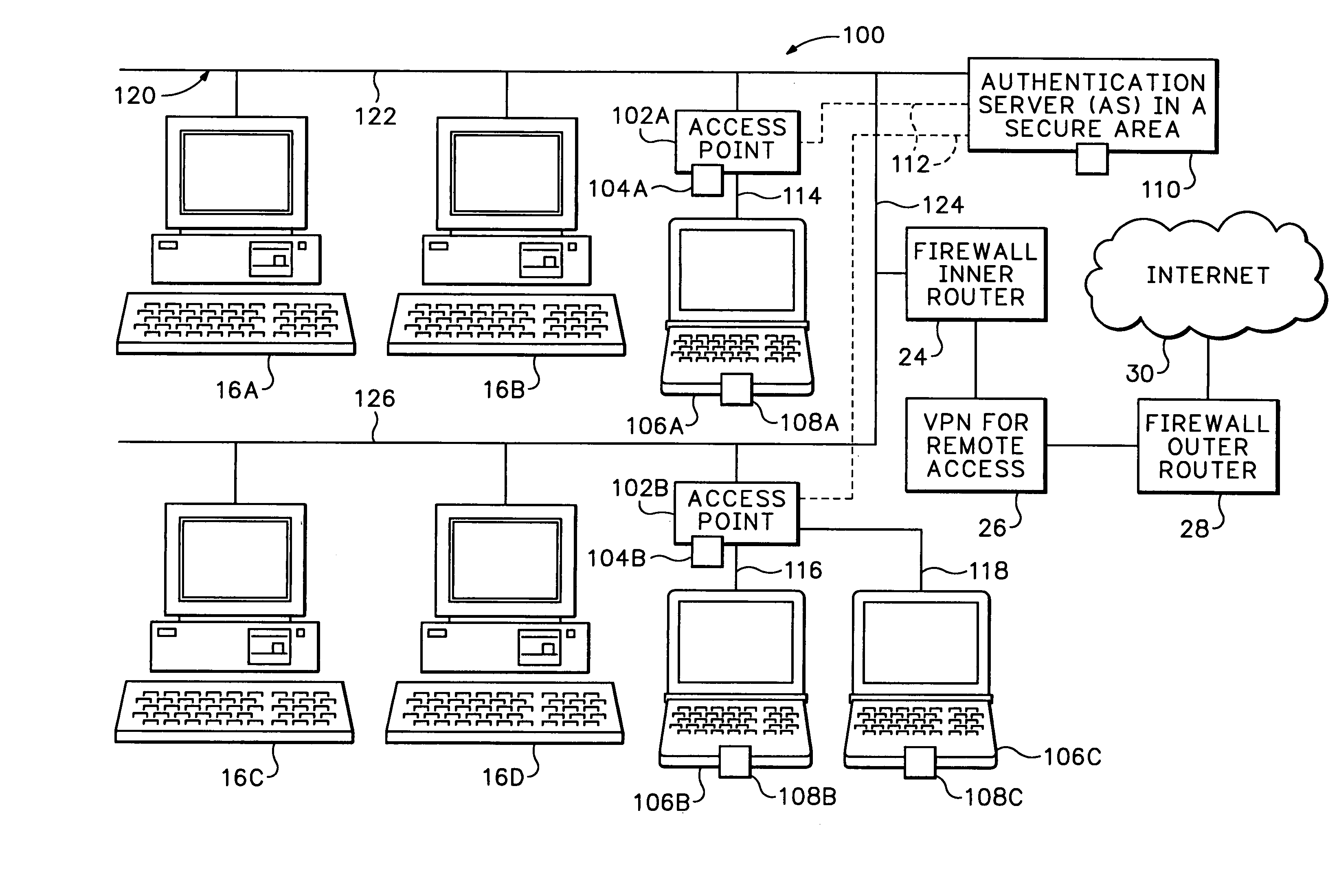
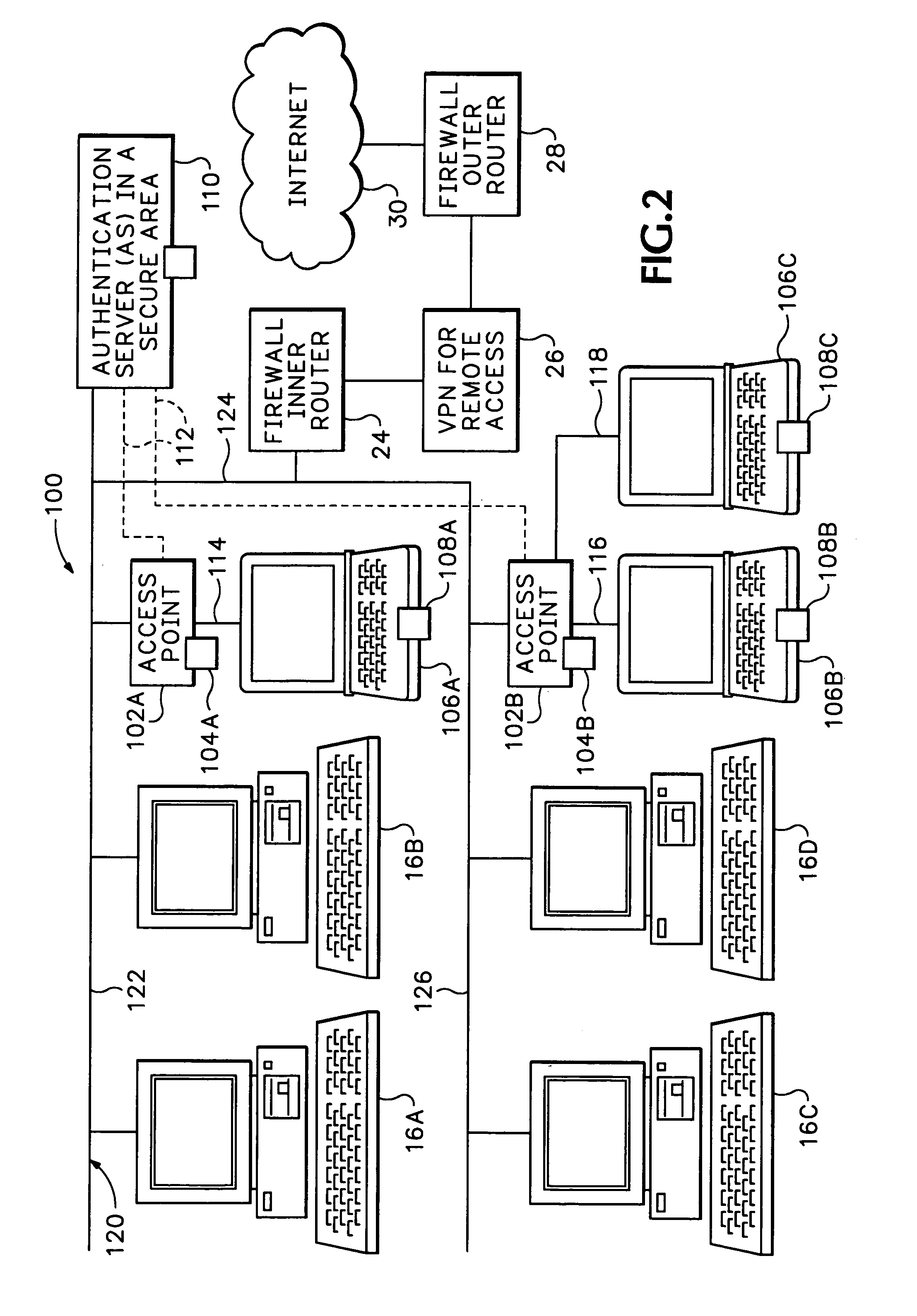
InactiveUS7174564B1Digital data processing detailsUser identity/authority verificationPasswordNetwork addressing
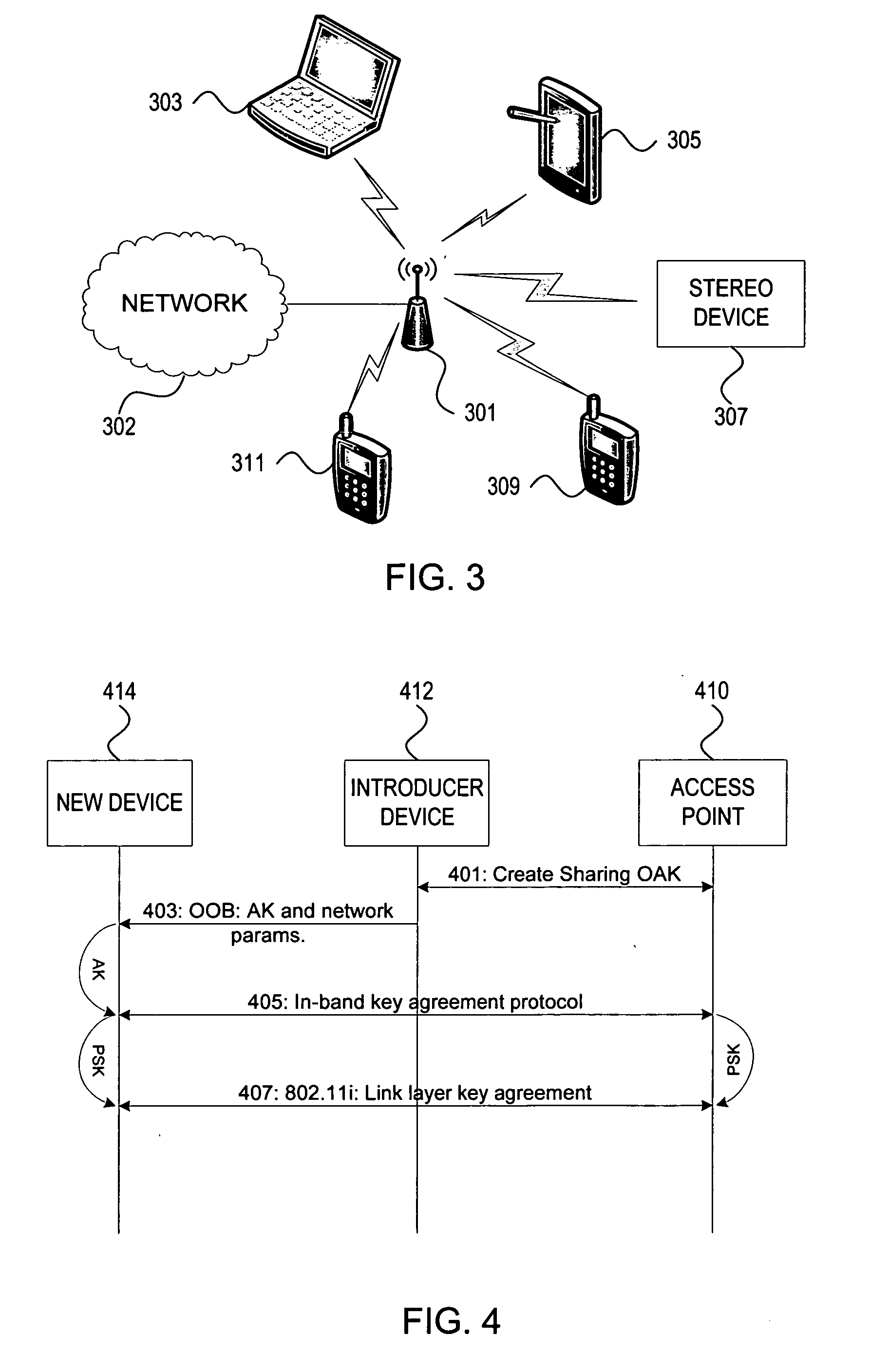
The secure wireless local area network of the present invention includes a single wired network that supports both wired and wireless devices. The network addresses security concerns by including an authentication server that services a plurality of access points. Each access point includes a first authentication device that generates and transmits a first authentication message to the corresponding wireless device over an air channel. The first authentication message includes encrypted validating information about the access point including an access point key that uniquely identifies the access point. Each wireless device includes a second authentication device. The wireless device receives the first authentication message and determines whether the access point is authorized to connect to the wired network. If the access point is valid, the second authentication device responds to the first authentication message by generating and transmitting a second authentication message to the access point. The second authentication message includes encrypted validating information about the wireless device and operator, e.g., a device key and the operator's logon name and password. The access point determines the authenticity of the wireless device by decrypting the portion of the second authentication message that includes the device key. If the wireless device is valid, the AP opens a control channel with the authentication server. The AP transmits the first and second authentication messages to the authentication server. If the authentication server validates the access point and the operator's logon name and password, it will authorize access to the wired network.
Owner:INTEL CORP
System and method for establishing network connection with unknown network and/or user device
InactiveUS7088727B1Soft handoffImprove throughputTime-division multiplexData switching by path configurationNetwork connectionNetwork addressing
Owner:NOMADIX INC
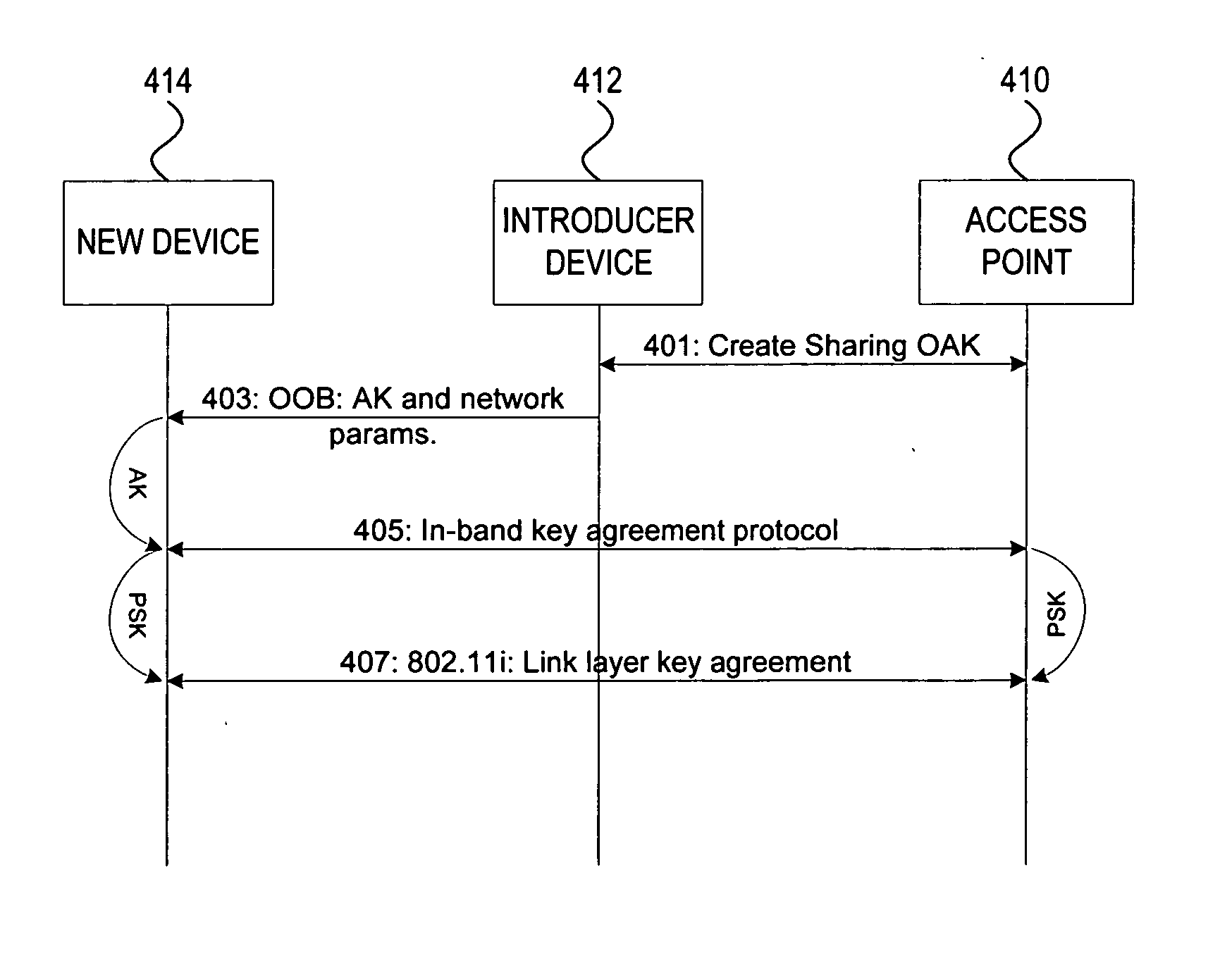
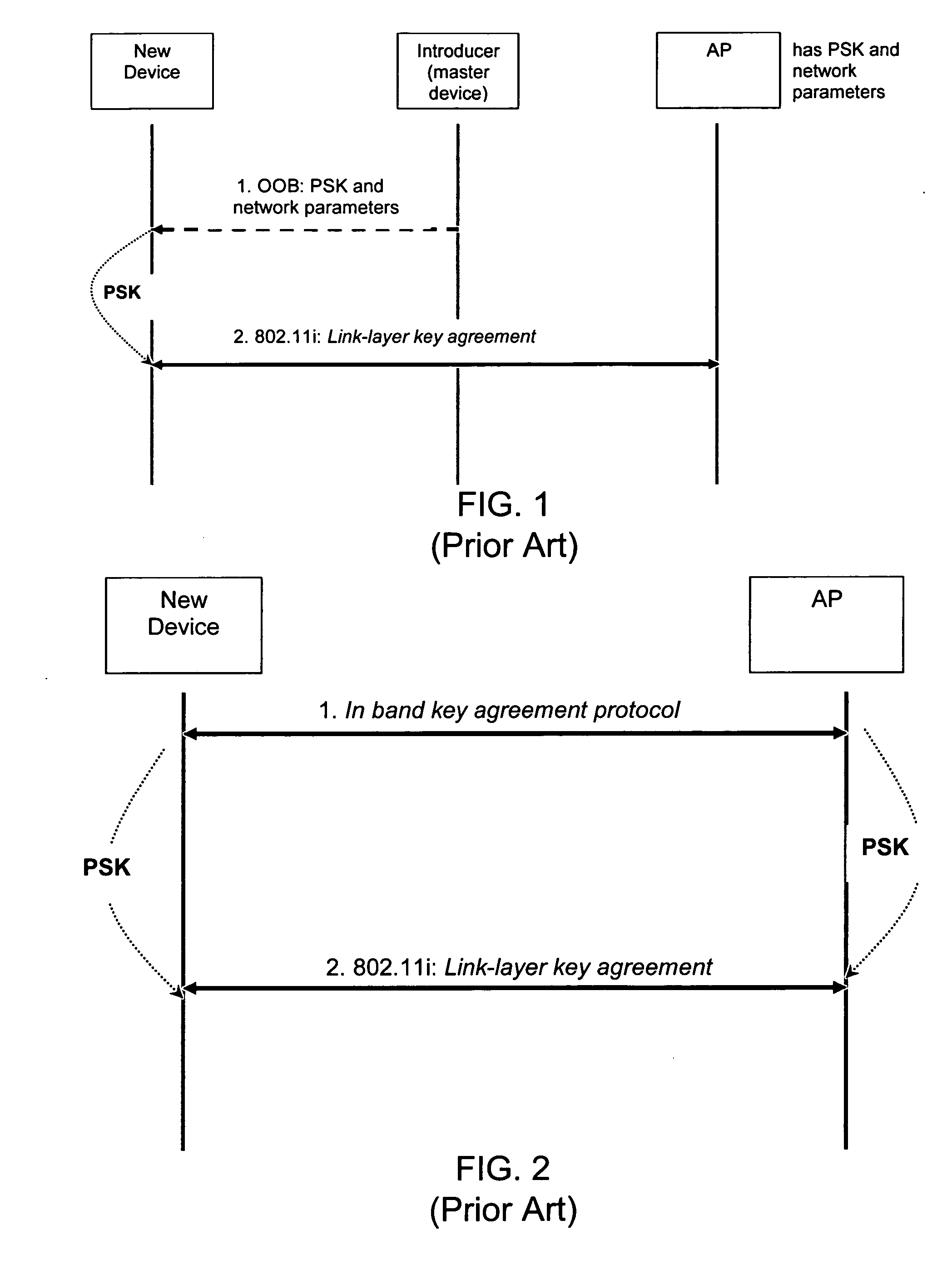
Administration of wireless local area networks
ActiveUS20060251256A1Improve securityImprove usabilityKey distribution for secure communicationAssess restrictionProbable CaseNetwork addressing
Methods and systems for managing access to a wireless local area network are provided. A wireless access point (AP) may use a unified approach that utilizes an out-of-band channel to communicate authentication key and network address information to a guest device, and utilizes an in-band channel to establish communications with the guest device, and also provides support for in-band setup on all devices. The ability to use out-of-band where possible provides for an increase to security and usability, and the possibility of delegating access from one device to another. The unified approach thereby also provides easy management of guest access to the WLAN.
Owner:NOKIA TECHNOLOGLES OY
Method and apparatus for secure content delivery over broadband access networks
InactiveUS7017188B1Expand accessAvoid leverageData processing applicationsDigital data processing detailsNetwork addressingNetwork address
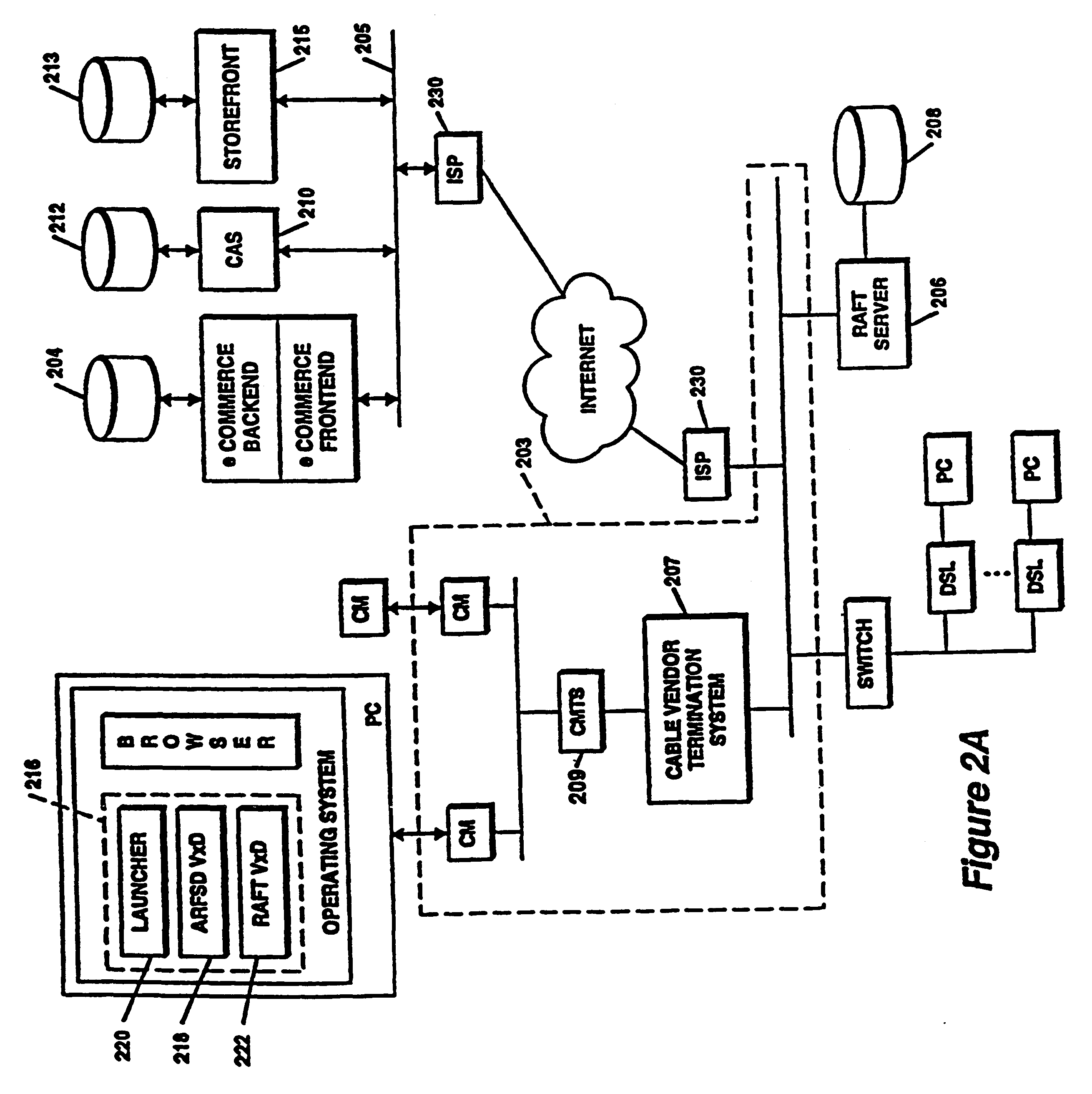
A system for secure delivery of on-demand content over broadband access networks utilizes a pair of servers and security mechanisms to prevent client processes from accessing and executing content without authorization. A plurality of encrypted titles are stored on a content server coupled to the network. An access server also coupled to the network contains the network addresses of the titles and various keying and authorization data necessary to decrypt and execute a title. A client application executing on a user's local computer system is required to retrieve the address, keying and authorization data from the access server before retrieving a title from the content server and enabling execution of the title on a user's local computer system.
Owner:MICROSOFT TECH LICENSING LLC
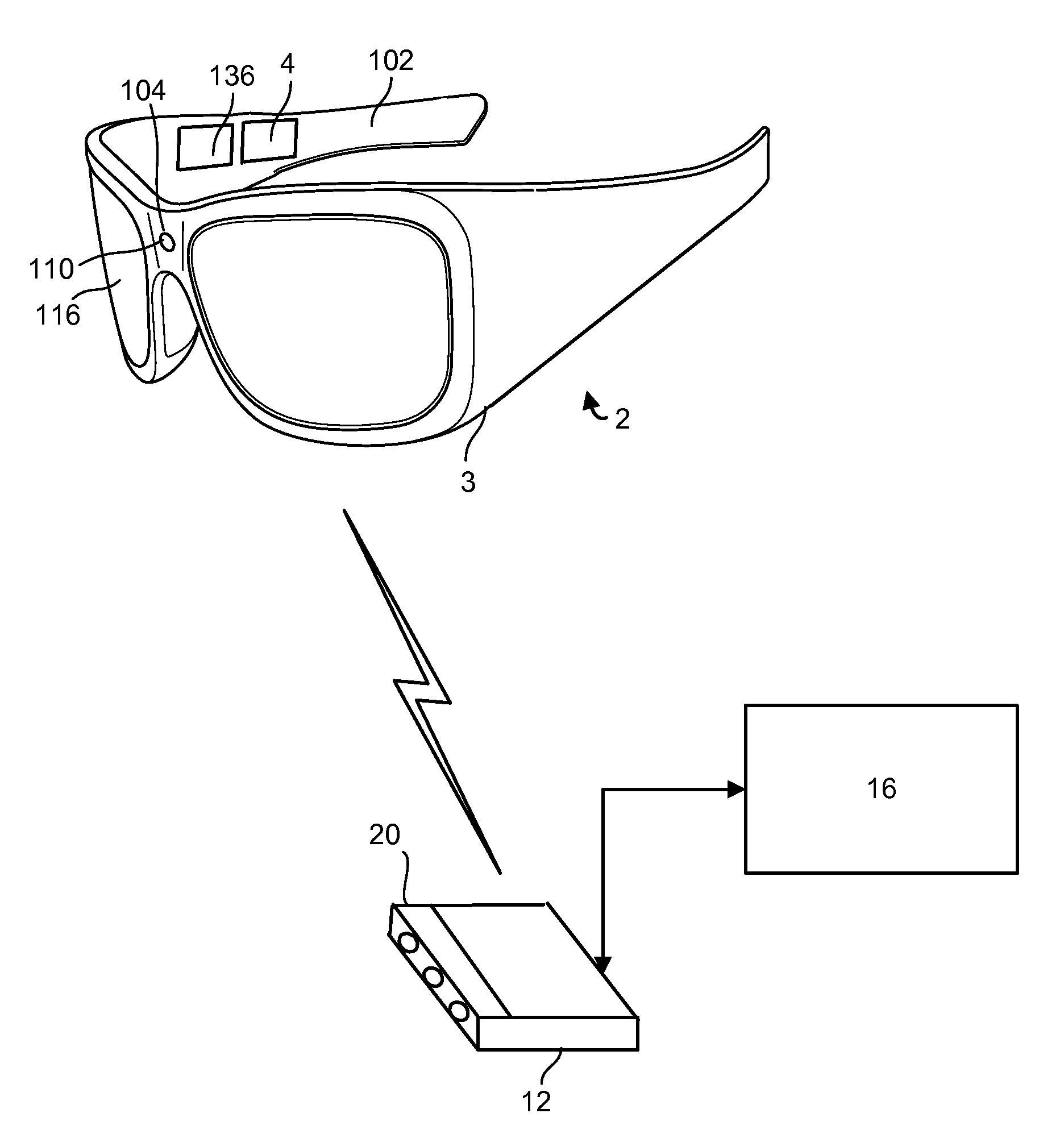
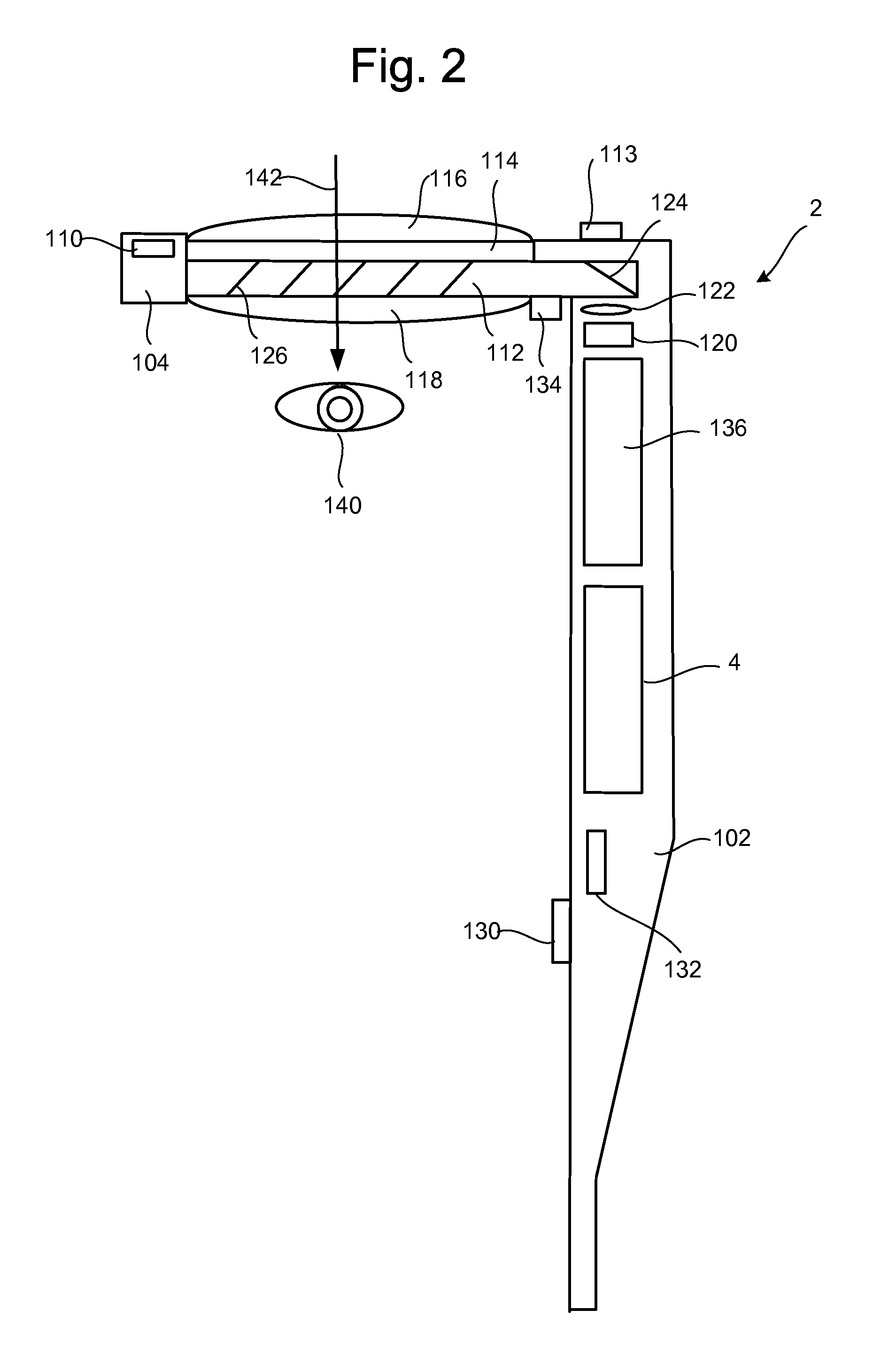
Connecting Head Mounted Displays To External Displays And Other Communication Networks
InactiveUS20130147686A1Not alleviating taskCathode-ray tube indicatorsInput/output processes for data processingComputer monitorDisplay device
An audio and / or visual experience of a see-through head-mounted display (HMD) device, e.g., in the form of glasses, can be moved to target computing device such as a television, cell phone, or computer monitor to allow the user to seamlessly transition the content to the target computing device. For example, when the user enters a room in the home with a television, a movie which is playing on the HMD device can be transferred to the television and begin playing there without substantially interrupting the flow of the movie. The HMD device can inform the television of a network address for accessing the movie, for instance, and provide a current status in the form of a time stamp or packet identifier. Content can also be transferred in the reverse direction, to the HMD device. A transfer can occur based on location, preconfigured settings and user commands.
Owner:MICROSOFT TECH LICENSING LLC
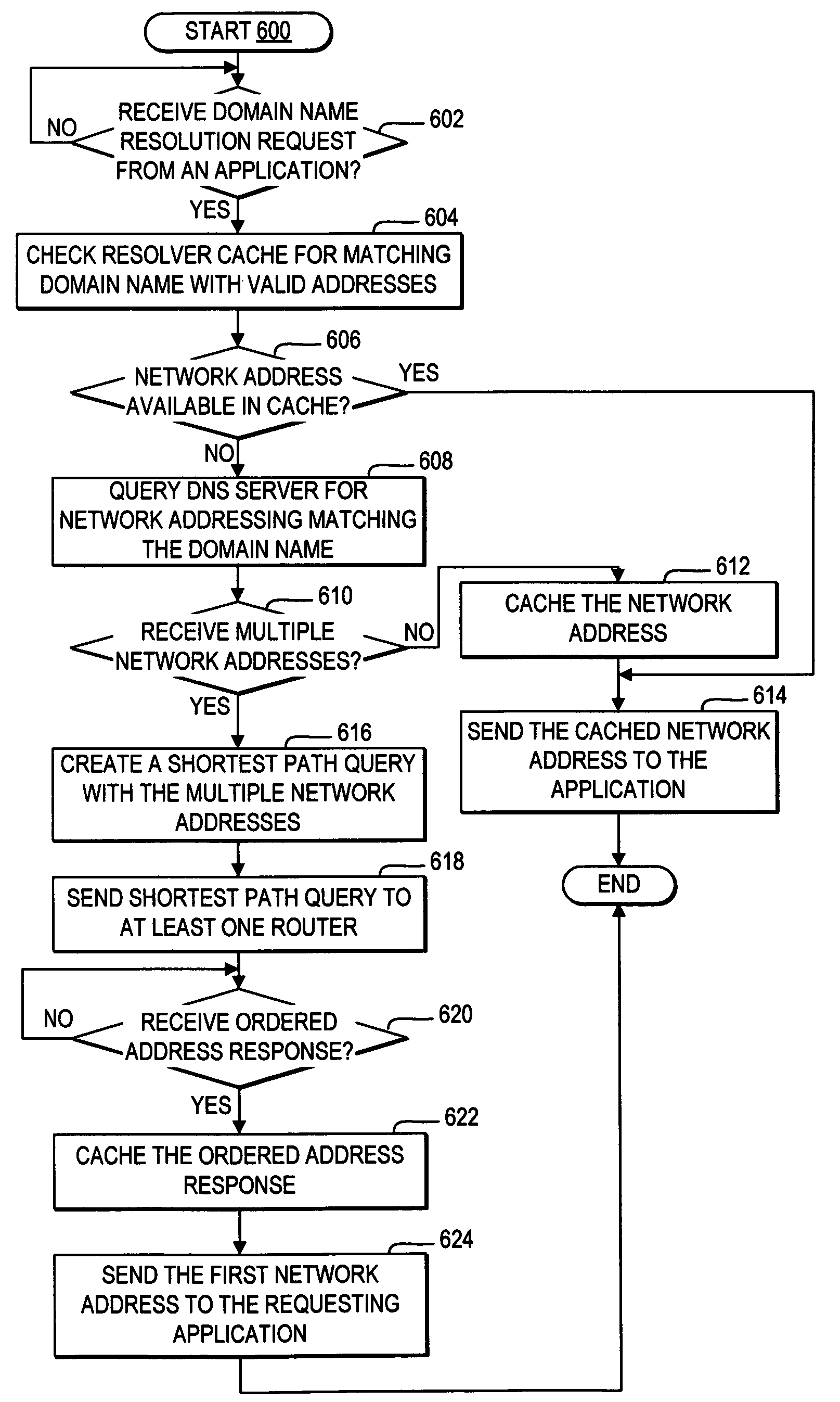
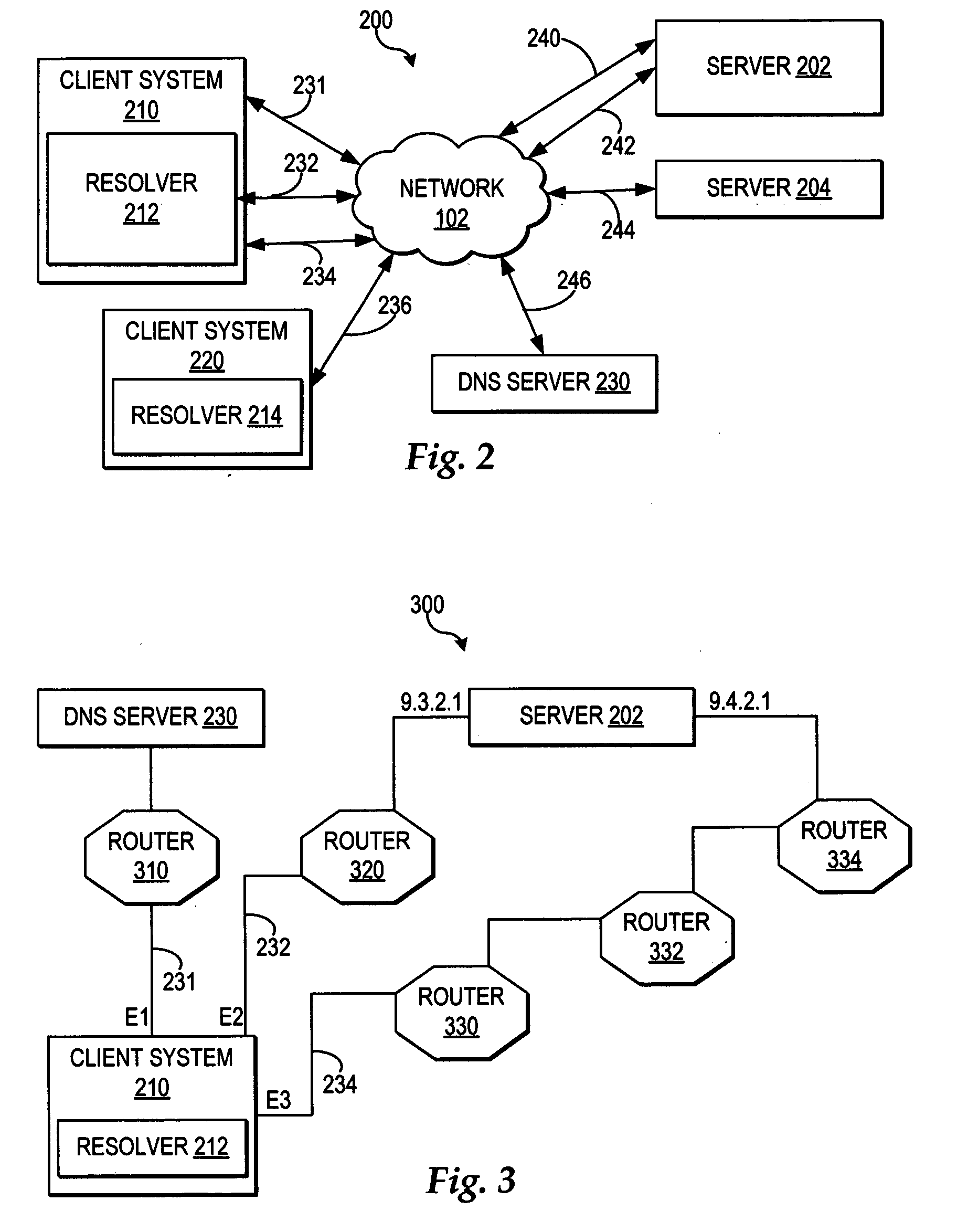
Resolver caching of a shortest path to a multihomed server as determined by a router
A resolver queries a DNS server for any network addresses associated with the particular domain name. If the resolver detects a response for the DNS server with multiple network addresses for a particular domain name, then the resolver creates and sends a shortest path query to at least one router enabled to receive and respond to shortest path queries. The shortest path query indicates at least one source address and the multiple destination addresses returned by the DNS server for the particular domain name. The router detects a separate length for each path accessible between each source address and each of the multiple destination addresses. The router then orders the destination addresses from shortest path to longest path and returns the ordered destination addresses to the requesting resolver. The resolver caches the ordered network addresses in the local cache in association with the particular domain name, such that for future requests for the particular domain name, the resolver retrieves from local cache the shortest path network address as ordered by the router. In addition, the resolver, responsive to receiving the ordered destination addresses, selects the shortest path network address for a response to an application requesting the resolution of the particular domain name.
Owner:IBM CORP
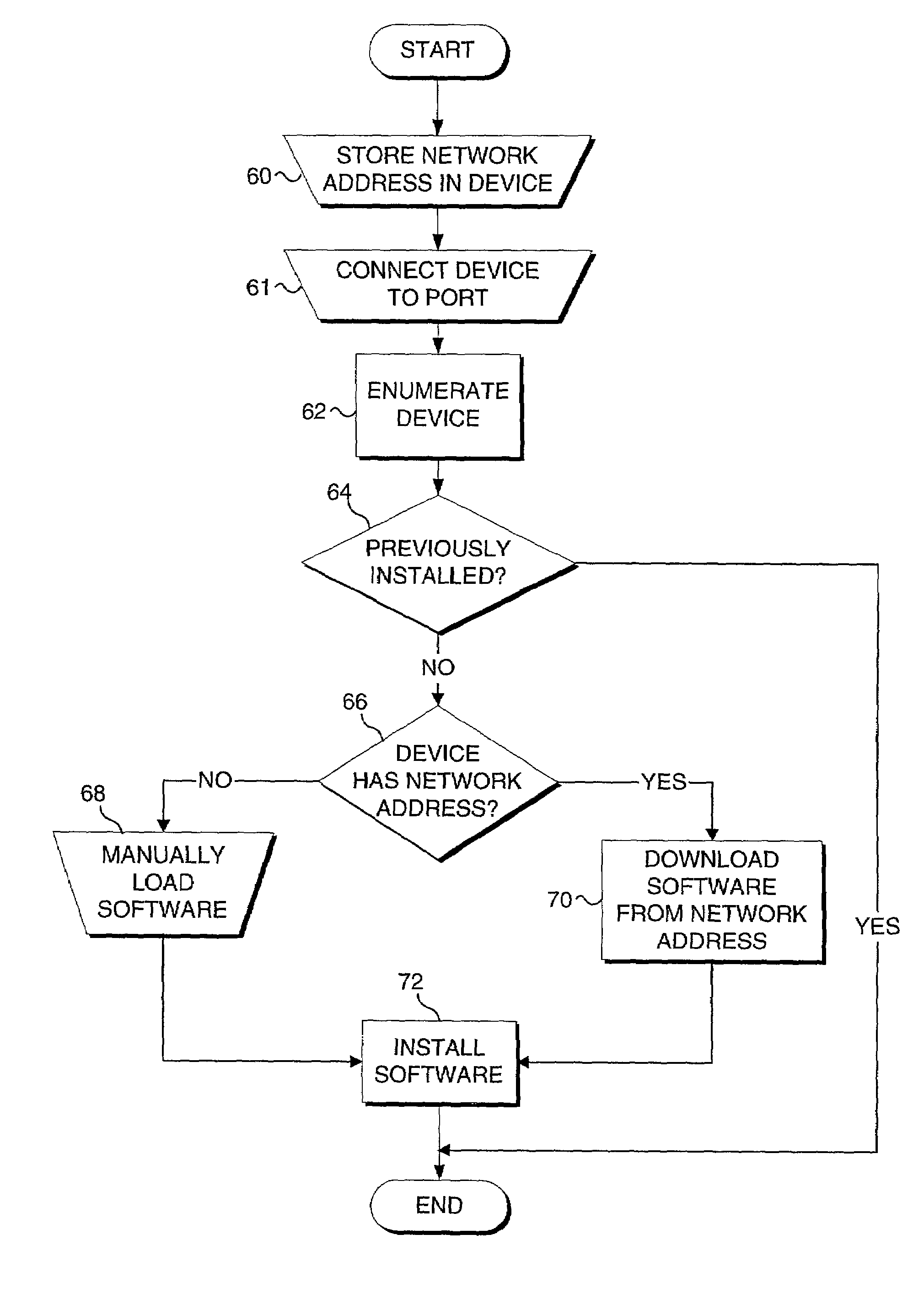
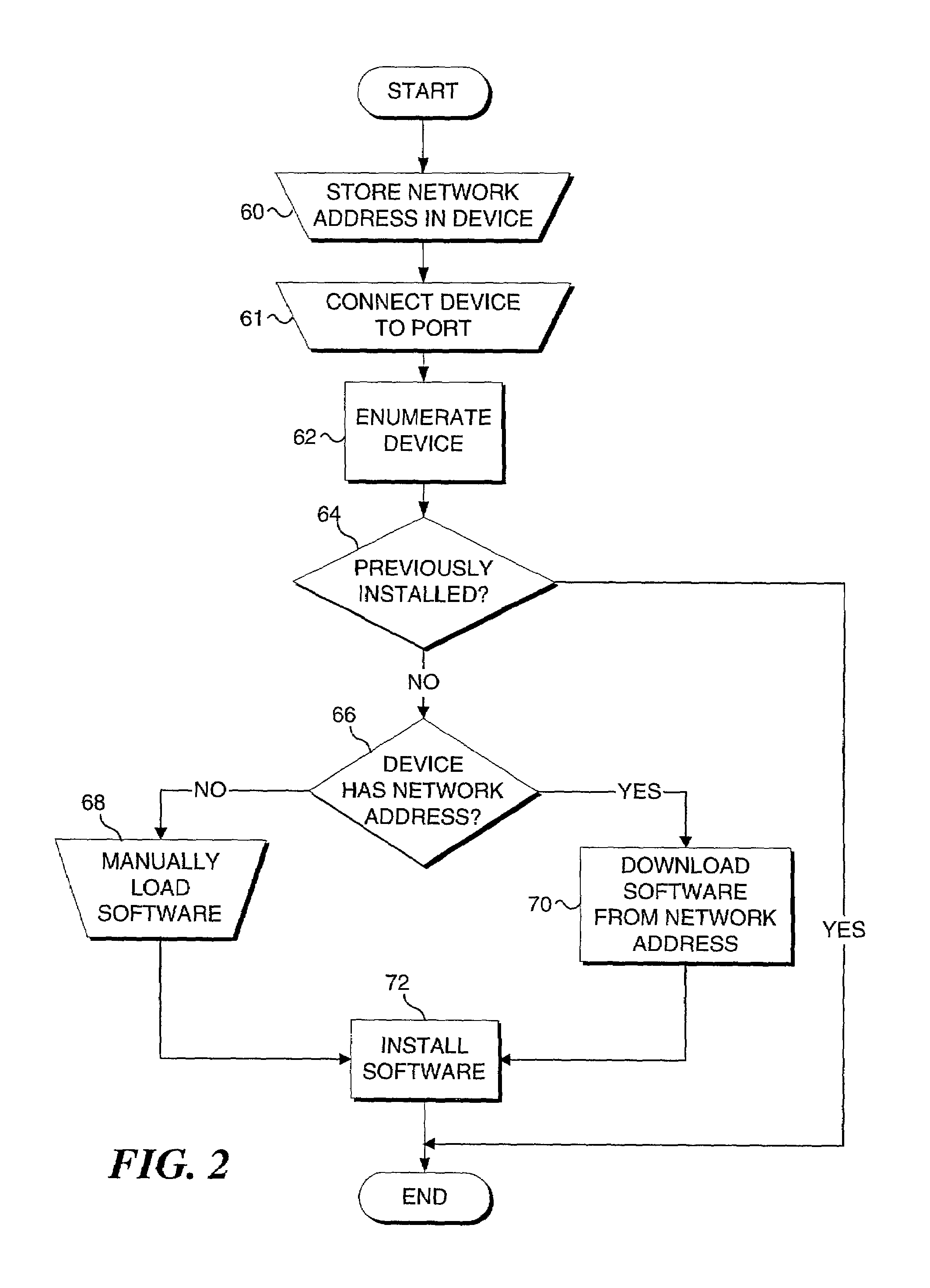
Method and system to access software pertinent to an electronic peripheral device based on an address stored in a peripheral device
InactiveUS7165109B2Multiple digital computer combinationsProgram loading/initiatingDocumentation procedureNetwork addressing
A method and system for obtaining a network address stored in a peripheral device, and accessing a remote device at the network address to obtain information related to the peripheral device. When the peripheral device is connected to a host computer, the stored network address is read by the host computer. The network address is preferably determined by the host computer when a peripheral device, such as a USB device, is initially connected to the host device, or when the host device with a newly connected USB is energized. The network address is then used by the host device to communicate with a remote device so that information pertaining to the peripheral device, such as a device driver for the peripheral device, can be accessed by the host device at the remote device. In addition, the host device can download or automatically execute a program stored at the remote device, download and install an application program relating to use of the peripheral device, display a Web page that includes information pertinent to the peripheral device, download documentation for the peripheral device, access help information, download and install firmware into the peripheral device and / or access other material related to the peripheral device. Access of the remote device can be fully automated or can optionally be implemented only with the permission of the user.
Owner:MICROSOFT TECH LICENSING LLC
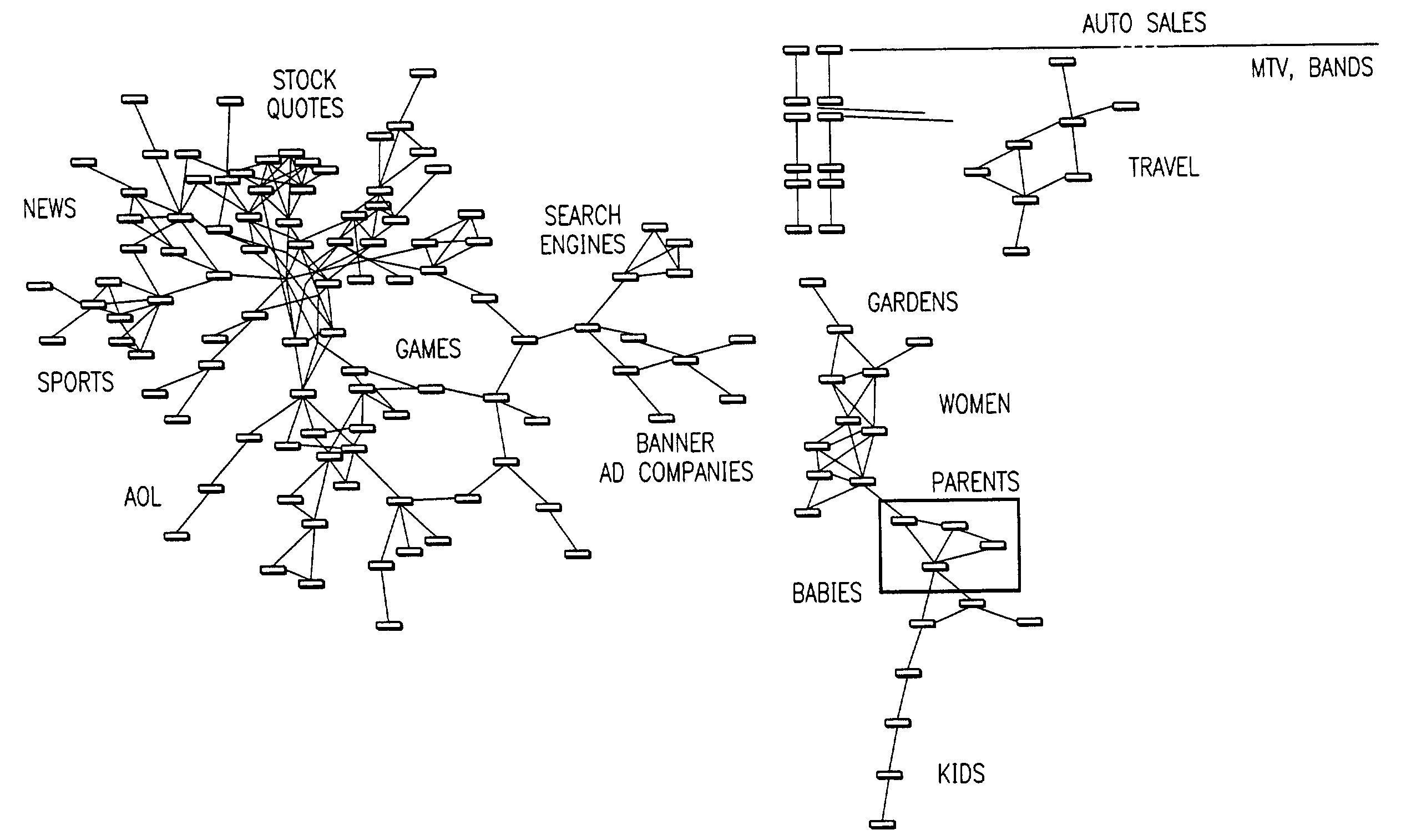
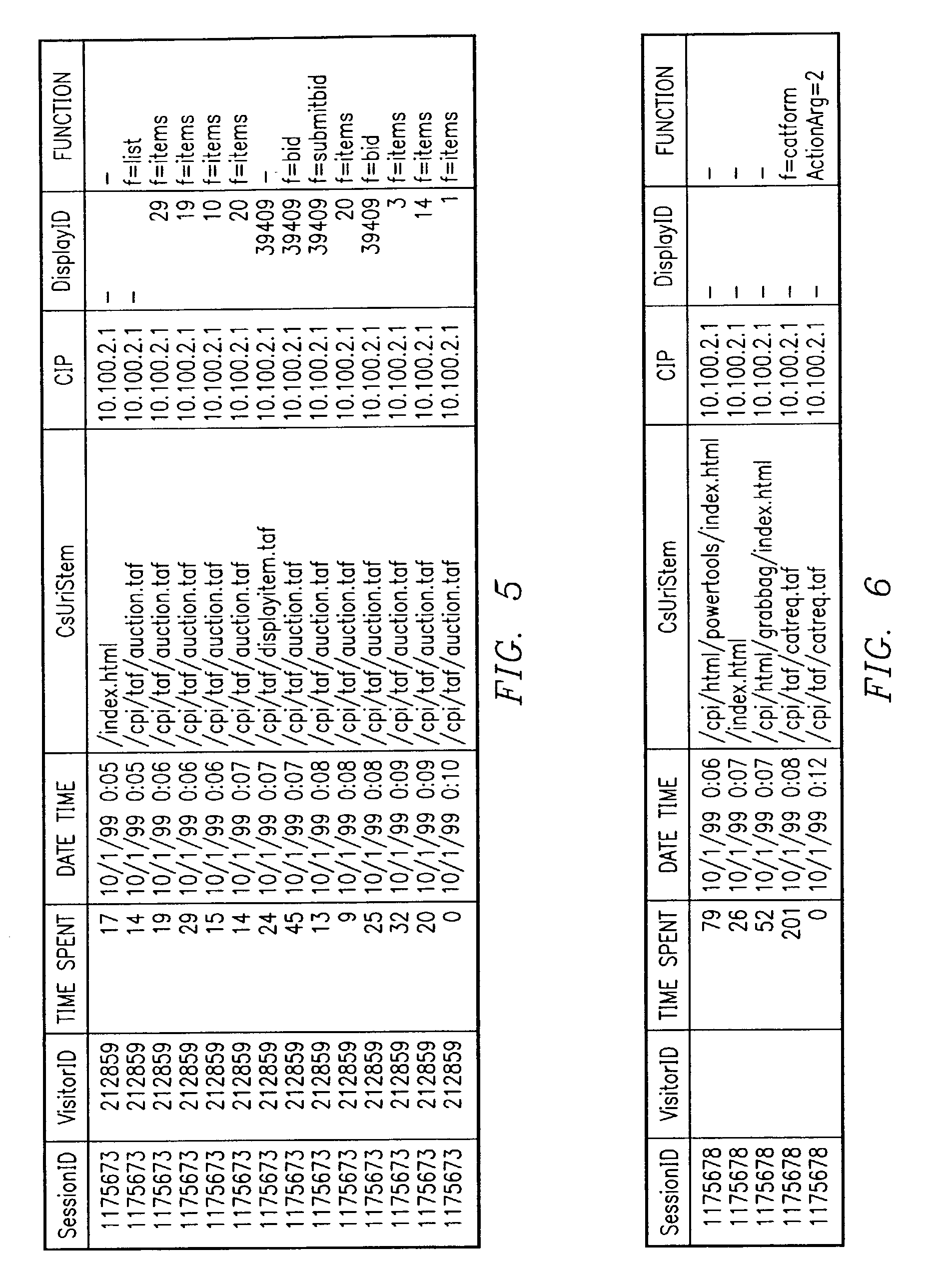
Visualization and analysis of user clickpaths
Methods and data processing system readable media have been created to graph user clickstream data over a network or at a network site to yield meaningful and visually esthetic information. In one set of embodiments, the method can comprise (i) performing a significance test on data from a network log and generating significance results. The method can also comprise (ii) determining which of network addresses and clicktrails between network addresses meet a traffic flow criterion. The data that meet a significance criterion, traffic criterion, or both can form (iii) graphable addresses and relationships. The method can further comprise (iv) generating statistics about the graphable addresses and relationships. The method can still further comprise (v) generating a graph based on the statistics about the graphable addresses and relationships, and (vi) changing any or all of the traffic flow, significance criterion, and statistics being computed, and regenerating the graph.
Owner:OPEN TEXT SA ULC
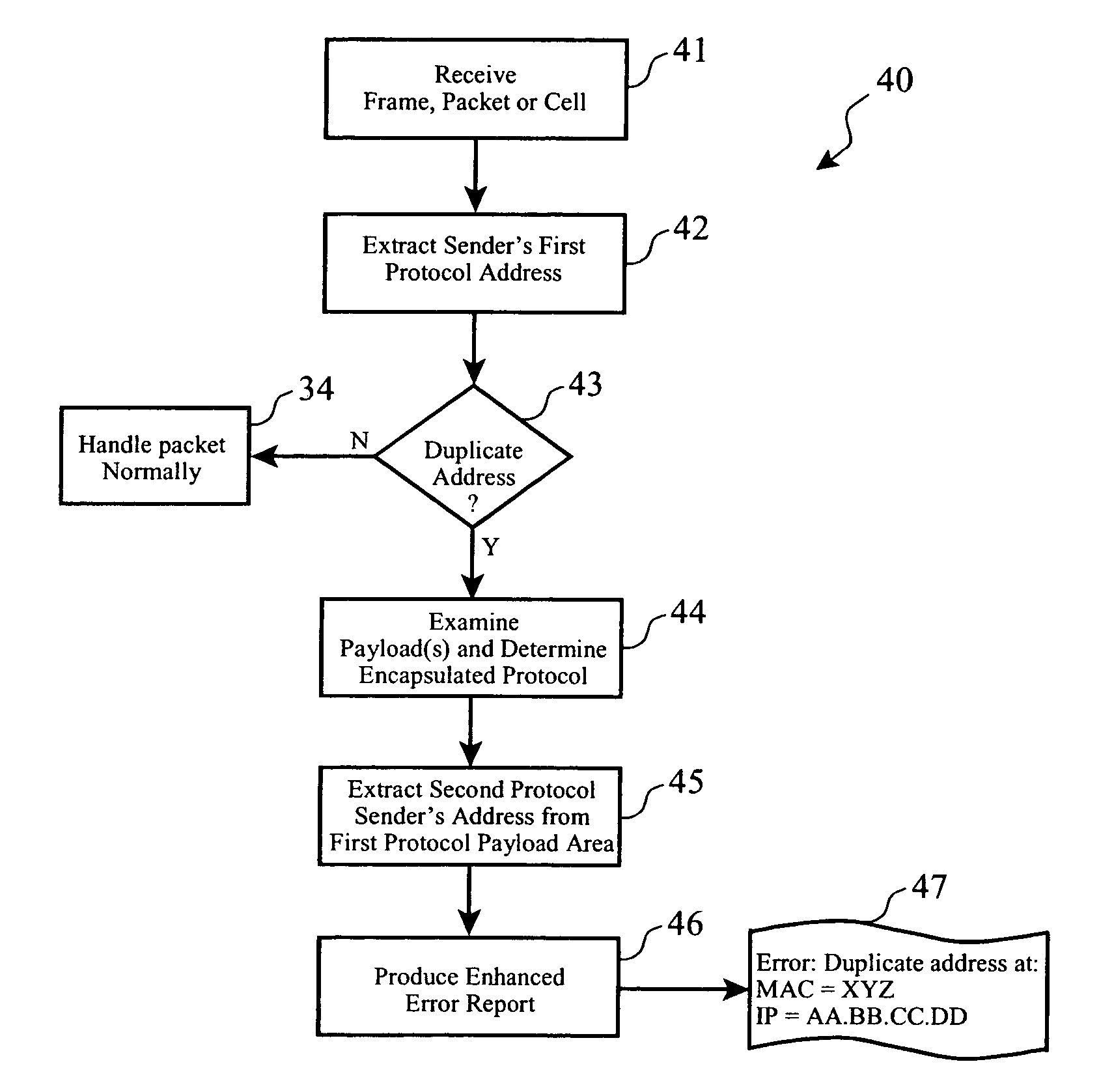
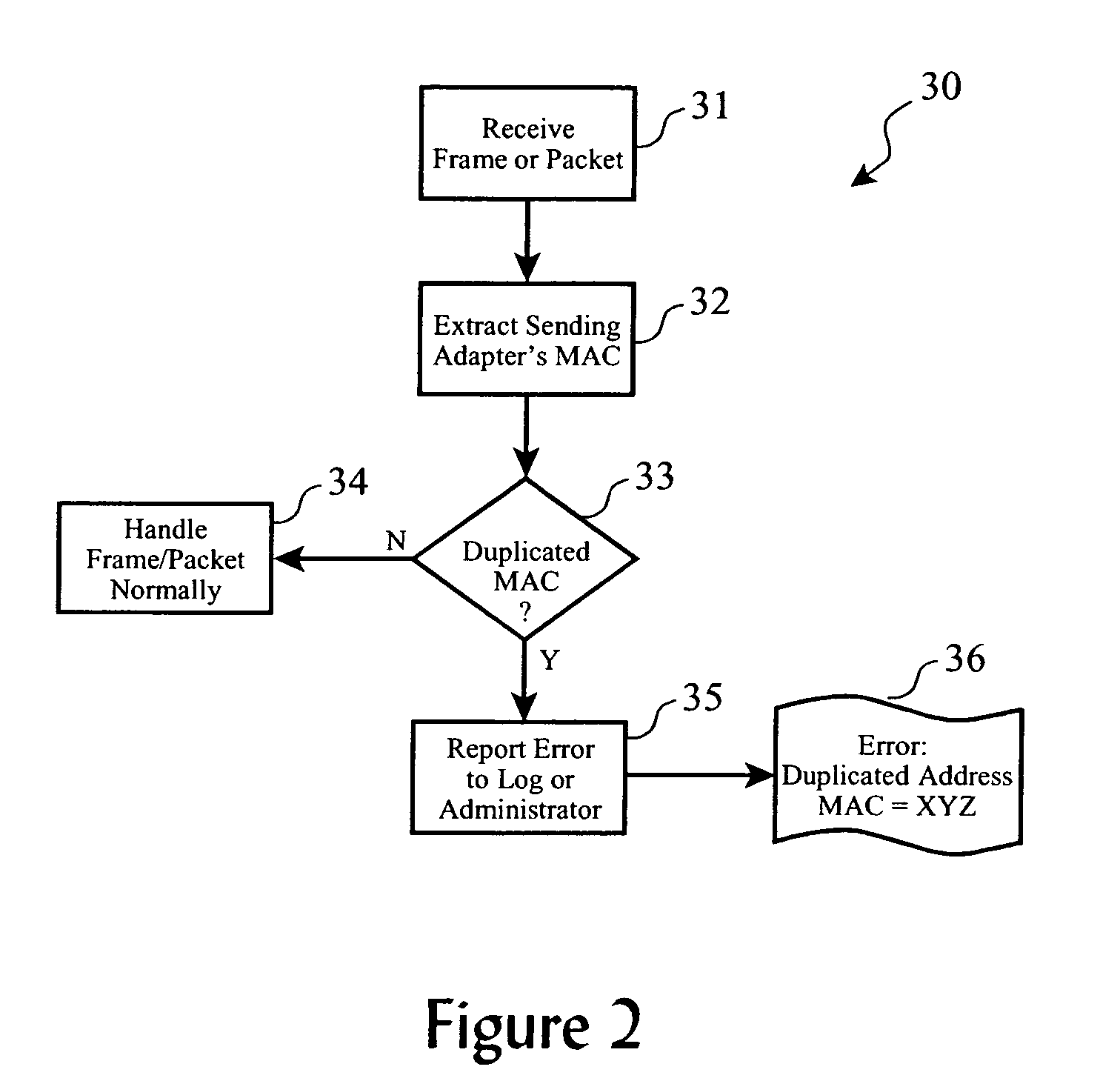
Duplicate network address detection
ActiveUS7246272B2Easy to detectError detection/correctionData switching by path configurationEncapsulated dataNetwork addressing
A plurality of data packets encoded according to a first protocol are received which encapsulate data encoded according to a second protocol. A first source address is extracted from the packets according to the first protocol, it is determined whether or not the first source address is a substantial duplicate of a known assigned address. If it is a duplicate, a second source address is extracted from the encapsulated data according to the second protocol, and the first source address and said second source address are provided in an enhanced error log so that a system administrator may correct the duplicate assigned address. Enhanced embodiments of the invention included analysis of data encapsulated by a third, fourth and subsequent protocols, and automatic determination of each protocol encoding format.
Owner:GOOGLE LLC
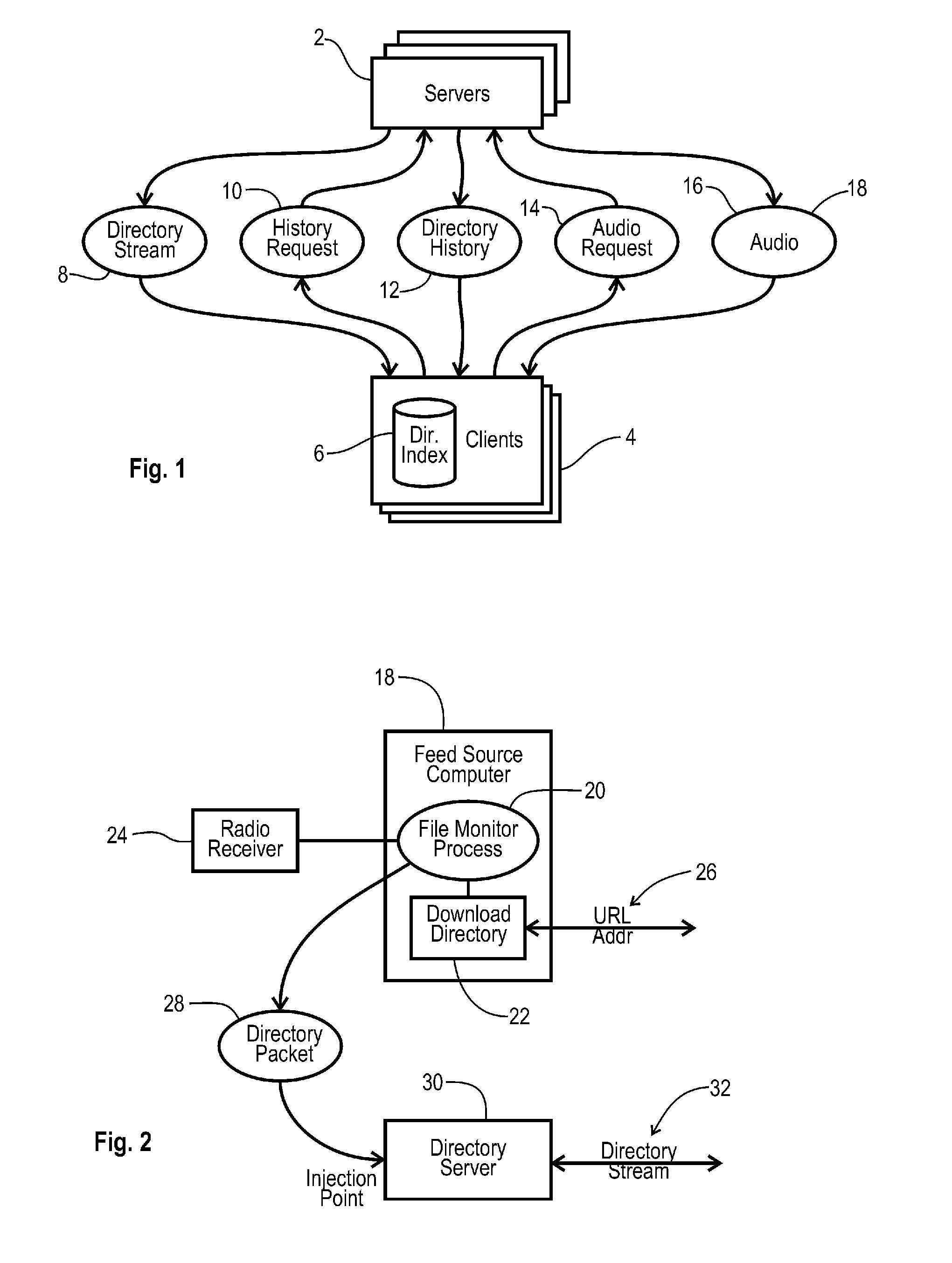
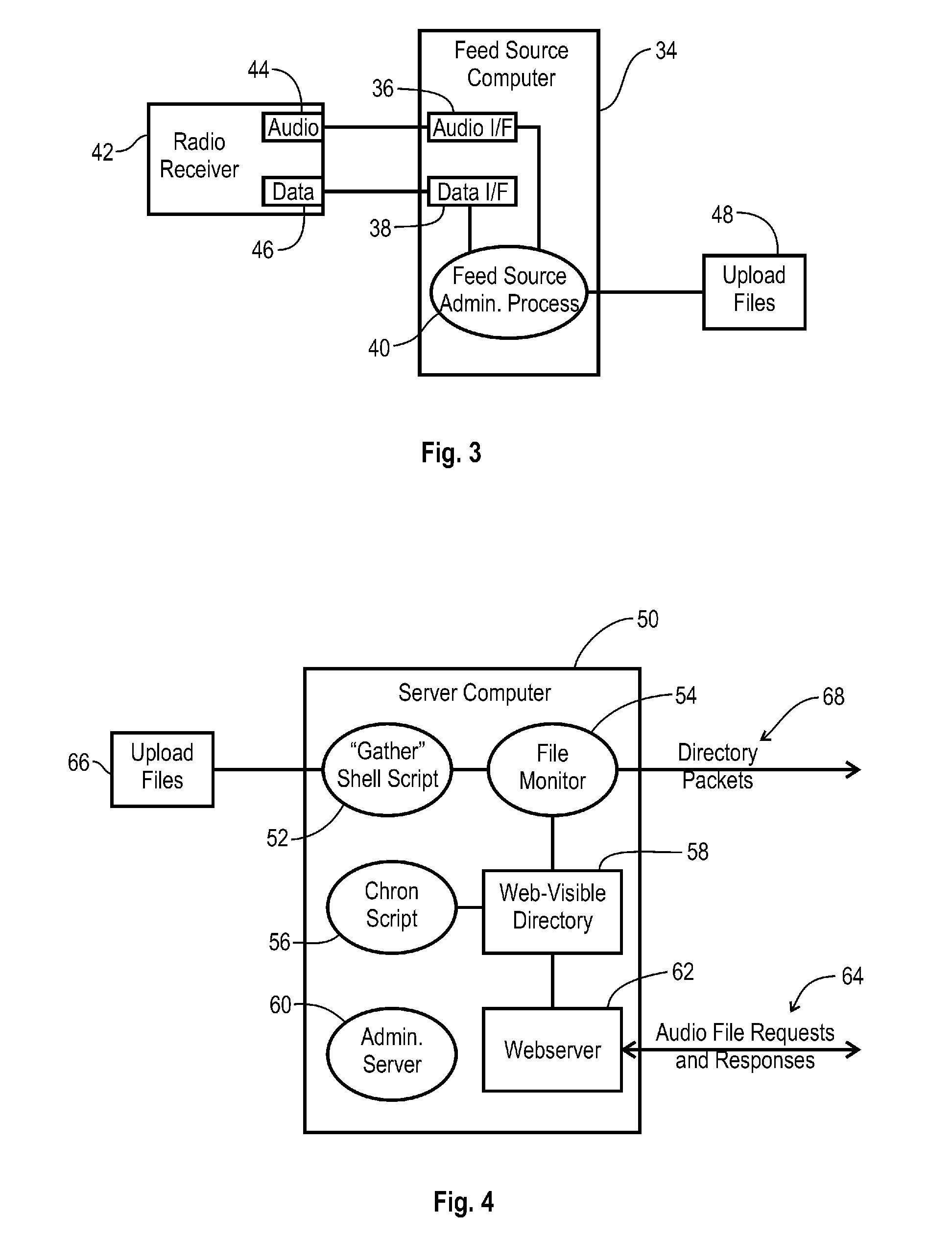
Network Audio Distribution System and Method
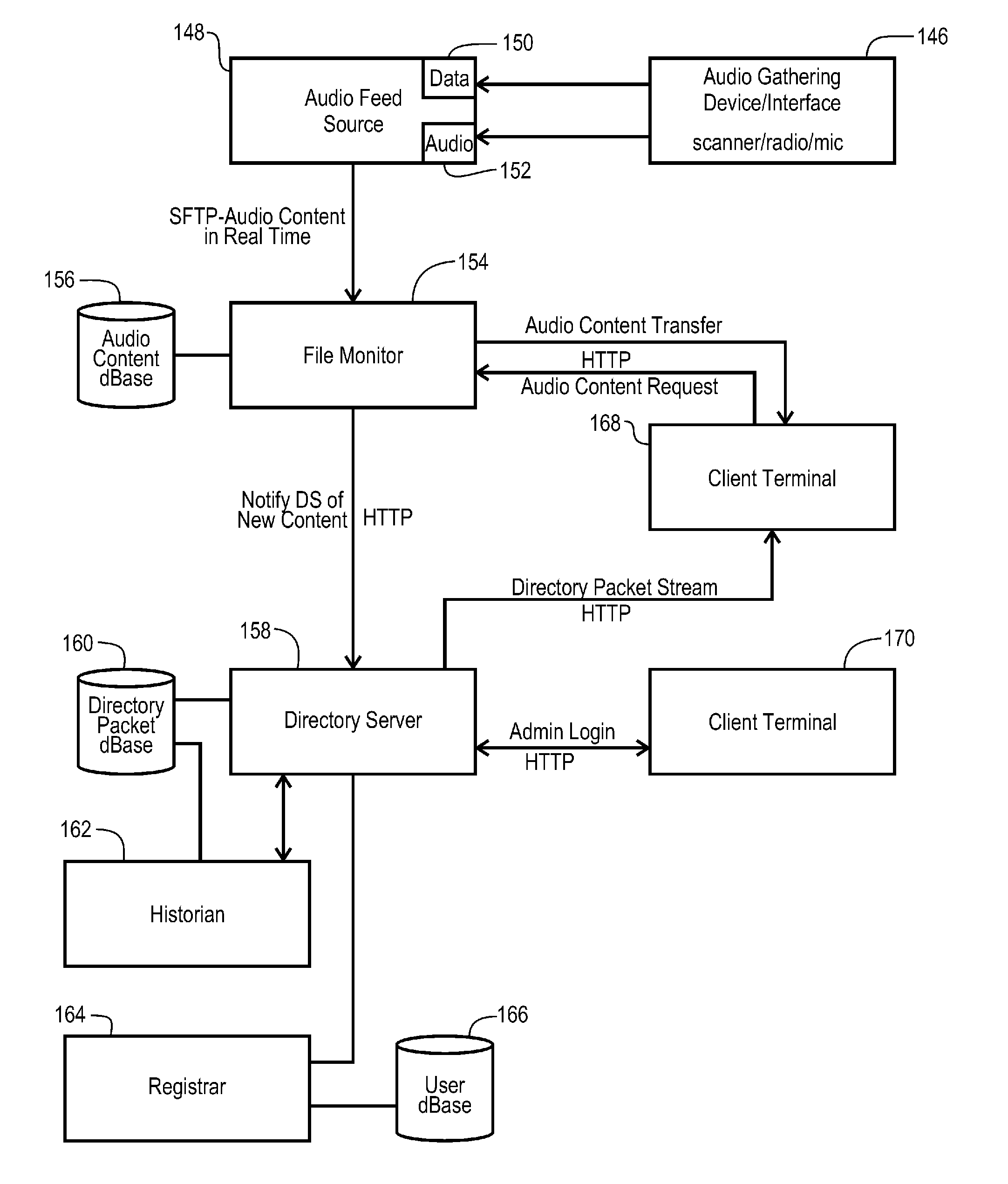
ActiveUS20100281178A1Obscuring predictabilityPulse modulation television signal transmissionMultiplex communicationComputer hardwareTimestamp
System and methods for distributing audio content from plural audio sources to plural client terminals located on a network. The system includes an audio source interface that is coupled to receive raw audio from a first audio source, and converts the raw audio into a digital audio clip that is incorporated into a digital audio packet, which further contains a timestamp and a channel identity corresponding to the first audio source. A network audio server is coupled to receive the digital audio packet from the audio source interface, and operates to format the digital audio packet into a digital audio file that is compliant with the network, and store the digital audio file at a network address. The network audio server generates a directory packet that includes the network address of the digital audio file, the channel identity, and the timestamp, and couples the directory packet to a directory server located on the network. The directory server receives the directory packet and generates a directory stream, including at least a portion of the directory packet, and couples the directory stream through the network to a first client terminal. The first client terminal receives the directory stream and selectively identifies the directory packet according to a client profile, and subsequently communicates an audio file request through the network, requesting the digital audio file from the network audio server. Then, upon receipt of the audio file request, the audio server responds by coupling the digital audio file to the client terminal through the network.
Owner:TELEGRAPH PEAK TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com