Patents
Literature
436 results about "Policy decision" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Policy Decisions is a modern, core platform that supports the full policy lifecycle for highly automated or heavily underwritten products on one platform, serving all user types for all distribution channels. Functionality.
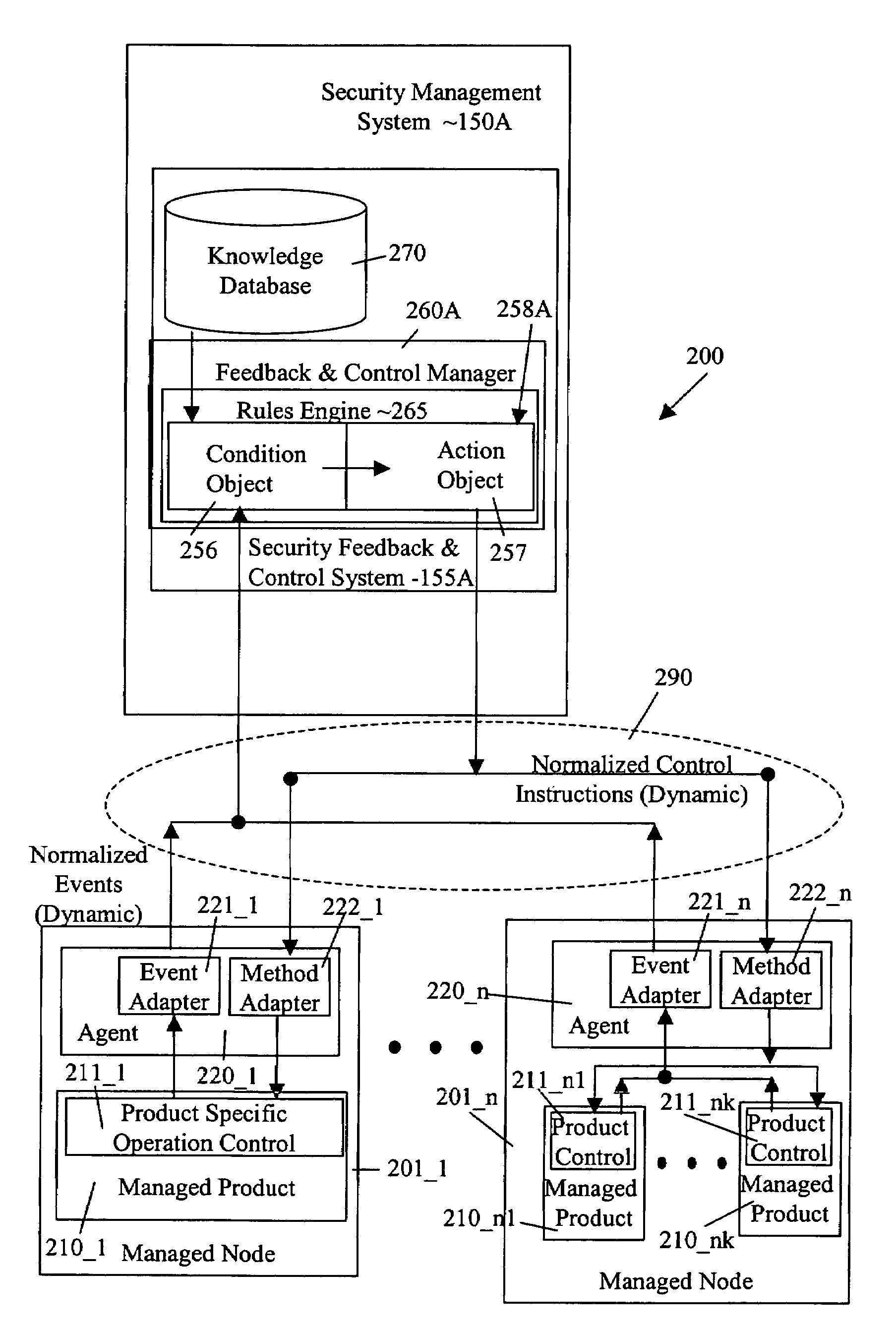
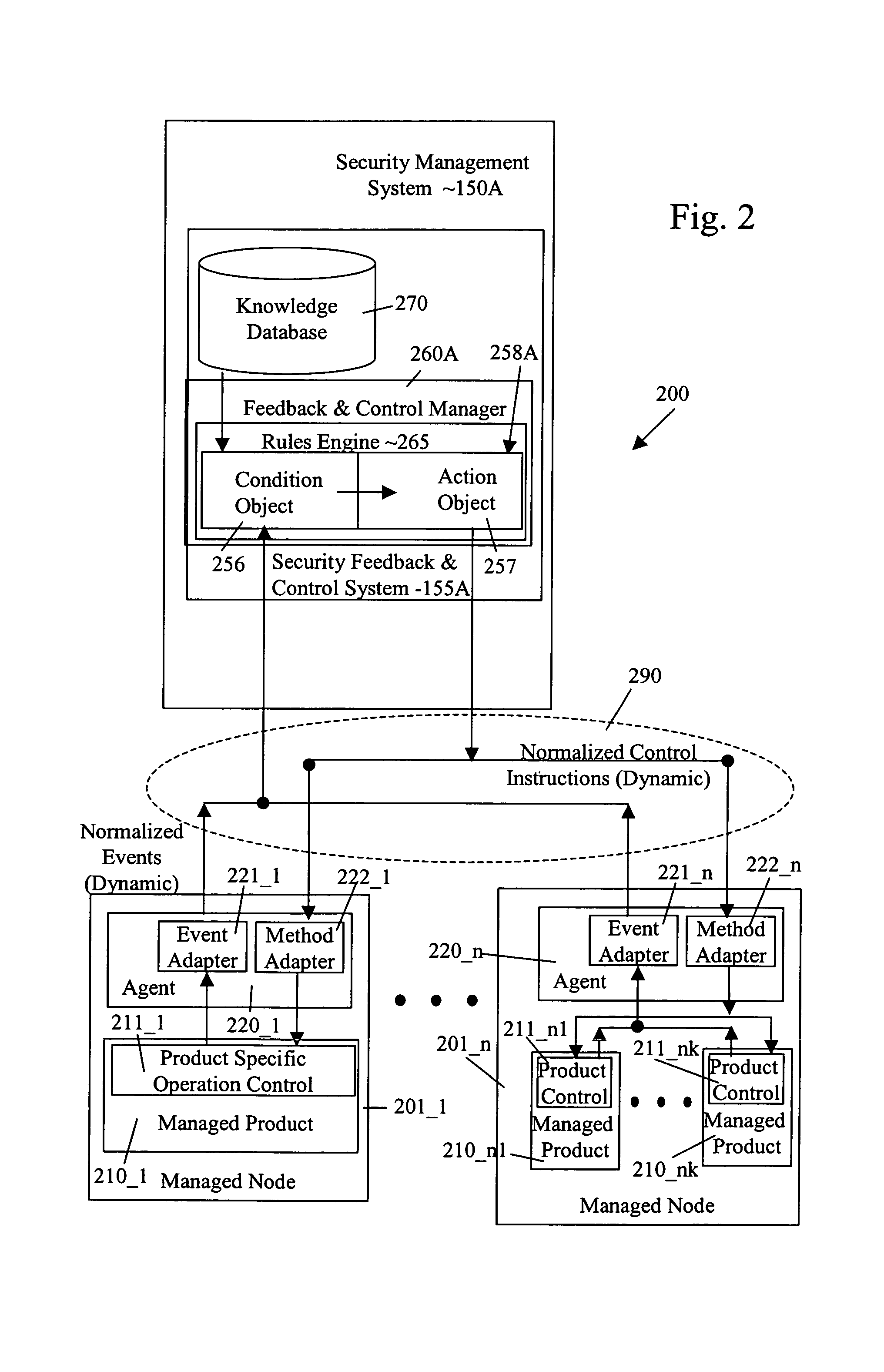
Security management system including feedback and control
InactiveUS7472422B1Memory loss protectionError detection/correctionPolicy decisionSafety management systems
A system uses automatic feedback and control to secure a network infrastructure by iterative convergence of the network's security structure to meet a security policy. Following initialization, a security feedback control system of the security management system makes dynamic adjustments to the system using bi-directional services that are controlled via policy decision components, without user intervention.
Owner:SYMANTEC CORP
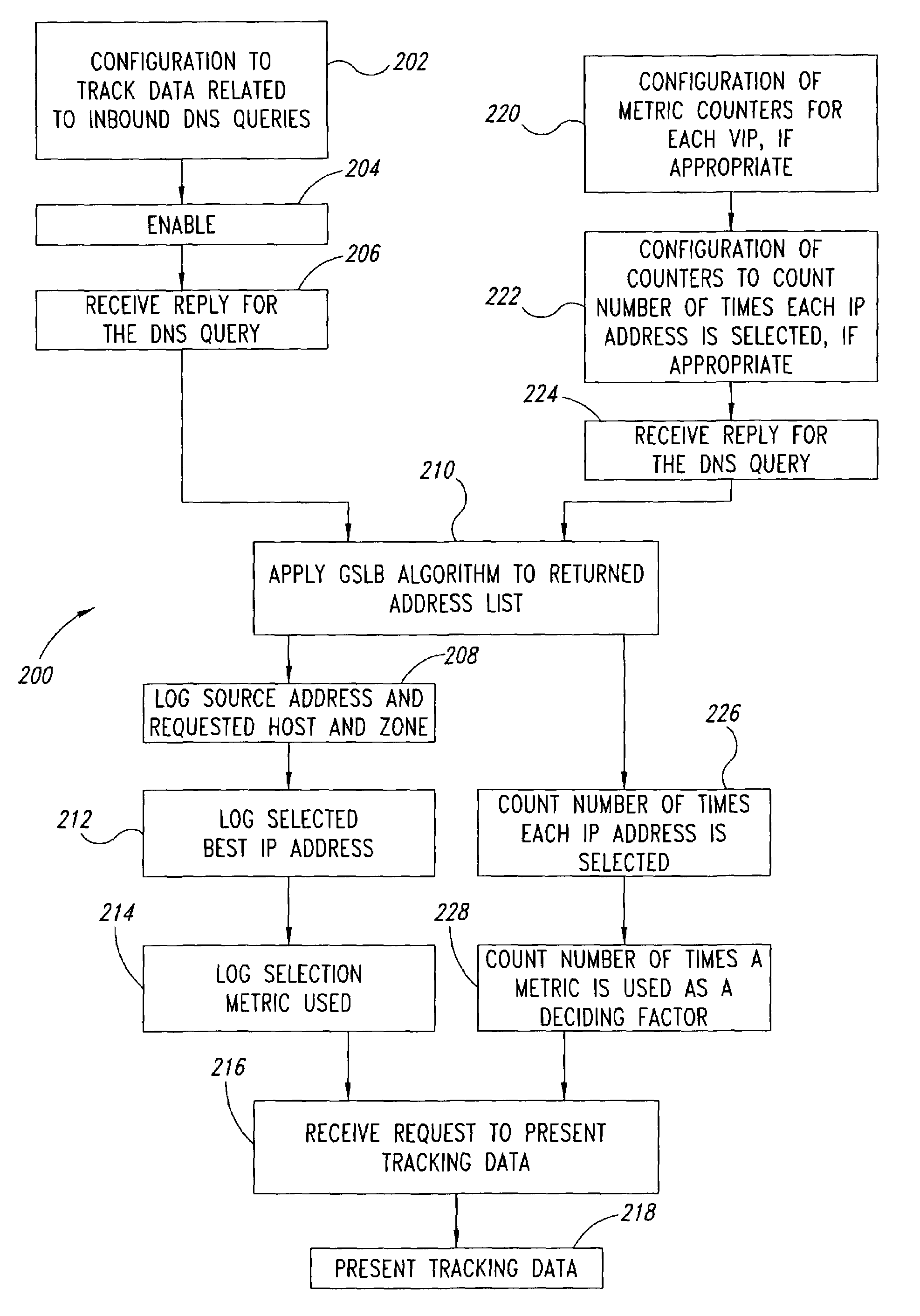
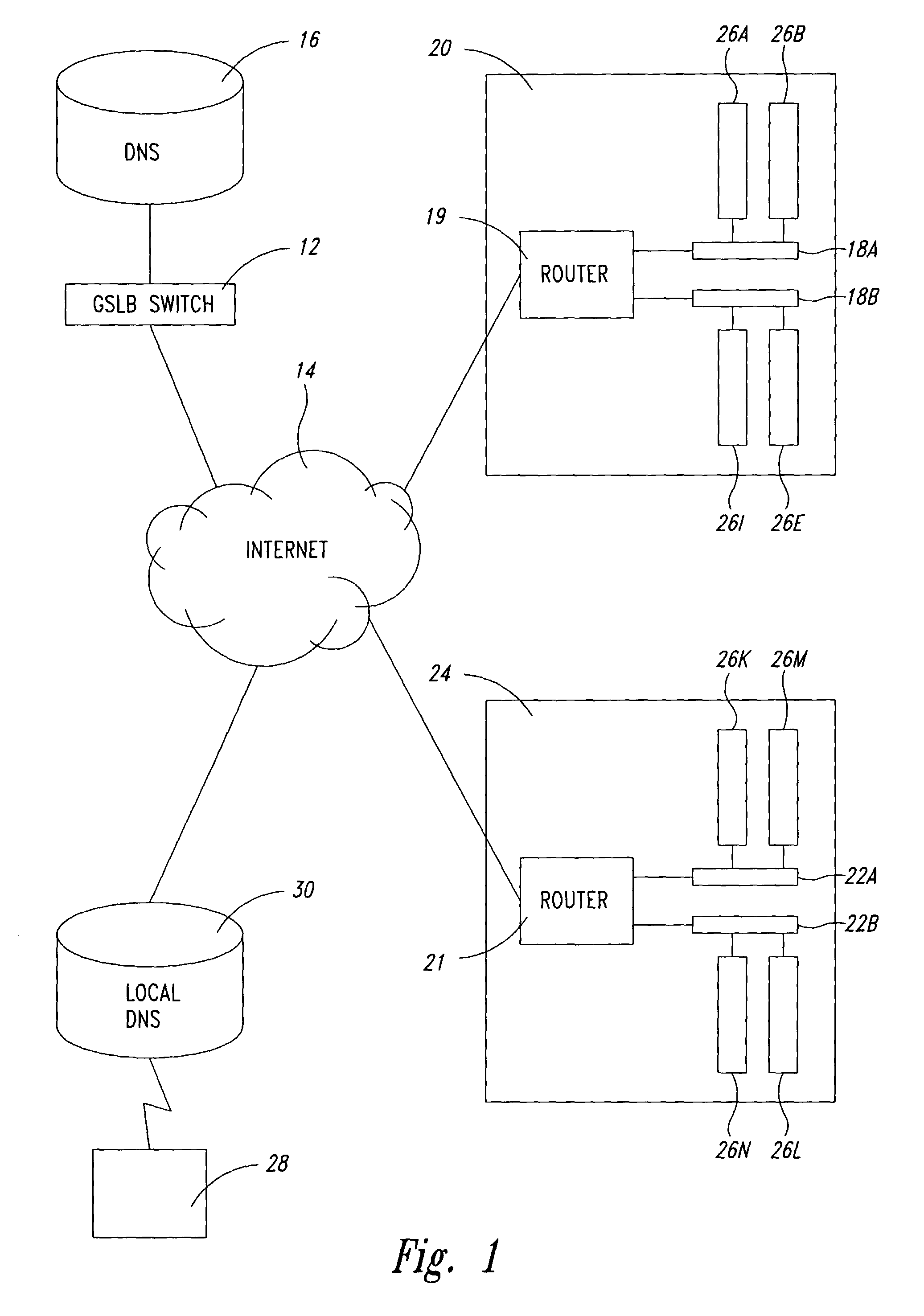
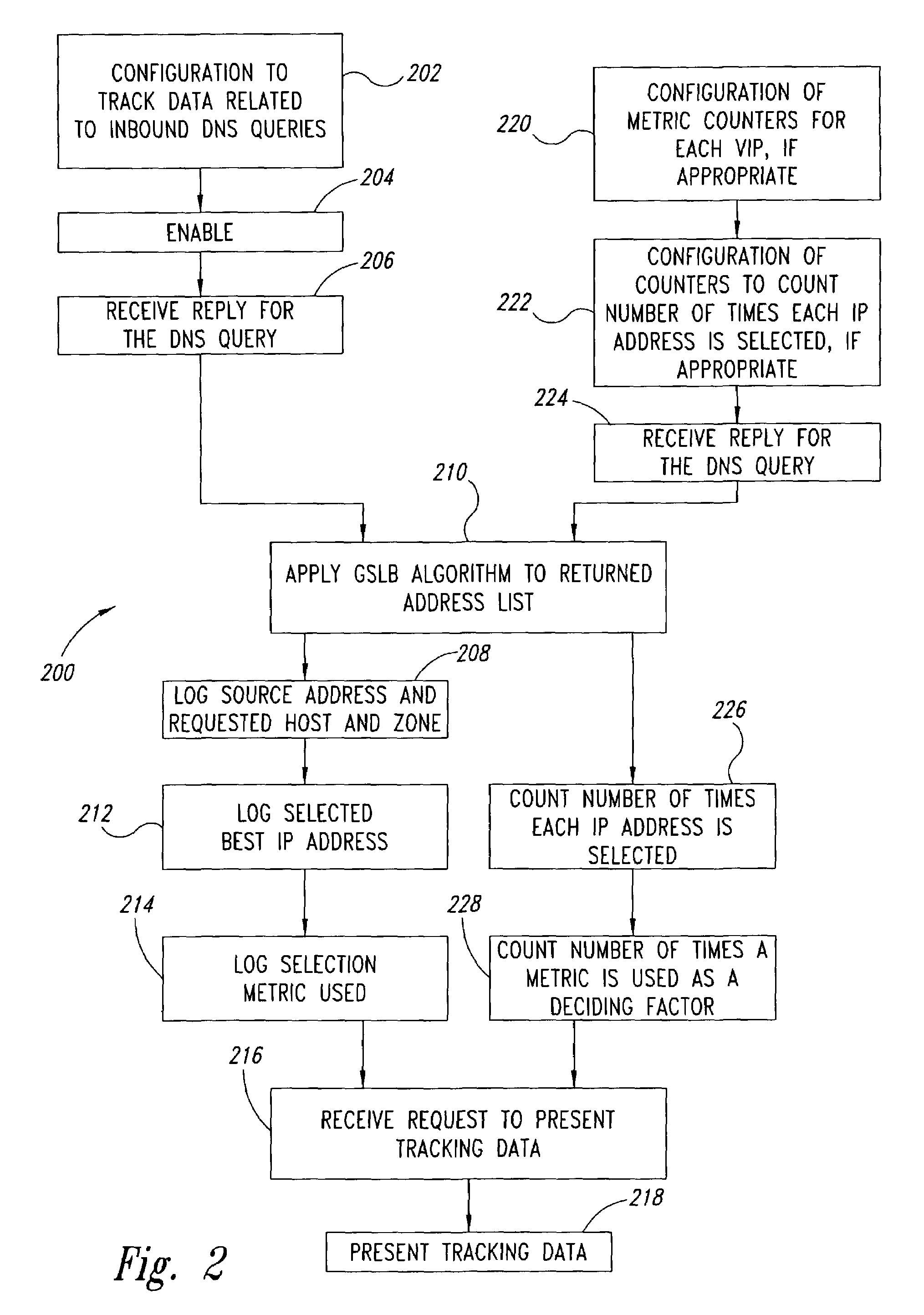
Statistical tracking of global server load balancing for selecting the best network address from ordered list of network addresses based on a set of performance metrics
ActiveUS7086061B1Multiprogramming arrangementsMultiple digital computer combinationsPolicy decisionIp address
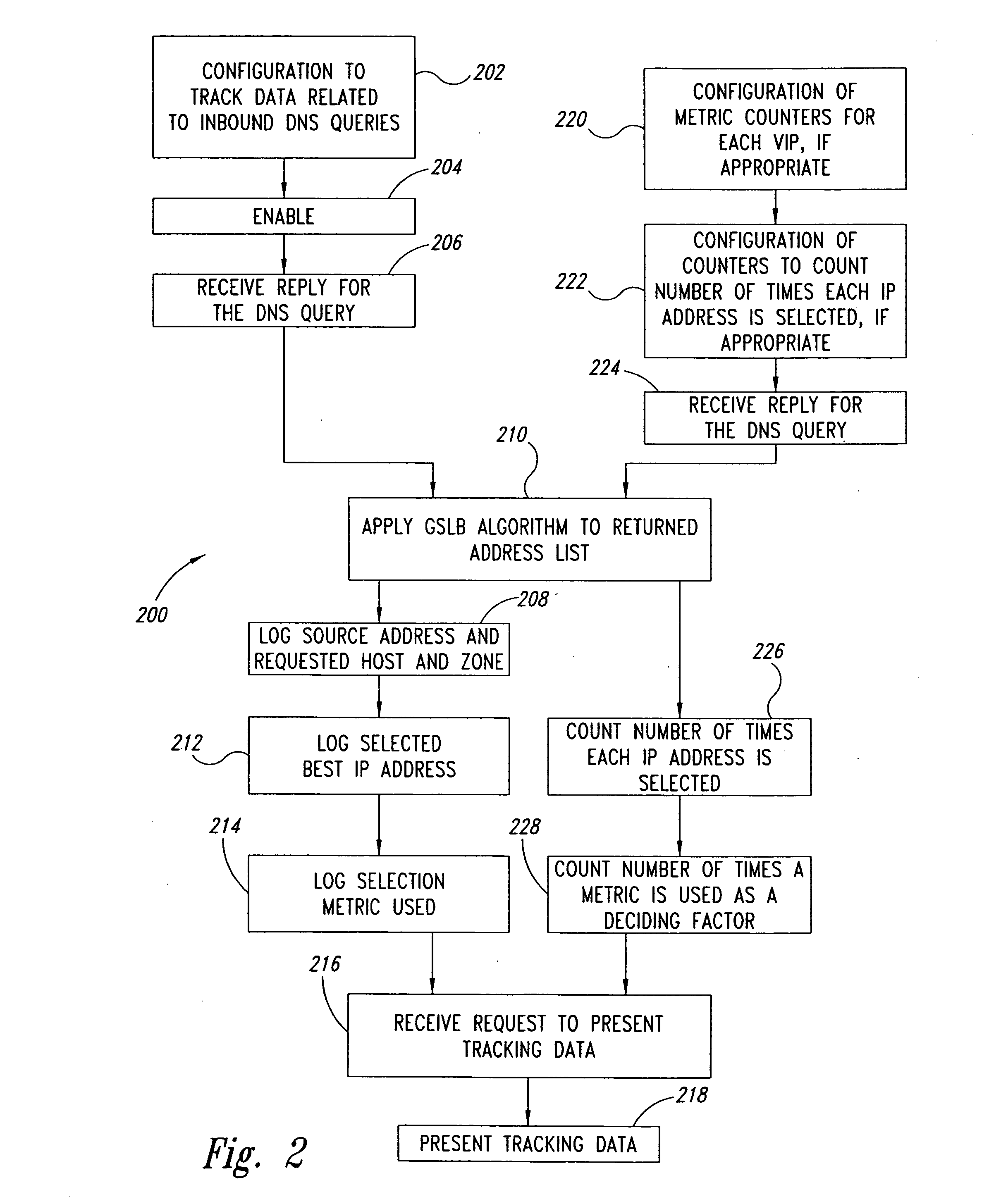
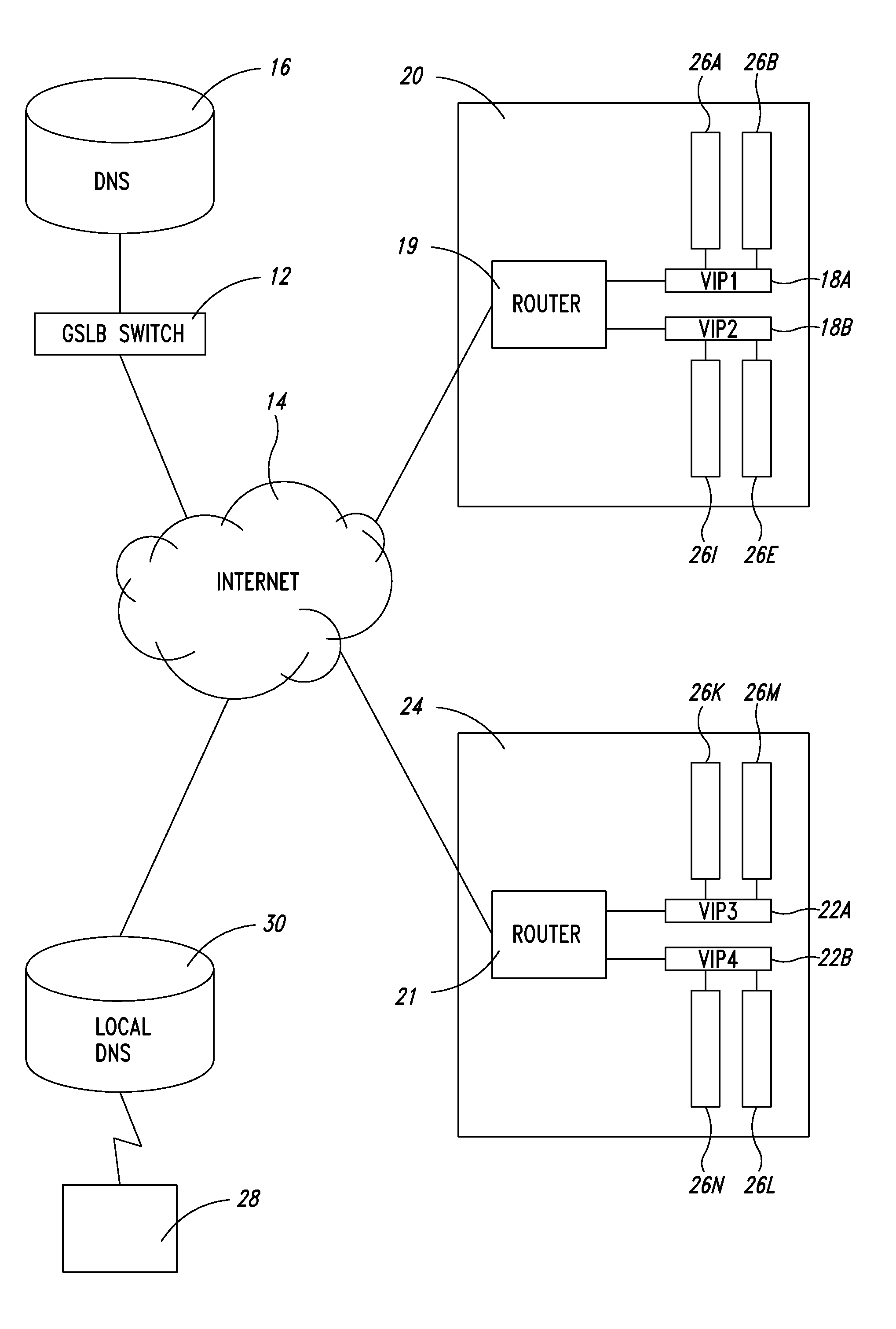
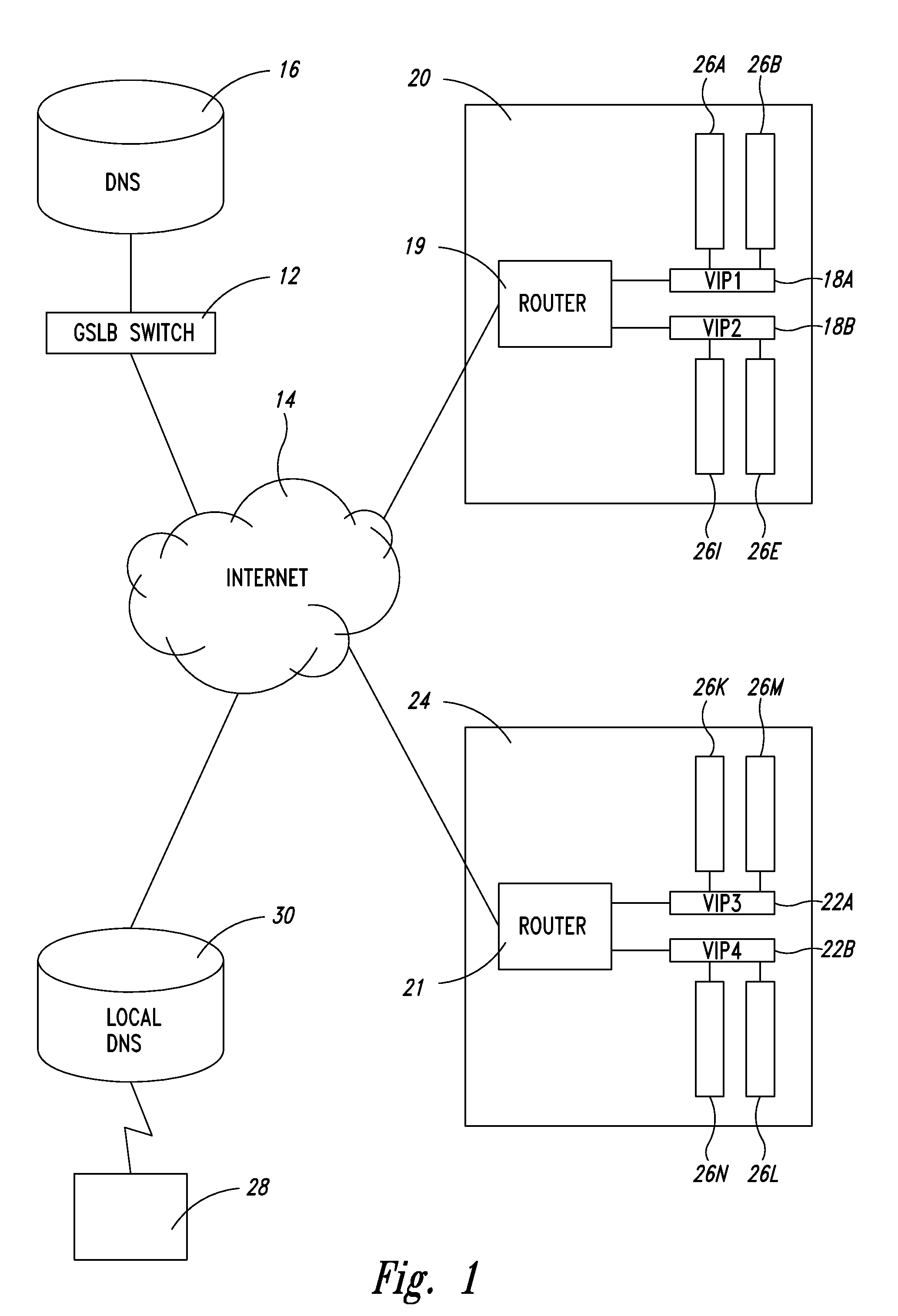
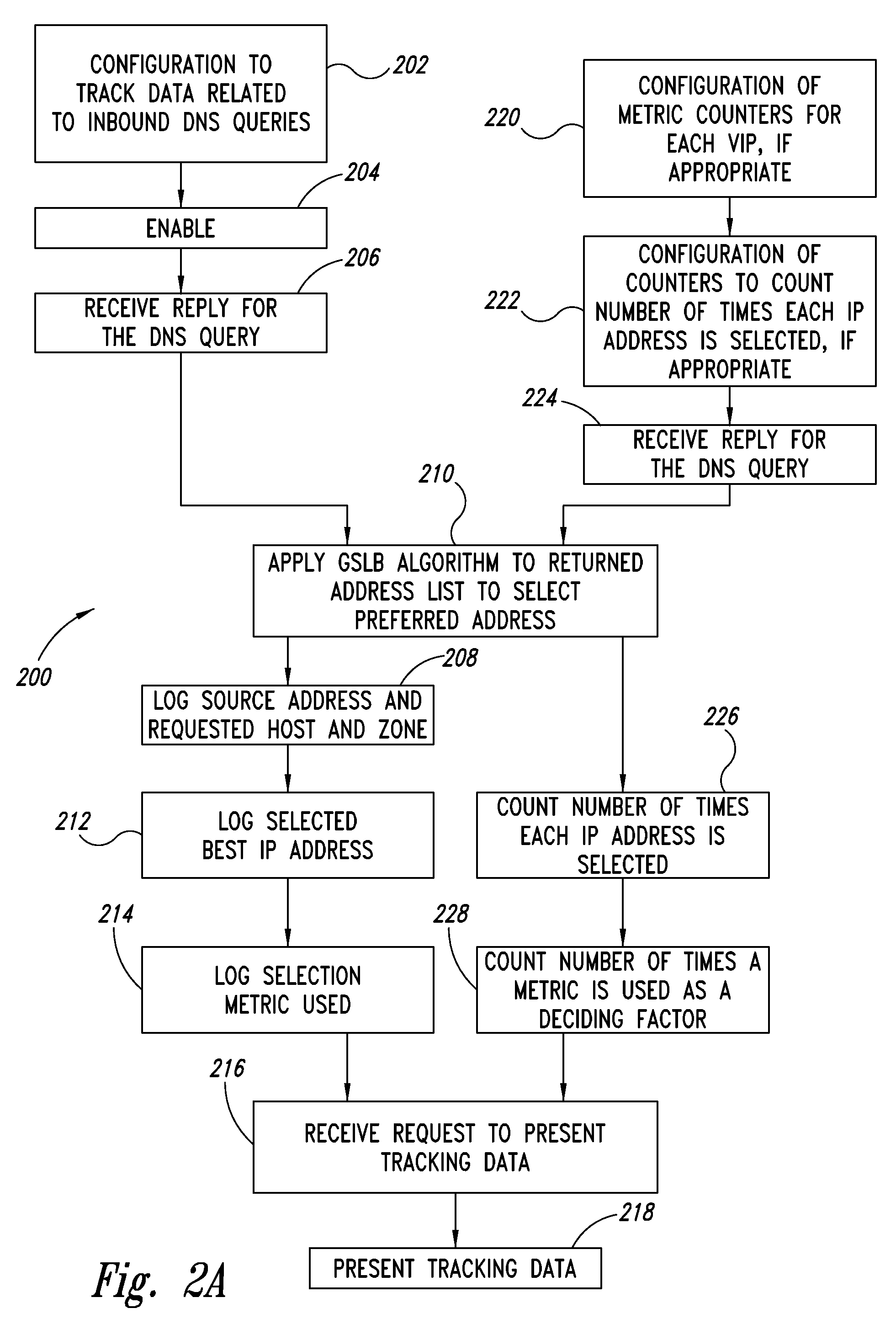
Server load-balancing operation-related data, such as data associated with a system configured for global server load balancing (GSLB) that orders IP addresses into a list based on a set of performance metrics, is tracked. Such operation-related data includes inbound source IP addresses (e.g., the address of the originator of a DNS request), the requested host and zone, identification of the selected “best” IP addresses resulting from application of a GSLB algorithm and the selection metric used to decide on an IP address as the “best” one. Furthermore, the data includes a count of the selected “best” IP addresses selected via application of the GSLB algorithm, and for each of these IP addresses, the list of deciding performance metrics, along with a count of the number of times each of these metrics in the list was used as a deciding factor in selection of this IP address as the best one. This tracking feature allows better understanding of GSLB policy decisions (such as those associated with performance, maintenance, and troubleshooting) and intelligent deployment of large-scale resilient GSLB networks.
Owner:AVAGO TECH INT SALES PTE LTD
Mechanisms for moving data in a hybrid aggregate
ActiveUS20100281230A1Improved performance characteristicsMemory architecture accessing/allocationMemory adressing/allocation/relocationPolicy decisionFile system
At least certain embodiments disclose a method, system and apparatus for relocating data between tiers of storage media in a hybrid storage aggregate encompassing multiple tiers of heterogeneous physical storage media including a file system to automatically relocate the data between tiers. The hybrid storage aggregate includes one or more volumes, each volume including a volume block number space spanning at least a first-tier of storage media and a second tier of storage media of the multiple tiers of heterogeneous physical storage media and the hybrid storage aggregate further includes a control module to cooperatively manage the tiers of the multiple tiers of heterogeneous physical storage media and a file system coupled with the control module, the file system including a policy module configured to make policy decisions based on a set of one or more policies and configured to automatically relocate data between different tiers of the multiple tiers of heterogeneous physical storage media based on the set of policies.
Owner:NETWORK APPLIANCE INC
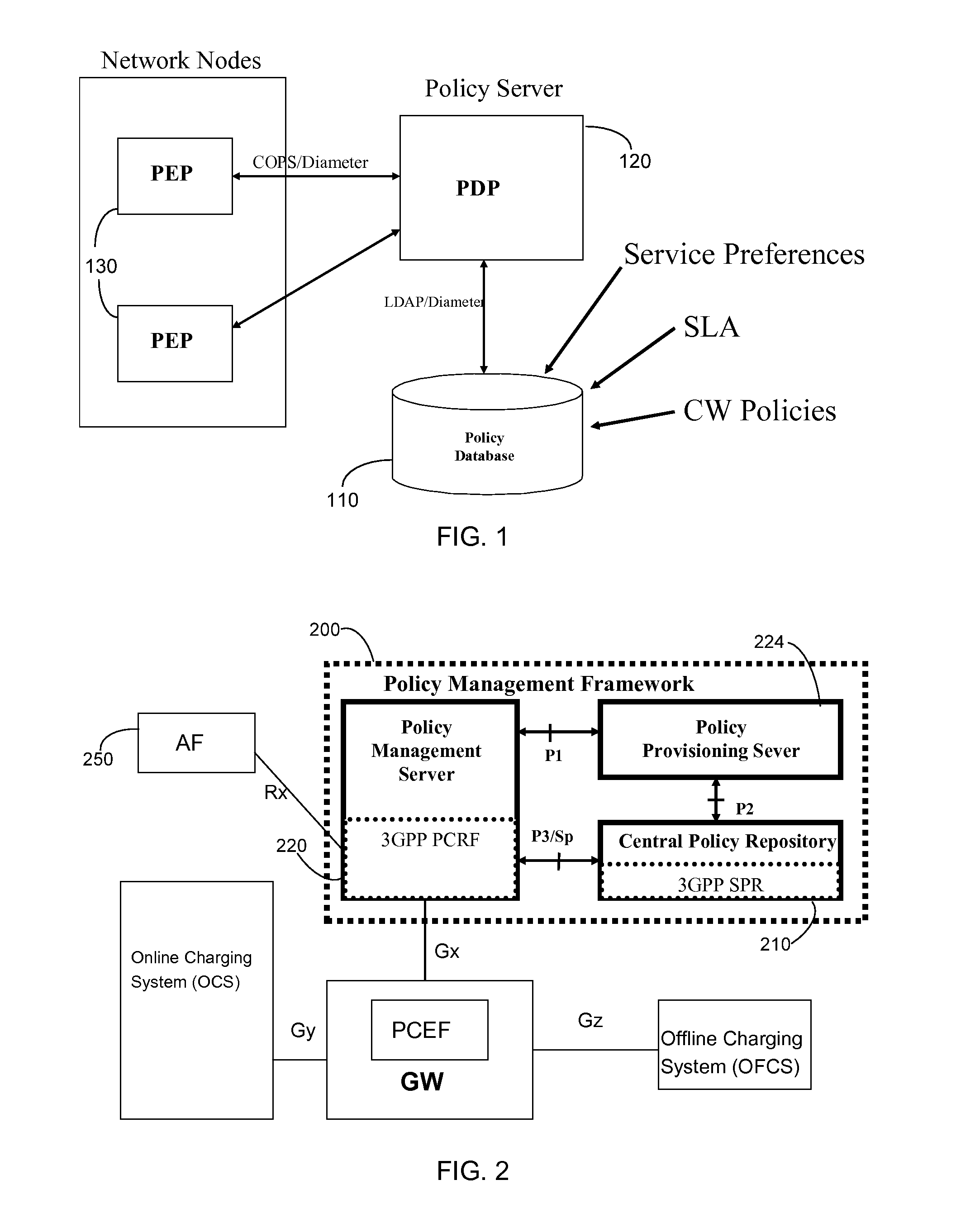
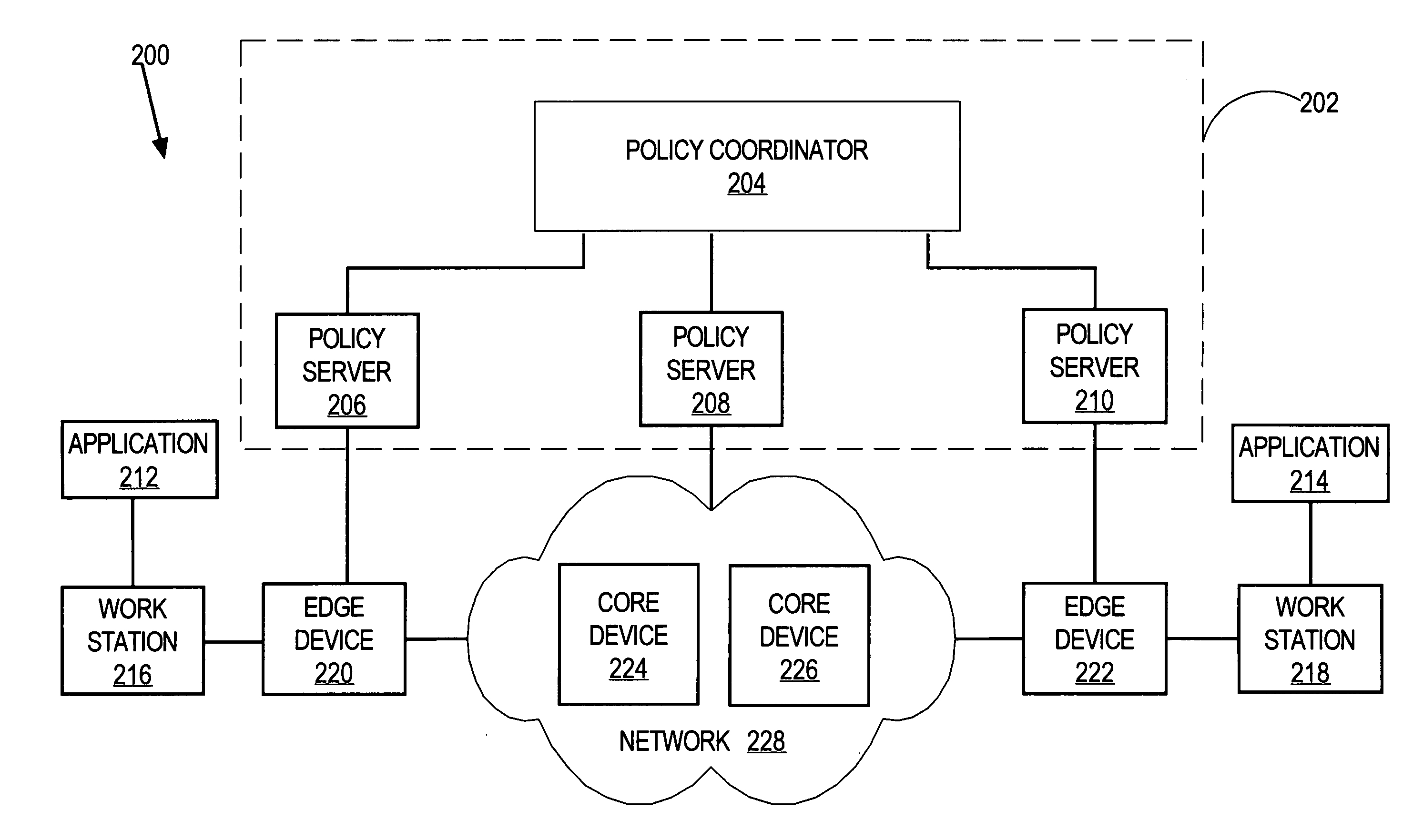
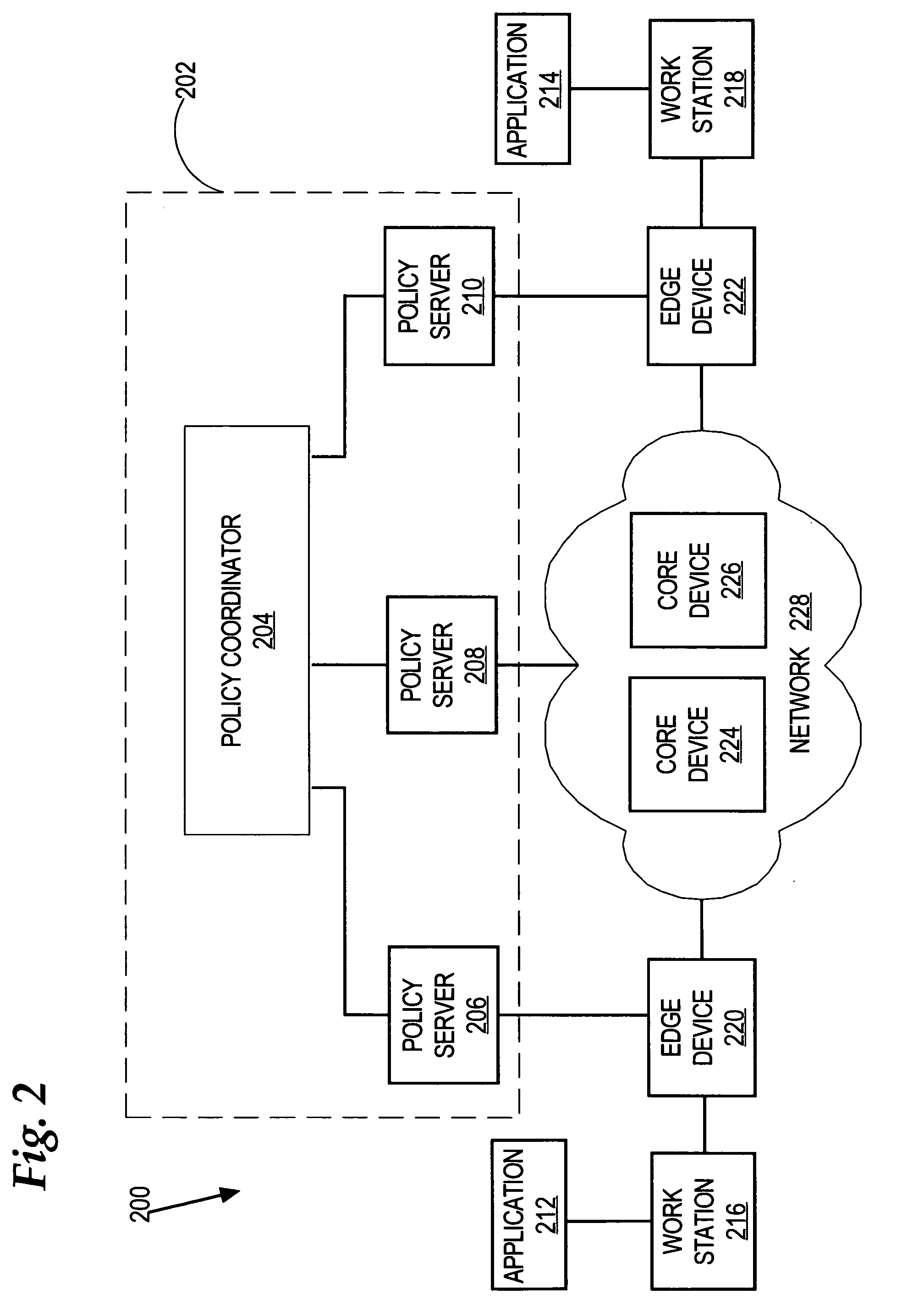
Generalized policy server
InactiveUS7272625B1Easy to handleMultiple digital computer combinationsTransmissionPolicy decisionTrust level
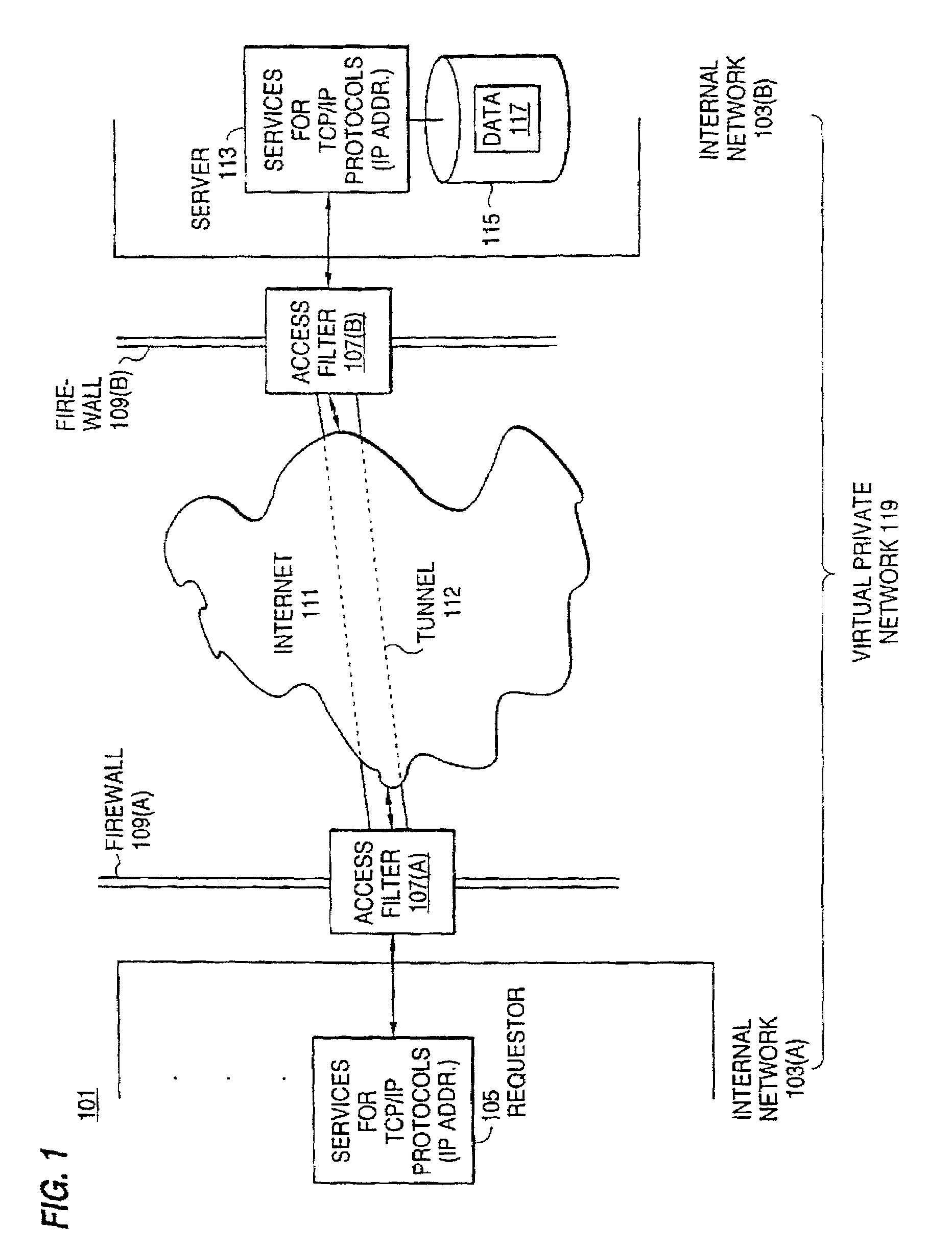
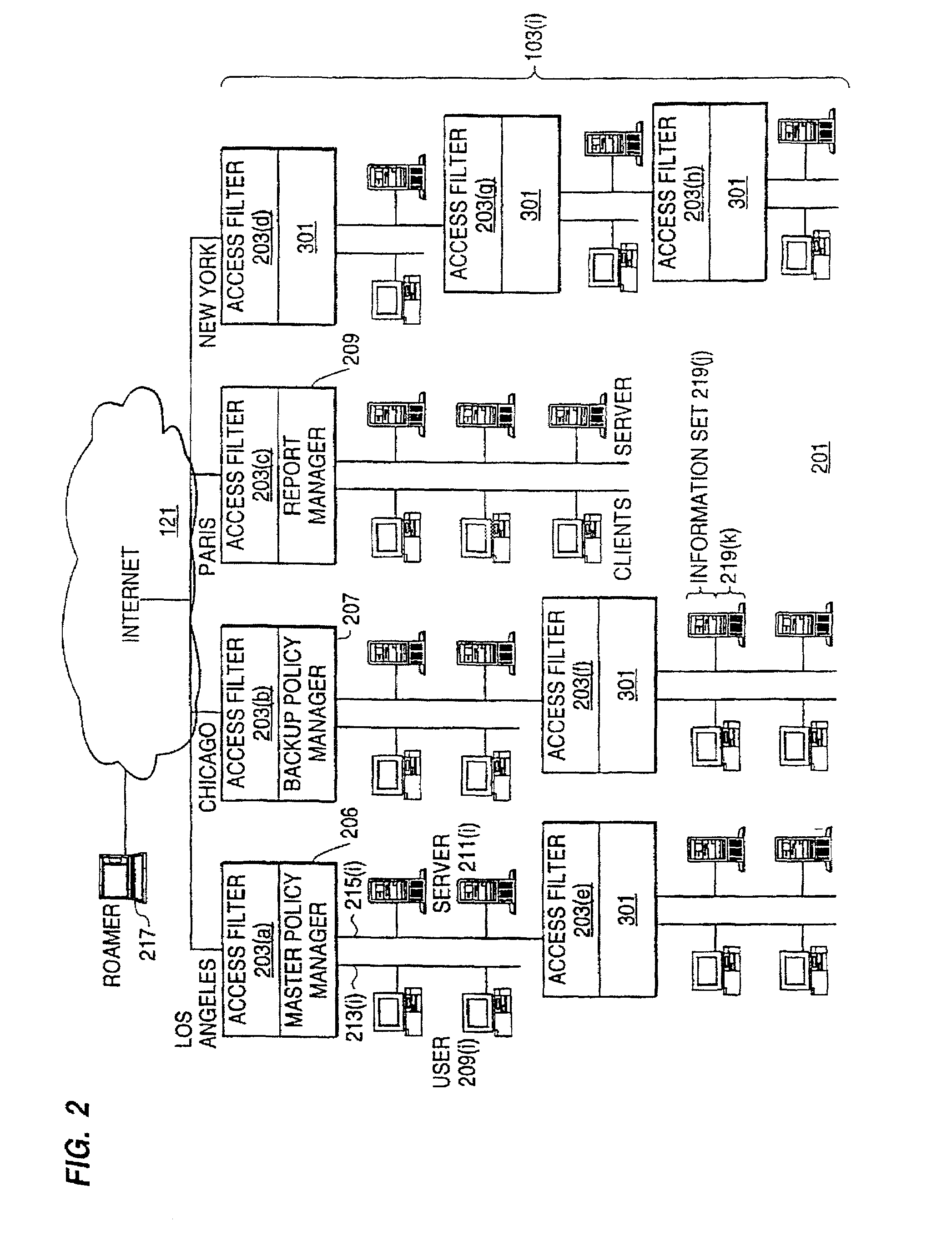
A policy system includes the policy server (2617); a policy database (2619) which located at policy decision point (2723); the access / response entity (2603); resource server (2711); policy message (2725) and policy enforcement point (2721). System connected through public network (2702) or internal network (103). The access filter (107, 203, 403) control access by use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Access is permitted or denied according to of access policies (307) which define access in terms of the user groups (FIGS. 9-12) and information sets (FIGS. 13A-18). The rights of administrators are similarly determined by administrative policies (FIGS. 23A-C). Access is further permitted only if the trust levels of the network by which is made by the sufficient access (FIGS. 25-29). A policy server component of the access filter has been separated from the access filter and the policies have been generalized to permit administrators of the policy server to define new types of actions and new types of entities. Policies may now further have specifications for time intervals during which the policies are in force and the entities may be associated with attributes that specify how the entity is to be used when the policy applies.
Owner:MARSHMAN RES +1
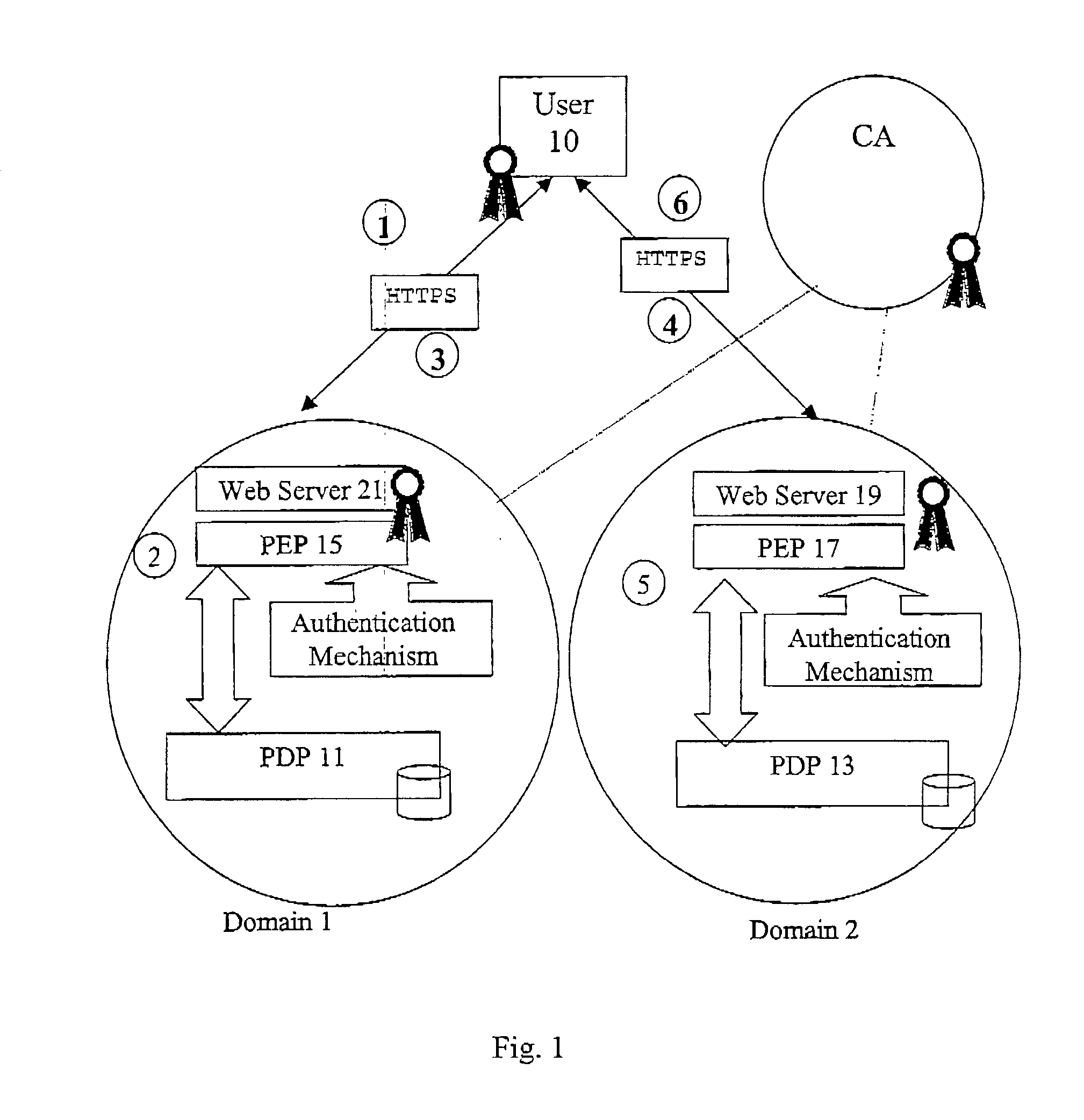
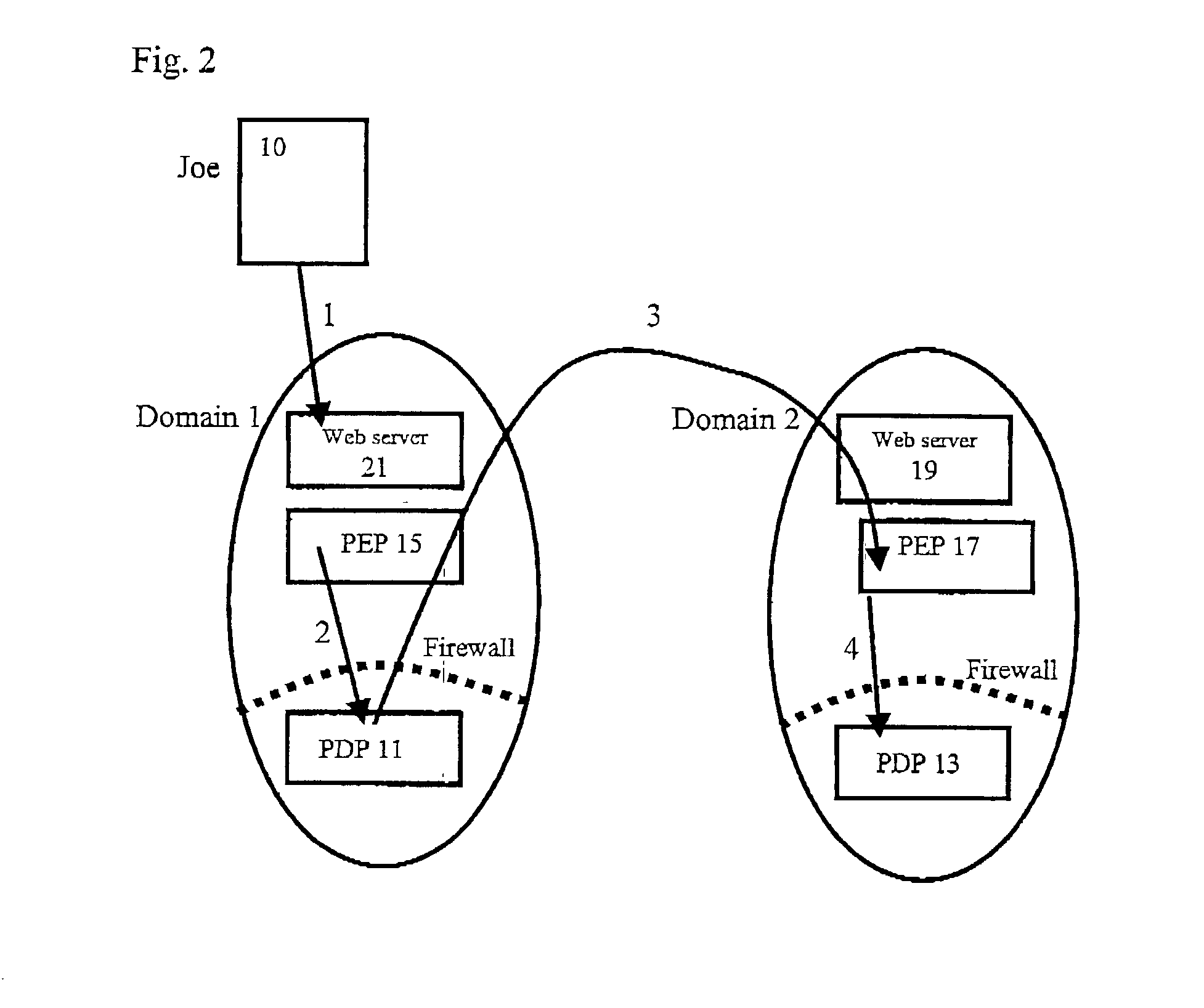
Multi-domain authorization and authentication
ActiveUS20030023880A1Special data processing applicationsSecuring communicationPolicy decisionAuthorization
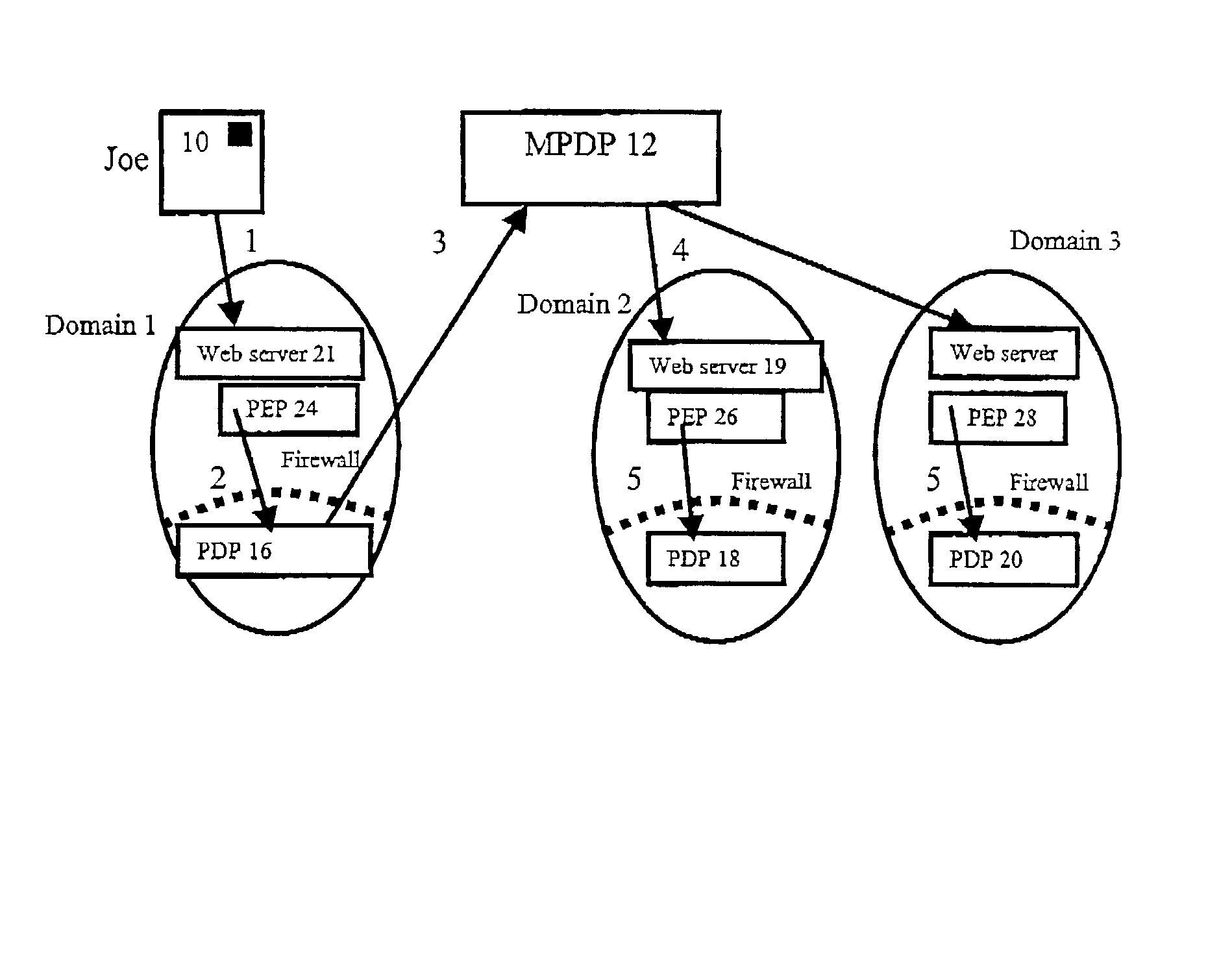
A method of multi-domain authorisation / authentication on a computer network comprises: a user making a request to a policy enforcement point of a computer for access to information on the computer; providing a location address for a user's authorisation and / or authentication information, a policy decision point of the service on the computer network then verifying the authorisation / authentication information; and the user being given access by the PEP to the information or the service requested, if the request is accepted, wherein the user's authorisation / authentication and / or further information is located on a meta policy decision point (MPDP).
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
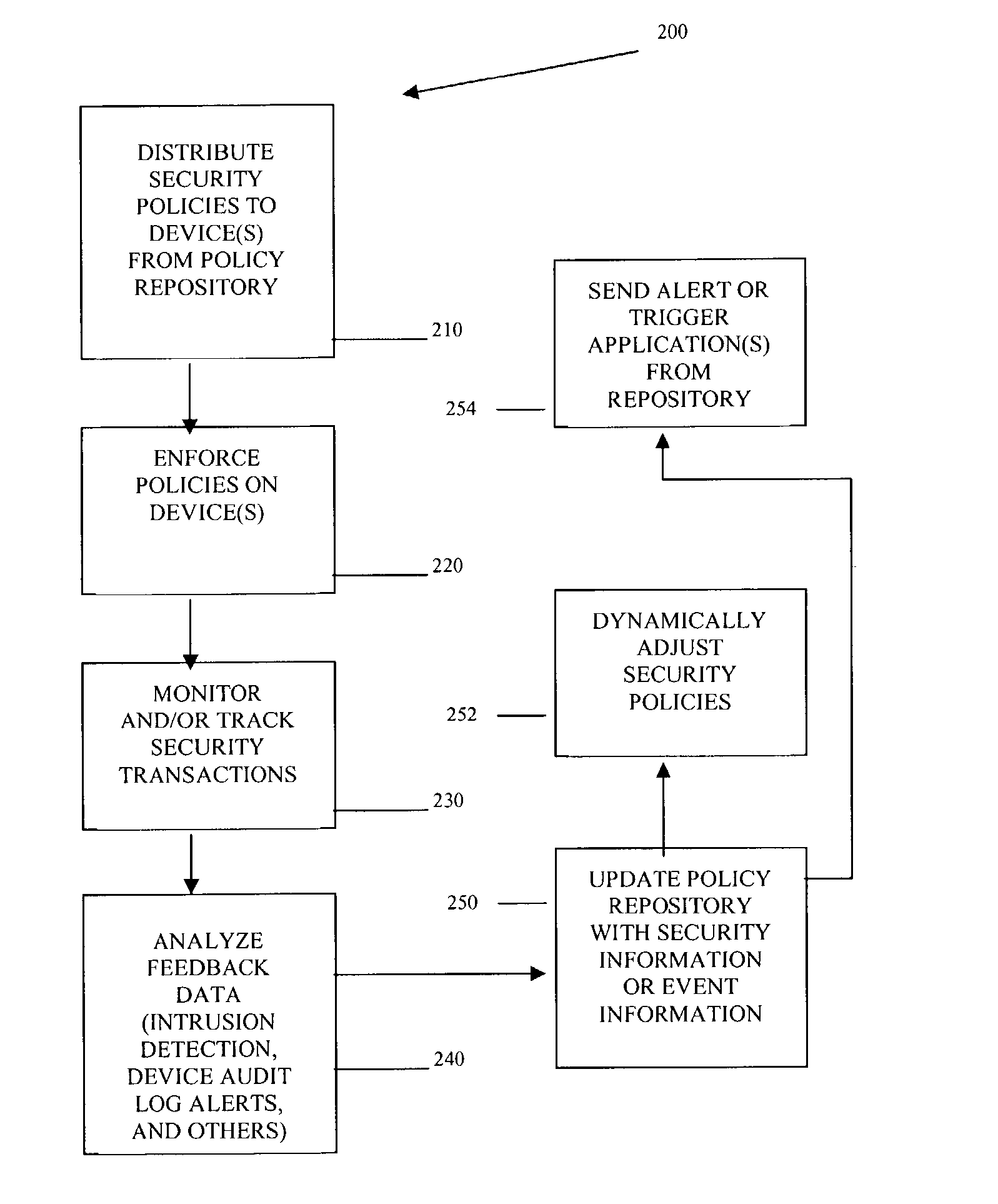
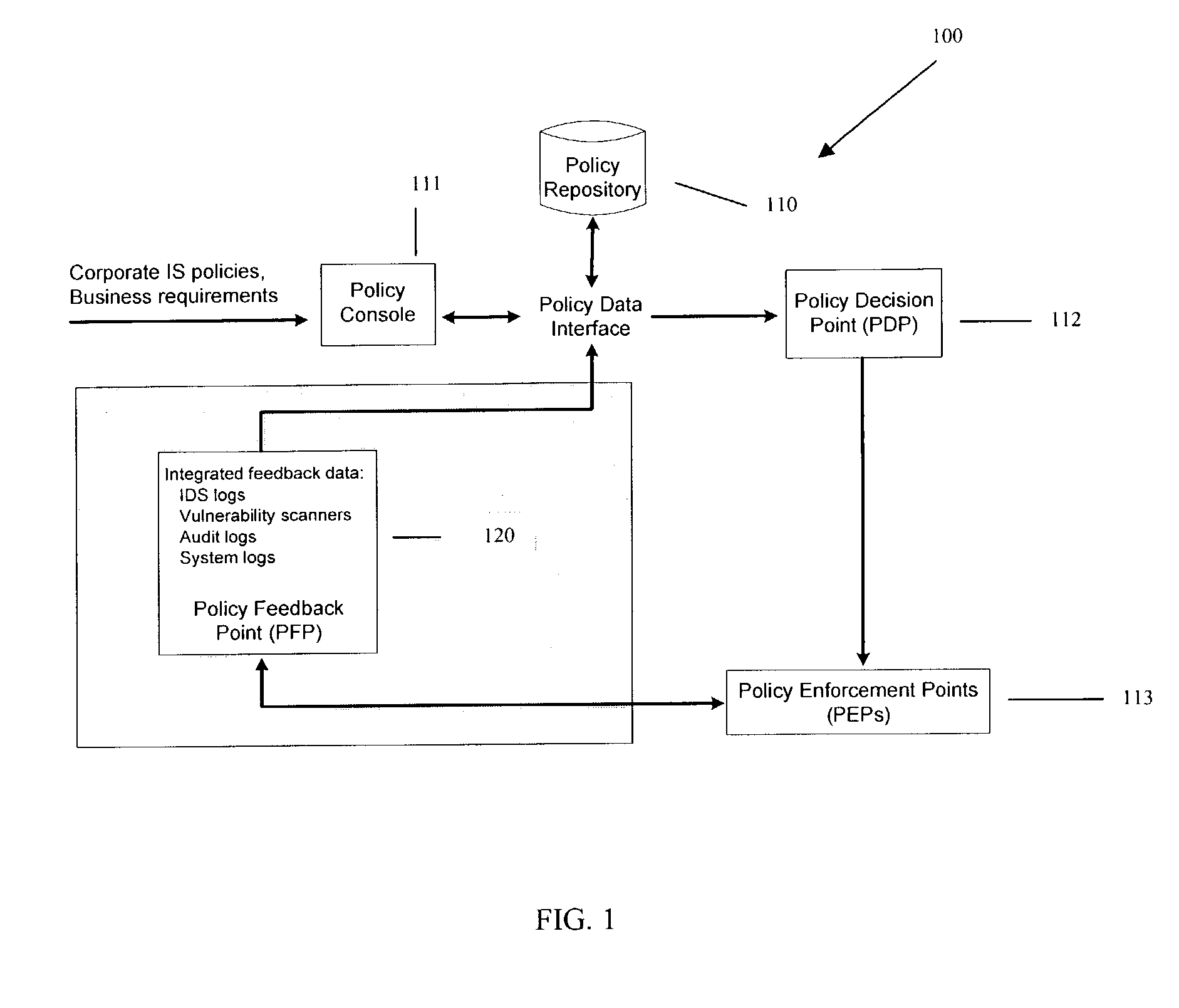
Methods and systems for managing security policies
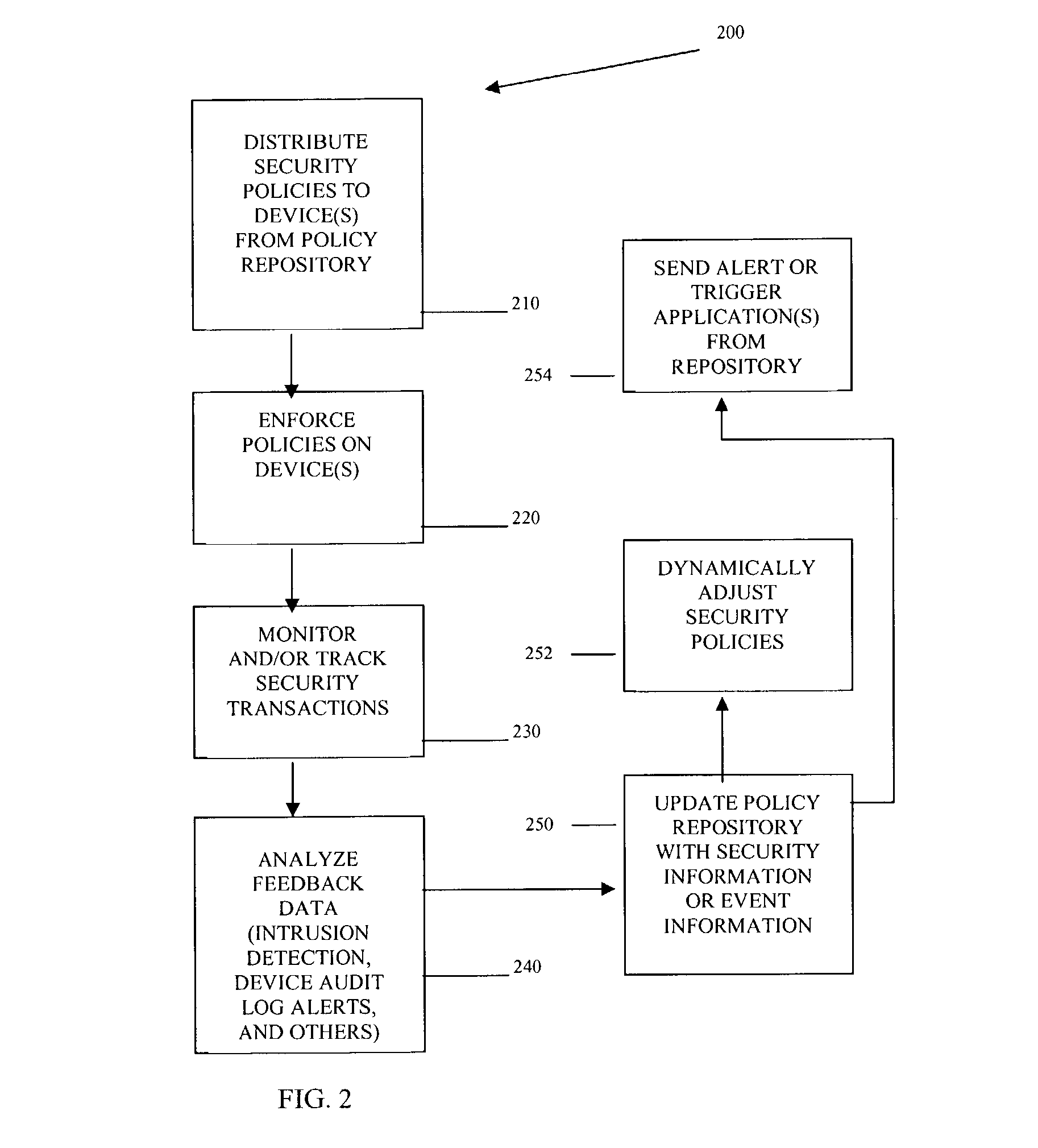
InactiveUS20040193912A1Data taking preventionDigital data processing detailsPolicy decisionSystems management
Methods, machines, and systems manage security policies of heterogeneous infrastructure and computing devices of a network. Security policy repository houses security policies that are pushed over the network by a policy decision point PDP to appropriate security-enabled devices (policy enforcement points (PEPs)) for enforcement. Using a closed feedback loop, a policy feedback point (PFP) collects and processes data from intrusions, alerts, violations, and other abnormal behaviors from a variety of PEPs or logs produced from PEPs. This data is sent as feedback to the policy repository. The PDP detects the data and analyzes it to determine if policy updates (which can be dynamic and automatic) need to be adaptively made and dynamically pushed to PEPs. The PDP can also send console messages or alerts to consoles or administrators.
Owner:INTEL CORP
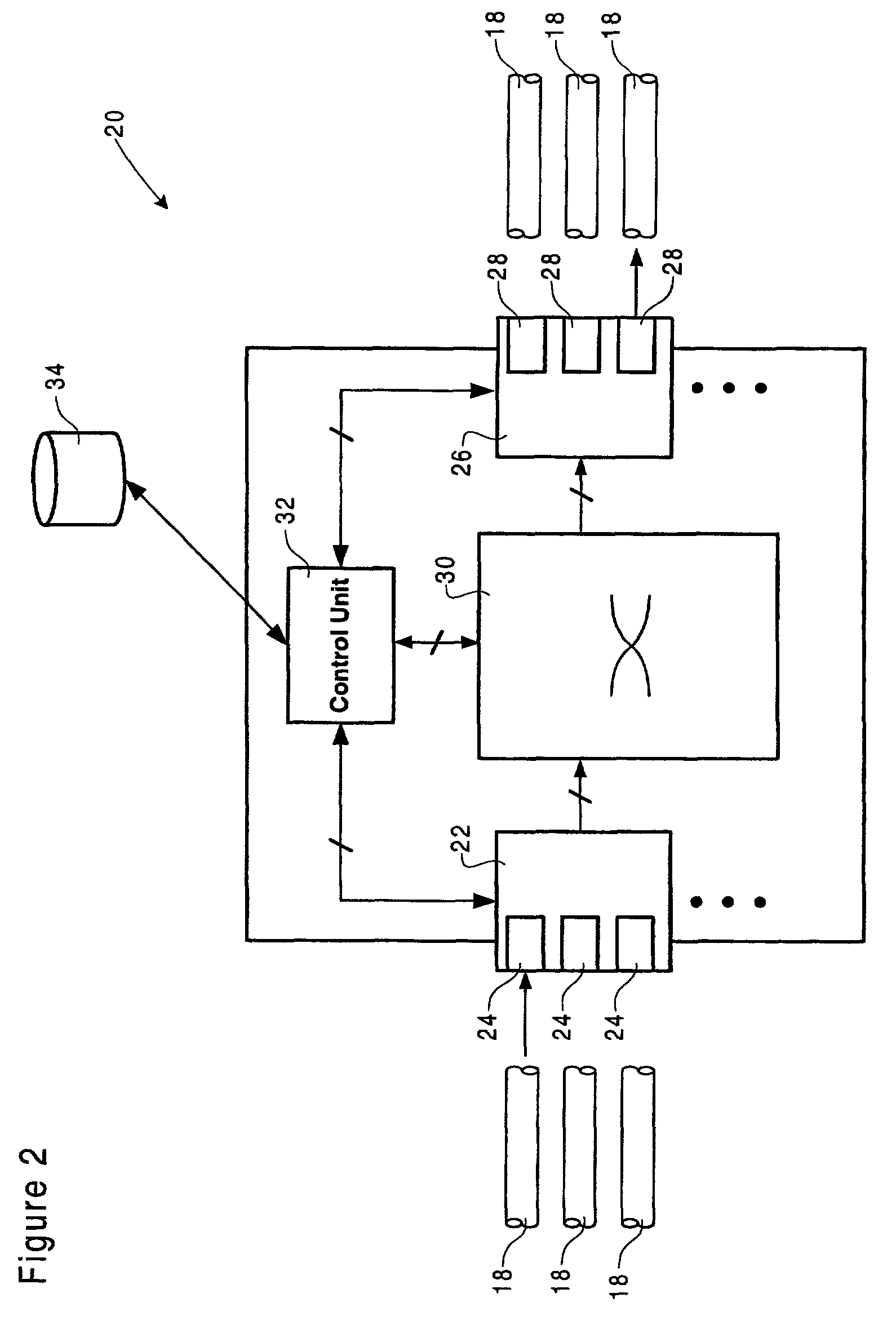
System for providing flexible charging in a network
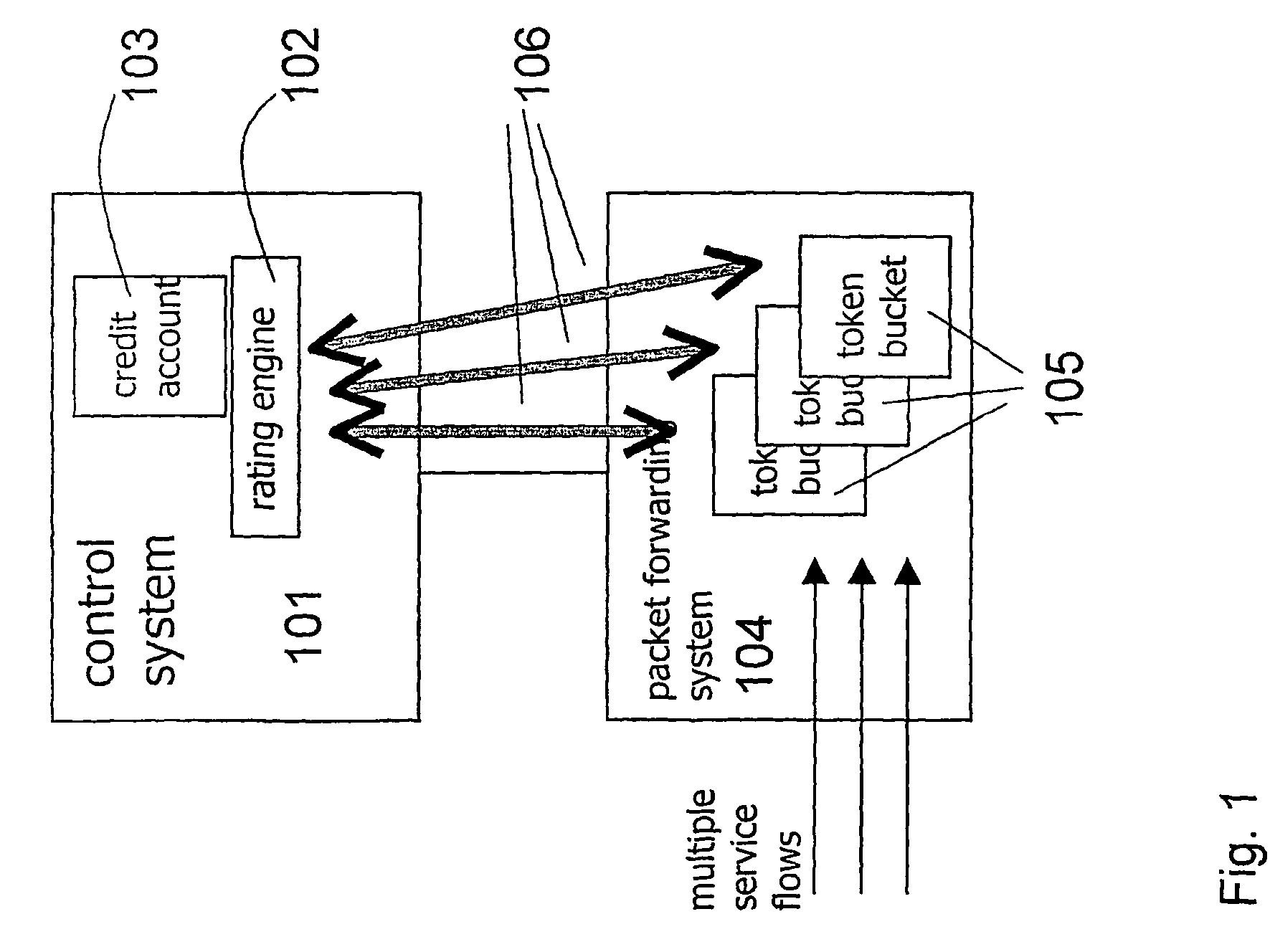
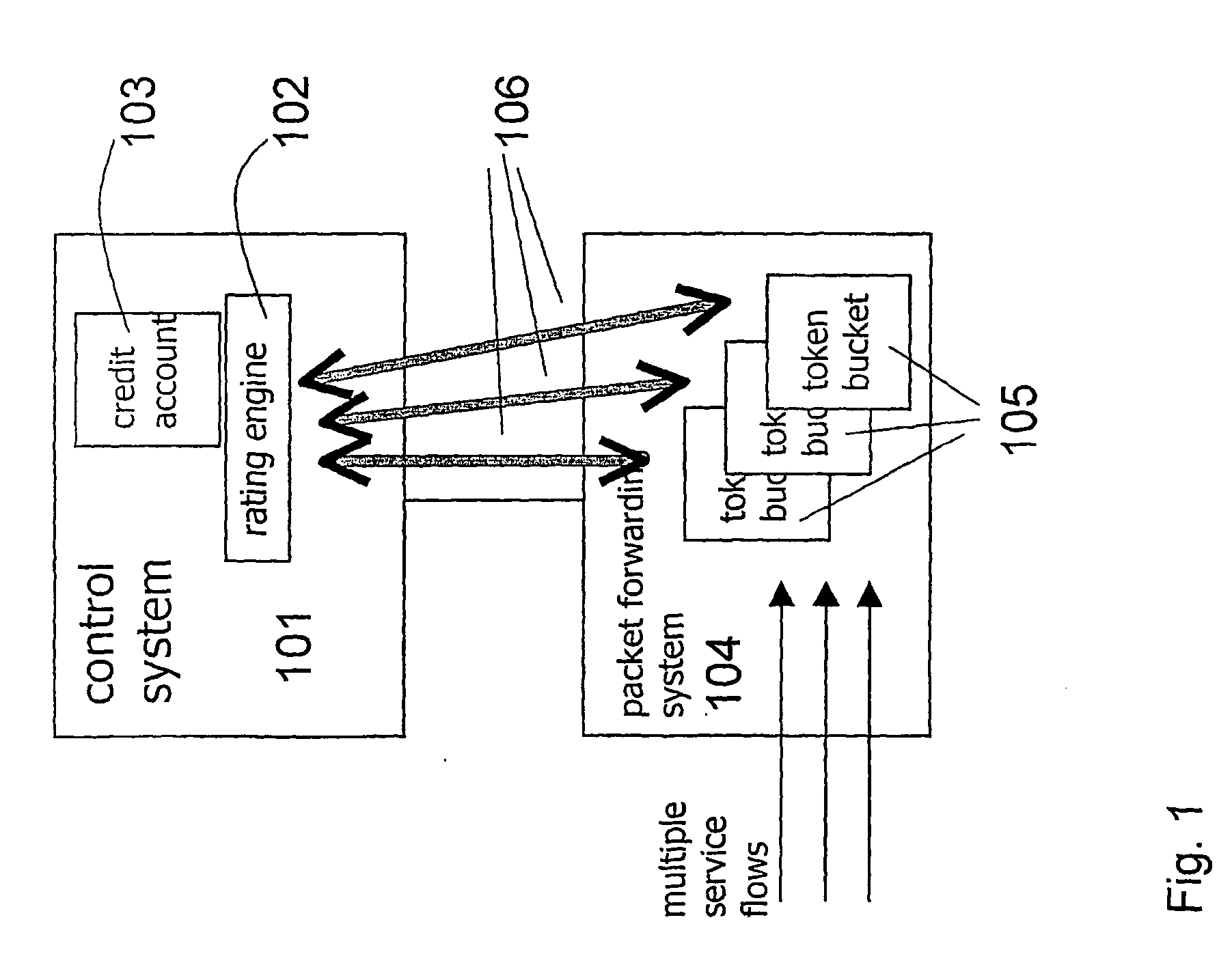
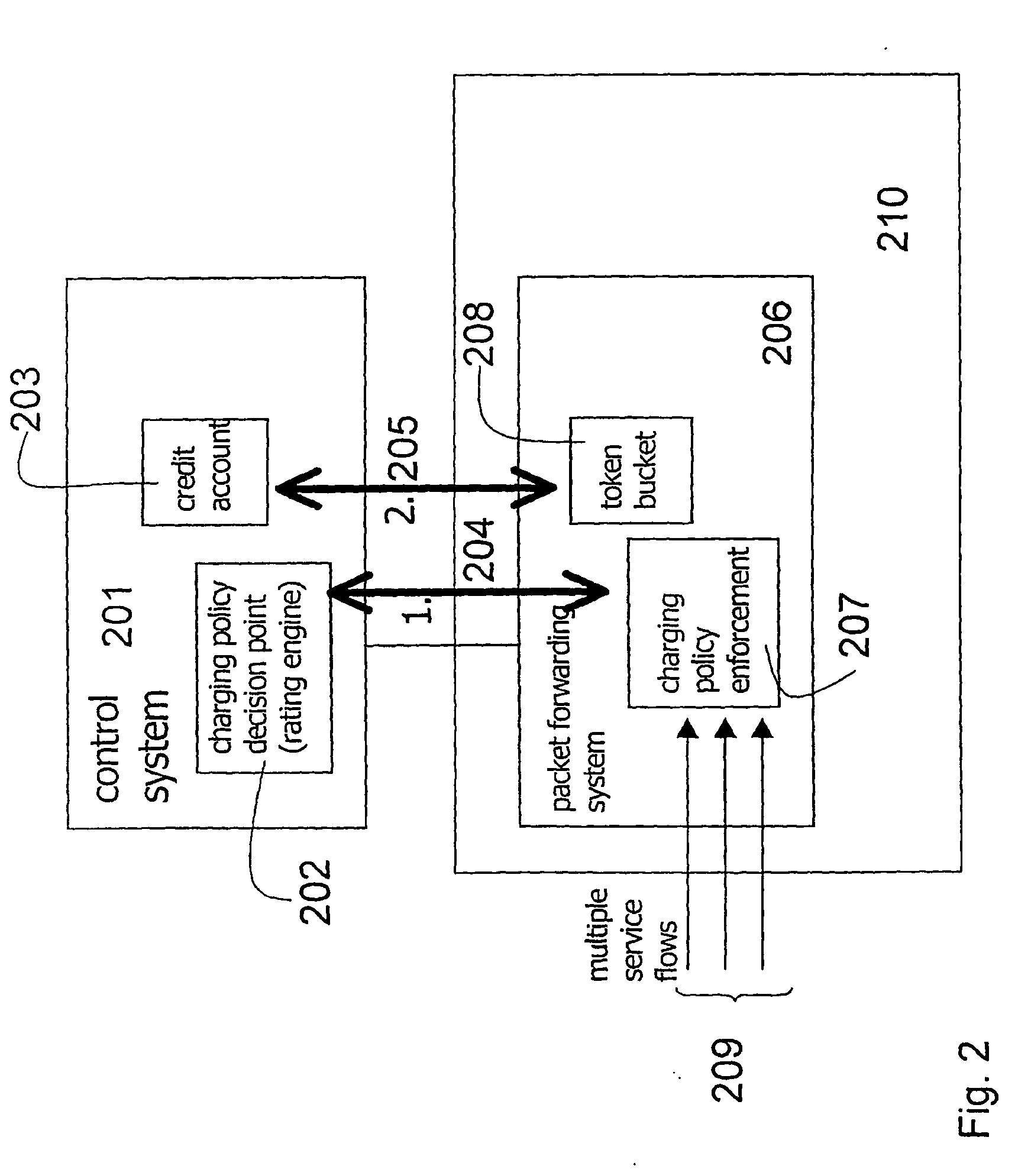
ActiveUS7450591B2Reduce signaling loadReduce reservationMetering/charging/biilling arrangementsData switching by path configurationService flowPolicy decision
Owner:TELEFON AB LM ERICSSON (PUBL)
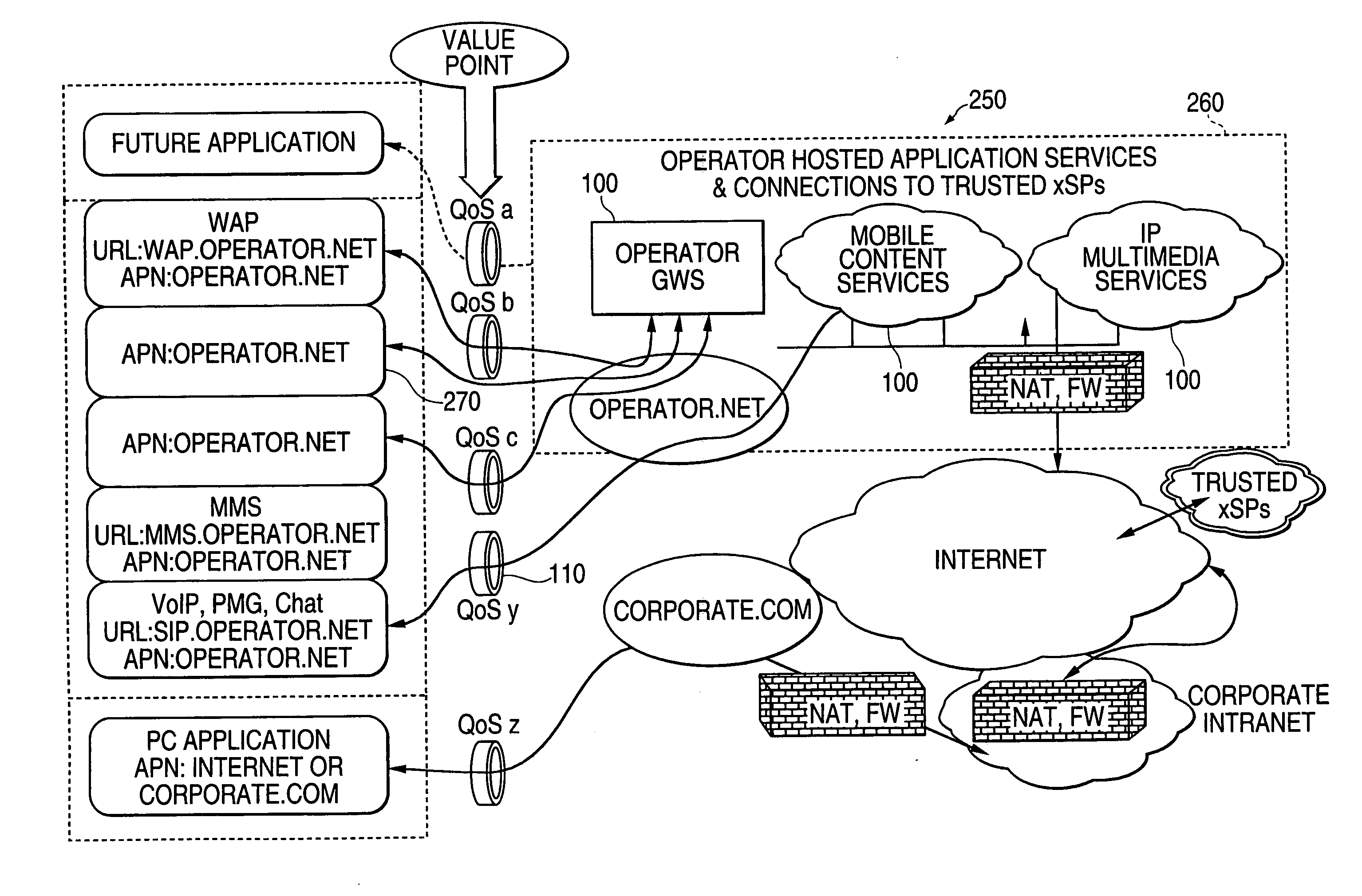
Multimedia next generation network architecture for IP services delivery based on network and user policy
InactiveUS7984130B2Network traffic/resource managementDigital computer detailsPolicy decisionService control
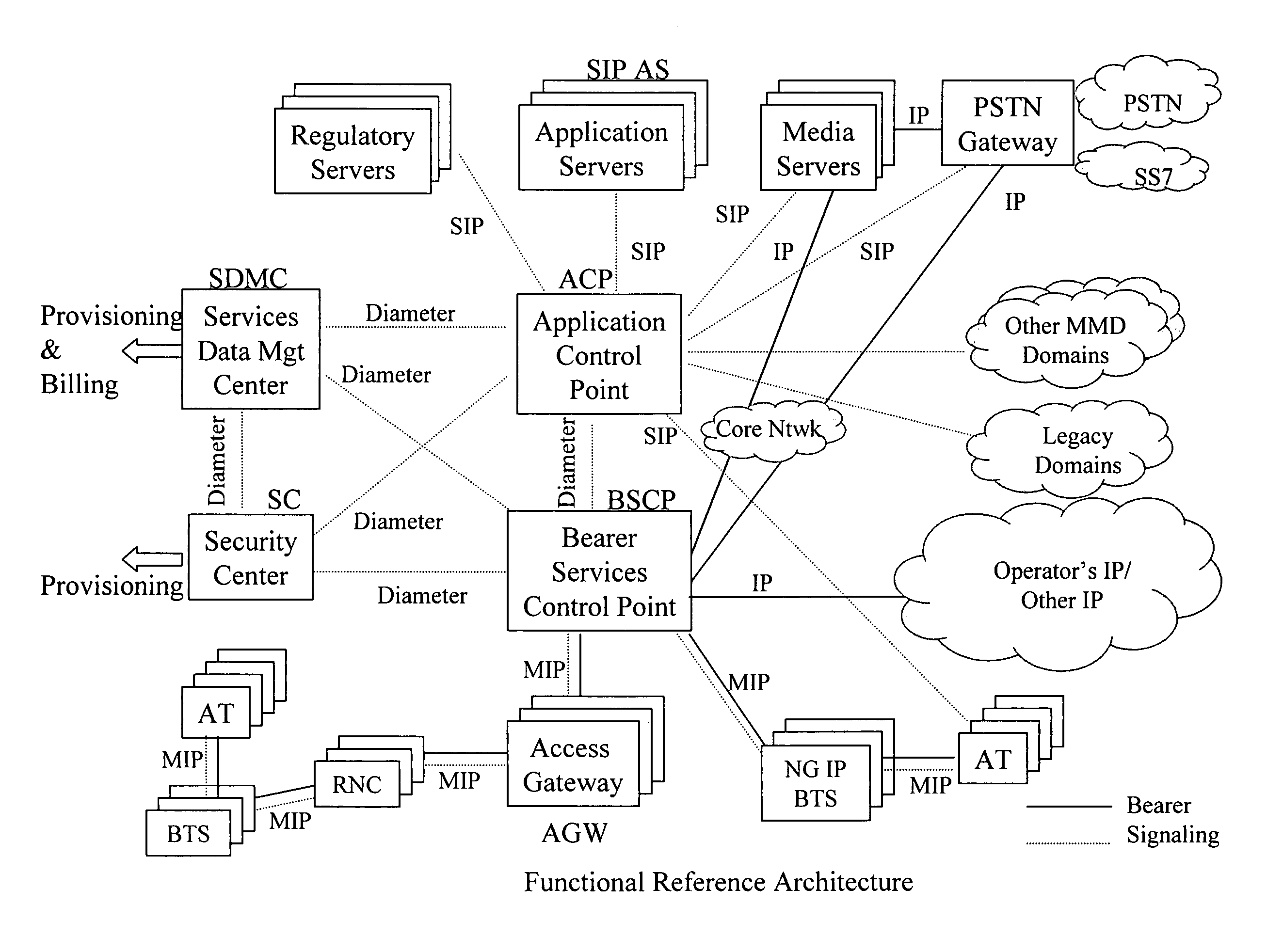
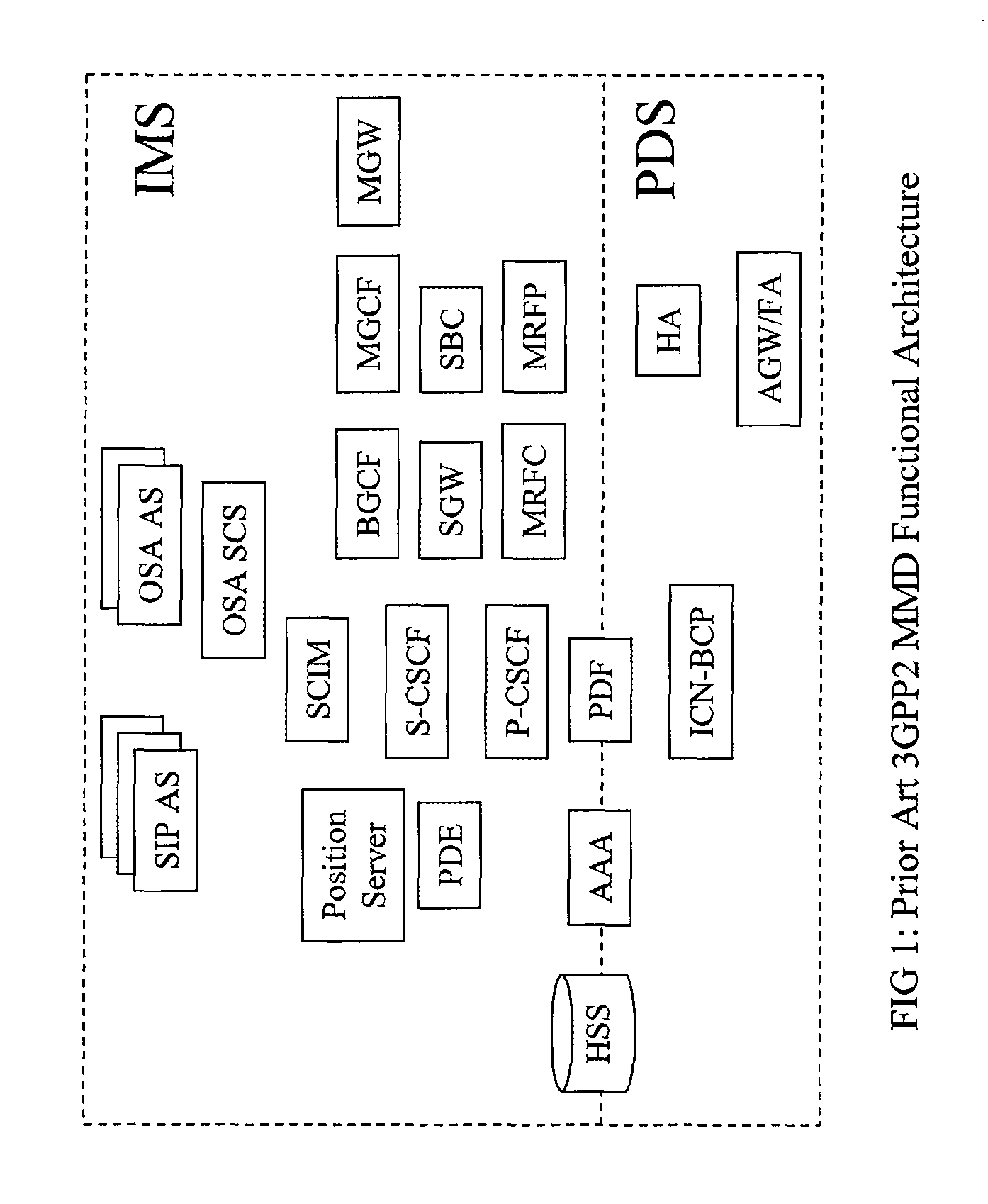
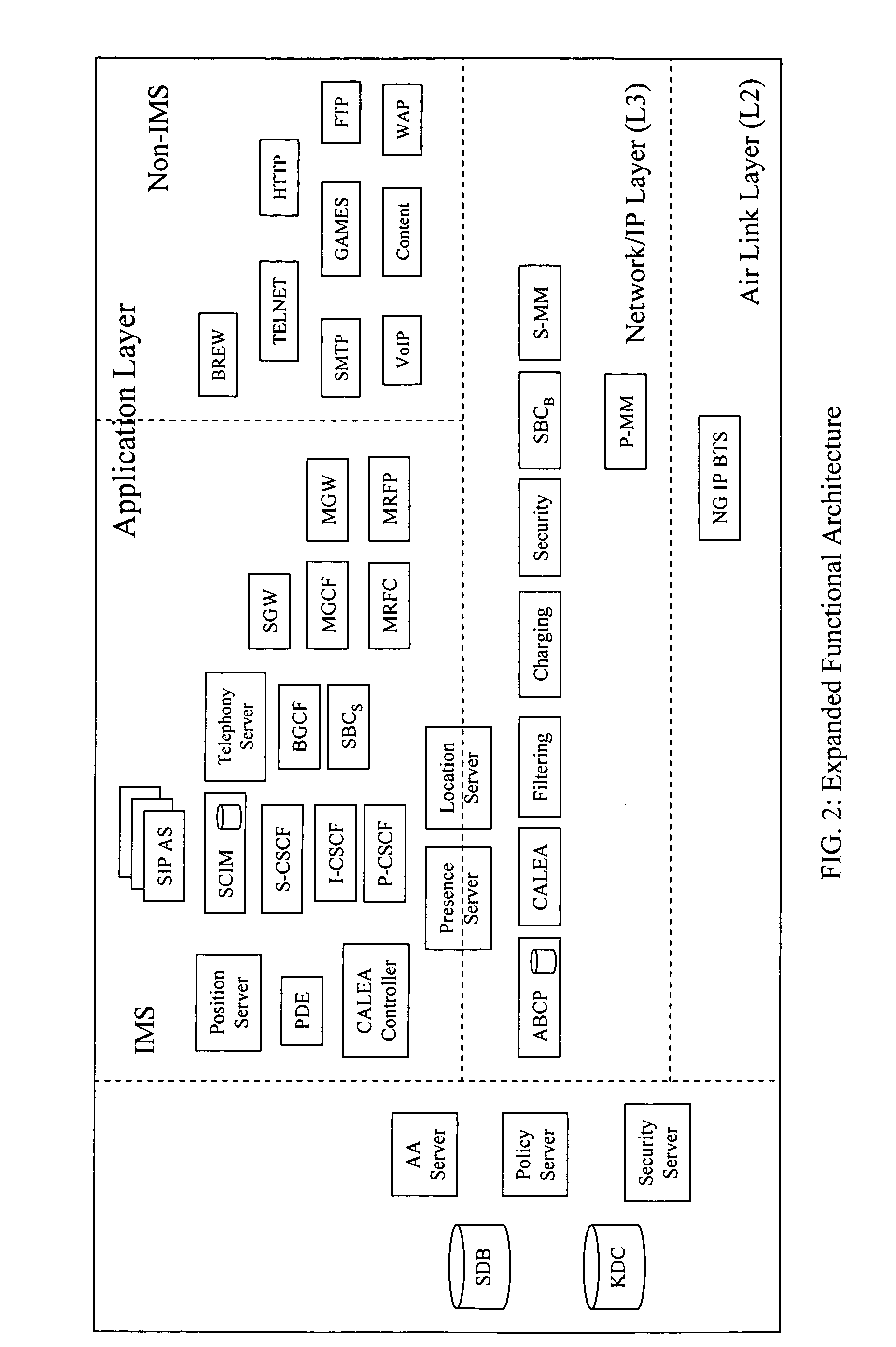
The exemplary Multimedia Next Generation Network architecture disclosed herein covers the entire next generation system, e.g. for wireless communication services, including application, signaling and bearer functionalities. The architecture addresses unification of subscriber databases for both SIP services and non-SIP services in a Services Data Management Center (SDMC). A Security Center (SC) provides a central repository for all security related databases and functions. An Application Control Point (ACP) provides a single point of services control for all active SIP services for all subscribers via state information and services interaction management. Policy decisions are made at the packet layer, for example in an Advanced Bearer Control Point (ABCP) clustered with other functions to form a Bearer Services Control Point (BSCP). Policy enforcement is implemented at various nodes at the network or packet layer (L3) and above, e.g. including the BSCP and ACP.
Owner:CELLCO PARTNERSHIP INC
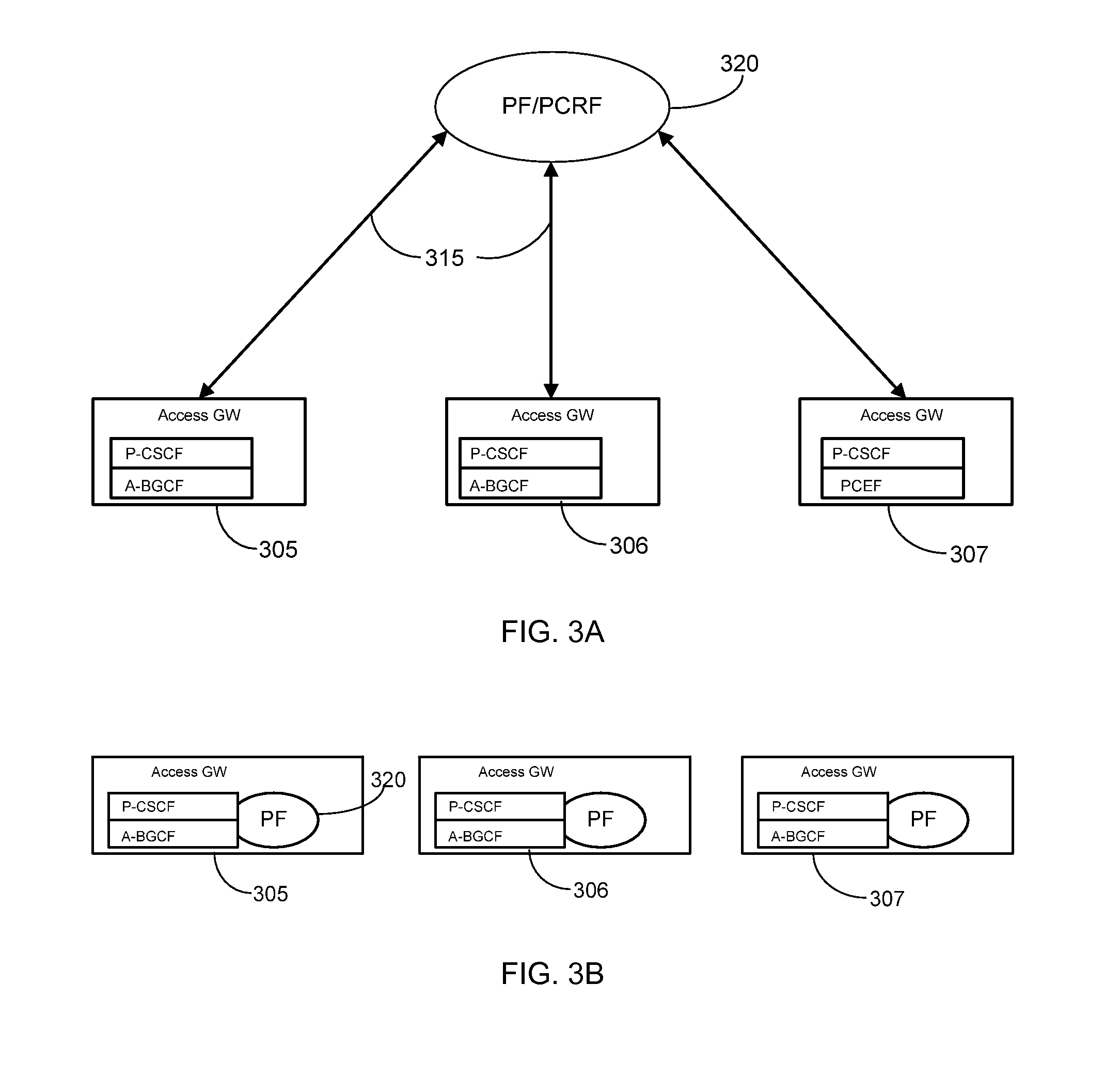
Cascading Policy Management Deployment Architecture
InactiveUS20090113514A1Improve performanceLimitation is enforcedError preventionTransmission systemsPolicy decisionWireless mesh network
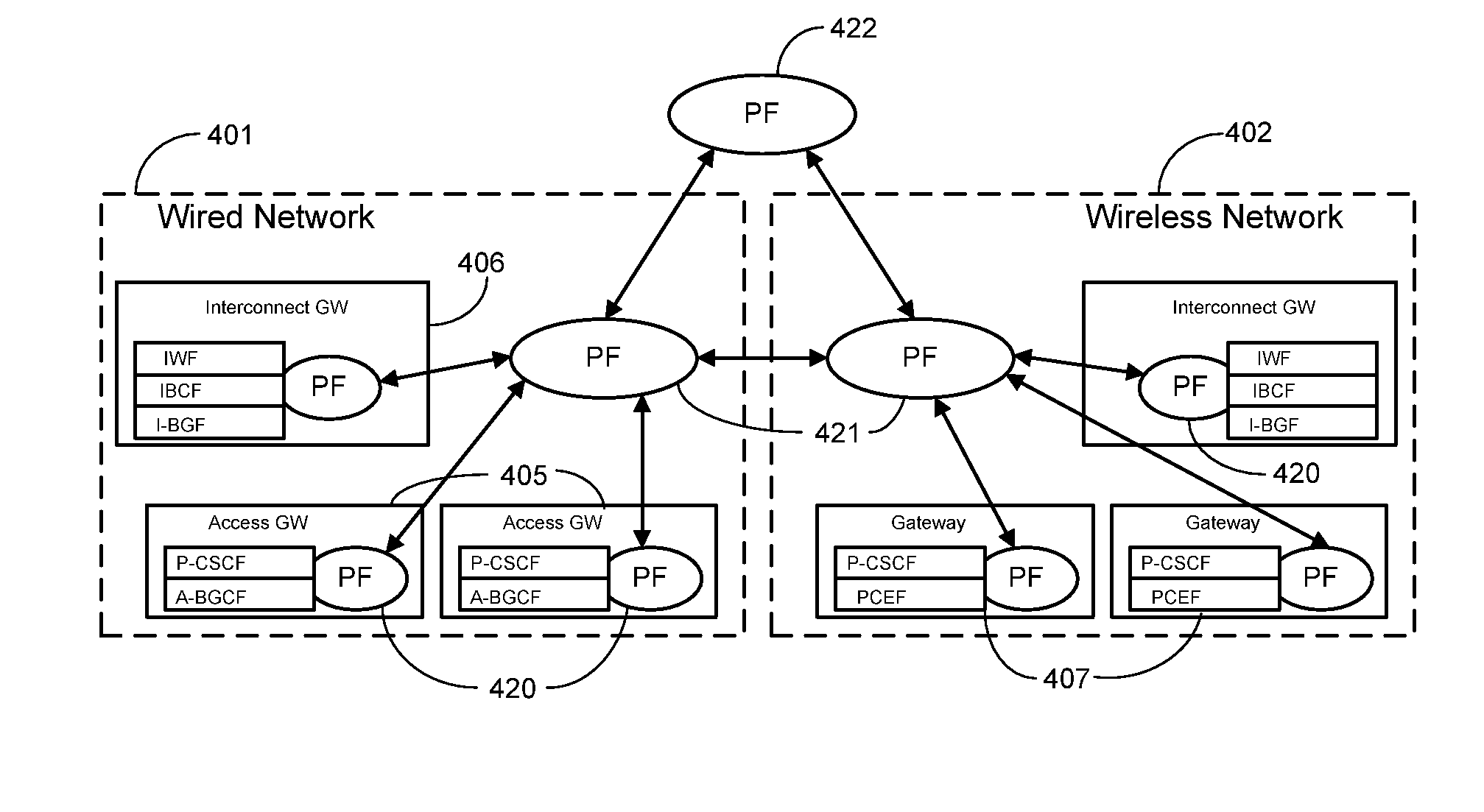
Systems and methods are provided to implement a dynamic and efficient cascading policy management framework architecture for both wired and wireless networks. A plurality of Policy Functions (PFs) are assigned to a plurality of Policy Enforcement Points (PEP). The PFs make decisions regarding local policy control at the specific PEP. The PFs then delegate the policy requests or IP flows to a separate PEP that is more conducive to enforcing that policy request. Thus, policy decisions are made at the point where the most information is available, leading to fewer policy requests traversing back and forth across a network. Additionally, this cascading Policy Management Framework Architecture allows for unified policy management across multiple types of networks, including wired (Internet) and wireless (UMTS).
Owner:AT&T MOBILITY II LLC
Statistical tracking for global server load balancing
InactiveUS20100223621A1Multiprogramming arrangementsMultiple digital computer combinationsPolicy decisionIp address
Server load-balancing operation-related data, such as data associated with a system configured for global server load balancing (GSLB) that orders IP addresses into a list based on a set of performance metrics, is tracked. Such operation-related data includes inbound source IP addresses (e.g., the address of the originator of a DNS request), the requested host and zone, identification of the selected “best” IP addresses resulting from application of a GSLB algorithm and the selection metric used to decide on an IP address as the “best” one. Furthermore, the data includes a count of the selected “best” IP addresses selected via application of the GSLB algorithm, and for each of these IP addresses, the list of deciding performance metrics, along with a count of the number of times each of these metrics in the list was used as a deciding factor in selection of this IP address as the best one. This tracking feature allows better understanding of GSLB policy decisions (such as those associated with performance, maintenance, and troubleshooting) and intelligent deployment of large-scale resilient GSLB networks.
Owner:AVAGO TECH INT SALES PTE LTD
Database for check risk decisions populated with check activity data from banks of first deposit
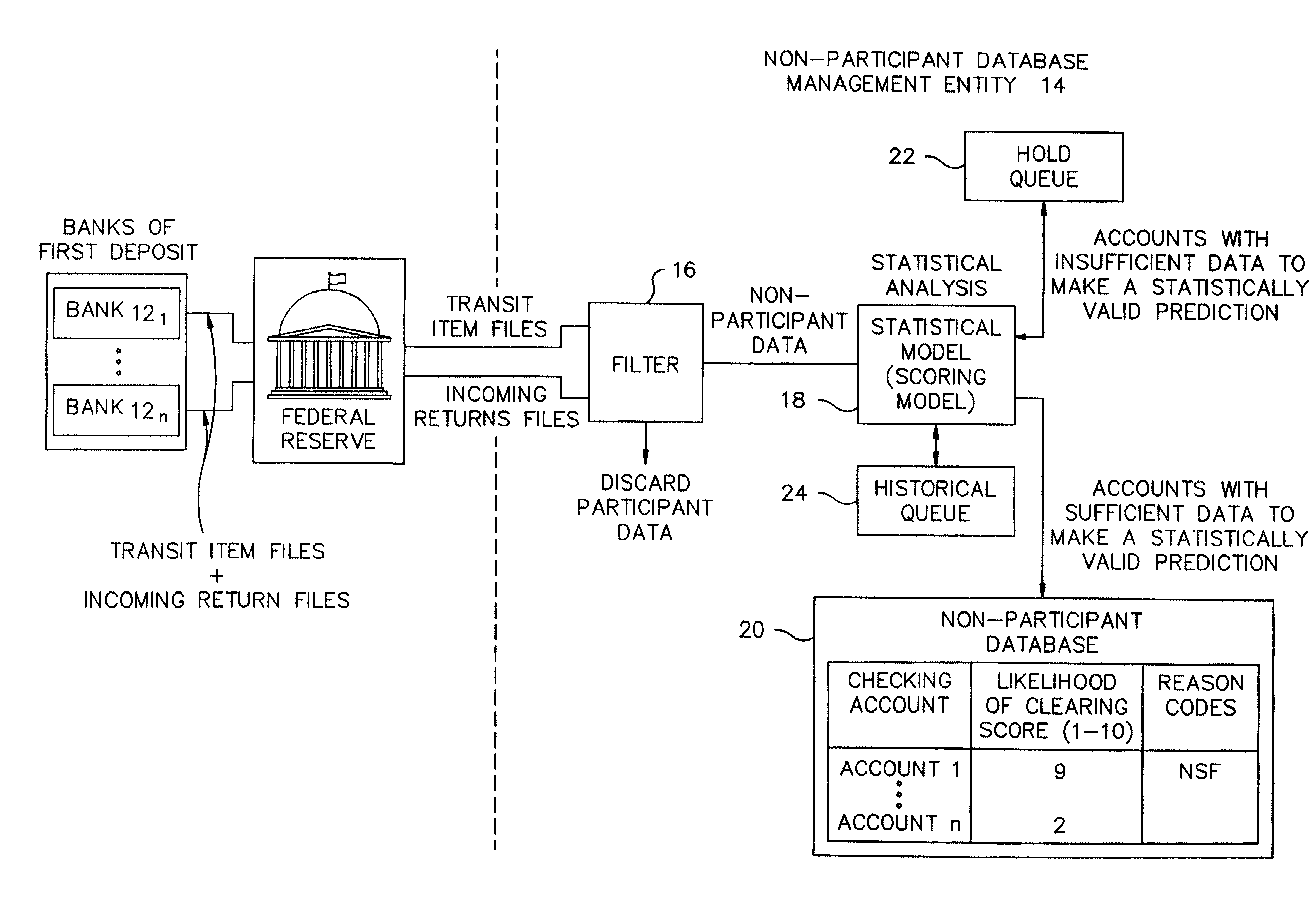
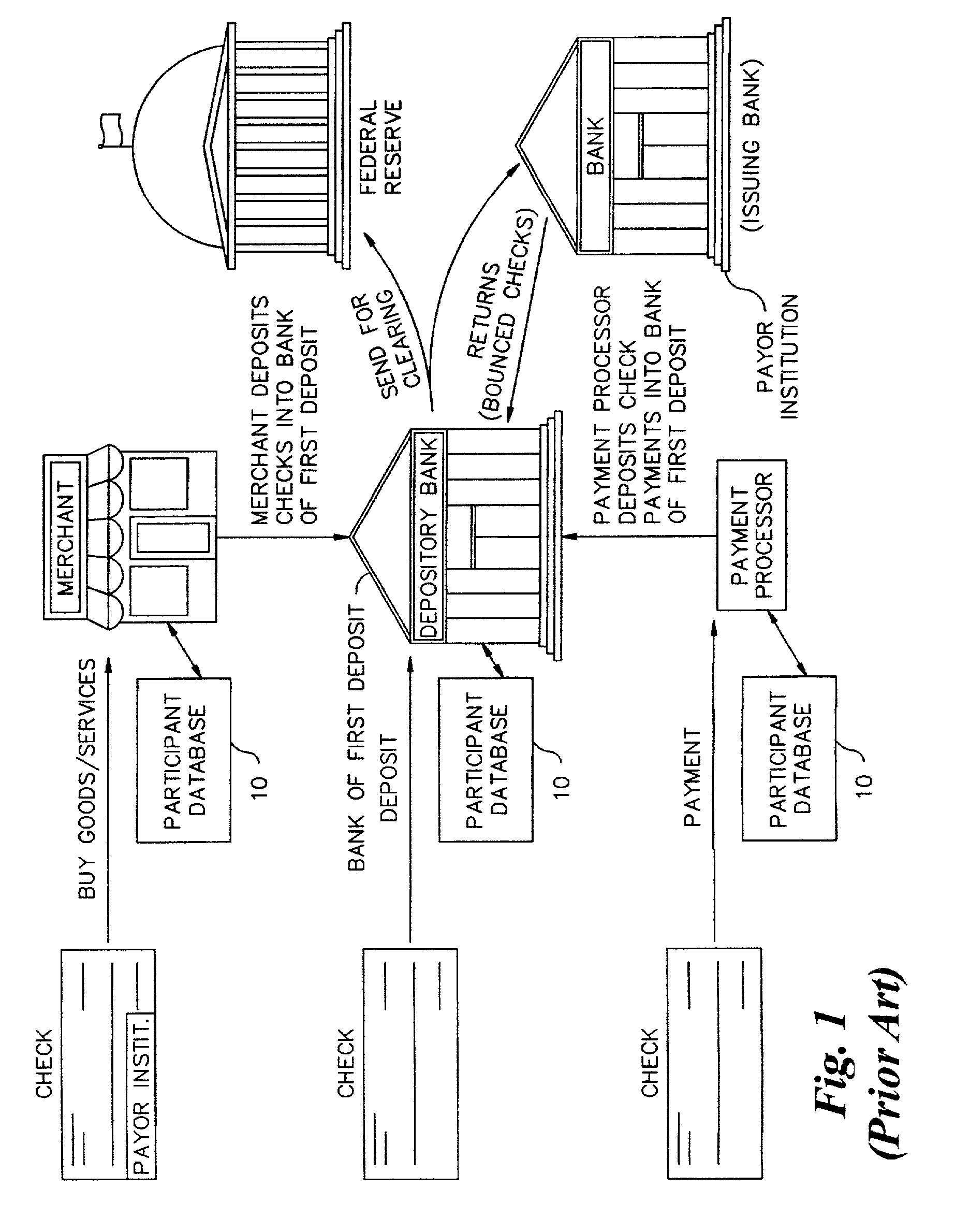
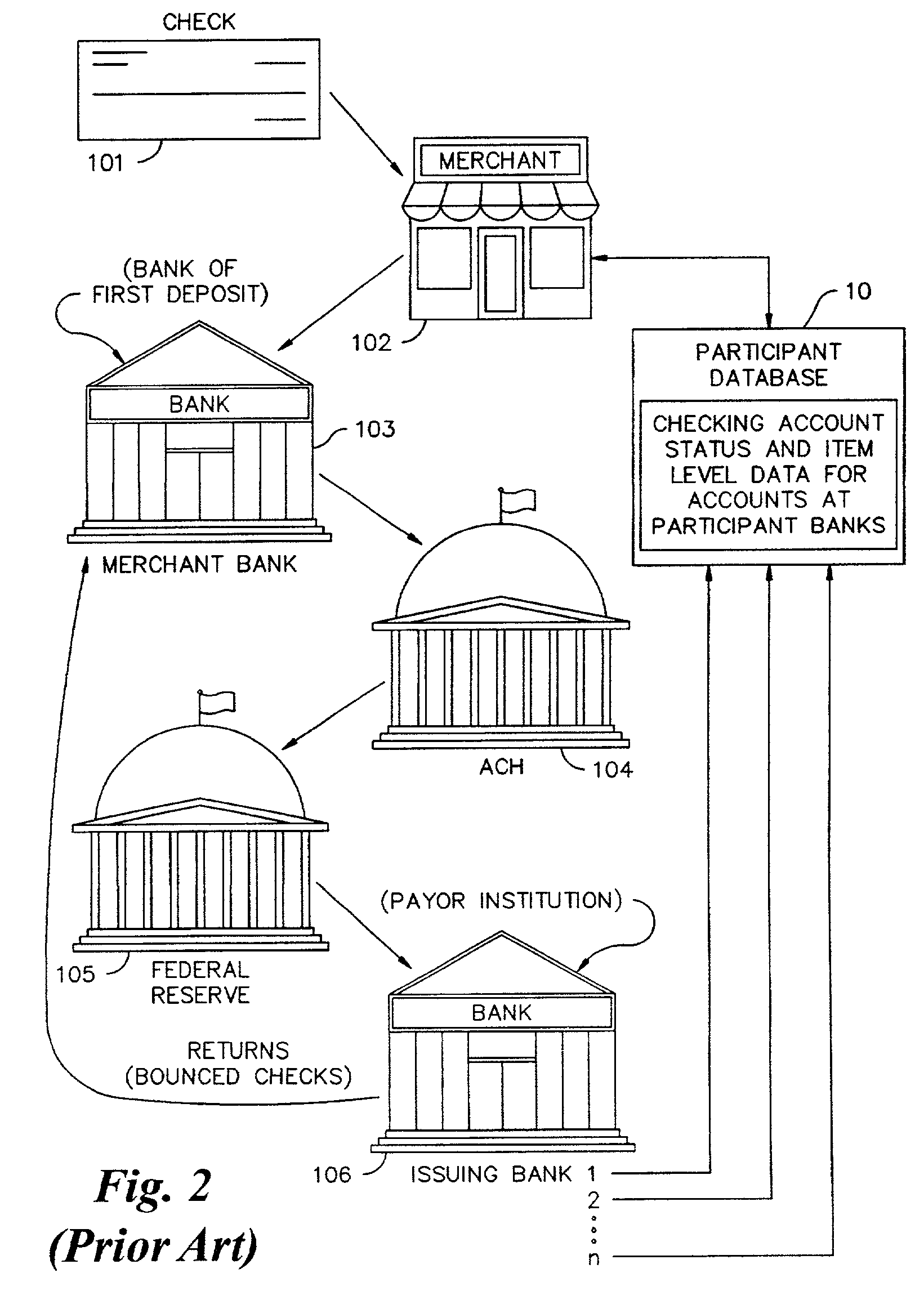
A plurality of banks of first deposit provide checking account activity data for both transit items (checks received for deposit that need to be cleared) and incoming returns (bounced checks) to a statistical model which determines from the data the likelihood that a check from a specific checking account will be returned. This data is used to populate a database of checking accounts to be used for making check risk decisions, such as check hold policy decisions, check acceptance decisions, and open to buy decisions.
Owner:EARLY WARNING SERVICES
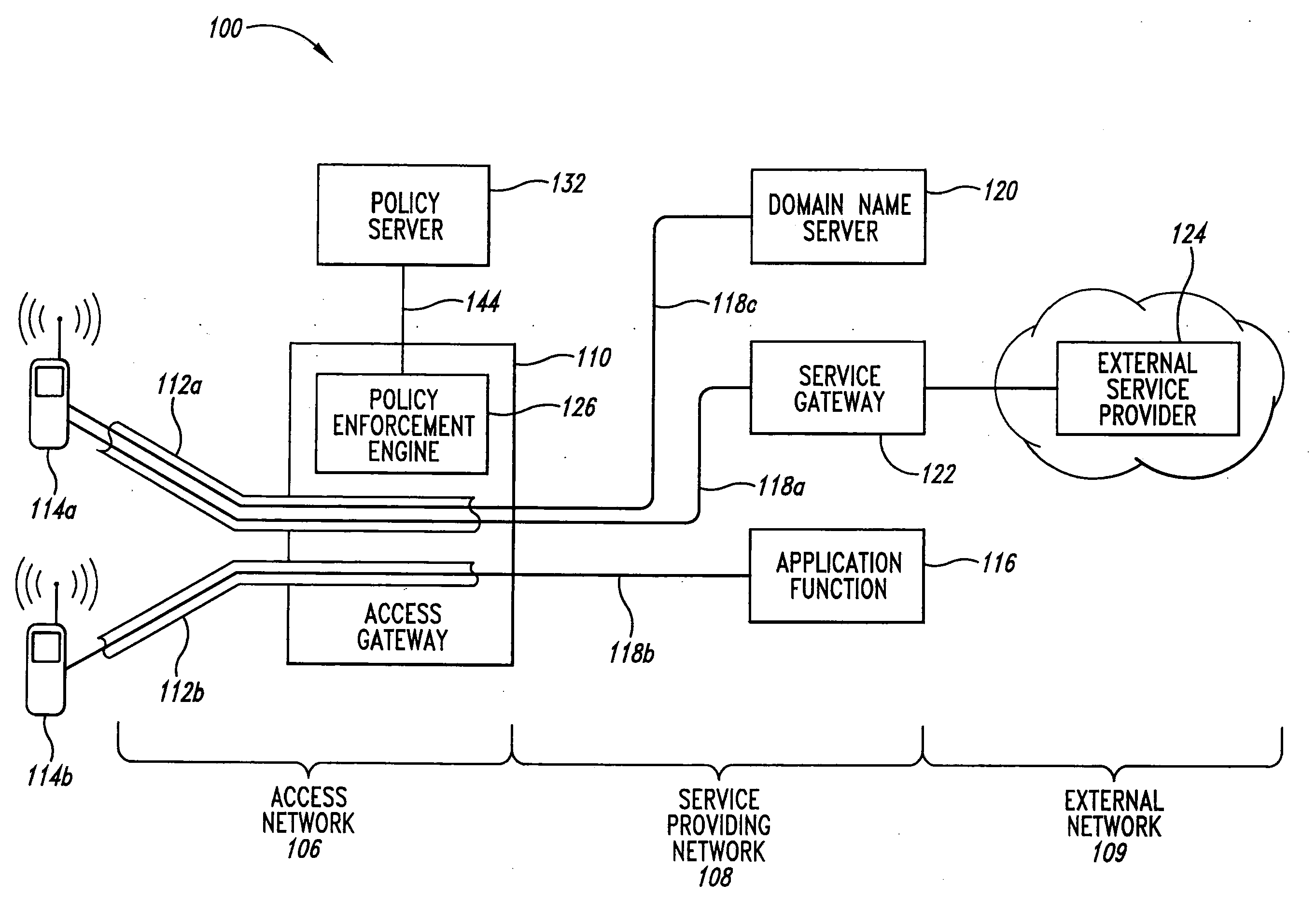
Method and apparatus for communicating network quality of service policy information to a plurality of policy enforcement points
A method is disclosed for communicating network quality of service policy information to a plurality of policy enforcement points. Active QoS configuration information is created and stored at a policy enforcement point, such as a router in a network. New configuration information is received and stored as an inactive configuration of the policy enforcement point. The policy enforcement point determines whether the inactive configuration information is properly functional in combination with the active QoS configuration information. The new configuration information is made active in place of the active QoS configuration information only in response to receiving an activation message. An inactive configuration may be signaled by a COPS protocol decision message from the policy decision point that identifies the configuration information as an inactive configuration by a specified flag bit in a message type value in a Context object that forms part of the decision message. Using the method, network quality of service policy information may be communicated to a plurality of policy enforcement points, with assurance that all receiving policy enforcement points can successfully deploy the configuration information. As a result, new QoS policy configuration information can be deployed to an entire network or to a large plurality of devices with assurance that all such information is received and deployed without adverse effects on the network or enforcement of policy information.
Owner:CISCO TECH INC
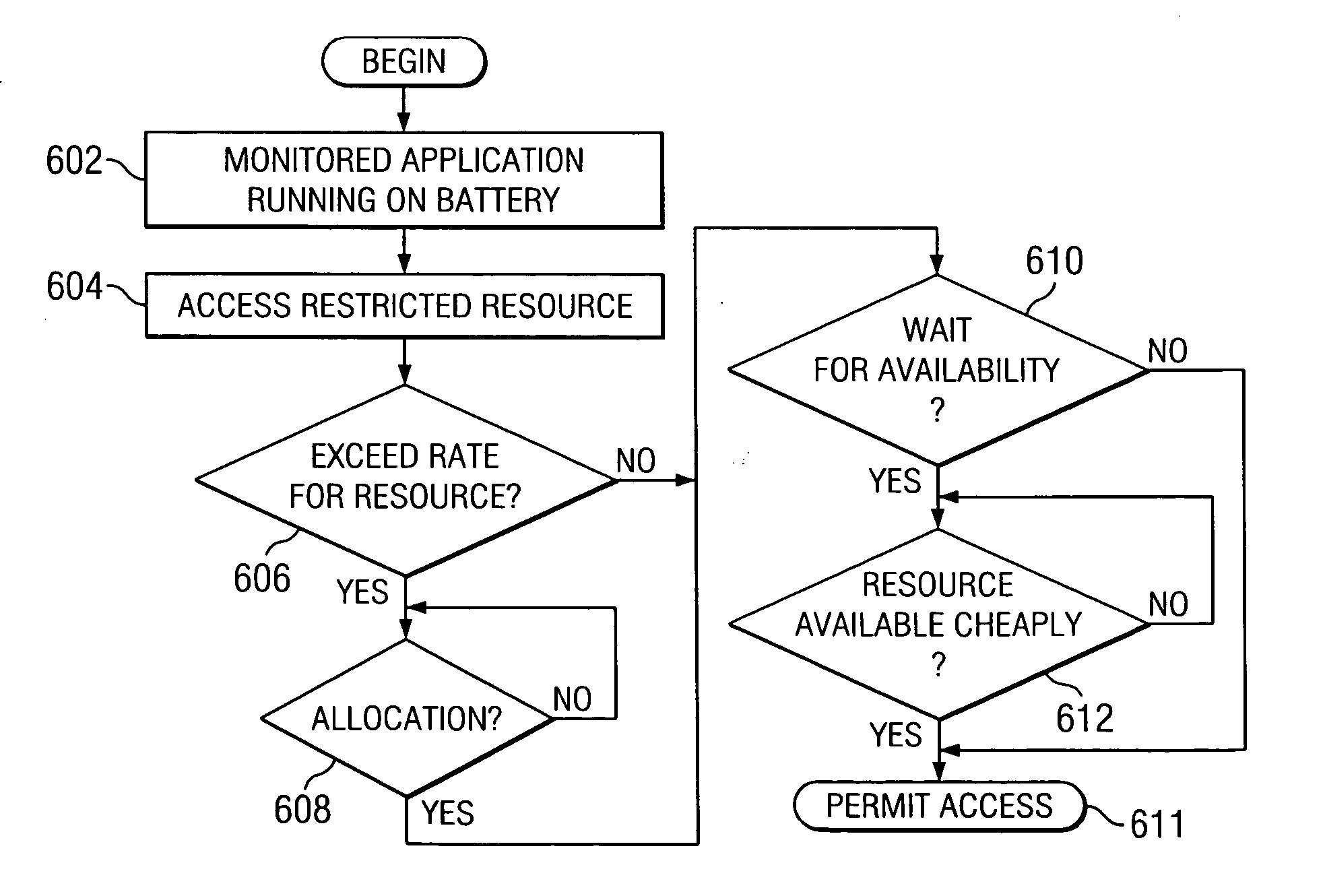
Method, apparatus, and program for adaptive control of application power consumption in a mobile computer
InactiveUS20050108075A1Energy efficient ICTPower supply for data processingPolicy decisionResource consumption
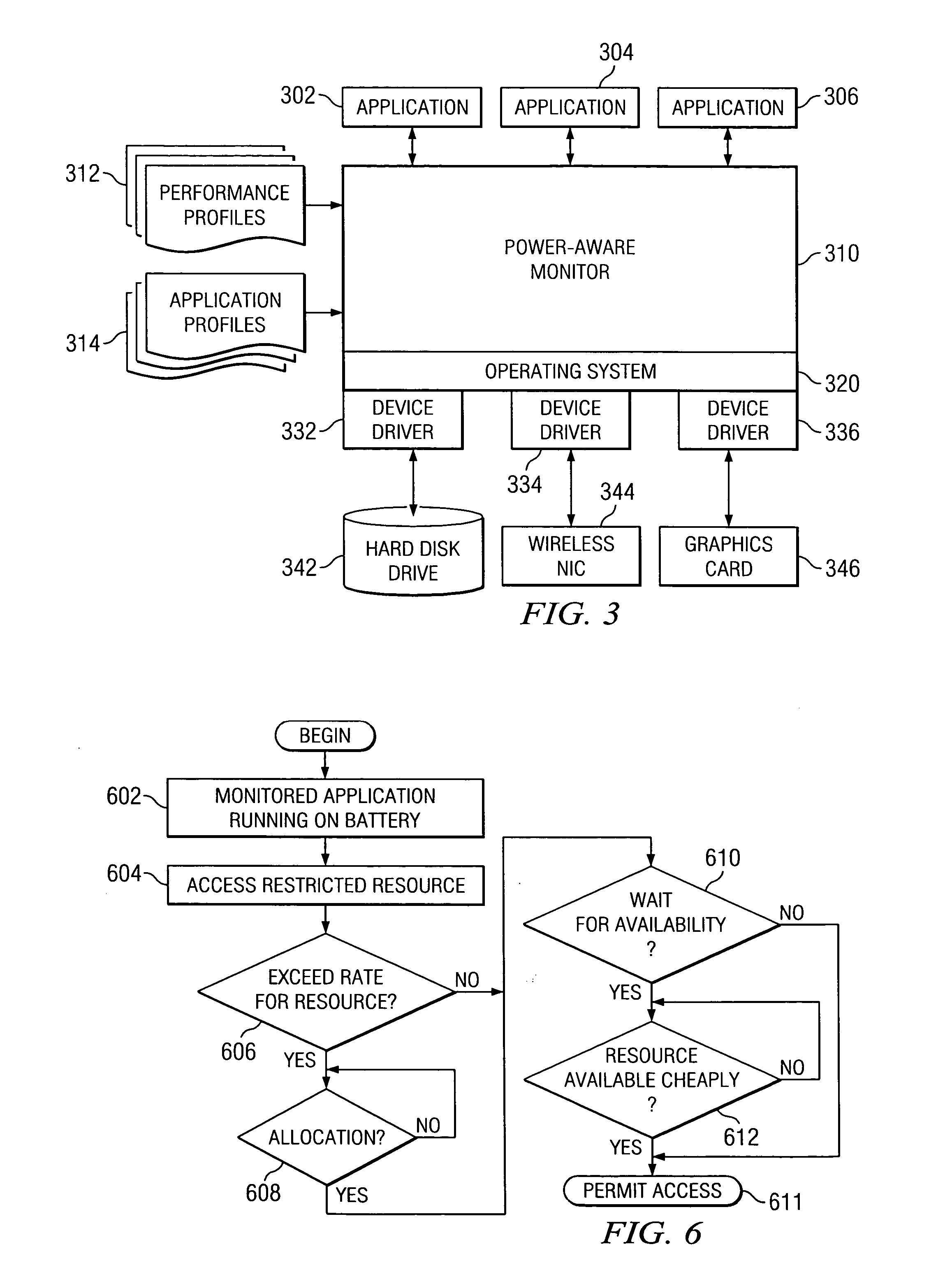
A power-aware monitor is provided for controlling the execution of state-unaware applications and optimizing their execution in light of power consumption issues. The power-aware monitor examines application usage to build profiles of resource consumption. When an application starts execution, the monitor determines the state of the battery to influence policy decisions. The monitor maintains a list of rules, which it uses in deciding policy. The user may modify these rules to override default behavior. The rules dictate whether an application executes unfettered, has its I / O, computation, or other activity restricted or delayed, or is completely aborted. When in doubt, the monitor may prompt the user for a decision.
Owner:LENOVO (SINGAPORE) PTE LTD
Policy-based forwarding in open shortest path first (OSPF) networks
A method and system enables policy-based traffic forwarding in a data network by implementing policy-based control over propagation of LSA messages through the data network. A route tag is asserted in respect of a link state advertisement (LSA) message advertising a network address. Propagation of the LSA through the data network is controlled using the asserted internal route tag. At each hop, a policy decision affecting the forwarding of the LSA is made. Exemplary policy decisions include, Pass and Discard. In addition, the forwarding table may be updated using the route and address information contained in the LSA. In this case, routes entered in the forwarding table may be tagged as an inclusion route or an exclusion route. This may be based on the value of an exclusion route flag, which can, for example, be provided as a binary “0” or “1” inserted into an unused portion of the options field of the LSA.
Owner:AVAYA MANAGEMENT LP
Enhanced QoS control
ActiveUS7209458B2Easy to controlNetwork traffic/resource managementData switching by path configurationPolicy decisionService information
The invention is a method and a system for the providing of service to user equipment (UE). A method of providing services to user equipment in accordance with the invention includes providing from a database (420) to a policy decision entity (405) subscriber information regarding permitted conditions for the users to obtain the services; providing service information from at least one network or server (100), regarding service offered by the at least one network or server to the user equipment, forming policy rules at the policy decision entity based upon the subscriber information and the service information. A requesting user equipment transmits a request for service to the communications network which is processed by the policy decision entity in accordance with the policy rules to determine if the service is to be allowed and if the service is allowed characteristics of the service to be provided to the requesting user equipment and the policy enforcement entity enforces at least one characteristic of an allowed service upon the communication network to insure that the allowed service obtained by the requesting user equipment has the at least one characteristic of the allowed service.
Owner:NOKIA TECHNOLOGLES OY
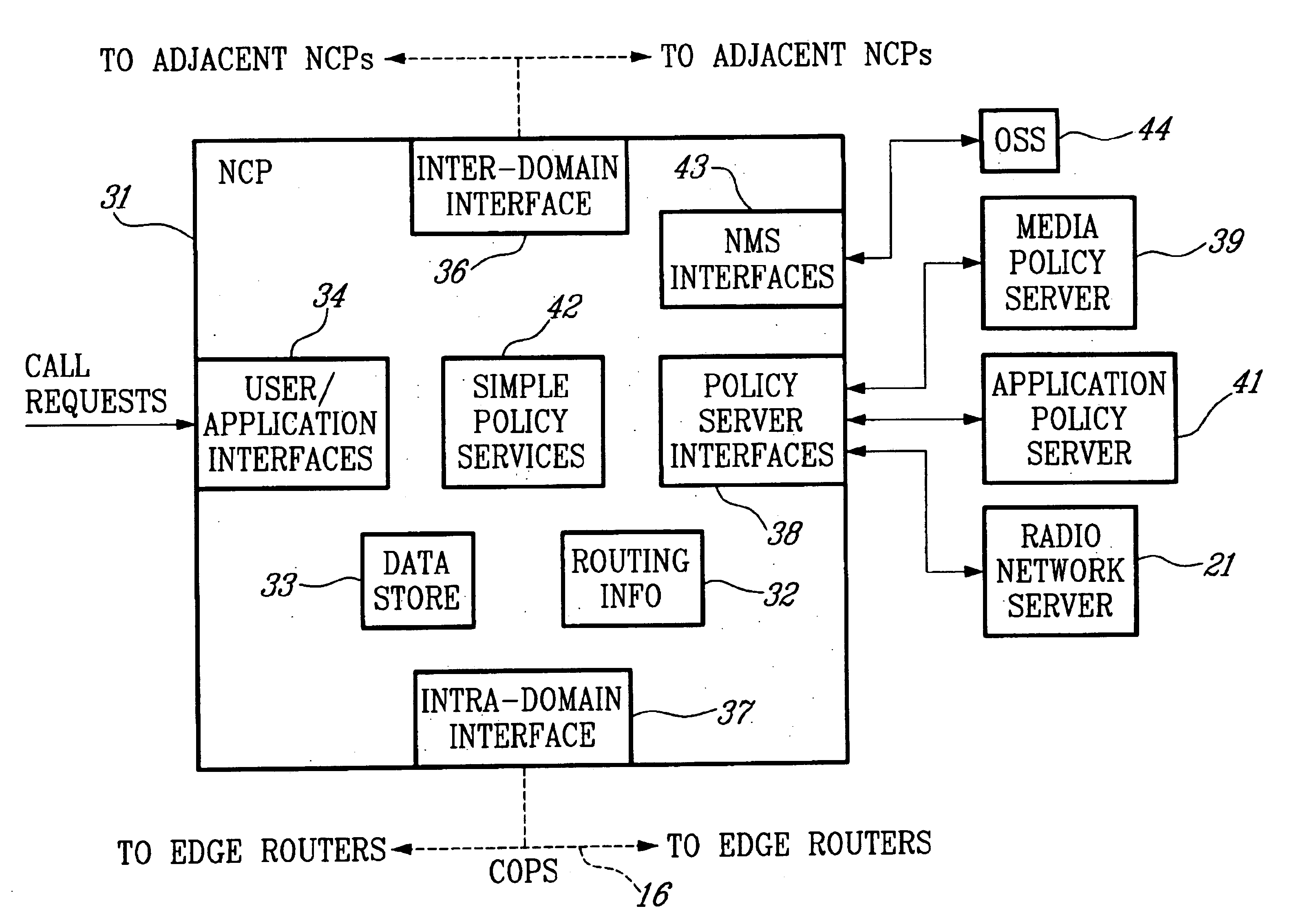
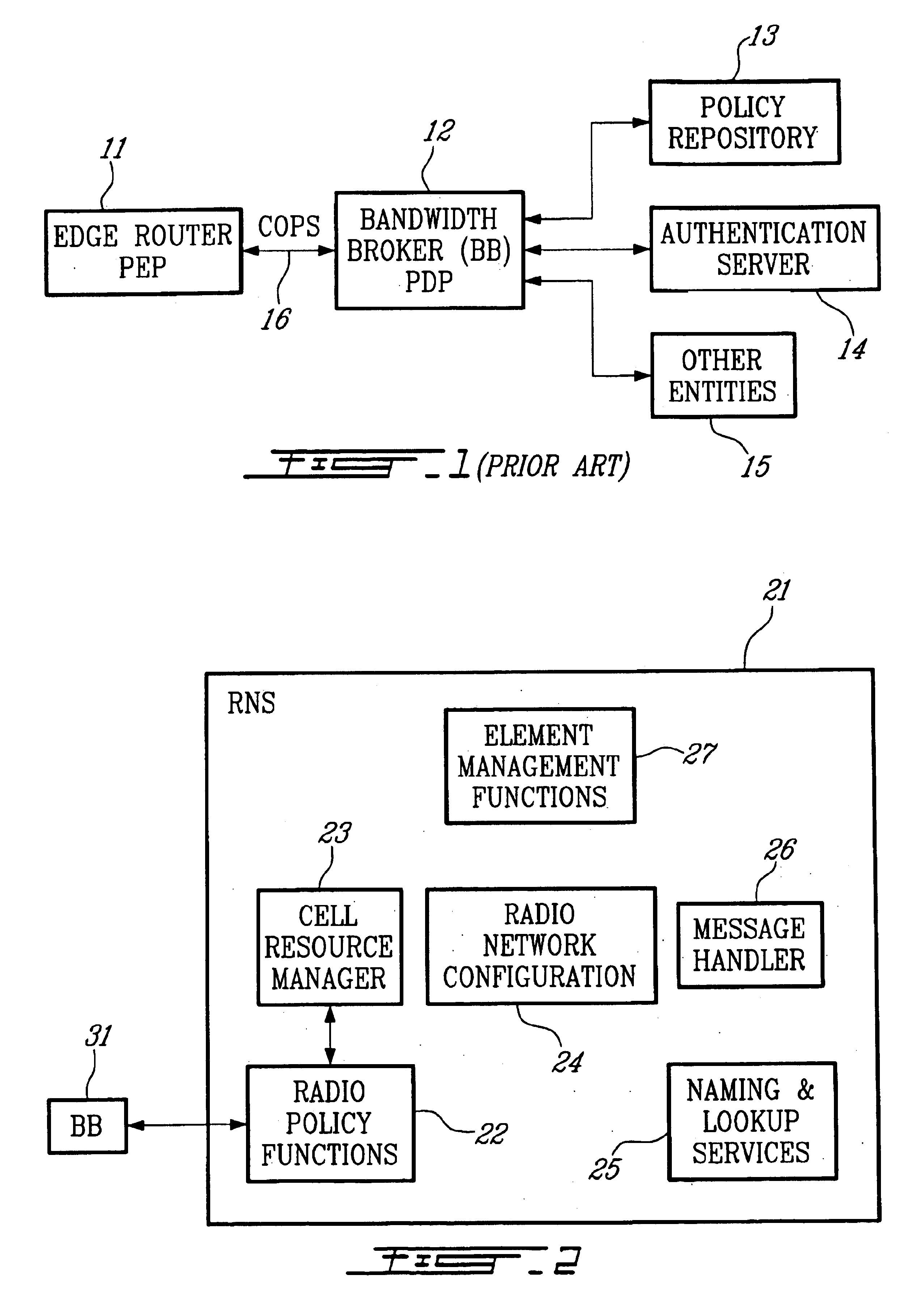
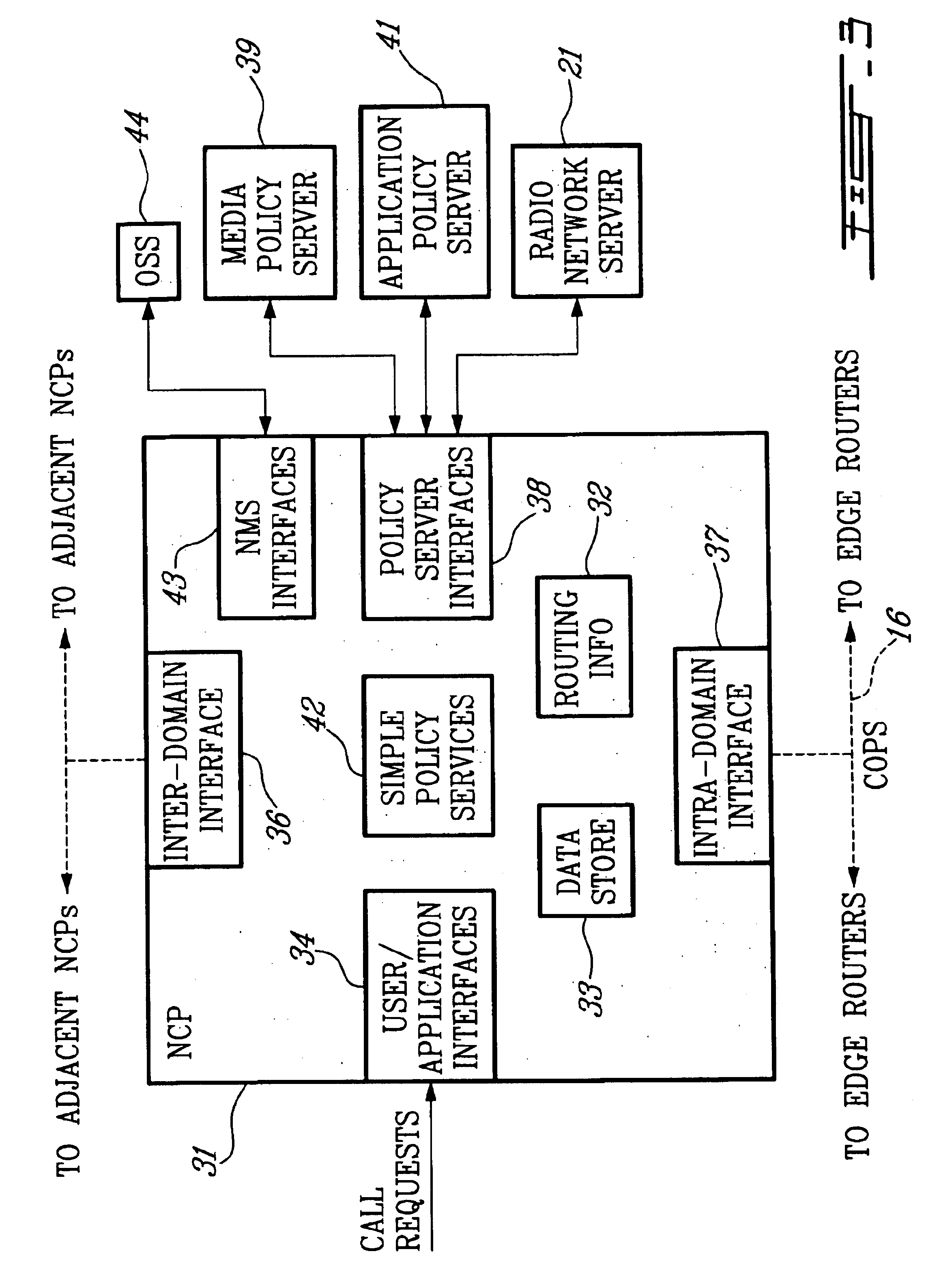
Policy server and architecture providing radio network resource allocation rules
A Radio Network Server (RNS) is modified to function as a policy server providing radio network resource allocation rules in an integrated third generation wireless IP network. The RNS determines a level of availability of radio network resources, and determines whether the level is sufficient to satisfy requests for resources in accordance with policy rules. The RNS informs a Bandwidth Broker (BB) whether the radio network resources are available. The BB functions as a Policy Decision Point (PDP) for its domain, and either allows or denies requests from users for network resources based on the input from the RNS. A plurality of edge routers in each domain interface with the BB utilizing the Common Open Policy Service (COPS) protocol interface. The edge routers function as Policy Enforcement Points (PEPs) for their domain to enforce policy decisions made by the BB. The BB may interface with BBs in other domains for calls that span multiple domains.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and system for routing control
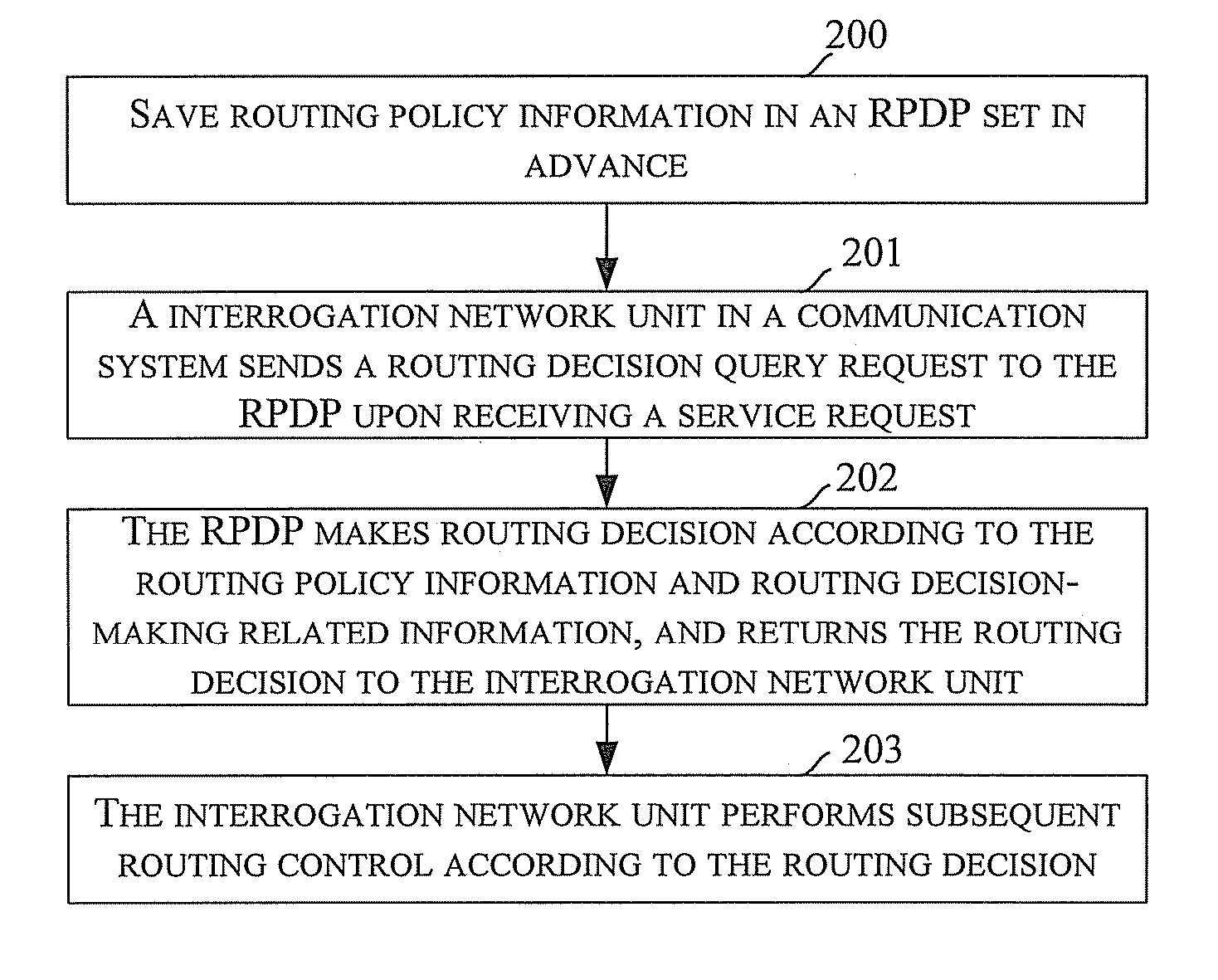
InactiveUS20080039104A1Routing decisionImprove user experienceWireless network protocolsRadio/inductive link selection arrangementsRouting decisionPolicy decision
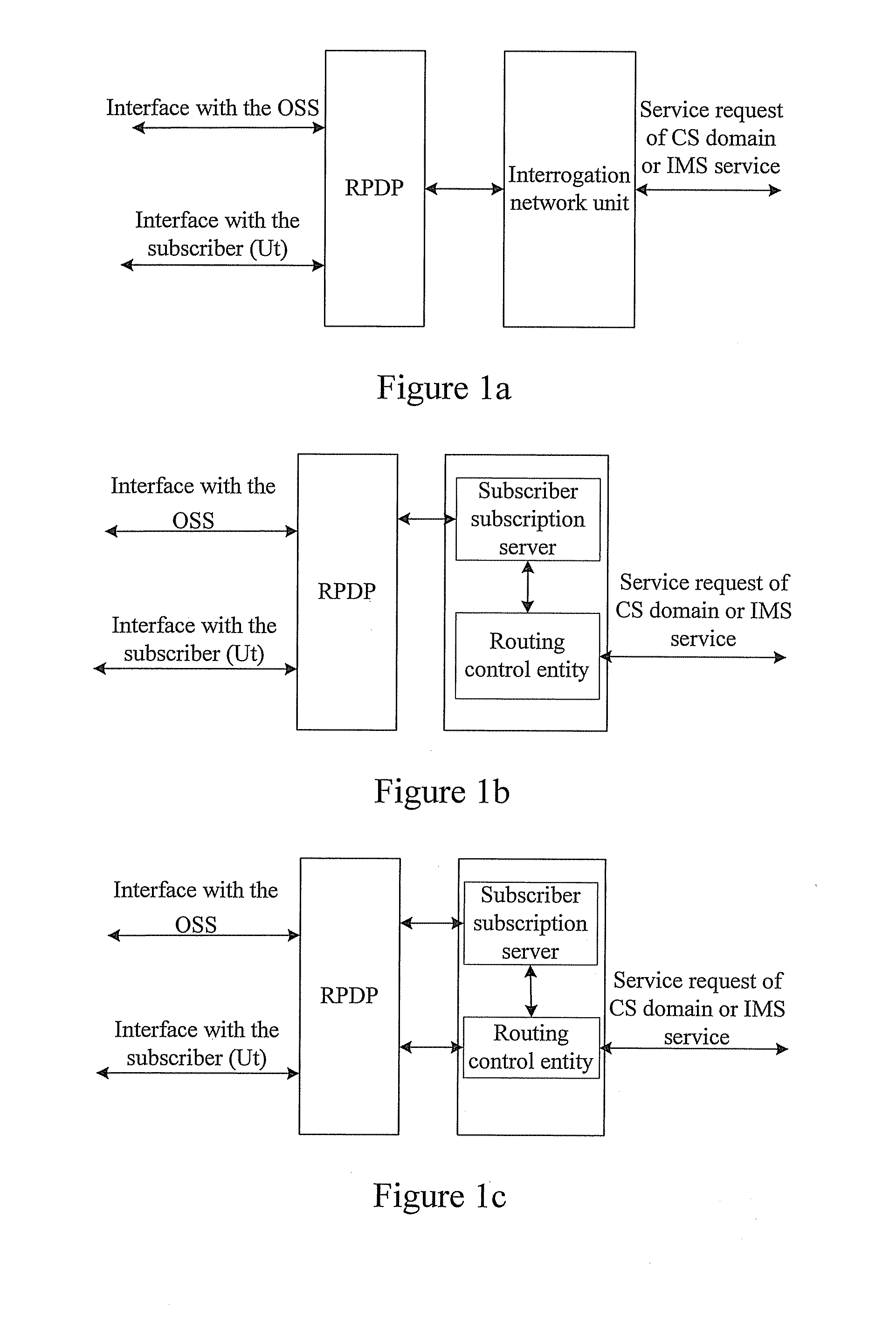
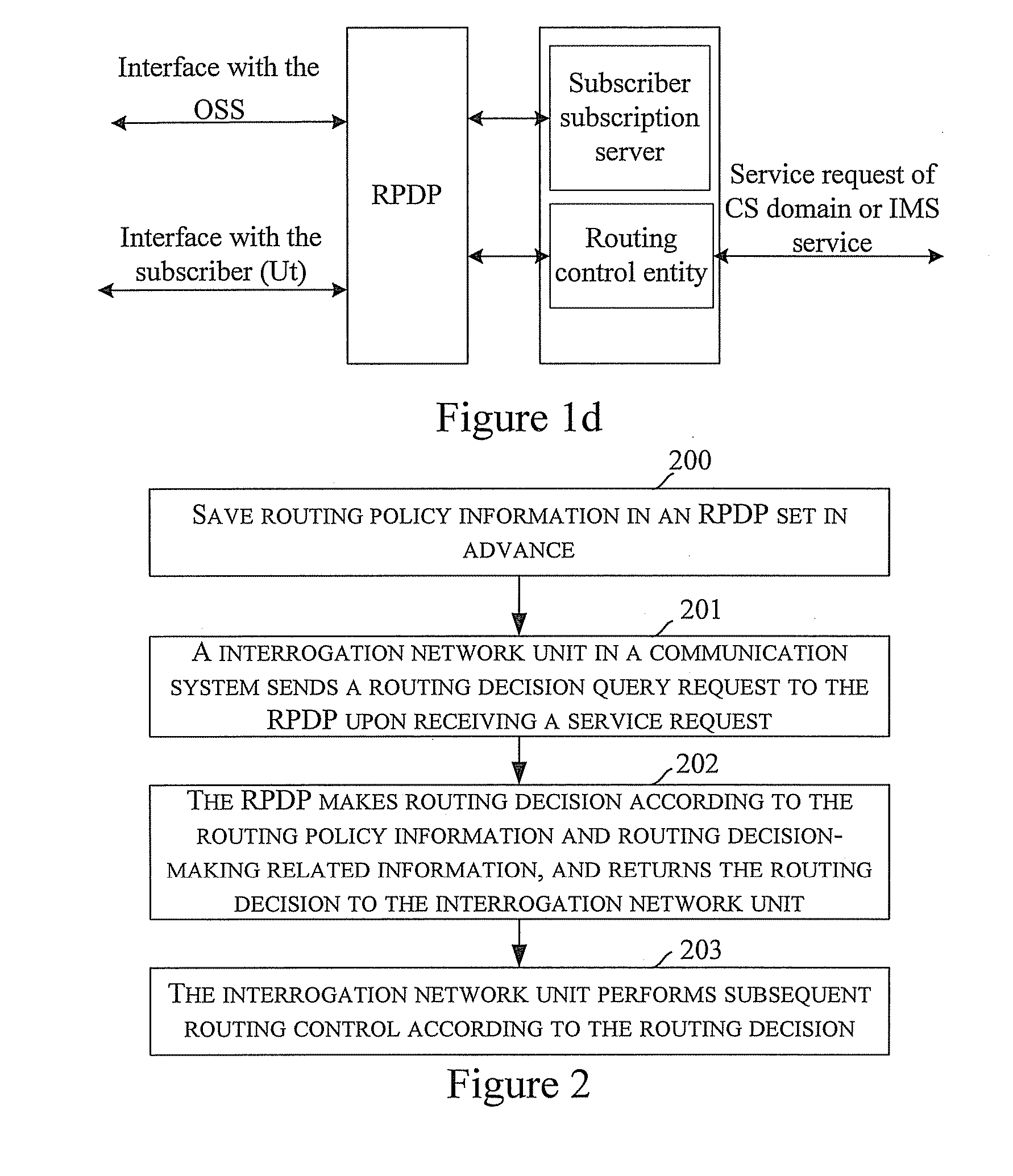
Embodiments of the present invention disclose a method for routing control applied to a communication system including a CS domain and an IMS and in which a Routing Policy Decision-making Point (RPDP) is set; and the method includes: initiating a routing query to the RPDP by an interrogation network unit in the communication system upon receiving a service request; making a routing decision by the RPDP according to routing decision-making related information and the routing policy information, returning the routing decision to the interrogation networking unit by the RPDP; and performing subsequent routing control by the interrogation network unit according to the routing decision. Embodiments of the present invention also disclose a system for routing control. In accordance with the embodiments of the present invention, across-domain routing control is thus realized in different network application environments according to different demands.
Owner:HUAWEI TECH CO LTD
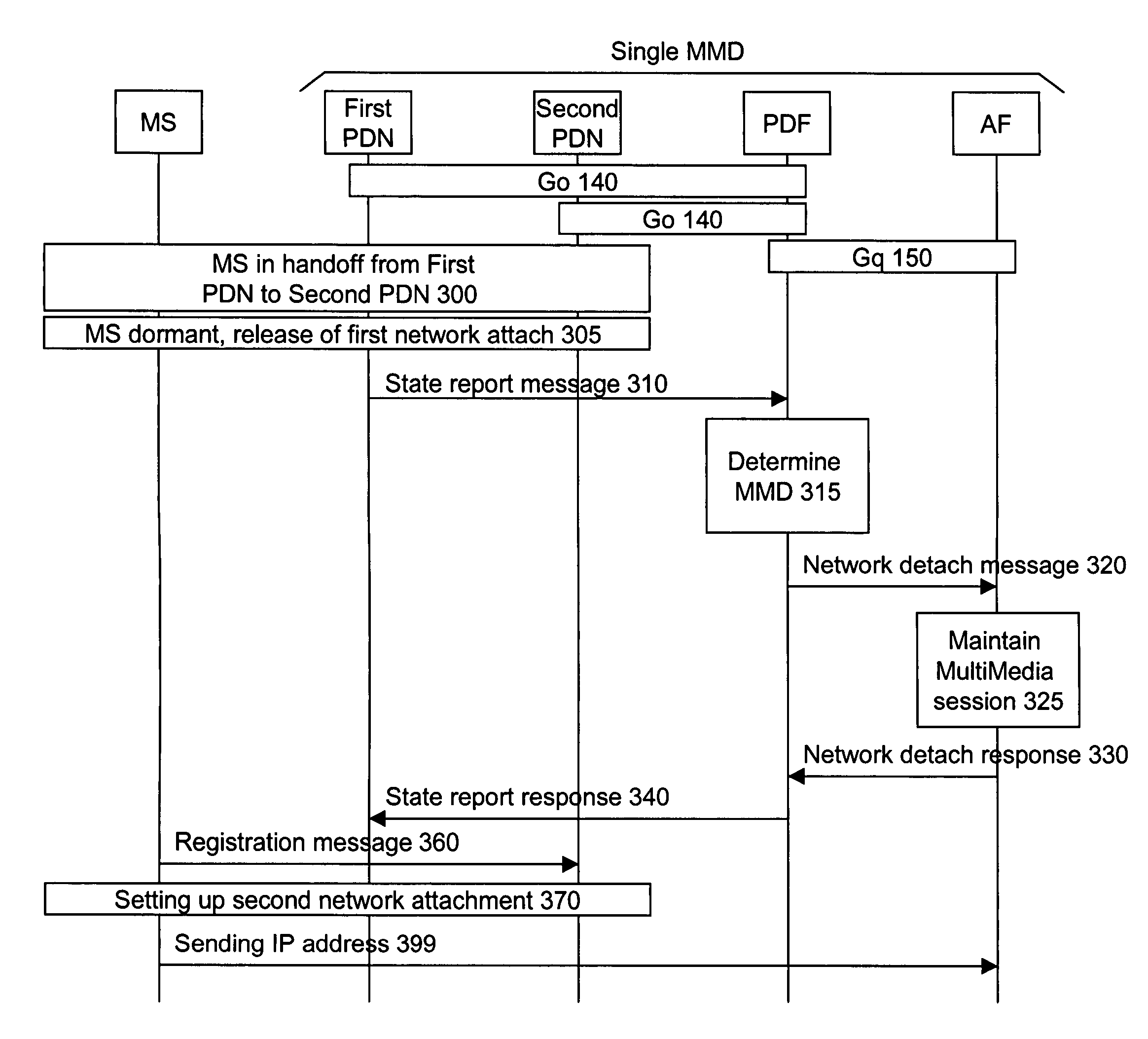
Seamless handoff for multimedia services
A method and Policy Decision Function node are provided for maintaining a multimedia session in an alive state for a mobile station following a release of a network attachment resulting from a handoff from a first Packet Data Node to a second Packet Data Node followed by a dormancy state of the mobile station. If both Packet Data Nodes are comprised into a same MultiMedia Domain, the Policy Decision Function informs an Application Function of the MultiMedia Domain that the multimedia session shall be maintained. Otherwise, if the two Packet Data Nodes are comprised into distinct MultiMedia Domains, a first Policy Decision Function, in addition to informing a first Application Function that the multimedia session shall be maintained, also fetches a context of the multimedia session. Further, the first Policy Decision Function transfers the context of the multimedia session to the first Packet Data Node, which in turn sends the context of the multimedia session to the second Packet Data Node. Subsequent to reactivation of the mobile station, a second Policy Decision Function transfers the context of the multimedia session from the second Packet Data Node to a second Application Function in a second MultiMedia Domain.
Owner:TELEFON AB LM ERICSSON (PUBL)
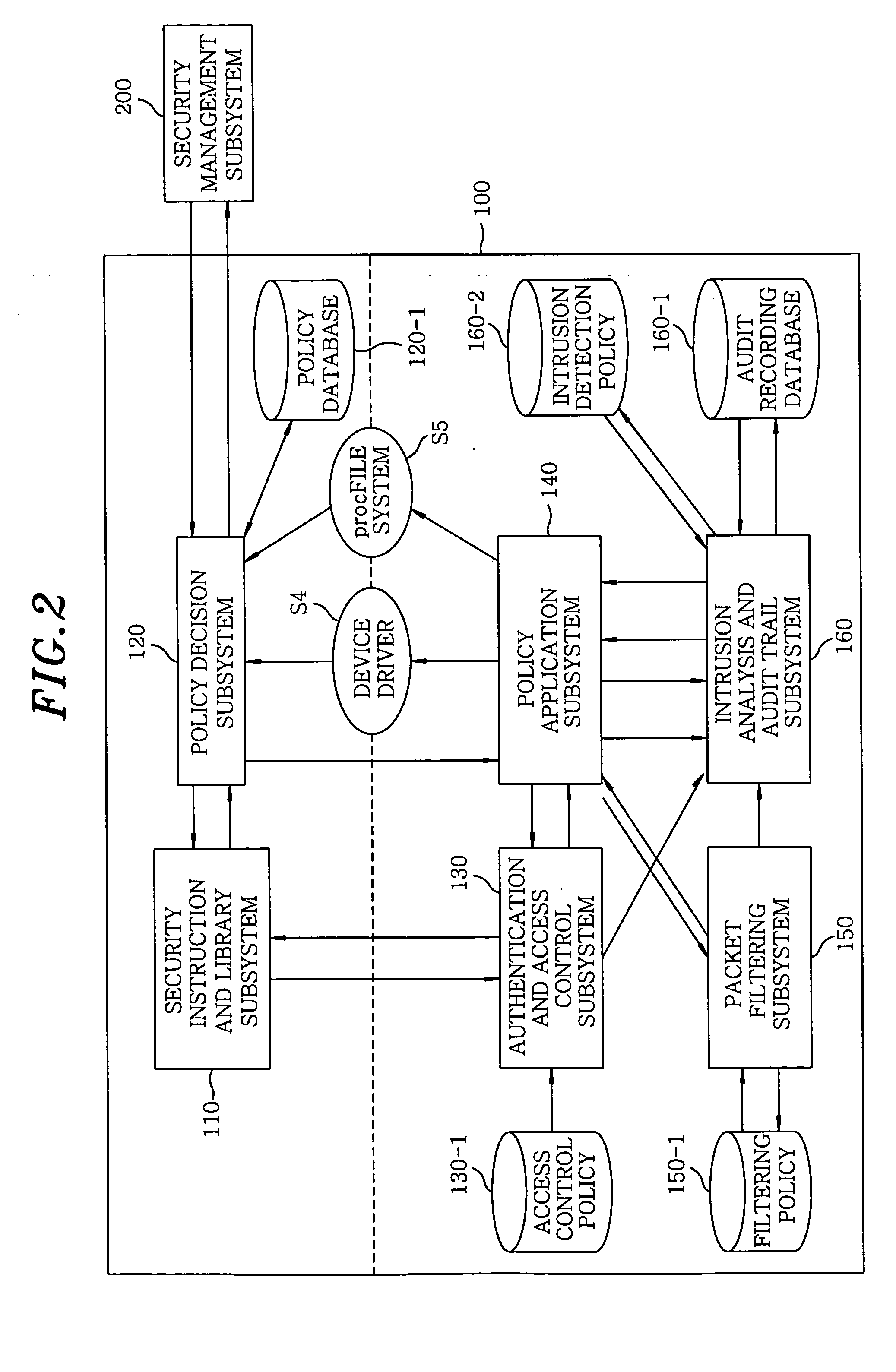
Method and apparatus for security engine management in network nodes
InactiveUS20050071650A1User identity/authority verificationDigital computer detailsPolicy decisionSystems management
In a security engine management apparatus in network nodes, a security instruction and library subsystem processes every application program and utility. A policy decision subsystem determines a filtering policy, an intrusion detection policy and an access control policy. An authentication and access control subsystem blocks an unauthorized user to access to a system and allows an authorized user to access thereto according to the access control policy. A policy application subsystem applies the policies. A packet filtering subsystem receives an allowed packet and denies a disallowed packet according to the filtering policy. An intrusion analysis and audit trail subsystem analyzes the intrusion according to the intrusion detection policy. A security management subsystem manages a security engine.
Owner:ELECTRONICS & TELECOMM RES INST
NETWORK ARCHITECTURE FOR DYNAMICALLY SETTING END-TO-END QUALITY OF SERVICE (QoS) IN A BROADBAND WIRELESS COMMUNICATION SYSTEM
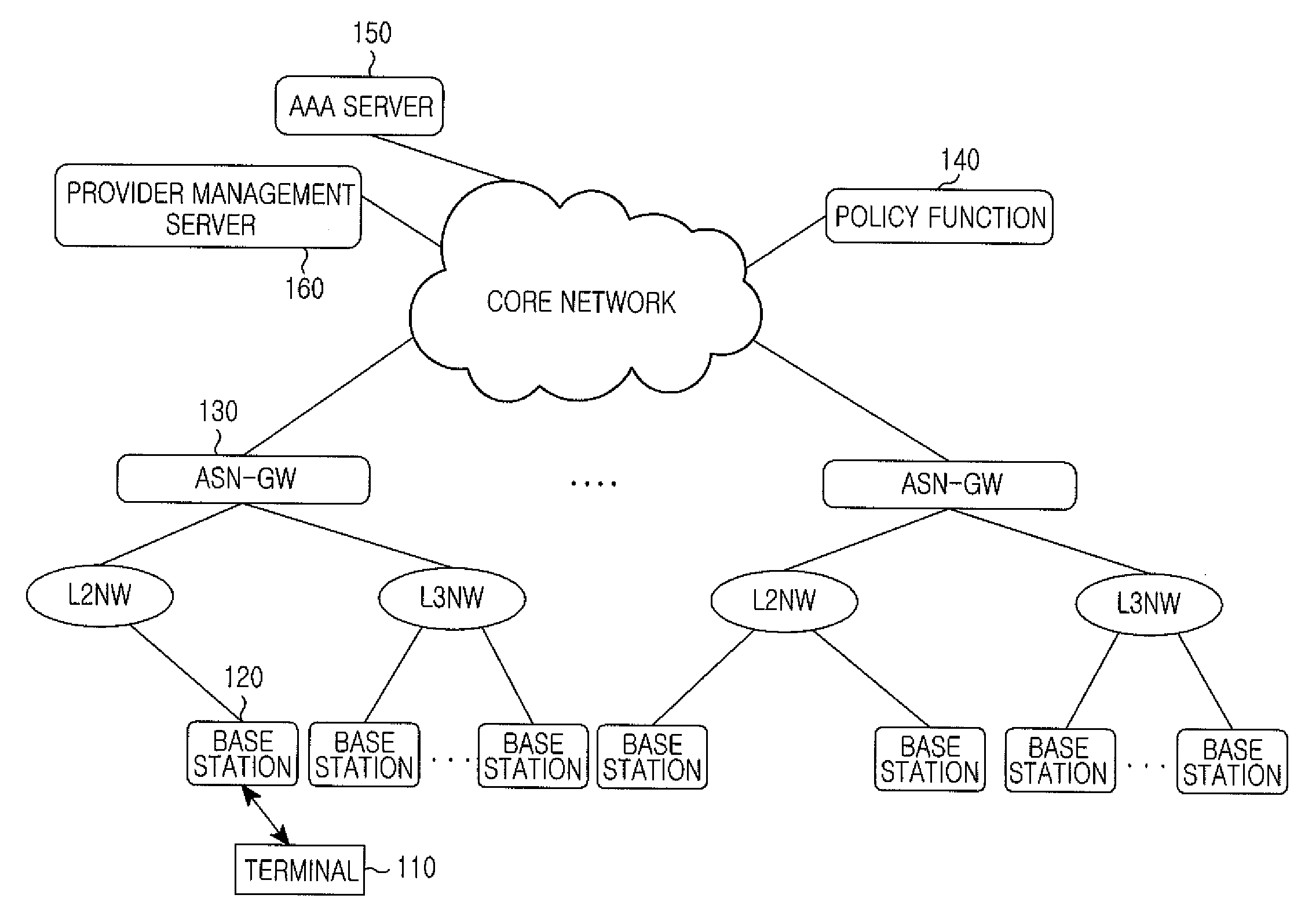
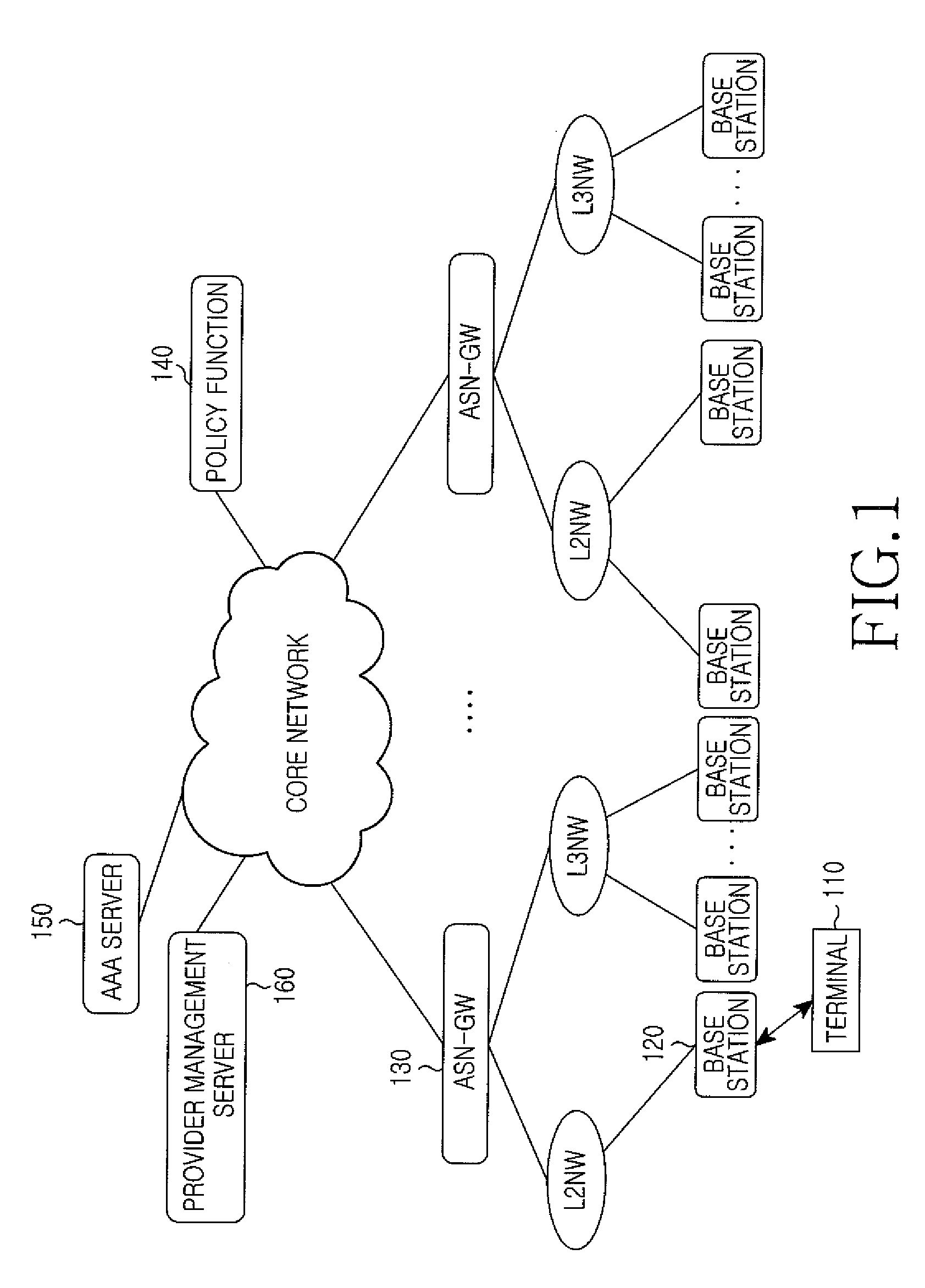
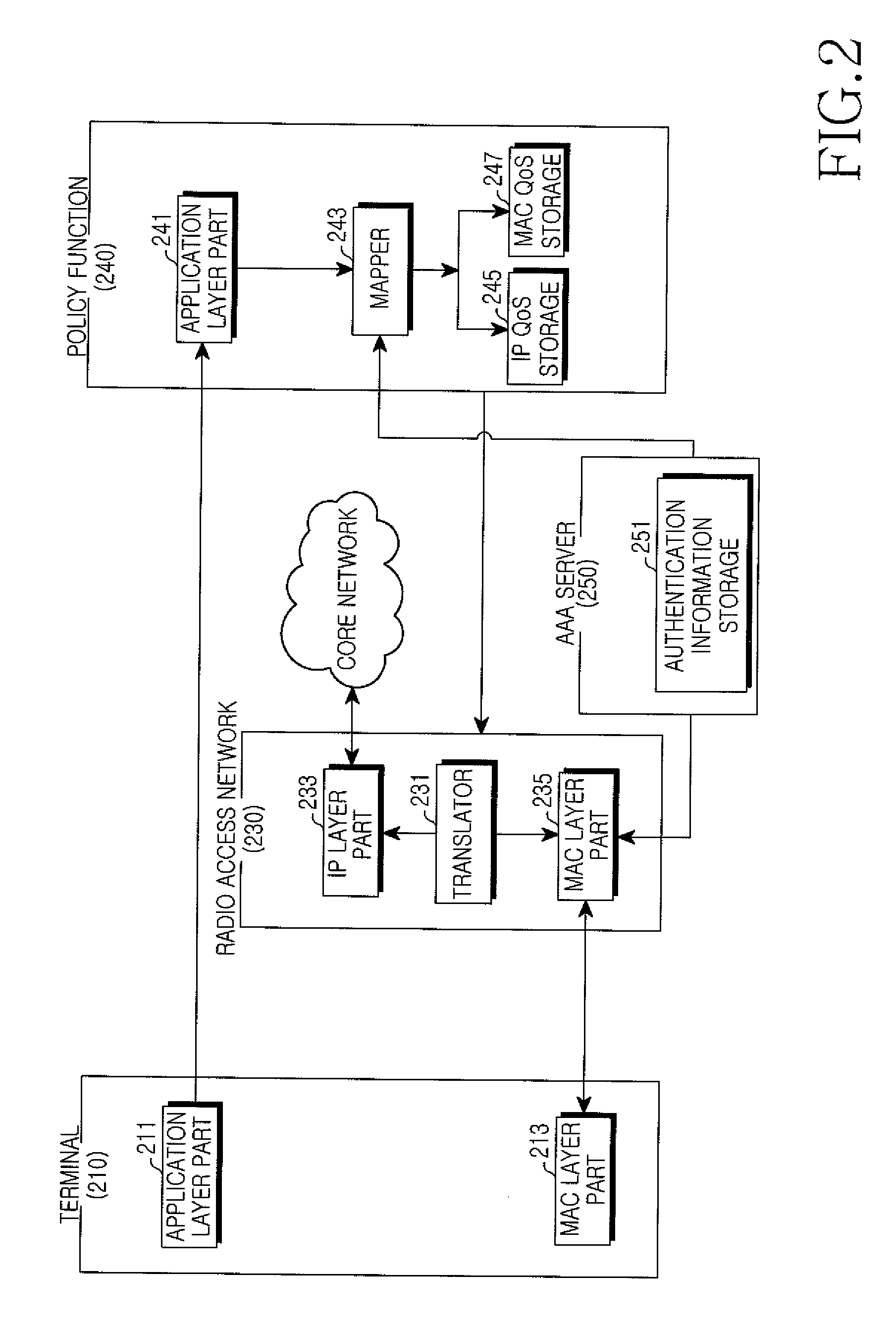
InactiveUS20080273520A1Efficient settingsNetwork traffic/resource managementTelephonic communicationQuality of servicePolicy decision
A communication network architecture including a broadband radio access network is provided. The architecture includes a terminal for transmitting an application layer service request message to request a service, a Policy Charging Rule Function (PCRF) for generating Quality of Service (QoS) parameters of an Internet Protocol (IP) layer using QoS parameters of an application layer contained in the application layer service request message, a first Policy Decision Function (PDF) for generating one or more QoS parameters of the IP layer in addition to the IP layer QoS parameters generated at the PCRF and a second PDF for generating a QoS parameter set of a radio access network using the IP layer QoS parameters generated at the PCRF and the one or more IP layer QoS parameters generated at the first PDF. The communication network guarantees an end-to-end QoS.
Owner:SAMSUNG ELECTRONICS CO LTD
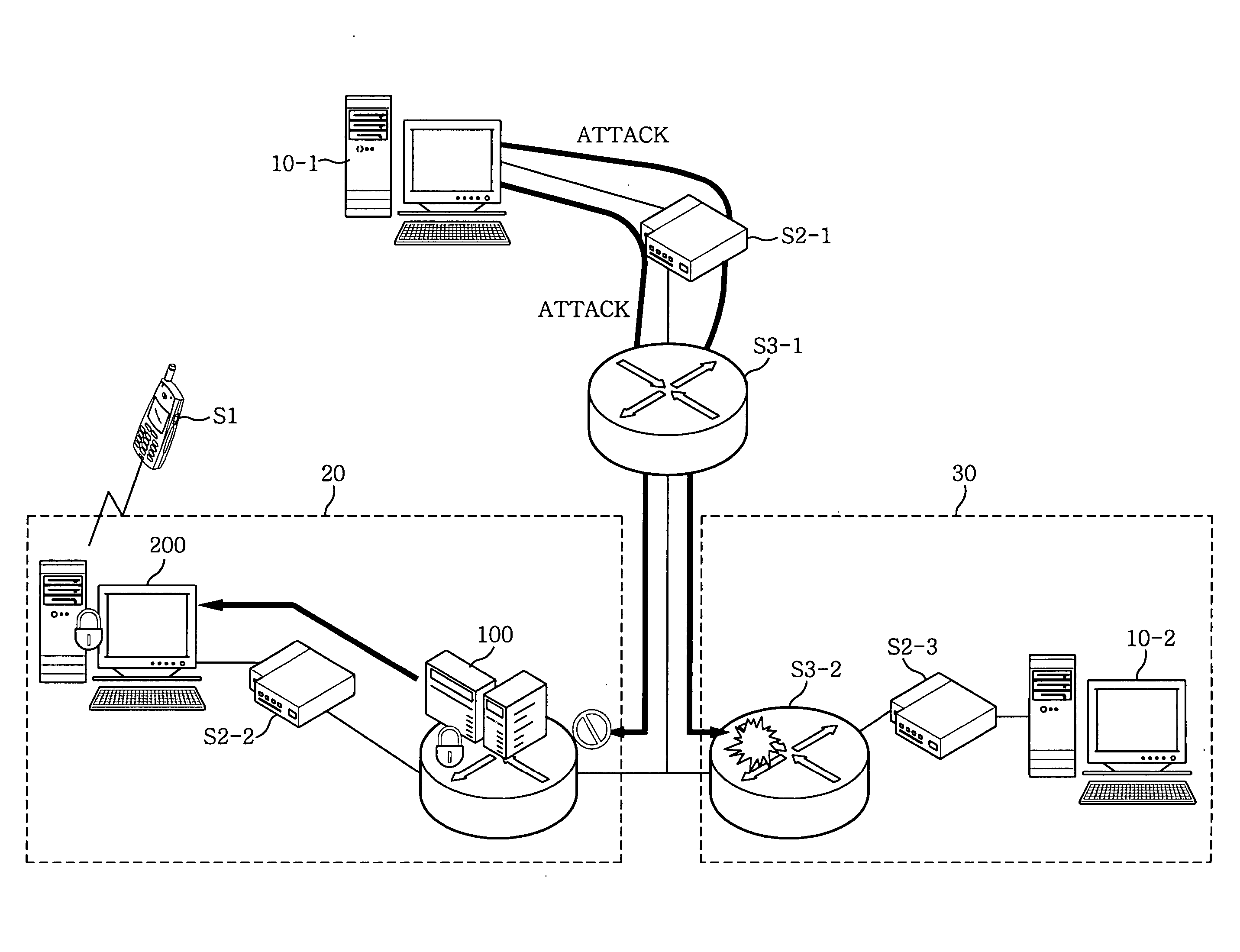
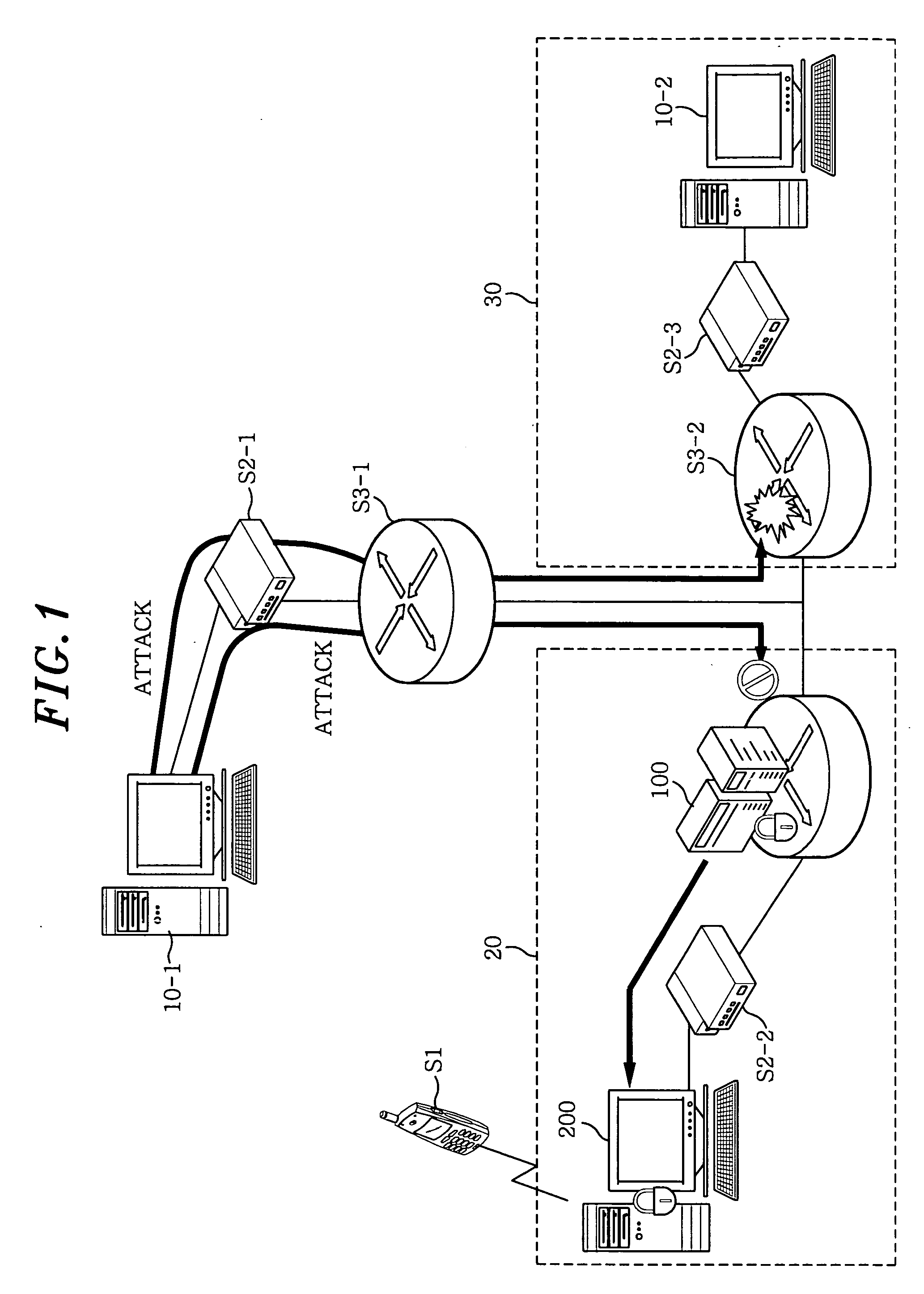
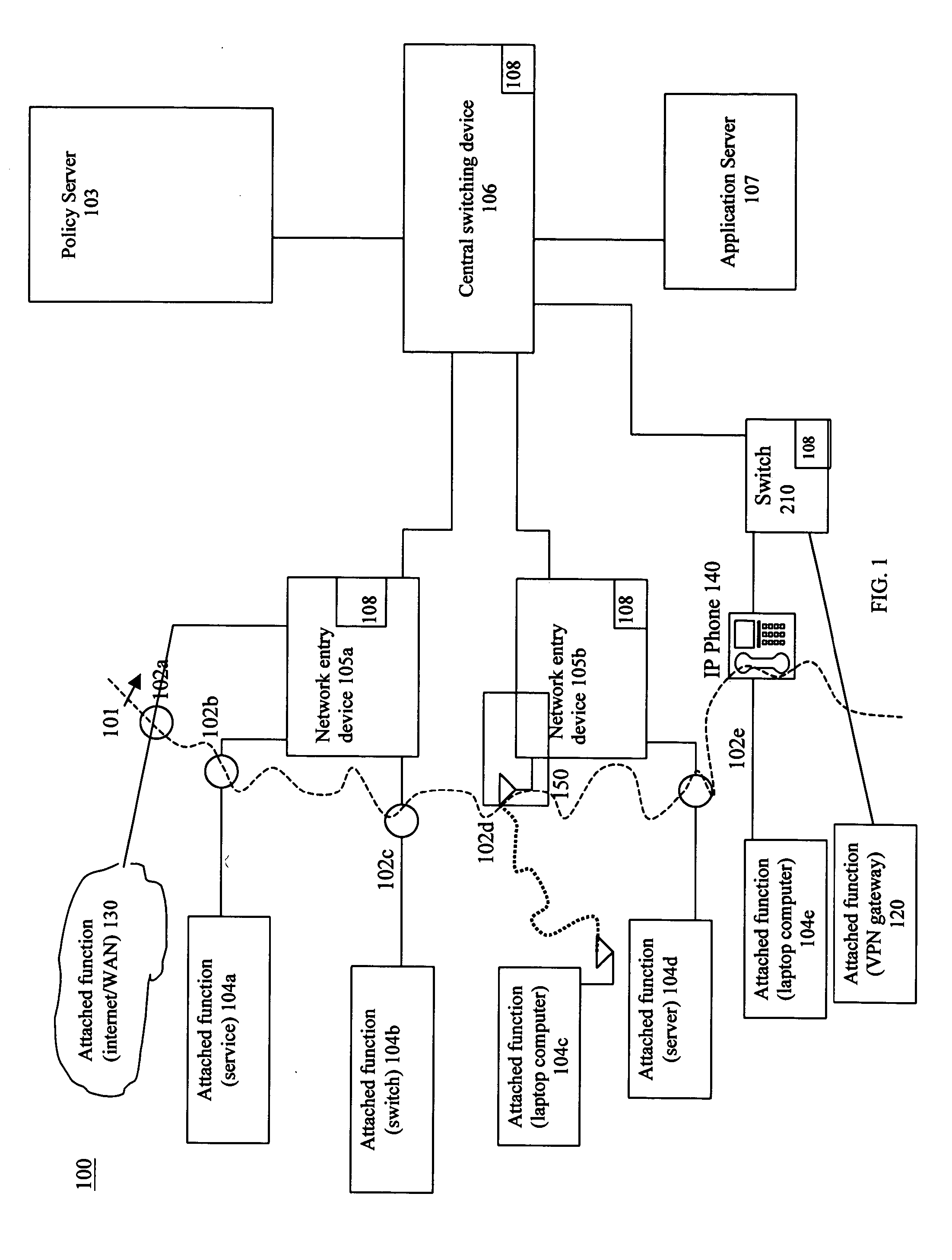
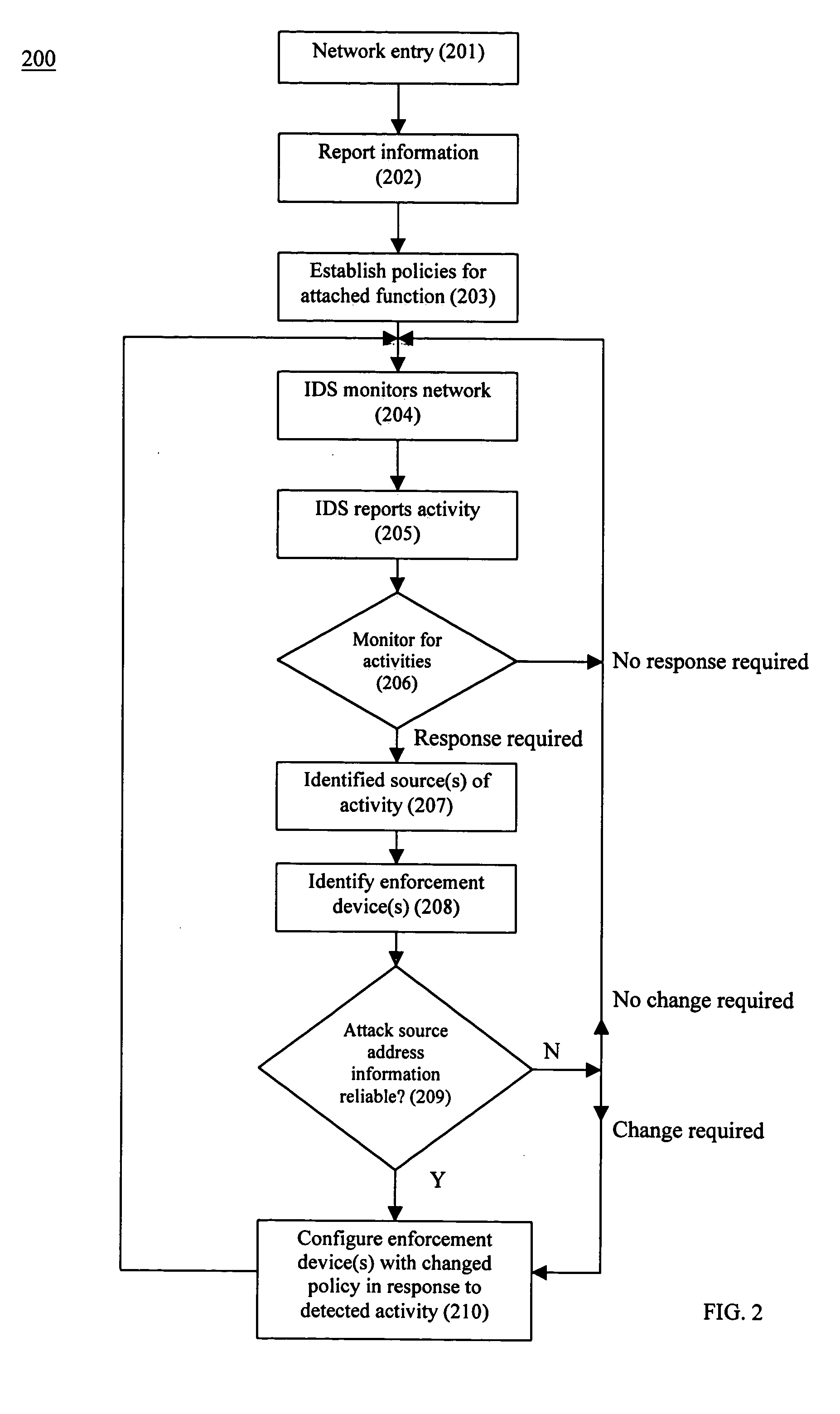
Distributed intrusion response system
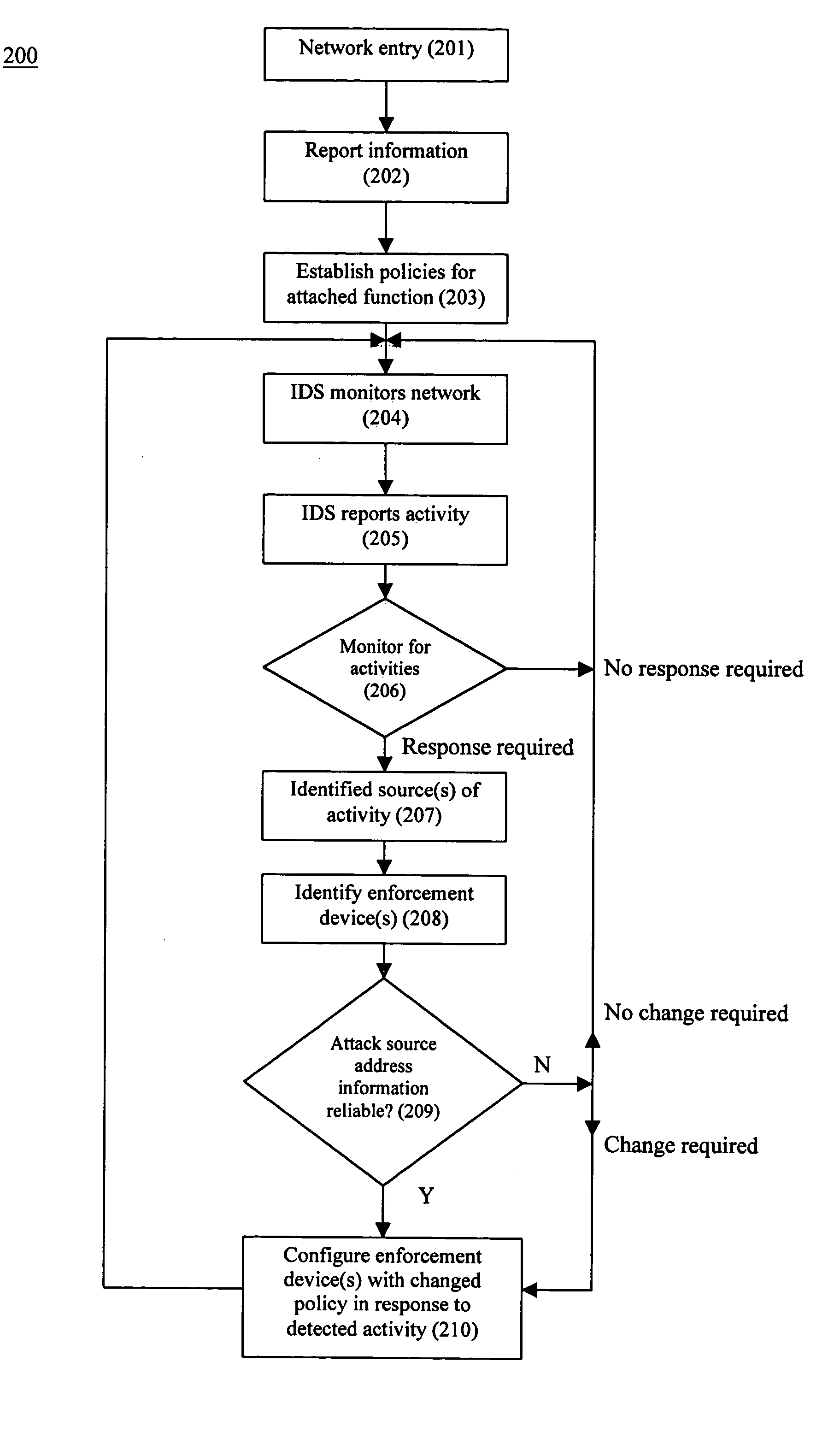
ActiveUS20050108568A1Good dynamic responseReduce harmMemory loss protectionDigital data processing detailsPolicy decisionIntrusion response systems
A system and method to respond to intrusions detected on a network system including attached functions and a network infrastructure. The system includes means for receiving from an intrusion detection function information about intrusions, a directory service function for gathering and reporting at least the physical and logical addresses of devices of the network infrastructure associated with the detected intrusions, and a plurality of distributed enforcement devices of the network infrastructure for enforcing policies responsive to the detected intrusions. A policy decision function evaluates the reported detected intrusions and makes a determination whether one or more policy changes are required on the enforcement devices in response to a detected intrusion. A policy manager function configures the distributed enforcement devices with the responsive changed policy or policies. Policy changes rules can vary from no change to complete port blocking on one or more identified enforcement devices associated with the detected intrusion, to redirecting the associated traffic including the intrusion and these policies may be modified or removed over time as warranted by network operation.
Owner:EXTREME NETWORKS INC
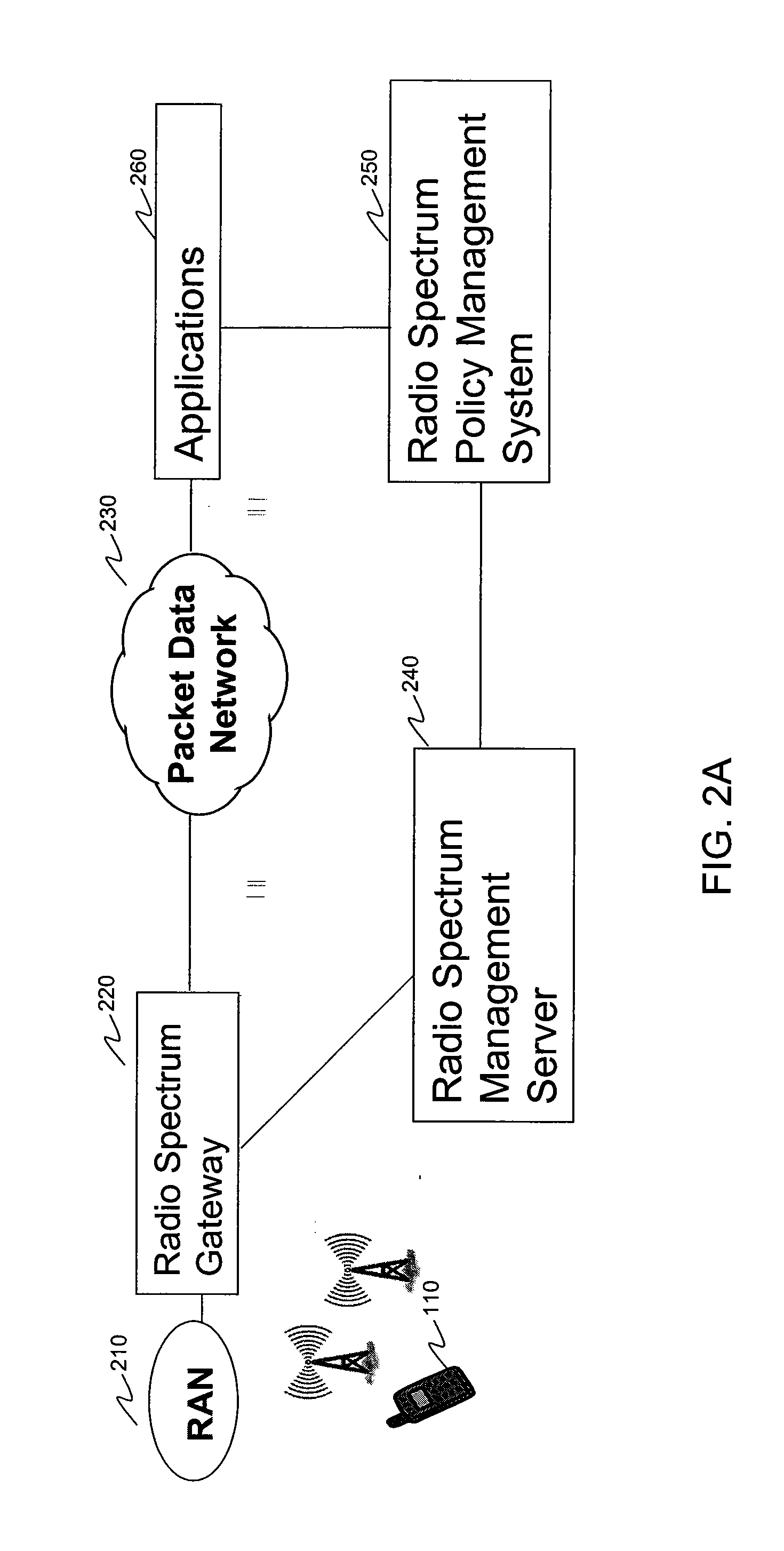
Systems and Methods for Subscriber-Centric Dynamic Spectrum Management
ActiveUS20080117869A1Promote generationReduce network operating costsError preventionTransmission systemsPolicy decisionFrequency spectrum
A radio spectrum management system is provided. In an embodiment, the radio spectrum management system includes a radio spectrum gateway, a radio spectrum management server and a radio spectrum policy decision server. The radio spectrum gateway is coupled to a radio access network that receives bandwidth requests from subscriber devices and provides bandwidth allocation decisions to the radio access network. The radio spectrum management server receives bandwidth requests from the radio spectrum gateway and provides bandwidth allocation decisions to the radio spectrum gateway based on radio resources and bandwidth policy decisions. The radio spectrum policy management server provides bandwidth policy decisions to the radio spectrum server. The bandwidth policy decisions are generated based on consideration of subscriber and / or application service provider characteristics. Methods for allocation of radio spectrum for a subscriber within a wireless network when the subscriber requests an application are also provided.
Owner:AMDOCS CANADIAN MANAGED SERVICES INC +1
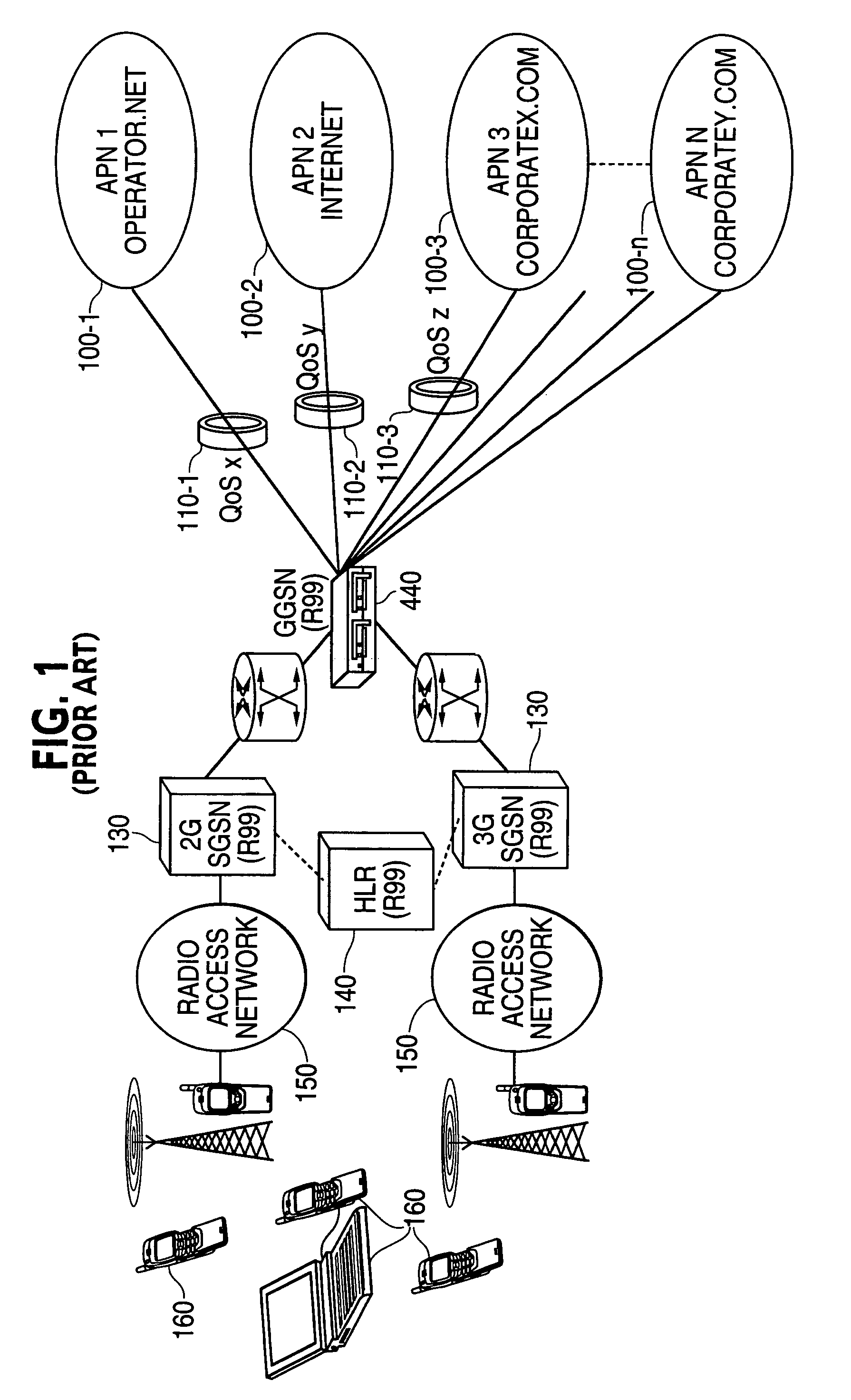
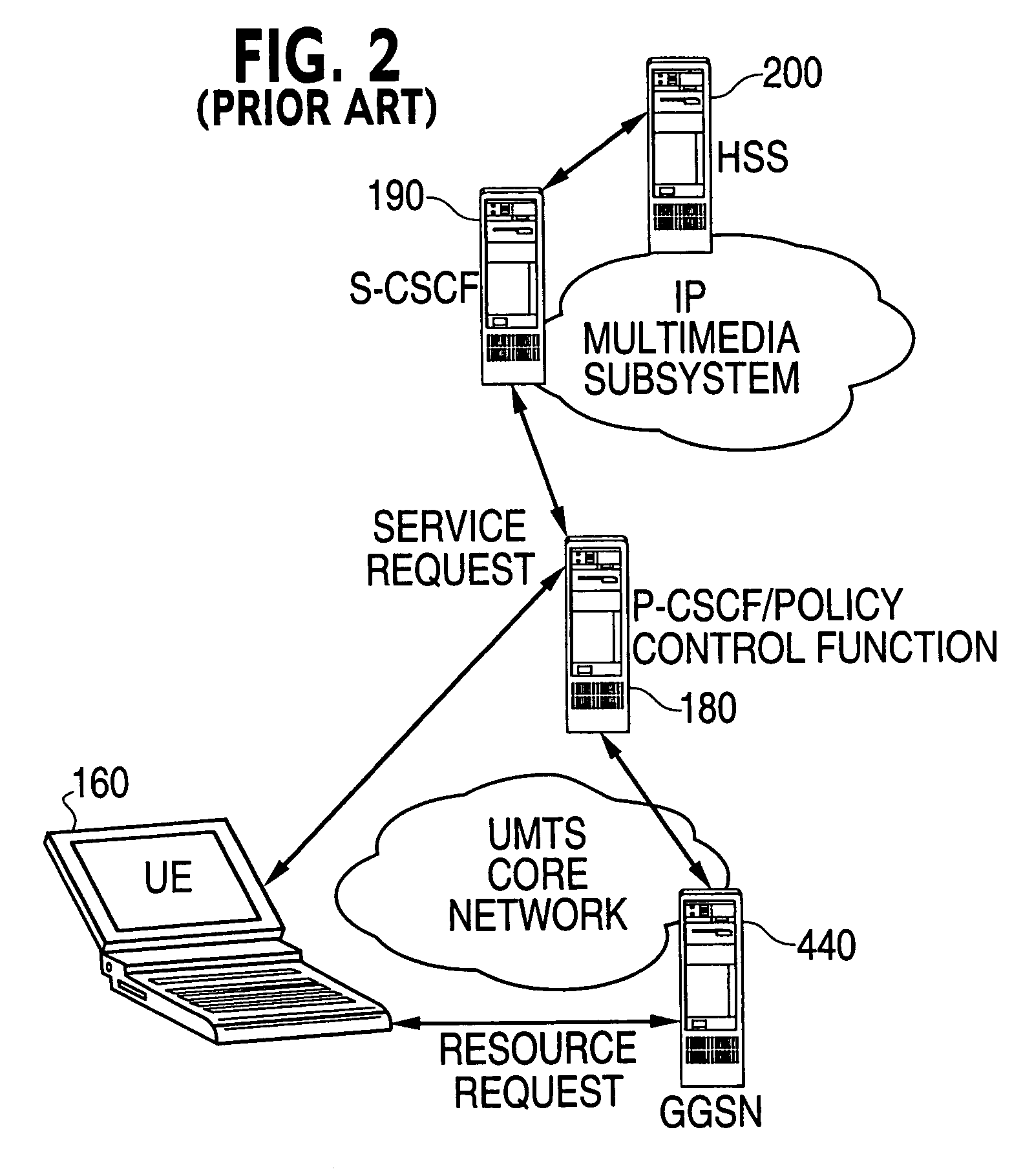
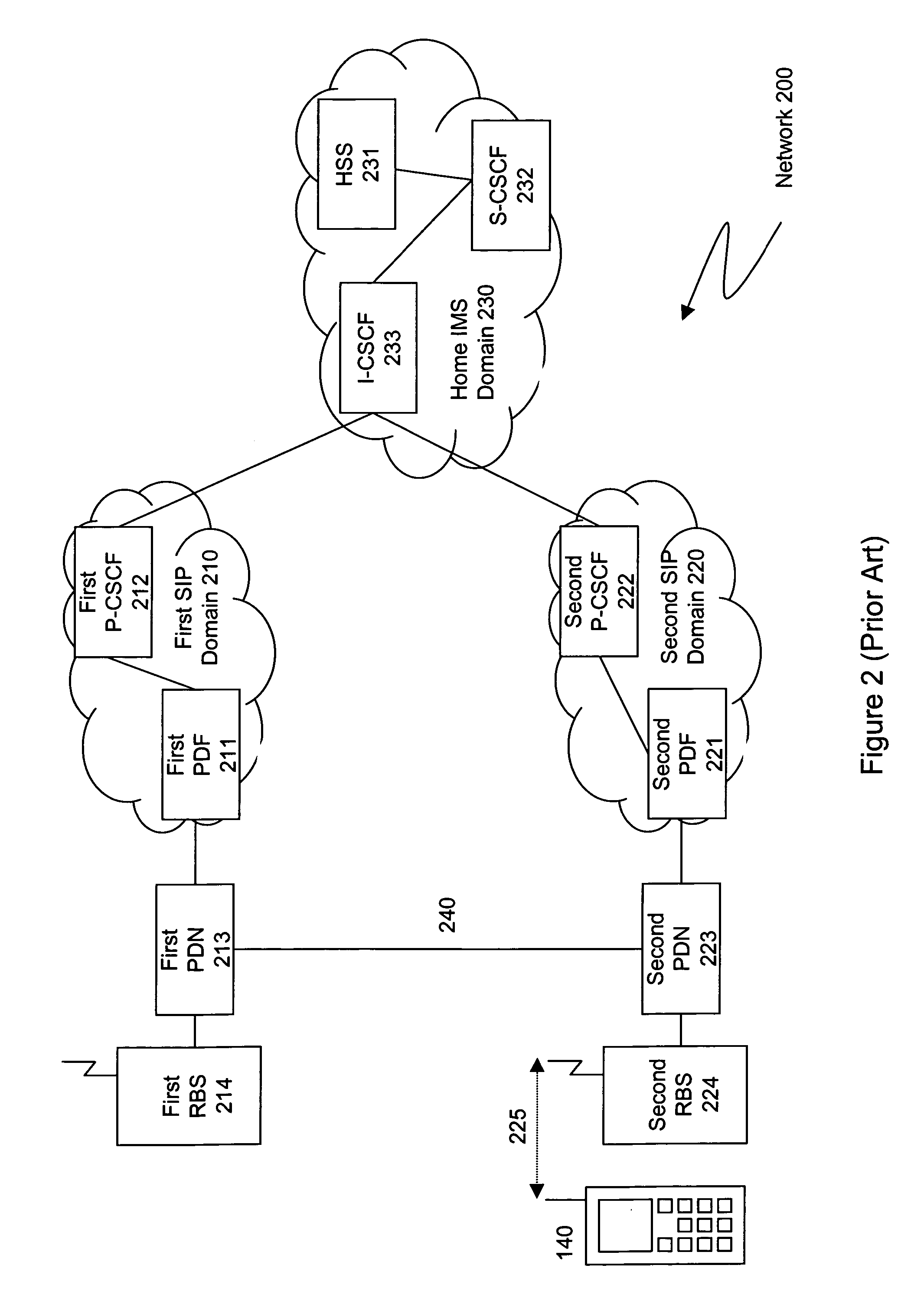
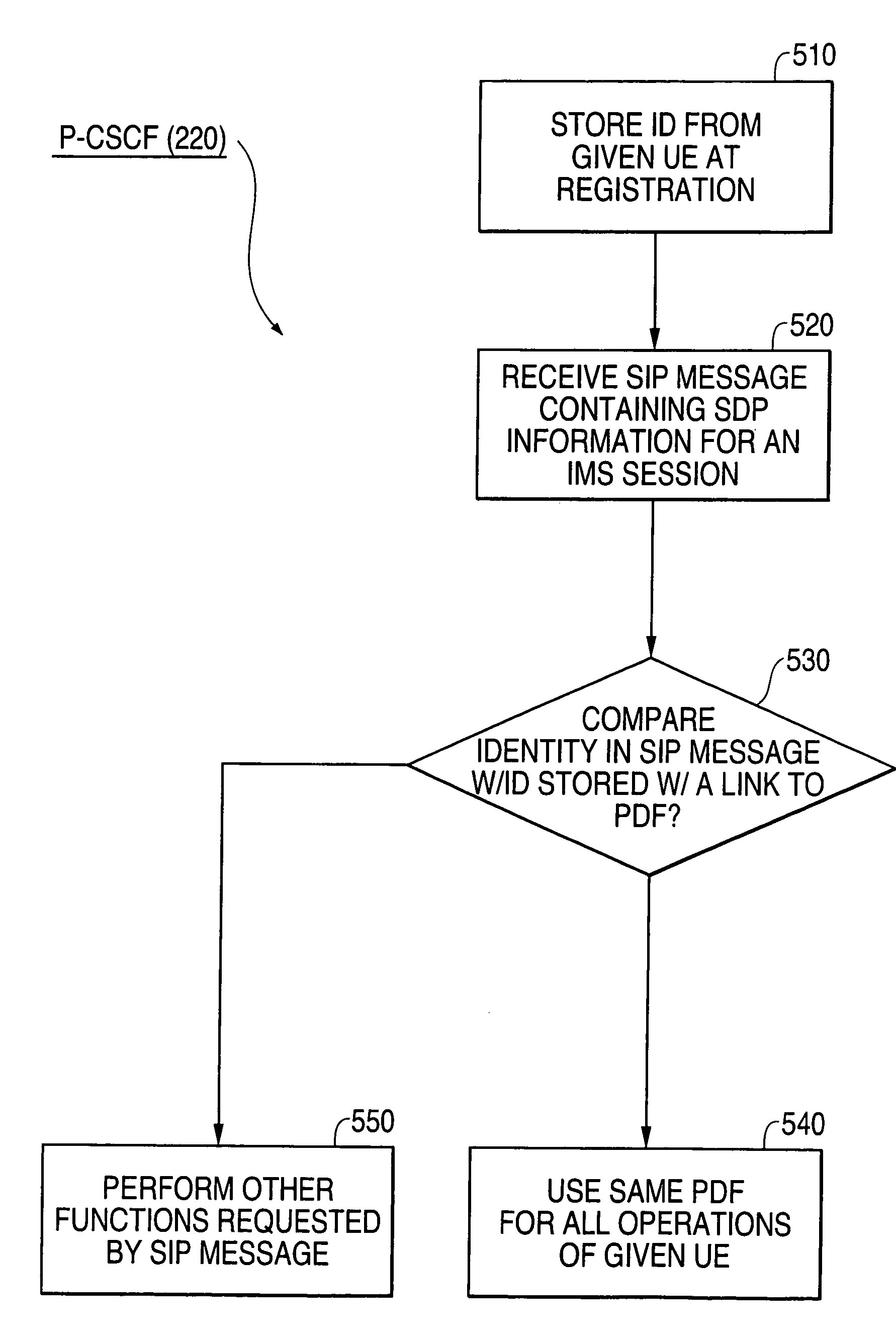
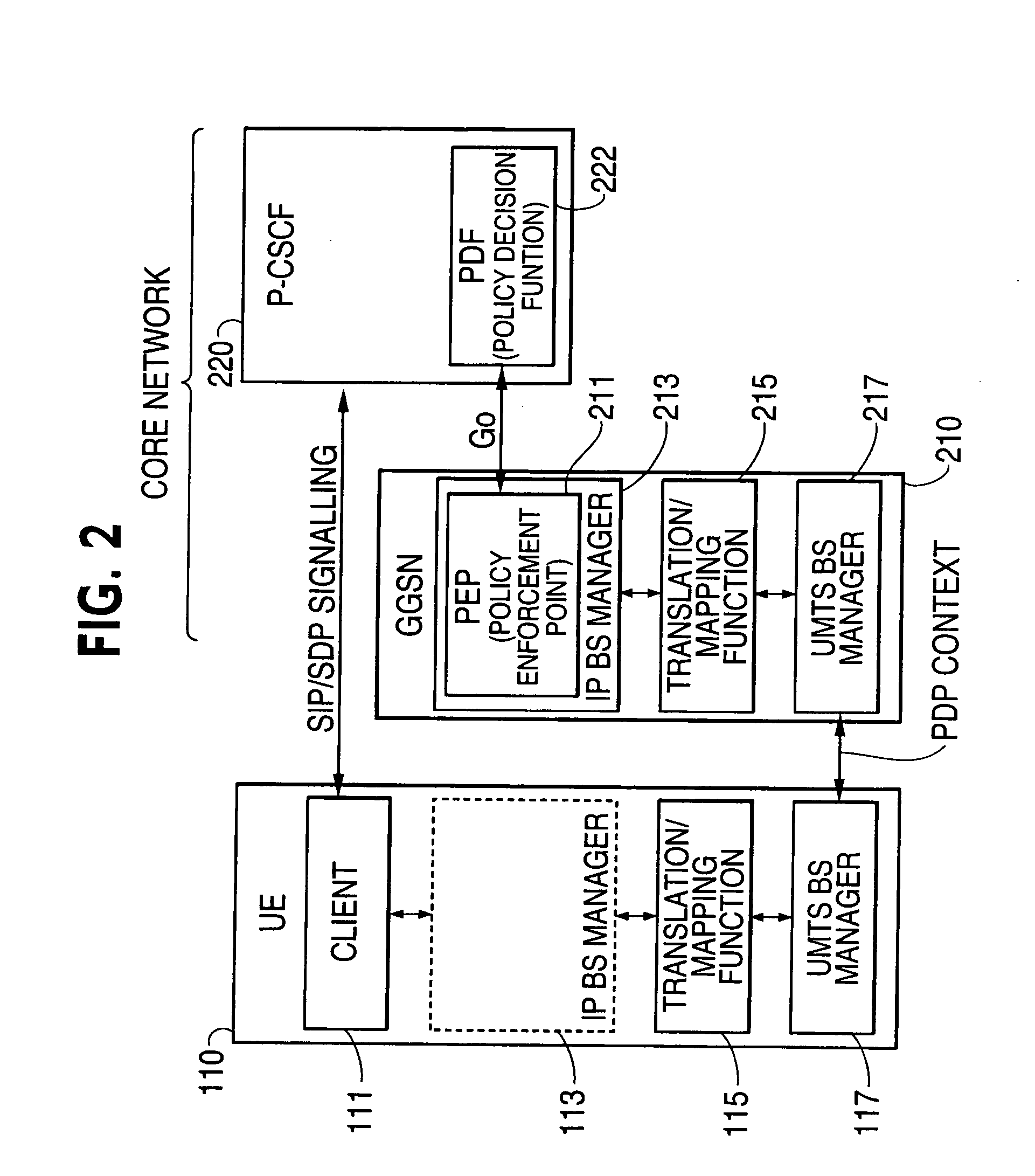
Mobile network having IP multimedia subsystem (IMS) entities and solutions for providing simplification of operations and compatibility between different IMS entities
InactiveUS20040187021A1User identity/authority verificationNetwork topologiesSession managementPolicy decision
An IP Multimedia Subsystem (IMS) architecture for IP multimedia services is provided with a given user equipment (UE); a gateway support node (GGSN) configured to handle packet transmission to / from the given UE; and a proxy call session control function (P-CSCF) configured to serve as a first contact point of the UE and provide session management services, including establishing a packet data protocol (PDP) context for IMS related signaling, registration, and other procedures for IMS sessions. The P-CSCF is also configured to perform the following: storing identification information from the given UE during registration in memory; receiving a SIP (Session Initiation Protocol) message from the given UE; comparing identity in the SIP message with the identification information stored with a link to a Policy Decision Function (PDF); and using the same PDF for all operations of the given UE, when the identity in the SIP messages matches the identification information stored in memory.
Owner:NOKIA CORP
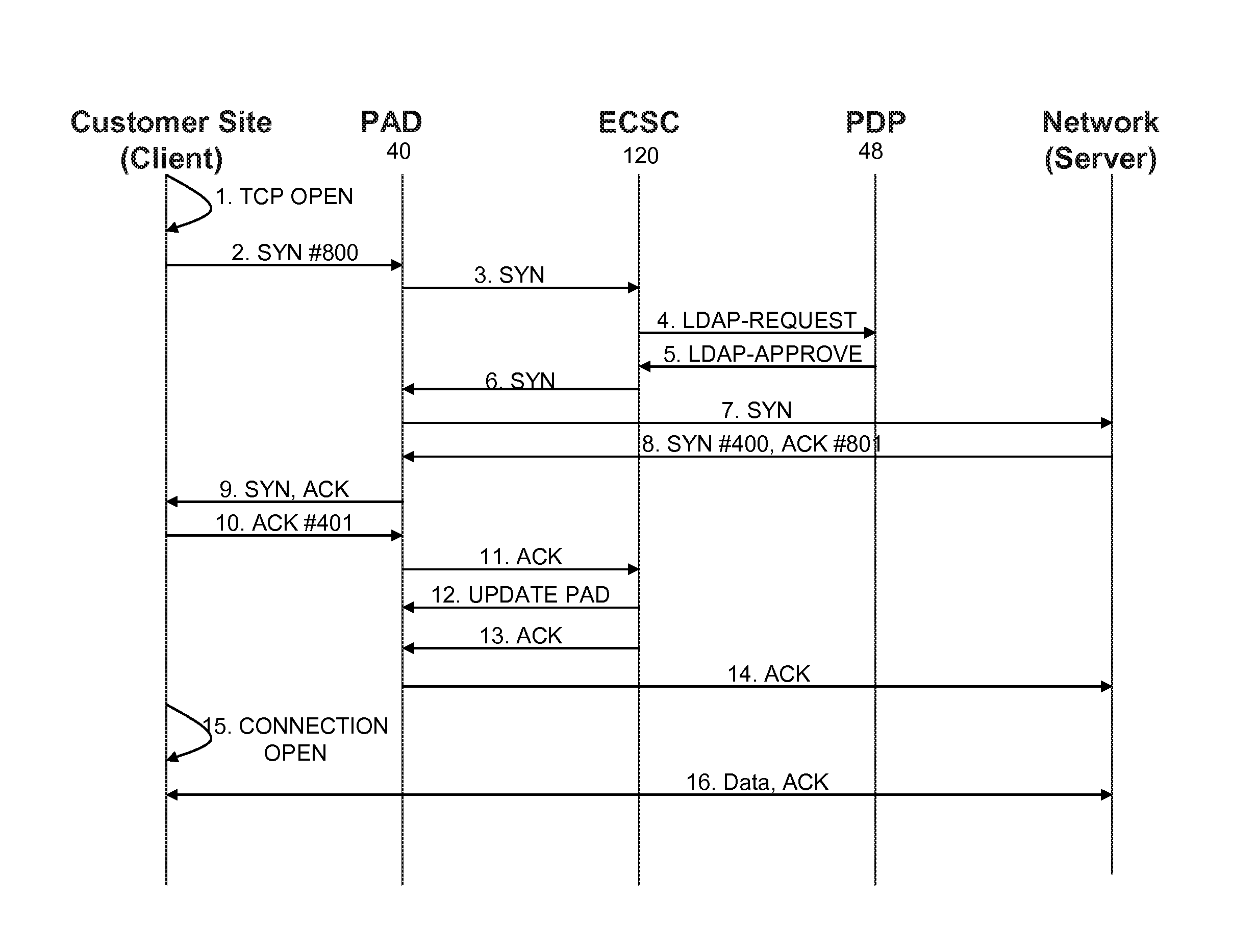
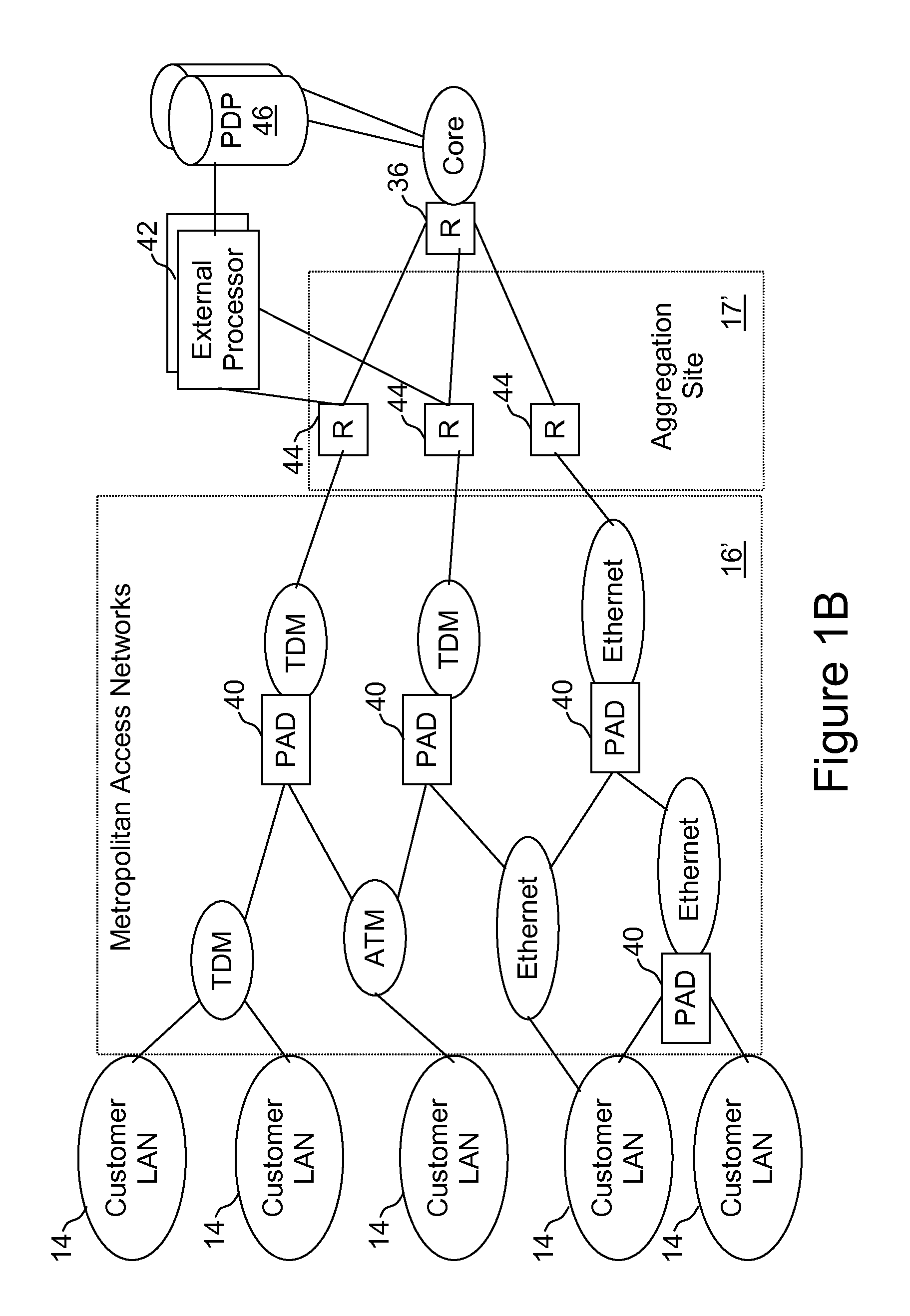
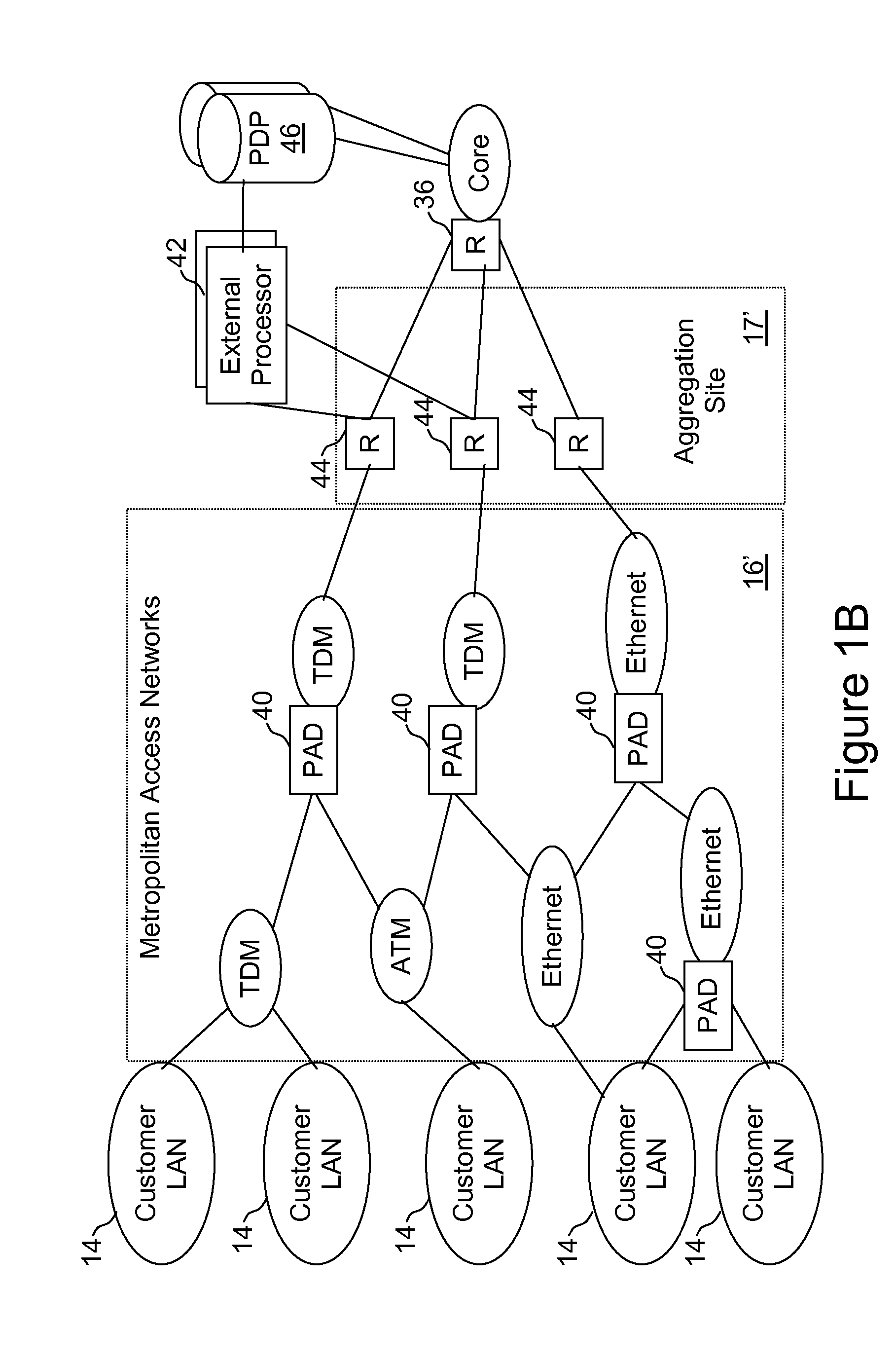
External processor for a distributed network access system
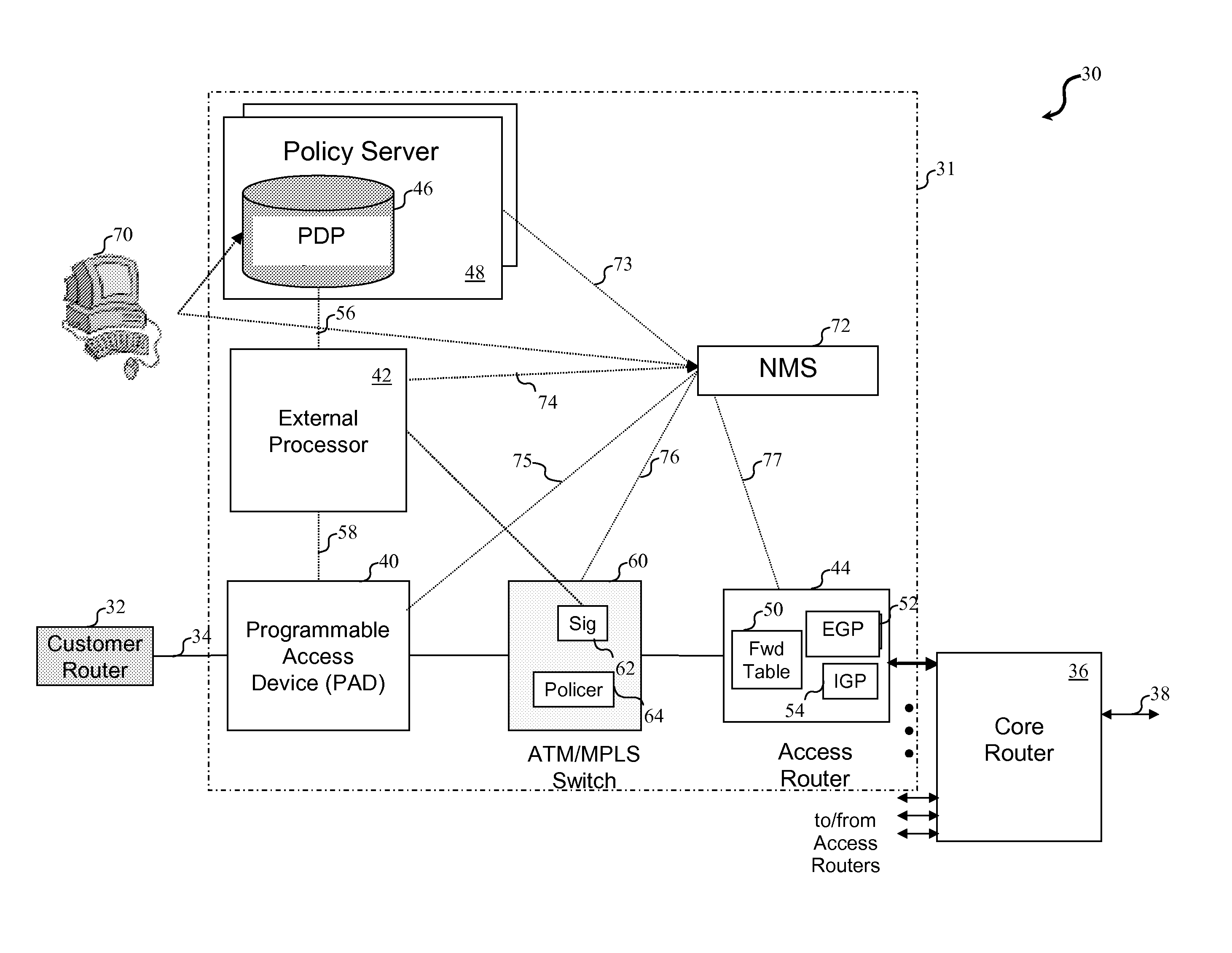
InactiveUS20100211678A1Good extensibilityIncrease flexibilitySpecial service provision for substationData switching by path configurationTraffic capacityPolicy decision
An external processor for a network access system having a programmable access device includes a service controller that provides at least one service for network traffic, a message processor that processes network messages for service processing by the service controller, and a programmable access device controller that programs the programmable access device in response to service controller processing. It is advantageous for the external processor to include primary and secondary service controllers for a particular service so that, if the primary service controller fails, the secondary service controller can provide the particular service for message received from the programmable access device. In preferred embodiments, the service controller further includes a reporting processor that provides an interface through which reporting messages received from the programmable access device can be communicated to the service controller and a signaling controller that transmits signals to configure network hardware to establish requested network connections. The external processor preferably further supports a service policy interface through which the service controller can request policy decisions from a possibly remote policy server.
Owner:VERIZON PATENT & LICENSING INC
Enhanced policy capabilities for mobile data services
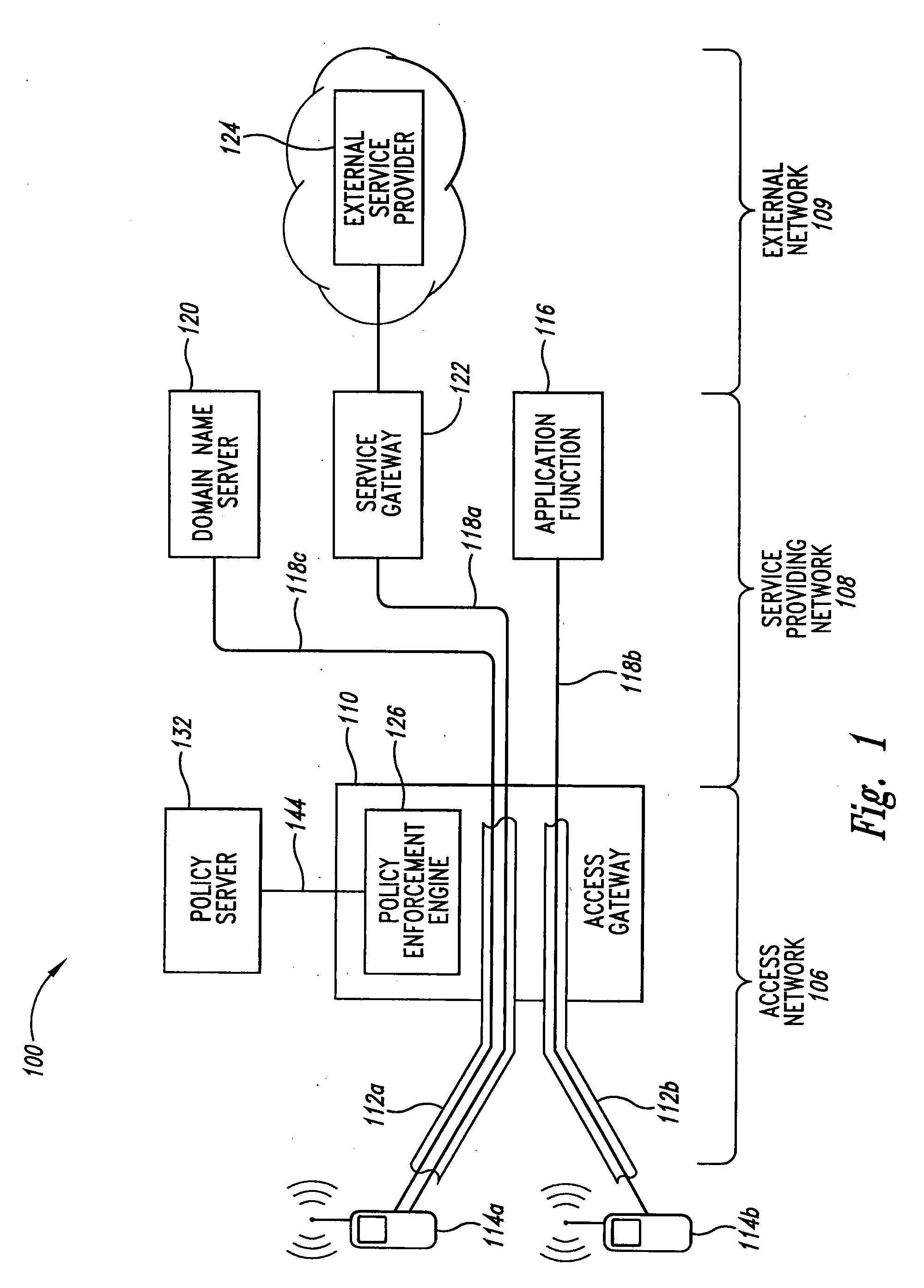
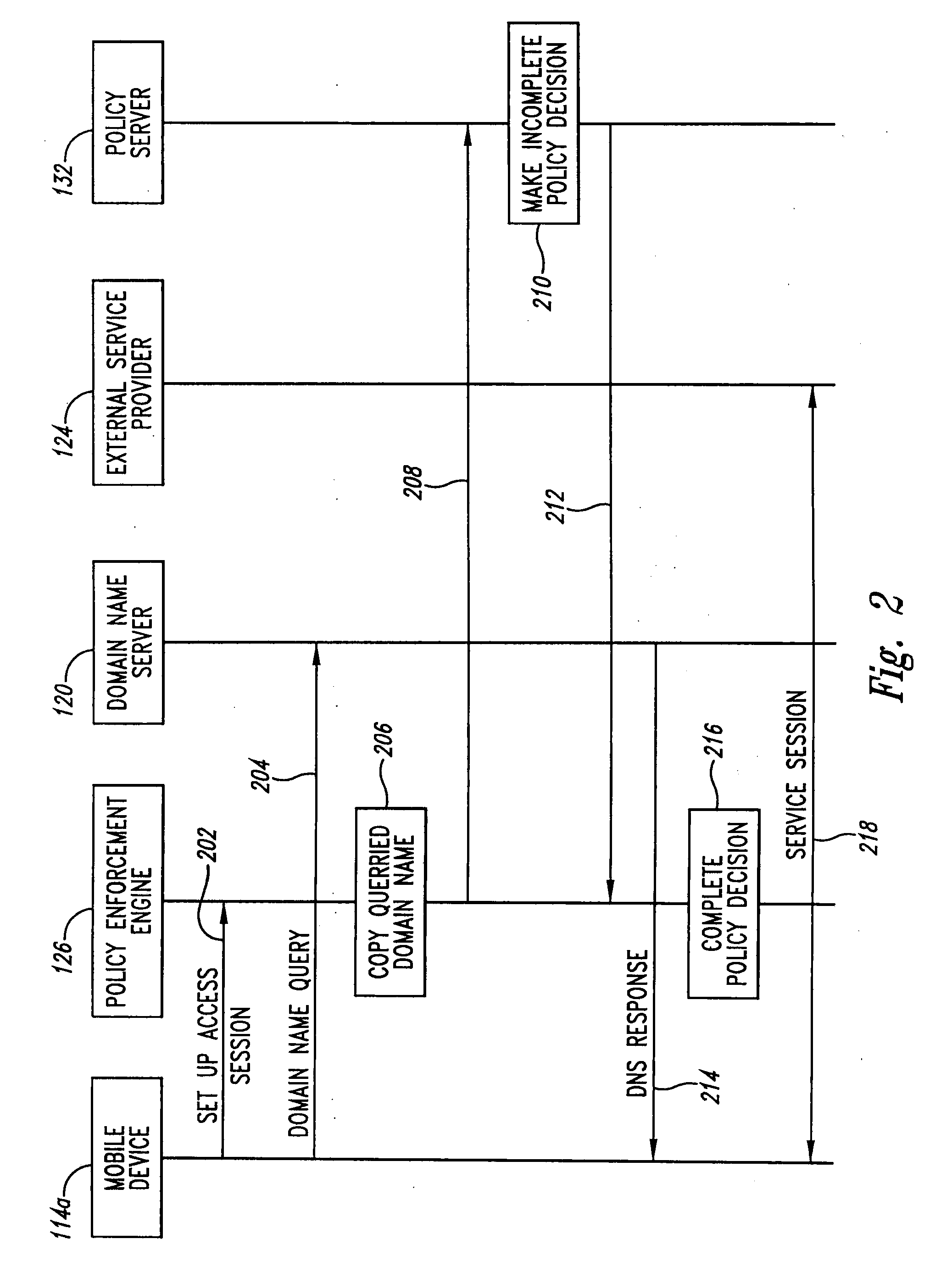
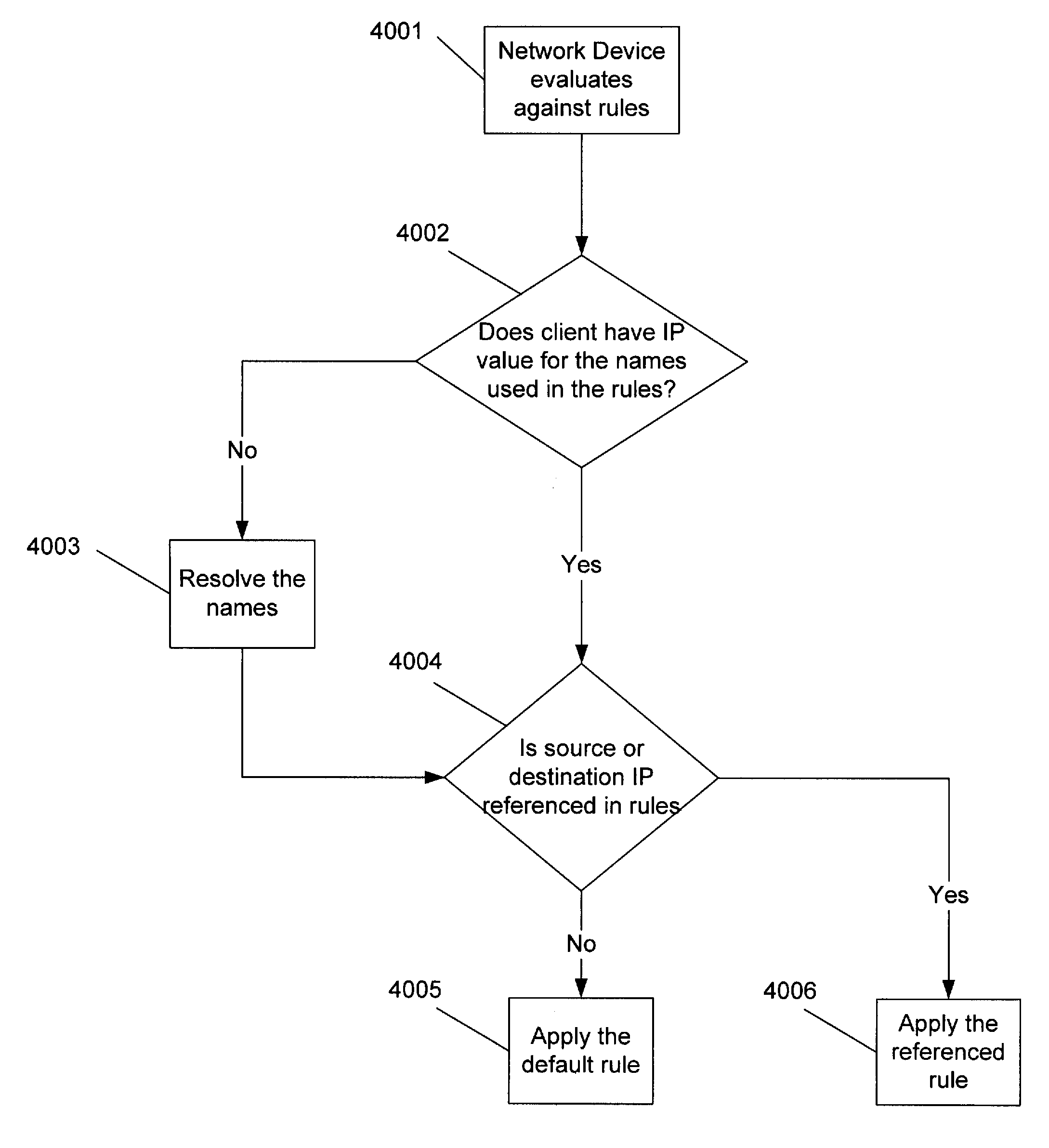
ActiveUS20090227228A1Metering/charging/biilling arrangementsAccounting/billing servicesPolicy decisionDomain name
A system and method for a mobile data access network to make policy control and charging decisions based on domain name queries. A mobile device sends a query about a domain name associated with a service a user of the mobile device wishes to engage. The access network carries the domain name query from a mobile device to a domain name server. The access network detects the domain name query and copies the queried domain name. The access network uses the queried domain name to make an incomplete policy decision. The policy decision is incomplete because one or more service data flow filters in the decision lack addresses for providers of the service. The access network detects a response to the domain name query and copies a service provider address from the response. The access network uses the service provider address to complete the policy decision.
Owner:AT&T MOBILITY II LLC
External processor for a distributed network access system
InactiveUS20110270956A1Good extensibilityIncrease flexibilitySpecial service provision for substationData switching by path configurationPolicy decisionTraffic capacity
An external processor for a network access system having a programmable access device includes a service controller that provides at least one service for network traffic, a message processor that processes network messages for service processing by the service controller, and a programmable access device controller that programs the programmable access device in response to service controller processing. It is advantageous for the external processor to include primary and secondary service controllers for a particular service so that, if the primary service controller fails, the secondary service controller can provide the particular service for message received from the programmable access device. In preferred embodiments, the service controller further includes a reporting processor that provides an interface through which reporting messages received from the programmable access device can be communicated to the service controller and a signaling controller that transmits signals to configure network hardware to establish requested network connections. The external processor preferably further supports a service policy interface through which the service controller can request policy decisions from a possibly remote policy server.
Owner:VERIZON PATENT & LICENSING INC
Method and system for propagating network policy
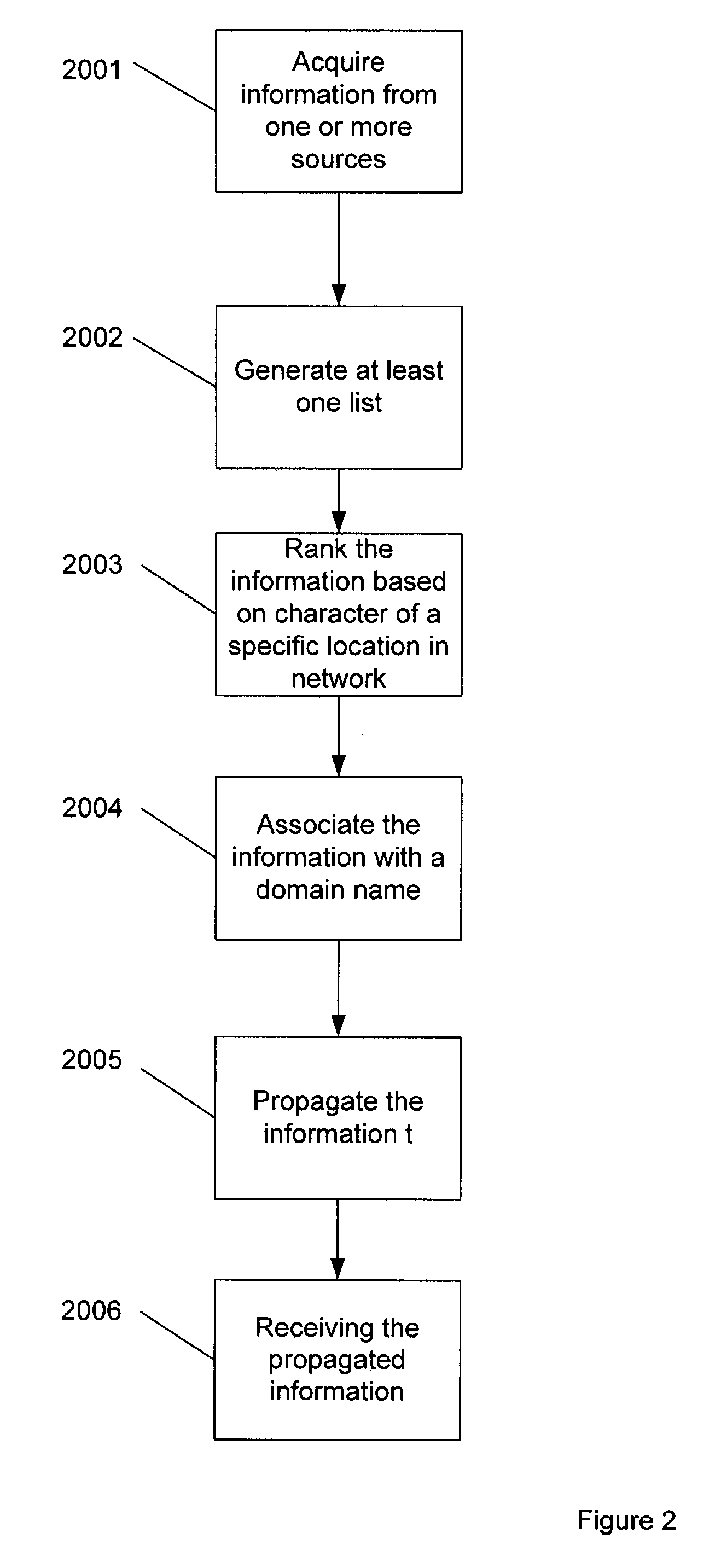
ActiveUS20080052758A1Increase profitFunction providedMemory loss protectionDigital data processing detailsPolicy decisionTraffic capacity
A method for acquiring and disseminating network node characteristics to enable policy decisions including receiving a resolution request from one or more clients in a network environment. Information, for example, network address, is then acquired from one or more sources regarding a specific location in a network, for example, a network node. A list of the network addresses is then generated and ranked based on one or more parameters that merit making traffic handling decisions. The network addresses are then associated with a host name on at least one directory server and then propagated to the one or more clients.
Owner:THREATSTOP
Method and system to clear counters used for statistical tracking for global server load balancing
Server load-balancing operation-related data, such as data associated with a system configured for global server load balancing (GSLB) that orders IP addresses into a list based on a set of performance metrics, is tracked. Such operation-related data includes inbound source IP addresses (e.g., the address of the originator of a DNS request), the requested host and zone, identification of the selected “best” IP addresses resulting from application of a GSLB algorithm, and the selection metric used to decide on an IP address as the “best” one. The data includes a count of the selected “best” IP addresses selected via application of the GSLB algorithm, and for each of these IP addresses, the list of deciding performance metrics, along with a count of the number of times each of these metrics in the list was used as a deciding factor in selection of this IP address as the best one. This tracking feature allows better understanding of GSLB policy decisions (such as those associated with performance, maintenance, and troubleshooting) and intelligent deployment of large-scale resilient GSLB networks. The counters can be cleared as needed and without having to reload the system.
Owner:AVAGO TECH INT SALES PTE LTD
System for providing flexible charging in a network
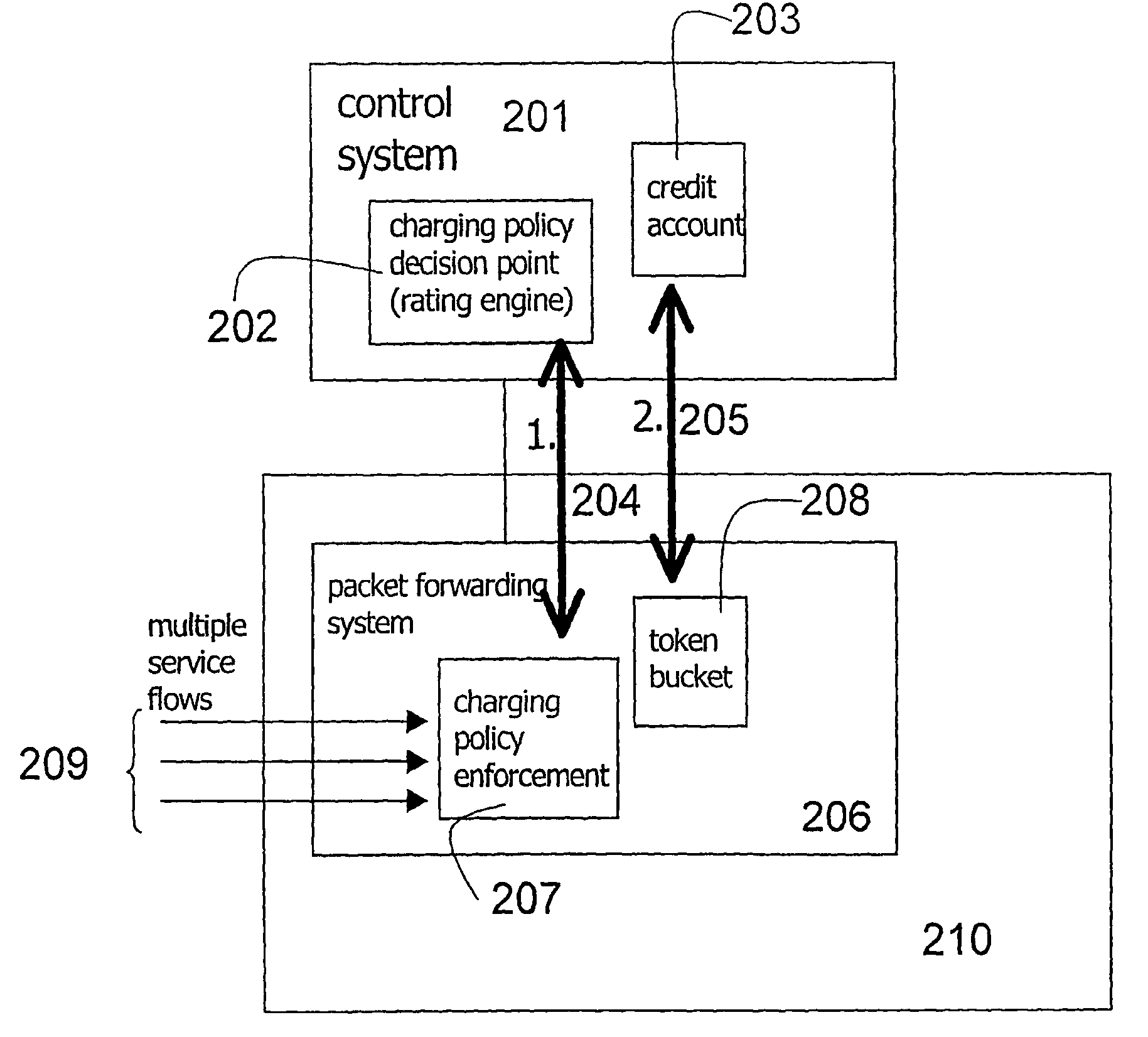
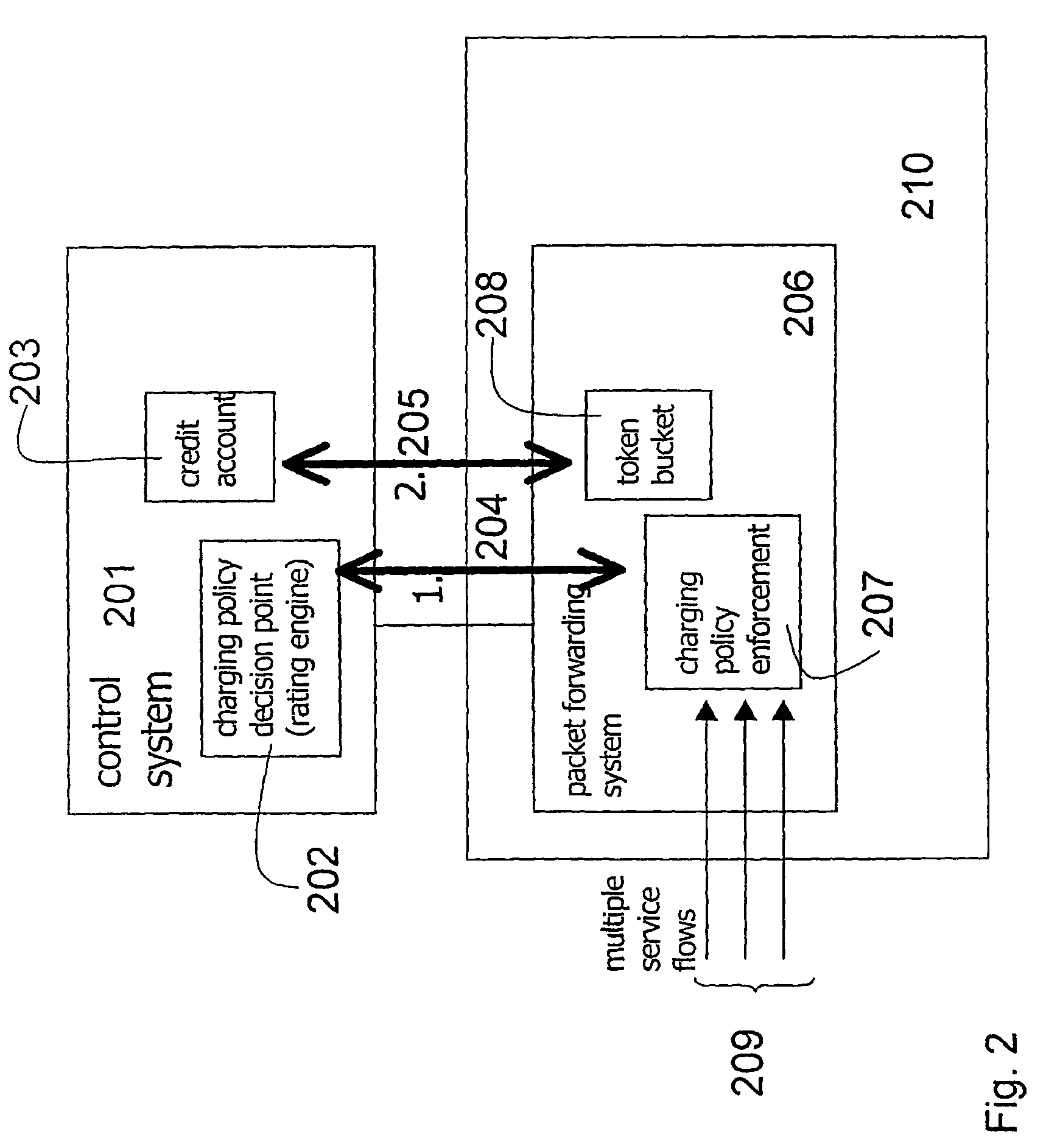
ActiveUS20060008063A1Reduce signaling loadReduce reservationMetering/charging/biilling arrangementsError preventionService flowPolicy decision
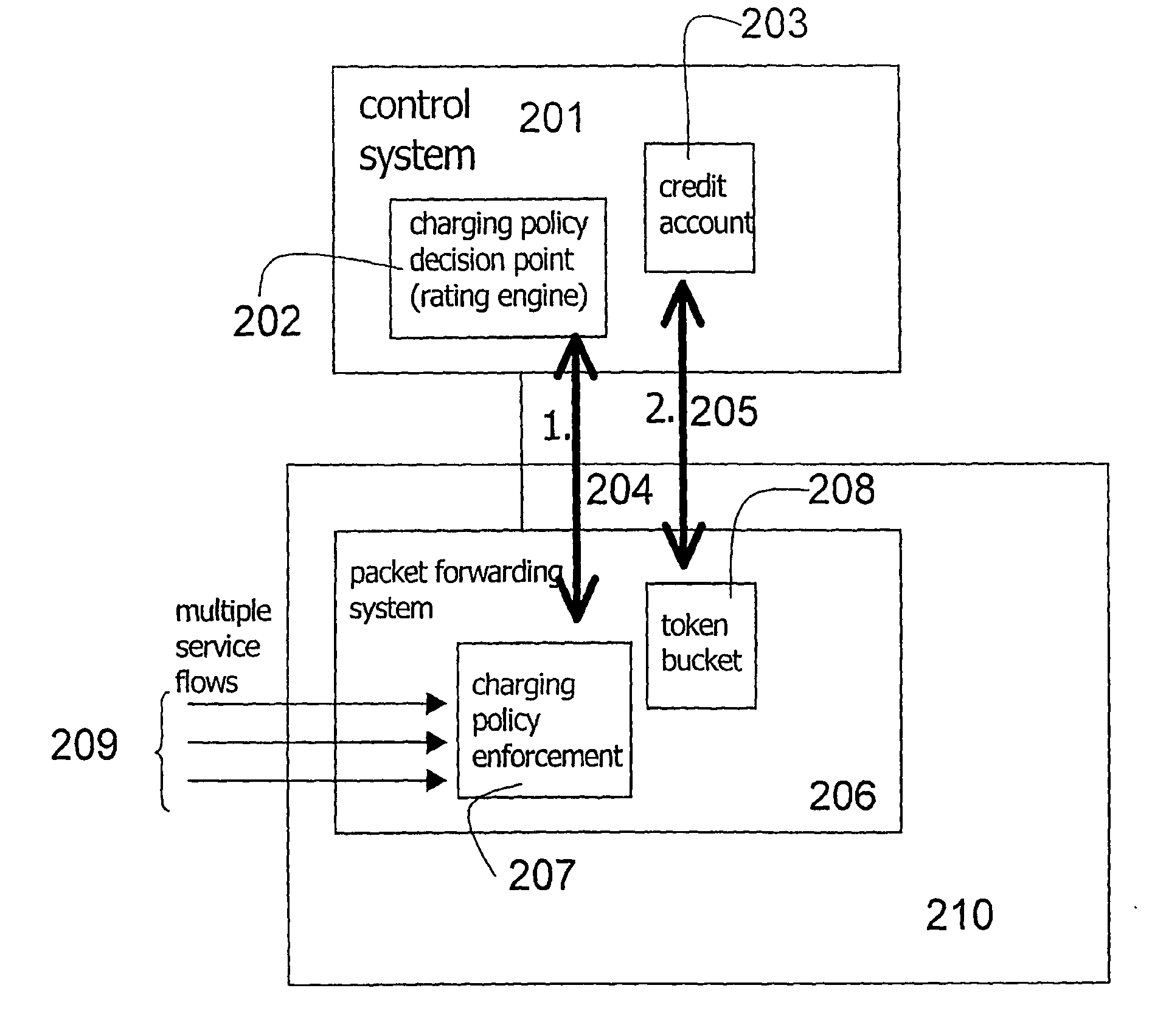
The present invention relates to arrangements for charging in a packet switched network. Packets are charged differently dependent on which service flow the packets belong to. The charging system comprises a control system and a serving element residing in a packet forwarding system wherein said control system comprises an account function adapted to manage an account of at least one user and a charging policy decision point arranged to calculate a charging policy for allowed services for the at least one user. Moreover, said serving element comprises a token bucket per user adapted to store reservations received from the account function of the user associated with the token bucket and a charging policy enforcement point arranged to perform charging for a plurality of the allowed services by reducing the stored reservation of the token bucket according to the calculated charging policy.
Owner:TELEFON AB LM ERICSSON (PUBL)
Fine-grained relational database access-control policy enforcement using reverse queries
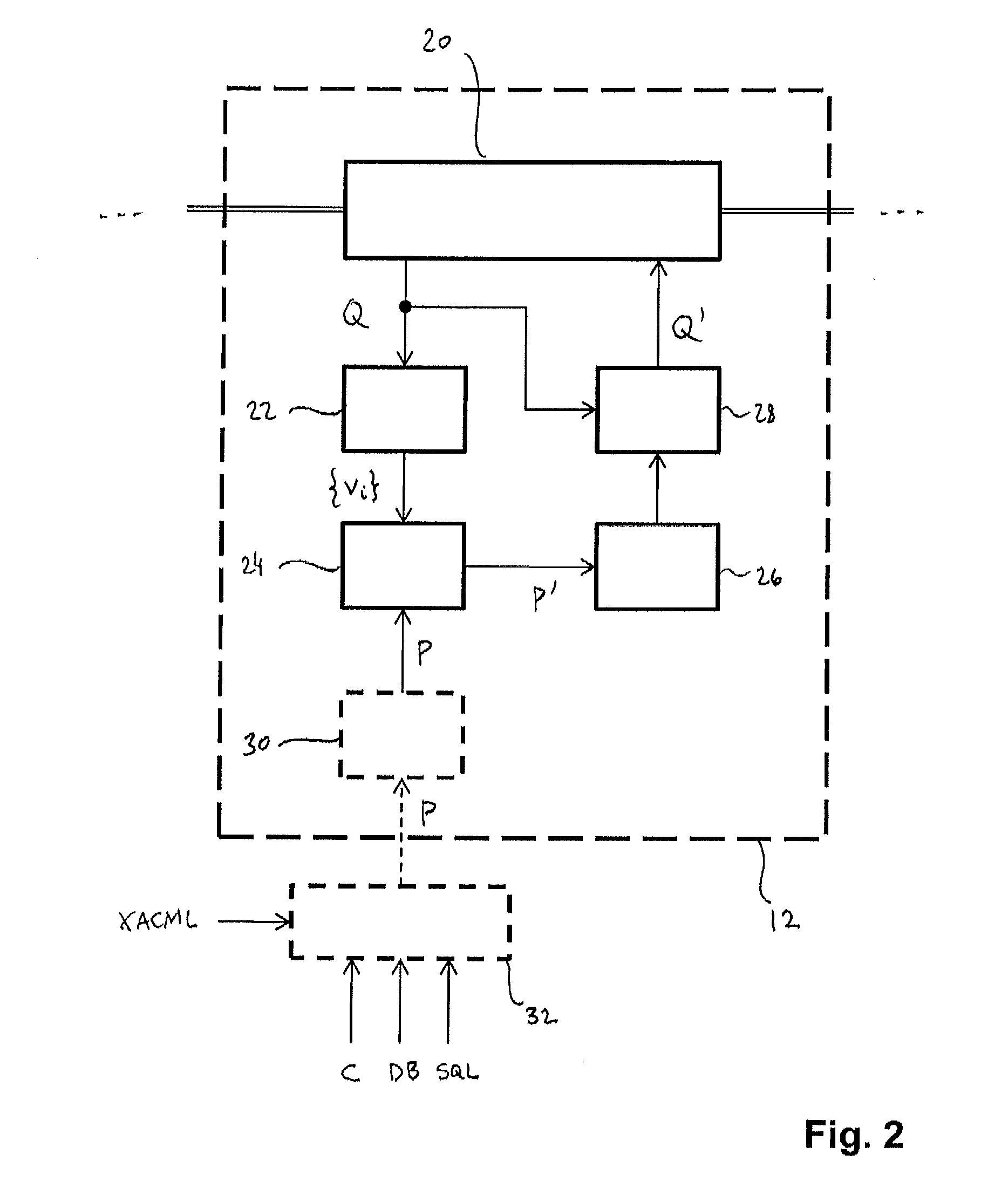
ActiveUS20140052749A1Accurately controllableIncreased latitudeDigital data information retrievalDigital data processing detailsDatabase queryPolicy decision
A method of providing access control to a relational database accessible from a user interface is implemented at a policy enforcement point, which is located between the database and the user interface and includes the steps of: (i) intercepting a database query from a user; (ii) assigning attribute values on the basis of a target table or target column in the query, a construct type in the query, or the user or environment; (iii) partially evaluating an access-control policy defined in terms of said attributes, by constructing a partial policy decision request containing the attribute values assigned in step ii) and evaluating the AC policy for this, whereby a simplified policy is obtained; (iv) deriving an access condition, for which the simplified policy permit access; and (v) amending the database query by imposing said access condition and transmitting the amended query to the database.
Owner:AXIOMATICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com