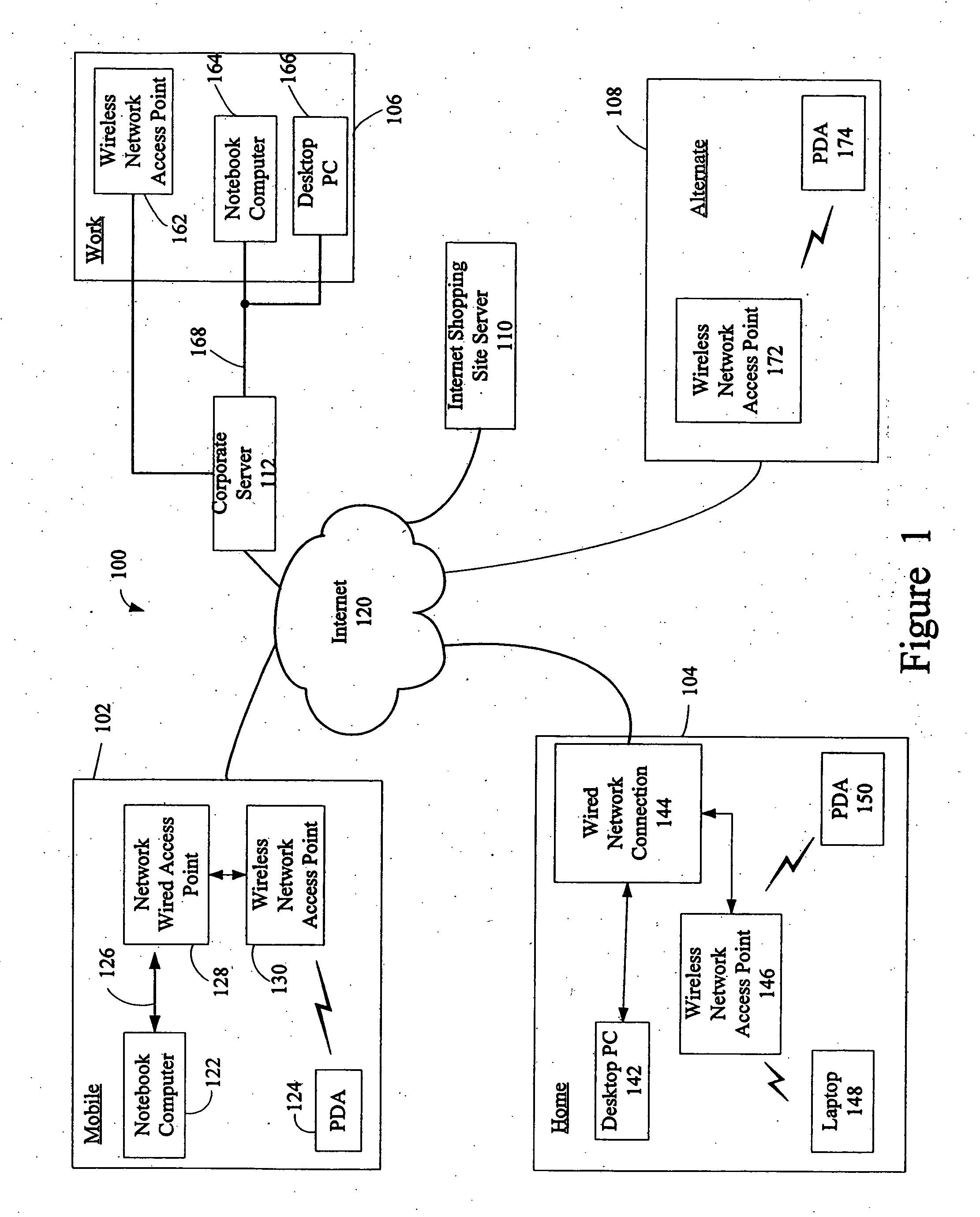
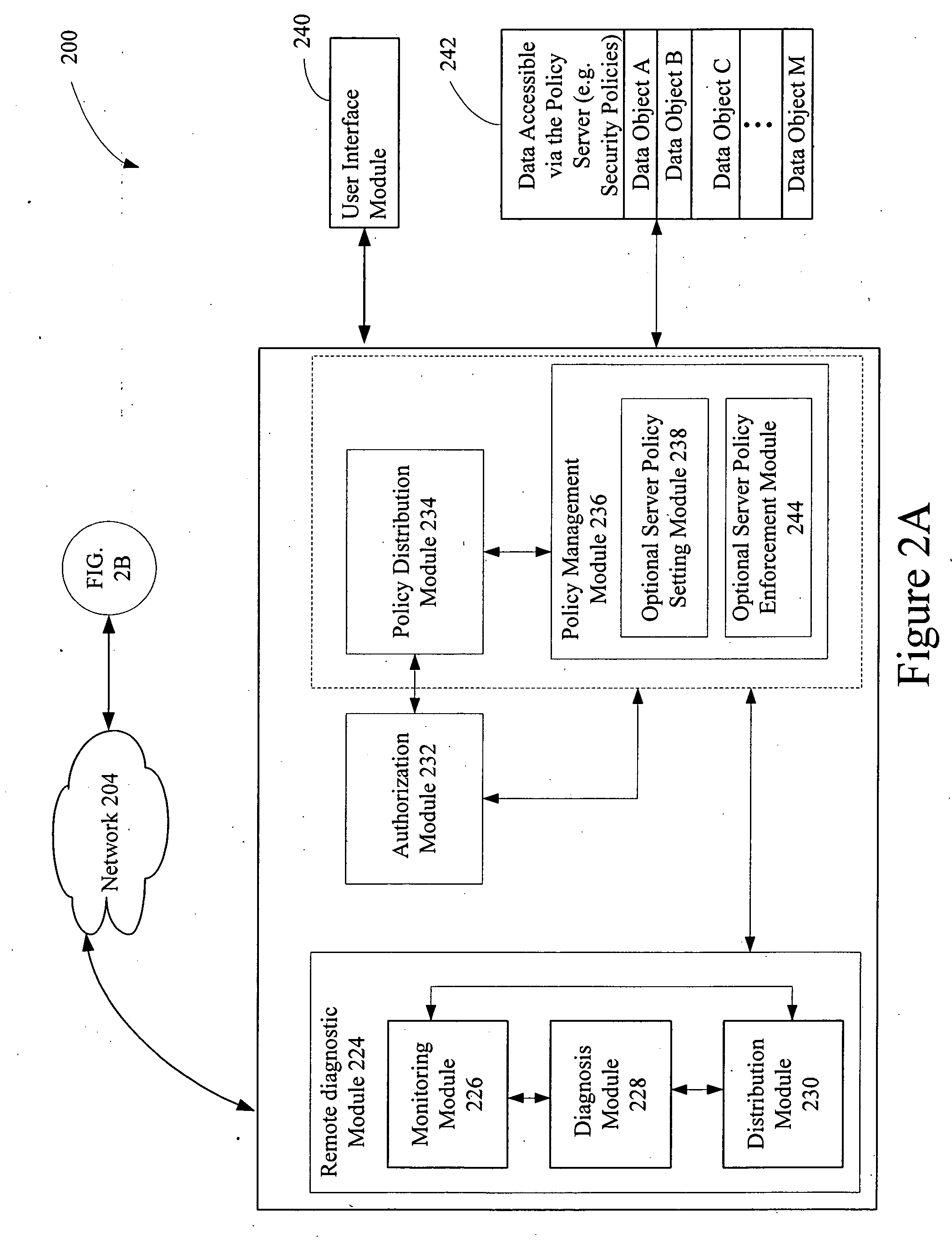
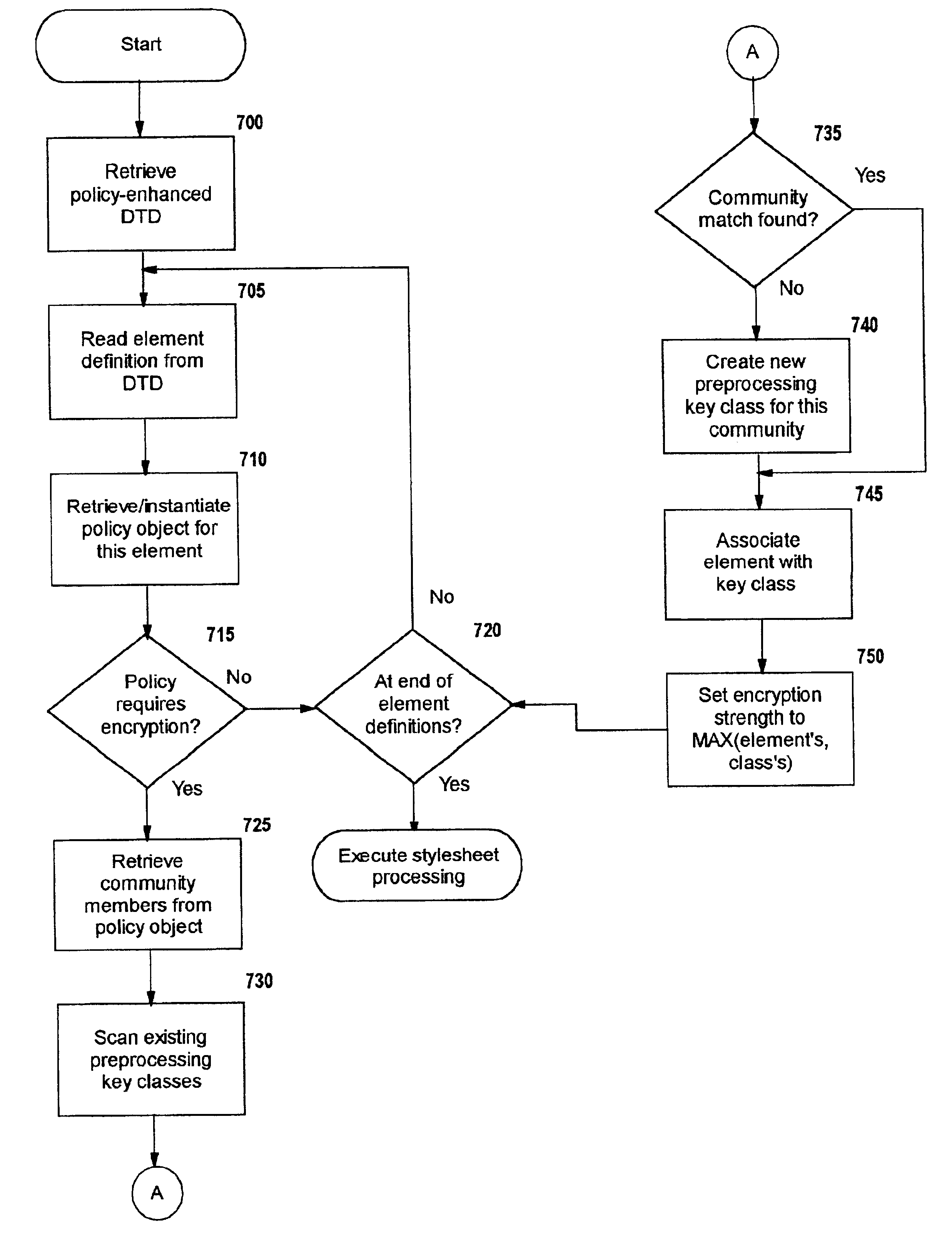
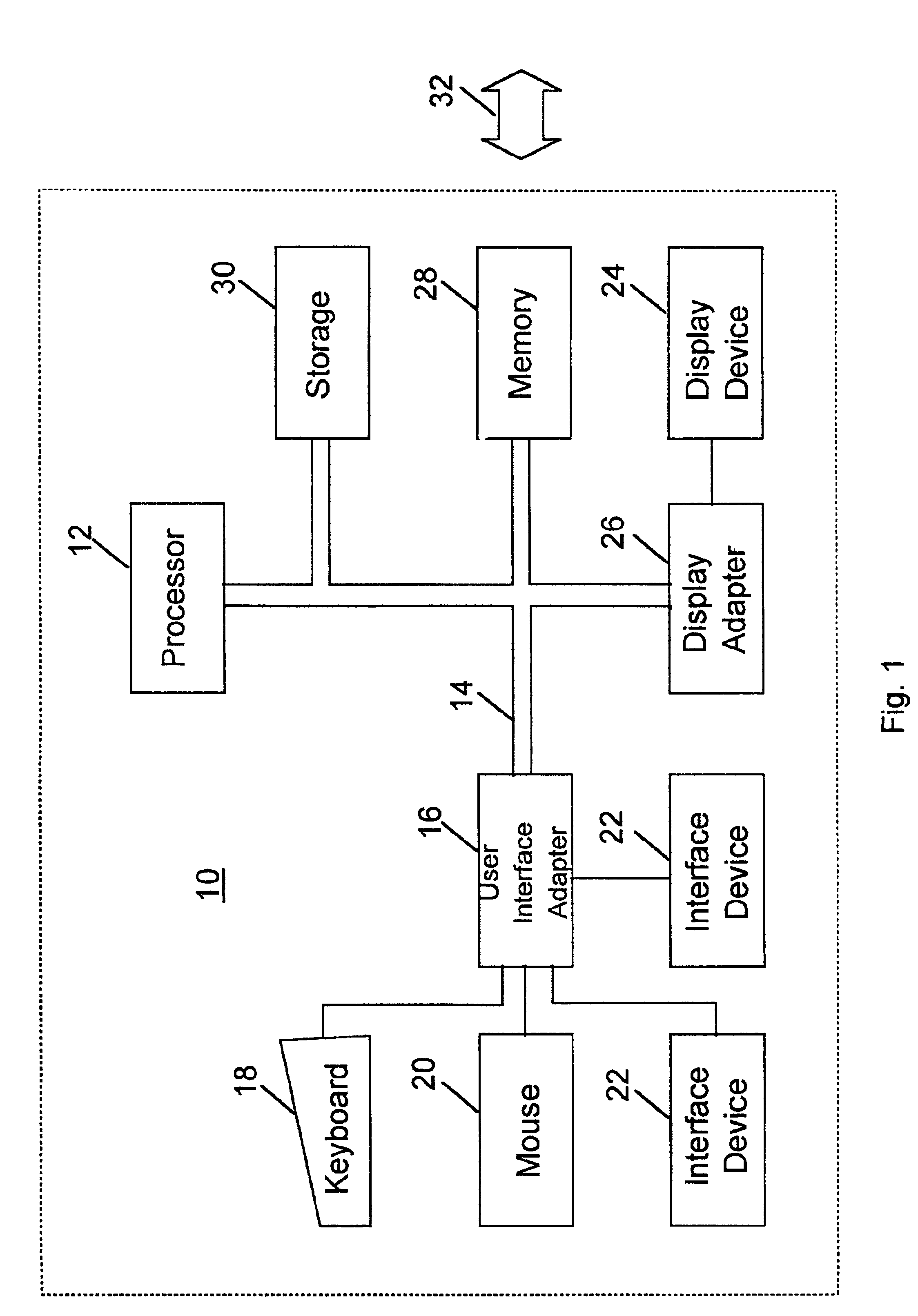
Patents
Literature
3237 results about "Security policy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security policy is a definition of what it means to be secure for a system, organization or other entity. For an organization, it addresses the constraints on behavior of its members as well as constraints imposed on adversaries by mechanisms such as doors, locks, keys and walls. For systems, the security policy addresses constraints on functions and flow among them, constraints on access by external systems and adversaries including programs and access to data by people.
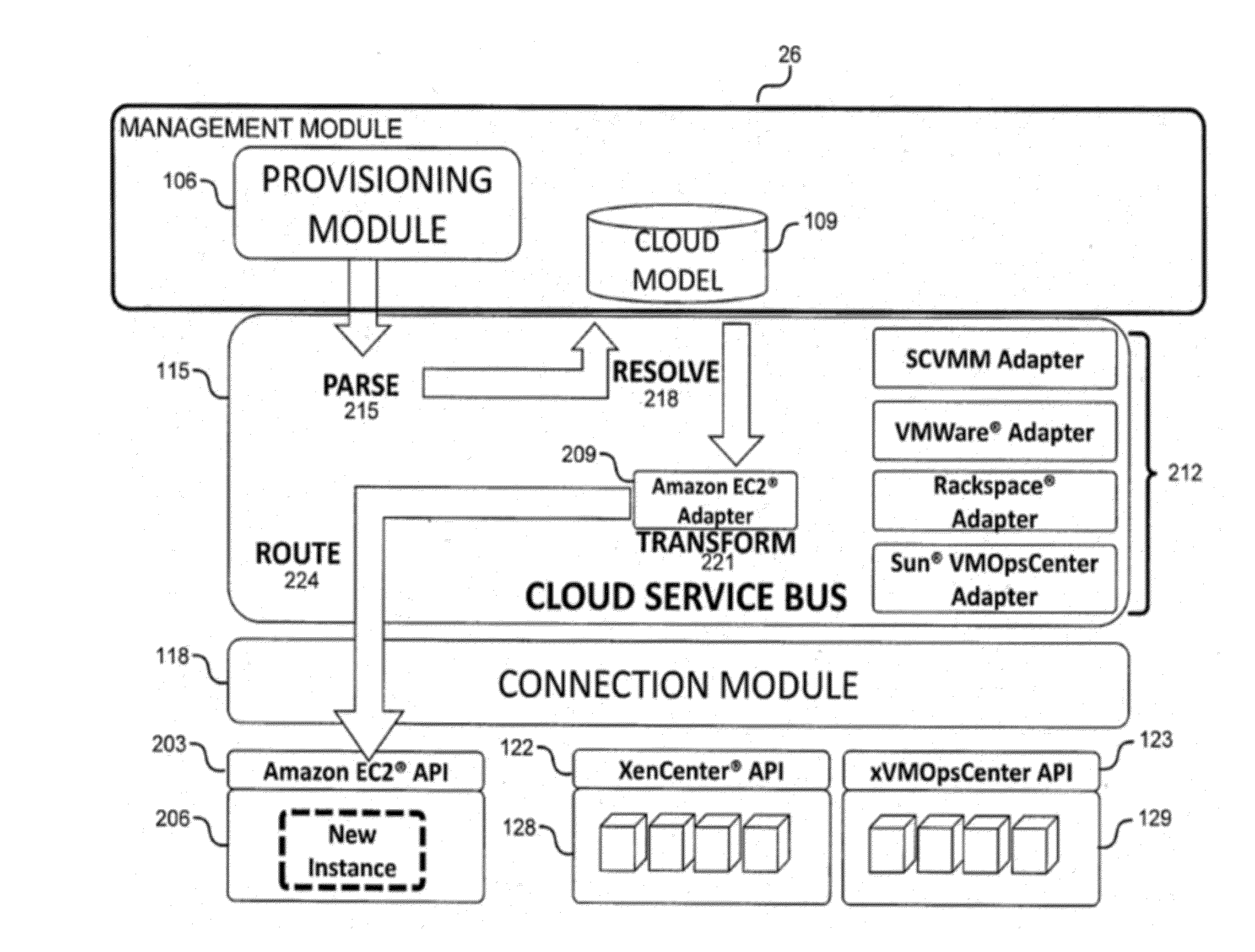
System and method for a cloud computing abstraction layer with security zone facilities
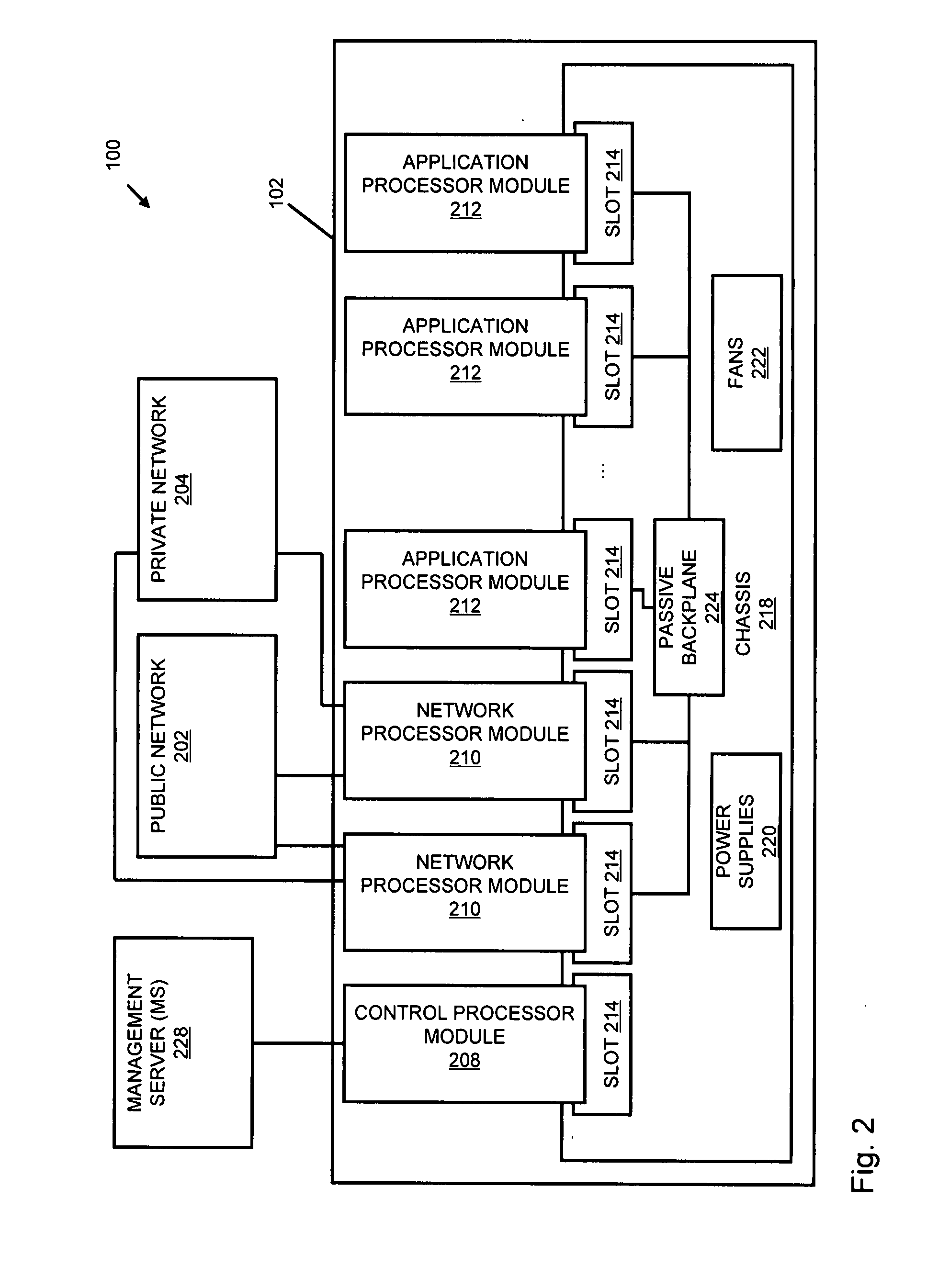
ActiveUS20120185913A1Rapid and dynamic deployment and scalingShorten the timeComputer security arrangementsHybrid transportVirtualizationAbstraction layer
In embodiments of the present invention improved capabilities are described for a virtualization environment adapted for development and deployment of at least one software workload, the virtualization environment having a metamodel framework that allows the association of a policy to the software workload upon development of the workload that is applied upon deployment of the software workload. This allows a developer to define a security zone and to apply at least one type of security policy with respect to the security zone including the type of security zone policy in the metamodel framework such that the type of security zone policy can be associated with the software workload upon development of the software workload, and if the type of security zone policy is associated with the software workload, automatically applying the security policy to the software workload when the software workload is deployed within the security zone.
Owner:DXC US AGILITY PLATFORM INC
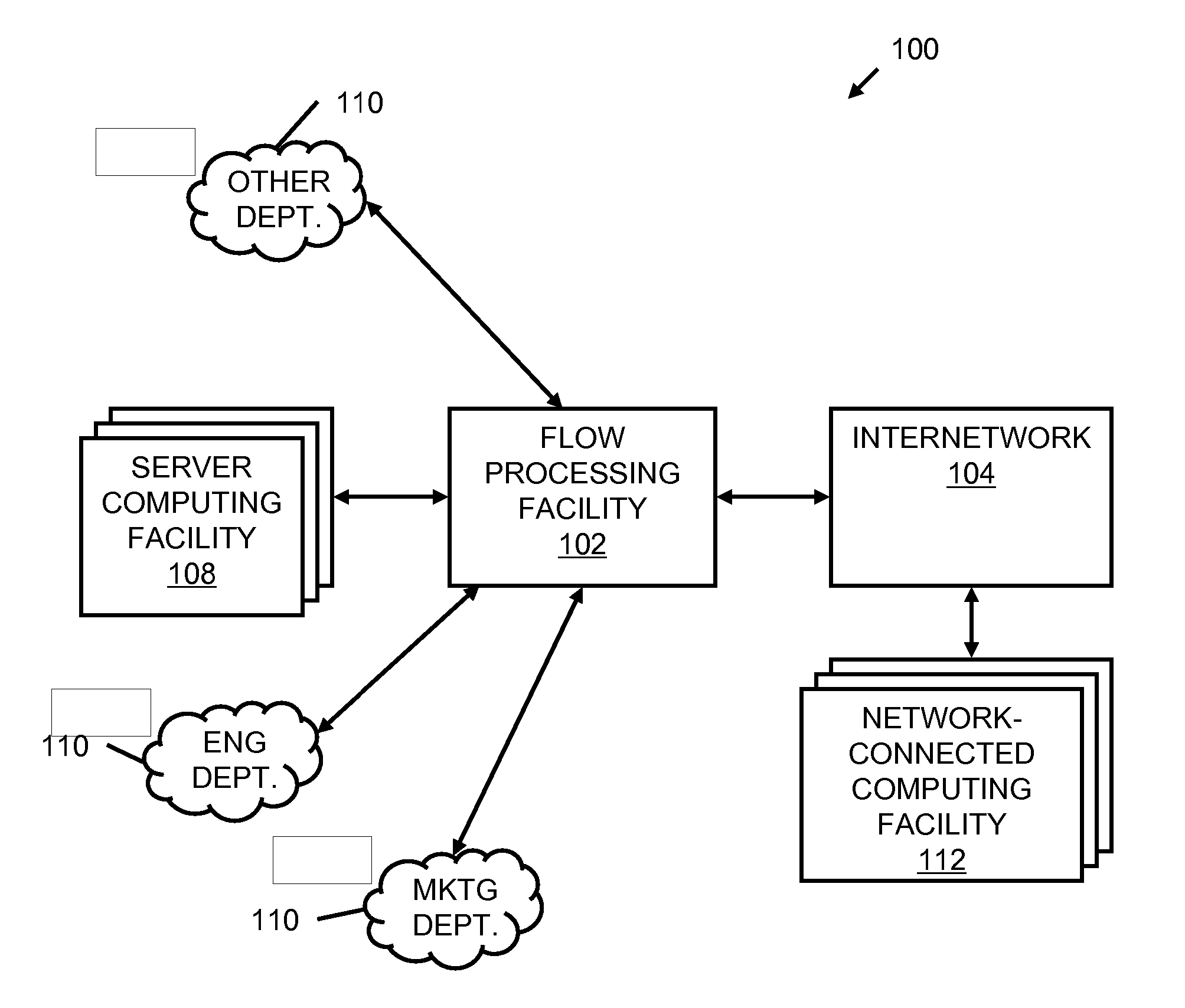
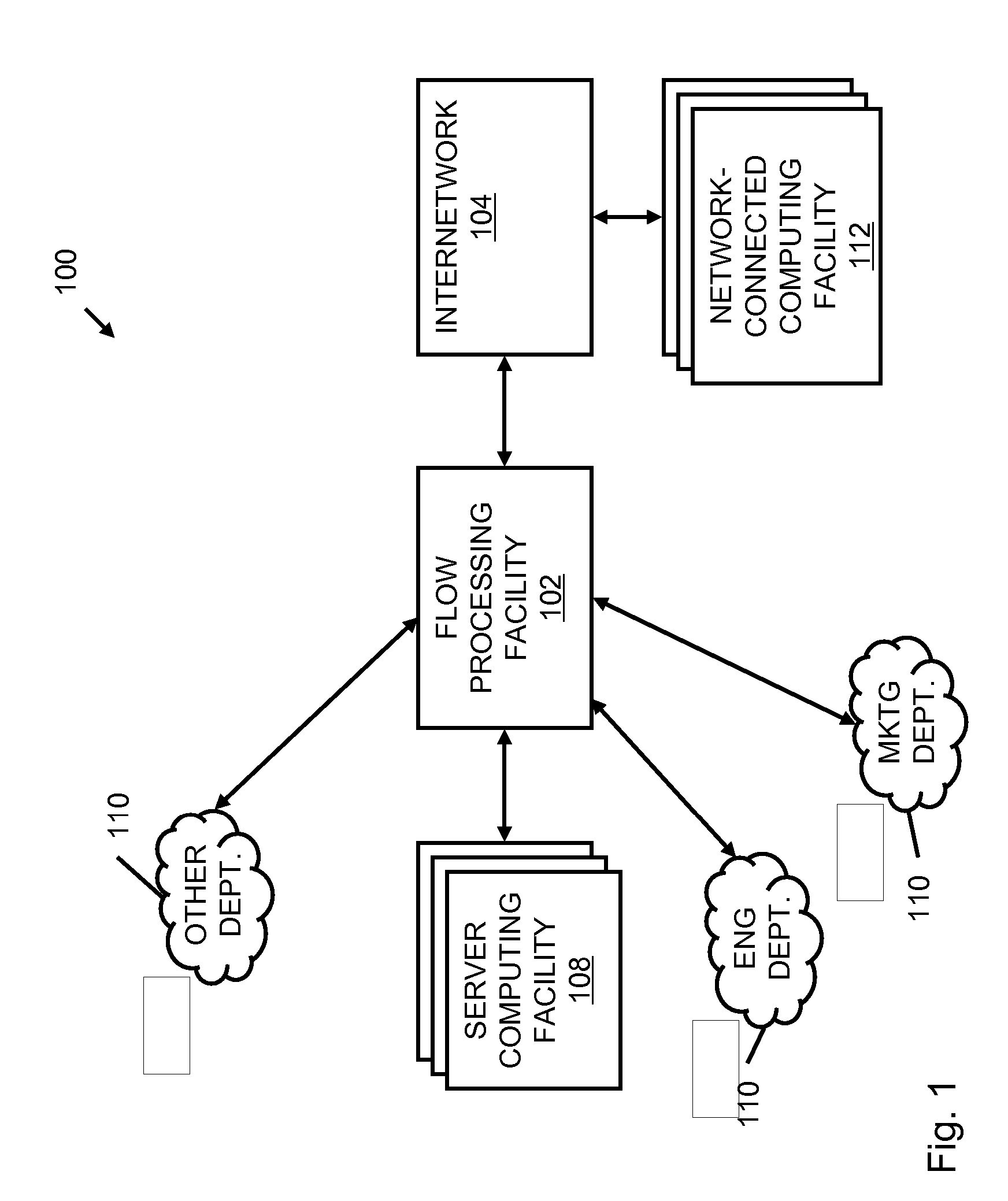
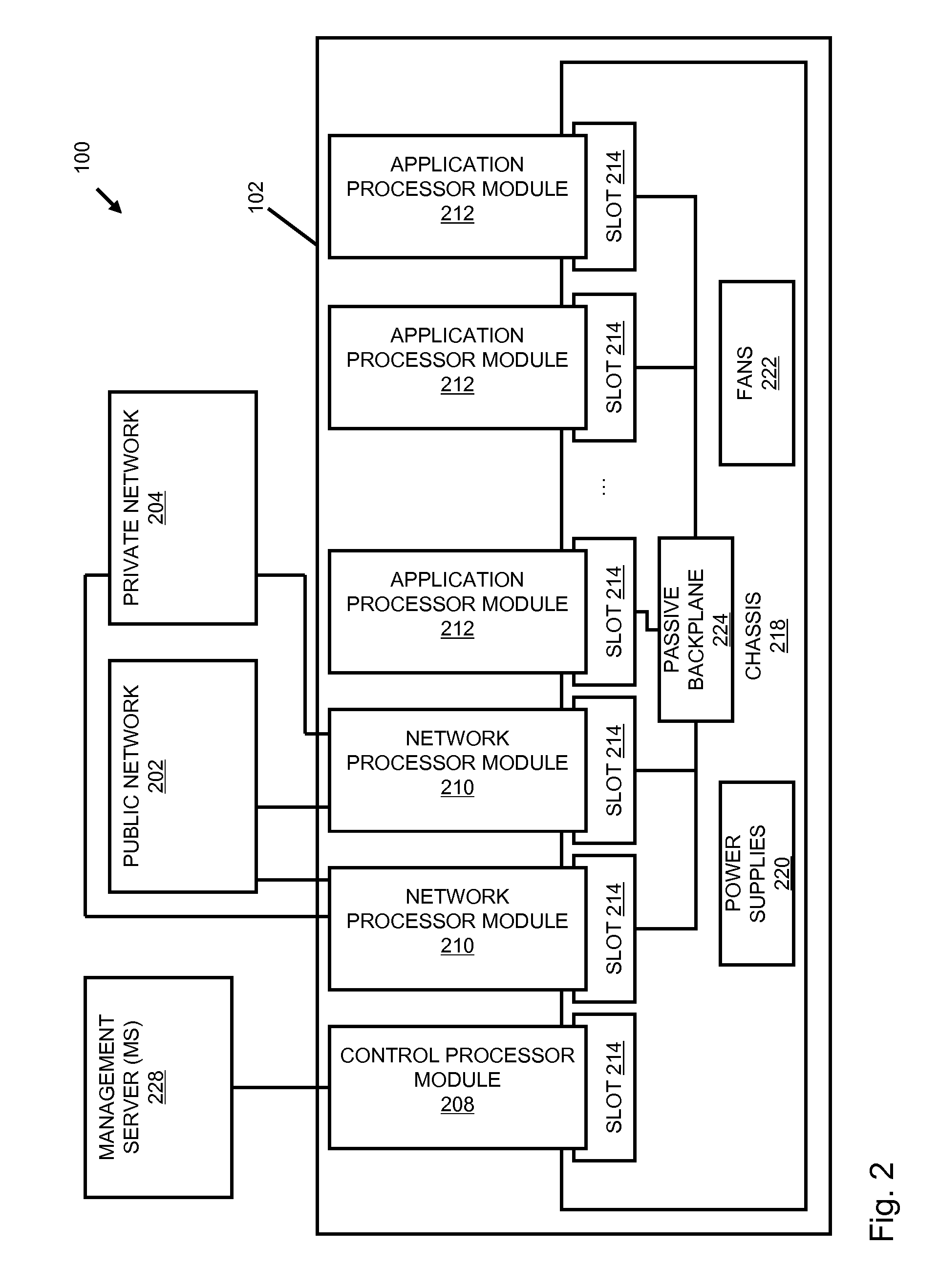
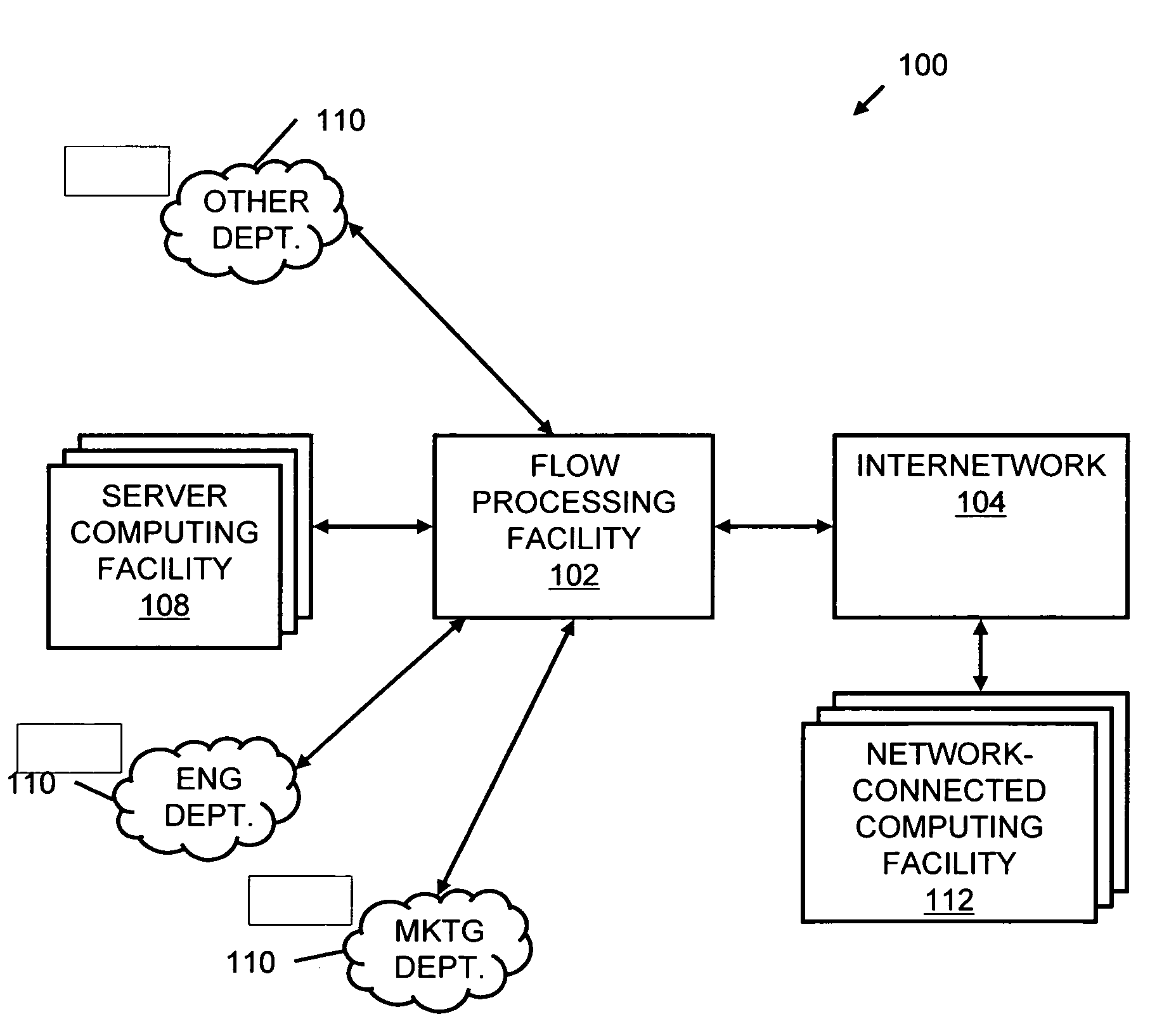
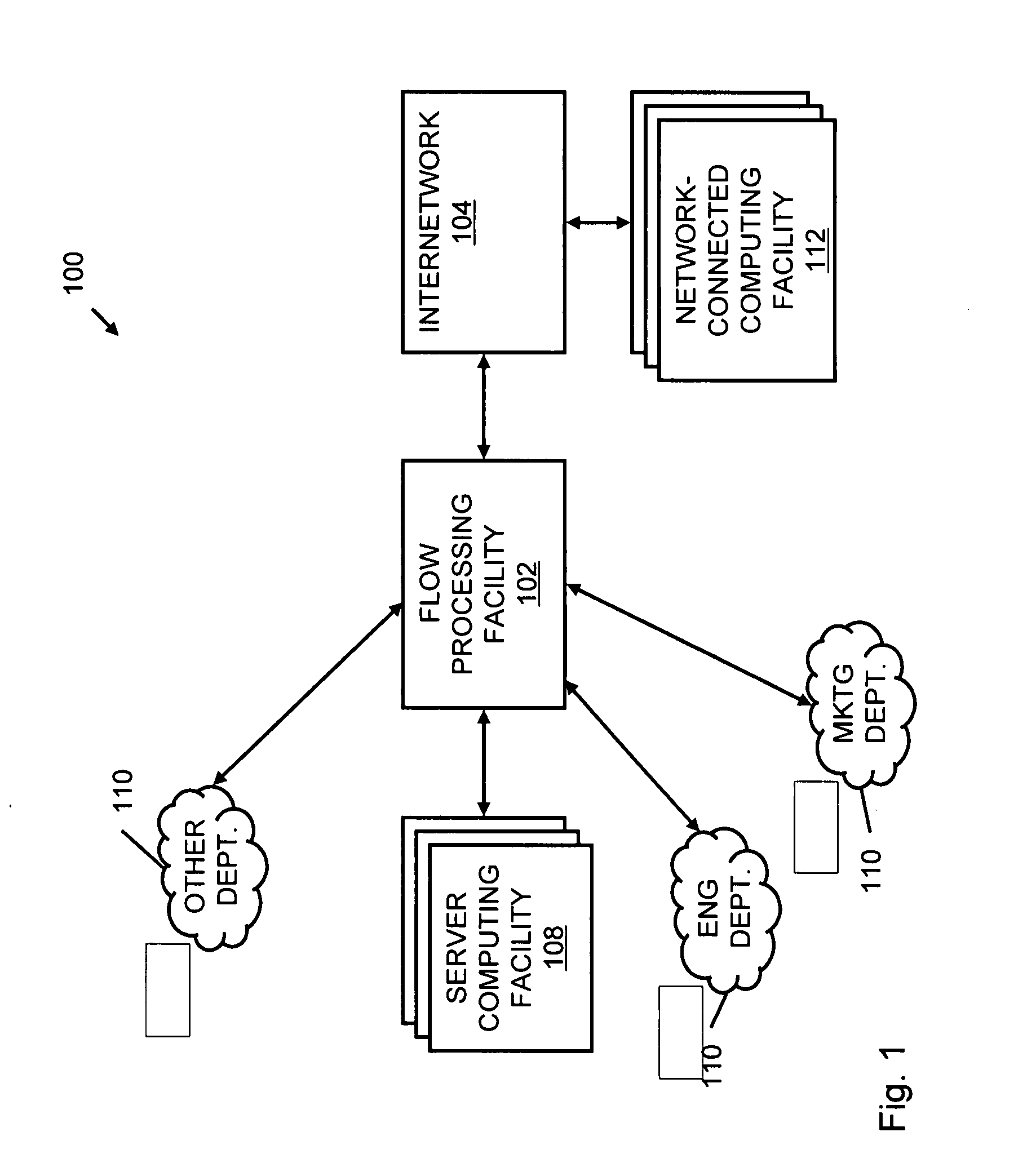
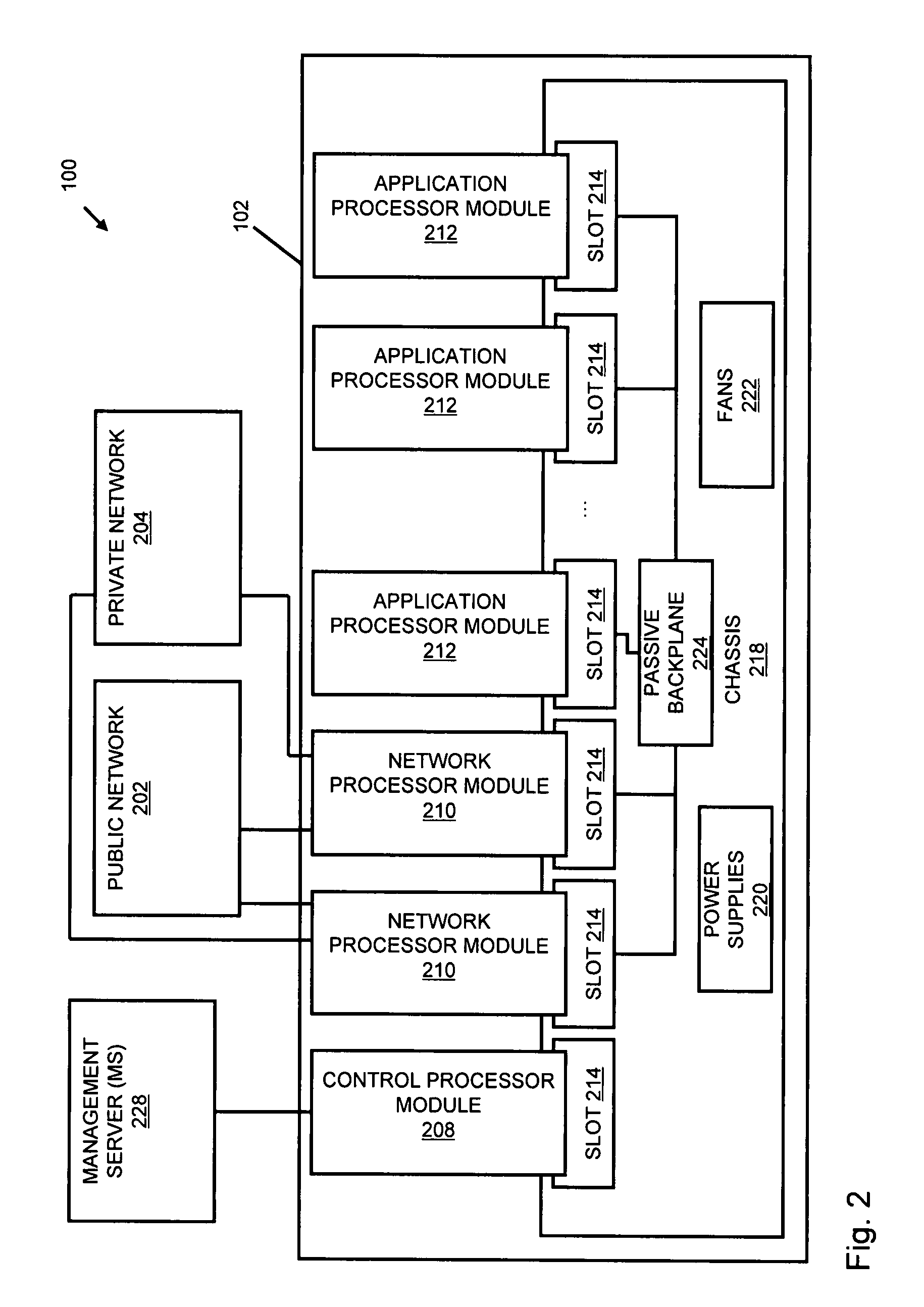
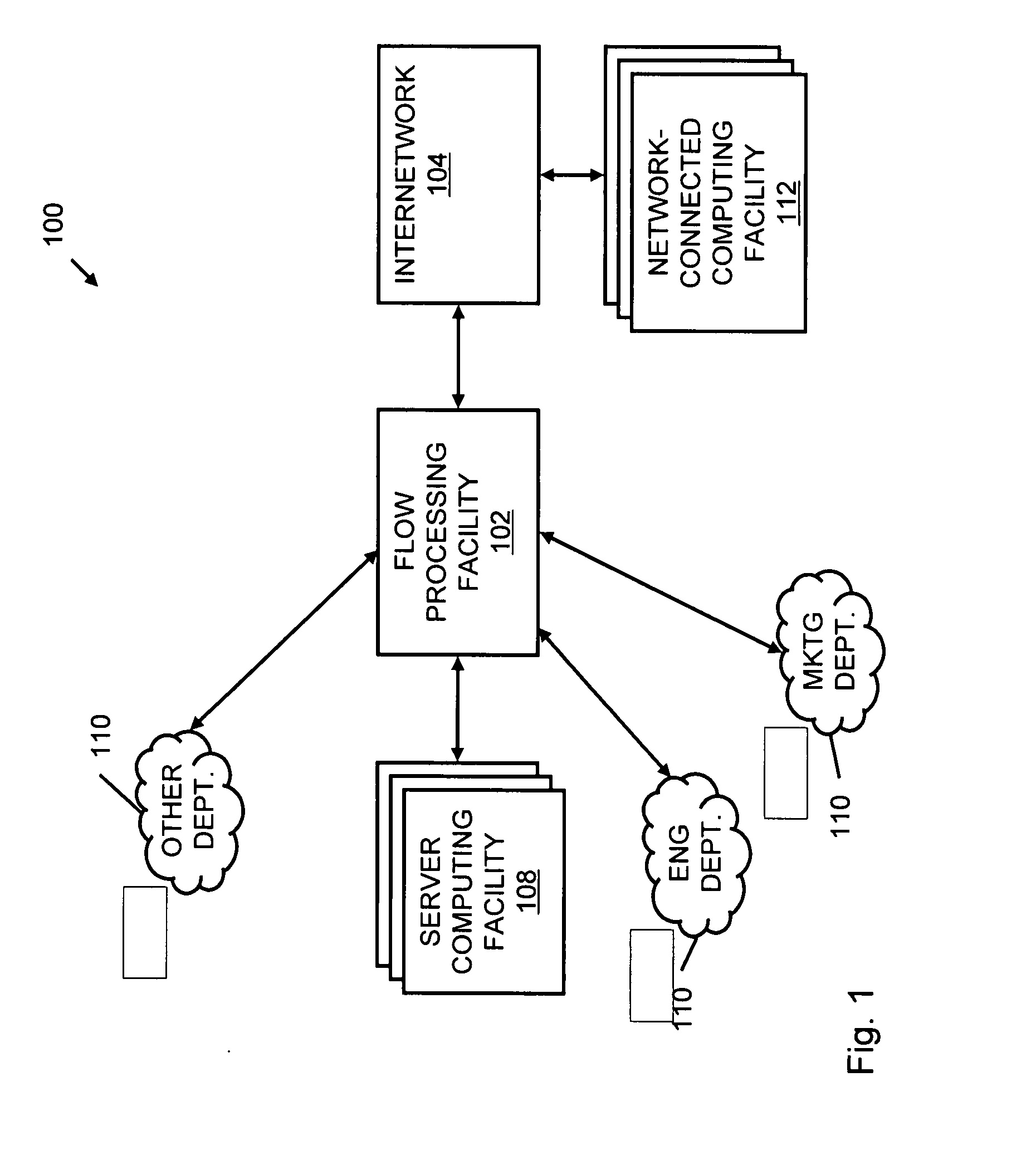
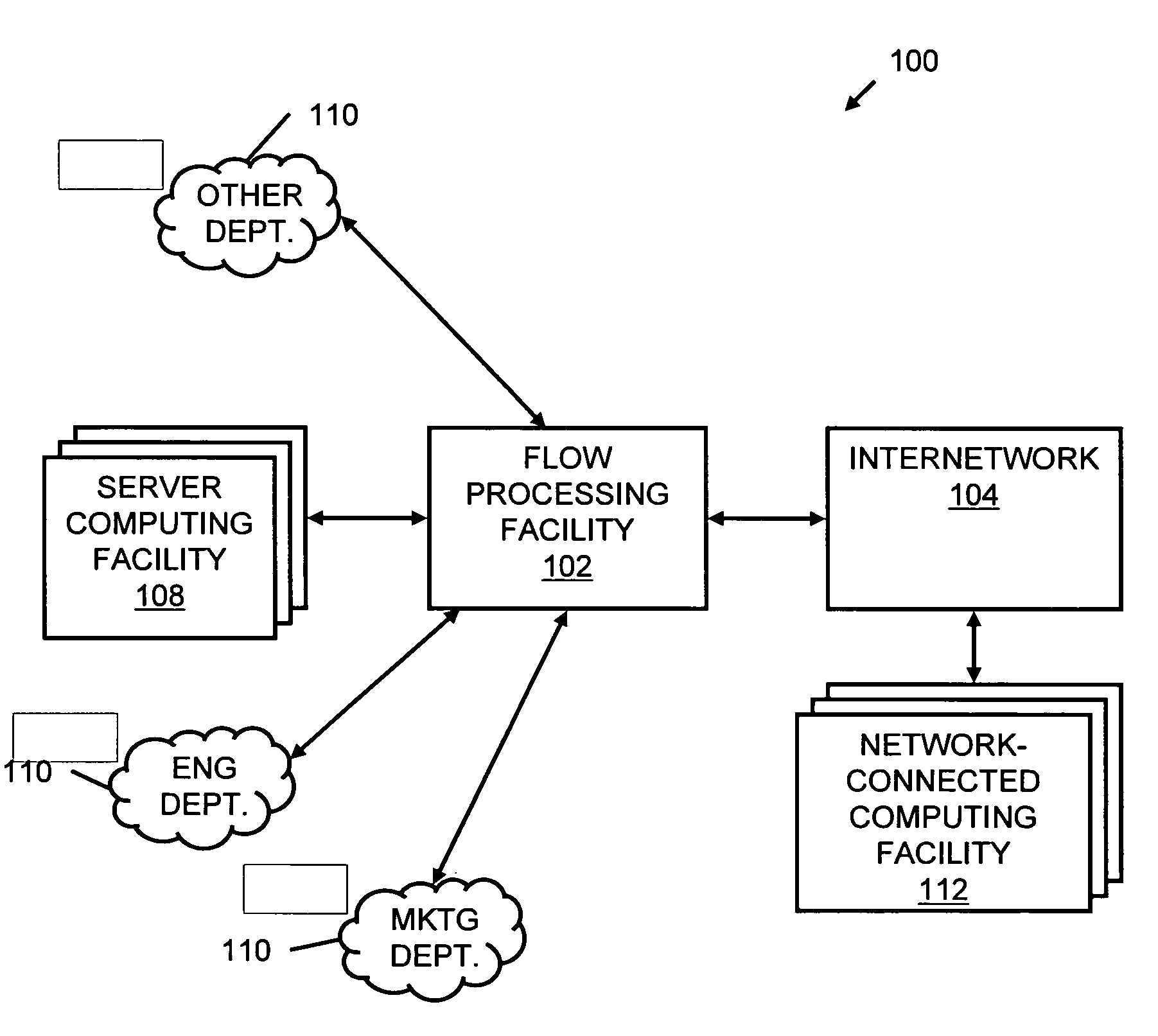
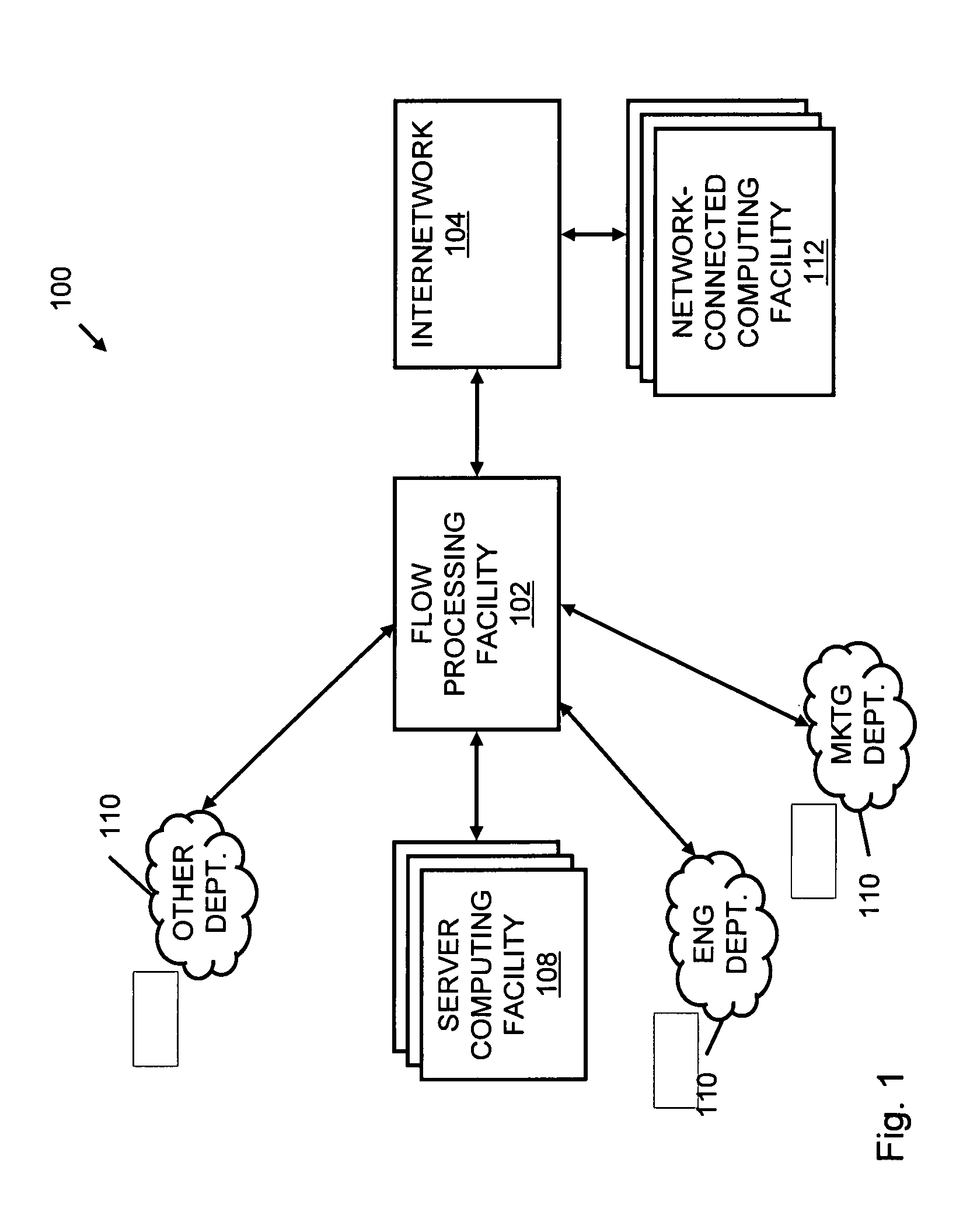
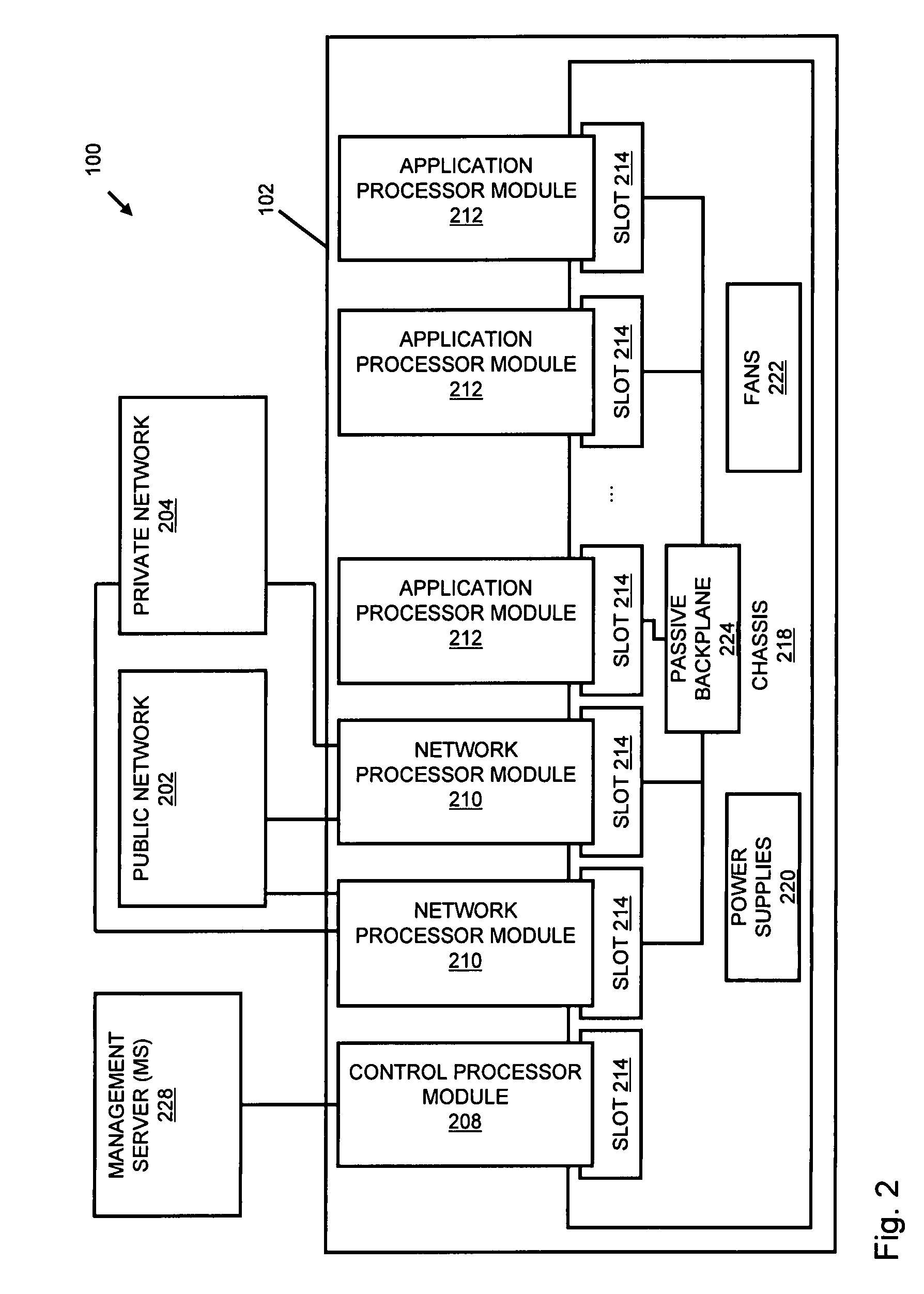
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
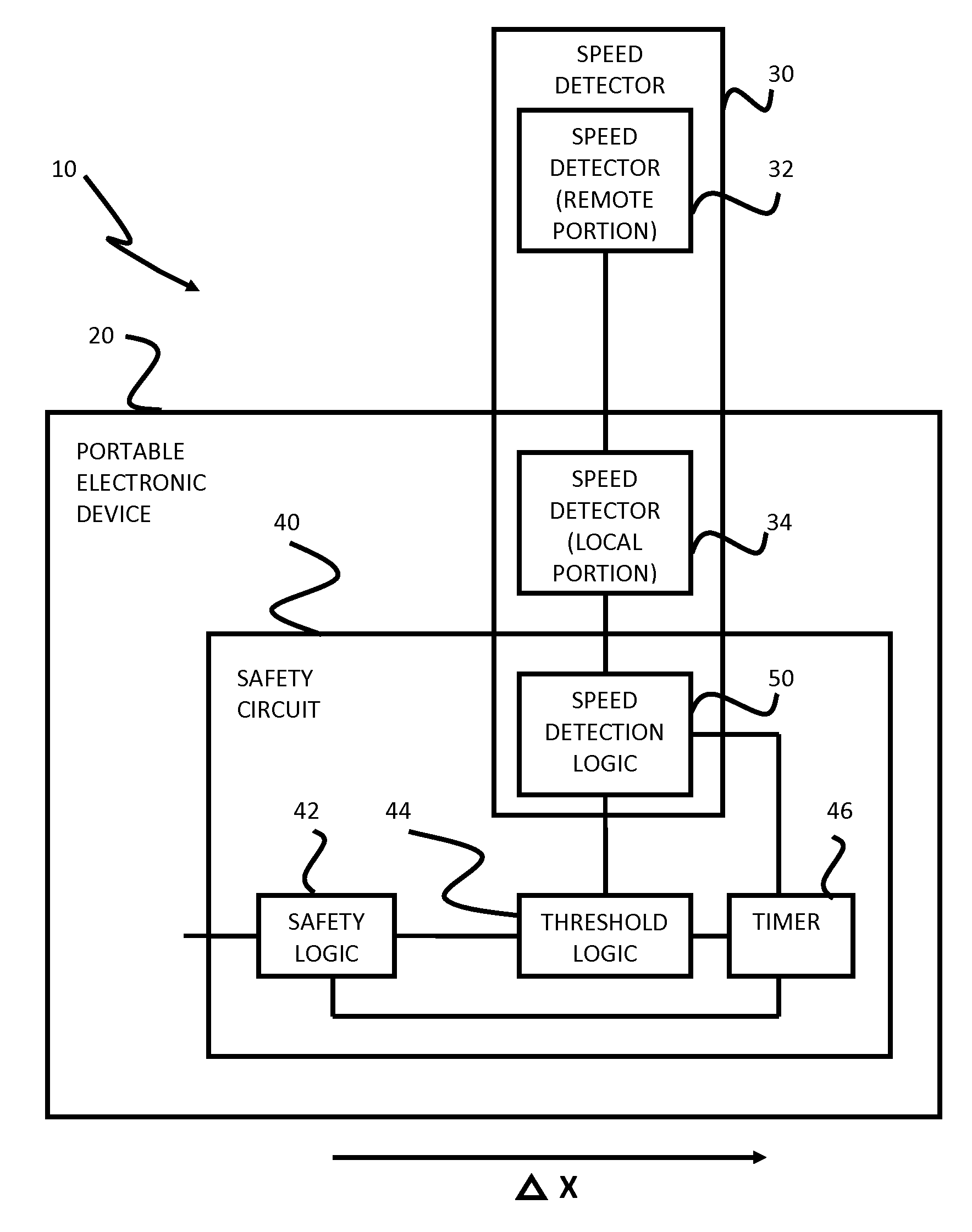
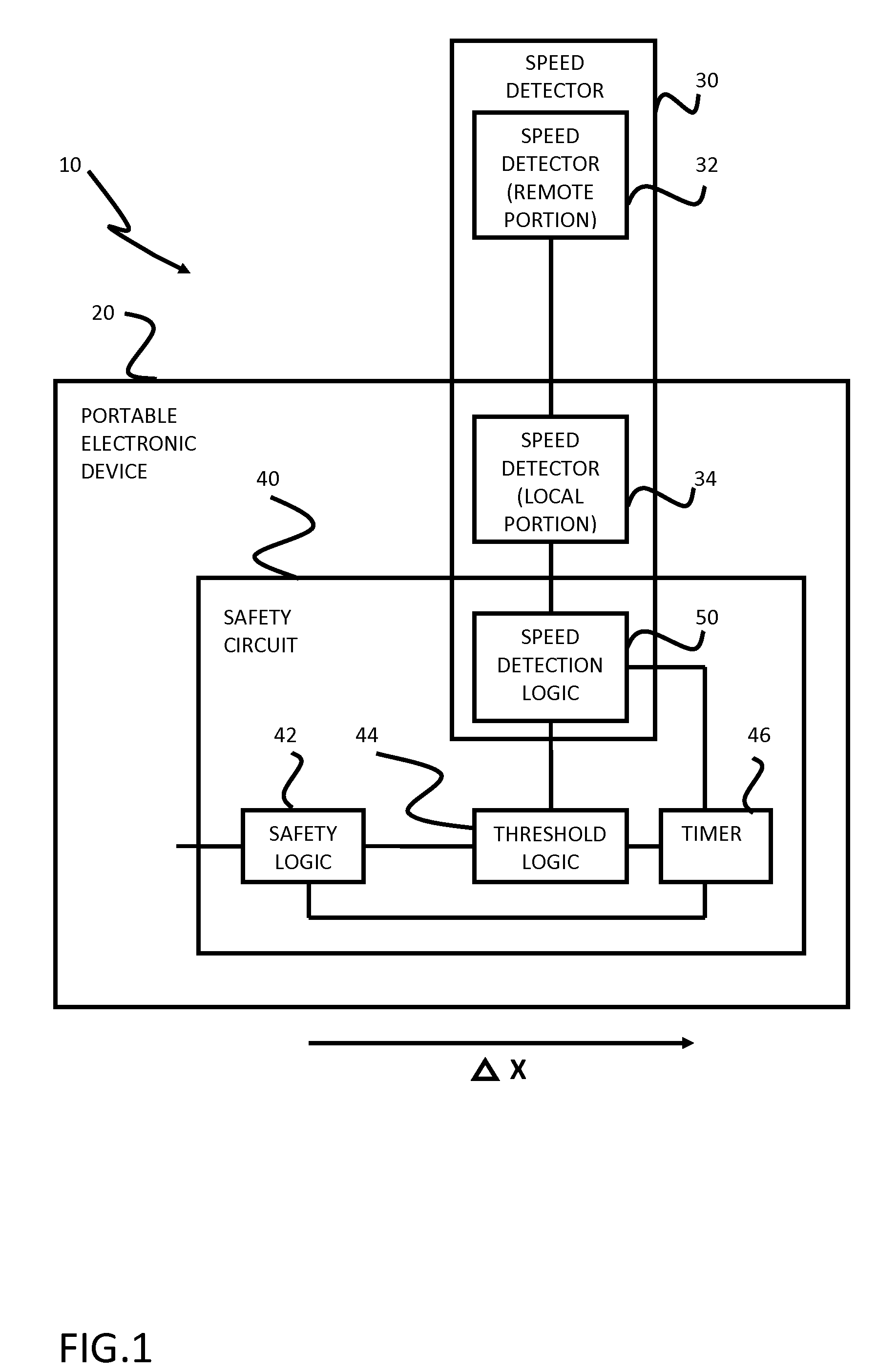
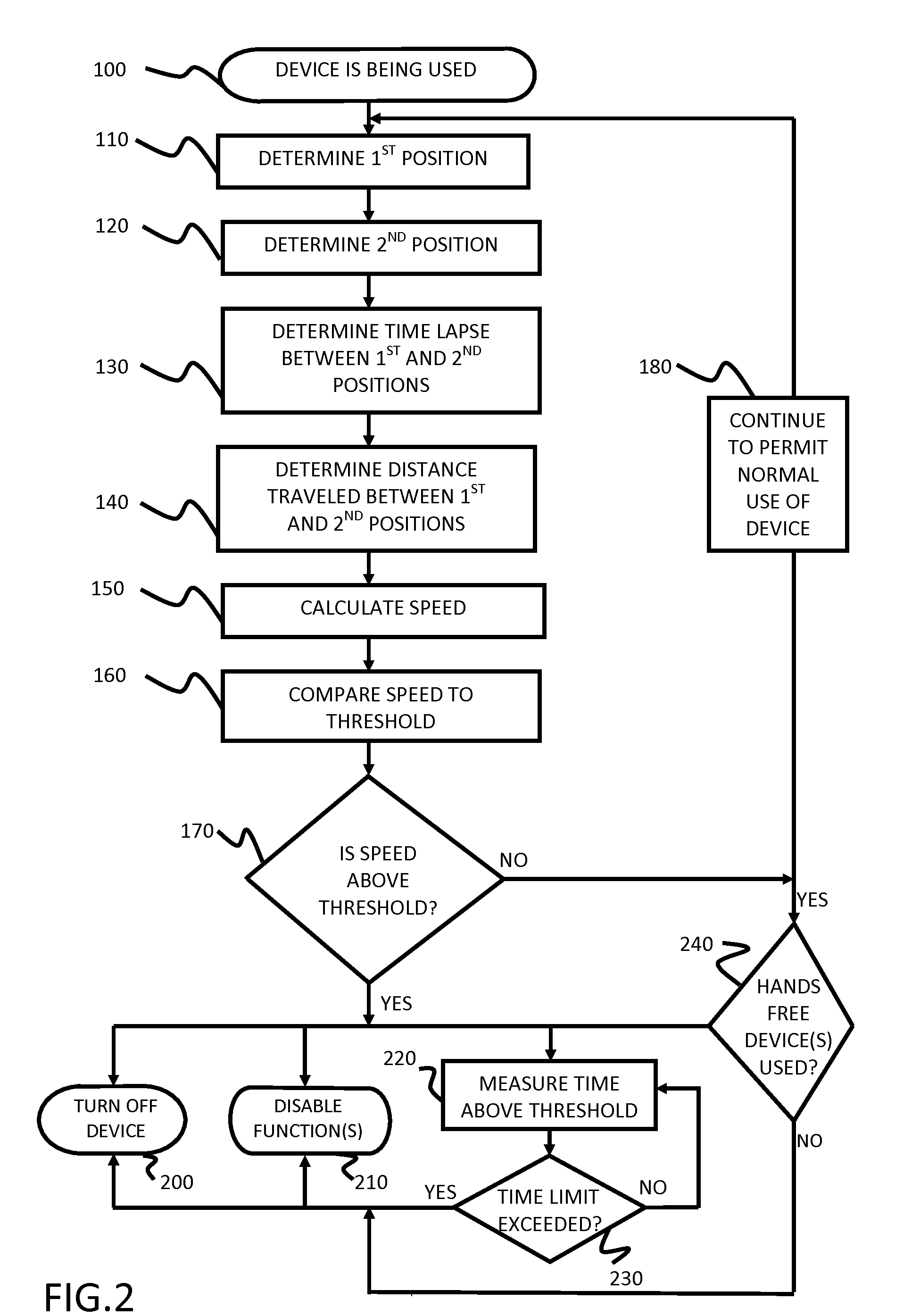
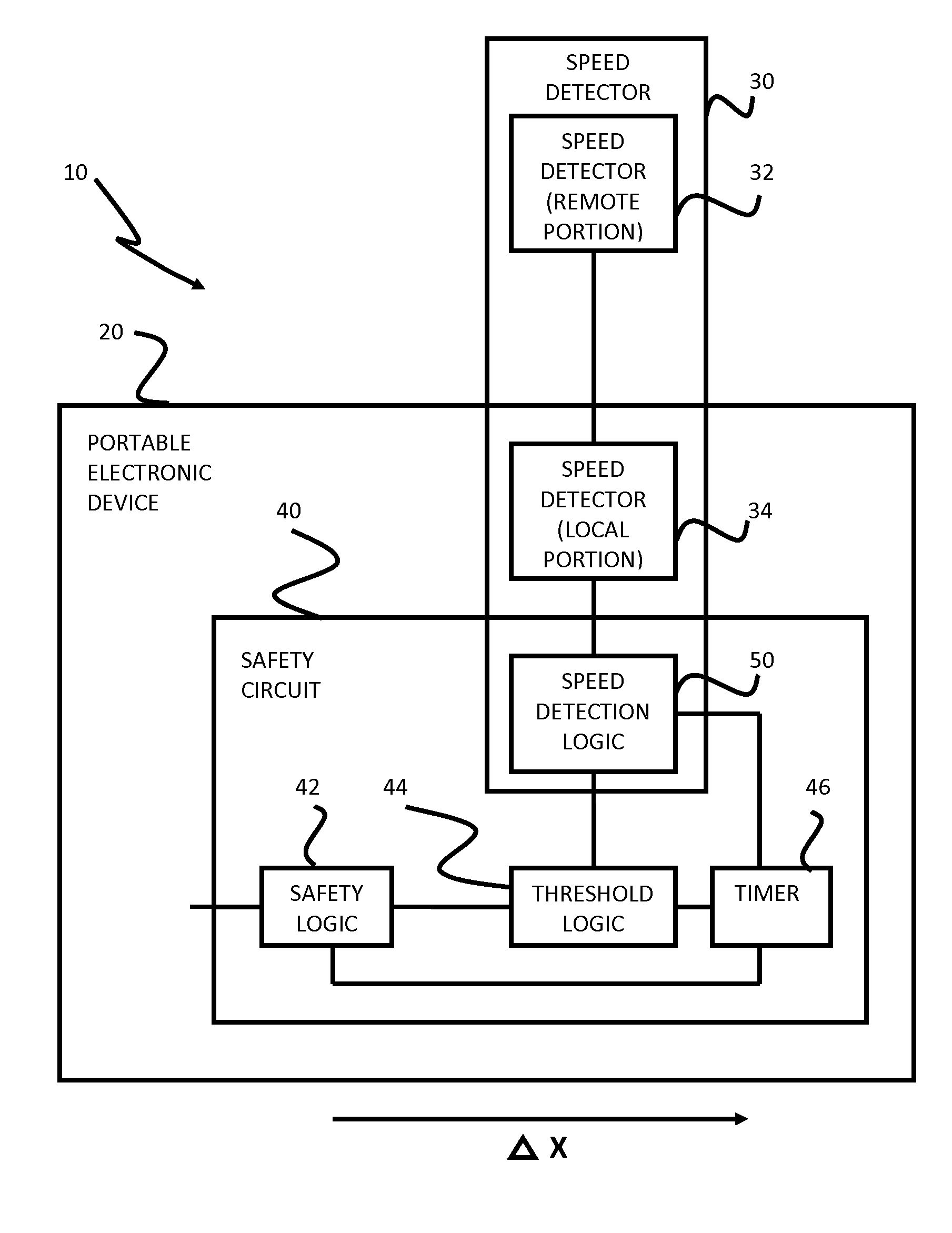
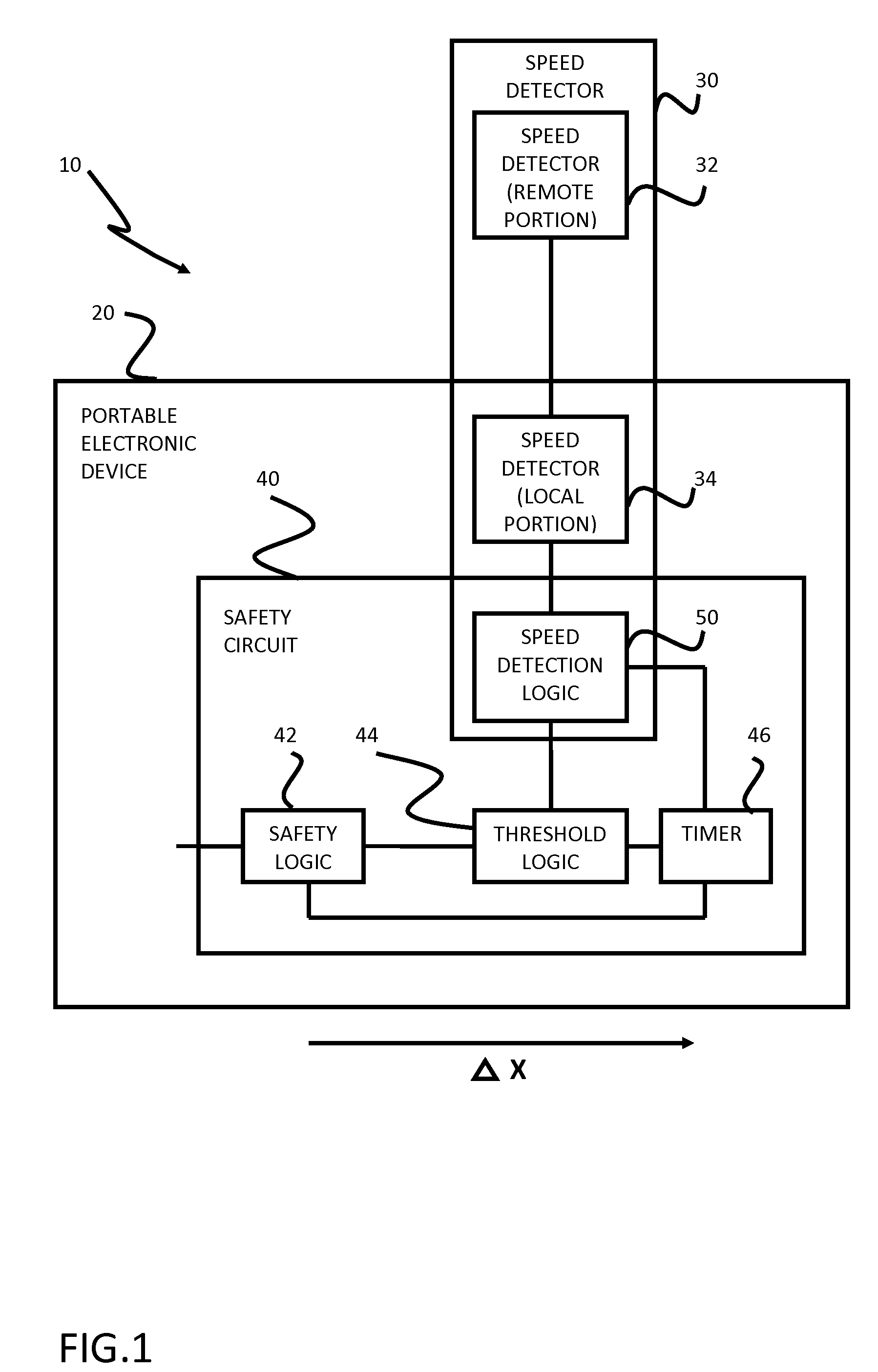
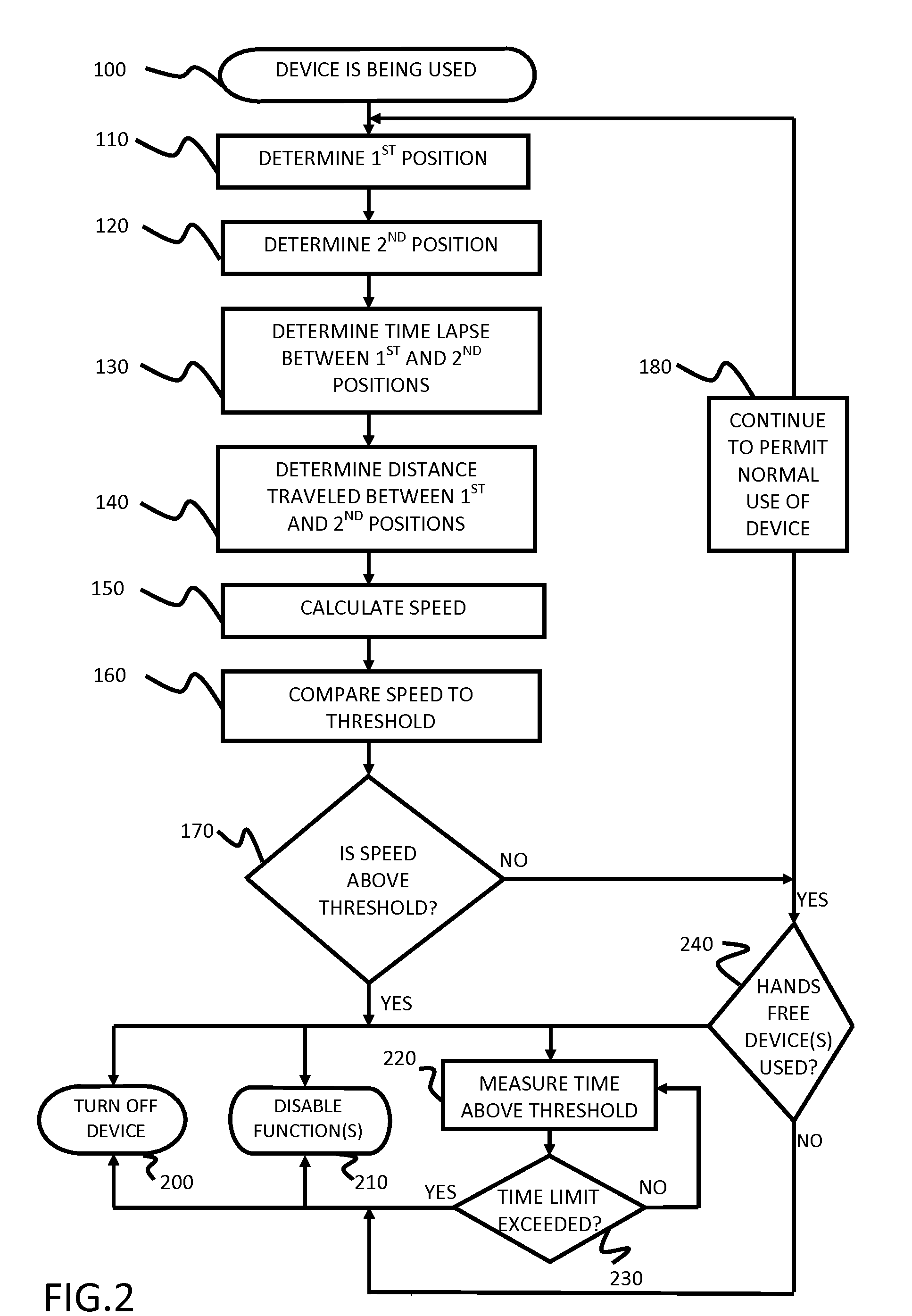
Safety features for portable electronic device
ActiveUS20100216509A1Unauthorised/fraudulent call preventionDevices with sensorHands freeSecurity policy
A portable device includes a safety feature that prevents some forms of use when the device is moving. The device may detect its speed or movement, compare that to a threshold, and provide a response or blocking function upon exceeding that threshold. The device may be a cell phone configured to disable transmission and reception of voice / text, conceal its display screen, and disable incorporated features and functions, if the cell phone is moving faster than walking speed or the movement is uncharacteristic of walking. The blocking function may be partially overridden based on a safety policy, which can be managed and customized. The introduction of hands-free devices may serve to override a blocking function and enable other functions.
Owner:AI-CORE TECH LLC
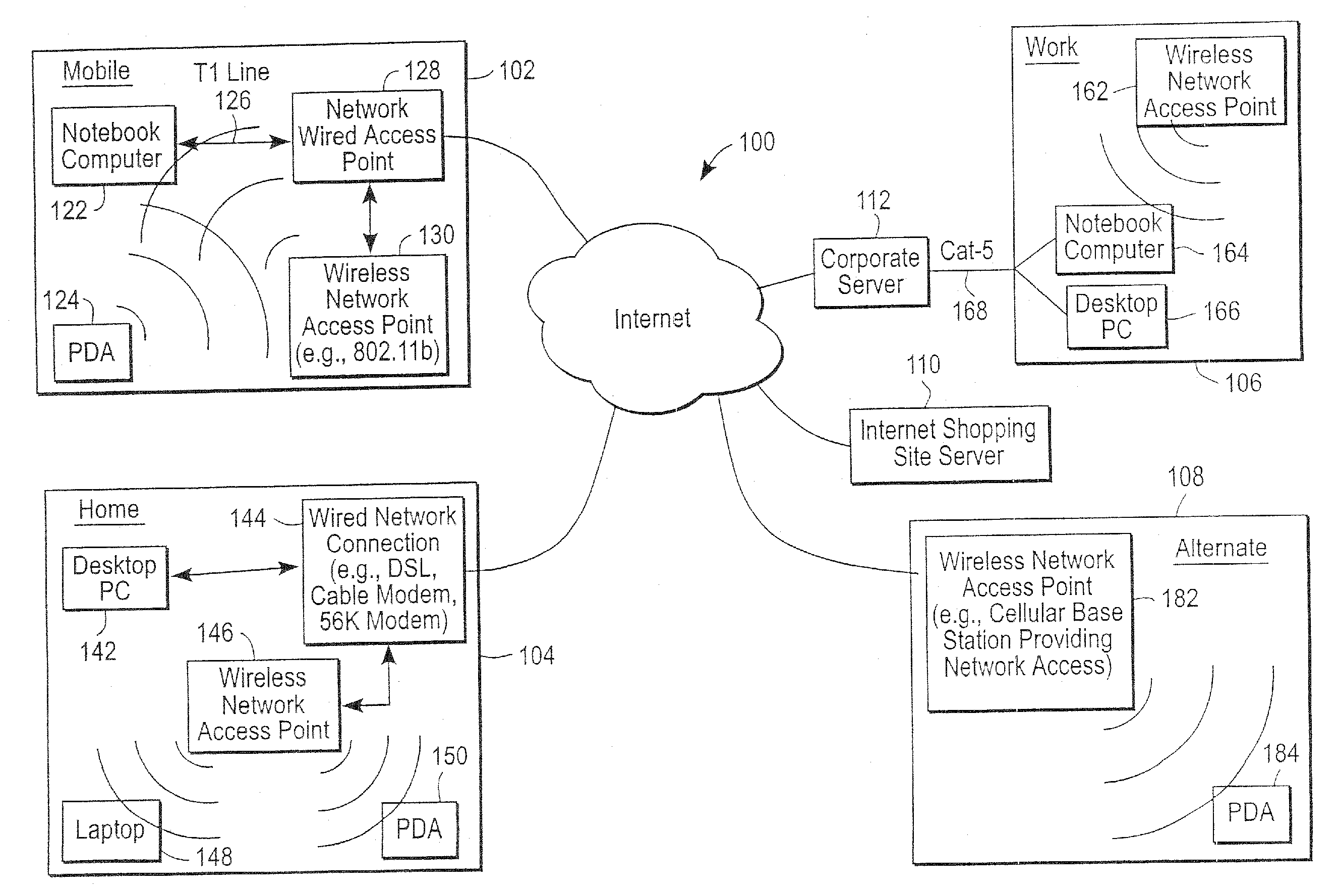
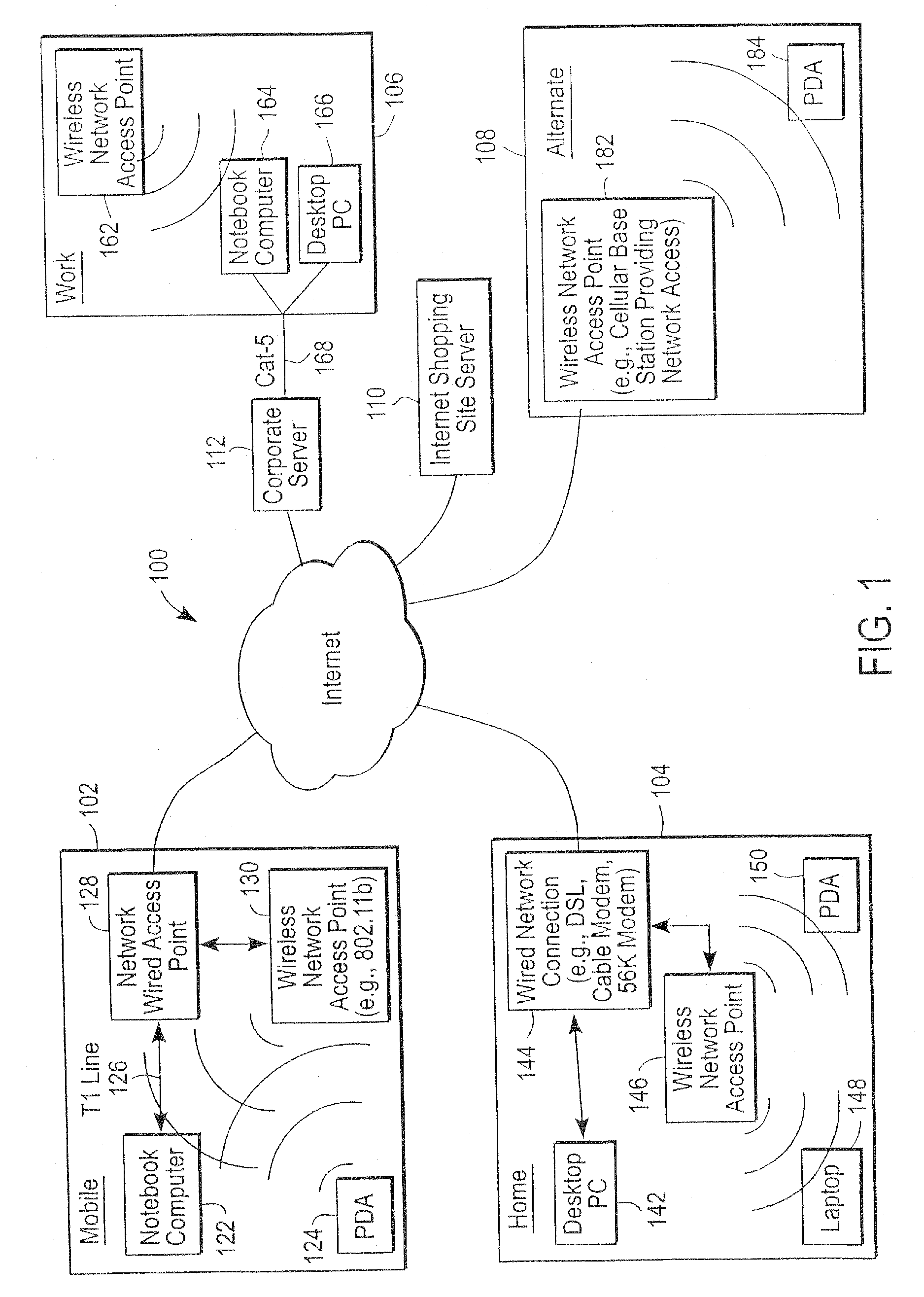
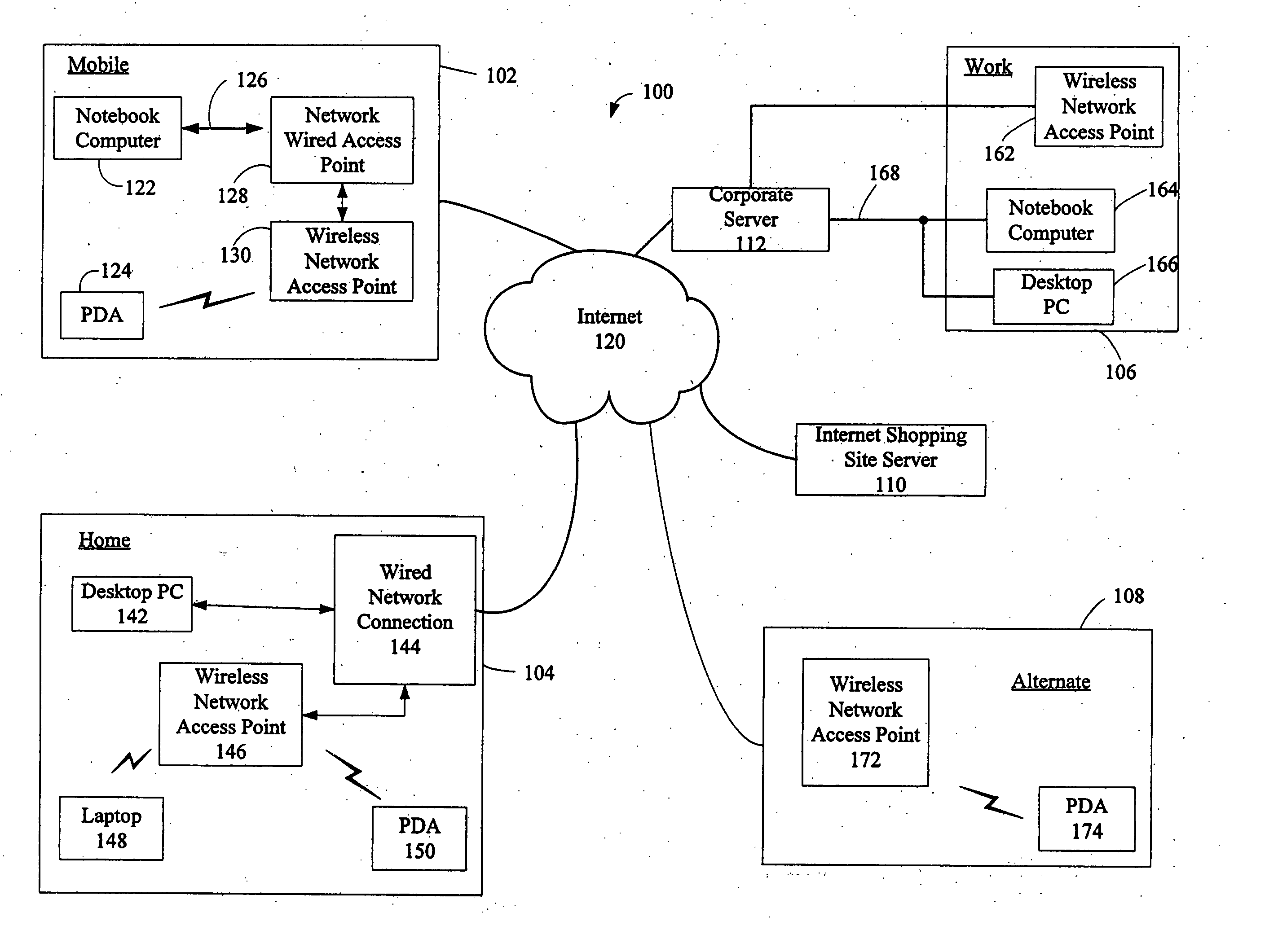
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
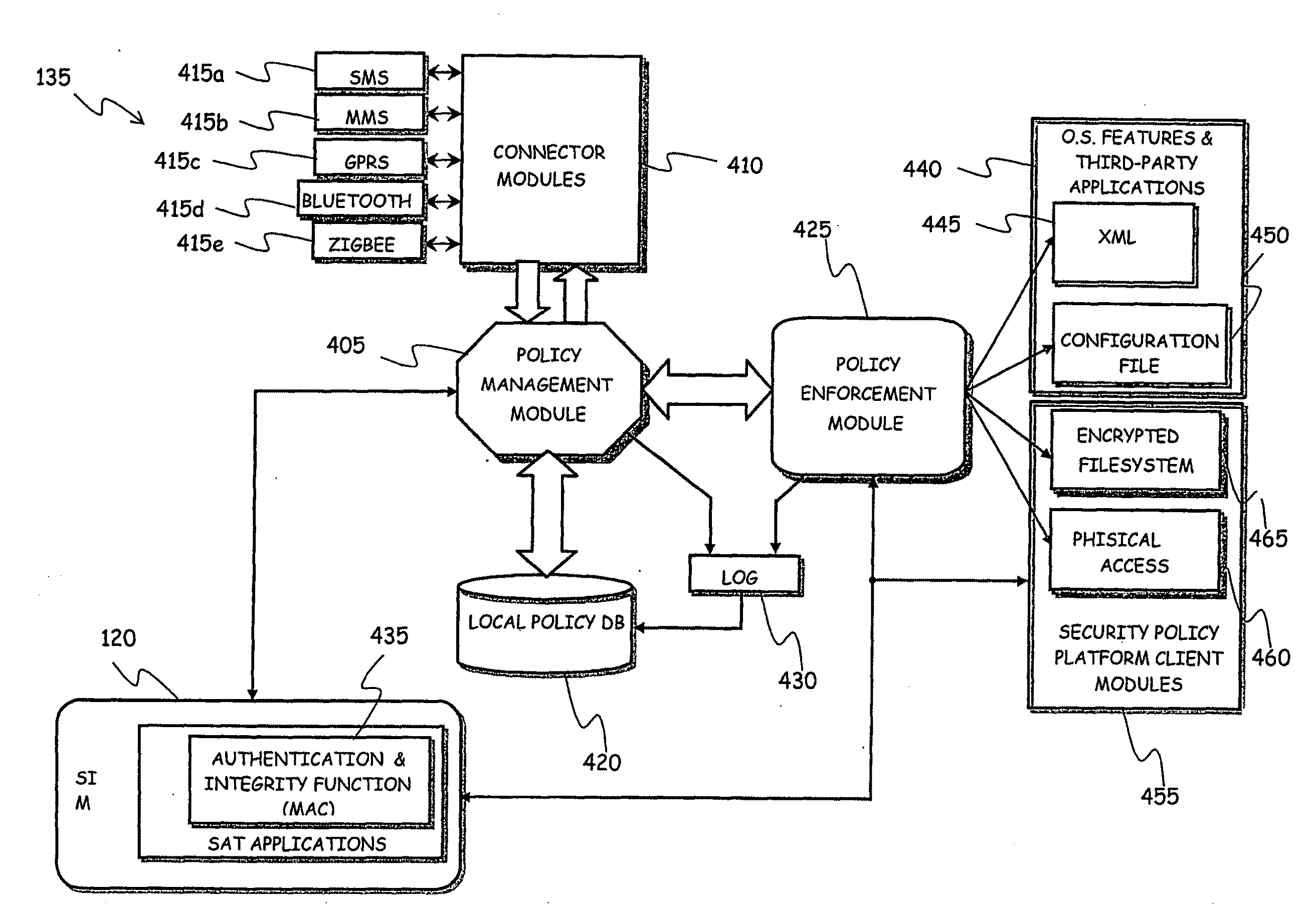
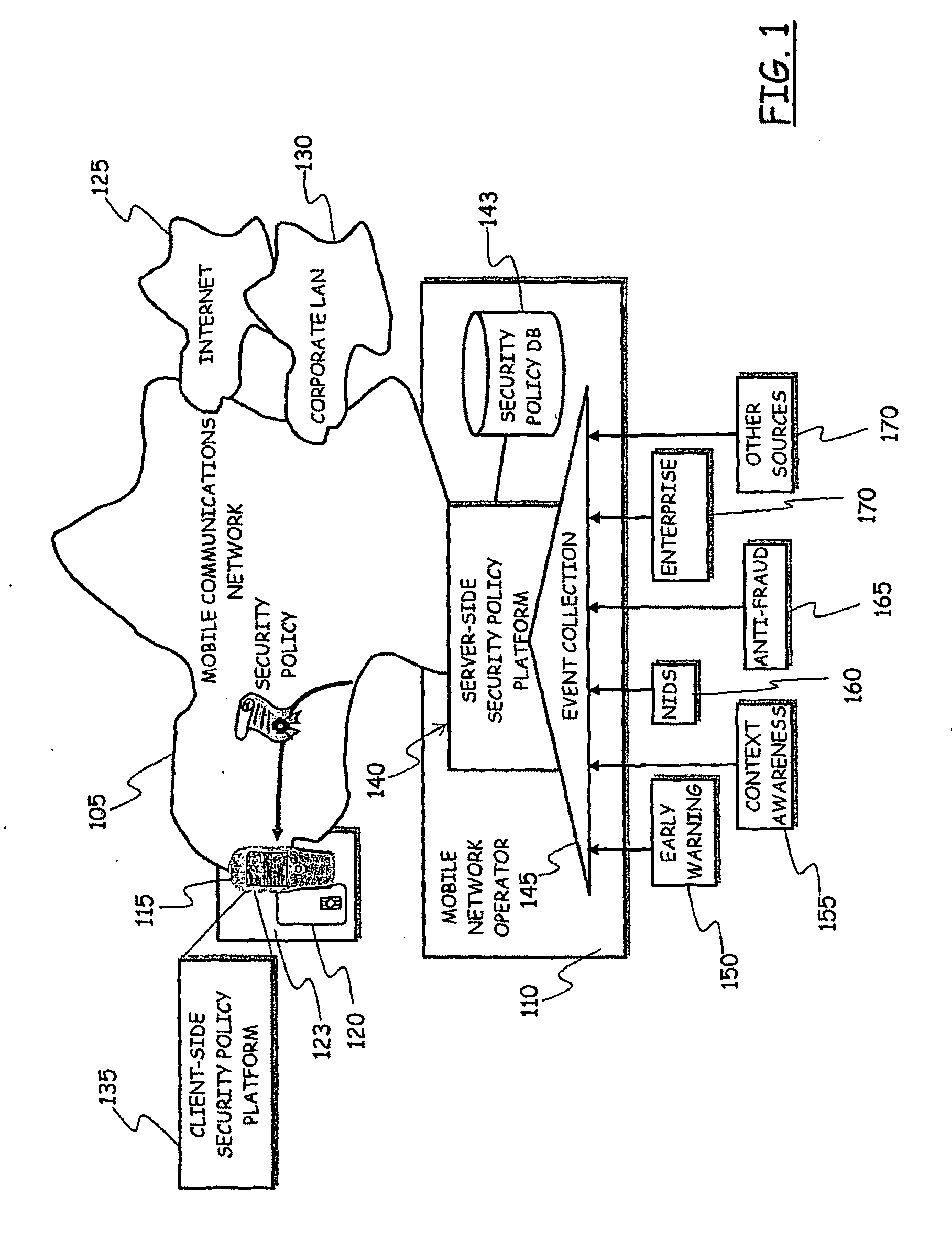
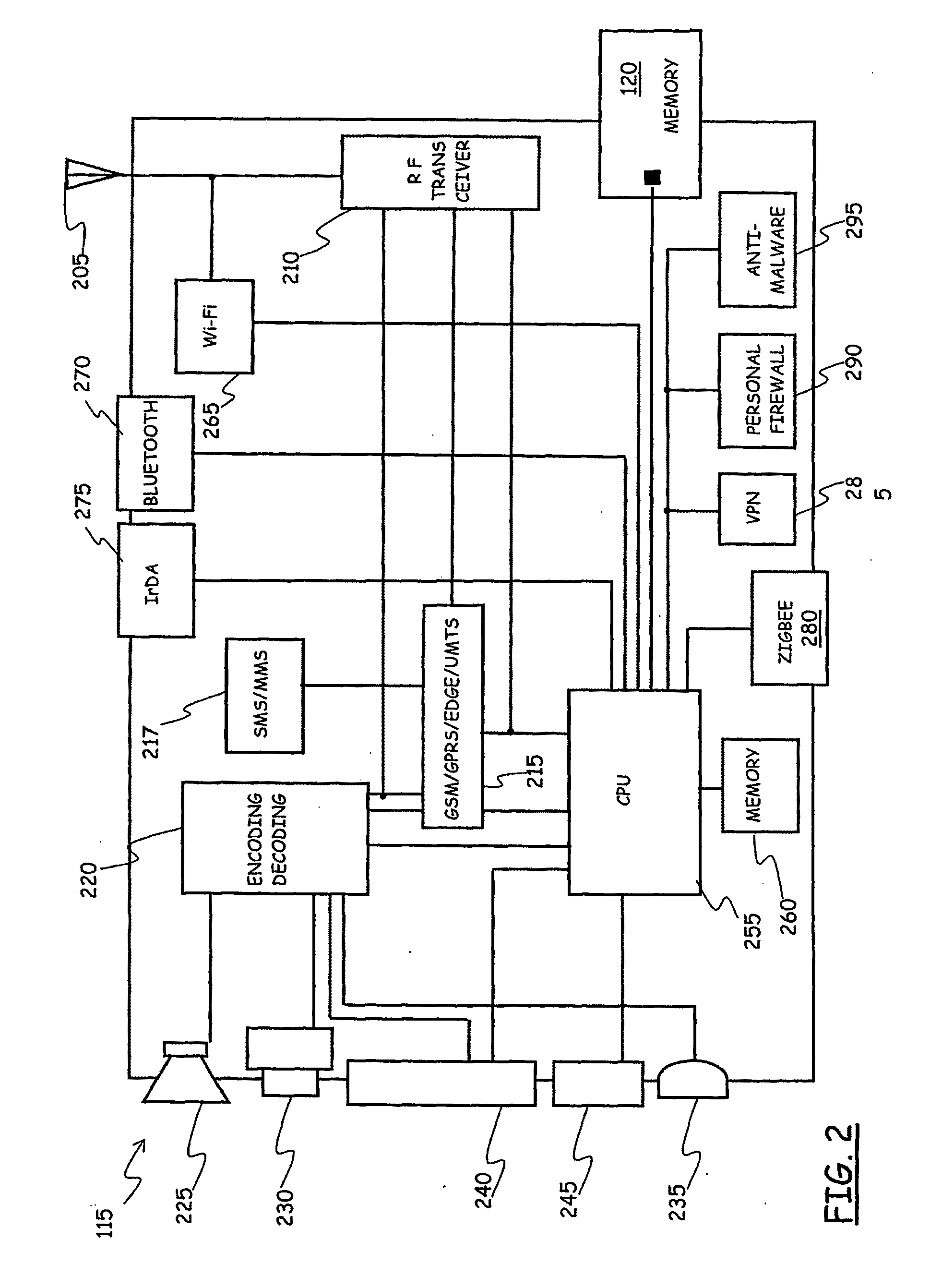
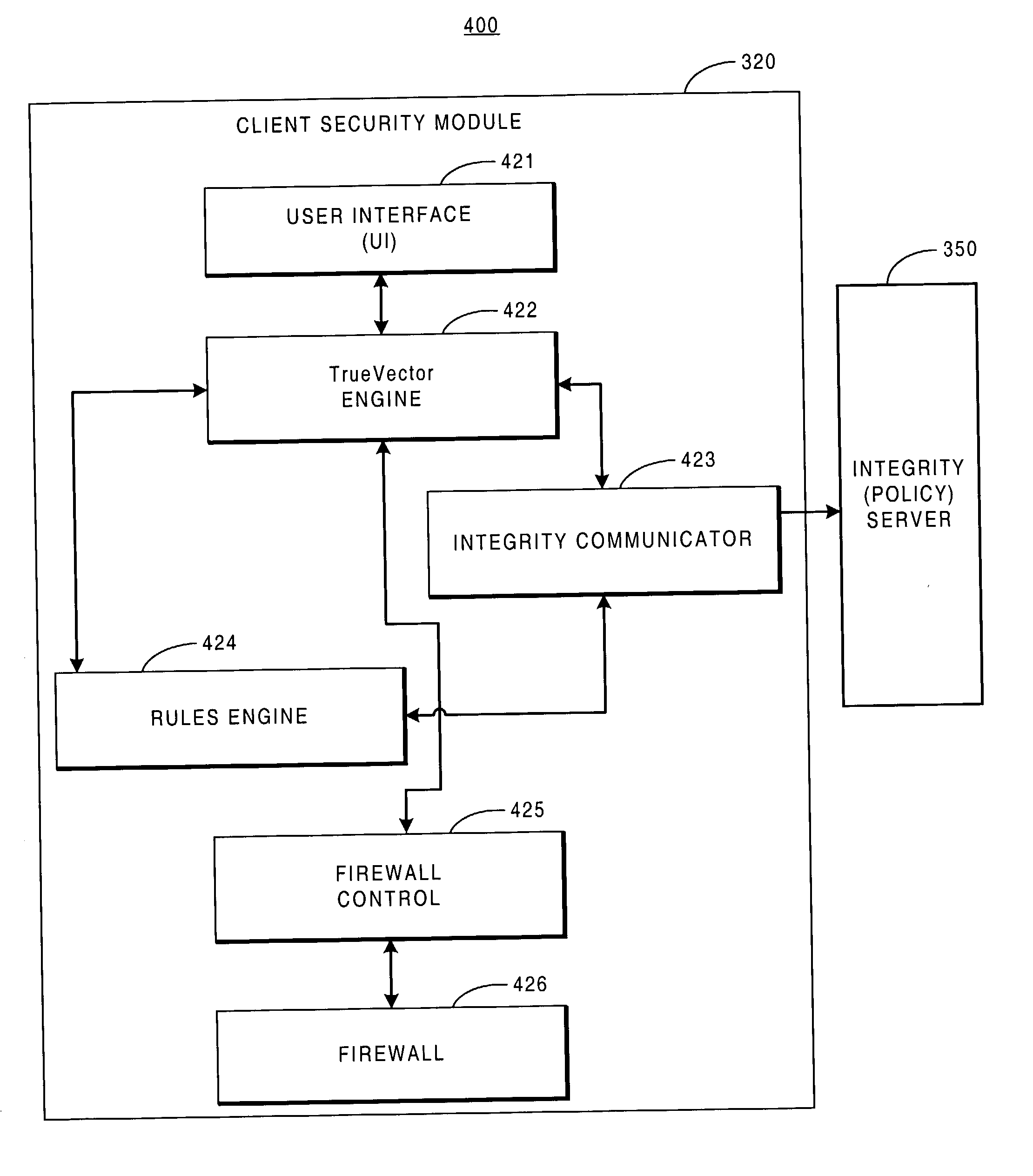
System for Enforcing Security Policies on Mobile Communications Devices
A system for enforcing security policies on mobile communications devices is adapted to be used in a mobile communications network in operative association with a subscriber identity module. The system having a client-server architecture includes a server operated by a mobile communications network operator and a client resident on a mobile communications device on which security policies are to be enforced. The server is adapted to determine security policies to be applied on said mobile communications device, and to send thereto a security policy to be applied. The client is adapted to receive the security policy to be applied from the server, and to apply the received security policy. The server includes a server authentication function adapted to authenticate the security policy to be sent to the mobile communications device; the client is further adapted to assess authenticity of the security policy received from the server by exploiting a client authentication function resident on the subscriber identity module.
Owner:TELECOM ITALIA SPA
System and methodology for security policy arbitration
ActiveUS20030177389A1Multiple digital computer combinationsProgram controlComputer networkSecurity policy
A system providing methods for a device to apply a security policy required for connection to a network is described. In response to receipt of a request from a device for connection to a particular network, a current policy to apply to said device for governing the connection to this particular network is determined from a plurality of available security policies available to the device. This current policy to apply to said device is generated by merging a plurality of security policies available for governing connections. After said current policy is applied to the device, the connection from the device to this particular network is allowed to proceed.
Owner:CHECK POINT SOFTWARE TECH INC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
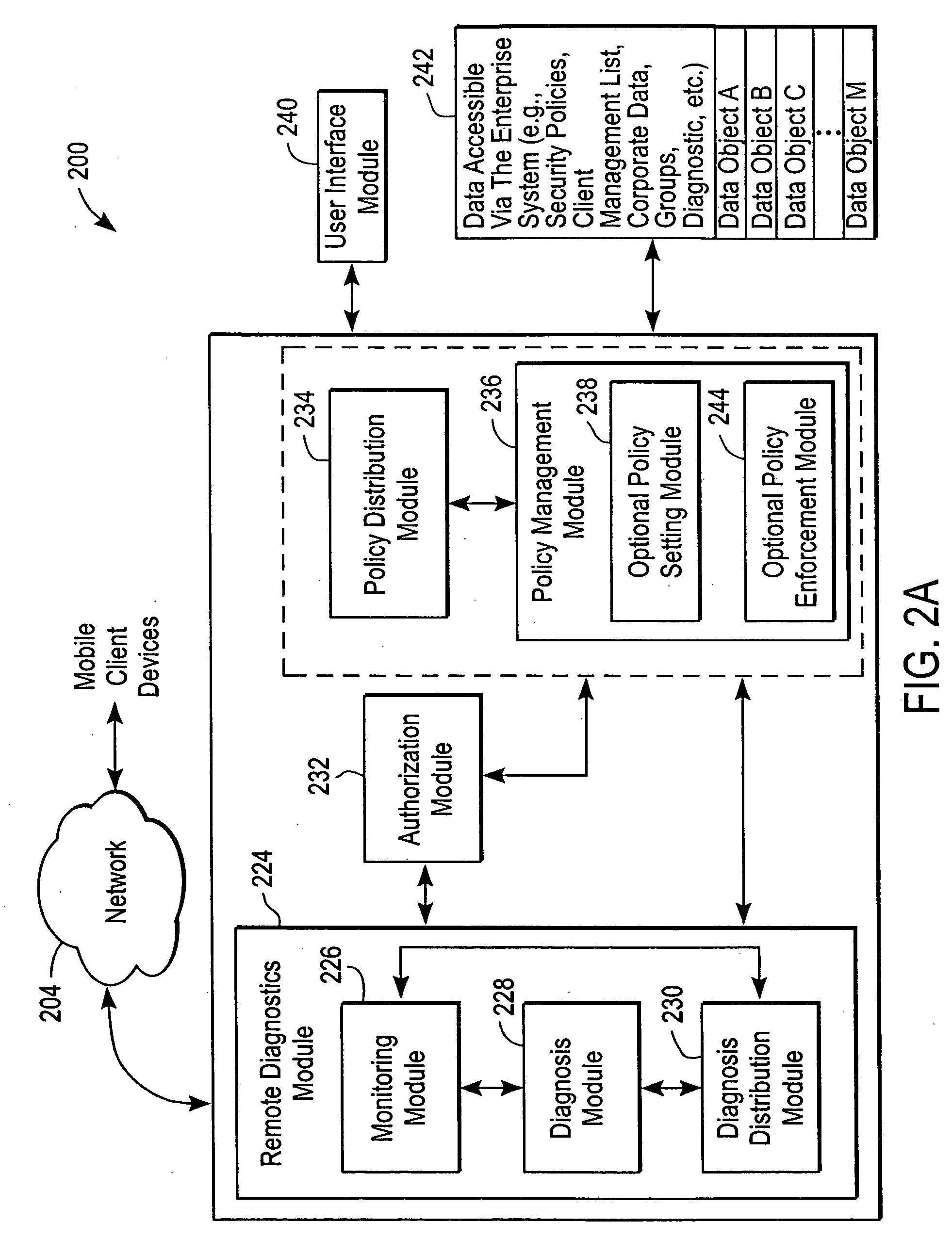
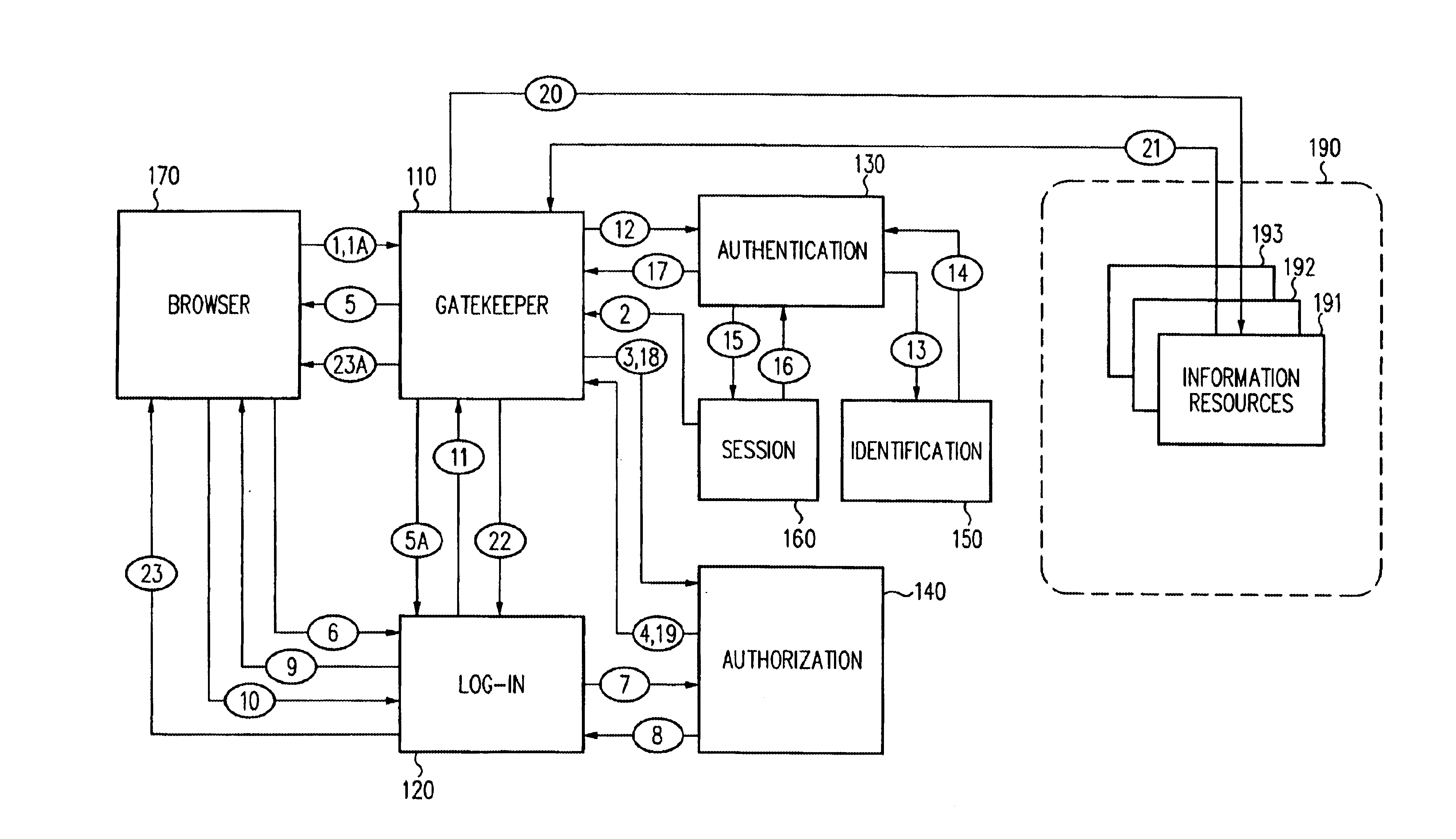
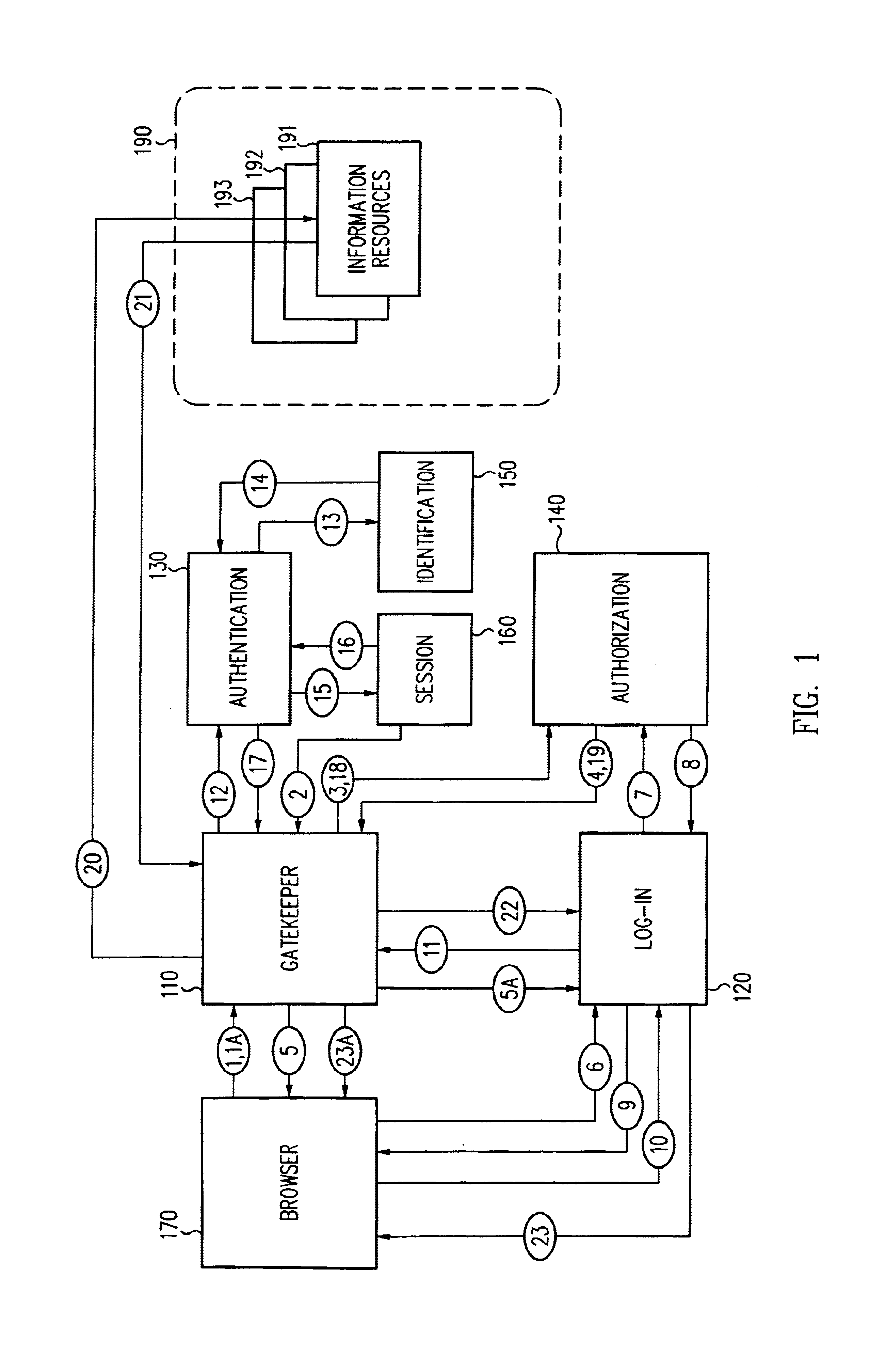
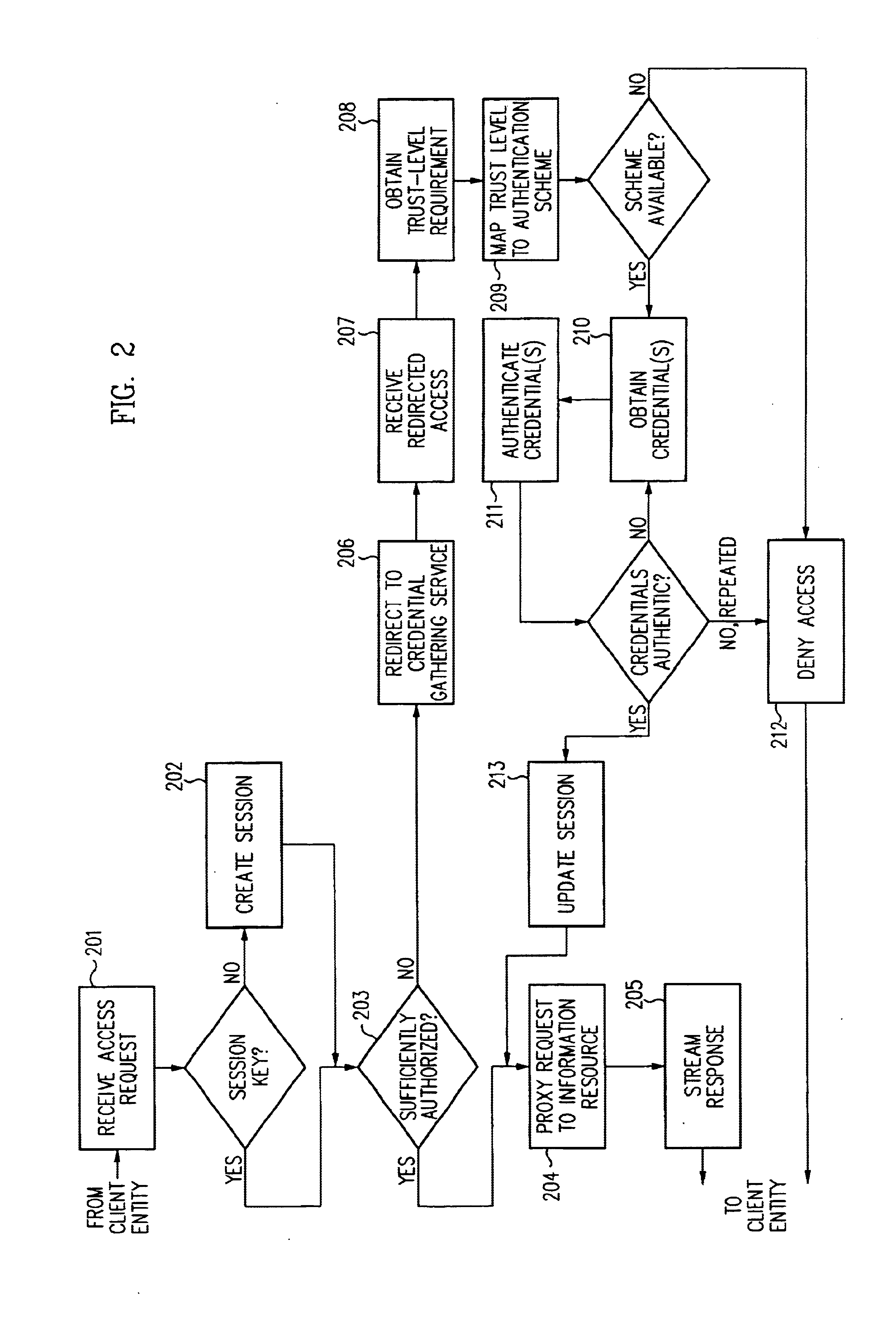
Security architecture with environment sensitive credential sufficiency evaluation
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
System and method for enforcing a security policy on mobile devices using dynamically generated security profiles
ActiveUS20070143824A1Eliminate needComplete banking machinesPayment architectureComputer networkSecurity parameter
A system and method for enforcing security parameters that collects information from a source relating to a mobile device (104). Based on the collected information, an identity status for the mobile device (104) is determined that uniquely identifies the mobile device (104) and distinguishes it from other mobile devices. The identity status of the mobile device (104) can be determined when the mobile device (104) connects to a computing node source (102) or when the mobile device (104) accesses a resource (124) within the network. A security profile based on the identity status of the mobile device (104) is generated and the security profile is applied to the mobile device (104).
Owner:TRUST DIGITAL
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
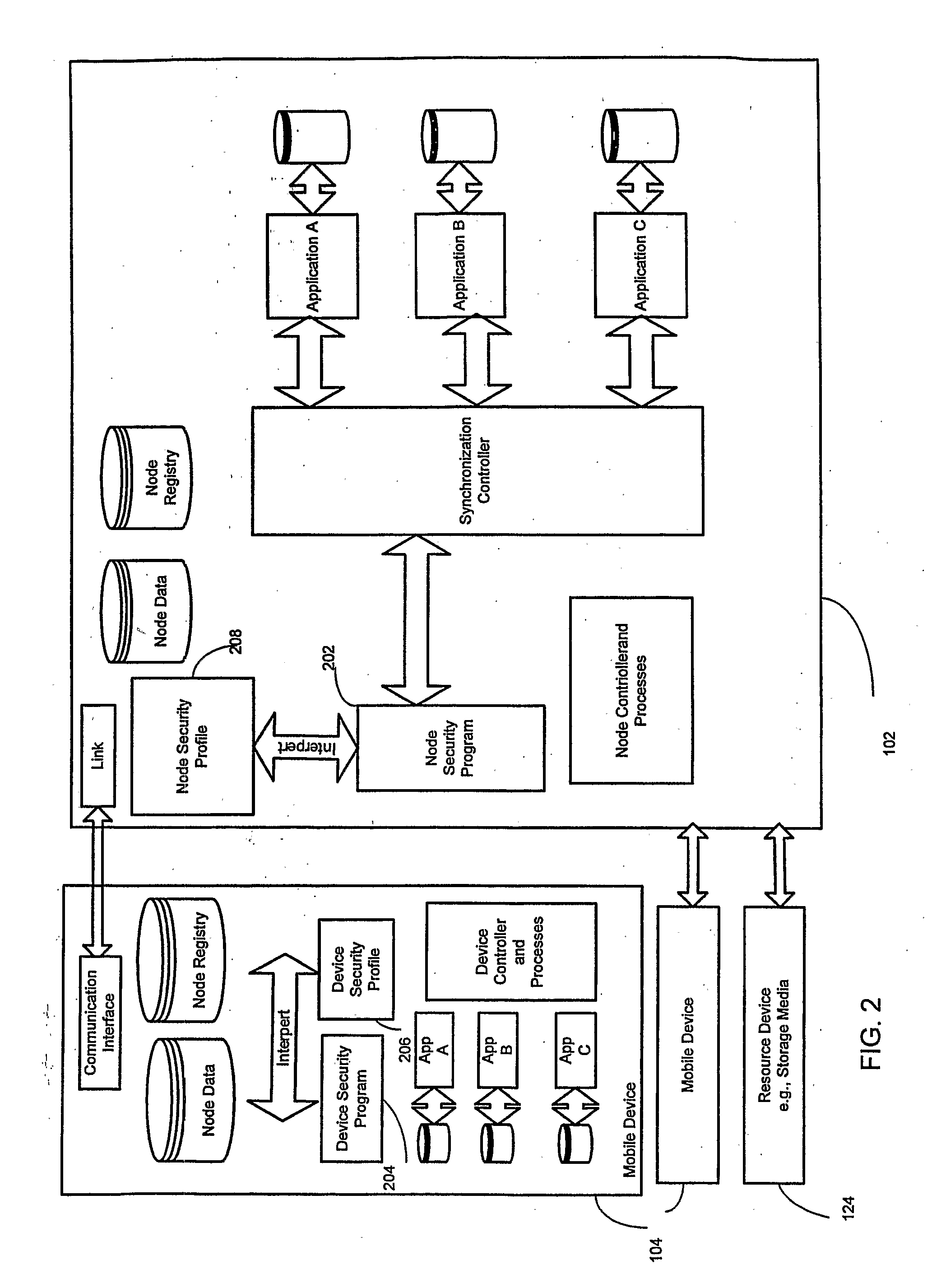
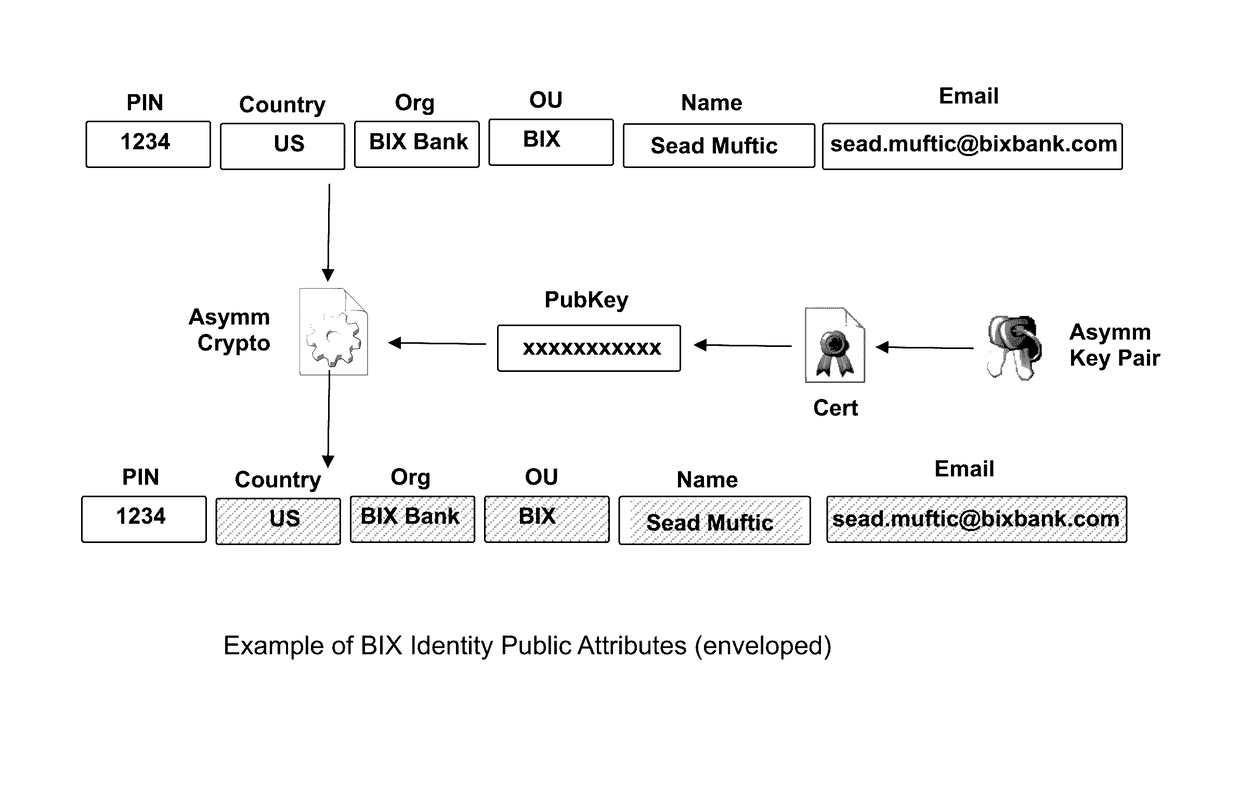
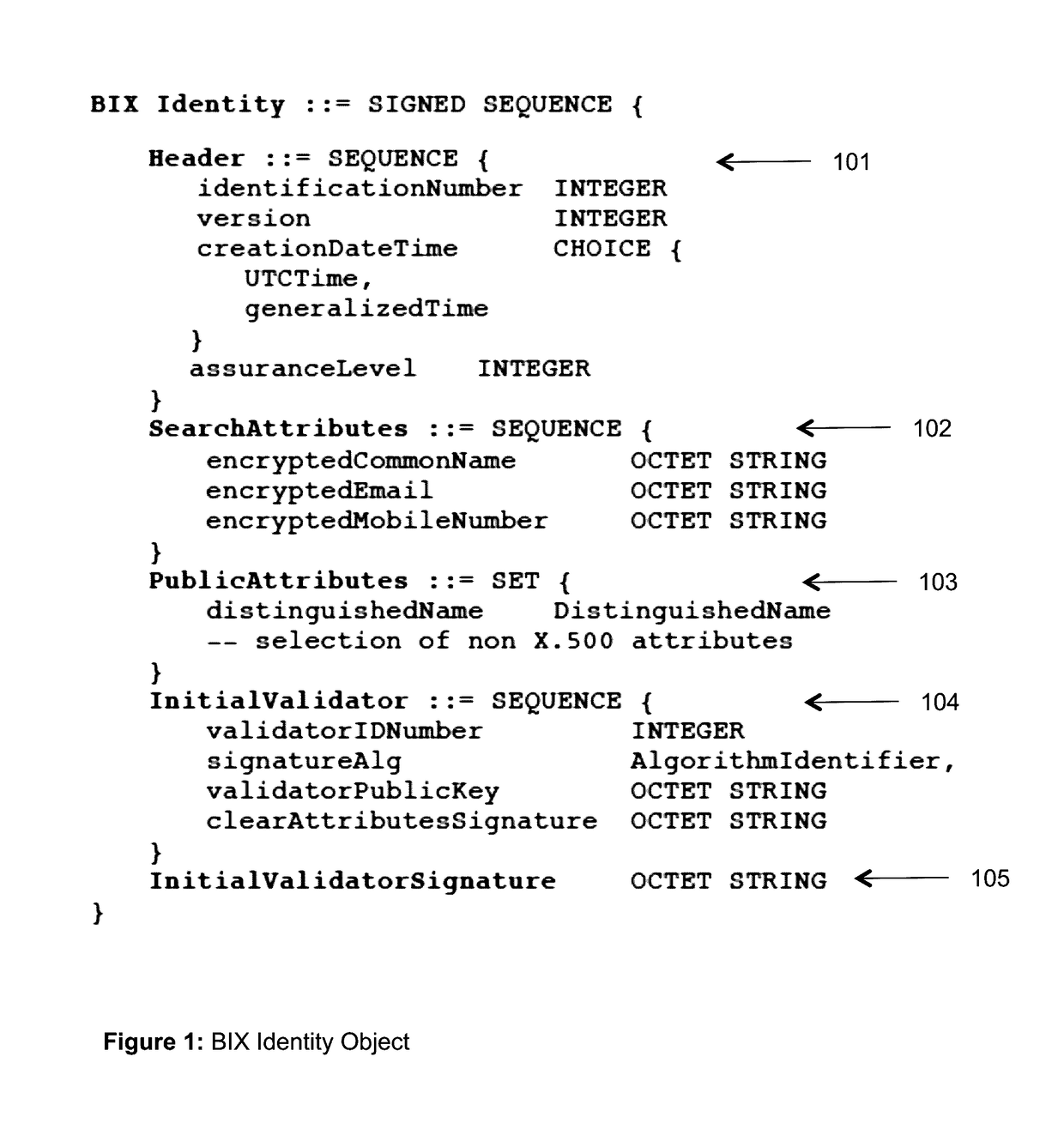
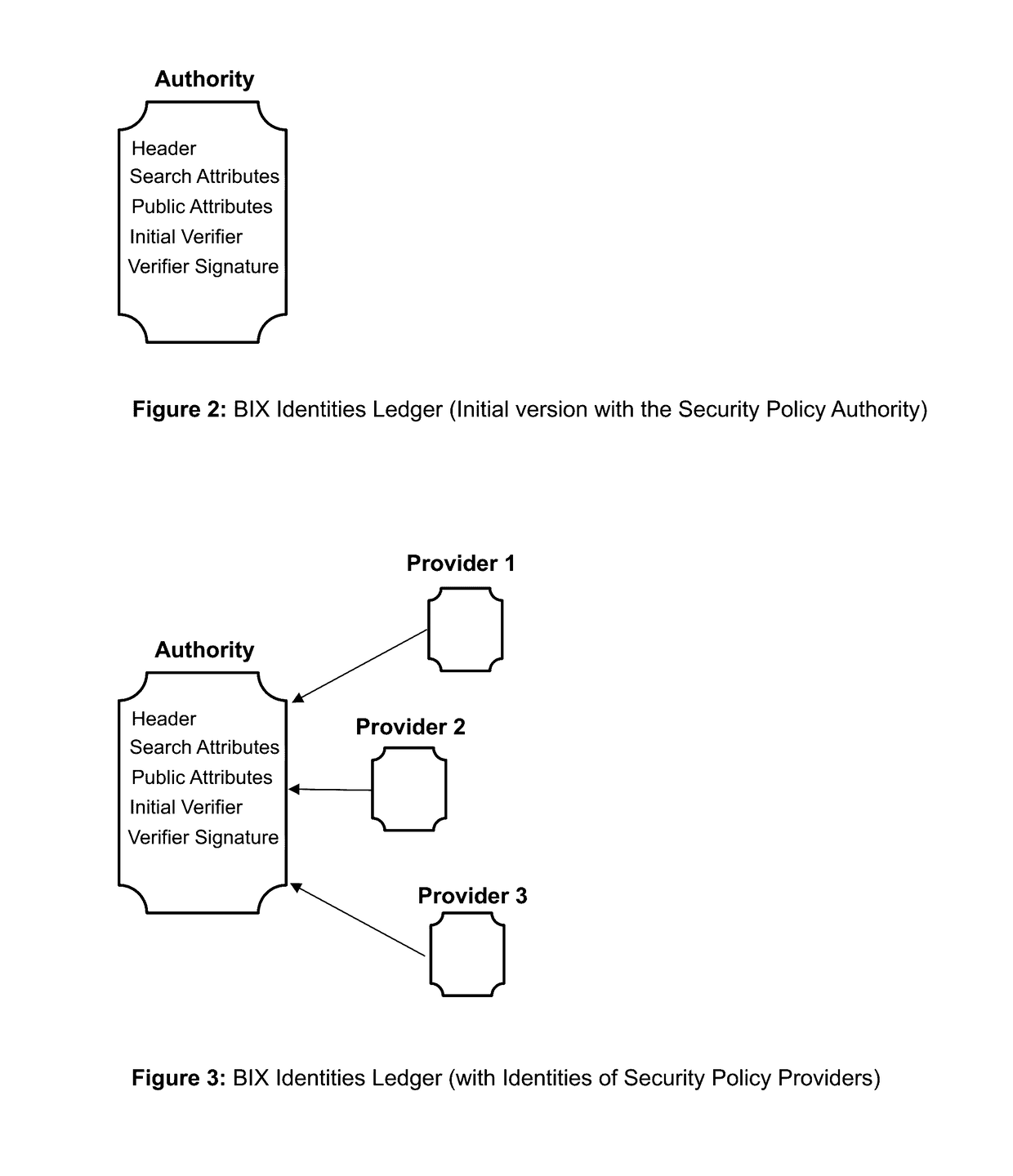
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
Safety features for portable electronic device
ActiveUS8270933B2Unauthorised/fraudulent call preventionDevices with sensorHands freeSecurity policy
A portable device includes a safety feature that prevents some forms of use when the device is moving. The device may detect its speed or movement, compare that to a threshold, and provide a response or blocking function upon exceeding that threshold. The device may be a cell phone configured to disable transmission and reception of voice / text, conceal its display screen, and disable incorporated features and functions, if the cell phone is moving faster than walking speed or the movement is uncharacteristic of walking. The blocking function may be partially overridden based on a safety policy, which can be managed and customized. The introduction of hands-free devices may serve to override a blocking function and enable other functions.
Owner:AI CORE TECH LLC
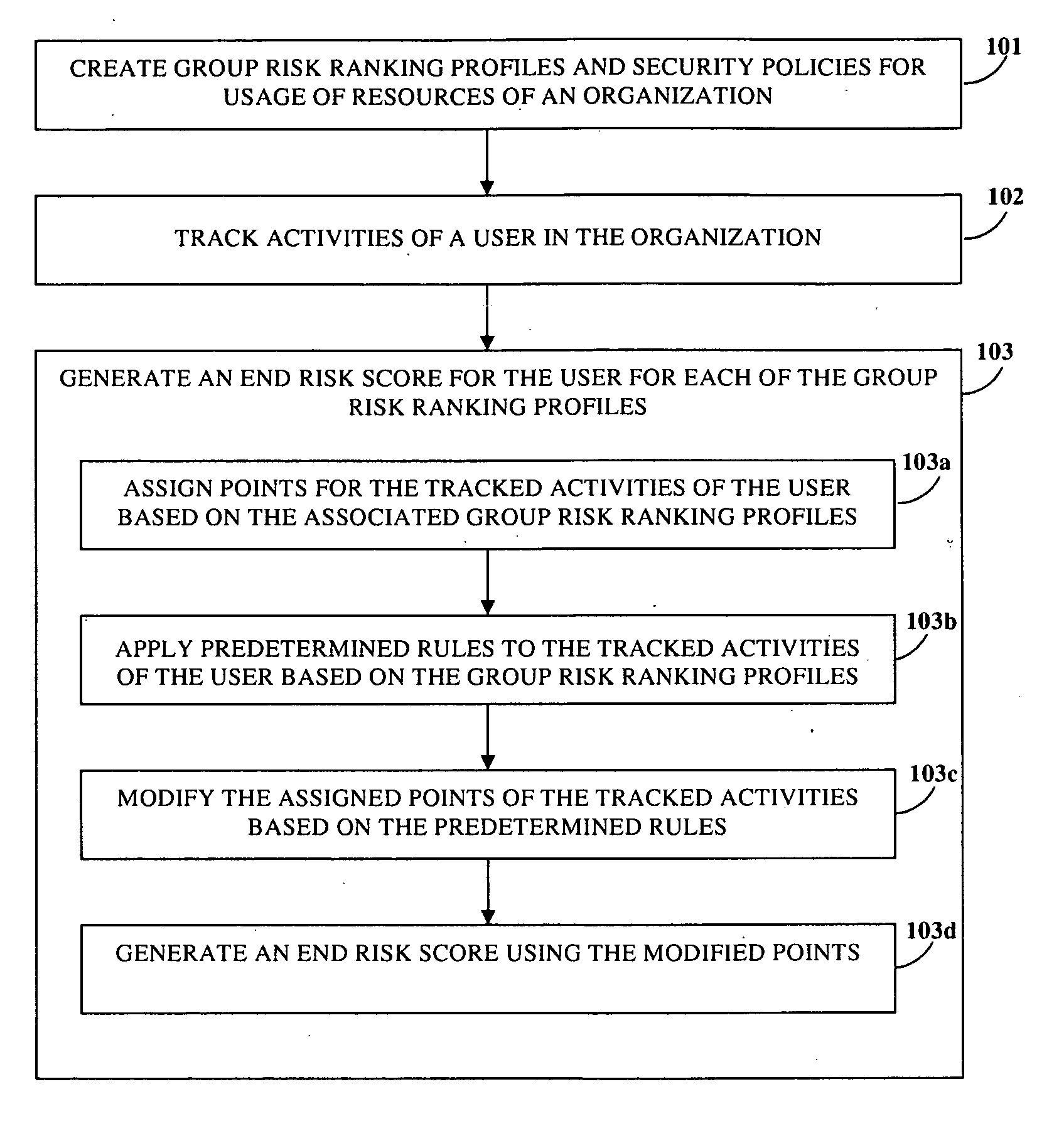
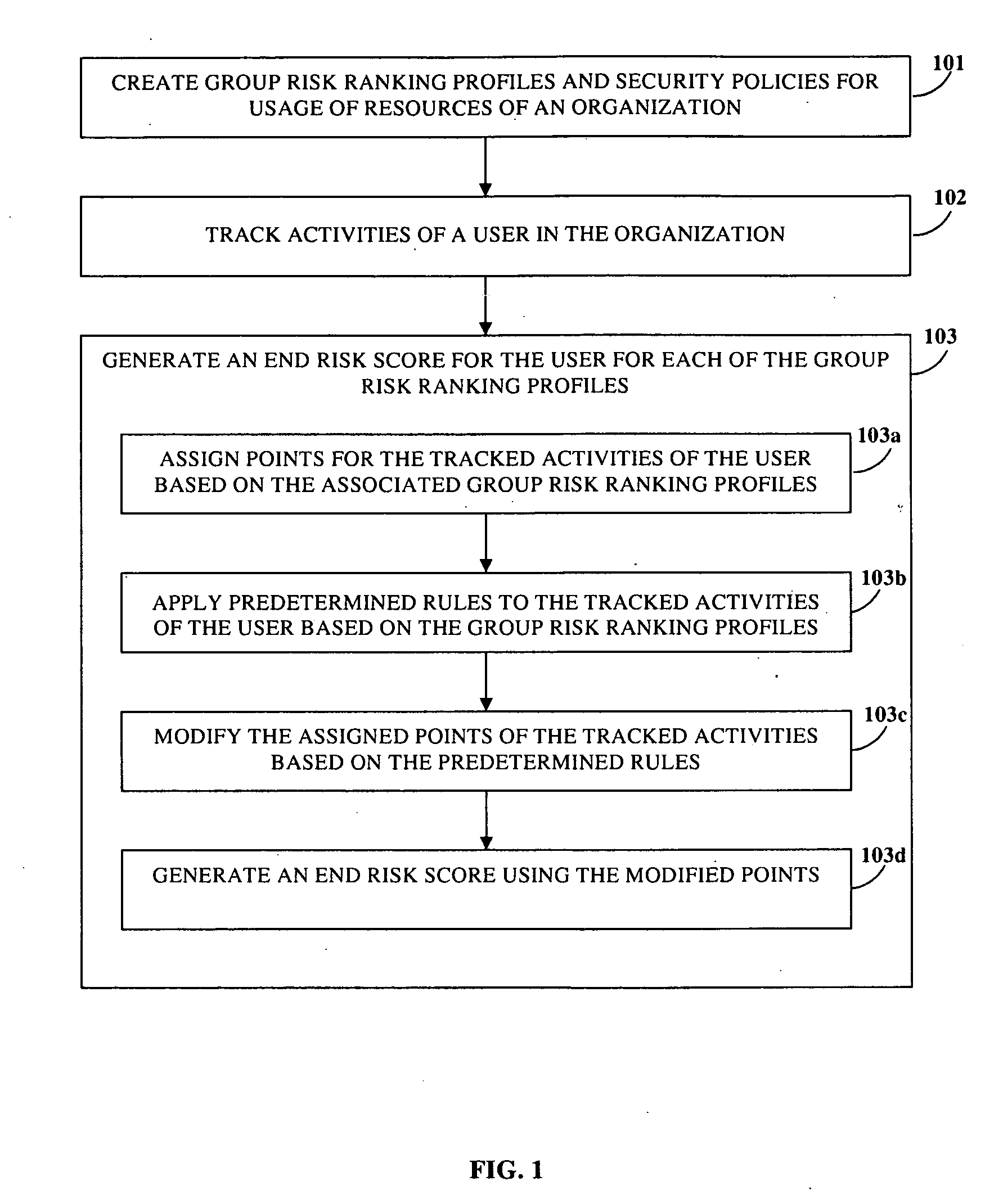
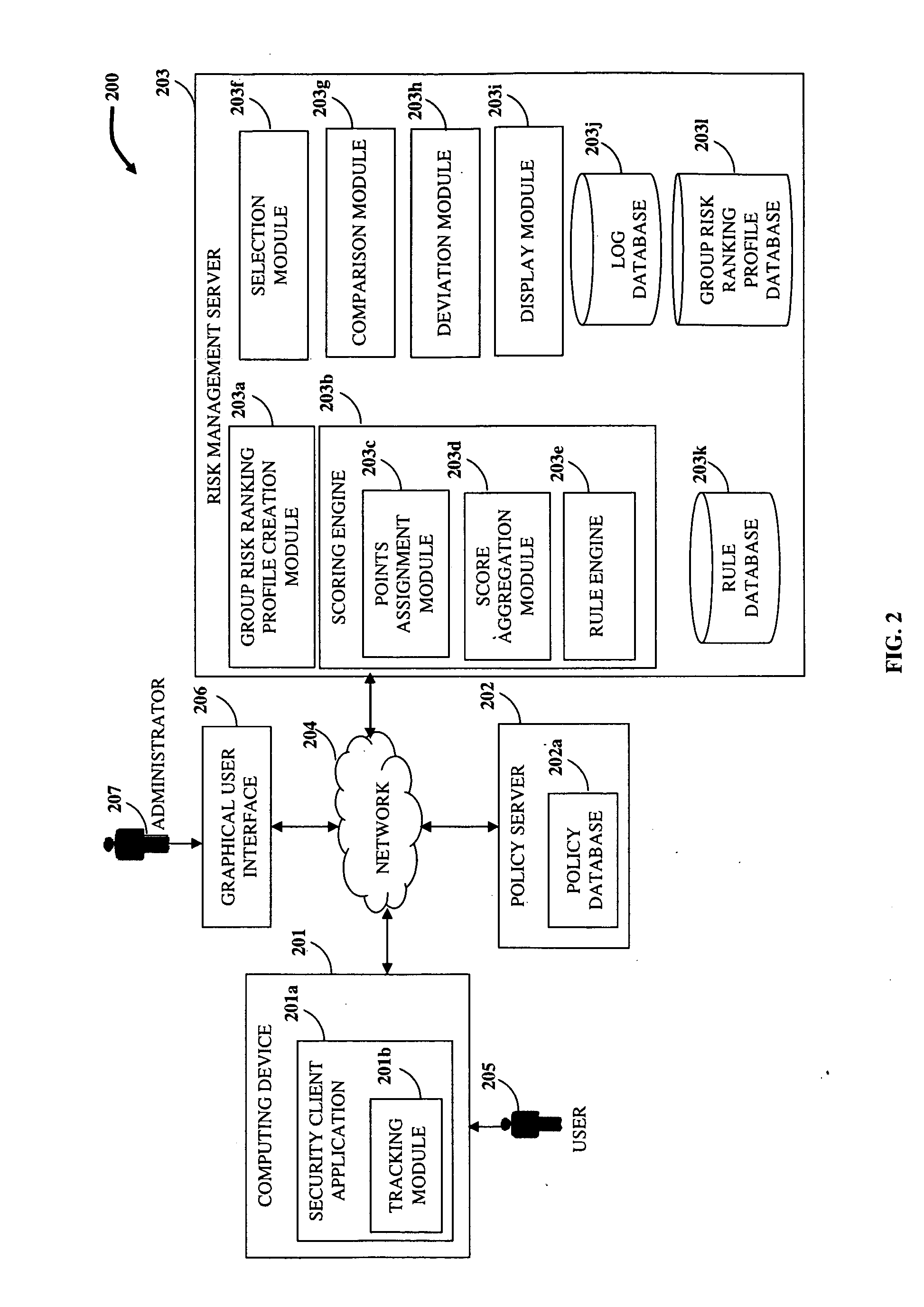
Risk Scoring Based On Endpoint User Activities
InactiveUS20100125911A1Minimize further violationMemory loss protectionError detection/correctionRisk rankingApplication software
Disclosed herein is a computer implemented method and system for ranking a user in an organization based on the user's information technology related activities and arriving at an end risk score used for determining the risk involved in activities performed by the user and for other purposes. Group risk ranking profiles and security policies for usage of the organization's resources are created. The user is associated with one or more group risk ranking profiles. A security client application tracks the user's activities. Points are assigned to the user's tracked activities based on each of the associated group risk ranking profiles. The assigned points are aggregated to generate a first risk score. The assigned points of the user's tracked activities are modified at different levels based on predefined rules. The modified points are aggregated to generate the end risk score which is used for compliance and governance purposes, optimizing resources, etc.
Owner:CISCO TECH INC
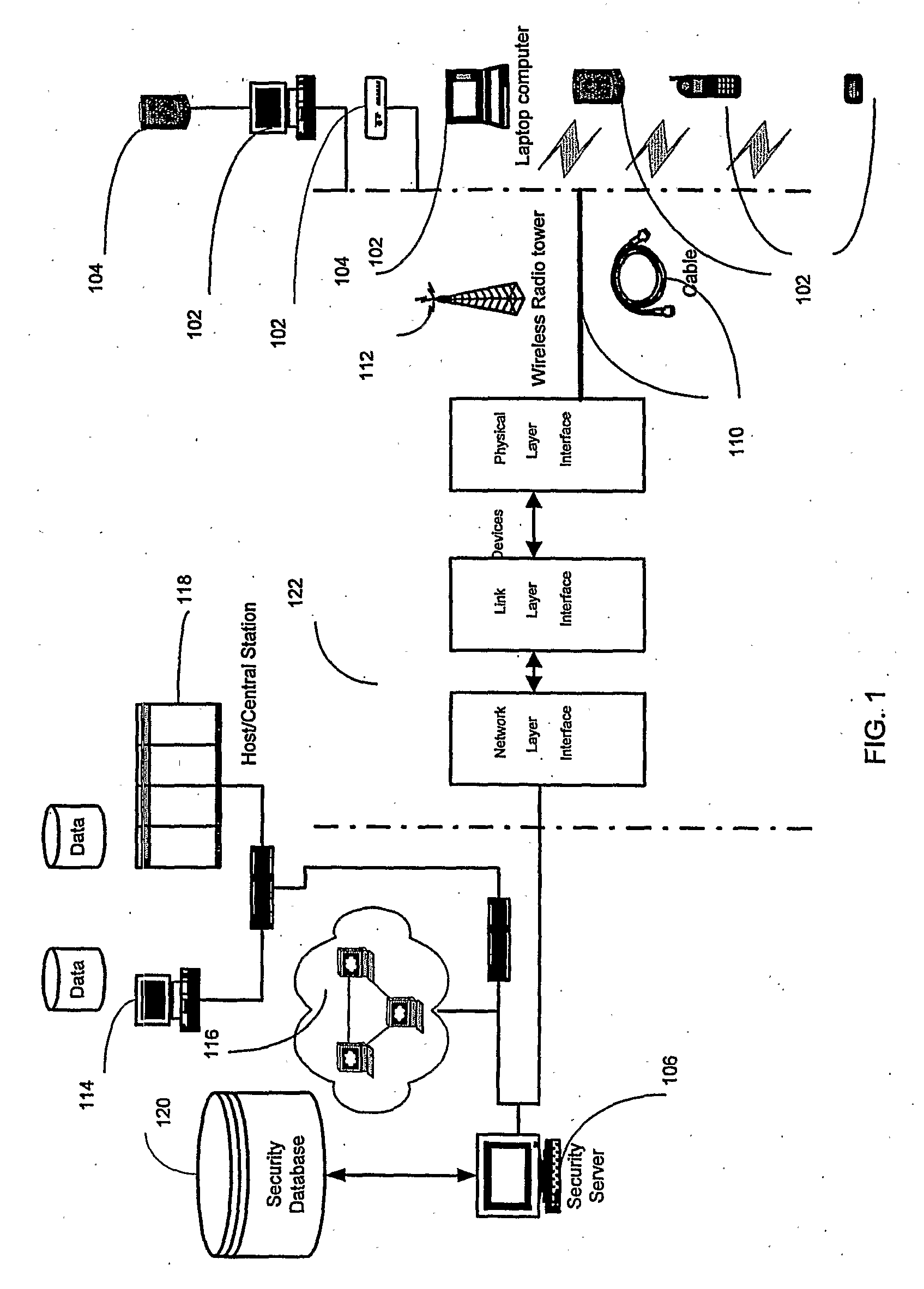
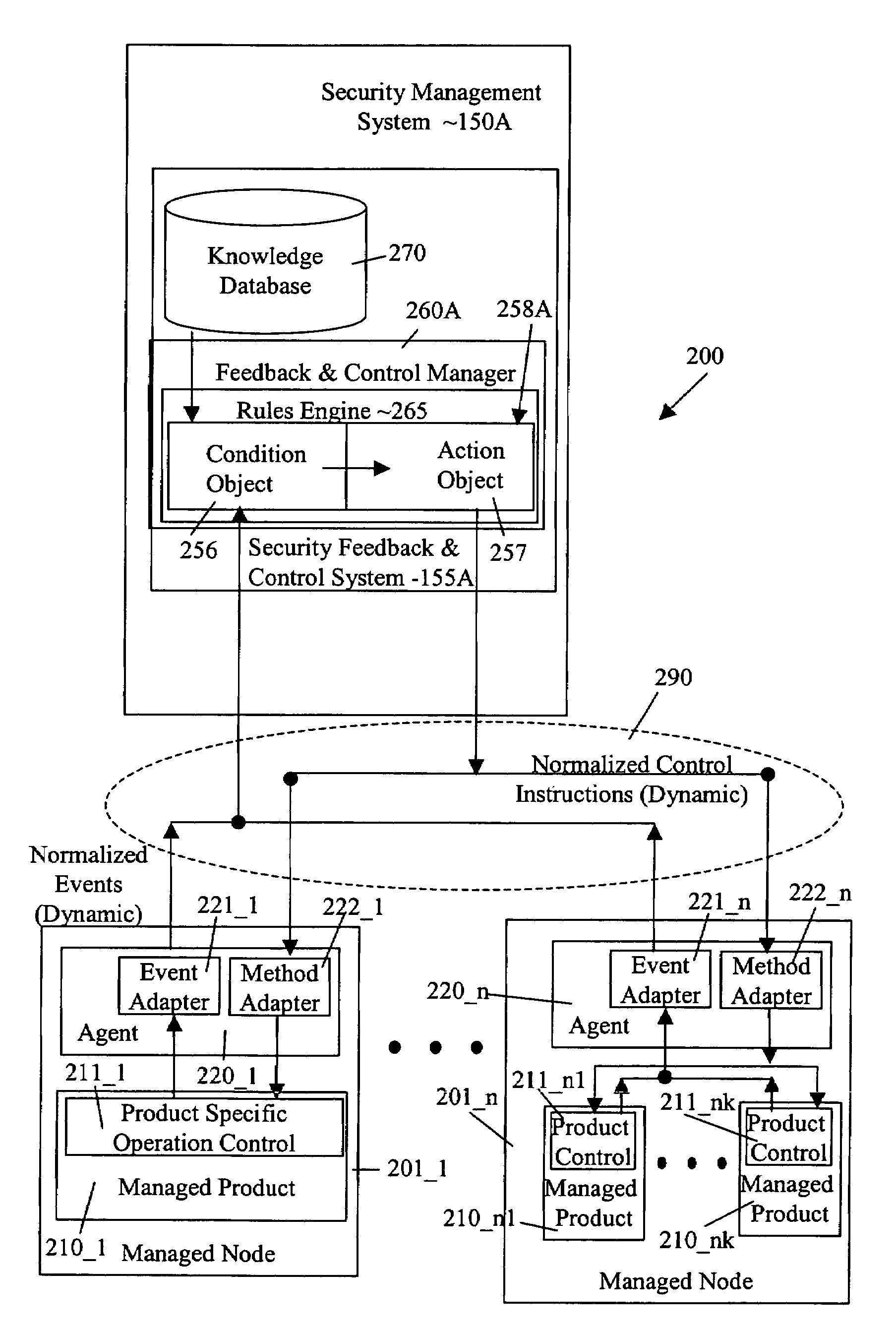
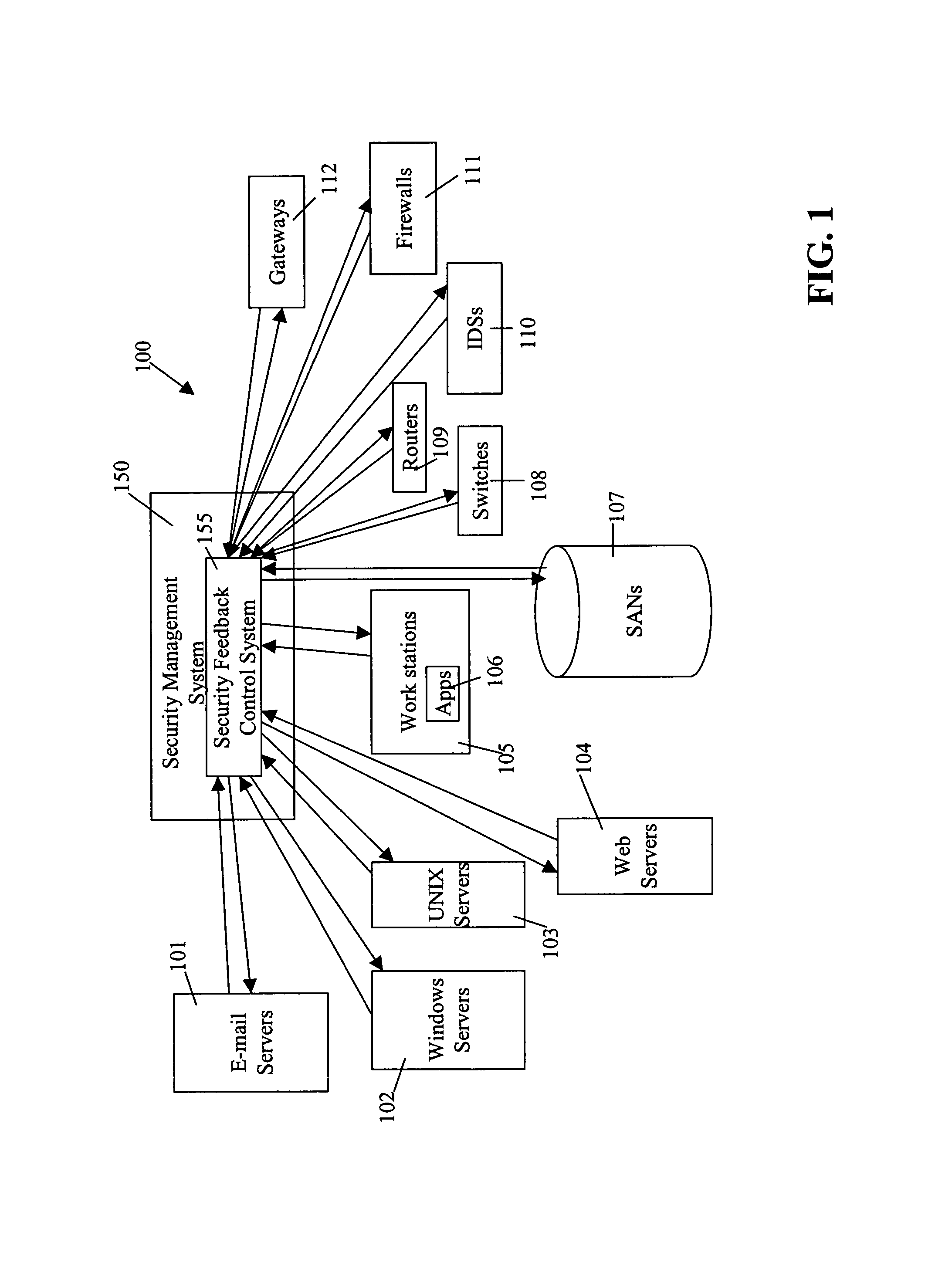
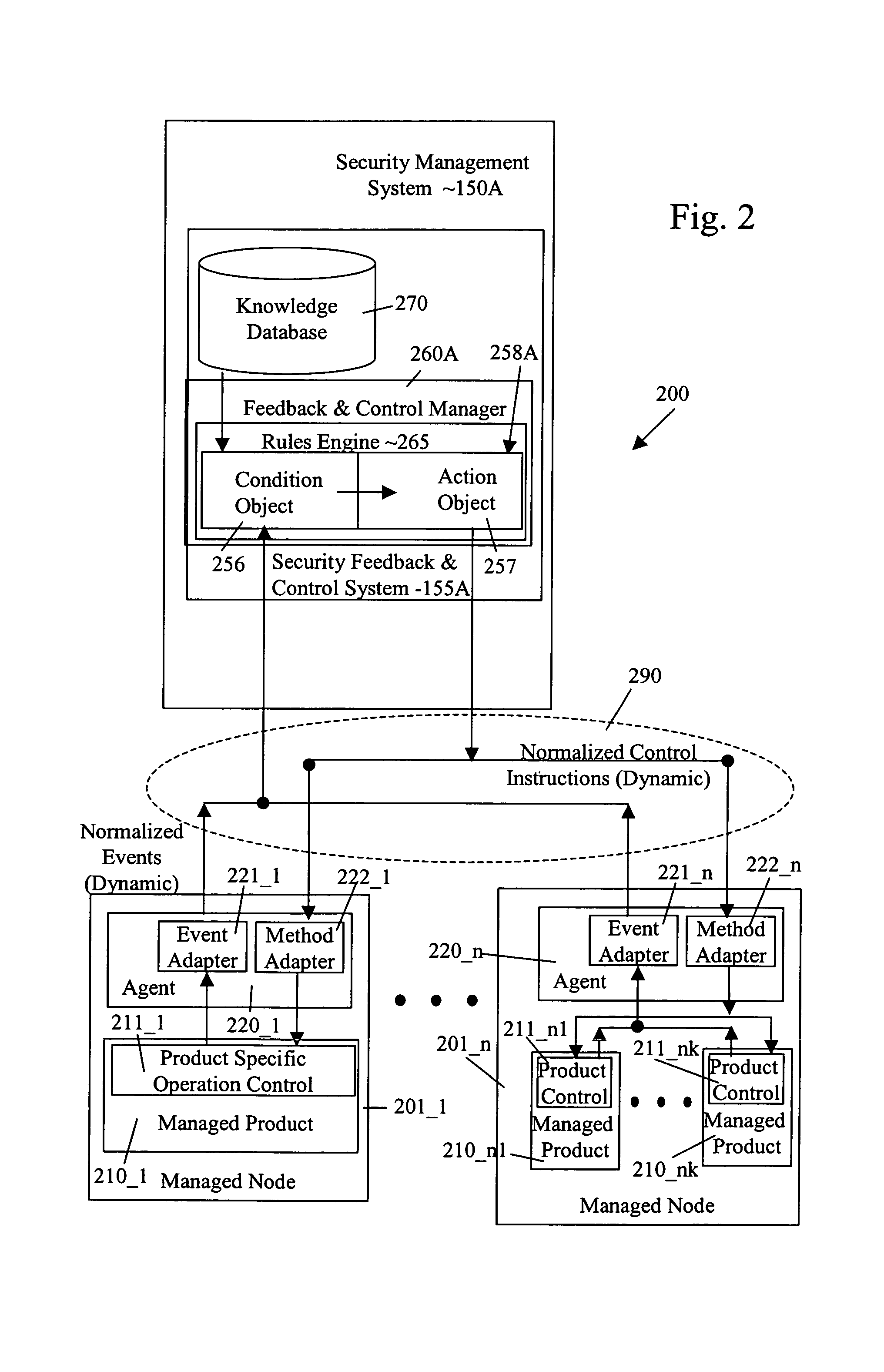
Security management system including feedback and control
InactiveUS7472422B1Memory loss protectionError detection/correctionPolicy decisionSafety management systems
A system uses automatic feedback and control to secure a network infrastructure by iterative convergence of the network's security structure to meet a security policy. Following initialization, a security feedback control system of the security management system makes dynamic adjustments to the system using bi-directional services that are controlled via policy decision components, without user intervention.
Owner:SYMANTEC CORP
System and methodology for security policy arbitration
ActiveUS7546629B2Multiple digital computer combinationsSecret communicationComputer networkSecurity policy
A system providing methods for a device to apply a security policy required for connection to a network is described. In response to receipt of a request from a device for connection to a particular network, a current policy to apply to said device for governing the connection to this particular network is determined from a plurality of available security policies available to the device. This current policy to apply to said device is generated by merging a plurality of security policies available for governing connections. After said current policy is applied to the device, the connection from the device to this particular network is allowed to proceed.
Owner:CHECK POINT SOFTWARE TECH INC
Administration of protection of data accessible by a mobile device
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
System and method for filtering access points presented to a user and locking onto an access point
ActiveUS20060094400A1Interconnection arrangementsUnauthorised/fraudulent call preventionSecurity policyComputer network
The present invention filters access points presented to a user and locks onto an access point. The present invention includes an access point filtering unit and an access point locking unit. The access point filtering unit determines the access points that are accessible by a client device and then filters them to present only the access points that are acceptable to under a security policy in force. The access point locking unit has a plurality of operating modes and can lock onto a user selected access point, a security policy prescribed access point, or the access point with the best signal profile. The present invention also includes several methods such as: a method for filtering access points for presentation to the user, a method for locking onto an access point selected by the user, a method for locking onto an access point with the best signal profile, and a method for locking onto an access point prescribed by a security policy for a given location.
Owner:APPLE INC
Selective data encryption using style sheet processing
InactiveUS6931532B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
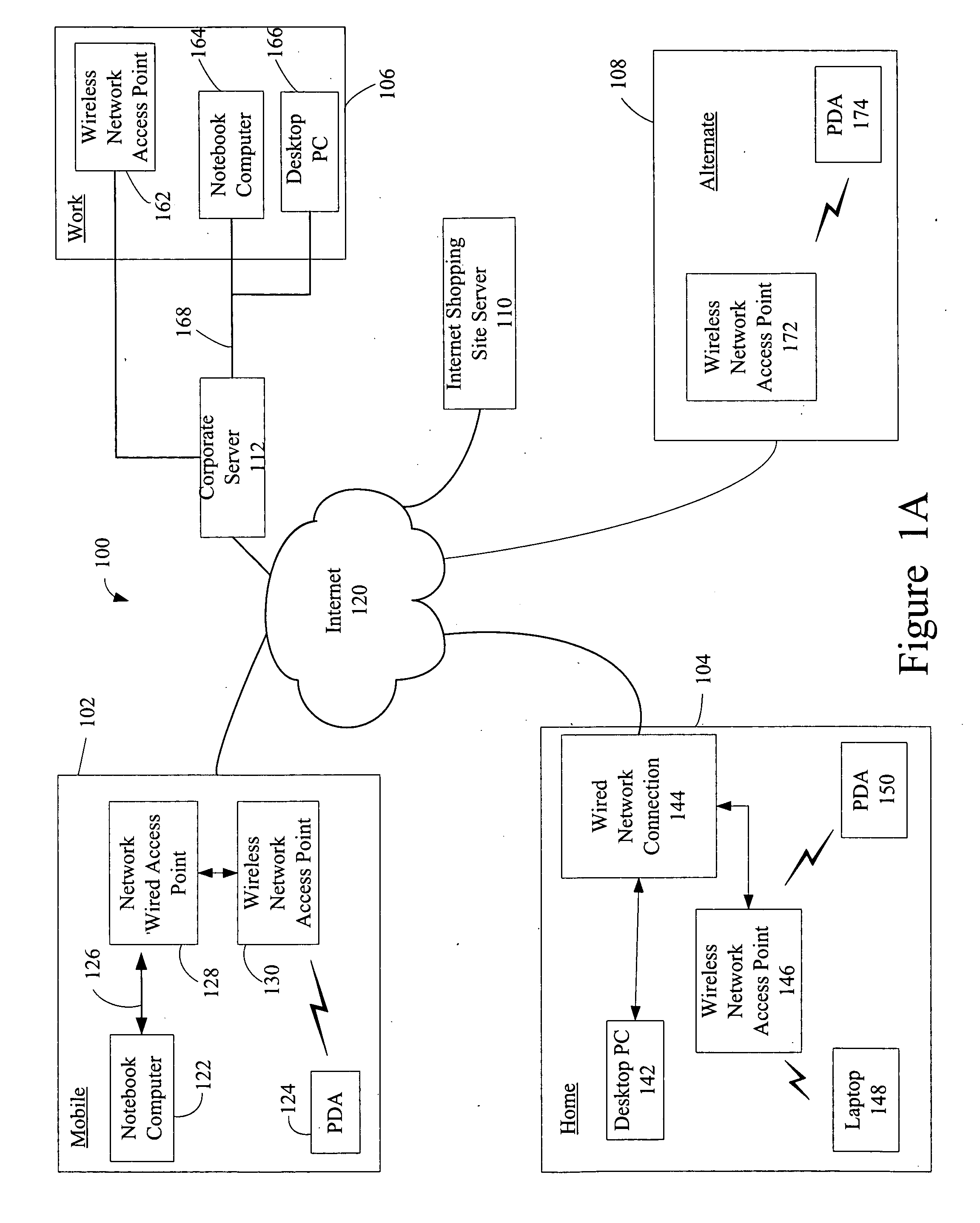
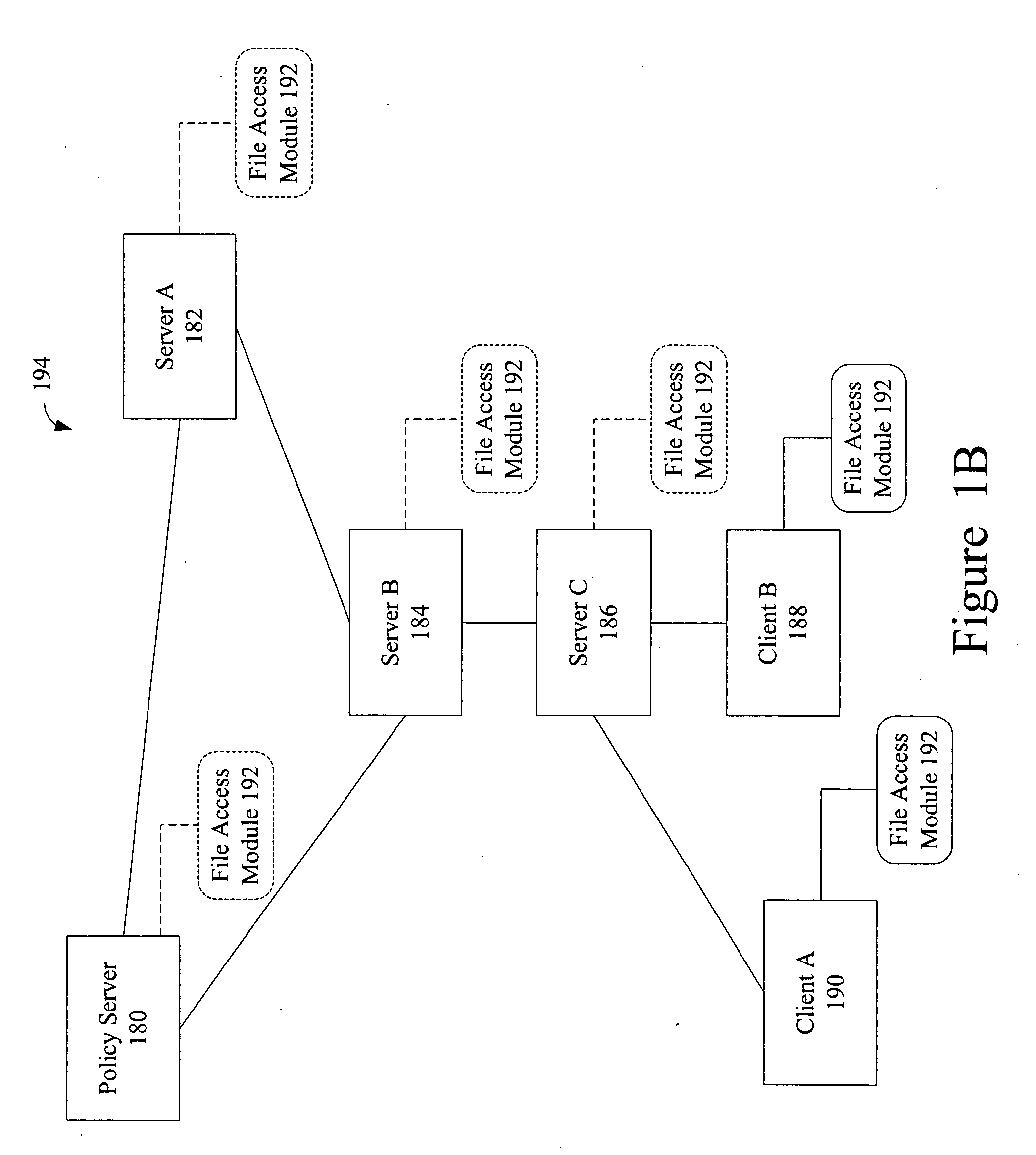
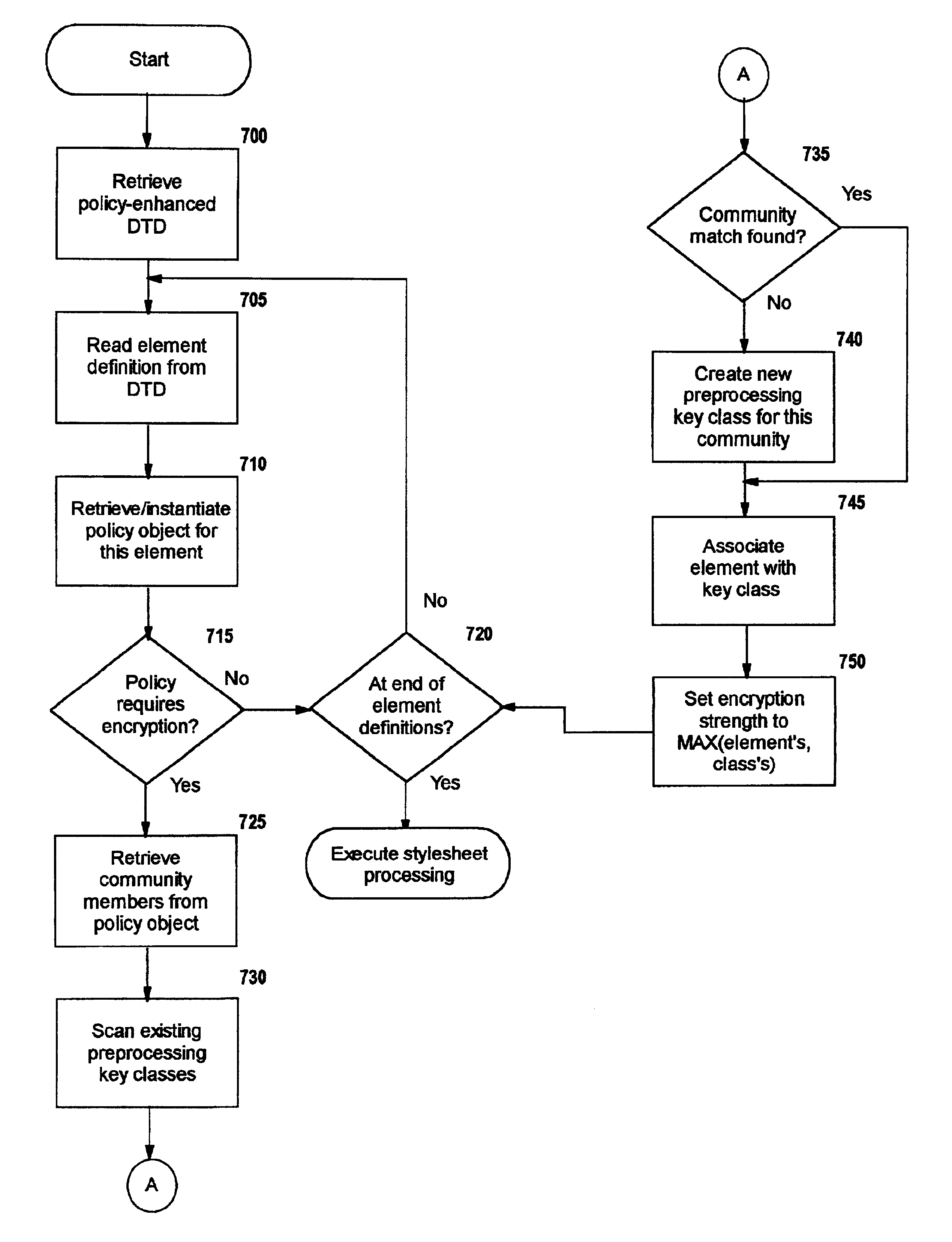
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Network appliance for securely quarantining a node on a network
InactiveUS20060164199A1Transformers/inductances magnetic coresData switching networksNetwork Access ControlSecurity policy
An apparatus, system, and method for managing dynamic network access control. The invention provides services and controlled network access that includes quarantining nodes so that they may be identified, audited, and provided an opportunity to be brought into compliance with a security policy. The invention is configured to detect a device seeking to join the network, and determine if the device is allowed to join the network. If the invention determines that the device is not to be allowed, the device may be quarantined using a VLAN. The suspect device may then be audited for vulnerabilities. If vulnerabilities are identified, remediation may be employed to guide the suspect device, a user, and / or administrator of the suspect device towards a resolution of the vulnerabilities, such that the device may be reconfigured for acceptance onto the network.
Owner:MCAFEE INC
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Firewall propagation
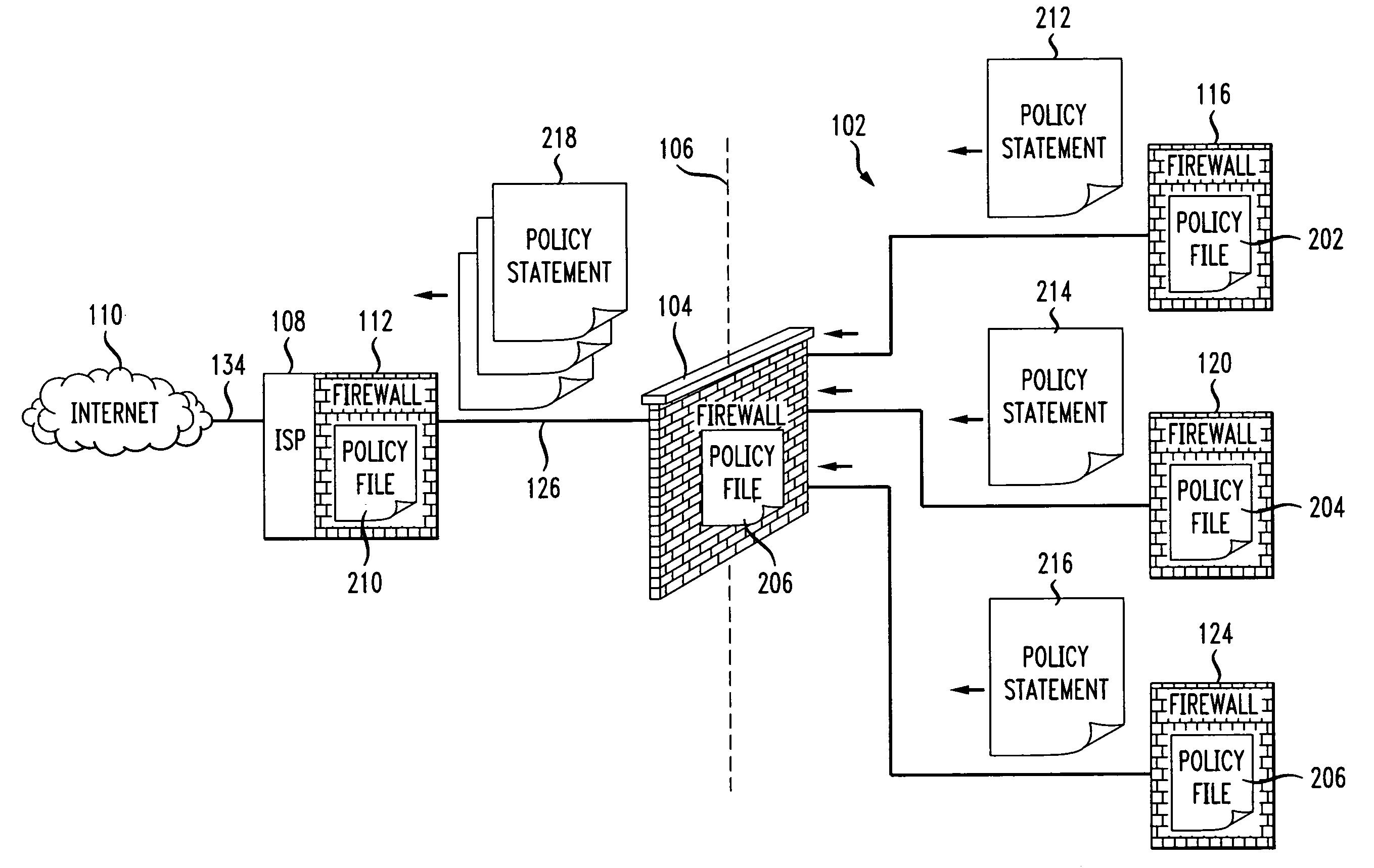
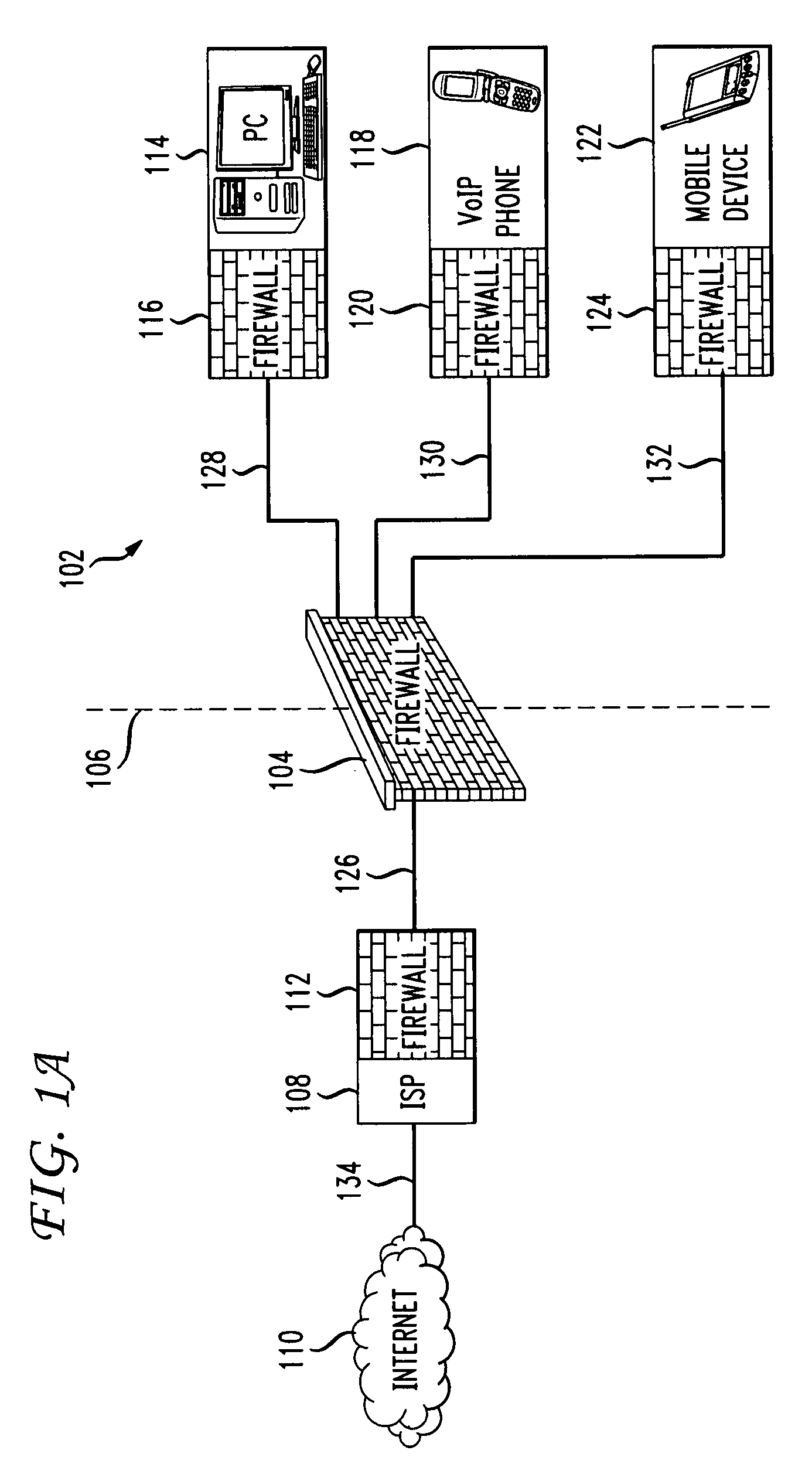
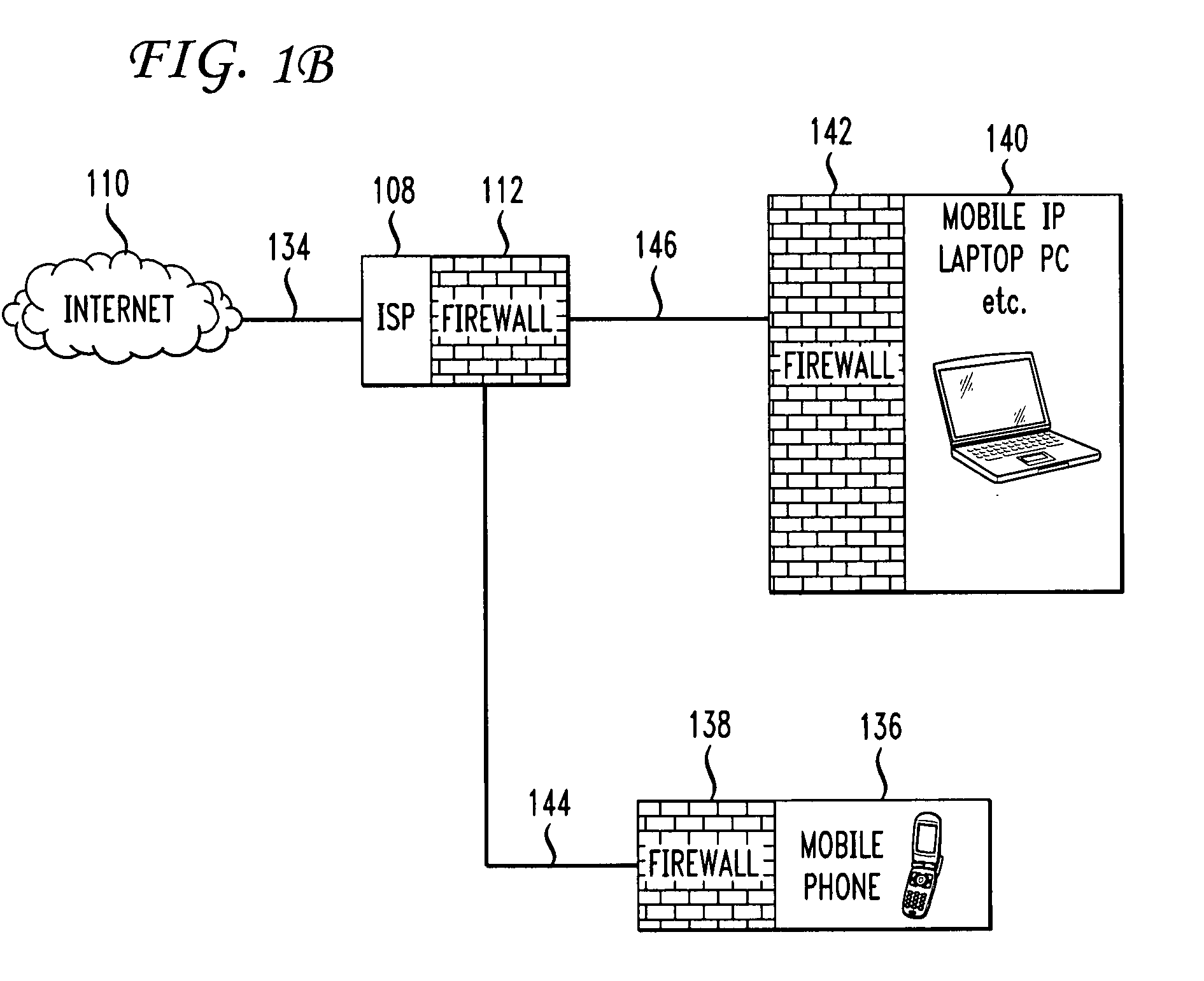
InactiveUS20080235755A1Unauthorized memory use protectionHardware monitoringSecurity ruleSecurity policy
Methods and systems for propagating data security policies and rules up a chain of network components, for example, from an end-user device having a firewall, to a network component at the “edge” of the network, such as a so-called “edge” firewall server, from where a policy statement can be transmitted to a service provider, such as an ISP, are described. A device, such as a computer or mobile phone, has, as part of its firewall software, a policy propagation file, that communicates with pre-existing firewall software. The firewall software creates a policy statement upon detecting a triggering event, which is transmitted from the device to the next data security component up the chain, “upstream,” in the network. In some cases this device may be a firewall server or a firewall policy server. The firewall server may combine policy statements from numerous end-user type devices and transmit the policy statement to an external network component, such as an ISP firewall server or similar device. The ISP or other service provider may then use the policy statement to implement date security rules for the devices in the network. In this manner, the firewall operated by the ISP implements rules and policies of a network owner or the owner of a stand-alone device, thereby preventing unwanted traffic from entering the network.
Owner:DIGICERT
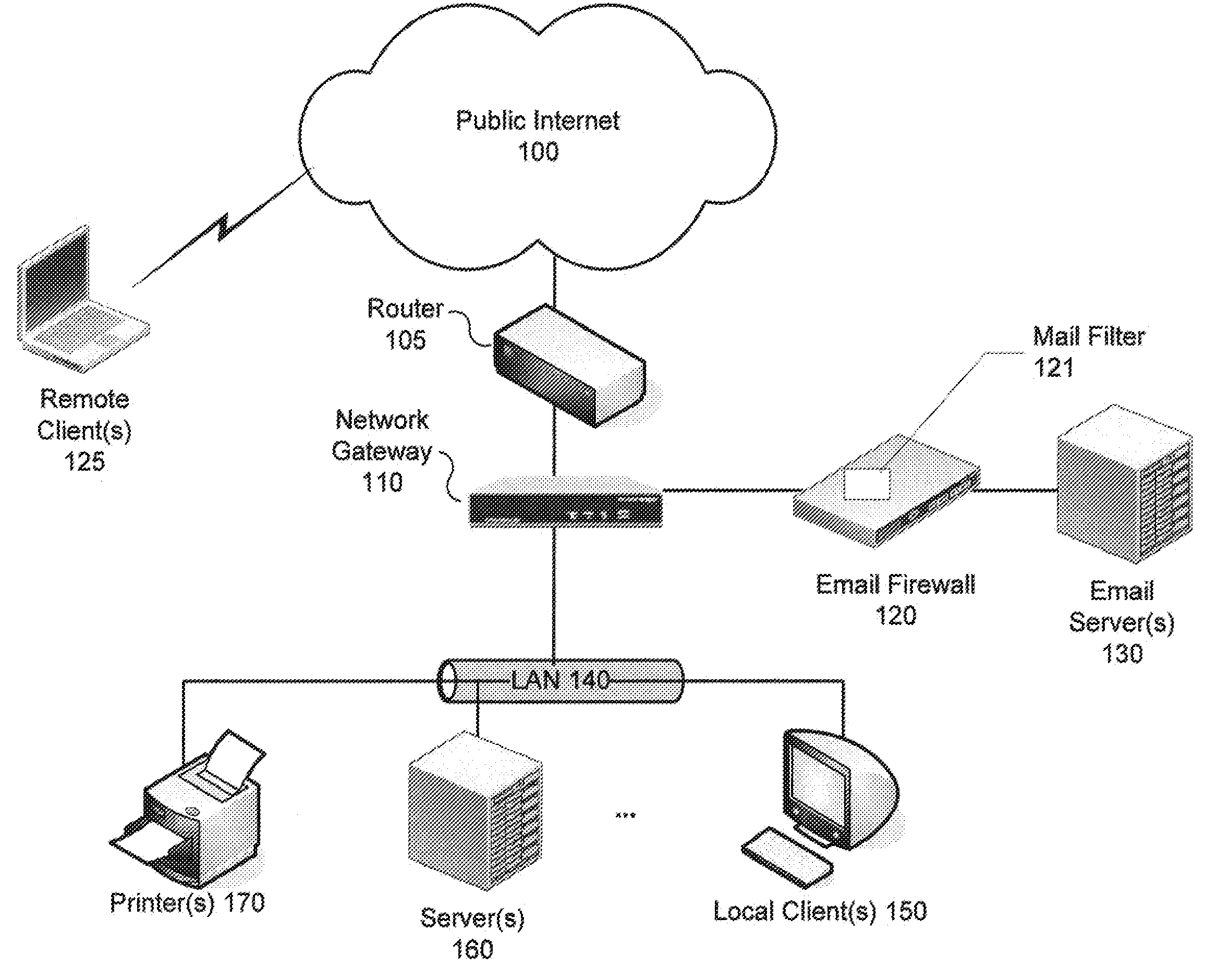
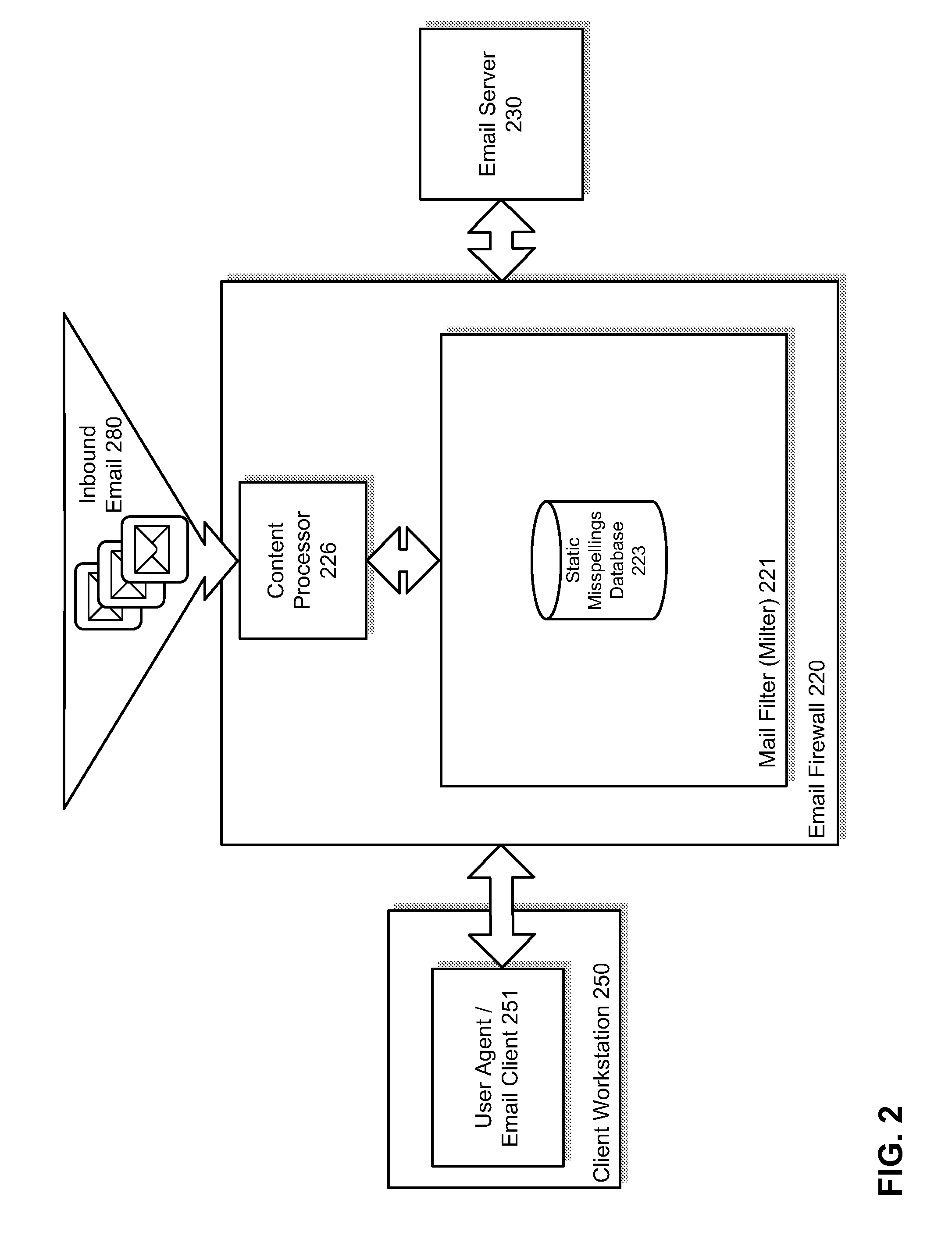
Heuristic detection of probable misspelled addresses in electronic communications
Methods and systems for detecting suspicious electronic communications, such as electronic mail (email) messages containing, originated or purportedly originated from misspelled and / or deliberately misleading addresses, are provided. According to one embodiment, an electronic communication, such as an electronic mail (email) message, is scanned to determine whether the electronic communication contains one or more suspicious addresses or represents a suspicious traffic pattern. If the electronic communication is determined to contain one or more suspicious addresses or is determined to represent a suspicious traffic pattern, then the electronic communication is handled in accordance with an electronic communication security policy associated with suspicious electronic communications. For example, an event may be logged, the electronic communication may be dropped or quarantined, the communication may be tagged as spam or possible phishing and / or an end user may be alerted to the existence of the one or more suspicious addresses.
Owner:FORTINET
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
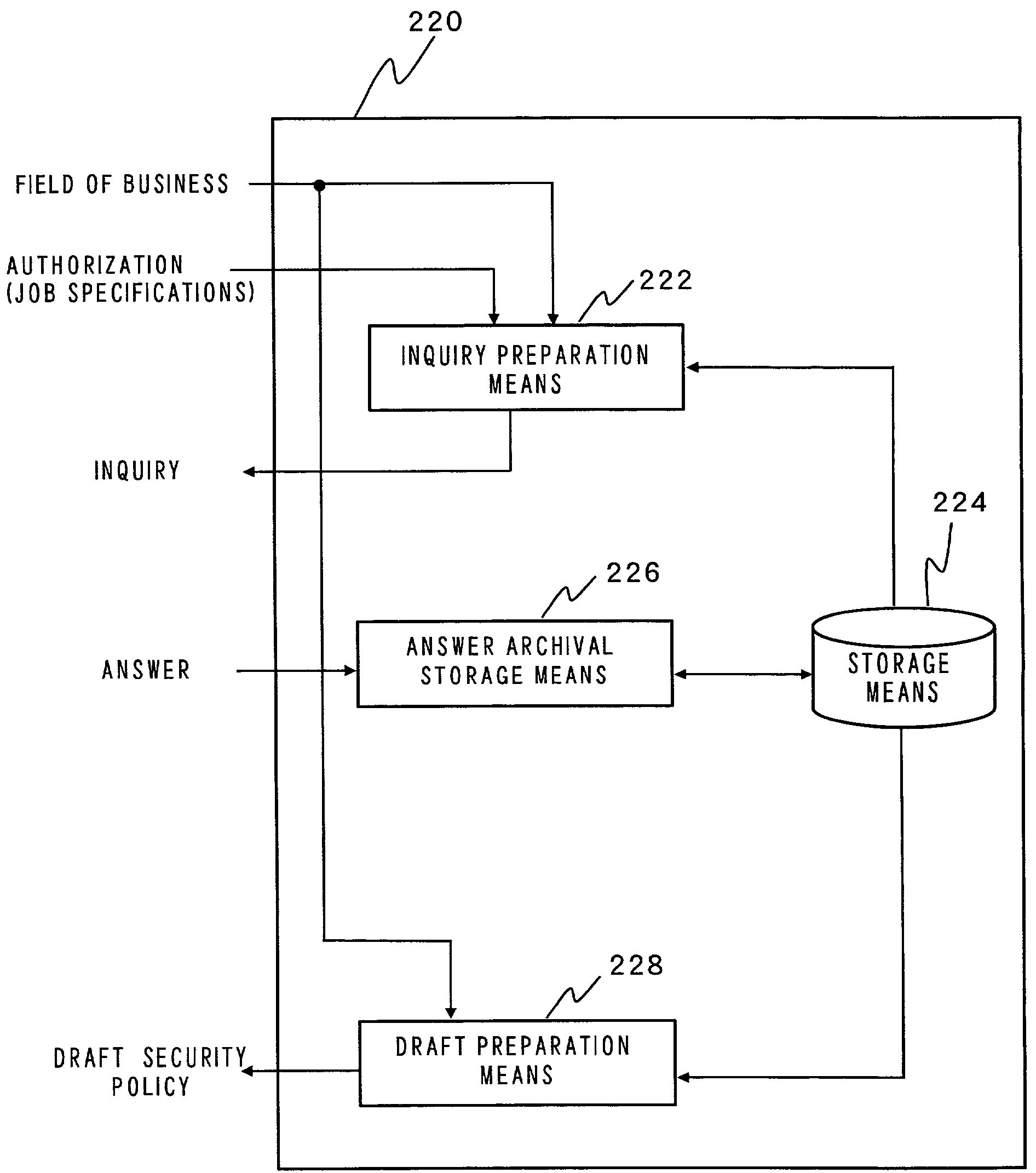
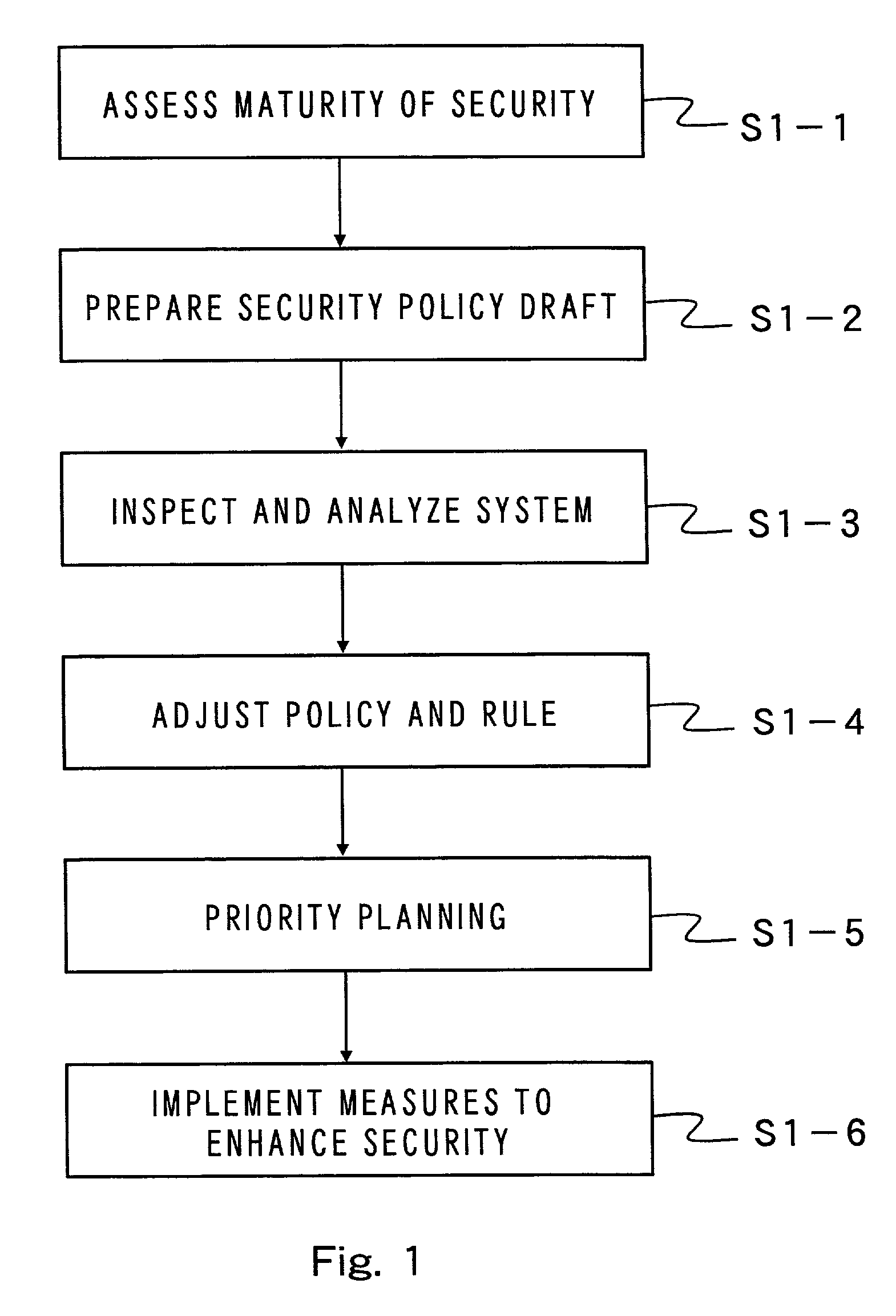
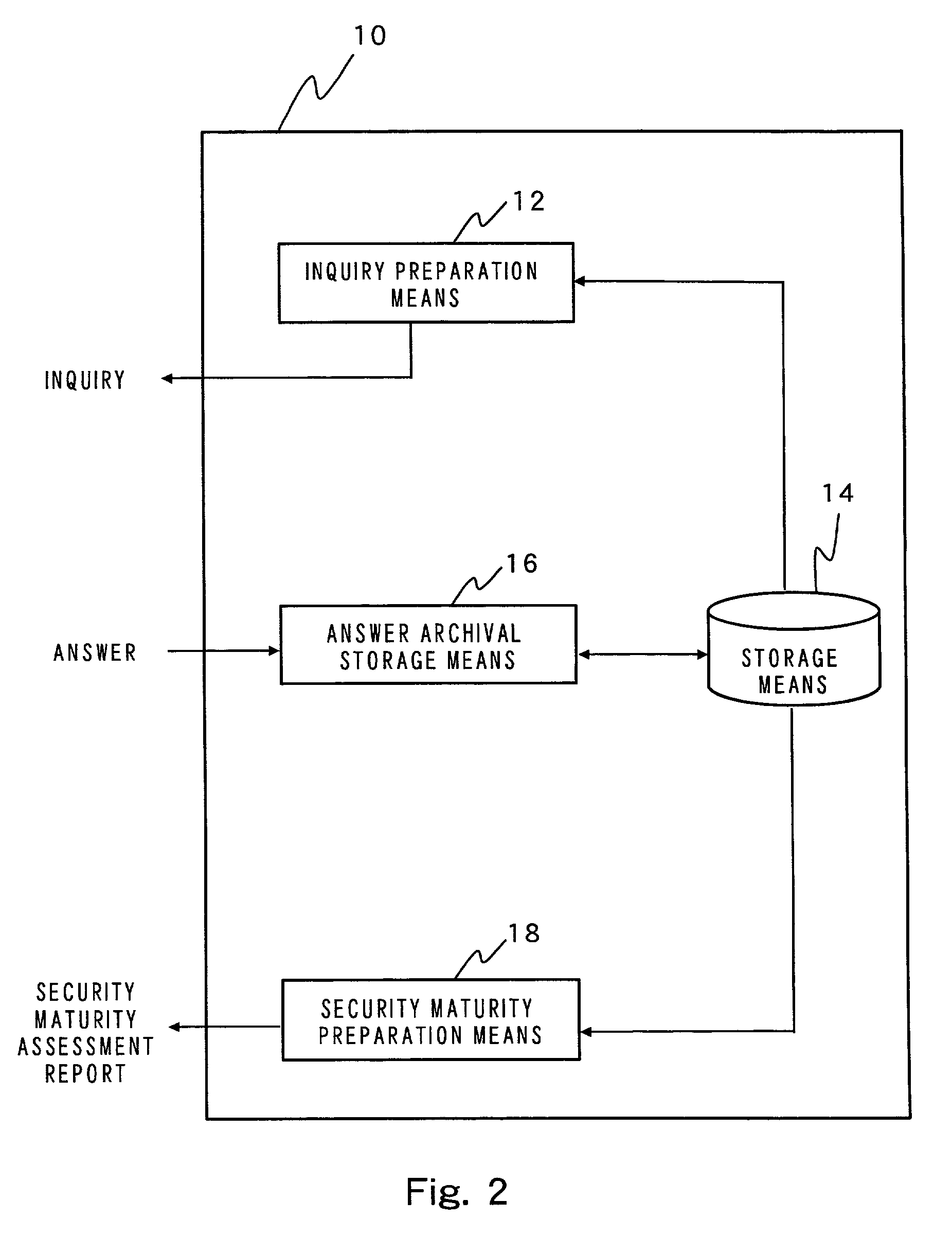
Method and apparatus for establishing a security policy, and method and apparatus for supporting establishment of security policy
ActiveUS7260830B2Efficient establishmentDigital data processing detailsComputer security arrangementsSecurity policy
There are provided a method of efficiently establishing a security policy and an apparatus for supporting preparation of a security policy. According to a method of establishing a security policy in six steps, a simple security policy draft is first prepared. The security policy draft is adjusted so as to match realities of an organization, as required, thus completing a security policy stepwise. Therefore, a security policy can be established in consideration of a schedule or budget of the organization.
Owner:ASGENT
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
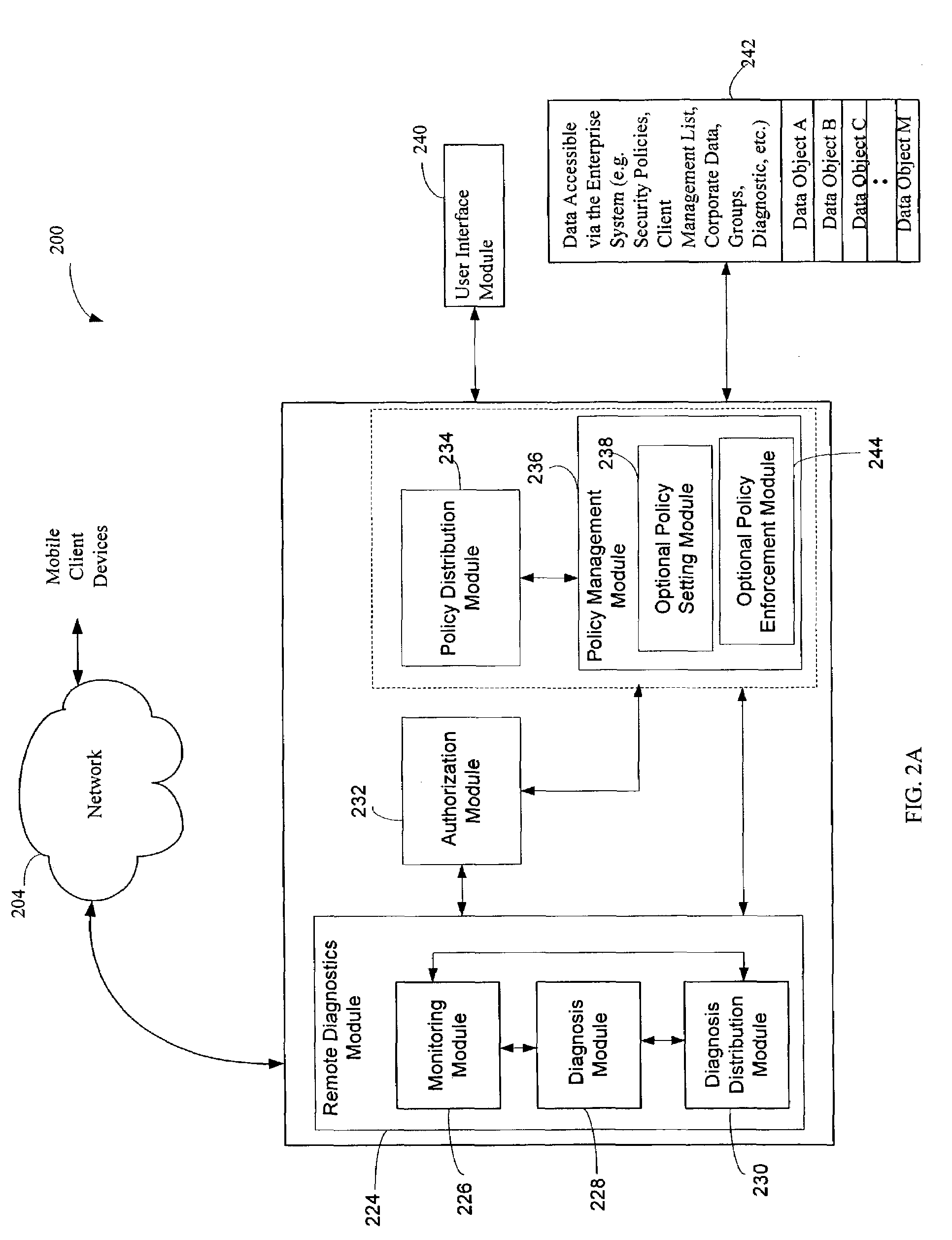
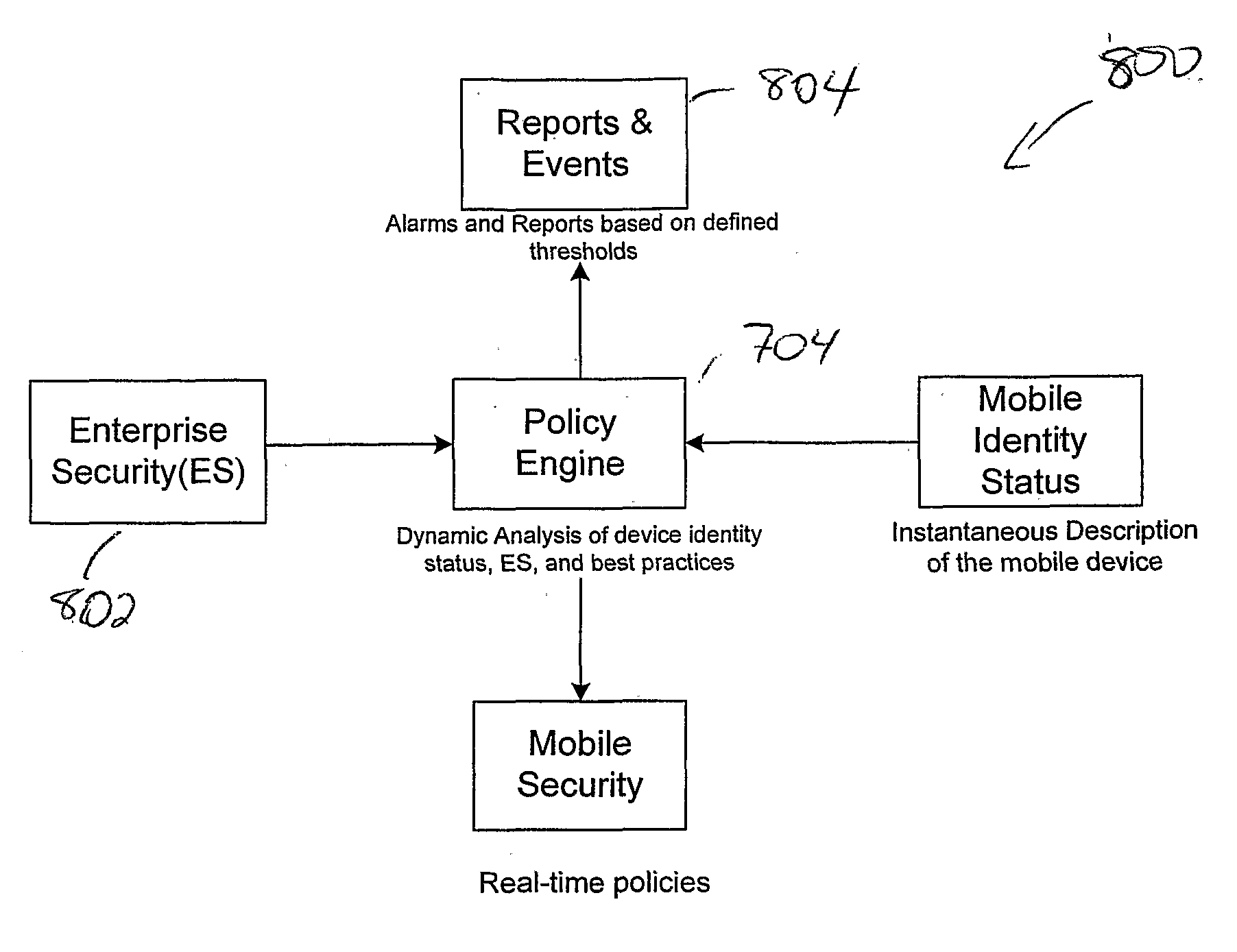
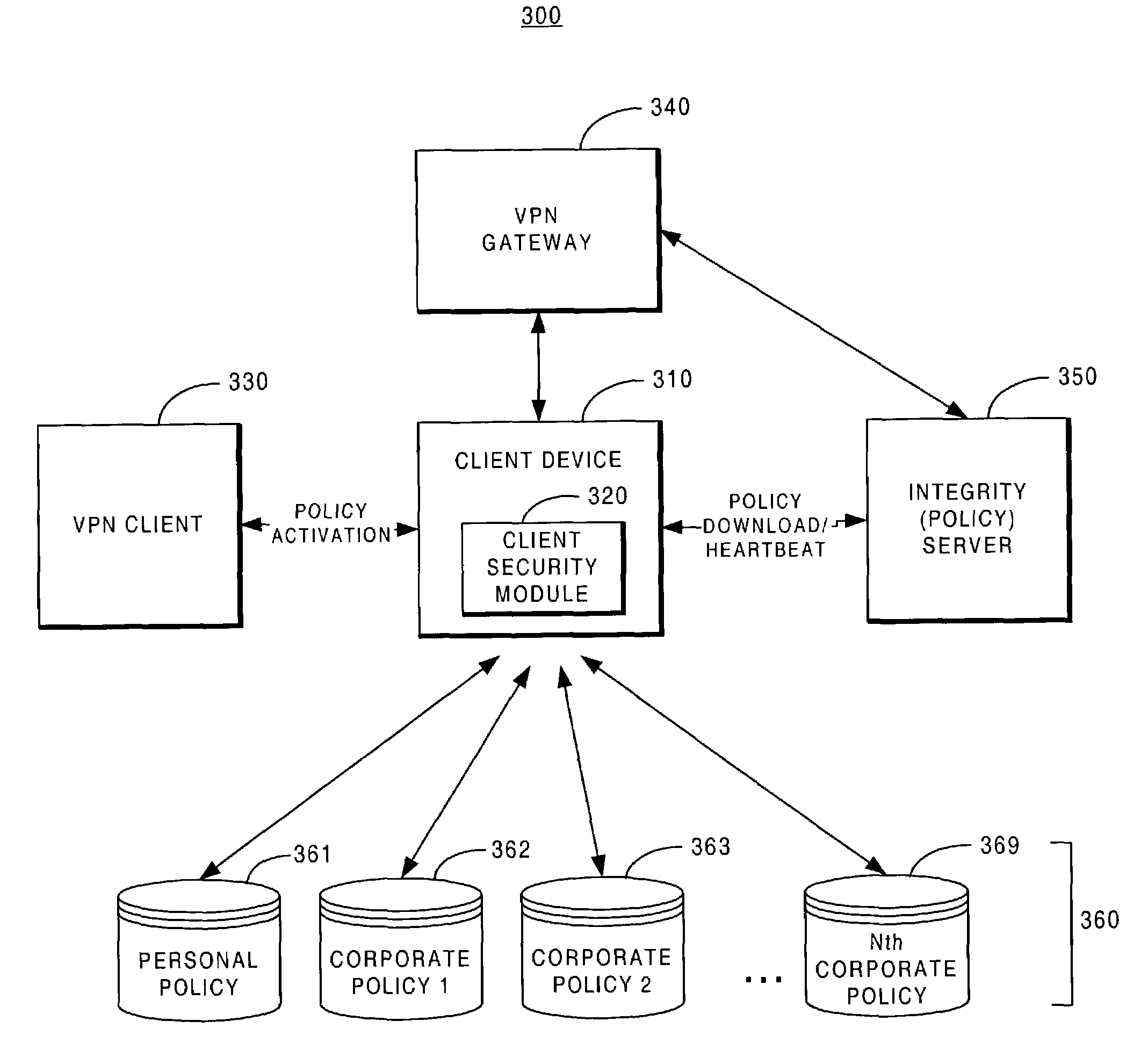
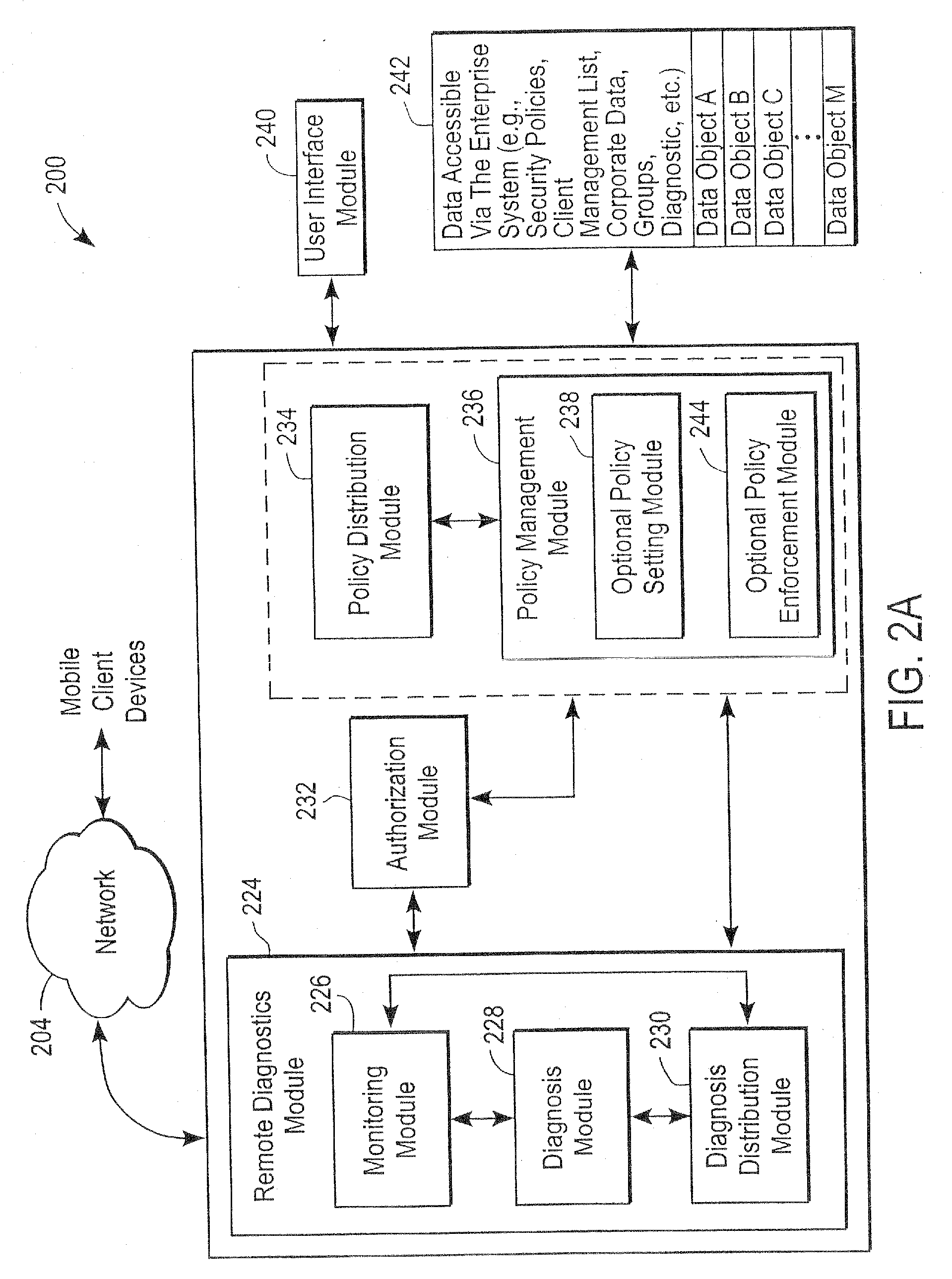
Centralized Dynamic Security Control for a Mobile Device Network
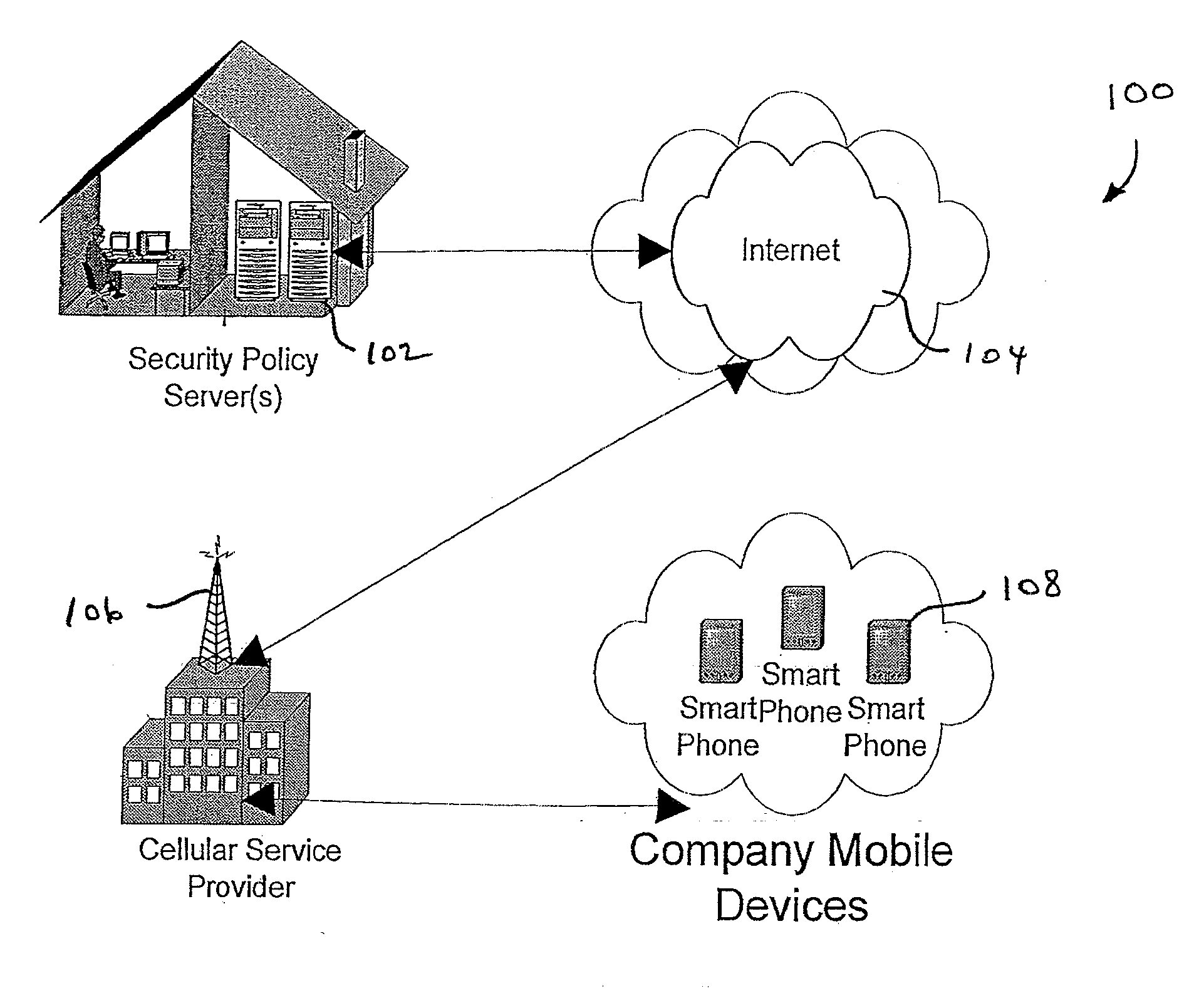
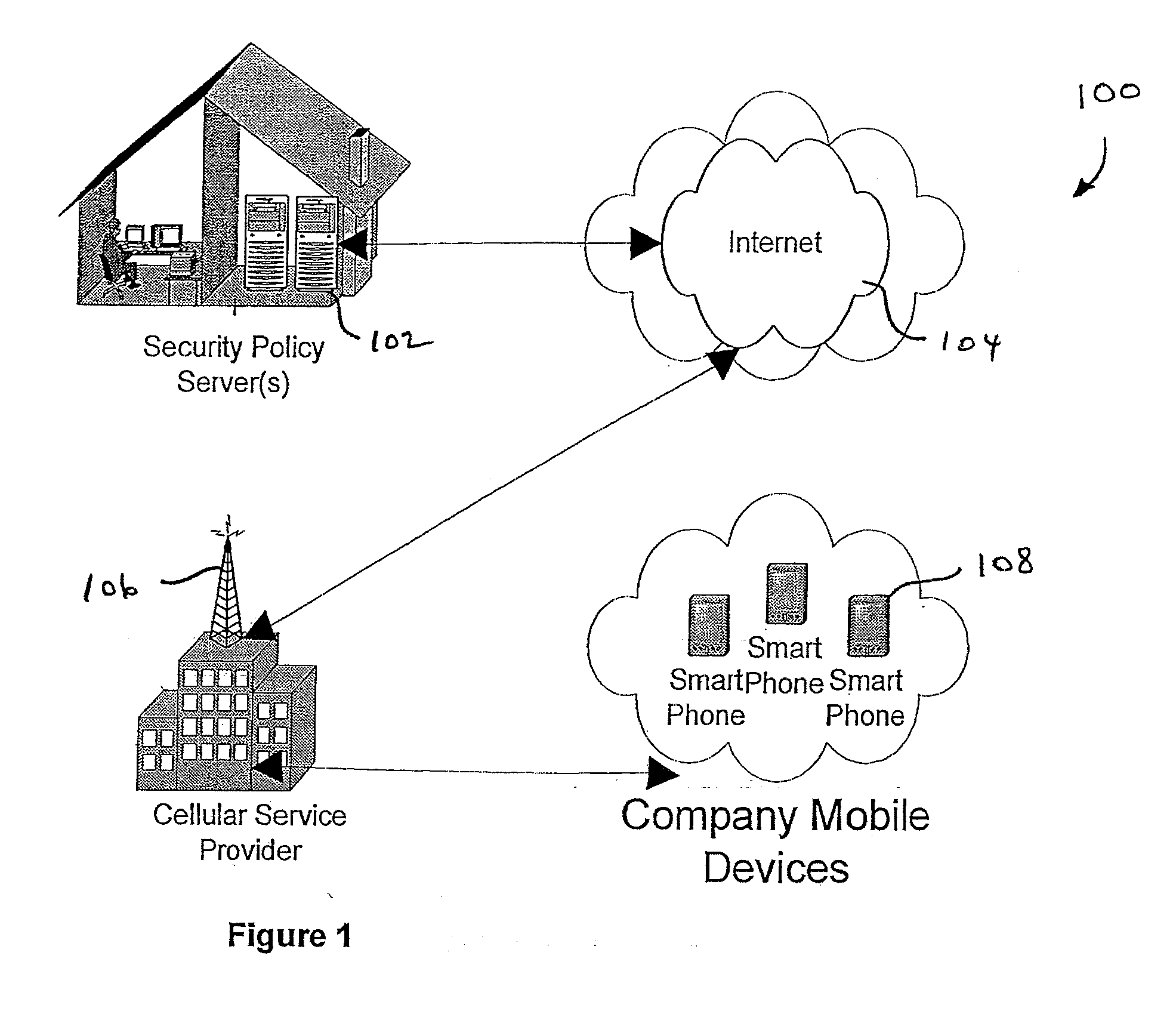
InactiveUS20070266422A1Well formedSecurity arrangementSpecial data processing applicationsTimerSecurity system
An security system for an enterprise network and data automates the revision, deployment, enforcement, auditing and control of security policies on mobile devices connected to said enterprise network, through automated communication between a security policy server and the mobile device. Control of the security system is centralized through administrative control of security policies stored on the security policy server. Automation of deployment of security policies to mobile devices occurs through transparent background communication and transfer of updated policies either triggered by a change in a security policy within the central repository of security policies or upon the expiration of a certain time period during which no policies were downloaded to the mobile device. When the mobile device is not in compliance with a security policy, a software security agent operating thereon limits access to said enterprise network and enterprise data. To aid in preventing the overwhelming of the enterprise network and the security policy server as a result of to many synchronization communications coming from too many mobile devices, a randomized timer is set by the software security agent upon receipt by the mobile device of a synchronization command from the security policy server.
Owner:SQUARE 1 BANK
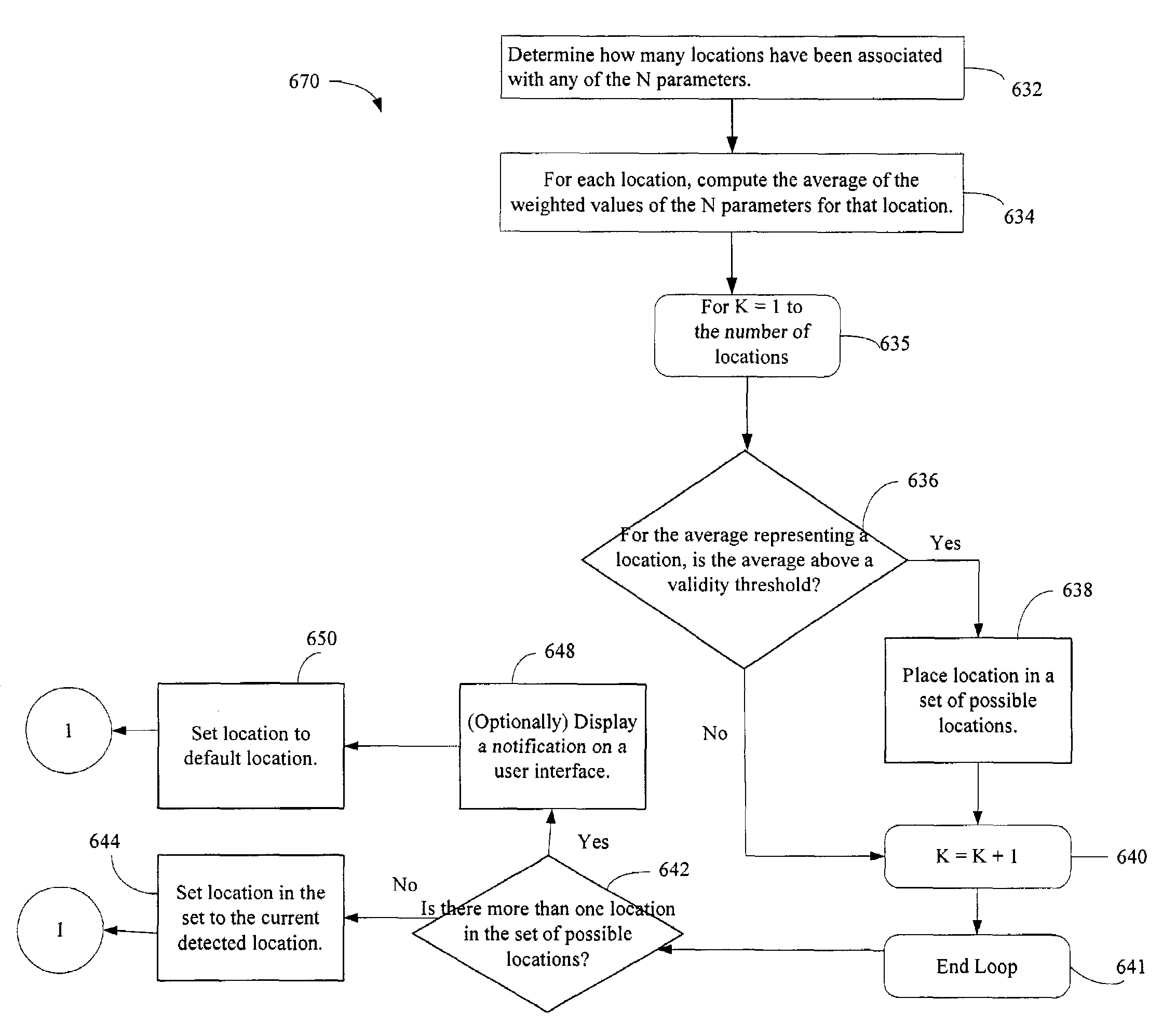
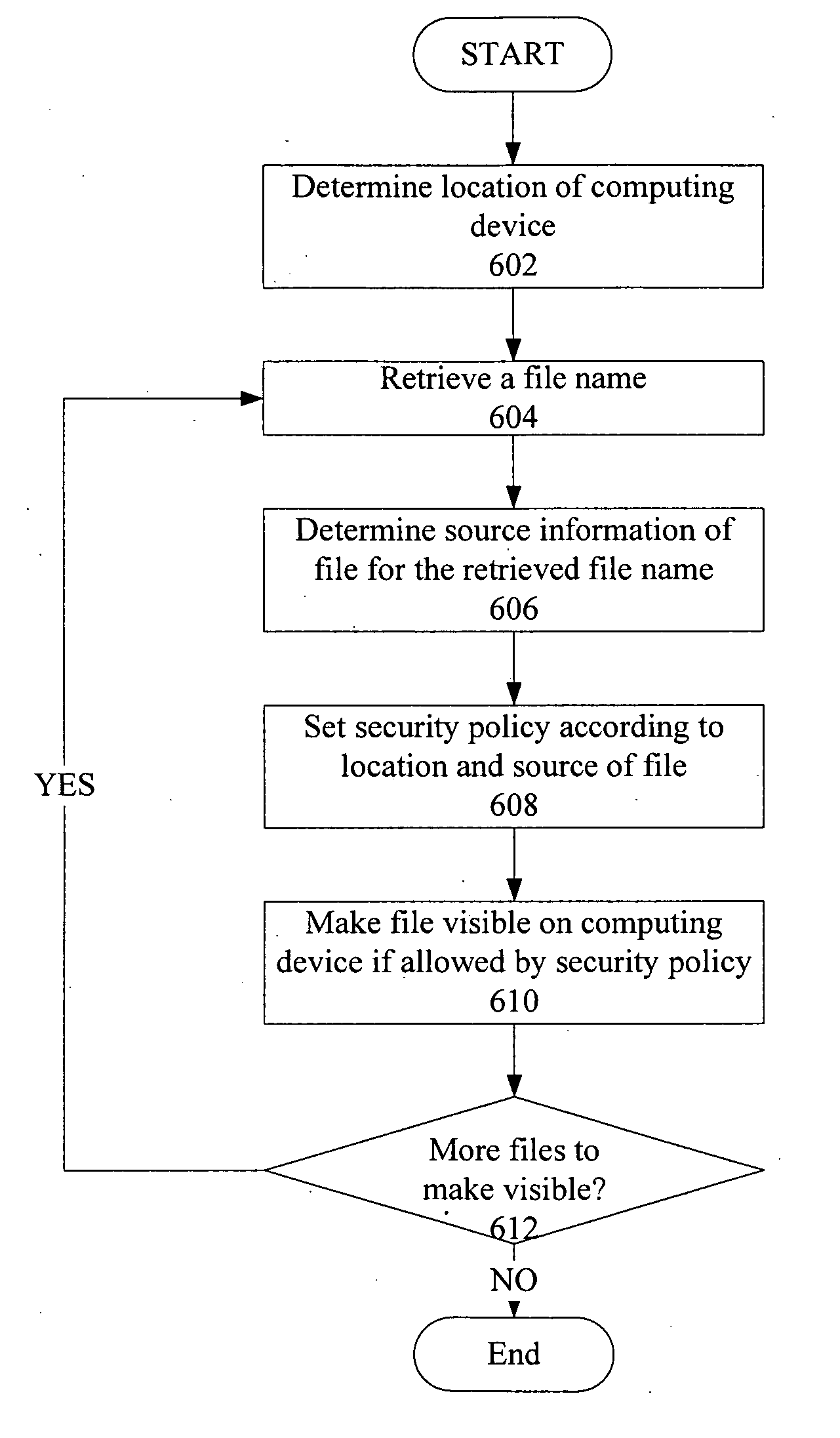
Access control to files based on source information
ActiveUS20060120526A1Digital data processing detailsUser identity/authority verificationWeb environmentSecurity policy
The present invention is a security tool for protection of data on a mobile computing device. The security tool provides a plurality of security policies to be enforced based on source information for the data and a location associated with a network environment in which a mobile device is operating. The security tool may be either located at the mobile computing device or at the server. The security tool includes a file access module for determining whether files are visible or accessible. The file access module comprises a tag generator, an association module, and a policy enforcement module. The tag generator creates source information for the file being accessed and the policy enforcement module determines what actions, if any, can be performed on the file and under what conditions such as location and network environment, type of file and other factors.
Owner:NOVELL INC
Selective data encryption using style sheet processing for decryption by a client proxy
InactiveUS6978367B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureDocument preparation
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Secure execution of a computer program
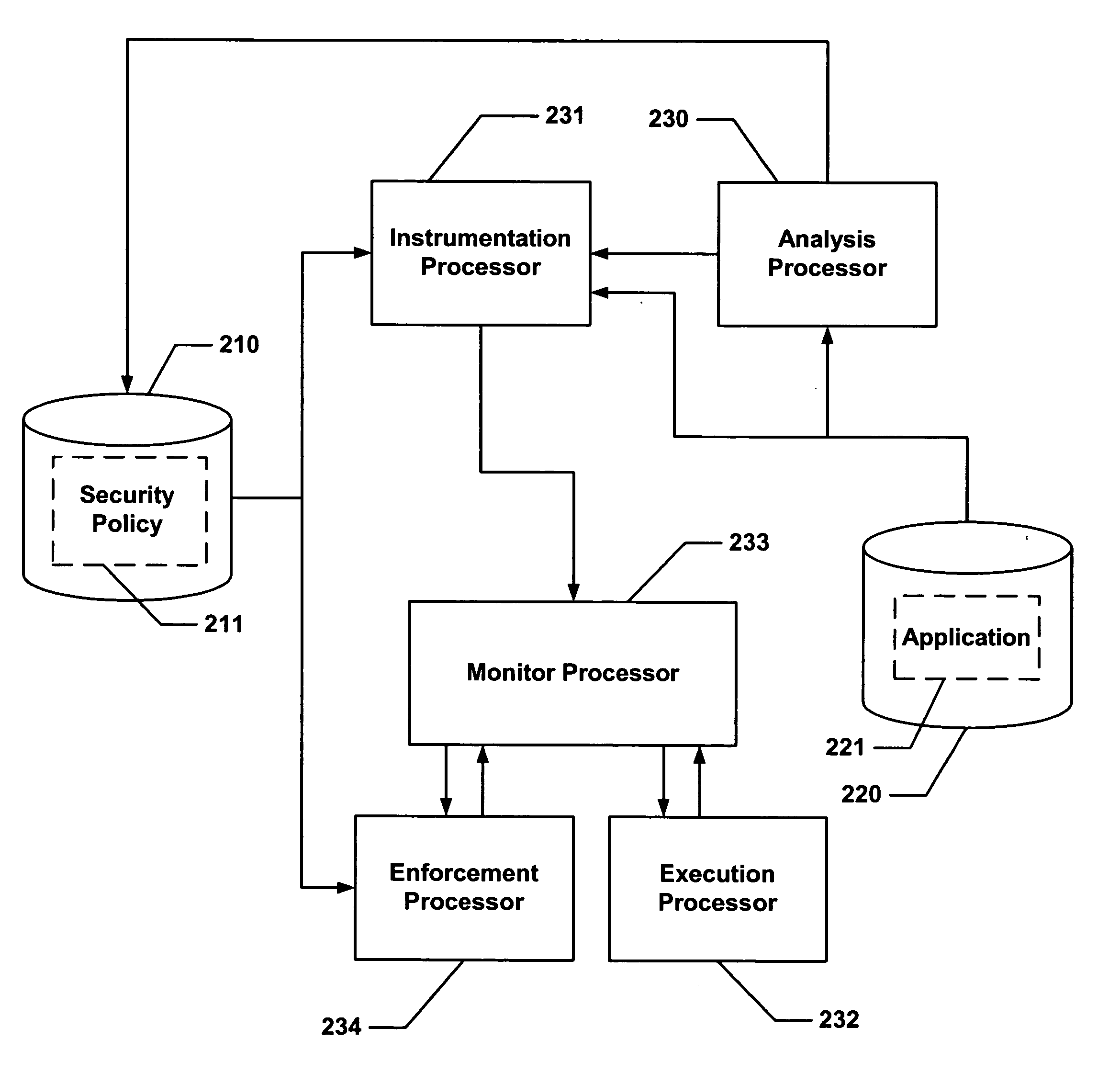
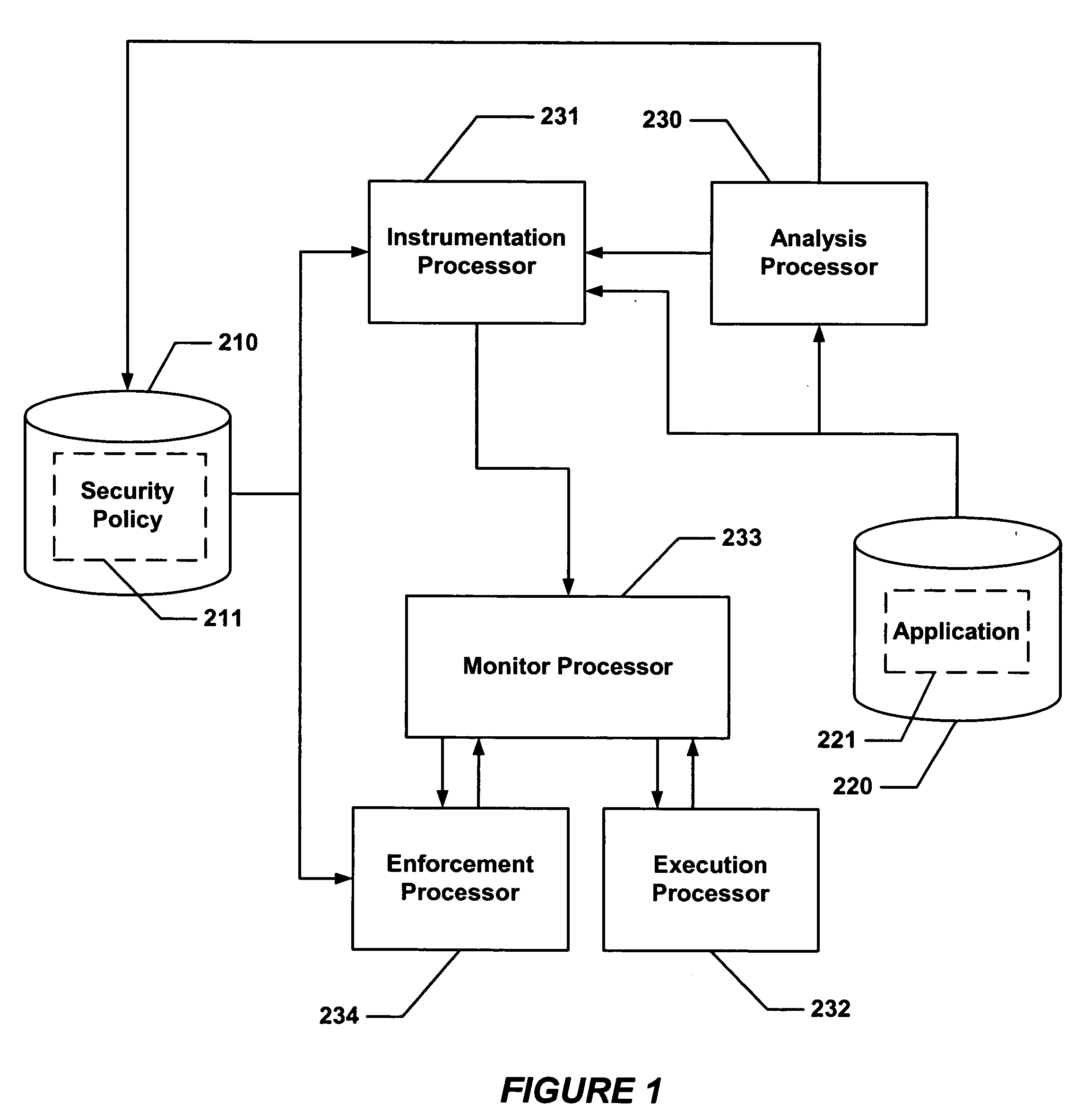
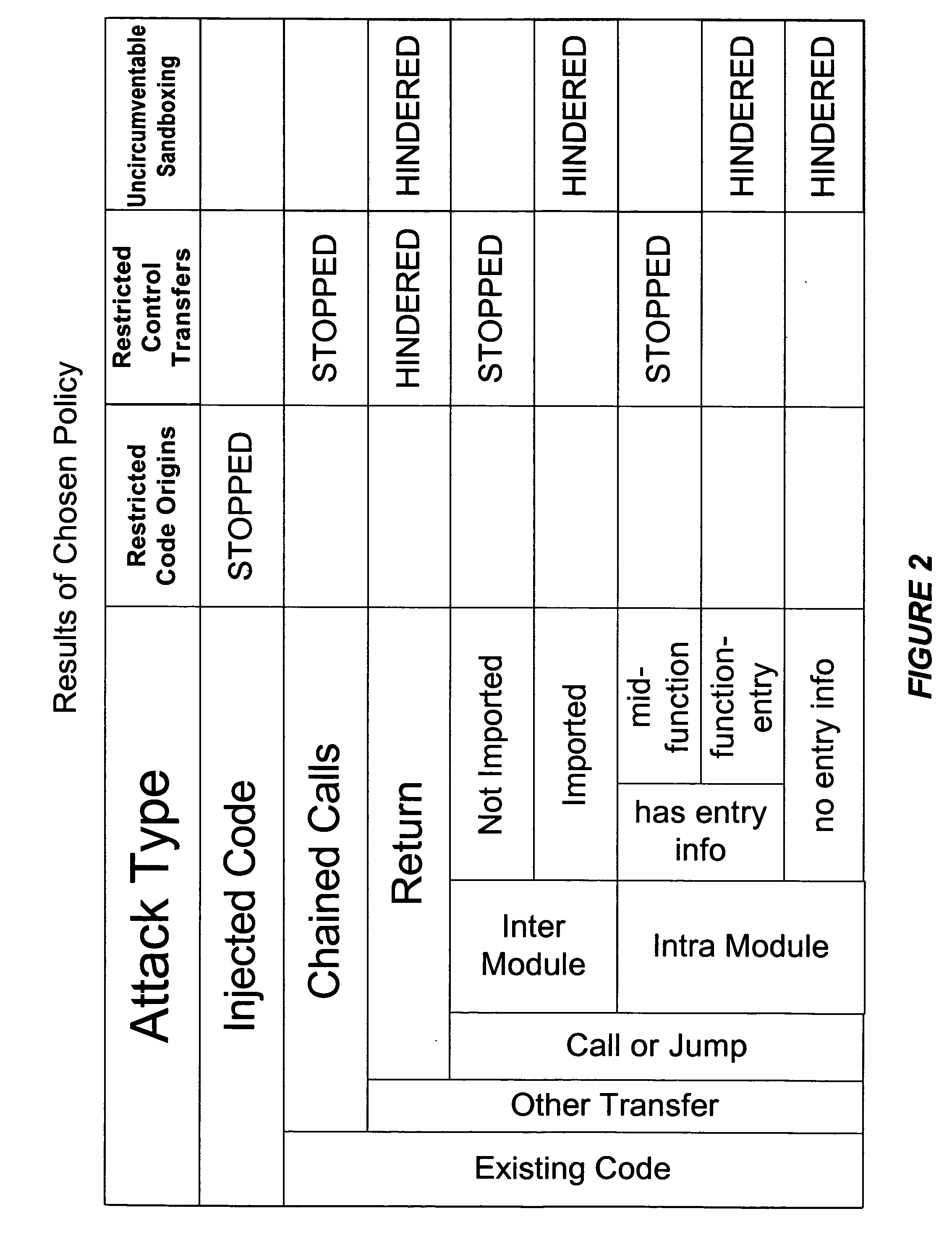
ActiveUS20040133777A1Digital data processing detailsUnauthorized memory use protectionControl flowApplication software
Hijacking of an application is prevented by monitoring control flow transfers during program execution in order to enforce a security policy. At least three basic techniques are used. The first technique, Restricted Code Origins (RCO), can restrict execution privileges on the basis of the origins of instruction executed. This distinction can ensure that malicious code masquerading as data is never executed, thwarting a large class of security attacks. The second technique, Restricted Control Transfers (RCT), can restrict control transfers based on instruction type, source, and target. The third technique, Un-Circumventable Sandboxing (UCS), guarantees that sandboxing checks around any program operation will never be bypassed.
Owner:MASSACHUSETTS INST OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com