Patents
Literature
730 results about "Network Access Control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
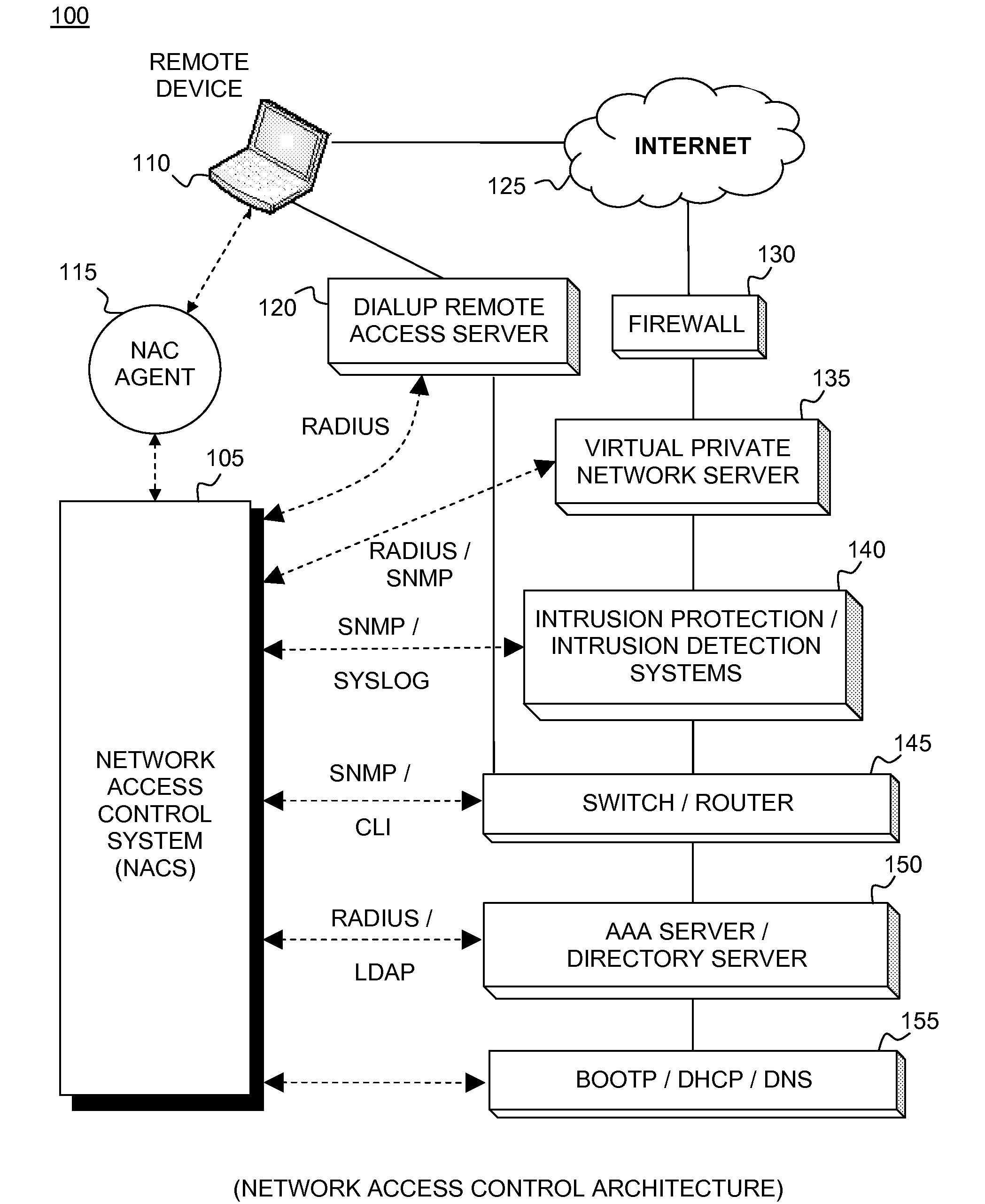
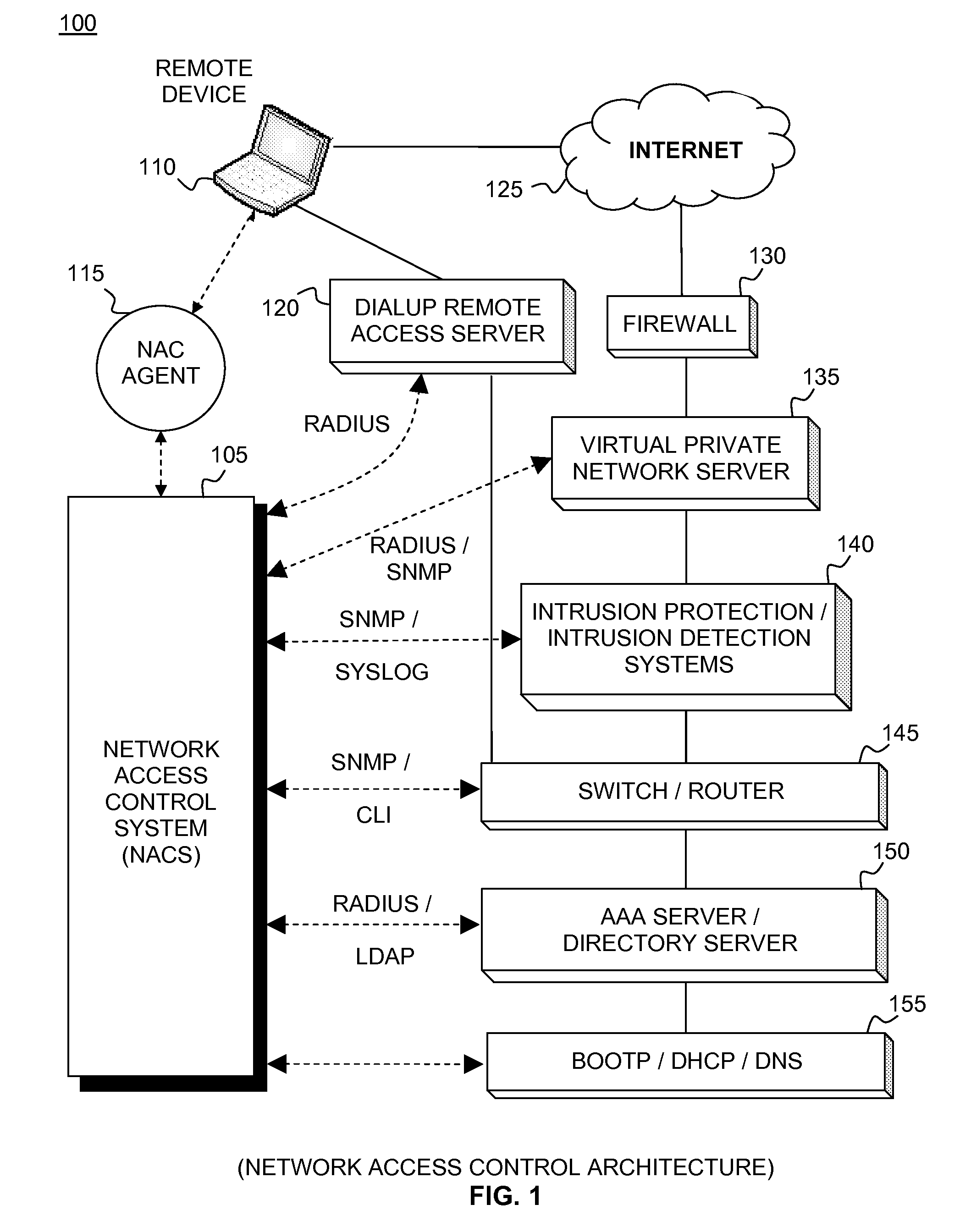
Network Access Control (NAC) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host intrusion prevention, and vulnerability assessment), user or system authentication and network security enforcement.
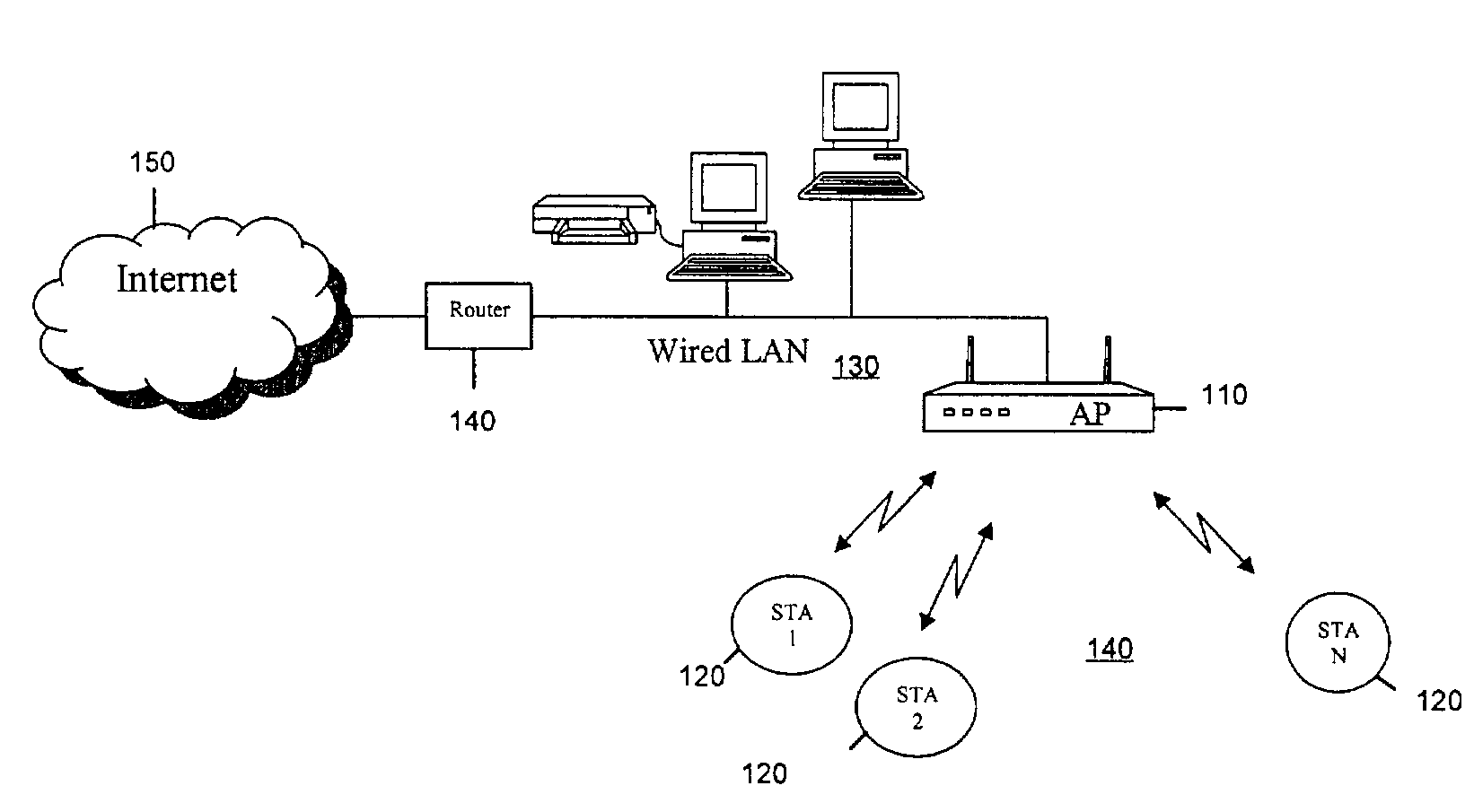
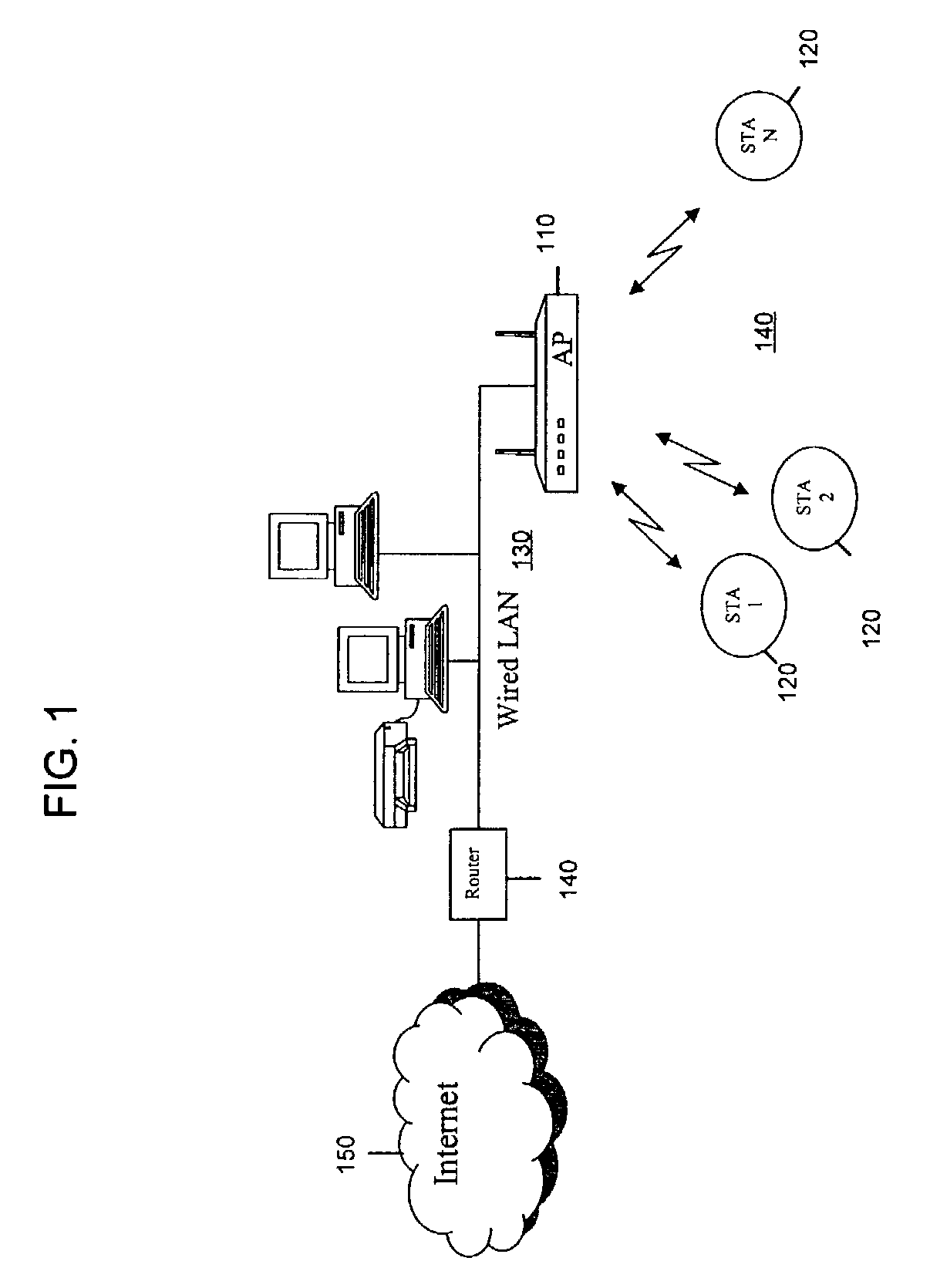
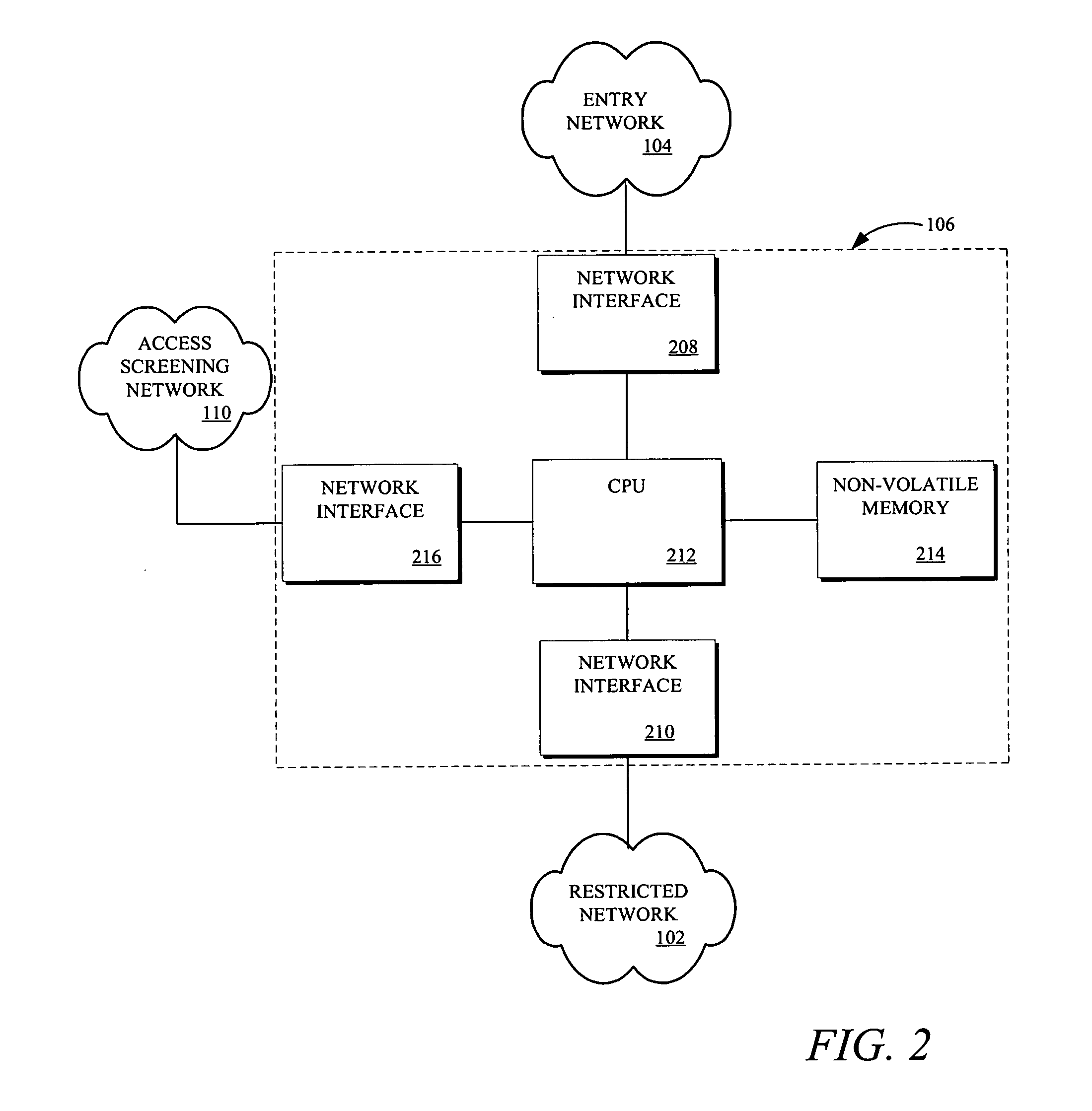
Network appliance for securely quarantining a node on a network
InactiveUS20060164199A1Transformers/inductances magnetic coresData switching networksNetwork Access ControlSecurity policy
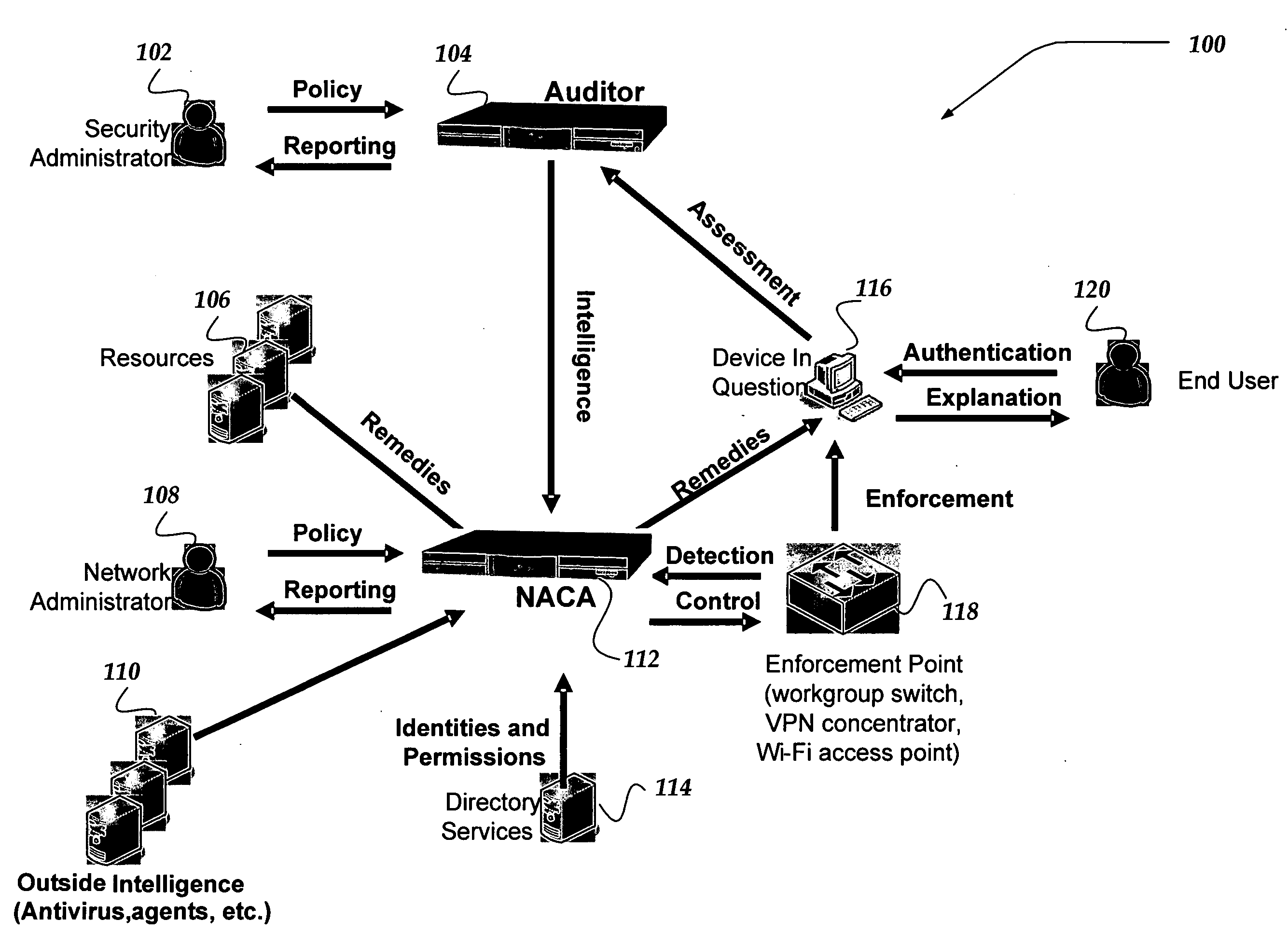
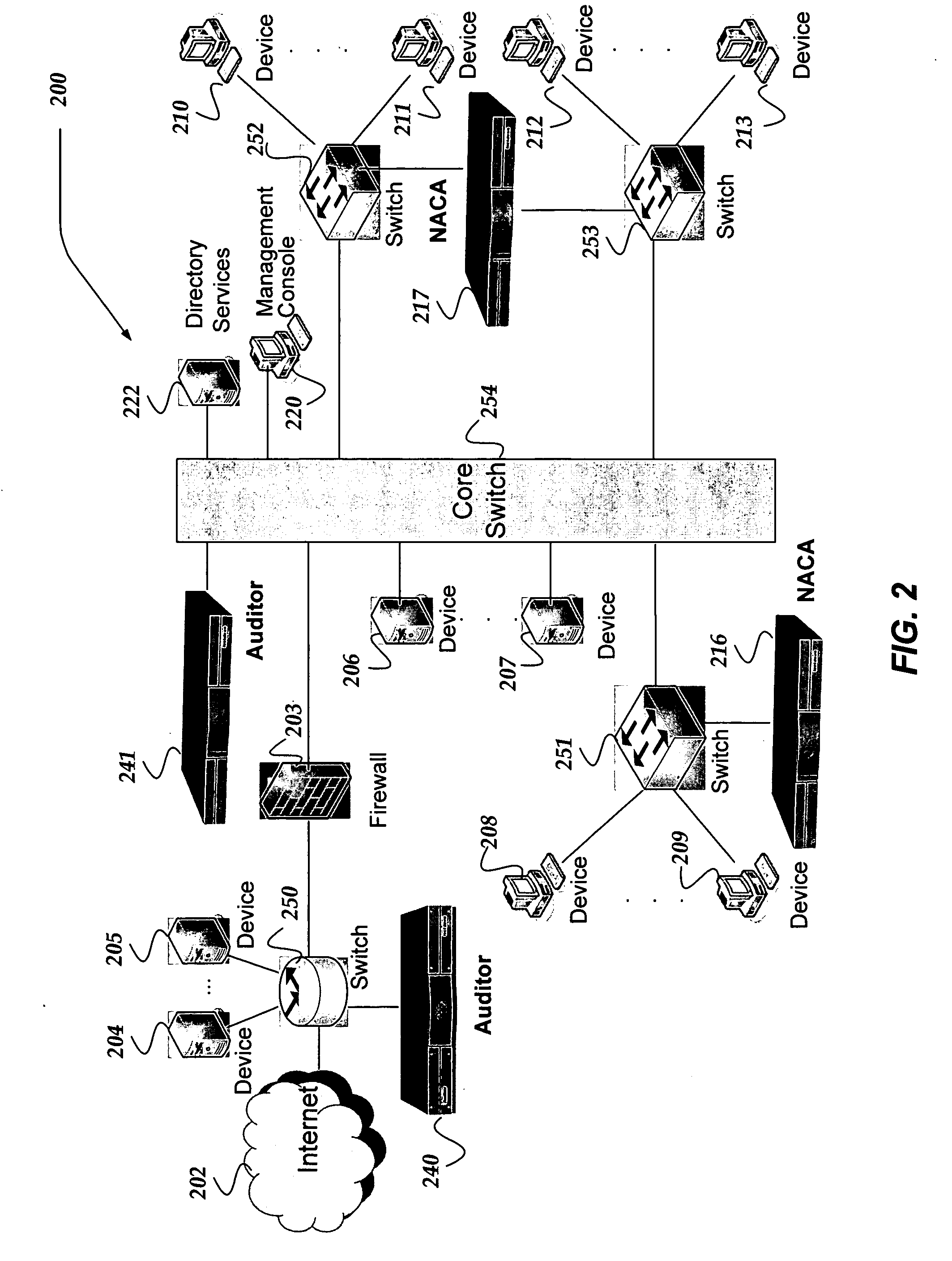
An apparatus, system, and method for managing dynamic network access control. The invention provides services and controlled network access that includes quarantining nodes so that they may be identified, audited, and provided an opportunity to be brought into compliance with a security policy. The invention is configured to detect a device seeking to join the network, and determine if the device is allowed to join the network. If the invention determines that the device is not to be allowed, the device may be quarantined using a VLAN. The suspect device may then be audited for vulnerabilities. If vulnerabilities are identified, remediation may be employed to guide the suspect device, a user, and / or administrator of the suspect device towards a resolution of the vulnerabilities, such that the device may be reconfigured for acceptance onto the network.
Owner:MCAFEE INC
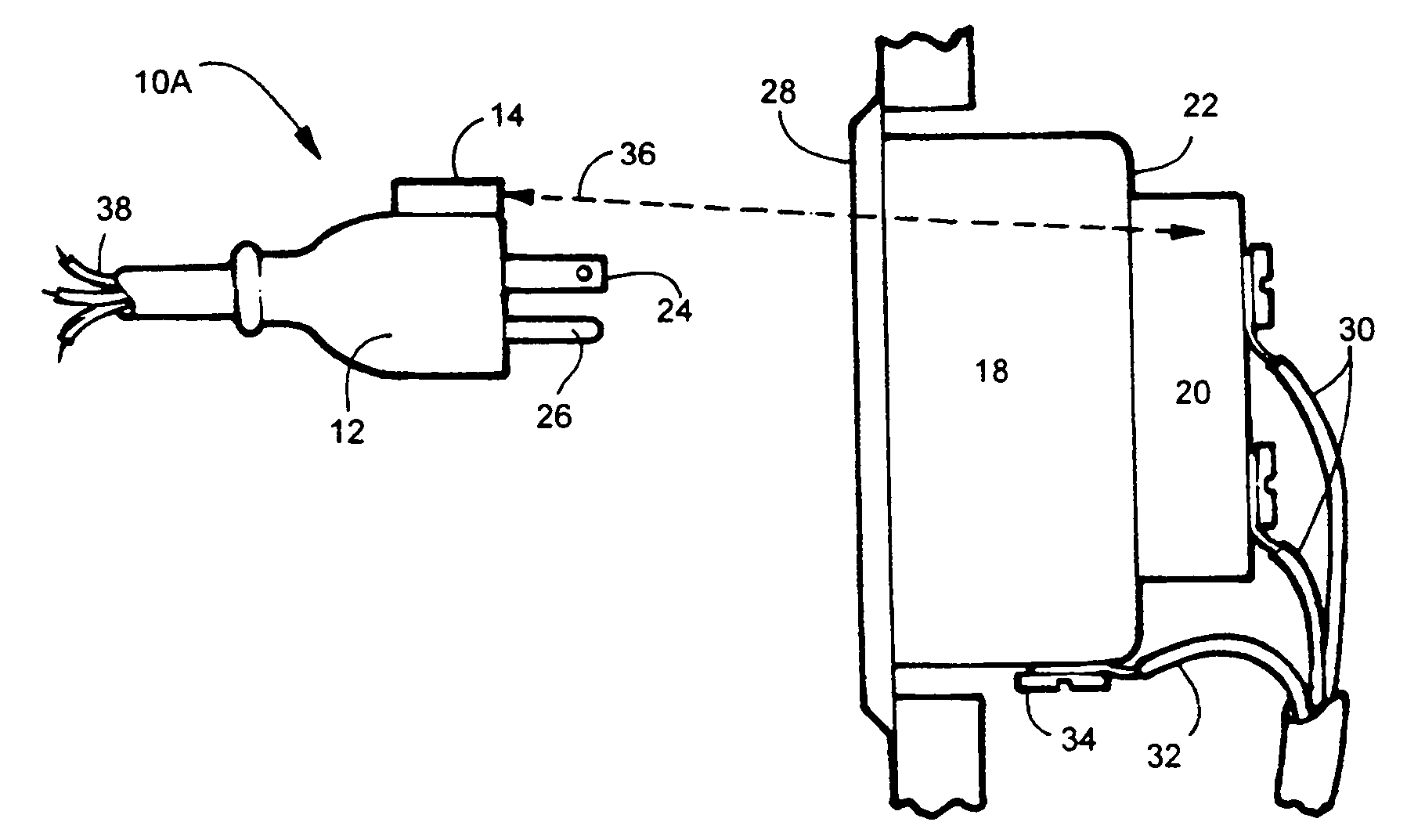
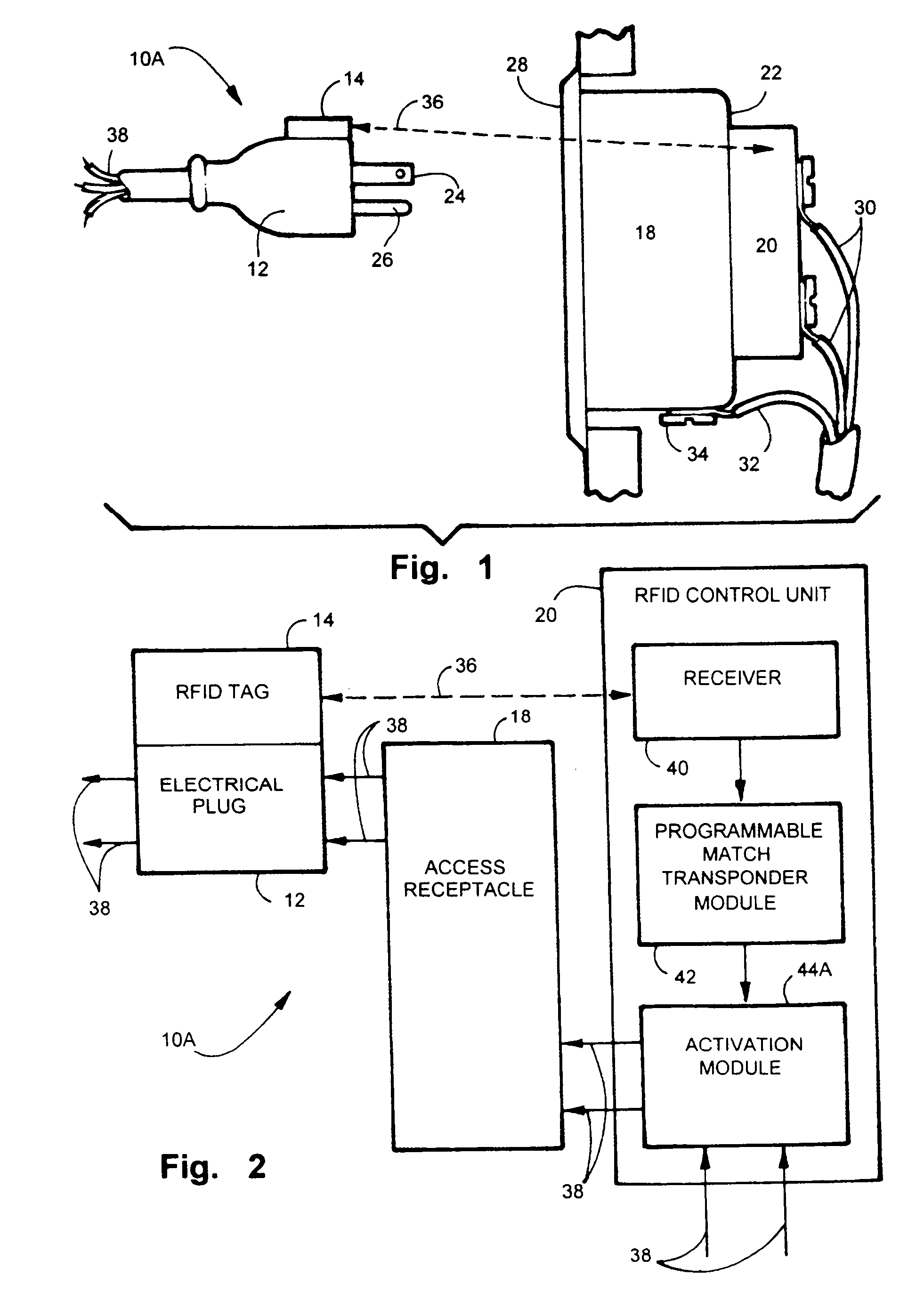
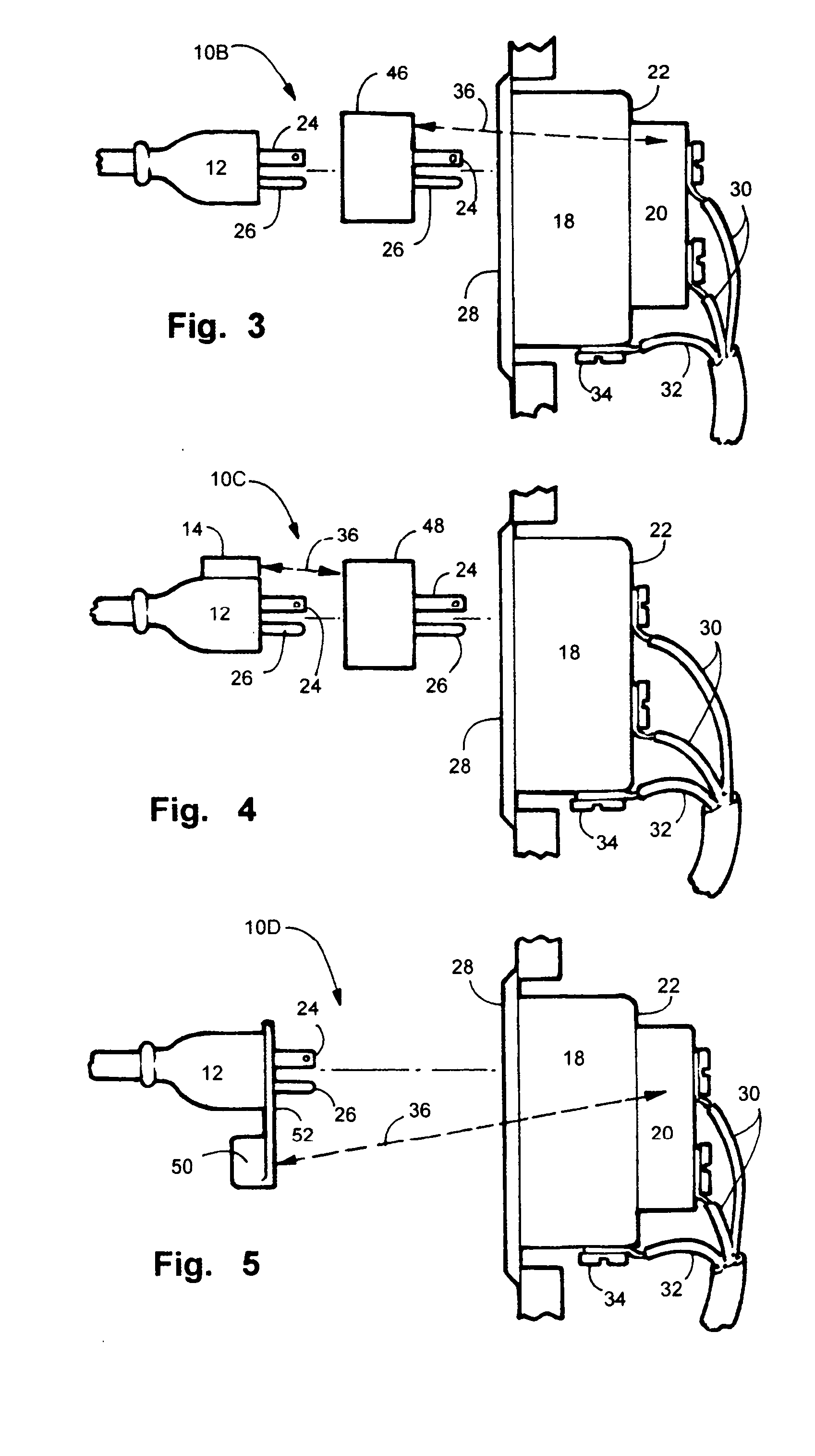
Electric, telephone or network access control system and method
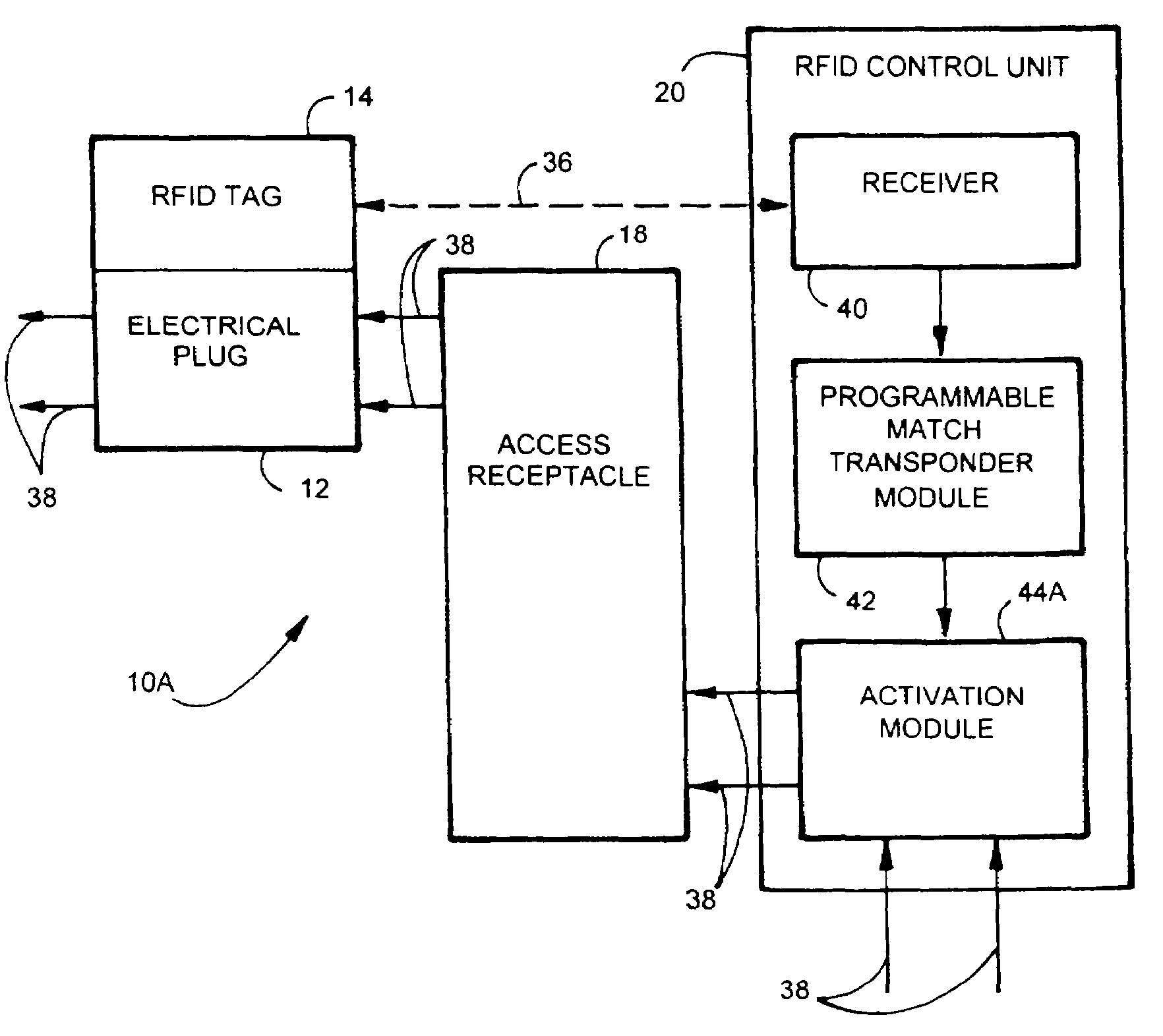
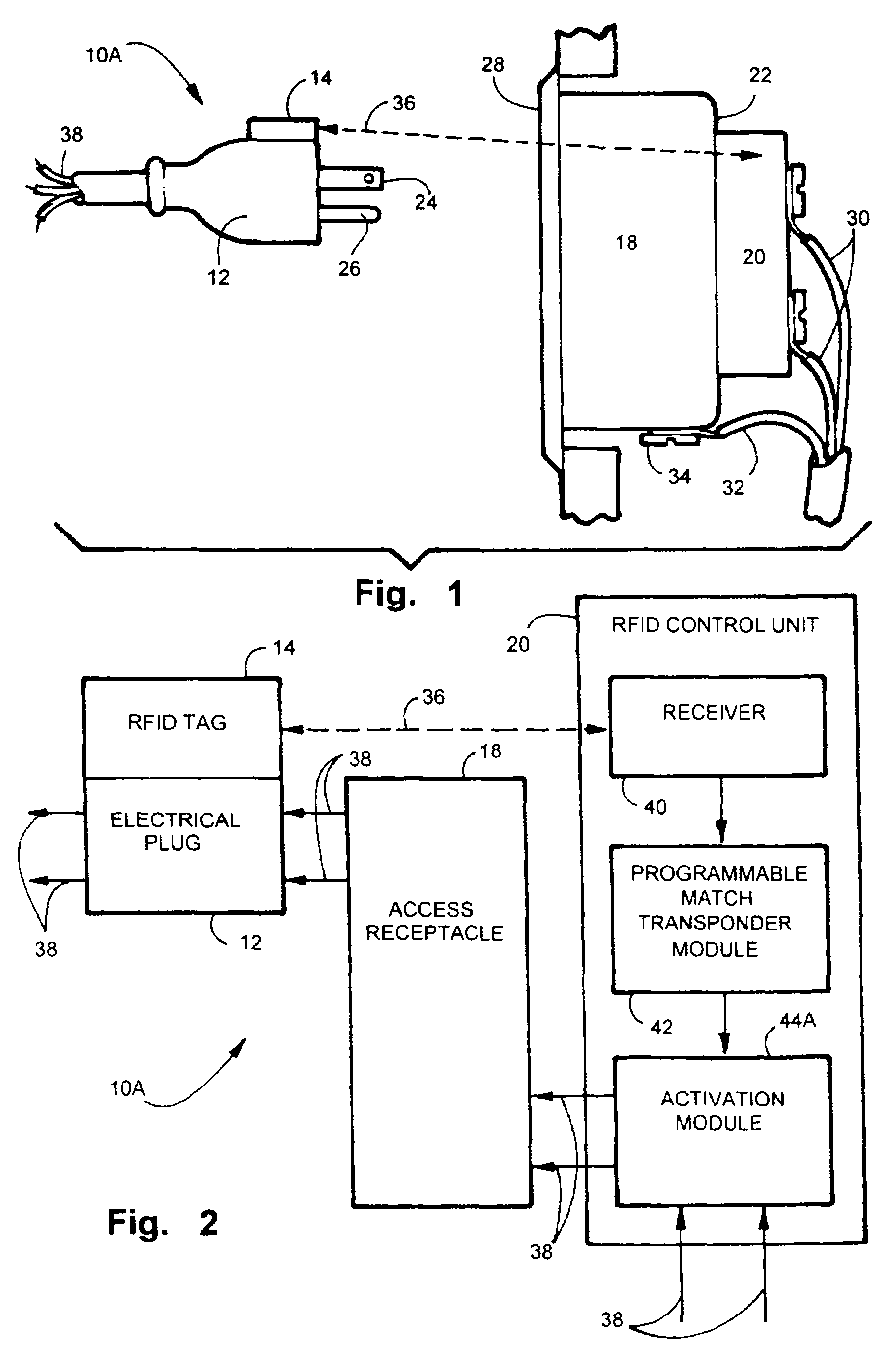
InactiveUS7167078B2EasilyEasy to installElectric signal transmission systemsMultiple keys/algorithms usageElectricityControl system
An apparatus and method for controlling user access to electrical receptacles and telephone and network communications receptacles. The device features a short range radio receiver and one or a plurality of RF energized radio identification tags with transmittable identification transponder codes. The receptacle contains circuitry that detects the immediate presence of energized transponders with proper identification codes and only enables the electric, telephone or network access from the receptacle to become active if the correct matching transponder identification code is present. The tag is a small flexible device having one side that may be attached to the plug or the receptacle or interfaced therebetween. Access to the power or network is allowed for a defined duration of time or only so long as the transponder remains energized and transmits the identification code.
Owner:POURCHOT SHAWN C
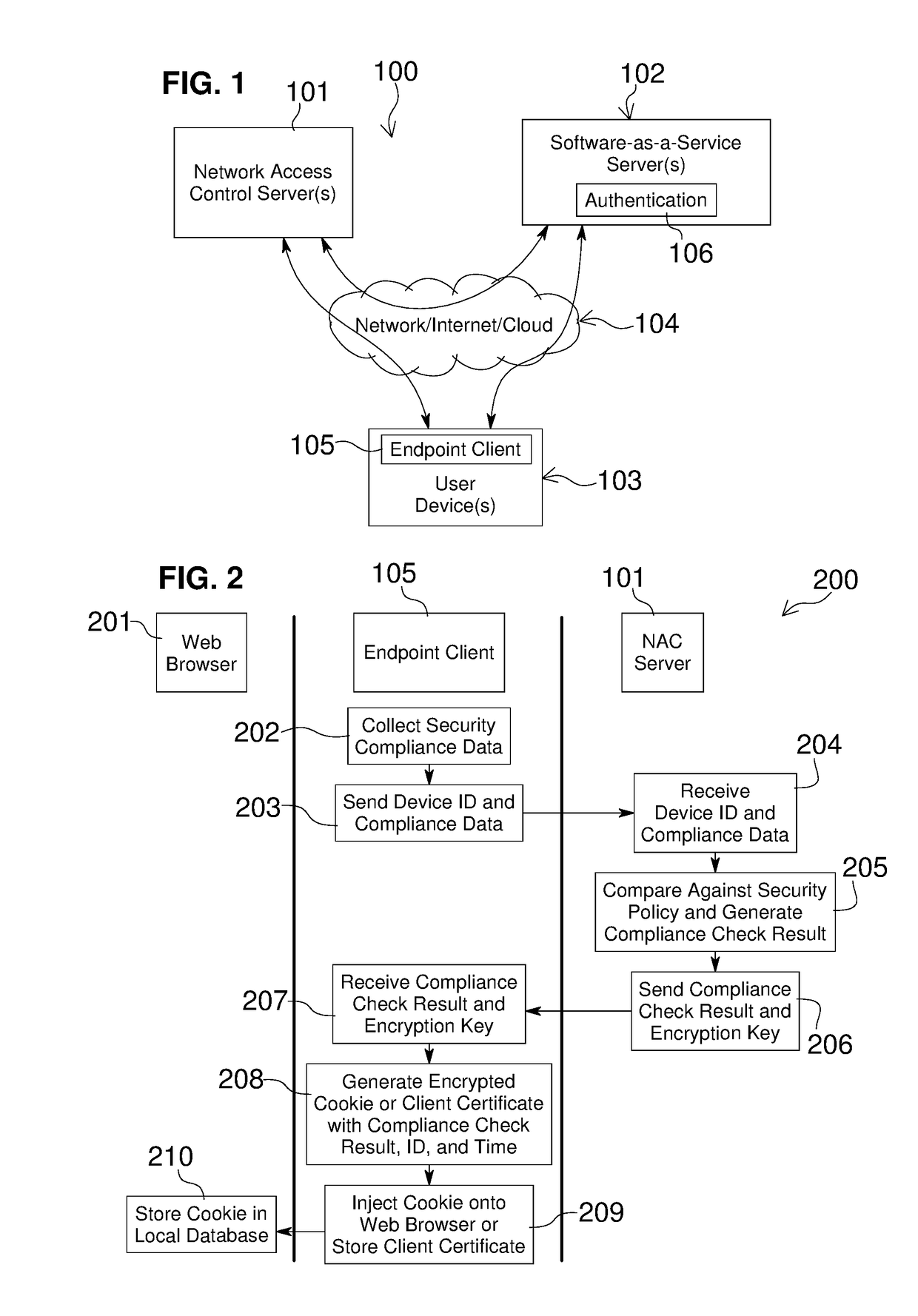
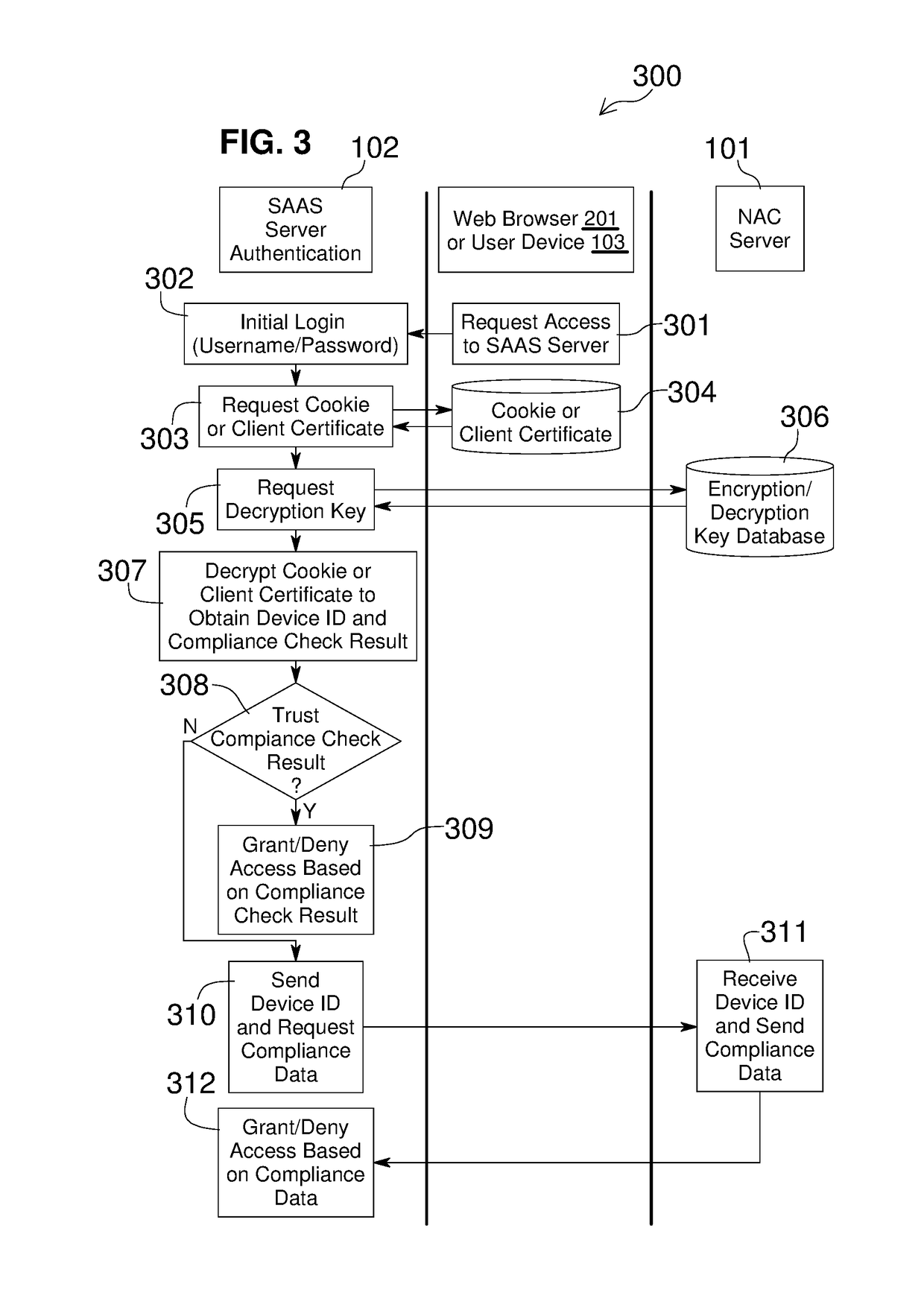
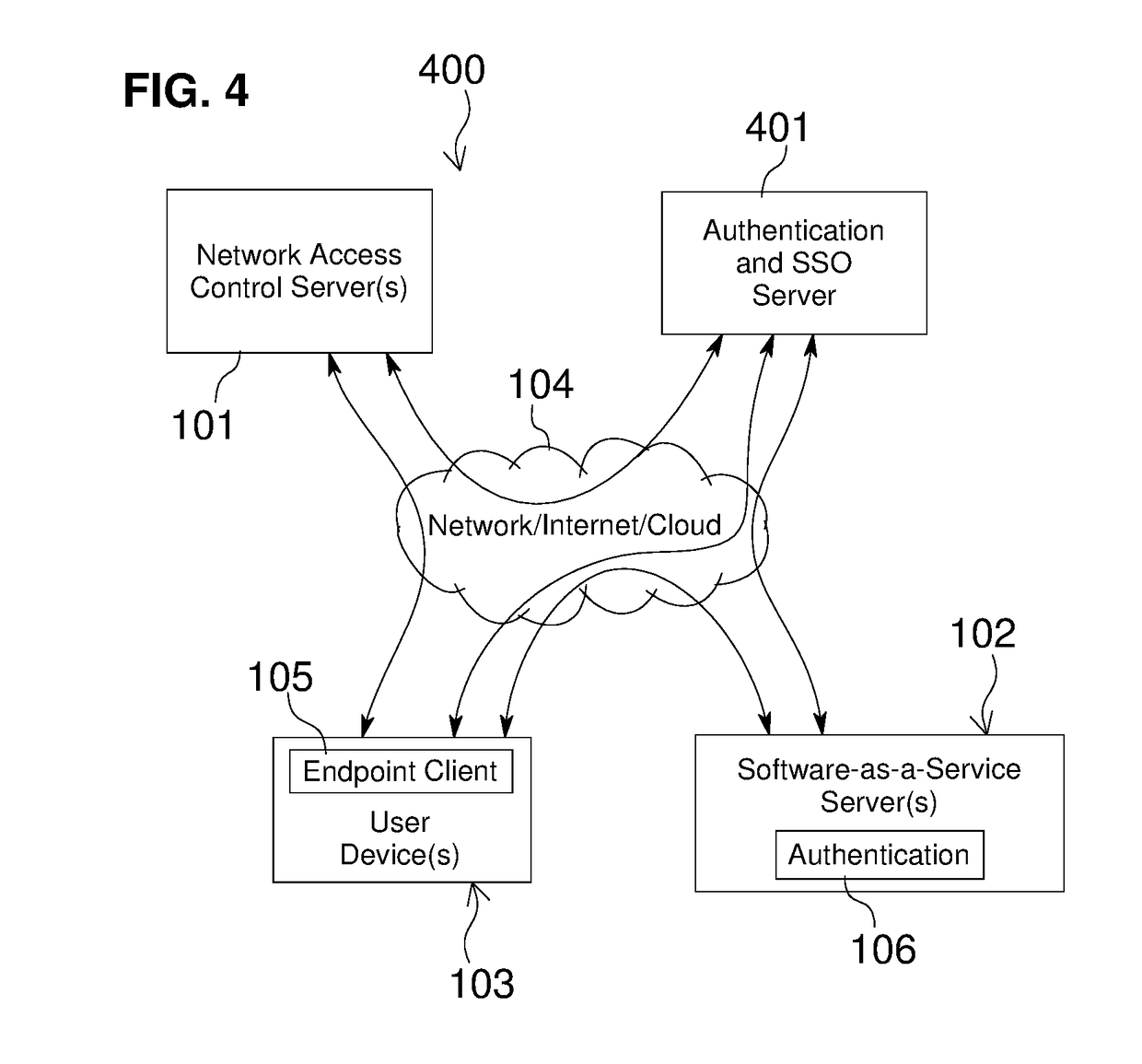
Network Access Control with Compliance Policy Check
Embodiments of the present invention include methods involving an authentication application, a client application, or a combination of a network access control server with the authentication application and the client application. The client application collects compliance data regarding the user device and communicates the compliance data to the network access control server. The network access control server generates a compliance check result based on whether the compliance data indicates that the user device is compliant with a security policy for the software-as-a-service server. The authentication application grants access by the user device when the compliance check result is positive; and the authentication application denies access by the user device when the compliance check result is negative. In some embodiments, the compliance check result or a user device identifier is stored in a web browser cookie or a client certificate on the user device.
Owner:OPSWAT INC
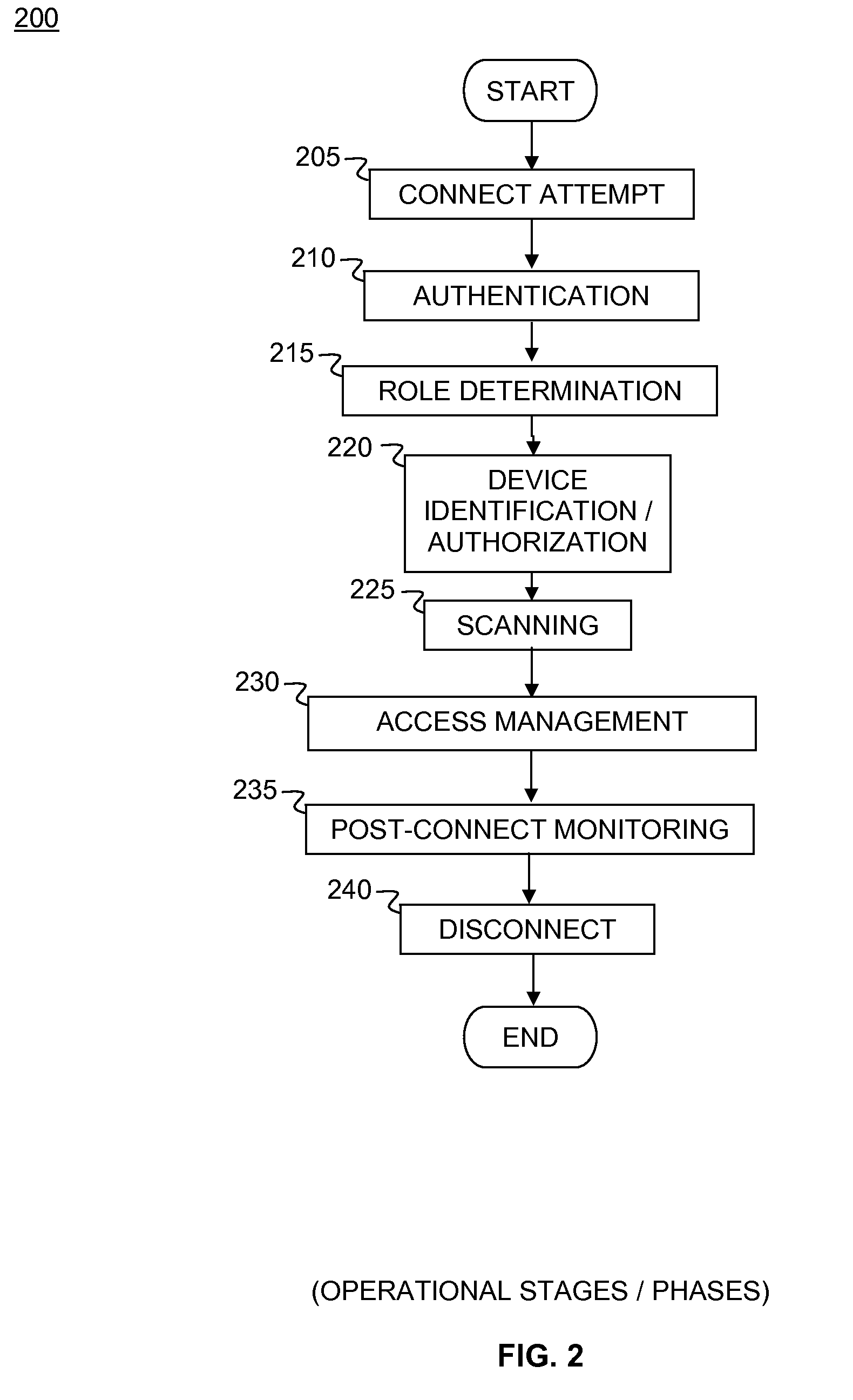
Network access control system and method for devices connecting to network using remote access control methods
ActiveUS20090307753A1Digital data processing detailsMultiple digital computer combinationsControl systemUser authentication
A system and method for network access control (NAC) of remotely connected devices is disclosed. In embodiments, agents support role mapping and policy-based scanning. Embodiments automatically perform authentication, assessment, authorization, provisioning, and remediation. Capabilities include user authentication, role-based authorization, endpoint compliance, alarms and alerts, audit logs, location-based rules, and policy enforcement. Processes collect information about the user as well as the host being used from sources including, but not limited to, LDAP, the remote access device, and the agent. Once this data has been obtained, embodiments construct a comprehensive model of the host. This model is subsequently used to govern the actual host's network access when it connects to the network. Passive monitoring includes vulnerability scanning to control access rights throughout the duration of the connection.
Owner:FORTINET
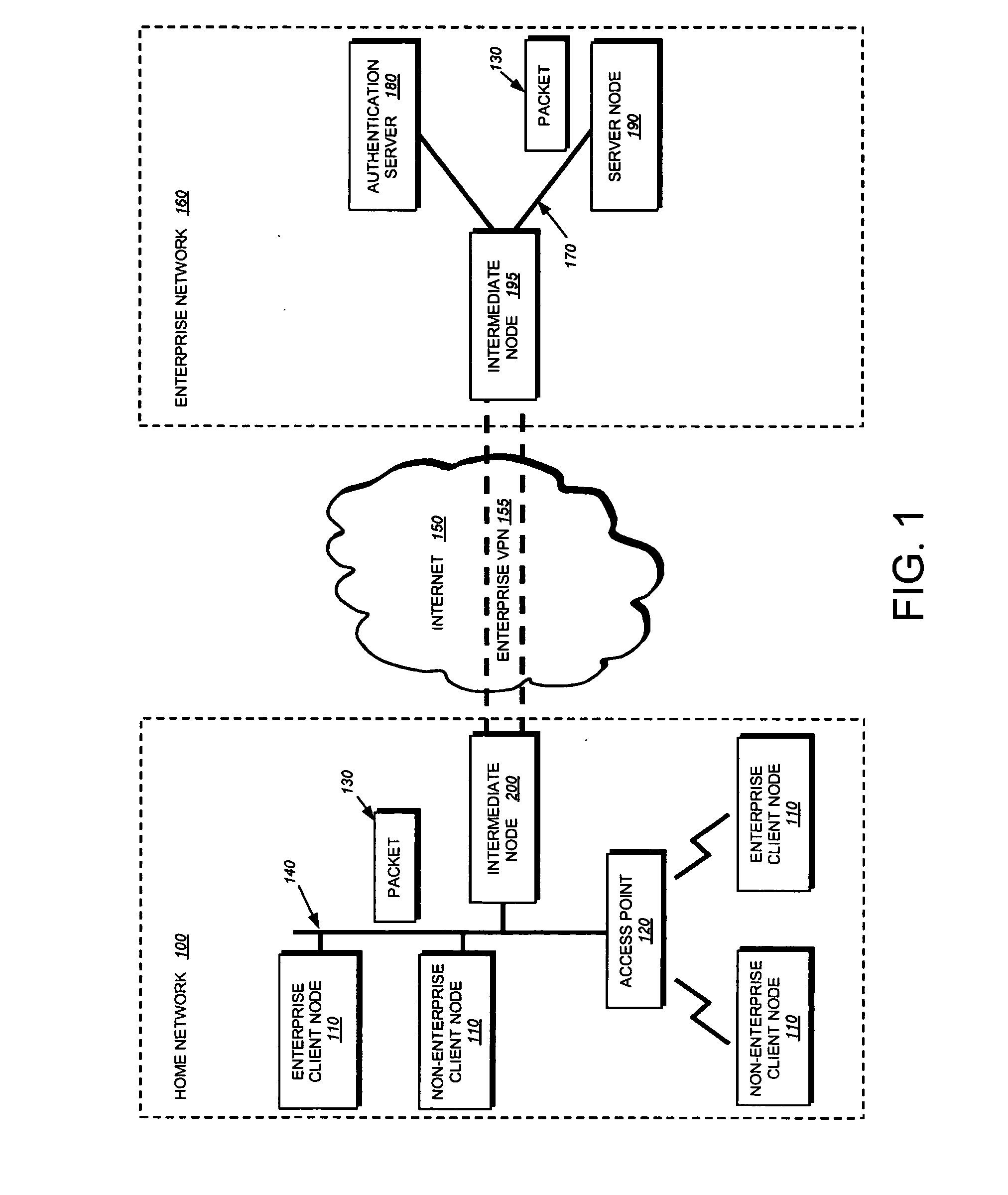
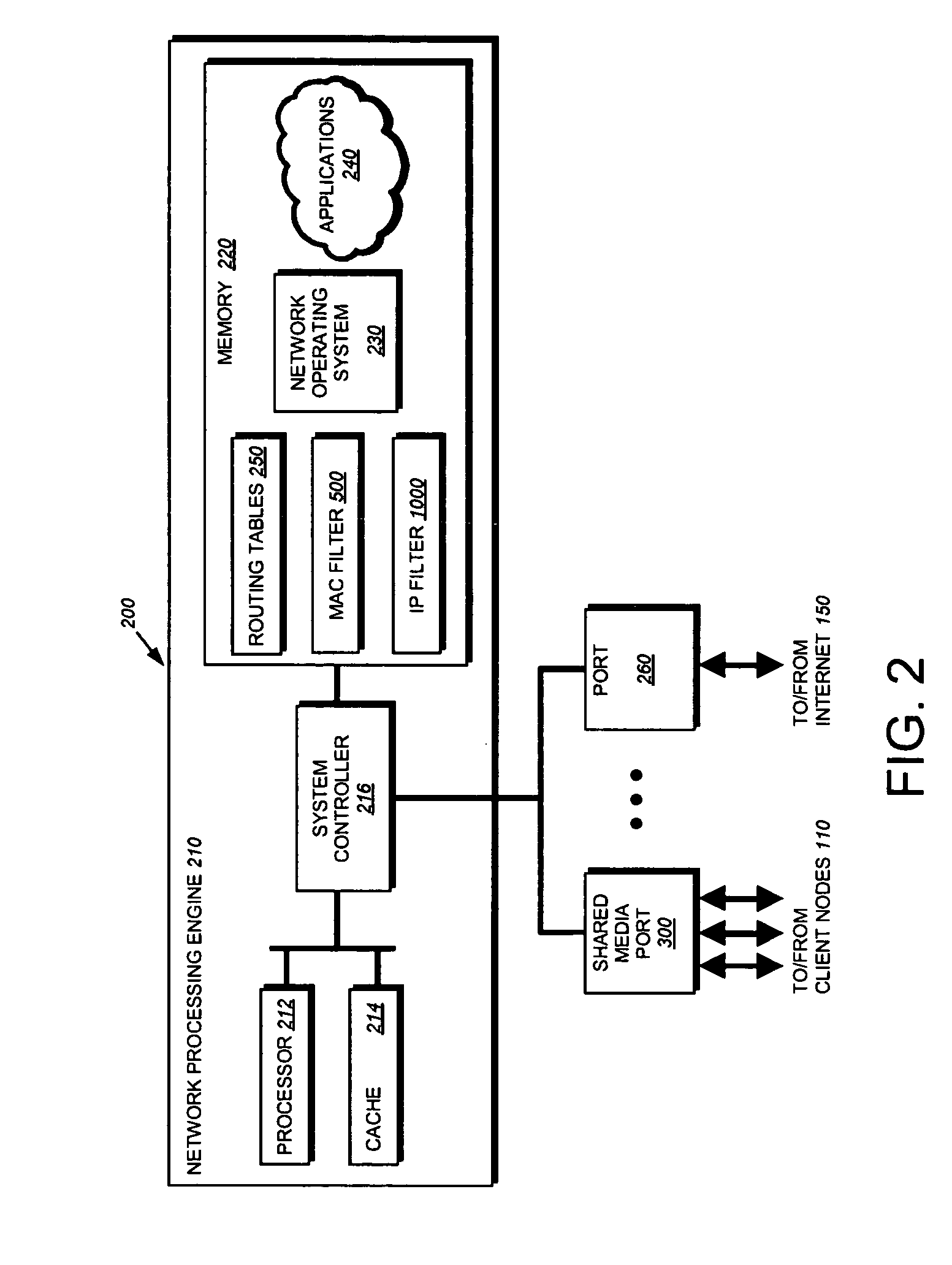
802.1X authentication technique for shared media
ActiveUS20050125692A1Increase network-access securityConvenient access controlDigital data processing detailsUser identity/authority verificationClient-sideNetwork Access Control
The present invention provides a technique for securely implementing port-based authentication on a shared media port in an intermediate node, such as a router. To that end, the invention provides enhanced port-based network access control that includes client-based control at the shared media port. Unlike previous implementations, the port does not permit multiple client nodes to access a trusted subnetwork as soon as a user at any one of those nodes is authenticated by the subnetwork. Instead, port-based authentication is performed for every client node that attempts to access the trusted subnetwork through the shared media port. As such, access to the trusted subnetwork is not compromised by unauthenticated client nodes that “piggy-back” over the shared media port after a user at another client node has been authenticated by the trusted subnetwork.
Owner:CISCO TECH INC
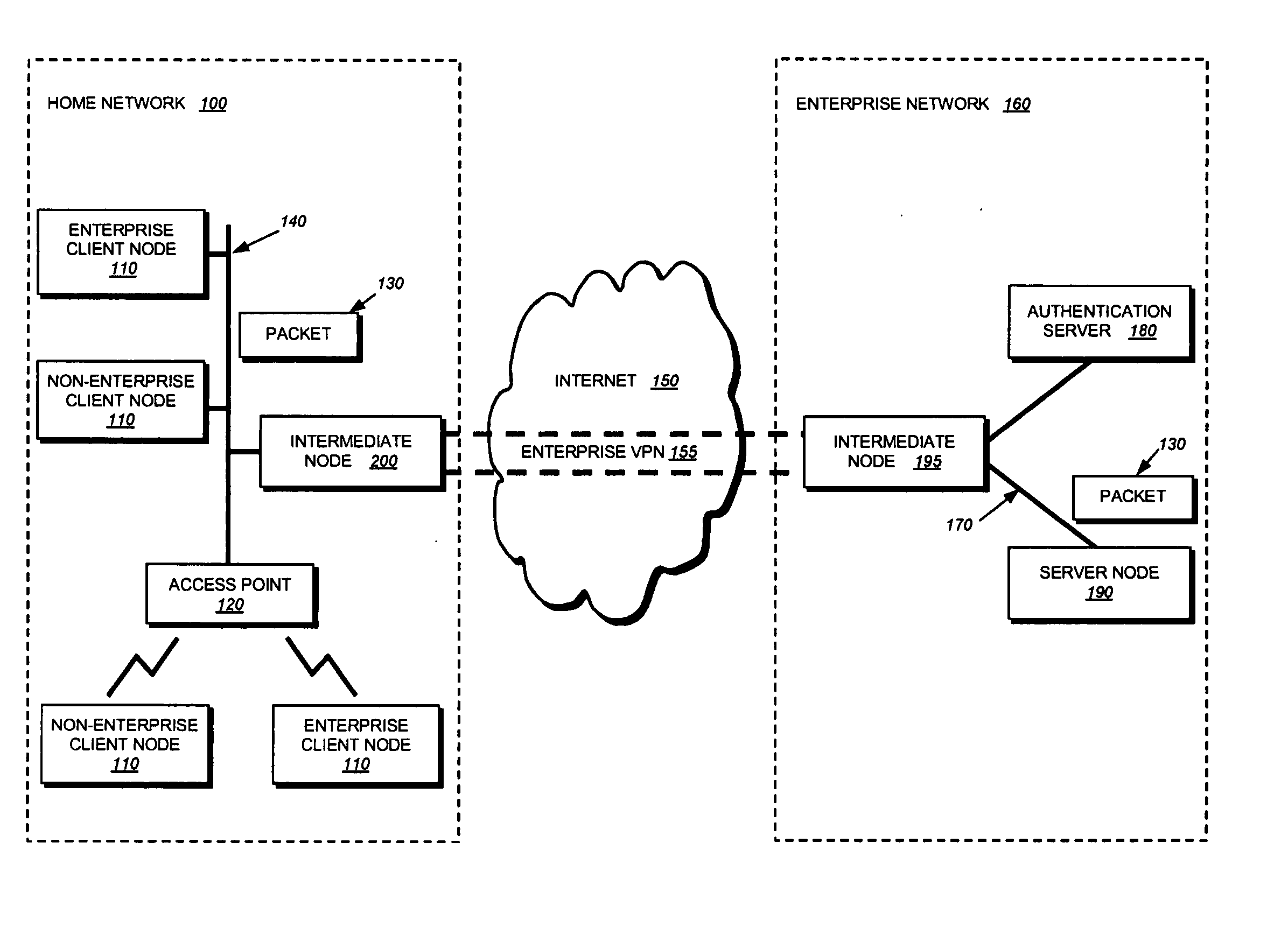
Method and system for enterprise network access control and management for government and corporate entities
InactiveUS20090254392A1Data processing applicationsComputer security arrangementsNetwork Access ControlIdentity management
A method, system, computer program product, and devices for enterprise network access control and management for Government and Corporate entities, including interagency identity management; connectors and controls; an interagency directory services transformation service; a user / duty position resolving service; role-based encryption key management; role-based business process modeling; and proximity-based access control enabled by user-role-track association.
Owner:ZANDER VAN S
Electric, telephone or network access control system and method
InactiveUS20050184856A1EasilyEasy to installElectric signal transmission systemsUnauthorised/fraudulent call preventionControl systemRadio receiver
An apparatus and method for controlling user access to electrical receptacles and telephone and network communications receptacles. The device features a short range radio receiver and one or a plurality of RF energized radio identification tags with transmittable identification transponder codes. The receptacle contains circuitry that detects the immediate presence of energized transponders with proper identification codes and only enables the electric, telephone or network access from the receptacle to become active if the correct matching transponder identification code is present. The tag is a small flexible device having one side that may be attached to the plug or the receptacle or interfaced therebetween. Access to the power or network is allowed for a defined duration of time or only so long as the transponder remains energized and transmits the identification code.
Owner:POURCHOT SHAWN C
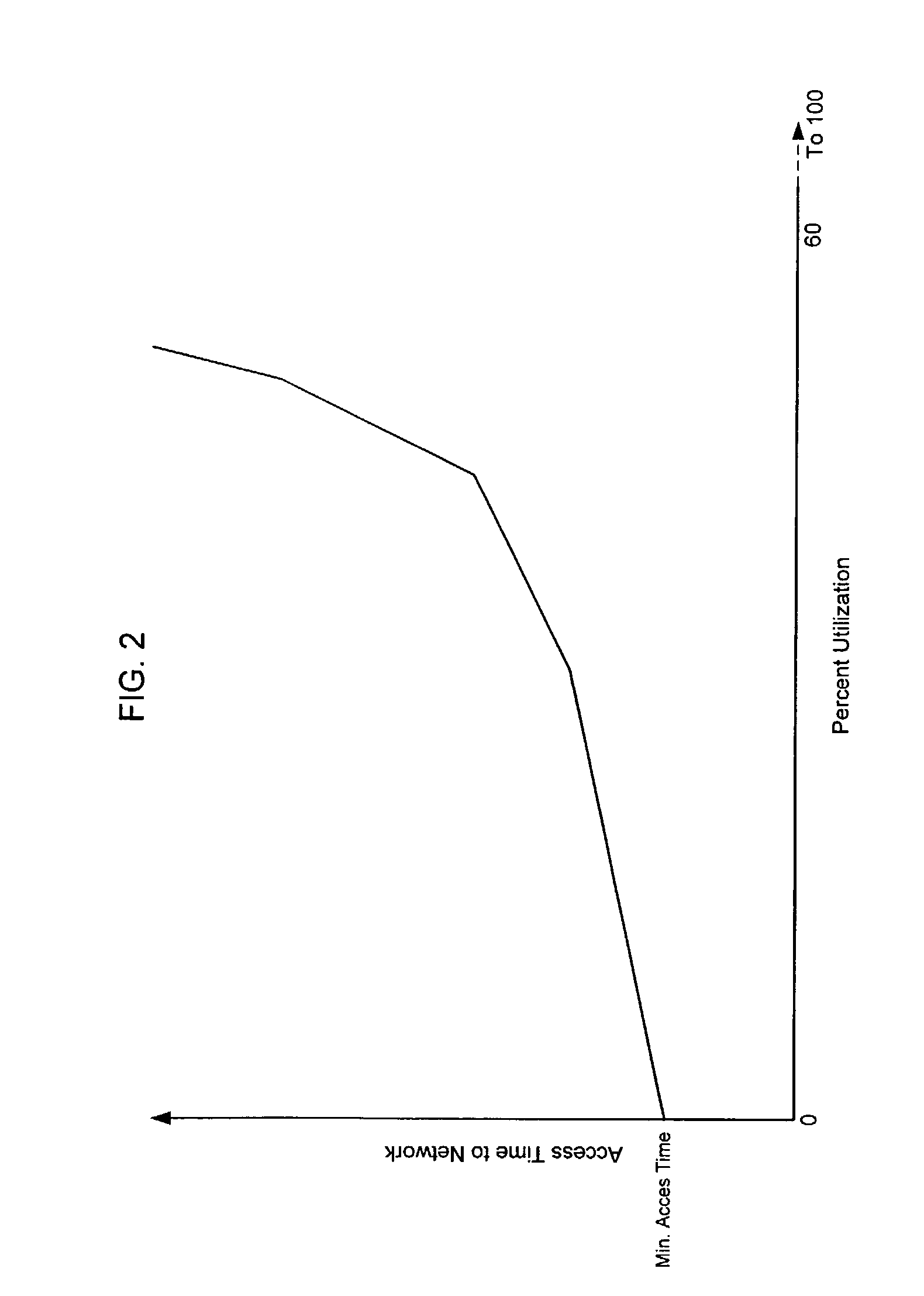
Throughput in multi-rate wireless networks using variable-length packets and other techniques
InactiveUS7248604B2Improve throughputImprove system throughputNetwork traffic/resource managementNetwork topologiesNetwork packetData rate
In a wireless communication network having a plurality of devices operating at different data rates that contend for access to the network, a method is provided that assigns network access parameters to one or more of the devices so as to control throughput on the network. Examples of network access control parameters are the maximum data packet size and the contention window size. Generally, the network access control parameter for slower data rate users is configured so that they do not occupy the network a disproportionate amount of time compared to faster data rate users.
Owner:IPR LICENSING INC
Multiple security layers for time-based network admission control
InactiveUS20100043066A1Reduce energy consumptionOptimize networkDigital data processing detailsUser identity/authority verificationComputer methodsNetwork Access Control
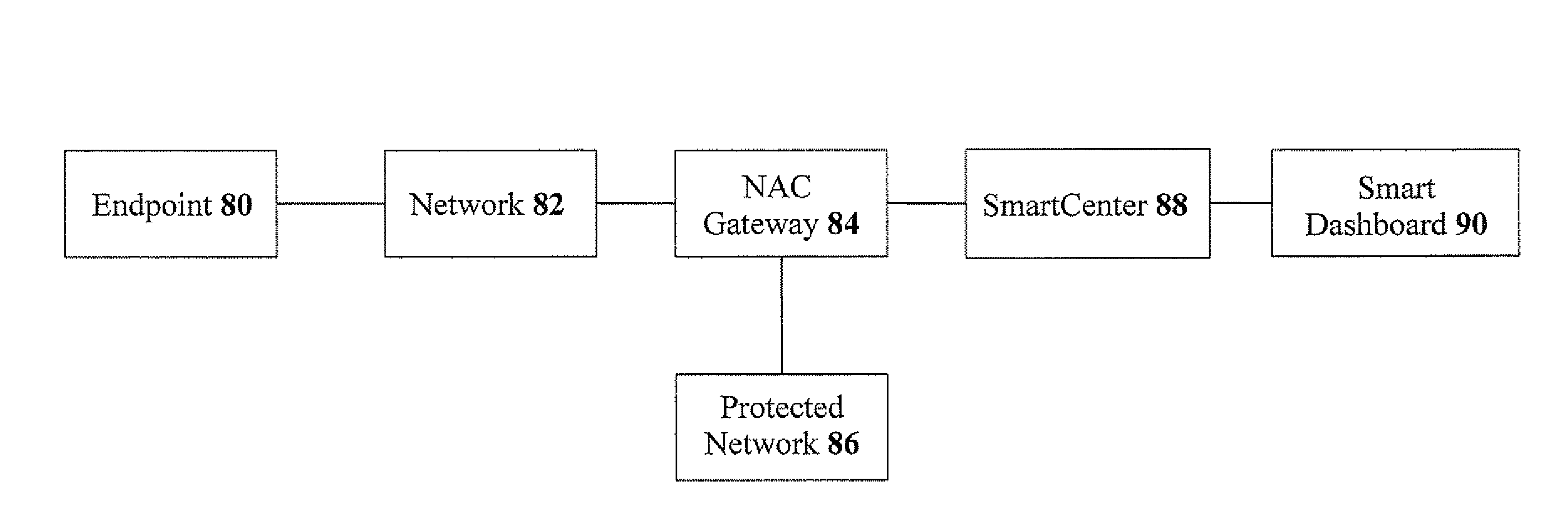
Embodiments of the present invention include a computer method of controlling access to a computer-based network comprising: (i) receiving an indication of an attempt to gain access to a computer-based network; (ii) applying a respective network access control policy to determine whether to allow the attempt to gain access to the computer-based network at each of multiple security layers; and (iii) allowing or blocking the attempt to gain access through the security layer to the computer-based network based on the application of the respective network access control policy at each security layer. Other embodiments include a computer method of controlling access to a computer-based network comprising: (a) scanning a host computer for viruses; (b) temporarily disabling a firewall of the host computer during an audit; and (c) shutting down high risk services running on the host computer.
Owner:NETCLARITY
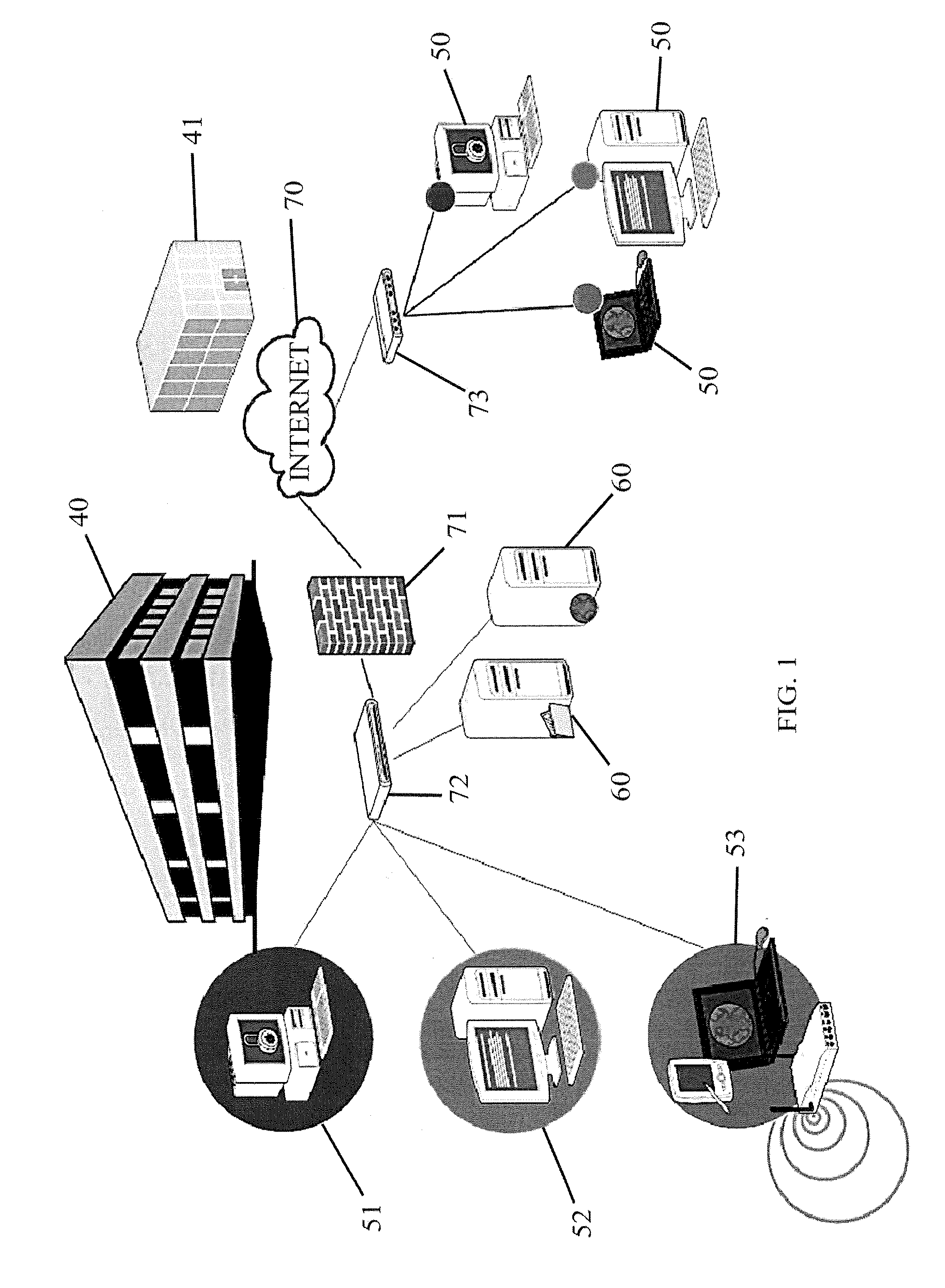
Interactive network access controller
InactiveUS20070220252A1Limited networkingUser identity/authority verificationNetwork Access ControlCommunication device
Methods (400, 500) and systems (100, 600) for interactively controlling access to a communication network (102) are disclosed. In one embodiment, a user is queried (600) on whether to allow a communication device (118) to access the network (102) and the communication device (118) is allowed access if the user actively gives permission (506). In one embodiment, the methods and systems of this invention allow interactive Media Access Control MAC address filtering of communication devices (118) attempting to access the network (102), for example wireless communication devices.
Owner:SINKO MICHAEL JOSEPH
System and method for a group-based network access control for a computer
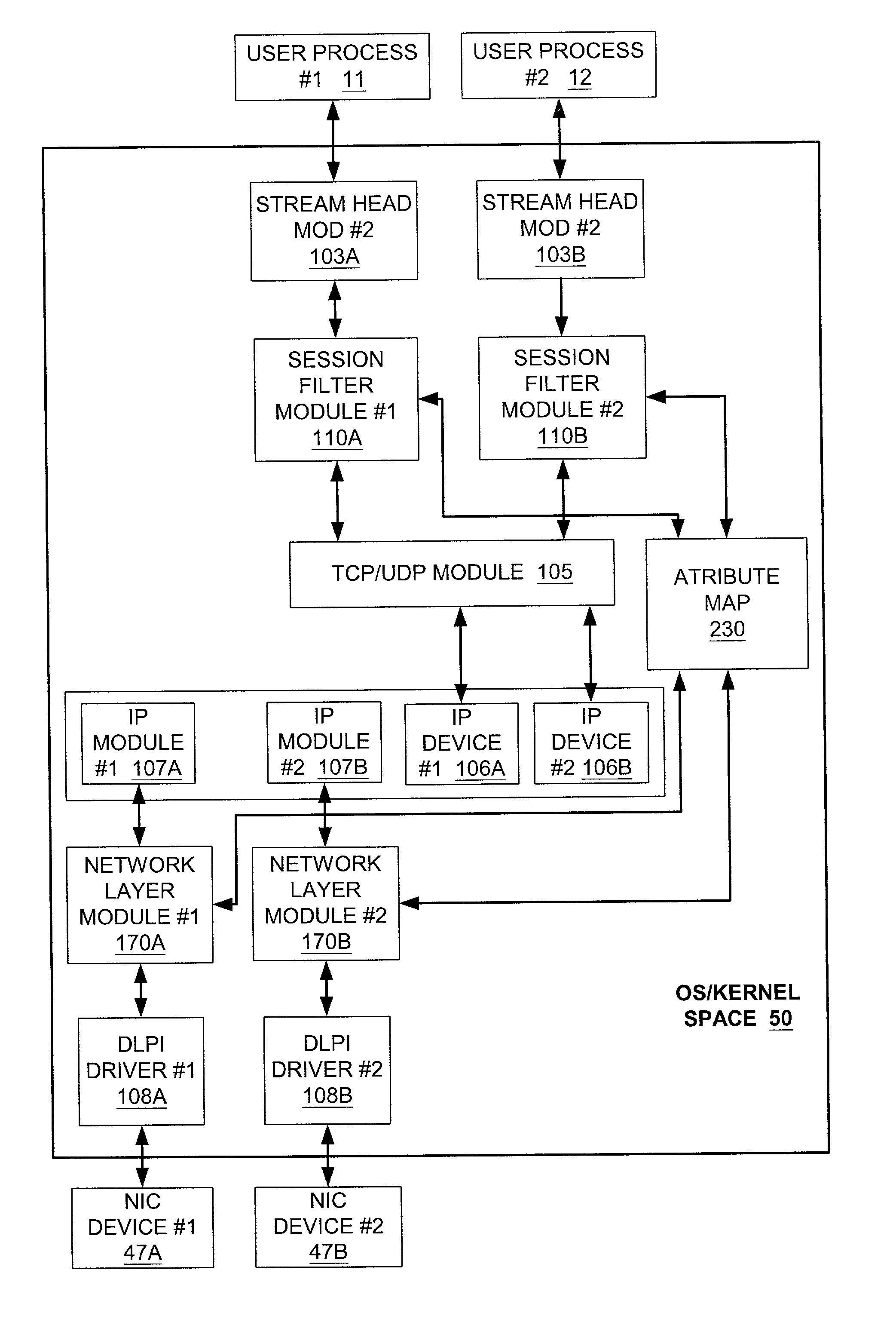
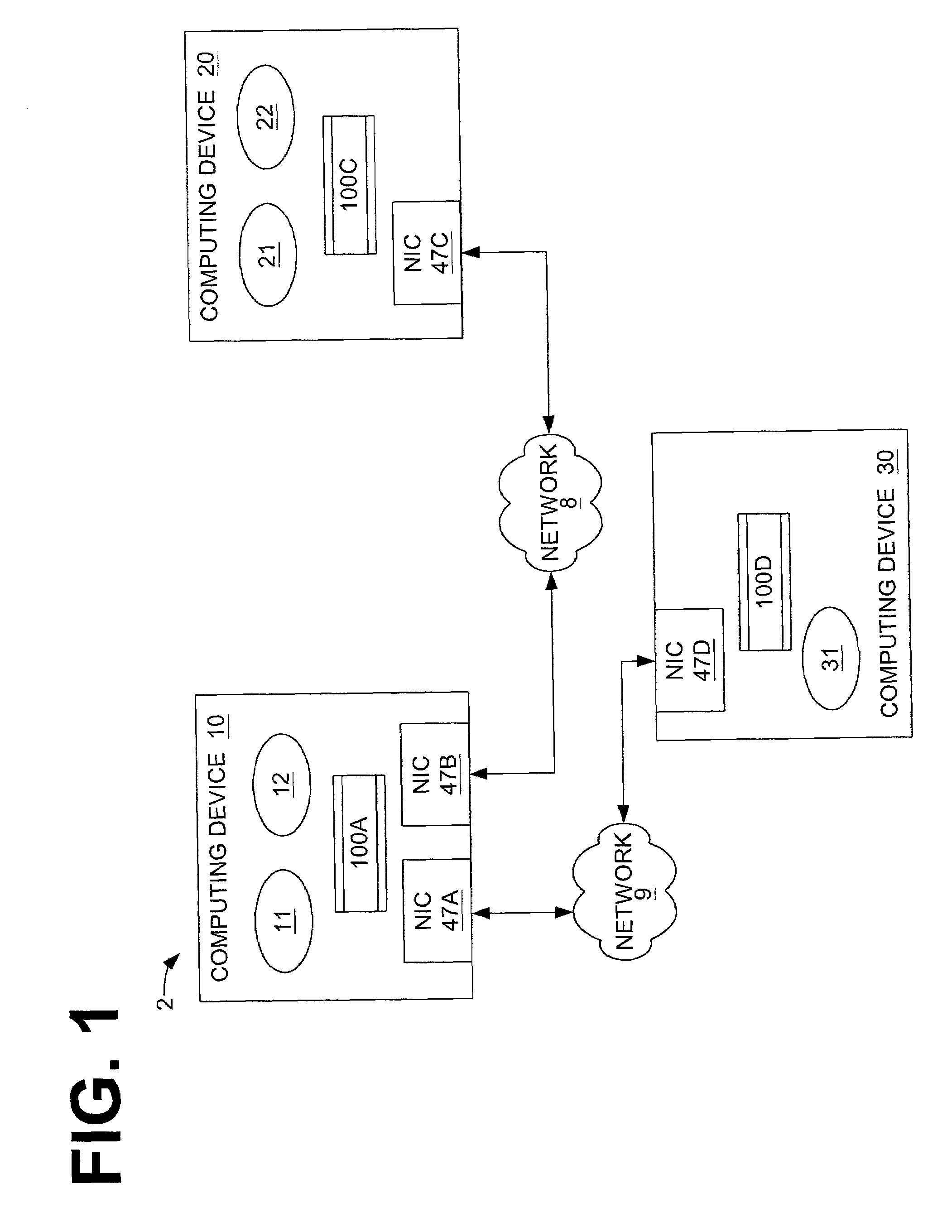
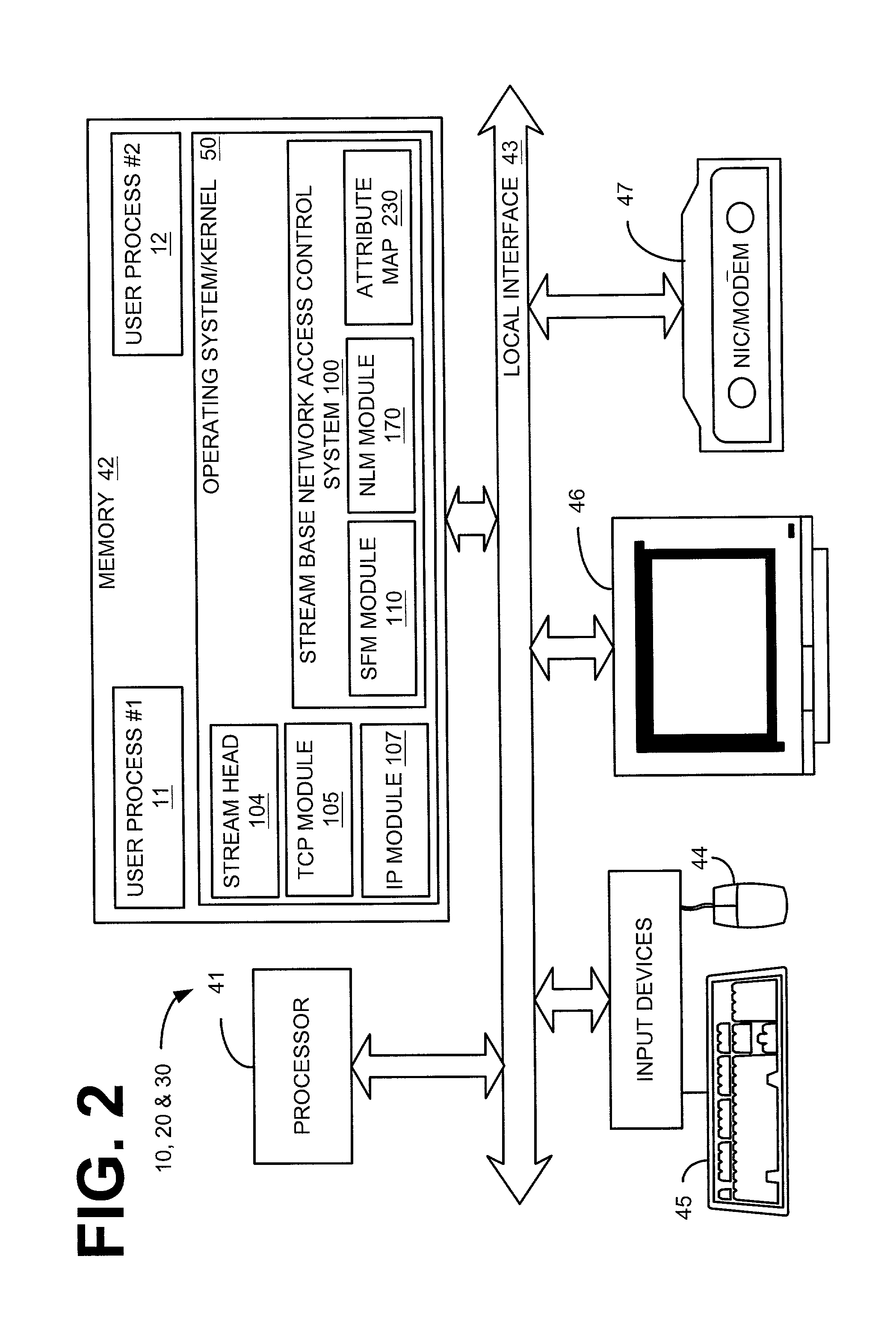
ActiveUS7032243B2Digital data processing detailsUnauthorized memory use protectionNetworking protocolControl system
Systems and methods for group-based network access control systems are provided. The group-based network access control system includes a software process operating on a computer. The software process is configured to communicate a packet through a group-based network protocol stack to a network interface card that includes an interface attribute. A table of network attributes, associated with a session filter module and a network filter module, compares the network endpoint attribute with the interface attribute in the table of network attributes to determine whether the software process can access the network interface card. Each network endpoint attribute comprises a primary group identifier and a supplemental group identifier list, and each interface attribute comprises a network group list. The method includes the steps of operating a software process that includes a network endpoint attribute. Next, packets are communicated through a network protocol stack to a network interface card, where the network interface card includes an interface attribute. Association between the network endpoint attribute and the interface attribute is established, and both the network endpoint attribute and the interface attribute are placed in a table. The network endpoint attribute is then compared with the interface attribute to determine whether the software process can access the network interface card. Each network endpoint attribute comprises a primary group identifier and a supplemental group identifier list, and each interface attribute comprises a network group list.
Owner:VALTRUS INNOVATIONS LTD
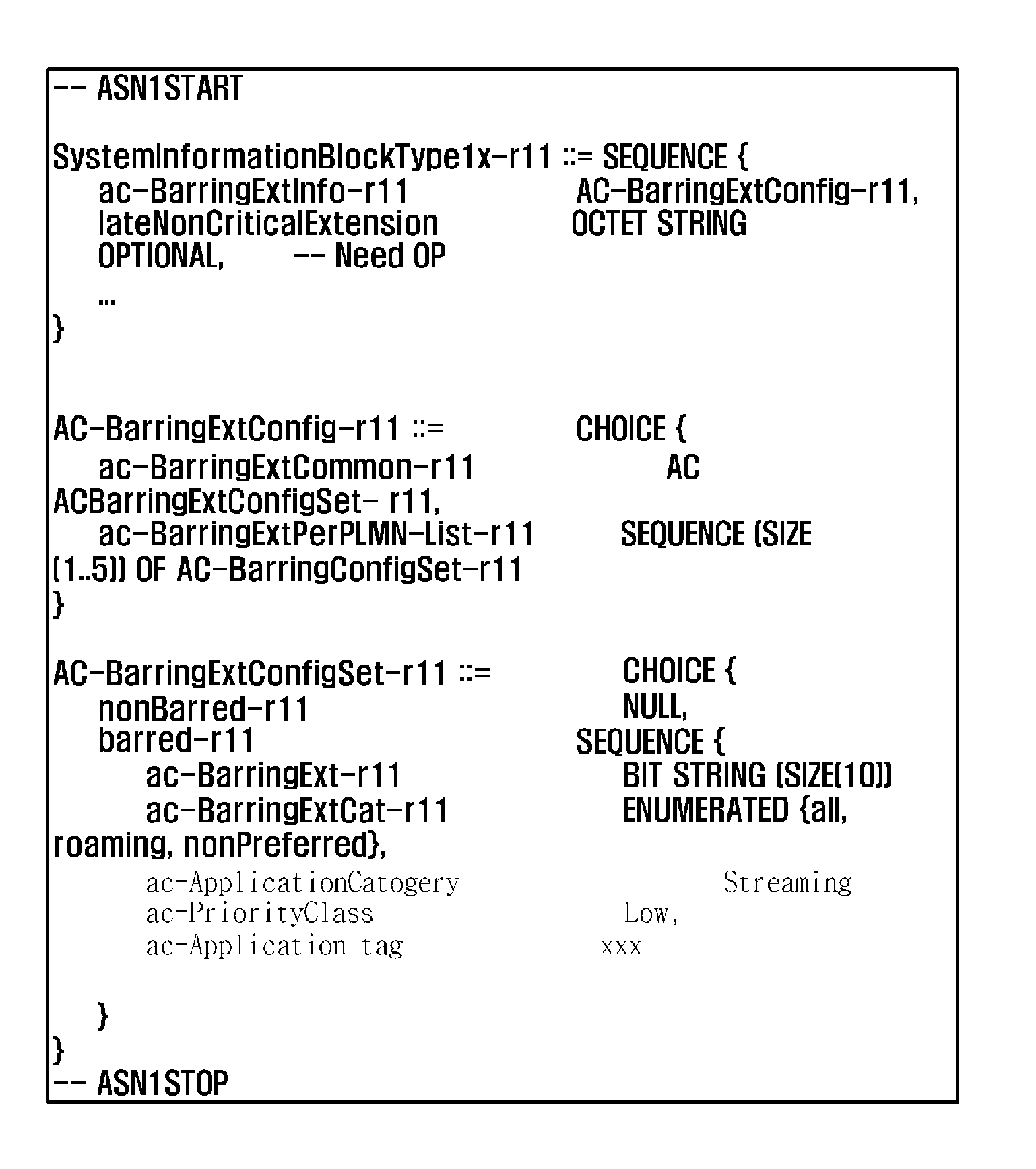
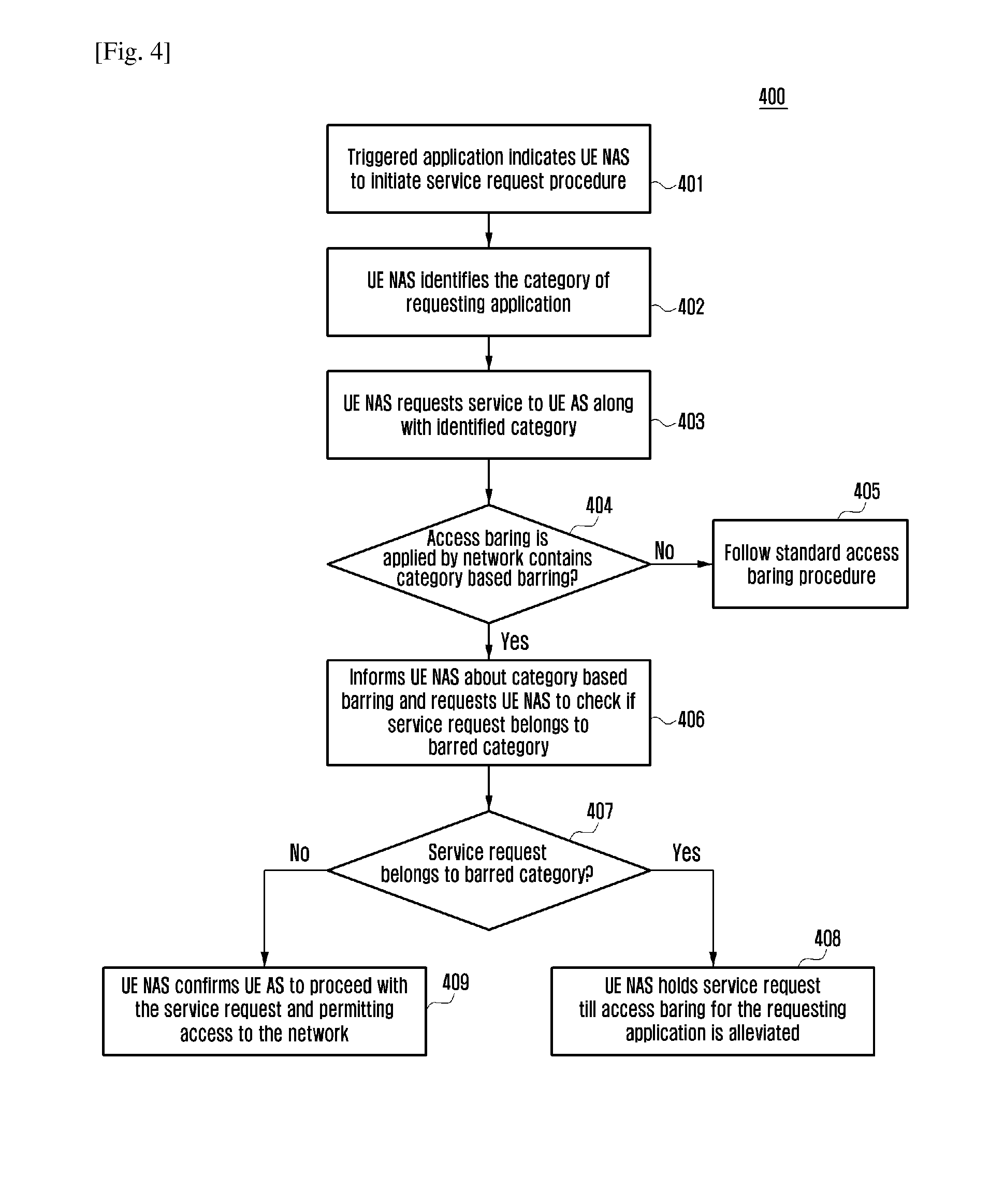
Granular network access control and methods thereof
A method and system that enhances the existing access barring mechanism as specified in the current 3GPP specification is disclosed. The method disclosed provides enhancing the access barring mechanism to accommodate application level barring between the User equipment (UE) and the network. The method disclosed individually restricts or permits access of network to every requesting application on the UE, based on granular category of the application and priority levels of the application within the granular category. The method disclosed also specifies handling of back-off timers; reject cause values and Access Point Name (APN) configuration by Access Stratum (AS) and Non Access Stratum (NAS) layer to support application level barring of UEs using the enhanced access barring mechanism. The enhanced access barring mechanism enables providing service to applications independent of other barred applications or priorities. The method disclosed provides a mechanism for access control for connected mode UEs.
Owner:SAMSUNG ELECTRONICS CO LTD
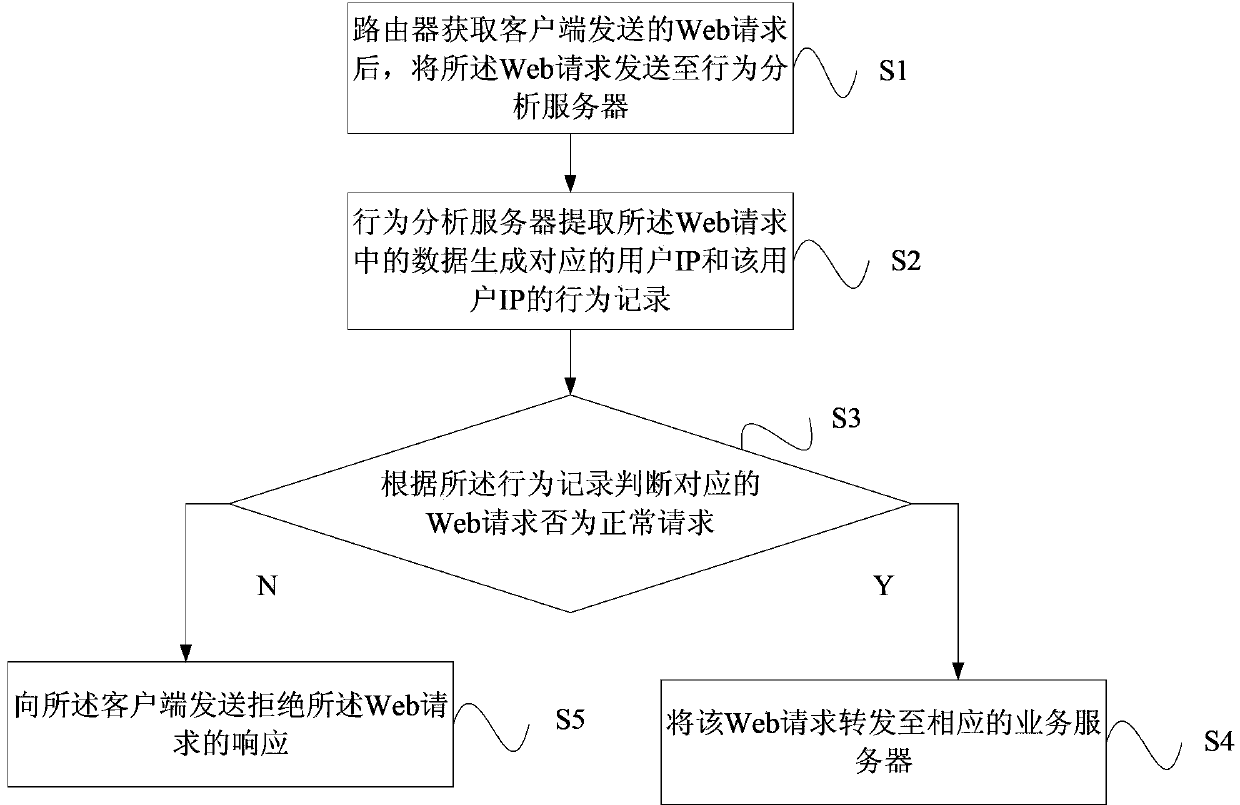
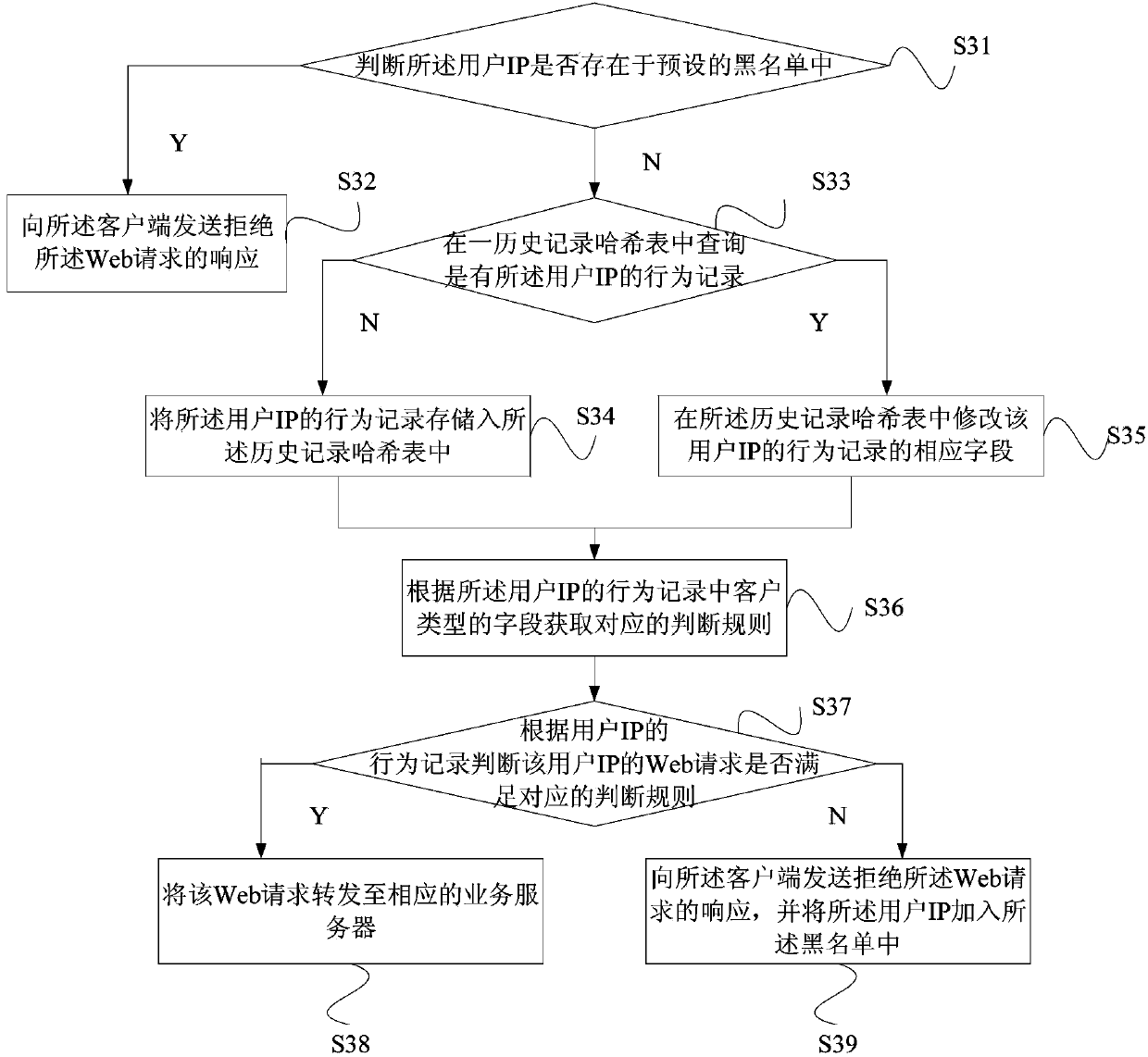
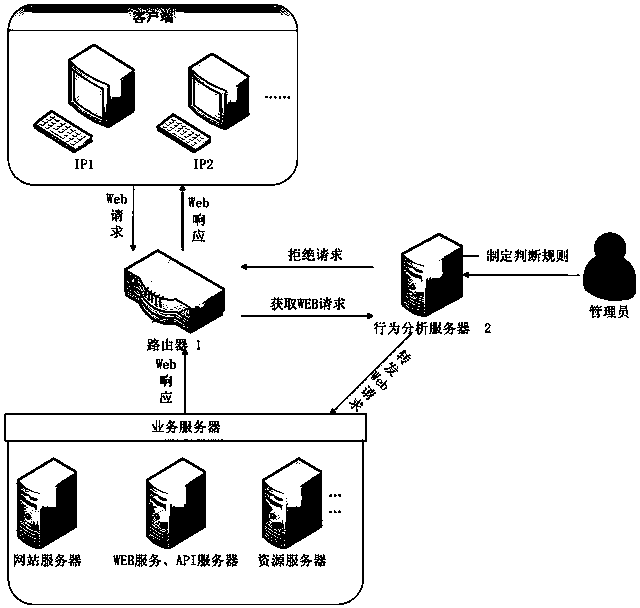
Network access control method and system based on IP access behaviors
ActiveCN103475637ASolve efficiency problemsSolve the cumbersome configurationTransmissionQuality of serviceData access control
The invention provides a network access control method and system based on IP access behaviors. The method includes: after a Web request sent by a client is acquired through a router, the Web request is sent to a behavior analyzing server; data in the Web request are extracted by the behavior analyzing server and a corresponding user IP and a behavior record of the user IP are generated and whether the Web request is a normal request is judged according to the behavior record; if the Web request is a normal request, then the Web request is forwarded to a corresponding service server and if not, then a response refusing the Web request is sent to the client so that access control on unknown IPs can be carried out dynamically and problems such as low efficiency, tedious configuration and poor dynamic instantaneity and the like in traditional IP access control are solved. At the same time, the network access control method and system also aim at restraining network attacks, regulating crawler behaviors, improving website or API service qualities and enhancing website stability and usability.
Owner:CTRIP COMP TECH SHANGHAI
Network access control
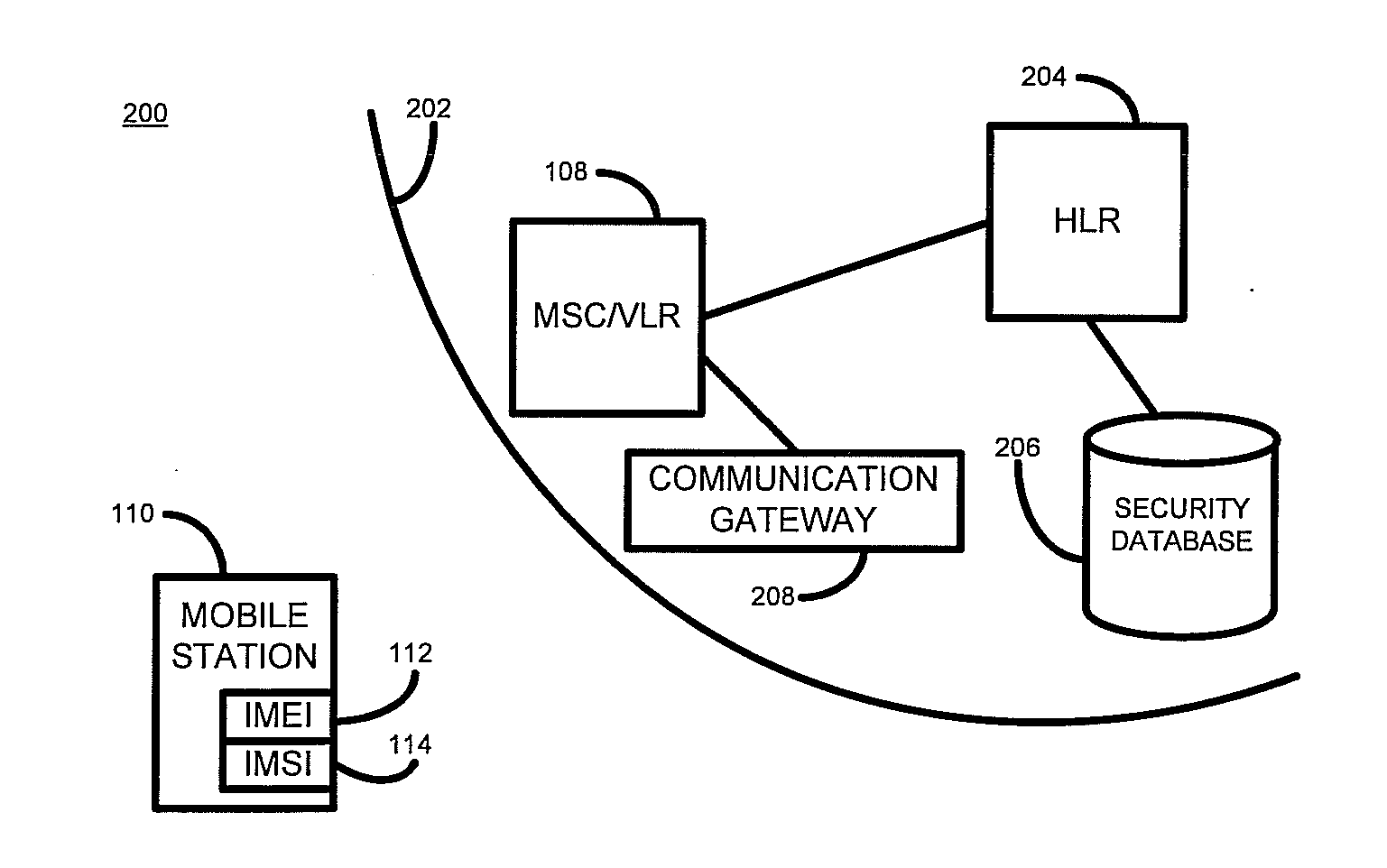
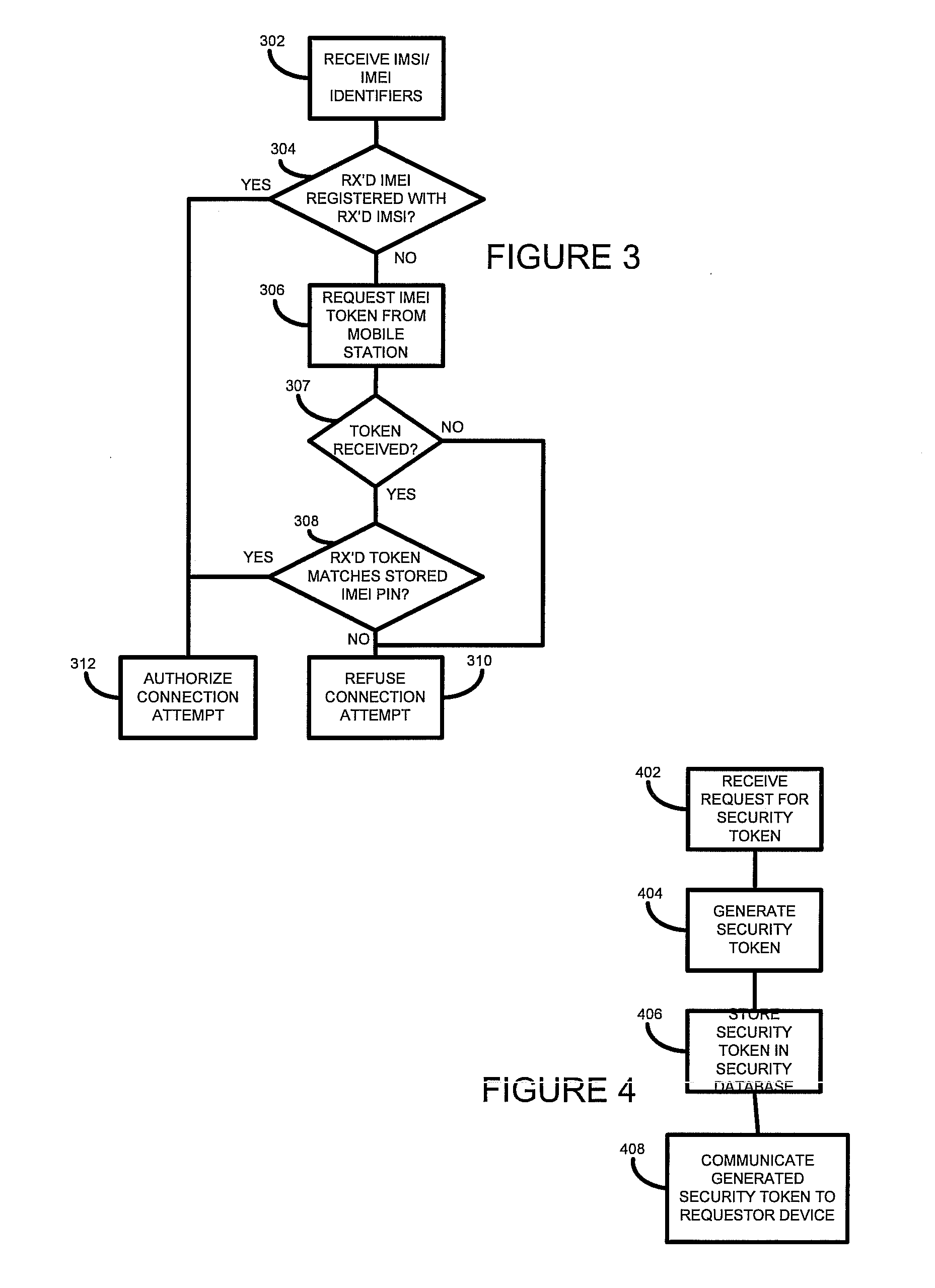
ActiveUS20110086612A1Reduce the valueAvoid security issuesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsData memoryUser identifier
According to one embodiment of the present invention, there is provided a method of authorizing a communication device to connect to a network. The method comprises receiving, at a processor, a communication device identifier and a subscriber identifier, determining, by the processor, whether the received communication device identifier is associated with the received subscriber identifier in a data store. Where it is determined that the received identifiers are not so associated the method further comprise requesting, by the processor, a security token associated with the communication device, receiving, at the processor, a security token, determining, by the processor, whether the received security token matches a stored security token associated with the received communication device identifier in the data store, and where it is so determined, authorizing the communication device to connect to the network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Behavior model generator system for facilitating confirmation of intention of security policy creator
InactiveUS20060005228A1Difficult to have consistencyImprove efficiencyTransmissionSpecial data processing applicationsNetwork Access ControlSecurity policy
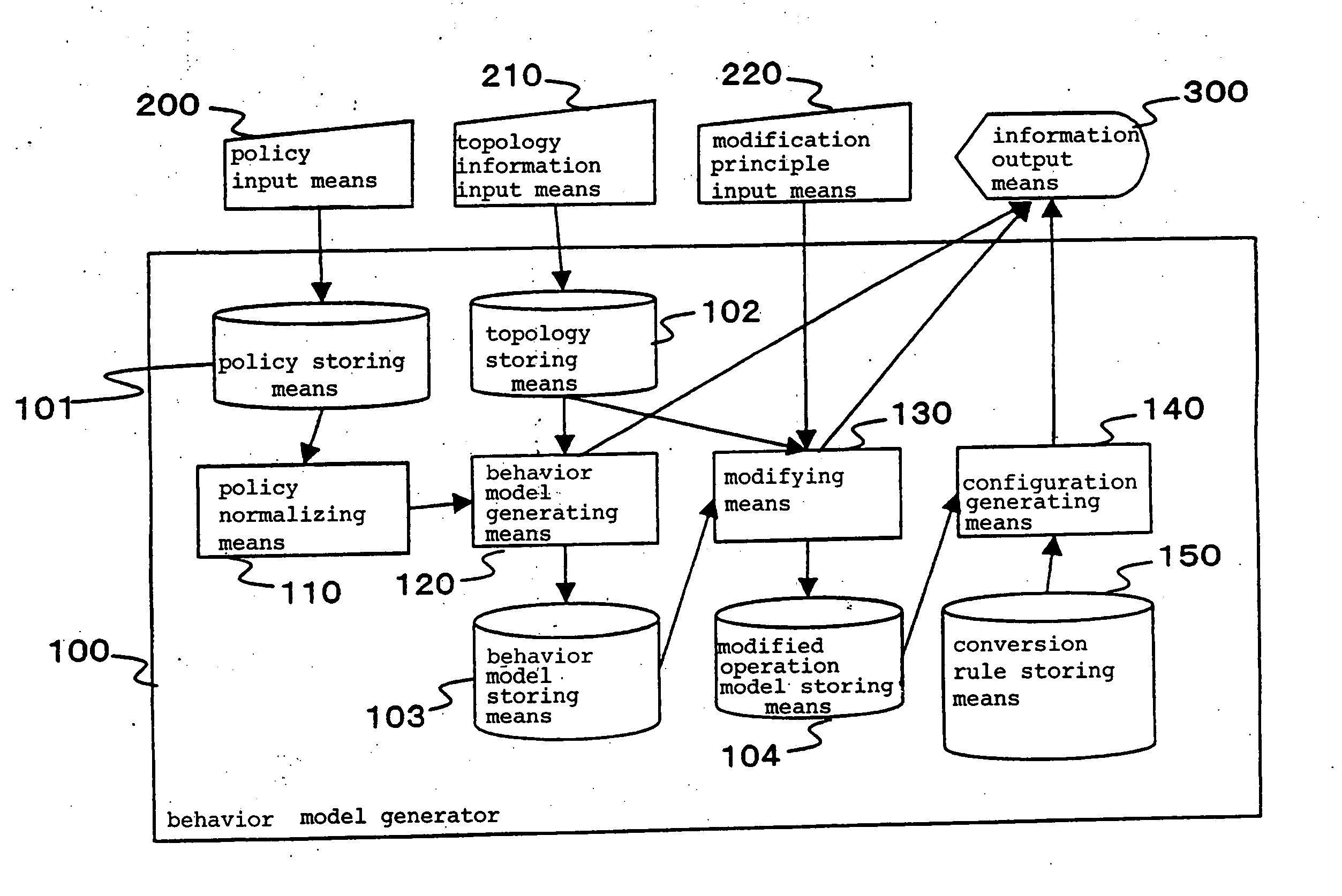
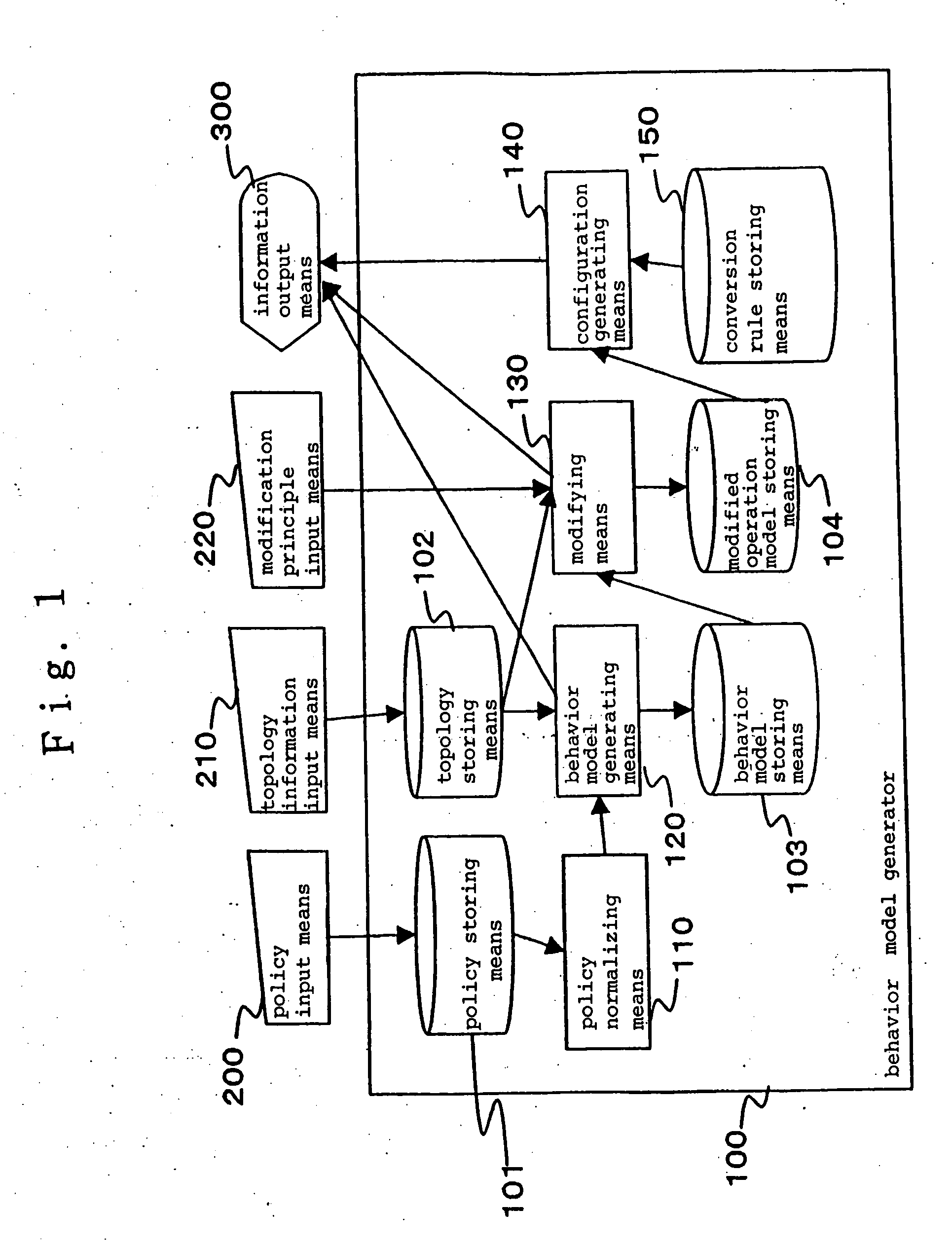
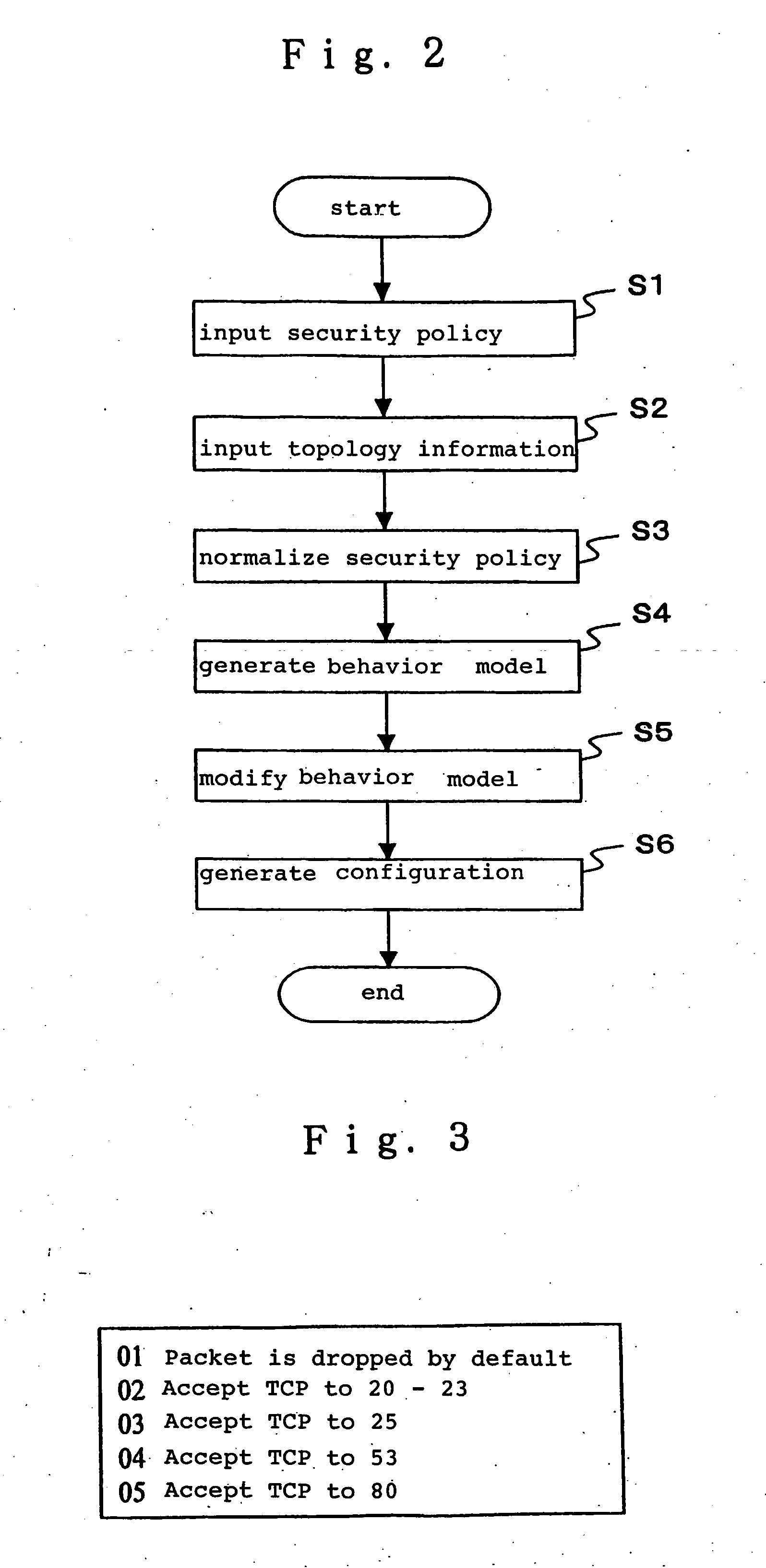
A policy normalizing means normalizes an entered security policy. Specifically, if the security policy does not include necessary items, the policy normalizing means compensates the security policy for the missing items by predefined values so that the security policy includes the necessary items. An behavior model generating means generates an behavior model representative of the operation of a network access controller based on the normalized security policy. In this event, the behavior model generating means generates an behavior model which is represented by a data structure that is not dependent on the type of the network access controller. A modifying means modifies the behavior model in accordance with a modification principle desired by an operator, and a configuration generating means generates configuration for the network access controller from the modified behavior model.
Owner:NEC CORP
Assessing risk based on offline activity history
ActiveUS8108923B1Memory loss protectionDigital data processing detailsNetwork Access ControlHost machine
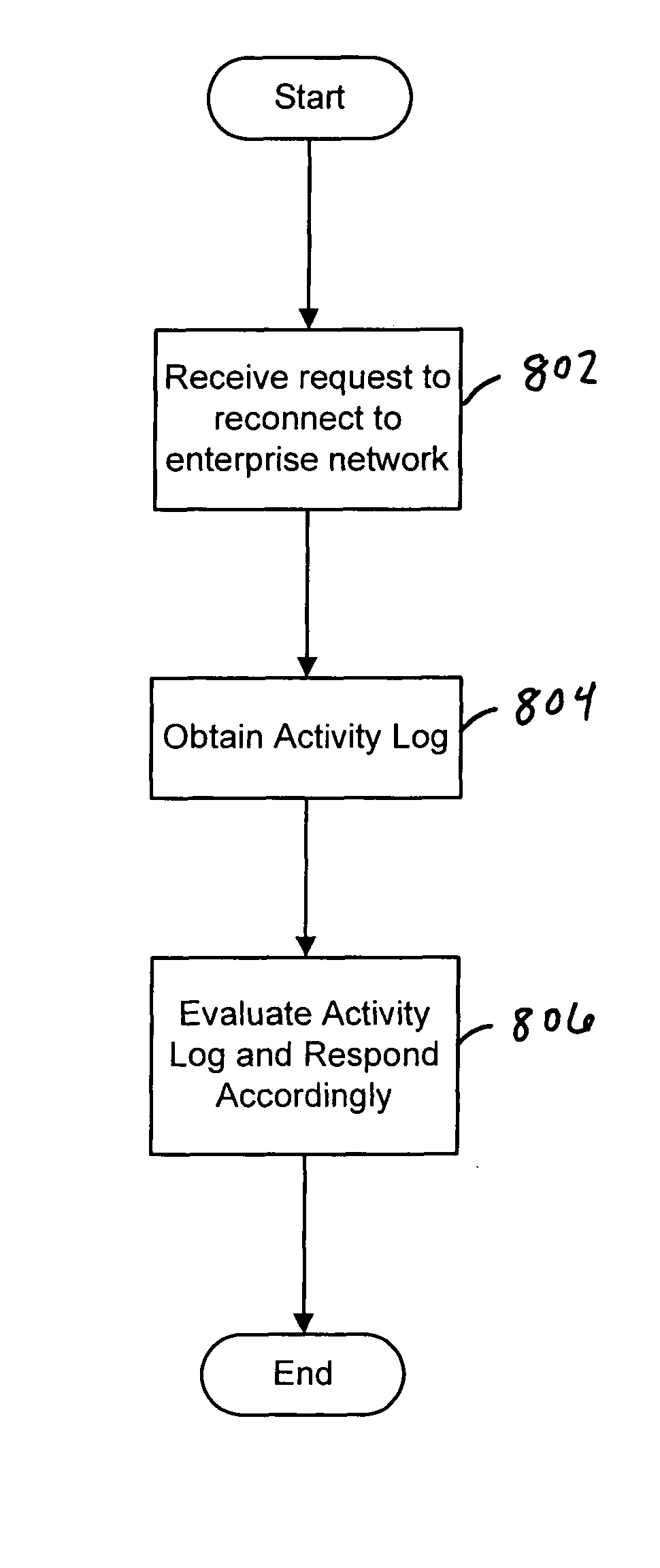
Controlling access to a protected network is disclosed. In some embodiments, one or more events that occur will a host is disconnected from the protected network are logged. The log is provided to one or more devices associated with the protected network when the host requests access to the protected network after a period in which it was not connected. In some embodiments, a network access control or other device or process uses the log to determine whether and / or an extent to which the host should be permitted to connect to the network.
Owner:CA TECH INC
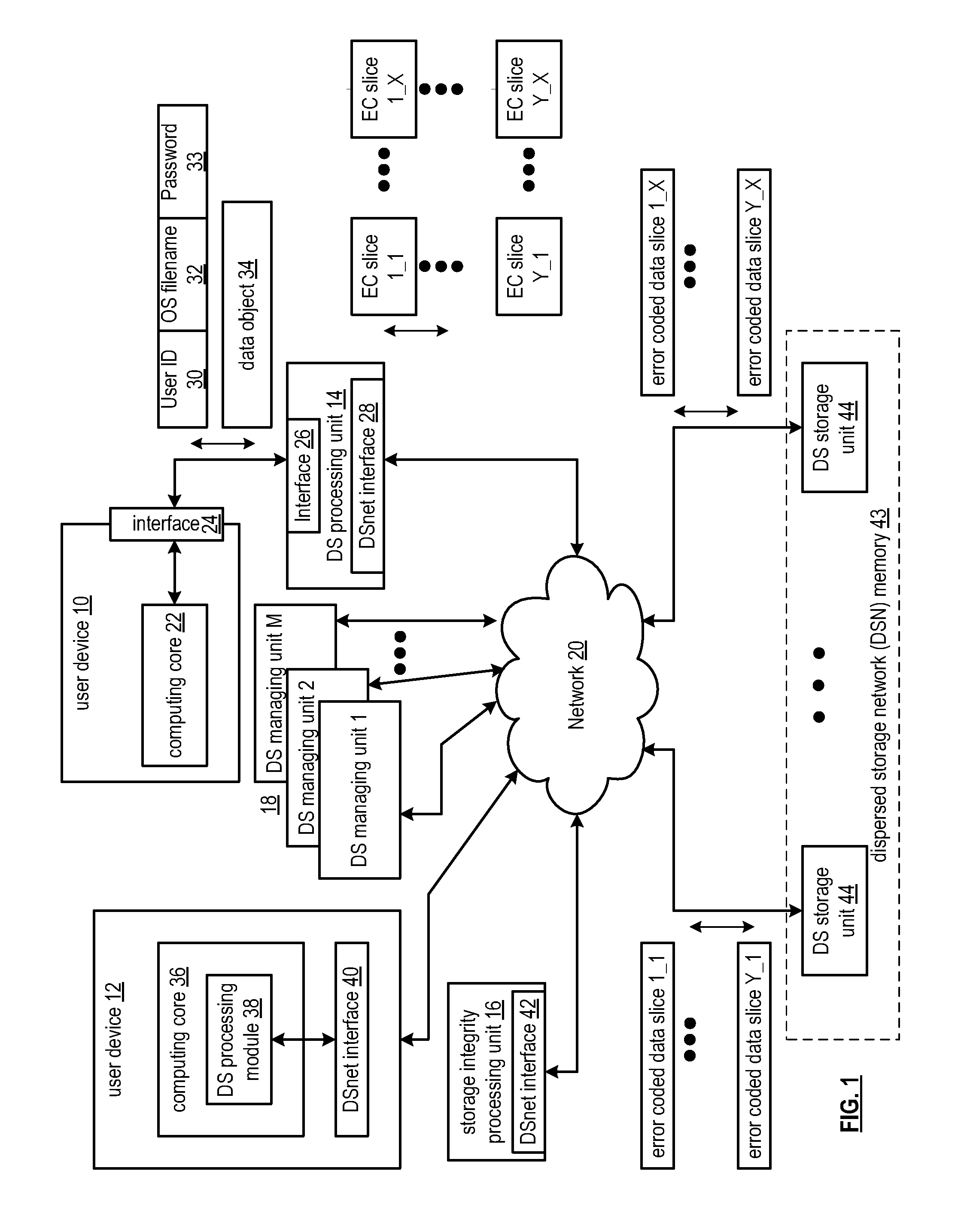
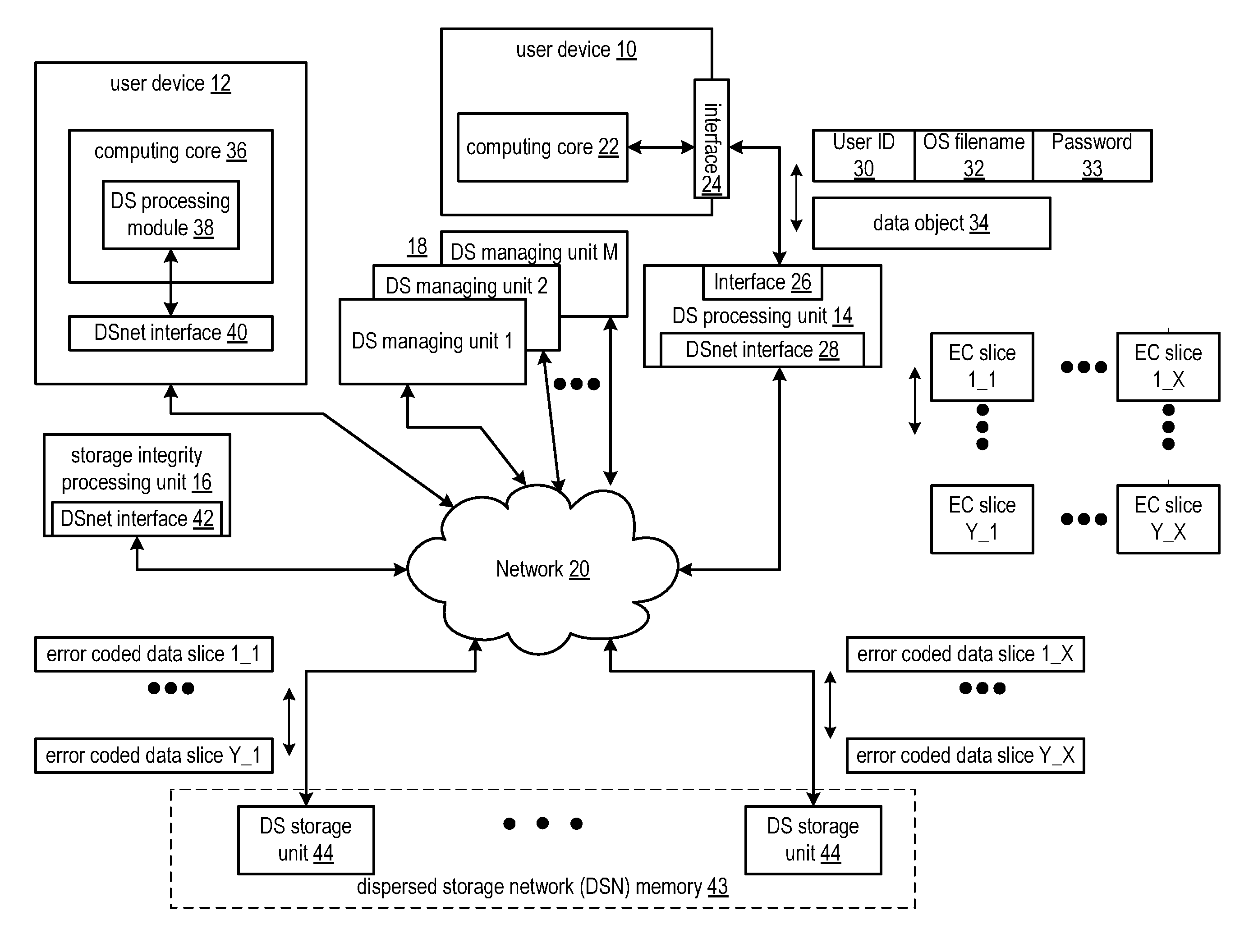
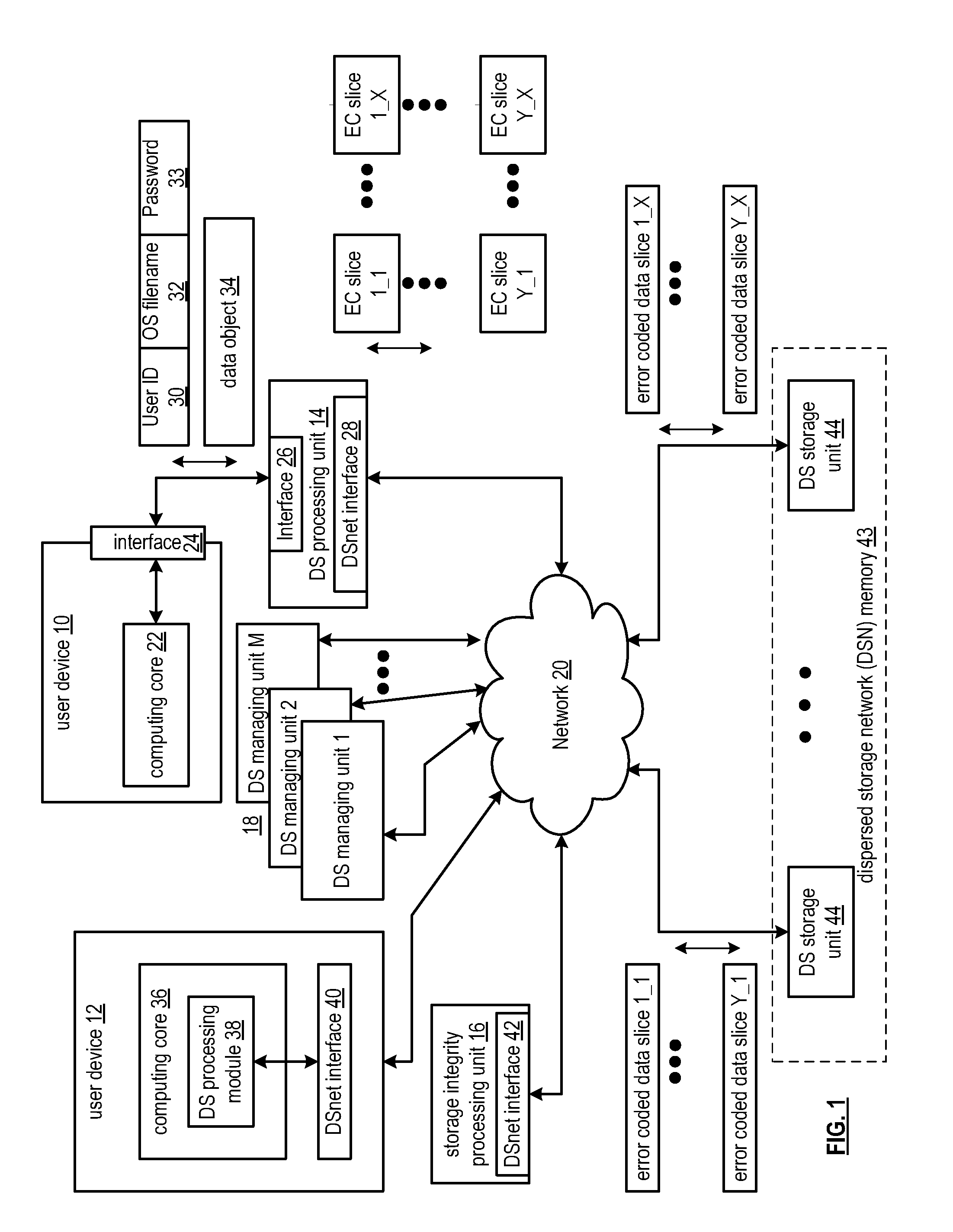
Verification of dispersed storage network access control information
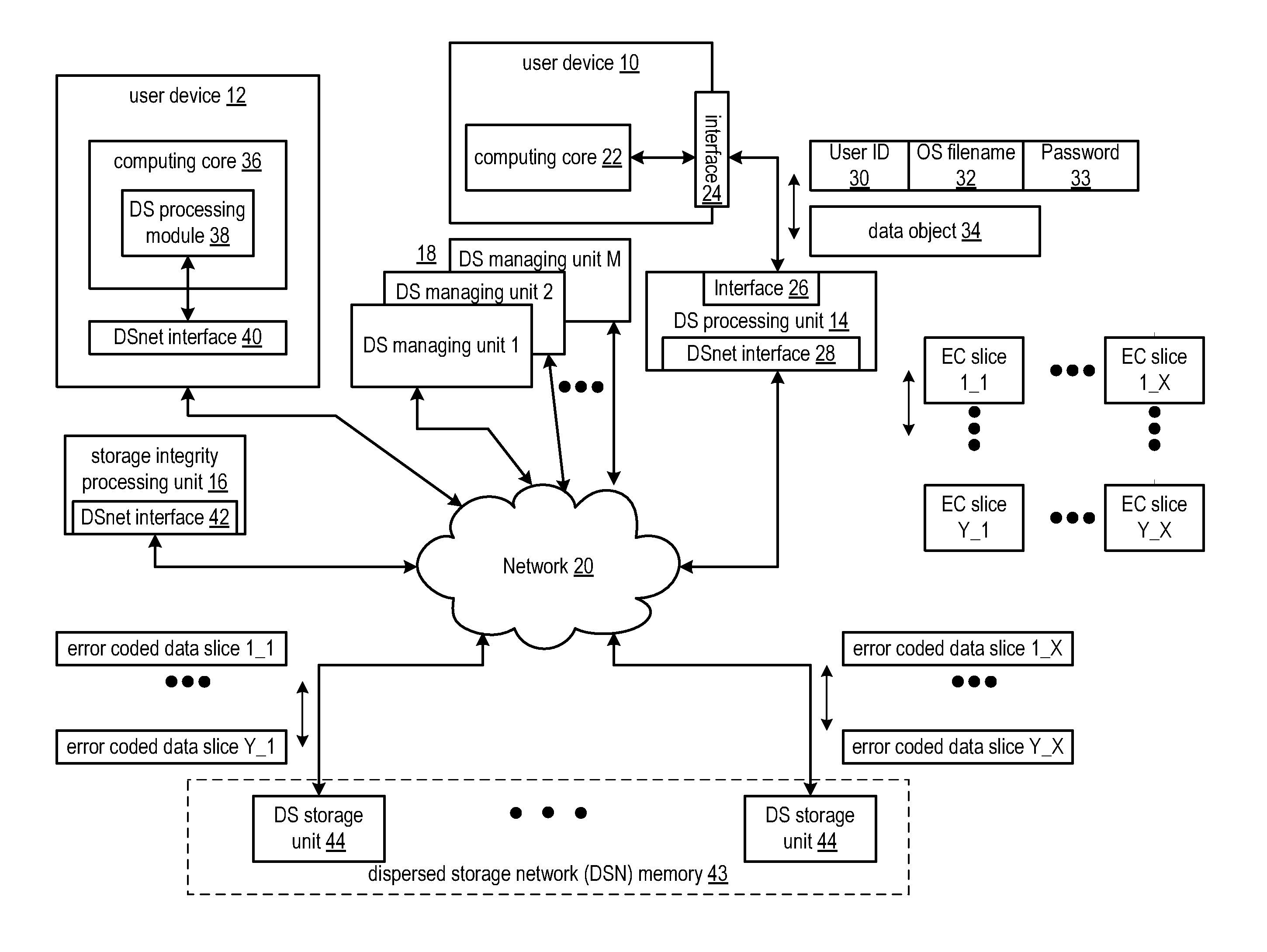
ActiveUS20110055578A1Digital data information retrievalError detection/correctionNetwork Access ControlComparator
In a dispersed storage network access control list information must be occasionally written out to system units across the network. A dispersed storage (DS) managing unit (18) combines (204) the access control list information with a clock stamp and hashes (206) that combined output. An encryptor (208) encrypts a security key (210) and the hash output to obtain a signature. A combiner (212) combines the signature and the output of combiner (204) and outputs to a publisher (214). Upon receipt of the output of the publisher (214) a dispersed storage unit (44) can reverse process and securely validate the access control list information provided by the publisher (214) to receive and store updated and valid access control list information. This processing is performed by the unit (44) using parsers (216), caches (218 and 228), hash operations (224), decryptors (222), comparators (226), logic (230), and key stores (220).
Owner:PURE STORAGE
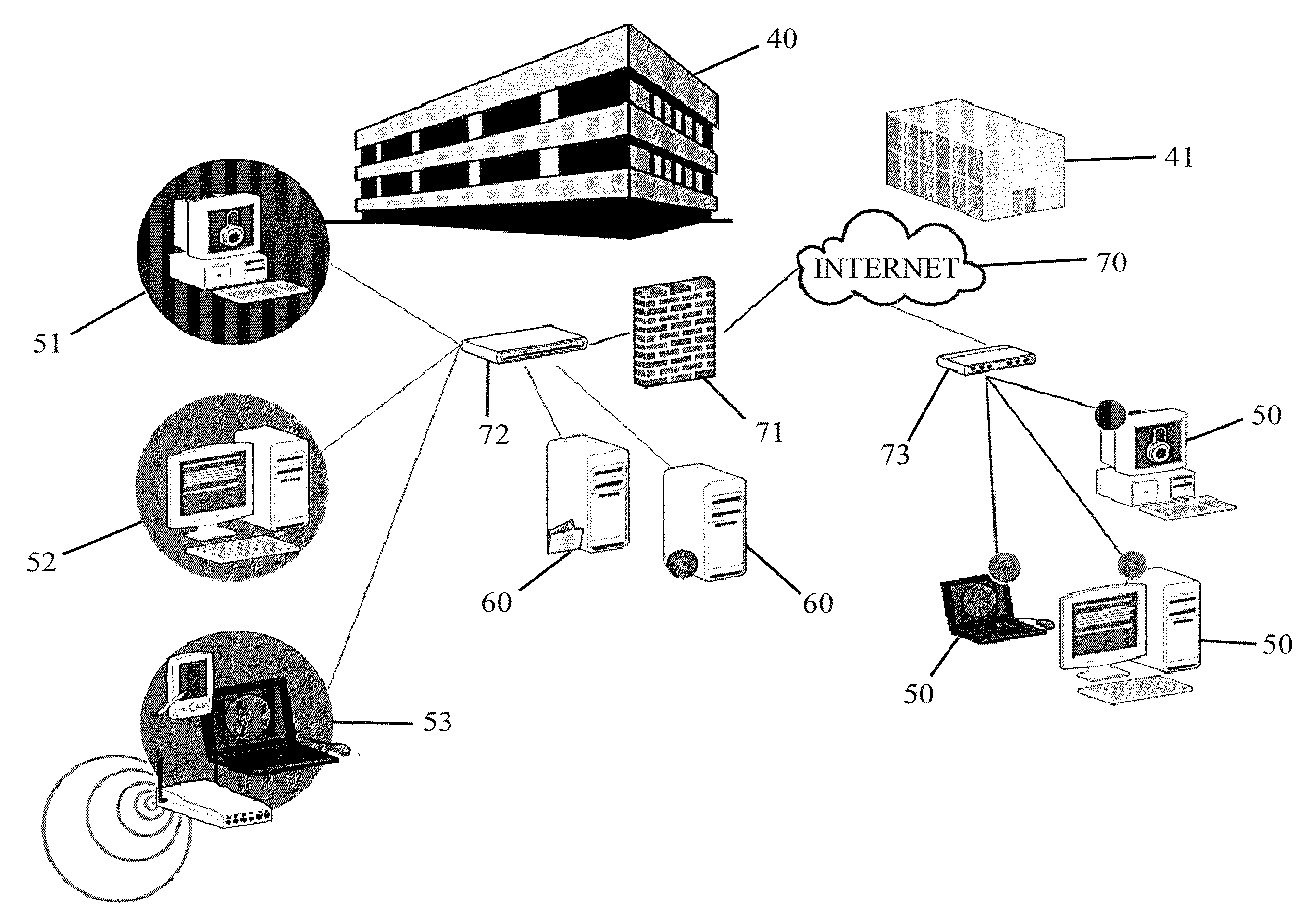
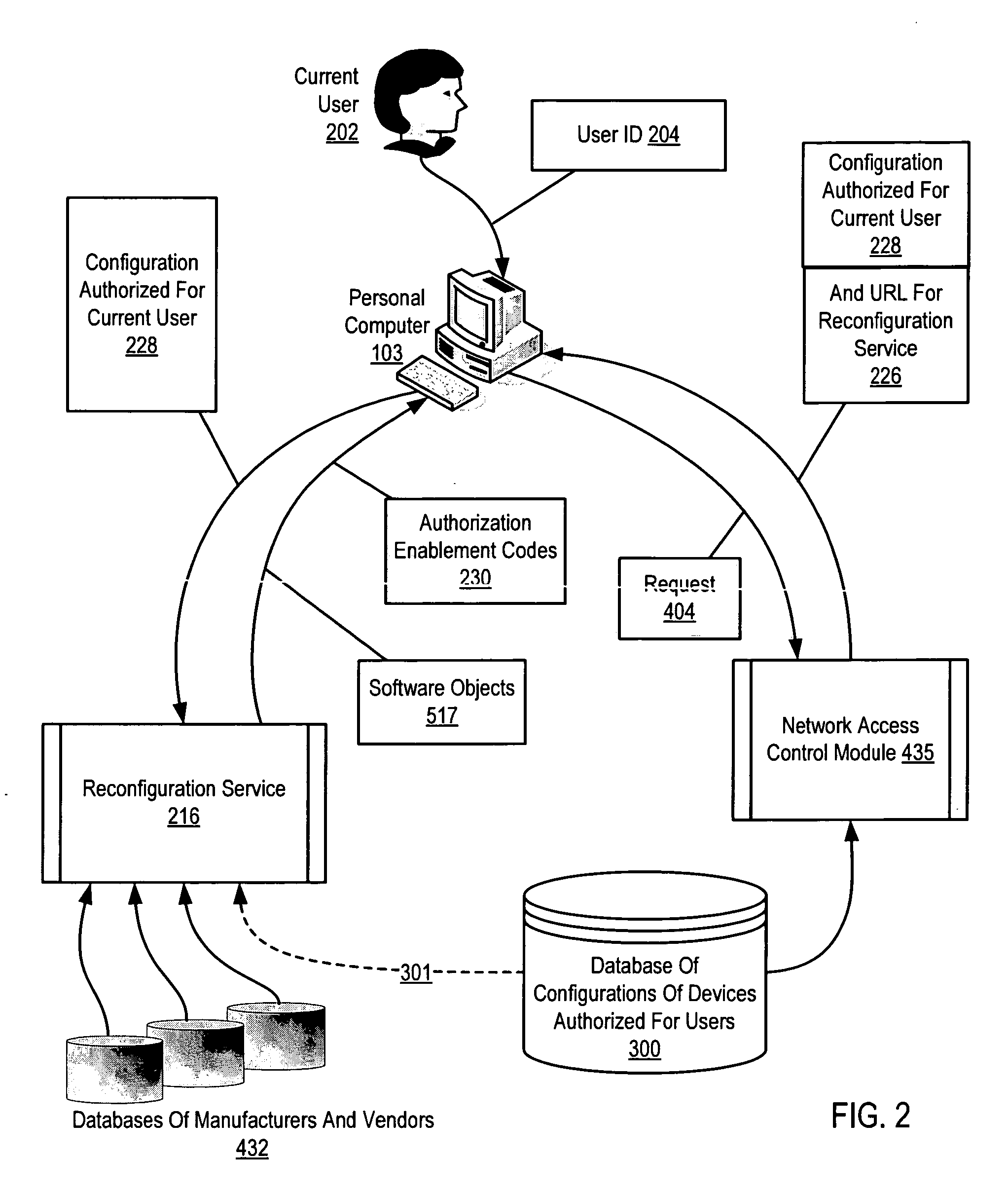
Administration of access to computer resources on a network
InactiveUS20060294580A1Cost-effectiveCost-effective configurationDigital data processing detailsUser identity/authority verificationComputer resourcesComputer network
Administration of access to computer resources on a network including receiving in a network access control module on a network, from a device communicatively coupled to the network, a request for access to resources on the network, the request including computer data representing an identity of the device, an identity of a current user of the device, and a current configuration of the device; and granting, by the network access control module to the device, access to resources on the network in dependence upon the identity of the device, the identity of the current user, the current configuration of the device, and a configuration of the device authorized for the current user.
Owner:IBM CORP
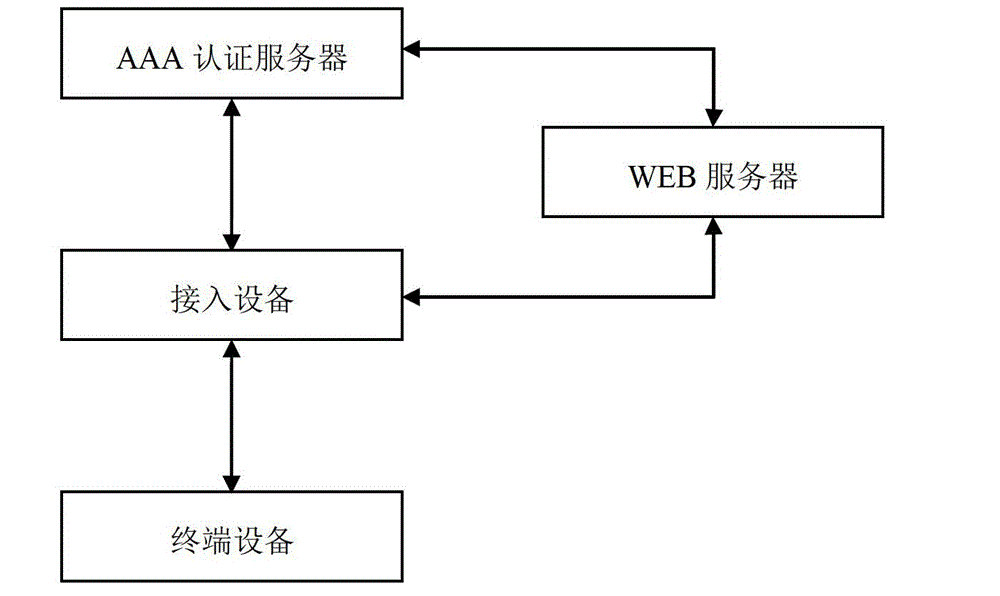
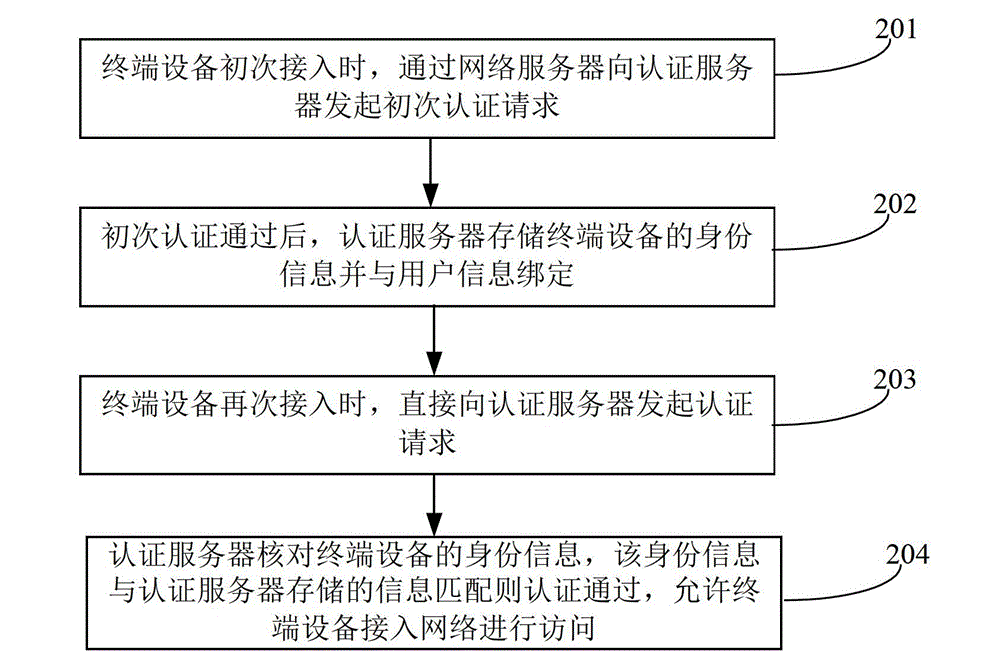
Network access control method and system
The invention relates to a network communication technology. Aiming at overcoming a defect that access speed is lower in the prior art, the invention discloses a network access control method and system, and increases the access speed and quantity of terminal devices. The network access control method comprises the steps that A, when the terminal devices access for the first time, a first-time authentication request is sent to an authentication server from a network server; B, after the first time authentication is passed, the authentication server stores identity information of the terminal devices and the identity information is bound with user information; C, when the terminal devices access again, an authentication request is sent to the authentication server directly; and D, the authentication server checks the identity information of the terminal devices, authentication is passed when the identity information is matched with the information stored in the authentication server, and the terminal devices are allowed to have an access to a network for a visit. The network access control system comprises the terminal devices, an access device, the network server and the authentication server. The method and the system simplify access control procedures and increase the access speed of a user to the network.
Owner:MAIPU COMM TECH CO LTD
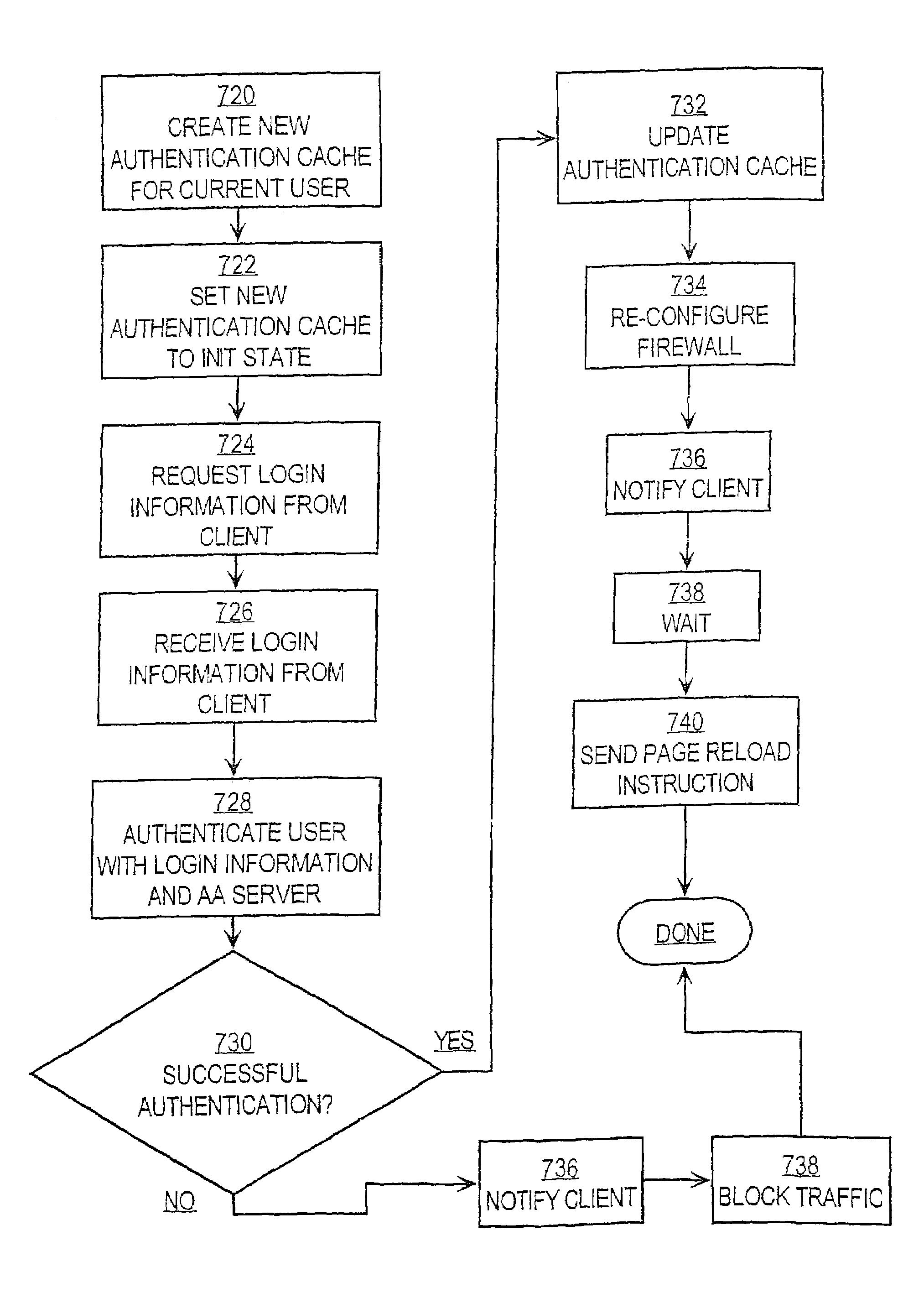
Local authentication of a client at a network device
A method and apparatus that provide network access control are disclosed. In one embodiment, a network device is configured to intercept network traffic initiated from a client and directed toward a network resource, and to locally authenticate the client. Authentication is carried out by comparing information identifying the client to authentication information stored in the network device. In one embodiment, an authentication cache in the network device stores the authentication information. If the client identifying information is authenticated successfully against the stored authentication information, the network device is dynamically re-configured to allow network traffic initiated by the client to reach the network resource. If local authentication fails, new stored authentication is created for the client, and the network device attempts to authenticate the client using a remote authentication server. If remote authentication is successful, the local authentication information is updated so that subsequent requests can authenticate locally. As a result, a client may be authenticated locally at a router or similar device, reducing network traffic to the authentication server.
Owner:CISCO TECH INC
System and method for multiple access control in satellite communications system
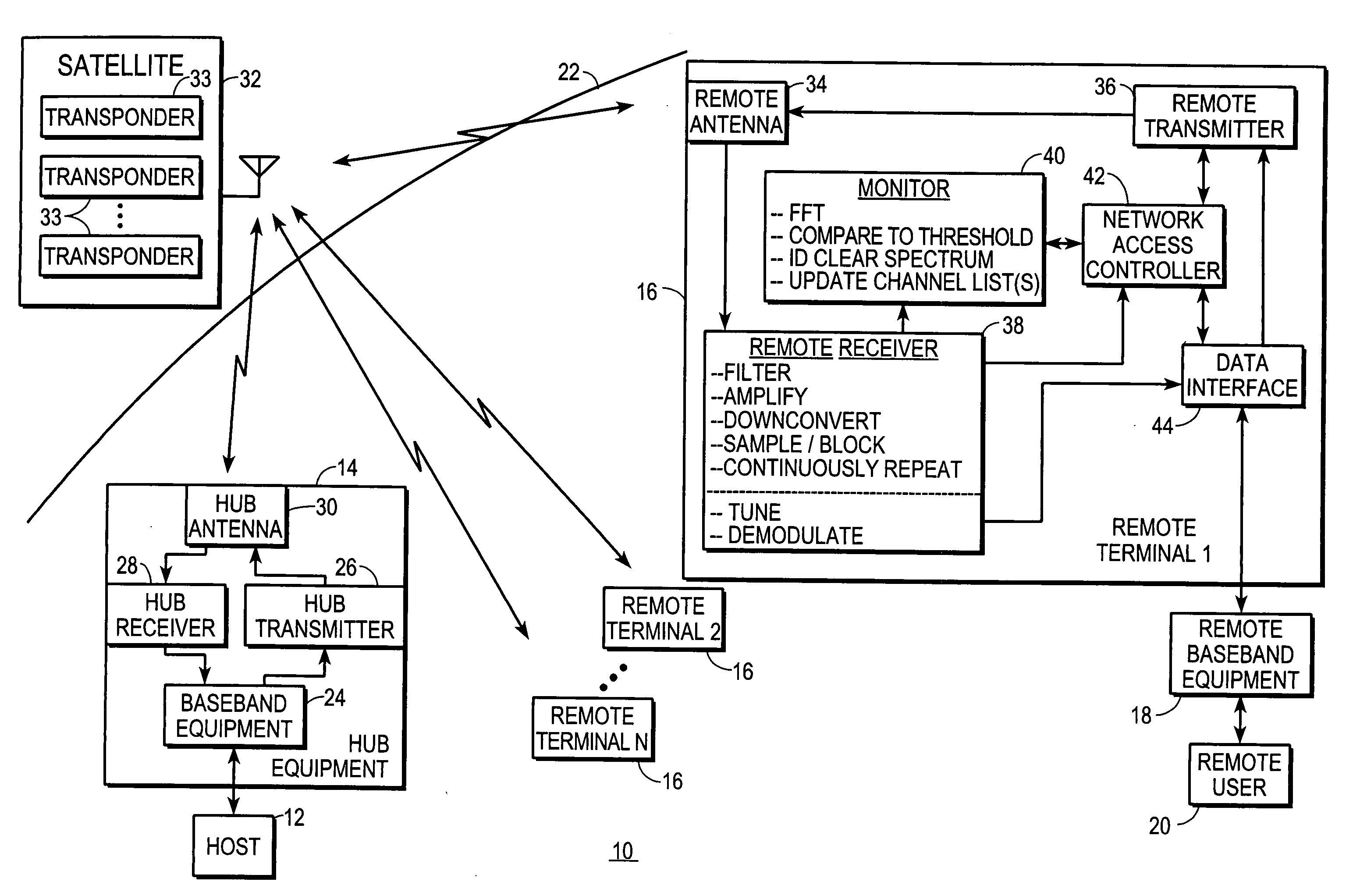
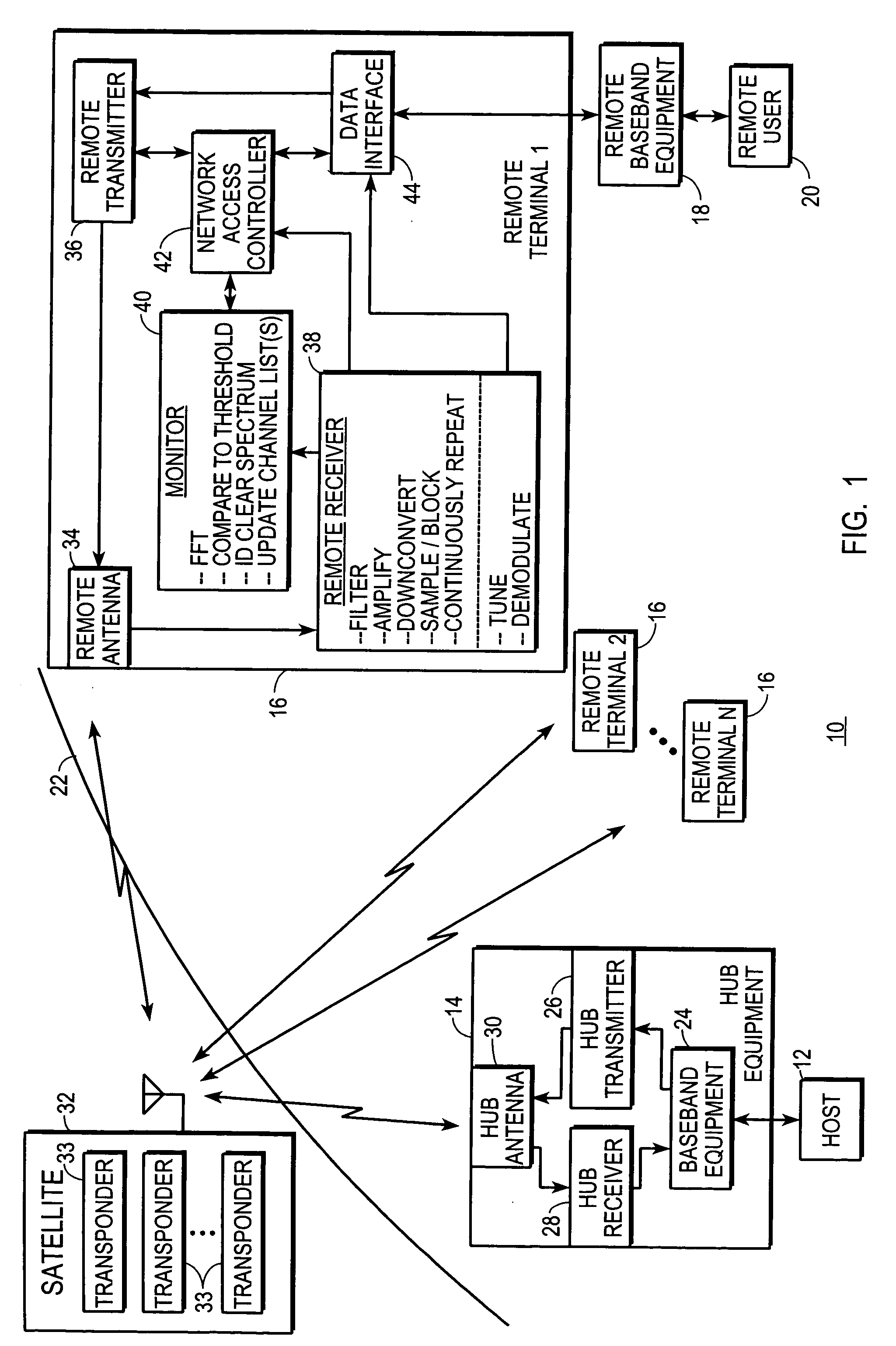
ActiveUS20060050660A1Guaranteed cost-effective operationUtilizes bandwidth efficientlyRadio transmissionWireless commuication servicesFrequency spectrumCommunications system
A satellite communications system (10) includes a hub (14), a satellite (32), and any number of remote terminals (16). Each remote terminal (16) includes a remote receiver (38), a monitor (40), and a network access controller (42). Each remote receiver (38) is configured to receive and down convert the system's entire spectrum of interest from which channels are accessed by the remote terminals (16). The monitors (40) independently perform FFT processes over this entire spectrum, but at a low frequency resolution which is no higher than needed to distinguish channels. Based on these spectral analyses, uplink / inbound channels are independently selected by the network access controllers (42) at each remote terminal (16). Remote terminals (16) immediately transmit data to the hub (14) as soon as they select an uplink / inbound channel.
Owner:NENABER TERRY +1
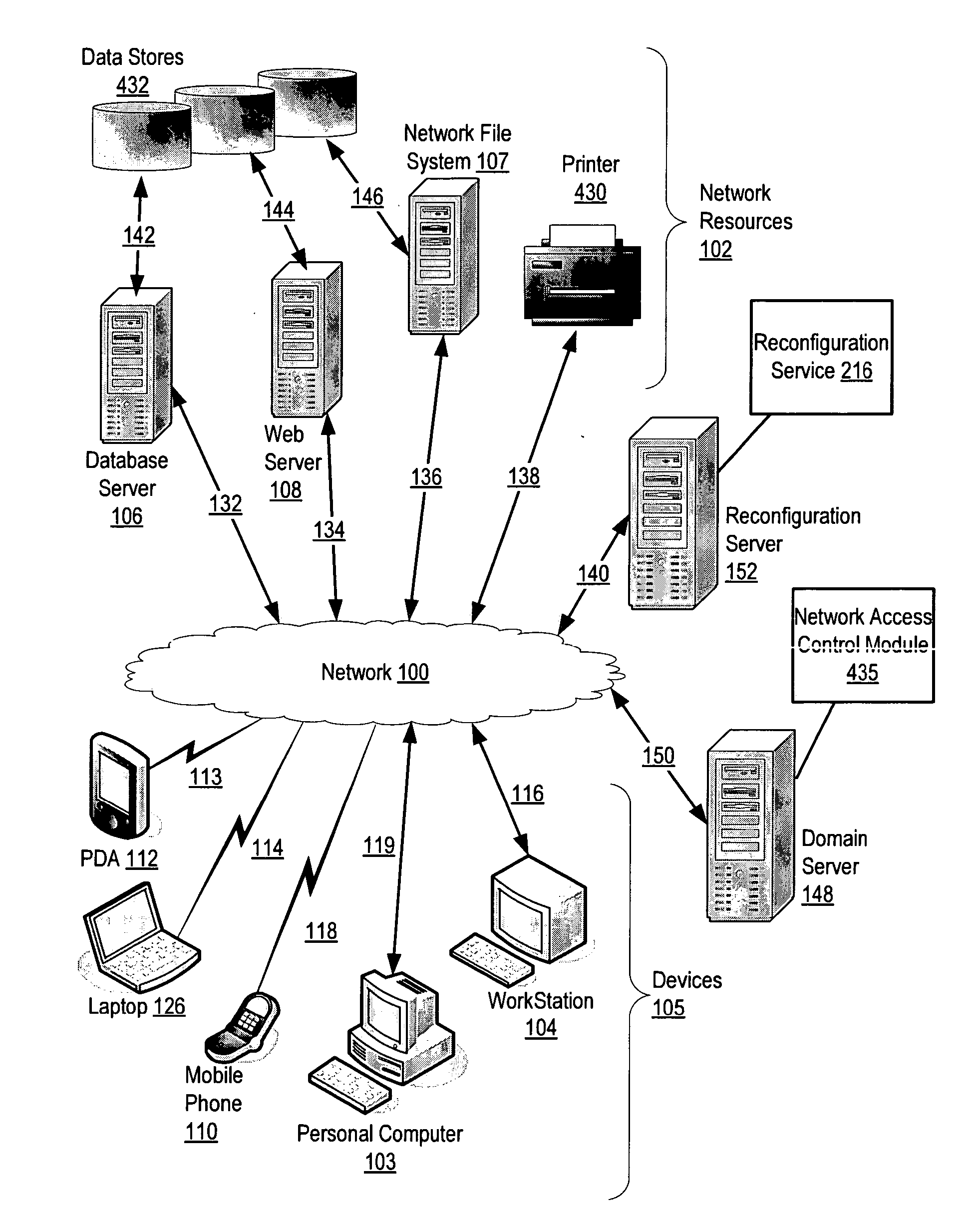
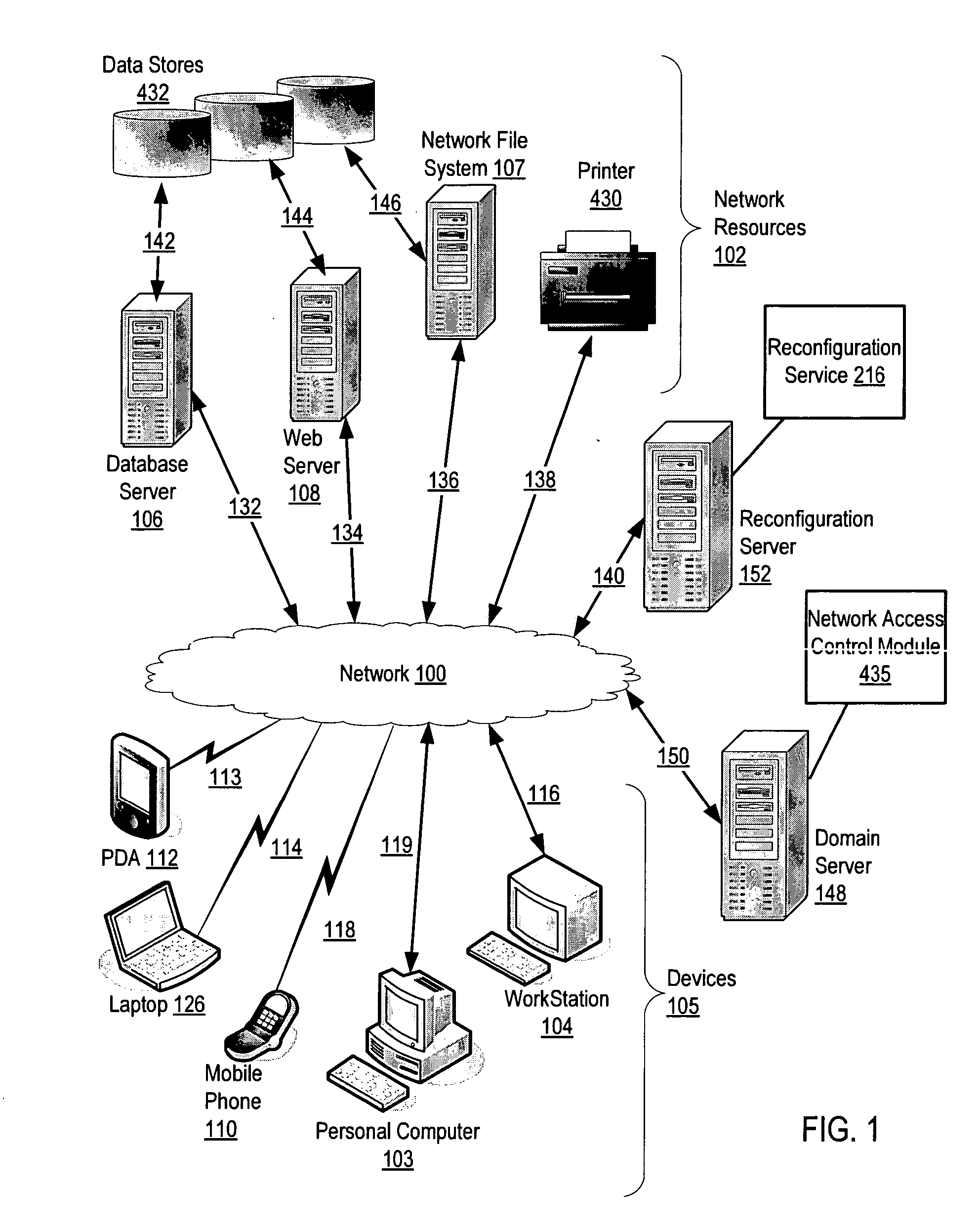
Method and apparatus for geographically regulating inbound and outbound network communications
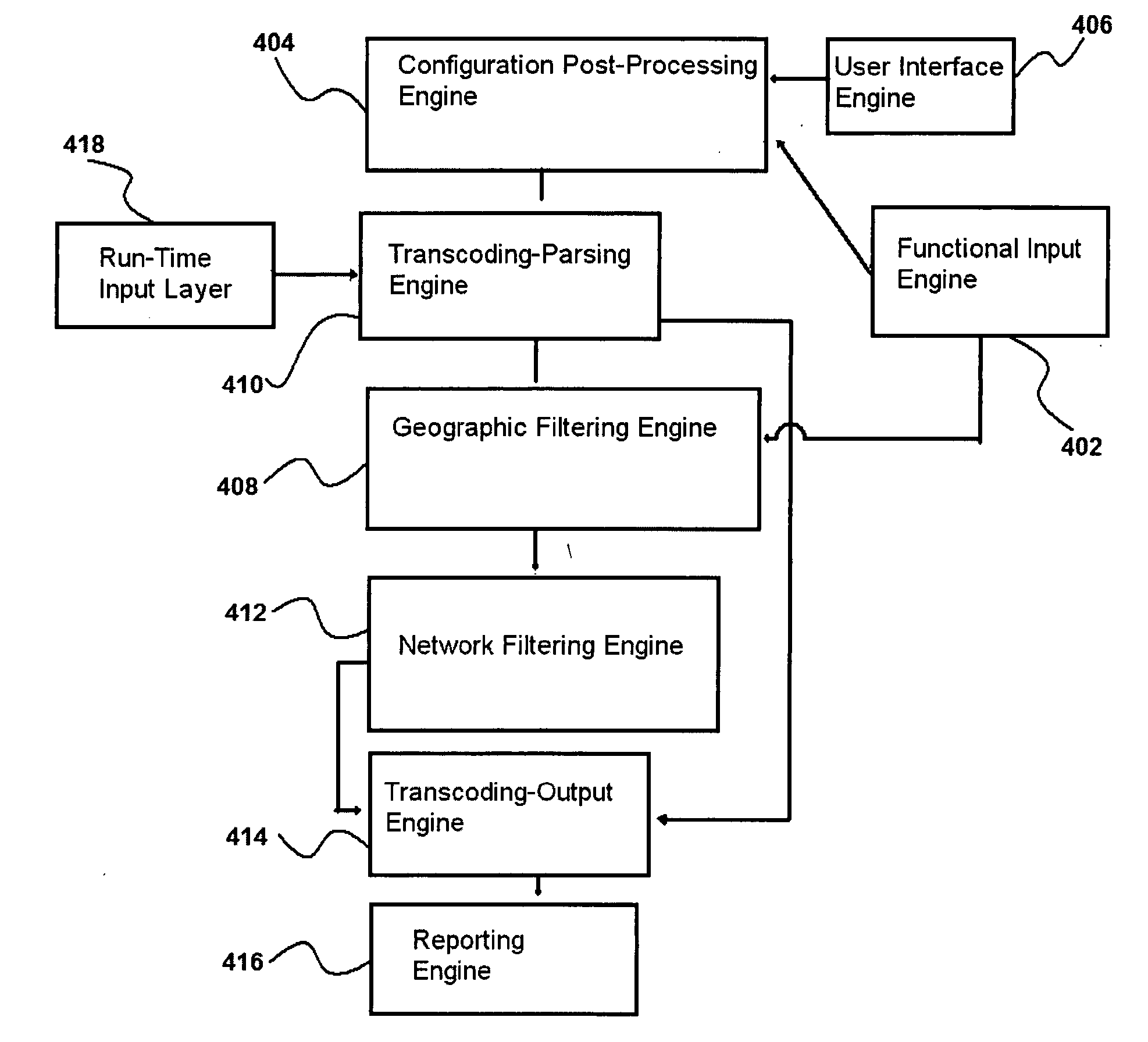
ActiveUS20070300296A1Multiple digital computer combinationsProgram controlGraphicsGraphical user interface
A system and method for regulating and analyzing inbound and outbound communications in and between computer networks on the basis of geographic security assertions are provided. Geographic information is collected, optimized, and shared between network objects to enforce network access control on the basis of configurable security assertions. Security assertions are configured and metrics displayed using maps and other geographic data in a graphical user interface.
Owner:IORHYTHM
System and method for managing security of general network
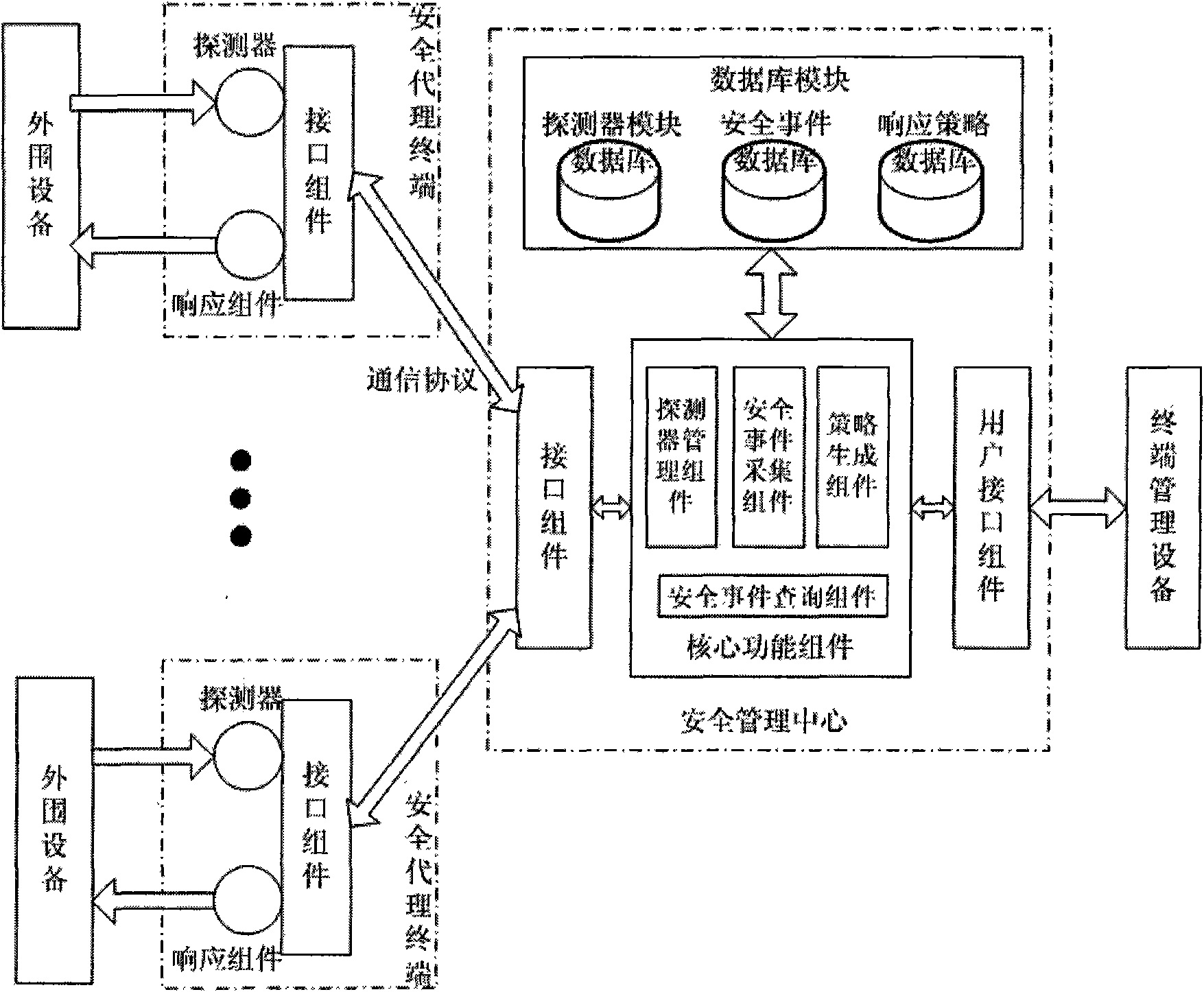
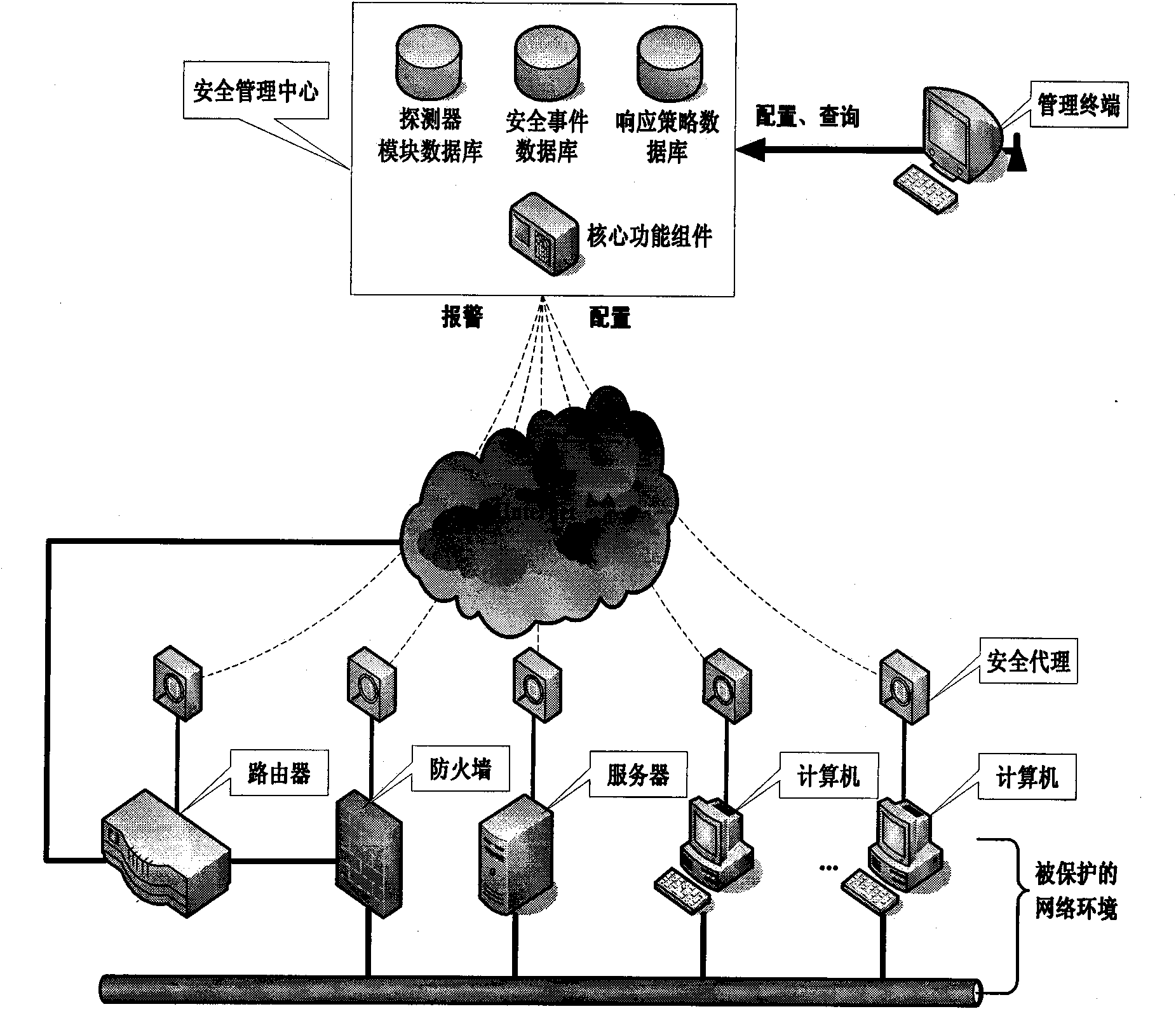
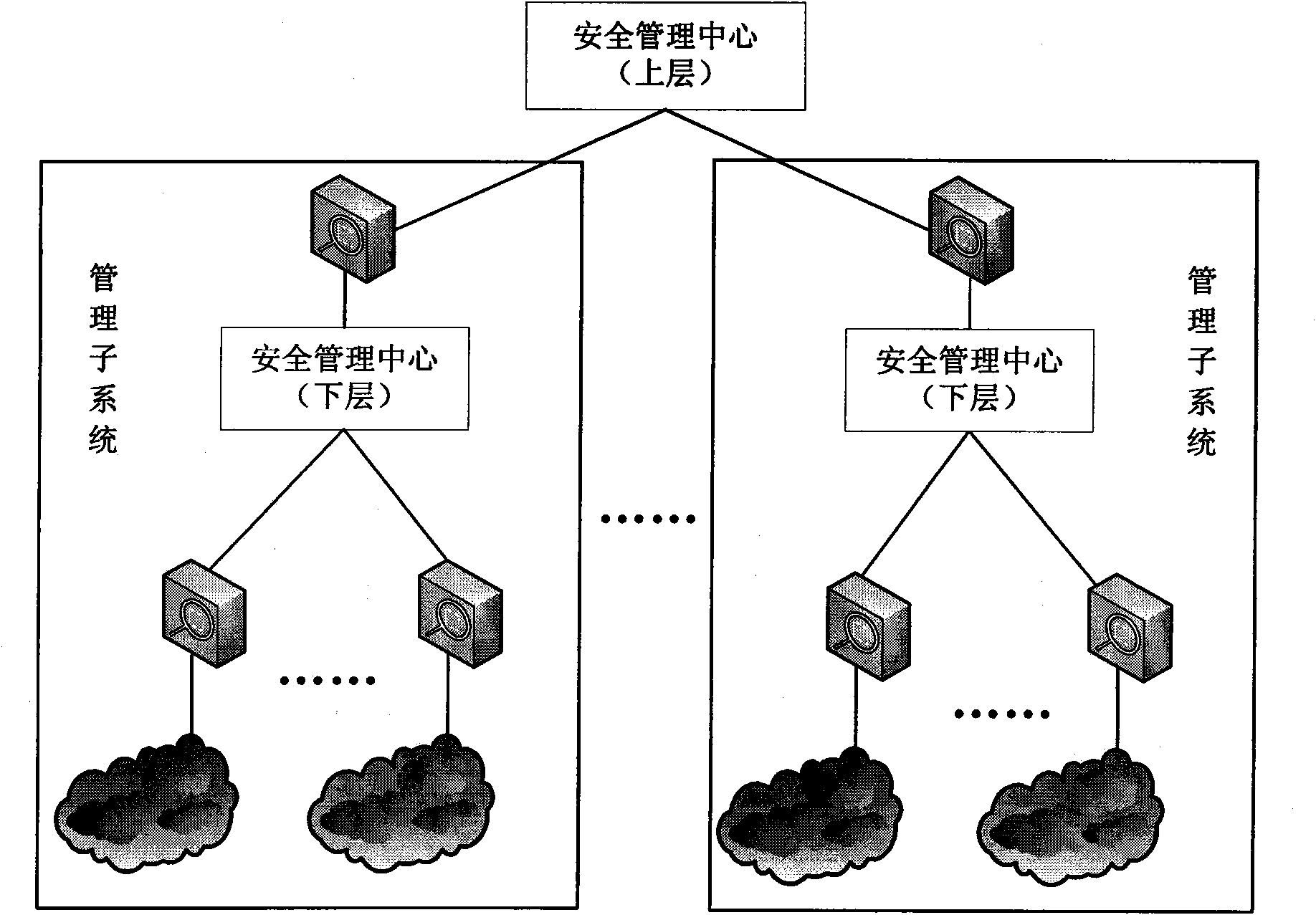
InactiveCN101582883AImprove general performanceIncrease opennessData switching networksDistributed securityProtection system
The invention discloses a system and a method for managing security of a general network, and mainly overcomes the defects of poor openness and expansibility and weak functional completeness existing in the prior network security management system. The system mainly comprises peripheral equipment, a security agent terminal, a security management center and terminal management equipment, wherein the security management center applies security technology of network access control, intrusion detection, virus detection and vulnerability management to the security agent terminal through an interface component, a data base module and a user interface component; and under the unified management and control, all security technology is mutually complemented and matched to detect and control network behaviors, so that a distributed security protection system structure in which security strategies are under central management and the security detection is separately distributed is formed. The system and the method have the advantages of flexible configuration, easy expansion, good openness, support of the different level management, and suitability for the security management and protection of the computer network in governments, colleges and universities, and large- and medium-sized enterprises.
Owner:XIDIAN UNIV
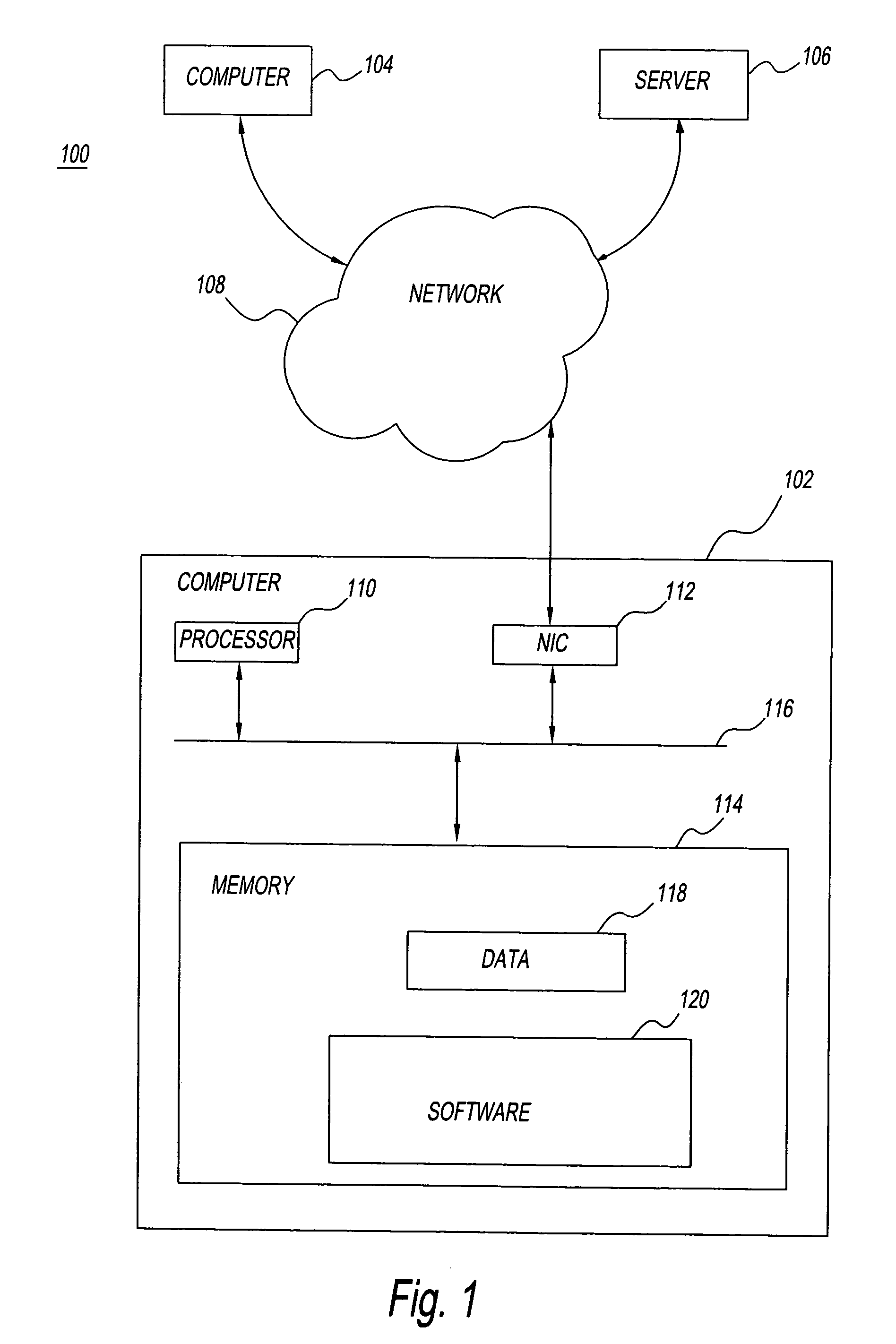
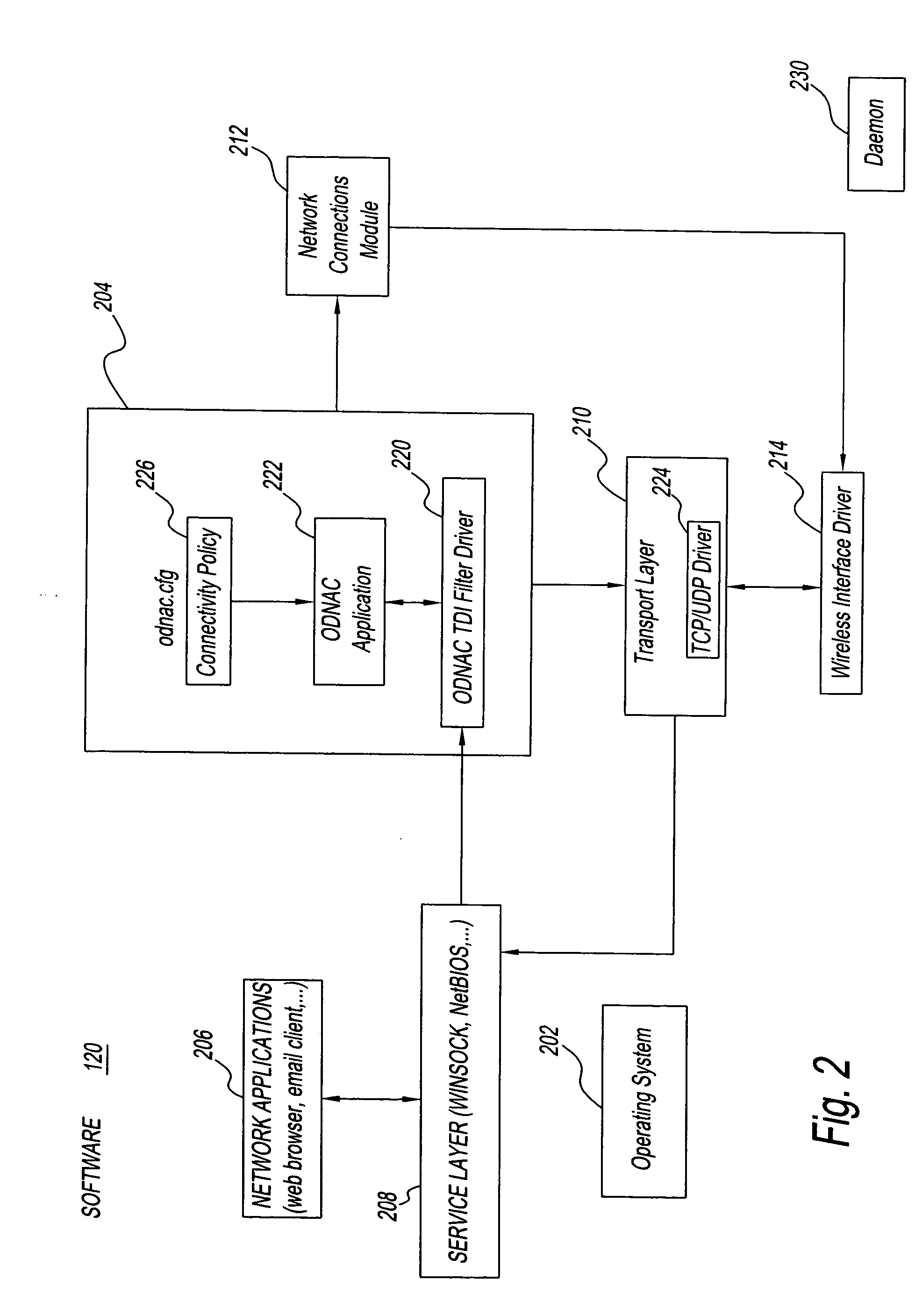
Computer and method for on-demand network access control
ActiveUS20060090023A1Shrink window of opportunityReduce power consumptionDigital computer detailsComputer security arrangementsNetwork activityApplication software
A computer and method that control access to a network. The computer includes an application that shrinks the window of opportunity for a network attack and reduces power consumption by automatically causing a computer to connect to the network when access is needed and to disconnect the computer from the network when access is not needed. The computer is automatically disconnected when it is deemed that network access is no longer needed, such as after a time period of no network activity. In turn, when the user, or the system, needs access to the network, the computer is automatically reconnected to the network. A software daemon on the computer may temporarily reconnect the computer to the network to access a server on the network to determine if attempts have been made to access the computer.
Owner:LENOVO PC INT
Updating dispersed storage network access control information
ActiveUS20110055277A1Digital data information retrievalDigital data processing detailsManagement unitNetwork Access Control
In a dispersed storage network where slices of secure user data are stored on geographically separated storage units (44), a managing unit (18) connected to the network (20) may seek to broadcast and update secure access control list information across the network (20). Upon a target device (e.g., devices 12, 14, 16, 18, or 44) receiving the broadcast the target device creates and sends an access control list change notification message to all other system devices that should have received the same broadcast if the broadcast is a valid request to update access control list information. The target device waits for responses from the other system devices to validate that the broadcast has been properly sent to a threshold number of other system devices before taking action to operationally change local data in accordance with the broadcast.
Owner:PURE STORAGE
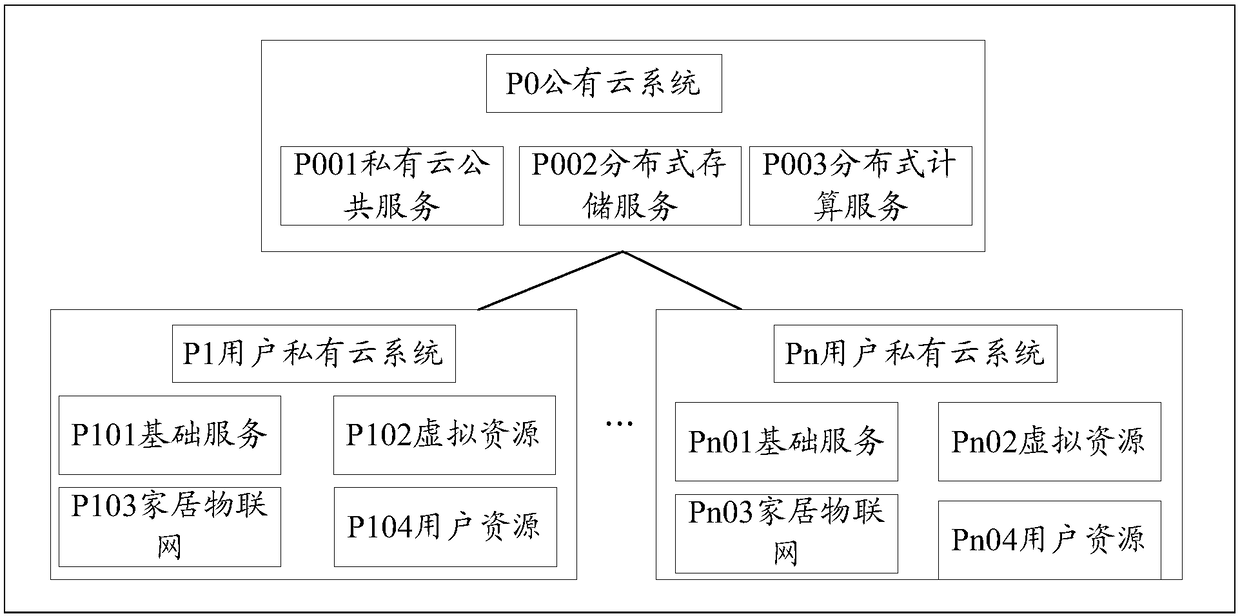
Internet-of-things control system based on mixed cloud
An internet-of-things control system based on mixed cloud comprises a public cloud system and a plurality of private cloud systems. The public cloud system is connected with the private cloud systemsto form a mixed cloud system, and the public cloud system is used for controlling the communication interaction of the private cloud systems and provides distributed storage and distributed computingcontrol for all nodes formed by all the private cloud systems; the private cloud systems provide network access control for user clients and various internet-of-things terminals and control local resources and meanwhile share a part of storage resources of local storage units and local hardware operation resources. The information isolated island problem of resources in user homes in the current internet-of-things system is solved, the problem that the user family object resources are independent and do not form a unified control coordination system, so that the existing internet-of-things system needs to construct huge system resources at the public end, and the system becomes huge, redundant and high in cost are solved, and the problem that the privacy of a user cannot be protected in ahigh-safety degree is solved.
Owner:北京算云联科科技有限公司
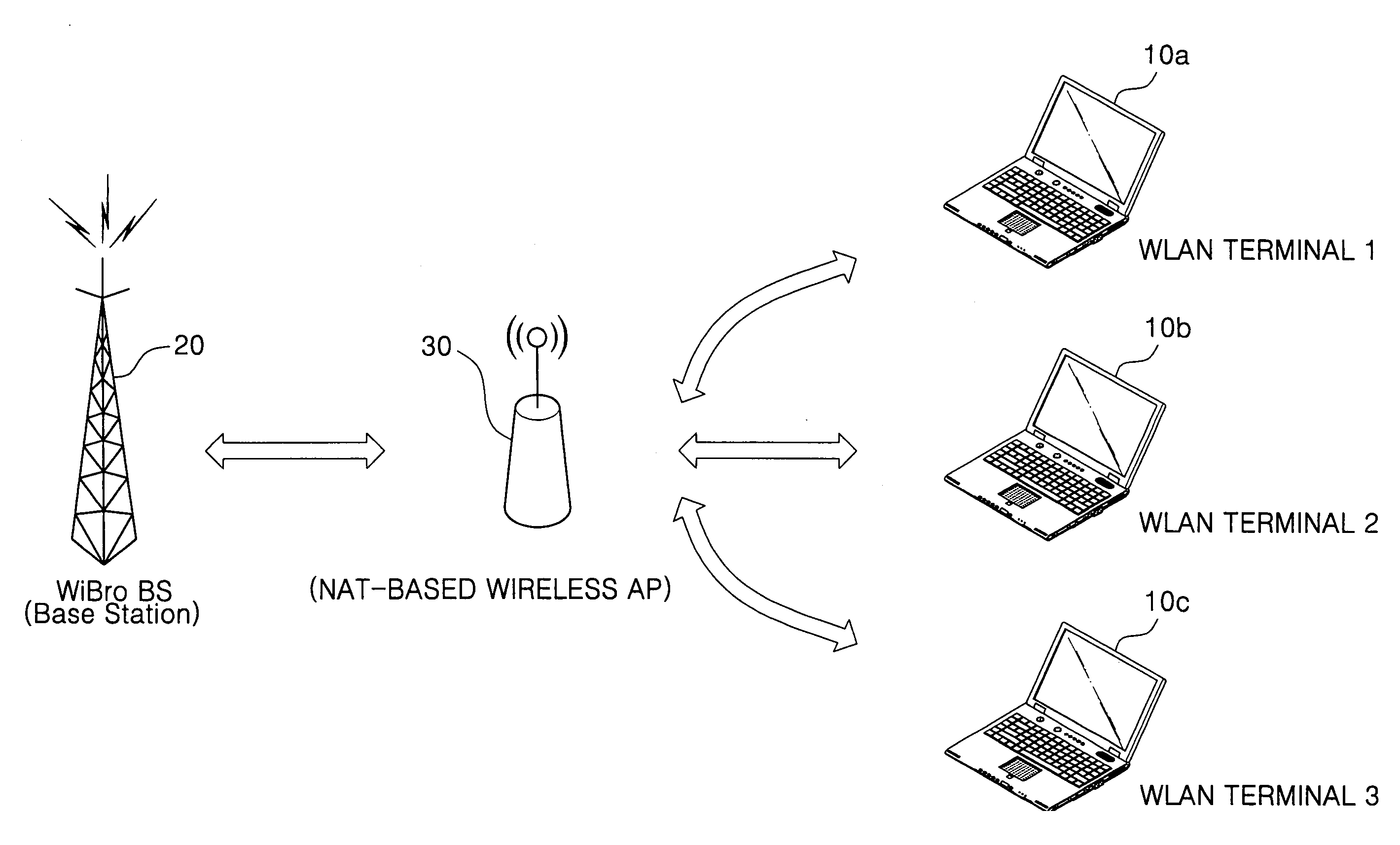
Method and system for authentication of WLAN terminal interworking with broadband wireless access network
ActiveUS20080219230A1Network topologiesRadio/inductive link selection arrangementsAccess networkUser authentication
A method and a system for interworking with a Broadband Wireless Access (BWA) network in a Wireless Local Area Network (WLAN) terminal. According to the method, a relay station for connecting the Wireless Local Area Network (WLAN) terminal with the Broadband Wireless Access (BWA) network sets a connection with the Broadband Wireless Access (BWA) network through an initialization process. A user authentication with the Wireless Local Area Network (WLAN) terminal is performed by the relay station in compliance with a Wireless Local Area Network (WLAN) protocol. A user authentication with a Broadband Wireless Access (BWA) network Access Control Router (ACR) is performed in compliance with a Broadband Wireless Access (BWA) network protocol by the relay station in place of the Wireless Local Area Network (WLAN) terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
Network access control system and method
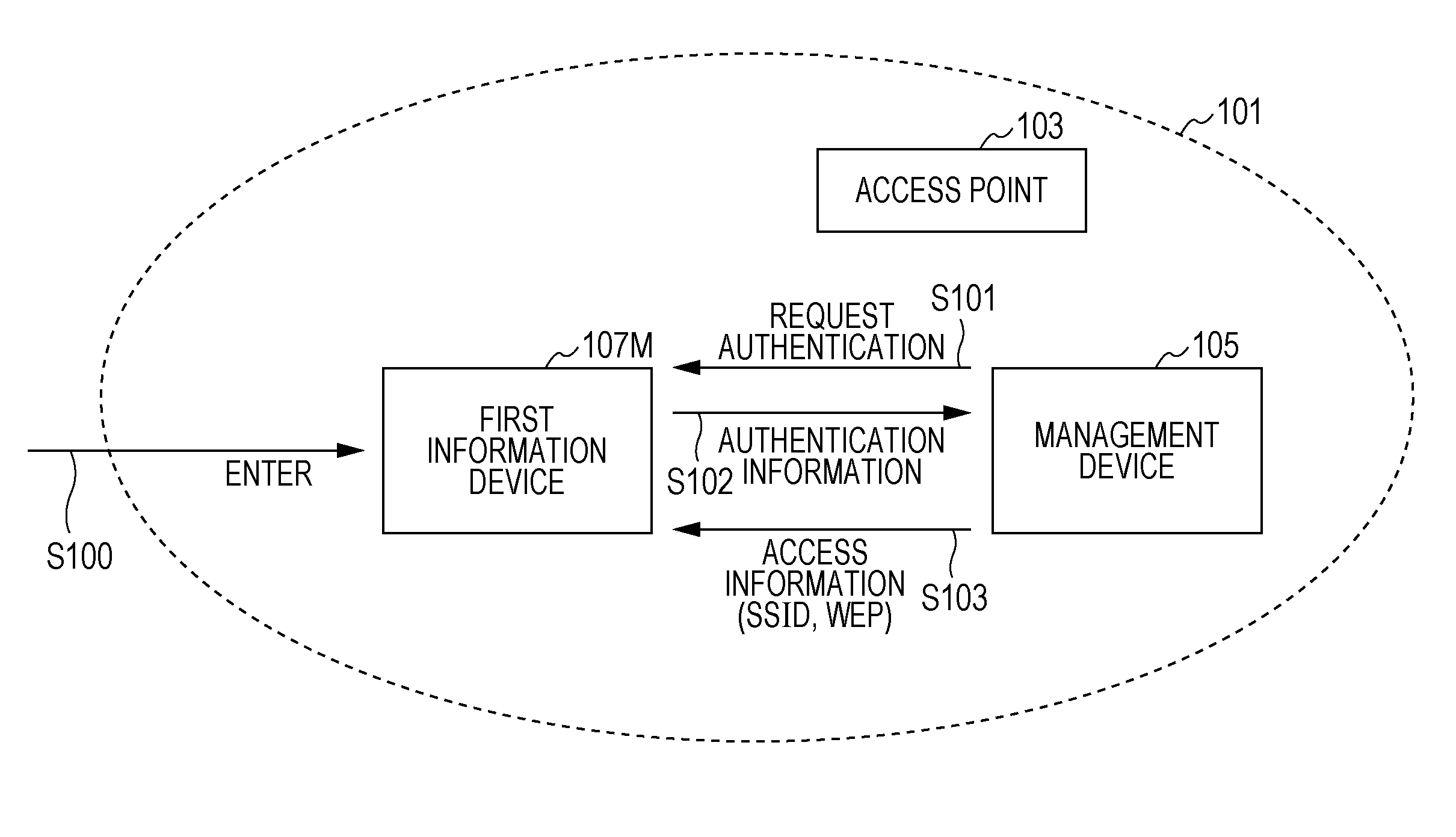
InactiveUS20100205655A1Easy accessDigital data processing detailsNetwork topologiesManagement unitControl system
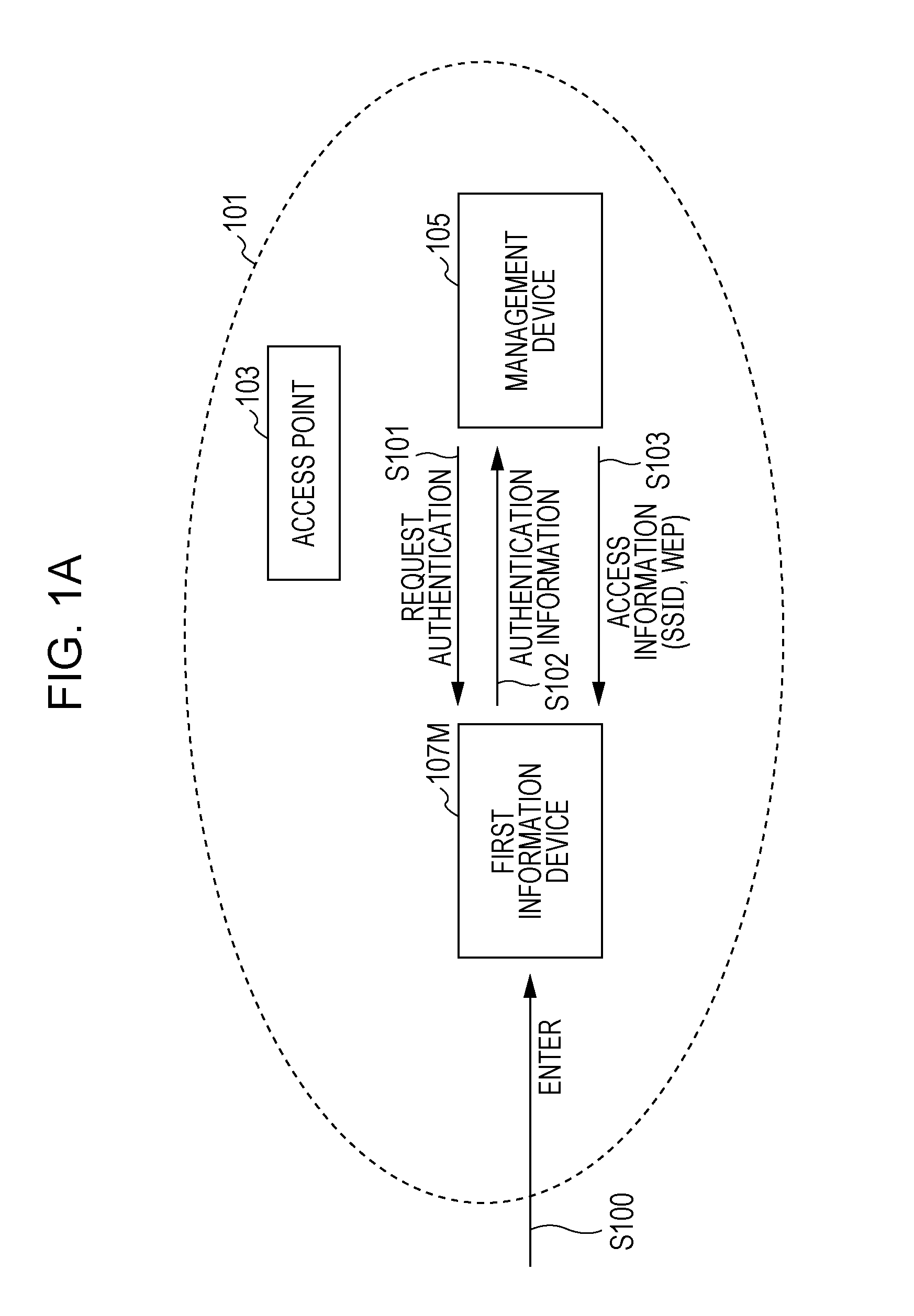
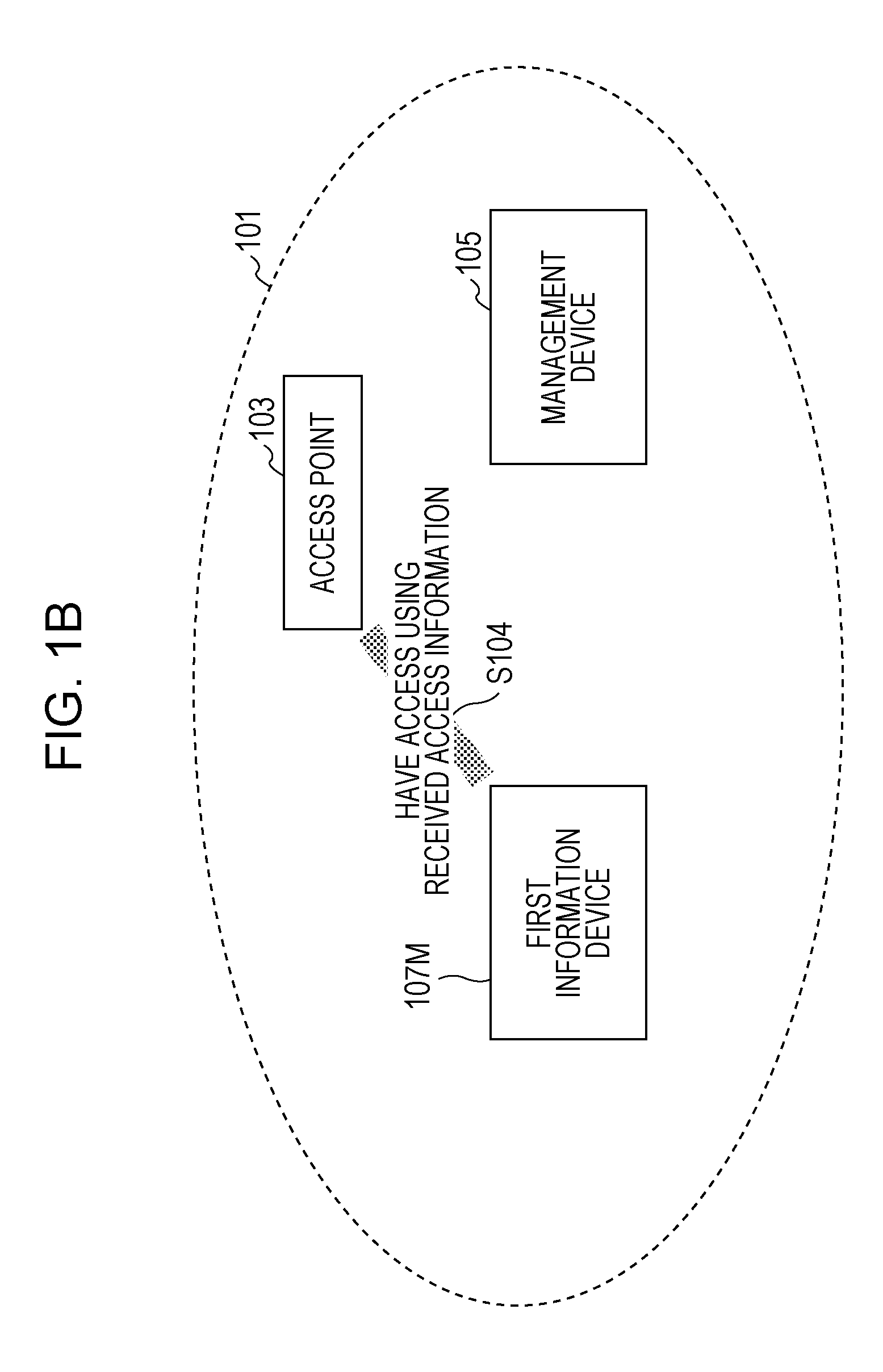
A network access control system includes an information device that has access to a relay device which relays communication in a communication network, by the use of access information, and performs communication via the relay device, and a management unit that finds information devices, wherein when the found information device has no access to the relay device and is a second information device which is allowed to have access to the relay device by a first information device, the management unit transmits the access information to the second information device without a request for authentication.
Owner:138 EAST LCD ADVANCEMENTS LTD
Methods and devices for enforcing network access control utilizing secure packet tagging
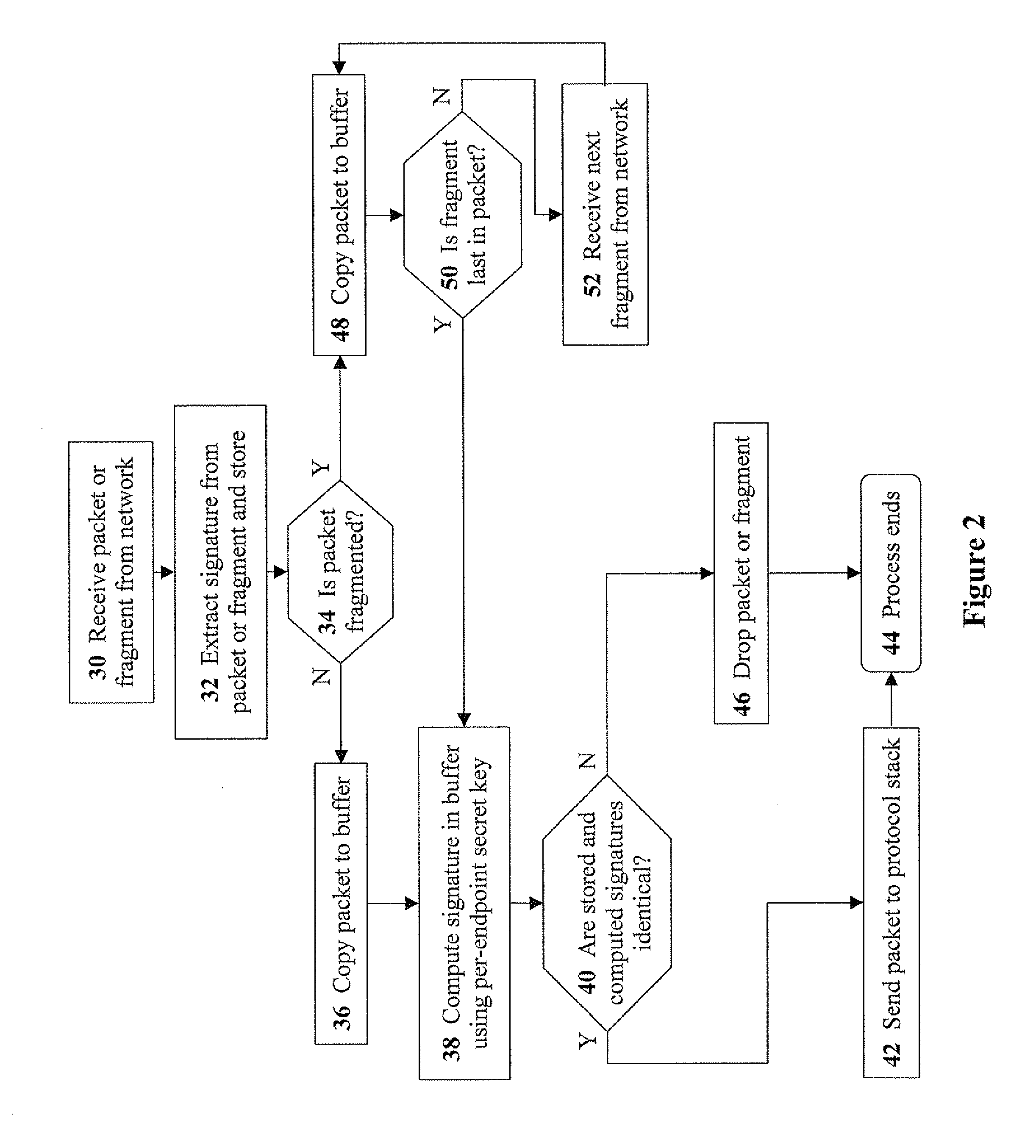
ActiveUS20090249466A1Keeping LAN traffic intactLevel of protectionUser identity/authority verificationMultiple digital computer combinationsNetwork Access ControlProtocol stack
Disclosed are methods, devices, and media for enforcing network access control, the method including the steps of: extracting a packet signature from a packet (or packet fragment) received from a network; storing the packet signature and the packet in a buffer; computing a buffer signature using a per-endpoint secret key; determining whether the packet signature and the buffer signature are identical; and upon determining the packet signature and the buffer signature are identical, transmitting the packet to a protocol stack. Preferably, the step of extracting includes extracting the packet signature from a field (e.g. identification field) of a header of the packet. Preferably, the method further includes the step of: upon determining the packet signature and the buffer signature are not identical, discarding the packet. Methods for receiving a packet from a protocol stack, and transmitting the packet to a network are disclosed as well.
Owner:CHECK POINT SOFTWARE TECH LTD
Network access control method and device thereof
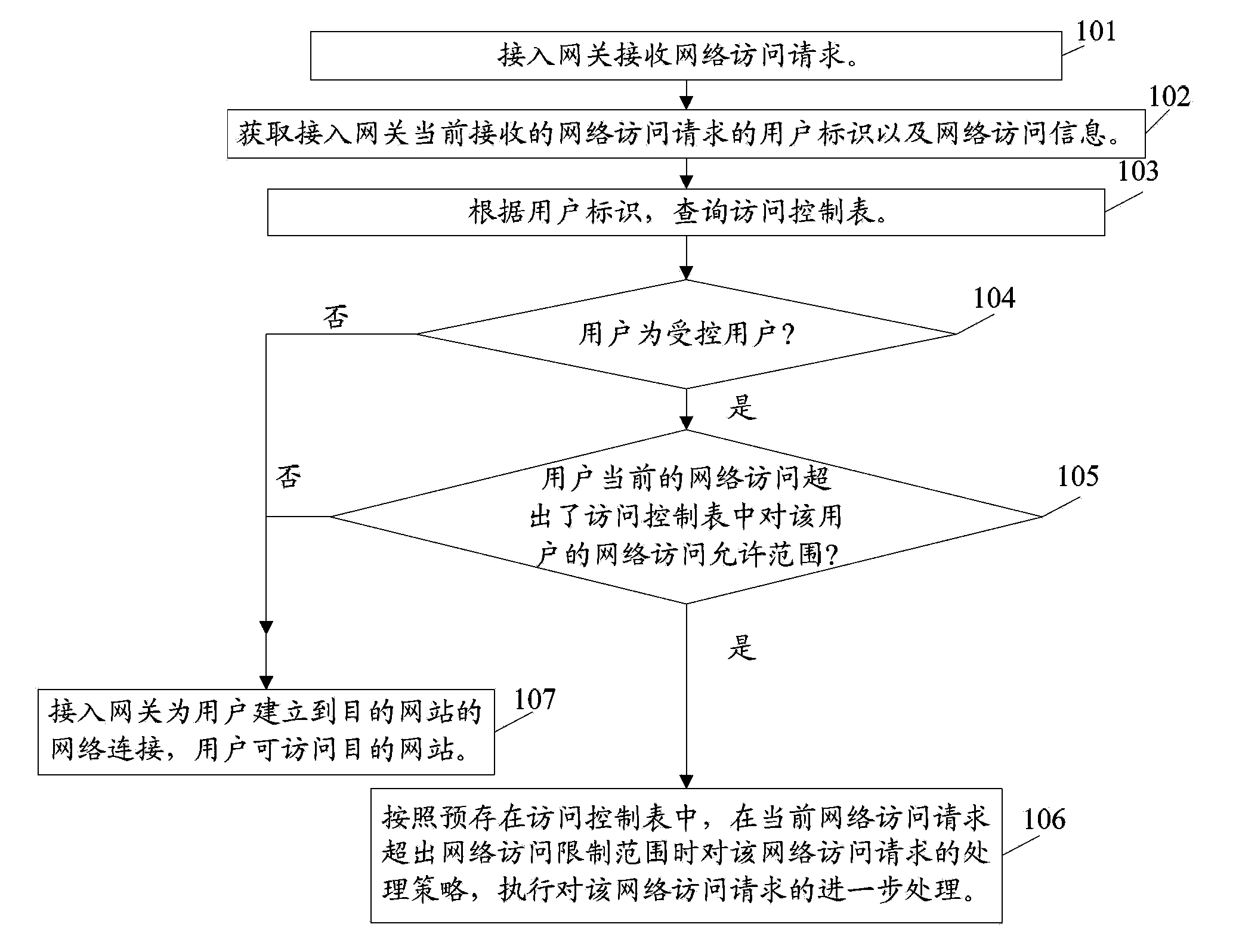
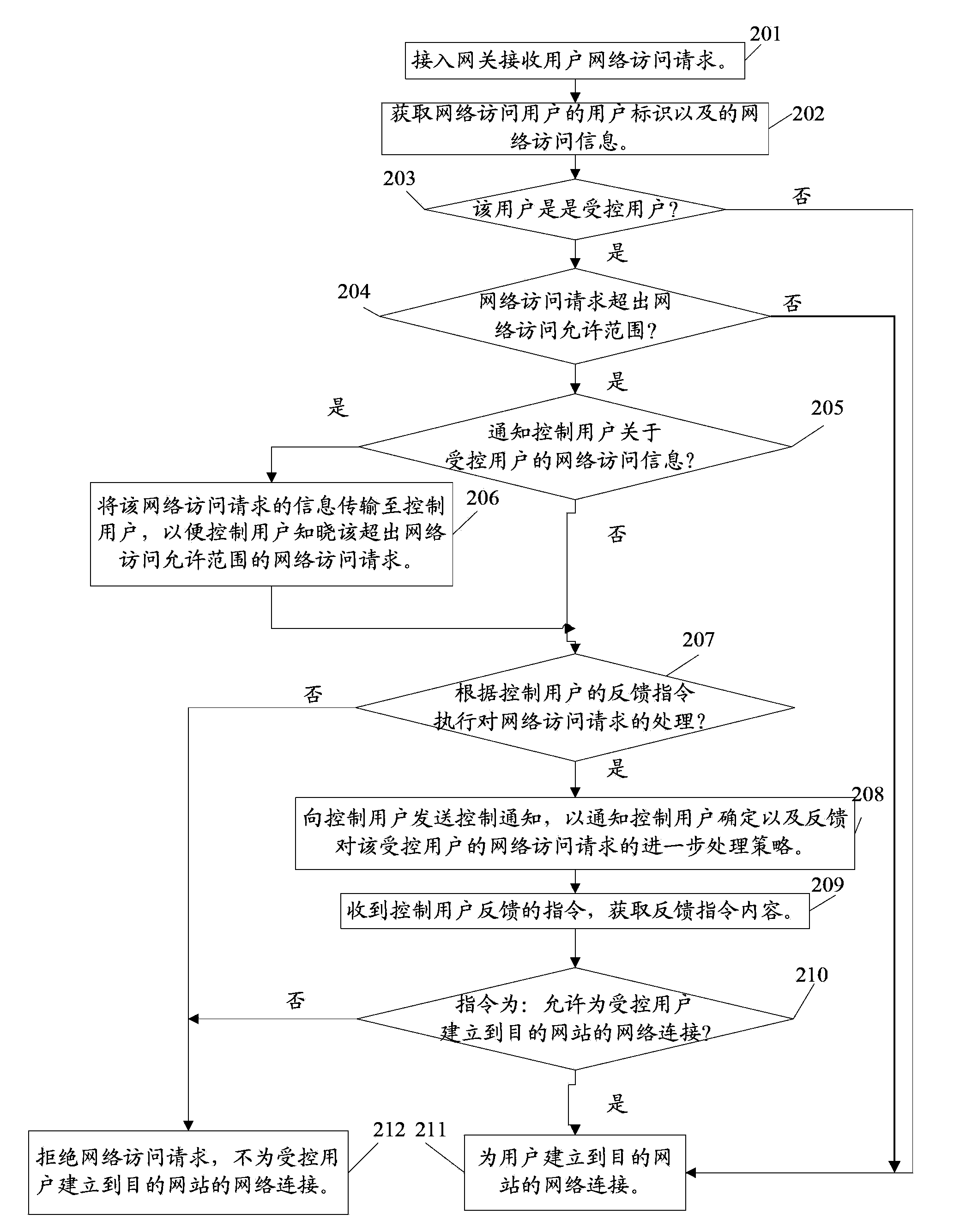
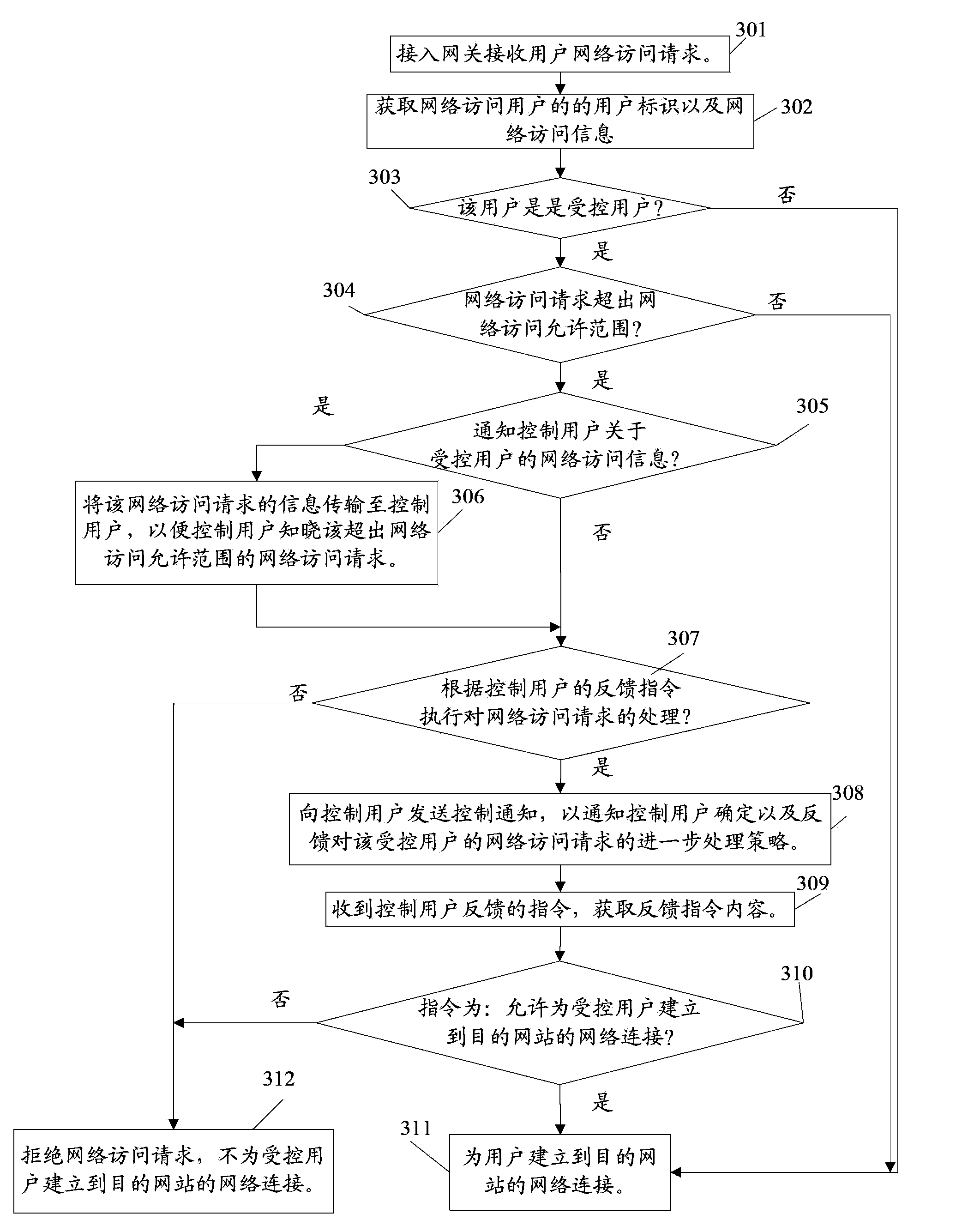
ActiveCN103516681AEffective and comprehensive controlFlexible controlTransmissionNetwork Access ControlAccess control
The invention relates to communication field, and discloses a network access control method and a device thereof. The network access control method comprises the following steps: acquiring a user identity in a network access request that is received by an access gateway; inquiring a prestored access control table according to the user identity and determining whether the user is a controlled user; if the user is the controlled user, acquiring the network access information of the controlled user; inquiring the access control table according to the network access information, determining whether the network access request exceeds a network access allowed range of the controlled user; if the network access request exceeds the network access allowed range of the controlled user, inquiring the access control table for acquiring a processing strategy to the network access request; and determining a network access control instruction according to the processing strategy, and transmitting the network access control instruction to the access gateway so that the access gateway performs processing to the network access request according to the network access control instruction. The network access control method according to the technical solution of the invention causes controlling for network access of the user more comprehensive, more flexible and more effective.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com