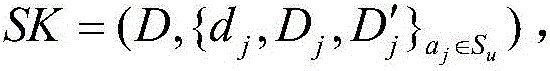Patents
Literature
646 results about "Data access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data Access Control gives customers the ability to customize and control what areas their users can access within Zuora. Data Access Control allows you do the following: Restrict what products and accounts your users can see within Zuora. Data Access Control is ONLY enforced on UI users, not API users.
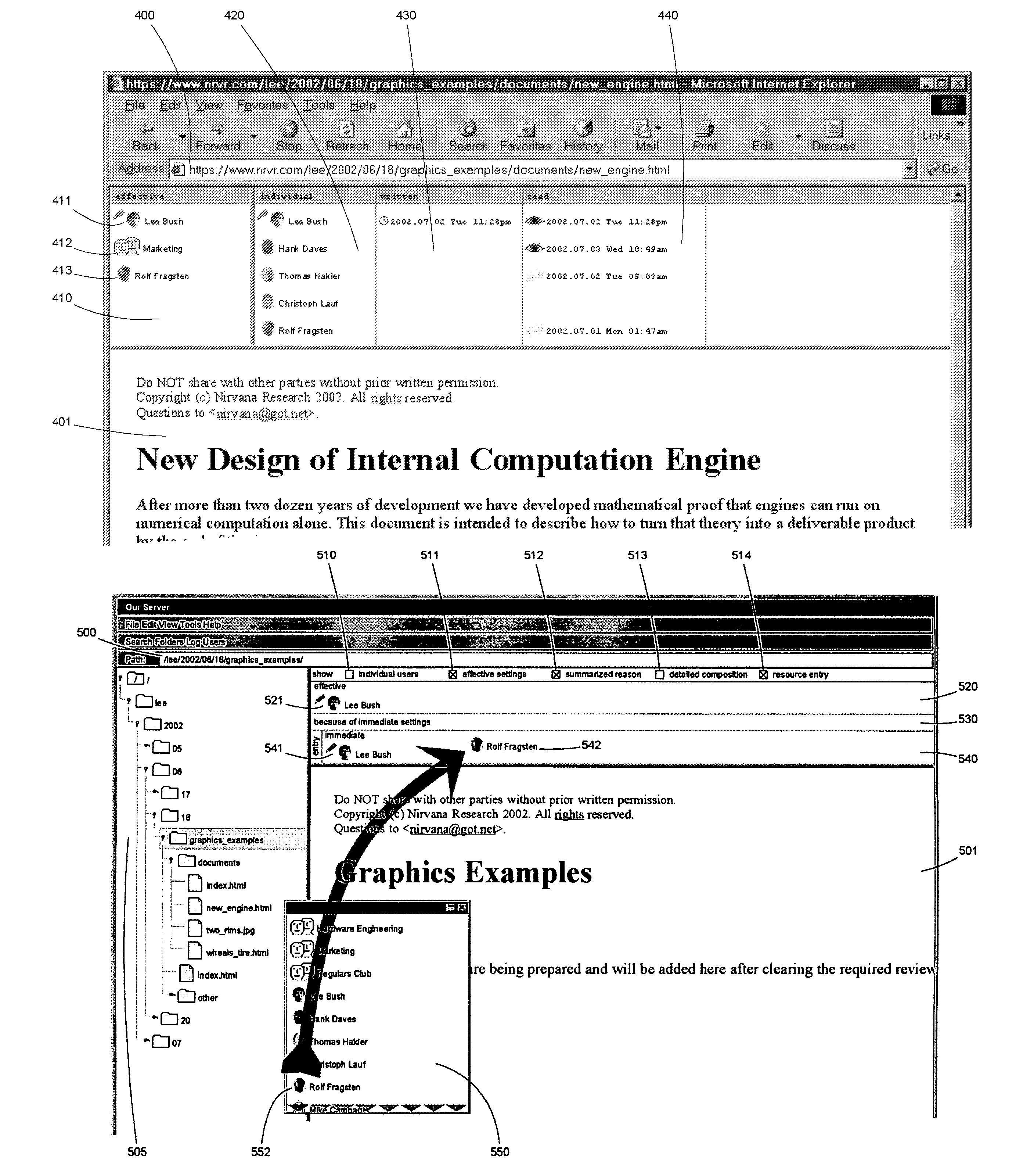
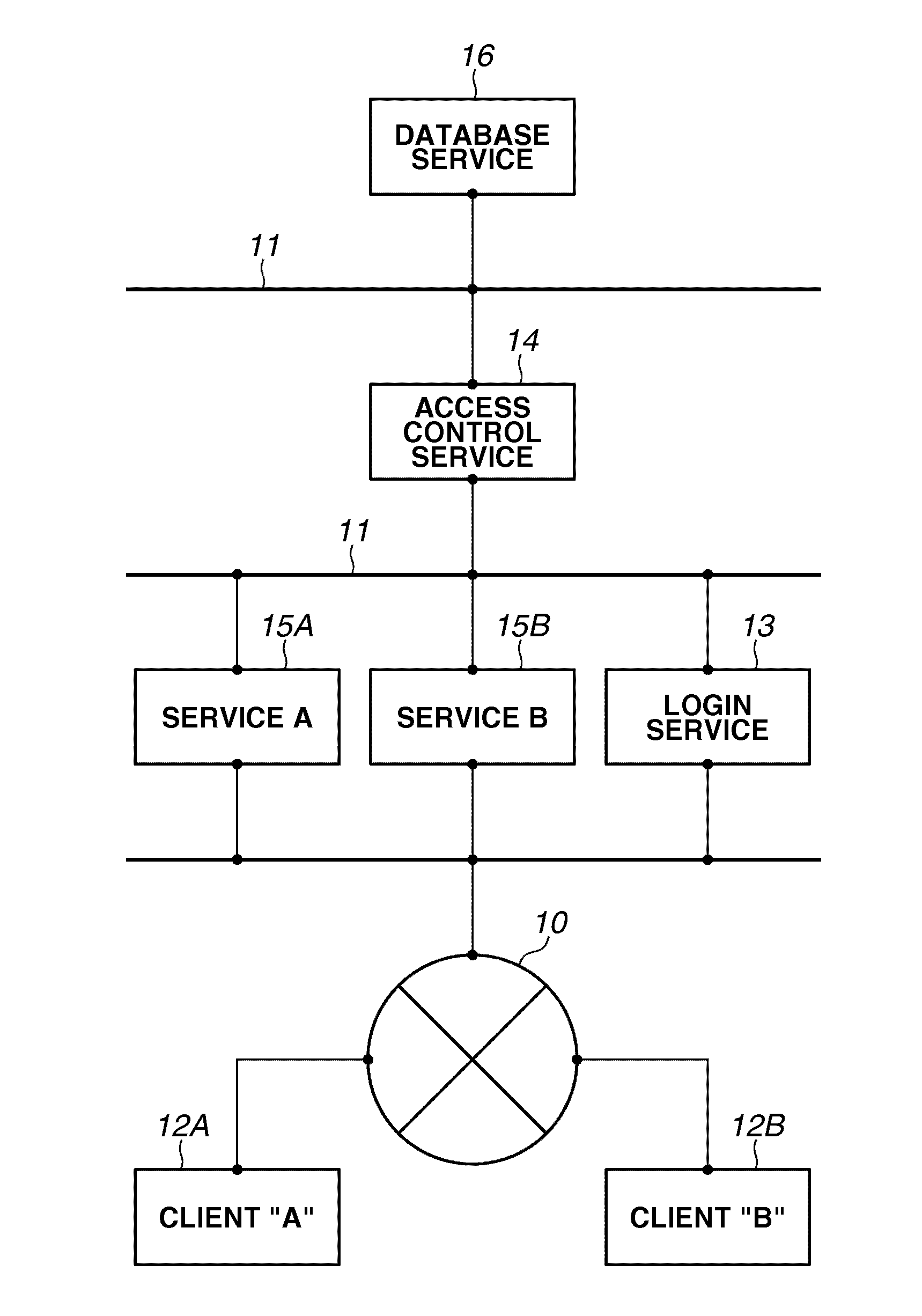
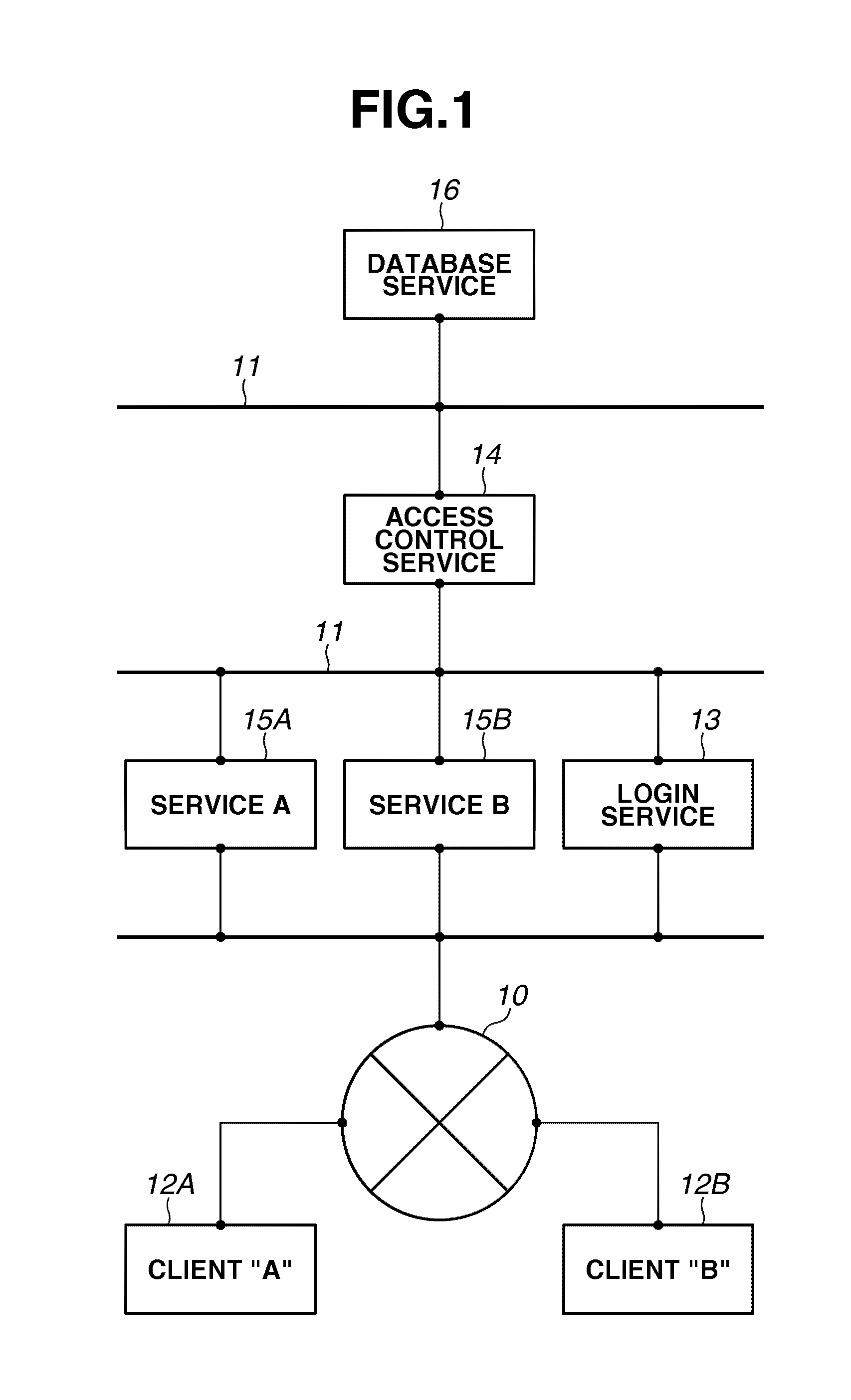
User interface driven access control system and method
InactiveUS9003295B2Digital data processing detailsAnalogue secracy/subscription systemsGraphicsWeb browser
Display regions for representations of results of transformations applied to access control settings for a resource appear integrated with a familiar representation of the resource, e.g. word processor, or Web browser. A number of functions modify layout and transformations, and those functions are available for invocation, e.g. through mouse gestures or key combinations. Users are graphically represented by displays comprising photographic likenesses. Groups can be shown as individual users. Giving someone access to a resource can be as easy as dragging that person's likeness. Access log information can be shown together with access control settings. Reviewing the subset of resources available to a user is made easier. Overflow indicators replace scroll bars. Macros effect snapshots of volatile sets of users. Sections within documents can be omitted automatically if a user lacks authorization. Access control settings for one resource can be linked to be dependent on settings for other resources.
Owner:NIRESIP
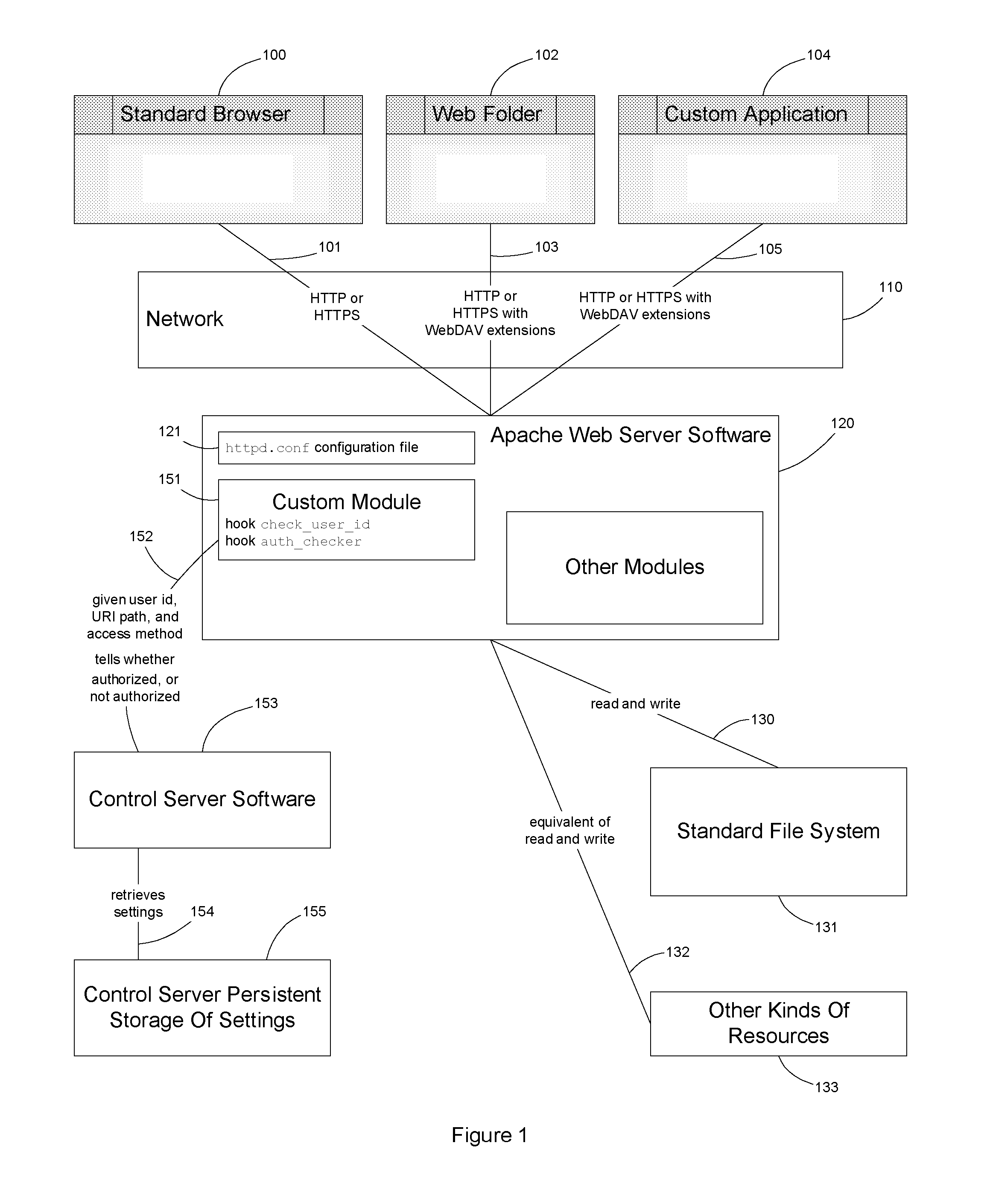
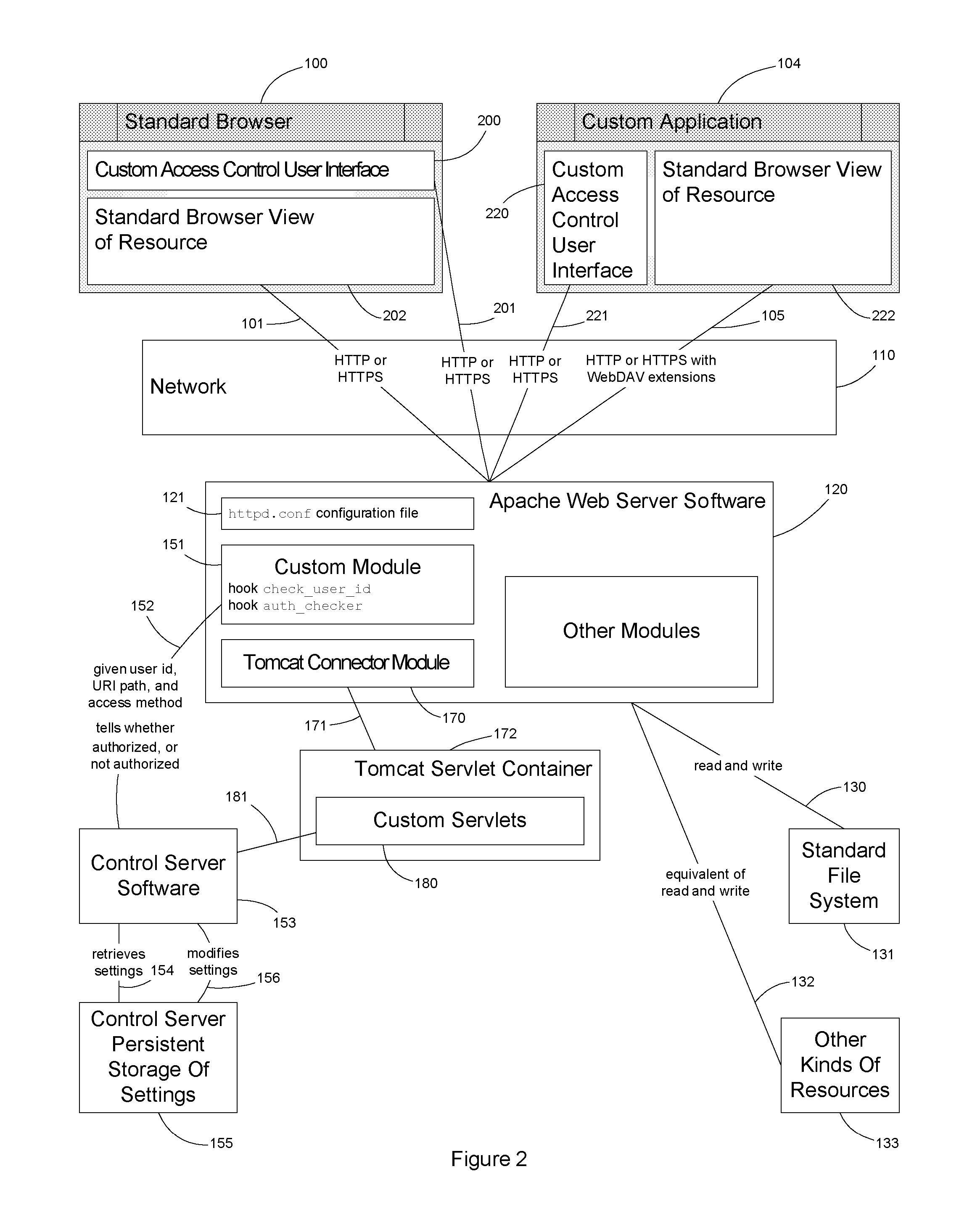
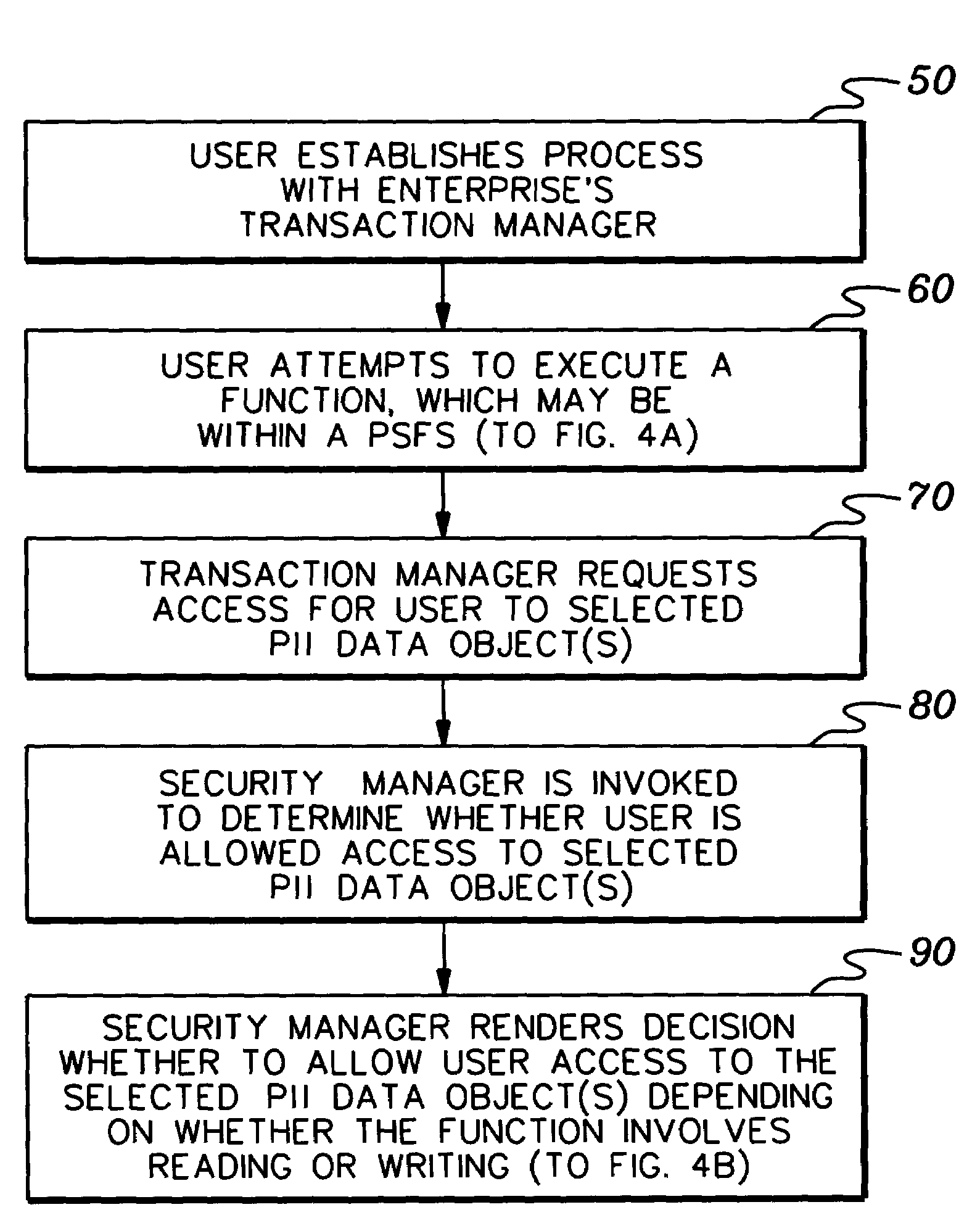
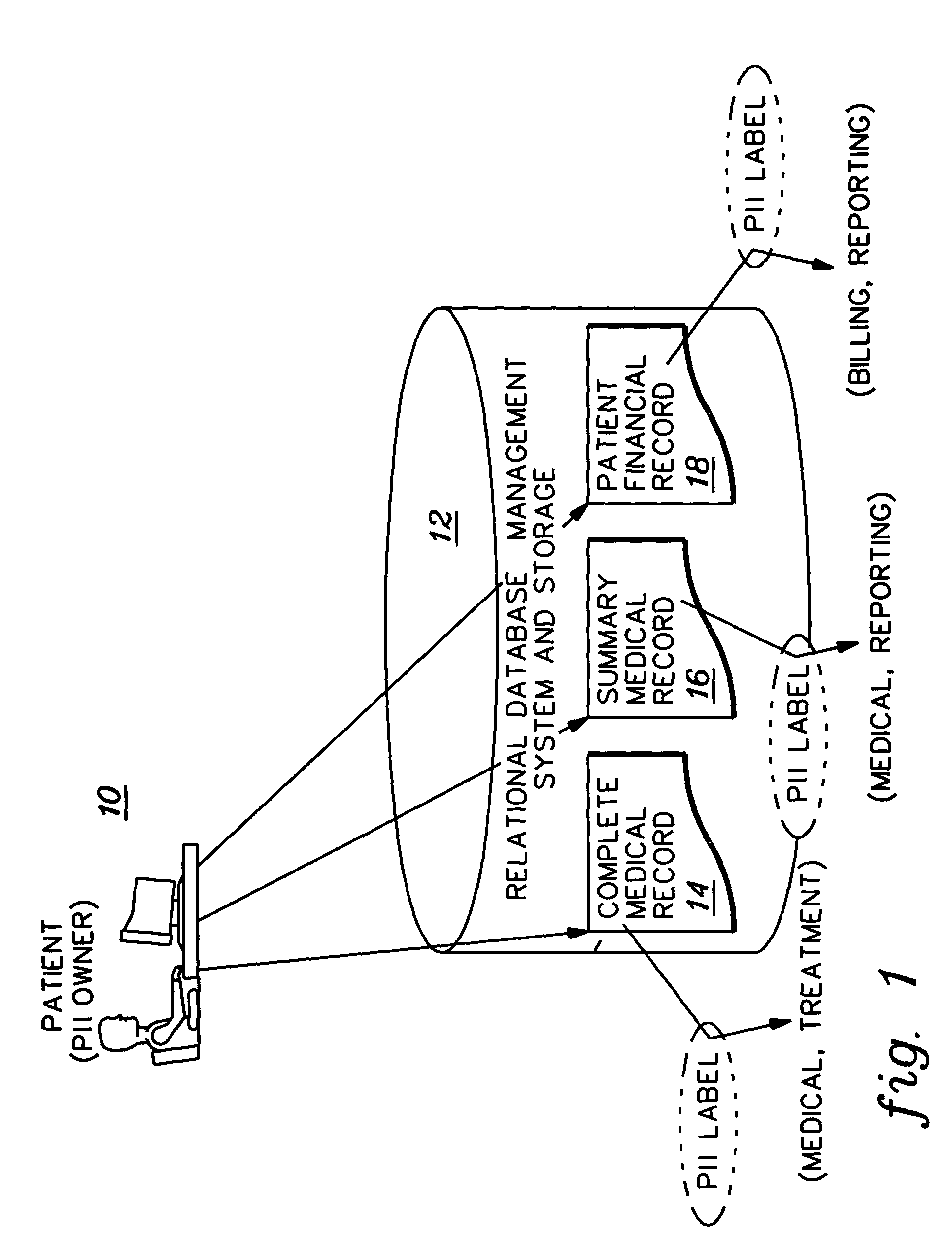
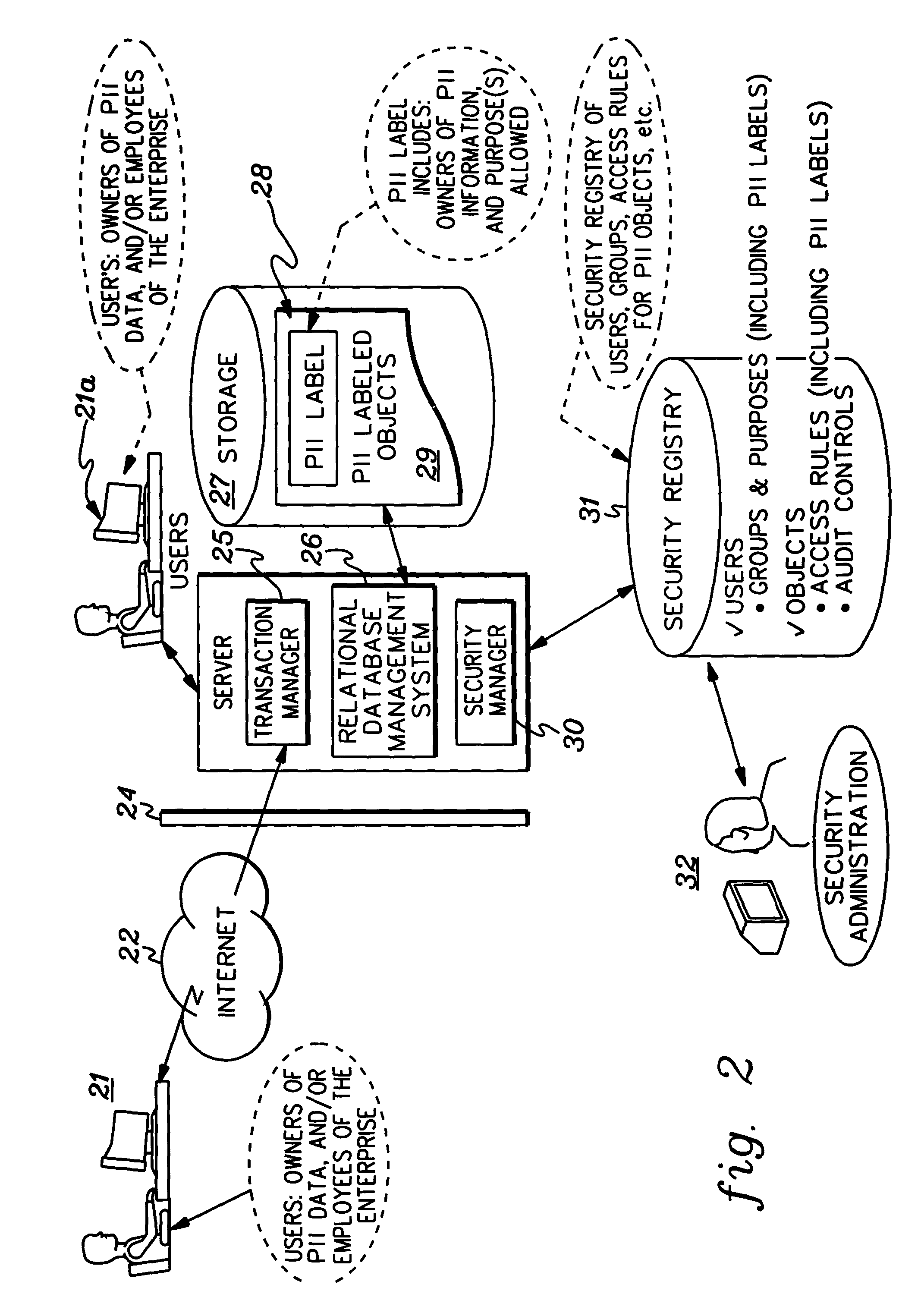
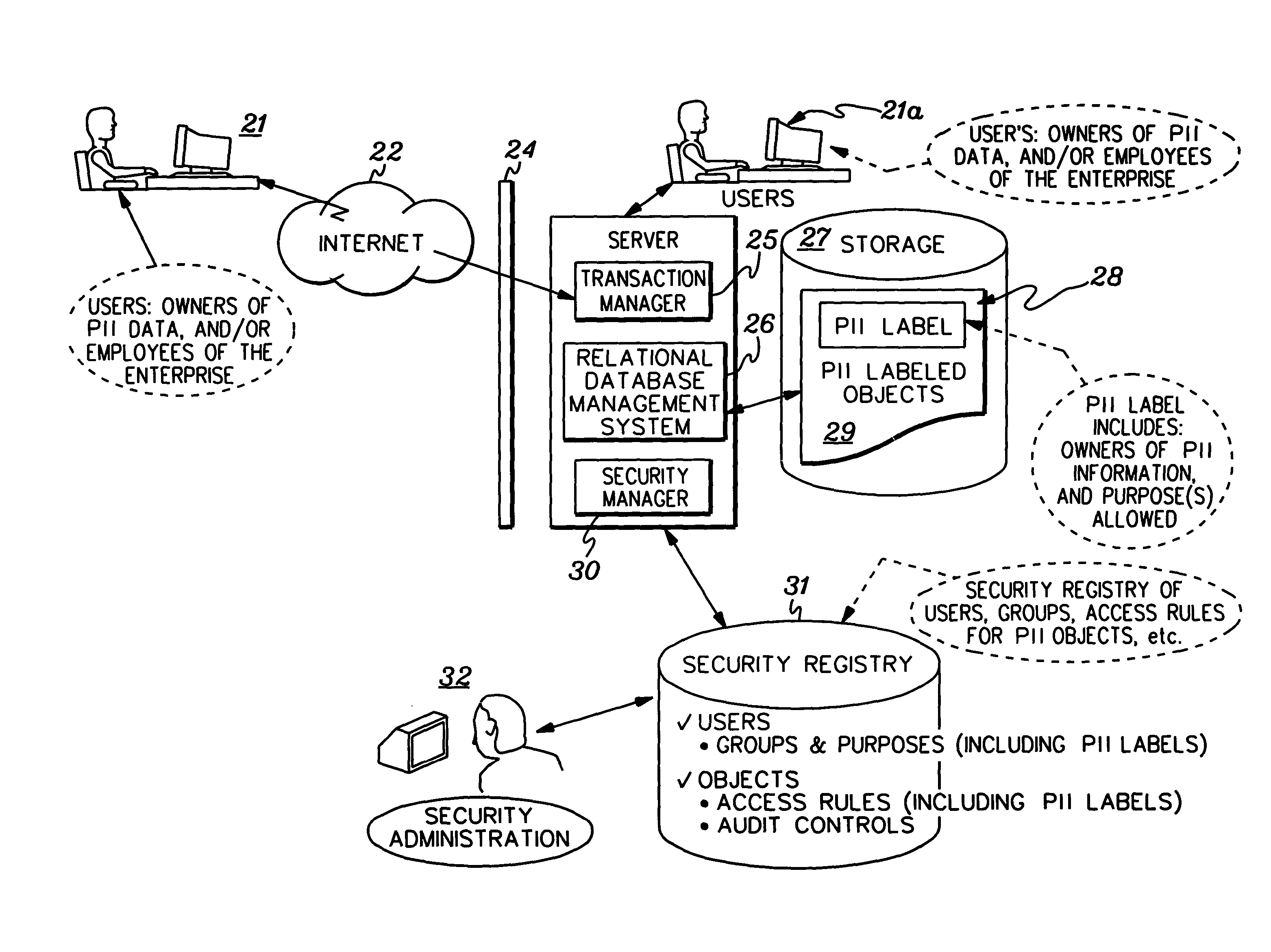
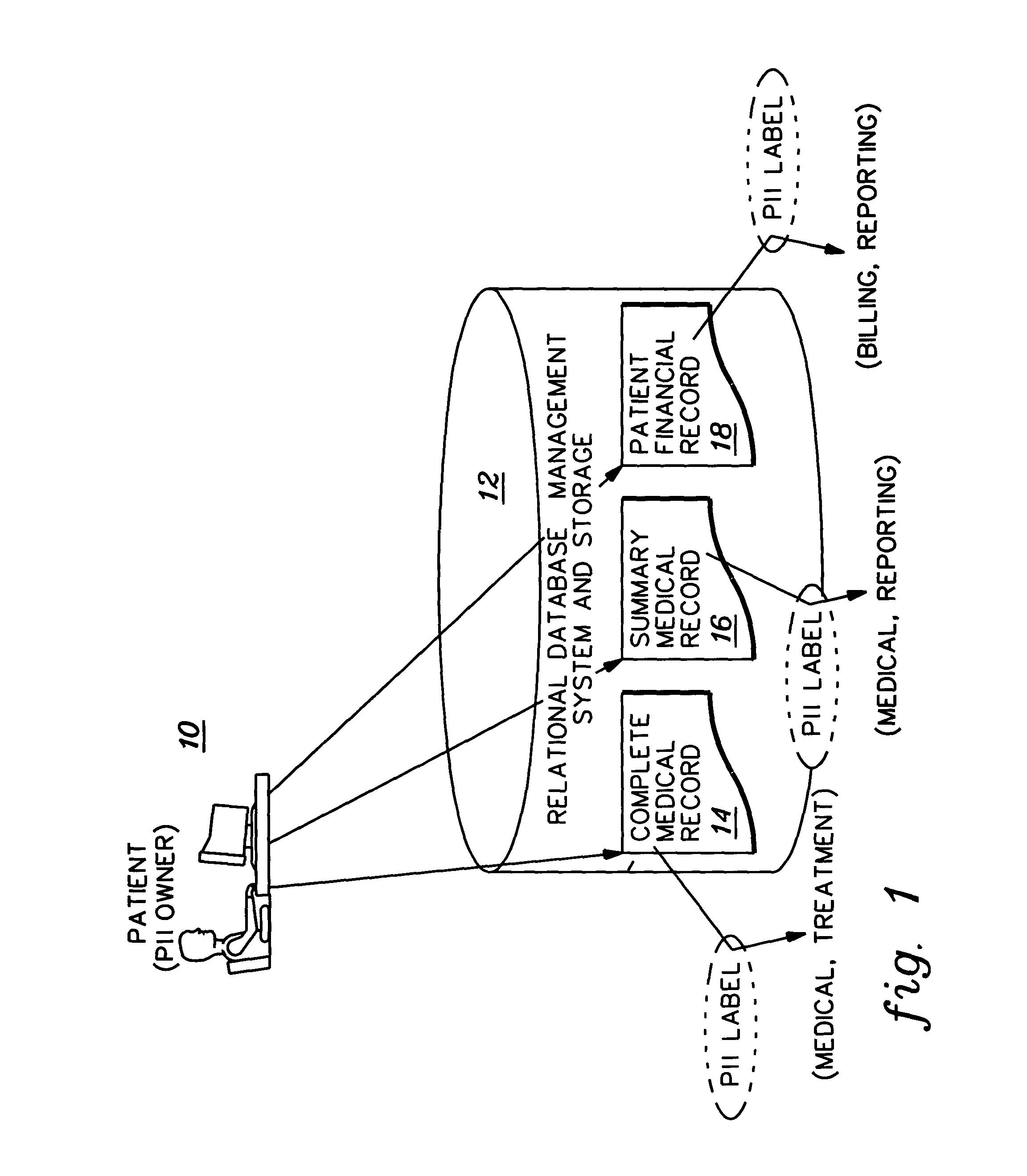
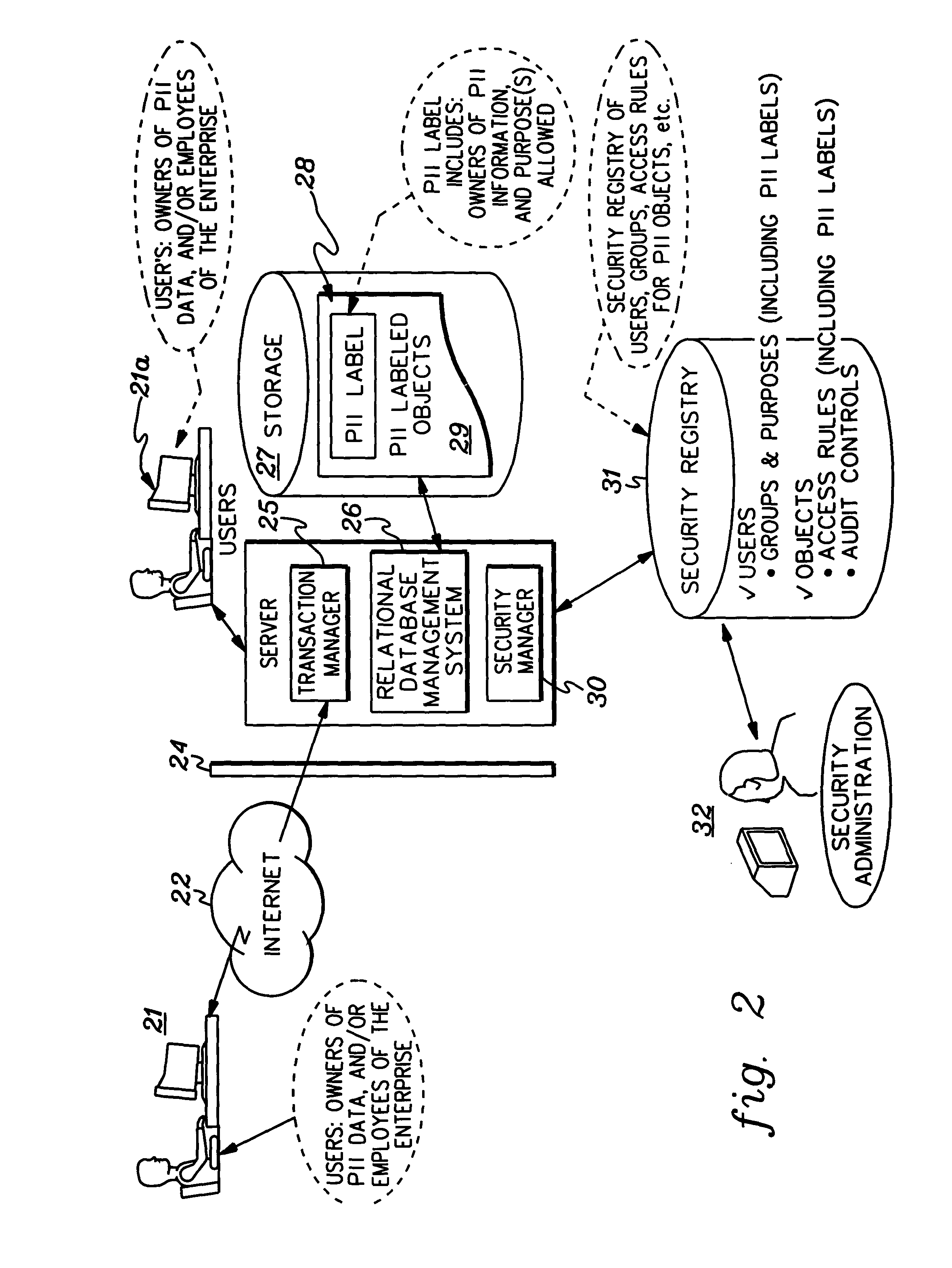
Implementation and use of a PII data access control facility employing personally identifying information labels and purpose serving functions sets
ActiveUS7302569B2Digital data processing detailsAnalogue secracy/subscription systemsFeature setInternet privacy
A data access control facility is implemented by assigning personally identifying information (PII) classification labels to PII data objects, with each PII data object having one PII classification label assigned thereto. The control facility further includes at least one PII purpose serving function set (PSFS) comprising a list of application functions that read or write PII data objects. Each PII PSFS is also assigned a PII classification label. A PII data object is accessible via an application function of a PII PSFS having a PII classification label that is identical to or dominant of the PII classification label of the PII object. A user of the control facility is assigned a PII clearance set which contains a list of at least one PII classification label, which is employed in determining whether the user is entitled to access a particular function.
Owner:SAILPOINT TECH HLDG INC
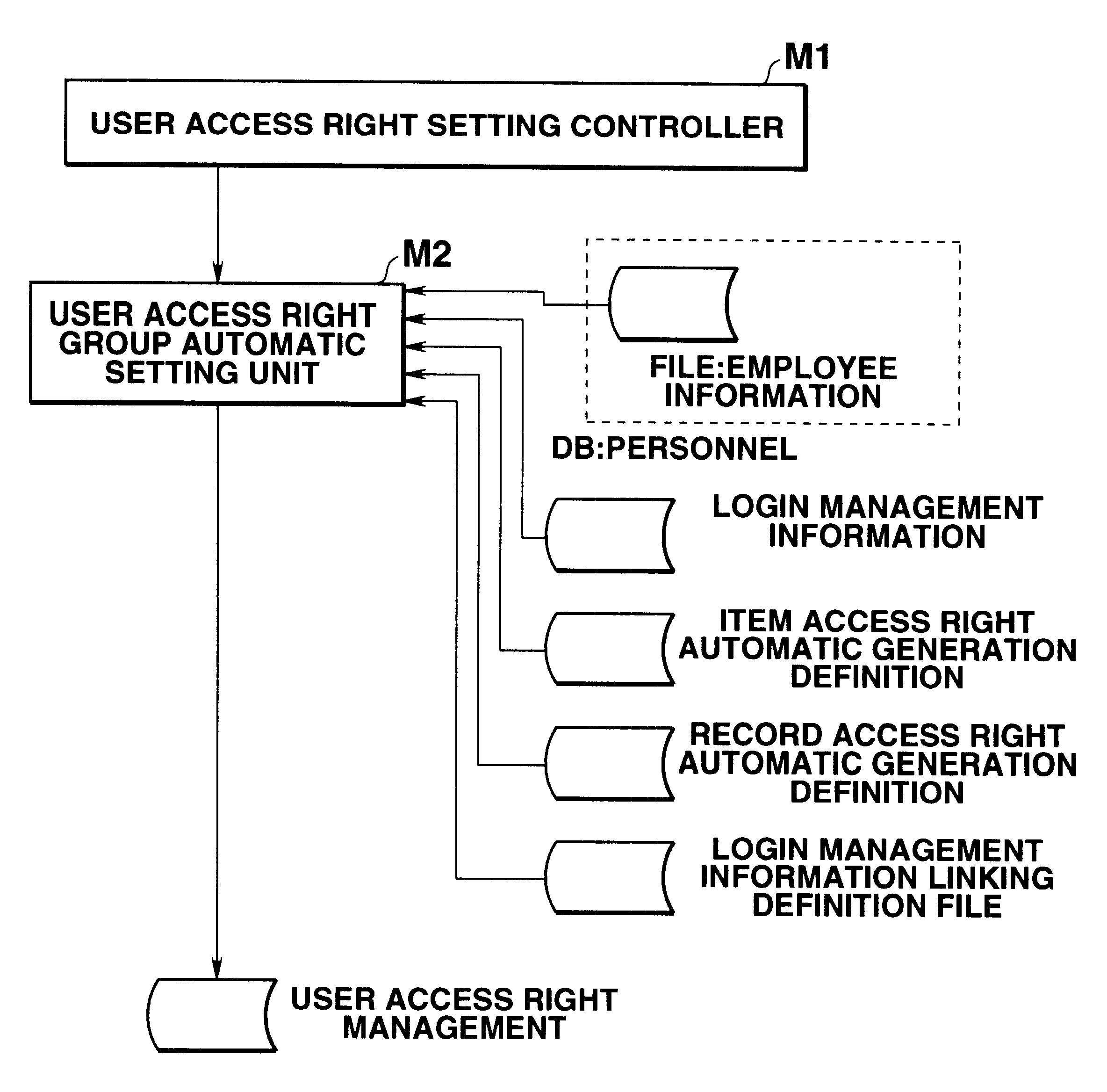
Data access control apparatus for limiting data access in accordance with user attribute
InactiveUS6275825B1Reduce loadPrevent setting errorsData processing applicationsDigital data processing detailsData access controlRights management
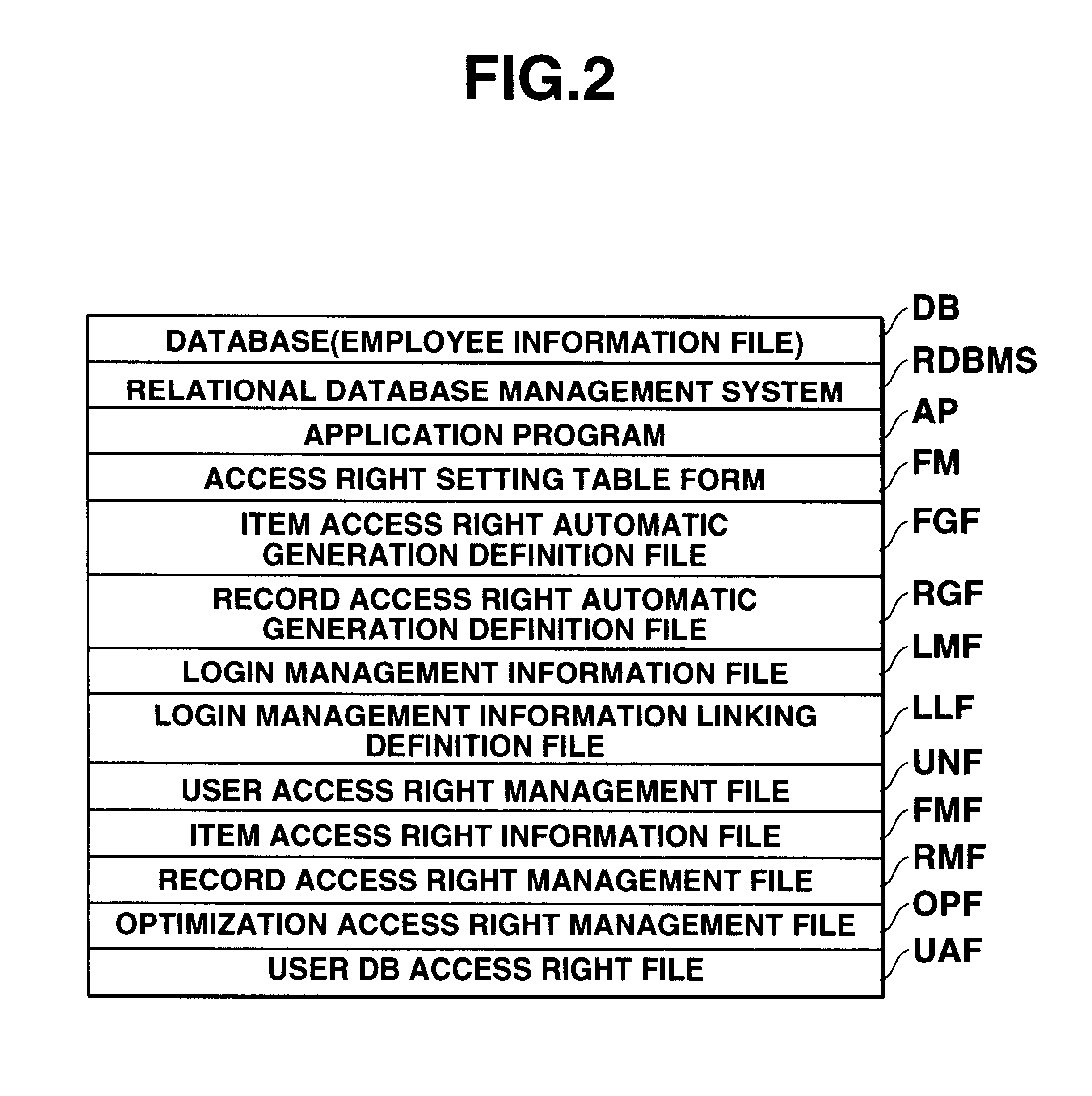
This invention provides a data access control apparatus arranged to automatically set access right information limiting data access, in accordance with a user attribute when a user accesses a database. In setting, for a plurality of users, access right information corresponding to each user, the load on an operator can be reduced, and access right information setting errors can be prevented. An automatic setting unit reads out information from a login management information file and an employee information file on the basis of definition information of a definition files to automatically generate a user access right management file which stores a login ID, an item access right, and a record access right group code for each user. When a login ID is input in accessing the employee information file, a setting controller refers to the management file to determine a user group to which the user belongs and an access enabled / disabled state of the data on the basis of the access right made to correspond to this user group.
Owner:CASIO COMPUTER CO LTD
Portable wireless terminal and its security system
InactiveUS20070281664A1Avoid interceptionSafe removalUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyRemote control
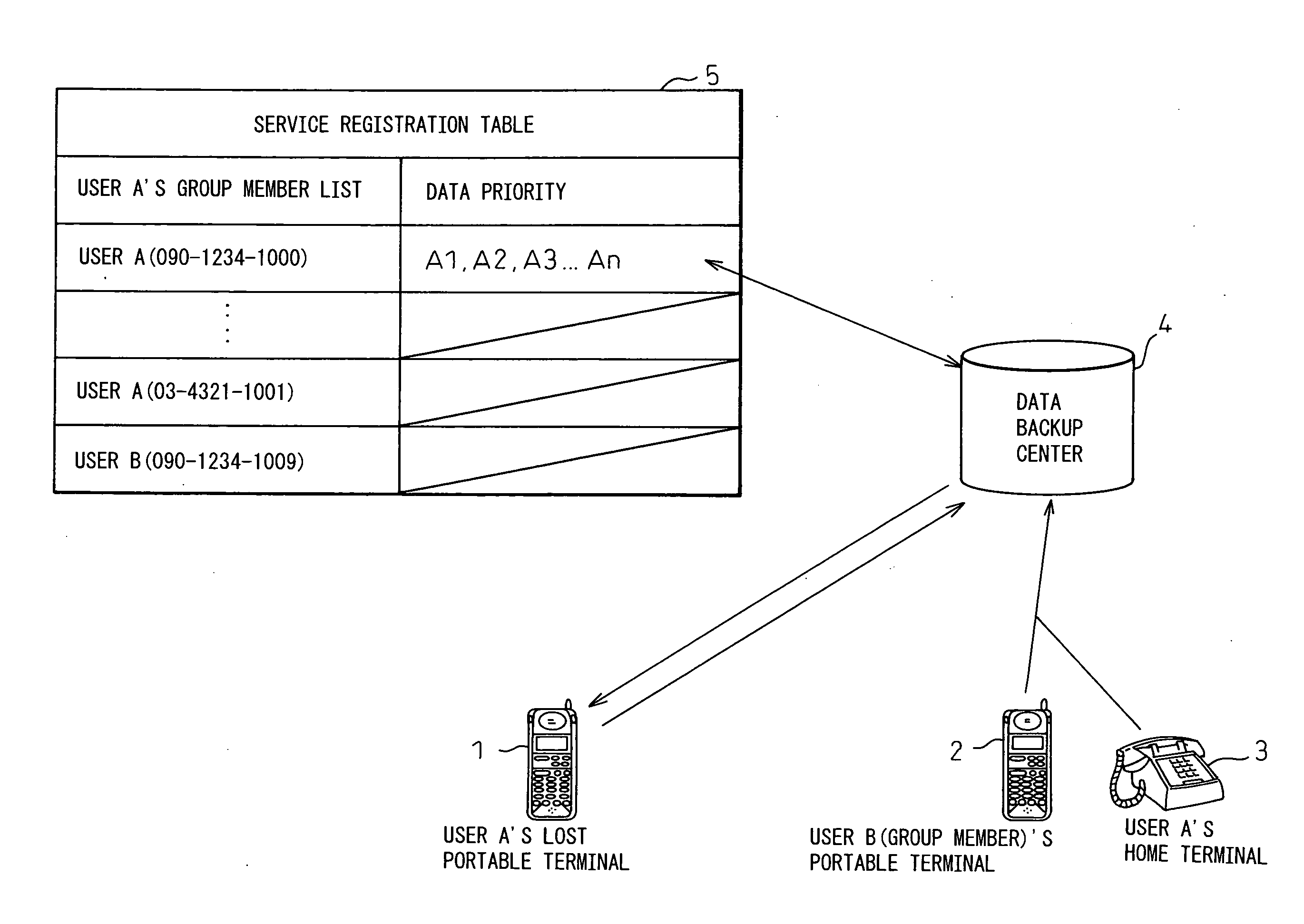
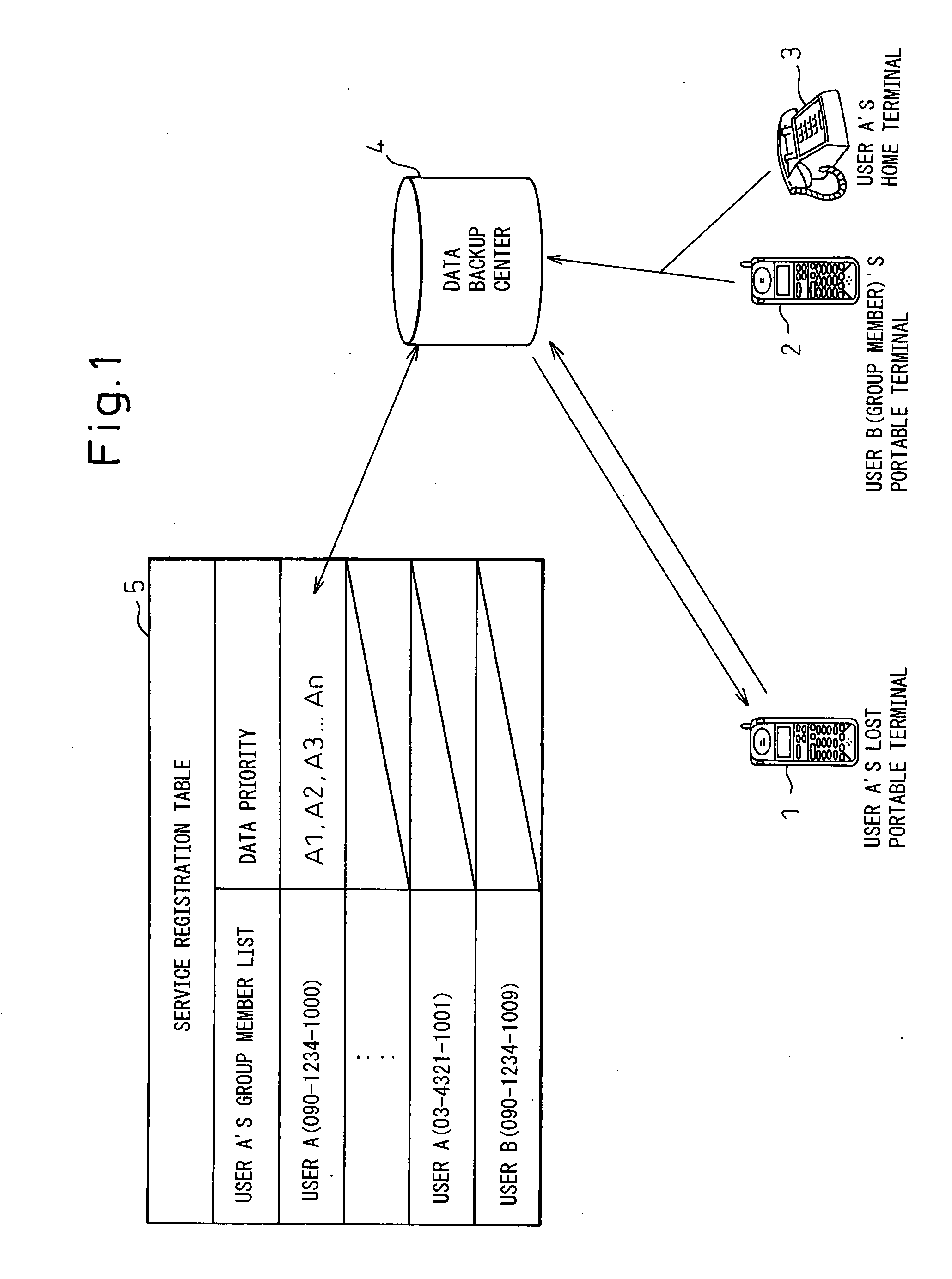
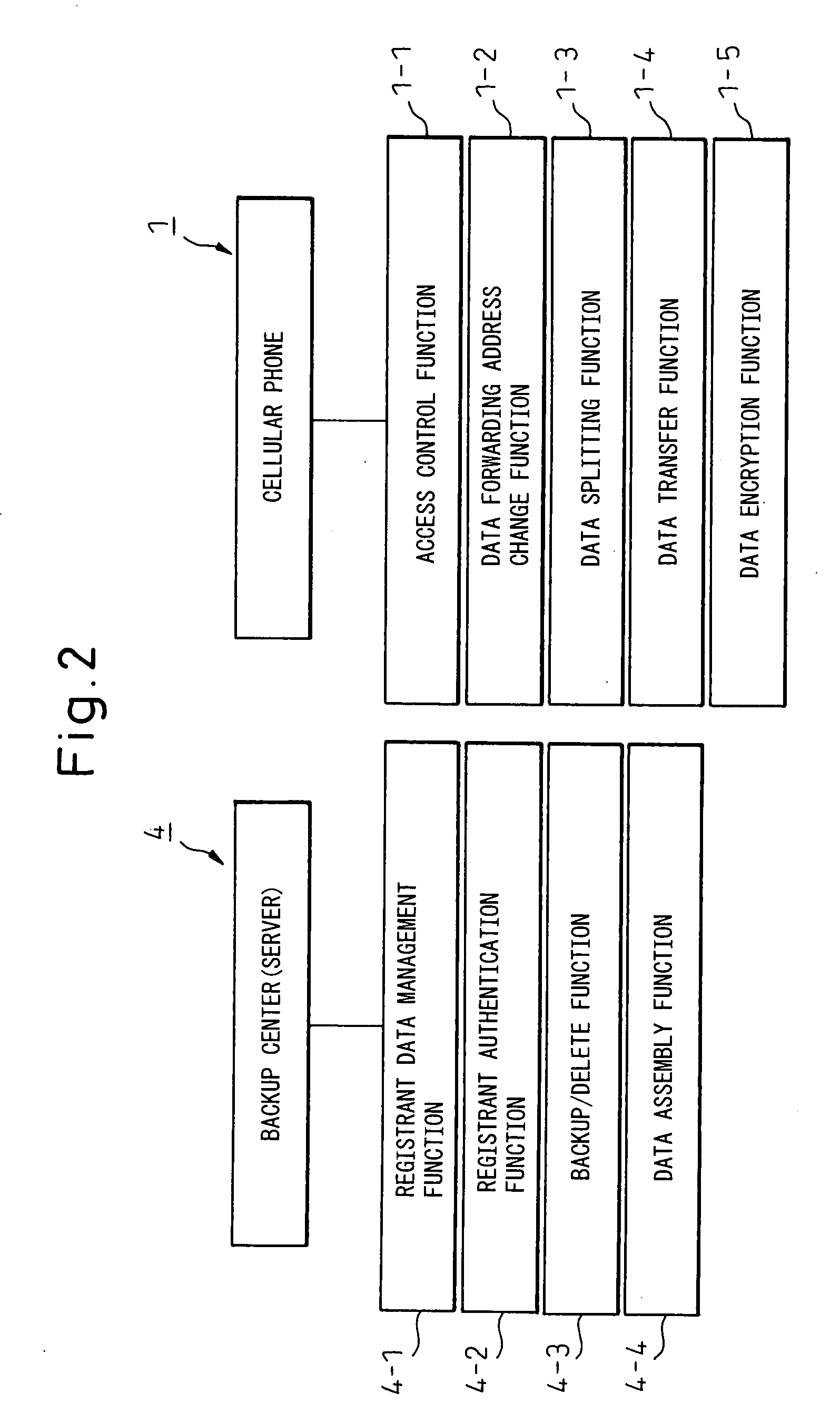
The present invention relates to a portable wireless terminal, and in particular, a portable wireless terminal such as a cellular phone, etc., and its security system that can reliably prevent, by remote control, improper use of the portable wireless terminal by a third party when it is lost or stolen. The portable wireless terminal that uploads backup data to a center by remote control from the center via a wireless network includes: a data access control section 1-1 that, in response to an instructions from the center, prohibits access to the backup data retained by a portable wireless terminal or deletes the backup data; an encryption section 1-5 that encrypts the backup data by using a public key notified from the center or a public key owned by the portable wireless terminal itself in response to instructions from the center; and a data transmission section 1-2 to 1-4 that transmits the backup data split into a plurality of data fragments on a plurality of communication paths to the center according to transmission priority of the backup data that is notified from the center or owned by the portable wireless terminal itself.
Owner:FUJITSU LTD
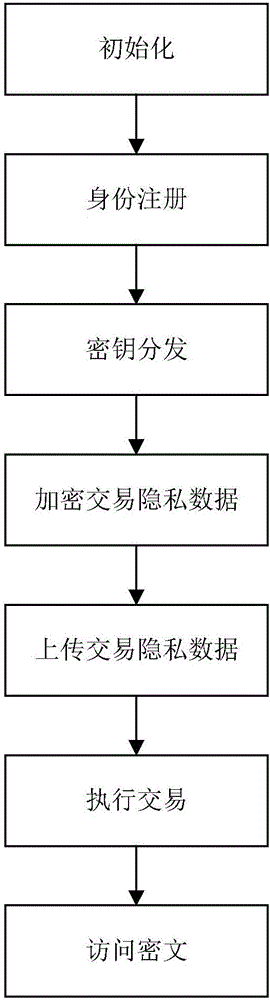
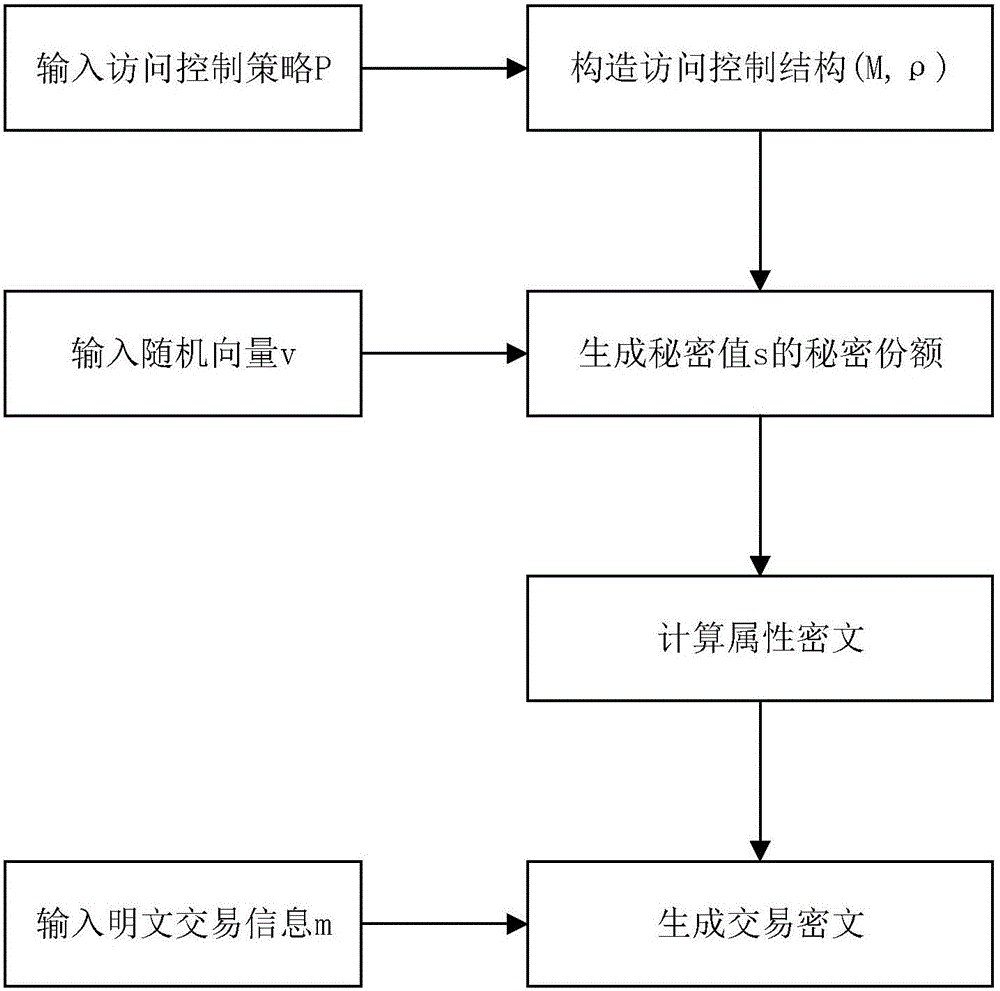
Block chain privacy data access control method based on attribute encryption
ActiveCN106503994AAddress privacy breachesRealize privacy protectionKey distribution for secure communicationDigital data protectionAttribute-based encryptionCiphertext
The invention discloses a block chain privacy data access control method based on attribute encryption, which mainly solves a problem in the prior art that the real identity of a user in the block chain is anonymously protected but the and transaction privacy information is not encrypted so as to cause privacy leakage. The method comprises the steps that 1. a system is initialized; 1, a user registers to obtain attribute information; 3, an authoritative center, according to the user attribute information, distributes a user private key; 4 a transaction party encrypts transaction privacy data and uploads the transaction privacy data to a block chain; 5, an accountant verifies the transaction information and performs the transaction; 6, a supervisory center is authorized to use the authorized private key to decrypt and check the transaction ciphertext. The method encrypts the transaction privacy information, avoids the leakage of data privacy and can be used for privacy protection of the virtual asset transaction data in the block chain.
Owner:XIDIAN UNIV
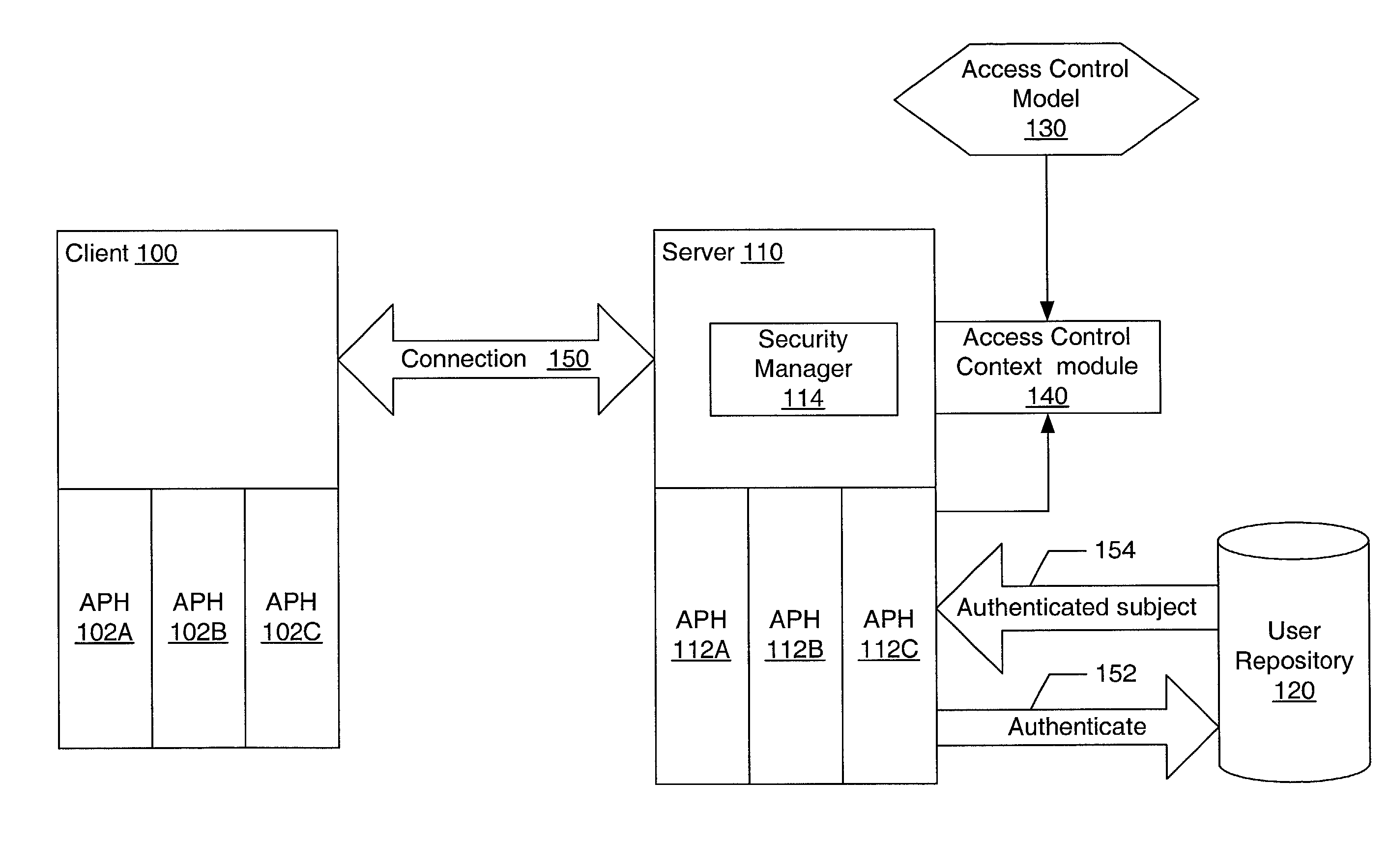
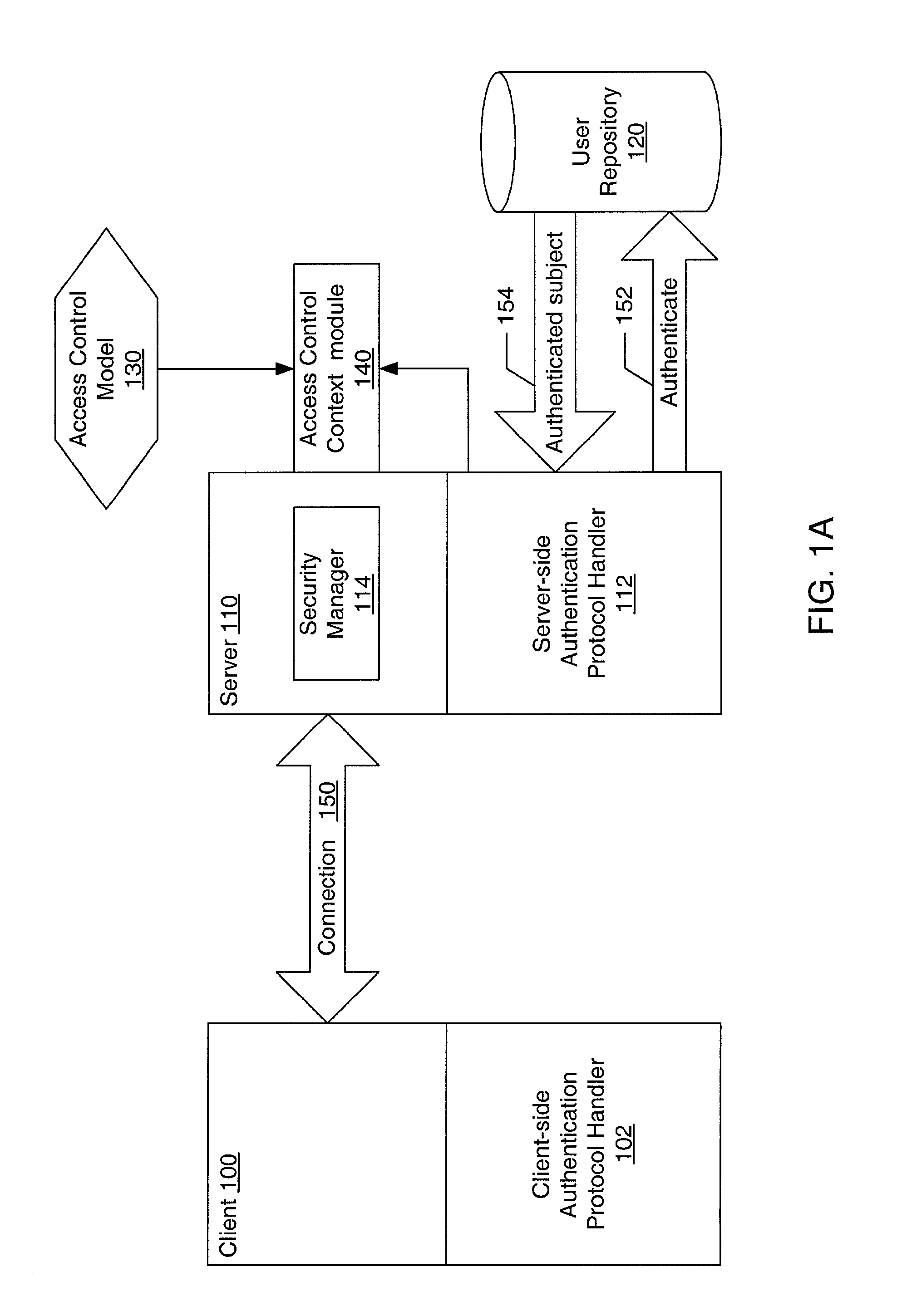
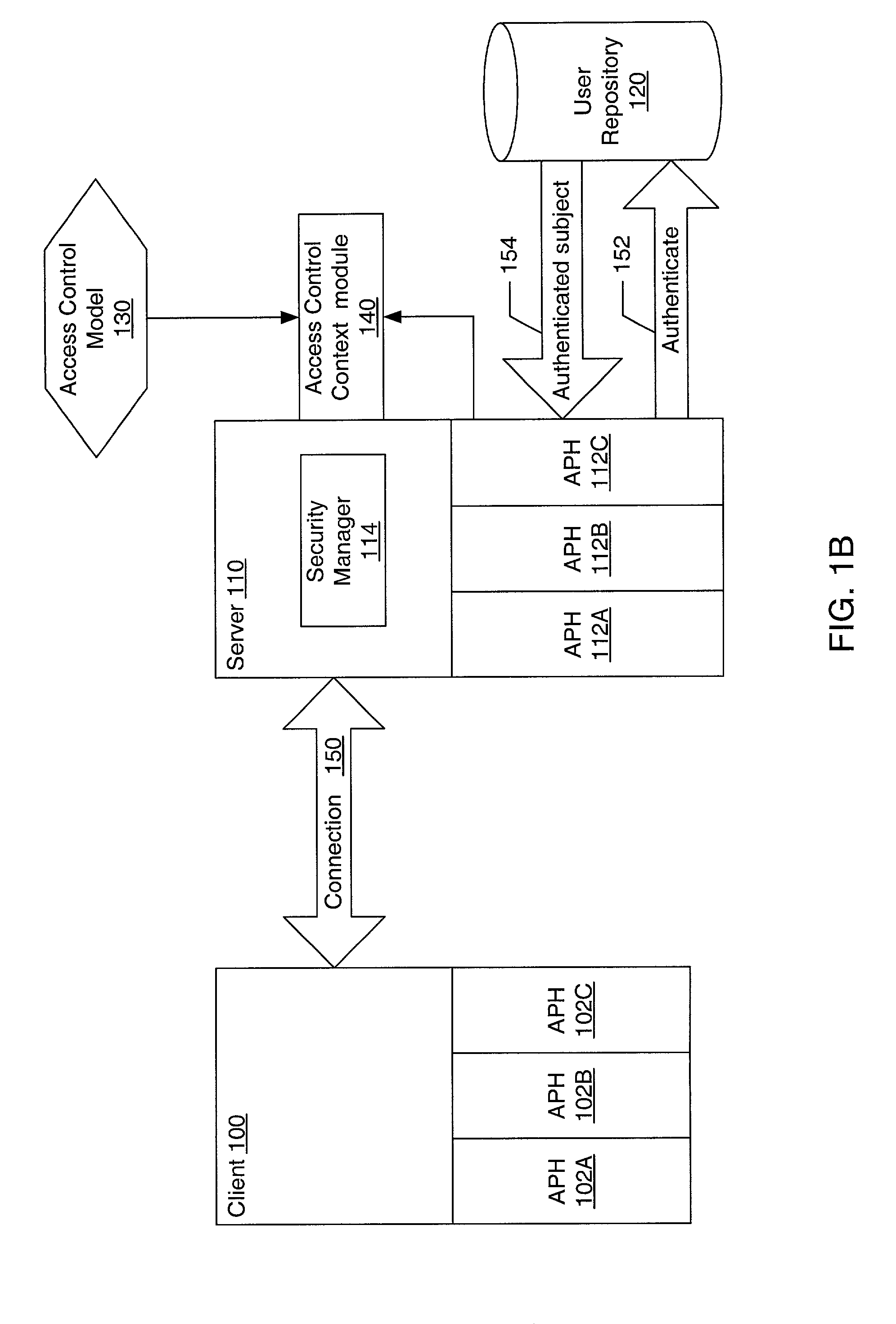
Pluggable authentication and access control for a messaging system
ActiveUS20030005117A1Memory loss protectionError detection/correctionData access controlComputerized system
A system and method for providing pluggable authentication and access control in computer systems and services are described. The authentication and access control process may be categorized into three components: an authentication protocol, a user repository and an access control model. In one embodiment, the authentication and access control mechanism may be implemented as three pluggable modules: an authentication protocol handler module for the authenticator side, an authentication protocol handler for the side to be authenticated, and an access control context module on the authenticator side. The pluggable modules may be exchangeable to support a variety of authentication types, user repositories, and access control models. The authentication protocol handlers provide symmetrical methods to handle requests and responses in the authentication process that reflect the symmetrical nature of the authentication process.
Owner:ORACLE INT CORP
Access control system, access control method, and access control program
ActiveUS7624424B2Efficient updateEffective controlDigital data processing detailsUser identity/authority verificationAccess control matrixData access control
Owner:NEC CORP
Access control for federated identities
ActiveUS7444519B2Digital data processing detailsMultiple digital computer combinationsThird partyData access control
An authentication process in a network environment provides a remote user with secured access to an enterprise network based on recognition of a third-party security token. The method includes authenticating the user against a plurality of third-party security tokens, wherein the third-party security tokens originate from a range of different partner home sites. The remote user, prior to obtaining secured access to the enterprise network, is not known to the enterprise network, and does not need to be associated with any security tokens previously originating from the enterprise network. The enterprise network is provided with the ability to rely upon third-party security tokens to authenticate the remote user.
Owner:GOOGLE LLC
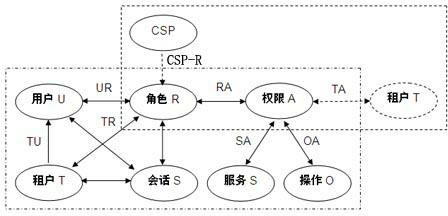
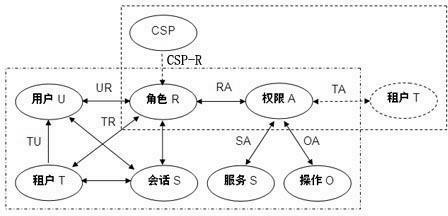
Cloud security access control model
InactiveCN102571821AReasonable designSimple structureData switching networksData access controlMedia access control
The invention discloses a cloud security access control model. The model is characterized in that: aiming at the multi-tenant architecture characteristic of cloud computing, by combining a role-based access control (RBAC) model, a tenant concept and a cloud service provider concept are introduced to an access control model, and a uniform tenant access control model and a user access control model are formed by defining model elements and formally describing model functions. The cloud security access control model can adapt to the characteristic of multi-tenant of the cloud computing, improves the flexibility of user authority management in a cloud computing environment, can reduce the complexity of authorization management and management overhead, and can effectively ensure the security and integrity of user data in the cloud computing environment.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
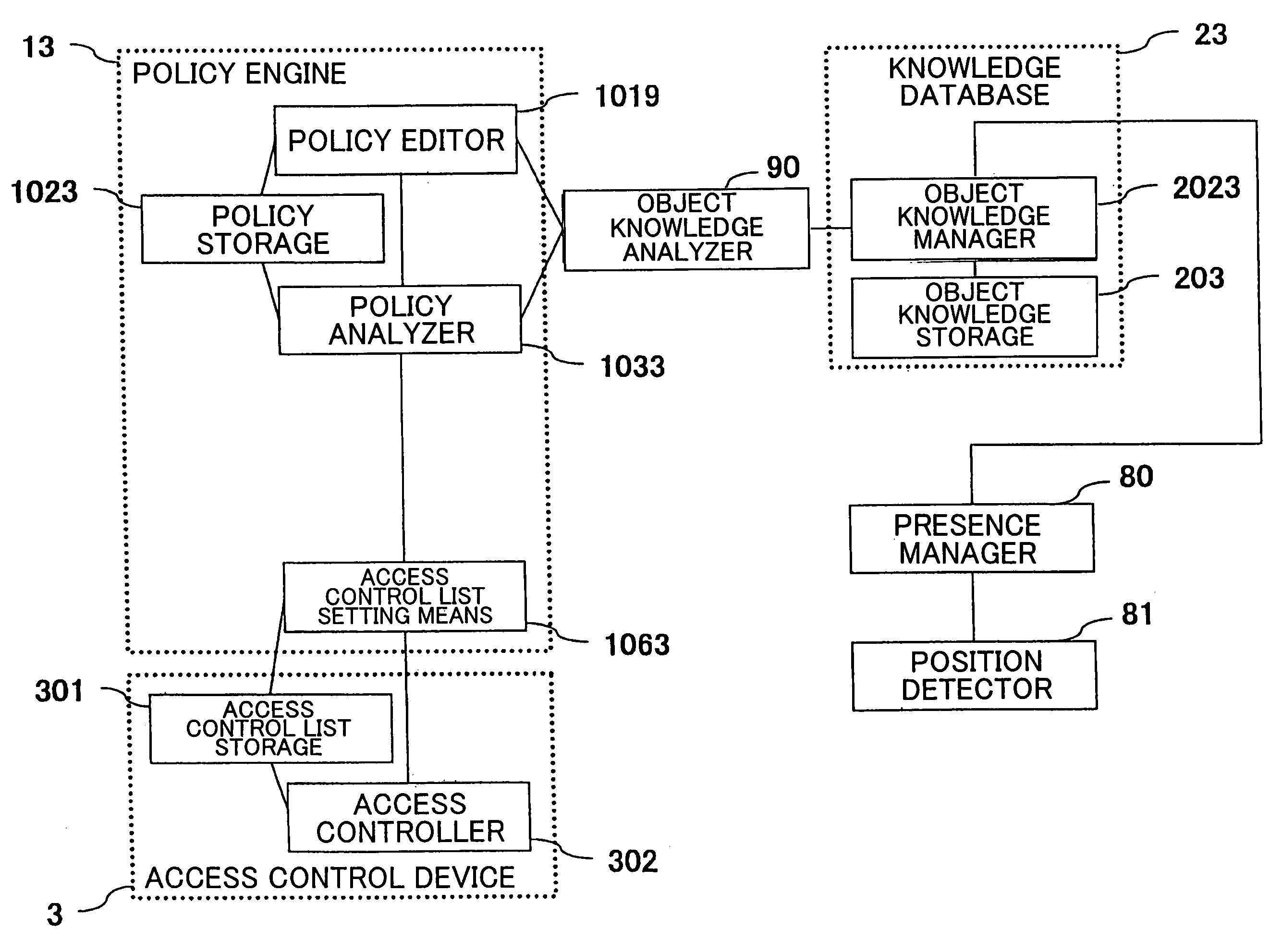
Specifying an access control policy
InactiveUS20110321122A1Avoid excessive errorEfficient solutionDigital data protectionPatient personal data managementData access controlExecution unit
A system for specifying an access control policy comprises: A user interface (13) for enabling a user to specify a plurality of policy rules comprising a subject attribute, an object, an action, and an authorization, the policy rules defining an access control policy (10). A translation means (9) for translating the access control policy into a machine readable data access control policy language to obtain a translated data access control policy (14). An output (11) for providing the translated data access control policy to an access control policy enforcing unit (50). A conflict detection means (2) for detecting at least two conflicting policy rules indicative of denial and allowance, respectively, of a possible access request. A conflict indication means (6) for indicating to a user information relating to the conflict. A conflict resolution input (7) for retrieving information from a user indicative of a conflict resolution.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
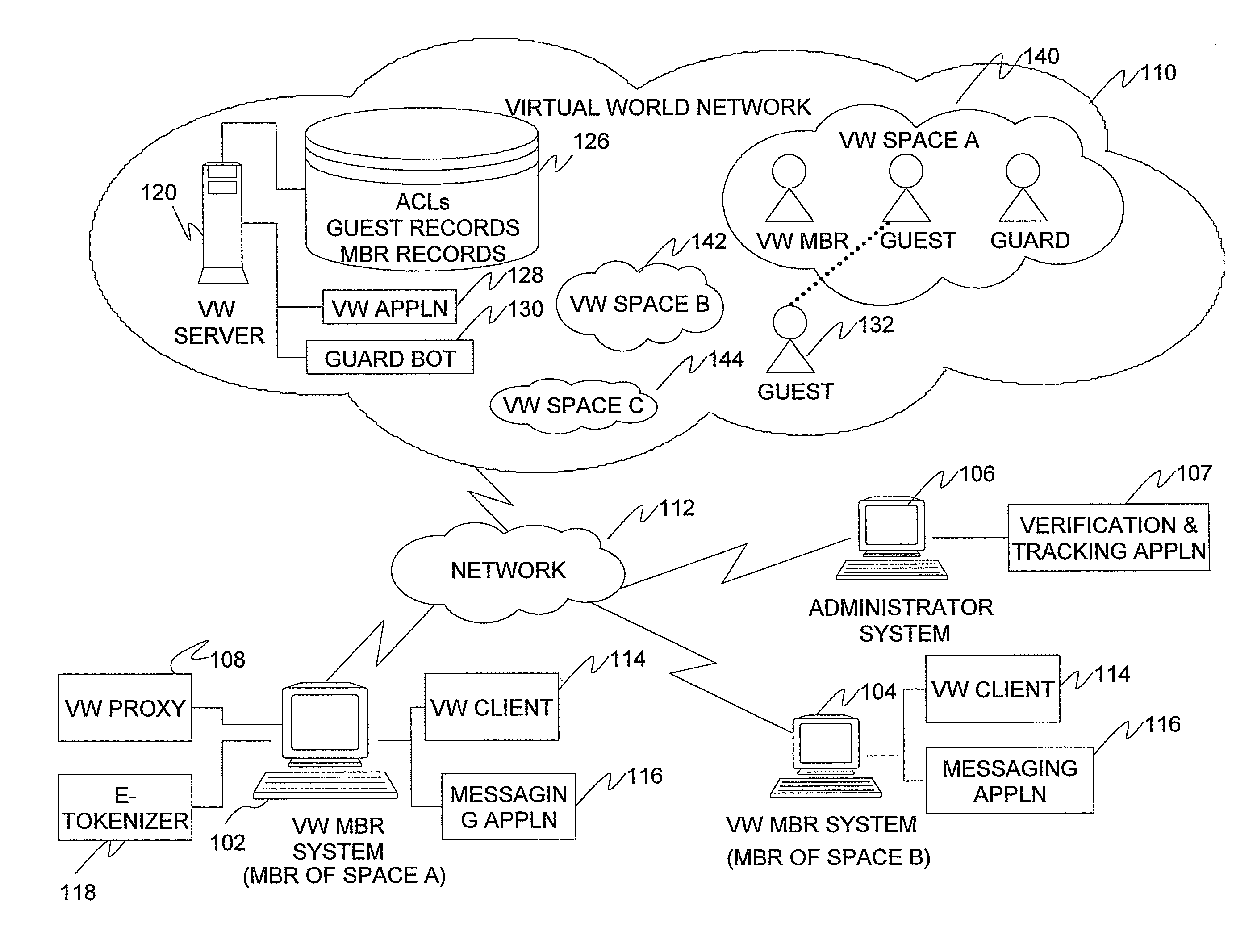
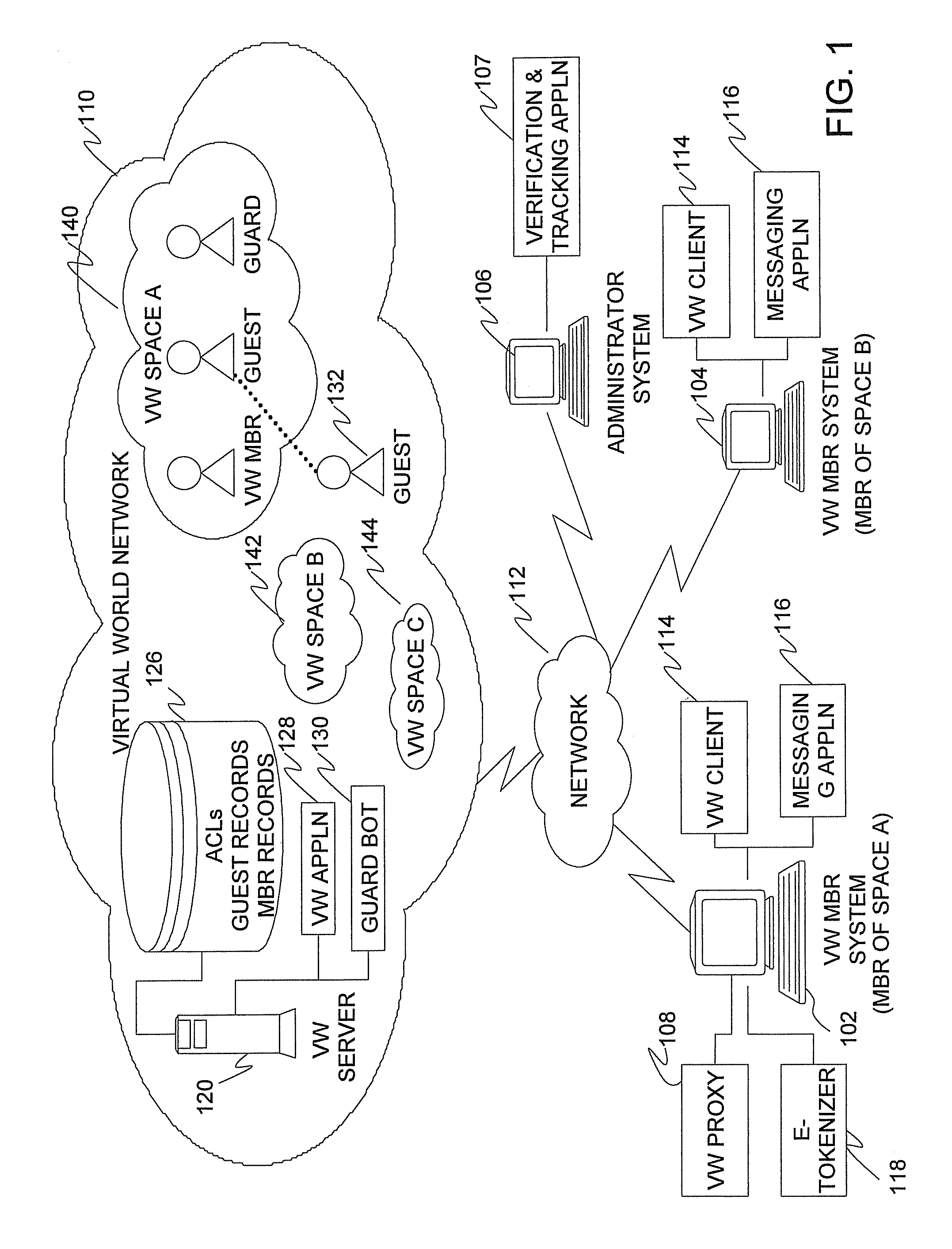
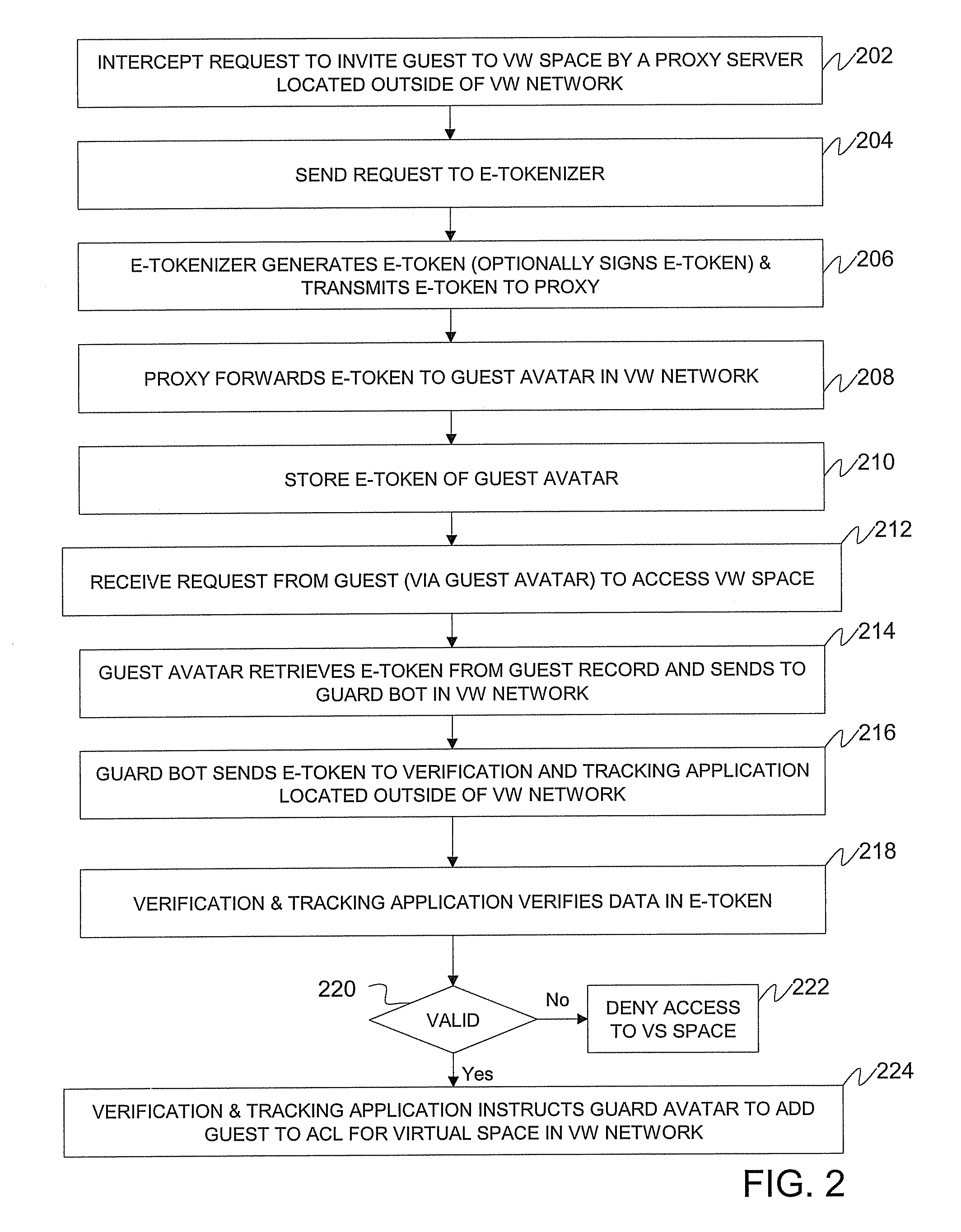
Method, system, and computer program product for providing e-token based access control for virtual world spaces
ActiveUS8132235B2Digital data processing detailsUser identity/authority verificationData access controlSecret code
A method for providing e-token based access control to virtual world (VW) spaces includes intercepting a request from a first VW member to invite a second VW member to a VW space within a VW network, the request intercepted outside of the VW network. The access controls also include using a secret code associated with the first member to generate an e-token that includes an identifier of the second member and the space. The access controls further include sending the e-token inside the network. In response to a request for access to the space, the access controls include sending the e-token outside of the network for verification. Upon successful verification of the e-token, the access controls include accessing the network and controlling a guard bot inside the network to grant access for the second member to the space. The guard bot adds the second member to an access control list.
Owner:ACTIVISION PUBLISHING
Data assessing control method based on blockchain
InactiveCN107103252AAccess subject to changeReduce sizeDigital data protectionTransmissionThird partyData access control
The invention discloses a data assessing control method based on a blockchain, and relates to the technical field of management and control of data of blockchains. According to the technical scheme, the technical problem in the prior art that the controllability in data assessing is poor and a block is large due to design boundedness of control authorities and storage structures of block data is solved. The data assessing control method based on the blockchain mainly comprises the steps that data of all users can be only accessed through users and agents, any third party who wants to access user data must send requests to the agents so that the third party can conduct accessing as the identity of the agents; all access logs of the user data can only be accessed by the agents and the users, any third party who wants to access logs must send requests through the agents so that the third party can conduct accessing as the identity of the agents. The data assessing control method based on the blockchain is used for designing a data sharing and accessing control system based on a large data environment.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
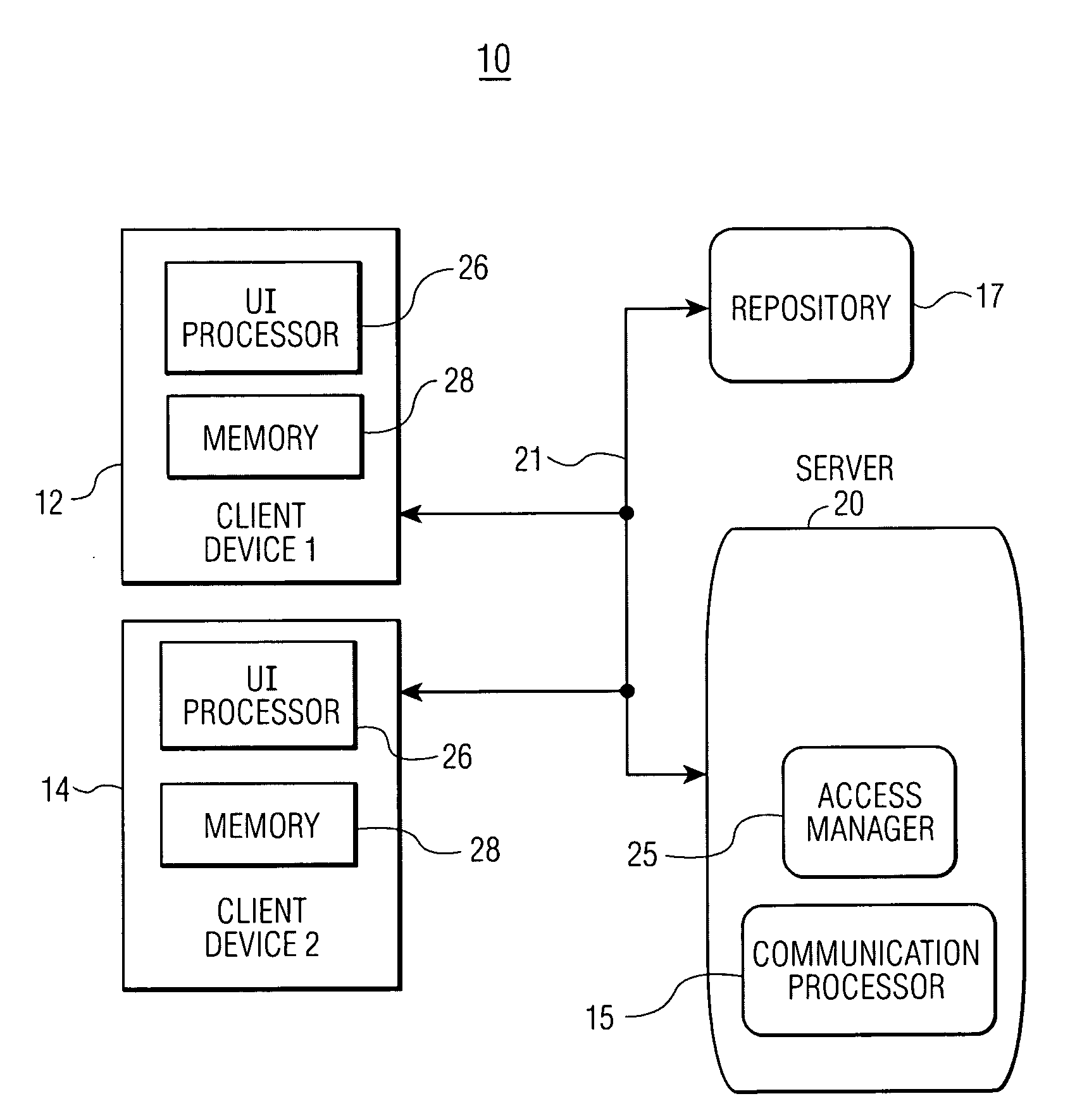
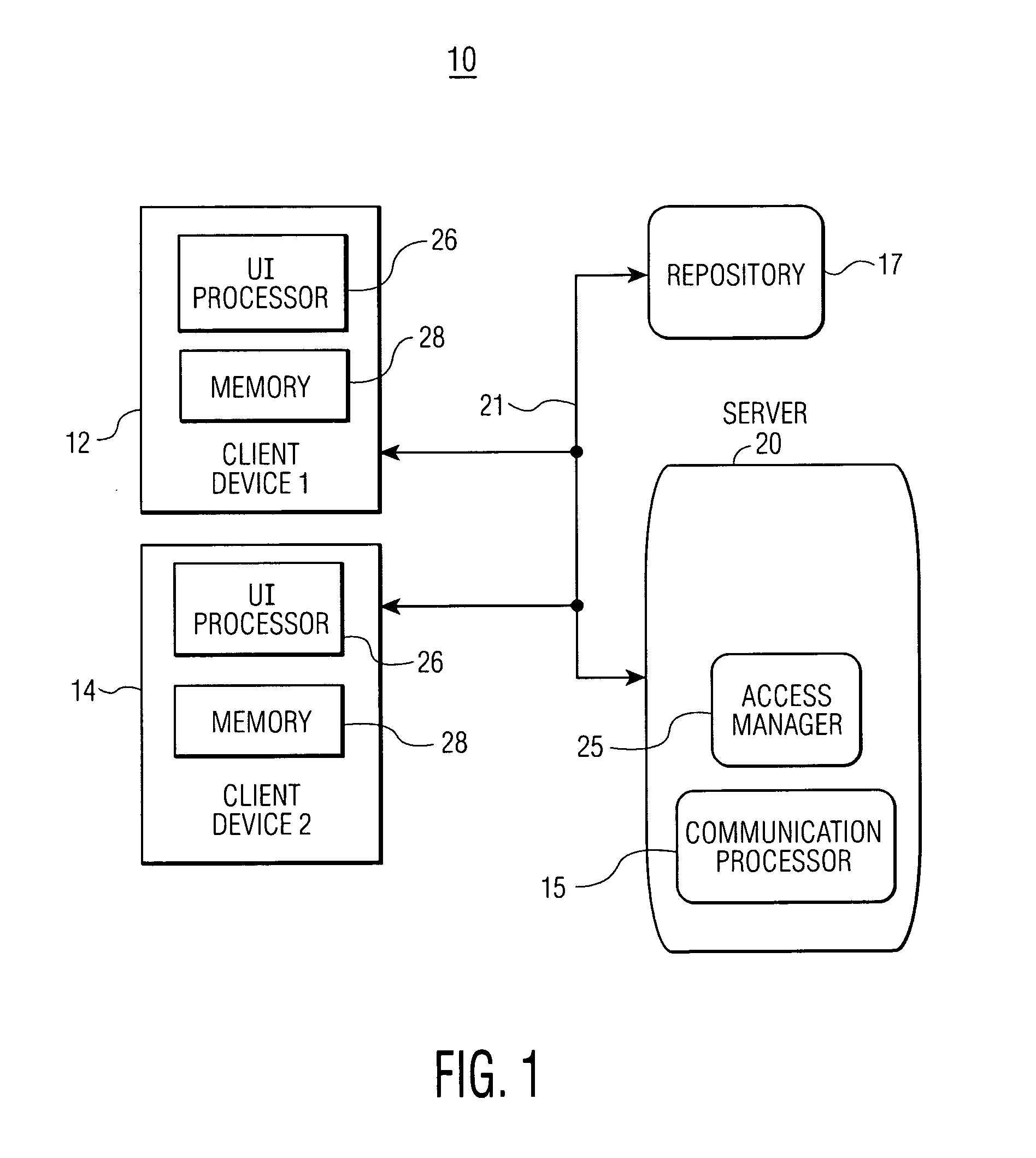
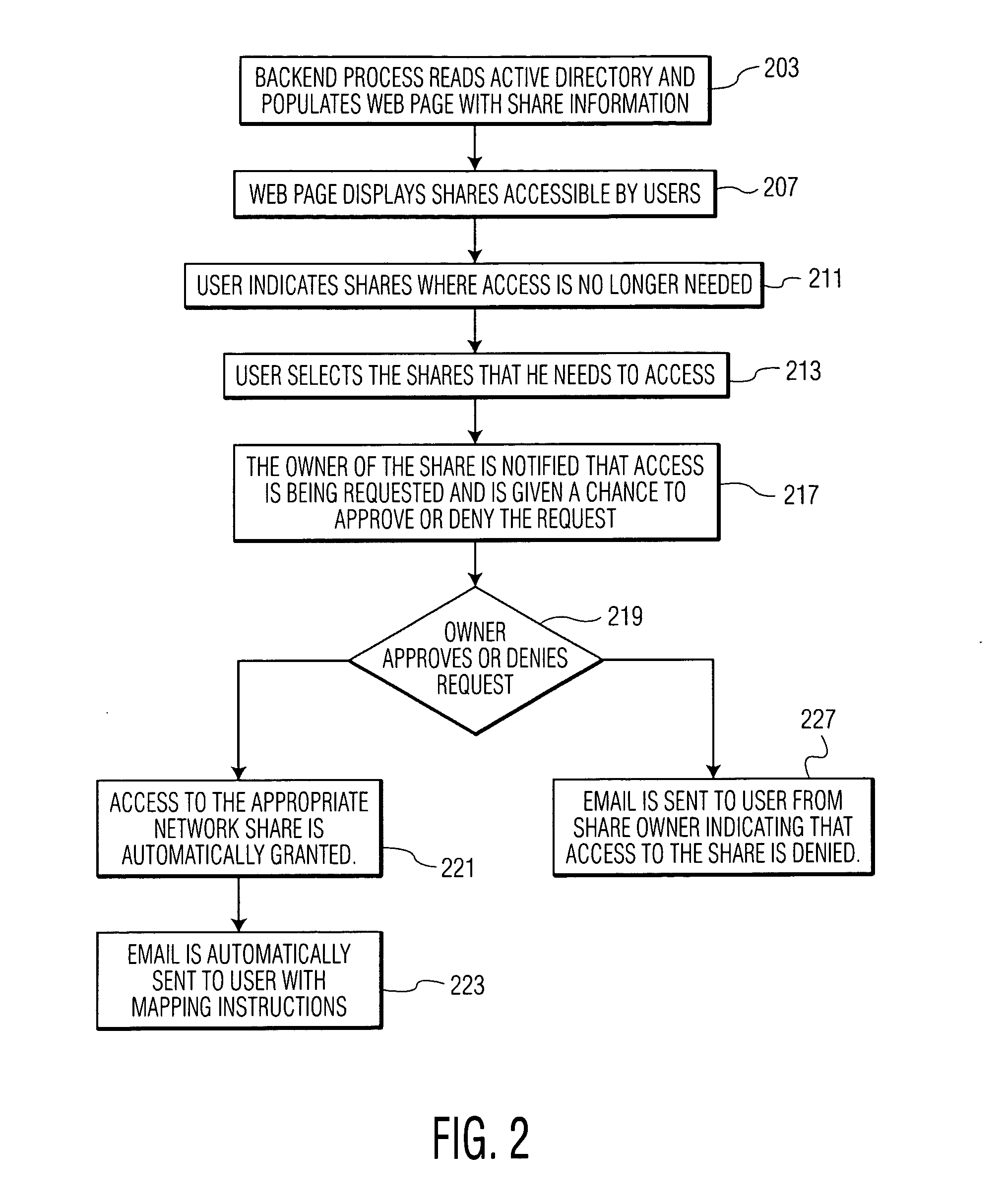
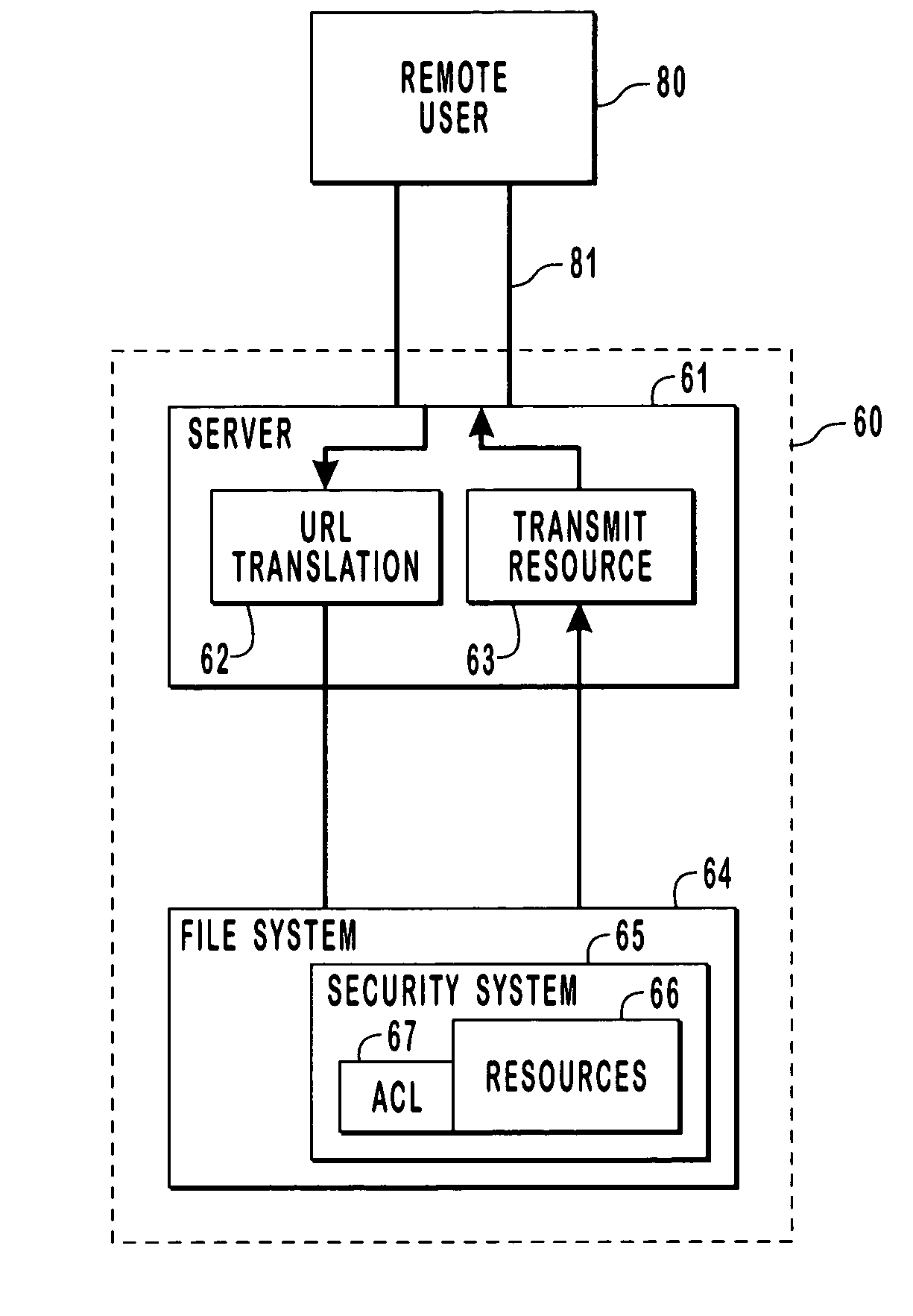
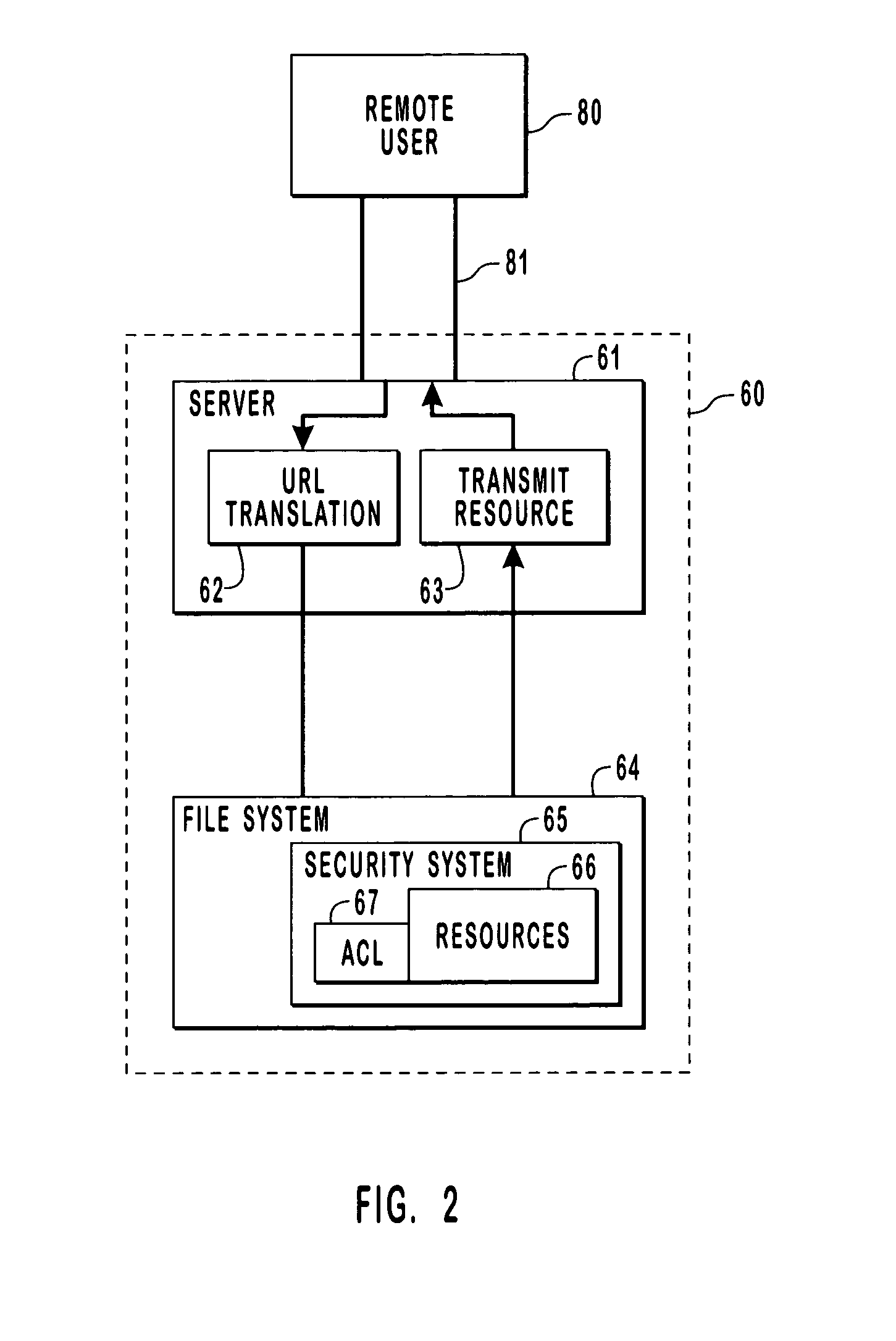
Data Access Control System for Shared Directories and Other Resources
InactiveUS20080256458A1Computer security arrangementsMultiple digital computer combinationsEmail addressControl system
A system manages directory access permissions without help-desk intervention. The system automatically manages user permissions to access processing system resources and includes a user interface providing data representing at least one display image enabling a user to request permission to access a particular processing system resource. A communication processor, in response to detection of a user request for permission to access a particular processing system resource, automatically, acquires a user identifier and user email address, determines an owner responsible for granting permission to access the particular processing system resource and an associated owner email address, emails a request message to the owner email address to grant the access of the user to the particular processing system resource and receives a response email message indicating grant of the access. An access manager, in response to a received grant of the access and updates access data to enable the user to access the particular processing system resource.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC
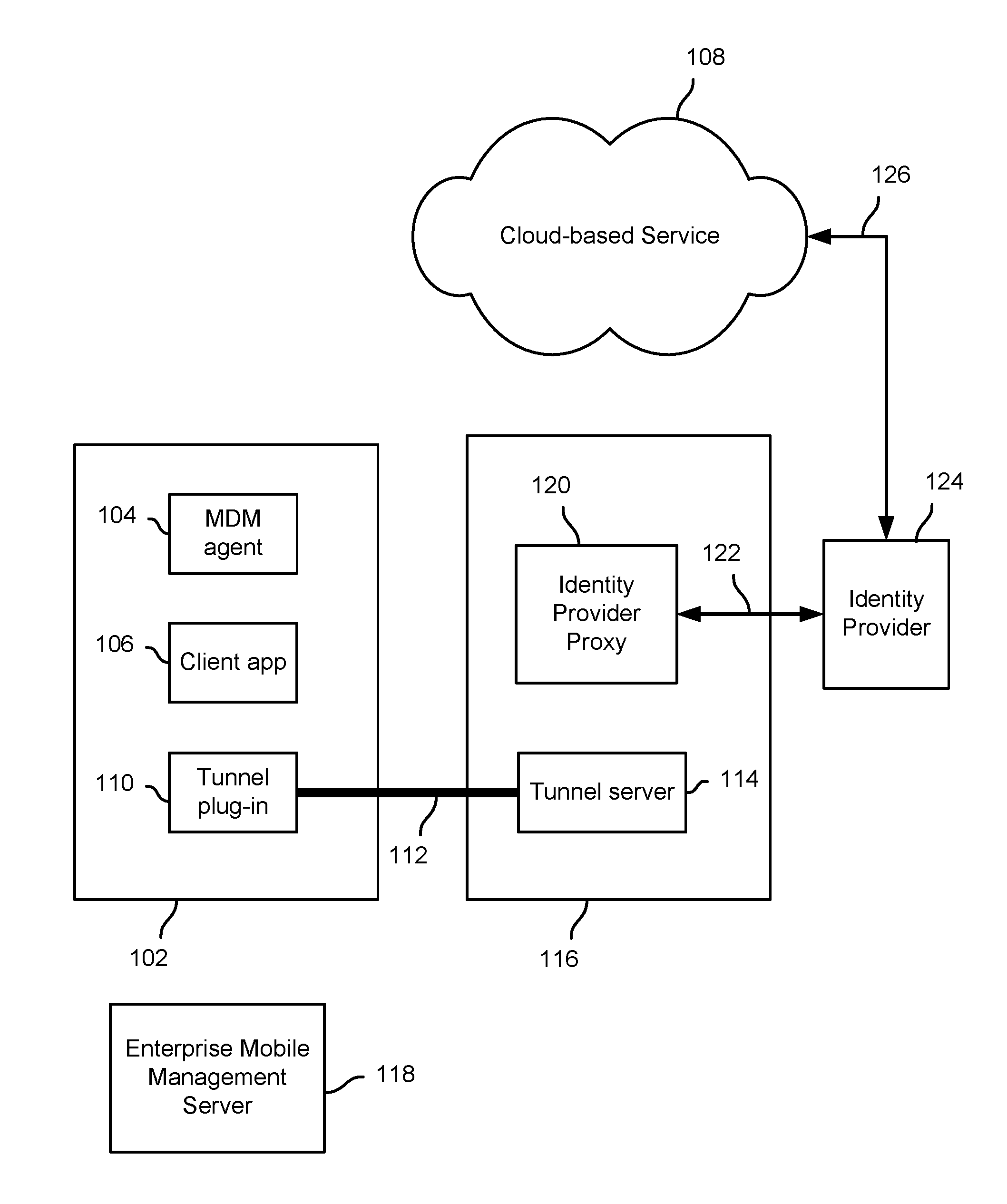
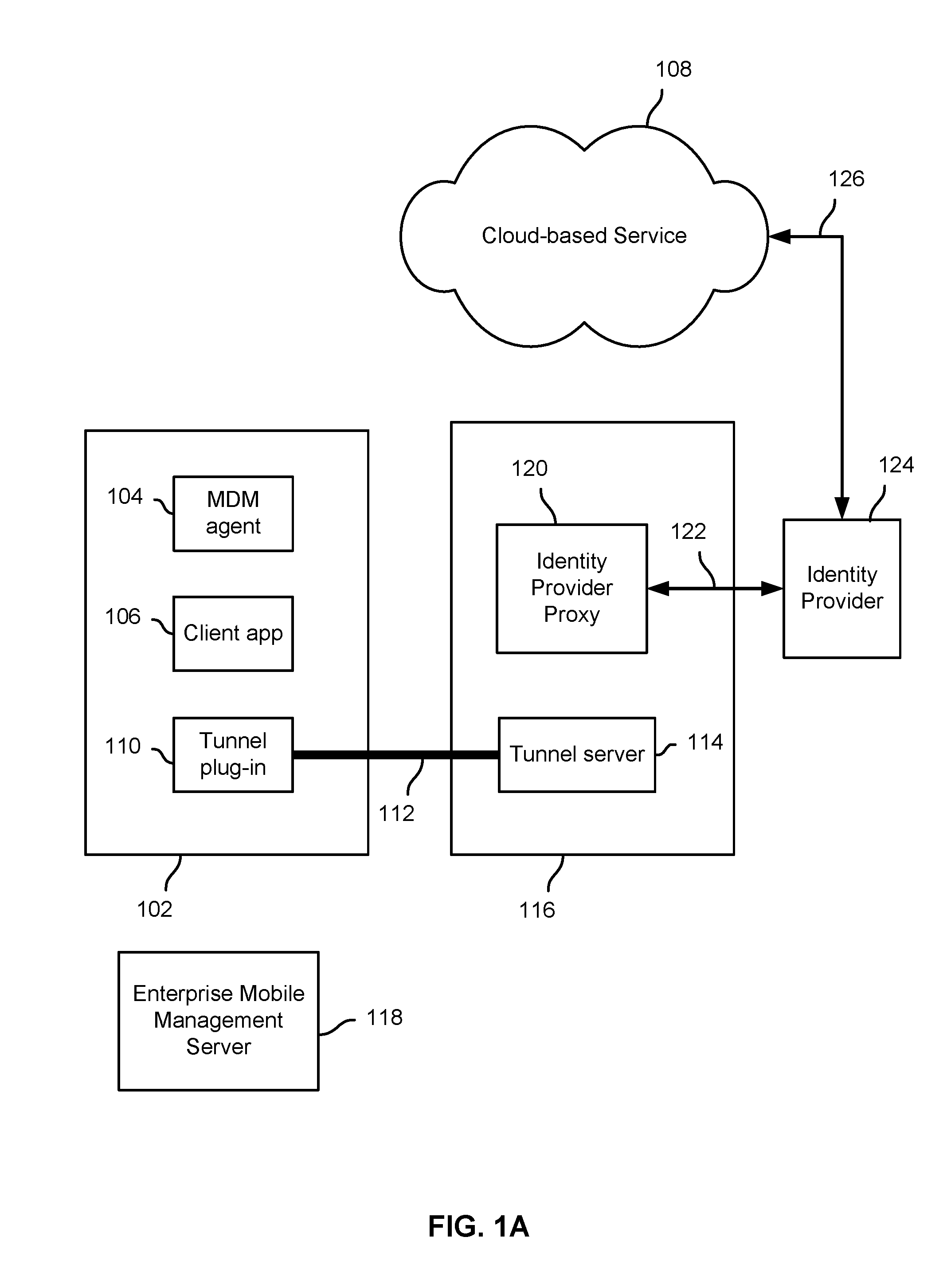
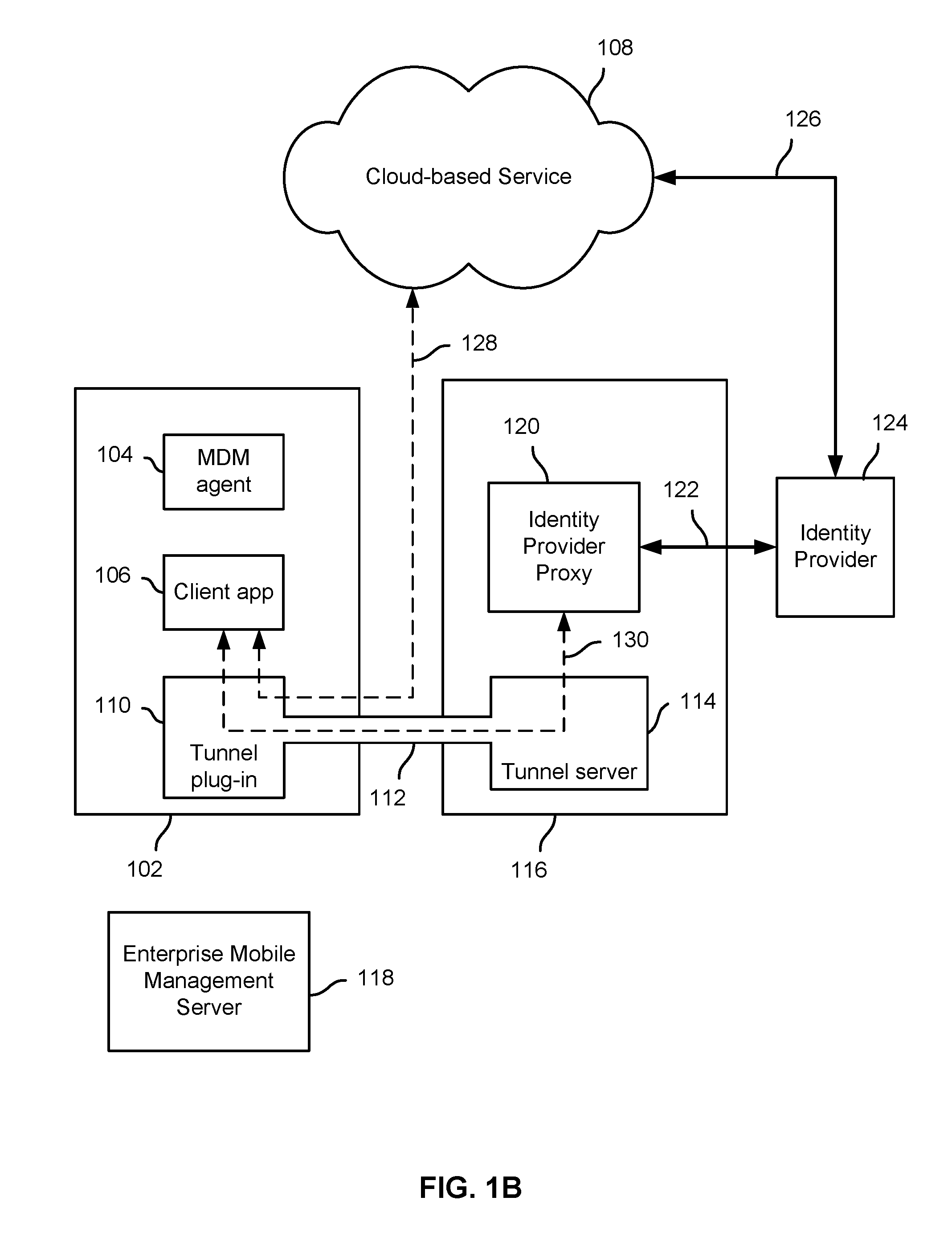
Identity proxy to provide access control and single sign on
Techniques to provide secure access to a cloud-based service are disclosed. In various embodiments, a request is received from a client app on a device to connect to a security proxy associated with the cloud-based service. A secure tunnel connection between the device and a node with which the security proxy is associated is used to establish the requested connection to the security proxy. Information associated with the secure tunnel is used to determine that the requesting client app is authorized to access the cloud-based service from the device and to obtain from an identity provider associated with the cloud-based service a security token to be used by the client app to authenticate to the cloud-based service.
Owner:IVANTI INC
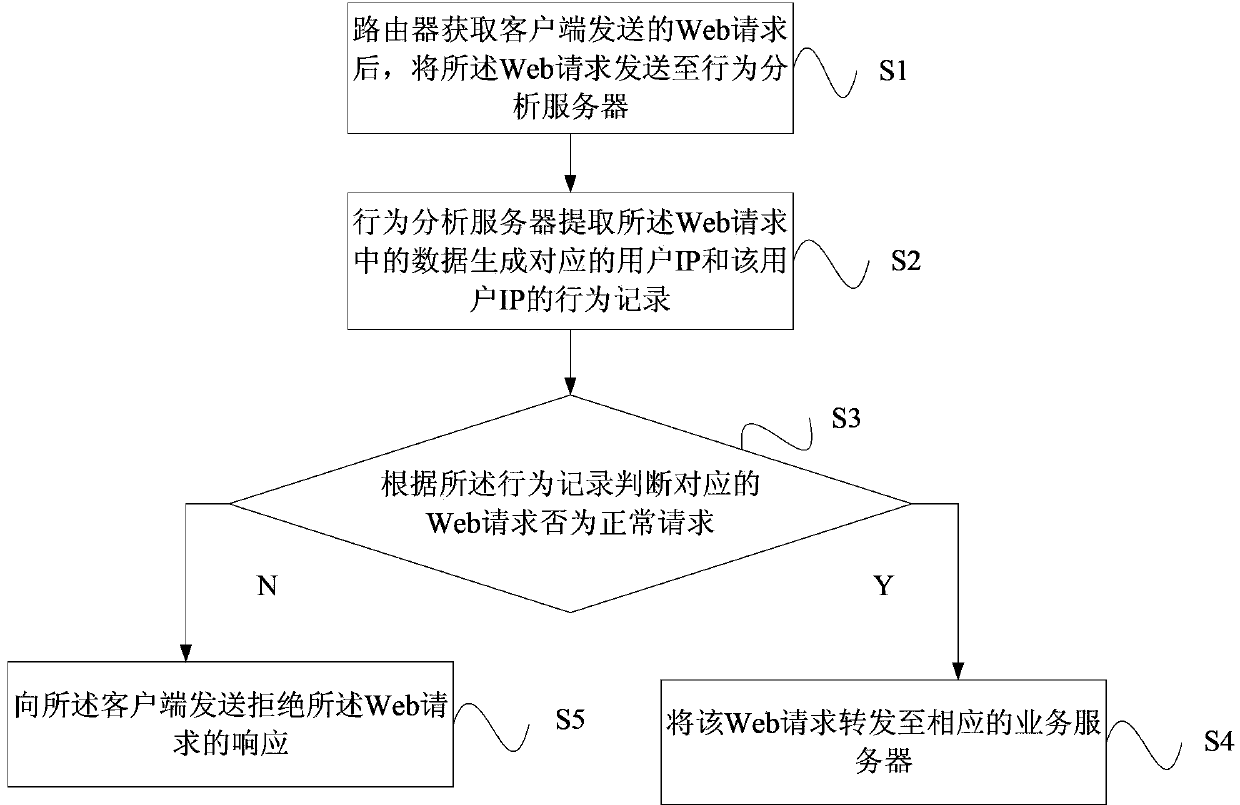
Network access control method and system based on IP access behaviors
ActiveCN103475637ASolve efficiency problemsSolve the cumbersome configurationTransmissionQuality of serviceData access control
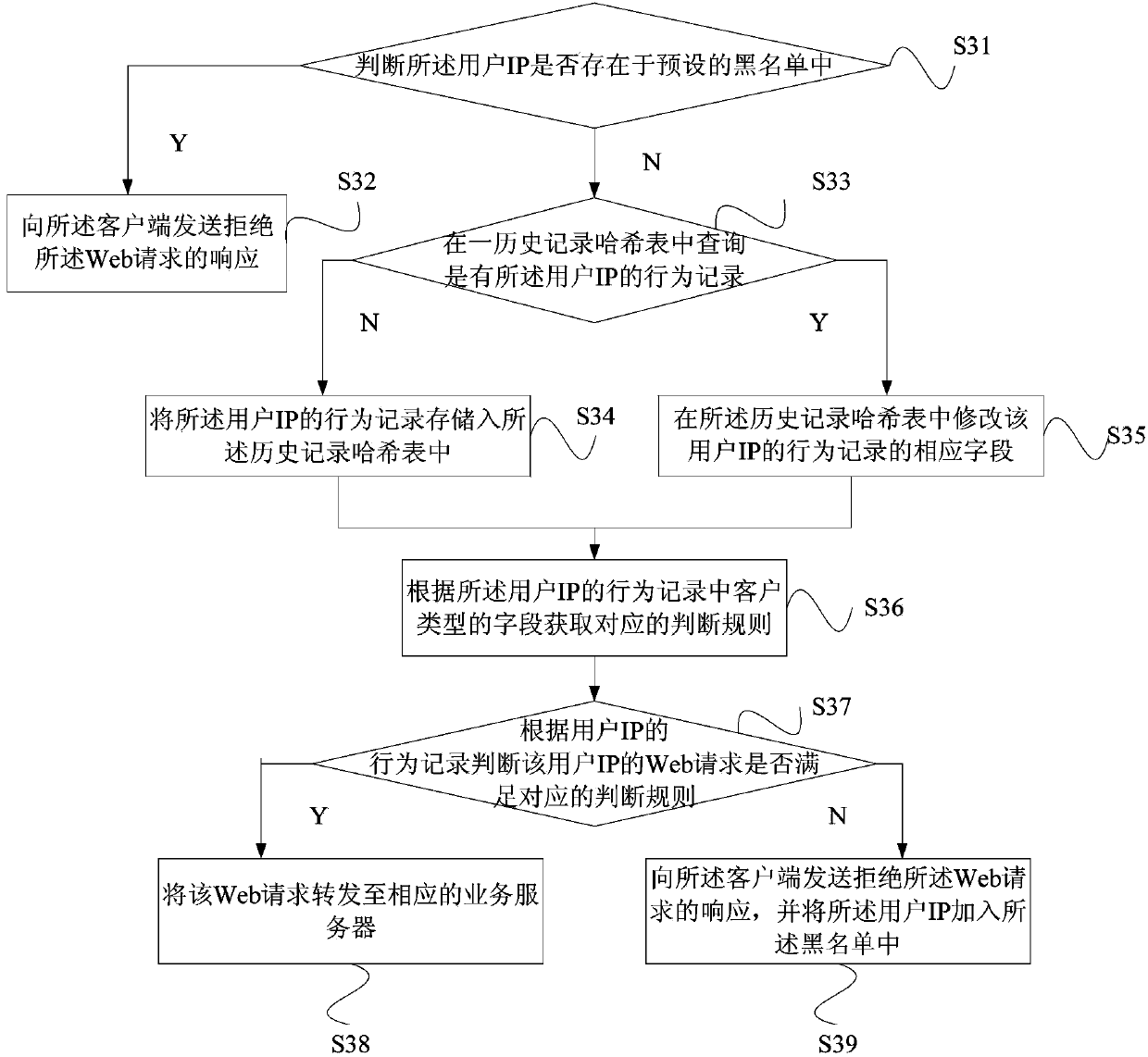
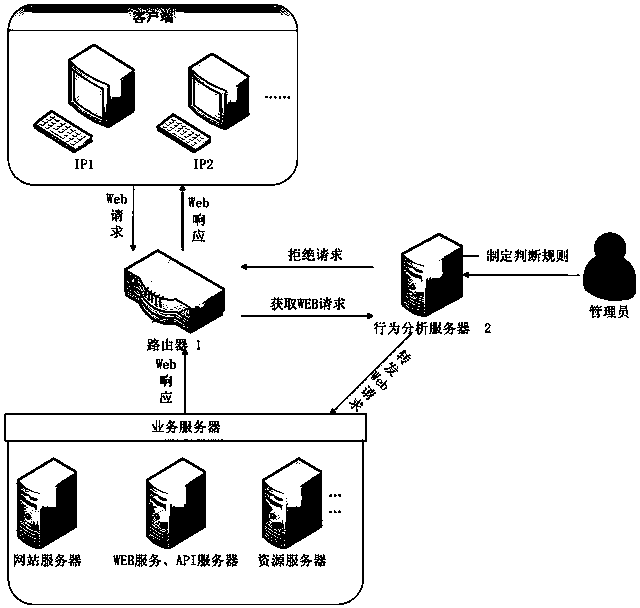
The invention provides a network access control method and system based on IP access behaviors. The method includes: after a Web request sent by a client is acquired through a router, the Web request is sent to a behavior analyzing server; data in the Web request are extracted by the behavior analyzing server and a corresponding user IP and a behavior record of the user IP are generated and whether the Web request is a normal request is judged according to the behavior record; if the Web request is a normal request, then the Web request is forwarded to a corresponding service server and if not, then a response refusing the Web request is sent to the client so that access control on unknown IPs can be carried out dynamically and problems such as low efficiency, tedious configuration and poor dynamic instantaneity and the like in traditional IP access control are solved. At the same time, the network access control method and system also aim at restraining network attacks, regulating crawler behaviors, improving website or API service qualities and enhancing website stability and usability.
Owner:CTRIP COMP TECH SHANGHAI
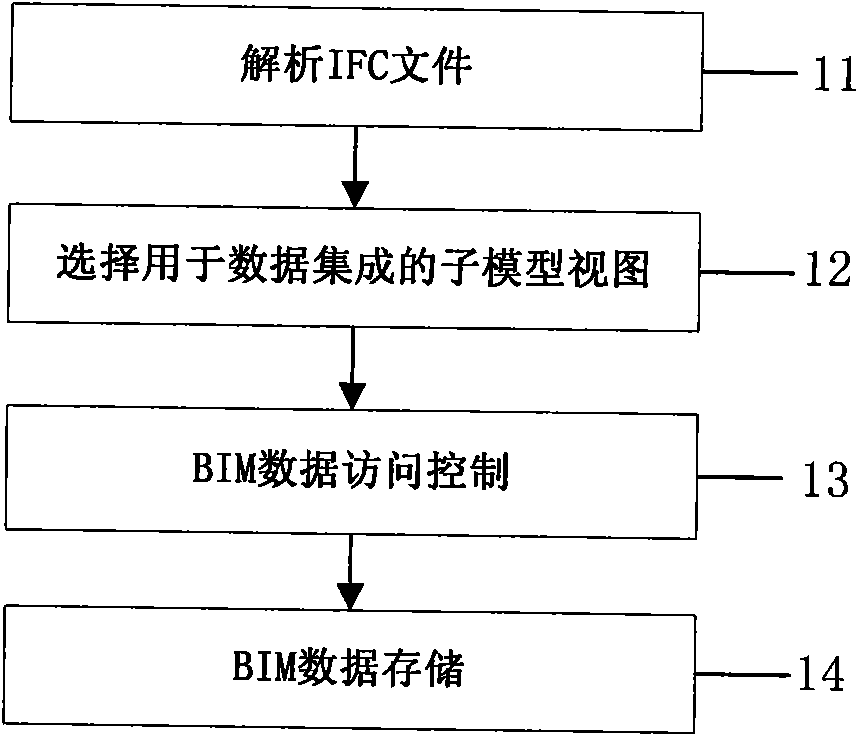
Engine device and method for data integration and exchange of building information mode based on IFC (industry foundation classes) standards
ActiveCN102609417AImprove integration efficiencyImprove exchange efficiencySpecial data processing applicationsBatch processingIntegrator
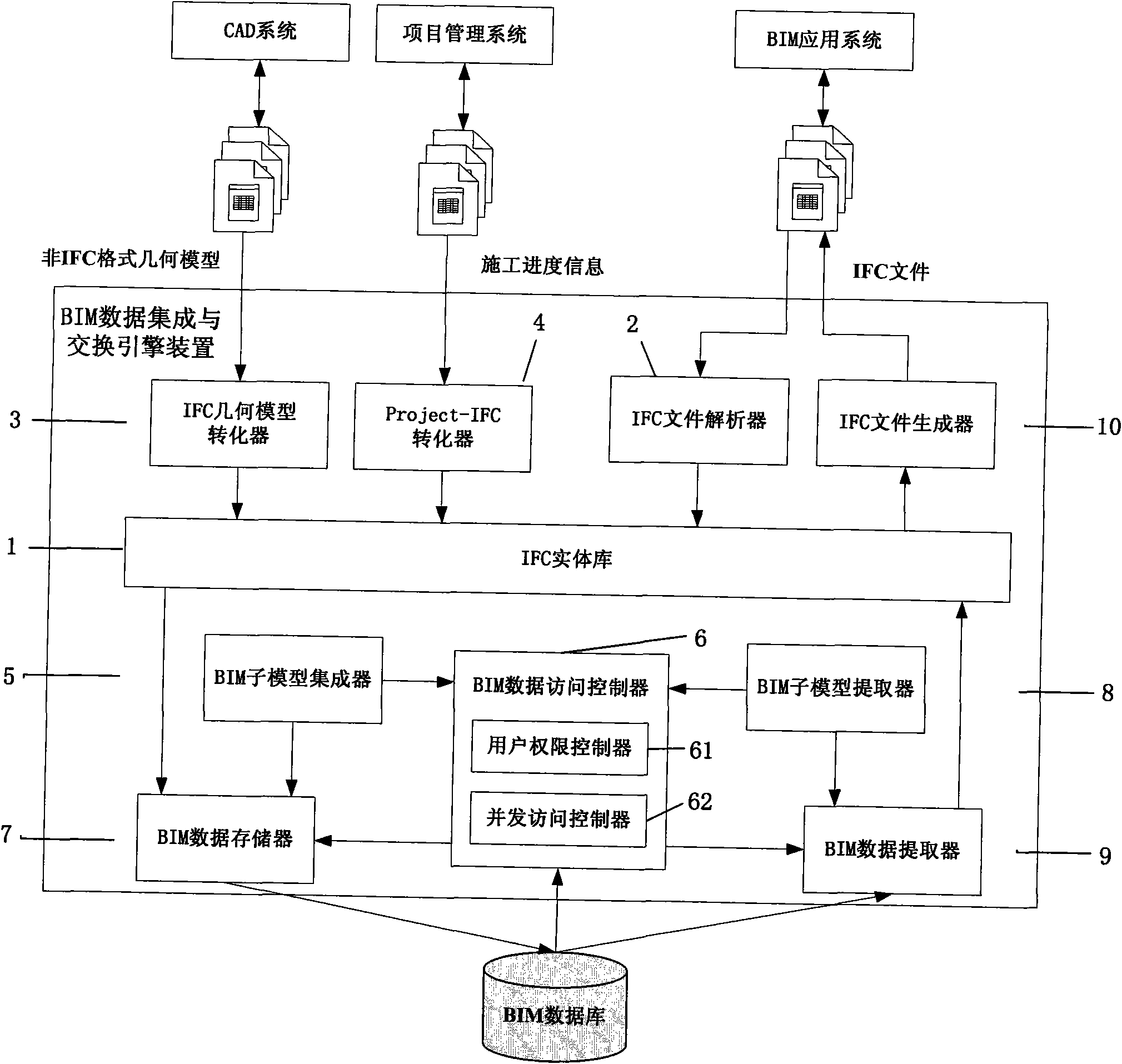
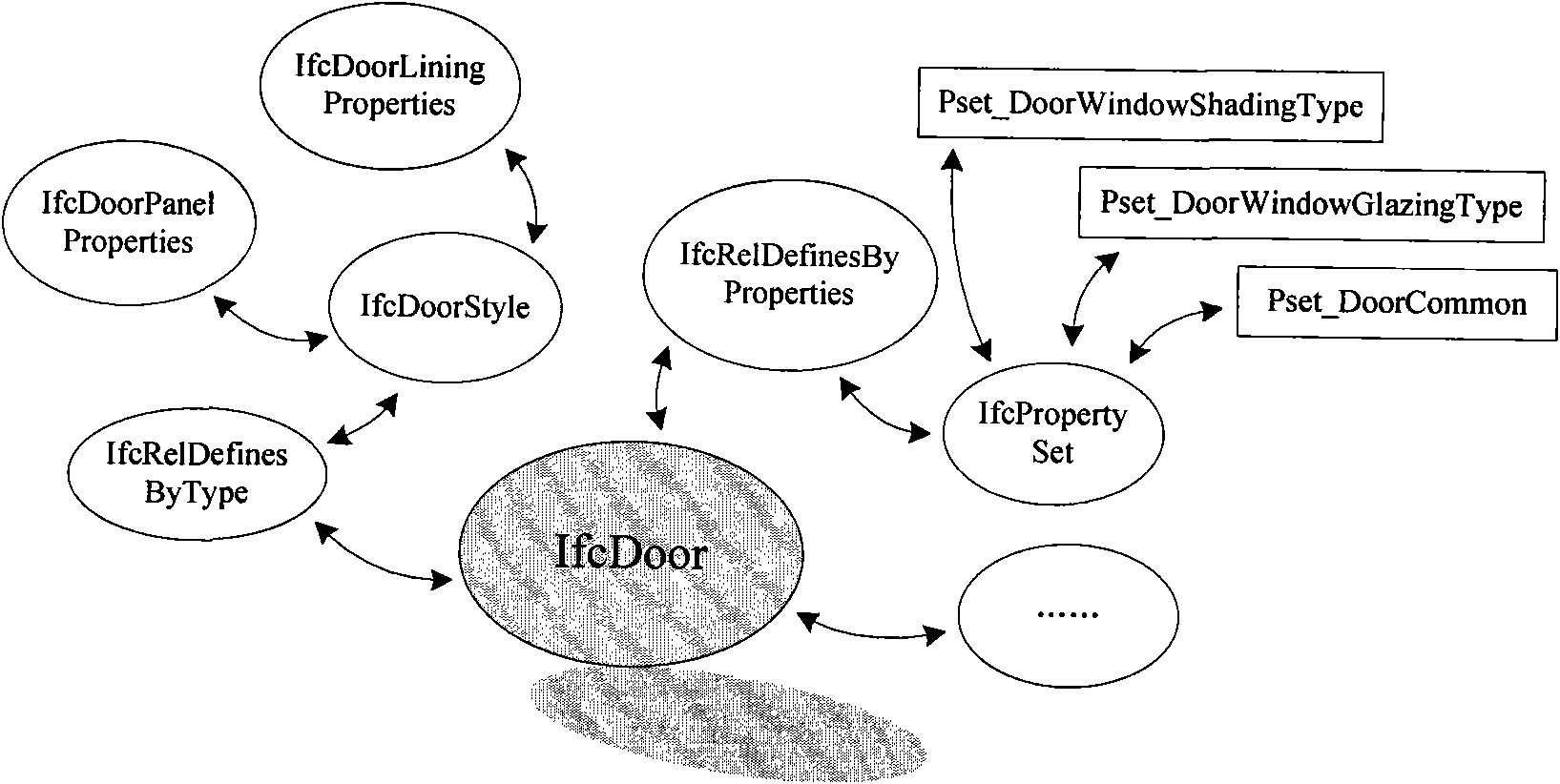
The invention belongs to the technical field of information of the building industry, and provides an engine device and a method for data integration and exchange of building information mode based on IFC (industry foundation classes) standards, which are used for creating and applying a building information model (BIM). The method is based on a BIM database created on the basis of the IFC standards and a relational database, and BIM resolution in an IFC format, conversion of building information in non-IFC formats, extraction and integration of BIM submodels and storage, exchange and access control of BIM data are realized. The engine device comprises an IFC entity library, an IFC file resolver, an IFC geometric model converter, a Project-IFC converter, a BIM submodel integrator, a BIM submodel extractor, a data access controller, a BIM data storage device, a BIM data extractor, an IFC file generator and the like. The building information model data integration and exchange engine device and the method support conversion of BIM data in various formats, and BIM data integration and exchange oriented to various stages of the life cycle of a building or different applications can be realized. In addition, BIM data integration and exchange efficiency is effectively improved by the aid of data batch processing technology.
Owner:TSINGHUA UNIV
Systems and methods for integrating access control with a namespace
InactiveUS7065784B2Digital data processing detailsUser identity/authority verificationComputer resourcesData access control
Provided are methods and systems for integrating the access controls of computer resources into a namespace or domain. For a remote user, a computer network or system is a namespace represented by a URL. In order to enforce the access controls of the computer network being accesses, a remote user is impersonated by a server of the computer system such that access requests to the resources of a system are made by the server in the security context of the remote user. By impersonating the remote user, the actual rights of the remote user are being presented to the access controls rather than the rights of the server. In this manner, the access control of the system can be enforced directly on the remote user and the access control is effectively extended to the namespace.
Owner:MICROSOFT TECH LICENSING LLC
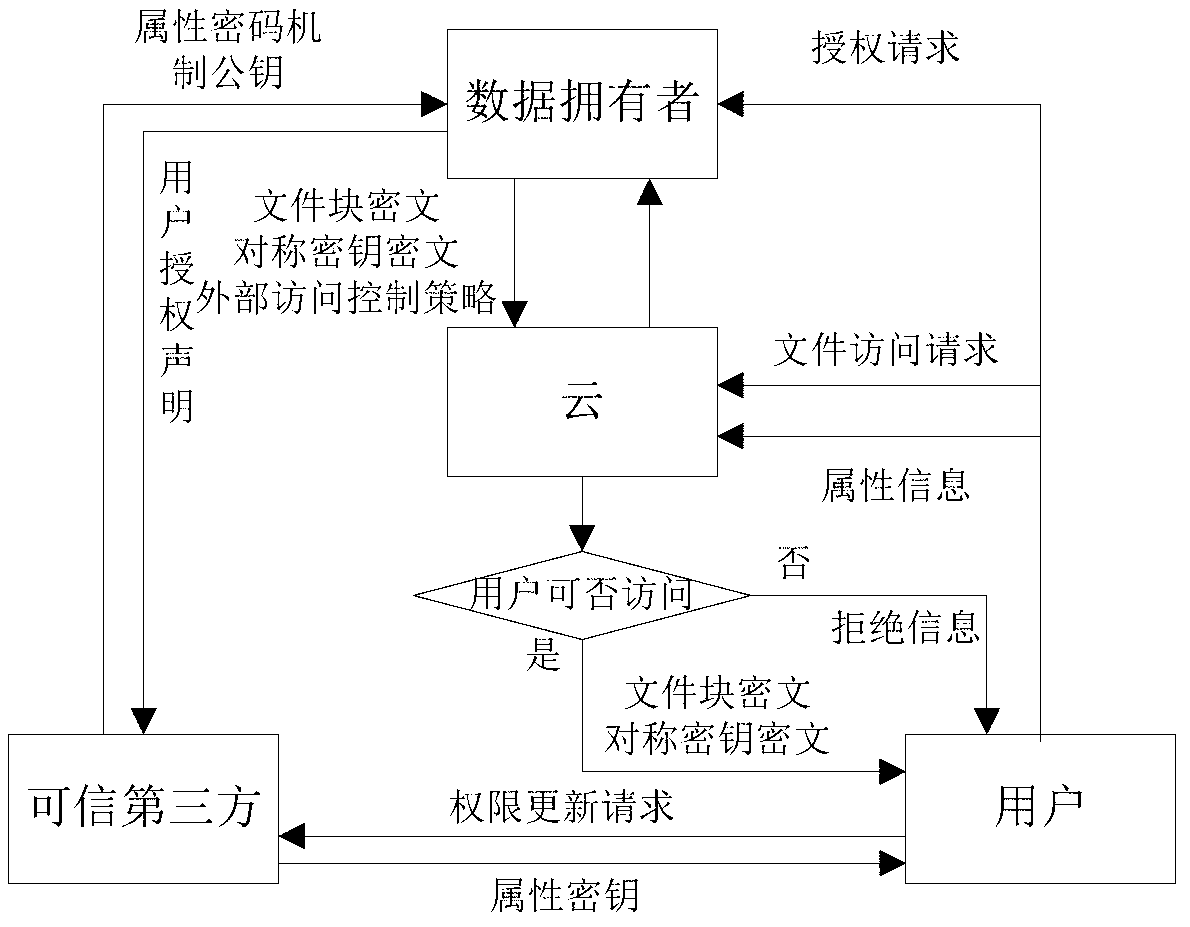
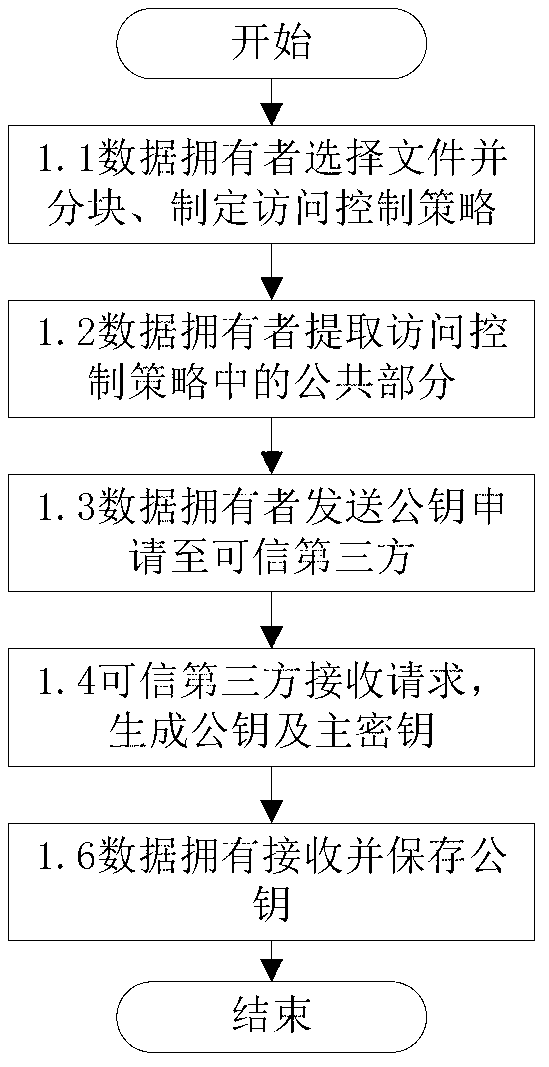
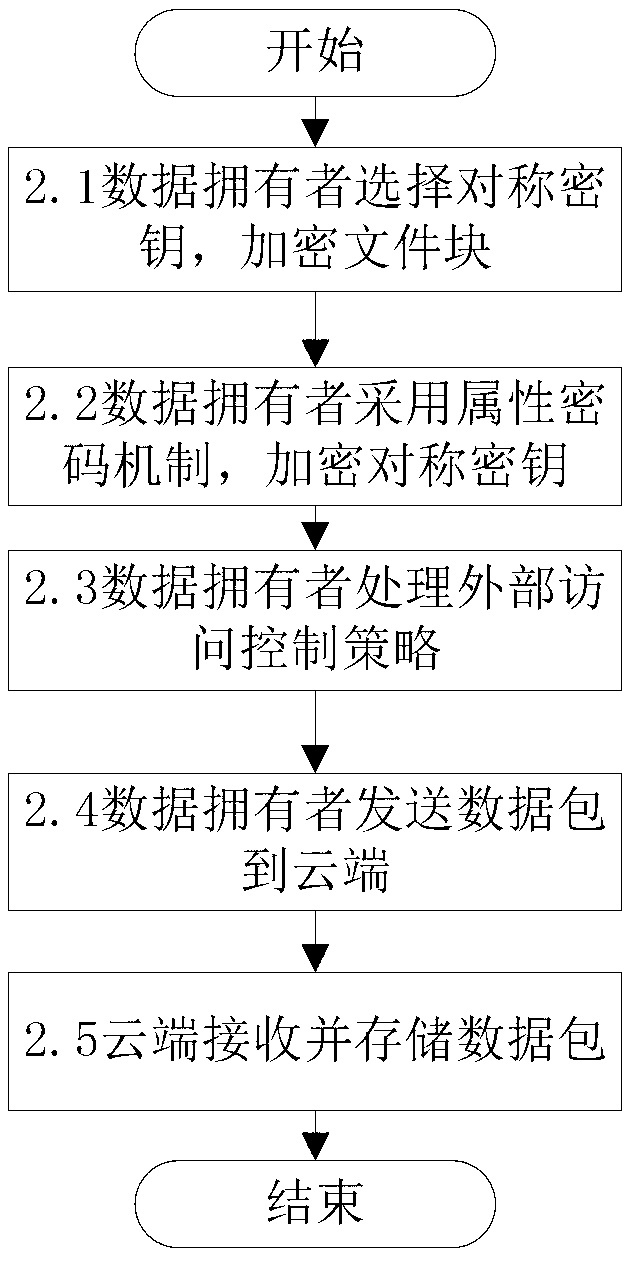
Fine-grained access control method for data in cloud storage
ActiveCN103179114AImplement access controlReduce overheadTransmissionUser PrivilegeAccess control matrix
The invention discloses a fine-grained access control method for data in cloud storage. The method includes the steps: firstly, a data owner blocking files and formulating an external access strategy of file blocks and an internal access strategy of the file blocks according an access control policy, and a trusted third party generating a public key and a master key according to an attribute password mechanism; the data owner utilizing a symmetric password mechanism to encipher the file blocks, utilizing the attribute password mechanism to encipher a symmetric key, and sending a cypher text of the file blocks and a cypher text of a secret key to the cloud; the data owner and the trusted third party utilizing the attribute password mechanism to authorize a user, and generating an attribute key and an attribute processed by an attribute encryption function for each attribute of the user; the data owner sending an user permission change statement to the trusted third party; and the trusted third party judging whether adding or deleting the user permission or not for the user according to the user permission change statement. Compared with the prior art, the method for the fine-grained data access control in the cloud storage has the access control with more fine-grained data under the condition of not increasing additional costs.
Owner:HUAZHONG UNIV OF SCI & TECH
Server system, control method, and storage medium for securely executing access to data of a tenant
ActiveUS20130007891A1Digital data processing detailsAnalogue secracy/subscription systemsData access controlOperating system
In a multitenant service, security of the entire service is guaranteed by logically separating data for each tenant, and performing control to prevent access to data of another tenant. In an operation of the multitenant service, there are some special cases in which an access to data of another tenant becomes necessary. Further, processing executable across tenants needs to be subjected to restrictions on an executor of the processing and a processing target in addition to restrictions on a processing content. In data access control of the multitenant service, a control operation to determine whether processing is executable across tenants for each API and a control operation to determine whether processing is executable across tenants according to tenant categories of the executor and the processing target are performed.
Owner:CANON KK
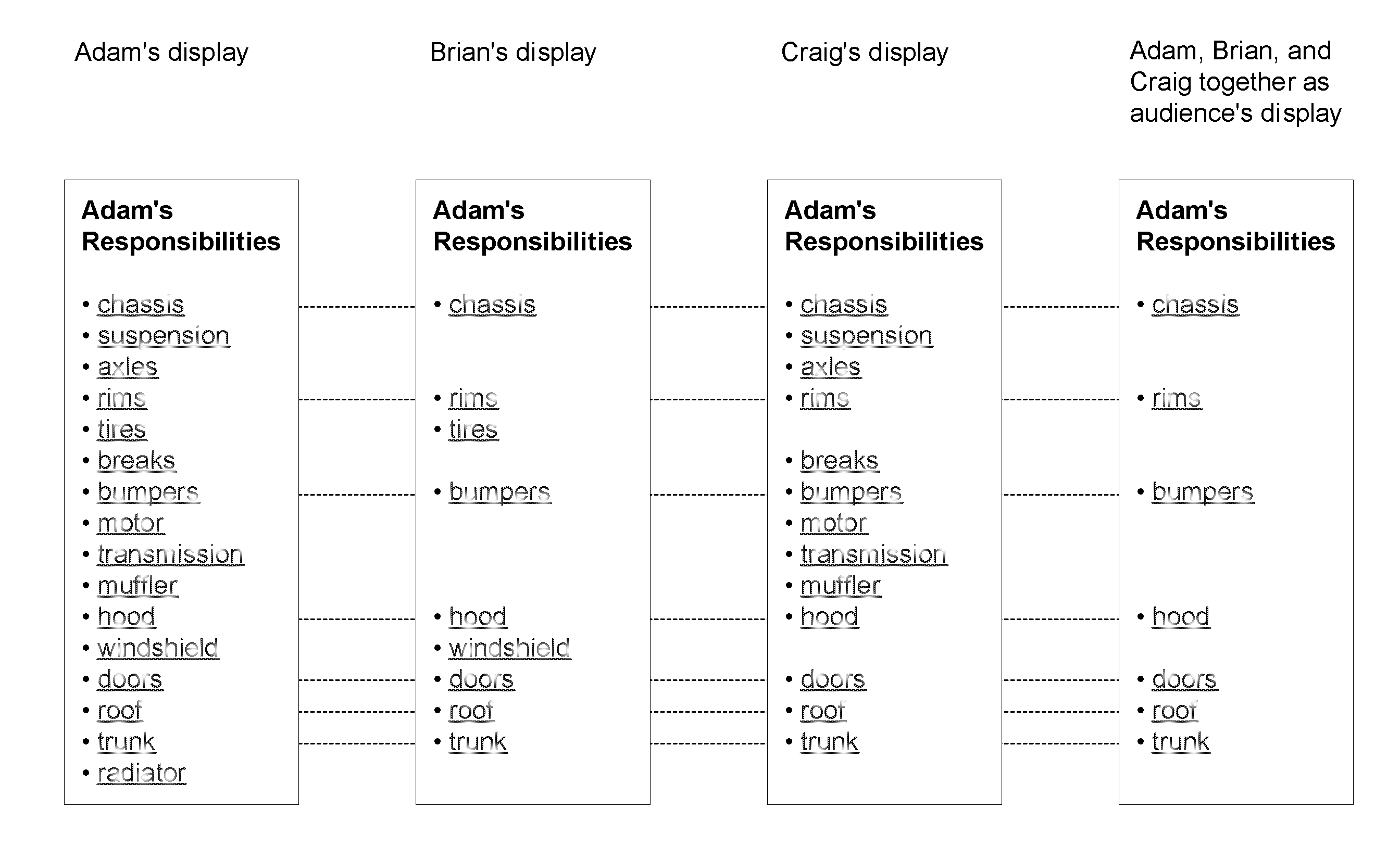
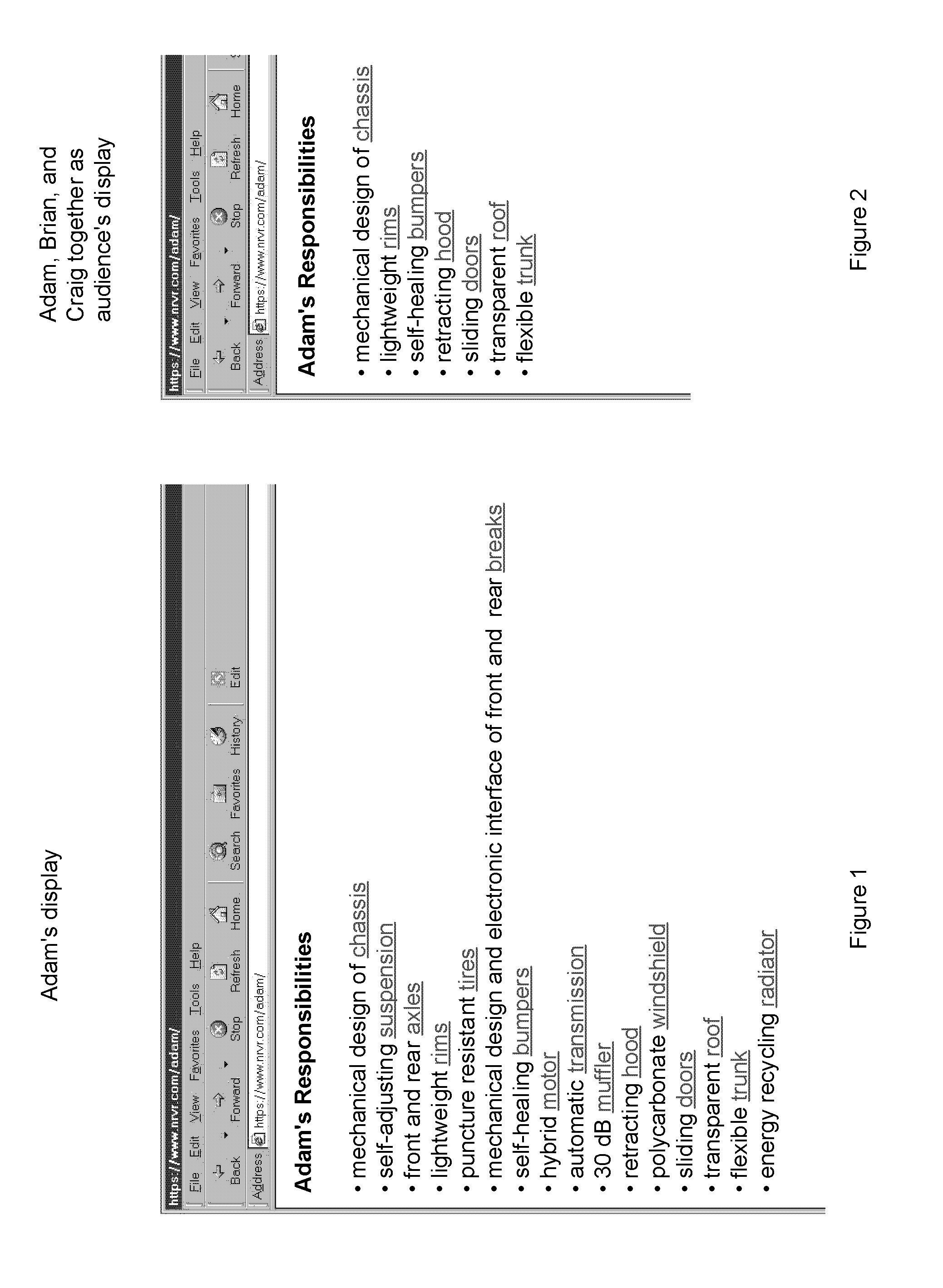
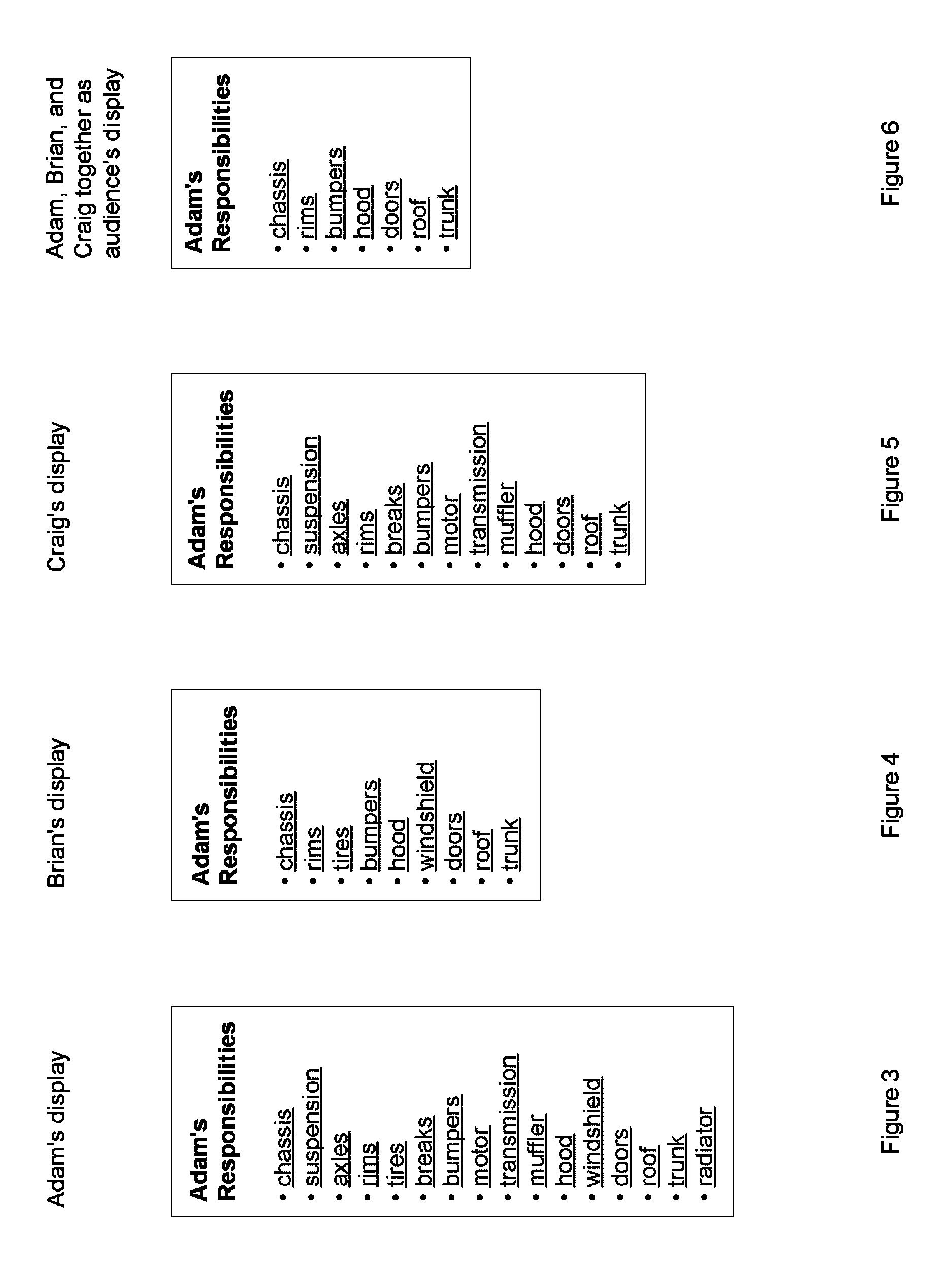
User interface driven access control system and methods for multiple users as one audience
InactiveUS9129088B1Easy to control and useAccurate measurementDigital data processing detailsMultiple digital computer combinationsControl systemData access control
An “audience” object describes a collection of users who are known to or expected to view a display. Access control and processing of access dependent contents for an audience are implemented so that information before being displayed is limited to what is authorized for every member in the audience to access. An operator can preview what an expected audience would see. The operator is aided in determining what the effects would be of a newcomer joining an audience. The operator is aided in determining who in an audience causes a difference in authorization. Hardware can be tied in with the access control software.
Owner:NIRESIP
Implementation and use of a PII data access control facility employing personally identifying information labels and purpose serving functions sets
ActiveUS20050044409A1Less security-becauseLess private-theDigital data processing detailsAnalogue secracy/subscription systemsFeature setInternet privacy
A data access control facility is implemented by assigning personally identifying information (PII) classification labels to PII data objects, with each PII data object having one PII classification label assigned thereto. The control facility further includes at least one PII purpose serving function set (PSFS) comprising a list of application functions that read or write PII data objects. Each PII PSFS is also assigned a PII classification label. A PII data object is accessible via an application function of a PII PSFS having a PII classification label that is identical to or dominant of the PII classification label of the PII object. A user of the control facility is assigned a PII clearance set which contains a list of at least one PII classification label, which is employed in determining whether the user is entitled to access a particular function.
Owner:SAILPOINT TECH HLDG INC
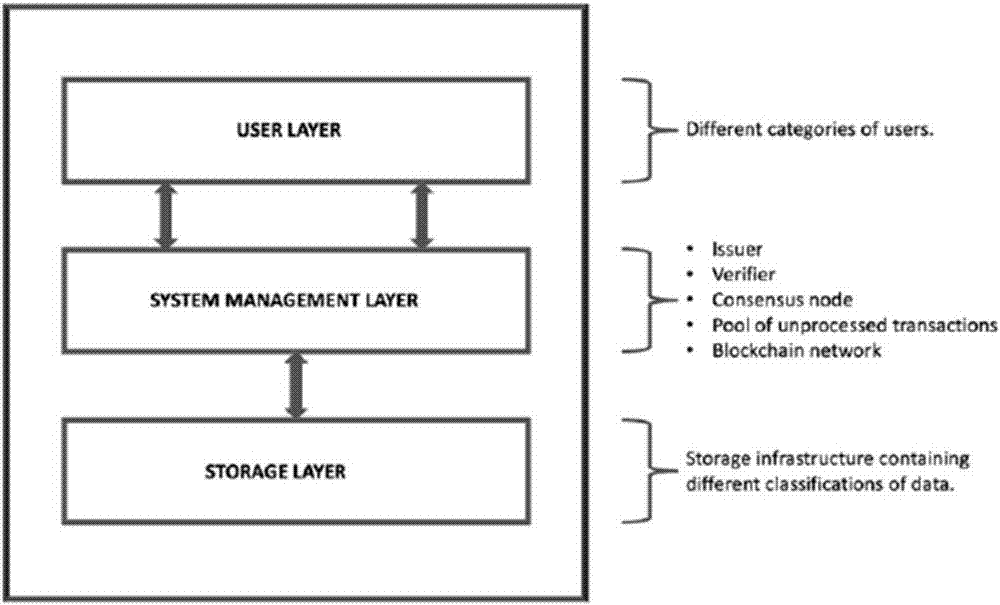
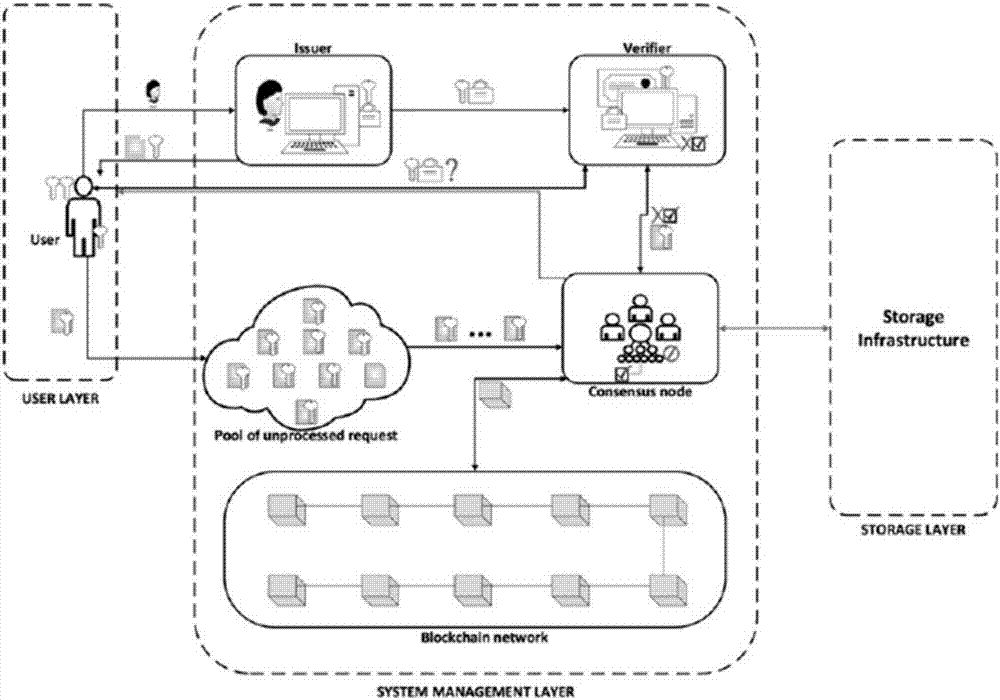
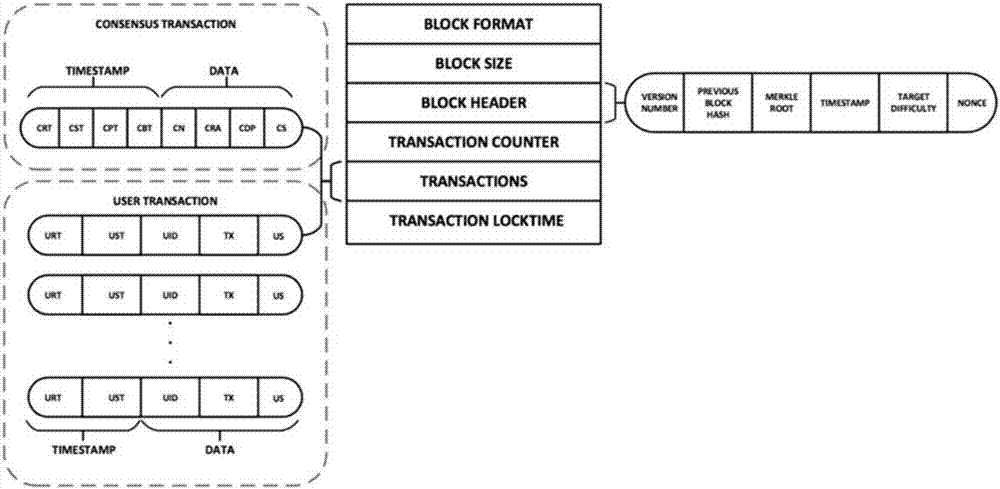
Block chain based data access control system
InactiveCN107070938AAchieve sharingSolve technical problems that are vulnerable to theftKey distribution for secure communicationUser identity/authority verificationSystems managementControl system
The invention discloses a block chain based data access control system. The block chain based data access control system comprises a user layer used for a user to send a registration application or a data access request to subordinates; a system management layer used for receiving the registration request or the data access request; and a storage layer used for the user layer to perform data access after the registration application and the data access request pass verification. When sending the registration application, password checking and verification between the system management layer and the user layer is carried out for three times, the system management layer generates a transaction public key and a transaction private key based on the last password and hands in the transaction public key to the system management layer for keeping; and when sending the data access request, the system management layer takes out and verifies a block of the data access request which is encrypted by the last password and signed by the transaction private key, and the user obtains the access permission of data stored in the storage layer after the successful verification. The block chain based data access control system solves the technical problem that user data are stolen easily due to adoption of a centralized deployment mode in the prior art.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
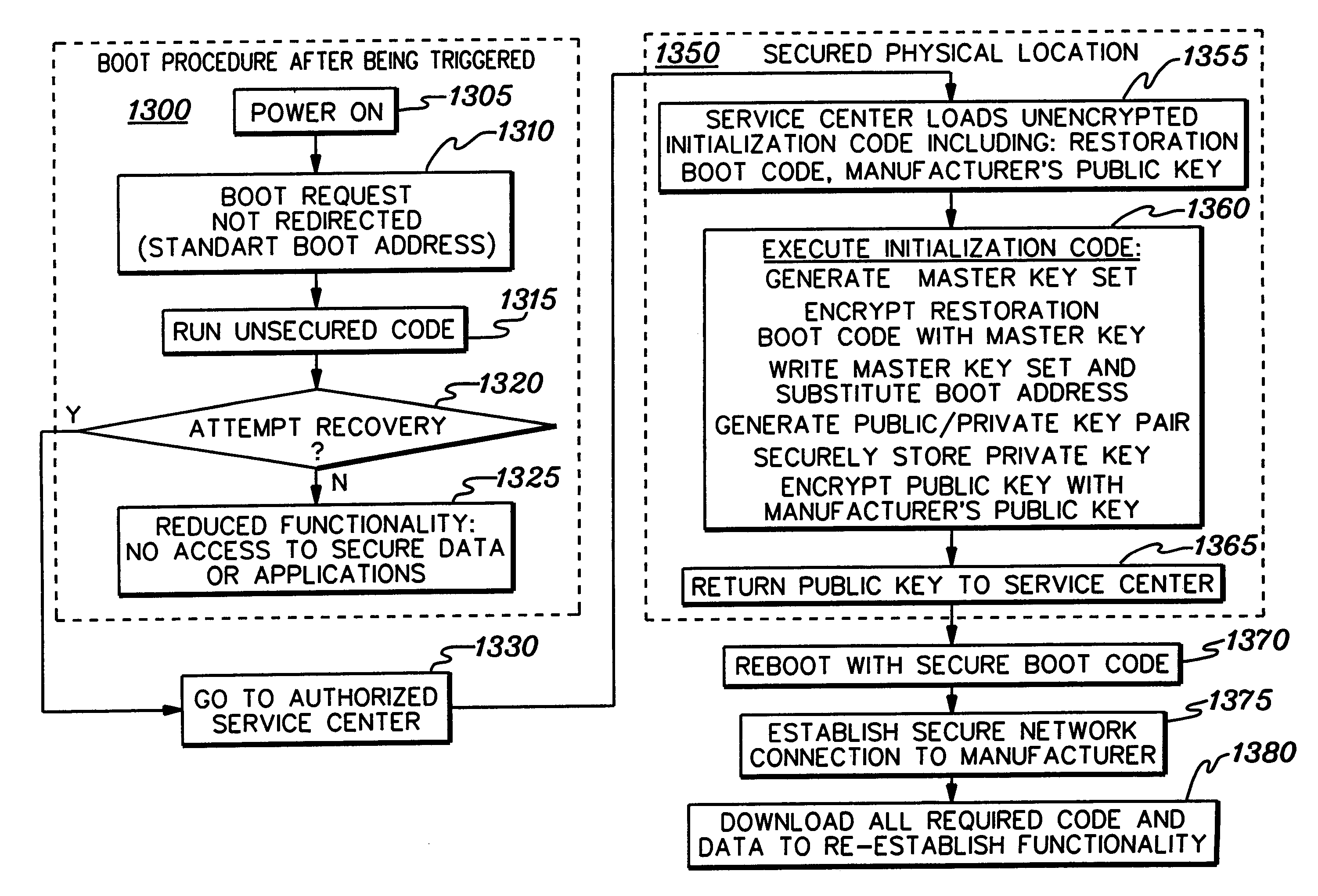
Initializing, maintaining, updating and recovering secure operation within an integrated system employing a data access control function
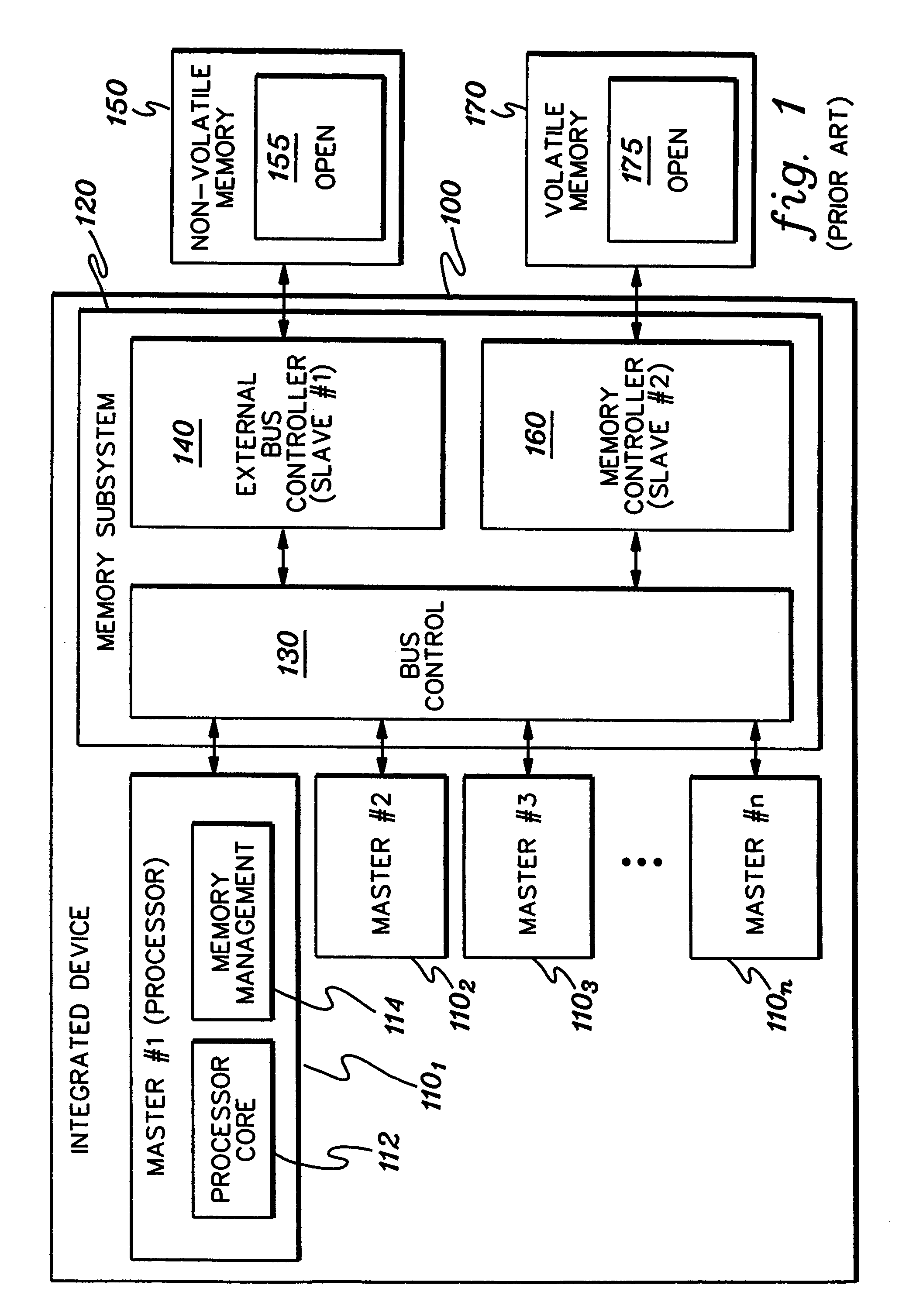
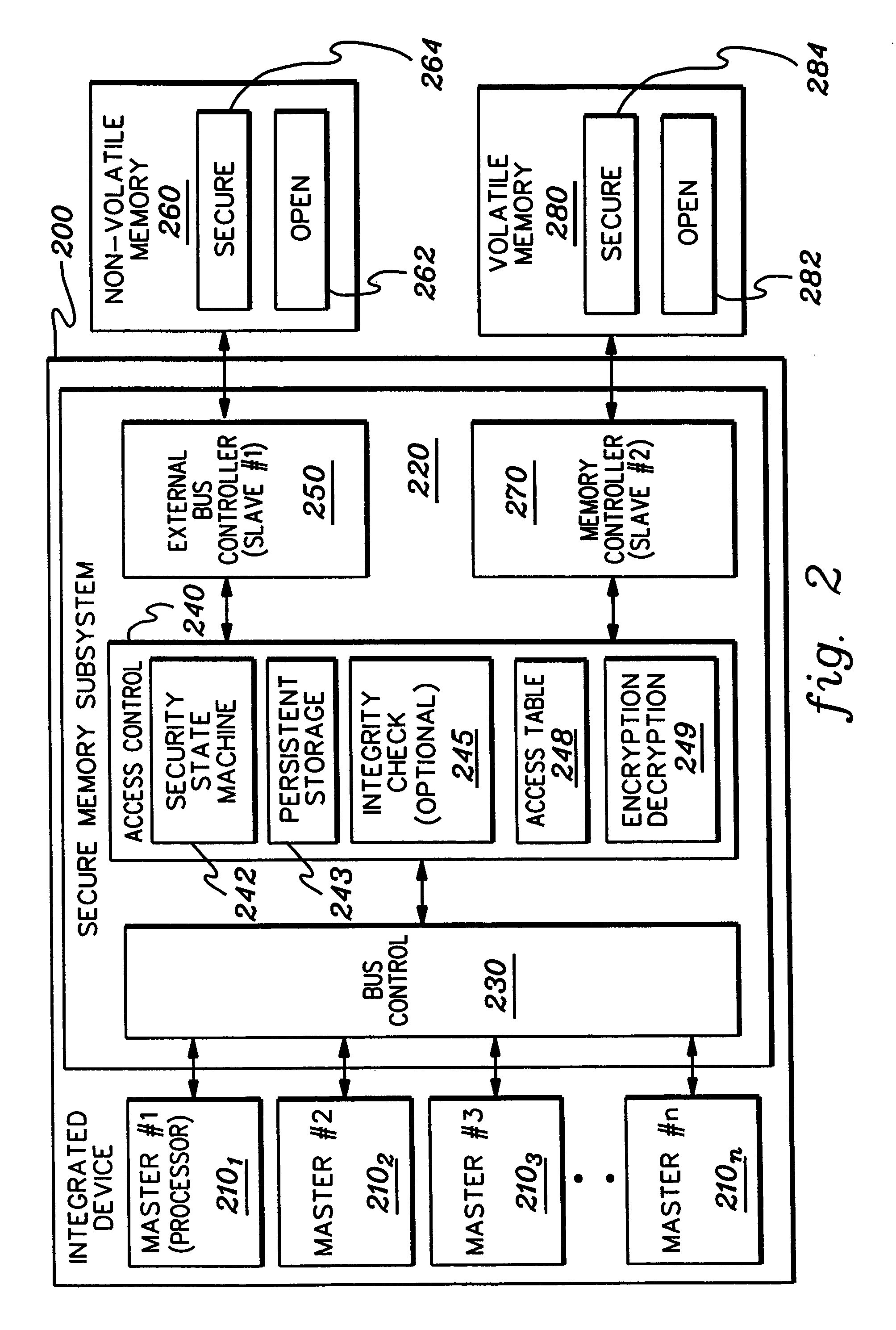
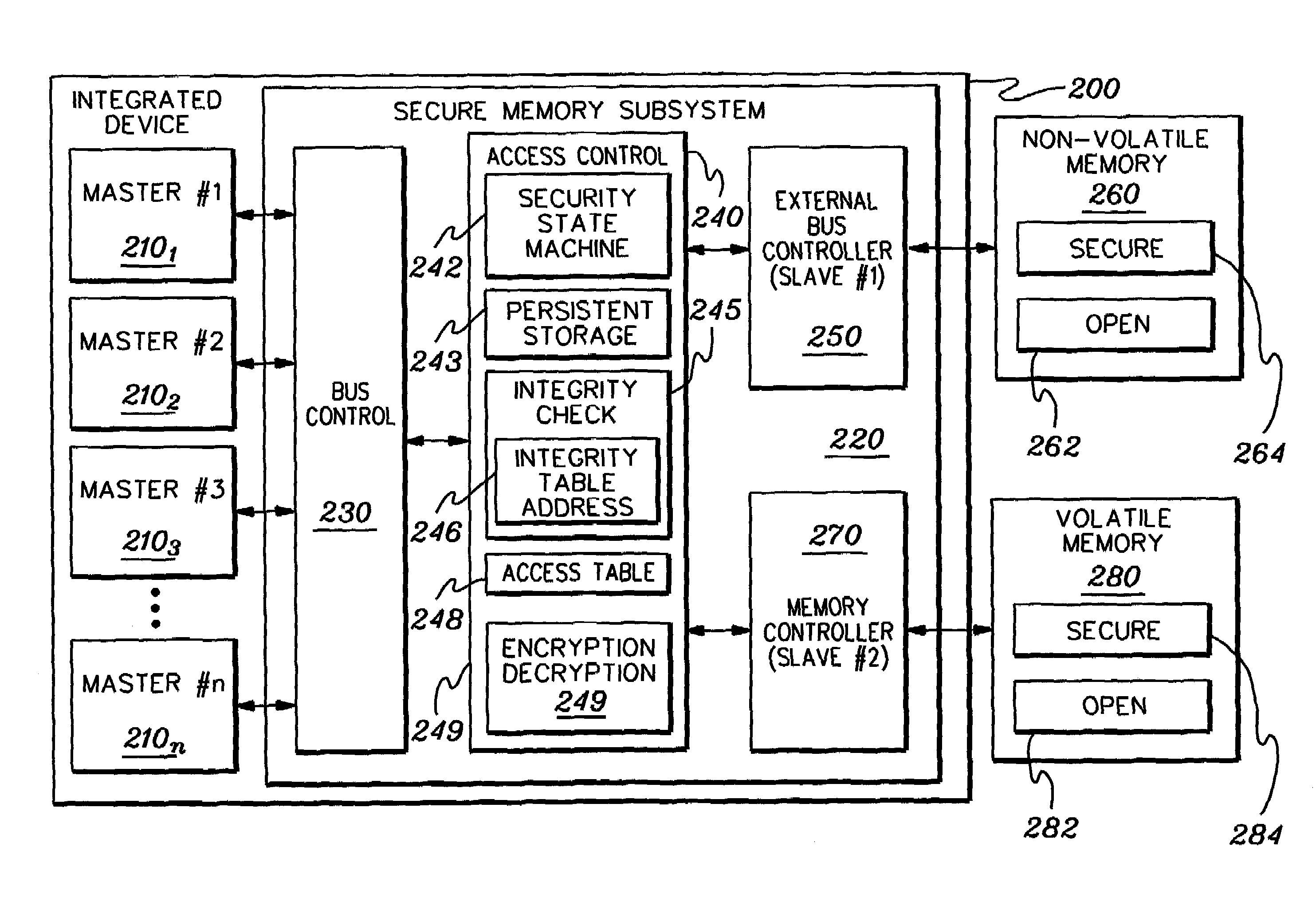
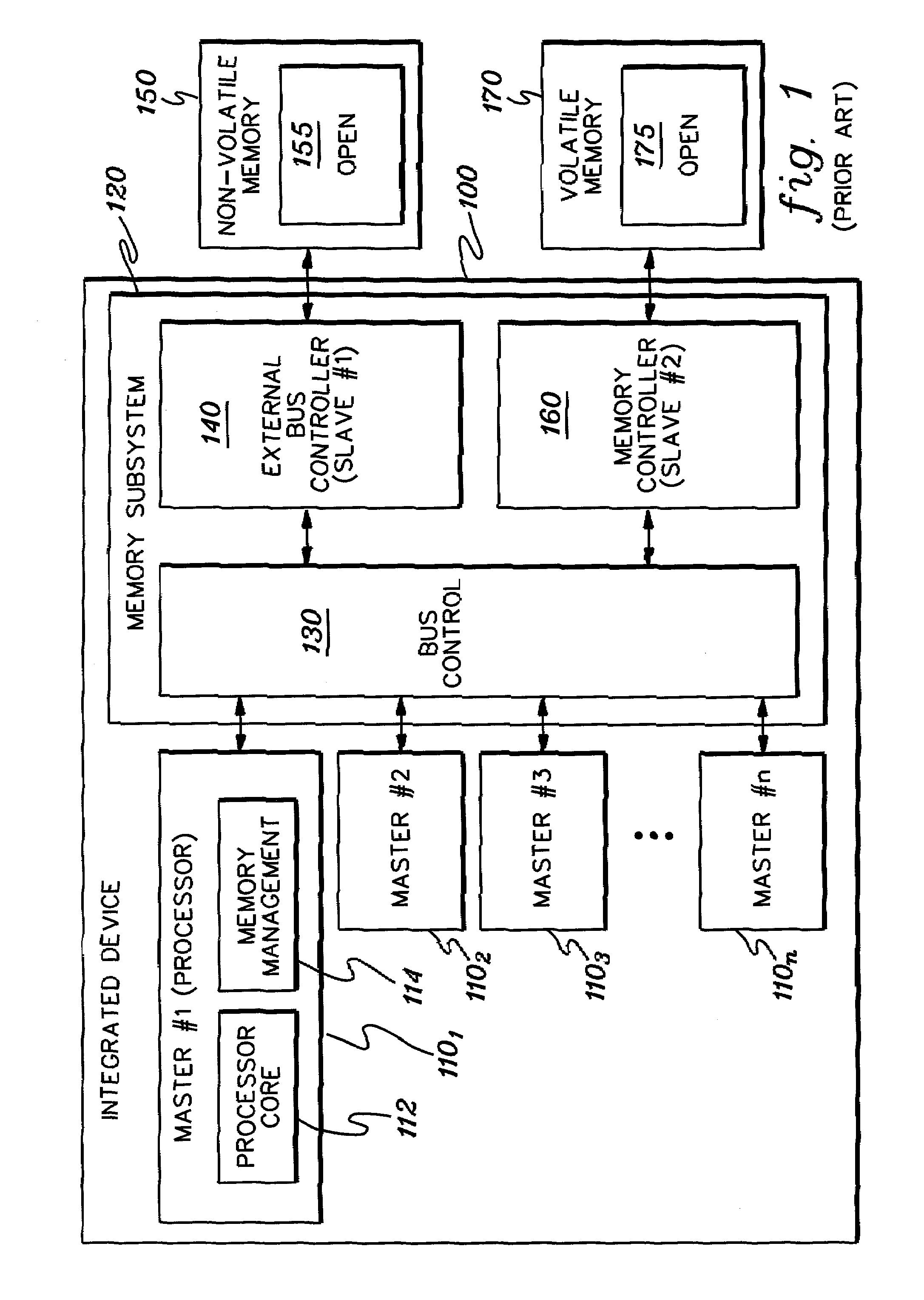
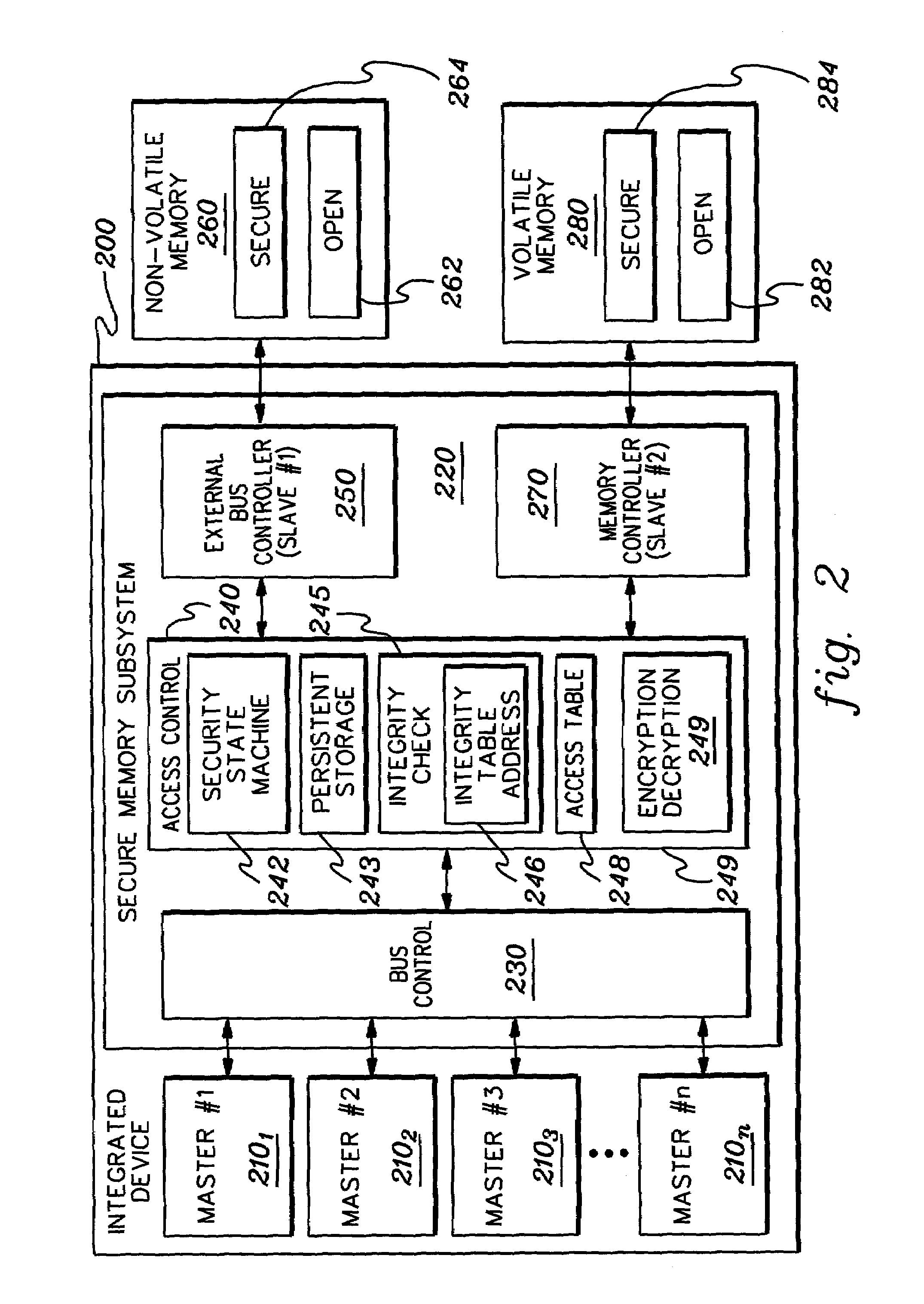
ActiveUS7356707B2Reduced level of functionalityUser identity/authority verificationDigital computer detailsData access controlSafe operation
Techniques are provided for initializing, maintaining, updating and recovering secure operation within an integrated system. The techniques, which employ a data access control function within the integrated system, include authenticating by a current level of software a next level of software within an integrated system. The authenticating occurs before control is passed to the next level of software. Further, an ability of the next level of software to modify an operational characteristic of the integrated system can be selectively limited via the data access control function. Techniques are also provided for initializing secure operation of the integrated system, for migrating data encrypted using a first key set to data encrypted using a second key set, for updating software and keys within the integrated system, and for recovering integrated system functionality following a trigger event.
Owner:DAEDALUS BLUE LLC
Control function implementing selective transparent data authentication within an integrated system
InactiveUS7266842B2Simplified integrity value calculationCode latency be minimizedRandom number generatorsUser identity/authority verificationData access controlData request
A data authentication technique is provided for a data access control function of an integrated system. The technique includes passing a data request from a functional master of the integrated system through the data access control function, and responsive to the data request, selectively authenticating requested data. The selective authentication, which can occur transparent to the functional master initiating the data request, includes employing integrity value generation on the requested data when originally stored and when retrieved, in combination with encryption and decryption thereof to ensure the authenticity of the requested data. As an enhancement, cascading integrity values may be employed to facilitate data authentication.
Owner:IBM CORP
Controlling client access to networked data based on content subject matter categorization
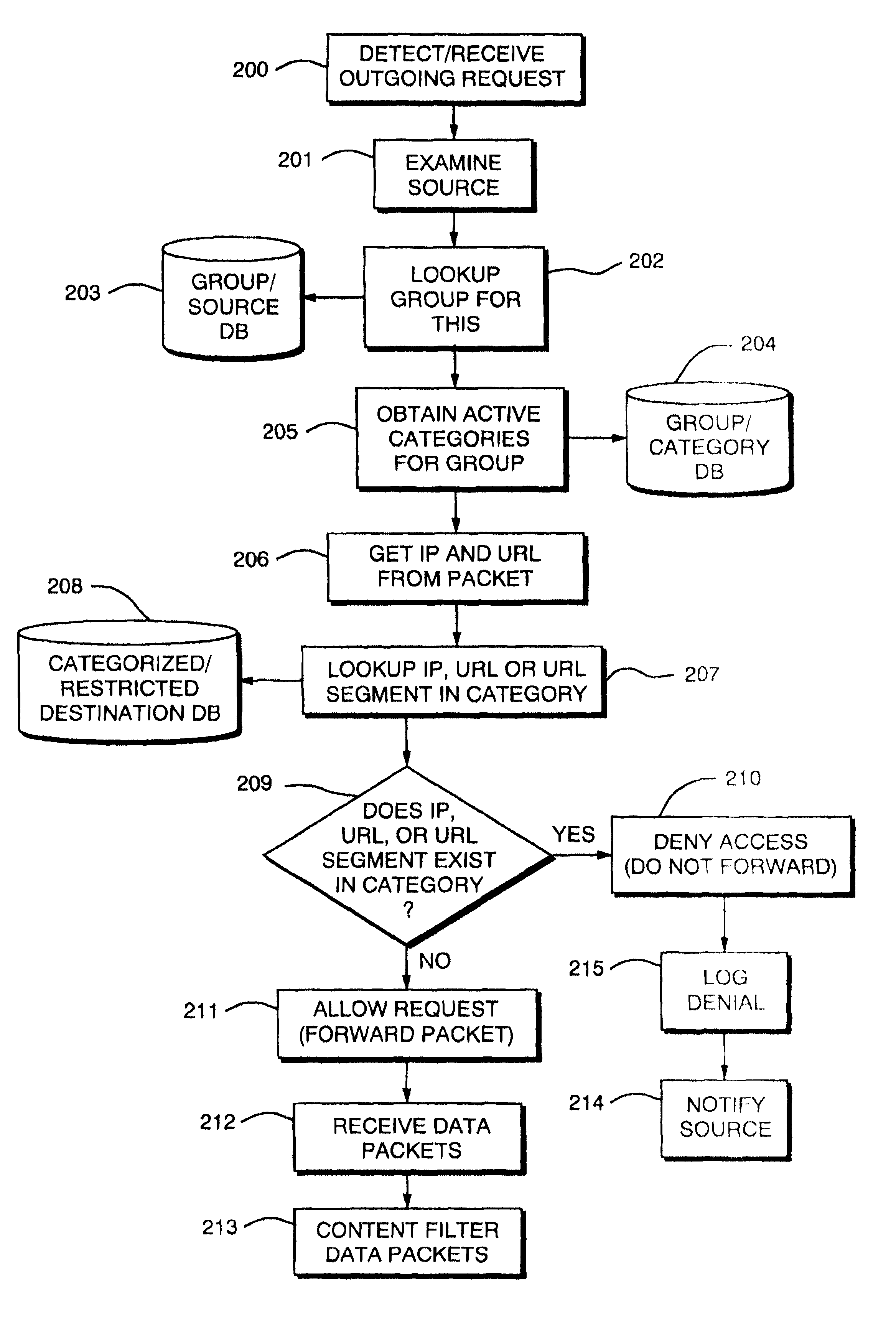
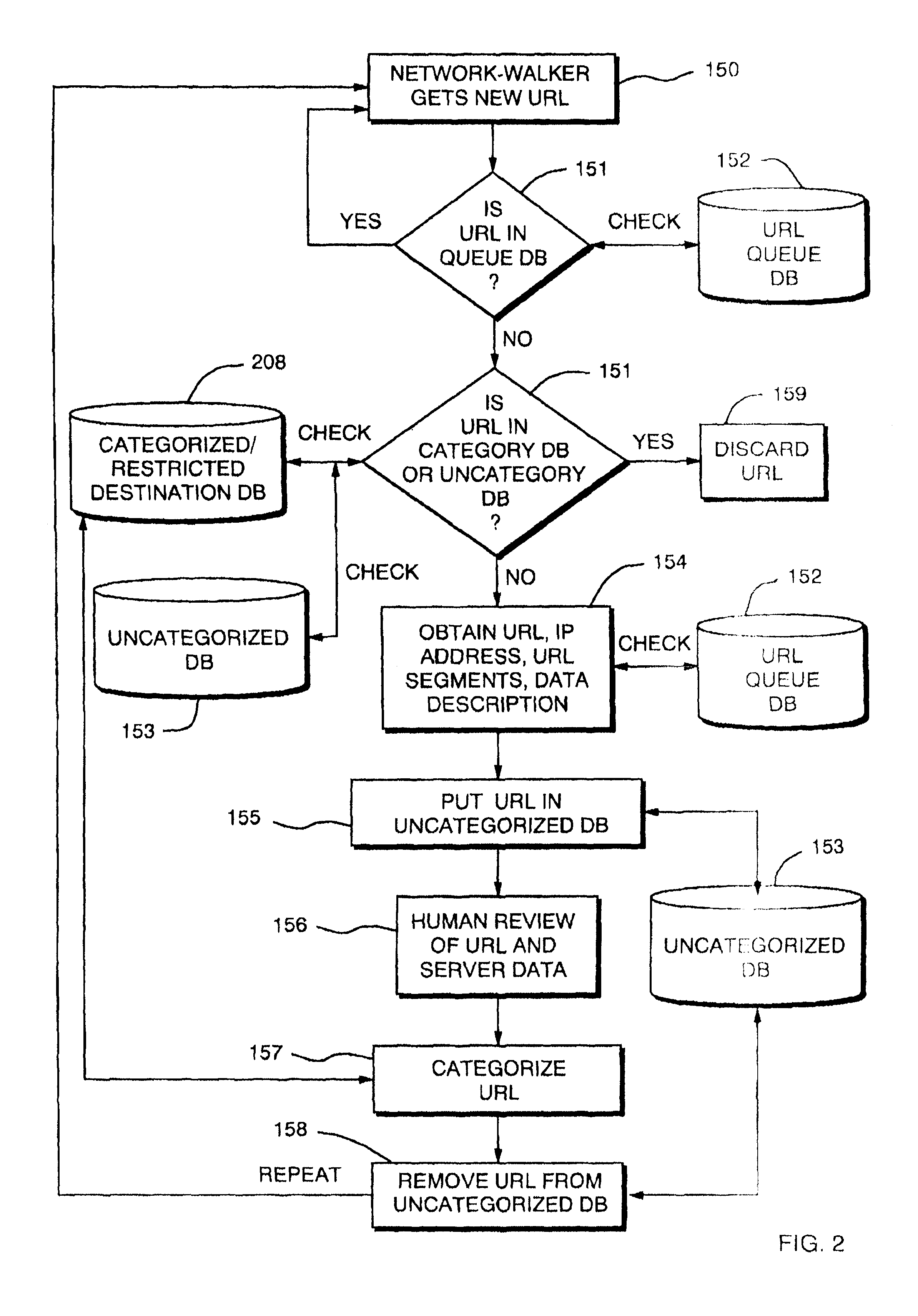
InactiveUSRE41168E1Constant maintenanceEasy accessMultiple digital computer combinationsTransmissionIp addressThe Internet
An access control technique to limit access to information content such as available on the Internet. The technique is implemented within a network device such as a proxy server, router, switch, firewall, bridge or other network gateway. The access control process analyzes data in each request from the clients and determines if the request should be forwarded for processing by a server to which it is destined. Access control may be determined by comparing client source information against a database of Uniform Resource Locators (URLs), IP addresses, or other resource identification data specifying the data requested by the client. The invention therefore provides access control not based only upon content, but rather, based primarily upon the identity of the computers or users making the requests. The technique further avoids the problems of the prior art which categories or filters the content of only web pages based solely upon objectionable words. This is because a category database is used by the network device to control access and is created via a process involving human editors who assist in the creation and maintenance of the category database.
Owner:CONTENT ADVISOR
IC card with radio interface function, antenna module and data processing apparatus using the IC card
InactiveUS20050006484A1Pivotable antennasAntenna supports/mountingsData access controlComputer science
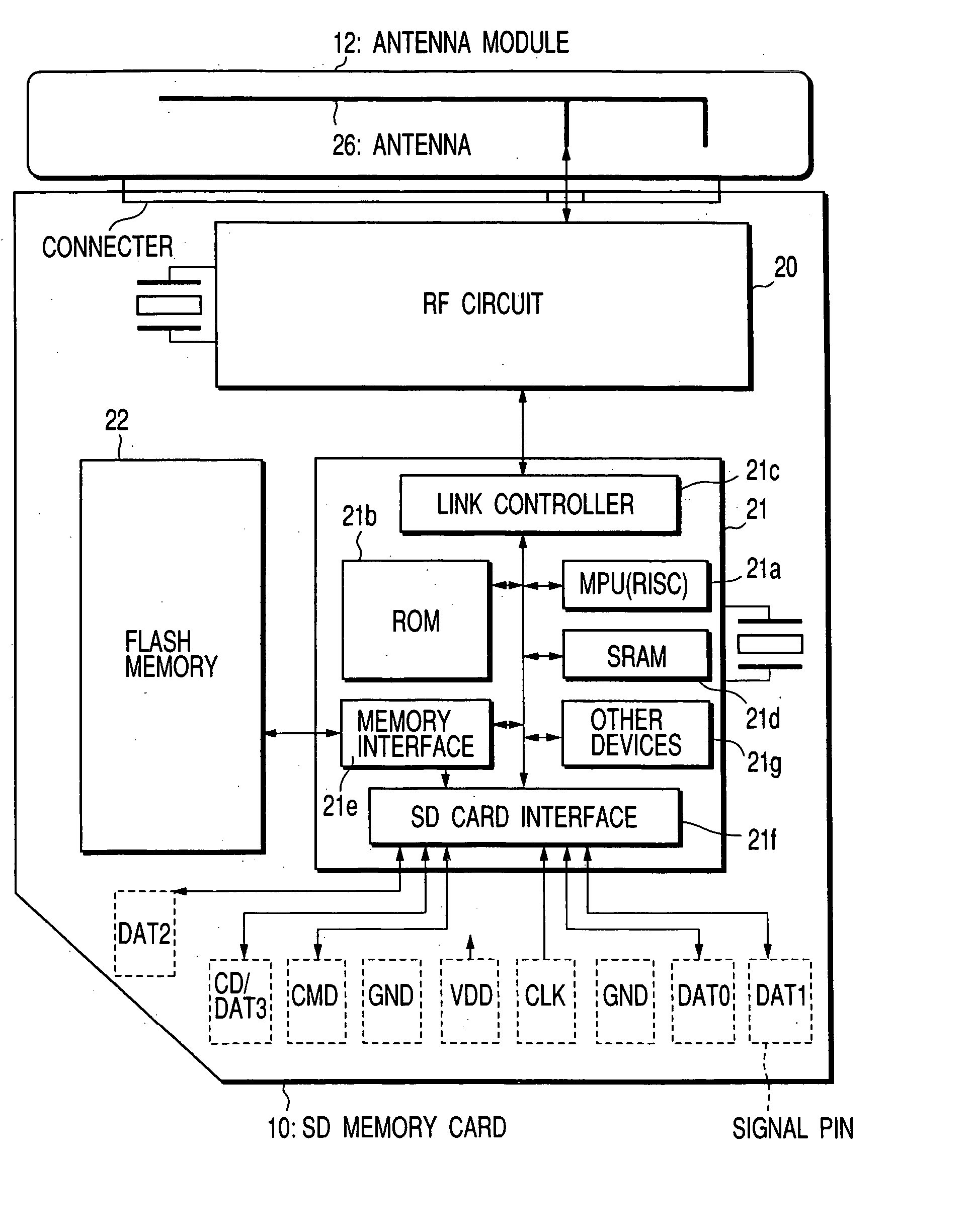
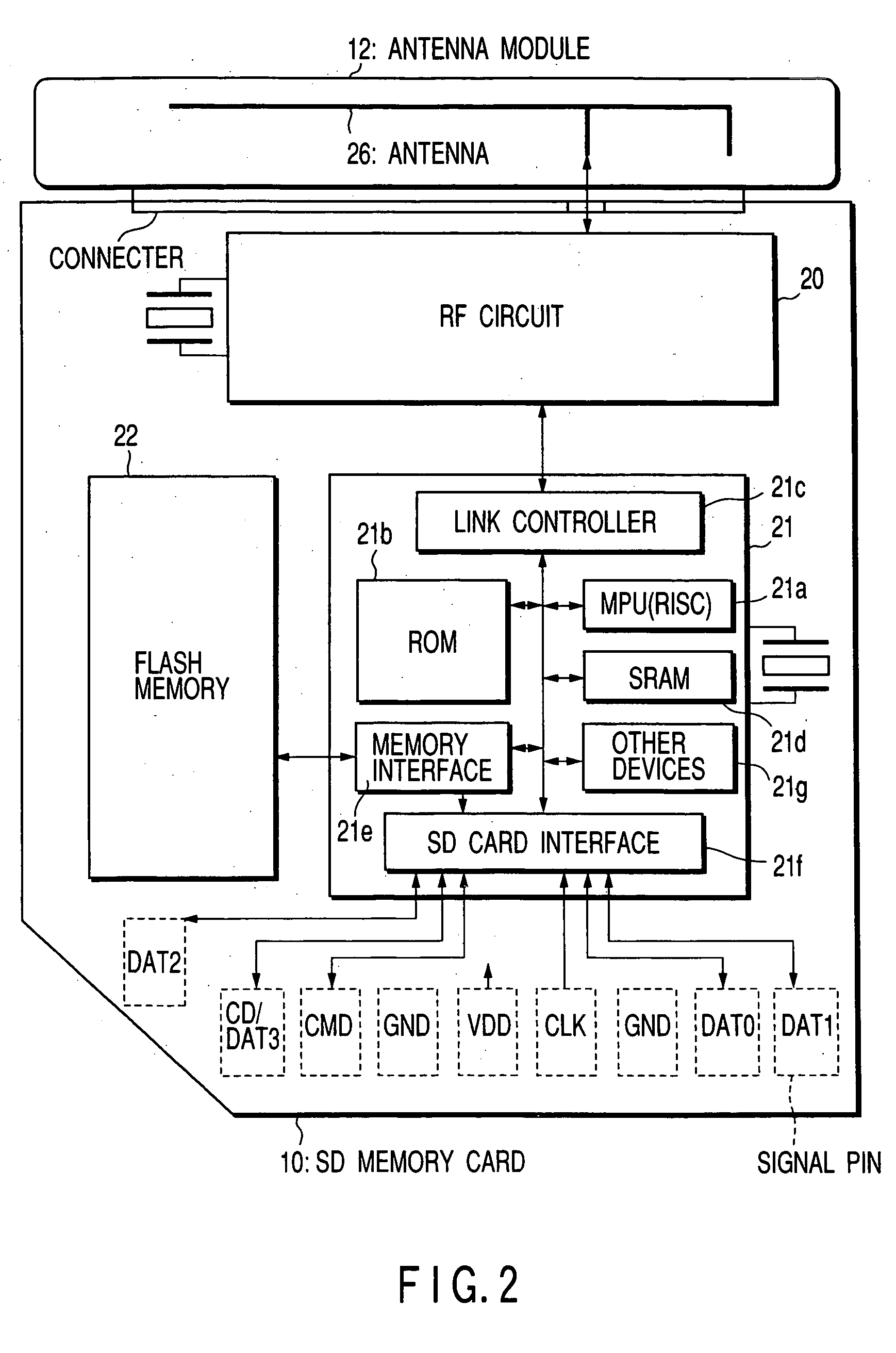
An SD memory card contains an RF circuit, a controller LSI and a flash memory. The RF circuit is connected to an antenna module attached to the SD memory card. The controller LSI executes radio interface control and interface control for the SD memory card. By running a protocol control program and an SD memory card interface control program stored in a ROM, using an MPU, the controller LSI executes upper-protocol control and SD memory card interface control (security data access control, flash memory access control).
Owner:TOSHIBA MEMORY CORP
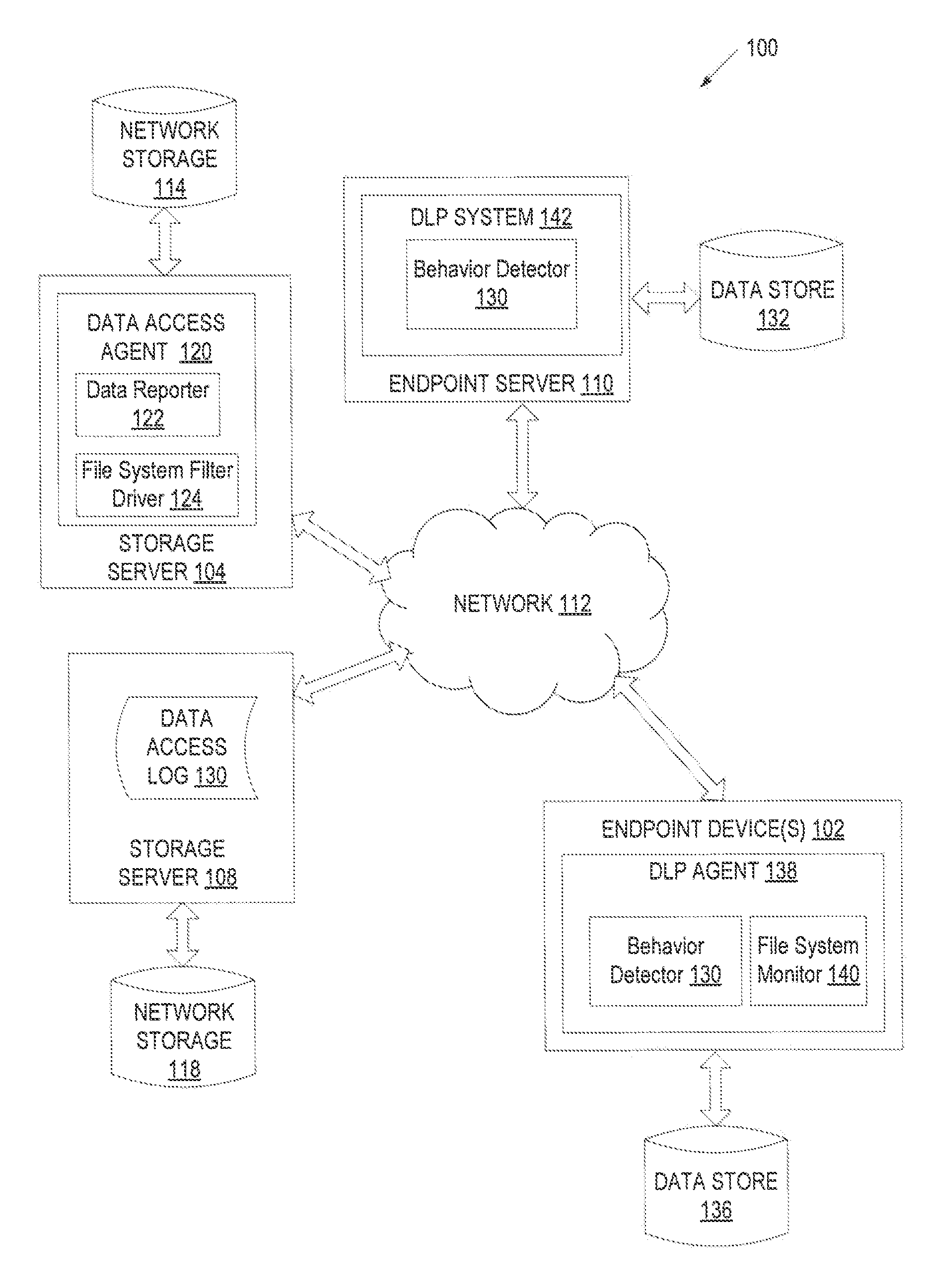
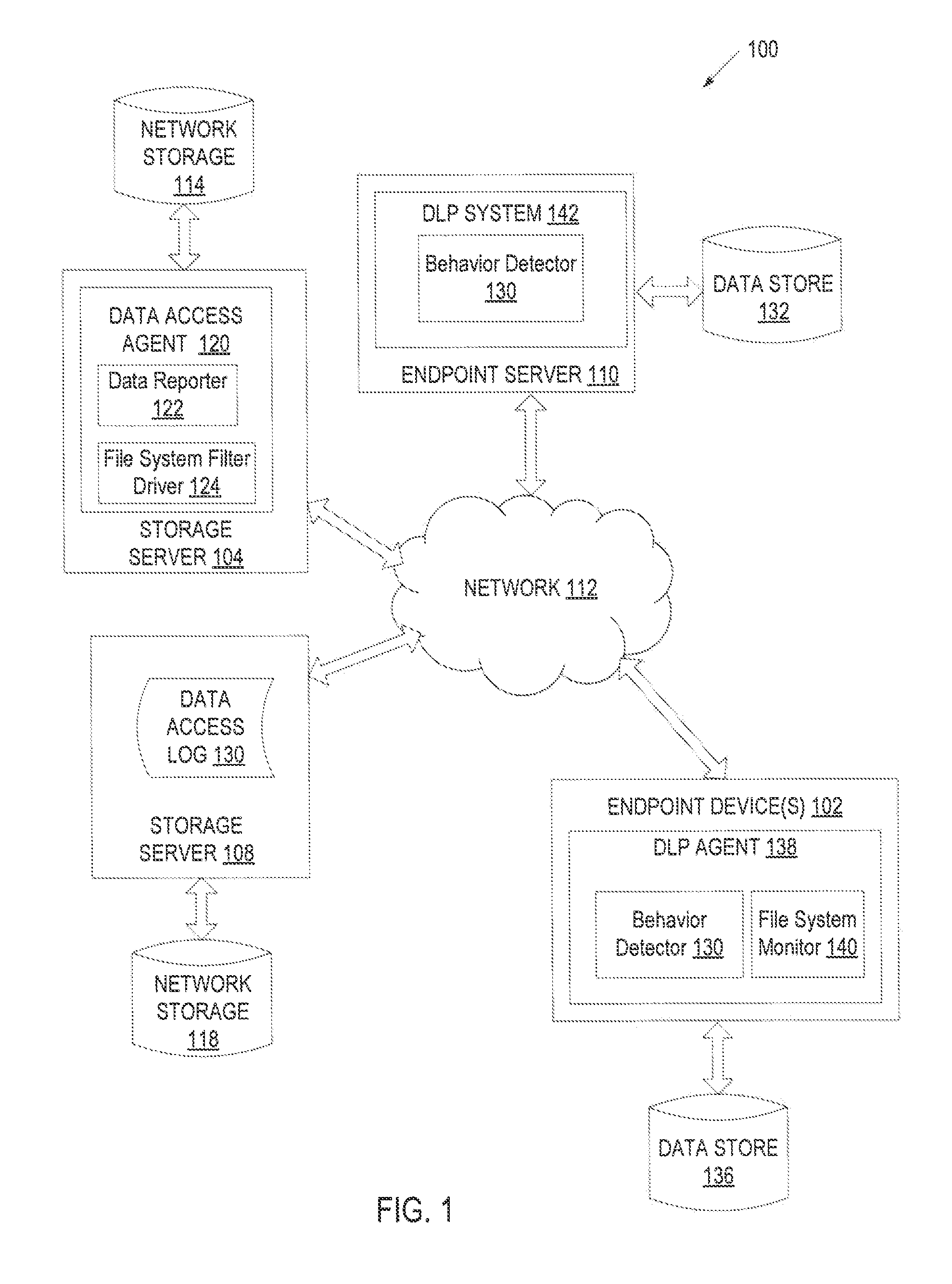
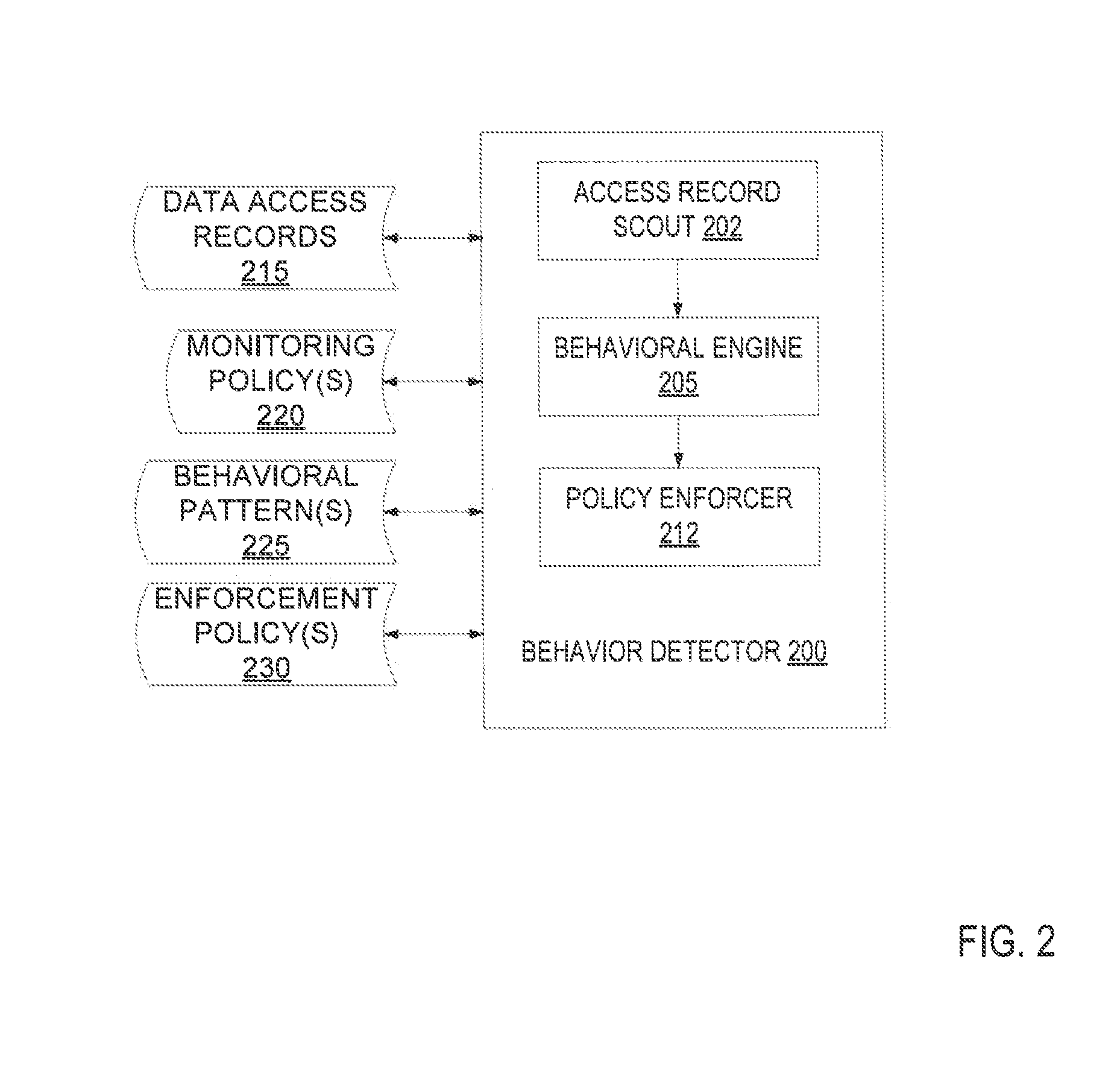
Behavioral engine for identifying anomalous data access patterns
ActiveUS9275065B1Digital data information retrievalComputer security arrangementsData access controlData mining
A computing device receives data access records and determines a user data access behavior pattern for a user based on the data access records. The computing device receives new data access records and identifies any deviation from the user data access behavior pattern based on the new data access records. Upon identifying deviation from the user data access behavior pattern, the computing device generates an alert indicating that the user has deviated from the user data access behavior pattern.
Owner:CA TECH INC
System and method for access control
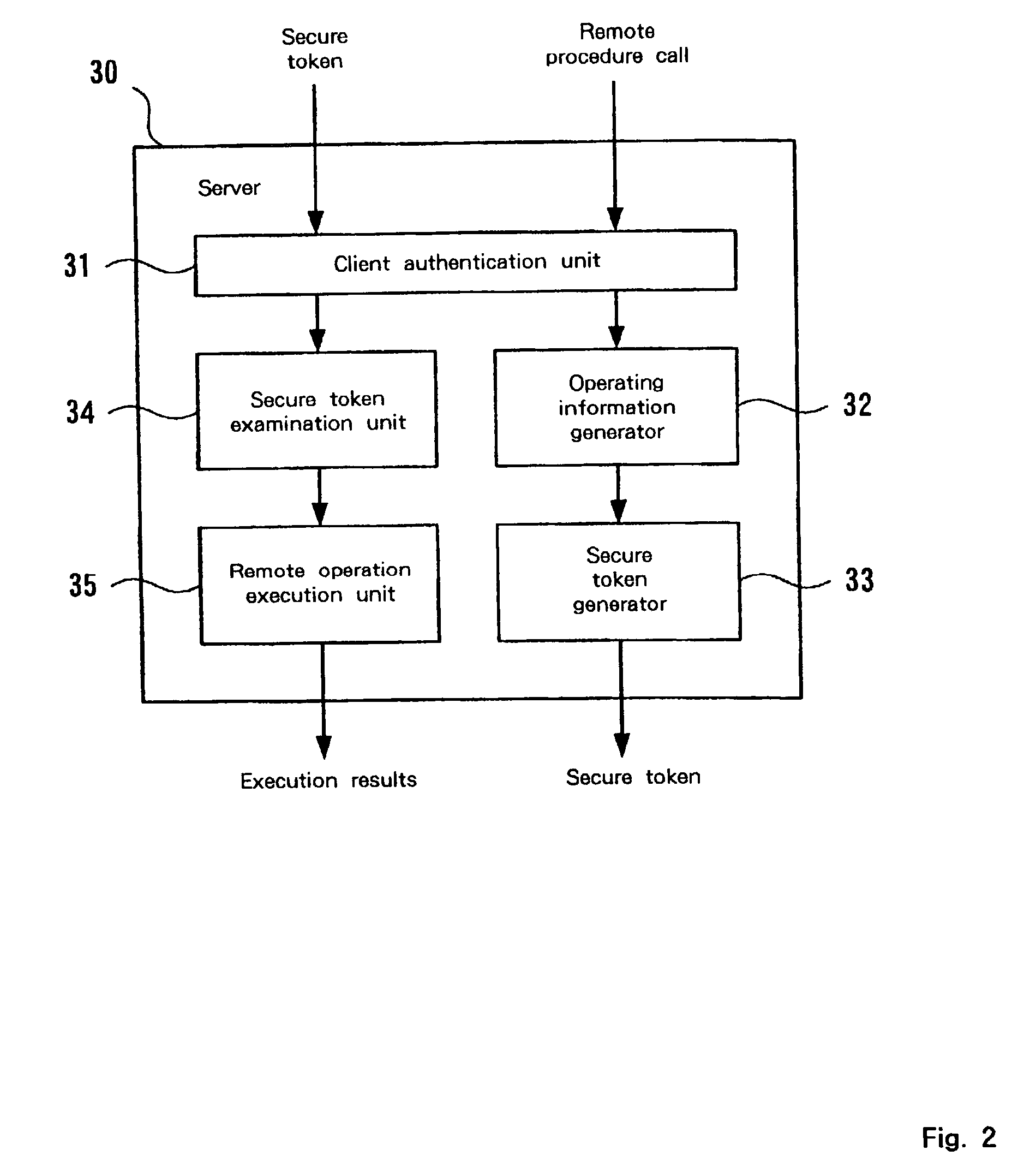
InactiveUS20030005333A1User identity/authority verificationUnauthorized memory use protectionData setAccess control matrix
A mechanism for access control based on remote procedure calls is established whereby server management costs for the processing associated with the authentication of client access rights and the provision of requested resources can be reduced by distributing these costs among clients. A first client, which has an access right to a server via a network, can issue a remote procedure call to the server. The first client can also communicate with a second client, which doesn't have an access right to the server. The first client requests the server to issue a token, which is a data set for permitting the second client a limited access to the server, and subsequently the token prepared by the server is transmitted to the second client. The second client originally has no access rights relative to the server. However, if the second client transmits a remote procedure call using the received token, limited access is granted. The server performs a process designated by the remote procedure call from the second client. The token includes operating information for designating an operation to be performed based on the remote procedure call, and identification information for identifying the second client.
Owner:IBM CORP
Internet of Things data privacy protection method based on block chain and trusted hardware
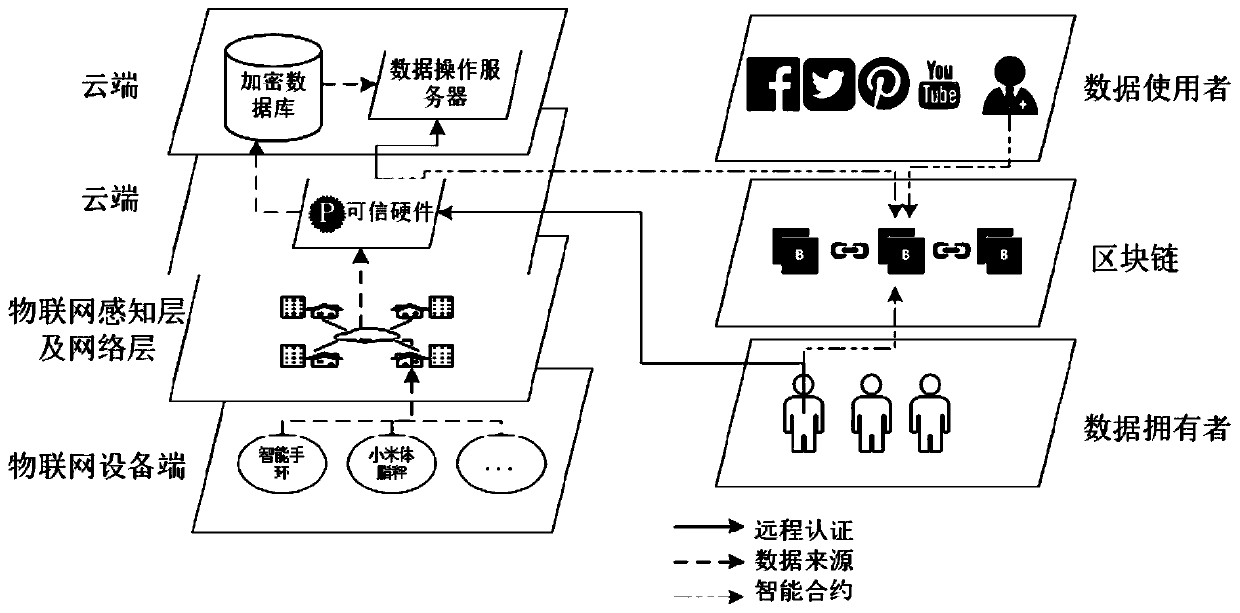
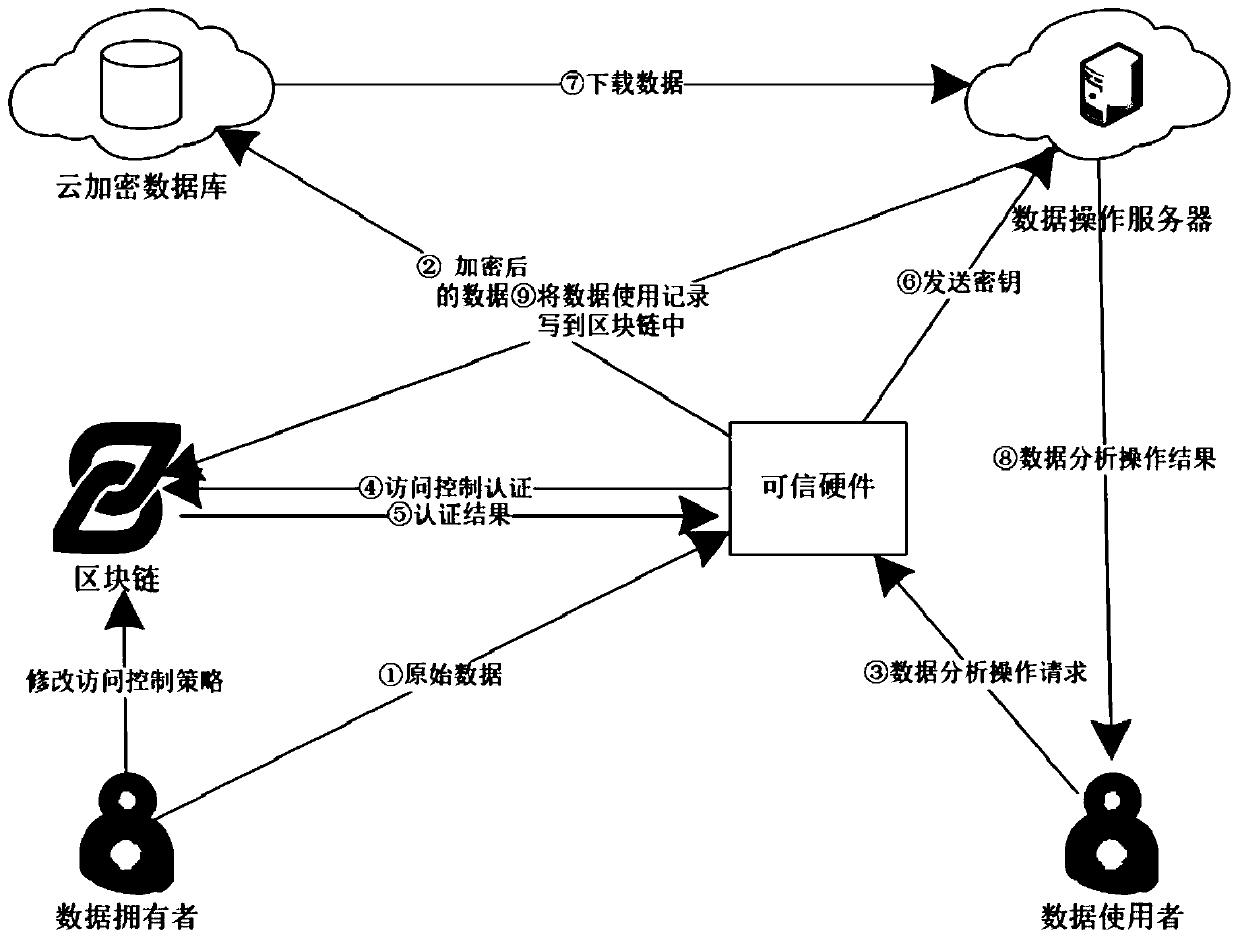
ActiveCN110086804AEnsure safetyGuaranteed reliabilityUser identity/authority verificationDigital data protectionData privacy protectionTrusted hardware
The invention relates to an Internet of Things data privacy protection method based on a block chain and the trusted hardware. The method comprises three stages of secret key management and data generation, data access control strategy definition and intelligent contract deployment and data access and intelligent contract execution, and Internet of Things data is encrypted by a hardware trusted entity IDA and uploaded to a cloud for storage; when there is an operation request, the trusted entity calls an access control authentication interface of the smart contract to carry out authority authentication; after the authority authentication passes, the trusted entity carries out security authentication on the operation execution server and sends the secret key to the data operation executionserver through a security channel; and the server downloads the data from the cloud, then decrypts the data and executes the operation, and writes the data use record into the block chain after the data analysis operation is completed. According to the scheme, the block chain is combined with the trusted entity, the data is effectively operated under the condition that the original data privacy isnot leaked, and the integrity and the safety of the data use records are guaranteed.
Owner:GUANGZHOU UNIVERSITY
System providing methodology for access control with cooperative enforcement
ActiveUS7590684B2Digital data processing detailsAnalogue secracy/subscription systemsData access controlClient-side
A system providing methodology for access control with cooperative enforcement is described. In one embodiment, for example, a method is described for authorizing a client to access a service based on compliance with a policy required for access to the service, the method comprises steps of: specifying a policy required for access to the service; detecting a request for access to the service from a client; attempting authentication of the client based on credentials presented by the client; if the client is authenticated based on the credentials, determining whether the client is in compliance with the policy based, at least in part, on attributes of the client; and if the client is determined to be in compliance with the policy, providing access to the service.
Owner:CHECK POINT SOFTWARE TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com