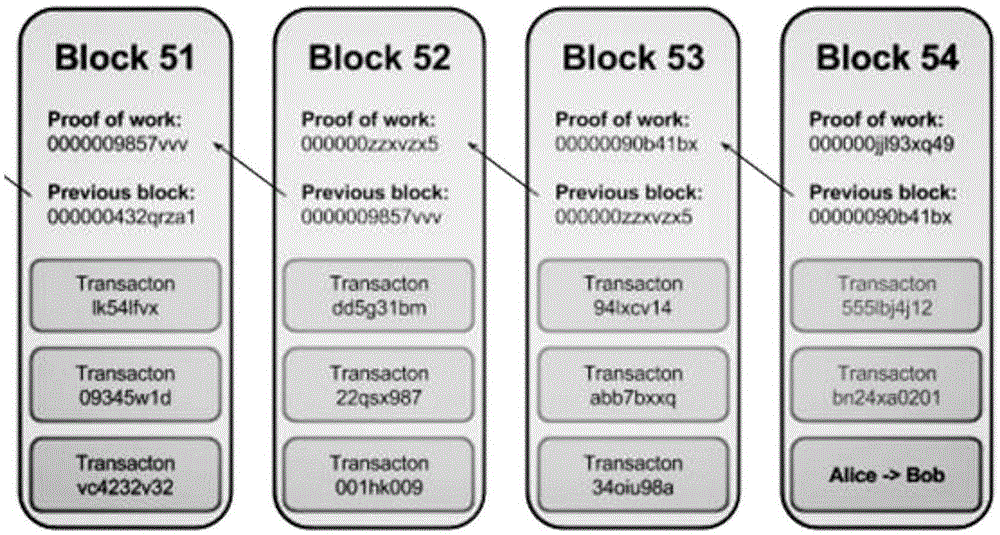
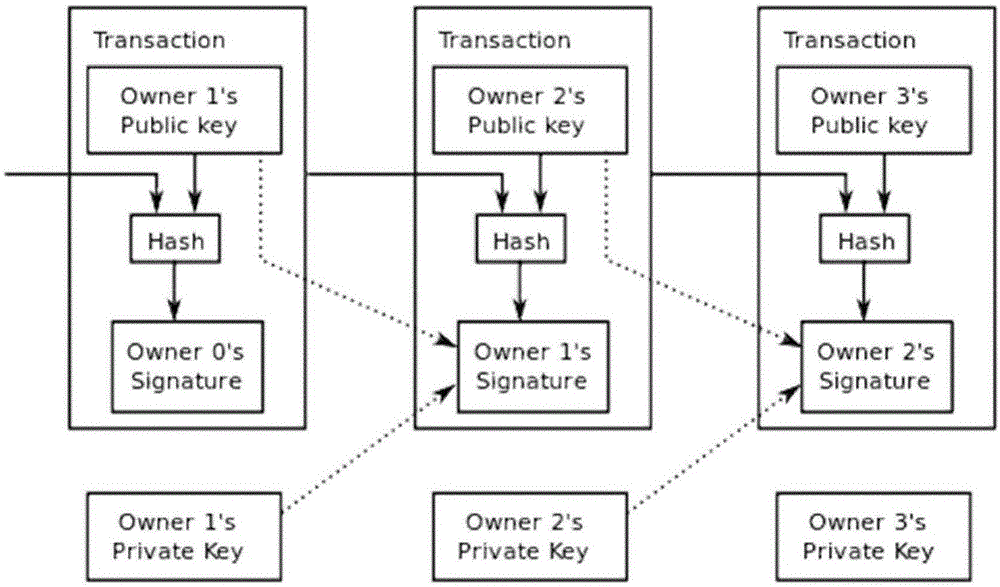
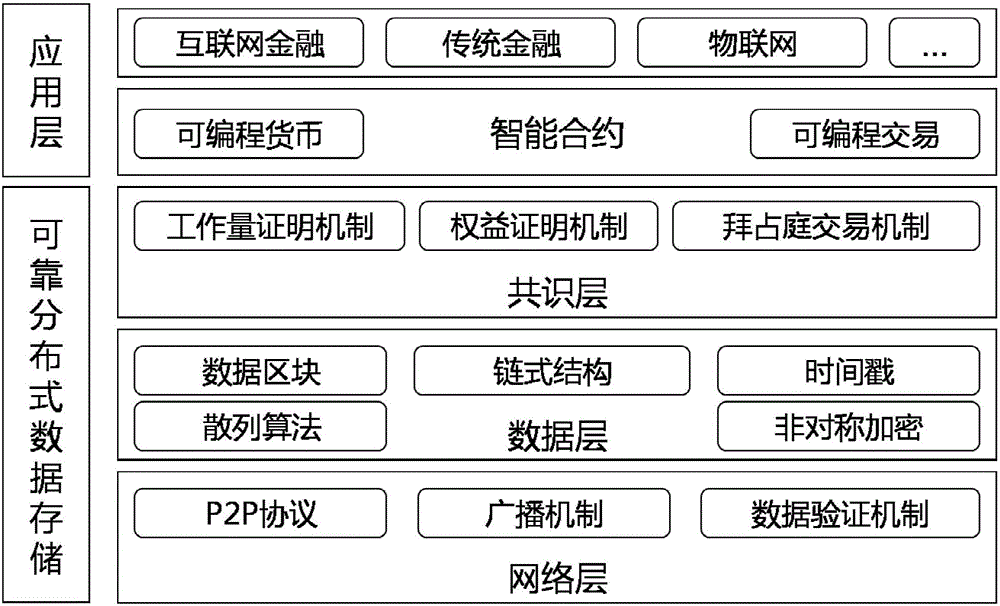
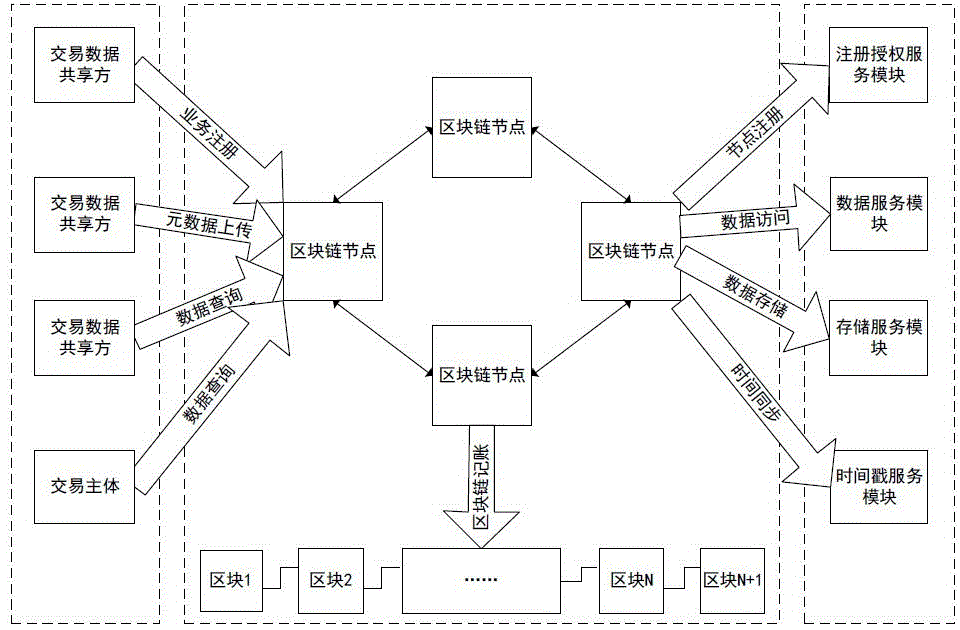
Patents
Literature
4387 results about "Data sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data sharing is the practice of making data used for scholarly research available to other investigators. Replication has a long history in science. The motto of The Royal Society is 'Nullius in verba', translated "Take no man's word for it." Many funding agencies, institutions, and publication venues have policies regarding data sharing because transparency and openness are considered by many to be part of the scientific method.
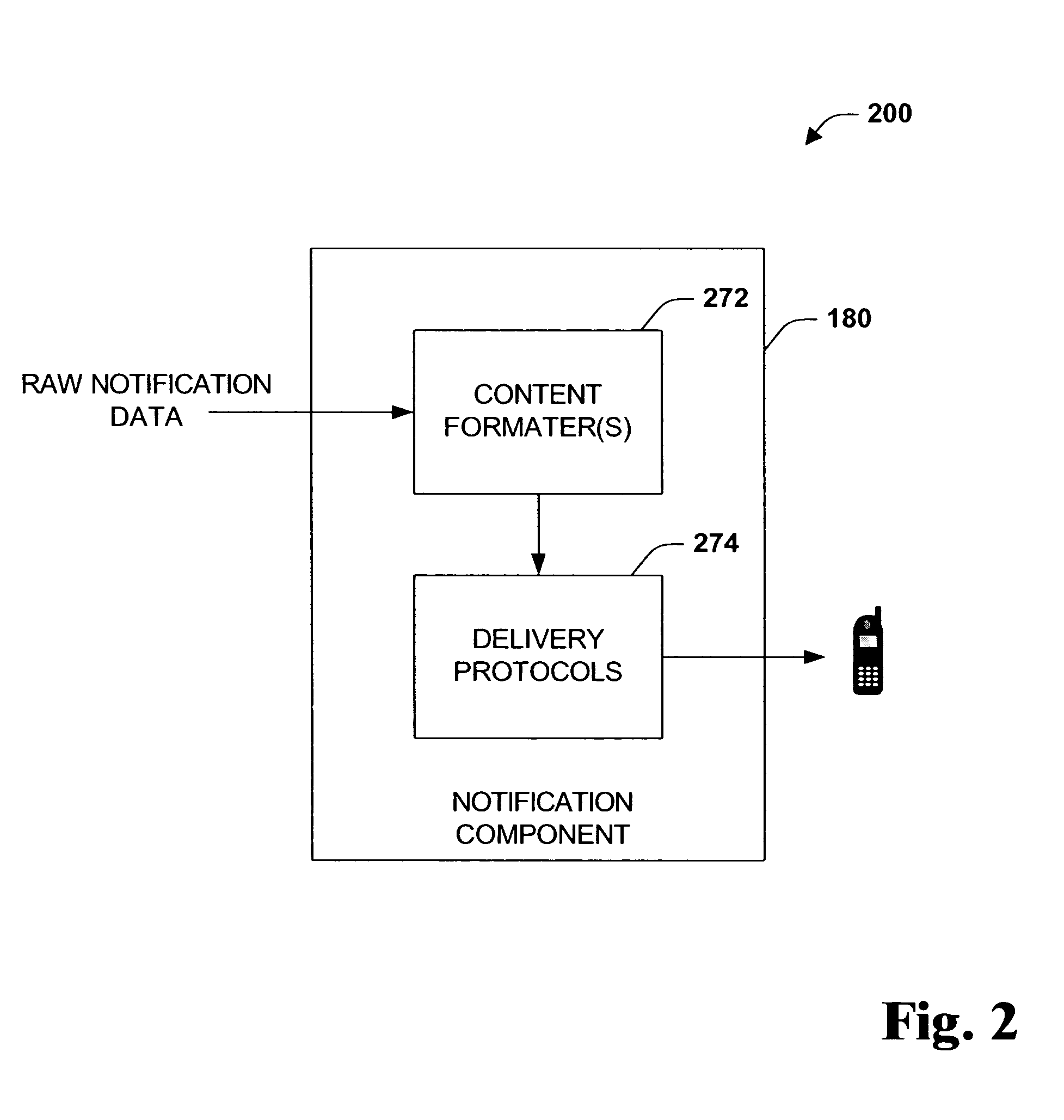
Policy-Based Application Management
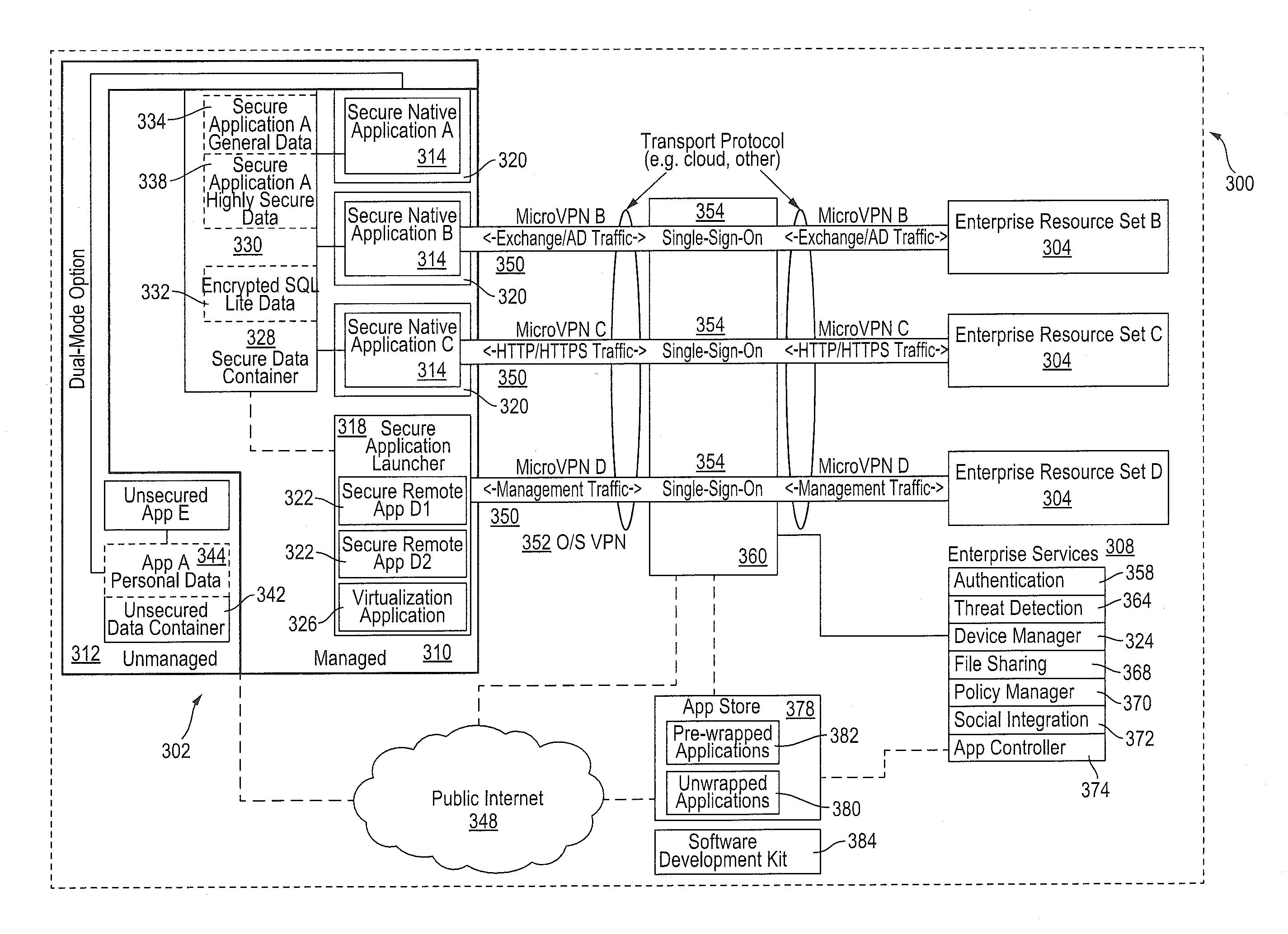
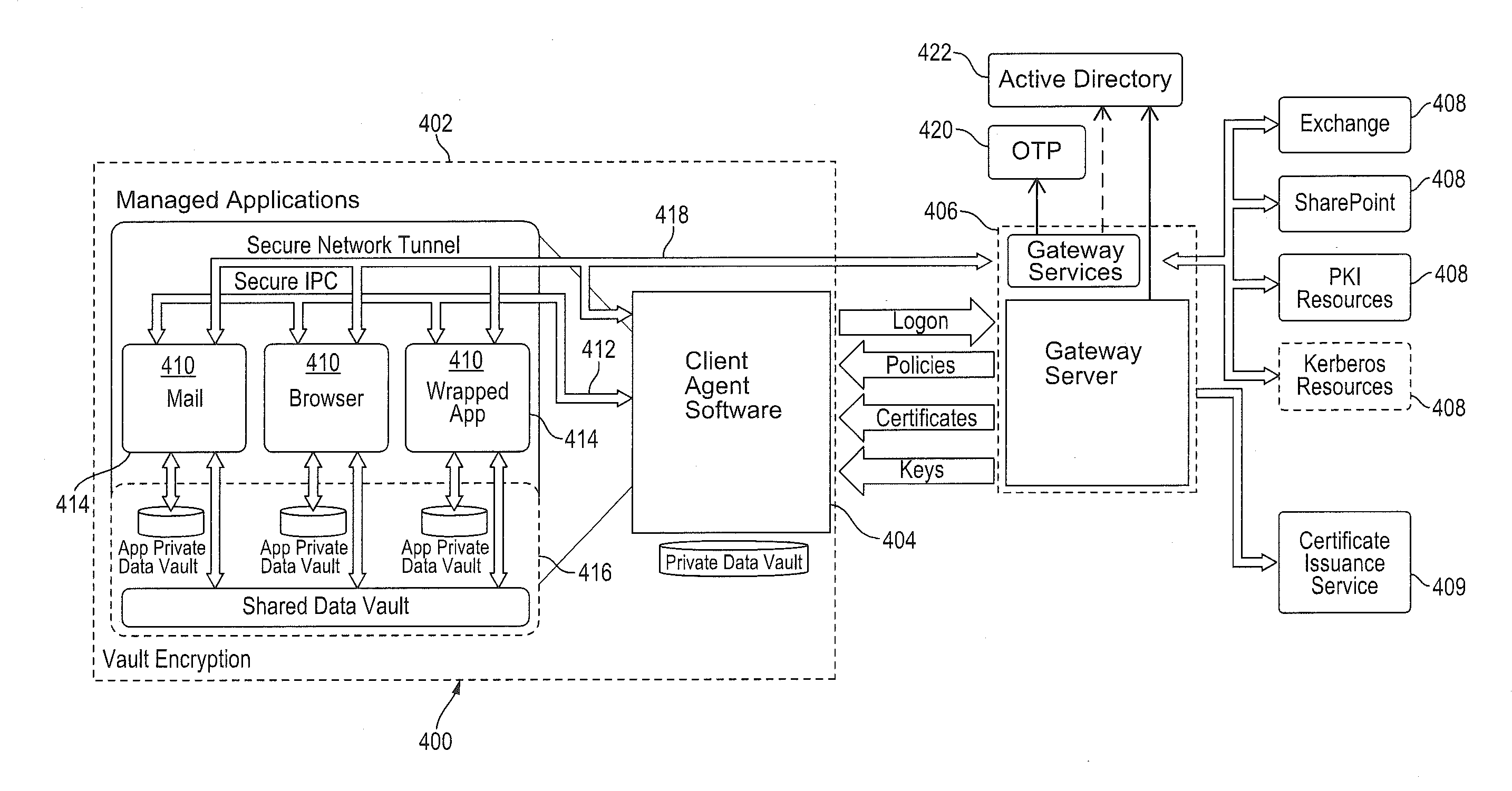
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
Policy-Based Application Management
ActiveUS20140032691A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
Systems and methods for improved data sharing and content transformation
InactiveUS20050234864A1Easy to shareNeed can be fittedDigital data information retrievalDigital data processing detailsThird partyInternet privacy
A user's personal computer can be turned into a personal network server for easily sharing personal digital information with other people using a wide variety of devices. There are a variety of alternative ways in which such file sharing on the user's computer can be implemented, such as with a client-side server approach, a hosted server approach, and an automated publish approach. Depending upon a variety of factors, the requested shared data may be intelligently and dynamically transformed to better fit the requesting party's needs. Programming interfaces are available to third parties that allow for access to the shared data and for providing customized instructions on what to do when transforming the data.
Owner:SHAPIRO AARON M
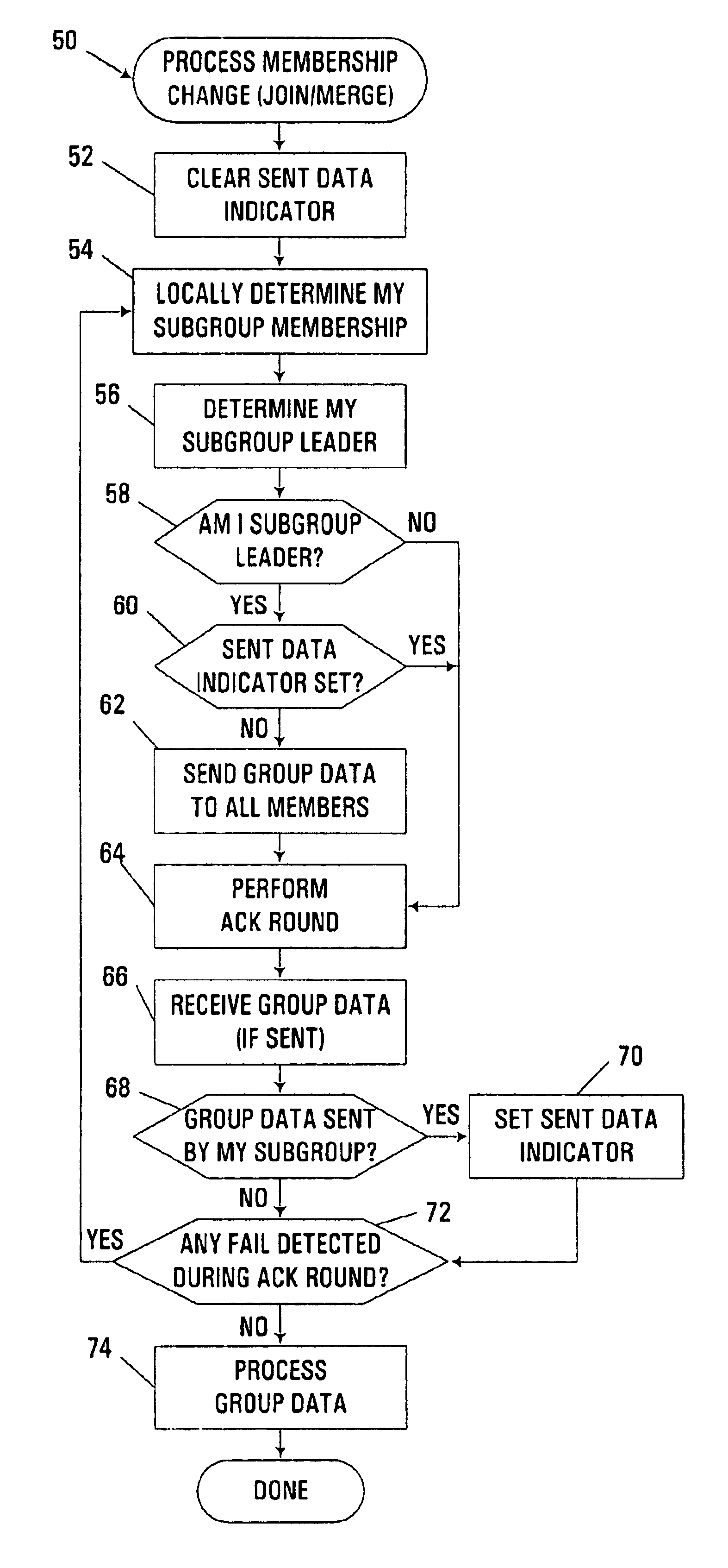
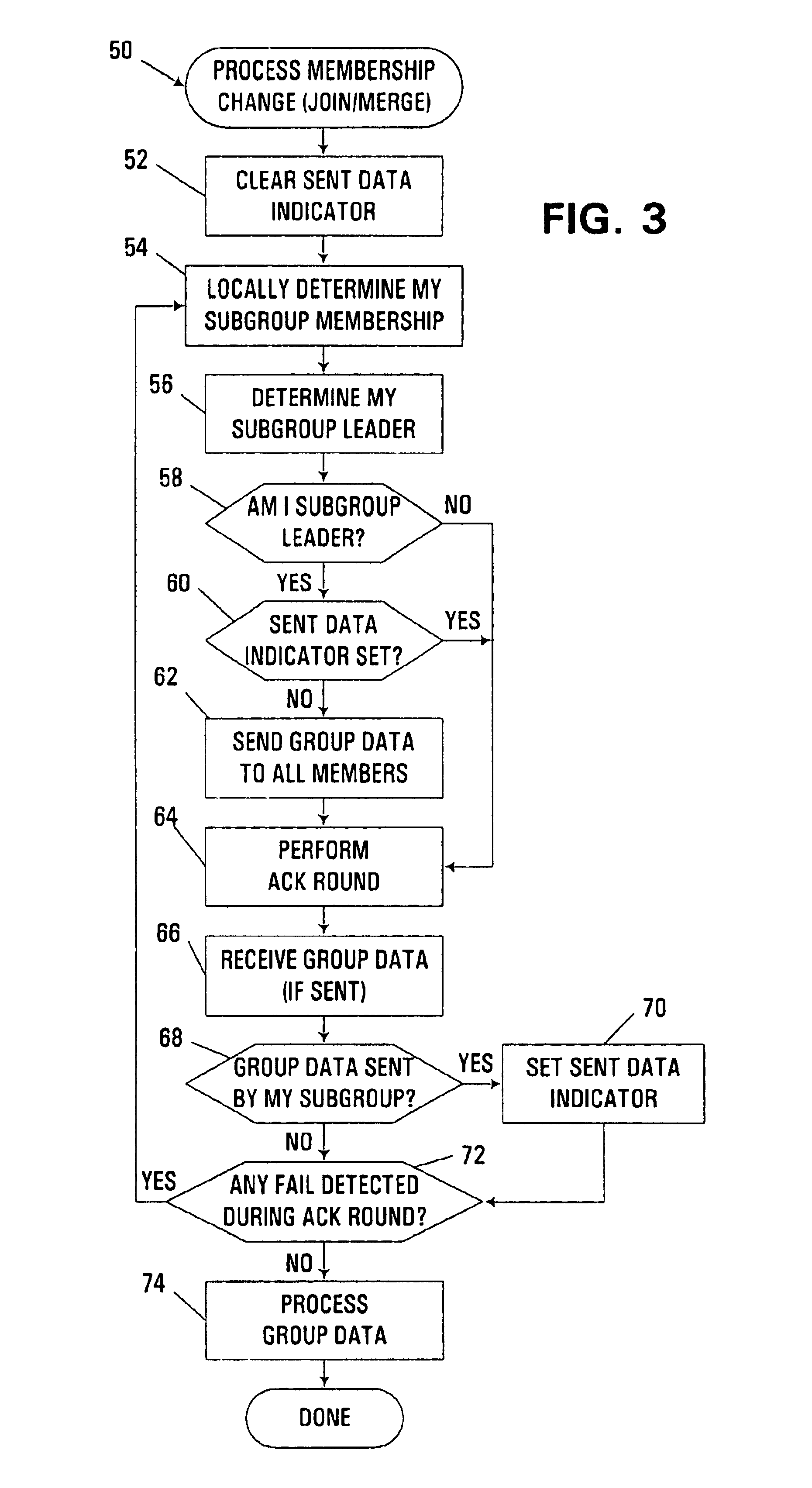
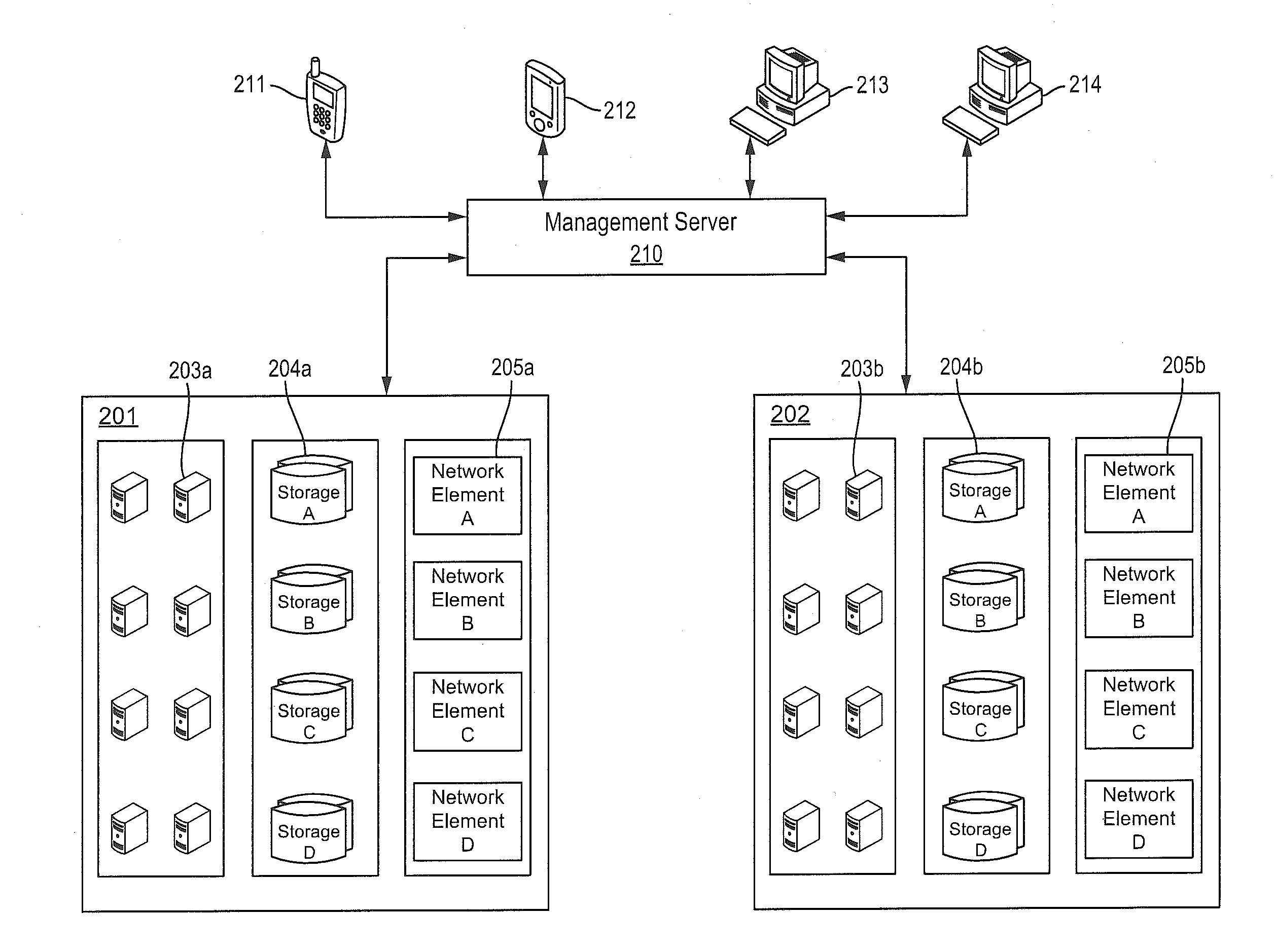
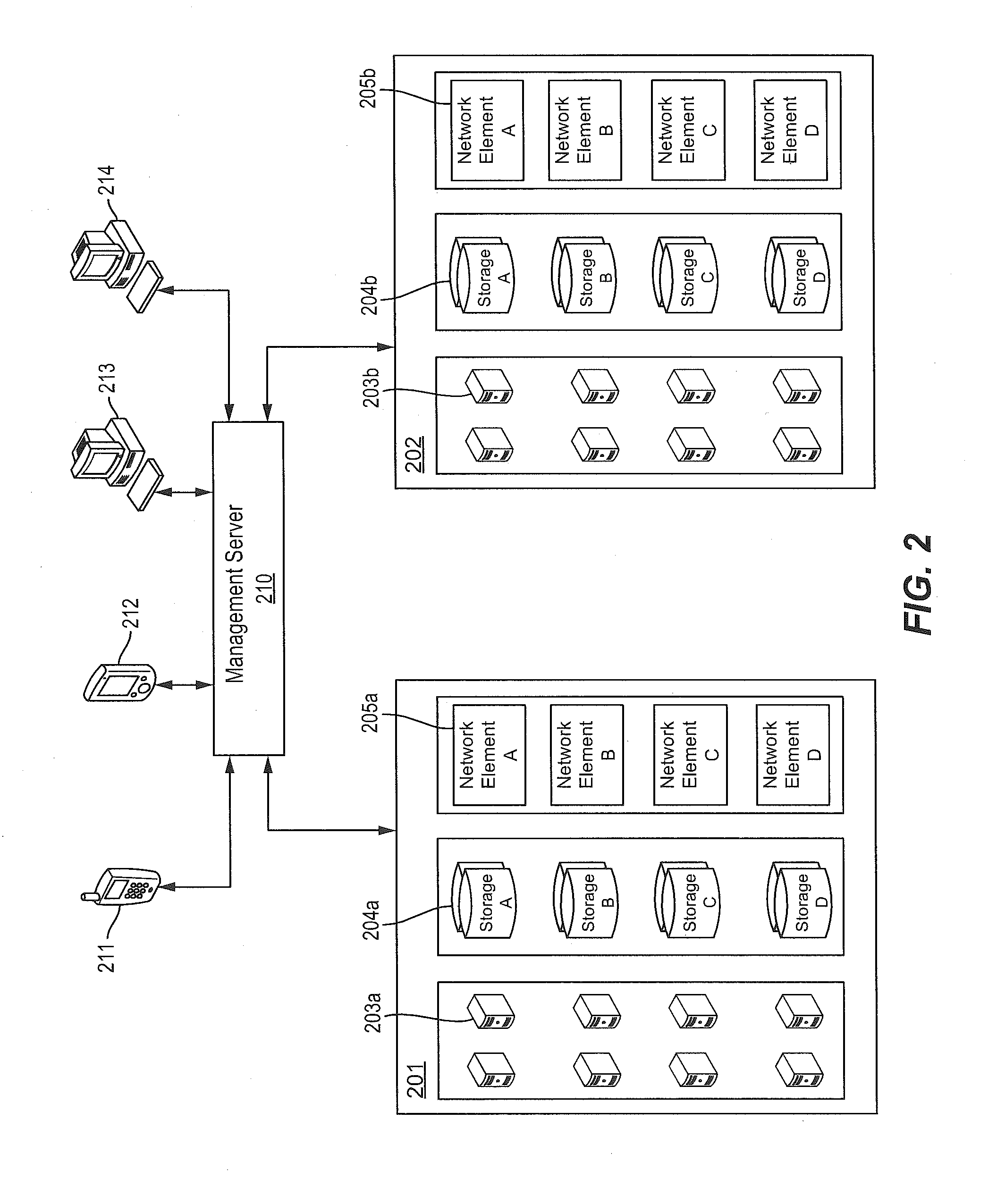
Group data sharing during membership change in clustered computer system
InactiveUS6839752B1Error preventionFrequency-division multiplex detailsComputerized systemData sharing
An apparatus, program product and method utilize subgroup-specific leader members to exchange group data between group members during the handling of a request to organize members into a group in a clustered computer system, e.g., when handling a membership change operation such as a merge or join. Such subgroup leaders may be determined locally within individual subgroup members, and moreover, the subgroup members may locally track the transmission status of group data for the various subgroups. Each subgroup includes one or more members that are known to store group data that is coherent among all subgroup members.
Owner:IBM CORP
Dynamic management of node clusters to enable data sharing
InactiveUS20060074940A1Digital data information retrievalDigital data processing detailsNode clusteringDynamic management
Owner:IBM CORP
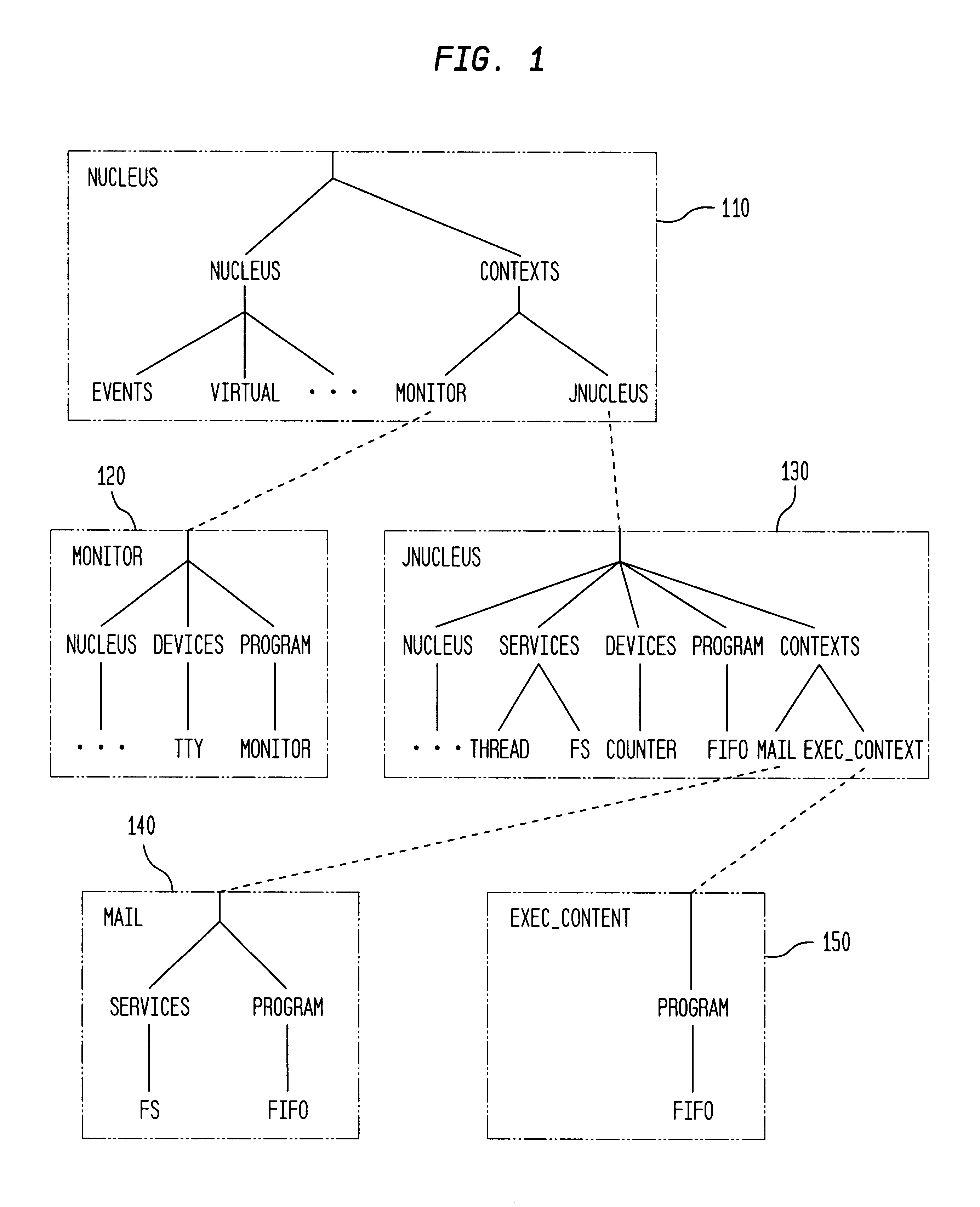
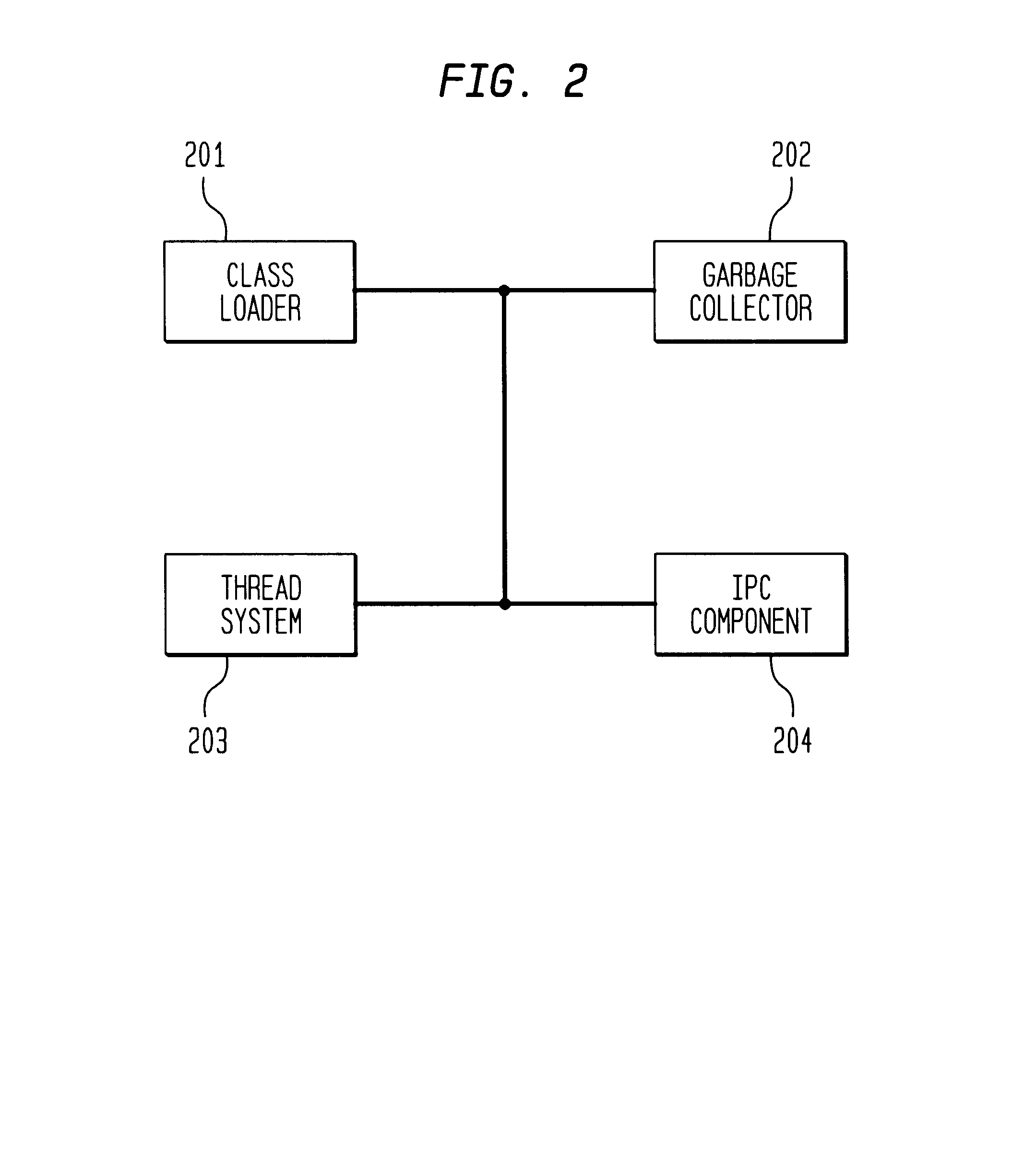
Integrating operating systems and run-time systems
InactiveUS6546546B1Specific access rightsMemory adressing/allocation/relocationOperational systemApplication software
The Virtual Machine is viewed by many as inherently insecure despite all the efforts to improve its security. This invention provides methods, apparatus, and computer products to implement a system that provides operating system style protection for code. Although applicable to many language systems, the invention is described for a system employing the Java language. Hardware protection domains are used to separate Java classes, provide access control on cross domain method invocations, efficient data sharing between protection domains, and memory and CPU resource control. Apart from the performance impact, these security measures are all transparent to the Java programs, even when a subclass is in one domain and its superclass is in another, when they do not violate the policy. To reduce the performance impact, classes are grouped and shared between protection domains and map data lazily as it is being shared. The system has been implemented on top of the Paramecium operating system used as an example of an extensible operating system application.
Owner:IBM CORP
Dynamically integrating disparate systems and providing secure data sharing
InactiveUS20050203892A1Digital data information retrievalDigital data processing detailsTime informationScripting language
Owner:FATPOT TECH
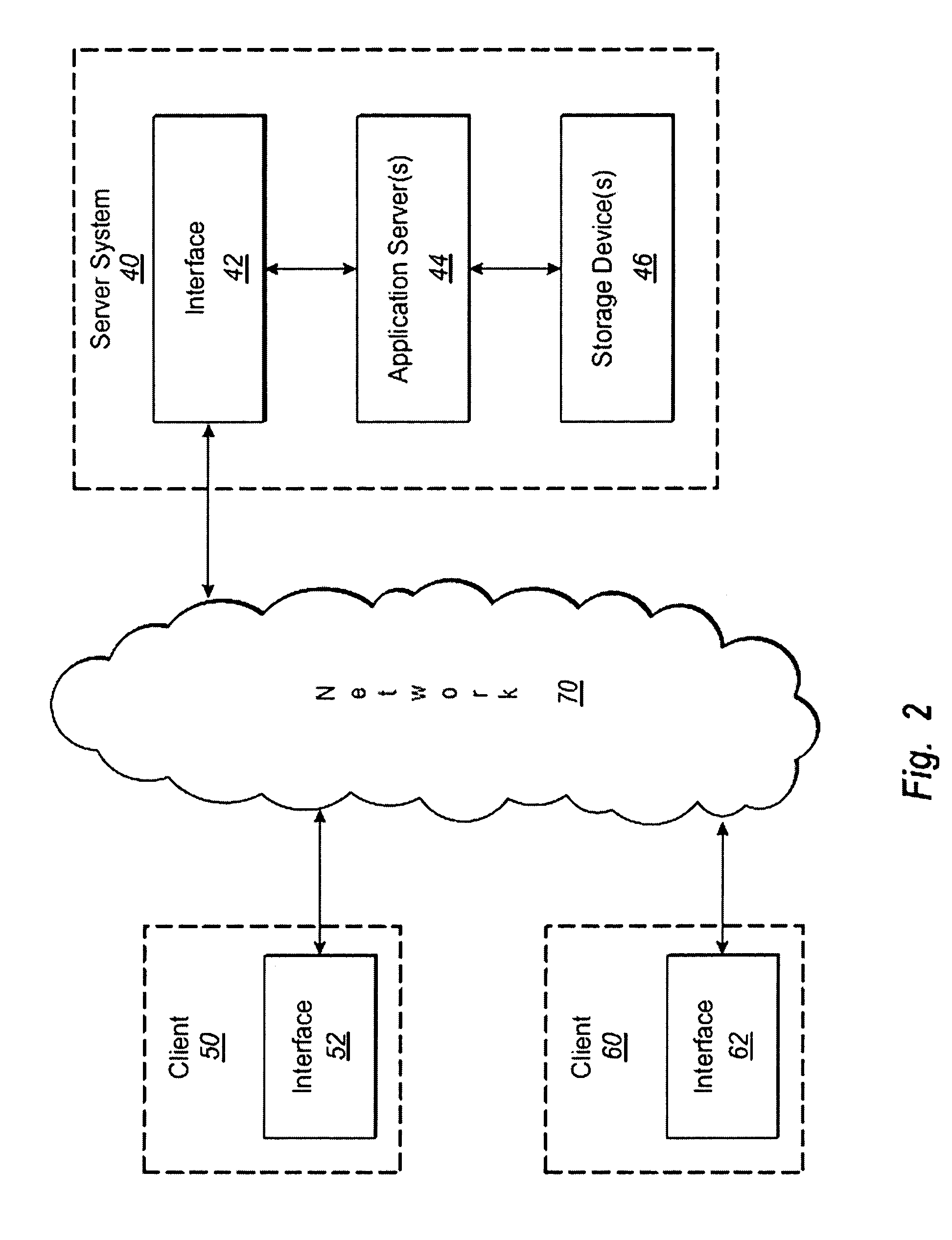
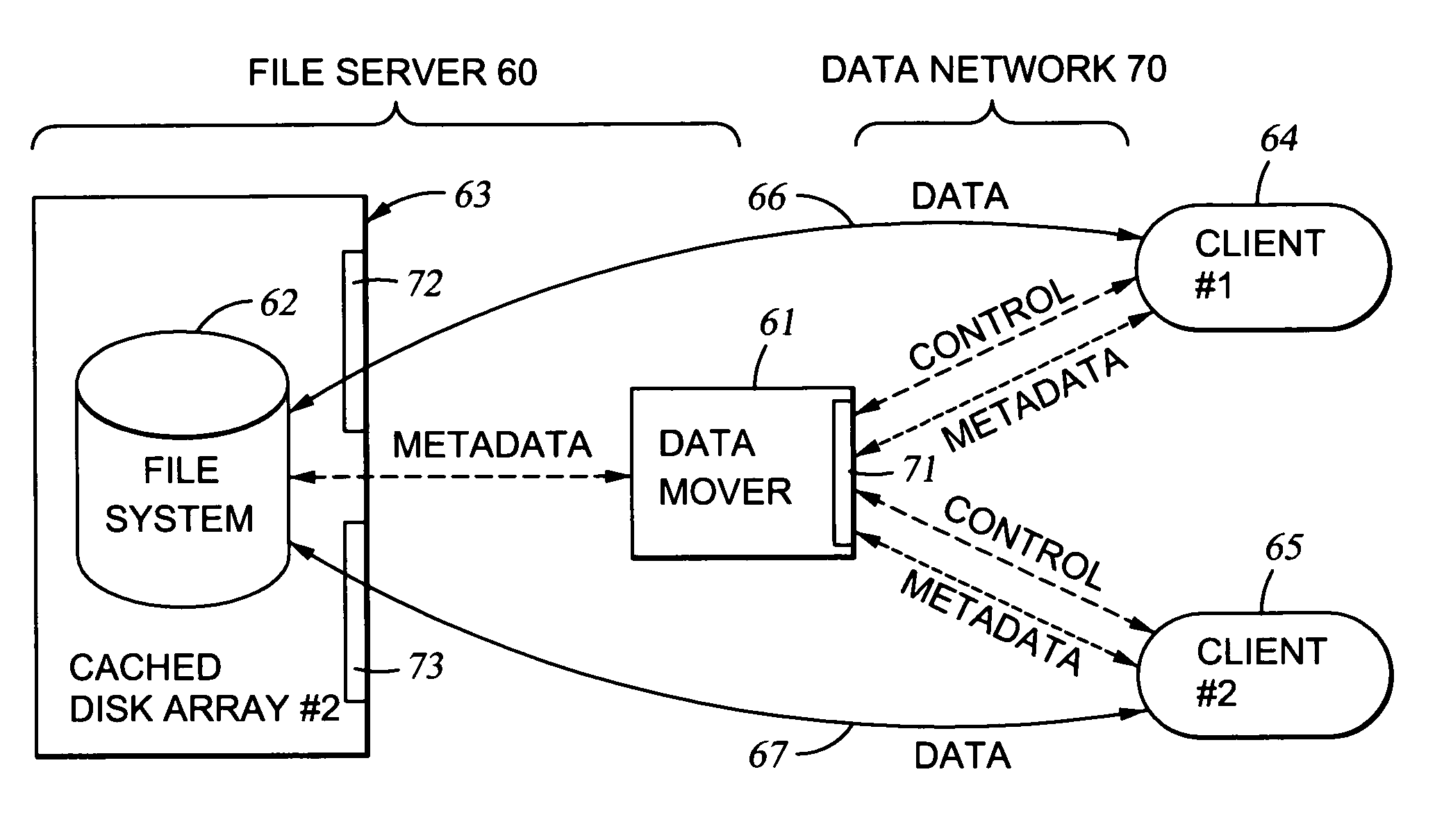
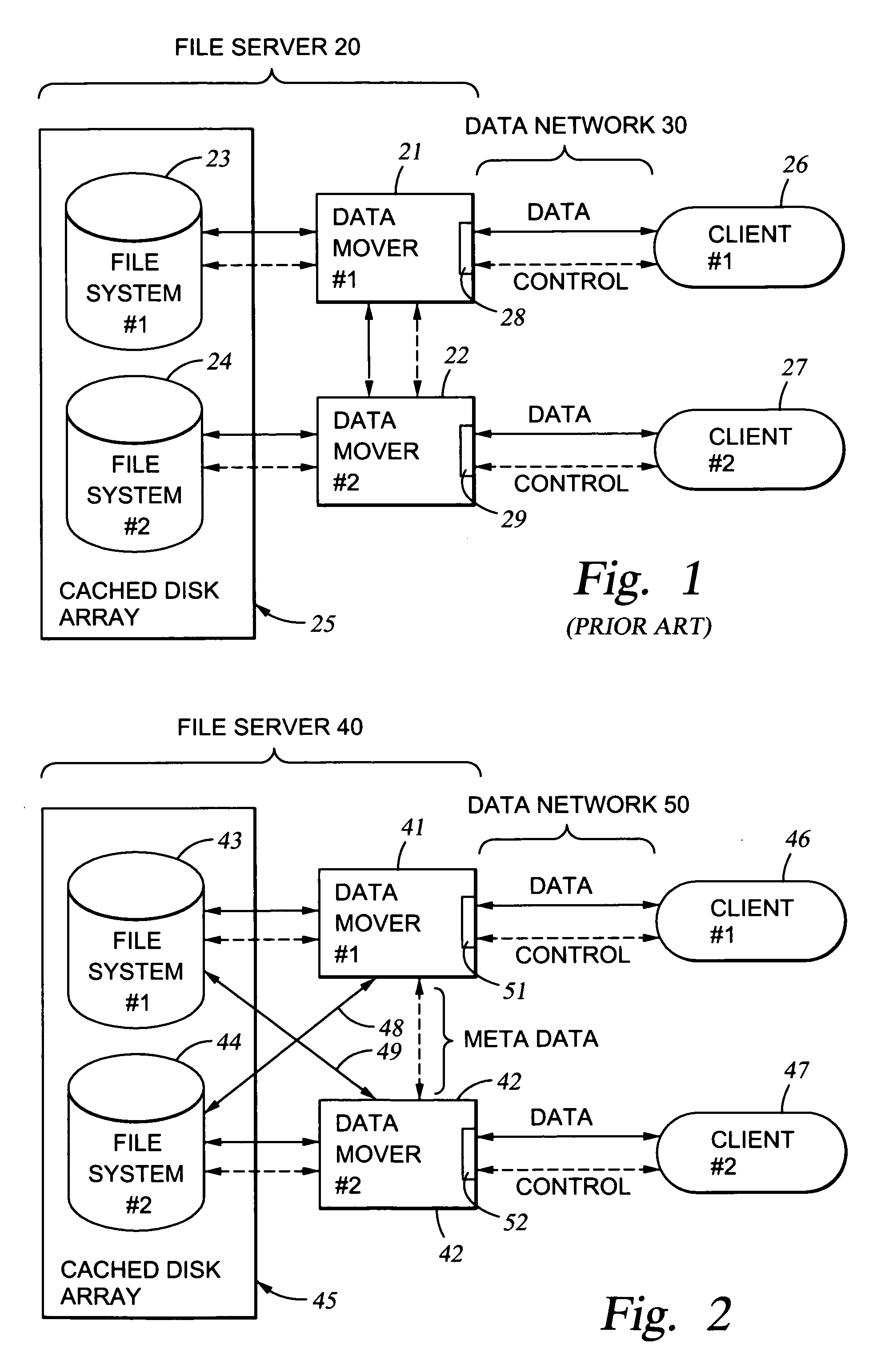
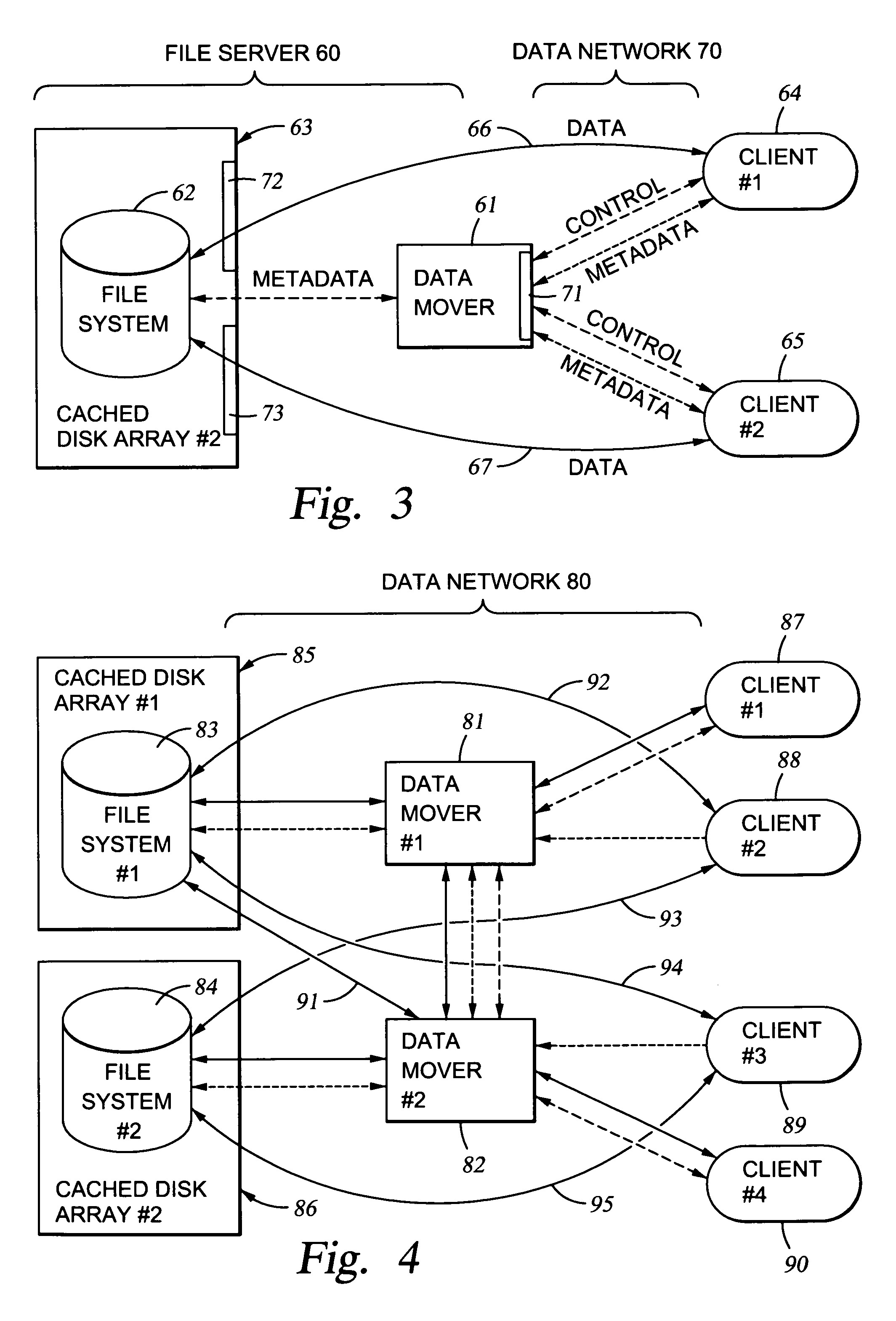
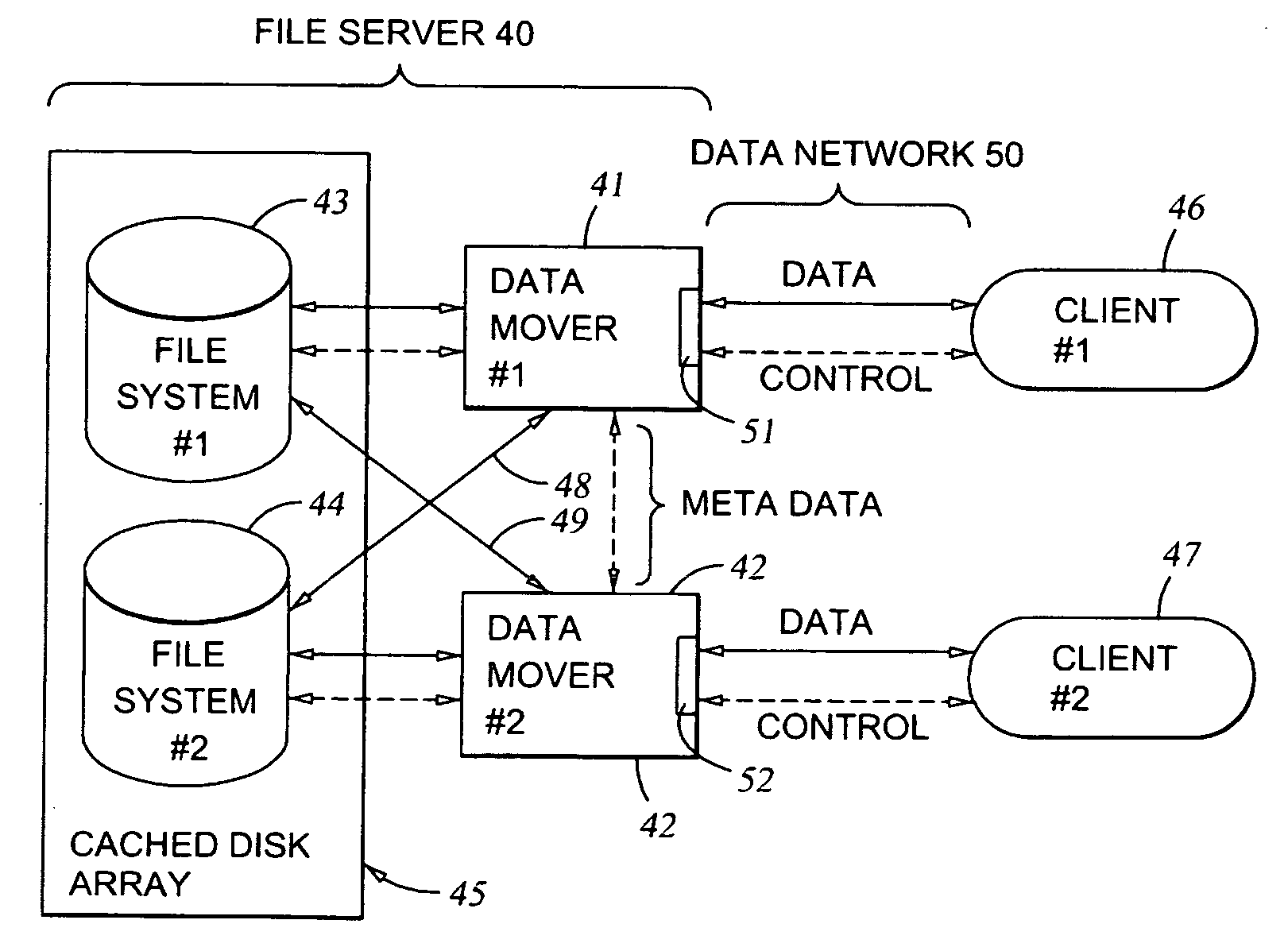
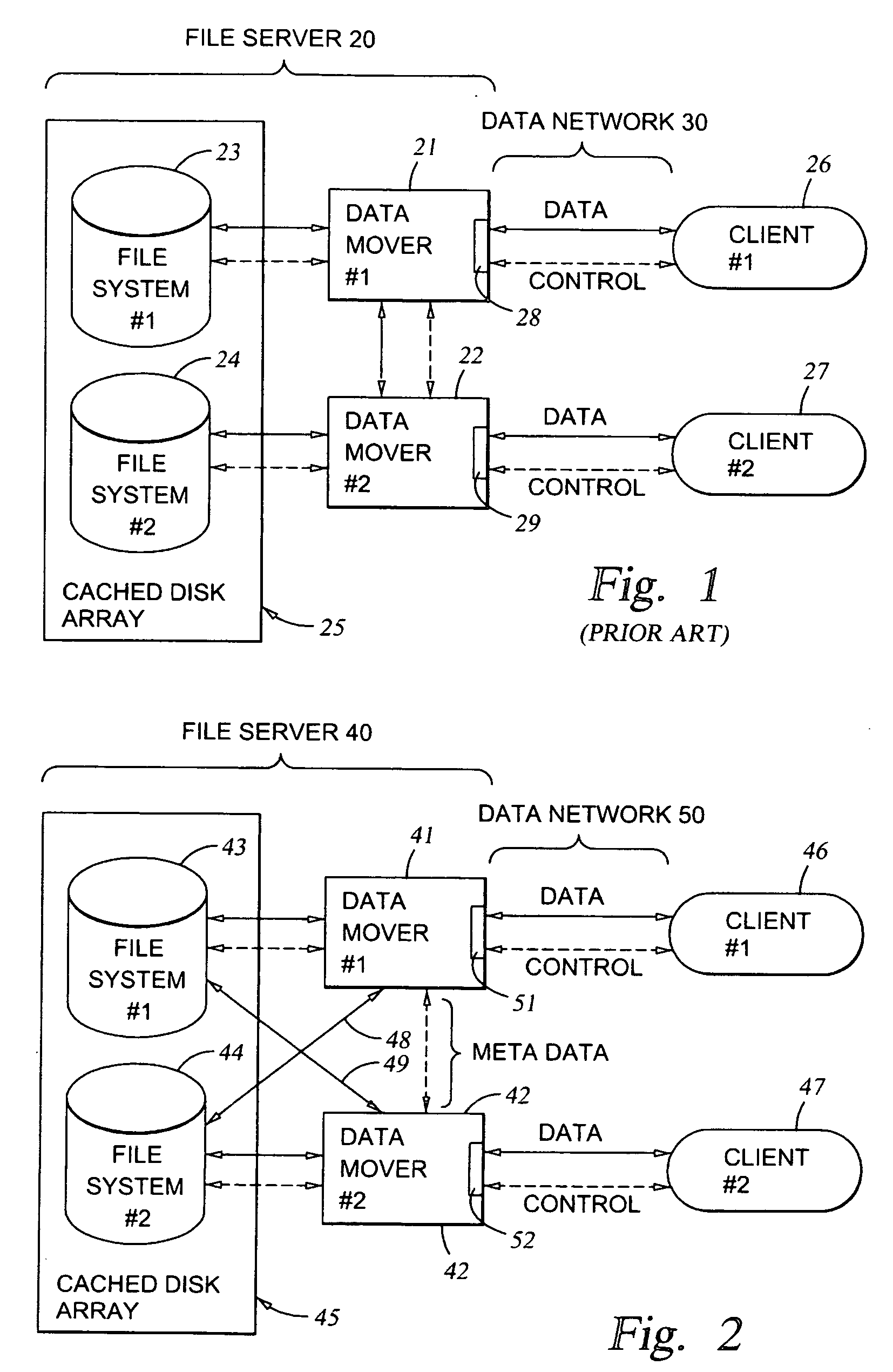
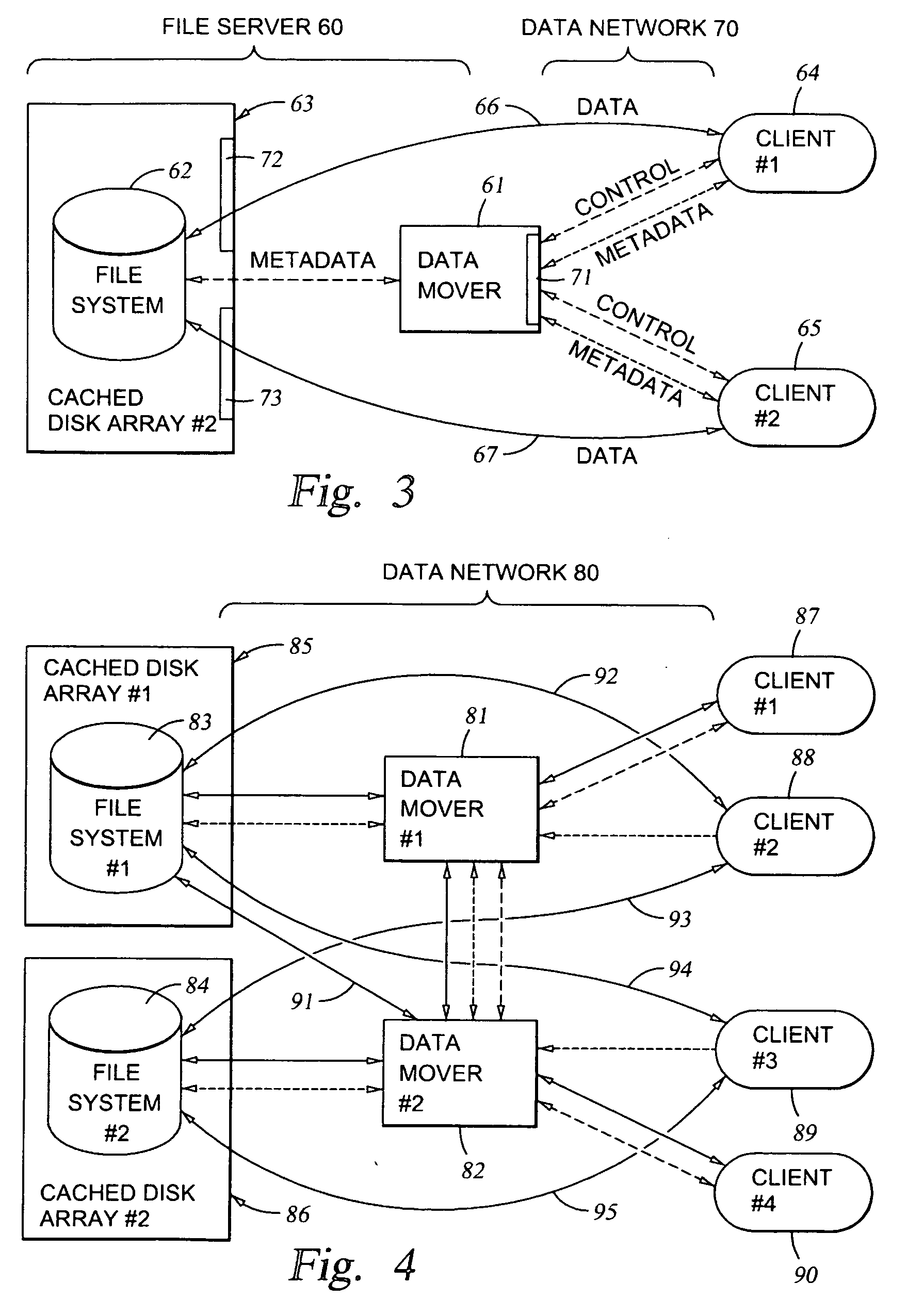
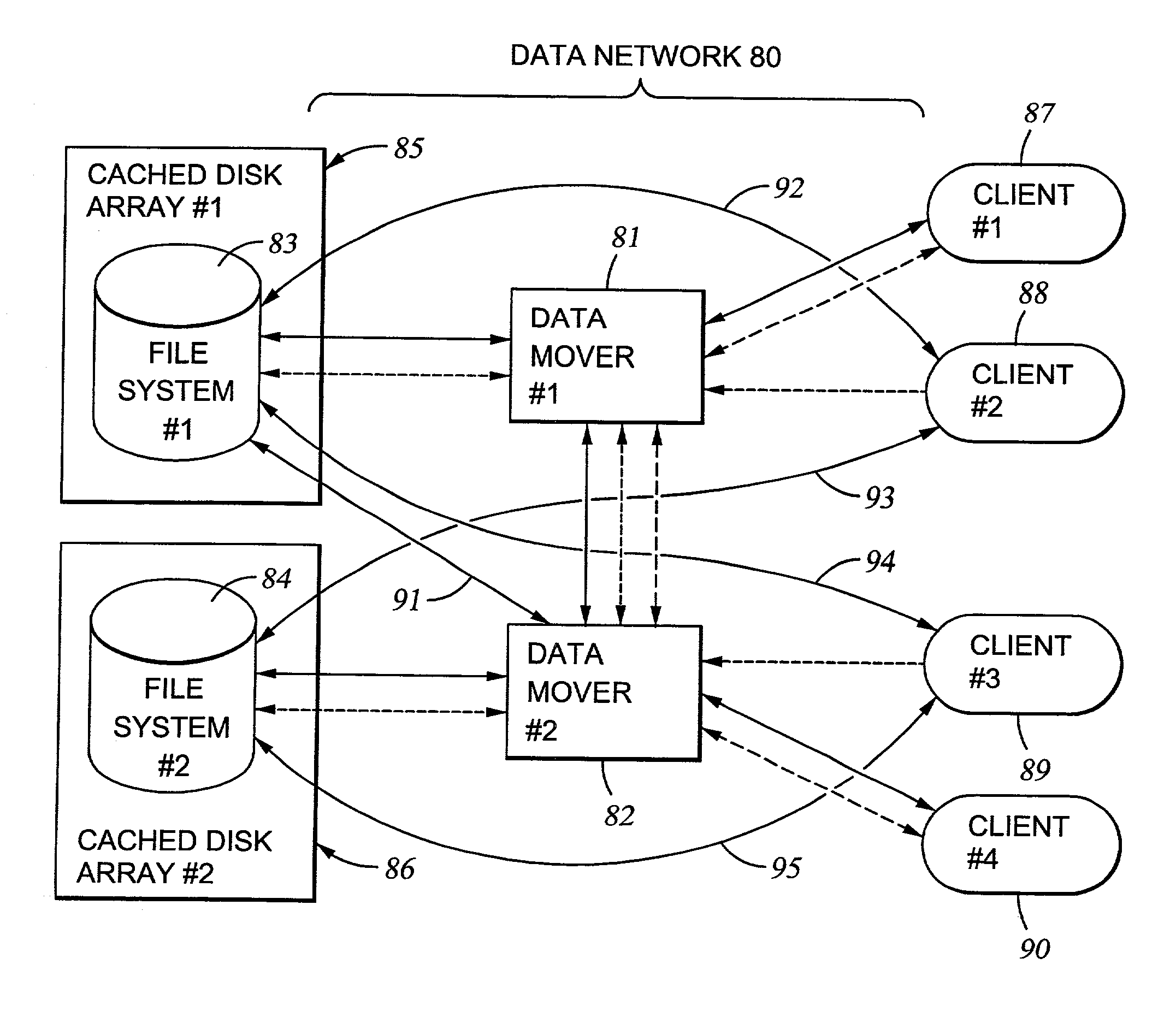
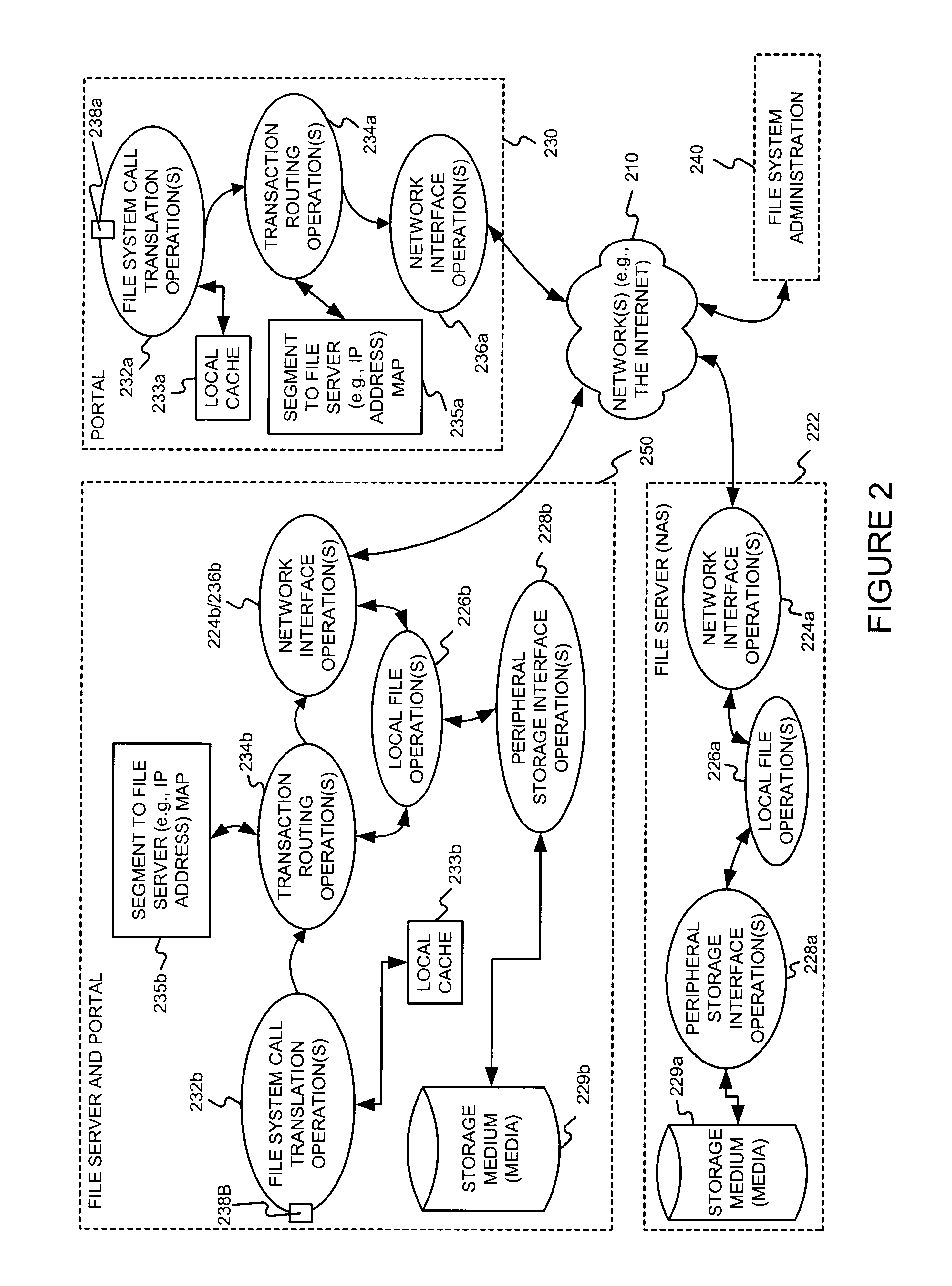
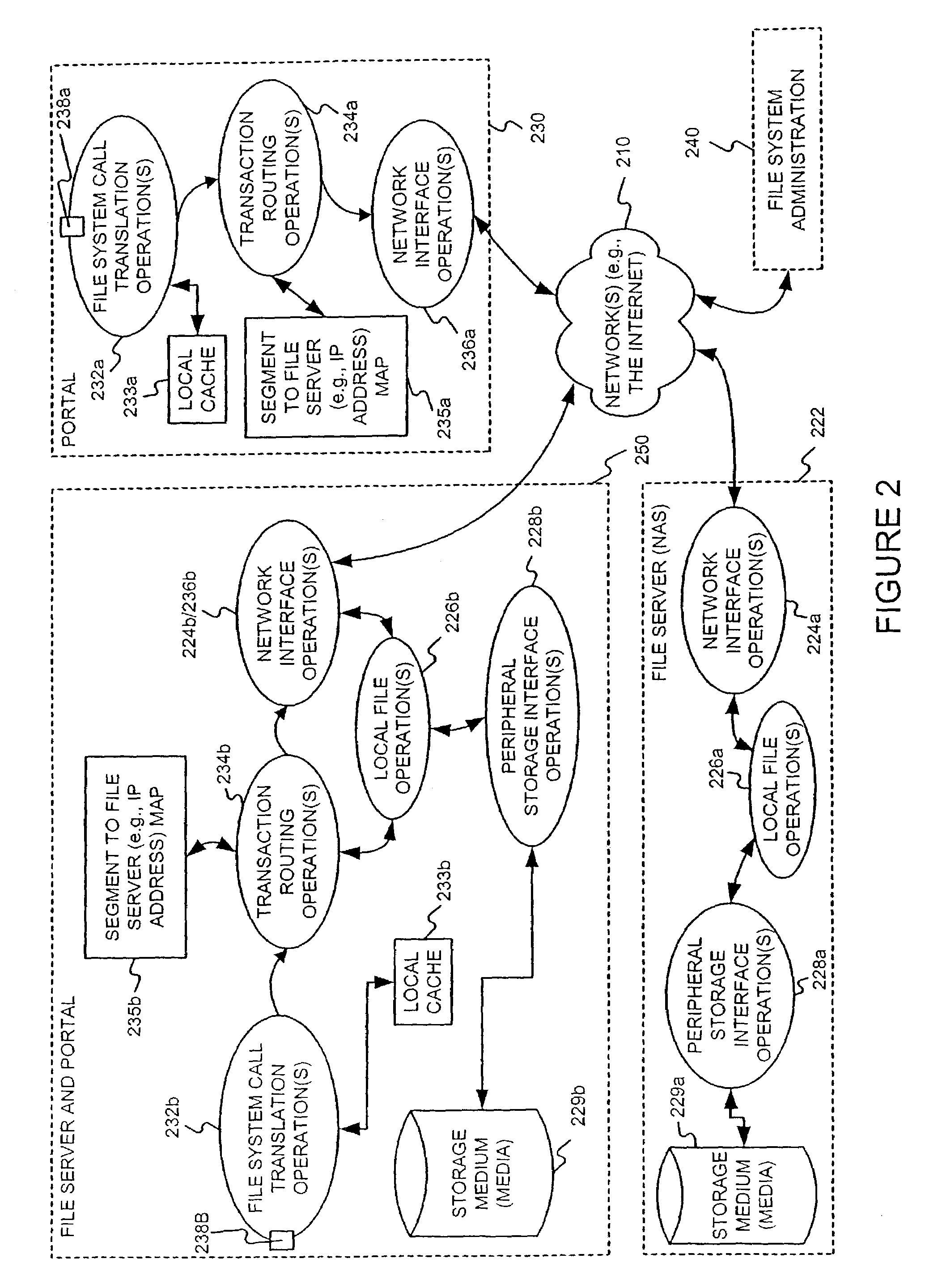
File server system providing direct data sharing between clients with a server acting as an arbiter and coordinator
InactiveUS6973455B1Digital data information retrievalData processing applicationsData accessNetwork data
A client is permitted to send data access commands directly to network data storage of a network file server after obtaining a lock on at least a portion of the file and obtaining metadata indicating storage locations for the data in the data storage. For example, the client sends to the file server at least one request for access to a file. In response, the file server grants a lock to the client, and returns to the client metadata of the file including information specifying data storage locations in the network data storage for storing data of the file. The client receives the metadata, and uses the metadata to produce at least one data access command for accessing the data storage locations in the network storage. The client sends the data access command to the network data storage to read or write data to the file. For a write operation, the client may modify the metadata. When the client is finished writing to the file, the client returns any modified metadata to the file server.
Owner:EMC IP HLDG CO LLC
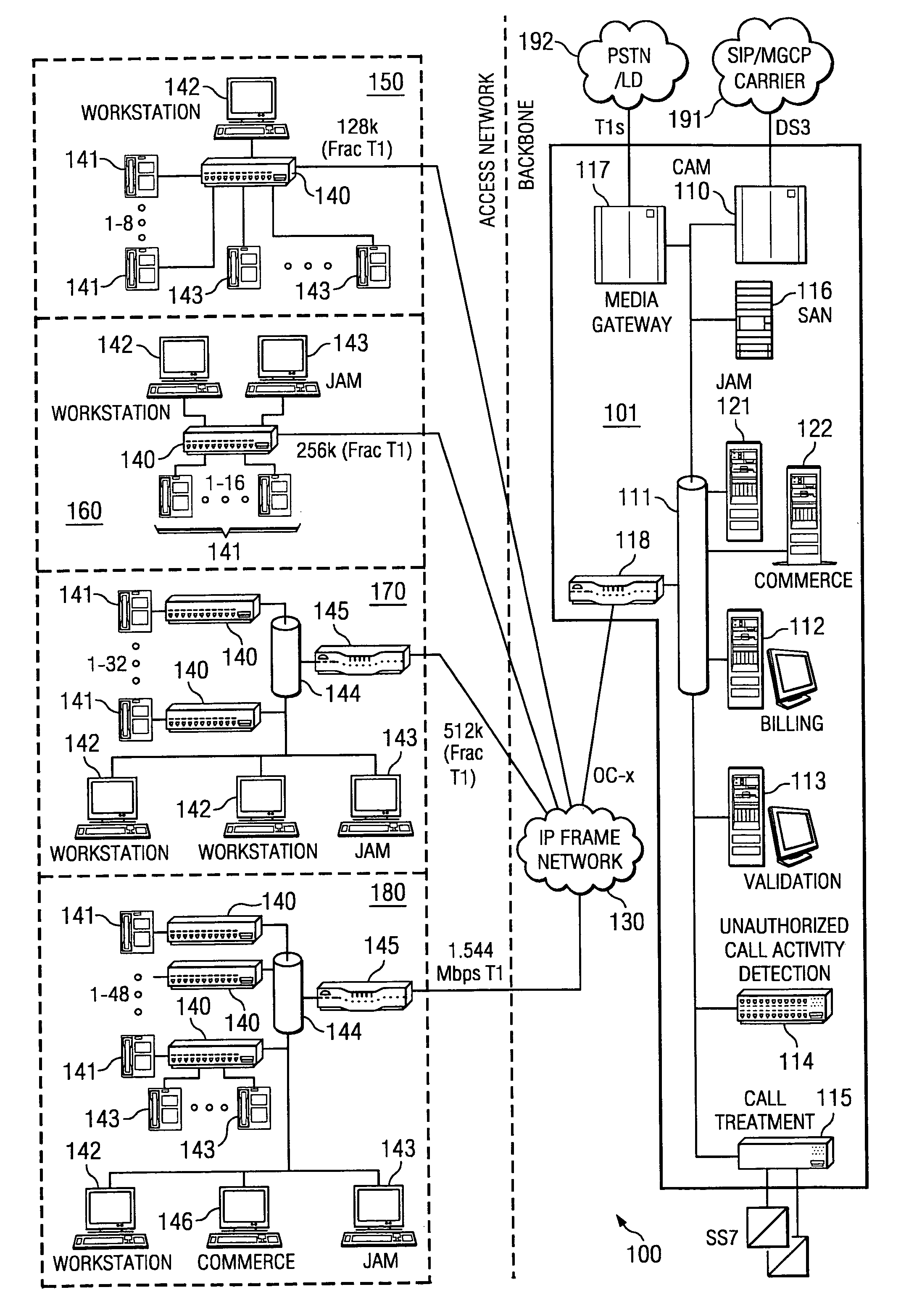
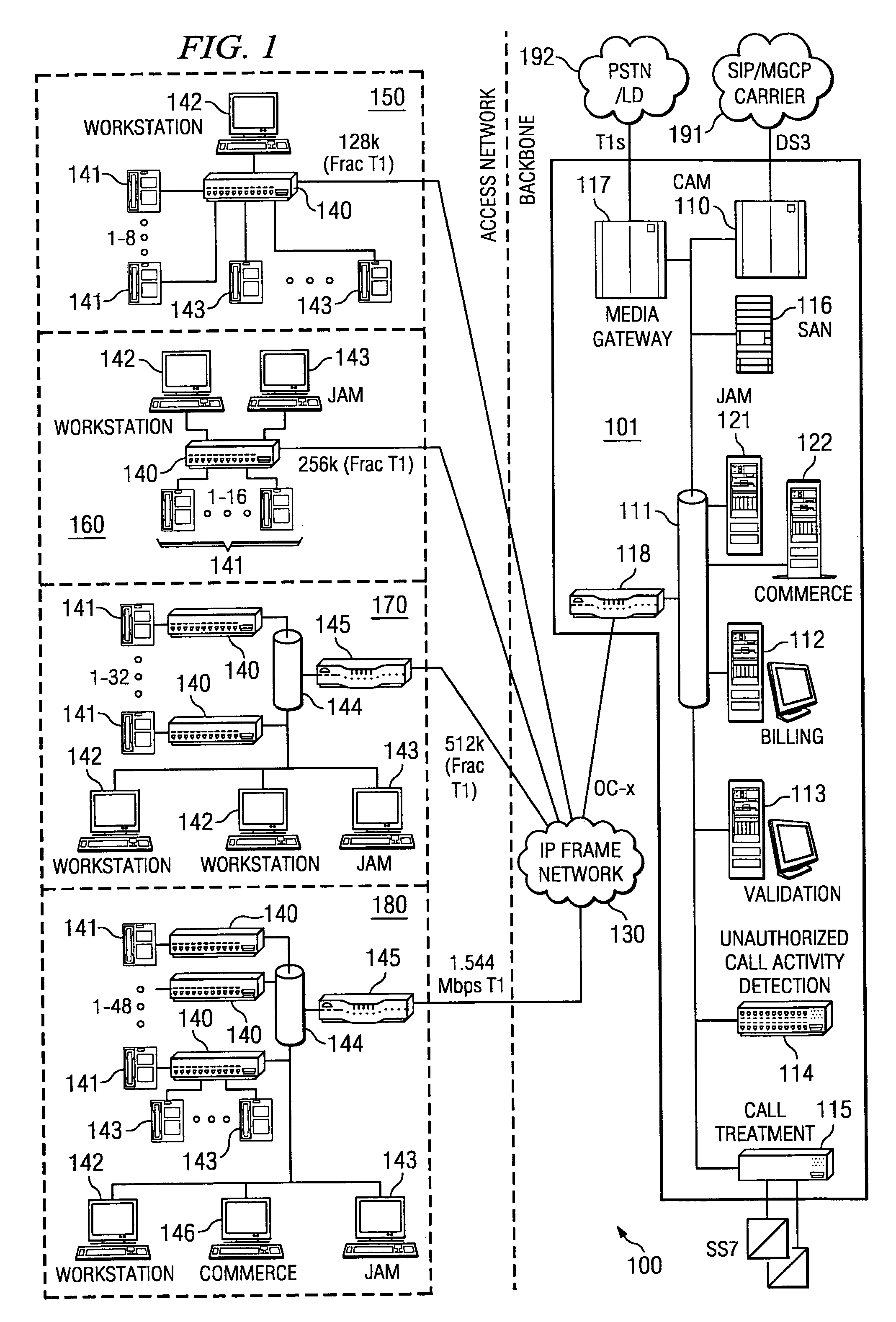
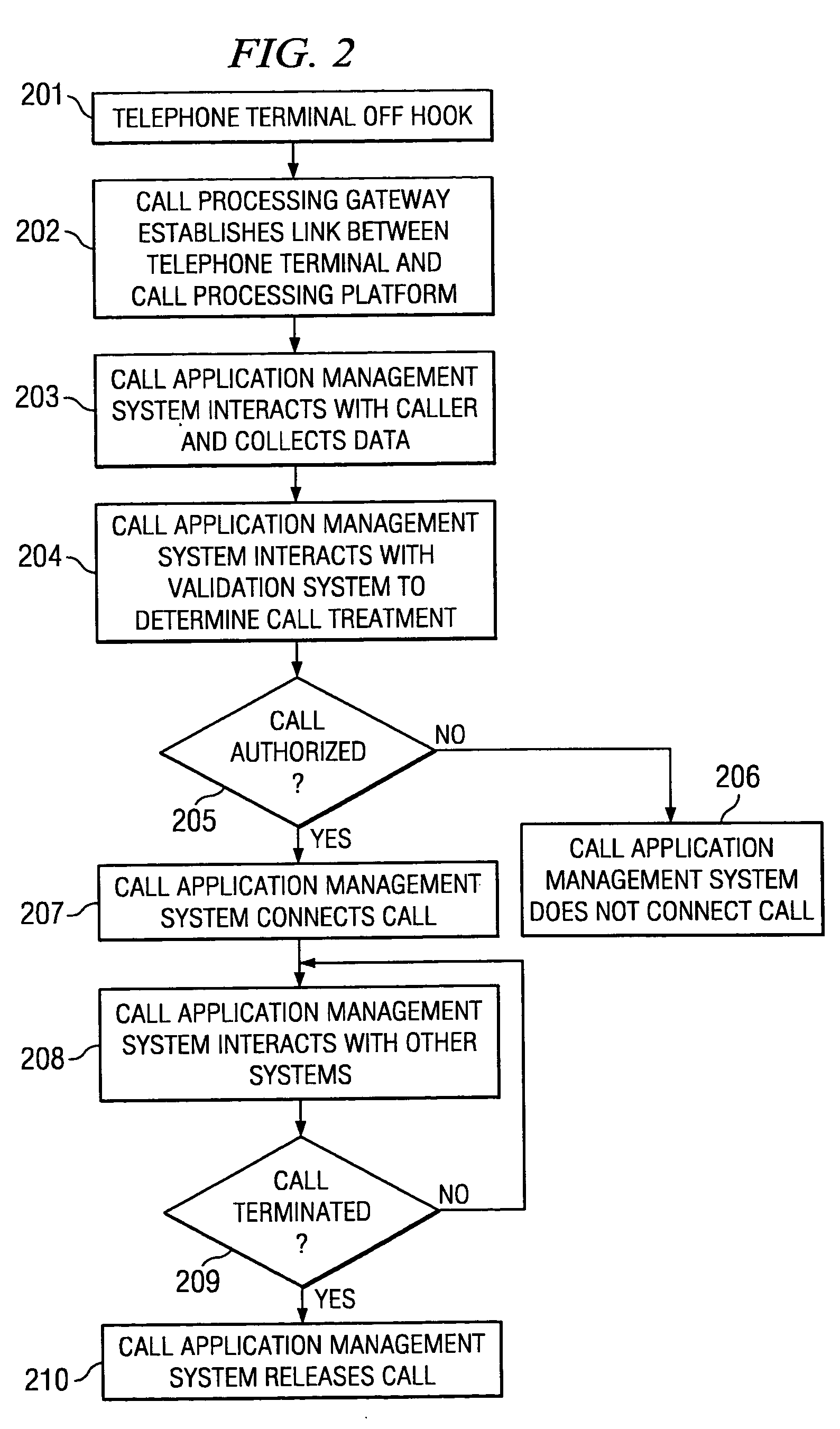
Centralized call processing
InactiveUS7899167B1Reduce data communicationLower connection costsSpecial service provision for substationMultiplex system selection arrangementsData sharingCall routing
Disclosed are systems and methods which provide a centralized architecture for call processing. Embodiments utilize voice over Internet protocols (VoIP) to carry calls from a location at which calling services are provided to a centralized call processing platform providing call processing functionality, such as calling party identification, call validation, call routing, and connection to the public switched telephone network (PSTN). Call processing gateways may be utilized to provide plain old telephone service (POTS) analog line interfaces for use with a plurality of telephone sets disposed for use at a location and at least one wide area network (WAN) interface for providing high speed data communication to a centralized call processing platform. PSTN interfacing by a call processing platform may be provided as a VoIP connection to the PSTN and / or as POTS trunking. Call processing platforms may provide for data sharing, aggregation, and / or analysis across multiple facilities served.
Owner:SECURUS TECH LLC
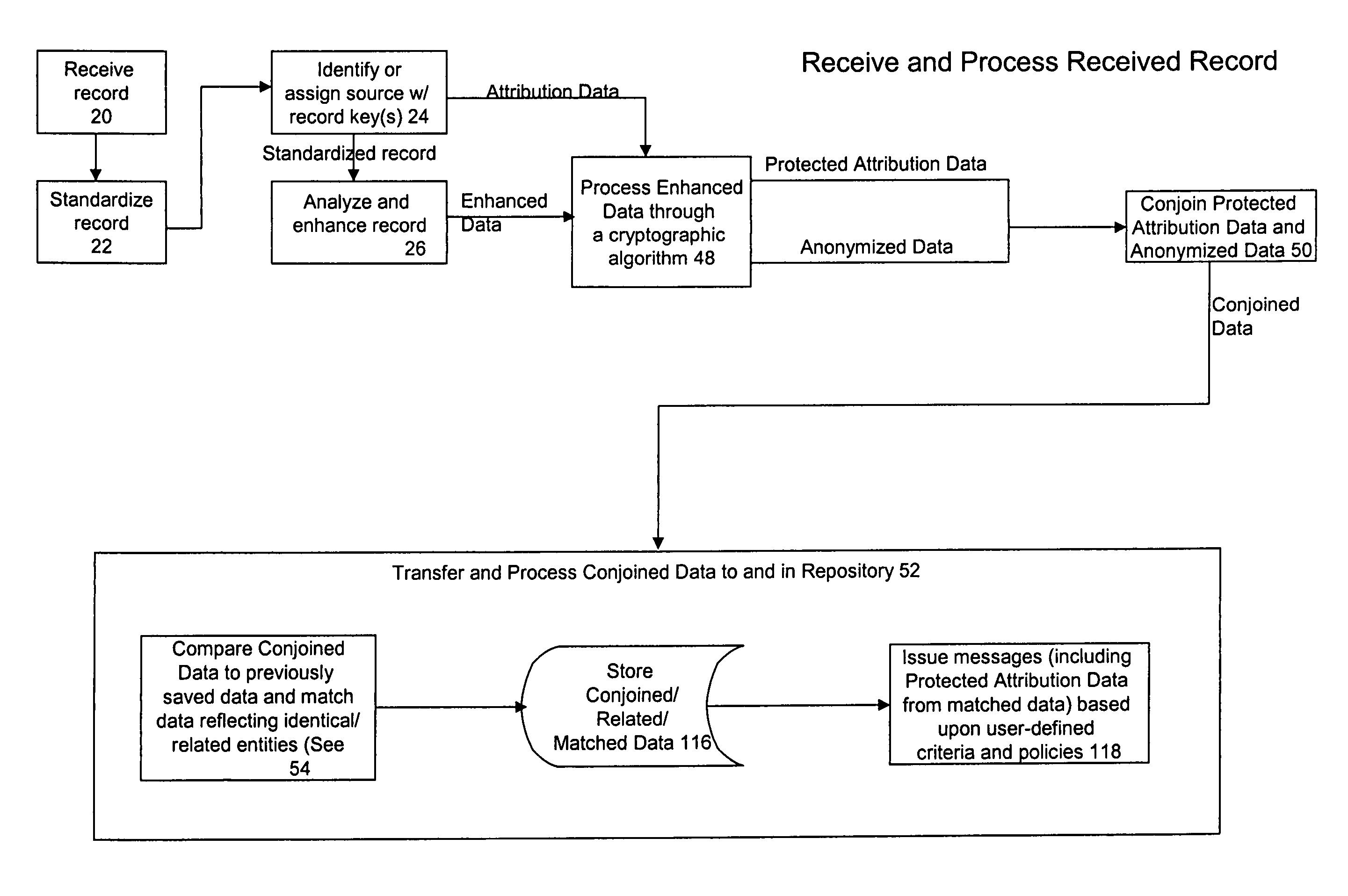
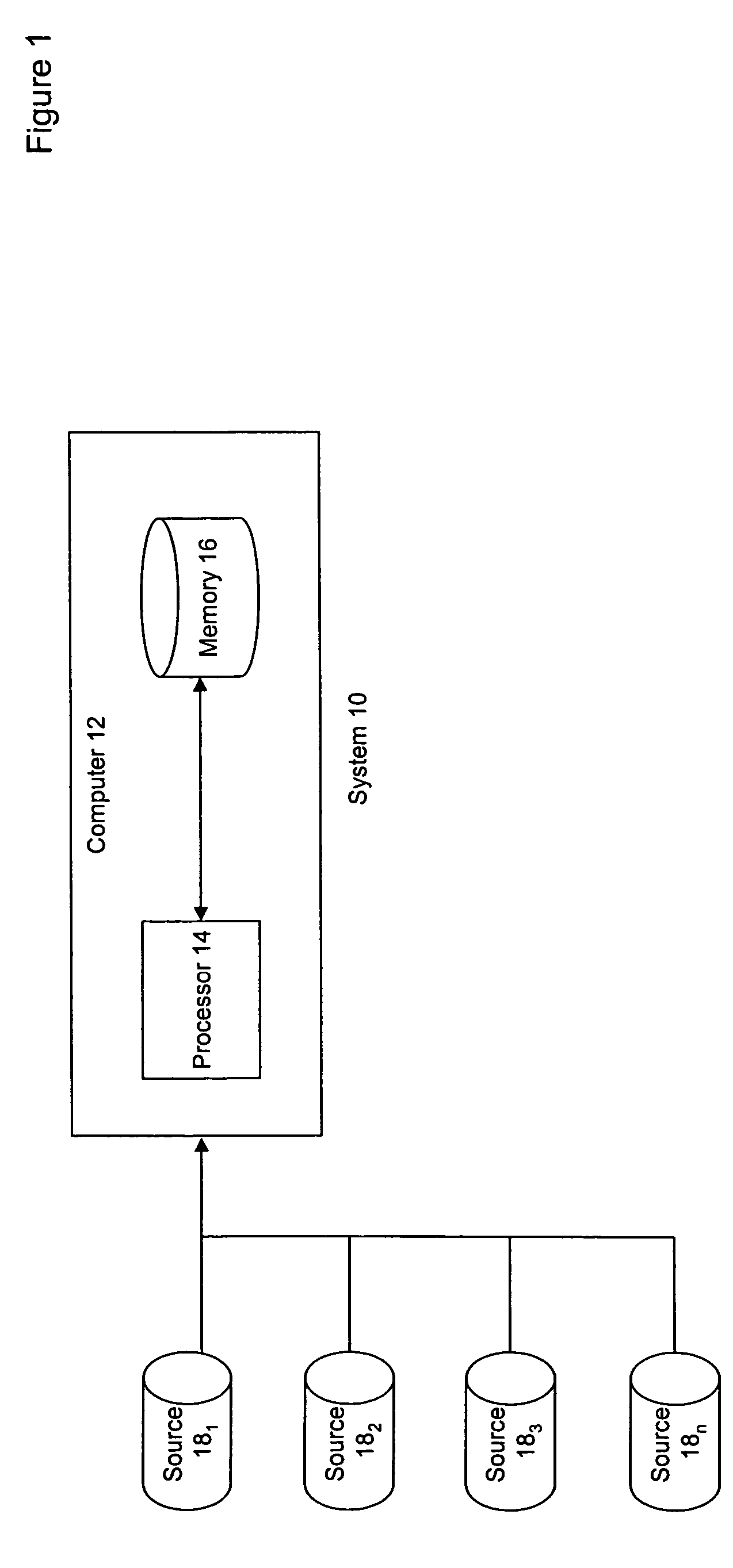
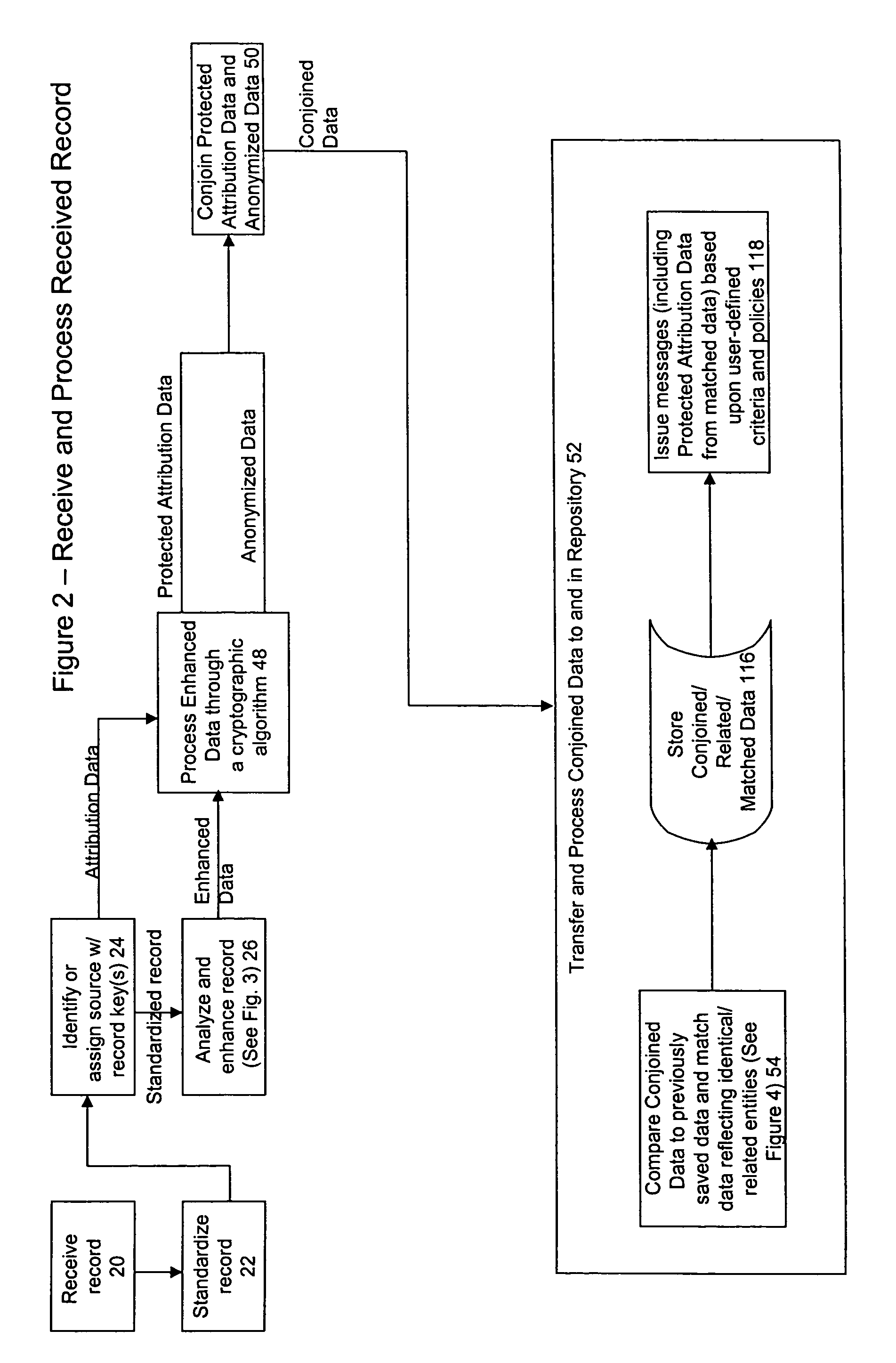
Confidential data sharing and anonymous entity resolution
ActiveUS7900052B2Easy to recordDigital data information retrievalDigital data processing detailsComputer hardwareData sharing
A method, program and system for processing data is disclosed. The data comprises identifiers of a plurality of entities. The method, program and system comprising the steps of: (a) receiving one or more records, each record having a plurality of identifiers, each record corresponding with at least one entity, (b) utilizing a cryptographic algorithm to process at least two of the plurality of identifiers in the record, (c) sometimes after transmitting the processed record to a separate system or database, comparing the processed record to previously stored data; (d) matching the processed record with previously stored data that is determined to reflect the entity, the previously stored data that is determined to reflect the entity comprising at least a portion of at least two previously received records and / or based upon another identifier; and / or (e) associating the processed record with previously stored data that is determined to reflect a relationship with the entity.
Owner:IBM CORP
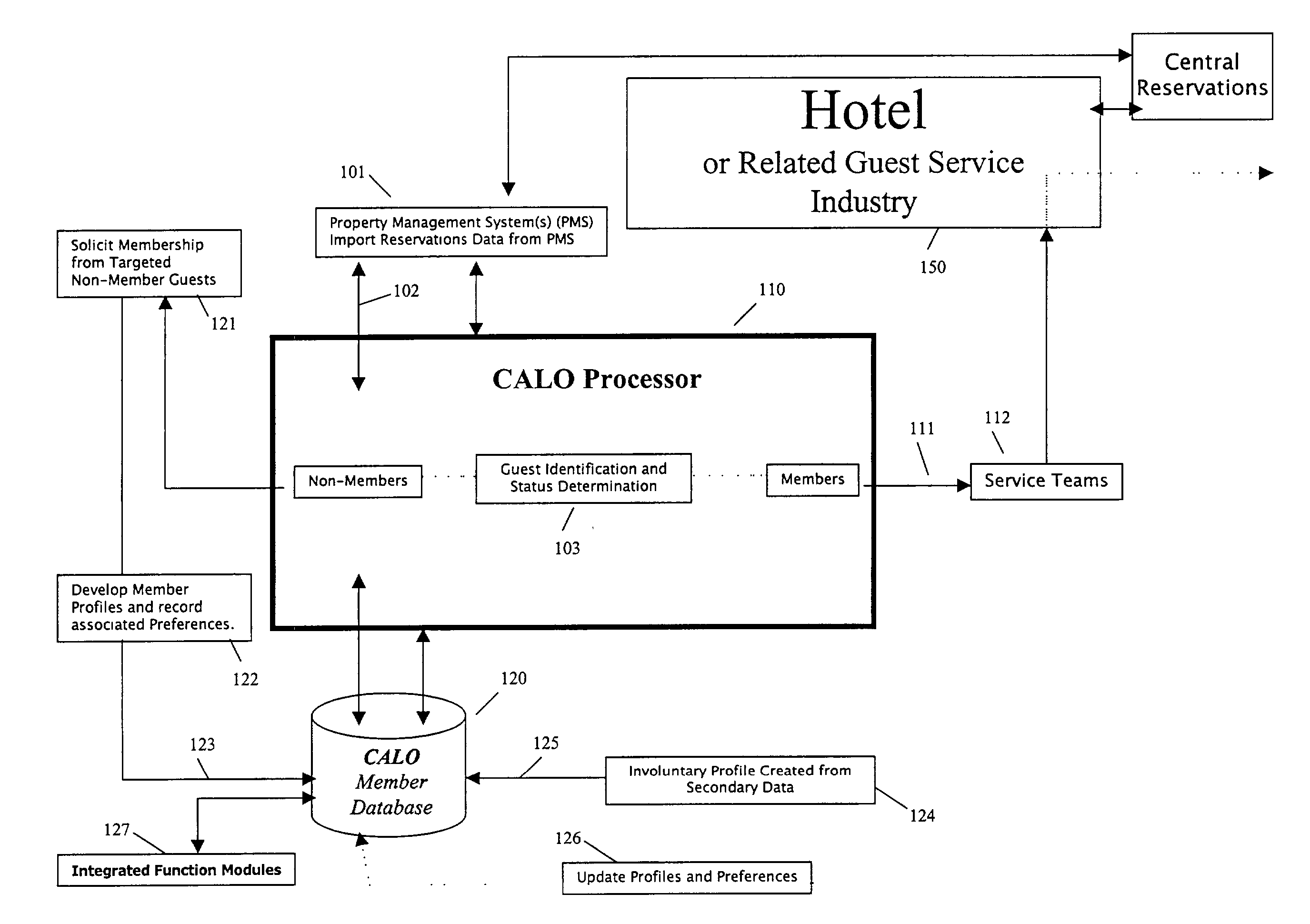
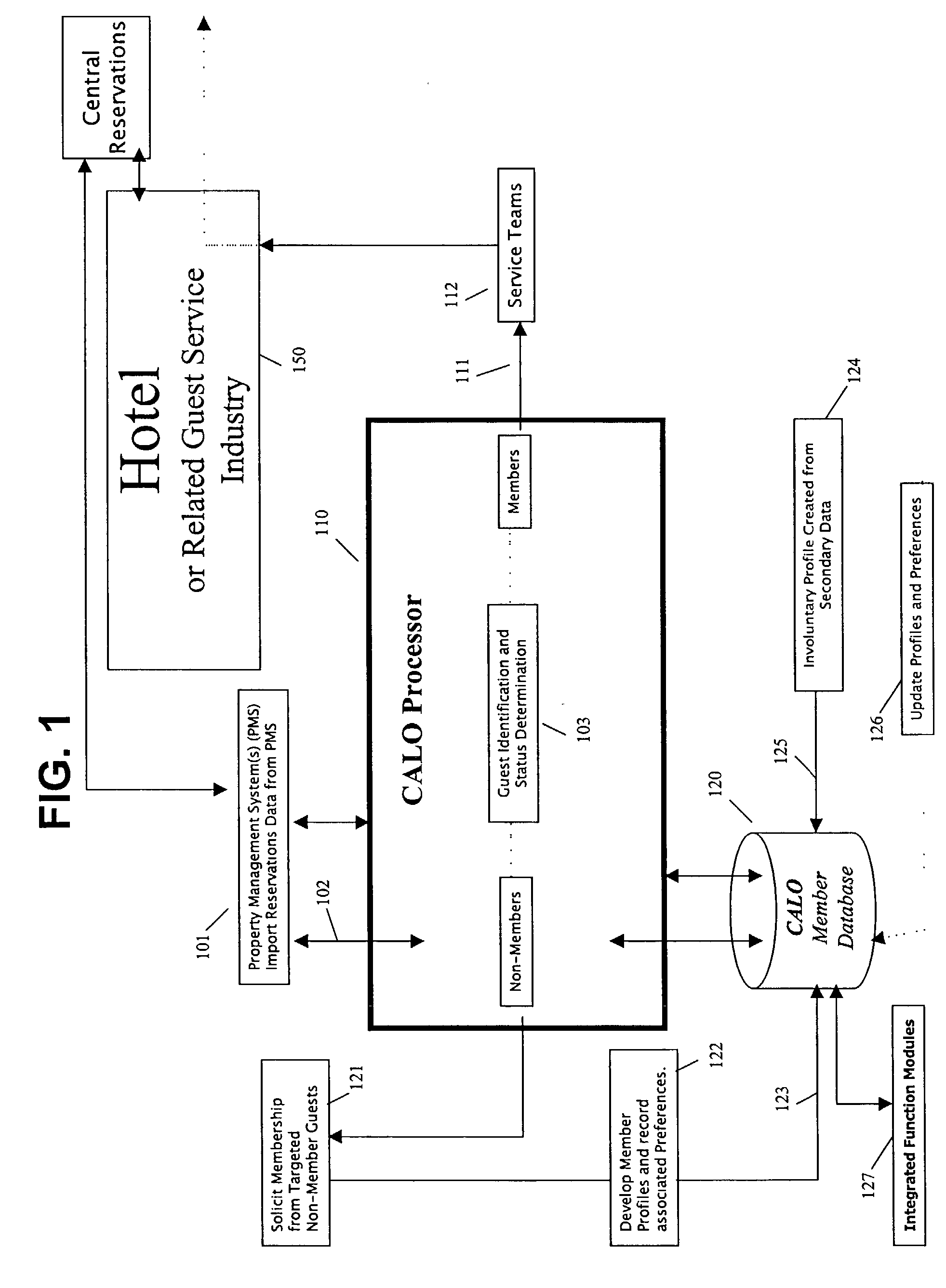
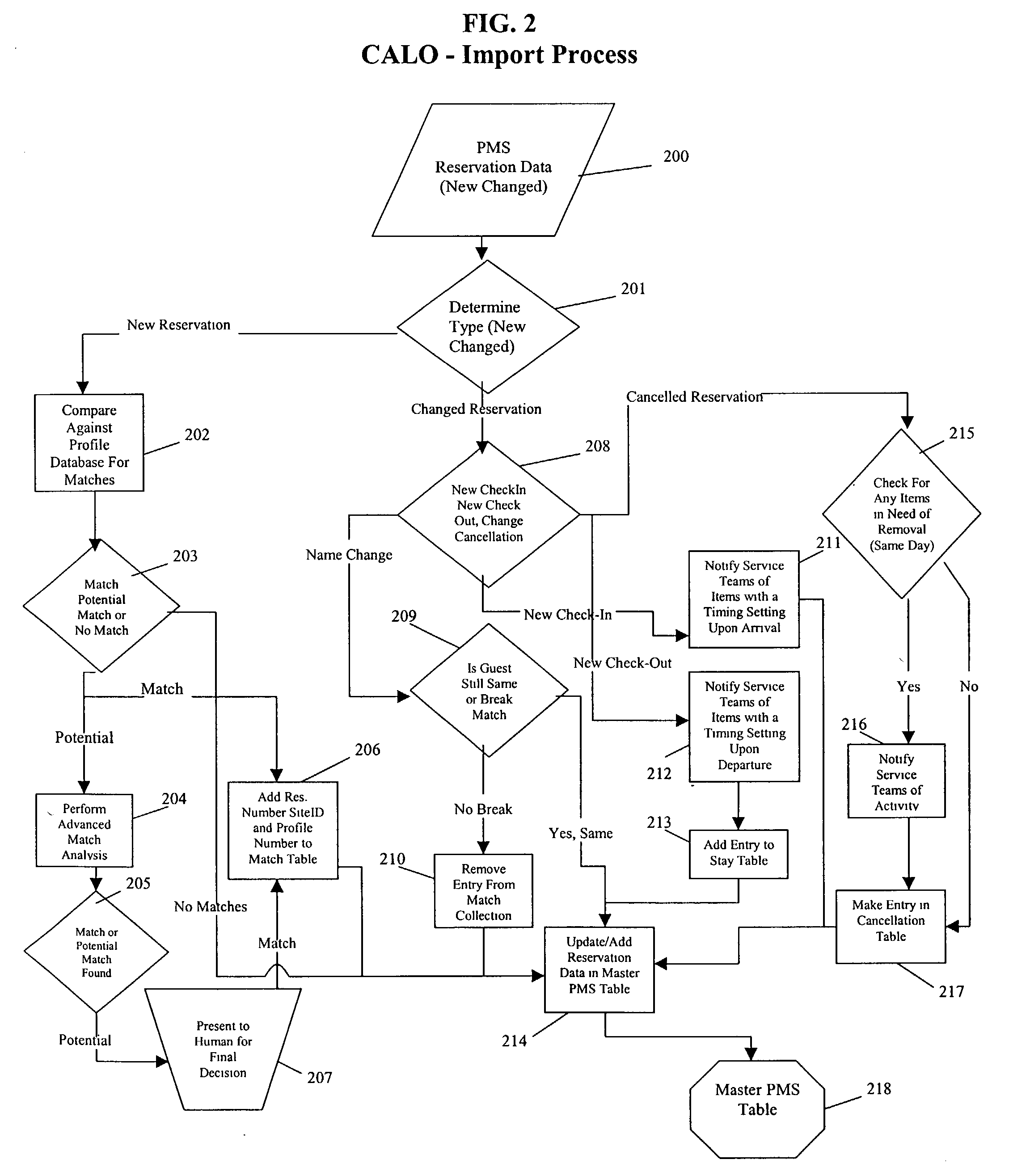
Guest relationship management system
A method for implementing a guest profiling program that utilizes guest profiles, which. are developed and expanded by information gathered from various sources and managed in a central Guest Relationship Management System (GRMS). The GRMS is a web-architected internet application. The primary interface between the GRMS and hotel systems is a connection to each hotel's property management system (PMS). The GRMS extracts data from PMSs. PMS data is updated to the central GRMS for processing. The core application logic includes capabilities to identify reservations with attributes and to match guest reservations extracted from each hotel's PMS with profiled guests. Both automated and user-initiated data manipulation processes utilize the central GRMS profiles and PMS data to generate outputs designed to increase the quality and timeliness of services and to assist marketing efforts. The web-based architecture of GRMS enables consistent data sharing and processing capabilities with a plurality of hotels.
Owner:GENGARELLA JOHN S
Policy-Based Application Management
ActiveUS20140033271A1Digital data protectionInternal/peripheral component protectionVirtualizationApp store
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
Block chain-based credit investigation data sharing and trading system
InactiveCN106651346APerfect risk control levelSolve imperfectionsPayment protocolsBuying/selling/leasing transactionsRisk ControlData provider
The invention relates to a block chain-based credit investigation data sharing and trading system. The credit investigation data sharing and trading system comprises at least two P2P network nodes; each network node comprises an underlying block chain system and a credit investigation data sharing platform running in the underlying block chain system; and the credit investigation data sharing platform comprises a data sharing module, a data query trading module, a member management module and a block chain adaption layer. According to the credit investigation data sharing and trading system, a trusted credit investigation data sharing and trading platform is established by using a block chain technology; and special data sharing mechanism, data query mechanism and data trading mechanism are used, so that credit investigation data owners and credit investigation data demanders can be attracted to perform use, credit investigation data providers can perform data trading under the condition that data is protected, and credit investigation data queriers can obtain the credit investigation data to improve risk control levels of themselves.
Owner:上海凯岸信息科技有限公司
Multi-party sharing transaction metadata method, device and system based on block chain
ActiveCN107180350AEnsure safetyEasy to operateFinanceBuying/selling/leasing transactionsDigital signatureTransaction data
The invention discloses a sharing transaction metadata method, device and system based on block chains; transaction metadata can be extracted from various party transaction data and written into the block chain, thus forming a distributed shearing transaction metadata block chain account book; the method comprises the following steps: issuing a digital signature certificate based on a PKI / CA system for block chain nodes and transaction various parties, recording transaction metadata, and signaturing the block in a secrete manner; desensitizing transaction main body information, extracting transaction metadata from original transaction data, uploading the transaction metadata to block chain nodes, allowing the transaction main body to confirm the transaction metadata, allowing the block chain node to write the confirmed transaction metadata into the block chain, and allowing data sharing parties to check the block chain information after authorization. In an authority issuing business scene, the original transaction and collateral data are encrypted and stored through a storage service module, and related transaction authorities are provided for the transaction sharing party, the transaction main body and the transaction main body opponent party.
Owner:唐晓领
File server system providing direct data sharing between clients with a server acting as an arbiter and coordinator
InactiveUS20050251500A1Data processing applicationsDigital data information retrievalData accessNetwork data
A client is permitted to send data access commands directly to network data storage of a network file server after obtaining a lock on at least a portion of the file and obtaining metadata indicating storage locations for the data in the data storage. For example, the client sends to the file server at least one request for access to a file. In response, the file server grants a lock to the client, and returns to the client metadata of the file including information specifying data storage locations in the network data storage for storing data of the file. The client receives the metadata, and uses the metadata to produce at least one data access command for accessing the data storage locations in the network storage. The client sends the data access command to the network data storage to read or write data to the file. For a write operation, the client may modify the metadata. When the client is finished writing to the file, the client returns any modified metadata to the file server.
Owner:EMC CORP
Secure and zero knowledge data sharing for cloud applications
Disclosed is a zero-knowledge distributed application configured to securely share information among groups of users having various roles, such as doctors and patients. Confidential information may be encrypted client-side, with private keys that reside solely client side. Encrypted collections of data may be uploaded to, and hosted by, a server that does not have access to keys suitable to decrypt the data. Other users may retrieve encrypted data from the server and decrypt some or all of the data with keys suitable to gain access to at least part of the encrypted data. The system includes a key hierarchy with multiple entry points to a top layer by which access is selectively granted to various users and keys may be recovered.
Owner:MASIMO CORP
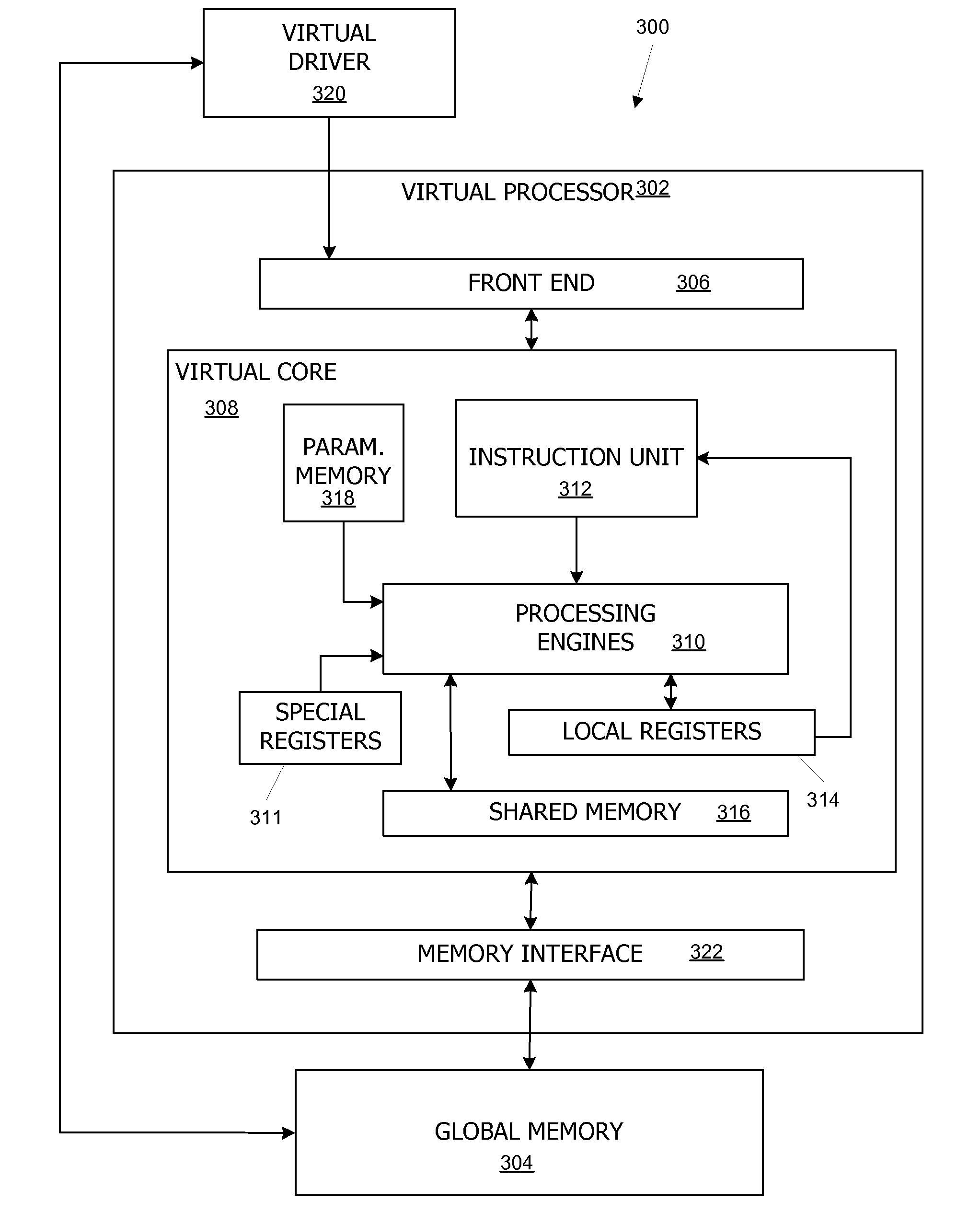
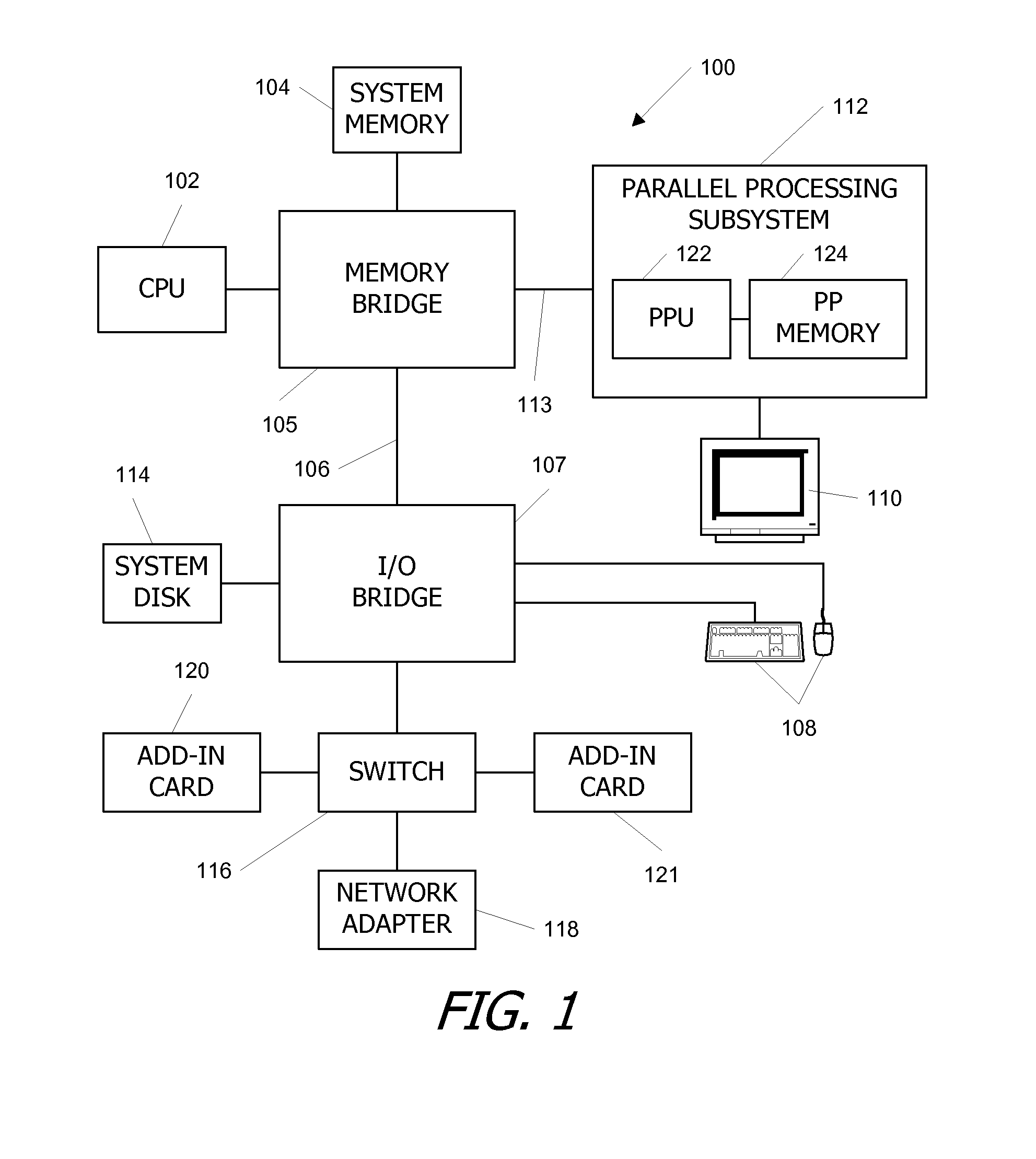
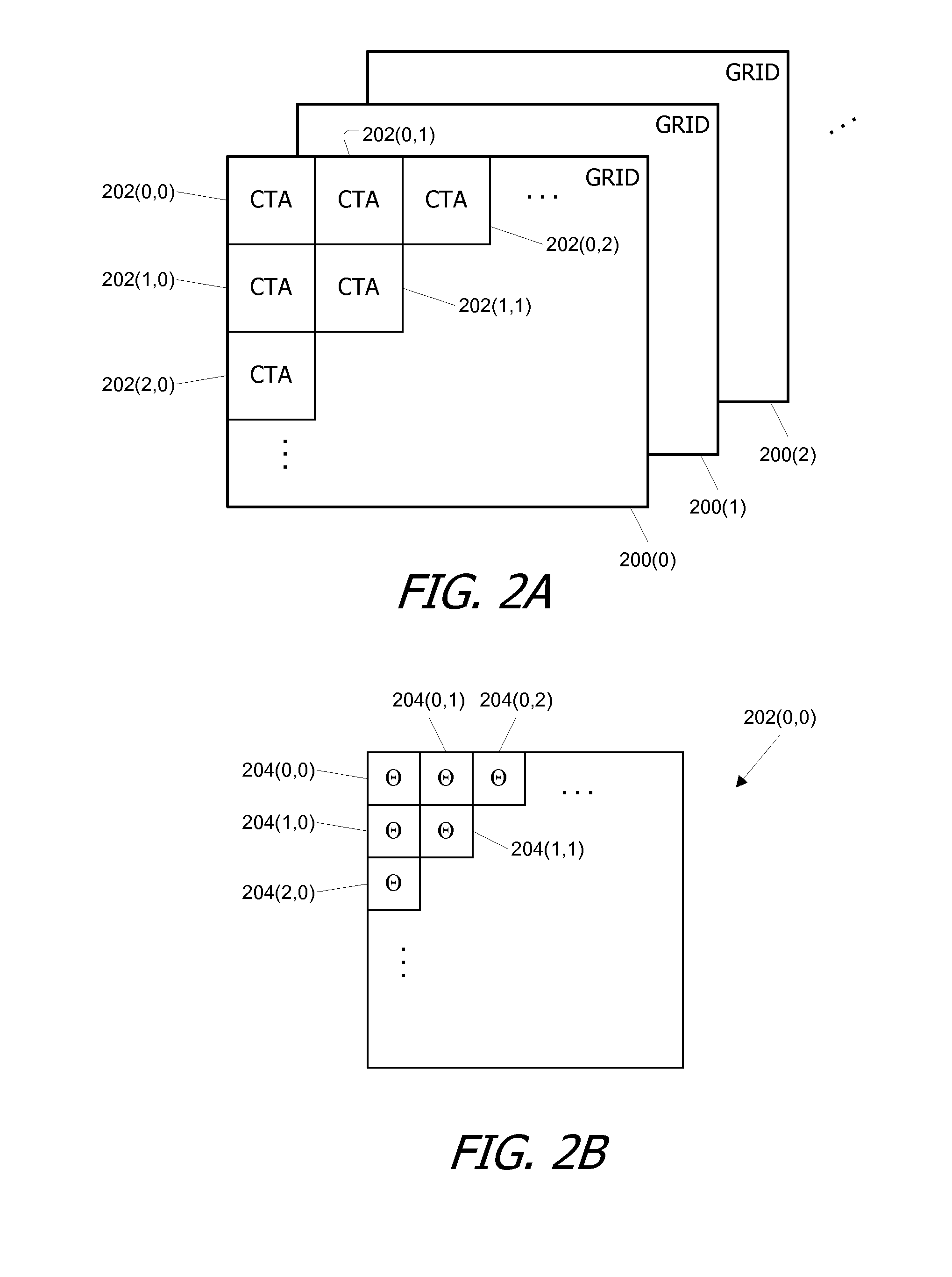
Virtual architecture and instruction set for parallel thread computing
ActiveUS20080184211A1Improve developmentImprove portabilityProgram control using stored programsSoftware engineeringApplication softwareData sharing
A virtual architecture and instruction set support explicit parallel-thread computing. The virtual architecture defines a virtual processor that supports concurrent execution of multiple virtual threads with multiple levels of data sharing and coordination (e.g., synchronization) between different virtual threads, as well as a virtual execution driver that controls the virtual processor. A virtual instruction set architecture for the virtual processor is used to define behavior of a virtual thread and includes instructions related to parallel thread behavior, e.g., data sharing and synchronization. Using the virtual platform, programmers can develop application programs in which virtual threads execute concurrently to process data; virtual translators and drivers adapt the application code to particular hardware on which it is to execute, transparently to the programmer.
Owner:NVIDIA CORP
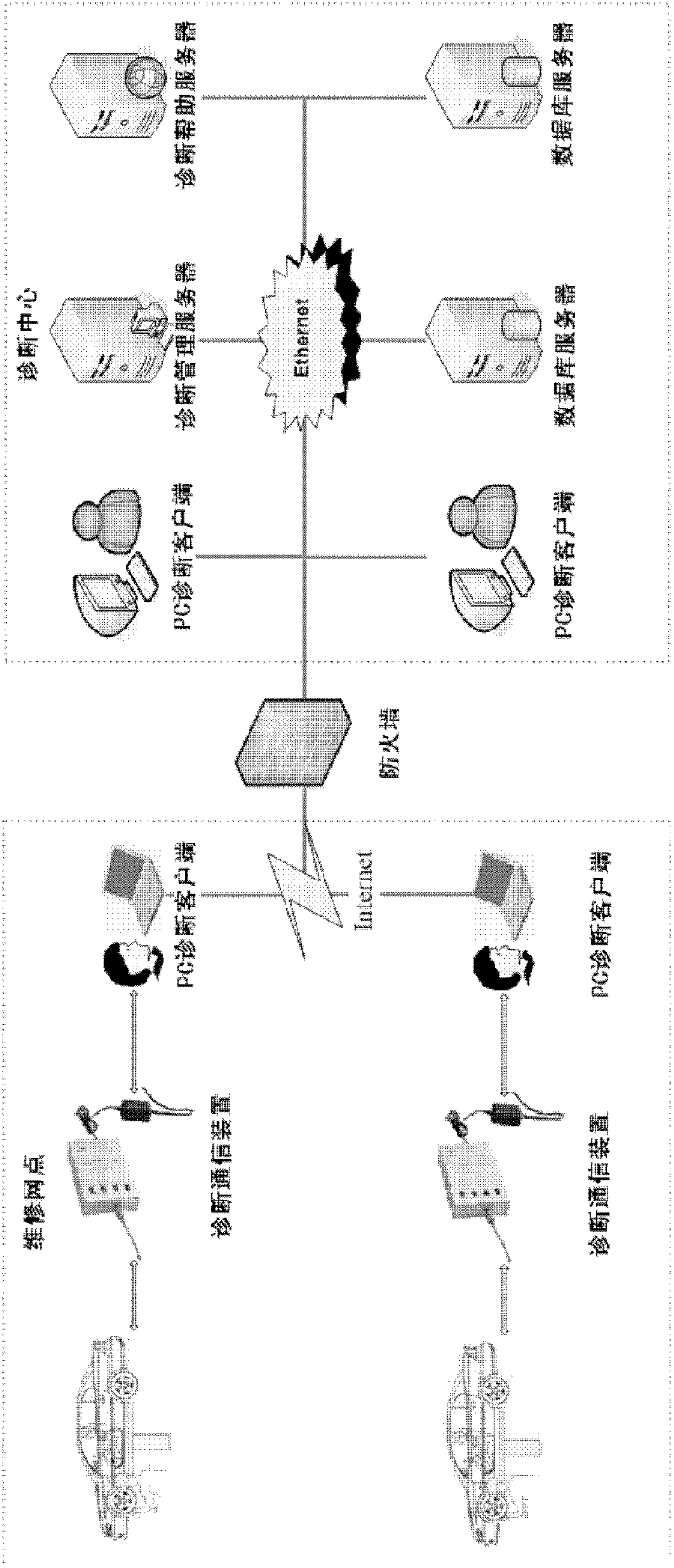
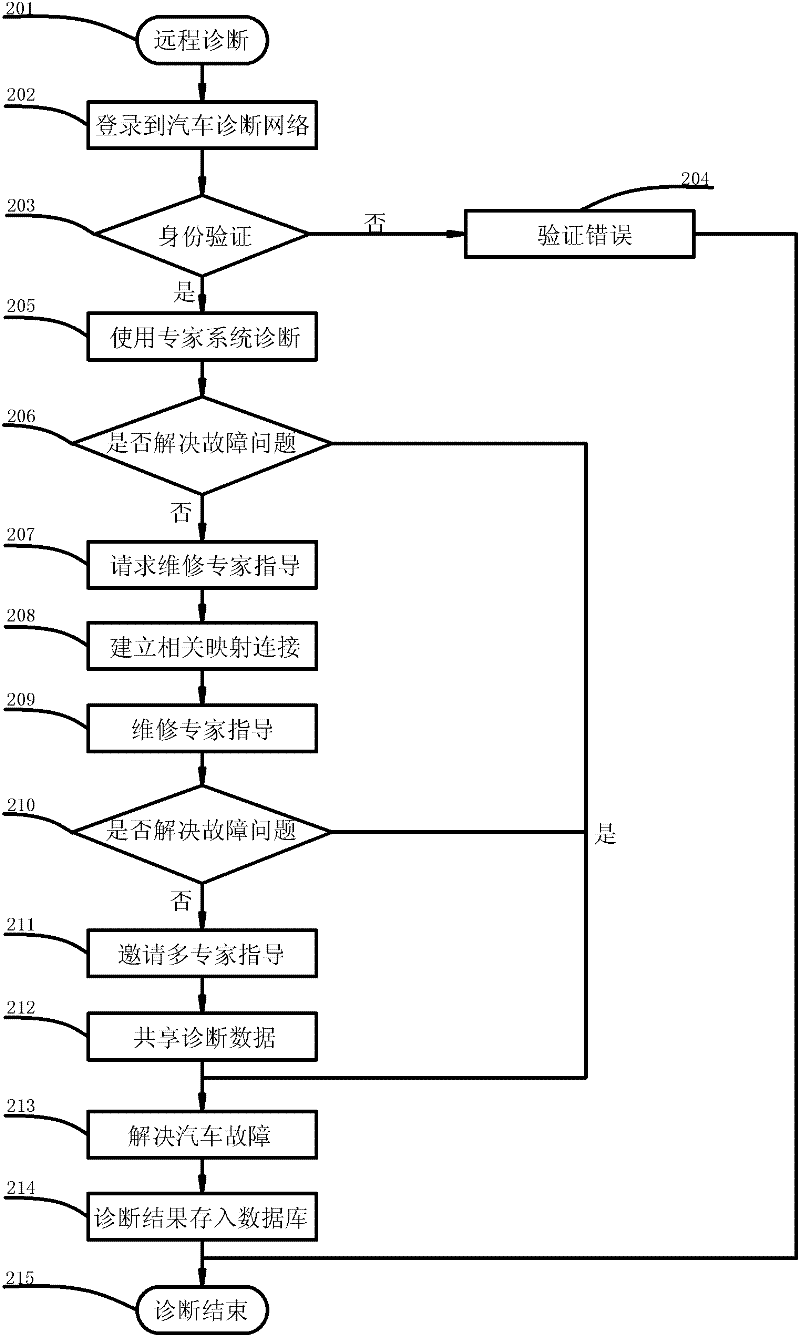
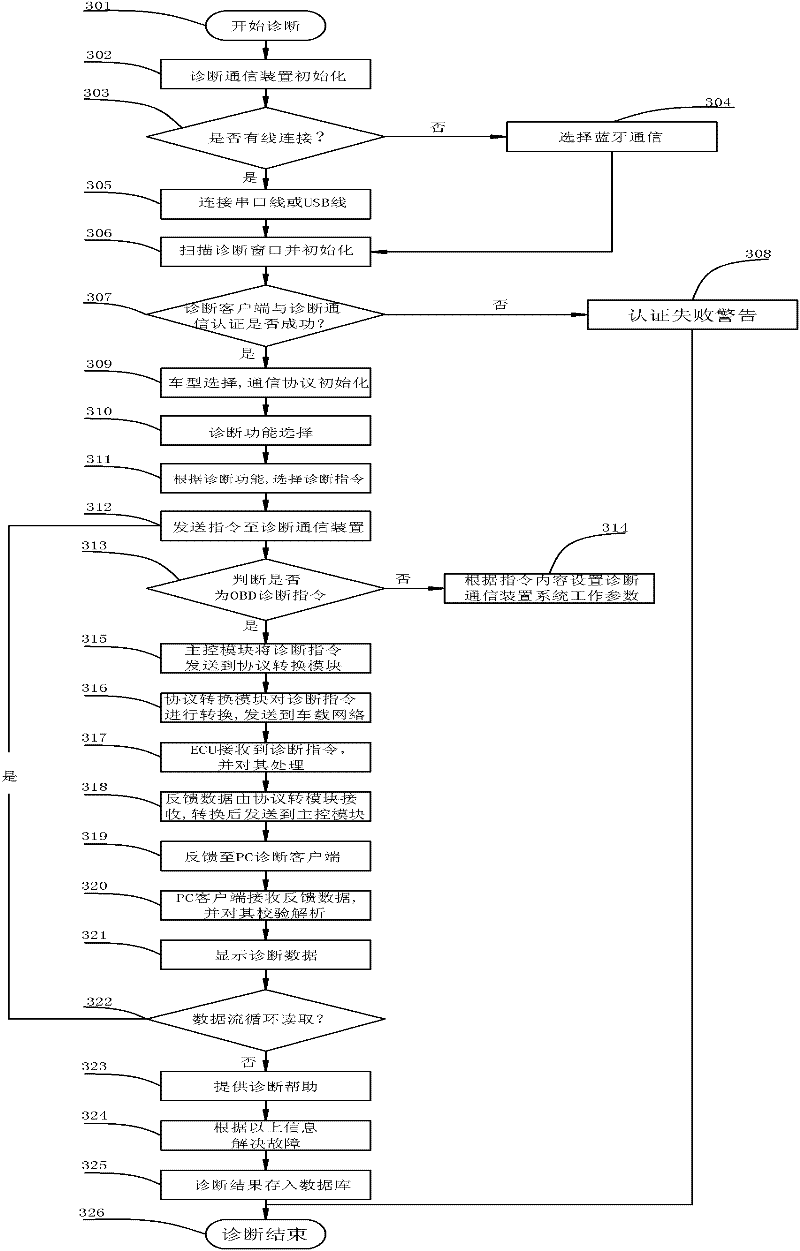
Multifunctional remote fault diagnosis system for electric control automobile
ActiveCN102183945AReduce the cost of after-sales serviceImprove the efficiency of after-sales serviceElectric testing/monitoringInteraction interfaceNetwork management
The invention relates to a multifunctional remote fault diagnosis system for an electric control automobile. The multifunctional remote fault diagnosis system comprises a remote fault diagnosis service center, PC (Personal Computer) diagnosis client sides and a diagnosis communication device. The remote fault diagnosis service center serves as a key of the system and is mainly used for realizing an automobile fault diagnosis network management function and an automobile remote fault diagnosis assistance function; the PC diagnosis client sides are mainly used for providing specific automobile diagnosis application functions and remote diagnosis interfaces for users with different rights through human-computer interaction interfaces; and the diagnosis communication device is mainly used for realizing the data communication between the PC diagnosis client sides and a vehicle-mounted network and providing diagnosis data service for upper applications. By means of the multifunctional remote fault diagnosis system, with the remote fault diagnosis service center as a core and all PC diagnosis client sides as nodes, an automobile fault diagnosis network is established; automobile diagnosis data sharing is realized by means of the diagnosis communication device; multifunctional automobile remote fault assistance and fault elimination help can be provided; automobile fault information is subjected to statistic analysis; and a reliable automobile quality report is provided for an automobile manufacturer.
Owner:WUHAN UNIV OF TECH +1
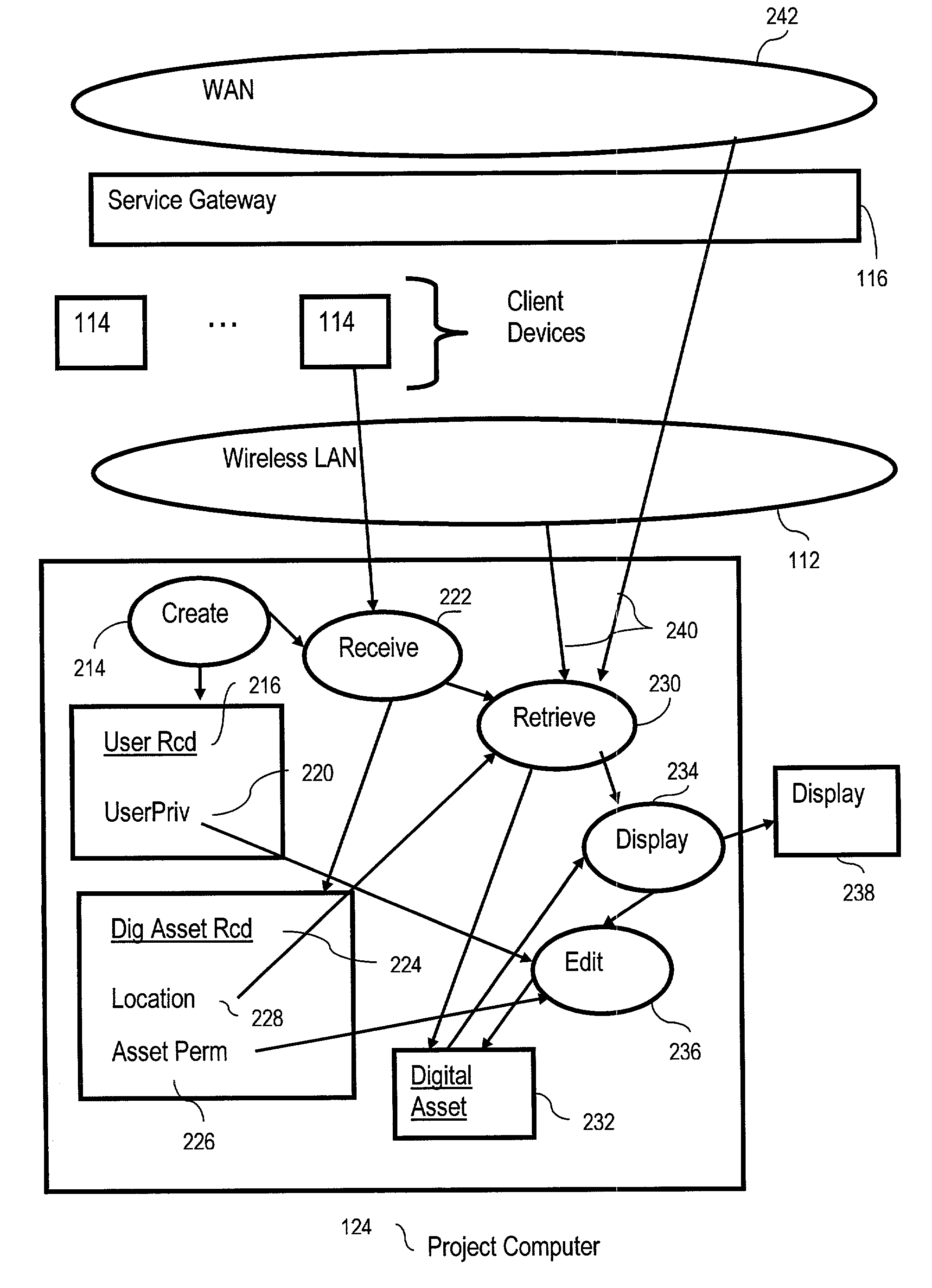
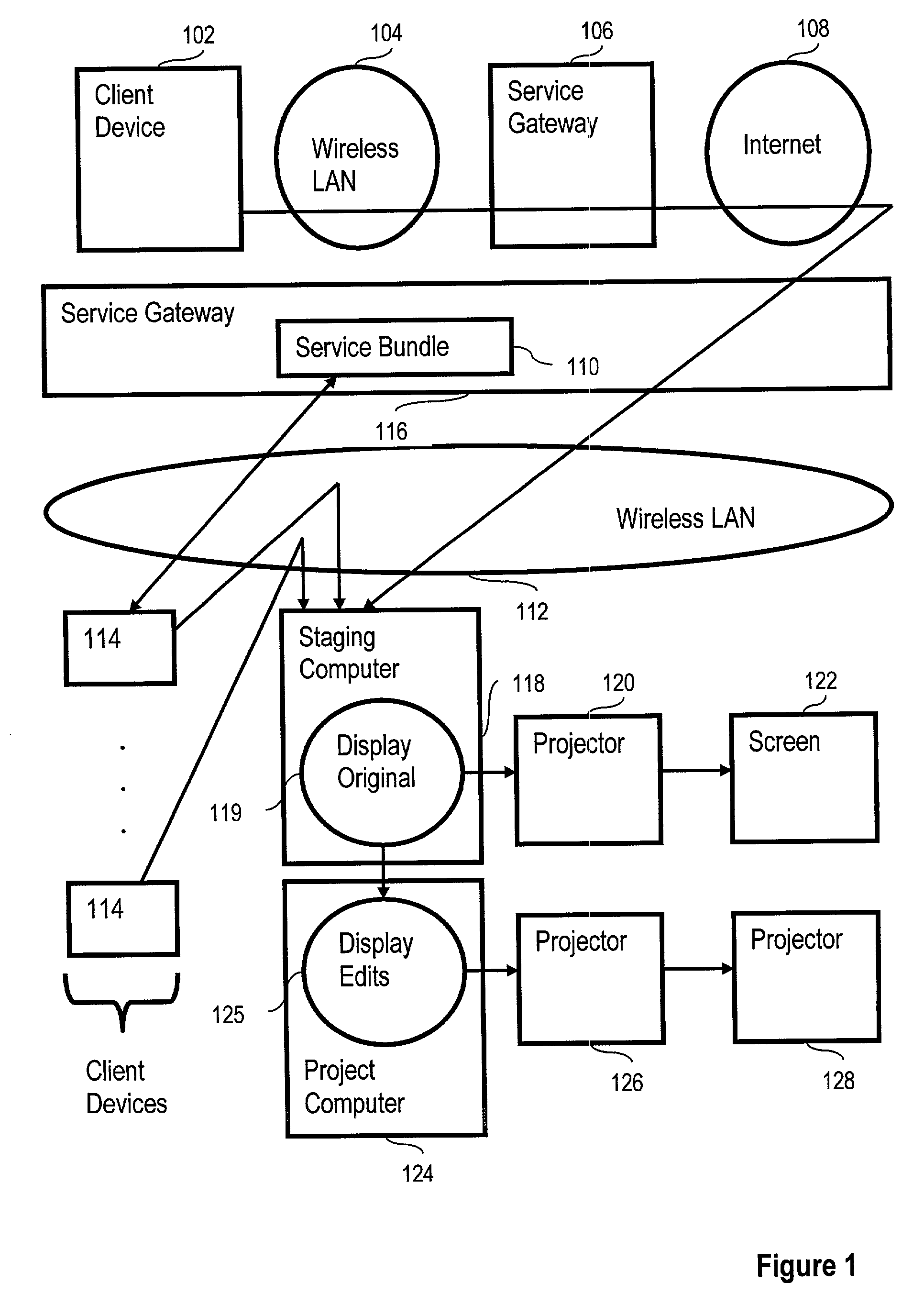
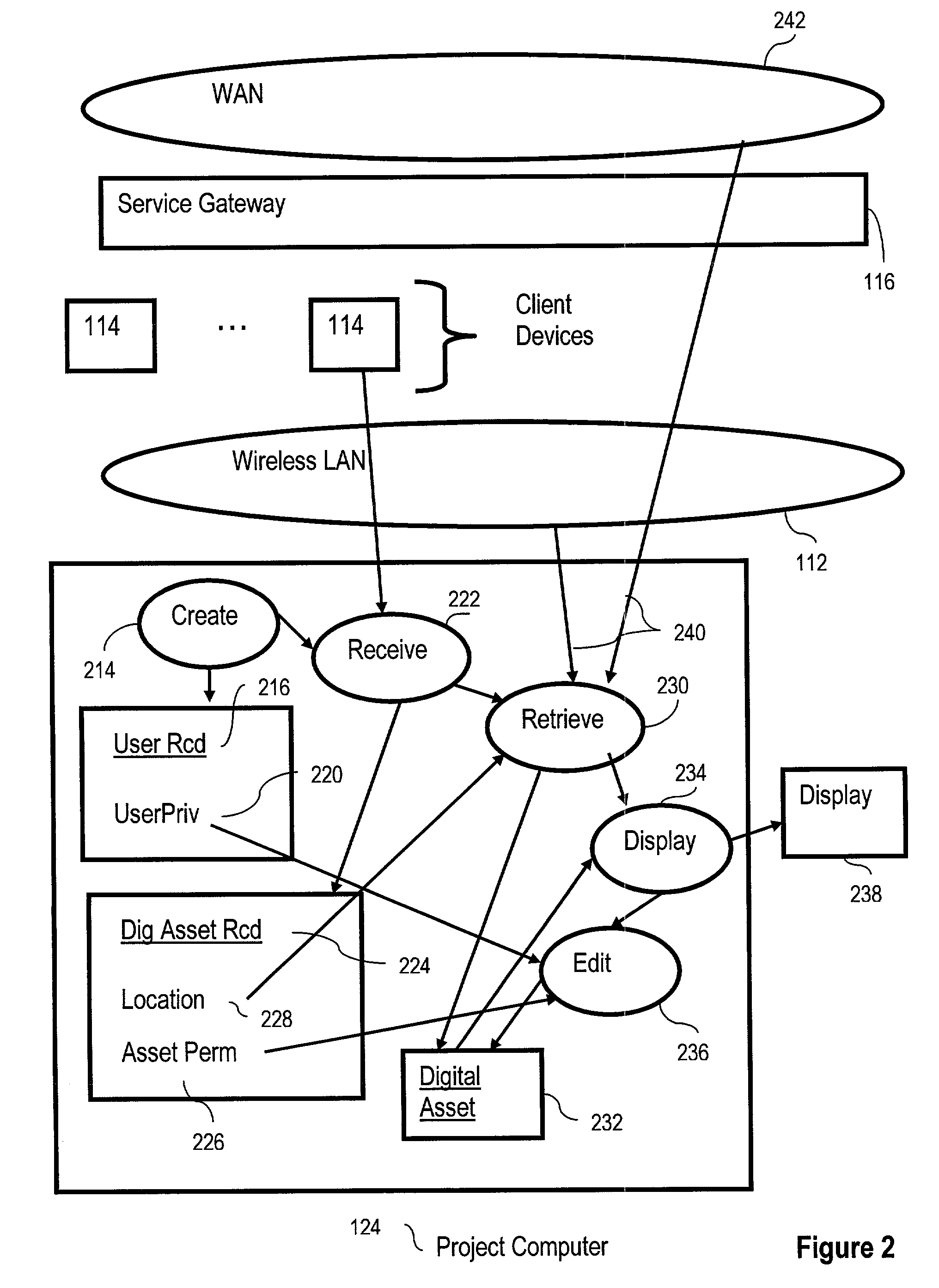
Ad hoc data sharing in virtual team rooms
ActiveUS7287053B2Digital data processing detailsMultiple digital computer combinationsClient-sideData sharing
A method of ad hoc data sharing for virtual teams rooms, including creating at least one user record representing a user granted access to digital assets, wherein each user has a client device, at least two of the client devices are wirelessly coupled for data communications to at least one computer, and each user record comprises a user access privilege field identifying for each user that user's user access privilege for access to digital assets. Embodiments also include receiving from client devices digital asset records representing digital assets, retrieving digital assets in dependence upon the location fields in the digital asset records, displaying the retrieved digital assets, and editing one or more of the retrieved digital assets, wherein the editing is carried out in dependence upon user access privilege and in dependence upon asset access permission.
Owner:ACTIVISION PUBLISHING
A data sharing exchange system and method based on a block chain
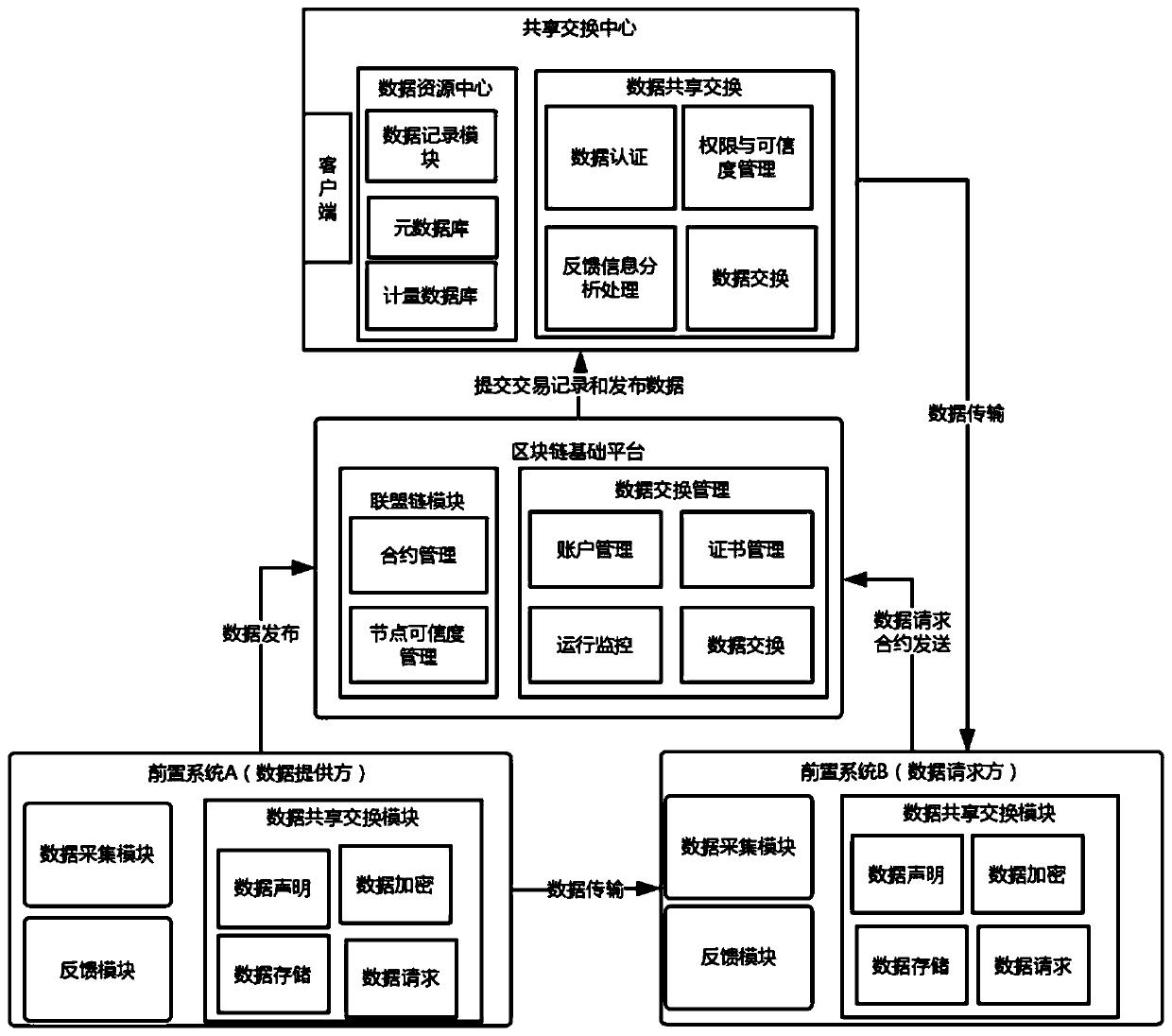
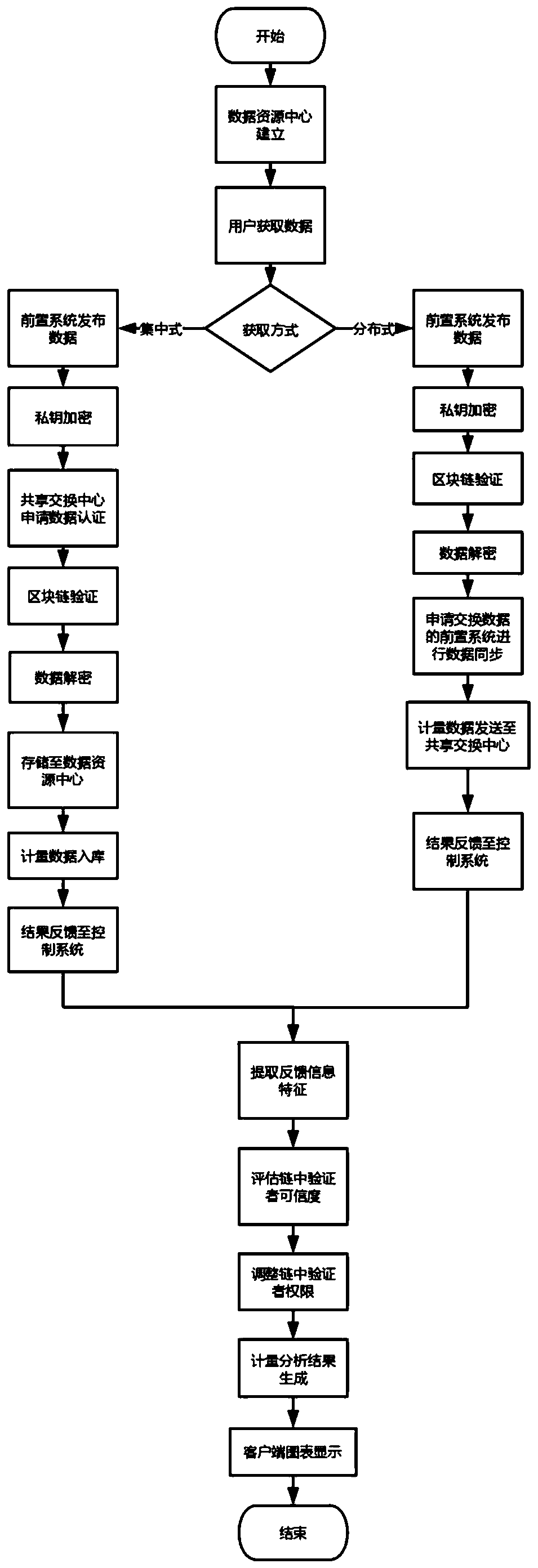
ActiveCN109729168AComply with shared exchange requirementsEasy to modifyUser identity/authority verificationDigital data protectionEnd systemControl system
The invention discloses a data sharing exchange system and method based on a block chain. The system comprises a data sharing exchange center, a front-end system and a block chain basic platform. Thedata sharing exchange center comprises a data sharing exchange control system, a data resource center and a client; The front-end system comprises a data acquisition system, a shared exchange module and a feedback module; The block chain basic platform comprises an alliance chain module and a data sharing exchange management module, the alliance chain module is responsible for intelligent contractand verifying credibility configuration of nodes, the intelligent contract generated in the data sharing exchange process is verified, and the data sharing exchange center communicates with the front-end systems in an alliance chain mode. According to the invention, the credit problem and the incentive problem of data sharing exchange in a multi-party participation environment are solved, the security and the reliability are ensured, the enthusiasm of a user for publishing and updating the sharing exchange data is promoted, and meanwhile, the guiding effect on user decision can be realized.
Owner:浙江成功软件开发有限公司
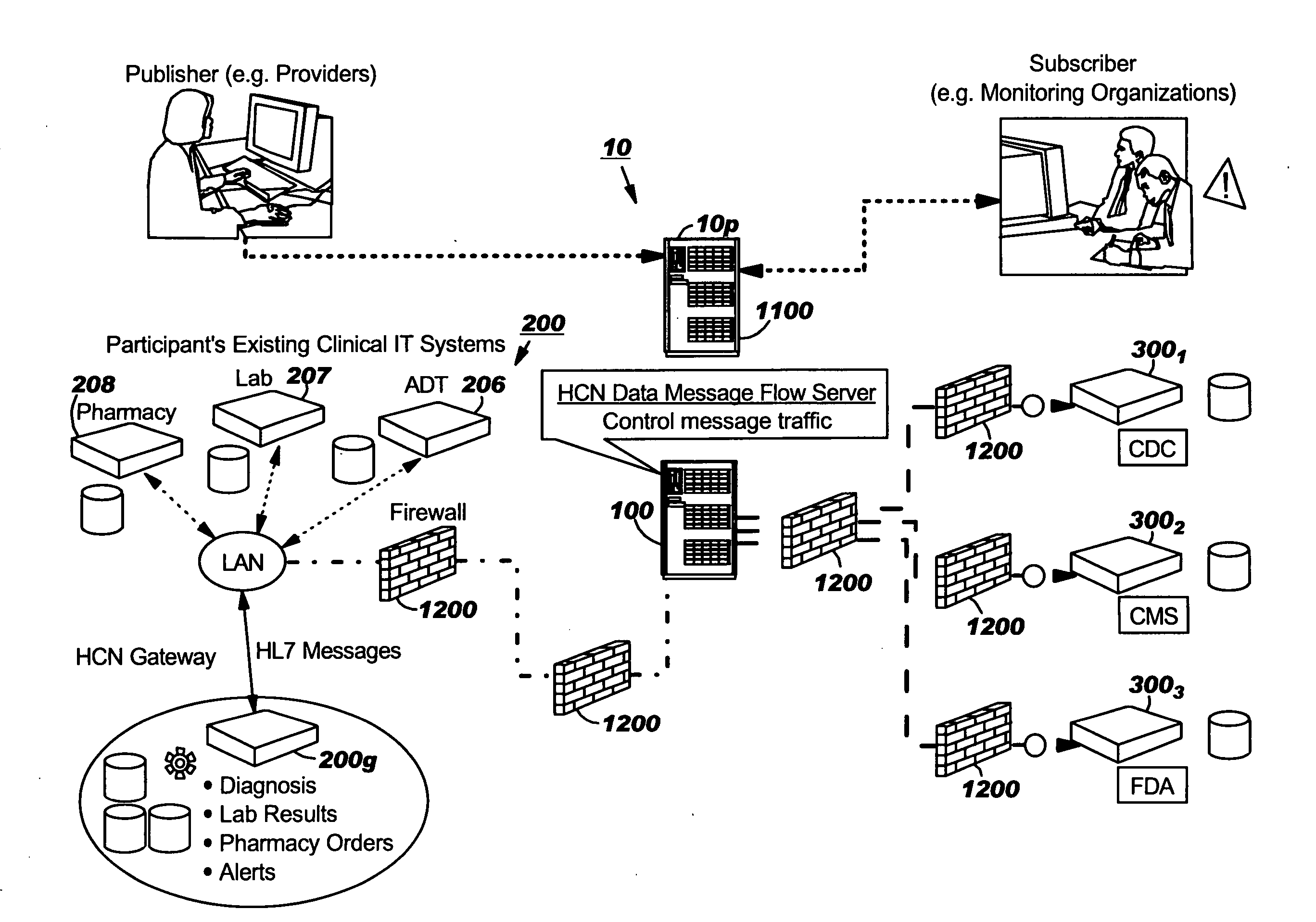
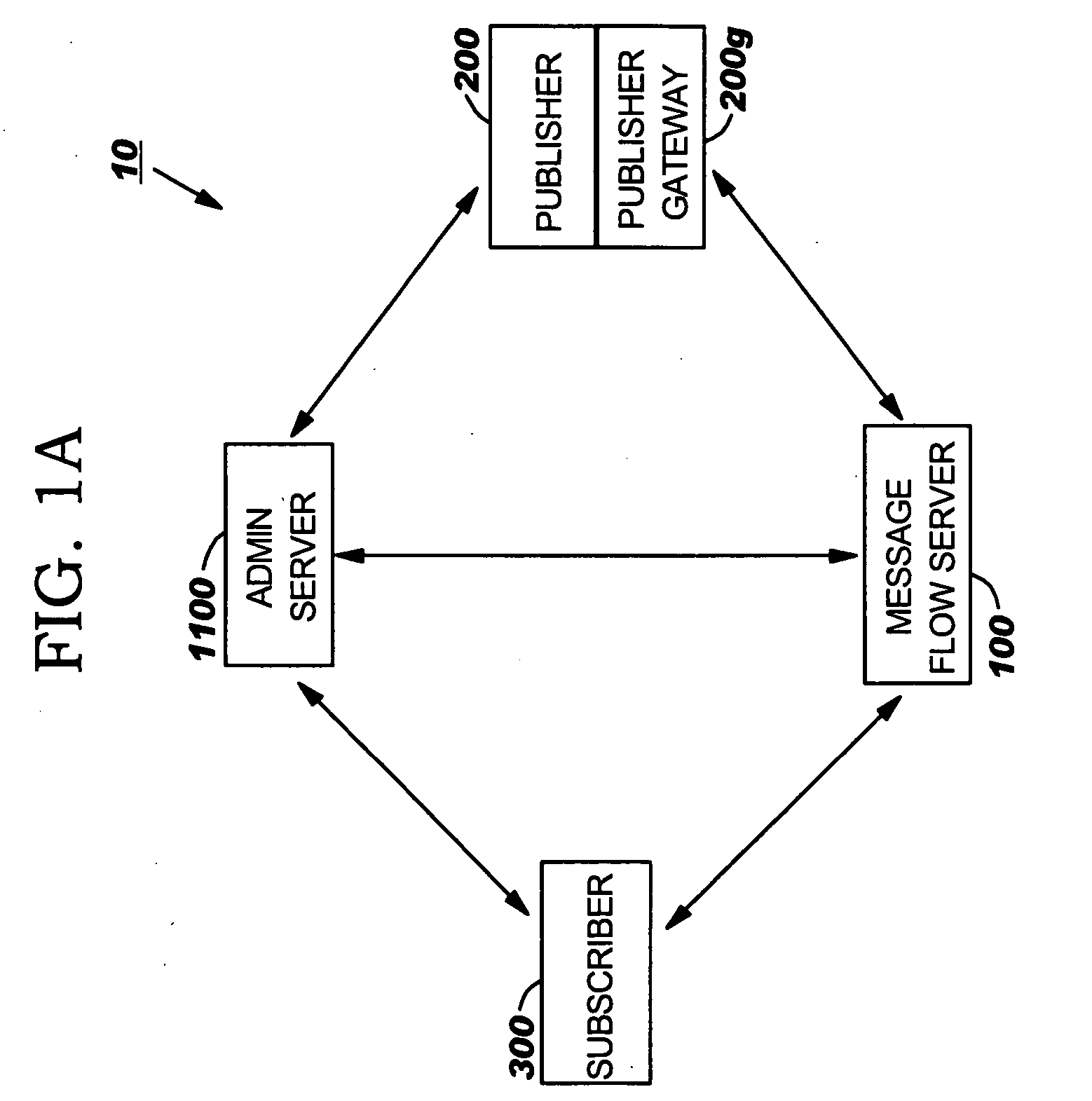
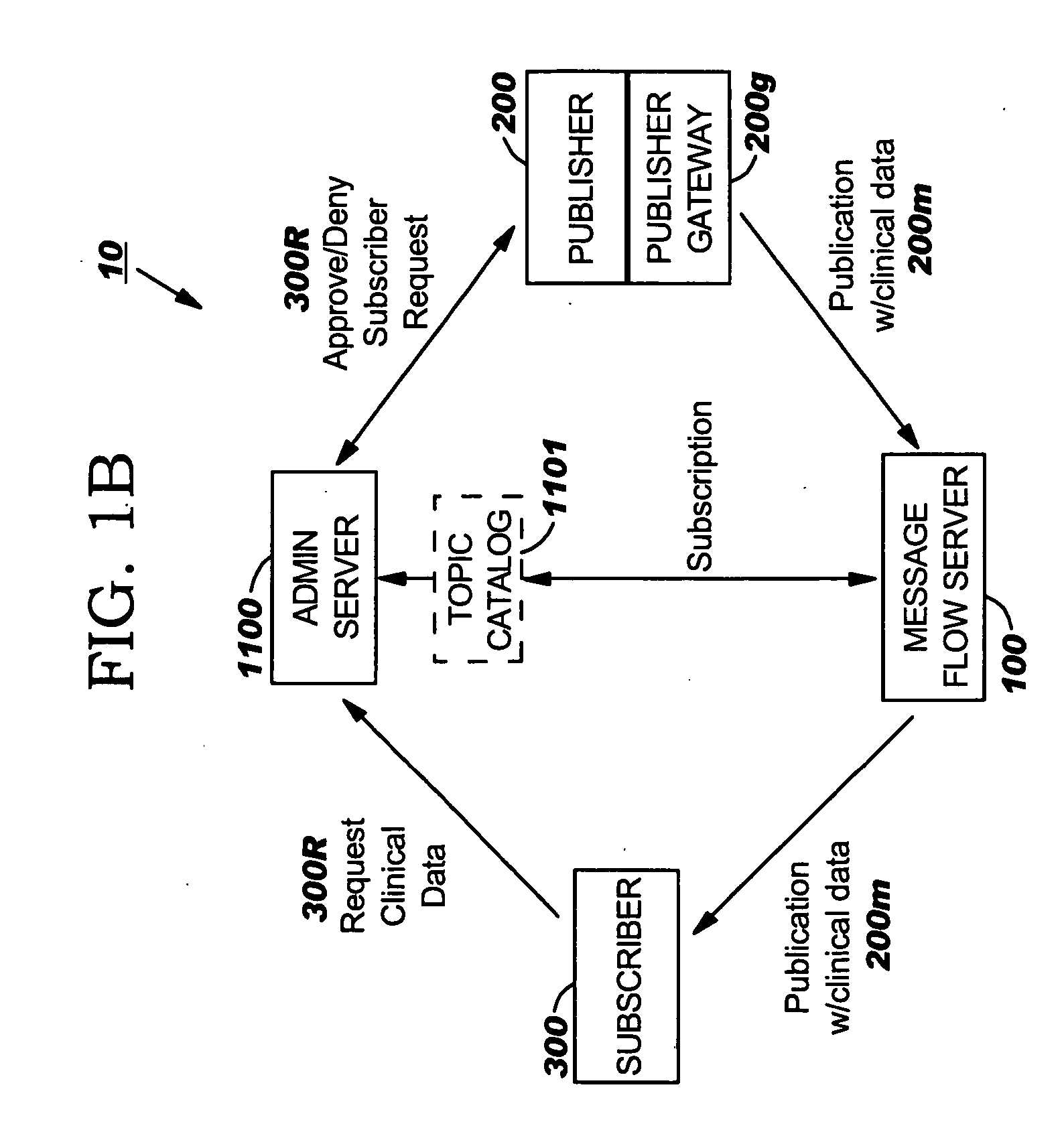
Publisher gateway systems for collaborative data exchange, collection, monitoring and/or alerting
A Publisher source of healthcare data is configured to communicate with an Internet-based data sharing system, the Publisher comprising a Publisher Gateway configured to electronically receive patient data from a plurality of data input sources, automatically correlate data from the plurality of input sources associated with respective patients into respective electronic patient data records having electronically searchable data fields, and electronically store the patient data records in a Publisher database.
Owner:IBM CORP
Personalized folders
InactiveUS20050091184A1Facilitate information exchangeEasy to shareDigital data information retrievalDigital data processing detailsPersonalizationData sharing
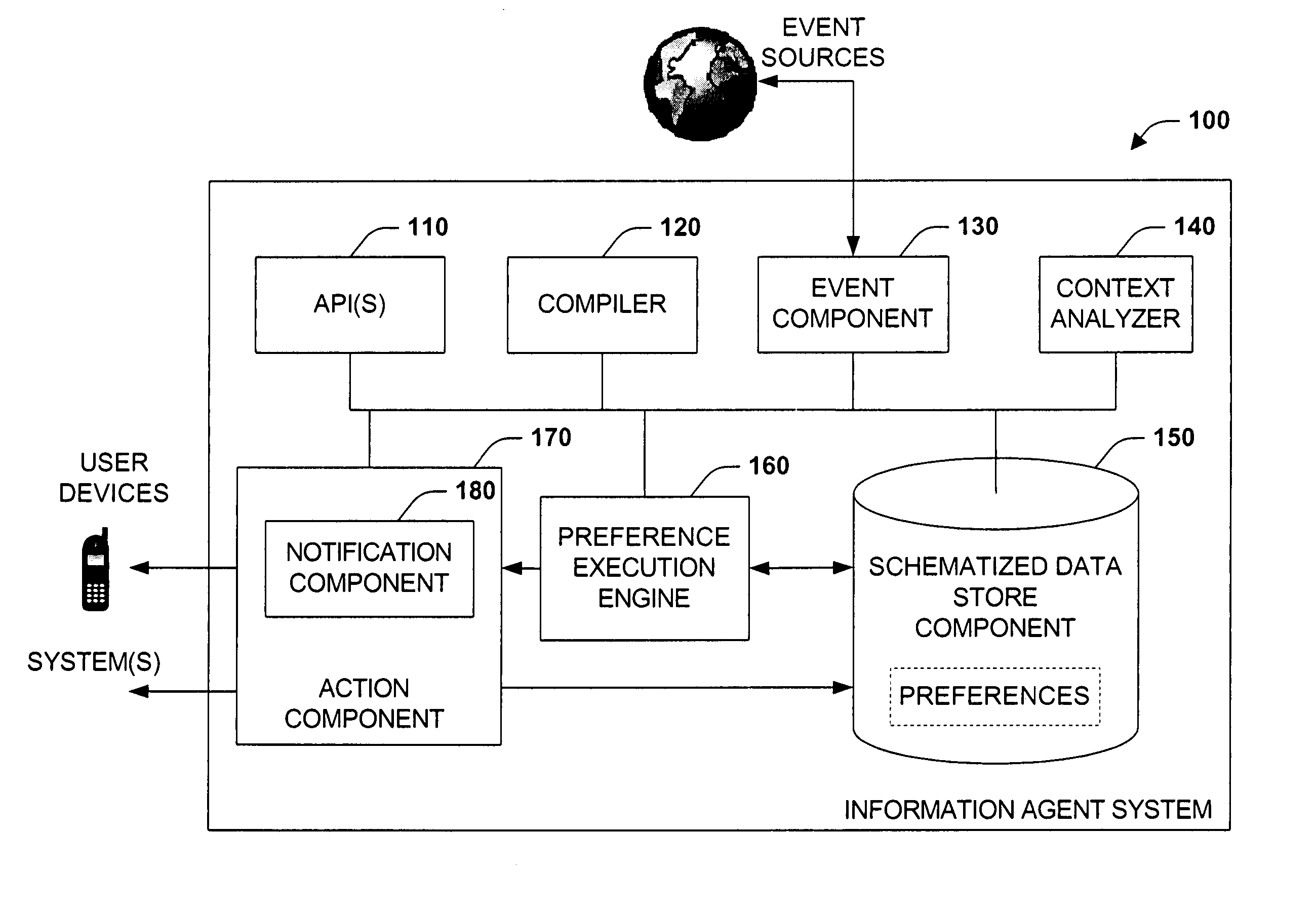
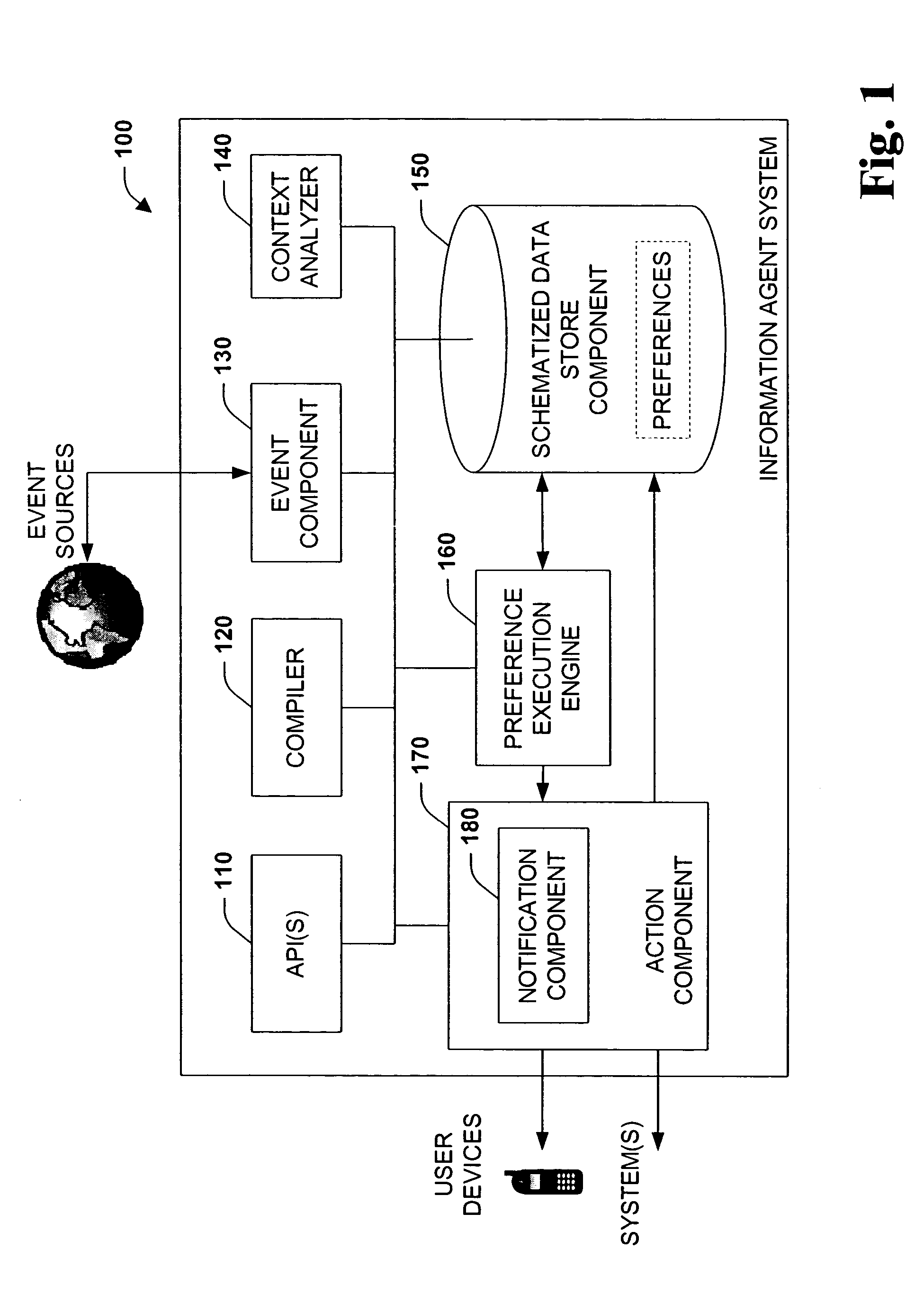
The present systems and methods disclose a system for personalizing computer functionality. End-users are provided with tools to easily write rich and complex preferences, for example, by using a plurality simple IF-THEN propositional logic. The preferences are then transformed into queries and executed efficiently on structured data. Preferences that are satisfied then execute actions such as providing notification or storing data in a particular folder. Furthermore, according to an aspect of the invention, data, logic, events, inter alia, are all schematized, thereby enabling sharing of data between application components and across applications.
Owner:MICROSOFT TECH LICENSING LLC
Policy-Based Application Management
InactiveUS20140032733A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
File server system providing direct data sharing between clients with a server acting as an arbiter and coordinator
InactiveUS7120631B1Data processing applicationsDigital data information retrievalData accessClient-side
A client is permitted to send data access commands directly to network data storage of a network file server after obtaining a lock on at least a portion of the file and obtaining metadata indicating storage locations for the data in the data storage. For example, the client sends to the file server at least one request for access to a file. In response, the file server grants a lock to the client, and returns to the client metadata of the file including information specifying data storage locations in the network data storage for storing data of the file. The client receives the metadata, and uses the metadata to produce at least one data access command for accessing the data storage locations in the network storage. The client sends the data access command to the network data storage to read or write data to the file. For a write operation, the client may modify the metadata. When the client is finished writing to the file, the client returns any modified metadata to the file server.
Owner:EMC CORP
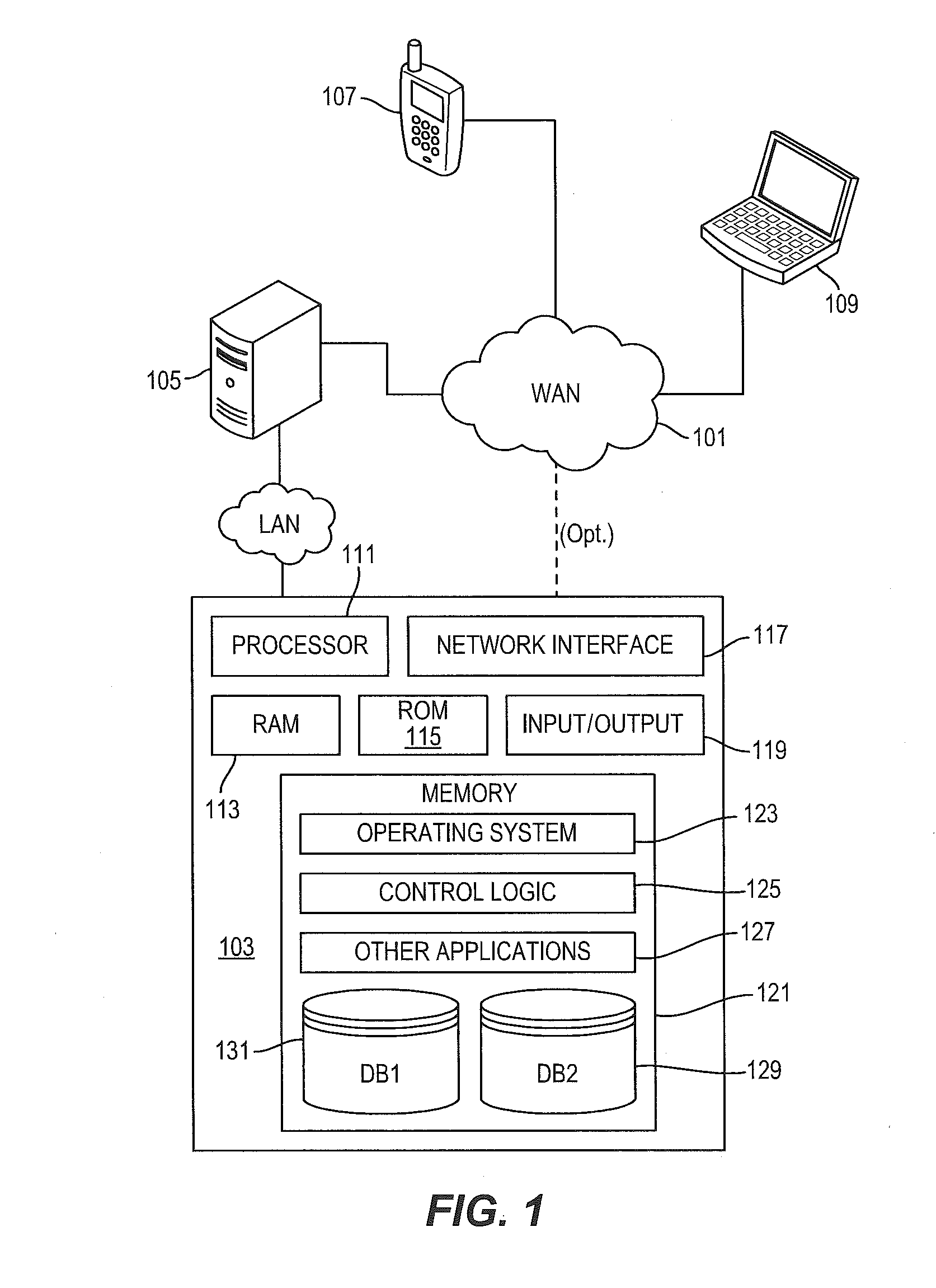
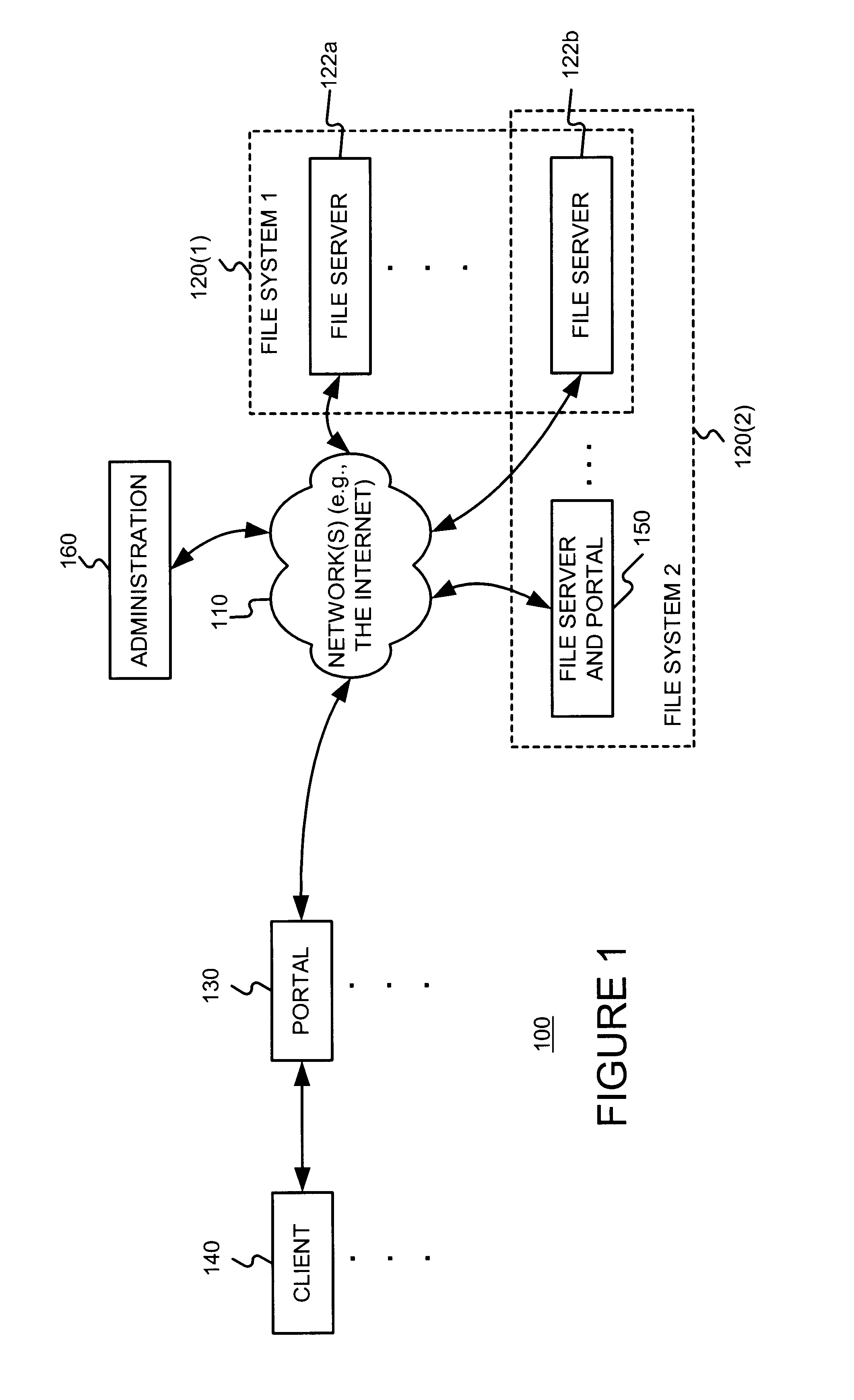
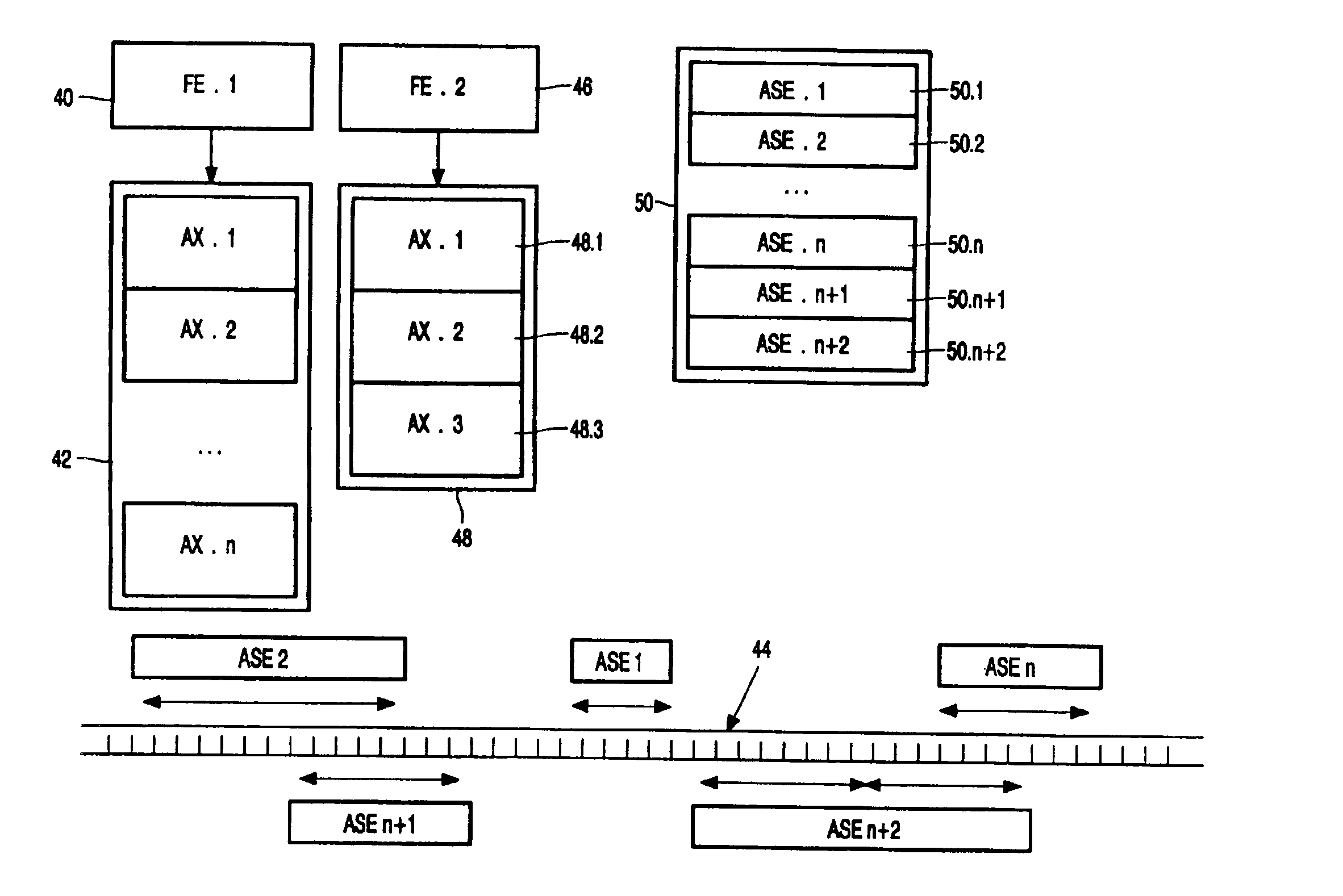
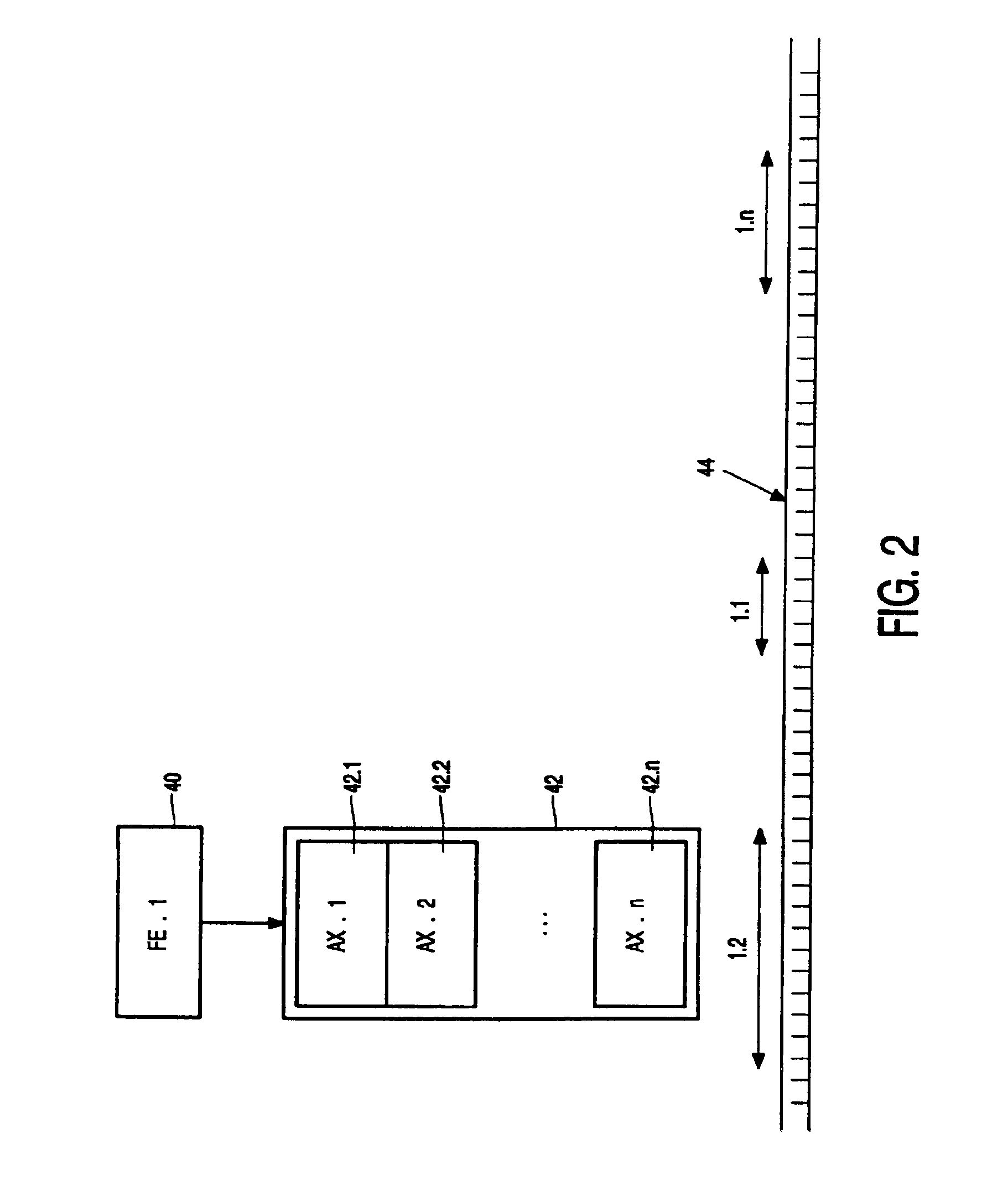
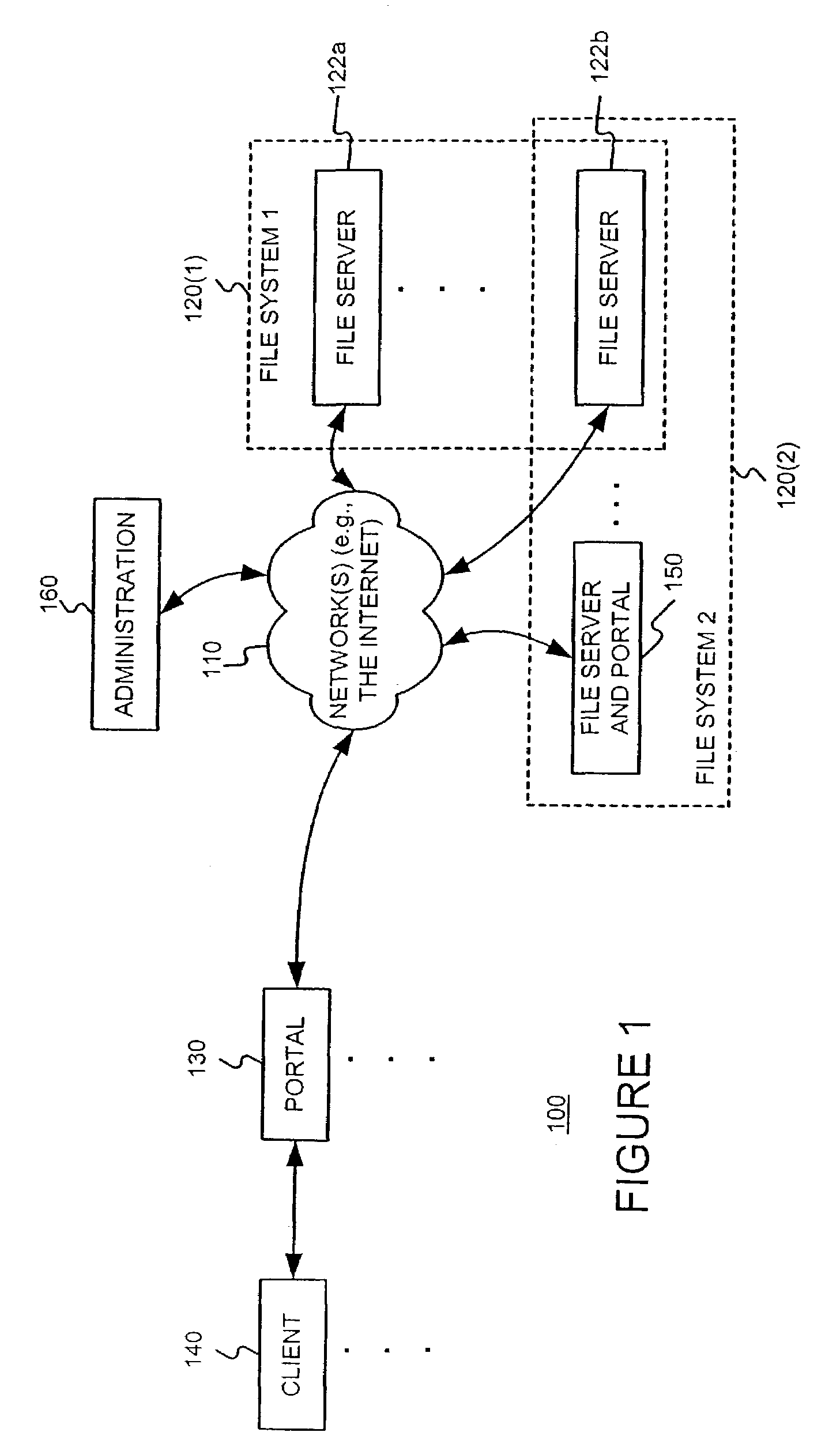
Distributing files across multiple, permissibly heterogeneous, storage devices
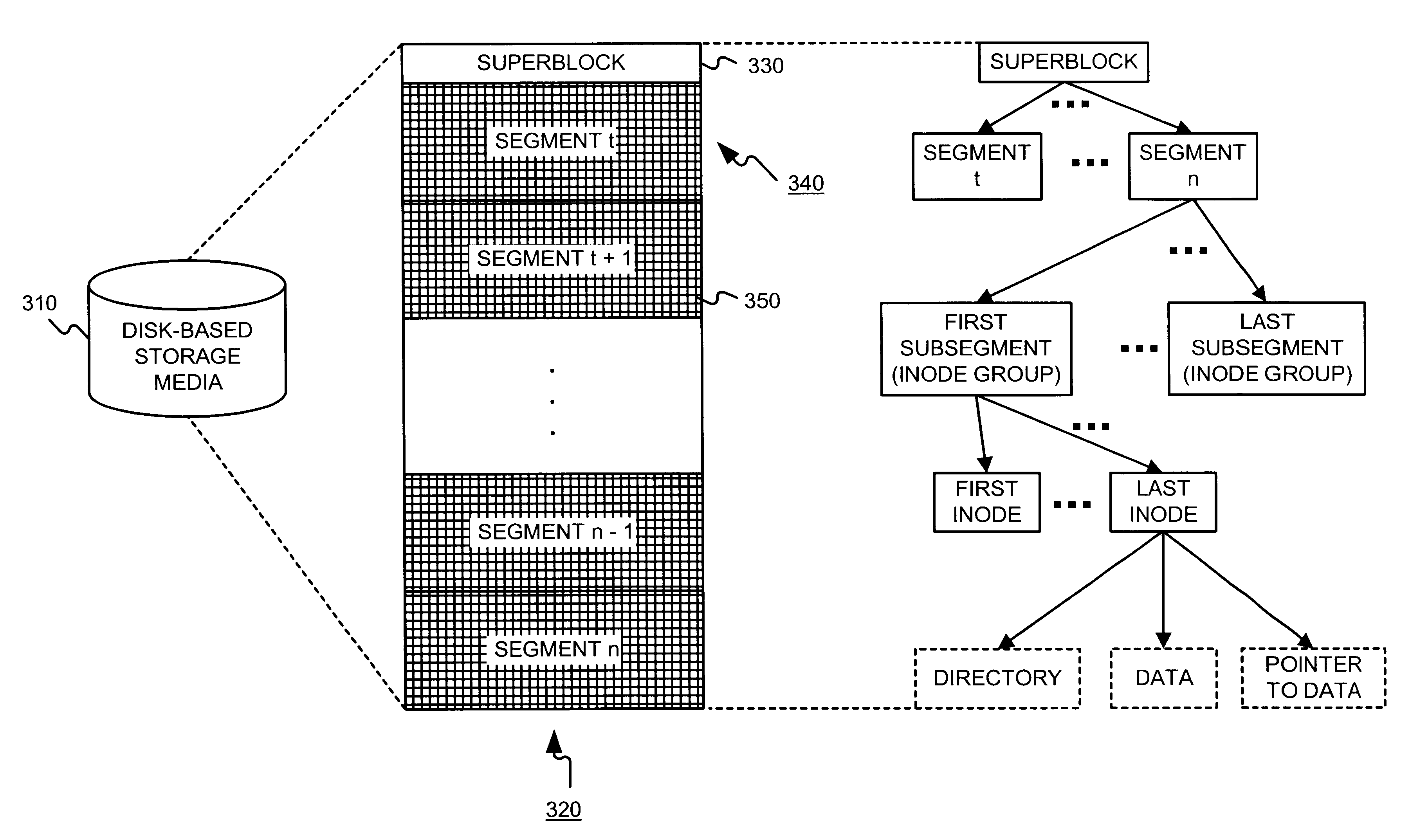
A file system (i) permits storage capacity to be added easily, (ii) can be expanded beyond a given unit, (iii) is easy to administer and manage, (iv) permits data sharing, and (v) is able to perform effectively with very large storage capacity and client loads. State information from a newly added unit is communicated (e.g., automatically and transparently) to central administration and management operations. Configuration and control information from such operations is communicated (e.g., automatically) back down to the newly added units, as well as existing units. In this way, a file system can span both local storage devices (like disk drives) and networked computational devices transparently to clients. Such state and configuration and control information can include globally managed segments as the building blocks of the file system, and a fixed mapping of globally unique file identifiers (e.g., Inode numbers) and / or ranges thereof, to such segments.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
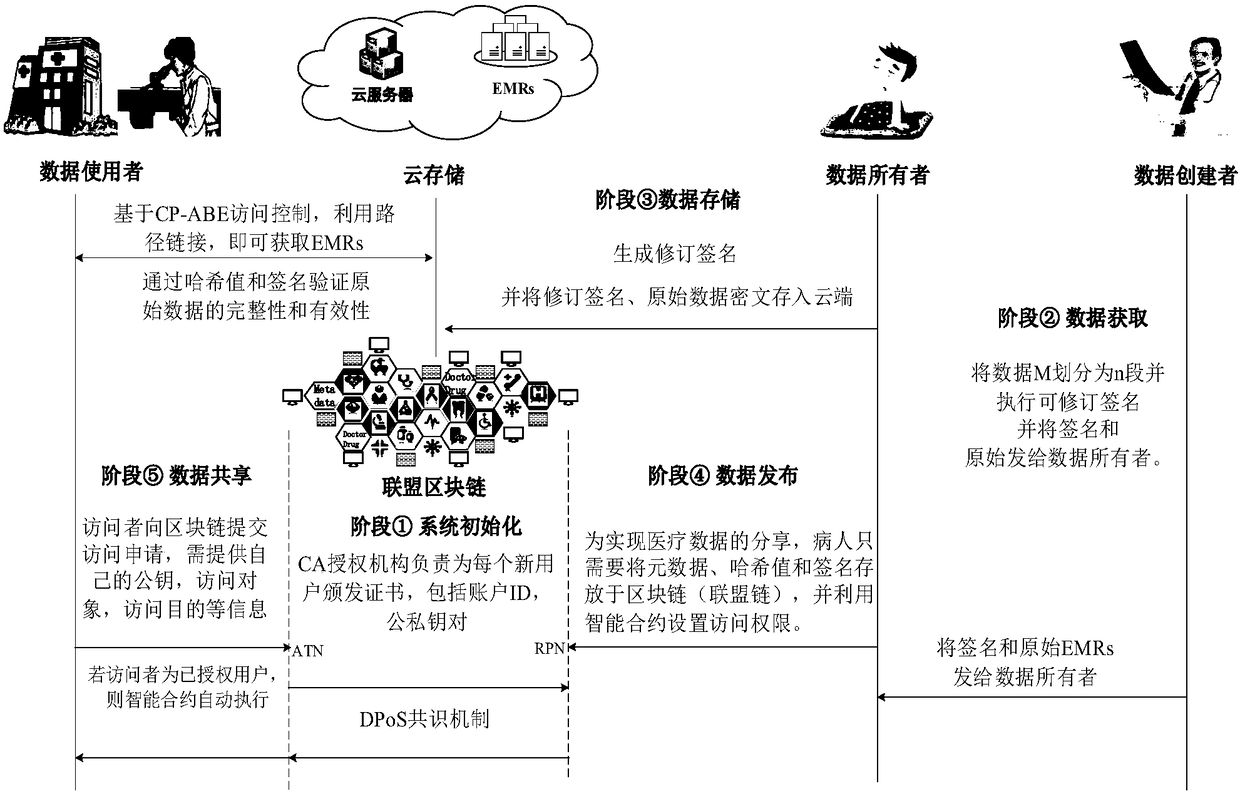
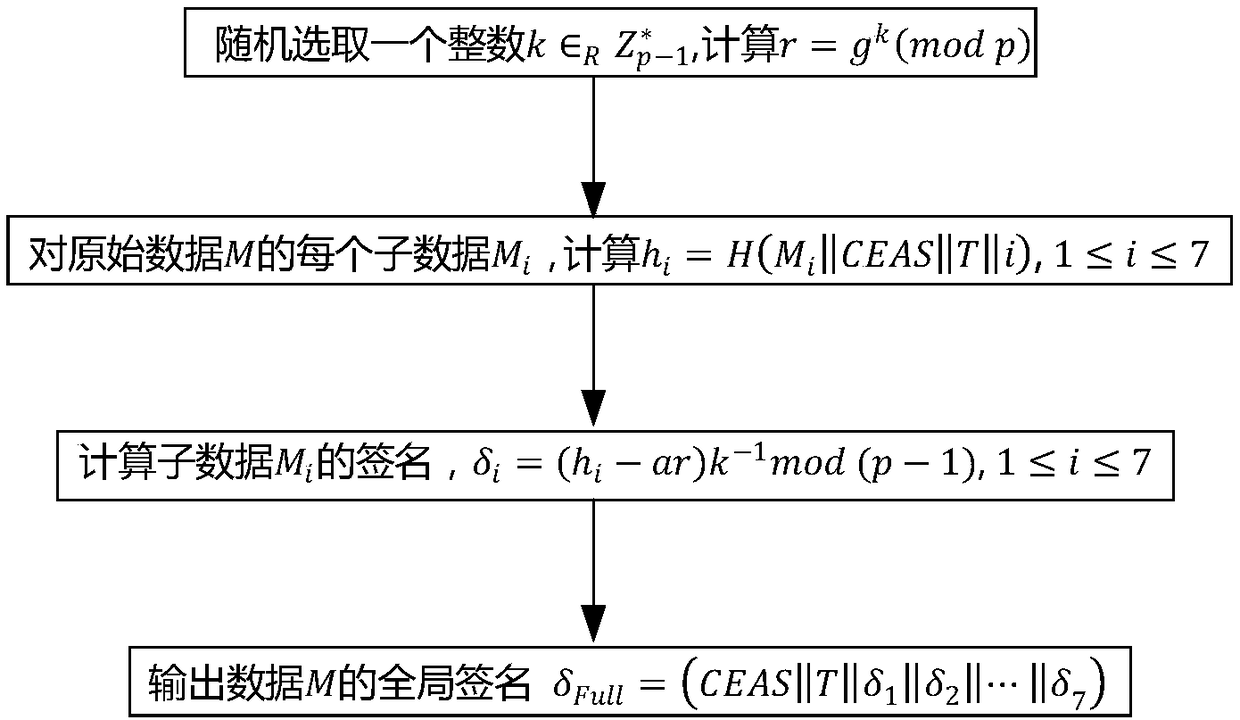
Electronic medical record storage and sharing model and method based on blockchains
ActiveCN109326337AEasy to controlImplement storage securityDigital data protectionPatient-specific dataPrivacy protectionData access
The invention discloses an electronic medical record storage and sharing model and method based on the blockchains and solves problems of patient's rights of access to personal medical data and insecure storage and sharing of sensitive medical data in the prior art. The model is characterized by comprising data creators, data owners, cloud storage, federated blockchains and data consumers, whereinthe blockchain is a control center. The method comprises steps that system initialization is performed; medical data are acquired, and data storage with intercepted signatures is employed; data publishing with the improved DPOS consensus mechanism is employed; data sharing based on smart contracts is performed. The method is advantaged in that security, reliability, privacy protection and securestorage are achieved, in combination with the cloud storage technology and the interceptable signature technology, in the federated blockchains, users can set sharing conditions through the smart contracts, safe and effective data sharing and access can be realized, and strong practicality is achieved.
Owner:XIDIAN UNIV
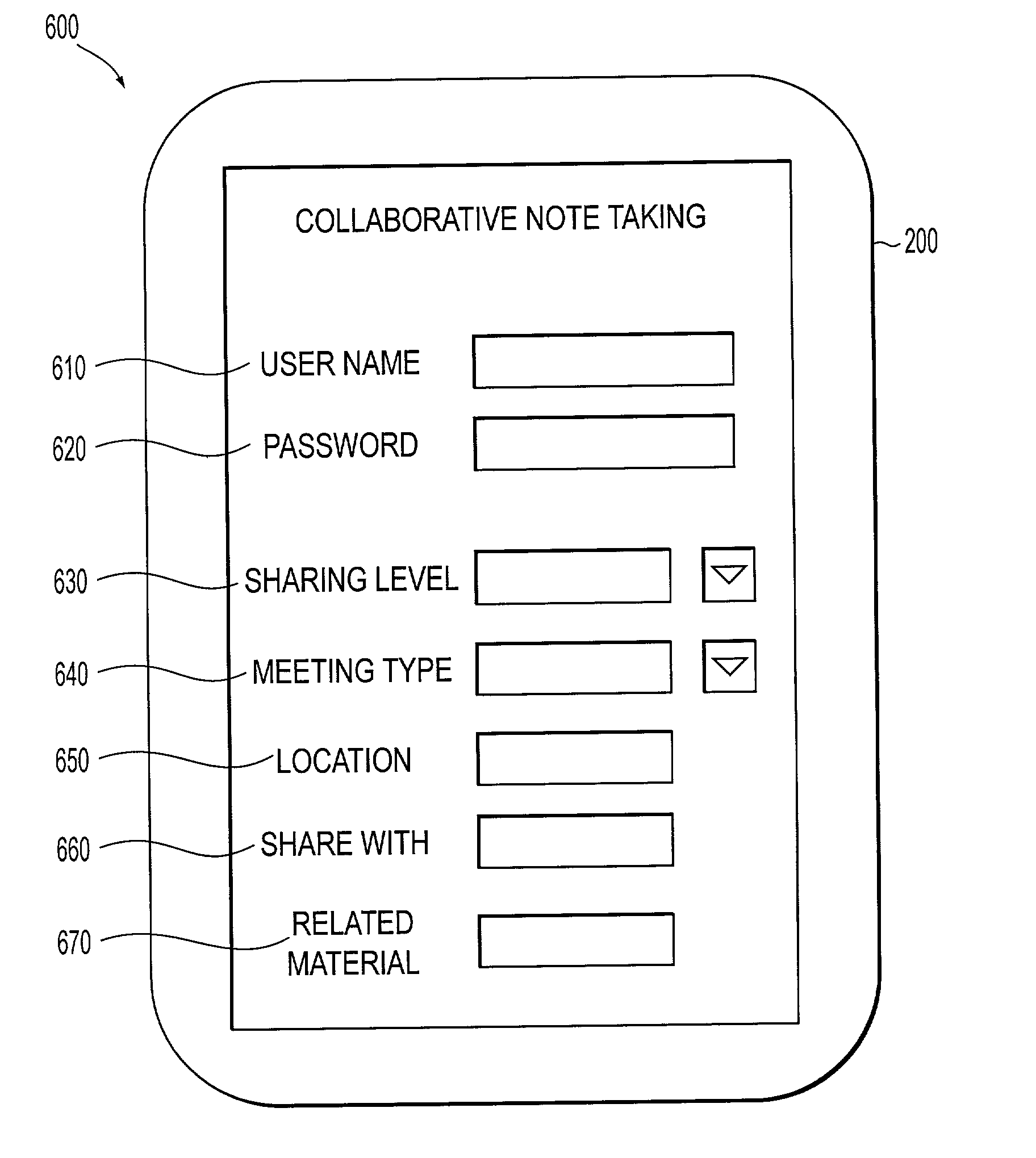
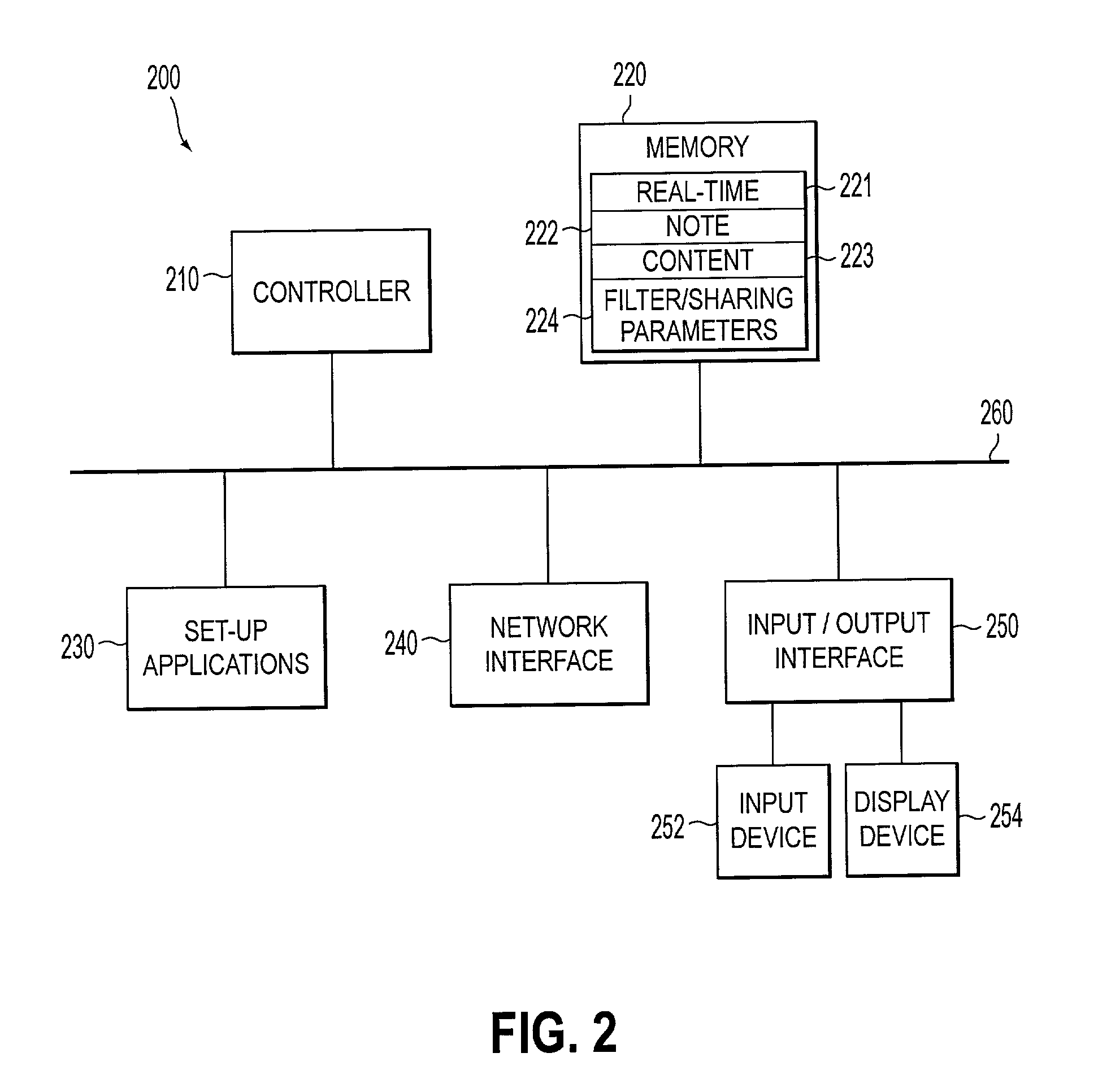
Systems and methods for displaying text recommendations during collaborative note taking
Multiple users access a collaborative data-sharing system during a data-sharing event. Each user can establish the level of sharing to be allowed with each other user and filtering criteria for filtering the data before it is provided to the other users. Data can be extracted from a number of different sources, including data input by other users and / or previously created information sources. For example, slides from a presentation on a similar topic may be identified and included by a user as a potential source of information to be used by other users. Shared data can be displayed on devices used by users to communicate with the collaborative data-sharing system. A user can selected data provided by the collaborative data-sharing system, which was obtained from the data input by other users and / or from the identified additional data sources and added to that user's data as data entered by that user.
Owner:FUJIFILM BUSINESS INNOVATION CORP
File systems supported data sharing
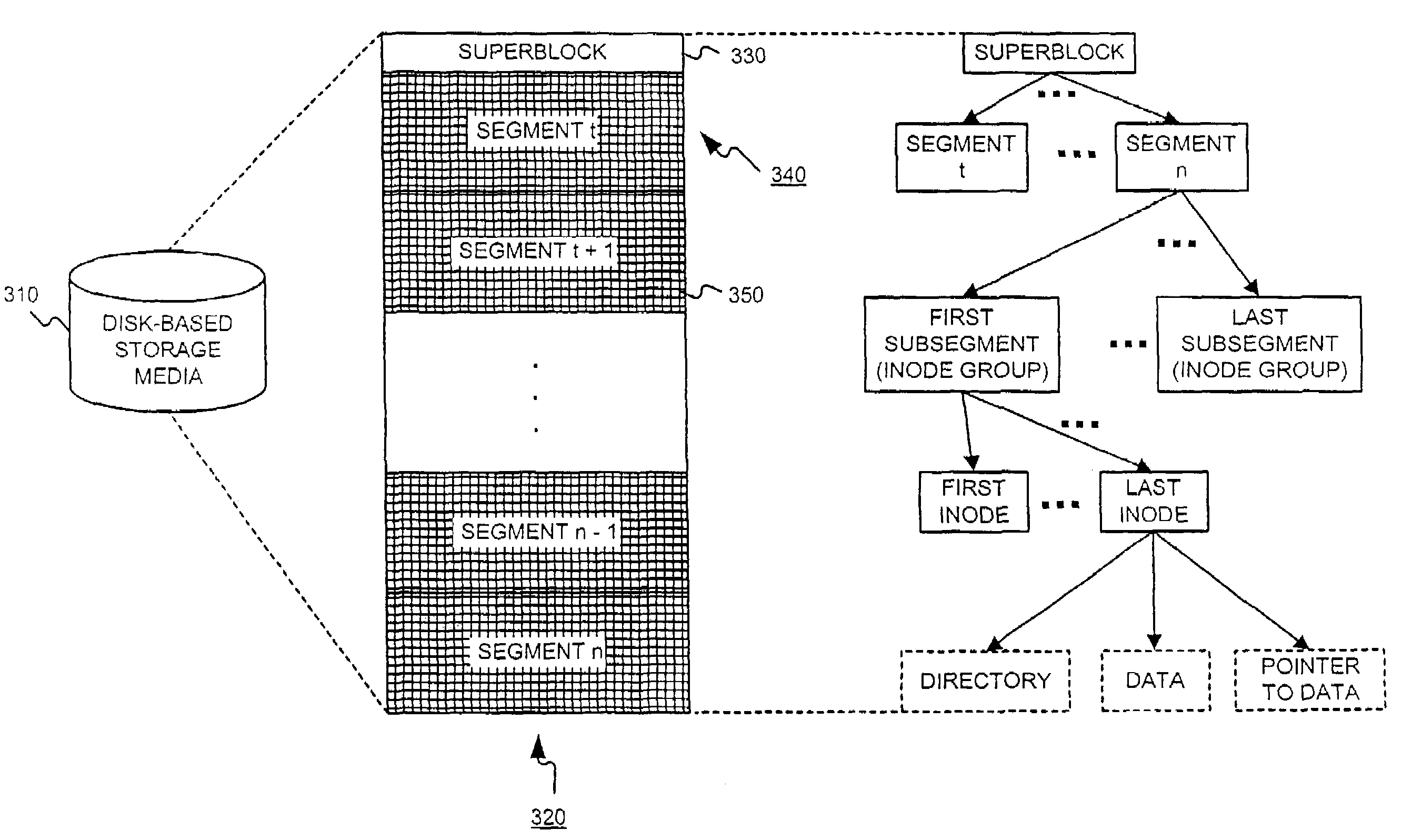
InactiveUS6934700B1Easy to operateGood flexibilityData processing applicationsInput/output to record carriersData segmentOptical disk storage
A storage file system is provided for data stored on a storage medium, and particularly for storage of data on optical disc storage medium. Each successive or alternate file of data included in the storage medium is represented by a respective allocation extent list with each allocation extent identifying locations of data segments for each file. Data in some data segments or portions of data segments may be shared by two or more files with each file having a respective allocation extent list entry referencing that segment and each such allocation extent maintaining byte-accurate pointers to the start and end of the data relevant to each file within the data segment. An allocation space table containing respective entries for each reference to a data segment or portion of a data segment, and optionally a free-space table identifying those data segments or portions of data segments available for rewriting, may be provided to allow for rapid reclamation of free within the storage medium.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Storage allocation in a distributed segmented file system
InactiveUS7406484B1Efficient executionStorage capacity can be easilyData processing applicationsTransmissionInodeData sharing
A file system (i) permits storage capacity to be added easily, (ii) can be expanded beyond a given unit, (iii) is easy to administer and manage, (iv) permits data sharing, and (v) is able to perform effectively with very large storage capacity and client loads. State information from a newly added unit is communicated (e.g., automatically and transparently) to central administration and management operations. Configuration and control information from such operations is communicated (e.g., automatically) back down to the newly added units, as well as existing units. In this way, a file system can span both local storage devices (like disk drives) and networked computational devices transparently to clients. Such state and configuration and control information can include globally managed segments as the building blocks of the file system, and a fixed mapping of globally unique file identifiers (e.g., Inode numbers) and / or ranges thereof, to such segments.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
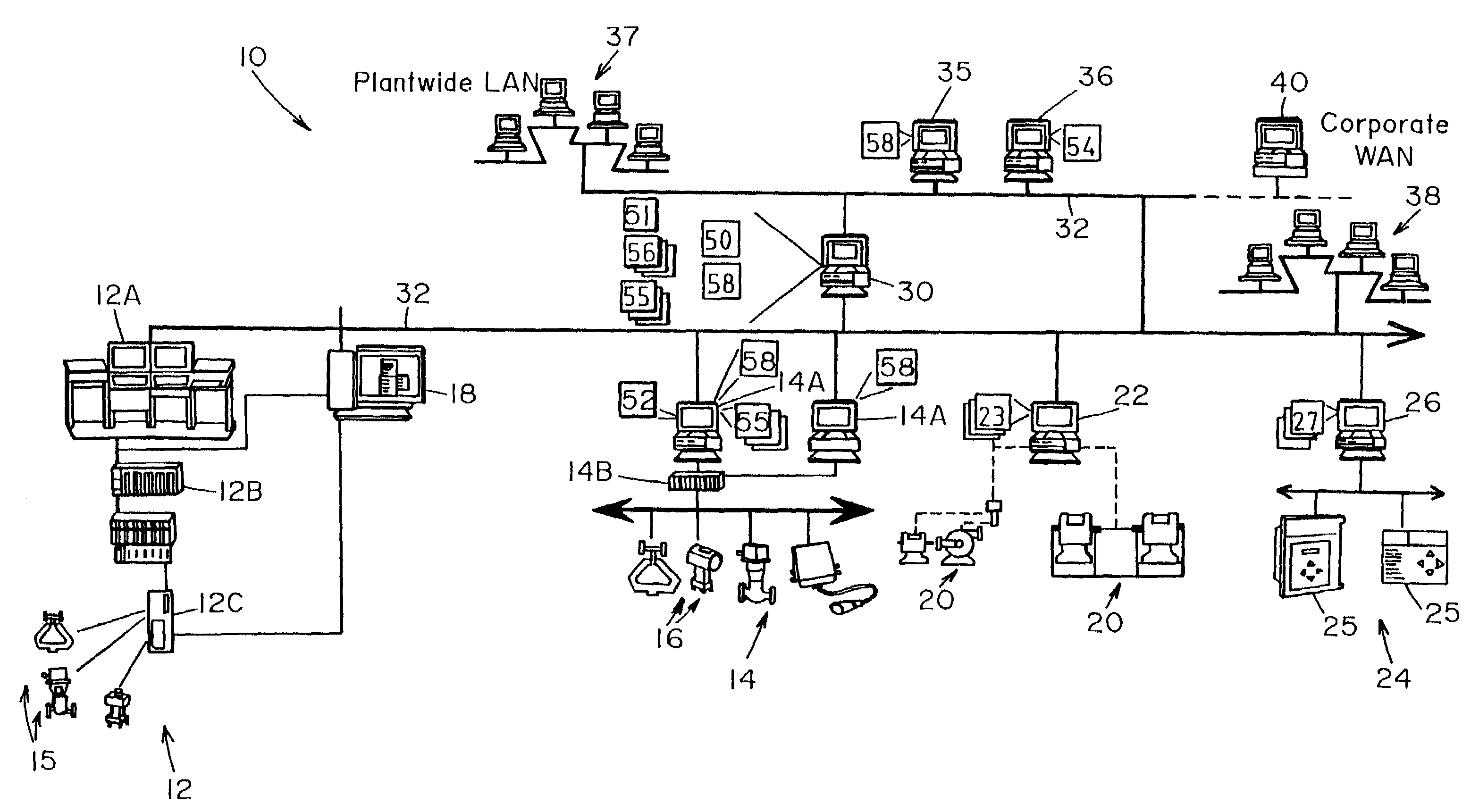
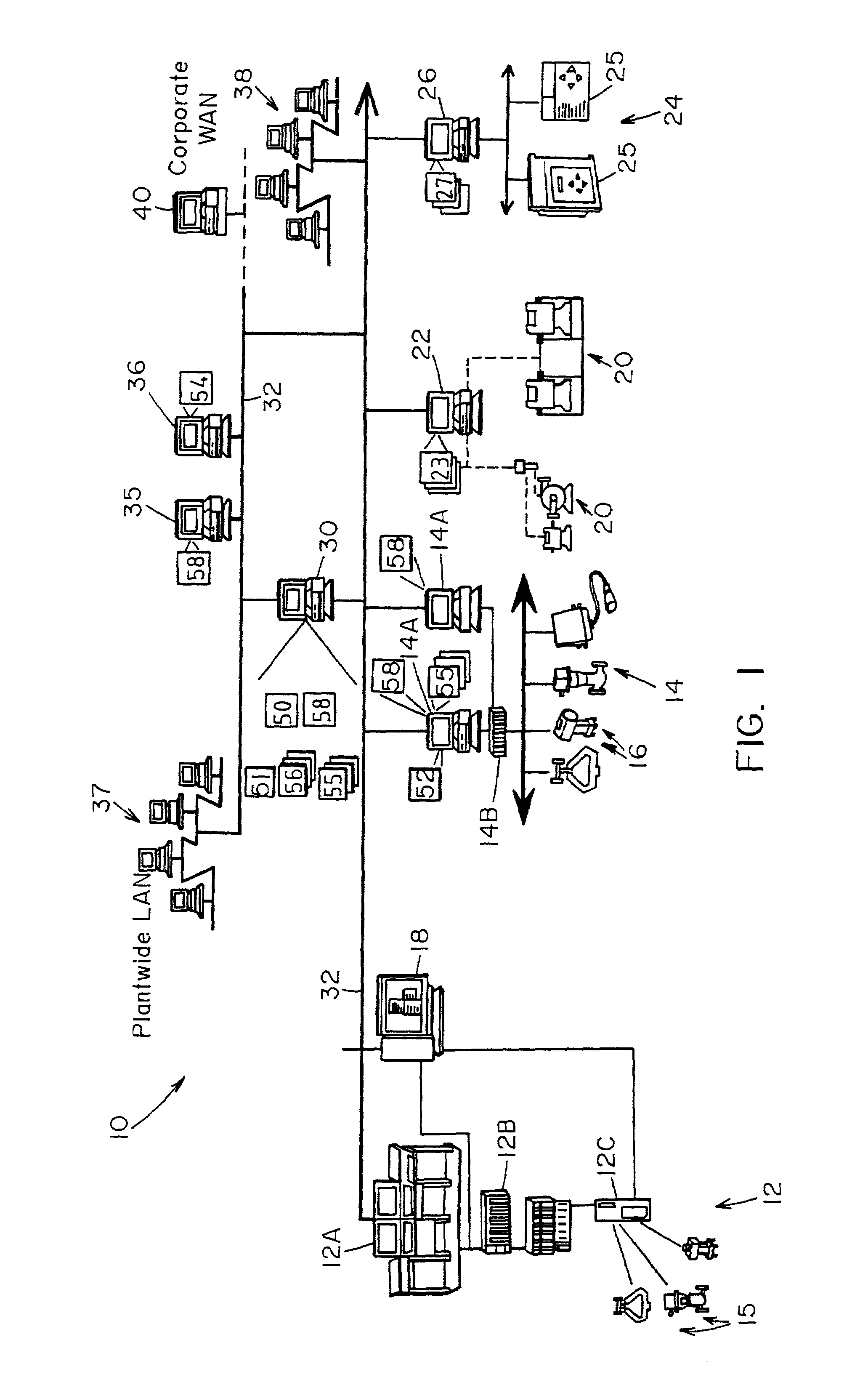
Data sharing in a process plant
InactiveUS7346404B2Sampled-variable control systemsComputer controlOptimal controlBusiness activities
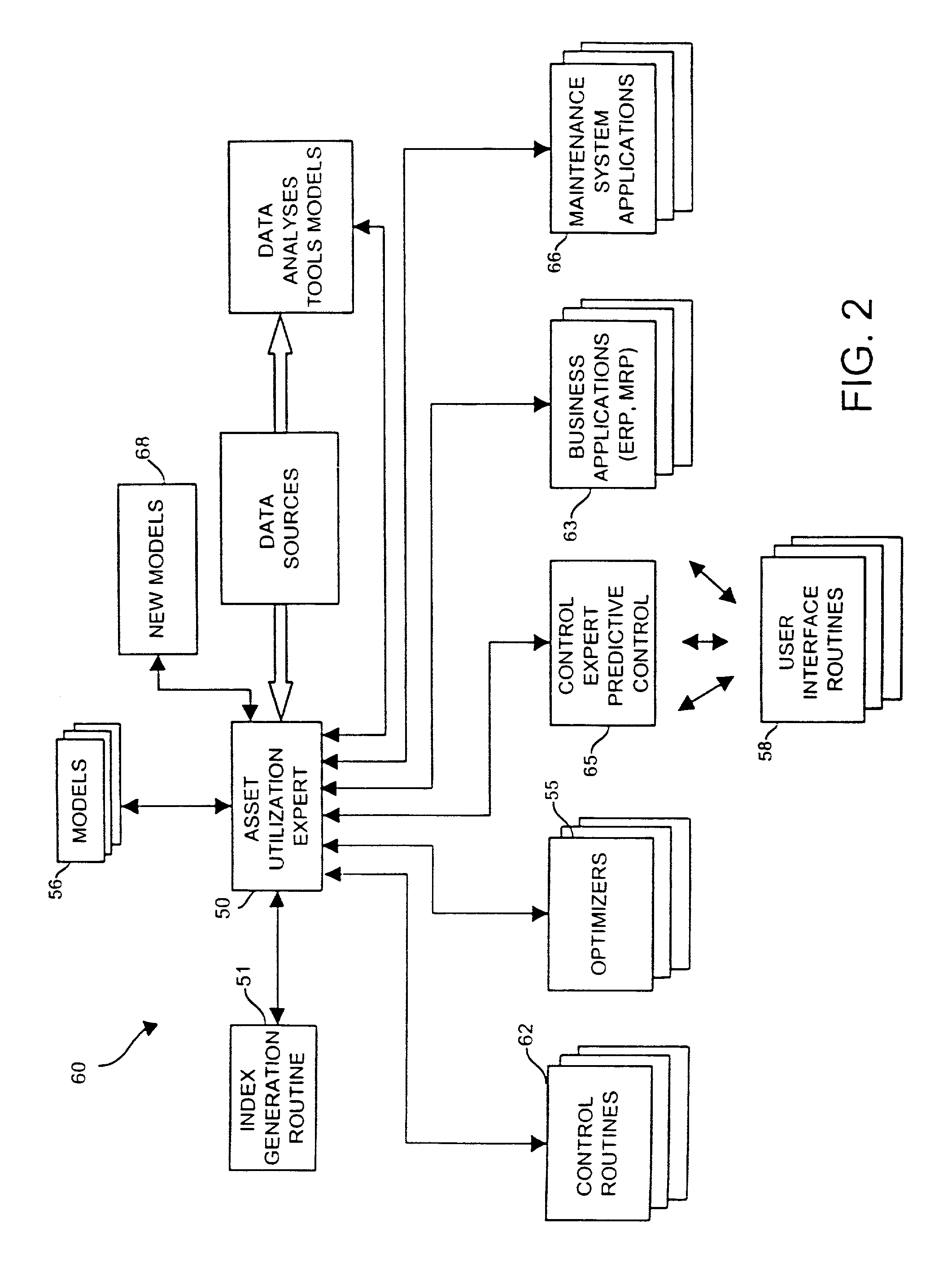
A process plant uses an asset utilization expert to collect data or information pertaining to the assets of the process plant from various sources or functional areas of the plant including, for example, the process control functional areas, the maintenance functional areas and the business systems functional areas. This data and information is stored in a database and is sent to and manipulated in a coordinated manner by tools, such as optimization and modeling tools. This data is also redistributed to other areas or tools where it is used to perform overall better or more optimal control, maintenance and business activities. Information or data may be collected by maintenance functions pertaining to the health, variability, performance or utilization of a device, loop, unit, etc. and this information may then be sent to and displayed to a process operator or maintenance person to inform that person of a current or future problem.
Owner:FISHER-ROSEMOUNT SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com