Patents
Literature
1724 results about "Network storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and methodology for optimizing delivery of email attachments for disparate devices
InactiveUS20020016818A1Digital data information retrievalMultiple digital computer combinationsDevice typeWireless handheld devices
An e-mail system that re-packages message attachments optimized for delivery to wireless handheld devices is described. The preferred embodiment provides an optimization of the e-mail deliveries to allow for the recipients to receive e-mail attachments at a time and in a size / format as desired. The preferred embodiment compares the size of attached images to the capabilities of the type of the recipient client device, and preempts delivery of the original format of those attachments if they are determined to be burdensome or overwhelming. In cases wherein these attachments would strain the capabilities of the recipient devices' wireless bandwidth and / or display features, the original attachments are removed from the messages and do not accompany the e-mail delivery. Any detached attachment is saved in a network media-sharing repository, and can be subsequently accessed via a link (e.g., URL) referencing that storage address. Recipients can specify their wireless handheld device types, and opt to receive transformations of this type of attachment as a default substitute in subsequent e-mail deliveries. In cases wherein the recipient has previously used multiple types of client devices when receiving messages from the system, the present invention applies a transformation on the current attachment that corresponds to the least capable in the set of those multiple devices. Recipients may also elect to receive the URL for the network storage address of copies of either the original and / or transformed attachments.
Owner:SYNIVERSE ICX CORP
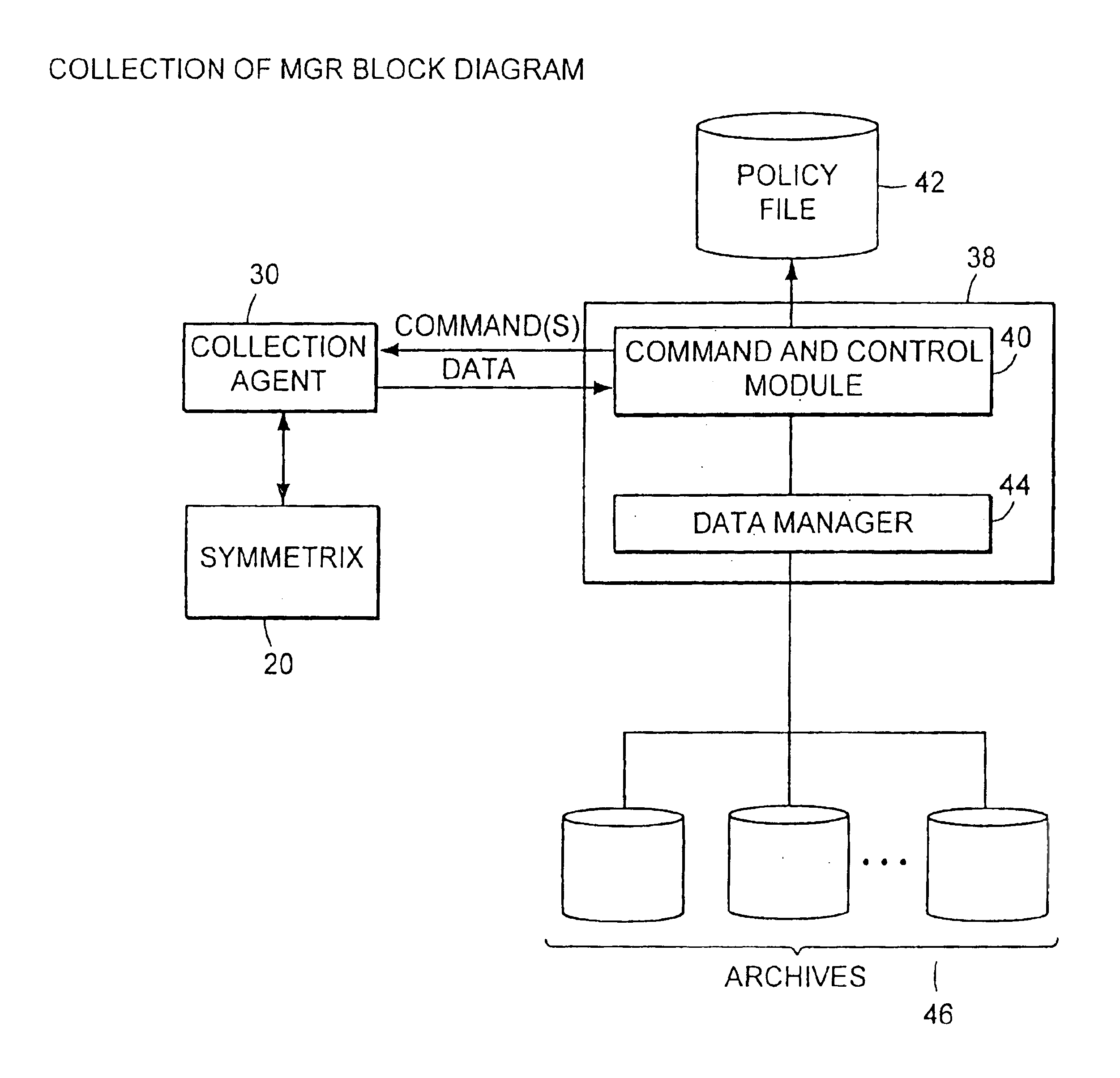
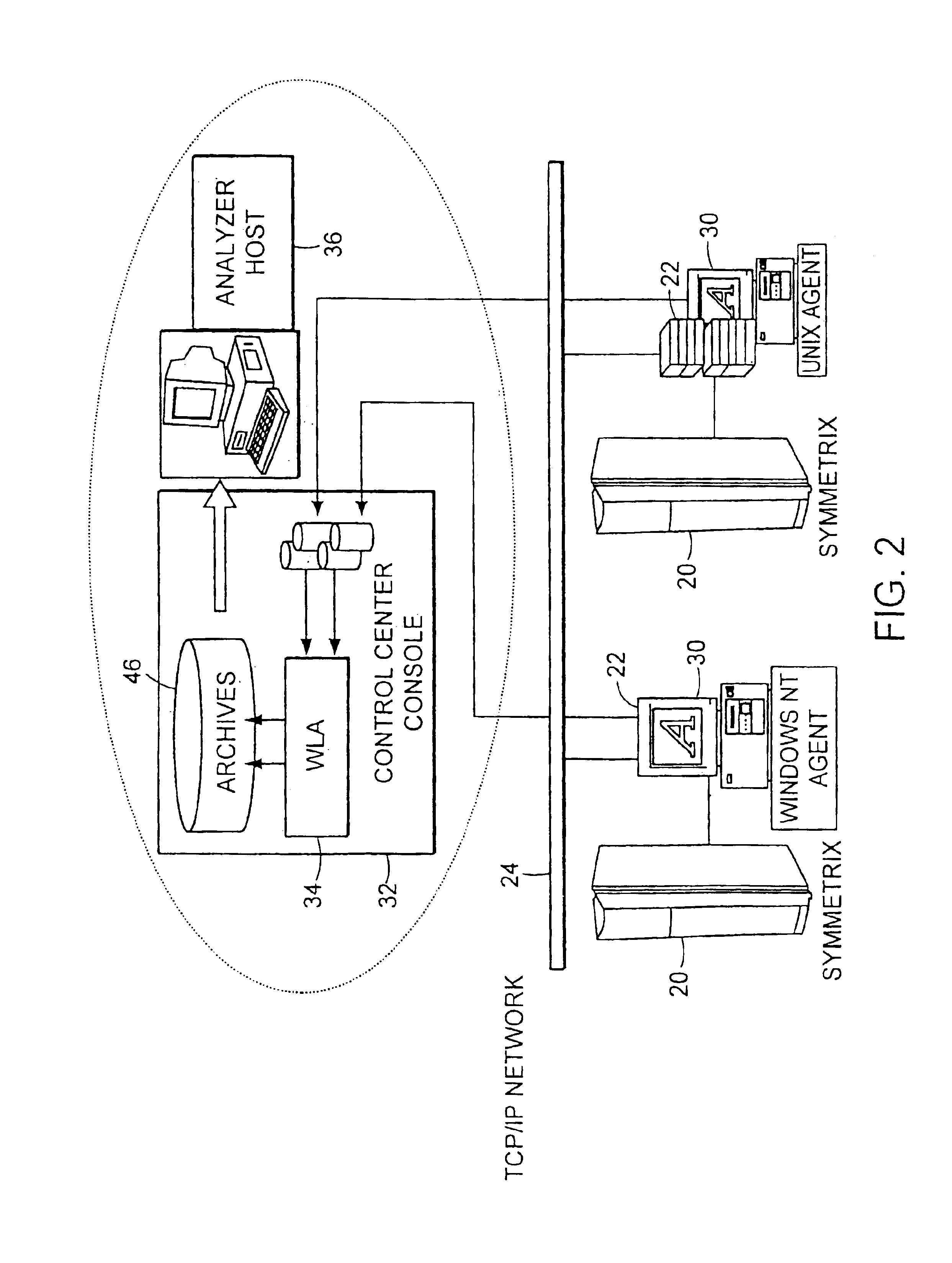
Method and apparatus for storage system metrics management and archive
InactiveUS6886020B1Promote generationEasy accessData processing applicationsDigital data information retrievalCommand and controlData management
A data management and archive method and apparatus, such as for implementation in an automated system to monitor and manage status, performance and configuration data for a plurality of networked storage components. Analysis and cross-correlation of data related to the plurality of storage components can be done individually, collectively and / or comparatively. A collection manager component of a workload analyzer is implemented to start and stop data collection in the context of a system comprising at least one storage component (or at least two networked storage components). The collection manager includes a command and control module that coordinates requests of data from at least one collection agent configured on at least one host connected to the storage component(s).
Owner:EMC IP HLDG CO LLC
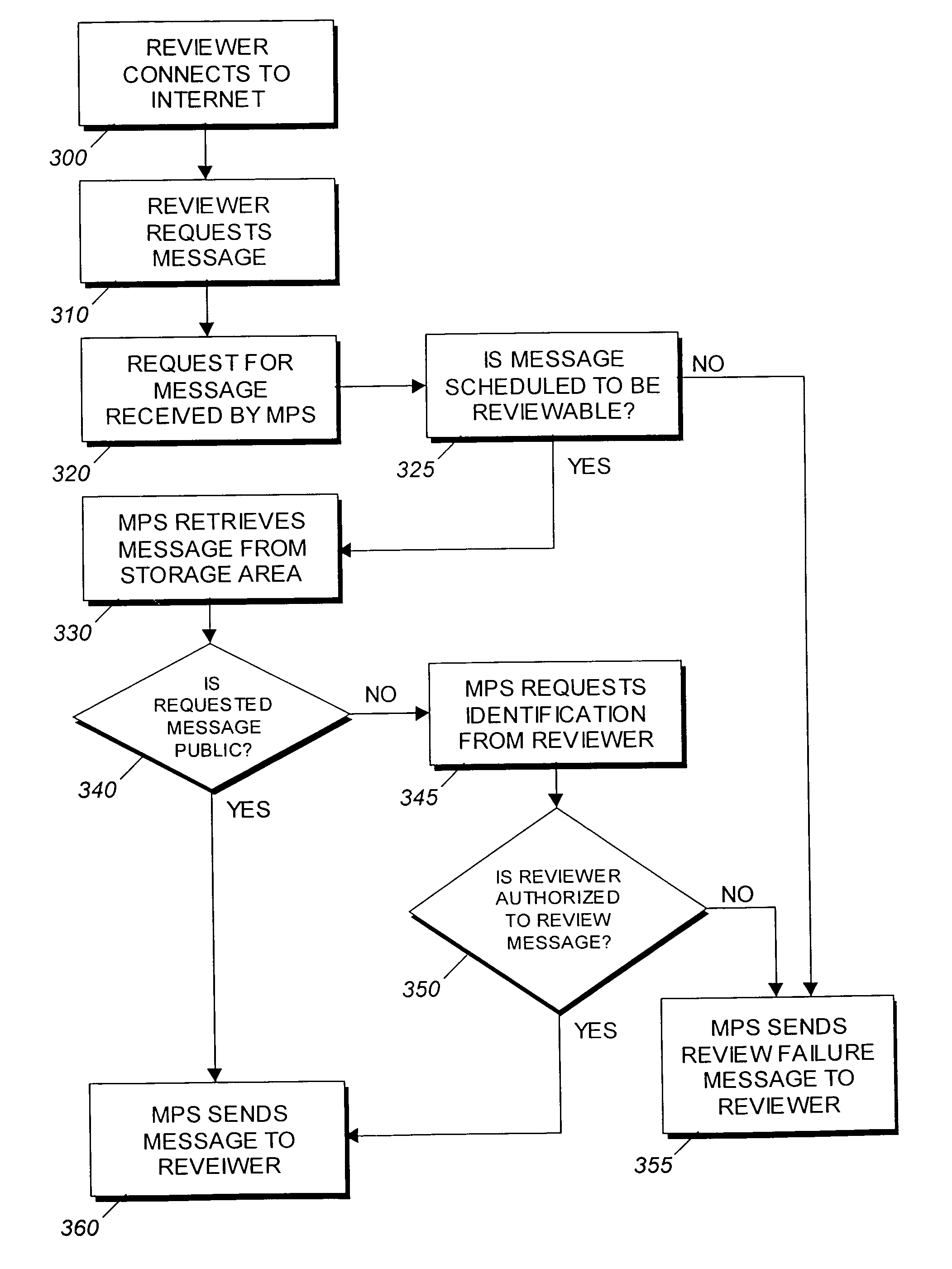
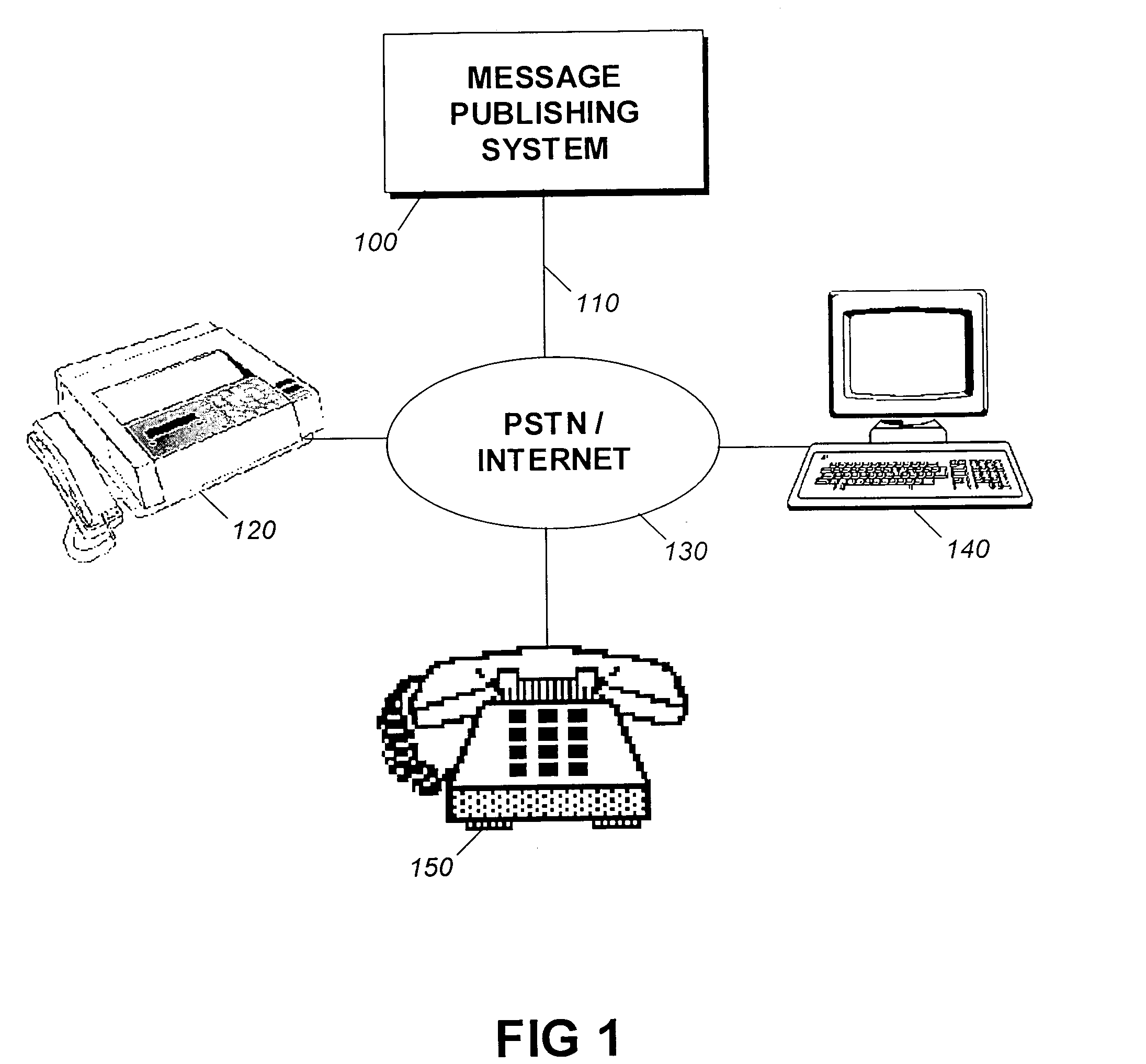
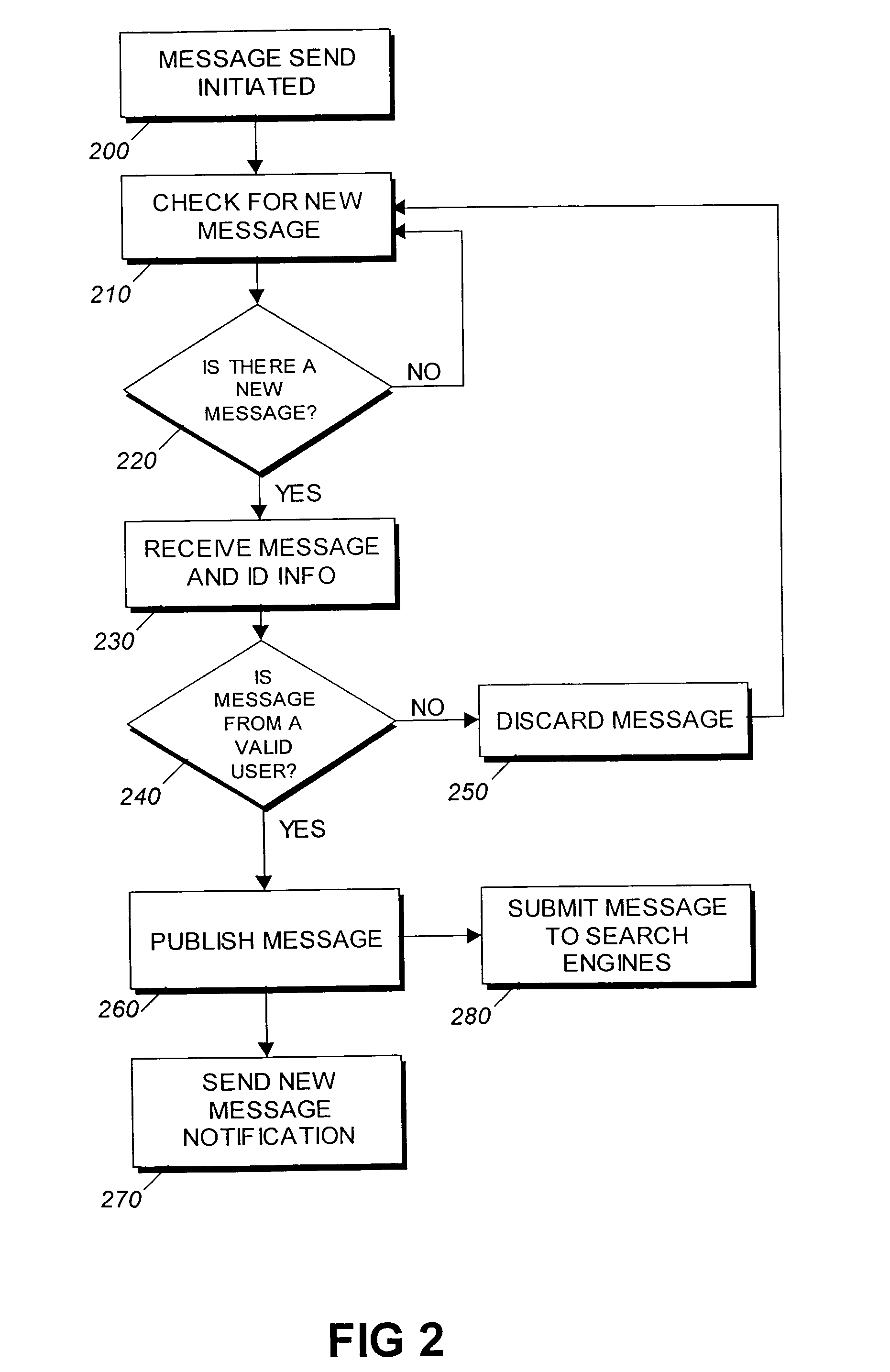
Message publishing system and method
InactiveUS7032030B1Easy to publishEasy and secure and economicalData processing applicationsUser identity/authority verificationWeb browserWeb service
A Message Publishing System (MPS) and method is disclosed. The MPS publishes a message, preferably on the Internet, that can be simultaneously reviewed by a mass audience. A user of the MPS sends the message to be published to the MPS. The MPS verifies that the sender of the message is an authorized user of the MPS before publishing the message. The MPS converts the received message into one or more formats, preferably webpage(s) for display on the Internet. The message is stored in a network storage area, preferably on an Internet web server. When the MPS receives a request for the message, it retrieves the requested message from the storage area and sends it to the requestor for review, preferably using a web browser.
Owner:EASYWEB INNOVATIONS
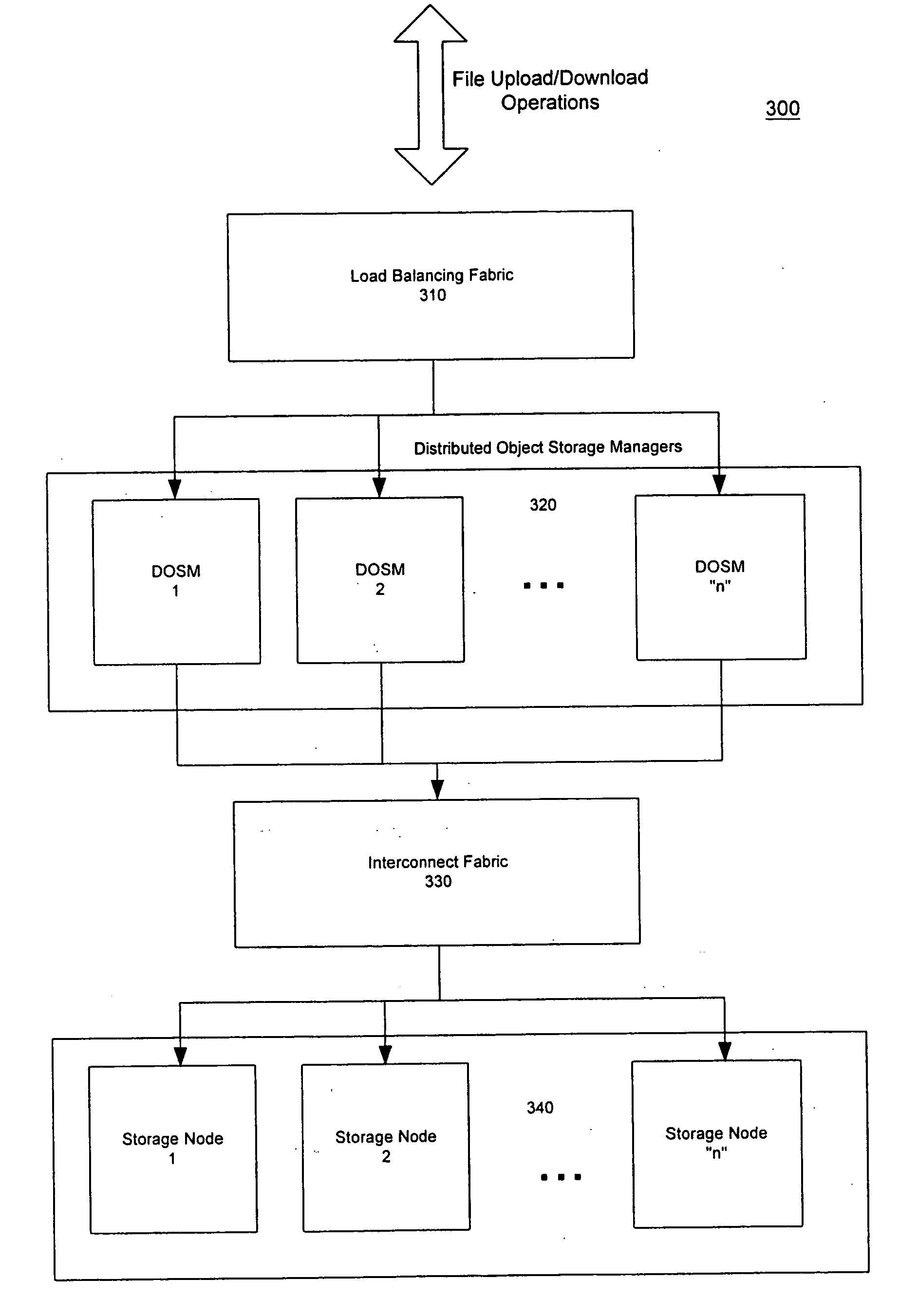
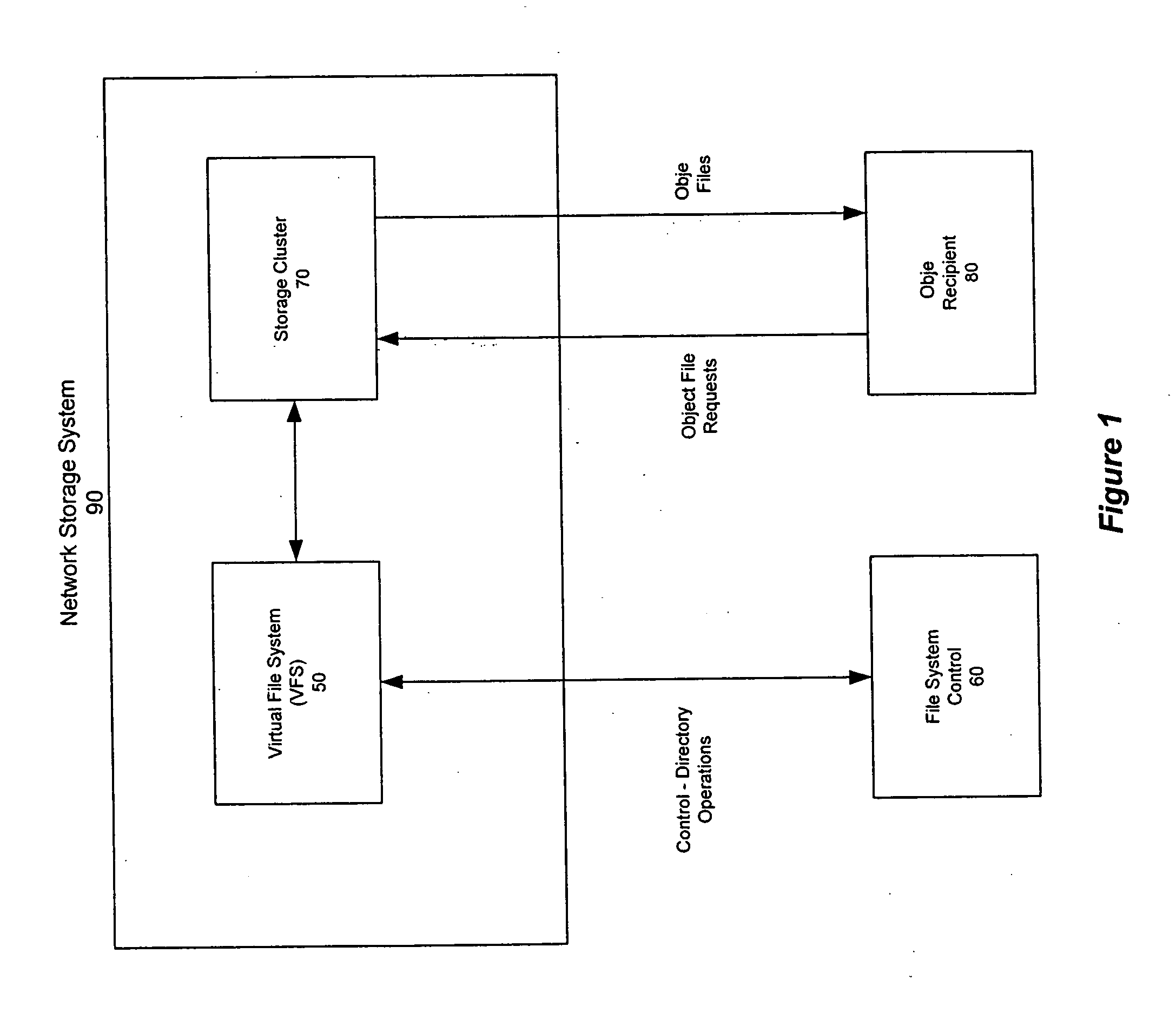
Distributed storage cluster architecture
InactiveUS20050246393A1Input/output to record carriersDigital data information retrievalVirtual file systemDistributed object
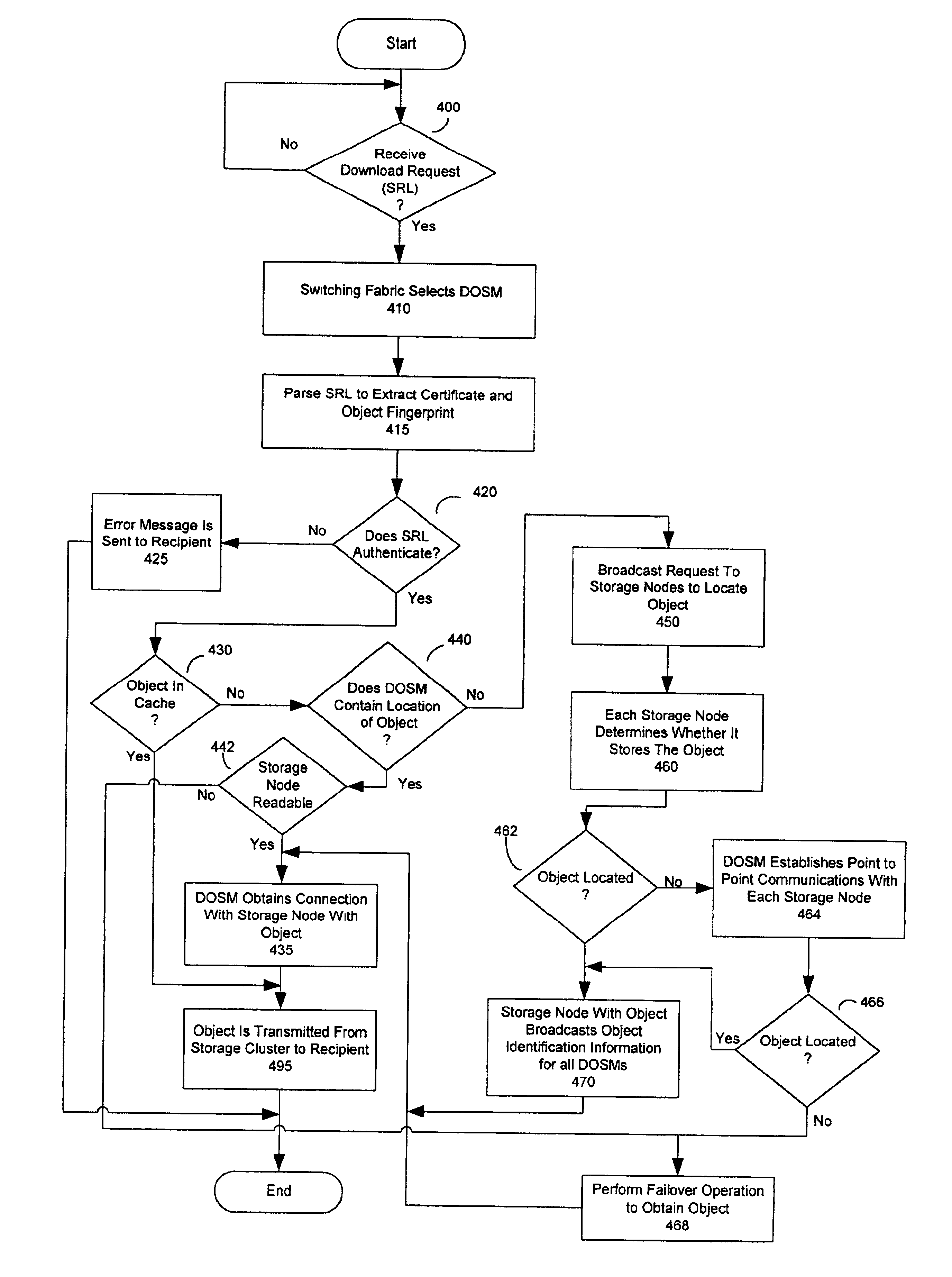
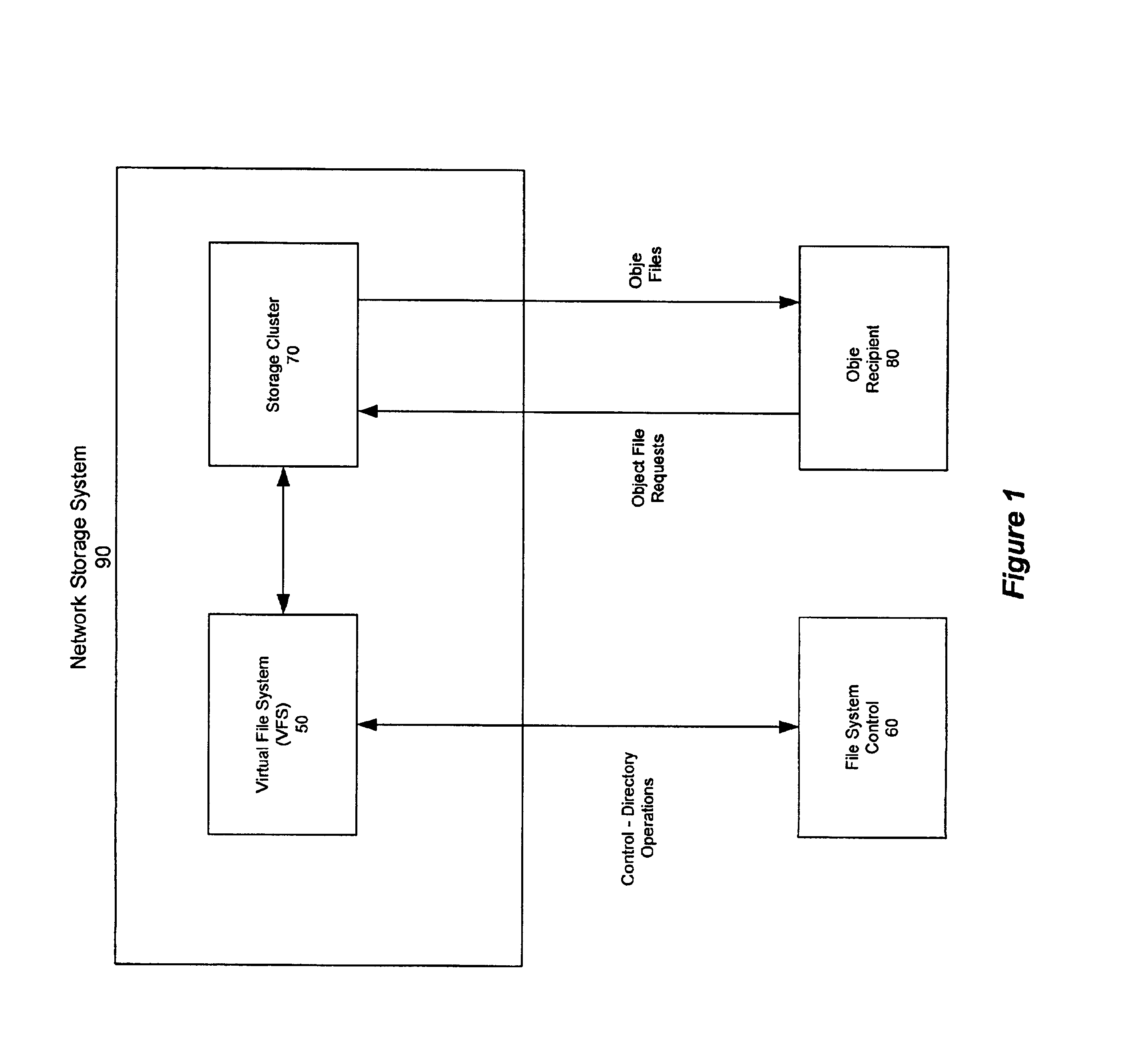
A network storage system includes a virtual file system (“VFS”) that manages the files of the network storage system, and a storage center that stores the files. The VFS and the storage center are separated, such that a client accesses the VFS to conduct file system operations and the client accesses the storage center to upload / download files. The client accesses the network storage system through one or more storage ports. The storage center includes a plurality of distributed object storage managers (DOSMs) and a storage cluster that includes a plurality of intelligent storage nodes. The network storage system includes additional storage centers at geographically disparate locations. The network storage system uses a multi-cast protocol to maintain file information at the DOSMs regarding files stored in the intelligent storage nodes, including files stored in disparate storage centers.
Owner:INTEL CORP
Networked content storage
InactiveUS20070124781A1Easy to useIncrease supplyAnalogue secracy/subscription systemsTwo-way working systemsComputer scienceOperating system
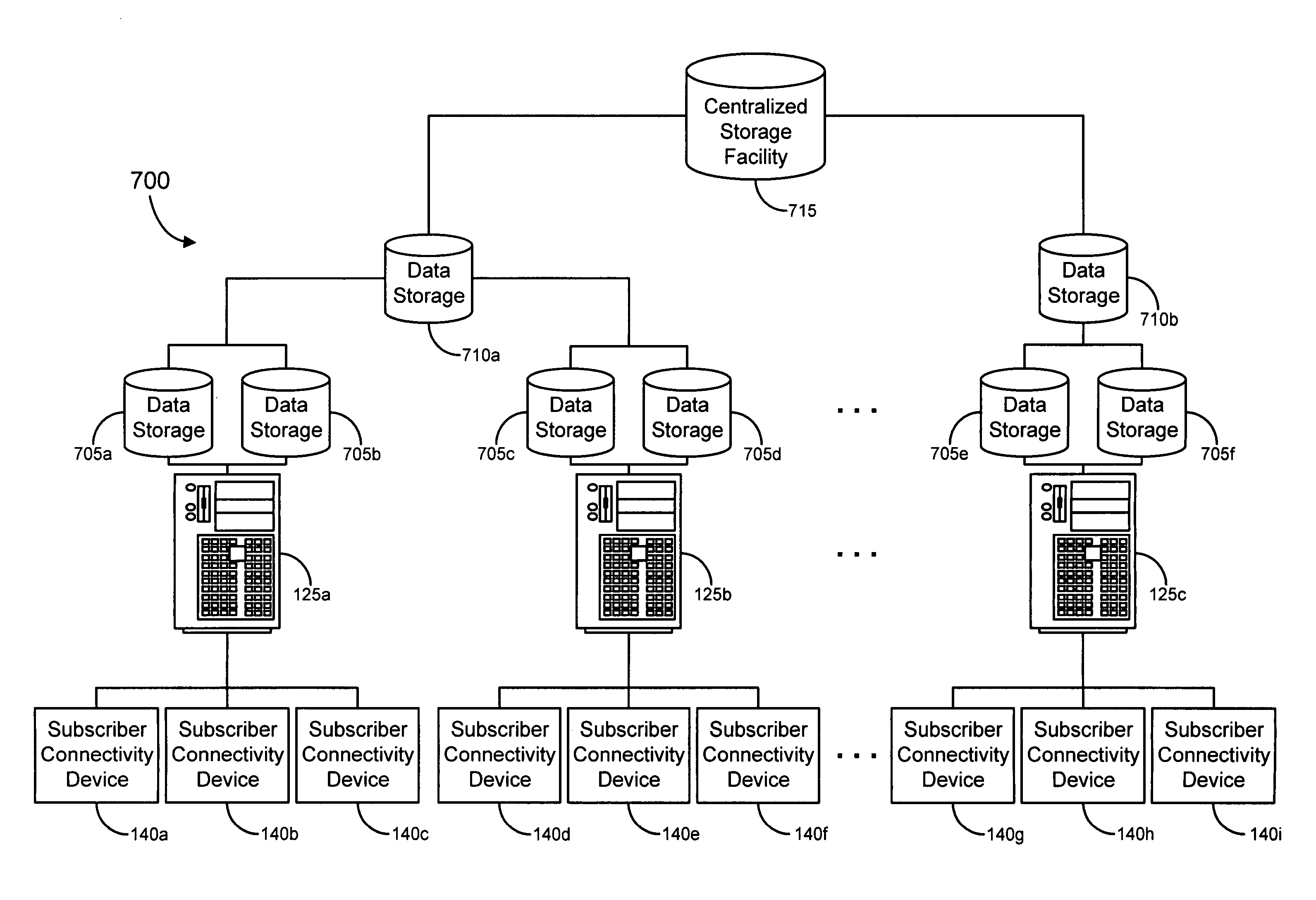
Embodiments of the invention provide networked storage of content, which can be used to allow the enhanced provision of real-time and / or on-demand content (such as video content, audio content, etc.) to a subscriber. Merely by way of example, in an aspect of some embodiments, a hierarchical storage structure may be used to cache content for provision to a plurality of subscribers. This can be used to balance competing concerns of efficiently using network and / or storage resources and providing expedient responses to subscribers' requests for content.
Owner:QWEST
Method and apparatus for accessing remote storage in a distributed storage cluster architecture
InactiveUS6952737B1Digital data information retrievalInput/output to record carriersVirtual file systemDistributed object
A network storage system includes a virtual file system (“VFS”) that manages the files of the network storage system, and a storage center that stores the files. The VFS and the storage center are separated, such that a client accesses the VFS to conduct file system operations and the client accesses the storage center to upload / download files. The client accesses the network storage system through one or more storage ports. The storage center includes a plurality of distributed object storage managers (DOSMS) and a storage cluster that includes a plurality of intelligent storage nodes. The network storage system includes additional storage centers at geographically disparate locations. The network storage system uses a multi-cast protocol to maintain file information at the DOSMs regarding files stored in the intelligent storage nodes, including files stored in disparate storage centers.
Owner:INTEL CORP
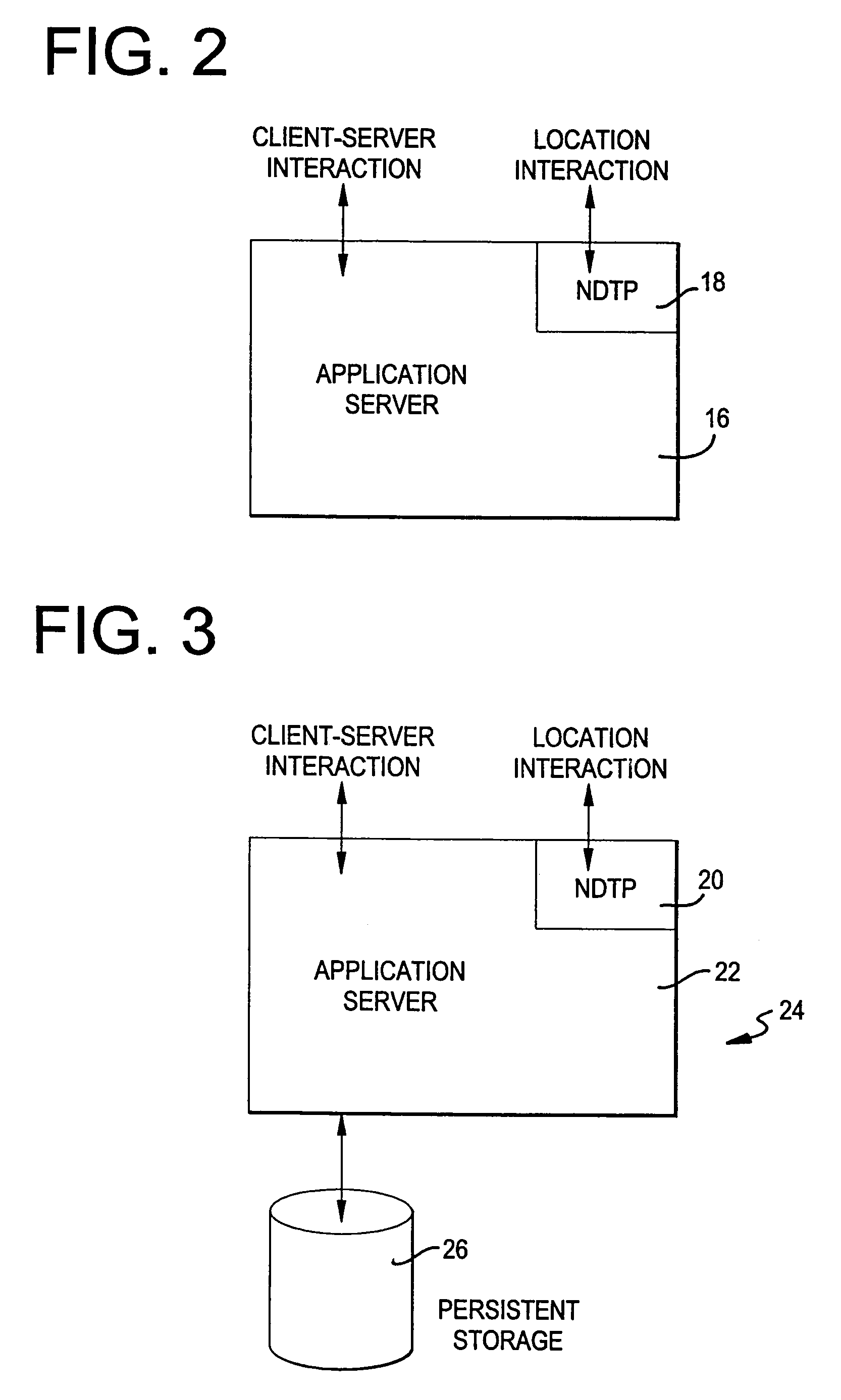
Method and apparatus for managing location information in a network separate from the data to which the location information pertains
InactiveUS7233978B2Multiple digital computer combinationsMetadata still image retrievalComputer scienceNetwork storage
A system and method for storing and retrieving location information across a network is disclosed. The system and method utilize a transfer protocol configured to transport an identifier / location relationship to allow one or more locations to be associated with an identifier in the location store of a location server, where the identifier represents a unique entity and the location represents a location of data pertaining to the identifier. The location server contains programming logic operative to provide responses to location queries and capable of scaling a plurality of location servers according to system performance and logistical requirements.
Owner:KOVE IO INC
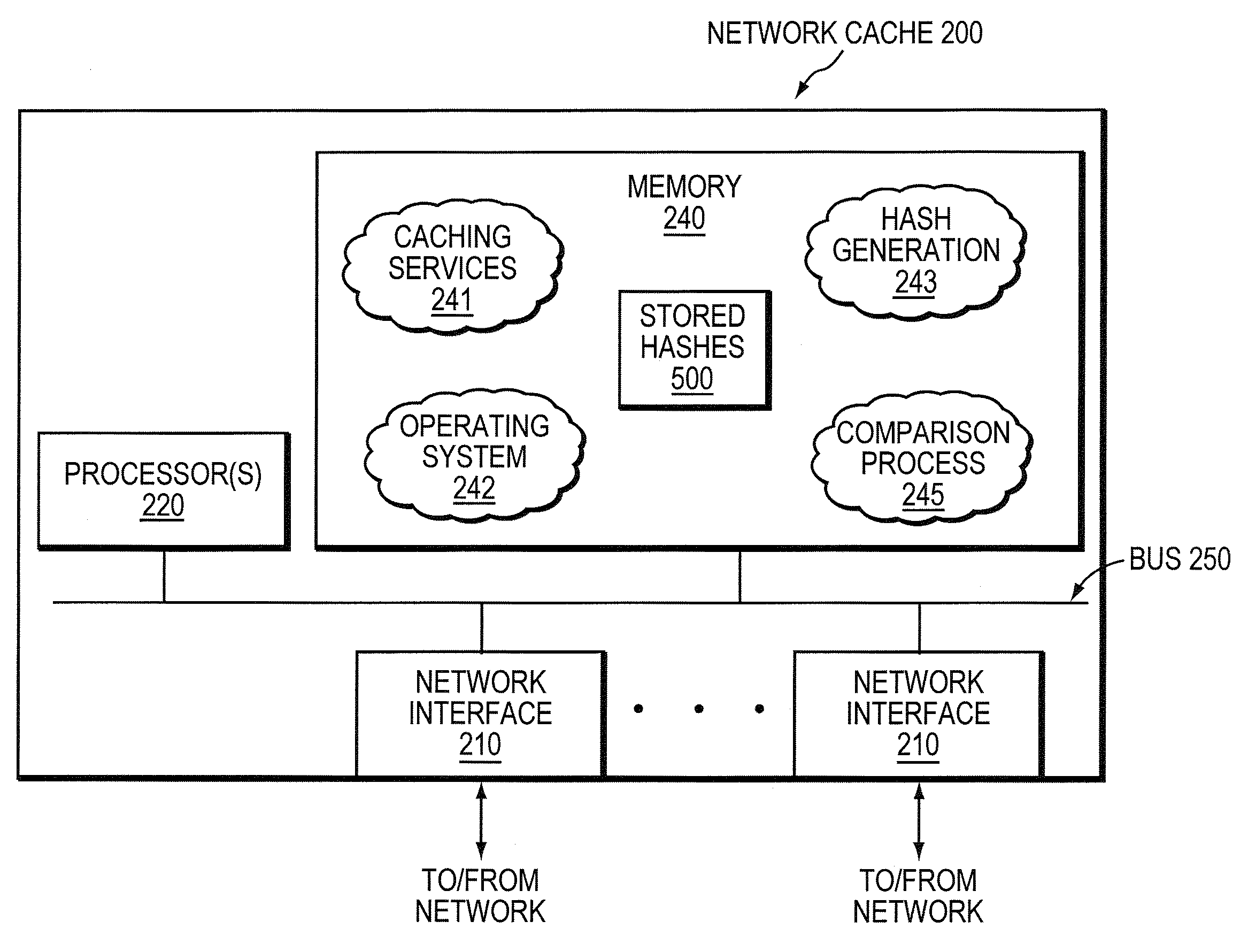
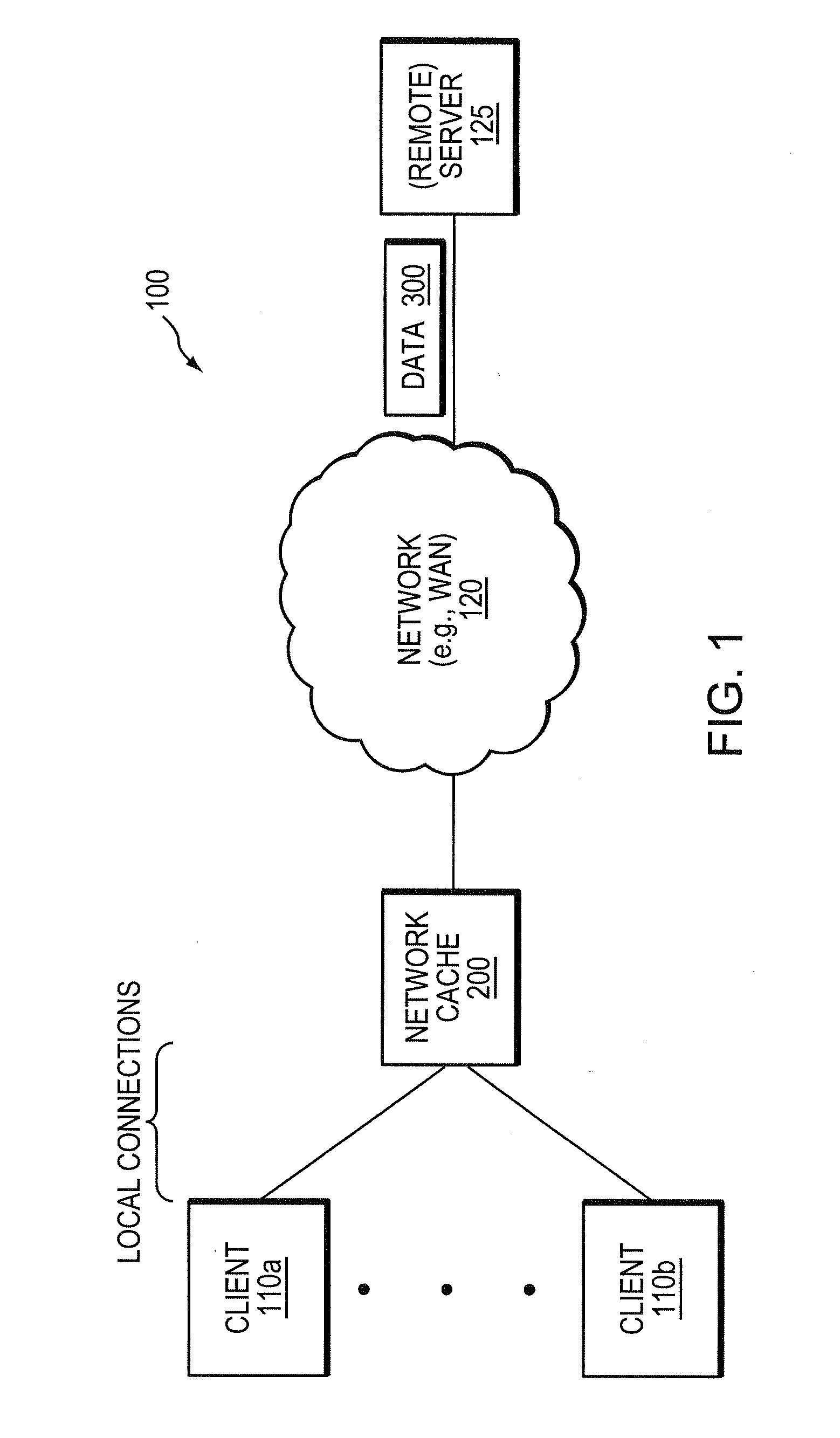
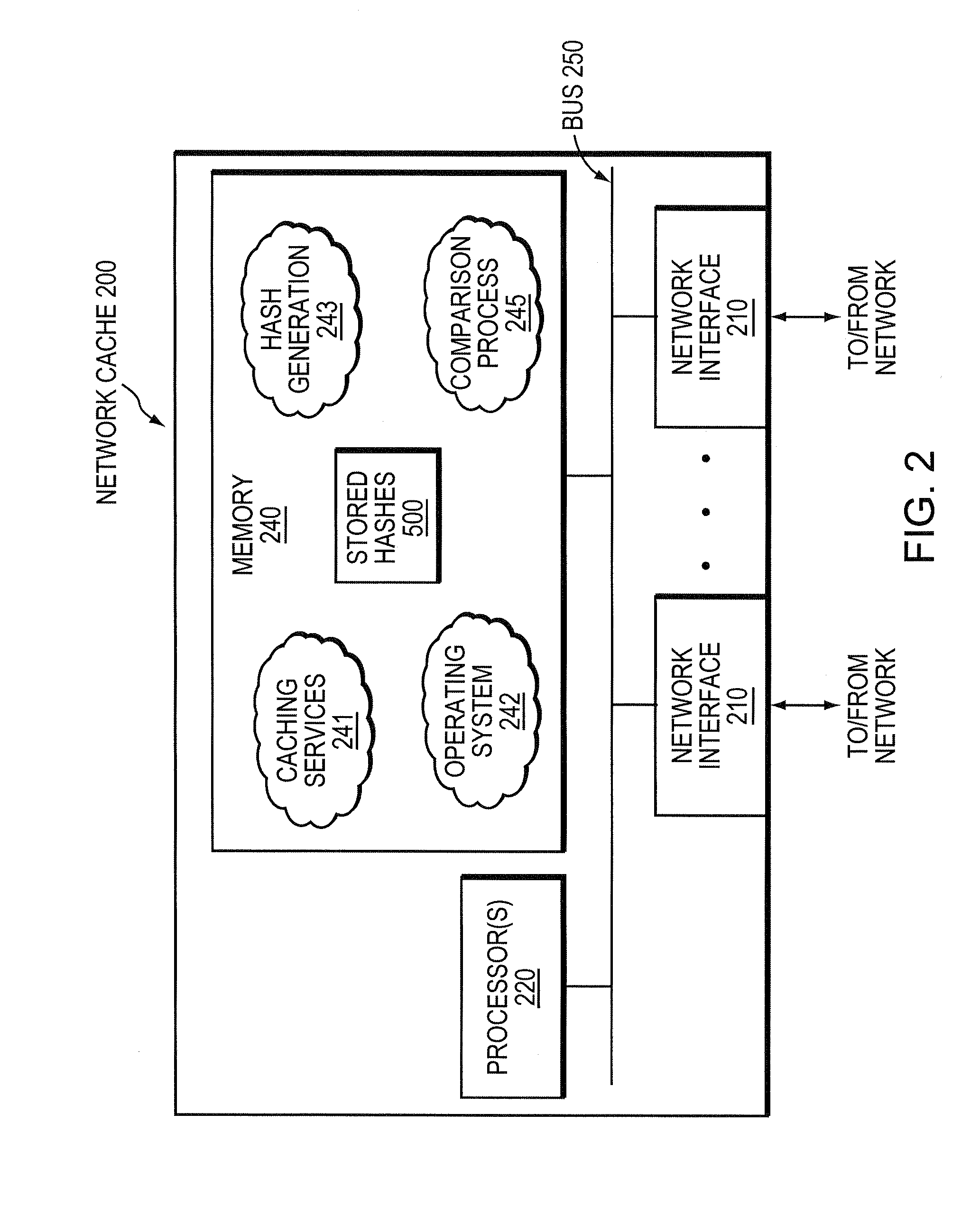
System and method for bandwidth optimization in a network storage environment
ActiveUS20080243992A1Optimized network bandwidth utilizationResource can be very expensiveMultiple digital computer combinationsSpecial data processing applicationsClient-sideData store
According to one or more embodiments of the present invention, a network cache intercepts data requested by a client from a remote server interconnected with the cache through one or more wide area network (WAN) links (e.g., for Wide Area File Services, or “WAFS”). The network cache stores the data and sends the data to the client. The cache may then intercept a first write request for the data from the client to the remote server, and determine one or more portions of the data in the write request that changed from the data stored at the cache (e.g., according to one or more hashes created based on the data). The network cache then sends a second write request for only the changed portions of the data to the remote server.
Owner:NETWORK APPLIANCE INC
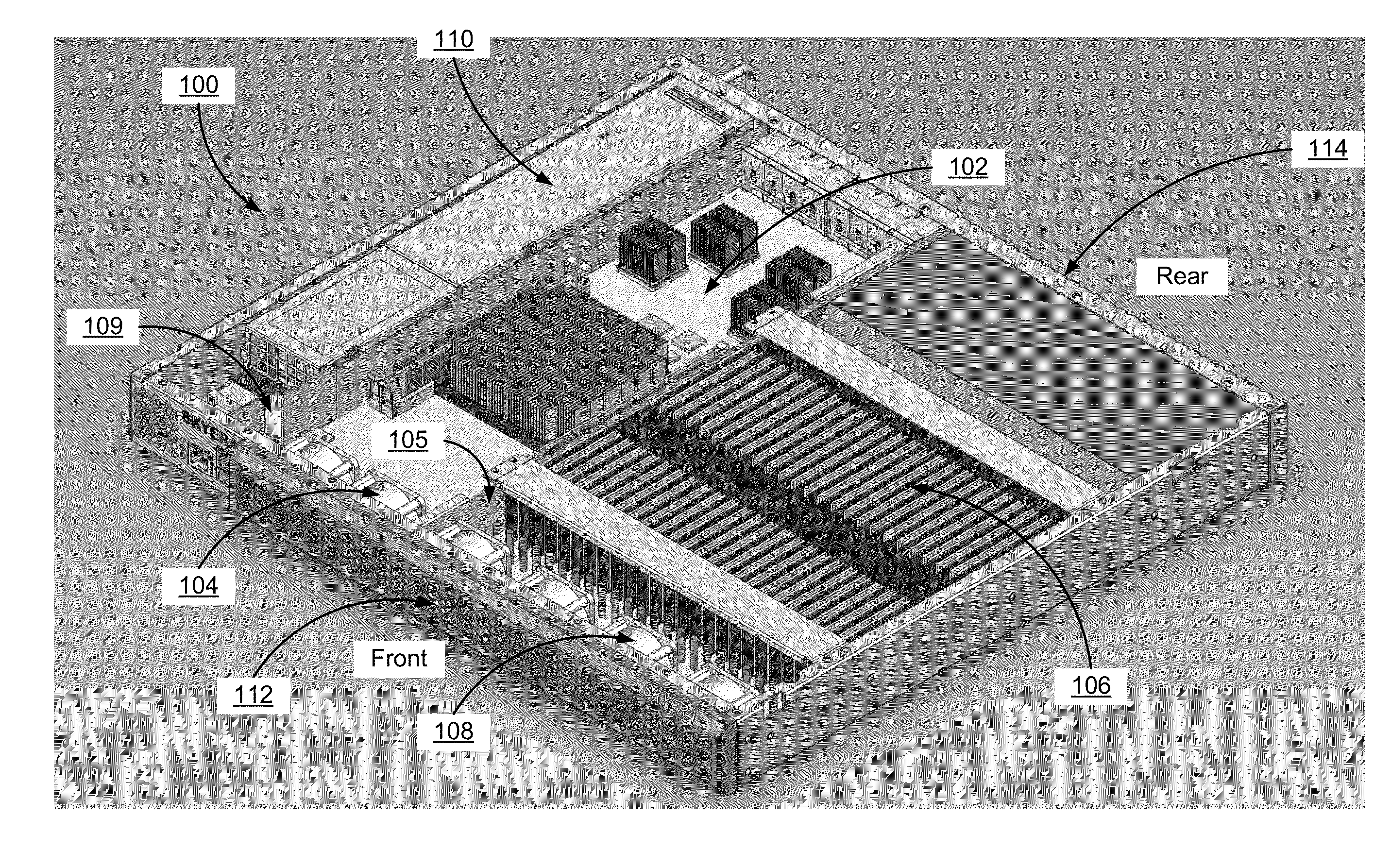
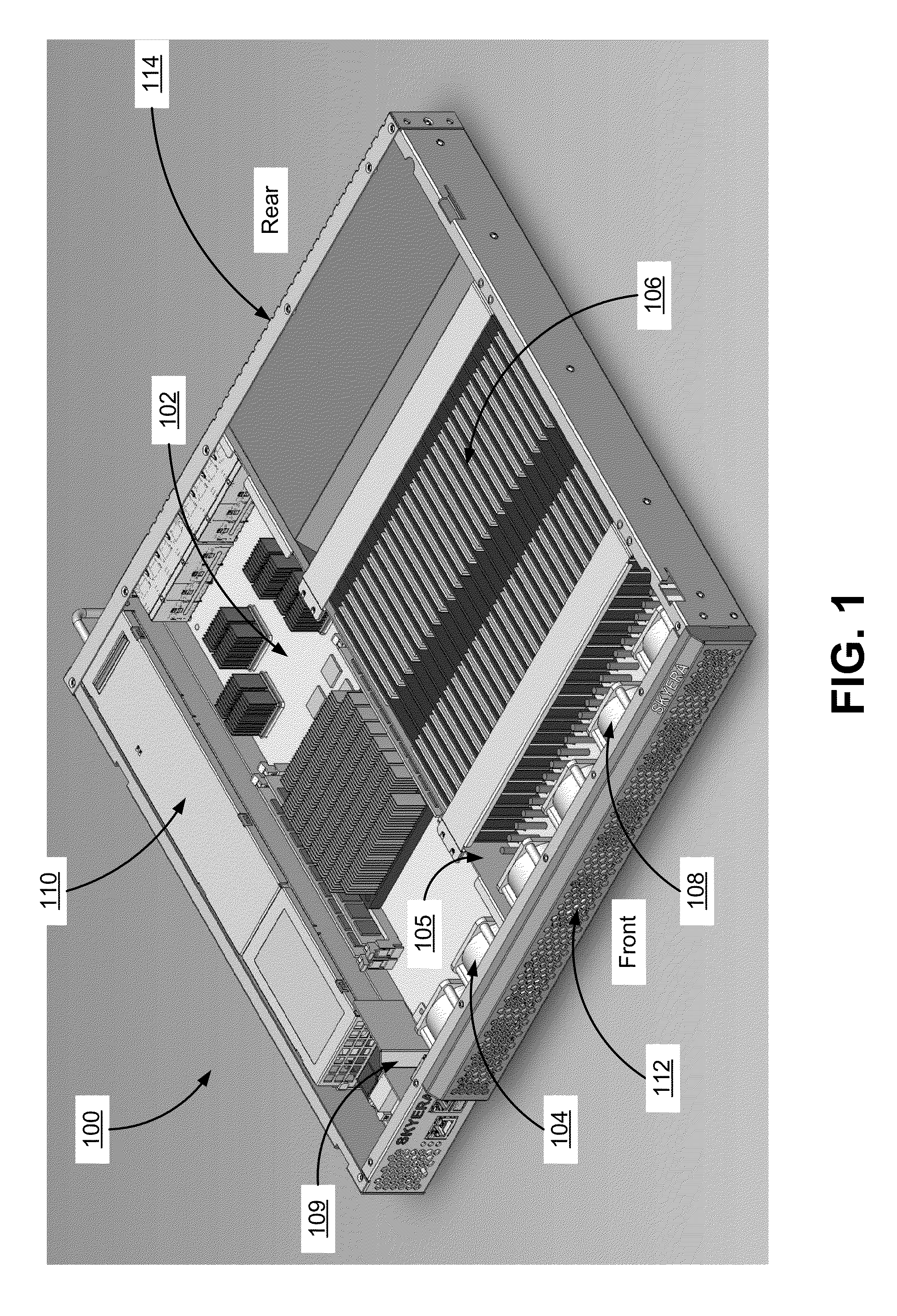
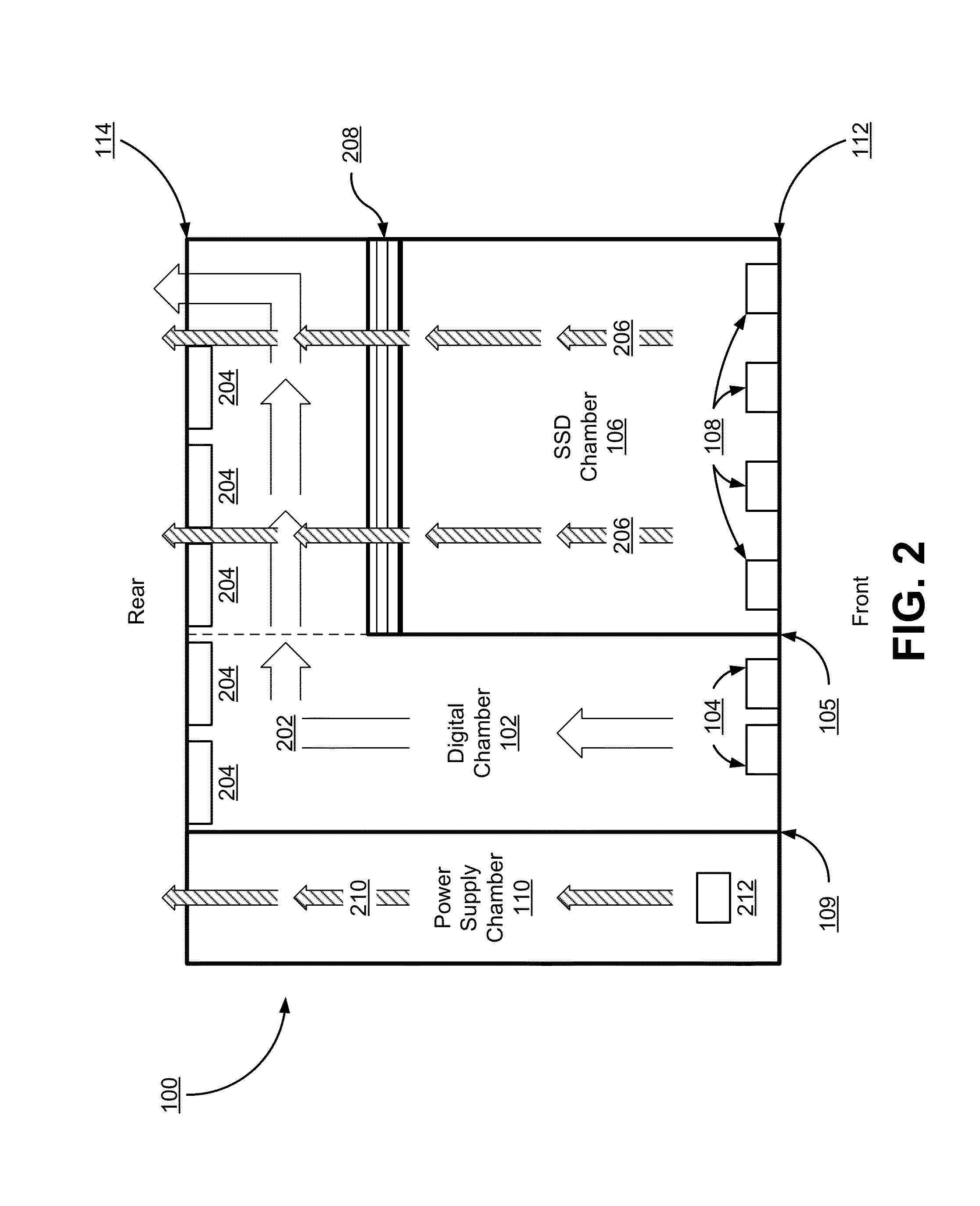
Chassis with separate thermal chamber for solid state memory
ActiveUS20140063721A1Extended service lifeServersTemperatue controlTemperature controlJunction temperature
A chassis for a network storage system contains a first thermal chamber that houses conventional electronic components and a second thermal chamber that houses non-volatile solid state memory such as flash memory. A cooling system keeps the electronics in first thermal chamber below their maximum junction temperature. Meanwhile, a temperature regulating system maintains the solid state memory in the second thermal chamber within a range of a preferred operating temperature selected to extend the lifetime and / or improve the reliability of the solid state memory. Thus, the chassis provides dual zone temperature control to improve performance of the network storage system.
Owner:WESTERN DIGITAL TECH INC
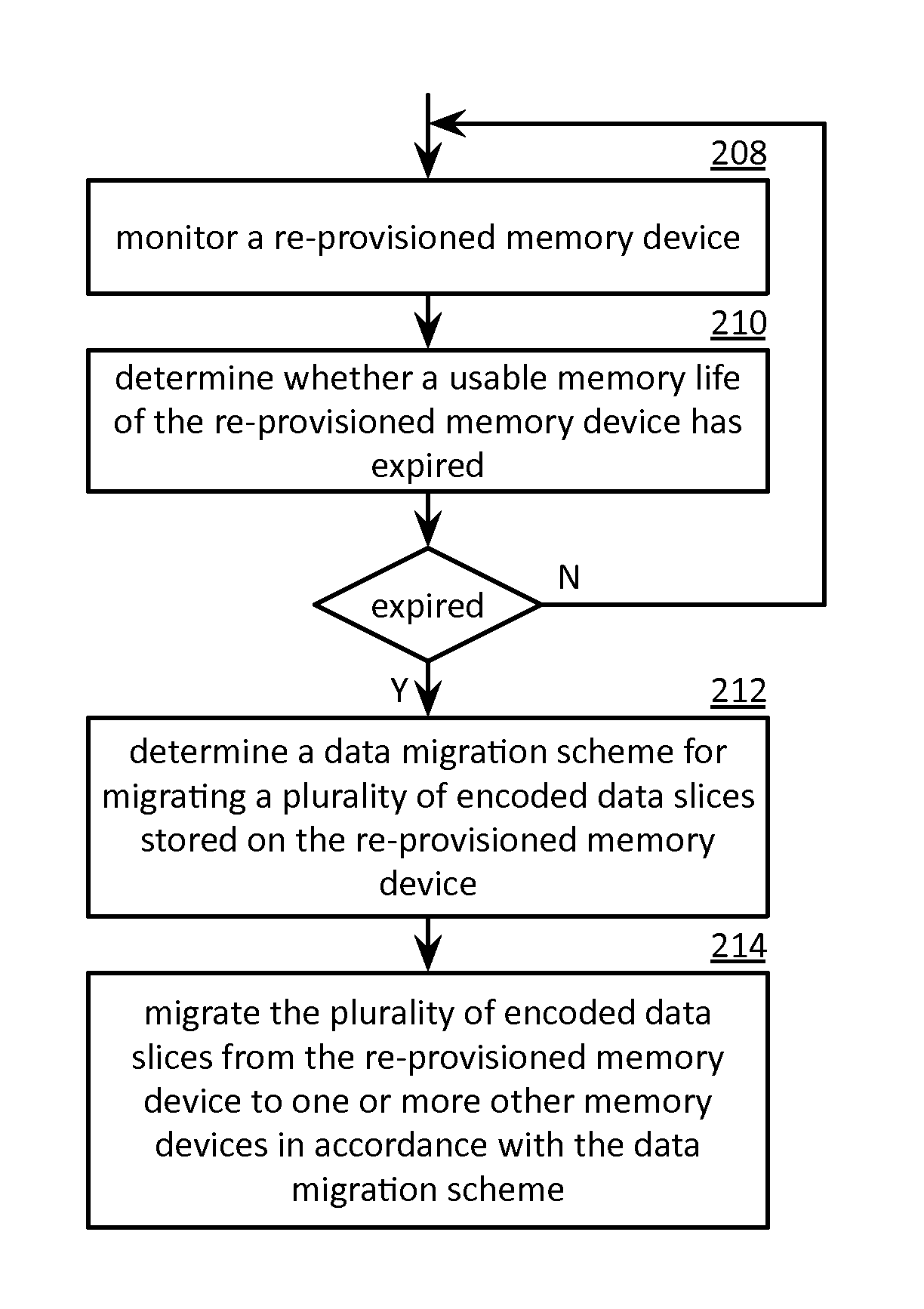
Migrating encoded data slices from a re-provisioned memory device of a dispersed storage network memory
A method begins by a processing module monitoring a reprovisioned memory device that has been reprovisioned from a legacy storage protocol to an error coding dispersed storage protocol. The method continues with the processing module determining a data migration scheme for migrating a plurality of encoded data slices stored on the reprovisioned memory device and migrating the plurality of encoded data slices from the reprovisioned memory device to one or more other memory devices in accordance with the data migration scheme when a usable memory life of the reprovisioned memory device in the error coding dispersed storage protocol has expired.
Owner:PURE STORAGE
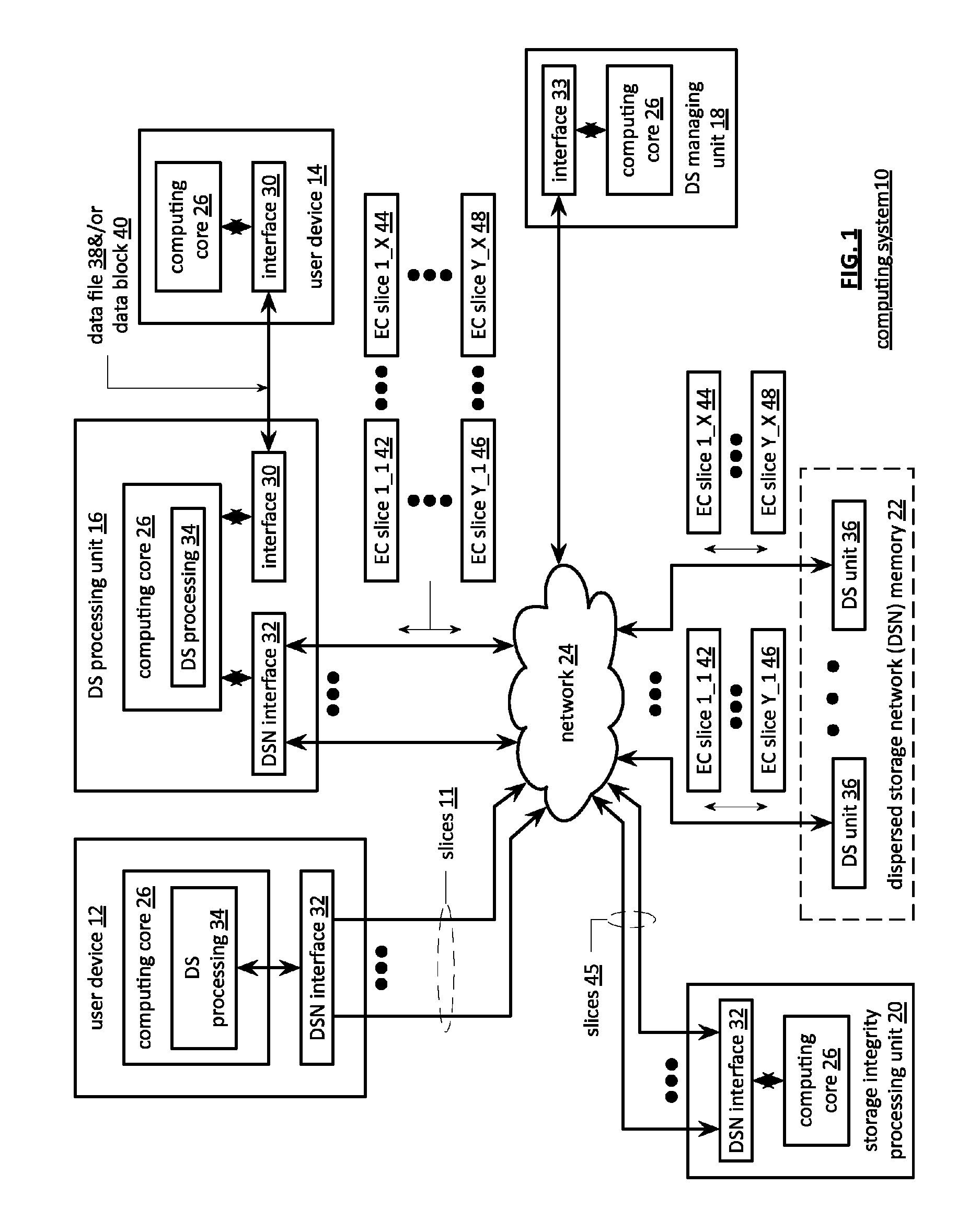
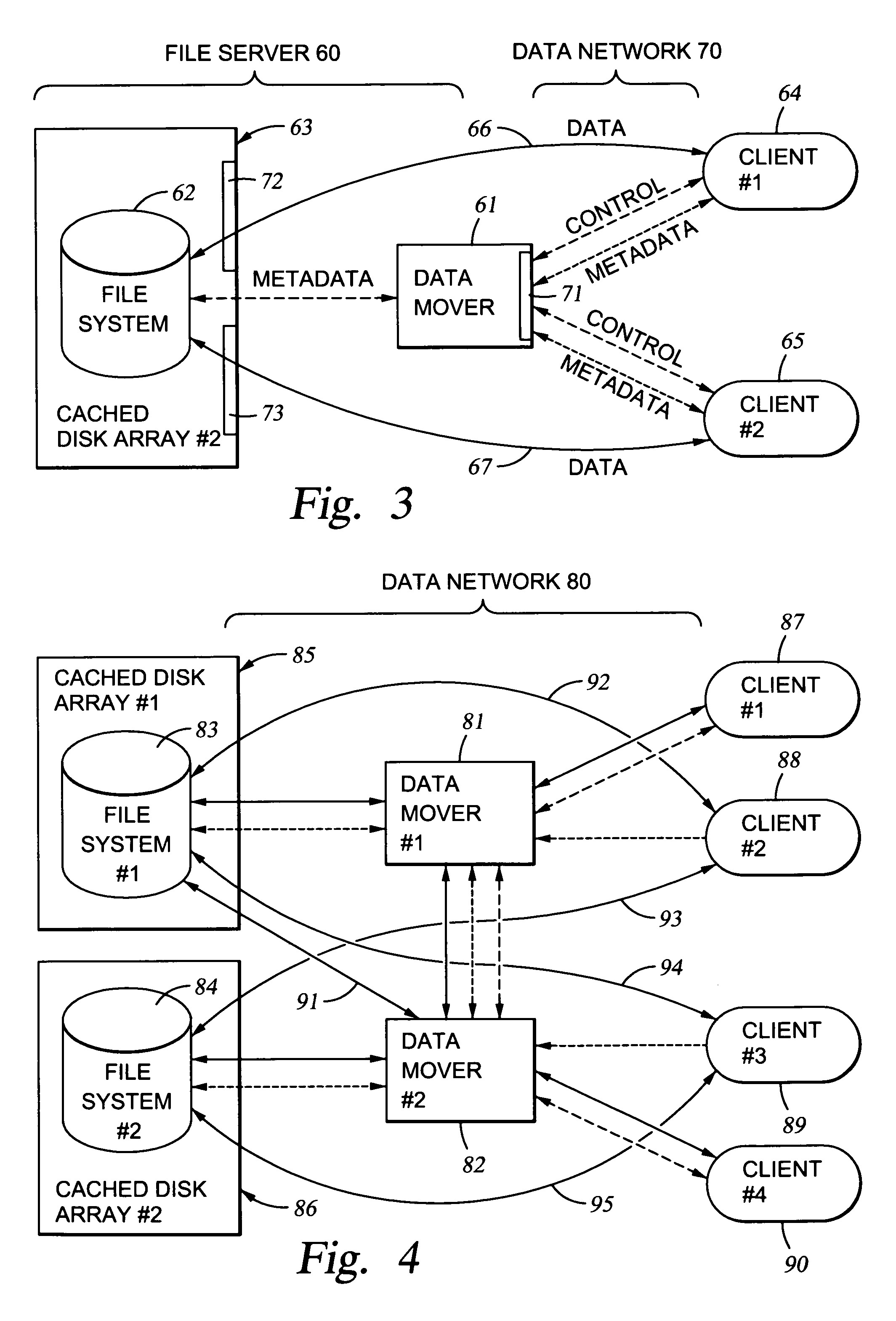
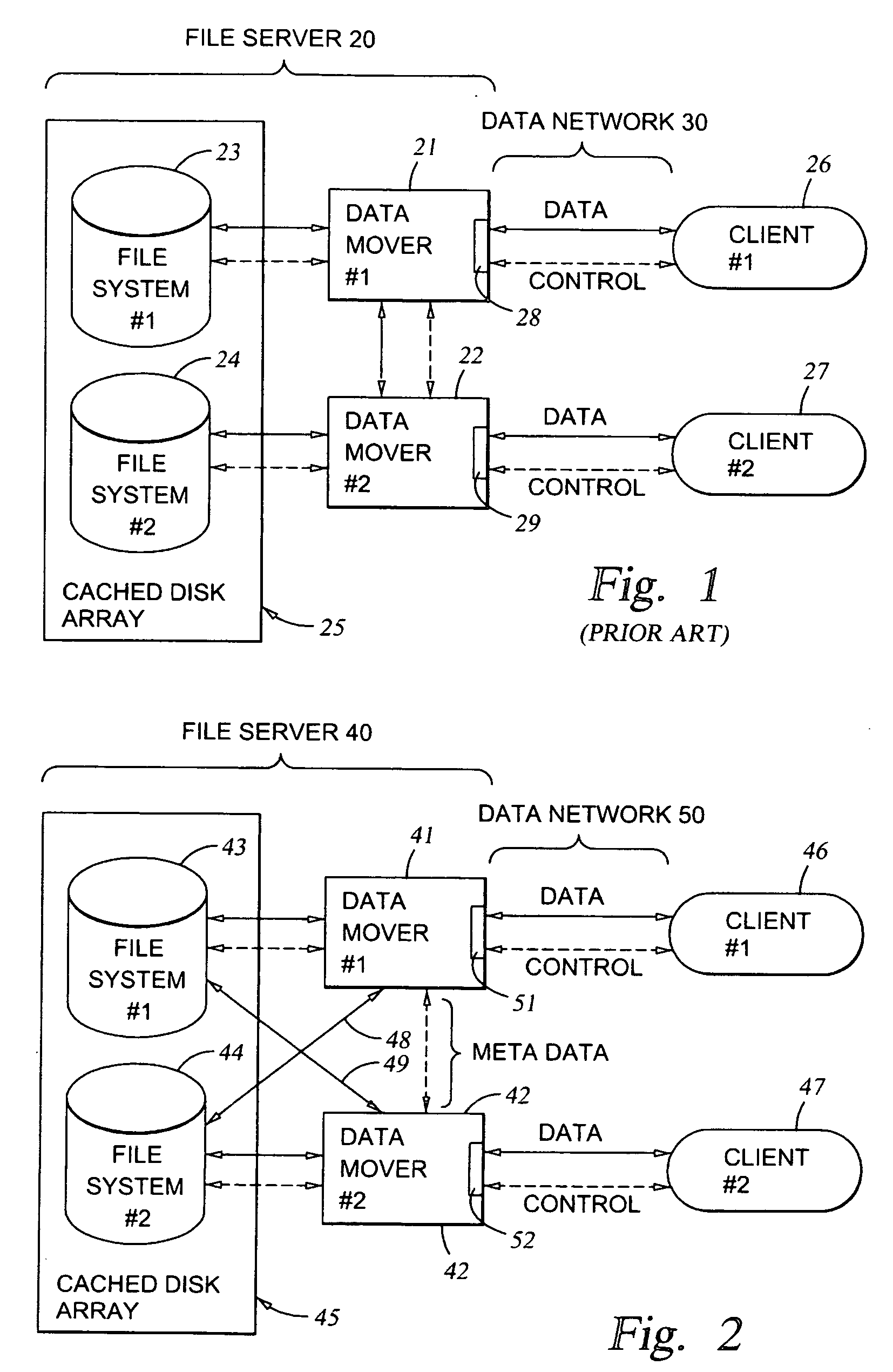
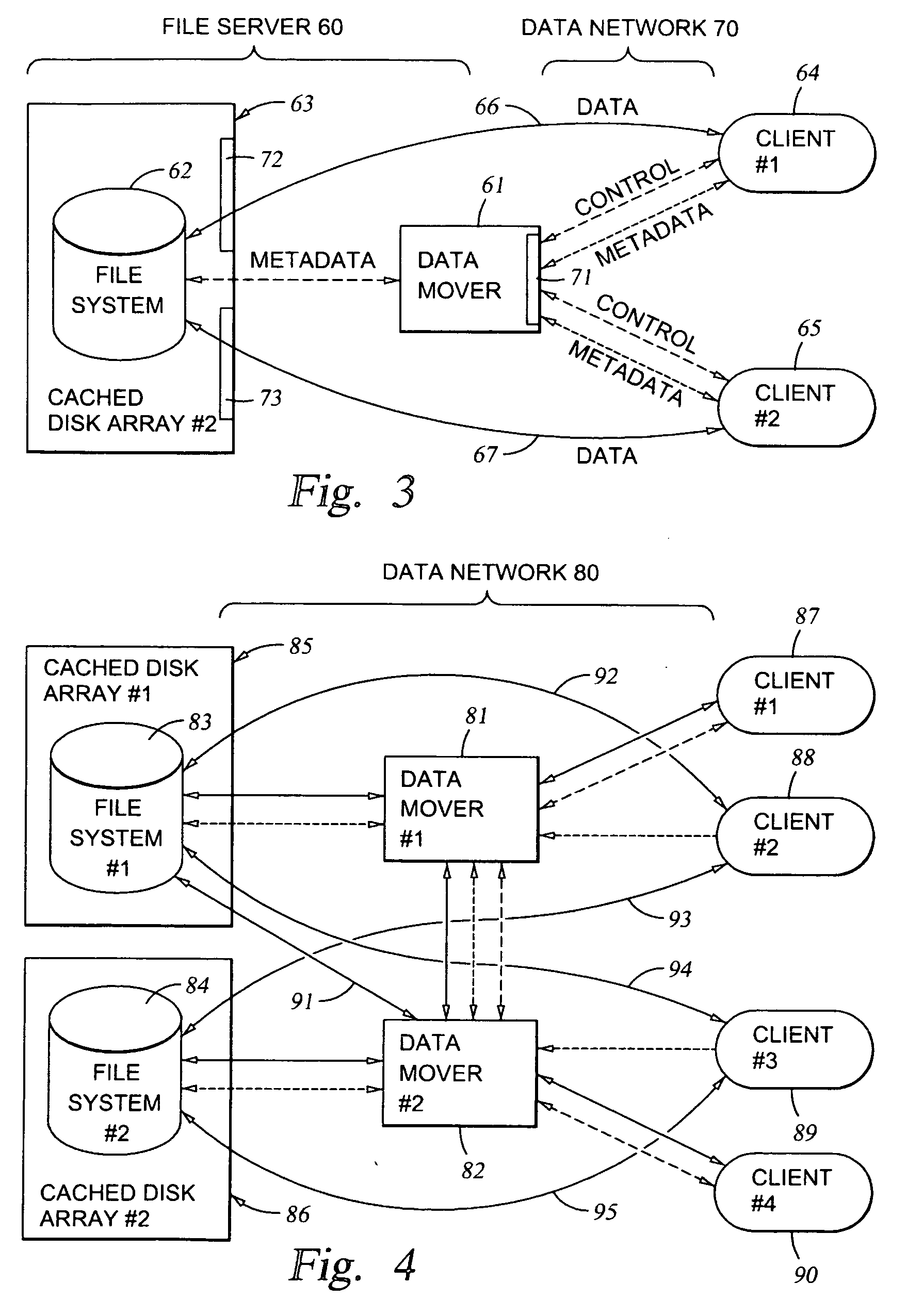
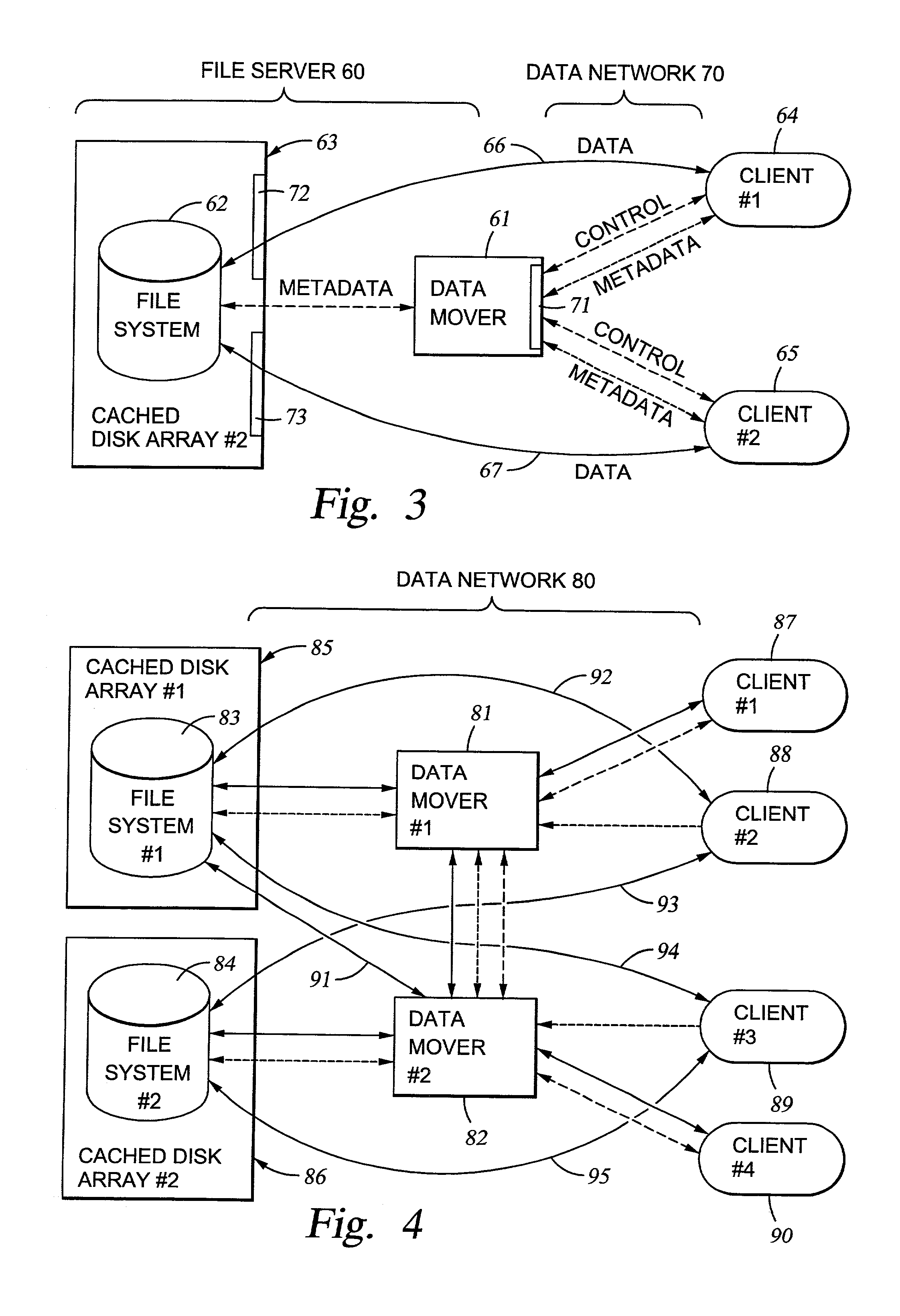
File server system providing direct data sharing between clients with a server acting as an arbiter and coordinator
InactiveUS6973455B1Digital data information retrievalData processing applicationsData accessNetwork data
A client is permitted to send data access commands directly to network data storage of a network file server after obtaining a lock on at least a portion of the file and obtaining metadata indicating storage locations for the data in the data storage. For example, the client sends to the file server at least one request for access to a file. In response, the file server grants a lock to the client, and returns to the client metadata of the file including information specifying data storage locations in the network data storage for storing data of the file. The client receives the metadata, and uses the metadata to produce at least one data access command for accessing the data storage locations in the network storage. The client sends the data access command to the network data storage to read or write data to the file. For a write operation, the client may modify the metadata. When the client is finished writing to the file, the client returns any modified metadata to the file server.
Owner:EMC IP HLDG CO LLC
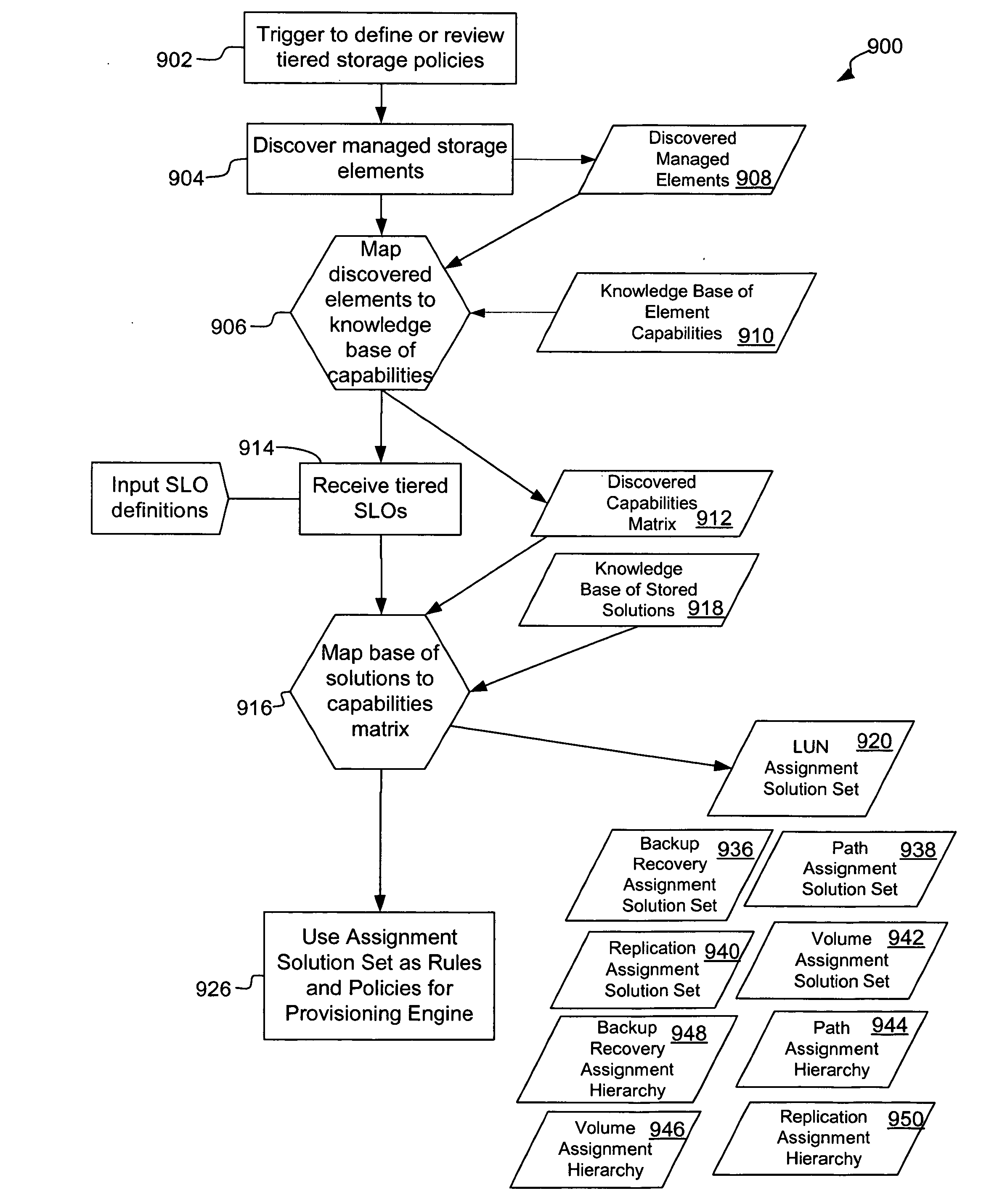
Systems and methods for adaptively deriving storage policy and configuration rules
InactiveUS20060236061A1Memory systemsInput/output processes for data processingFile systemService level objective
In one embodiment, the invention relates to an adaptive engine for creating provisioning policies and rules for network storage provisioning, which can be driven by service level objectives. The service level objectives can be defined for a given quality of service (“QoS”) for one or more users or user groups, file systems, databases, or applications, or classes of file systems, databases, or applications. In addition, the service level objectives can define the cost, availability, time to provision, recoverability, performance and accessibility objectives for the file system, database or application.
Owner:HEWLETT PACKARD DEV CO LP
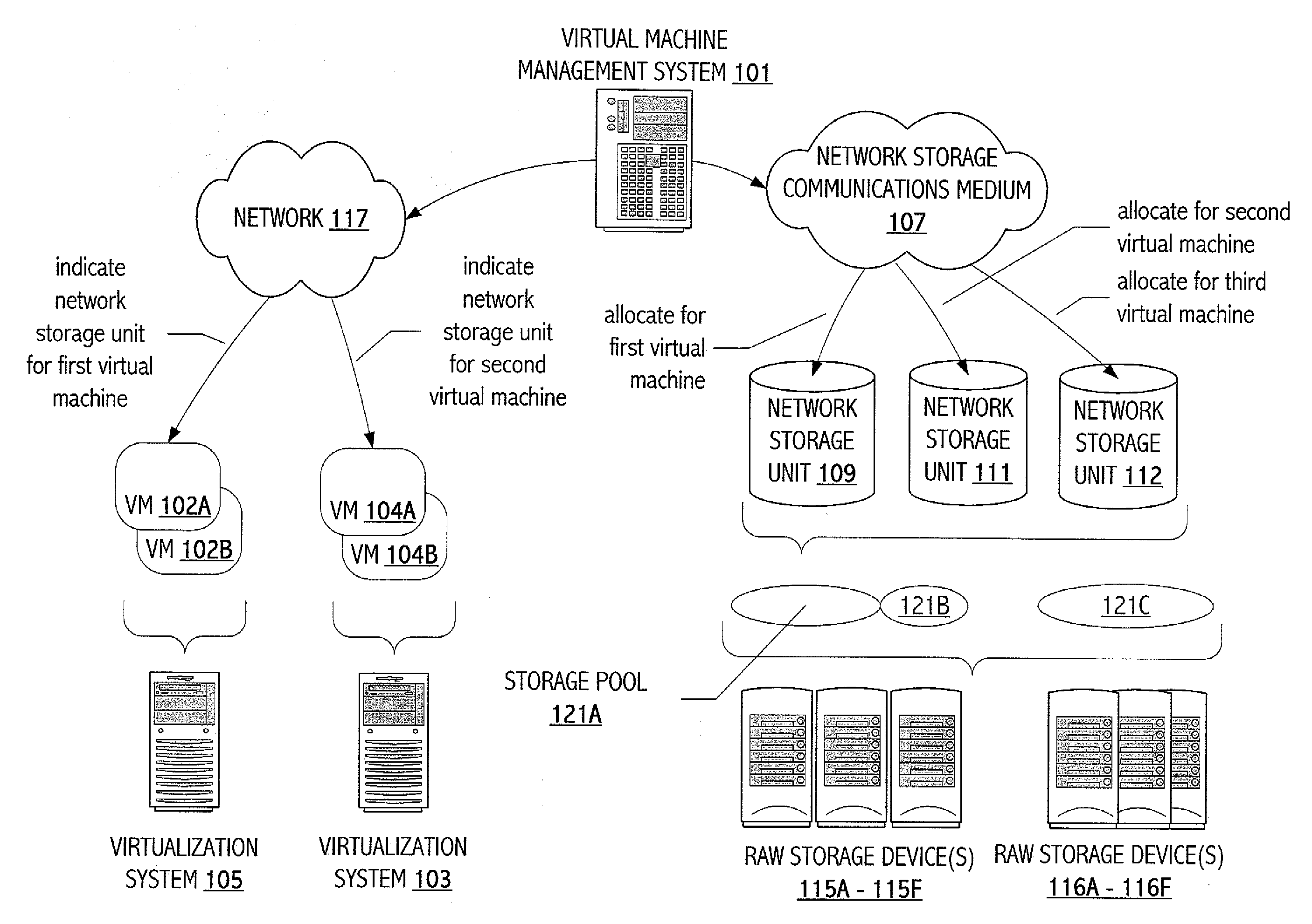
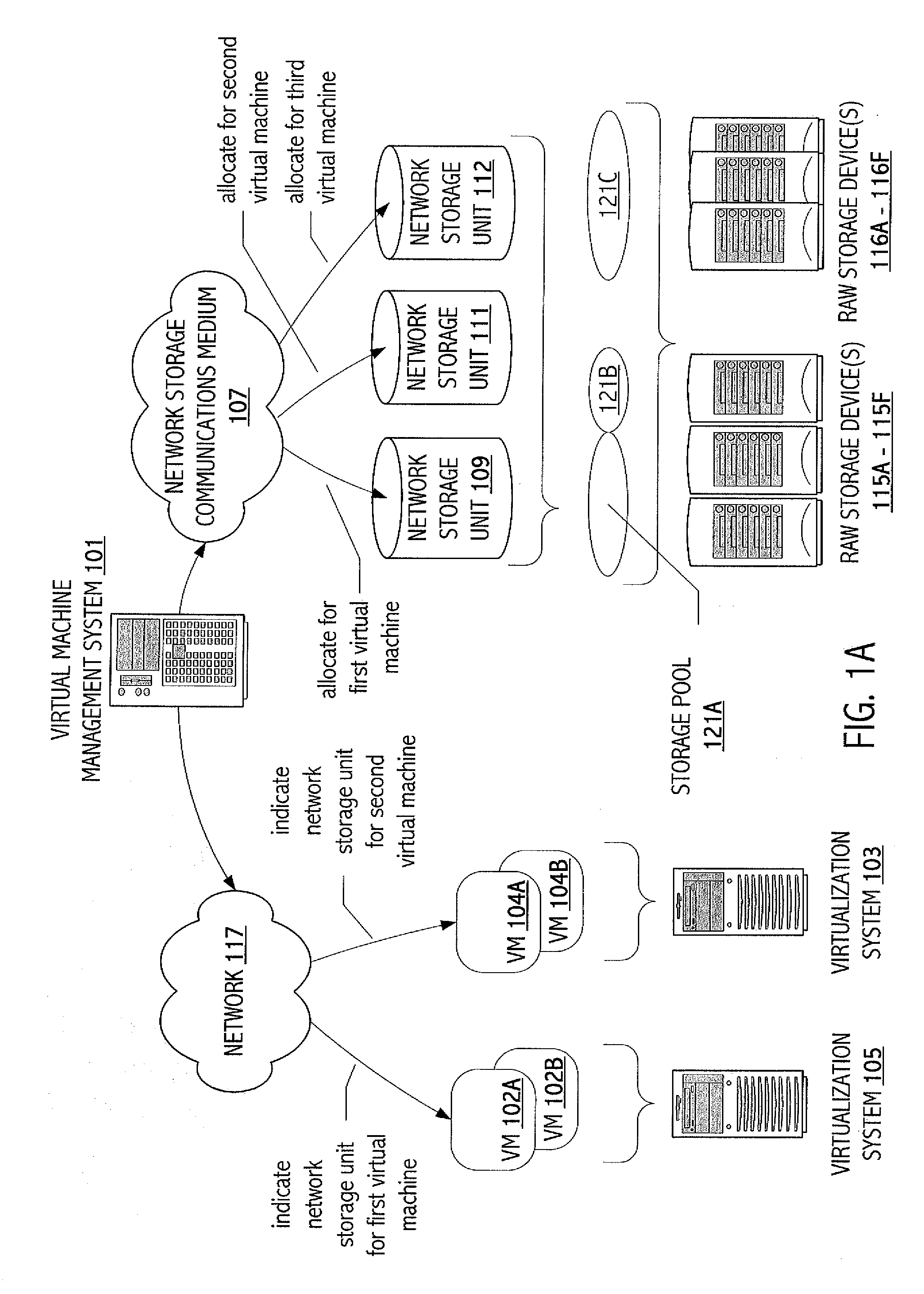
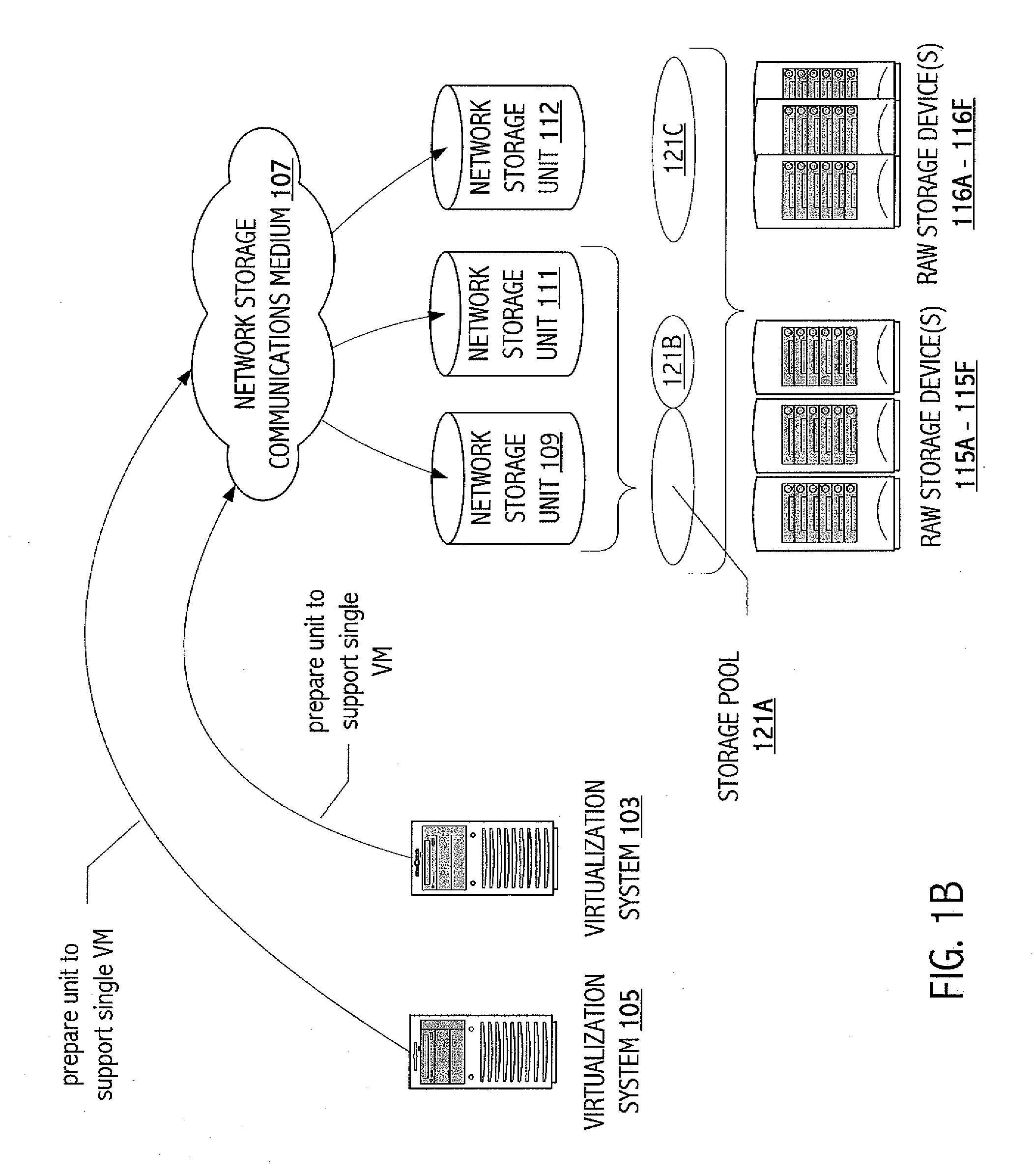
Implementation of Virtual Machine Operations Using Storage System Functionality
One embodiment of the present invention includes a method comprising: (a) representing at least state data of a virtual machine in a unit of network storage of a network storage system; and (b) employing data manipulation functionality of the network storage system to implement a virtual machine operation that manipulates at least the state data of the virtual machine.
Owner:VMWARE INC
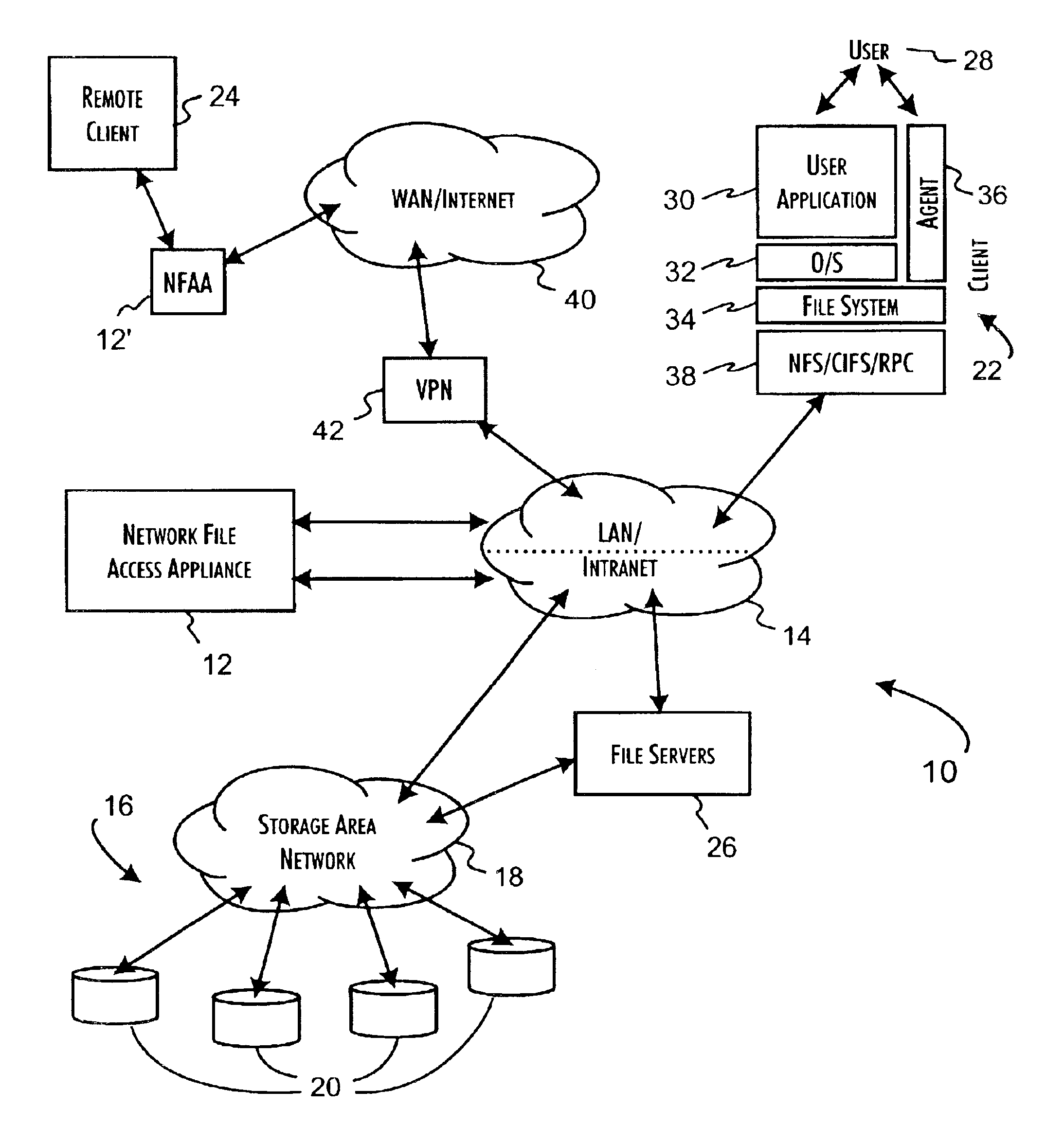
Secure network file access controller implementing access control and auditing
InactiveUS6931530B2Ensure integritySafe storageDigital data processing detailsUser identity/authority verificationReference mapSecure transmission
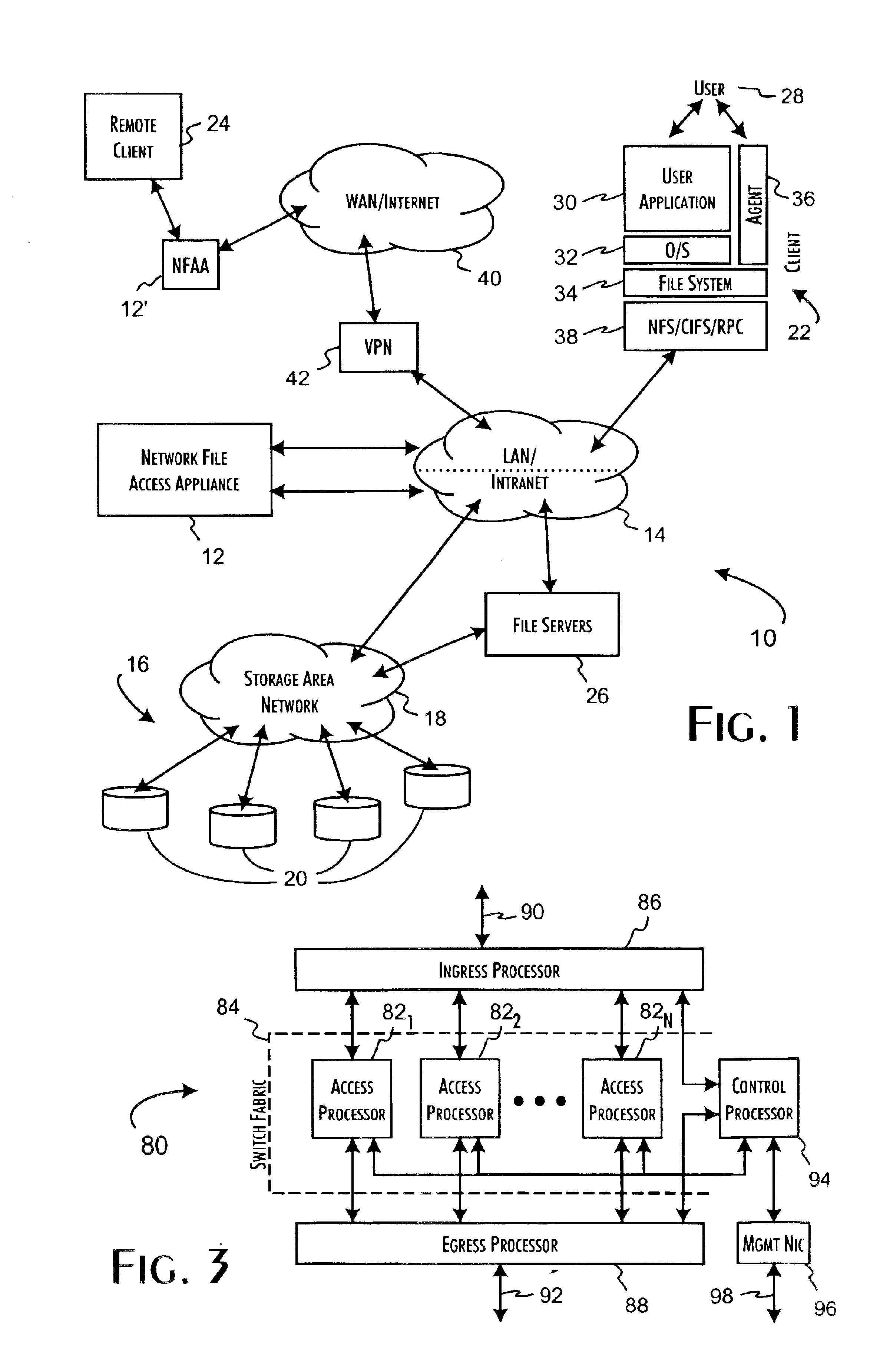
A network file access appliance operates as a secure portal for network file access operations between client computer systems and network storage resources. The file access appliance terminates network file access transactions, identified by packet information including client system, mount point, and file request identifiers, between client systems and mount points supported by the access controller. A policy parser determines, based on the packet information, to selectively initiate network file access transactions between the access controller and network storage resources to enable completion of selected network file access transactions directed from the clients to the network file access appliance. The network file access transactions directed to the network storage resources are modified counterparts of policy selected client network file access transactions modified to reference mapped network storage resource mount points and support the secure transfer and storage of network file data.
Owner:THALES DIS CPL USA INC
Non-Volatile Memory Backup for Network Storage System
InactiveUS20060080515A1Improve resource utilizationImprove efficiencyError detection/correctionMemory systemsStandby powerData storing
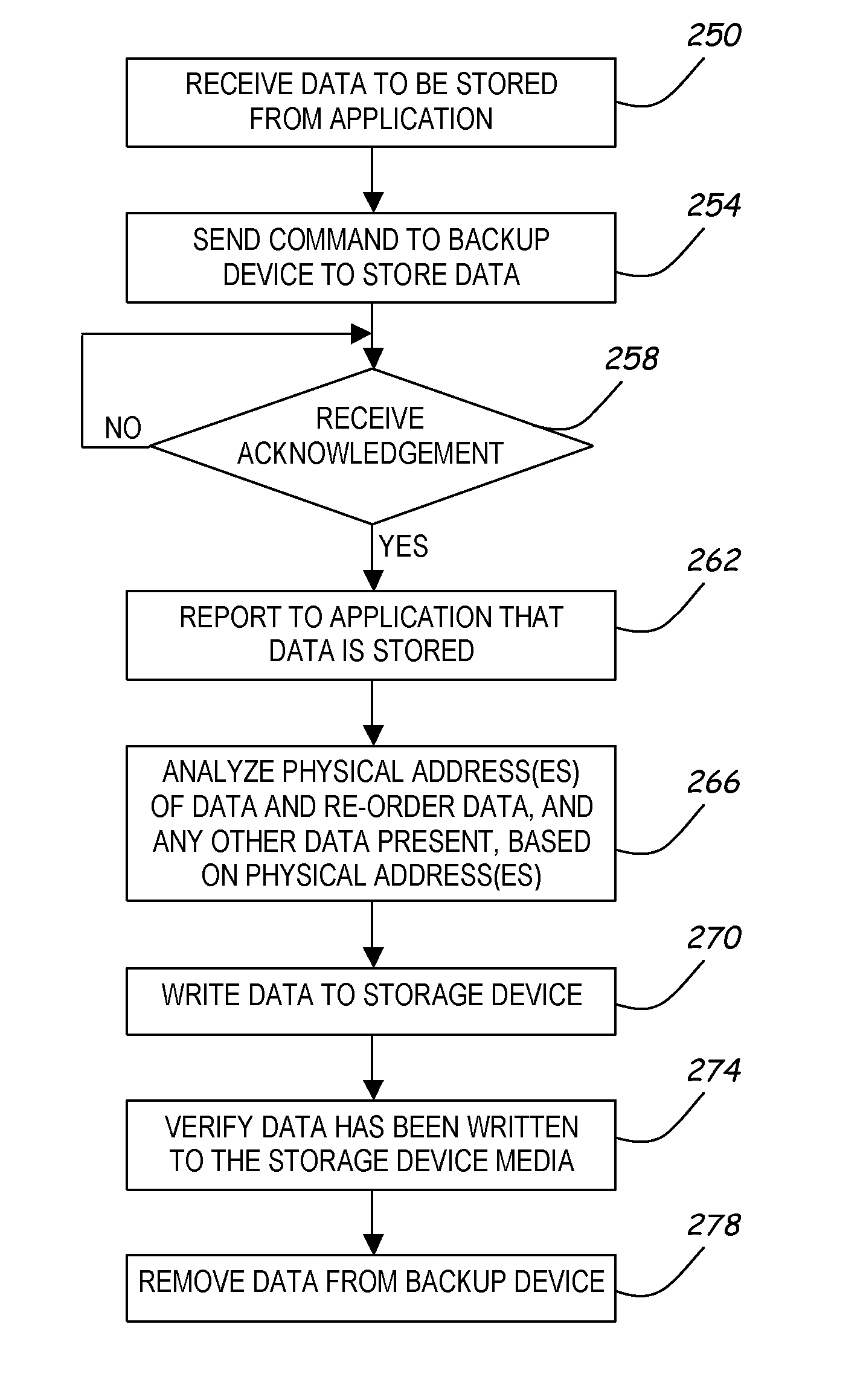
A data storage system including a primary data storage device and a backup data storage device stores data with enhanced performance. The primary data storage device has a primary data storage device memory for holding data, and the backup data storage device has a backup volatile memory, a backup non-volatile memory, and a processor. The backup storage device processor causes a copy of data provided to the primary data storage device to be provided to the backup data storage device volatile memory, and in the event of a power interruption moves the data from the backup volatile memory to the backup non-volatile memory. In such a manner, data stored at the backup data storage device is not lost in the event of a power interruption. The backup data storage device further includes a backup power source such as a capacitor, a battery, or any other suitable power source, and upon detection of a power interruption, switches to the backup power source and receives power from the backup power source while moving the data from the backup volatile memory to the backup non-volatile memory.
Owner:HEWLETT PACKARD DEV CO LP
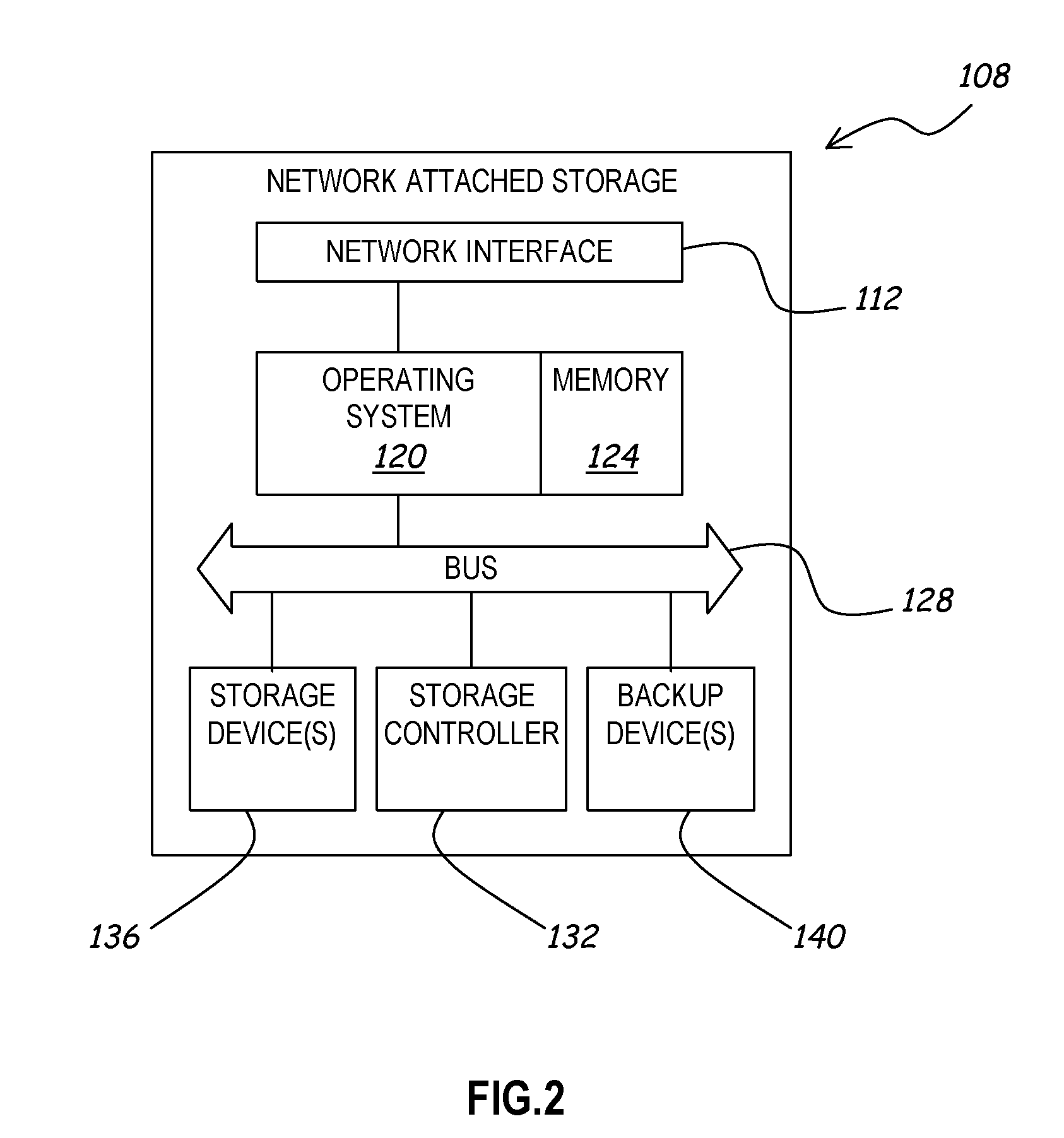
System for Providing Multi-path Input/Output in a Clustered Data Storage Network
ActiveUS20060277383A1Avoid problemsImprove performanceDigital computer detailsTransmissionClustered dataStorage area network
A distributed network storage system provides capability to send and receive storage information from multiple network storage servers in a storage area network using iSCSI commands. A storage server system comprising at least two data storage servers stores one or more logical volumes of data. A host computer receives a storage command from a host application, and determines one or more data storage servers has information to complete the storage command. The host computer generates one or more iSCSI network commands to carry out the storage command, and transmits the iSCSI network commands directly to each data storage server having necessary information. The storage servers receive iSCSI network commands, and return a response to the host. The host and storage servers verify the configuration of the storage network and are capable of correcting or updating the configuration as required.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
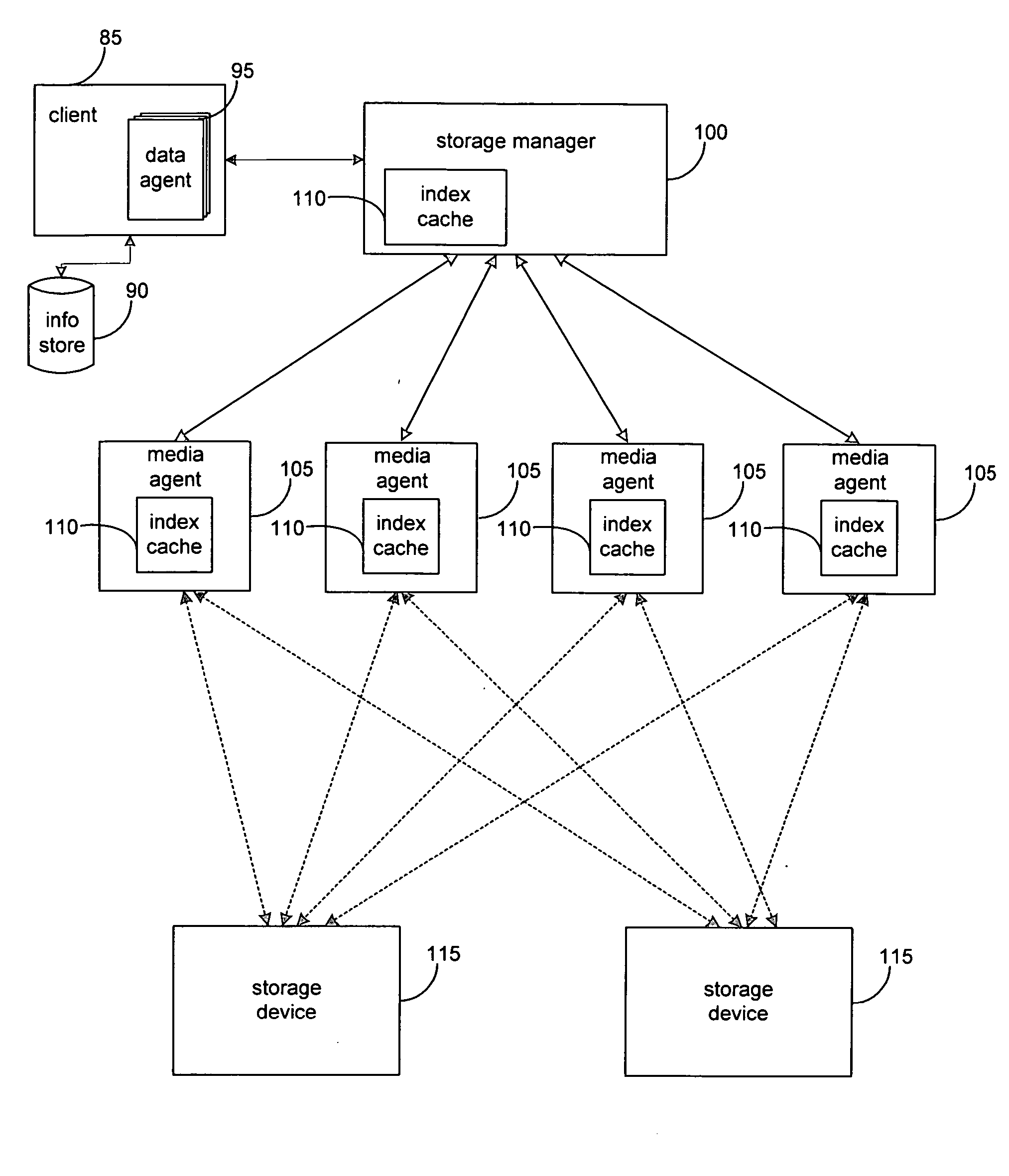
System and method for dynamically performing storage operations in a computer network
ActiveUS20050044114A1Data processing applicationsInput/output to record carriersLogical networkOperating system
Methods and systems are described for performing storage operations on electronic data in a network. In response to the initiation of a storage operation and according to a first set of selection logic, a media management component is selected to manage the storage operation. In response to the initiation of a storage operation and according to a second set of selection logic, a network storage device to associate with the storage operation. The selected media management component and the selected network storage device perform the storage operation on the electronic data.
Owner:COMMVAULT SYST INC
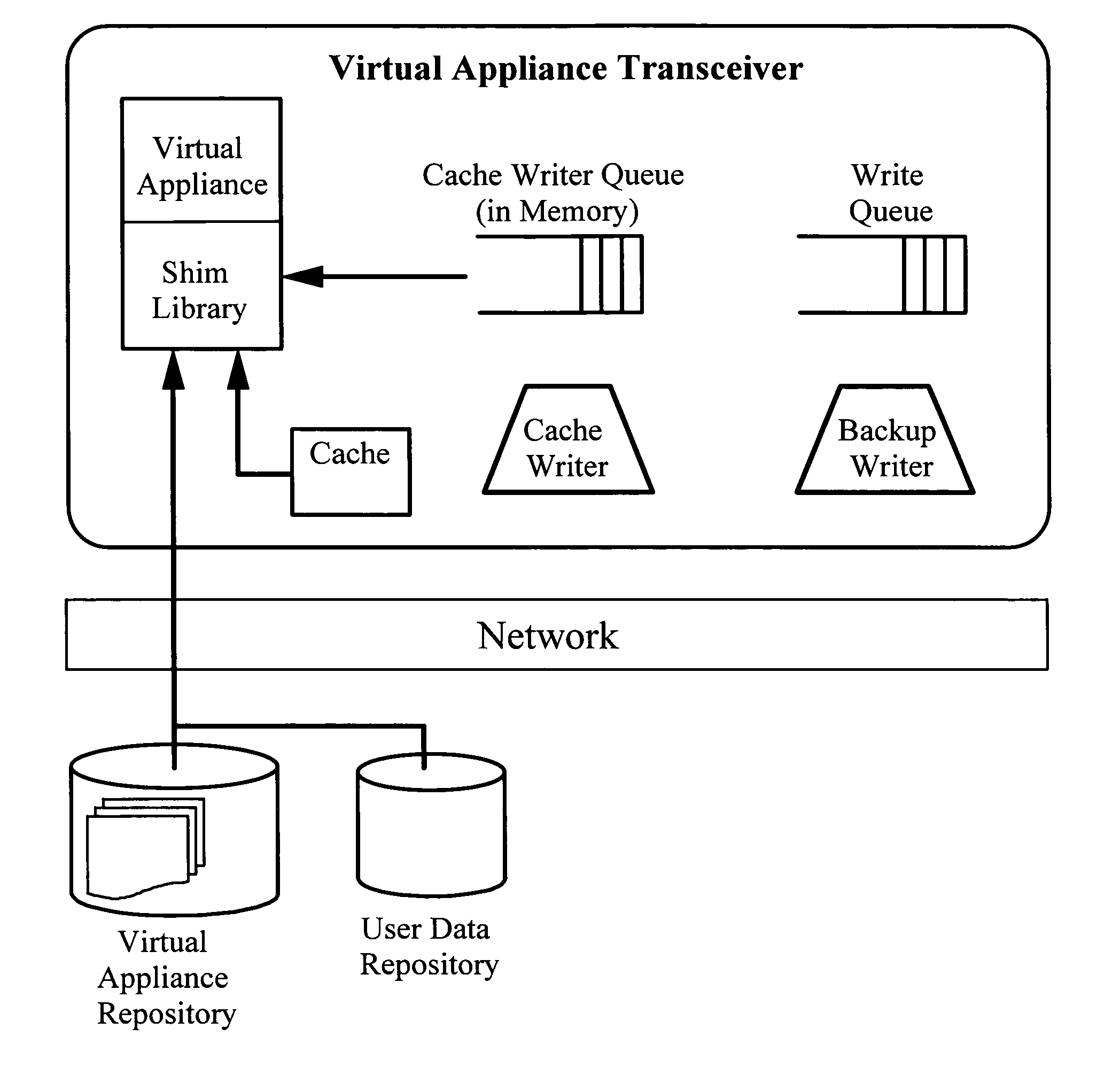
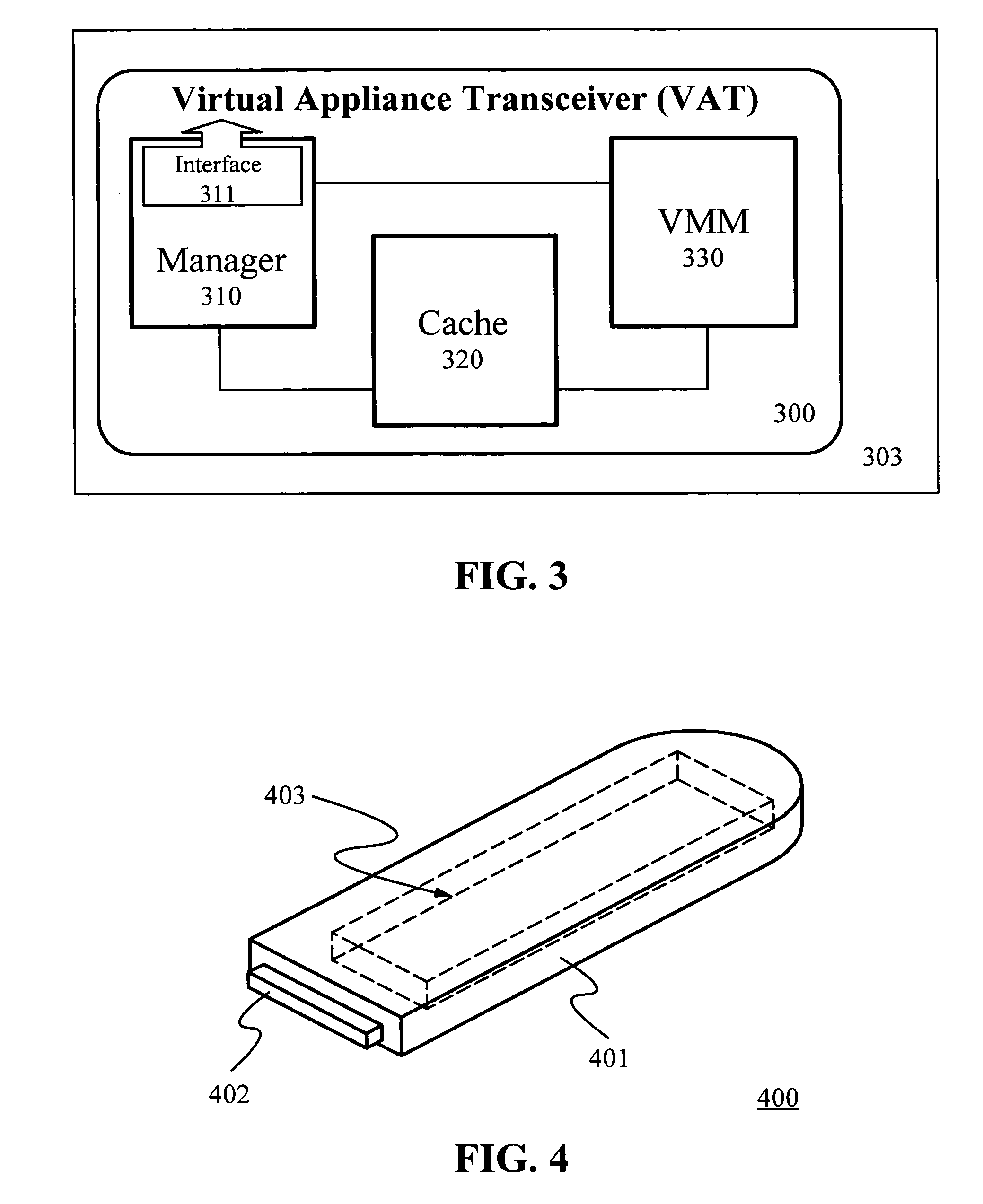
Cache-based system management architecture with virtual appliances, network repositories, and virtual appliance transceivers
ActiveUS20050125513A1Adversely affecting system performanceError detection/correctionDigital computer detailsTransceiverSystems management
A cache-based system management architecture named “the Collective” automates system management and supports mobile computing. The Collective manages systems by manipulating virtual appliances, each encapsulating a system state. A virtual appliance (VA) may comprise a virtual network of VAs. Distributed repositories separately storing the VAs and user data. Publishers create and maintain VAs. A user plugs a bootable portable storage device implementing a VA transceiver (VAT) into a host computer. The VAT, comprising a Manager, a Cache Client, and a virtual machine monitor (VMM), authenticates the user, retrieves a copy of the latest version of a subscribed VA from the appropriate network repository, obtains user data, and automatically backs up the user data over the network in the background while running the subscribed VA. Multiple VAs can be run at the same time. With the novel caching protocol and cache charging process, the Collective performs well and has numerous advantages.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
File server system providing direct data sharing between clients with a server acting as an arbiter and coordinator
InactiveUS20050251500A1Data processing applicationsDigital data information retrievalData accessNetwork data
A client is permitted to send data access commands directly to network data storage of a network file server after obtaining a lock on at least a portion of the file and obtaining metadata indicating storage locations for the data in the data storage. For example, the client sends to the file server at least one request for access to a file. In response, the file server grants a lock to the client, and returns to the client metadata of the file including information specifying data storage locations in the network data storage for storing data of the file. The client receives the metadata, and uses the metadata to produce at least one data access command for accessing the data storage locations in the network storage. The client sends the data access command to the network data storage to read or write data to the file. For a write operation, the client may modify the metadata. When the client is finished writing to the file, the client returns any modified metadata to the file server.
Owner:EMC CORP
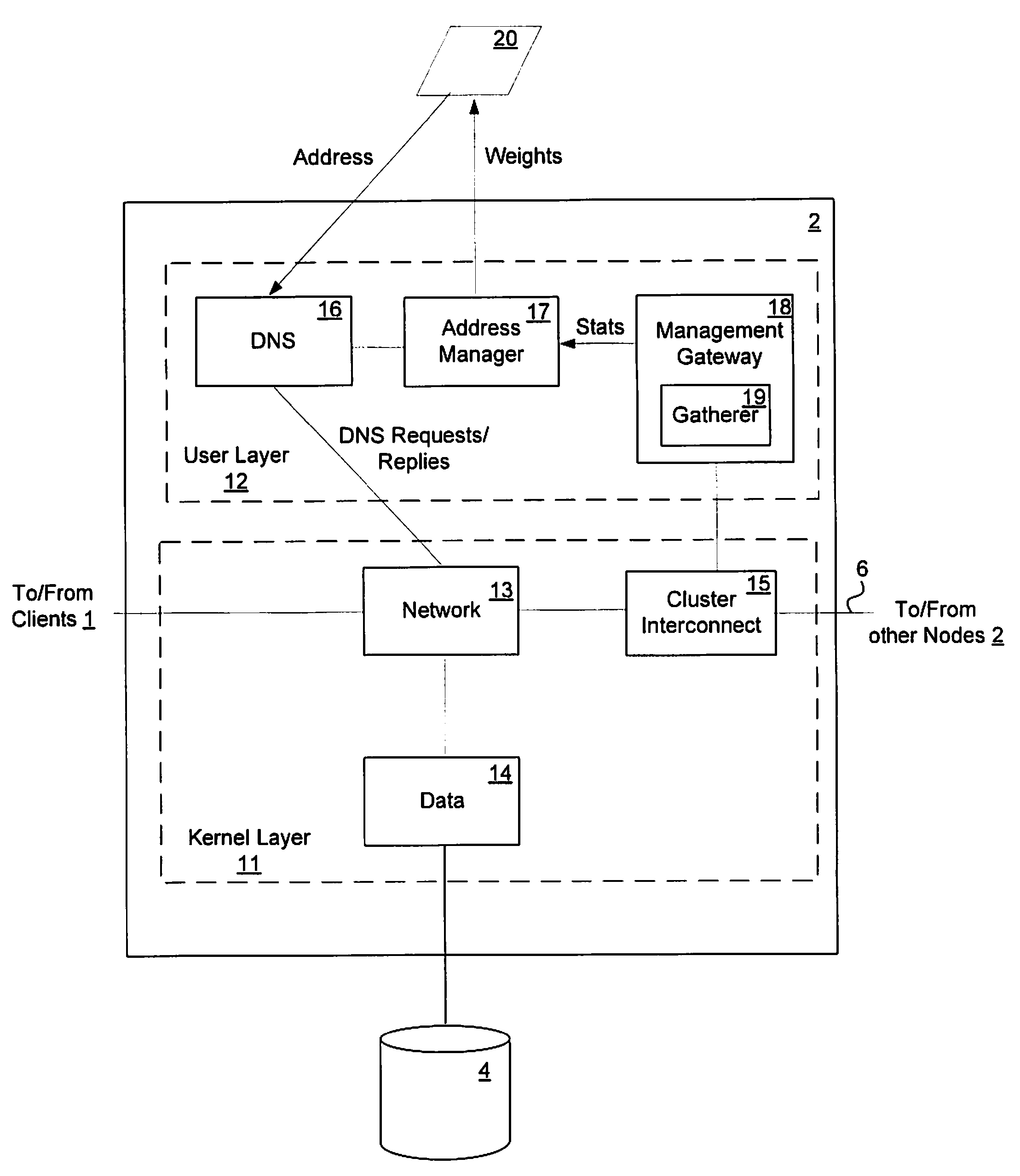
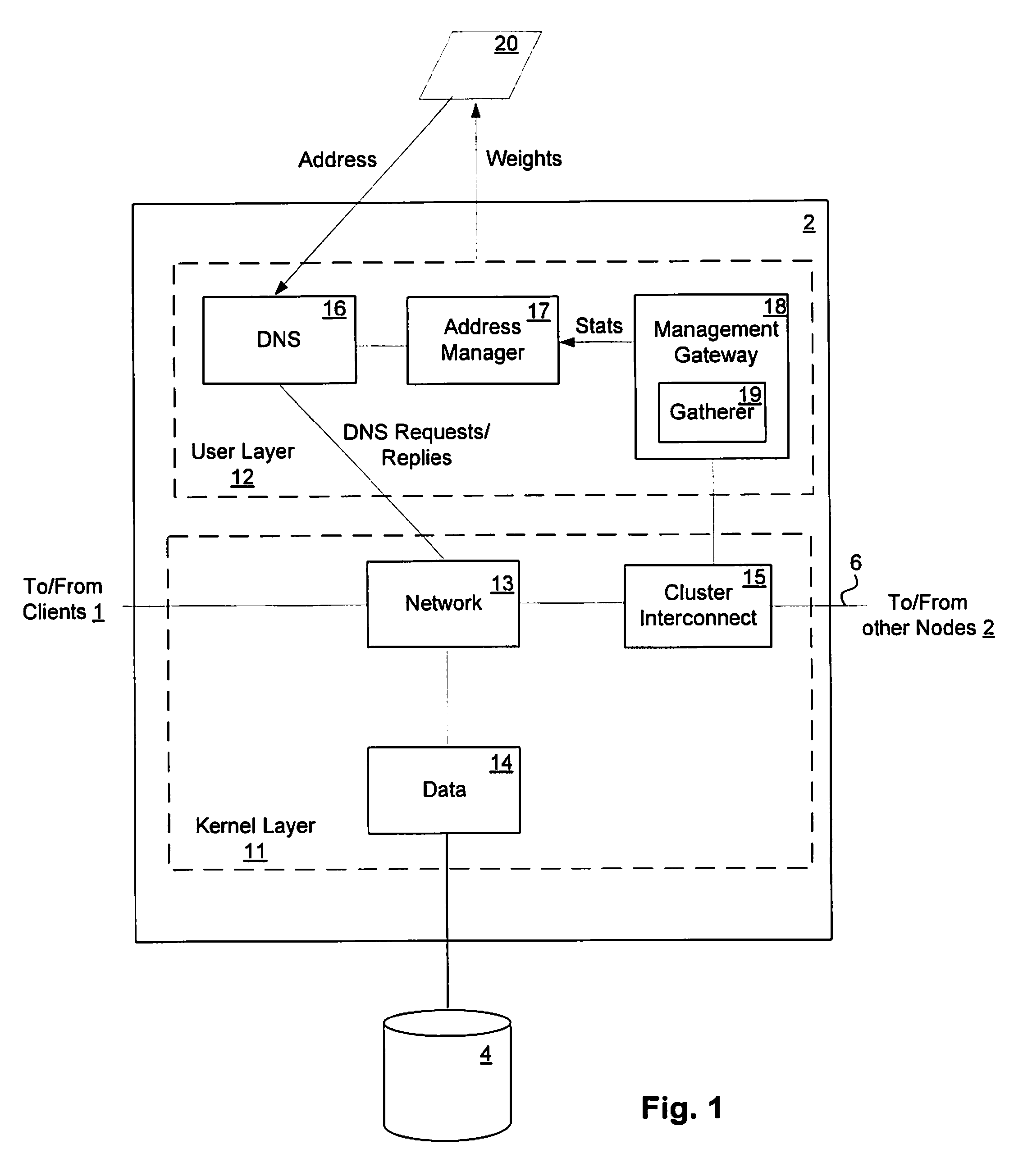
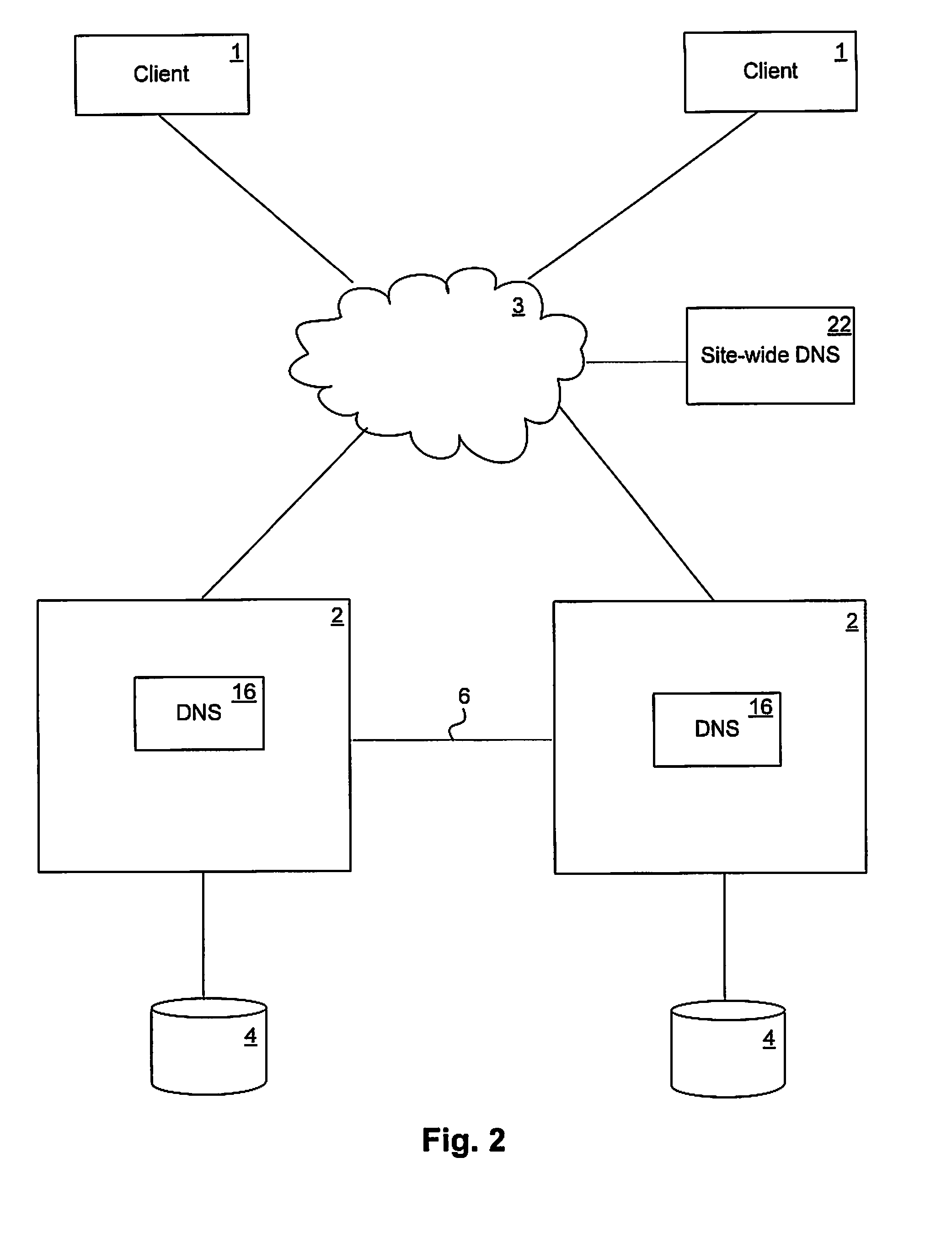
Load-derived probability-based domain name service in a network storage cluster
ActiveUS20100023621A1Multiprogramming arrangementsMultiple digital computer combinationsDomain nameIp address
DNS name resolution is integrated into each node in a network storage cluster, to allow load balancing of network addresses, using a weighted random distribution to resolve DNS requests. A node in the cluster gathers statistics on utilization of resources, such as CPU utilization and throughput, on nodes in the cluster and distributes those statistics to all other nodes. Each node uses the same algorithm to generate weights for the various IP addresses of the cluster, based on the statistics distributed to it. The weights are used to generate a weighted list of available network addresses. In response to a DNS request, a DNS in a given node randomly indexes into the weighted address list to resolve requests to a network address. The weights are chosen so that the DNS is likely to pick an IP address which has a low load, to balance port and node usage over time.
Owner:NETWORK APPLIANCE INC
Method and System of Degital Content Sharing Among Users Over Communications Networks , Related Telecommunications Network Architecture and Computer Program Product Therefor
ActiveUS20070243860A1Improve performanceEasy to manageTransmissionSpecial data processing applicationsAccess networkTelecommunications network
A method and a system for digital content sharing between individual users in a peer-to-peer fashion, wherein each user is connected to a respective local access network through a transport network. The method and system provide local network storage areas associated with each user arranged for archiving digital contents, and carry out the transferring of contents via the transport network from a storage area associated with a user holding requested contents to a remote network storage area associated with a requesting user on a different access network according to the connectivity available on the transport network. The shared contents are made available for access by the requesting user on its local network storage area. A telecommunications network architecture includes the system so that there is a plurality of services of content sharing between pairs of individual users implementing the above method.
Owner:TELECOM ITALIA SPA
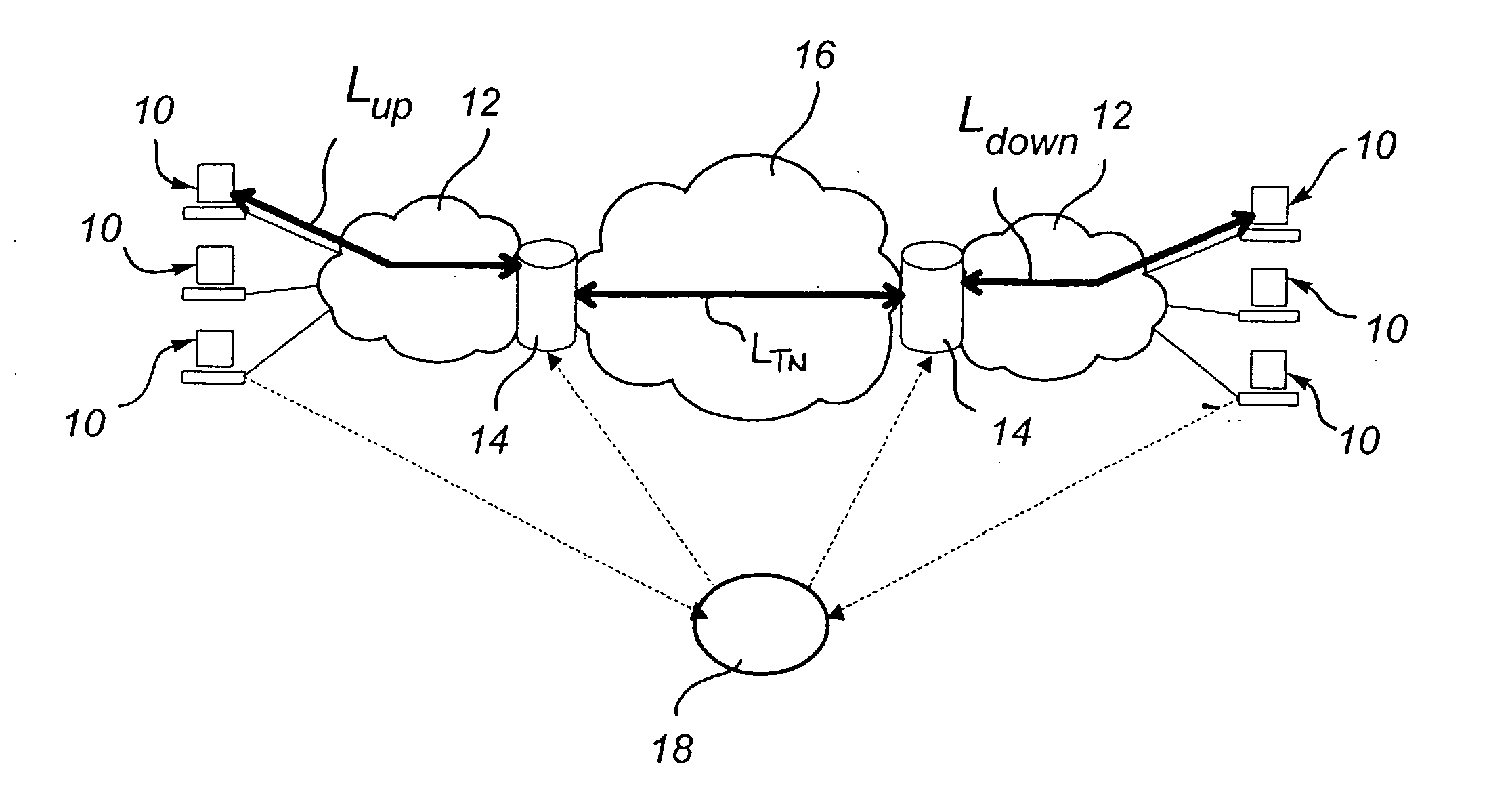
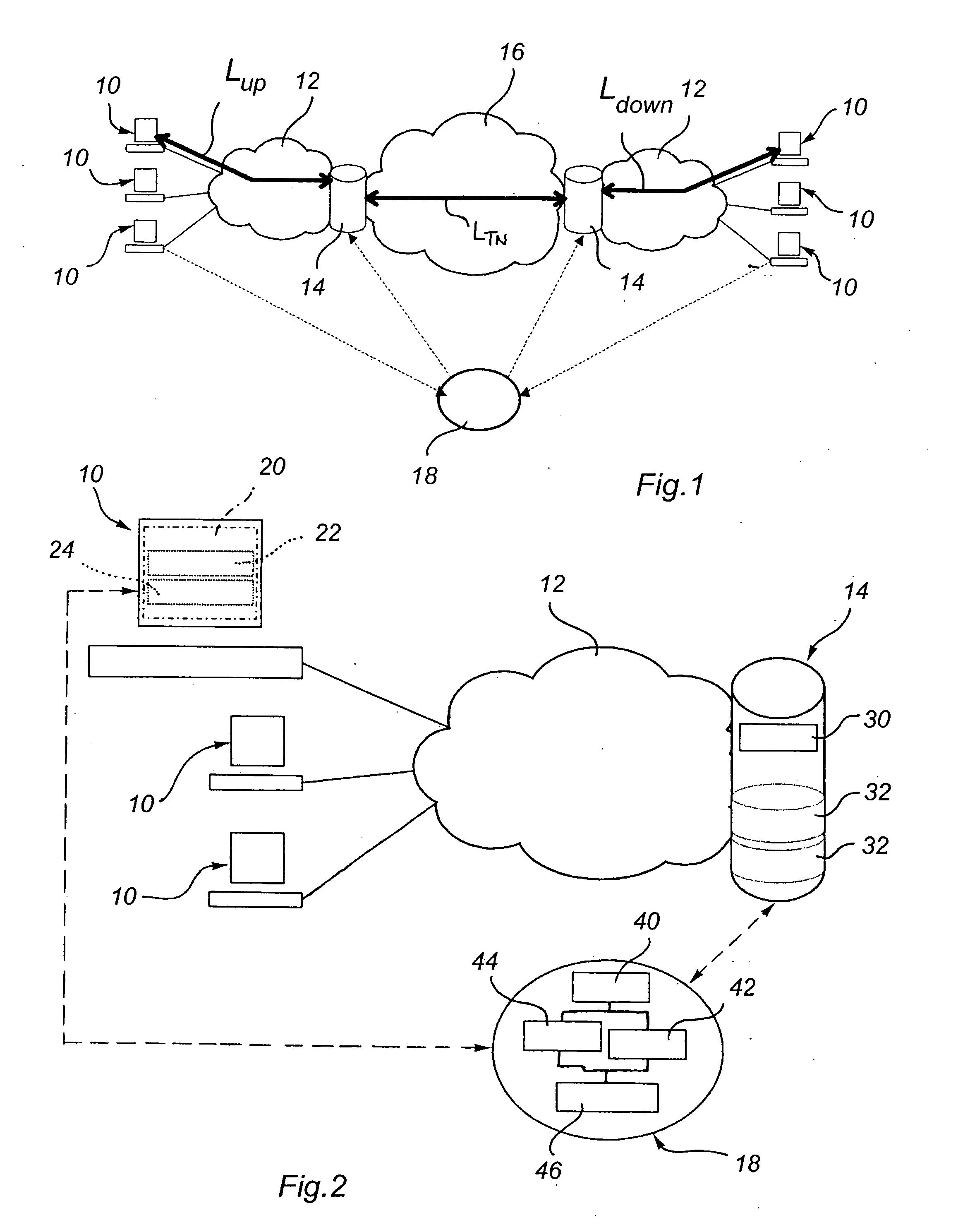
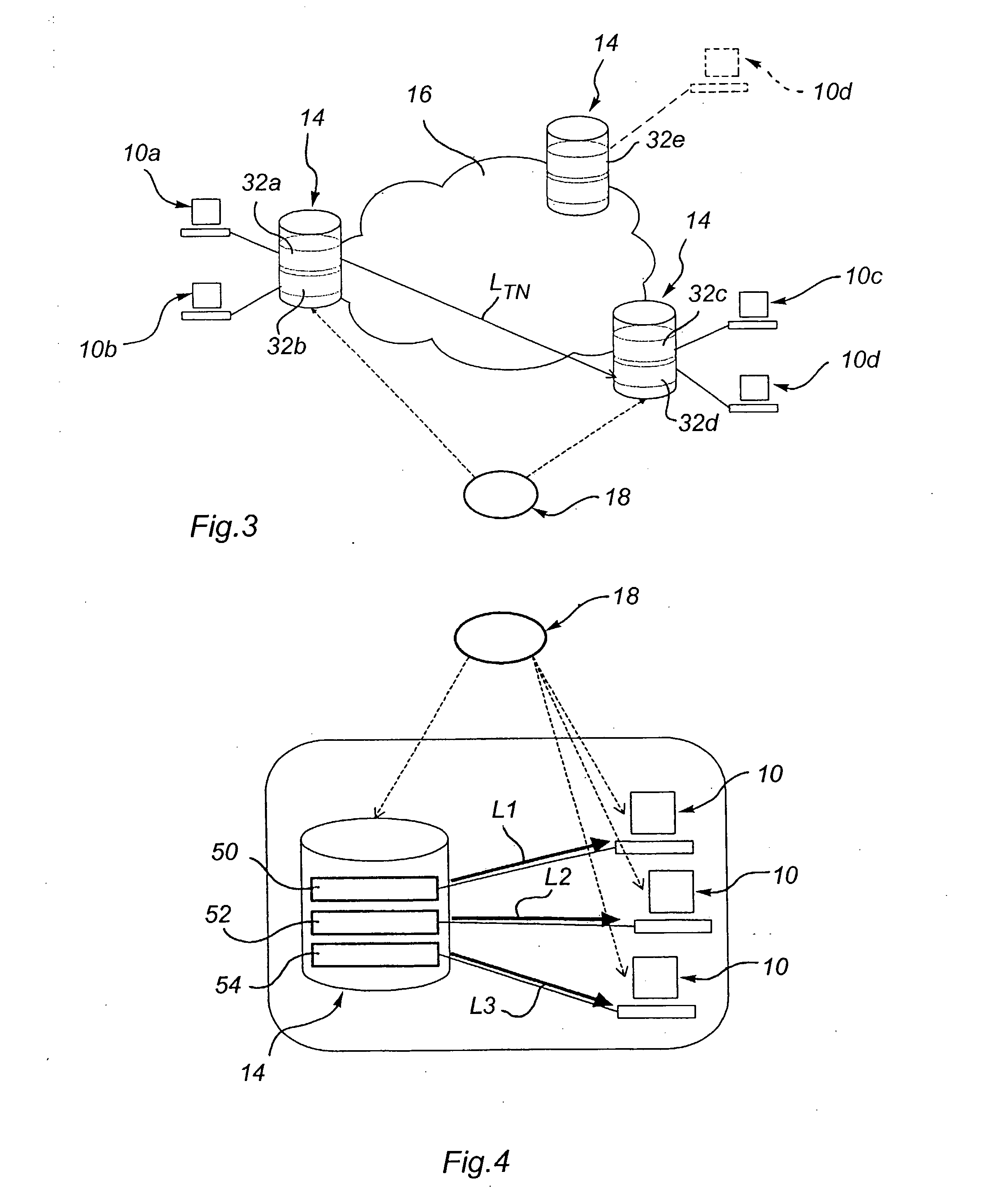
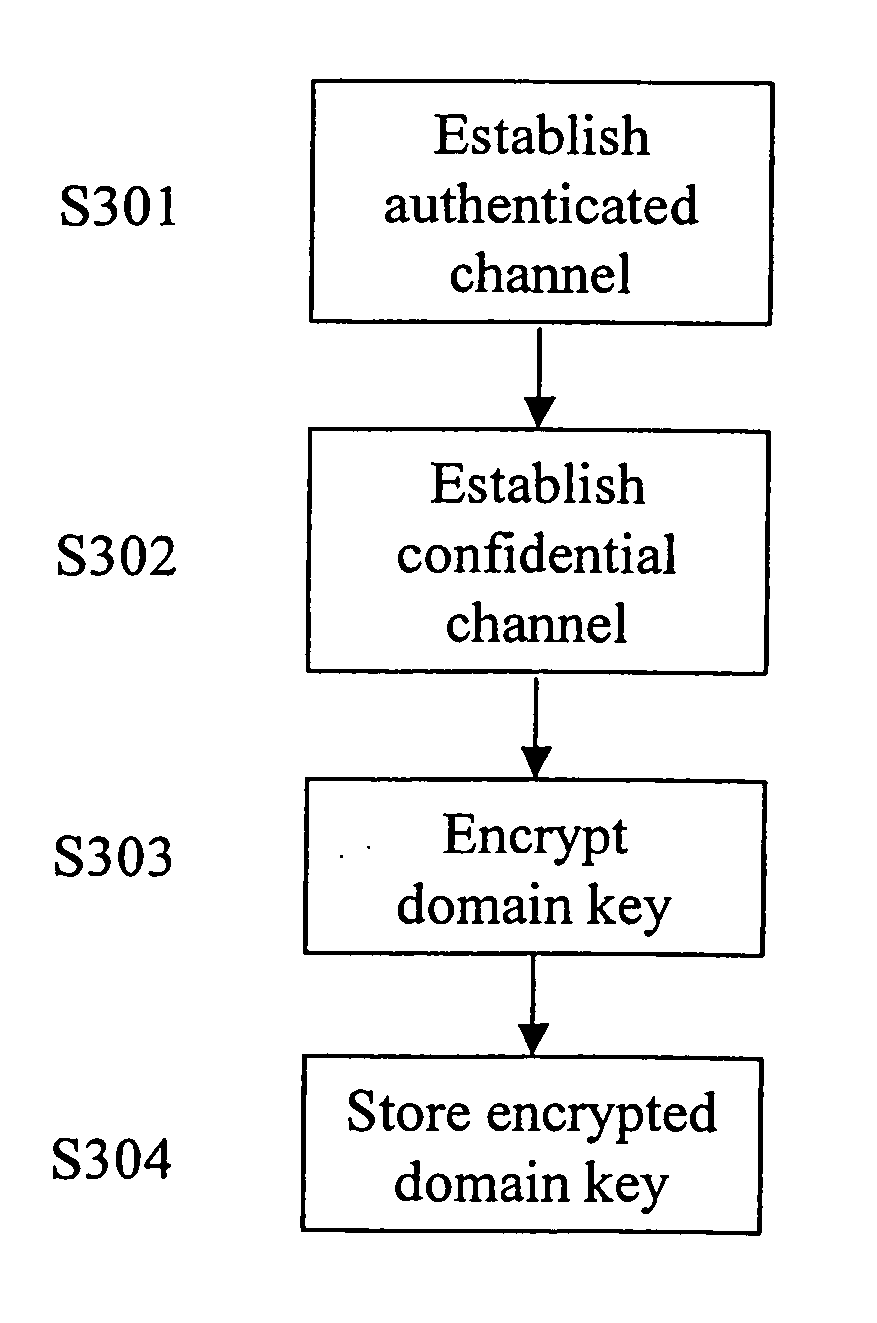
Accessing protected data on network storage from multiple devices
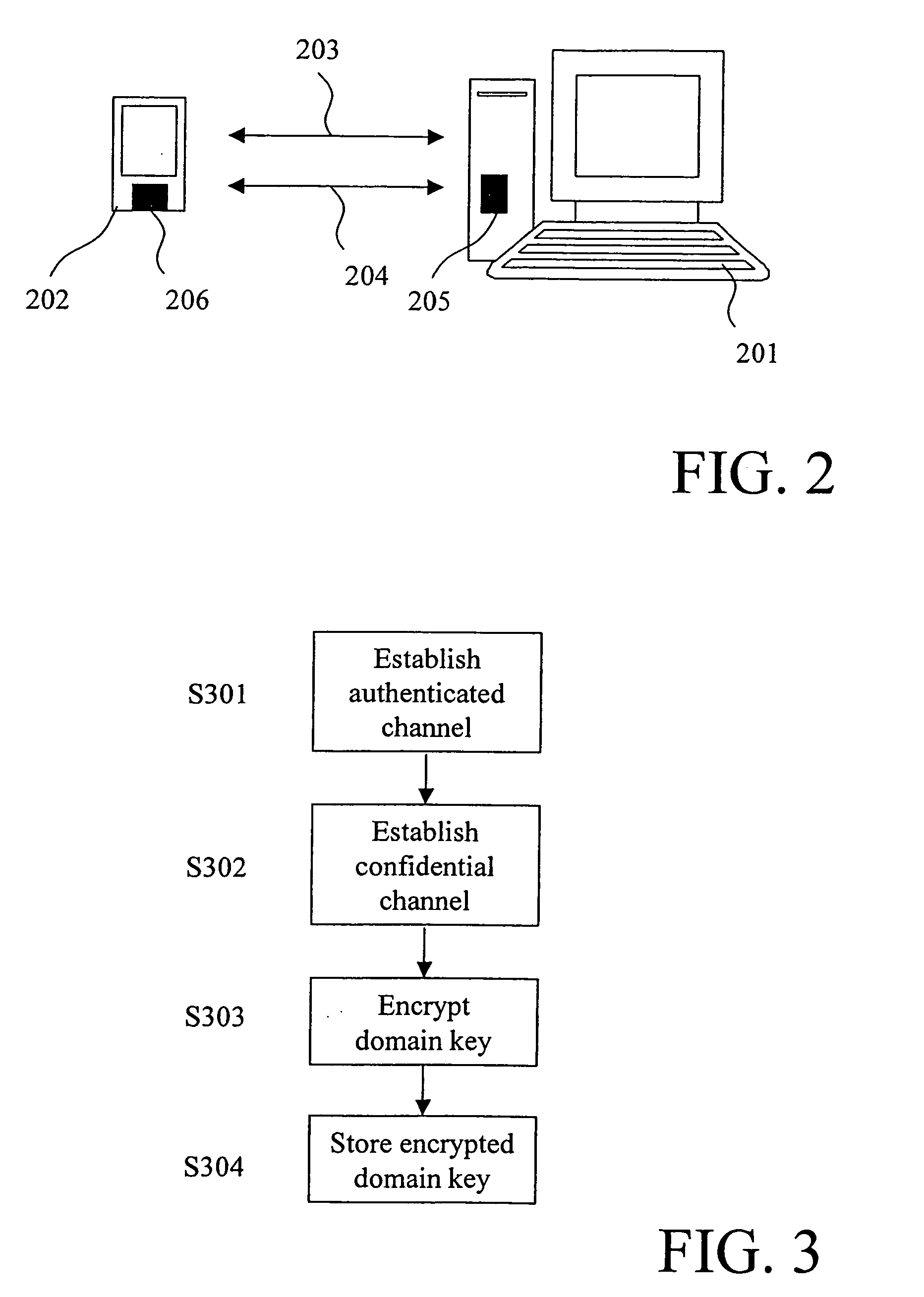
ActiveUS20050193199A1Easy to manageKey distribution for secure communicationData taking preventionPlaintextAuthorized domain
The present invention relates to a method and a system of securely storing data on a network (100) for access by an authorized domain (101, 102, 103), which authorized domain includes at least two devices that share a confidential domain key (K), and an authorized domain management system for securely storing data on a network for access by an authorized domain. The present invention enables any member device to store protected data on the network such that any other member device can access the data in plaintext without having to communicate with the device that actually stored the data.
Owner:NOKIA TECHNOLOGLES OY
File server system providing direct data sharing between clients with a server acting as an arbiter and coordinator
InactiveUS7120631B1Data processing applicationsDigital data information retrievalData accessClient-side
A client is permitted to send data access commands directly to network data storage of a network file server after obtaining a lock on at least a portion of the file and obtaining metadata indicating storage locations for the data in the data storage. For example, the client sends to the file server at least one request for access to a file. In response, the file server grants a lock to the client, and returns to the client metadata of the file including information specifying data storage locations in the network data storage for storing data of the file. The client receives the metadata, and uses the metadata to produce at least one data access command for accessing the data storage locations in the network storage. The client sends the data access command to the network data storage to read or write data to the file. For a write operation, the client may modify the metadata. When the client is finished writing to the file, the client returns any modified metadata to the file server.
Owner:EMC CORP
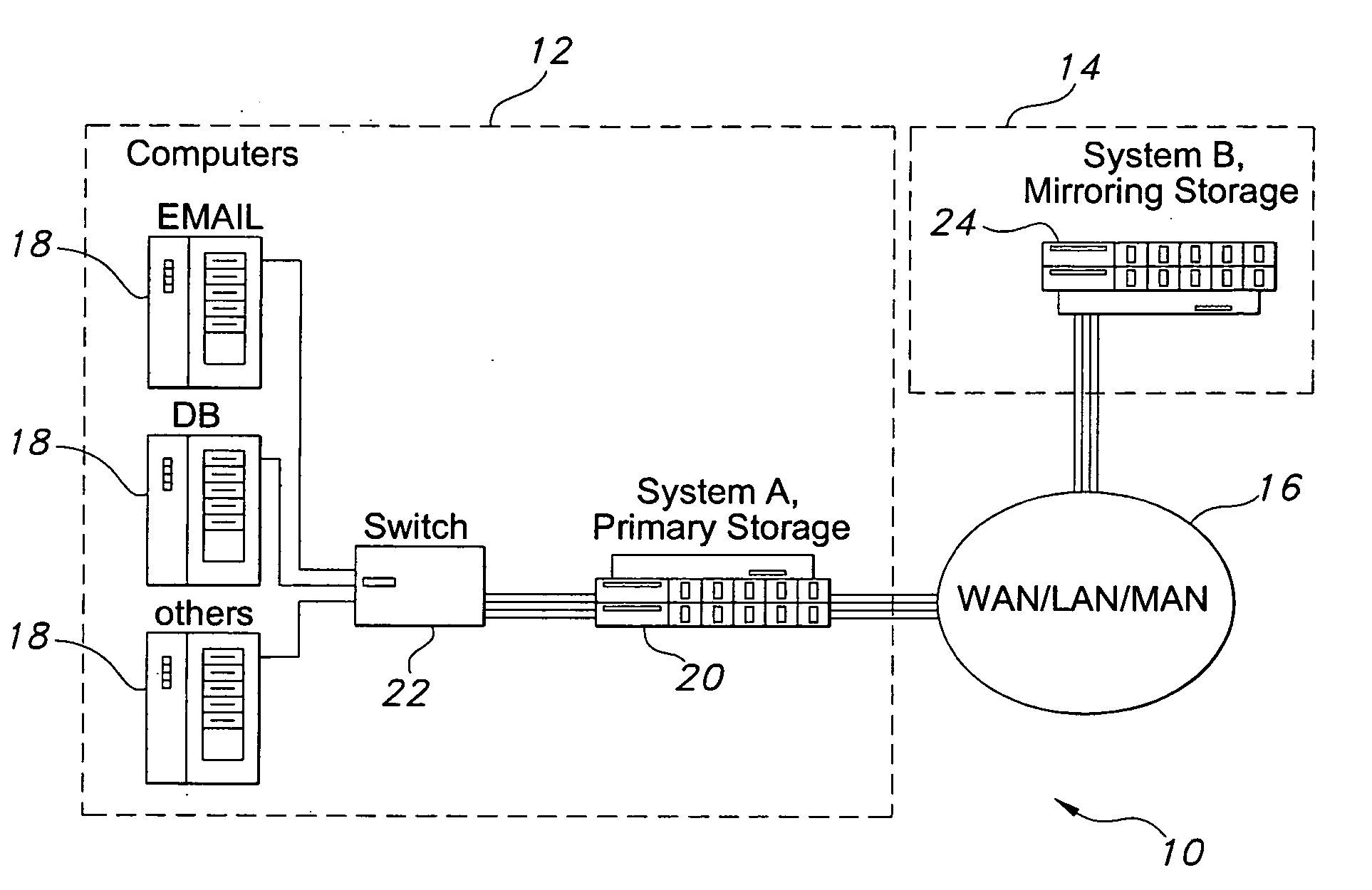
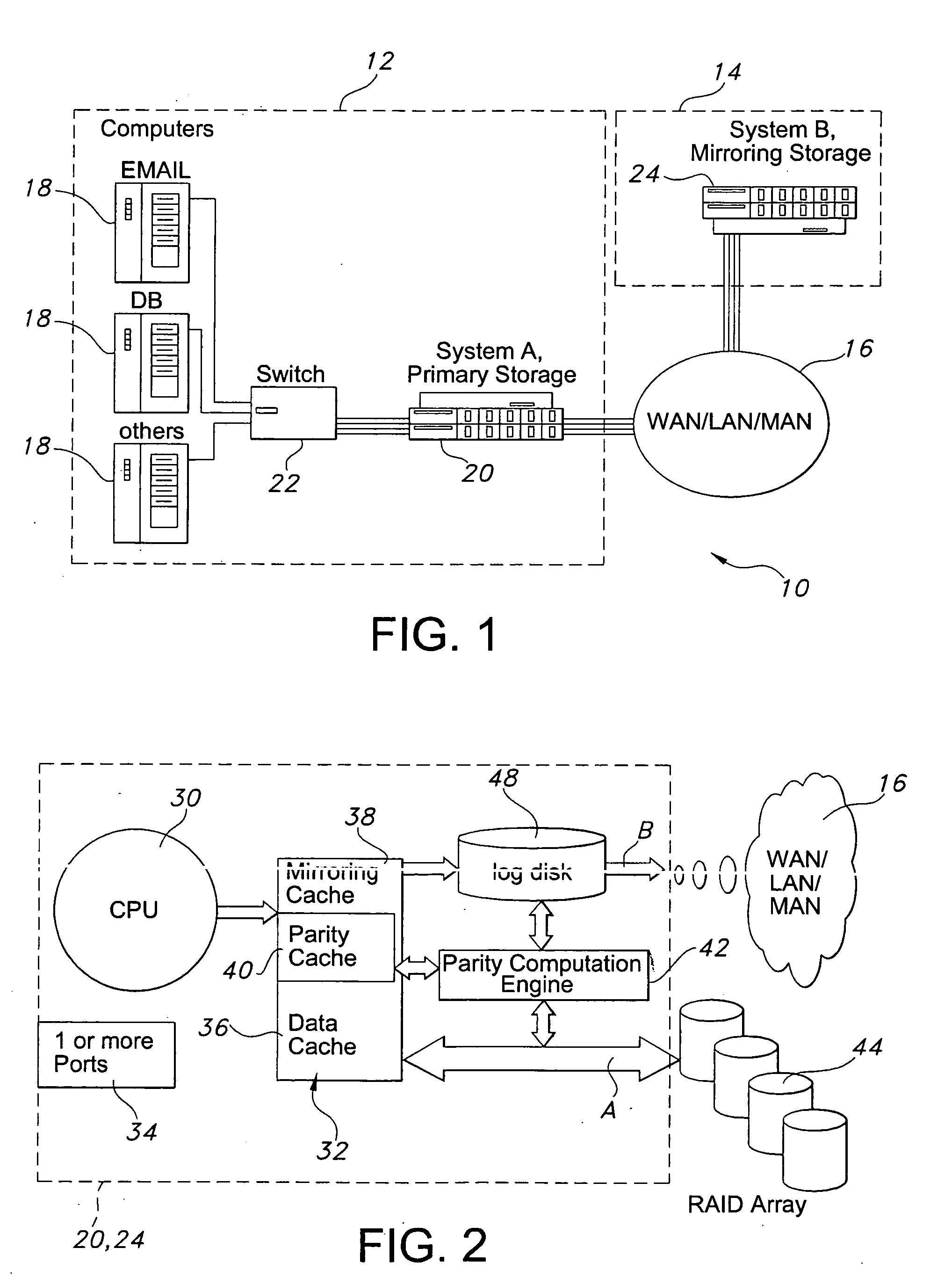
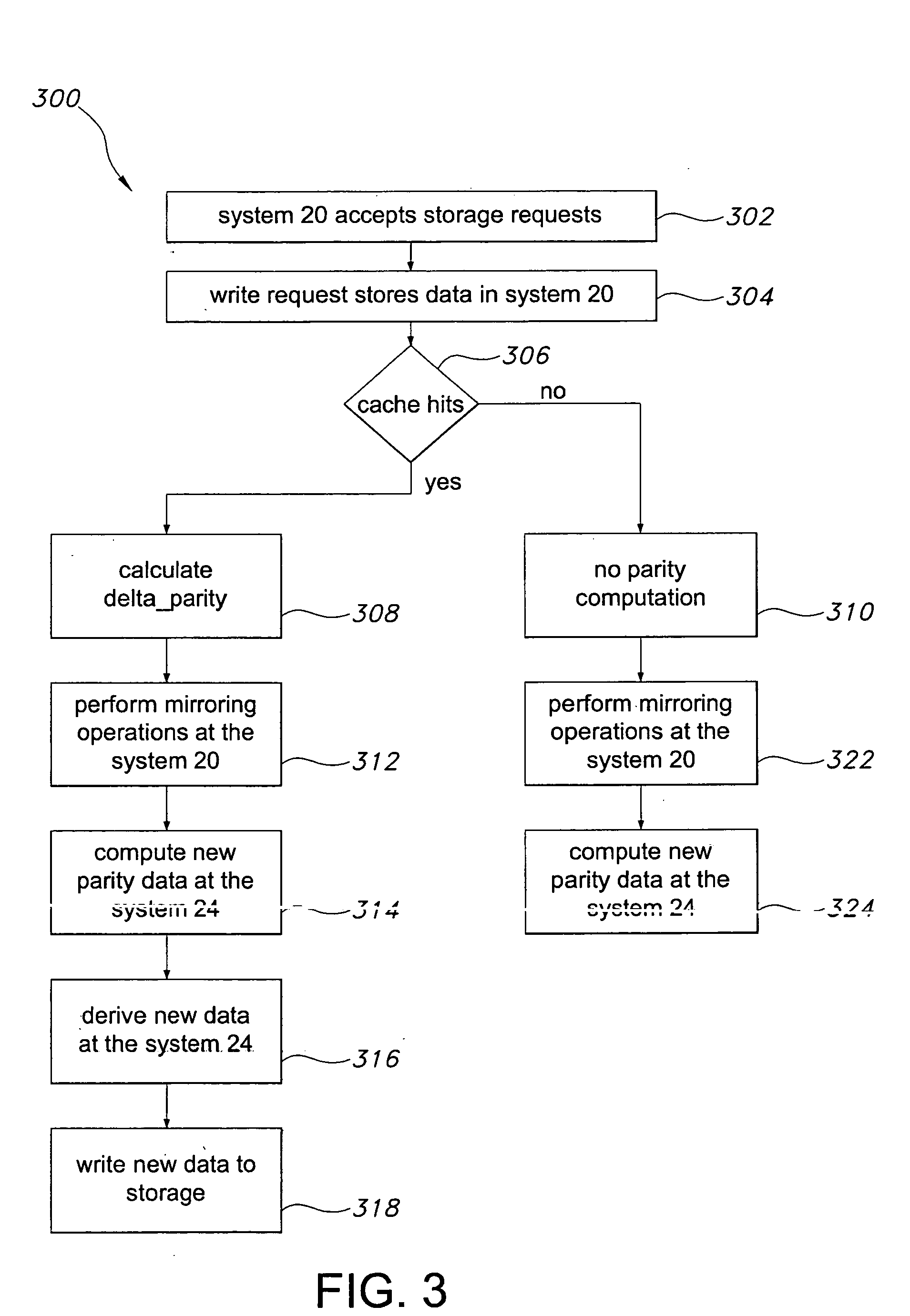
Data replication method over a limited bandwidth network by mirroring parities
A method dramatically reduces the amount of data to be stored and transferred in a networked storage system. Preferably, the network storage system provides continued data protection through mirroring / replication, disk-to-disk backup, data archiving for future retrieval, and Information Lifecycle management (ILM). The idea is to leverage the parity computation that exists in RAID systems. By caching, transferring, and storing data parity or delta bytes of changes on a block as opposed to data block itself, substantial data reduction is possible without using sophisticated compression algorithms at the production side to minimize performance impacts upon production servers. Data can be computed using the parity / delta and previously existing data at mirror side, replication side, backup storage, or at retrieval time upon events such as failures or ILM operations.
Owner:ZOLL CIRCULATION +1
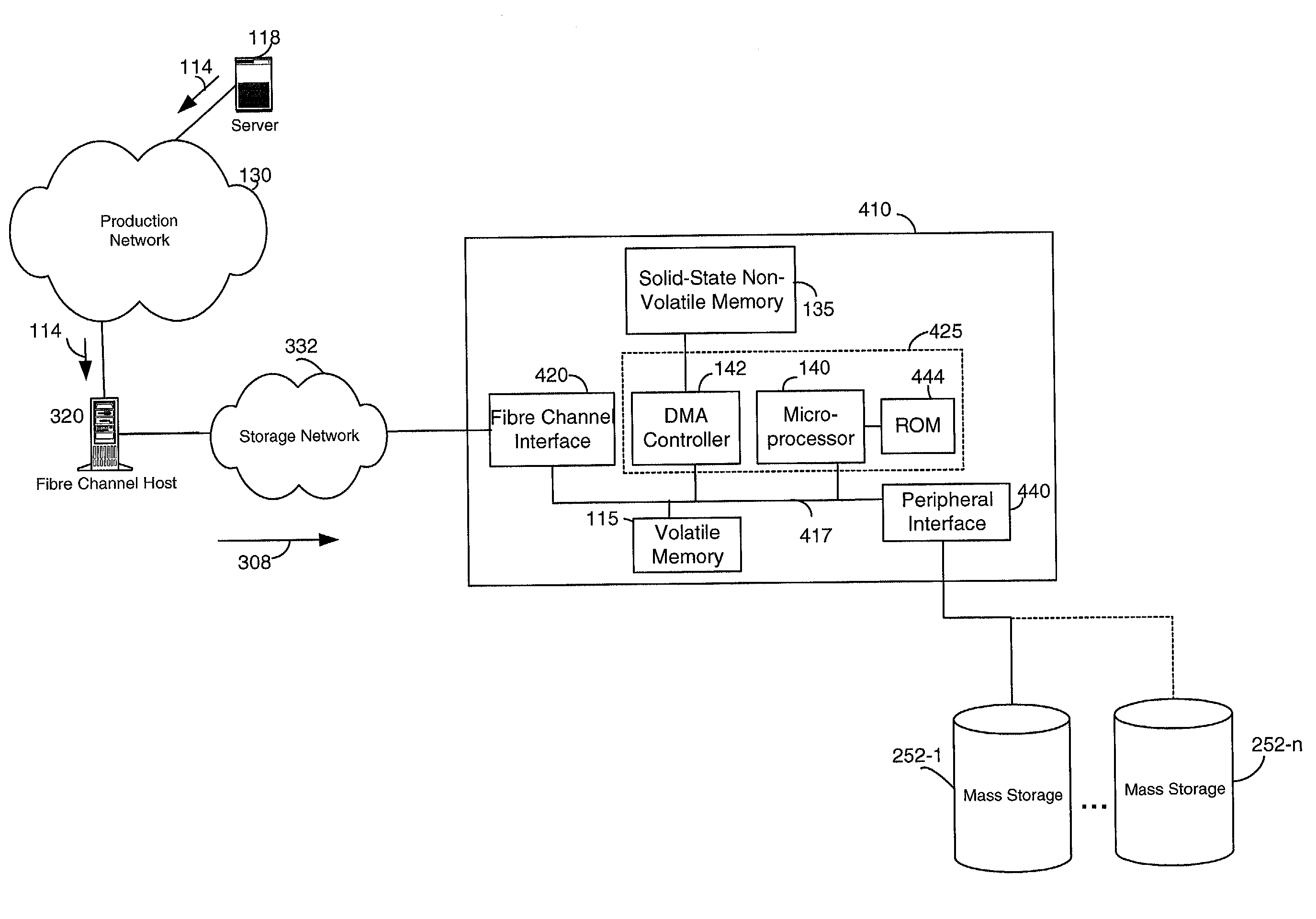
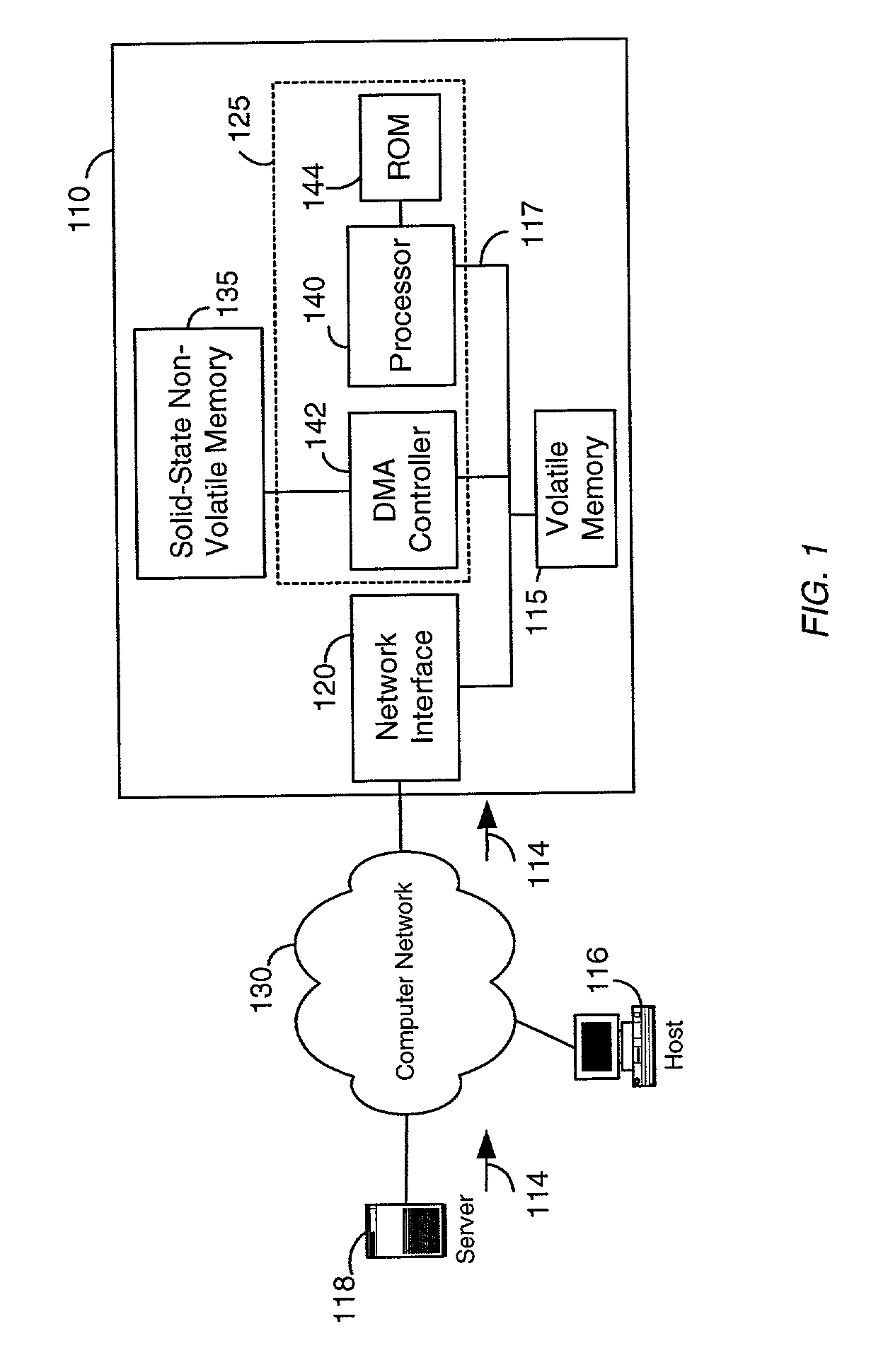
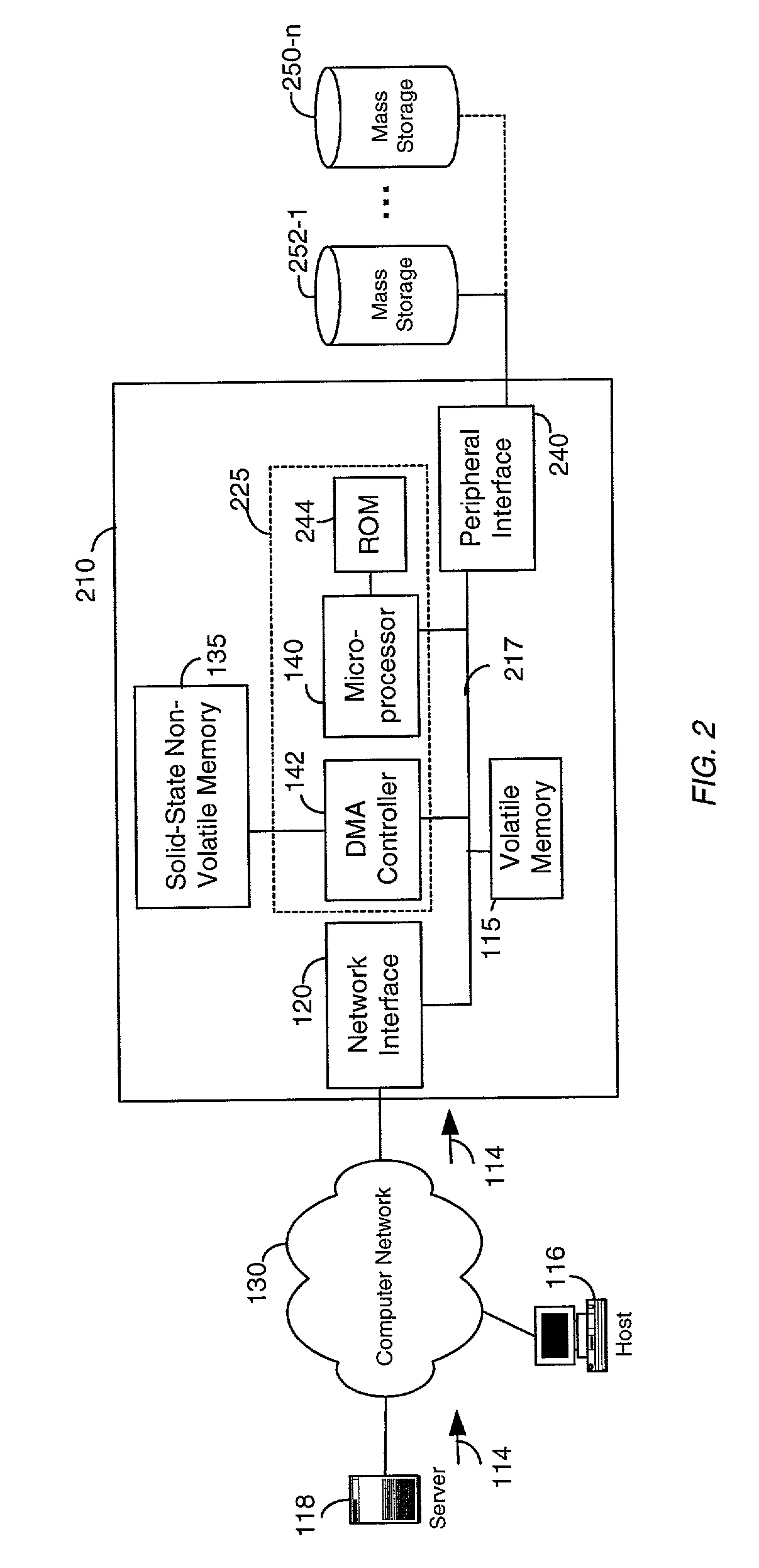
Network storage device having solid-state non-volatile memory
InactiveUS6981070B1Great access timeSmall currentMemory architecture accessing/allocationInput/output to record carriersMass storageRAID
A network storage device. In one embodiment, the network storage device of the present invention uses solid-state non-volatile memory (e.g., flash-memory) as a storage medium, and has at least one interface configured for coupling to a computer network. The network storage device of the present invention is accessible to client(s) and / or server(s) of the computer network, and uses solid-state non-volatile memory to store data received therefrom. The network storage device may also be configured to include a memory for caching data to be written to the solid-state non-volatile memory. In order to provide additional storage, the network storage device may also include a peripheral interface or another network interface for coupling to a mass storage device (e.g., a RAID system), and / or another network interface for coupling to a network of mass storage devices. The network storage device may be a stand-alone unit, or may be implemented as part of a network server, or as part of a mass storage device.
Owner:BITMICRO LLC
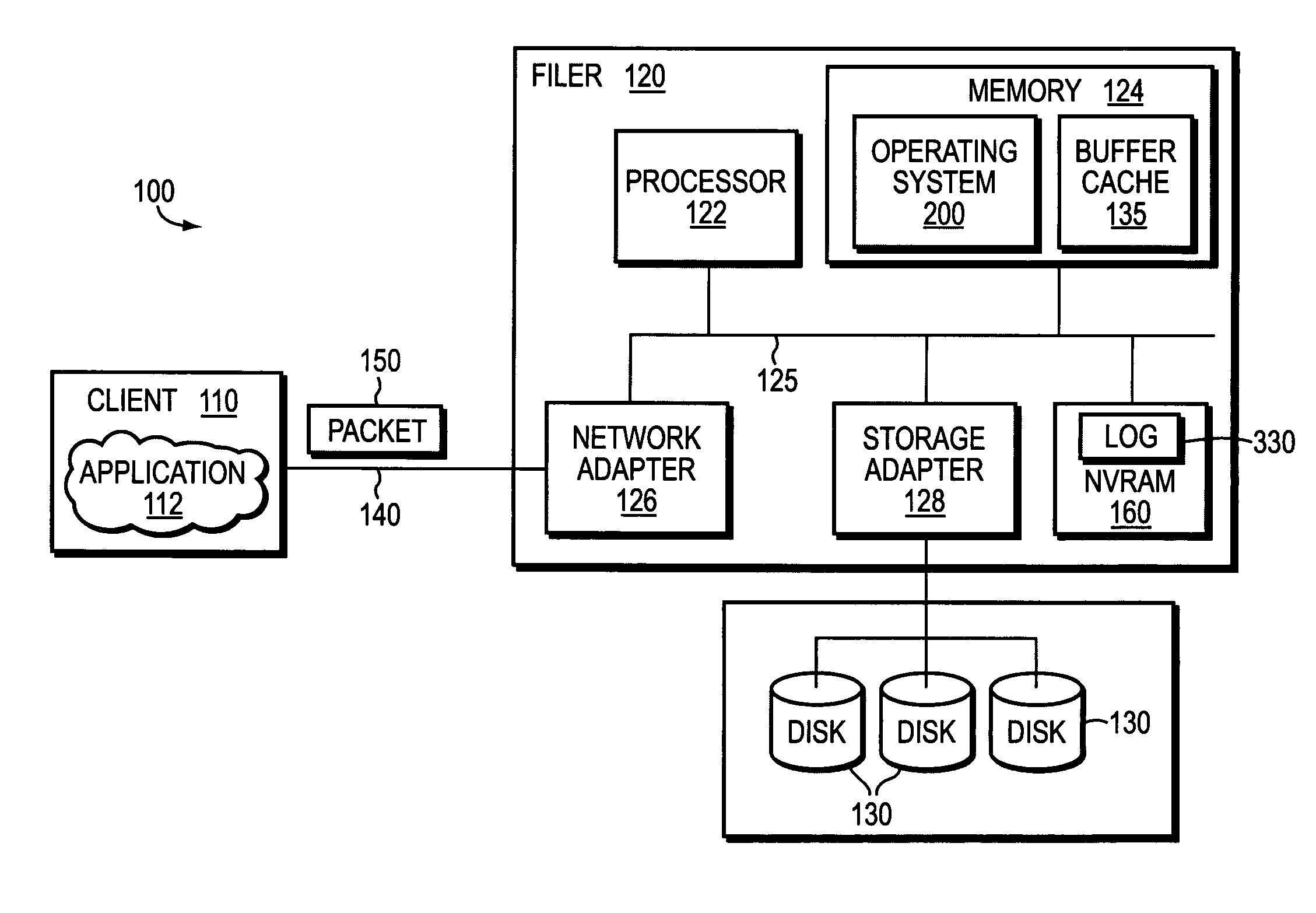
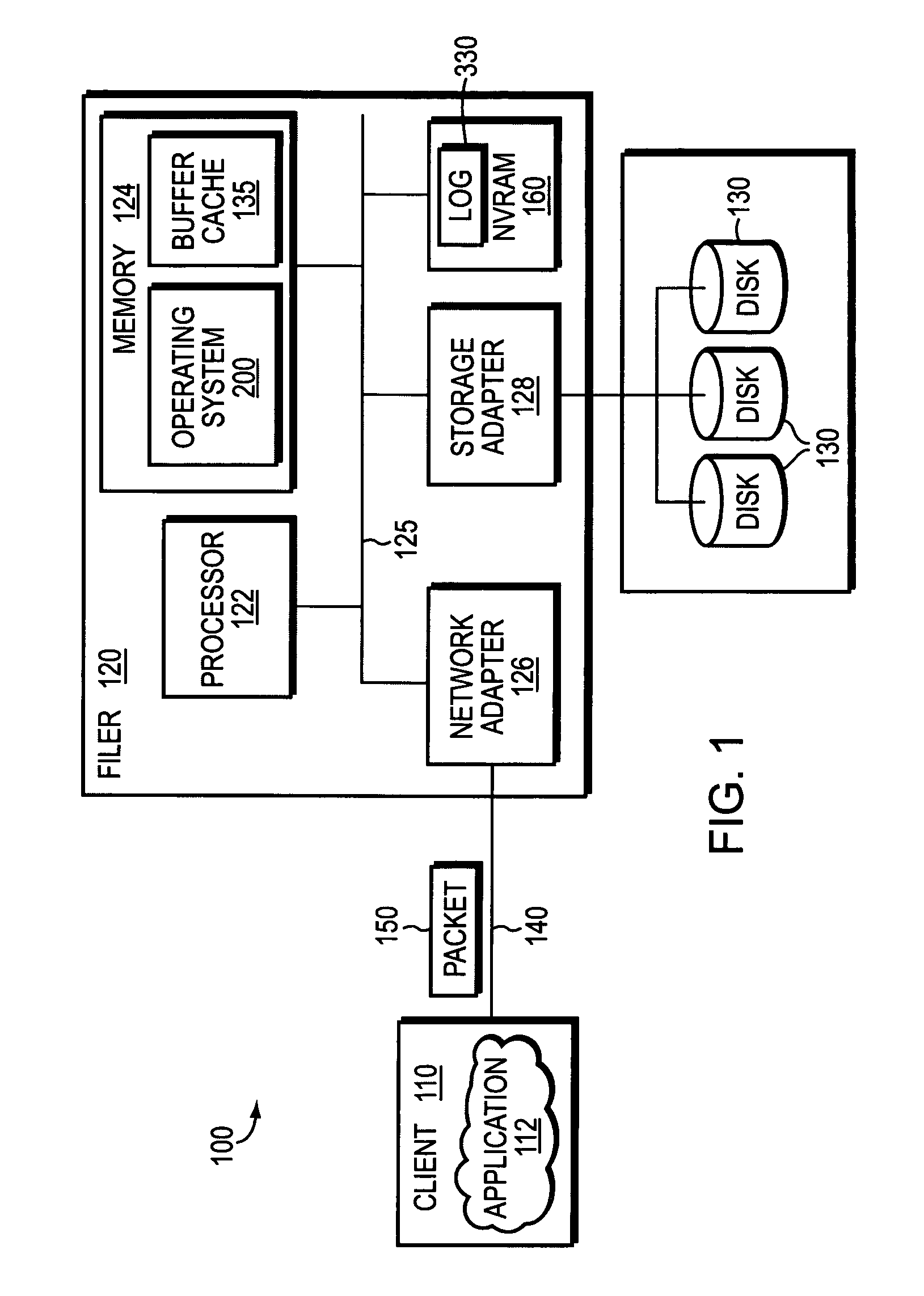
System and method for parallelized replay of an NVRAM log in a storage appliance
InactiveUS7249150B1Avoid mistakesError detection/correctionSpecial data processing applicationsFile systemClient-side
A system and method for enabling parallel replay of a backup memory log of client transaction request entries to a network storage appliance file system is provided. The backup memory is typically implemented as a non-volatile random access memory (NVRAM). An initiator establishes a swarm of messages with a plurality of transaction blocks pointing to logged request entries and related states associated therewith. The states represent the various phases of file system recovery and disk storage including a retrieval of disk information (data and meta-data), typically in the form of a LOAD, and a subsequent modify phase. The swarm is transferred to the file system for parallel disk information-retrieval in an interleaved process. Any transactions that cannot be performed due to a required prerequisite action (e.g. a prior file-create) are returned to the initiator for reloading once the prerequisite action has occurred.
Owner:NETWORK APPLIANCE INC
Apparatus and method for deterministically killing one of redundant servers integrated within a network storage appliance chassis
InactiveUS20050246568A1Potentially reliableReliable methodNon-redundant fault processingFault response safety measuresSignal onControl store
An apparatus for deterministically killing one of redundant servers integrated into a network storage appliance chassis along with at least one storage controller is disclosed. Each server can generate a kill signal on a backplane of the chassis to the other server in response to a stopped heartbeat of the other server in order to disable the I / O ports of the other server on a network so the live server can reliably take over the identity of the other server on the network. Unlike conventional kill paths, such as an Ethernet cable connecting the two servers in separate chassis, the present invention does not require the failed server to be operational since the kill path is substantially a direct reset to the I / O ports of the failed server. One server raises a shield before killing the other server to avoid both servers killing each other simultaneously.
Owner:DOT HILL SYST
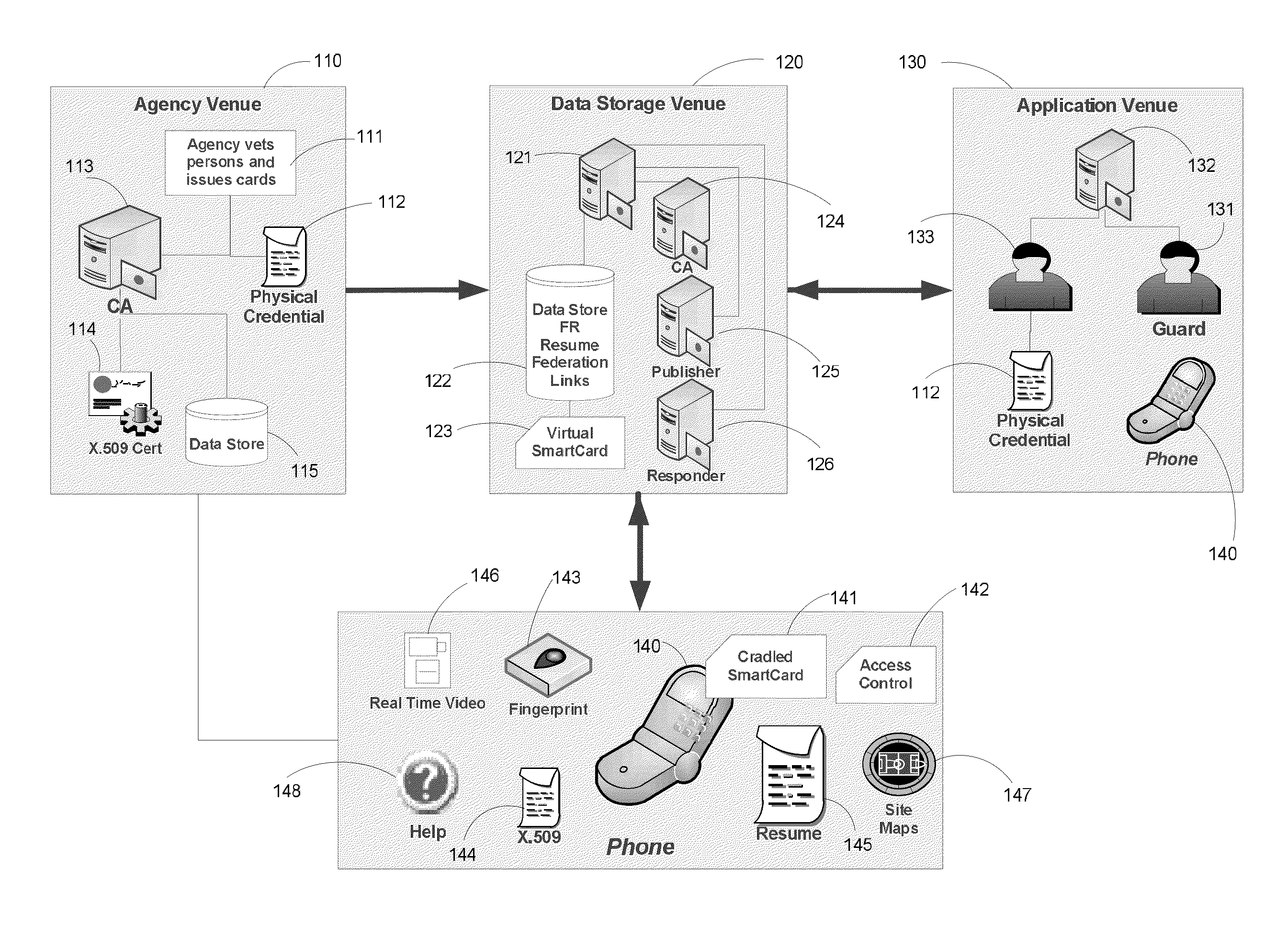
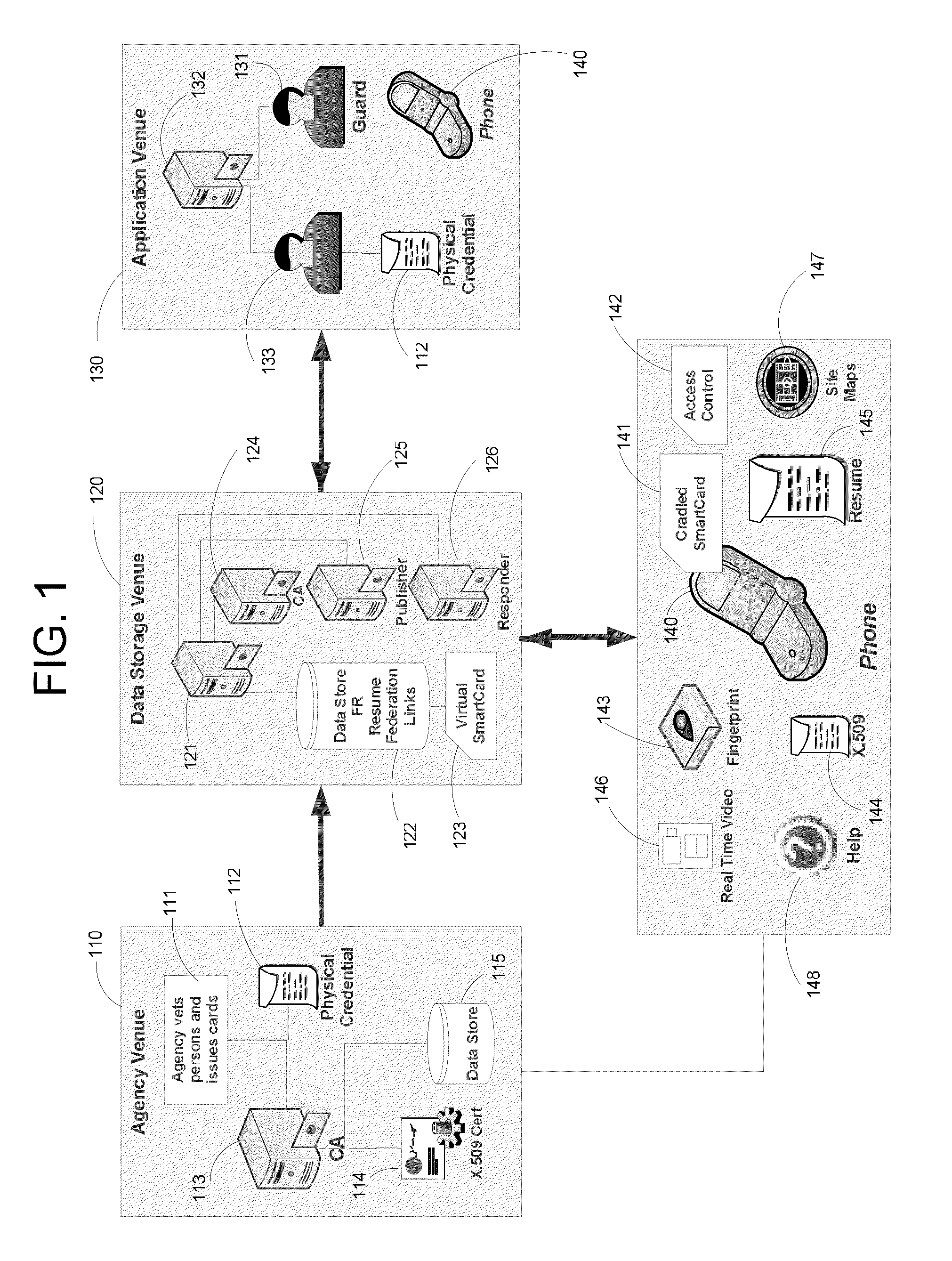
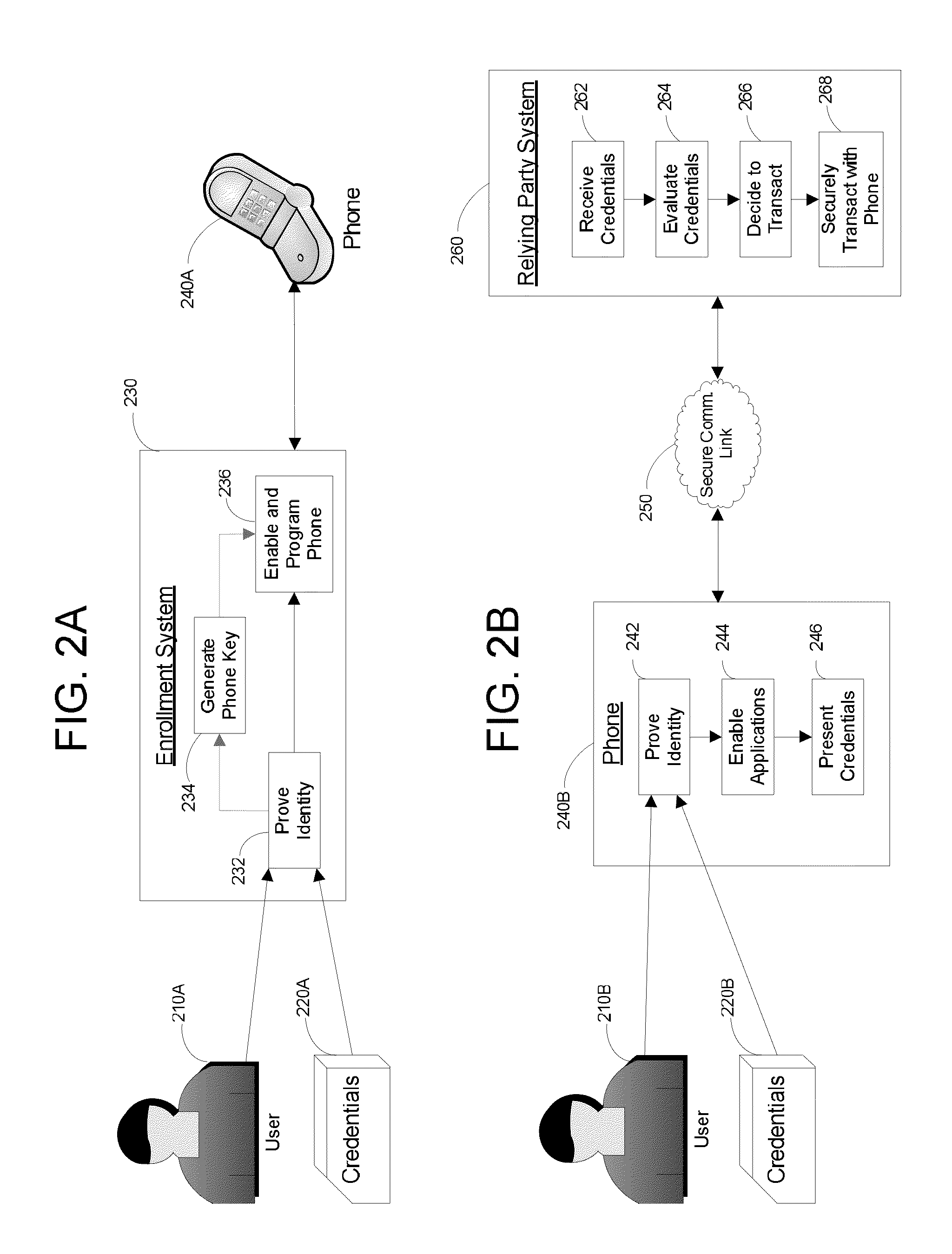
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20130061055A1Reduce computing power requirementsIncrease the number ofDigital data processing detailsUser identity/authority verificationCredit cardHardware security module
A virtual smartcard and methods for creating the same are provided. A virtual smartcard is a set of computer-implemented processes, associated with an individual, which simulate the behavior of a physical smartcard or other authentication token containing a hardware security module. In one embodiment, a computer receives credential data derived from the physical credential and authentication data pertinent to the individual such as a biometric imprint, and creates a virtual smartcard by storing the credential data in association with the authentication data in a network storage. The credential data may later be used for identification and encryption purposes upon the individual providing the authentication data to the network storage, even if the physical credential itself has been lost. Thus, the virtual smartcard provides a network-based method for backing up a passport, driver's license, credit card, public transportation card, or other such identification card or device.
Owner:INFERSPECT
Diagnostic Oral Health Care Implement and System
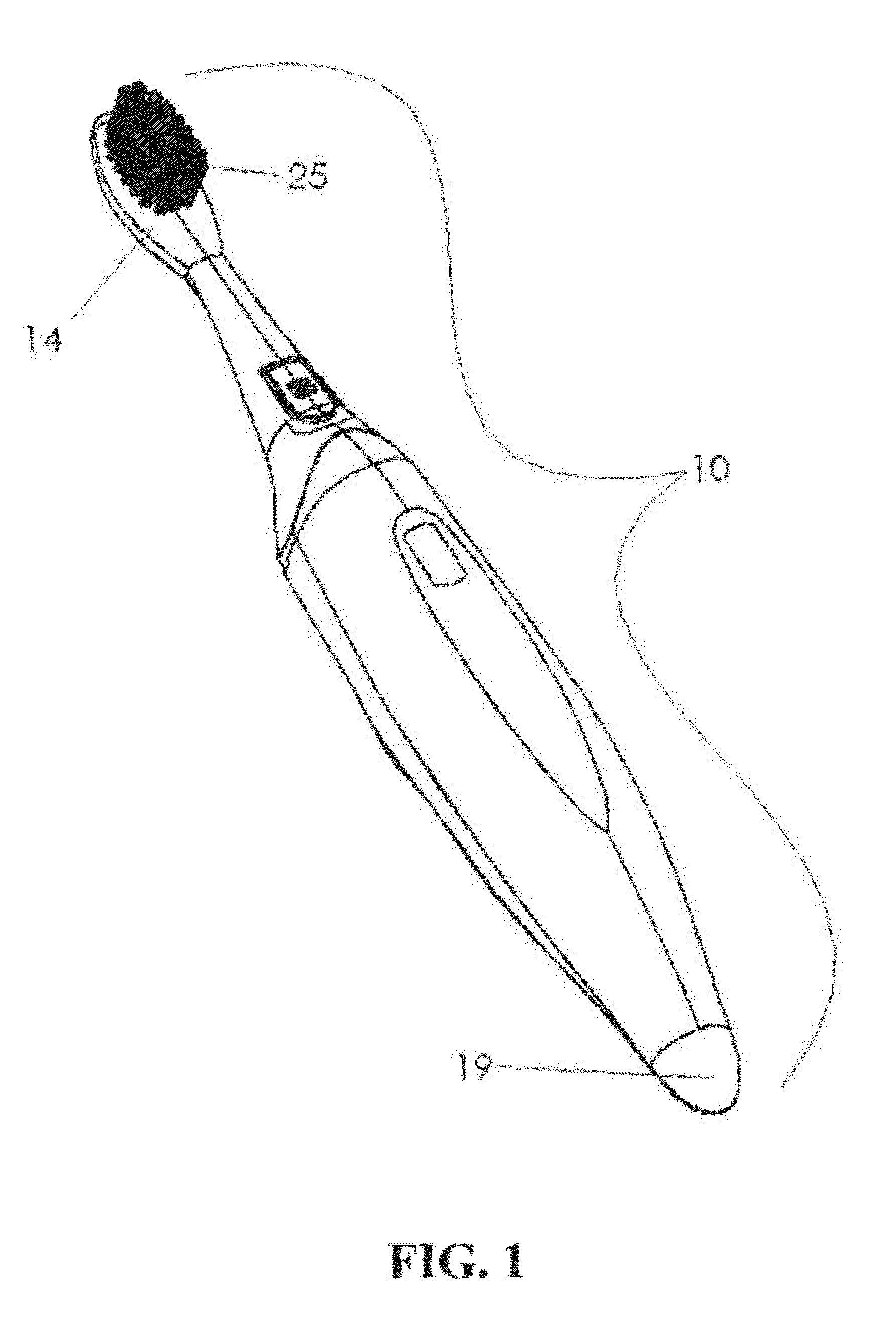
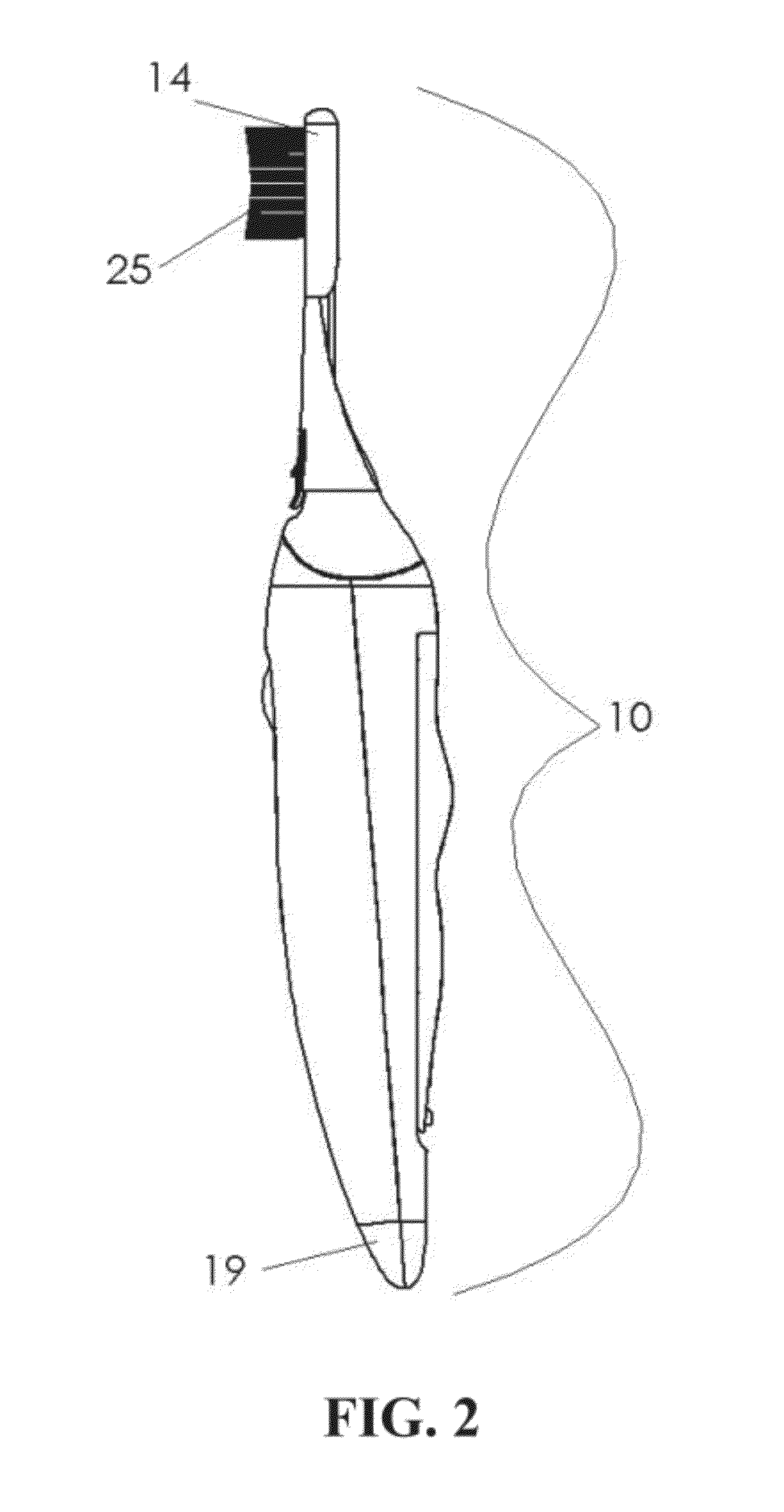
A diagnostic oral health care implement and system are provided for use during oral health care activities. The diagnostic oral health care implement has a diagnostic sensor. The diagnostic sensor provides diagnostic measurements in a plurality of formats including the biofilm thickness of dental plaque. The diagnostic oral health care system has a diagnostic oral health care implement and a first data transfer medium. The system optionally has any combination of a second data transfer medium, a network storage device, and a third data transfer medium. The system provides for the collection of diagnostic measurements and transmission of the data into a readable, usable form for the user via an oral health care implement.
Owner:BEAM TECH
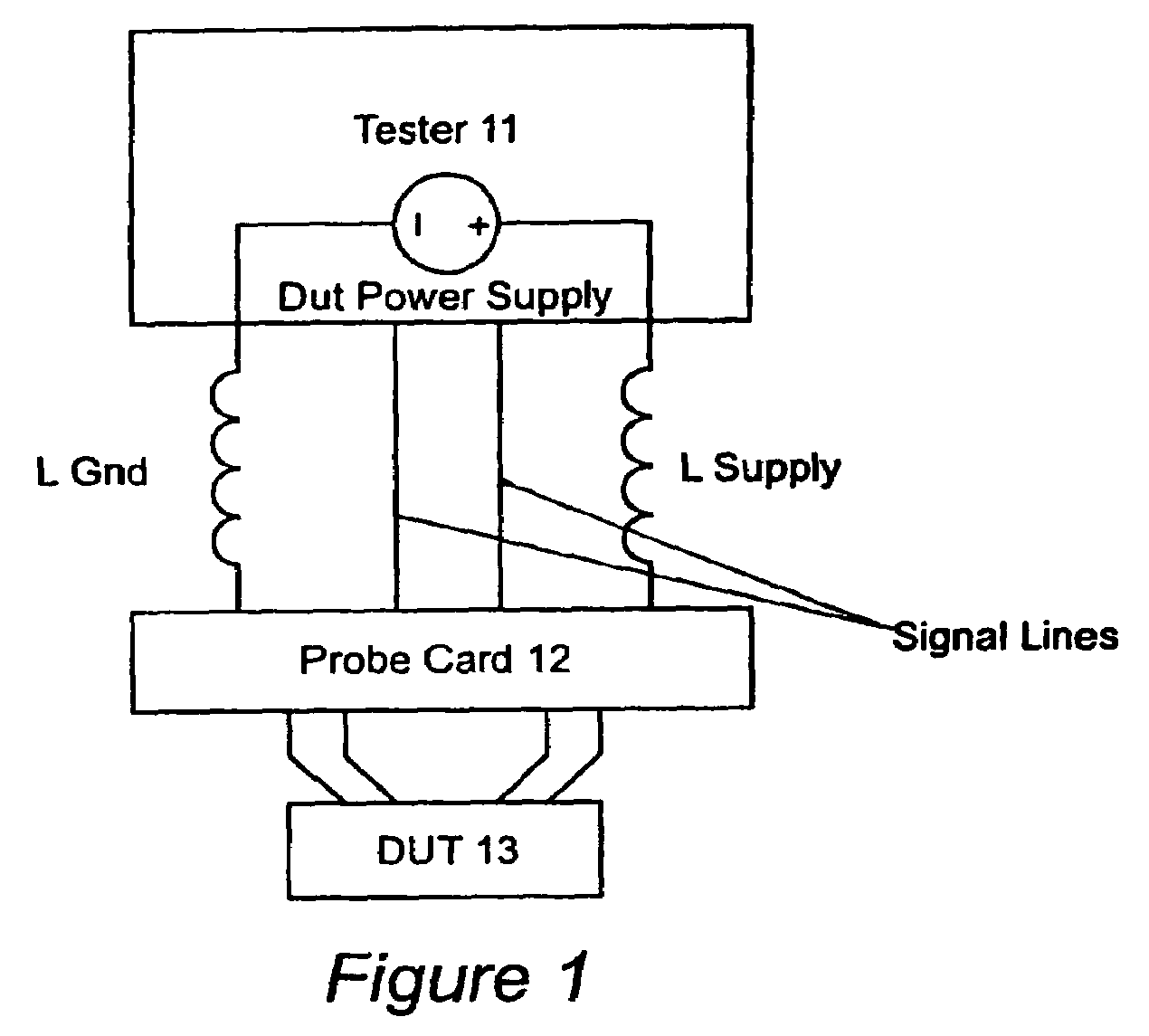
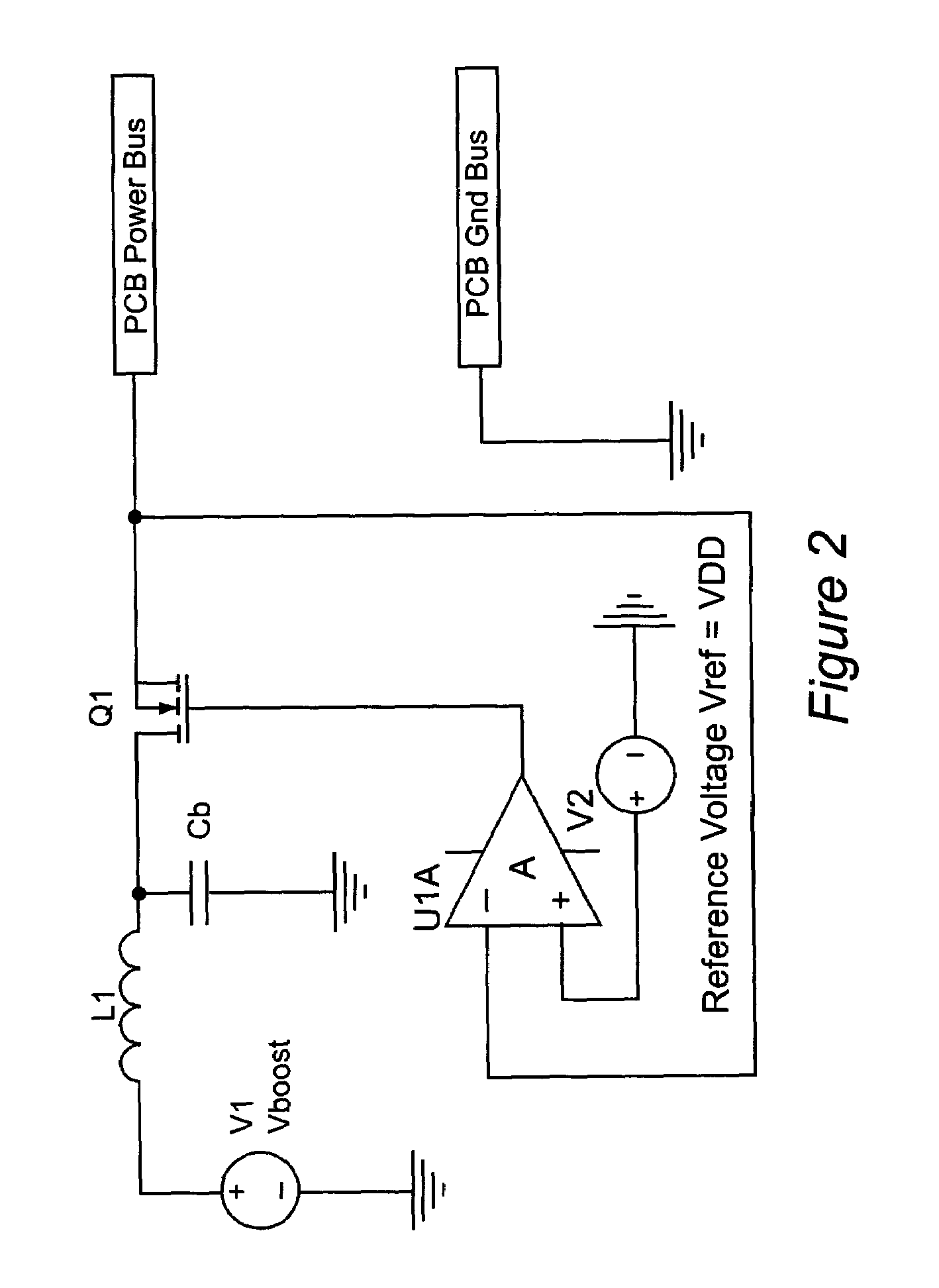
Device for probe card power bus noise reduction
InactiveUS7005879B1Reducing probe card power supply spikeEasy to superviseElectronic circuit testingIndividual semiconductor device testingCapacitancePhysical space
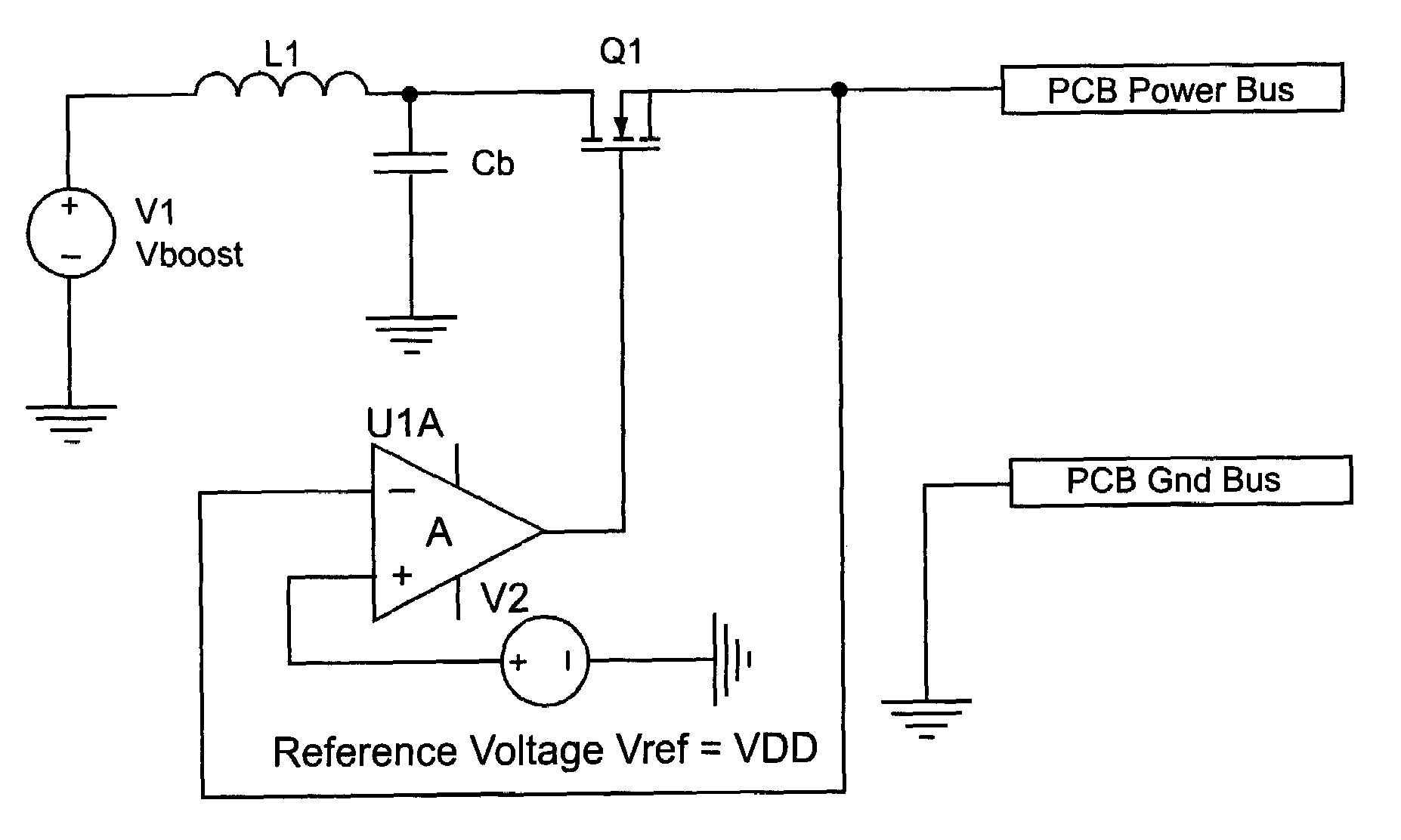
Noise reduction for application of structural test patterns to a Device Under Test (DUT) is accomplished with a capacitor “booster” bypass network on the probe card in which the capacitors are charged to a much higher voltage Vboost than the DUT power supply voltage VDD. Charging the capacitors to a voltage N×VDD allows the buster network to store N times the charge of a conventionally configured capacitance network, and effectively provides N times the capacitance of the original network in the same physical space.
Owner:GLOBALFOUNDRIES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com