Patents
Literature
53 results about "Authorized domain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
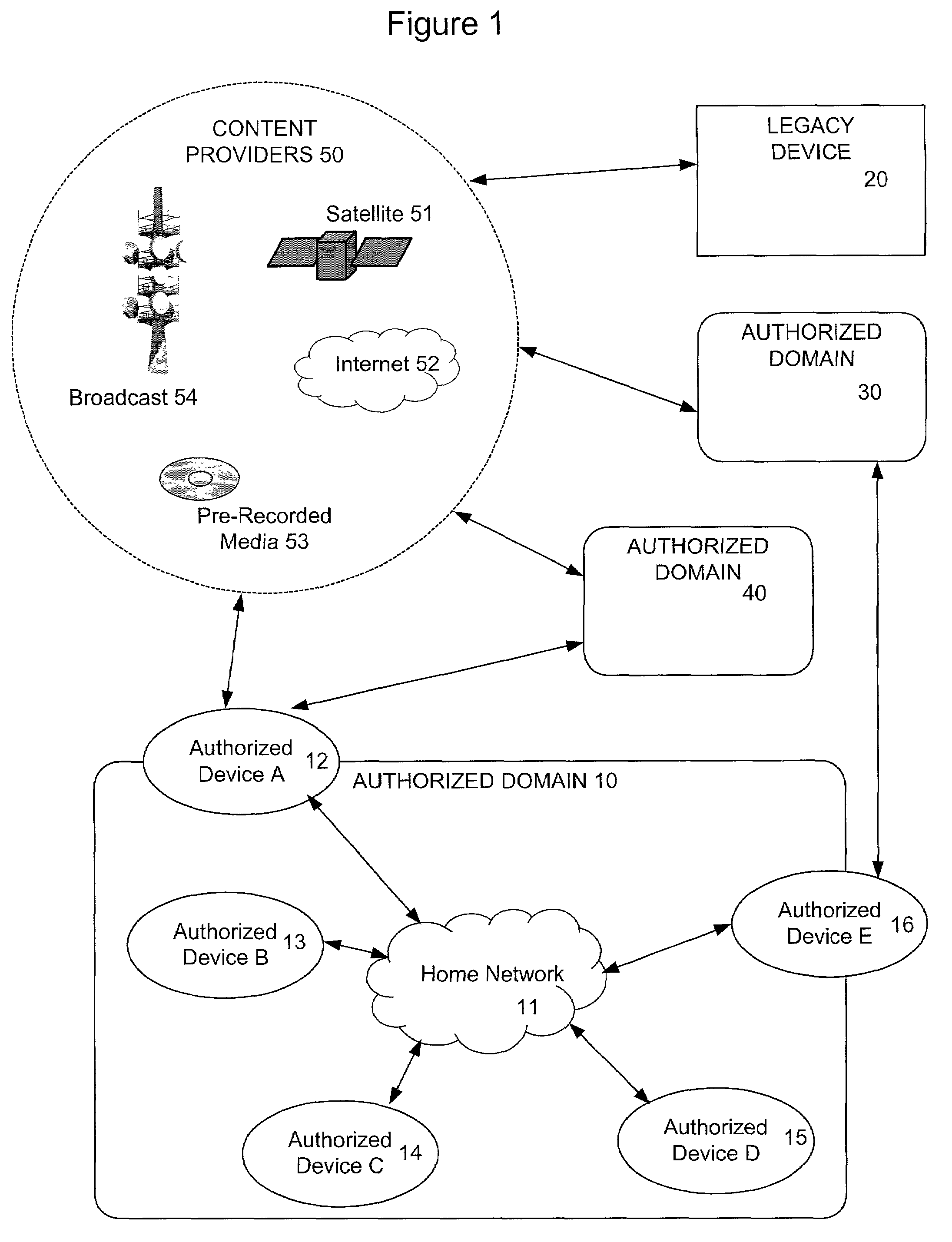
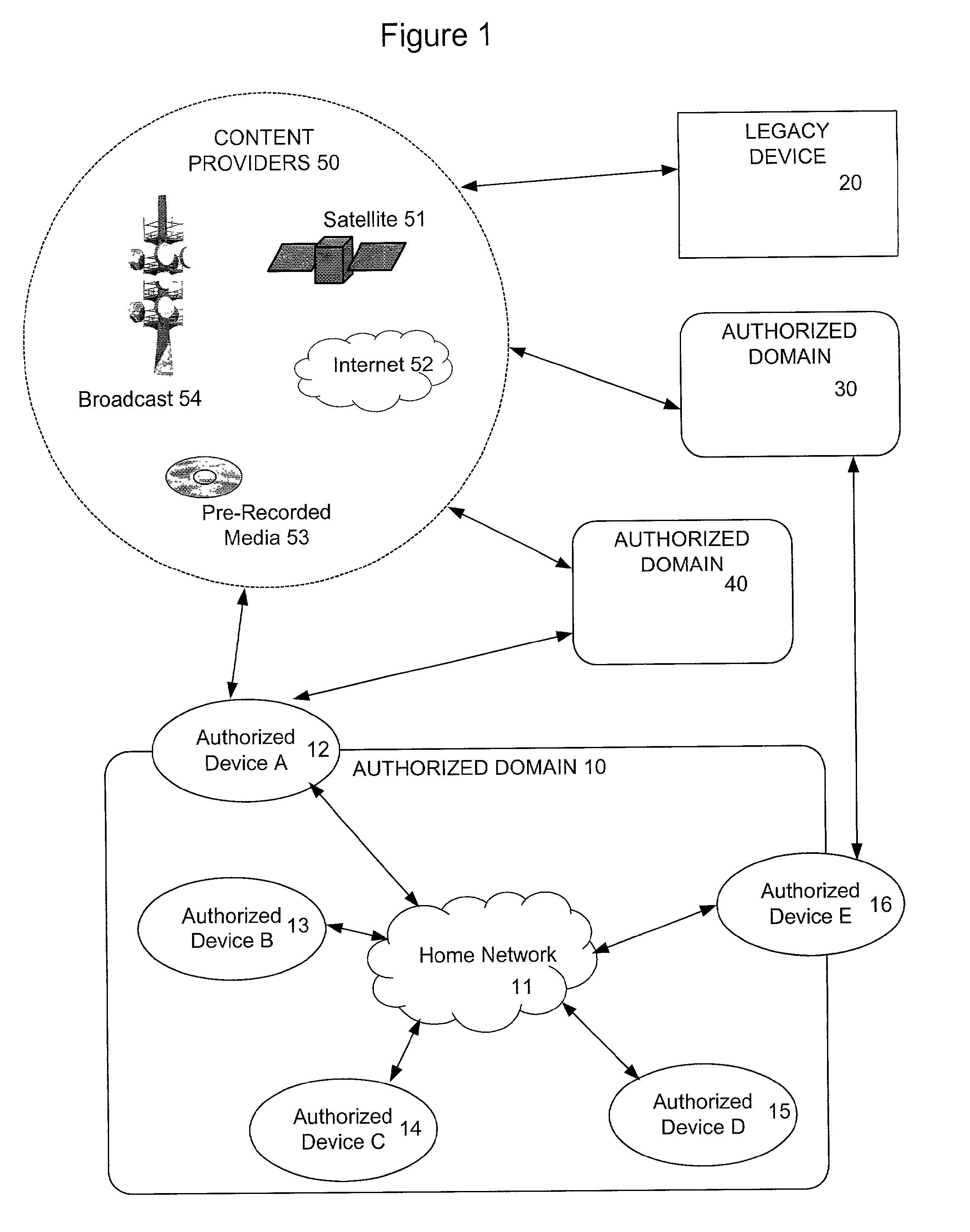
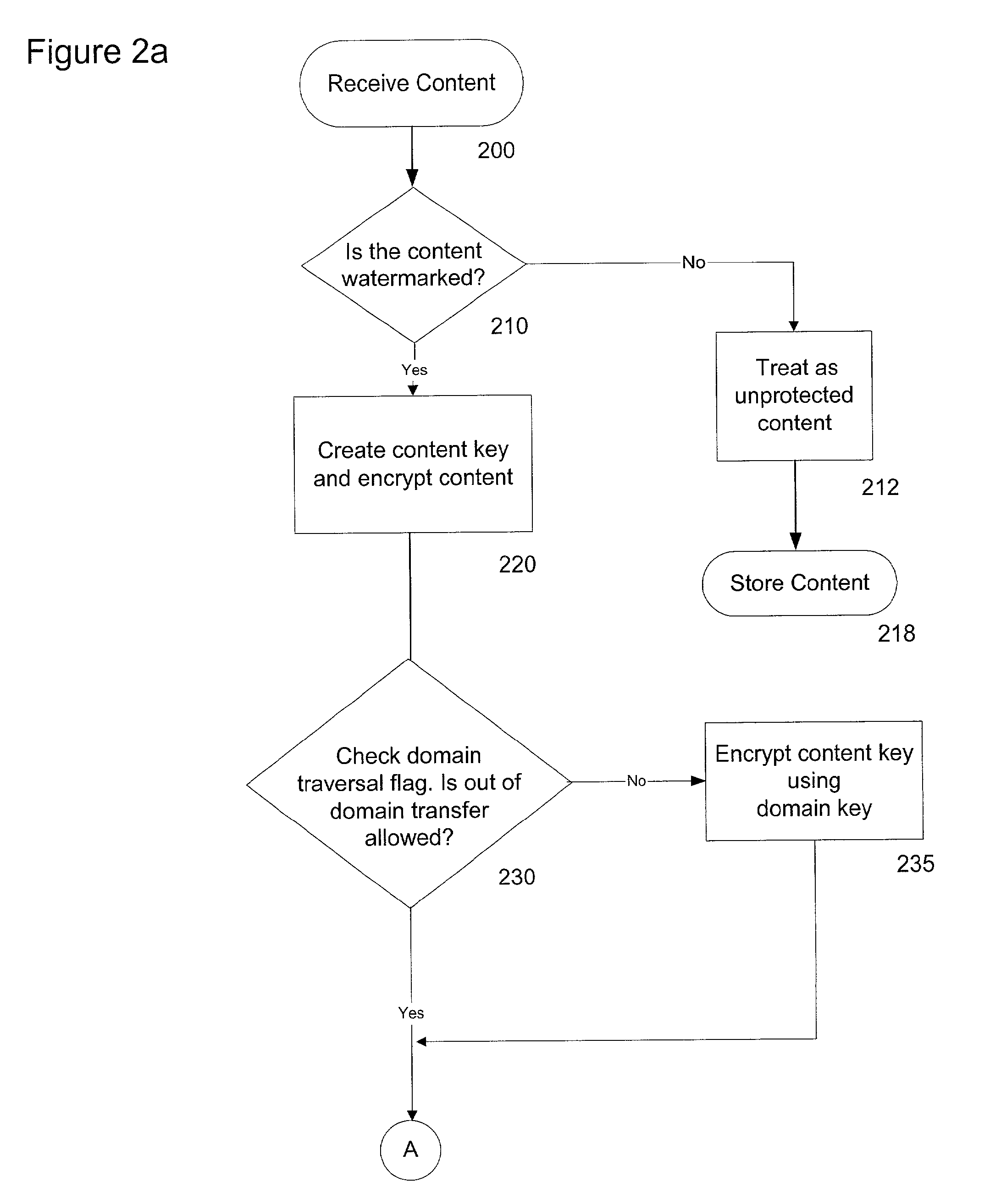
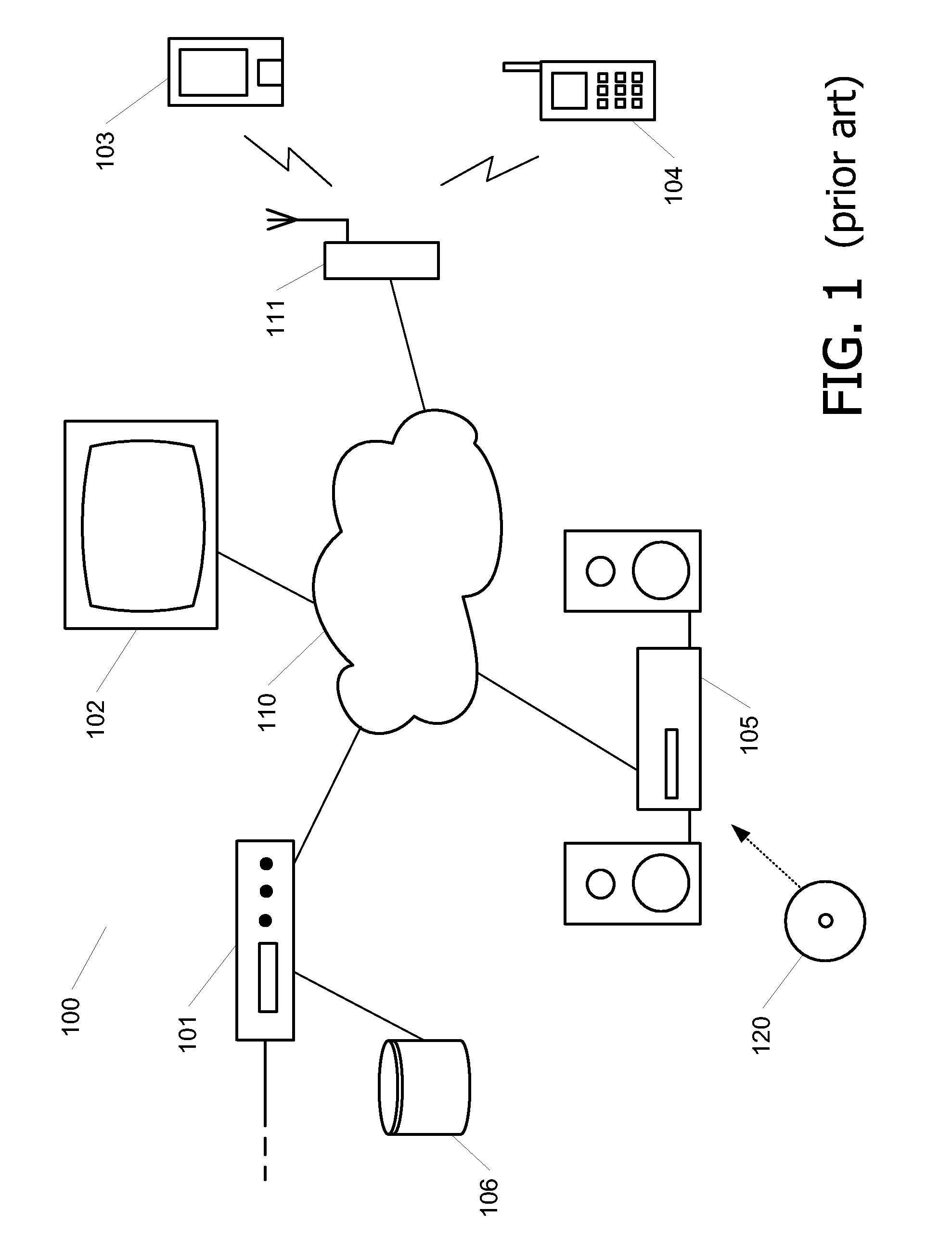
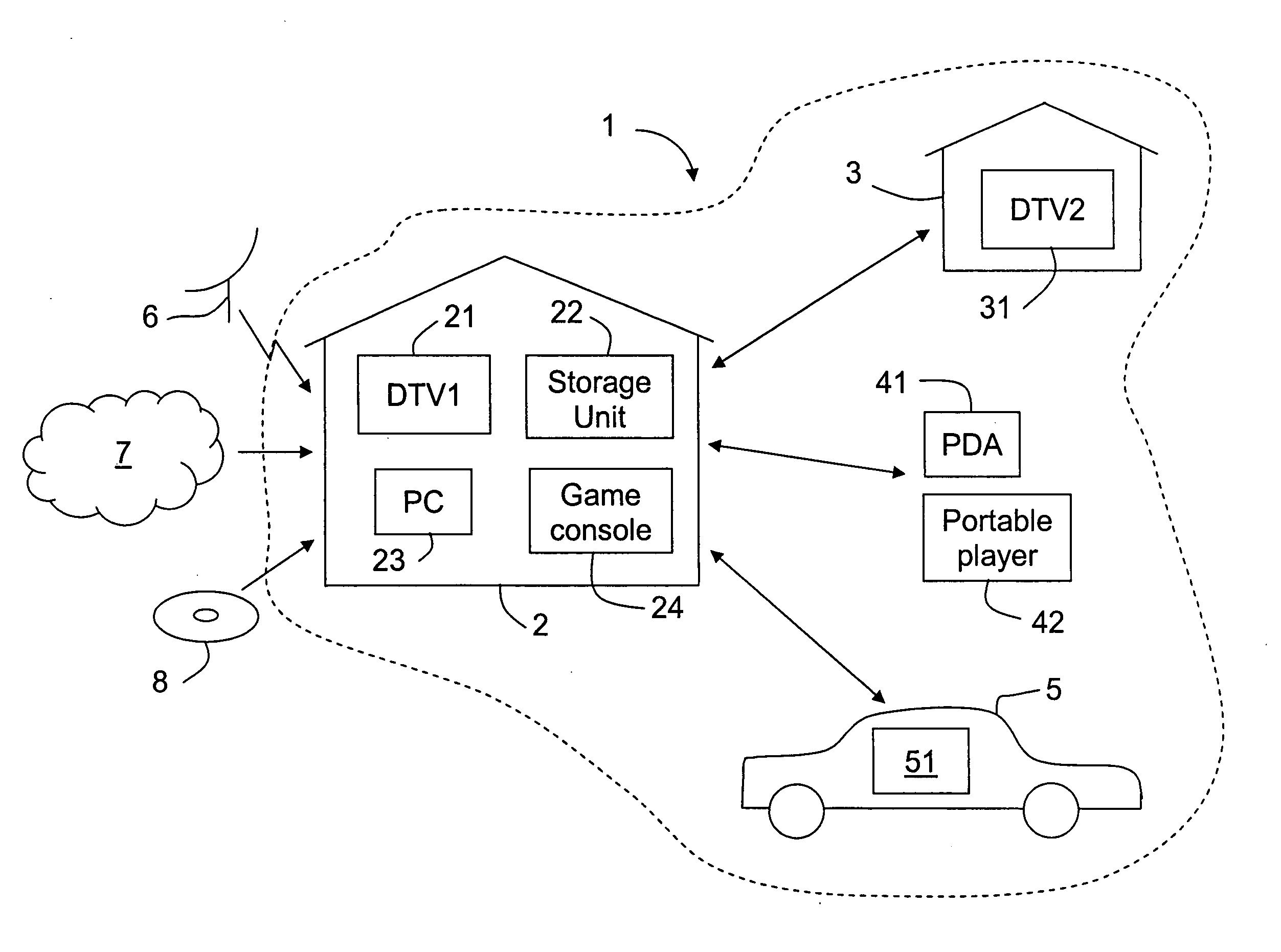
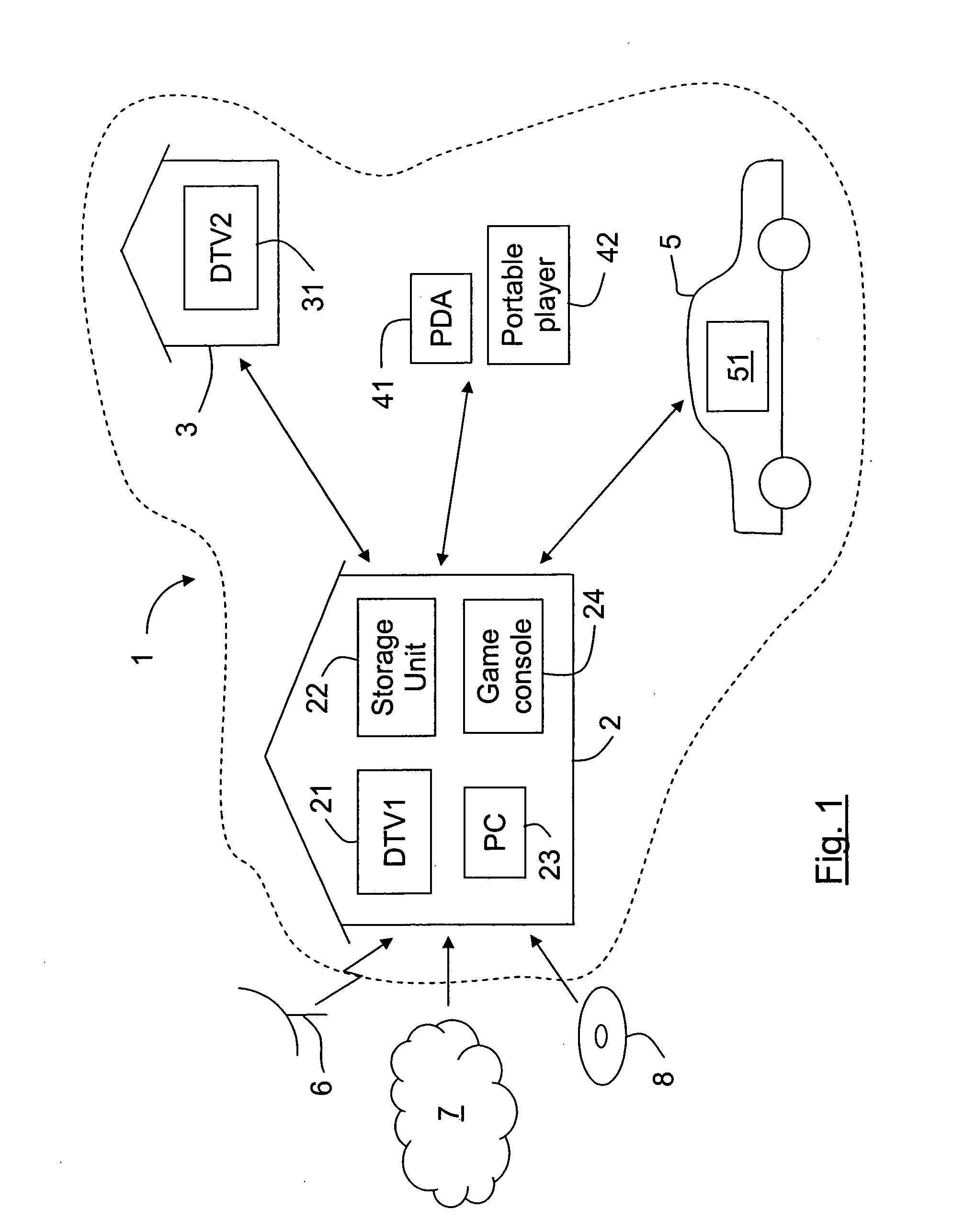
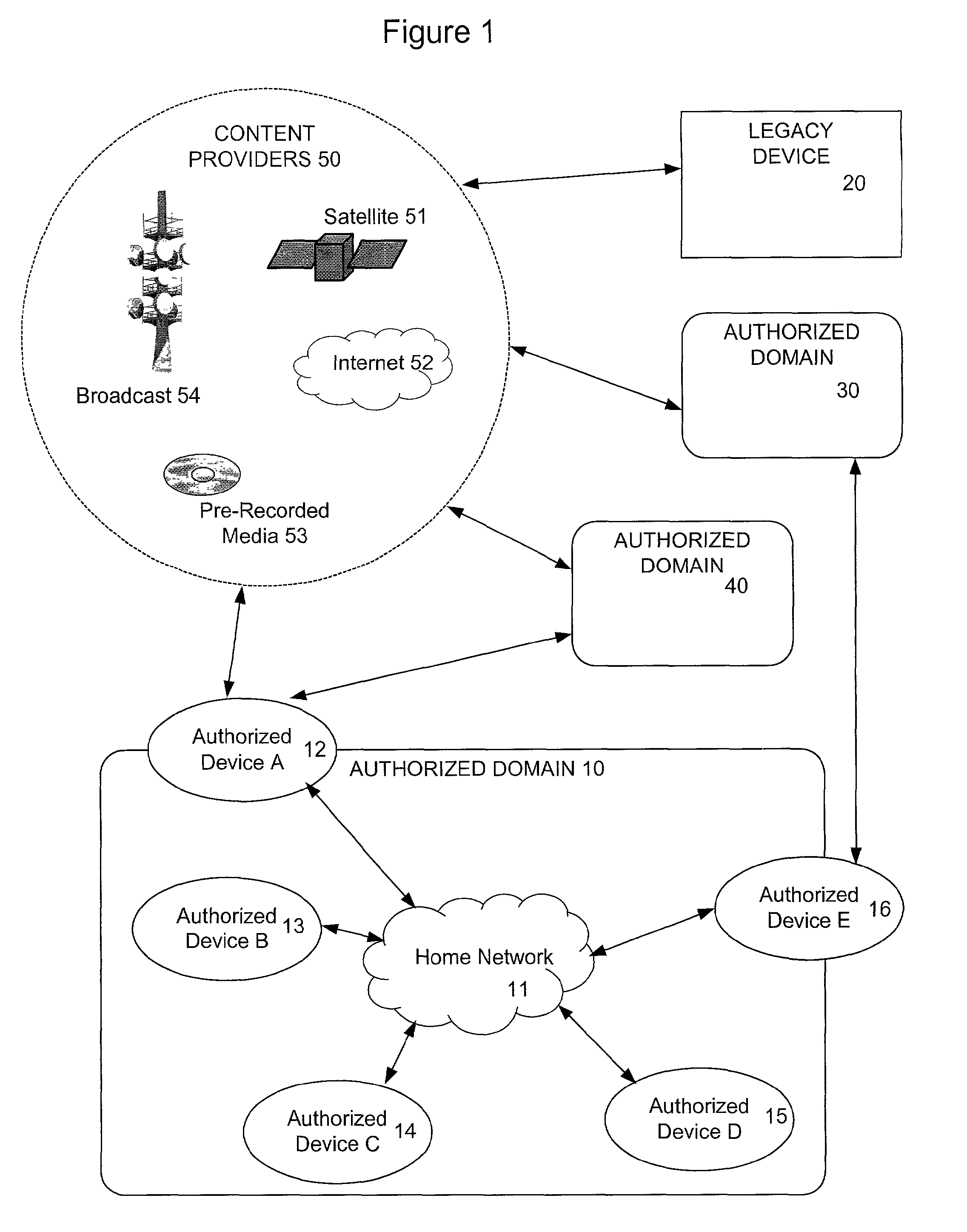
In the DVB Project's Content Protection and Copy Management (CPCM) scheme, an Authorized Domain is a set of CPCM-compliant devices that "are owned, rented or otherwise controlled by members of a single household", according to the DVB Project. Industry observers saw Authorized Domain as having the potential either to loosen or to tighten restrictions on the use of copyrighted works. Detractors felt it might raise the price of content consumption for end-users and damage their ability to duplicate copies of works. Supporters of Authorized Domain, on the other hand, said it is neutral to such concerns, because it doesn't favor one content distribution business model over another.
Enforcing authorized domains with domain membership vouchers
InactiveUS20050102513A1Simplifies sharing of contentSimple contentKey distribution for secure communicationUser identity/authority verificationVoucherAuthorized domain
Domain membership vouchers are transmitted to devices in response to domain membership requests and domain joining requests. These vouchers include domain identifiers and domain keys encrypted with the public keys of the requesting devices. Once received, the domain membership vouchers establish the devices as members of authorized domains. Such authorized domains allow the sharing of protected content among devices within a particular authorized domain.
Owner:NOKIA CORP
Separation of copy protection rules
InactiveUS20050071669A1Digital data processing detailsAnalogue secracy/subscription systemsDigital rights management systemCopy protection
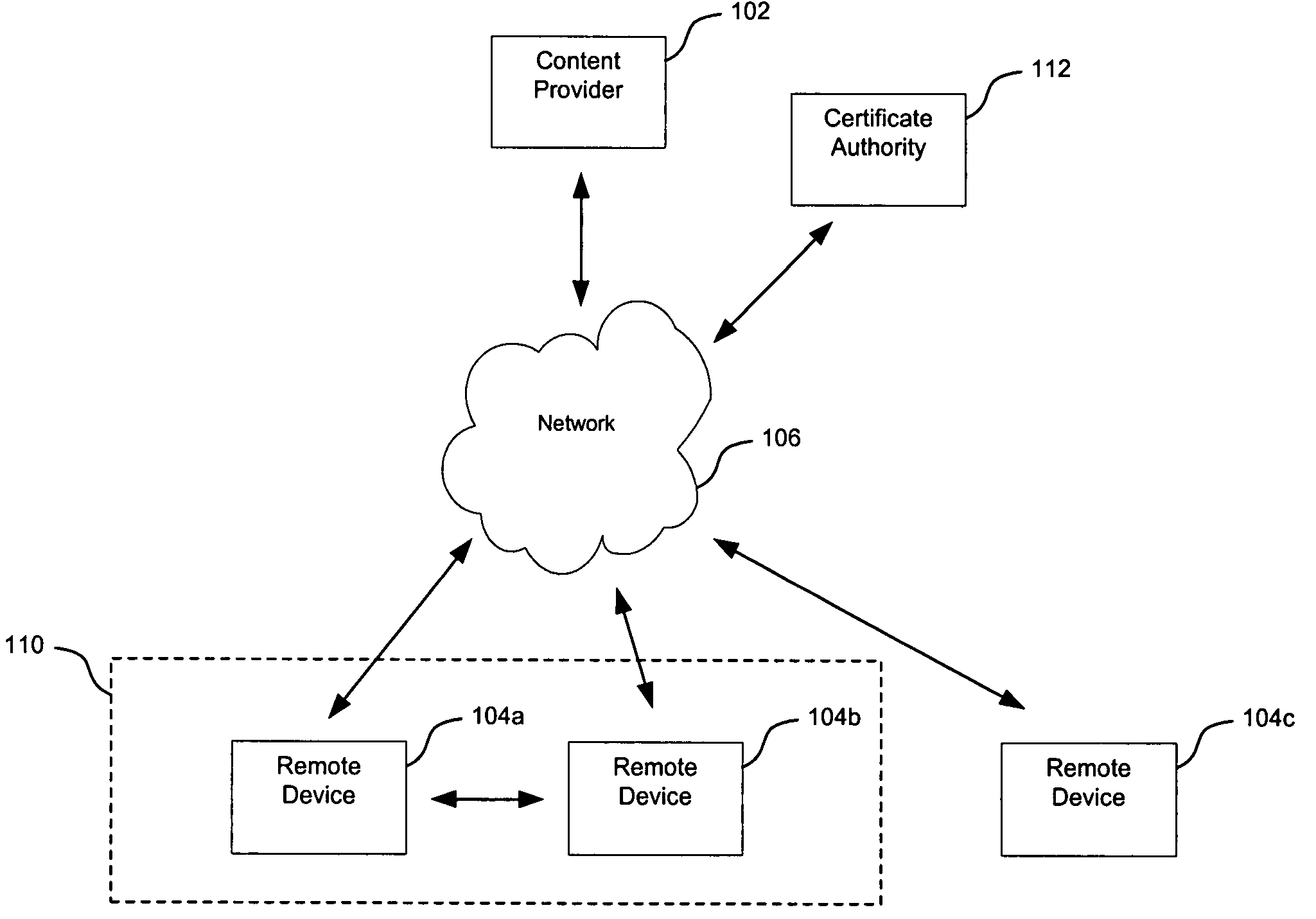
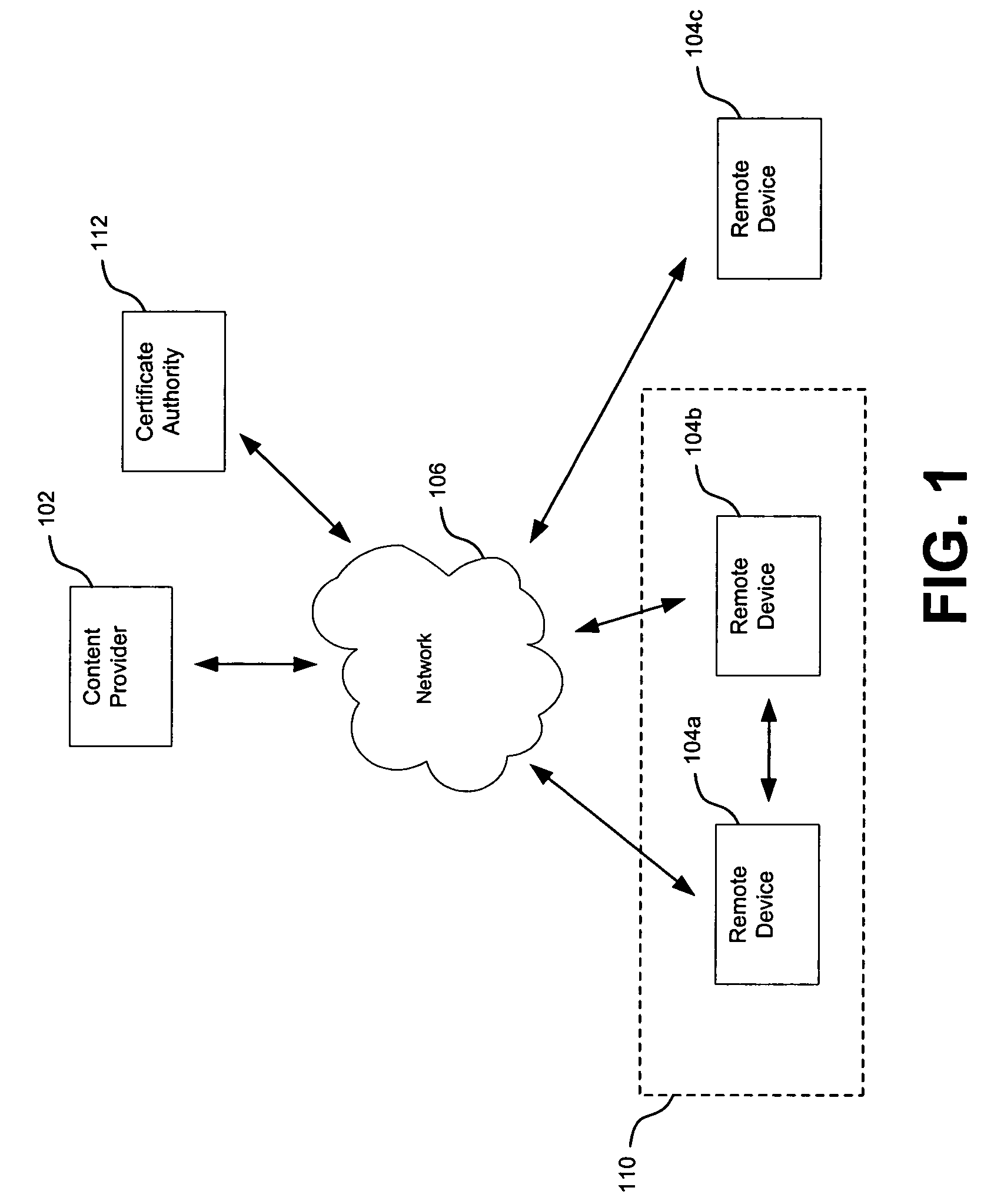
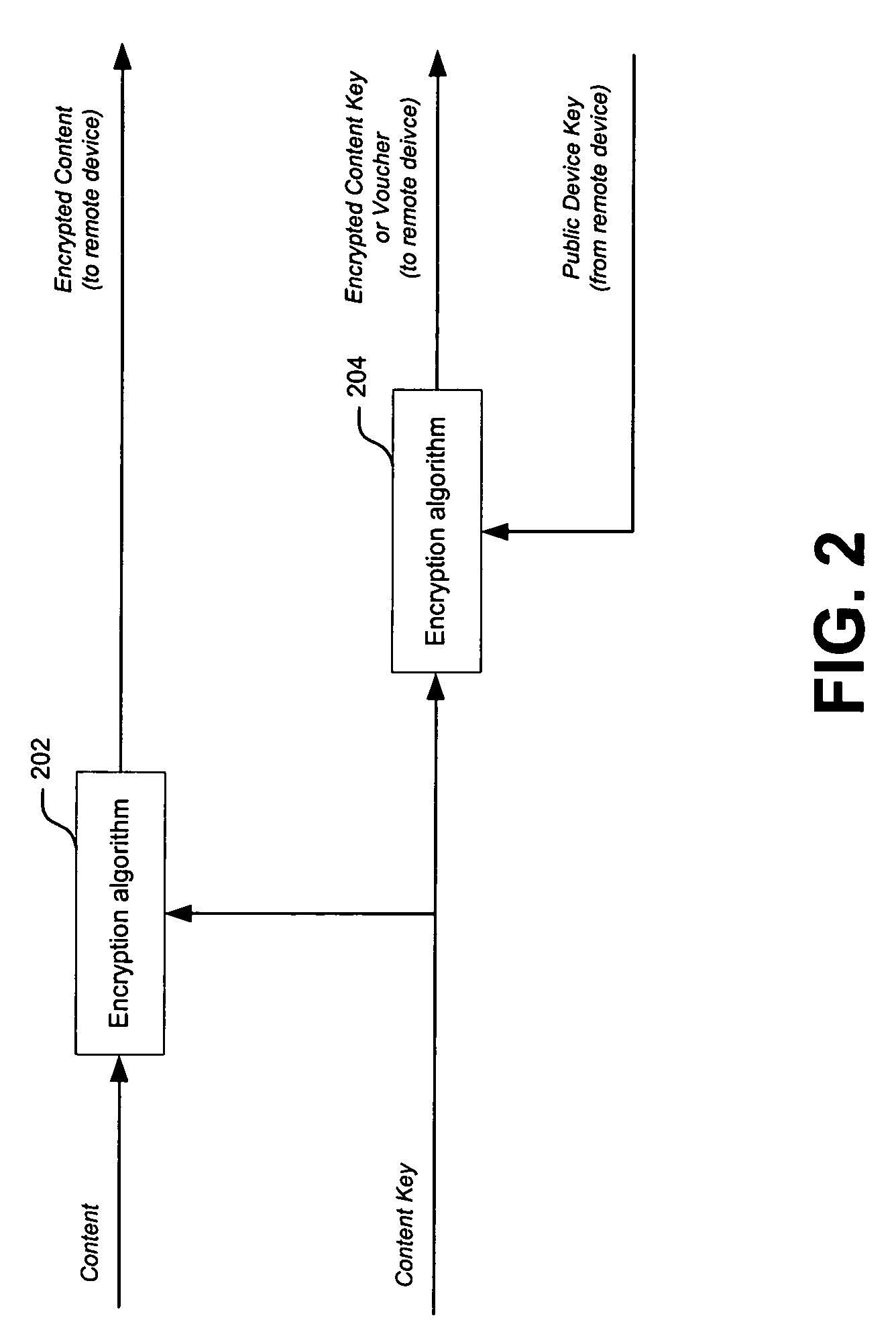
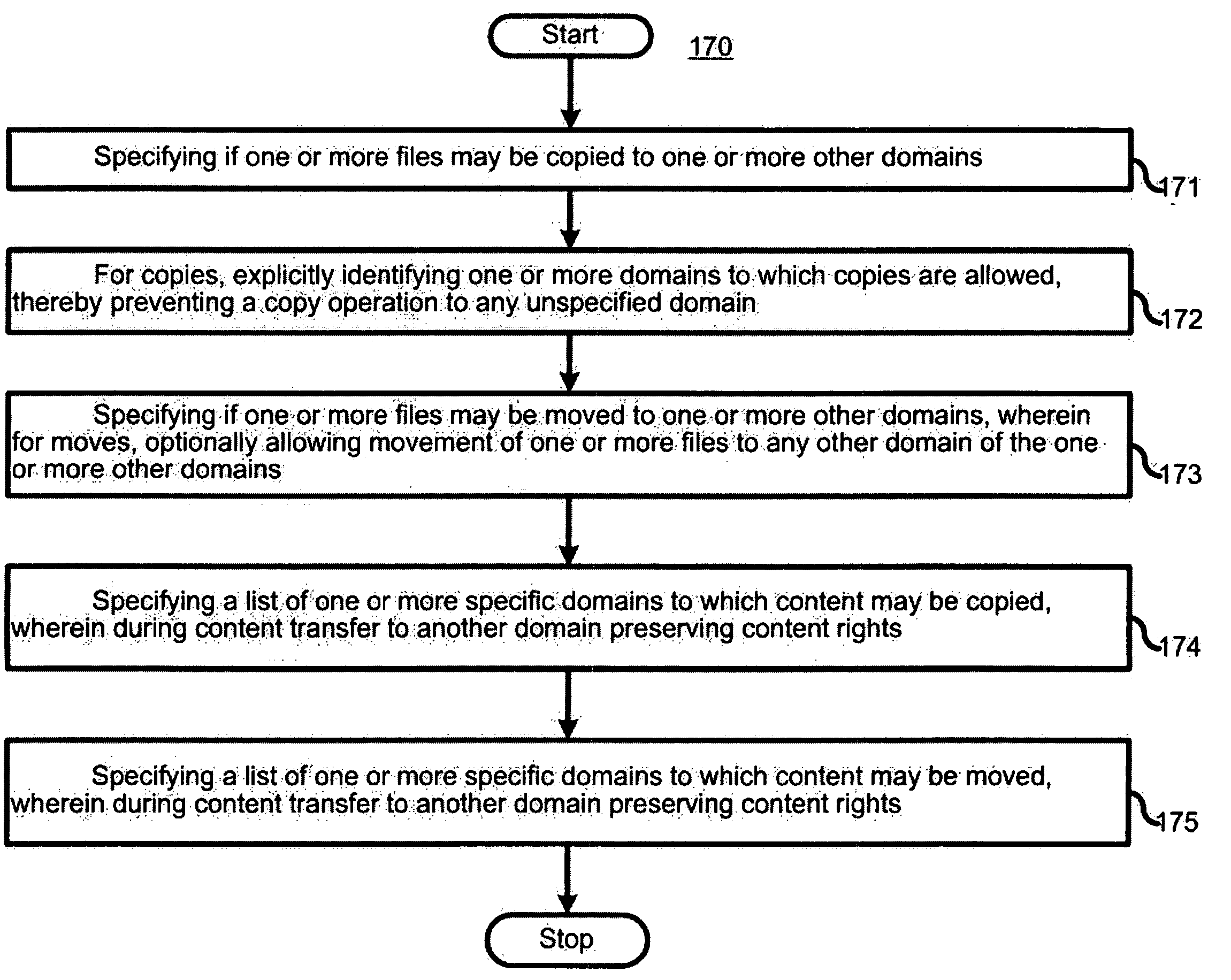
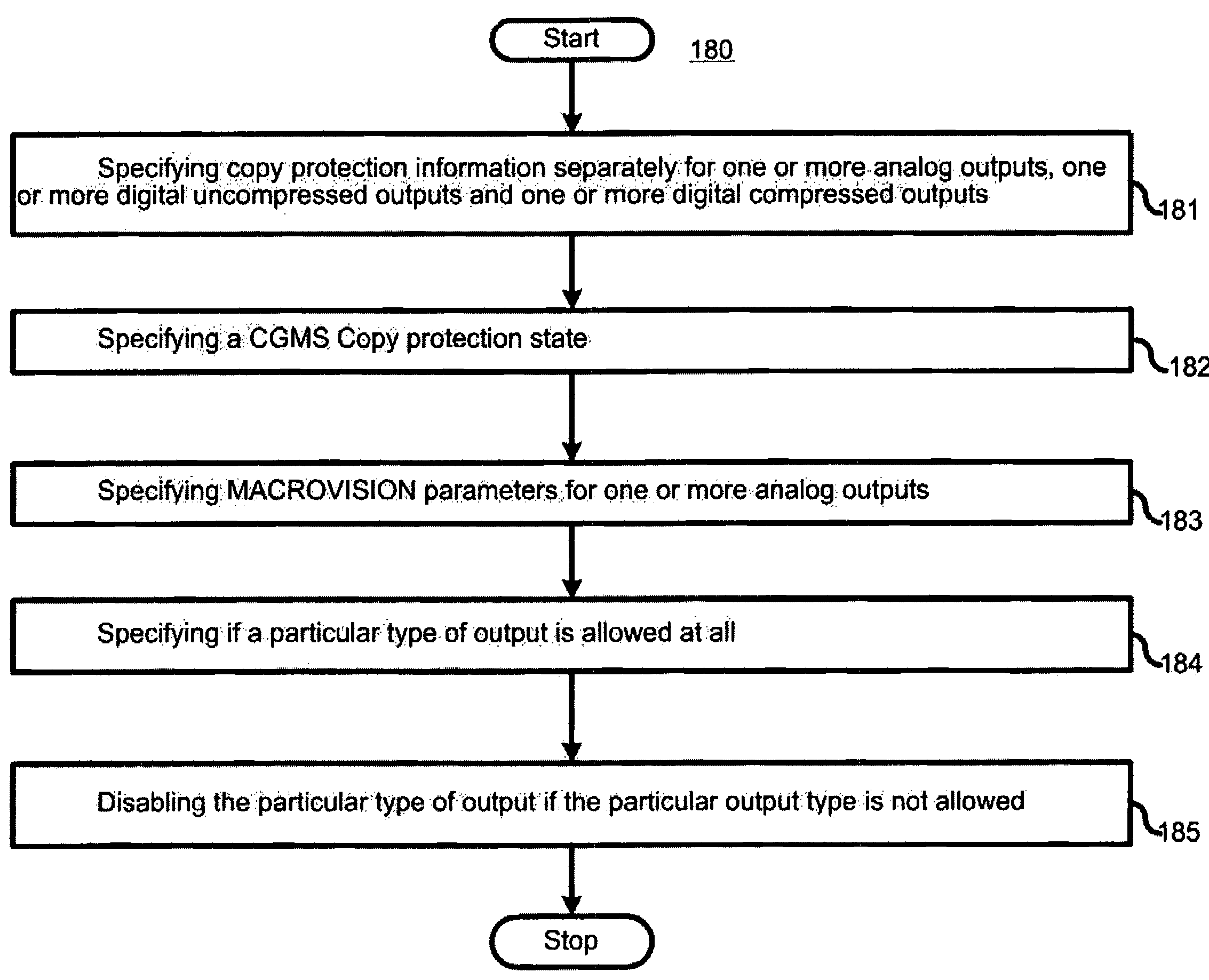
A copyright protection method (150) and apparatus (190) employs (151) a first protection scheme (160) within a single authorized domain (195), in which all interfaces (194a-c) are protected with digital rights management system and employs (152) a second protection scheme (170) for use in inter-domain file transfers. The method (150) and apparatus (190) may employ (153) a third protection scheme (180) for external outputs (197a-c) not protected by a digital rights management system. The first protection scheme (160) includes specifying (161) whether a copy of files is allowed to be stored anywhere within the single authorized domain; specifying (162) whether files may be stored only on specific devices within the single authorized domain; or specifying (163) how many simultaneous rendering devices are permitted when rendering files. The second protection scheme (170) may include: specifying (171) if the files may be copied to other domains; and explicitly identifying (172) domains to which copies are allowed; specifying (173) if files may be moved to other domains, and optionally allowing movement of files to any other domain; specifying (174) a list of specific domains to which content may be copied, and preserving content rights during content transfer to another domain; or specifying (175) specific domains to which content may be moved, and preserving content rights during content transfer. The third protection scheme (180) may include: specifying (181) copy protection information separately for analog, digital uncompressed and digital compressed outputs; specifying (182) a CGMS Copy protection state; specifying (183) MACROVISION parameters for analog outputs; specifying (184) if a particular type of output is allowed at all; or disabling (185) the particular type of output if the particular output type is not allowed.
Owner:GOOGLE TECH HLDG LLC
Accessing protected data on network storage from multiple devices
ActiveUS20050193199A1Easy to manageKey distribution for secure communicationData taking preventionPlaintextAuthorized domain
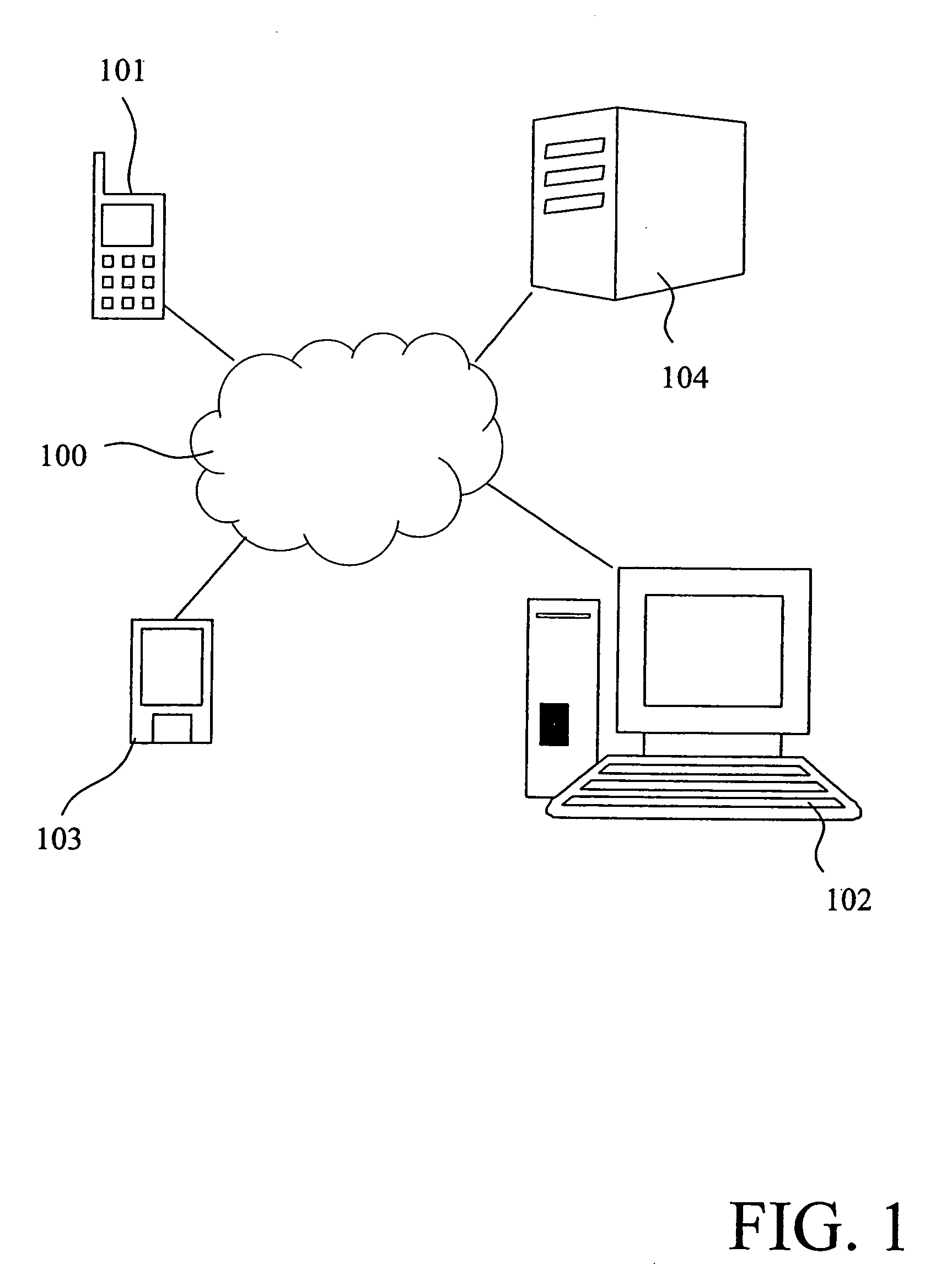
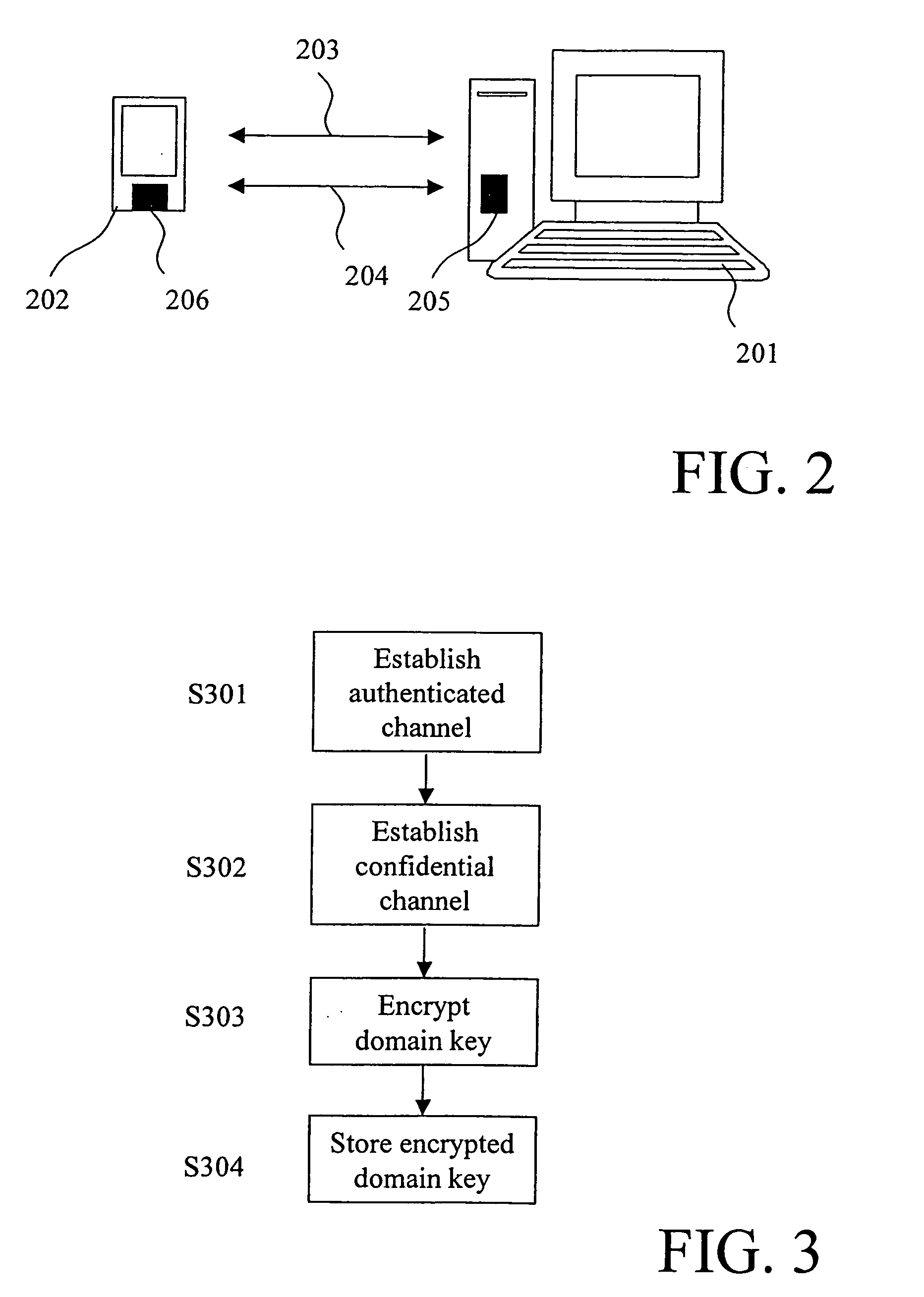
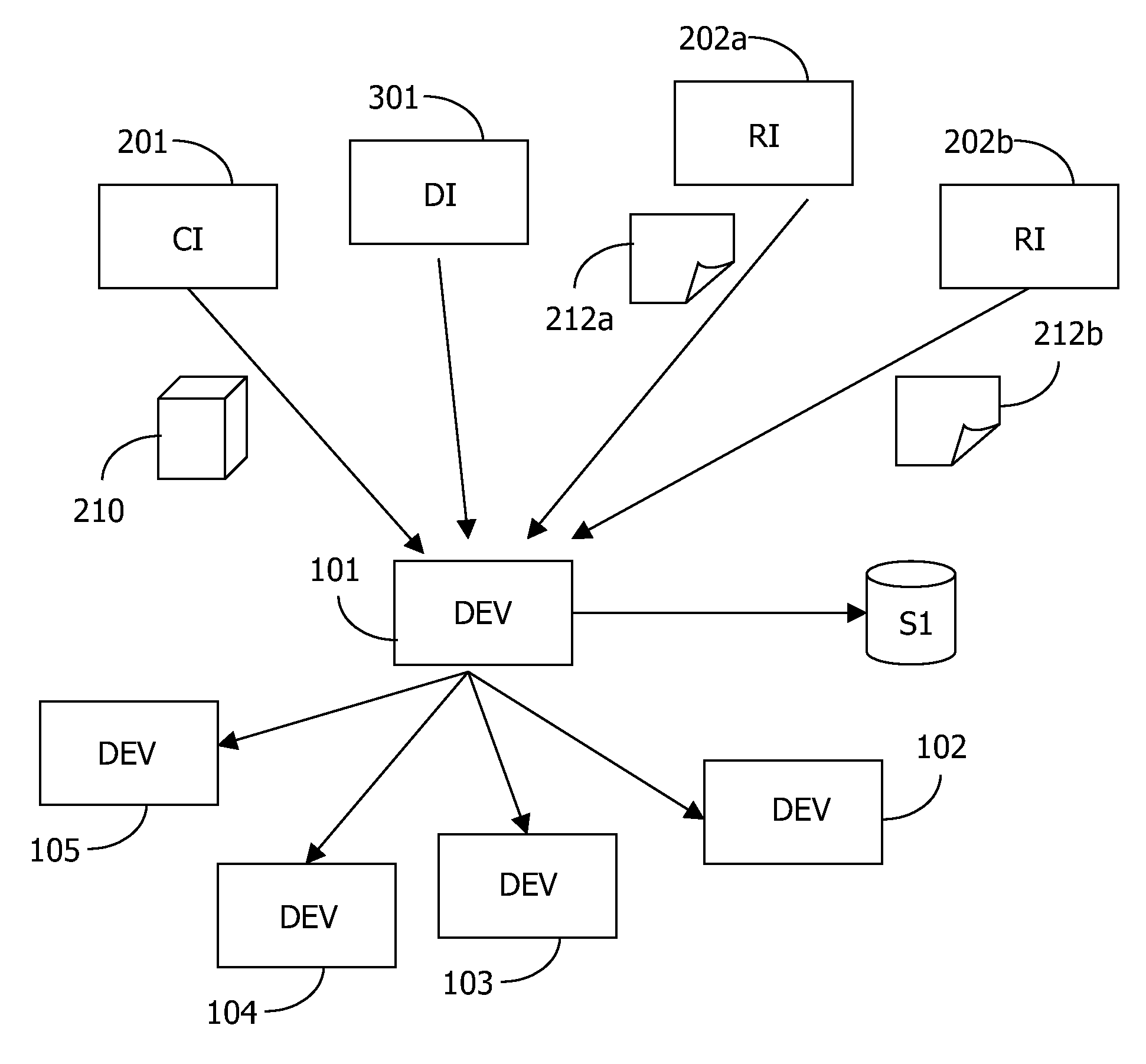
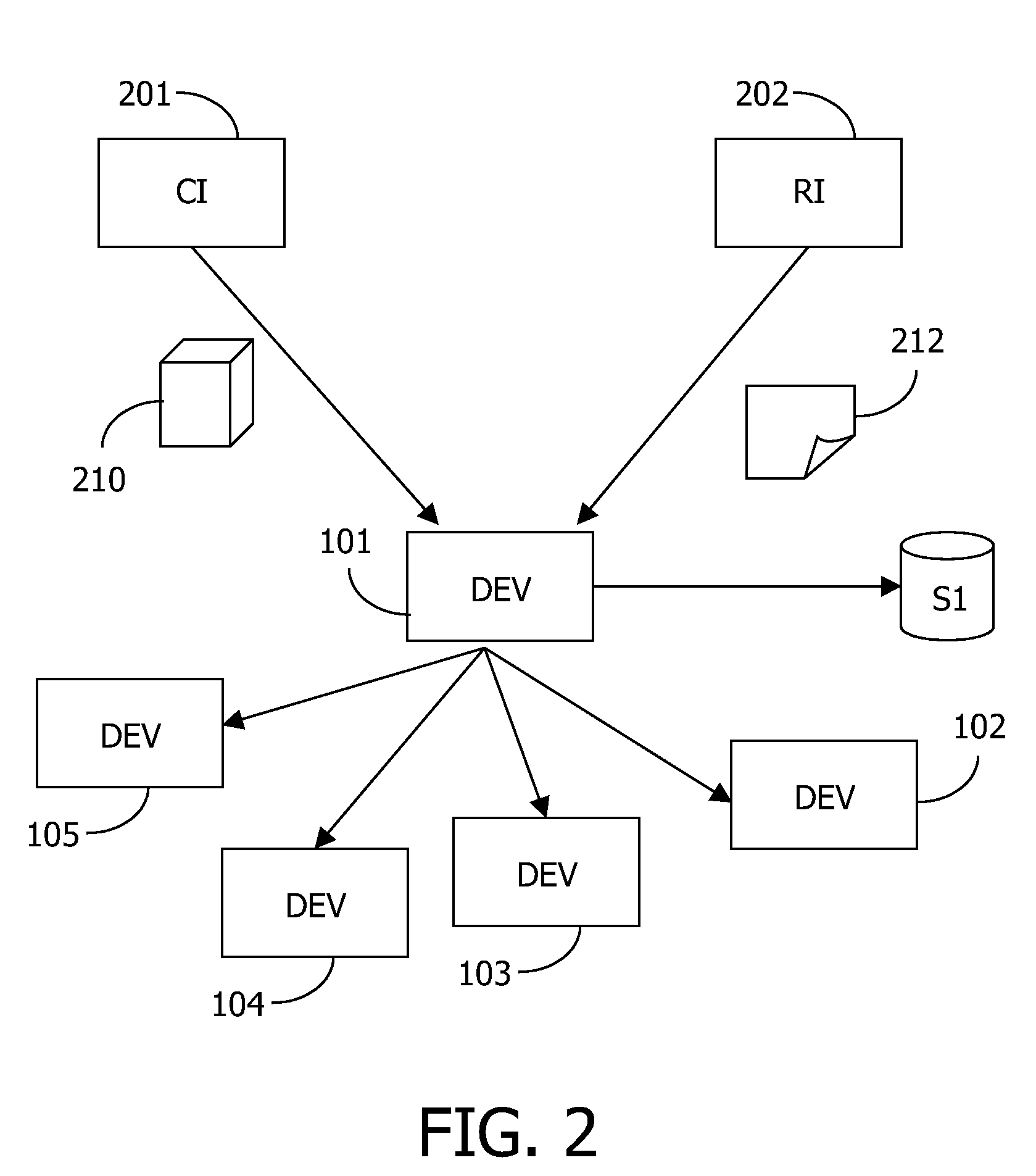
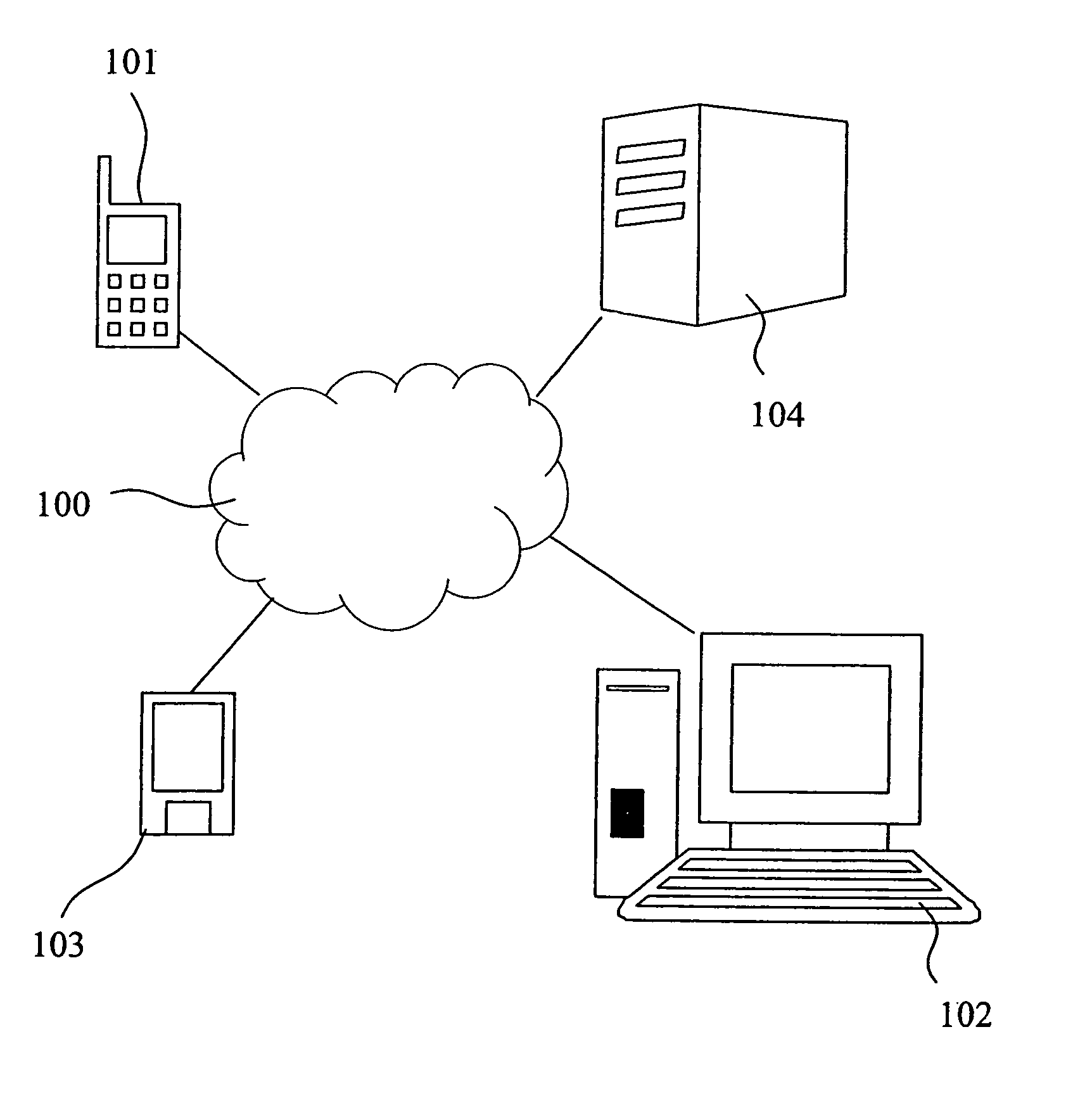
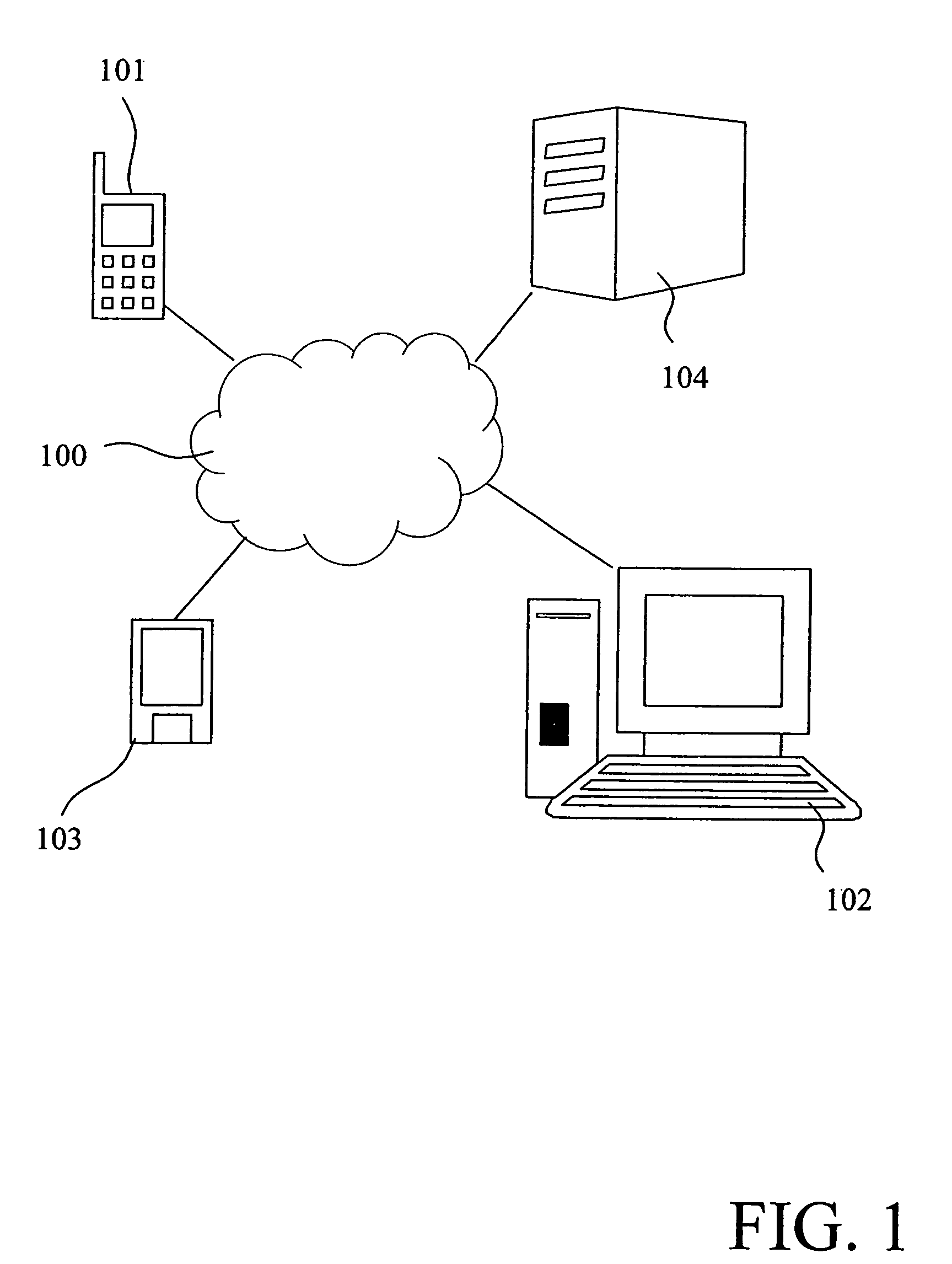
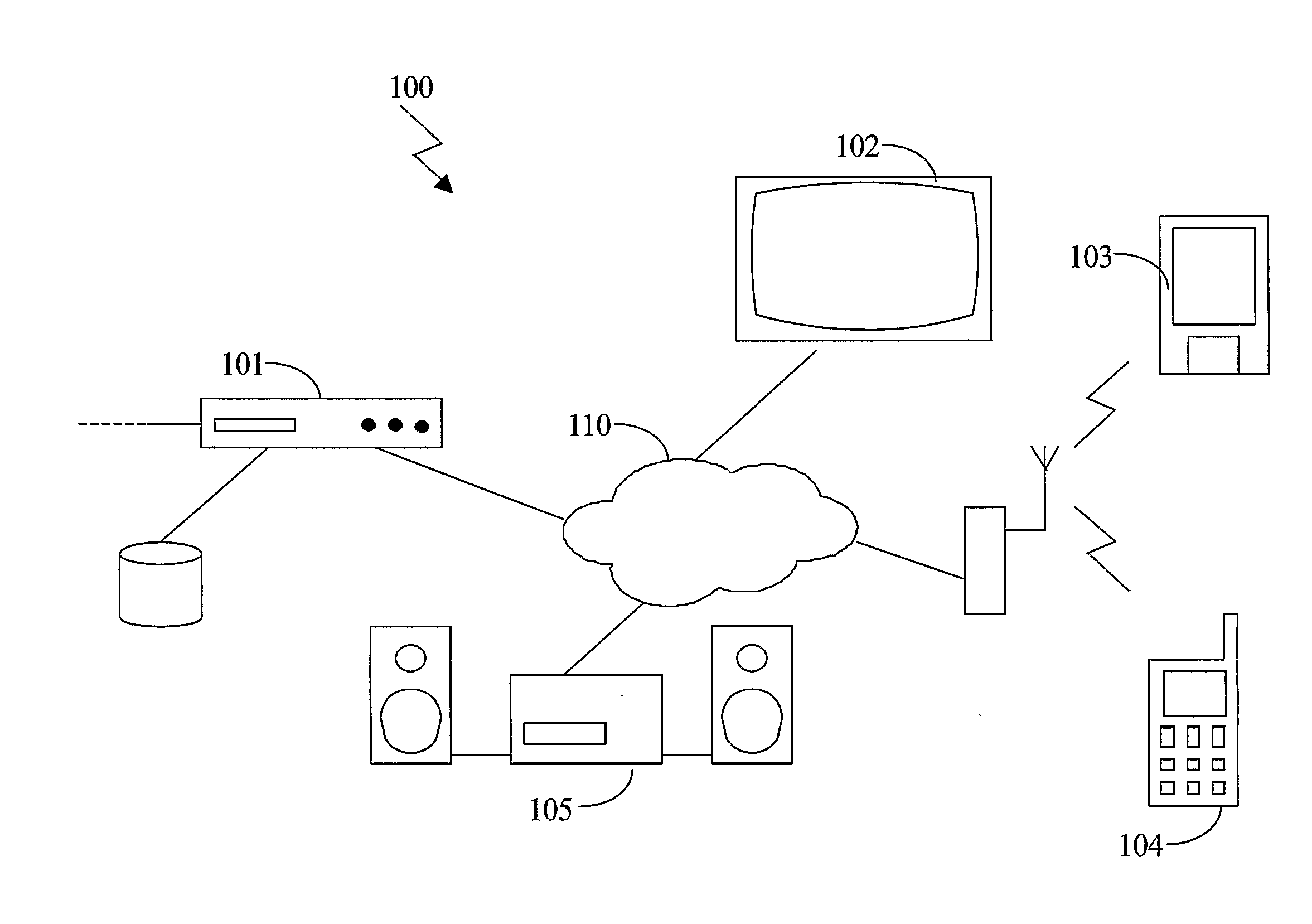
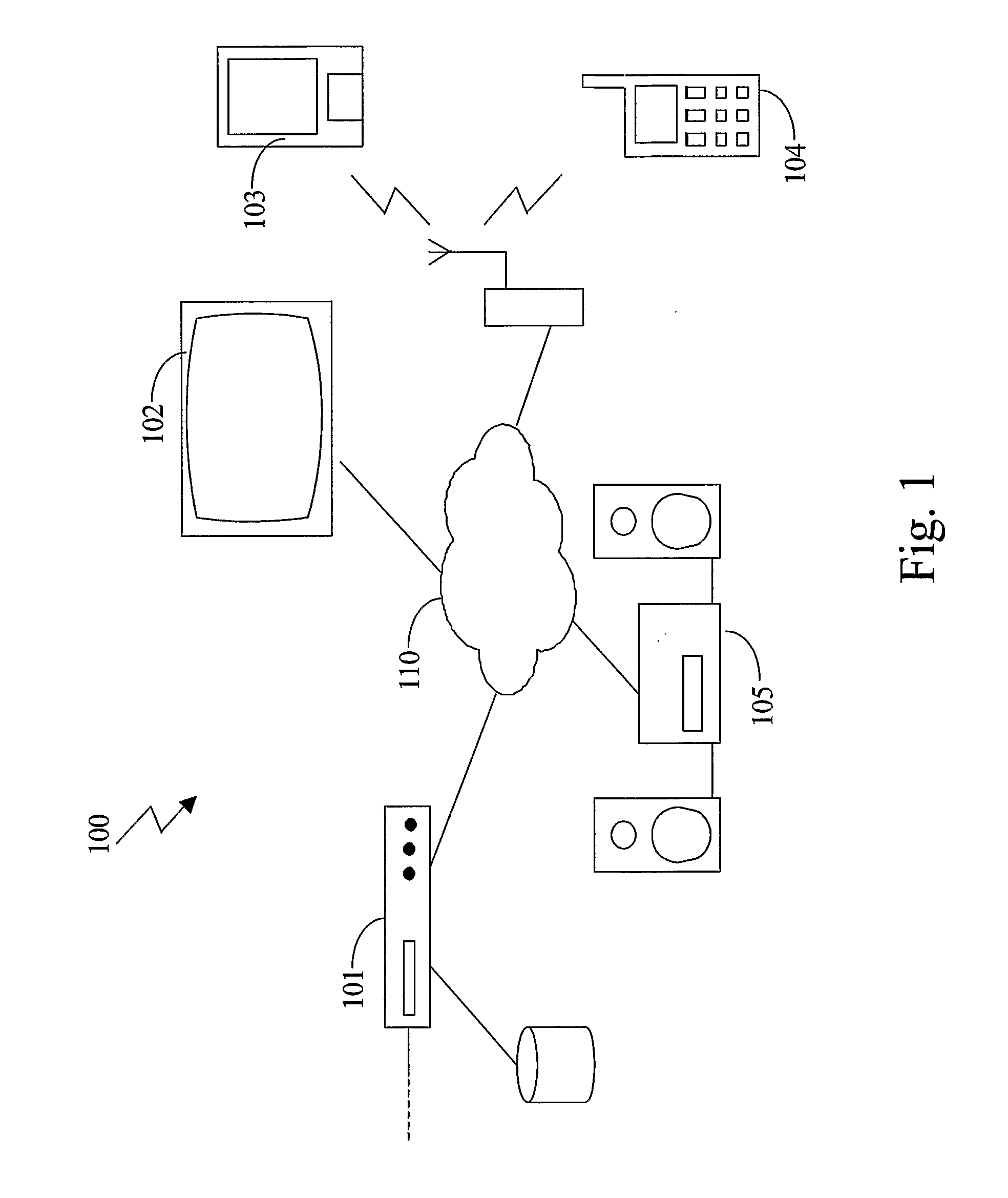
The present invention relates to a method and a system of securely storing data on a network (100) for access by an authorized domain (101, 102, 103), which authorized domain includes at least two devices that share a confidential domain key (K), and an authorized domain management system for securely storing data on a network for access by an authorized domain. The present invention enables any member device to store protected data on the network such that any other member device can access the data in plaintext without having to communicate with the device that actually stored the data.
Owner:NOKIA TECHNOLOGLES OY
Separation of copy protection rules for digital rights management
InactiveUS20050071663A1Digital data processing detailsAnalogue secracy/subscription systemsRights managementDigital rights management
Management of rights to content is provided within an authorized domain. In a single authorized domain, where a plurality of domain interfaces are protected using a common rights management system, a copy of particular content may be allowed to be provided on all devices or only on specific devices coupled to the domain via the interfaces. Copy protection information, for outputs to external devices not protected by the common rights management system, is also specified. Rules can be provided for specifying whether particular content may be copied or moved to another protected domain. A number of rendering devices permitted to render the content simultaneously may be specified. Content rules are provided for use in managing rights to content within an authorized domain. Such rules can be associated with content that is persistently stored by a consumer device, as well as with content that is only rendered by a consumer device.
Owner:GENERAL INSTR CORP +1
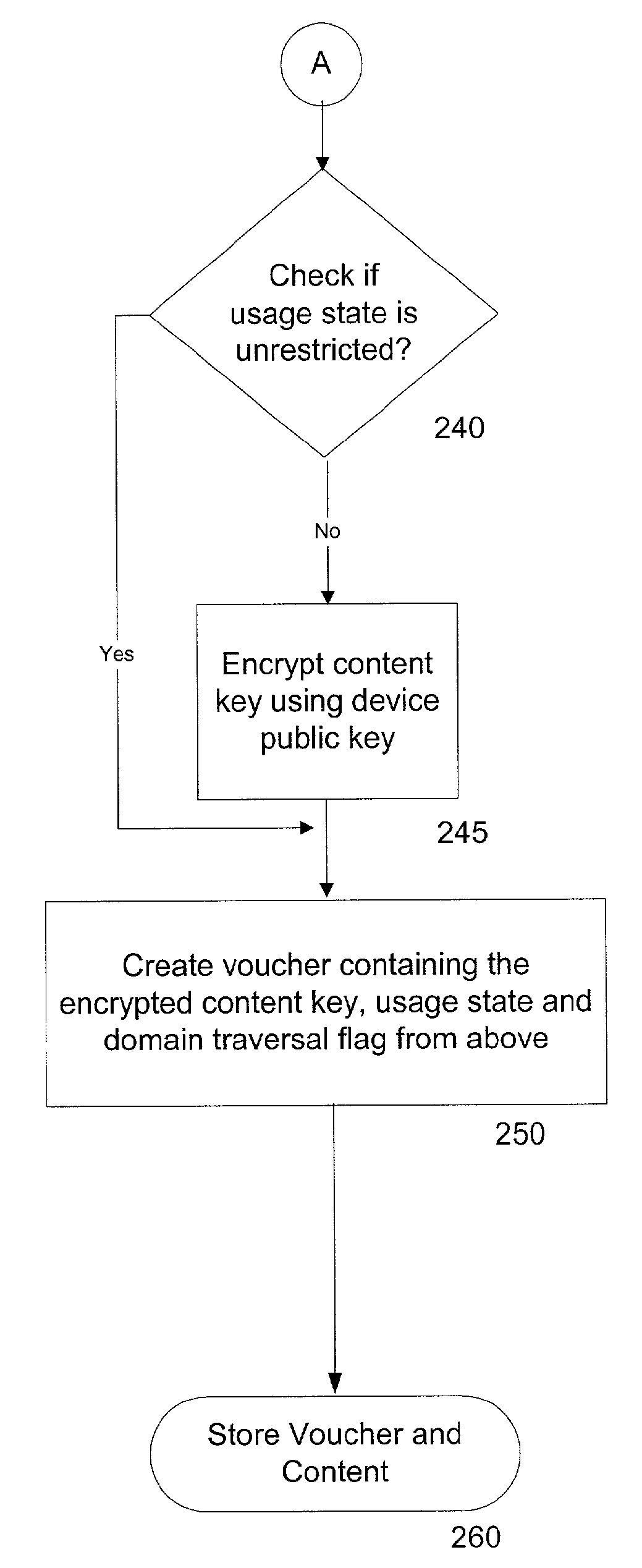
System and method for controlled copying and moving of content between devices and domains based on conditional encryption of content key depending on usage
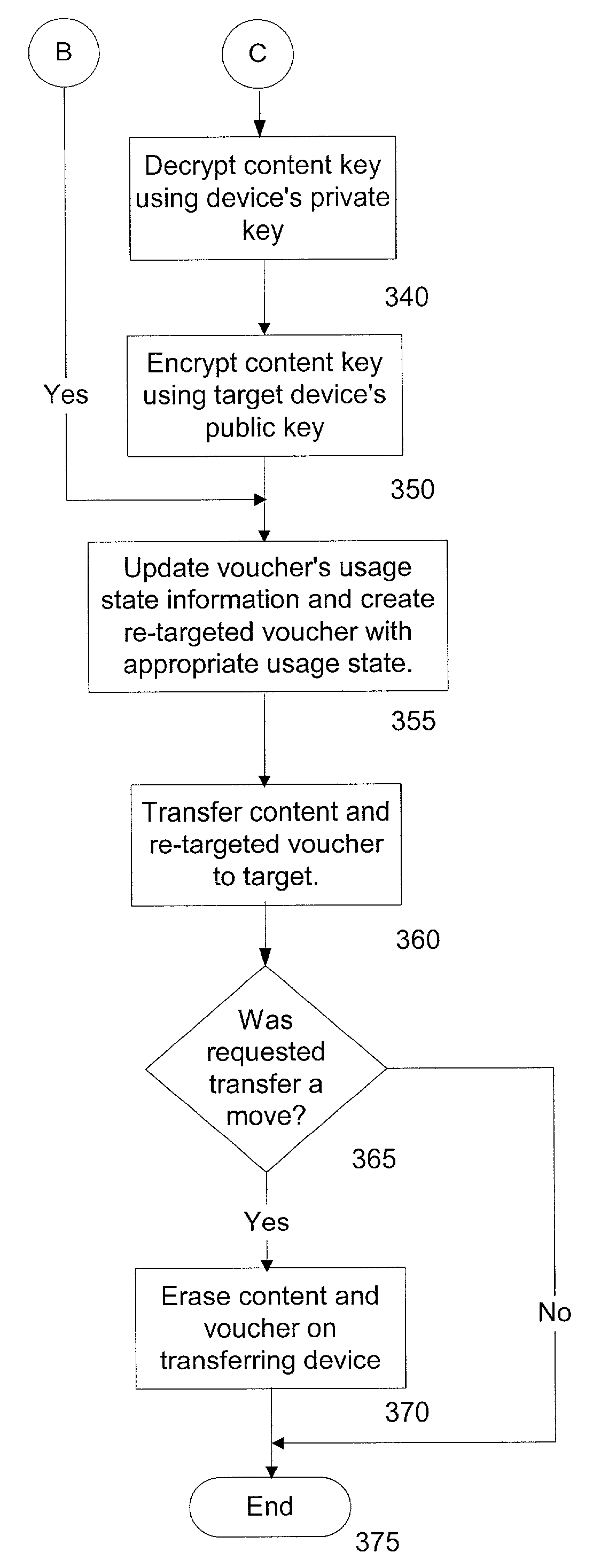
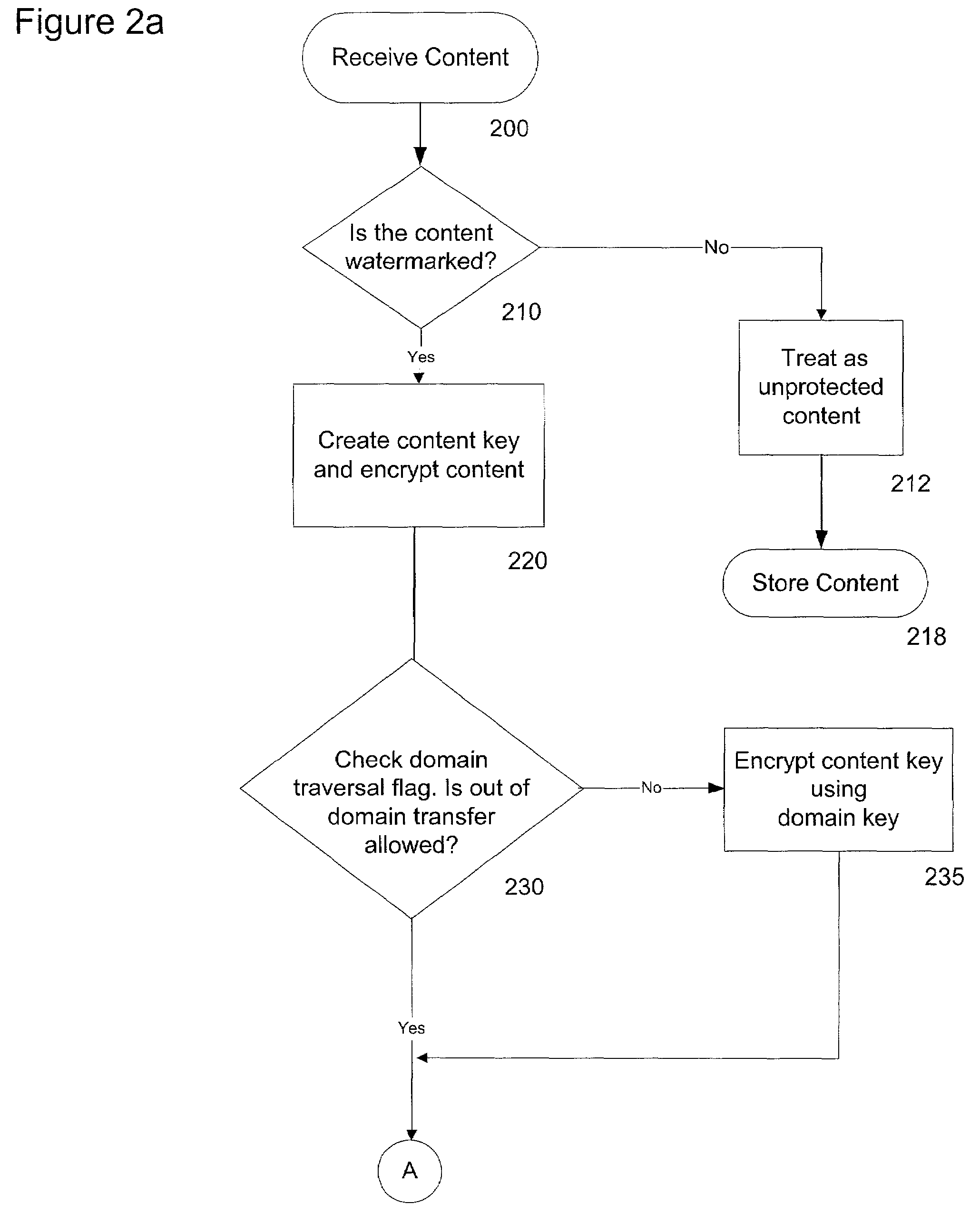
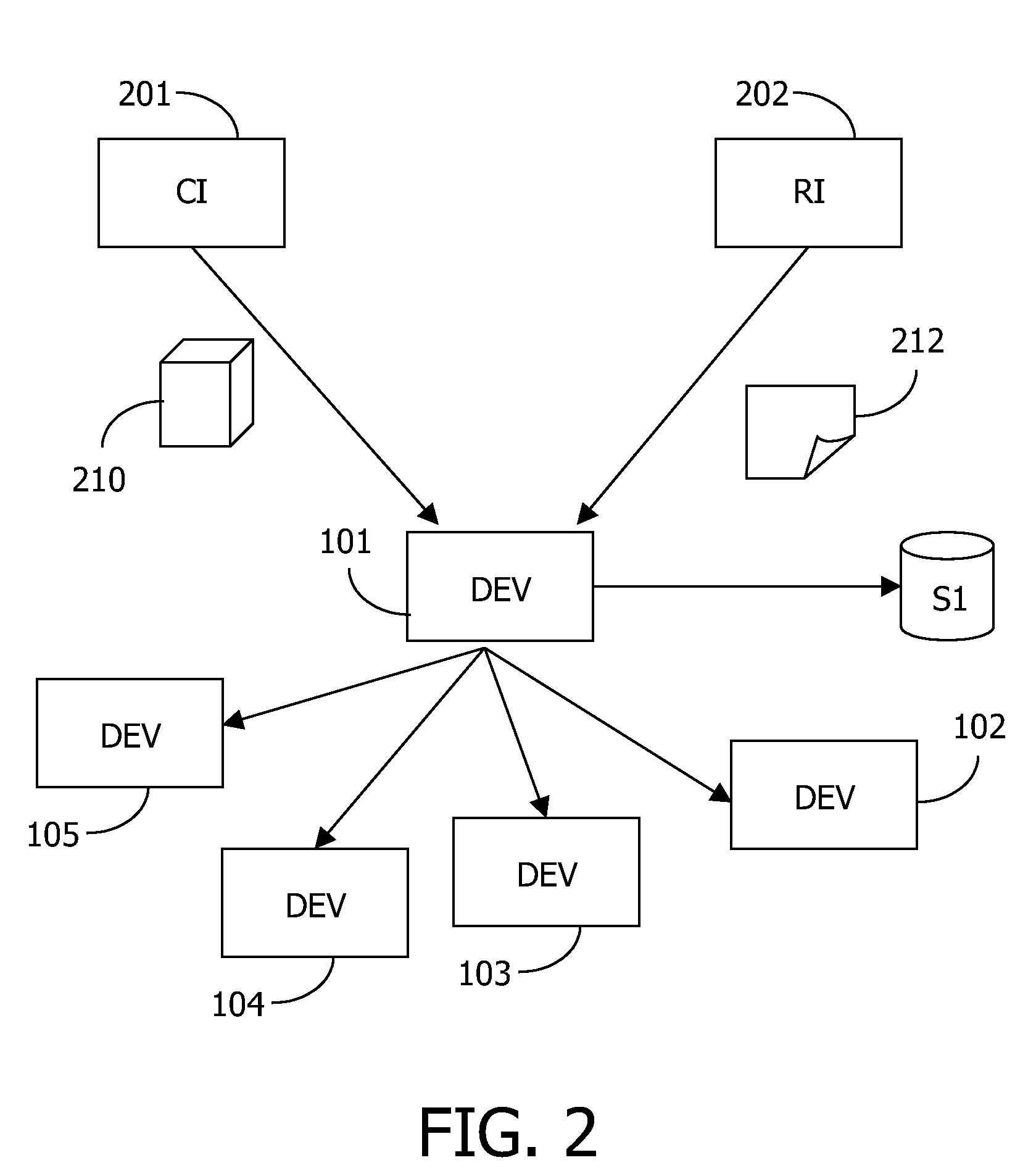
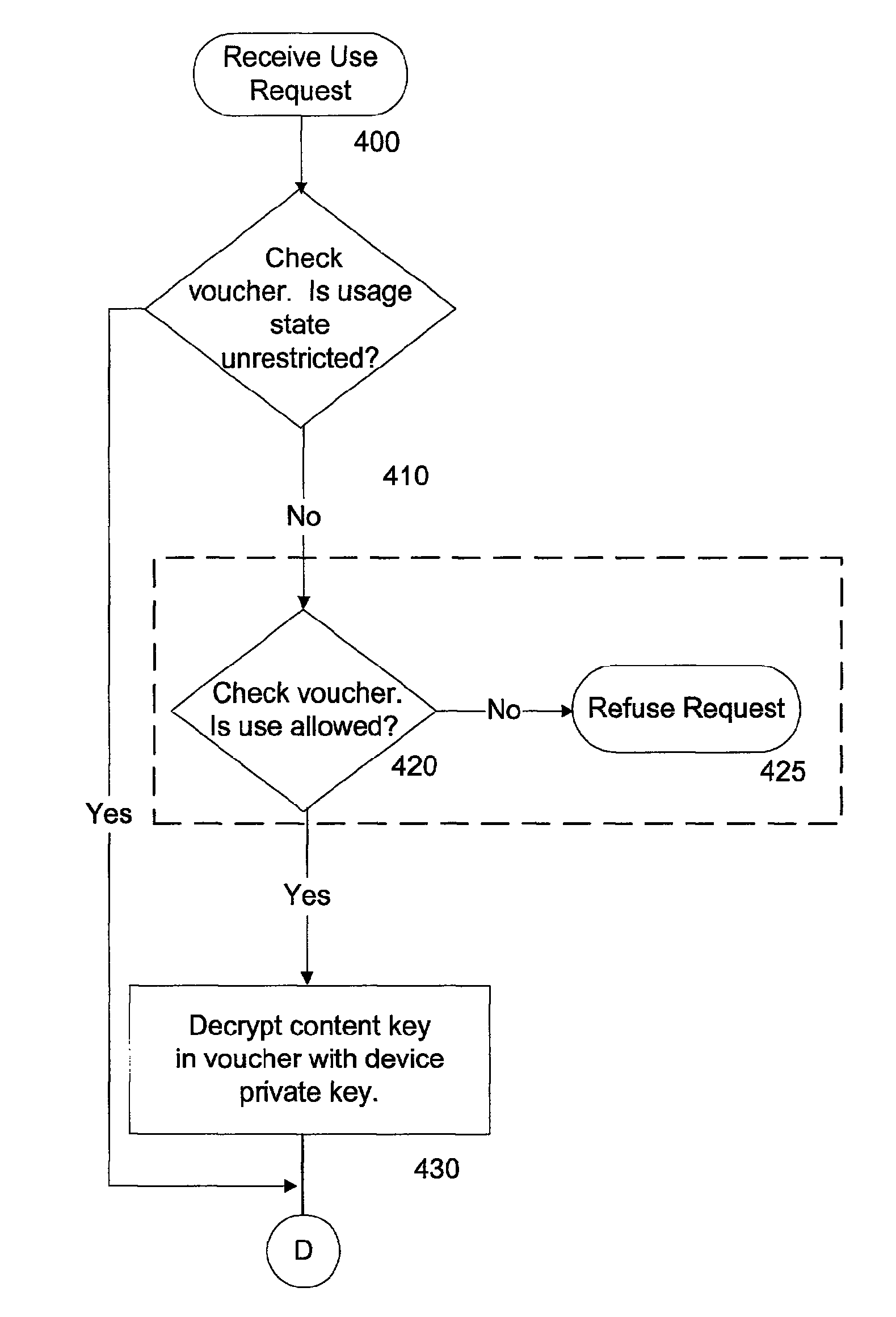
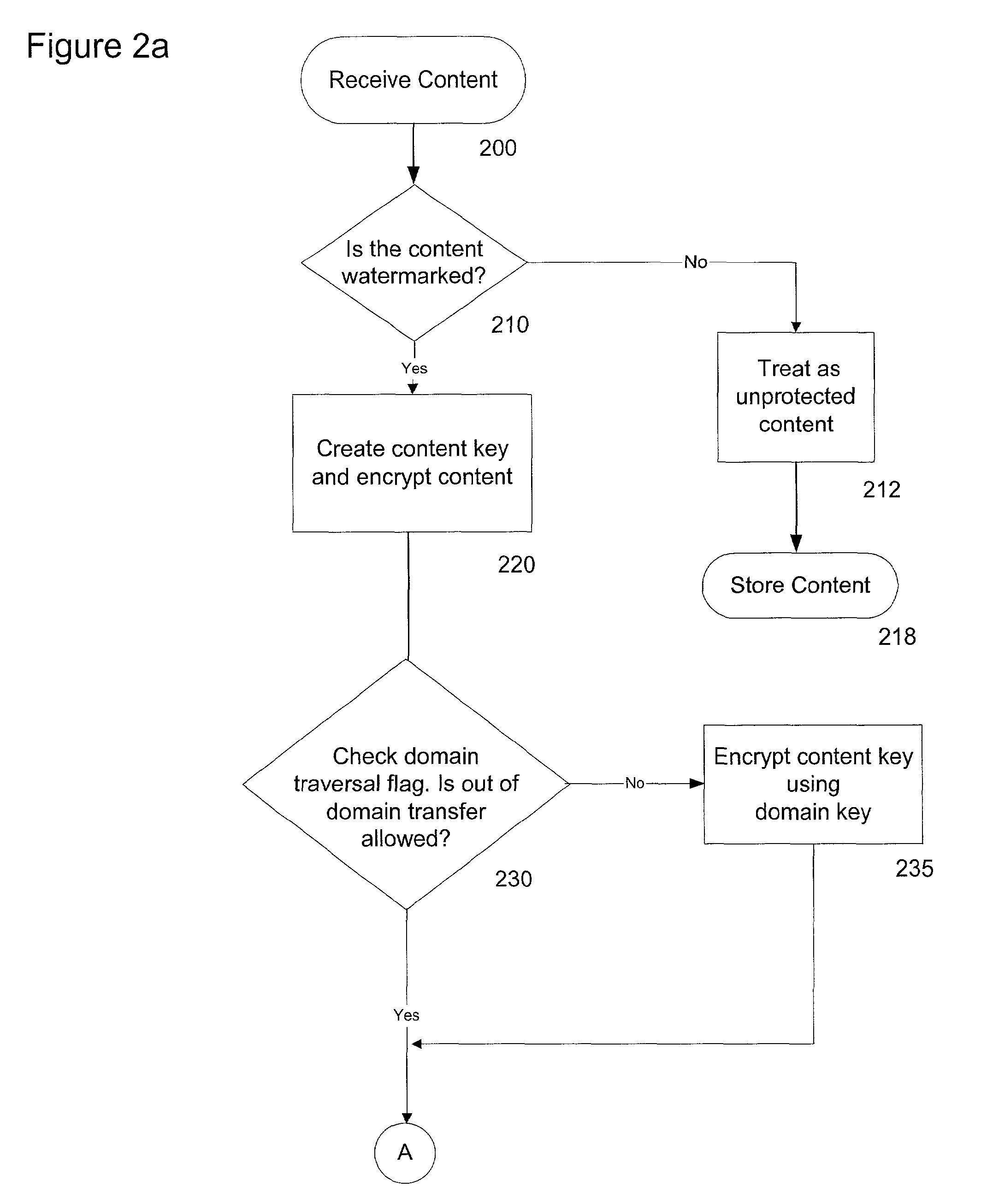
ActiveUS7487363B2Avoid easy removalEasy transferTelevision system detailsUser identity/authority verificationMobile contentAuthorized domain
A system and method is disclosed for allowing content providers to protect against widespread copying of their content, while enabling them to give their customers more freedom in the way they use the content. In accordance with one embodiment, content providers identify their content as protected by watermarking the content. Consumers use compliant devices to access protected content. All of a user's compliant devices, or all of a family's devices, can be organized into an authorized domain. This authorized domain is used by content providers to create a logical boundary in which they can allow users increased freedom to use their content.
Owner:NOKIA TECHNOLOGLES OY
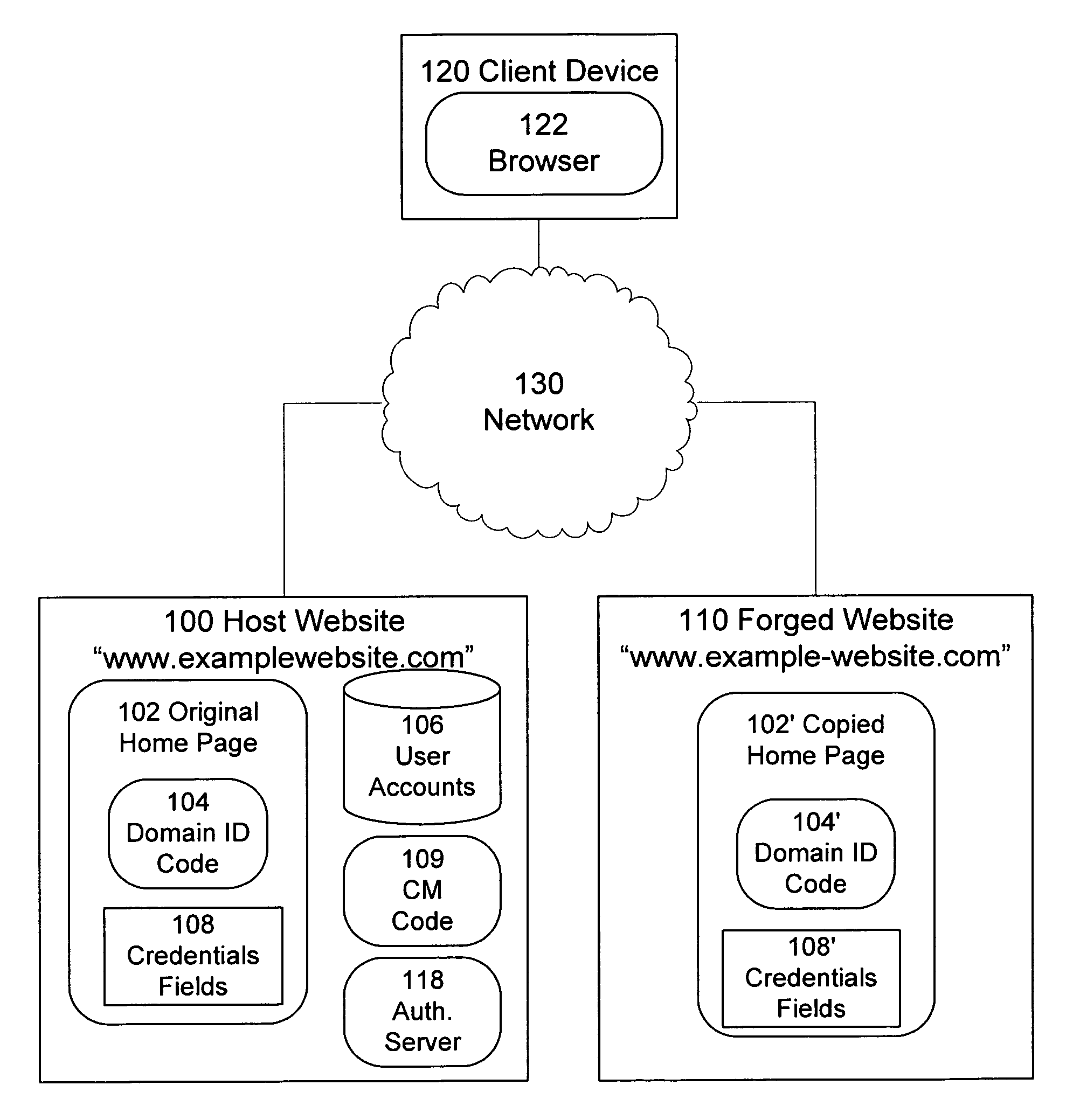
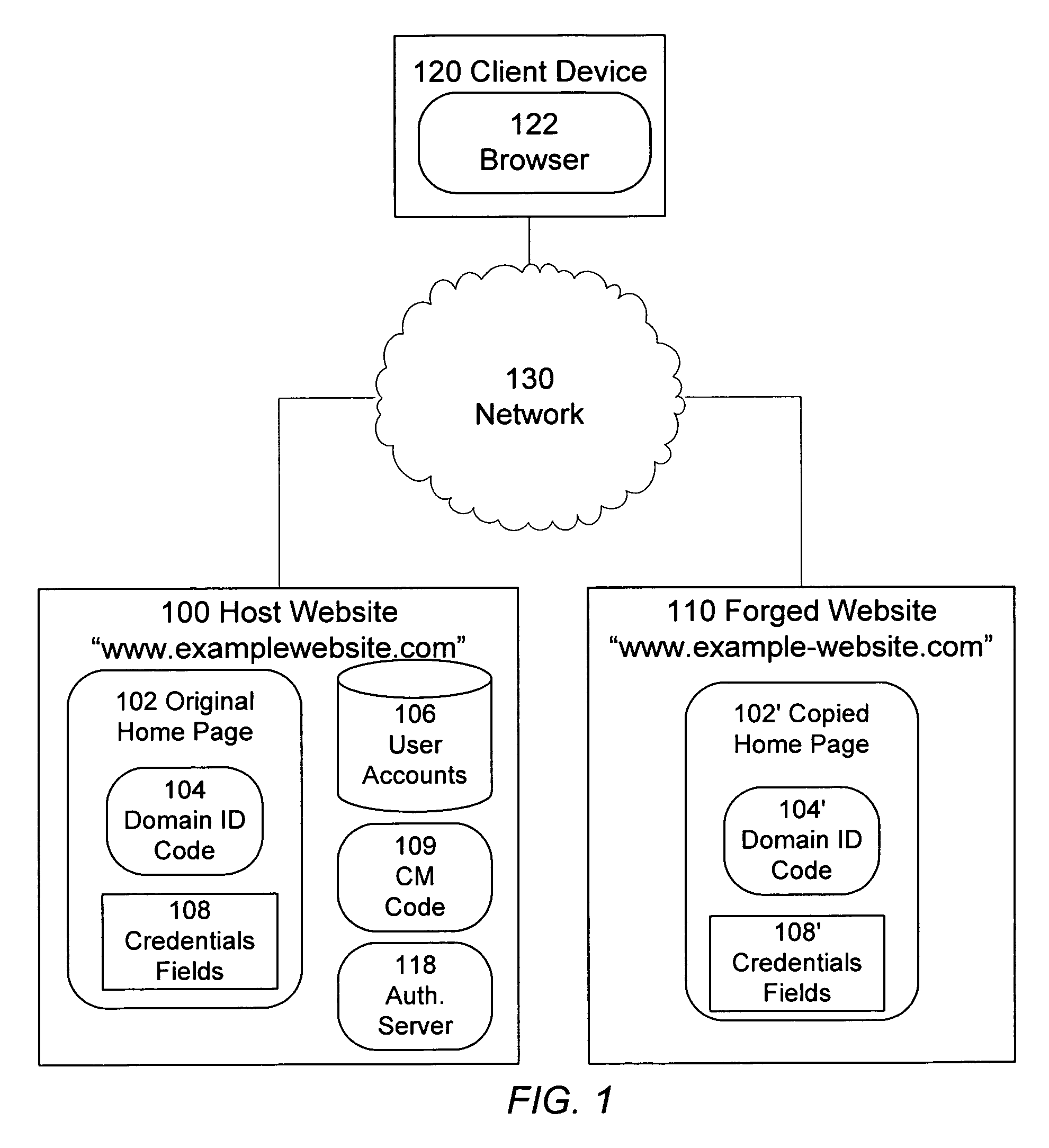
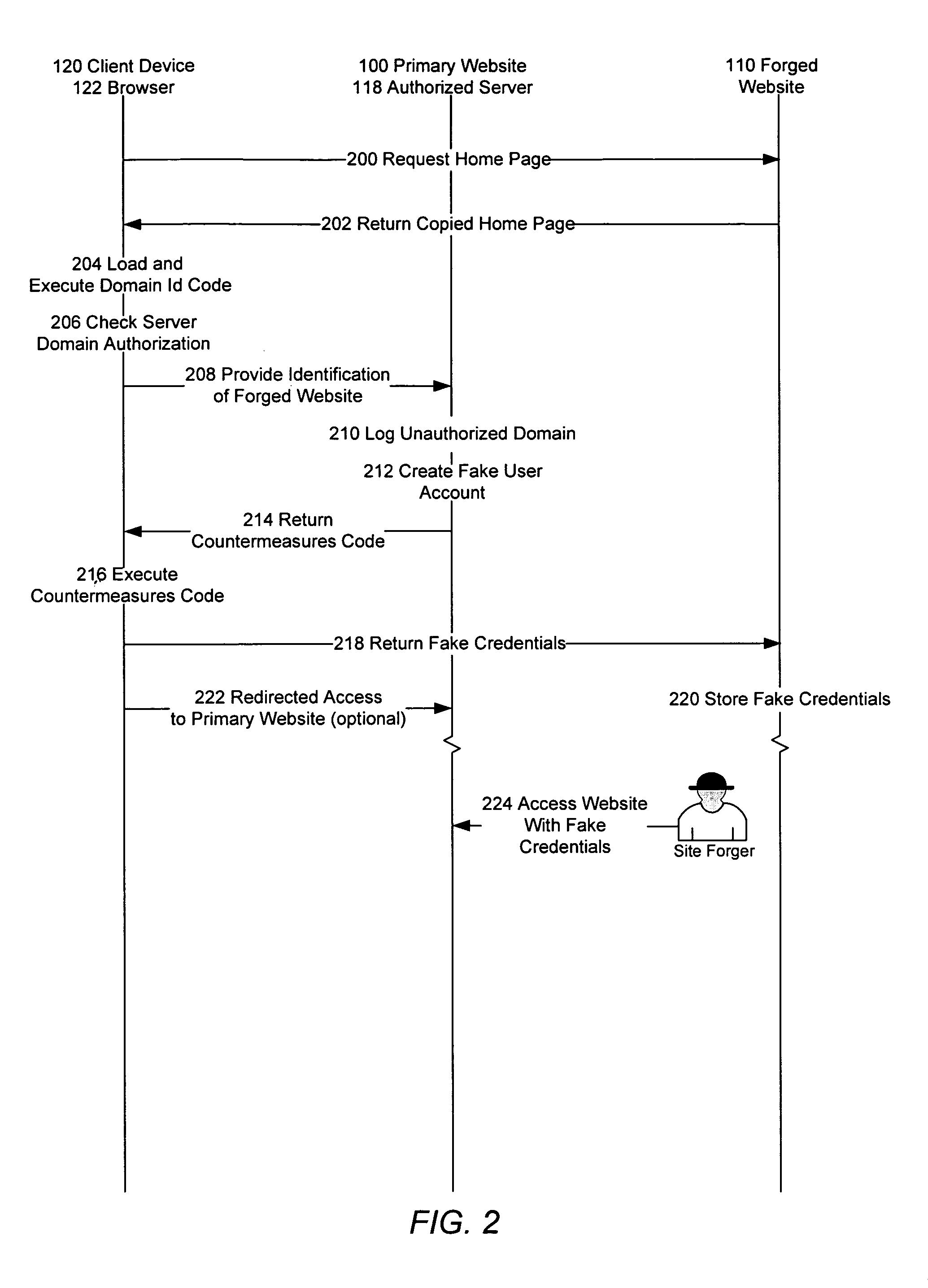
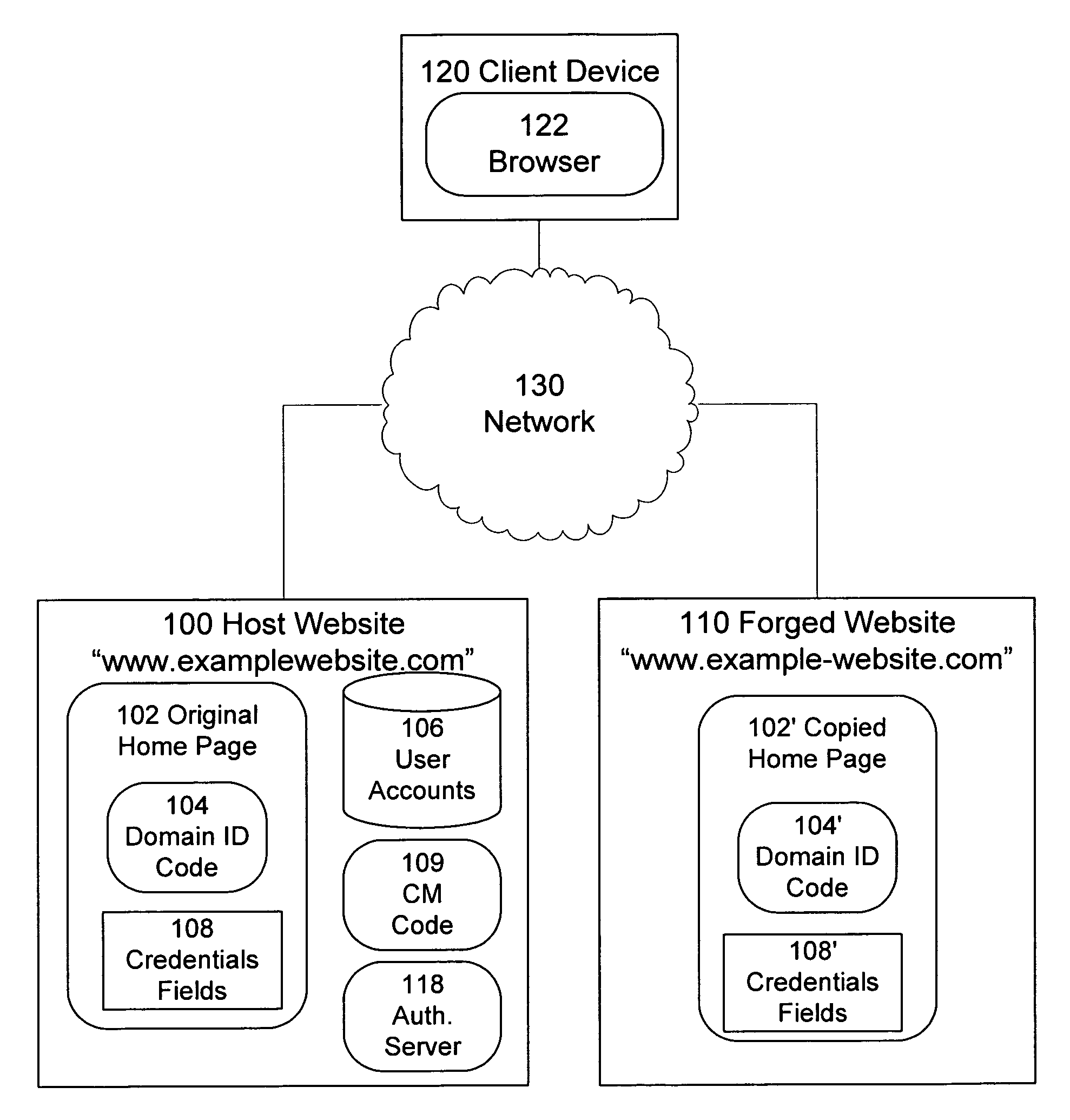
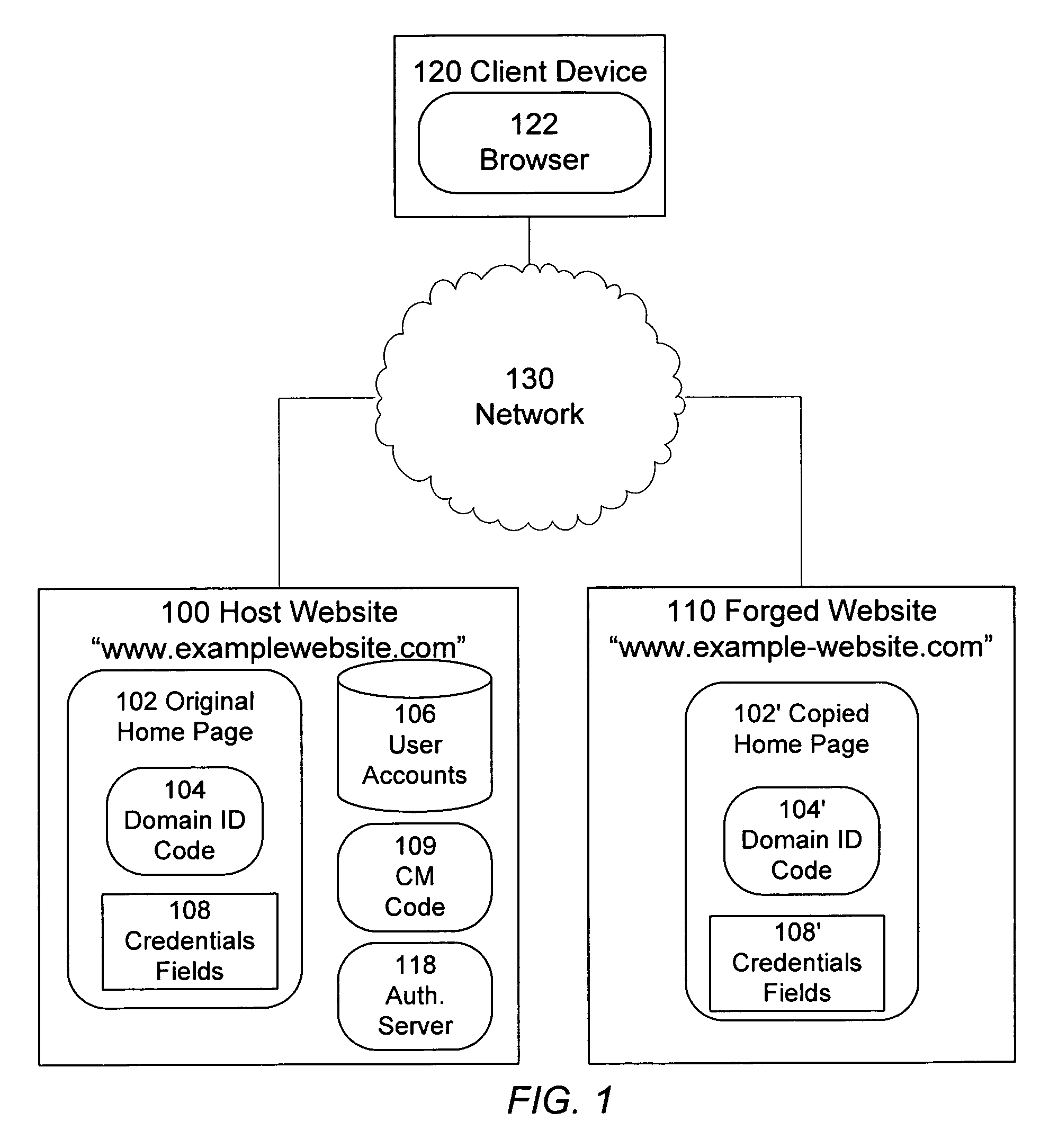
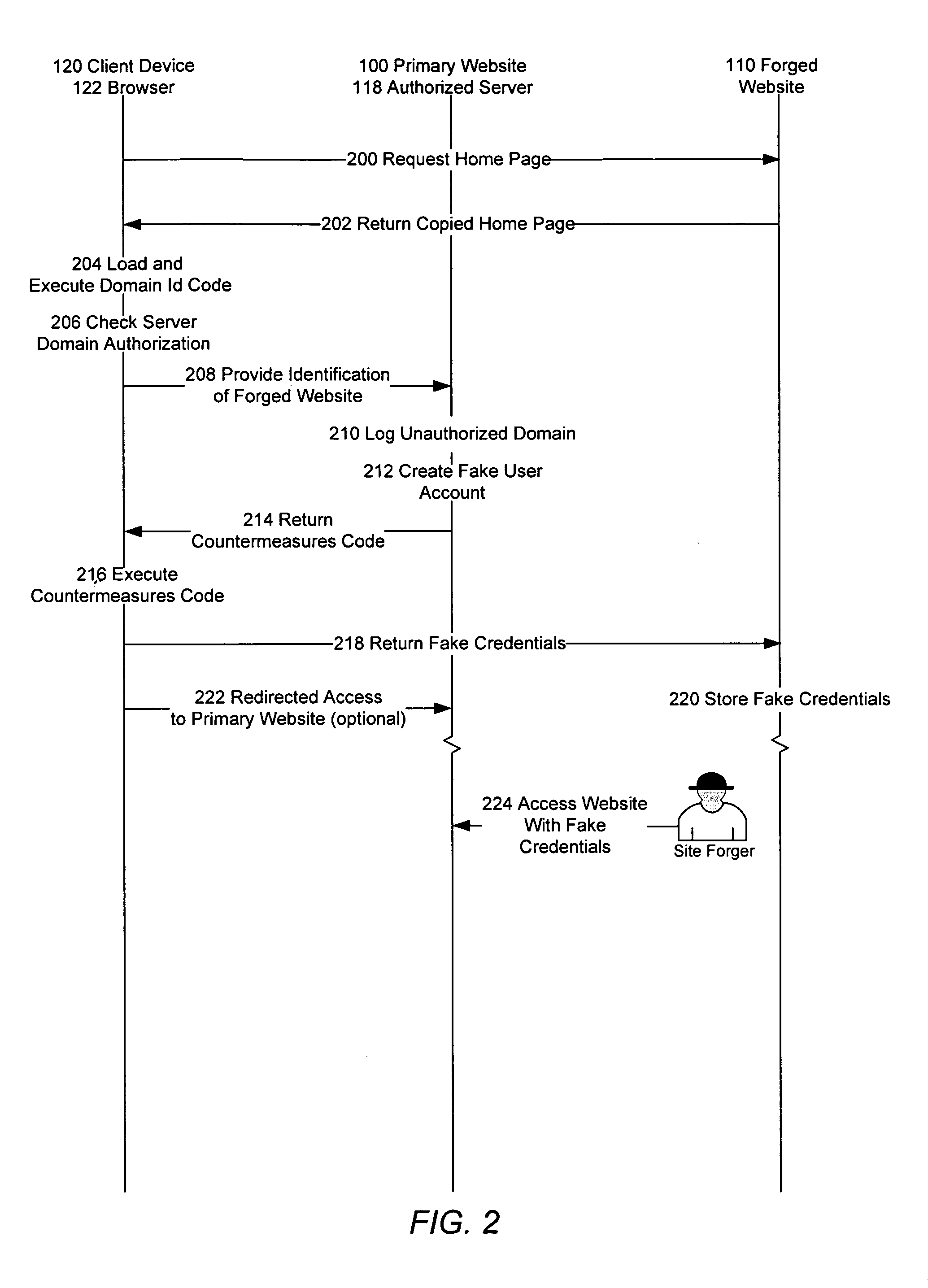
Identification of and countermeasures against forged websites
A system, a method, and computer program product identify a website that is a forgery of a primary website. Client side executable code is included in a page of the primary website, which page is copied in the forged website. The client side code, when executed by a client device, determines whether the domain from which the page is served is an authorized domain. Where the serving domain is not authorized, the client device is configured to alter the execute countermeasures against the forged website, such as altering operation of the forged page.
Owner:META PLATFORMS INC
Identification of and Countermeasures Against Forged Websites
ActiveUS20090228780A1Digital data processing detailsMultiple digital computer combinationsWeb siteCountermeasure
A system, a method, and computer program product identify a website that is a forgery of a primary website. Client side executable code is included in a page of the primary website, which page is copied in the forged website. The client side code, when executed by a client device, determines whether the domain from which the page is served is an authorized domain. Where the serving domain is not authorized, the client device is configured to alter the execute countermeasures against the forged website, such as altering operation of the forged page.
Owner:META PLATFORMS INC
Access to authorized domains
InactiveUS20090132811A1Easy to controlKey distribution for secure communicationUser identity/authority verificationA domainOne-way function
In a domain comprising a plurality of devices, the devices in the domain sharing a common domain key, a method of enabling a entity that is not a member of the domain to create an object that can be authenticated and / or decrypted using the common domain key, the method comprising providing to the entity that is not a member of the domain a diversified key that is derived using a one-way function from at least the common domain key for creating authentication data related to said object and / or for encrypting said object, the devices in the domain being configured to authenticate and / or decrypt said object using the diversified key.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
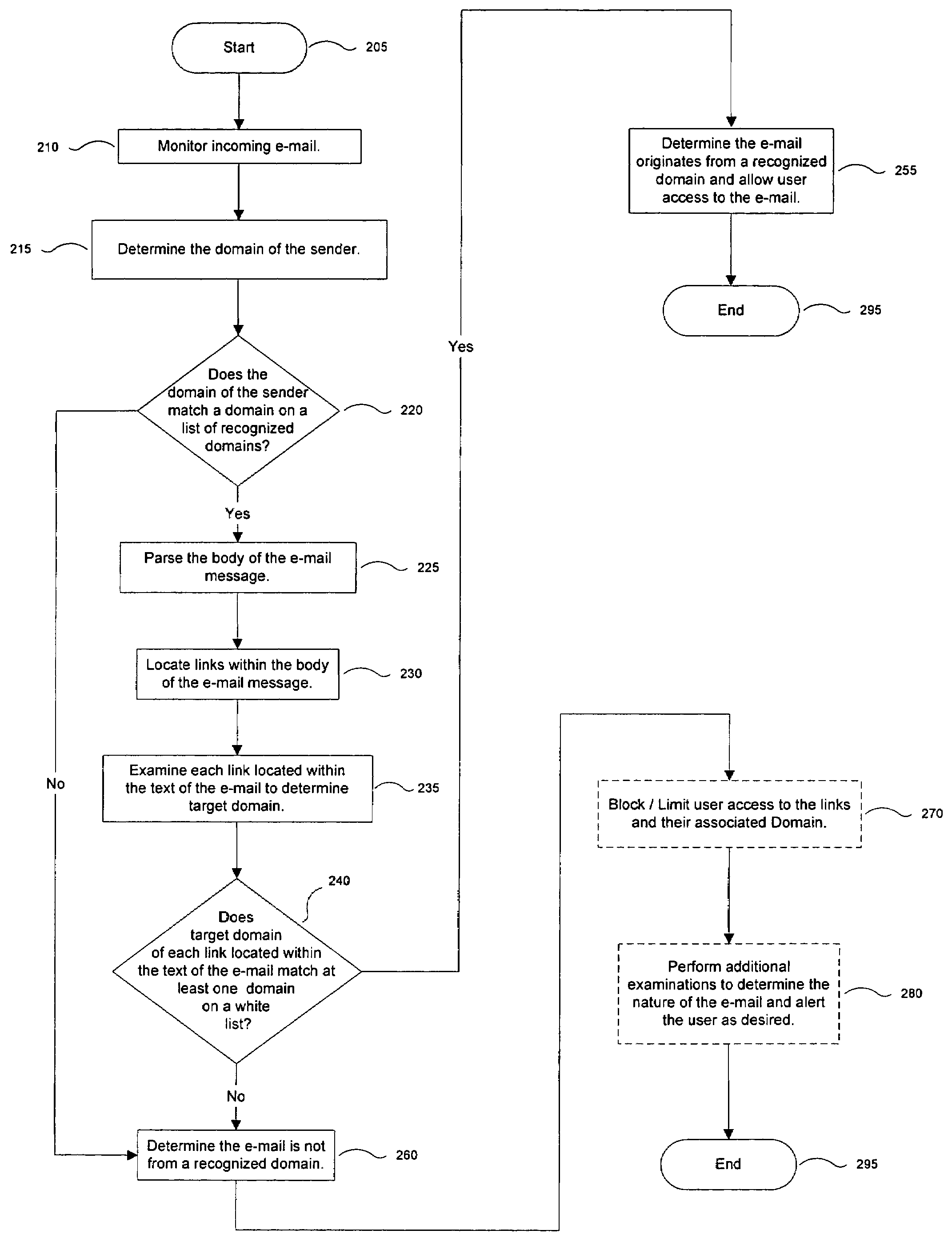
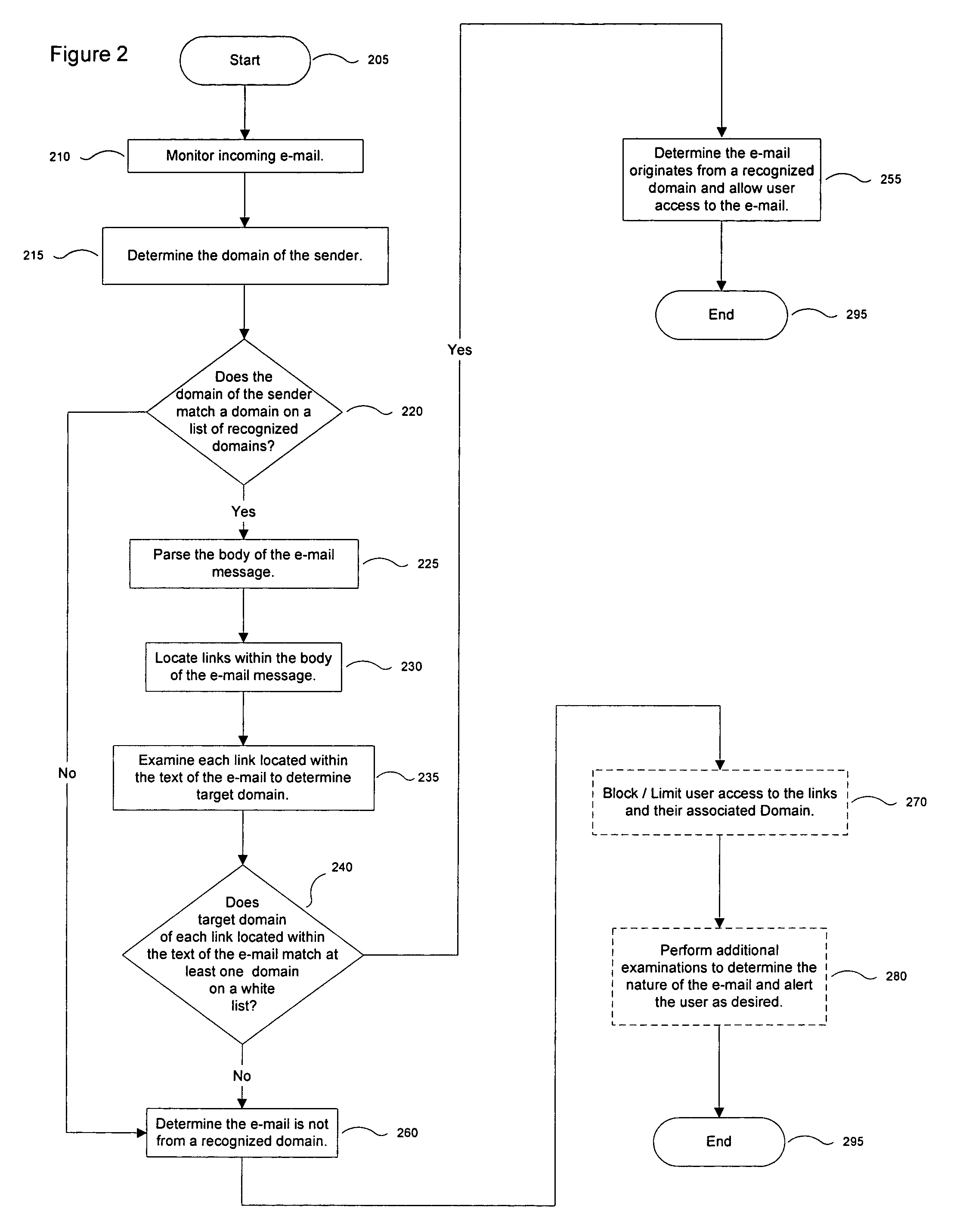
Determining whether e-mail messages originate from recognized domains
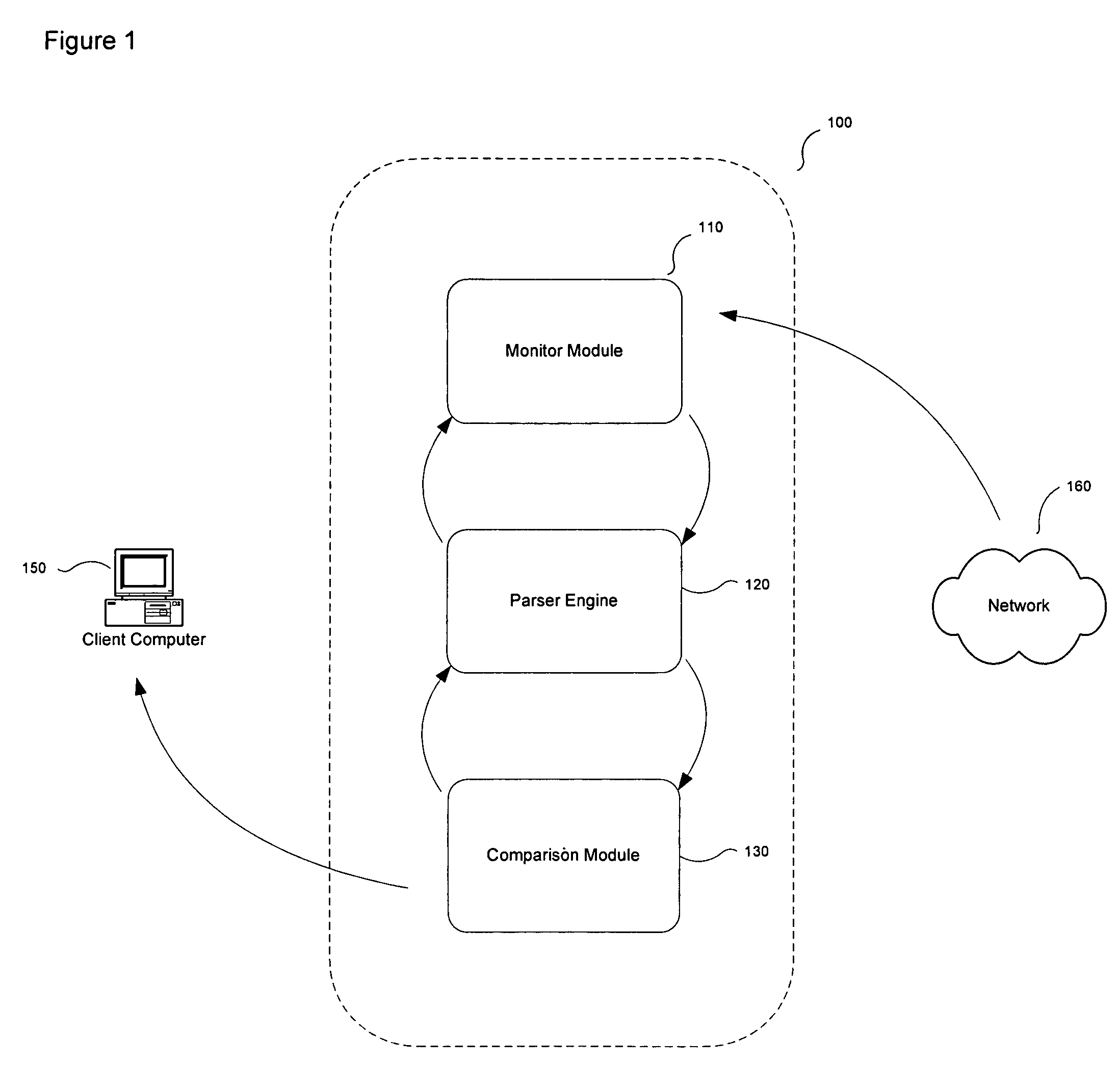
ActiveUS7496634B1Multiple digital computer combinationsData switching networksInternet privacyAuthorized domain
A message manager monitors incoming e-mail messages. The message manager determines whether the from field of each incoming e-mail message indicates that the e-mail message originates from a recognized domain. Responsive to determining that the from field indicates that the e-mail originates from a recognized domain, the message manager compares at least one domain associated with at least one link found embedded in the text of the e-mail message to a list of authorized domains. Based on the results of the comparison, the message manager determines whether the e-mail message originates from a recognized domain.
Owner:NORTONLIFELOCK INC
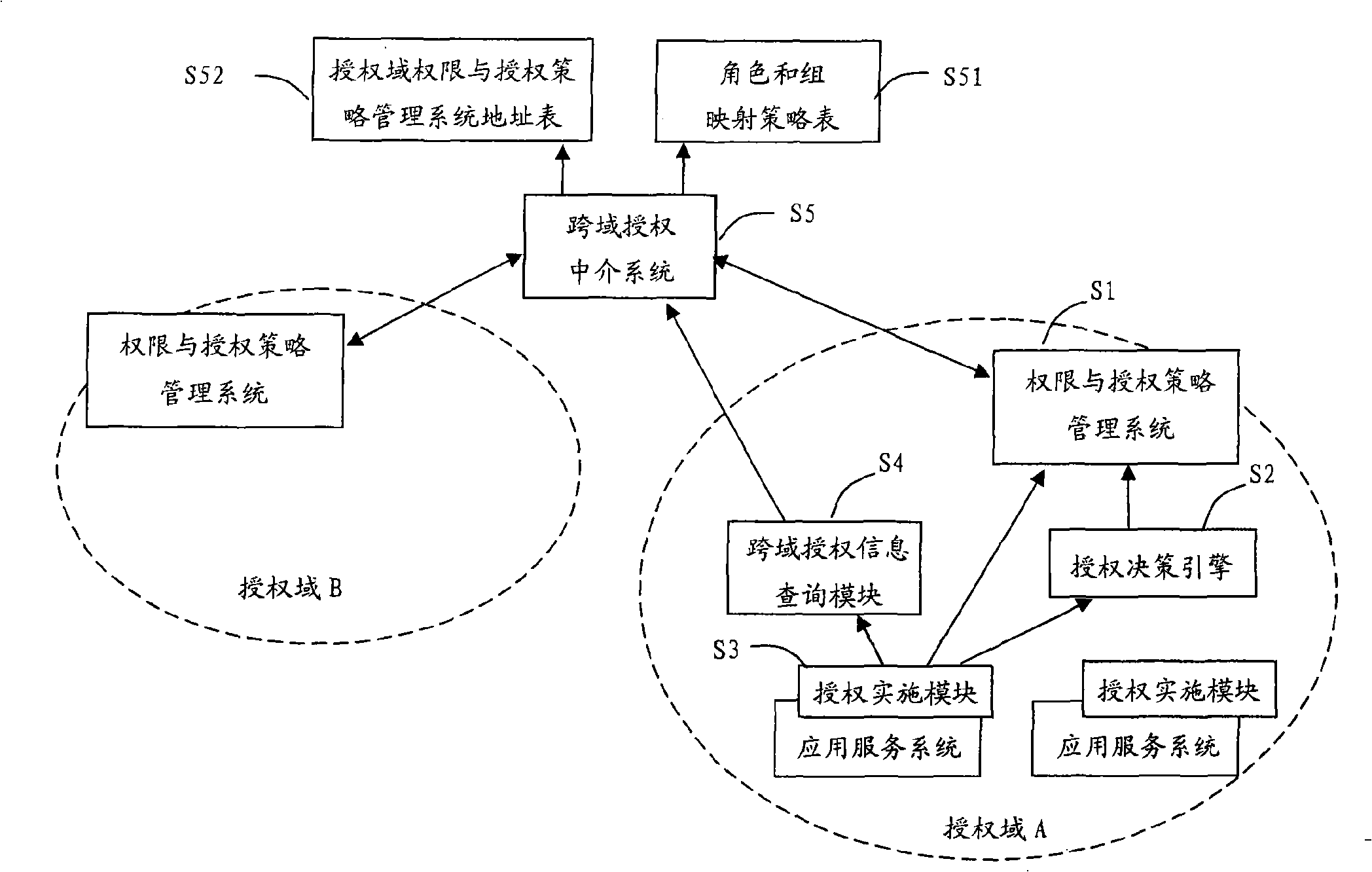
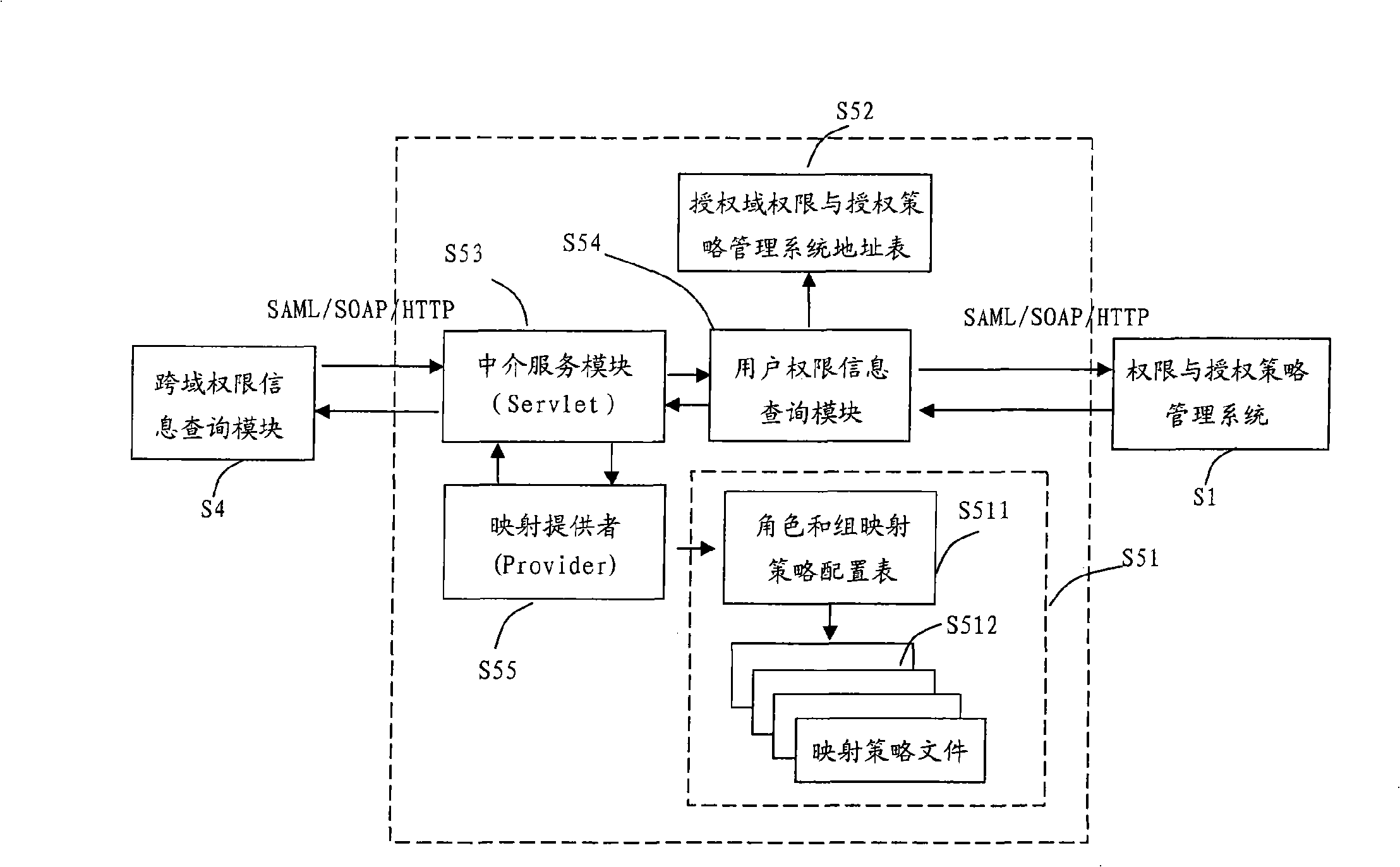
A cross-domain access control system for realizing role and group mapping based on cross-domain authorization
InactiveCN101262474ASuitable for cross-domain access controlUser identity/authority verificationControl systemSystem maintenance
The invention relates to a cross-domain access control system for role implementation and group mapping on the basis of cross-domain authorization medium. The cross-domain access control system of the invention maintains one role and group mapping strategy table through one cross-domain authorization medium system, wherein, the strategy table is provided with a serials of mapping strategies, and one mapping strategy defines the mapping relationship of roles and groups from one authorization domain to another. When the users of one authorization domain access another authorization domain, the medium system of cross-domain authorization provides roles and groups in the target authorization domain to be accessed, corresponding to the roles and groups in the original authorization domain and on the basis of roles and groups strategy, leading user limit of authorization in one domain to be converted or correspondingly matched to another domain, thereby realizing cross-domain access control based on RBAC or ACL. The cross-domain access control system of the invention is not only suitable for the cross-domain access control based on RBAC and based on ACL, but also suitable for the cross-domain access control based on inter-domain of RBAC and ACL.
Owner:WUHAN UNIV OF TECH +1
System and method for controlled copying and moving of content between devices and domains based on conditional encryption of content key depending on usage state
InactiveUS20080313741A1Easy transferAvoid easy removalTelevision system detailsEncryption apparatus with shift registers/memoriesMobile contentAuthorized domain
A system and method is disclosed for allowing content providers to protect against widespread copying of their content, while enabling them to give their customers more freedom in the way they use the content. In accordance with one embodiment, content providers identify their content as protected by watermarking the content. Consumers use compliant devices to access protected content. All of a user's compliant devices, or all of a family's devices, can be organized into an authorized domain. This authorized domain is used by content providers to create a logical boundary in which they can allow users increased freedom to use their content.
Owner:NOKIA CORP
Accessing protected data on network storage from multiple devices
ActiveUS8059818B2Easy to manageKey distribution for secure communicationData taking preventionPlaintextAuthorized domain
The present invention relates to a method and a system of securely storing data on a network (100) for access by an authorized domain (101, 102, 103), which authorized domain includes at least two devices that share a confidential domain key (K), and an authorized domain management system for securely storing data on a network for access by an authorized domain. The present invention enables any member device to store protected data on the network such that any other member device can access the data in plaintext without having to communicate with the device that actually stored the data.
Owner:NOKIA TECHNOLOGLES OY
Transmission/reception system
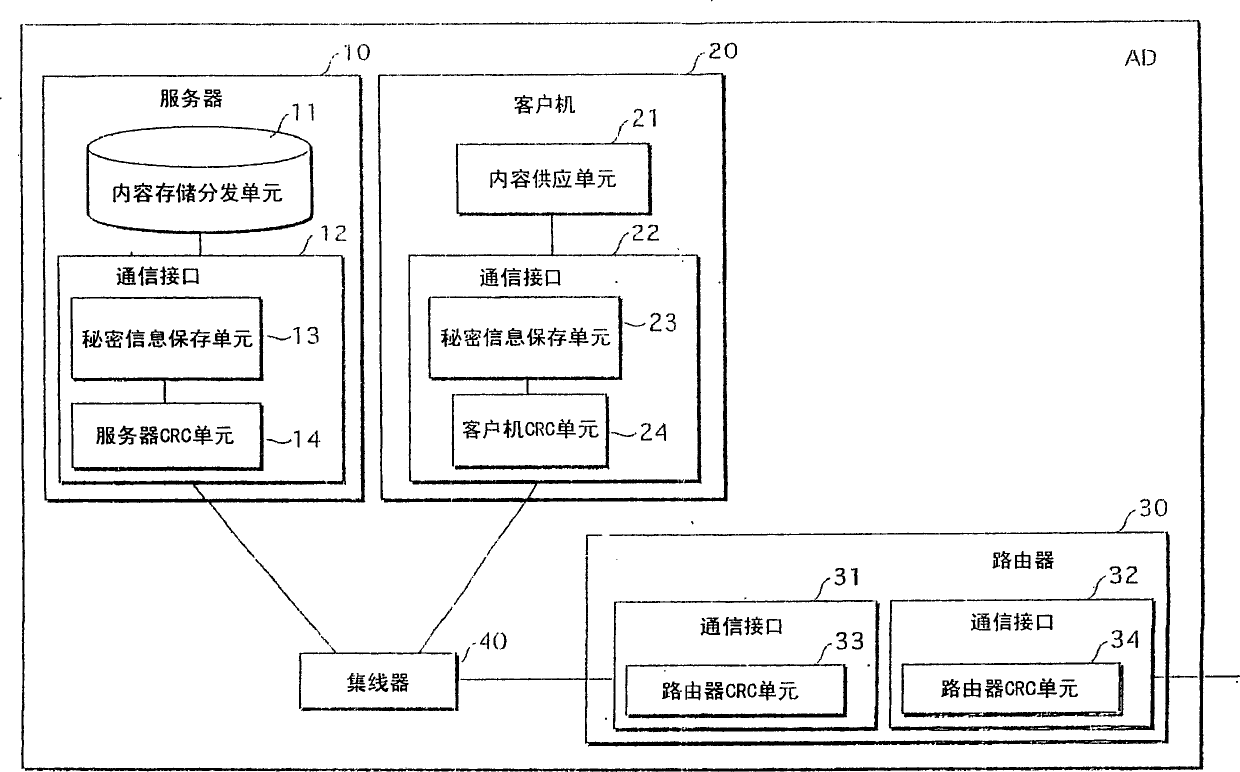
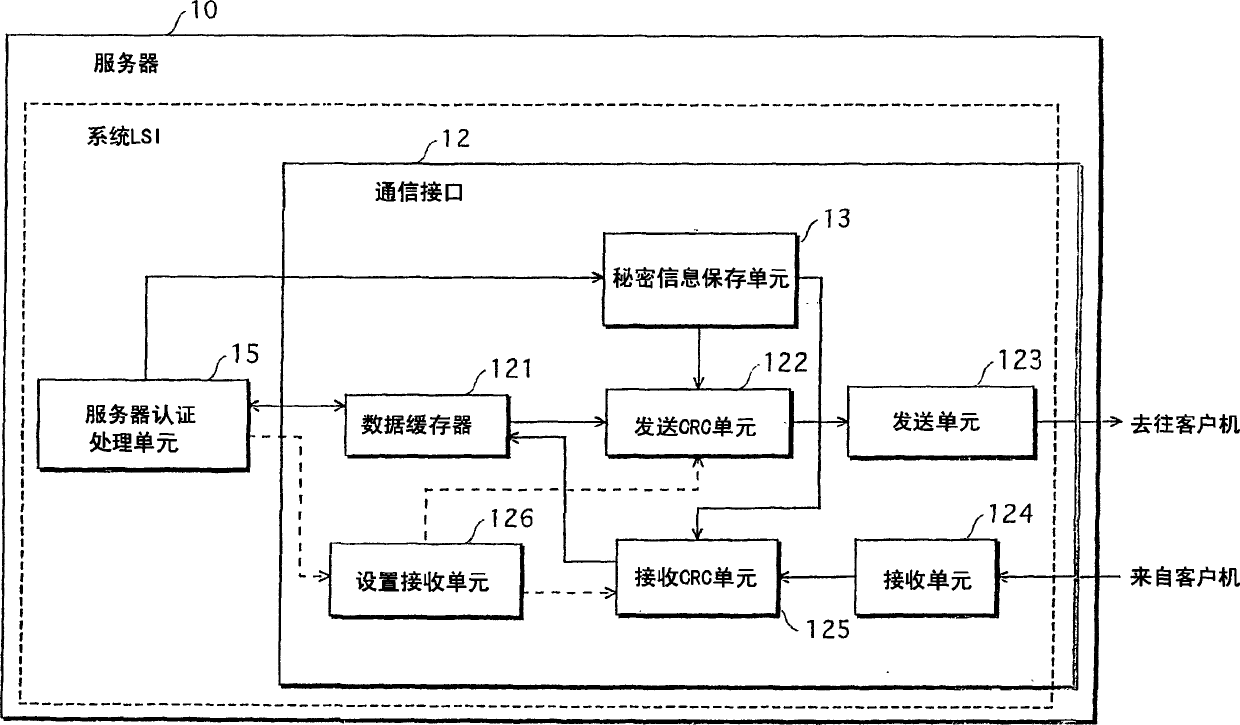
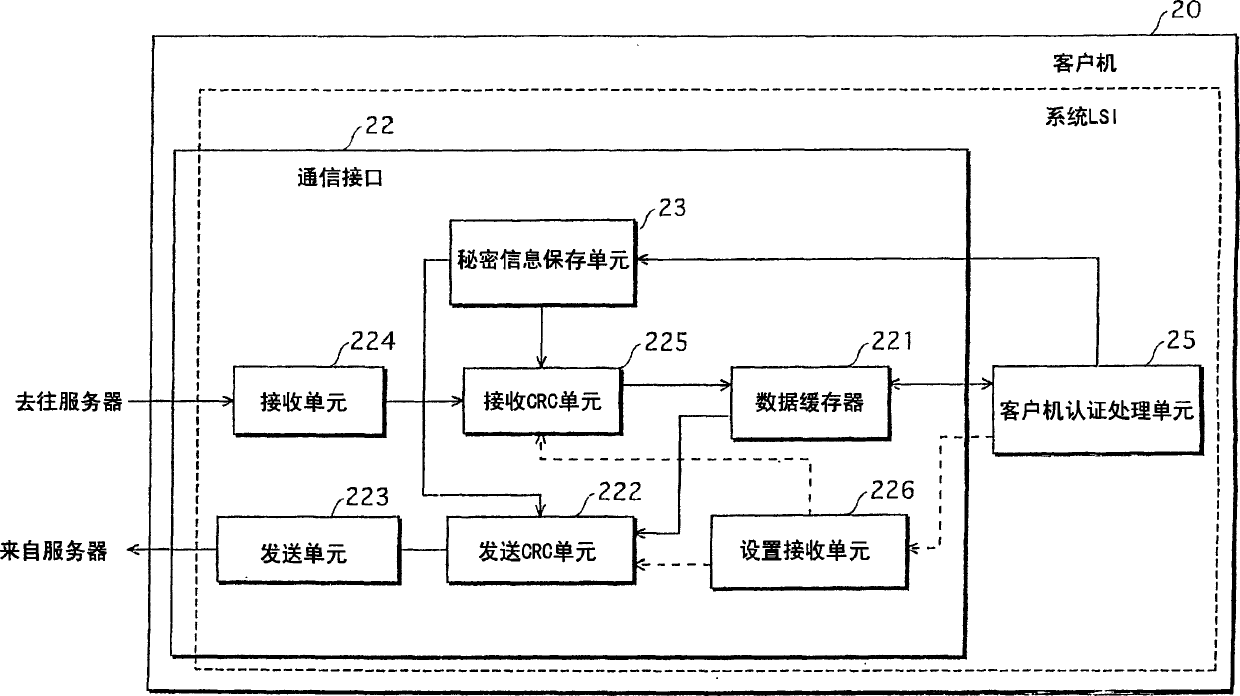
InactiveUS7457410B2Authentication processing is reliableInhibit transferKey distribution for secure communicationError preventionClient-sideAuthorized domain
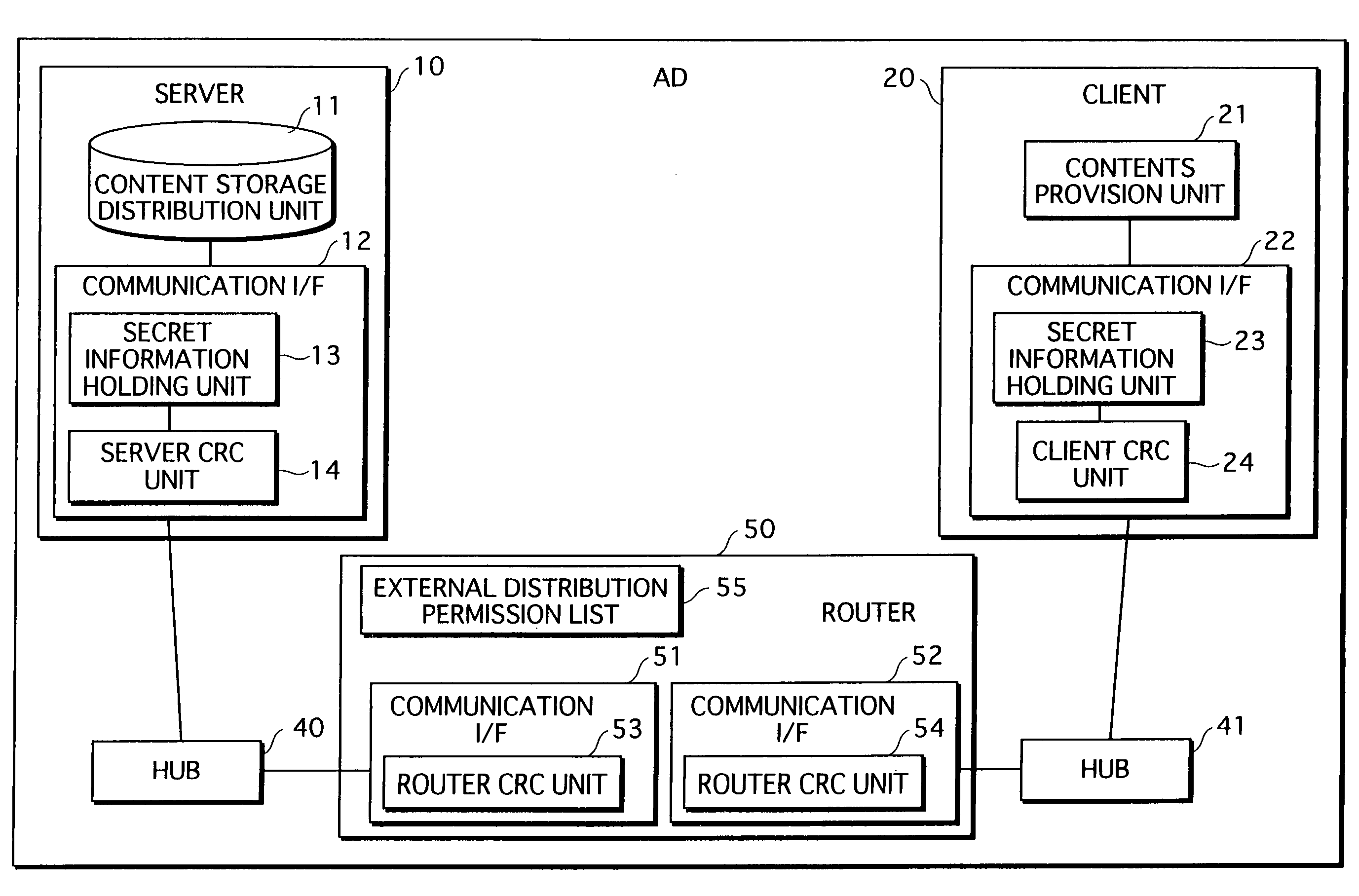
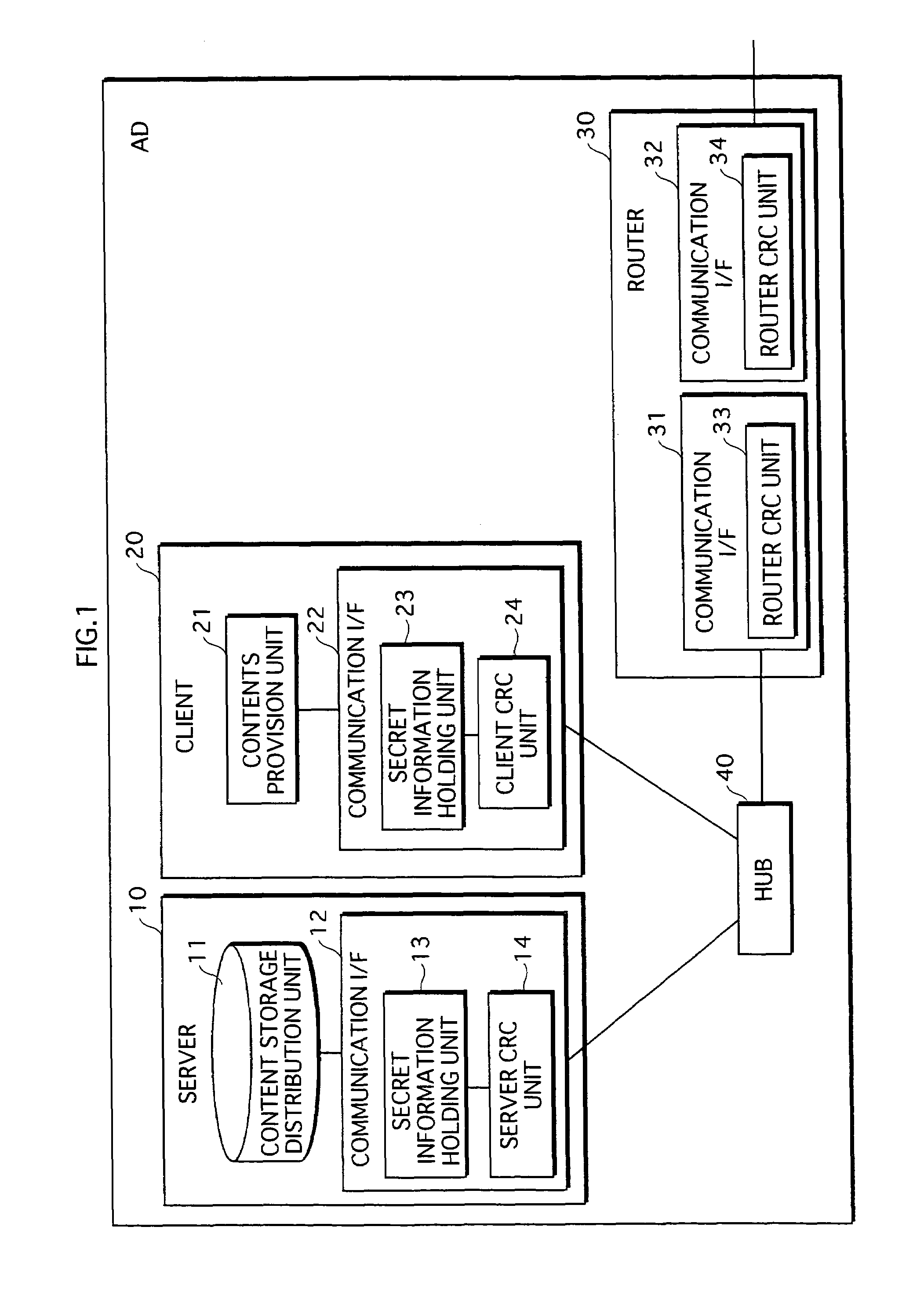
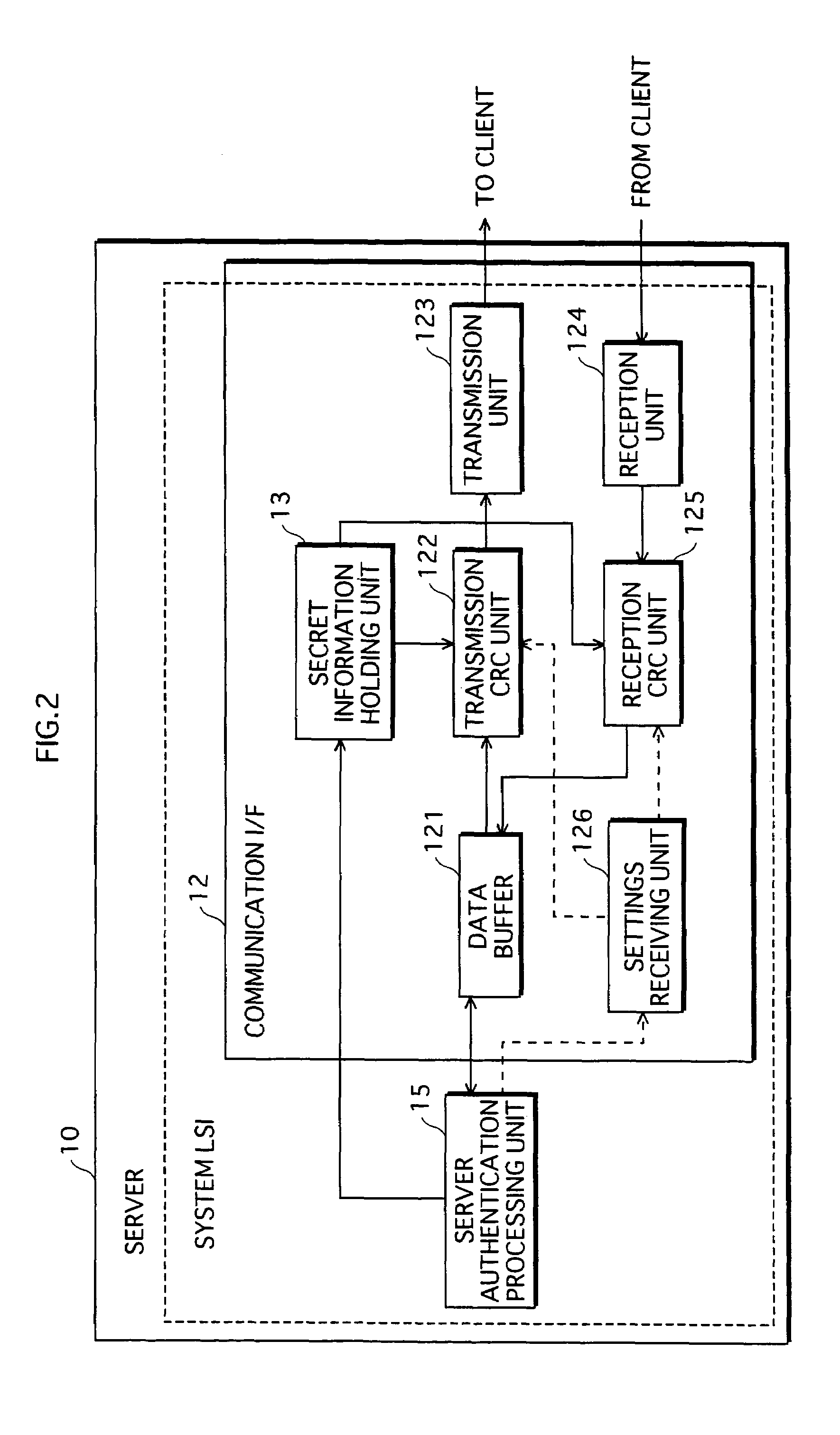
A server and a client hold common secret information in respective secret information holding units. A server Cyclic Redundancy Check (CRC) unit in the server generates a CRC code after adding the secret information to communication data, and transmits the communication data with the CRC code attached. A client CRC unit of the client generates a CRC code after adding the secret information to communication data, and checks whether or not an error has occurred in the communication data on the communication path. Since the client holds the secret information, the client determines that an error has not occurred, and obtains the communication data. On the other hand, a router, which does not hold the secret information, is unable to obtain the communication data. This prevents the communication data from being transferred to devices outside an authorized domain.
Owner:PANASONIC CORP
Data carrier belonging to an authorized domain
InactiveUS20070056040A1Input/output to record carriersDigital data processing detailsCarrier signalData content
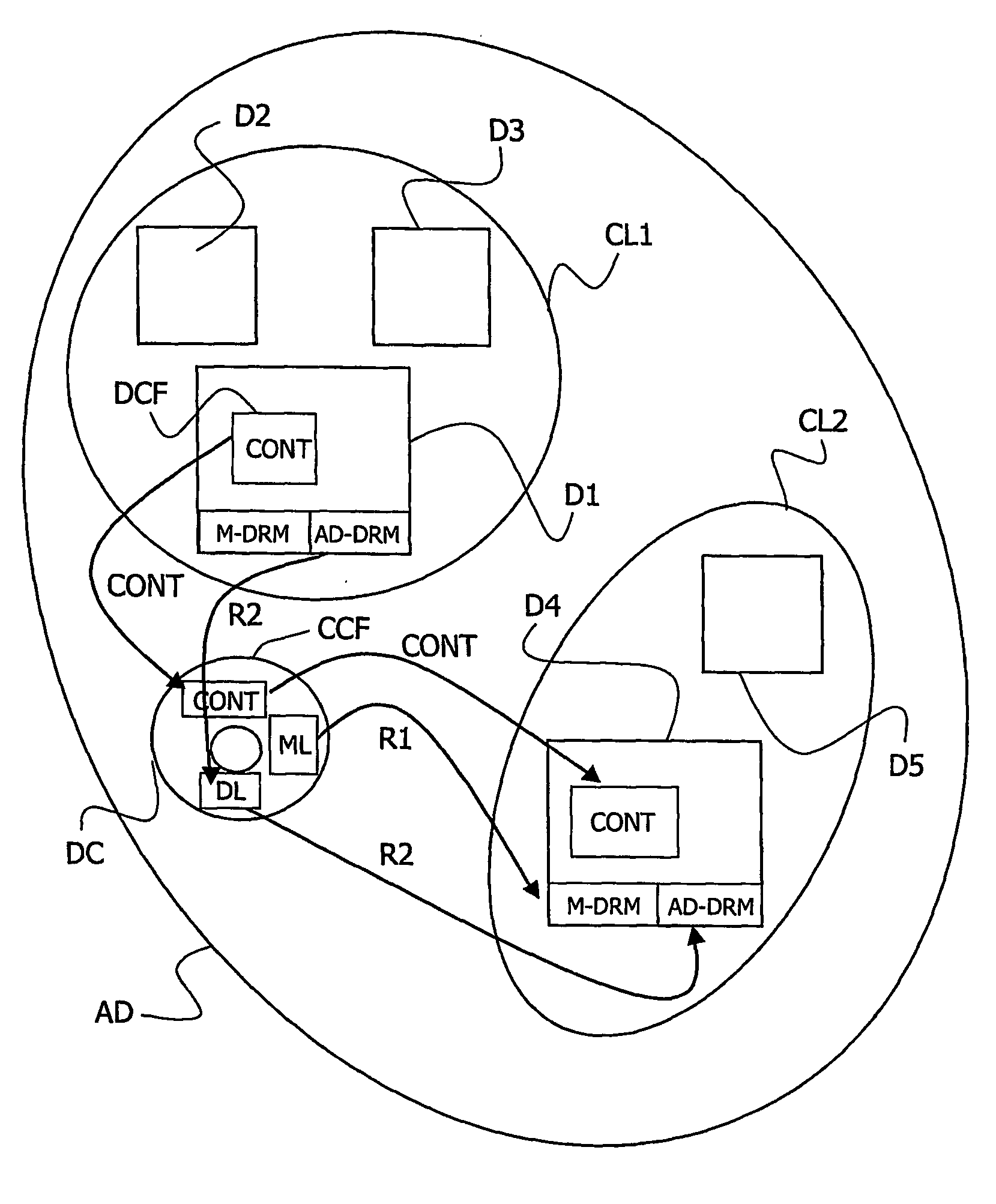
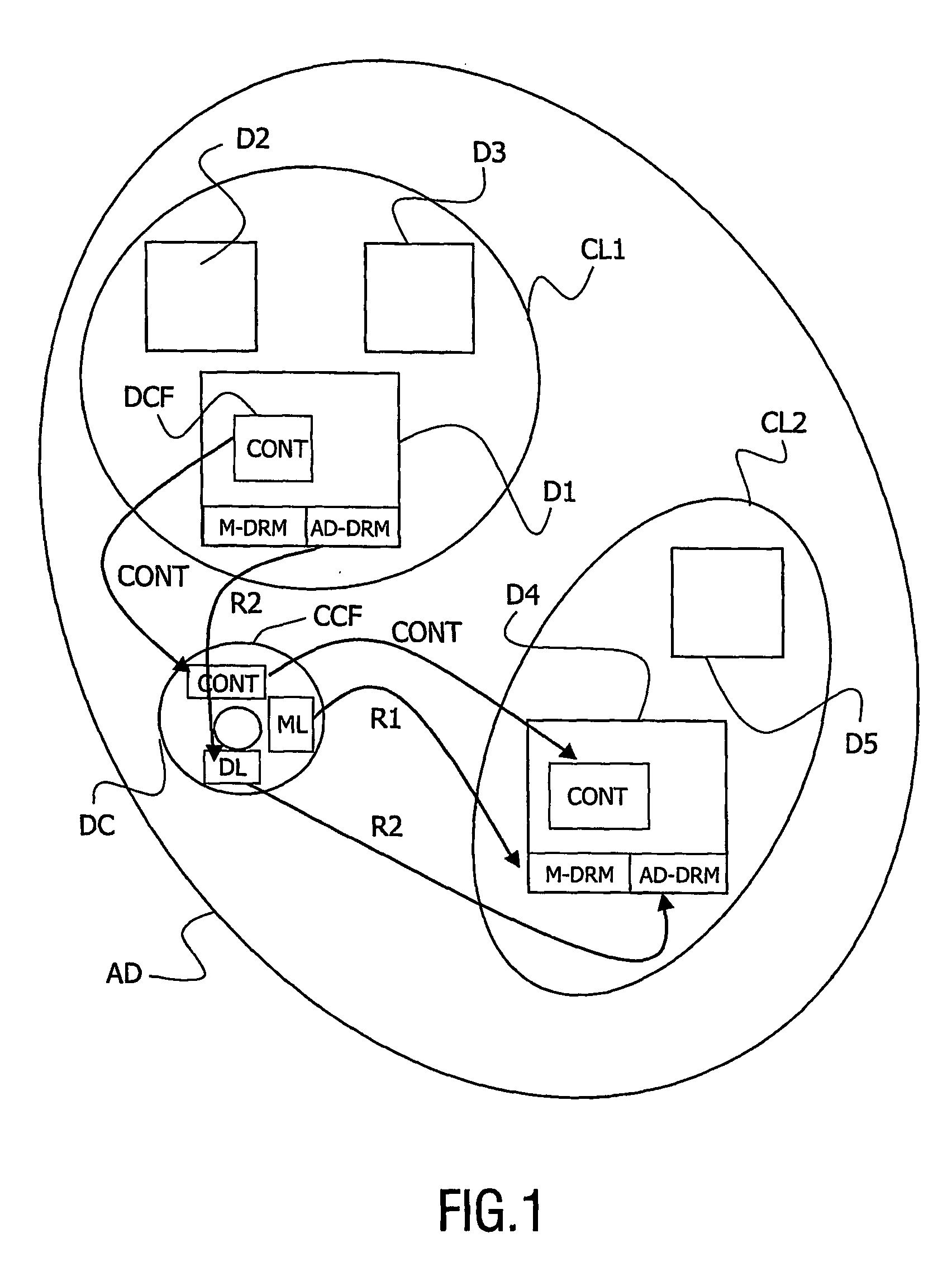
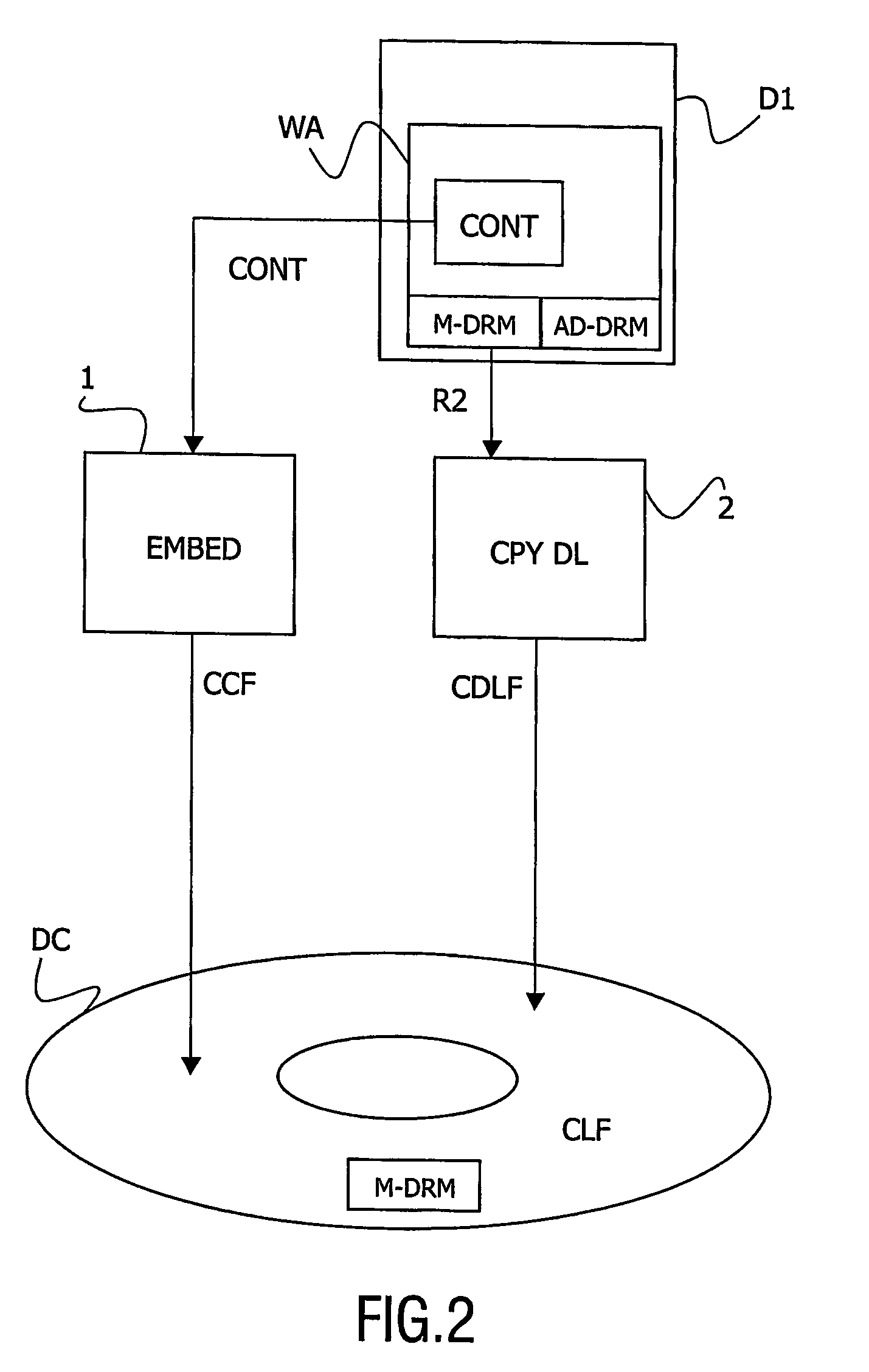
The invention relates to a data carrier (DC) for carrying a data content (CONT) belonging to an authorized domain (AD). Said data carrier (DC) comprises a data carrier data right management system (M-DRM) ruled by first rights (R1) of exporting said data content (CONT) to a reading apparatus (RA). Said authorized domain comprises a domain data right management system (AD-DRM) ruled by second rights (R2) of exporting said data content (CONT) to a reading apparatus (RA), said second rights depending on whether the reading apparatus belongs to the authorized domain. The data carrier (DC) comprises said data content (CONT) stored within a data carrier data content file (CCF) having a data carrier format specified by said data carrier data right management system (M-DRM), a data carrier license (ML) comprising said first rights (R1) and a domain license (DL) comprising said second rights (R2), said domain license (DL) being stored as a data carrier domain license file (CDLF) having said data carrier format.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Separation of copy protection rules
InactiveUS7551738B2Digital data processing detailsAnalogue secracy/subscription systemsDigital rights management systemCopy protection
A copyright protection method and apparatus employ a first protection scheme within a single authorized domain, in which all interfaces are protected with digital rights management system, and employ a second protection scheme for use in inter-domain file transfers. The method and apparatus employ a third protection scheme for external outputs not protected by a digital rights management system.
Owner:GOOGLE TECH HLDG LLC
System and methods for reduction of unwanted electronic correspondence
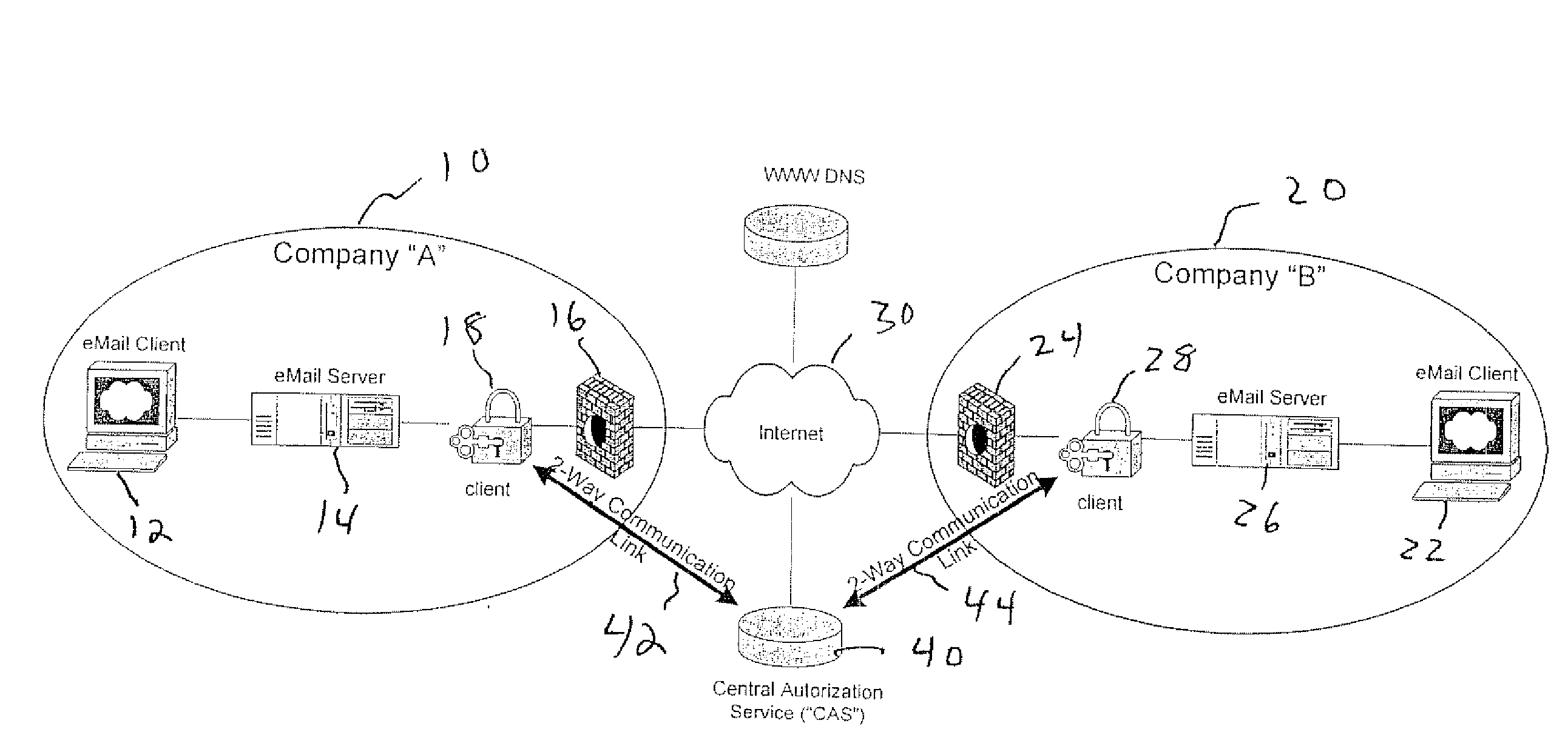
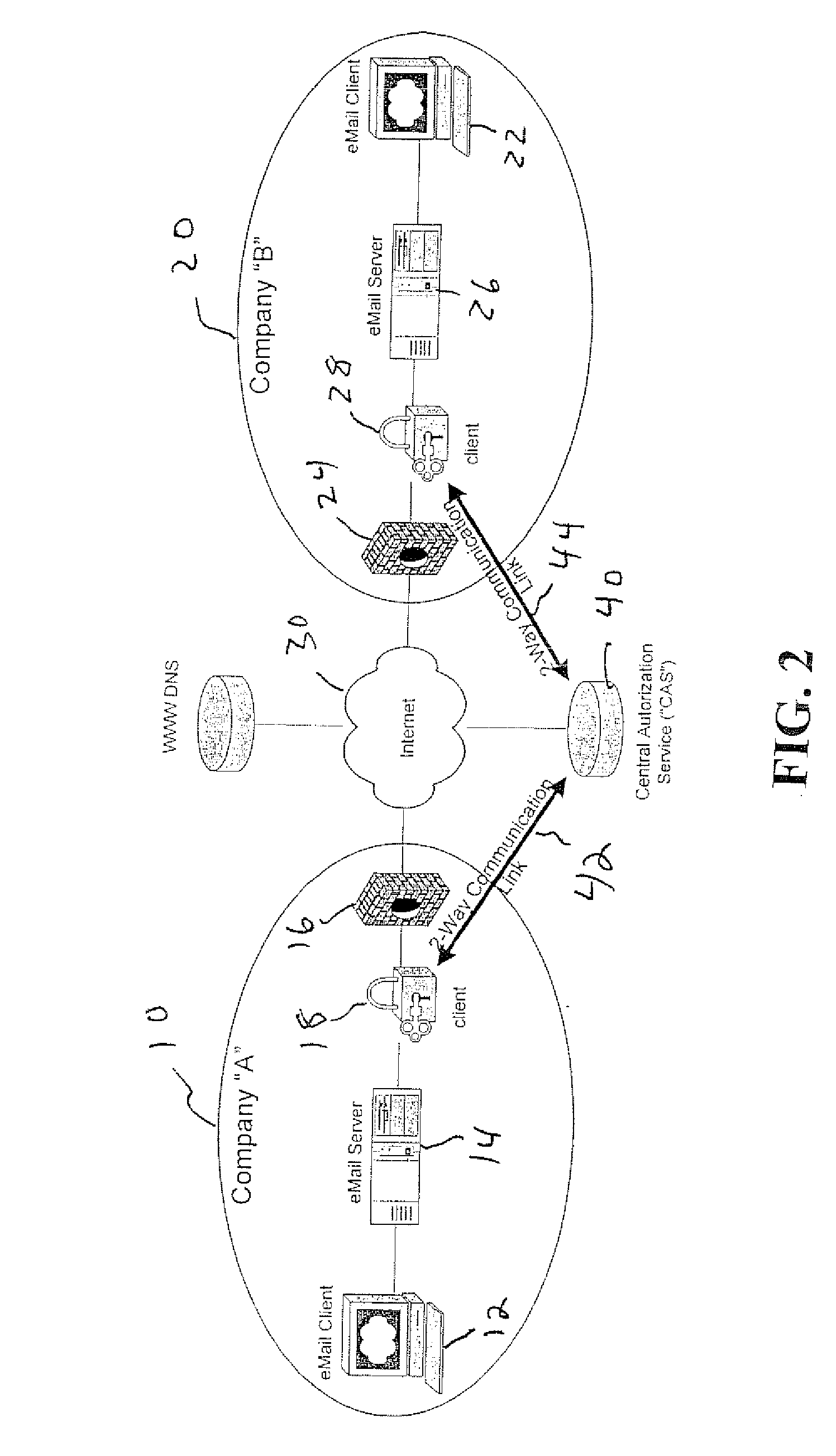
InactiveUS20080168536A1Digital data processing detailsMultiple digital computer combinationsClient-sideAuthorized domain
A system for authenticating electronic correspondence includes a sender, a recipient, and a central authorization service. The sender includes a correspondence client at which electronic correspondence is composed, a correspondence server for routing proposed correspondence, and a sender client. The recipient includes a correspondence client at which electronic correspondence is viewed, a correspondence server that delivers the correspondence to the correspondence client, and a recipient client. The central authorization service has a two-way communication link to each of the sender client and the recipient client. The sender client is configured to determine whether composed correspondence to be sent originates from at least one of an authorized server and an authorized domain before sending the correspondence and informs the central authorization service if a determination is made if the correspondence does not originate from an authorized server or an authorized domain. The recipient client determines the authenticity of received correspondence and only upon a determination of authenticity forwards the message to the correspondence server for routing to the recipient client.
Owner:MITCHELL TECH
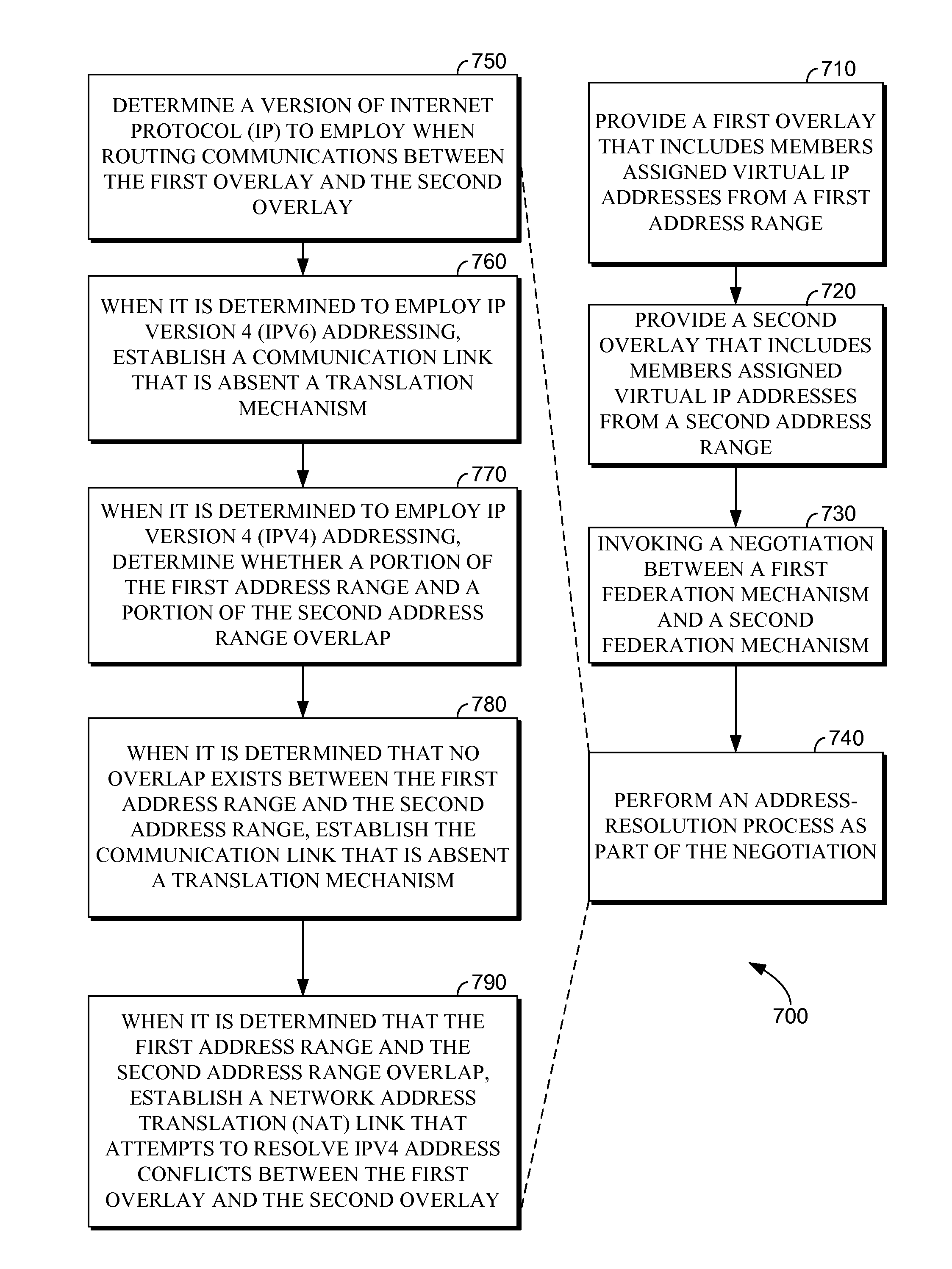
Federation among services for supporting virtual-network overlays
ActiveUS8688994B2Simplifies provisioning security policyUser identity/authority verificationTime-division multiplexTelecommunications linkVirtual network
Computerized methods, systems, and computer-readable media for promoting cooperation between a first and second virtual network overlay (“overlay”) are provided. The first overlay is governed by a first authority domain and includes members assigned virtual IP addresses from a first address range. The second overlay is governed by a second authority domain, which is associated with a second federation mechanism, for negotiating on behalf of the second overlay. The second federation mechanism is capable of negotiating with, or soliciting delegation of authority from, a first federation mechanism that is associated with the first authority domain. When negotiations are successful or authority is delegated, the second federation mechanism establishes a communication link between the second overlay and the first overlay or joins a member of the second overlay to the first overlay. Joining involves allocating a guest IP address from the first address range to the member.
Owner:MICROSOFT TECH LICENSING LLC
Authorized Domain Policy Method
ActiveUS20080271158A1Maximum flexibilityIncrease competitionDigital data processing detailsAnalogue secracy/subscription systemsA domainAuthorized domain
The present invention relates to a method and a device for determining access to multimedia content from an entry identifier, in a domain which comprises a number of entry identifiers, and where the multimedia content is assigned an access number n indicating the number of entry identifiers which may access the multimedia content. This is obtained by accessing a domain list indicating at least some of said entry identifiers in said network domain and by further determining that the entry identifier may access said multimedia content if said entry identifier is between the n entries in said domain list determined by an evaluation rule.
Owner:INTERTRUST TECH CORP
Method and Apparatus for Controlling the Number of Devices Installed in an Authorized Domain
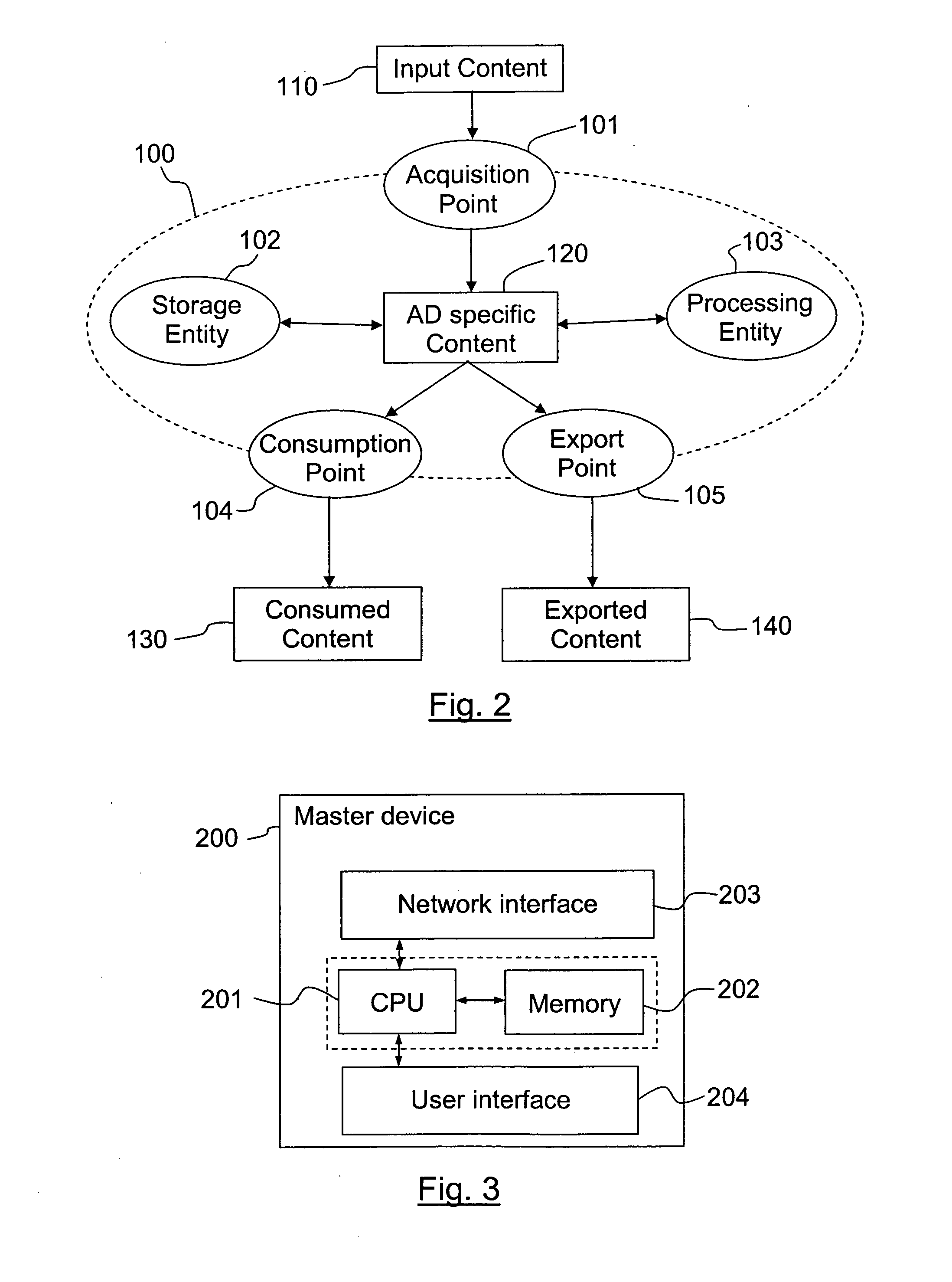
ActiveUS20100306823A1Pulse modulation television signal transmissionDigital data processing detailsEngineeringAuthorized domain
The number of devices installed in an Authorized Domain is controlled by a master device functionality. This master devices stores ceiling values for the total number Totaljimit of devices to be installed in the AD; the total number Localjimit of devices to be installed in a local proximity with the master device and the total number Remotejimit of devices to be installed remotely from said master device. The master device also stores current values of the number Local_count of devices installed in the AD in local proximity with the master device; and the number Remote_count of devices installed in the AD remotely from said master device. When a new device is to be installed in the AD, the ceiling values are checked with respect to the current values and it is checked whether the device is in local proximity with the master device to authorize or not its installation in the AD, either locally or remotely.
Owner:INTERDIGITAL CE PATENT HLDG
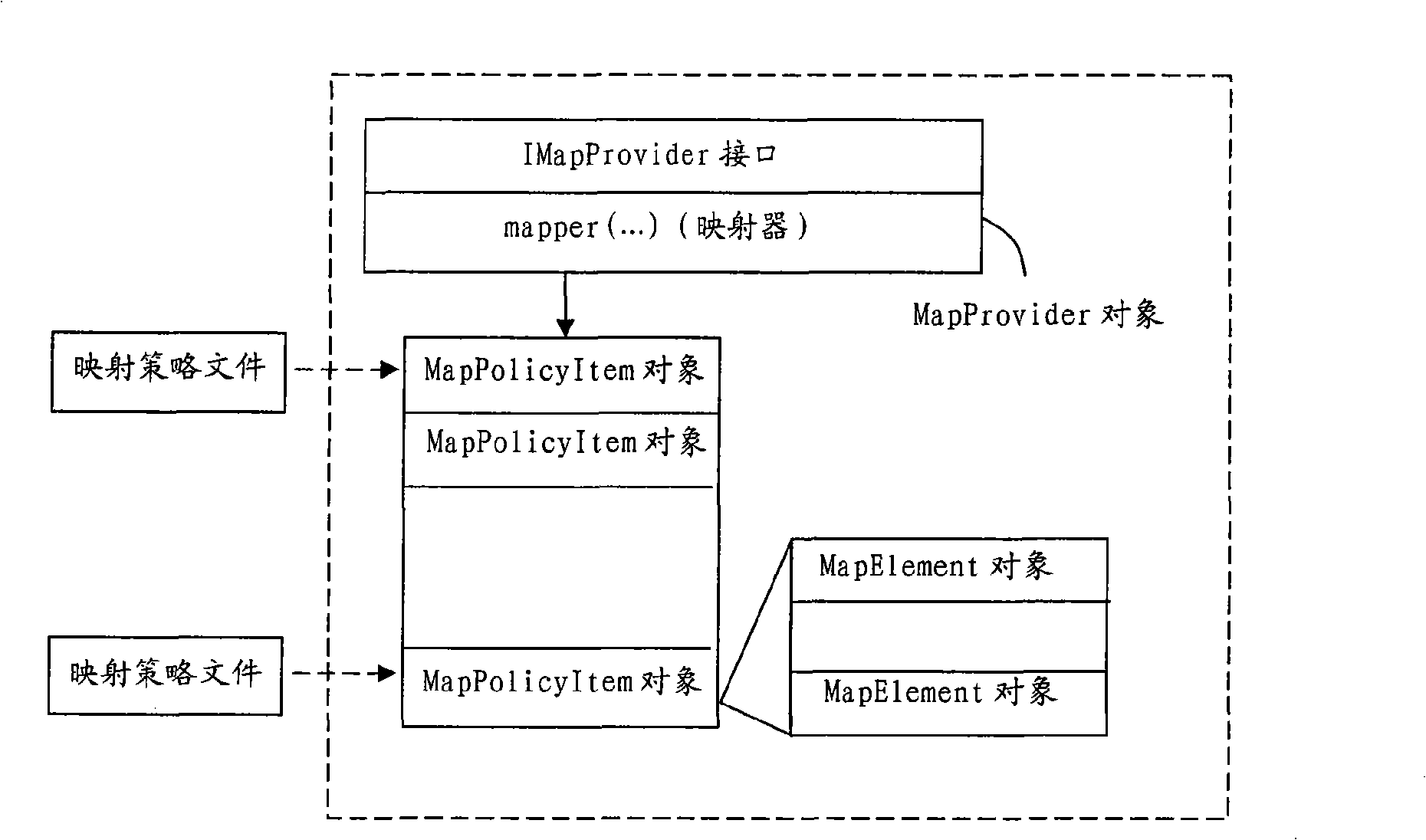
Distributed Authorized Domain Management
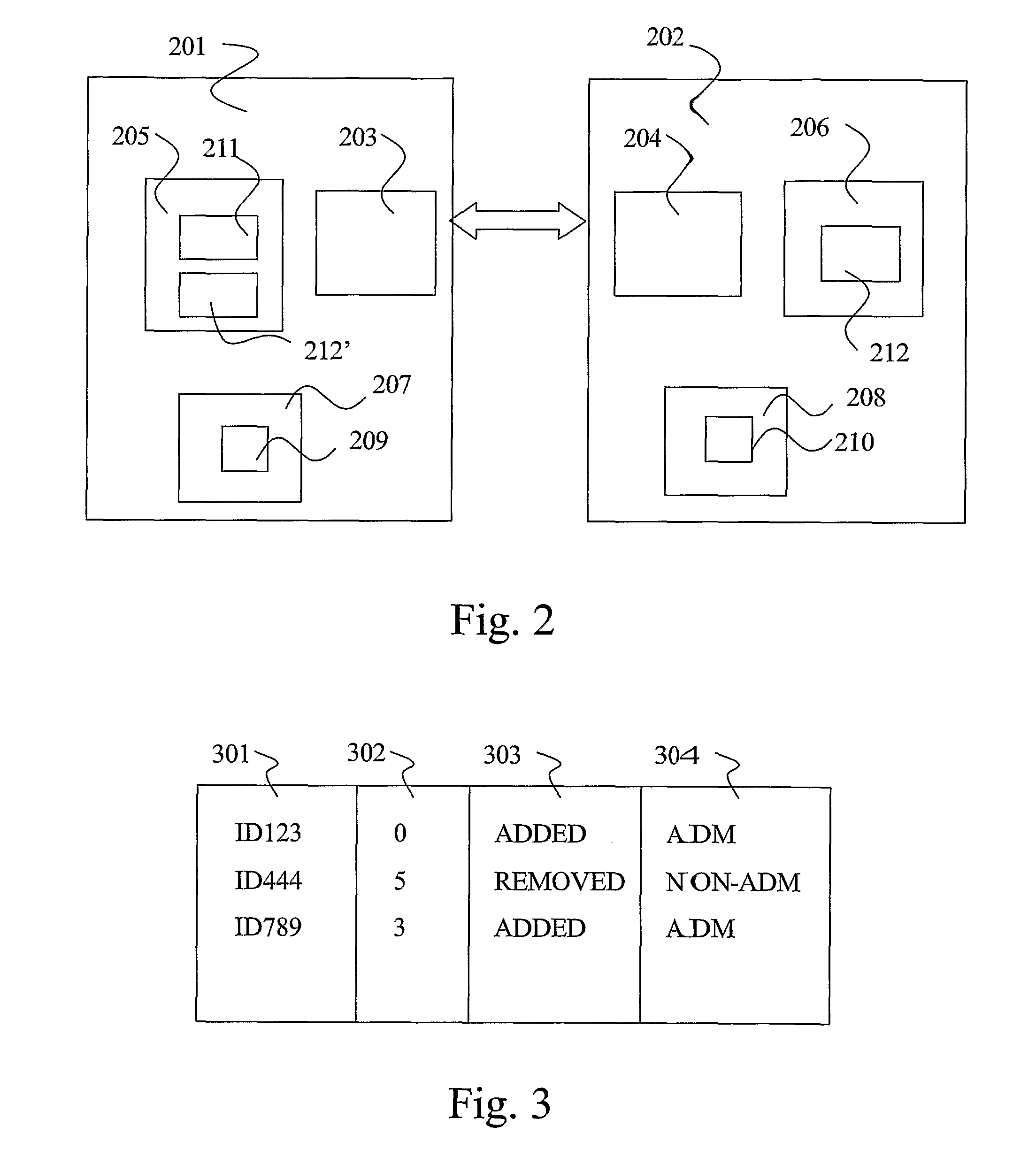
InactiveUS20070226372A1Television system detailsData processing applicationsAuthorized domainWorld Wide Web
The present invention relates to an authorized domain including a plurality of Authorized Domain Managers (ADMs). The plurality of ADMs contrary to a single ADM solution enables portable ADMs, that do not have to be continuously connected to the AD. The invention provides a solution for keeping the ADMs synchronized. For this purpose, inter alia, each ADM is provided with a map, which comprises an identifier area for containing identifiers corresponding to other devices, and at least one property area for containing properties of the identifiers. The property area is mapped on the identifier area. The properties are arranged to provide information about updates thereof. By obtaining map contents of another ADM, and comparing the contents of the own map with the map contents of the other ADM, it is possible for an ADM to determine whether to perform any updates of the own map.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
CDN optimal scheduling method based on local DNS
InactiveCN108989487AImprove access experienceAccurate schedulingData switching networksDomain nameUser needs
The invention relates to a CDN optimal scheduling method based on local DNS, comprising: an ICP content user experience optimization system and an Internet content user experience optimization system.IN the ICP Content User Experience Optimization System, fora domain name often visited by users, ICP's Authorized Domain Name Server is deployed next to the ICP User Experience Optimization system,aforwarding server is configured as the address of ICP authorized domain name server on ICP user experience optimization system, and the resource is obtained directly through domain name forwarding, and the local dialing test result is obtained through Tesse global resource library, and the optimal resource list is returned according to the user's strategy. The user experience is enhanced; local DNS service capabilities are enhanced; fault content source second-level switching is performed; the backbone network bandwidth of operators is saved. On the one hand, the access experience of users isenhanced, and the competitiveness of operators is enhanced; on the other hand, the backbone network bandwidth of the operators is greatly saved and the cost of the operators is reduced.
Owner:BEIJING TESTOR TECH
Cache optimization method and system for resisting continuous variable-domain name prefix attack
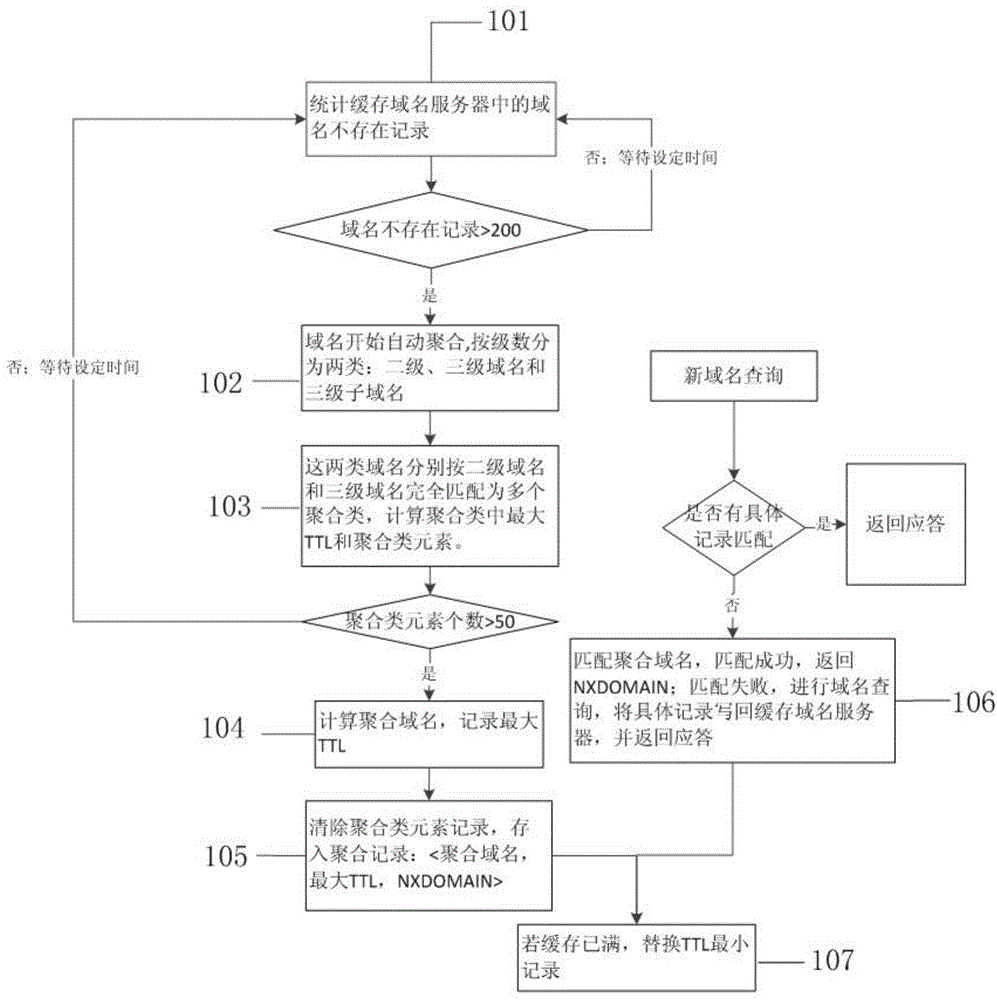
ActiveCN104618354AGuaranteed real-timeReduce false positive rateTransmissionDomain nameCache optimization
The invention relates to a cache optimization method and system for resisting continuous variable-domain name prefix attack. The method includes that regularly counting domain name absence records according to a set time period through a domain name cache server, when the domain name absence records surpass a set threshold, beginning to automatically gather the domain names; dividing the domain names into a plurality of aggregate classes according to the complete matching between second-level domain names and third-level domain names, if the element number of the aggregate class surpasses a set threshold, aggregating all the domain names in the aggregate class into an aggregate domain name with prefix *; for a new domain name query request, if there is no corresponding concrete record in the domain name cache server, matching with the aggregate domain name, if the matching is successful, returning a domain name absence response, otherwise, performing domain name query in an authorization domain name server. The cache optimization method for resisting the continuous variable-domain name prefix attack has advantages of strong cache stability, high timeliness, cache space saving and the like.
Owner:INST OF INFORMATION ENG CAS
Transmission/reception system
InactiveCN1836398AKey distribution for secure communicationError preventionComputer hardwareMessage authentication code
A server 10 and a client 20 hold common secret information in respective secret information holding units 13 and 23. A server CRC unit 14 in the server 10 generates a CRC code after adding the secret information to communication data, and transmits the communication data with the CRC code attached. A client CRC unit 24 of the client 20 generates a CRC code after adding the secret information to communication data, and checks whether or not an error has occurred in the communication data on the communication path. Since the client 20 holds the secret information, the client 20 determines that an error has not occurred, and obtains the communication data. On the other hand, a router 30, which does not hold the secret information, is unable to obtain the communication data. This prevents the communication data from being transferred to devices outside an authorized domain.
Owner:PANASONIC CORP
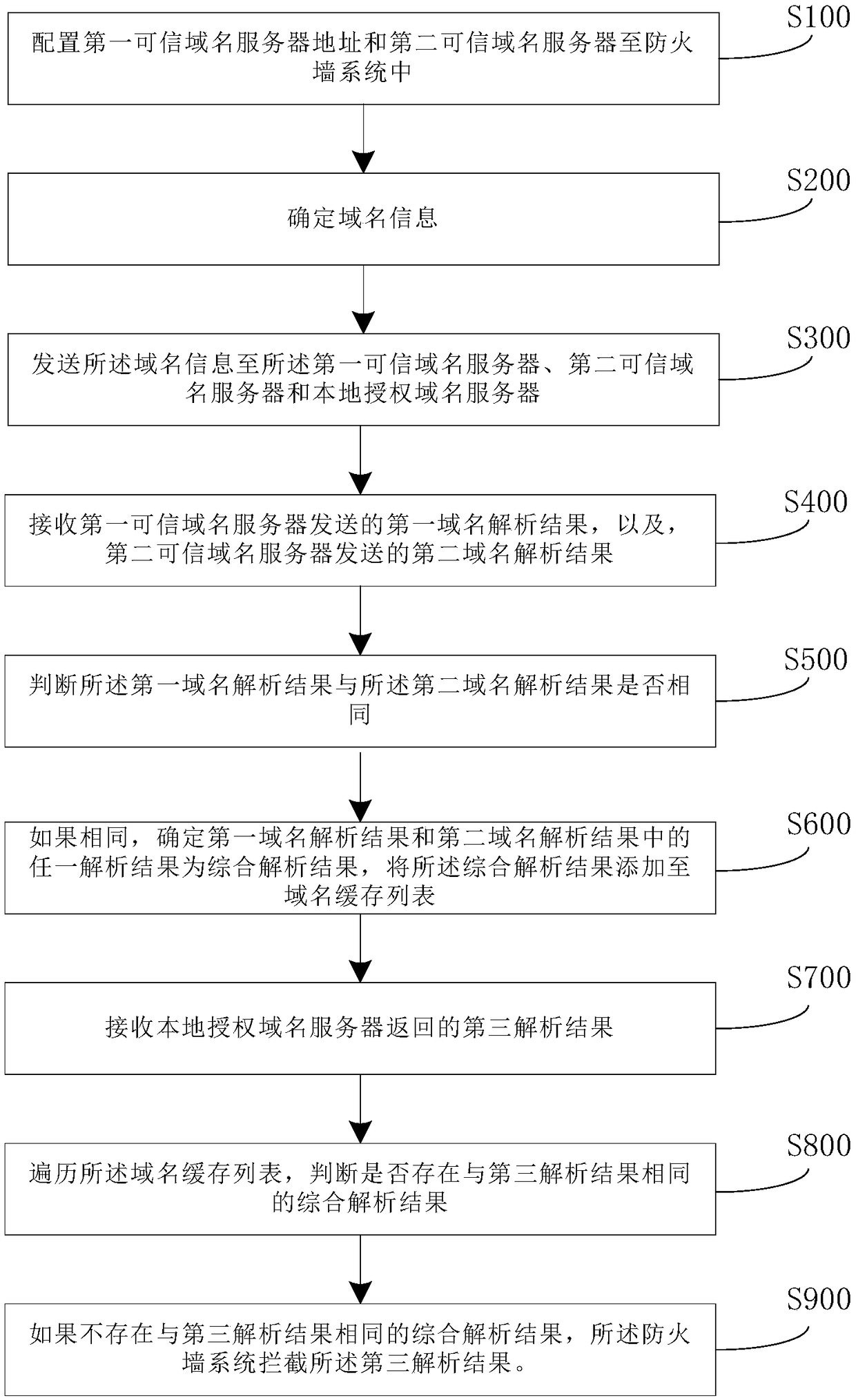
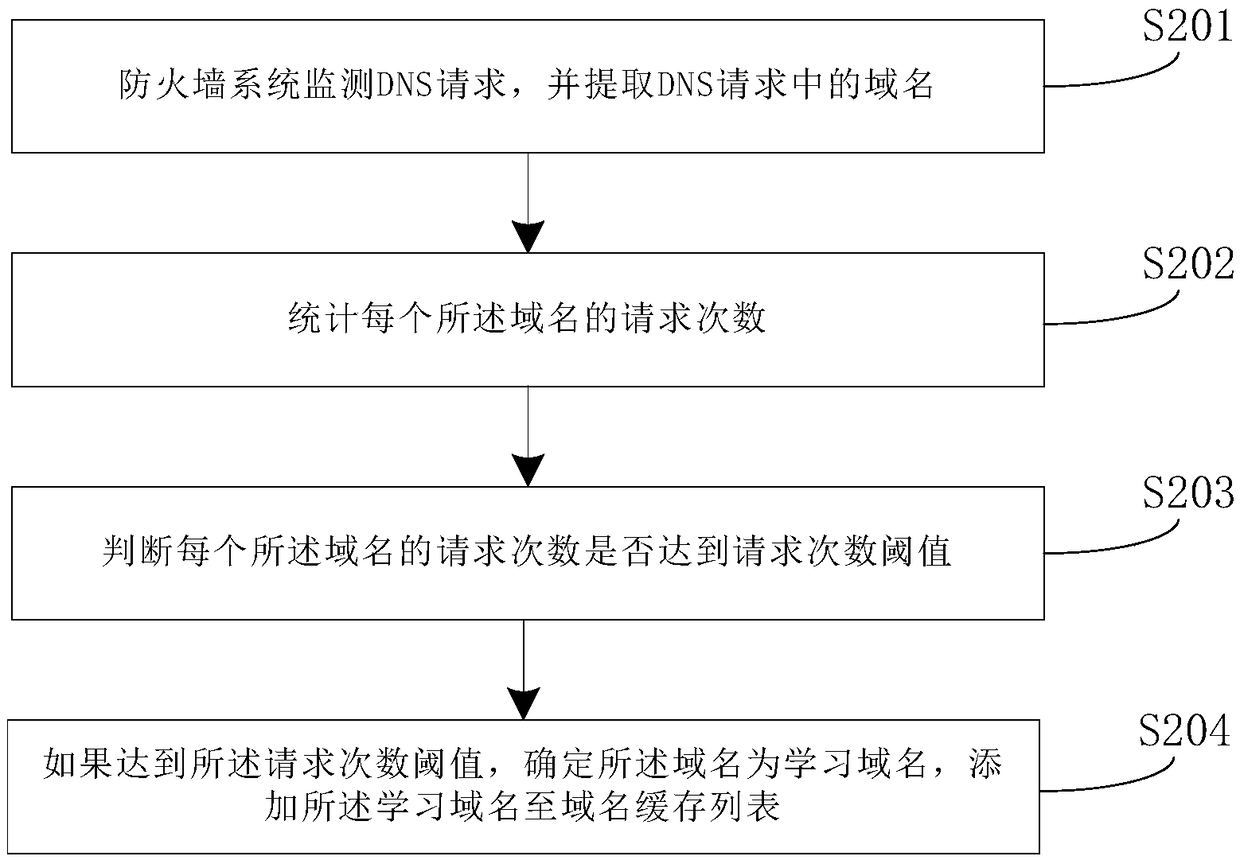
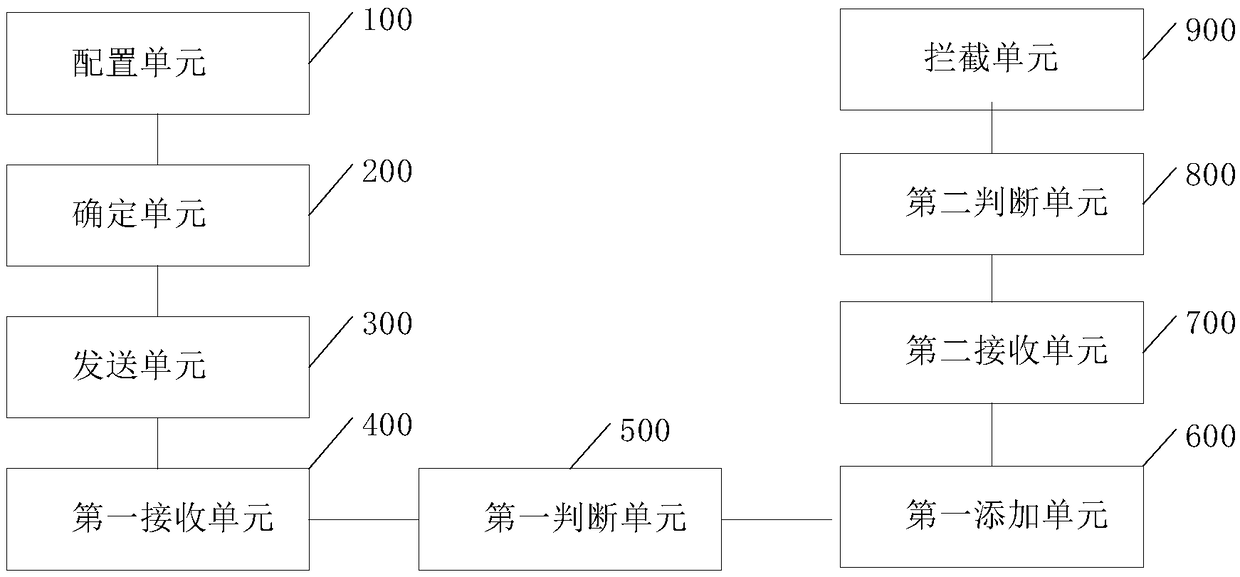
DNS hijack defending method, device and system based on firewall system
InactiveCN109361676ARealize the defense function of hijackingRealize the defense functionTransmissionDomain nameThird party
The application discloses a DNS hijack defending method, device and system based on a firewall system. The method comprises the following steps: configuring a first credible domain name server and a second credible domain name server; judging whether parsing results relevant to domain name information returned by the first credible domain server and the second credible domain server are the same or not; if so, storing the parsing results in a domain cache list; comparing whether a third parsing result returned by a local authorized domain name server is the same as the parsing results in the domain name cache list or not; and if not, hijacking a third parsing result by the firewall system since the third parsing result is hijacked. Third parties, namely, the first credible domain name server, the second credible domain name server and the local authorized domain name server are used for confirmation to realize the defending function of the firewall system for DNS hijacks, so that DNS hijack attack behaviors can be detected and intercepted reasonably and effectively, and harm to a user caused by phishing sites is avoided.
Owner:天津睿邦安通技术有限公司
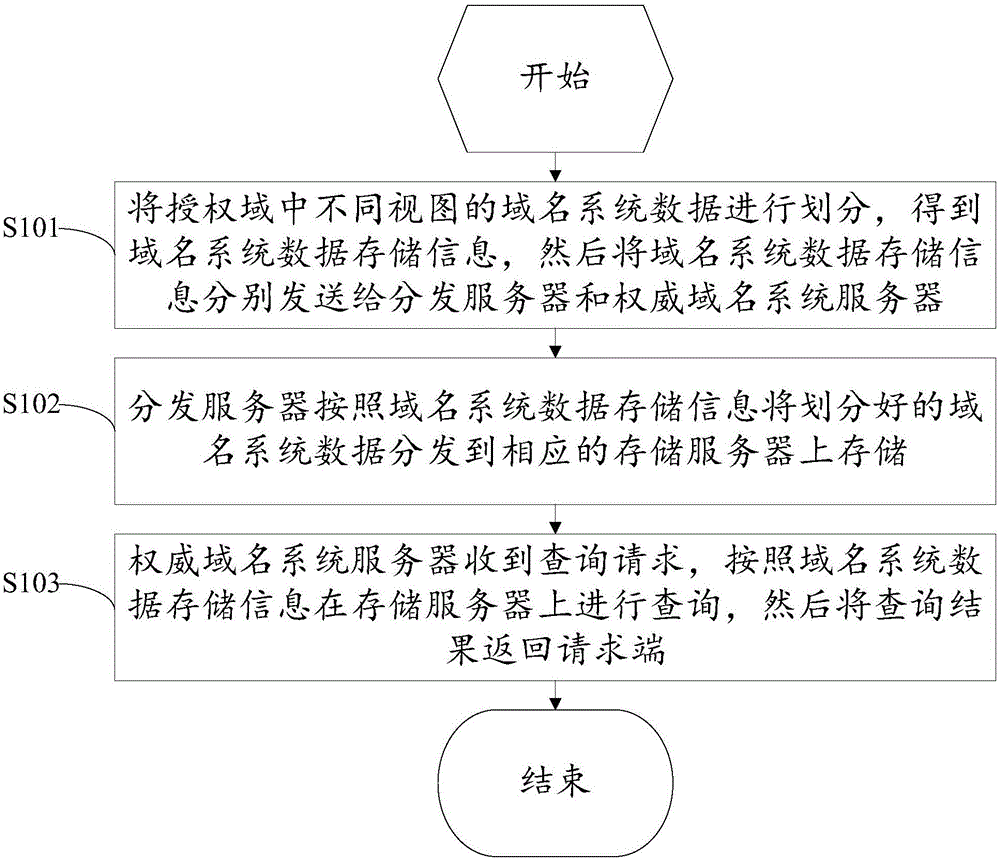
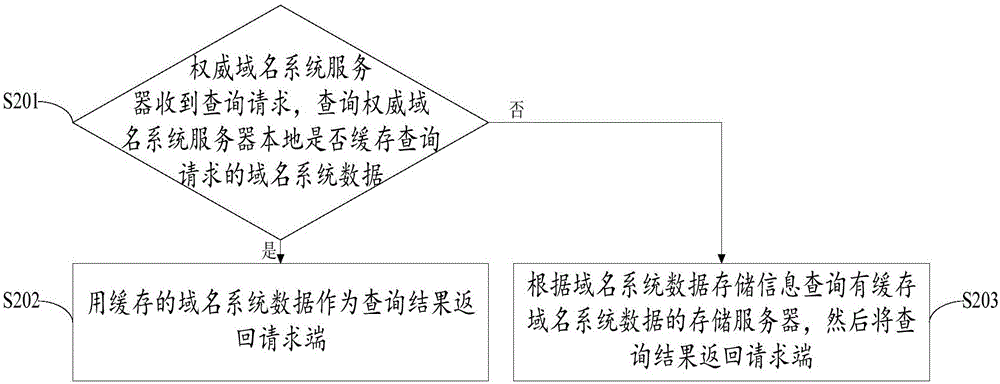
Method and system for storing and managing data of authoritative domain name system server
ActiveCN106534390AReduce data volumeImprove storage space utilizationTransmissionDomain nameAuthorized domain
The invention discloses a method and a system for storing and managing data of an authoritative domain name system server. The method comprises the following step of dividing domain name system data of different views in an authorized domain to obtain domain name system data storage information, and then sending the domain name system data storage information to a distribution server and the authoritative domain name system server respectively; distributing the well-divided domain name system data to corresponding storage servers for storage based on the domain name system data storage information by the distribution server; and after the authoritative domain name system server receives a query request, querying at the storage servers according to the domain name system data storage information and returning the query result to a requesting terminal. The problems of storage bottleneck and query efficiency reduction of the authoritative domain name system server caused by sharp increase of domain names and views and the problem of resource waste in data distribution and storage of a domain name system are solved; and the correctness of the query result of the domain name system is ensured while the reasonable optimization.
Owner:CHINANETCENT TECH
Accessing protected data on network storage from multiple devices
InactiveCN1939028AImprove securityKey distribution for secure communicationData taking preventionPlaintextAuthorized domain
The present invention relates to a method and a system of securely storing data on a network (100) for access by an authorized domain (101, 102, 103), which authorized domain includes at least two devices that share a confidential domain key (K), and an authorized domain management system for securely storing data on a network for access by an authorized domain. The present invention enables any member device to store protected data on the network such that any other member device can access the data in plaintext without having to communicate with the device that actually stored the data.
Owner:NOKIA TECH OY
Method, apparatus and computer program enabling the counting of devices in an authorized domain
InactiveUS20080139174A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareLoudspeaker
The exemplary embodiments include a method that involves determining a logical device count for individual ones of a plurality of devices in an authorized domain; calculating a sum of the logical device counts; and comparing the sum with a maximum allowable number of devices for the authorized domain, where the logical device count for a device may be equal to one, less than one, or greater than one. The logical device count is a value greater than one when a particular device is includes multiple consumption points, where a value of the logical device count equals a number of consumption points for the particular device, and the logical device count is a value less than one when a particular consumption point includes multiple devices, such as when a plurality of speakers are used to express content.
Owner:NOKIA CORP
Authorized domain policy method
ActiveUS8752190B2Maximum flexibilityIncrease competitionDigital data processing detailsAnalogue secracy/subscription systemsA domainAuthorized domain
Owner:INTERTRUST TECH CORP
Access to authorized domains
InactiveUS8761398B2Easy to controlDigital data processing detailsUser identity/authority verificationOne-way functionA domain
In a domain comprising a plurality of devices, the devices in the domain sharing a common domain key, a method of enabling a entity that is not a member of the domain to create an object that can be authenticated and / or decrypted using the common domain key, the method comprising providing to the entity that is not a member of the domain a diversified key that is derived using a one-way function from at least the common domain key for creating authentication data related to said object and / or for encrypting said object, the devices in the domain being configured to authenticate and / or decrypt said object using the diversified key.
Owner:KONINK PHILIPS ELECTRONICS NV
System and method for controlled copying and moving of content between devices and domains based on conditional encryption of content key depending on usage state
InactiveUS7844821B2Avoid easy removalEasy transferTelevision system detailsUser identity/authority verificationMobile contentAuthorized domain
A system and method is disclosed for allowing content providers to protect against widespread copying of their content, while enabling them to give their customers more freedom in the way they use the content. In accordance with one embodiment, content providers identify their content as protected by watermarking the content. Consumers use compliant devices to access protected content. All of a user's compliant devices, or all of a family's devices, can be organized into an authorized domain. This authorized domain is used by content providers to create a logical boundary in which they can allow users increased freedom to use their content.
Owner:NOKIA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com