Transmission/reception system
A technology for receiving systems and senders, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., and can solve problems such as inability to restrict devices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0121]
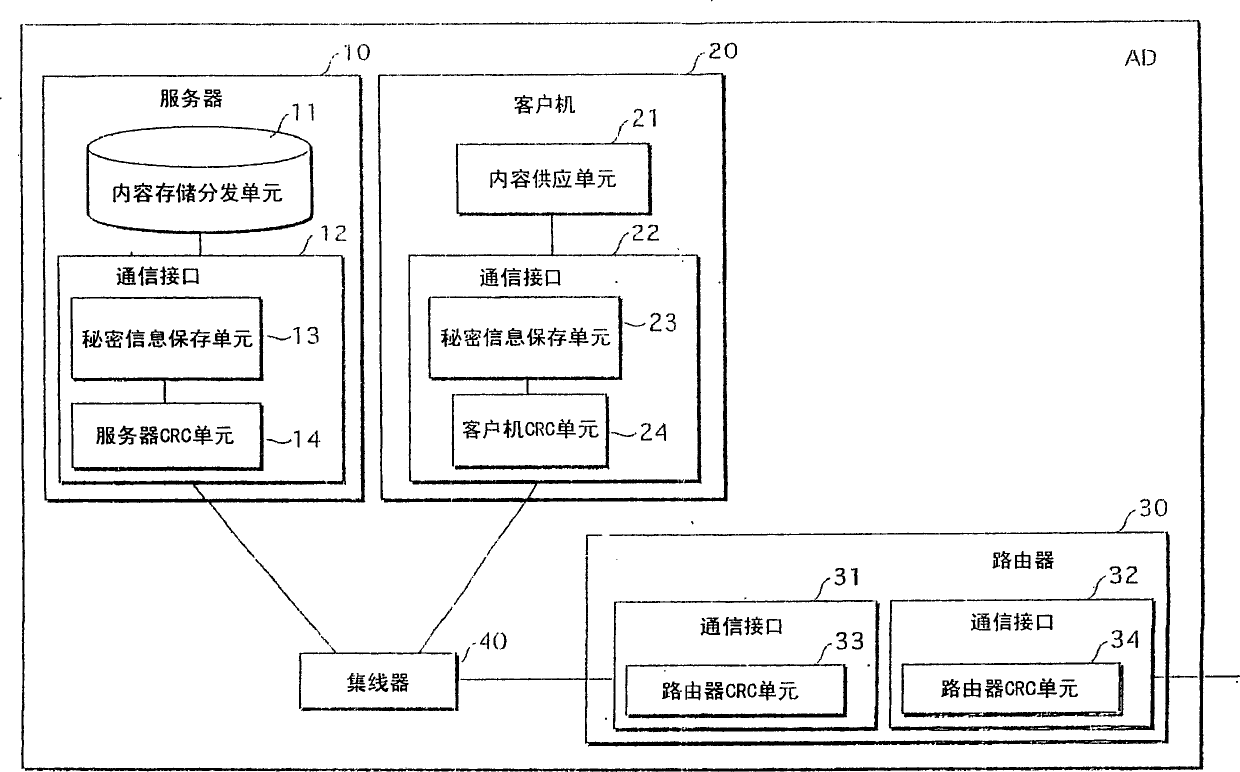
[0122] Fig. 1 shows the outline of AD of the first embodiment.
[0123] The AD includes a server 10, a client 20, a router 30, and a hub 40, and the server 10 and the client 20 are connected in a star shape around the hub 40. It should be noted that other clients than the client 20 may be connected to the hub 40, but are omitted from the drawing. Furthermore, it is assumed that the hub 40 does not perform CRC code error detection.
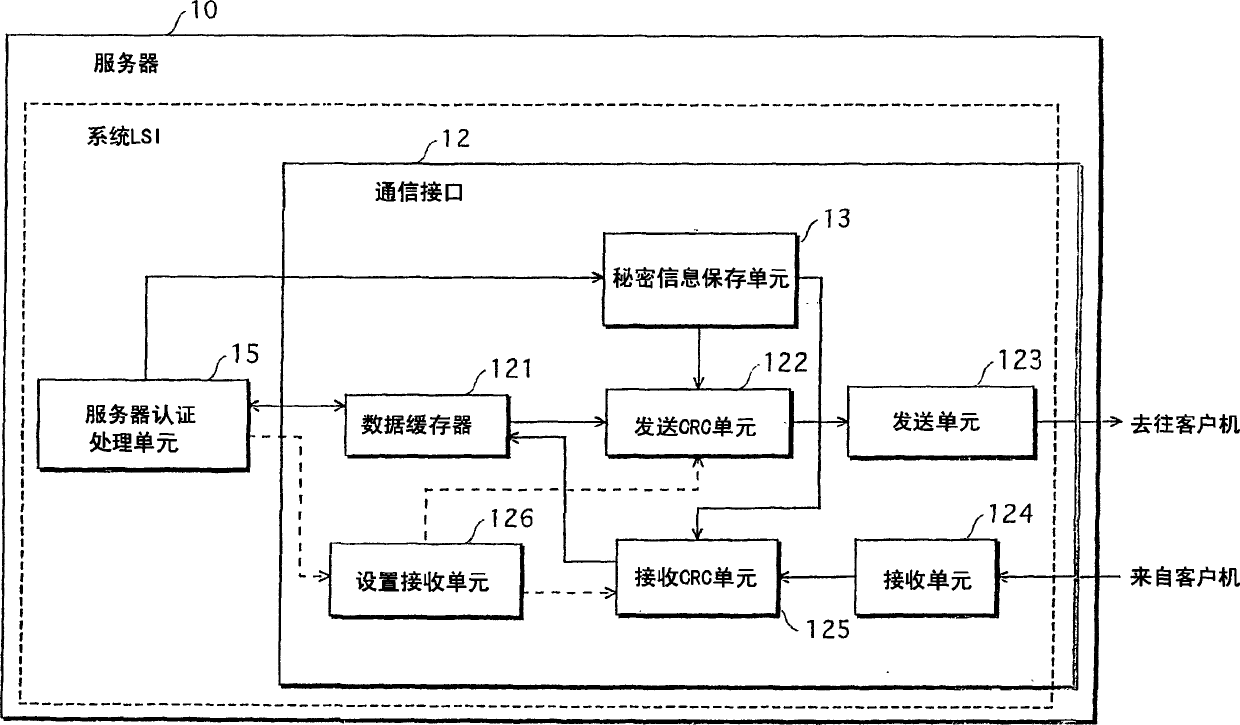
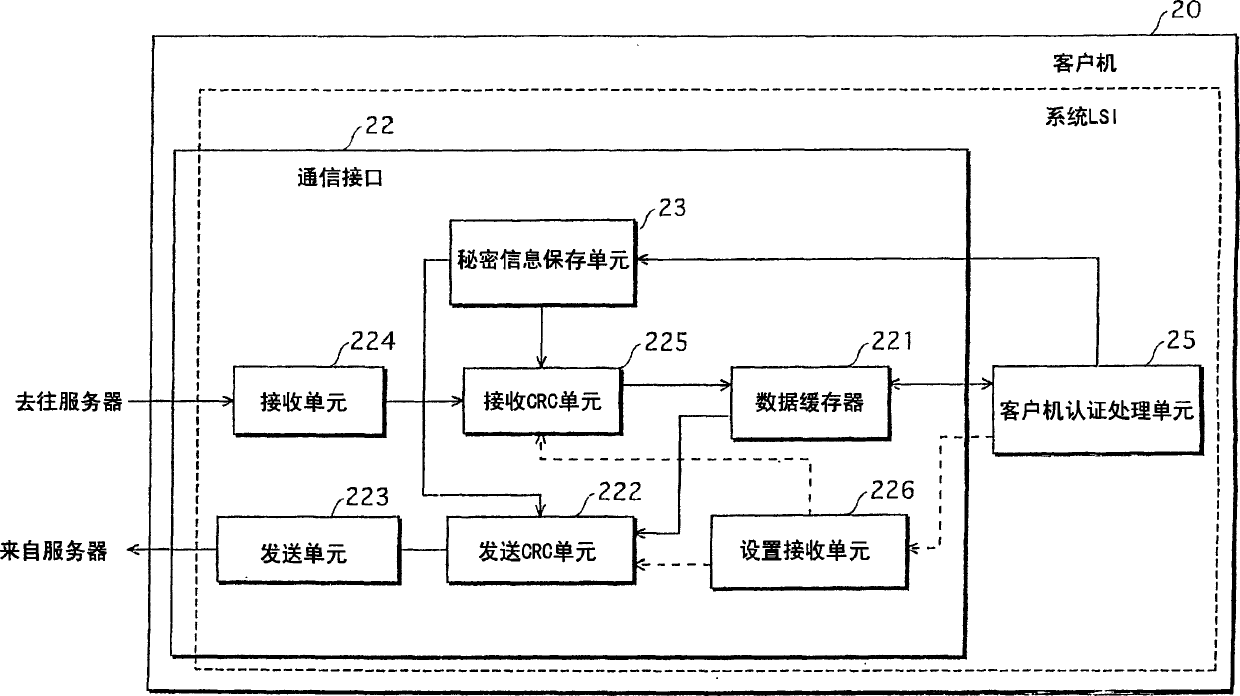
[0124] The router 30 is the only device in the AD network connected to a network outside the AD (hereinafter also referred to as an external network). The server 10 acquires content from an external network through the router 30 and stores the content in the content storage and distribution unit 11 . When receiving a content distribution request from the client 20, the server 10 first confirms that the client 20 is a device in the AD according to the authentication process, and then distributes the content to the client 20. The distri...
no. 2 example
[0249]
[0250] In the described first embodiment, authentication frames are prevented from passing through router 30 to other networks during the authentication process. This means that the content stored in the server 10 is shared only in one subnet attached to the router 30 . From another point of view, it can be considered that the scope of AD is limited to a subnet.
[0251] However, if the scope of AD is limited to one subnet, there will be problems, for example, users who operate different networks upstairs or downstairs in their home will not be able to use the server stored downstairs in the upstairs device in the content.
[0252] For this purpose, in this embodiment, the MAC addresses of the server and the client are registered in the router in advance, and if a frame for one registered MAC address is received, it is transmitted without error detection using the CRC code the frame. This means that when an authentication frame is sent by the server to the client...
no. 3 example
[0294]
[0295] In the second embodiment, the router registers the MAC addresses of the server and the client in advance, and when receiving a frame for a registered MAC address, transmits the frame without performing an error check using a CRC code . This prevents frames sent by the server to the client via the router from being discarded by the router, even if the router's communication interface does not support the special CRC mode.
[0296] However, with this method, even if an error occurs on the communication path, the router transmits the frame from the server to the router without performing error checking. This is especially problematic in a busy network environment.
[0297] In consideration of this problem, the present embodiment allows special CRC mode error checking in routers by providing communication interfaces in routers that support special CRC modes. This prevents the router from transmitting frames in which errors have occurred. As in the first embodi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com