Patents
Literature
8842results about "Public key for secure communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
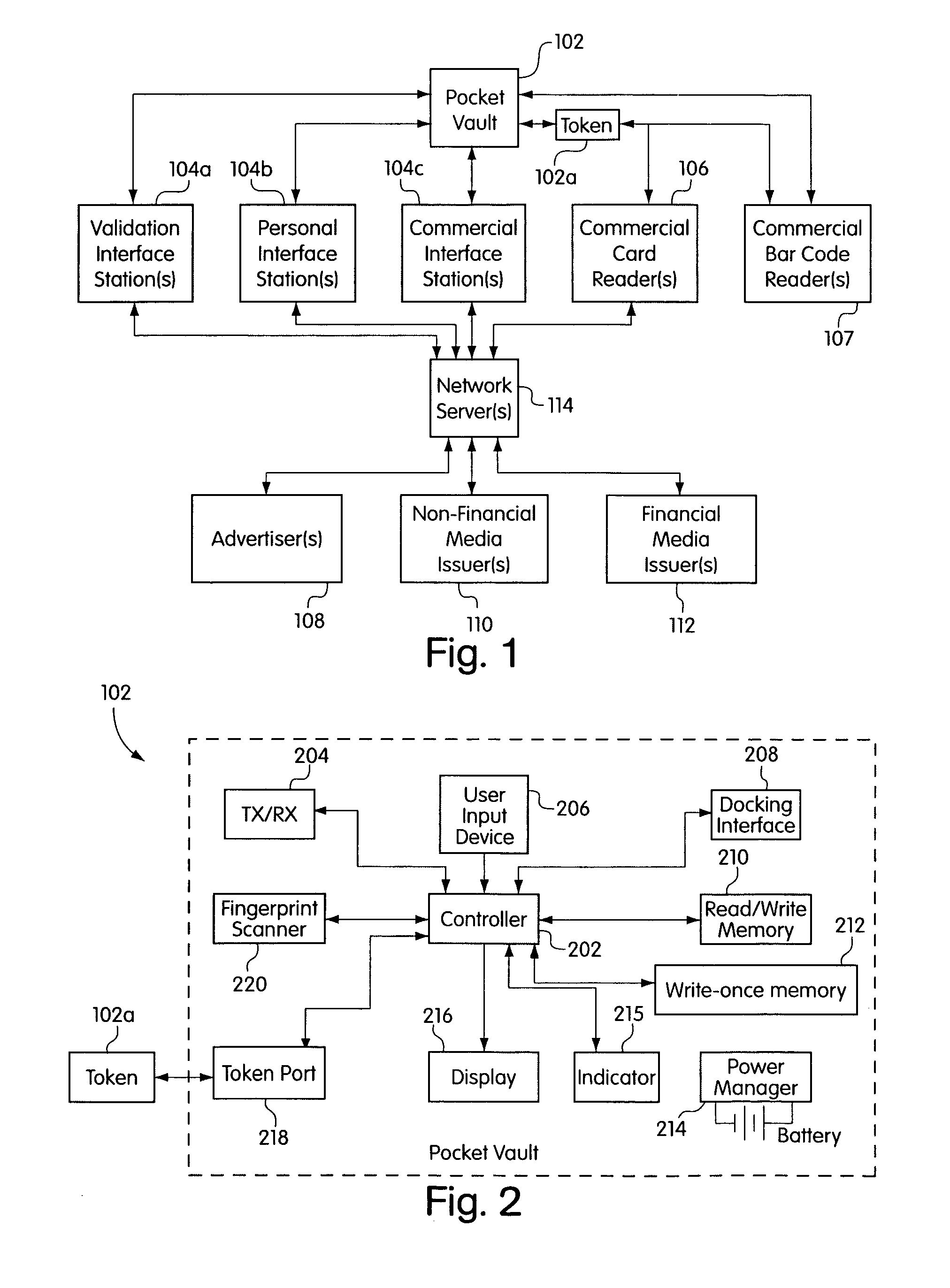
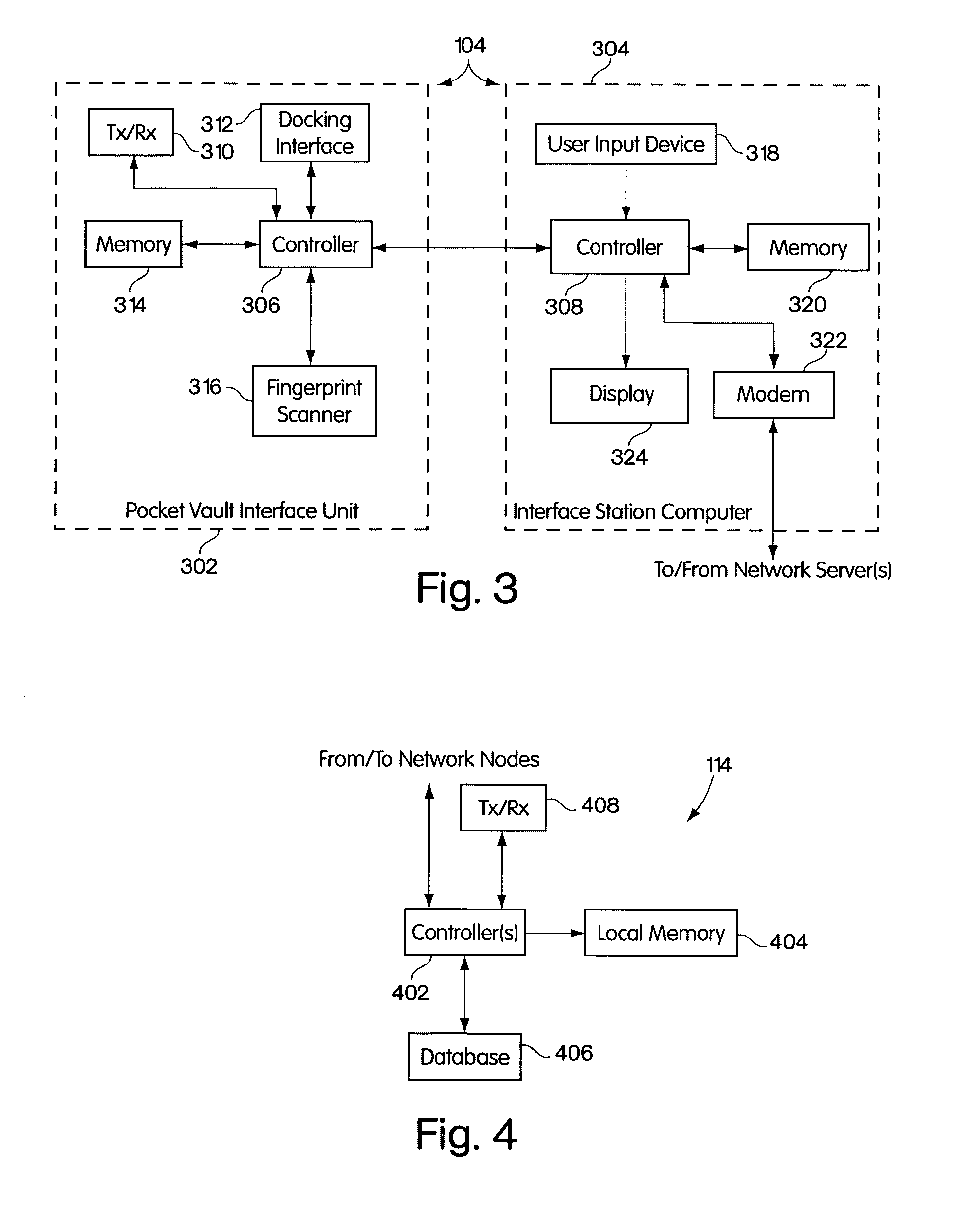
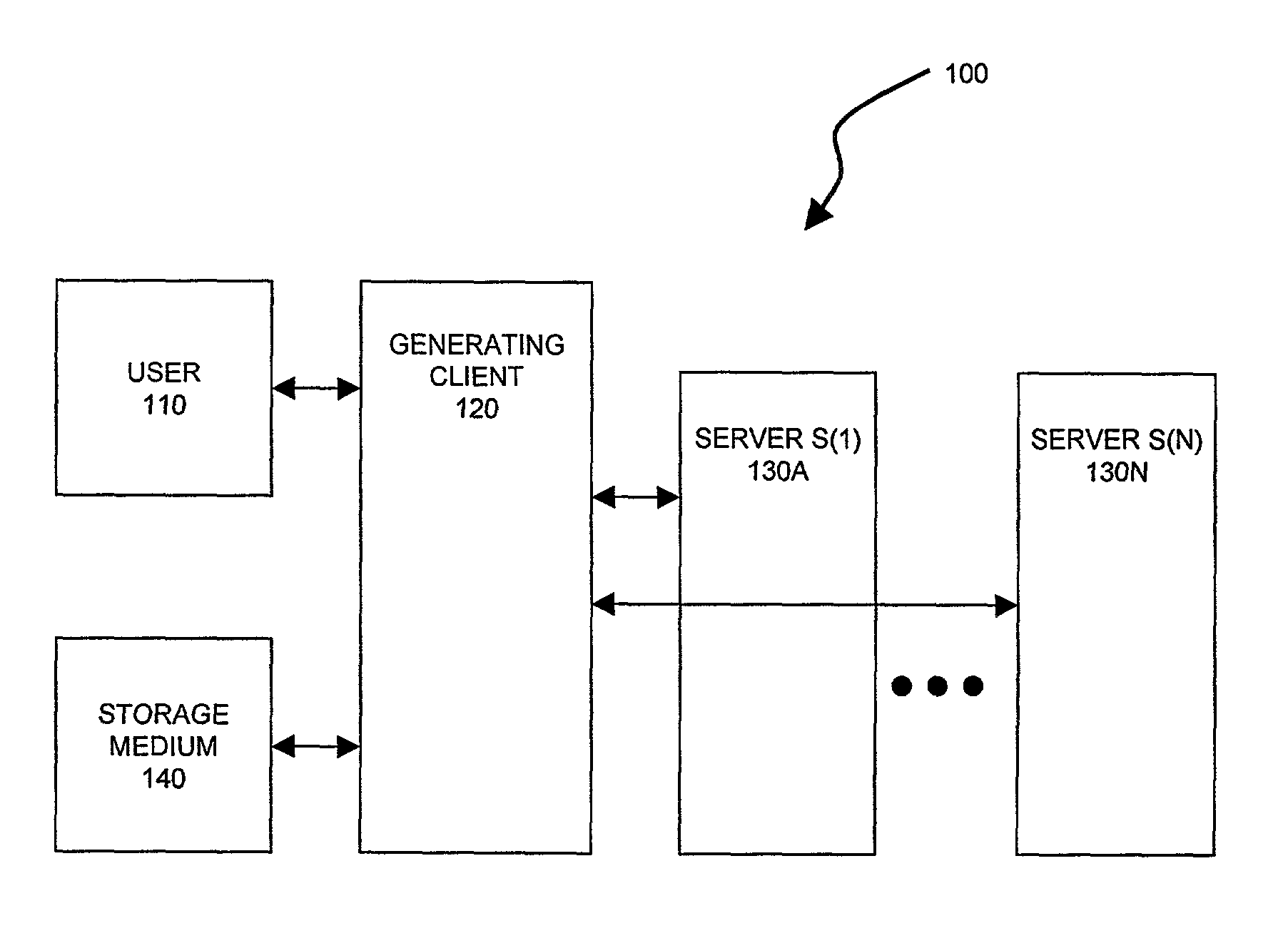
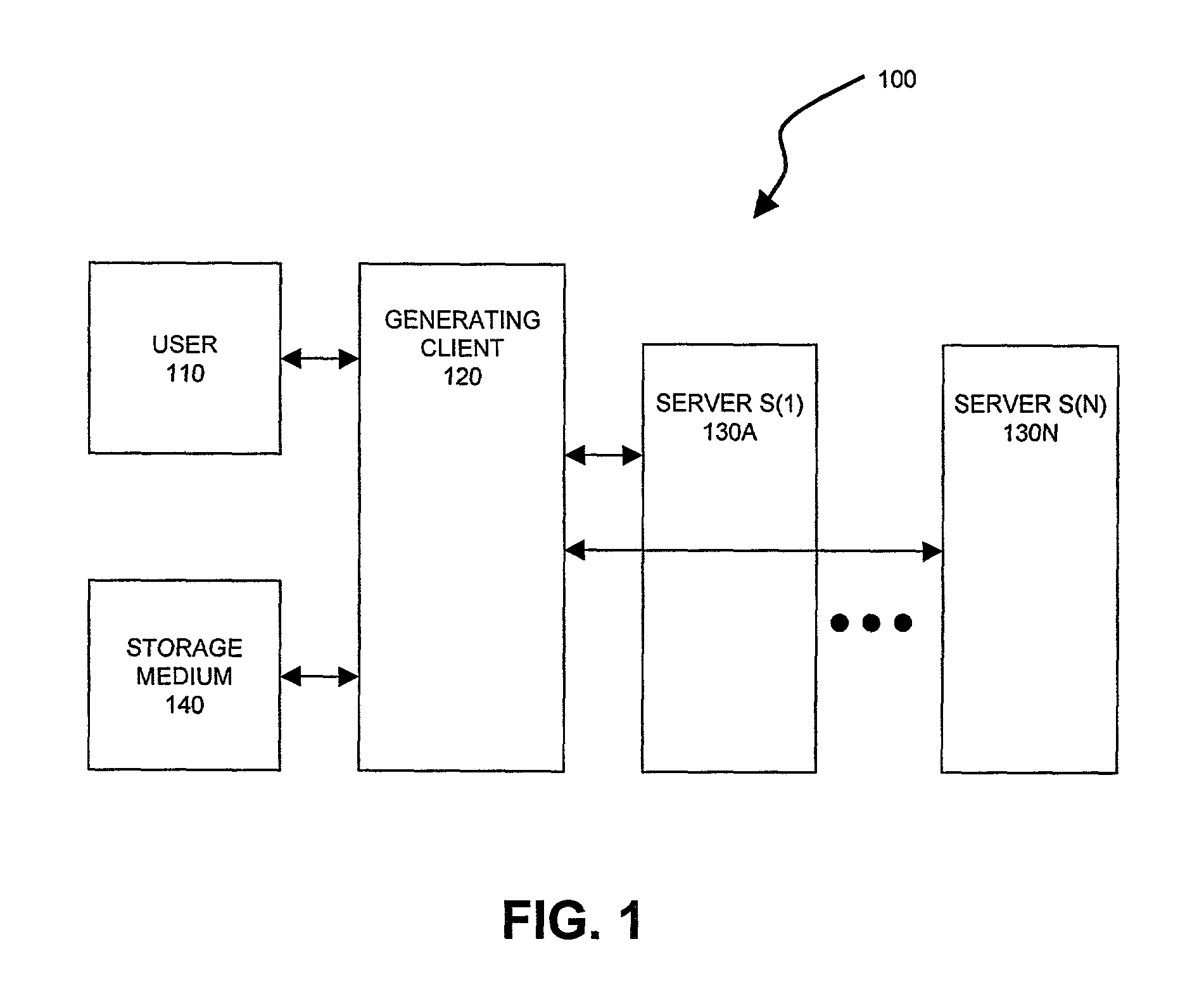
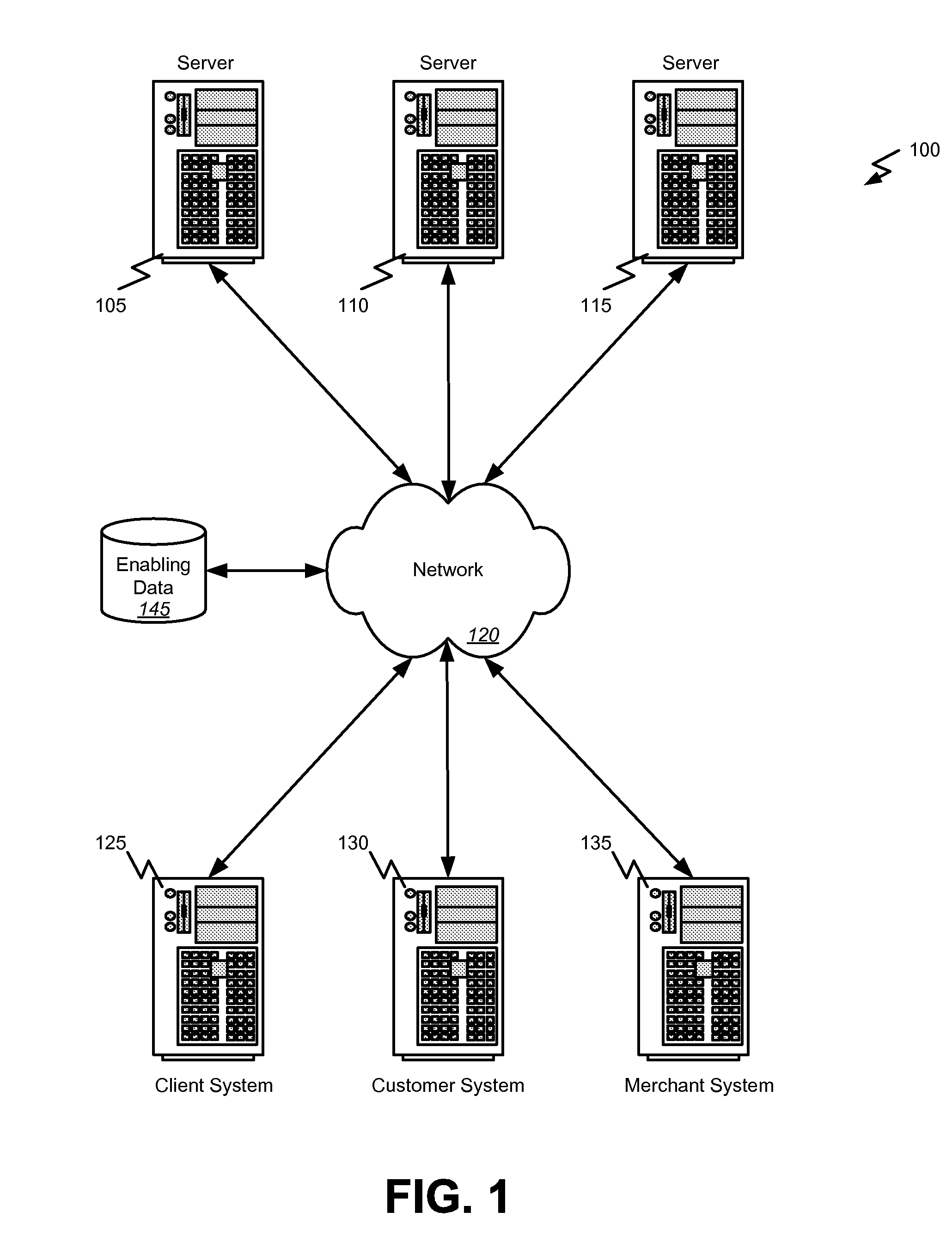
Electronic content delivery system
InactiveUS6226618B1Key distribution for secure communicationDigital data processing detailsDelivery systemSystem safety
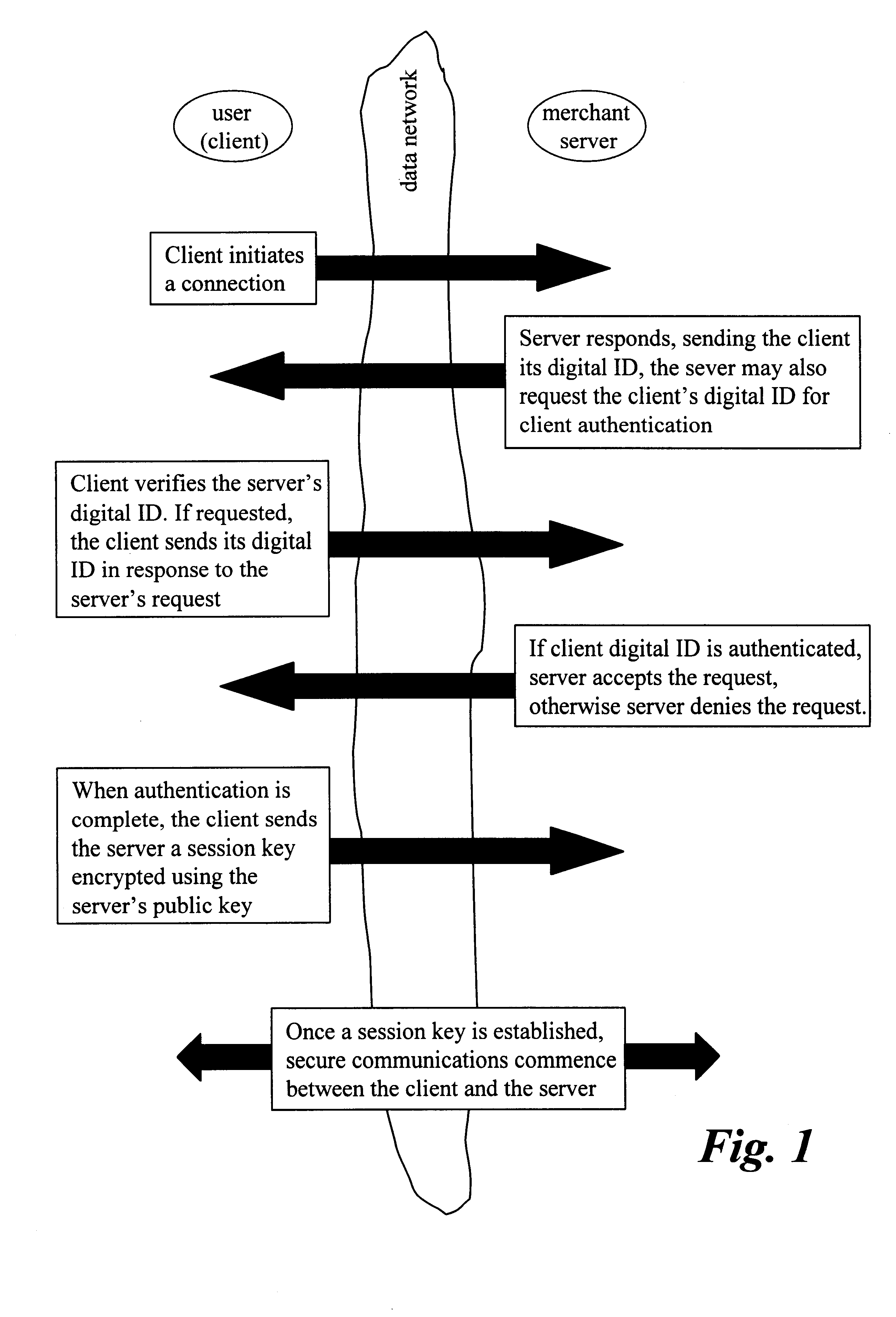
Disclosed is a method and apparatus of securely providing data to a user's system. The data is encrypted so as to only be decryptable by a data decrypting key, the data decrypting key being encrypted using a first public key, and the encrypted data being accessible to the user's system, the method comprising the steps of: transferring the encrypted data decrypting key to a clearing house that possesses a first private key, which corresponds to the first public key; decrypting the data decrypting key using the first private key; re-encrypting the data decrypting key using a second public key; transferring the re-encrypted data decrypting key to the user's system, the user's system possessing a second private key, which corresponds to the second public key; and decrypting the re-encrypted data decrypting key using the second private key.
Owner:LEVEL 3 COMM LLC
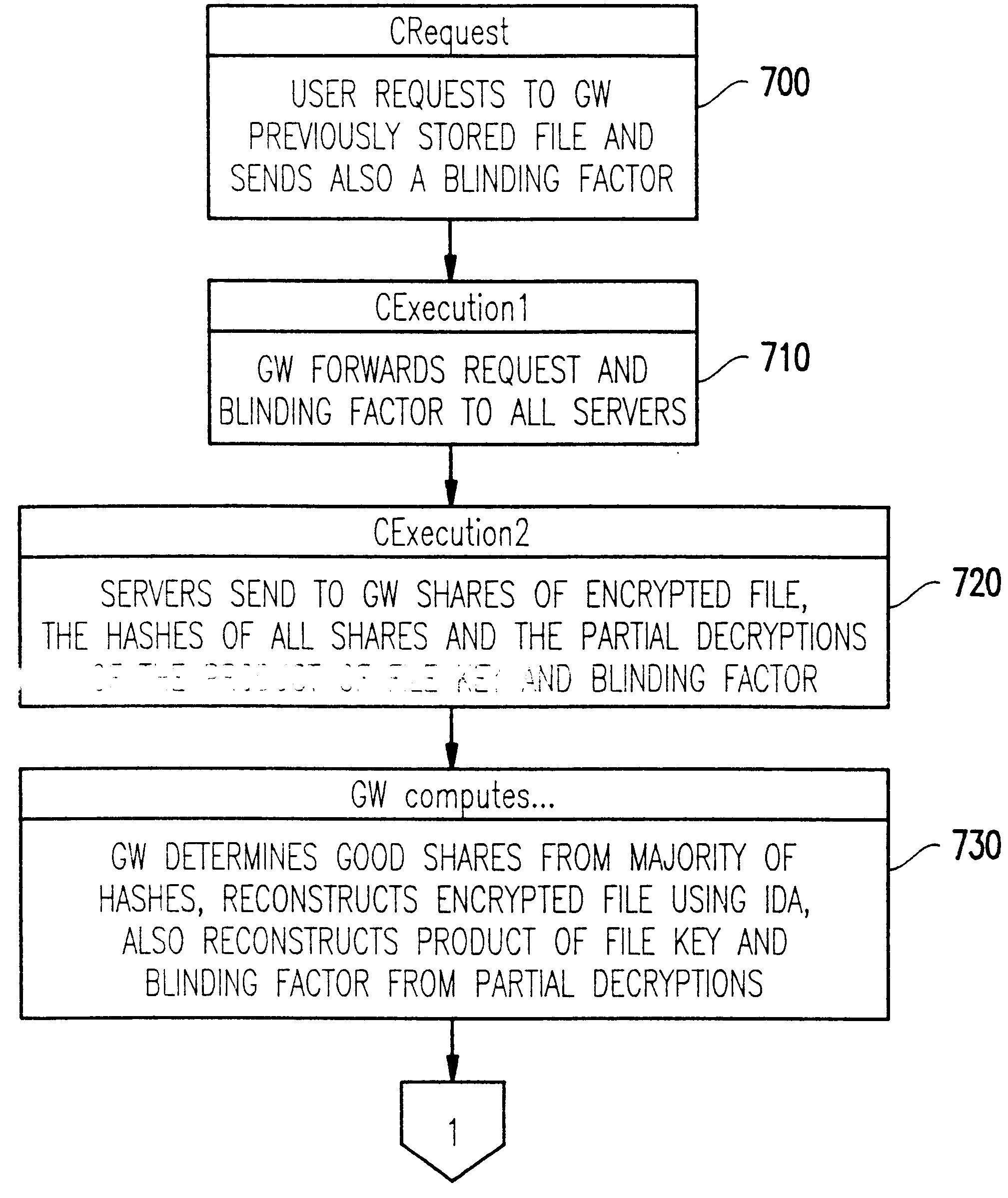
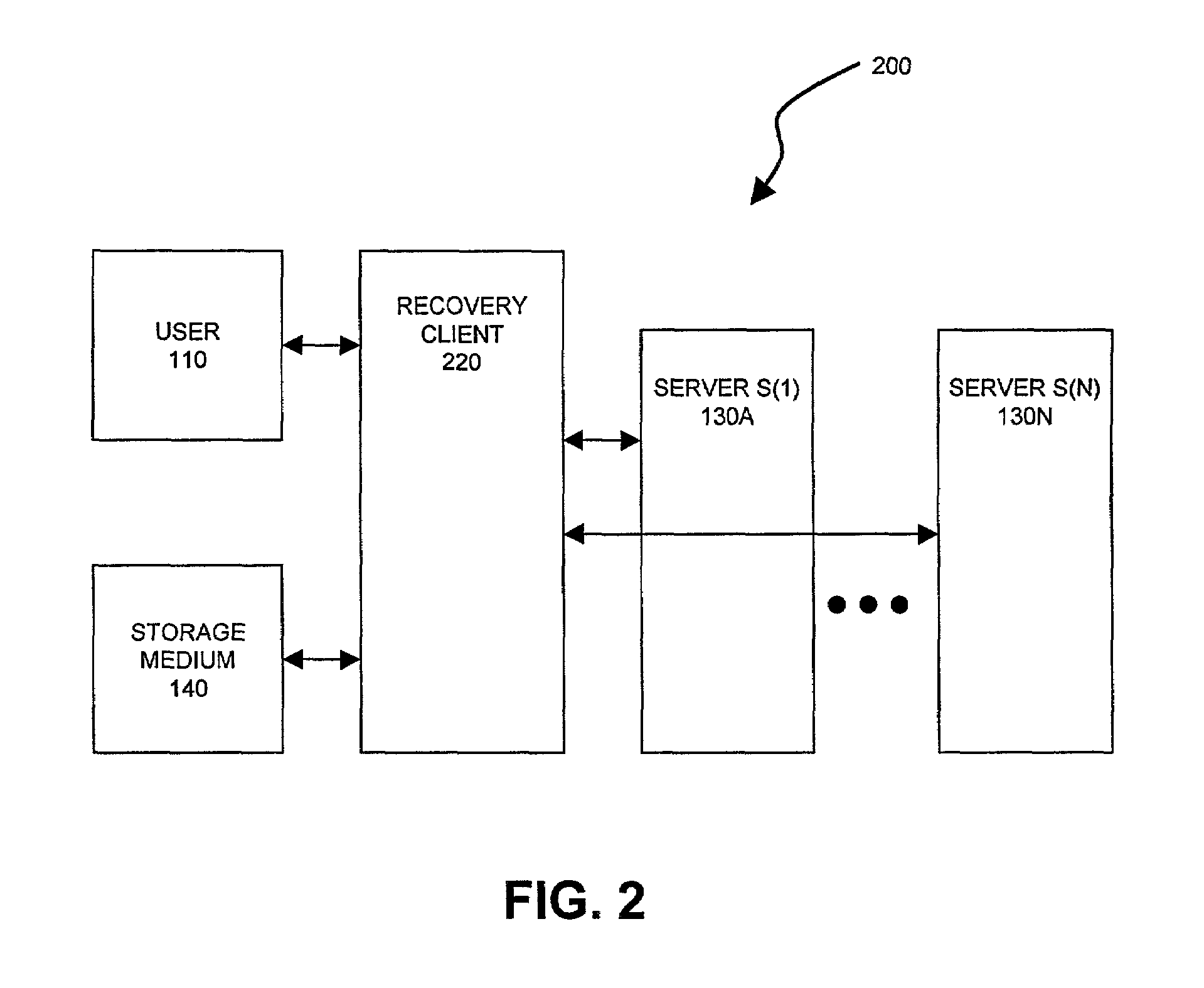
Method and apparatus for the secure distributed storage and retrieval of information
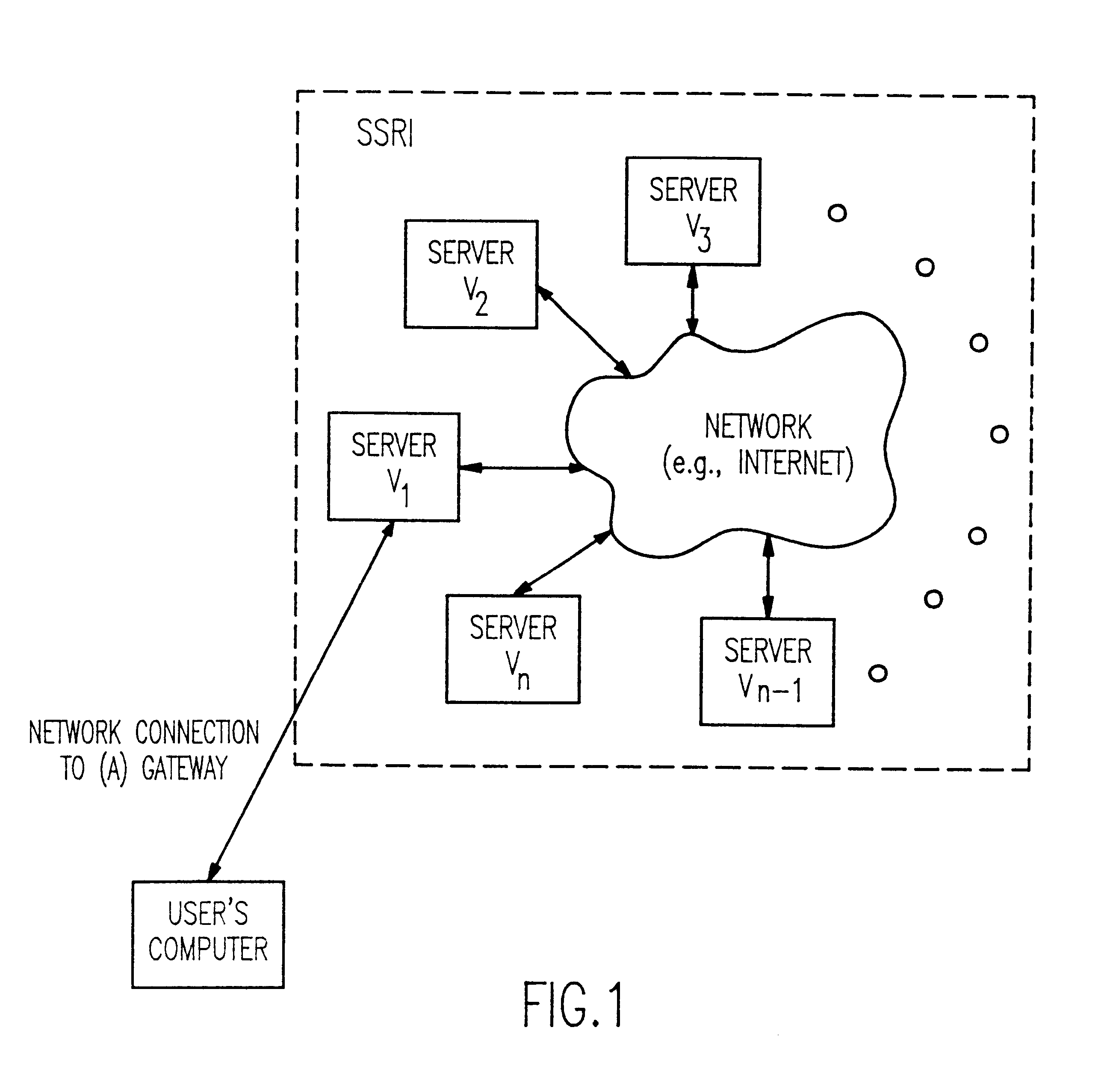
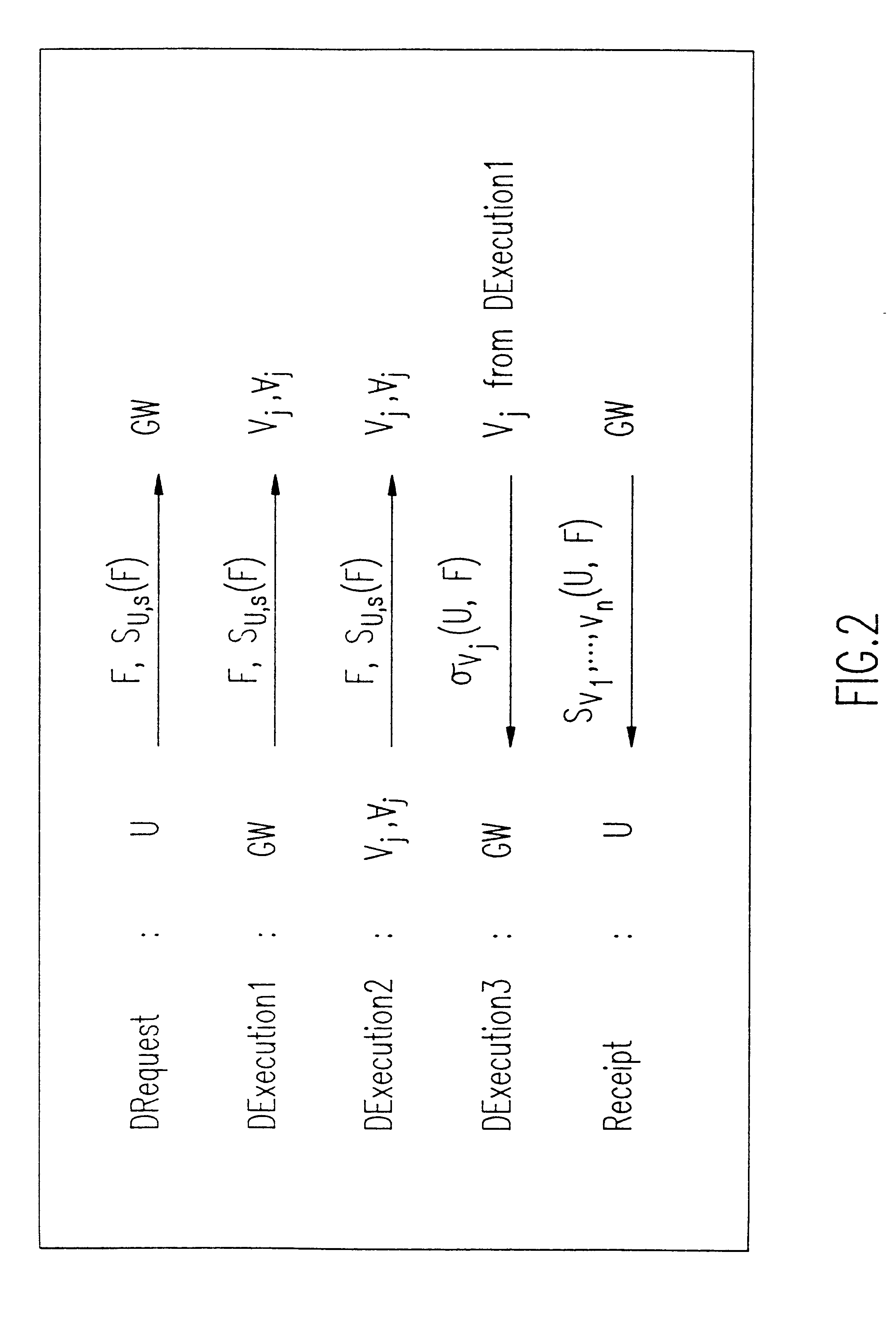
InactiveUS6192472B1Data processing applicationsPublic key for secure communicationActive faultConfidentiality
A solution to the general problem of Secure Storage and Retrieval of Information (SSRI) guarantees that also the process of storing the information is correct even when some processors fail. A user interacts with the storage system by depositing a file and receiving a proof that the deposit was correctly executed. The user interacts with a single distinguished processor called the gateway. The mechanism enables storage in the presence of both inactive and maliciously active faults, while maintaining (asymptotical) space optimailty. This mechanism is enhanced with the added requirement of confidentiality of information; i.e., that a collusion of processors should not be able to learn anything about the information. Also, in this case space optimality is preserved.
Owner:IBM CORP
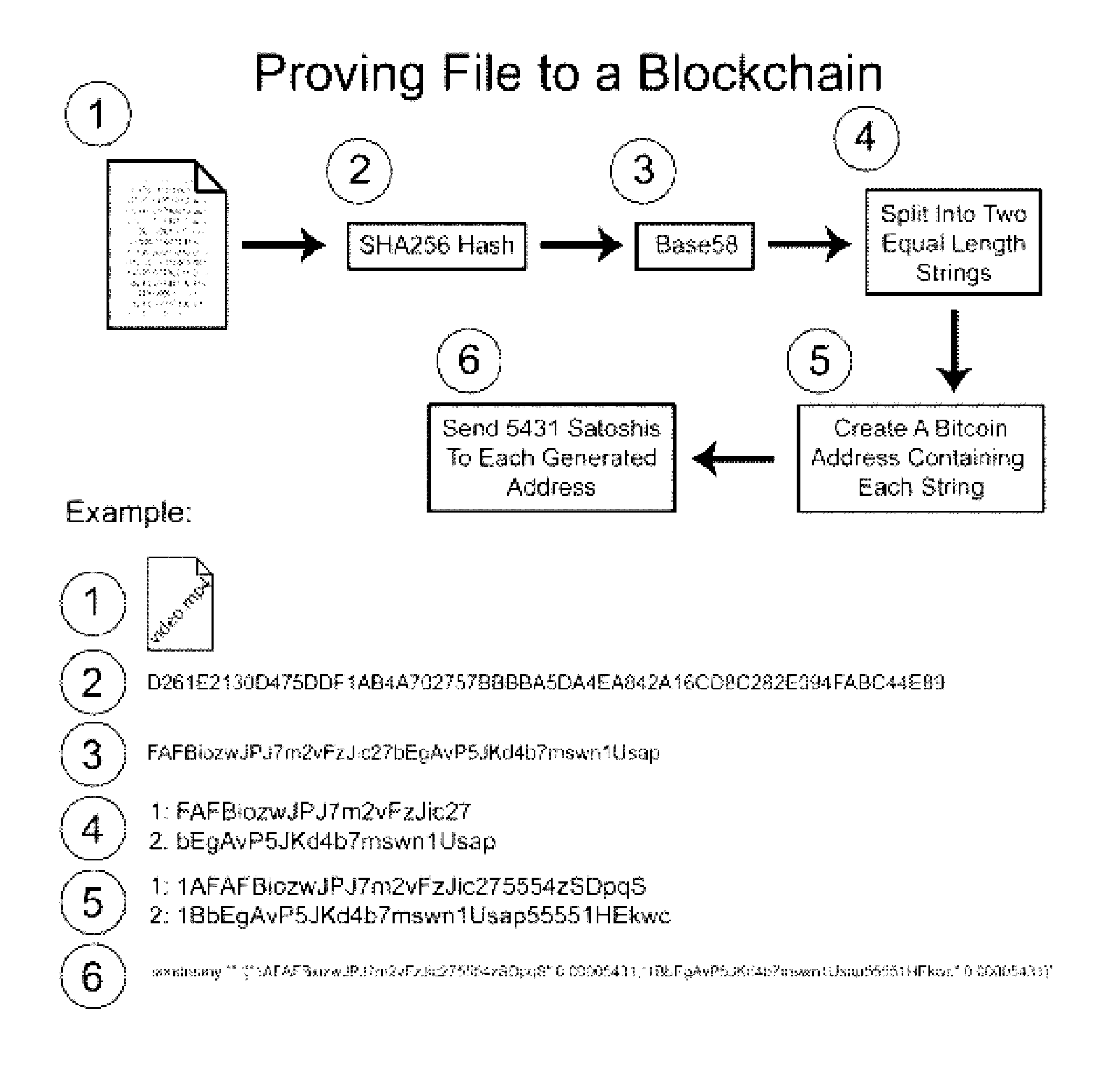
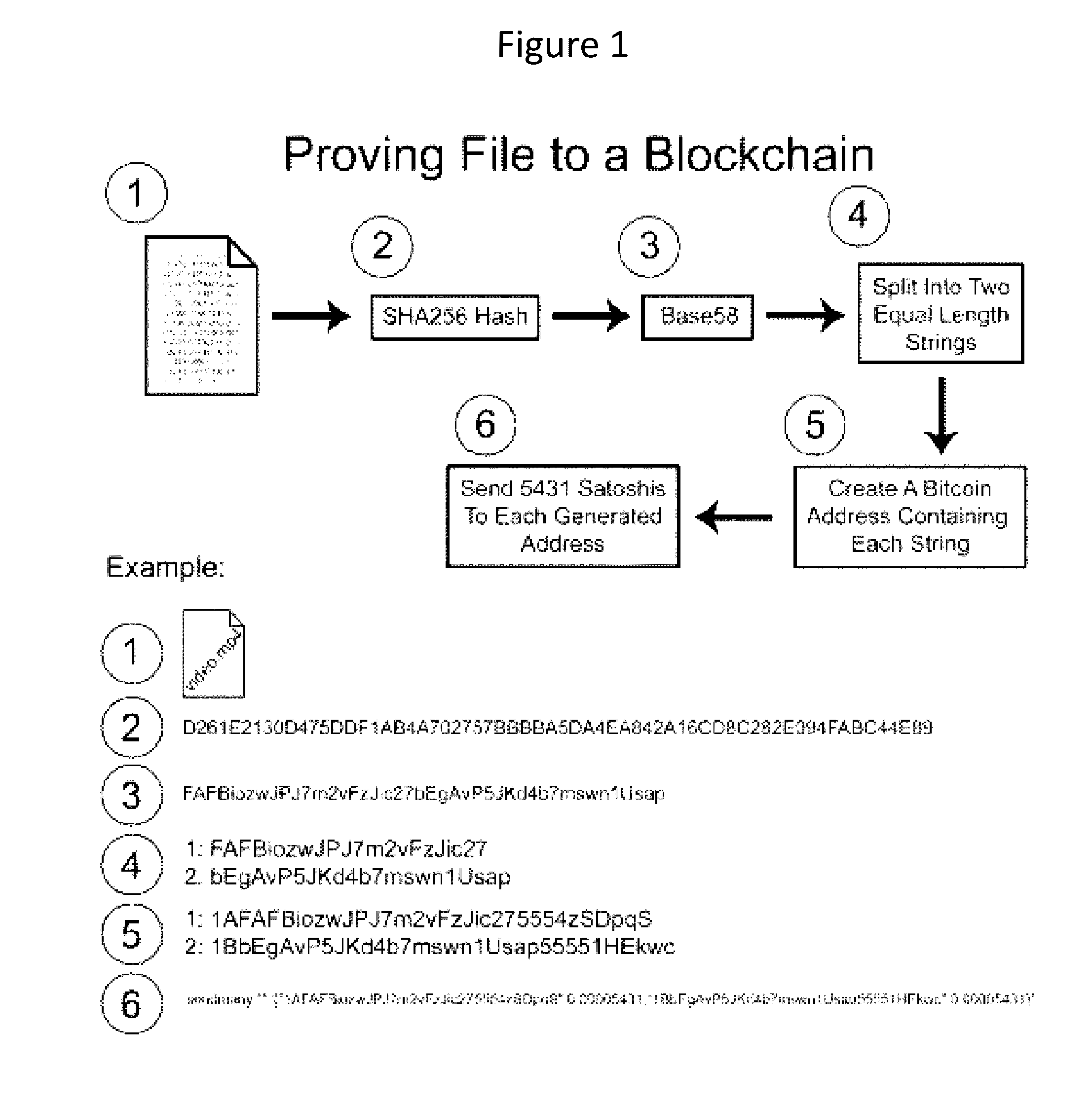
Authentication and verification of digital data utilizing blockchain technology
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
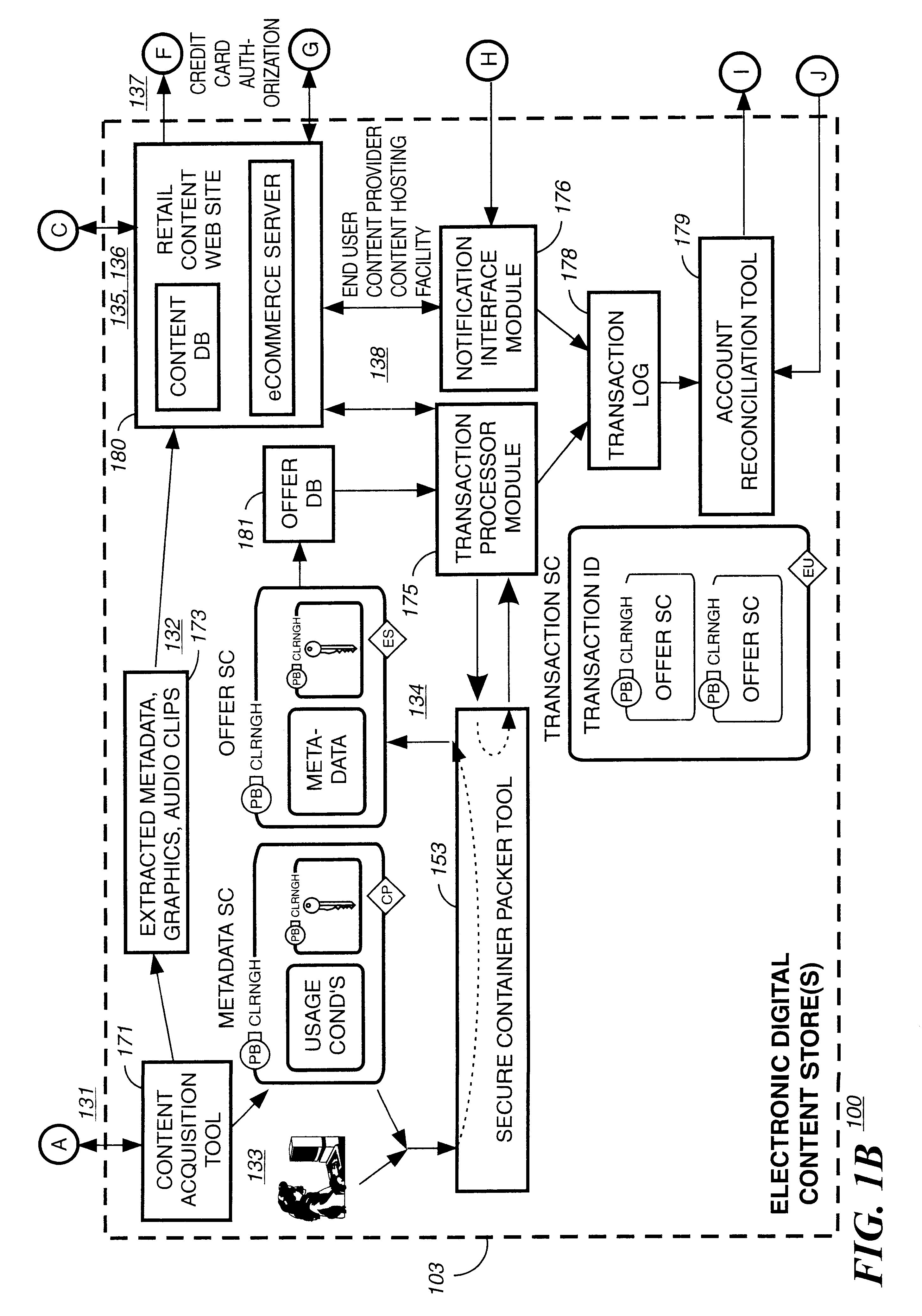
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
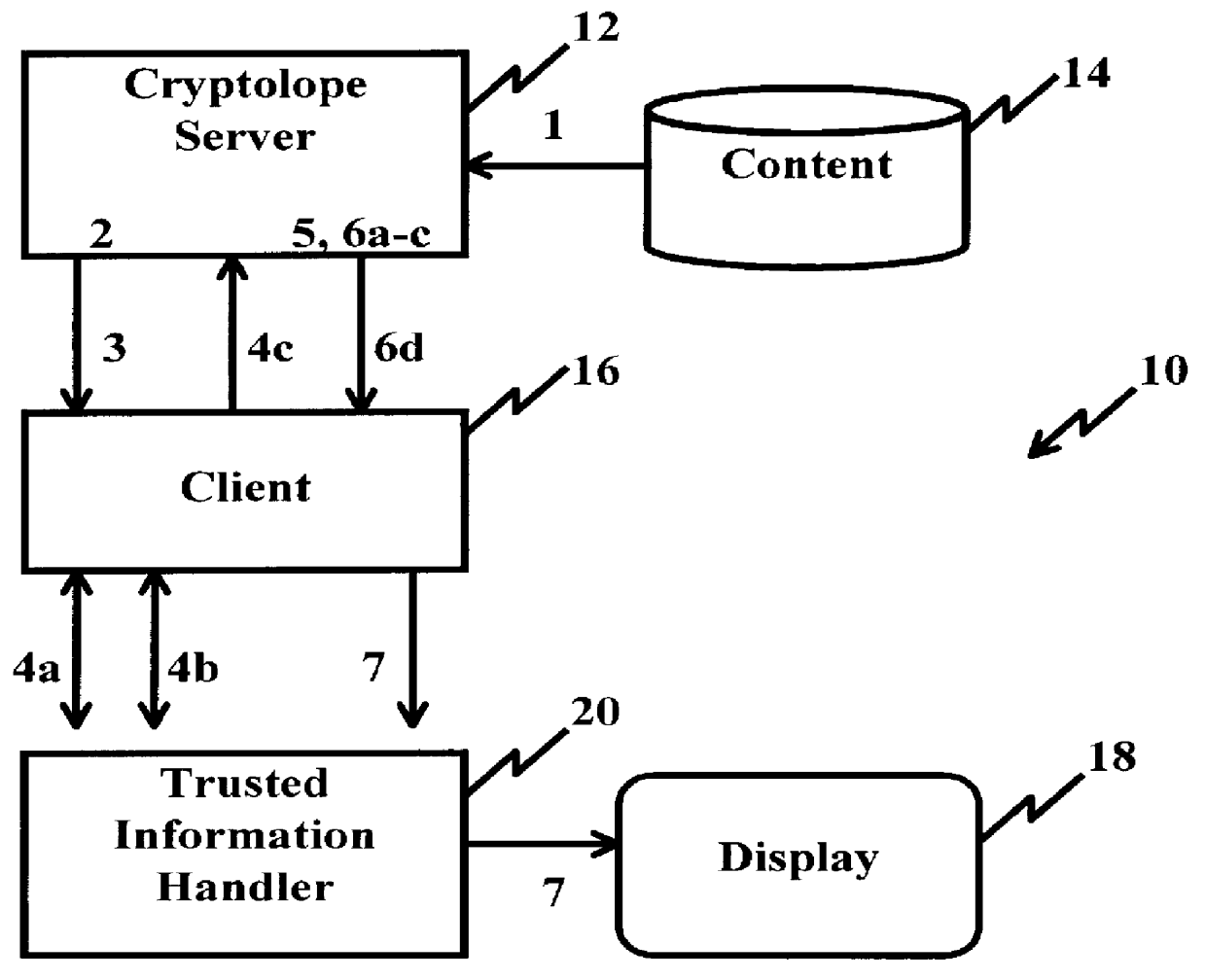
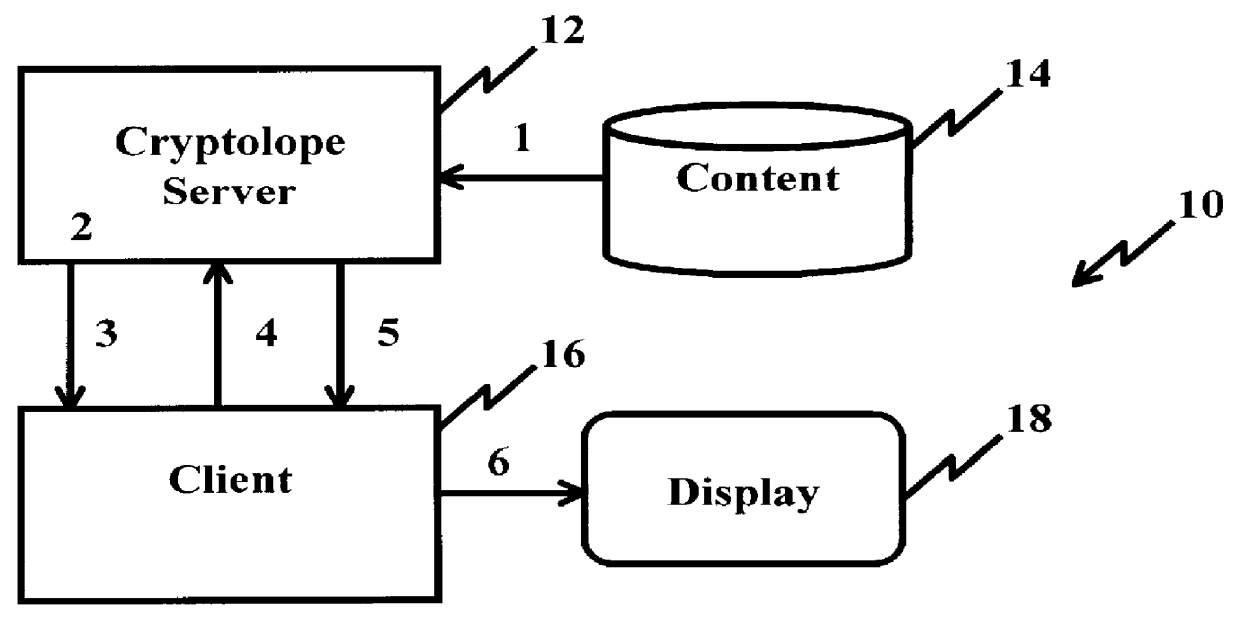
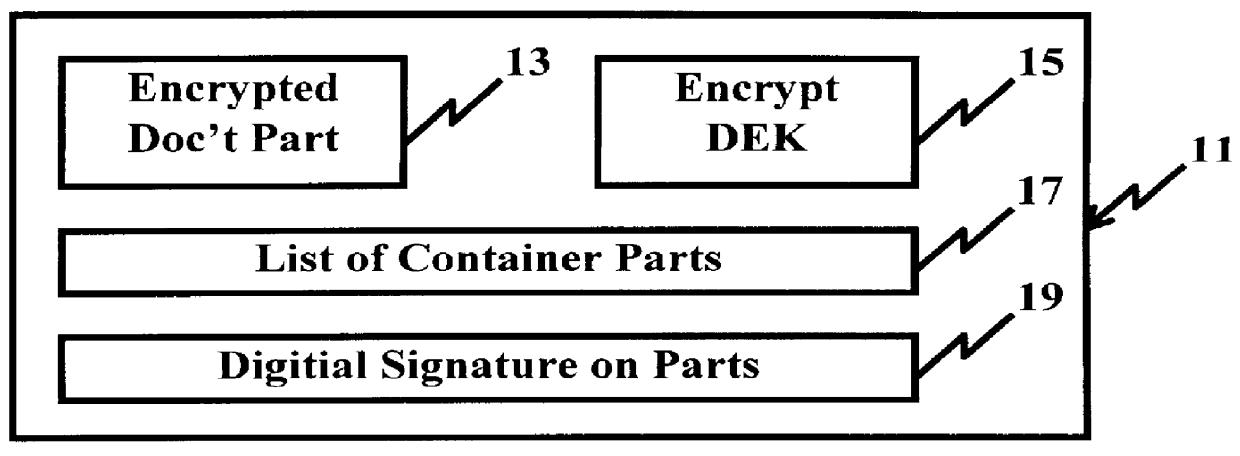
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
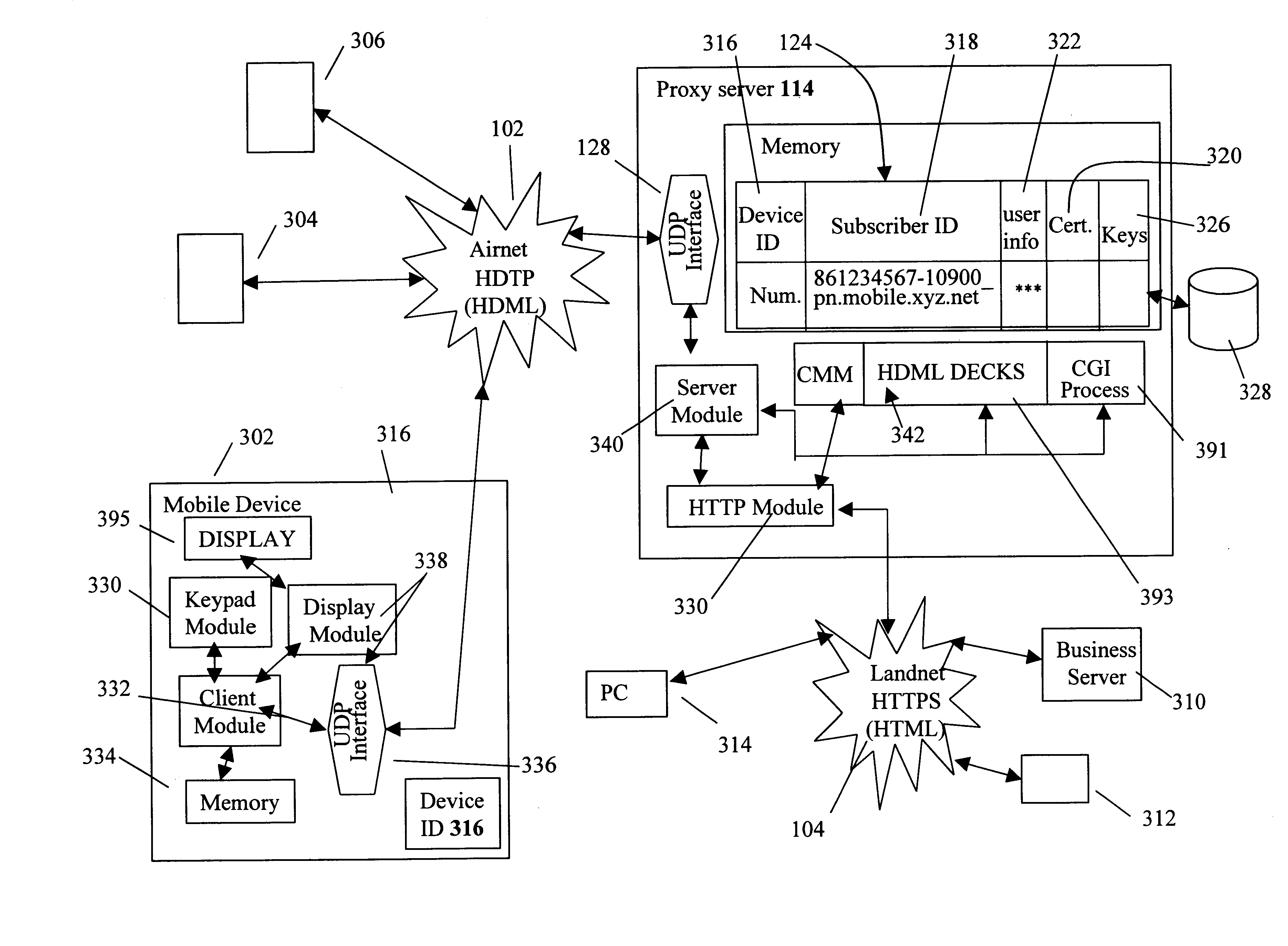
Centralized certificate management system for two-way interactive communication devices in data networks
InactiveUS6233577B1Key distribution for secure communicationData processing applicationsServer applianceCommunication device
The present invention discloses a central certificate management system for thin client devices in data networks and has particular applications to systems having a large number of the thin clients serviced by a proxy server through which the thin clients communicate with a plurality of secure server computers over a data network. According to one aspect, the present invention provides a certificate management module that causes the server device to manage digital certificates for each of the thin client devices. To minimize the latency of obtaining certificates for each of the thin client devices, the certificate management module reserves a fixed number of free certificates signed by a certificate authority and their respective private keys in a certificate database and frequently updates the free certificate according to a certificate updating message. Whenever a user account is created for a thin client device, the certificate management module fetches one or more free certificates from the certificate database and associate the fetched certificates to the created account and meanwhile the certificate management module creates new free certificates with the certificate authority to fill in the certificate database. Apart from the tradition of obtaining certificates locally in client devices that normally have sufficient computing power, the present invention uses the computing resources in a server device to carry out the task of obtaining and maintaining certificates asynchronously in the proxy server and further. These and other features in the present invention dramatically minimize the demands for computing power and memory in thin client devices like mobile devices, cellular phones, landline telephones or Internet appliance controllers.
Owner:UNWIRED PLANET
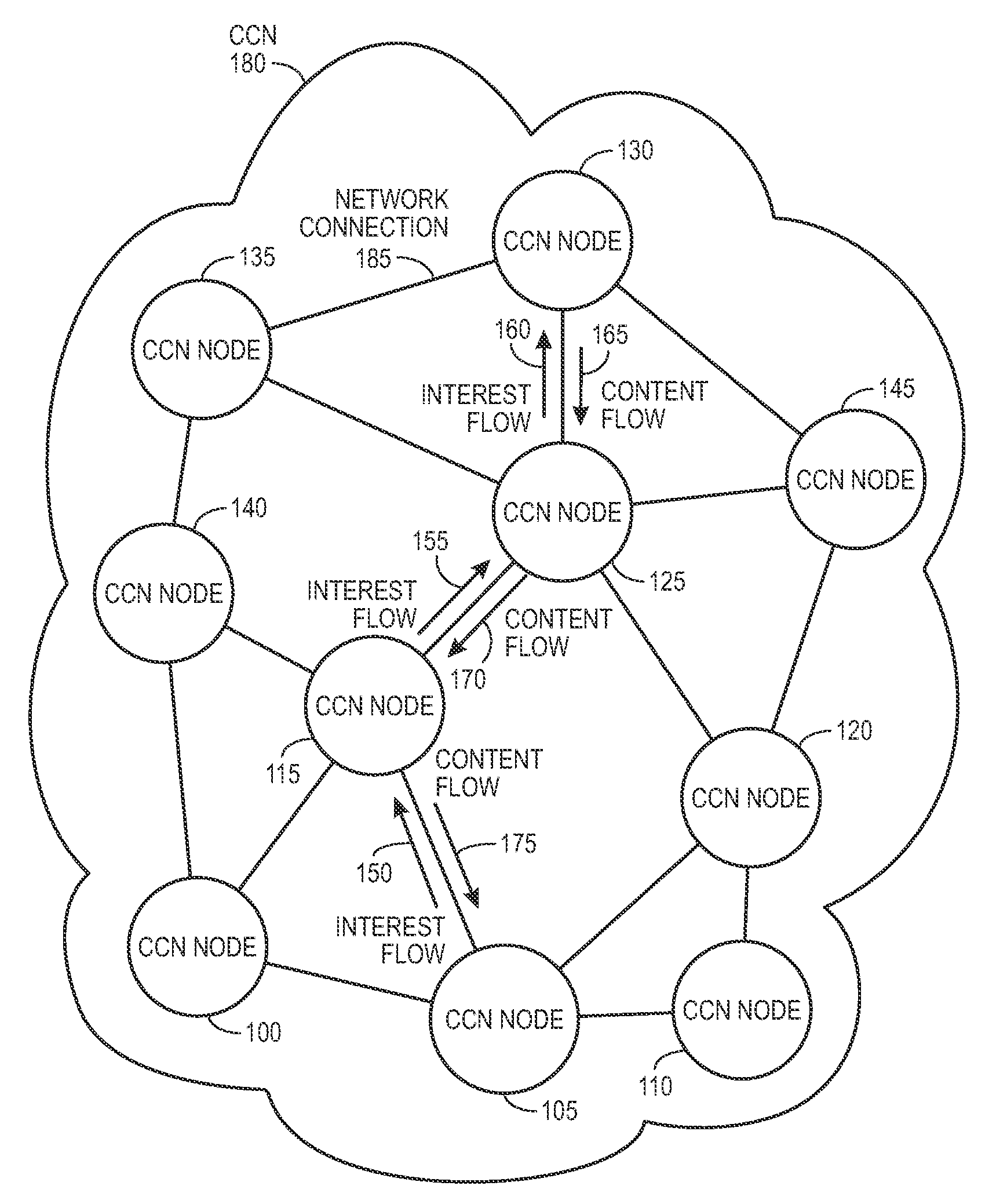
Controlling the spread of interests and content in a content centric network
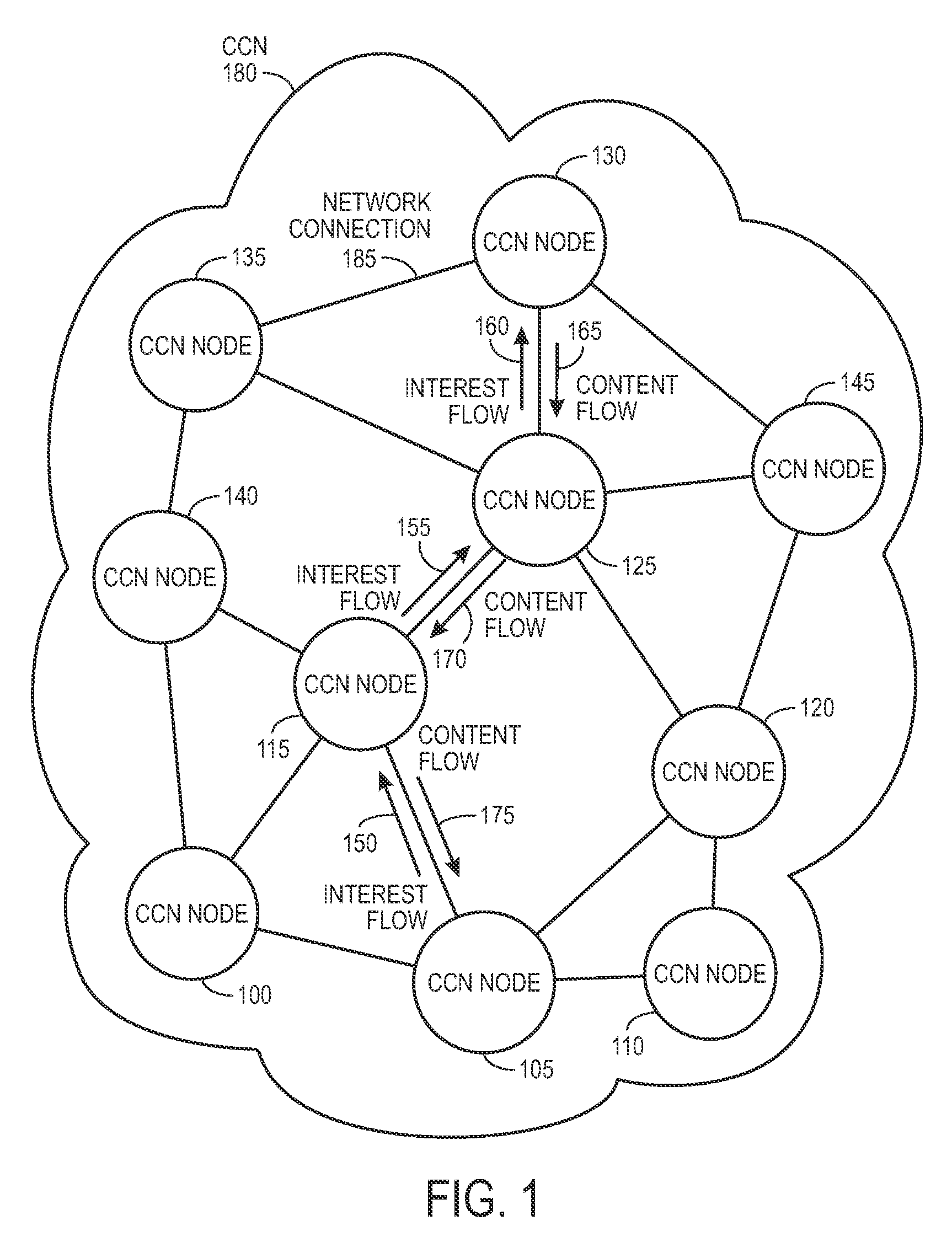
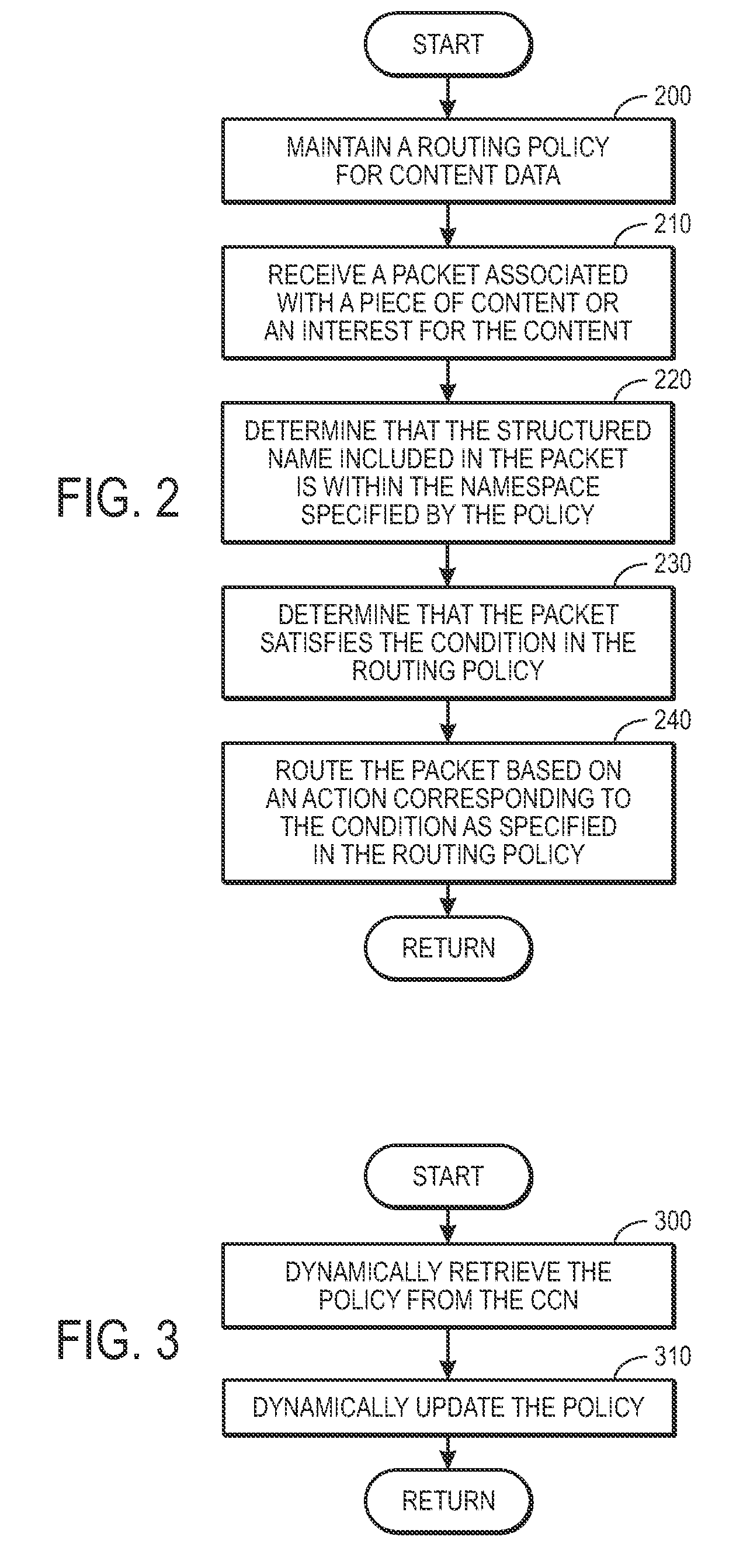
ActiveUS20090288163A1Easy flow controlExpected levelMemory loss protectionMultiple keys/algorithms usageContent centricSystem maintenance
One embodiment of the present invention provides a system for controlling the spread of interests and content in a content centric network (CCN). During operation, the system maintains a routing policy for content data. The system also receives a packet associated with a piece of content or an interest for the content. Next, the system determines that the structured name included in the packet is within the namespace specified in the routing policy. The system further determines that the packet satisfies the condition in the routing policy. Subsequently, the system routes the packet based on in part the action corresponding to the condition as specified in the routing policy.
Owner:CISCO TECH INC
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
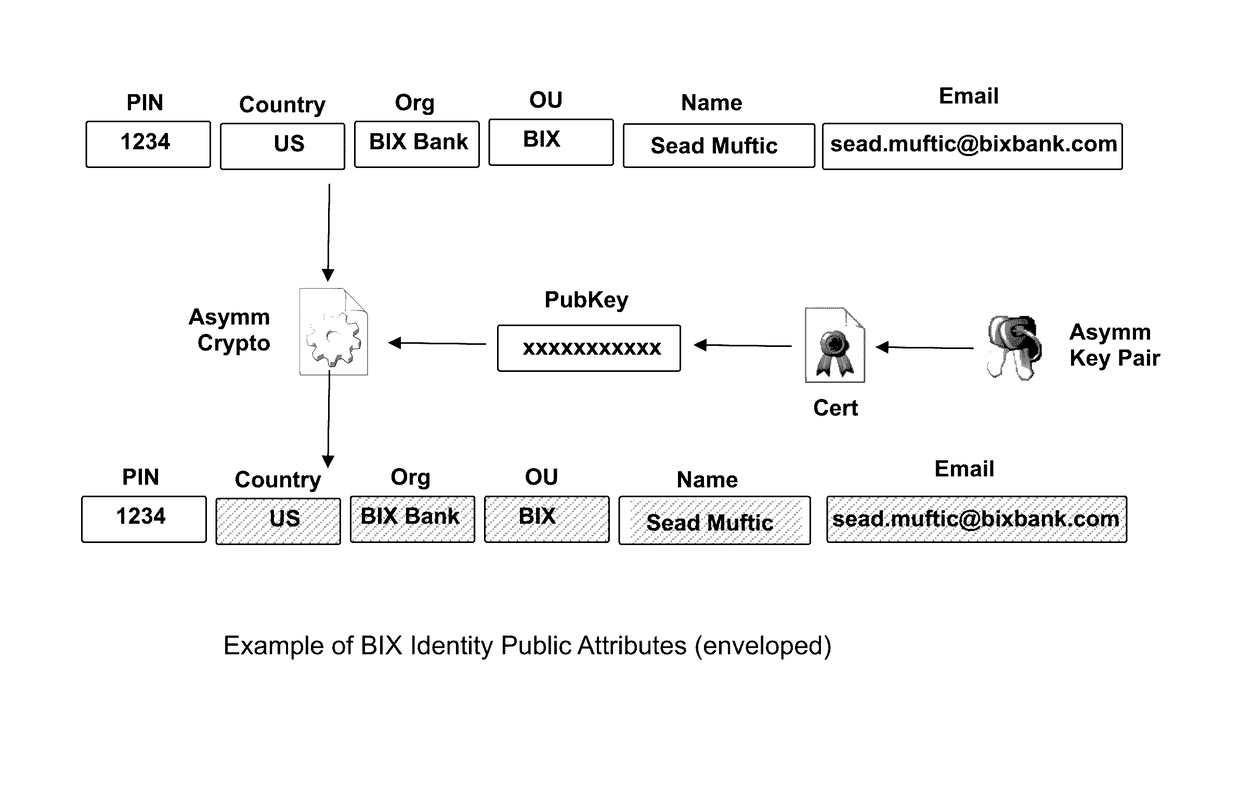
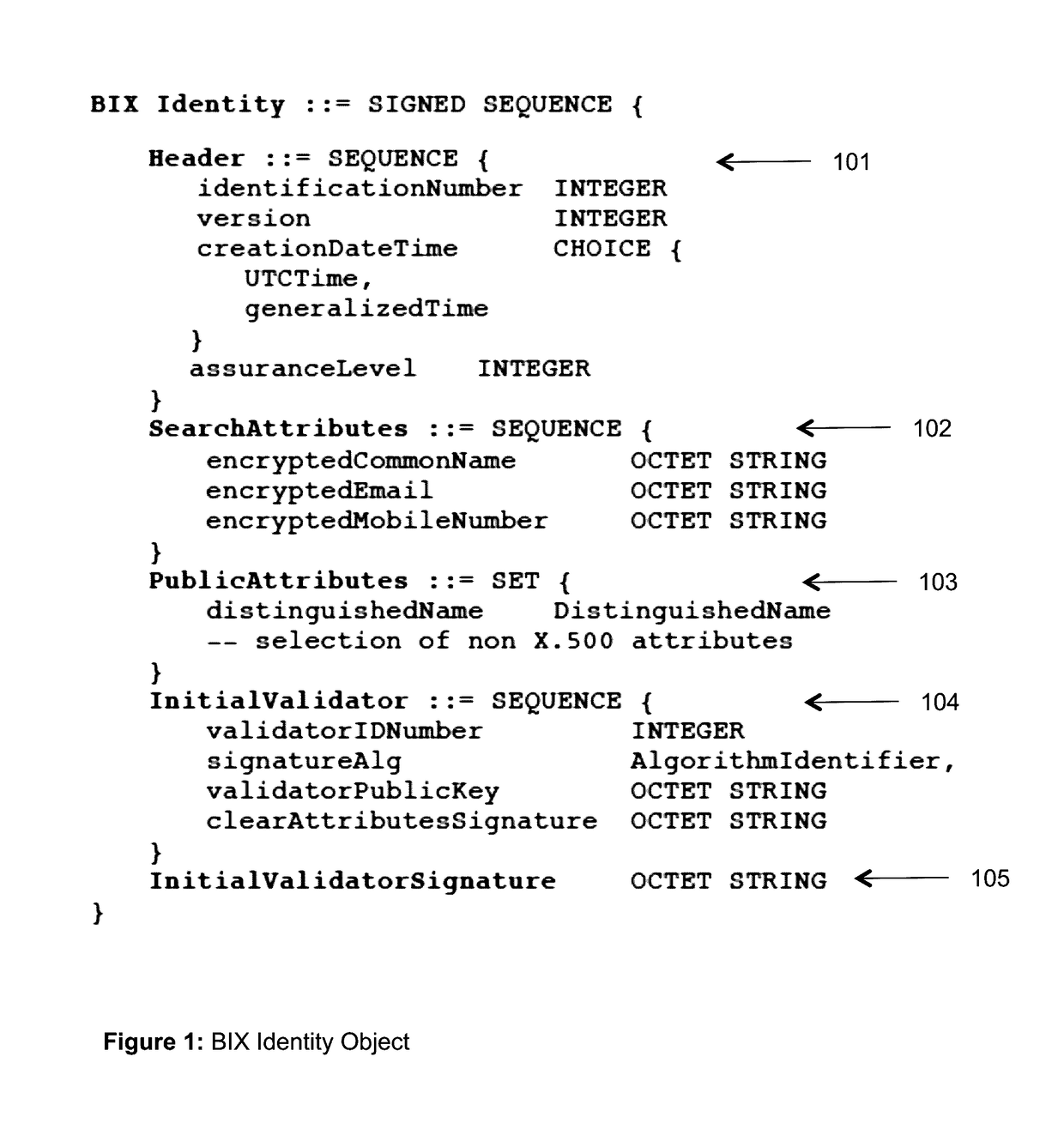
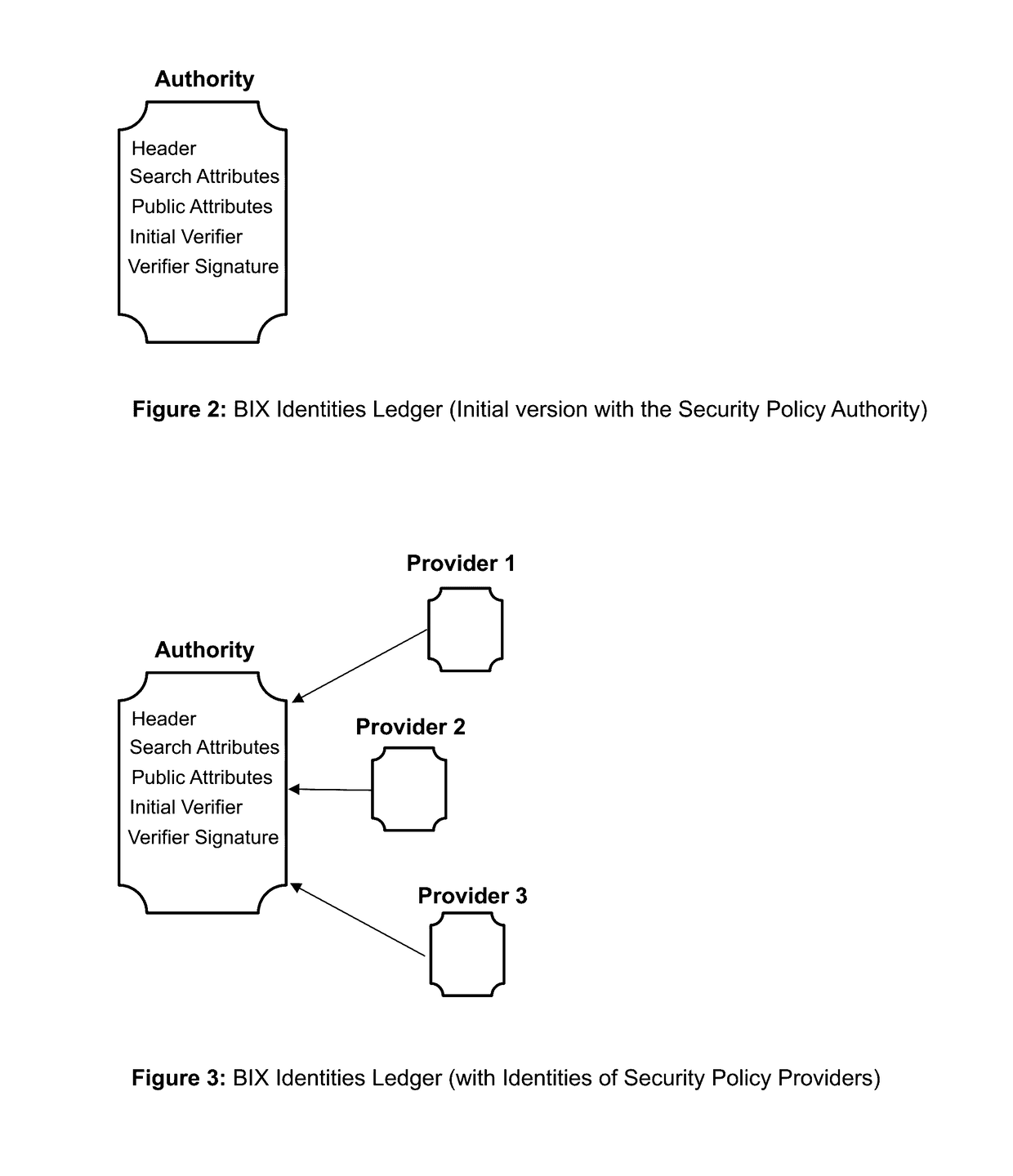
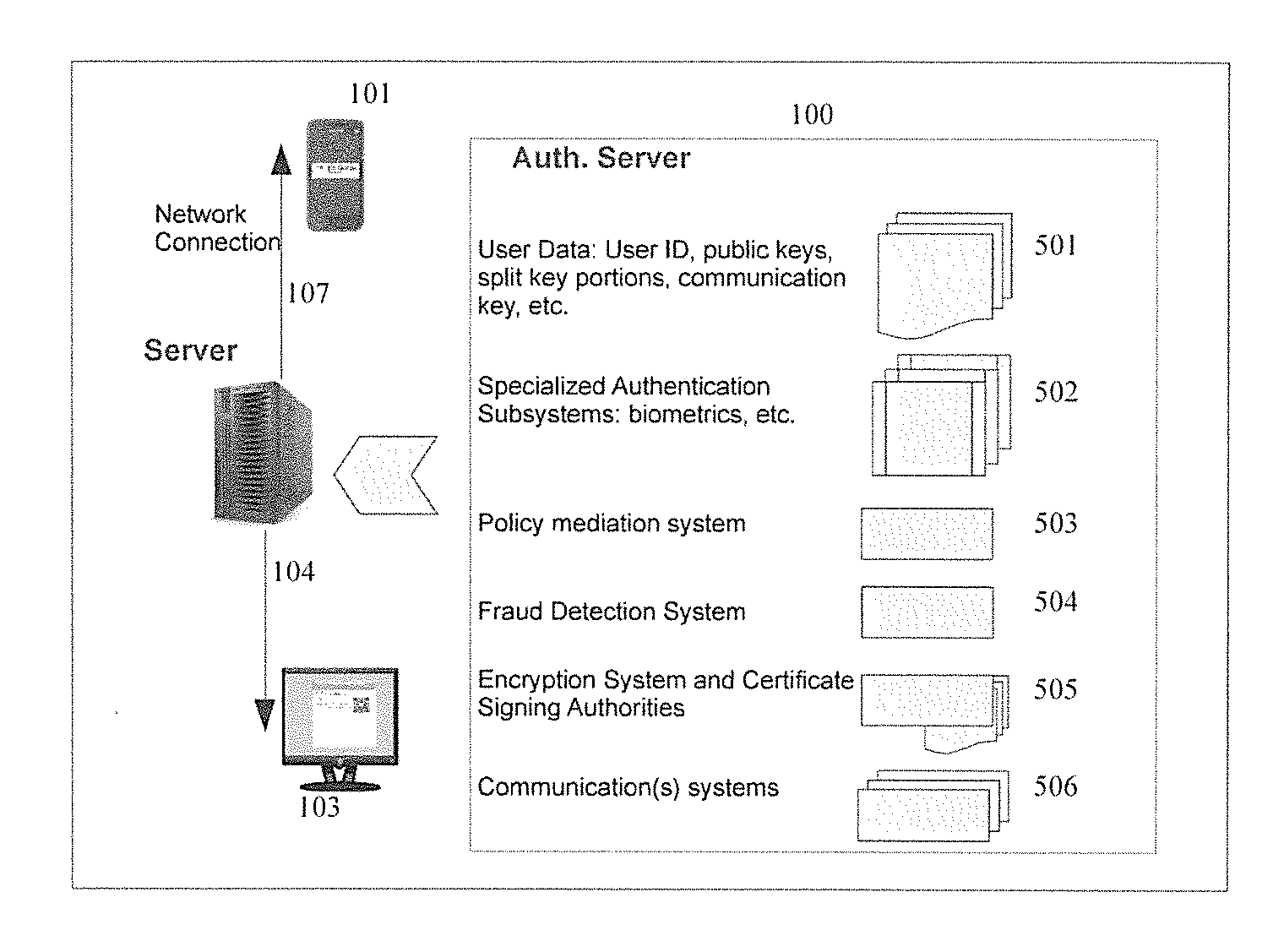
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
Secure authentication in a multi-party system
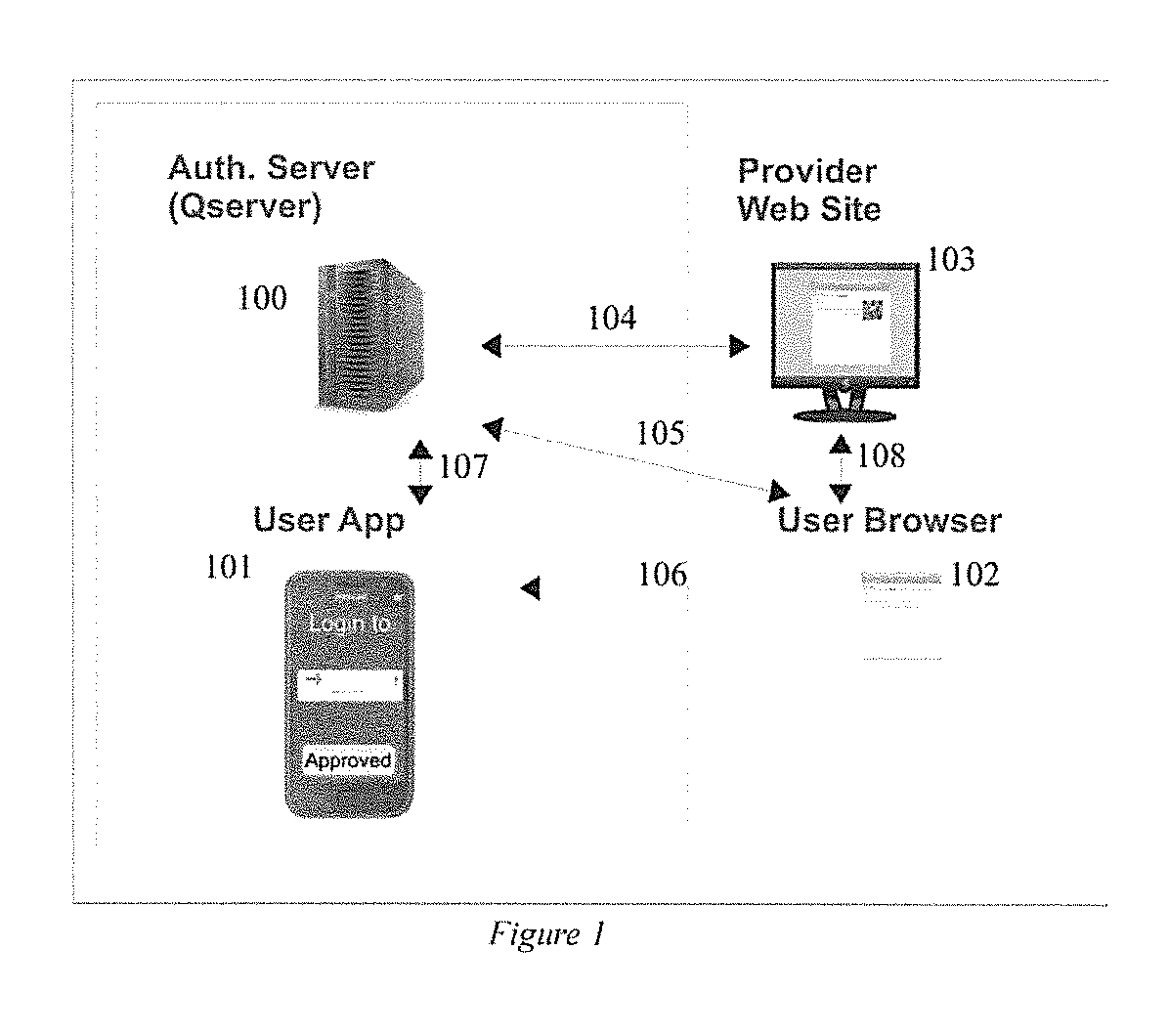
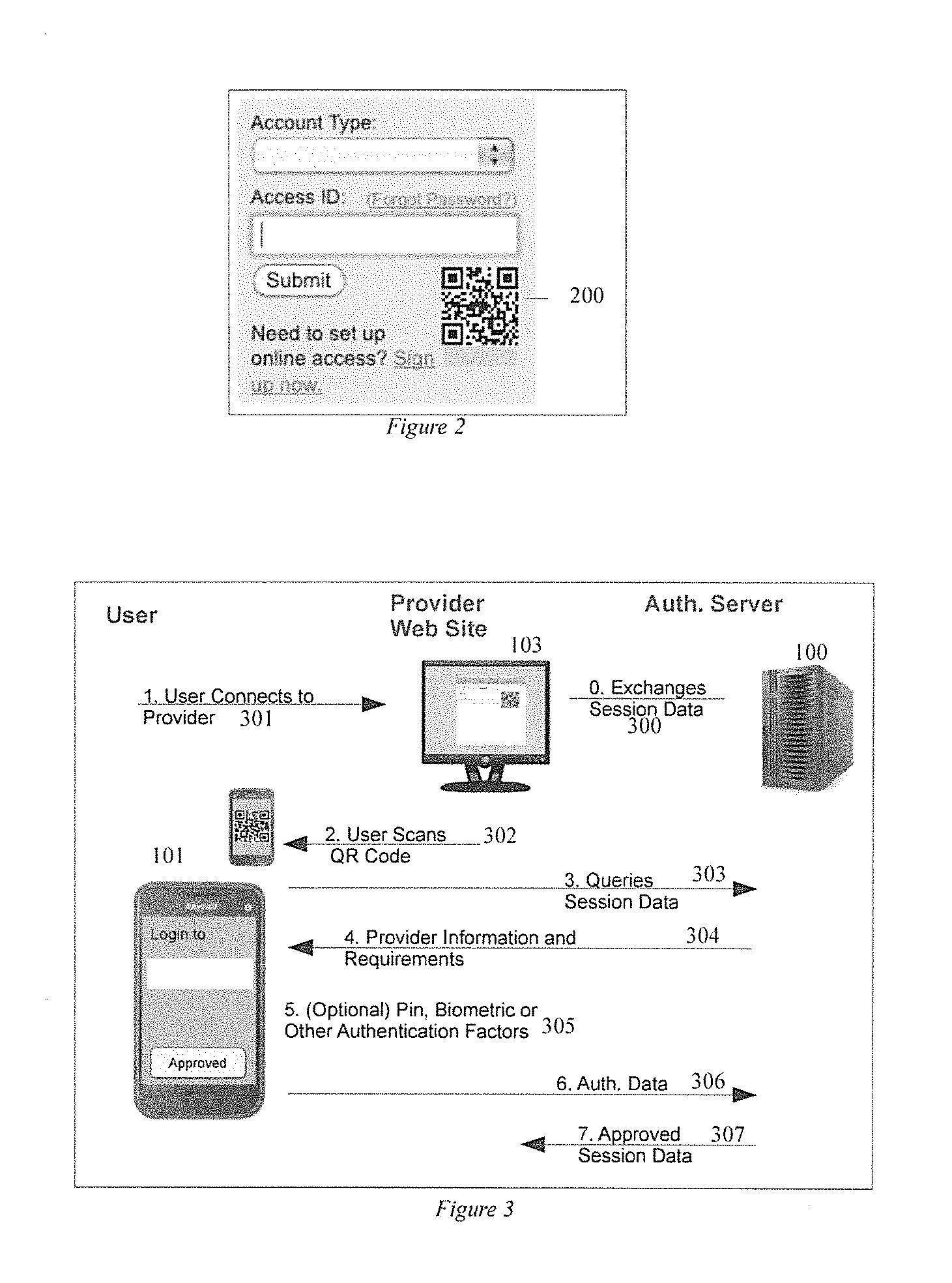
ActiveUS20130262857A1Web data indexingPublic key for secure communicationUser inputAuthentication server
A network user is authenticated to another network entity by using a first program to receive user input validation information, and store a user credential. A second program receives information, such as a random number, from the other entity. The first program receives an input transferring the information to it, transmits the information to the authentication server, and receives an identifier of the other entity, other information, and authentication policy requirements from the authentication server. It then transmits the input validation information corresponding to the received authentication policy requirements to the authentication server, and in response receives a request for a user credential. It signs a message, including the transferred information and the received other information, with the stored user credential, and transmits the signed message to the authentication server to authenticate the user.
Owner:PAYFONE
Automated Access, Key, Certificate, and Credential Management
ActiveUS20150222604A1Effective rotationLow costMultiple keys/algorithms usagePublic key for secure communicationCredential managementTrust relationship
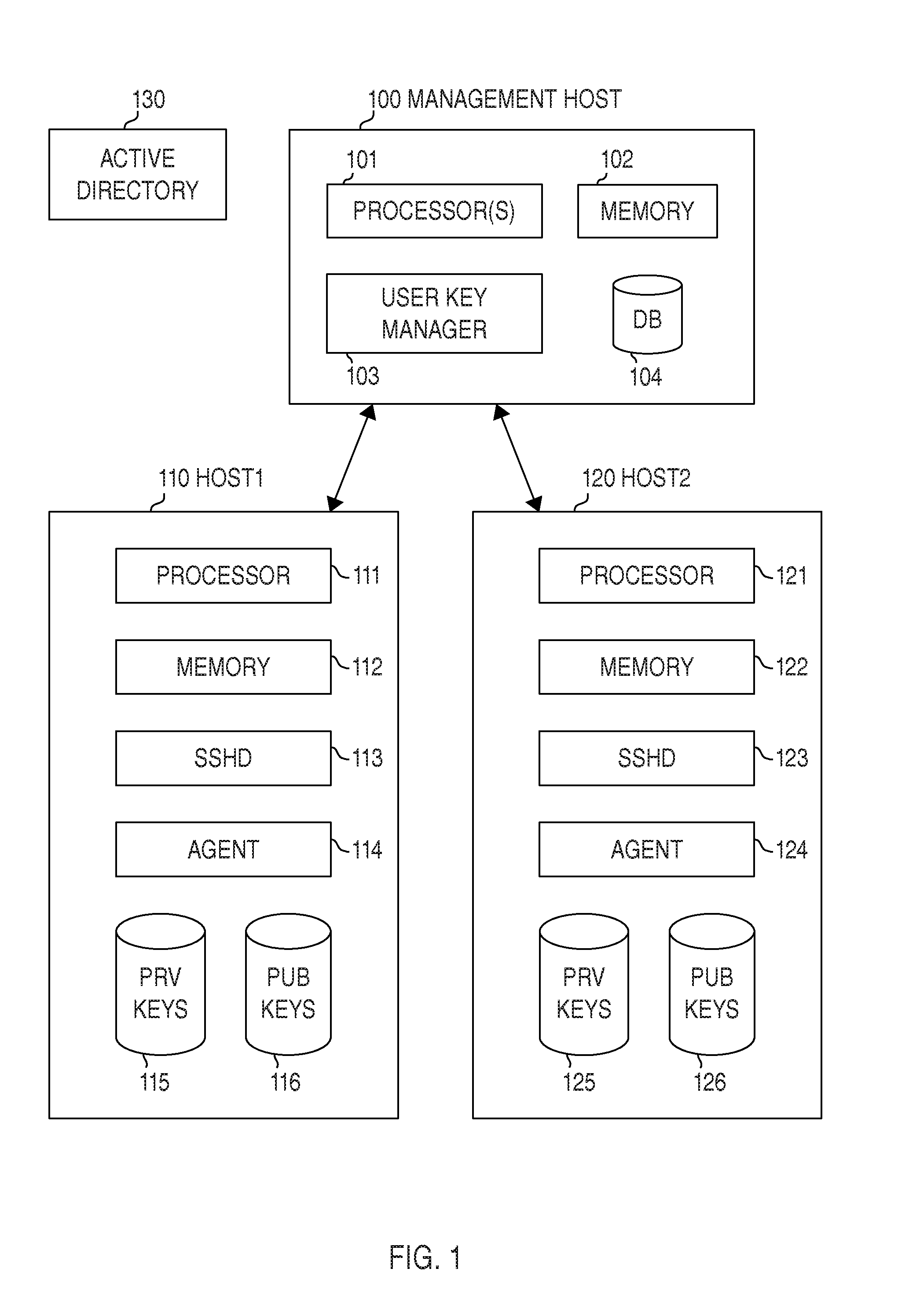
Certain embodiments provide means for managing automated access to computers, e.g., using SSH user keys and other kinds of trust relationships. Certain embodiments also provide for managing certificates, Kerberos credentials, and cryptographic keys. Certain embodiments provide for remediating legacy SSH key problems and for automating configuration of SSH keys, as well as for continuous monitoring.
Owner:SSH COMMUNICATIONS SECURITY
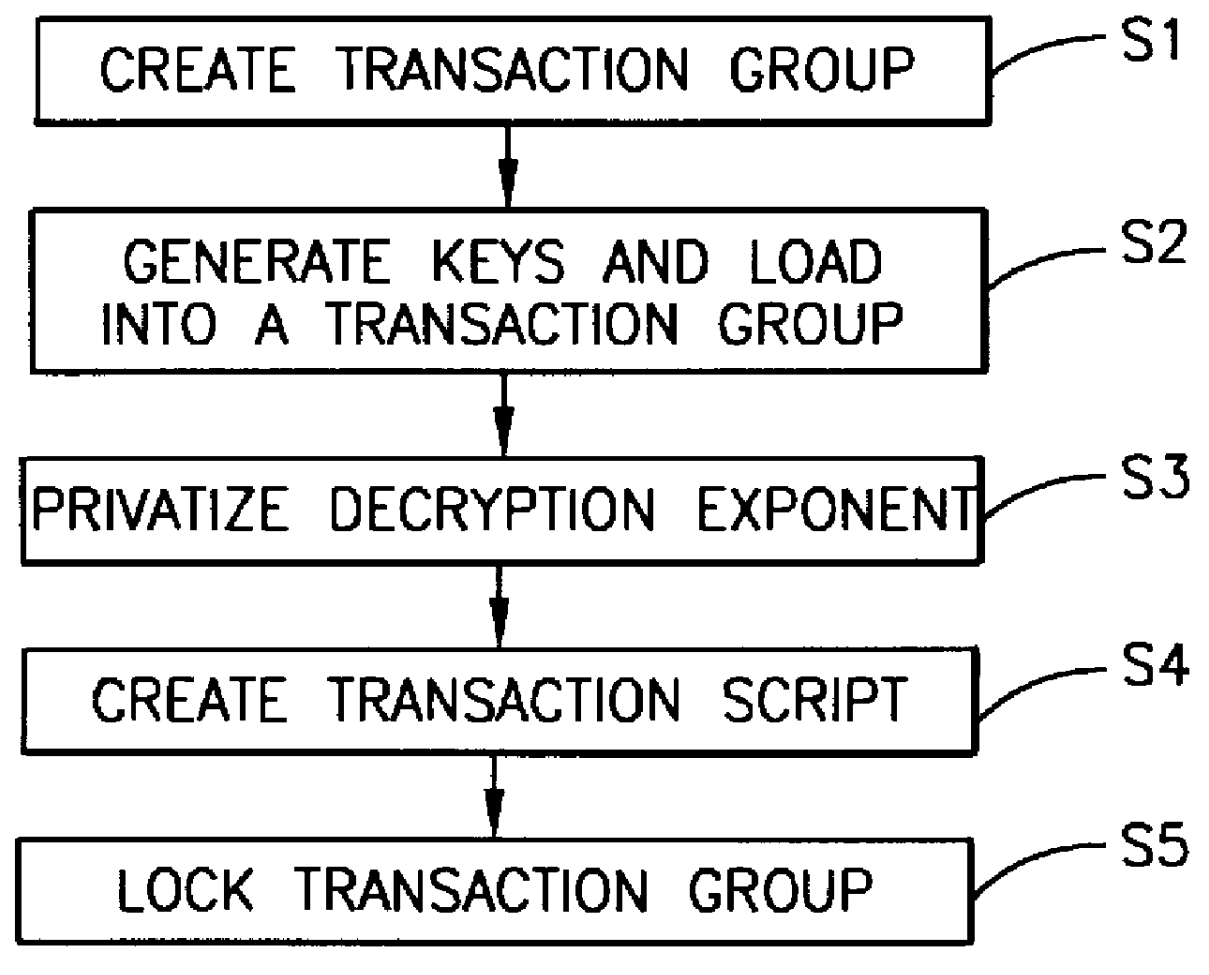
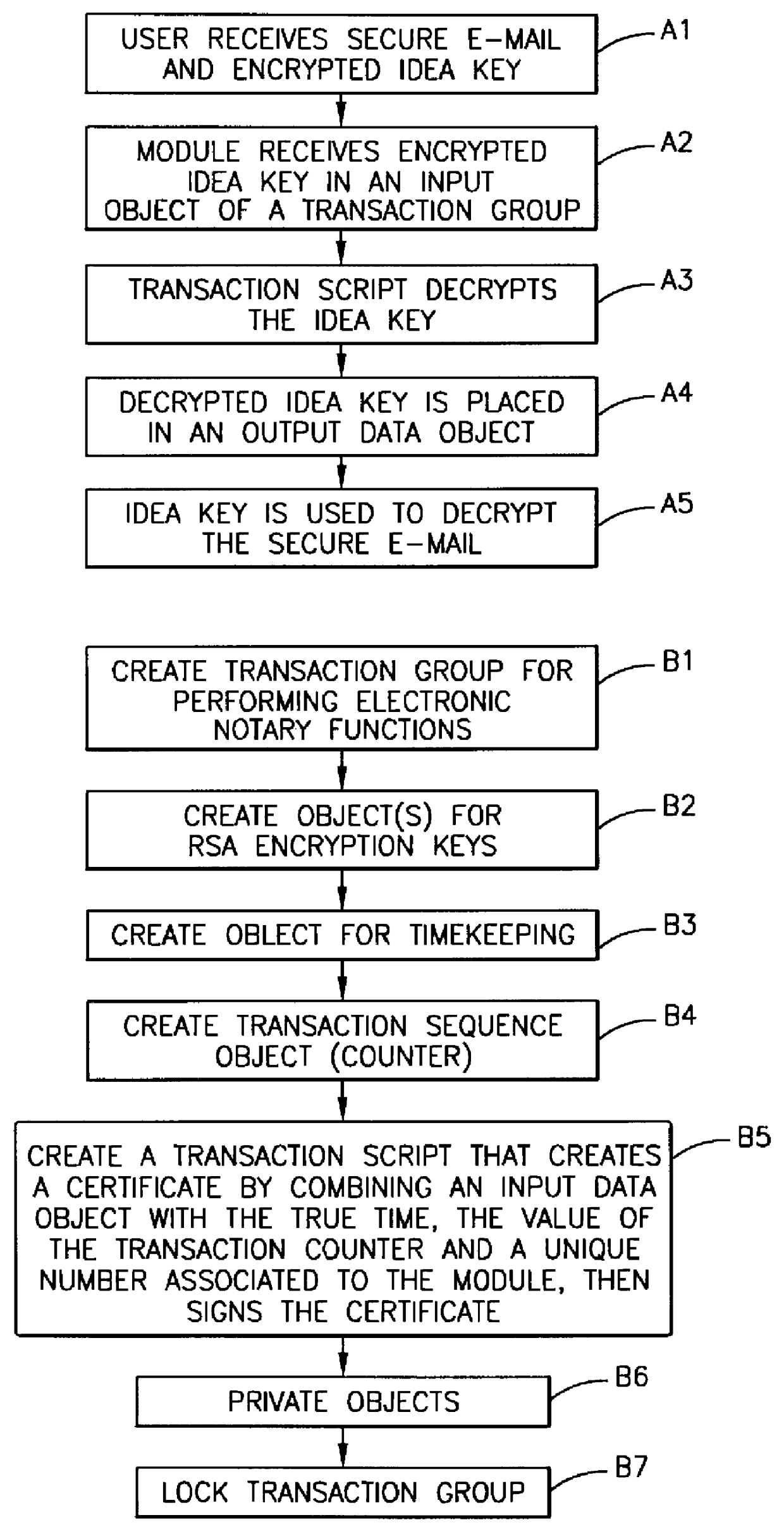
Method, apparatus, system and firmware for secure transactions
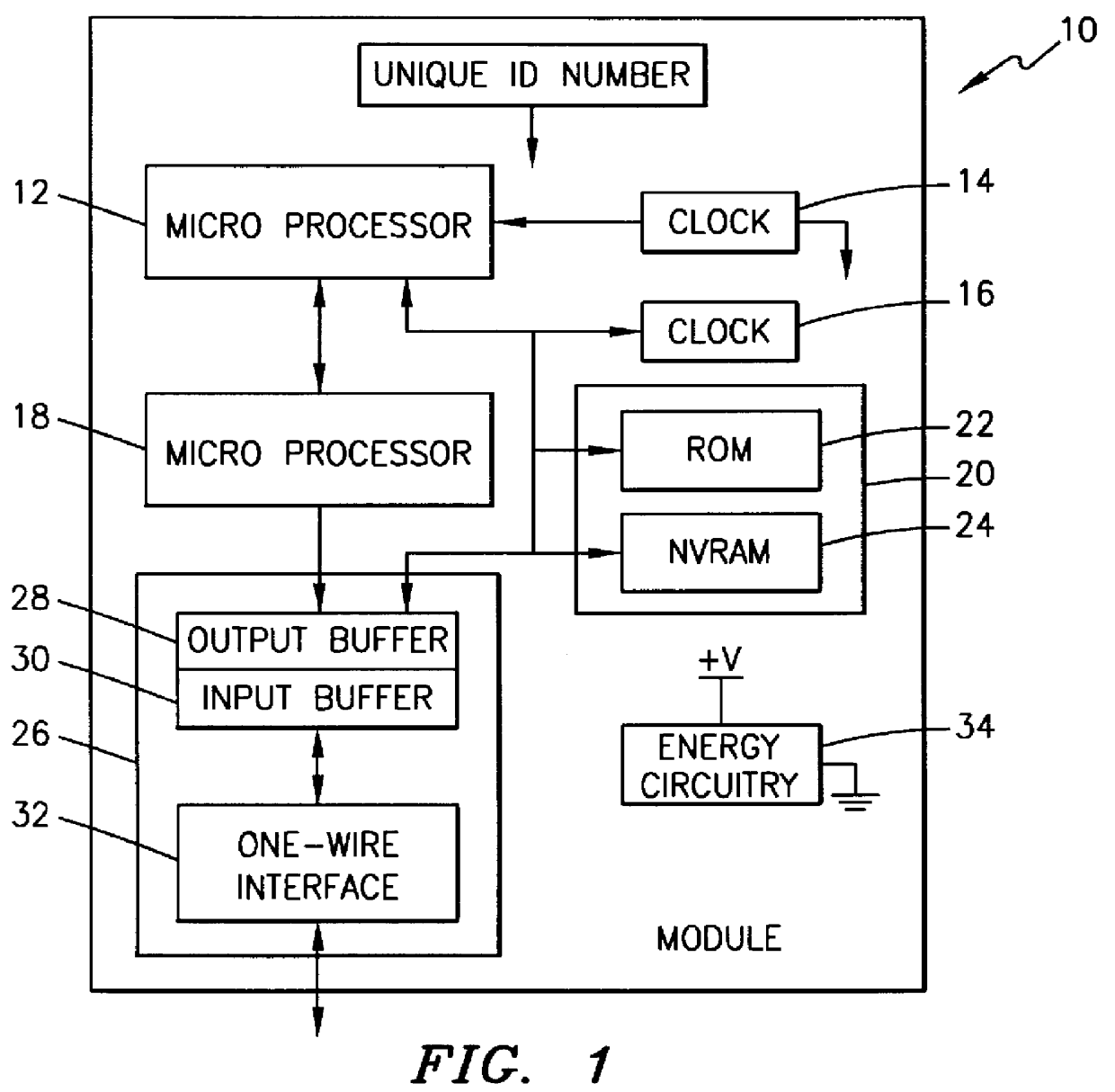
The present invention relates to an electronic module used for secure transactions. More specifically, the electronic module is capable of passing information back and forth between a service provider's equipment via a secure, encrypted technique so that money and other valuable data can be securely passed electronically. The module is capable of being programmed, keeping track of real time, recording transactions for later review, and creating encryption key pairs.
Owner:MAXIM INTEGRATED PROD INC
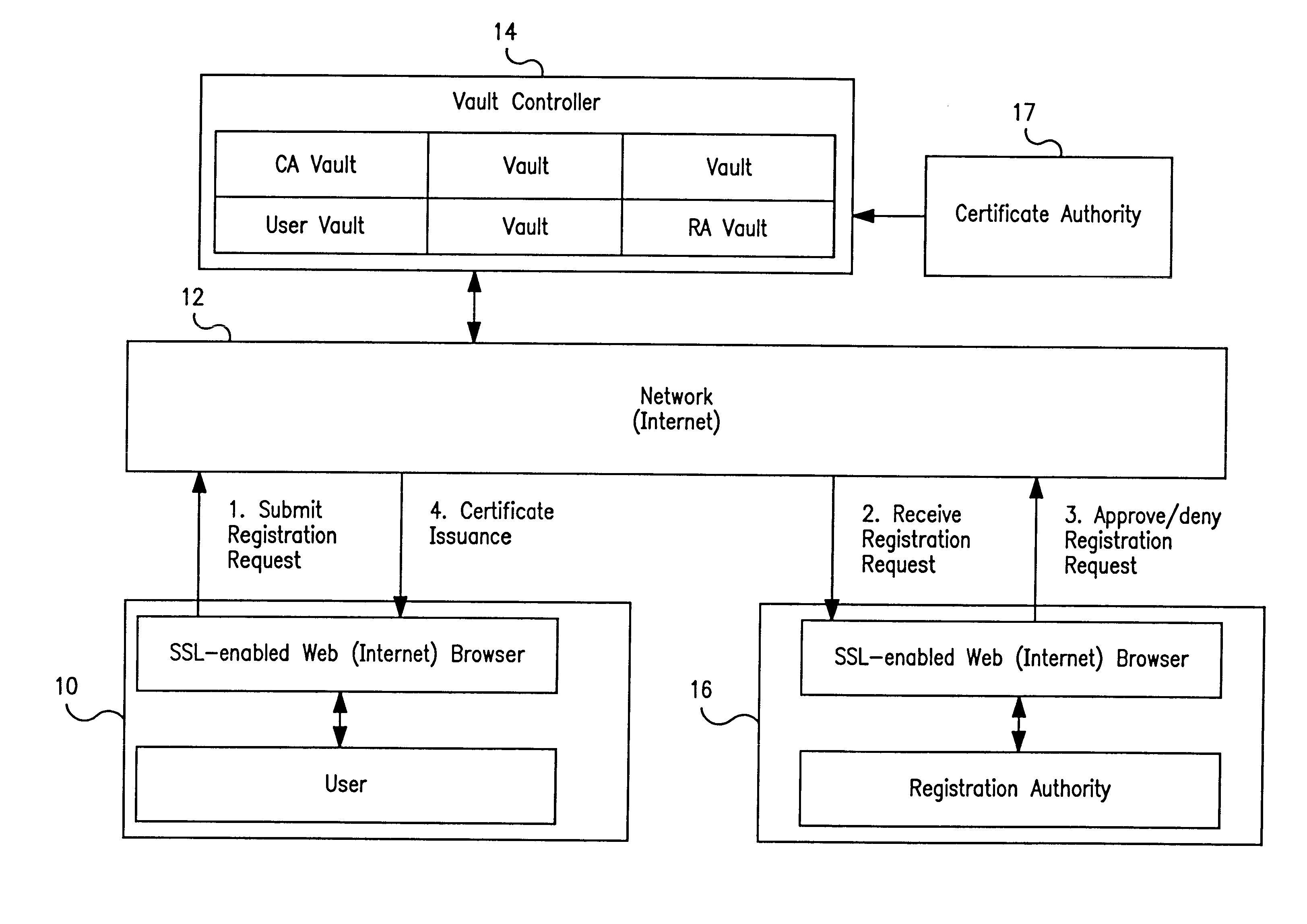
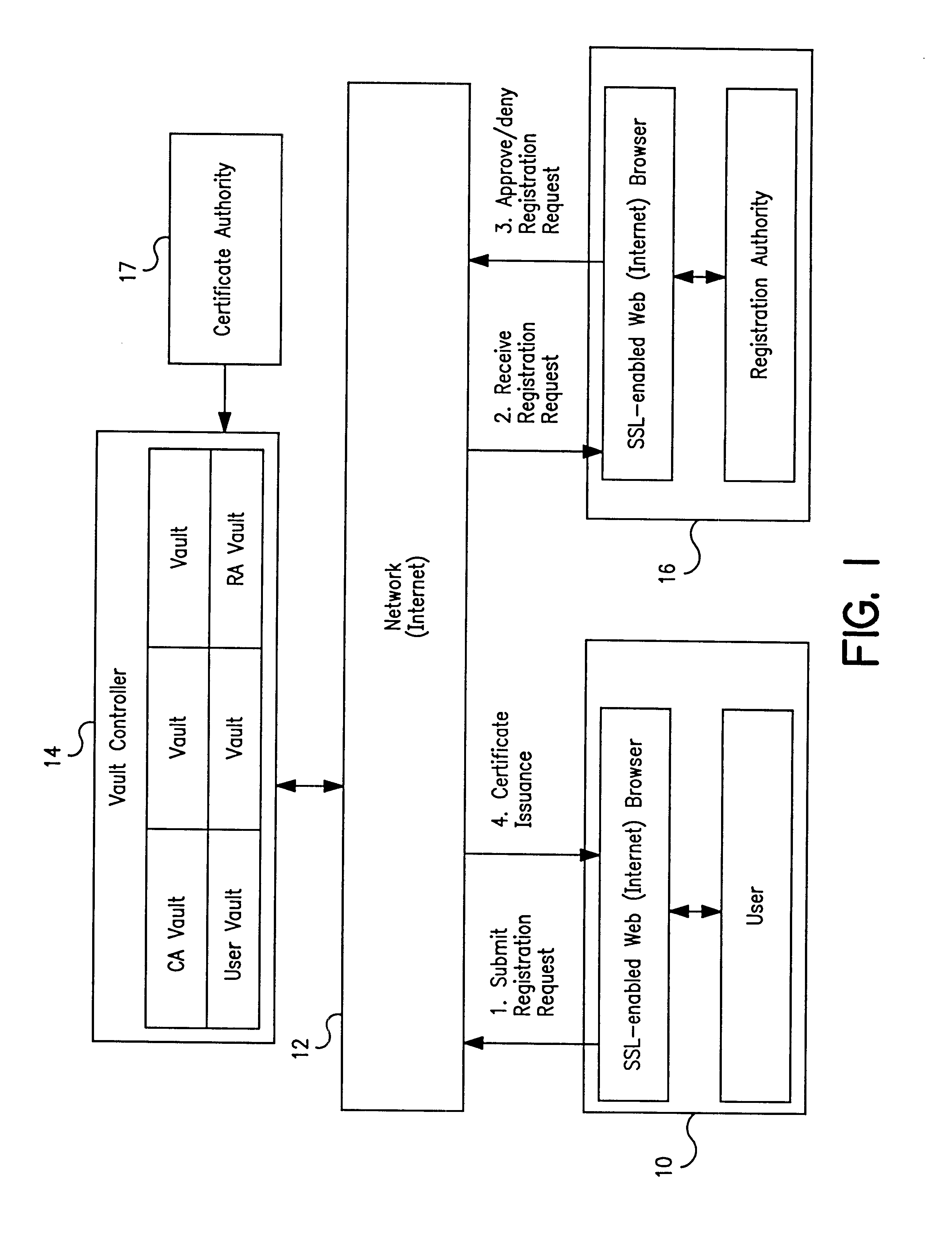
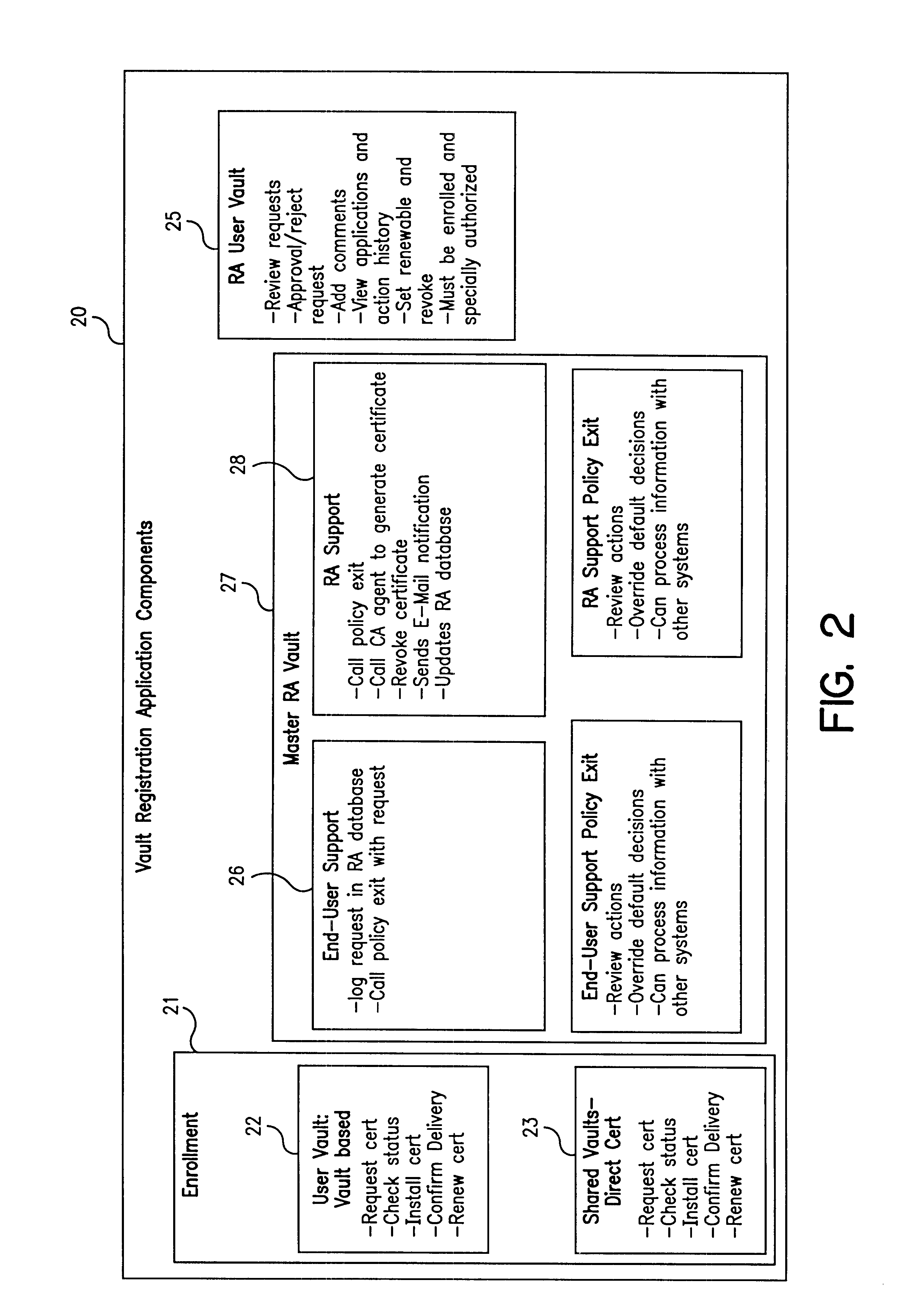
Vault controller based registration application serving web based registration authorities and end users for conducting electronic commerce in secure end-to-end distributed information system
InactiveUS6438690B1FinanceDigital data processing detailsRegistration authorityCommunications system
A secure end-to-end communications system includes a vault controller based registration application for managing the issuance and administration of digital certificates for use in conducting electronic commerce in the system. The system includes an end user terminal and a registration authority terminal coupled to a vault controller through the system. A registration application executable in the controller utilizes SSL and dedicated vaults to process requests for digital certificates from end users on an automated or manual basis. The registration application includes an enrollment module which implements the process of applying for and receiving certificates; an RA desk top module which allows an administrator to review certificate requests and manage certificates; a master Registration Authority (RA) module which conducts the processing of requests and the generation of certificates; and an RA (Registration Authority) database serves as a repository of information about applicants, certificate requests, and their processing history.
Owner:IBM CORP
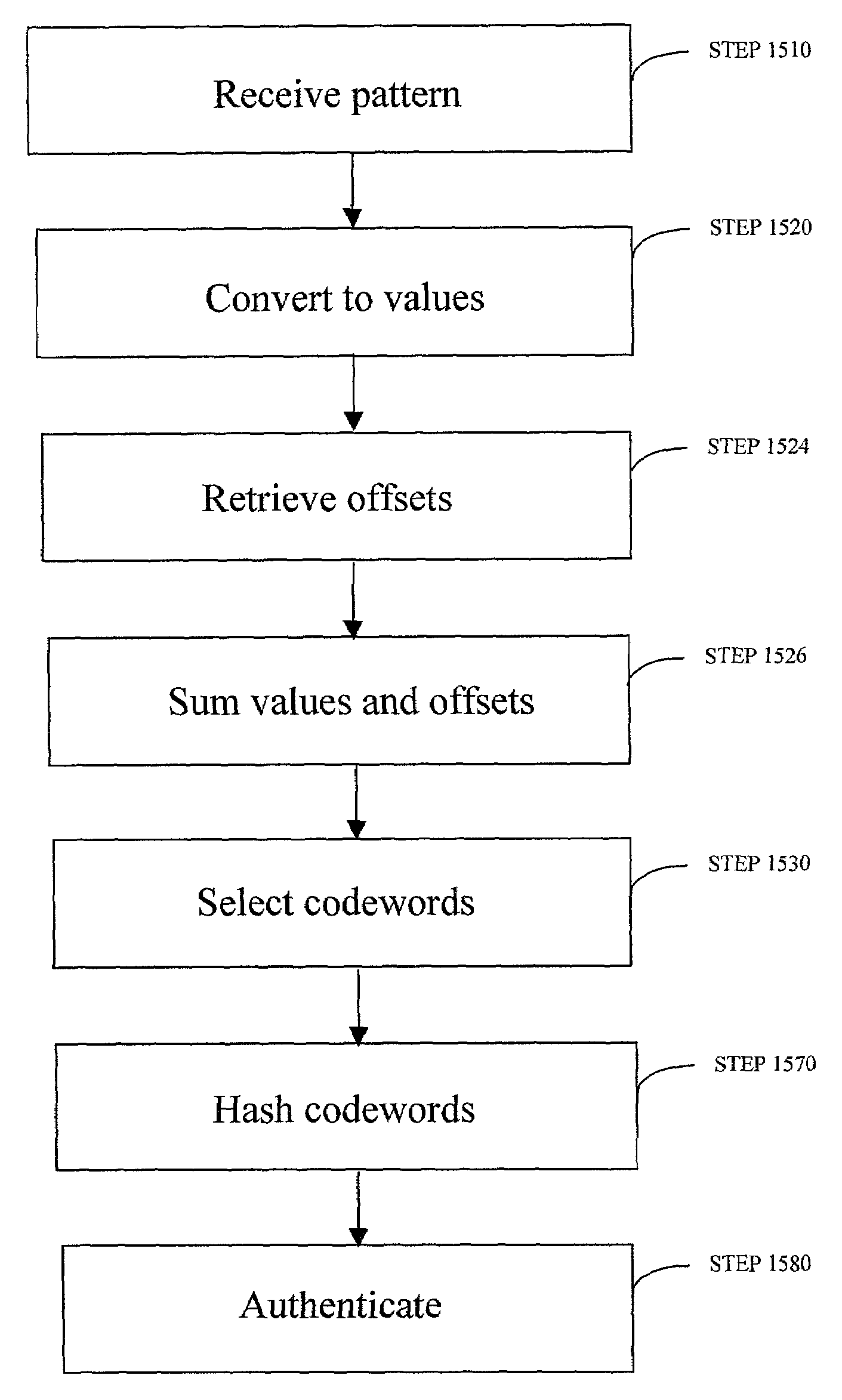
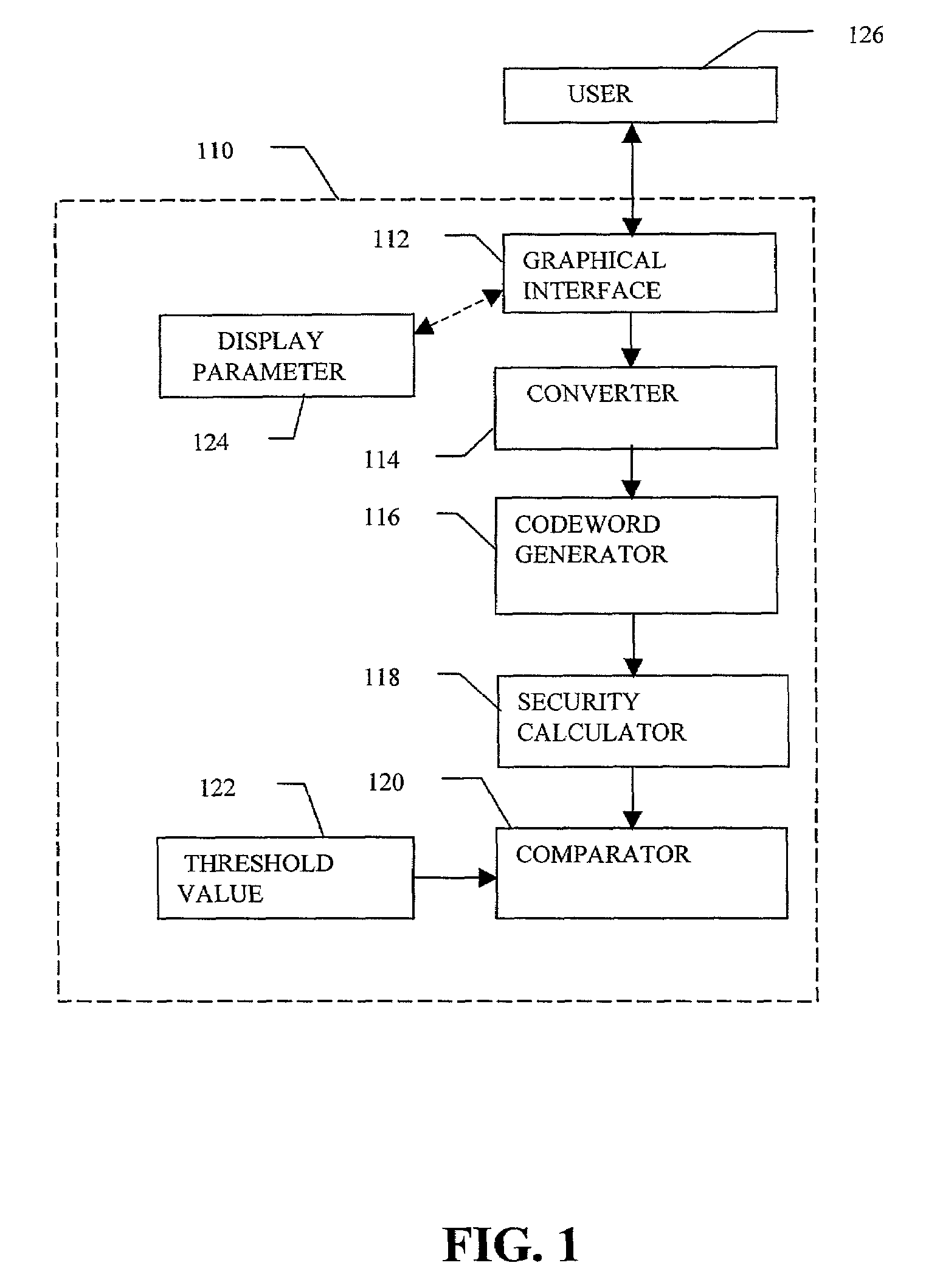
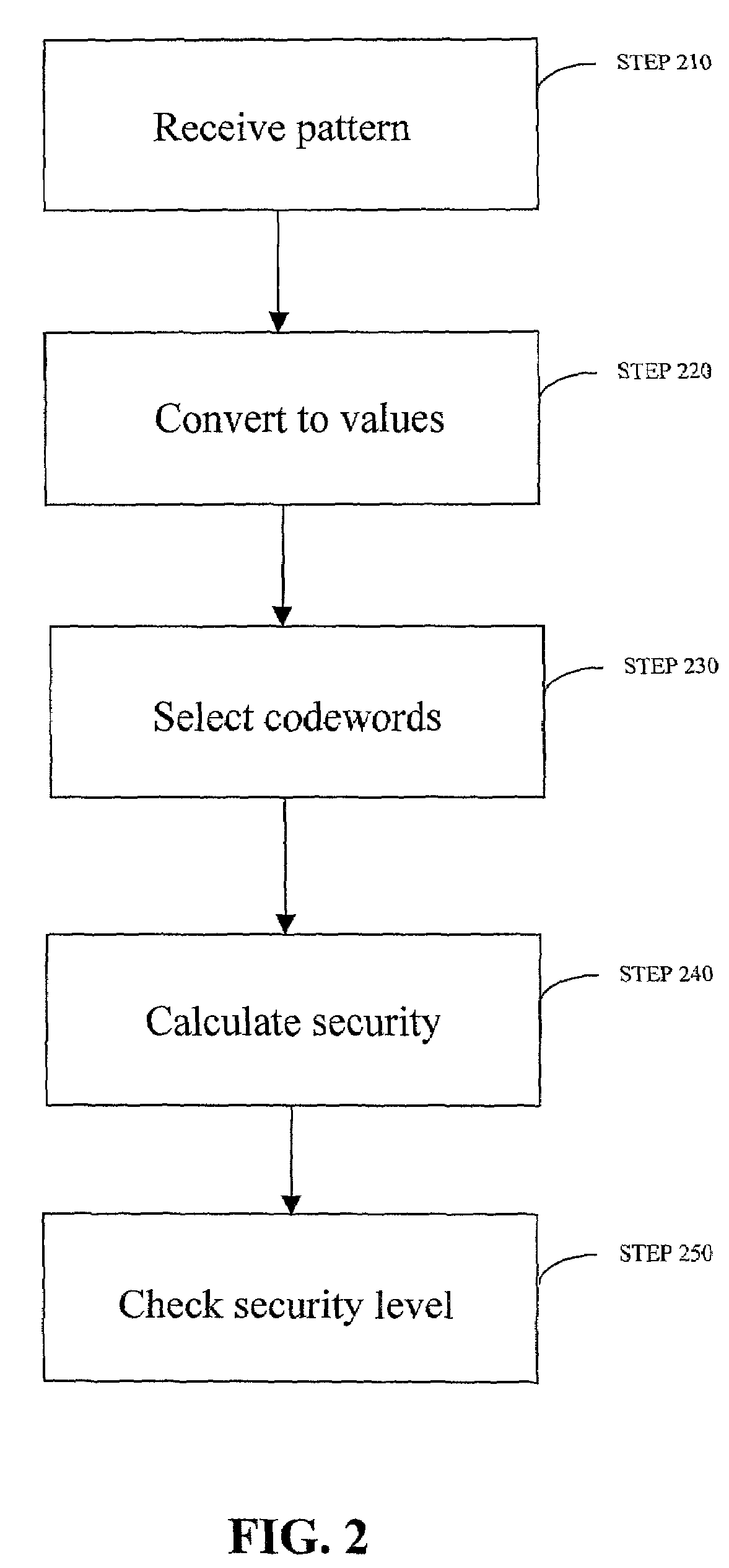
Robust visual passwords
InactiveUS7219368B2Easy to rememberKey distribution for secure communicationPublic key for secure communicationGraphicsUser input
Enrollment and authentication of a user based on a sequence of discrete graphical choices is described. A graphical interface presents various images and memory cues that a user may associate with their original graphical choices. Enrollment may require the input to have a security parameter value that meets or exceeds a threshold. An acceptable sequence of graphical choices is converted to a sequence of values and mapped to a sequence of codewords. Both a hash of the sequence of codewords and a sequence of offsets are stored for use in authenticating the user. An offset is the difference between a value and its corresponding codeword. Authentication requires the user to enter another sequence of discrete graphical choices that is approximately the same as original. The offsets are summed with the corresponding values before mapping to codewords. Authentication requires the sequence of codewords, or a hash thereof, to match.
Owner:RSA
Access system utilizing multiple factor identification and authentication
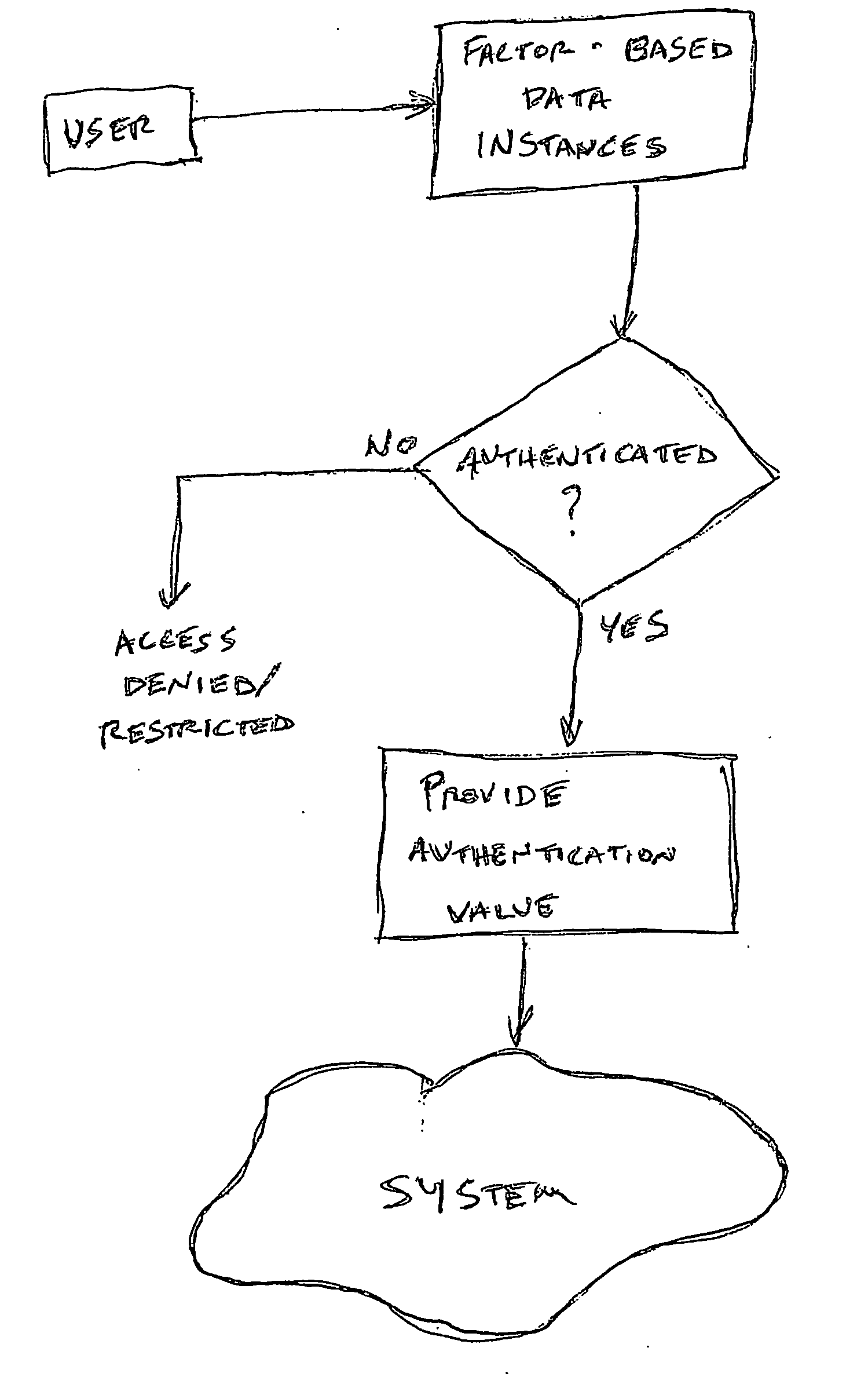
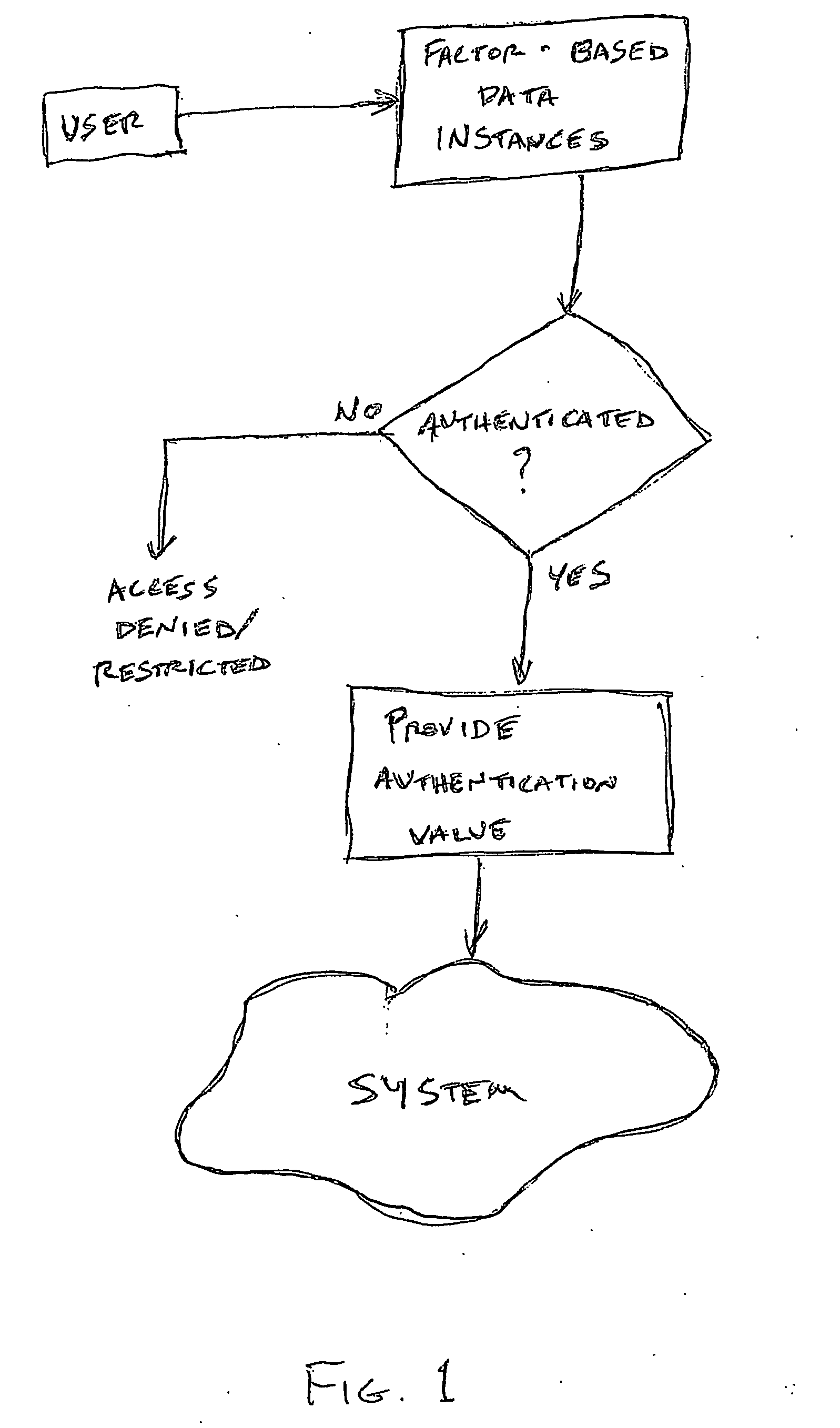
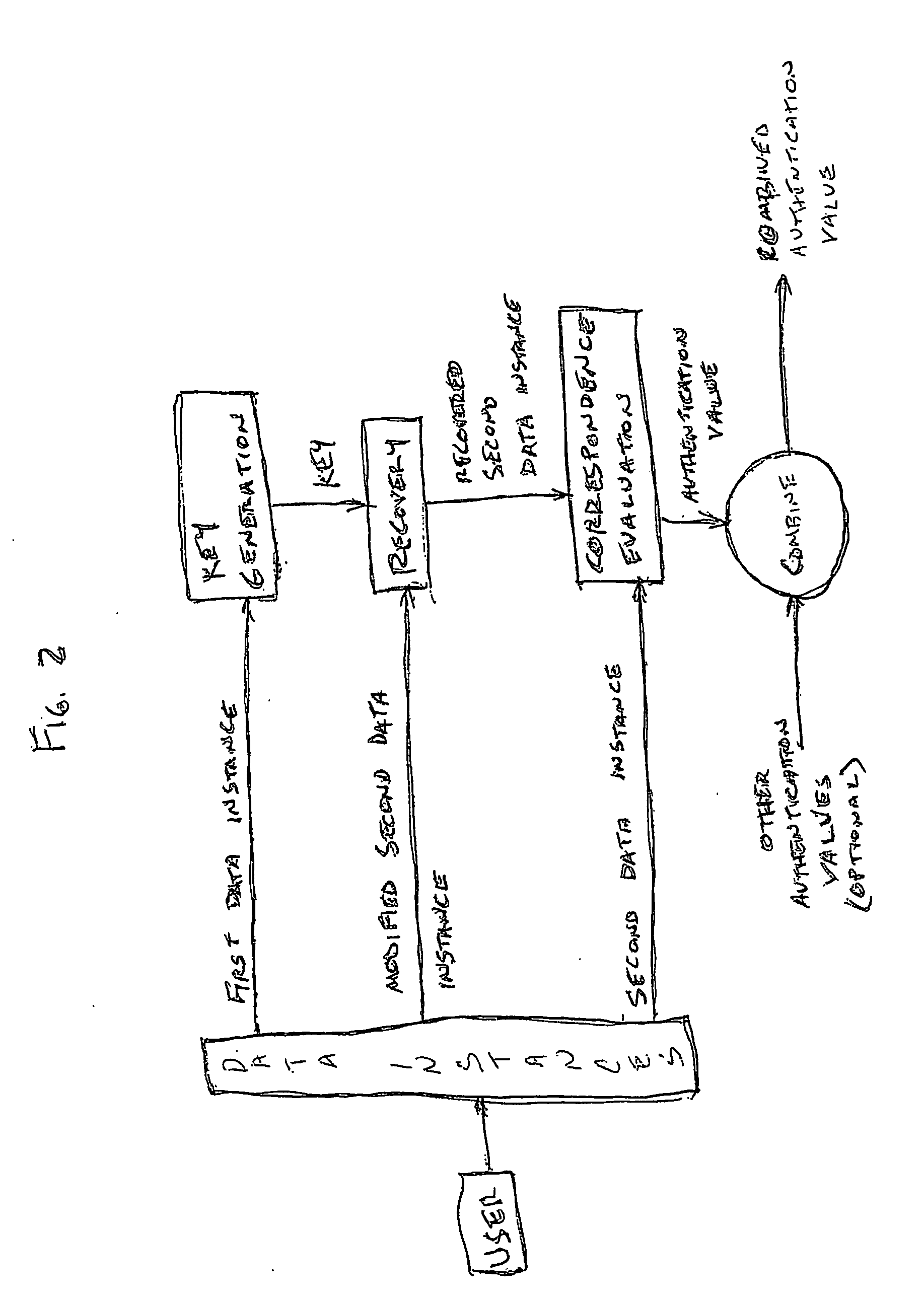
InactiveUS20050235148A1Flexible approachEasy to useKey distribution for secure communicationPublic key for secure communicationTransfer systemPassword
A method of authenticating a user to use a system includes using a provider token to generate a random value. The token generates a derived key based at least in part on a token-provided salt value and a user-provided password. The provider generates a token unlock key based at least in part on the derived key and sends it to the token. First and second challenge data instances are generated by the provider and the token, respectively, and the process is terminated if the challenge data instances are determined not to match. If the challenge data instances are determined to match, then an encrypted data transfer system is established between the token and the provider, and the token unlocks locked private data stored on the token. The user is authenticated for secured use of the system based at least in part on the unlocked private data.
Owner:TECSEC
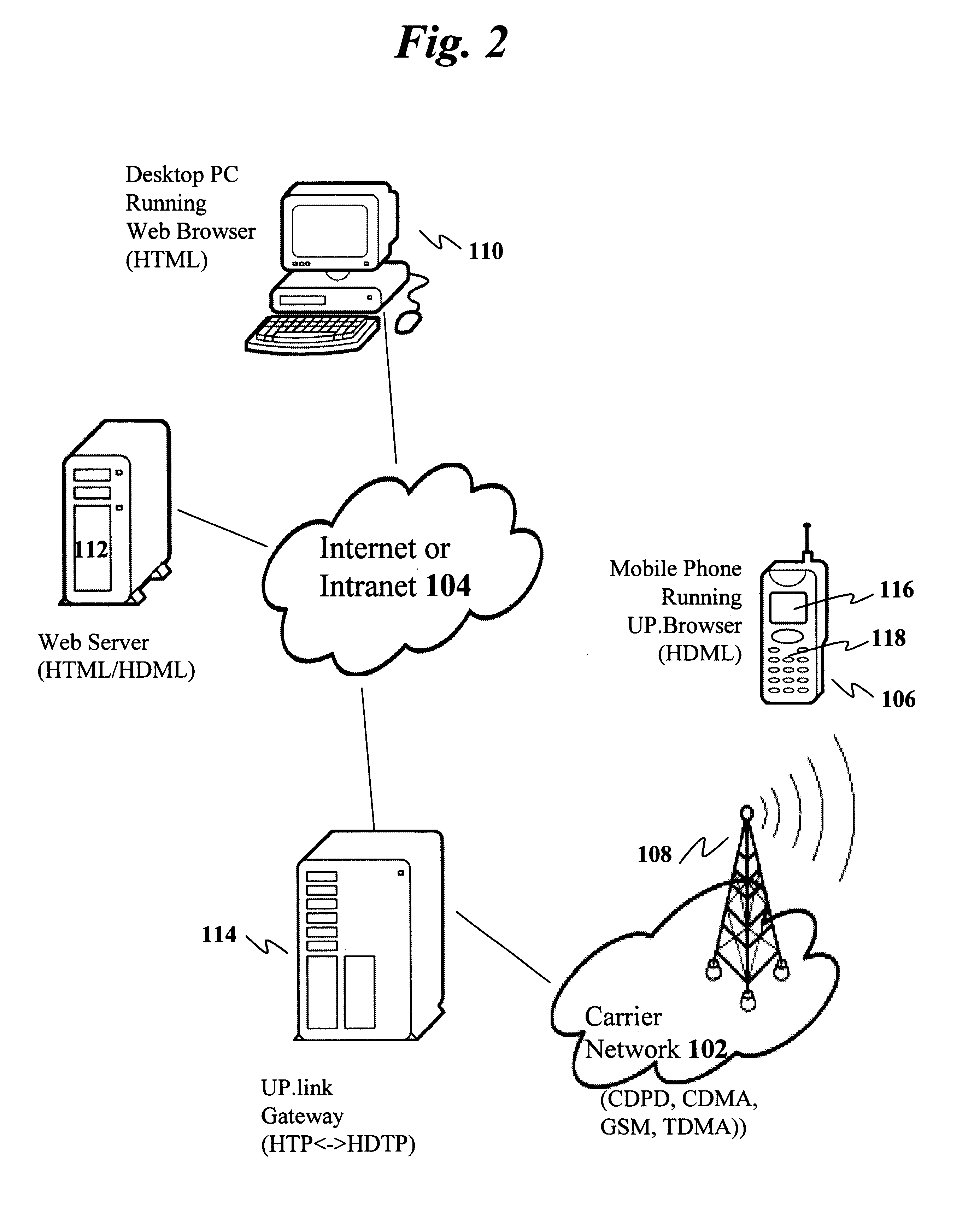
Method and apparatus for establishing dynamic tunnel access sessions in a communication network
InactiveUS7117526B1Key distribution for secure communicationPublic key for secure communicationTelecommunications linkCommunication link
A method and apparatus for implementing dynamic tunnel access sessions at a network device within a communications network. The tunnel access sessions are created between a network device, typically a gateway device and a network service, such as the Internet or a corporate intranet. The dynamic tunnel access sessions provide for subscriber-transparent tunneling. The present invention does not require special client-side software to be loaded on the remote host of the subscriber, and does not require any manual configuration of the remote host. A subscriber is capable of establishing more than one tunnel access session to more than one network service during a network session. Additionally, more than one subscriber who accesses the communication network via the network device is able to establish a communication link with a pre-existing tunnel.
Owner:NOMADIX INC
System and method for secure electronic communication services
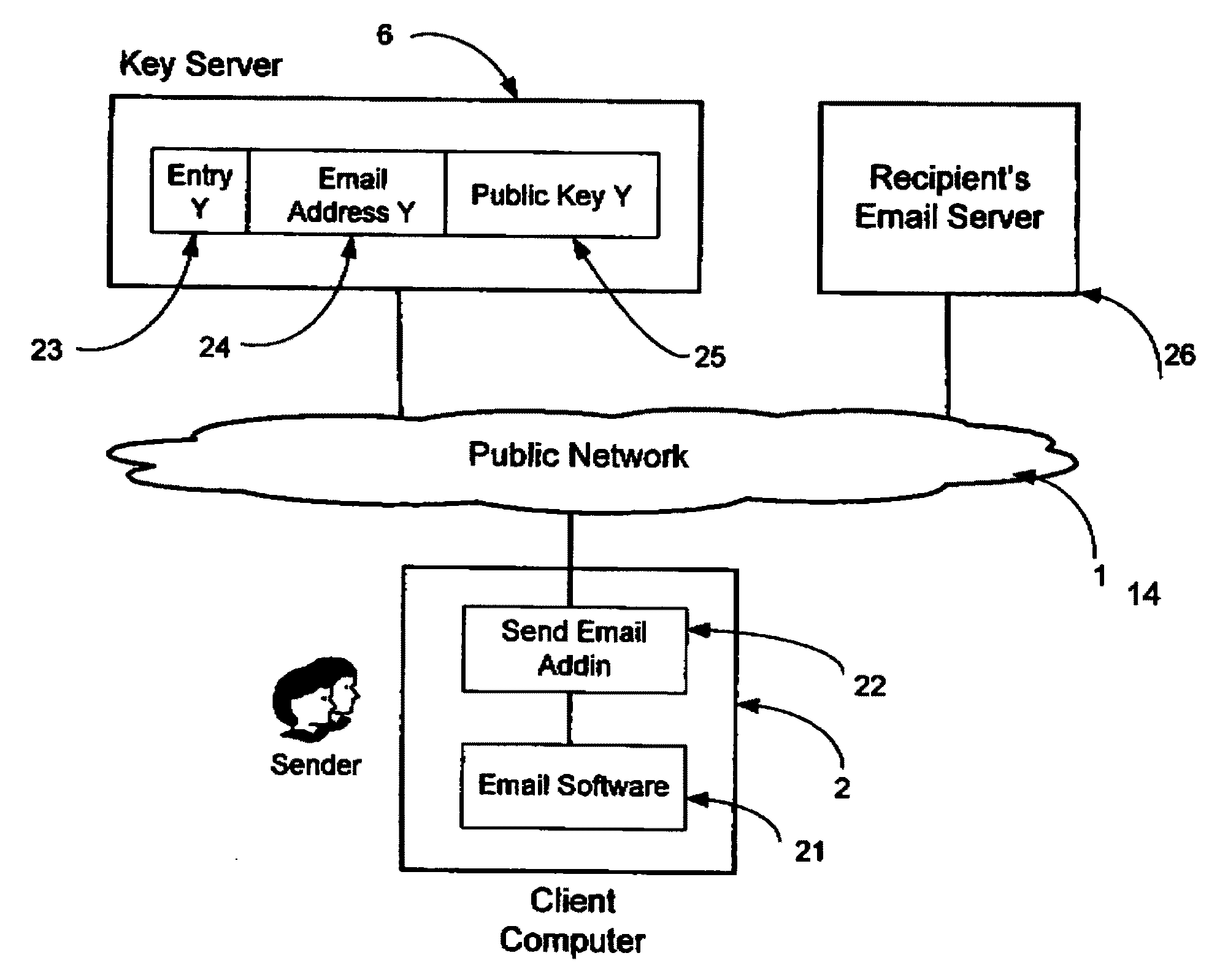
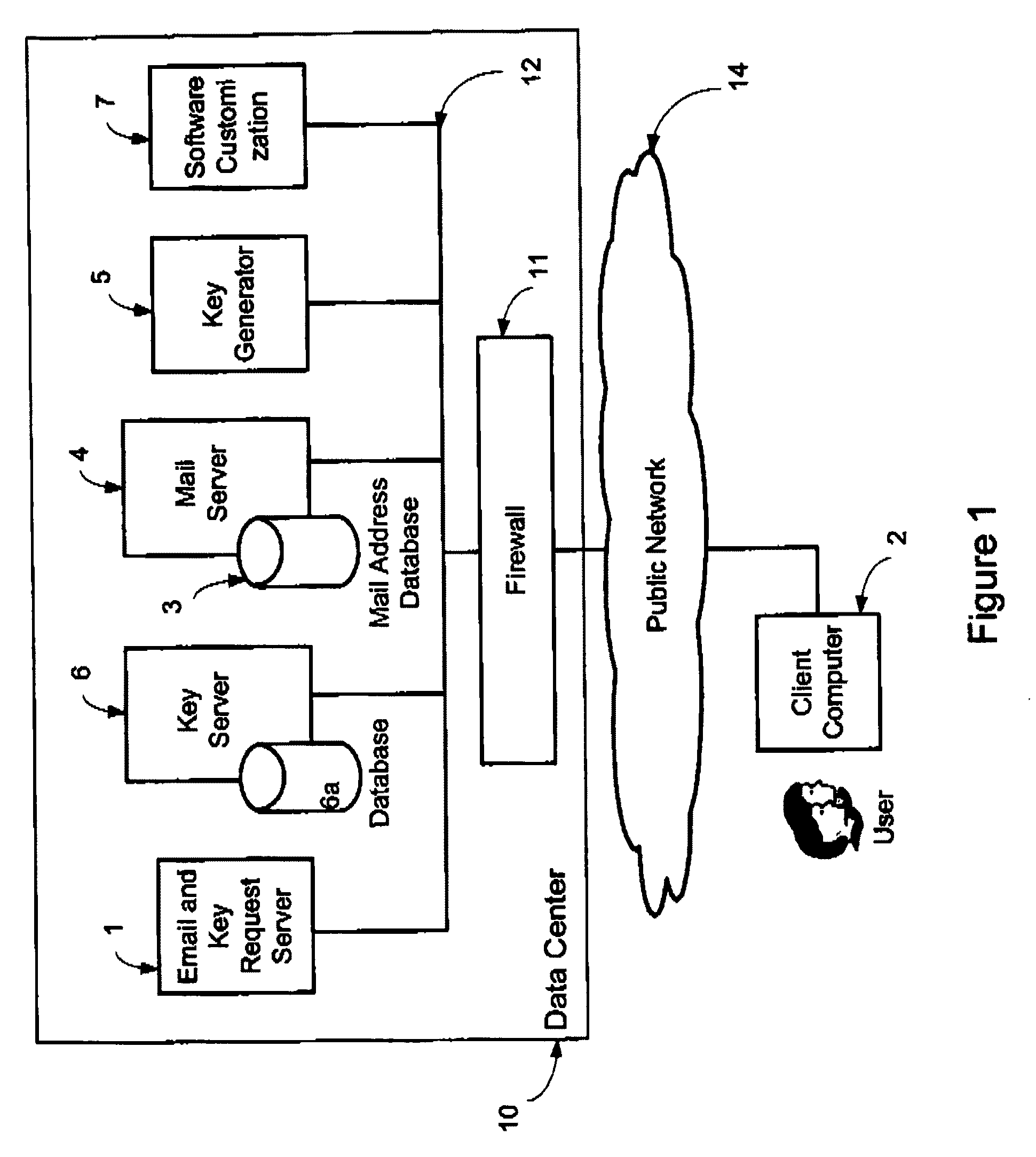
InactiveUS20090198997A1Easy accessSecure transmissionKey distribution for secure communicationMultiple keys/algorithms usageScalable systemEmail address
A system, method and software module for secure electronic communication services, wherein a public key (25) of private-public-key pair (30,25) is associated with an email address (24), internet name or other registered unique identifier; the registered user of the unique identifier holds the private-key (30) securely, and the respective public-key (25) is made accessible on a key server (6) for look-up and retrieval by other users, for encryption of communications to be sent to the holder of the private-key, and optionally for message confidentiality, message integrity and authentication of sender and recipient, without requiring certificates. A distributed and scalable system is provided by a server network (600; 401, 501) for registration, key distribution and management preferably using a kDNS server hierarchy (601,602,603) or a key-DNS server hierarchy (701,702,) and associated protocols so that public-keys of recipients can be searched and retrieved over the internet based on the recipients email address or other unique identifier, thus facilitating secure communication between users in different network domains and organizations.
Owner:TOPOSIS CORP
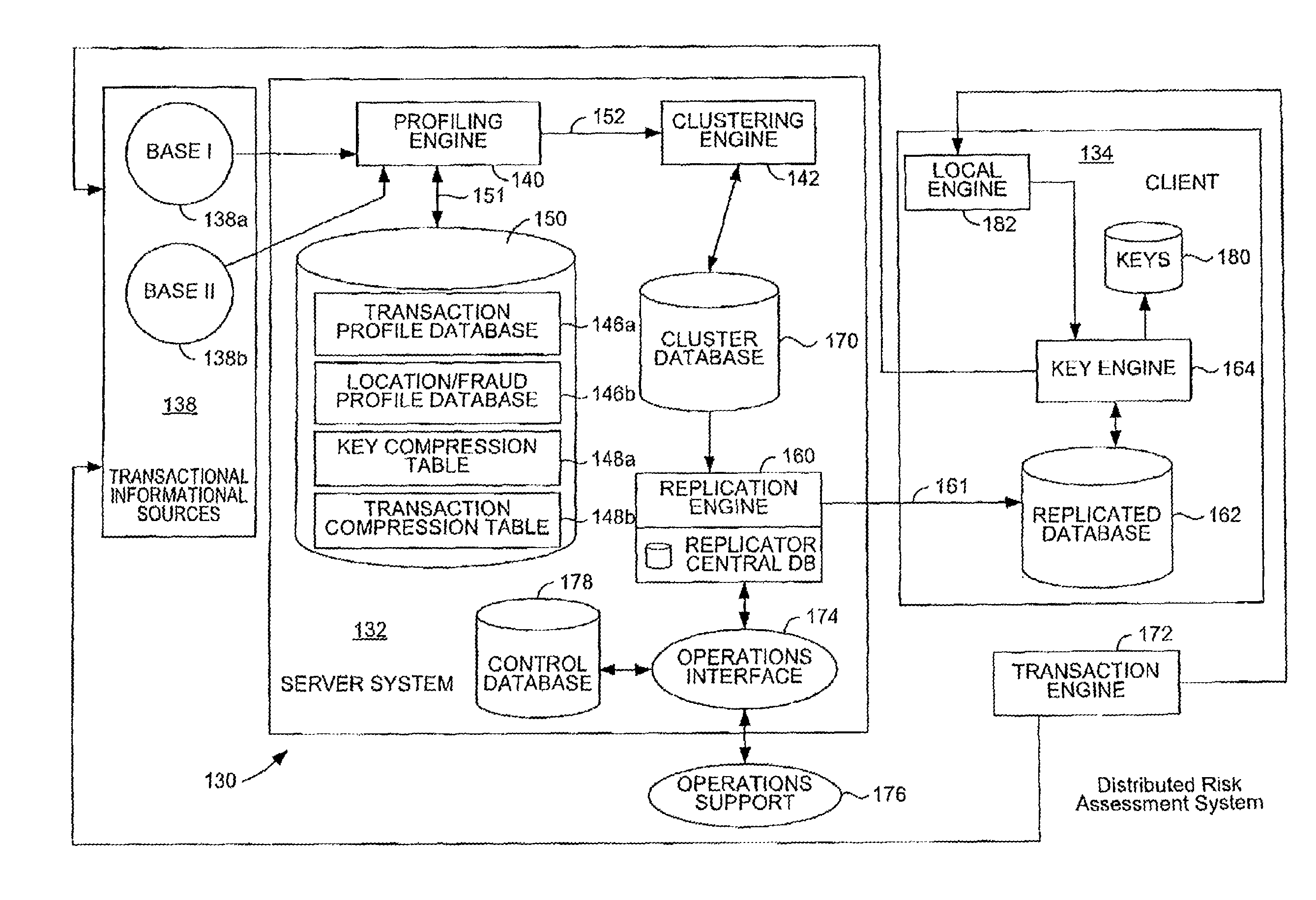
Distributed Quantum Encrypted Pattern Generation And Scoring
InactiveUS20100057622A1Informed decisionPrivacy protectionFinancePublic key for secure communicationPattern generationClient-side
Transaction scoring is performed in a distributed manner across a client-server computing system. A computing system for processing a transaction includes a server system and a client system. The server system is arranged to process information associated with the transaction, while the client system communicates with the server system and includes a key engine which is arranged to generate keys. The client system and the server system are arranged to cooperate to make probabilistic determinations associated with the transaction. The client is arranged to send the keys generated by the key engine as a transaction to the server system.
Owner:VISA USA INC (US)
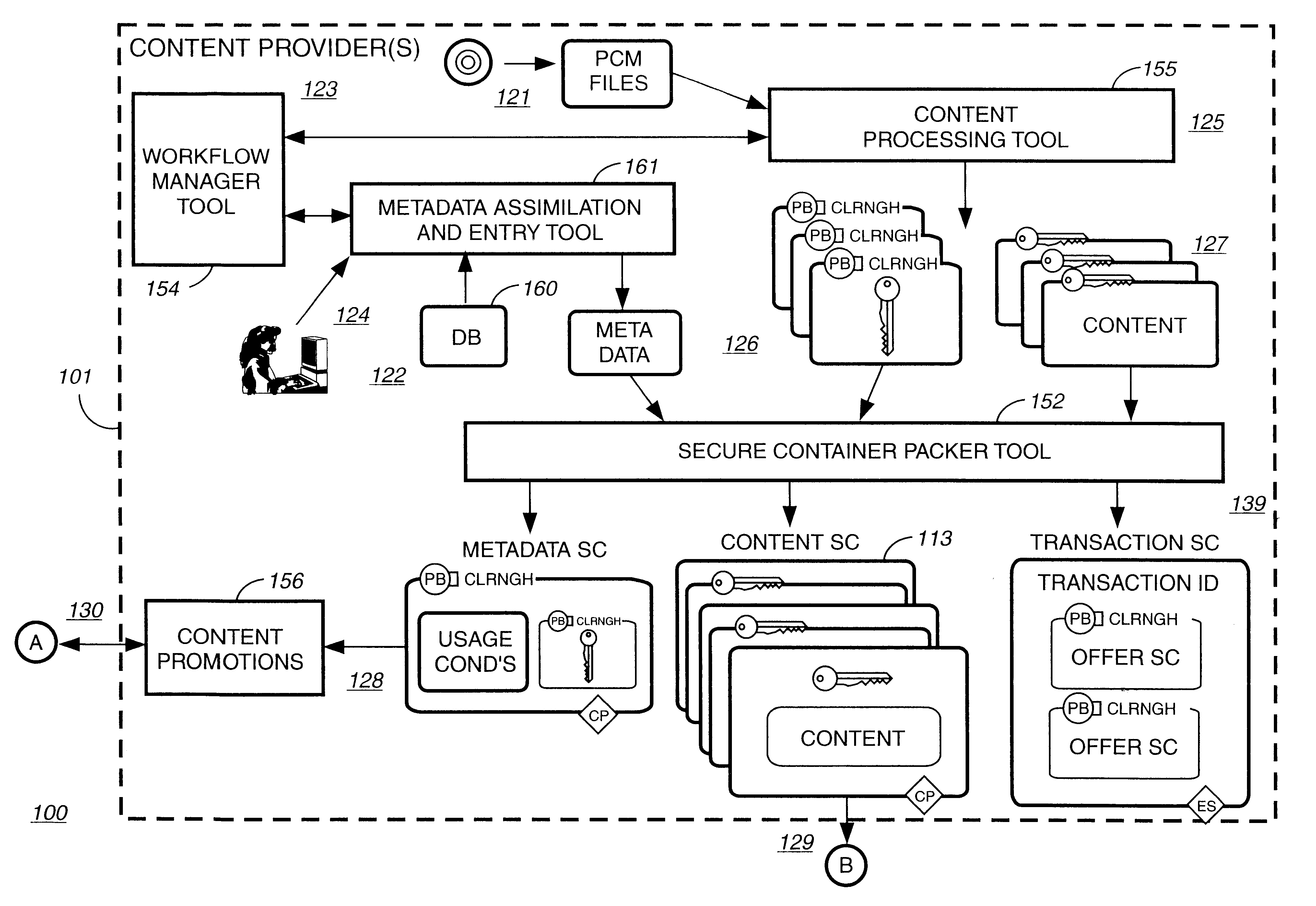
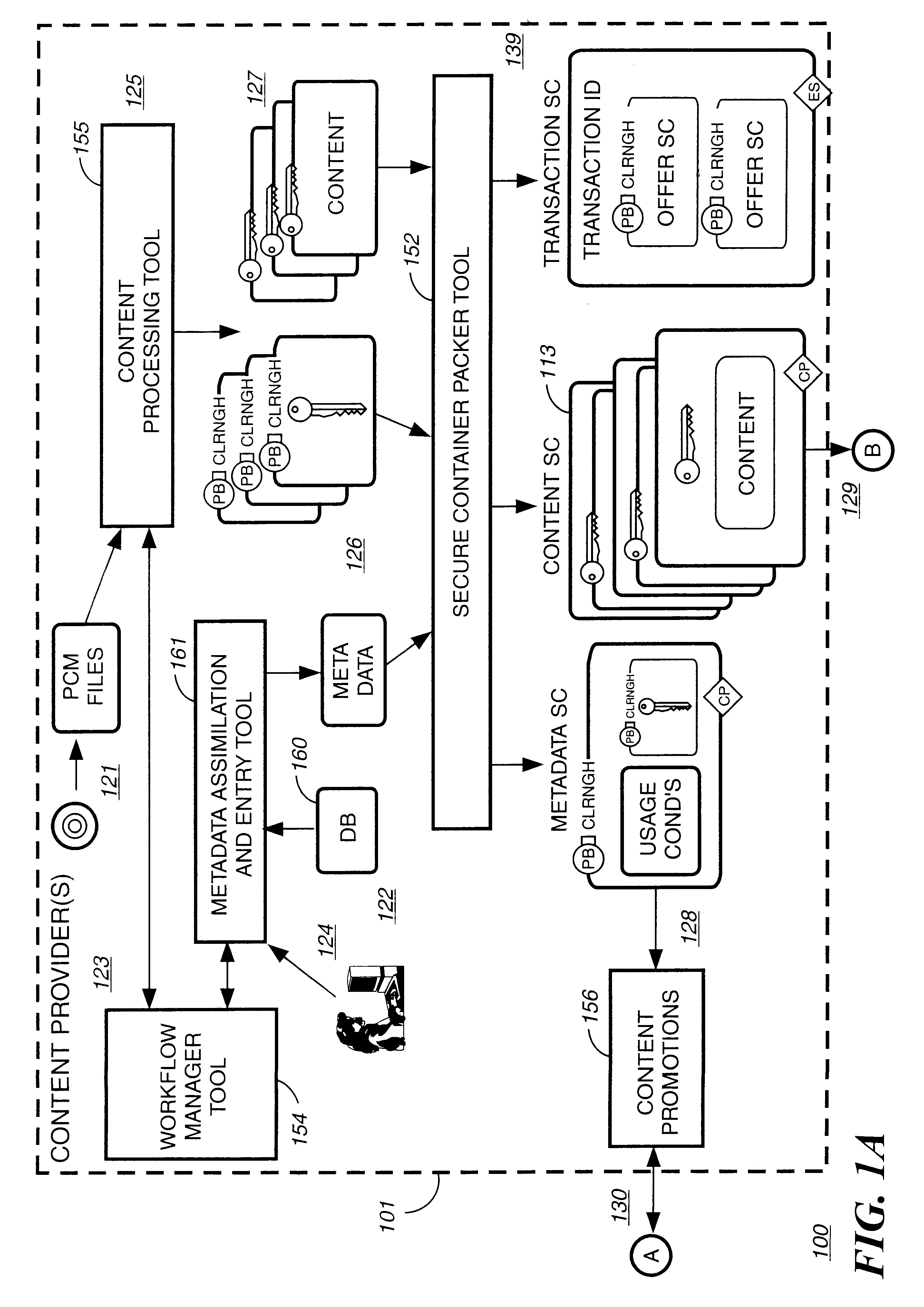
Digital content preparation system
InactiveUS6959288B1Key distribution for secure communicationPublic key for secure communicationDigital contentNumber content
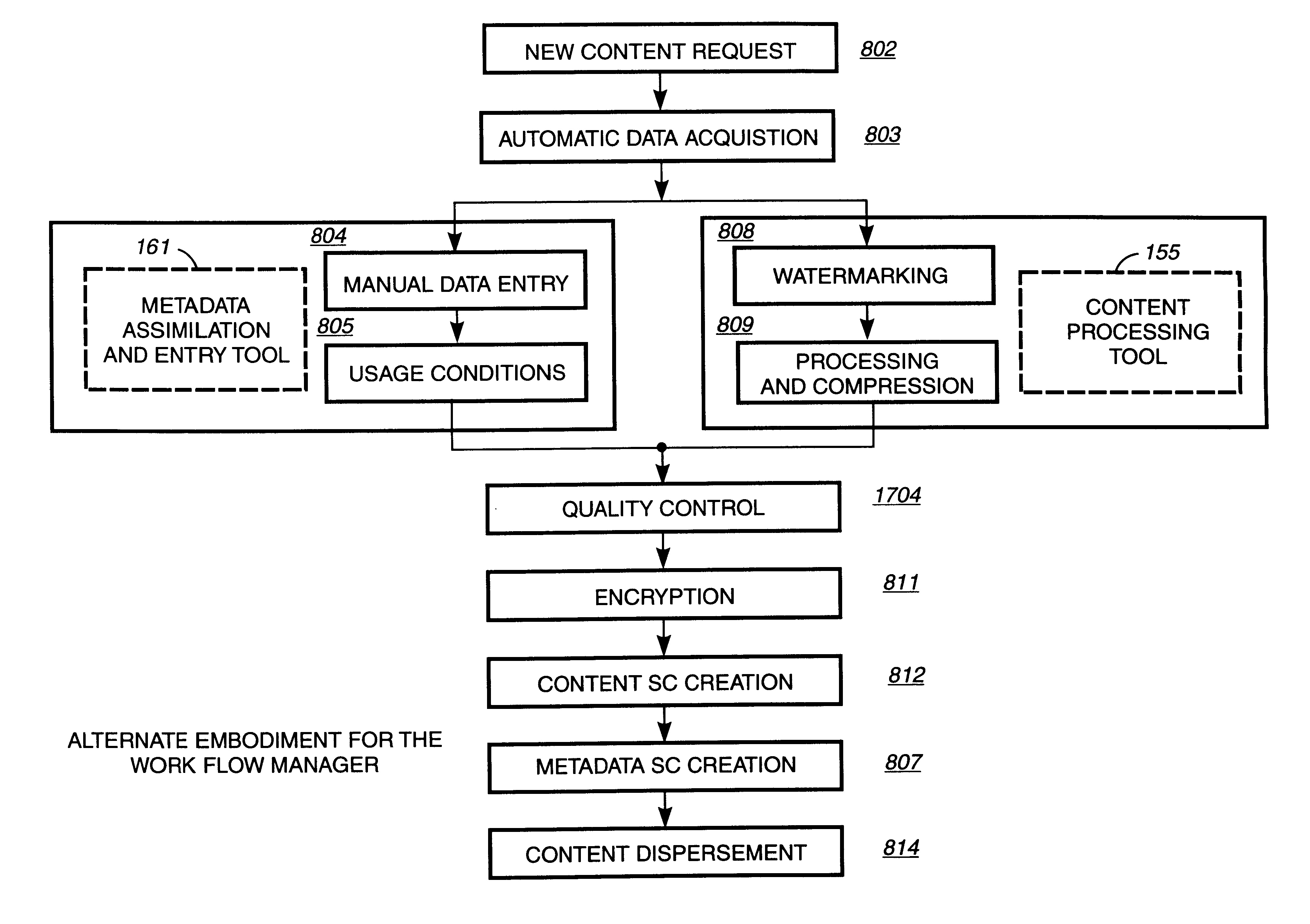
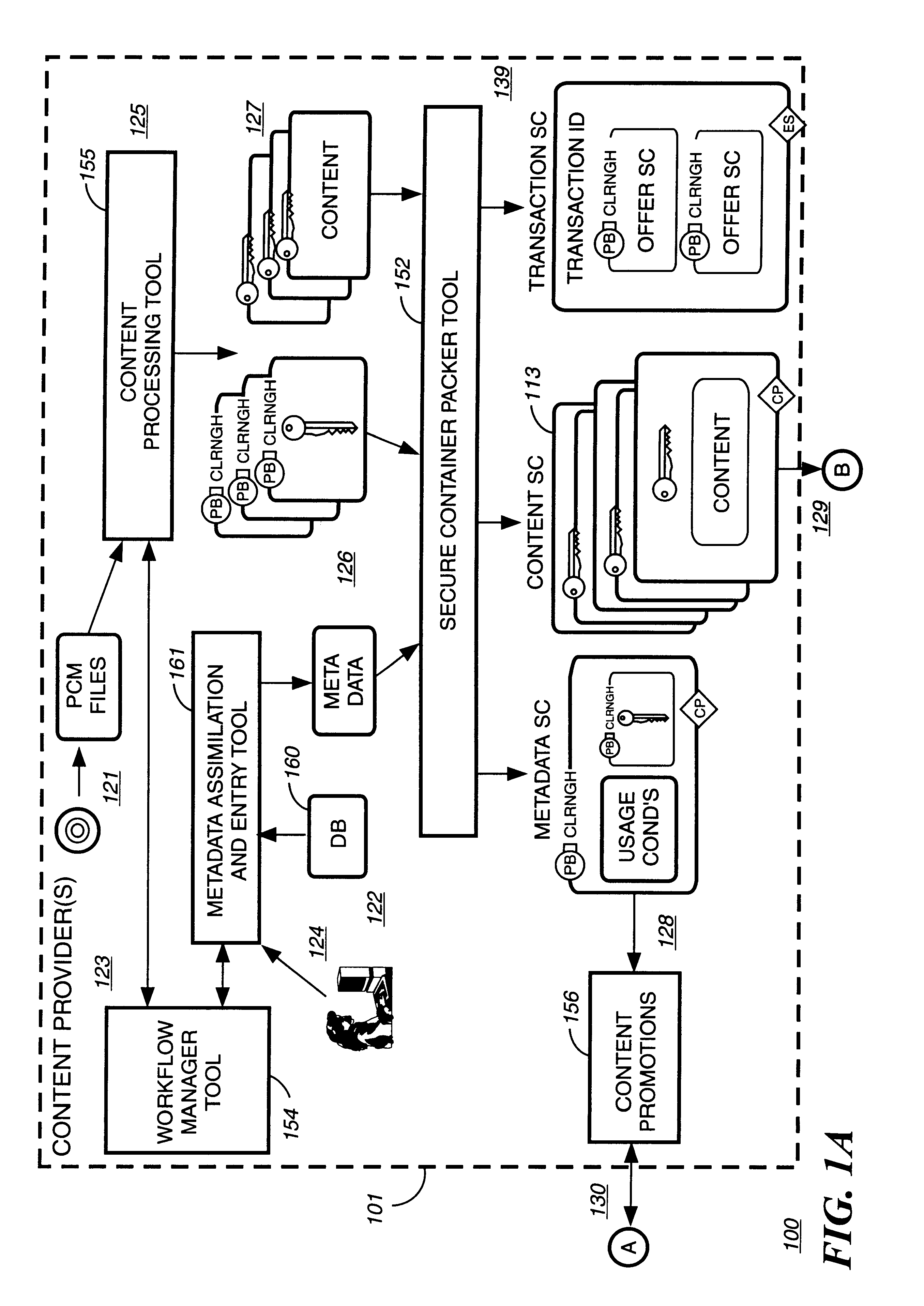
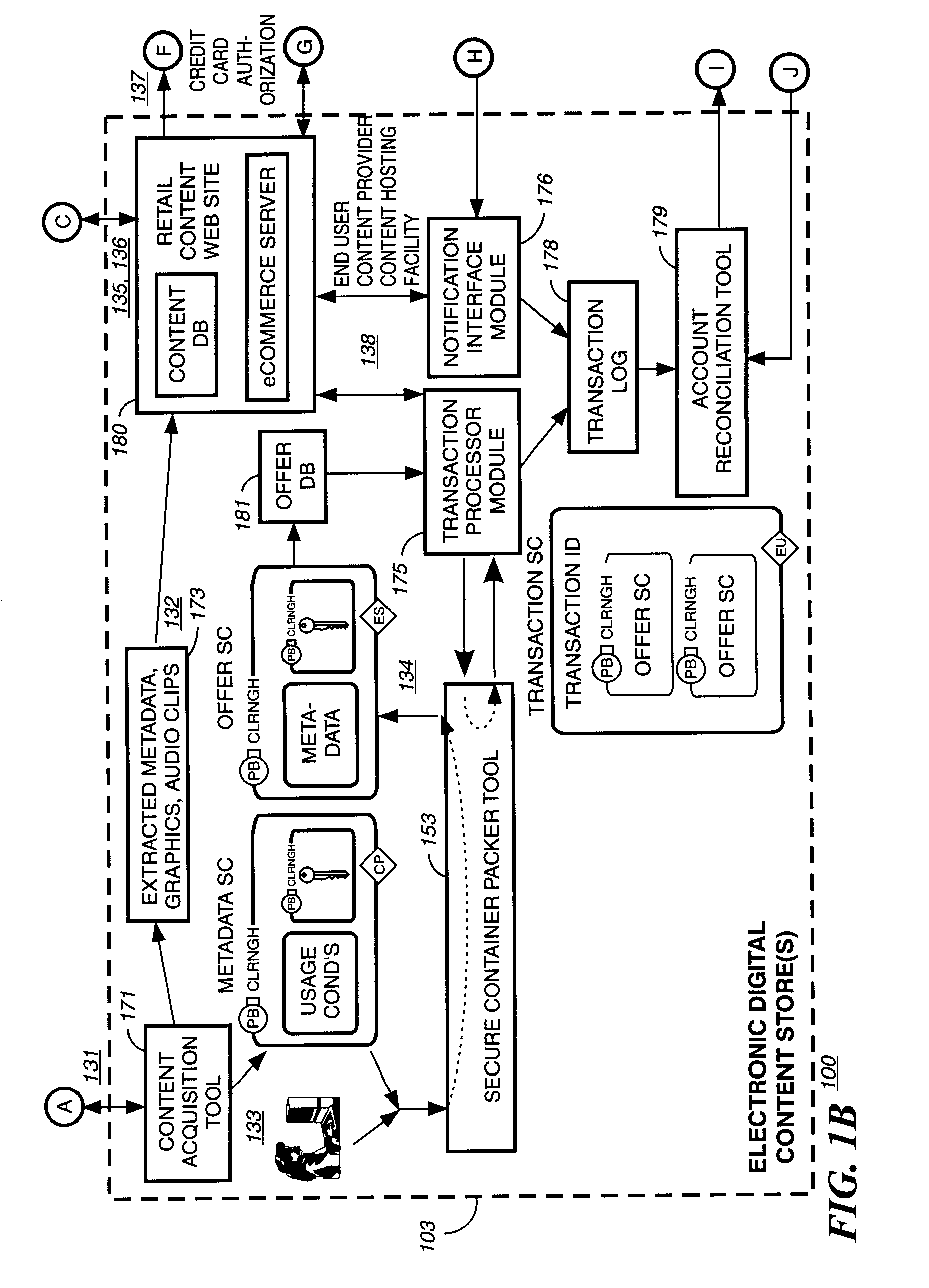
A digital content preparation system that includes a metadata acquisition tool for acquiring metadata associated with the digital content, and a digital content processor for processing the digital content by performing at least one of watermarking, encoding, and encrypting. A work flow manager manages processings by the metadata acquisition tool and the digital content processor. In one preferred embodiment, the metadata acquisition tool includes an automatic metadata acquisition tool and a manual metadata acquisition tool, and the digital content processor includes an encoder and an encrypter. The present invention also provides a method for preparing digital content. According to the method, metadata associated with the digital content is acquired, and the digital content is processed by at least one of watermarking, encoding, and encrypting. Processings in the acquiring step and the processing step are managed. In a preferred method, the acquiring step includes automatically retrieving at least a portion of the metadata and allowing manual entry of at least a portion of the metadata, and the processing step includes encoding the digital content and encrypting the encoded digital content.
Owner:IBM CORP
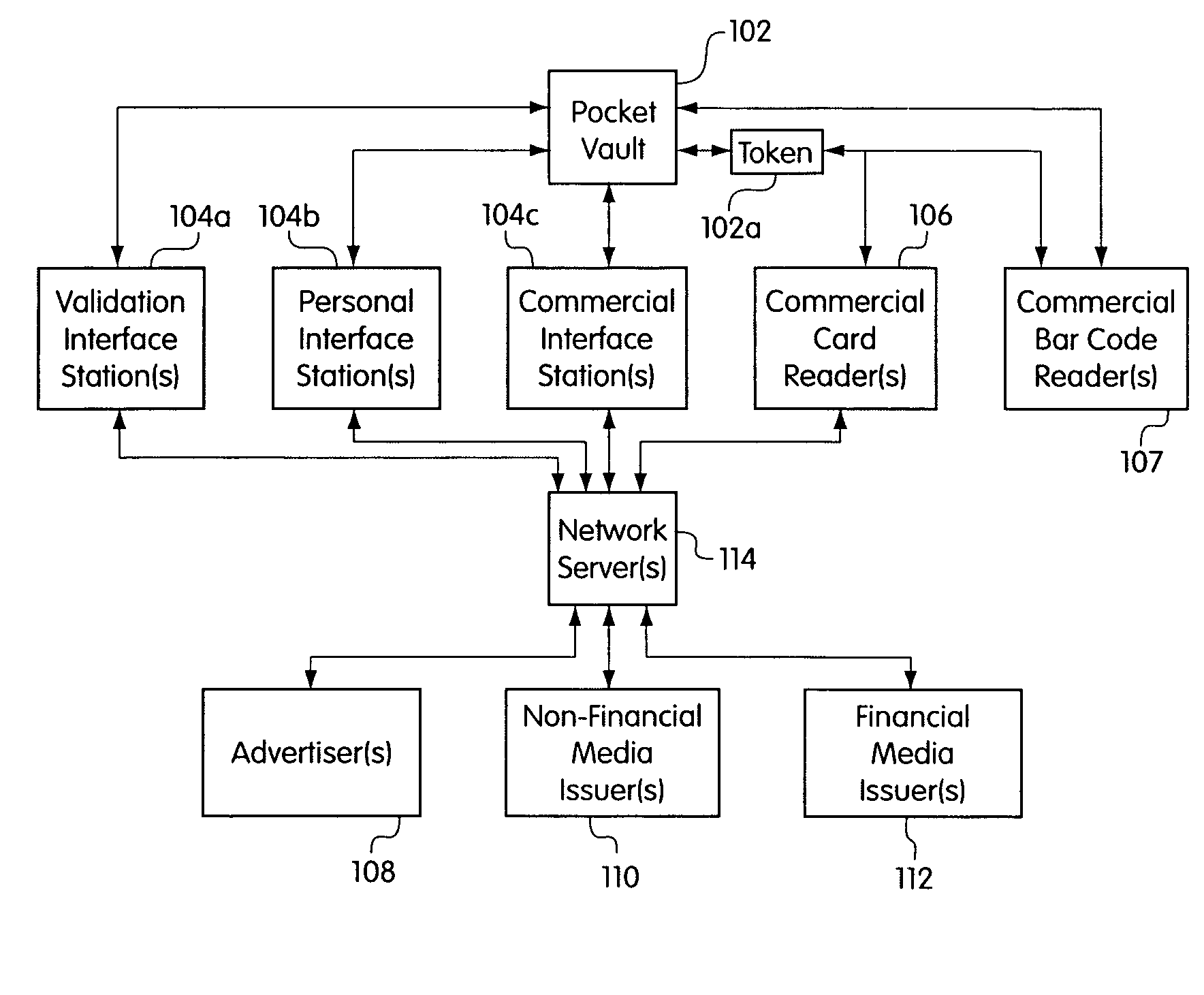
Portable electronic authorization system and method
Owner:KIOBA PROCESSING LLC
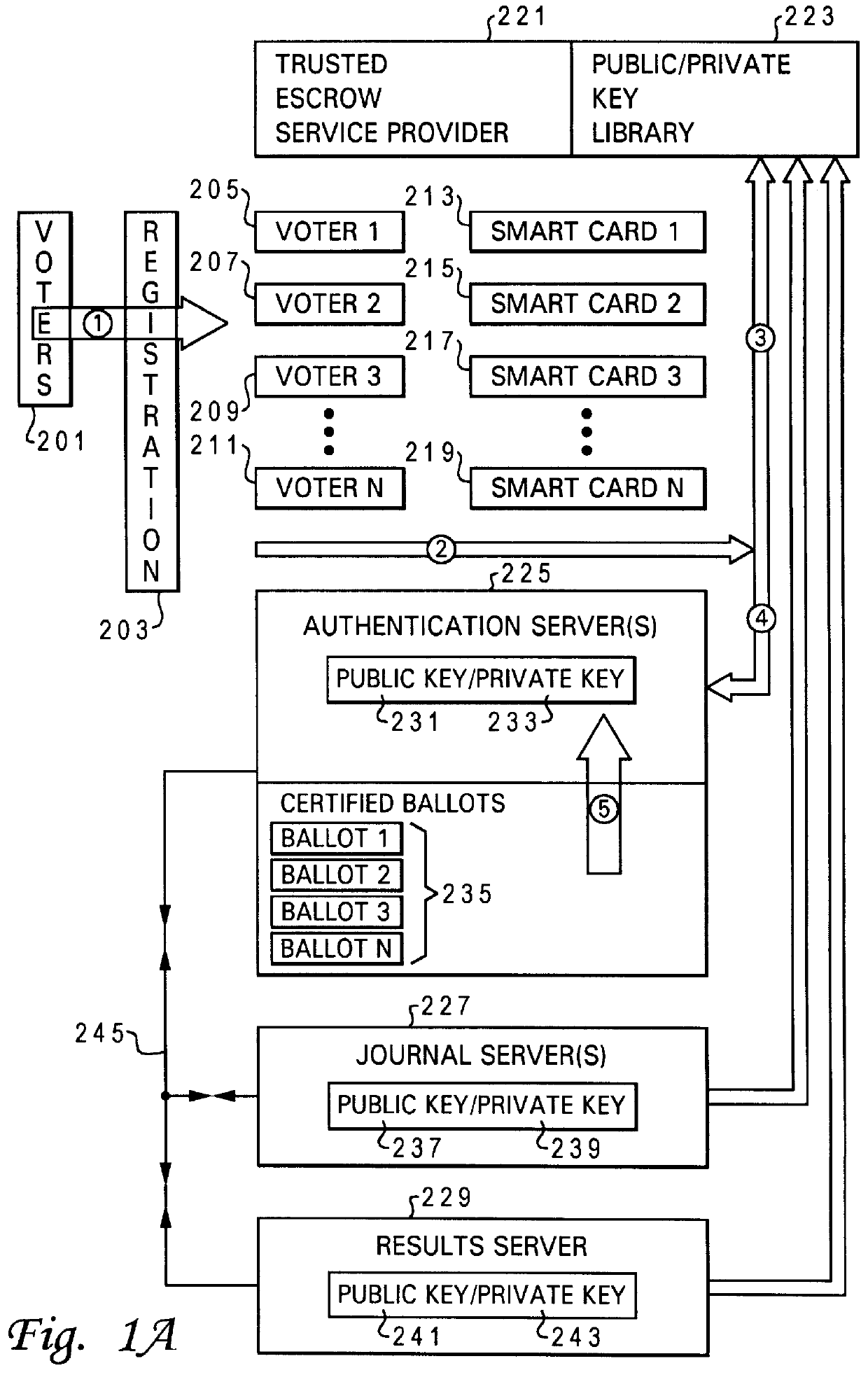
Method and system for secure computer moderated voting
InactiveUS6081793AVoting apparatusMultiple keys/algorithms usageData processing systemAuthentication server
A method and system is provided for improved electronic voting. The system optionally allows paper type ballots to be utilized. A plurality of cryptographic routines are utilized in a distributed data processing system to maximize the privacy of both the voter's identity and the content of completed ballots. An authentication server is utilized to interact with a voter to issue electronic ballots and receive completed electronic ballots in a manner which determines the authenticity of the identification of the voter, while maintaining the content of the completed ballot confidential. The distributed data processing system further includes a results server which tabulates the content of completed ballots in a manner which maintains the identity of the voters associated with the particular ballots confidential. The distributed data processing system may further include a journal server which records completed ballots, in a manner which facilitates the challenge of ineligible votes and the correction of erroneous votes.
Owner:LENOVO PC INT
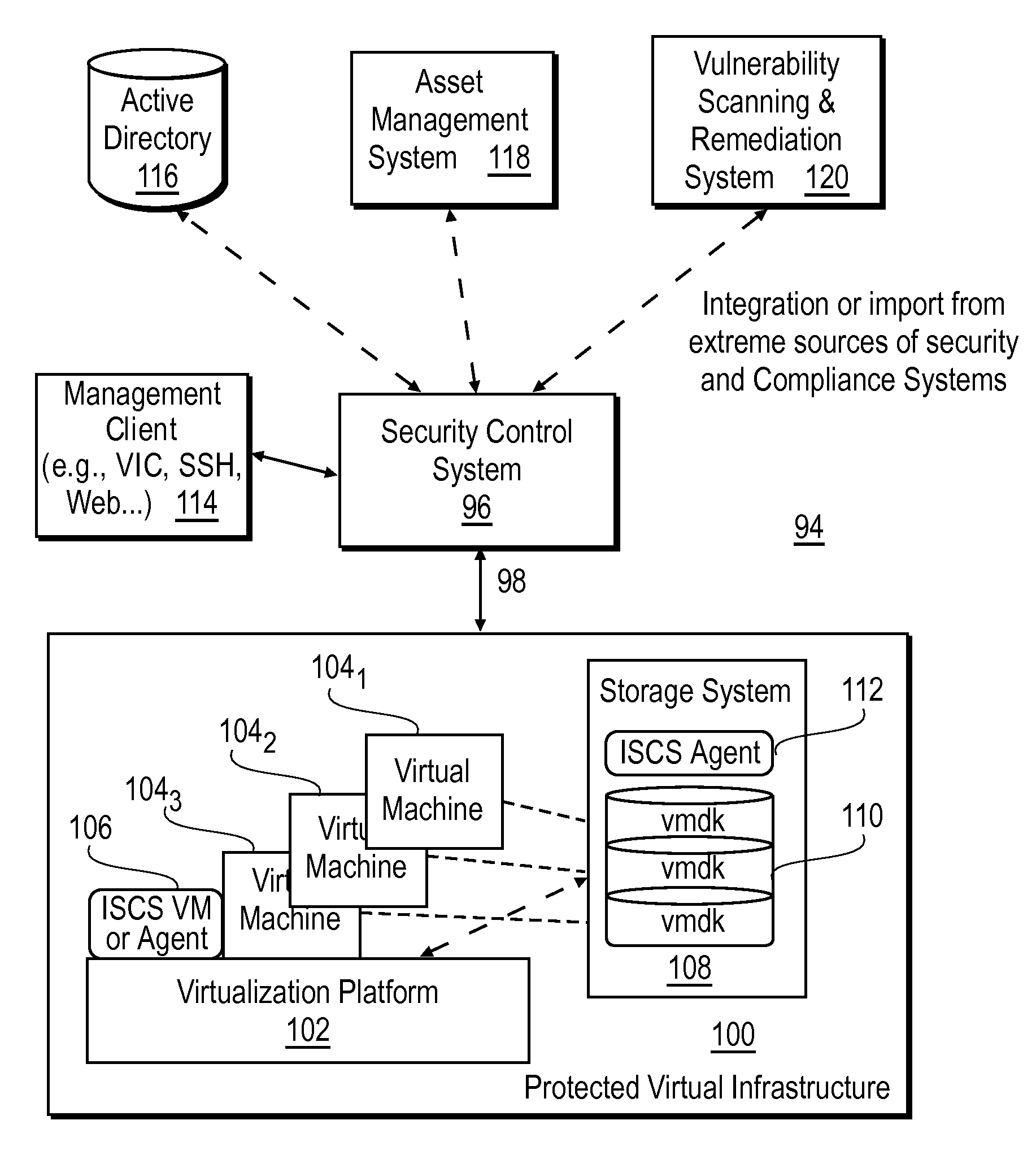
Intelligent security control system for virtualized ecosystems
ActiveUS20100169948A1Digital data processing detailsPublic key for secure communicationObject handlingVirtualization
Resources of a virtualized ecosystem are intelligently secured by defining and analyzing object handling security control information for one or more logical resources in the virtualized ecosystem and deriving therefrom object properties for each of the logical resources involved in the execution of a virtual machine in any given context within the virtualized ecosystem.
Owner:HYTRUST
Communication device and communication method
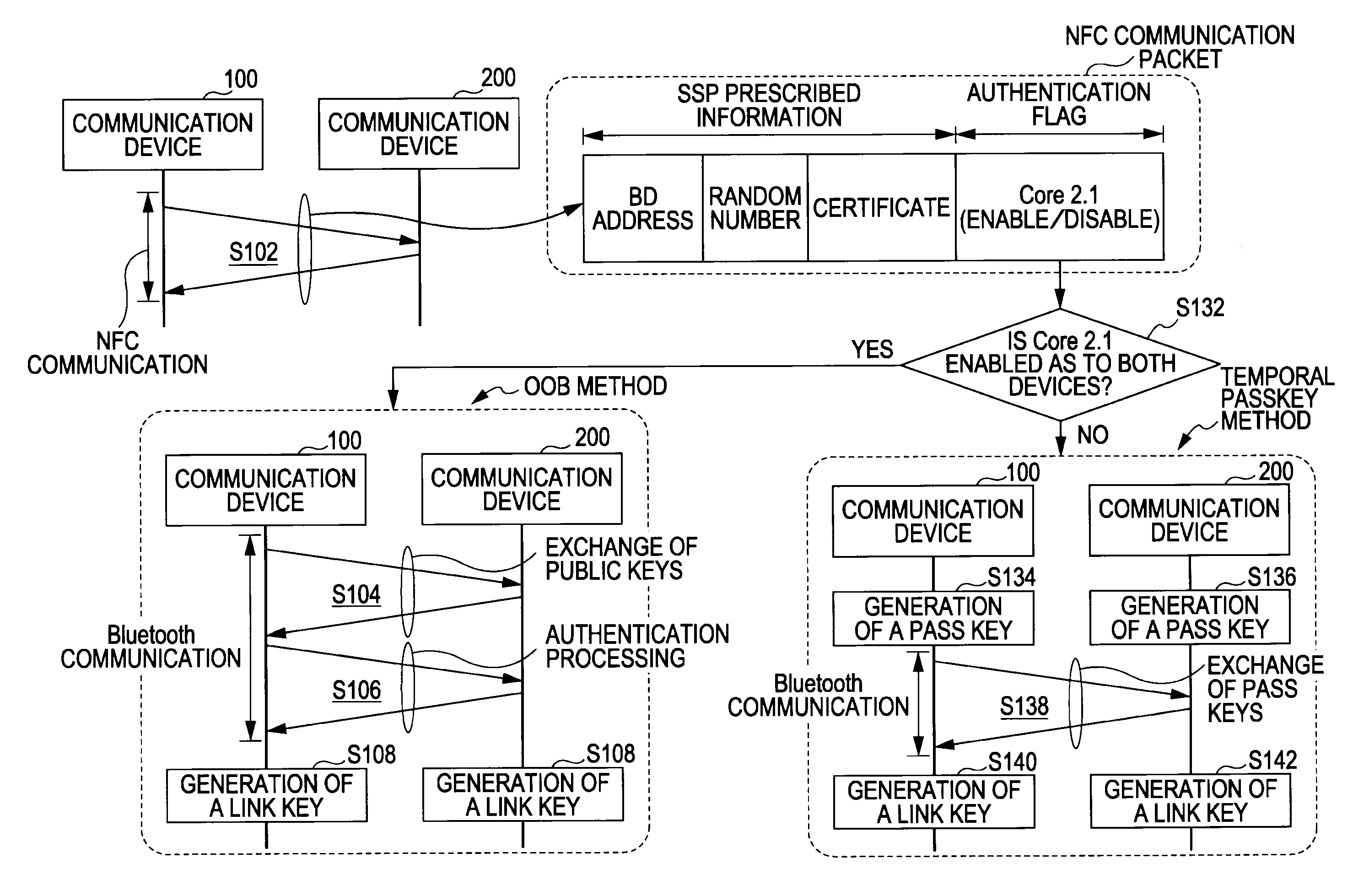
ActiveUS20090222659A1Reduce user burdenReduce the burden onKey distribution for secure communicationPublic key for secure communicationComputer hardwareCommunication unit
A communication device for performing communication by employing first and second communication units, includes: a reception unit for receiving a communication packet including a random number generated for every connection with another communication device, a certificate calculated with the random number, and authentication method information indicating whether or not an authentication method at the second communication unit is compatible with the public key system, through the first communication unit; and a method determining unit for determining whether or not an originator of the communication packet accepts public key encryption based on the authentication method information included in the communication packet; wherein in a case of the method determining unit determining that the originator of the communication packet does not accept the public key system, the random number included in the communication packet is replied to the originator as the identification information of the device itself.
Owner:SONY CORP
Internet-based shared file service with native PC client access and semantics and distributed access control
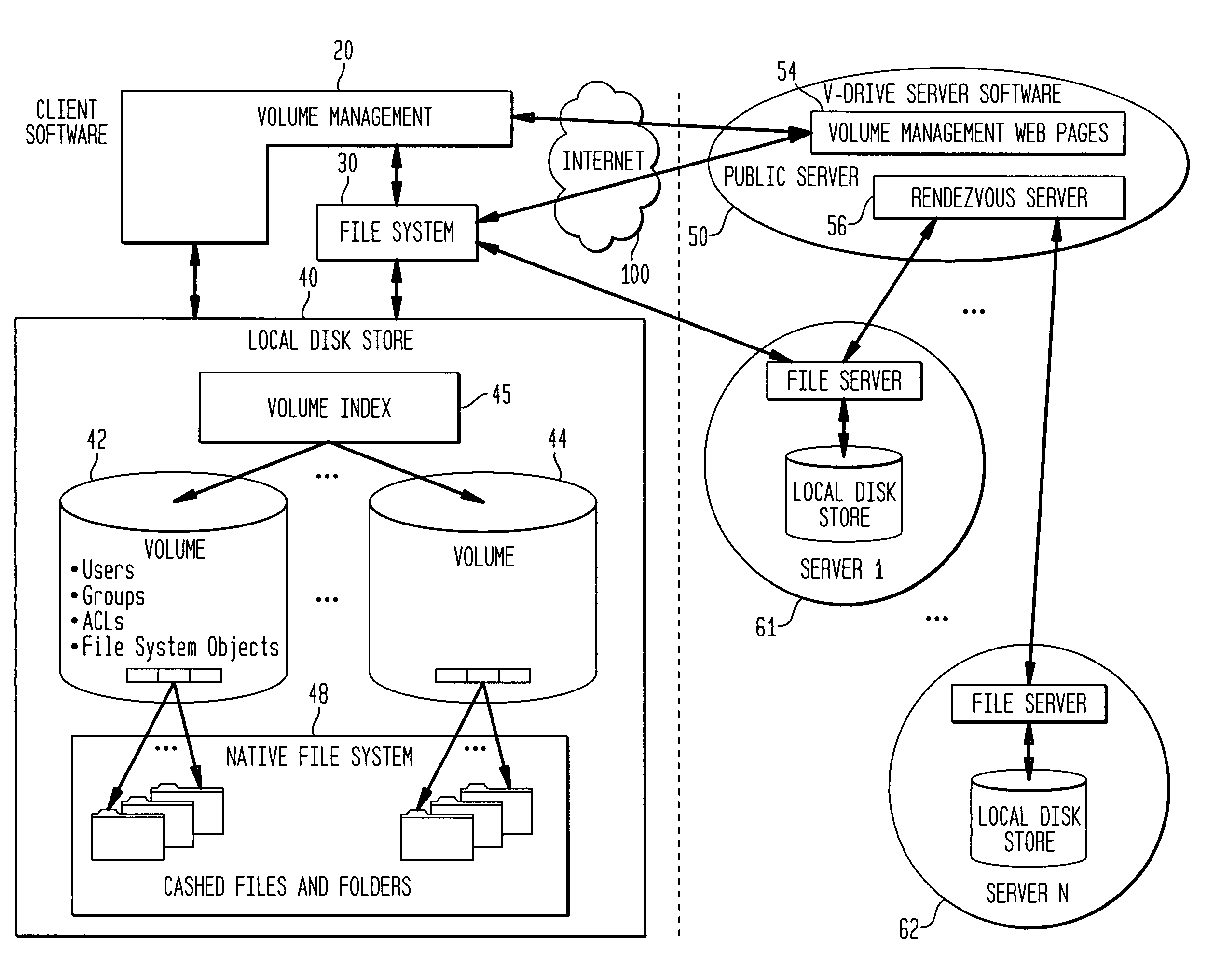
InactiveUS7136903B1Web data retrievalPublic key for secure communicationWide area networkAccess control
A multi-user file storage service and system enable each user of a pre-subscribed user group to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Additionally, an encrypted key is transferred from the file server node to a particular client node via a secure channel. The encrypted key uses an encryption function and a decryption function not known locally at the remote file server. Furthermore, both privileged access control rights and file sharing mode access control to a particular file of the group of files are delegated to one or more distributed nodes other than the remote file server node which provides the data.
Owner:GOOGLE LLC
System and methods for maintaining and distributing personal security devices
InactiveUS7111172B1Key distribution for secure communicationPublic key for secure communicationInternet privacyClient-side
This invention relates to methods and apparatus for securely accessing and providing information including the use of a personal security device on a client where the client is subject to compromise.
Owner:EMC IP HLDG CO LLC
Interactive multimedia advertising and electronic commerce on a hypertext network
A system and method for providing targeted, interactive, multimedia advertisements and electronic commerce capability on a hypertext network. Advertising software from a server is loaded on a user's client computer through a browser at the user's request. The display screen of the client computer is partitioned into a browser area, which retains the full functionality of the underlying browser, and advertising area. Controls affecting the presentation and content of the advertisements streamed from the server to the client computer are available to the user in the advertising area, as are secure purchase and electronic coupon controls.
Owner:TWITTER INC
Server-assisted regeneration of a strong secret from a weak secret
InactiveUS7359507B2Resist attackKey distribution for secure communicationPublic key for secure communicationPasswordCipher
Methods for regenerating a strong secret for a user, based on input of a weak secret, such as a password, are assisted by communications exchanges with a set of independent servers. Each server holds a distinct secret value (i.e., server secret data). The strong secret is a function of the user's weak secret and of the server secret data, and a would-be attacker cannot feasibly compute the strong secret without access to both the user's weak secret and the server secret data. Any attacker has only a limited opportunity to guess the weak secret, even if he has access to all messages transmitted in the generation and regeneration processes plus a subset (but not all) of the server secret data.
Owner:RSA
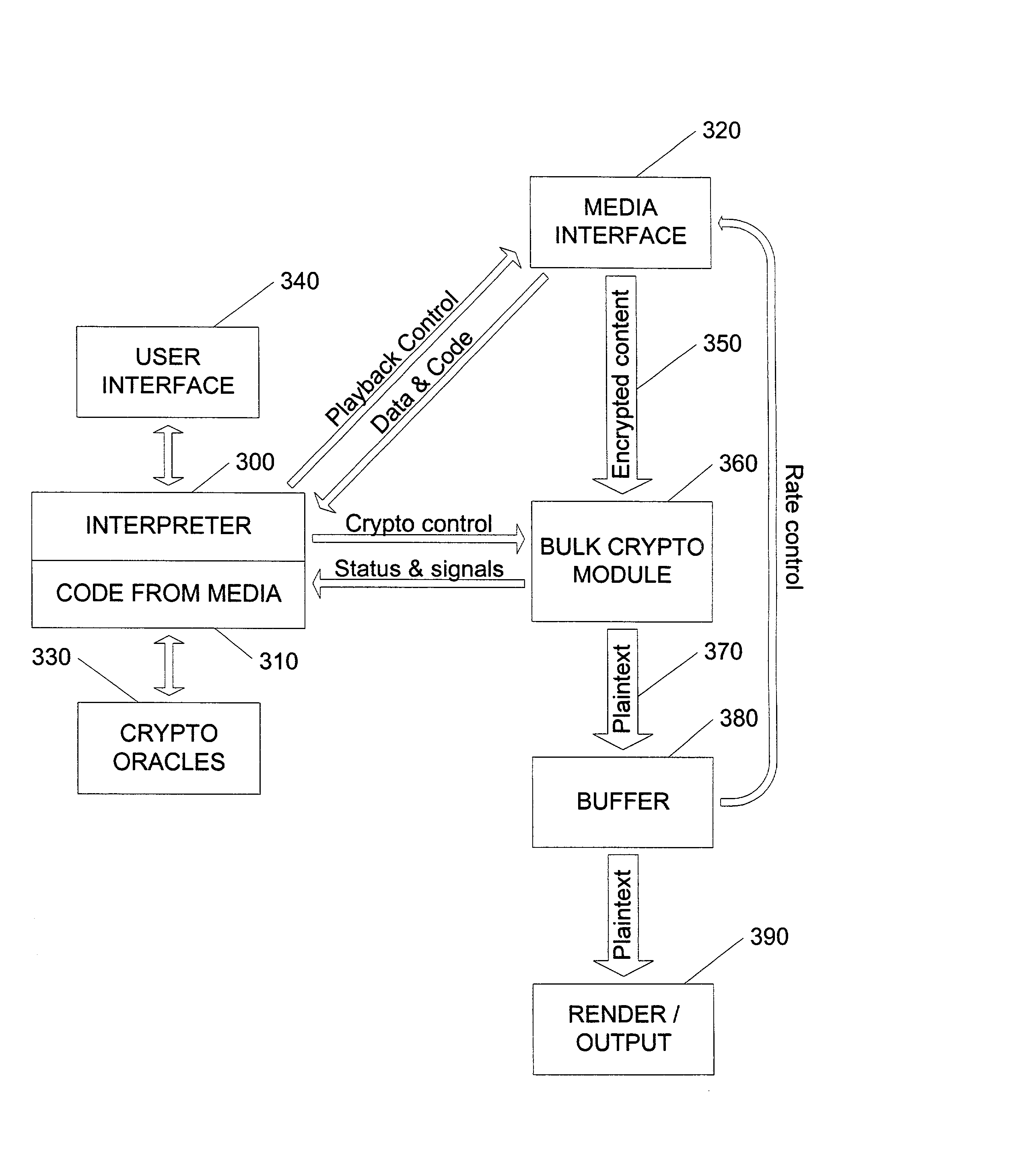
Content security layer providing long-term renewable security
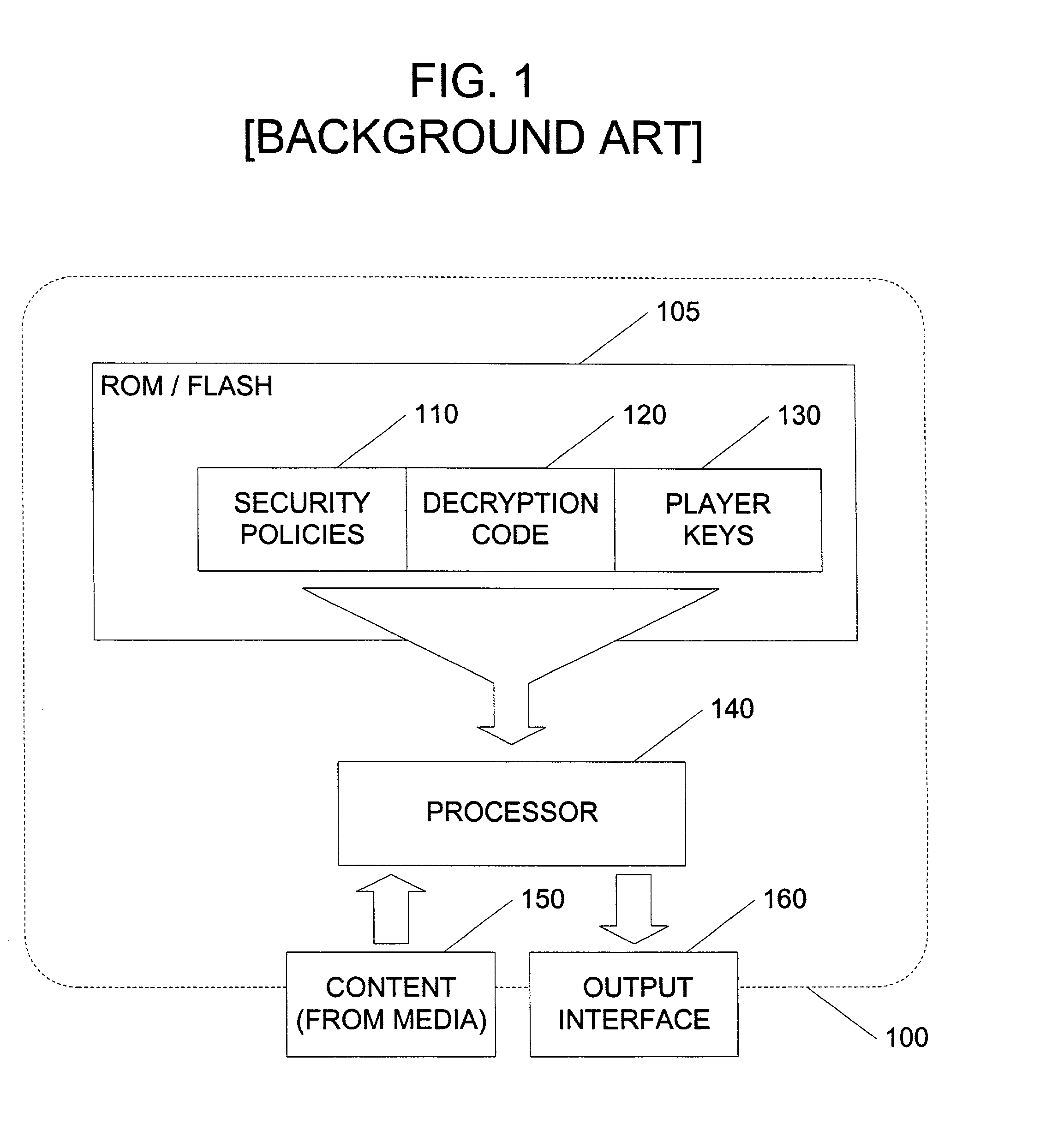
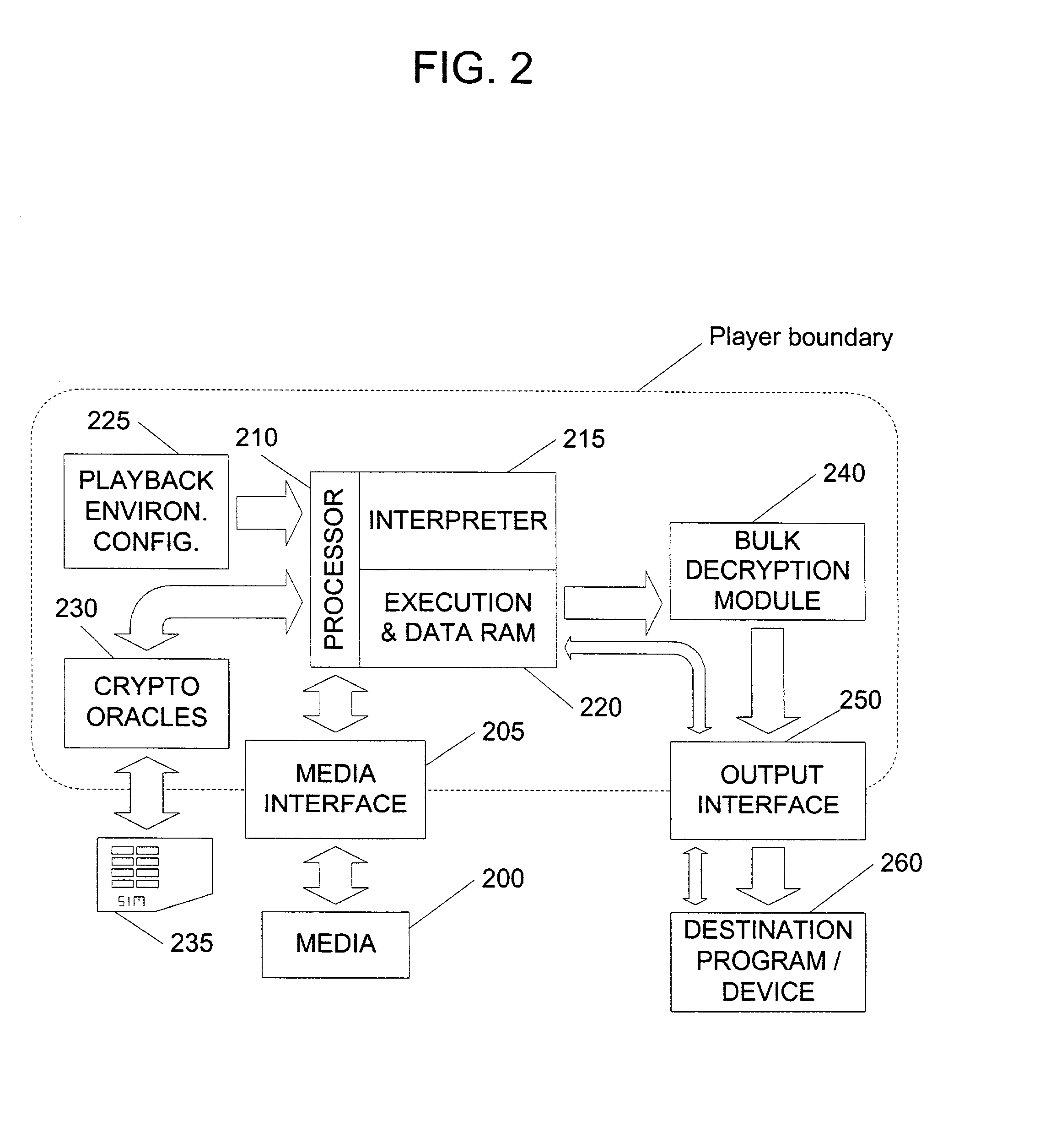
InactiveUS20020141582A1Unparalleled flexibilityIncrease sampling rateTelevision system detailsKey distribution for secure communicationAttackMediaFLO
In an exemplary embodiment, digital content is mastered as a combination of encrypted data and data processing operations that enable use in approved playback environments. Player devices having a processing environment compatible with the content's data processing operations are able to decrypt and play the content. Players can also provide content with basic functions, such as loading data from media, performing network communications, determining playback environment configuration, controlling decryption / playback, and / or performing cryptographic operations using the player's keys. These functions allow the content to implement and enforce its own security policies. If pirates compromise individual players or content titles, new content can be mastered with new security features that block the old attacks. A selective decryption capability can also be provided, enabling on-the-fly watermark insertion so that attacks can be traced back to a particular player. Features to enable migration from legacy formats are also provided.
Owner:ROVI SOLUTIONS CORP
Storage array access control from cloud-based user authorization and authentication
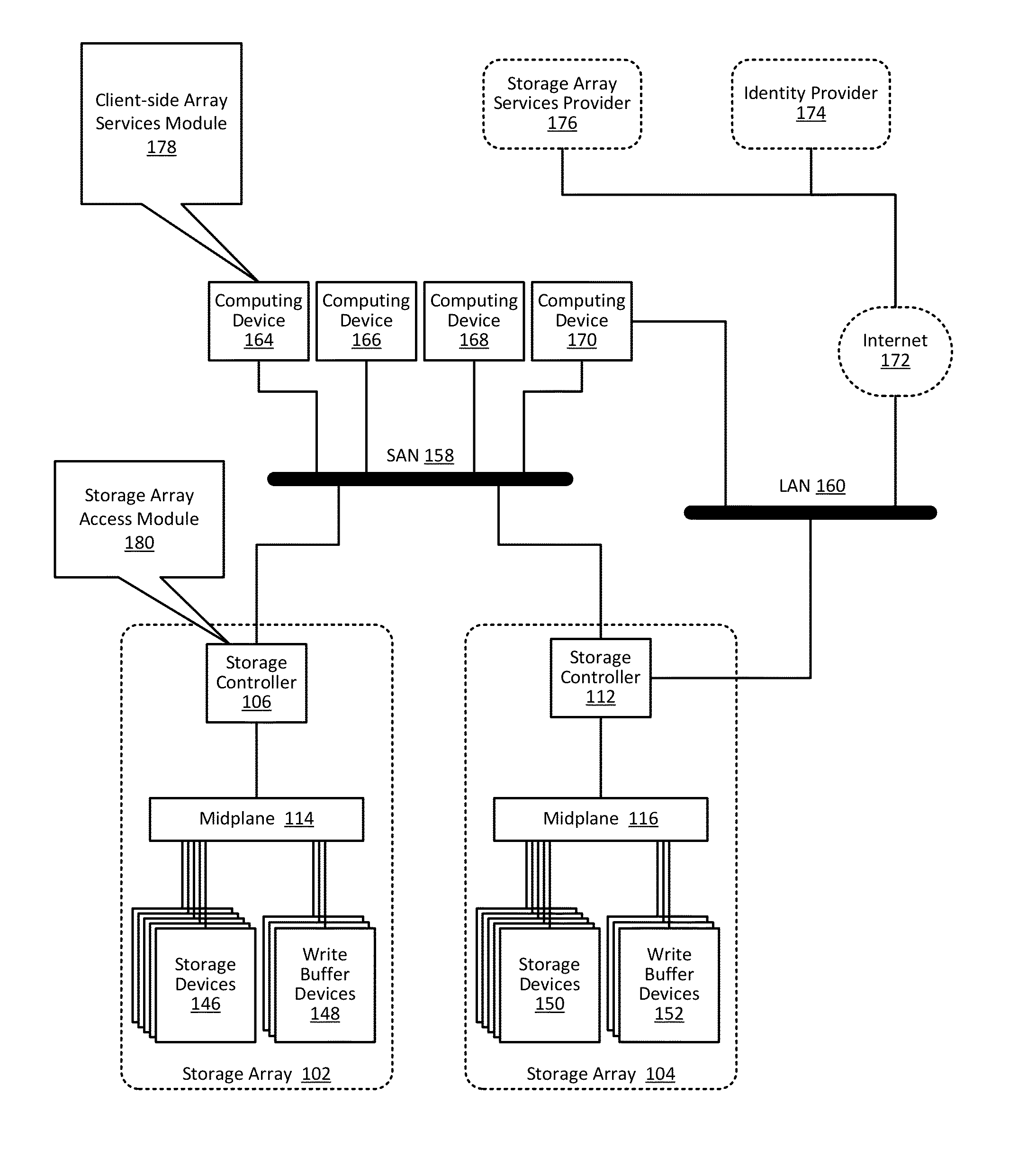
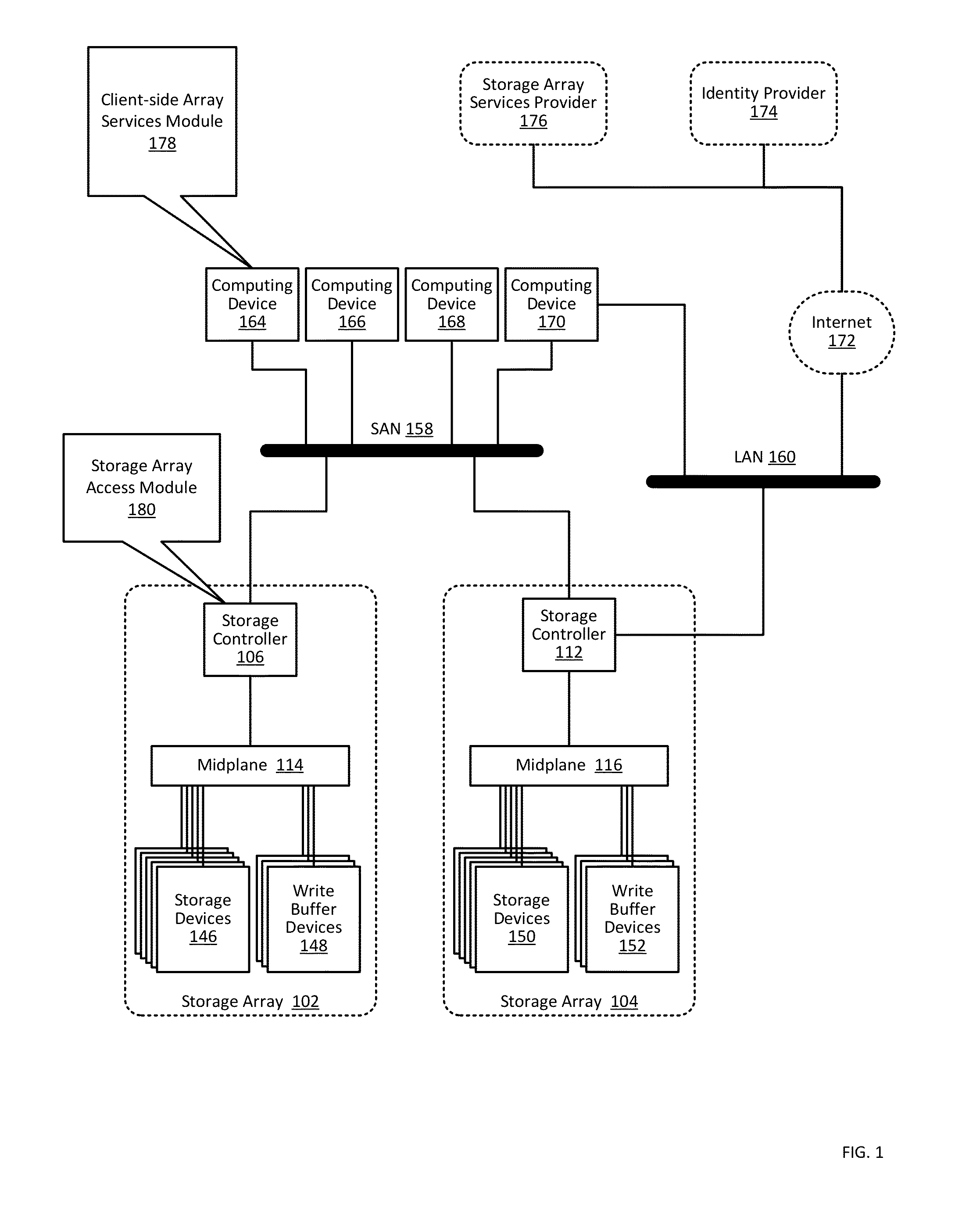
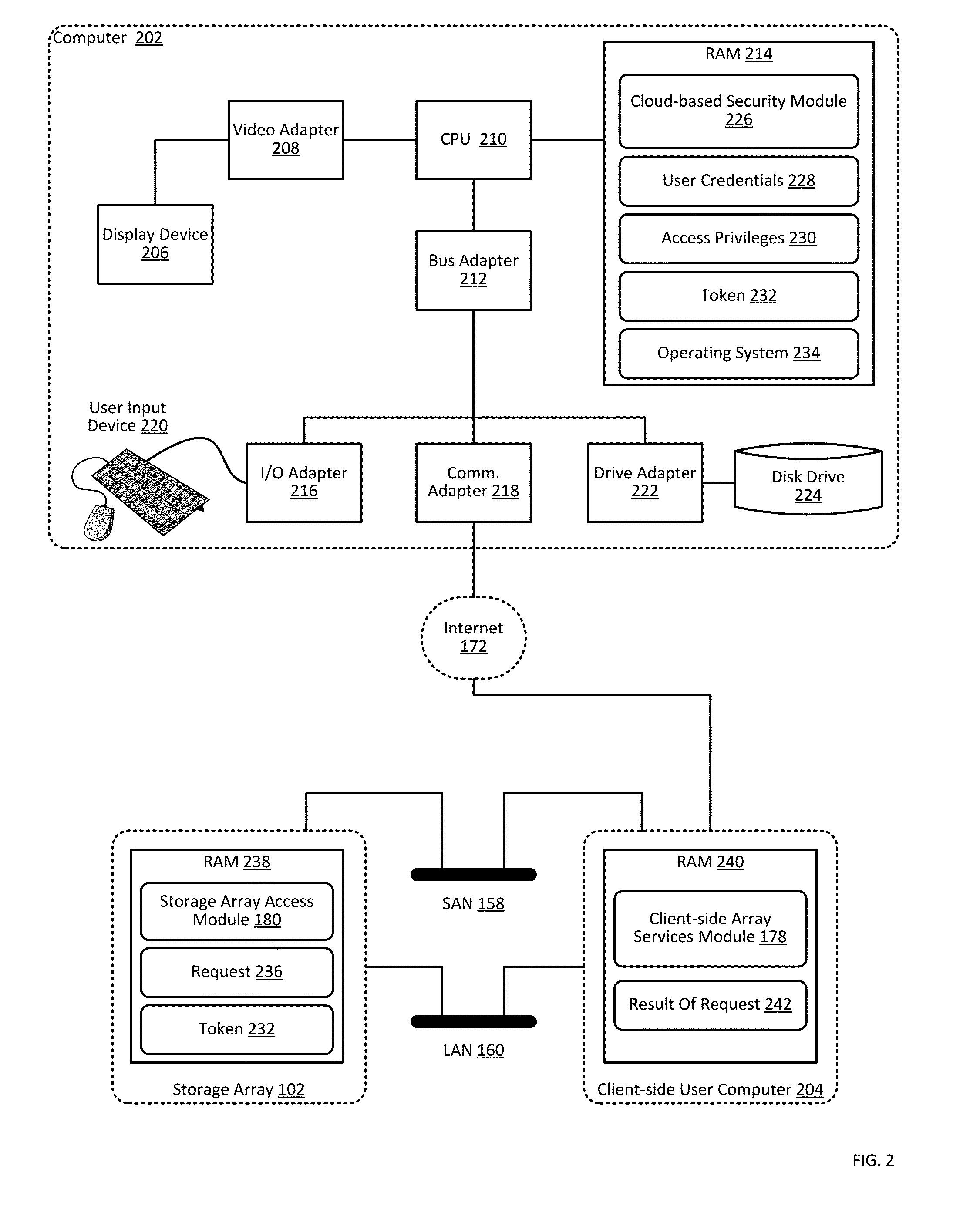
ActiveUS9444822B1Public key for secure communicationDigital data processing detailsCloud baseClient-side
Owner:PURE STORAGE
Tamper-protected hardware and method for using same
ActiveUS20140108786A1Execution of malicious code is preventedPreventing executionKey distribution for secure communicationMultiple keys/algorithms usageTamper proof hardwareComputer module
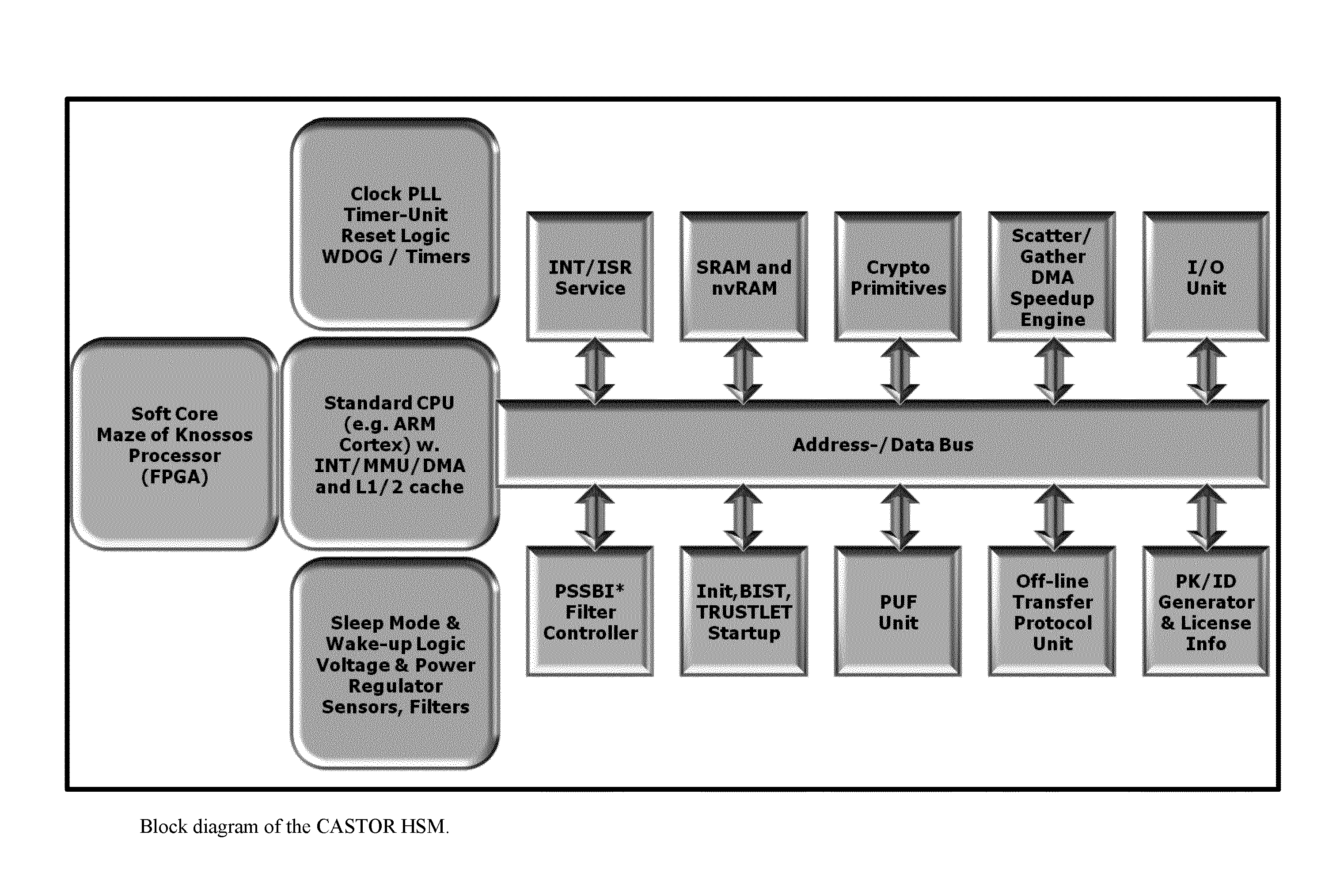
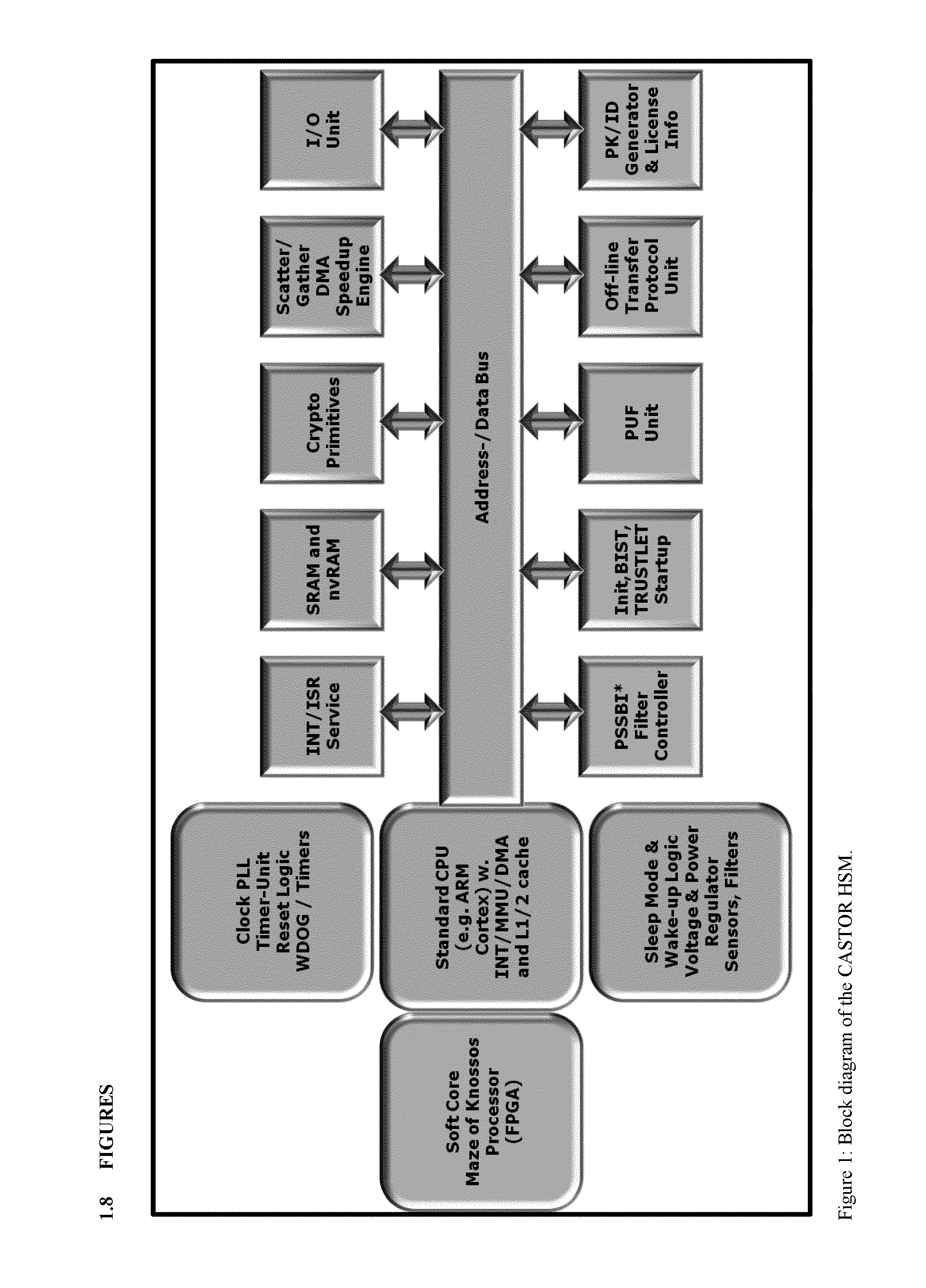
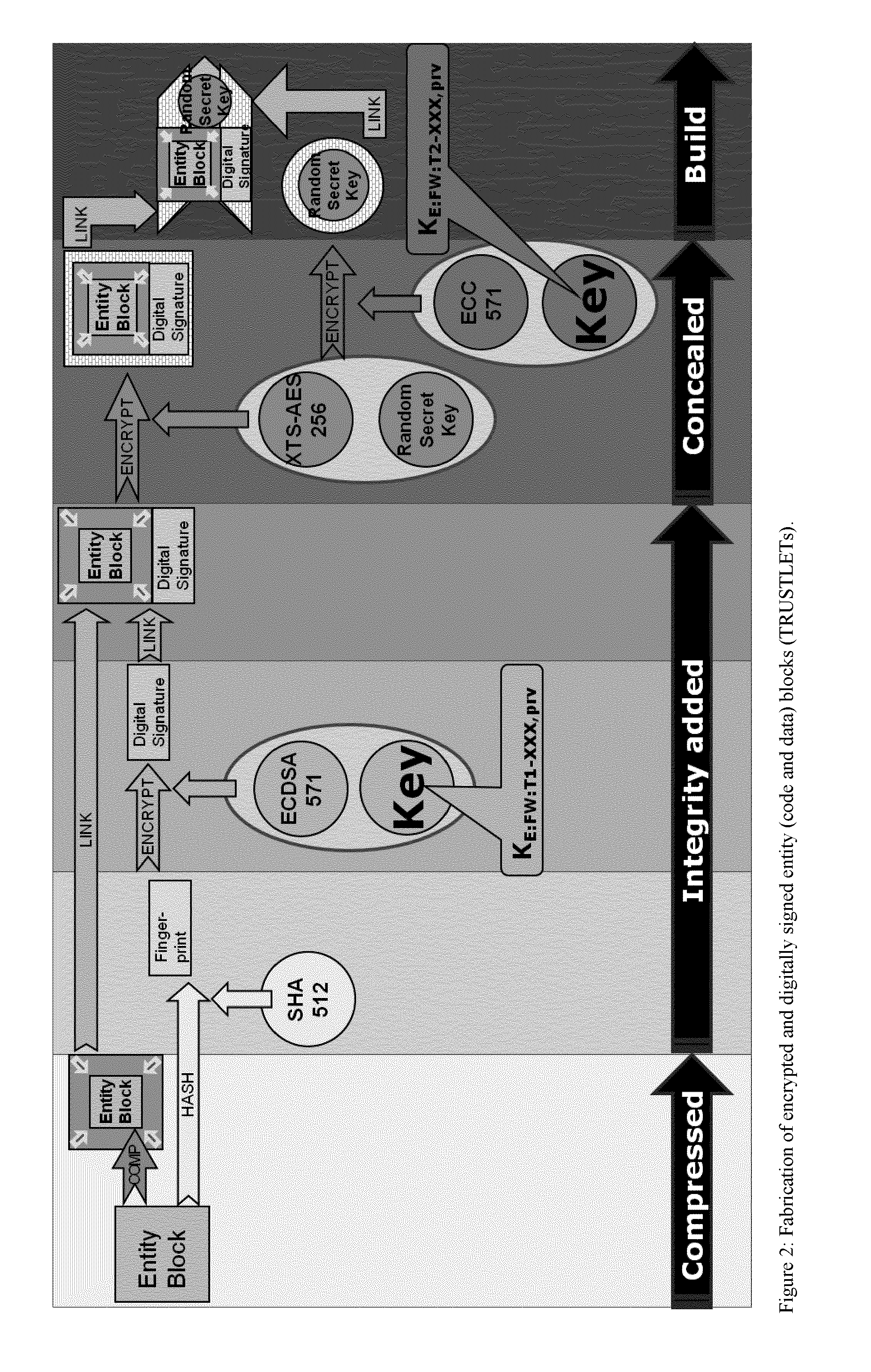
One of the various aspects of the invention is related to suggesting various techniques for improving the tamper-resistibility of hardware. The tamper-resistant hardware may be advantageously used in a transaction system that provides the off-line transaction protocol. Amongst these techniques for improving the tamper-resistibility are trusted bootstrapping by means of secure software entity modules, a new use of hardware providing a Physical Unclonable Function, and the use of a configuration fingerprint of a FPGA used within the tamper-resistant hardware.
Owner:EMSYCON
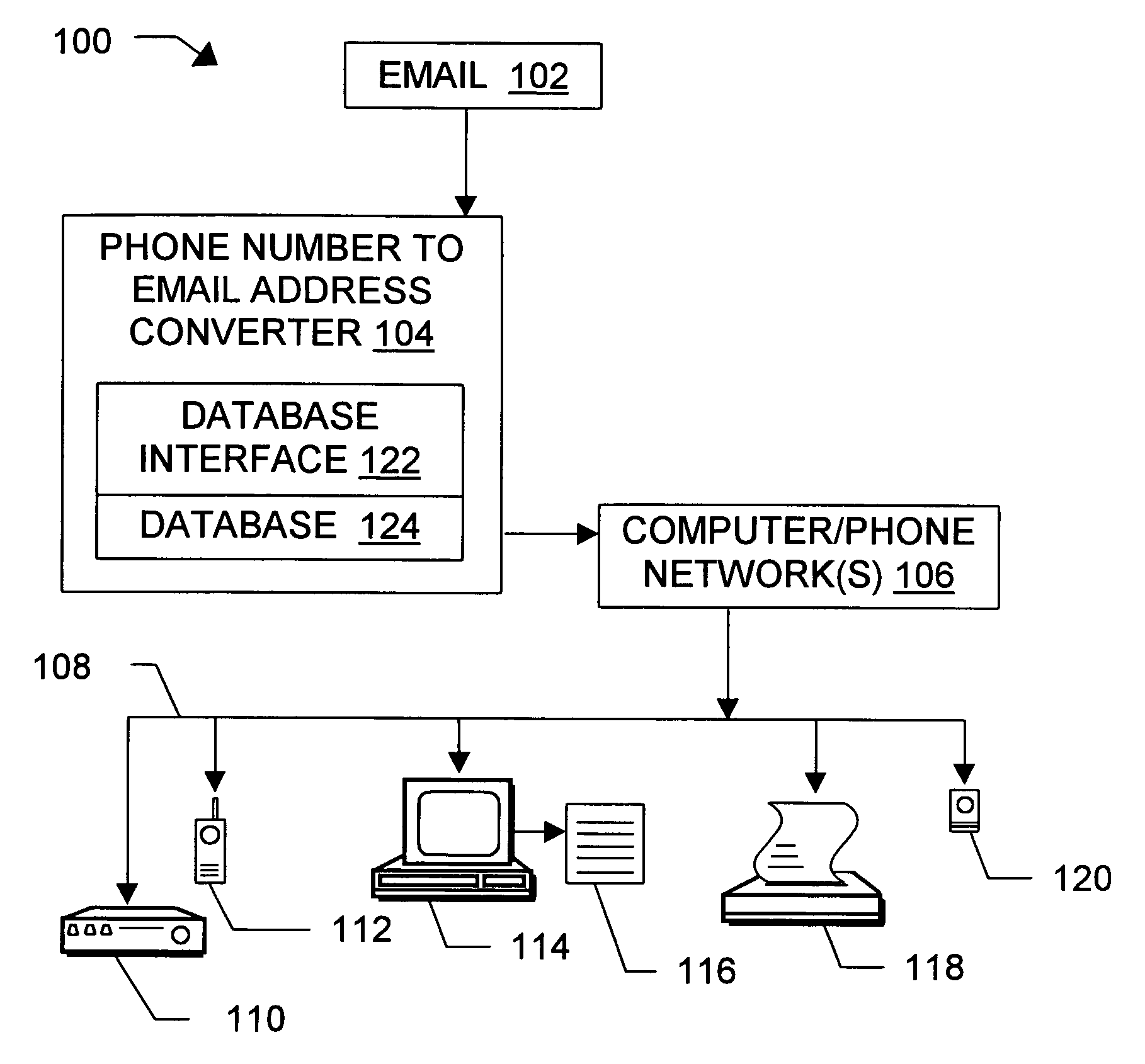
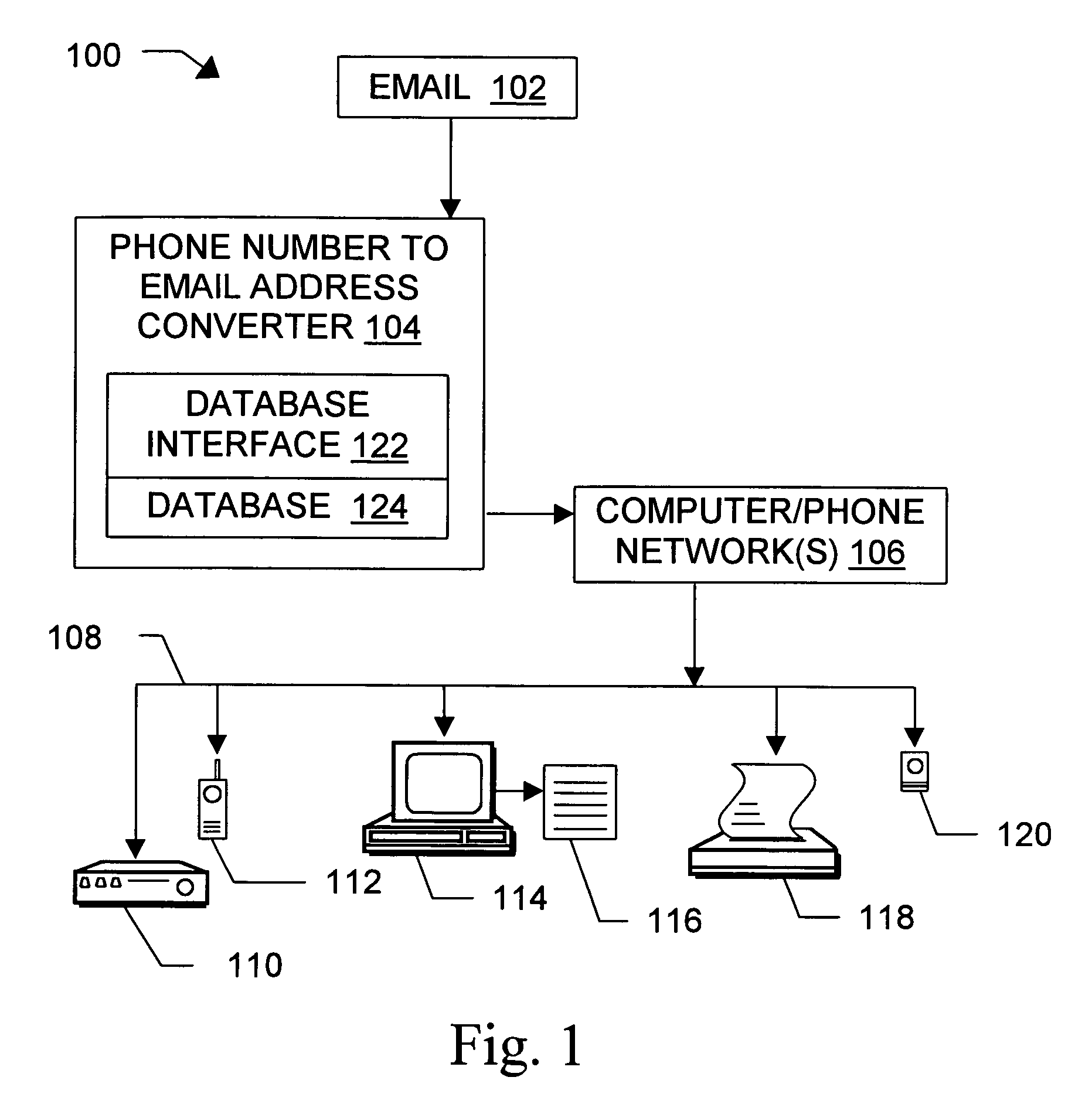
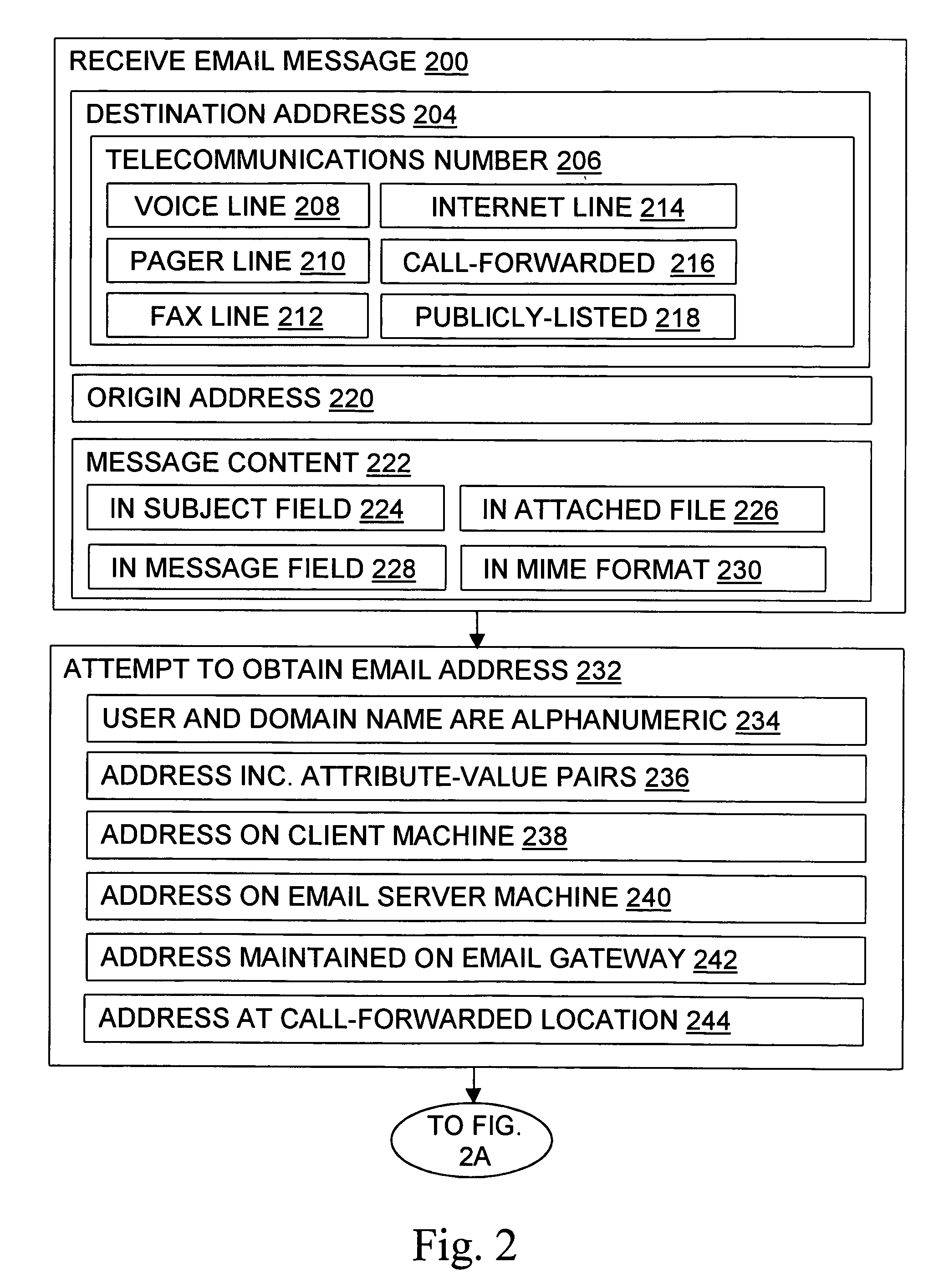
Message routing
InactiveUS6981023B1Easy to getRemove the burdenInterconnection arrangementsPublic key for secure communicationEmail addressSelective calling
Methods, devices, signals, and systems are provided in a message routing architecture which provides improved capabilities for integrating “digital” communication through email messages with “analog” communication through voice and / or fax or pager messages. Email can be addressed using nothing more than a standard telephone or fax number. If the registered owner of the telephone or fax number has a corresponding email address, then the invention converts the telephone or fax number to the email address for delivery and uses standard email delivery systems to deliver the message. If no conventional delivery email address is known, or if the message sender or recipient specify multiple delivery modes, then the email message content is transformed into voice, pager and / or fax content and delivered to the recipient using the telephone or fax number which was specified as the email address. Familiar telecommunications services such as call forwarding and selective call blocking can also be used with messages that originate as email. The invention also supports use of telecommunications numbers as indexes into databases which contain public key certificates, to make it unnecessary for a proposed message recipient to provide its public key expressly in advance to each particular proposed message originator.
Owner:HAMILTON MICHAEL +1
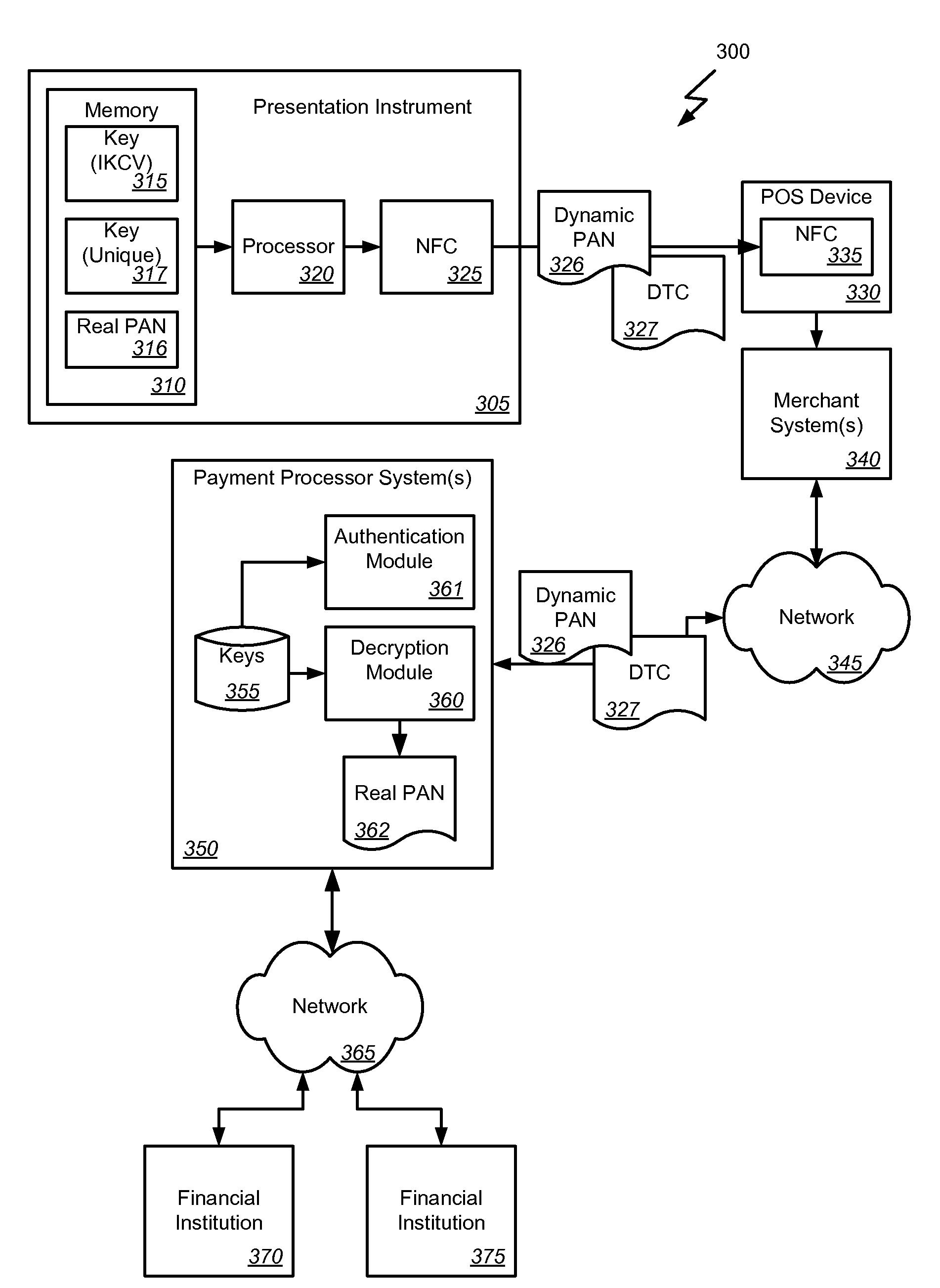
Dynamic primary account number (PAN) and unique key per card
Methods, systems, and machine-readable media are disclosed for handling information related to a financial transaction including utilizing dynamic cryptograms. According to one embodiment, a method of processing a financial transaction related to a financial account can comprise detecting initiation of the transaction with a device used as a presentation instrument in the transaction. A Dynamic Transaction Cryptogram (DTC) and a dynamic PAN can be generated at the device. The DTC can be used to authenticate the transaction and the dynamic PAN can comprise an encrypted form of a real PAN of the financial account that is valid for a single transaction. The DTC and the dynamic PAN can be provided by the device for use in the transaction.
Owner:FIRST DATA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com