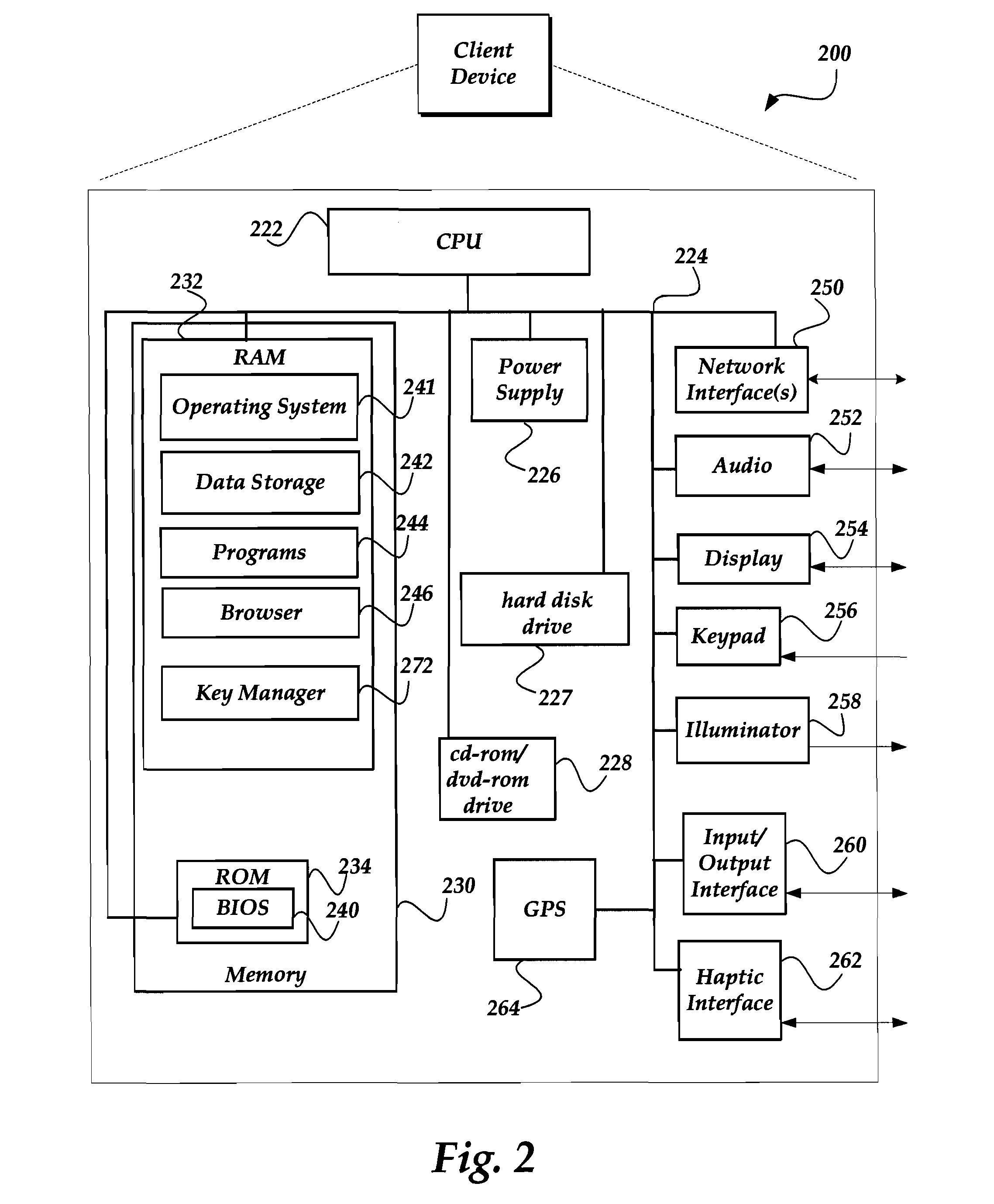
Patents
Literature
148 results about "Registration authority" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
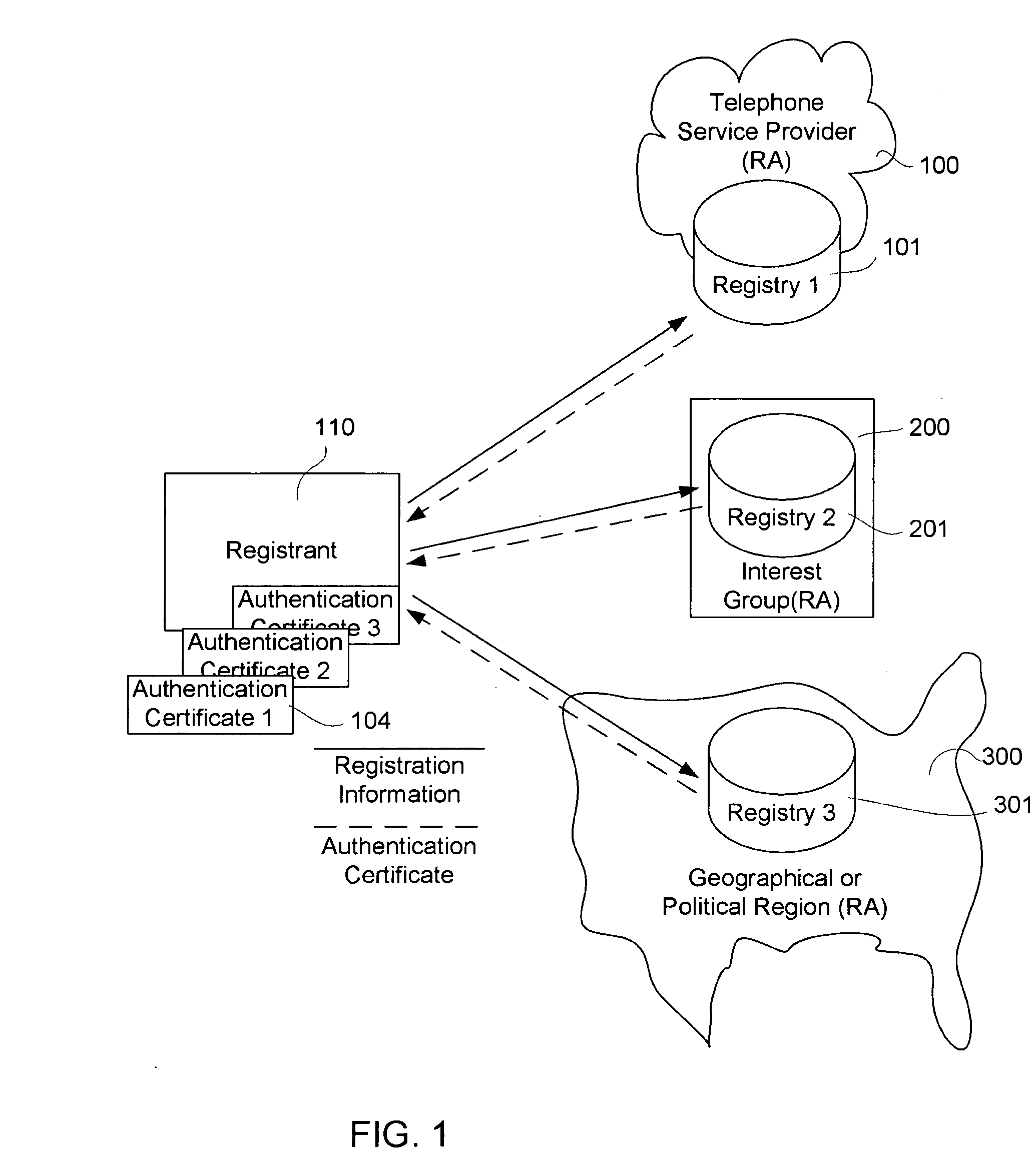
Registration authorities exist for many standards organizations, such as ANNA (Association of National Numbering Agencies for ISIN), the Object Management Group, W3C, IEEE and others. In general, registration authorities all perform a similar function, in promoting the use of a particular standard through facilitating its use. This may be by applying the standard, where appropriate, or by verifying that a particular application satisfies the standard's tenants. Maintenance agencies, in contrast, may change an element in a standard based on set rules – such as the creation or change of a currency code when a currency is created or revalued (i.e. TRL to TRY for Turkish lira). The Object Management Group has an additional concept of certified provider, which is deemed an entity permitted to perform some functions on behalf of the registration authority, under specific processes and procedures documented within the standard for such a role.
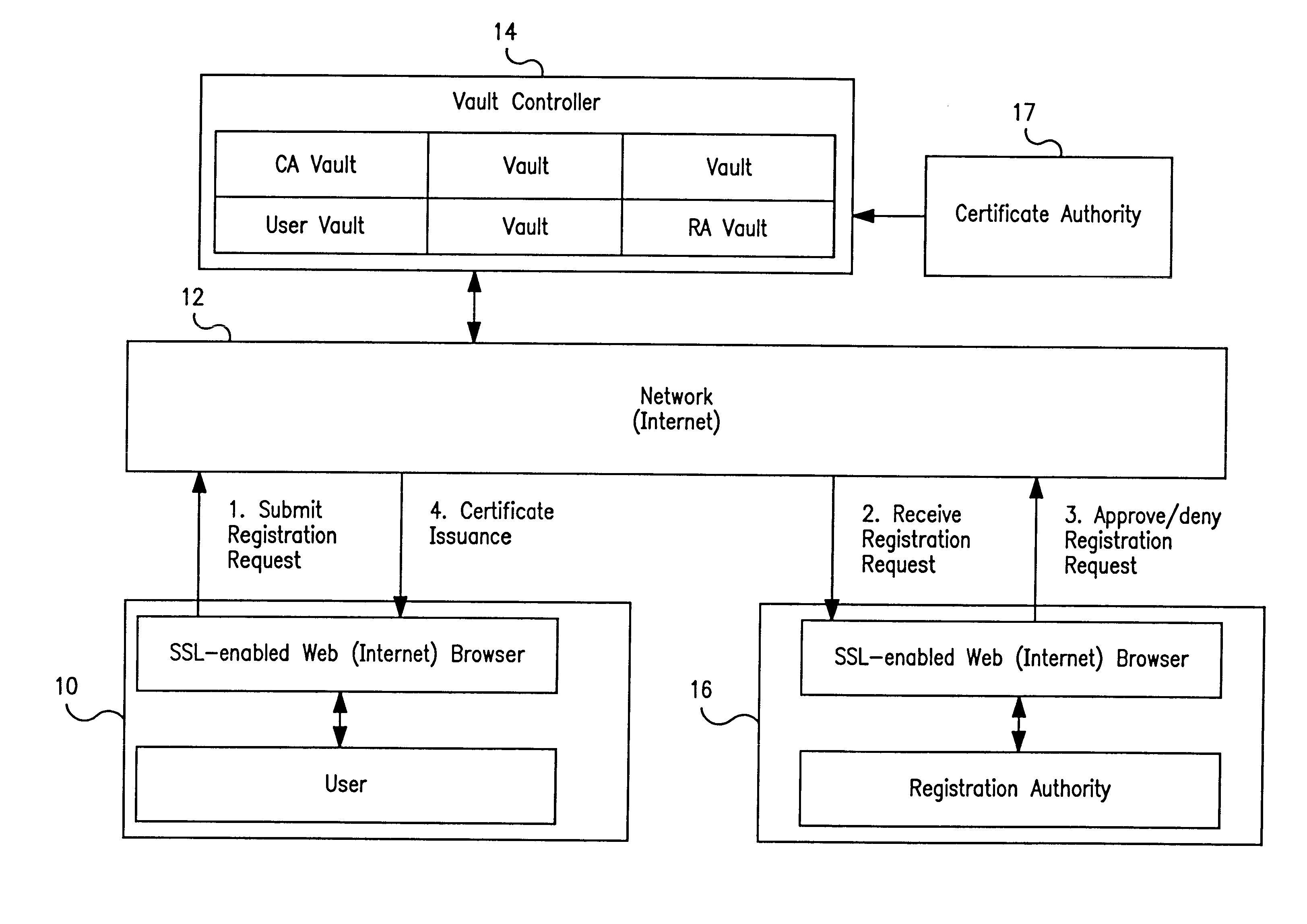
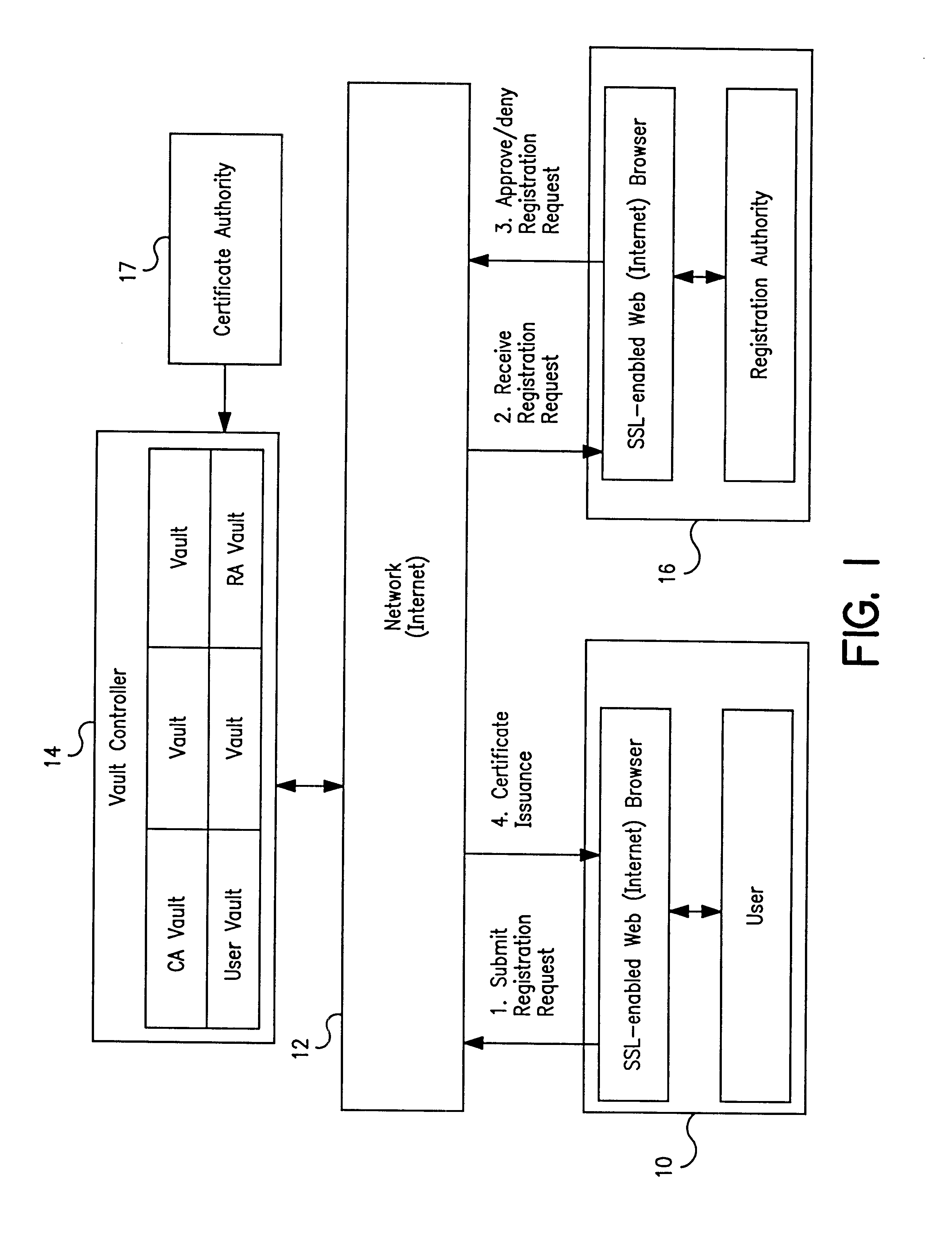
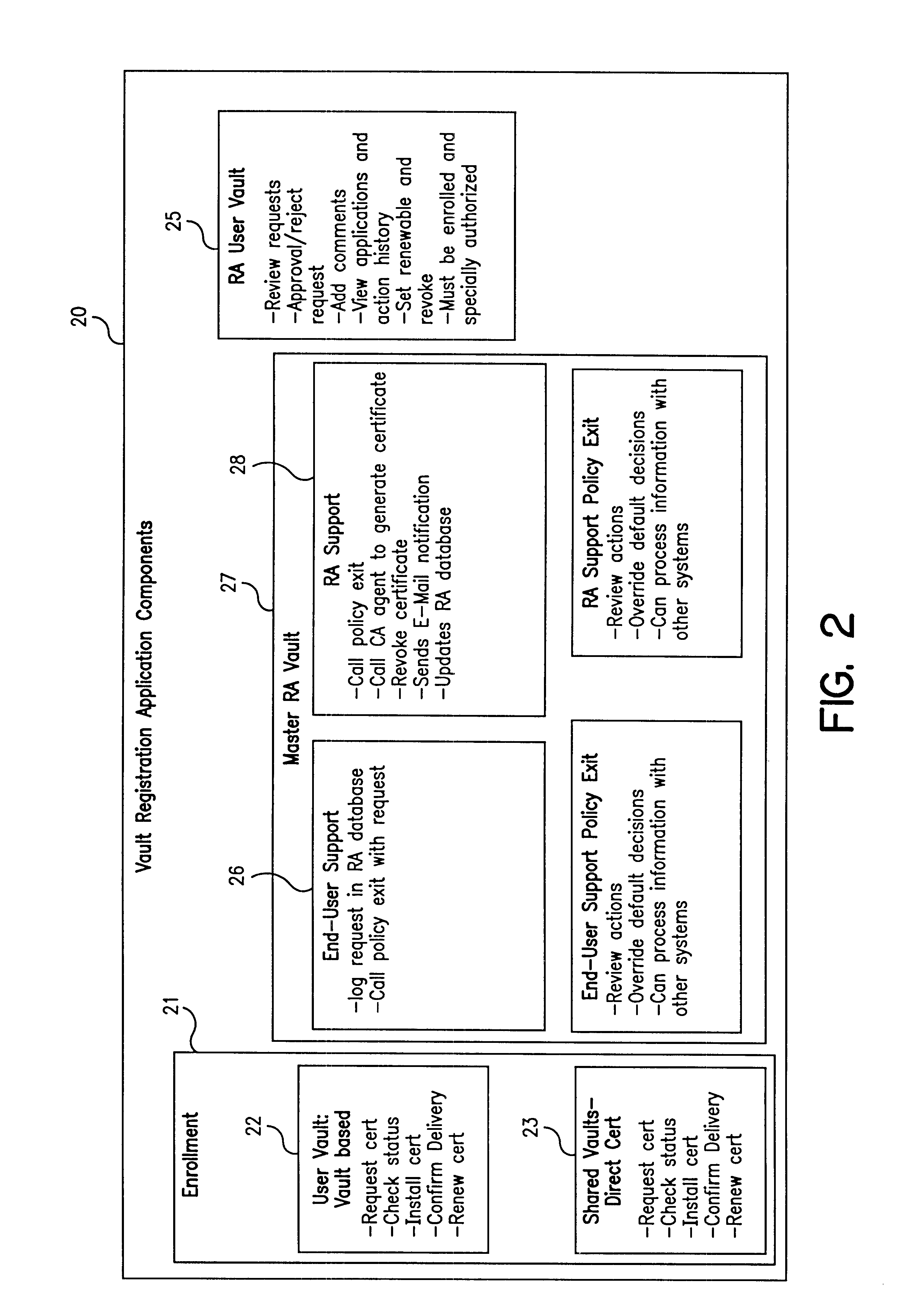
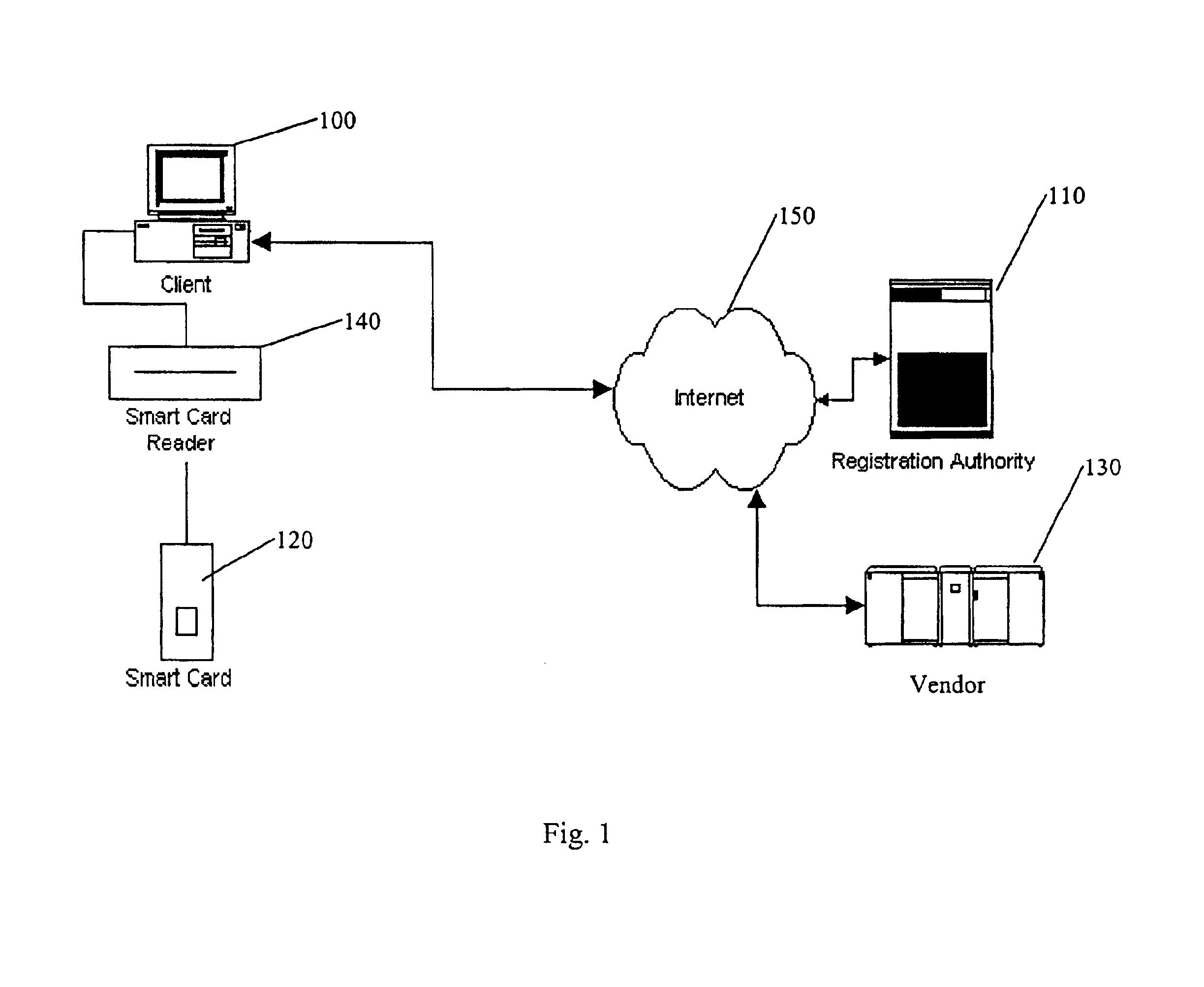
Vault controller based registration application serving web based registration authorities and end users for conducting electronic commerce in secure end-to-end distributed information system
InactiveUS6438690B1FinanceDigital data processing detailsRegistration authorityCommunications system
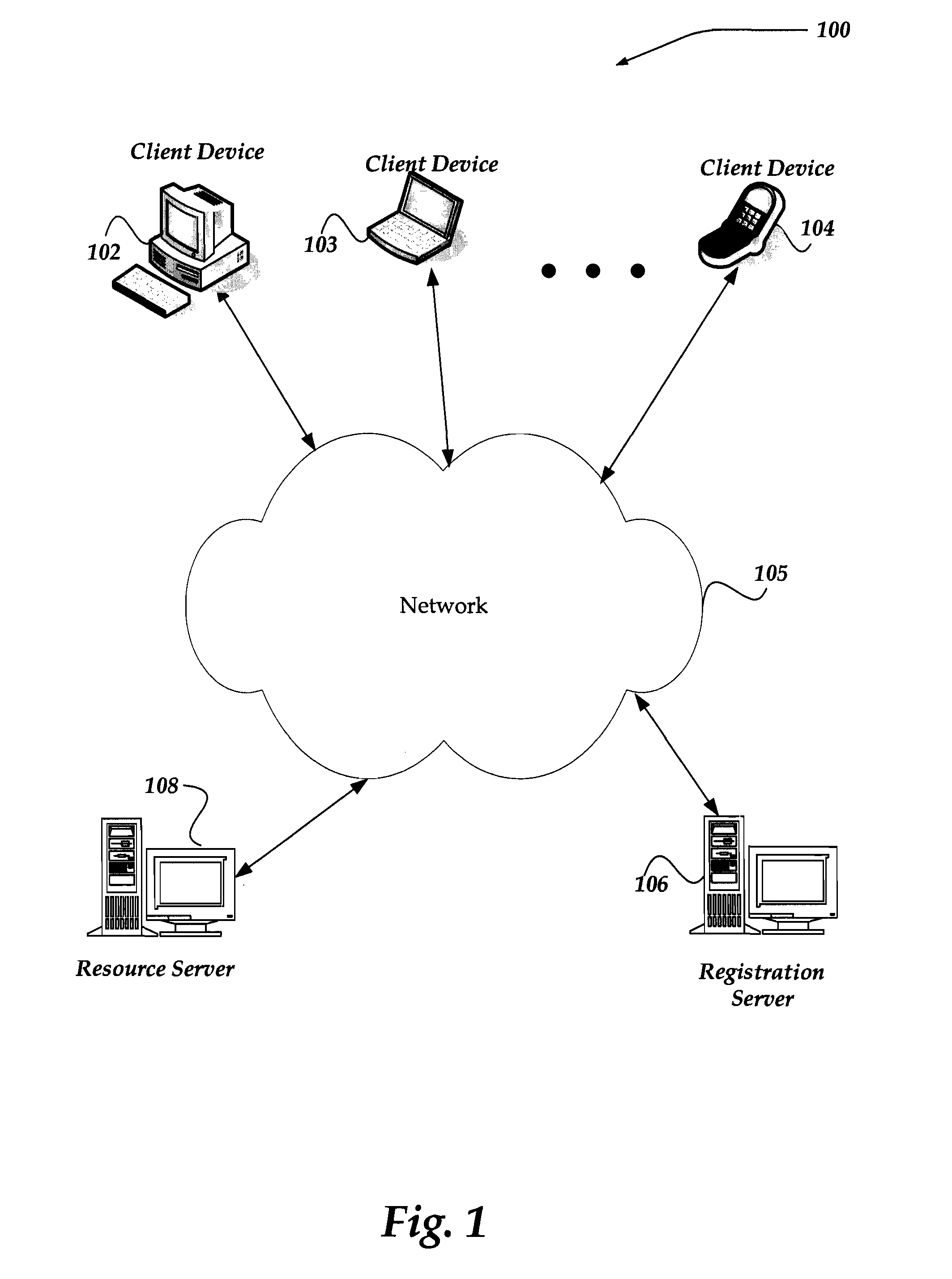
A secure end-to-end communications system includes a vault controller based registration application for managing the issuance and administration of digital certificates for use in conducting electronic commerce in the system. The system includes an end user terminal and a registration authority terminal coupled to a vault controller through the system. A registration application executable in the controller utilizes SSL and dedicated vaults to process requests for digital certificates from end users on an automated or manual basis. The registration application includes an enrollment module which implements the process of applying for and receiving certificates; an RA desk top module which allows an administrator to review certificate requests and manage certificates; a master Registration Authority (RA) module which conducts the processing of requests and the generation of certificates; and an RA (Registration Authority) database serves as a repository of information about applicants, certificate requests, and their processing history.
Owner:IBM CORP
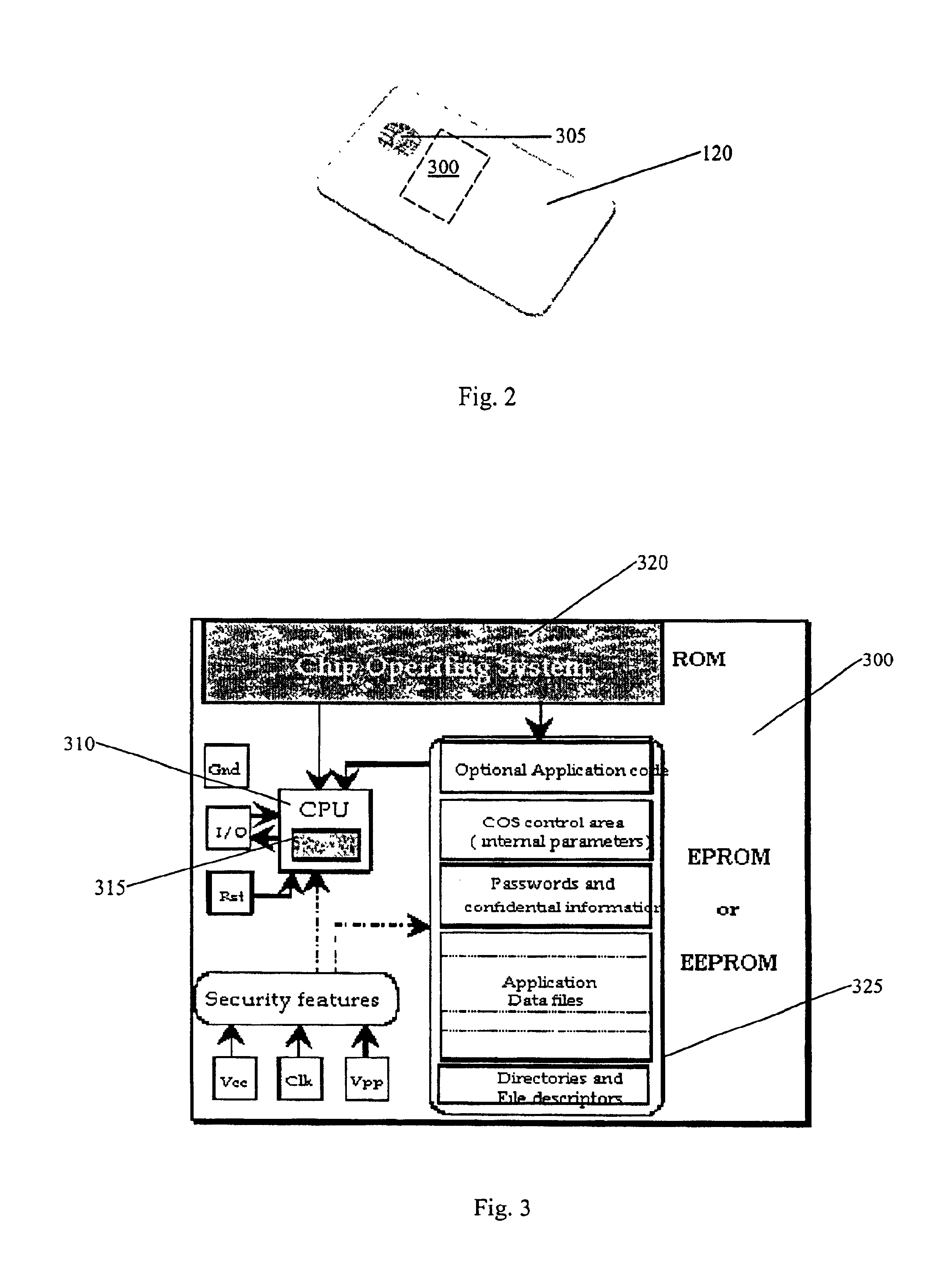
System and method for preventing unauthorized access to electronic data
InactiveUS6857067B2Prevent unauthorized accessVolume/mass flow measurementUser identity/authority verificationRegistration authorityData storing
A system and method are provided for preventing unauthorized access to electronic data stored on an electronic device. A portable licensing medium is configured to communicate with the electronic device for storing license data. The license data is used to determine whether to allow access to the electronic data. A registration authority communicates with the electronic device. The registration authority has a database of verification data for verifying the license data stored on the licensing medium and provides updated license data to the licensing medium.
Owner:UNILOC 2017 LLC
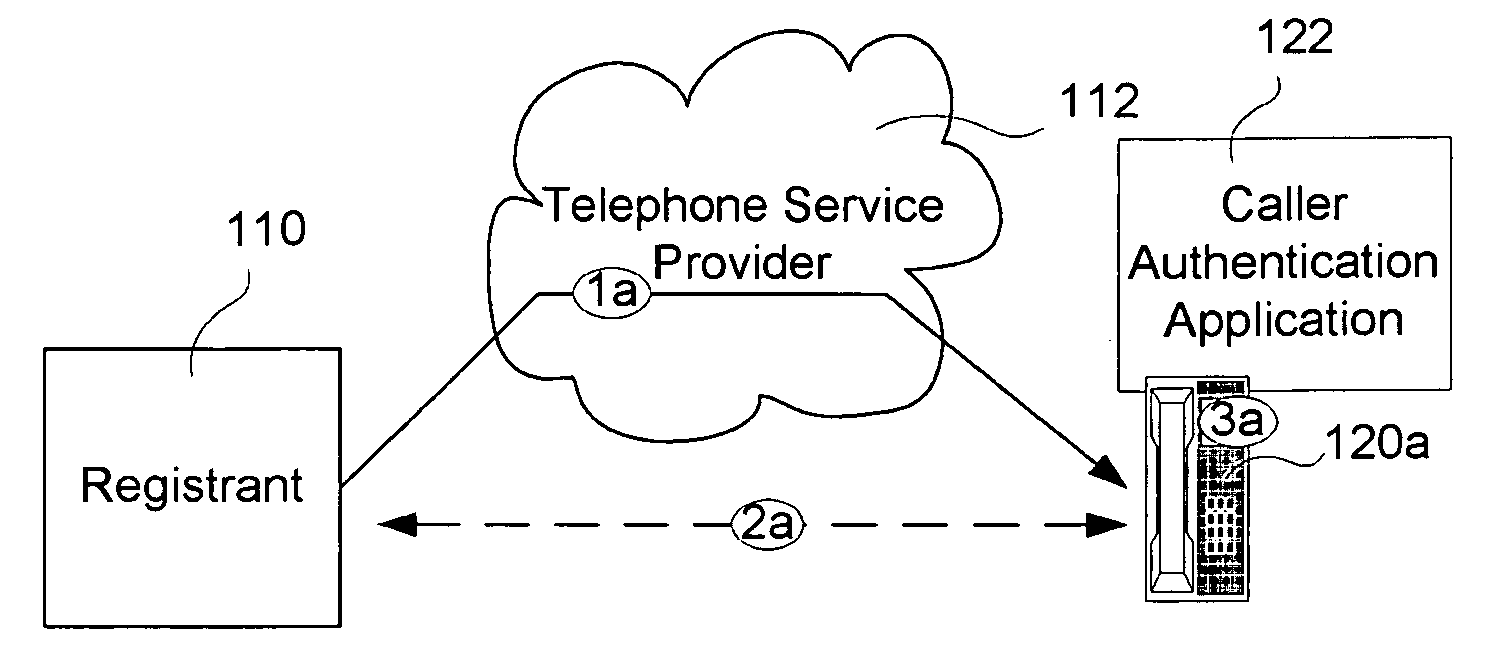
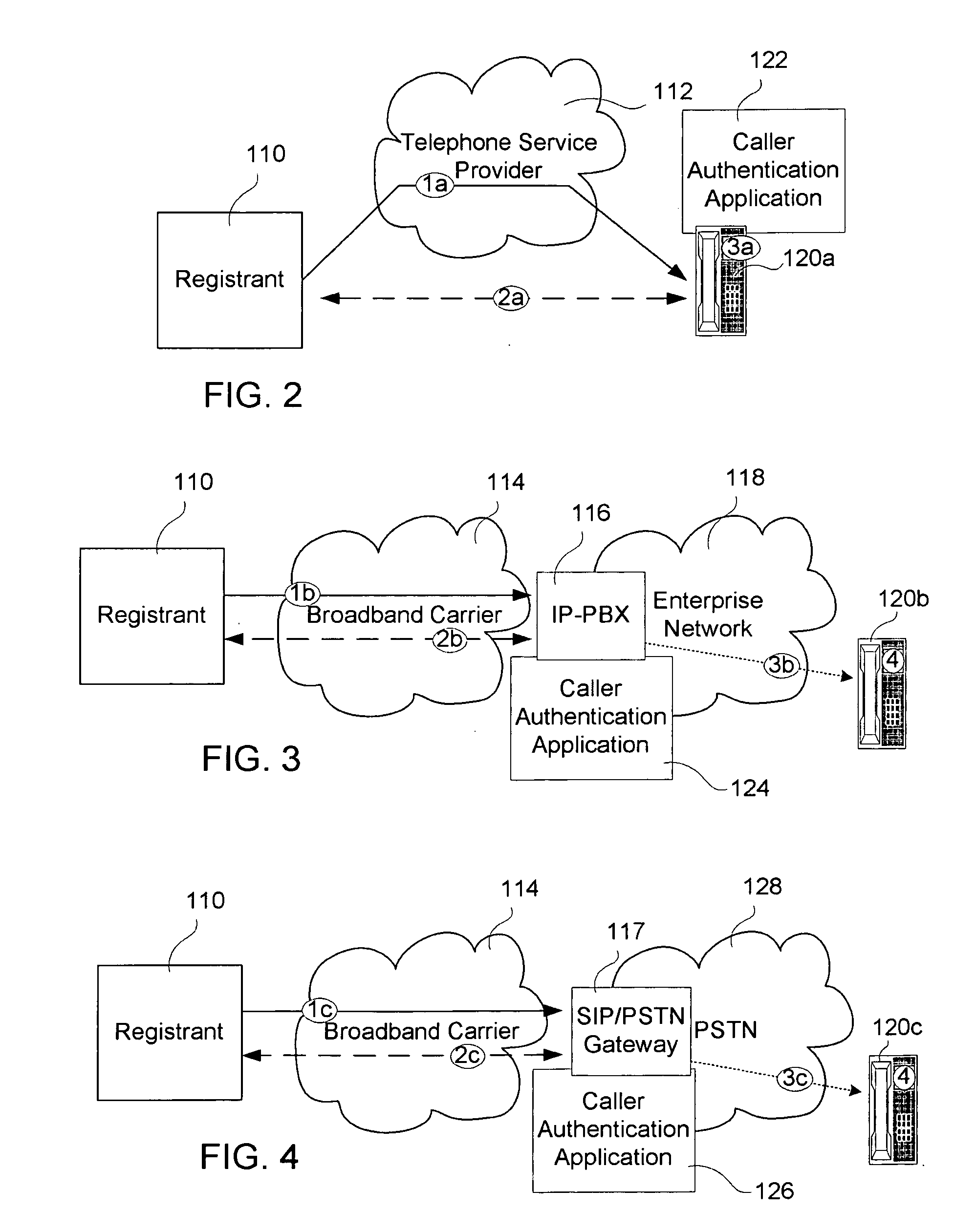
Caller name authentication to prevent caller identity spoofing
InactiveUS20080181379A1Multiplex system selection arrangementsCalling susbscriber number recording/indicationRegistration authorityCall setup
Caller name is authenticated using authentication certificates issued by a registration authority that registers callers who wish to terminate calls to callers subscribed to the registration authority. In one embodiment, the authentication certificates are sent to a called device or a proxy for the called device via a path that is separate from the call setup path. An indication is conveyed to the called party to indicate whether the caller name was successfully authenticated.
Owner:ALCATEL LUCENT SAS
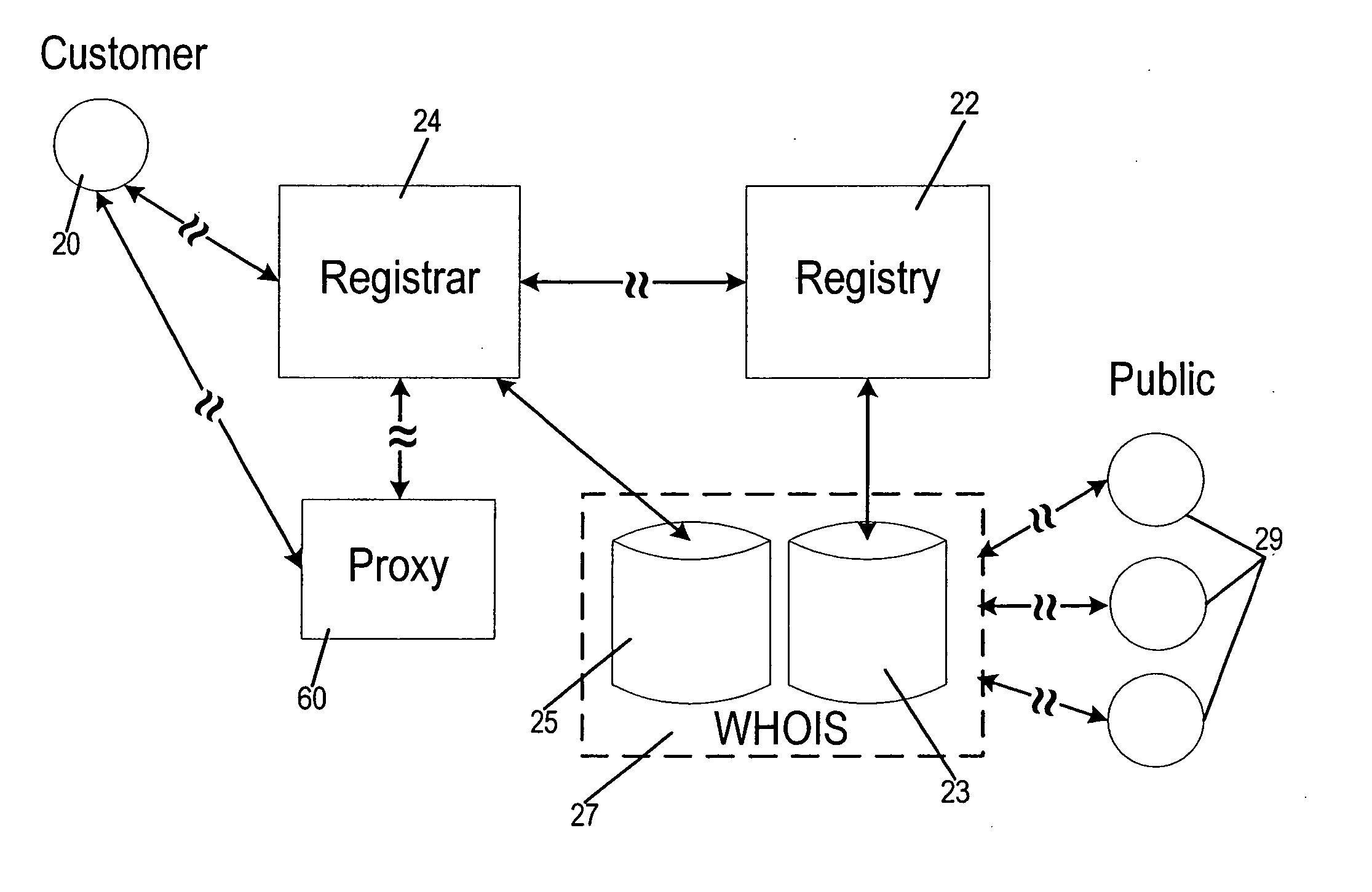
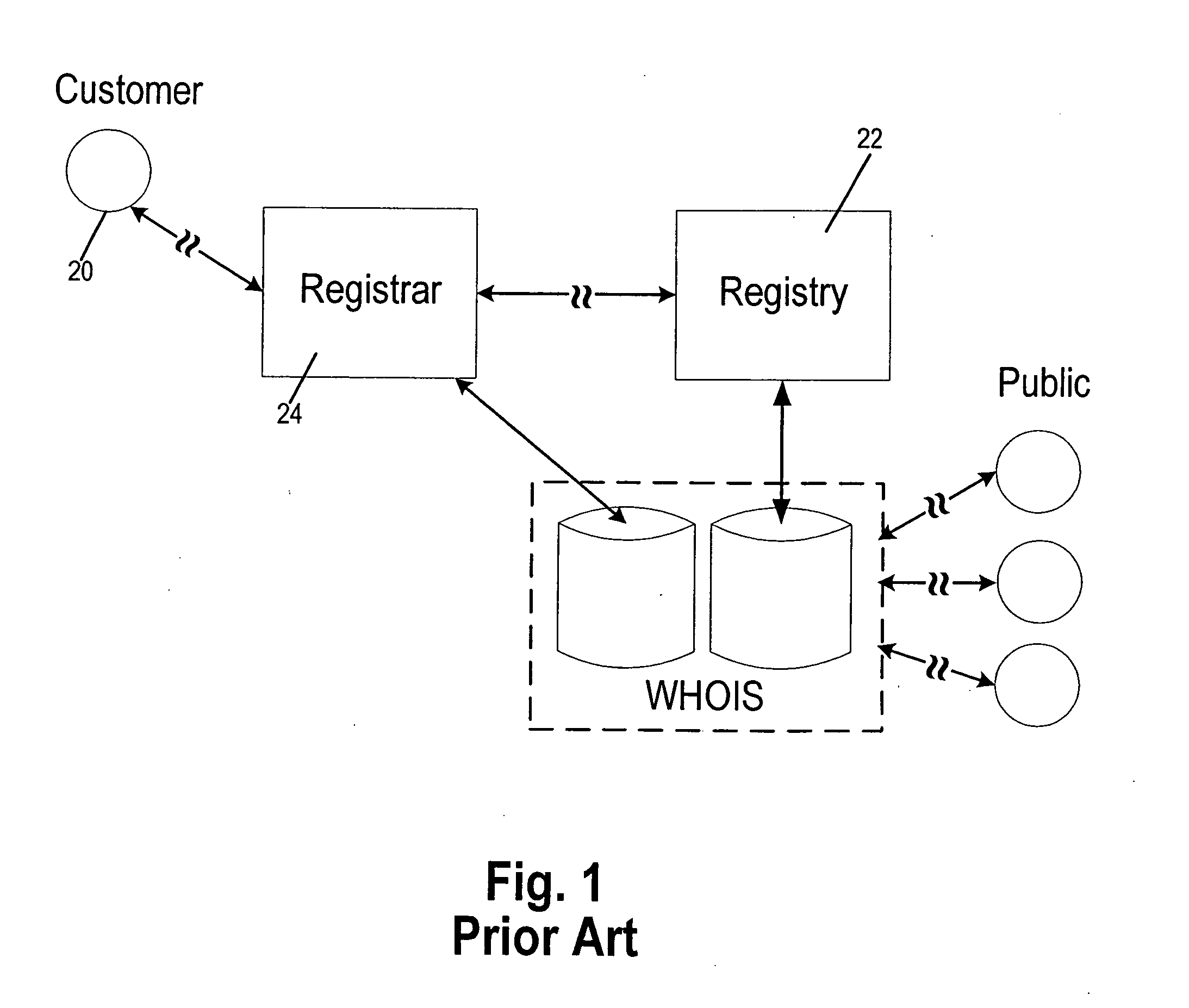
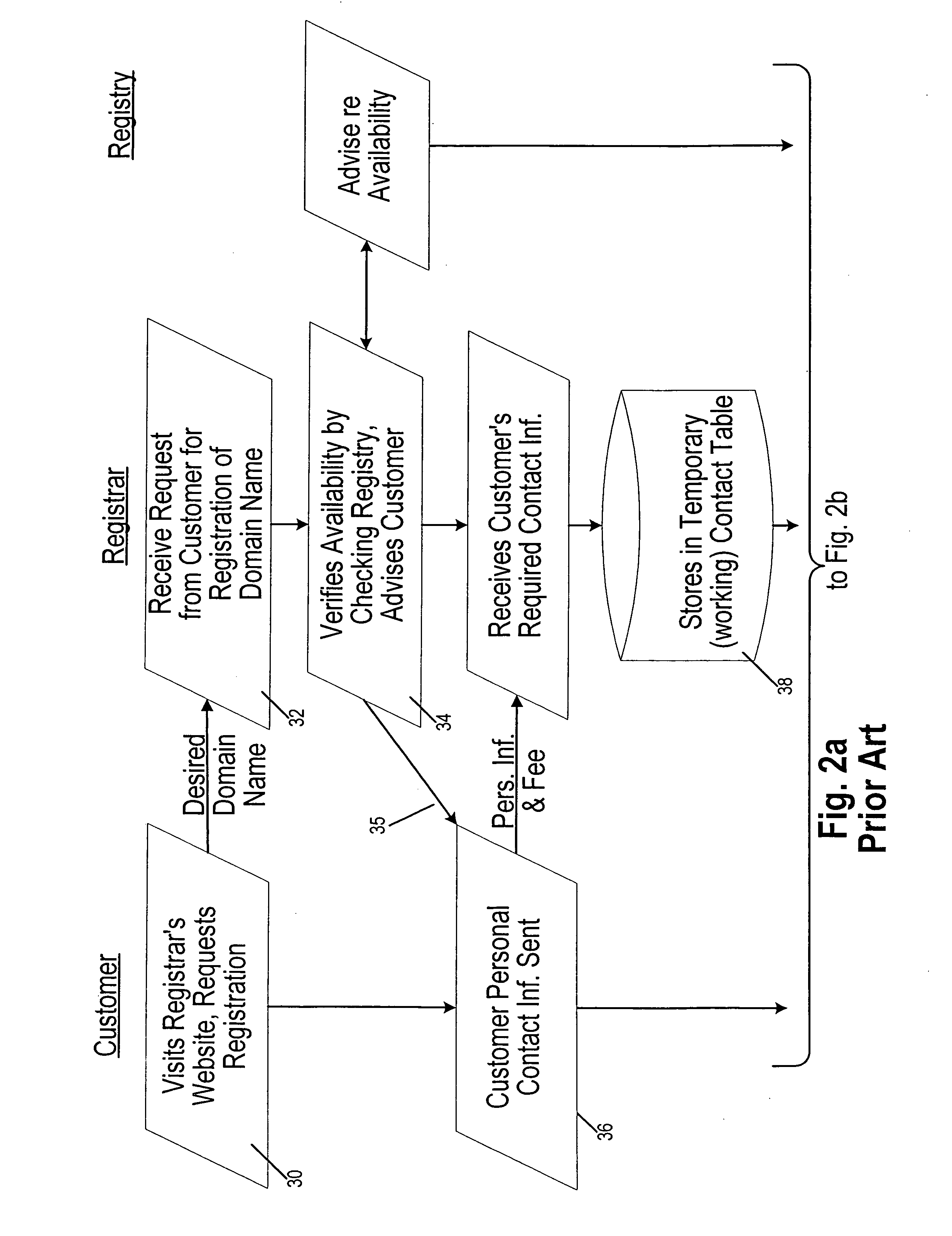
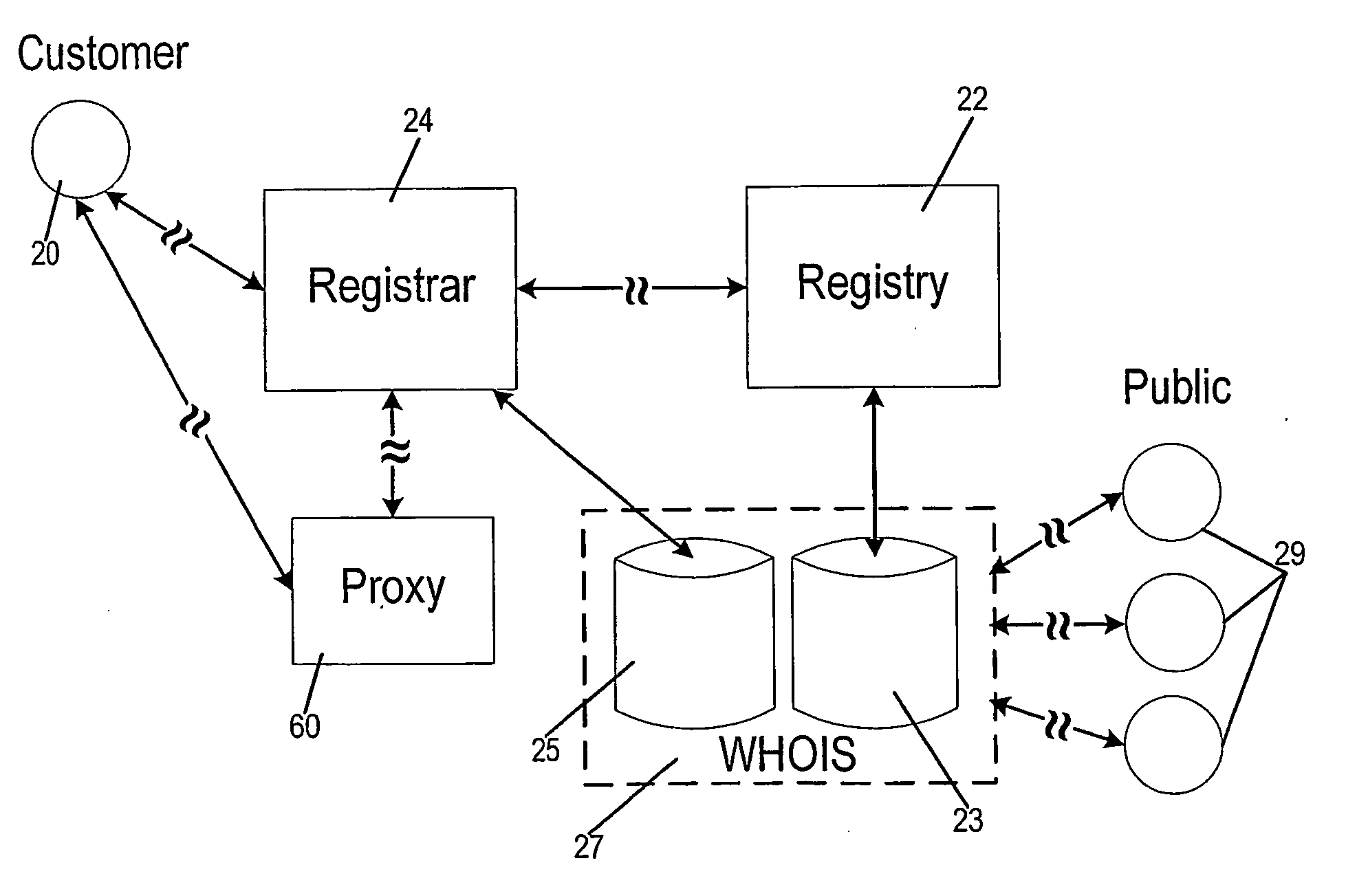
Systems and methods for domain name registration by proxy
InactiveUS20060271668A1Multiple digital computer combinationsTransmissionDomain nameRegistration authority
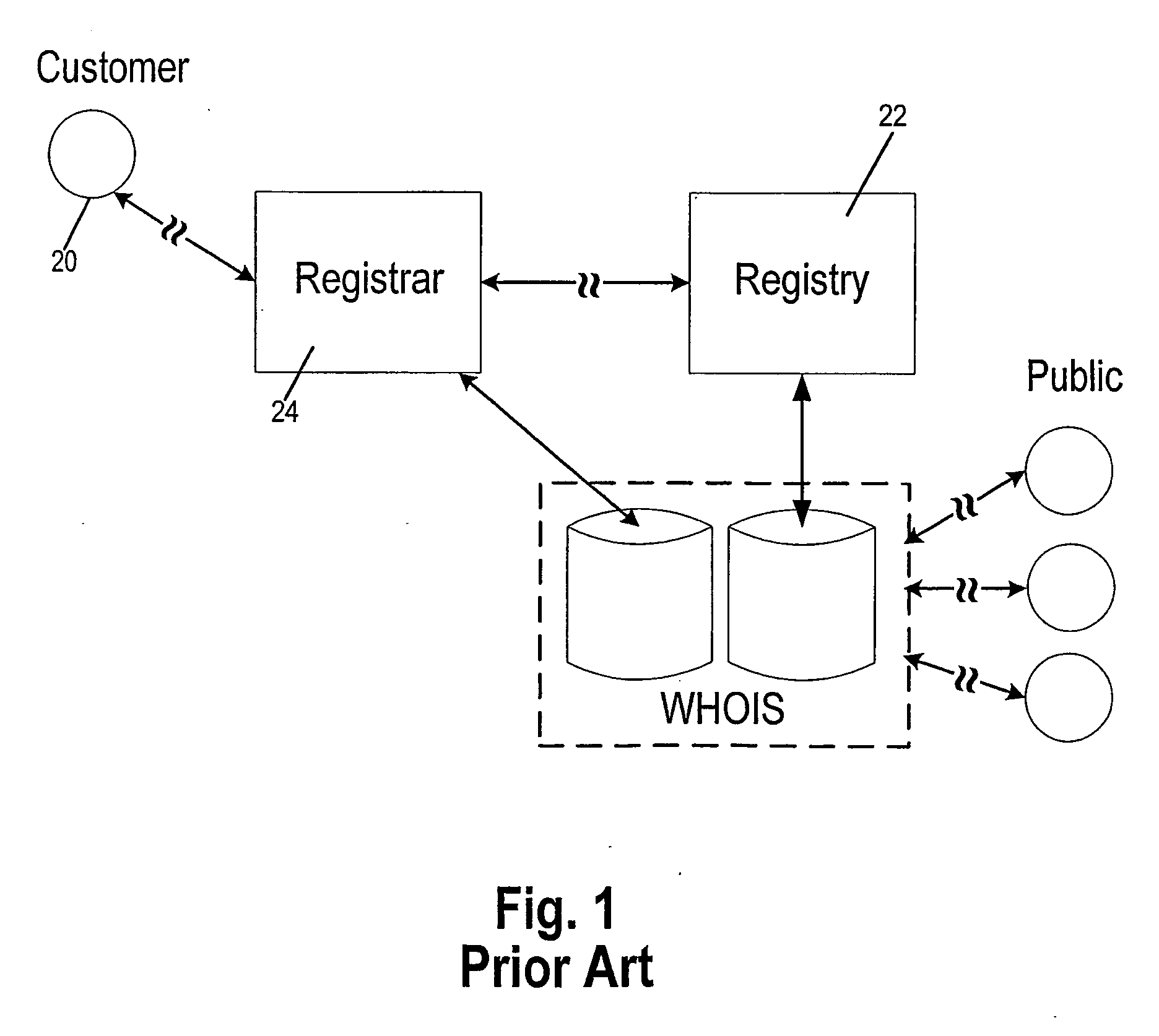
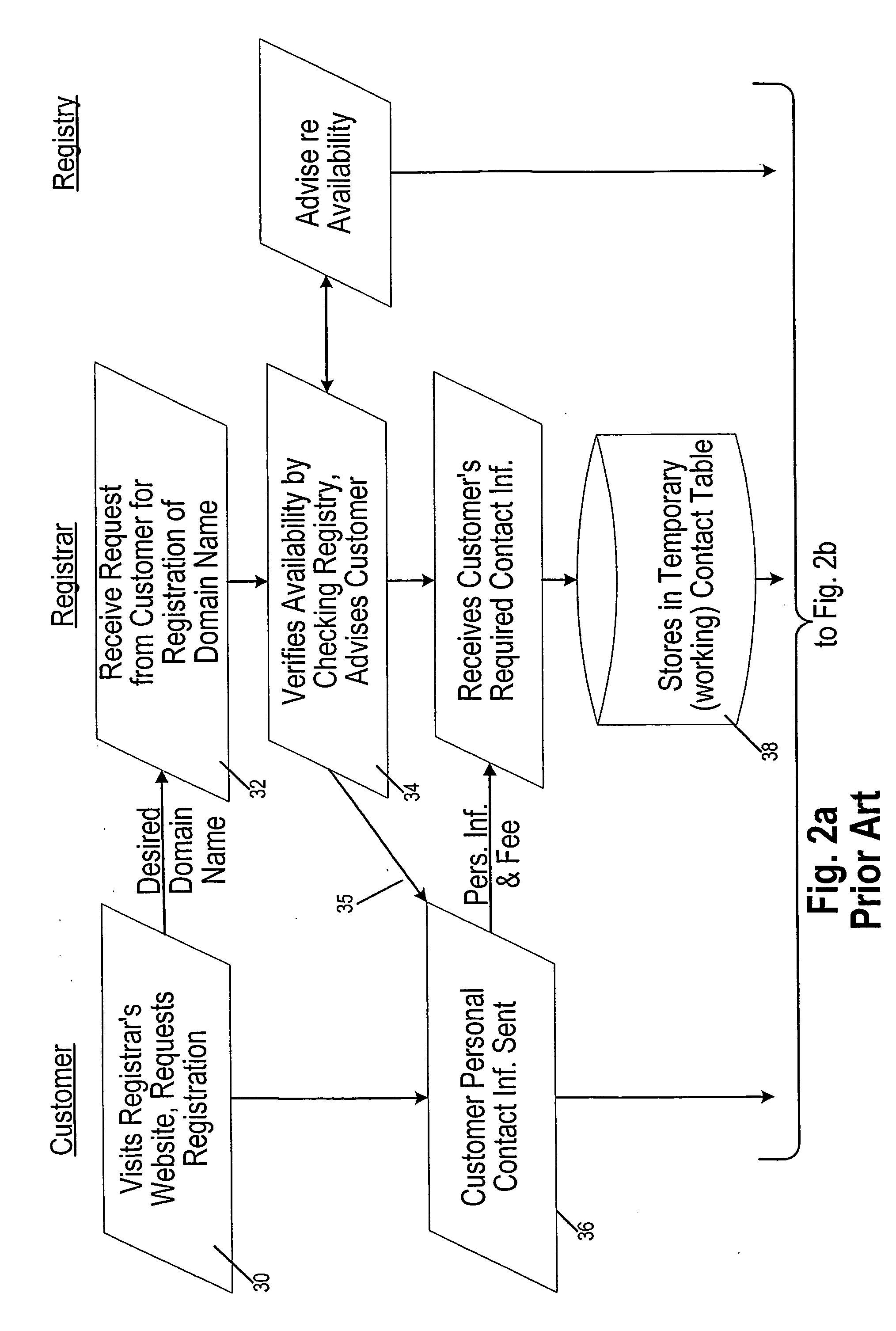
A system and method of proxy domain name registration permits a would-be domain name registrant anonymity. A registrar affords customers the opportunity to use the proxy registration. If the customer seeking registration of a domain name requests, the registrar obtains contact information needed for registration from a proxy entity established for this purpose. The registrar completes the registration of the domain name with the appropriate registry (i.e. “.com, .net” etc.). The contact information published in WHOIS is that of proxy entity. Contractually the customer is afforded control over the domain name. Emails intended for the customer are received by the proxy entity who may filter them if the customer requests. Emails sent by the customer are sent to the proxy entity who in turn sends them to the indicated addressee.
Owner:GO DADDY OPERATING
System and methods for managing the distribution of electronic content
InactiveUS7580988B2Improve integrityDigital data processing detailsUser identity/authority verificationRegistration authorityElectronic information
The present invention provides systems and methods for transfering electronic information from one location to another such that only one original work exists at a given time. The methods and systems of the present invention allow distribution of originals without requiring a registration authority or other entity to vouch for what constitutes an “original” piece of information, thus reducing (or eliminating entirely) the need to centrally record changes in ownership each time originals change hands.
Owner:INTERTRUST TECH CORP
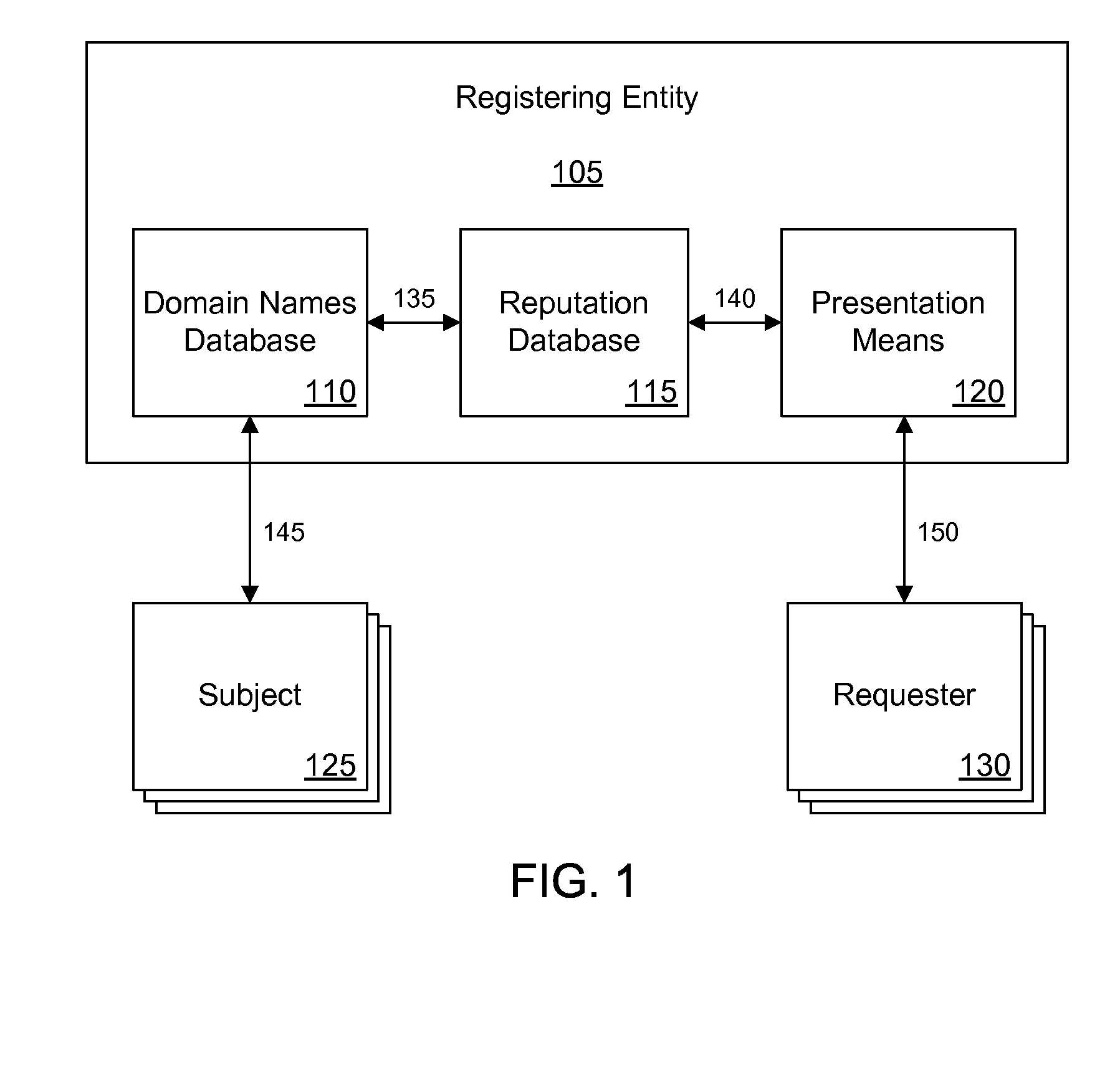
Tracking domain name related reputation
InactiveUS20080028100A1Multiple digital computer combinationsElectric digital data processingThird partyDomain name
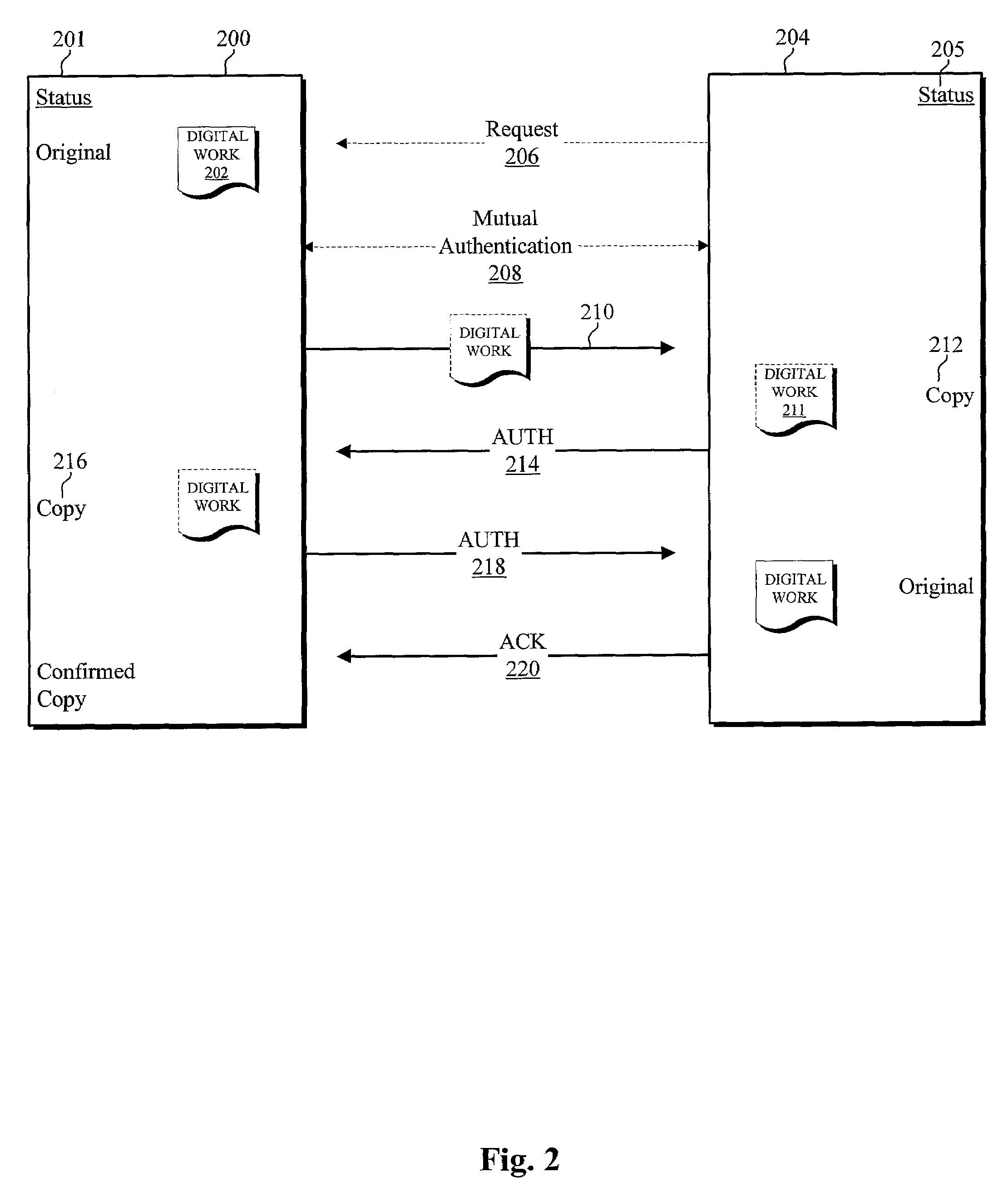
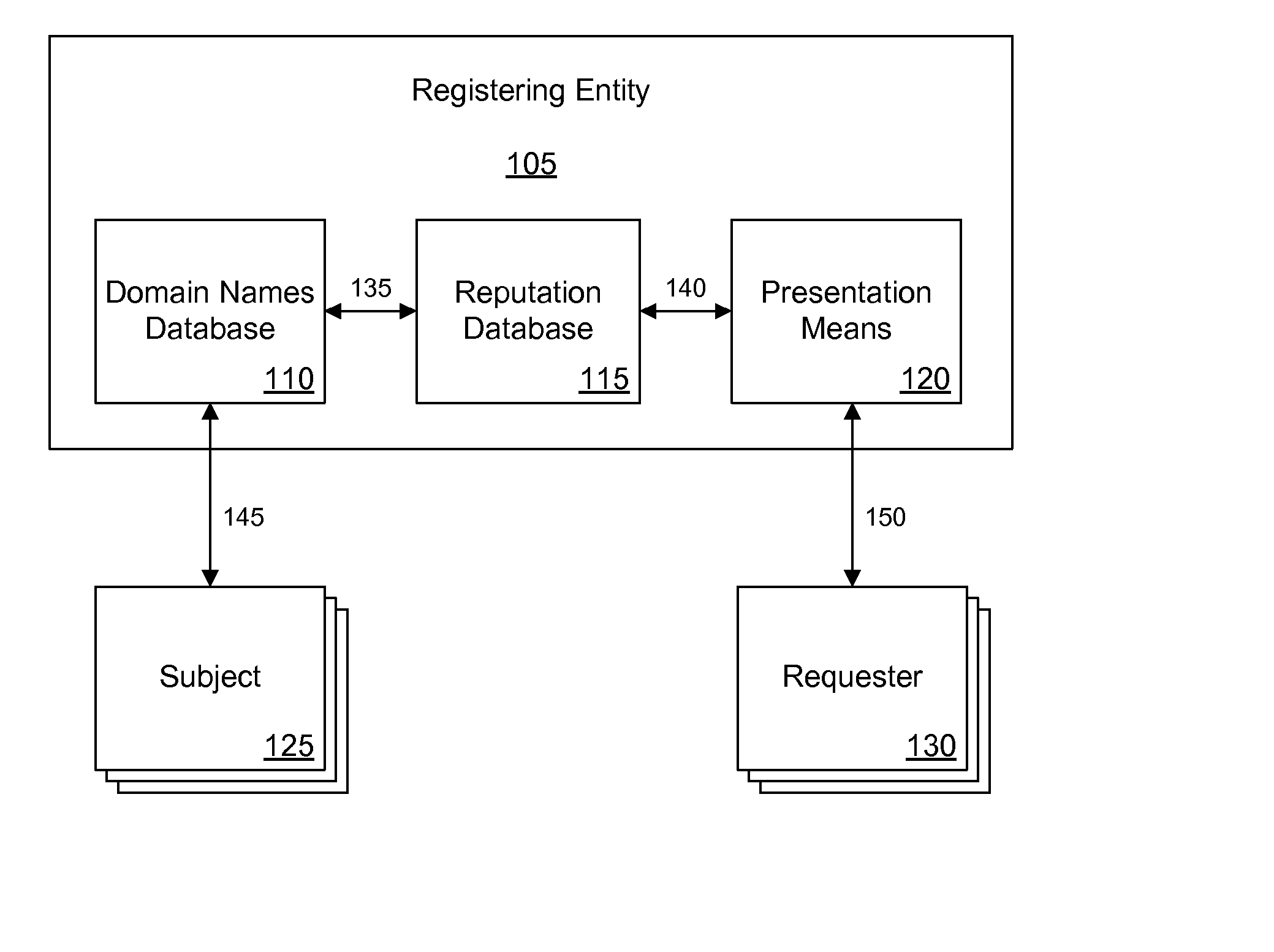
Disclosed systems and methods provide for tracking of domain name related reputation by a domain name Registering Entity (e.g. Registry, Registrar, Reseller, etc.). The Registering Entity maintains a database with reputation data that can be accessed by the requesters. A domain name may be registered through the Registering Entity or a third party. The reputation data may be tracked on the domain name itself, URLs, domain name purchaser or registrant, or email addresses associated with the domain name. The reputation data may include various categories, such as email practices, website content, privacy policies and practices, fraudulent activities, domain name related complaints, digital certificates associated with the domain name, overall reputation, etc. The reputation data may be digitally signed for authenticity. The requester may decide whether to allow email messages or to visit URLs based on the domain name related reputation.
Owner:GO DADDY OPERATING
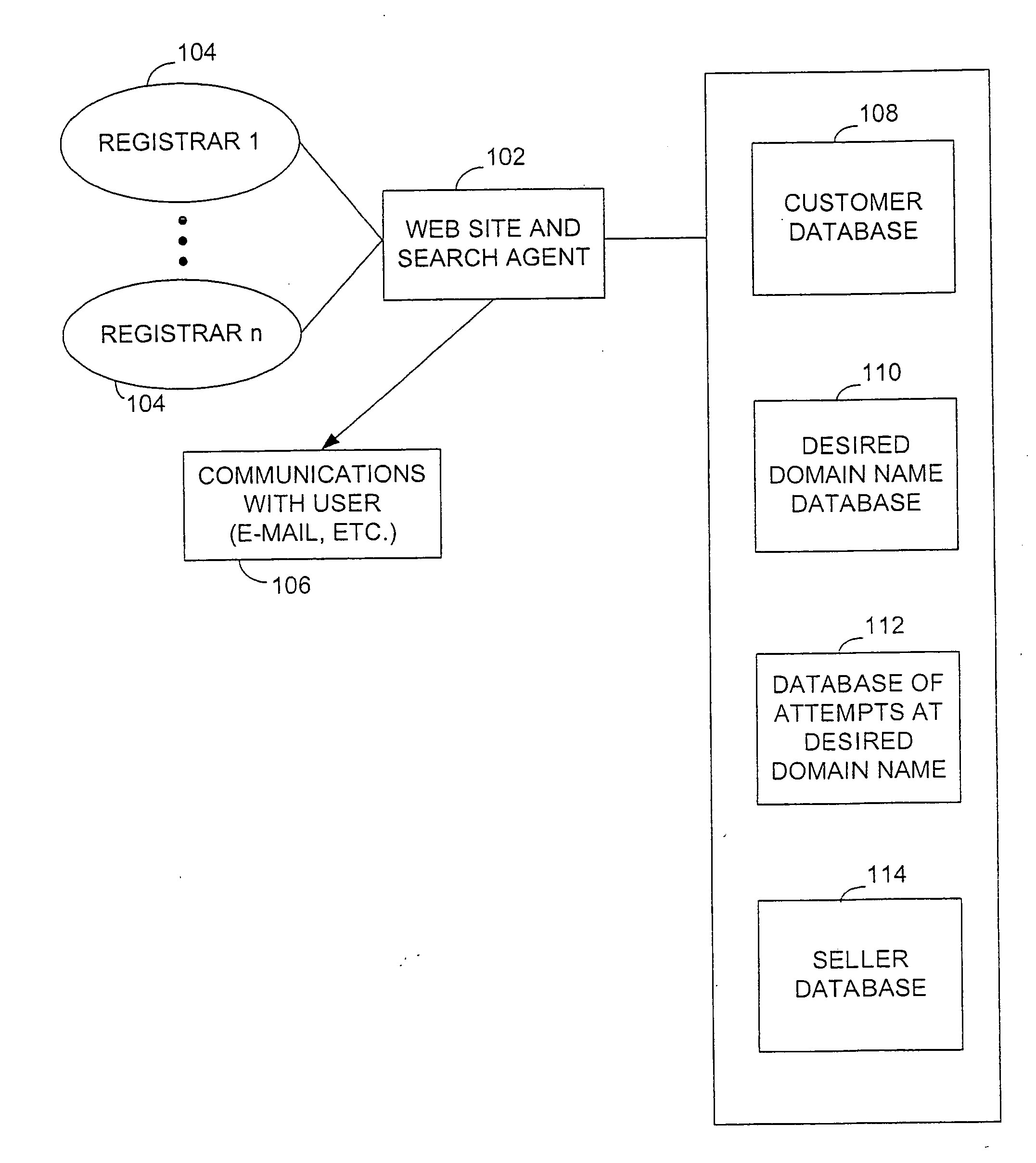
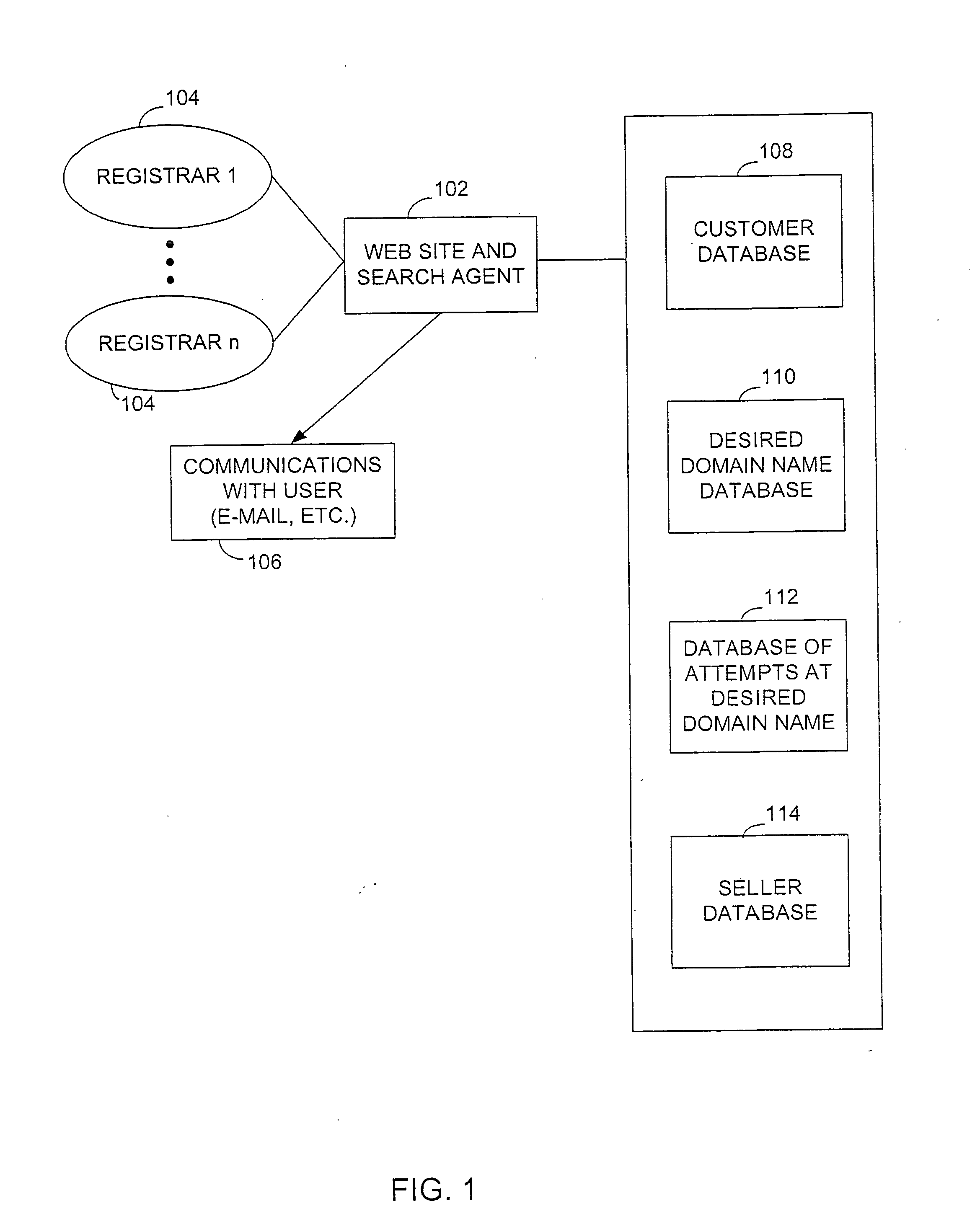
Domain name acquisition and management system and method
InactiveUS20060161682A1Facilitate auctionFinanceDigital data processing detailsRegistration authorityDomain name
A preferred embodiment of the present invention can accept an indication of a domain name or set of domain names from interested entity. The desired domain names are names that an interested entity desires to register through a domain name registration system or systems, such as that operated by a registry-accredited registrar. The system can closely monitor the domain name registry or registrar databases used to provide domain name resolution or registration over a distributed network, such as the Internet, and determine the expiration or availability of the name or names supplied by the interested entity. When a desired domain name appears to be available, the system can register or re-register the domain name through a domain registration service. If there is more than one interested entity for a domain name, the system can also facilitate an auction for the domain name.
Owner:WEB COM GRP
Secure tracking system and method for video program content
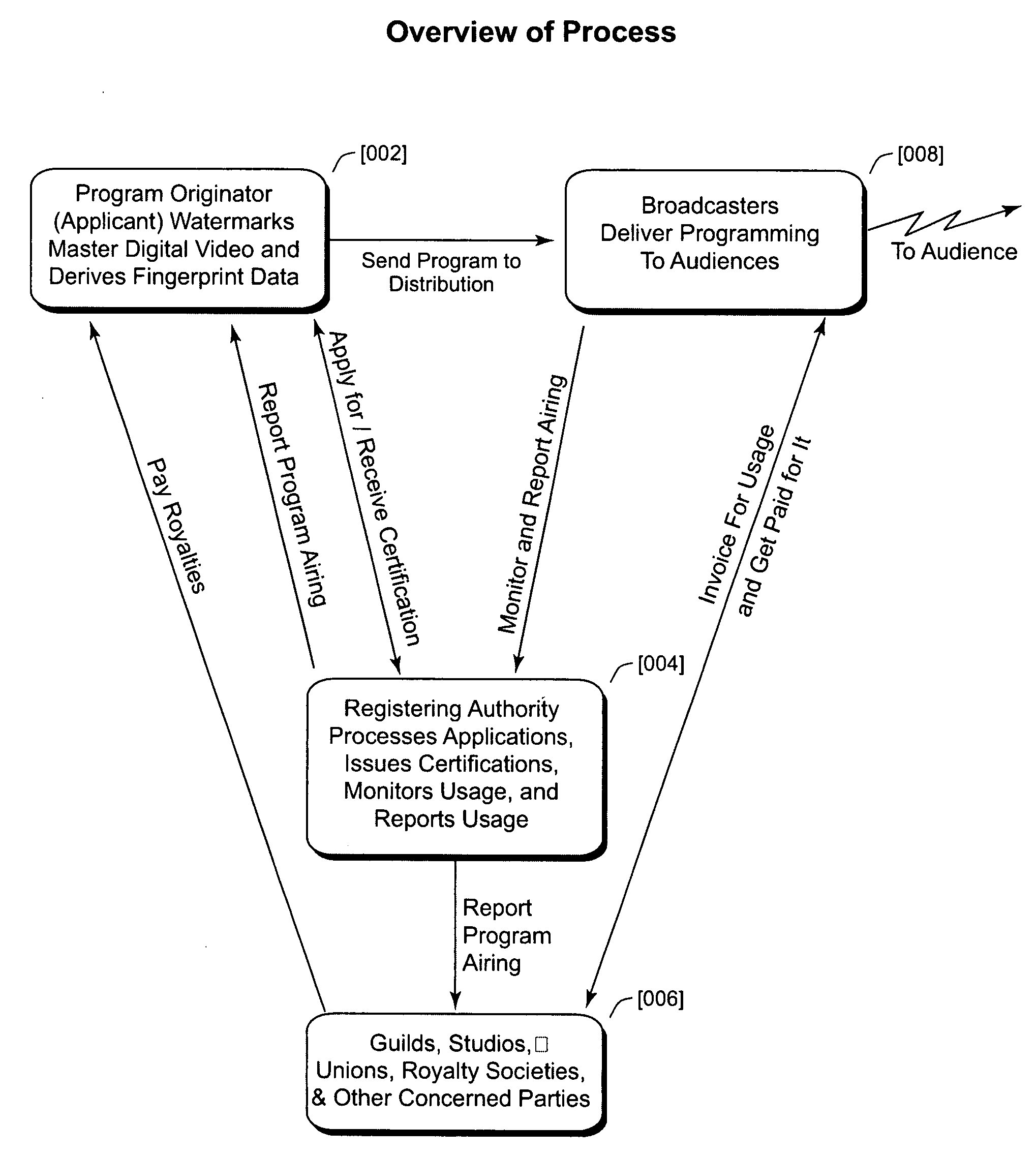
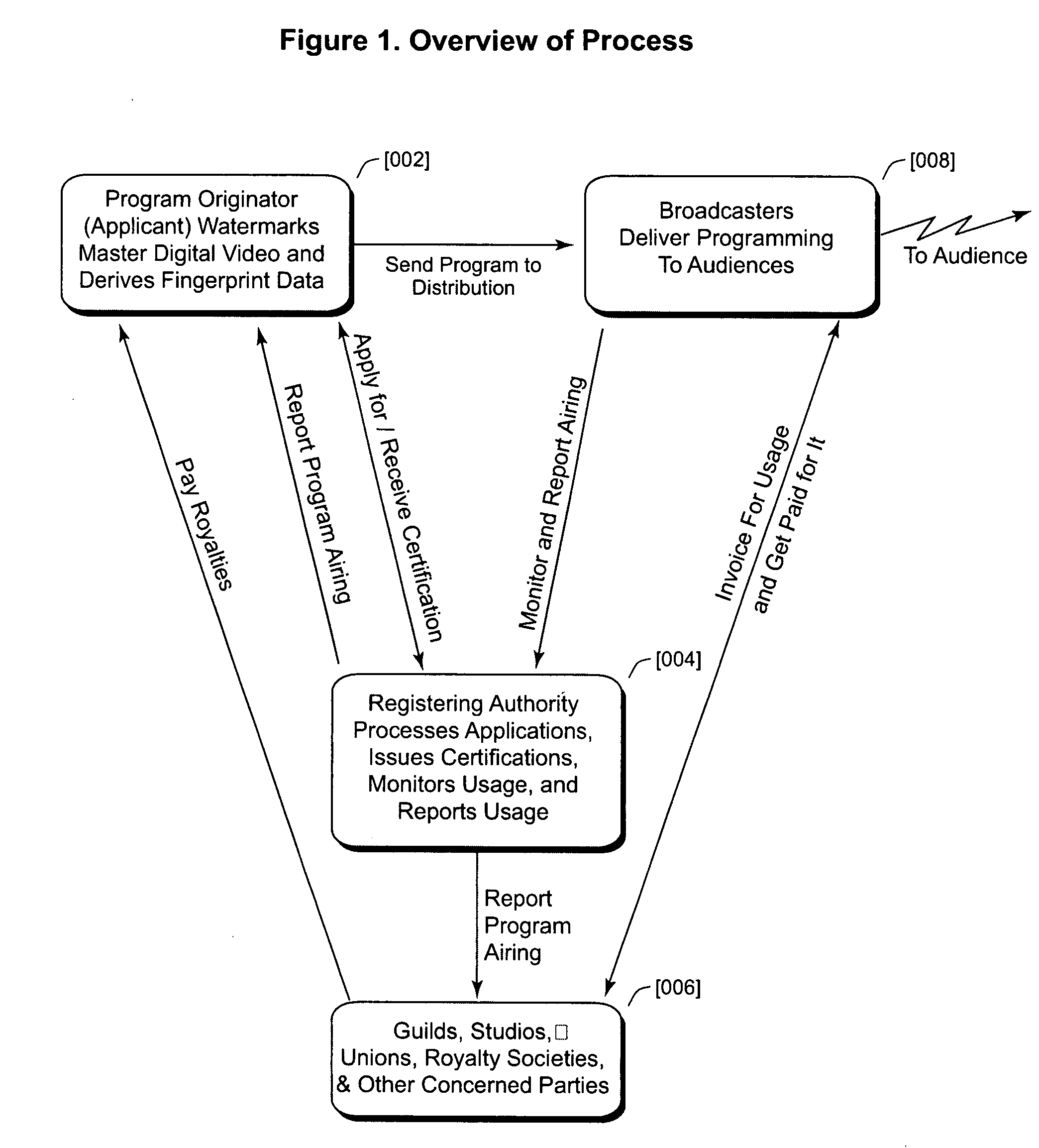
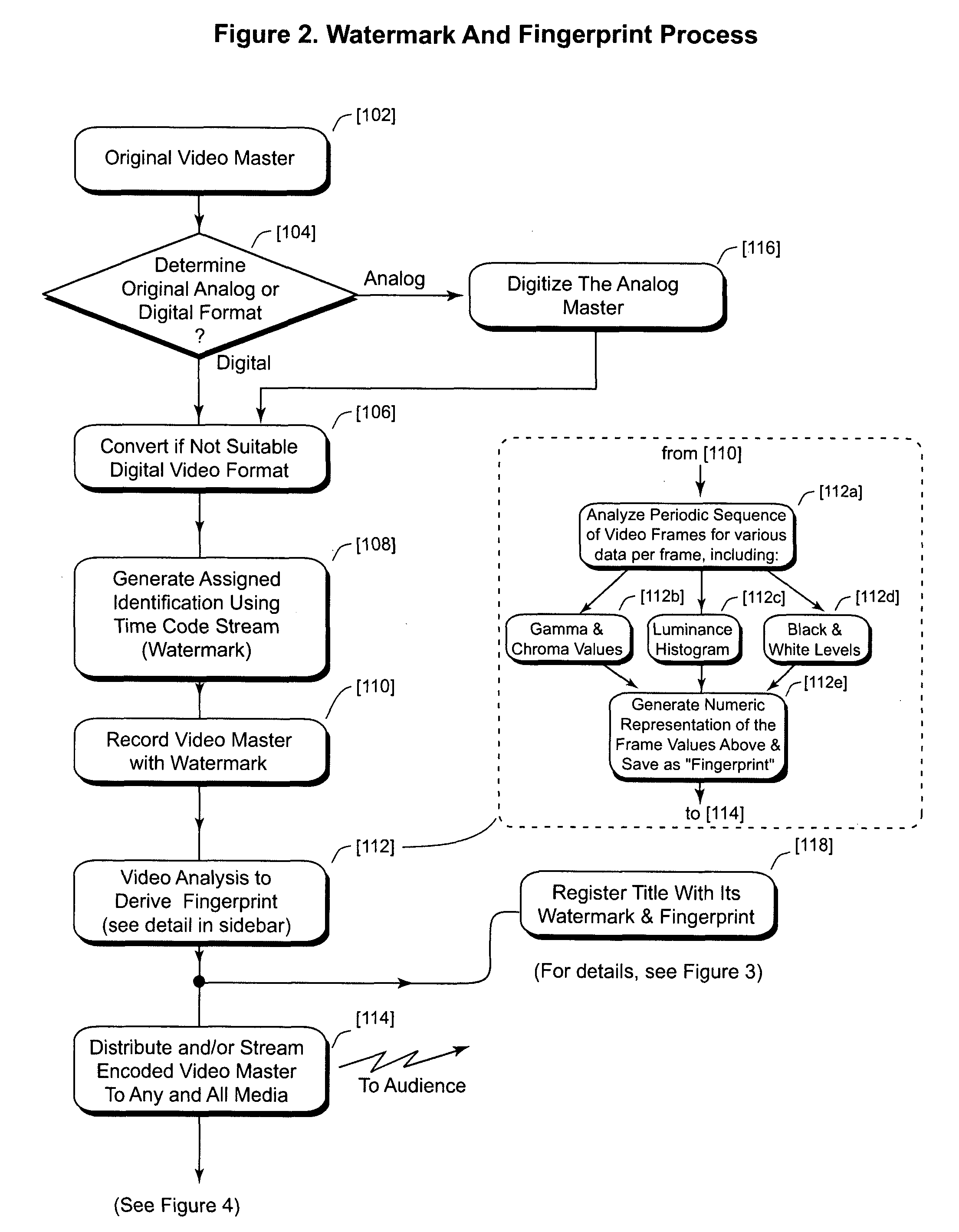
InactiveUS8601504B2Facilitates automatic detectionAccurate and complete reporting of program usageUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareRegistration authority
A secure tracking system for video program content places a special code (watermark) within the broadcast program, preferably via the user bits of the SMPTE time code already used on virtually all film and video production systems. A registering authority provides proof of a program broadcast by detecting watermarking and fingerprinting on various broadcast media around the world and reporting it back to a central database.
Owner:IP ACQUISITIONS LLC
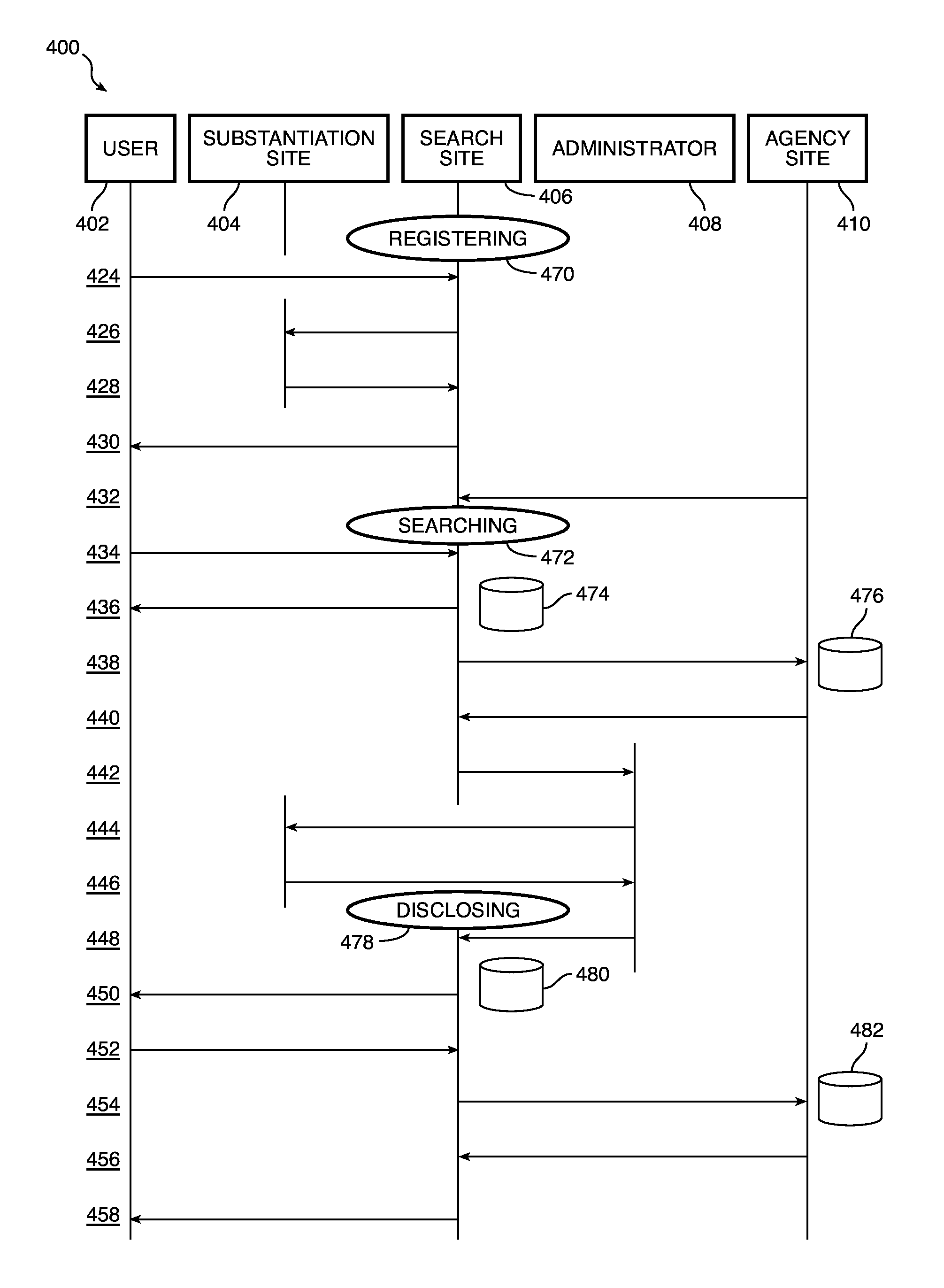
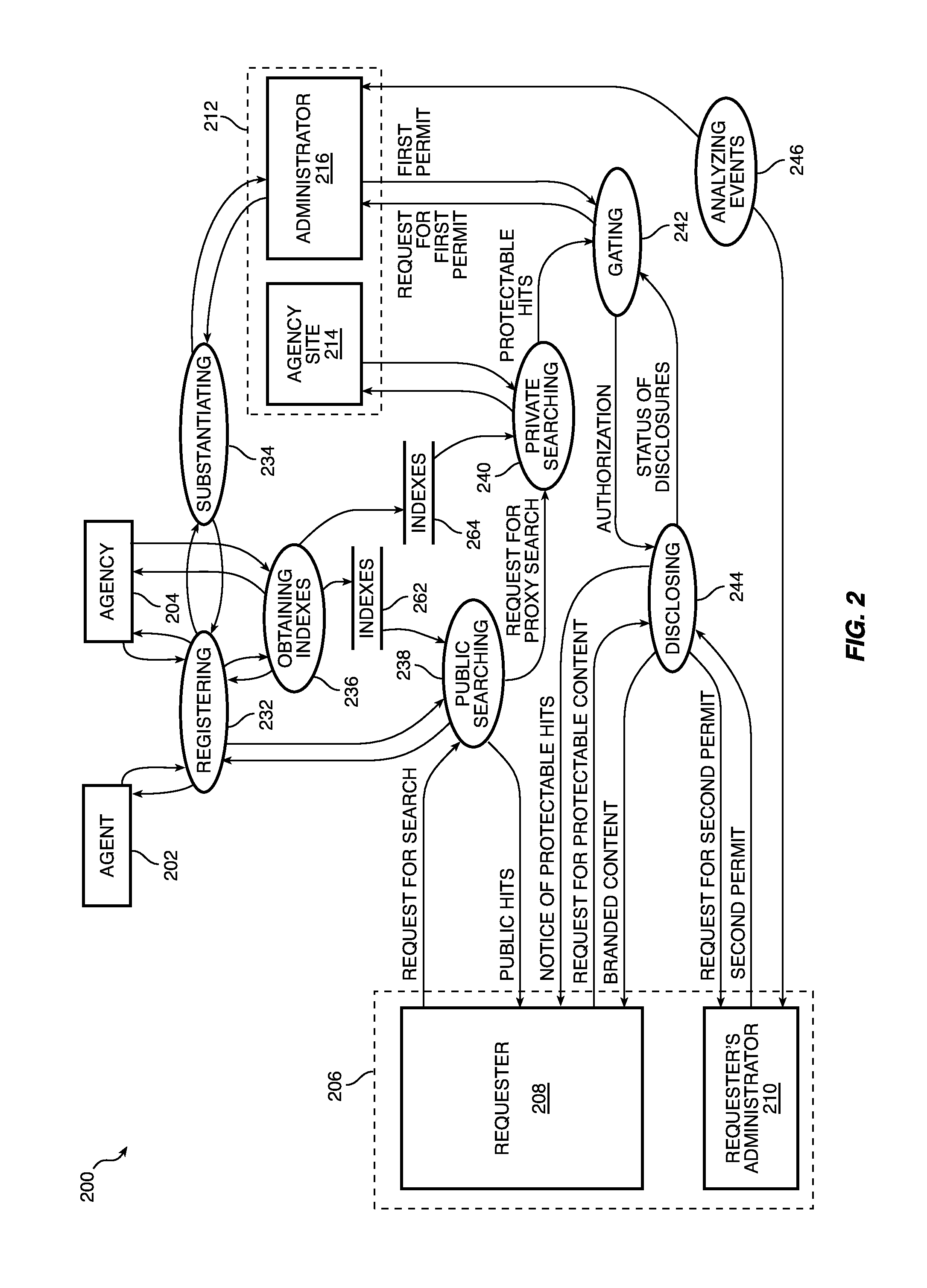
Systems and methods for managing disclosure of protectable information
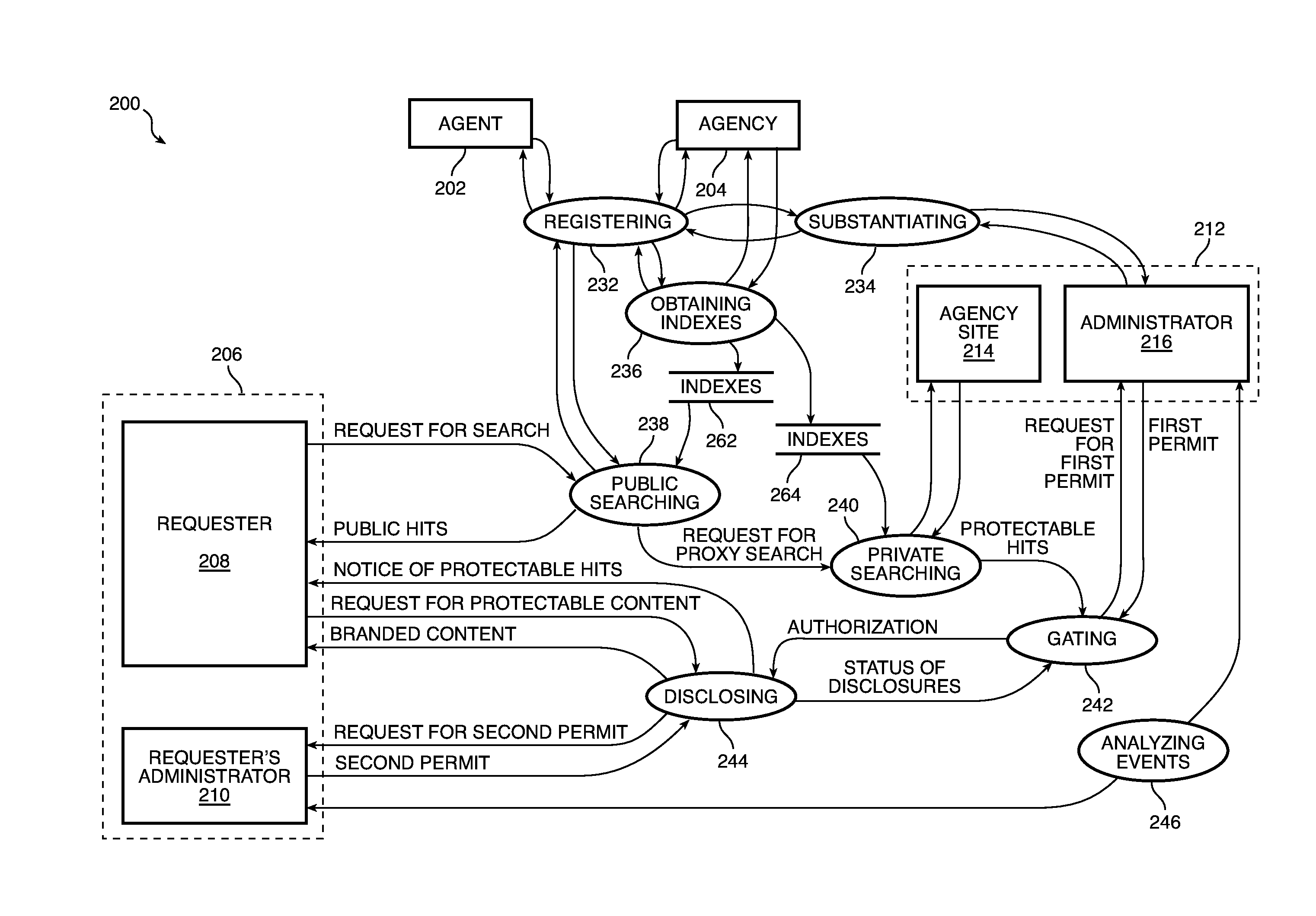
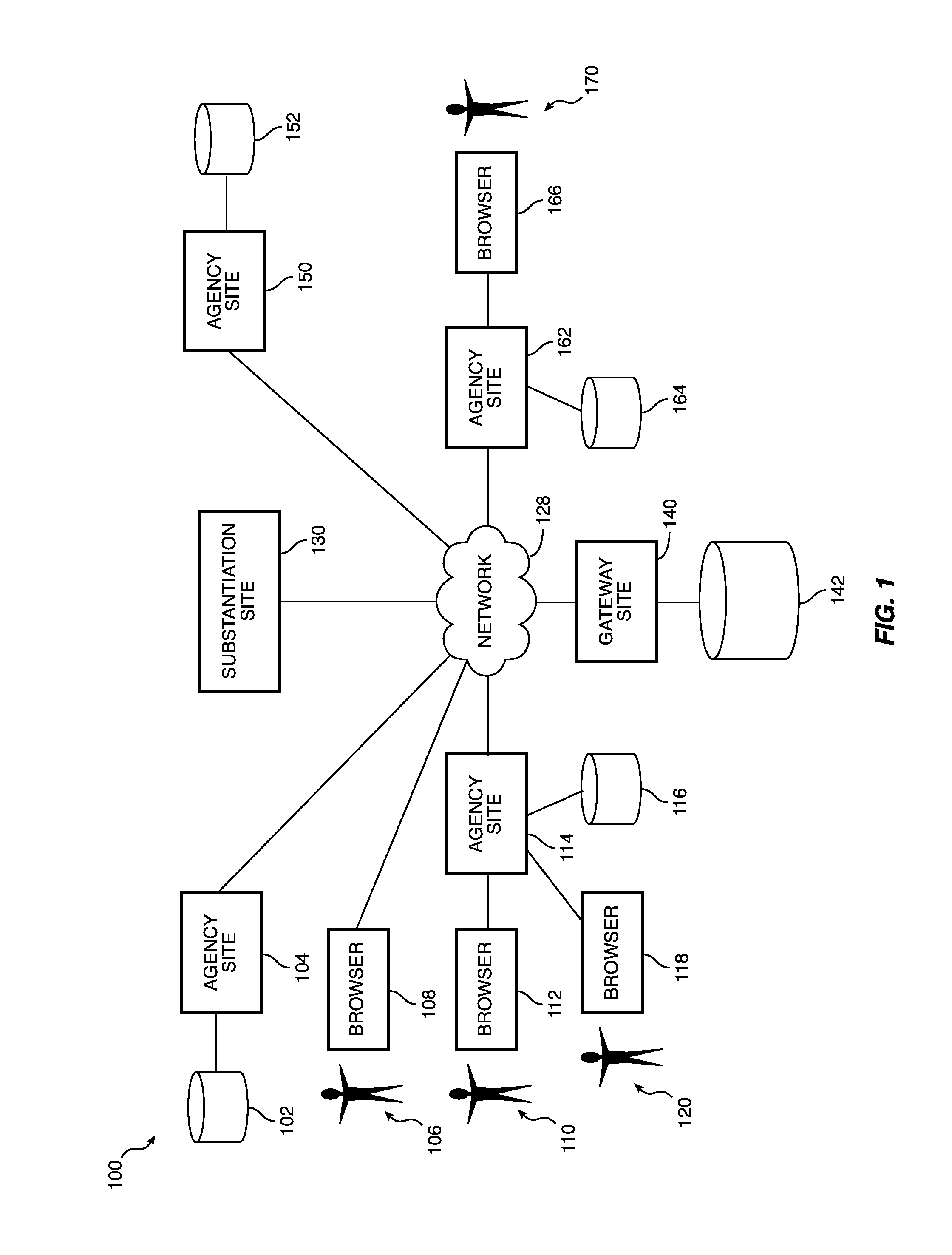
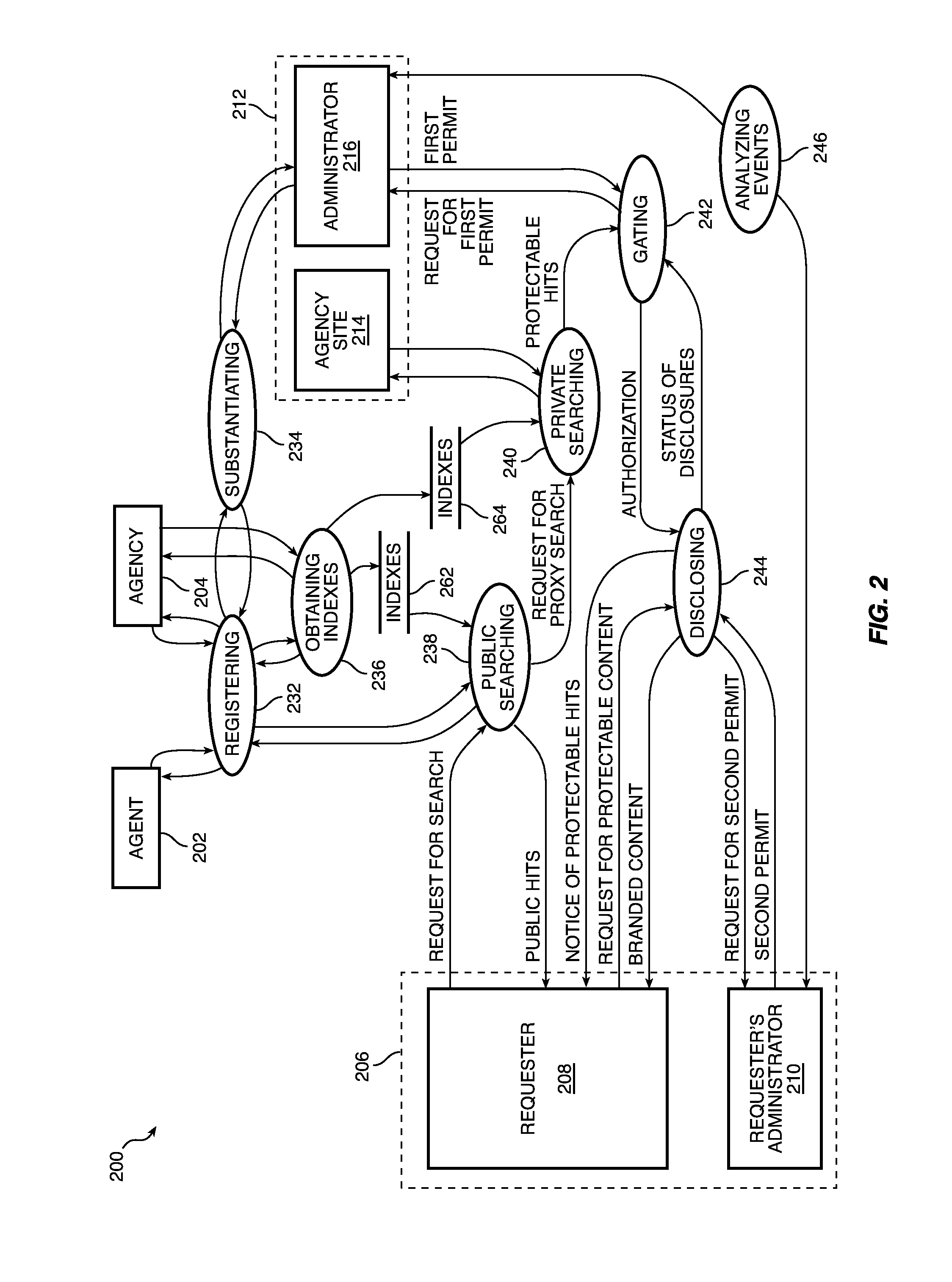
ActiveUS9058499B1Key distribution for secure communicationWeb data indexingRegistration authorityDatabase
A server and one or more portals cooperate with a first registered agency, an administrator of the first registered agency, a second agency, and an administrator of the second registered agency to determine whether access to protectable information should be granted to a registered requester.
Owner:TASER INT INC
Public key validation service
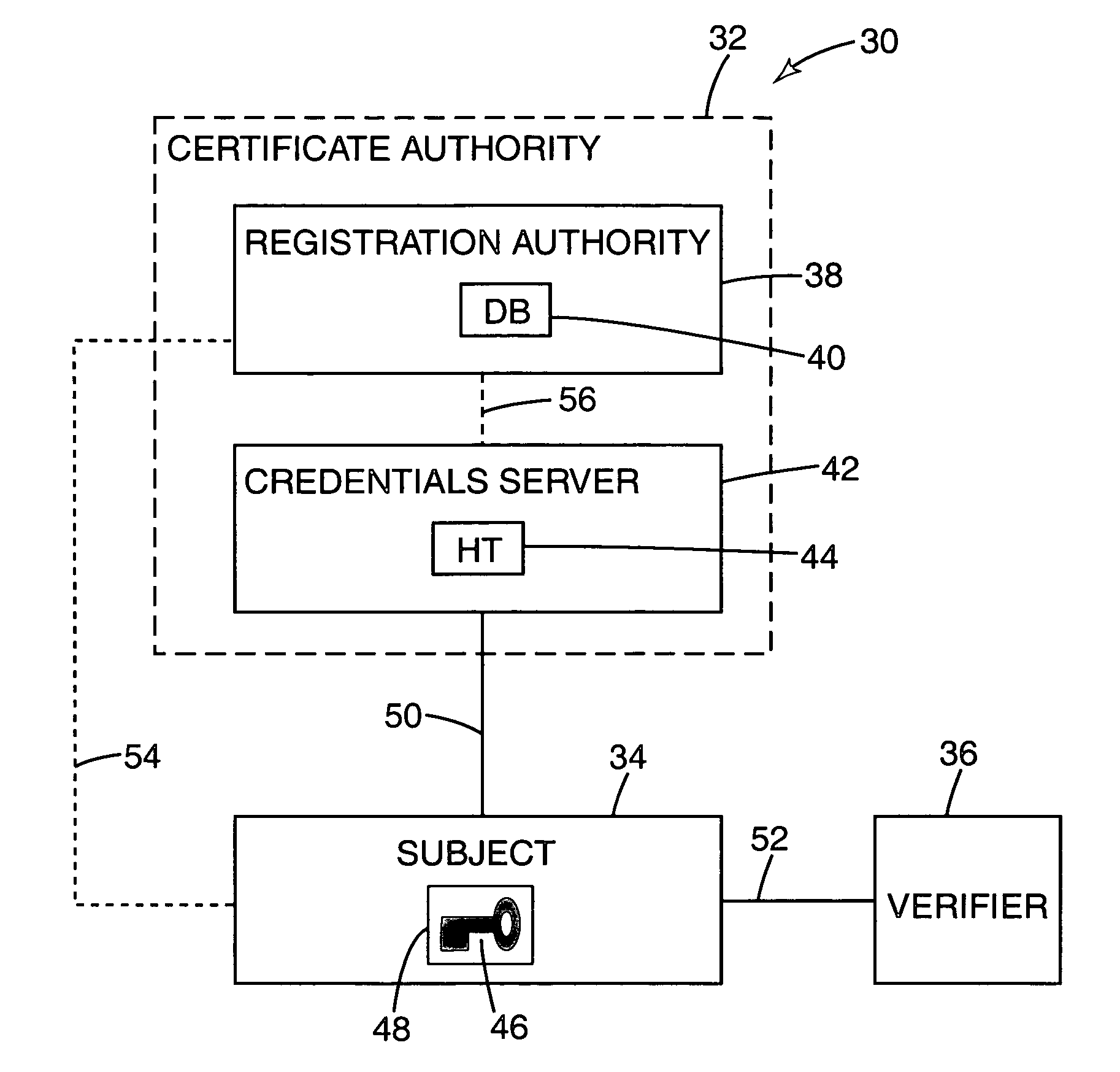
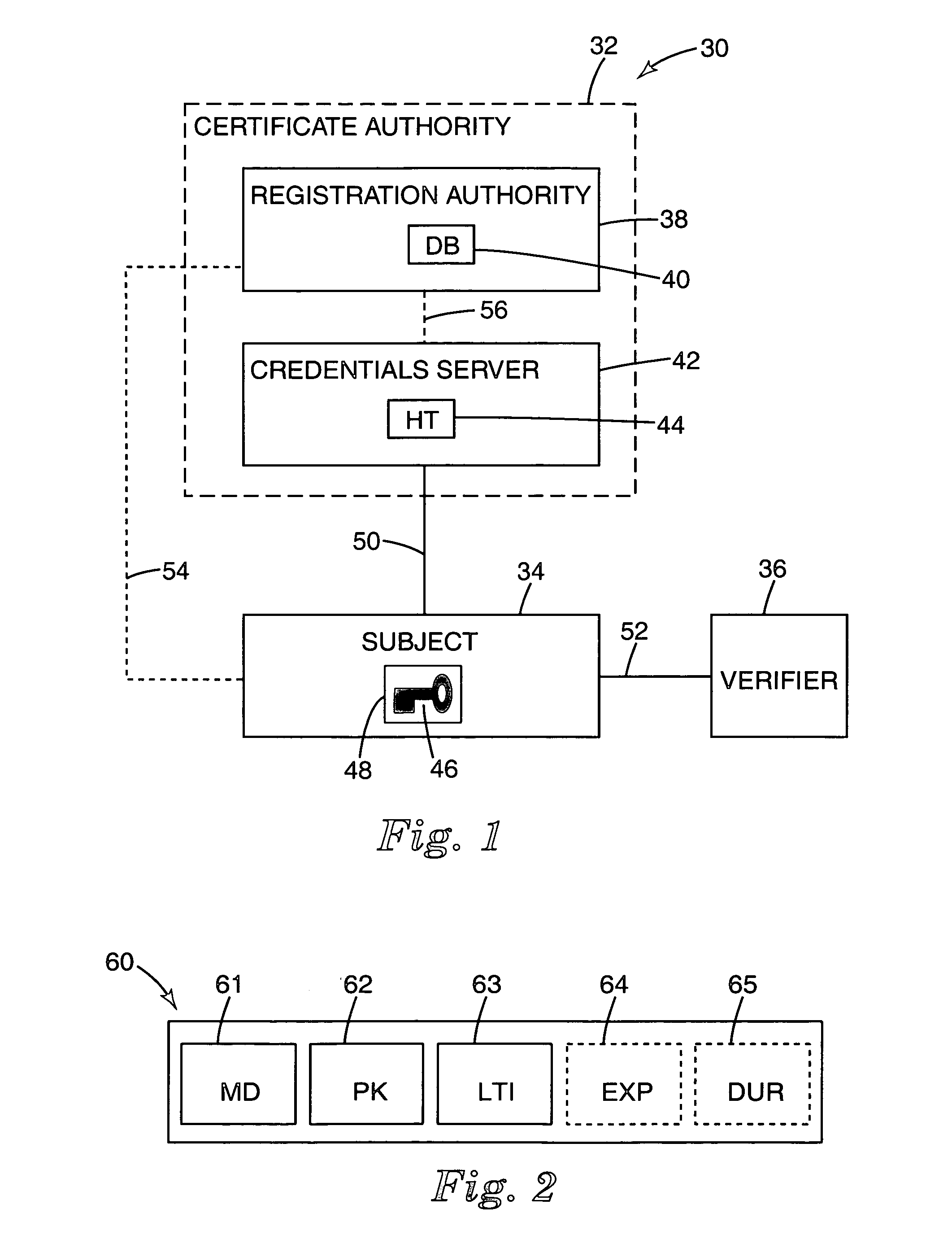
InactiveUS7010683B2Key distribution for secure communicationDigital data processing detailsRegistration authoritySerial code
A public key validation agent (PKVA) includes a registration authority which issues a first unsigned public key validation certificate (unsigned PKVC) off-line to a subject that binds a public key of the subject to a first public key serial number (PKVN). The registration authority maintains a certificate database of unsigned PKVCs in which it stores the first unsigned PKVC. A credentials server issues a disposable public key validation certificate (disposable PKVC) on-line to the subject. The disposable PKVC binds the public key of the subject from the first unsigned PKVC to the first PKVN from the first unsigned PKVC. The credentials server maintains a table that contains entries corresponding to valid unsigned PKVCs stored in the certificate database. The PKVA can be employed in a public key validation service to validate the public key of the subject before a private / public key pair of the subject is used for authentication purposes.
Owner:HEWLETT PACKARD DEV CO LP
Internet domain name registration system
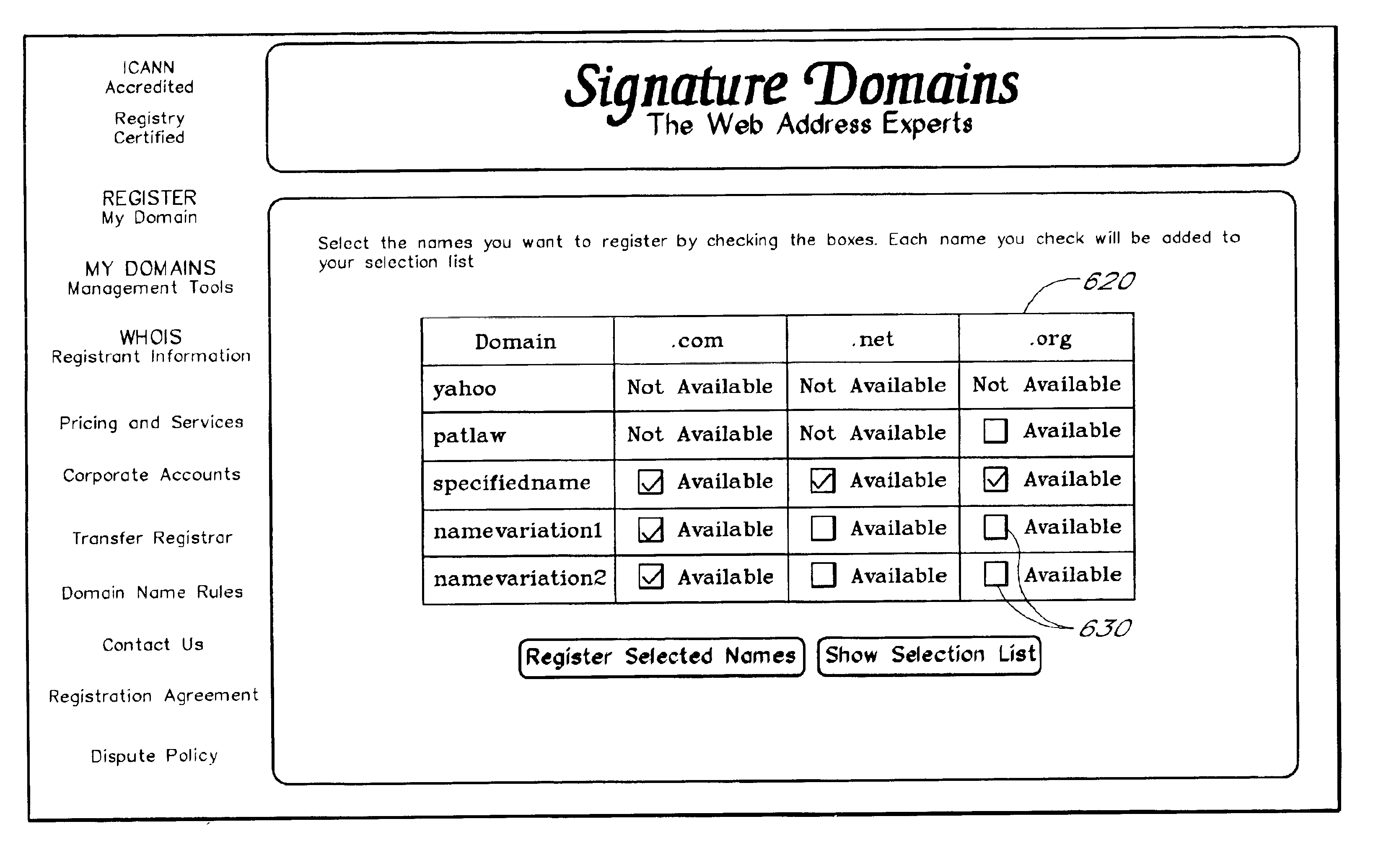
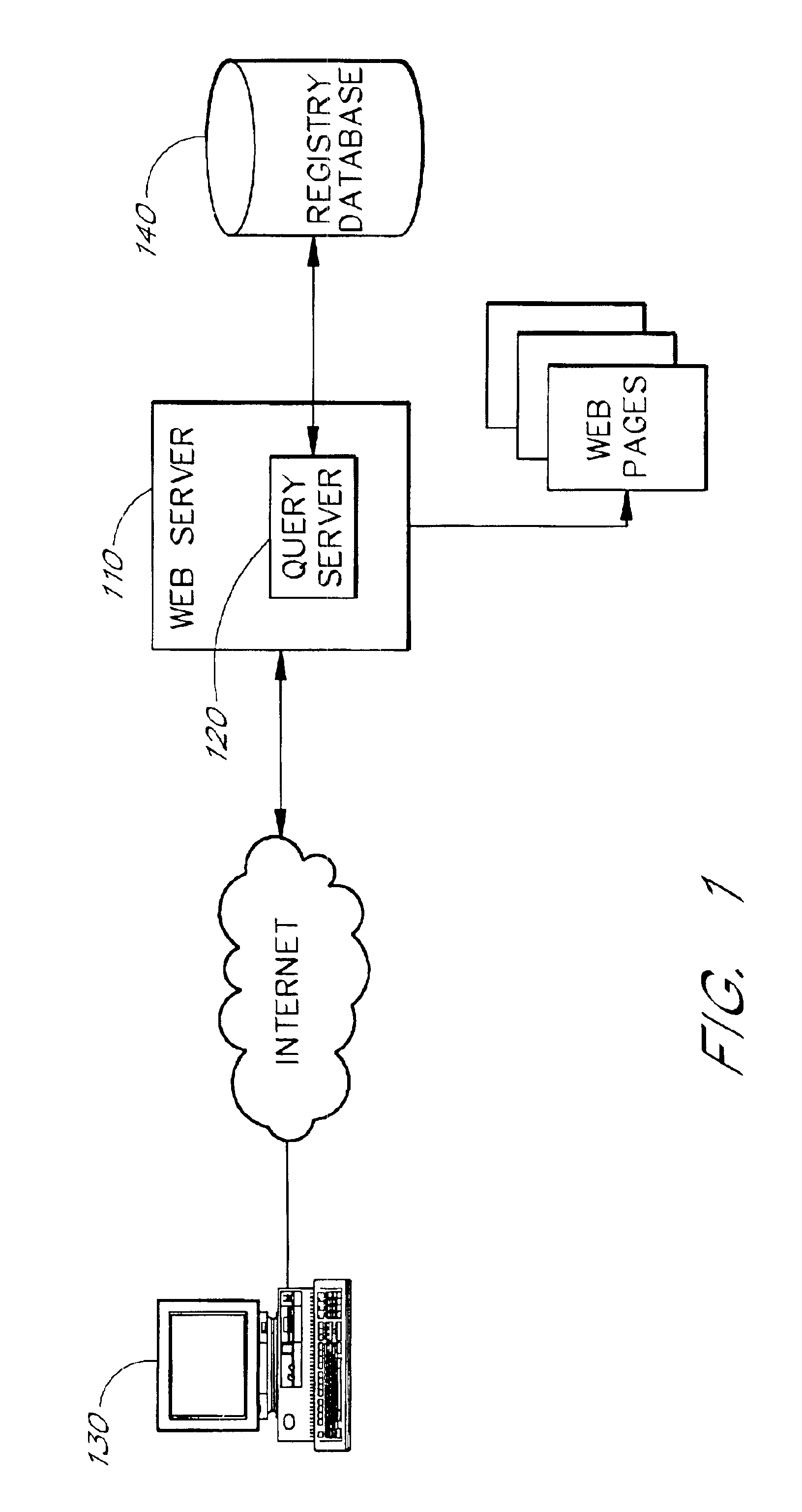
InactiveUS6980990B2Convenient queryReduce amountData processing applicationsDigital data processing detailsDomain nameRegistration authority
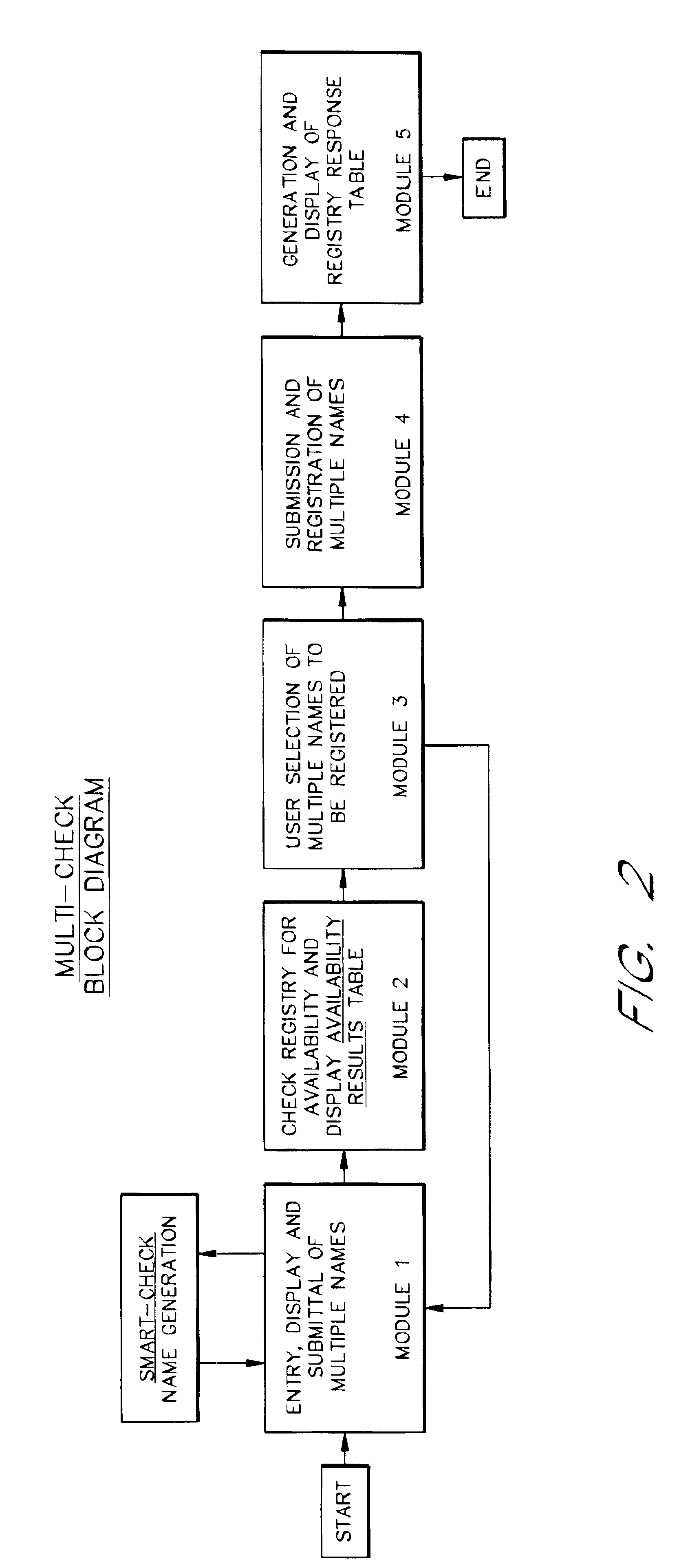
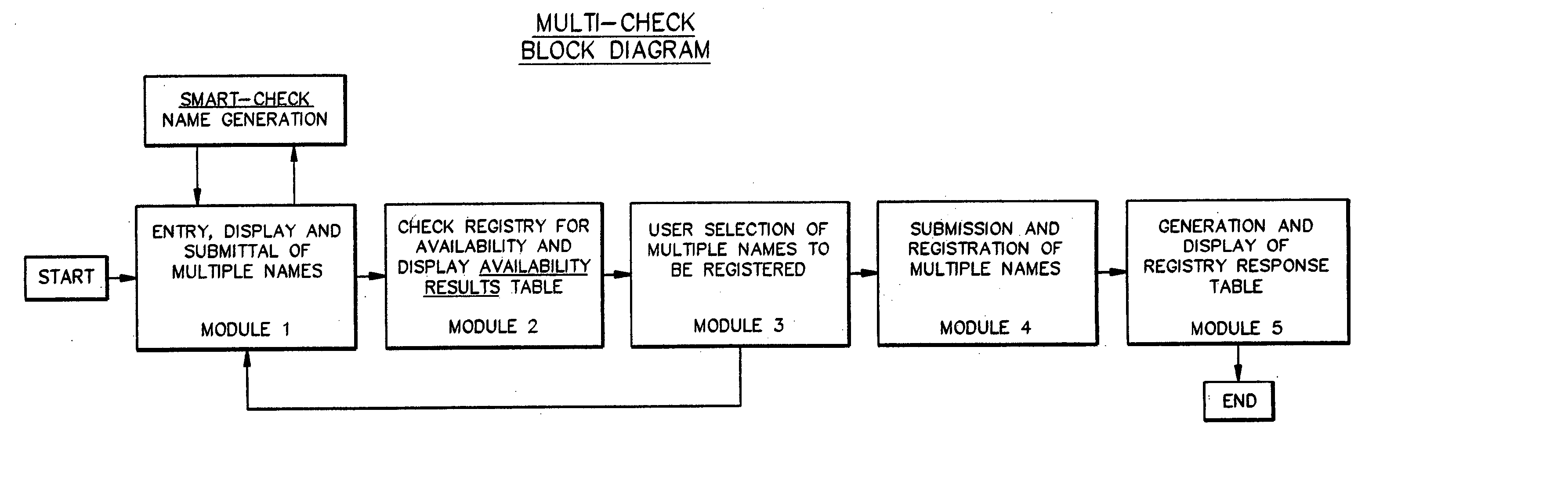
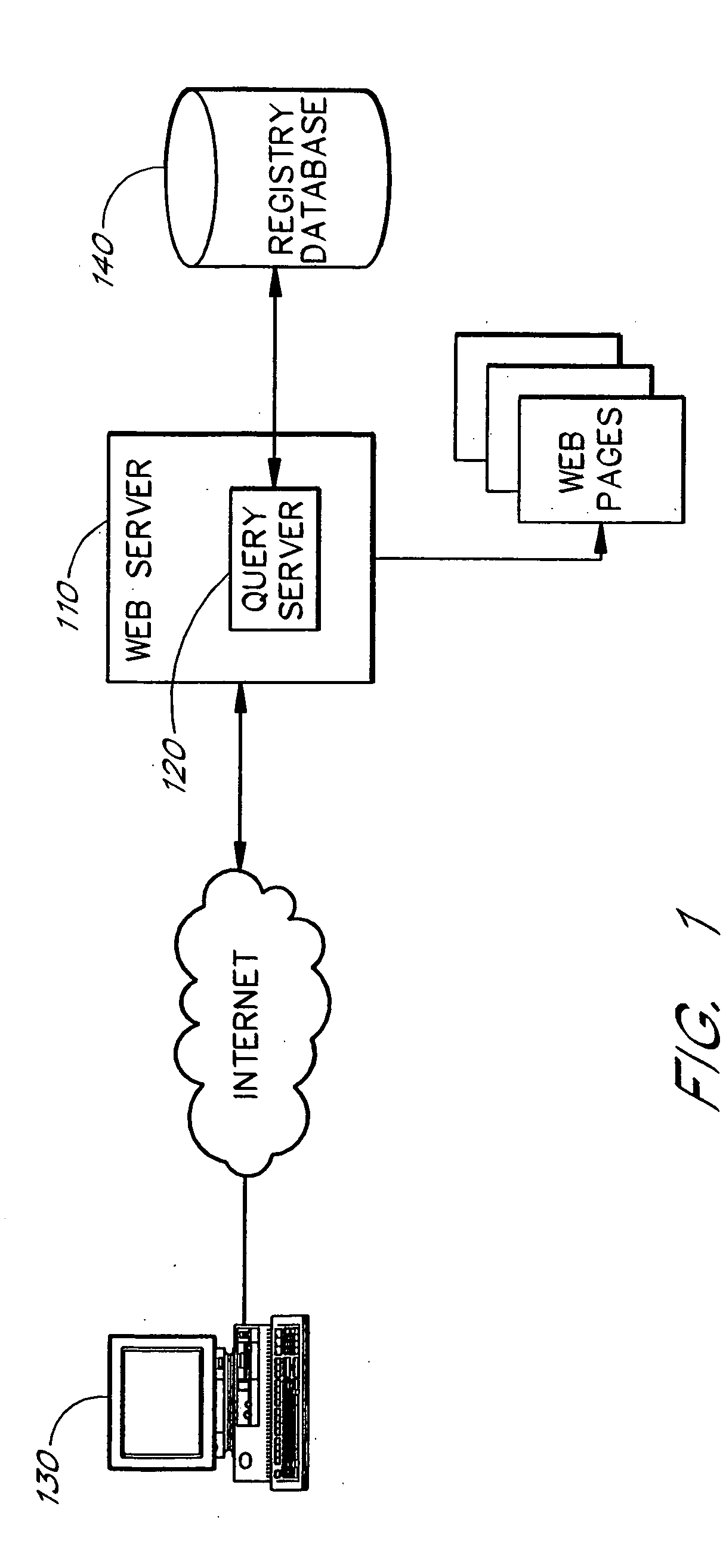
A domain name registration system includes a user interface through which a user can submit multiple names to a query server to determine the availability of the names for domain name registration. After the query results are returned for each of the multiple names submitted, the user is presented with a table listing the availability of each name in combination with multiple Top-Level Domain (TLD) extensions. The user is able to select one or more names from the table for registration in the registry database. After the query server has attempted to register each of the selected names, the user is presented with a Registry Response Table indicating which of the selected names were successfully registered as domain names. Thus, the system and method increases the speed and productivity of querying and updating a domain name registry or other database.
Owner:MULTICHECK SYST
Cryptographic methods and systems for managing digital certificates
ActiveUS20190123915A1Low costImprove securityMultiple keys/algorithms usagePublic key for secure communicationRegistration authorityCertificate authority
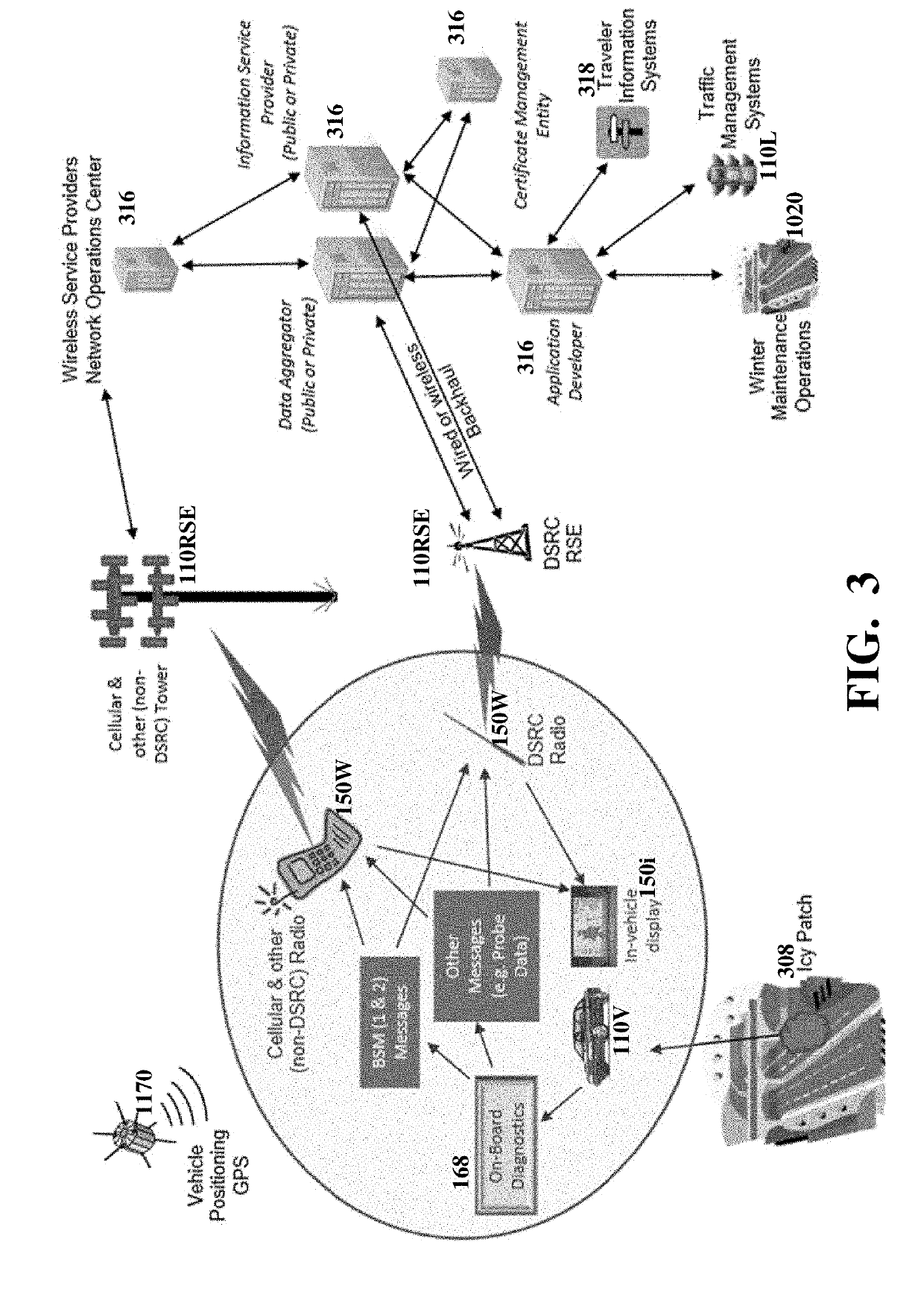
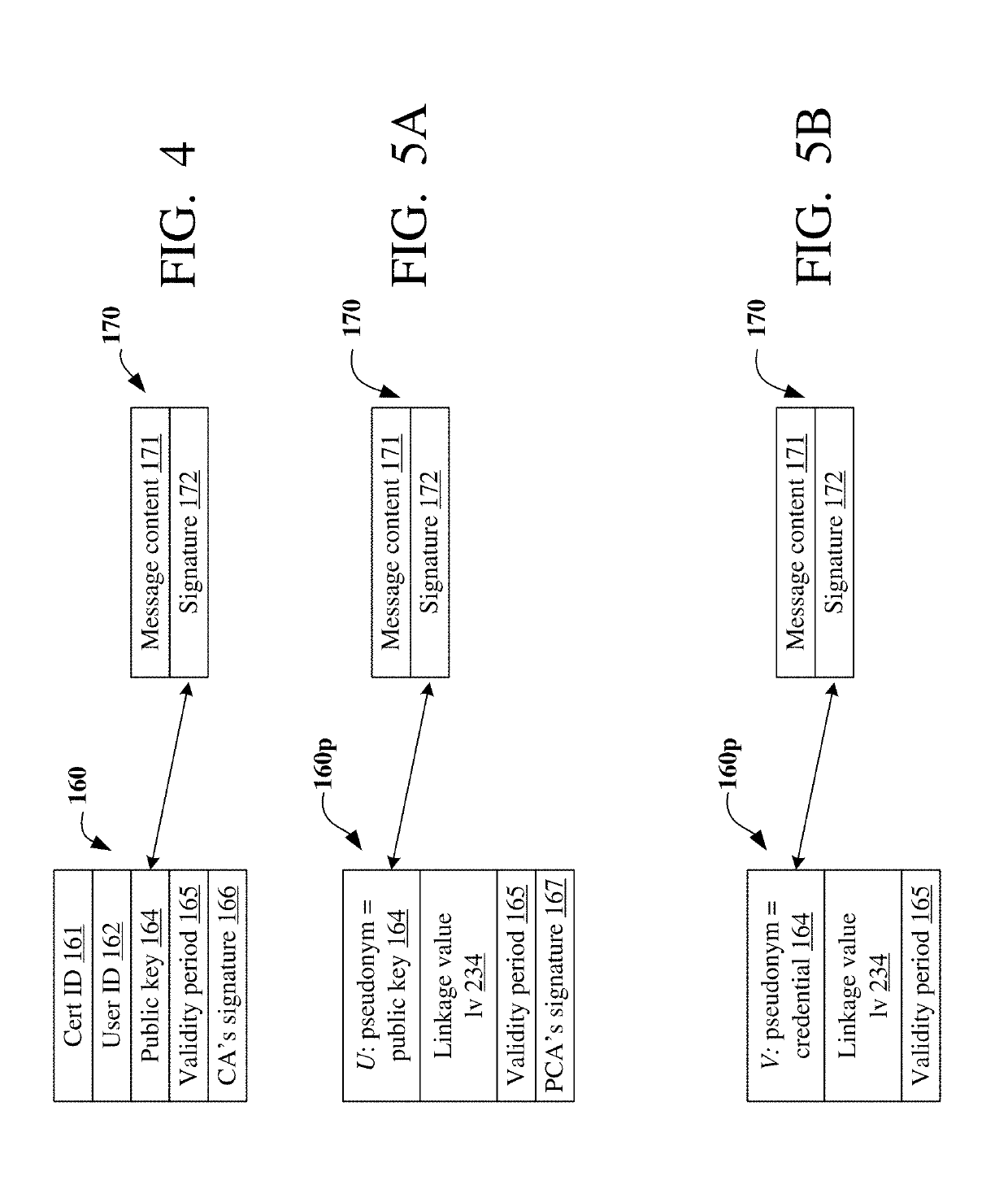
Pseudonym digital certificates (160p) are generated for devices (110 / 150) by a Pseudonym Certificate Authority (PCA), which communicates with devices via another entity—registration authority (RA)—so that the PCA and RA cannot associate certificates with devices. Each certificate is associated with a public signature key, and with a public encryption key used by PCA to encrypt the certificate to hide it from the RA. Both keys are derived by PCA from a single key. For example, the signature key can be derived from the public encryption key rather than generated independently. However, high security is obtained even when the PCA does not sign the encrypted certificate. Reduced bandwidth and computational costs are obtained as a result. Other embodiments are also provided.
Owner:LG ELECTRONICS INC +1
Generic public key infrastructure architecture
InactiveUS20080016336A1Rich varietyPublic key infrastructure trust modelsHome automation networksRegistration authorityClient-side
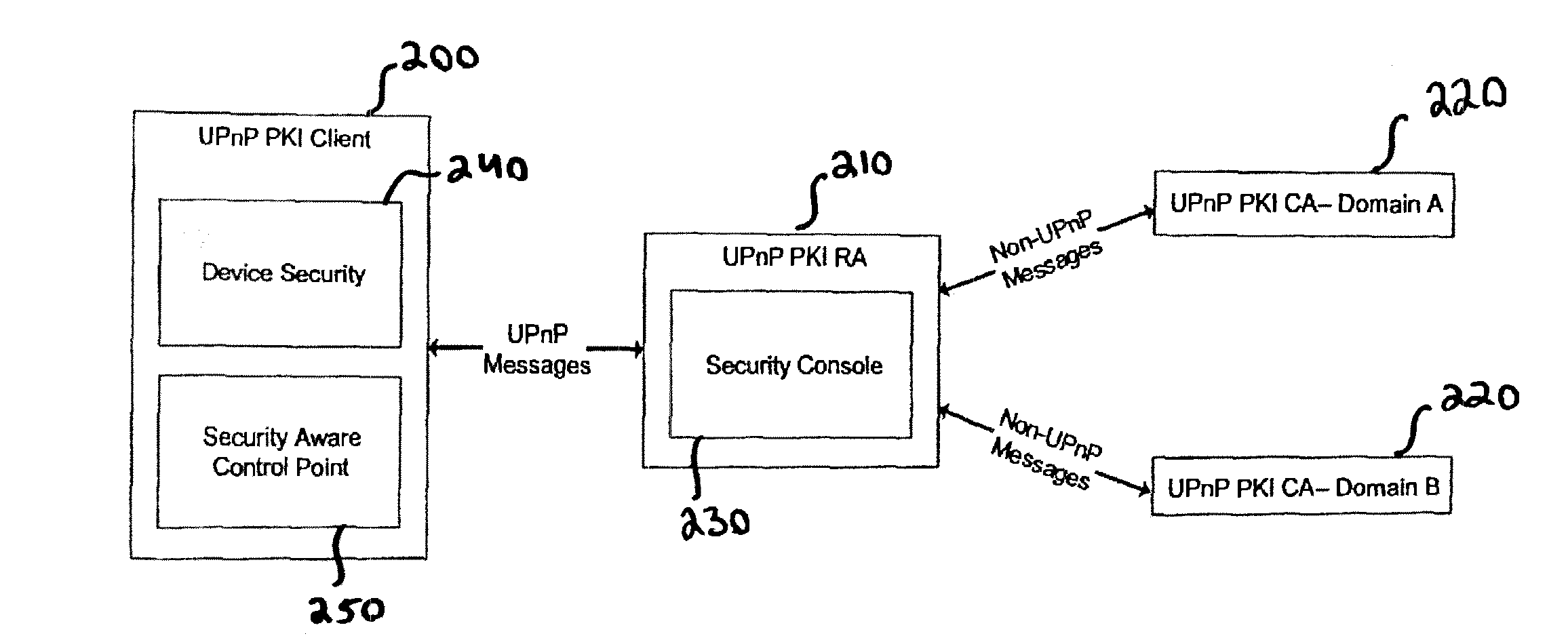
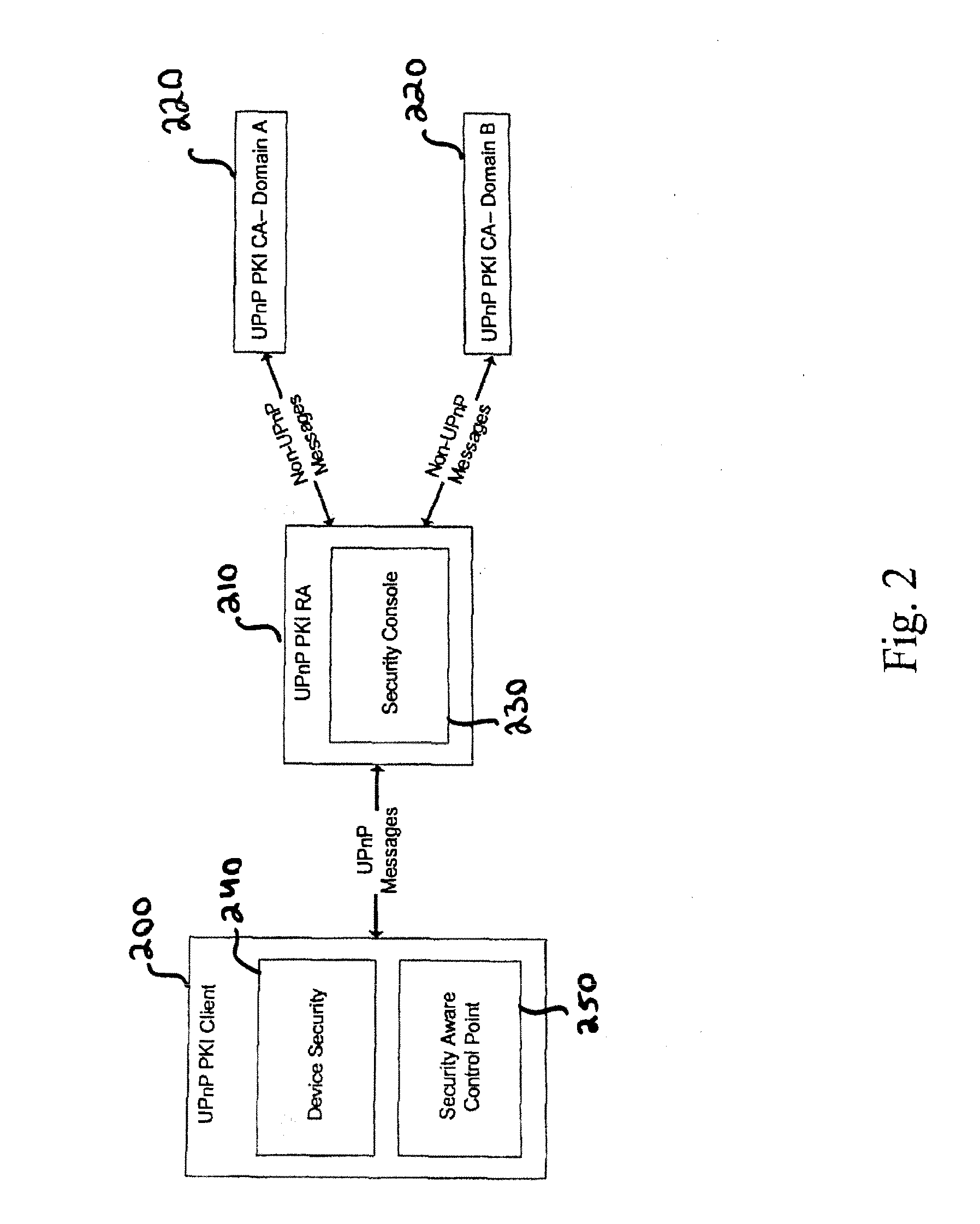
Methods, apparatuses and modules for creation of a generic public key infrastructure by use of established trust, wherein trust between a client and a registration authority is established, and an enrolled certificate is furnished in a secure manner to the client by use of the established trust. The present invention also address correspondingly configured servers and / or terminals, client and / or registration authorities and / or certificate authority entities, as well as device security, security-aware control points and security console units, provided with such modules and functions enabling the aspects of the method / s to be carried out. Respective computer programs and circuit arrangements for carrying out the aspects of the methods and / or for operating hardware to carry out the aspects of the above methods are also provided.
Owner:NOKIA CORP
Method of customizing a user's browsing experience on a World-Wide-Web site
In accordance with a first aspect of the present invention, a method of customizing the browsing experience of a user of a Web site comprised of a plurality of Web pages is provided. Each Web page is indexed using at least one coding system. A user record for each user is maintained on the Web site, which contains personal information of the user coded in accordance with said coding system. The user's browsing experience on the site may thus be readily customized using the user's personal information via code comparison. In accordance with a second aspect of the present invention, a method of ensuring the privacy of the user's personal information is provided through use of a unique Universal Anonymous Identifier (UAI) assigned to each user by a third party registration authority.
Owner:PERSONALPATH SYST
Public-key-encryption data-communication system and data-communication-system forming method
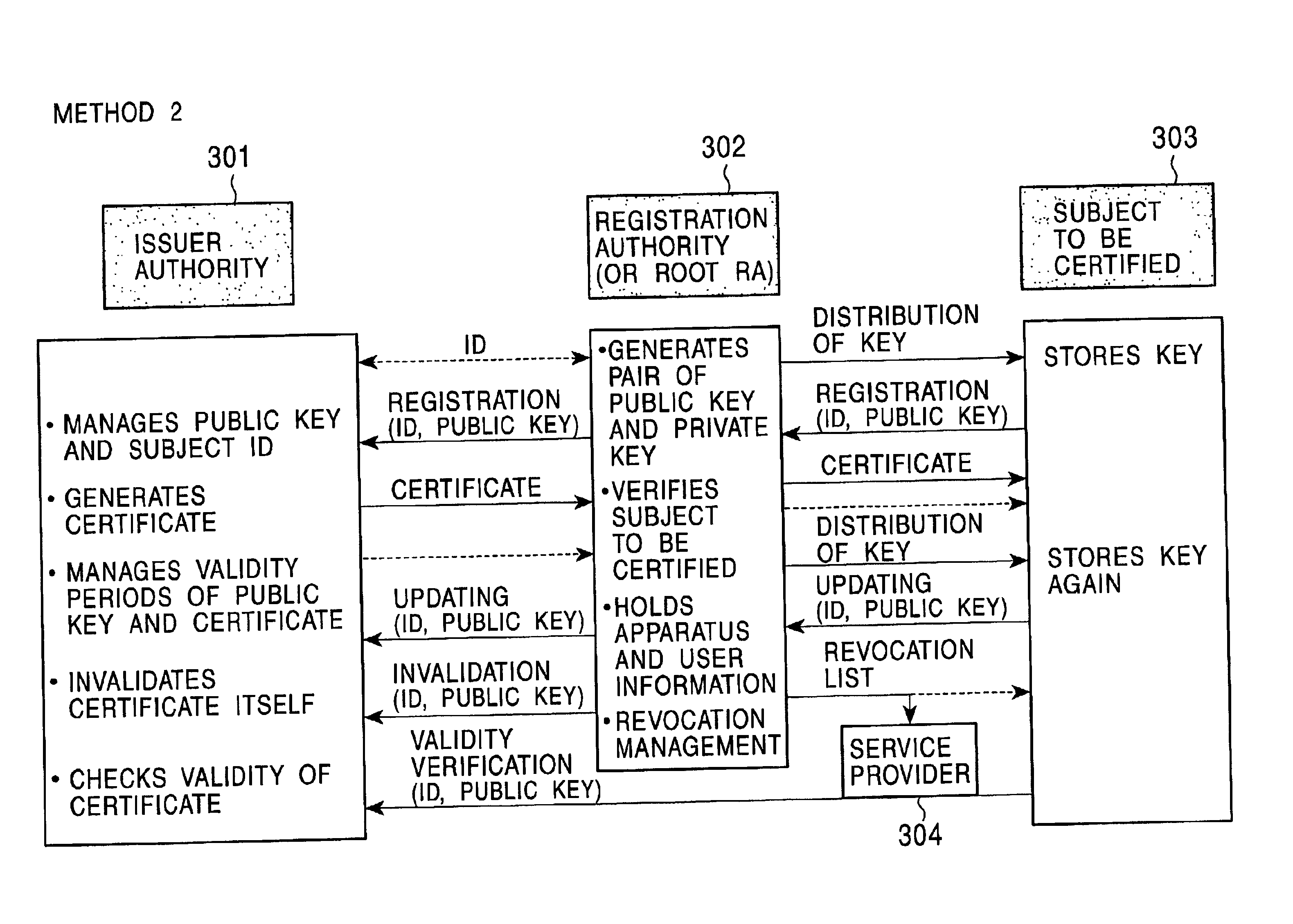
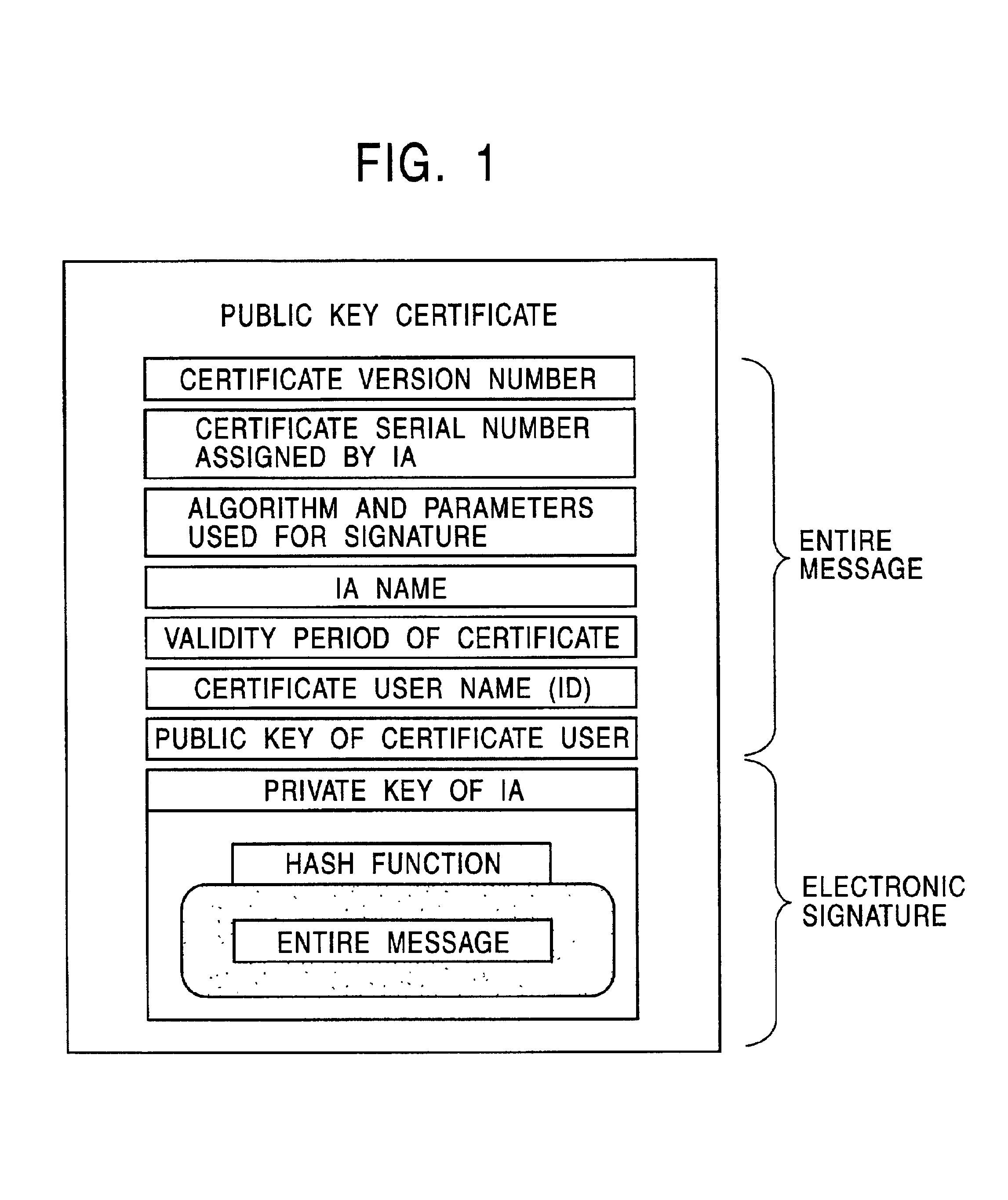
InactiveUS6990583B2Simple processEasy to useKey distribution for secure communicationDigital data processing detailsRegistration authorityCommunications system
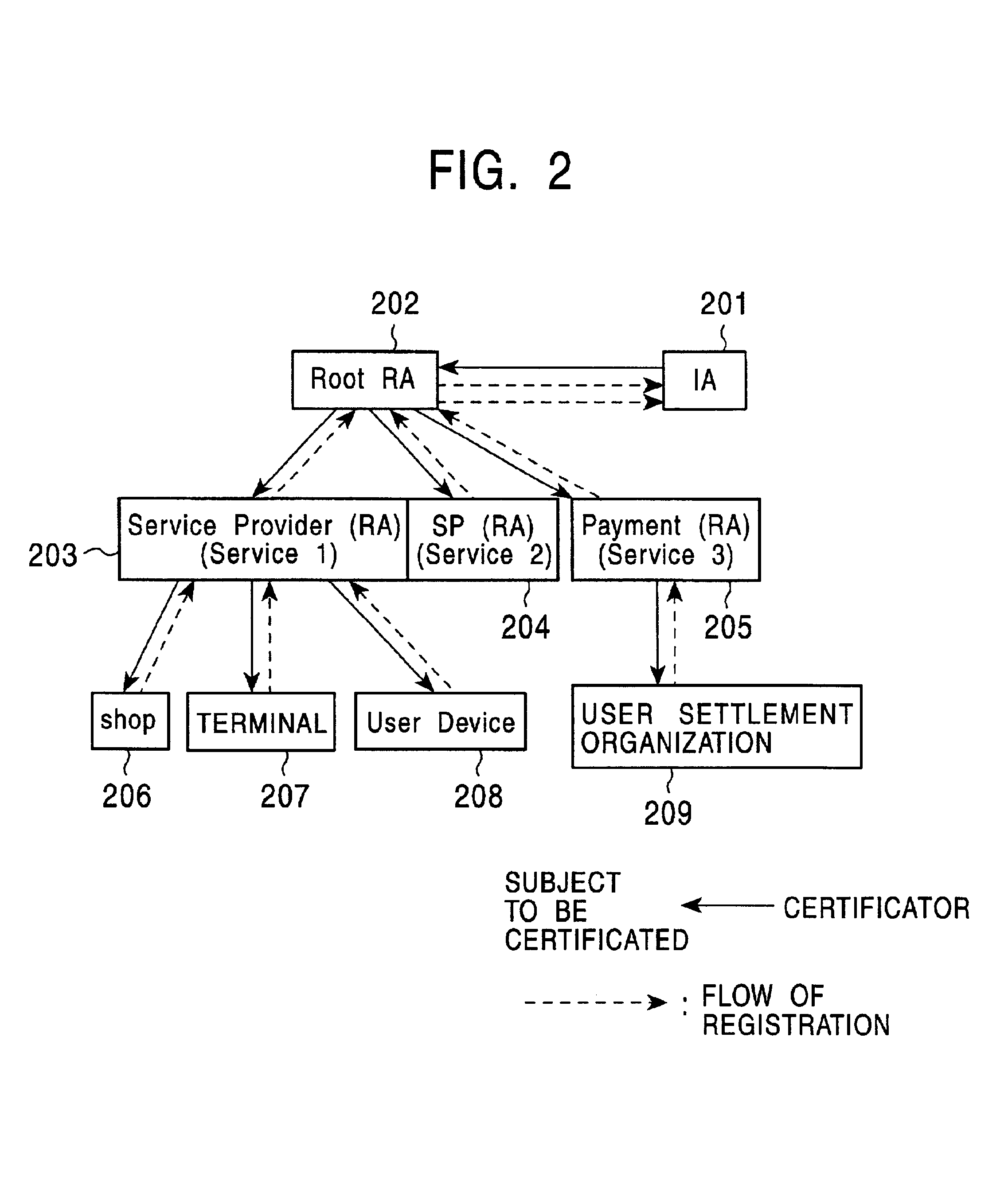
A public-key-encryption data-communication system includes a public-key-certificate issuer authority. The public-key-certificate issuer authority performs the issuance of a public key certificate and management operations, certification of a subject to be certificated, which is a certificate issuing request, and management such as registration processing are executed by a root registration authority or each registration authority. The public-key-certificate issuer authority performs processing for validating, invalidating, and deleting the certificate in accordance with a request from the root registration authority. The root registration authority accepts a request for issuing a public key certificate corresponding to the subject to be certificated which is under the control of a certificated registration authority, and transfers it to the public-key-certificate issuer authority in a form in which a signature is added to it. Processes by the public-key-certificate issuer authority, the root registration authority, the registration authority are separated, whereby the need for new implementation of user recognition, certificate issuance, registration, and management is eliminated.
Owner:SONY CORP
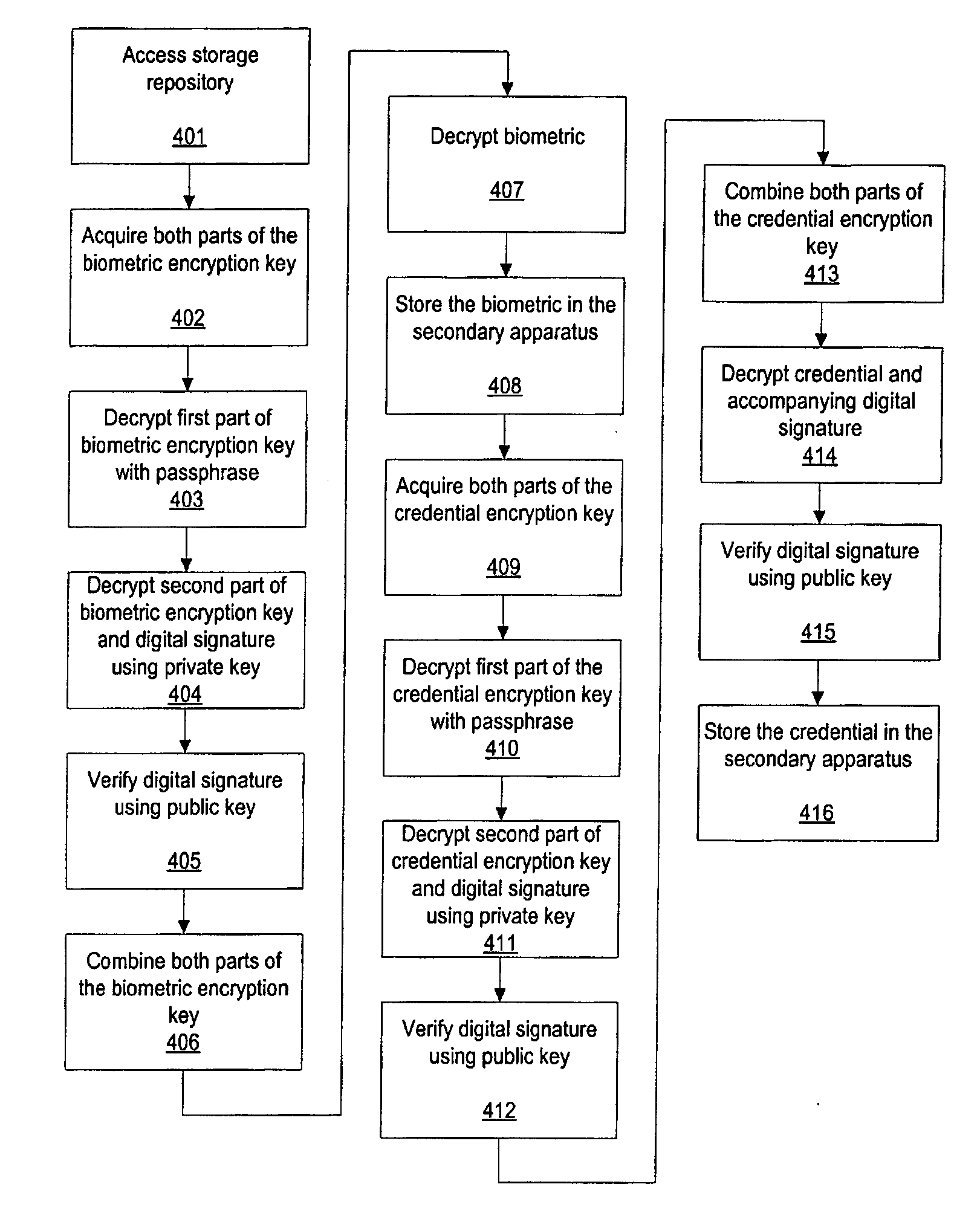
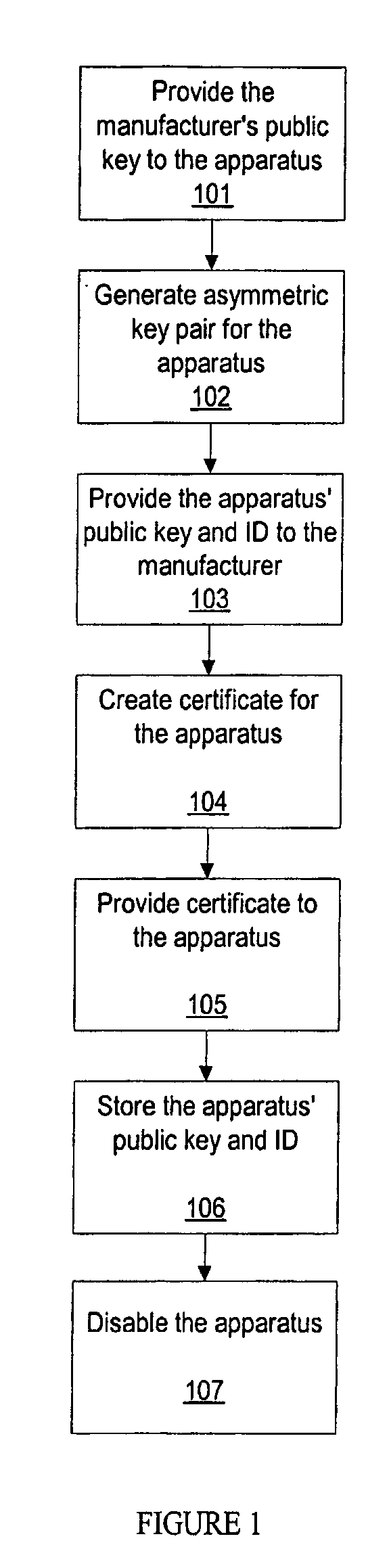
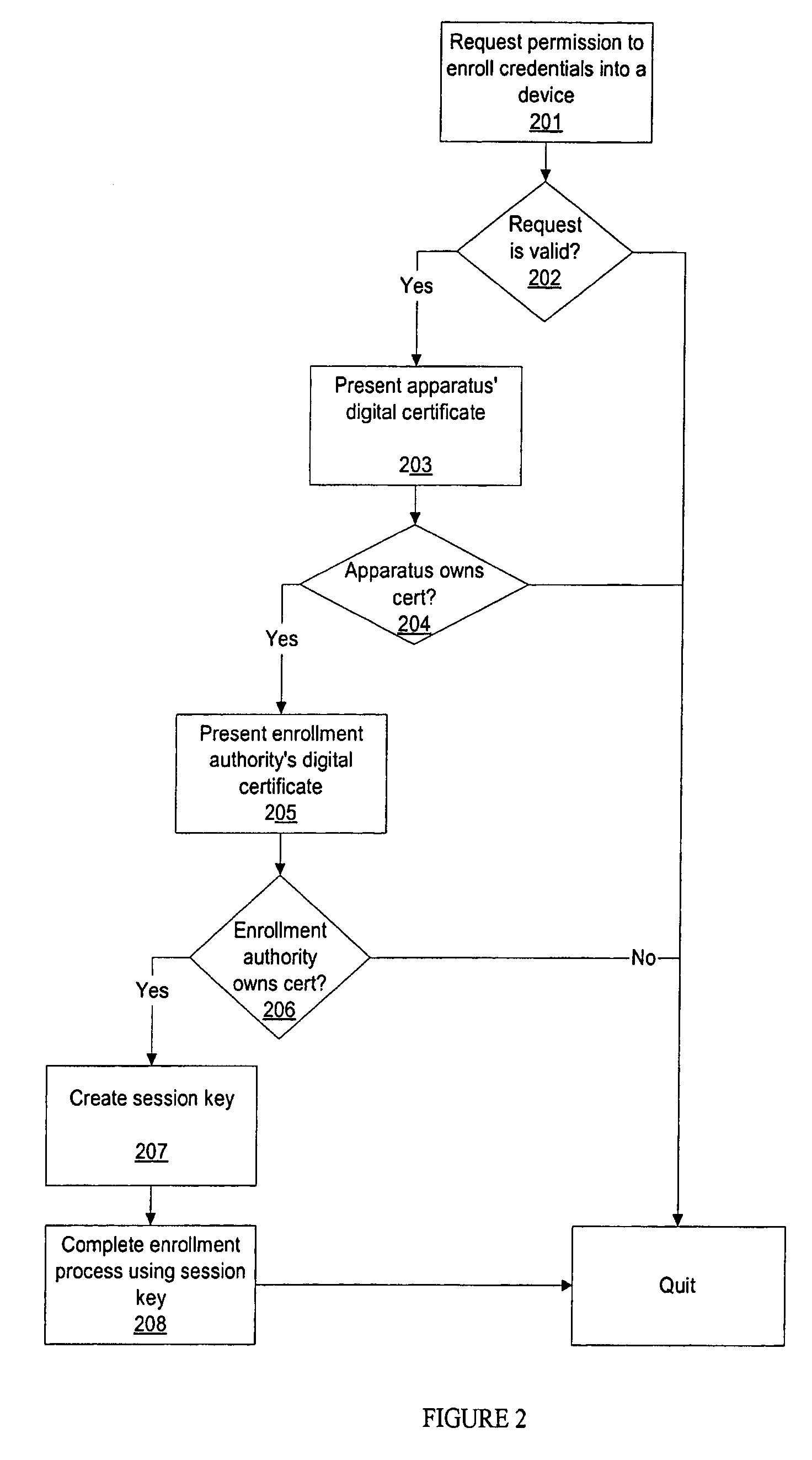
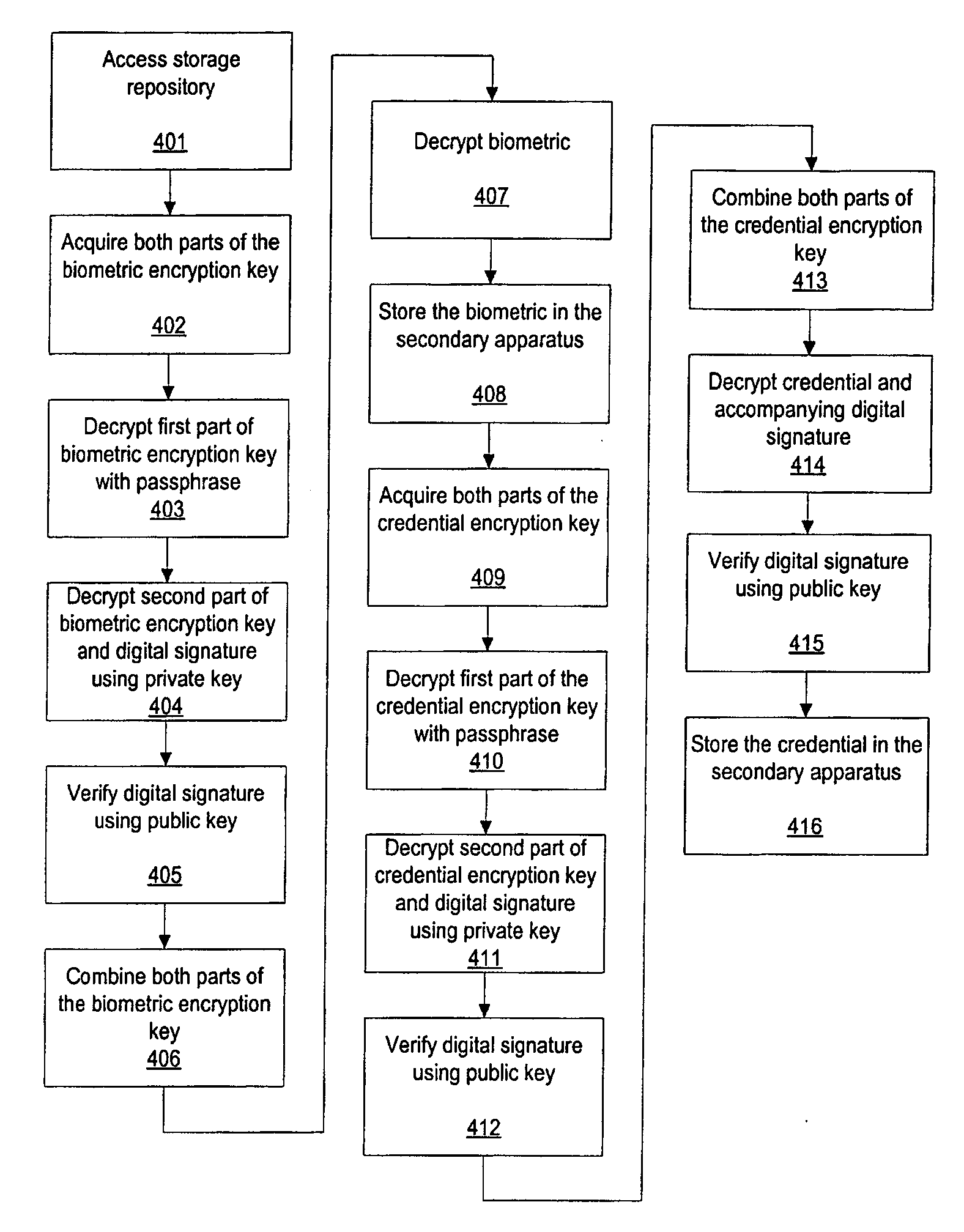
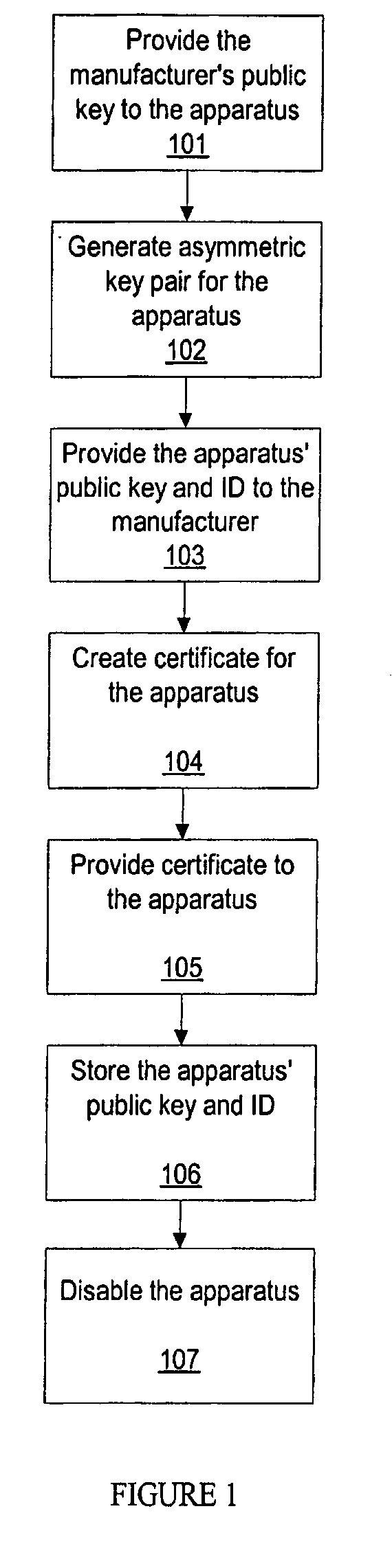
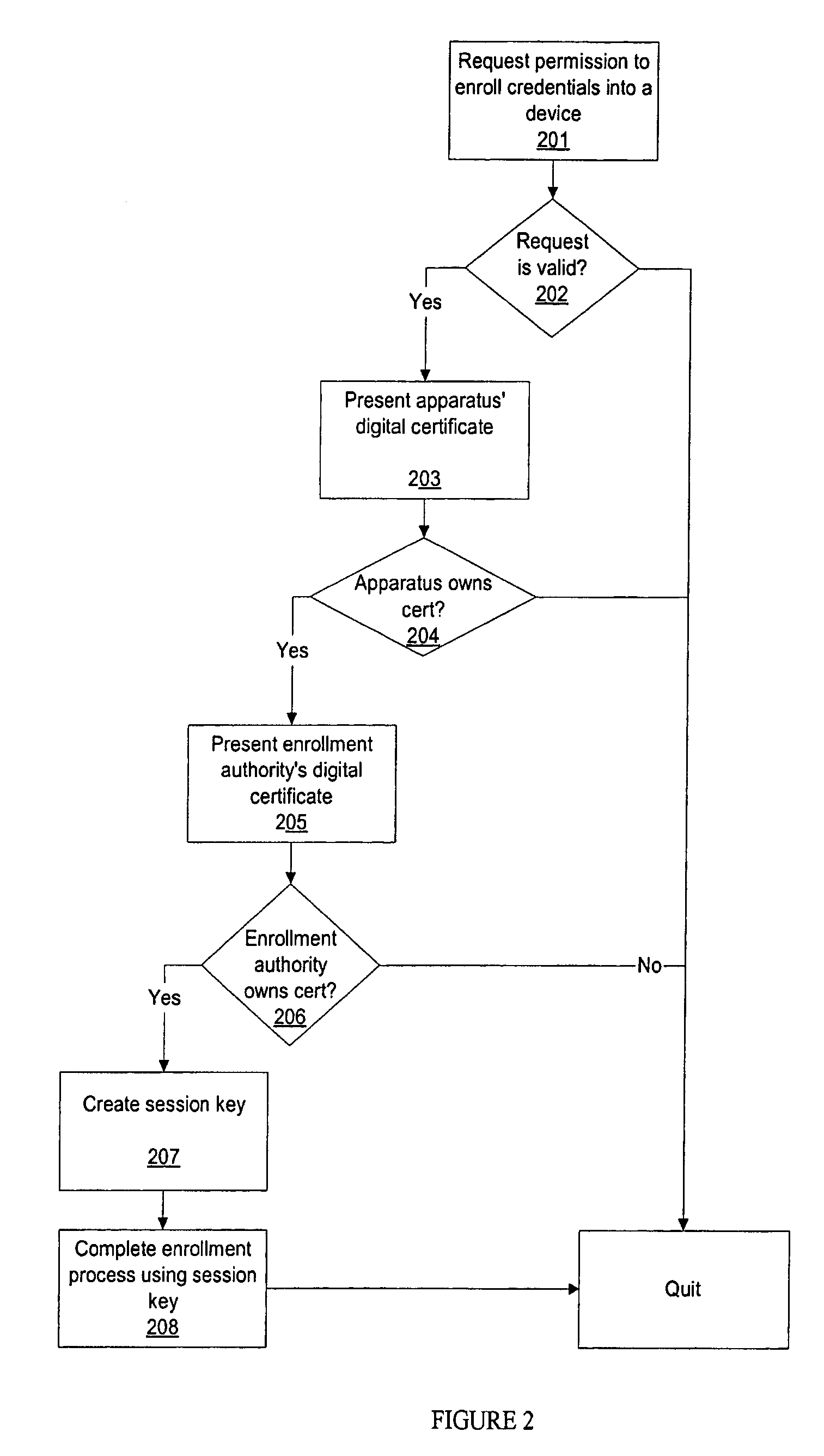
Methods for secure enrollment of personal identity credentials into electronic devices
InactiveUS20090031140A1Electric signal transmission systemsKey distribution for secure communicationRegistration authorityUnique identifier
A method and system for securely enrolling personal identity credentials into personal identification devices. The system of the invention comprises the manufacturer of the device and an enrollment authority. The manufacturer is responsible for recording serial numbers or another unique identifier for each device that it produces, along with a self-generated public key for each device. The enrollment authority is recognized by the manufacturer or another suitable institution as capable of validating an individual before enrolling him into the device. The enrollment authority maintains and operates the appropriate equipment for enrollment, and provides its approval of the enrollment. The methods described herein discuss post-manufacturing, enrollment, backup, and recovery processes for the device.
Owner:APPLE INC
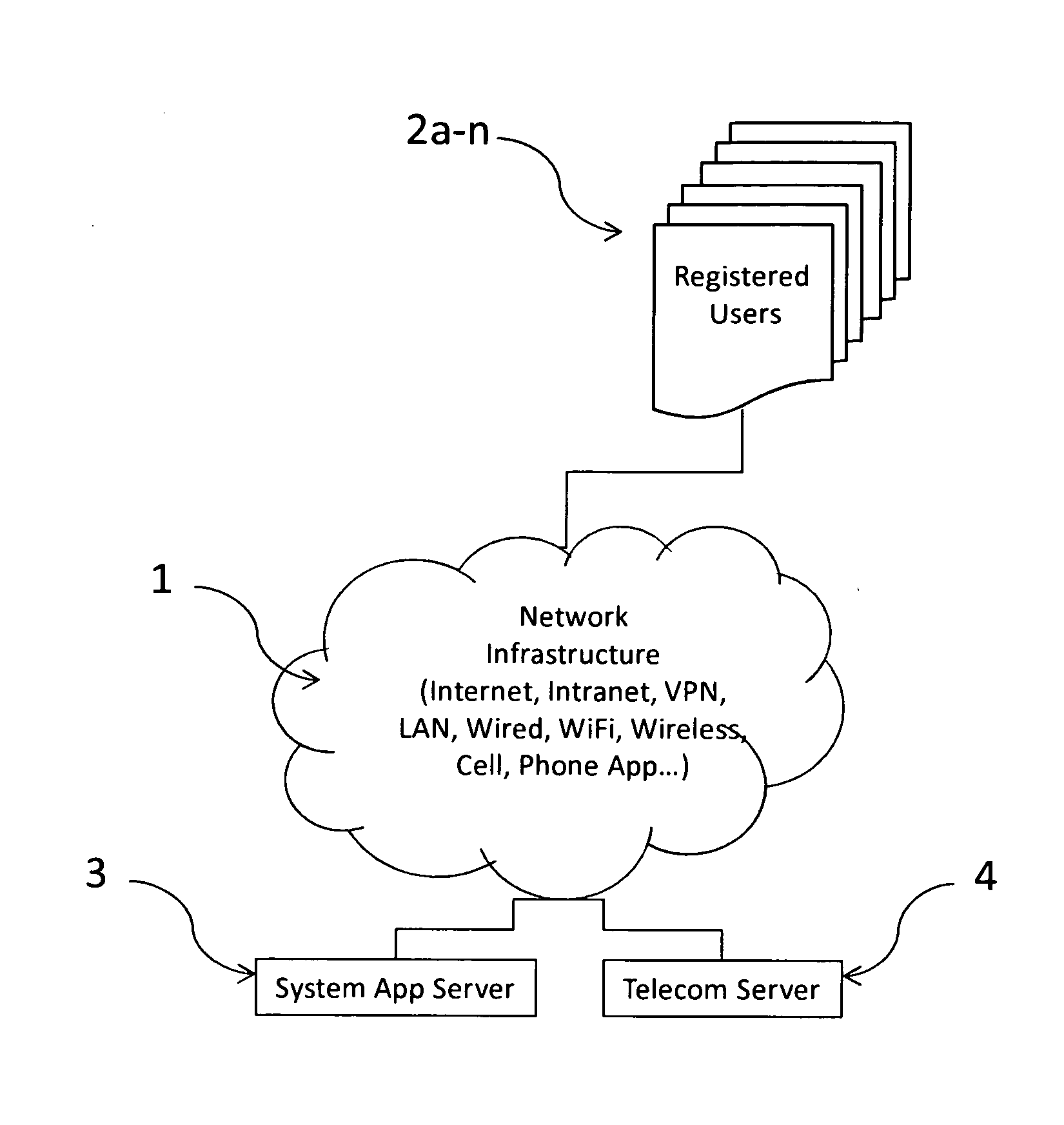
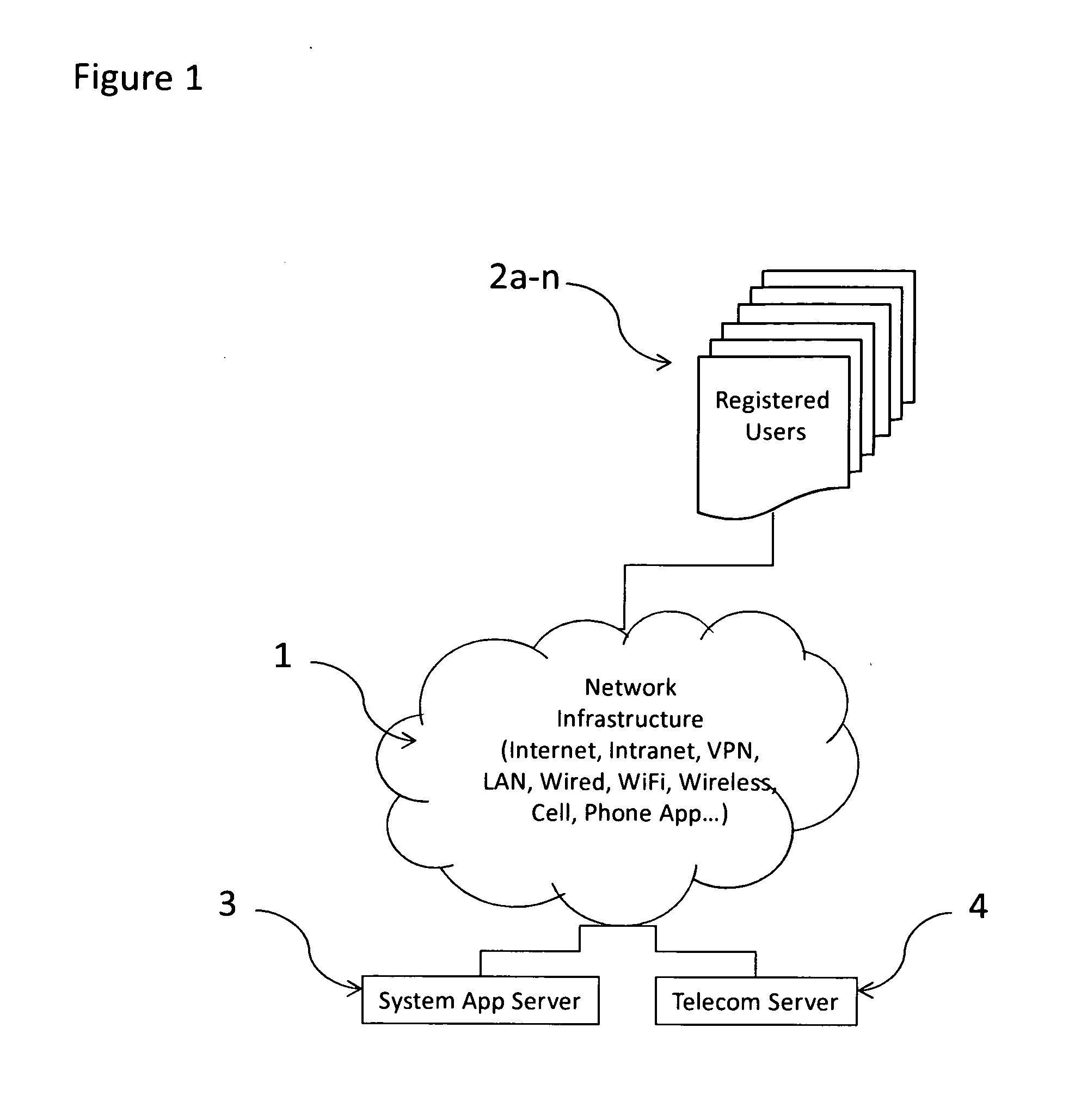
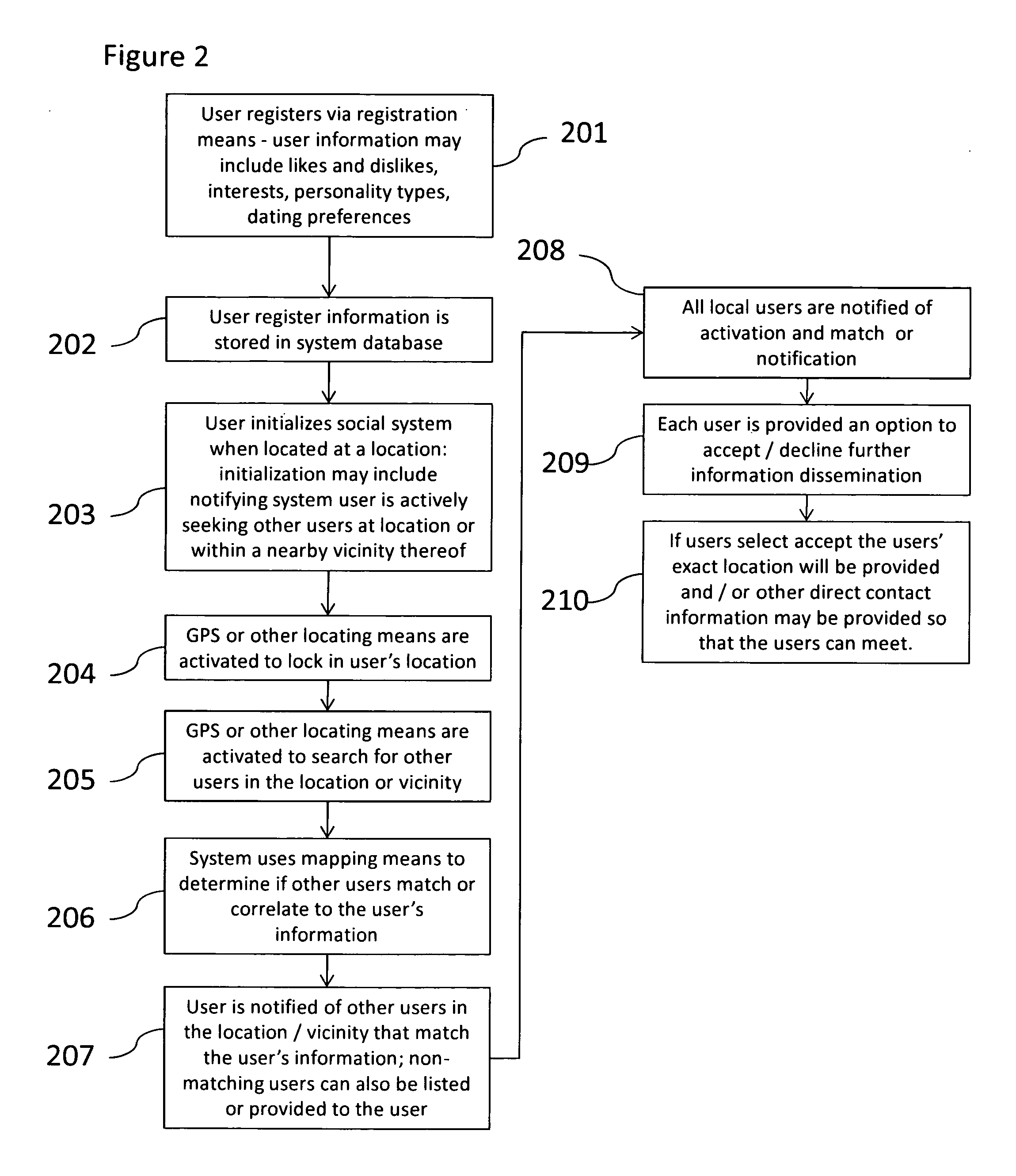
System for enabling interactive socialization of users at a location or geographic radius thereof
InactiveUS20130122936A1Improve abilitiesServices signallingLocation information based serviceRegistration authorityComputer compatibility
A system enables interactive socialization of users having a wireless device at a venue. The system includes a registration mechanism for registering a user. A location determination mechanism comprises a global positioning system that identifies the longitude and latitude of other users. An on-location update mechanism publishes the availability of the service at a given venue. A data mechanism runs a list of active sessions against a user compatibility engine. A notification is transmitted to each user that contains a compatibility match listing compatible users at the venue. Intercommunication among users is provided through the system / application, whereby a user receives the compatibility match notification and can respond with a message, block or ignore based on a compatibility assessment. The subject system or application may be used for a dating aid for meeting others, or to create networking opportunities.
Owner:HUDSON ROBERT P +1
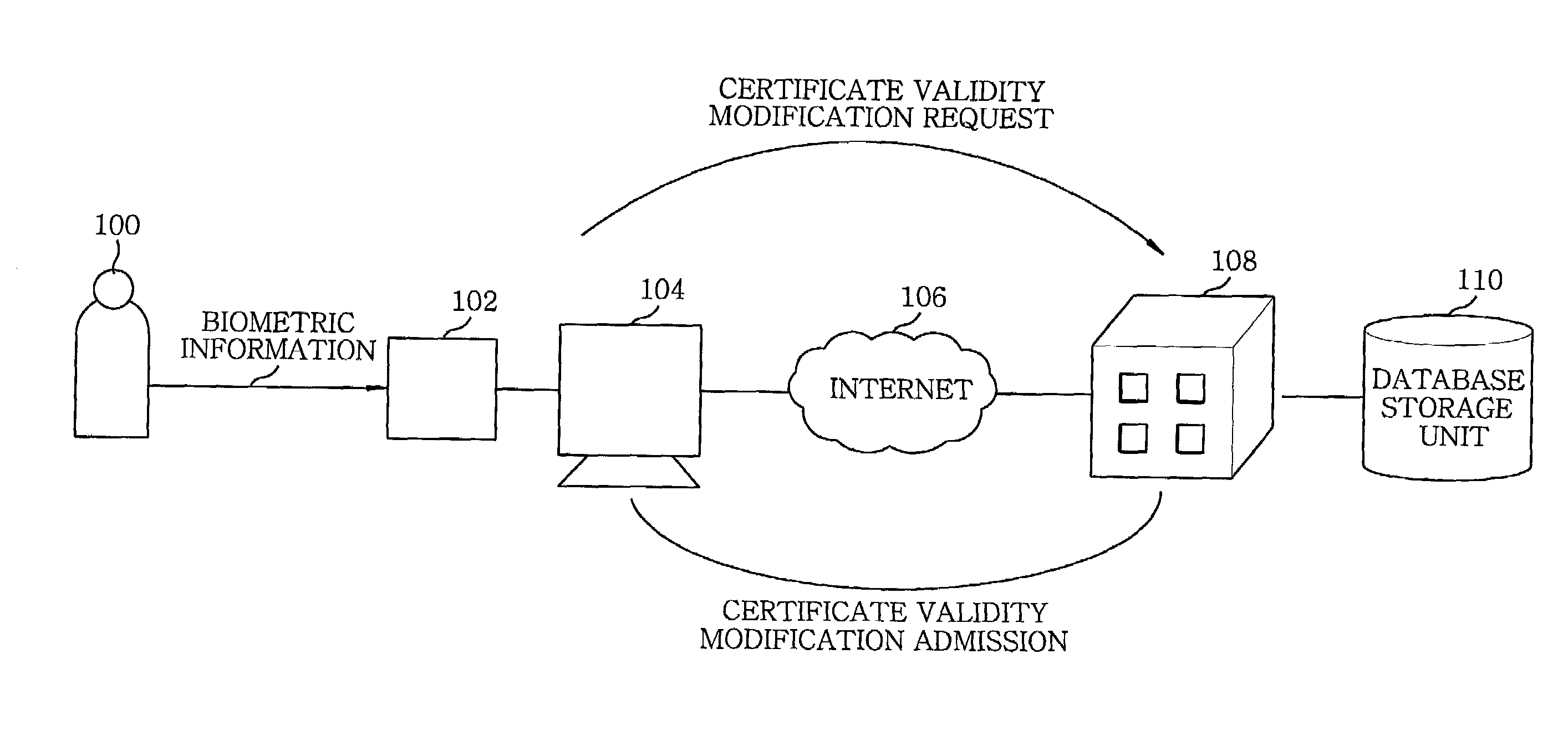
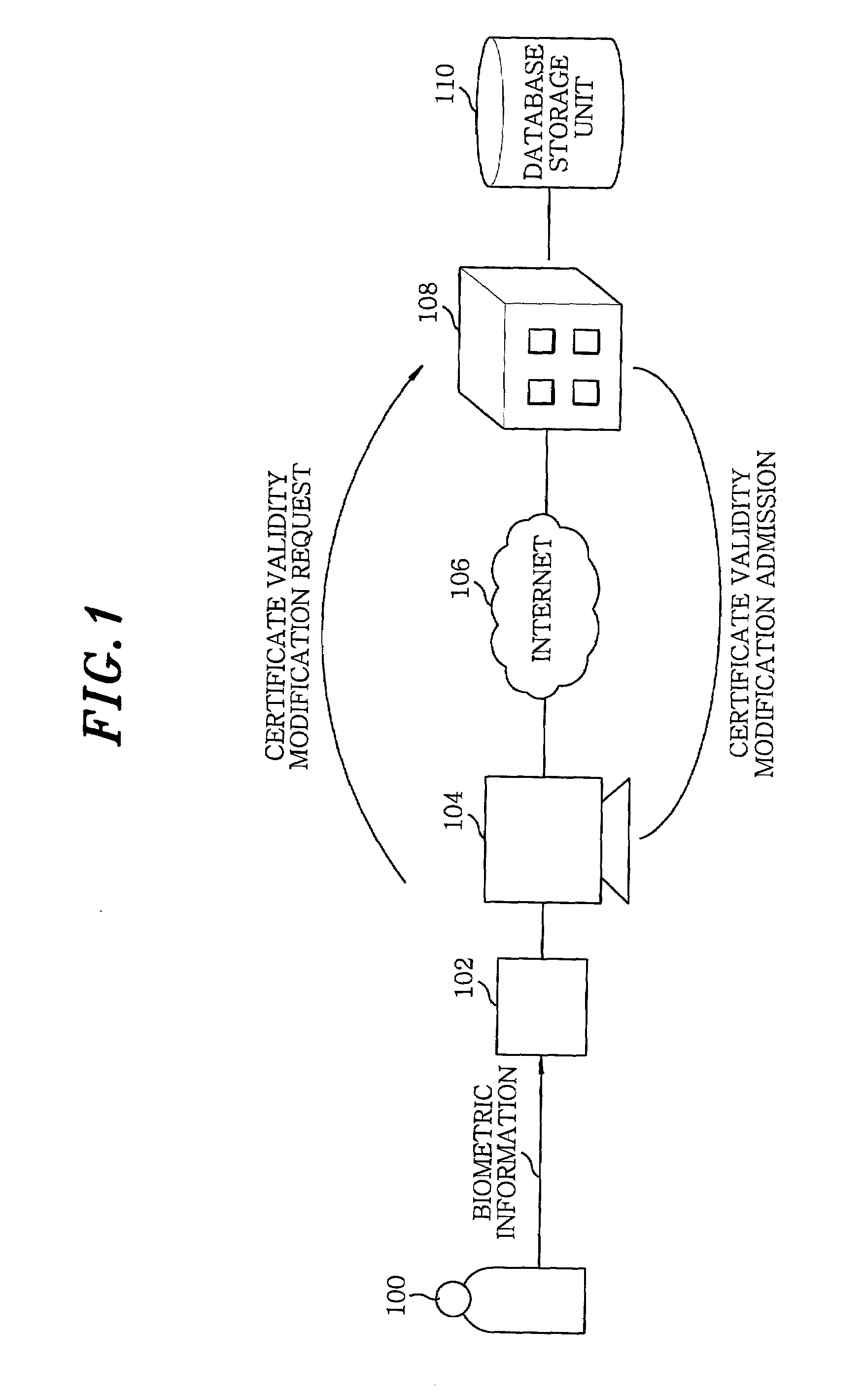
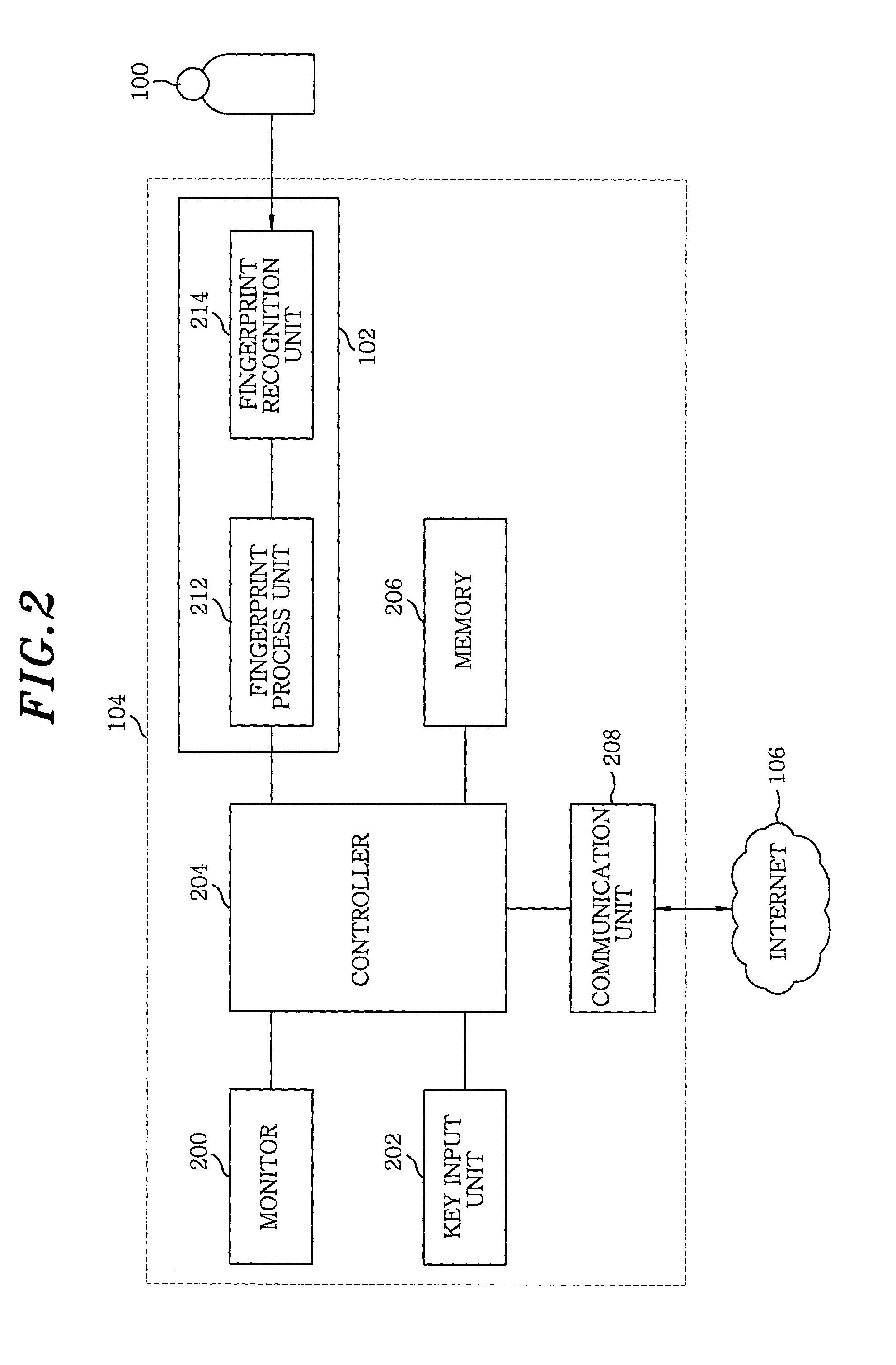
Method for modifying validity of a certificate using biometric information in public key infrastructure-based authentication system
InactiveUS7366904B2Key distribution for secure communicationMultiple keys/algorithms usageRegistration authorityUser authentication
The present invention provides a method for modifying validity of a certificate in a public key infrastructure (PKI)-based authentication system, which is capable of performing online suspension, recovery and revocation of a certificate between a user system and a certificate authority by executing user authentication with guaranteed reliability using user biometric information. Accordingly, there is no need for the user to personally visit a registration authority or certificate authority to modify the certificate validity. The user can easily modify the certificate validity using his / her user system connected online to the certificate authority.
Owner:ELECTRONICS & TELECOMM RES INST
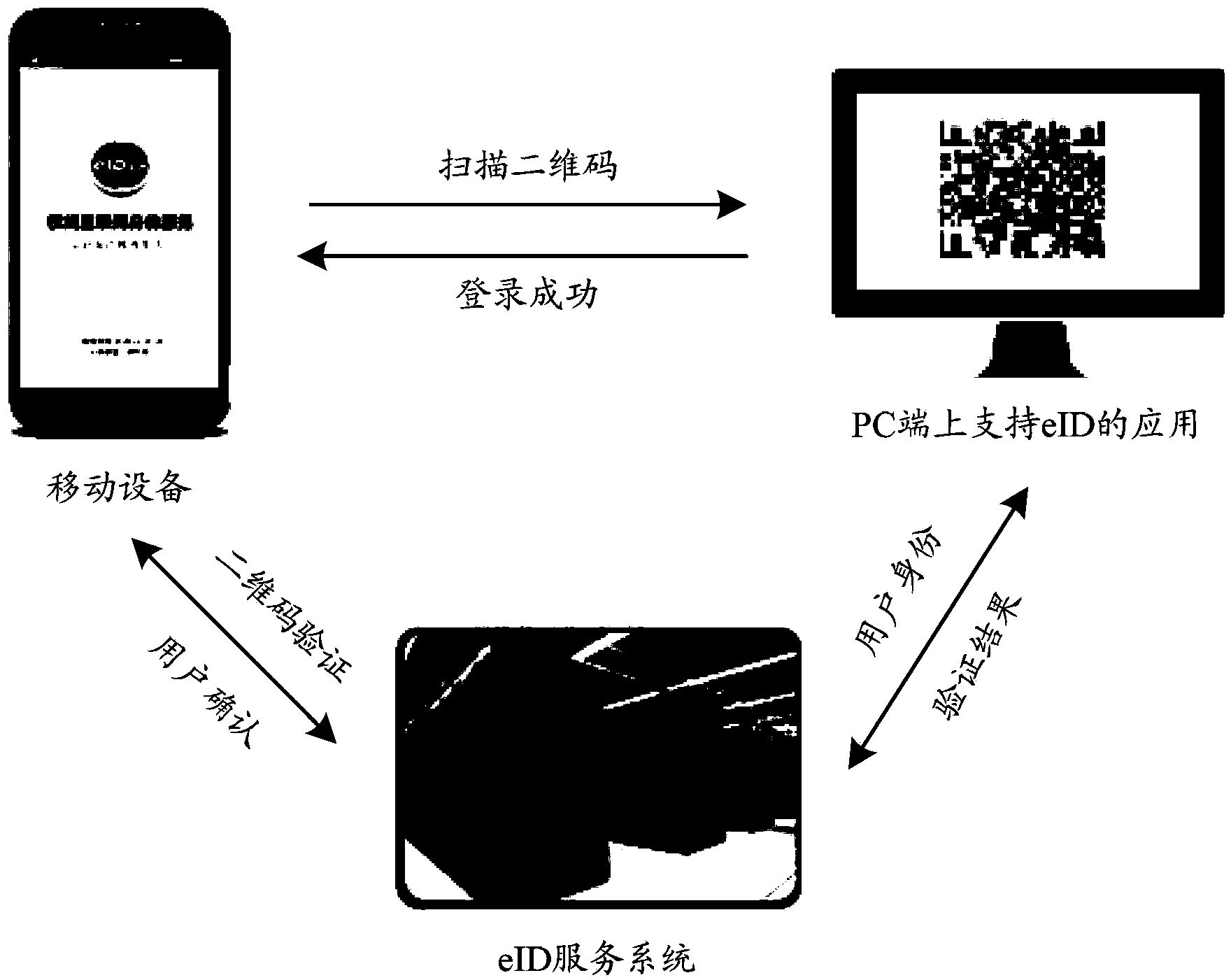
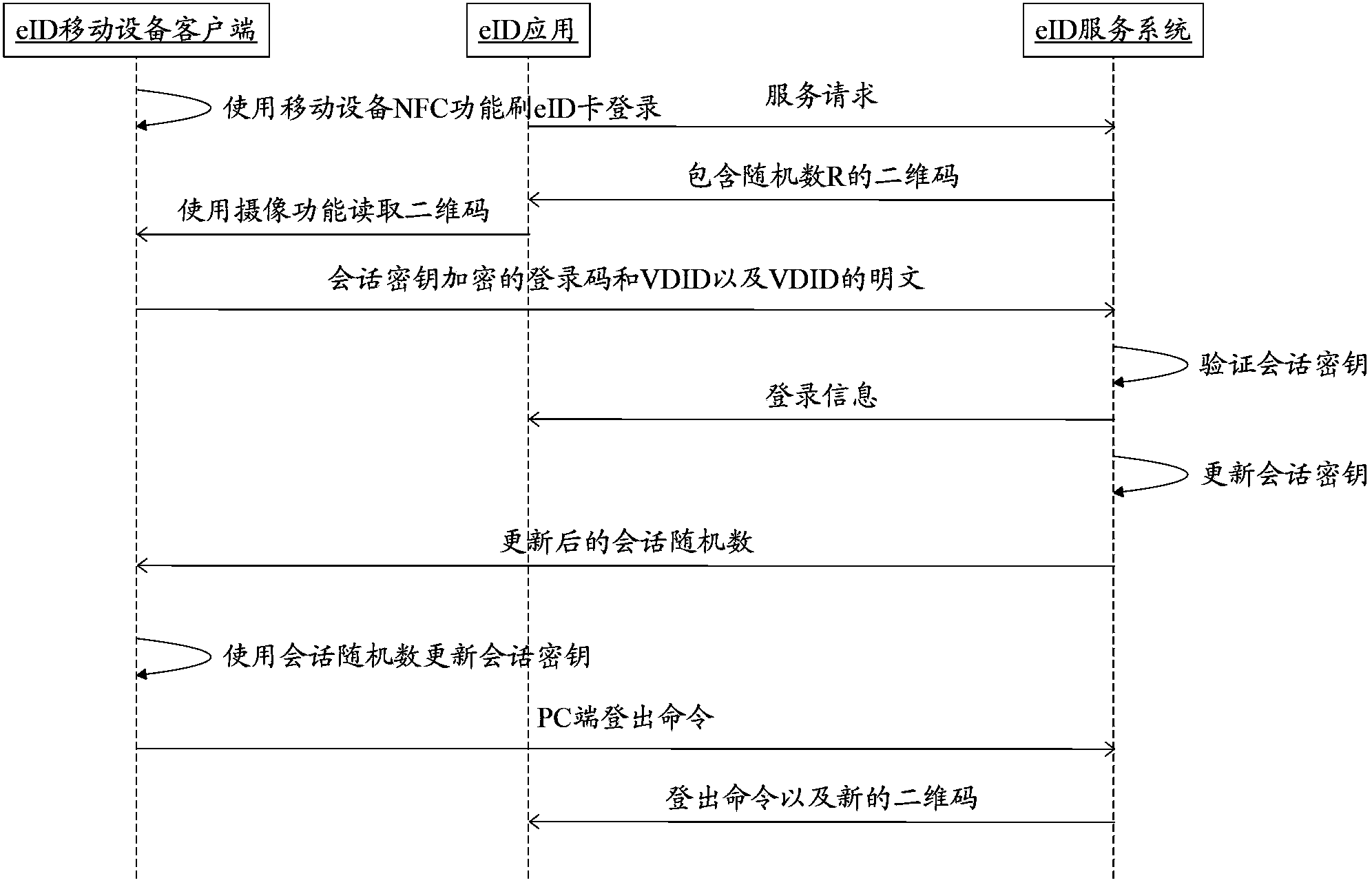
Two-dimensional code based method for realizing extended authentication control of smart card on mobile equipment
ActiveCN103366111AReduce instabilityReduce dependenceUser identity/authority verificationDigital data authenticationRegistration authoritySmart card
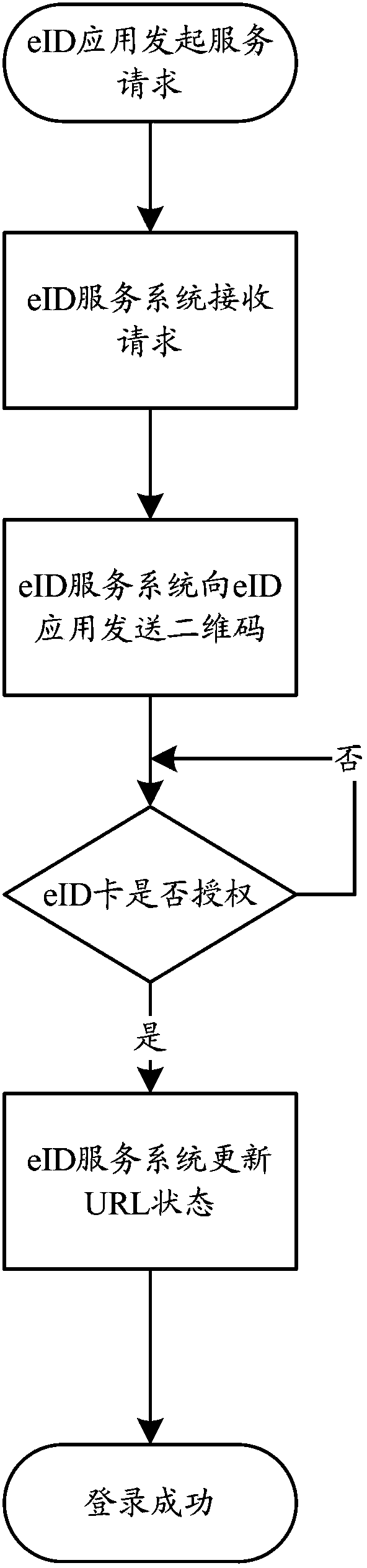
The invention relates to a two-dimensional code based method for realizing extended authentication control of a smart card on mobile equipment. The method comprises the following steps: an eID application program sends a service request to an eID service system; the eID service system returns a two-dimensional code including registry key information to the eID application program and monitors the status of the registry key information; the two-dimensional code is scanned; information acquisition is conducted; whether an eID card is registered or not is checked; the registration authority information of the eID card is read or encrypted and then sent to the eID service system; the eID service system achieves eID registration authority treatment; the session key is updated according to the result; the eID application program receives application service provided by the eID service system. By adopting the two-dimensional code based method for realizing extended authentication control of the smart card on mobile equipment, the dependence of the smart card on a traditional card reader is reduced, the identity authentication is safe and reliable, the use is convenient, quick and safe, the working performance is stable and reliable and the application range is relatively wide.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Edge computing node identity authentication method based on AES algorithm
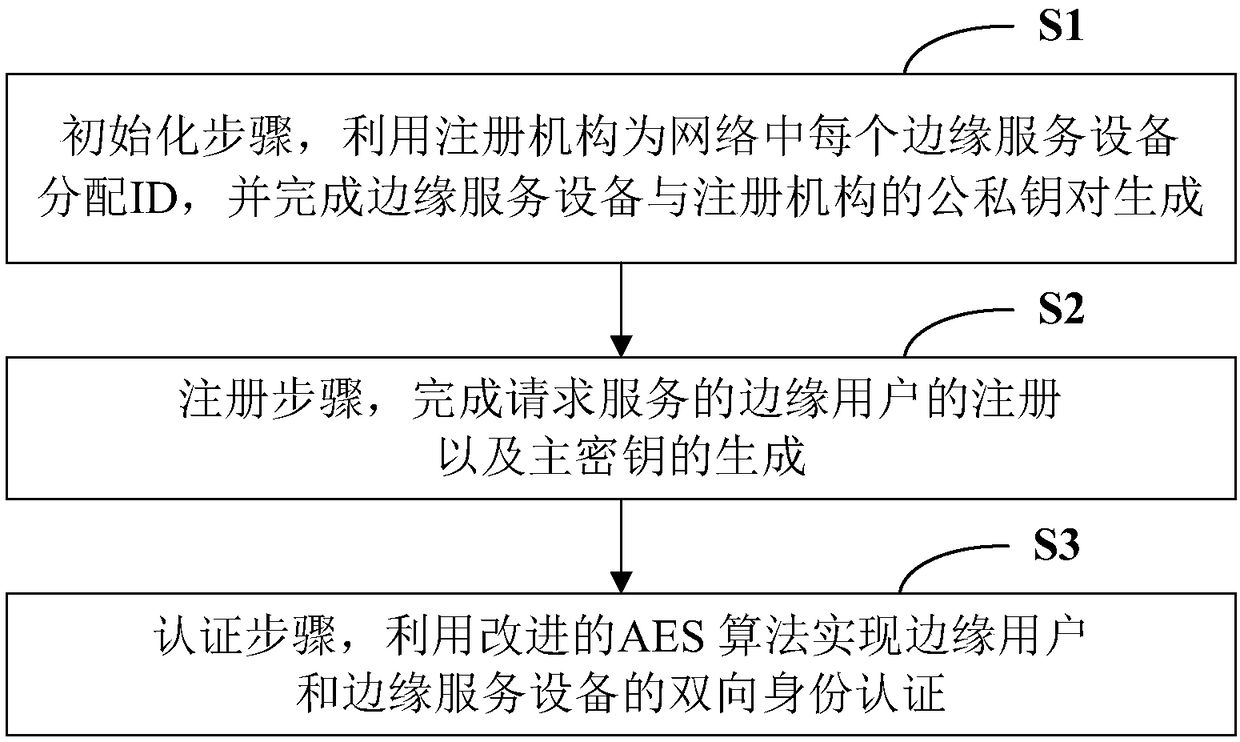
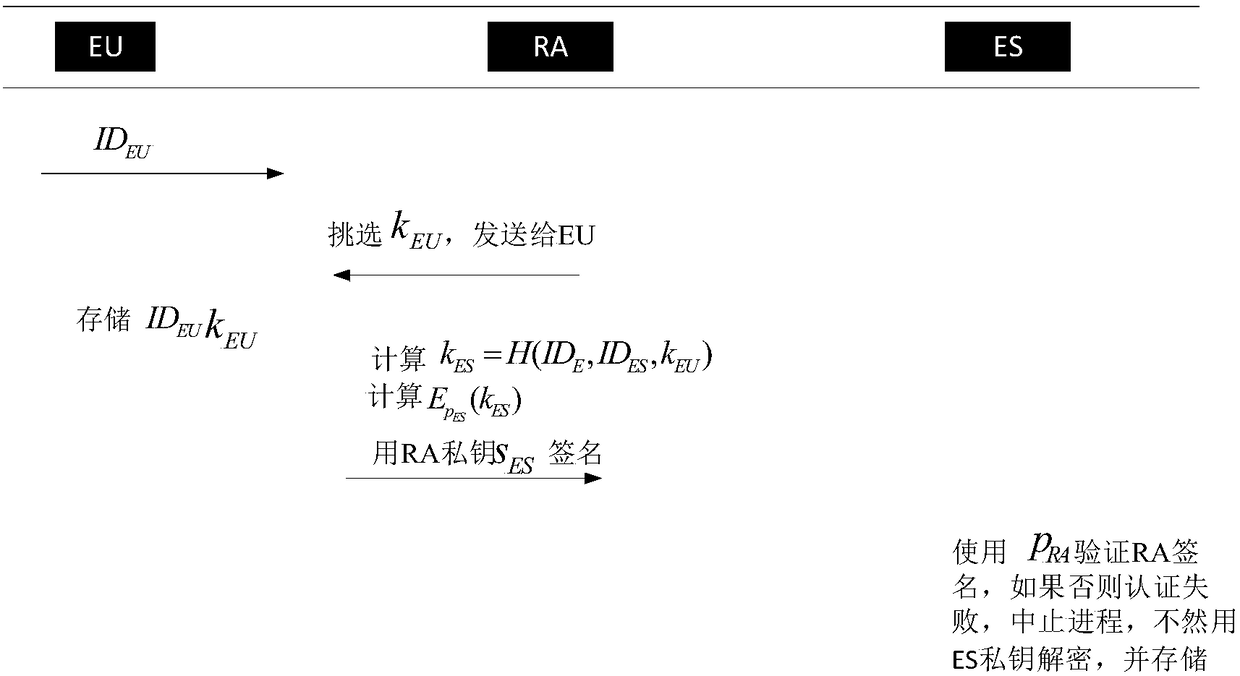
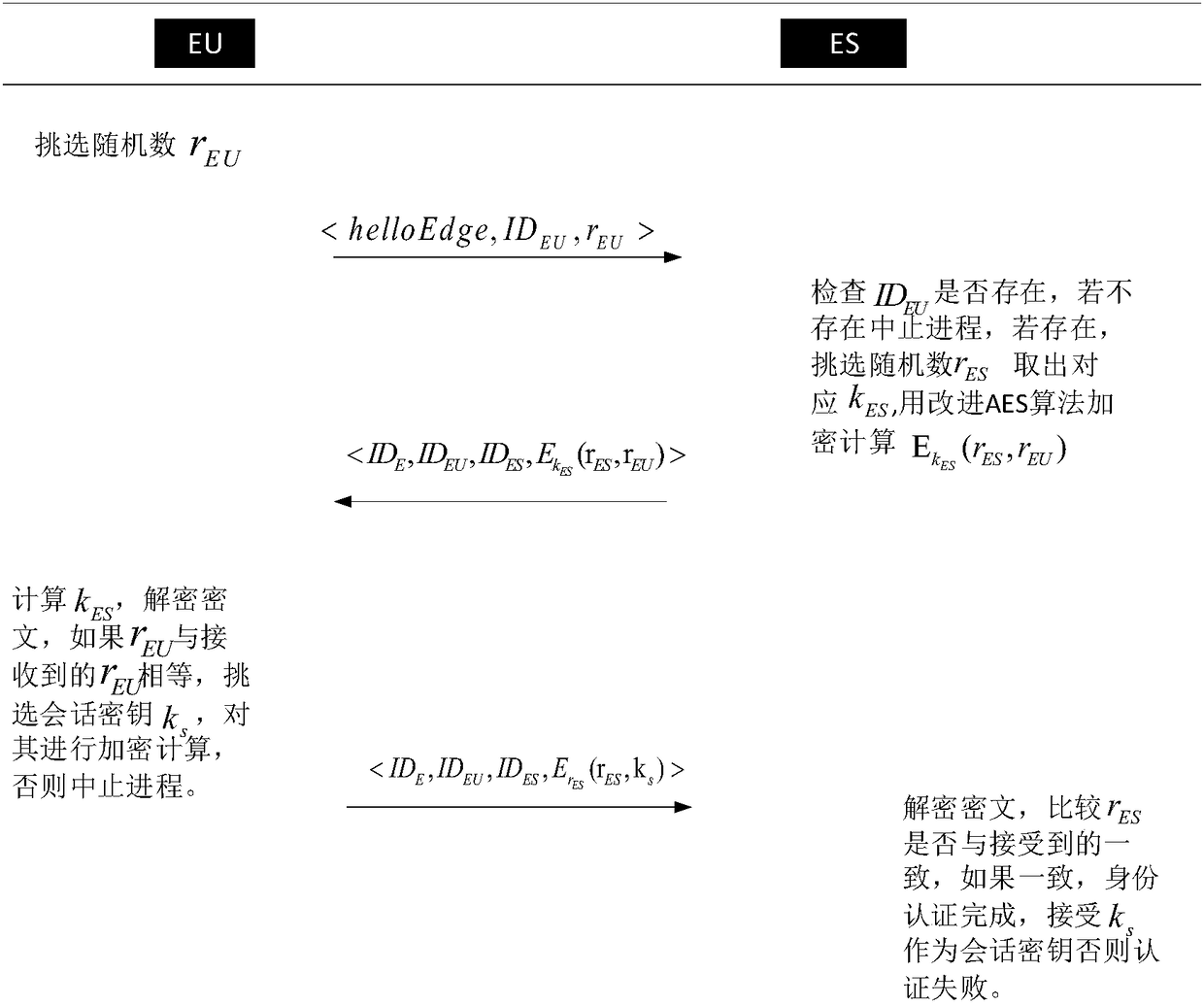
InactiveCN108173882ASolve the two-way authentication problemSafe and Efficient CommunicationKey distribution for secure communicationRegistration authorityTime delays
The invention provides an edge computing node identity authentication method based on an AES algorithm. The method comprises the following steps: an initialization step: allocating ID to each edge service device in a network by utilizing a register mechanism, and finishing generation of a public / private key pair of each edge service device and the register mechanism; a register step: finishing registration of an edge user requesting for service and generation of a master key; and an authentication step: realizing two-way identity authentication of the edge user and each edge service device byutilizing an improved AES algorithm. The technical scheme solves the problem of two-way identity authentication of an edge computing node, ensures safe and efficient communication of the edge node, and can meet requirements for high dynamic and low time delay of edge calculation.
Owner:UNIV OF SCI & TECH BEIJING
Method and system for secure connected vehicle communication
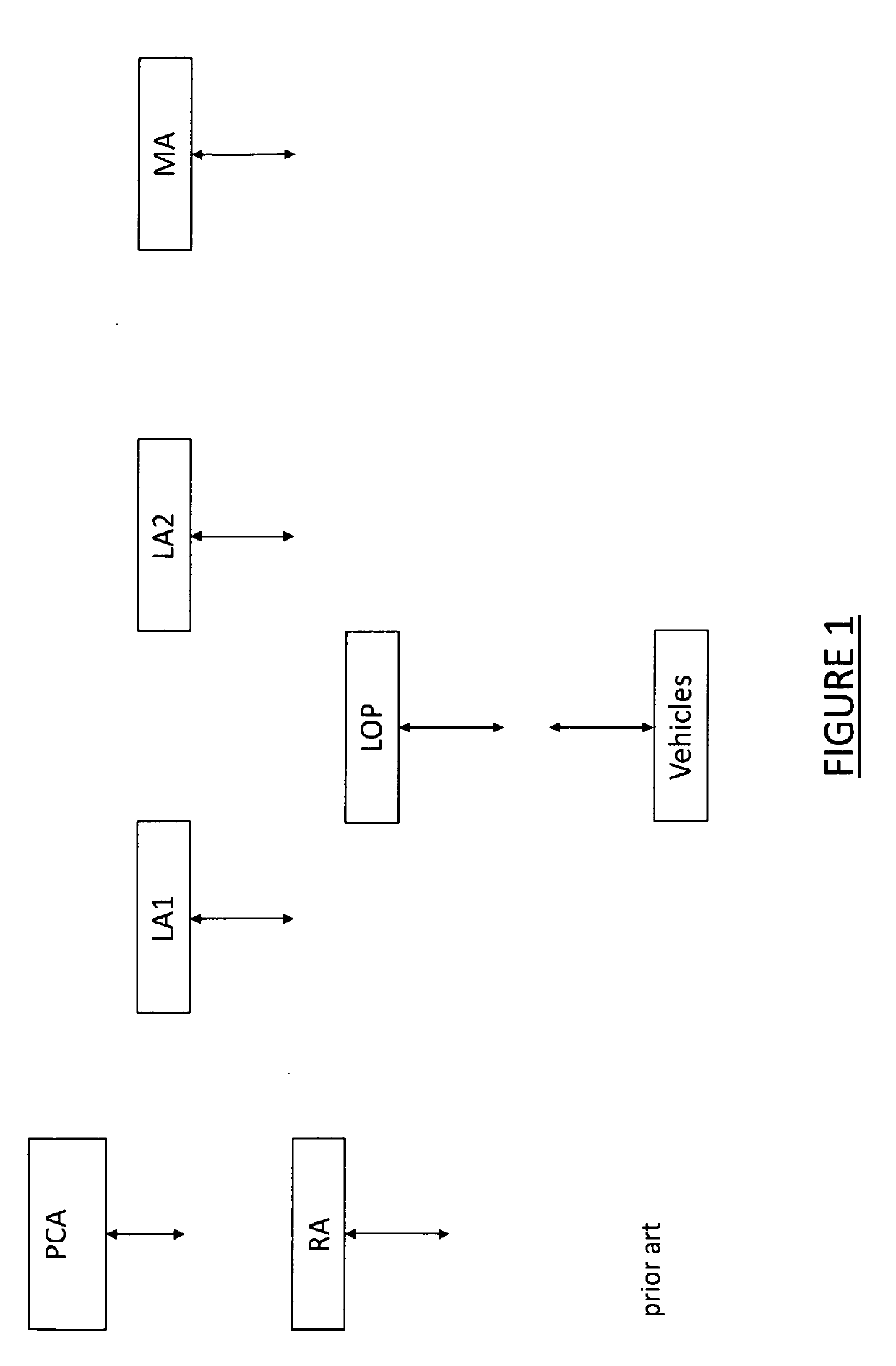
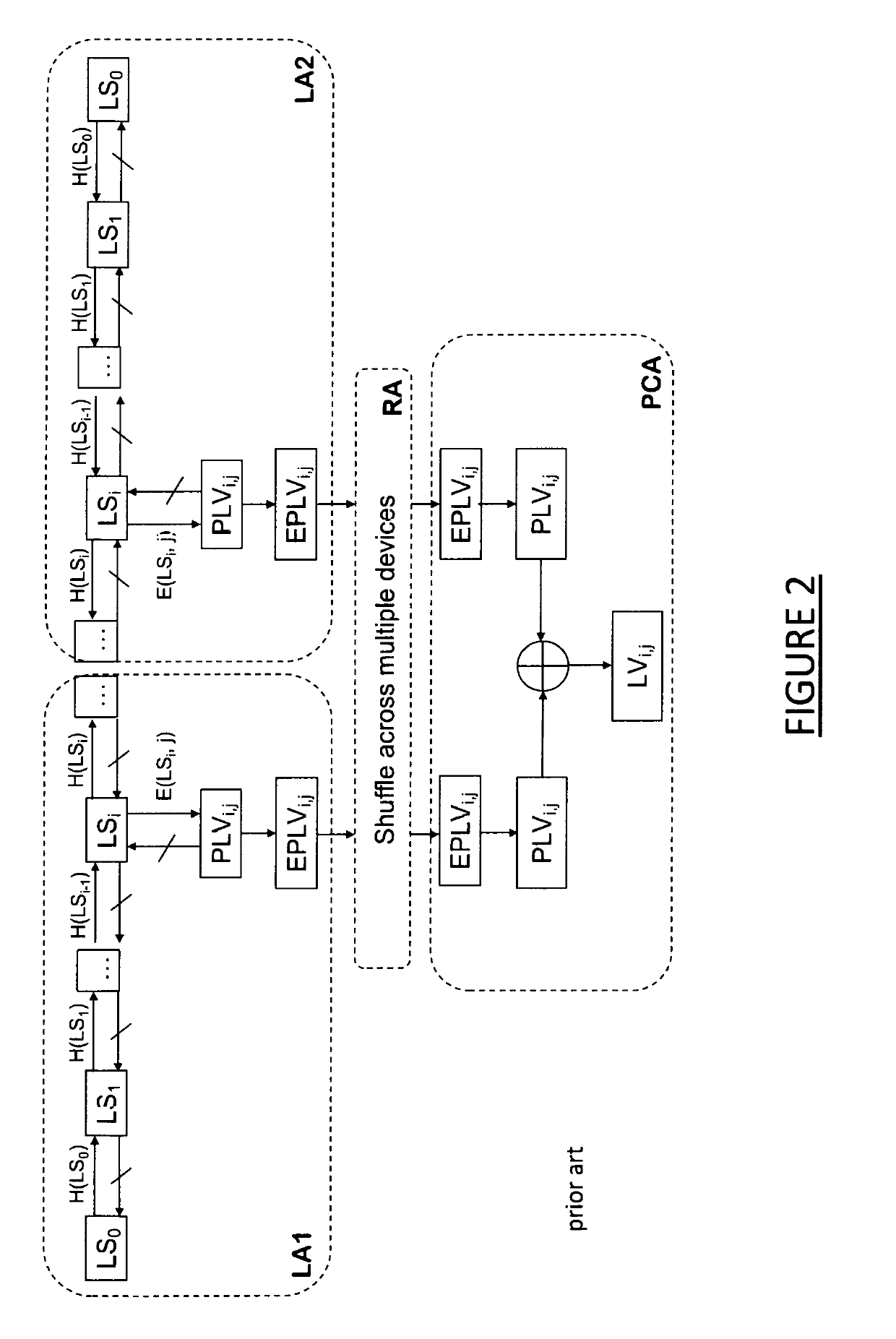
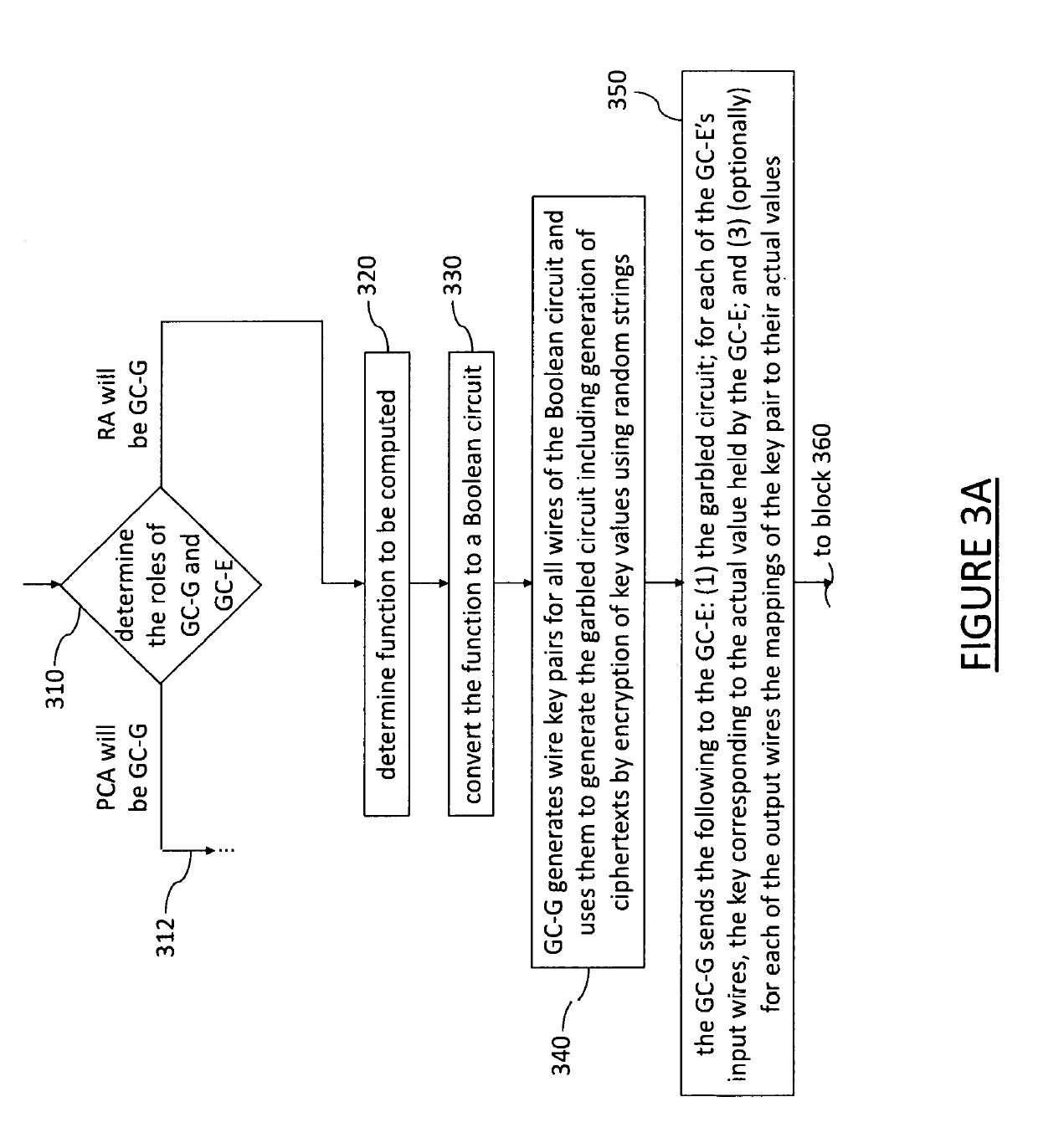
ActiveUS20190116048A1Improve efficiencyImprove securityKey distribution for secure communicationParticular environment based servicesRegistration authorityBoolean circuit
A method for producing linkage values to be contained within pseudonym digital certificates of a security credential management system for connected vehicles, including the following steps: providing a linkage value function that expresses linkage values as a function of a number of input parameters that include a linkage seed input from a pseudonym certificate authority processor entity and a plurality of inputs from a registration authority processor entity including a vehicle identifier and at least one index relating to a time period for the linkage value; producing a Boolean circuit representative of the function for a particular combination of the number of input parameters; and executing a garbled circuit protocol on the Boolean circuit between the registration authority processor entity and the pseudonym certificate authority processor entity, whereby the pseudonym certificate authority processor entity privately derives a linkage value for the particular combination of the number of input parameters.
Owner:ONBOARD SECURITY INC
Proxy email method and system
ActiveUS20060015868A1Automatic call-answering/message-recording/conversation-recordingProgram loading/initiatingDomain nameRegistration authority
A system and method of proxy (60) domain name registration permits a would-be domain name registrant anonymity. A registrar (24) affords customers (20) the opportunity to use the proxy registration. If the customer seeking registration of a domain name requests, the registrar obtains contact information needed for registration from a proxy entity established for this purpose. The registrar completes the registration of the domain name with the appropriate registry (22) (i.e. “.com, .net” etc.). The contact information published in WHOIS (27) is that of proxy entity. Contractually the customer is afforded control over the domain name. Emails intended for the customer are received by the proxy entity who may filter them if the customer requests. Emails sent by the customer are sent to the proxy entity who in turn send them to the indicated addressee.
Owner:GO DADDY OPERATING
Systems And Methods For Managing Disclosure Of Protectable Information
ActiveUS20150229630A1Key distribution for secure communicationWeb data indexingRegistration authorityKnowledge management
A server and one or more portals cooperate with a first registered agency, an administrator of the first registered agency, a second agency, and an administrator of the second registered agency to determine whether access to protectable information should be granted to a registered requester.
Owner:TASER INT INC
Pre-binding and tight binding of an on-line identity to a digital signature
ActiveUS8321677B2Multiple keys/algorithms usageUser identity/authority verificationRegistration authorityN application
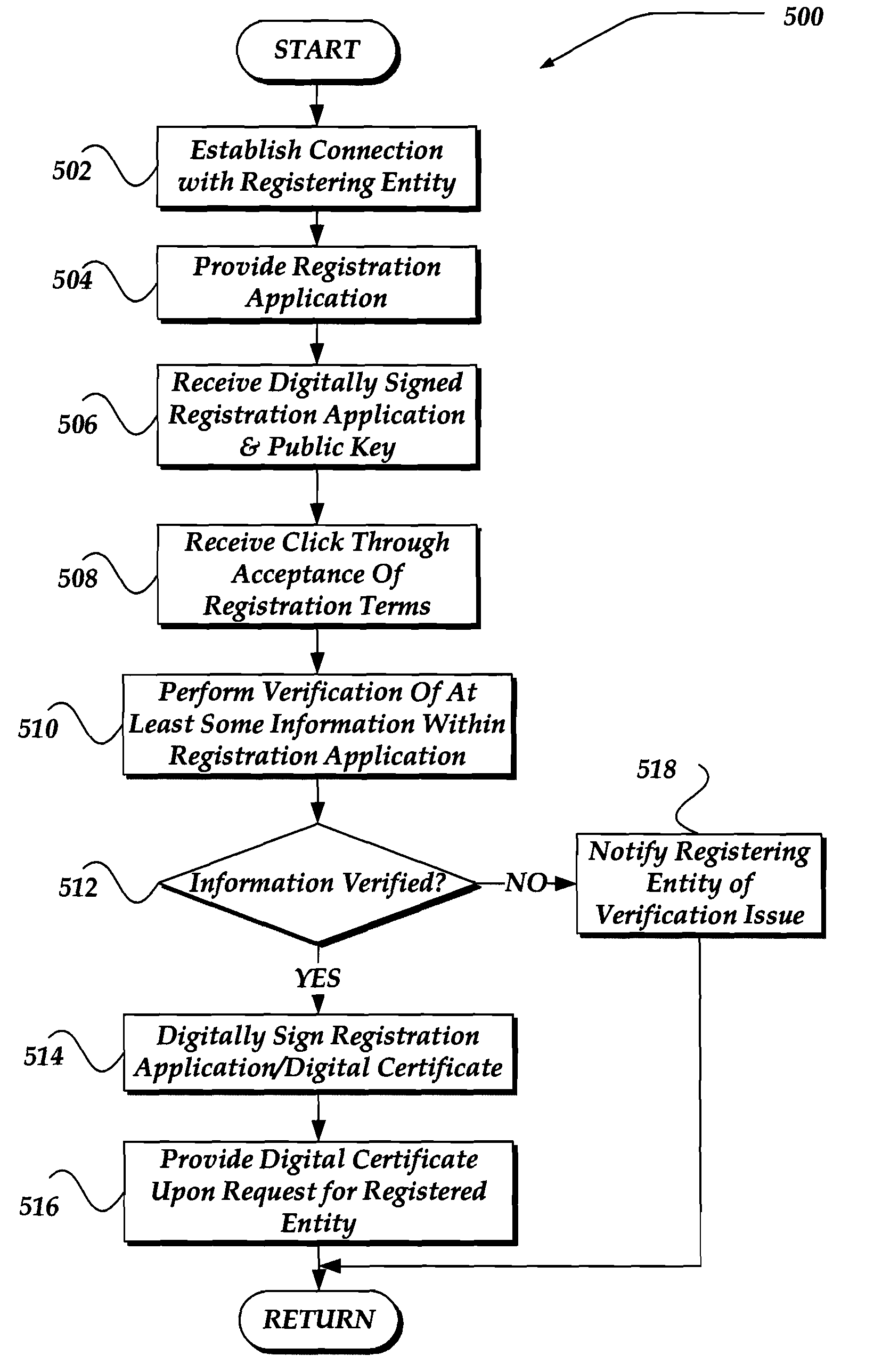
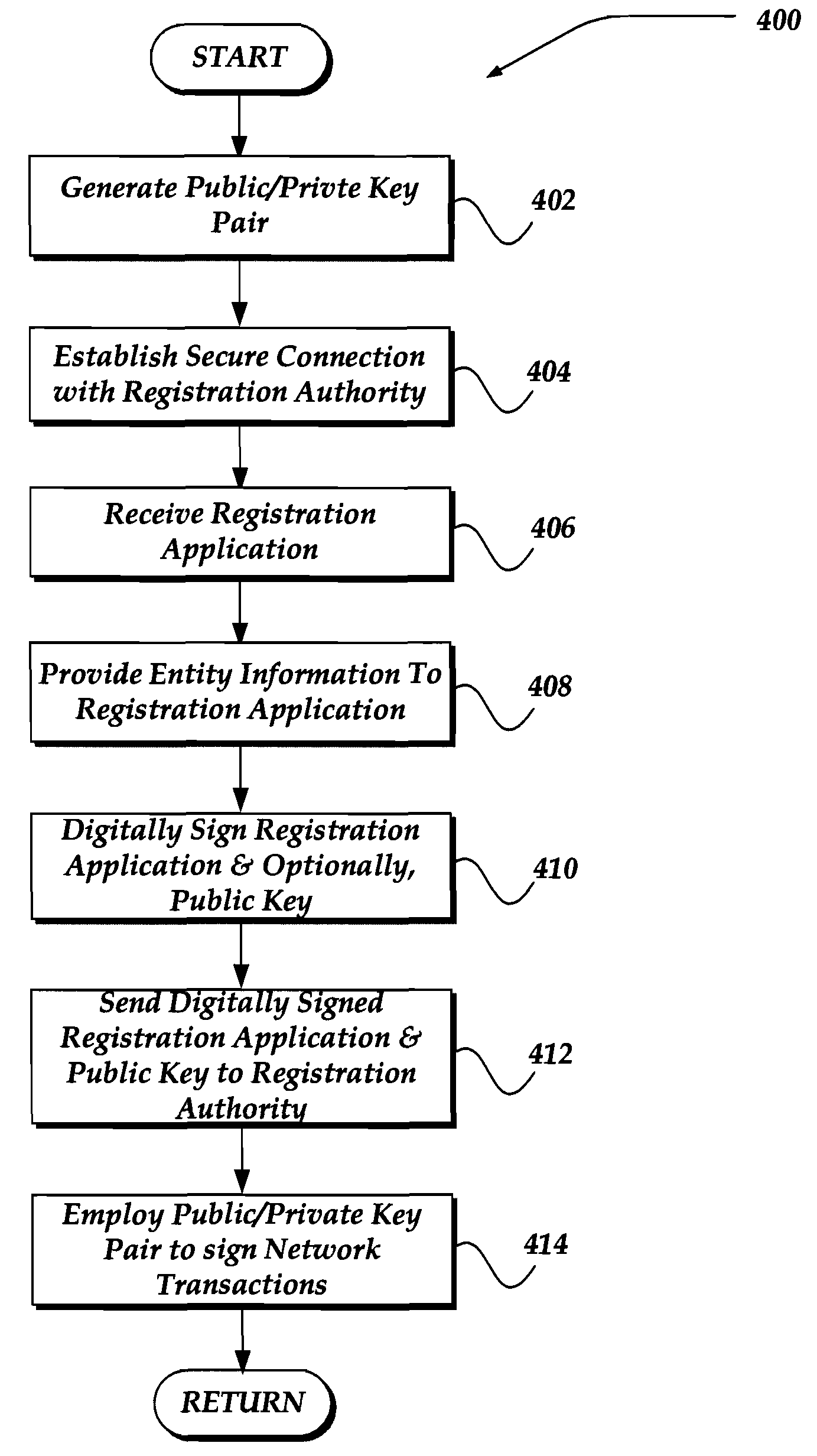
A method, apparatus, and system are directed towards generating a public / private key pair prior to registration. The generation of the public / private key pair is performed by the entity to which the key pair is to be associated. The entity may then complete n application. The entity may then employ the generated public / private key pair to digitally sign the application. In one embodiment, the public key is provided with the application to a registration authority. Upon request, the public key and at least some of the application information may be provided to requester for use in identification, authentication, integrity, and / or non-repudiation of the registered entity. In another embodiment, the registration authority or other entity may verify the identity of the registering entity using the application. In one embodiment, the registration authority may select to digitally sign the application to indicate that the information has been verified.
Owner:GOOGLE LLC
Internet domain name registration system
InactiveUS20050256853A1Convenient queryReduce amountData processing applicationsDigital data processing detailsRegistry dataResponse table
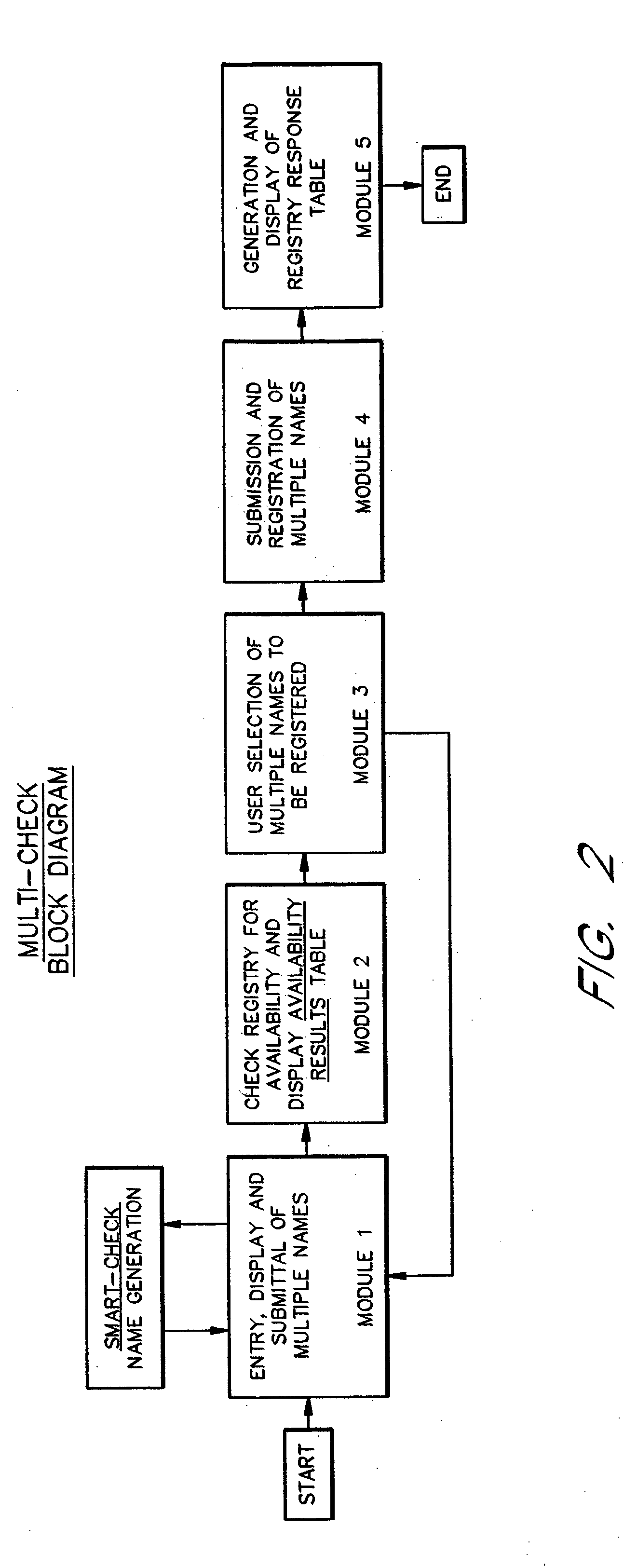
A domain name registration system includes a user interface through which a user can submit multiple names to a query server to determine the availability of the names for domain name registration. After the query results are returned for each of the multiple names submitted, the user is presented with a table listing the availability of each name in combination with multiple Top-Level Domain (TLD) extensions. The user is able to select one or more names from the table for registration in the registry database. After the query server has attempted to register each of the selected names, the user is presented with a Registry Response Table indicating which of the selected names were successfully registered as domain names. Thus, the system and method increases the speed and productivity of querying and updating a domain name registry or other database.
Owner:MULTICHECK SYST
Methods for secure restoration of personal identity credentials into electronic devices
InactiveUS20090037746A1Key distribution for secure communicationElectric signal transmission systemsRegistration authorityUnique identifier
A method and system for securely enrolling personal identity credentials into personal identification devices. The system of the invention comprises the manufacturer of the device and an enrollment authority. The manufacturer is responsible for recording serial numbers or another unique identifier for each device that it produces, along with a self-generated public key for each device. The enrollment authority is recognized by the manufacturer or another suitable institution as capable of validating an individual before enrolling him into the device. The enrollment authority maintains and operates the appropriate equipment for enrollment, and provides its approval of the enrollment. The methods described herein discuss post-manufacturing, enrollment, backup, and recovery processes for the device.
Owner:APPLE INC
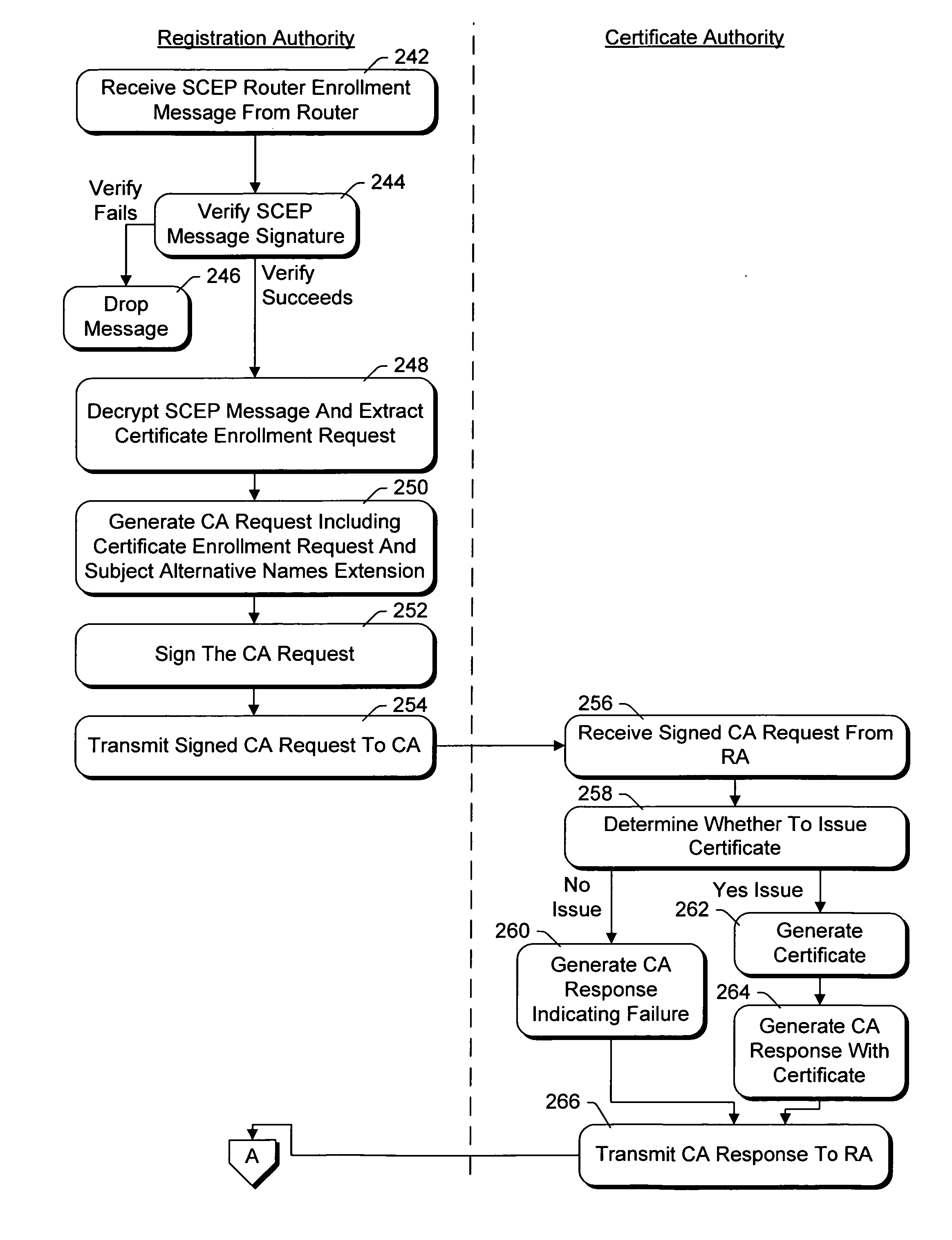
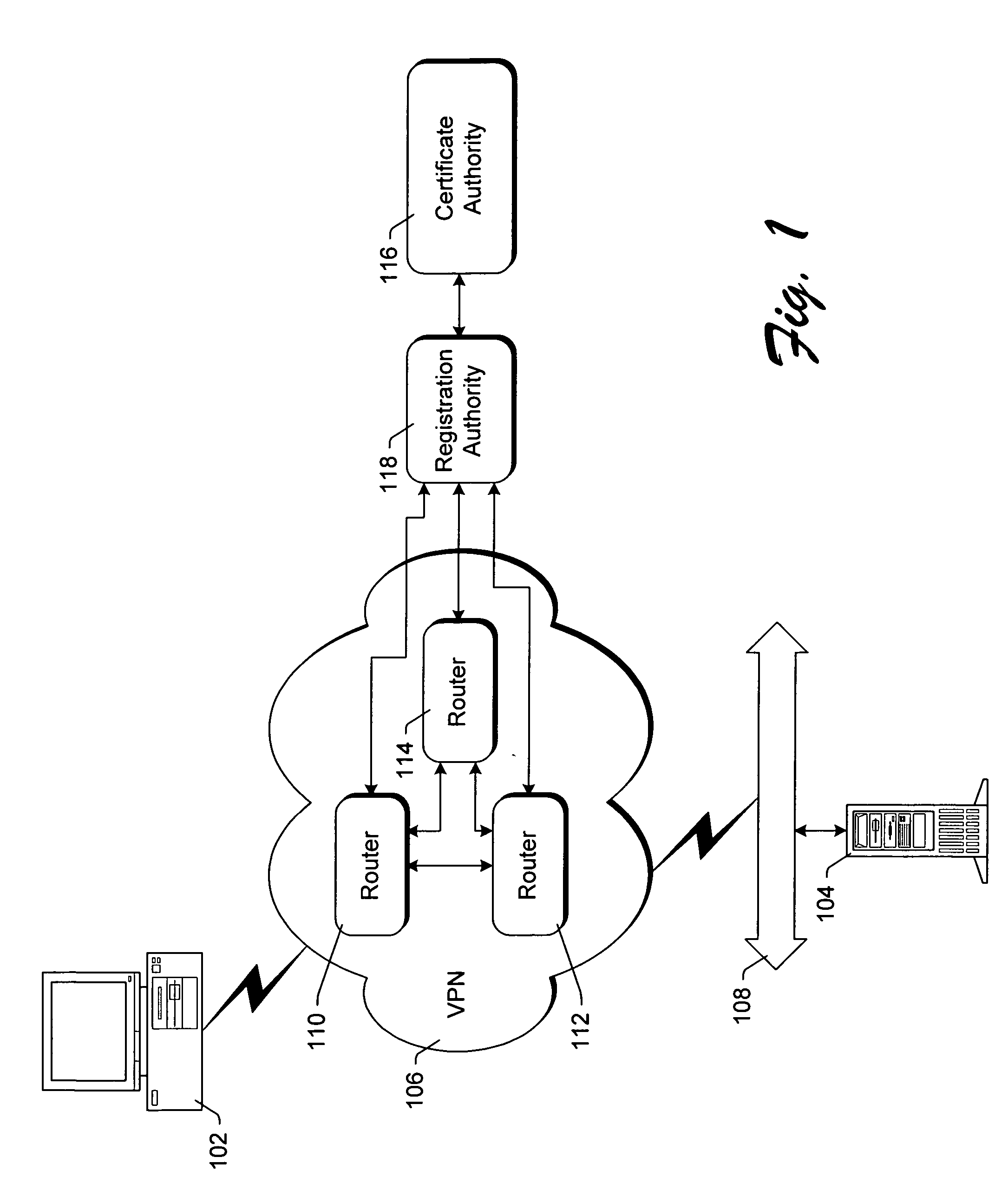
VPN enrollment protocol gateway
InactiveUS20050210237A1Digital data processing detailsUser identity/authority verificationRegistration authorityPrivate network
Owner:MICROSOFT TECH LICENSING LLC
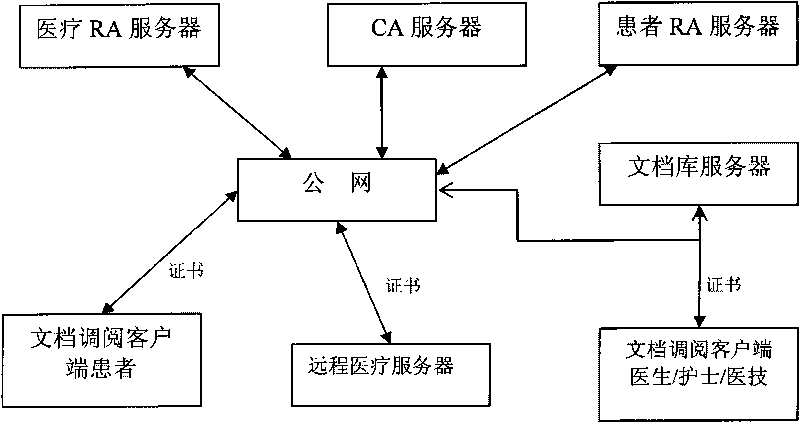
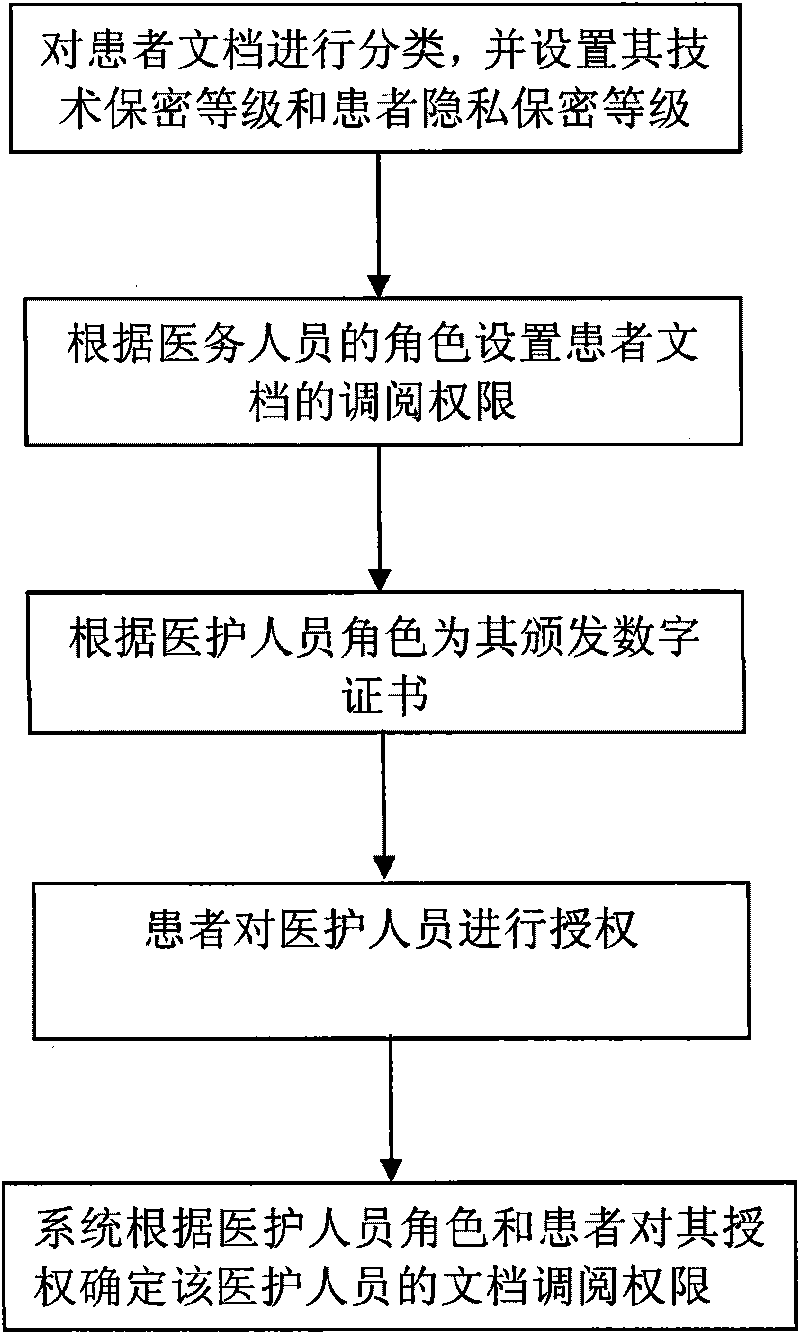
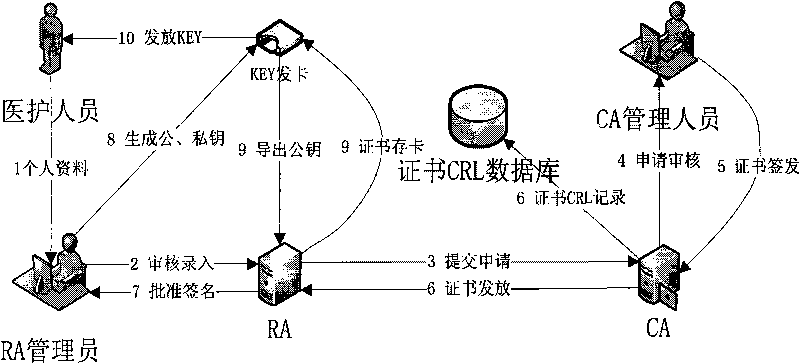
Patient document retrieval authorization control method and system
ActiveCN101727534AEasy to useProtect intellectual propertySpecial data processing applicationsRegistration authorityIntellectual property
The invention discloses patient document retrieval authorization control method and system, belonging to the technical field of computer software. The method comprises the following steps of: firstly, classifying patient documents, setting access rights to the documents for medical personnel according to the roles of the medical personnel and issuing corresponding digital certificates to the medical personnel; then signing own documents by patients and meanwhile setting diagnosis activity participation roles and the access time of the medical personnel; and finally, determining the document retrieval rights of the medical personnel according to the roles, the diagnosis activity participation roles and the access time of the medical personnel by the system. The system comprises a medical personnel certificate registration mechanism, a patient certificate registration mechanism, a certificate authorization mechanism, a safety service interface, an access control module, a document retrieval client and a document base server. Compared with the prior art, the invention not only protects the individual privacy information of patients and the intellectual property of medical units, but also are convenient for the medical personnel to conveniently use the documents of the patients.
Owner:NEW FOUNDER HLDG DEV LLC +1
Secure electronic voting system based on identity signature
InactiveCN103903325AIncrease opennessReduce the burden onVoting apparatusDigital data authenticationRegistration authorityLarge scale network
The invention discloses a secure electronic voting system based on an identity signature. The secure electronic voting system comprises a registration mechanism, a notary mechanism, a voter, a vote checking center and a flight ticket center. The voting system comprises an identity-based signature scheme, a matrix homomorphic encryption scheme, a matrix fully-homomorphic encryption scheme and a matrix commissioned calculation scheme, and comprises the following steps of: a series of initialization work of the notary mechanism before election; a series of operations of the voter for completing voting; votes checking and counting by a vote counting mechanism ; and statistical results decoding and election results announcing by the notary mechanism. By adopting the technical scheme disclosed by the invention, firstly the electronic voting scheme is a secure electronic voting scheme, secondly the size of the votes can be freely determined, so that the secure electronic voting system can be used for large-scale network voting for election, and thirdly all links of the election are more open and transparent.
Owner:SUZHOU UNIV
Pre-binding and tight binding of an on-line identity to a digital signature
ActiveUS20080126806A1Multiple keys/algorithms usageUser identity/authority verificationRegistration authorityDigital signature
A method, apparatus, and system are directed towards generating a public / private key pair prior to registration. The generation of the public / private key pair is performed by the entity to which the key pair is to be associated. The entity may then complete n application. The entity may then employ the generated public / private key pair to digitally sign the application. In one embodiment, the public key is provided with the application to a registration authority. Upon request, the public key and at least some of the application information may be provided to requester for use in identification, authentication, integrity, and / or non-repudiation of the registered entity. In another embodiment, the registration authority or other entity may verify the identity of the registering entity using the application. In one embodiment, the registration authority may select to digitally sign the application to indicate that the information has been verified.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com