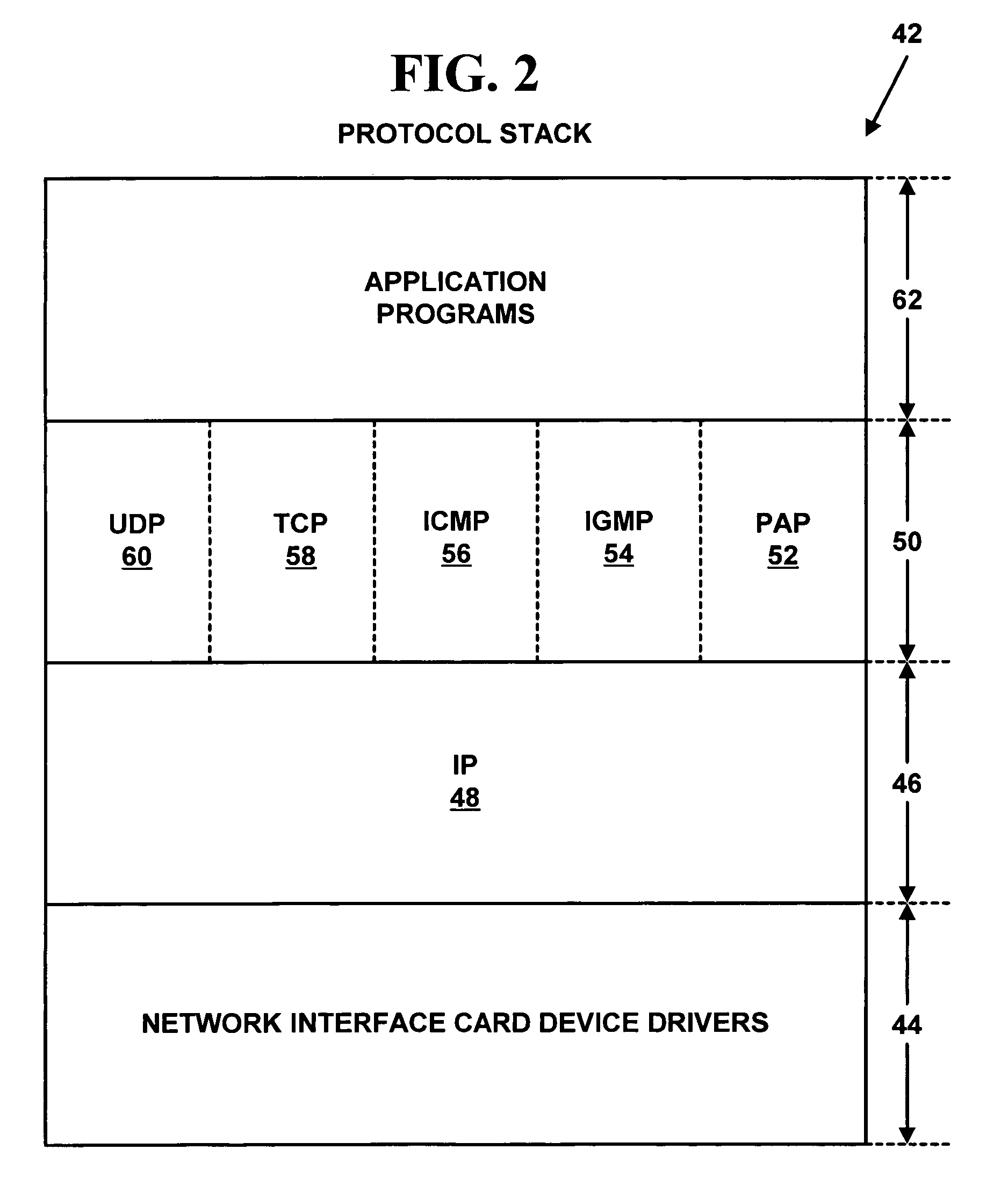
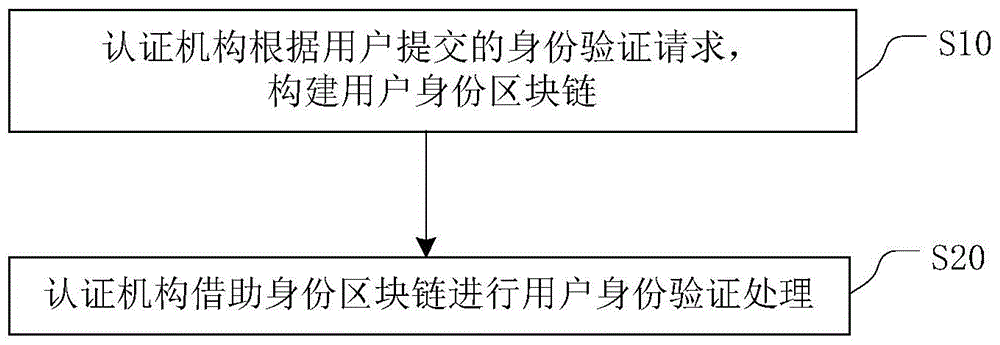
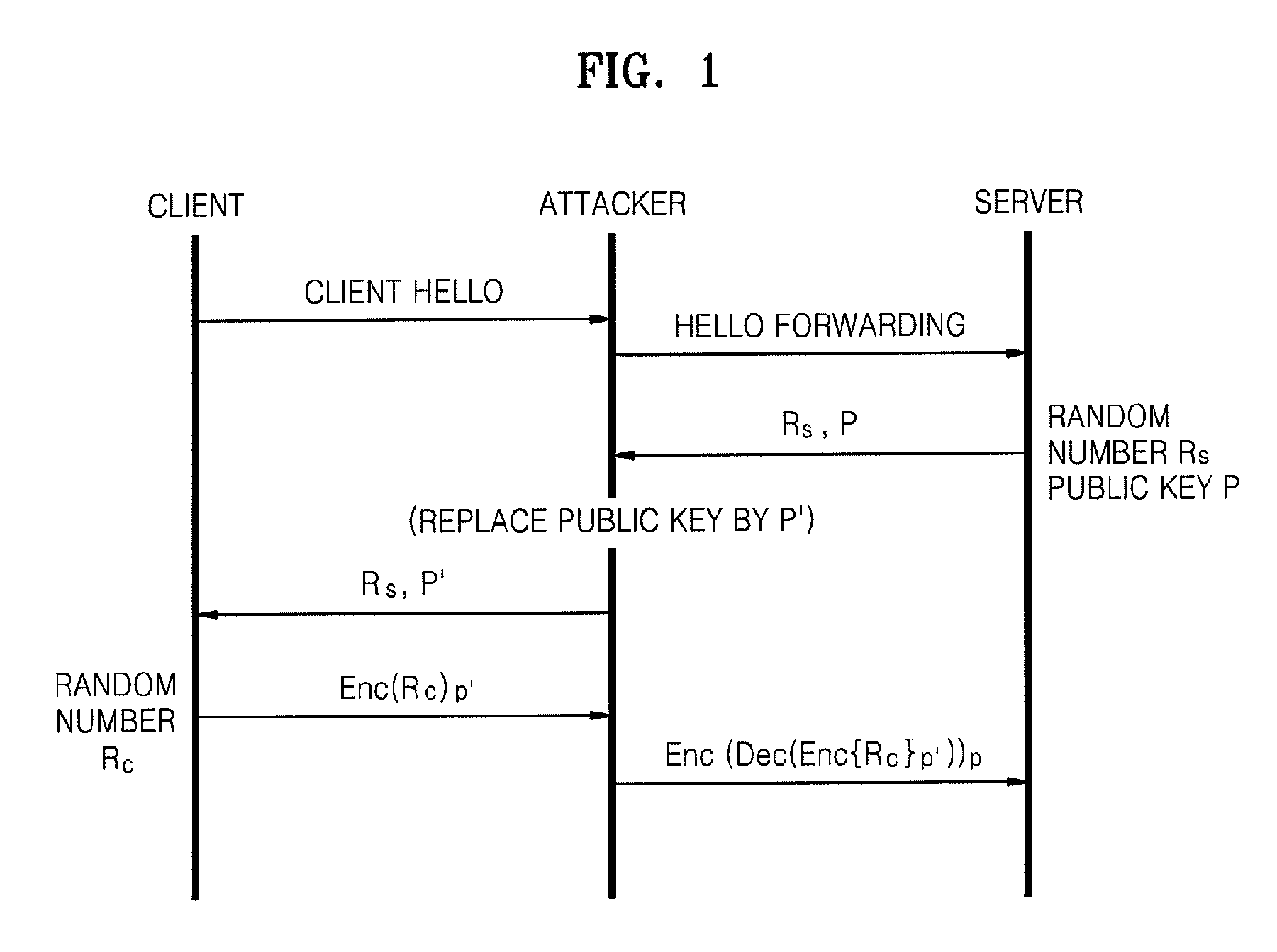
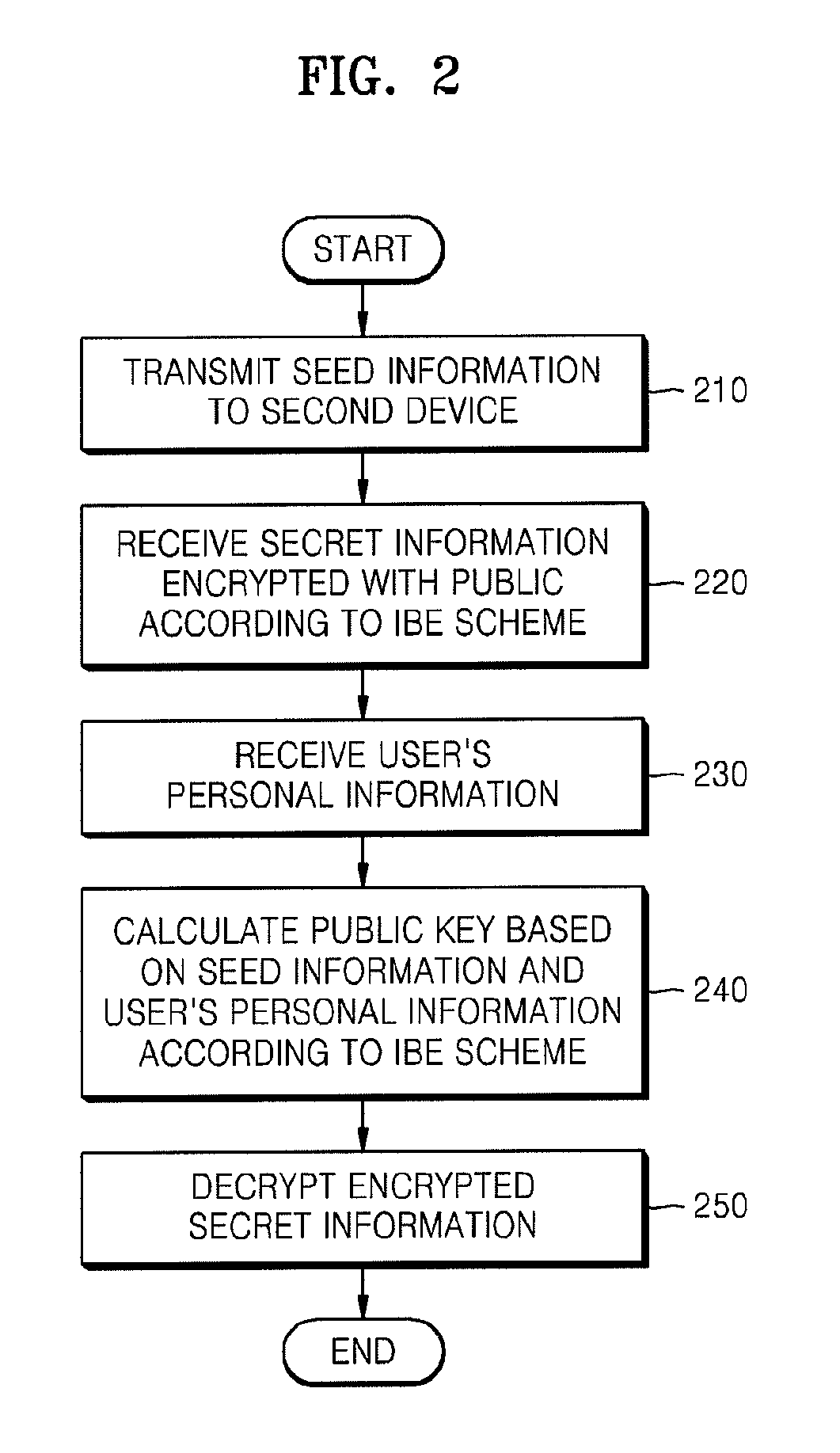
Patents
Literature
833 results about "Certificate authority" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
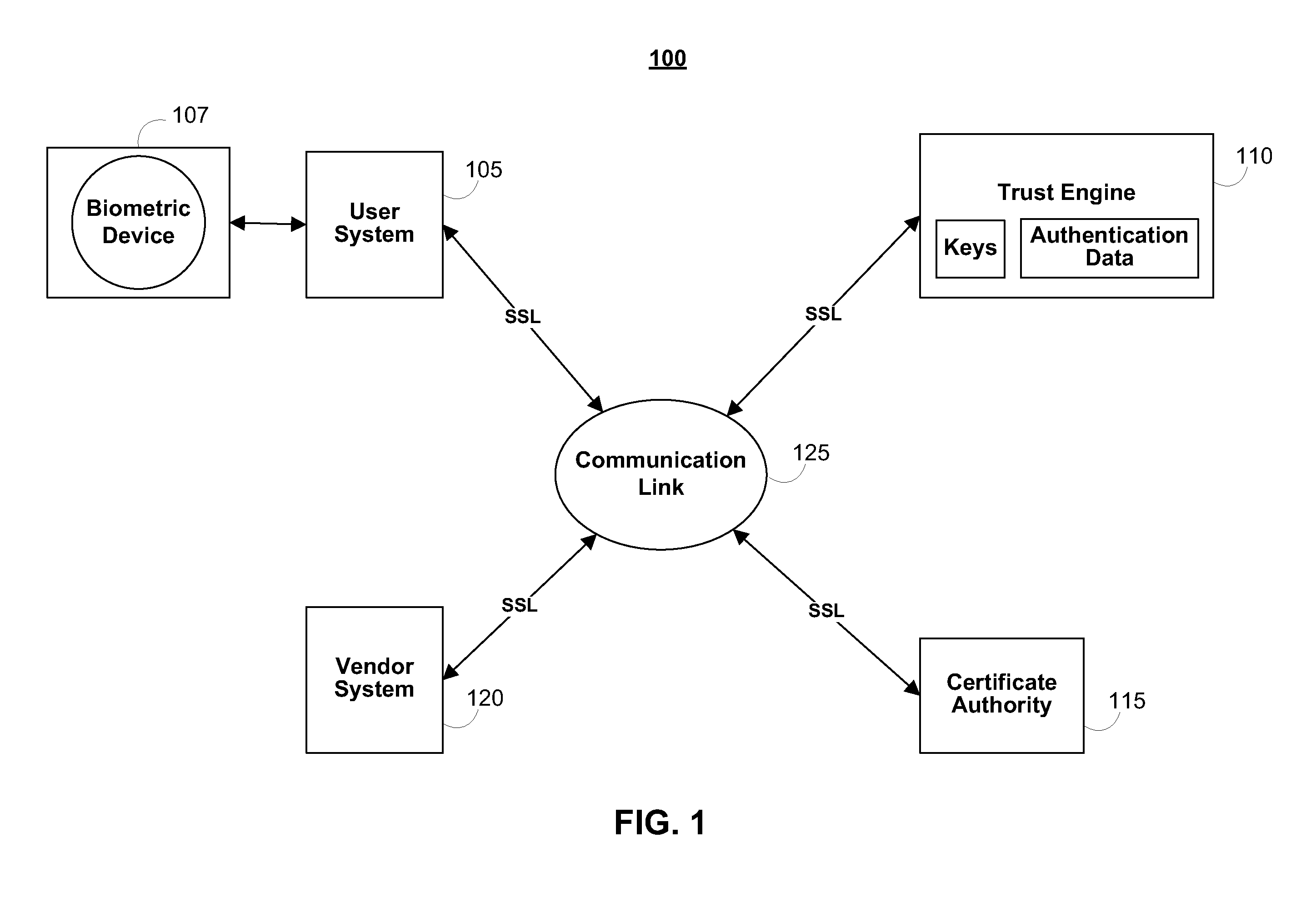
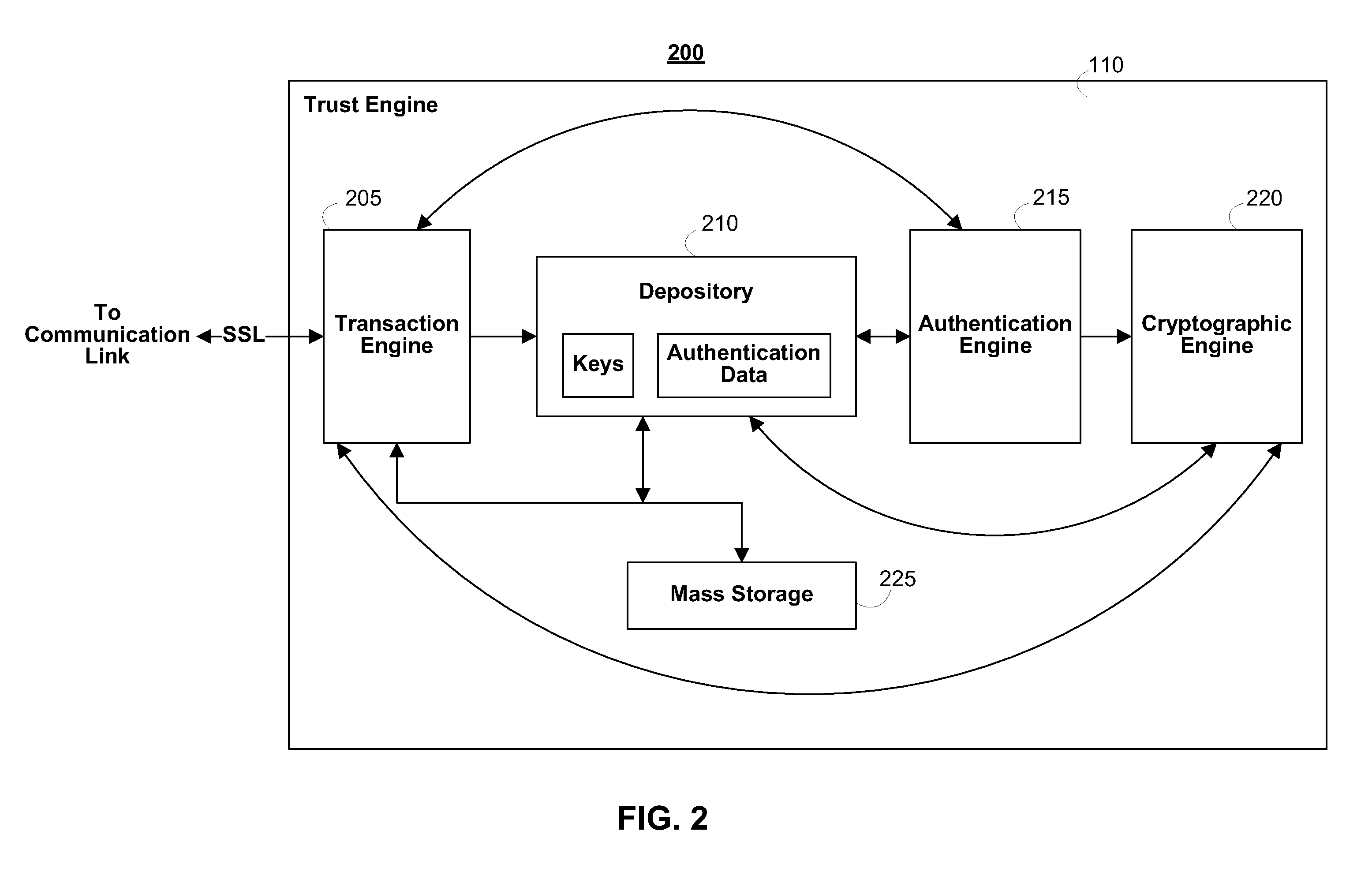
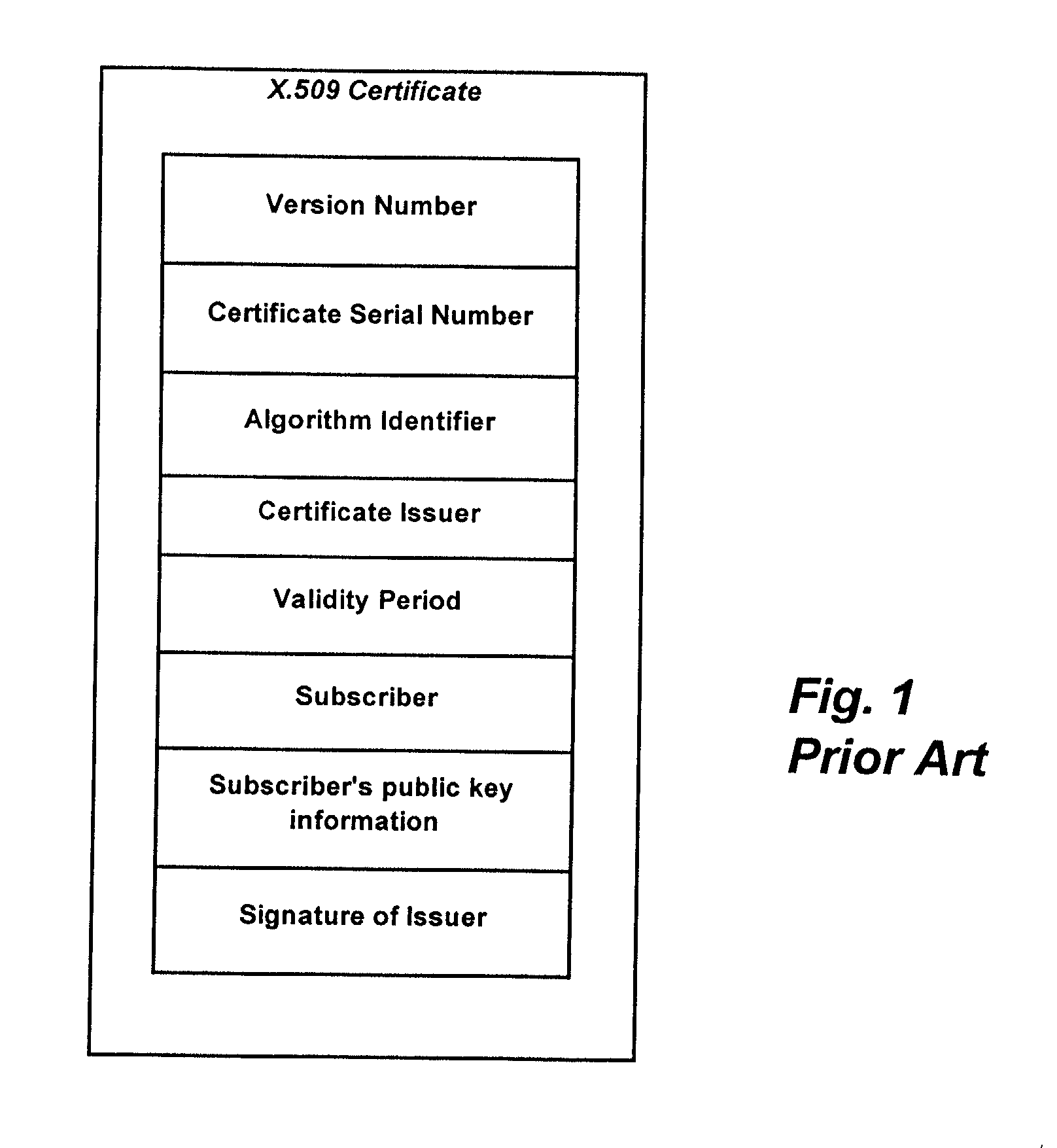
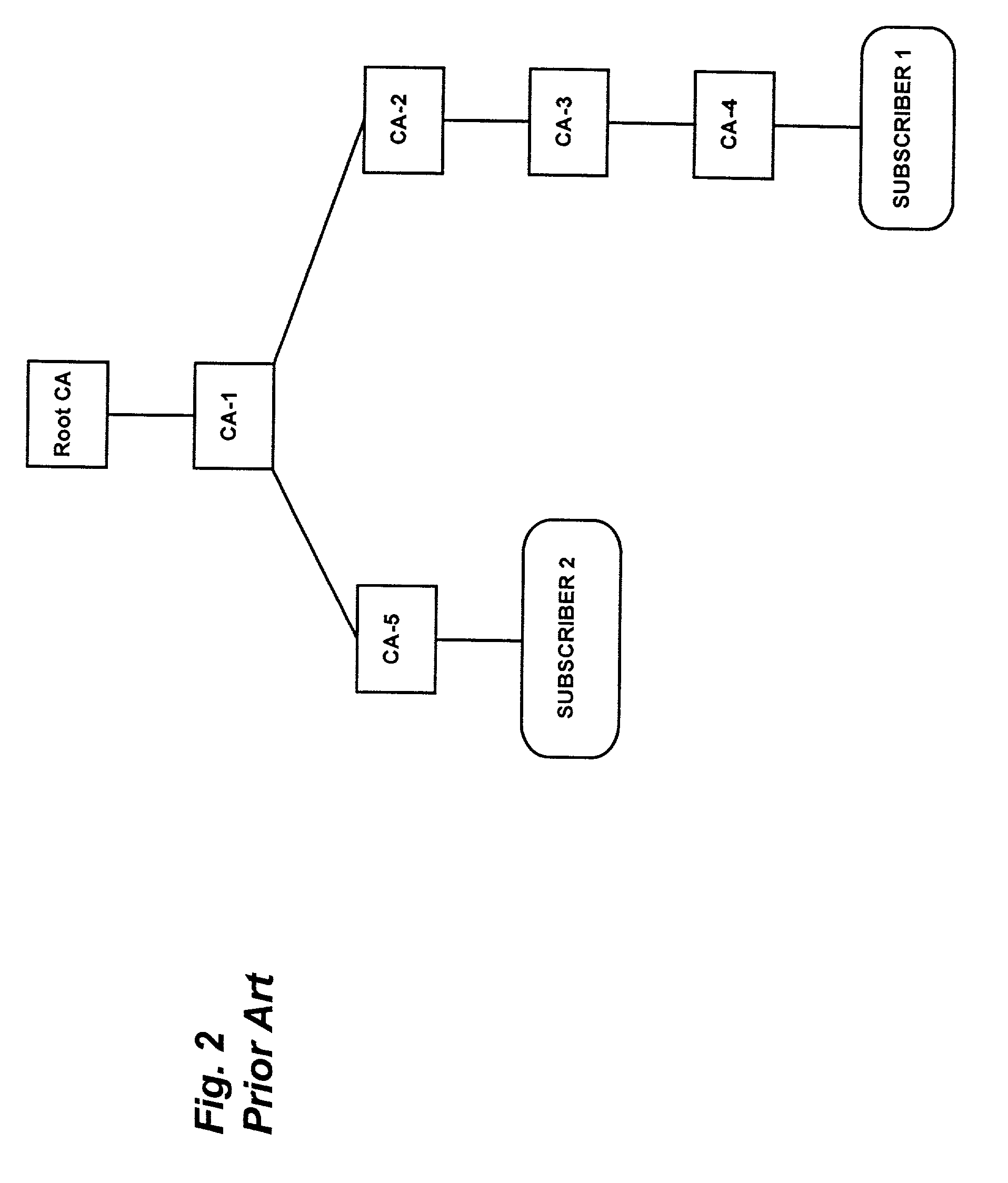
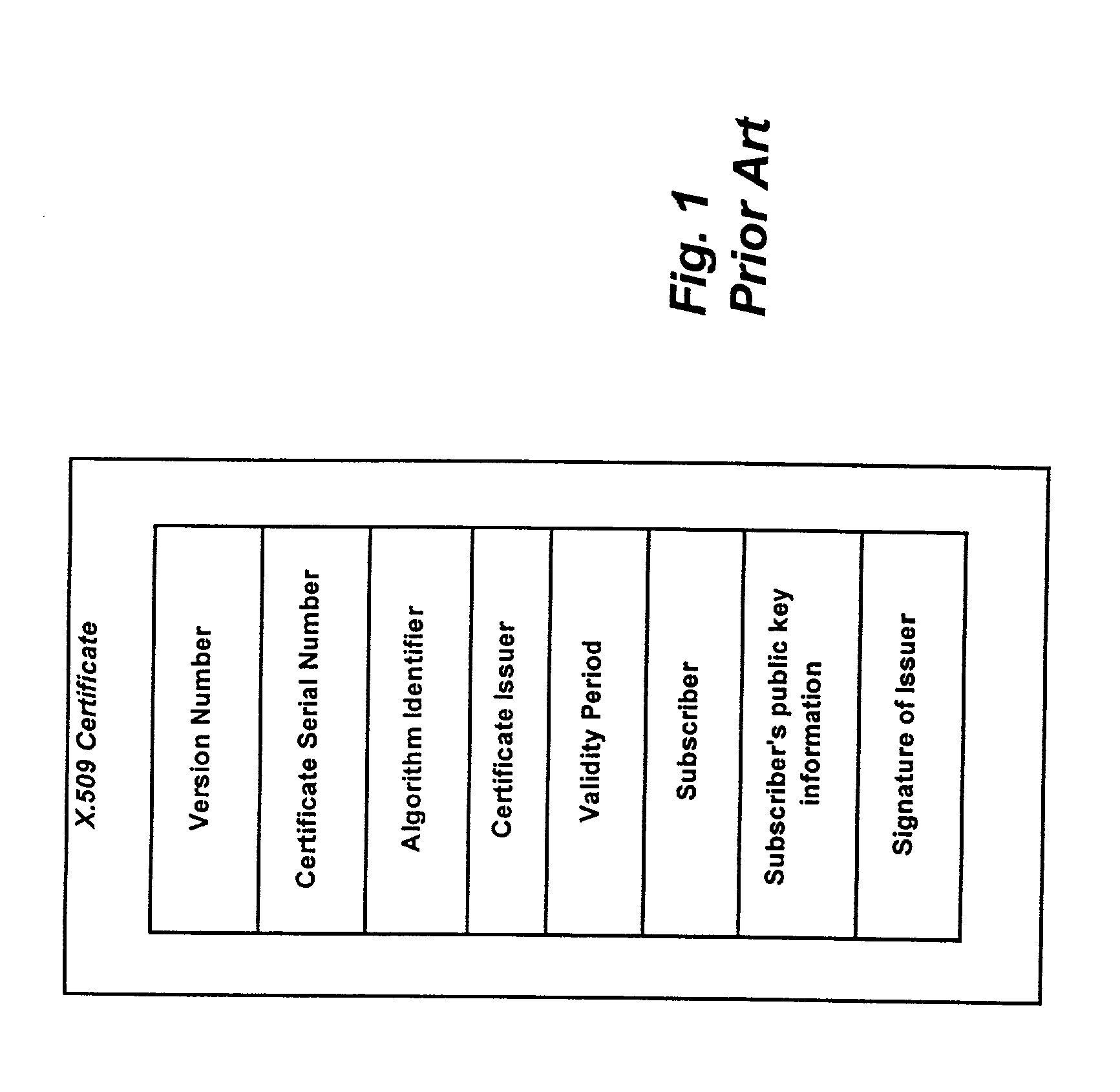
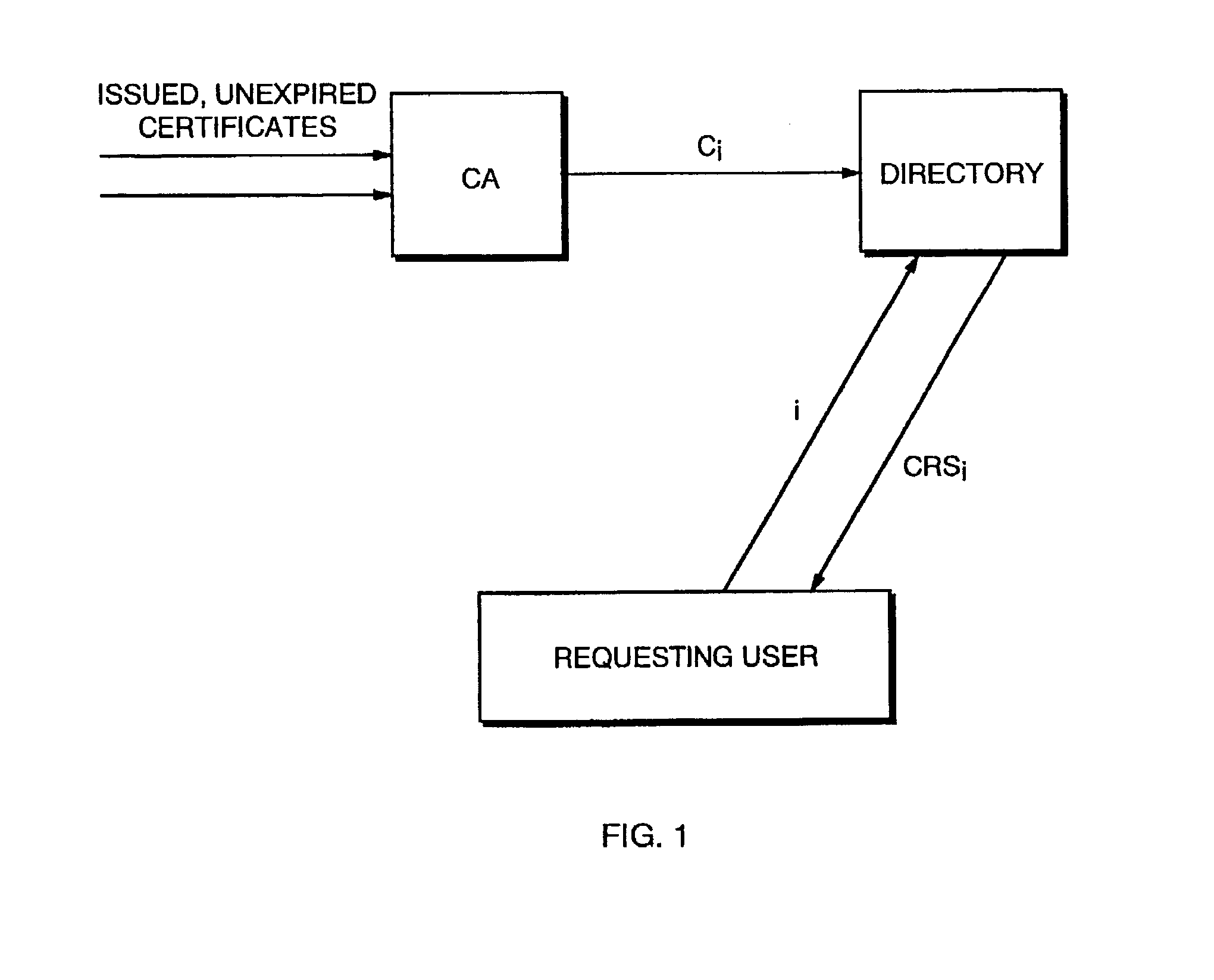
In cryptography, a certificate authority or certification authority (CA) is an entity that issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate. The format of these certificates is specified by the X.509 standard.
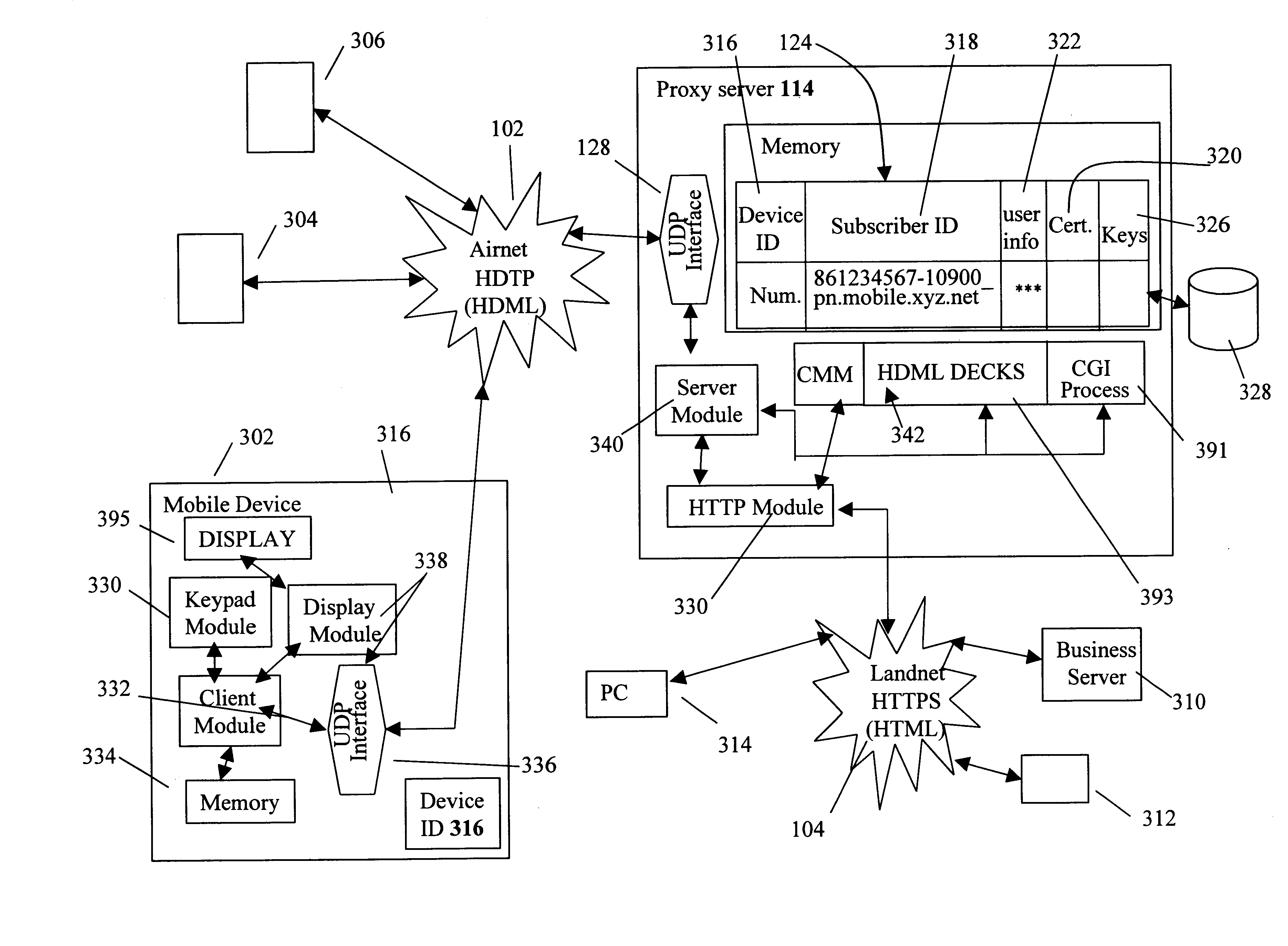
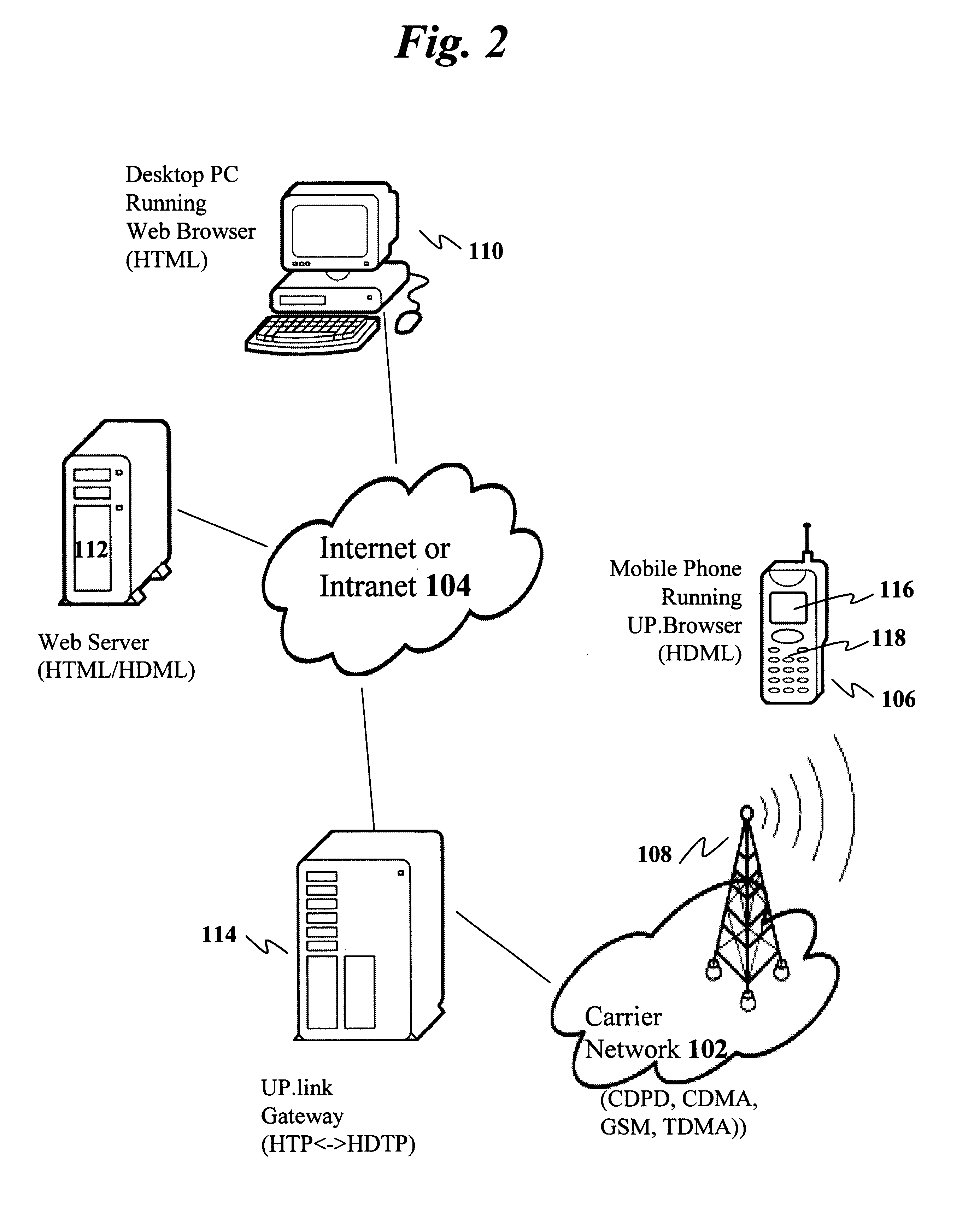
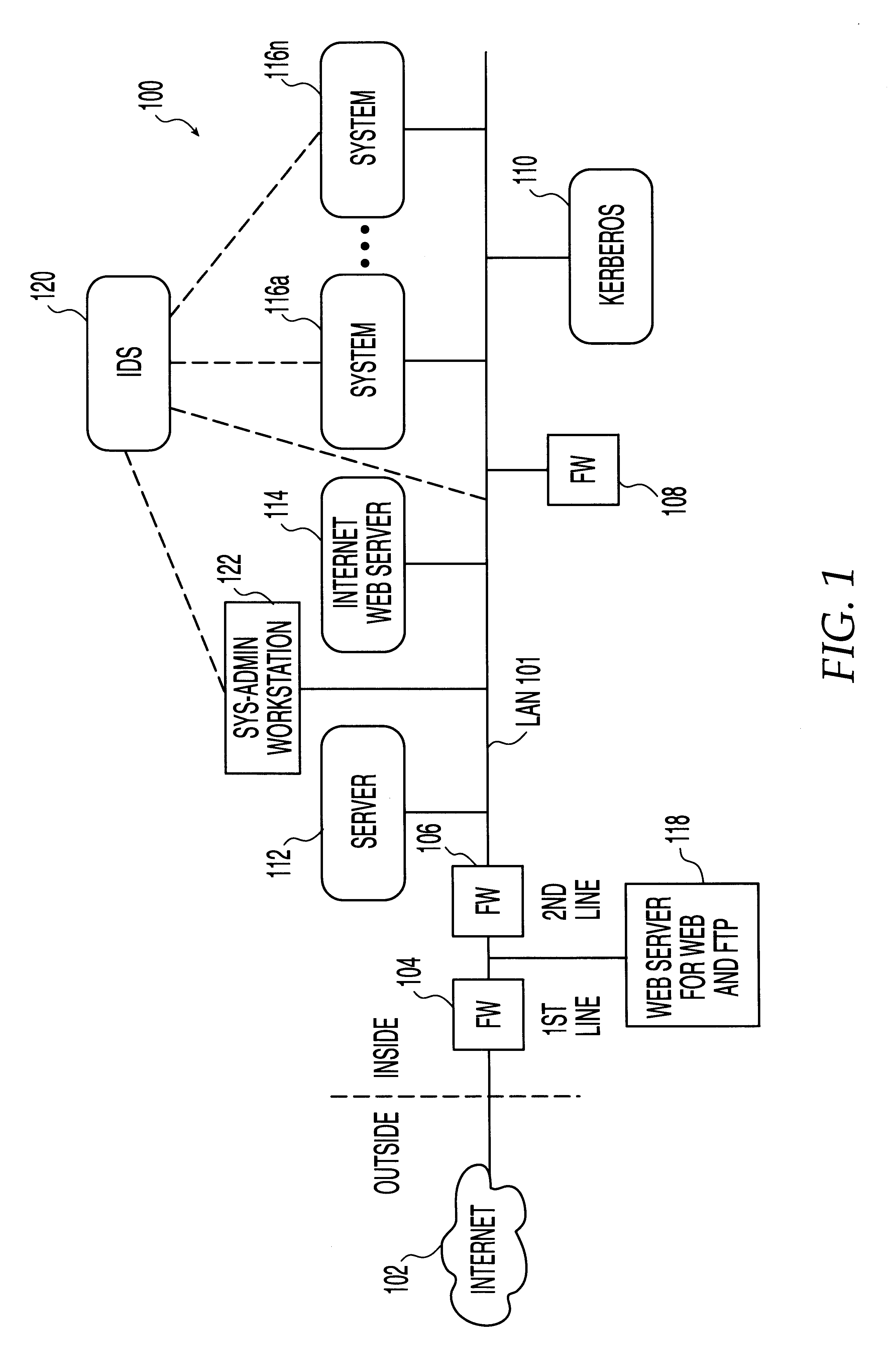
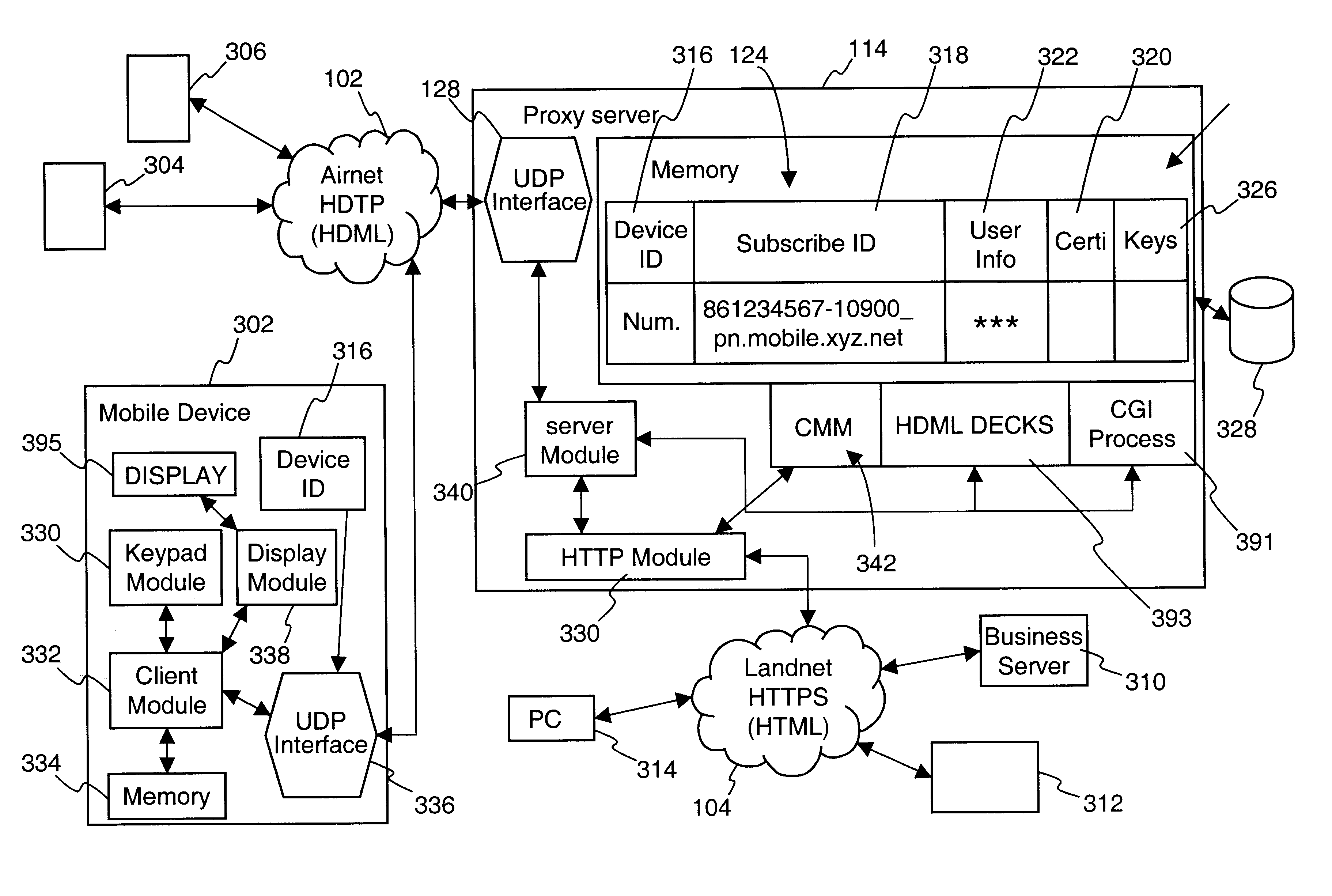
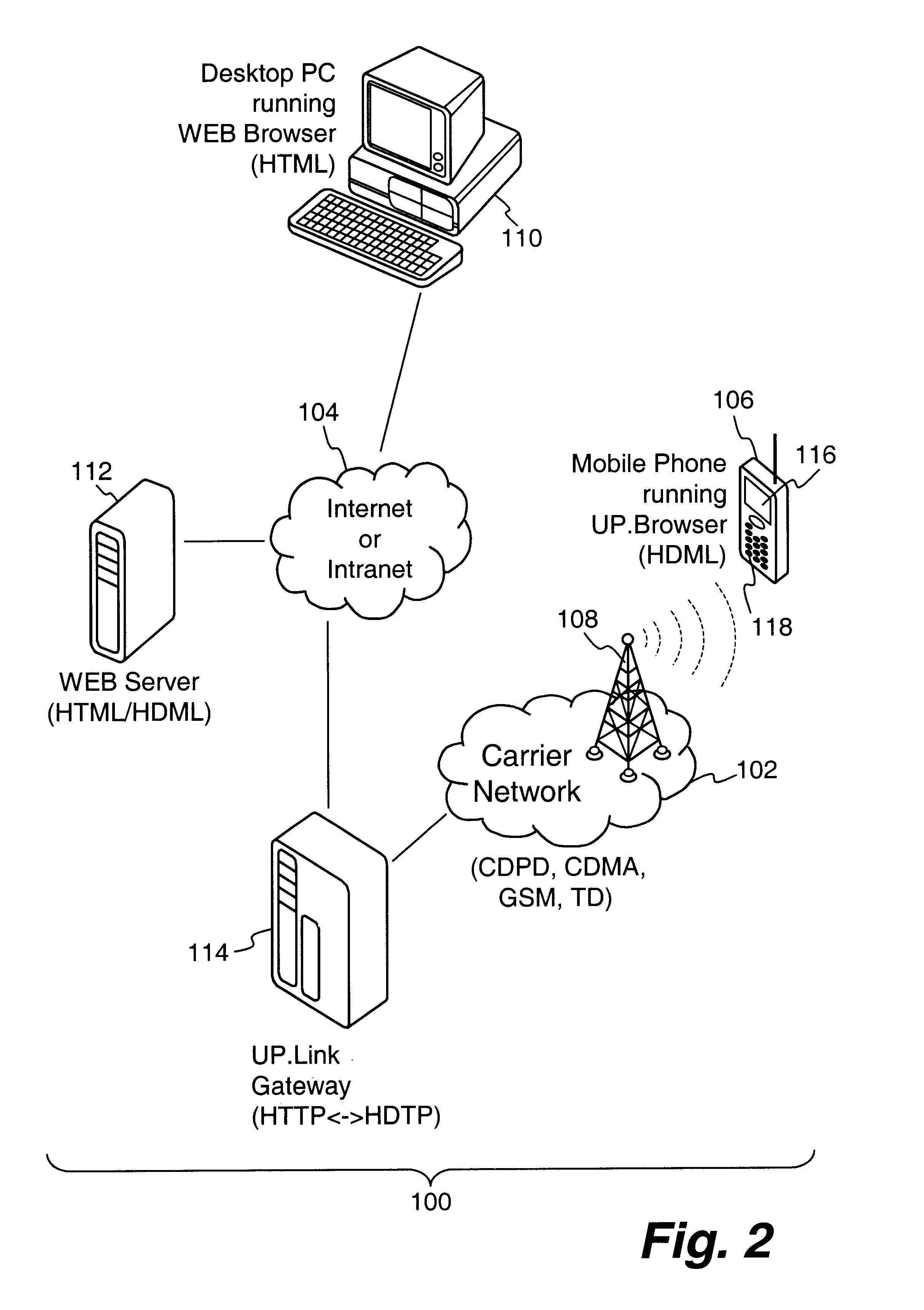
Centralized certificate management system for two-way interactive communication devices in data networks
InactiveUS6233577B1Key distribution for secure communicationData processing applicationsServer applianceCommunication device
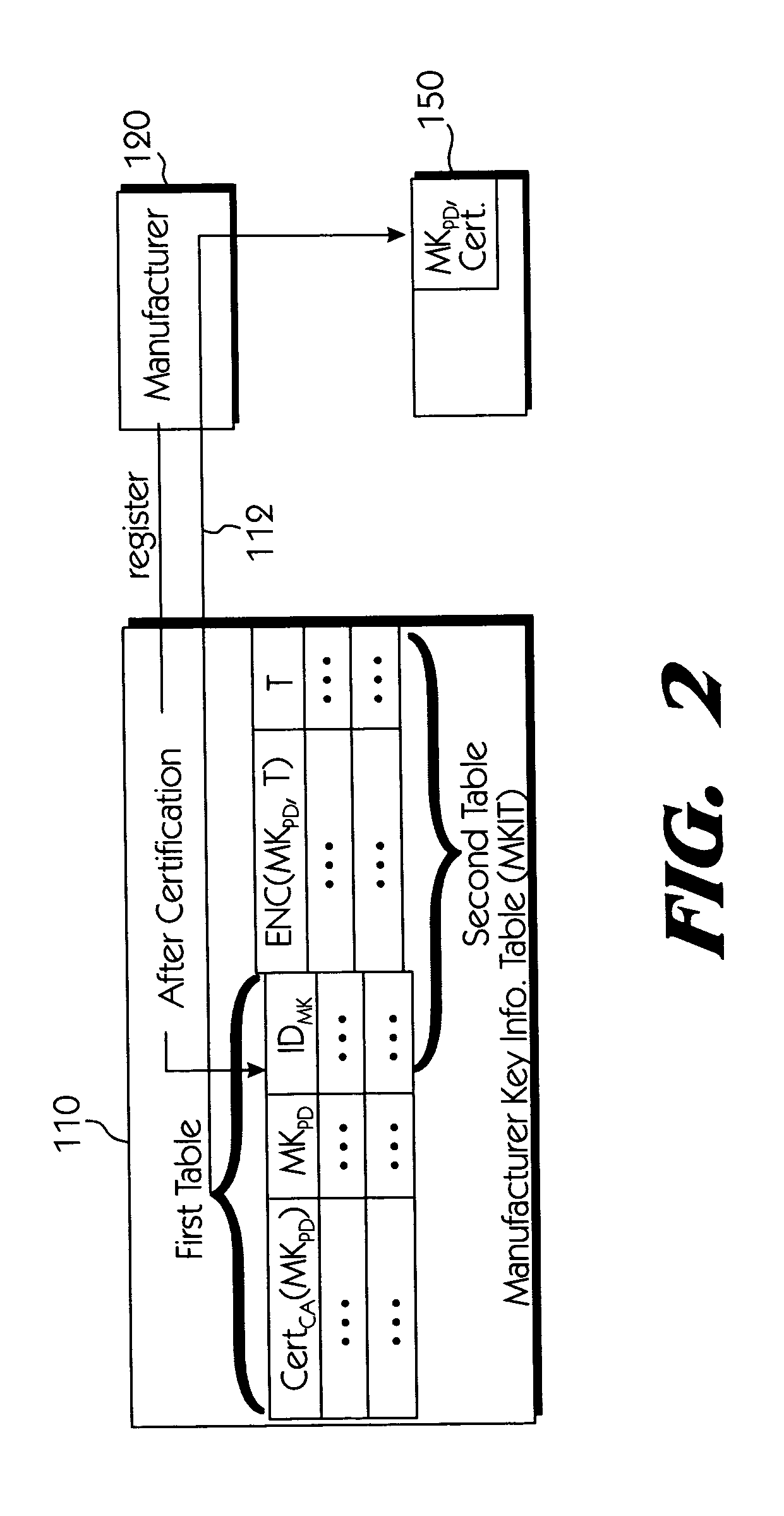
The present invention discloses a central certificate management system for thin client devices in data networks and has particular applications to systems having a large number of the thin clients serviced by a proxy server through which the thin clients communicate with a plurality of secure server computers over a data network. According to one aspect, the present invention provides a certificate management module that causes the server device to manage digital certificates for each of the thin client devices. To minimize the latency of obtaining certificates for each of the thin client devices, the certificate management module reserves a fixed number of free certificates signed by a certificate authority and their respective private keys in a certificate database and frequently updates the free certificate according to a certificate updating message. Whenever a user account is created for a thin client device, the certificate management module fetches one or more free certificates from the certificate database and associate the fetched certificates to the created account and meanwhile the certificate management module creates new free certificates with the certificate authority to fill in the certificate database. Apart from the tradition of obtaining certificates locally in client devices that normally have sufficient computing power, the present invention uses the computing resources in a server device to carry out the task of obtaining and maintaining certificates asynchronously in the proxy server and further. These and other features in the present invention dramatically minimize the demands for computing power and memory in thin client devices like mobile devices, cellular phones, landline telephones or Internet appliance controllers.
Owner:UNWIRED PLANET
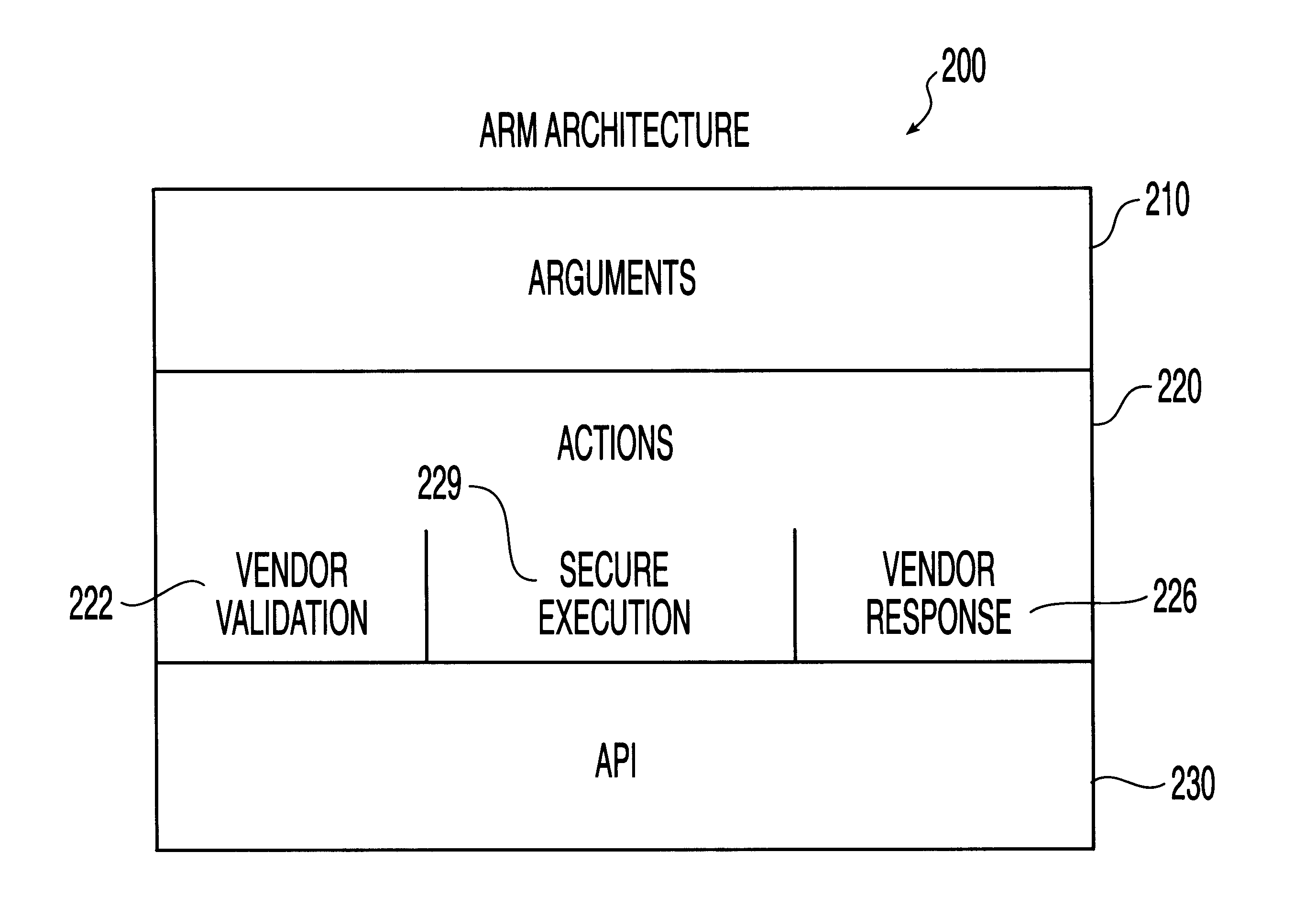
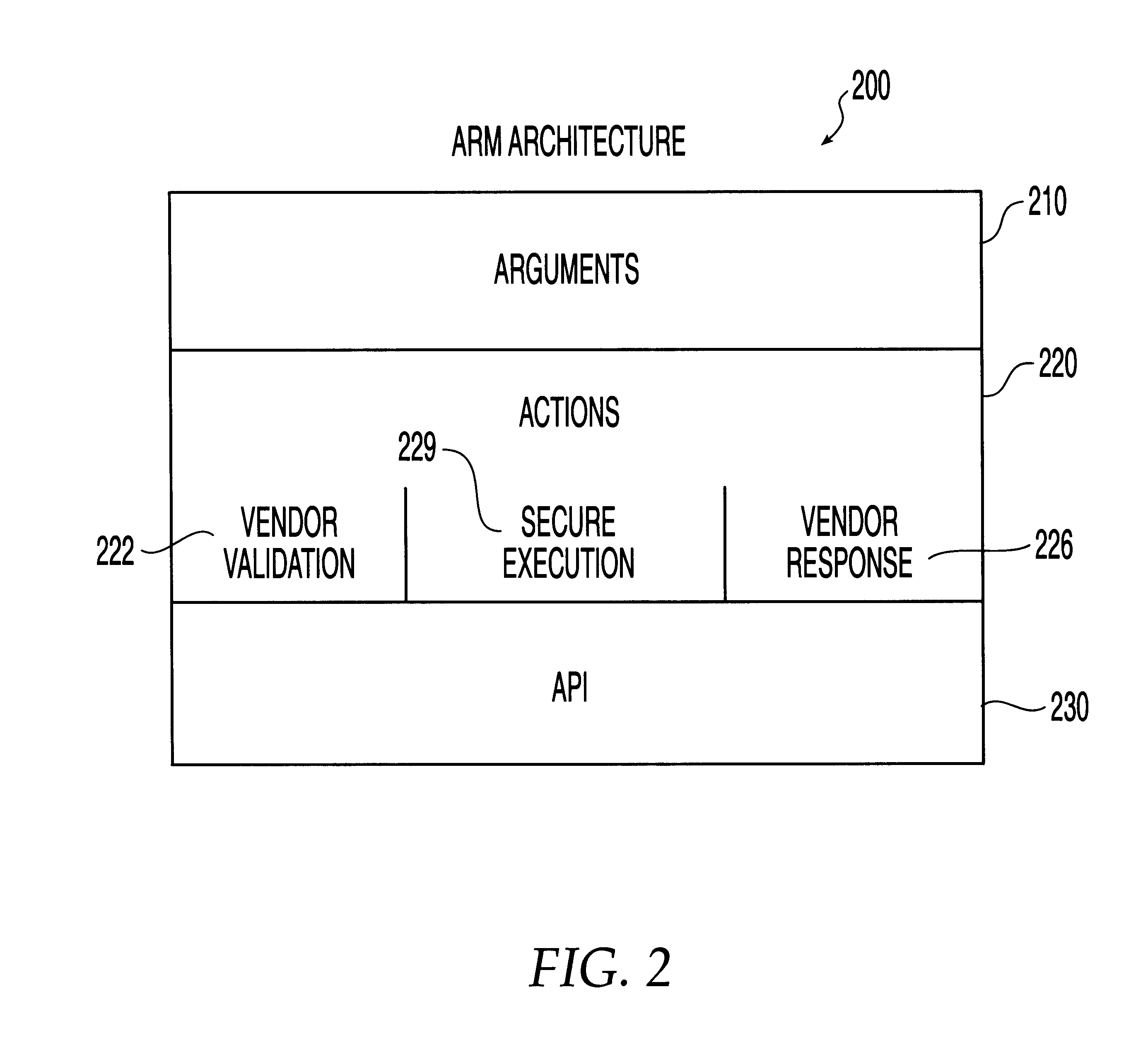
System, method and computer program product for automatic response to computer system misuse using active response modules
InactiveUS6275942B1Rapid responseMemory loss protectionDigital data processing detailsSoftware engineeringSecurity level
A system, method and computer program product for automatic response to computer system misuse using active response modules (ARMs). ARMs are tools that allow static intrusion detection system applications the ability to dynamically increase security levels by allowing real-time responses to detected instances of computer misuse. Several classes of ARMs exist which allow them to interface with several types of network elements found within a computing environment (e.g., firewalls, web servers, Kerberos severs, certificate authorities, etc.). The ARMs, once defined, are deployed in a "plug and play" manner into an existing intrusion detection system within a computing environment. A user (e.g., system administrator) may then configure the ARMs by linking them to specific computer misuses. Upon receipt of an instance of the computer misuse from the intrusion detection system, each ARM linked to the misuse collects pertinent data from the intrusion detection system and invokes a response specified by the ARM class and the collected pertinent data.
Owner:MCAFEE LLC +1
Method and system for distributed network address translation with network security features
InactiveUS7032242B1Digital data processing detailsUser identity/authority verificationSecurity associationIp address
A method and system for distributed network address translation with security features. The method and system allow Internet Protocol security protocol (“IPsec”) to be used with distributed network address translation. The distributed network address translation is accomplished with IPsec by mapping a local Internet Protocol (“IP”) address of a given local network device and a IPsec Security Parameter Index (“SPI”) associated with an inbound IPsec Security Association (“SA”) that terminates at the local network device. A router allocates locally unique security values that are used as the IPsec SPIs. A router used for distributed network address translation is used as a local certificate authority that may vouch for identities of local network devices, allowing local network devices to bind a public key to a security name space that combines a global IP address for the router with a set of locally unique port numbers used for distributed network address translation. The router issues security certificates and may itself be authenticated by a higher certificate authority. Using a security certificate, a local network device may initiate and be a termination point of an IPsec security association to virtually any other network device on an IP network like the Internet or an intranet. The method and system may also allow distributed network address translation with security features to be used with Mobile IP or other protocols in the Internet Protocol suite.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Copy protection system for portable storage media
InactiveUS6950941B1Limited abilityKey distribution for secure communicationData processing applicationsDevice formDigital content
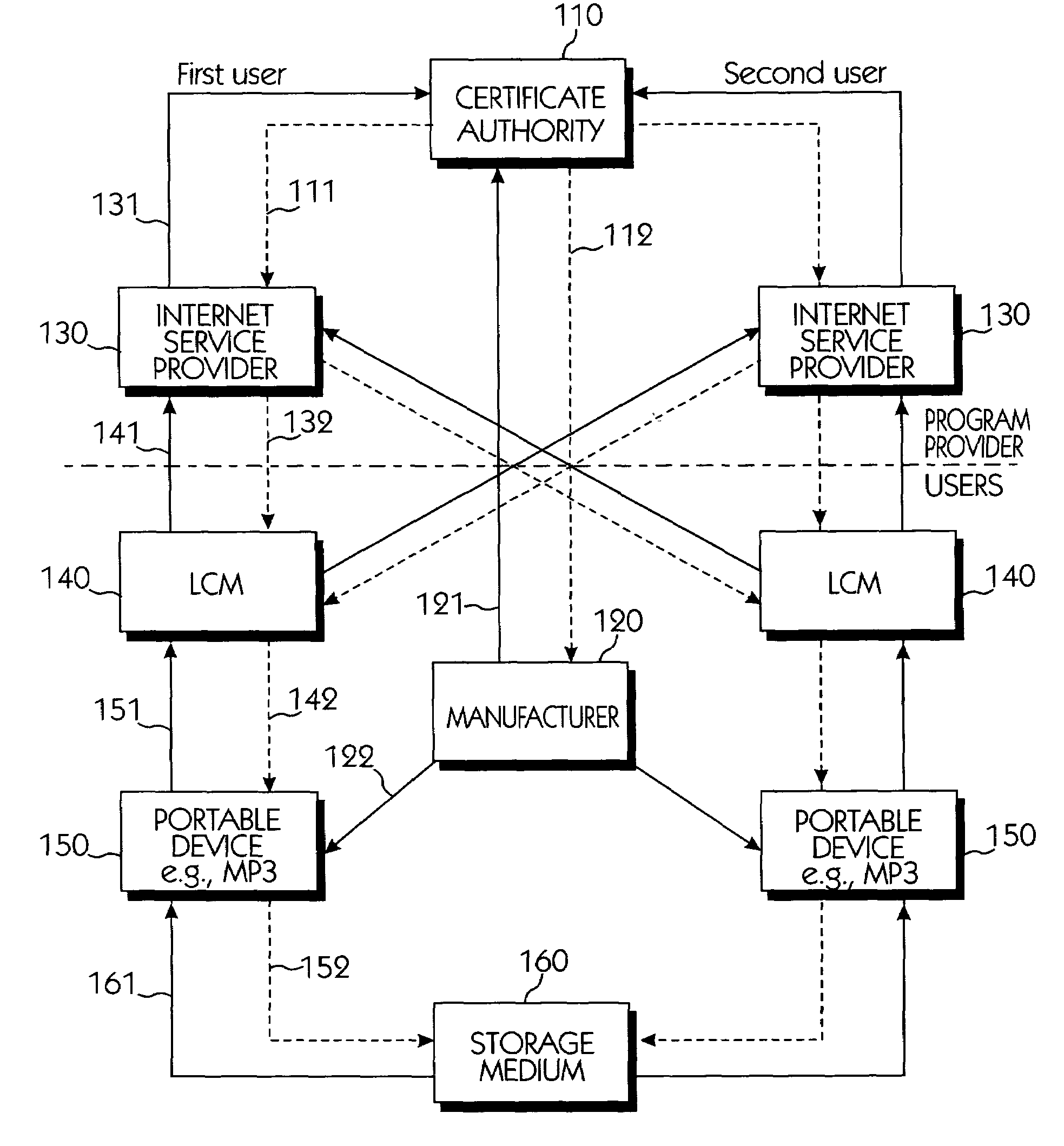
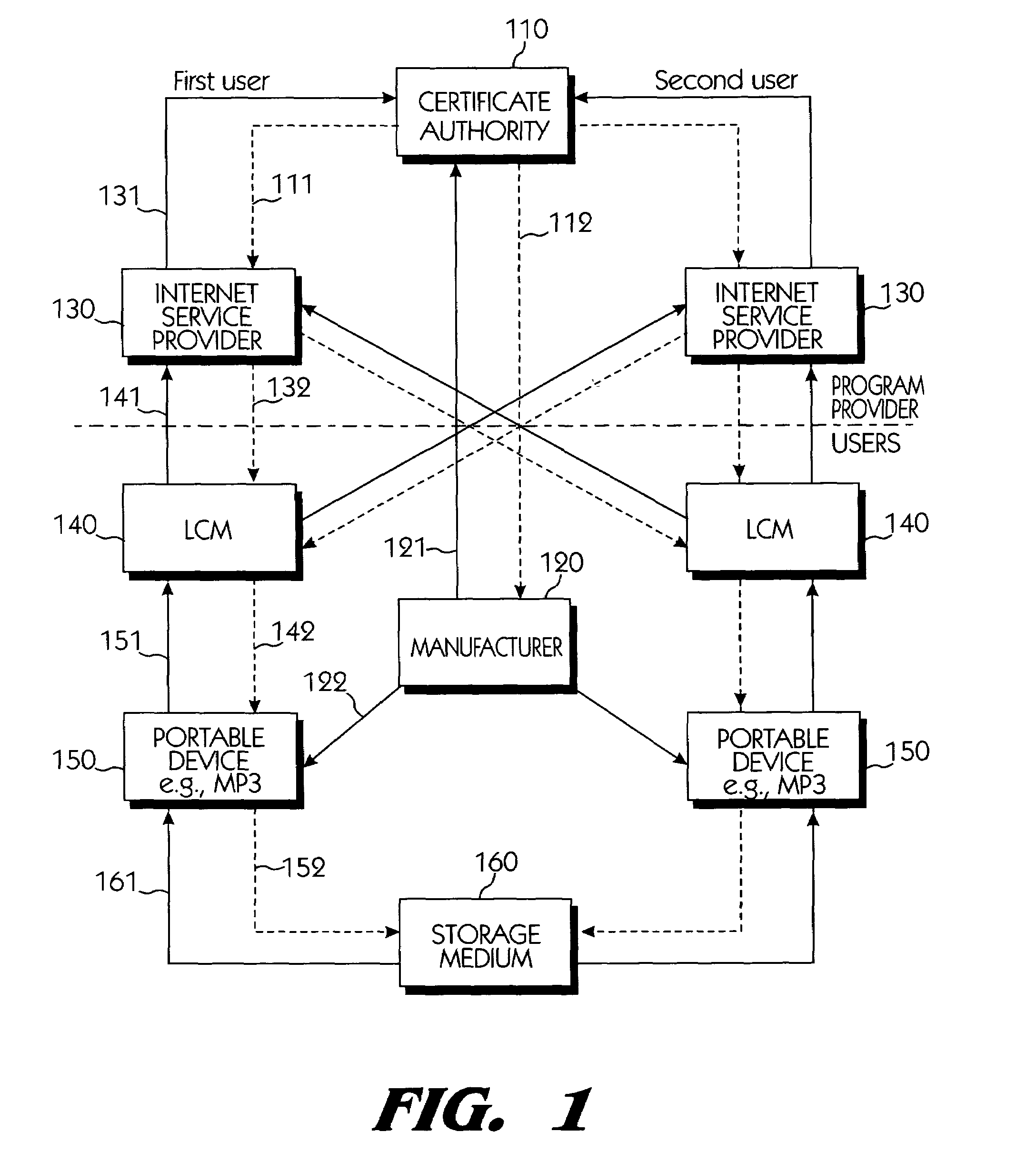
Systems connected to users generate a plurality of keys which are mutually shared, and download and upload digital contents by using secret channels formed between the systems. An information provider receives an authorization from a certificate authority. A licensed SDMI compliant module (LCM) is authenticated through the information provider, and the information provider and the LCM form a channel. A portable device is authenticated from the information provider through the LCM, and the LCM and the portable device form a channel. The digital content between the LCM and the portable device is downloaded and uploaded according to respective control state data of the LCM and the portable device. The system can use a physical address of a bad sector formed in the portable medium during the manufacturing process for preventing an illegal copy of the downloaded digital contents through the portable device after the digital contents have been downloaded.
Owner:SAMSUNG ELECTRONICS CO LTD
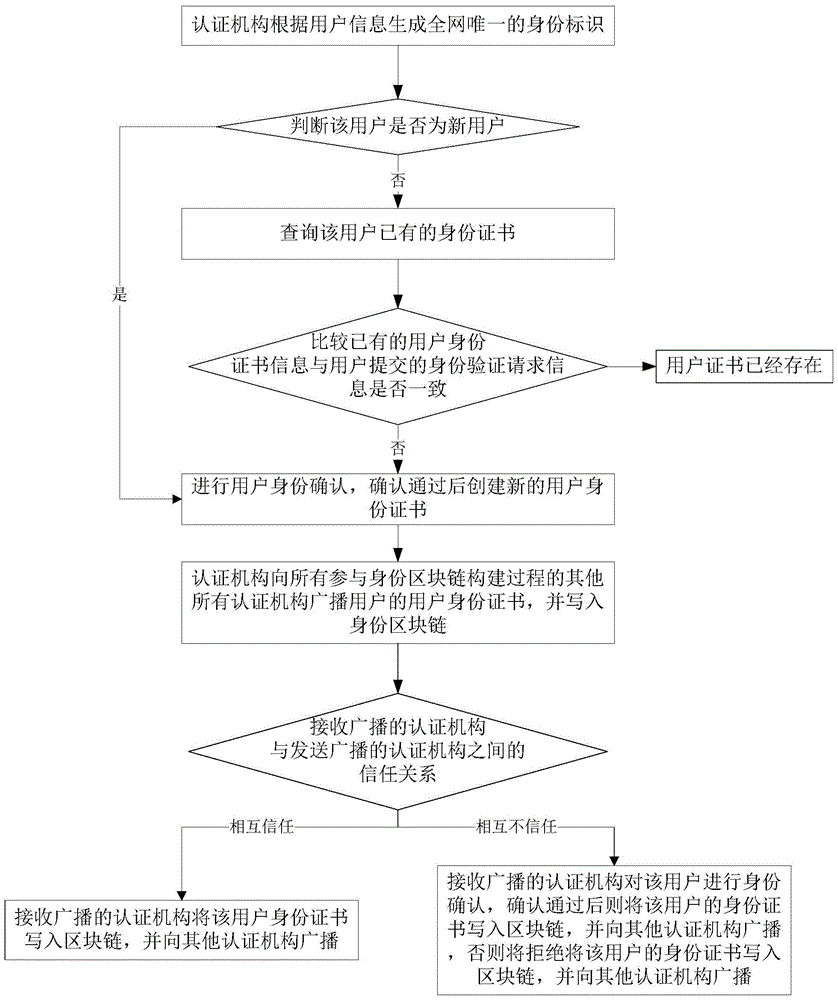
Block chain identity construction and verification method
ActiveCN105701372AImprove authentication efficiencyDoes not affect accuracyDigital data authenticationValidation methodsThe Internet
The present invention relates to identity construction and verification on the Internet, and provides a block chain identity construction and verification method. The method comprises the following steps: a certificate authority constructs a user identity block chain according to an identity verification request submitted by a user; and the certificate authority performs user identity verification processing by means of the identity block chain. According to the method provided by the present invention, user identity information is written into the block chain, and multiple certificate authorities jointly complete confirmation and storage of the identity information by means of an agreement mechanism, and then the user can conveniently perform identity verification by using the block chain. The method is not only capable of improving efficiency of user identity verification, but also will not affect accuracy of the user identity information due to the problem of an individual certificate authority, thereby greatly improving security of an identity verification process.
Owner:BUBI BEIJING NETWORK TECH CO LTD +1
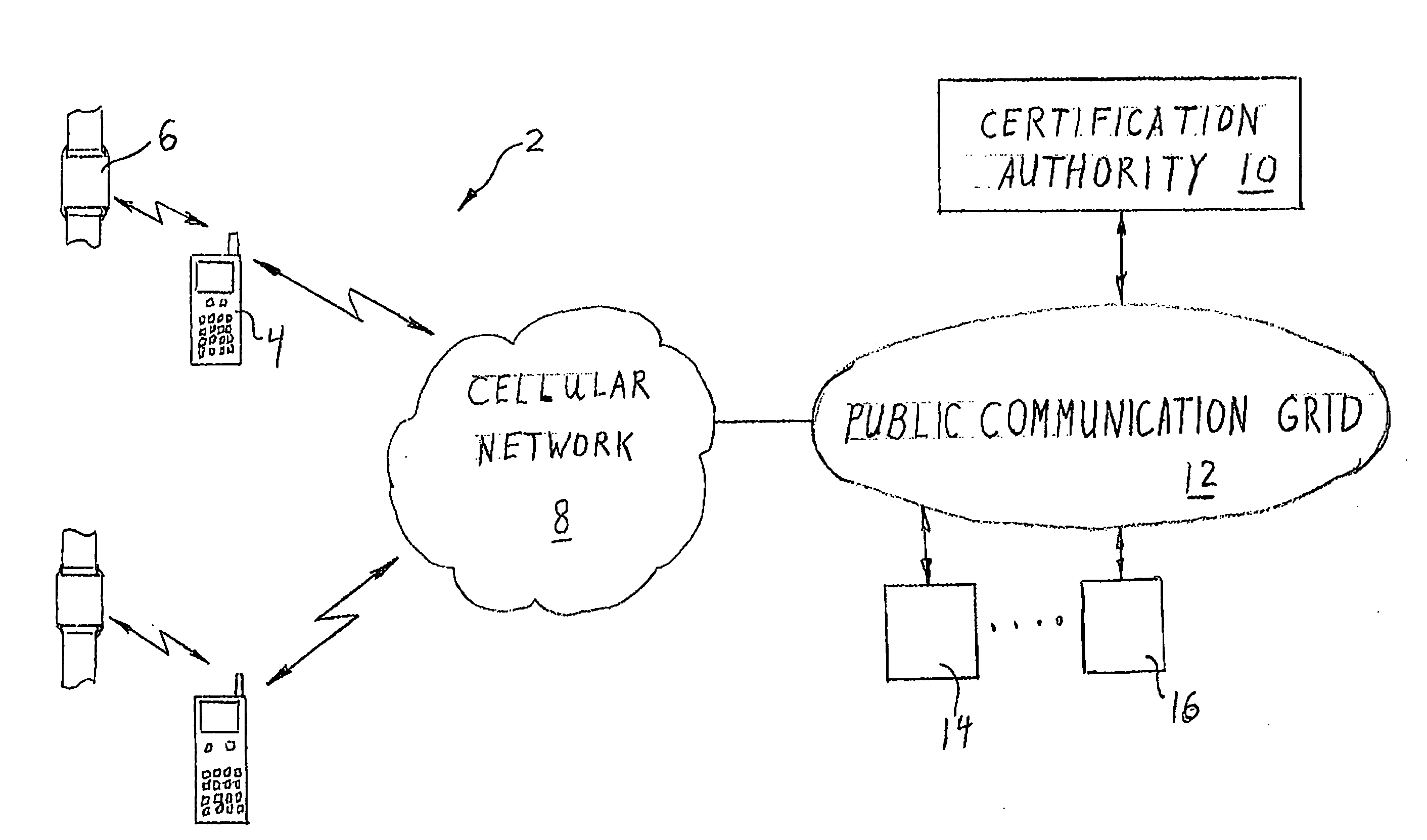
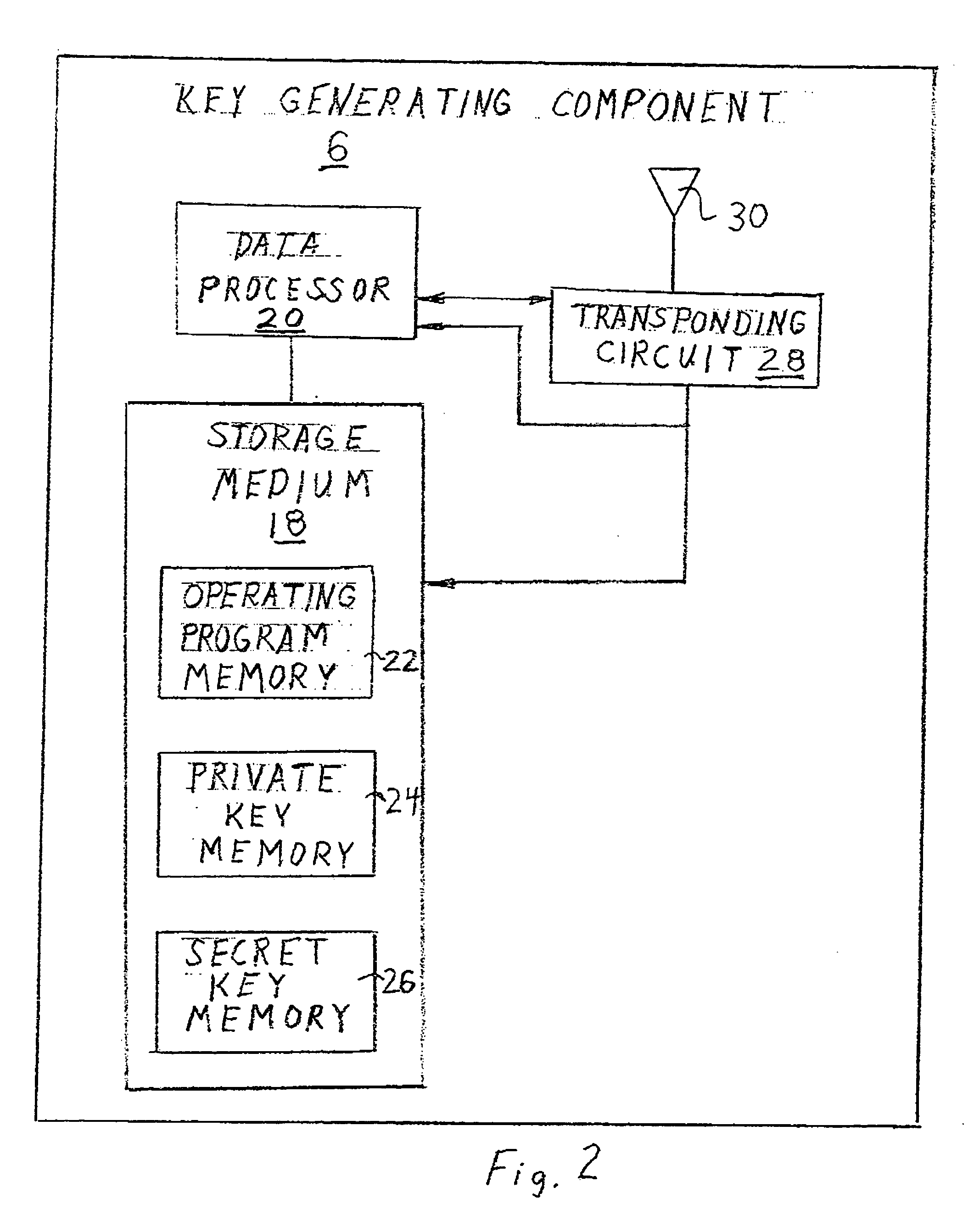
Security system for handheld wireless devices using-time variable encryption keys
ActiveUS20080022089A1Least costOperational securityNetwork topologiesPublic key infrastructure trust modelsCommunications systemWireless broadcasting
In one embodiment, the invention provides a portable wireless personal communication system for cooperating with a remote certification authority to employ time variable secure key information pursuant to a predetermined encryption algorithm to facilitate convenient, secure encrypted communication. The disclosed system includes a wireless handset, such as PDA, smartphone, cellular telephone or the like, characterized by a relatively robust data processing capability and a body mounted key generating component which is adapted to be mounted on an individual's body, in a permanent or semi-permanent manner, for wirelessly broadcasting, within the immediate proximity of the individual, a secret or private key identifying signal corresponding to a time variable secure key information under the control of the certification authority. The key identifying signal is generated in a format that facilitates secure wireless communication with the individual in accordance with a predetermined encryption algorithm including a PKI encryption algorithm. The disclosed system may be used with a console for coordinating access to a variety of different communication system and networks.
Owner:MLR
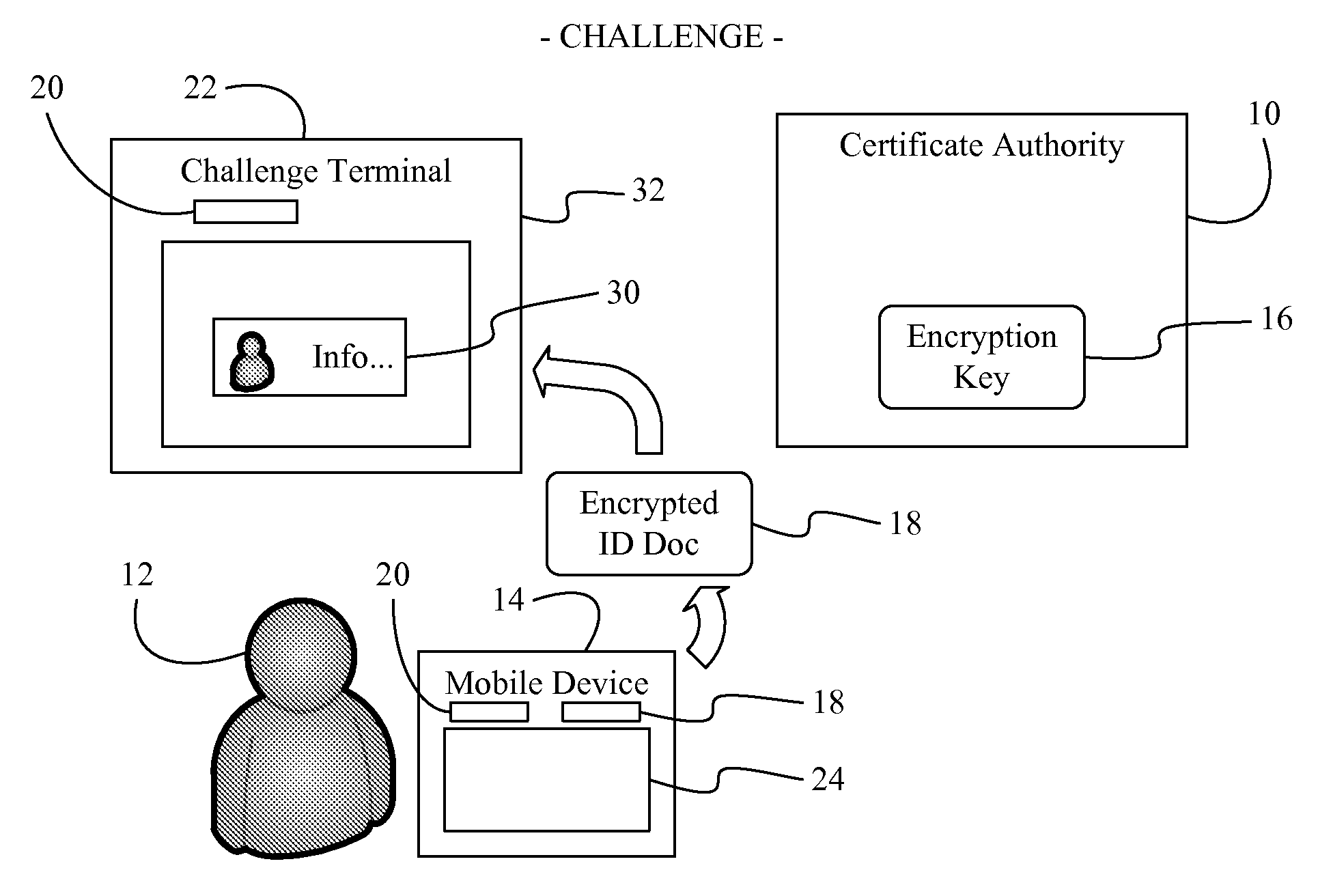
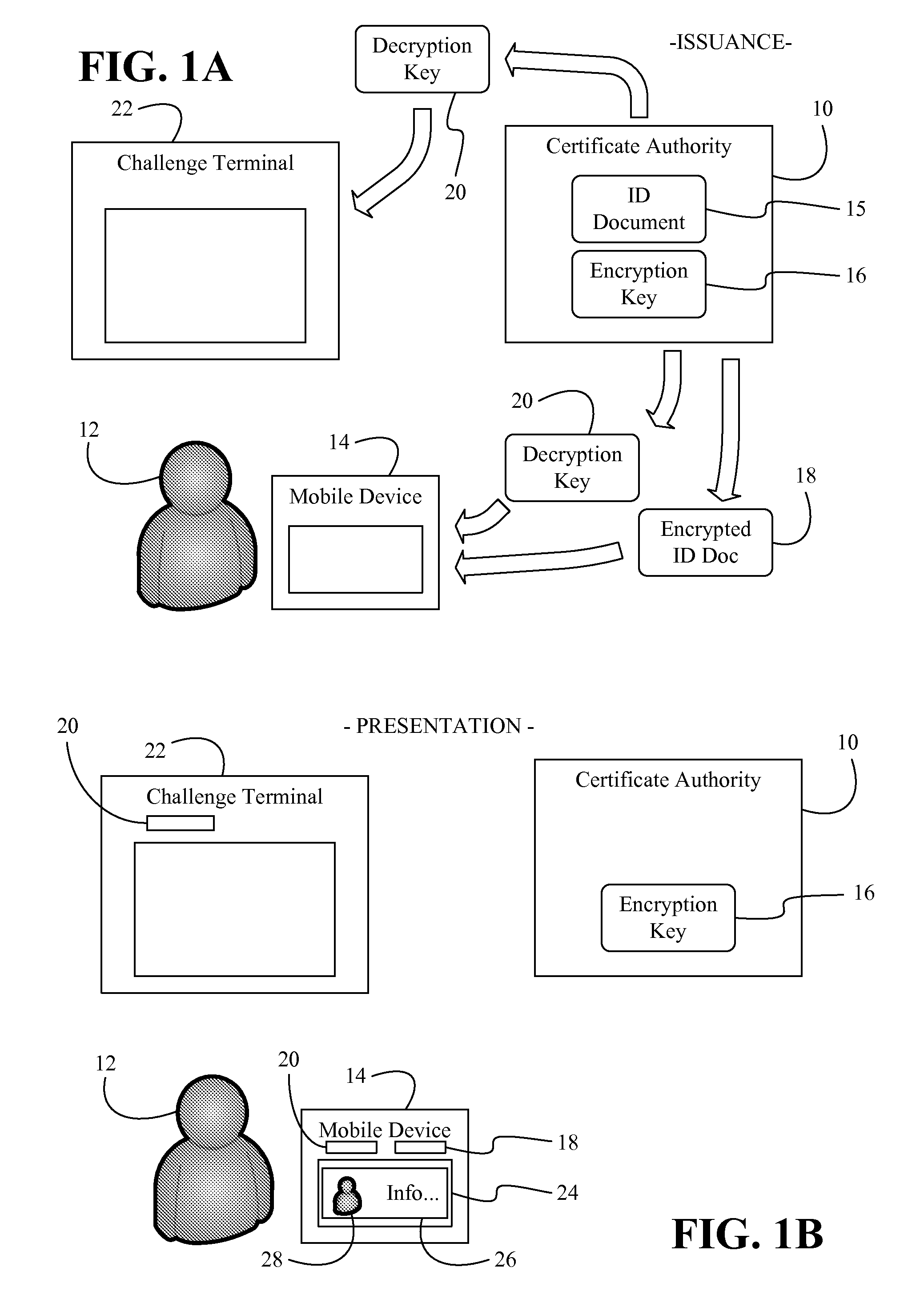
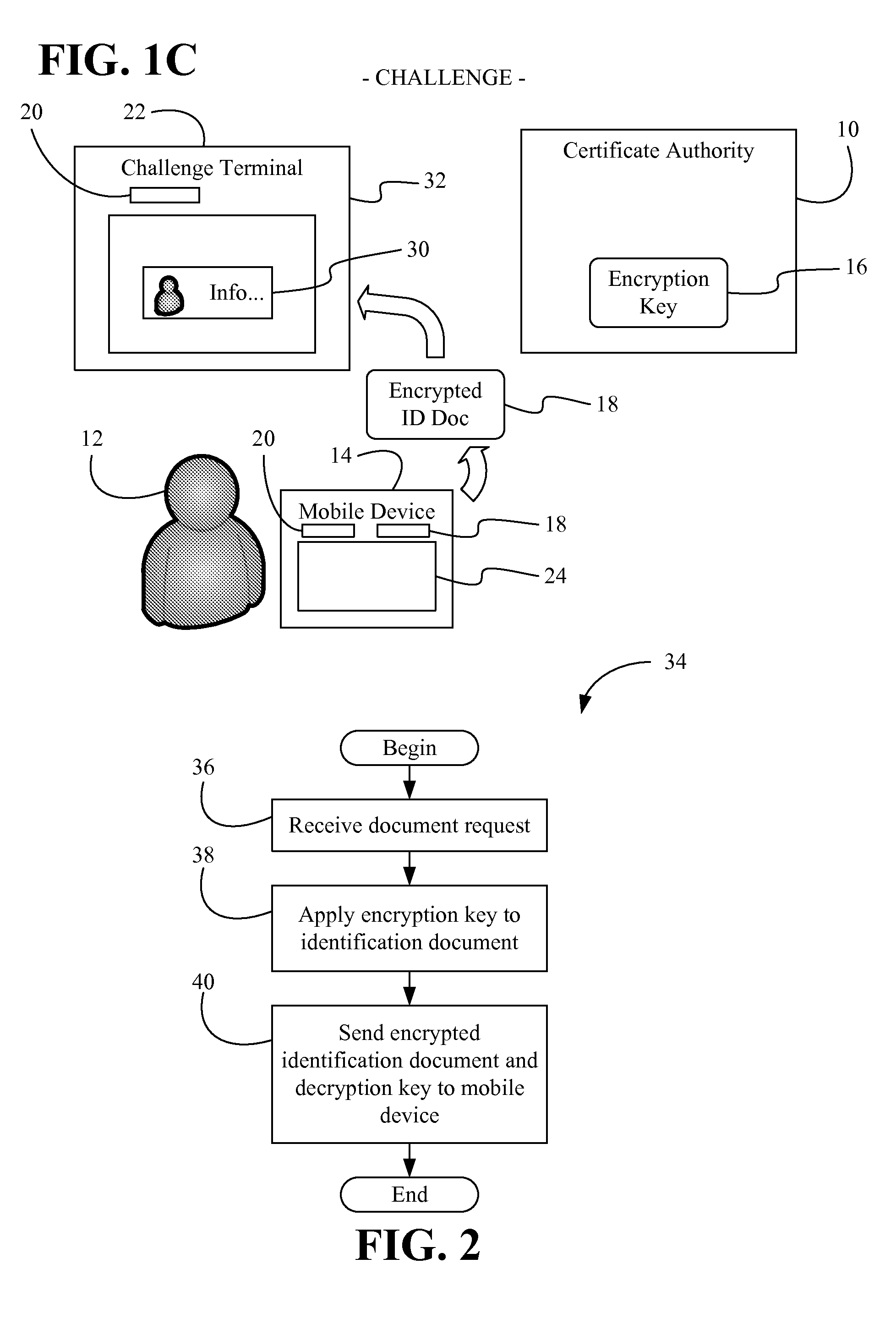
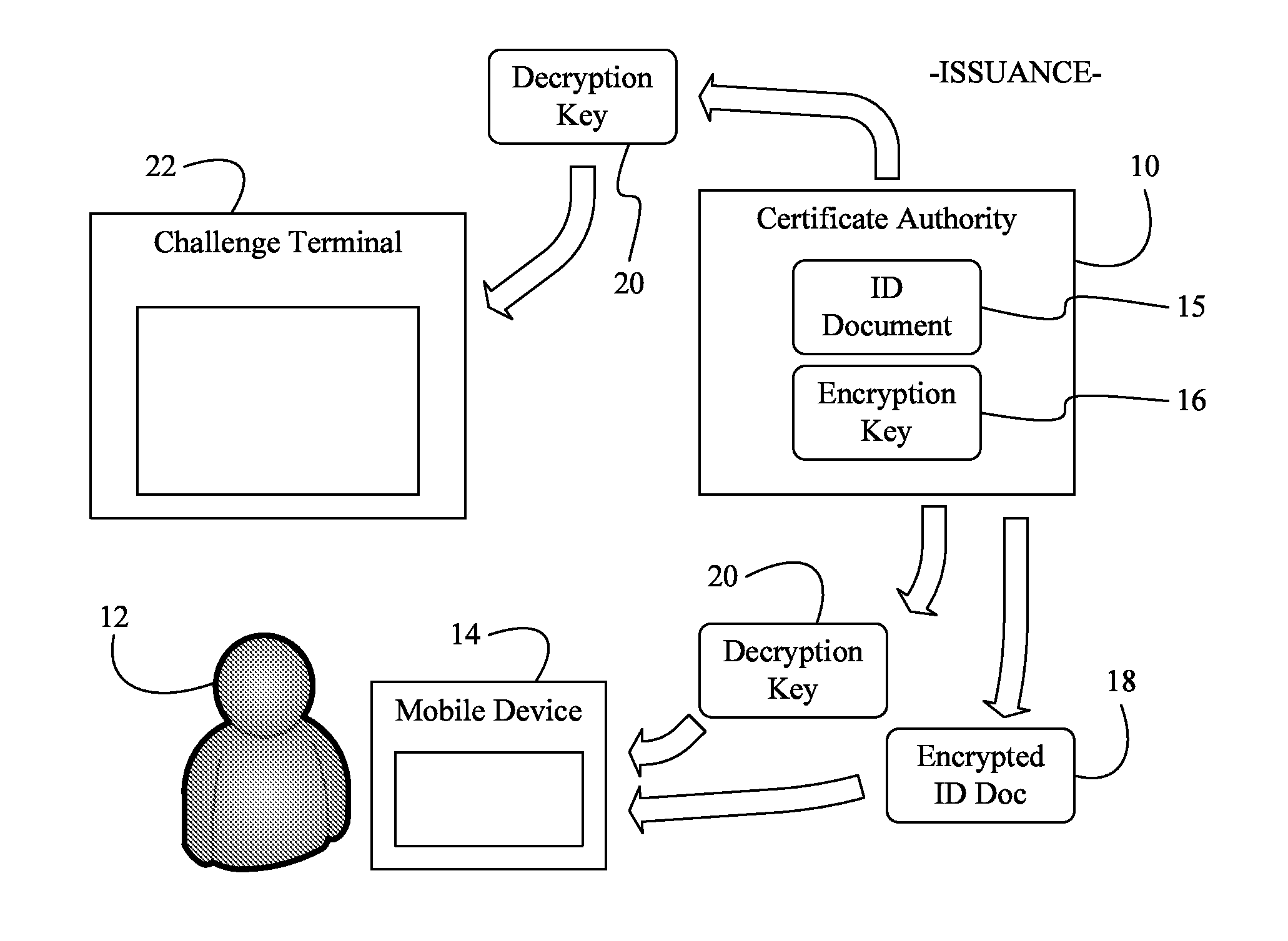
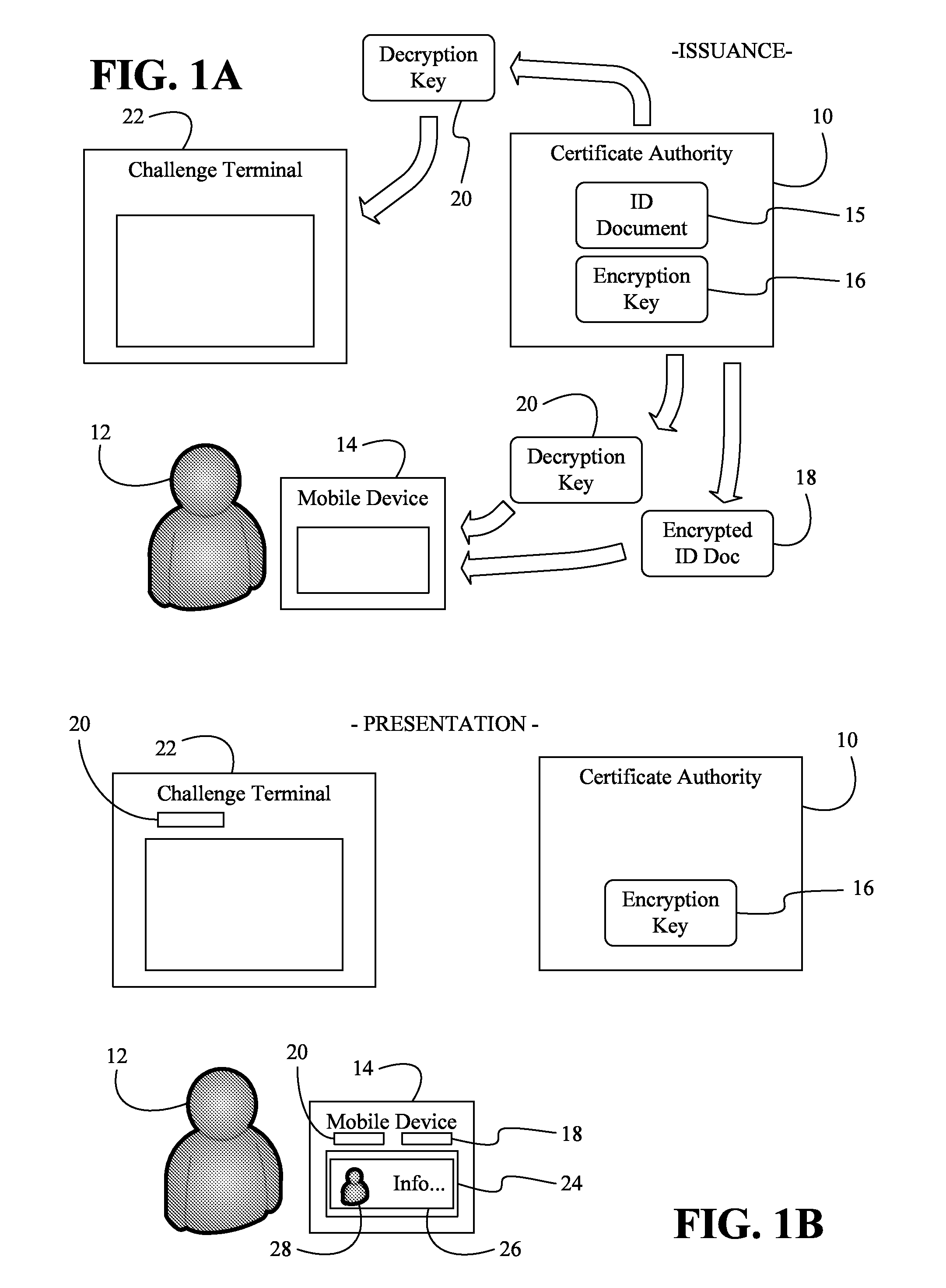
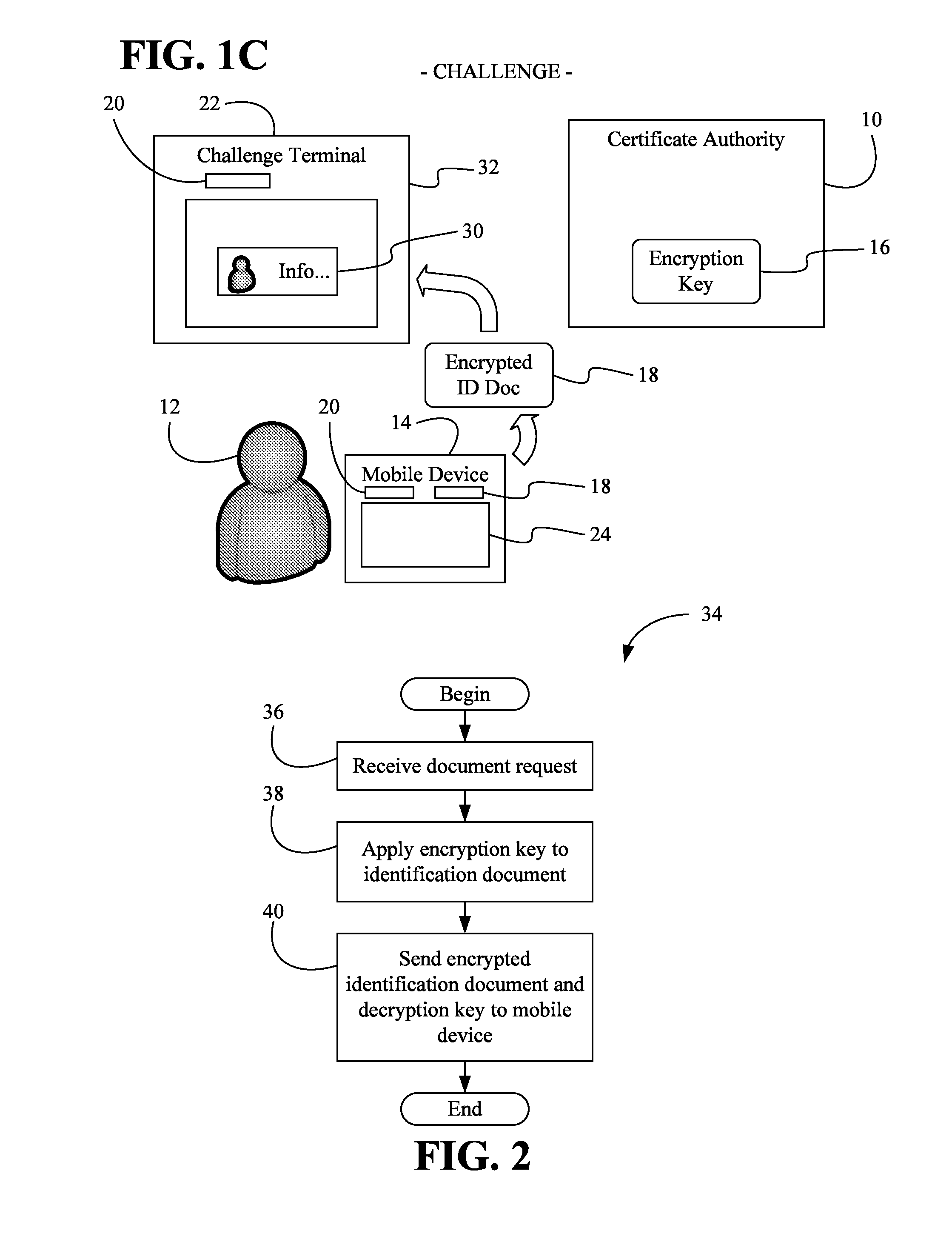
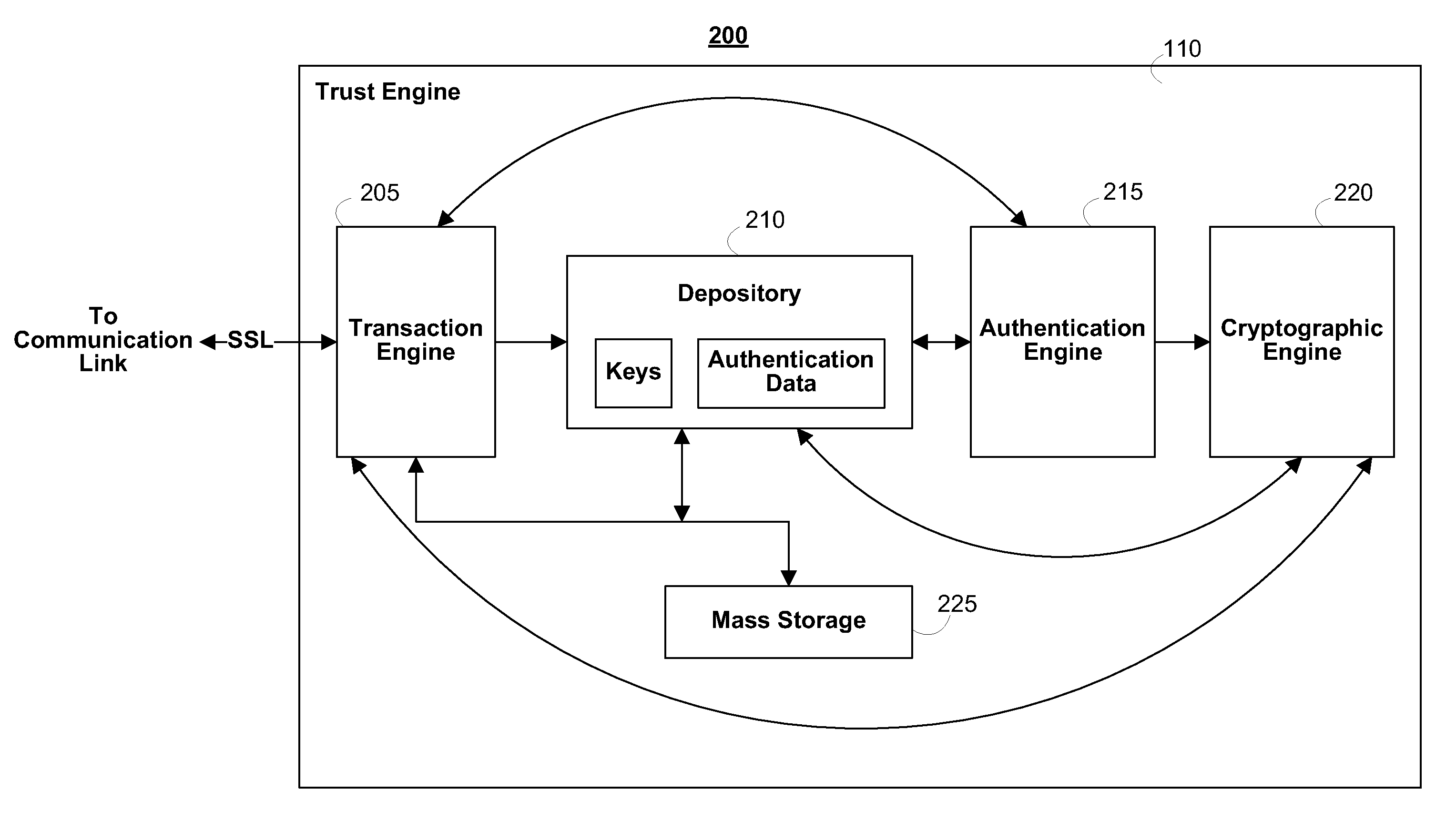
Issuing, presenting and challenging mobile device identification documents
Methods and systems of authenticating electronic identification (ID) documents may provide for receiving a decryption key and an encrypted ID document from a certificate authority server at a mobile device, wherein the encrypted ID document includes a read only document having a photograph of an individual. Additionally, the decryption key may be applied to the encrypted ID document to obtain a decryption result in response to a display request. The decryption result can be output via a display of the mobile device, wherein the encrypted ID document can be sent to a challenge terminal if a challenge request is received.
Owner:EDISON VAULT LLC
Issuing, presenting and challenging mobile device identification documents
Methods and systems of authenticating electronic identification (ID) documents may provide for receiving a decryption key and an encrypted ID document from a certificate authority server at a mobile device, wherein the encrypted ID document includes a read only document having a photograph of an individual. Additionally, the decryption key may be applied to the encrypted ID document to obtain a decryption result in response to a display request. The decryption result can be output via a display of the mobile device, wherein the encrypted ID document can be sent to a challenge terminal if a challenge request is received.
Owner:EDISON VAULT LLC
Systems and methods for securing data in motion
ActiveUS20110202755A1Computer security arrangementsData switching networksCertificate authorityKey establishment
Two approaches are provided for distributing trust among a set of certificate authorities. Both approaches are equally secure. In each approach, a secure data parser is integrated with any suitable encryption technology. Each approach may be used to secure data in motion. One approach provides methods and systems in which the secure data parser is used to distribute trust in a set of certificate authorities during initial negotiation (e.g., the key establishment phase) of a connection between two devices. Another approach of the present invention provides methods and systems in which the secure data parser is used to disperse packets of data into shares. A set of tunnels is established within a communication channel using a set of certificate authorities, keys developed during the establishment of the tunnels are used to encrypt shares of data for each of the tunnels, and the shares of data are transmitted through each of the tunnels. Accordingly, trust is distributed among a set of certificate authorities in the structure of the communication channel itself.
Owner:SECURITY FIRST INNOVATIONS LLC
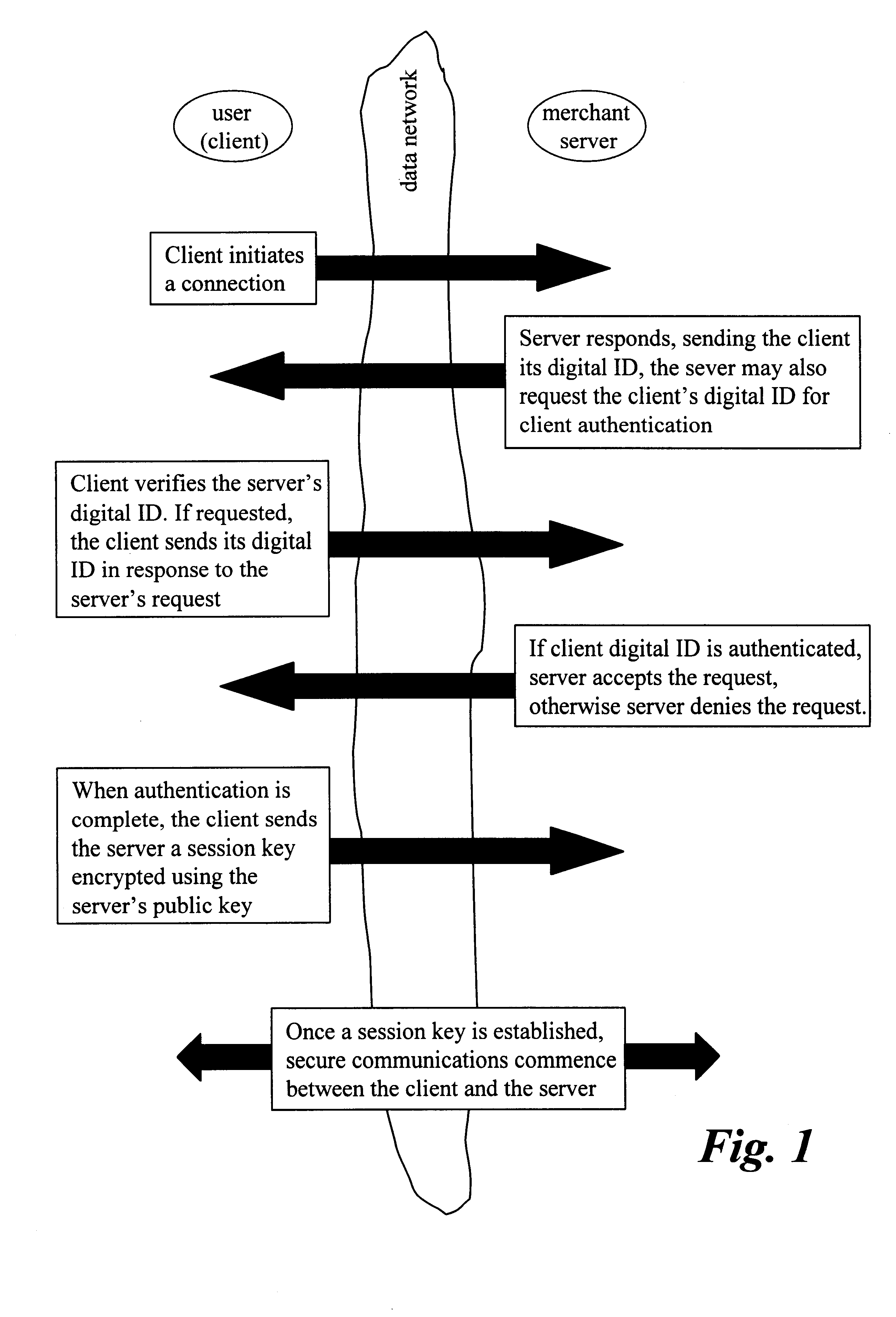
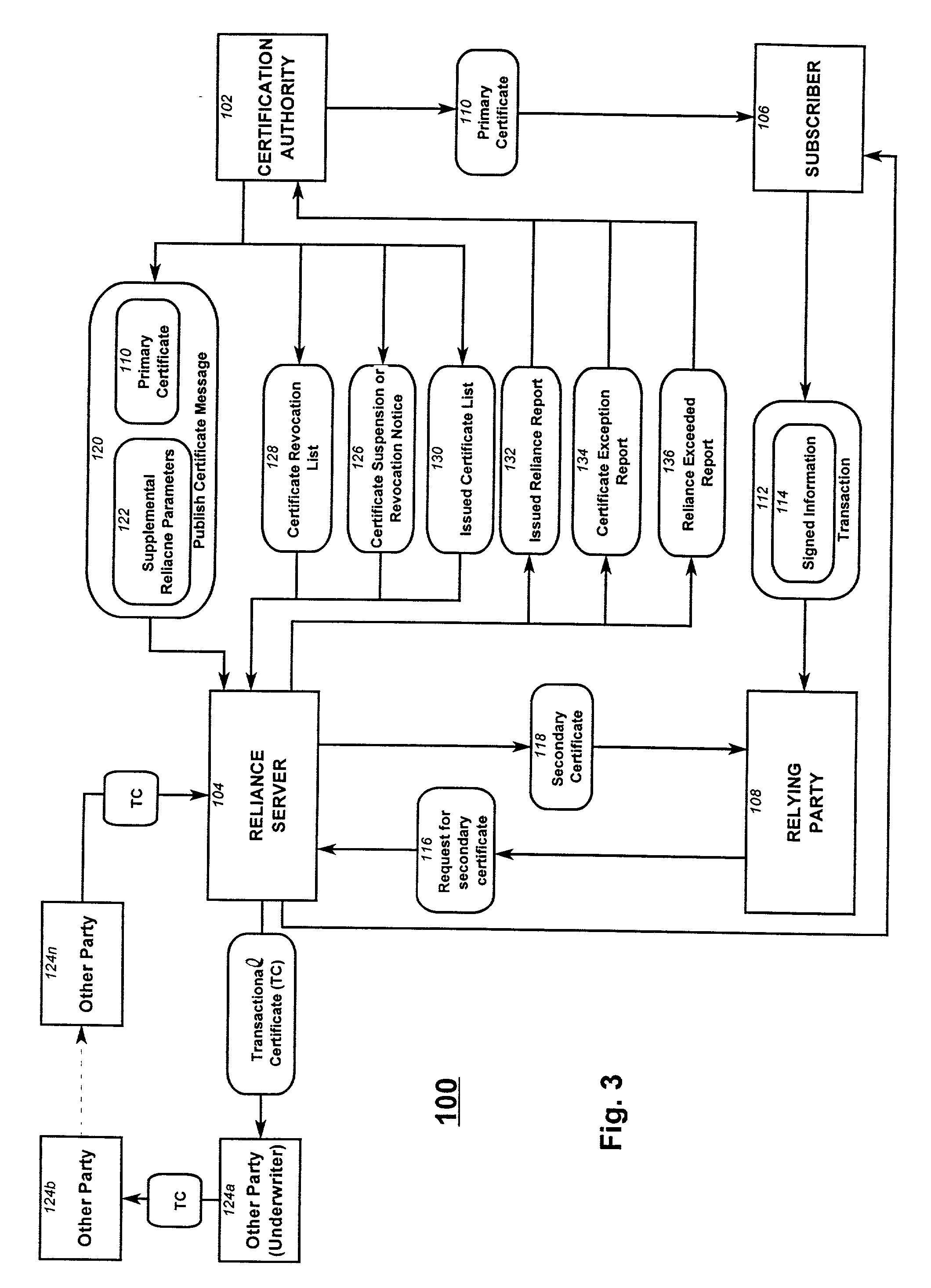
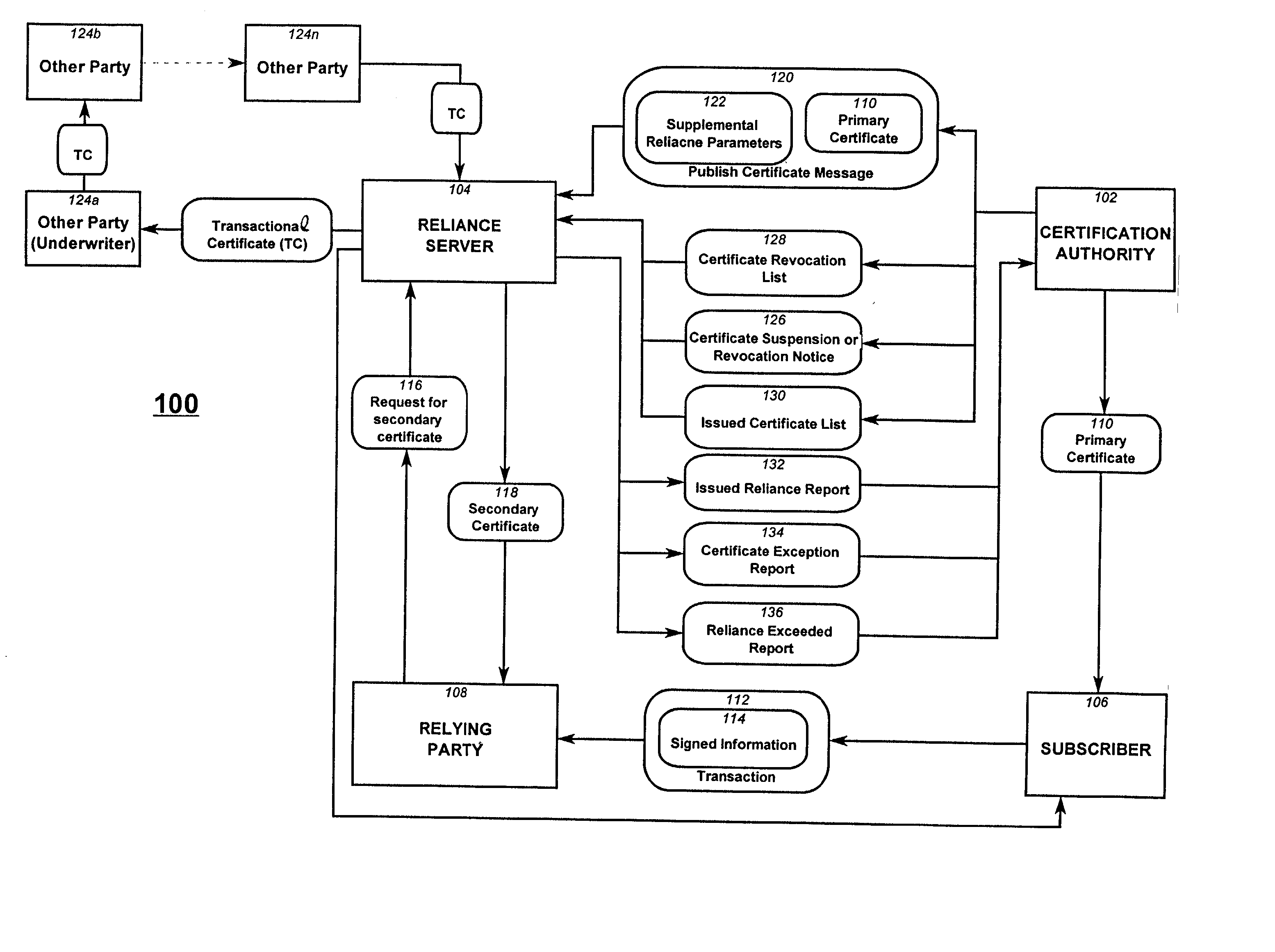
Reliance management for electronic transaction system
InactiveUS20010011255A1Complete banking machinesPublic key for secure communicationProxy certificateCertificate authority
A method of managing reliance in an electronic transaction system includes a certification authority issuing a primary certificate to a subscriber and forwarding to a reliance server, information about the issued primary certificate. The reliance server maintains the forwarded information about issued primary certificate. The subscriber forms a transaction and then provides the transaction to a relying party. The transaction includes the primary certificate or a reference thereto. The relying party sends to the reliance server a request for assurance based on the transaction received from the subscriber. The reliance server determines whether to provide the requested assurance based on the information about the issued primary certificate and on the requested assurance. Based on the determining, the reliance server issues to the relying party a secondary certificate providing the assurance to the relying party.
Owner:CERTCO
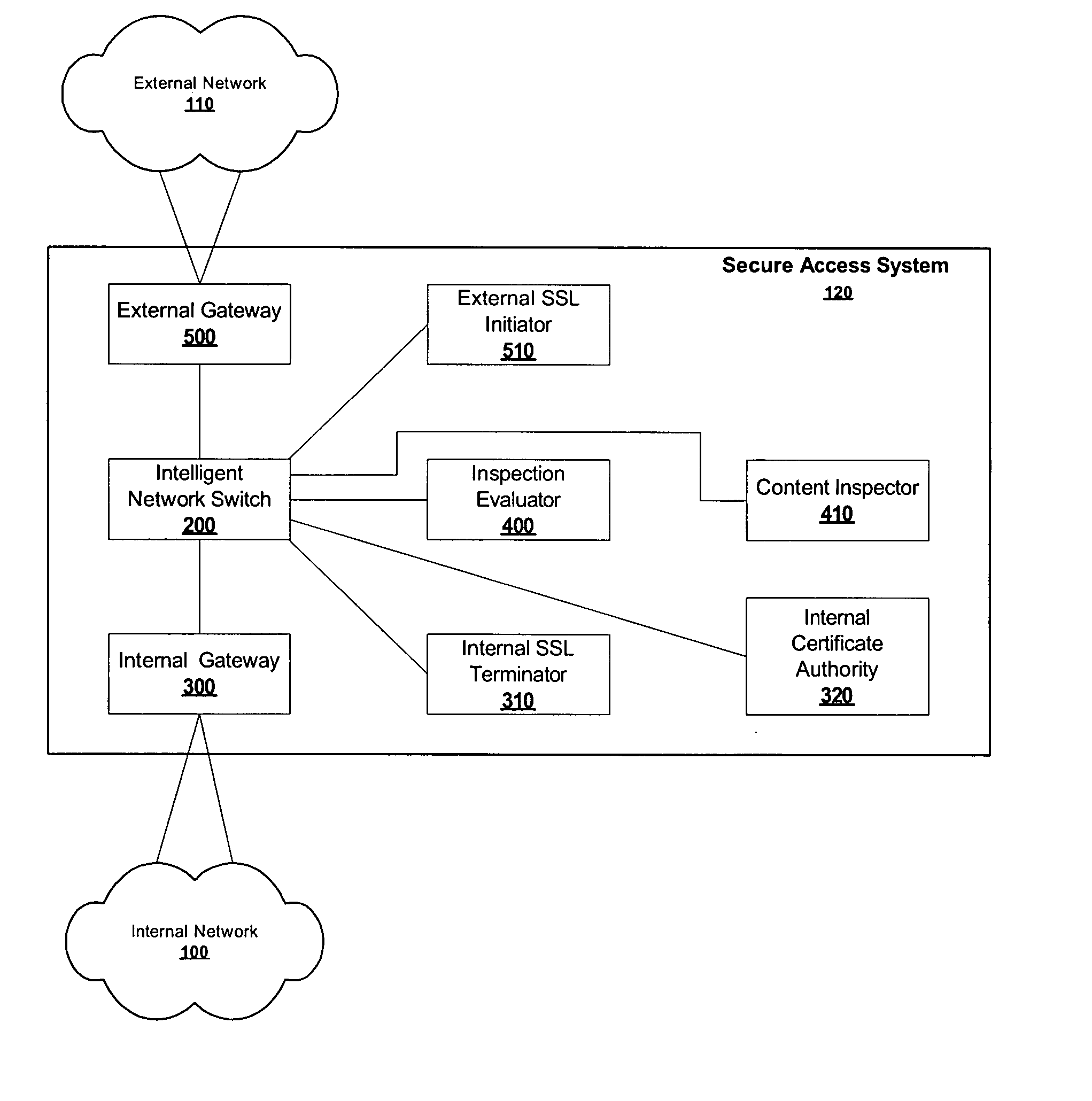
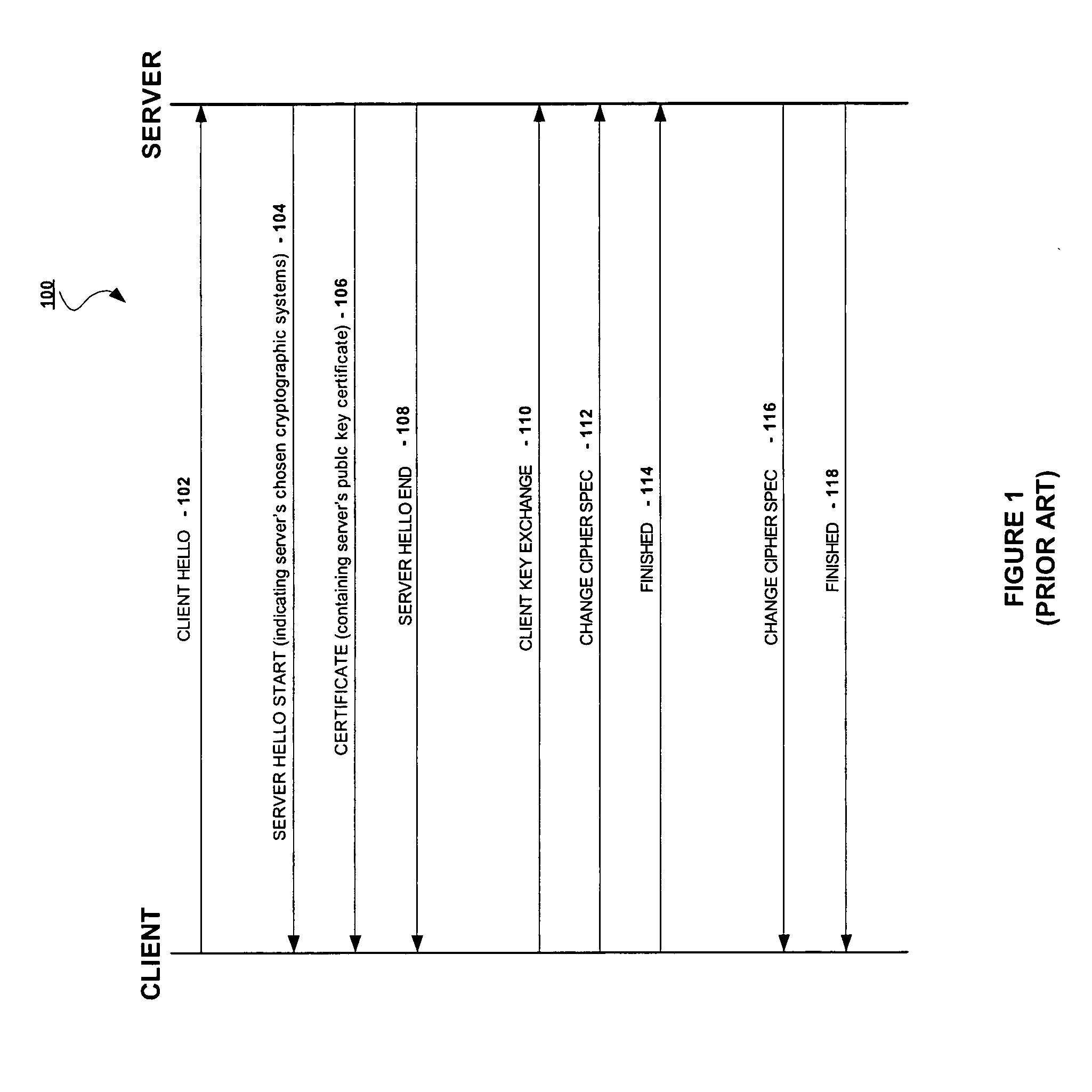
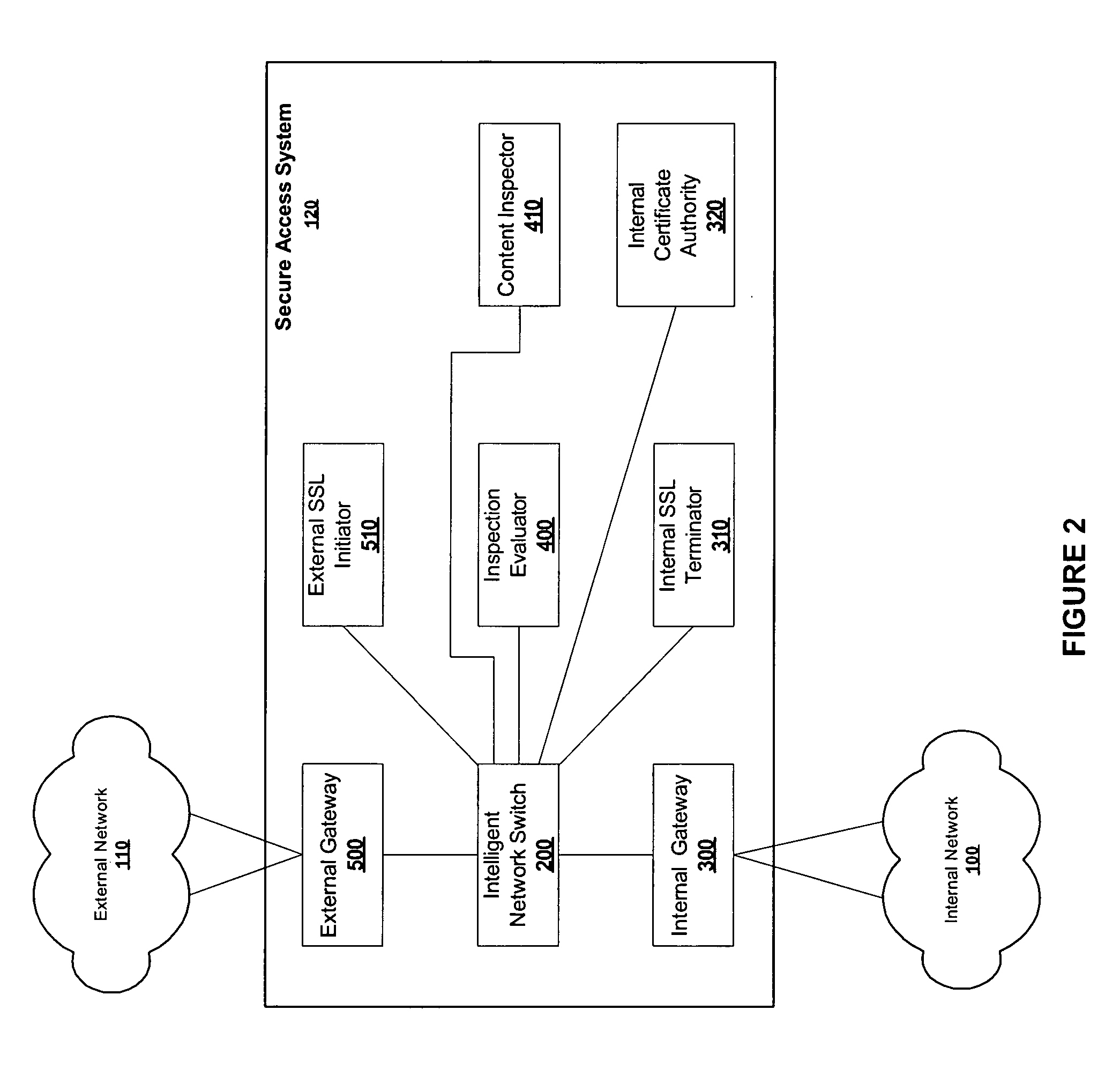
Content inspection in secure networks
ActiveUS20050050362A1Digital data processing detailsUser identity/authority verificationData packThe Internet
A secure access system is used to connect an internal network, such as a private LAN, to an external network, such as the Internet. The system is provided with internal and external gateways, for connecting to the respective networks, as well as an inspection evaluator, content inspector, internal certificate authority, internal SSL terminator and external SSL initiator. Packets routed through the access system are inspected before they are forwarded from one gateway to the other, except those packets of designated users of the internal network which are directly forwarded without inspection. Encrypted packets received by the access system are decrypted, inspected, and then re-encrypted before they are forwarded.
Owner:RADWARE
Group key distribution
InactiveUS6038322AEfficient additionLow costKey distribution for secure communicationPublic key for secure communicationTimestampNetwork addressing
A method for distributing a secret key from a key holder H to intended group members M. The method assumes that during the distribution process each party, a group member M and the key holder H, can decrypt and encrypt exchanged information such that the encrypter knows that the decrypter will be the intended party. The method preferably uses a public key / private key encryption technique in which, for example, a trusted Certificate Authority in a public key infrastructure signs the certificates to provide the public keys involved in the encryption. Alternatively, the method, together with a symmetric cipher, uses a shared secret, established in an authenticated mechanism that is outside the information exchanges of the invention. Additionally, the method uses a strong mixing function that takes several items of data as input and produces a pseudo-random authentication (or digest). Inputs to the mixing function include identity stamps that are generated by each member M and key holder H. These inputs can be the identity of the stamp generator, such as a network address, port, or protocol, a timestamp, and / or a secret value that is known only to the stamp generator. The stamps include information to bind member M if generated by key holder H, and to bind key holder H if generated by member M. Consequently, the invention authenticates each communication exchange between member M and key holder H.
Owner:CISCO TECH INC
Trusted infrastructure support systems, methods and techniques for secure electronic commerce transaction and rights management
InactiveUS7165174B1Improve efficiencyIncrease flexibilityPublic key for secure communicationDigital data processing detailsTransaction managementBusiness management
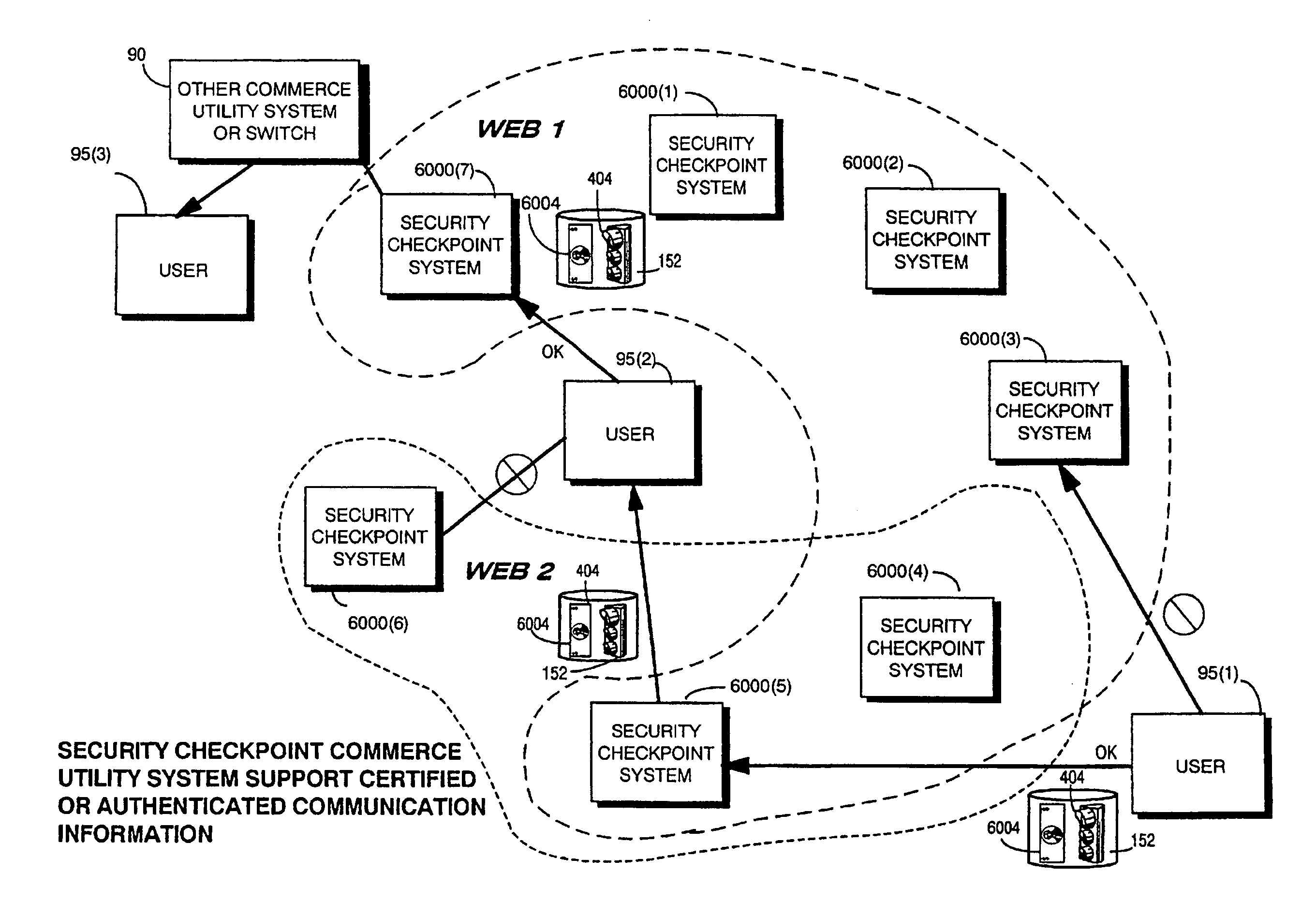
The present inventions provide an integrated, modular array of administrative and support services for electronic commerce and electronic rights and transaction management. These administrative and support services supply a secure foundation for conducting financial management, rights management, certificate authority, rules clearing, usage clearing, secure directory services, and other transaction related capabilities functioning over a vast electronic network such as the Internet and / or over organization internal Intranets.These administrative and support services can be adapted to the specific needs of electronic commerce value chains. Electronic commerce participants can use these administrative and support services to support their interests, and can shape and reuse these services in response to competitive business realities.A Distributed Commerce Utility having a secure, programmable, distributed architecture provides administrative and support services. The Distributed Commerce Utility makes optimally efficient use of commerce administration resources, and can scale in a practical fashion to accommodate the demands of electronic commerce growth.The Distributed Commerce Utility may comprise a number of Commerce Utility Systems. These Commerce Utility Systems provide a web of infrastructure support available to, and reusable by, the entire electronic community and / or many or all of its participants.Different support functions can be collected together in hierarchical and / or in networked relationships to suit various business models and / or other objectives. Modular support functions can combined in different arrays to form different Commerce Utility Systems for different design implementations and purposes. These Commerce Utility Systems can be distributed across a large number of electronic appliances with varying degrees of distribution.
Owner:INTERTRUST TECH CORP
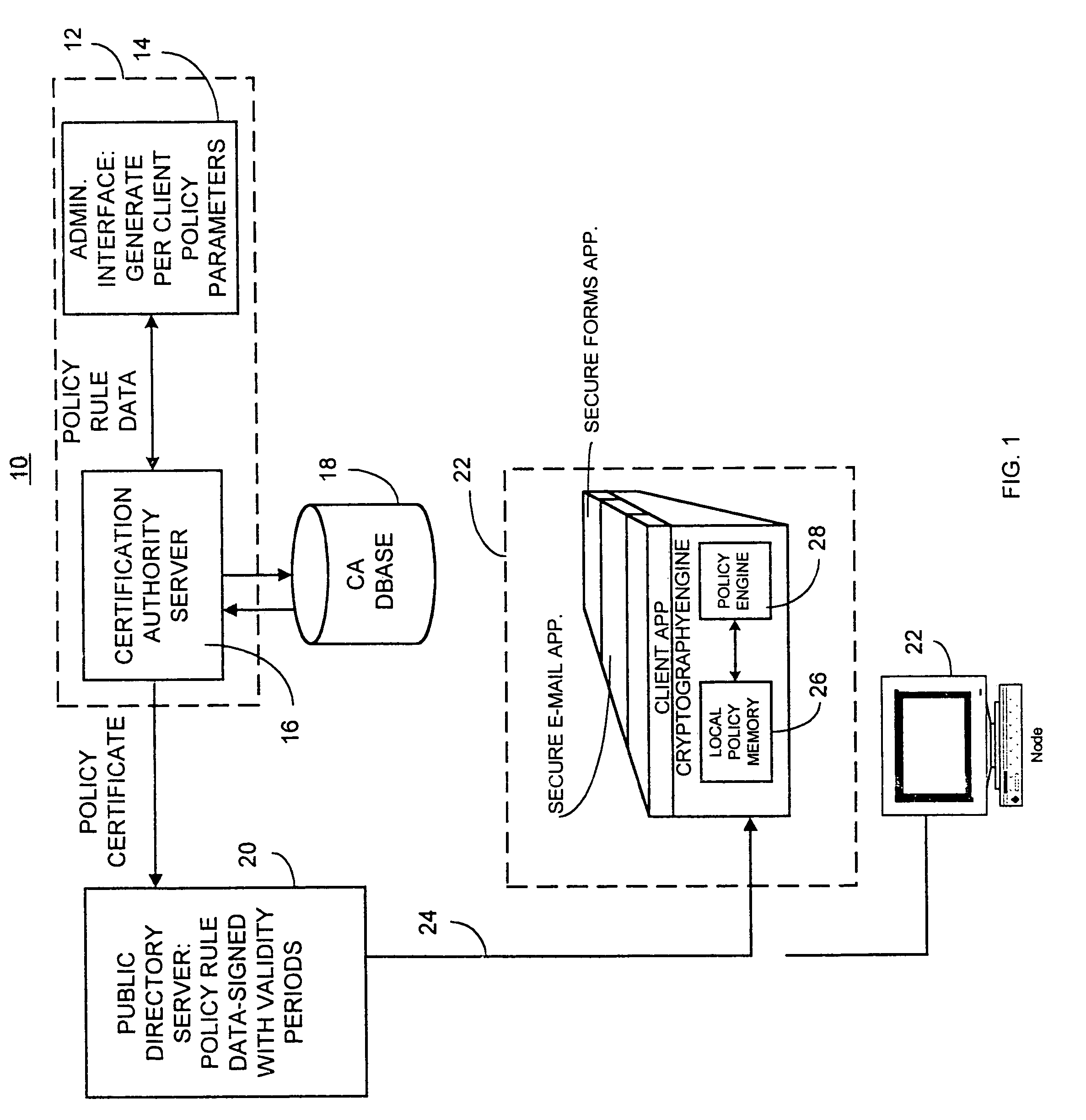
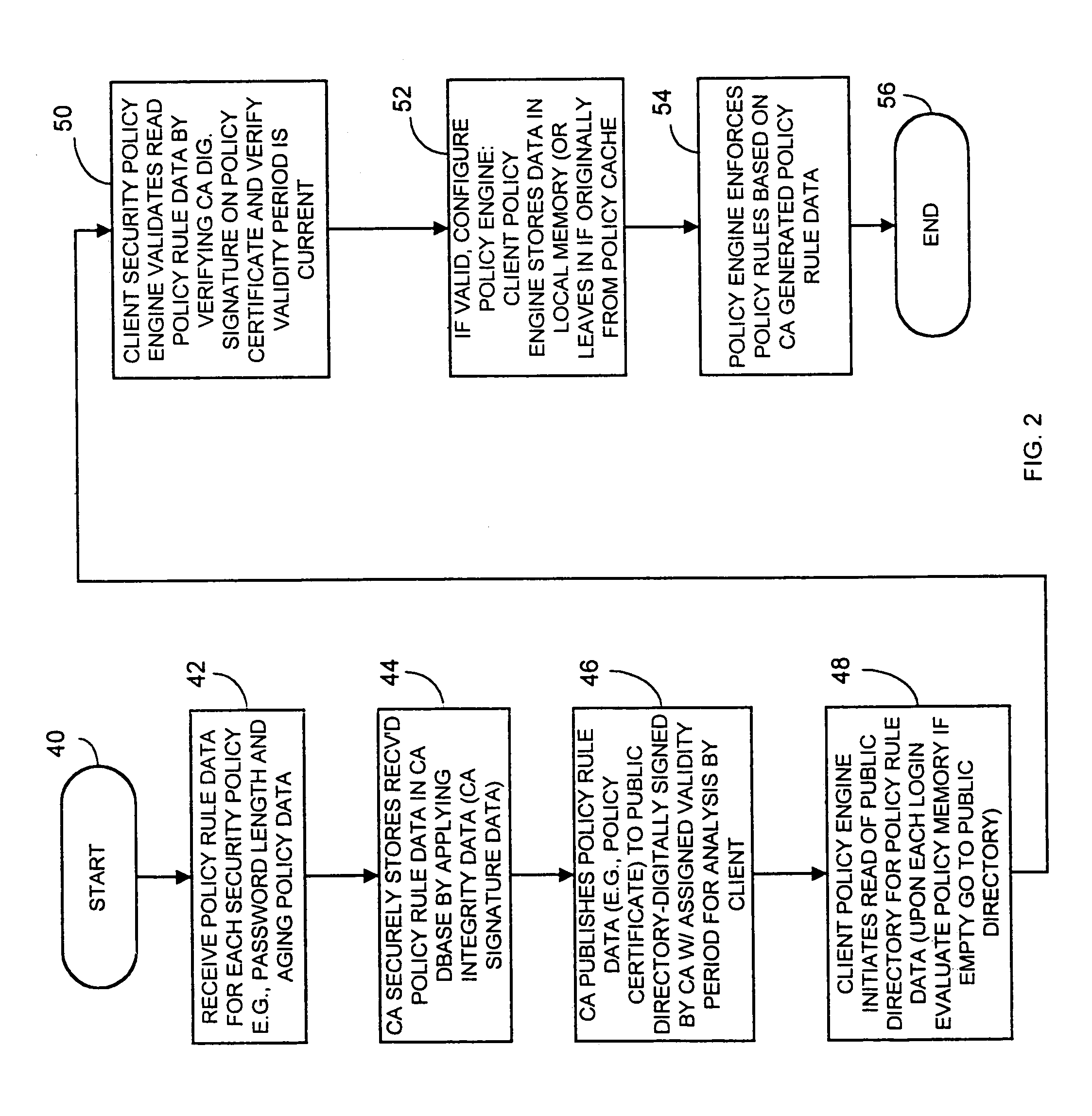
Computer network security system and method having unilateral enforceable security policy provision
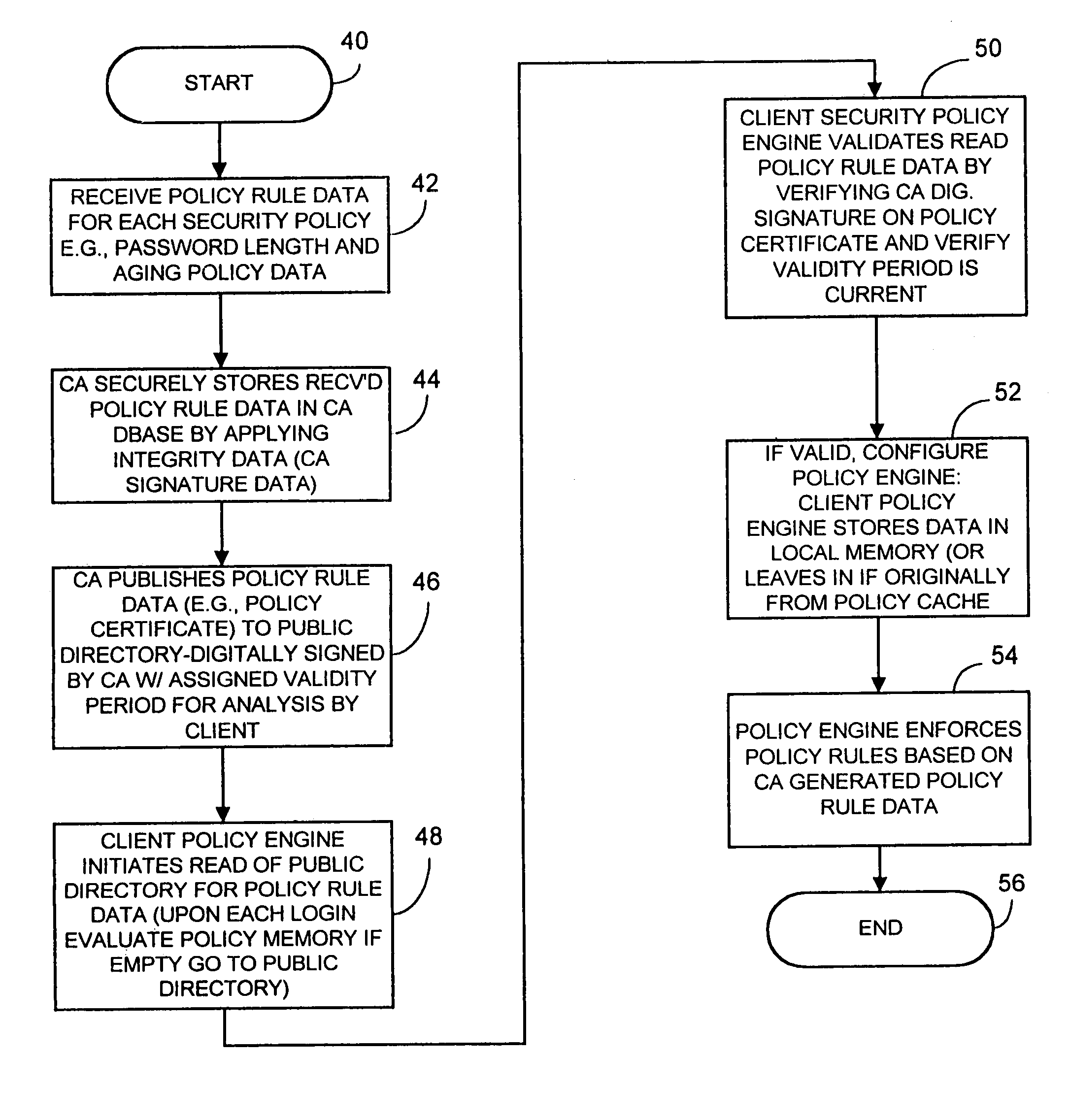
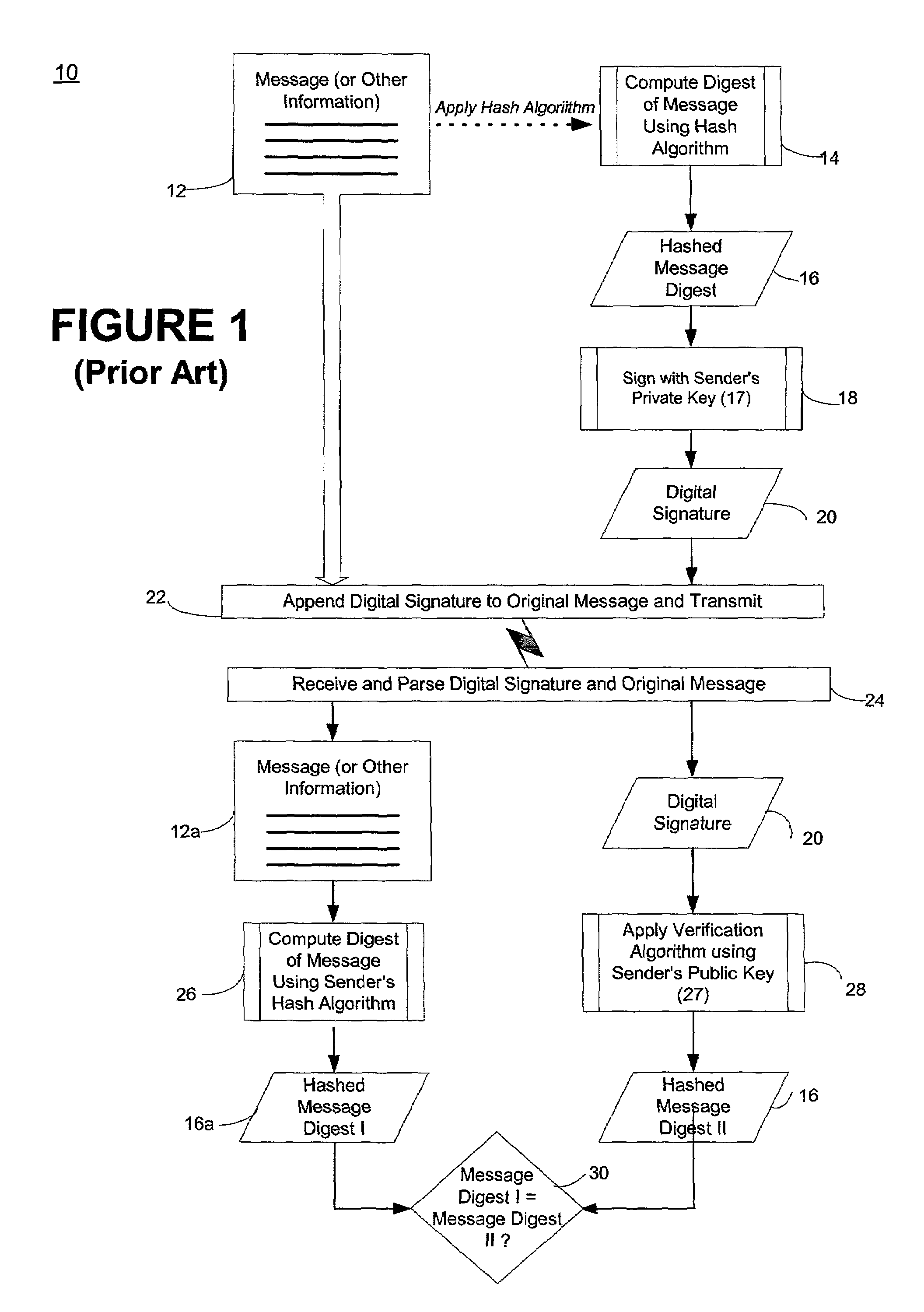
InactiveUS7174563B1Digital data processing detailsUser identity/authority verificationDigital signaturePassword
A computer network security system and method utilizes digitally signed and centrally assigned policy data, such as password length rules, that is unilaterally enforced at network nodes by node policy enforcement engines. The policy data may be variable on a per client or network node basis through a centralized authority, such as a certification authority. The computer network security system provides variable security policy rule data for distribution to at least one network node through a central security policy rule data distribution source, such as the certification authority. The central security policy rule data distribution source associates a digital signature to the variable security policy rule data to ensure the integrity of the policies in the system. Each network node uses a policy rule data engine and policy rule table to decode policy rule data and enforce the policy rules as selectively determined through the central authority.
Owner:ENTRUST
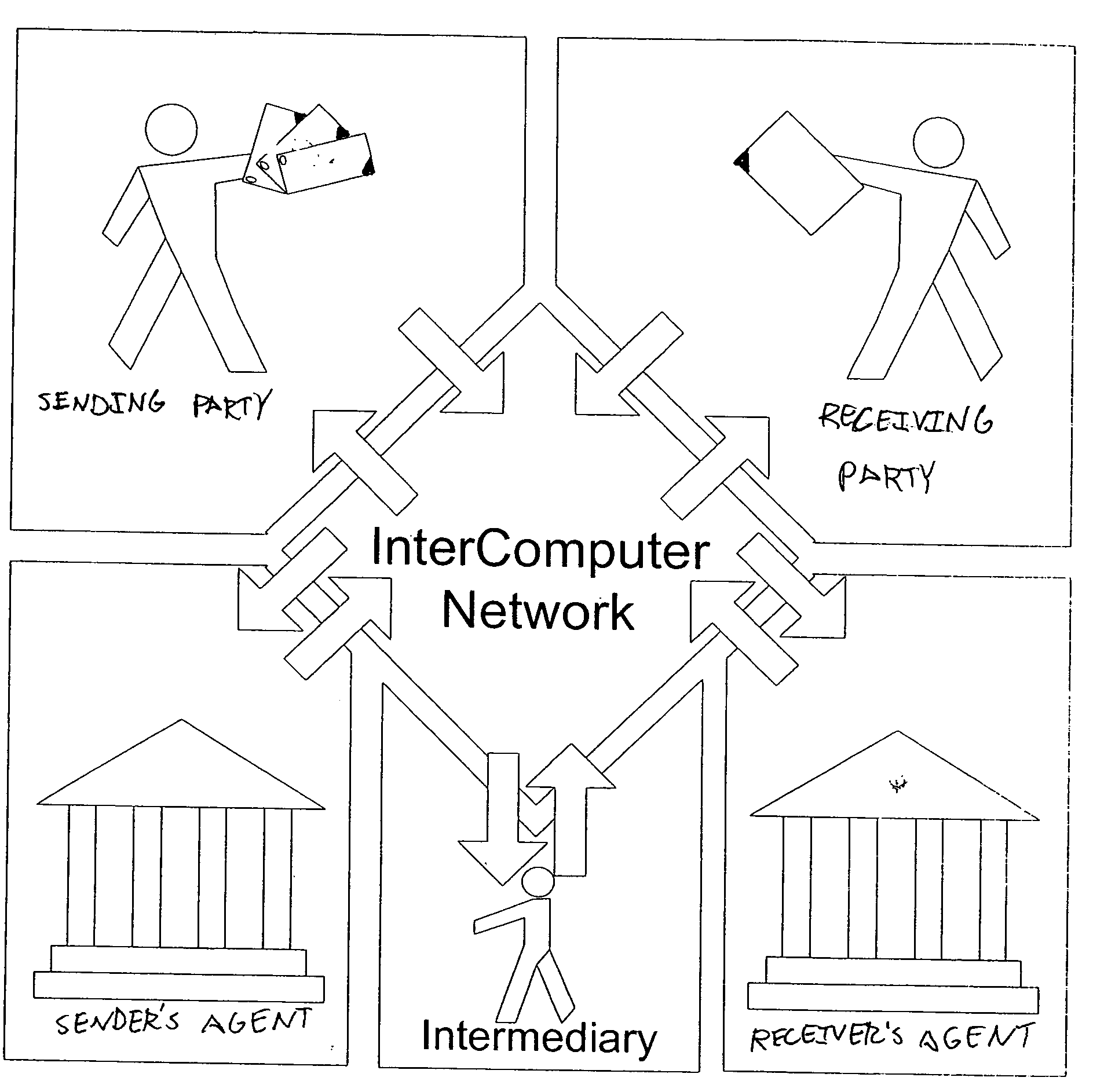
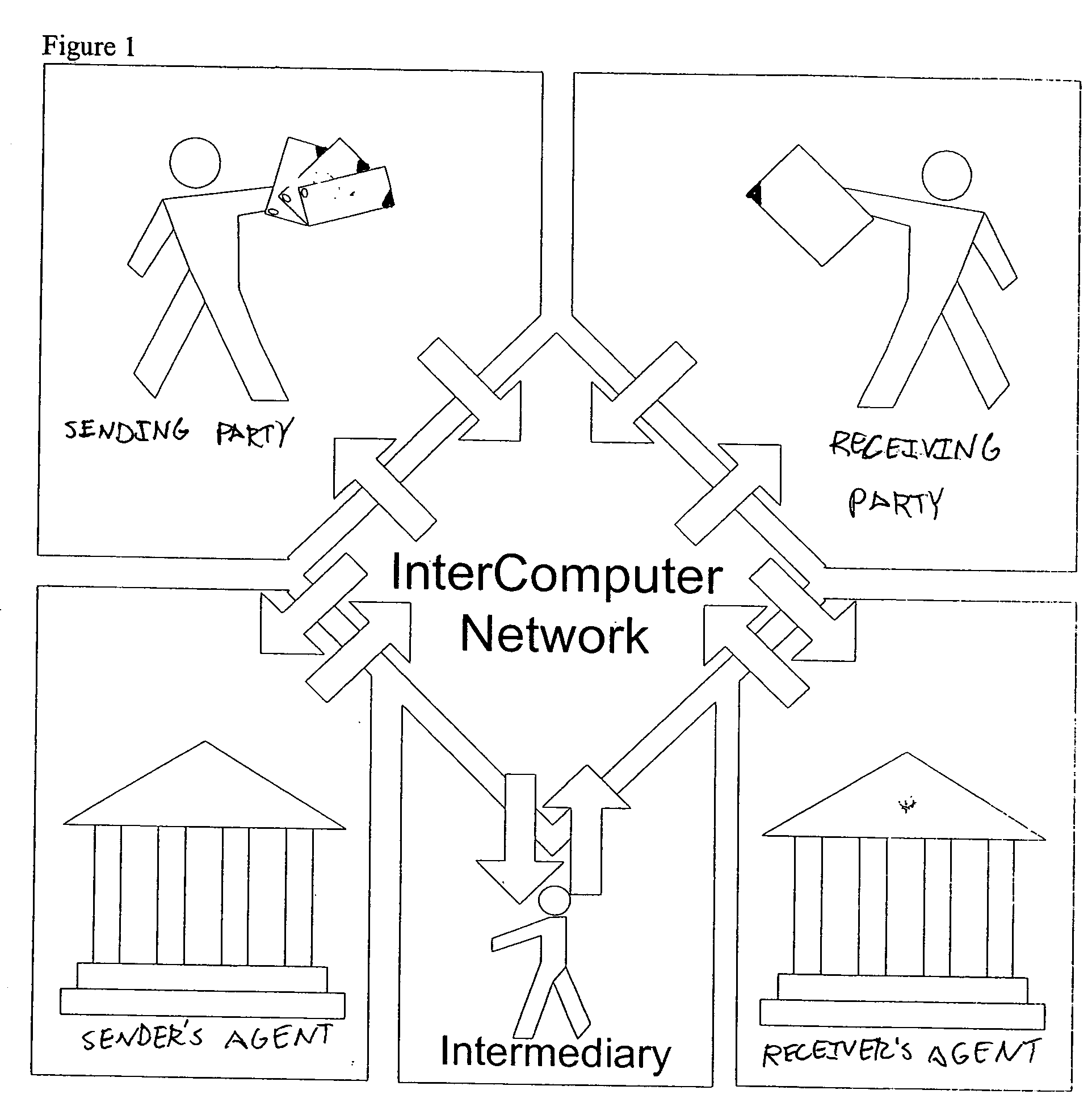
Secure messaging system
InactiveUS20050257045A1Guaranteed smooth progressUser identity/authority verificationPayment circuitsTransfer systemDocumentation
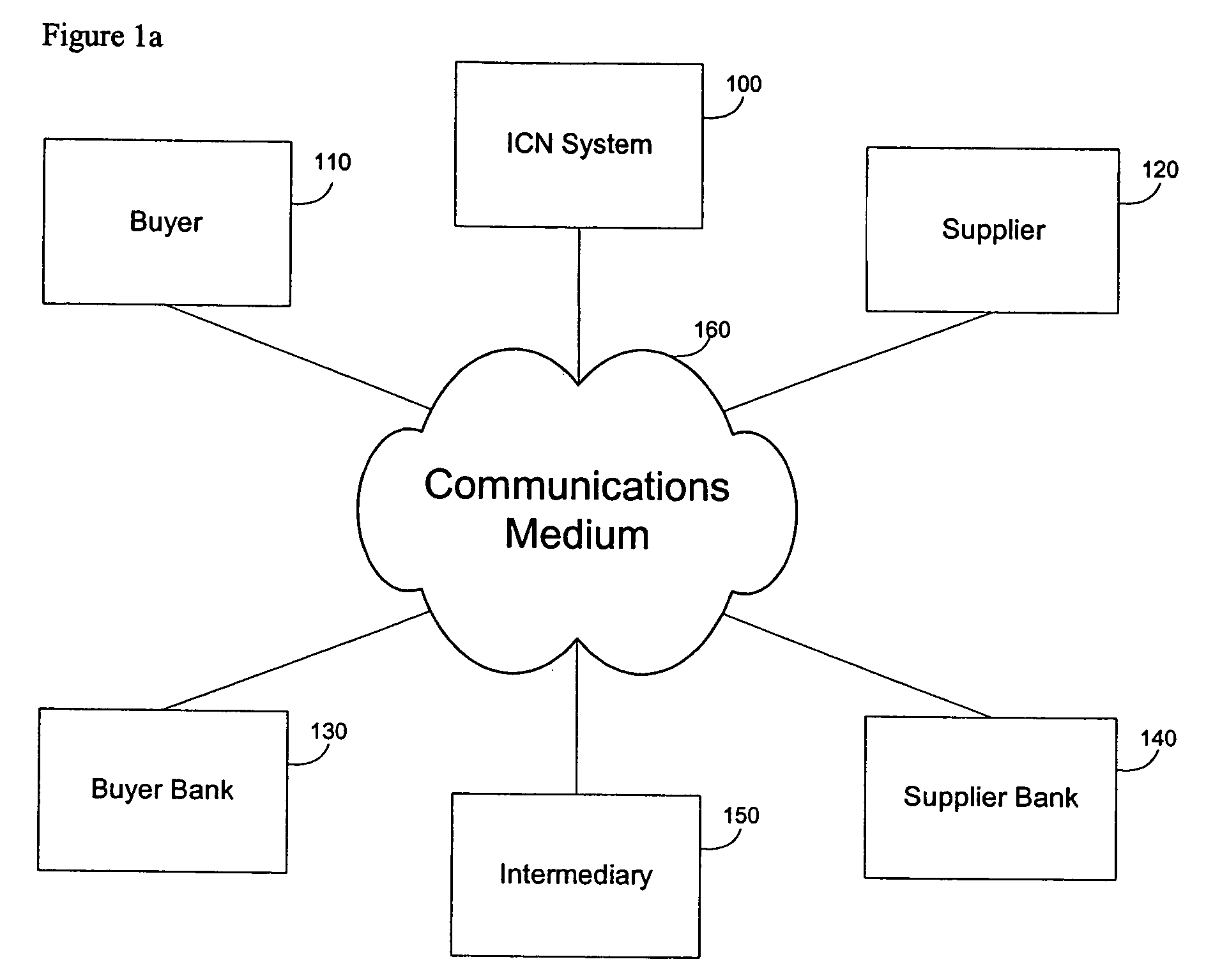
A method for secure data transactions over a computer network is described. In one embodiment, the act of generating at the first party a document, which authorizes the data transaction to proceed is performed. In one embodiment, the document content is signed using a computer network with audit-level encryption digital certificates. In one embodiment, a signed digital message (and / or document) is sent from the first party to the network transfer system electronically, and can be authenticated via the ICN certificate authorities to demonstrate the authorities of the signer of the signed document in assent to the transaction. In one embodiment, a copy of the signed digital document can be stored in a database associated with the transfer network system. In one embodiment, the system uses rules (patterns) of exchange agreed upon within and between organizations. These rules enable the exchange to progress smoothly and drive systematically the attention of participants to demands and problems etc. as a given transaction goes along.
Owner:INTERCOMP CORP
Reliance server for electronic transaction system
InactiveUS20020062438A1Complete banking machinesUser identity/authority verificationProxy certificateCertificate authority
Owner:CERTCO
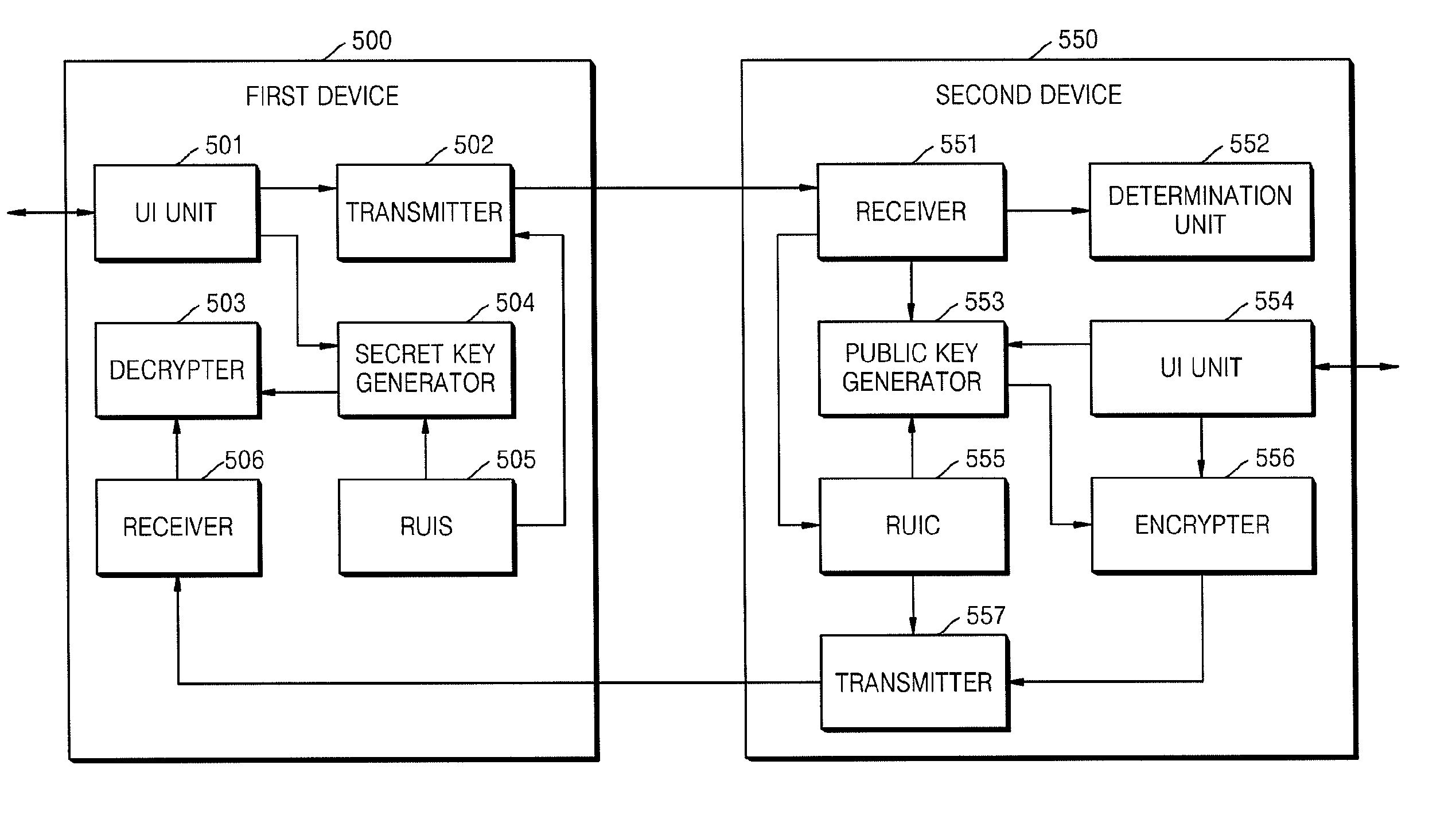
Method of and apparatus for sharing secret information between device in home network
InactiveUS20090055648A1Reduce traffic problemsAvoid complex calculationsKey distribution for secure communicationPublic key for secure communicationID-based encryptionPassword
A method and apparatus for sharing secret information between devices in a home network are provided. In the method and apparatus, home network devices receive a password (credential) input by a user and encrypt secret information based on the credential by using keys generated according to a predetermined identity-based encryption (IBE) scheme. Accordingly, it is possible to securely share the secret information between home network devices without any certificate authority or certificate.
Owner:SAMSUNG ELECTRONICS CO LTD
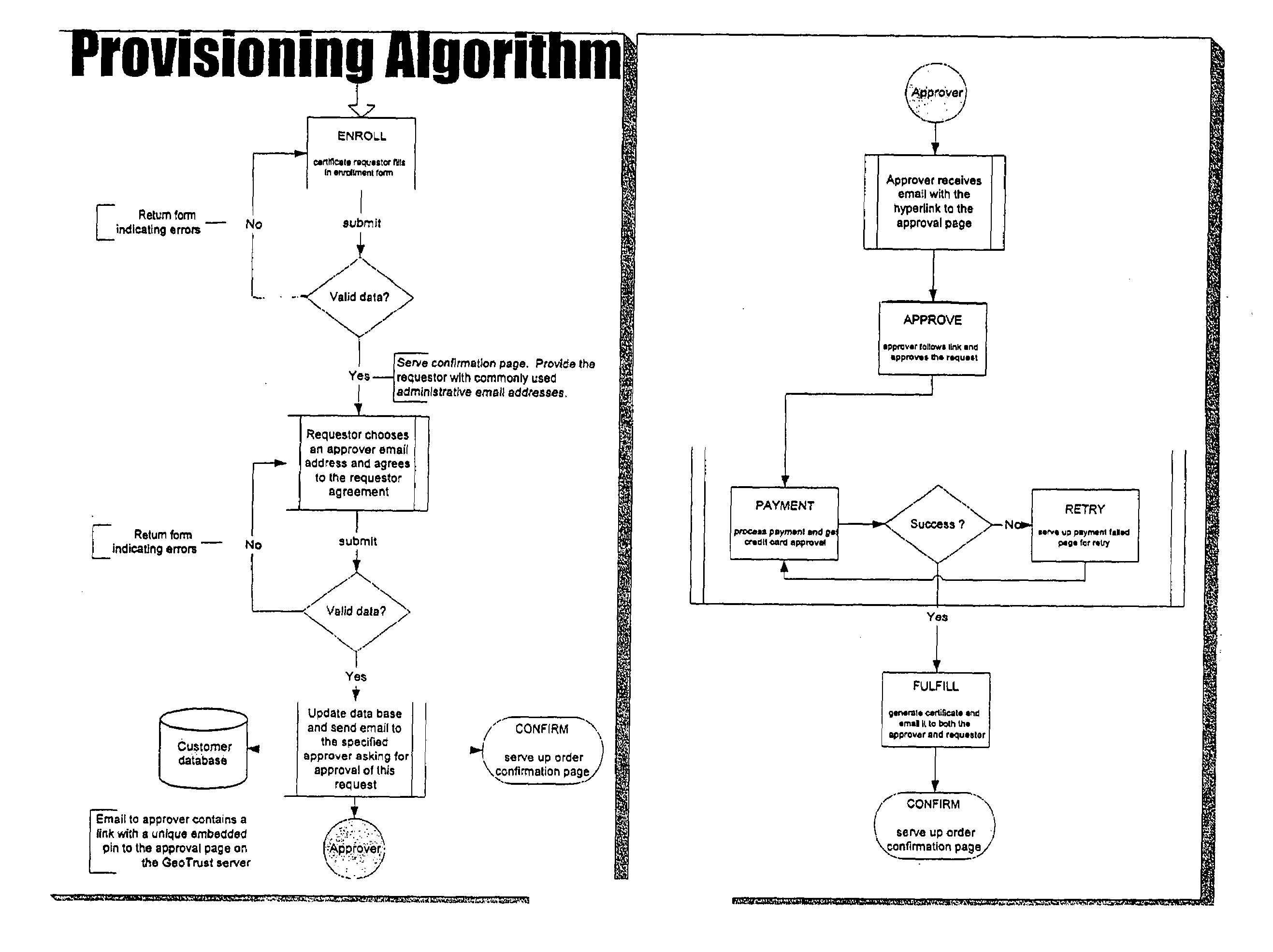
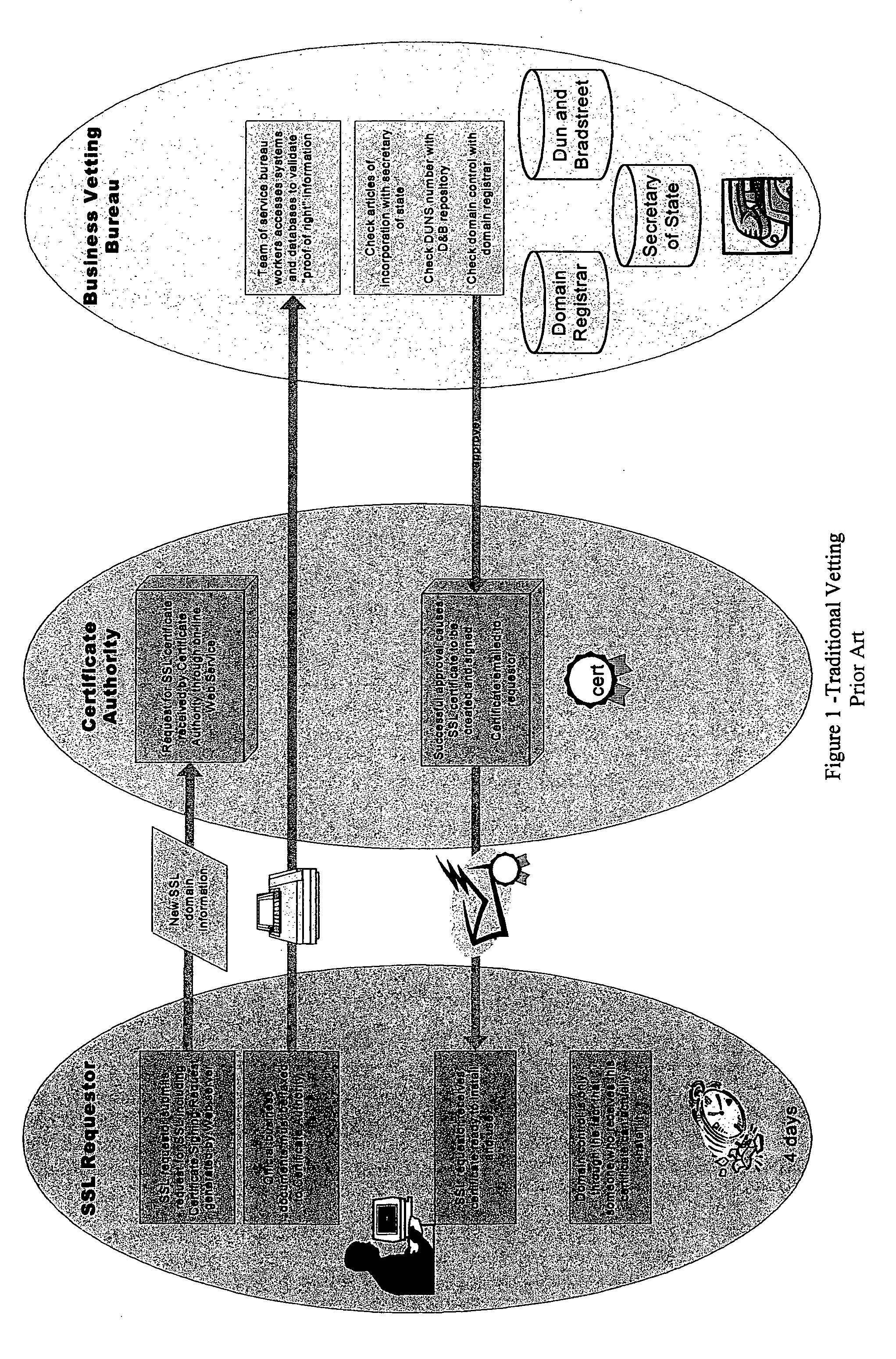
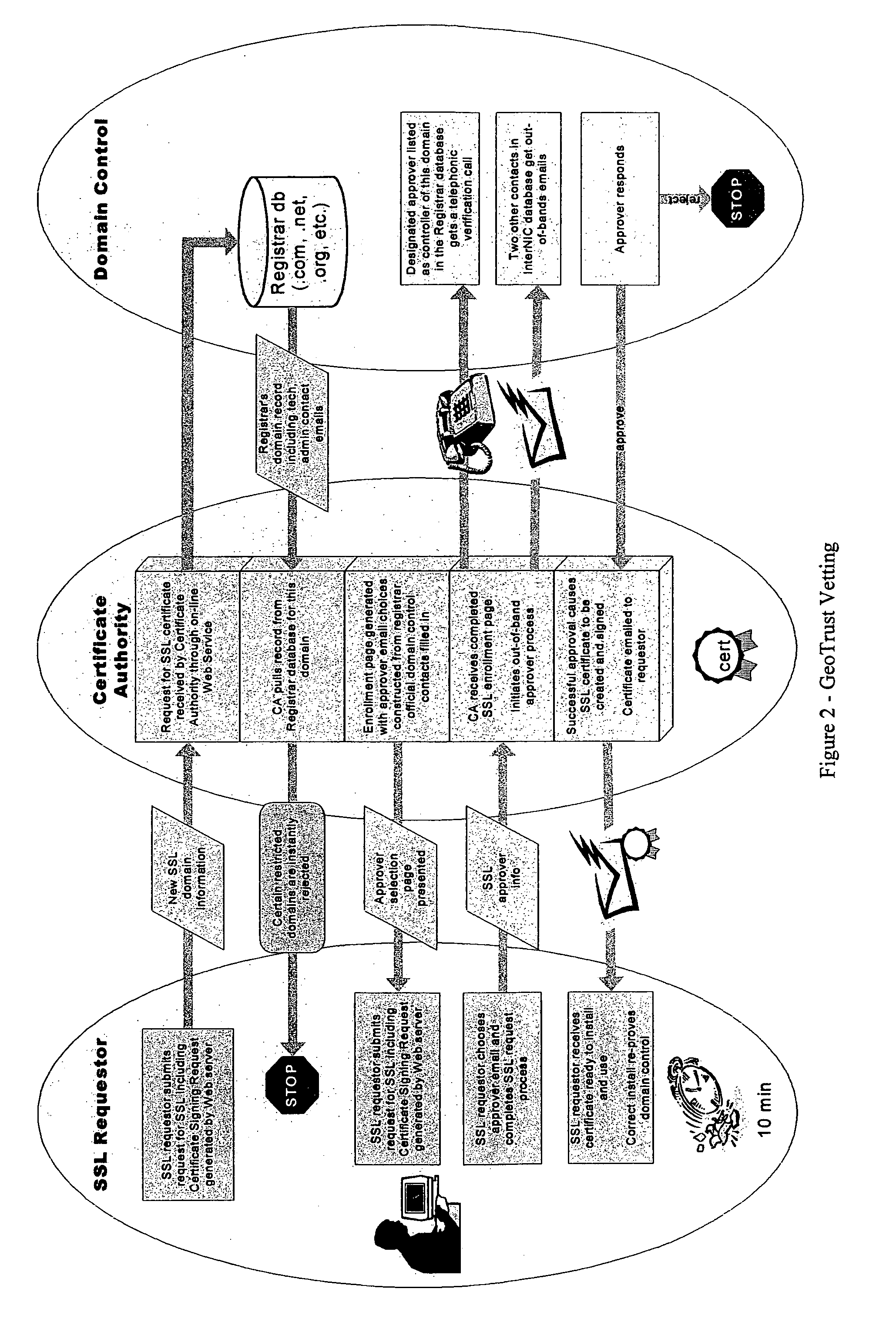
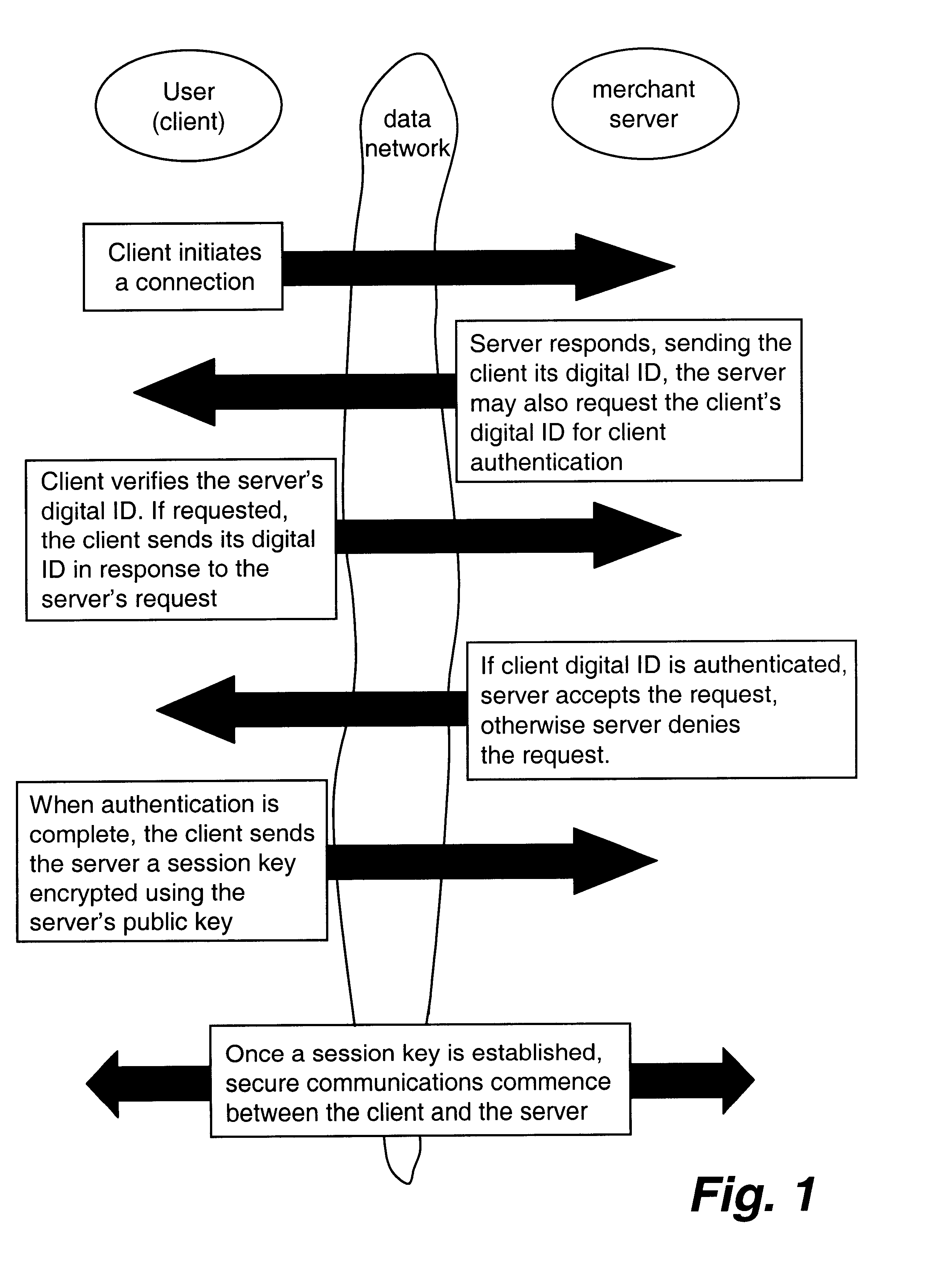
Methods and systems for automated authentication, processing and issuance of digital certificates
InactiveUS7003661B2User identity/authority verificationComputer security arrangementsEmail addressWeb service
In a computer system and process for automated identification, processing and issuance of digital certificates, web server domain-control vetting is employed in issuance of server certificates. A Requestor requests a web server certificate from a certificate authority, the certificate authority receives the request. Based on domain information the certificate authority generates Approver email addresses, and the Requestor is required to select an Approver email address or addresses. The certificate authority contacts the Approver using the selected email address or addresses and requests that the Approver approve issuance of the certificate. If approved, the certificate authority accepts the request, and creates and signs the certificate and the signed certificate is sent to the Requestor.
Owner:DIGICERT
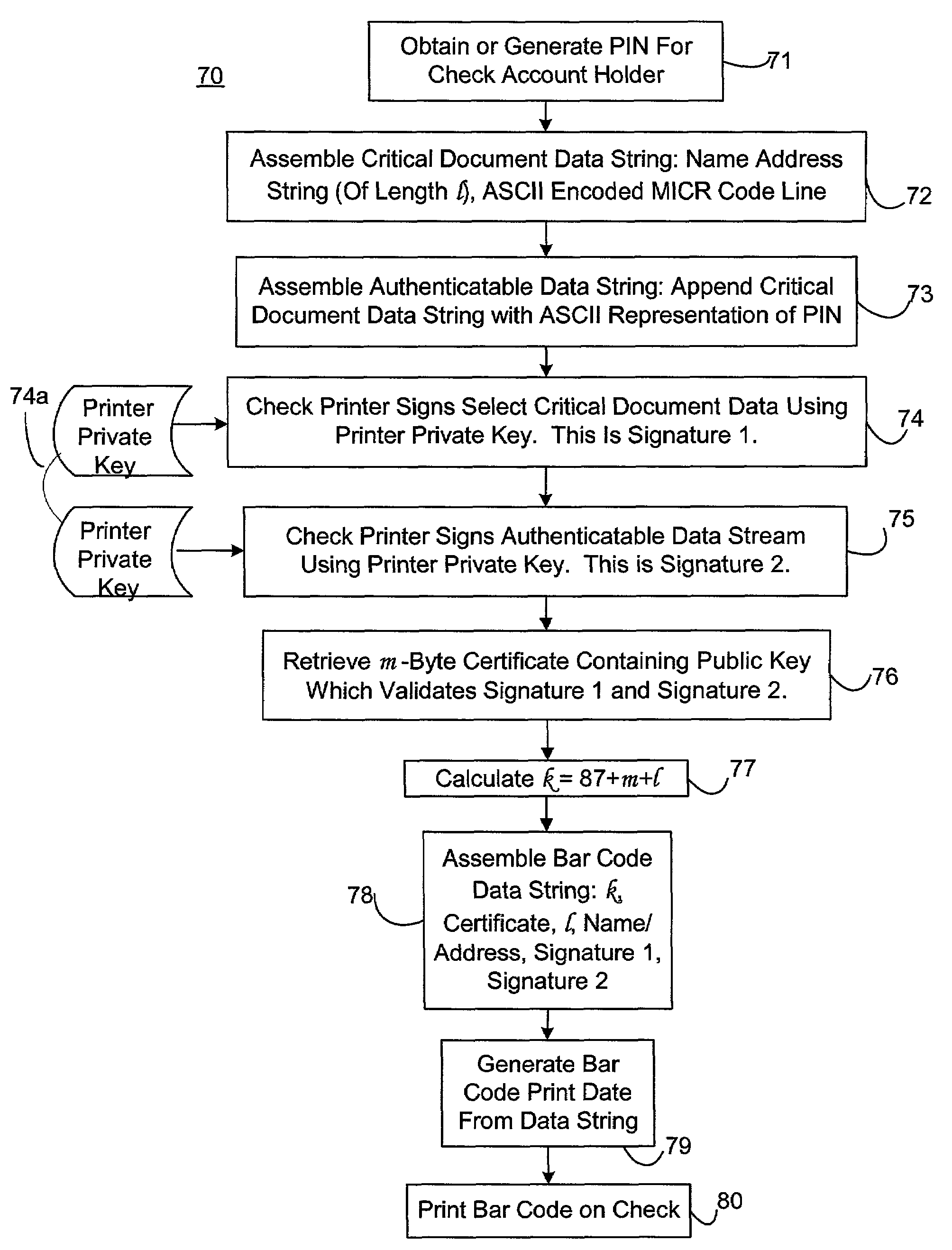
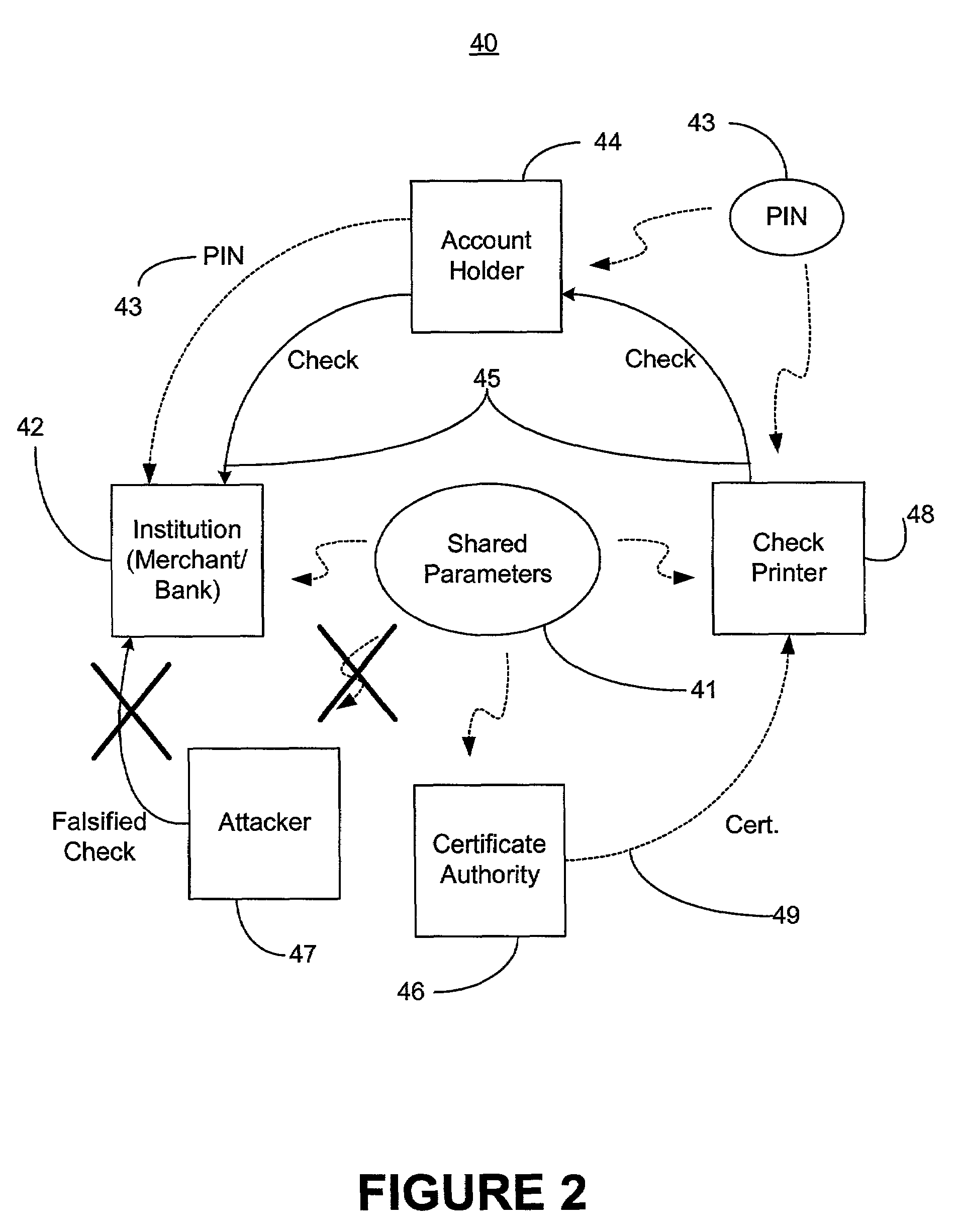
Self-authentication of value documents using digital signatures
ActiveUS7051206B1Low costImprove reliabilityKey distribution for secure communicationPaper-money testing devicesCredit cardPublic key certificate
An encryption-free technique for enabling the self-authentication of value documents (including personal and commercial checks) presented at a point of purchase or financial institution. Certain data contained on the value document may be signed with a first digital signature and authenticated with a public key certificate issued from a trusted certificate authority. The signed data and public key certificate are stored on the value document, preferably in a two-dimensional bar code data format. In the case of certain personal value documents (such as checks, credit cards, passports, birth certificates, Social Security cards, etc.), a unique personal identification number (PIN) also may be included in the document data that is signed by a second digital signature. At a point of purchase, a merchant or teller can scan and read the data stored in the two-dimensional bar code and other magnetically recorded information, and together with the PIN the customer provides, can authenticate the value document thus presented using the second digital signature. Alternatively, if the customer is not present, if the personal value document contains the second digital signature, the document may be verified using a PIN-generating algorithm or other method that generates all permutations of PINs. The first digital signature alone may be used to authenticate selected data within the personal value document even when the PIN is not available. Similarly, in the case of a commercial value documents, authentication of pre-printed data may be based entirely upon only the first digital signature.
Owner:UNISYS CORP
Centralized certificate management system for two-way interactive communication devices in data networks
InactiveUS6516316B1Key distribution for secure communicationData processing applicationsServer applianceCommunication device
The present invention discloses a centralized certificate management system for thin client devices in data networks and has particular applications to systems having a large number of the thin clients serviced by a proxy server through which the thin clients communicate with a plurality of secure server computers over a data network. According to one aspect, the present invention comprises a certificate management module that causes the server device to manage digital certificates for each of the thin client devices. To minimize the latency of obtaining certificates for each of the thin client devices, the certificate management module reserves a fixed number of free certificates signed by a certificate authority and their respective private keys in a certificate database and frequently updates the free certificate according to a certificate updating message. Whenever a user account is created for a thin client device, the certificate management module fetches one or more free certificates from the certificate database and associate the fetched certificates to the created account and meanwhile the certificate management module creates new free certificates with the certificate authority to fill in the certificate database. Apart from the tradition of obtaining certificates locally in client devices that normally have sufficient computing power, the present invention uses the computing resources in a server device to carry out the task of obtaining and maintaining certificates asynchronously in the proxy server and further. These and other features in the present invention dramatically minimize the demands for computing power and memory in thin client devices like mobile devices, cellular phones, landline telephones or Internet appliance controllers.
Owner:UNWIRED PLANET
Authentication system and process
InactiveUS6230266B1Reducing authentication system securityEliminate needUser identity/authority verificationAuthentication systemCertificate authority
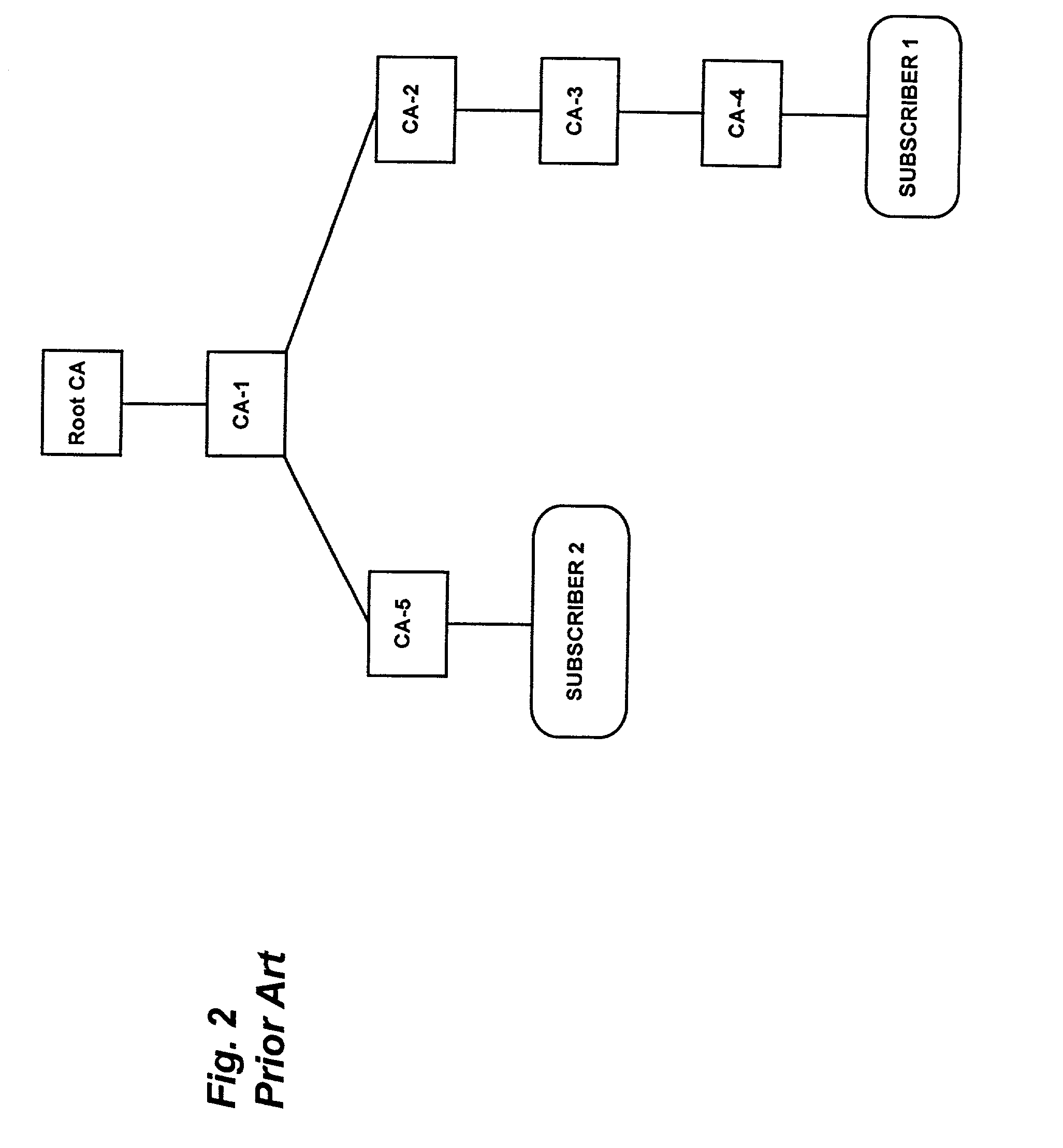
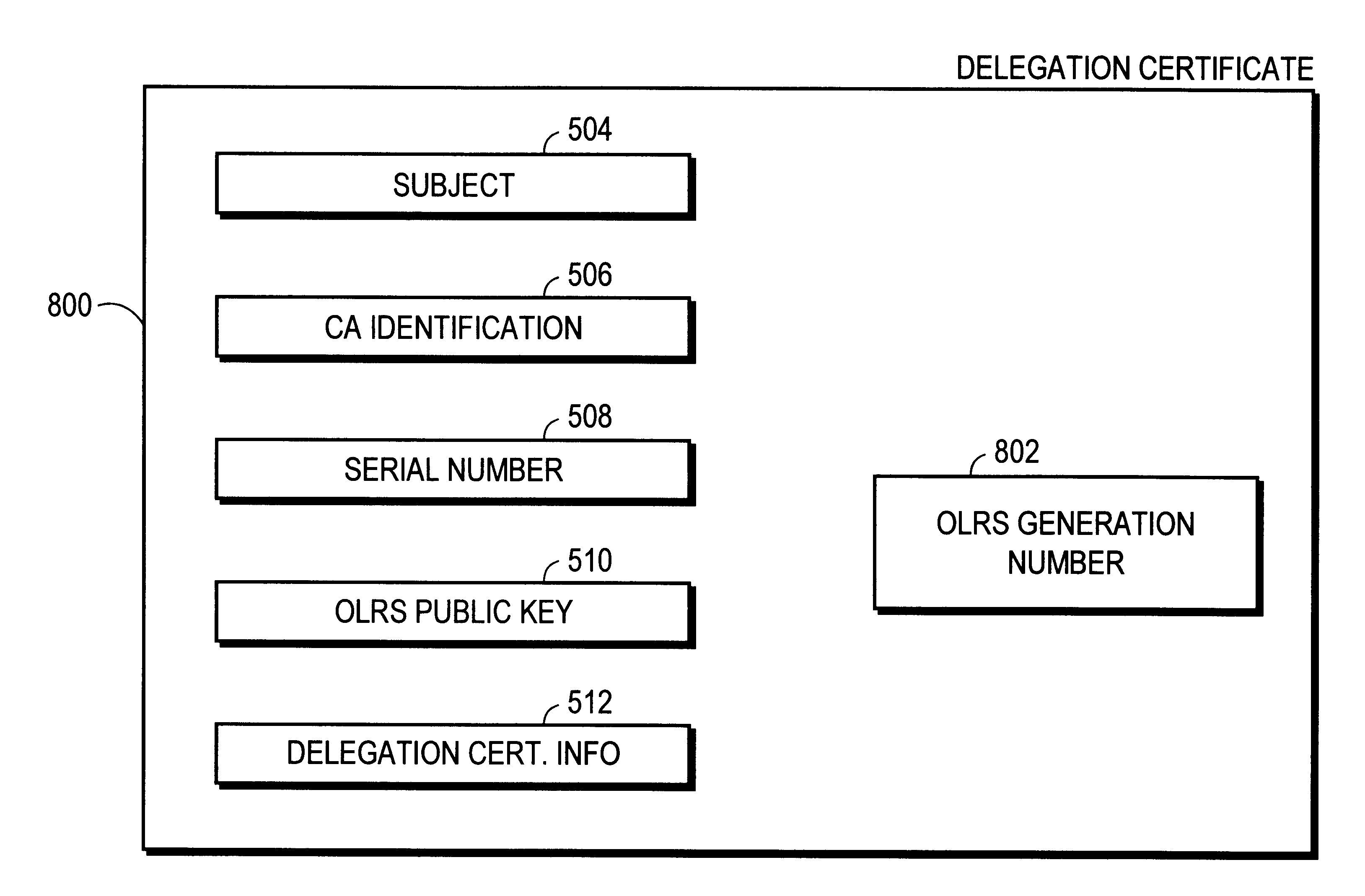
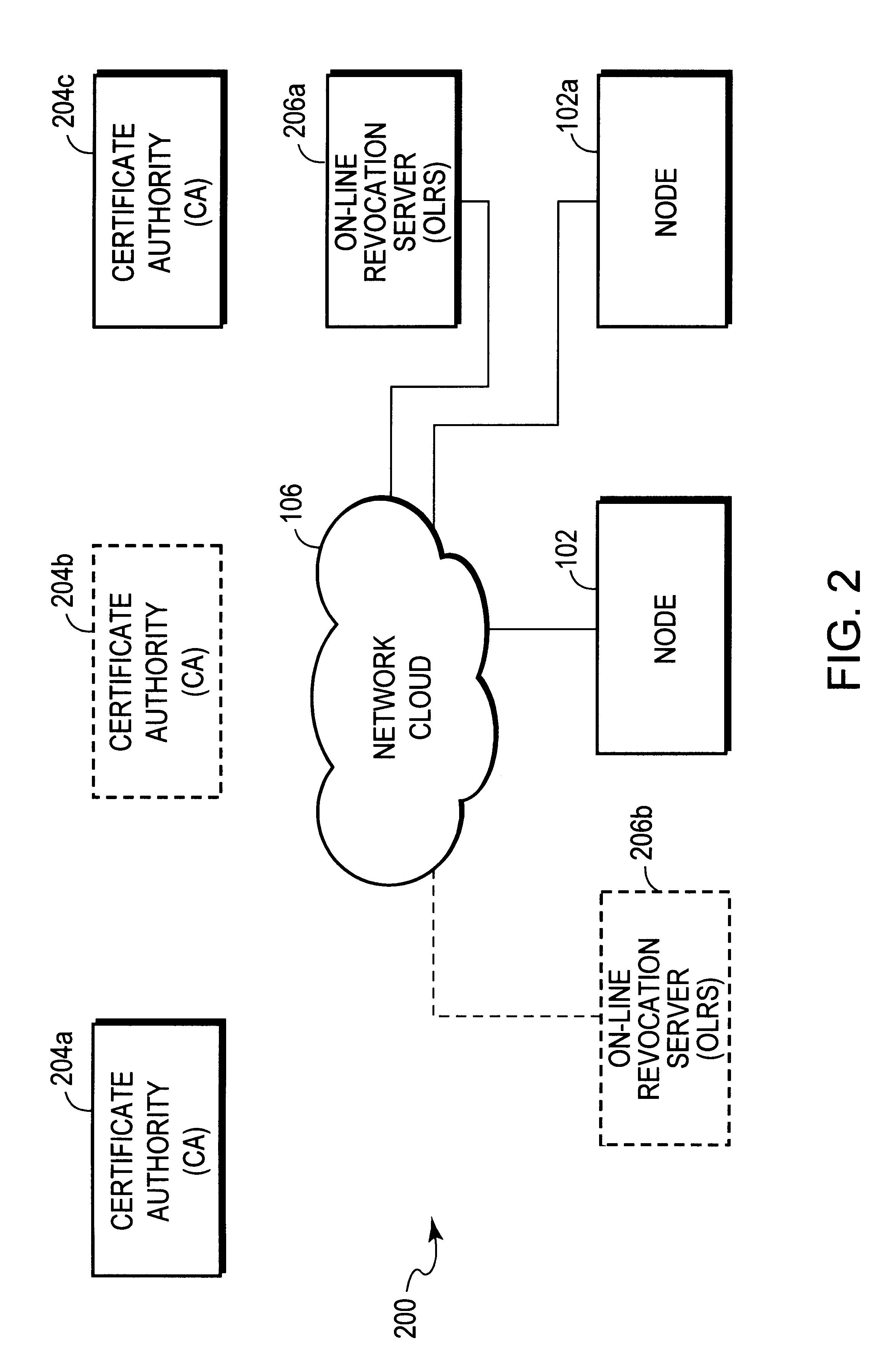
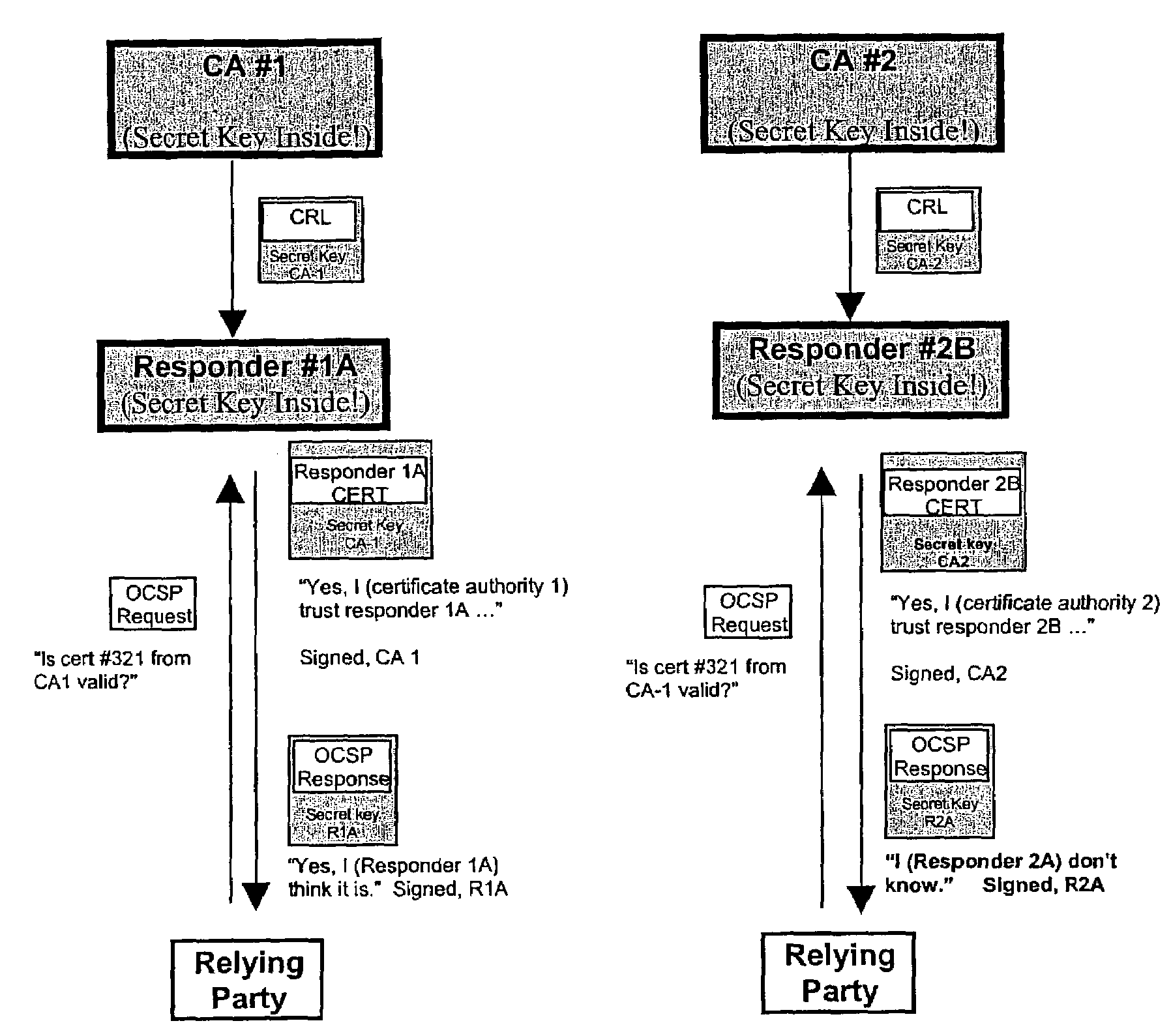
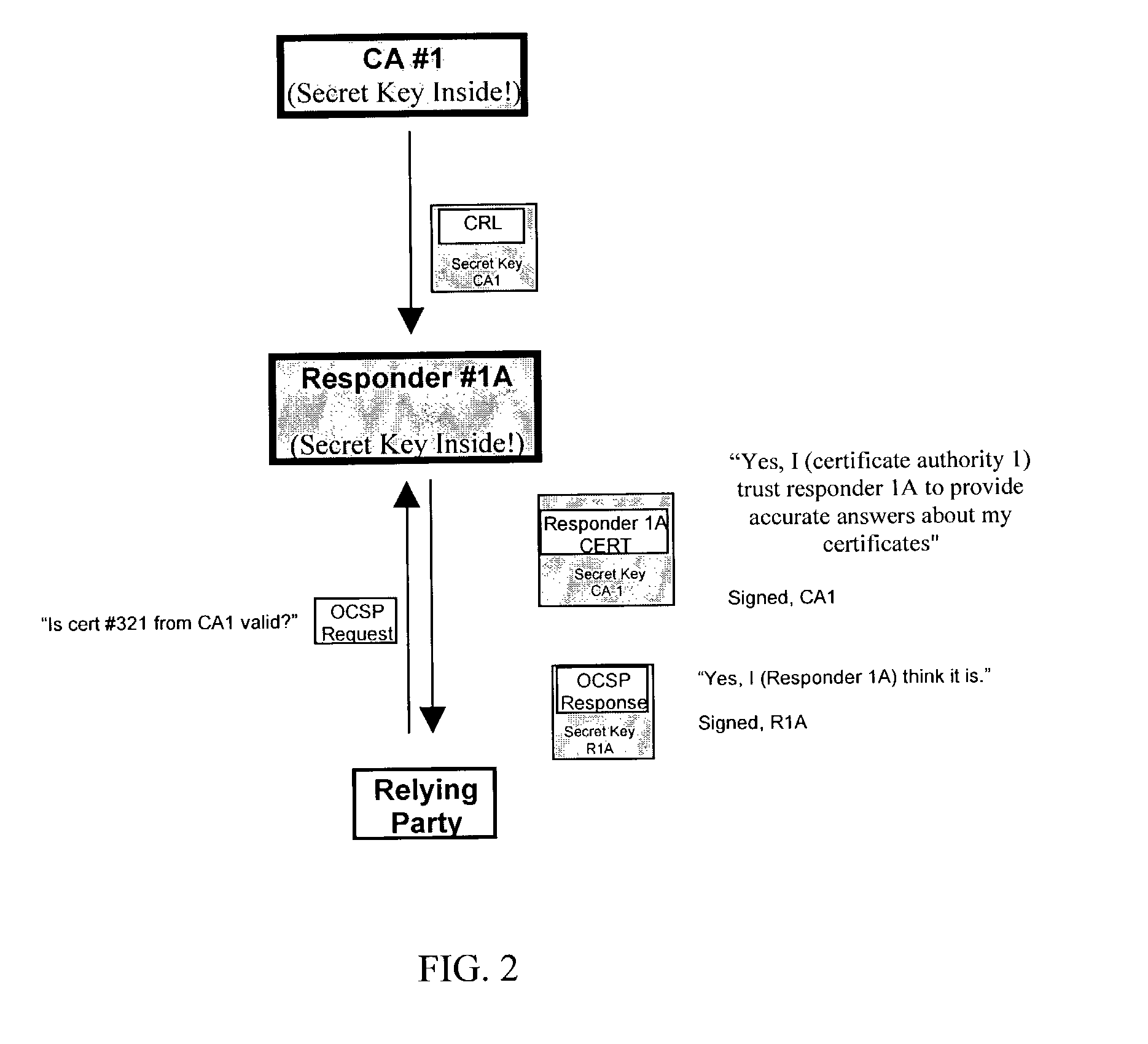
An authentication method and process are provided. One aspect of the process of the present invention includes authorizing a first on-line revocation server (OLRS) to provide information concerning certificates issued by a certificate authority (CA) that have been revoked. If the first OLRS is compromised, a second OLRS is authorized to provide certificate revocation information, but certificates issued by the CA remain valid unless indicated by the second OLRS to be revoked.
Owner:ORACLE INT CORP
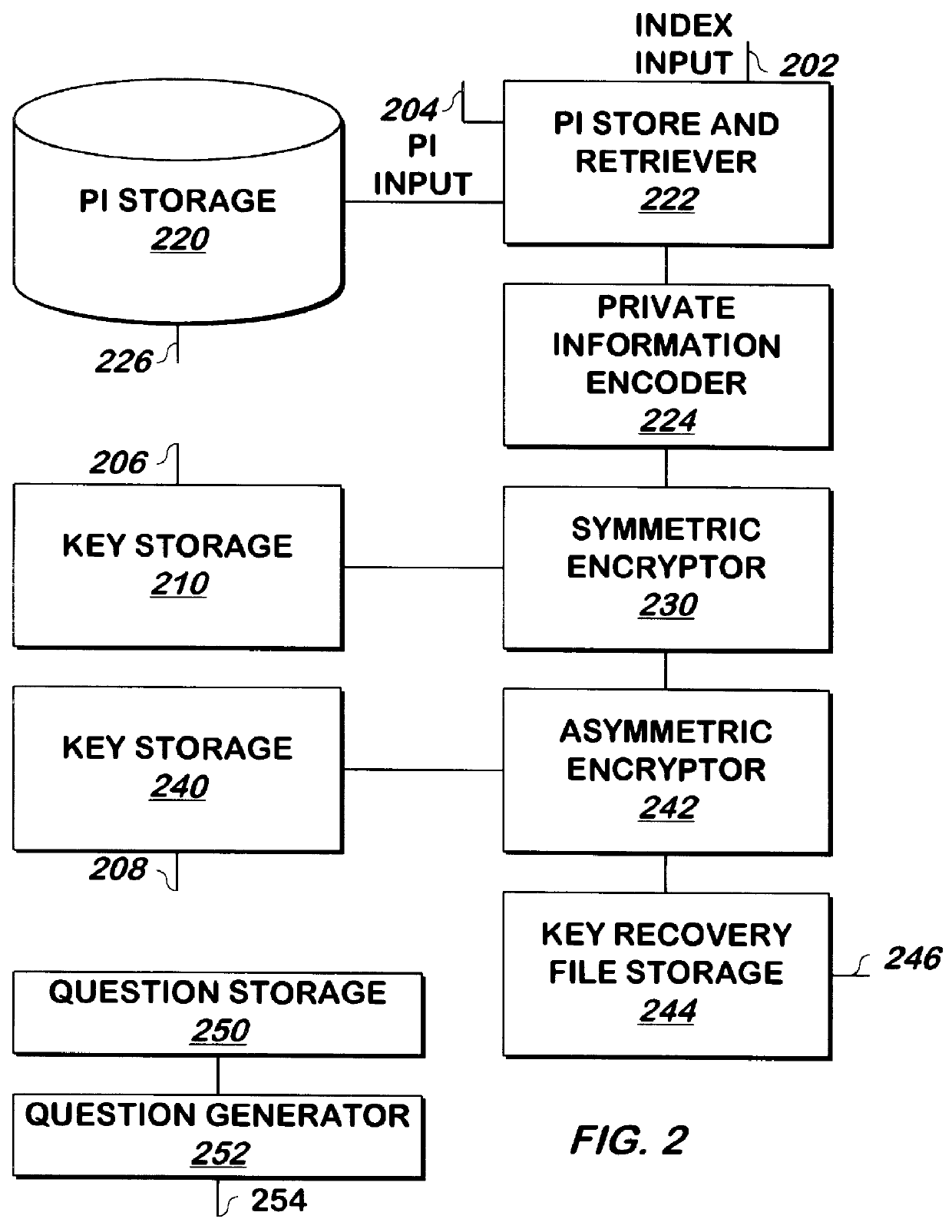
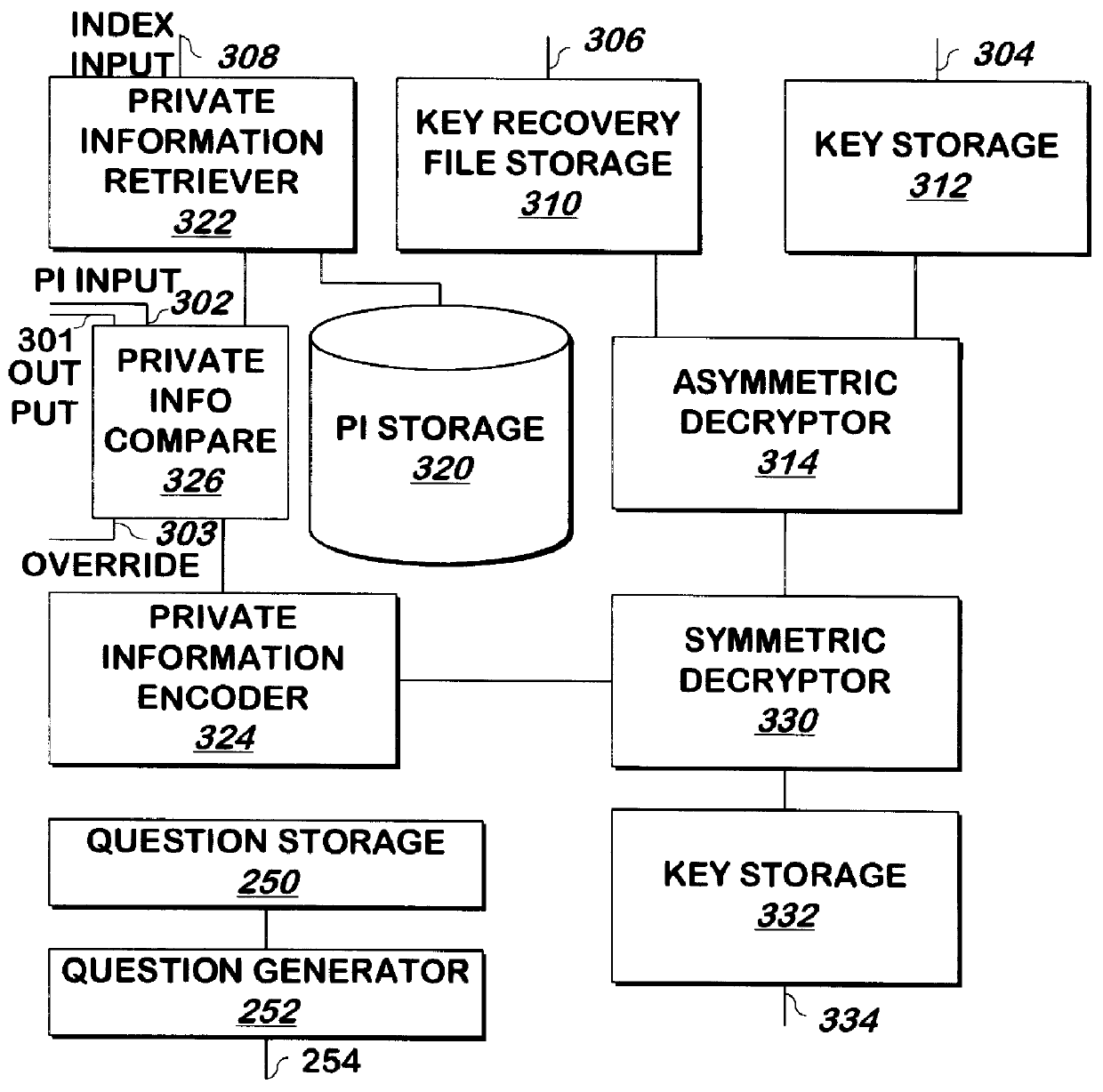
Methods and apparatus for recovering keys
A key such as a private key or key password of a private key is encrypted for storage, and may be decrypted if the private key becomes lost or unavailable. The key is encrypted by encoding, for example, by hashing, private information such as mother's maiden name and social security number, and the result is used as a key to encrypt the private key using DES or another symmetric encryption technique. The encrypted key is again encrypted, for example using asymmetric encryption, using the public key of a trusted party such as the certificate authority that generated the private key. The result may be stored as a key recovery file by the principal of the private key or another party. To decrypt the key recovery file, the private key corresponding to the public key used to encrypt the key recovery file is used to decrypt the key recovery file, for example by asymmetric decryption. The result is symmetrically decrypted using a key obtained by encoding, for example, by hashing, the private information in the same manner as was used to encrypt the key. The result of this decryption is the key.
Owner:ORACLE INT CORP
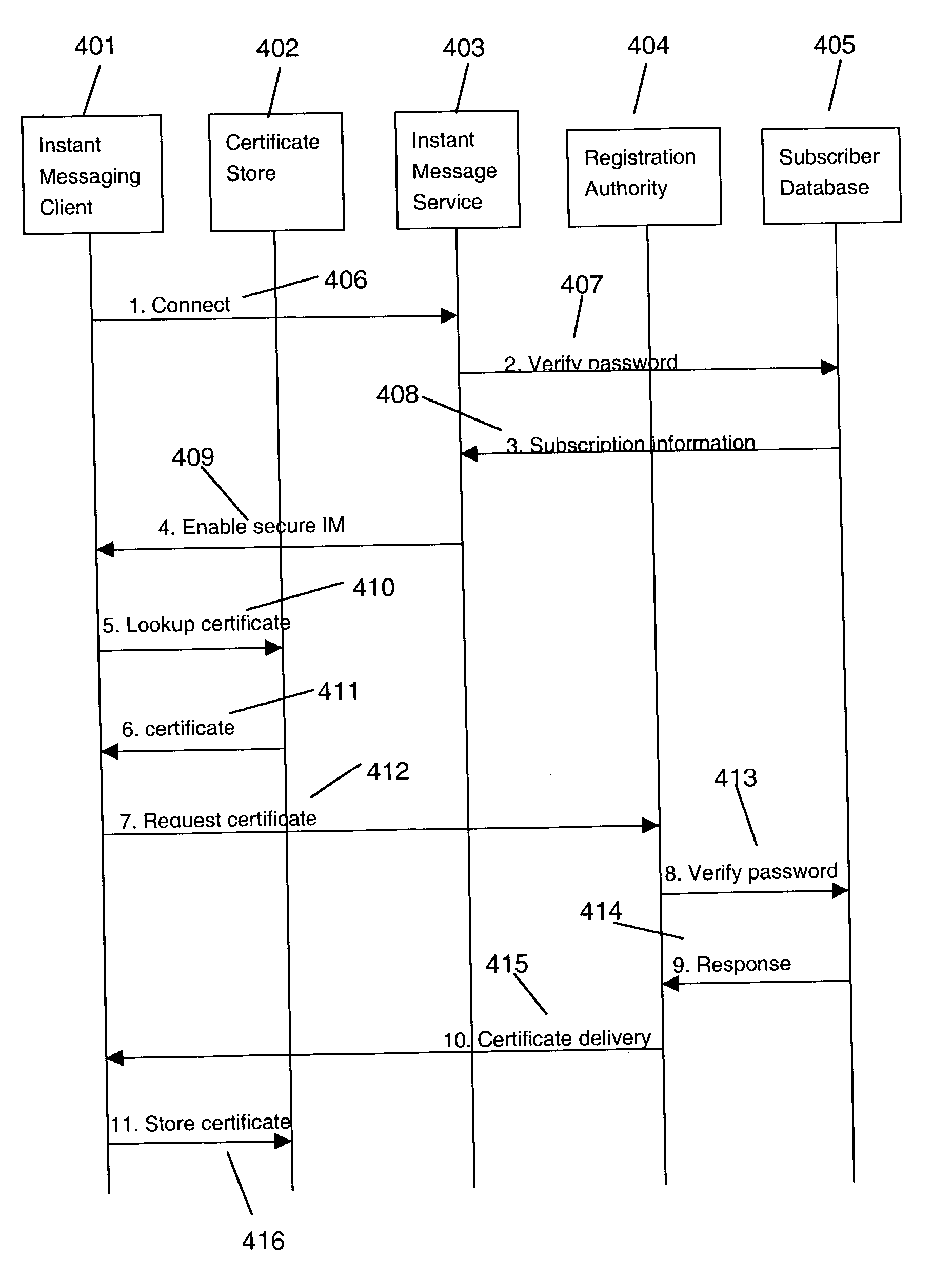
Secure instant messaging system
ActiveUS7131003B2Multiple keys/algorithms usagePublic key for secure communicationRelevant informationSecure state
A secure instant messaging system integrates secure text instant messaging and secure file transfers into existing instant messaging systems. At least one certificate authority (CA) is provided that issues a security certificate to a user that binds the user's instant messaging screen name to a public key which is used by other users to encrypt messages and files sent to the user and by the user to decrypt the received messages and files. A subscriber database is used by the CA to keep track of valid users and their associated information, such as: user screen names, user subscription expiration dates, and enrollment agent information. A user sends his certificate to the invention's instant messaging server which publishes the user's certificate to other users by creating a hash value of the user's certificate and sending it to the other users which allows the recipients to decide if they need to update their caches with a new copy of the user's certificate. Instant messages and files are encrypted by a sending user using an encryption algorithm and the recipient's certificate. The sending user can sign instant messages using his private signing key. The security status of each received instant message is displayed to the user.
Owner:GOOGLE LLC
Trusted infrastructure support systems, methods and techniques for secure electronic commerce, electronic transactions, commerce process control and automation, distributed computing, and rights management
InactiveUS20060218651A1Improve powerIncrease flexibilityTelevision system detailsPulse modulation television signal transmissionTransaction managementElectronic network
The present inventions provide an integrated, modular array of administrative and support services for electronic commerce and electronic rights and transaction management. These administrative and support services supply a secure foundation for conducting financial management, rights management, certificate authority, rules clearing, usage clearing, secure directory services, and other transaction related capabilities functioning over a vast electronic network such as the Internet and / or over organization internal Intranets. These administrative and support services can be adapted to the specific needs of electronic commerce value chains. Electronic commerce participants can use these administrative and support services to support their interests, and can shape and reuse these services in response to competitive business realities. A Distributed Commerce Utility having a secure, programmable, distributed architecture provides administrative and support services. The Distributed Commerce Utility makes optimally efficient use of commerce administration resources, and can scale in a practical fashion to accommodate the demands of electronic commerce growth. The Distributed Commerce Utility may comprise a number of Commerce Utility Systems. These Commerce Utility Systems provide a web of infrastructure support available to, and reusable by, the entire electronic community and / or many or all of its participants. Different support functions can be collected together in hierarchical and / or in networked relationships to suit various business models and / or other objectives. Modular support functions can combined in different arrays to form different Commerce Utility Systems for different design implementations and purposes. These Commerce Utility Systems can be distributed across a large number of electronic appliances with varying degrees of distribution.
Owner:INTERTRUST TECH CORP
Physical access control
InactiveUS7353396B2Digital data processing detailsUser identity/authority verificationHash functionGranularity
A system and method are disclosed for controlling physical access through a digital certificate validation process that works with standard certificate formats and that enables a certifying authority (CA) to prove the validity status of each certificate C at any time interval (e.g., every day, hour, or minute) starting with C's issue date, D1. C's time granularity may be specified within the certificate itself, unless it is the same for all certificates. For example, all certificates may have a one-day granularity with each certificate expires 365 days after issuance. Given certain initial inputs provided by the CA, a one-way hash function is utilized to compute values of a specified byte size that are included on the digital certificate and to compute other values that are kept secret and used in the validation process.
Owner:ASSA ABLOY AB
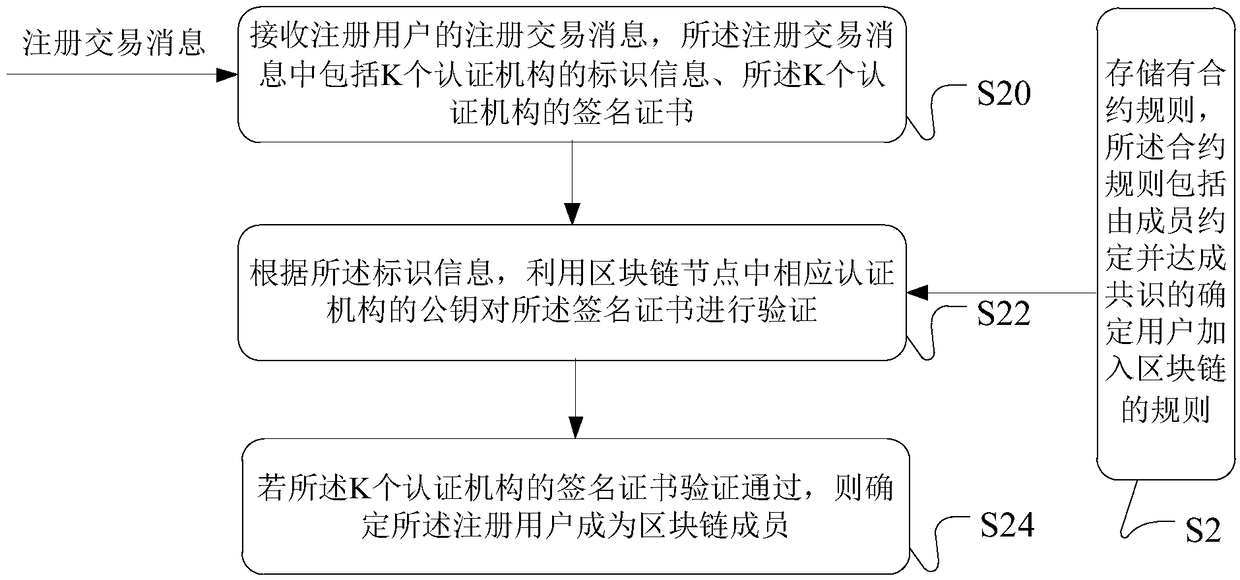
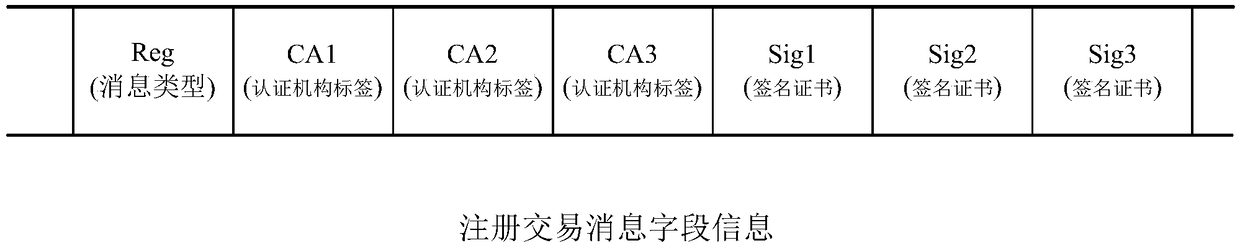
Data processing method and apparatus of blockchain member management, server and system
ActiveCN108667618AAchieve self-managementAchieve autonomyUser identity/authority verificationPayment architectureCertificate authorityAuthentication
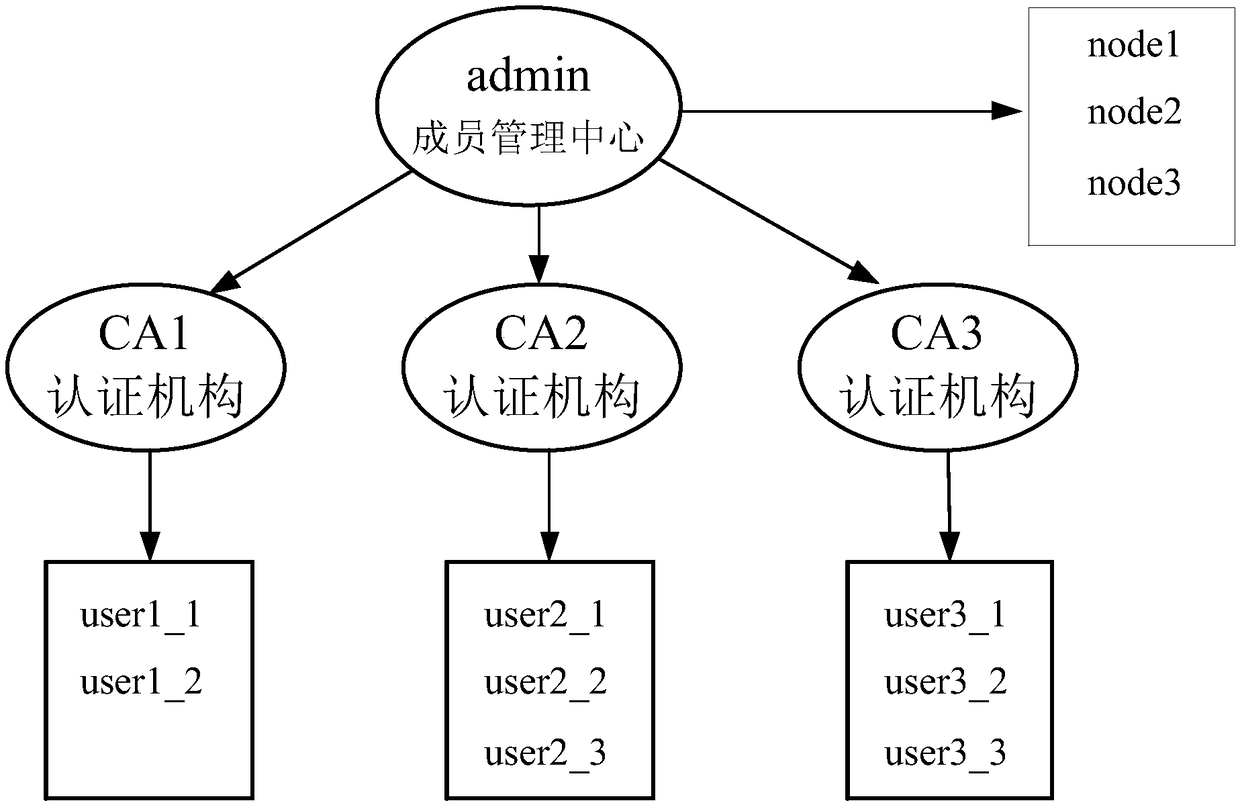
The embodiment of the invention discloses a data processing method and apparatus of blockchain member management, a server and a system. The verification of a user to join in a blockchain can be automatically performed based on a contract rule in the blockchain, and when a blockchain node receives a registration request of a user, the blockchain node verifies the registration request by using a public key of a corresponding certificate authority in the registration request. If the verification is passed, it can be determined that the registered user is a blockchain member. The contract rule can be agreed by the members in advance, a signature certificate of the certificate authority is obtained in the certificate authority under a user chain, the signature certificate is submitted during registration, and the blockchain node can determine the user as the blockchain member after verifying the signature certificate by using the public key of the corresponding certificate authority. By adoption of the method provided by the embodiment of the invention, the centralized member authentication management mode is removed, and the self-management of the blockchain members is achieved by thecontract rule.
Owner:ADVANCED NEW TECH CO LTD
Certificate issuing system based on block chain
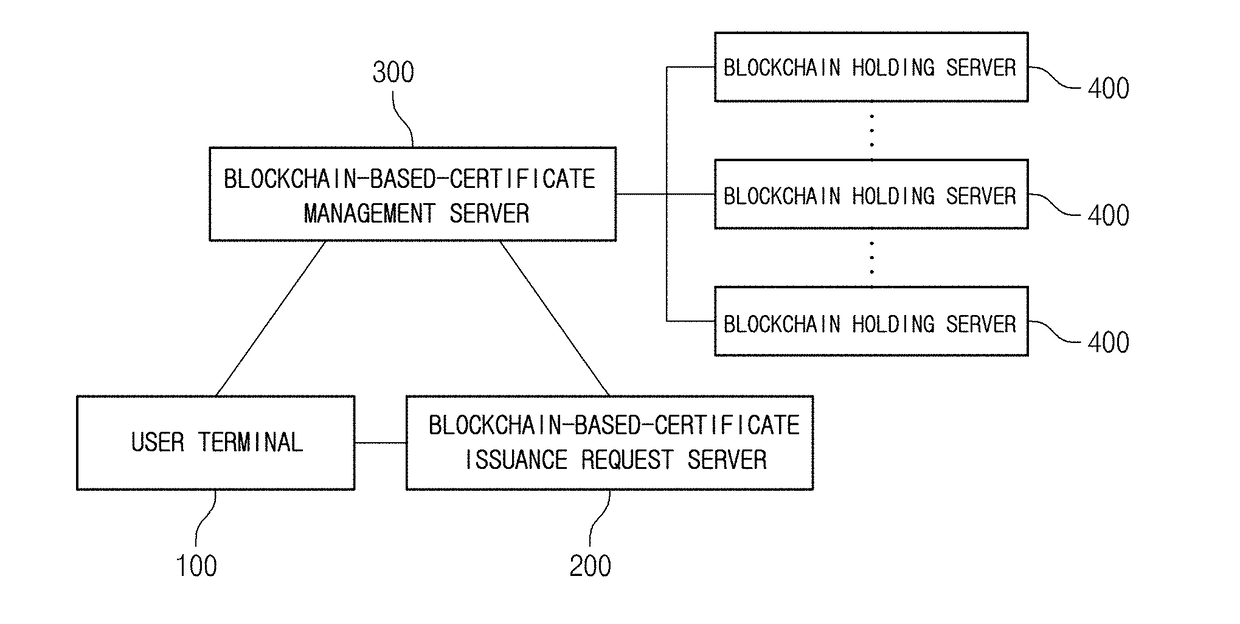
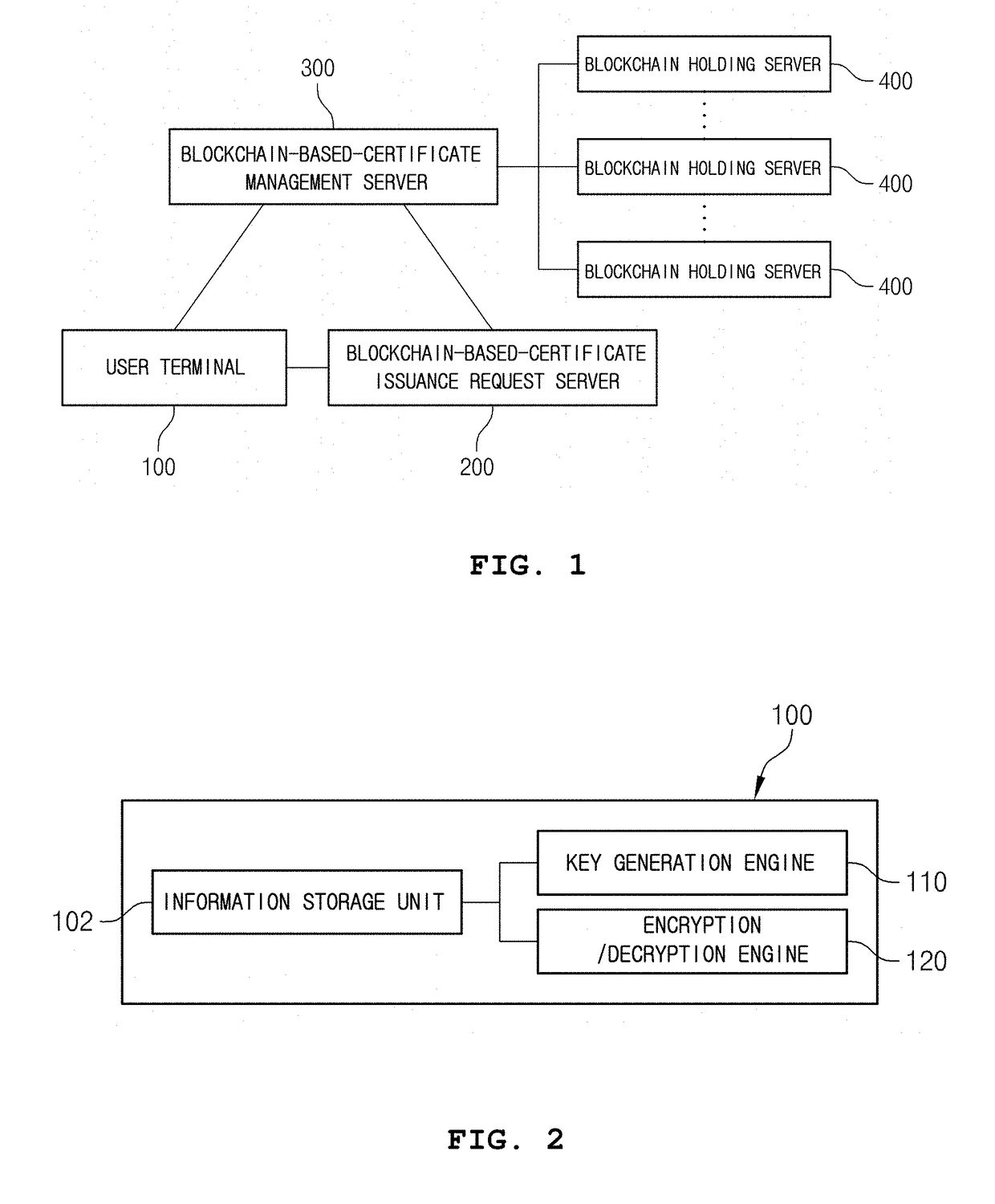
ActiveUS20180227293A1Prevent leakageLow costKey distribution for secure communicationFinanceComputer terminalDistributed database
The present invention provides a certificate issuing system based on a block chain, the system having a means for directly generating a certificate-specific public key and a certificate-specific private key in a user terminal operated by a user, guiding the certificate-specific public key and the certificate-specific private key so as to be generated in a state in which a network in the user terminal is blocked, and eliminating the costs incurred for constructing, operating, and maintaining the certificate issuing system having a high-grade security system linked therewith so as to block hacking, which occurred in the past, as much as possible, since the certificate-specific public key requiring maintenance is stored and managed in an electronic wallet, installed in servers that hold block chains, through a peer-to-peer network (P2P)-based distributed database, not by a server run by a certificate authority (CA).
Owner:COINPLUG LNC
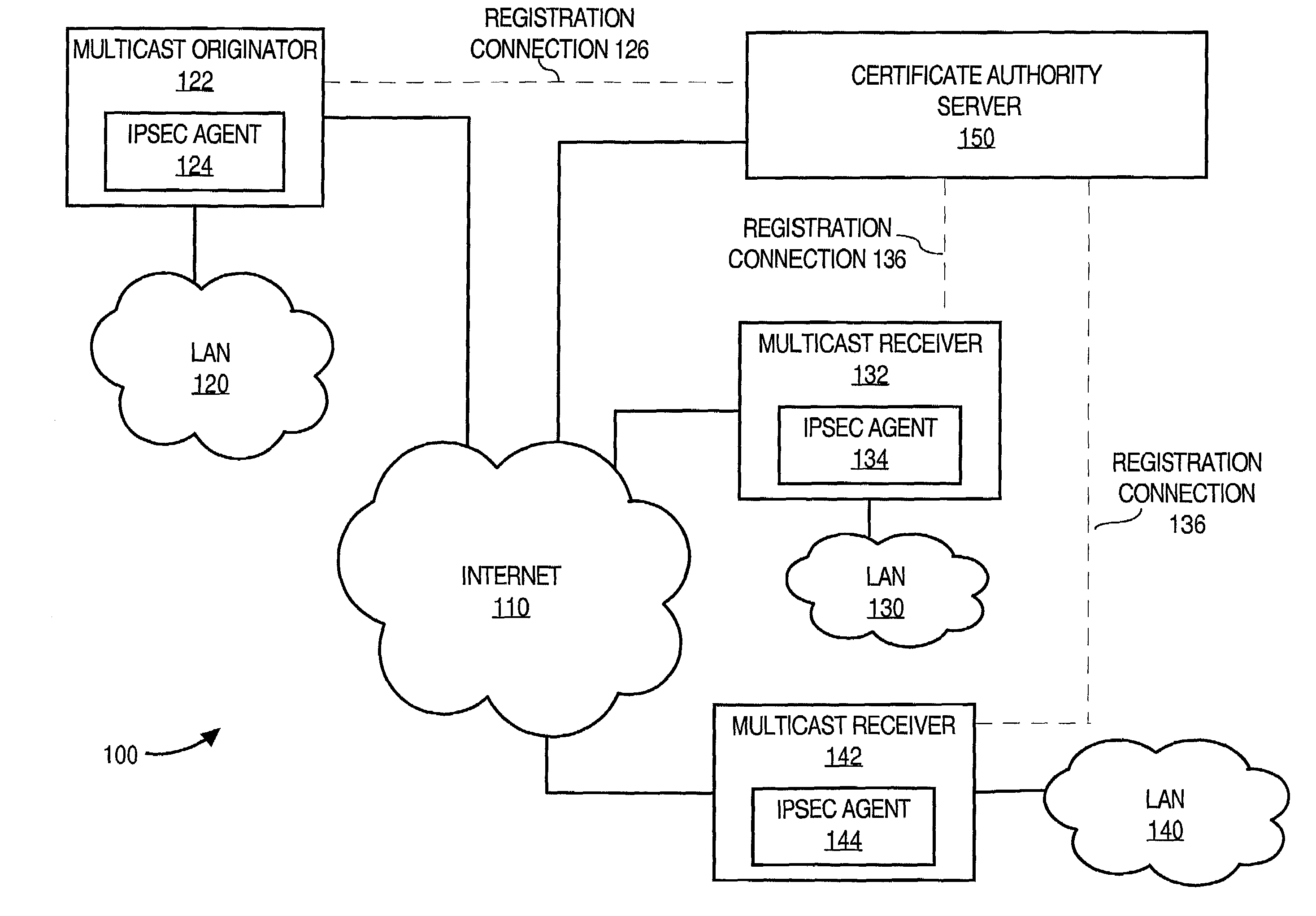
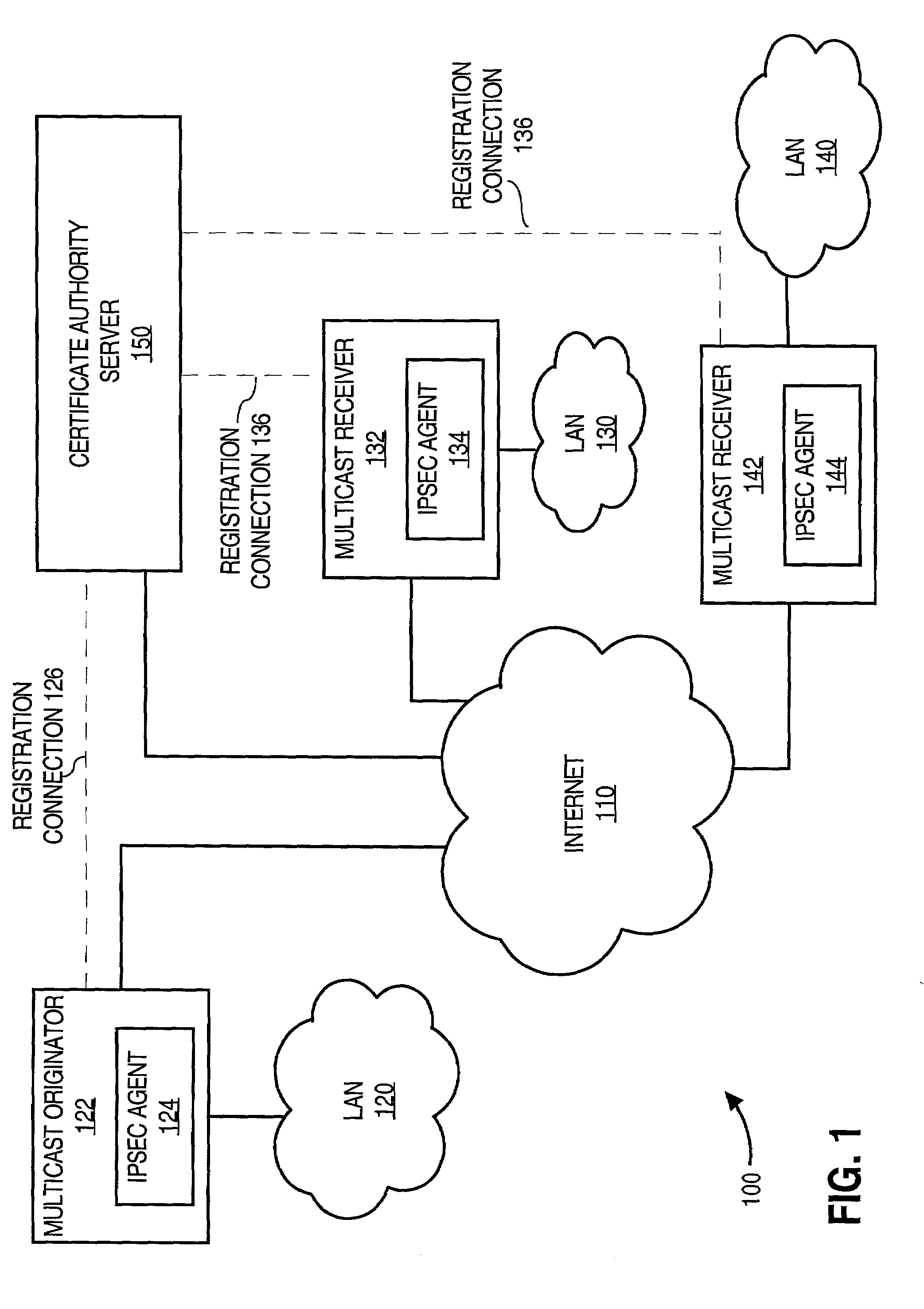
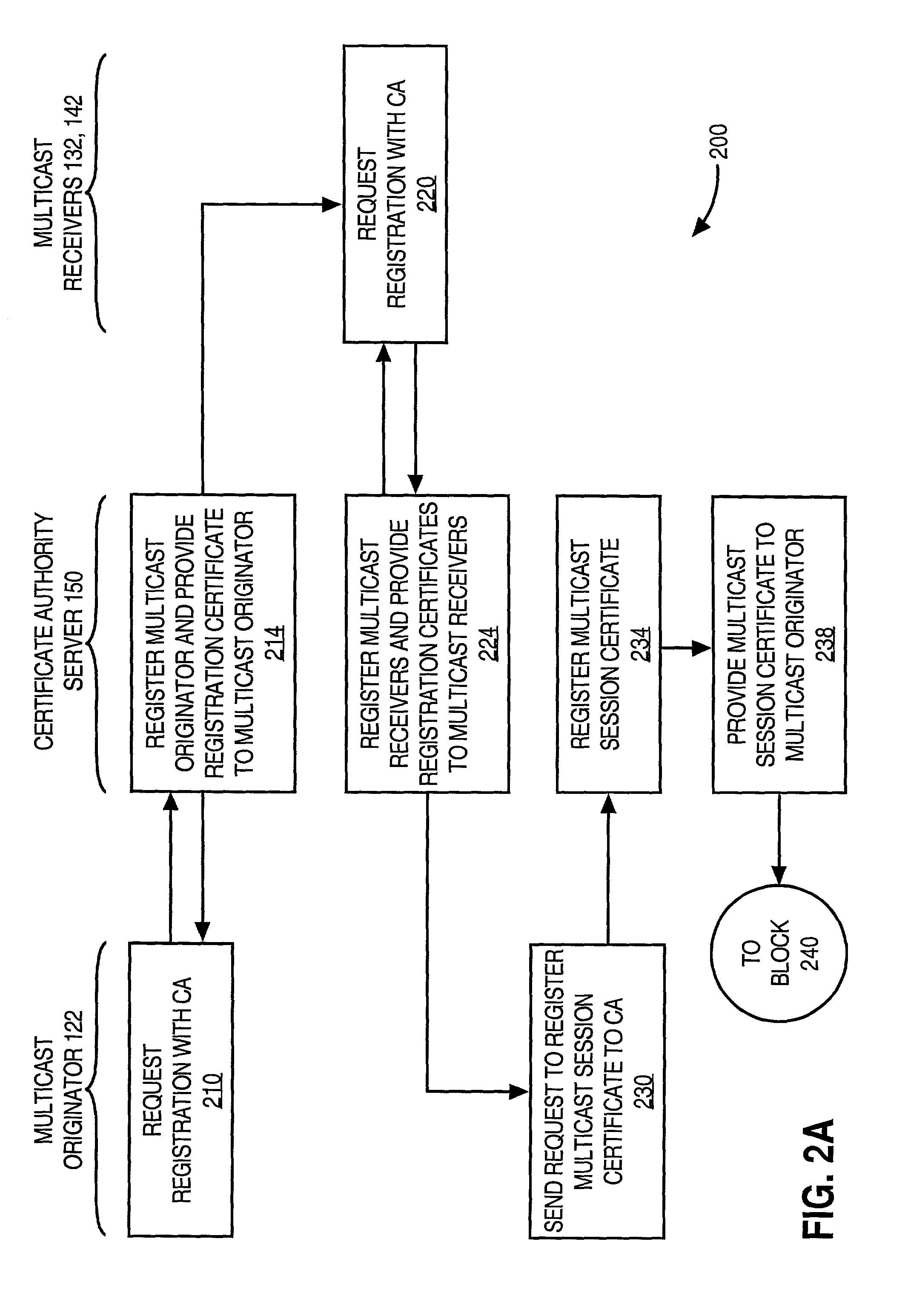
Facilitating secure communications among multicast nodes in a telecommunications network
An approach for facilitating secure communications among multicast nodes in a telecommunications network is disclosed. A source node sends an encryption key and an identifier to an authoritative node that stores the encryption key and associates the identifier with the encryption key. The source node encrypts data using the encryption key and sends the encrypted data with the identifier in a multicast. The multicast destination nodes retrieve the encryption key from the authoritative node based on the identifier and then decrypt the multicast. A list of administrative nodes, a list of authorized nodes, and an expiration time may be used to manage the encryption key. The authoritative node may be a certificate authority or key distribution center, and the source node may encrypt the multicast using the Internet security protocol (IPsec) or secure socket layer (SSL). Thus, communications among multicast nodes may be efficiently secured in a scalable manner.
Owner:CISCO TECH INC
Method for a Web site with a proxy domain name registration to receive a secure socket layer certificate
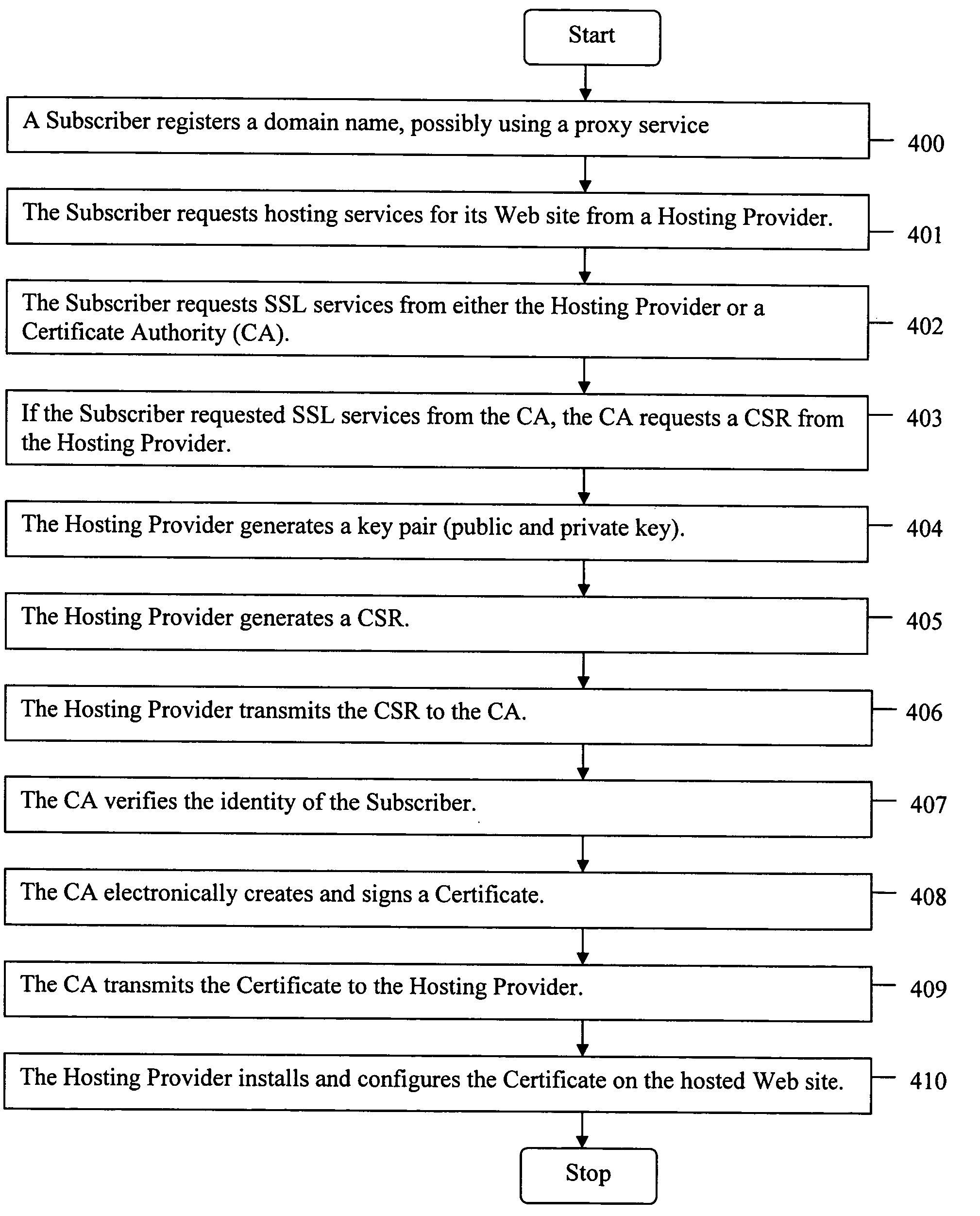
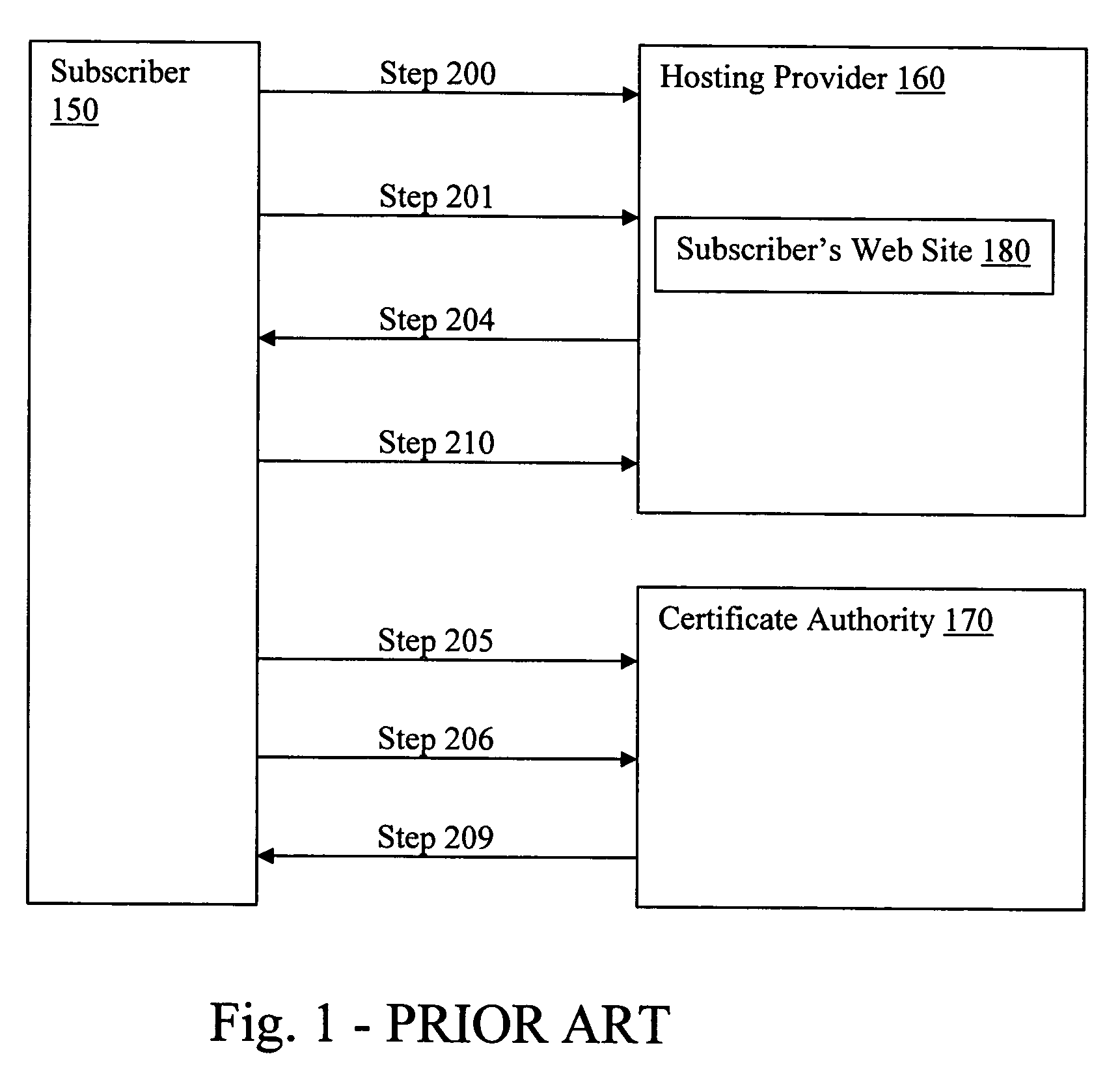
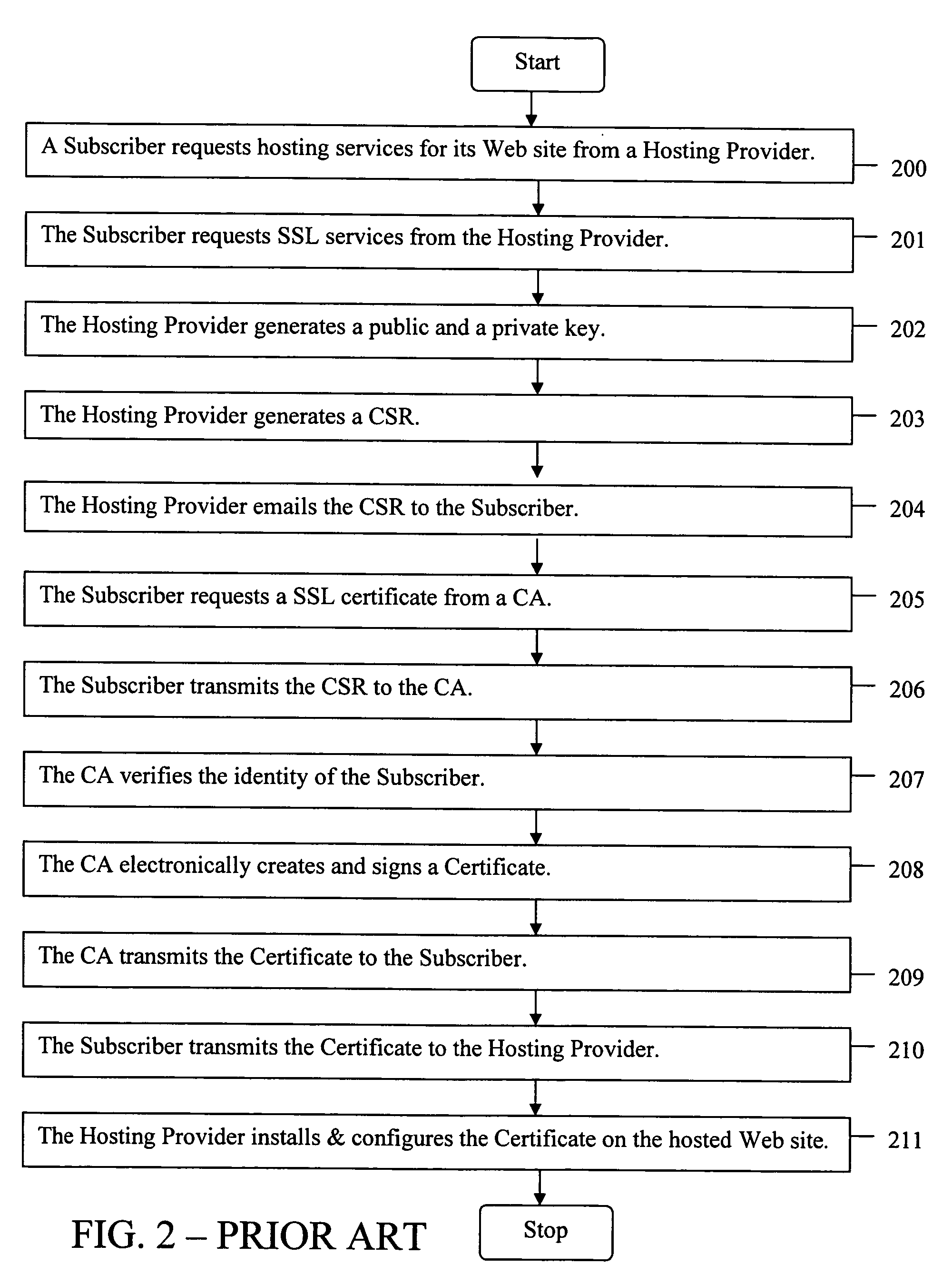
ActiveUS20050289084A1Improve securityMaximize efficiencyUser identity/authority verificationPayment architectureDomain nameWeb site
The present invention provides systems and methods for enabling encrypted communication capabilities for a Subscriber's Web Site, thereby allowing Customers to access the Subscriber's Web Site in a secure manner. The Subscriber may register a domain name associated with the Subscriber's Web Site using a proxy domain name service, thereby hindering its Customers ability to verify the owner of the Subscriber's Web Site. A Hosting Provider hosts the Subscriber's Web Site and a Certificate Authority (CA) verifies the identity of the Subscriber. In combination the Hosting Provider and CA provide the Subscriber's Web Site with Secure Sockets Layer (SSL) encrypted communications capability. The Hosting Provider and CA communicate directly with each other as needed, typically via the Internet, without using the Subscriber as an intermediary in their communications.
Owner:GO DADDY OPERATING
Email access control scheme for communication network using identification concealment mechanism
InactiveUS7188358B1Digital data processing detailsUser identity/authority verificationSecure communicationPersonalization
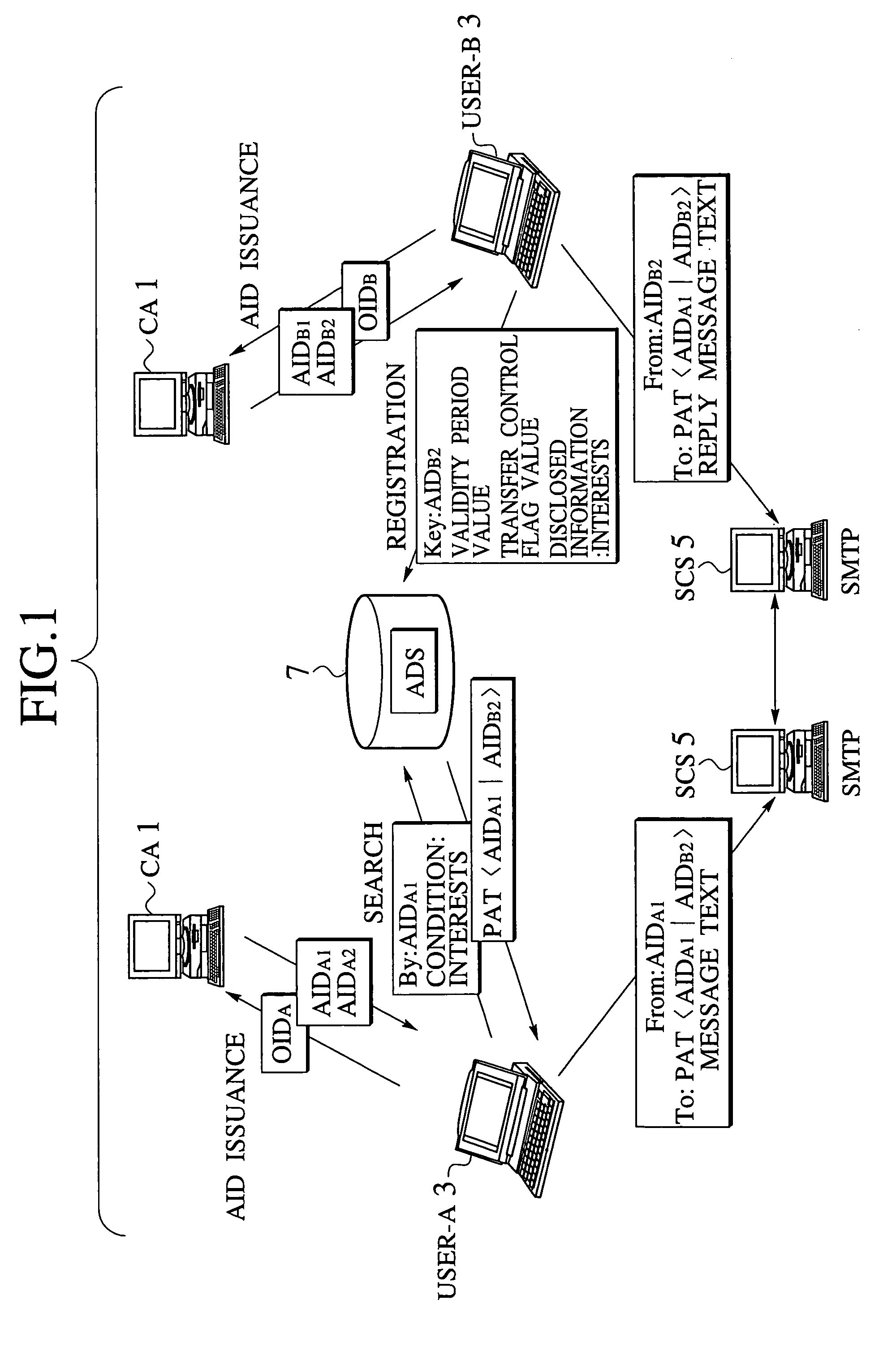
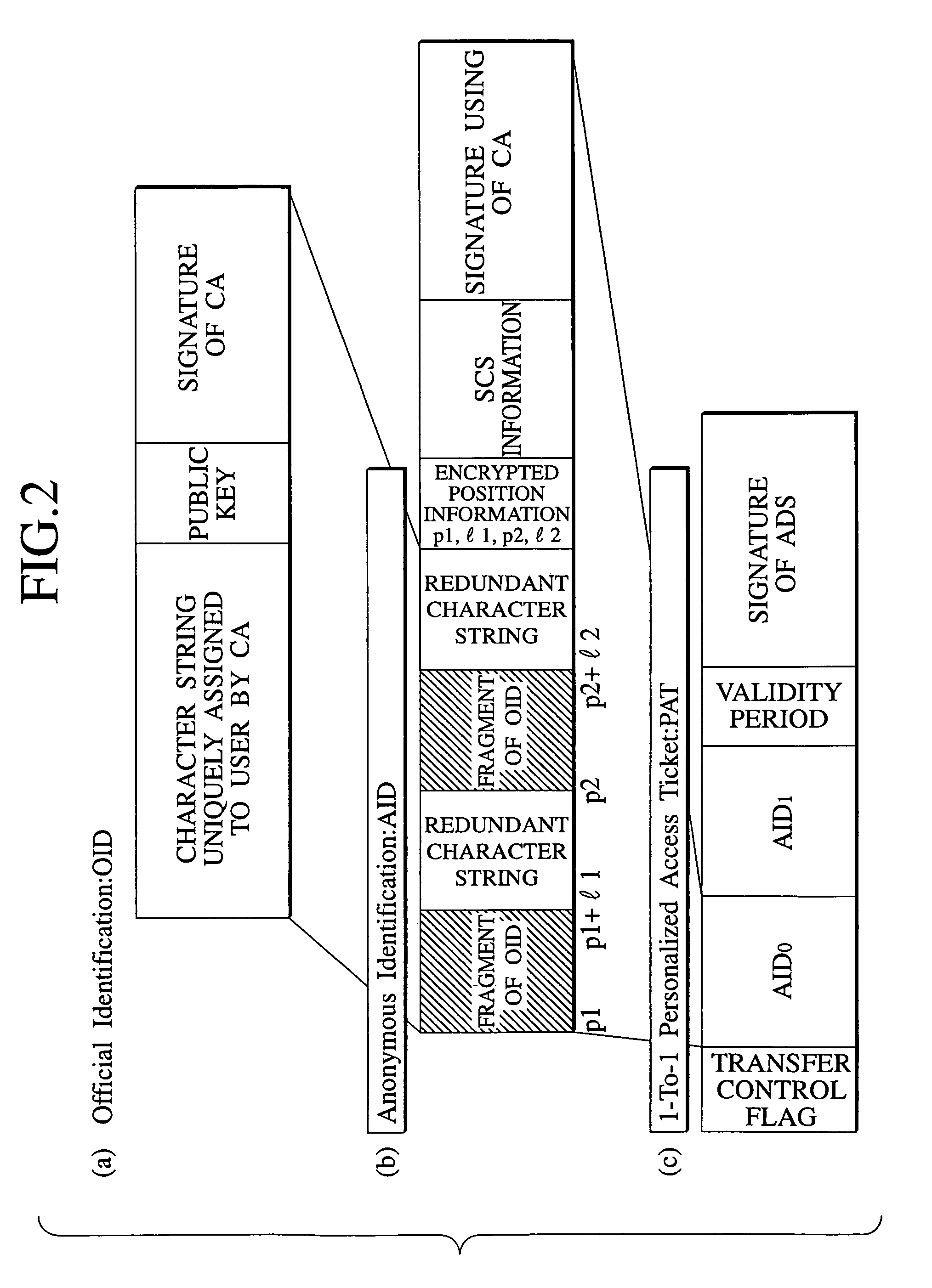
An email access control scheme capable of resolving problems of the real email address and enabling a unique identification of the identity of the user while concealing the user identification is disclosed. A personalized access ticket containing a sender's identification and a recipient's identification in correspondence is to be presented by a sender who wishes to send an email to a recipient so as to specify the recipient as an intended destination of the email. Then, accesses between the sender and the recipient by verifying an access right of the sender with respect to the recipient according to the personalized access ticket at a secure communication service. Also, an official identification of each user by which each user is uniquely identifiable by a certification authority, and an anonymous identification of each user containing at least one fragment of the official identification are defined, and each user is identified by the anonymous identification of each user in communications for emails on a communication network.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com