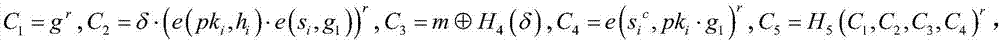Patents
Literature
38 results about "Proxy certificate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
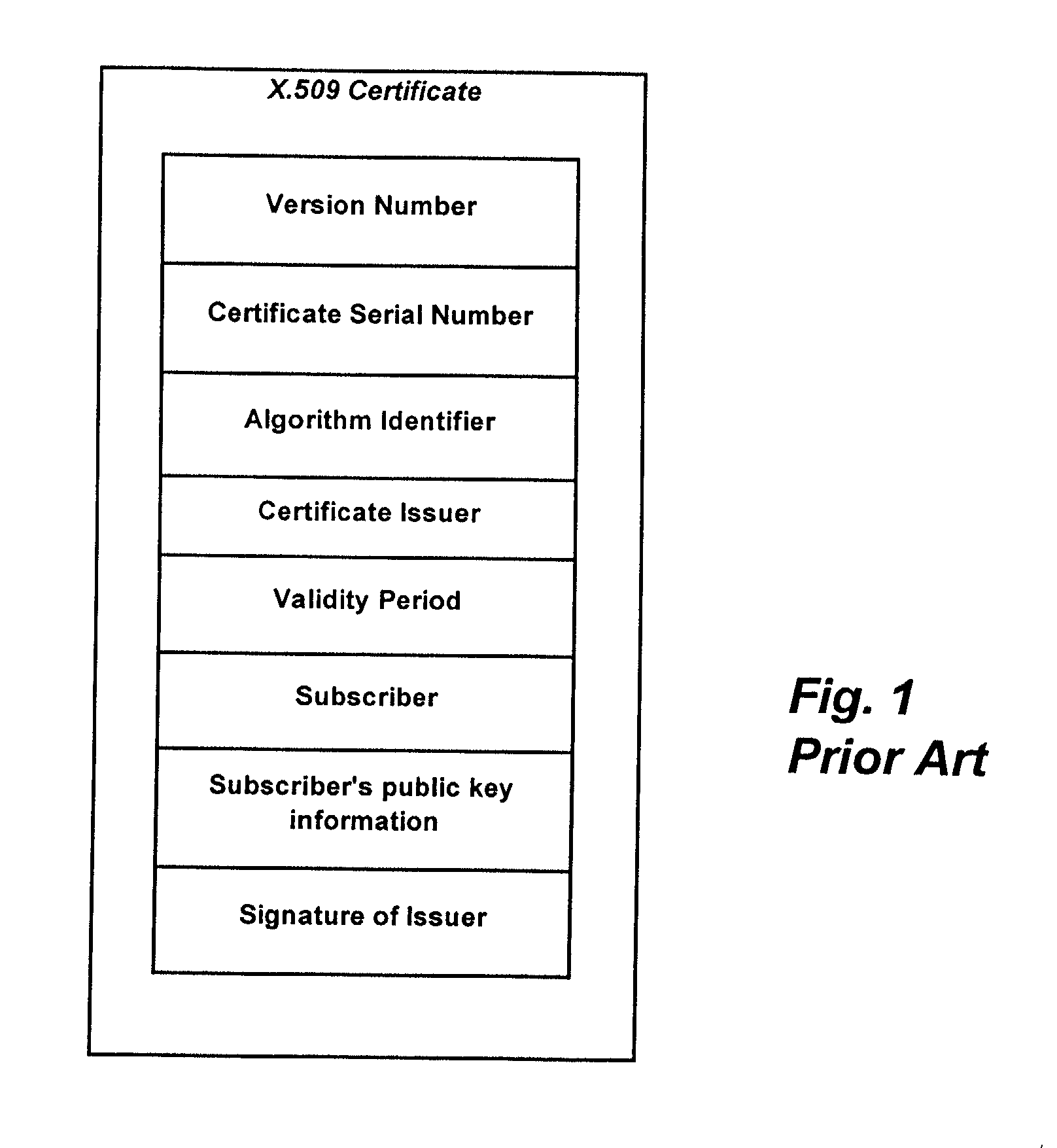
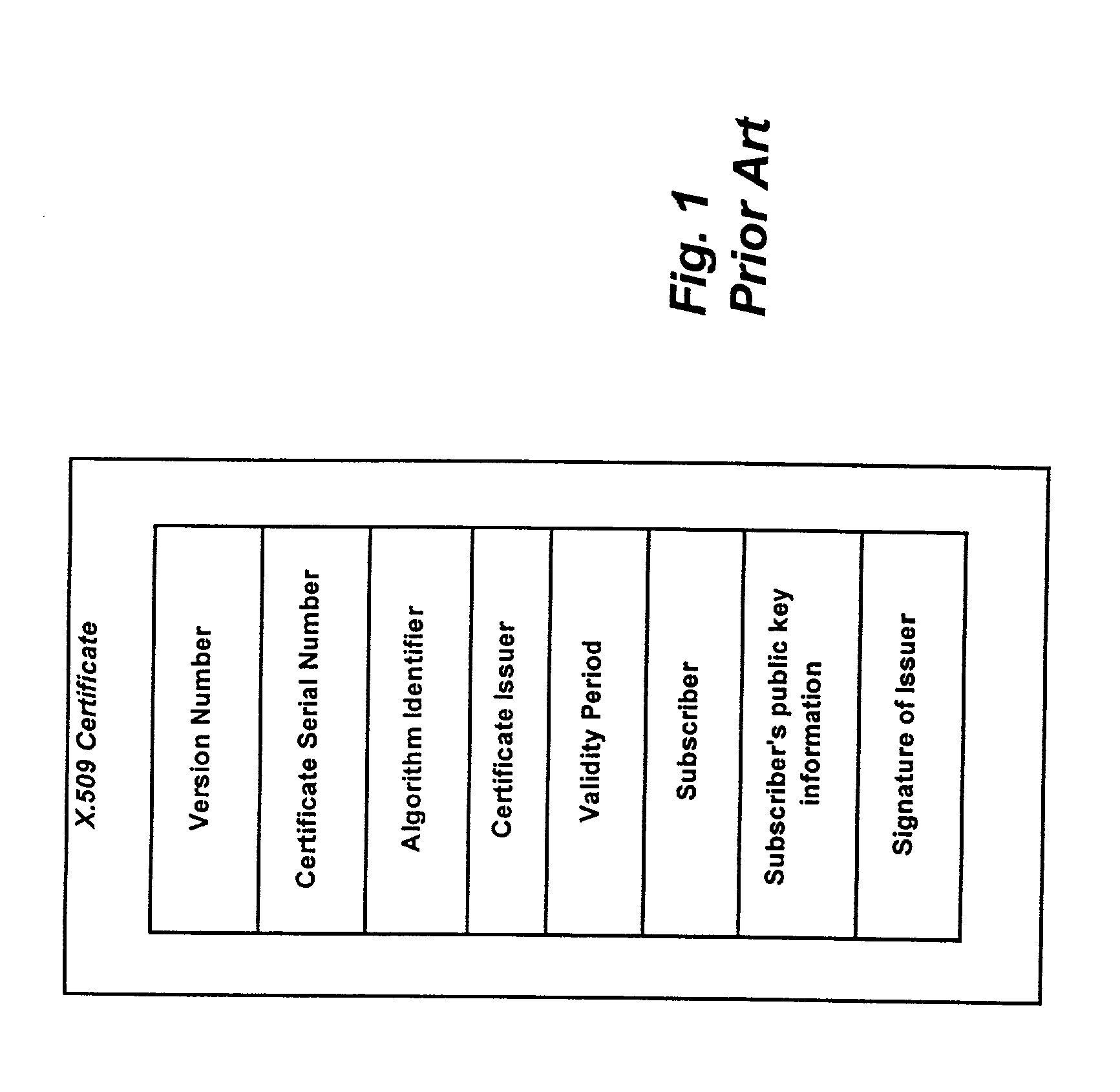
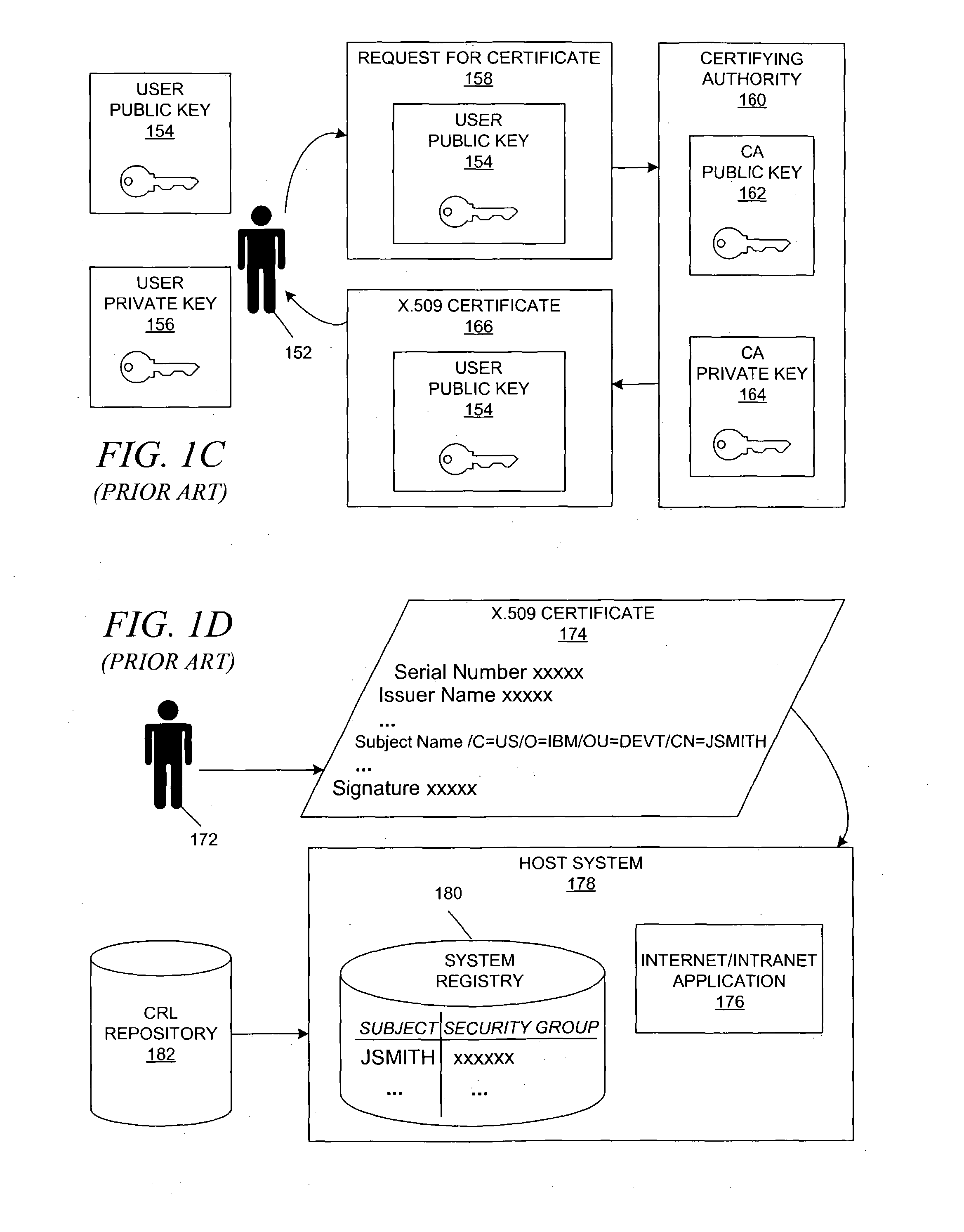
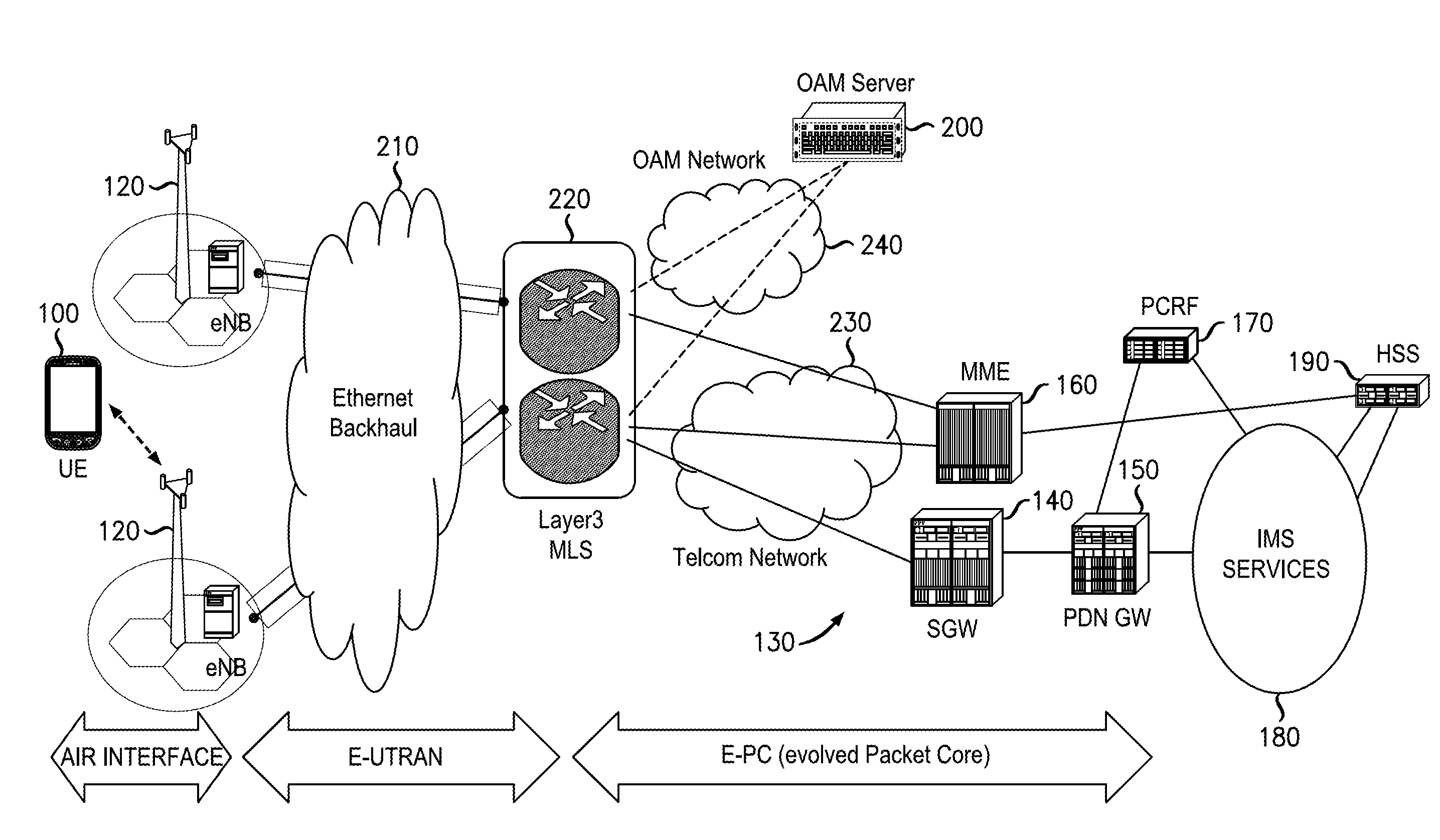
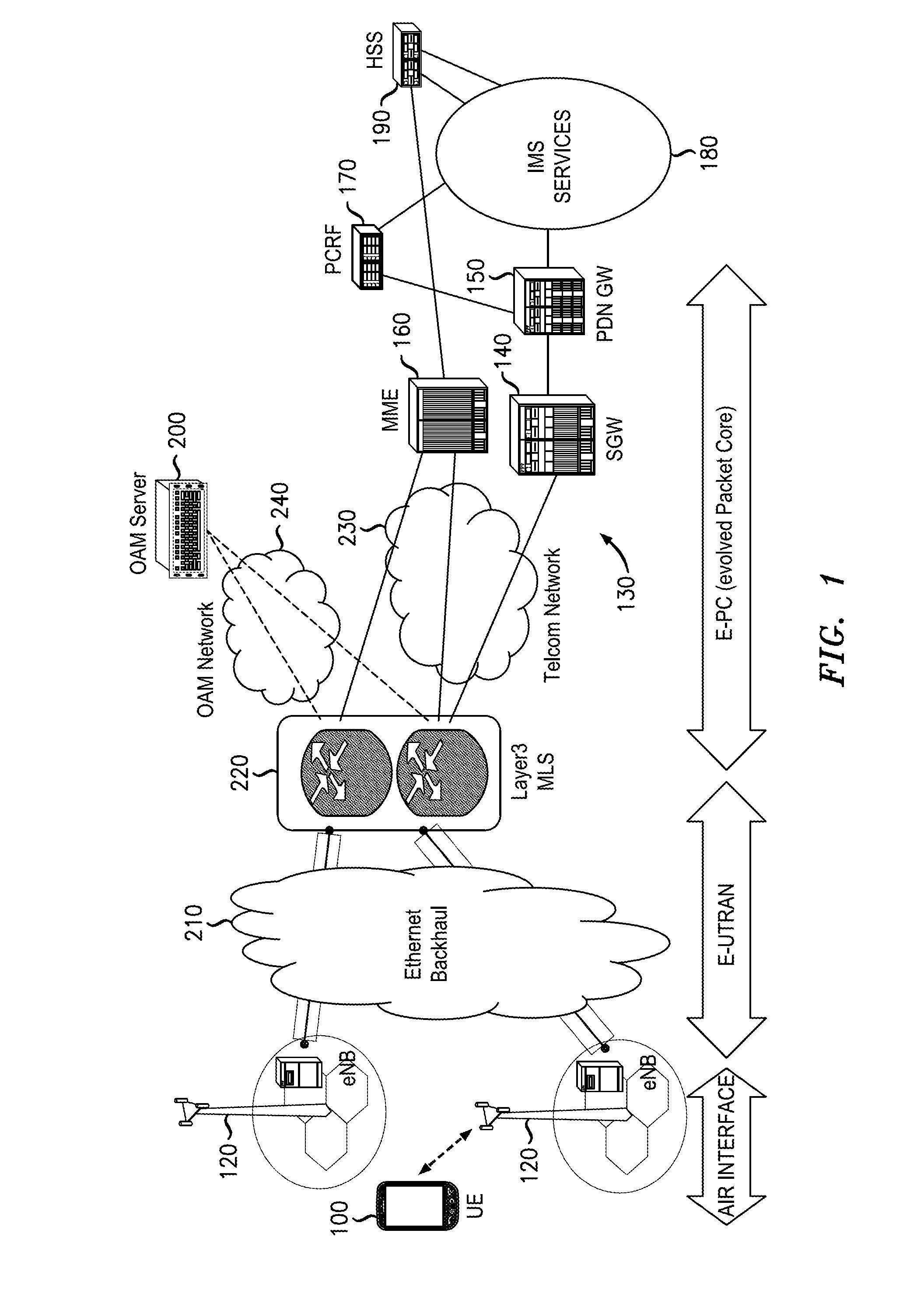
The term Proxy Certificate is used to describe a certificate that is derived from, and signed by, a normal X.509 Public Key End Entity Certificate or by another Proxy Certificate for the purpose of providing restricted proxying and delegation within a PKI based authentication system.
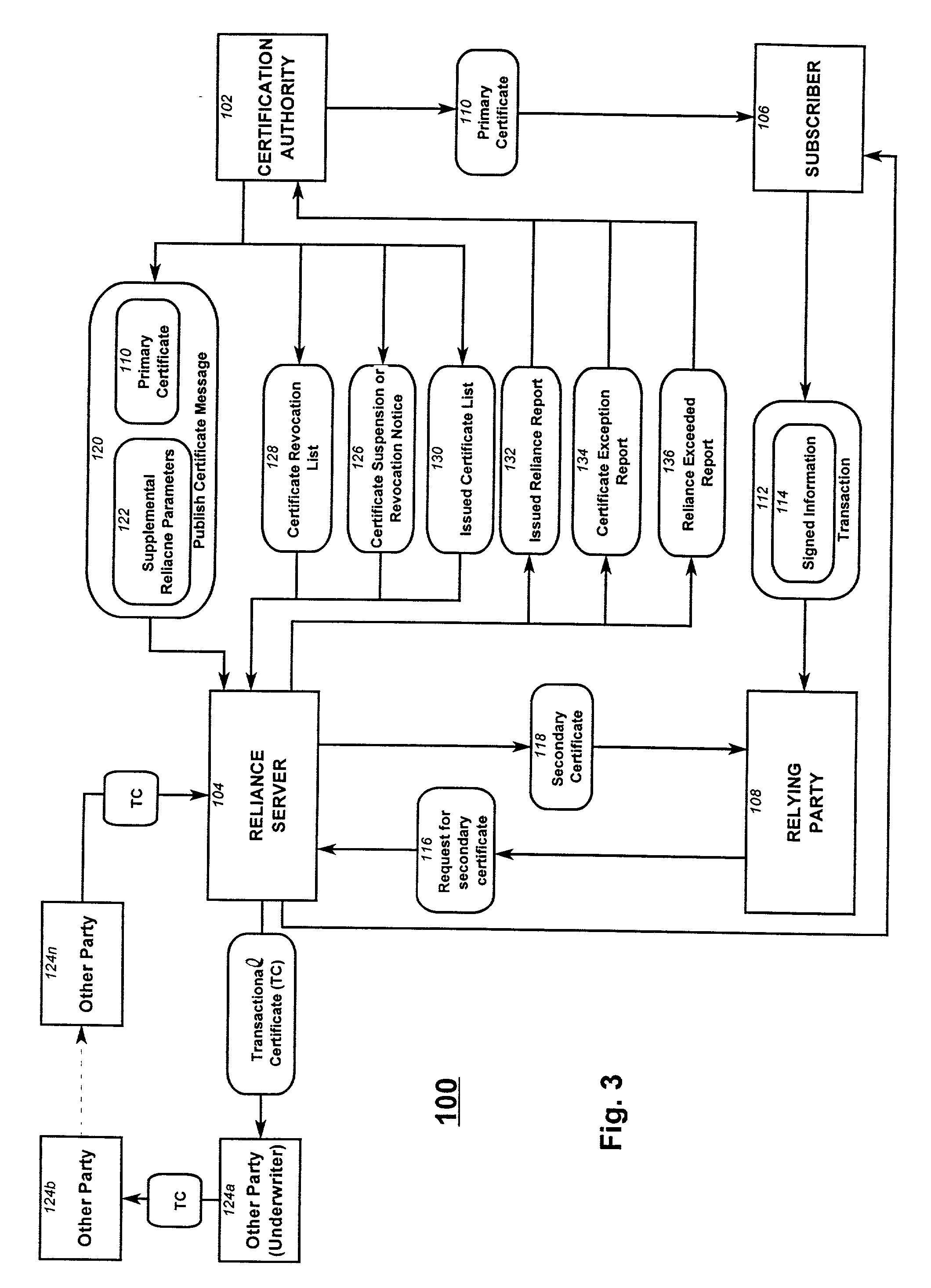
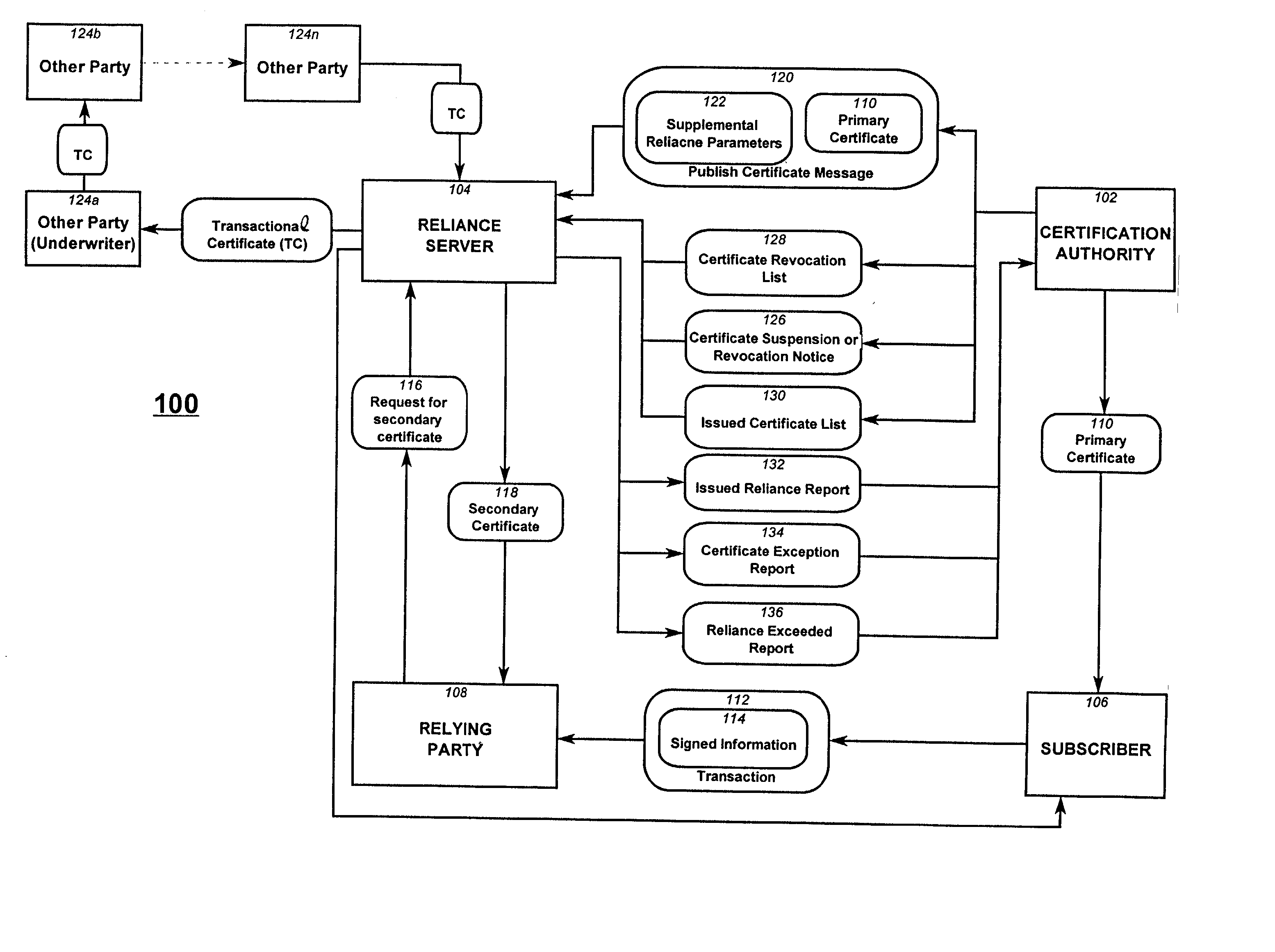
Reliance management for electronic transaction system
InactiveUS20010011255A1Complete banking machinesPublic key for secure communicationProxy certificateCertificate authority
A method of managing reliance in an electronic transaction system includes a certification authority issuing a primary certificate to a subscriber and forwarding to a reliance server, information about the issued primary certificate. The reliance server maintains the forwarded information about issued primary certificate. The subscriber forms a transaction and then provides the transaction to a relying party. The transaction includes the primary certificate or a reference thereto. The relying party sends to the reliance server a request for assurance based on the transaction received from the subscriber. The reliance server determines whether to provide the requested assurance based on the information about the issued primary certificate and on the requested assurance. Based on the determining, the reliance server issues to the relying party a secondary certificate providing the assurance to the relying party.
Owner:CERTCO
Reliance server for electronic transaction system
InactiveUS20020062438A1Complete banking machinesUser identity/authority verificationProxy certificateCertificate authority
Owner:CERTCO
Method and system for a single-sign-on operation providing grid access and network access
InactiveUS20050021956A1User identity/authority verificationMultiple digital computer combinationsSuccessful completionUser device
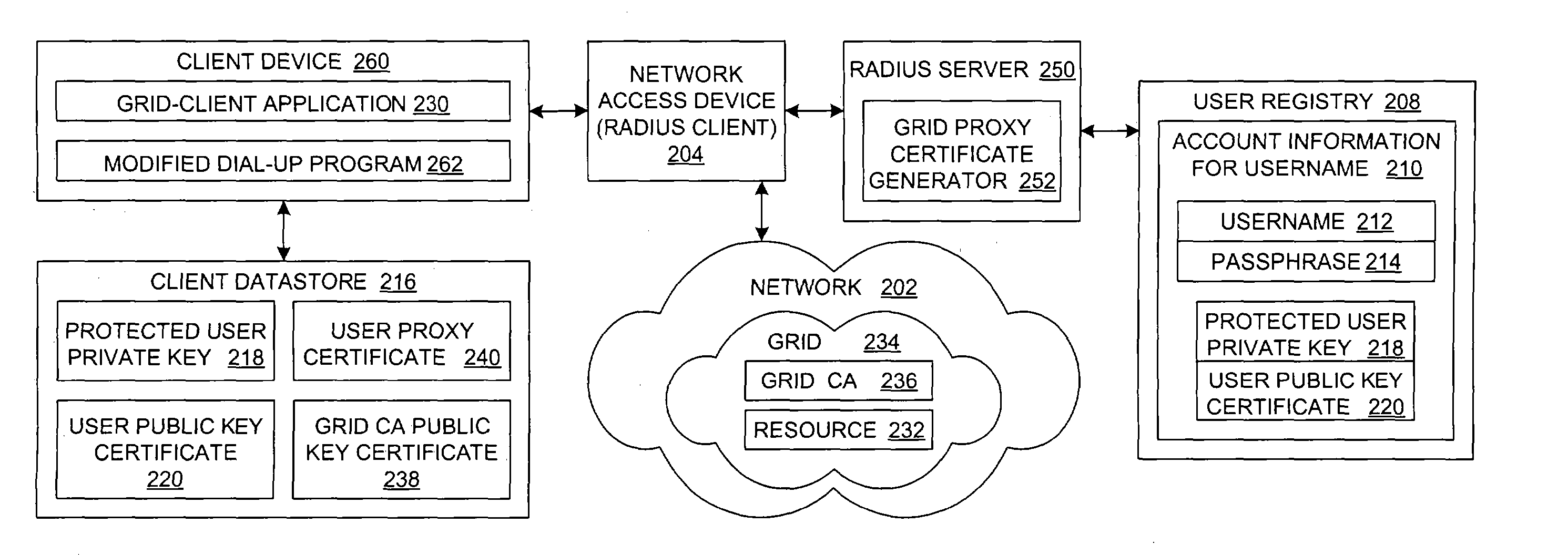
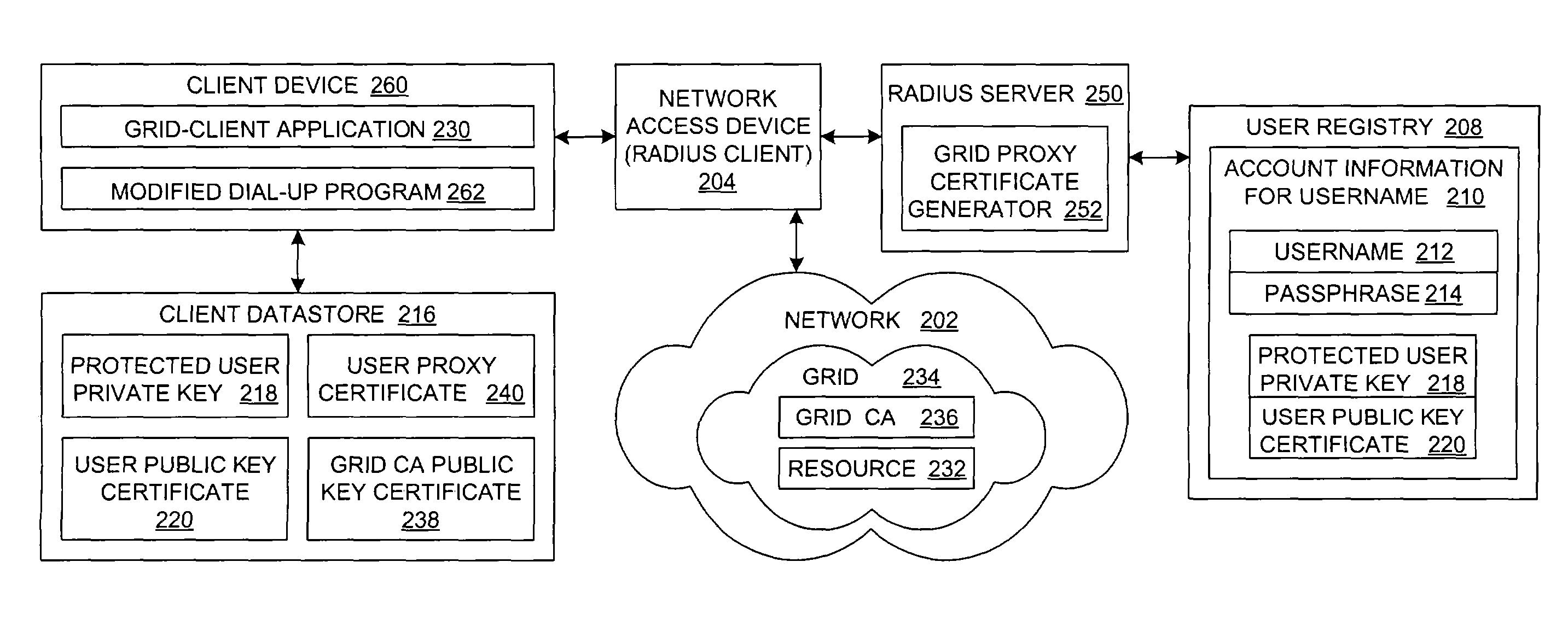
A user device initiates a network access authentication operation via a network access device with a network access authentication server, e.g., a Remote Authentication Dial-In User Service (RADIUS) server, which also generates an X.509 proxy certificate and includes the proxy certificate with the information, such as a set of network access parameters, that is returned to the user device in response to a successful completion of the network access authentication operation. The user device extracts and stores the proxy certificate. The network access parameters are used by the user device to communicate via the network access device on a network, which supports a grid. When the user device accesses a resource in the grid, the proxy certificate is already available, thereby obviating the need to generate a new proxy certificate and allowing a user of the user device to experience an integrated single-sign-on for network access and grid access.
Owner:IBM CORP
License management system and method
ActiveUS20090013177A1Efficient managementUser identity/authority verificationProgram/content distribution protectionComputer networkProxy certificate
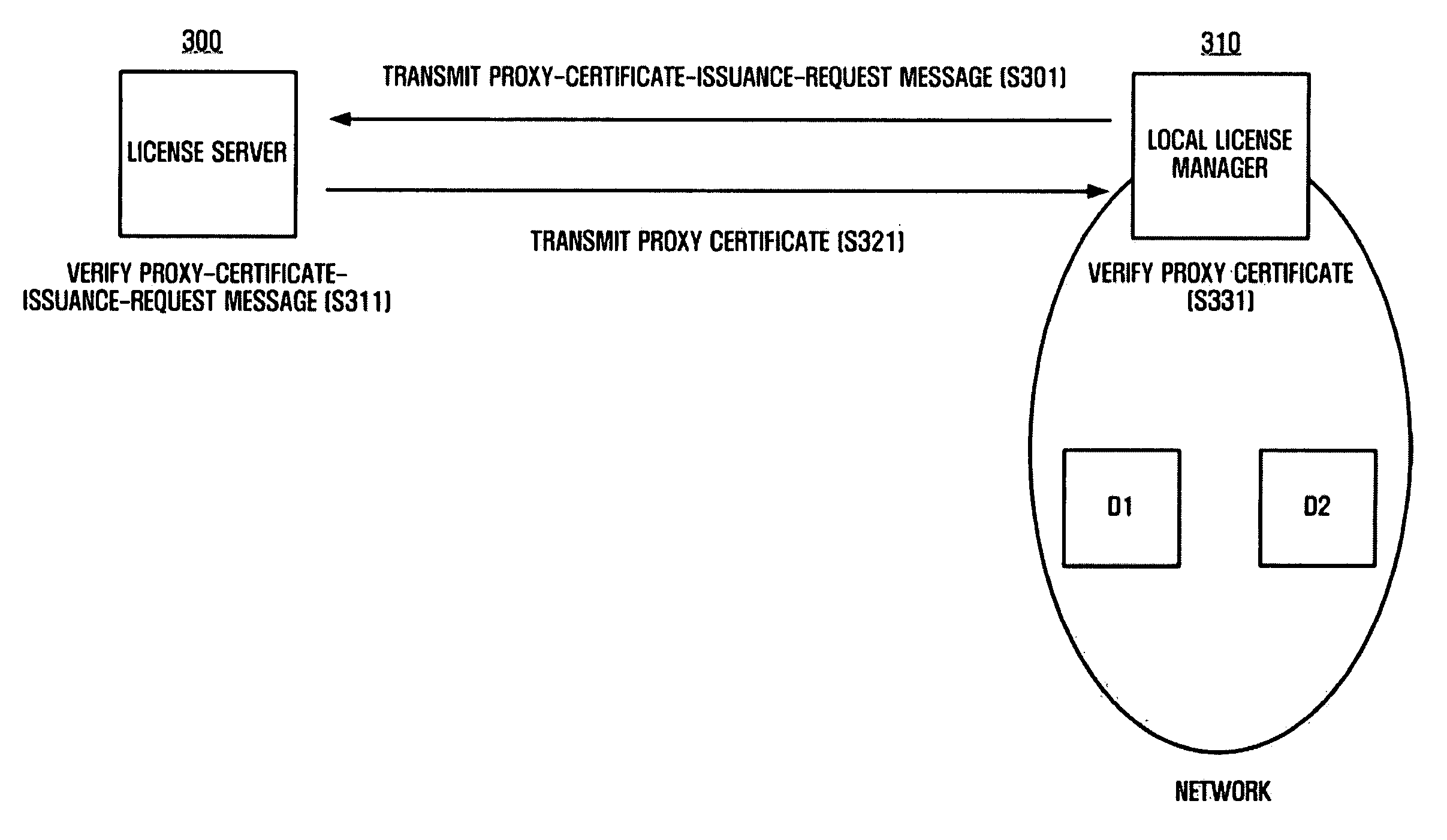
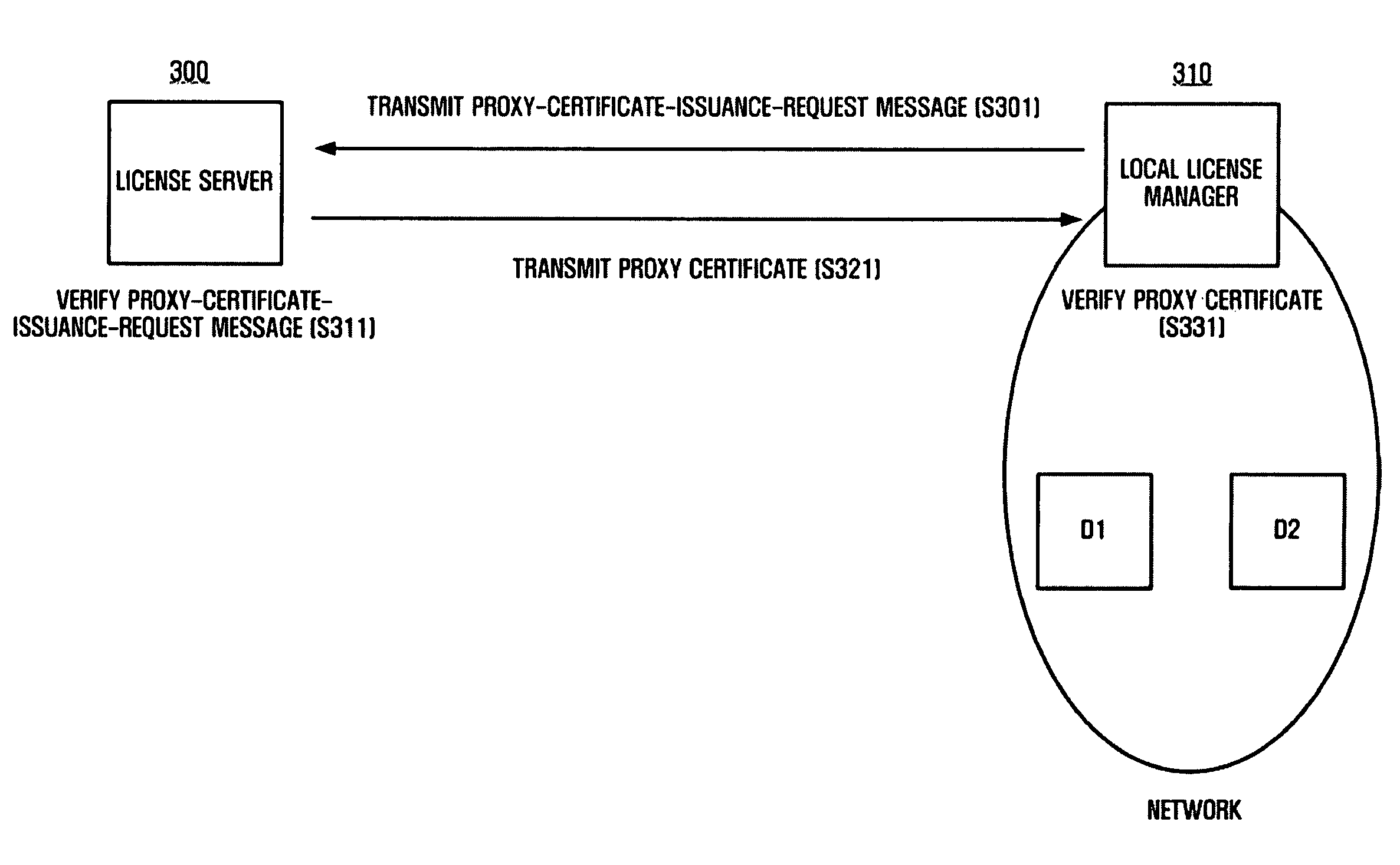
A license-management system and method is provided. A method of issuing a proxy certificate includes transmitting a proxy-certificate-issuance-request message to a license server in order for the local license manager to acquire an authority to issue a license by a local license manager; enabling the license server to verify the proxy-certificate-issuance-request message; if the proxy-certificate-issuance-request message is valid, transmitting a proxy certificate to the local license manager by the license server, the proxy certificate including information regarding the authority to issue a license; and verifying the proxy certificate by the local license manager.
Owner:SAMSUNG ELECTRONICS CO LTD
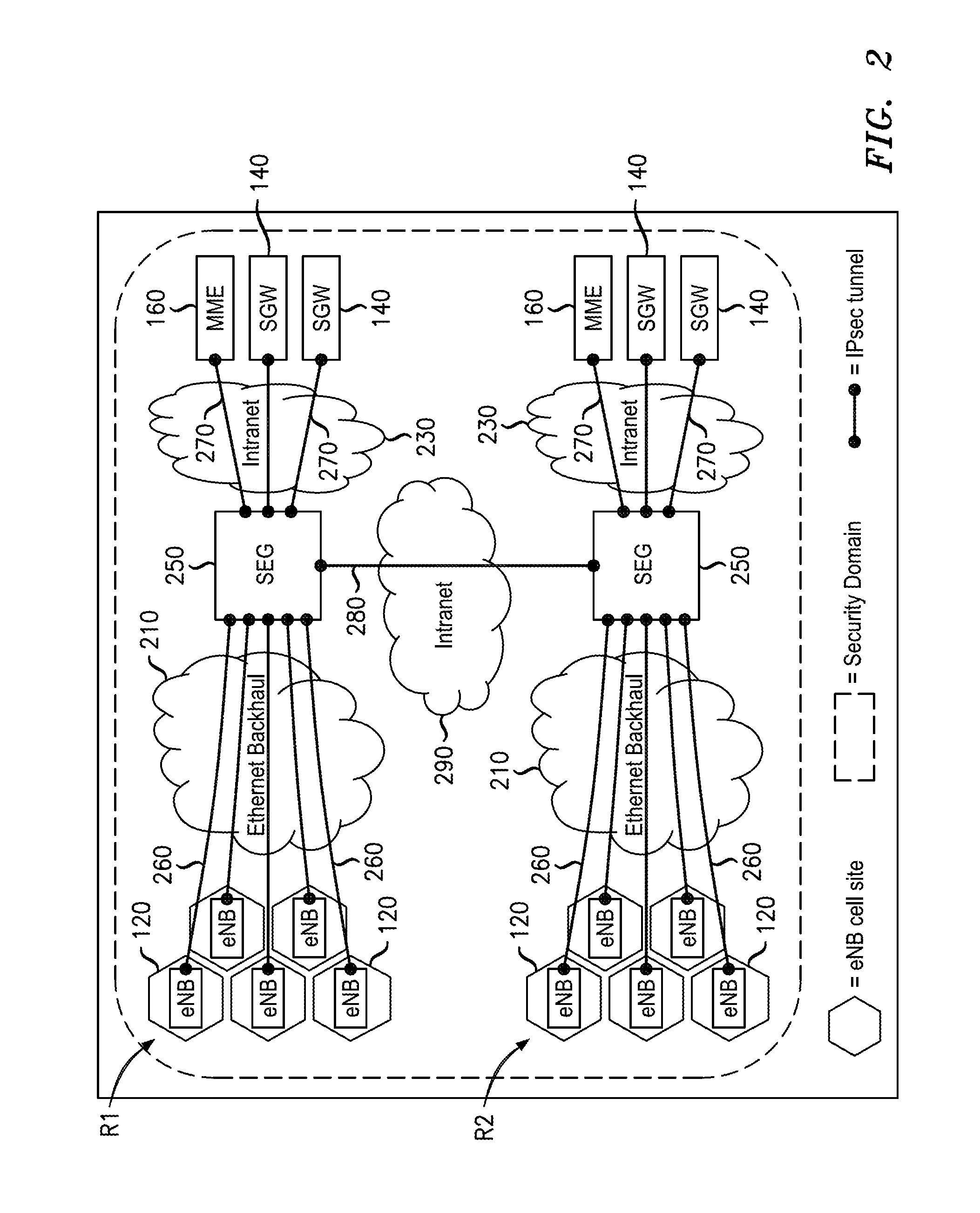
Flexible System And Method To Manage Digital Certificates In A Wireless Network
InactiveUS20120246466A1User identity/authority verificationPublic key infrastructure trust modelsRoot certificateWireless mesh network
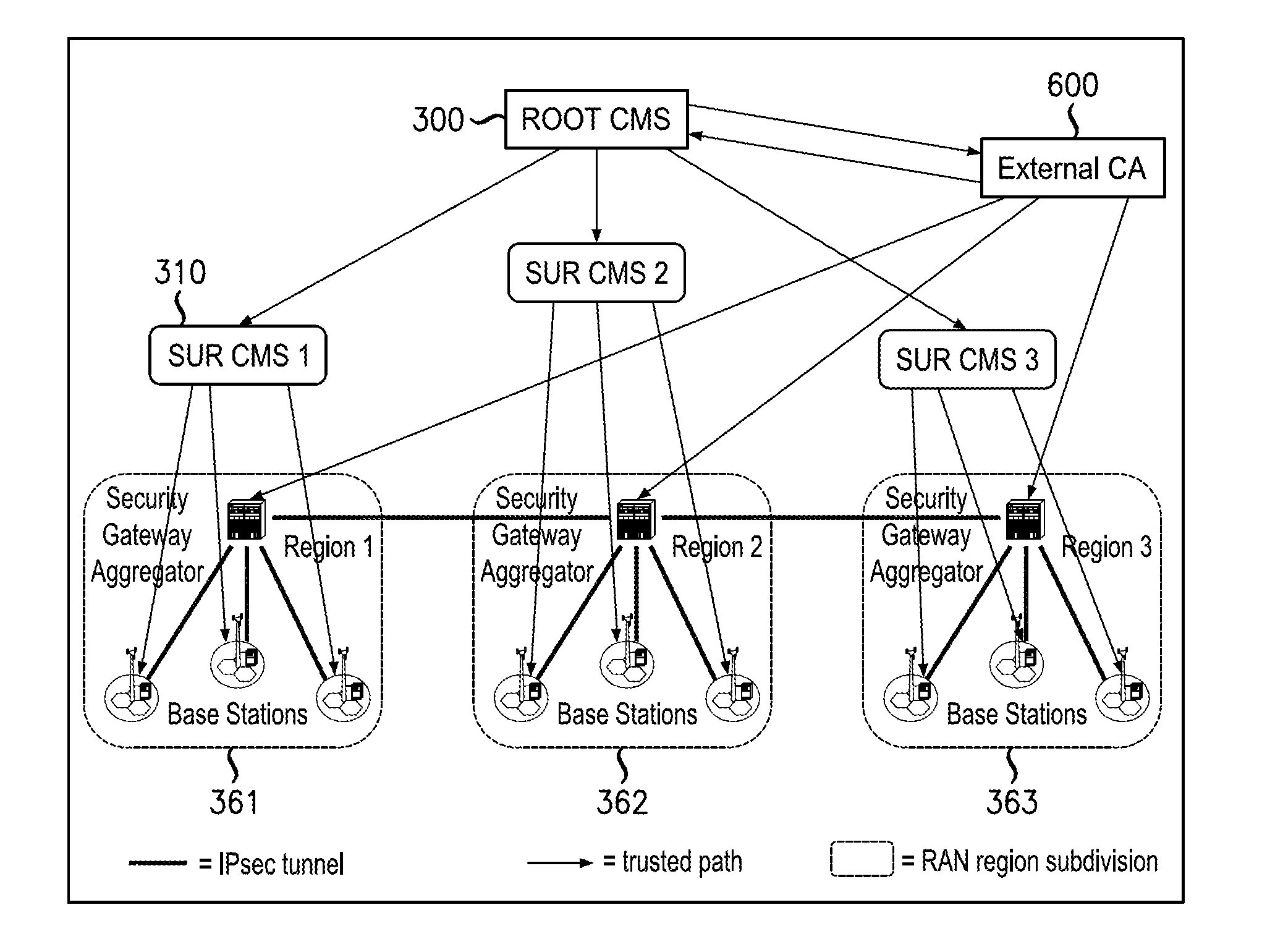
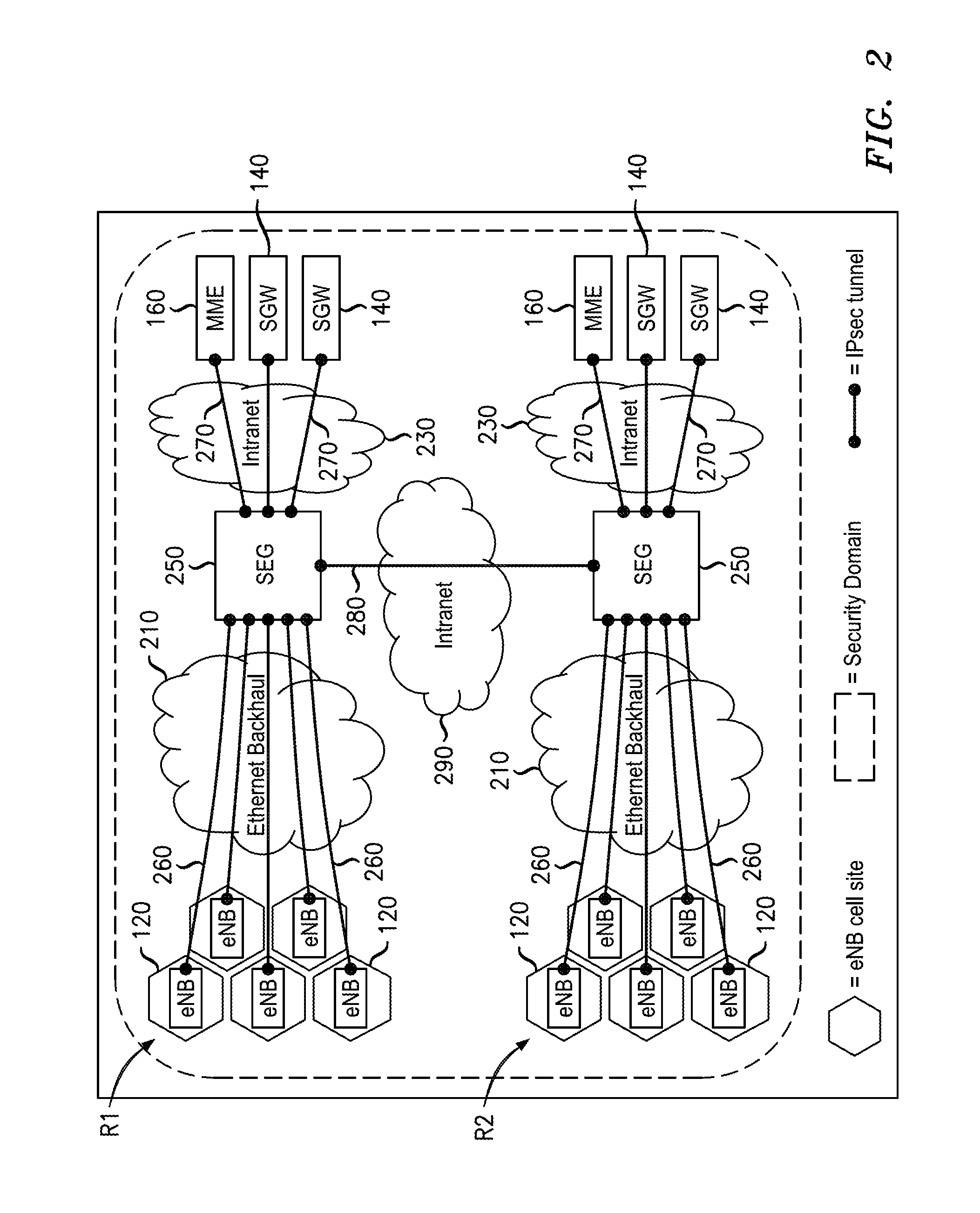
An infrastructure is provided for managing the distribution of digital certificates for network security in wireless backhaul networks. In embodiments, a root certificate management system (root CMS) processes requests for digital certificates, issues root certificates, automatically authenticates surrogate certificate management systems (sur-CMSs), and automatically processes certificate requests and issues certificate bundles to sur-CMSs that are successfully authenticated. The infrastructure includes sur-CMSs to which are assigned base stations within respective regions. Each sur-CMS automatically authenticates its own base stations and automatically processes certificate requests and issues certificate bundles to base stations that are successfully authenticated. A certificate bundle issued to a base station includes a digital certificate, signed by the issuing sur-CMS, of a public key of such base station, and at least one further digital certificate, including a self-signed certificate of the root CMS.
Owner:ALCATEL LUCENT SAS
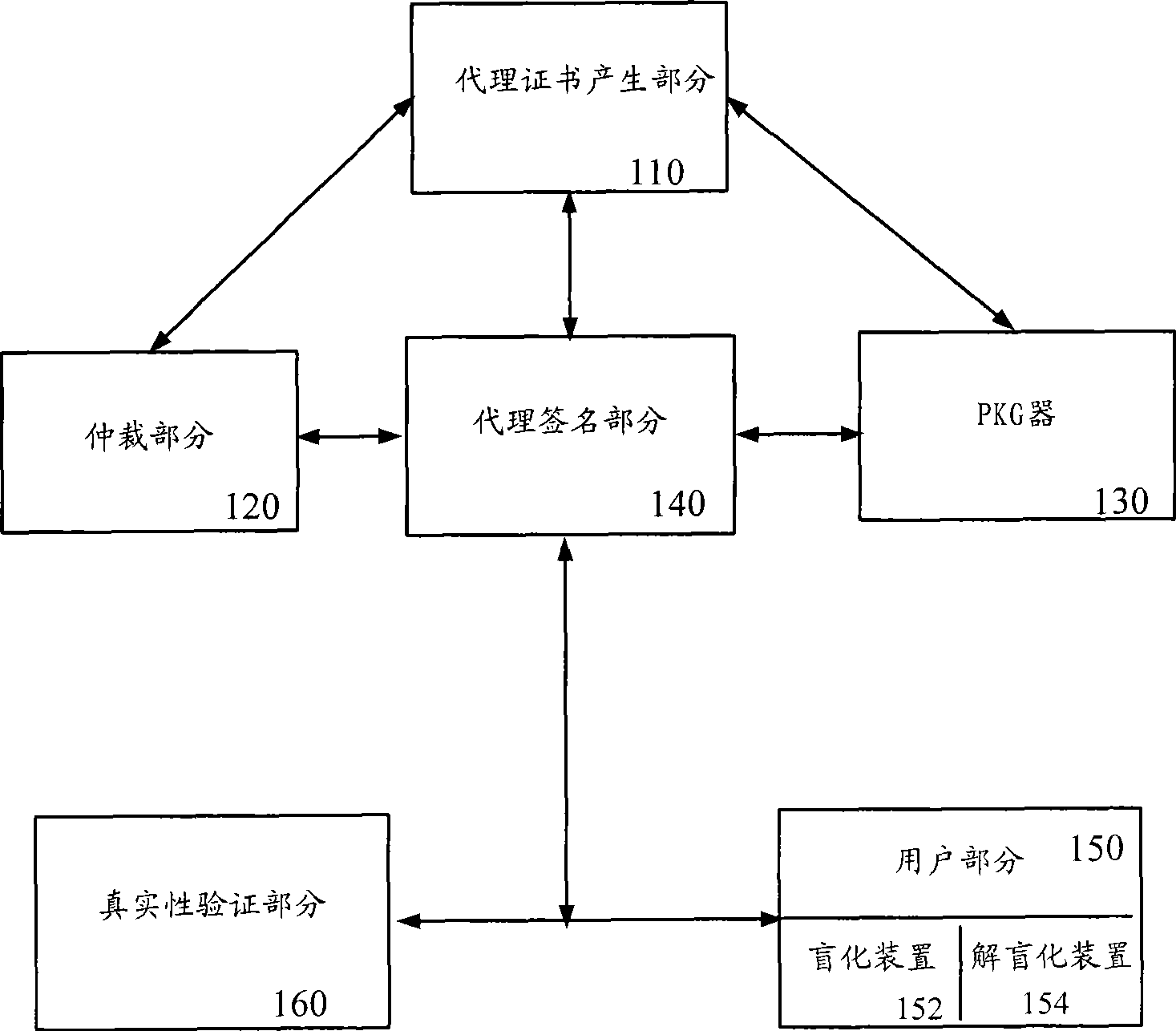
Proxy blind signing system and method based on identification
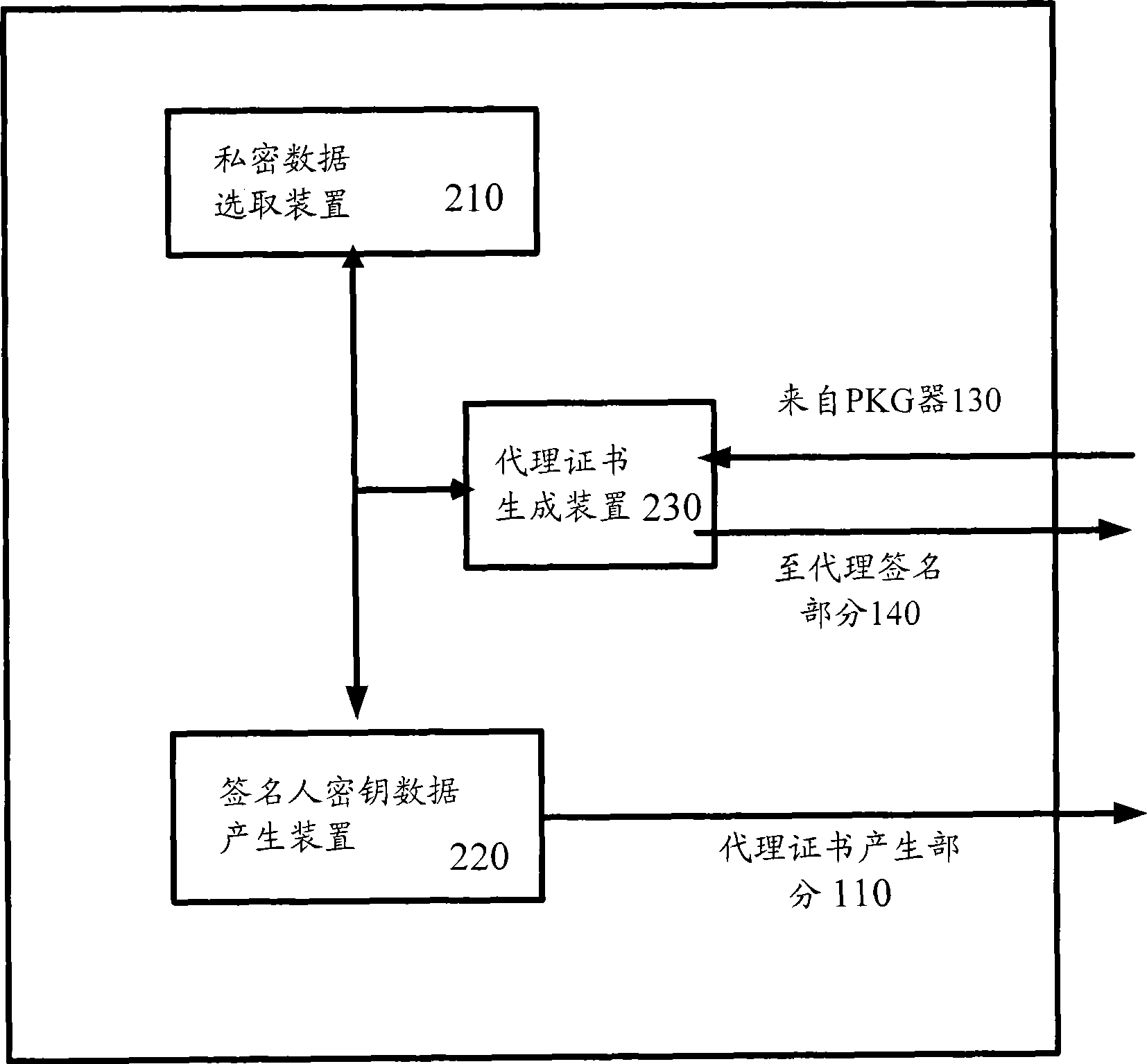
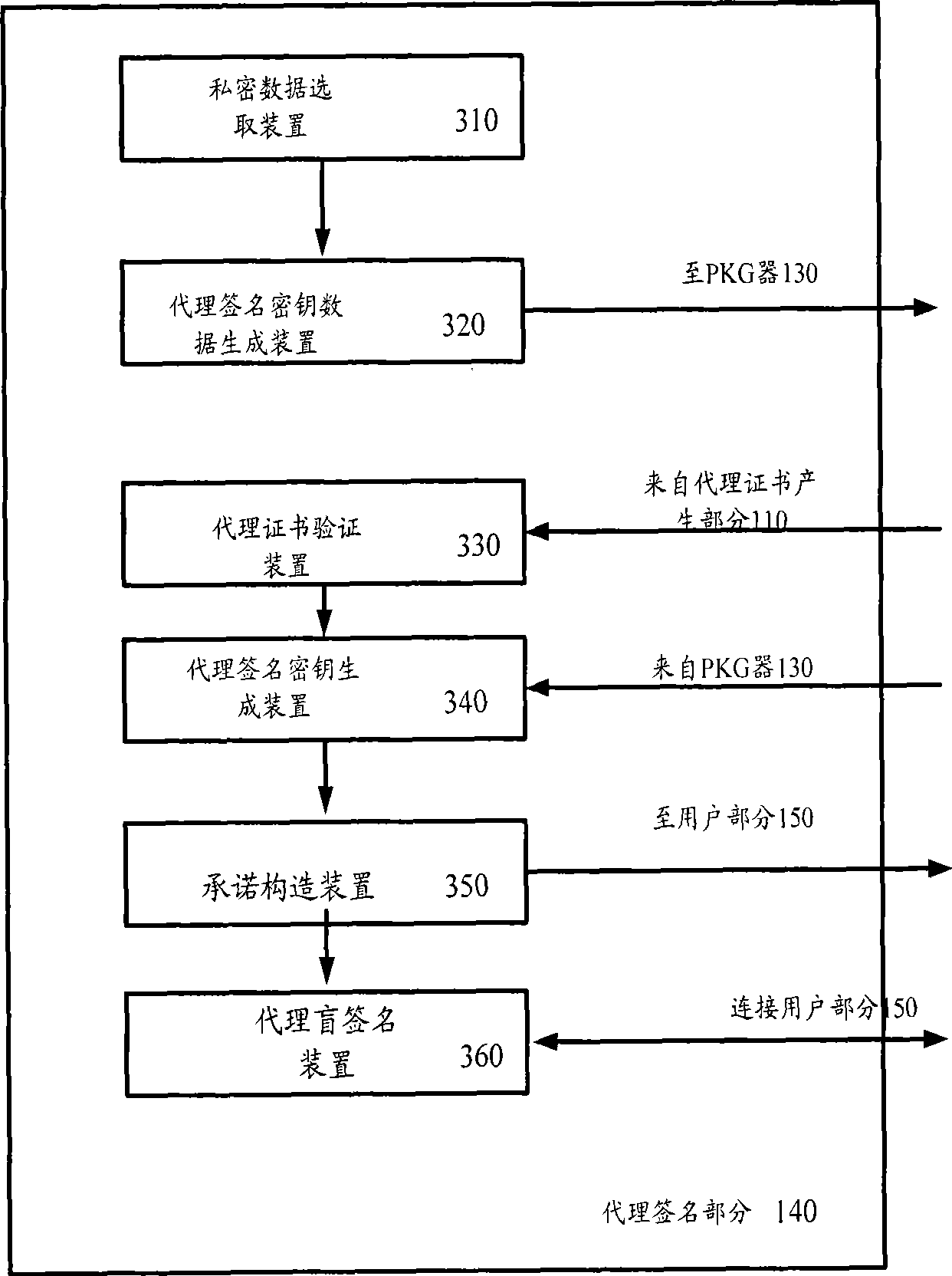
The invention provides an ID-based proxy blind signature system of an incredible private key generator and a method. The system comprises the key generator used for calculating the key according to the obtained key data so as to utilize the signature of the key on a message m to verify the reliability of the message m; a proxy certificate generation part used for generating the key data used by a signer according to the private data of the user and transmitting the key data to the private key generator to calculate the private key SA of the signer and constructing a certificate m Omega and signaling on the certificate m Omega by the private key, so that a proxy certificate W A-B is obtained; and a proxy signature part used for selecting proxy private data to generate corresponding private data and sending the private data to the private key generator to calculate a proxy private key SB and obtaining a proxy signature key according to the private key SB and a proxy public key W A-B, and constructing a premise according the proxy signature key and the proxy certificate W A-B, thereby leading the signature algorithm to satisfying the performances of non-forgery and non-repudiation.
Owner:SONY CHINA
Grid mutual authorization through proxy certificate generation
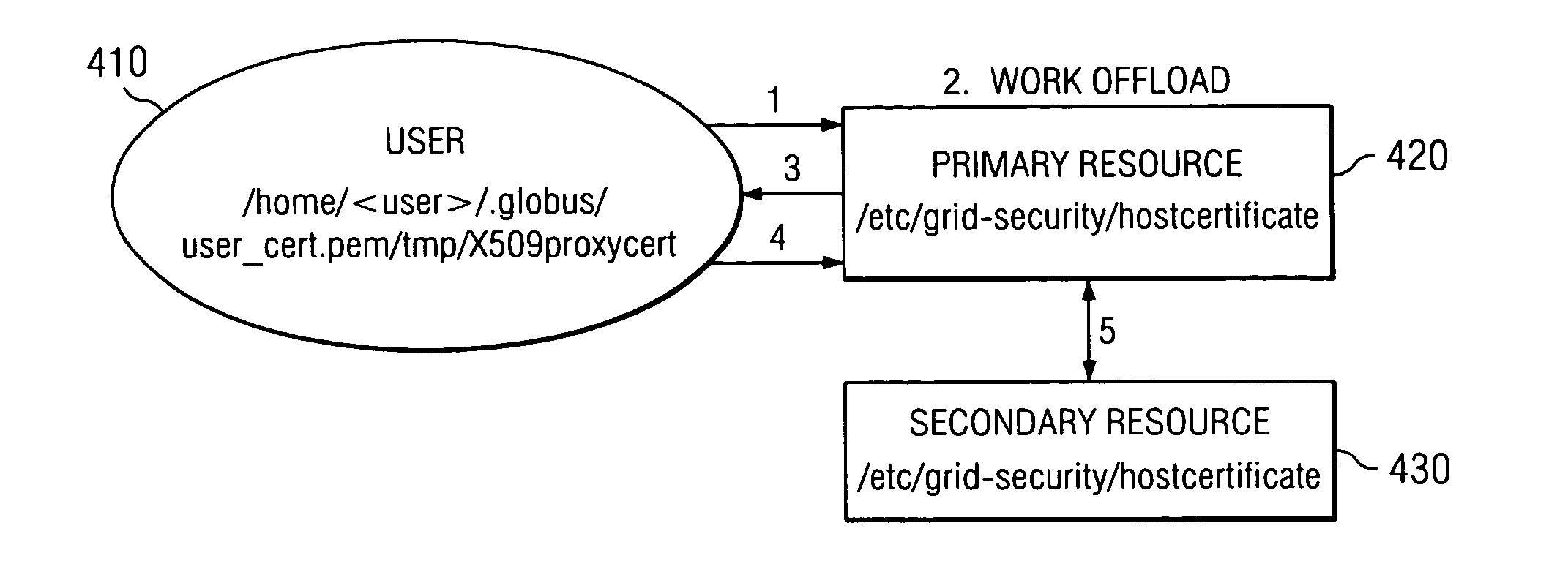
ActiveUS20050216733A1Recognize disadvantageUser identity/authority verificationGeneral purpose stored program computerProxy certificateAuthorization
A mechanism for mutual authorization of a secondary resource in a grid of resource computers is provided. When a primary resource attempts to offload a grid computing job to a secondary resource, the primary resource sends a proxy certificate request to the user machine. Responsive to a proxy certificate request, the user machine performs authorization with the secondary resource. If authorization with the secondary resource is successful, the user machine generates and returns a valid proxy certificate. The primary resource then performs mutual authentication with the secondary resource. If the authorization with the secondary resource fails, the user machine generates and returns an invalid proxy certificate. Mutual authentication between the primary resource and the secondary resource will fail due to the invalid proxy certificate. The primary resource then selects another secondary resource and repeats the process until a resource is found that passes the mutual authorization with the user machine.
Owner:IBM CORP
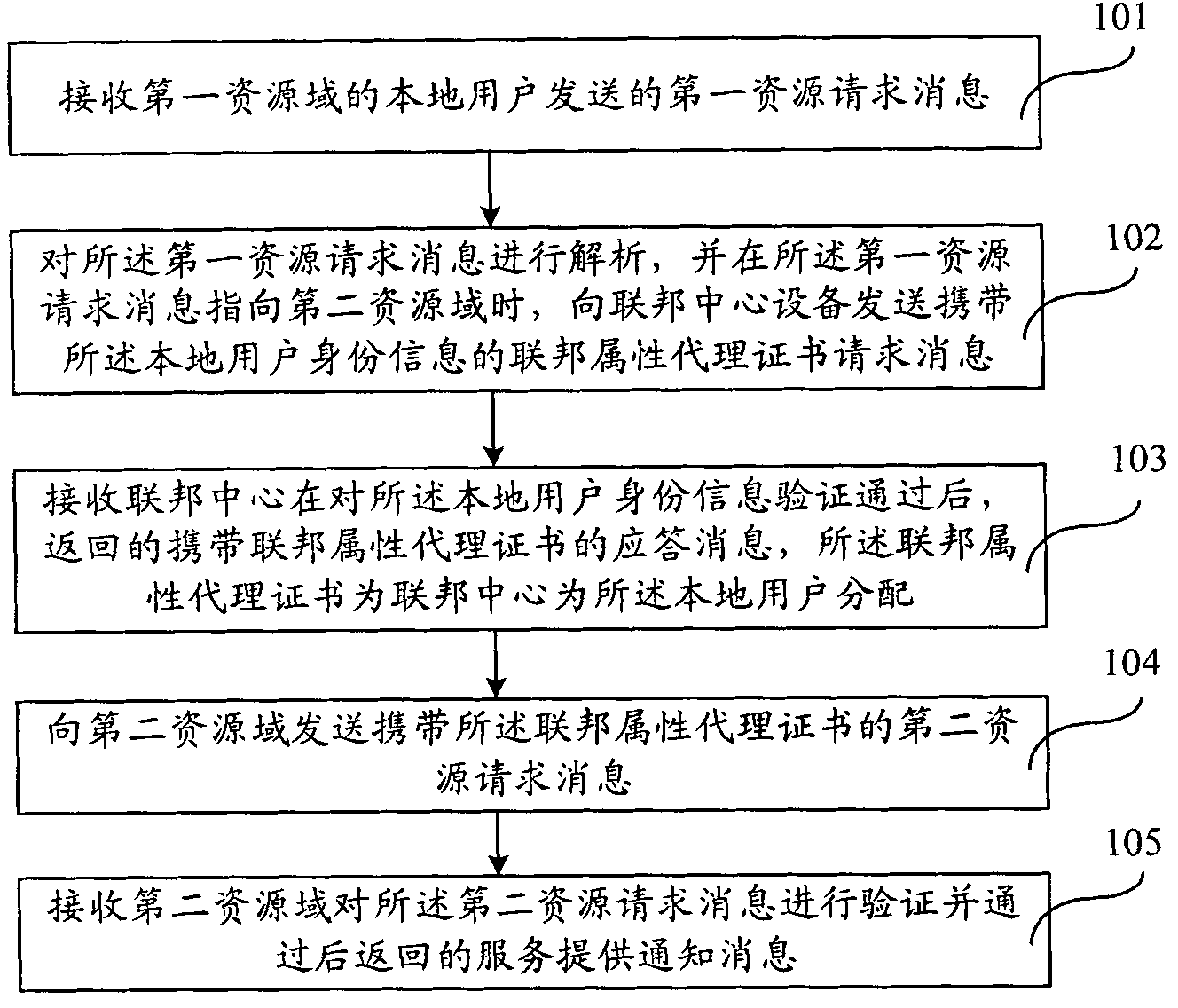
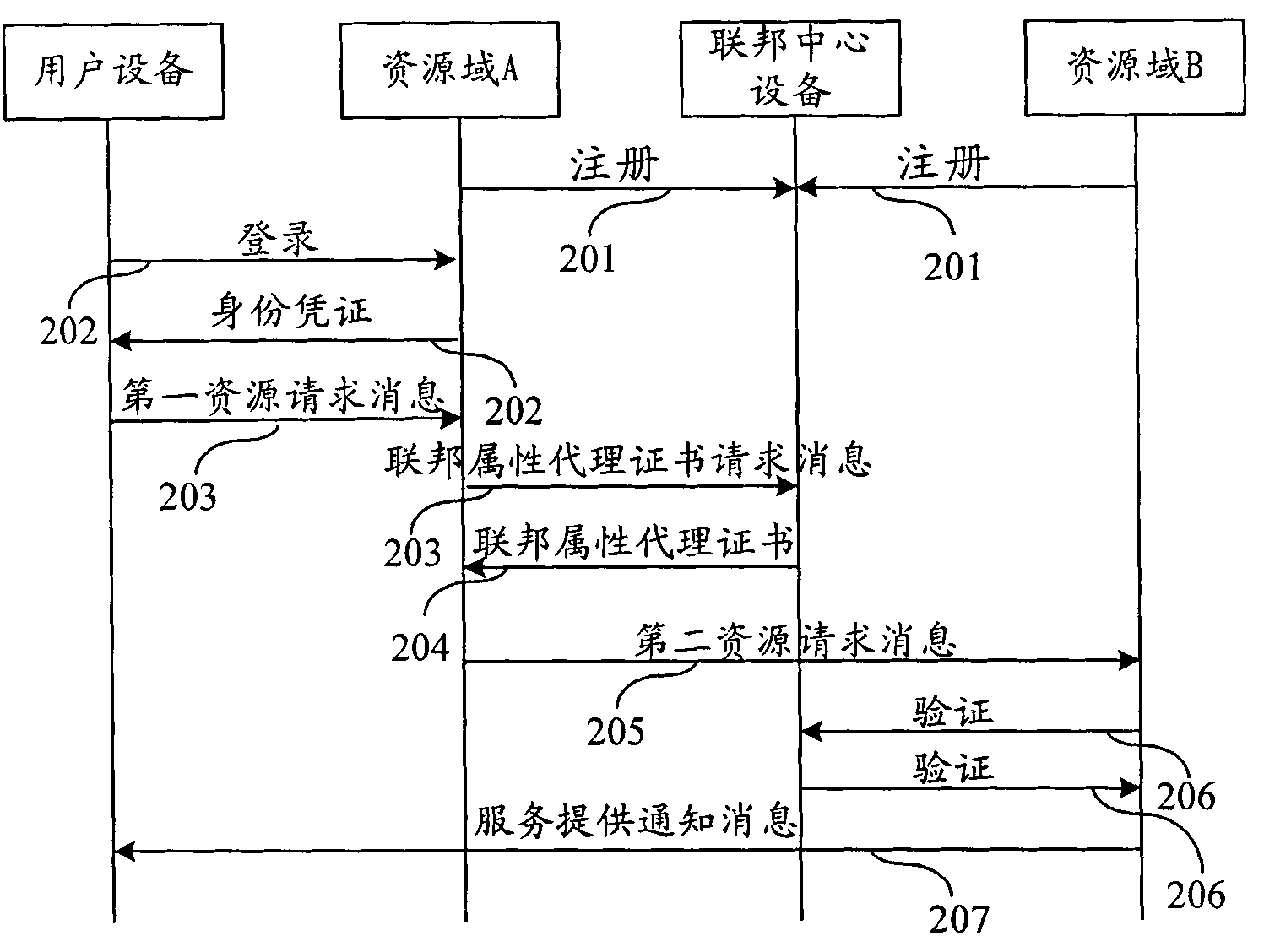
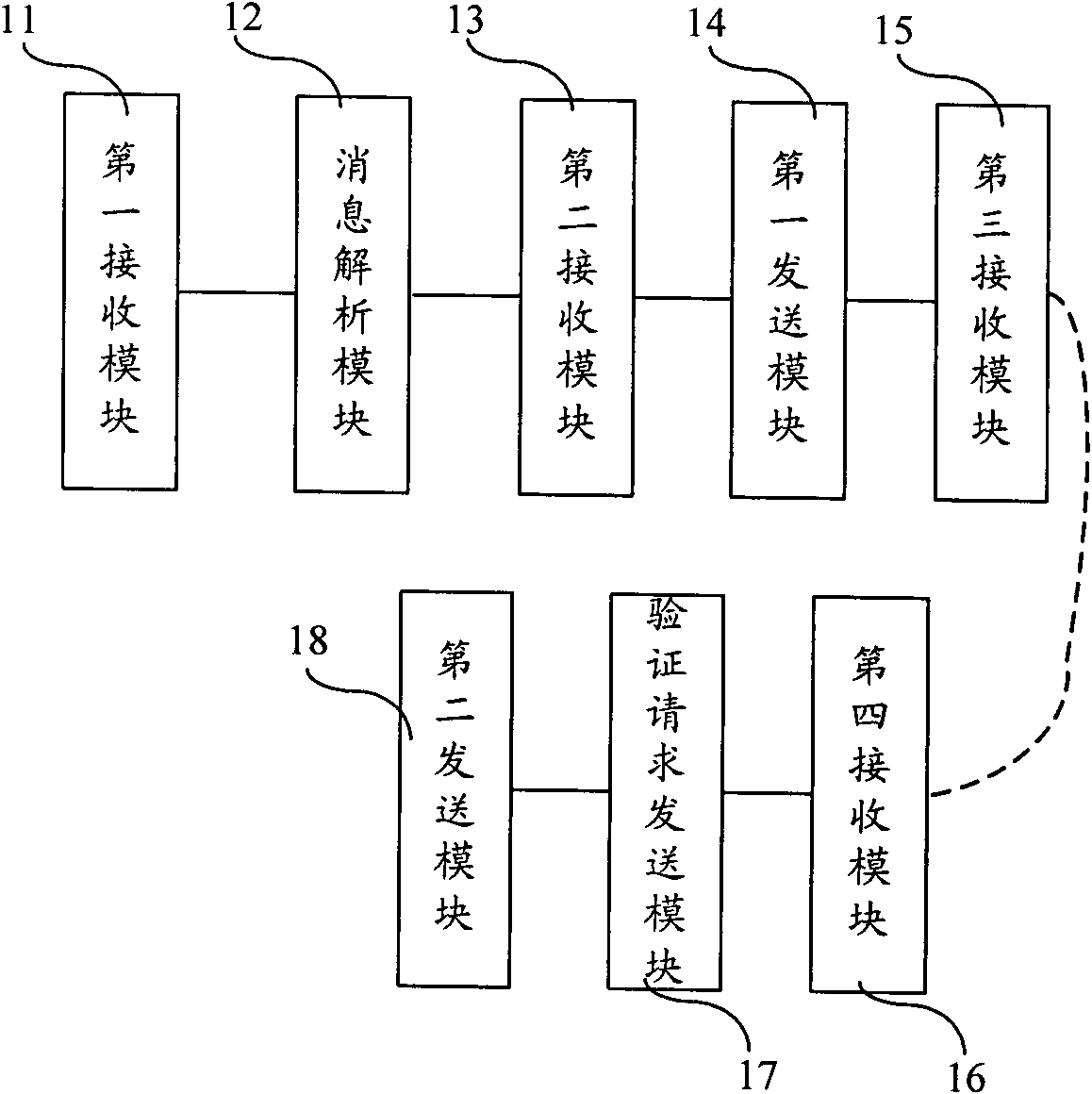
Method and system for safely accessing cross-resource pool resources based on federal center
The invention provides a method, a system and a device for safely accessing cross-resource pool resources based on a federal center, and federal center equipment. The method comprises the following steps of: receiving a first resource request message sent by a local user in a first resource domain; analyzing the first resource request message, and sending a federal attribute proxy certificate request message which carries identity information of the local user to the federal center equipment when the first resource request message points to a second resource domain; receiving a response message which carries a federal attribute proxy certificate and is returned by the federal center equipment after the identity information of the local user passes verification, wherein the federal attribute proxy certificate is allocated to the local user by the federal center; sending a second resource request message which carries the federal attribute proxy certificate to the second resource domain; and receiving a service provision notification message returned by the second resource domain after the second resource domain verifies the second resource request message and the second resource request message passes verification. Through the technical scheme, cross-resource domain resources can be called.
Owner:BEIHANG UNIV
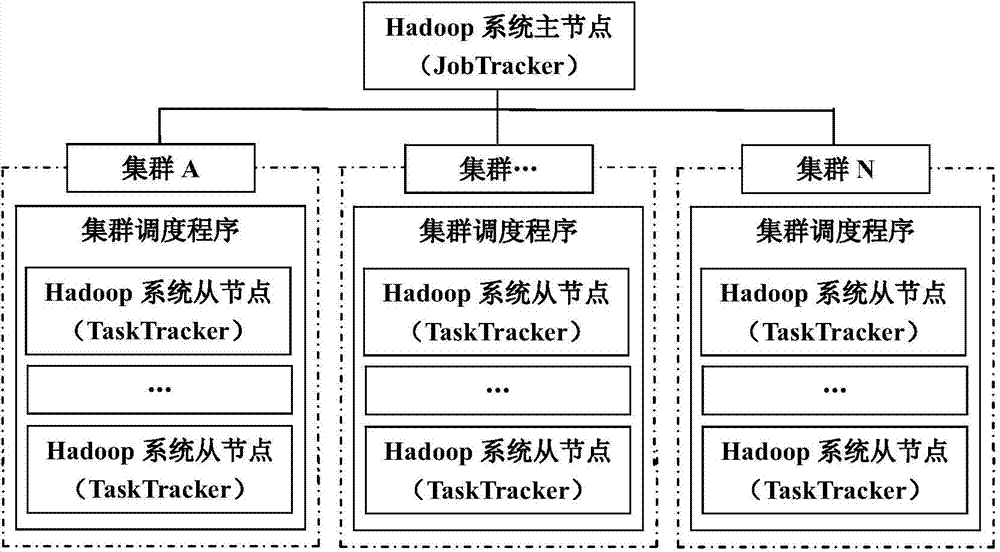
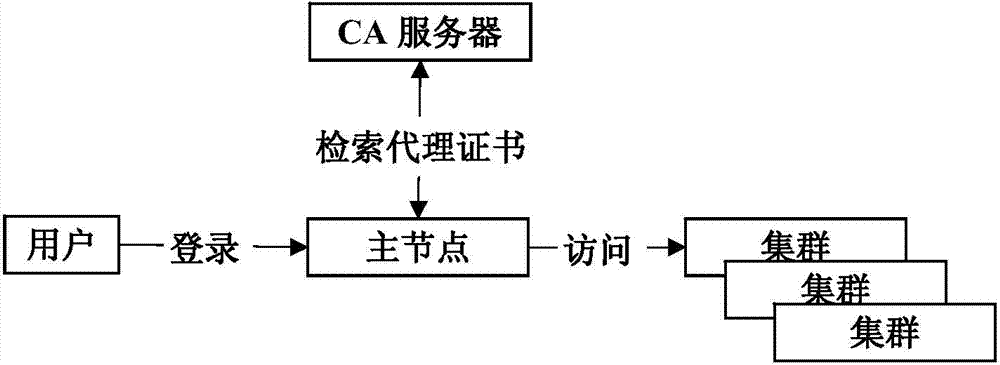
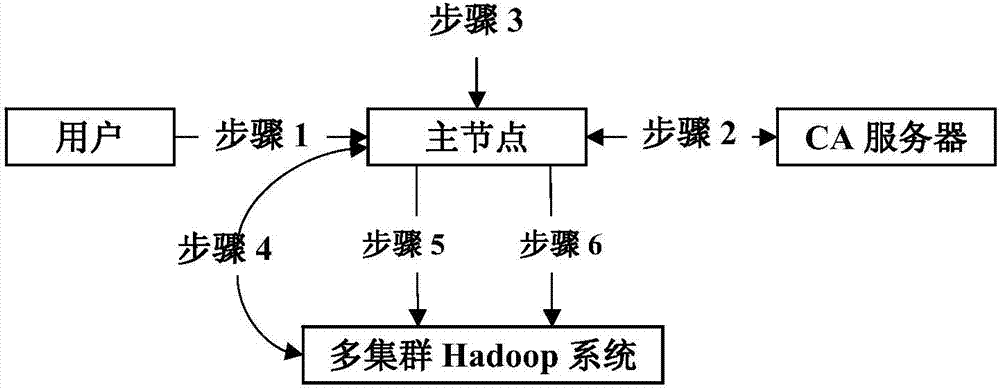
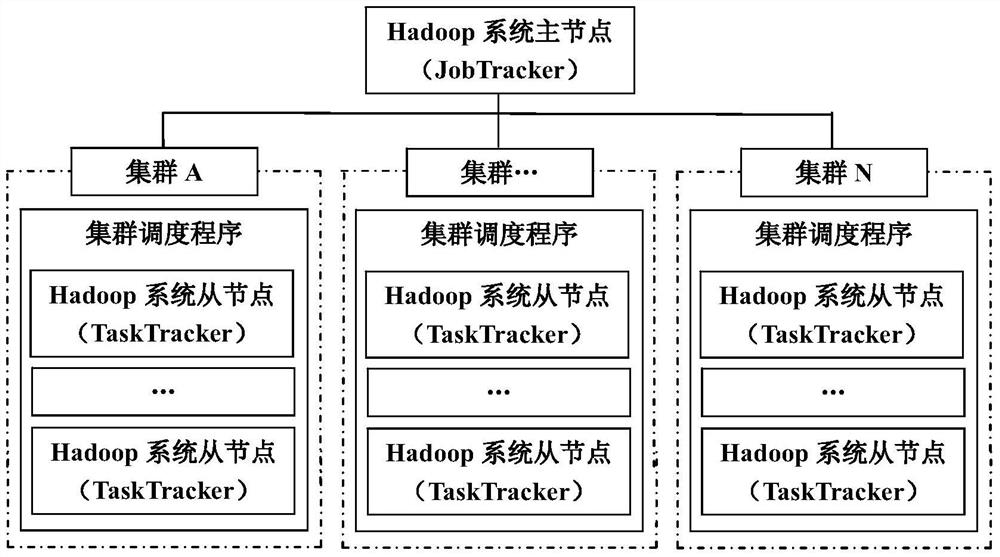
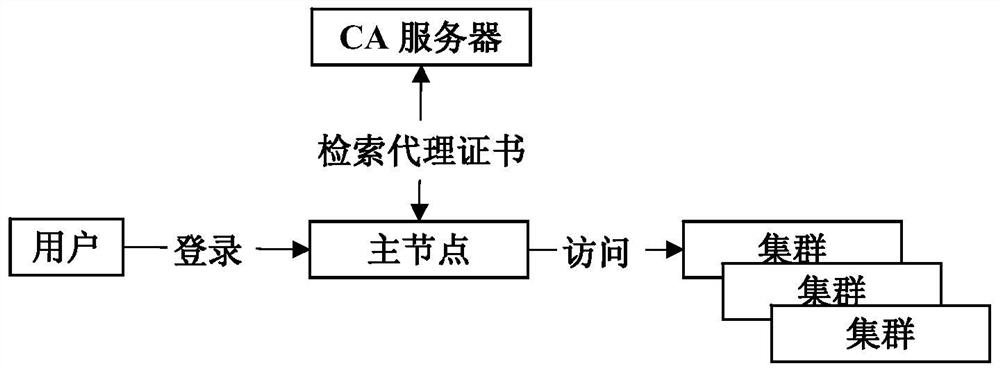
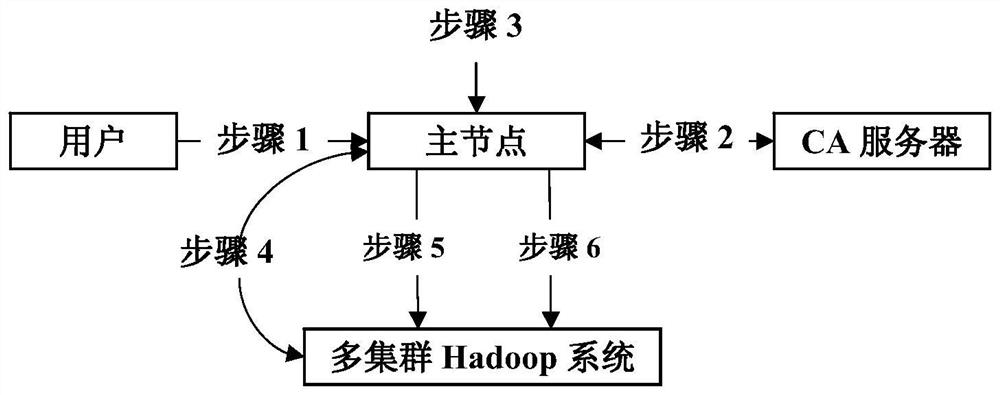
Public key algorithm and SSL (security socket layer) protocol based method of optimizing security of multi-cluster Hadoop system
ActiveCN104735087AAchieve protectionPublic key for secure communicationUser identity/authority verificationMulti clusterSingle cluster
The invention provides a public key algorithm and SSL (security socket layer) protocol based method of optimizing security of a multi-cluster Hadoop system. The method includes the steps of authenticating identity of a user when the user logs in to a master node; allowing the master node to submit a request to a CA (certificate authority) server to acquire a proxy certificate; allowing the master node to create a slave node list and determine identity of the master node; allowing bidirectional authentication between the master node and slave nodes; allowing the multi-cluster Hadoop system to execute a task submitted by the user; stopping the user from submitting tasks. The method has the advantages that user authentication and network attack protection are effectively achieved for the Hadoop system running across multiple cluster environments, the defect of the original security mechanism of the single-cluster Hadoop system running in the multiple cluster environments is made up, and the network attack protection with the original security mechanism of the single-cluster Hadoop system forms complete security protection for the multi-cluster Hadoop system.
Owner:STATE GRID CORP OF CHINA +2
Implementing method of network security system capable of self-updating letter of representation
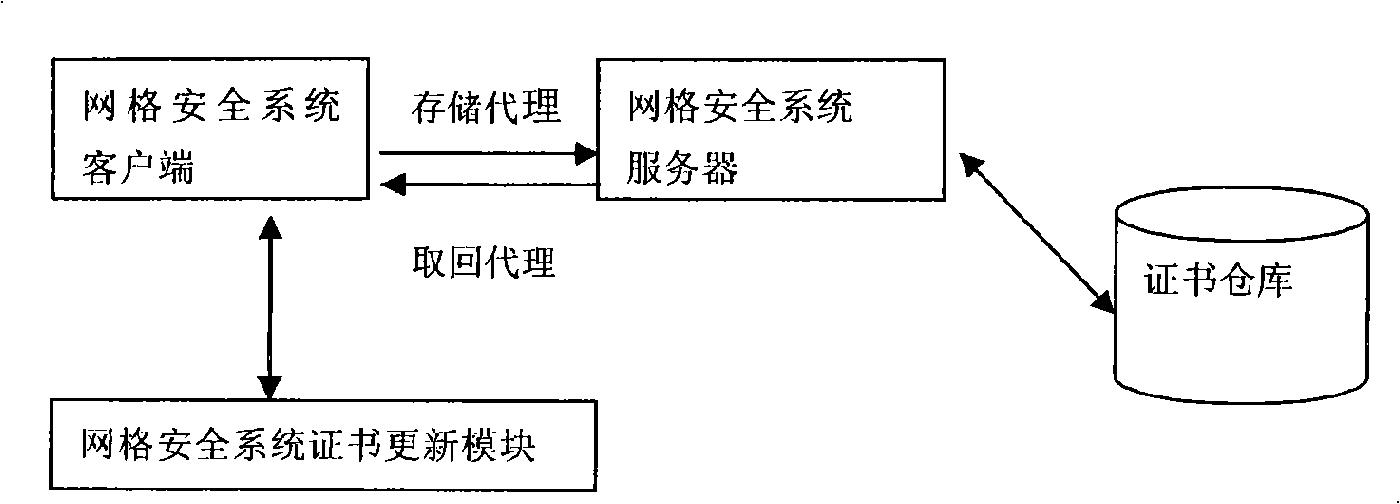
InactiveCN101309146AEasy to storeEnsure safetyUser identity/authority verificationMultiple digital computer combinationsComputer moduleNetwork security policy
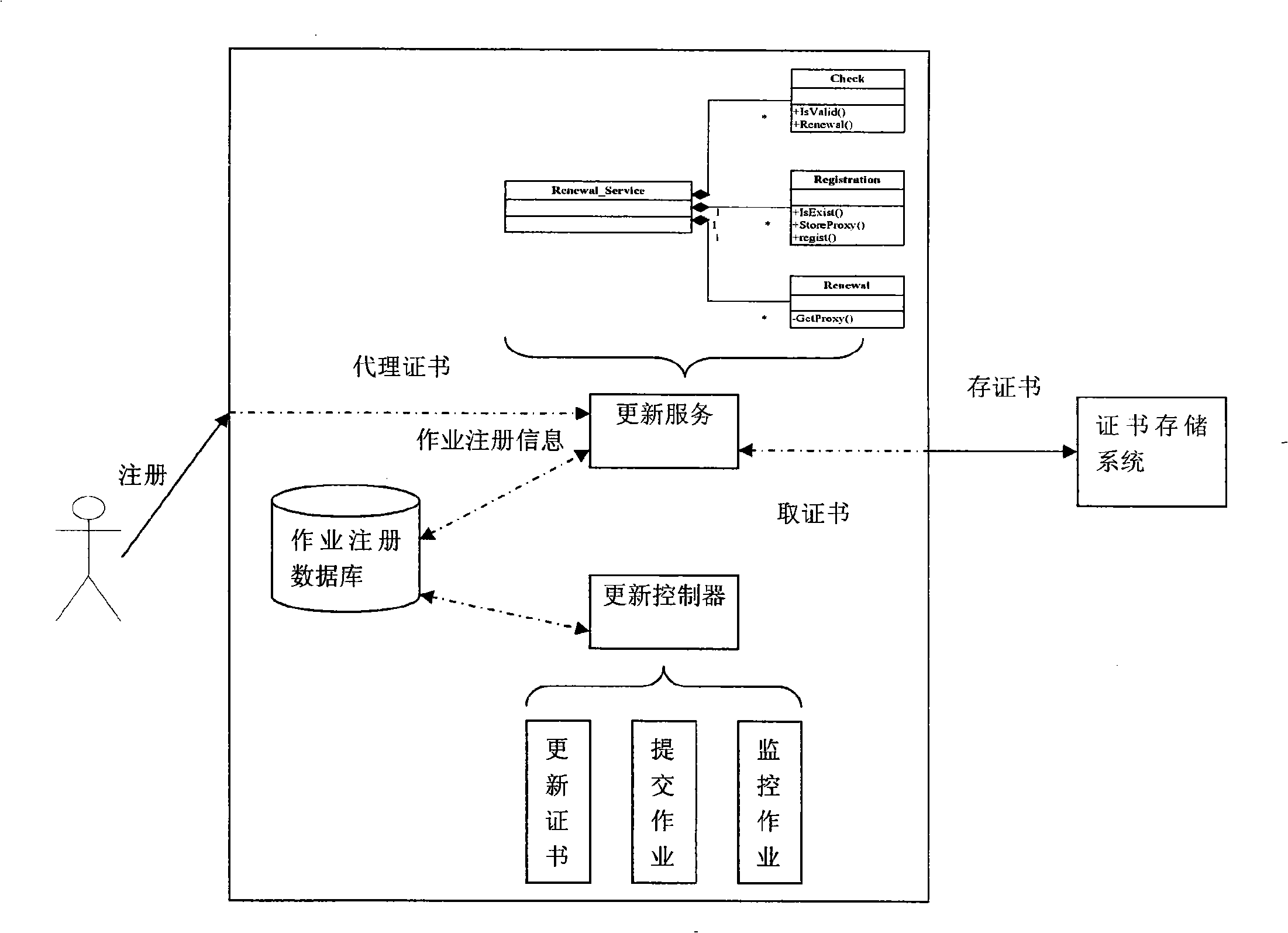
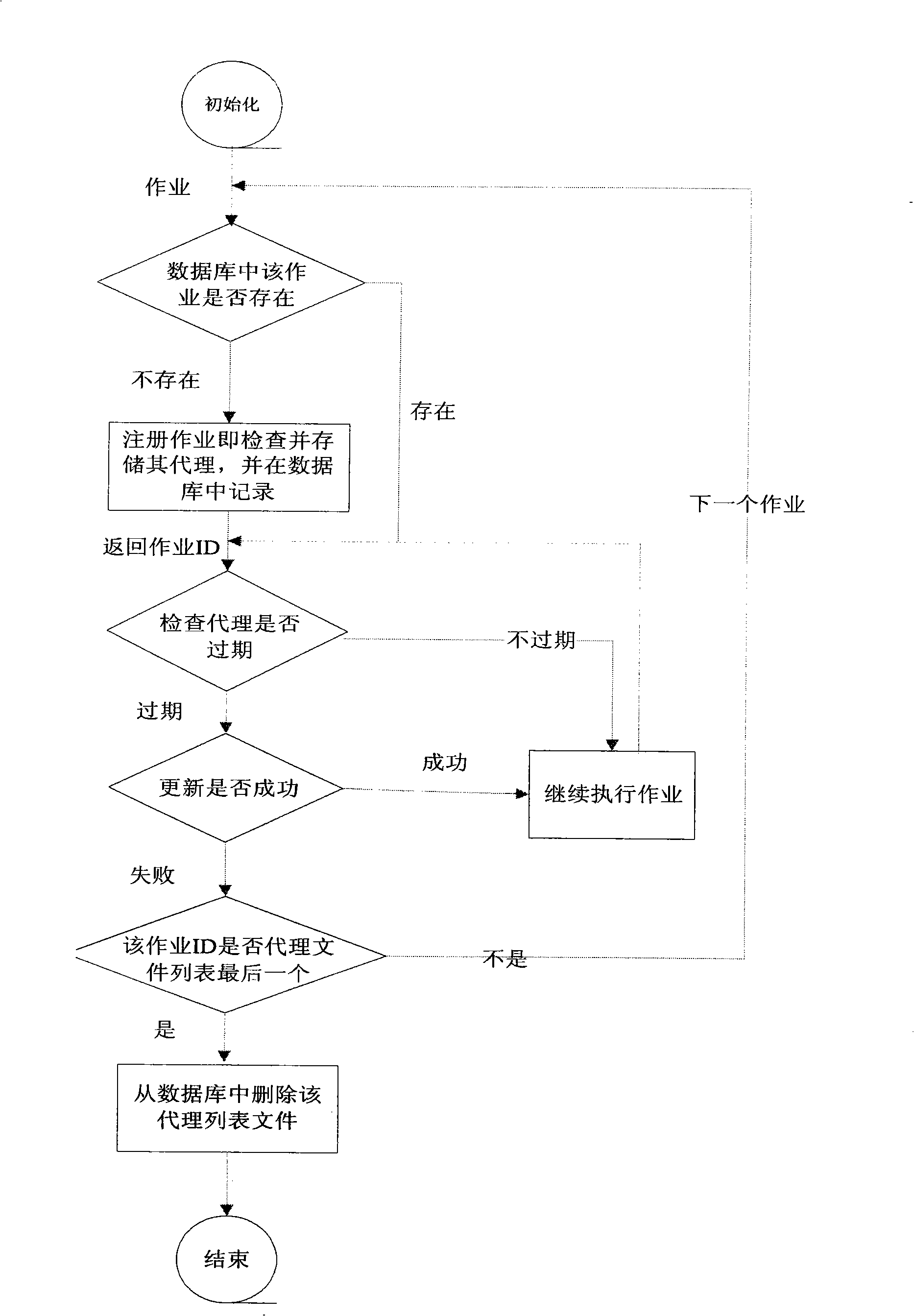
Disclosed is an implementation method of a grid security system which can update the proxy certificate automatically; the implementation method is a strategic method and adopts a regular check mechanism to check the proxy certificate of the operation continuously; once the overdue proxy certificate is detected and the proxy is updated automatically to ensure the normal running of the operation. The grid security system which can update the proxy certificate automatically is mainly composed of a grid security system client, a grid security system server, a grid security system certificate updating module and a certificate repository; the proxy updating service uses the function provided by the certificate repository. From the logical viewpoint, the service can be considered as a module of the operation management system; the module records and manages the proxy certificates of the submitted operations and the operations require the proxy to be updated; therefore, the operation maintained by the service remains the validity through the way; the updated proxy is searched back from the certificate repository periodically to replace the proxy which is about to be overdue.
Owner:NANJING UNIV OF POSTS & TELECOMM
Flexible system and method to manage digital certificates in a wireless network
InactiveUS8627064B2Digital data processing detailsUser identity/authority verificationRoot certificateSelf-signed certificate
An infrastructure is provided for managing the distribution of digital certificates for network security in wireless backhaul networks. In embodiments, a root certificate management system (root CMS) processes requests for digital certificates, issues root certificates, automatically authenticates surrogate certificate management systems (sur-CMSs), and automatically processes certificate requests and issues certificate bundles to sur-CMSs that are successfully authenticated. The infrastructure includes sur-CMSs to which are assigned base stations within respective regions. Each sur-CMS automatically authenticates its own base stations and automatically processes certificate requests and issues certificate bundles to base stations that are successfully authenticated. A certificate bundle issued to a base station includes a digital certificate, signed by the issuing sur-CMS, of a public key of such base station, and at least one further digital certificate, including a self-signed certificate of the root CMS.
Owner:ALCATEL LUCENT SAS
Communication system and method in public key infrastructure
InactiveUS7797533B2User identity/authority verificationCoding/ciphering apparatusRoot certificateCommunications system
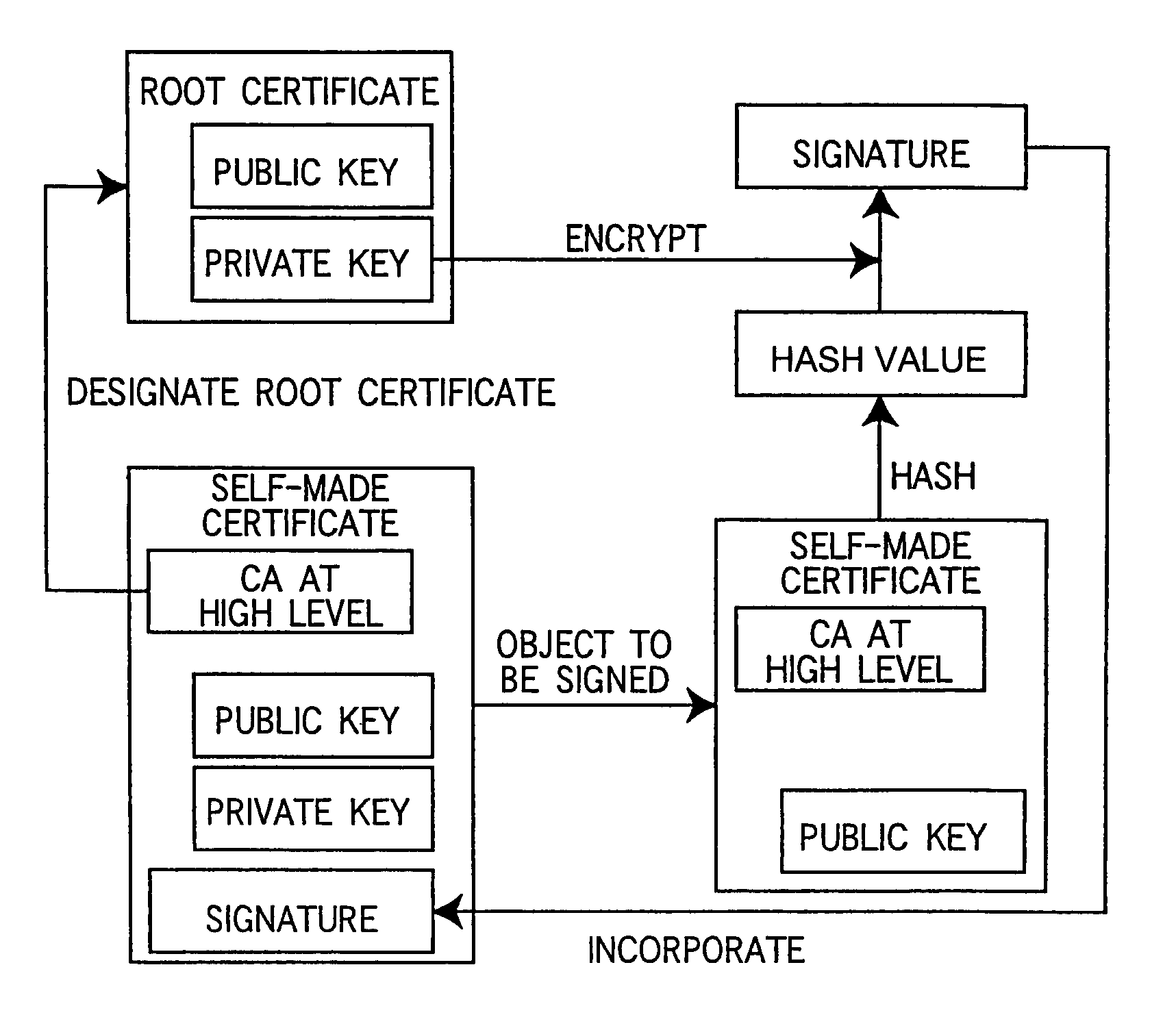
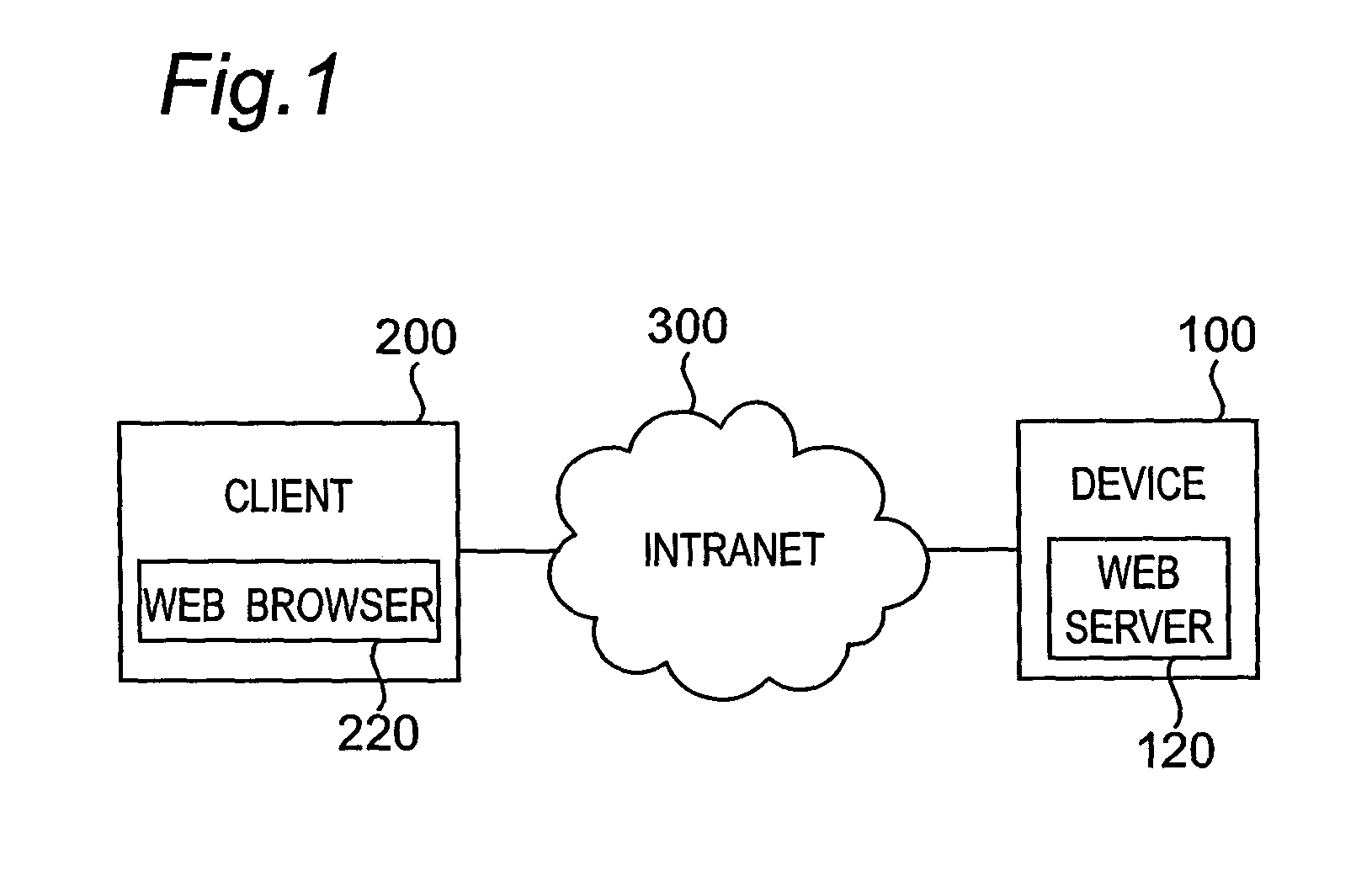
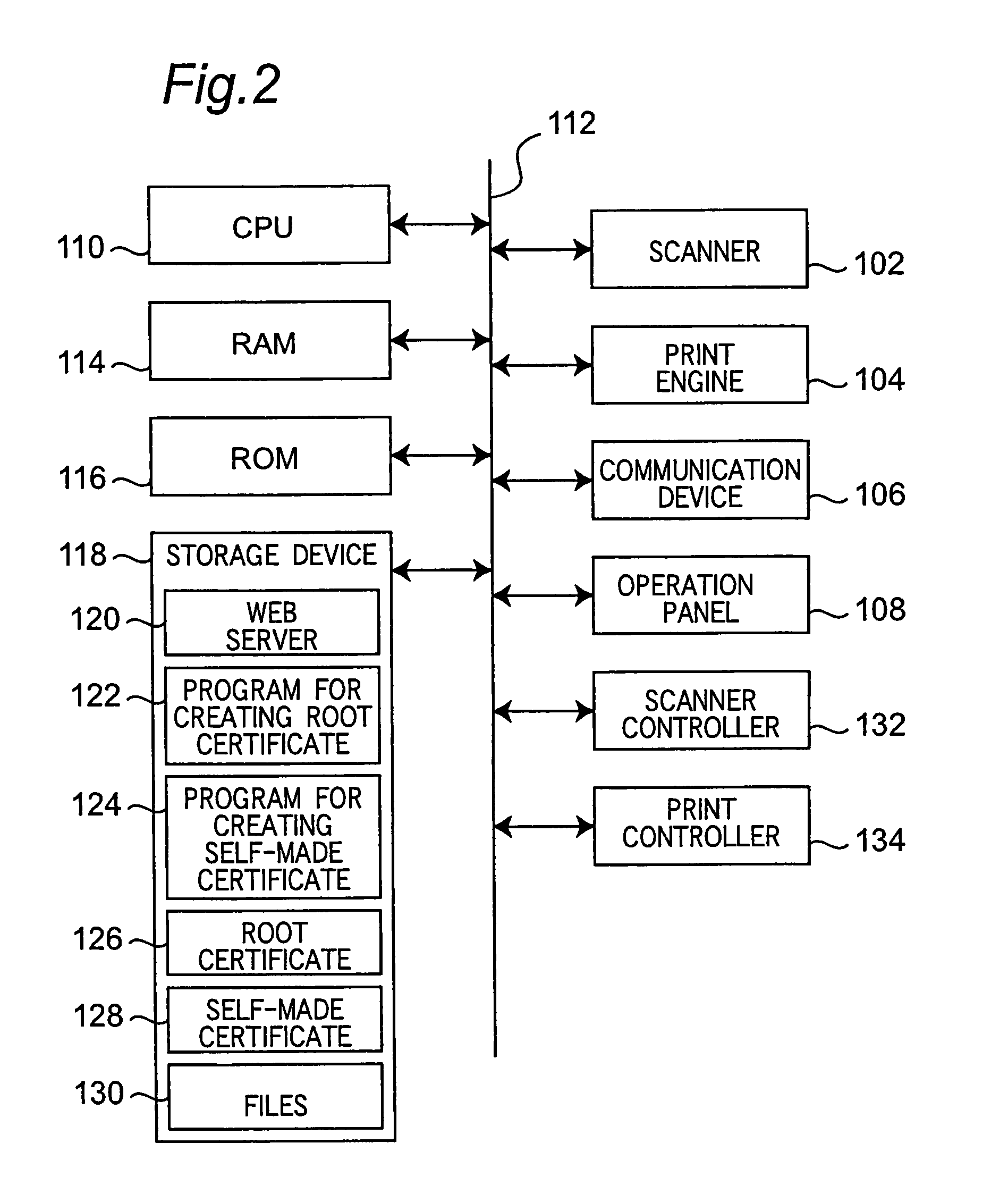
In a communication system wherein a device and a client communicate data with each other through a network, the device holds a root certificate including a public key in a pair of the public key and a private key and signed with the public key. When data is sent, a certificate creator creates a second certificate including the root certificate designated as a certificate authority at a higher level and signed with the root certificate, and the second certificate is sent to the client. In the client, the root certificate has been stored beforehand, and a verifier verifies the signature of the second certificate with the root certificate.
Owner:MINOLTA CO LTD
Method and system for a single-sign-on operation providing grid access and network access
InactiveUS7496755B2User identity/authority verificationMultiple digital computer combinationsSuccessful completionUser device
A user device initiates a network access authentication operation via a network access device with a network access authentication server, e.g., a Remote Authentication Dial-In User Service (RADIUS) server, which also generates an X.509 proxy certificate and includes the proxy certificate with the information, such as a set of network access parameters, that is returned to the user device in response to a successful completion of the network access authentication operation. The user device extracts and stores the proxy certificate. The network access parameters are used by the user device to communicate via the network access device on a network, which supports a grid. When the user device accesses a resource in the grid, the proxy certificate is already available, thereby obviating the need to generate a new proxy certificate and allowing a user of the user device to experience an integrated single-sign-on for network access and grid access.
Owner:INT BUSINESS MASCH CORP
Grid mutual authorization through proxy certificate generation
ActiveUS7467303B2User identity/authority verificationGeneral purpose stored program computerProxy certificateComputer science
A method for mutual authorization of a secondary resource in a grid of resource computers is provided. When a primary resource attempts to offload a grid computing job to a secondary resource, the primary resource sends a proxy certificate request to the user machine. Responsive to a proxy certificate request, the user machine performs authorization with the secondary resource. If authorization with the secondary resource is successful, the user machine generates and returns a valid proxy certificate. The primary resource then performs mutual authentication with the secondary resource. If the authorization with the secondary resource fails, the user machine generates and returns an invalid proxy certificate. Mutual authentication between the primary resource and the secondary resource will fail due to the invalid proxy certificate. The primary resource then selects another secondary resource and repeats the process until a resource is found that passes the mutual authorization with the user machine.
Owner:IBM CORP
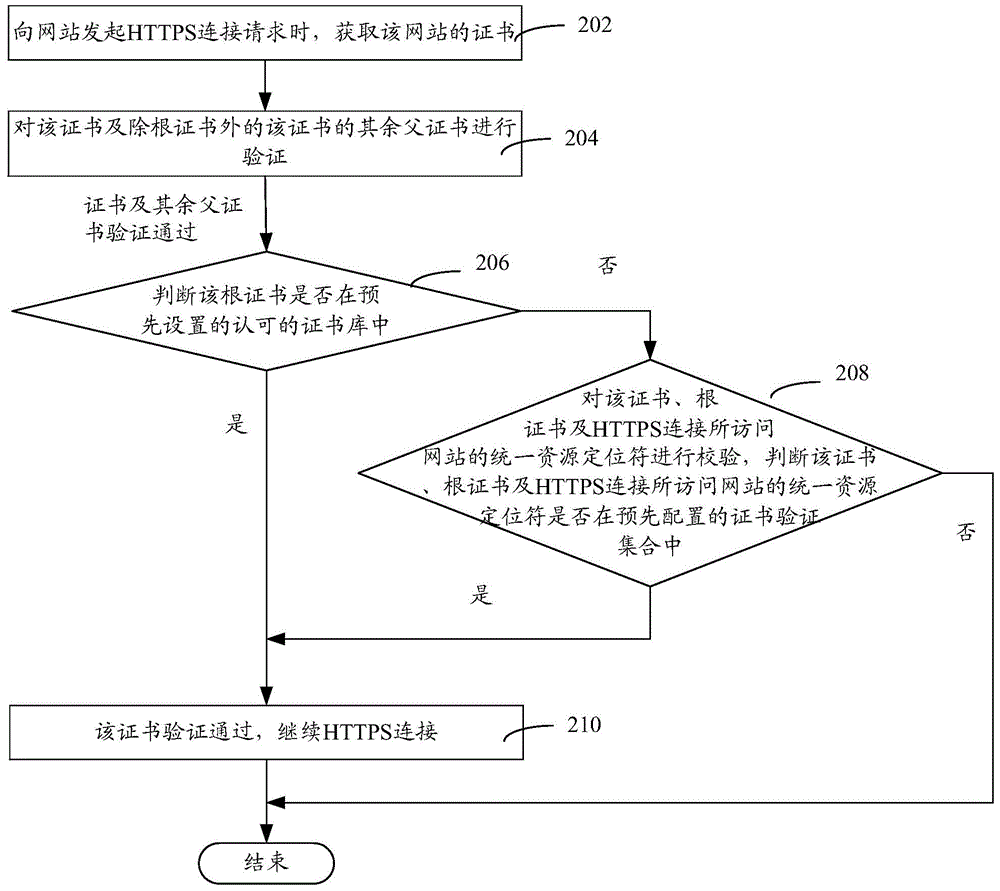
HTTPS connection verification method and device
The invention relates to an HTTPS connection verification method and device. The method comprises the following steps: when an HTTPS connection request is initiated to a website, a certificate of the website is obtained; the certificate and other father certificates of the certificate except for a root certificate are verified; if verifications of the certificate and the other father certificates are passed, whether the root certificate is in a preset approval certificate library is judged; if the root certificate is in the preset approval certificate library, the certificate verifications are passed, HTTPS connection is continued; if the root certificate is not in the preset approval certificate library, the certificate, the root certificate and a uniform resource locator of the website accessed by the HTTPS connection are verified, whether the certificate, the root certificate and the uniform resource locator of the website accessed by the HTTPS connection are in a preconfigured certificate verification set; if the certificate, the root certificate and the uniform resource locator of the website accessed by the HTTPS connection are in the preconfigured certificate verification set, the certificate verifications are passed, and the HTTPS connection is continued; and, if the certificate, the root certificate and the uniform resource locator of the website accessed by the HTTPS connection are not in the preconfigured certificate verification set, the process is ended. The HTTPS connection verification method and device do not need to install the root certificate, prevent a system from a threat, and improve safety of the system.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Methods for client certificate delegation and devices thereof
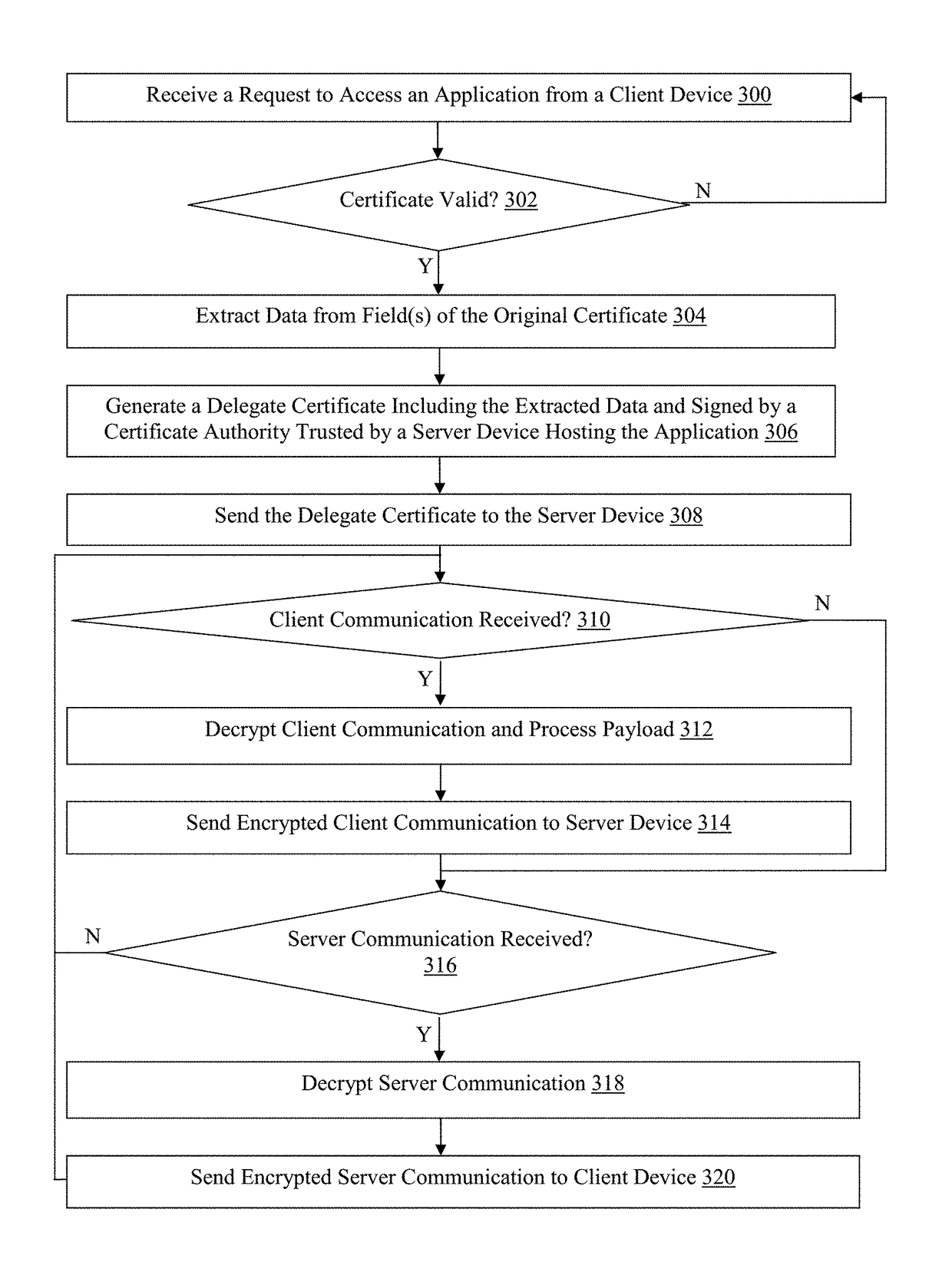
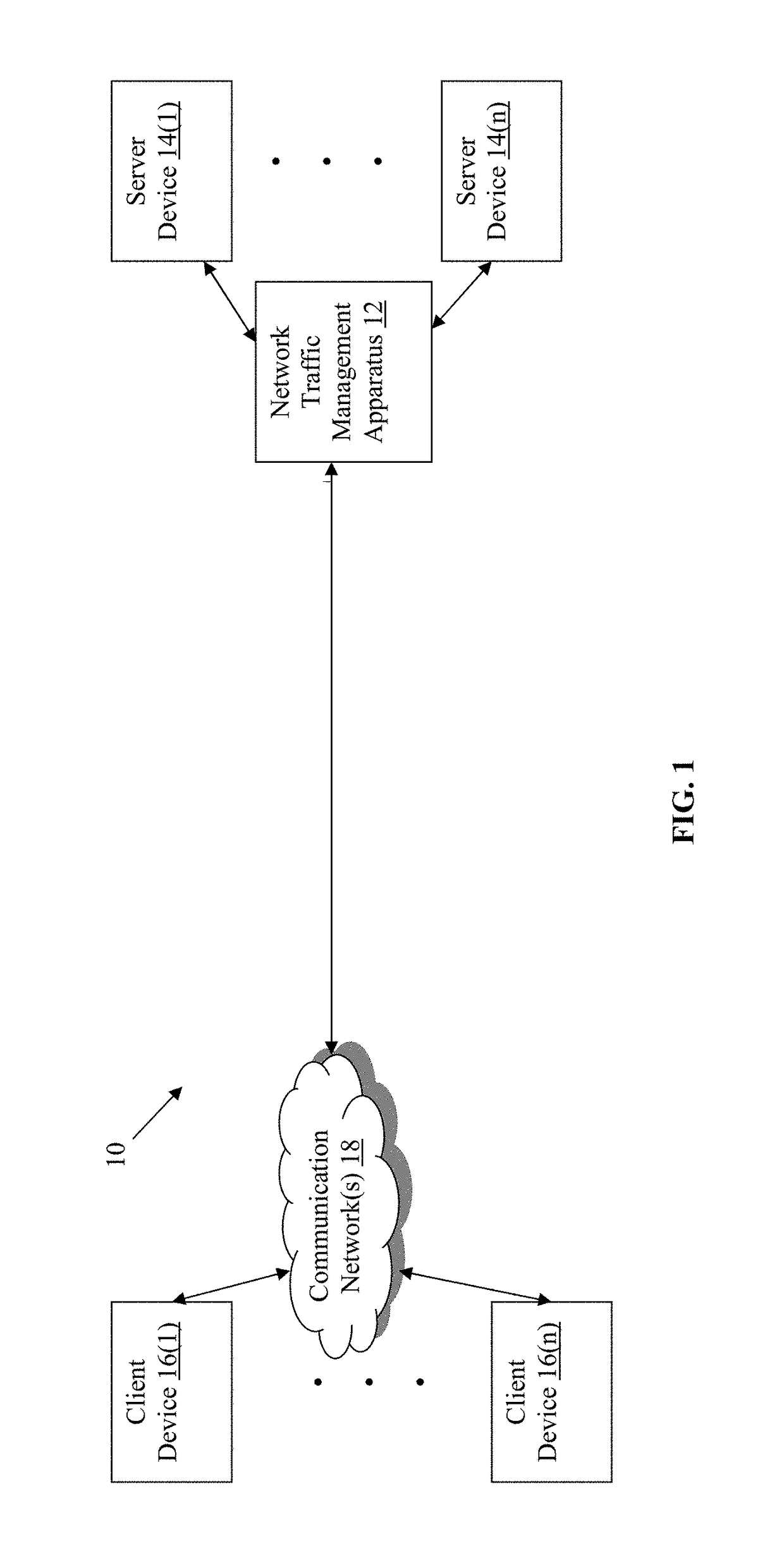
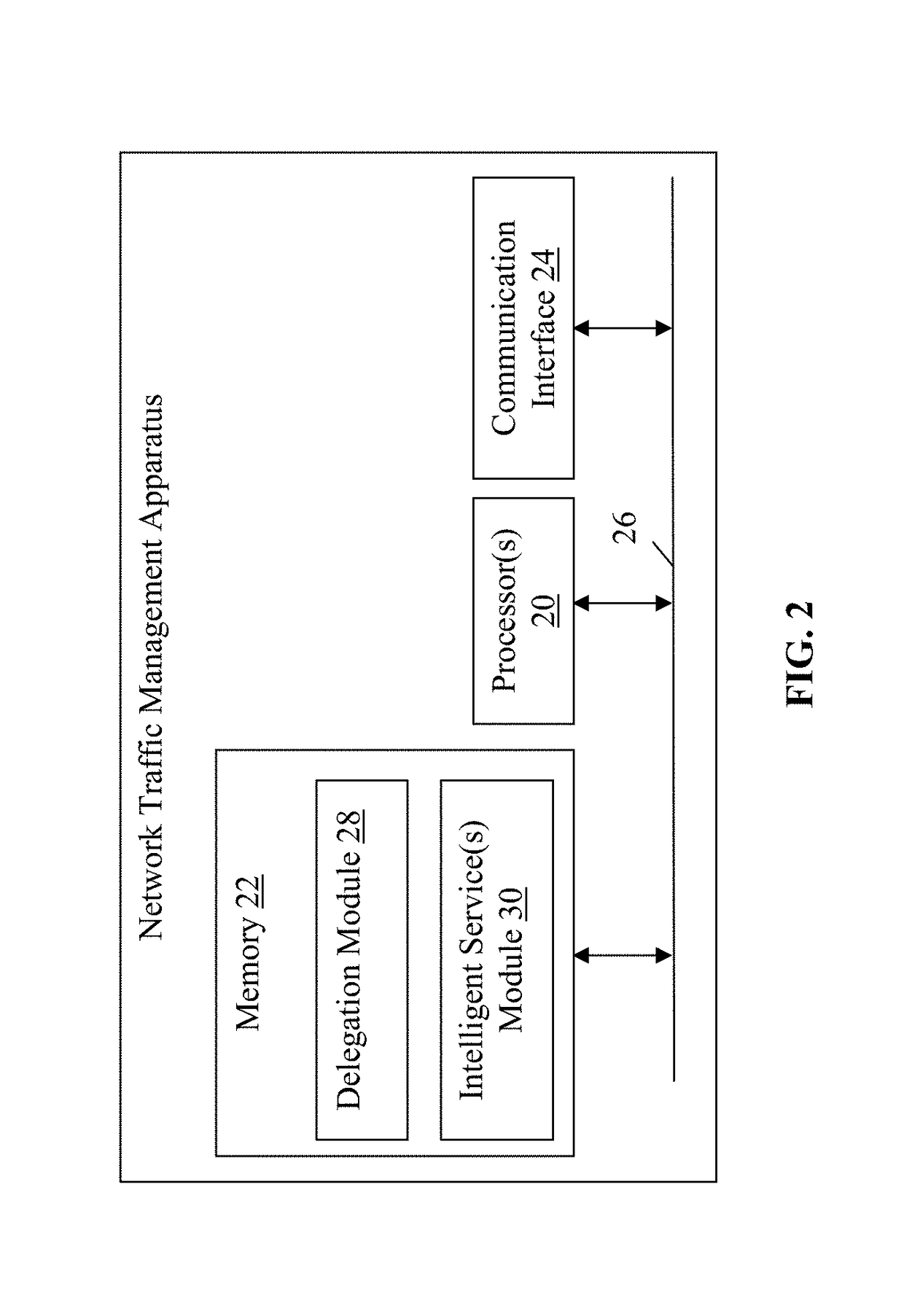
ActiveUS9800568B1Improve securityConnection securityTransmissionApplication softwareProxy certificate
Methods, non-transitory computer readable media, and network traffic management apparatuses that receive a request from a client device to access an application. The request comprises an original certificate. A determination is made when the certificate is valid. Data is extracted from one or more fields of the certificate, when the determining indicates that the user certificate is valid. A delegate certificate comprising the data and signed by a certificate authority trusted by a server device hosting the application is generated. The delegate certificate is sent to the server device. With this technology, network traffic management apparatuses can secure SSL connections using PFS-capable ciphers, while also inspecting payload data in network traffic exchanged between client and server devices in order to provide intelligent services in the network.
Owner:F5 NETWORKS INC
Credential protection handling method facing service
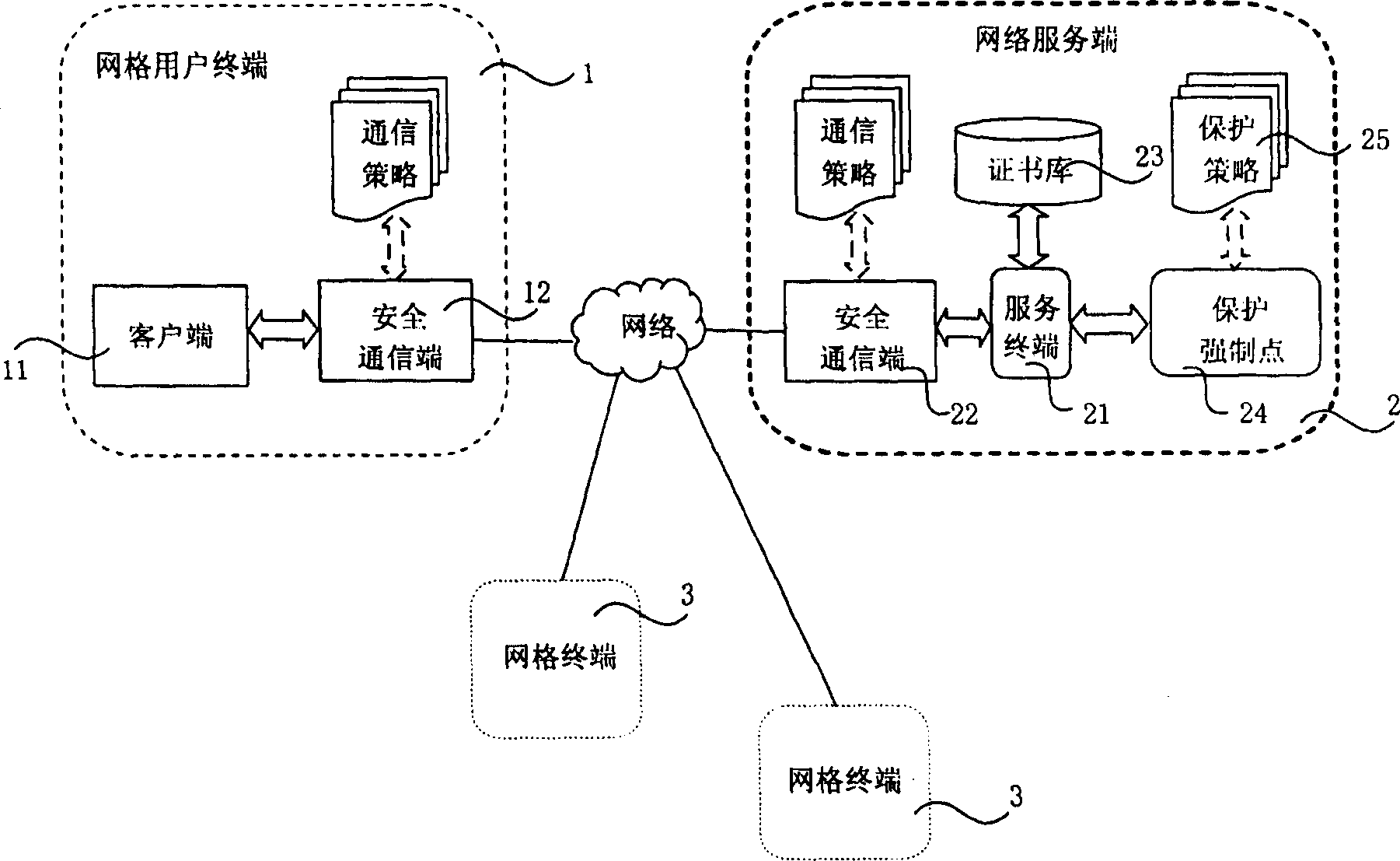
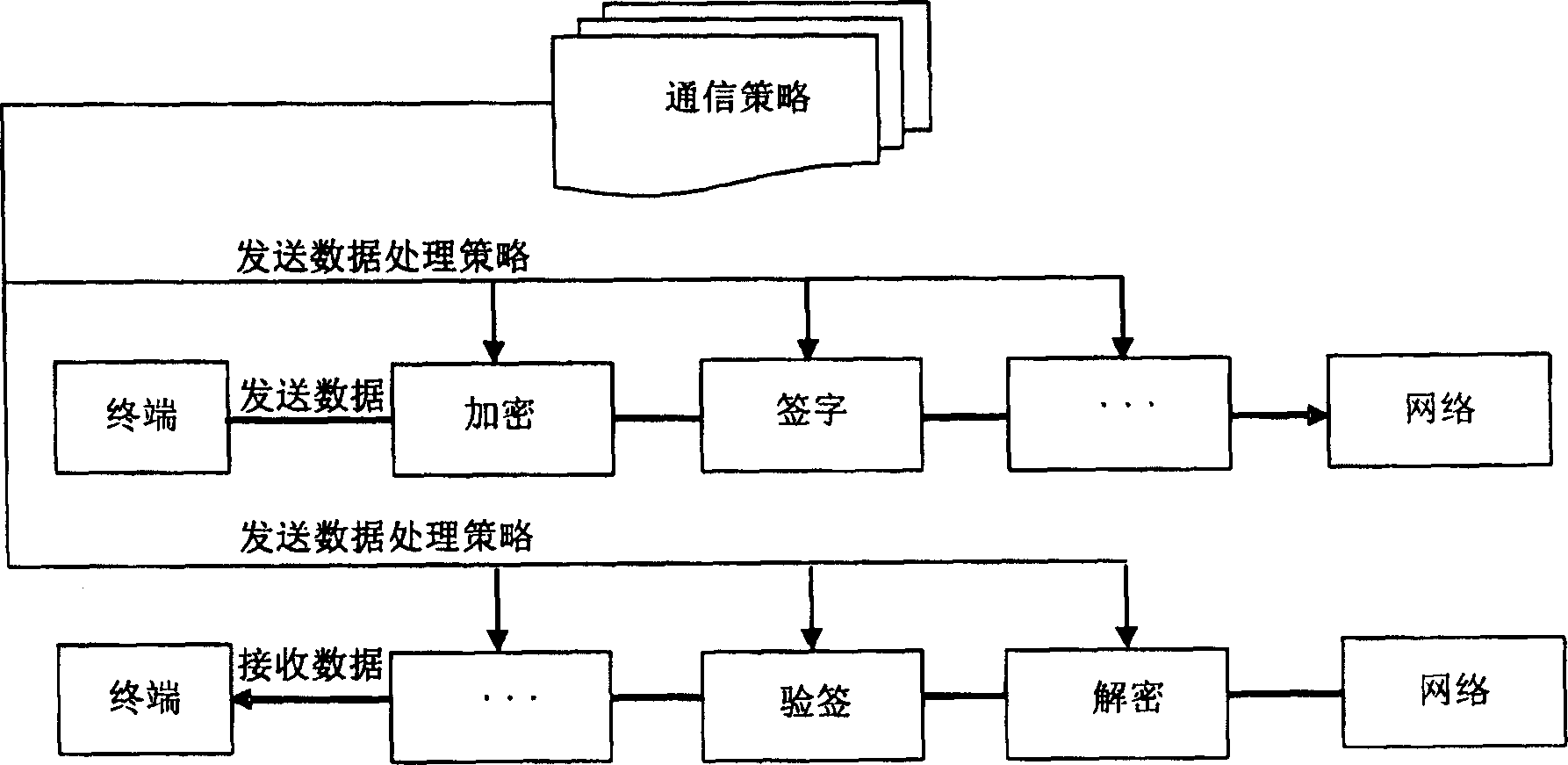
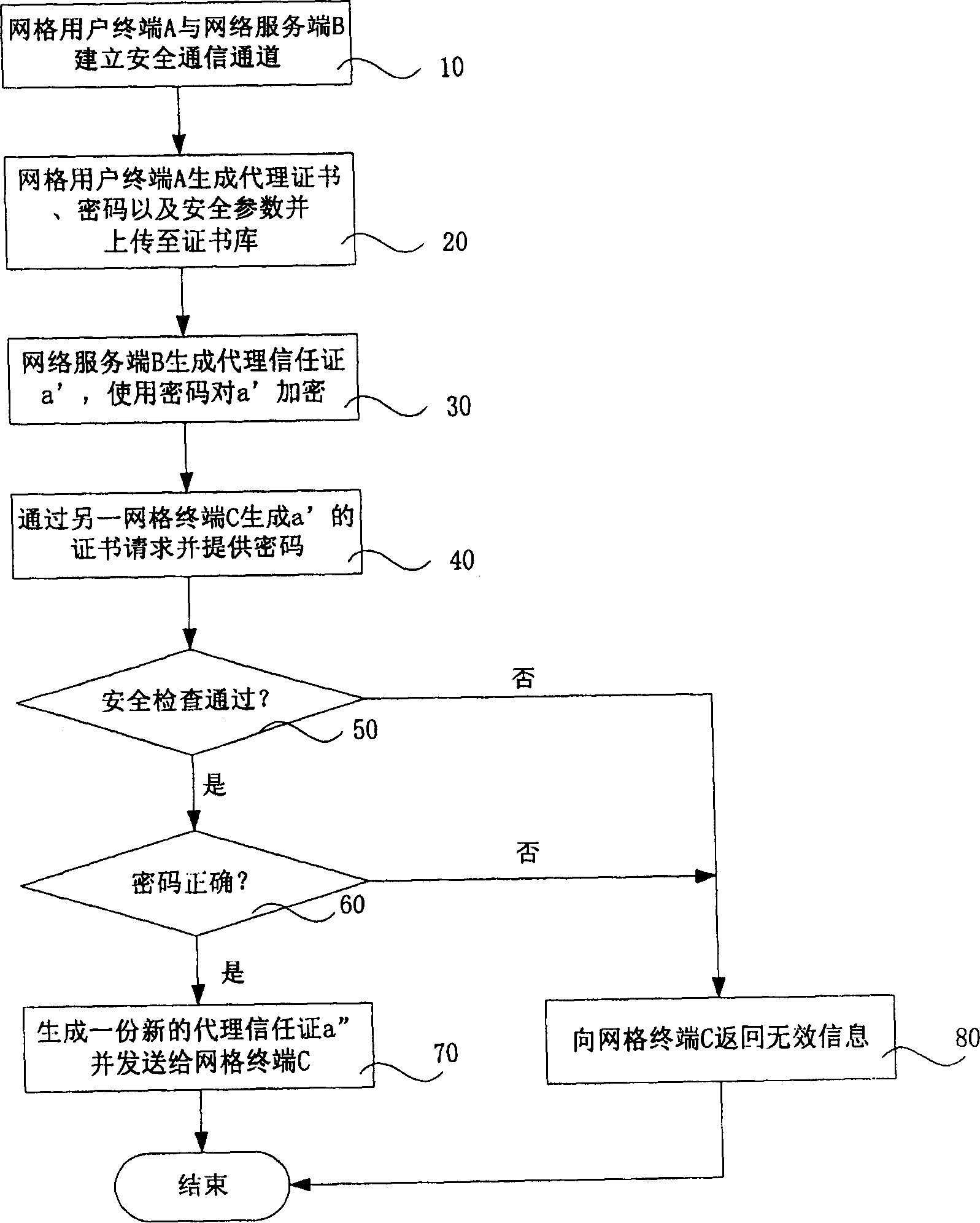
InactiveCN1791116AFlexible choiceIncrease flexibilityTransmissionSecure communicationProtection mechanism
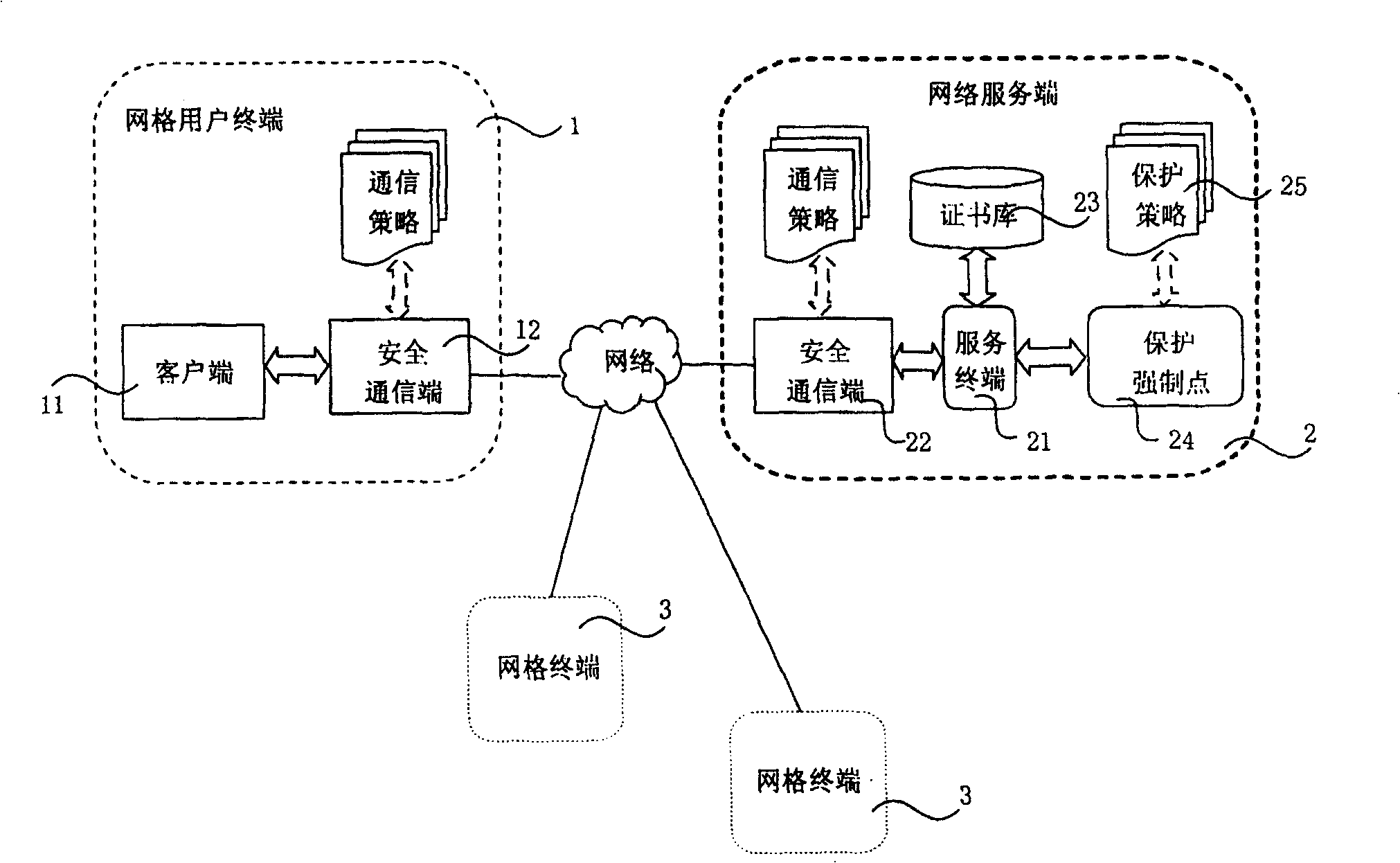
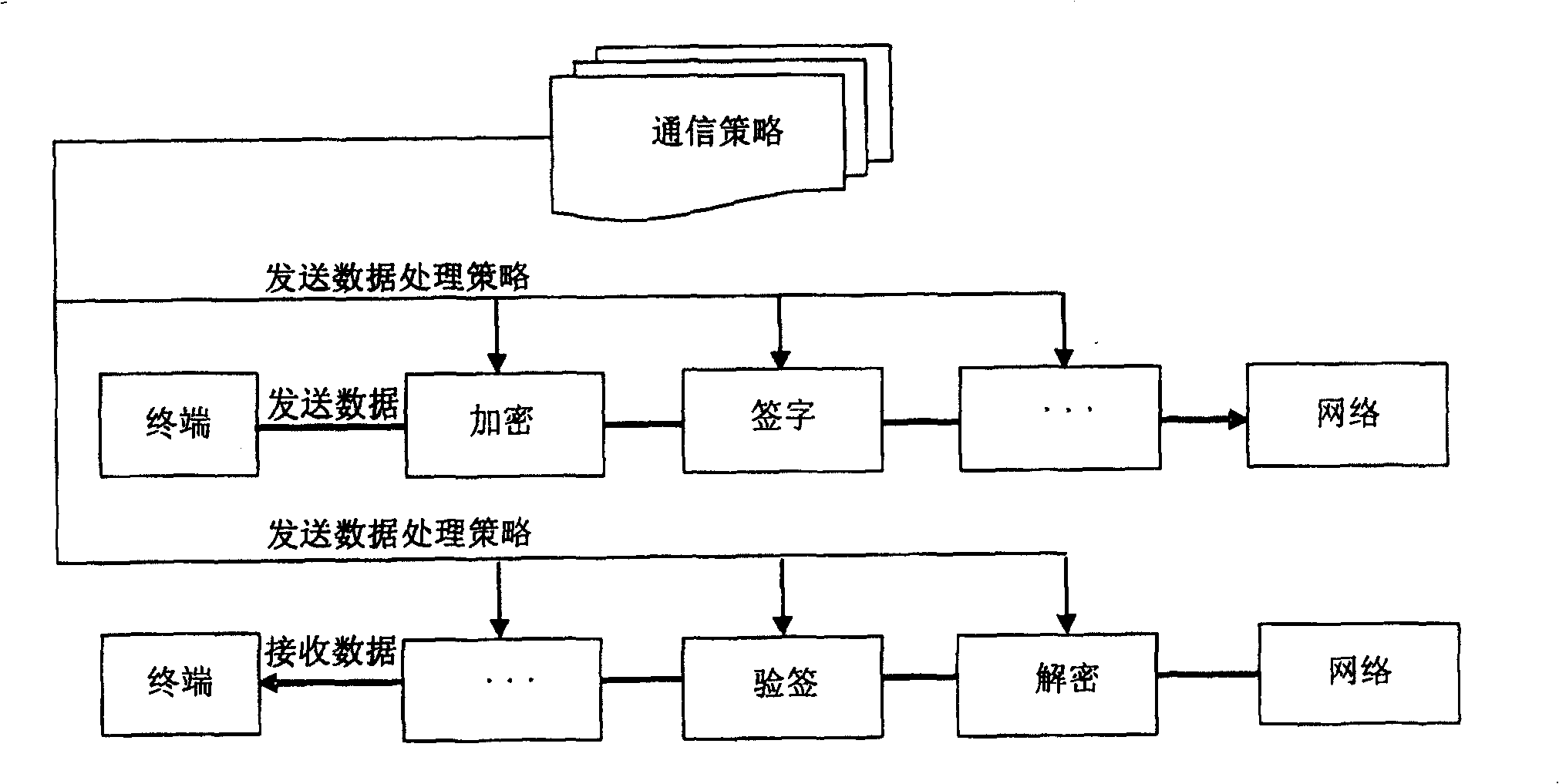
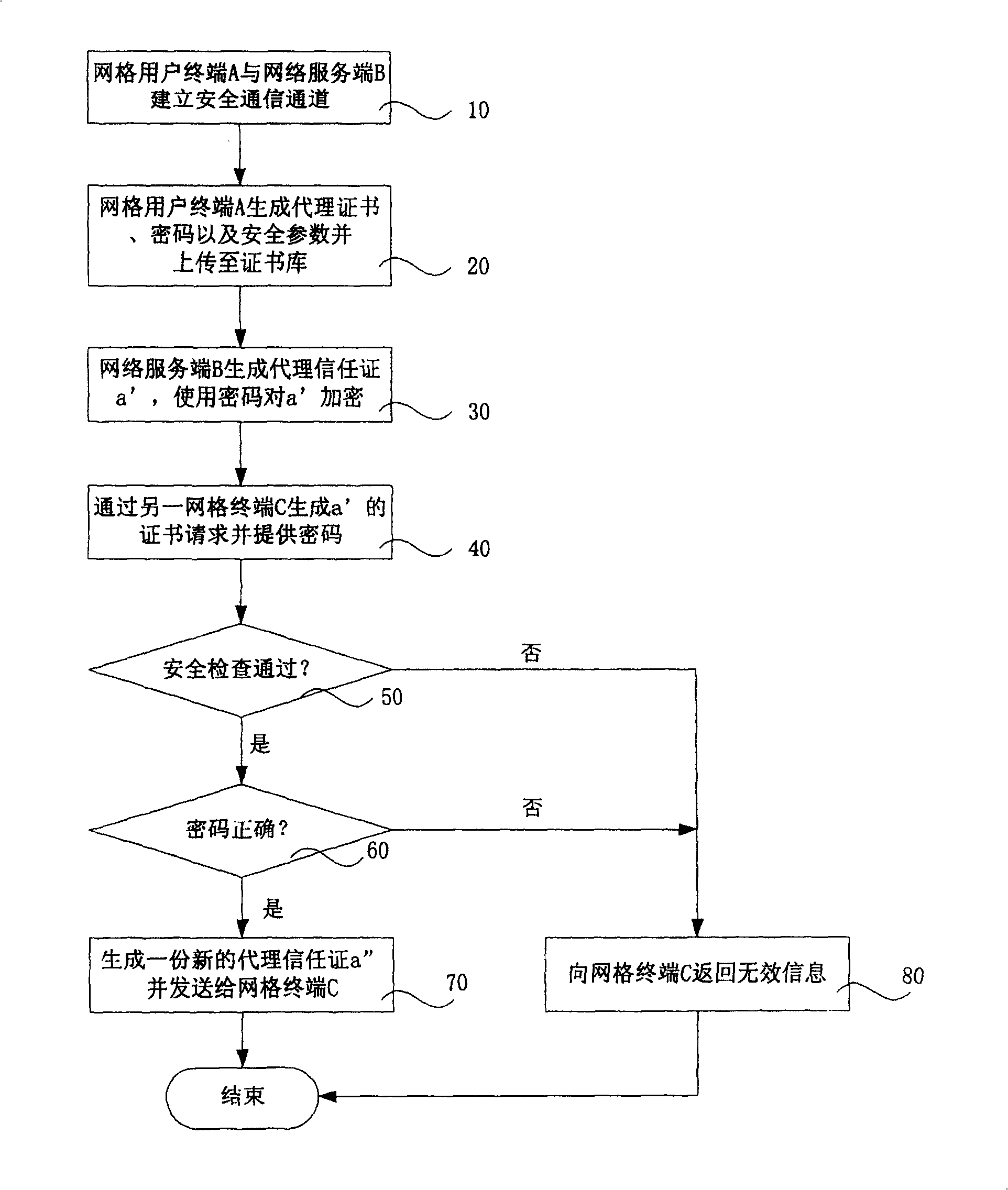
The invention discloses a protective treatment method for trust certificate faced service. Wherein, the user terminal builds a security communication channel with network server and uploads agent certificate and cipher and security parameter all generated by it self; the server generates and enciphers agent trust certificate to preserve with security parameter; the terminal visits the certificate library and provides cipher; the server checks and validates the cipher, if pass, generates a new agent trust certificate to send to terminal. This invention fuses trust certificate into WSRF frame, and enhances flexibility for protection.
Owner:BEIHANG UNIV
License management system and method
ActiveUS8006085B2Efficient managementUser identity/authority verificationProgram/content distribution protectionComputer networkProxy certificate
A license-management system and method is provided. A method of issuing a proxy certificate includes transmitting a proxy-certificate-issuance-request message to a license server in order for the local license manager to acquire an authority to issue a license by a local license manager; enabling the license server to verify the proxy-certificate-issuance-request message; if the proxy-certificate-issuance-request message is valid, transmitting a proxy certificate to the local license manager by the license server, the proxy certificate including information regarding the authority to issue a license; and verifying the proxy certificate by the local license manager.
Owner:SAMSUNG ELECTRONICS CO LTD
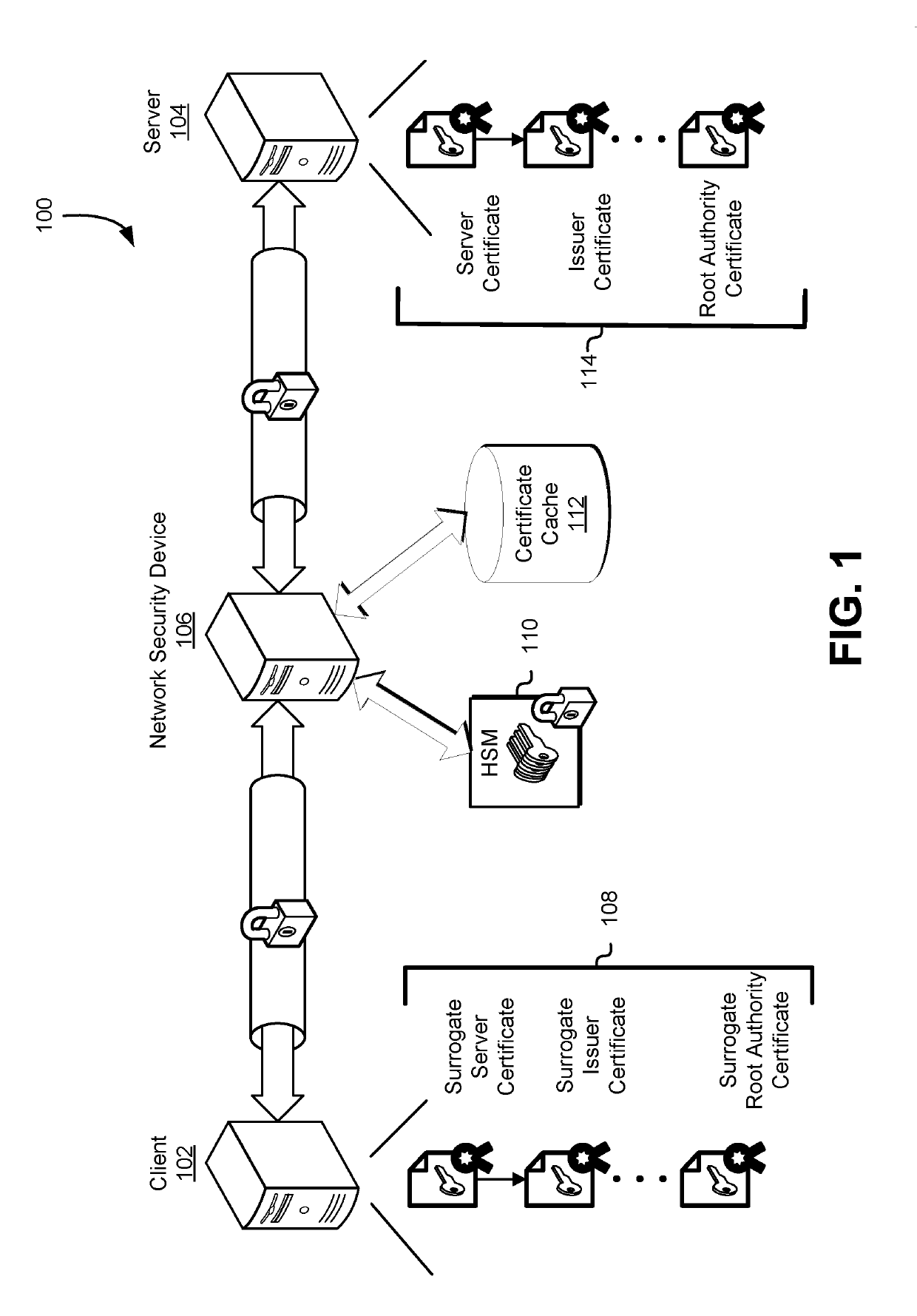
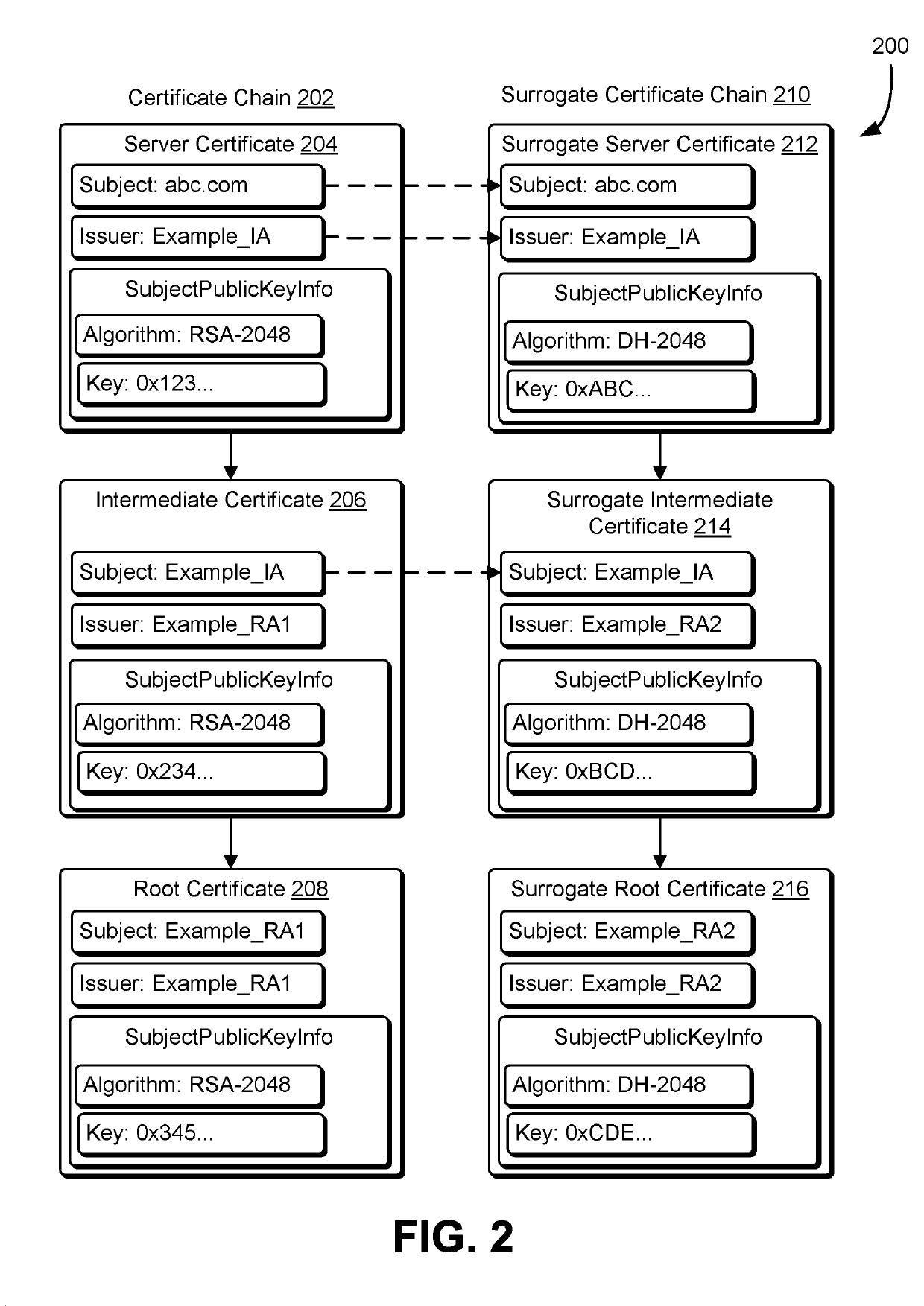
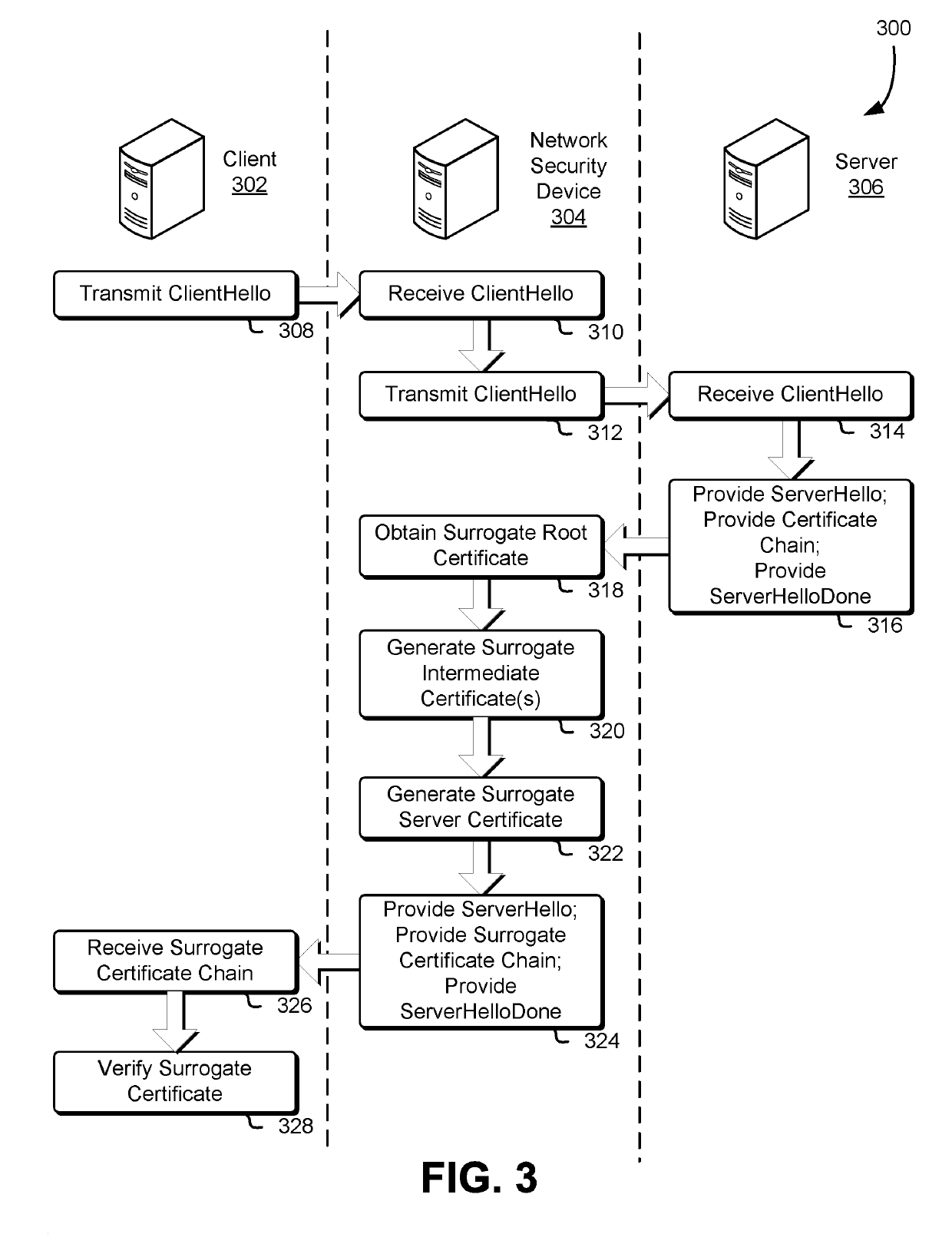
Network security with surrogate digital certificates
A computing device such as a network security device receives one or more digital certificates in a certificate chain and generates one or more surrogate digital certificates that form a surrogate certificate chain. A surrogate certificate may be generated using certificate information from a corresponding digital certificate of the received certificate chain. In some cases, the received certificate chain may have a trusted root certificate that is a trust anchor for the received certificate chain and the generated surrogate certificate chain may have a different trusted root certificate that is the trust anchor for the surrogate certificate chain. Cryptographic keys of the certificate chains may be used to establish cryptographically protected communication sessions. The computing device may monitor network traffic utilizing cryptographic keys included in the certificate chains to encrypt data. The encrypted data may be decrypted and inspected to determine whether sensitive information is transmitted in an improper manner.
Owner:AMAZON TECH INC
Communication method and system in IaaS system
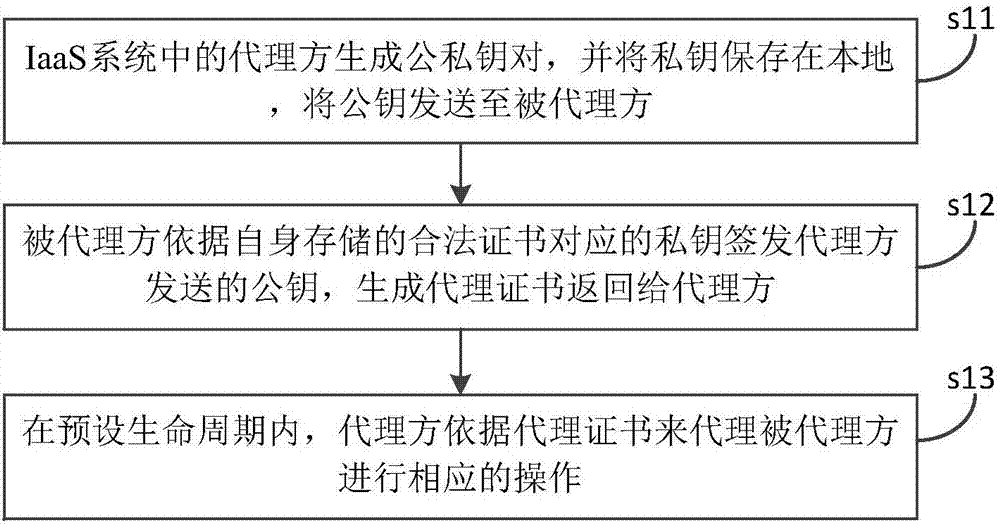
ActiveCN107172172AGuaranteed legalityImprove securityKey distribution for secure communicationCommunications systemProxy certificate
The invention discloses a communication method and a communication system in an IaaS system, based on a public key infrastructure (PKI). The method comprises the steps as follows: a proxy side in the IaaS system generates a public and private key pair, stores a private key locally, and sends a public key to a proxied side; the proxied side signs and issues the public key sent by the proxy side according to the private key corresponding to a legal certificate stored by itself, generates a proxy certificate and returns the proxy certificate to the proxied side; and the proxy performs a corresponding operation as proxy for the proxied side according to the proxy certificate within a preset life cycle. According to the method and the system provided by the invention, the proxy side can carry the proxy certificate with specific legal validity sent by the proxied side to perform the proxy operation, and legality and security of the proxy operation in the IaaS system are ensured.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Trusted content access management using multiple social graphs across heterogeneous networks
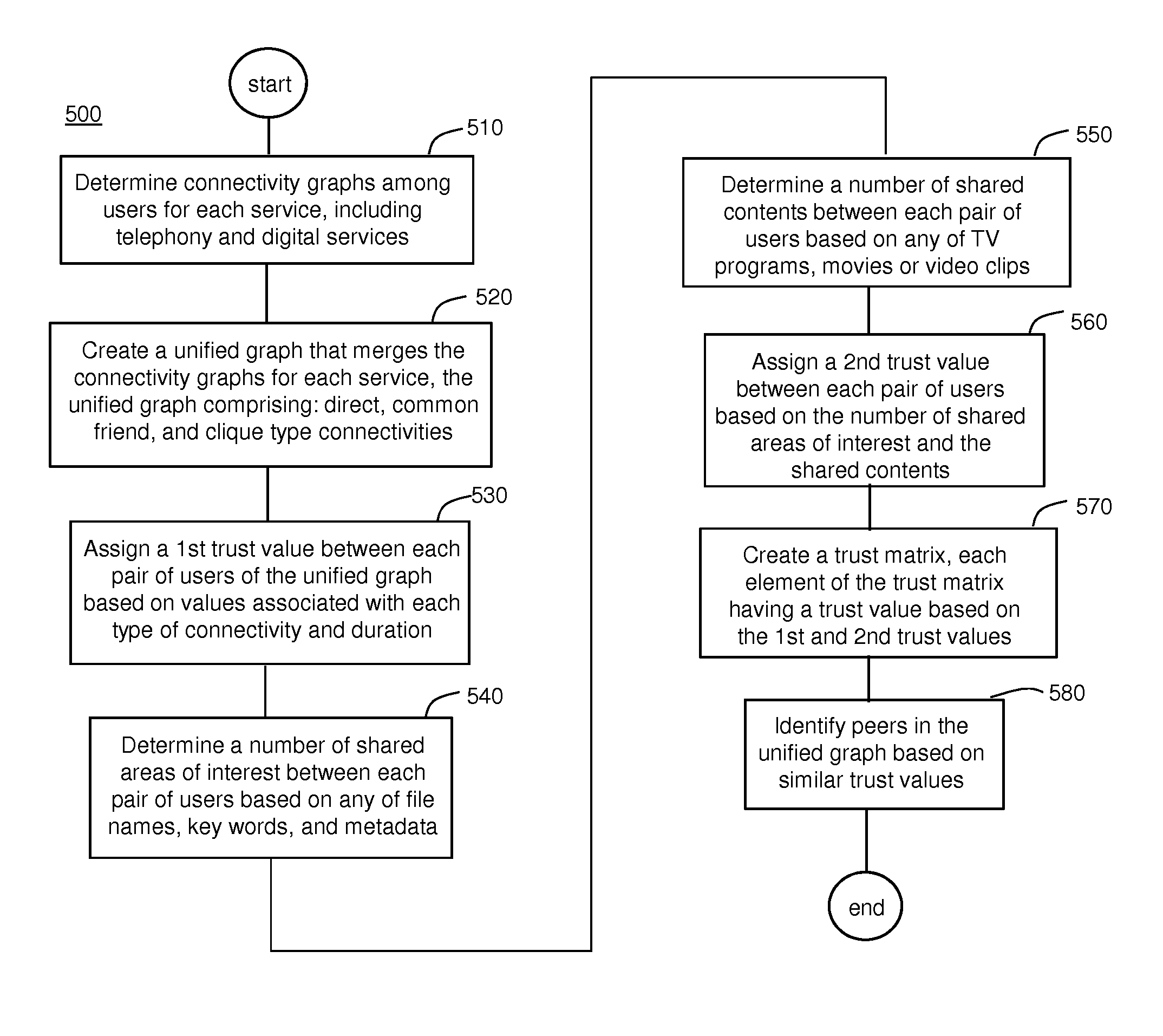
InactiveUS8561101B2Digital data processing detailsDigital computer detailsHeterogeneous networkContent management
A method, system, and computer readable storage device (that stores the method) extract connectivity information from multiple telecommunication services, provided by a single multiple service provider. The method, system, and device merge the separate connectivity information from each service in a unified graph of telephone service users and digital service users (including common users of both services). The method, system, and device assigne trust values based on the connectivity information and shared data content between users. The method, system, and device may also issue a proxy certificate of authority (CA), by a trusted CA residing within the digital service, to provide digital service to a user of the telephone service in the unified graph, when the trusted CA is a nearest trusted CA in the unified graph.
Owner:IBM CORP
Internet data collection method and system based on man-in-the-middle
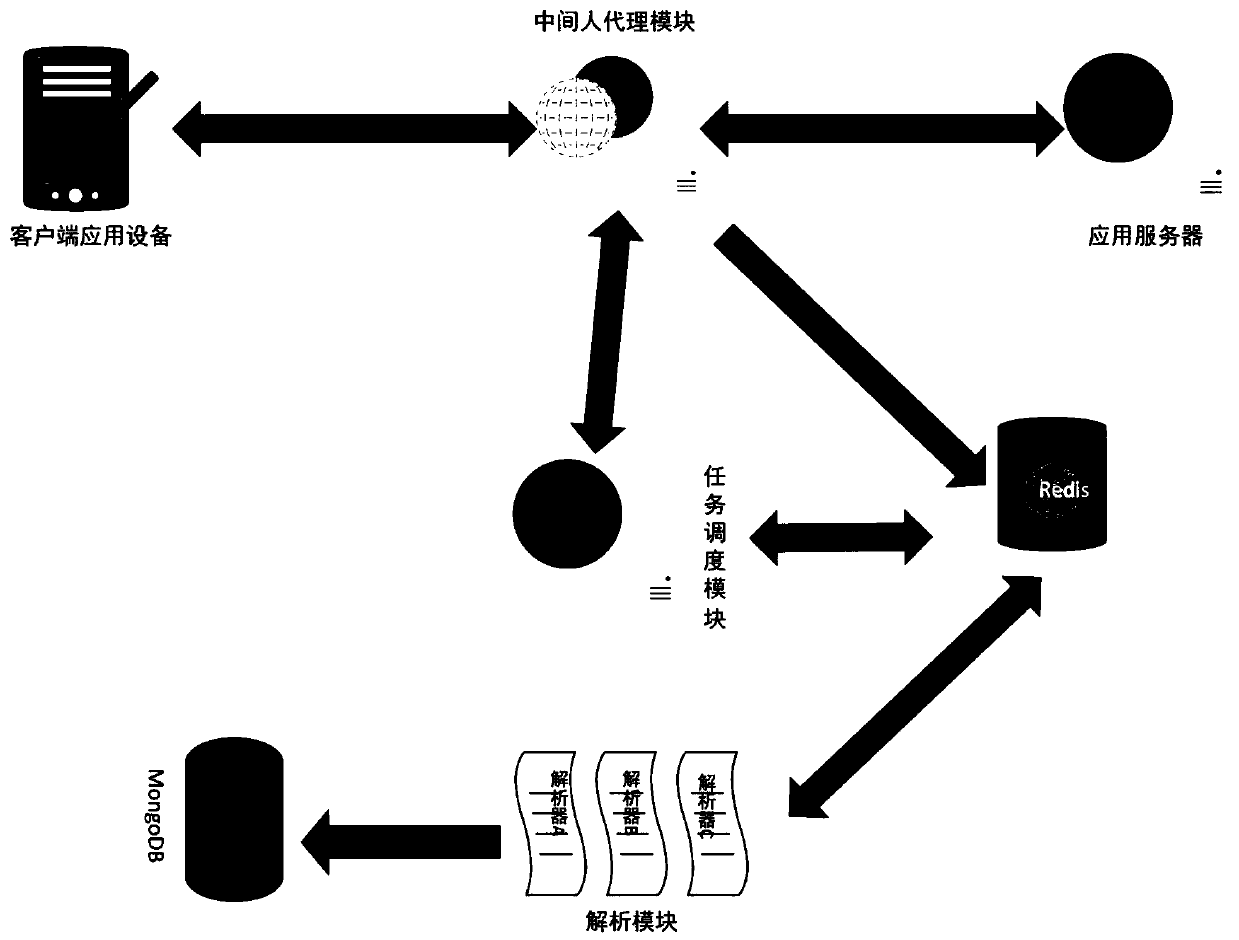
PendingCN110781367AImprove crawling efficiencyFlexible configuration of structured data analysisWeb data indexingSpecial data processing applicationsAcquisition apparatusInternet traffic
The invention provides an Internet data collection method and system based on a man-in-the-middle. The method comprises the steps that a man-in-the-middle proxy certificate is installed to webpage information collection equipment, a man-in-the-middle of the webpage information collection equipment is established, and when the webpage information collection equipment accesses webpage information inthe Internet, the man-in-the-middle proxy certificate acts on all network traffic of the webpage information collection equipment; the man-in-the-middle acquires an collection task accommodating a URL regular expression of a to-be-acquired webpage, captures traffic conforming to the URL regular expression in all network traffic as intermediate traffic, injects the collection task into an HTML page of the intermediate traffic to obtain a to-be-analyzed page, and stores the to-be-analyzed page into a first database; and the analysis module distributes the to-be-analyzed page to the analyzer instance for analysis according to the URL information of the to-be-analyzed page in the first database, acquires a webpage collection result accommodating the structured data from the analyzer instanceand stores the webpage collection result into the second database. According to the invention, data collection of all applications which provide information by integrating browser kernel functions canbe supported.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
A security optimization method for multi-cluster hadoop system based on public key algorithm and ssl protocol
ActiveCN104735087BAchieve protectionPublic key for secure communicationUser identity/authority verificationAlgorithmTheoretical computer science
Owner:STATE GRID CORP OF CHINA +2
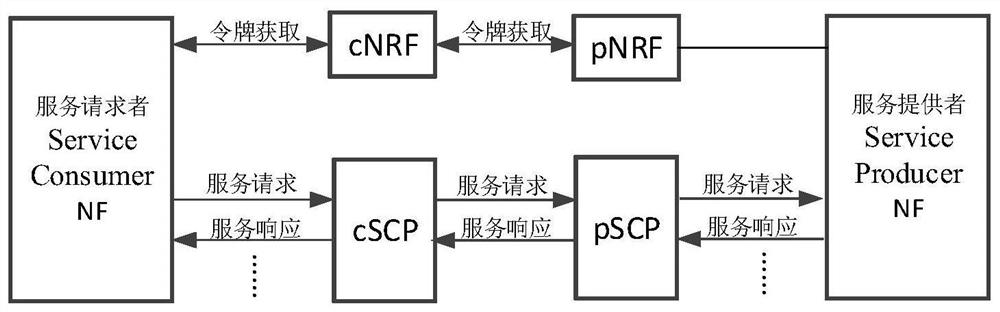
A method for service-oriented architecture authorization
ActiveCN112822678BAchieve legitimacyUser identity/authority verificationSecurity arrangementEngineeringProxy certificate
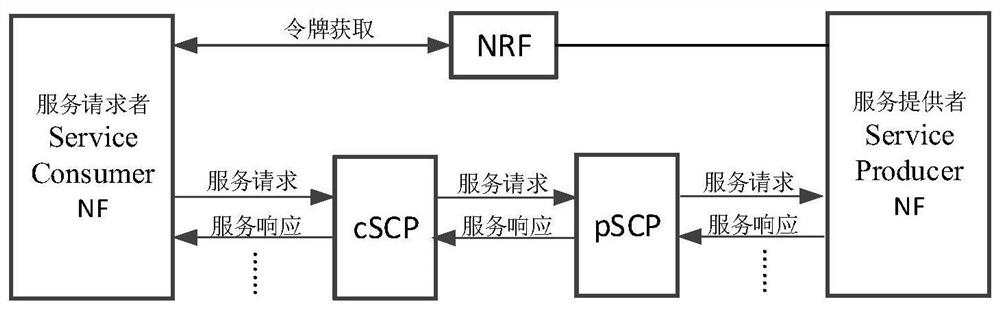
The embodiment of the present application discloses a method and device for service-oriented architecture authorization. The method includes: a first network storage function network element generates a token after receiving a token request, and the first network storage function is included in the token Write the SCP certificate information of the service communication agent, and return the token carrying the certificate information to the sender of the token request; the service provider network function receives the service request, and the service request carries the token containing the SCP certificate information card or carry the token and the verification result of the certificate information; if the service request does not contain the verification result of the certificate information, the service provider network function verifies the certificate information of the SCP; if the verification result is successful Then continue the authorization process. Through the above technical solution, the problem that the network function of the service provider cannot verify the certificate information in the token after the introduction of the service communication proxy can be solved.
Owner:HUAWEI TECH CO LTD
Credential protection handling method facing service
InactiveCN100456770CFlexible choiceIncrease flexibilityTransmissionSecure communicationProtection mechanism
The invention discloses a protective treatment method for trust certificate faced service. Wherein, the user terminal builds a security communication channel with network server and uploads agent certificate and cipher and security parameter all generated by it self; the server generates and enciphers agent trust certificate to preserve with security parameter; the terminal visits the certificate library and provides cipher; the server checks and validates the cipher, if pass, generates a new agent trust certificate to send to terminal. This invention fuses trust certificate into WSRF frame, and enhances flexibility for protection.
Owner:BEIHANG UNIV
Method and device for multi-proxy signature without certificate
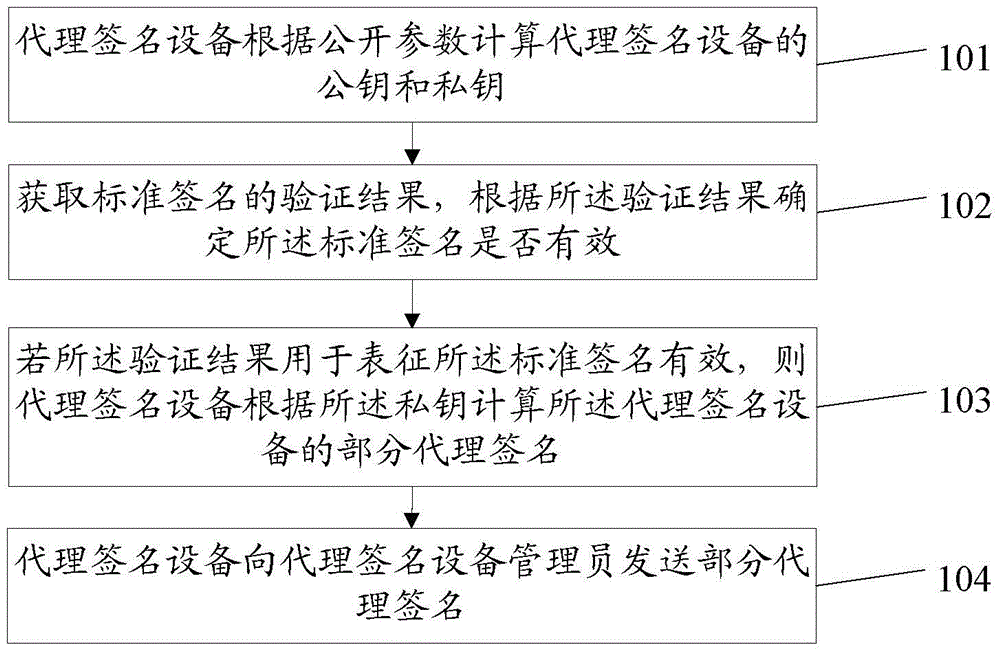
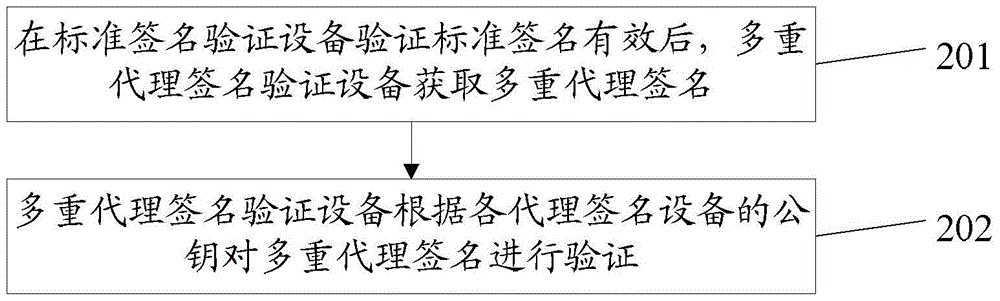
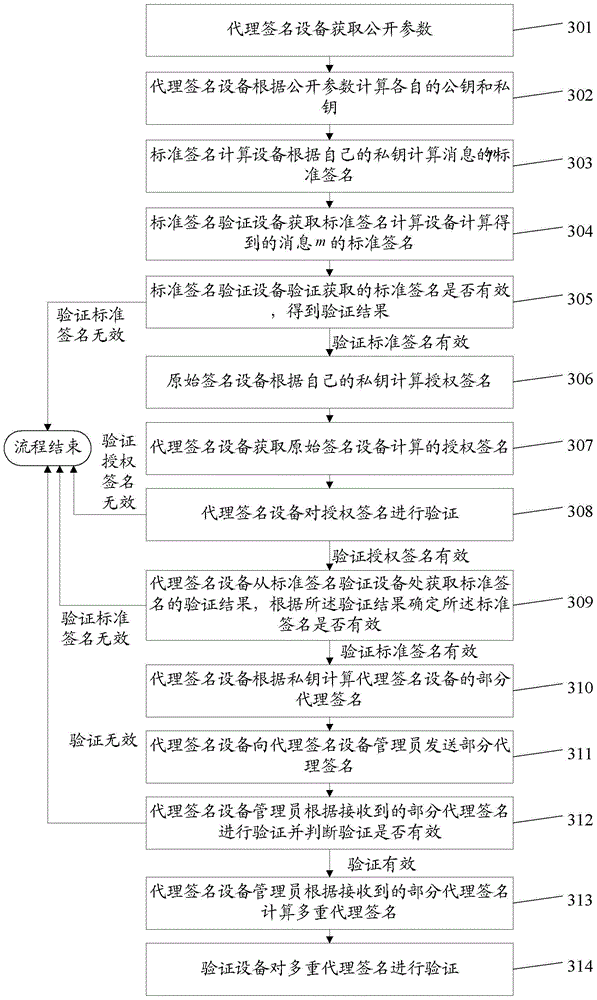
ActiveCN104468476BSmall amount of calculationReduce computing timeUser identity/authority verificationProxy certificateMulti proxy
The invention discloses a method and device for multi-proxy signature without certificate, relates to the technical field of communication, and solves the problem of large amount of calculation for multi-proxy signature without certificate by using bilinear pairing. The method of the present invention may specifically include: the proxy signature device calculates the public key and private key of the proxy signature device according to the public parameters, and the public key corresponds to the private key; obtains the verification result of the standard signature, and determines whether the standard signature is valid according to the verification result; if The verification result is used to indicate that the standard signature is valid, and the partial proxy signature of the proxy signature device is calculated according to the private key; the partial proxy signature is sent to the proxy signature device administrator, so that after the proxy signature device administrator calculates multiple proxy signatures based on the partial proxy signature , the multi-proxy signature verification device verifies the multi-proxy signature. Applicable to certificateless multi-proxy signatures.
Owner:HUAWEI DEVICE CO LTD
Implementation scheme of two-factor login manner capable of opening and closing freely
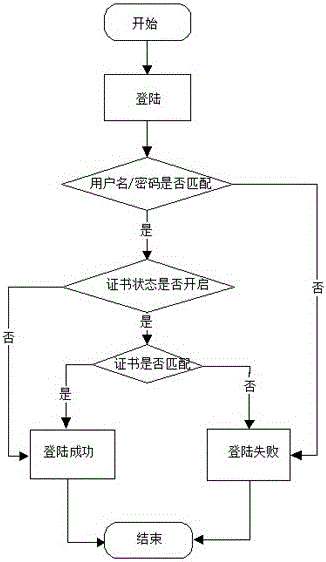
The present invention discloses an implementation scheme of a two-factor login manner capable of opening and closing freely. The two-factor login refers to login based on a user name / password and a personal certificate. The two-factor login manner is able to open and close freely. The personal certificate is realized by using a keytool of Java JDK. The process is as follows: firstly, a trusted certificate bank is generated according to a command; then a personal certificate is generated, and the trusted certificate is exported from the personal certificate; and finally, the trusted certificate is imported into the certificate bank. Authentication of the certificate can be performed by a user, and the authentication of the certificate can be started and closed freely.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
A system and method for proxy re-encryption based on certificateless conditions
ActiveCN105025024BControl re-encryption capabilitiesFlexible online re-encryptionMultiple keys/algorithms usageCryptosystemKey escrow
The invention discloses a certificateless-condition-based proxy re-encryption system and method. A certificateless public key system and a proxy re-encryption system are combined together, so that certificate management is avoided and problems in secrete key distribution and escrow are eliminated. In a condition of ensuring encryption safety, online re-encryption is performed flexibly and the re-encryption capability of a proxy center is controlled, so that only ciphertext meeting specific conditions can be re-encrypted effectively. At the same time, since the certificateless public key system is used, the system and method provided by the invention have advantages of traditional public key encryption and identify-based encryption and are good in performance and convenient in application in an open network environment. The novel system and method provided by the invention are safe and efficient.
Owner:HOHAI UNIV
A method and system for proxy re-encryption based on certificate condition
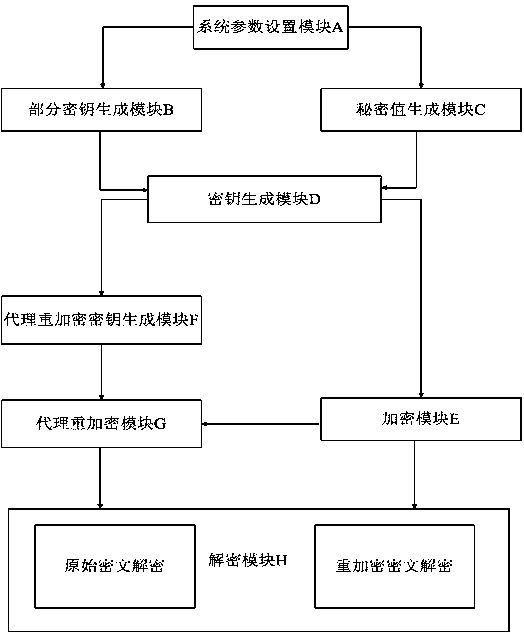
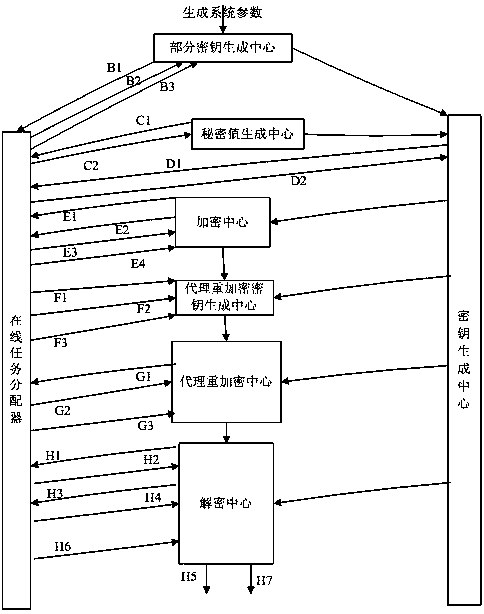
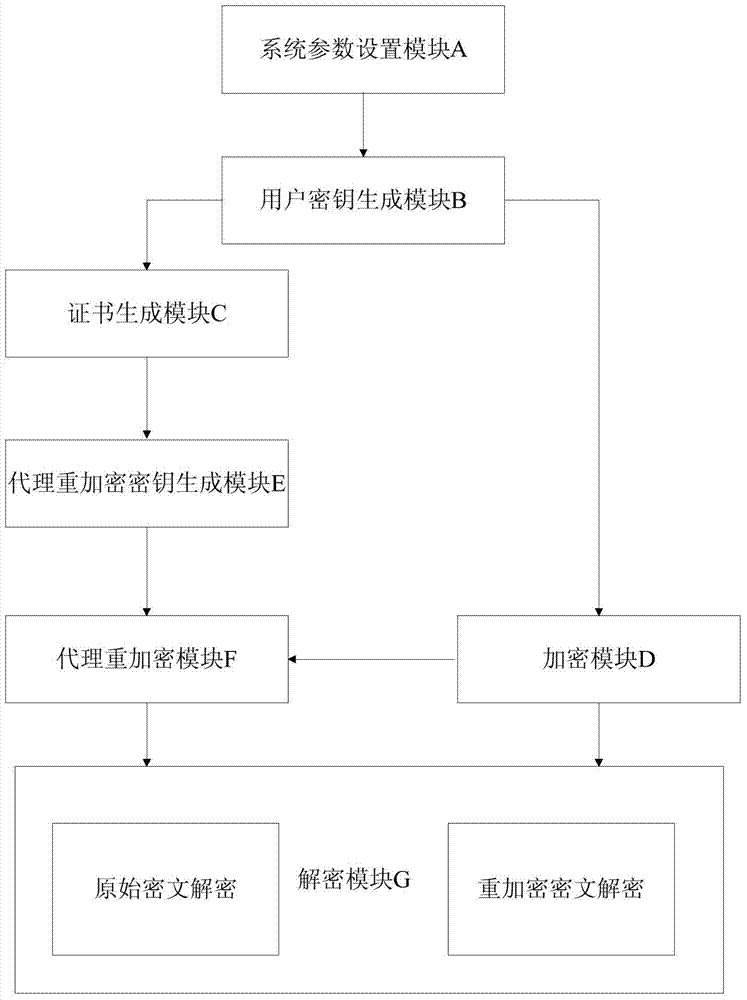
InactiveCN104363218BSimplify the management processControl re-encryption capabilitiesTransmissionPlaintextCryptographic key generation
The invention discloses a proxy re-encryption system on the basis of certificate conditions. The proxy re-encryption system comprises a system parameter setting module, a user key generation module, a certificate generation module, an encryption module, a proxy re-encryption key generation module, a proxy re-encryption module and a decryption module, wherein the system parameter setting module generates a system master key and system public parameters; the user key generation module generates public keys and private key pairs of various users; the certificate generation module endorses the identity of the users and the public keys and generates certificates of the users; the encryption module is used for encrypting messages and transmitting the messages to the decryption module and the proxy re-encryption key generation module; the proxy re-encryption key generation module generates proxy re-encryption keys and transmits the same to the proxy re-encryption module; the proxy re-encryption module re-encrypts original cryptographs to generate re-encryption cryptographs to be transmitted to the decryption module; the decryption module restores corresponding plaintexts. The invention further discloses a proxy re-encryption method on the basis of certificate conditions. On the premise of guaranteeing safety of the system, the original cryptographs can be flexibly subjected to proxy re-encryption, and rights of proxies are strictly controlled.
Owner:HOHAI UNIV
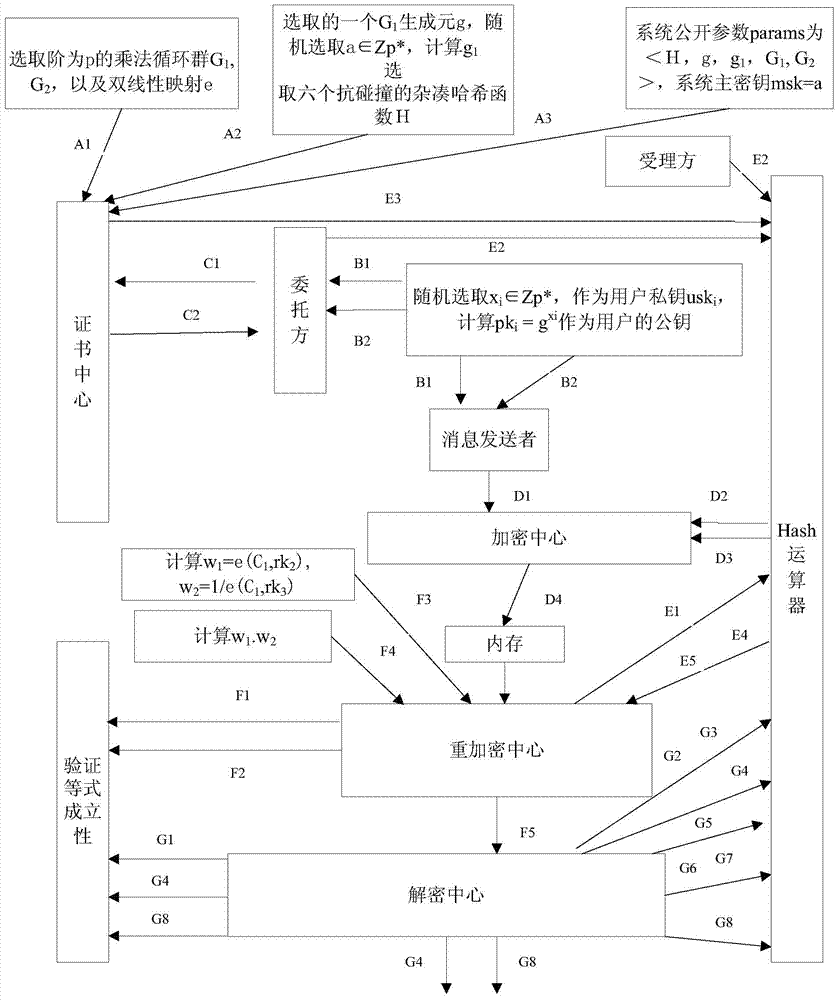
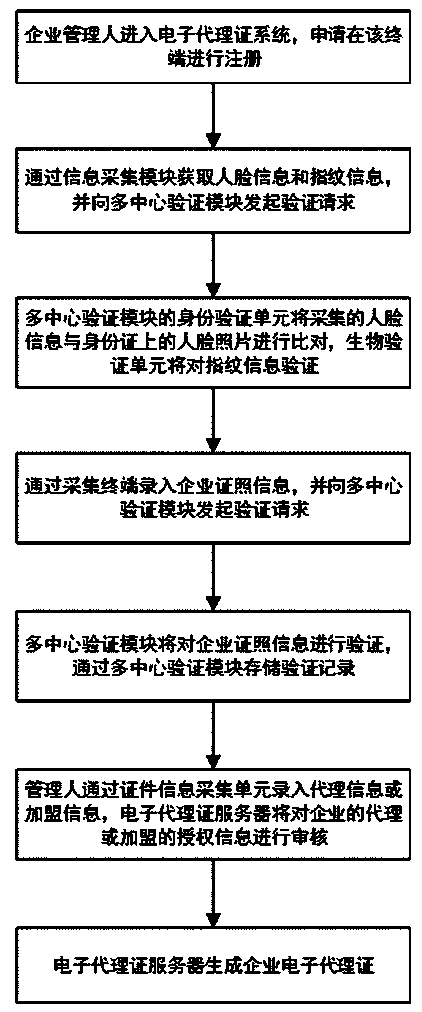
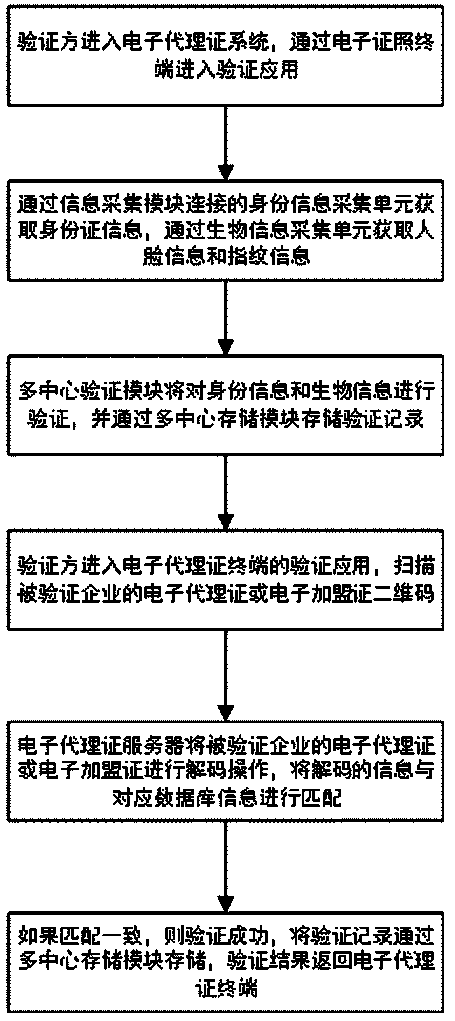
Certificate chain electronic agent certificate system
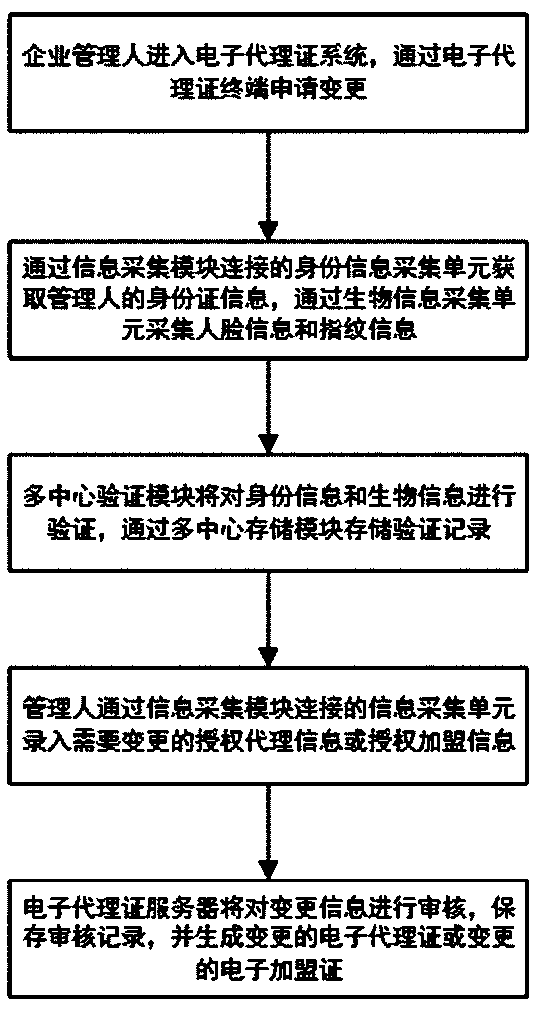
InactiveCN109635654AMonitor sales in real timePrevent being forgedMatching and classificationCommerceProxy certificateAuthorization
A certificate chain electronic agent certificate system carries out identity verification, biological verification and certificate verification on enterprise managers through a multi-center verification module, and verification records are stored through a multi-center storage module. A manager initiates a request for generating an electronic agent certificate or an electronic franchischer certificate at an electronic agent certificate terminal; the electronic agent certificate server receives the request. An authorized enterprise electronic certificate ID and an authorized enterprise electronic certificate ID are acquired through a multi-certificate center module. The electronic certificate ID of the enterprise is authorized. A unique enterprise electronic agent certificate or an enterprise electronic franchise certificate is generated by combining an encryption algorithm with a combination mode of a random number according to the ID and the authorization information of the authorizedenterprise electronic certificate, a verifier can verify the authenticity of the electronic agent certificate and verify the identity information of a certificate holder in real time, and the phenomenon that the agent certificate is forged and tampered is eradicated.
Owner:GLOBAL PRESTIGE INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com