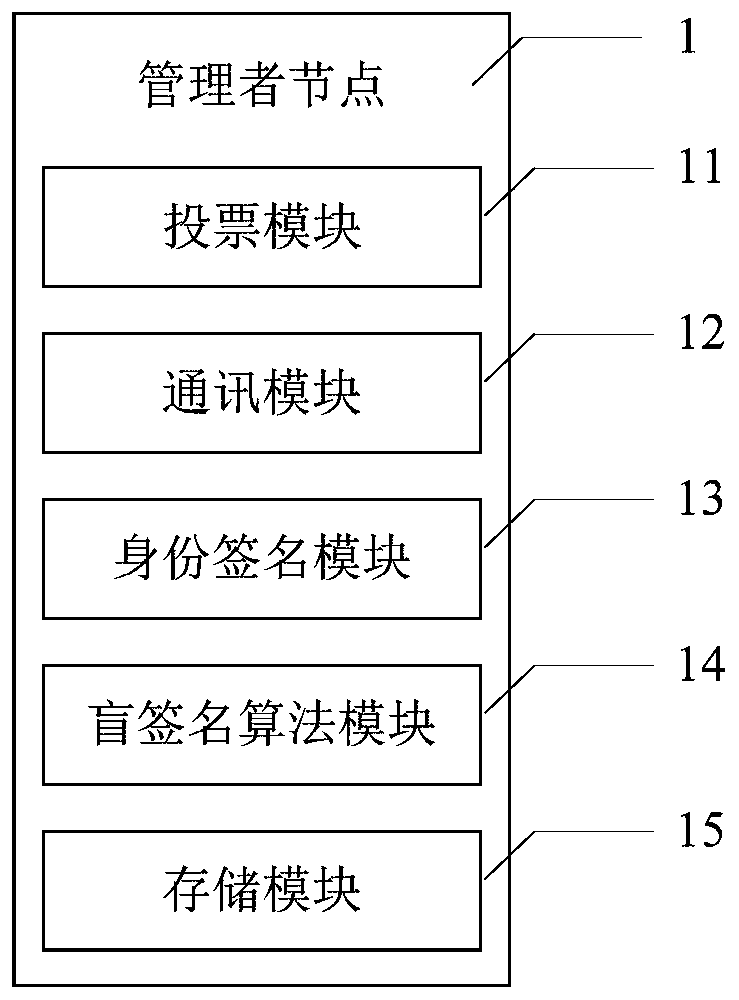
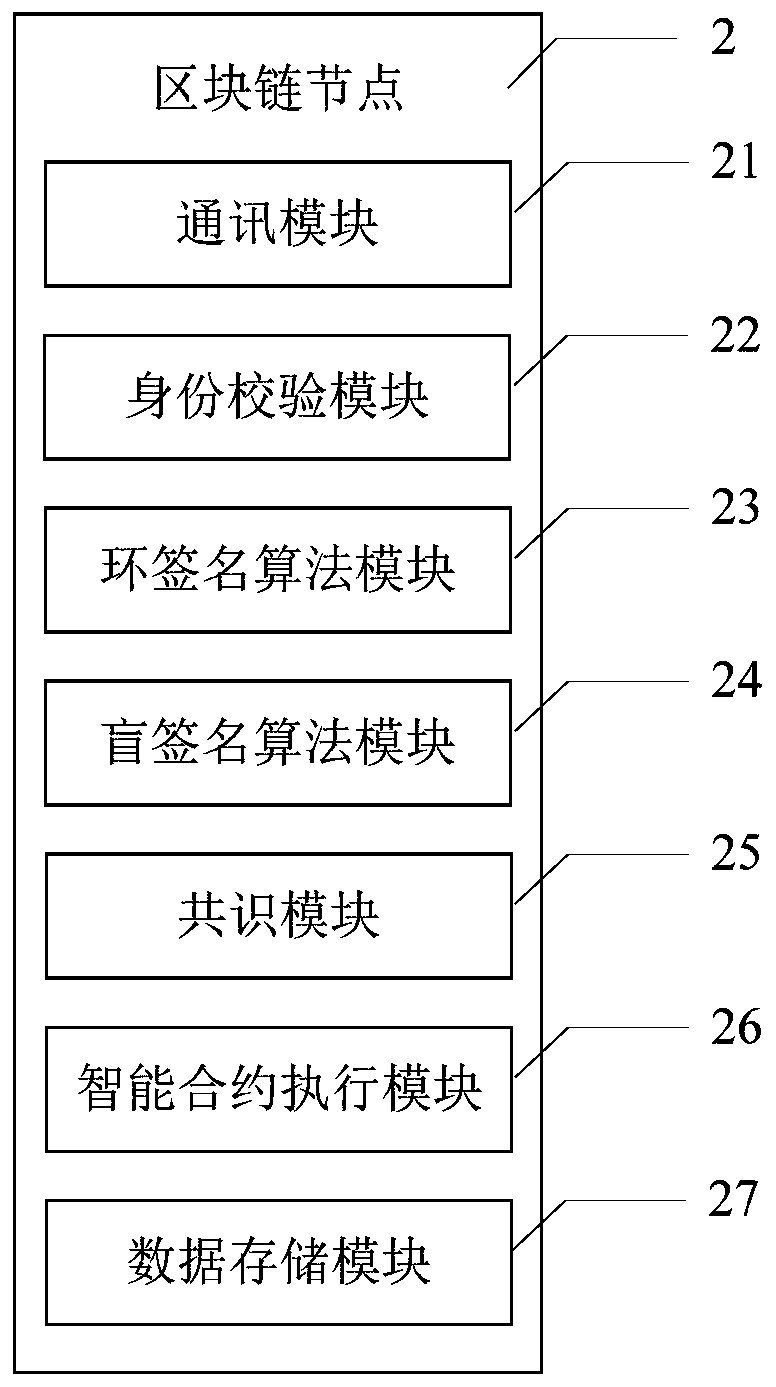
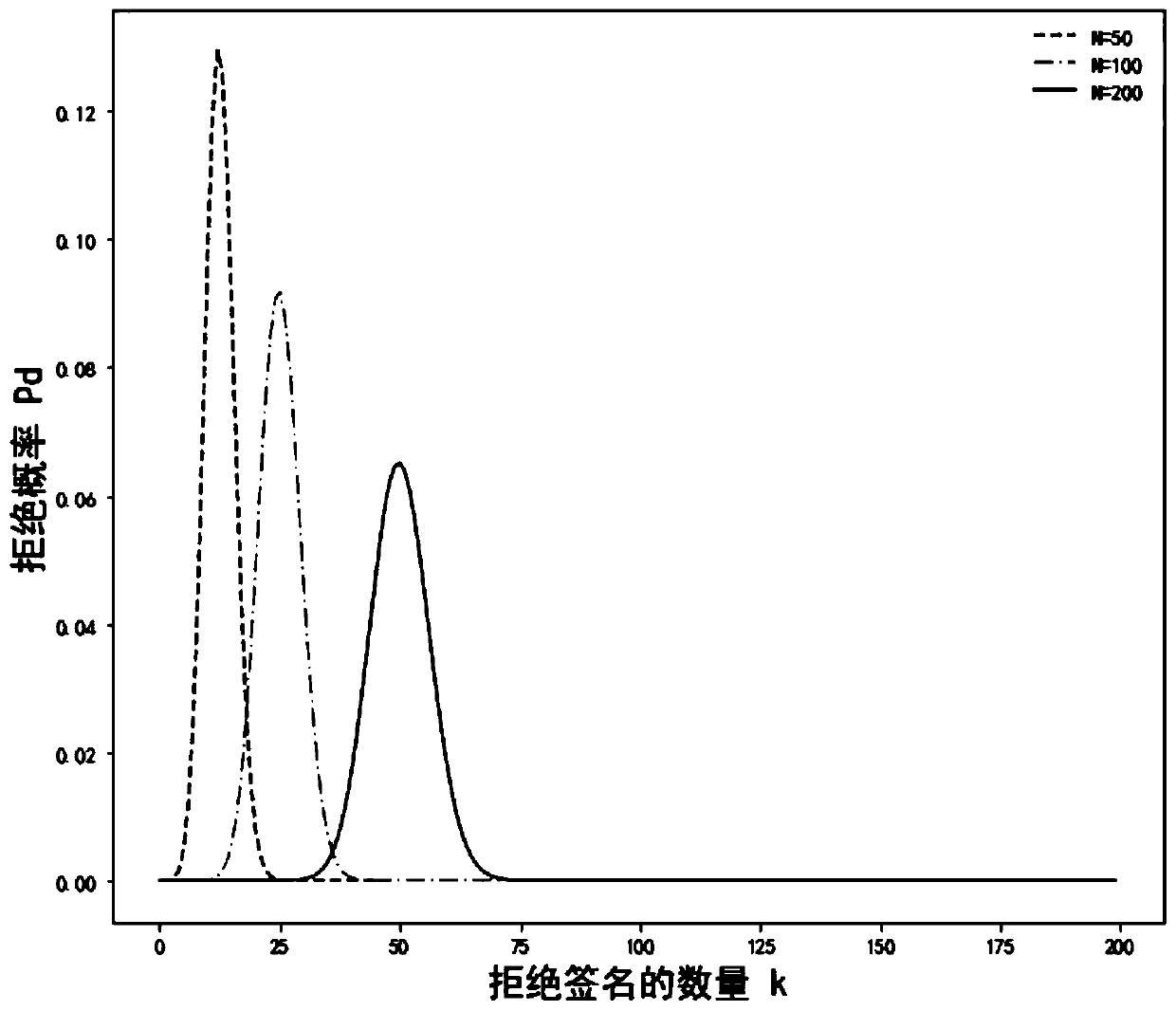
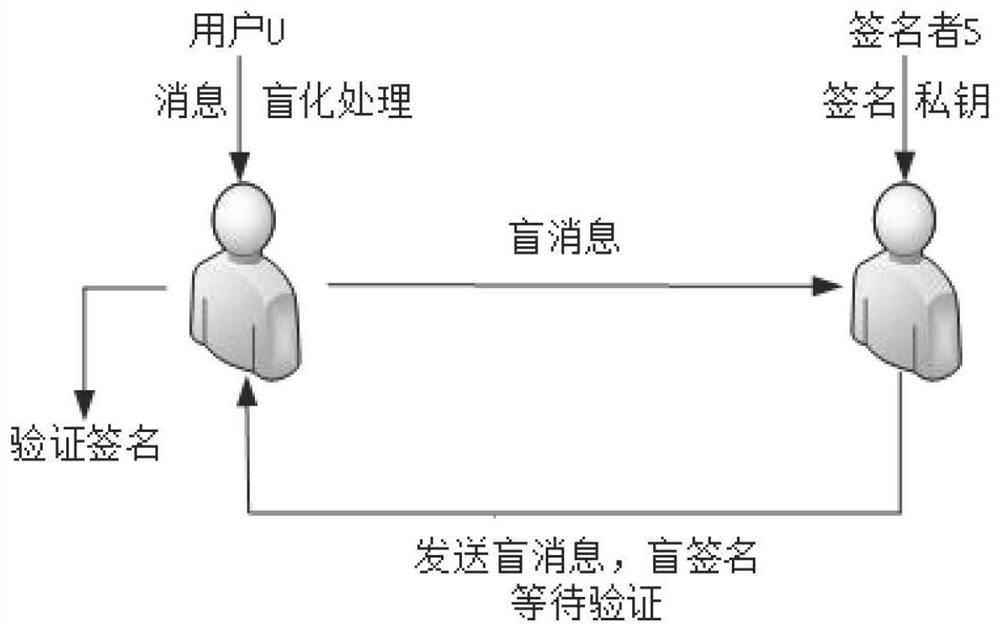
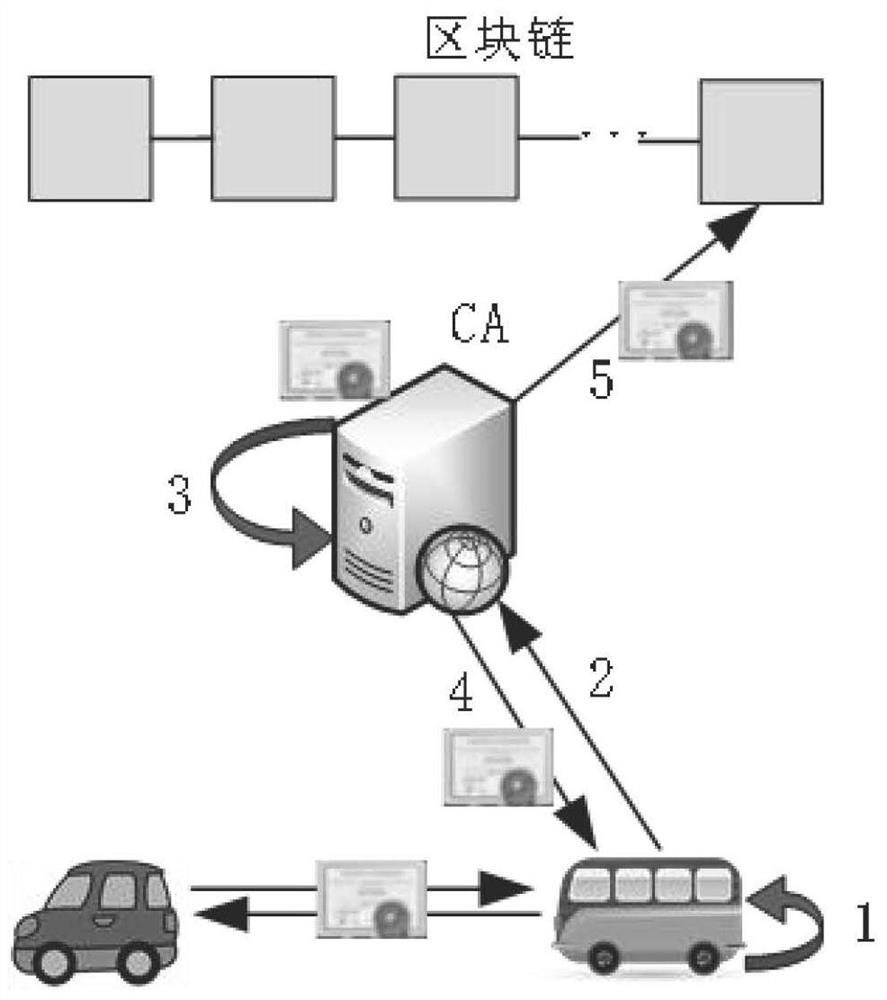
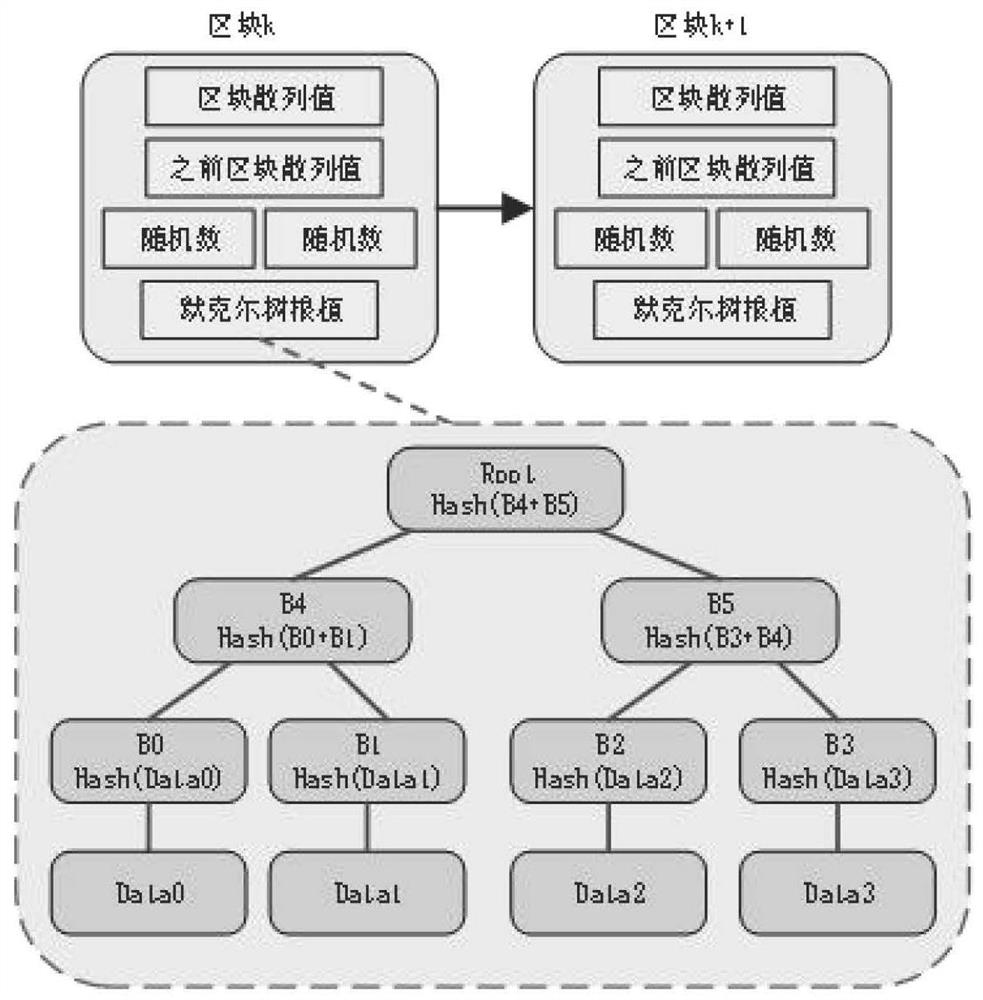
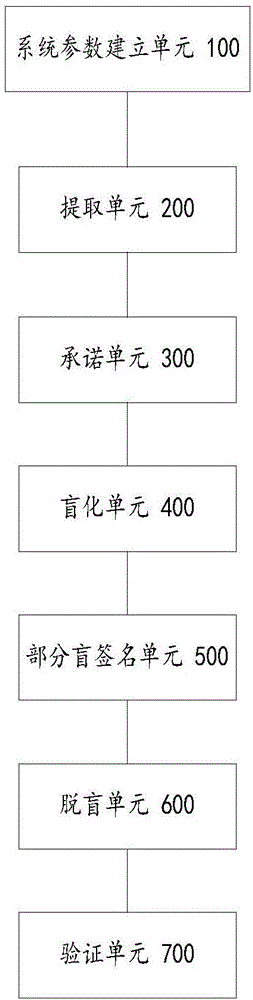
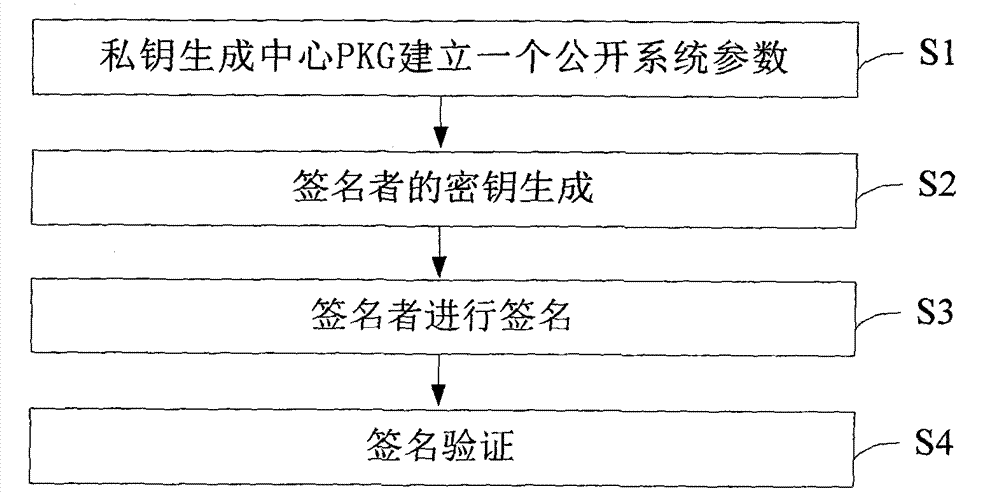
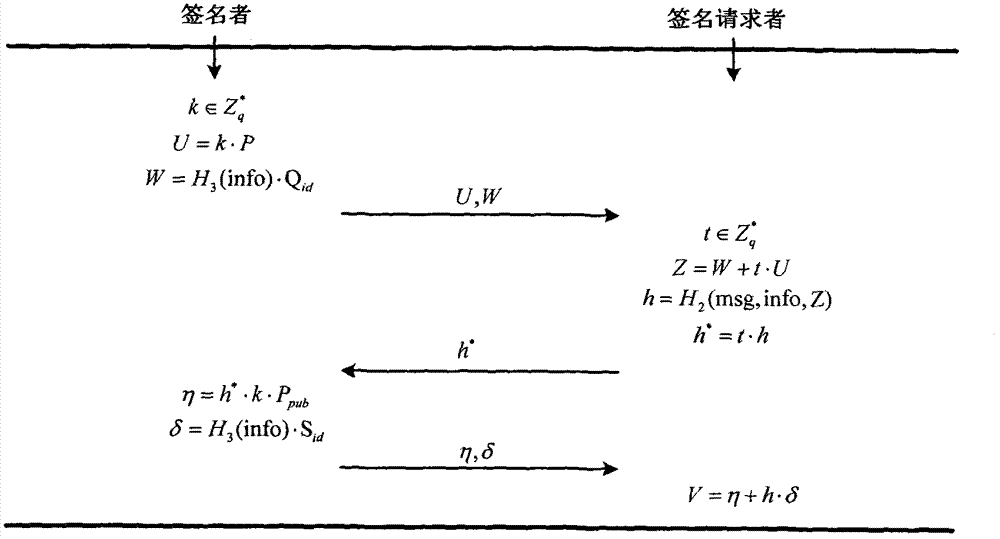
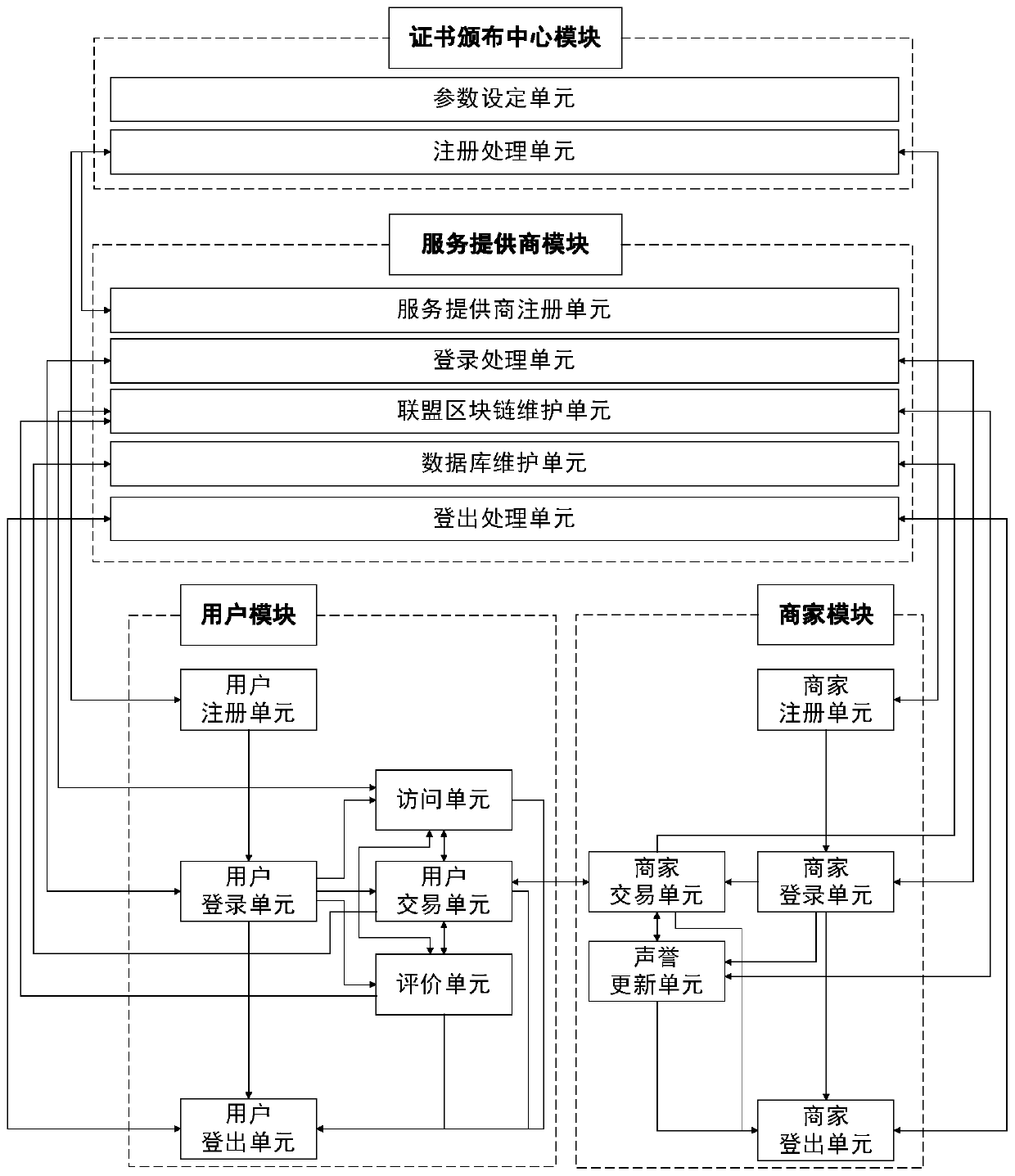
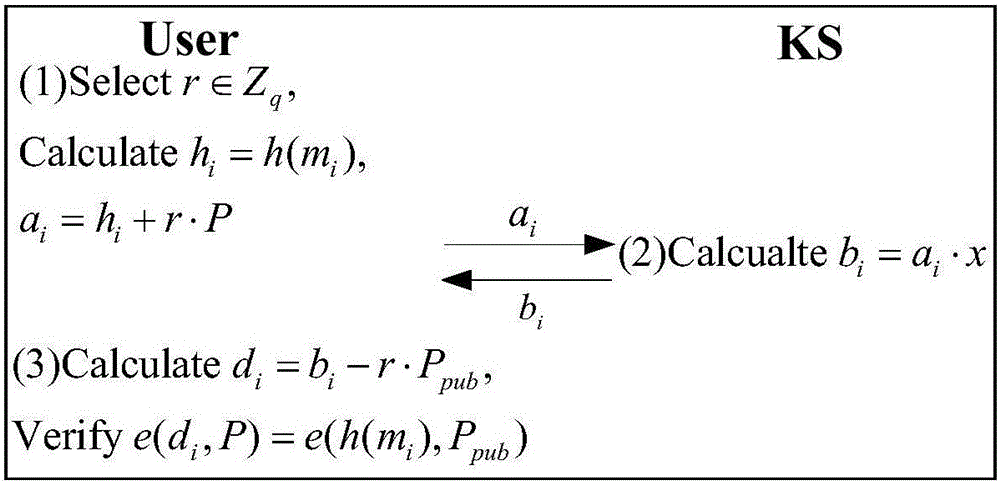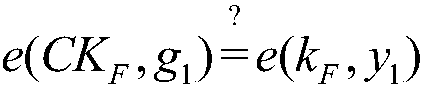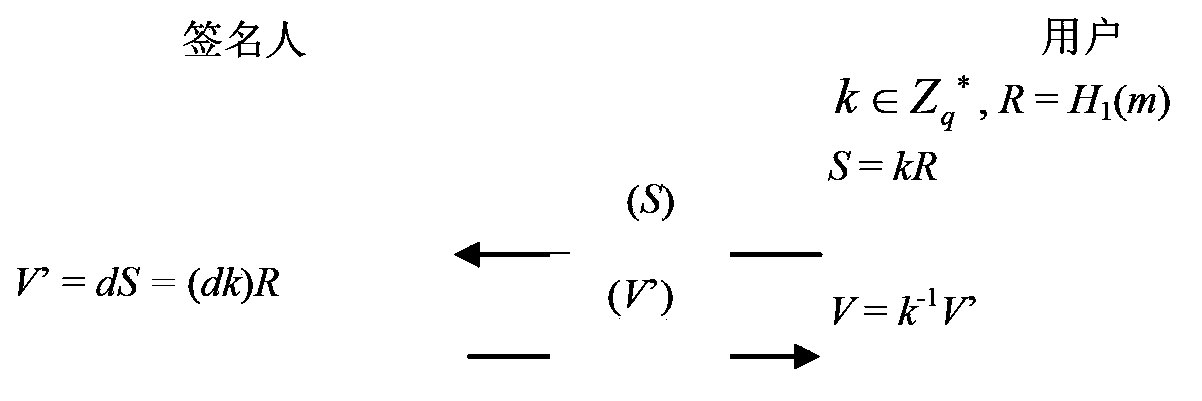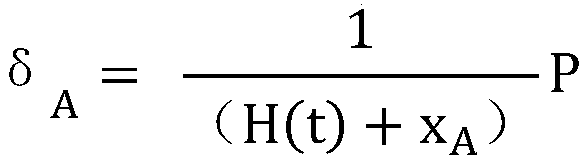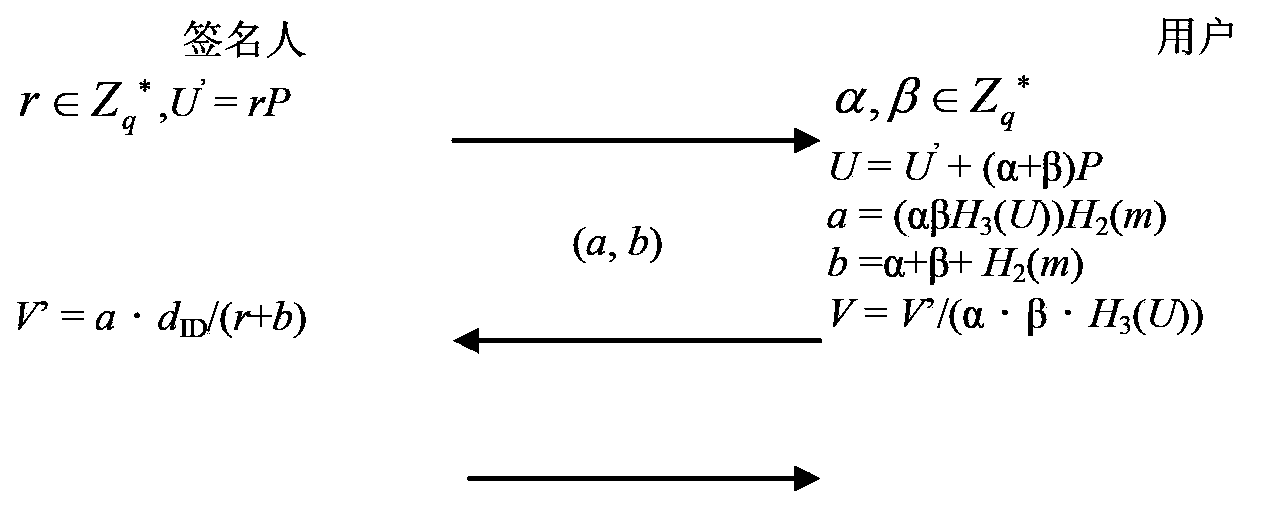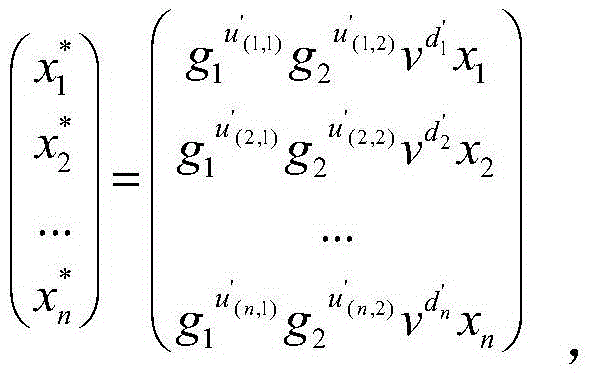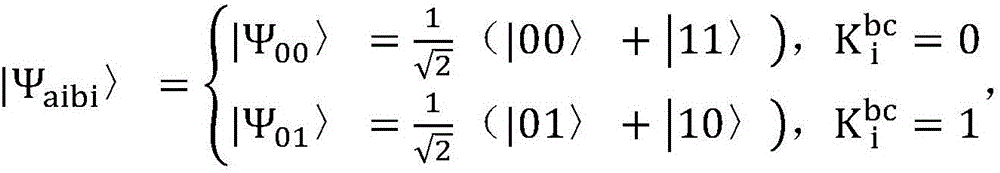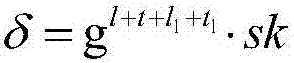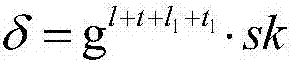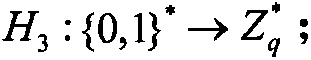Patents
Literature
145 results about "Blind signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
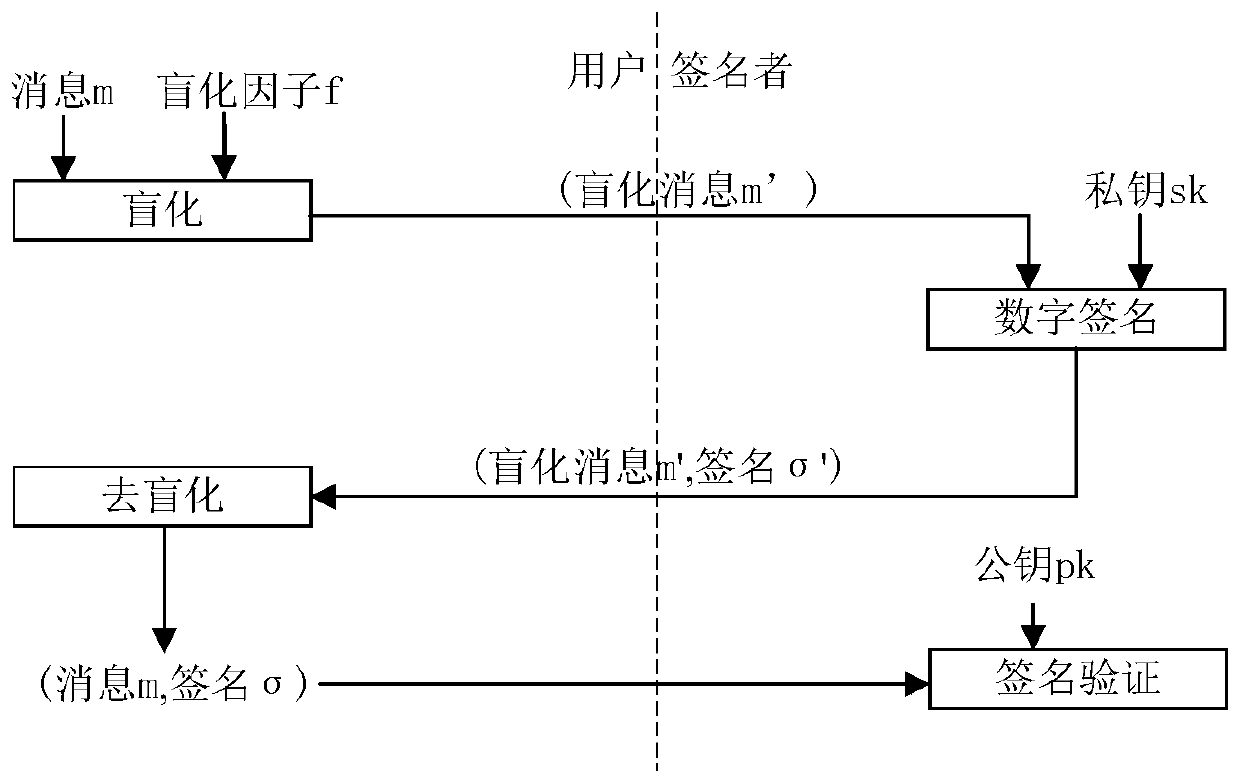
In cryptography a blind signature, as introduced by David Chaum, is a form of digital signature in which the content of a message is disguised (blinded) before it is signed. The resulting blind signature can be publicly verified against the original, unblinded message in the manner of a regular digital signature. Blind signatures are typically employed in privacy-related protocols where the signer and message author are different parties. Examples include cryptographic election systems and digital cash schemes.
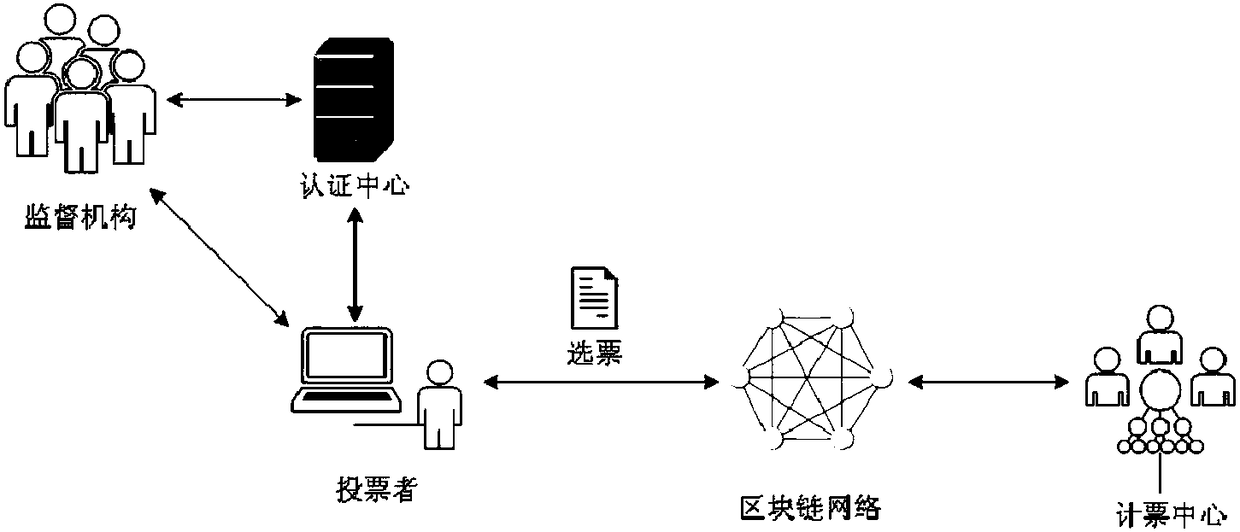
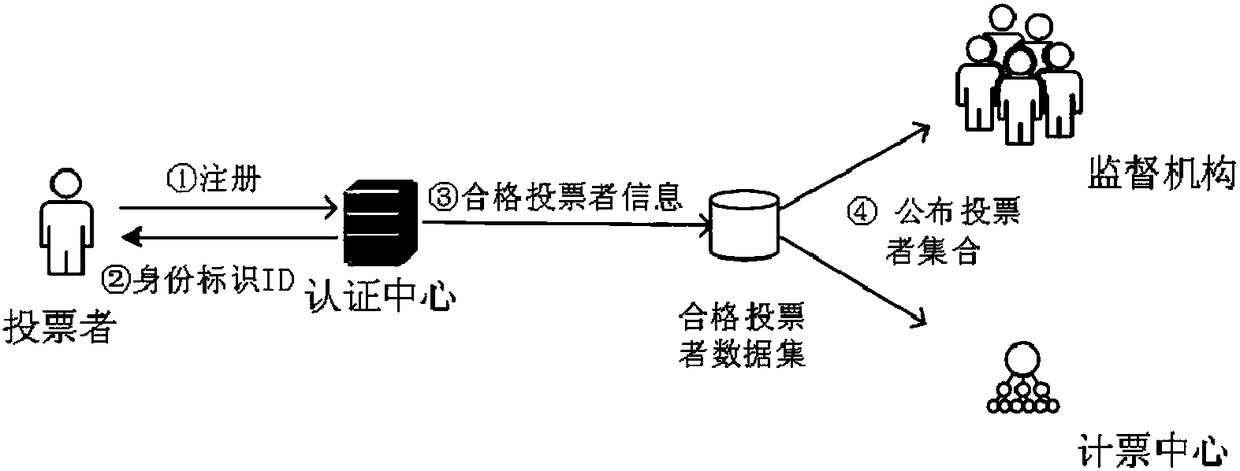
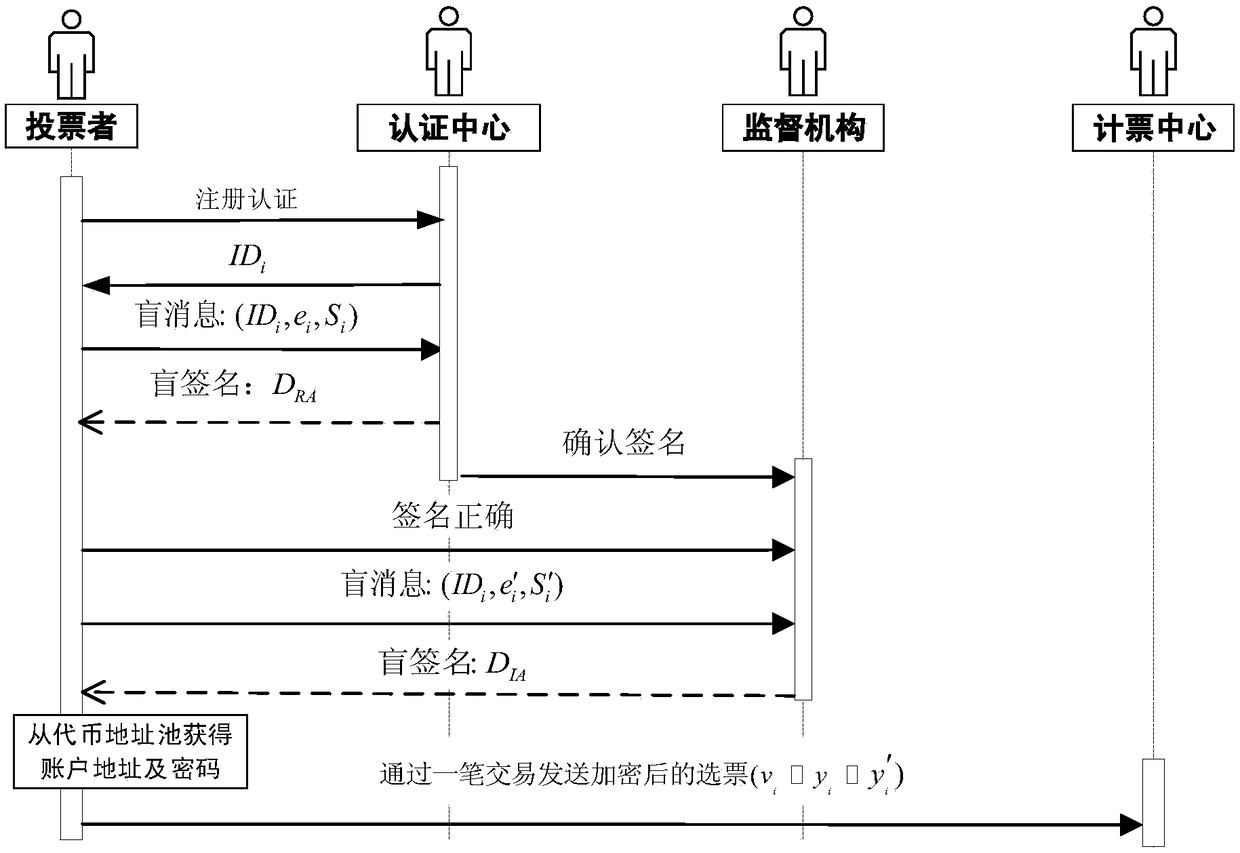
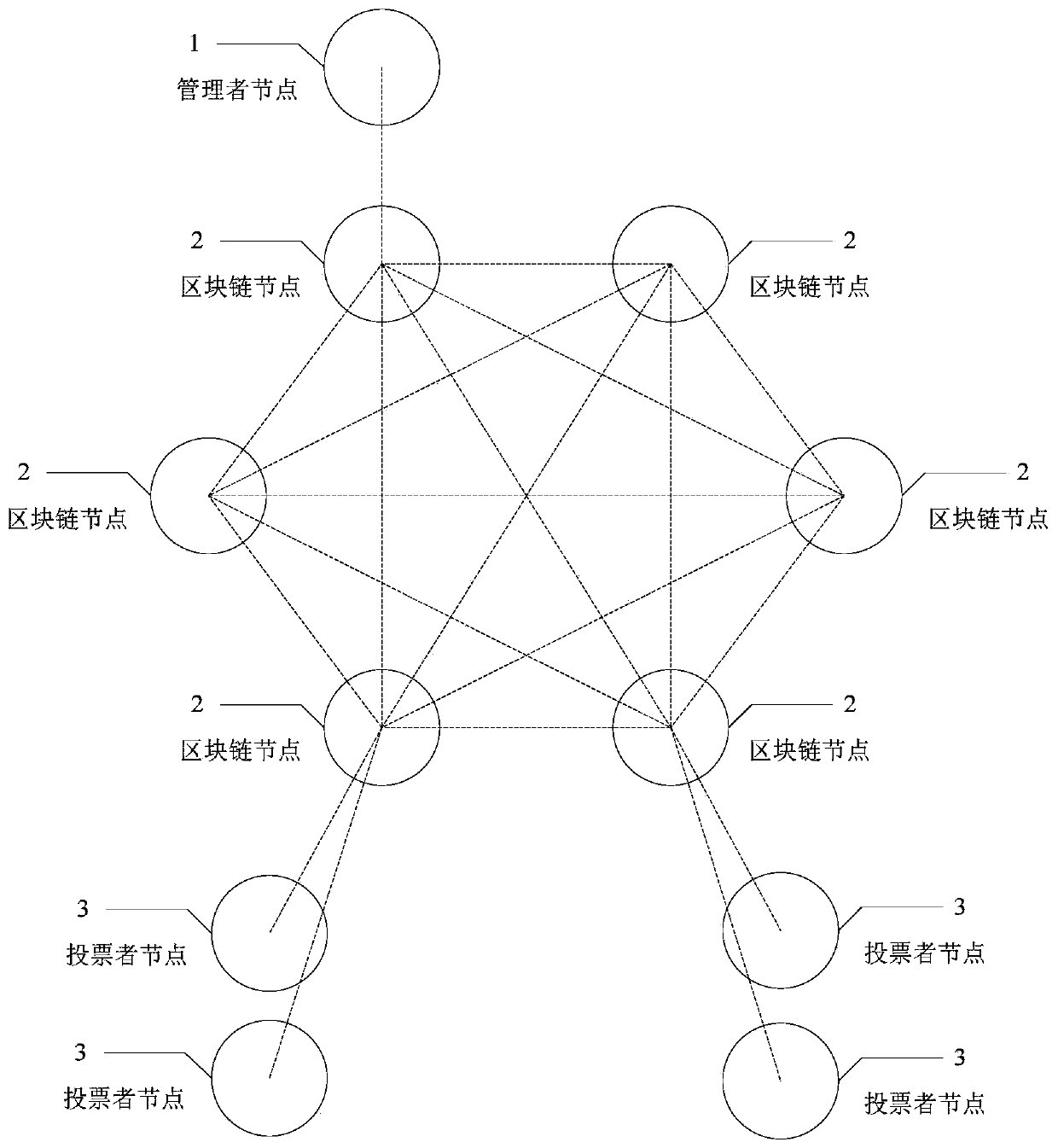
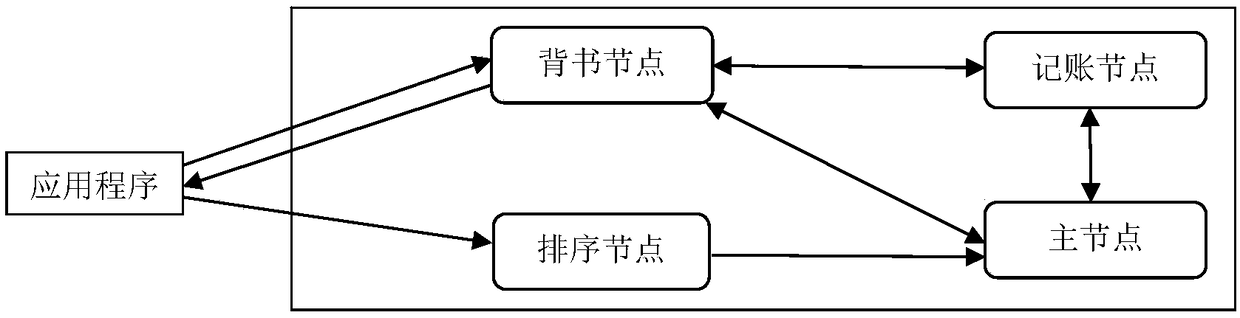
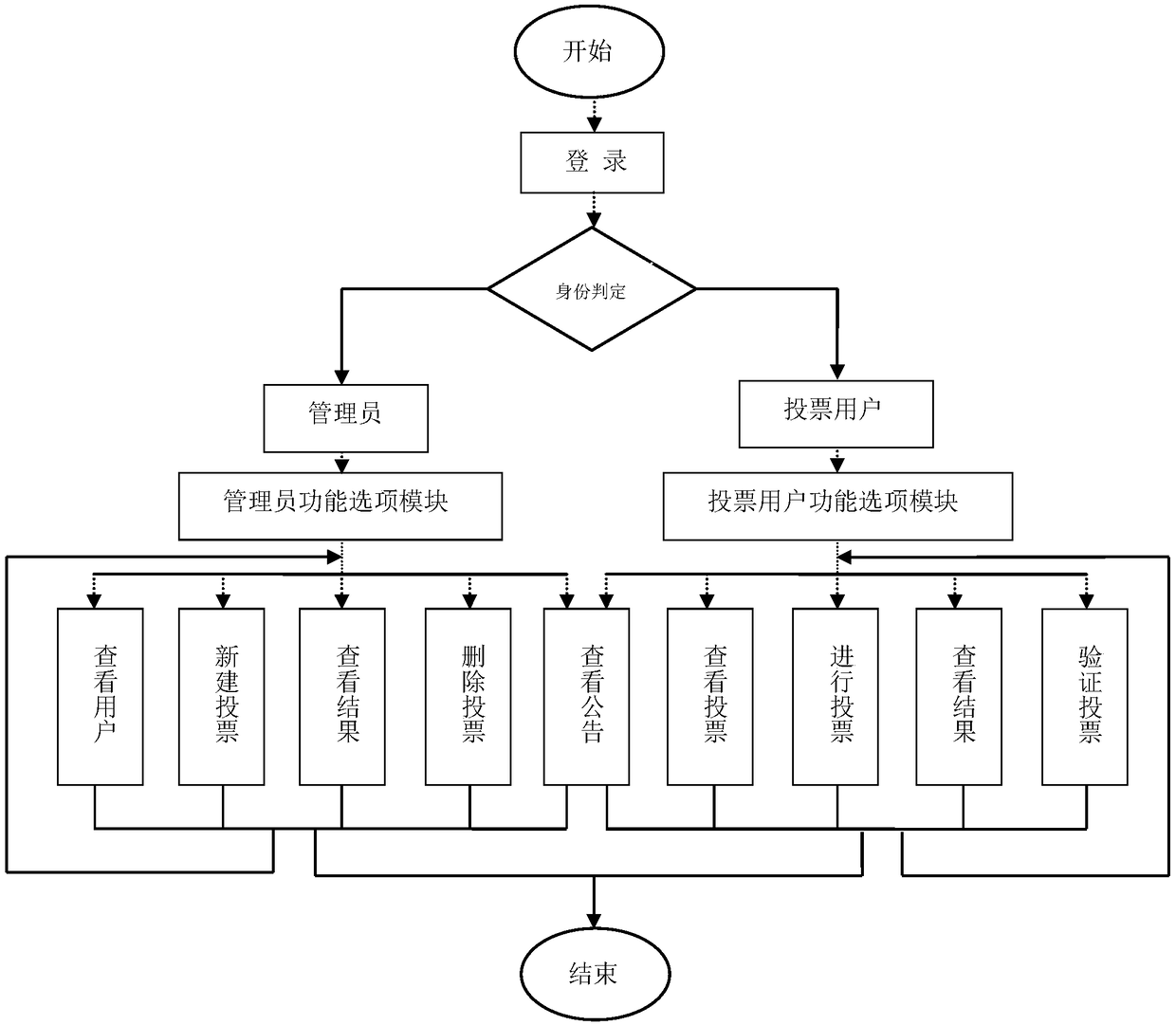
Anonymous electronic voting method based on blockchain
InactiveCN108109257AProtect anonymityPrivacy protectionVoting apparatusUser identity/authority verificationTransaction dataBlind signature
Owner:HANGZHOU DIANZI UNIV
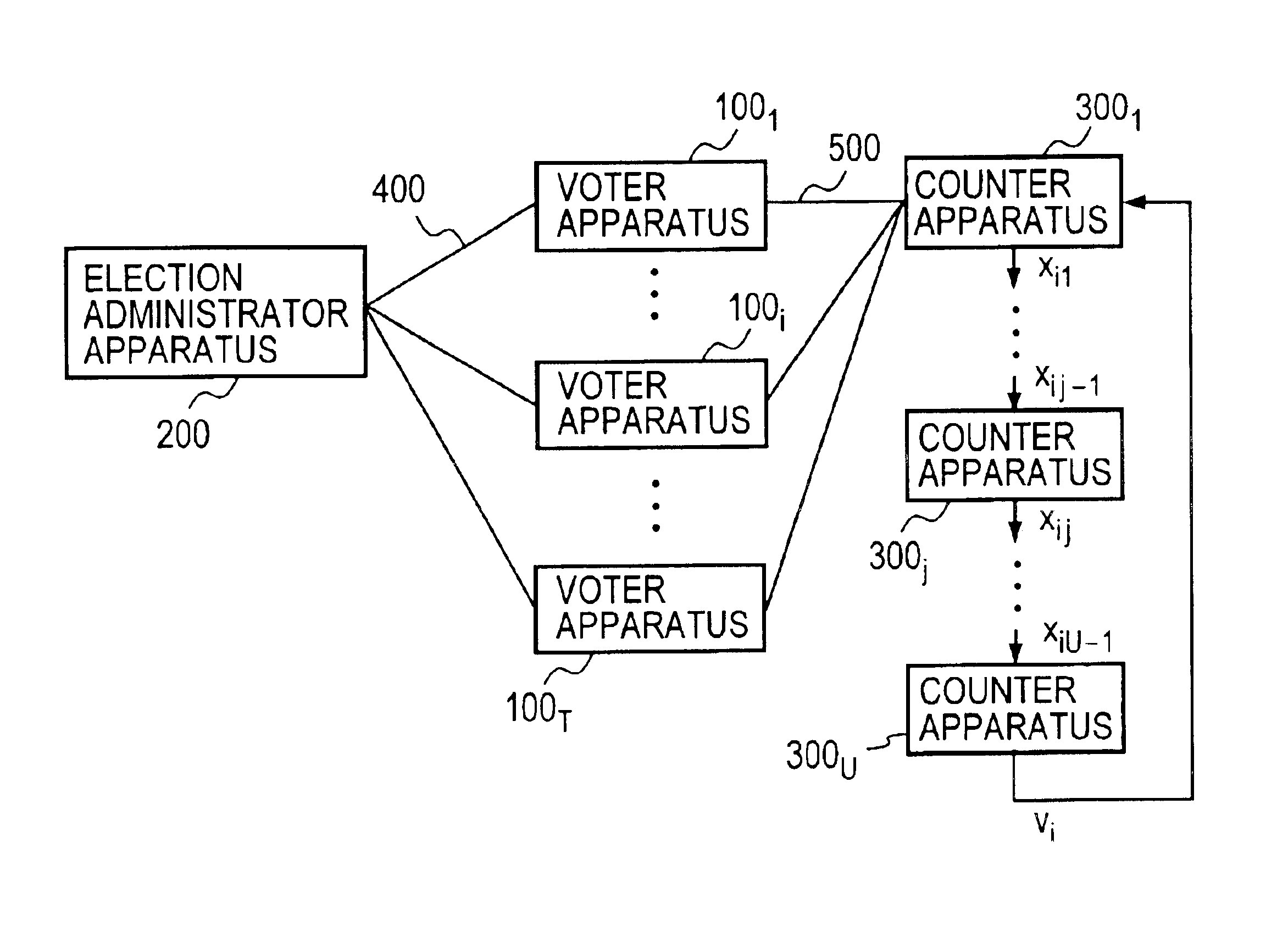
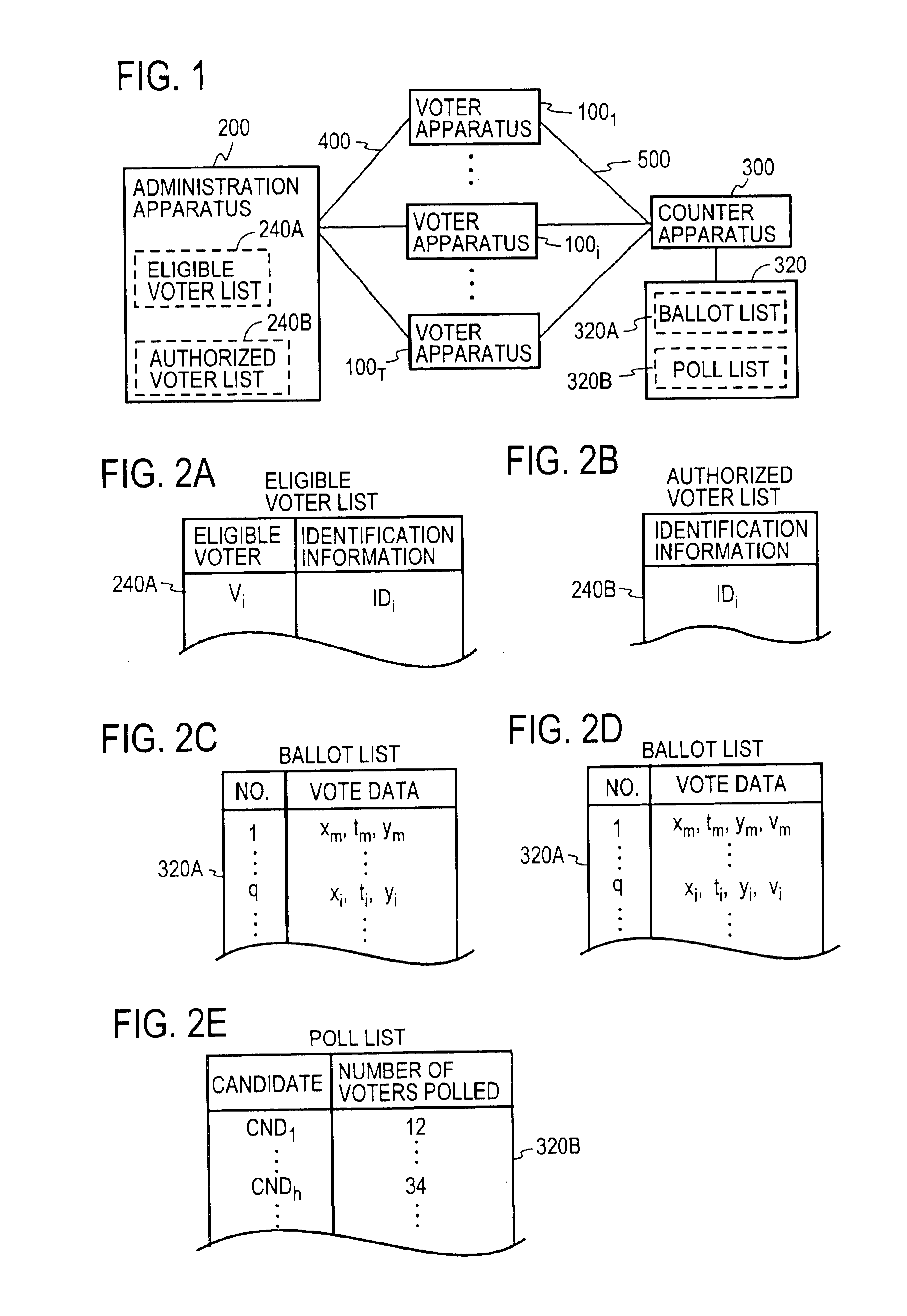
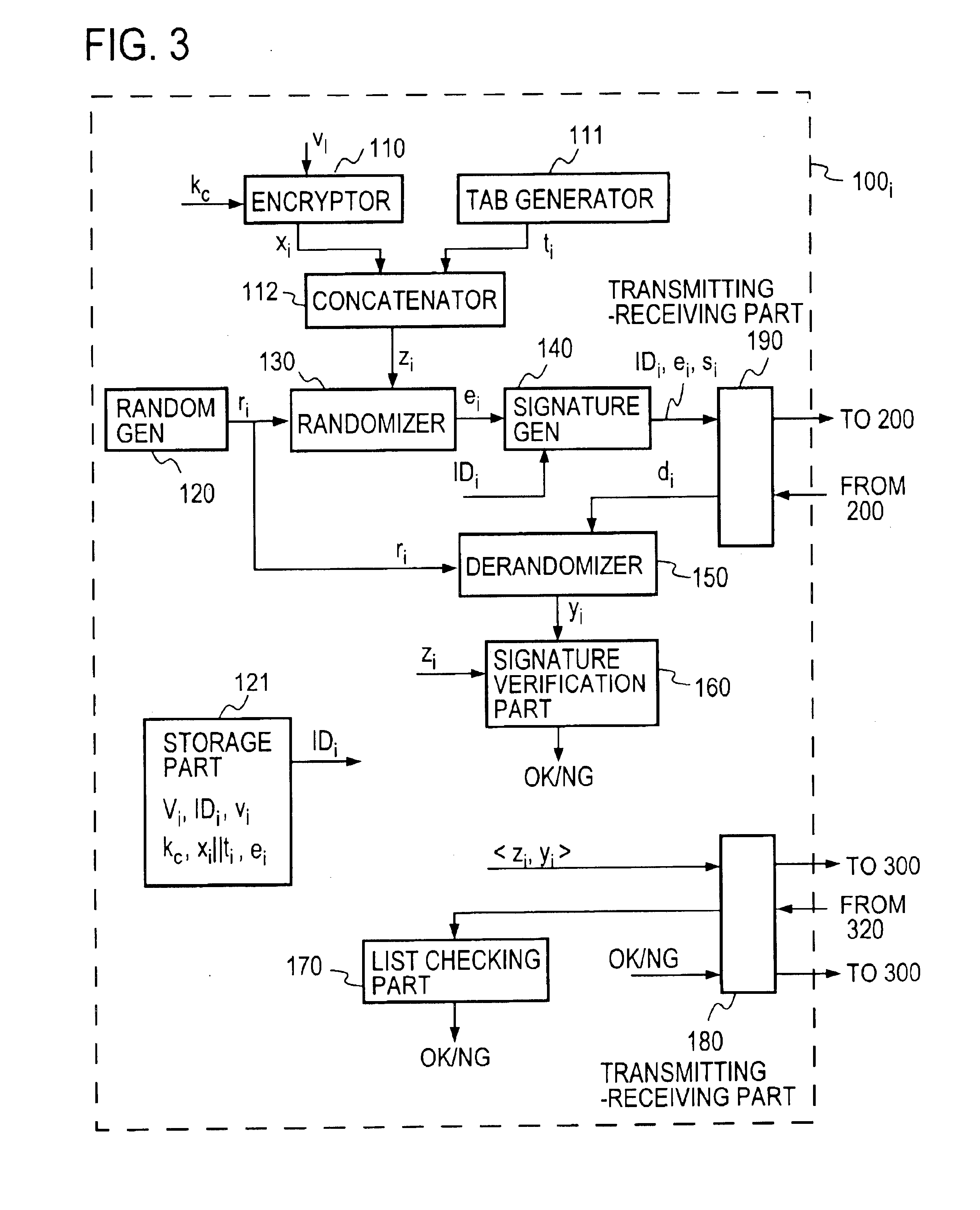
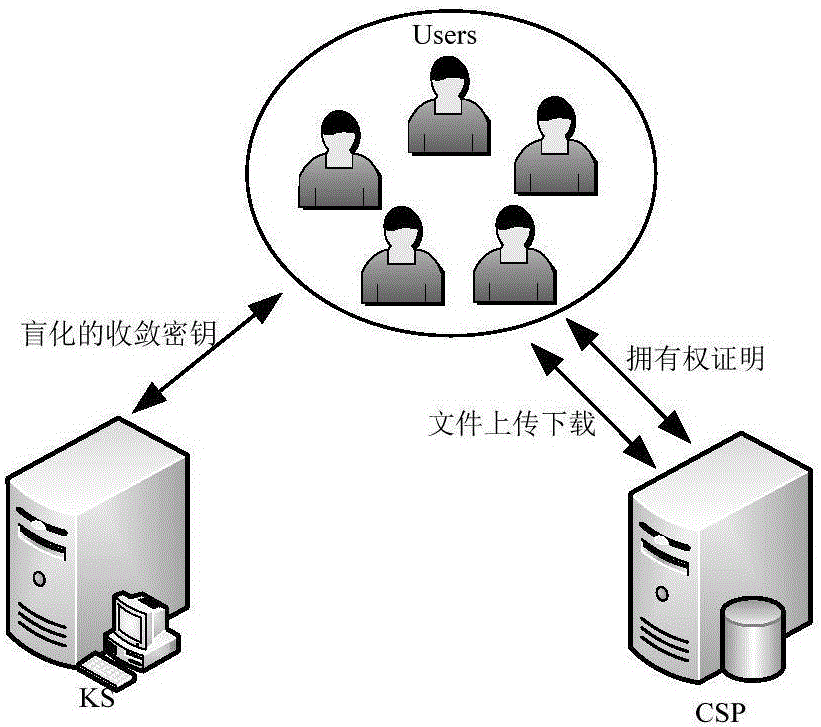
Electronic voting method and system and recording medium having recorded thereon a program for implementing the method
InactiveUS6845447B1Ensuring privacyEasy to optimizeVoting apparatusError detection/correctionBlind signatureRecording media
A voter Vi encrypts his vote content vi with a public key kPC of a counter C, then concatenates the encrypted vote content xi with a tag ti to obtain a ballot zi, then randomizes it with a random number ri to create a preprocessed text ei, and sends it and a signature si therefor to an election administrator A. The administrator A generates a blind signature di for the preprocessed text ei and sends it back to the voter Vi. The voter Vi excludes the influence of the random number ri from the blind signature di to obtain administrator signature yi, and sends vote data <zi, yi> to a counter C. The counter C verifies the validity of the administrator signature yi and, if valid, generates and publishes a vote list containing the data <zi, yi> to the voter Vi. The voter Vi checks the vote list to make sure that it contains the data <zi, yi> with his tag ti held in the ballot zi. The counter C decrypts the encrypted vote content xi in the ballot zi to obtain the vote content vi, and counts the number of votes polled for each candidate.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
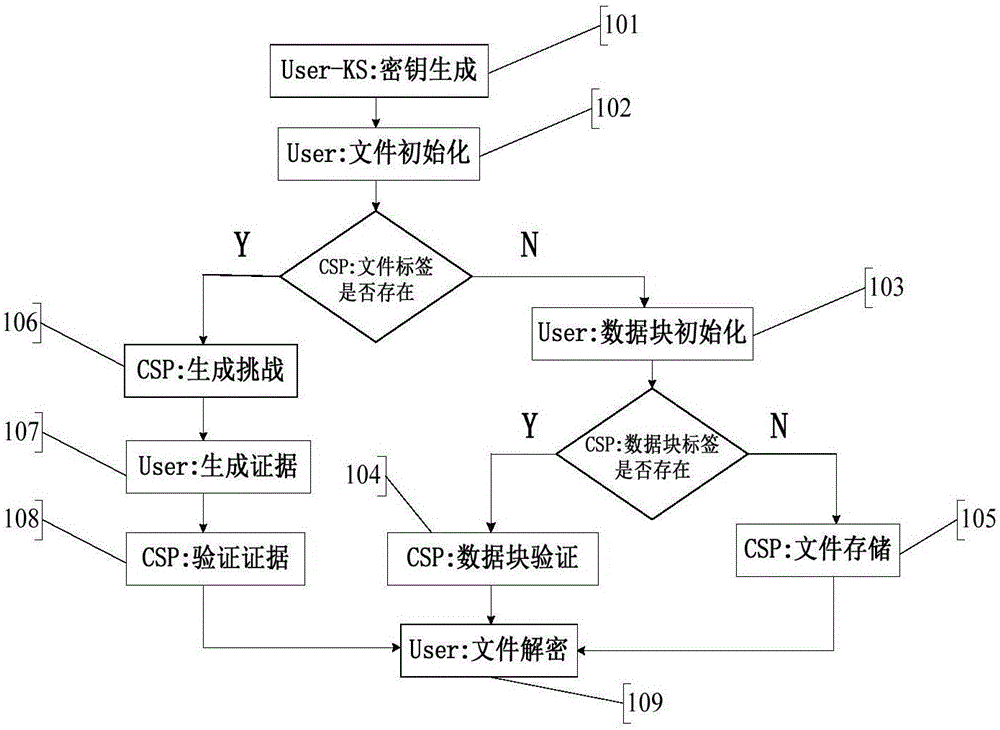
Client secure deduplication method of ciphertext data in cloud storage
ActiveCN105939191AProtection securityAvoid attackKey distribution for secure communicationUser identity/authority verificationCiphertextBlind signature
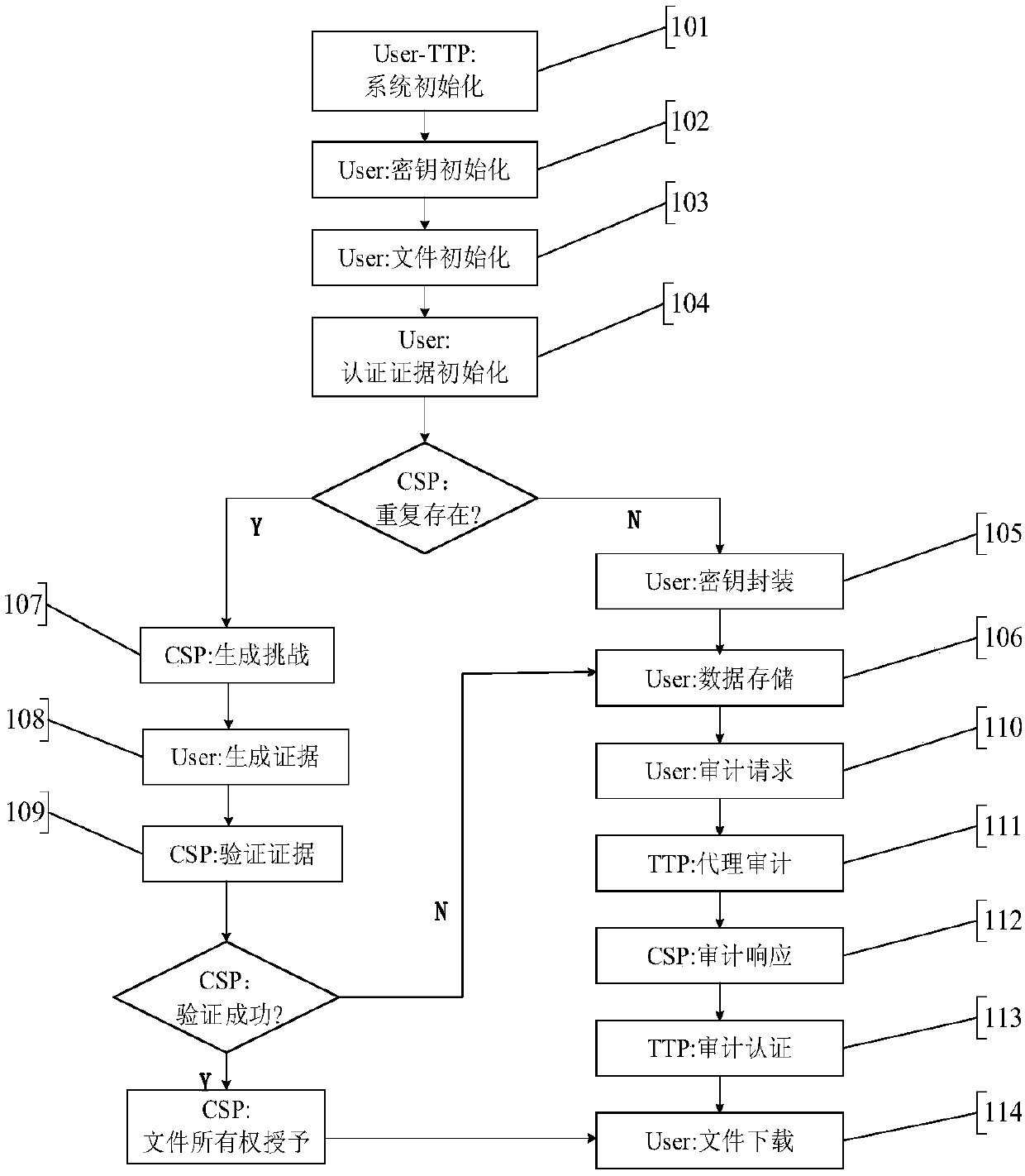
The invention discloses a client secure deduplication method of ciphertext data in cloud storage. The method comprises the following steps of: (1) key generation; (2) file initialization; (3) data block initialization; (4) data block verification; (5) file storage; (6) challenge generation; (7) proof generation; (8) proof verification; and (9) file decryption. According to the method of the invention, a secure key generation protocol is constructed based on blind signature, and therefore, secondary encryption of convergence keys is realized, and the security of the keys can be ensured; and a signature-based ownership proving method is put forward based on the above encryption, and with the method adopted, it can be ensured that a user can prove his or her ownership of a certain file in the could storage to a could server in a safer and more efficient way, and file-level and block-level deduplication of a ciphertext file can be realized.
Owner:NANJING UNIV OF SCI & TECH
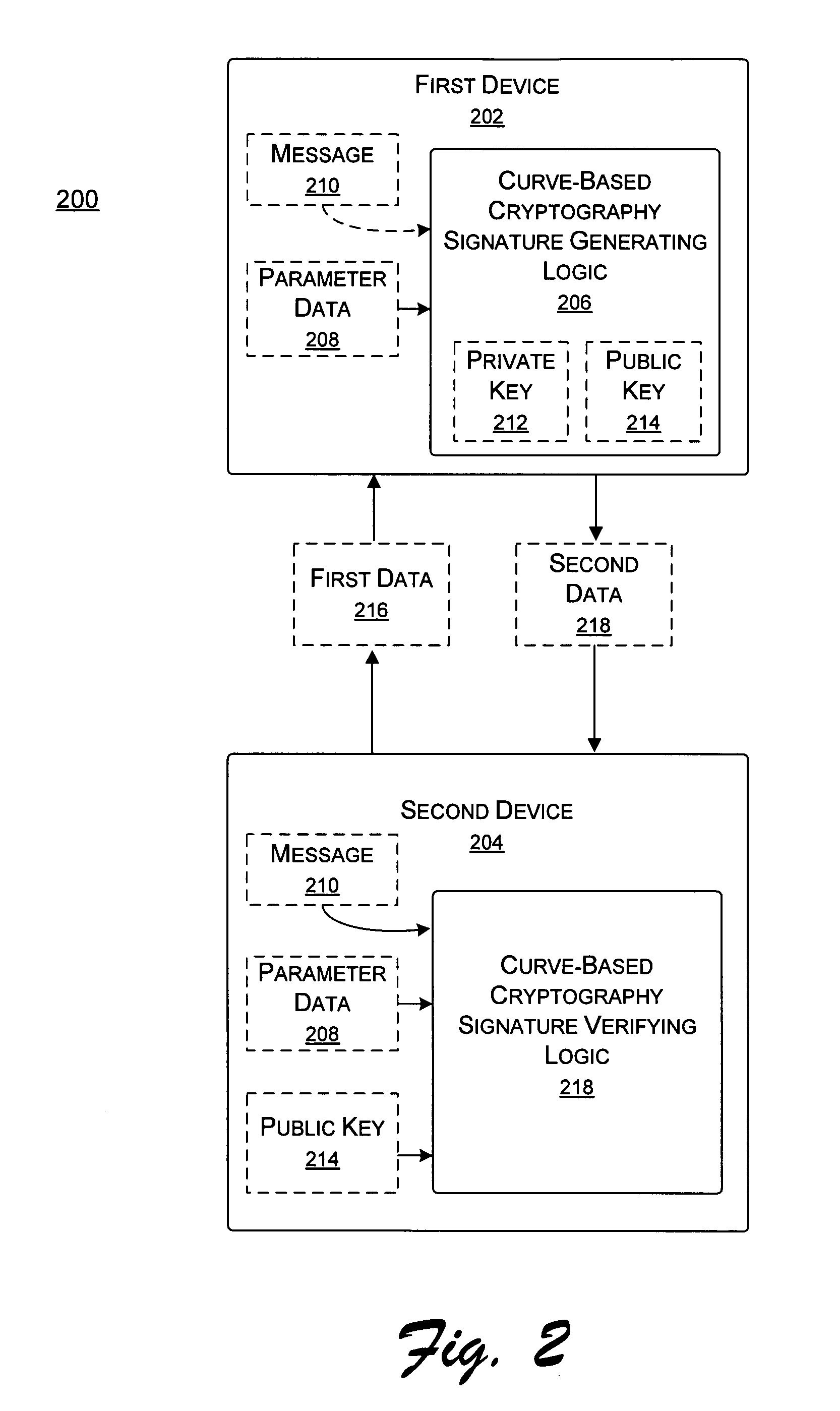
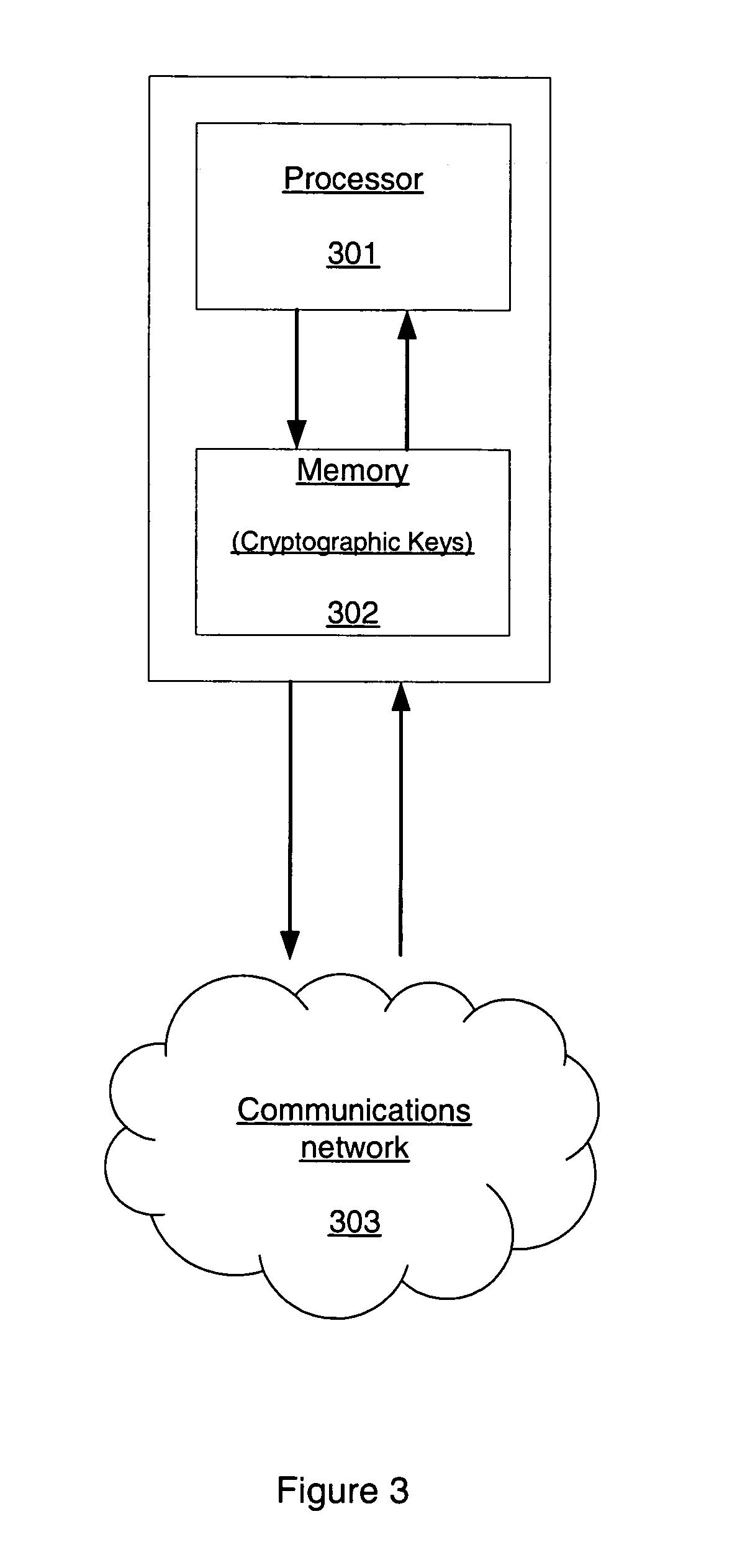
Methods and apparatuses for providing blind digital signatures using curve-based cryptography
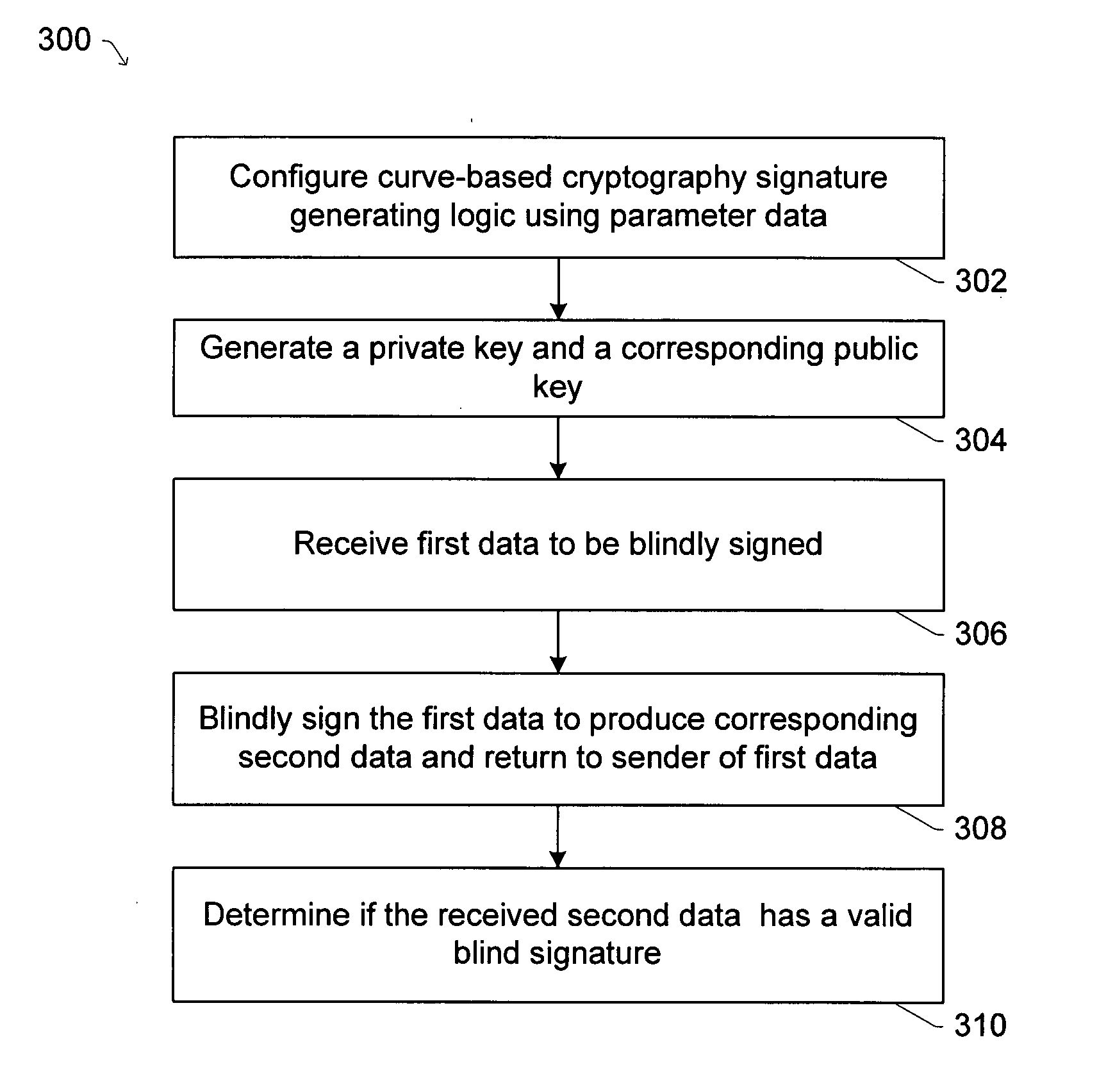
Methods and apparatuses are provided for generating blind digital signatures using curve-based cryptography techniques. One exemplary method includes establishing parameter data for use with signature generating logic that encrypts data based on a Jacobian of at least one curve. Here, the parameter data causes the signature generating logic to select at least one Gap Diffie-Hellman (GDH) group of elements relating to the curve. The method also includes receiving first data that is to be blindly signed, determining private key data and corresponding public key data using the signature generating logic, and generating second data by signing the first data with the private key data using the signature generating logic. The second data includes the corresponding blind digital signature. In other implementations, the method may also include having additional logic, for example, in one or more other devices, determine if the blind digital signature is valid.
Owner:MICROSOFT TECH LICENSING LLC
Cloud data duplication elimination and integrity auditing method based on convergence encryption
ActiveCN107800688ASafe and efficient managementTo achieve deduplicationKey distribution for secure communicationUser identity/authority verificationCloud dataTrusted third party
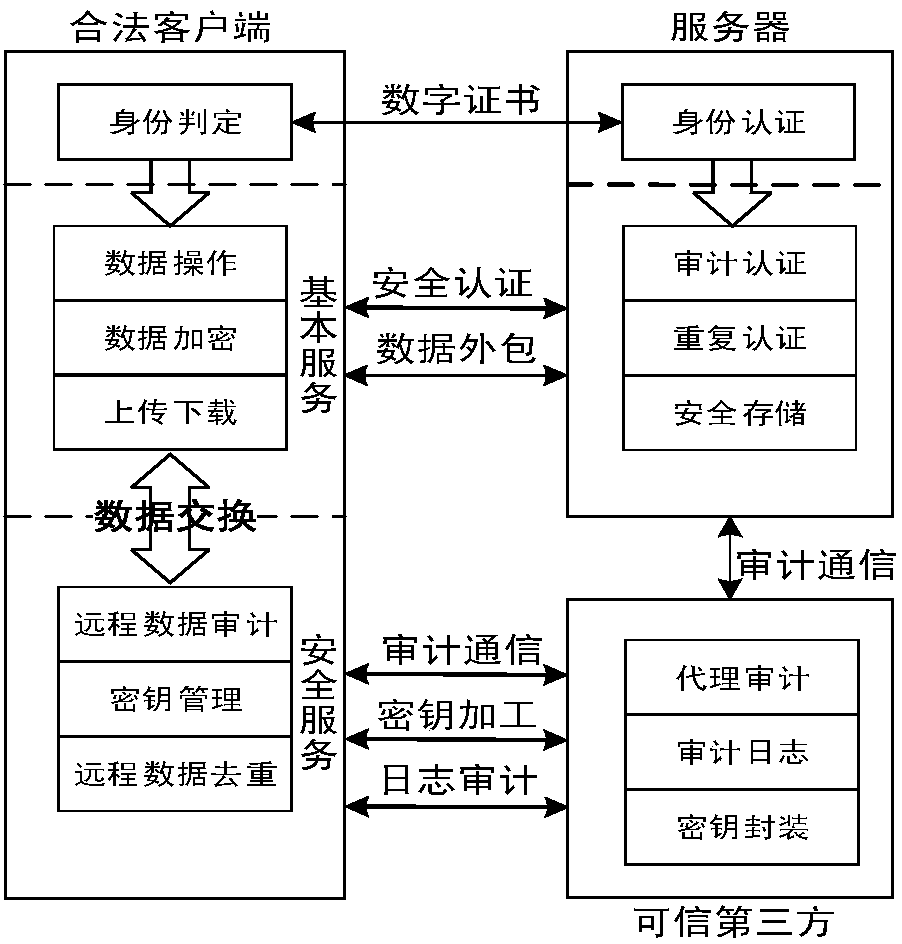
The invention discloses a cloud data duplication elimination and integrity auditing method based on convergence encryption. According to the method, through adoption of a convergence key encapsulation / de-encapsulation algorithm based on blind signatures, convergence keys can be securely stored and moreover convergence key duplication elimination can be realized; and through utilization of a BLS signature algorithm based on the convergence keys, auditing public keys are stored by a trusted third party TTP, the TTP carries out proxy auditing, and duplication elimination of auditing signatures and the auditing public keys is realized. The method comprises the specific steps of carrying out system initialization; carrying out key initialization; carrying out file initialization; carrying out authentication evidence initialization; carrying out key encapsulation; carrying out data storage; carrying out duplication challenge; carrying out duplication response; carrying out duplication authentication; carrying out request auditing; carrying out proxy auditing; carrying out auditing response; carrying out auditing authentication; and carrying out file downloading. According to the method,a utilization rate of a cloud storage space is improved, the duplication elimination of auditing signatures and the auditing public keys is realized, and the storage and computing cost of a client arereduced.
Owner:NANJING UNIV OF SCI & TECH
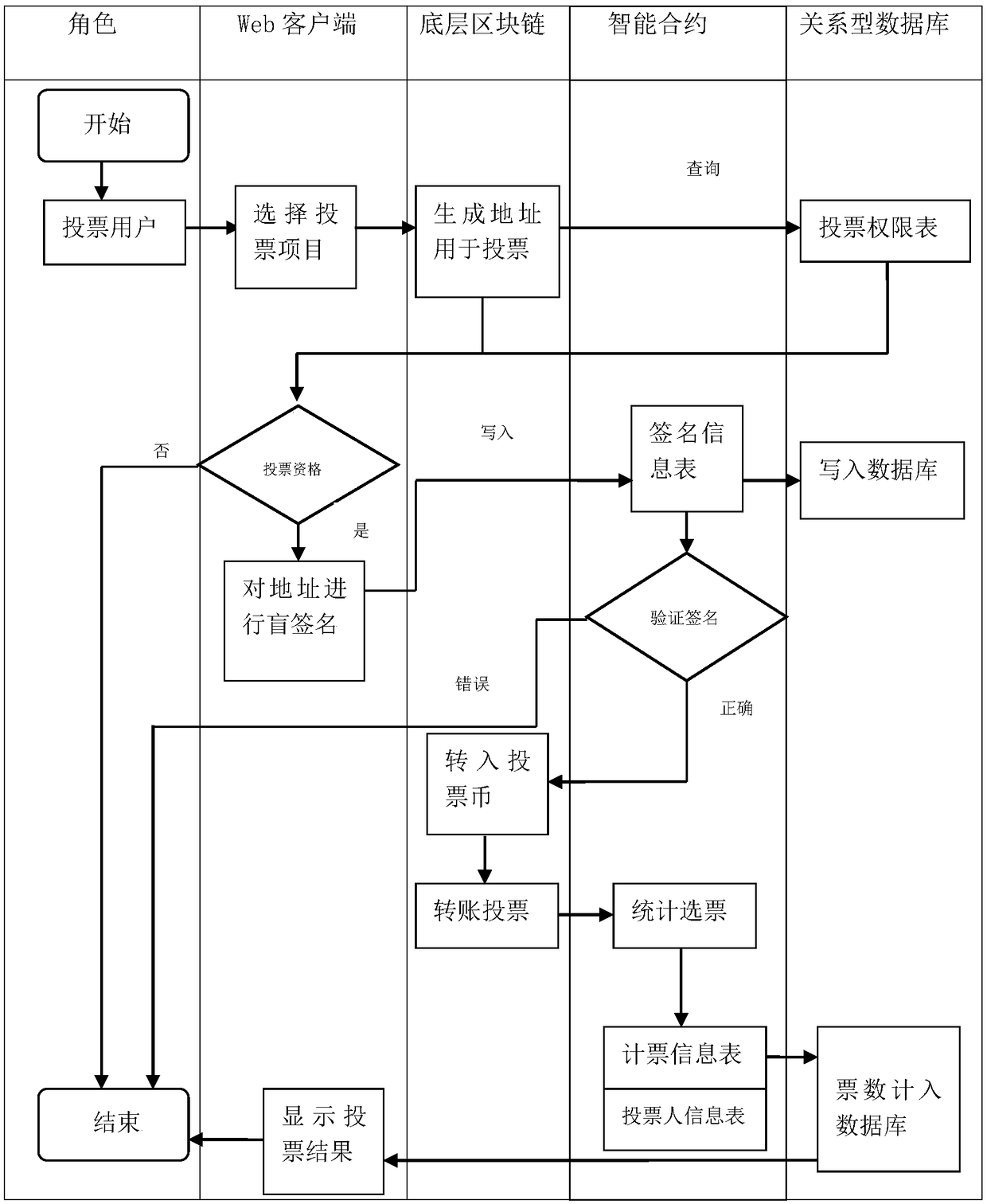
Blockchain anonymous voting system and method
ActiveCN110391911ASolve human cheatingSolve machine failureKey distribution for secure communicationFinanceRing signatureBlind signature
The invention provides a blockchain anonymous voting system and method. A voting system is realized by using a block chain; voting logic is put into an intelligent contract for operation; voting datacan be publicized and transparentized; a centralized node does not exist, even if a single node fault occurs, the overall operation of the system is not influenced;, the voting data in the blockchaincan be tampered by any person, and moreover, by introducing cryptographic technologies such as blind signature and ring signature into the blockchain, details such as identity information and voting intention of voters are hidden on the premise of ensuring the openness and legality of necessary voting data, so that the effect of protecting the privacy of users is achieved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
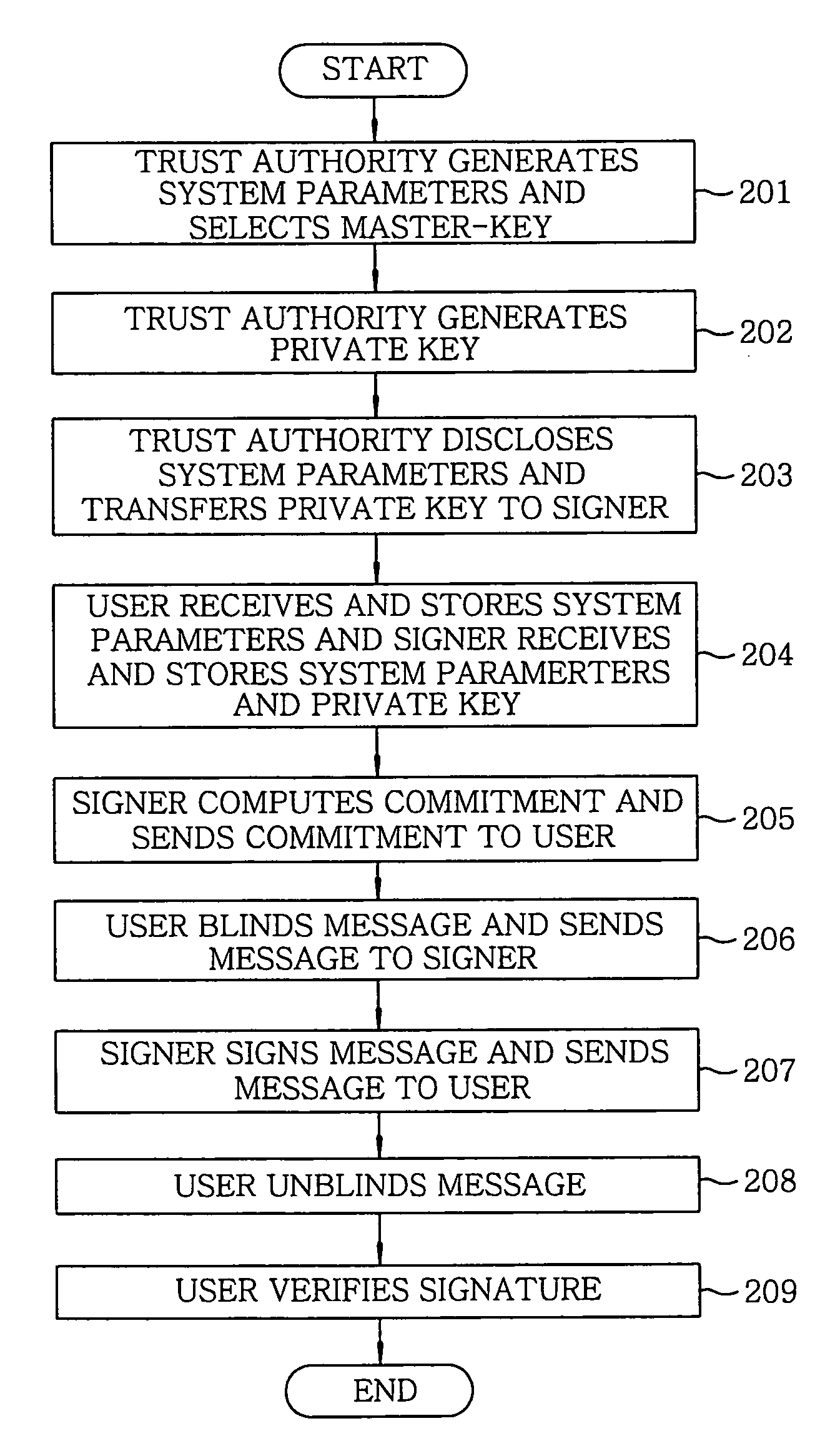
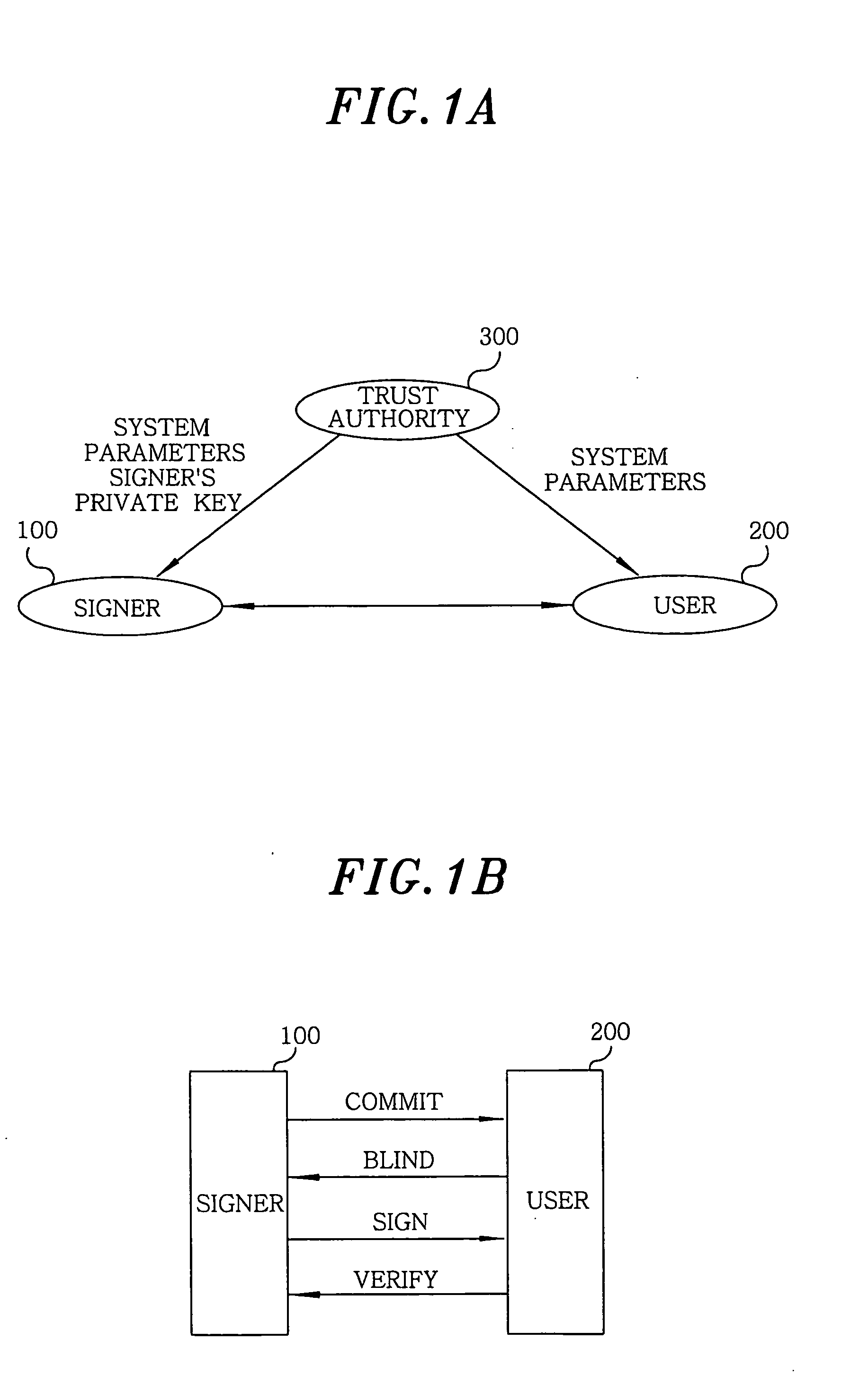
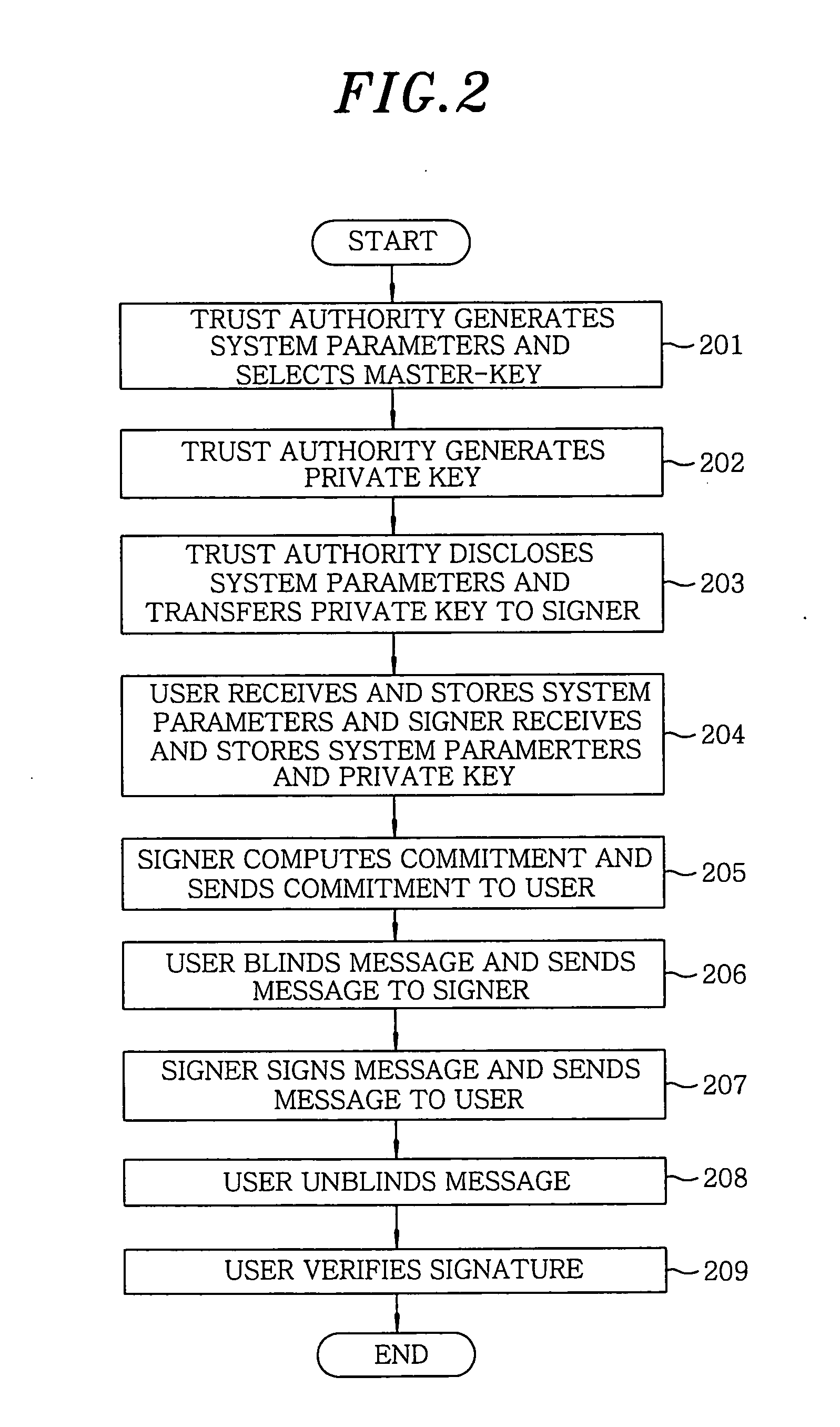
Apparatus and method for generating and verifying ID-based blind signature by using bilinear parings
InactiveUS20050005125A1Multiple keys/algorithms usageUser identity/authority verificationTrusted authorityBlind signature
In an apparatus and a method for generating and verifying an identity based blind signature by using bilinear parings, a trust authority generates system parameters and selects a master key. Further, the trust authority generates a private key by using a signer's identity and the master key. The signer computes a commitment and sends the commitment to the user. The user blinds a message and sends the blinded message to the signer. The signer signs the blinded message and sends the signed message to the user. Thereafter, the user unblinds the signed message and then verifies the signature.
Owner:INFORMATION & COMM UNIV EDUCATIONAL FOUND
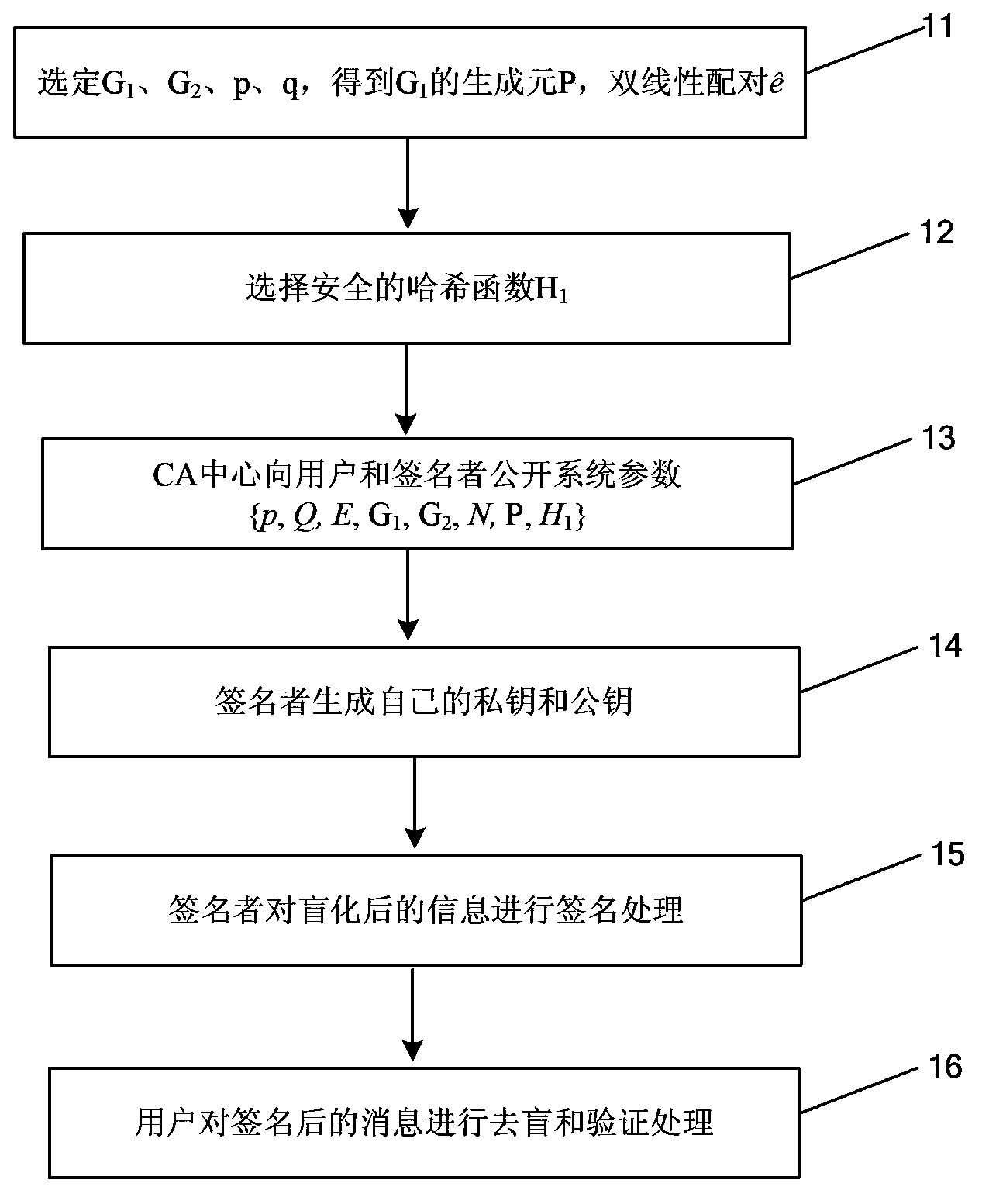
Blind signature method based on elliptic curve and device thereof
ActiveCN103780385AShorten the lengthImprove throughputPublic key for secure communicationUser identity/authority verificationMessage lengthHash function
The invention provides a blind signature method based on an elliptic curve and a device thereof. The method mainly comprises the following steps: (1) a sending user randomly selects a blind factor k belonging to Zq*, formulas R=H1(m) and S=kR are calculated, m is a (0,1) string with any length in information to be signed, S is a blinded message, q is a set large prime number, Zq* represents integers in a range from 1 to (q-1), H1 is a one-way Hash function, Fp is a domain formed by integers from 0 to (p-1), p is a set large prime number, and q is the prime factor of (p+1); (2) a signer uses a private key d of the signer to sign S, a formula V'=dS= (dk)R is calculated, and V' is sent to a receiving user; (3) the receiving user receives V', a formula V=k-1V' is calculated, and the X coordinate of V is the signature of the message m. According to the blind signature method based on the elliptic curve of the embodiment of the invention, the blind signature message length is only the X coordinate of an elliptic curve point, the throughput of system operation is increased, and the method and the device are suitable for a communication environment with a limited bandwidth.
Owner:AEROSPACE INFORMATION
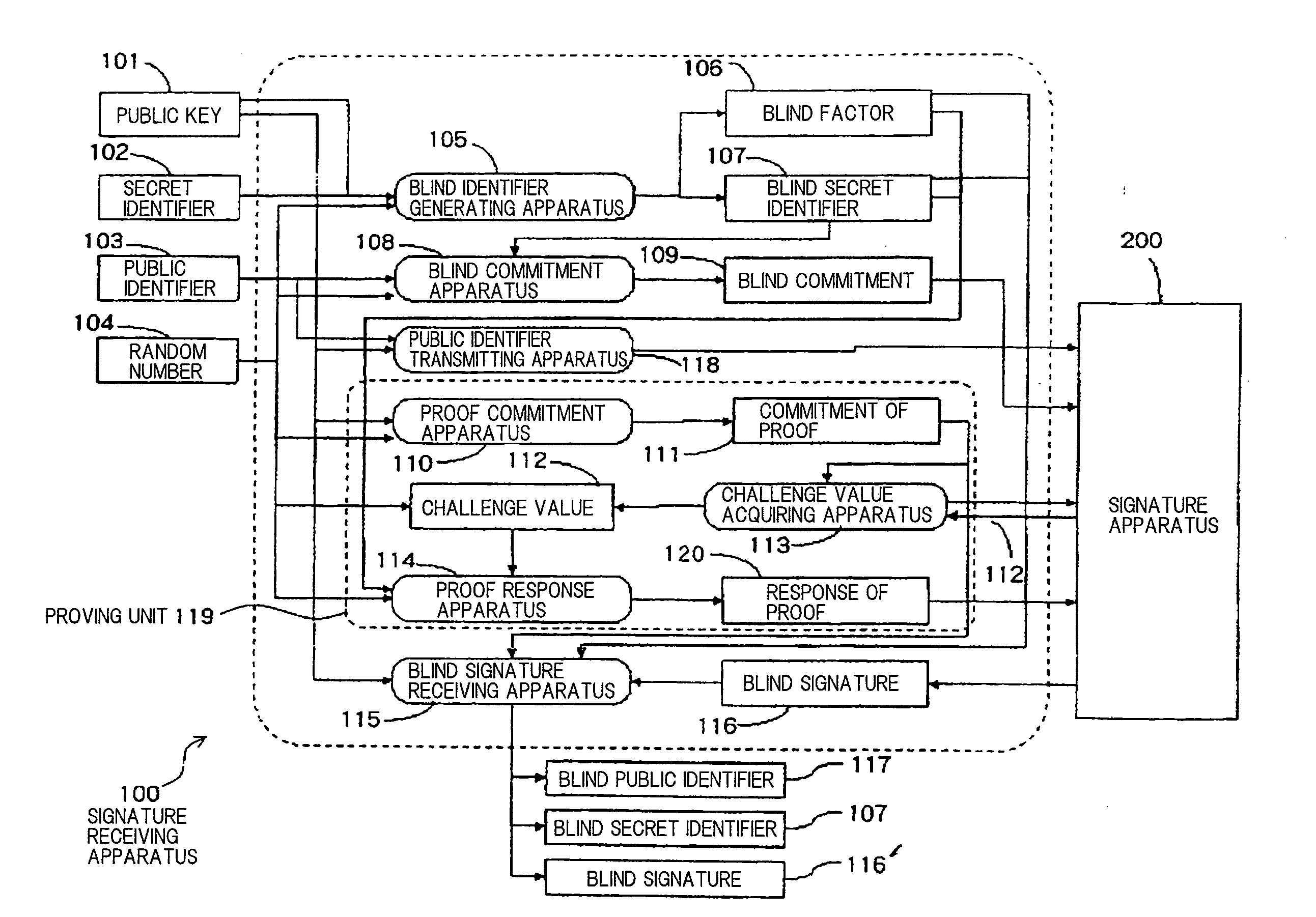
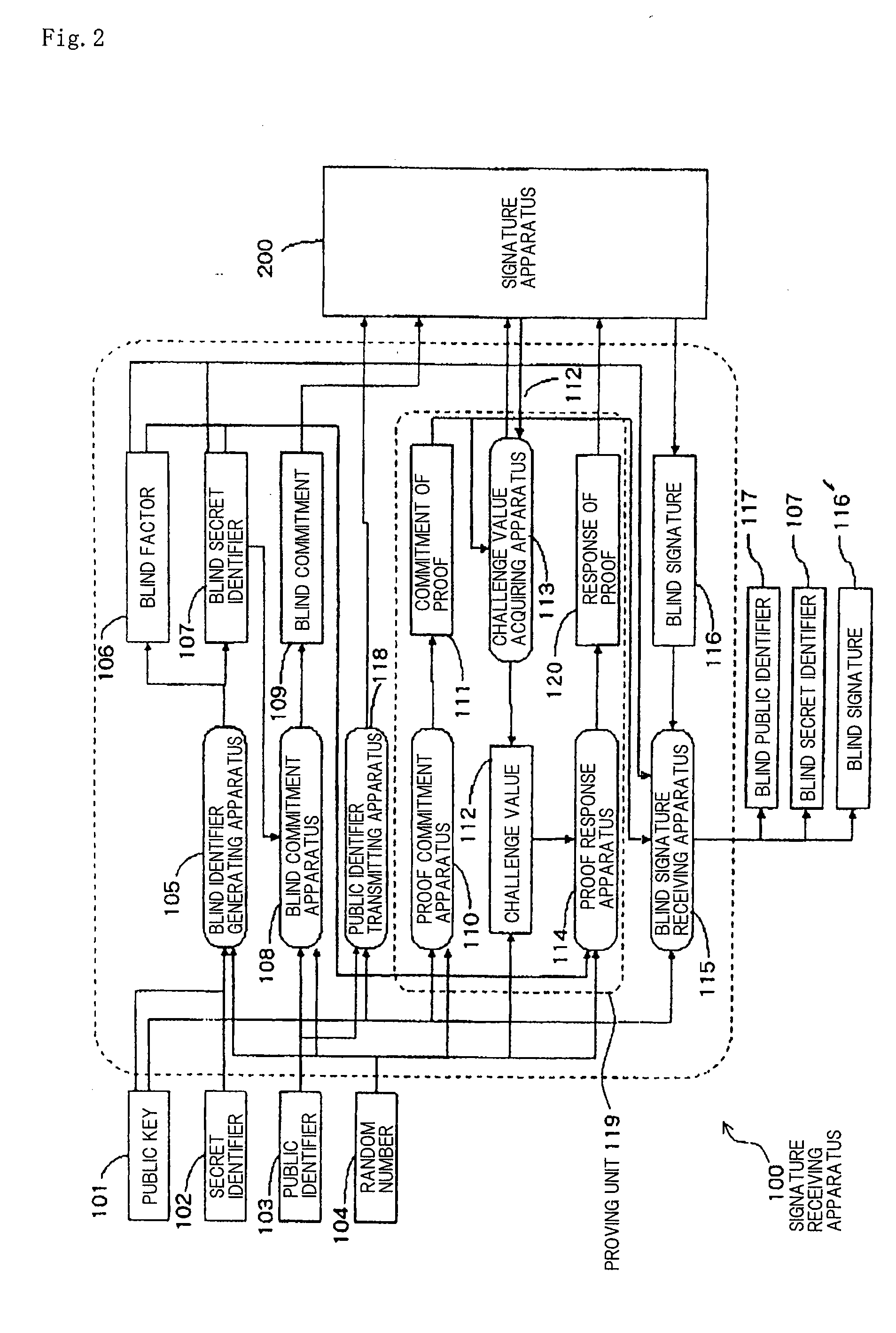
Limited Blind Signature System
InactiveUS20080141035A1Reduce the possibilityUser identity/authority verificationRandom oracleBlind signature
The present invention is aimed at the proposal of a limited blind signature system which is highly safe such that its safety can be proven without the assumption of a random oracle model. A signature presenting apparatus is supplied with a public key, a blind secret identifier, a blind public identifier, a blind signature, and a random number. A signature verifying apparatus outputs “valid” if the signature presenting apparatus is supplied with the data and otherwise outputs “invalid”.
Owner:NEC CORP
Blind signature based privacy preservation method for admissible block chains
The invention discloses a permission block chain privacy protection method based on blind signature. For transaction content, the transaction information m is encrypted blindly by Hash function, and then the transaction is signed by the address private key of both parties to ensure that the transaction information can only be viewed by both parties, and then only the unique DAID of digital assets,the blind signature of the transaction and the endorsement public key of the endorsing node are recorded on the block chain; the transaction information m is encrypted blindly by Hash function, and then the transaction is signed by both parties' address private keys. For the identity information of the transaction user, the information written into the block chain has only the blind signature andthe third-party public key address which provides the blind signature, and the ID of the digital asset. The latter two have nothing to do with the transaction information and the user information, and the blind signature is unforgeable and unextractable, so the privacy of the identity information of the user can be protected. The invention can not only protect the identity information privacy ofboth sides of the transaction, but also protect the information of the transaction during the transaction of the licensing block chain.
Owner:GUANGXI NORMAL UNIV
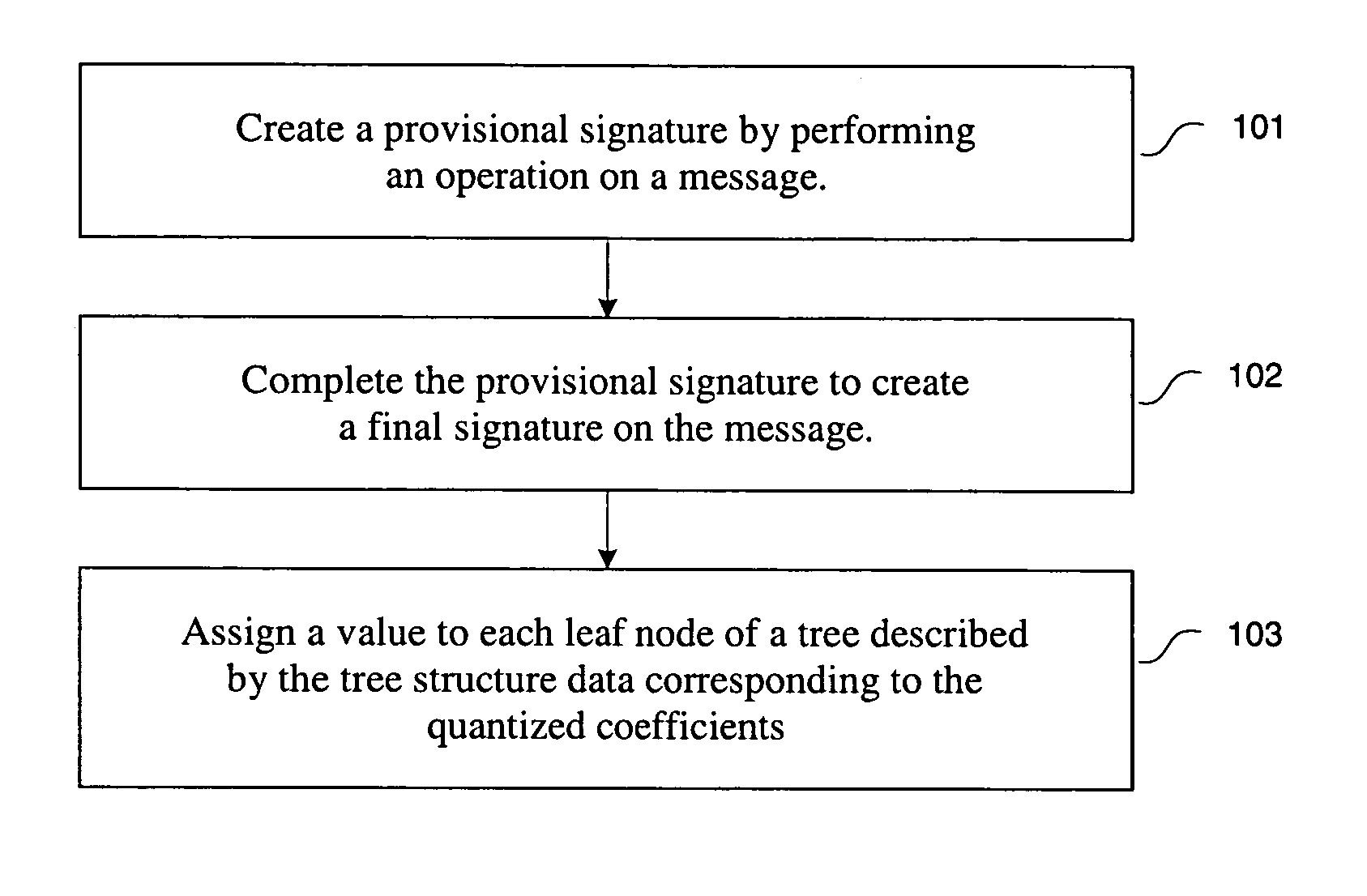
Provisional signature schemes
InactiveUS7730319B2User identity/authority verificationSecret communicationBlind signatureComputer security
A method and apparatus for implementing portions of a provisional signature scheme are disclosed. In one embodiment, the method comprises creating a provisional signature by performing an operation on a message and completing the provisional signature to create a final signature on the message. Such a scheme may be used for server assisted signature schemes, designated confirmer signature schemes and blind signature schemes.
Owner:NTT DOCOMO INC
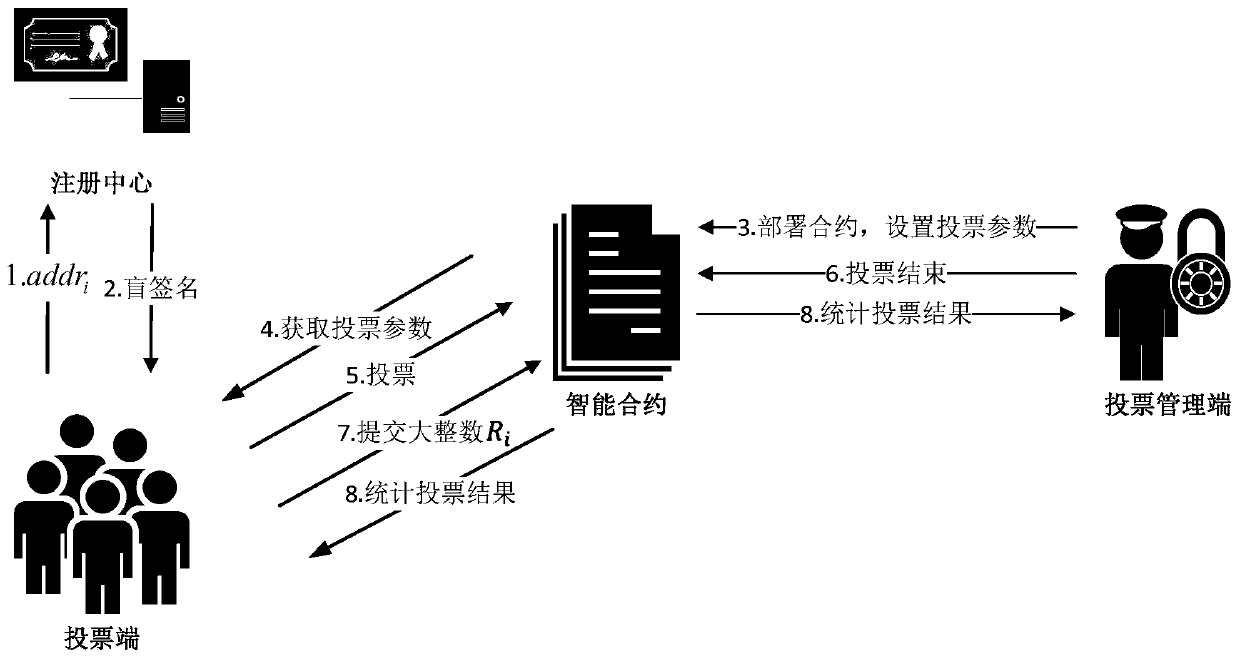
Blockchain-based anonymous electronic voting method and system
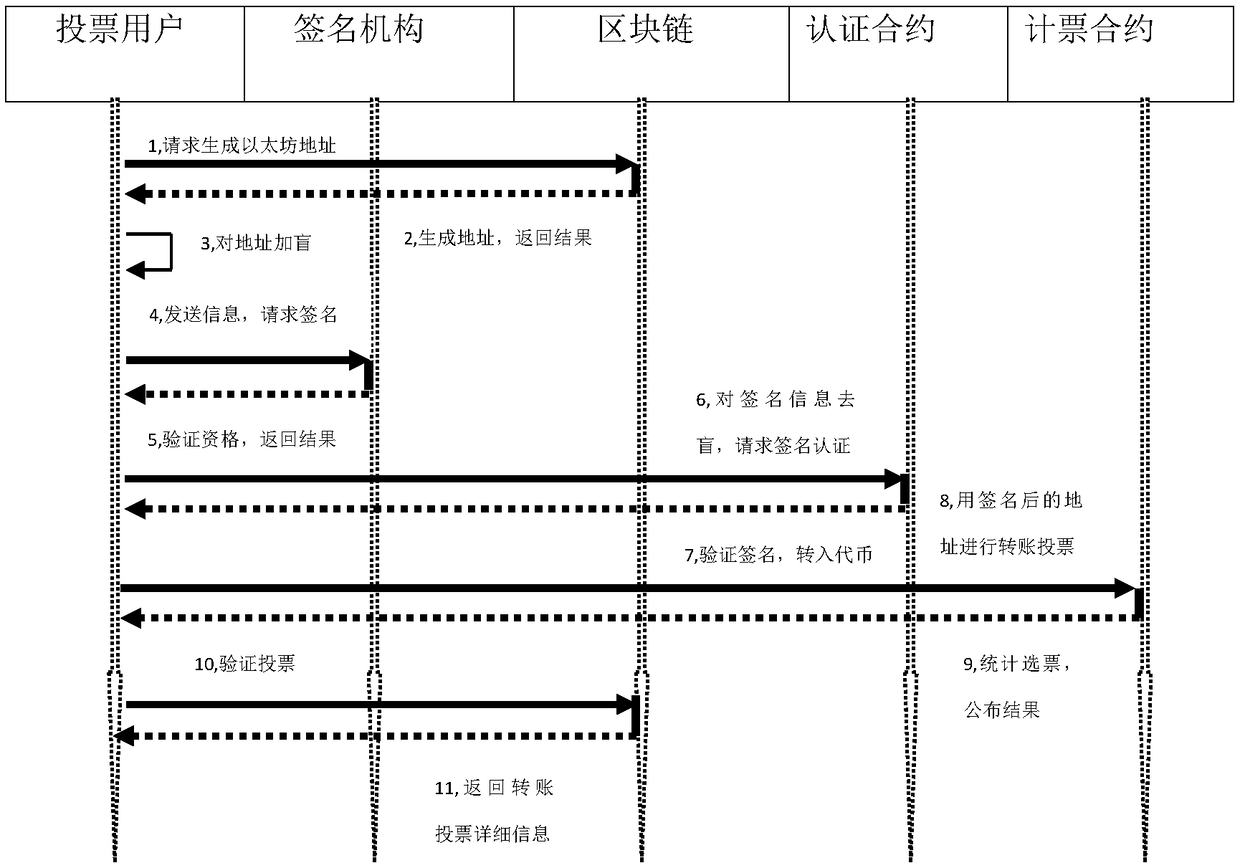
ActiveCN110232764AImprove fairnessProtect personal privacyVoting apparatusPublic key for secure communicationBlind signatureSmart contract
The invention discloses a blockchain-based anonymous electronic voting method and a system thereof. The method comprises the following steps: voting terminal identity information and Ethereum accountaddress are sent to the registration center by the voting terminal, and a blind signature is generated at the registration center and sent to the voting terminal, and a voting right signature is output by the voting terminal; voting parameters are generated by a voting managing terminal, the parameters are included to a smart contract and sent to the blockchain network in a transaction manner forinformation announcement, the smart contract voting contents are obtained by the voting terminal, and vote messages at the voting terminal are issued to the smart contract of the voting managing terminal, and then a voting process is finished. When the set voting end time is reached, the voting managing terminal stops receiving votes in a smart contract manner and statistical results are obtained.The voting records can be checked at any time and cannot be falsified, and the voting fairness is improved. The ballots are separated from the true identity of the voting party, and the double anonymity protection of the voting terminal and the voting is realized, and the personal privacy of the voting terminal is better protected.
Owner:JINAN UNIVERSITY
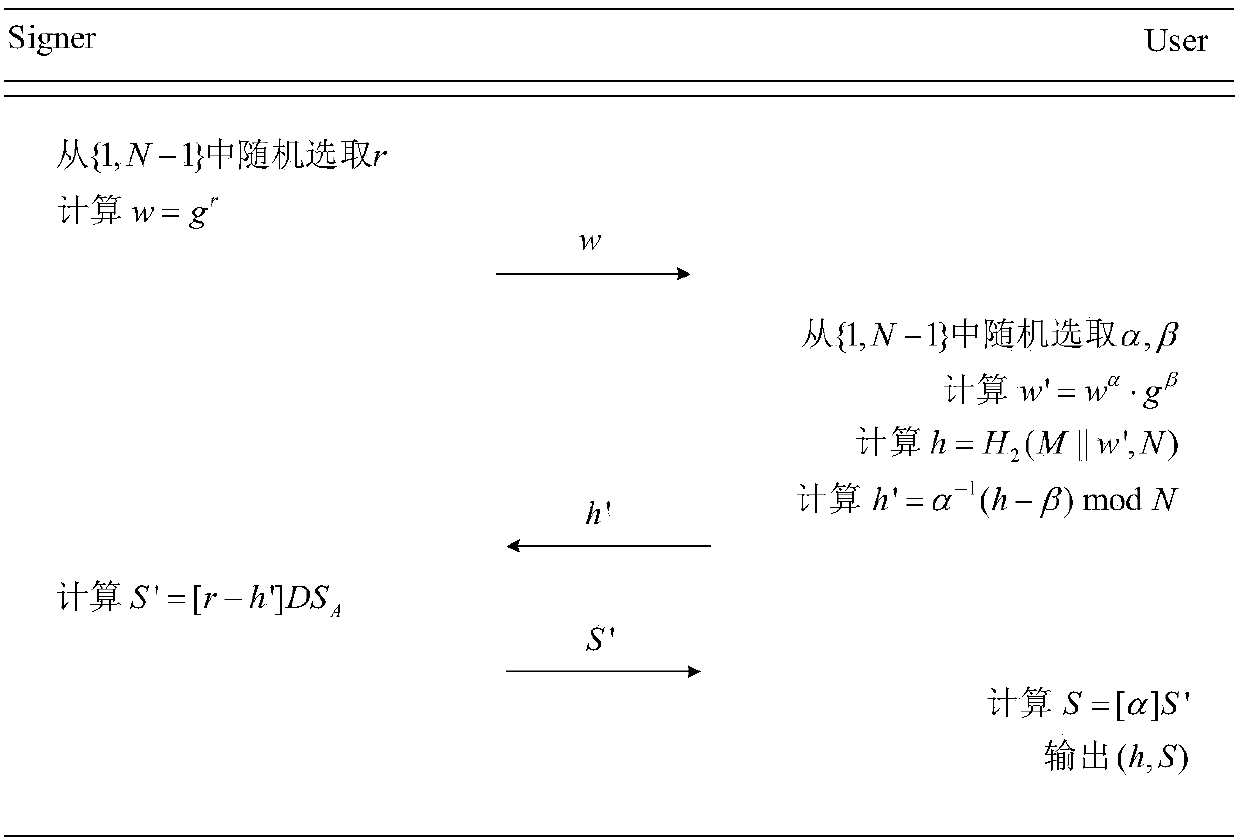
Blind signature generation method and system based on SM9 digital signature
ActiveCN108551392AGuaranteed correctnessGuaranteed privacyPublic key for secure communicationUser identity/authority verificationGeneration processTemporary variable
The invention discloses a blind signature generation method and system based on SM9 digital signature. The method comprises the following steps: 1) a key generation center KGC generates a signature private key DSA of a Signer; 2) the Signer calculates a first temporary variable w and sends the w to a User; 3) after the User receives the w, a second temporary variable w' and a hash value h) of a to-be-signed message M are generated, and a third temporary variable h' is calculated and sent to the Signer finally; 4) after the Signer receives the h', the temporary signature S' is calculated and sent to the User; 5) the User receives the S' and then calculates a signature value S, and outputs the signature (h, S). The method has the characteristics of low complexity, high security, easy verification, etc. The signature generation process must have both Signer and User participating simultaneously, and the process of generating the SM9 blind signature does not leak the signed message to thesigner, thus ensuring the security of the message, and improving the fairness of the SM9 digital signature generation.
Owner:WUHAN UNIV
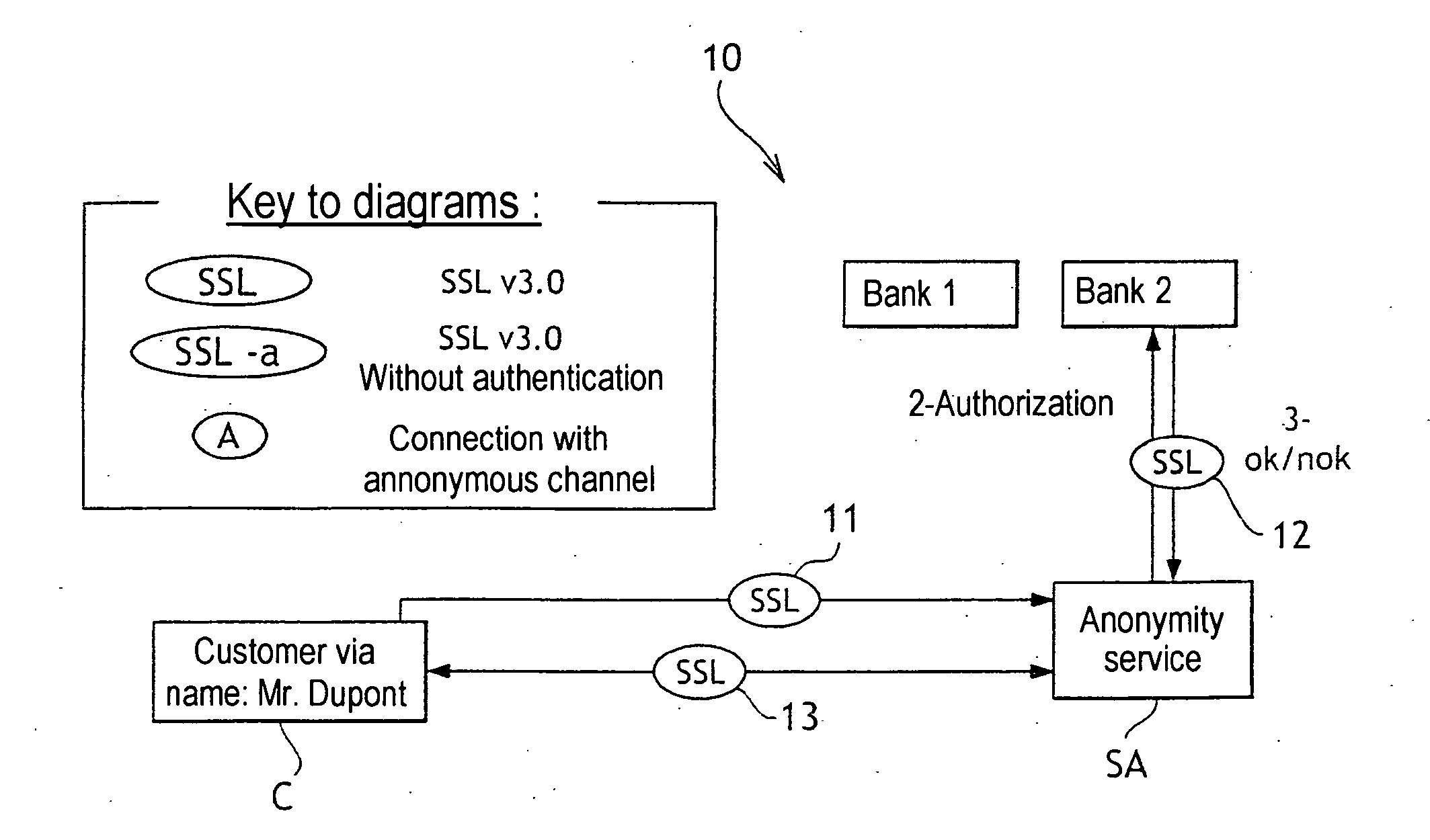
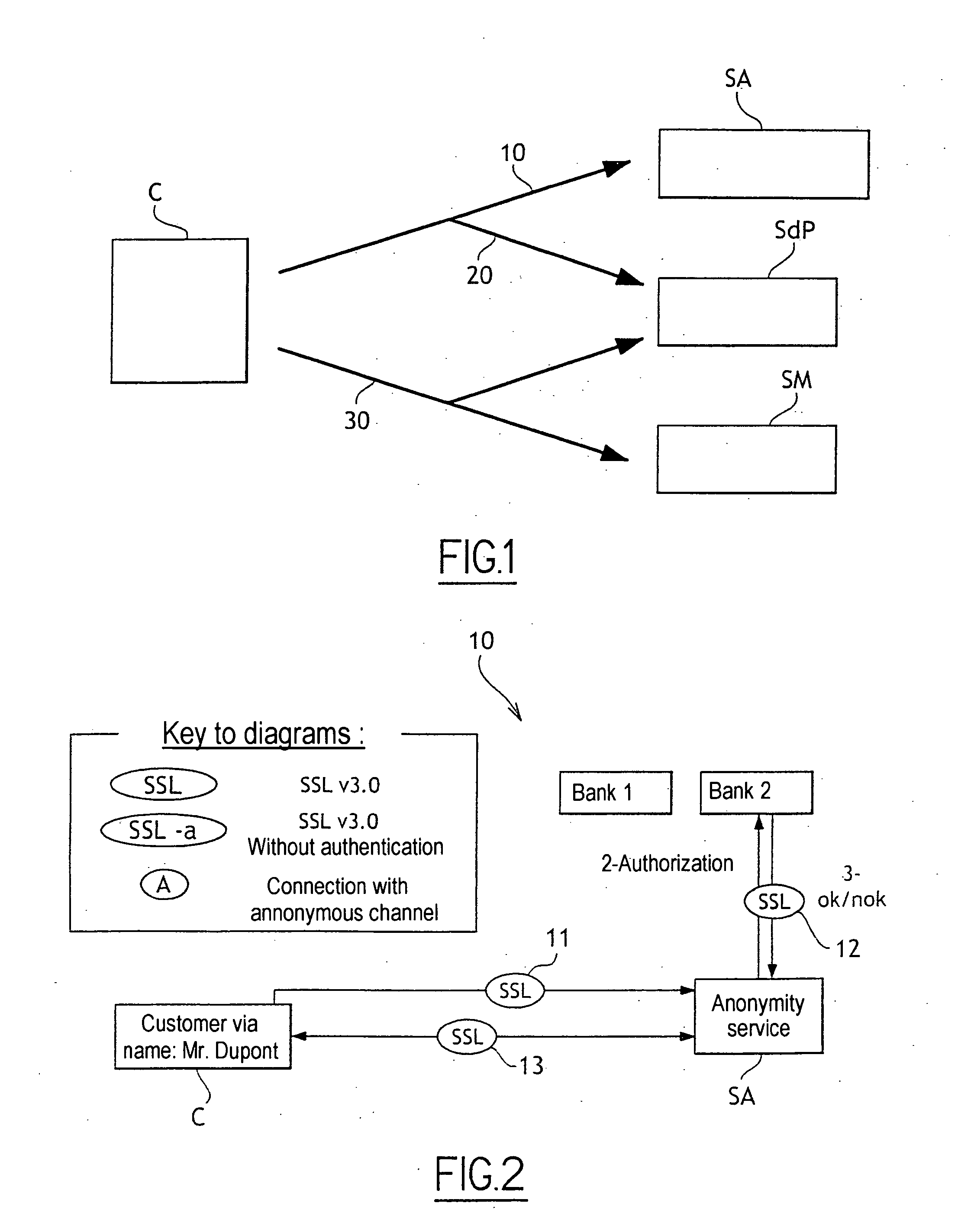
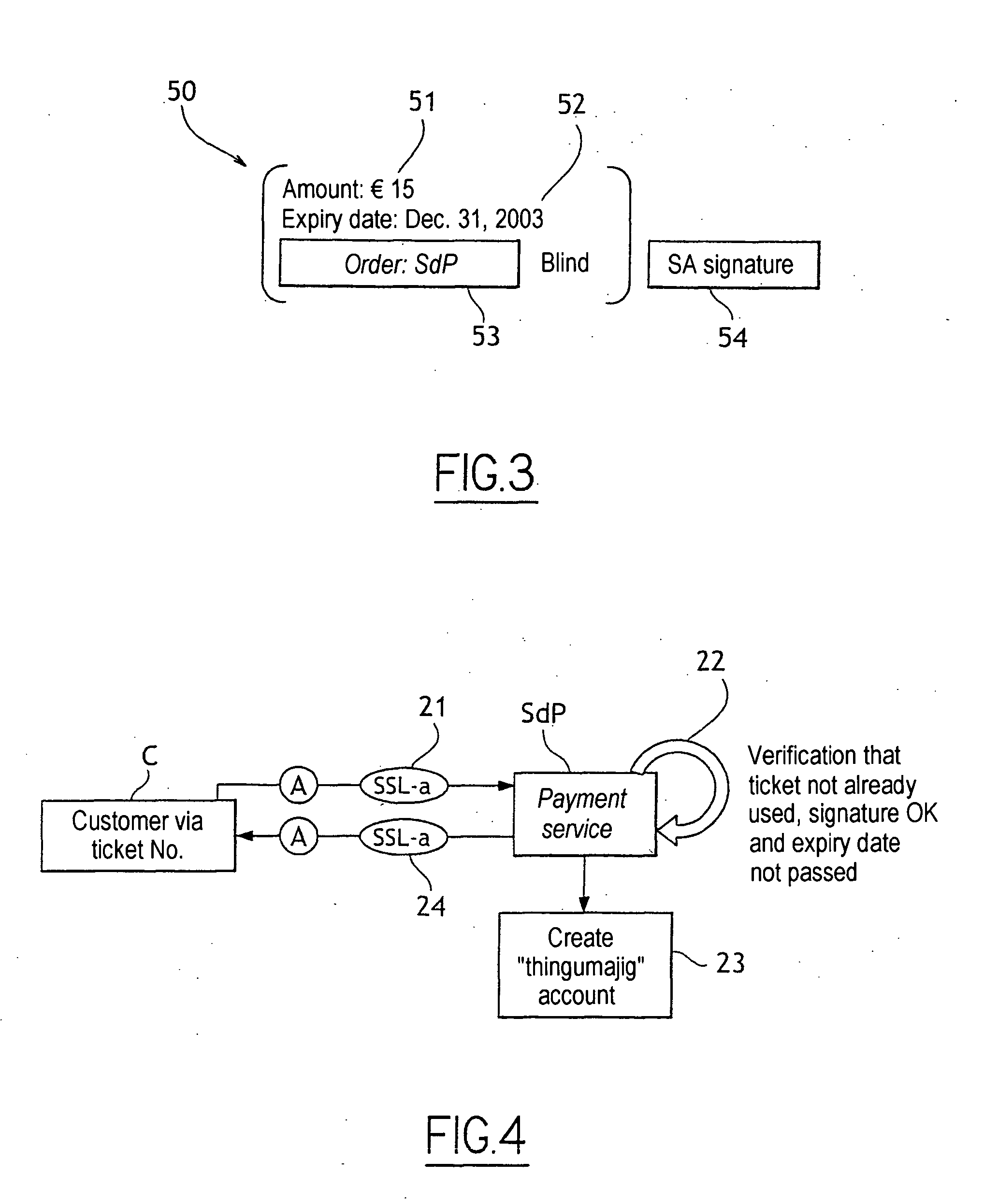
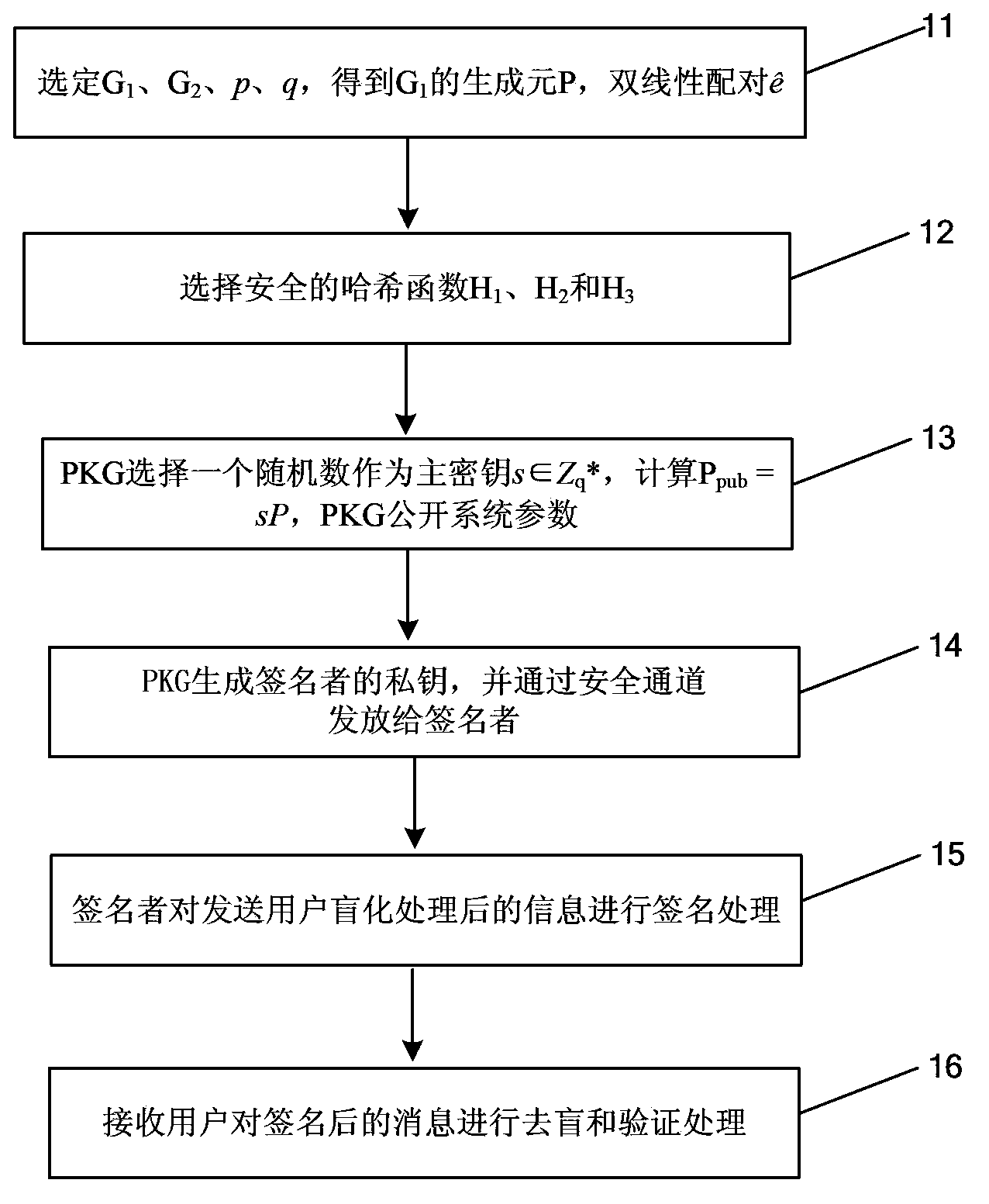
Anonymous and Secure Internet Payment Method and Mobile Devices
An anonymous and secure on-line payment system and method based on the partially blind signature cryptographic method with revocable anonymity. To this end, an Anonymity Server (SA) enables the Customer (C) to acquire on-line anonymous payment means on the basis of a protocol that does not enable the Anonymity Server to link the payment means to the Customer (C). The Payment Server (SdP) comprises means for opening an anonymous account using the anonymous payment means (50). A Customer (C) can make an on-line purchase from a Merchant Site (SM) without having to give a bank card number and remaining anonymous to the merchant and more generally to any entity present in the transaction or absent therefrom. However, this anonymity may be revoked by a trusted entity in the event of fraud on the Customer. Finally, a Customer can make payments when on the move.
Owner:FRANCE TELECOM SA
Blind signature method based on identity and device thereof
ActiveCN103780386AShorten the lengthImprove throughputUser identity/authority verificationMessage lengthGreek letter beta
The invention provides a blind signature method based on an identity and a device thereof. The method comprises the following steps: (1) a signer chooses a random number r belonging to Zq*, a formula U'=rP is calculated, Zq* represents integers in a range from 1 to (q-1), q is a set large prime number, P is the generator of G1, and p is a set large prime number; (2) a sending user randomly selects a blind factor (alpha, beta) belonging to Zq*, a formula U=U'+(alpha+beta)P is calculated, a= (alpha*beta*H3(U)) H2 (m), b= alpha+beta+H2(m), H2 and H3 are one-way Hash functions, and m is plain text information to be signed; (3) the signer uses a private key dID=sQID of the signer to sign (a, b), a formula V'=a*dID / (r+b) is calculated, H1 is a one-way Hash function, and s is a random number as a main cipher key; (4) a receiving user calculates a formula V=V' / (alpha*beta*H3(U))=H2(m)*dID / (r+b), and the coordinate X of V is the signature of a message m. According to the blind signature method based on an identity of the embodiment of the invention, a blind signature message length is only the X coordinate of an elliptic curve point, and the throughput of system operation is increased.
Owner:AEROSPACE INFORMATION
Blind signature method and a blind signature system
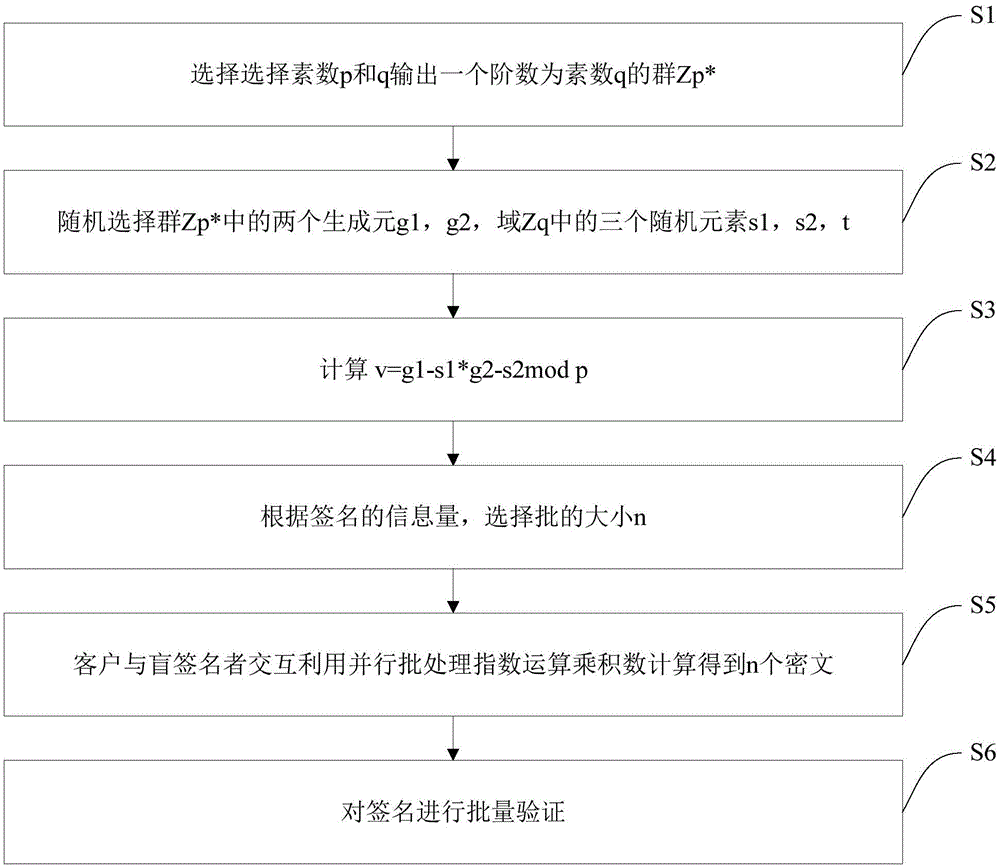
ActiveCN105681045ASmall amount of calculationReduce computing timeUser identity/authority verificationPayment protocolsBatch processingTheoretical computer science
The invention discloses a blind signature method and a blind signature system. The method comprises the steps of selecting prime numbers p and q, and outputting a group Zp* with the order of the prime number q; randomly selecting two generators g1 and g2 in the group Zp*, and three random elements s1, s2 and t in a domain Zq; working out v according to a FORMULA; according to the information amount of signatures, selecting the size n of a batch; and working out n cryptographs through interactively using parallel batch processing index computation products by a client and a blind singer; and verifying the signatures in batches. The blind signature method has the advantages as follows compared with the general batch processing index computation product, about 25% computation quantity is saved, thus the computational pressure is effectively relieved; and during the verifying process, the n signatures are simultaneously verified by a batch verifying method, the computation time is effectively saved, only about 70% of the time of the general method is needed, and the efficiency is high.
Owner:BEIHANG UNIV
Anonymous electronic voting method based on block chain technology
ActiveCN109274505AImprove integrityTo achieve openness and transparencyUser identity/authority verificationTrusted third partyBlind signature
The invention discloses an anonymous electronic voting method based on block chain technology, which combines block chain technology with traditional encryption algorithm to design a new anonymous voting method. As an important application innovation technology, block chain provides a set of decentralized, safe and reliable distributed database technology scheme which needs to be collectively maintained, and makes it have obvious advantages in solving many application problems. The invention adopts the intelligent contract in the block chain of Ethernet Square to replace the trusted third party, the voting process is implemented by transactions of account numbers in the block chain, Blind signature algorithm is used to protect the anonymity of voting, and the whole voting process and voting results will be recorded in the block chain of Ethernet Square, thus a new electronic voting method based on block chain technology is designed, which can realize the transparency of voting and improve the security of voting.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
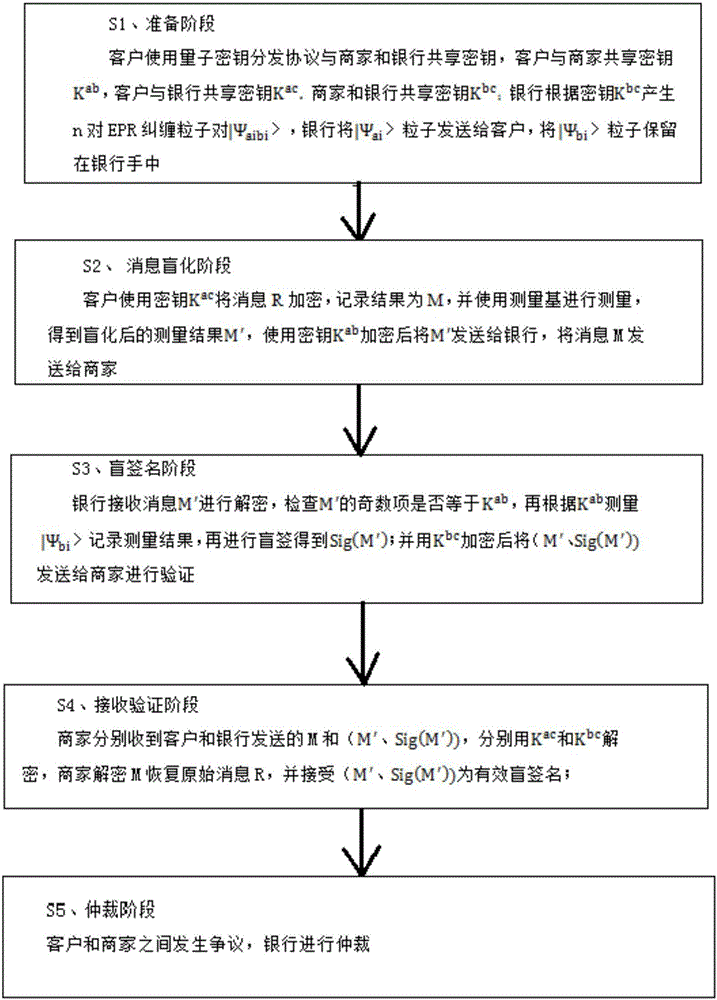
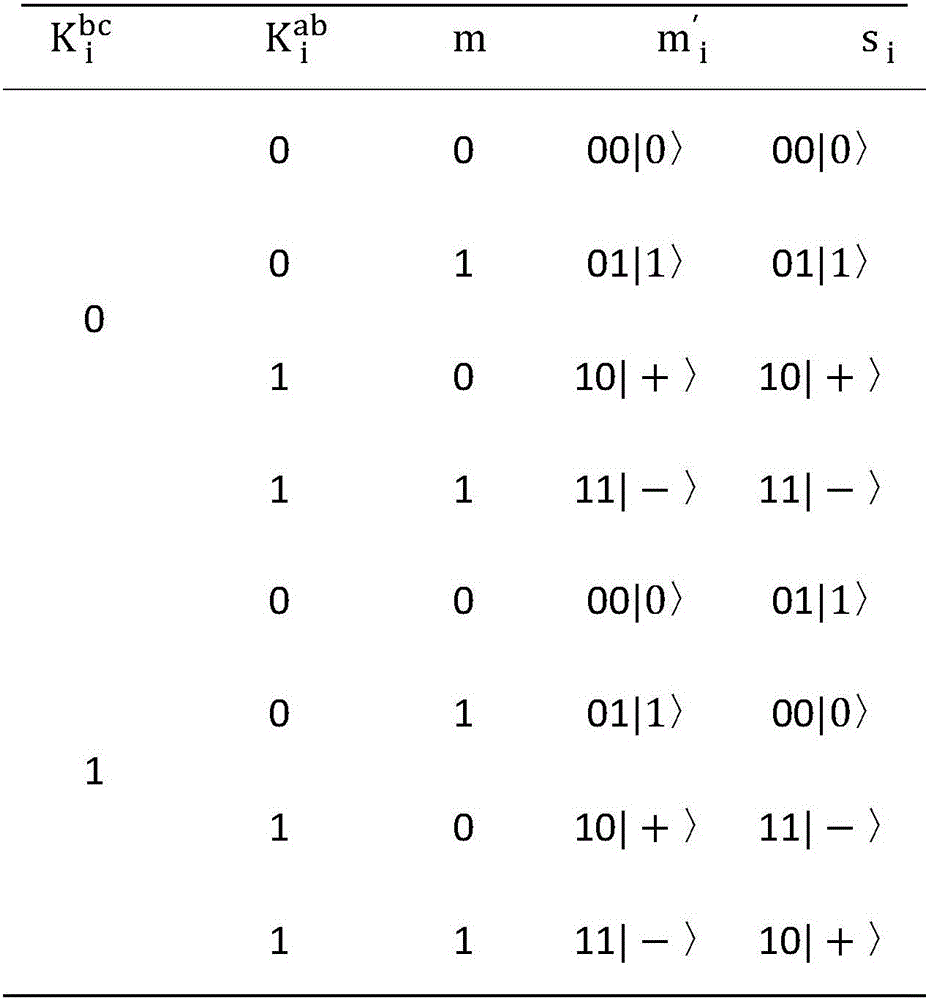
Quantum blind signature message authenticity protection method
InactiveCN106452768AGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationBlind signaturePreparation stage
The invention discloses a quantum blind signature message authenticity protection method which sequentially includes a preparation stage, a message blinding stage, a blind signature stage, a receiving verification stage and an arbitration stage. A customer respectively shares a key with other customers and sellers by the aid of a quantum key distribution protocol and applies for signature from a bank after encrypting and blinding messages by the key, the messages are transmitted to the sellers after blind signature of the bank, and the sellers accept valid blind signature after verification. When the customer and the sellers are in dispute, the bank is introduced as a trustworthy arbitrator for arbitration, judges the condition of even bits according to the key and then compares odd bits, and the signature is regarded as invalid signature if one bit does not conform to rules. When the signature of application messages or blind messages is modified, the signature can be verified, and blind signature message authenticity is ensured.
Owner:HUNAN UNIV OF ARTS & SCI
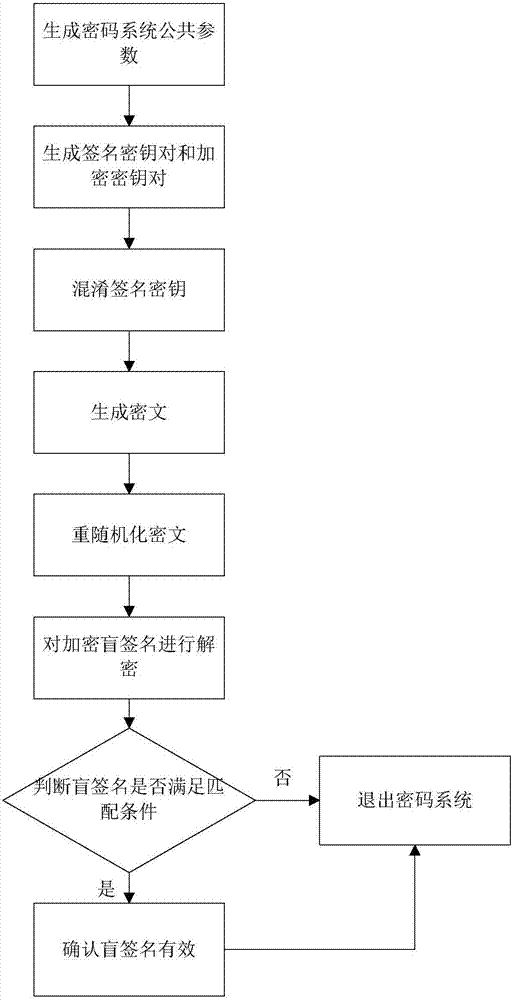
Encrypted blind signature method based on obfuscation technology
ActiveCN107070662AImprove securitySignature key protectionUser identity/authority verificationObfuscationCiphertext
The invention discloses an encrypted blind signature method based on an obfuscation technology. The method comprises the specific realization steps of 1, generating cipher system public parameters; 2, generating a signature key pair and an encryption key pair; 3, obfuscating signature keys; 4, generating a ciphertext; 5, re-randomizing the ciphertext; 6, decrypting an encrypted blind signature; 7, judging whether the blind signature satisfies a blind signature matching condition or not; 8, confirming that the blind signature is valid by a user; and 9, logging out a cipher system. According to the method, the obfuscation technology is adopted, a signer obfuscates the keys, so the signature keys of the signer are effectively protected, and the security of the encrypted blind signature is improved. According to the method, the ciphertext is re-randomized by a receiver, so the data volume processed by the receiver is greatly reduced. According to the method, the blind signature matching condition is simple, so the performance efficiency of judging the validity of the blind signature is greatly improved.
Owner:XIDIAN UNIV
File encryption method based on blockchain bidding and tendering system
InactiveCN111130793AGuaranteed validityGuaranteed operabilityEncryption apparatus with shift registers/memoriesUser identity/authority verificationAlgorithmBlind signature
The invention discloses a file encryption method based on a blockchain bidding and tendering system, comprising the following steps: 1) a bidder imports a bidding file F into a client, and the clientrandomly generates an AES key and encrypts the F by using an AES algorithm to generate F '; 2) the client uploads F'to an IPFS, the client takes a hash value of F 'to obtain Hf, a random number uuid is added behind Hf to obtain m, a blind signature algorithm is applied to blinding the m, and m' is obtained; 3) the client sends m' to a server for signature, and the server signs m' by using a private key to obtain s'; 4) the client sends s' to the intelligent contract, and the intelligent contract is used for verify the validity of the signature of the bidding party; if the signature is valid, the client removes blindness of the s' to obtain s; if the signature is invalid, step 3) is executed; 5) the client sends s and m to the intelligent contract for verification; if the verification succeeds, m is stored in the blockchain. The method disclosed in the invention ensures safe storage of the bidding documents.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
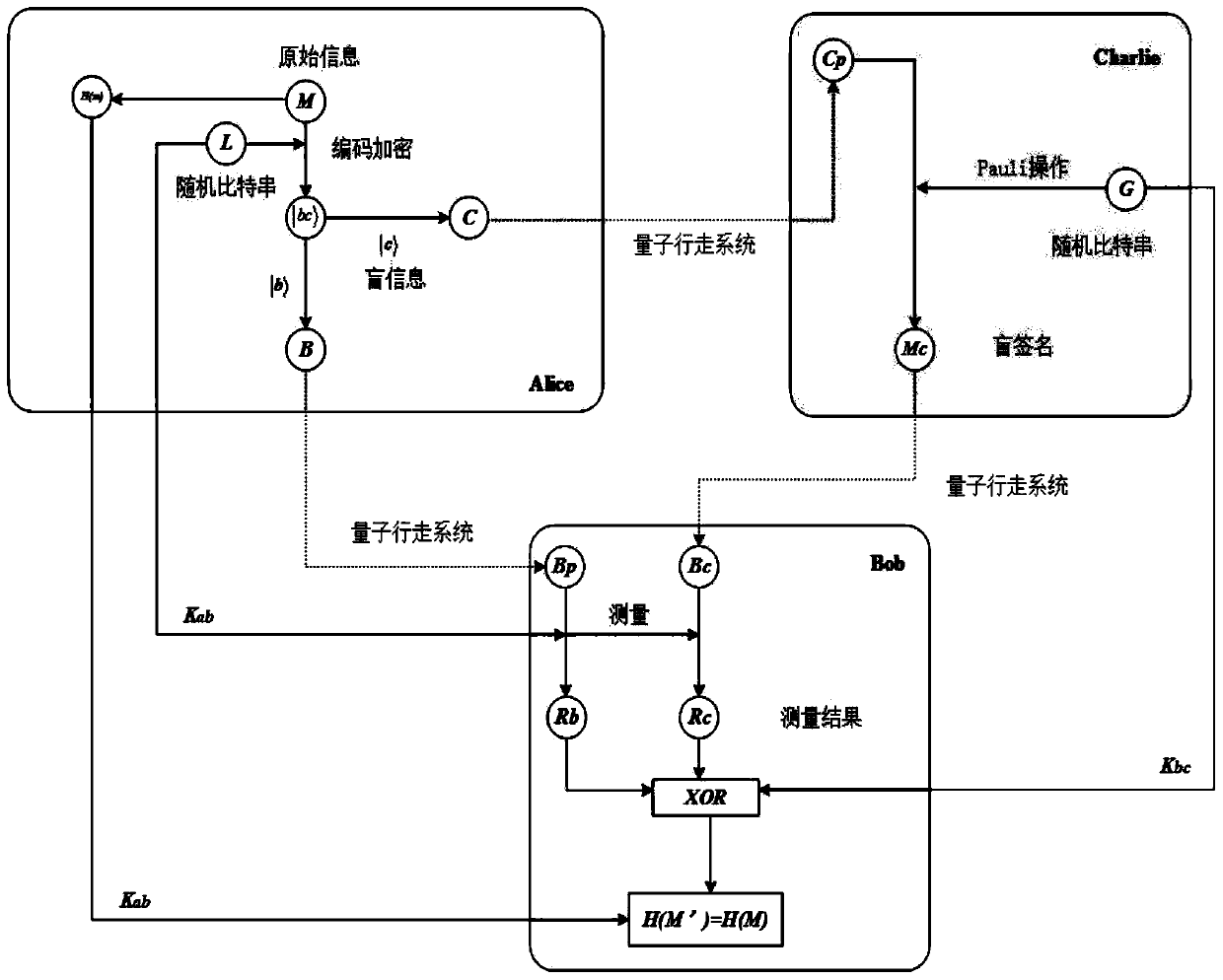
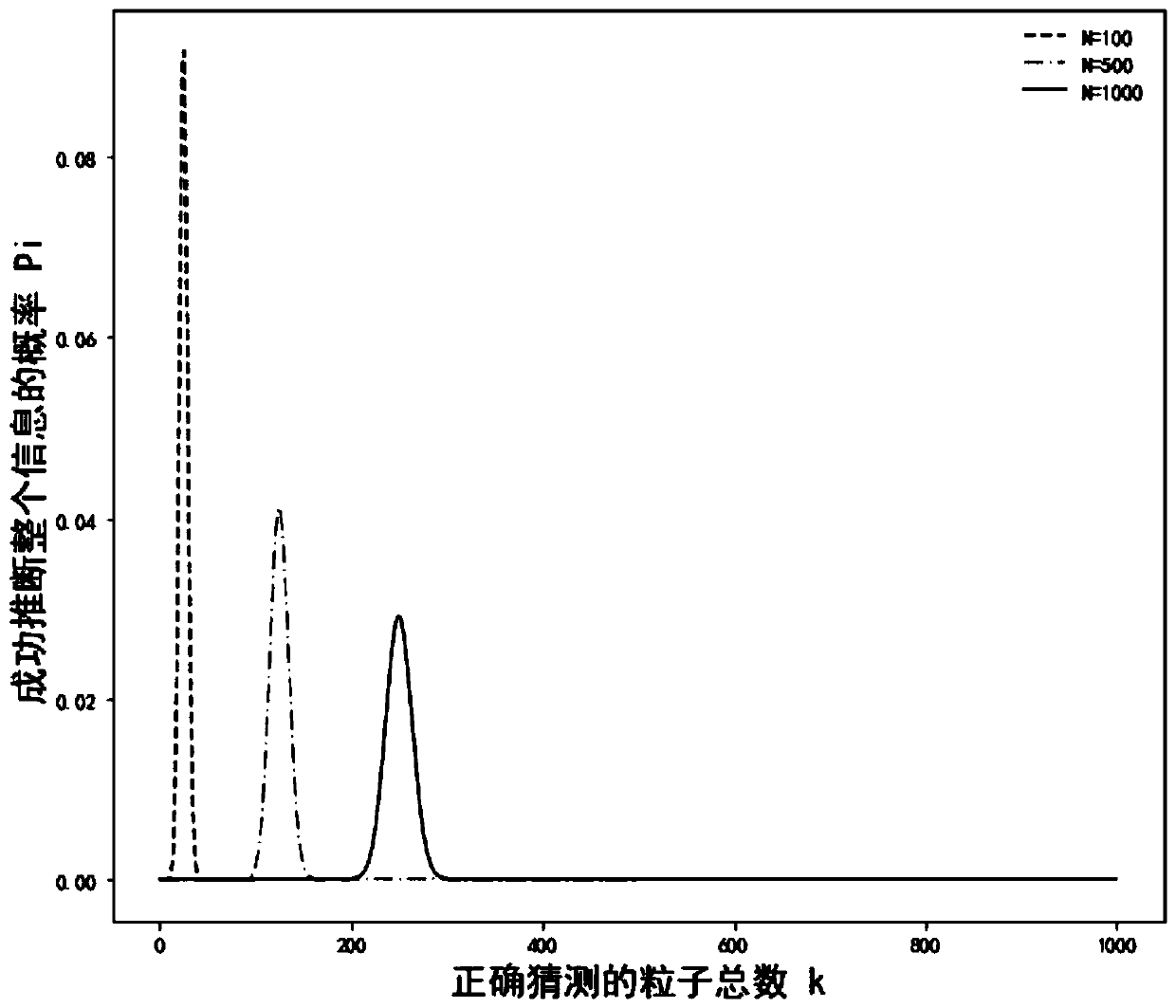
Unentangled quantum blind signature method and system based on quantum walking
ActiveCN110213060AProven robustnessAchieve the effect of one-time pad (OTP)Key distribution for secure communicationUser identity/authority verificationE-commerceBlind signature
The invention belongs to the technical field of quantum information processing, and discloses an unentangled quantum blind signature method and system based on quantum walking, and the method comprises the steps: carrying out the coding and blind information through employing four single event states in combination with a blind coding rule of a message in the coding stage of the message; in the invisible transmission process of the coded particles, using quantum walking to achieve invisible transmission of the coded particles, wherein entanglement is spontaneously generated on the invisible transmission seed particles, which is used for resisting negative attacks of signers and denial attacks of verifiers and further used for preventing attackers from forgery signatures. The method comprises secret key updating, the effect of one-time encryption (OTP) is achieved, and therefore a next execution scheme does not need secret key redistribution any more; security analysis shows that the scheme of the invention satisfies the characteristics of unforgeability, undeniable property and blindness, can also resist entanglement attack, and is very suitable for use in electronic commerce or electronic payment systems.
Owner:芽米科技(广州)有限公司
Vehicle privacy protection method based on blockchain and blind signature
PendingCN111756547AEnsure fairnessLookup inefficiencyUser identity/authority verificationPrivacy protectionEngineering
The invention discloses a vehicle privacy protection method based on a blockchain and a blind signature, and belongs to the field of Internet of Things. The method comprises: firstly, a public and private key pair generated by a vehicle is obtained, and a digital certificate is obtained from a digital certificate authentication mechanism through a blind signature algorithm and an anonymous certification mode; meanwhile, the digital certificate authentication mechanism enables the obtained certificates to be in one-to-one correspondence with the public keys of the vehicle; when the CA issues adigital certificate to the vehicle, the public key of the vehicle is stored in the blockchain; when communication occurs between vehicles, in order to confirm the legality of the identity of the vehicle, a receiver needs to use a public key of a sender to perform hash operation to obtain a Merkel root value, and compares the calculated root value with the root value in the blockchain in an anonymous authentication mode to confirm the legality of the vehicle. According to the method, the blockchain technology is applied to vehicle privacy protection, the problems of vehicle identity informationprivacy, vehicle certificate storage and vehicle identity authentication in a vehicle network are solved, and the method is an effective vehicle privacy protection method.
Owner:KUNMING UNIV OF SCI & TECH
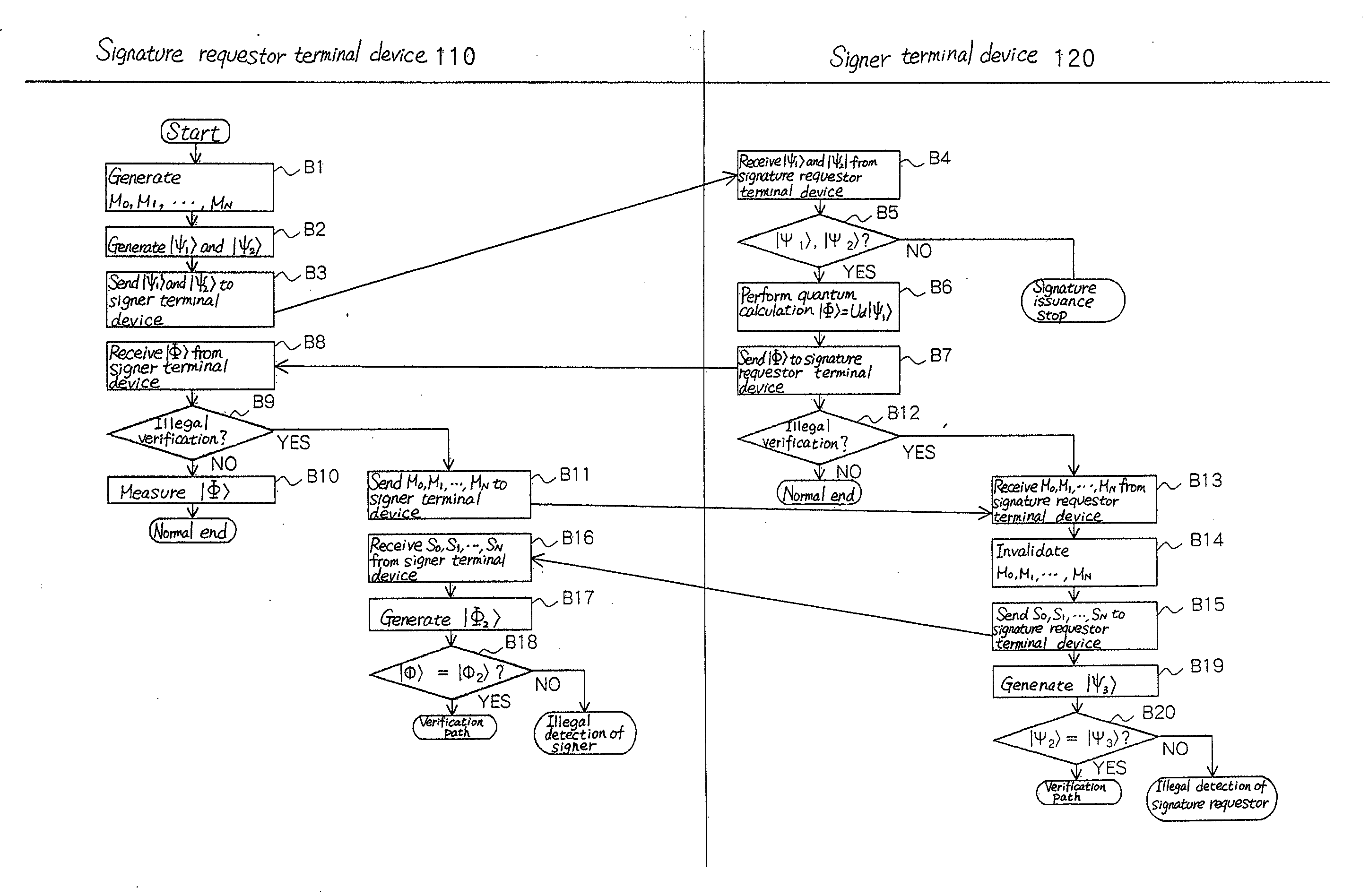
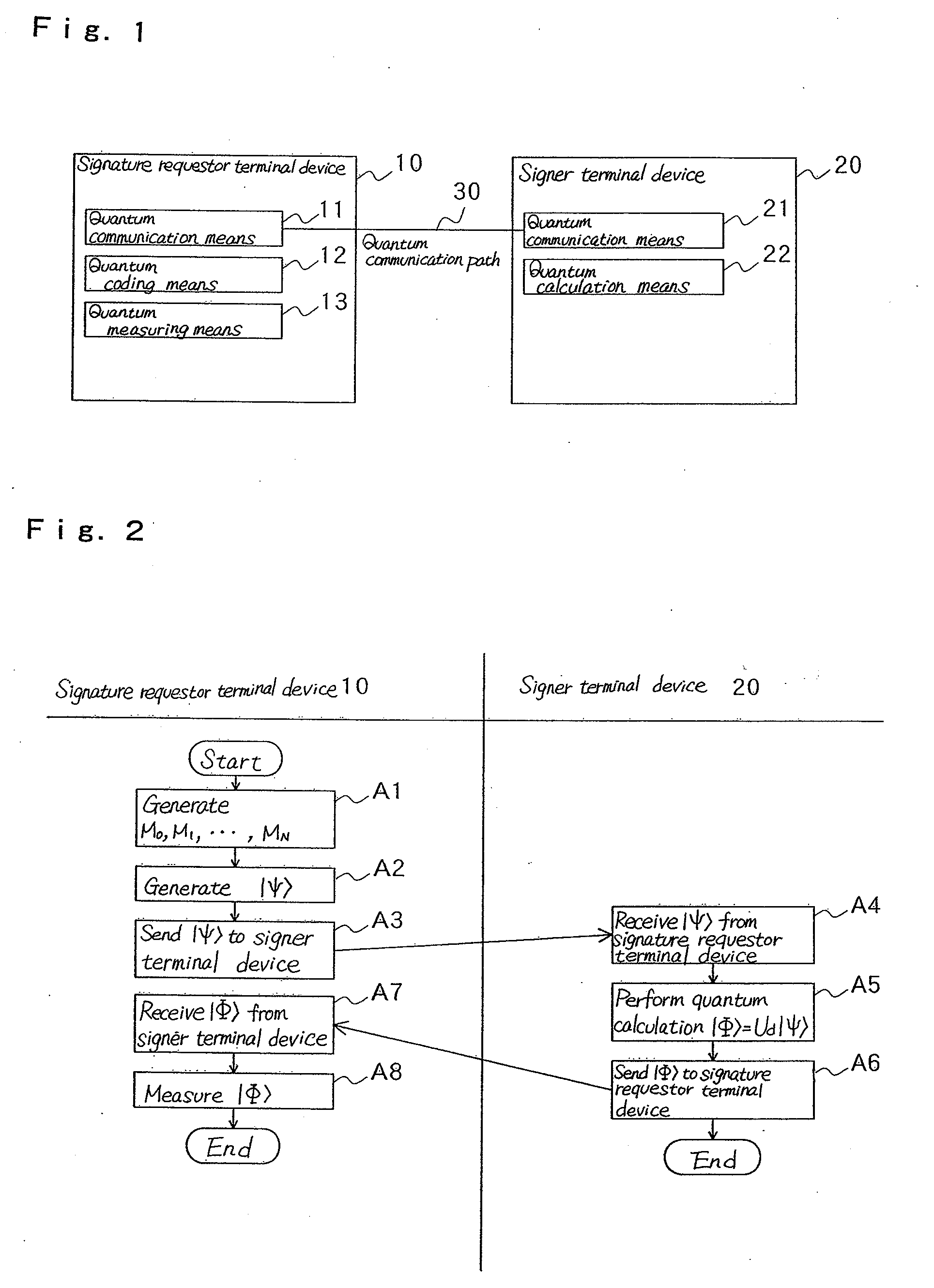
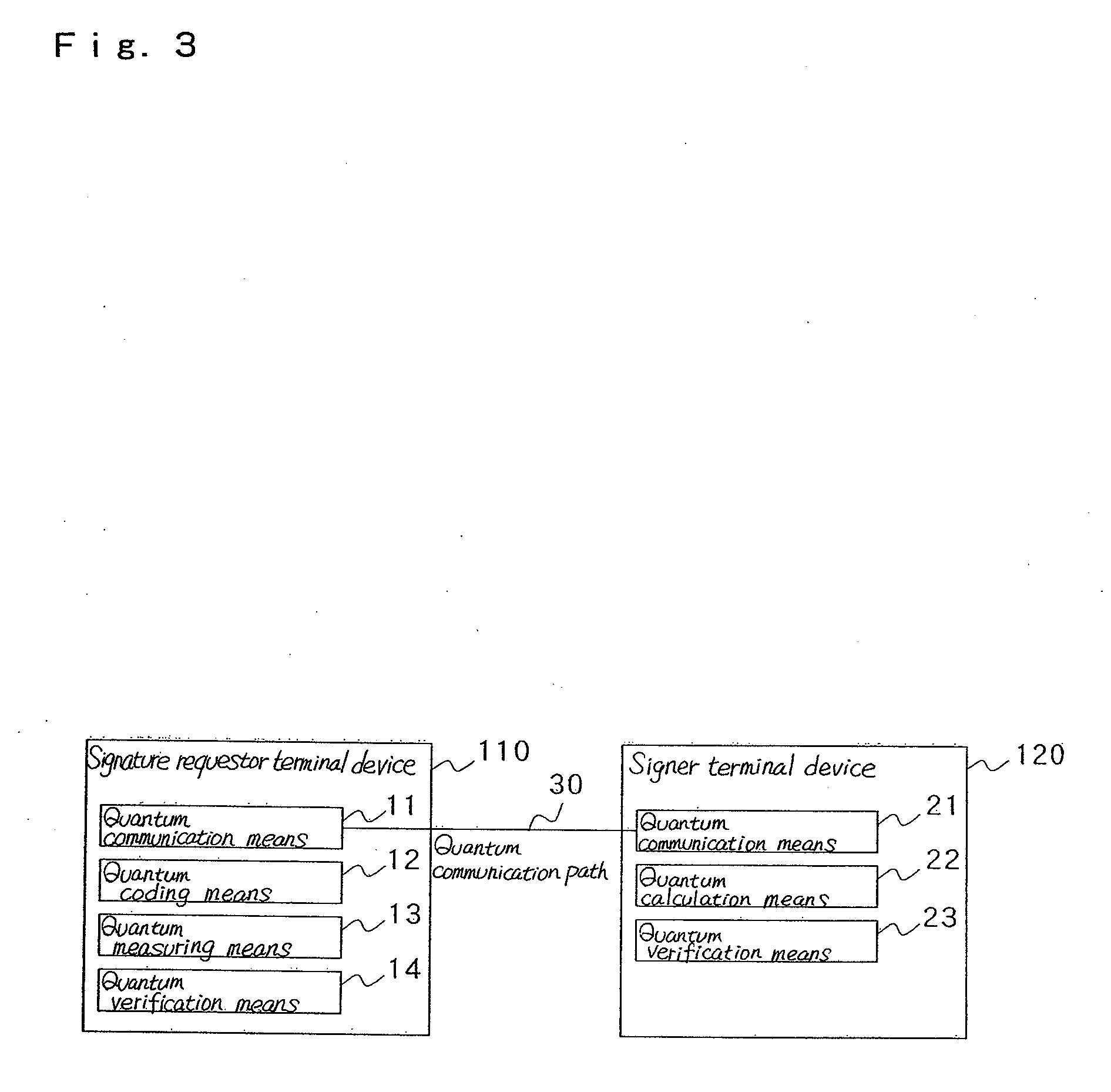
Blind signature method and its system
InactiveUS20090031137A1Accurate measurementUser identity/authority verificationTerminal equipmentBlind signature
Signature requestor terminal device (10) codes a plurality of messages to a quantum state and transmits it to signer terminal device (20). Signer terminal device (20) issues a blind signature for the plurality of the messages coded to the quantum state, codes the messages and the signature to a quantum state and sends them back to signature requestor terminal device (10).
Owner:NEC CORP
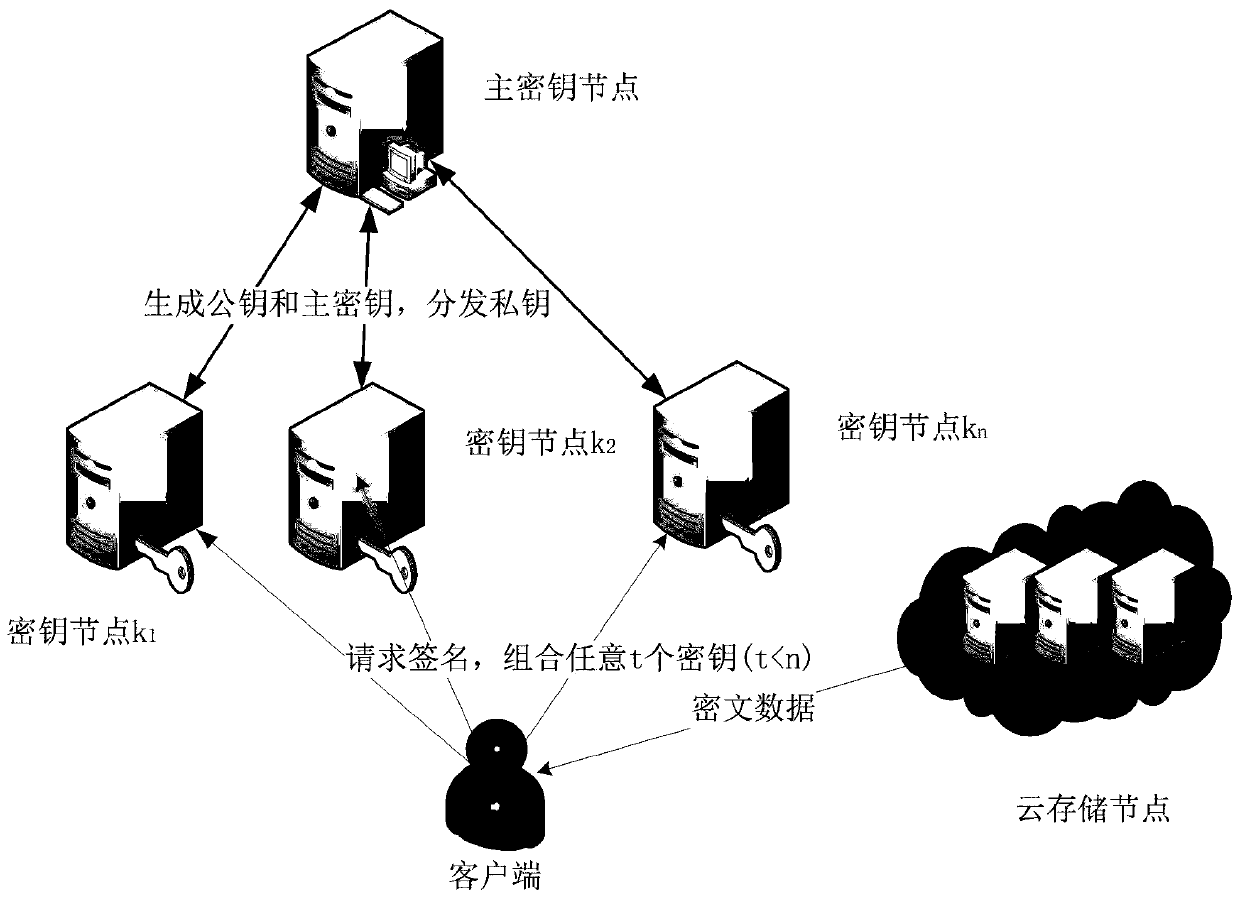
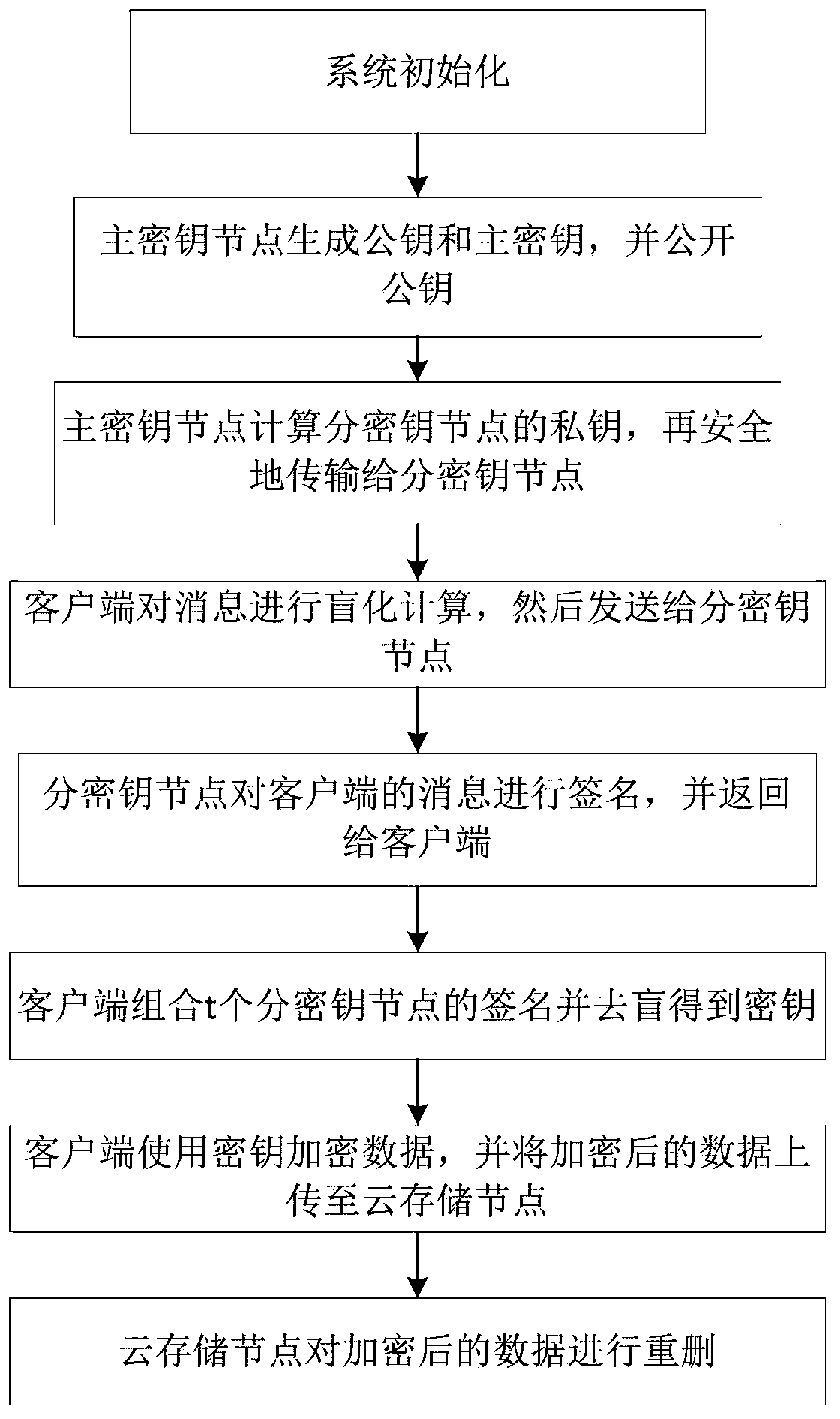
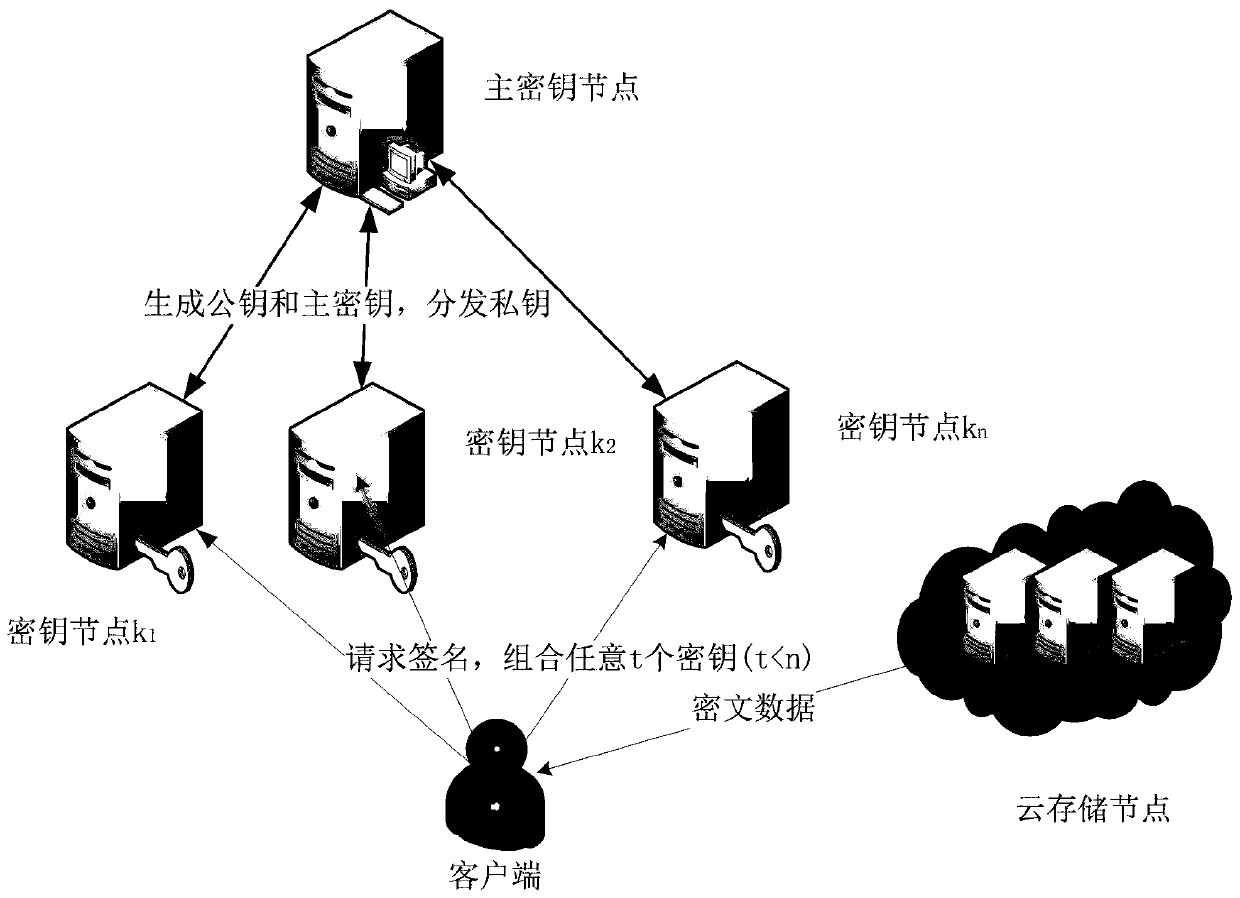
Data security duplicate removal method based on threshold blind signature
ActiveCN109962769AImprove securityNo single point of failureKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextBlind signature
The invention discloses a data security duplicate removal method based on a threshold blind signature. The invention relates to the field of digital signatures in information security, and solves theproblems that n key management nodes are adopted to perform blind signing on messages at the same time, a large amount of information needs to be interacted among the key management nodes, and the calculation overhead for verifying signatures is large. System initialization is firstly performed, and a main key node generates a public key and a public key; the n sub-key nodes are numbered as k1, k2,..., kn, and a t-1-order polynomial is constructed: f(x)=a0+a1x+...+a<t-1>x<t-1>; partial private keys corresponding to each sub-key node: f(k1), f(k2),...,f(kn), are calculated and safely transmitted to the sub-key nodes; and then the client blinds the message, and sends the blinded message to the sub-key node. And the sub-key node signs the message and returns the message to the client. And theclient uploads the ciphertext data to the cloud server. According to the method provided by the invention, a single-point fault problem does not exist, the main key node can be offline after initialization is completed, and the n sub-key nodes only need at least t available sub-key nodes to complete subsequent steps.
Owner:CHANGCHUN UNIV OF SCI & TECH
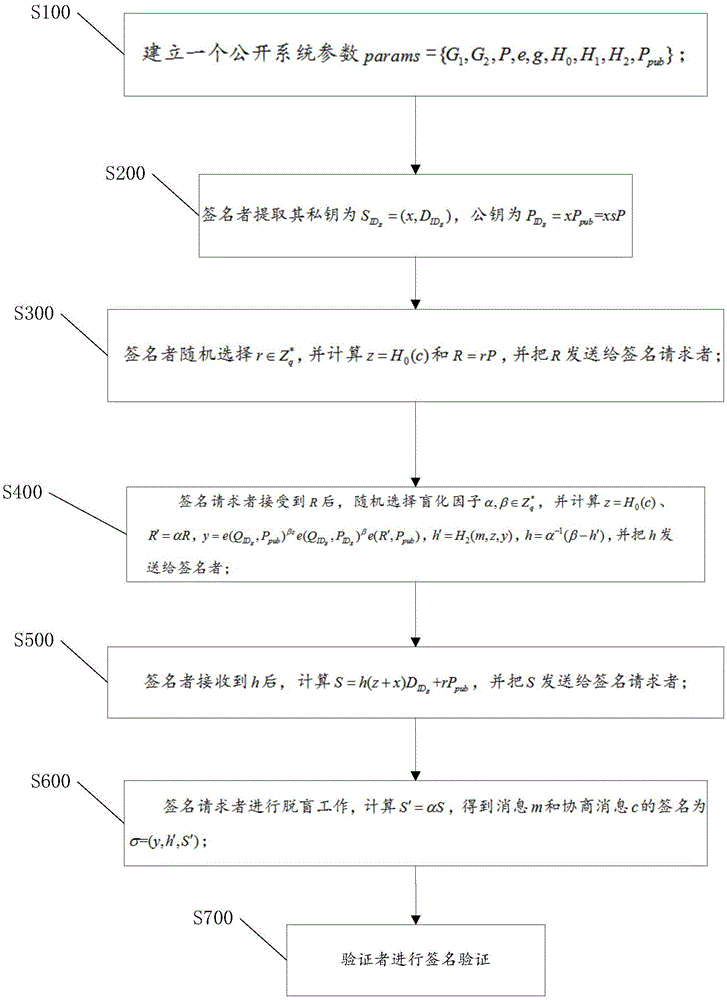
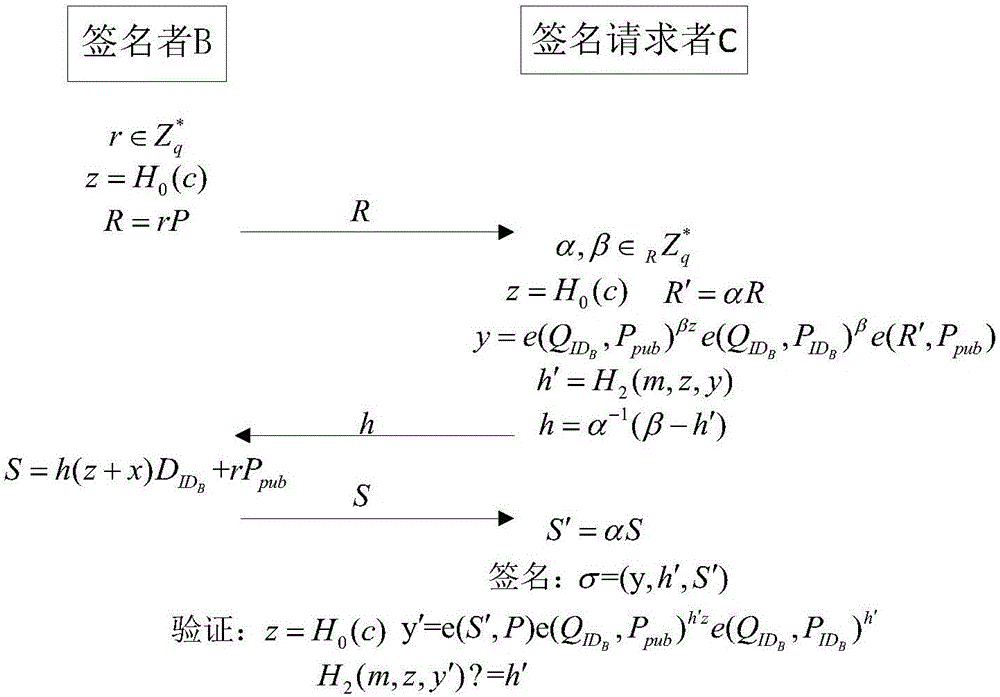
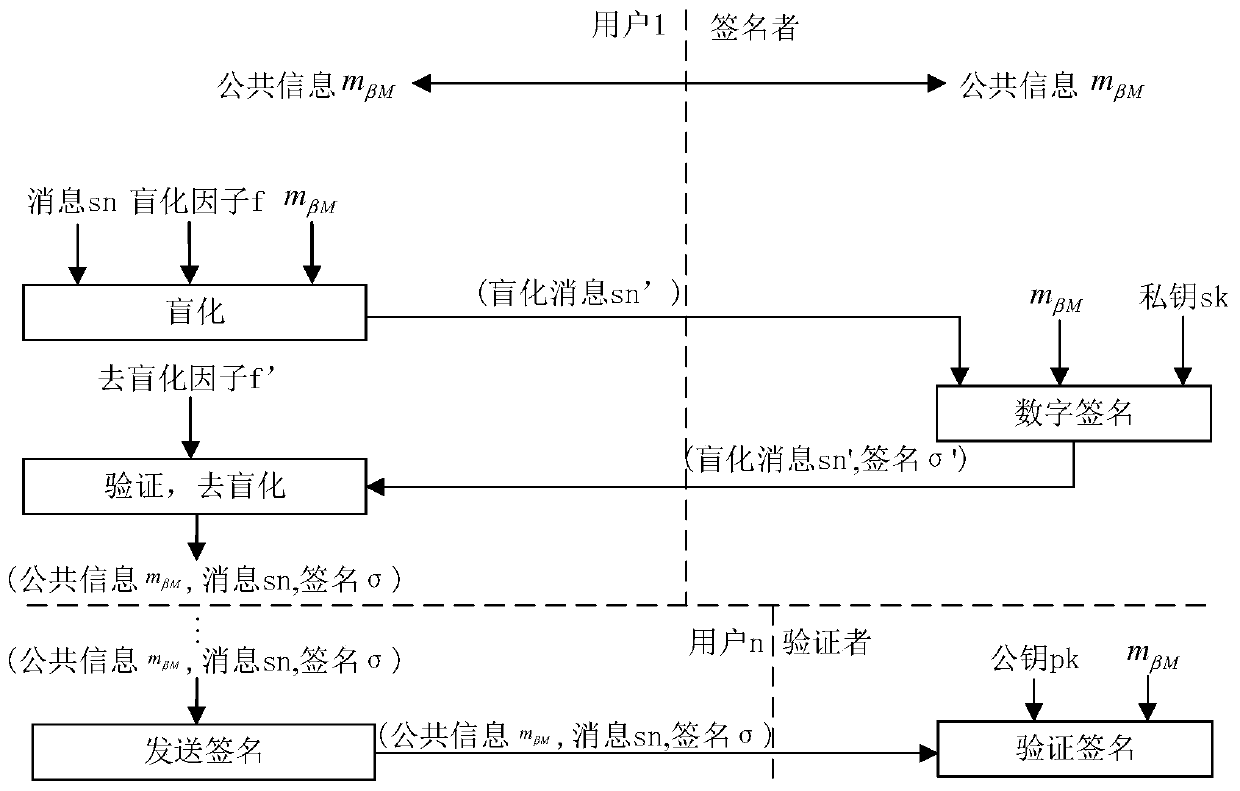
CL-PBS (certificateless partially blind signature) method and device
ActiveCN106789019AFix security issuesKey distribution for secure communicationUser identity/authority verificationGreek letter sigmaBlind signature
The invention is applicable to the technical field of information security and provides a CL-PBS (certificateless partially blind signature) method. The method comprises the steps as follows: a public system parameter params=[G1, G2, P, e, g, H0, H1, H2, Ppub] is established; a signer extracts a private key shown in the specification and a public key shown in the specification; a signer randomly selects an icon shown in the specification, calculates z=H0(c) and R=rP and sends R to a signature requester; the signature requester randomly selects a blinding factor shown in the specification after receiving the R, calculates formulas shown in the specification and sends h to the signer; the signer calculates a formula shown in the specification and sends S to the signature requester after receiving h; the signature requester conducts de-blinding work and calculates S'=alphaS to obtain a signature sigma=(y, h', S') of a message m and a consultation message c; a verifier verifies the signature. The method effectively solves the security problems caused by tapering of consultation public information in CL-PBS.
Owner:SHENZHEN UNIV
Anonymous secure payment channel method and device
ActiveCN110378690AReduce the burden onSimple compositionFinanceProtocol authorisationPaymentThe Internet
The invention discloses an anonymous secure payment channel method and a device, and the method comprises the steps: enabling two transaction parties to communicate on the Internet, determining the willingness of a transaction, selecting a path, determining a transaction man-in-the-middle, and building deployment intelligent contracts with the transaction man-in-the-middle, so as to build a channel; transmitting a virtual channel opening certificate between the two transaction parties and the transfer intermediary; controlling two transaction parties to perform transaction, and sending transaction certificates to each other; sending a final result of a transaction to a transaction intermediary through a first transaction user; and performing calculation by the transaction intermediary, sending a blind signature certificate for closing settlement to the first transaction user after confirmation, performing exchange with a certificate for closing the channel with the first transaction user, and the first transaction user carries out blind removal processing on the received blind signature certificate and forwards the blind signature certificate to the second transaction user for closing the channel. The method can realize non-linkable identities of both parties in a transaction process, and is suitable for most blockchain networks supporting smart contracts.
Owner:BEIHANG UNIV
Partially blind signature method based on identity
InactiveCN104333453AEliminate demandReduce allocationUser identity/authority verificationComputation complexityElectronic cash
The invention provides a partially blind signature method based on identity and relates to the technical field of information security. The partially blind signature method based on identity is capable of reducing the calculation complexity and improving the execution efficiency. The method comprises the following steps: public system parameters {G1, q, 1, P, G2, e, H1, H2, H3, QPKG} are established by PSK and an integer sPKG is randomly selected as a private key for secret storage from the integral multiplicative group as shown in the description of mod q; a signer sends own identity information as shown in the description to a private key generation center, the private key generation center generates the private key Did of the signer and sends the private key Did to the signer via a security authentication channel, and then the signal obtains the private key Sid and confirms that the private key is generated by the private key generation center; next, the signer signs; a verifier verifies the validity of the signature by use of the public key of the signer. The partially blind signature method based on identity can be applied to electronic cash, electronic voting and electron transactions.
Owner:XIDIAN UNIV
Reputation evaluation method and system for privacy protection based on block chain
ActiveCN110020541AMake it publicPrevent illegal tamperingDigital data protectionMarketingPrivacy protectionFinancial transaction
The invention relates to a reputation evaluation method and system for privacy protection based on a block chain, and belongs to the technical field of blind signatures, secure multi-party signaturesand block chains. After the user and the merchant finish the online transaction, anonymous evaluation is carried out on the merchant to generate an evaluation transaction, the evaluation transaction is sent to the alliance block chain network, each service provider carries out partial decryption on the evaluation in the evaluation transaction and sends the evaluation to the block chain network, and the merchant updates the reputation of the merchant according to the partial decryption information. Specifically, the method comprises the following steps: a user, a merchant and a service providerregister with a trusted party to obtain corresponding keys; and the user accesses the reputation of the merchant under each service provider, evaluates the service provider after online transaction,broadcasts the reputation in a block chain transaction form, and the service provider serves as a miner of the block chain network, calculates the obtained evaluation for all merchants and updates themerchants. The method and the system have the advantages of reputation publicity, reputation availability, data audit and effective privacy protection for user evaluation.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Blind digital signature system and method based on braid group and computer product
ActiveCN101807990APublic key for secure communicationUser identity/authority verificationFactor baseBlind signature
The invention provides blind digital signature system and method based on a braid group. The system comprises a key generating device, an information blinding device, a signing device and a signature de-blinding device, wherein the key generating device is used for generating public keys and private keys based on system parameters; the information blinding device is used for selecting blinding factors based on the system parameters and calculating the selected blinding factors and information to be signed based on the conjugation operation to generate a blinding information braid; the signing device is used for calculating the private keys generated by the key generating device and the blinding information braid to be signed based on the conjugation operation to generate a blinding signature braid; and the signature de-blinding device is used for calculating the blinding factors and the blinding signature braid based on the conjugation operation to generate a signature braid and combining the information to be signed and the de-blinded signature braid into a whole signature, therefore, the blind digital signature based on the braid group can be verified in the aspect of safety, hopefully stands against the known quantum analysis, and is more suitable for the application scenes of the blind digital signature, such as electronic money and the like.
Owner:BEIJING UNIV OF POSTS & TELECOMM
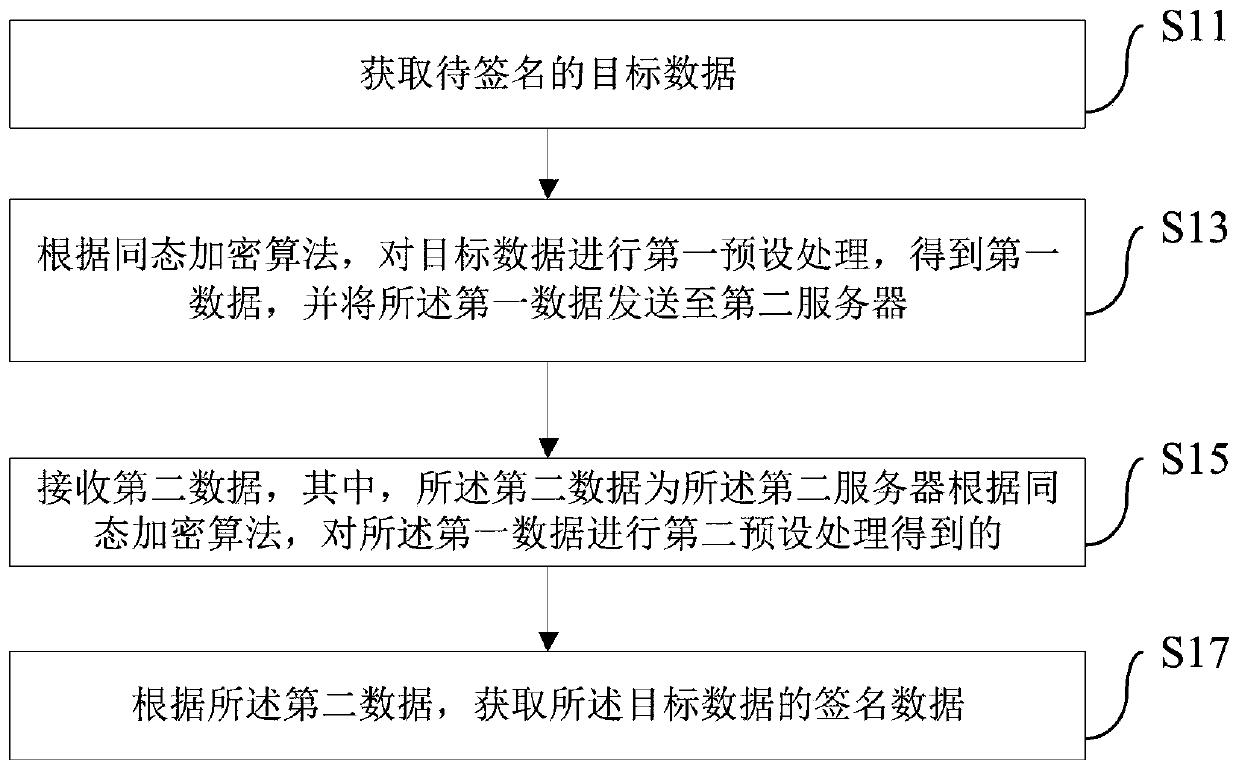
Blind signature acquisition method and device and server
ActiveCN109818730AAvoid gettingAvoid trackingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareBlind signature
The embodiment of the invention provides a blind signature obtaining method and device and a server, and the method comprises the steps: obtaining to-be-signed target data; performing first preset processing on the target data according to a homomorphic encryption algorithm to obtain first data, and sending the first data to a second server; receiving second data and acquiring the second data by the second server through carrying out second preset processing on the first data according to a homomorphic encryption algorithm; and obtaining signature data of the target data according to the second data. According to the scheme, blind processing is performed on the target data on the basis of the SM2 by using a homomorphic encryption algorithm; and the processed data is sent to the second server for blind signature, the second server cannot obtain specific content contained in the target data, and meanwhile, the signature carried out by the second server cannot be tracked, so that the technical problem that the data privacy of a user and a signer cannot be protected in the existing method is solved.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com