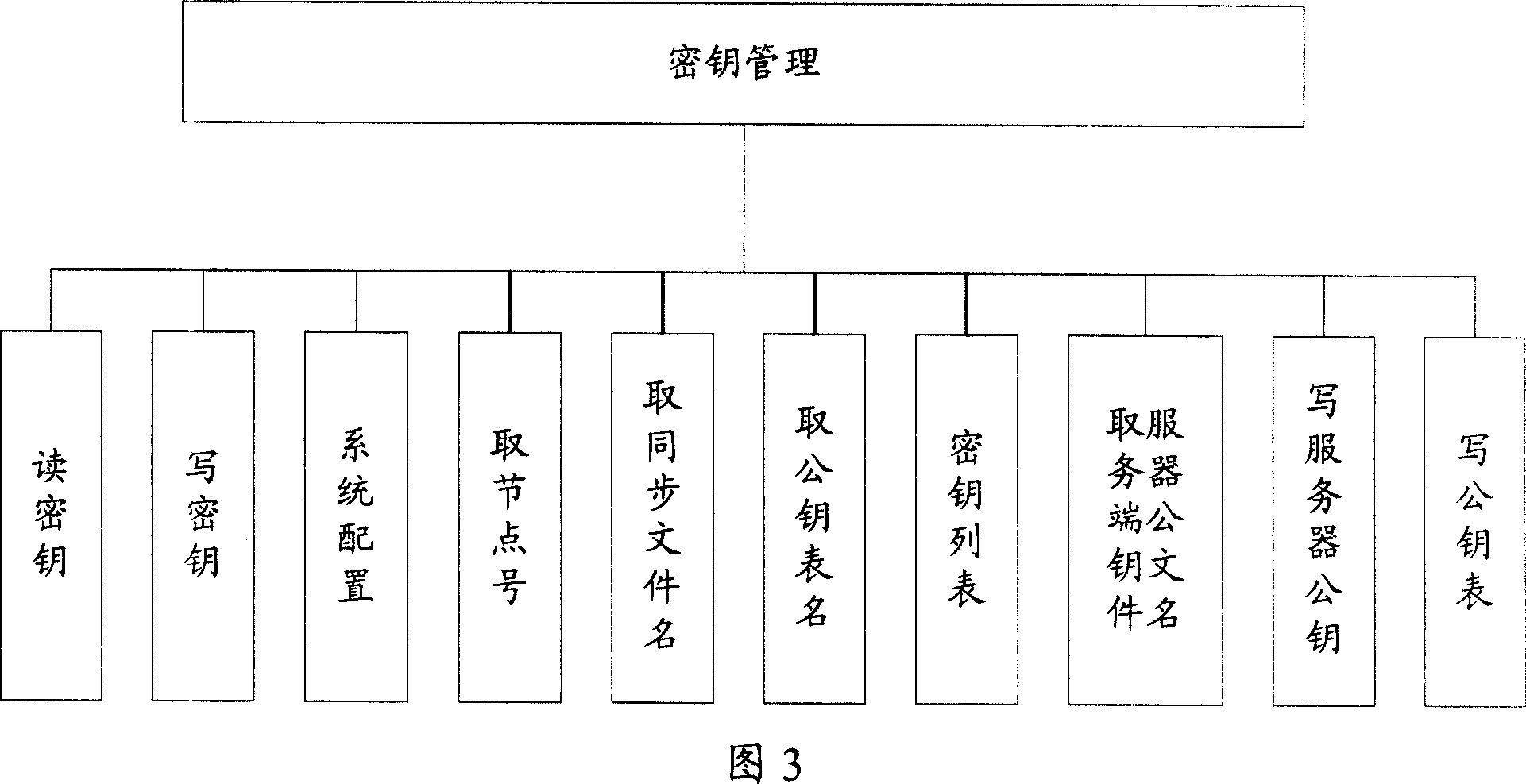
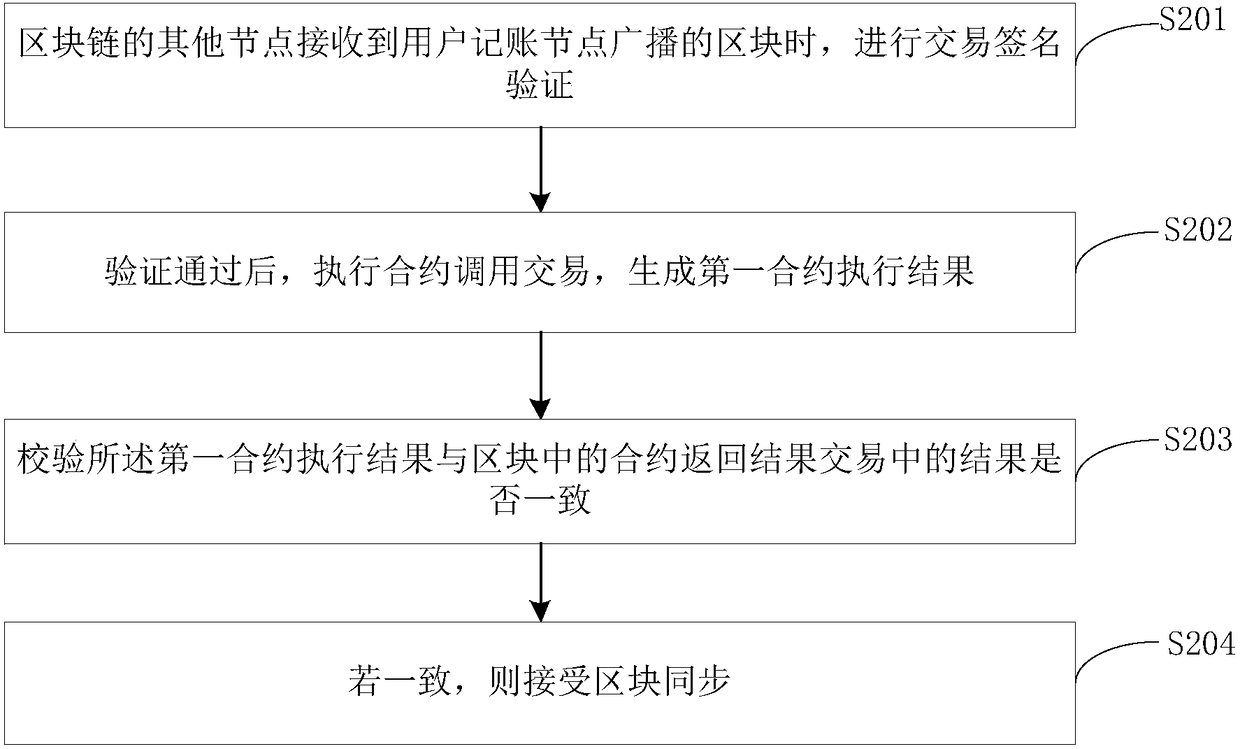
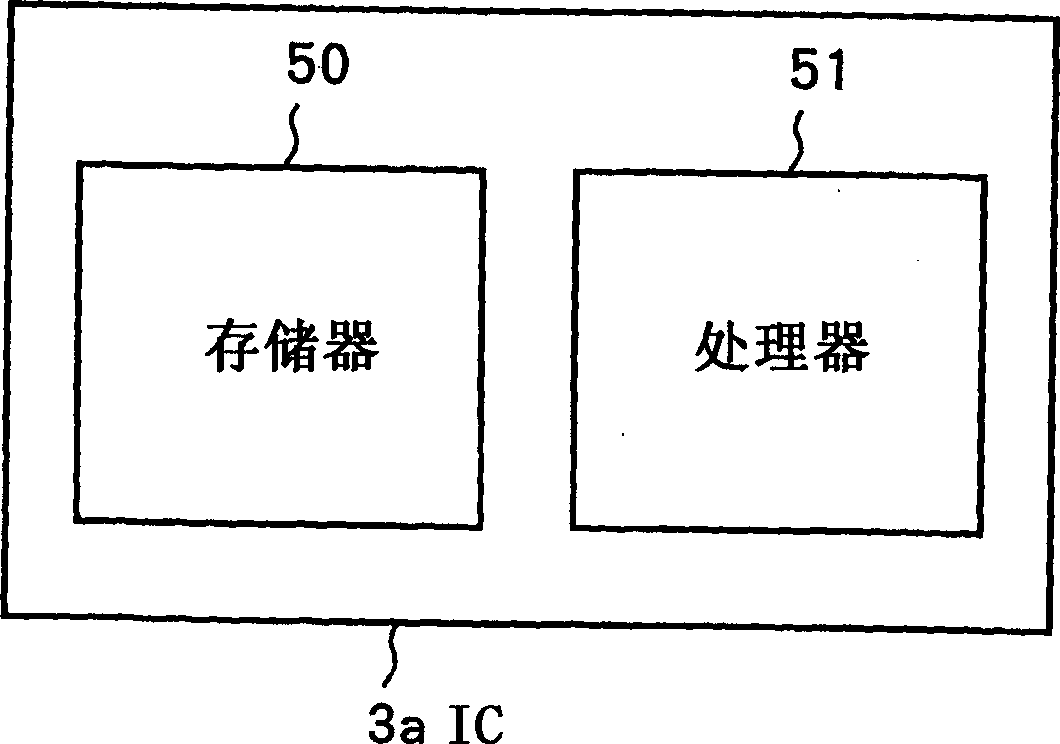
Patents
Literature
127results about How to "Prevent illegal tampering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
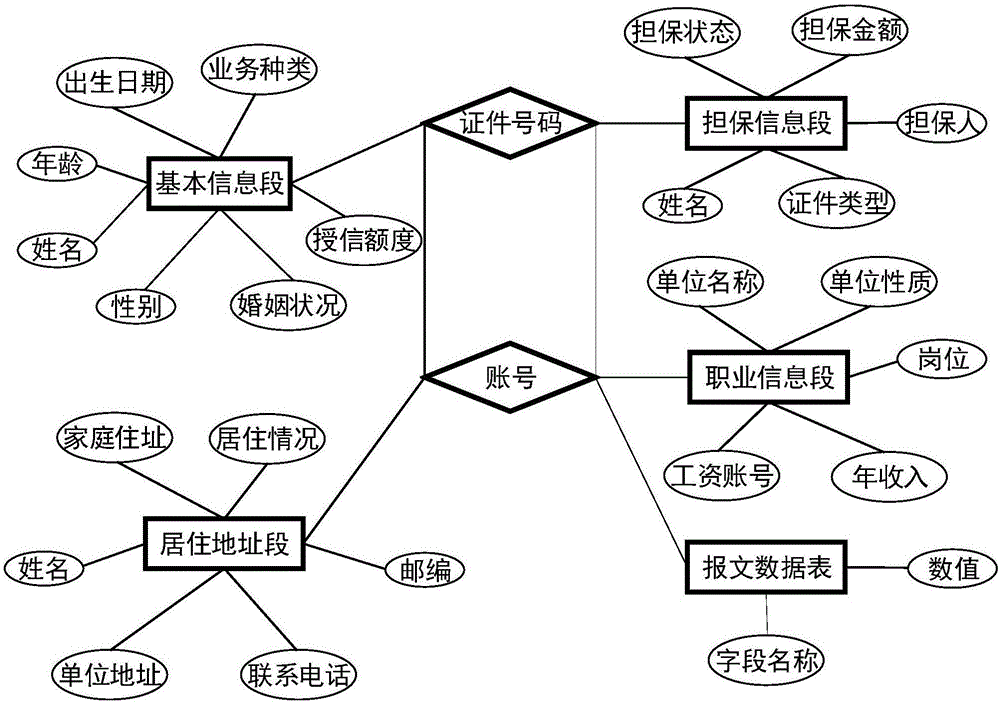
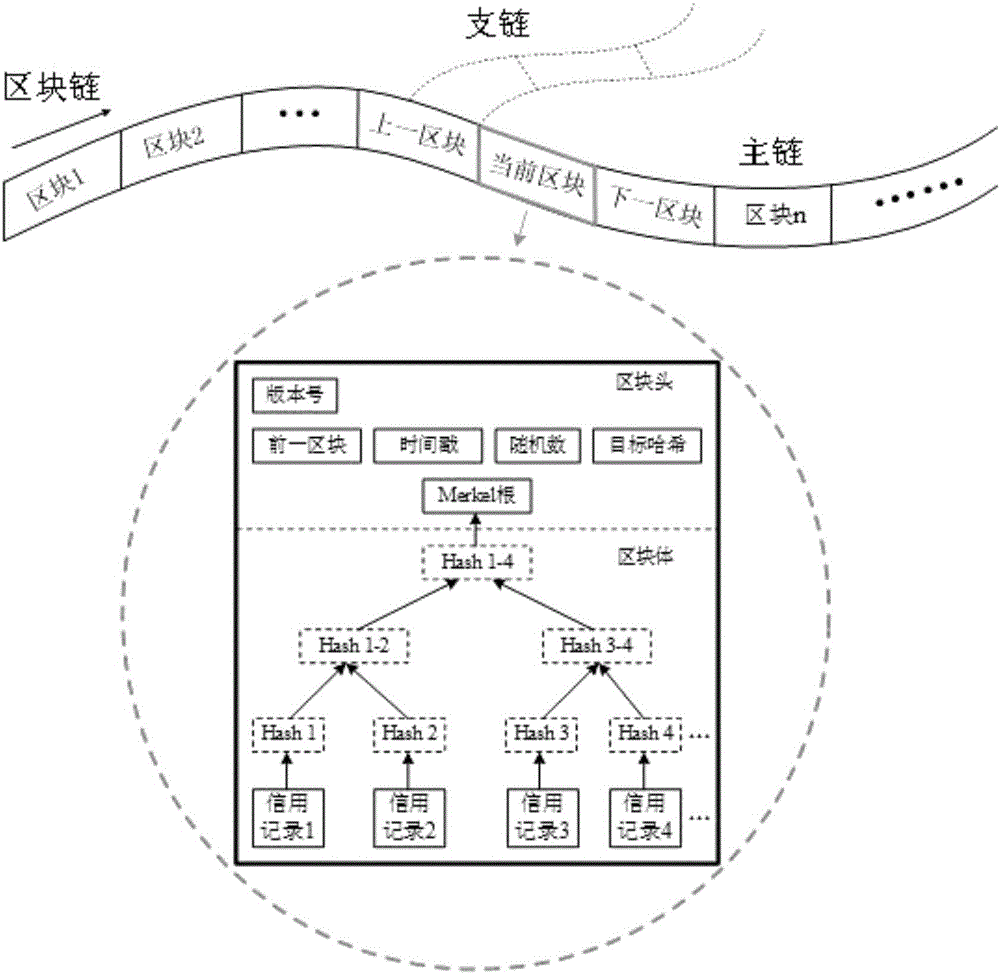
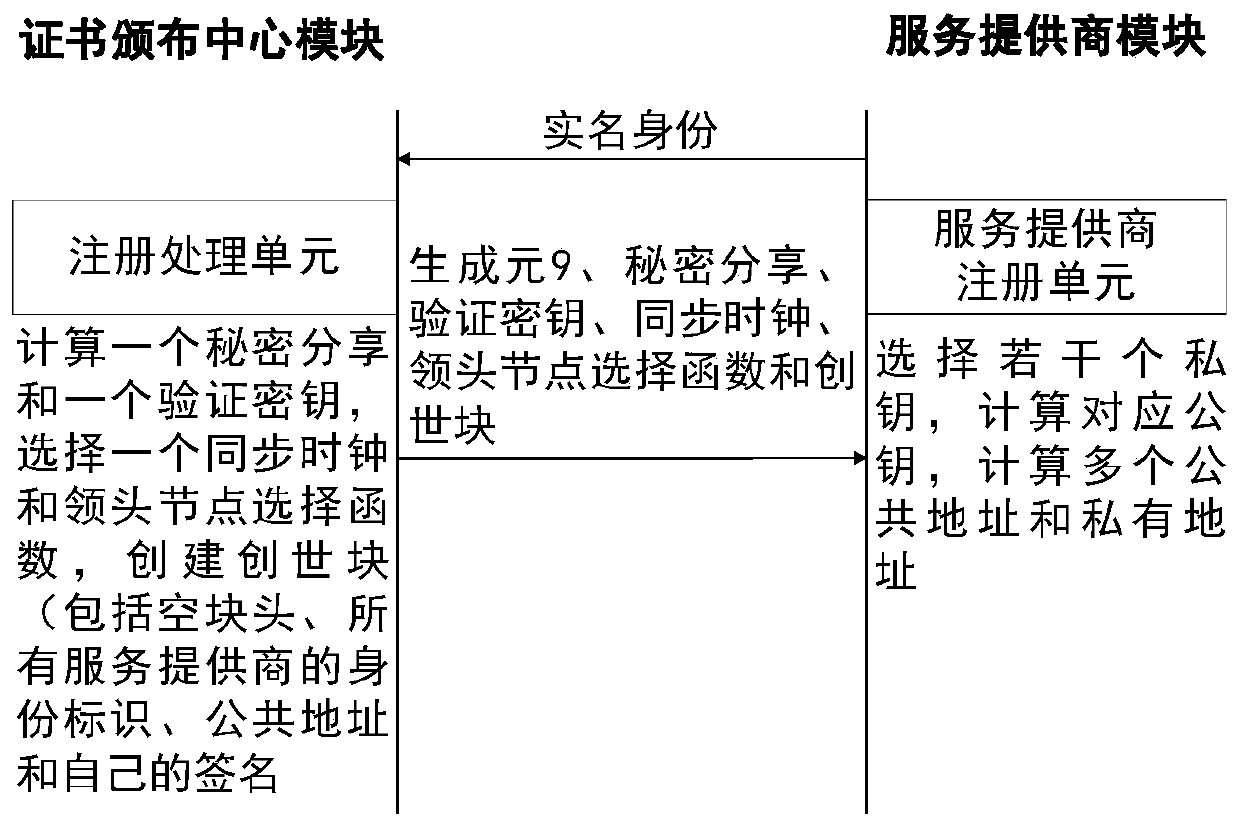
Individual credit reporting system establishment method based on block chain technology
InactiveCN106230808ARealize distributed managementAchieve sharingFinanceTransmissionData informationModel system
The invention discloses an individual credit reporting system establishment method based on a block chain technology. Block encapsulation and distributed management are carried out on individual credit data information by utilization of features of the block chain technology, and the defect that a management center is heavy in load and low in efficiency under intensive management of an individual credit reporting system can be removed. Moreover, an RSA asymmetric cryptographic algorithm is applied to a block chain, the system is very difficult to break by traversing all possible keys, the security of the individual credit reporting system is greatly ensured, and illegal tampering of the credit data can be effectively avoided. According to the method, high-security distributed data sharing among multiple credit databases can be realized, establishment of an intensive individual credit management center can be avoided, and the credit reporting cost is reduced. According to a model system structure with the complete block chain, the method has very wide application prospect in the field of individual credit reporting.
Owner:HANGZHOU YUNXIANG NETWORK TECH
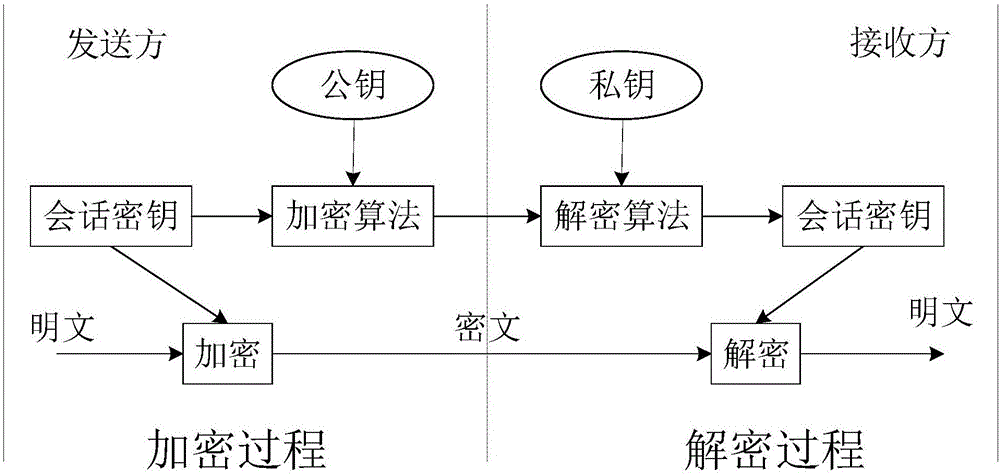
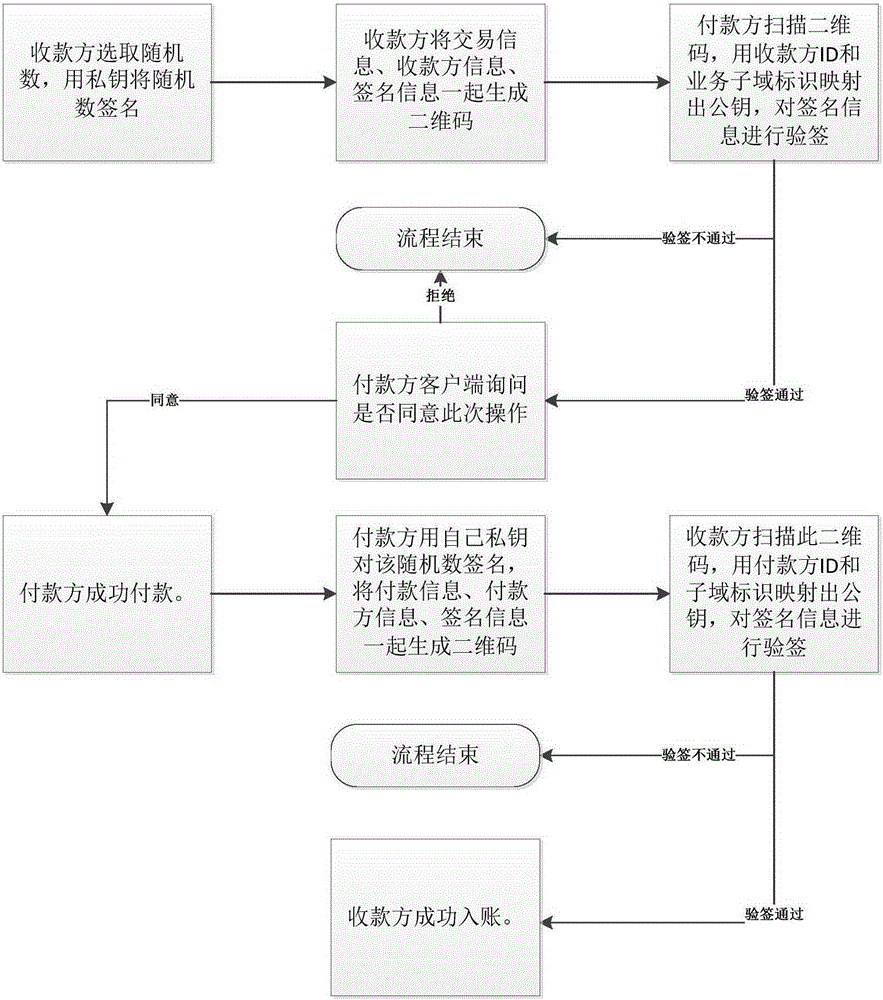
Novel offline payment method
InactiveCN105205664AConvenient paymentPrevent illegal tamperingPayment architecturePaymentMobile device
The invention discloses a novel offline payment method. The method comprises the steps that account numbers of an accountee party and a receiving party serve as IDs, and a corresponding public key and private key are mapped according to business sub-domain identifications; a random number is selected from the receiving party, signature is conducted on the random number through the private key, and a two-dimension code is generated; the two-dimension code is scanned through the accountee party, the public key is mapped by means of the receiving party ID and the service sub-domain identification, and attestation is conducted on a signing message; if attestation succeeds, the accountee party successfully pays according to transaction information; signature is conducted on the random number by the accountee party through the private key after payment to generate a two-dimension code; the receiving party scans the two-dimension code, the public key is mapped through the accountee party ID and the business sub-domain identification, and attestation is conducted on a signing message; if attestation succeeds, posting is successfully conducted on the receiving party. According to the novel offline payment method, payment does not rely on the support of a network any more, payment is achieved on various mobile equipment, and the payment process is greatly facilitated. The two-way authentication process based on the identifications is adopted by the two payment parties, the legality of transactions is fully guaranteed, and illegal manipulation of information and information disguising are prevented.
Owner:CHINA SMARTCITY TECH
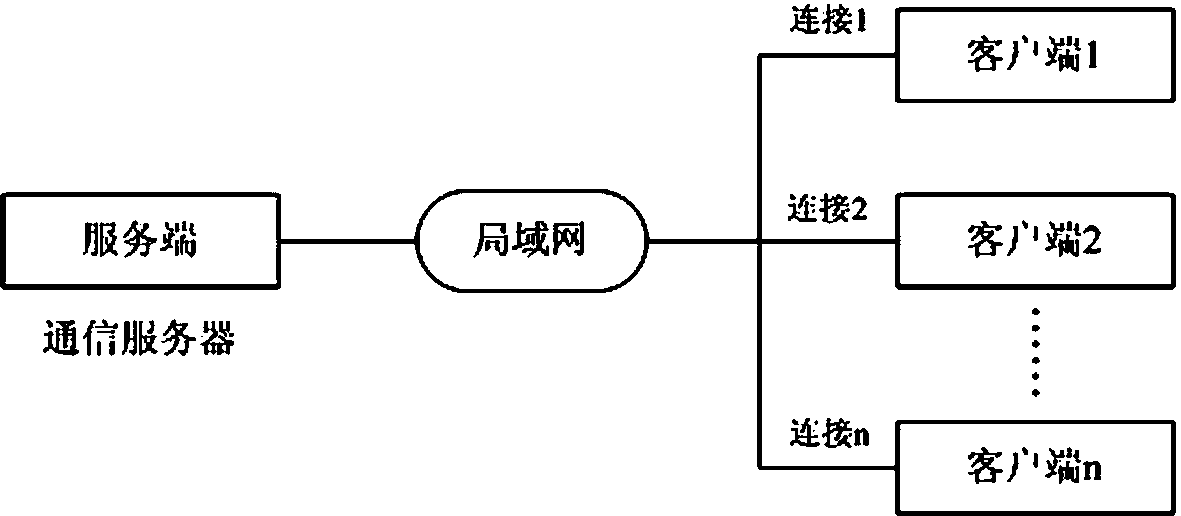
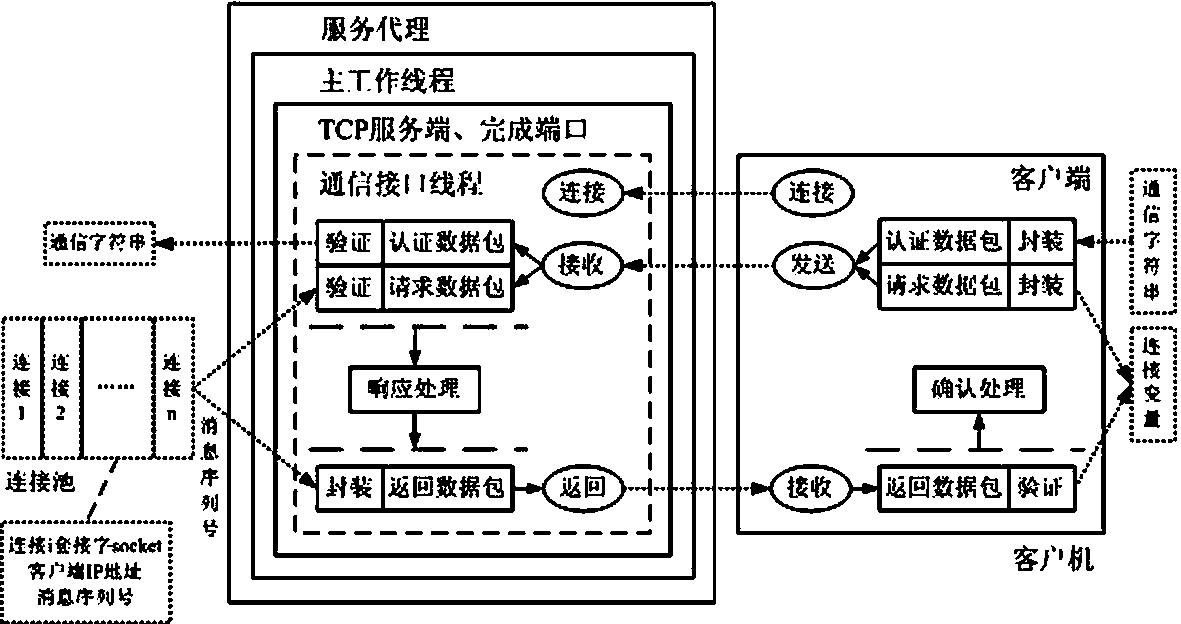
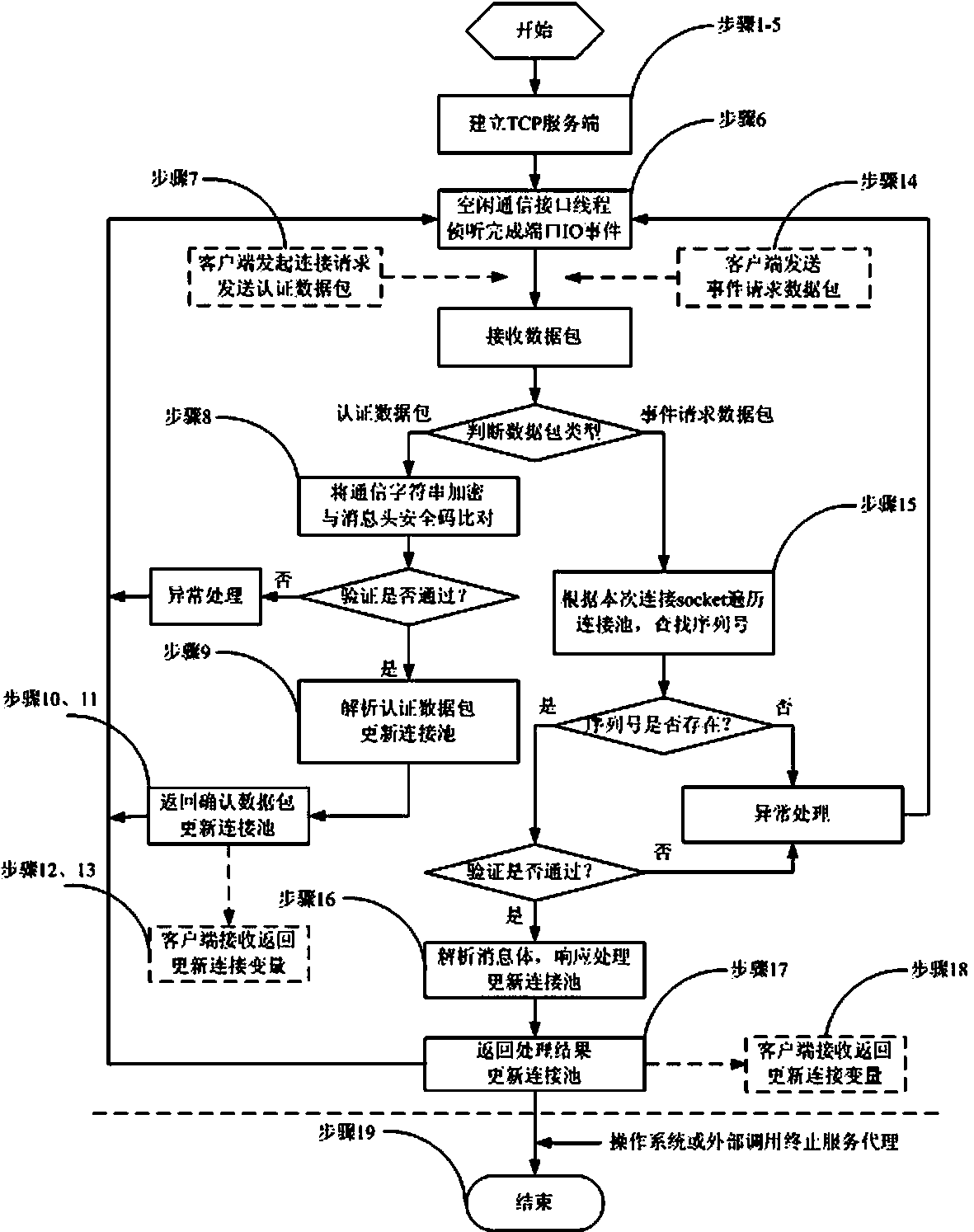
Multilink safety communication method based on completion port model
InactiveCN103391289AImprove scalabilityEasy to implementError preventionSecure communicationCommunication interface
The invention provides a method for supporting multilink concurrence safety communication between a server and multiple clients and relates to a multilink safety communication method based on a completion port model. The method includes that a main worker thread at a communication server is embedded into an application service of a Windows system to run, a transmission control protocol (TCP) communication server is built according to the completion port model, meanwhile a fixed number of communication interface threads are built to conduct communication with the clients in an asynchronous mode, and the parallel processing capability of the server is improved. In an interaction process, after any client builds the TCP connection, two communication parties must adopt a handshake mechanism to ensure connection legality and adopt connection pool queues or local variables to dynamically maintain message serial numbers in the following data receiving and transmitting process, data transmitted by any party on the legal connection are packaged again according to the data package structure definition, and the receiving party adopts a safety verification algorithm to verify the data packages and regroup the plurality of data packages according to the precedence order of the message serial numbers.
Owner:中船凌久高科(武汉)有限公司
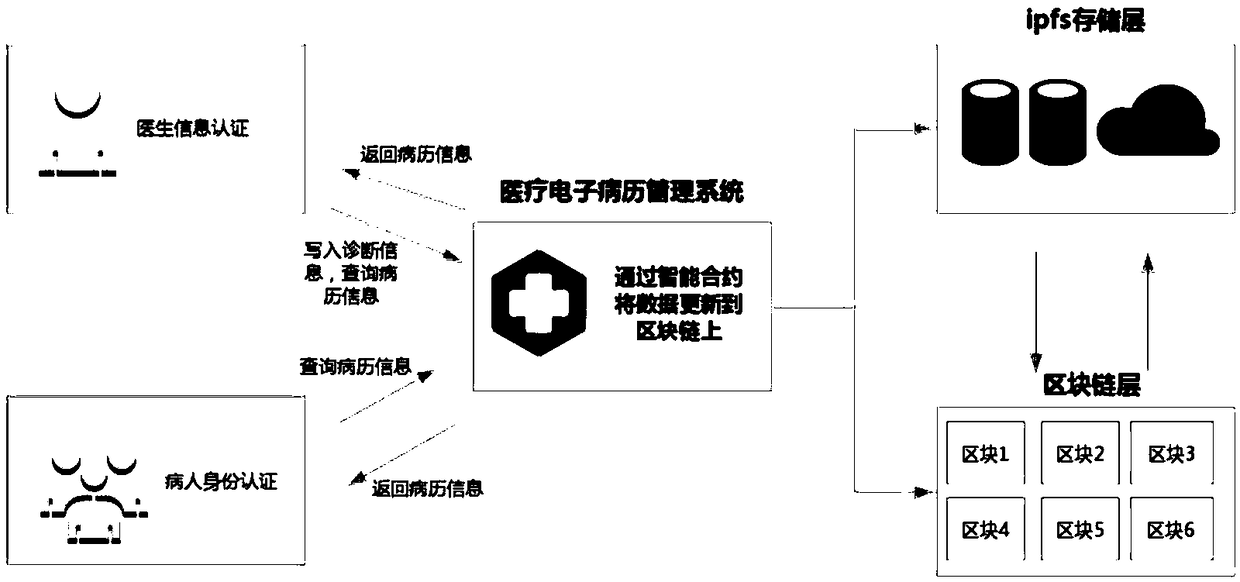
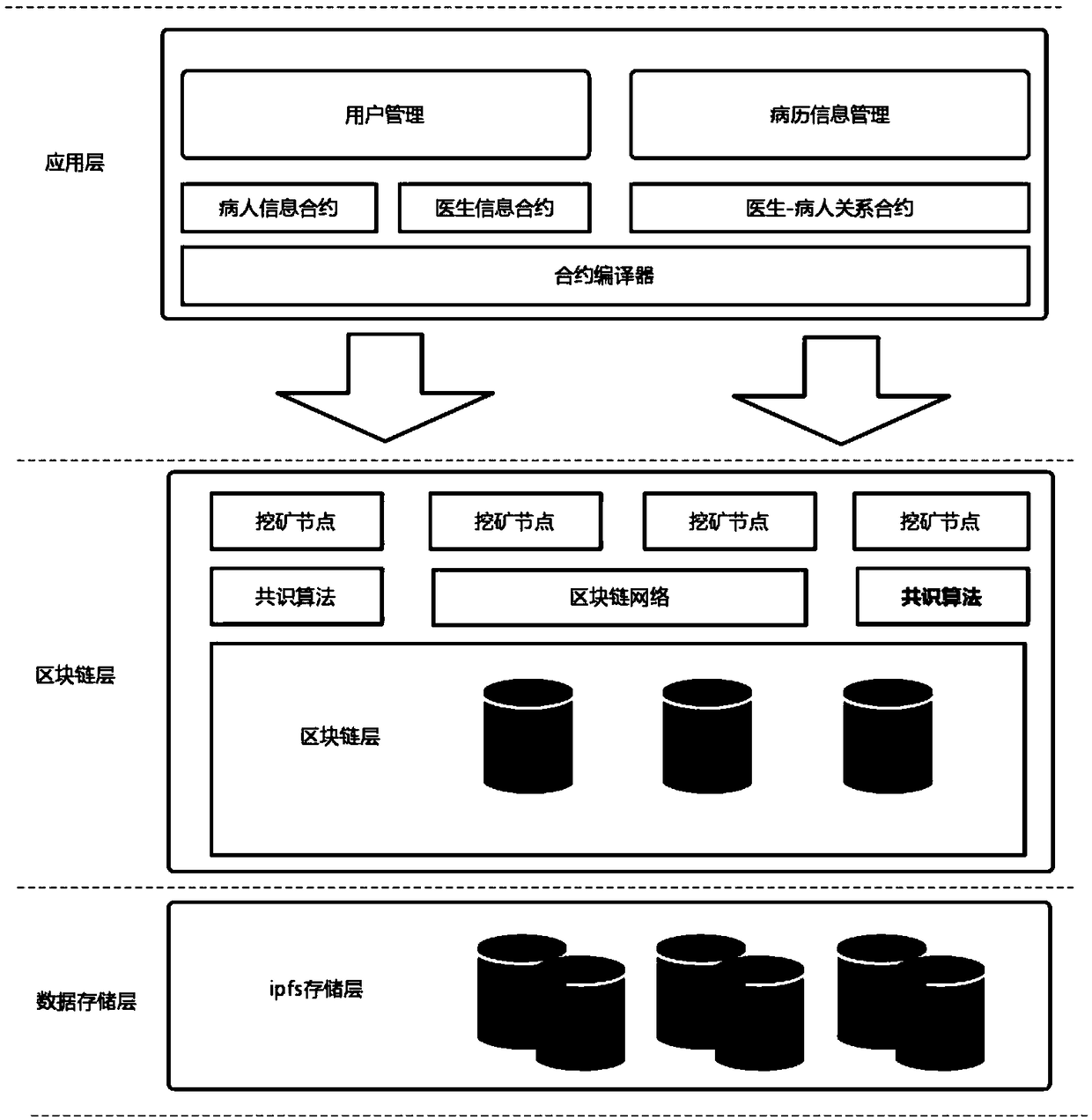
Blockchain-based medical electronic medical record distributed management system and construction method thereof
InactiveCN109215751AAvoid lostReduce maintenance costsMedical communicationDigital data protectionMedical recordSystem maintenance
The invention discloses a blockchain-based medical electronic medical record distributed management system and a construction method thereof. According to the blockchain-based medical electronic medical record distributed management system and the construction method thereof, the diagnosis processes of patients, such as medical records and prescriptions, are written into a blockchain in the form of smart contracts, so that a relevant hospital does not need to rely on a centralized server to manage the medical record information of the patients, and single-point failures common to the centralized server can be avoided; the data stored in the blockchain cannot be tempered and are traceable, and therefore, illegal tampering can be prevented; and a series of information such as the physical health, medical histories, and personal data of the patients, which concern personal privacy, can be effectively protected through an ABE encryption algorithm. With the system and method of the invention adopted, data loss caused by the single-point failures can be avoided, system maintenance cost can be decreased, and a condition that the diagnosis records of the patients are falsified during medical disputes can be avoided.
Owner:JINAN UNIVERSITY
Method for signature and seal central management and trust authorized electronic signature and seal
InactiveCN1588385AEasy to useAchieve logoutOffice automationData switching networksRights managementSecurity question
The present invention is safe centralized electronic stamping management and submitted stamping method, and relates to information technology. The present invention provides centralized stamping server in OA system for remote centralized stamping service and stamp management. The user side provides control for local document verification and the archived document verification and communicates via special interface with the role authority distribution in the OA system, so that the management of electronic stamps is integrated to the role authority management in the OA system to realize the centralized electronic stamping management and submitted stamping. The present invention has high safety, simple structure, flexible mode and easy integration.
Owner:SHANGHAI JIAO TONG UNIV +1
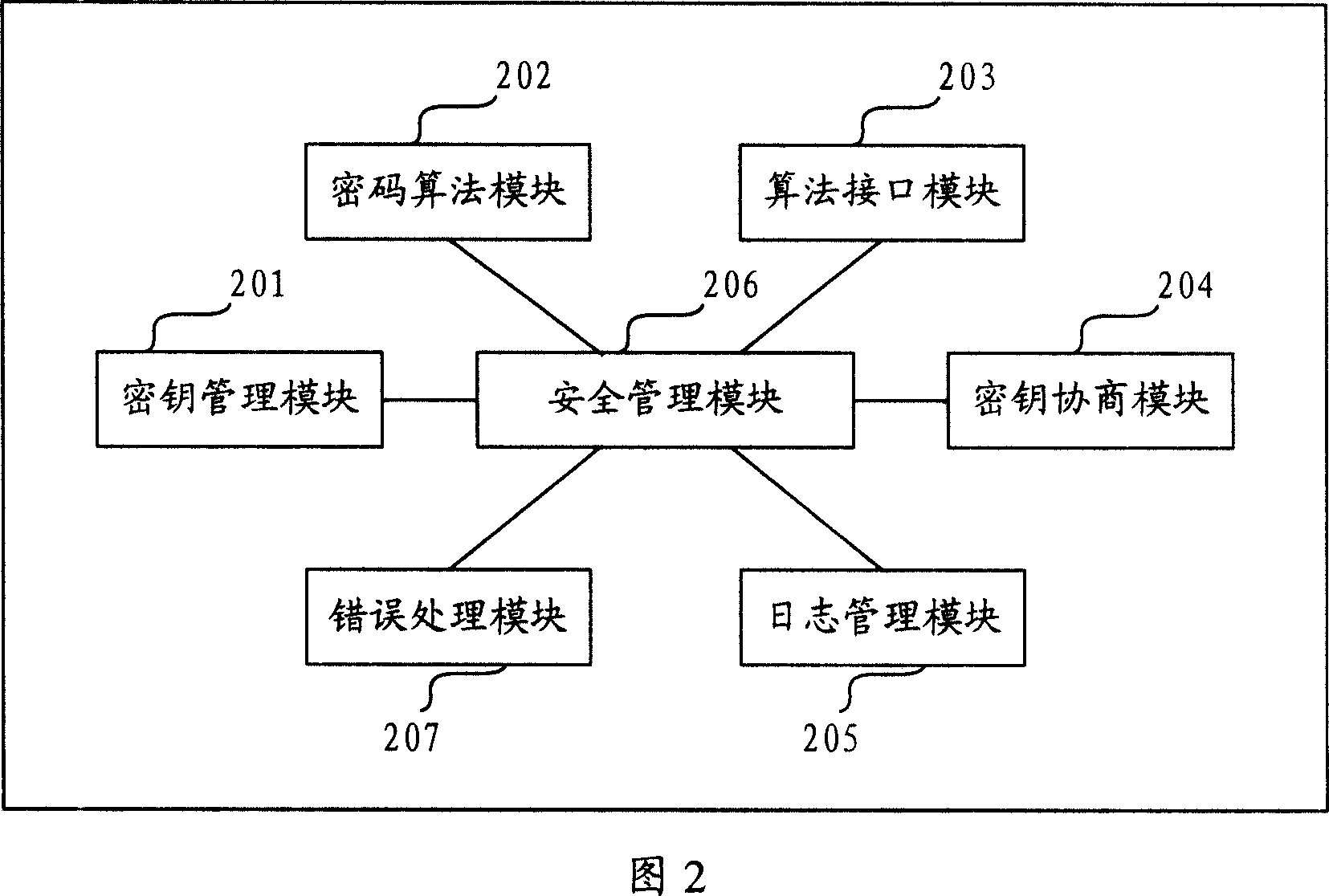
Information security control system
InactiveCN101043335AImplement encrypted transmissionAvoid illegal acquisitionUser identity/authority verificationError processingConfidentiality
The invention provides a control system for the information safety to solve the safe problems existed in the business system, and prevent the important data from leakage and illegal interpolation. The system includes: key management module, key negotiation module, code interface module, log management module, security management module and mistake processing module. The control system for the information safety provided by the invention can combine with the business system closely, and it is classified following the business system on the structure design, the business logic of every hierarchy has the corresponding security control to protect the every aspects of business, and the business safety technical measures cover the every aspect of business system that includes data transmission, data storage, database, files, logs and operation certification and so on, and it can assure the confidentiality, integrality, anti-aggression, usability, anti-repudiation, ID identify and authority control of business system.
Owner:CHINA CONSTRUCTION BANK
Method for establishing a secure communication link in a multi-UAV environment
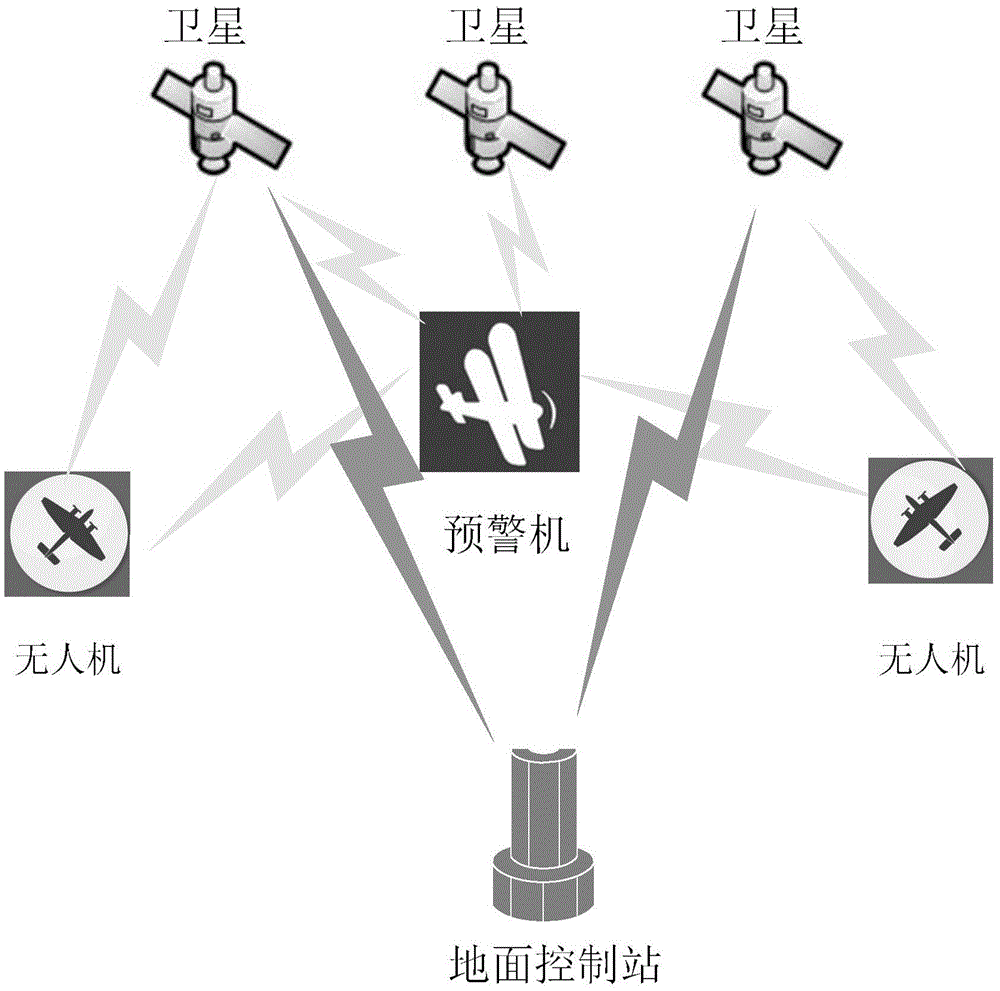
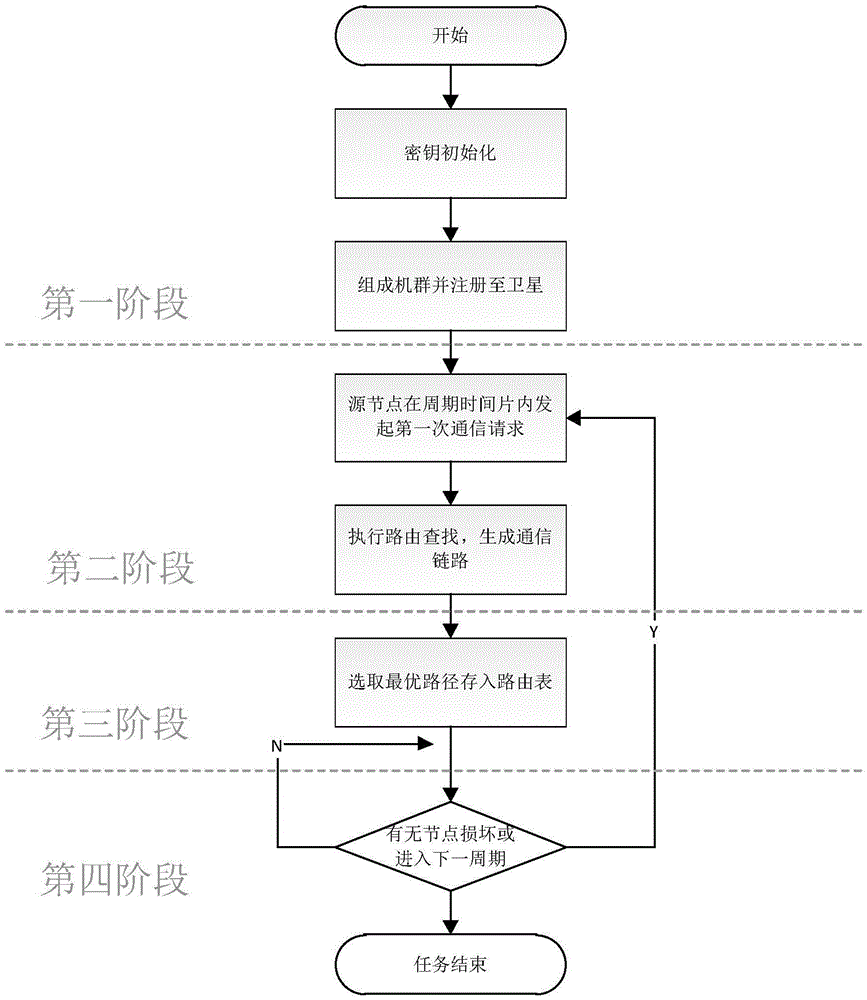
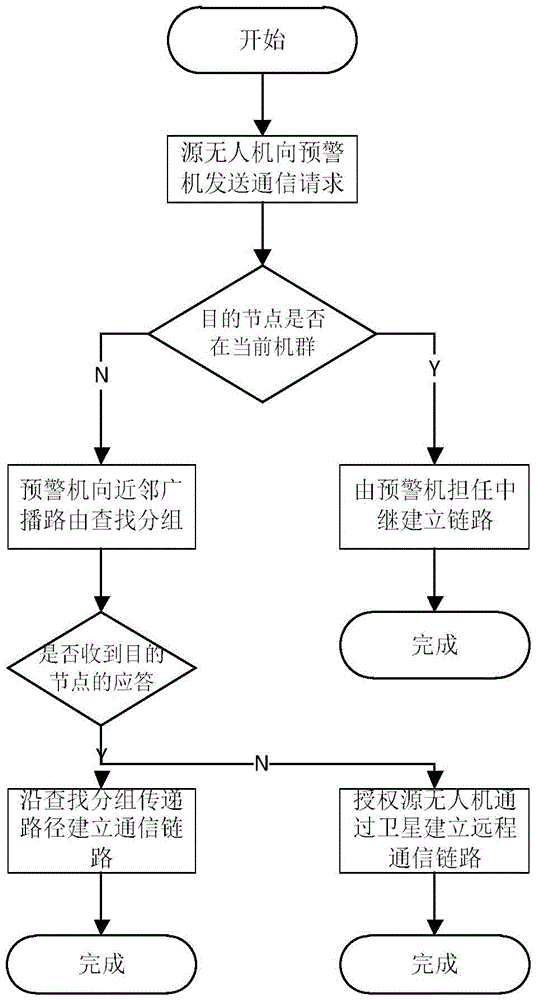
ActiveCN105491564AThe communication link is stablePrevent illegal tamperingConnection managementRadio transmissionData transmissionSecure communication
The present invention discloses a method for establishing a secure communication link in a multi-UAV environment and mainly solves the problems that the link state is unstable and data is easily captured, deleted and even tampered by a third party due to frequent changes for a network topology in the existing Unmanned Aerial Vehicle (UAV) communication technology. The technical scheme of the present invention is as follows: satellites and Airborne Early Warning Aircrafts (AEW) are efficiently utilized to manage UAV nodes in terms of data transmission requirements for the UAV; a reliable link look-up and establishing method for the UAV communication is designed; a reliable interaction protocol is used when establishing the communication link so as to avoid the false communication requests and responses and prevent the link information from being tampered by malicious nodes; and data is encrypted with a private key allocated by a ground station so as to ensure the safety of messages and improve the stability and security for the UAV communication; meanwhile, the survivability of the system is enhanced by providing effective solutions for the condition of damaged link. The method provided by the invention can be used for establishing a secure communication link in a multi-UAV environment.
Owner:XIDIAN UNIV +1
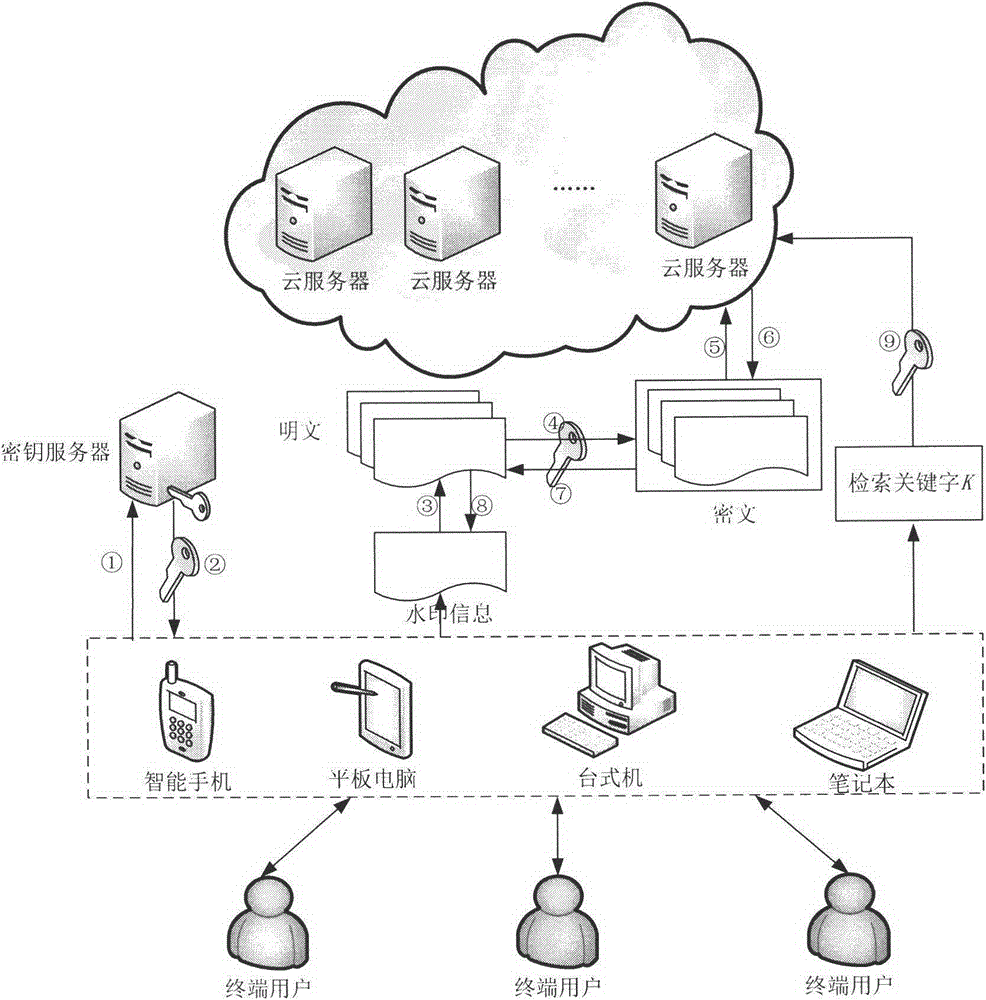
Cloud data security protection method adopting fully homomorphic encryption technology and multiple digital watermarking technology
InactiveCN105323209AEnsure transmission securityEnsure storage securityTransmissionThird partyStorage security
The present invention discloses a cloud data security protection method adopting a fully homomorphic encryption technology and a multiple digital watermarking technology. The cloud data security protection method is characterized in that in a cloud computing environment, a trusted third-party organization distributes a key to a user, after the user stores the key, a fully homomorphic encryption scheme is adopted to encrypt to-be-uploaded data at a user side, then the encrypted data is uploaded to a cloud side, thereby ensuring transmission security and storage security of data; in addition, when the user searches for data, direct search for ciphertext can be performed after a search keyword is encrypted, thereby improving search efficiency; and moreover, before the data is uploaded to the cloud side, a fragile watermarking and a robust watermarking are respectively embedded into the to-be-uploaded data, the purpose of embedding of the fragile watermarking is to prevent illegal modification of the data, so as to achieve authentication for integrity of the data, and the purpose of embedding of the robust watermarking is to protect copyright of the data, so as to achieve authentication for copyright of the data.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
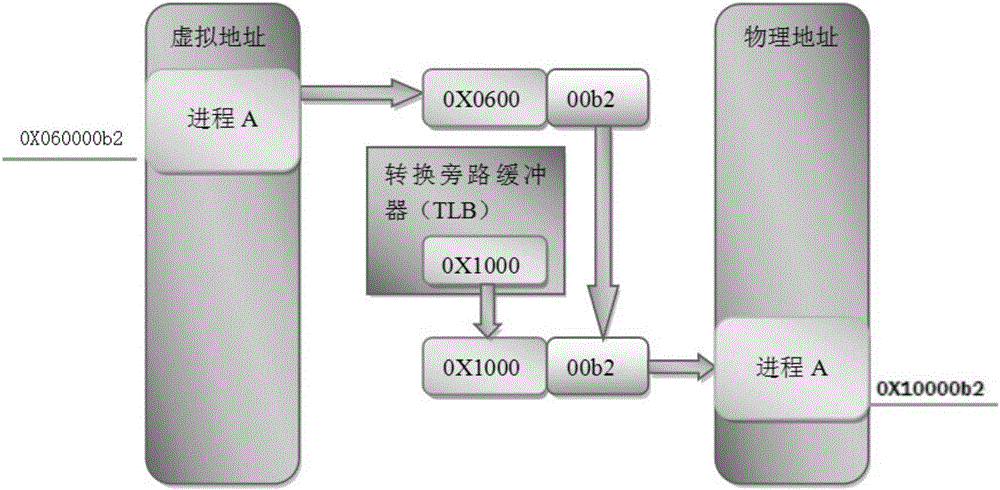
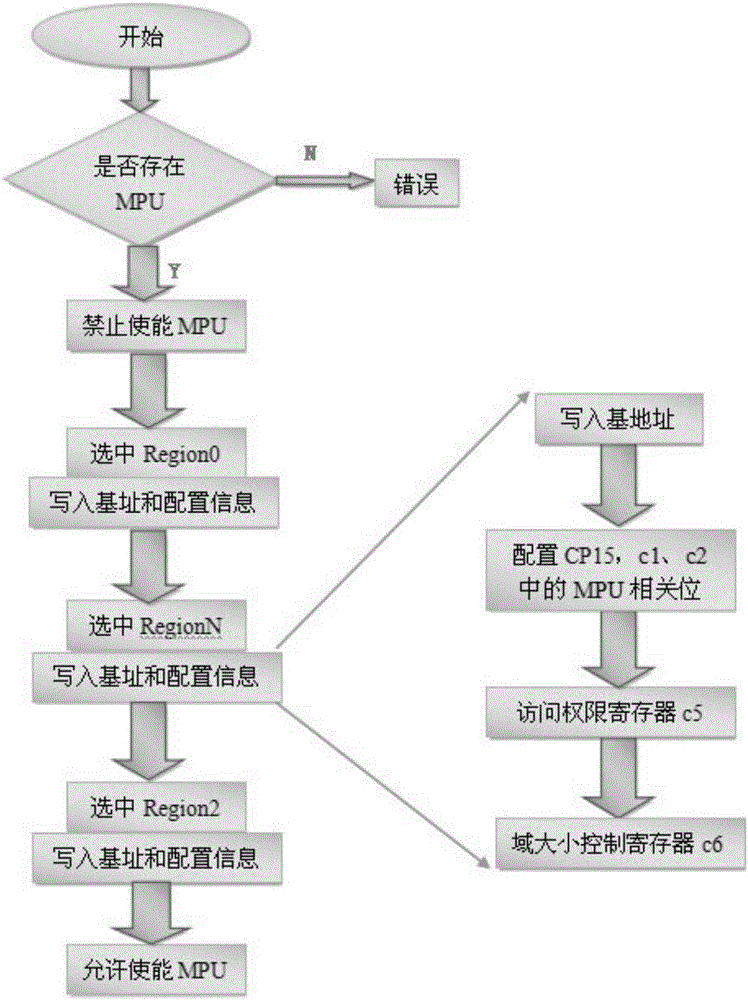
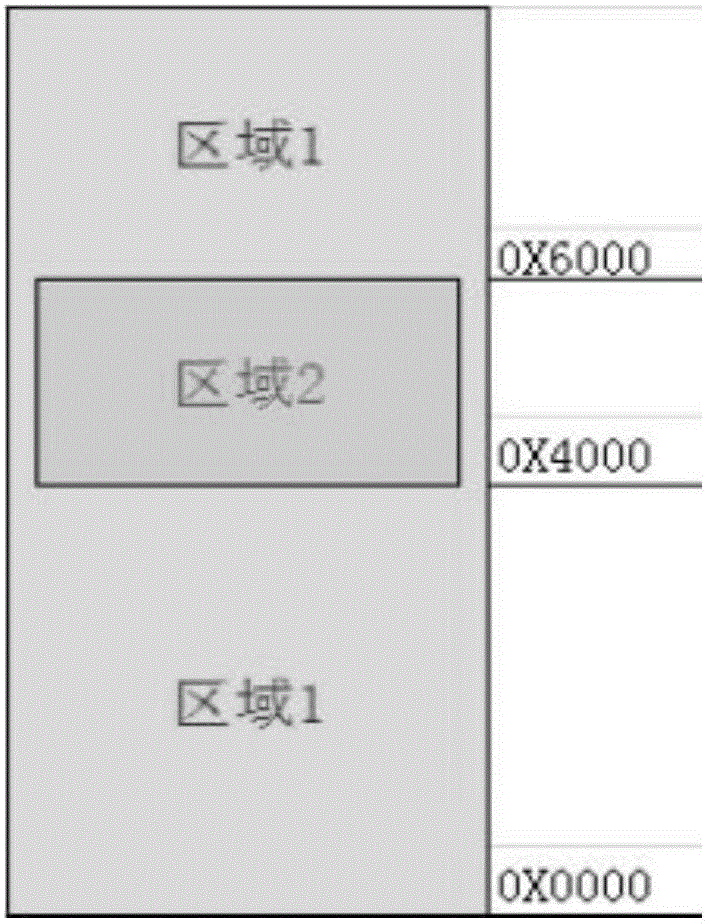
Method for technically controlling secure access to embedded system memory
ActiveCN105787360ARealize dynamic switchingEnsure legitimate accessInternal/peripheral component protectionPlatform integrity maintainanceWrite bufferOperational system
The invention discloses a method for technically controlling secure access to an embedded system memory. The method includes the following steps of initially designing a system of a memory secure access mechanism, wherein an MPU memory protection unit is introduced, domain attributes of different grades are distributed, and an access attribute and a system initiating progress are set; secondly, designing the secure access to the memory for switching of embedded operation system process context, wherein a domain control module is set, the system process context is set, and switching of the system process content is achieved in the domain control module. The illegal access of all address space resources are detected and limited through a processor MPU hardware mechanism, the boundary control and context switching of any task of the embedded real-time multi-task operation system for accessing resources of other tasks is achieved, distributing and designing of cache, writing buffer and MPU attributes of different storage spaces in the system are achieved, and the control over secure access to all background domains in the memory is ensured.
Owner:HANGZHOU BYTE INFORMATION TECH CO LTD
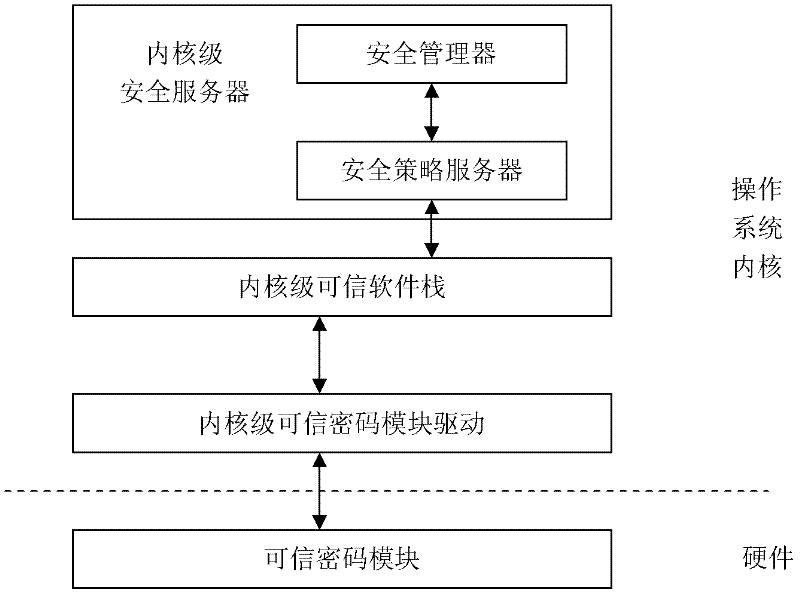
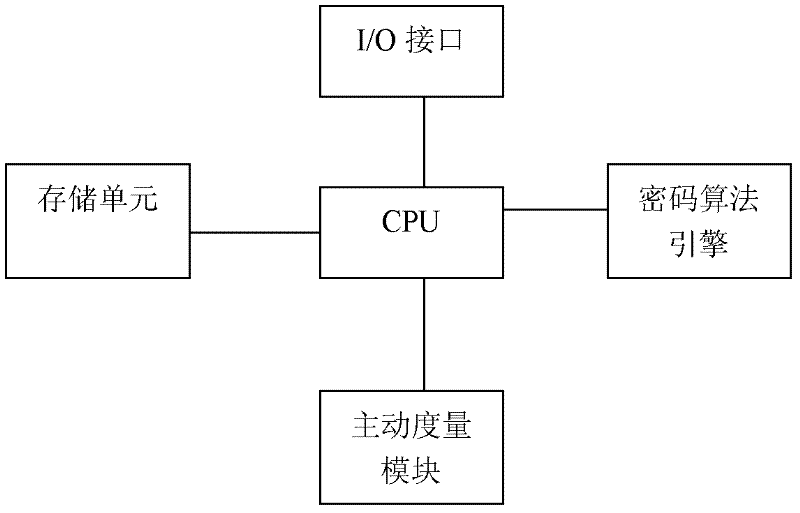
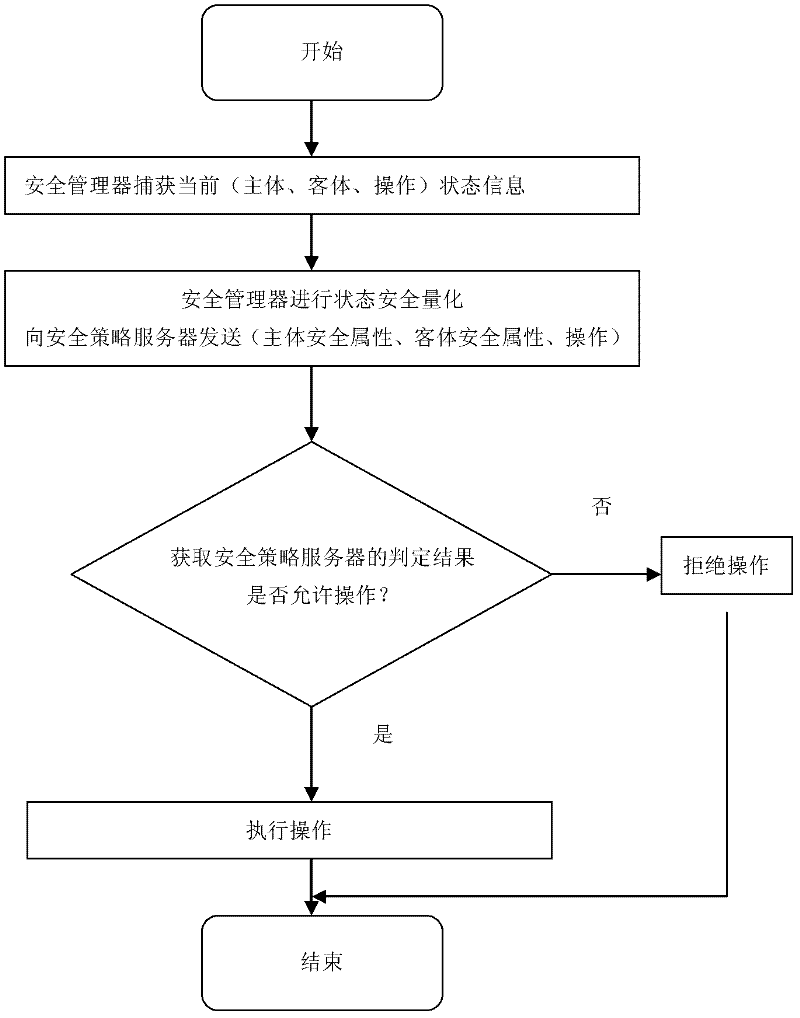
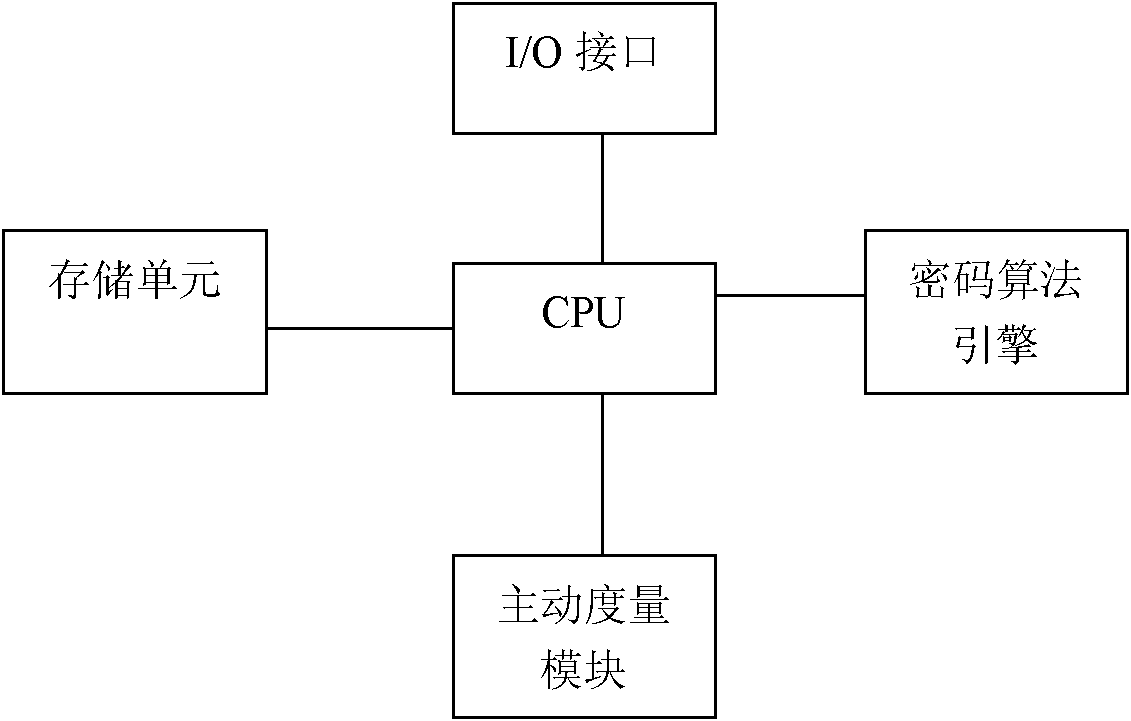
A Trusted Software Base for Proactive Security Services
InactiveCN102270287APrevent unauthorized operationsPrevent unauthorized modificationPlatform integrity maintainanceActive safetyBIOS
The invention discloses a trusted software base providing an active security service, comprising a trusted password module and an operating system kernel. The operating system kernel is provided with a kernel-level trusted password module driver, a kernel-level trusted software stack and a kernel-level security service module; a security manager and a security strategy server are arranged in the kernel-level security service module; the trusted password module provides a hardware engine for encryption operation and hash operation, and verifies integrity of a trusted BIOS (Basic Input / Output System); the trusted BIOS is used for verifies the integrity of PC hardware devices and an MBR (Master Boot Record); the MBR is used for guiding an OS (Operating system) Loader, and verifies the integrity of the OS Loader; and the kernel-level security service module captures security related information at a key security control point in a kernel layer of the operating system, and performs access control and least privilege control. The trusted software base effectively prevents unauthorized operations and rogue programs from performing unauthorized modification on application codes and configurations, and prevents secret disclosure of application resources, thereby guaranteeing the privacy and the integrity of an application environment.
Owner:中国人民解放军海军计算技术研究所
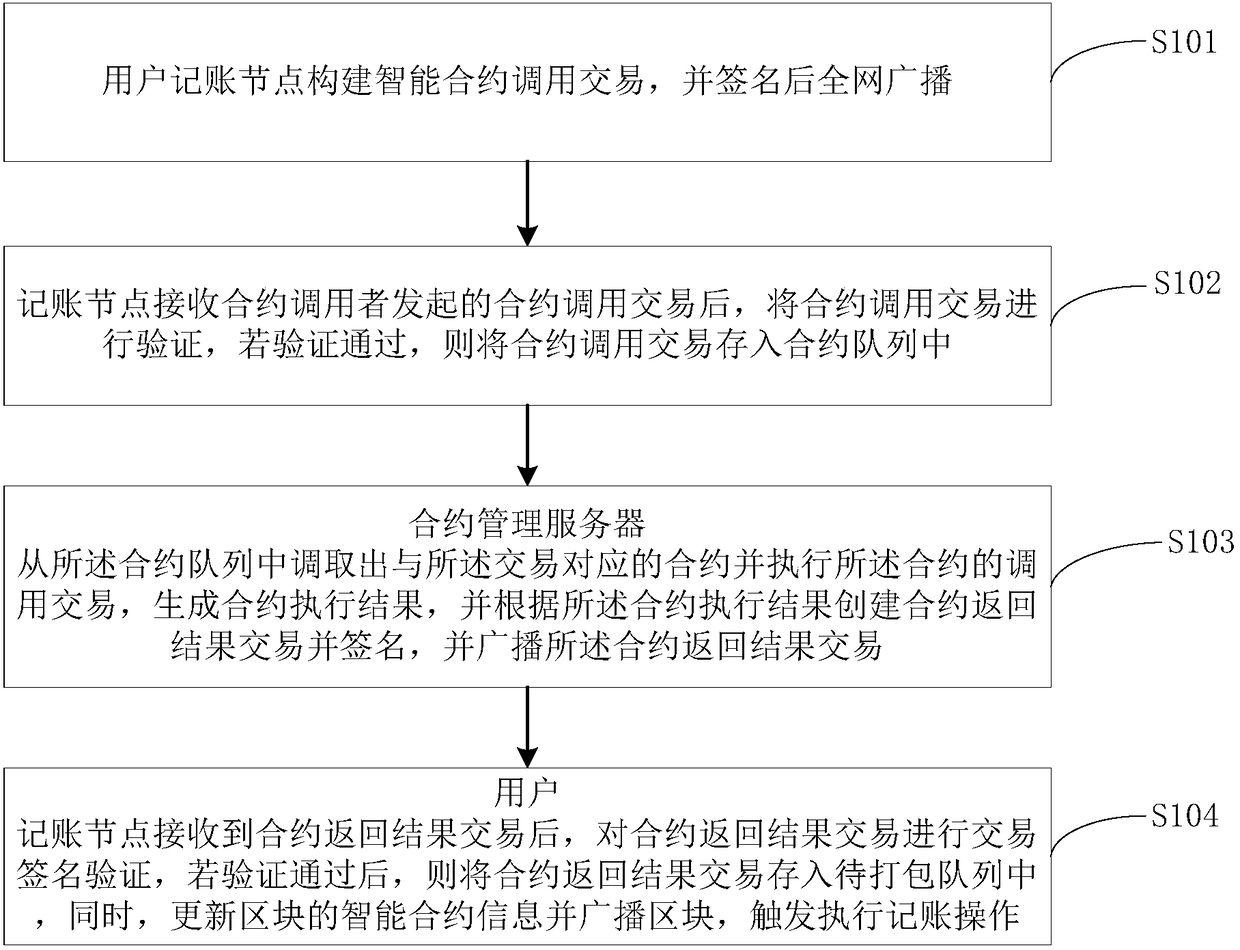
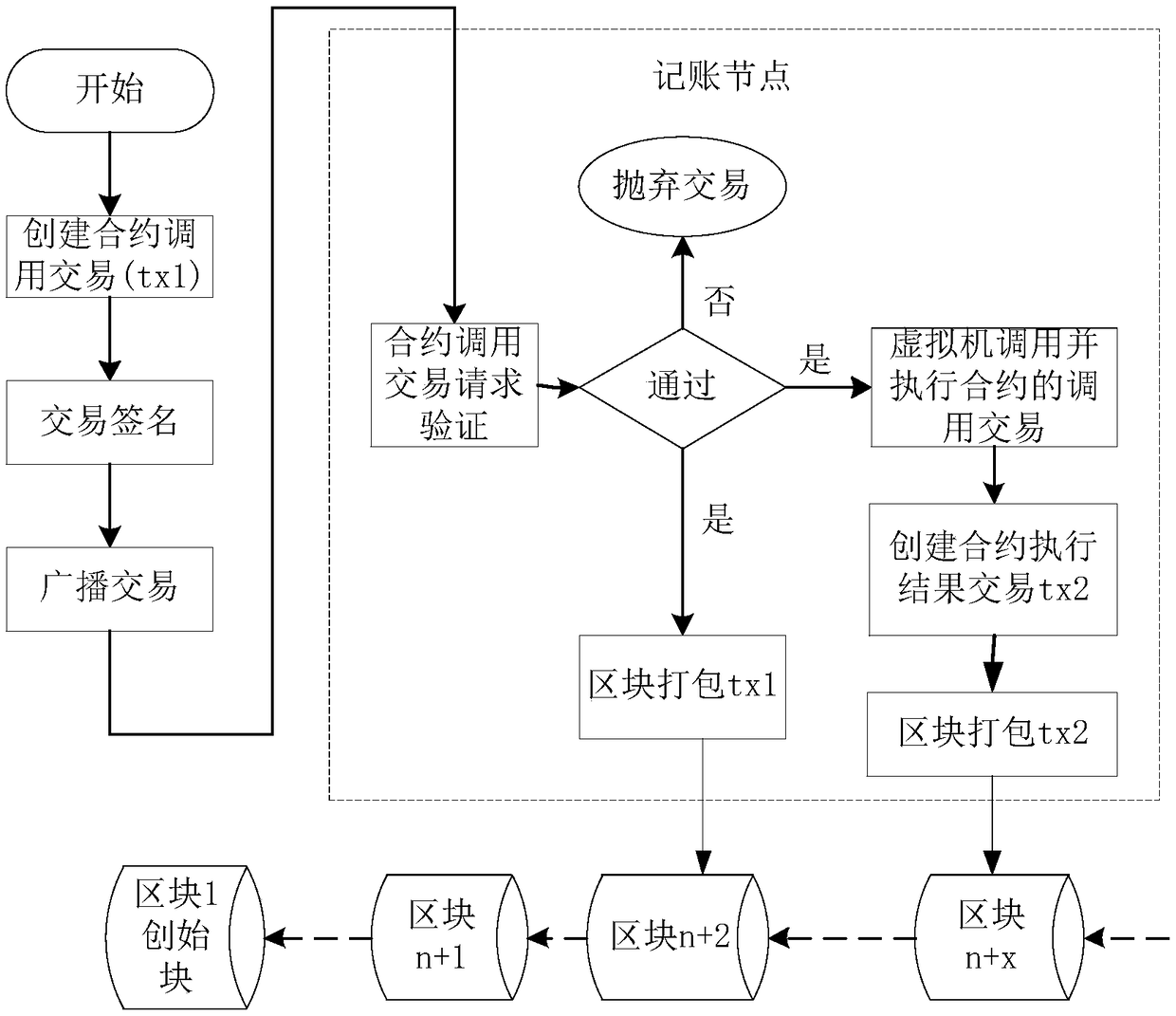
Intelligent contract bookkeeping method, computer device and readable storage medium
ActiveCN109064334AEnsure legalityEnsure effectivenessFinancePayment protocolsService efficiencySmart contract
The invention is applicable to the field of computer technology, and provides an intelligent contract bookkeeping method, a computer device and a readable storage medium. The method comprises the following steps: a user bookkeeping node constructs an intelligent contract calling transaction, and broadcasts the transaction throughout the network after signing; The bookkeeping node verifies the contract call transaction after receiving the contract call transaction, and stores the contract call transaction into the contract queue after the verification is passed; At the same time, the contract management server transfers out the contract corresponding to the transaction from the contract queue and executes the contract, generates the contract execution result, and creates the contract returnresult transaction according to the contract execution result and broadcasts after signing; The bookkeeping node performs transaction signature verification after receiving the contract return resulttransaction, stores the contract return result transaction into the queue to be packed after verification, updates the intelligent contract information of the block and broadcasts the block, triggersthe bookkeeping operation. The bookkeeping operation safety of the invention is good, and the intelligent contract can be more focused on the service of the service data, thereby improving the service efficiency.
Owner:WEALEDGER NETWORK TECH CO LTD
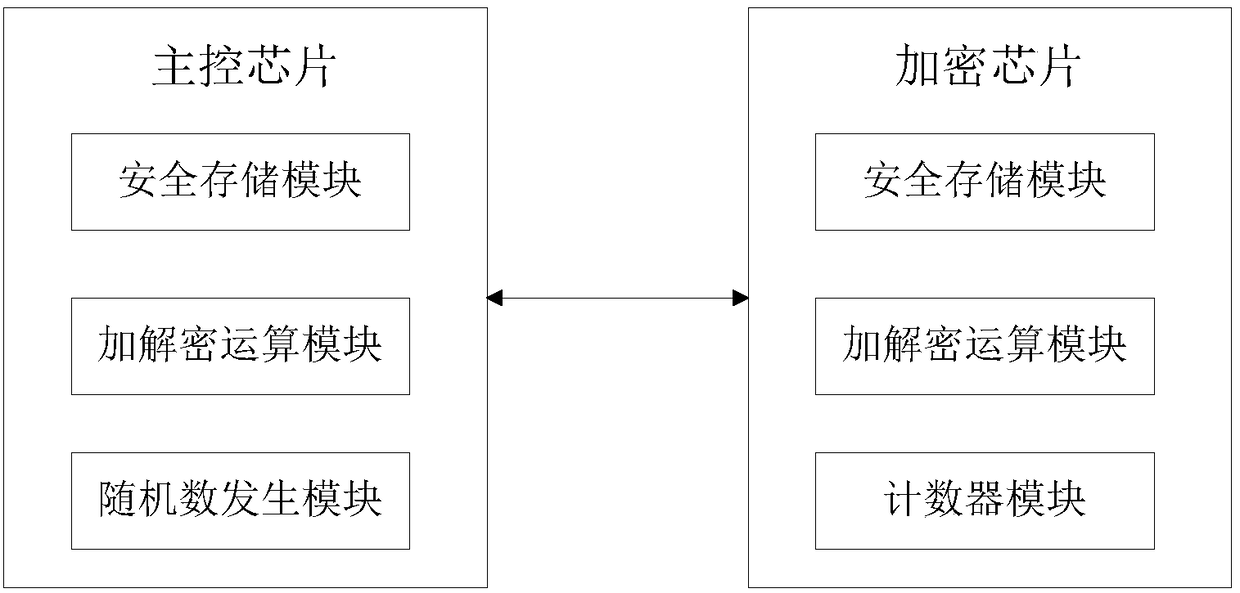
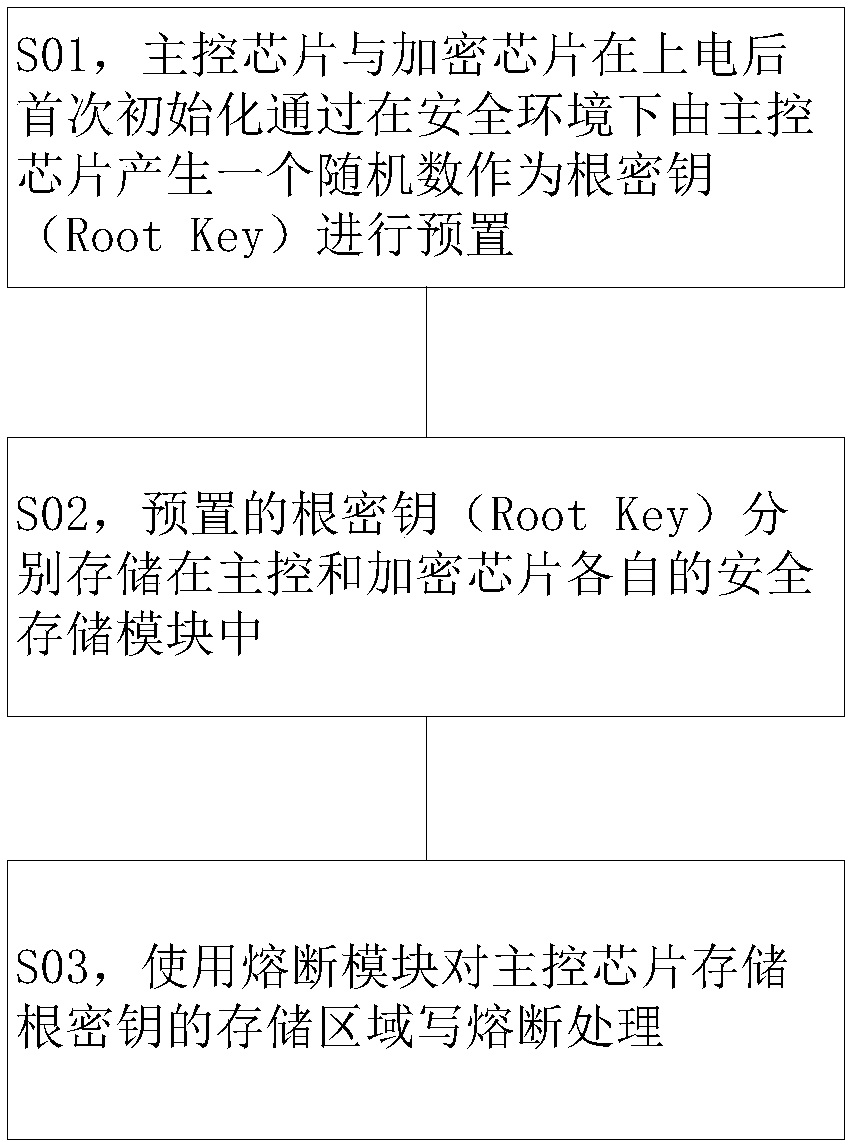
Secure communication system and method of main control chip and encryption chip
ActiveCN108234132APrevent illegal tamperingProtection securityKey distribution for secure communicationUser identity/authority verificationData transmissionChallenge response
The invention discloses a secure communication system of a main control chip and an encryption chip. The system comprises the main control chip and the encryption chip, wherein the main control chip is connected with the encryption chip; the main control chip and the encryption chip perform authentication via challenge response; the main control chip comprises a random number generation module, afirst encryption and decryption operation module and a first secure storage module; and the encryption chip comprises a counter module, a second encryption and decryption operation module and a secondsecure storage module. The invention also discloses a secure communication method of the main control chip and the encryption chip. The invention relates to the technical field of secure communication, and in particular relates to the secure communication system and method of the main control chip and the encryption chip. The main control chip and the encryption chip perform authentication via challenge response, the chip is effectively prevented from being illegally tampered, a random number is used as a key, communication data between the main control chip and the encryption chip is subjected to encryption treatment and decryption treatment by using the encryption and decryption operation modules, the data transmission security is effectively ensured, and the data exchange security is ensured.
Owner:深圳市中易通安全芯科技有限公司
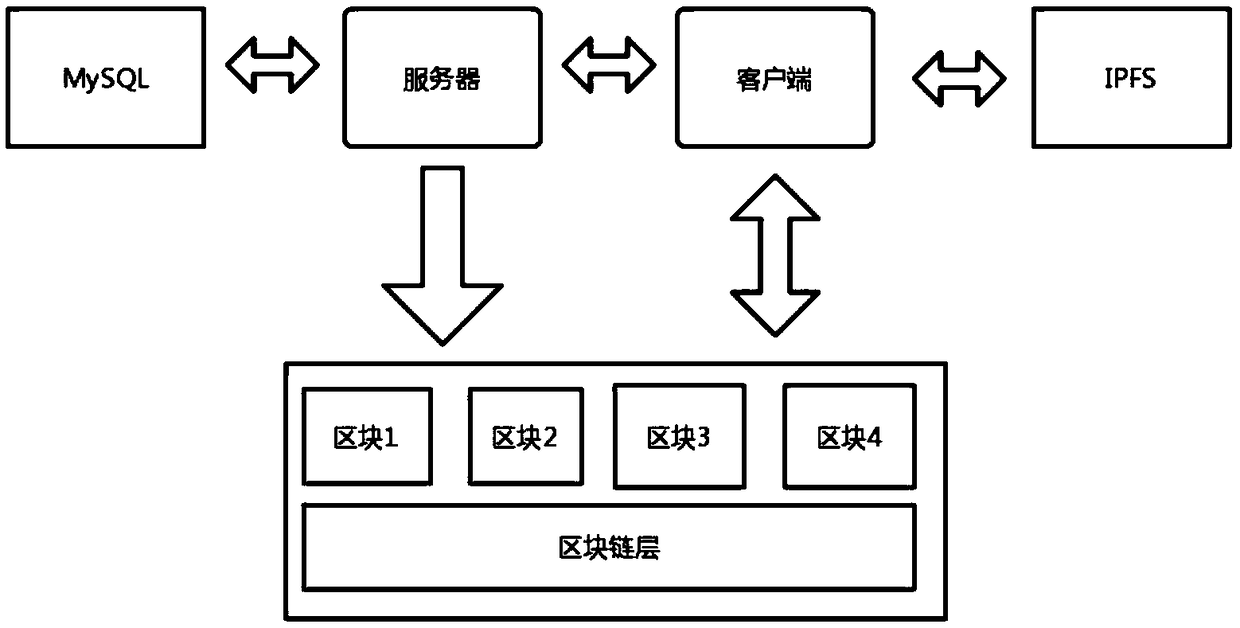
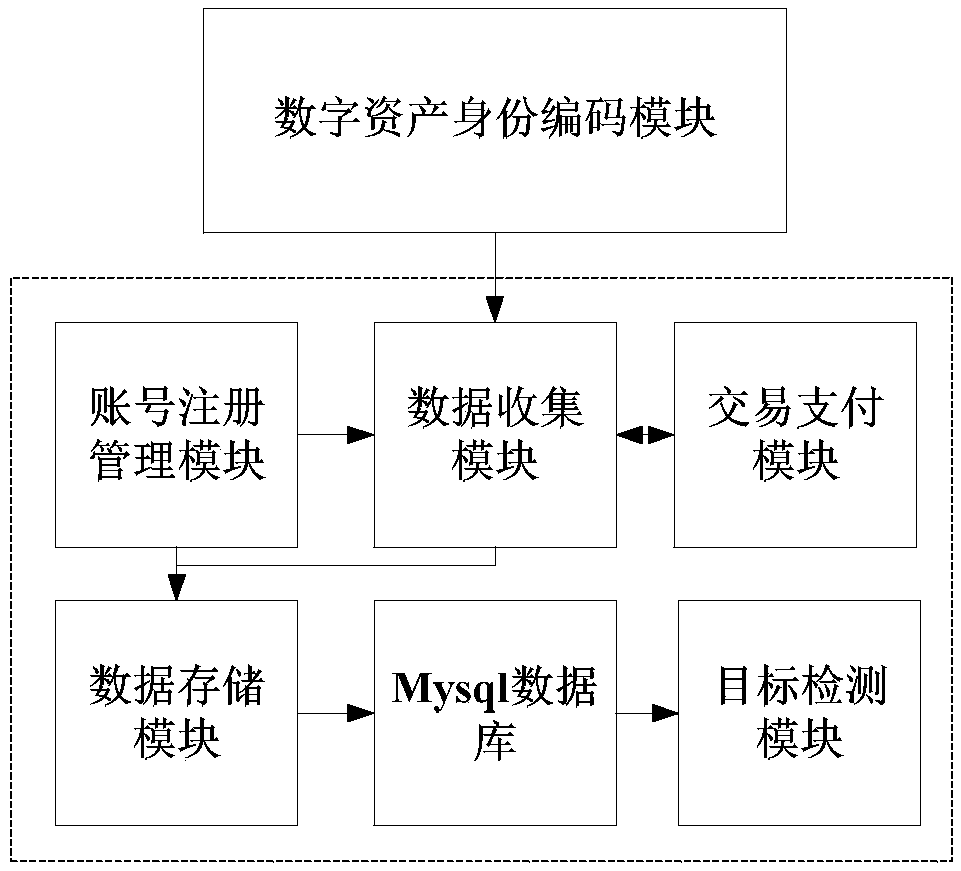
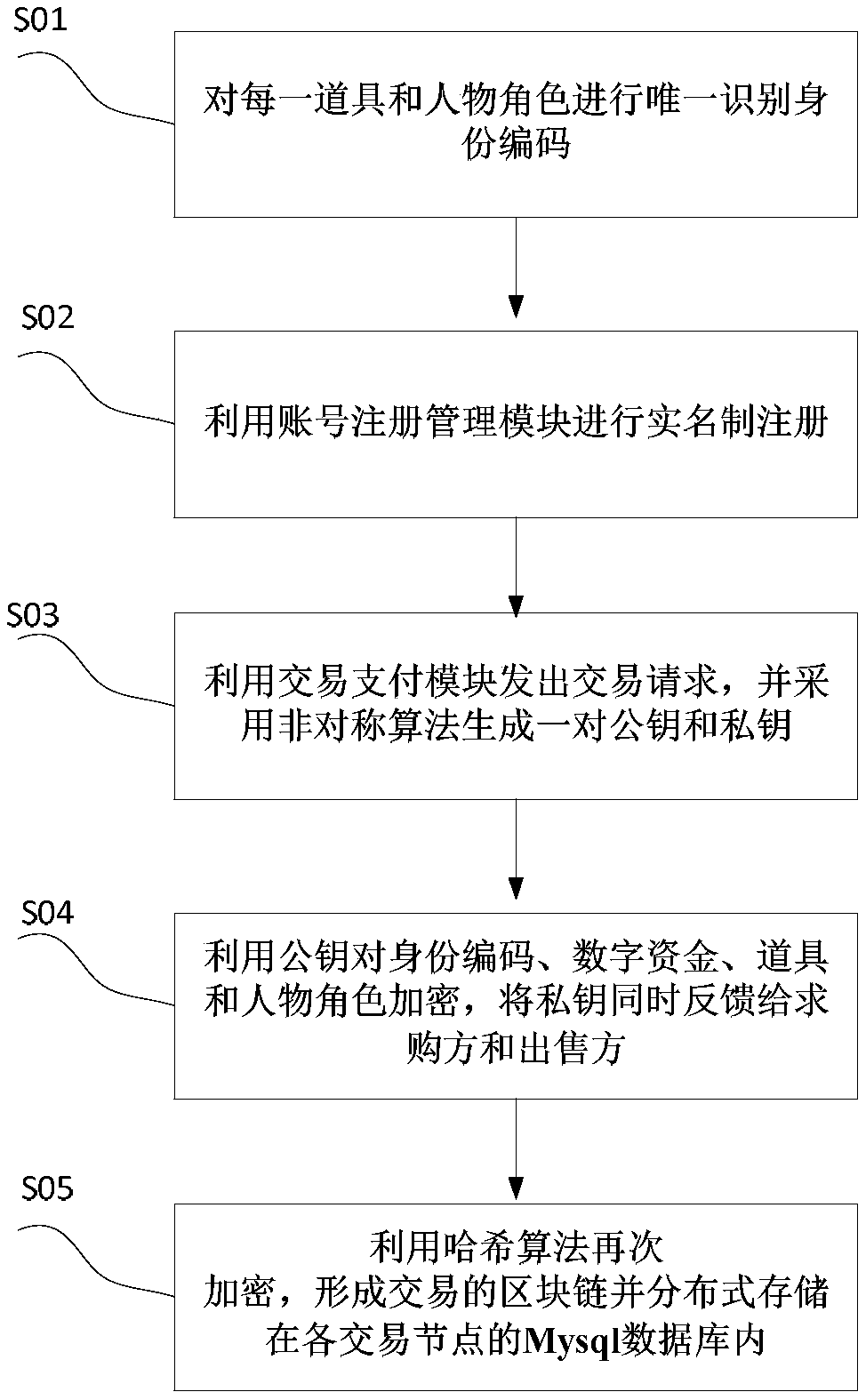
Digital asset right confirmation transaction method based on block chain technology
ActiveCN108764877AGuarantee safe and reliableRealize remote point-to-point secure interactionPayment protocolsPaymentDigital fingerprint
The invention discloses a digital asset right confirmation transaction method based on a block chain technology. The method comprises the following steps of carrying out unique identification identitycoding on each stage property and character role; carrying out real-name system registration through utilization of an account registration management module; sending out a transaction request through utilization of a transaction payment module, and generating a pair of public key and private key through adoption of an asymmetric algorithm; encrypting identity codes, digital funds, the stage properties and the character roles through utilization of a pubic key and feeding back a private key to a buyer and a seller; encrypting the identity codes, the digital funds, the stage properties and the character roles through utilization of a Hash algorithm after the identity codes, the digital funds, the stage properties and the character roles are encrypted through utilization of the pubic key,and generating a digital fingerprint; and storing the digital fingerprint to Mysql databases, forming a transaction block chain, and storing information to the Mysql database of each transaction nodein a distributed mode. The method has the advantages that the method is secure and reliable, is convenient for query and is reliable in data storage, and illegal tampering is avoided. The method has very high practical value and popularization value in the technical field of digital asset right confirmation transaction.
Owner:密钥科技(深圳)有限公司
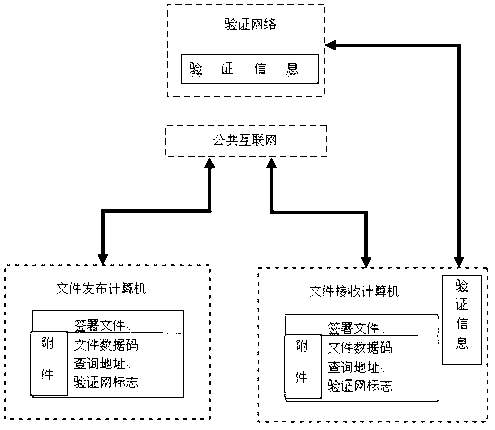
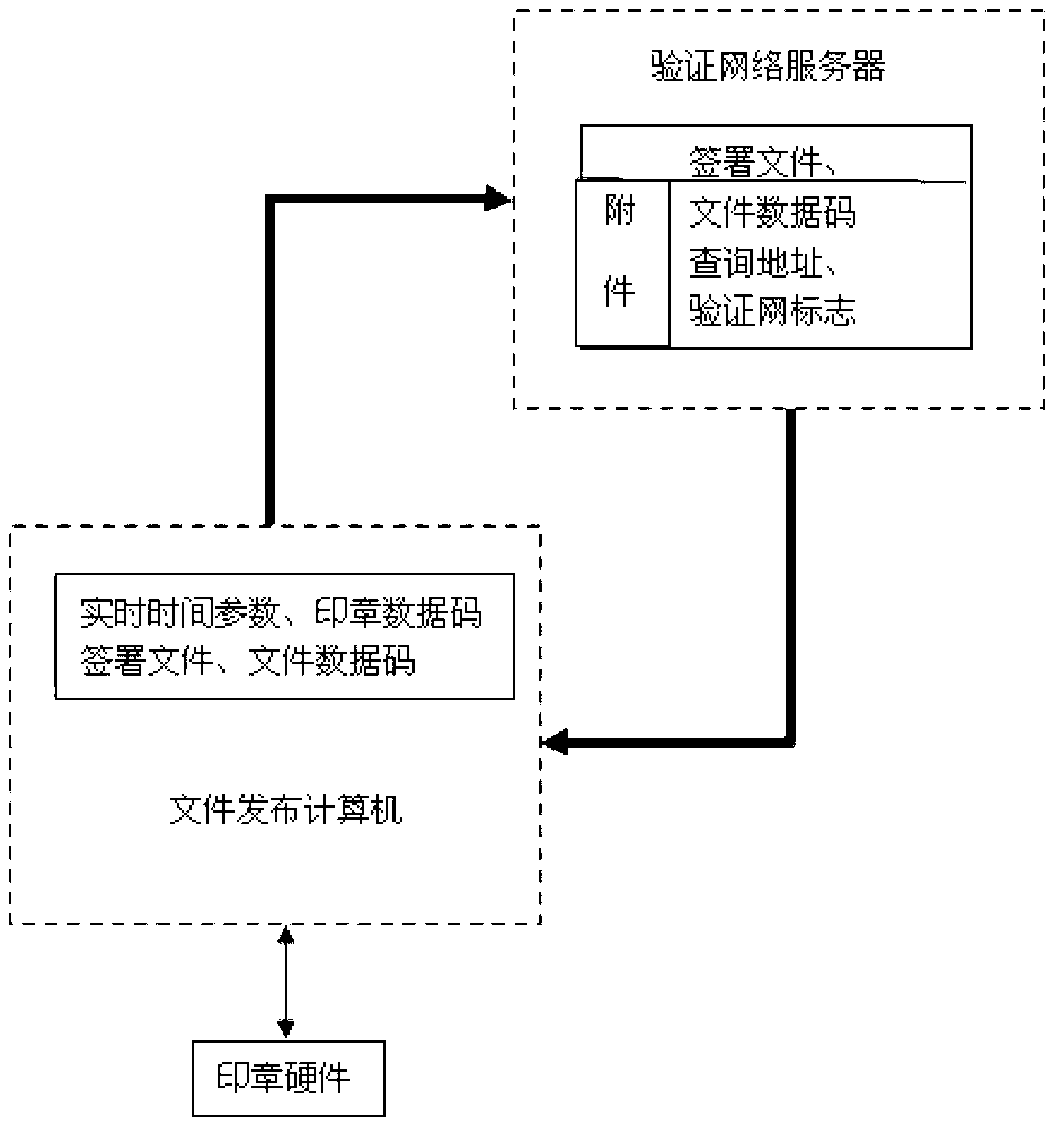
Verification method of electronic seal pattern and verification method of file containing electronic seal
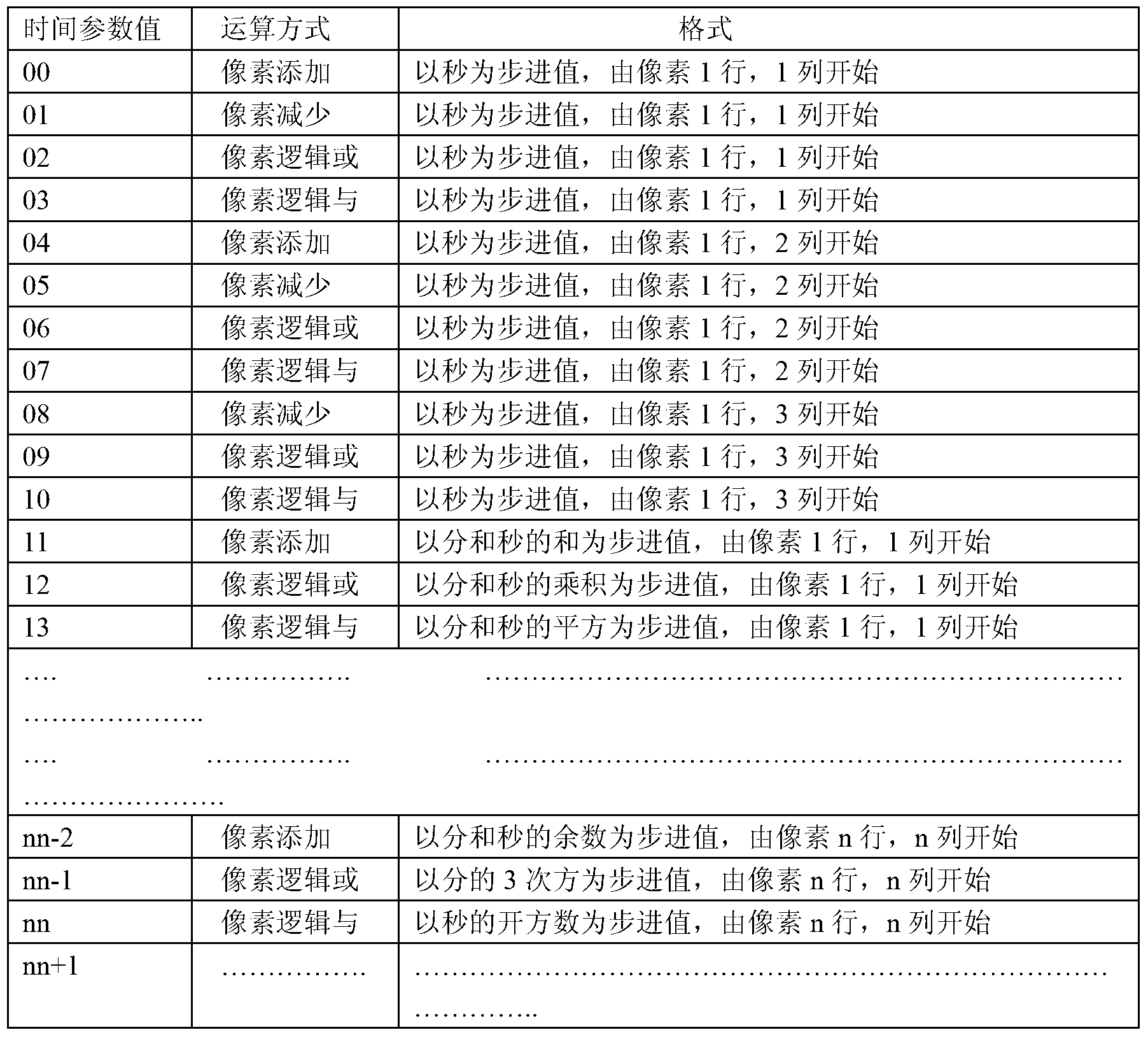
The invention discloses a verification method of an electronic seal pattern and a verification method of a file containing an electronic seal. A time parameter of the moment when the seal signs is converted into data and taken as a variable, the data and pixel data of the seal pattern of seal hardware perform combination operation, and data obtained after the combination operation are subjected to operation of a hash function, so that a hardware seal verification code is obtained; the hardware seal verification code and the time parameter of the moment when the seal signs are stored, encrypted and transmitted to a verification network by a computer; the verification network receives and decodes the hardware seal verification code and the time parameter of the moment when the seal signs, the time parameter of the moment when the seal signs is converted into data and taken as a variable, the data and pixel data of the seal pattern of the verification network are subjected to combination operation, and data obtained after the combination operation are subjected to operation of the hash function, so that a network seal verification code is obtained; and consistency of the hardware seal verification code and the network seal verification code is compared, so that the primitiveness of the seal pattern is verified, and seal verification information is generated.
Owner:西安华力国盾信息技术有限公司
Flash memory data management method and device and computer readable storage medium
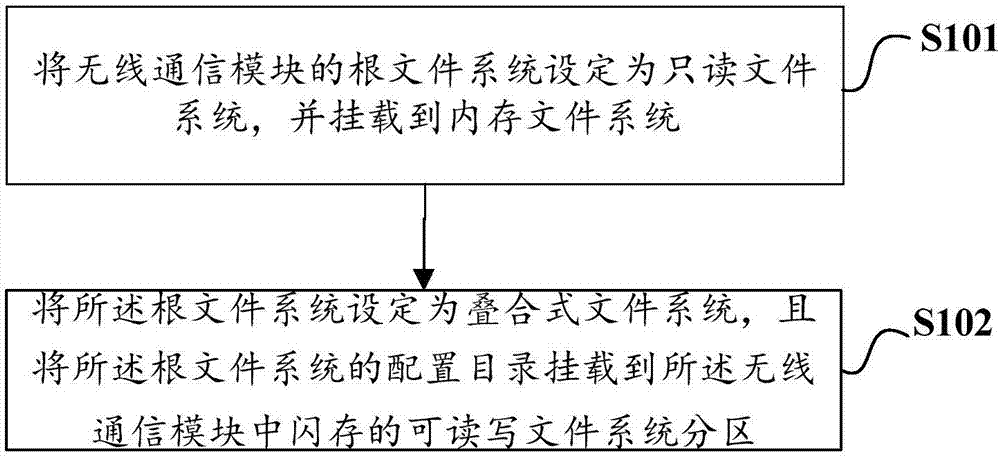
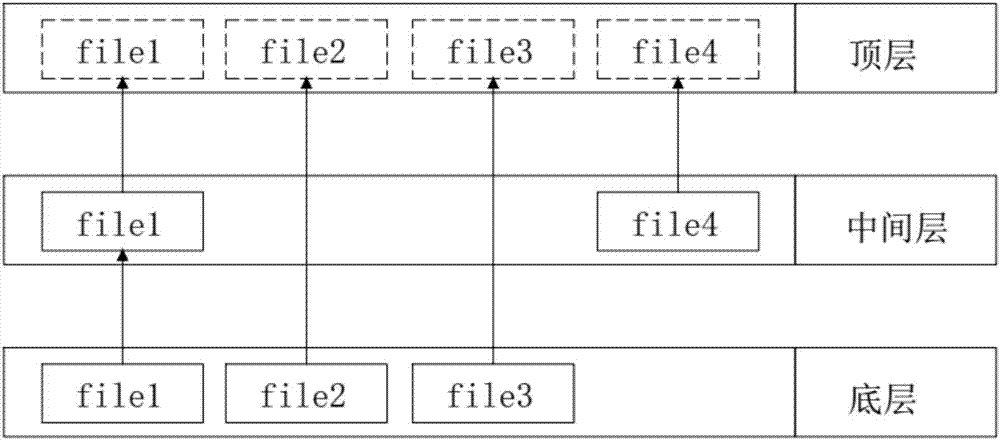
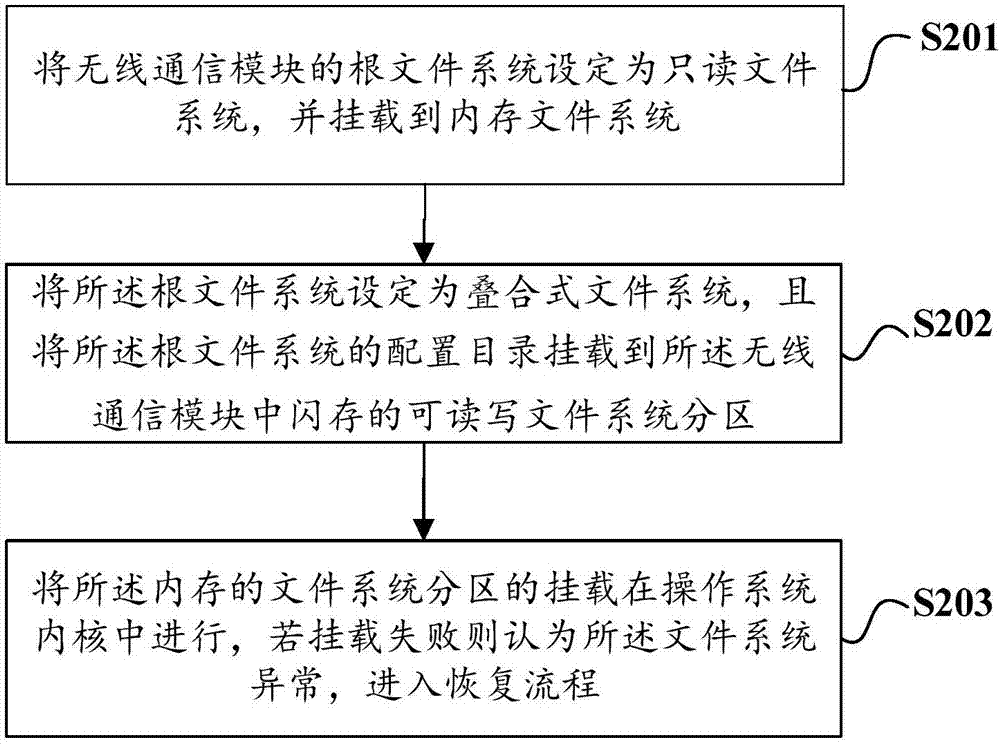
InactiveCN107479922AImprove stabilityImprove reliabilityEMI or RFI carrier shieldingProgram loading/initiatingFile systemStorage management
The invention discloses a flash memory data management method and device and a computer readable storage medium, and relates to the technical field of data storage management. The flash memory data management method and device and the computer readable storage medium aims at solving the technical problem of an existing wireless communication device that the module stability and reliability are influenced since flash memory data is abnormal. The flash memory data management method comprises the following steps of setting a root file system of a wireless communication module as a read-only file system and mounting a laminated file system to a memory; setting the root file system as the laminated file system and mounting a configuration catalogue of the root file system into a readable and writable file system partition of a flash memory in the wireless communication module. According to the flash memory data management method and device and the computer readable storage medium, the laminated file system and a recovery mechanism of the file system are adopted to improve the stability and reliability of the wireless communication module, and after-sales maintenance work of a product of the type of the wireless communication module is also reduced.
Owner:高新兴物联科技股份有限公司
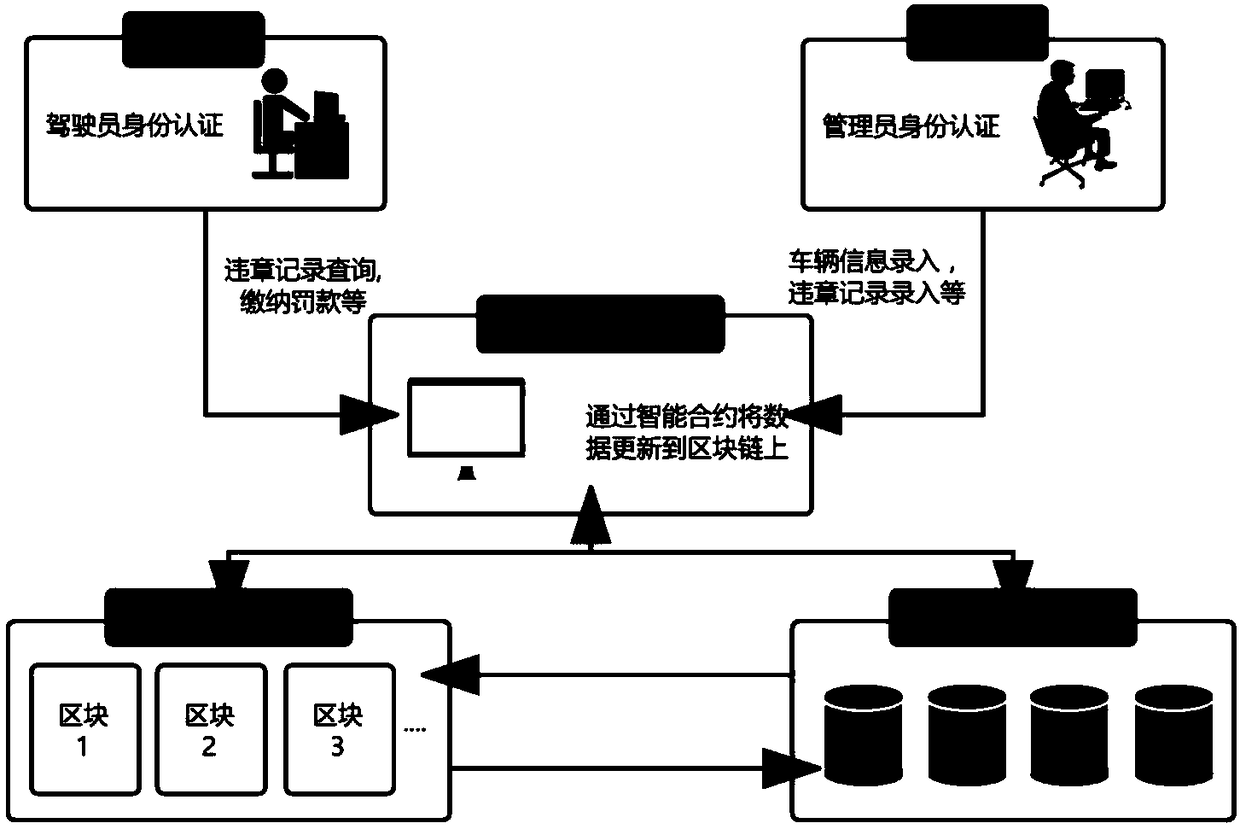
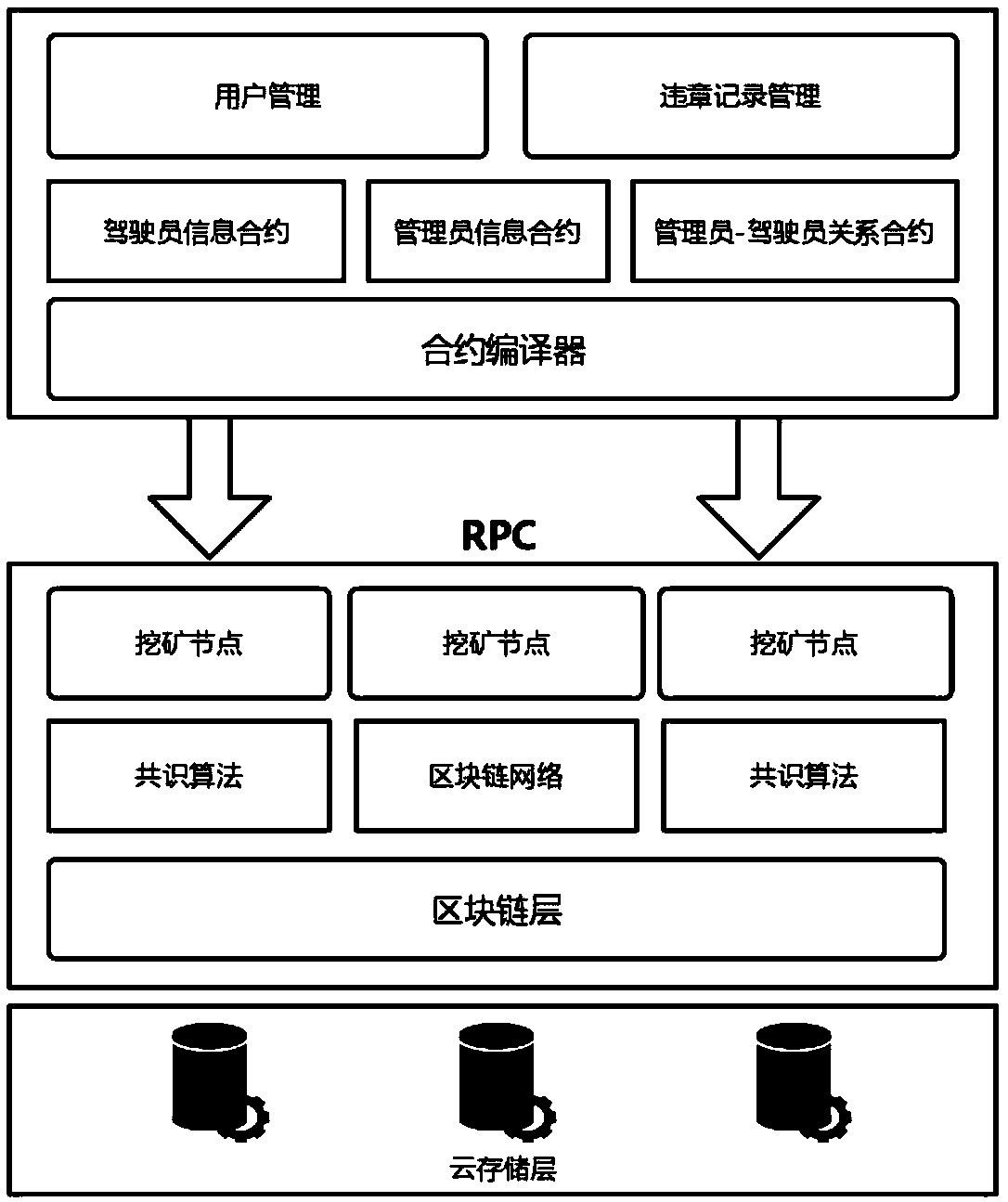
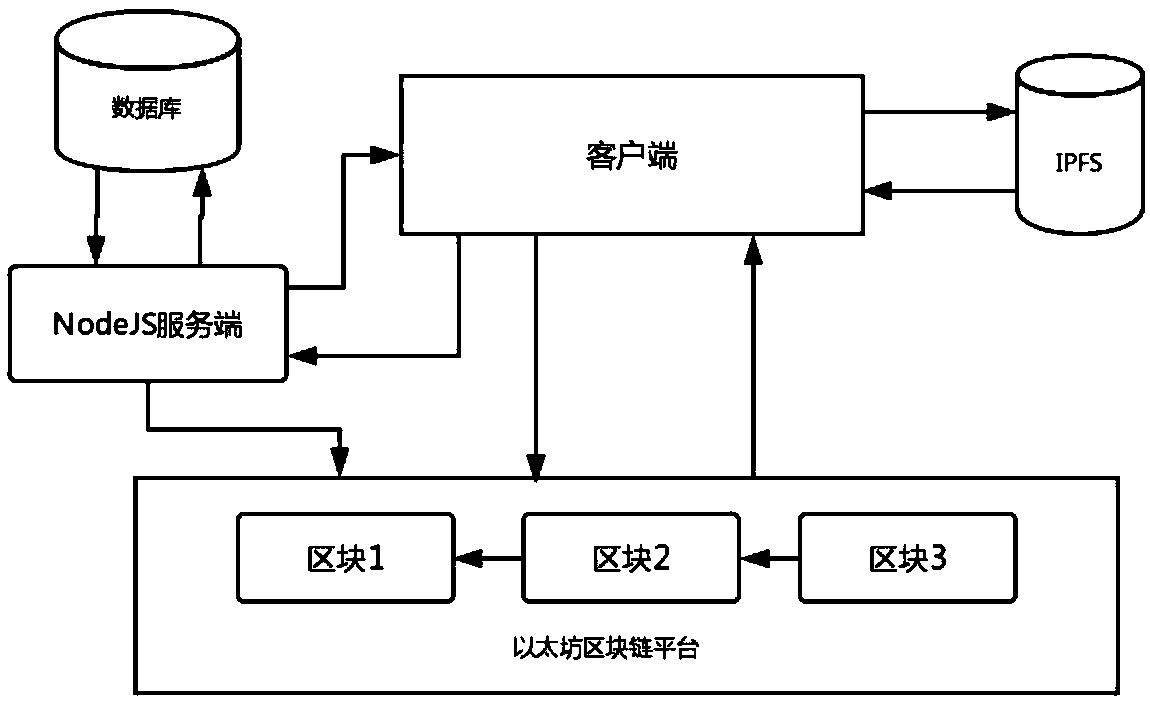
Block chain technology-based motor vehicle violation management system construction method
InactiveCN108614683AAvoid lostReduce maintenance costsFinanceSoftware designPaymentSystem maintenance
The invention discloses a block chain technology-based motor vehicle violation management system construction method. According to the method, motor vehicle violations are registered and the process of violation payment is written into a block chain in an intelligent contract form, so that related government sectors do not need to depend on a centralized server to manage the motor vehicle violation information, thereby avoiding the common single point fault problem of the centralized server; and the data stored in the block chain cannot be tampered and traced, so that illegal tampering can beprevented. Moreover, information, such as identity cards and driving licenses of drivers, referred to personal privacy is effectively protected by utilizing an ABE encryption algorithm. Through the method, data loss caused by single point faults can be avoided to reduce the system maintenance cost, and the violation records can be prevented from being illegally tampered.
Owner:JINAN UNIVERSITY
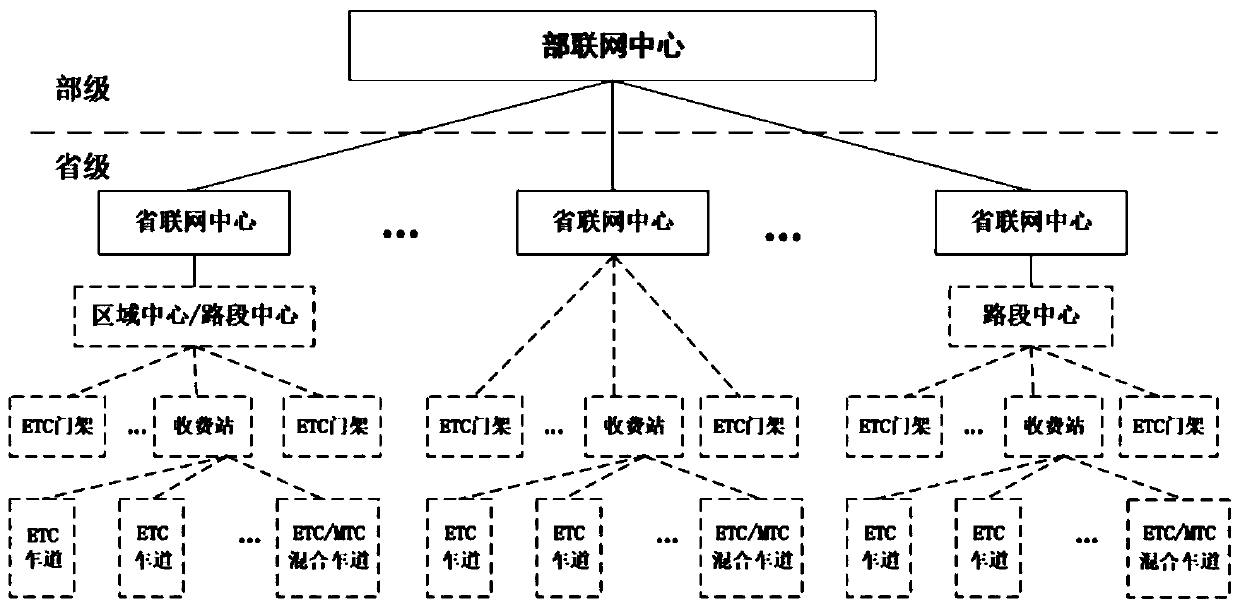
High-speed charging method and system based on block chain
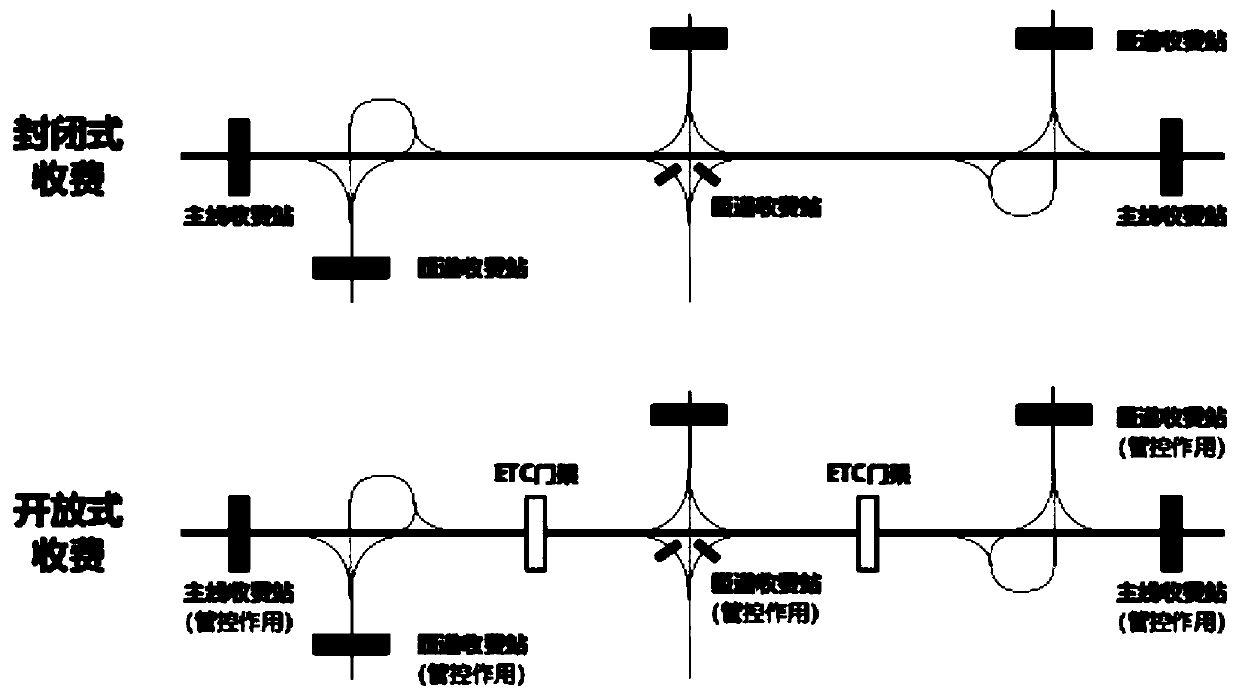
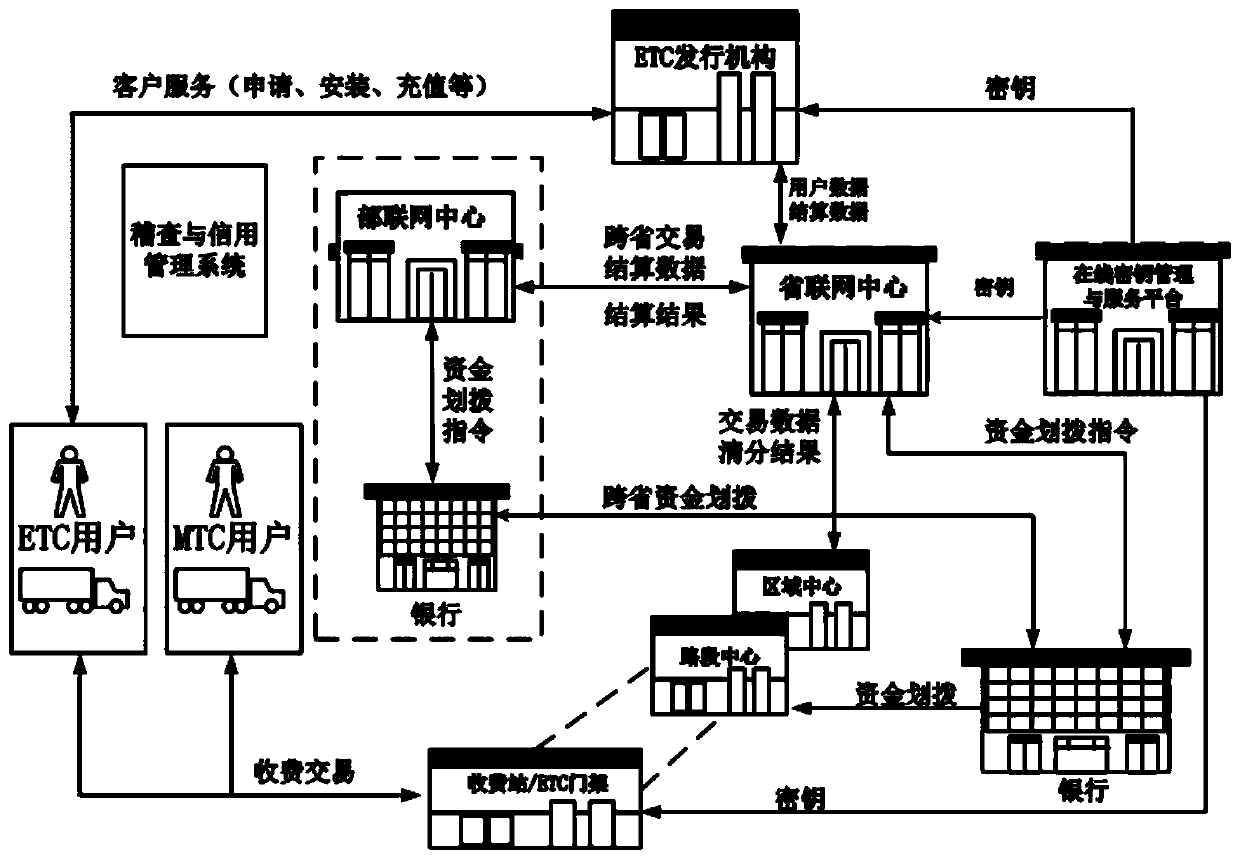
PendingCN110992499ARealize distributed storageAvoid lossTicket-issuing apparatusIndividual entry/exit registersSimulationFinancial transaction
The invention discloses a high-speed charging method and system based on a block chain, and the method comprises the steps: S100, obtaining the vehicle information of a vehicle when the vehicle passesthrough an entrance of a toll station, generating first transaction flow data, and uploading the first transaction flow data to a road section center to which the toll station belongs; s200, when thevehicle passes through the ETC portal frame, acquiring and uploading path information and cost information of the vehicle to a road section center to which the ETC portal frame belongs; and S300, when the vehicle passes through an exit of the toll station, acquiring path information and cost information of the vehicle and uploading the information to a road section center to which the toll station belongs. The block chain technology and the high-speed CPC charging technology are combined, distributed storage of data is achieved, the data security level is improved, data loss and illegal tampering are prevented, point-to-point data transmission of the center of a road section is achieved, the path backtracking speed is increased, and the path query network pressure is reduced.
Owner:WATCHDATA SYST
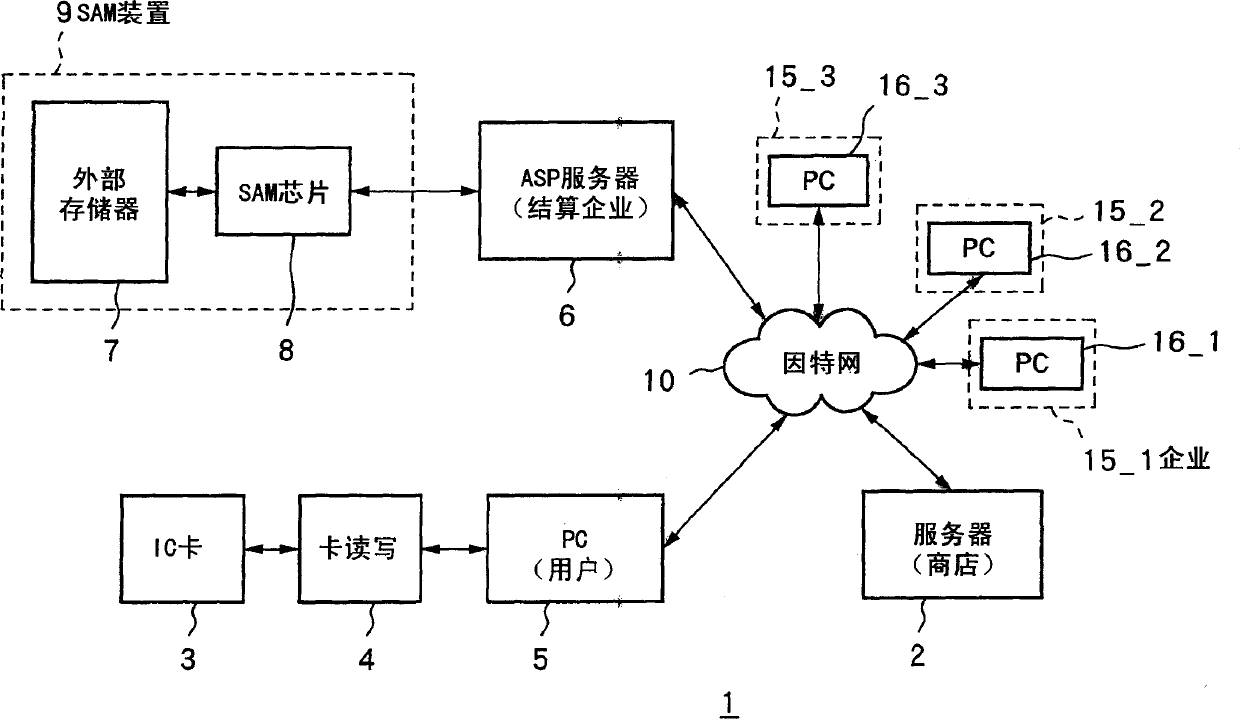
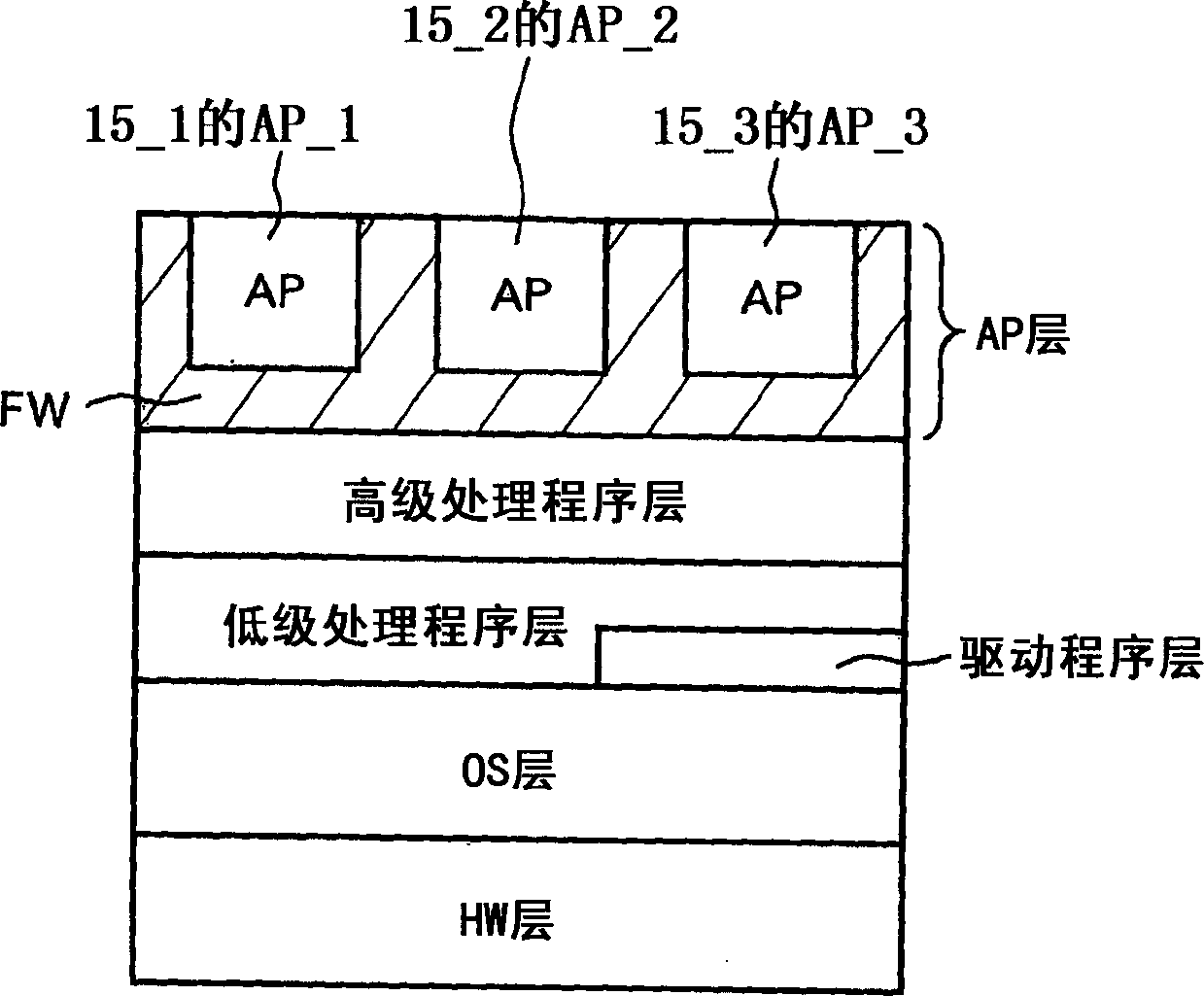
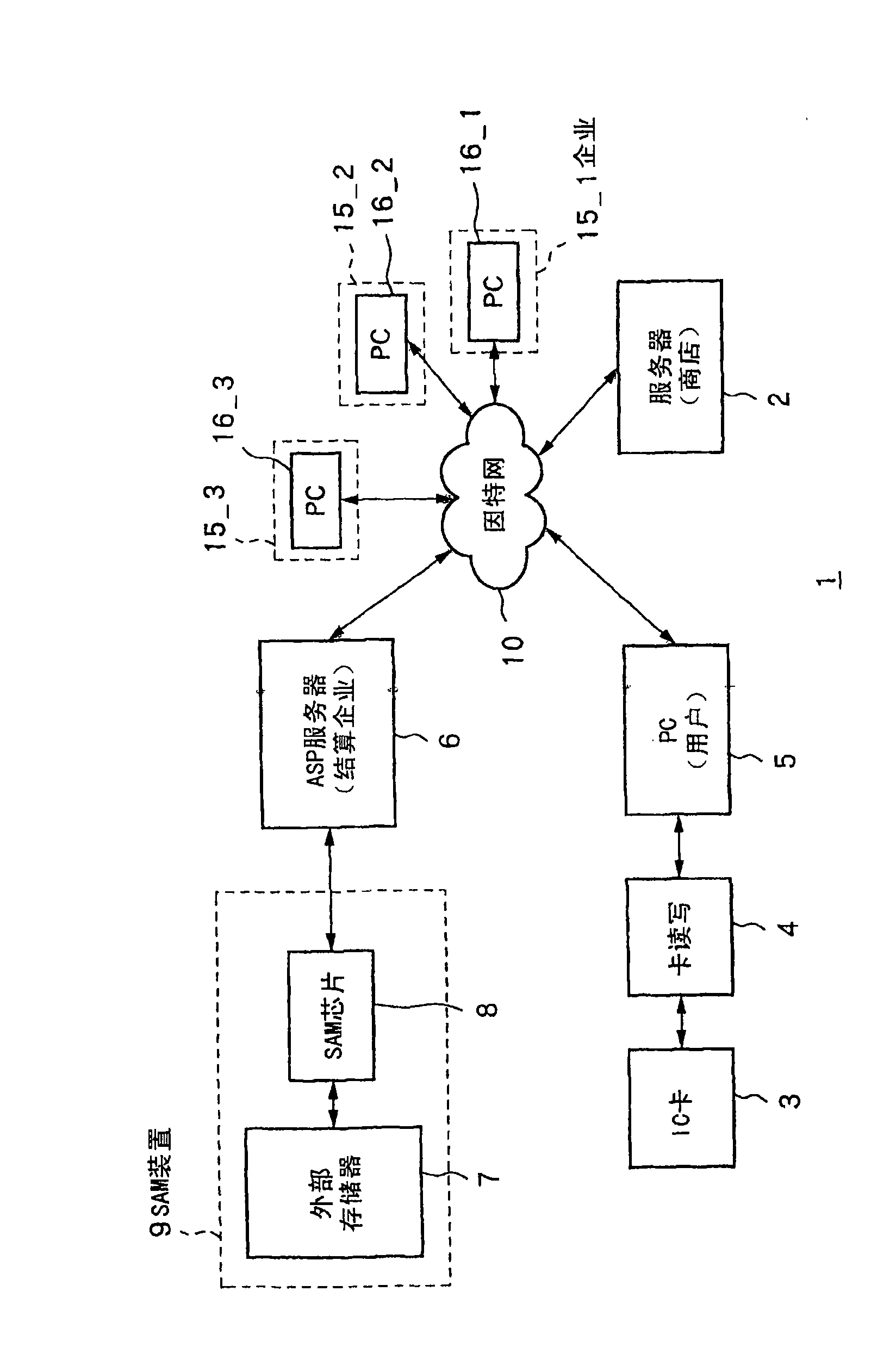
Data processing method and its apparatus
InactiveCN1465008APrevent illegal tamperingPrevent surveillanceAcutation objectsDigital data processing detailsChip selectParallel computing
In accordance with a plurality of processing requests, a SAM chip generates IC card entity data including job execution order data showing an order of execution of a plurality of jobs forming processing in accordance with a processing request and status data showing a state of progress of execution of said plurality of jobs for each of said processing requests. Further, the SAM chip selects one entity data from said plurality of entity data, selects and executes the job to be executed next based on the status data and processing order data of said selected entity data, and updates the status data in accordance with execution of said job.
Owner:SONY CORP
PE loader-based software packing protection method
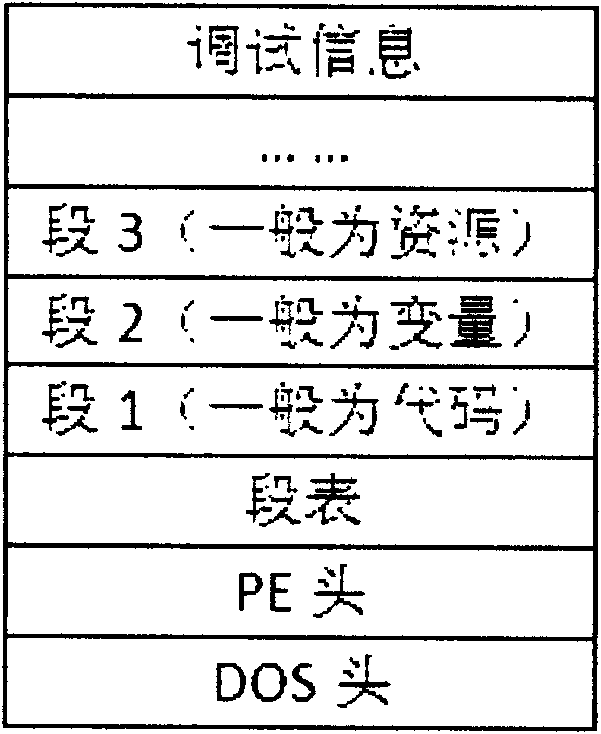
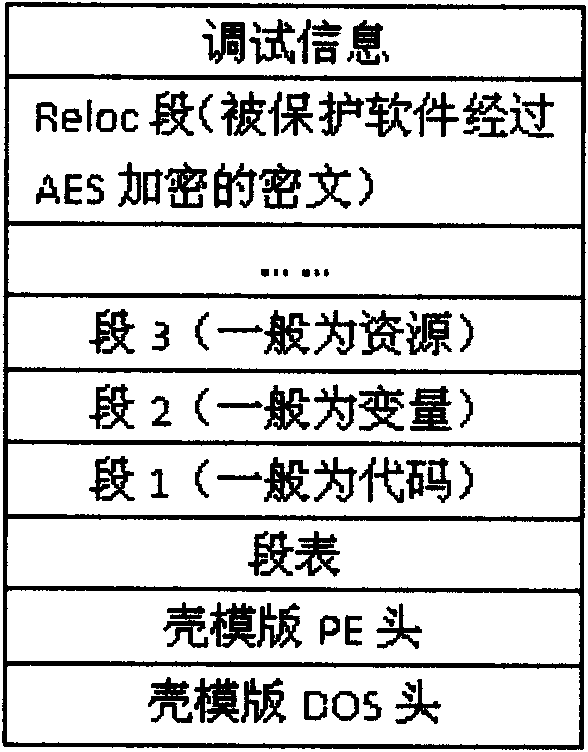
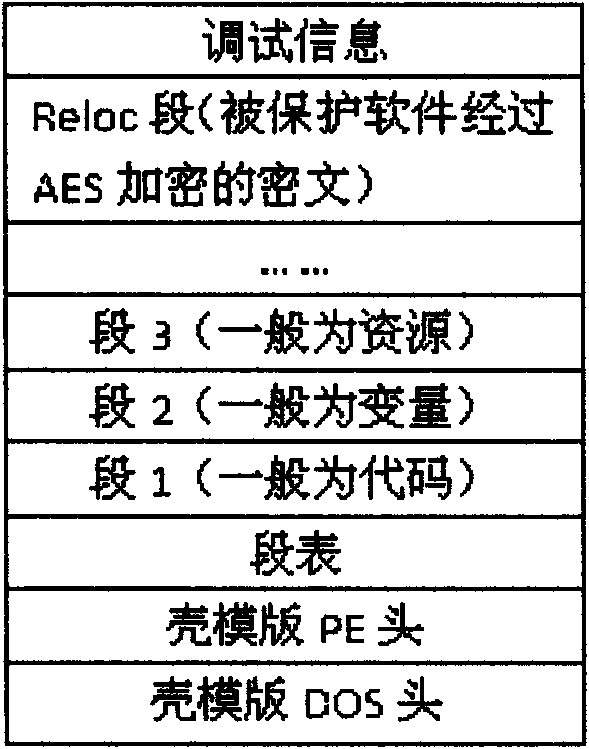
InactiveCN101964040APrevent disassembly crackingPrevent illegal tamperingPlatform integrity maintainanceData ingestionInternal memory
The invention relates to a PE loader-based software packing protection method. The method comprises the following steps of: mapping a shell template into an internal memory, repositioning the base address of the shell template by simulating a PE loader of Windows and calculating a relative virtual address (RVA) of a segment where the entry point of the shell template is positioned and the size of the segment, wherein the calculated RVA value of the segment and the size value of the segment are taken as parameters and a hash value calculated by a secure hash algorithm (SHA) is taken as a key of an advanced encryption standard (AES) encryption algorithm; mapping protected software into the internal memory and encrypting the protected software by the AES encryption algorithm by using calculated key; adding encrypted data into a Reloc segment of the shell template; processing a special resource in the software to be protected and extracting additional data of the special resource, attaching the special resource and the additional data to the end of a shell template file respectively and modifying a corresponding data item related to the special resource in the PE structure of the shell template; and repeating the modified shell template from the internal memory to a disc so as to obtain protected software. The method remarkably enhances the safety of the software.
Owner:XIAN UNIV OF TECH
6LoWPAN-based intelligent fire-fighting service system for colleges and universities and design method
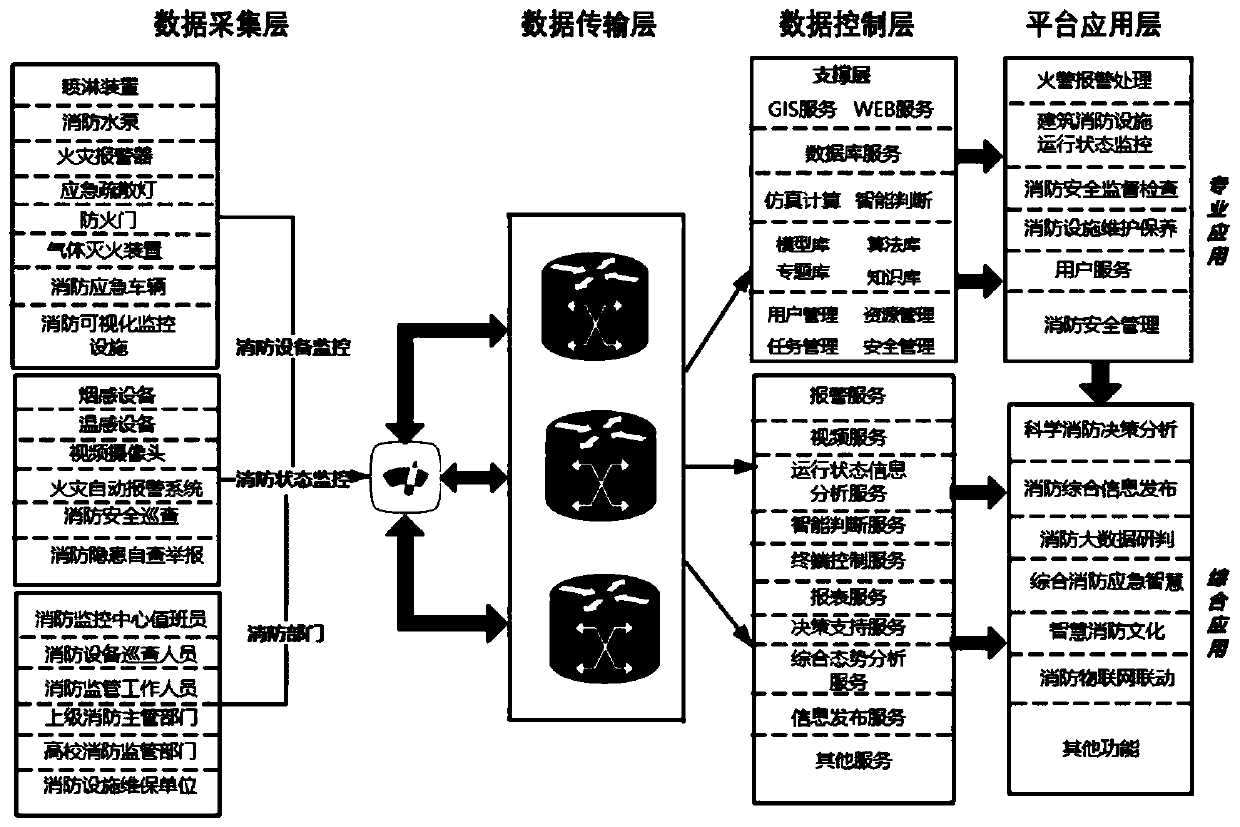
InactiveCN110996285APrevent illegal tamperingAvoid monitoringParticular environment based servicesTransmissionData acquisitionFire prevention
The invention discloses a 6LoWPAN-based intelligent fire-fighting service system for colleges and universities and a design method of the 6LoWPAN-based intelligent fire-fighting service system. The service system comprises a data acquisition layer, a data transmission layer, a data control layer and a system application layer, good interoperability of the 6LoWPAN can solve information isolation, the 6LoWPAN supports the intercommunication with other IEEE (Institute of Electrical and Electronic Engineers) 802.15. 4 equipment and supports the interconnection with other IP networks; through designing a data control layer based on fire-fighting big data, intelligentized analysis of data, intelligent control on fire-fighting equipment, a visual service platform is established; through analyzingand mining fire-fighting big data, the fire situation is predicted and a solution is formulated, the fire prevention and control efficiency is improved, the intelligence of a service platform is realized, the purposes of equipment management centralization, fire-fighting construction underlying data management intellectualization and management system platformization are achieved, and the systemhas the characteristics of high feasibility, convenience in networking and easiness in maintenance and upgrading.
Owner:CENT SOUTH UNIV +1
Reputation evaluation method and system for privacy protection based on block chain
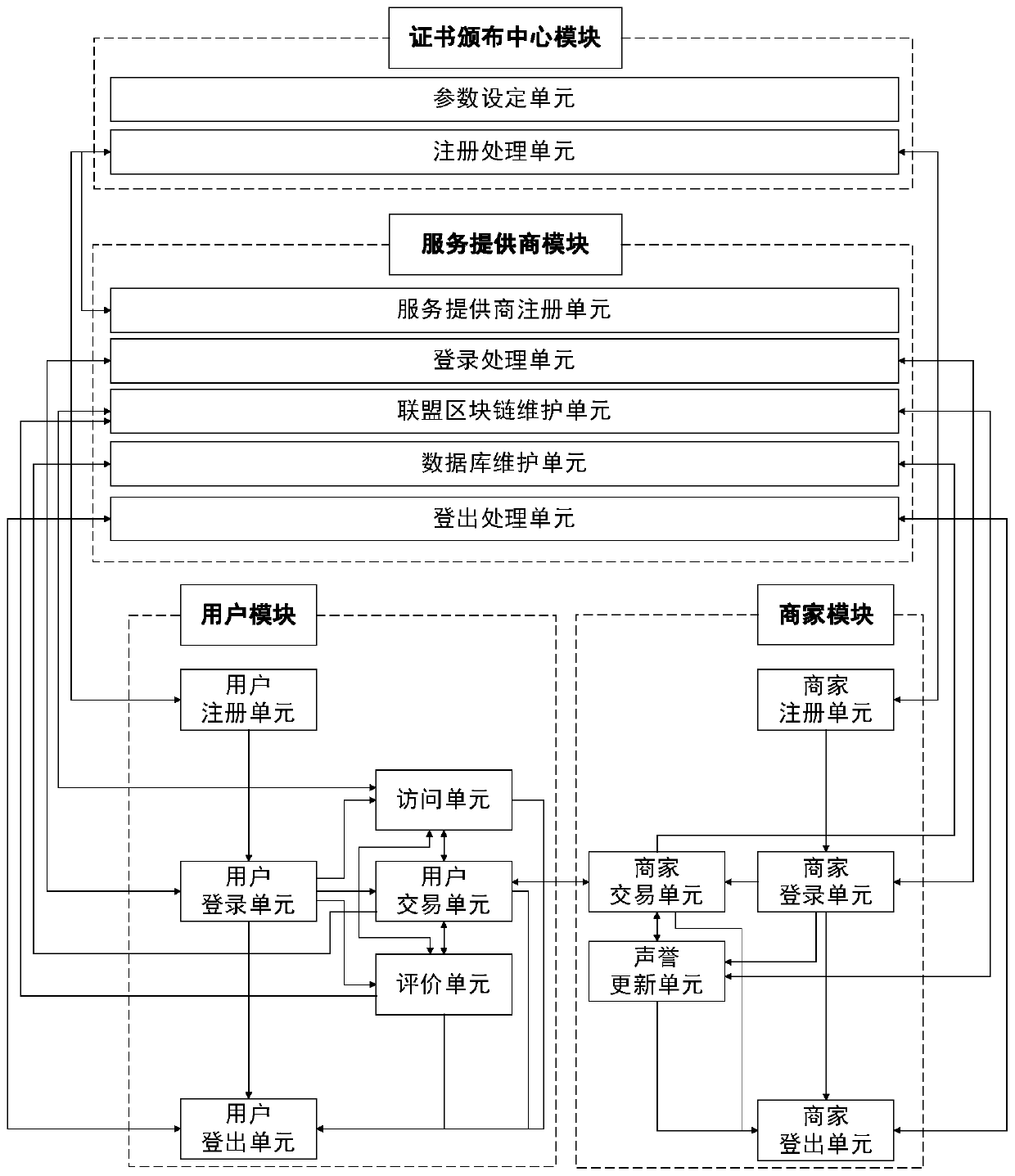
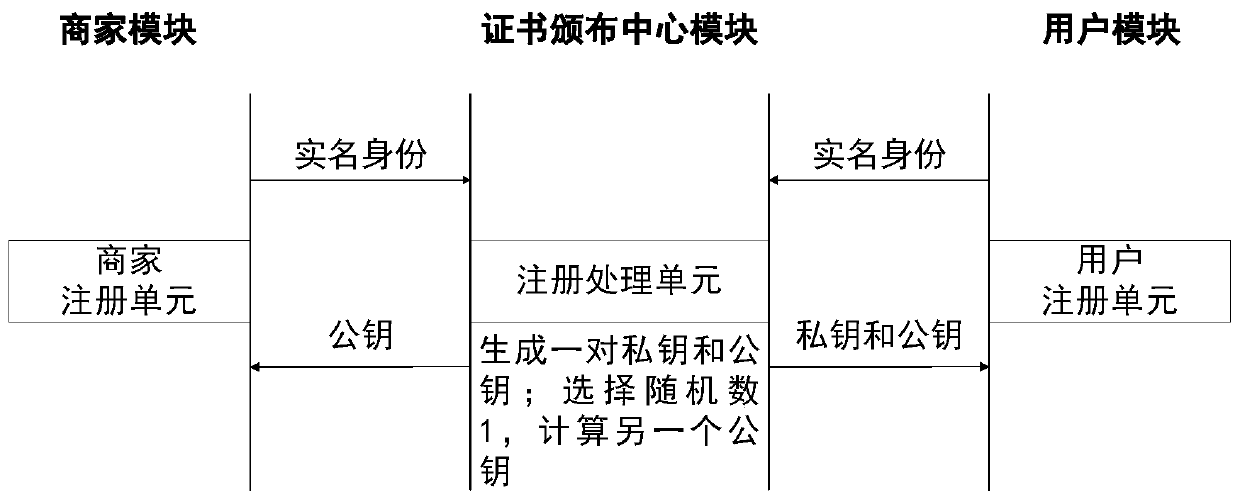
ActiveCN110020541AMake it publicPrevent illegal tamperingDigital data protectionMarketingPrivacy protectionFinancial transaction
The invention relates to a reputation evaluation method and system for privacy protection based on a block chain, and belongs to the technical field of blind signatures, secure multi-party signaturesand block chains. After the user and the merchant finish the online transaction, anonymous evaluation is carried out on the merchant to generate an evaluation transaction, the evaluation transaction is sent to the alliance block chain network, each service provider carries out partial decryption on the evaluation in the evaluation transaction and sends the evaluation to the block chain network, and the merchant updates the reputation of the merchant according to the partial decryption information. Specifically, the method comprises the following steps: a user, a merchant and a service providerregister with a trusted party to obtain corresponding keys; and the user accesses the reputation of the merchant under each service provider, evaluates the service provider after online transaction,broadcasts the reputation in a block chain transaction form, and the service provider serves as a miner of the block chain network, calculates the obtained evaluation for all merchants and updates themerchants. The method and the system have the advantages of reputation publicity, reputation availability, data audit and effective privacy protection for user evaluation.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
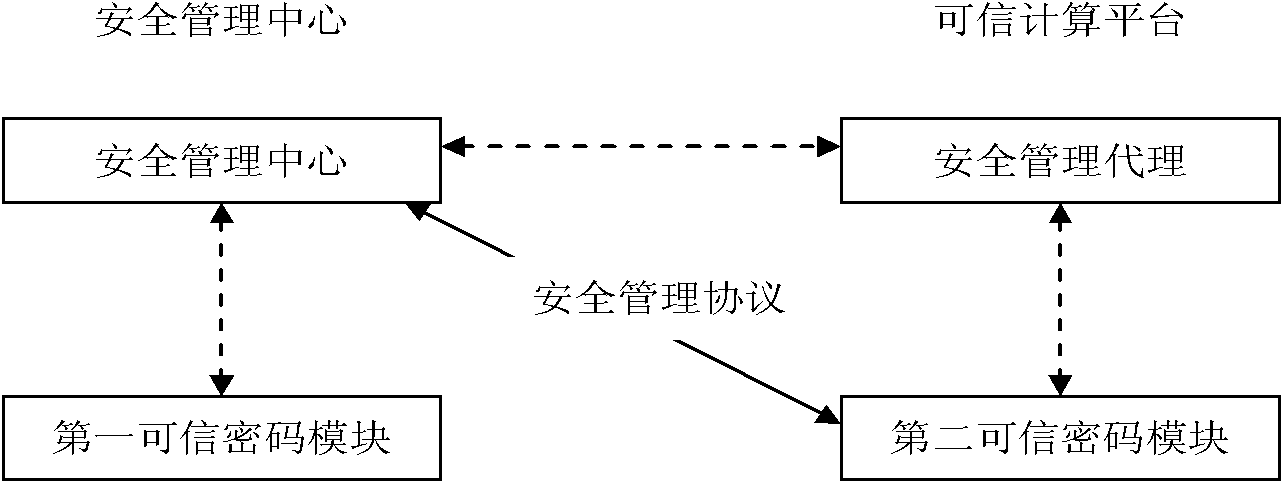
Security management system and method of dependable computing platform
InactiveCN102340500AGuarantee authenticityIntegrity guaranteedUser identity/authority verificationCode moduleSafety management systems
The invention discloses a security management system and method of a dependable computing platform. The security management system comprises a dependable code module, a security management center module, a security management agent module and a security strategy management protocol module; the security strategy management protocol module between the security management center module and the dependable code module is realized on basis of the dependable code module so that the security of the transmission of a security management strategy is ensured; the security protection of a security strategy at a security management center is realized on basis of the dependable code module; and a security strategy at the dependable computing platform is stored in the dependable code module, and the security of the security strategy is protected by the dependable code module so that the security of the storage of the security management strategy is ensured. The security management method based on the dependable computing platform comprises a step of generating a security strategy management protocol and steps of producing, extracting and deleting a new security strategy by the security management center and has the advantages of fulfilling the protection of encryption and integrity verification of security strategy data and preventing data leakage and unauthorized tampering of the security strategy data from an attacker.
Owner:中国人民解放军海军计算技术研究所
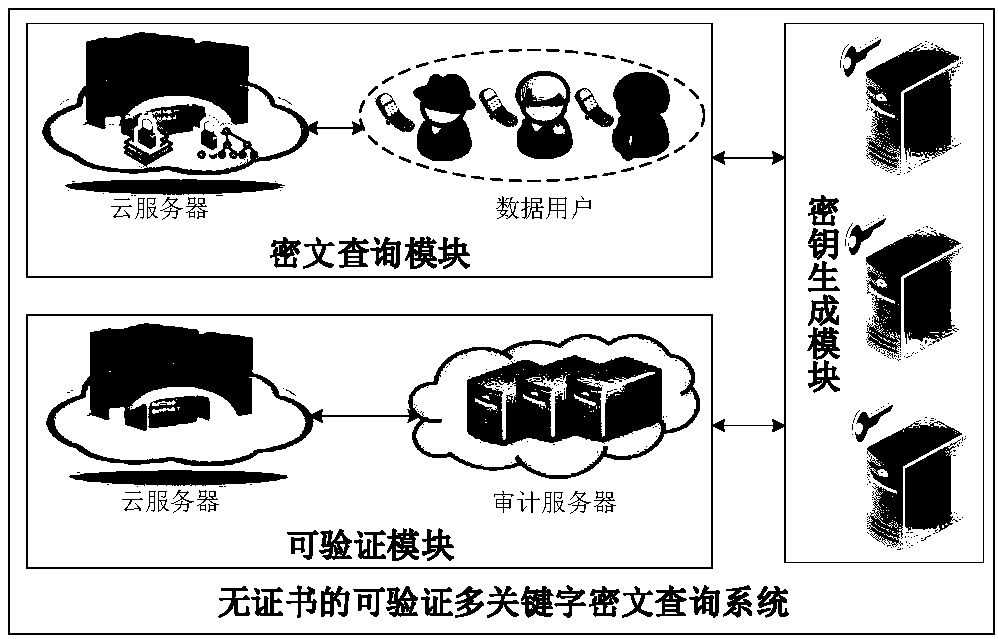
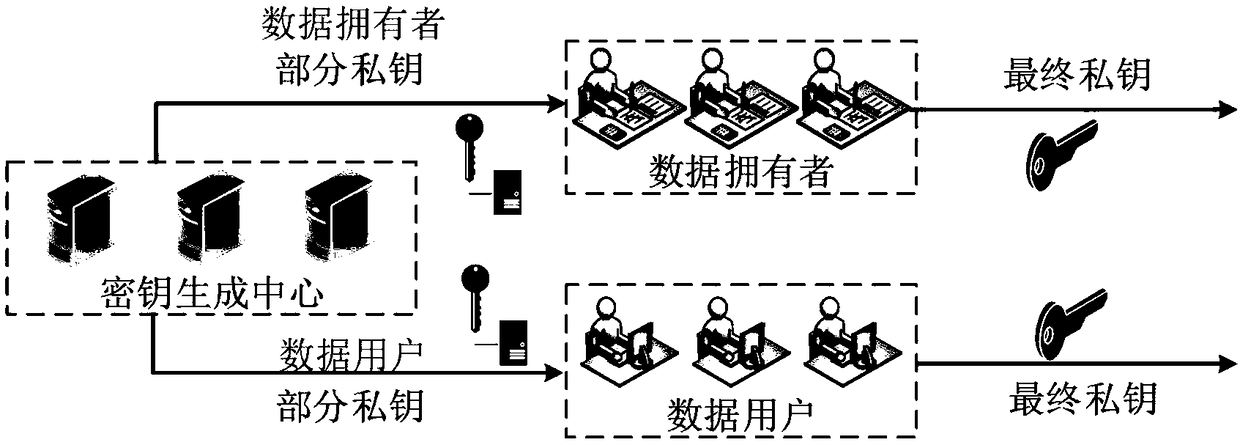
Certificateless verifiable multi-keyword ciphertext inquiring system and method
InactiveCN108156139AAvoids the overhead of certificate management and solves hosting challengesSolve hosting challengesUser identity/authority verificationCollocationData integrity
The invention discloses a certificateless verifiable multi-keyword ciphertext inquiring system and method. The system mainly comprises three modules: a key generation module, a ciphertext inquiring module and a verifiable module; under the cloud storage background, the system supports multi-keyword ciphertext retrieval by using the searchable encryption technology, and quickly positions to the interested ciphertext document of the user; the system solves the problems of certificate management and private key collocation by using the certificateless encryption technology, and performs correctness verification on an inquiring result by using public auditing technology, thereby guaranteeing the data integrity. By using the certificateless encryption technology, the system disclosed by the invention enables a key generation center to generate partial private key according to data user identity information, the data user generates the complete private key according to the partial private key and a secret value; the key generation center cannot obtain the data user private key; the certificate management expenditure is avoided, and the private key collocation problem is solved.
Owner:XIDIAN UNIV
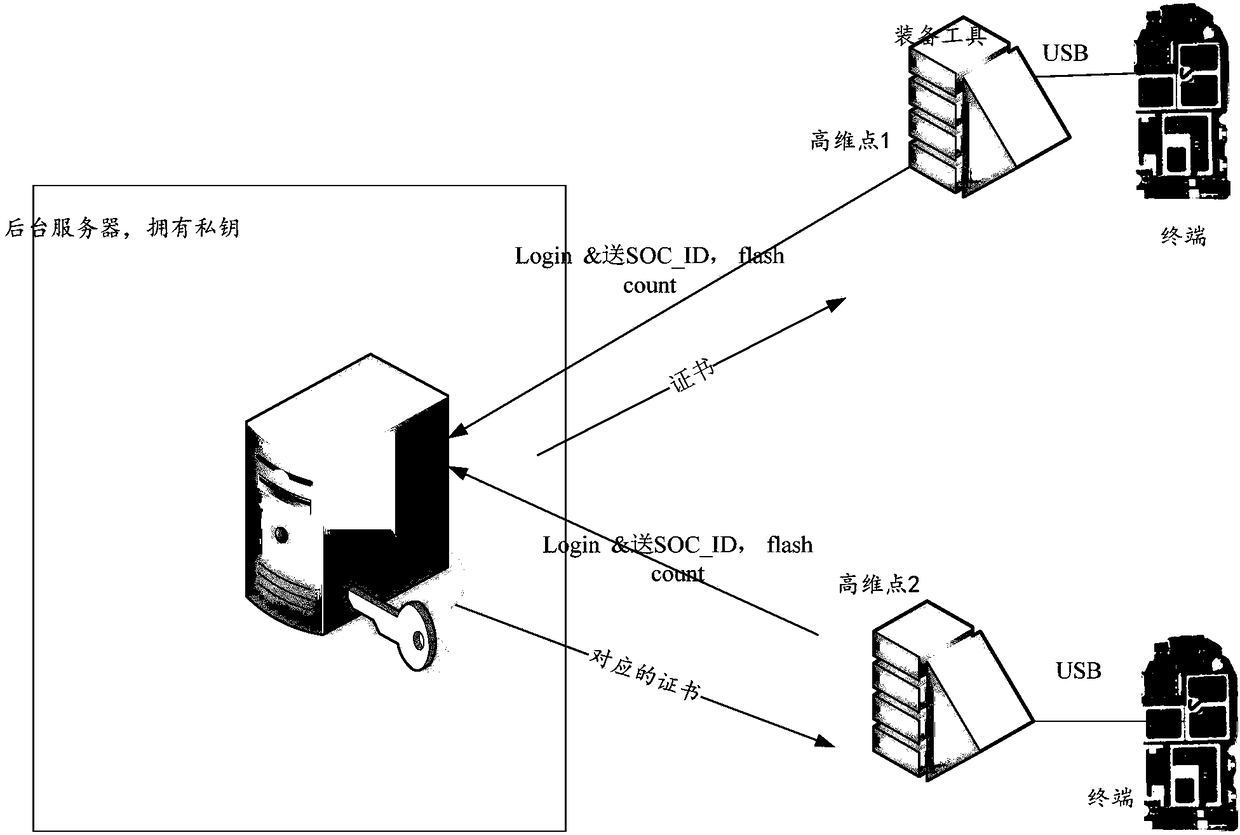
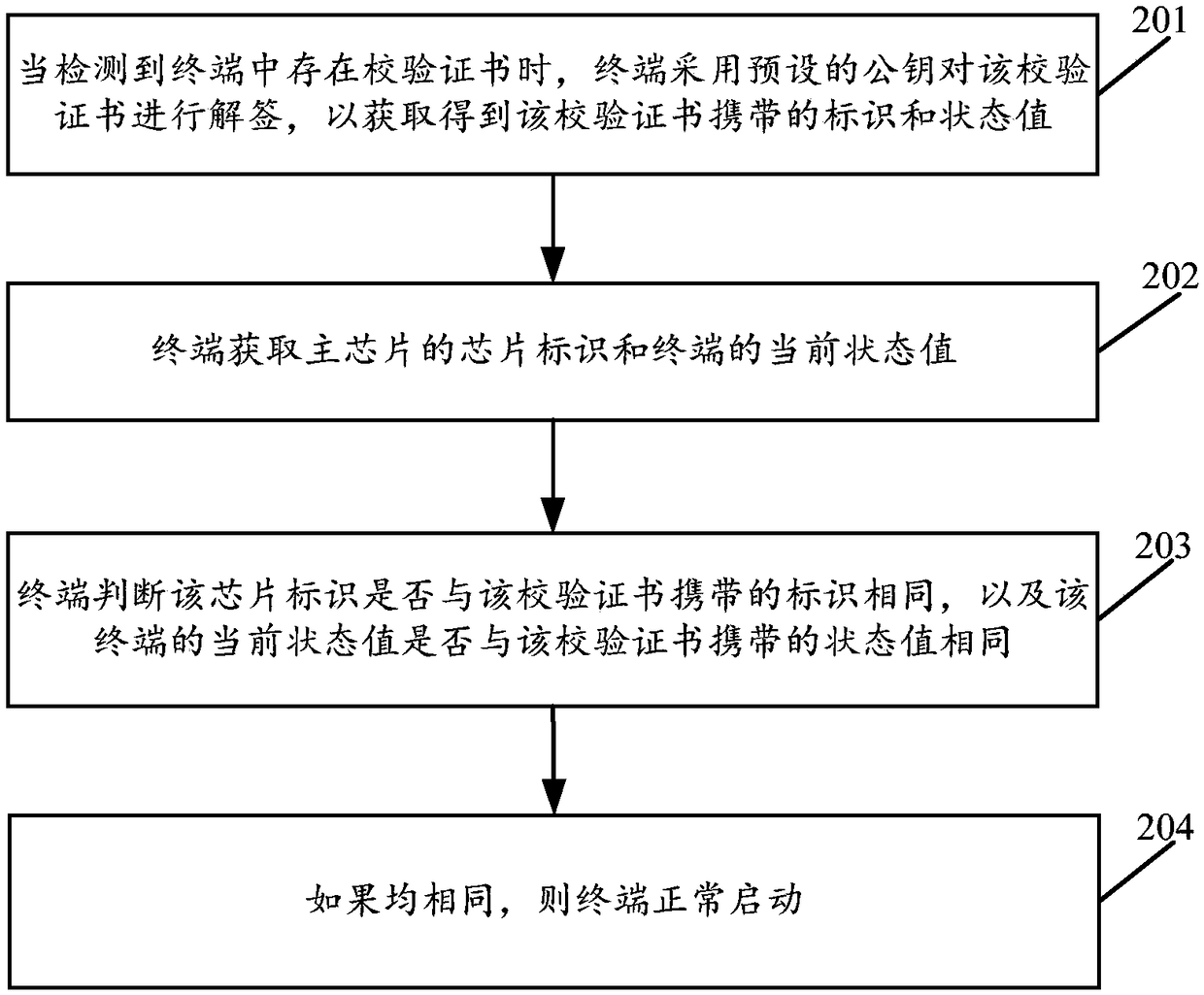
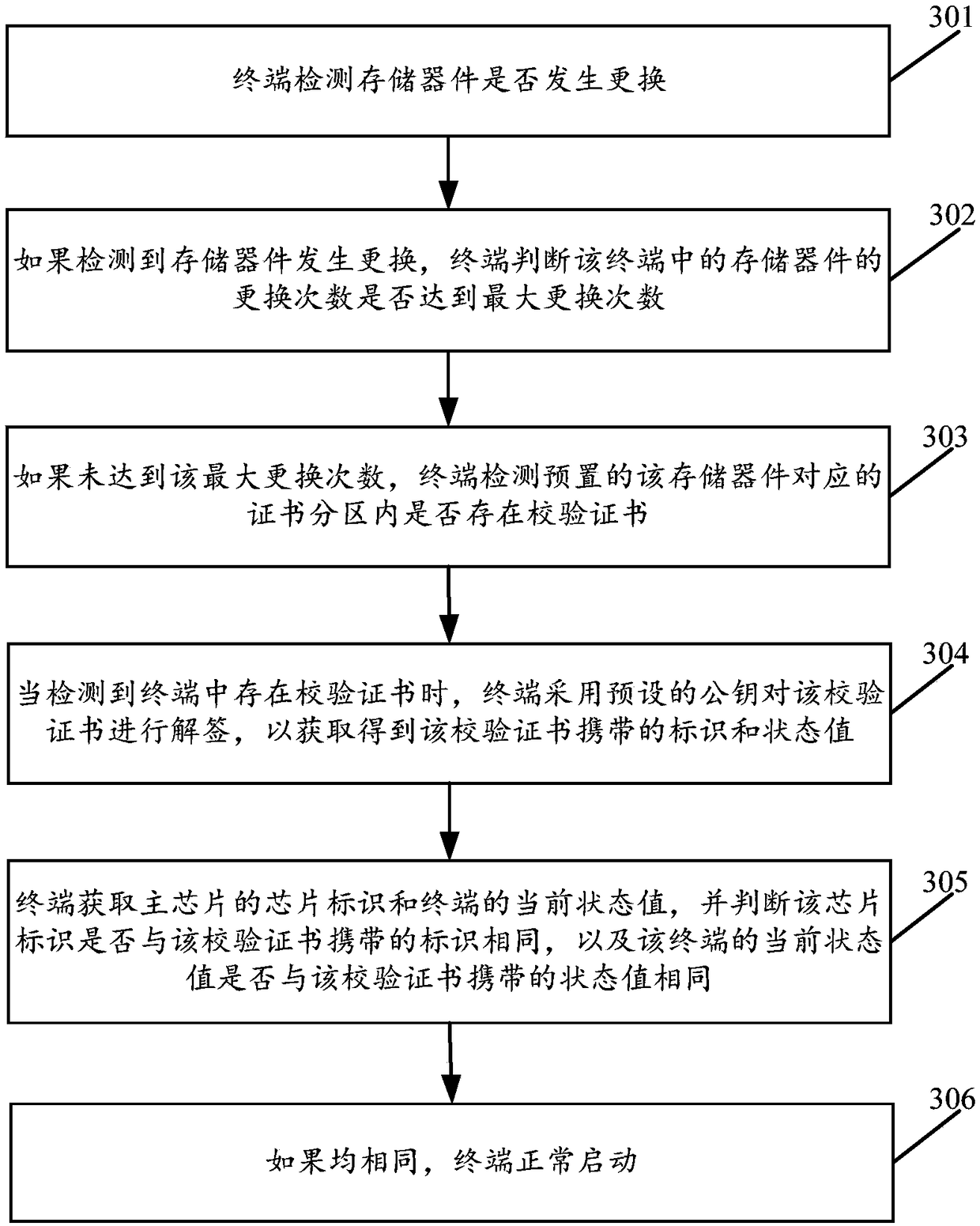
Terminal startup method, terminal, and signature device
ActiveCN109492370AImprove securityPrevent illegal tamperingKey distribution for secure communicationInternal/peripheral component protectionComputer terminalComputer engineering
The invention discloses a terminal startup method, a terminal and a signature device. The method comprises the following steps: when a verification certificate is detected in a terminal, the terminalunsigns the verification certificate by using a preset public key to obtain an identification and a status value carried by the verification certificate; when the verification certificate is detected,the terminal unsigns the verification certificate by using a preset public key to obtain a status value carried by the verification certificate. Wherein the verification certificate is written into the terminal after the signing device signs through the preset private key; the terminal obtains a chip identification of a main chip and a current state value of the terminal; the terminal judges whether the chip identifier is the same as the identifier carried by the verification certificate and whether the current state value is the same as the state value carried by the verification certificate. If all are the same, the terminal starts normally. By adopting the application, the program start control of the terminal can be carried out by introducing a verification certificate, the anti-theftreliability is improved, a special circuit is not required to be introduced, and the cost is low.
Owner:HUAWEI TECH CO LTD
Data processing method and the device thereof
InactiveCN101526982APrevent illegal tamperingPrevent surveillanceResource allocationDigital data processing detailsChip selectComputer module
The presemt invention relates to a data processing method and the device thereof. In accordance with a plurality of processing requests, a SAM chip generates IC card entity data including job execution order data showing an order of execution of a plurality of jobs forming processing in accordance with a processing request and status data showing a state of progress of execution of said plurality of jobs for each of said processing requests. Further, the SAM chip selects one entity data from said plurality of entity data, selects and executes the job to be executed next based on the status data and processing order data of said selected entity data, and updates the status data in accordance with execution of said job.
Owner:SONY CORP
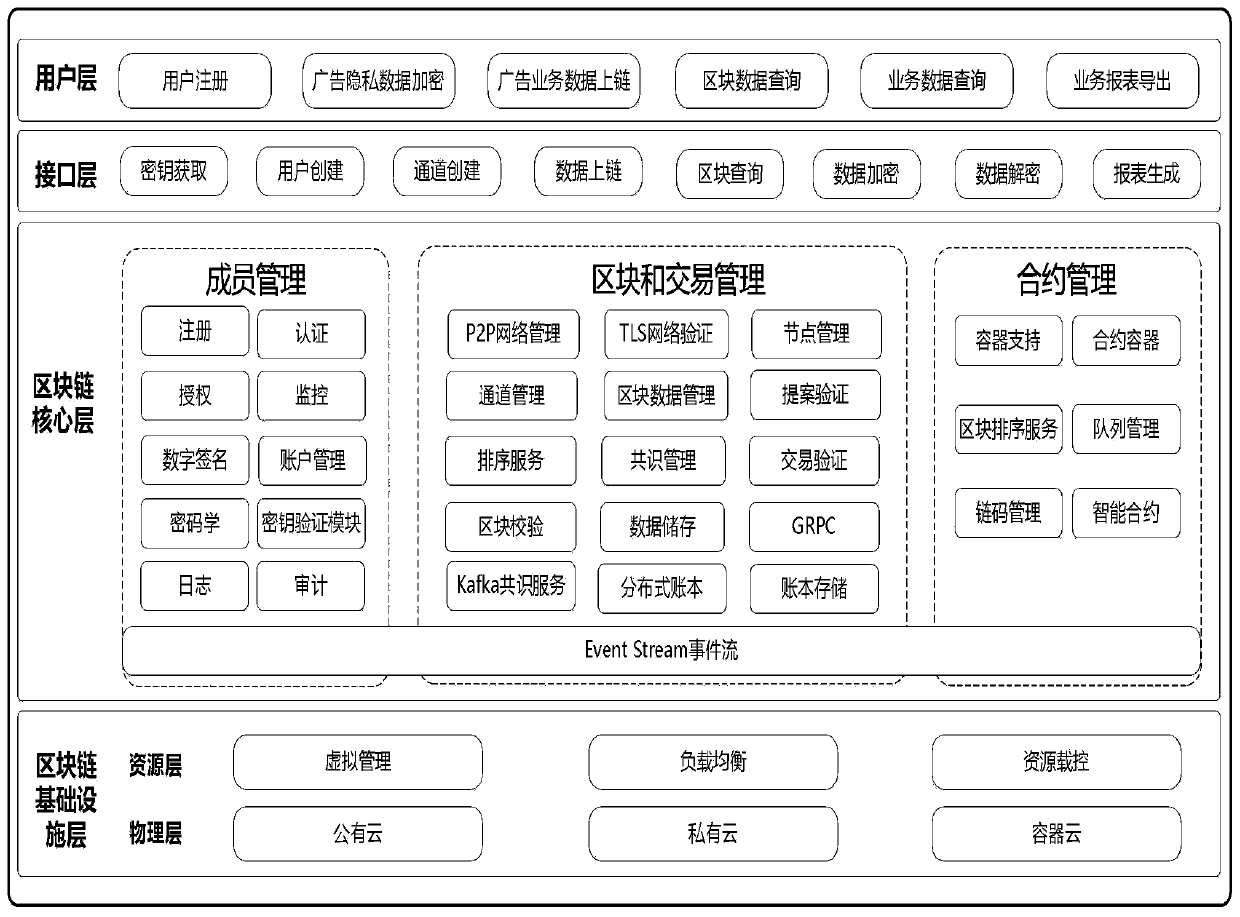
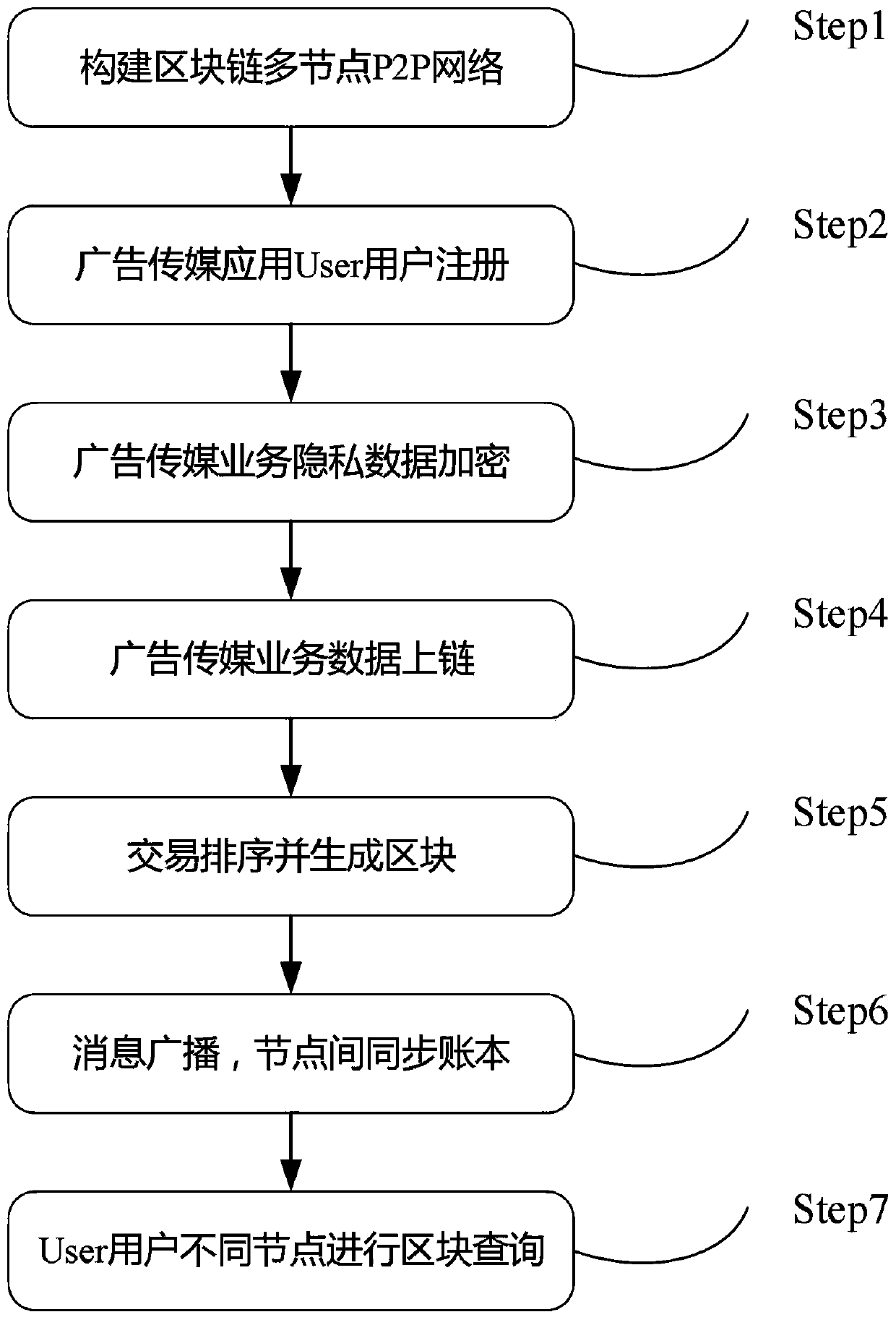
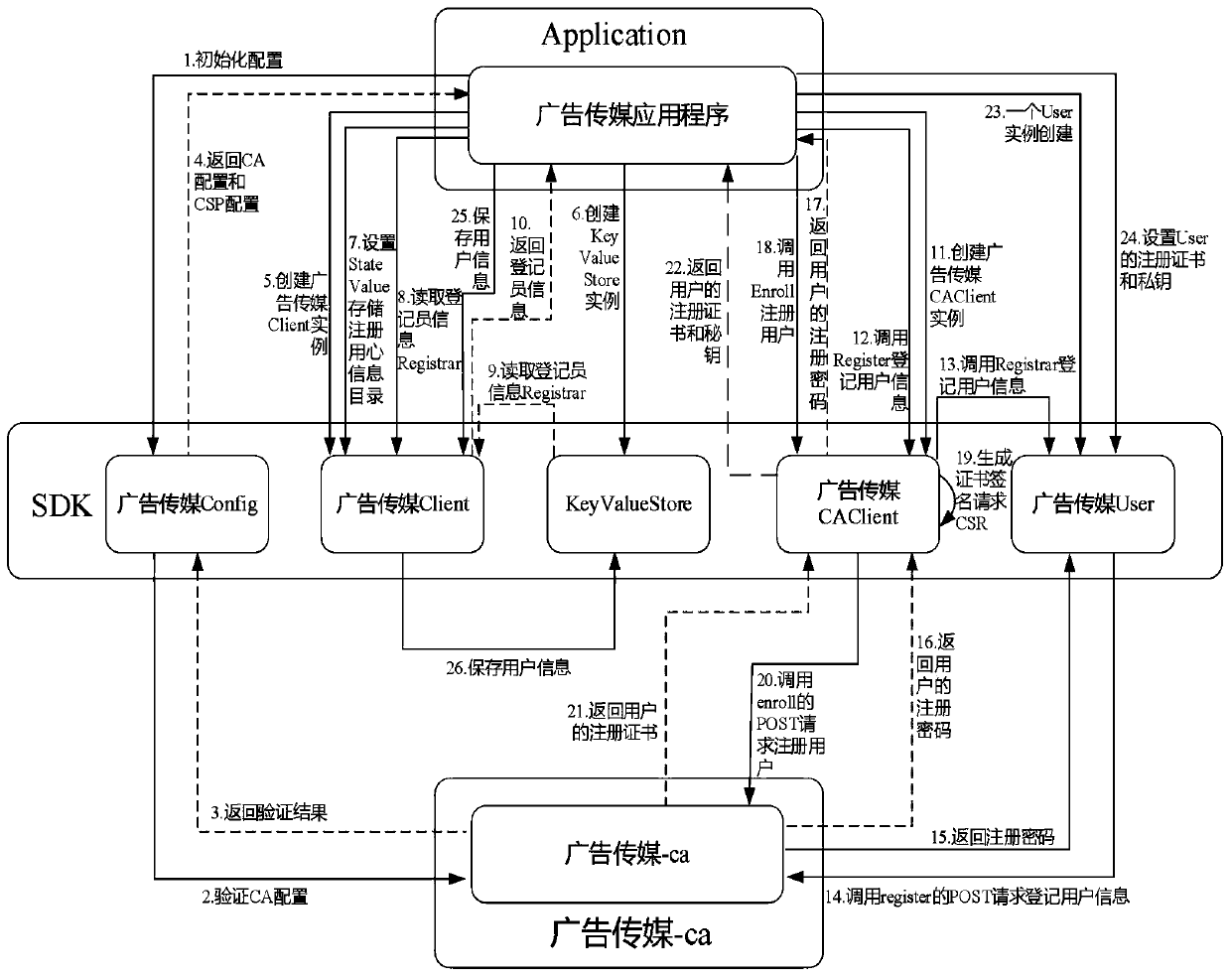
Advertisement media business data credible storage system based on block chain
InactiveCN110022217AProtection securityRealize depositUser identity/authority verificationMarketingTamper resistanceBusiness data
The invention discloses an advertisement media service data credible storage system based on a block chain, which can more comprehensively protect the safety of advertisement media service data. The method comprises the following steps: firstly, selectively encrypting advertisement media business privacy data through a symmetric encryption algorithm; secondly, storing the data in the block chain,permanently storing important data in the chain, meanwhile, ensuring the tamper resistance of the advertisement media service data stored in the chain by combining an elliptic curve algorithm of the block chain, and meanwhile, ensuring the privacy of the advertisement media service privacy data. The method can effectively prevent the advertisement media business data from being tampered, has the advantage of high security, and provides a credible evidence storage method for the advertisement media business data.
Owner:深圳大通实业股份有限公司
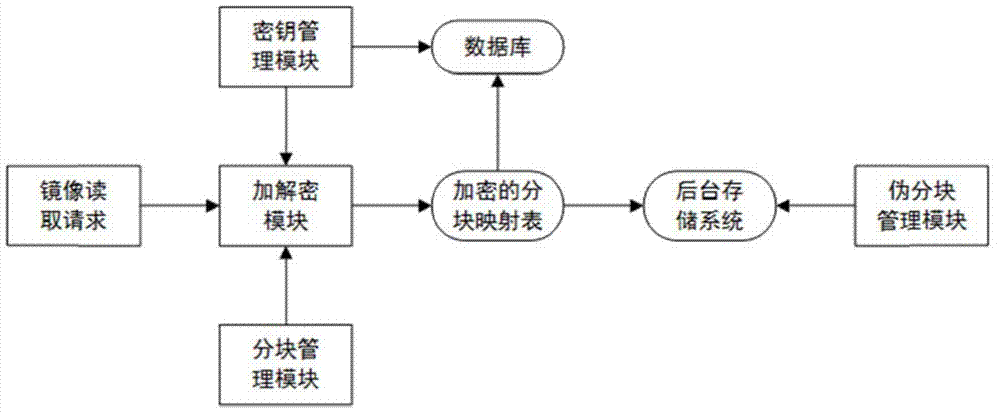
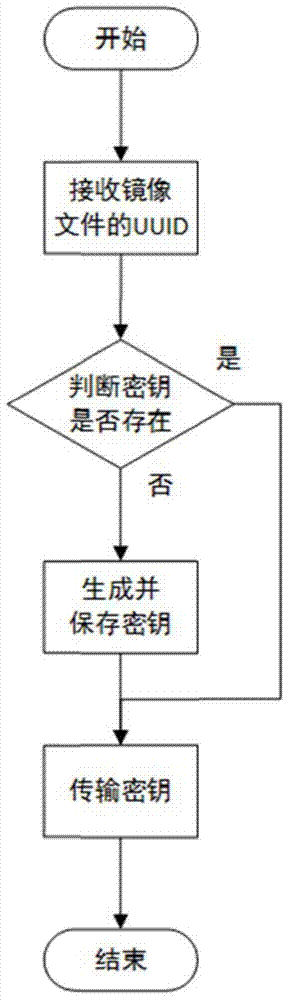
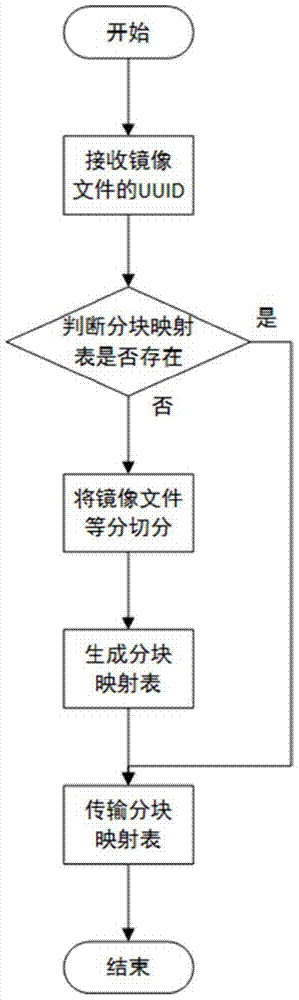
Lightweight mirror image file encryption system and method
ActiveCN104780048APrevent illegal tamperingReduce the possibility of brute-forcingKey distribution for secure communicationUser identity/authority verificationBrute forceMirror image
The invention discloses a lightweight mirror image file encryption system and a lightweight mirror image file encryption method and belongs to the technical field of cloud computing of computers. A mirror image file in a cloud computing system is encrypted, stored and managed. The encryption system comprises a key management module, a mirror image file block management module, an encryption / decryption module, a pseudo partitioning management module, a database and a background storage system. The encryption method comprises a key acquisition stage, a mirror image file partitioning stage, a mirror image file storage stage, a mirror image file reading stage and a pseudo partitioning maintenance stage. The mirror image file block management module is used for equally segmenting all mirror image files and then protecting the mirror image files through an encryption block mapping table. The safety of the mirror image files is ensured, and the encryption / decryption time cost is lower. Meanwhile, by creating and managing pseudo blocks in an idle storage space, the possibility of brute force is further reduced, and the safety is improved. The lightweight mirror image file encryption system and the lightweight mirror image file encryption method are applicable to any cloud computing system relating to mirror image file management.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
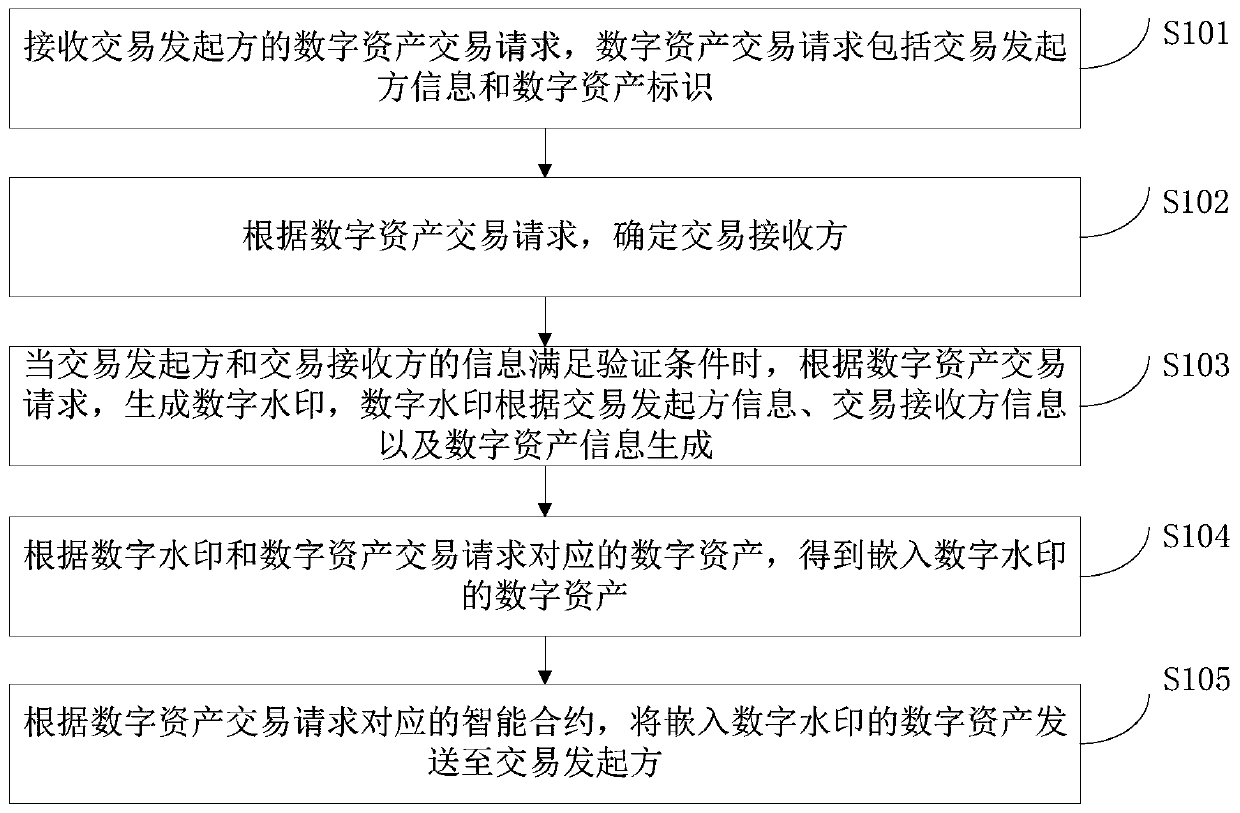
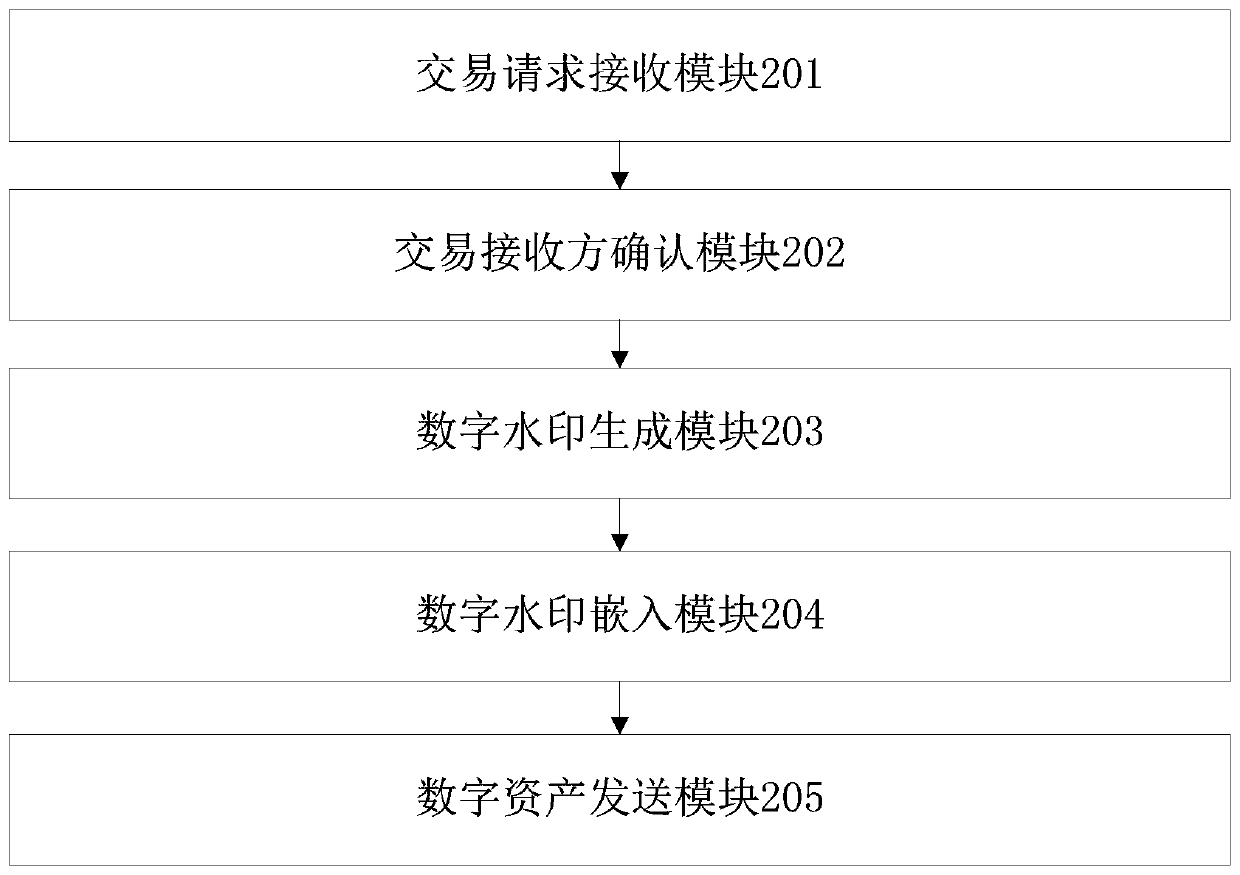
Digital asset transaction method and device based on block chain, and storage medium
ActiveCN111538784AReduce the cost of rights protectionPrecise positioningFinanceDatabase distribution/replicationEngineeringFinancial transaction
The invention provides a digital asset transaction method and device based on a block chain, and a storage medium. The method comprises the following steps: receiving a digital asset transaction request of a transaction initiator, wherein the digital asset transaction request comprises the information of the transaction initiator and a digital asset identifier; determining a transaction receiver according to the digital asset transaction request; when the information of the transaction initiator and the transaction receiver meets the verification condition, generating a digital watermark according to the digital asset transaction request, and generating a digital watermark according to the information of the transaction initiator, the information of the transaction receiver and the digitalasset information; obtaining digital assets embedded with digital watermark according to the digital watermark and the digital asset corresponding to the digital asset transaction request; and sending the digital asset embedded with the digital watermark to the transaction initiator according to the intelligent contract corresponding to the digital asset transaction request. An infringement userwho leaks the digital asset can be accurately positioned, and the digital asset right protection cost is reduced.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
Operation data tamper-proofing method based on block chain
InactiveCN111125776ACredible identityAvoid single point of failure problemsDigital data protectionPlatform integrity maintainanceTamper resistanceCiphertext
The invention discloses an operation data tamper-proofing method based on a block chain and provides a data tamper-proofing method based on a block chain used for monitoring illegal modification of adata system. According to the system, a business system and a tamper-proof supervision system are managed separately, ciphertext of data is synchronously uploaded while the data is input into a locallibrary of the business system, and meanwhile, all operations of the business system on a database are uploaded and traceable through the supervision system, so that illegal operations are hidden andcomprehensively supervised. An existing data storage technology is solved. If someone modifies the database, deletes the system log and modifies the backup file at the same time, the file before modification can hardly be found, serious consequences are easily caused in the fields of finance, judicial administration and the like, and an existing scheme adopting a block chain only provides a data evidence storage function and can not restore the data.
Owner:CHENGDU SEFON SOFTWARE CO LTD
Method for preventing tampering of identity information in real name authentication
ActiveCN105187219AAdd verification linkPrevent illegal tamperingUser identity/authority verificationRadio frequencyStatus changed
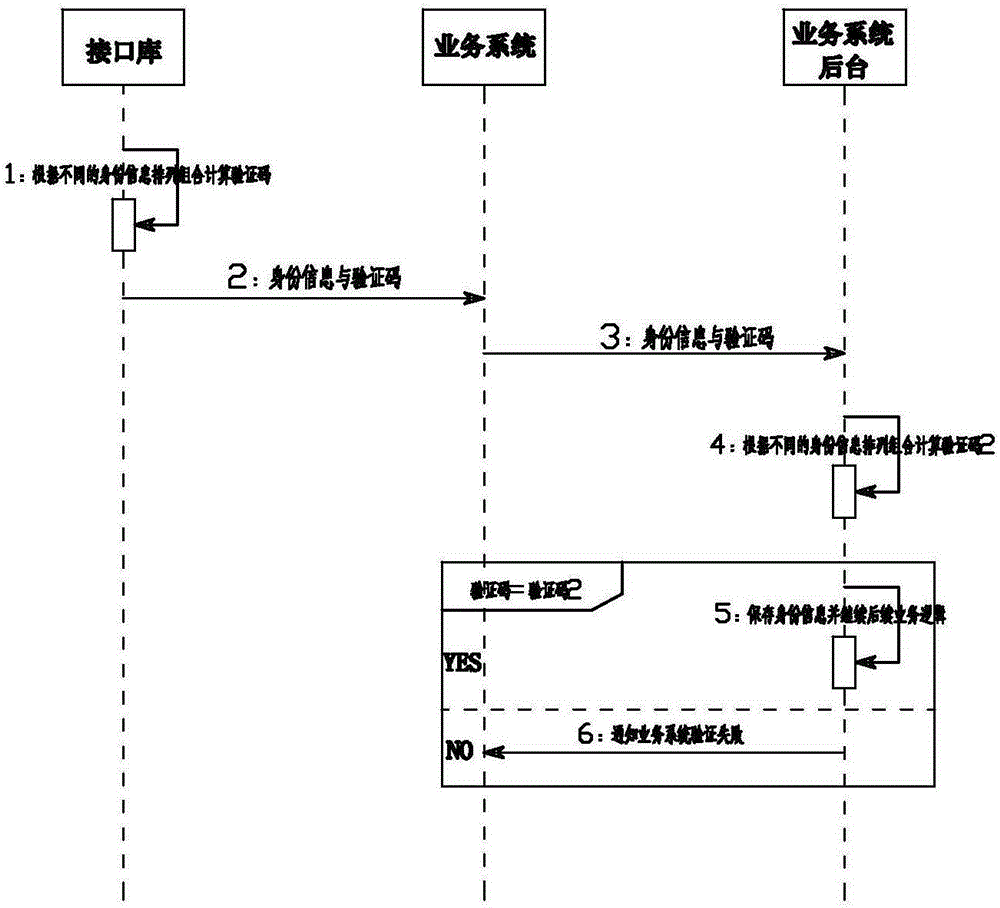
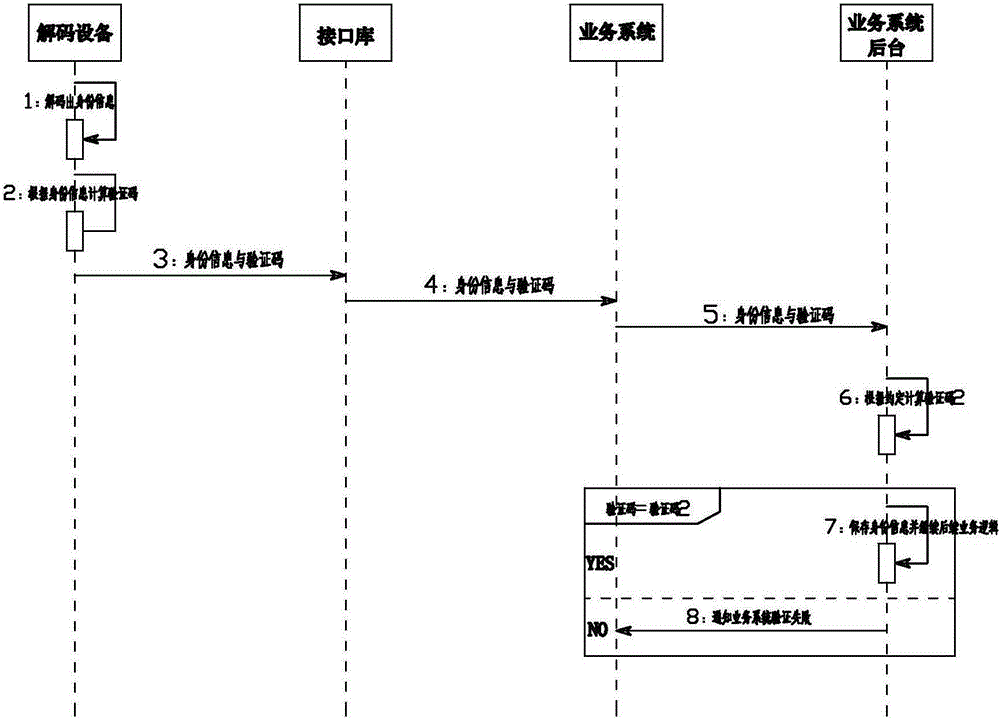
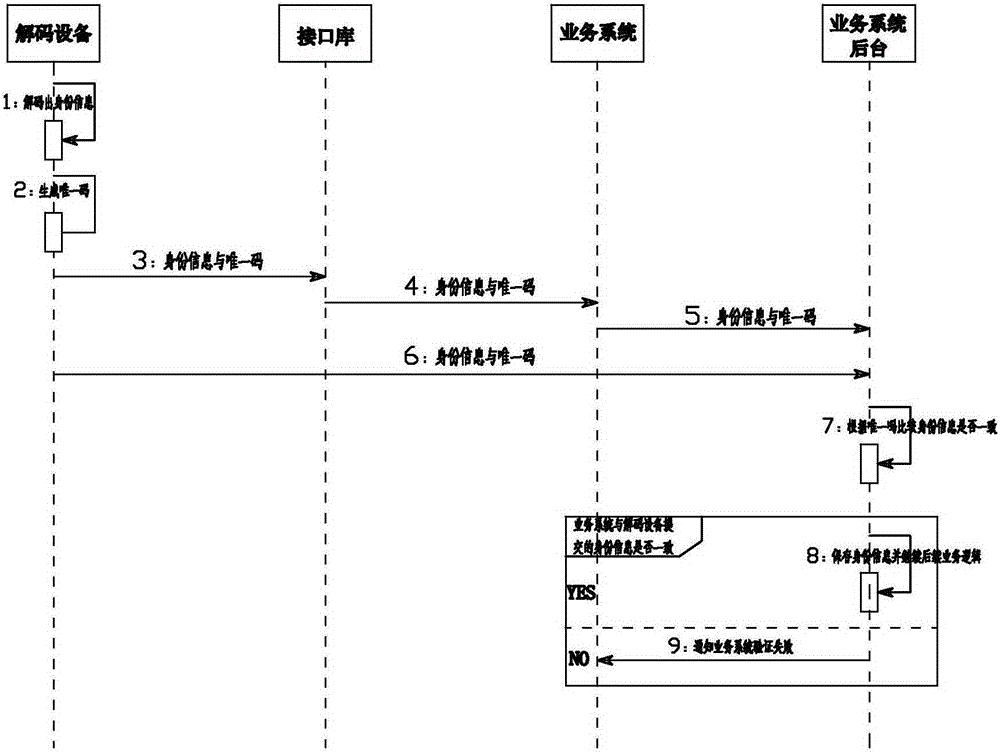
The invention provides a method for preventing tampering of identity information in real name authentication, and belongs to the field of methods for preventing tampering of identity information. A service system is provided. The service system is connected with radio-frequency equipment, and used for reading encrypted identity information in an identity card through the radio-frequency equipment, and decoding the encrypted identity information through decoding equipment at the other end of a network. Decoded identity information is returned to the service system. The method comprises the following steps that: the service system controls the radio-frequency equipment to acquire the encrypted identity information through an interface library, and transmits the encrypted identity information to the decoding equipment through a TCP / IP (Transmission Control Protocol / Internet Protocol) network; the decoding equipment decodes the received identity information, calculates a feature code with content in the identity information, and transmits the feature codes to the service system; and the service system verifies whether the identity information is tampered or not with the feature code. Through adoption of the method, the identity information can be effectively prevented from being tampered.
Owner:SHANDONG SENTER ELECTRONICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com