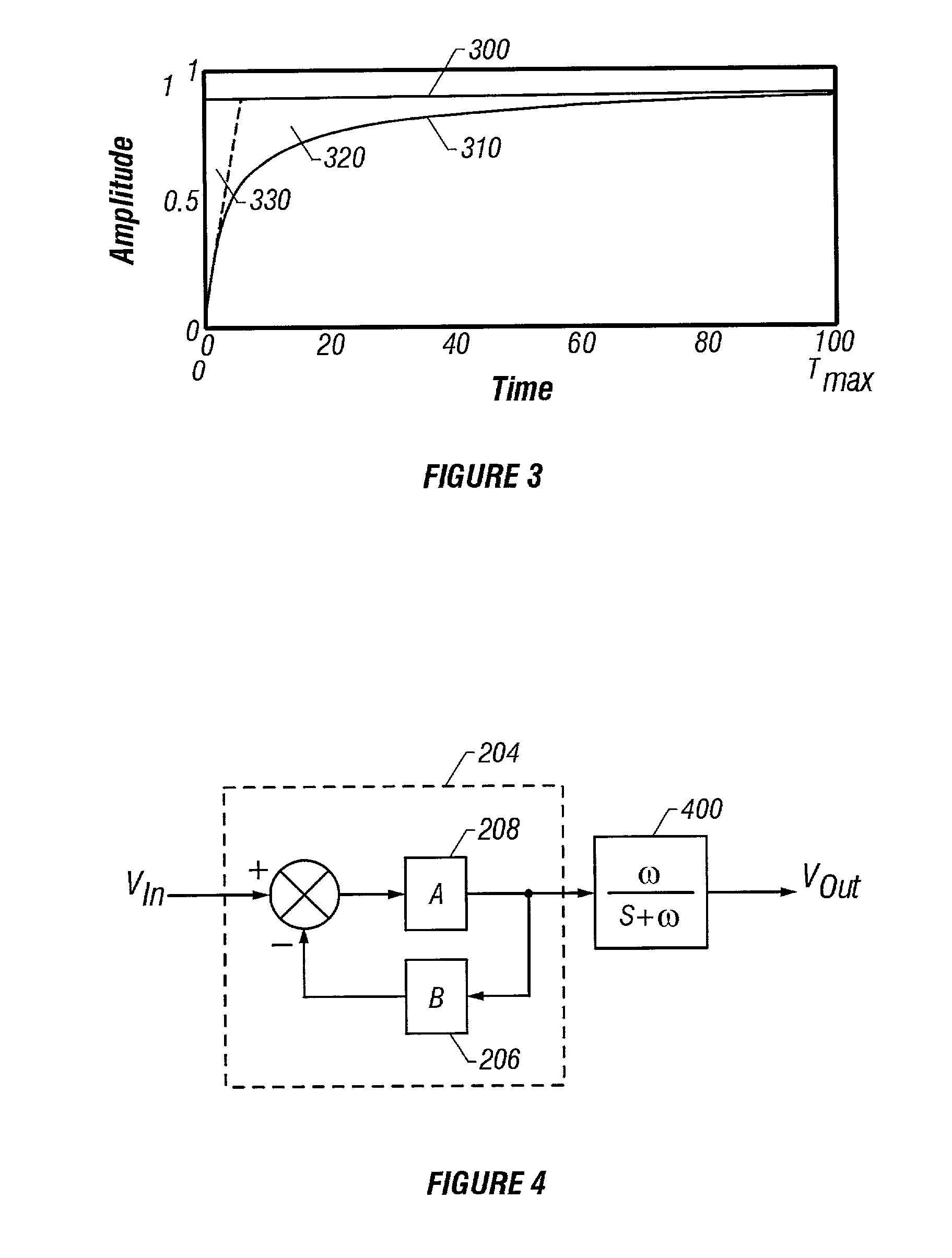
Patents
Literature
470 results about "Brute force" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
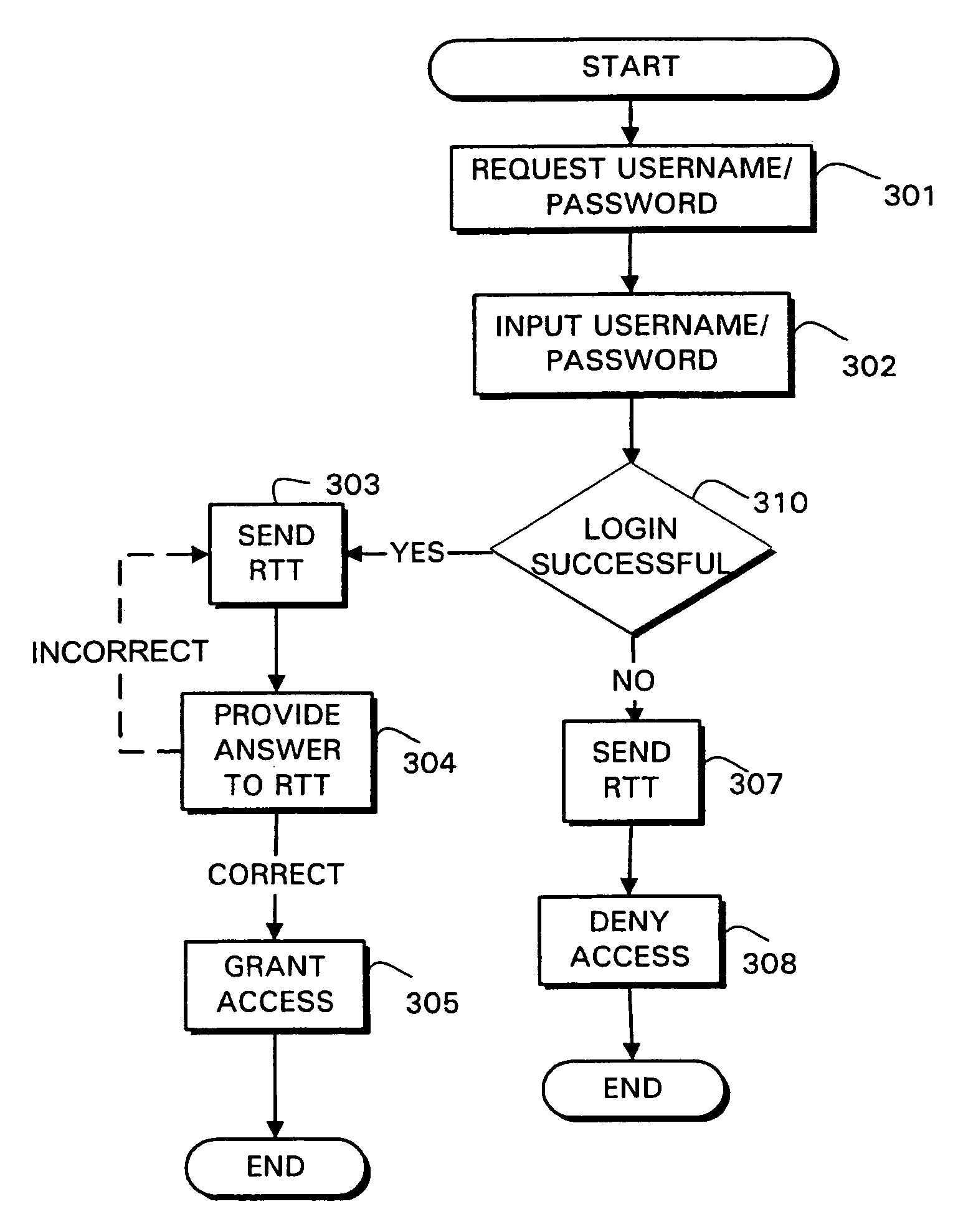
Secure authentication systems and methods
InactiveUS7383570B2Digital data processing detailsUser identity/authority verificationBrute forcePassword
Systems and methods are provided for authentication by combining a Reverse Turing Test (RTT) with password-based user authentication protocols to provide improved resistance to brute force attacks. In accordance with one embodiment of the invention, a method is provided for user authentication, the method including receiving a username / password pair associated with a user; requesting one or more responses to a first Reverse Turing Test (RTT); and granting access to the user if a valid response to the first RTT is received and the username / password pair is valid.
Owner:INTERTRUST TECH CORP
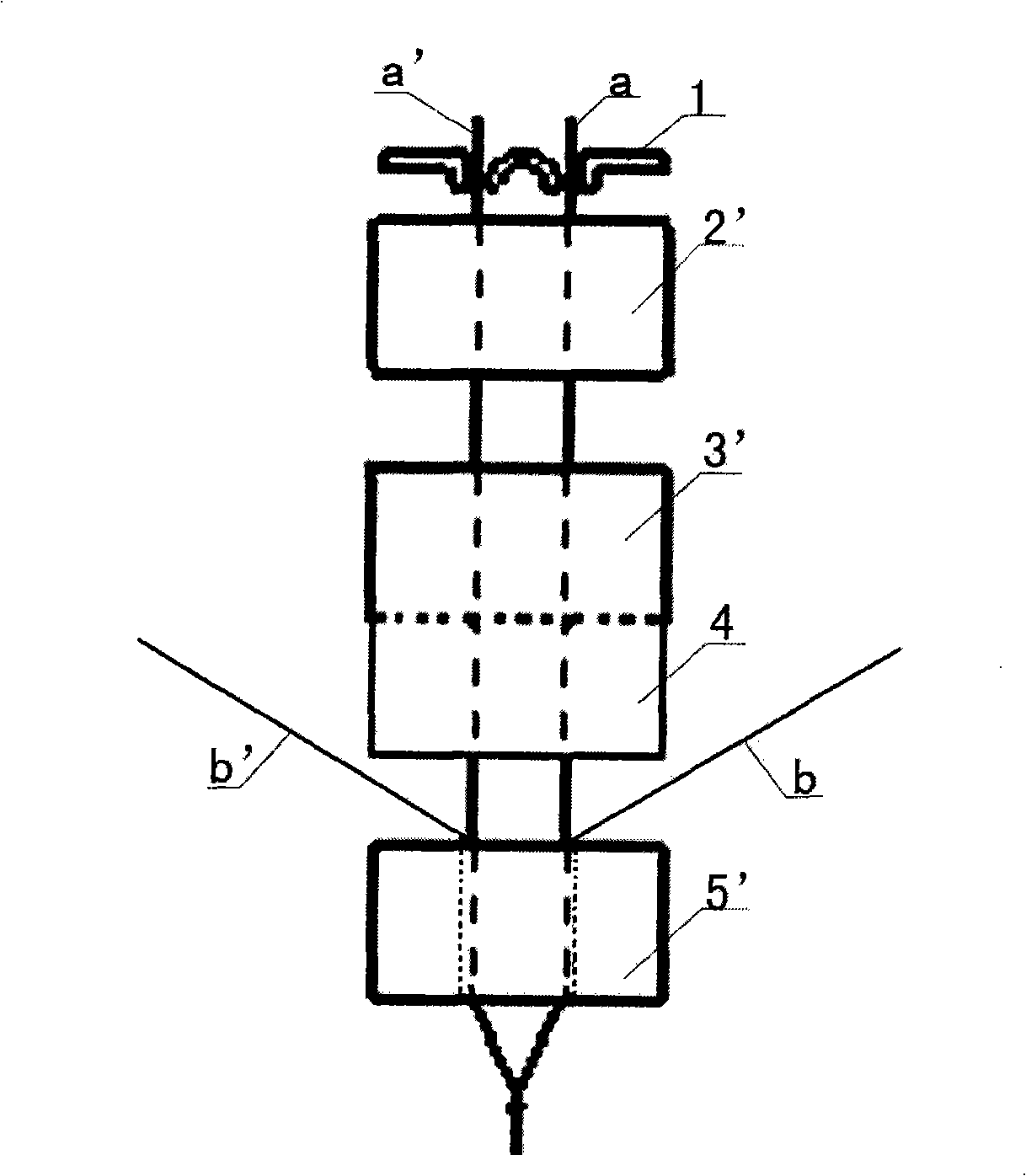
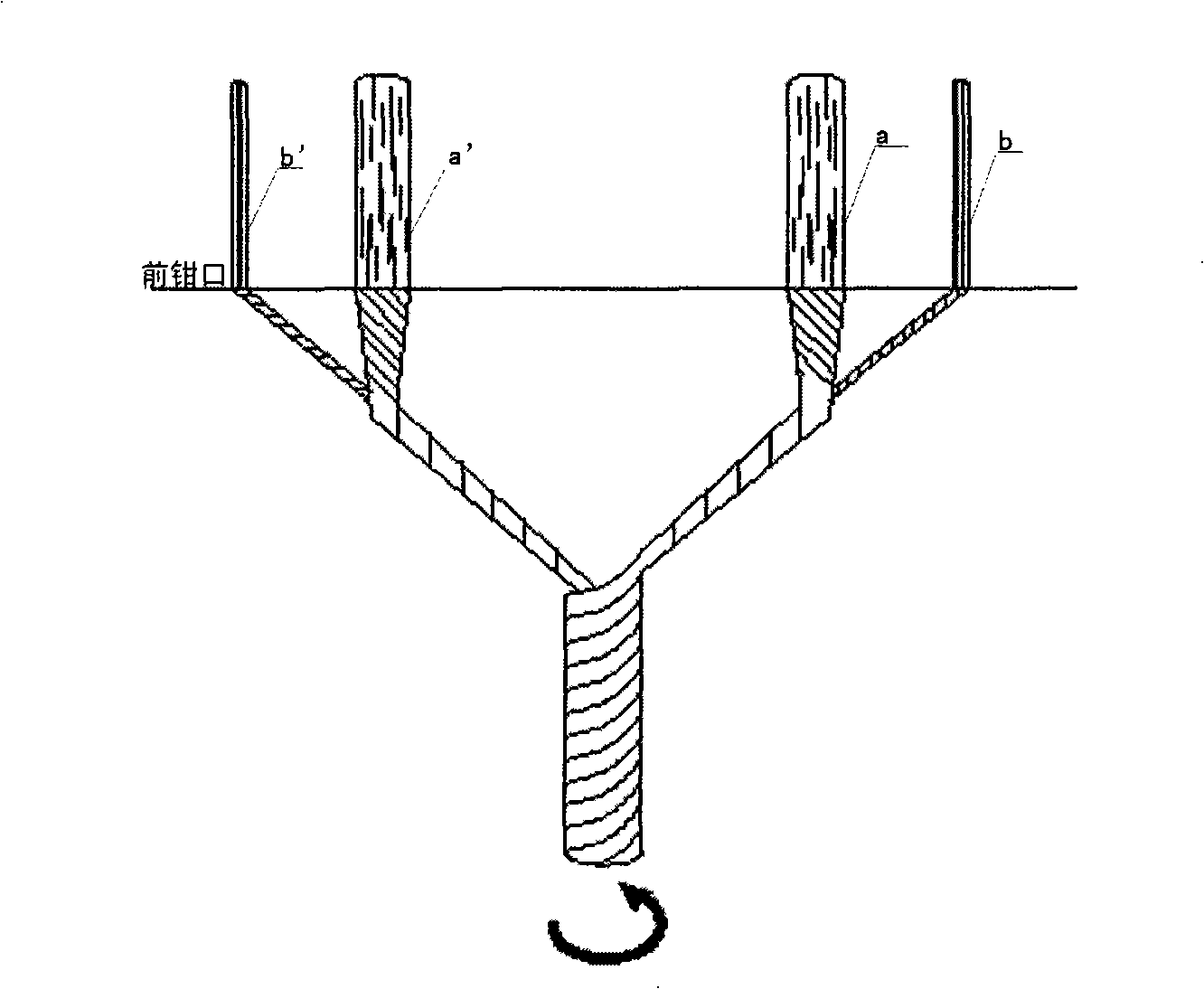
Positioning spinning method of embedded system
InactiveCN101492843ACompact structurePlay a reinforcing roleDrafting machinesContinuous wound-up machinesYarnFiber
Owner:WUHAN TEXTILE UNIV +2
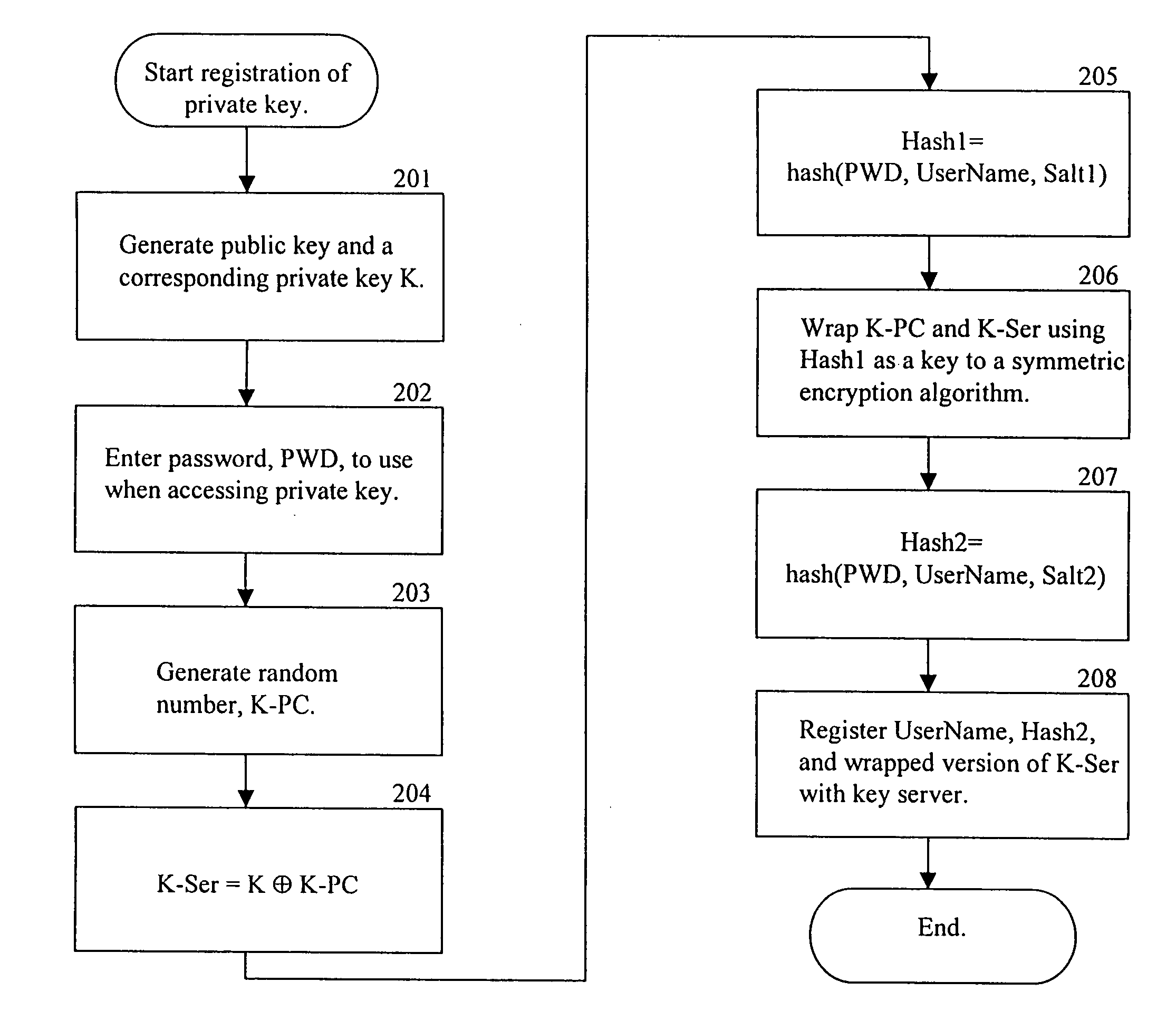
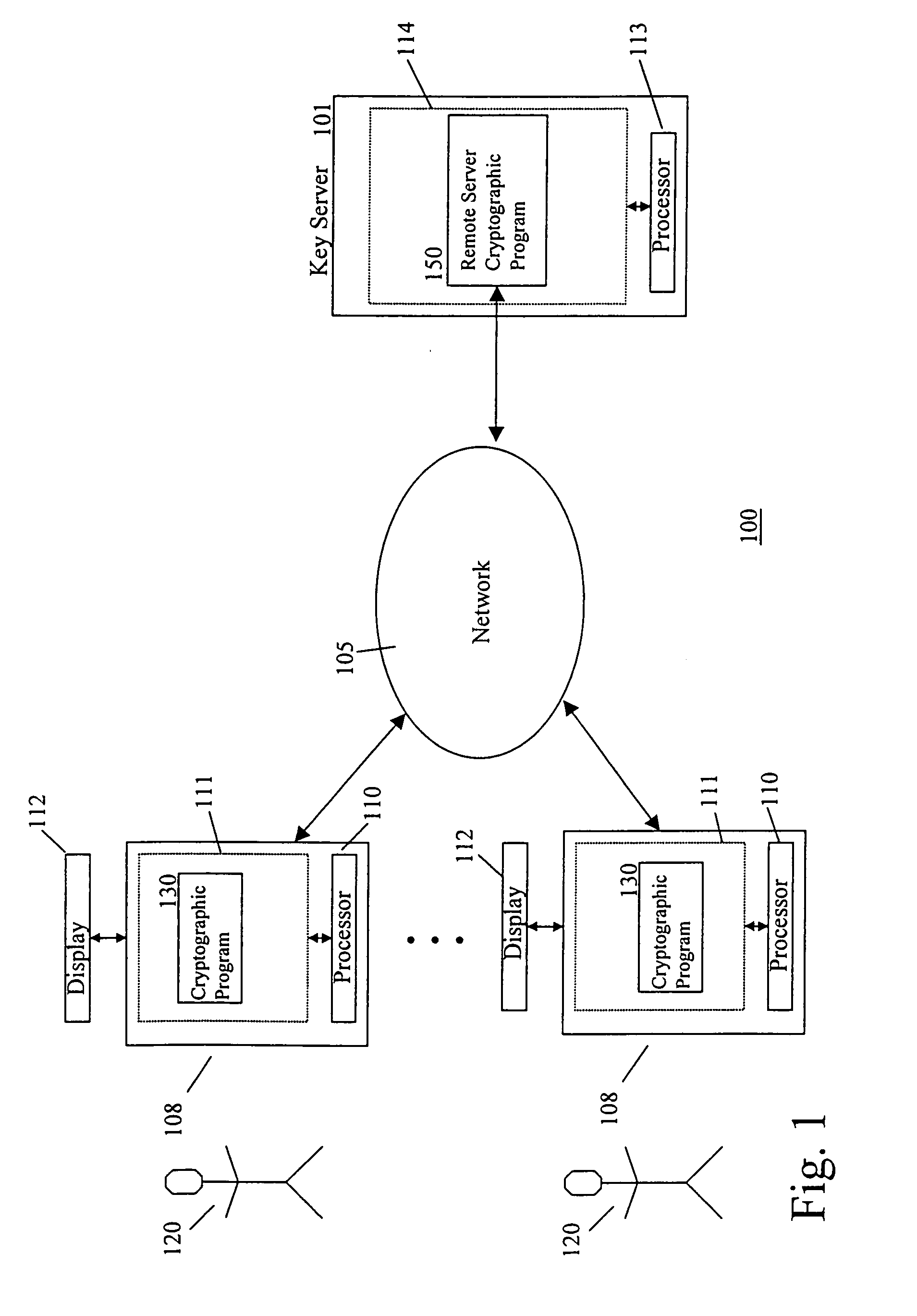
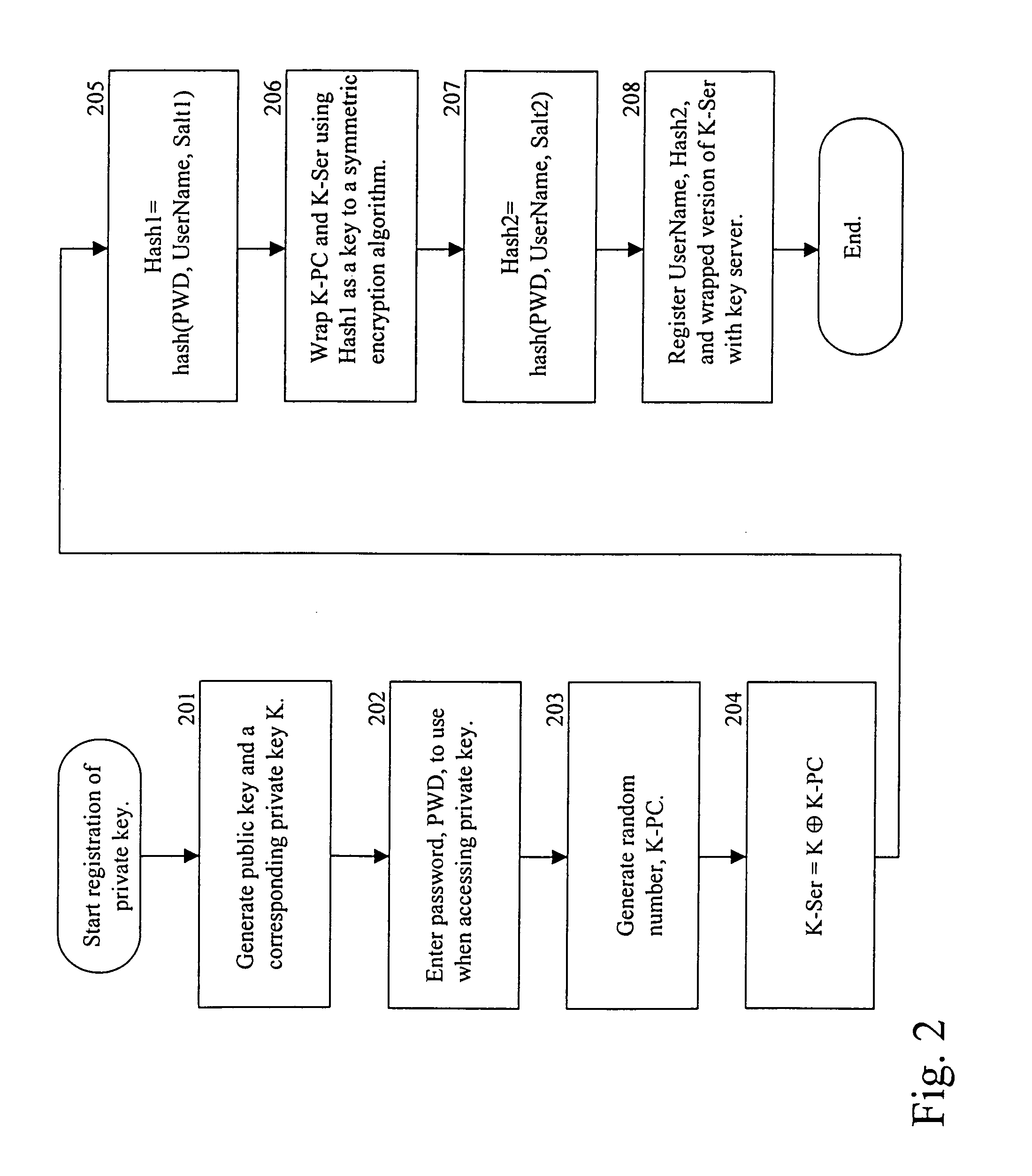
Secure storage of private keys
InactiveUS6950523B1Key distribution for secure communicationData processing applicationsBrute forcePassword
To protect a private cryptographic key, two values are derived. The two values together can reconstruct the key. One value is sent to a server and deleted from the local machine. The other value is held by the local machine. To use the key, the user will enter a password, which will be used to authenticate the user to the server, and retrieve the value from the server. The password is also used to unlock the value held by the local machine. The private cryptographic key is thus protected against brute force password attacks without changing the behavior of the user.
Owner:INTEL CORP
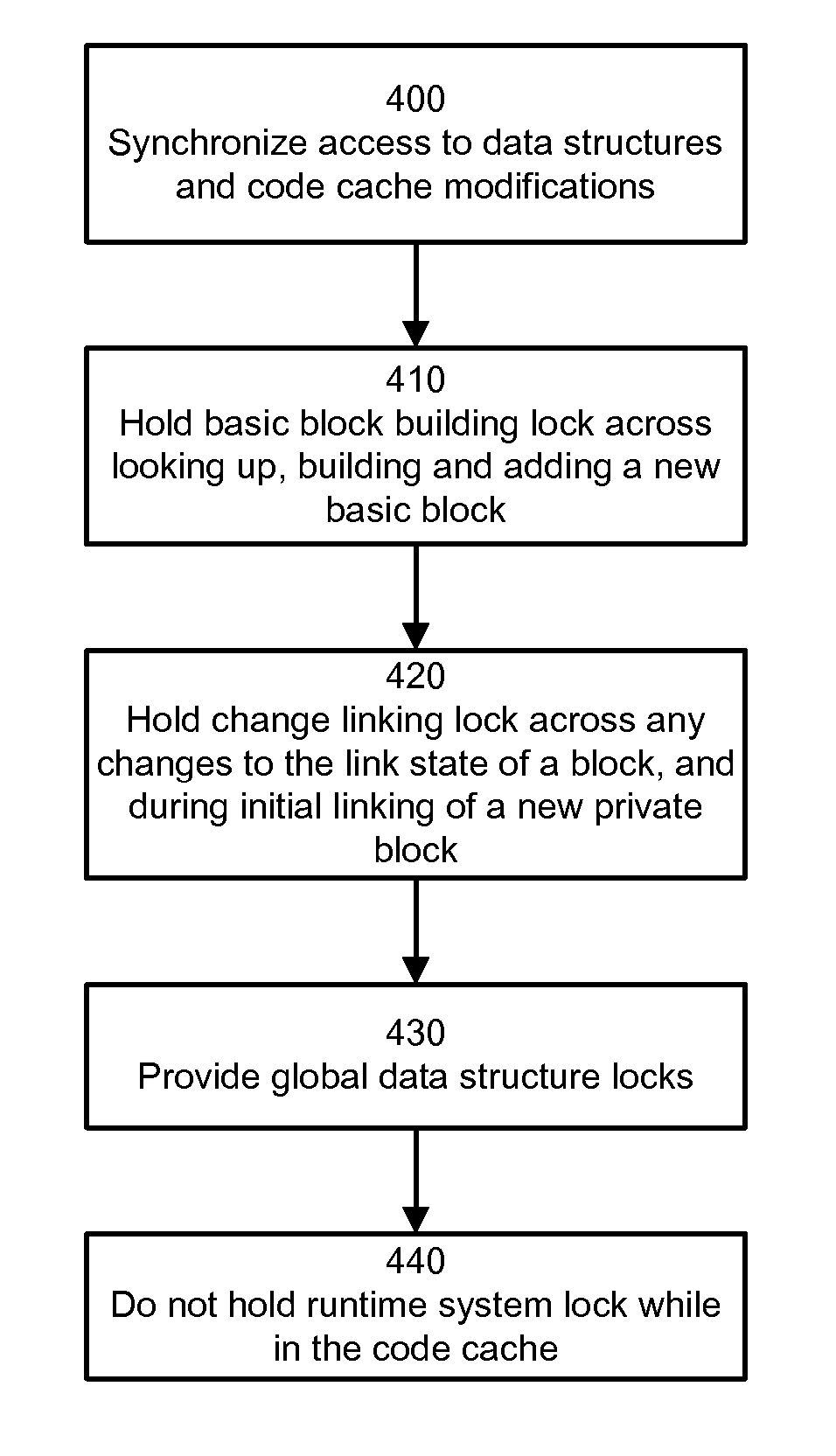
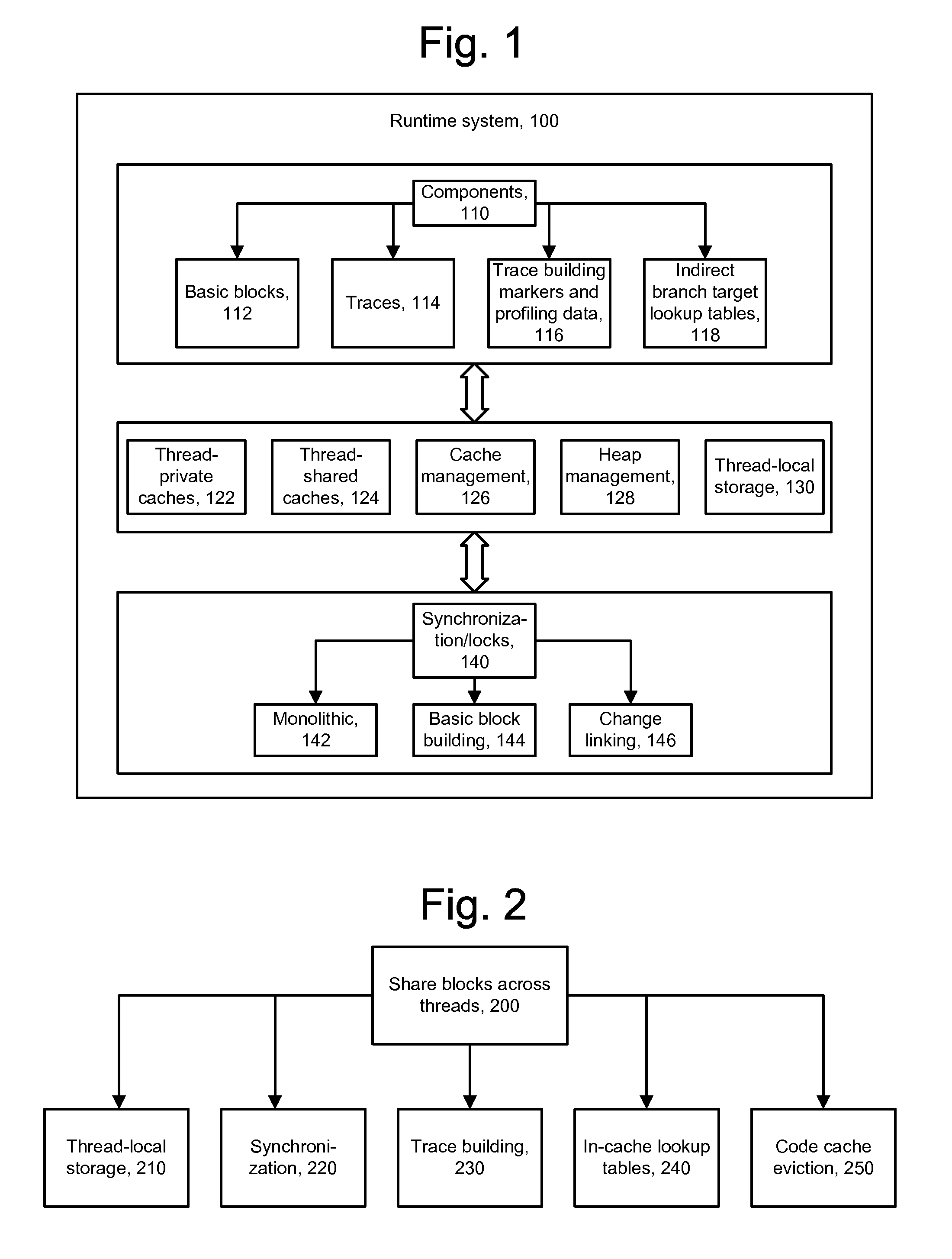
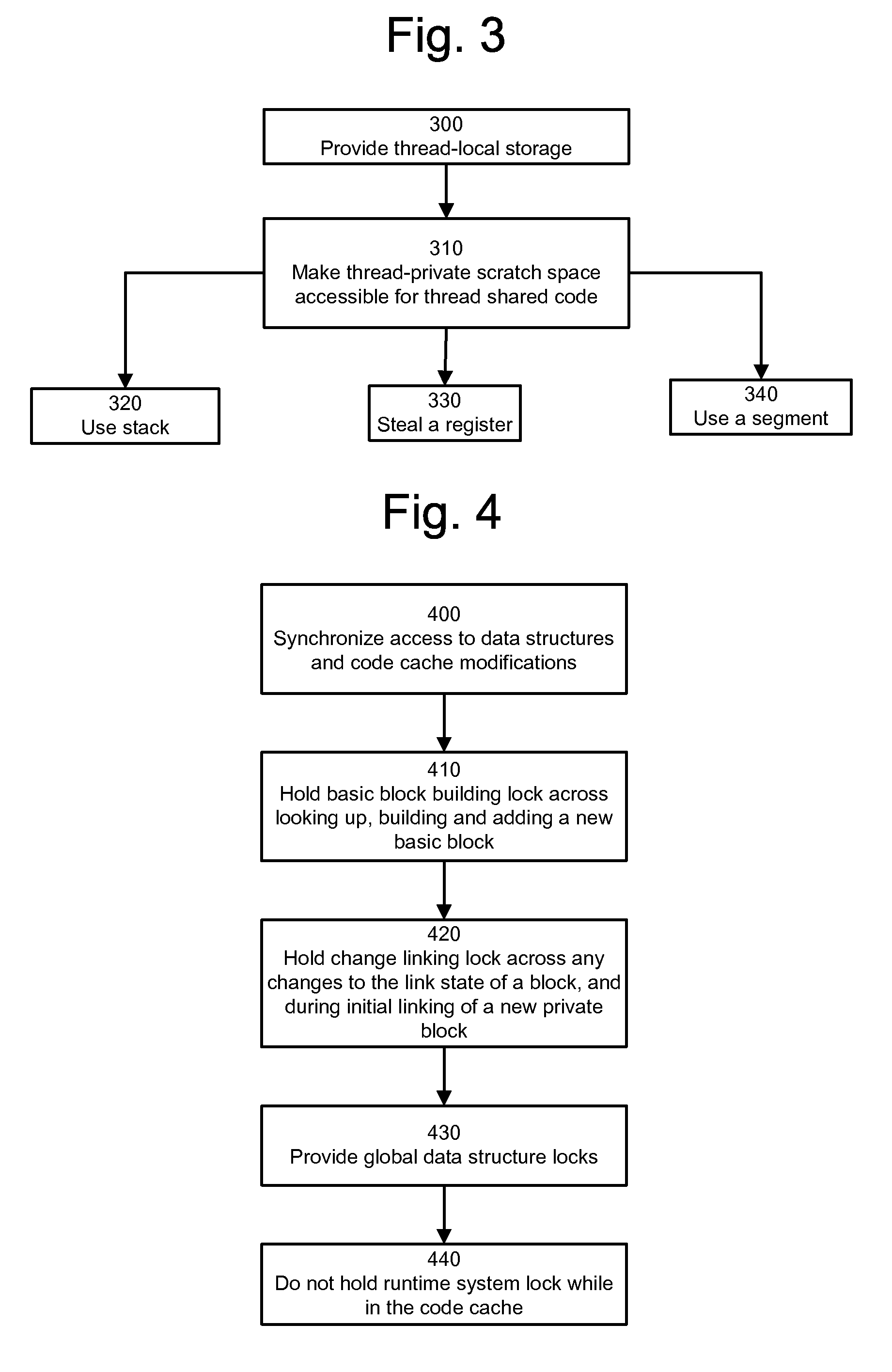
Thread-shared software code caches
ActiveUS20070067573A1Avoiding brute-force all-thread-suspensionAvoiding monolithic global locksMemory adressing/allocation/relocationMultiprogramming arrangementsTimestampBrute force
A runtime system using thread-shared code caches is provided which avoids brute-force all-thread-suspension and monolithic global locks. In one embodiment, medium-grained runtime system synchronization reduces lock contention. The system includes trace building that combines efficient private construction with shared results, in-cache lock-free lookup table access in the presence of entry invalidations, and a delayed deletion algorithm based on timestamps and reference counts. These enable reductions in memory usage and performance overhead.
Owner:VMWARE INC
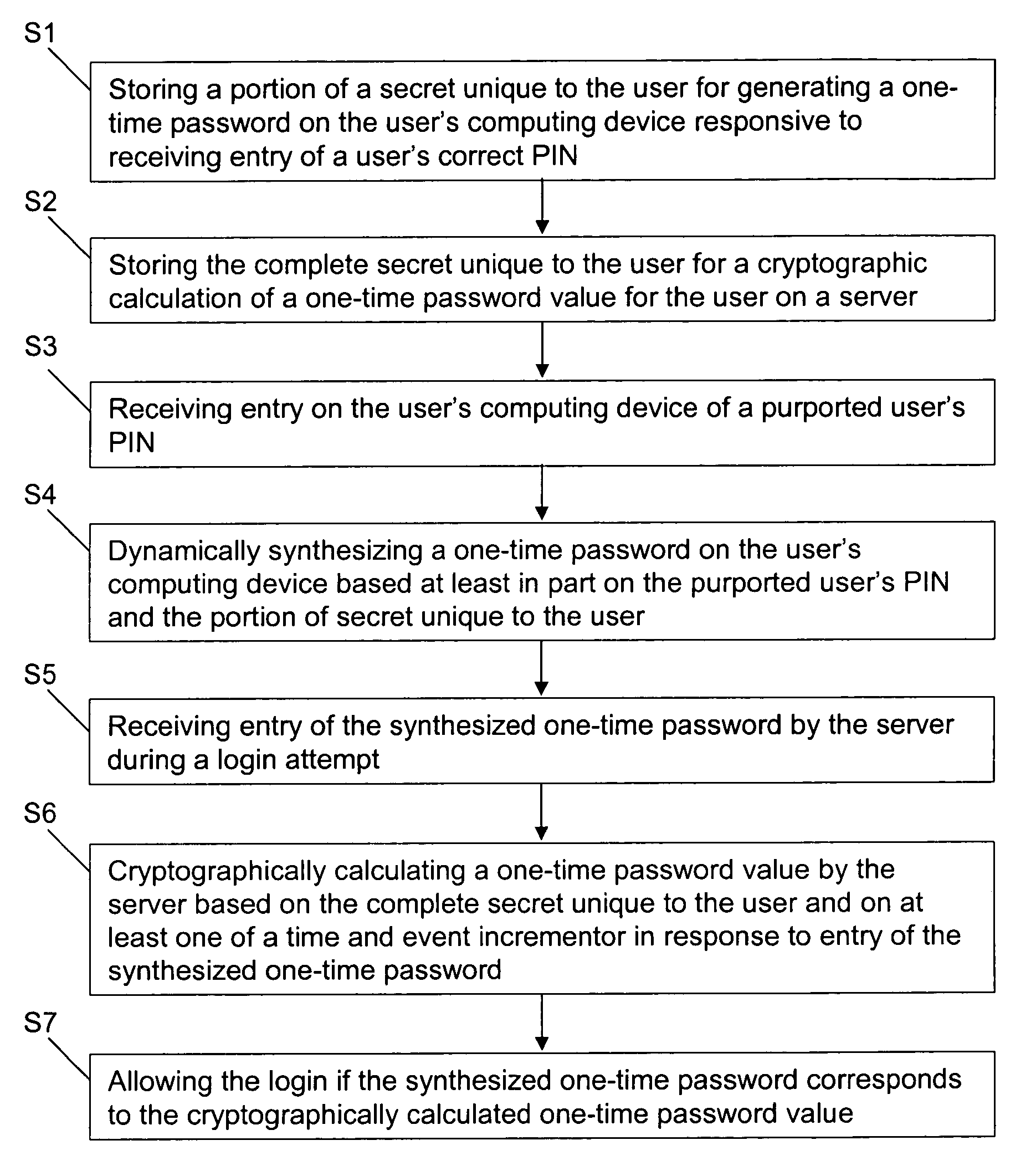
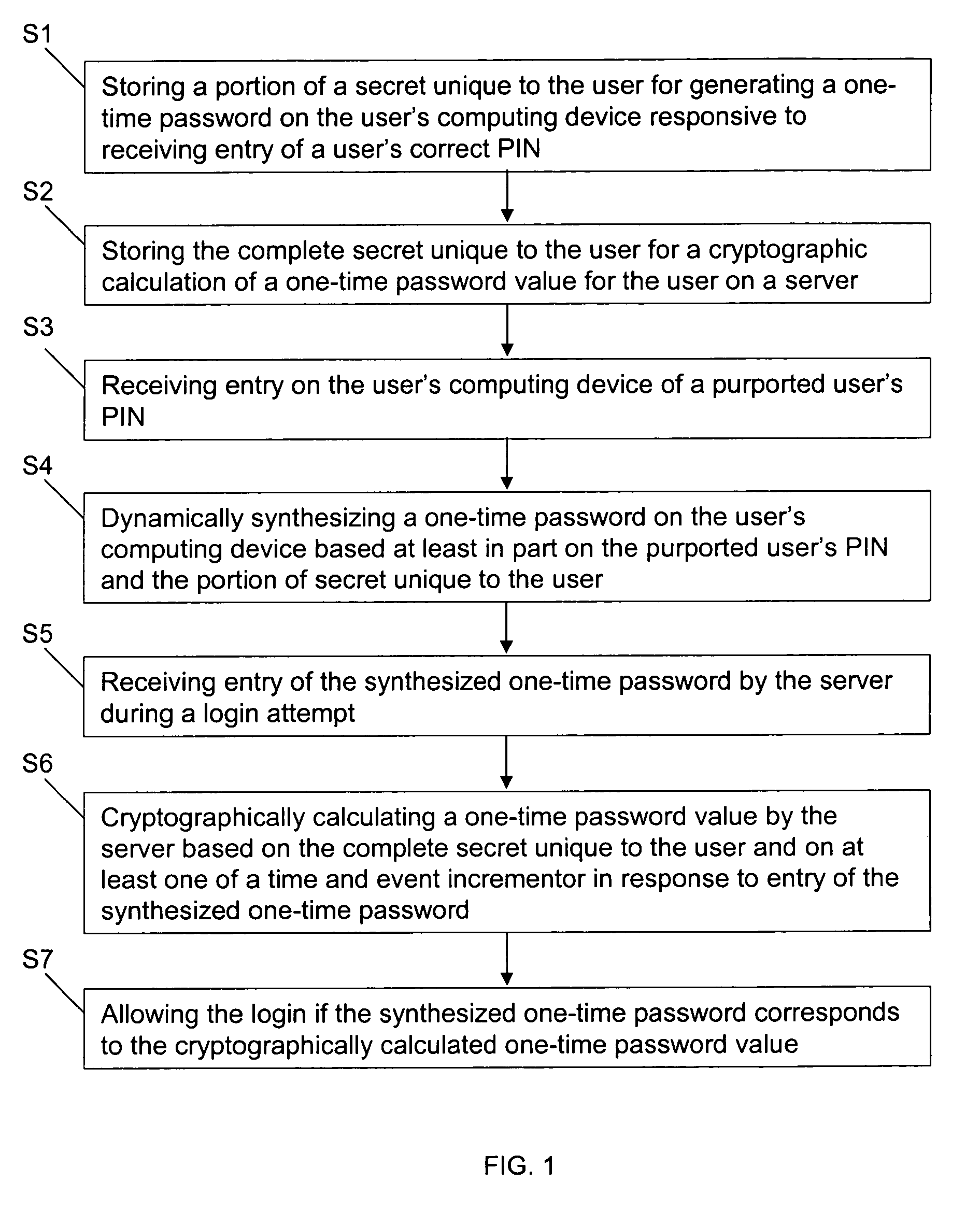
Methods and systems for secure user authentication
ActiveUS7904946B1Reduce in quantityDefeat threatDigital data processing detailsMultiple digital computer combinationsBrute forceUser authentication
Methods and systems for secure user authentication utilizes OTP generation and validation techniques in which the shared secret for generating the OTP is not stored in the user's mobile device but instead is dynamically synthesized based on a PIN that activates the OTP generation and the personalized OTP data. The client software has no knowledge of what the correct PIN should be and always generates a normal looking OTP based on whatever PIN is entered, and the only way to learn whether or not the OTP is correct is to submit it during user login. By limiting the number of failed login attempts before the account is locked, brute-force attacks via the online channel will fail, and further, brute-force attacks to uncover the correct PIN for generating the correct OTP offline will also fail even if a hacker steals the user's mobile device and extracts the data inside for offline hacking, because there is nothing on the client that contains the PIN or encrypted by the PIN.
Owner:CITICORP CREDIT SERVICES INC (USA)
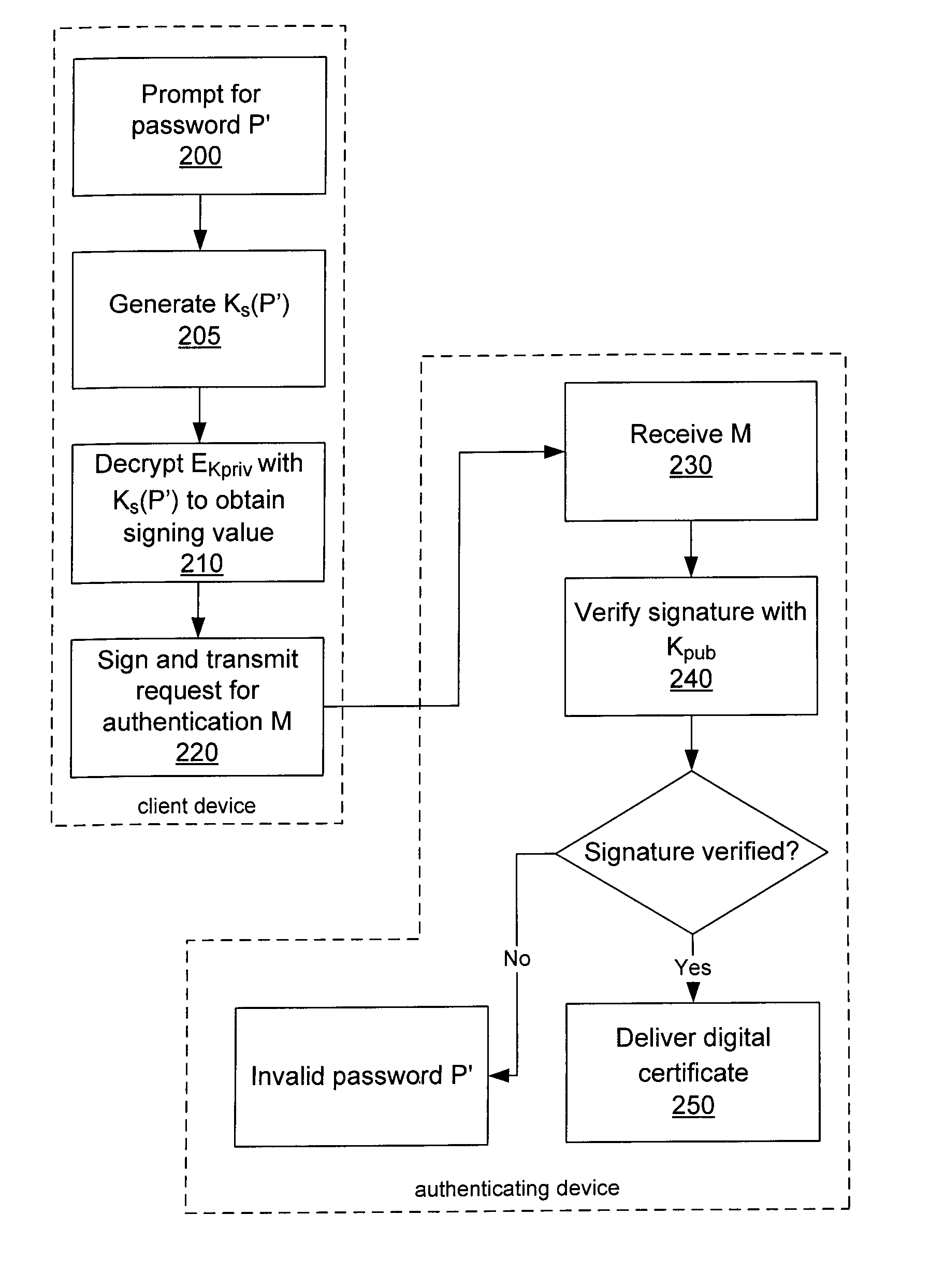
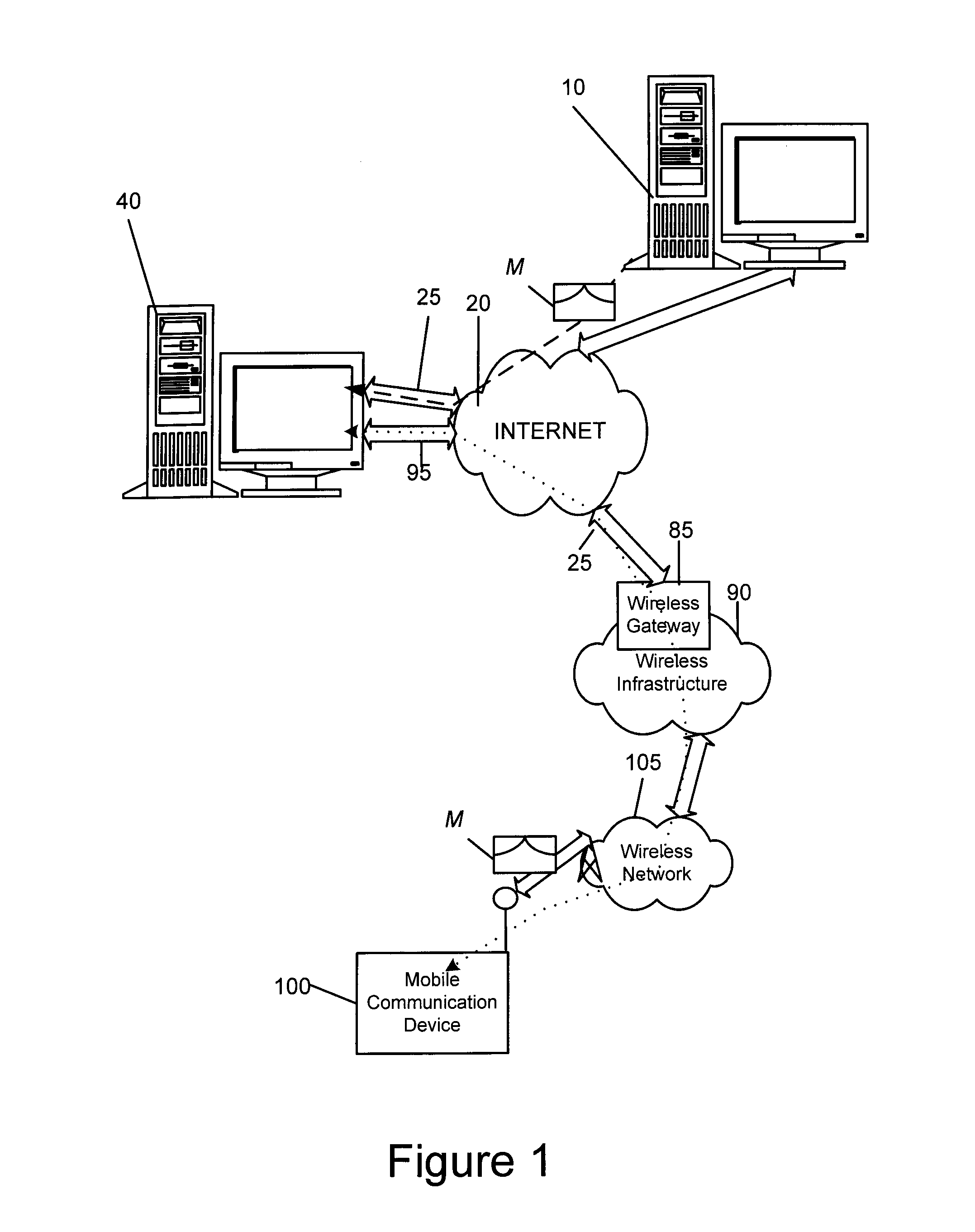
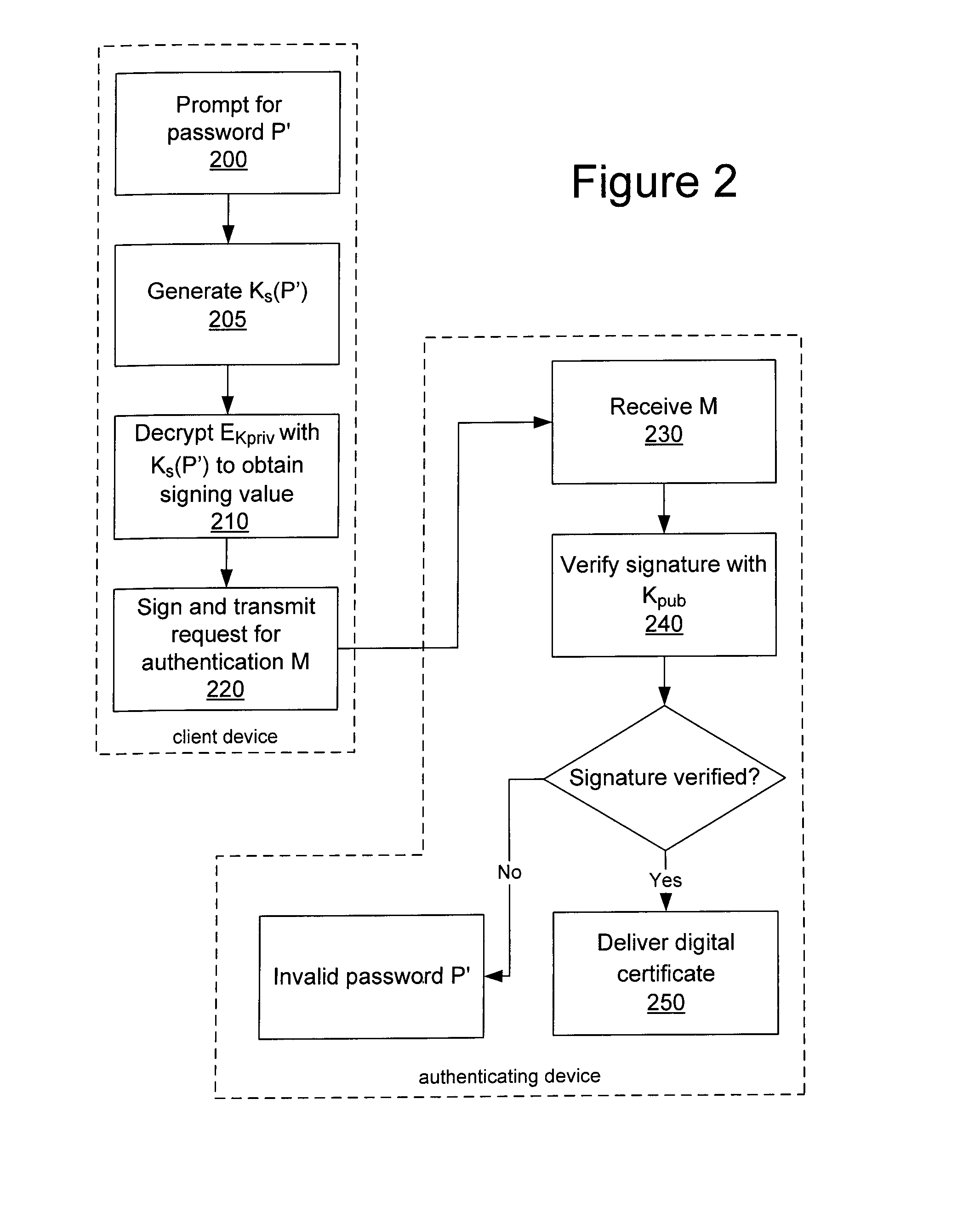
System and method for protecting a password against brute force attacks
ActiveUS20080120504A1User identity/authority verificationCryptographic attack countermeasuresBrute forcePassword
In a system and method for authenticating a client device by an authentication device, the client device user is assigned a PIN generated by the authentication device. The user provides the PIN and a password to the client device, from which the client device generates a symmetric key and further generates a public / private key pair. The private key is encrypted using the symmetric key and stored in encrypted form only. The public key and a message authentication code generated from the PIN are provided to the authentication device, which stores the public key. Subsequently, when the user seeks to be authenticated, the user enters a password at the client device, which is used to generate a symmetric key to decrypt the encrypted private key. A message to the authentication device is signed using the resultant value. The authentication device uses the public key to verify the signature of the message.
Owner:MALIKIE INNOVATIONS LTD
Medical chitosan fibre and preparation method thereof
ActiveCN101250759AHigh molecular weightEnough aminoFilament manufactureArtificial filament washing/dryingAcetic acidBrute force
The invention relates to medical chitosan fiber in the textile processing field and a preparing method thereof, the method for preparing spinning fluid comprises the following steps: arranging the chitosan powder in glacial acetic acid water solution and slowly dissolving by stirring under the condition of controlling temperature and time, wherein the dissolution temperature is 10-30DEG C, the dissolution time is 10-48h, and the stirring speed is 60-180r / min, wherein the chitosan powder occupies 3%-10%, dissolvent glacial acetic acid occupies 1%-5% and the other is water in the spinning raw materials, the chitosan content is more than 99.9% in chitosan fiber, and the chitosan fiber has higher molecular weight, sufficient amido, steady fiber structure, and good antibacterial property, brute force and hygiene security property.
Owner:HISMER BIO TECH
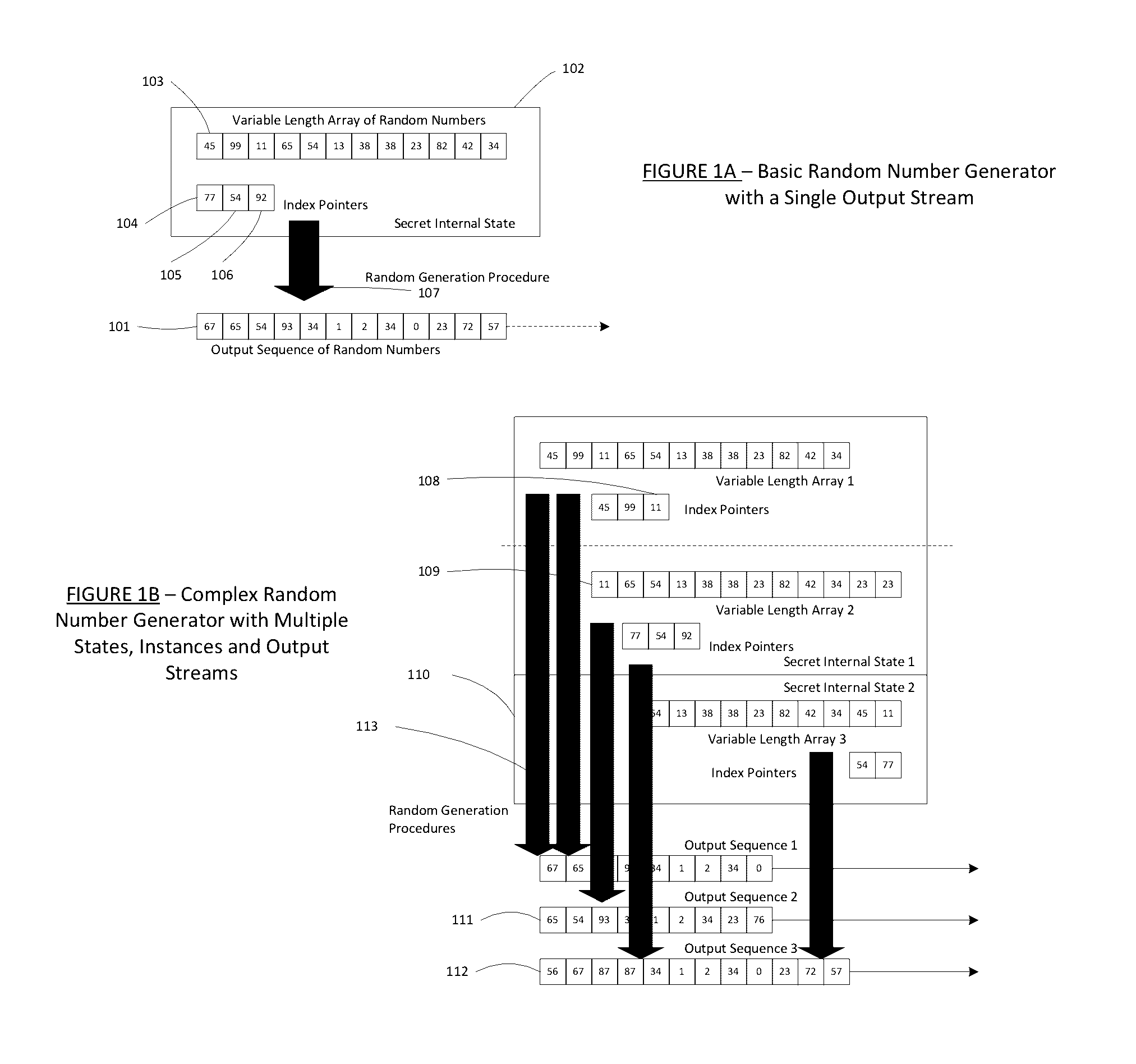
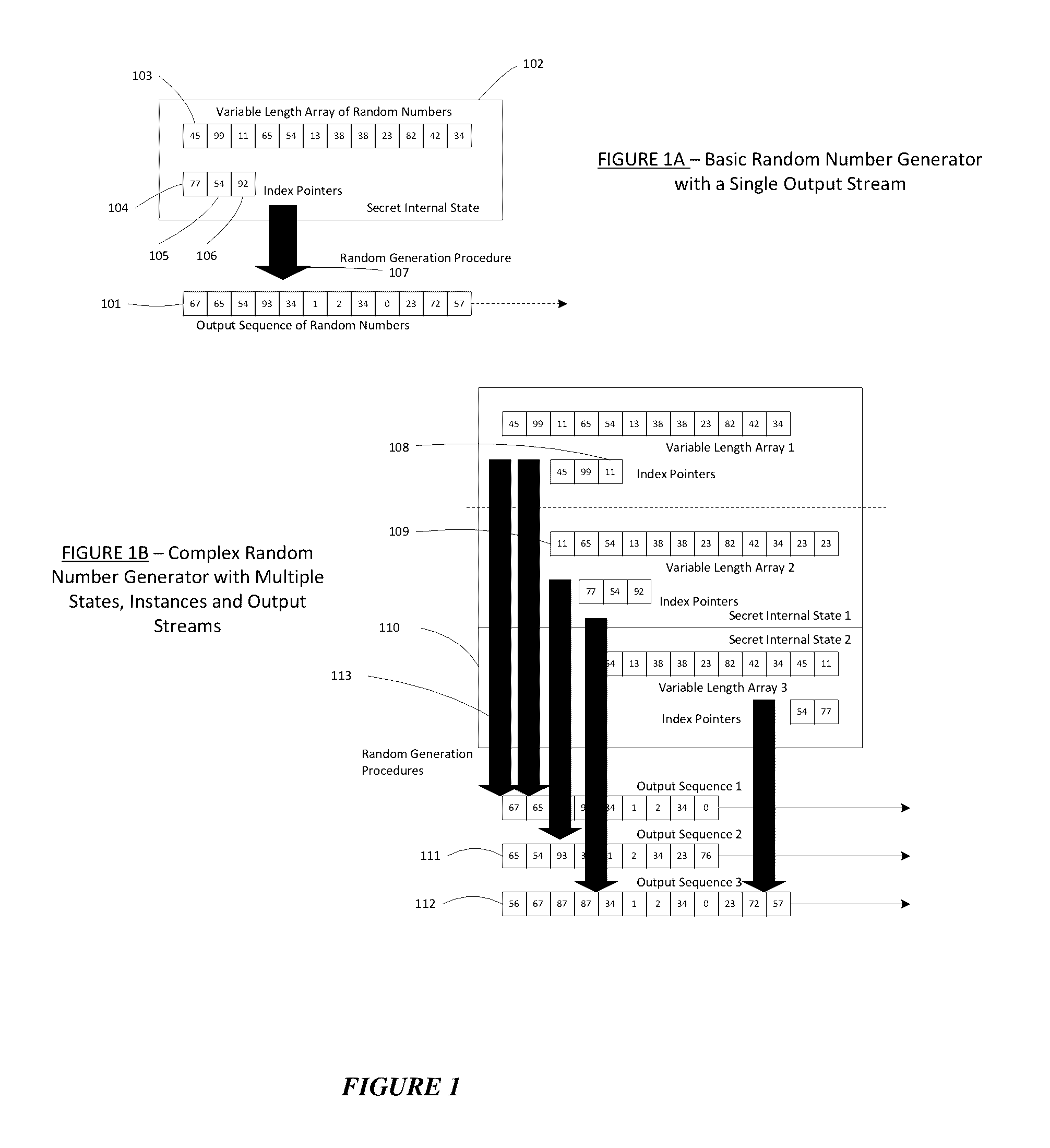
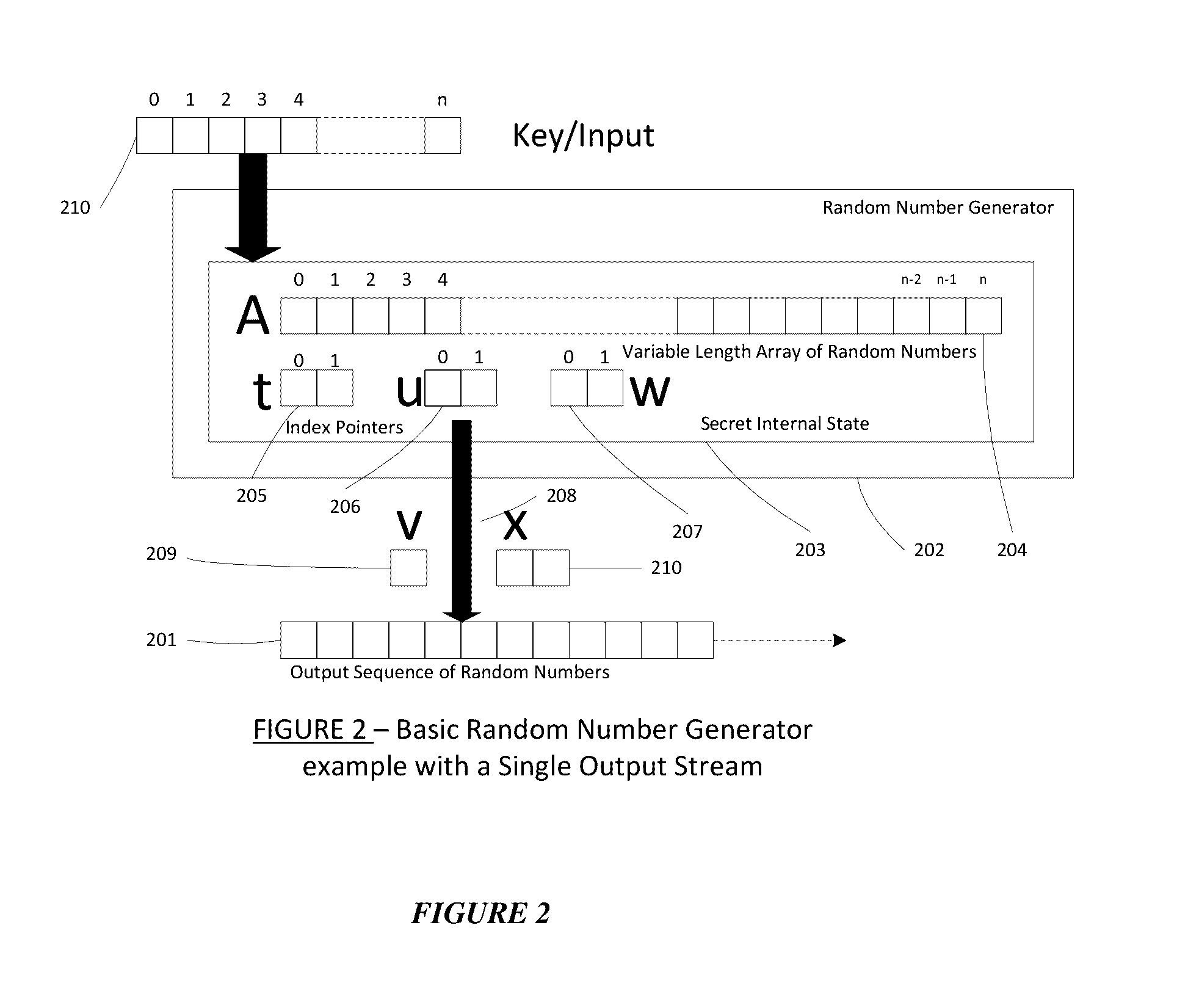
Method for a Dynamic Perpetual Encryption Cryptosystem
A dynamic computer communication security encryption method or system using an initial seed key and multiple random number generators of a specific design, whereby a sequence of independent random entropy values is produced by one set of random number generators and encrypted along with the message stream using the initial seed key, or the output of a second set of random number generators initialized with the initial seed key, and following the subsequent transmission of the variable encrypted entropy / message block, the entropy values are used to symmetrically or identically augment or increase the current uncertainty or entropy of the cryptosystem at both the sender and the receiver, prior to the next encryption block operation. The encryption process effectively entailing the use of multiple encryption ciphers, and the entropy augmentation process entailing the encryption or application of various logical mathematical operations on the already dynamic but deterministic internal state values of the second set of random number generators, effectively altering their deterministic outputs in a random probabilistic manner.Random length message value sequences from one or more data sources is combined with one or more random length entropy value sequences from an independent source, following which the entropy “updates” may also be used to alter, or change any cryptosystem variable, value or component in a randomly determined manner. In addition, whilst ensuring synchronization, the random entropy sequences also serve to “pollute” the cipher-stream and thereby hinder most current forms of cryptanalysis, whilst simultaneously injecting additional entropy into the cryptographic system and allowing for its propagation to affect any connected system nodes, and thereby introducing unpredictable entropy into the system pseudorandom number generator outputs, and thereby ensuring the perpetual generation of unpredictable random numbers.Super-encryption mechanics are independent of the user data, simple, fast and efficient, and can incorporate compression, error correction and asymmetric encryption authentication routines. But most importantly, super-encryption ensures resistance to brute force attacks (not possible to verify if a message was even sent), an ability to exceed “perfect secrecy” requirements, and an improvement on previous super-encipherment design, since overhead can be dramatically reduced from 100% overhead.Communication links previously established by system nodes with central authorities may be used for secure node authentication and registration, whilst allowing the central authority to broker and synchronize communication channels and providing mutual authentication and other security functions between the system nodes.
Owner:FIGUEIRA HELDER SILVESTRE PAIVA
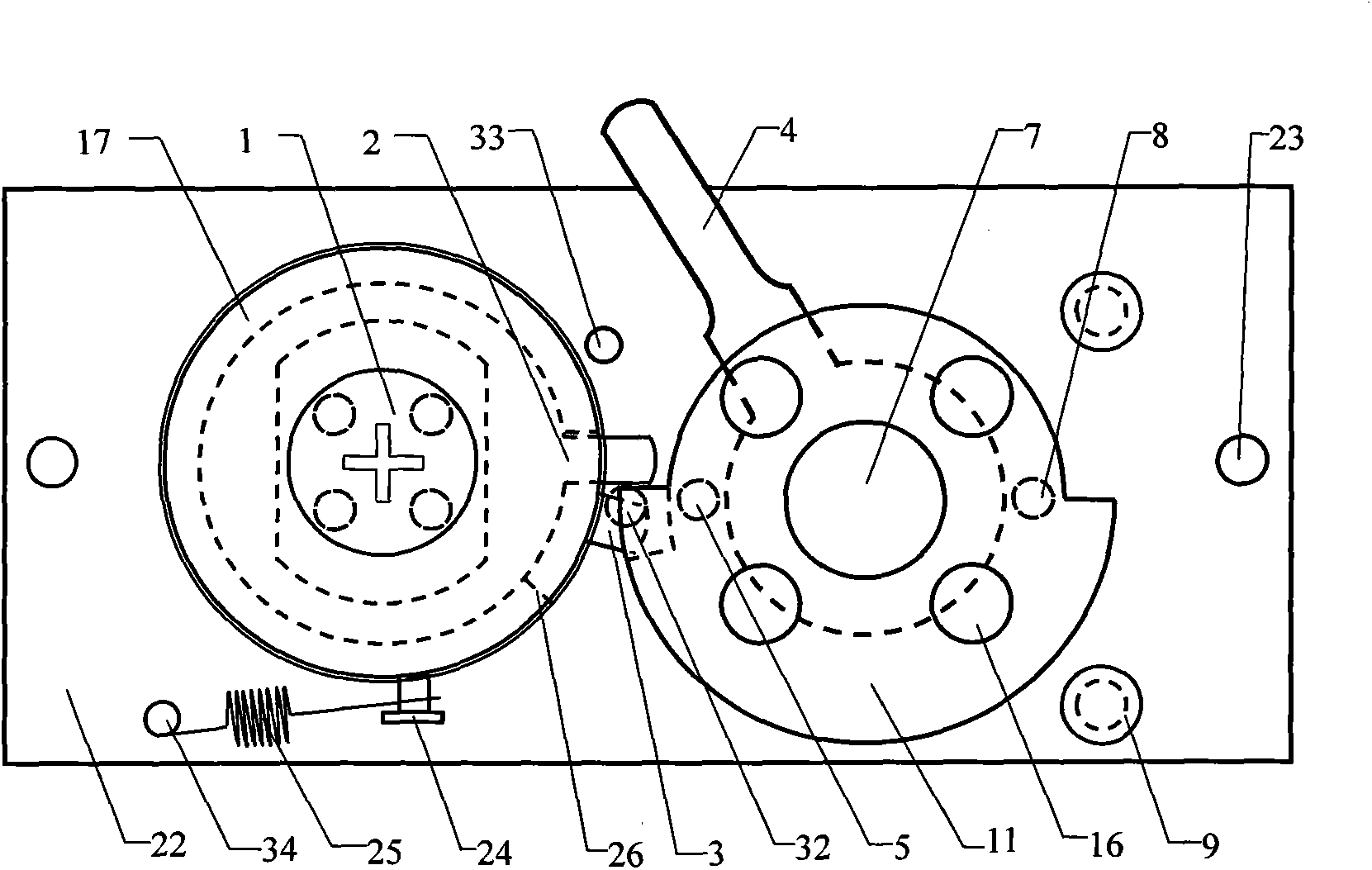
Cross mechanical anti-theft lock with fixed lock cylinder
The invention relates to a cross mechanical anti-theft lock with a fixed lock cylinder. The lock comprises a prying resistant plate, a drilling resistant piece, a backboard, a lock cylinder, an inner rotary ring, an outer rotary ring, a dialing ring, a moment limiter, a cam shaft and a matched key. The lock is mainly characterized in that the lock cylinder is fixedly assembled between the prying resistant plate and the backboard and cannot move. Driven by the cam, the inner and outer rotary rings at the periphery of the lock cylinder synchronously rotate an angle of 15 degrees first and are staggered with the lock cylinder, and then the outer rotary ring continuously rotates independently and unlocks, so that the lock cannot be unlocked technically. The prying resistant plate is located outside the lock cylinder, and a cross hole is formed in a position corresponding to the prying resistant plate, so that the lock is prevented from being destructively unlocked by a forced unlocking tool. The moment limiter can idle when a handle is rotated with brute force, so that the lock is prevented from being damaged and cannot be unlocked. The unlocking process comprises the following steps: inserting the key without rotating the key and rotating the handle for 90 degrees. The lock is locked without the key and in a way of reversely rotating the handle for an angle of 50 degree.
Owner:吕雪寒
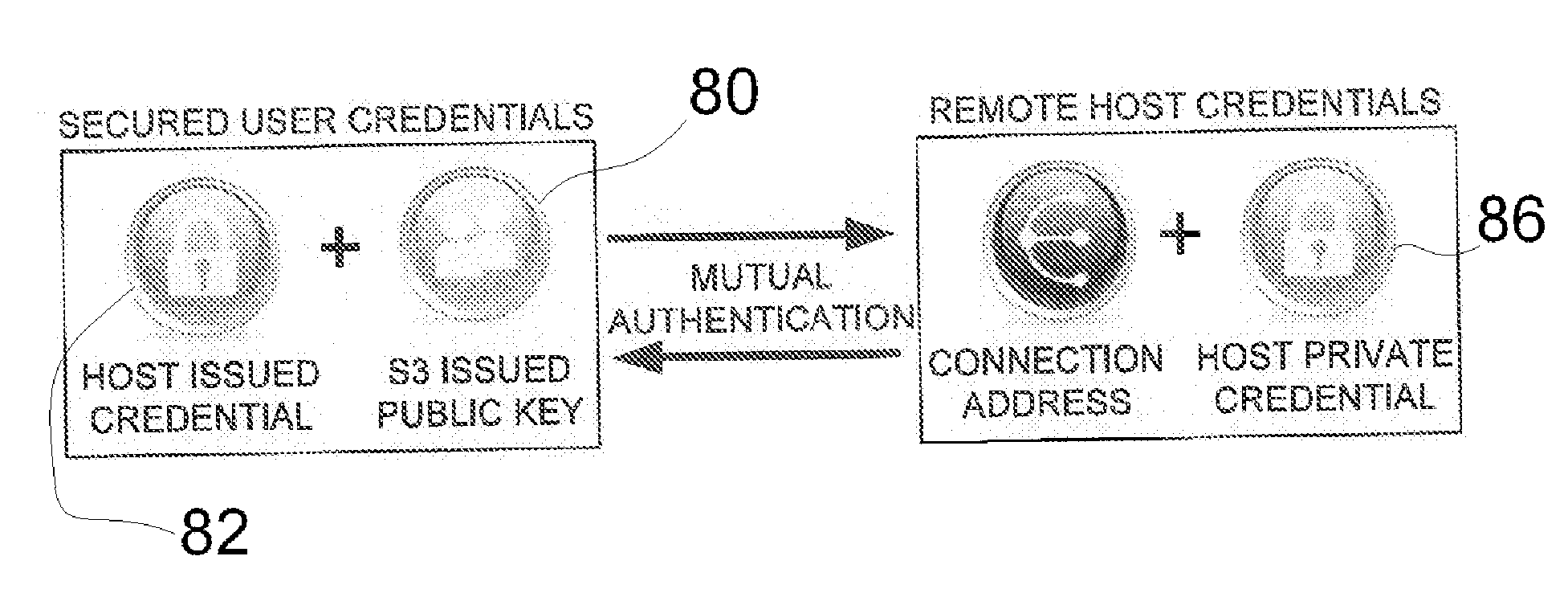
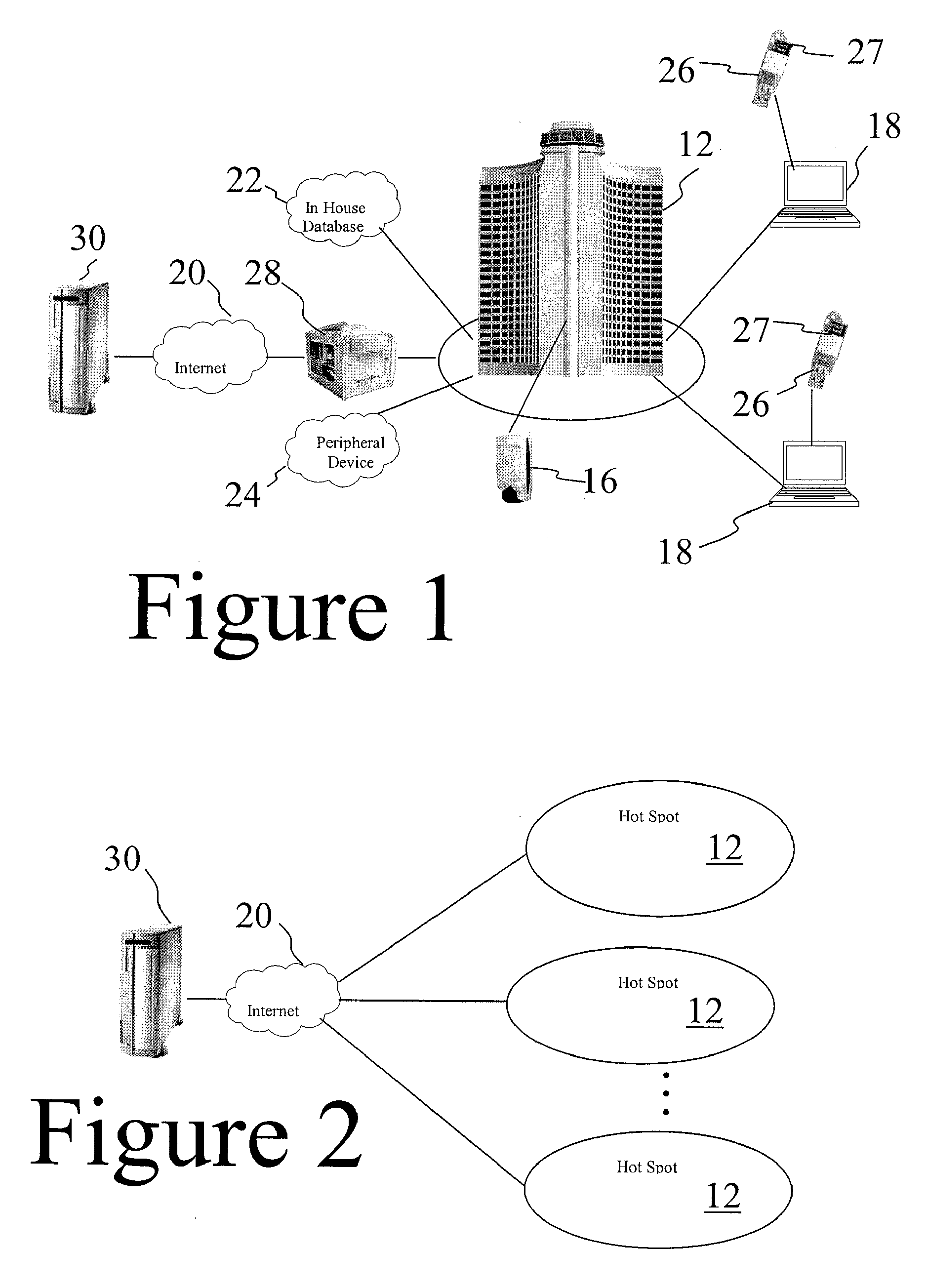
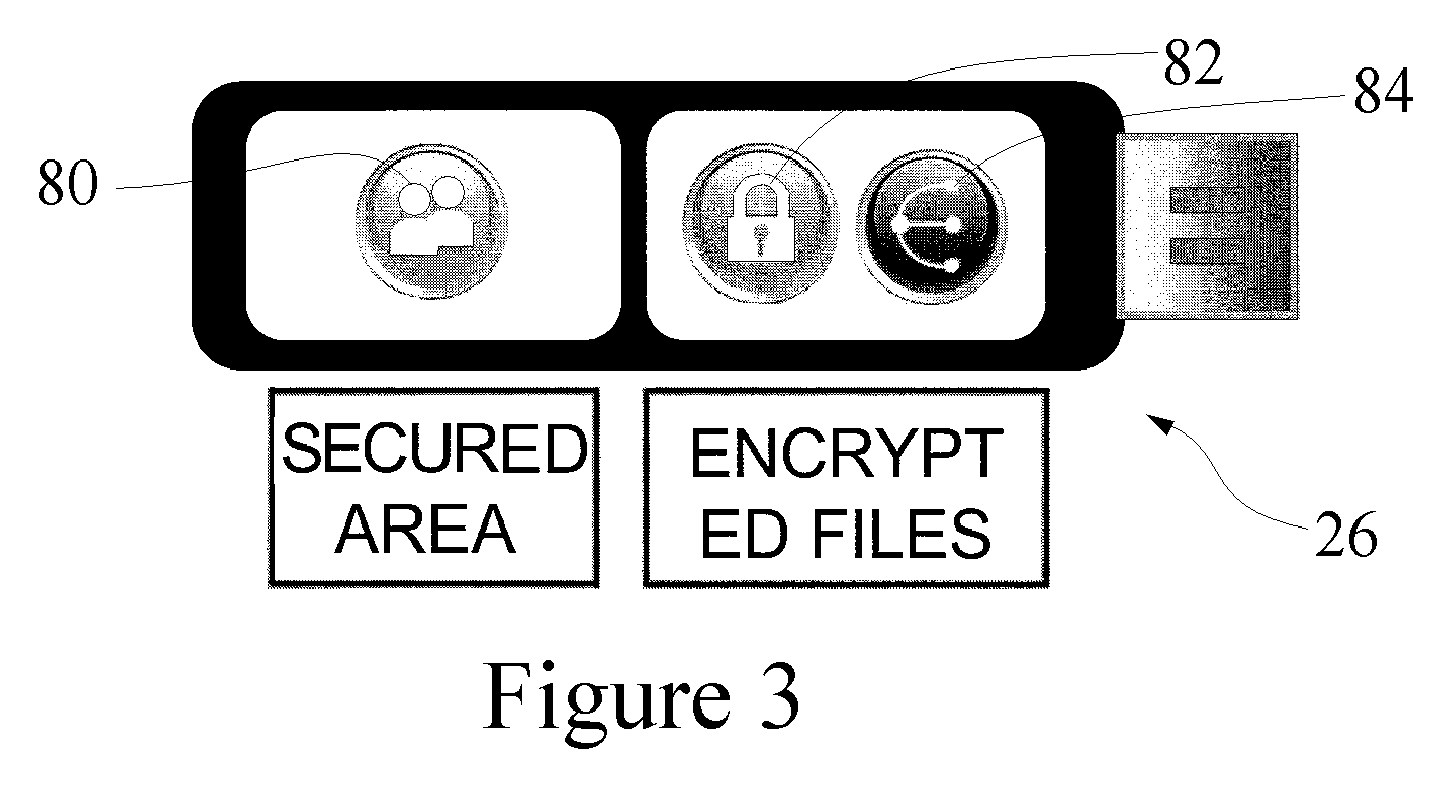
Token based two factor authentication and virtual private networking system for network management and security and online third party multiple network management method
InactiveUS20070186099A1Efficient and effectiveNetwork topologiesDigital data authenticationBrute forcePrivate network
A two-factor network authentication system uses “something you know” in the form of a password / Pin and “something you have” in the form of a key token. The password is encrypted in a secure area of the USB device and is protected from brute force attacks. The key token includes authentication credentials. Users cannot authenticate without the key token. Four distinct authentication elements that the must be present. The first element is a global unique identifier that is unique to each key. The second is a private credential generated from the online service provider that is stored in a secure area of the USB device. The third element is a connection profile that is generated from the online service provider. The fourth element is a credential that is securely stored with the online service provider. The first two elements create a unique user identity. The second two elements create mutual authentication.
Owner:DIRECTPOINTE
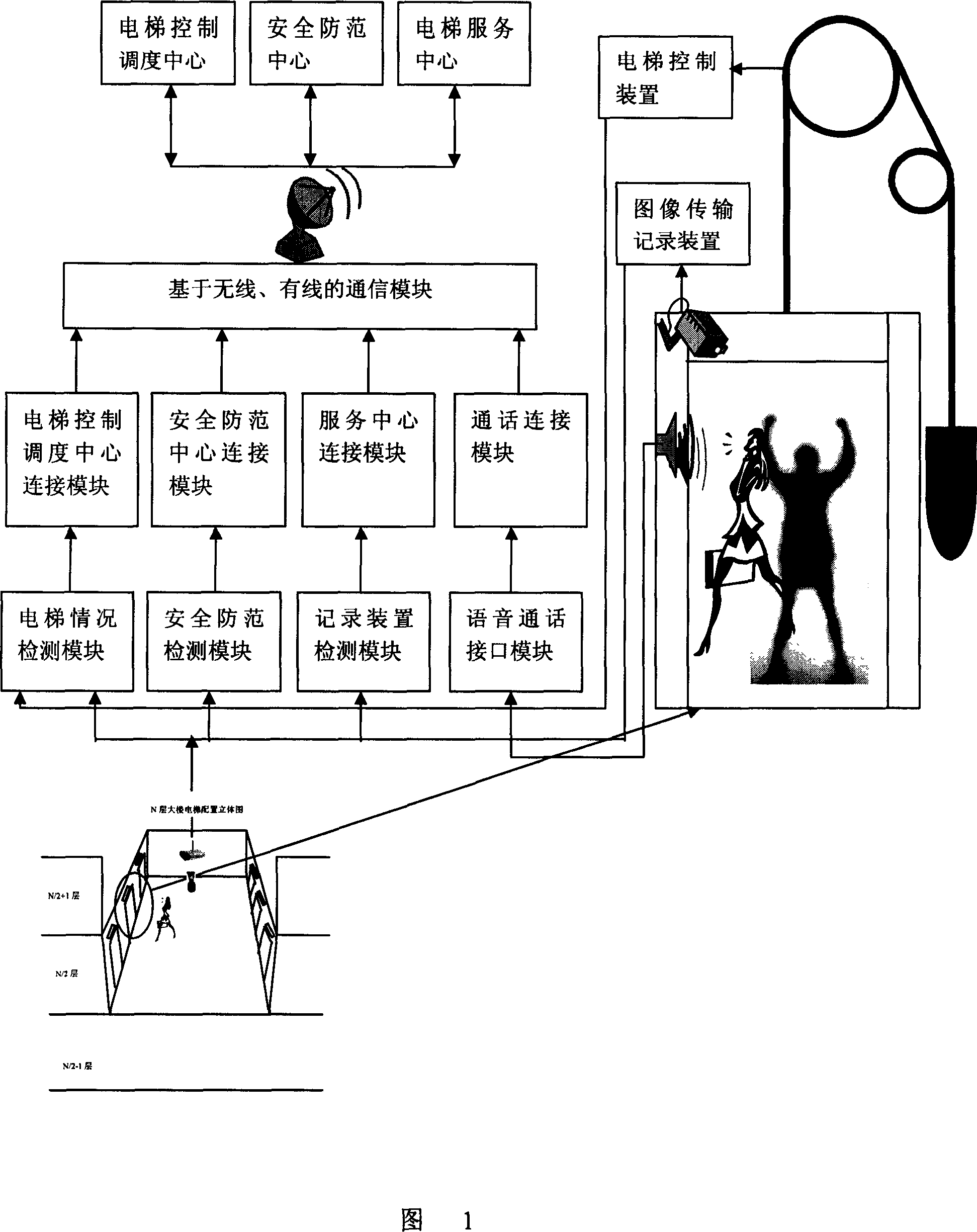
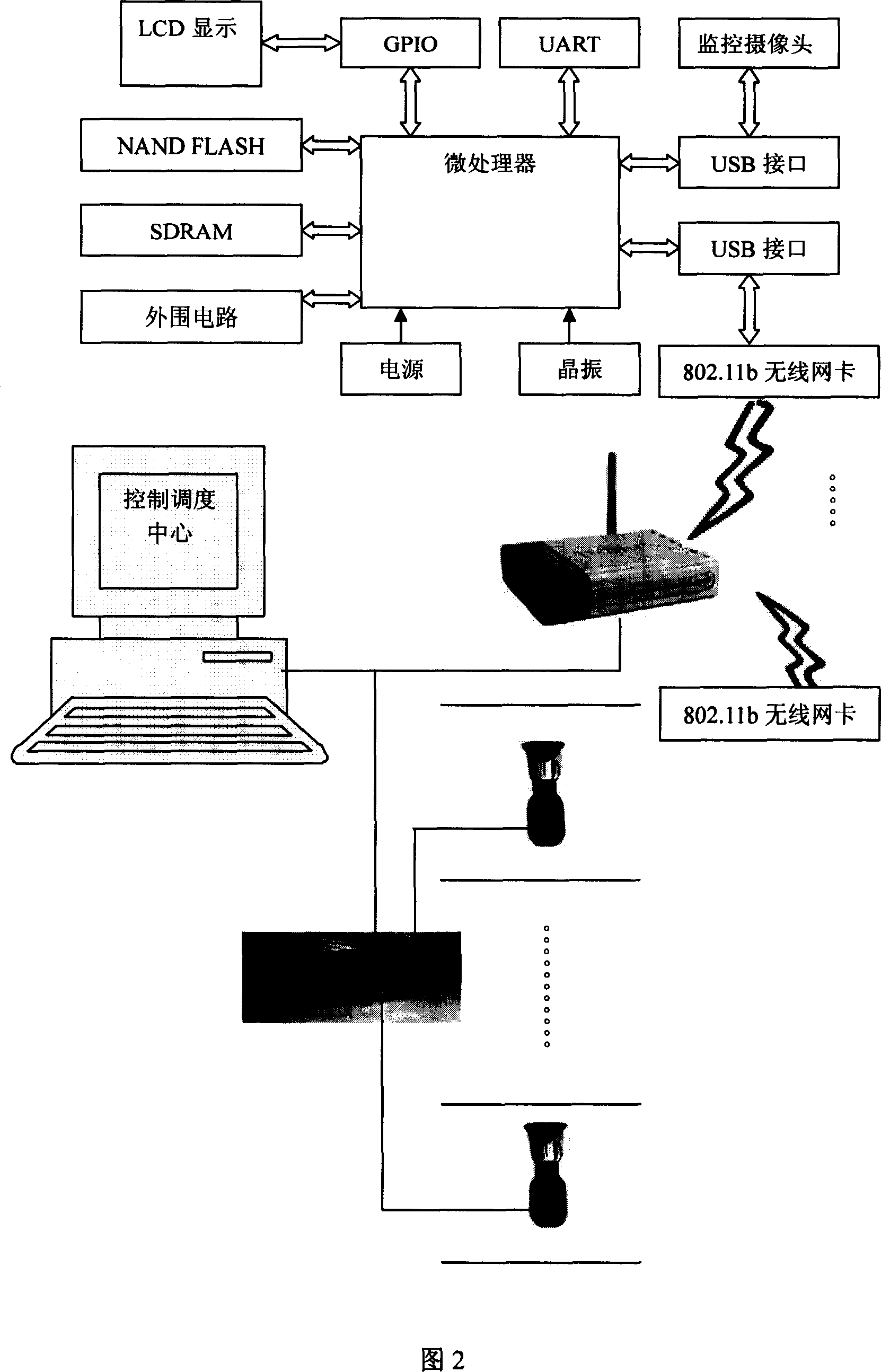
Elevator inner violence-proof apparatus based on image and speech recognition technique
The invention discloses an elevator inner-brute force device based on image and voice recognizing technology, which comprises the following parts: video sensor, voice receiver and monitor central computer to monitor elevator, wherein the video sensor and voice receiver connects monitor center computer through wireless network equipment, which contains display mode to display real-time elevator video data, the video sensor connects monitor central computer through wireless network exchanging equipment, which is warless LAN center, the computer contains microprocessor with image reading mode, image variation calculating mode, connecting area calculating mode, judging mode in the elevator to judge whether the accident occurs.
Owner:ZHEJIANG UNIV OF TECH
Enabling Faster Full-Text Searching Using a Structured Data Store
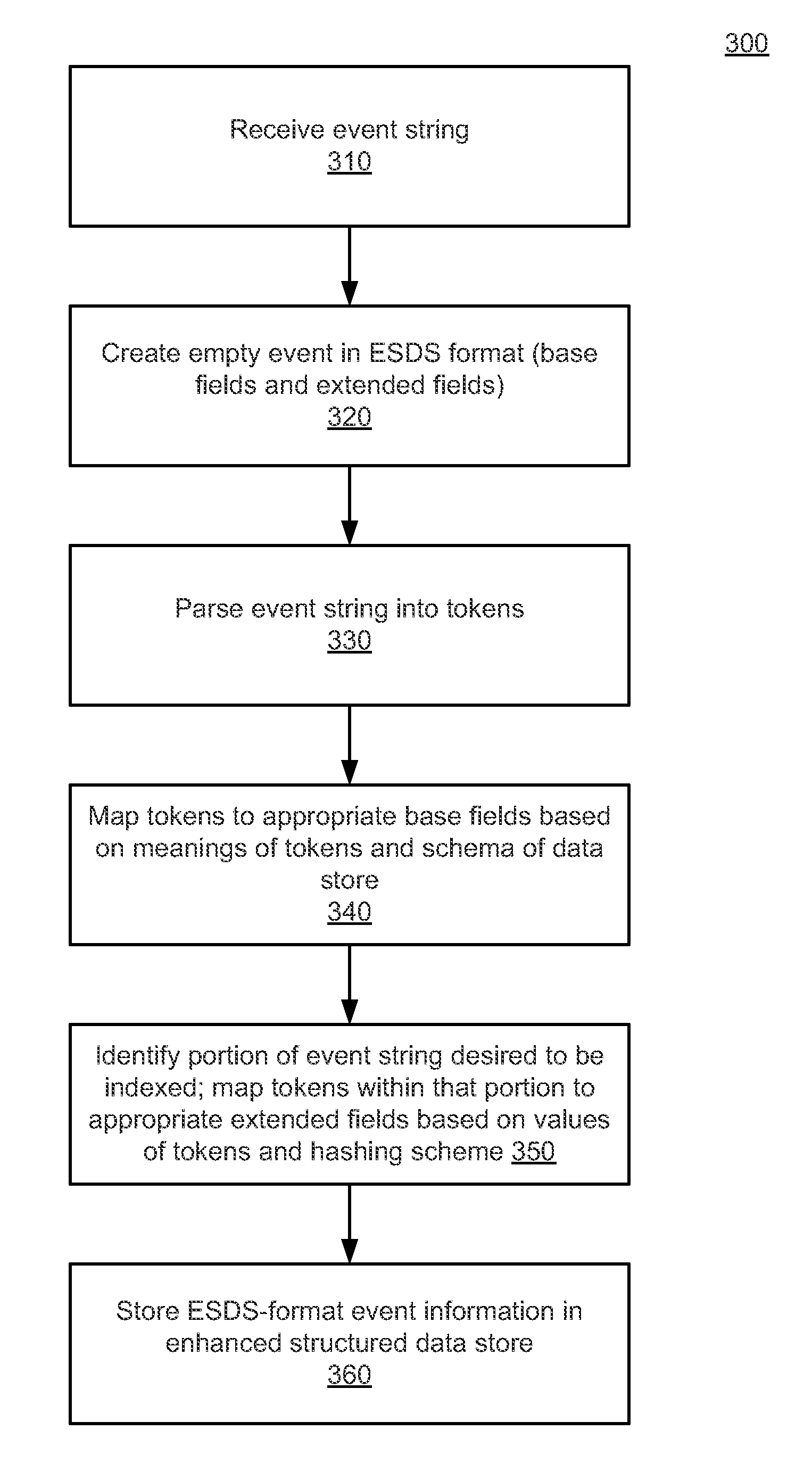
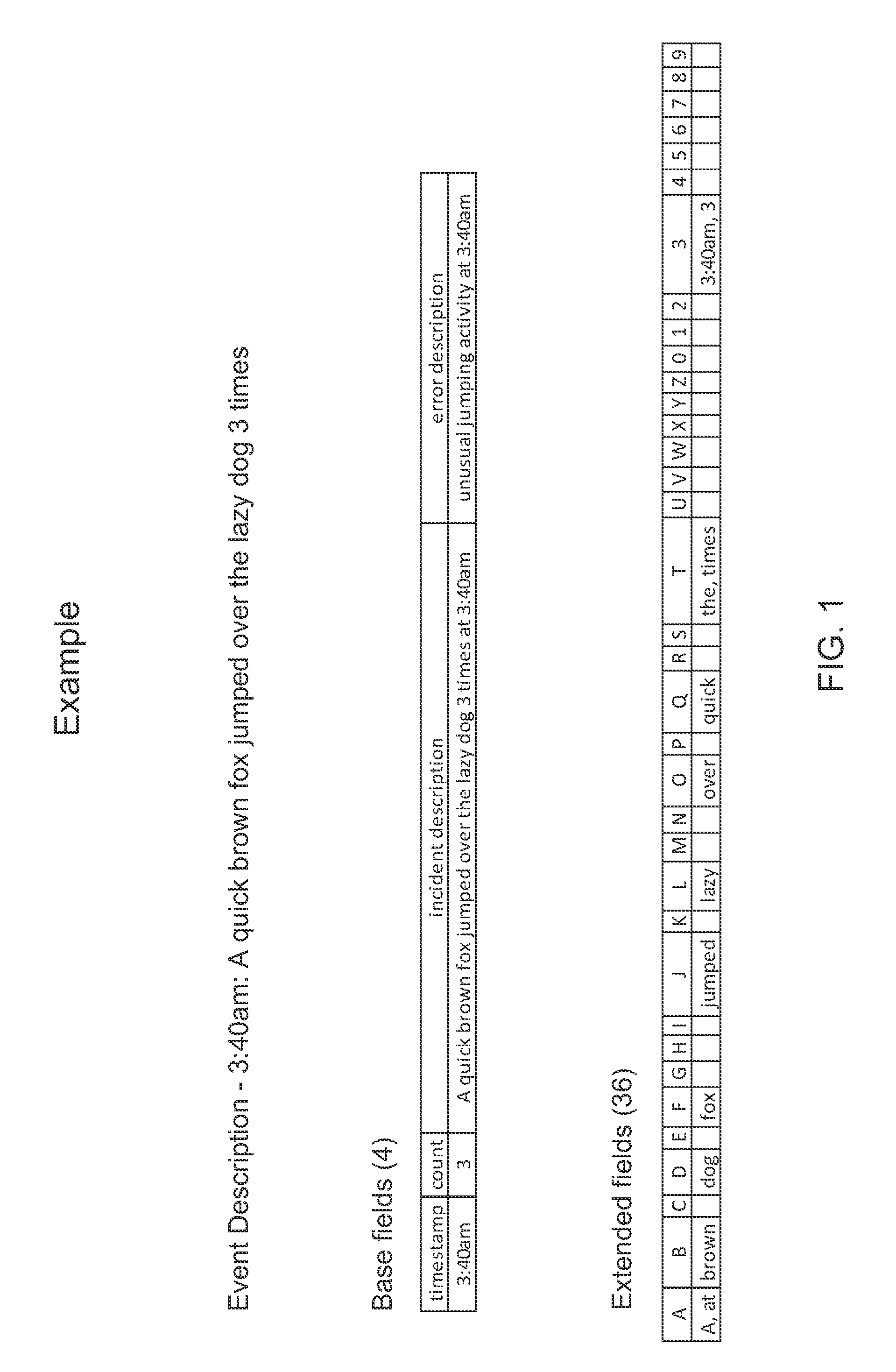
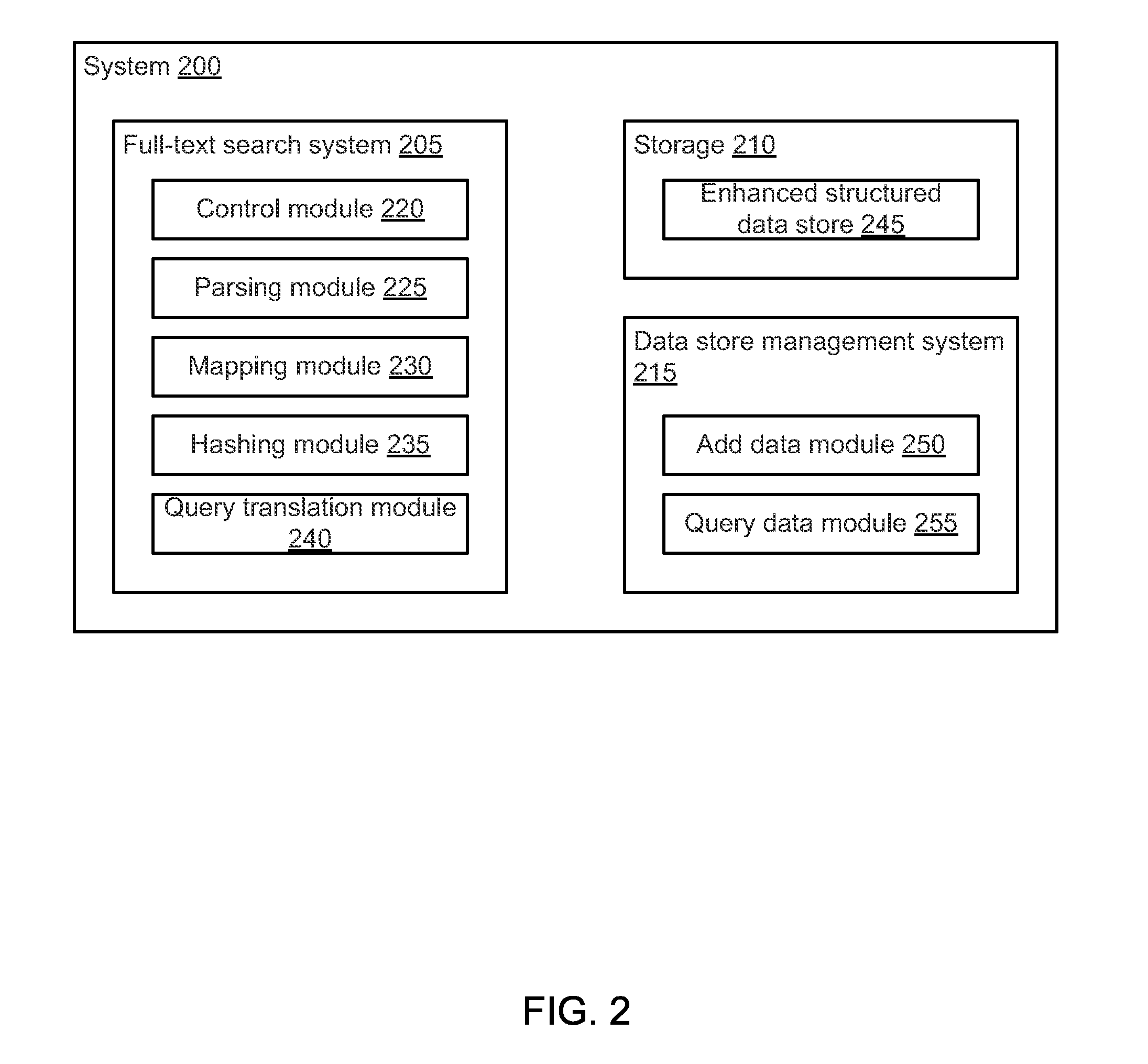
InactiveUS20110113048A1Avoid overheadIncrease data storageDigital data information retrievalComparison of digital valuesSyntaxBrute force
A traditional structured data store is leveraged to provide the benefits of an unstructured full-text search system. A fixed number of “extended” columns is added to the traditional structured data store to form an “enhanced structured data store” (ESDS). The extended columns are independent of any regular columnar interpretation of the data and enable the data that they store to be searched using standard full-text query syntax / techniques that can be executed faster (as opposed to SQL syntax). In other words, the added columns act as a search index. A token is stored in an appropriate extended column based on that token's hash value. The hash value is determined using a hashing scheme, which operates based on the value of the token, rather than the meaning of the token. This enables subsequent searches to be expressed as full-text queries without degrading the ensuing search to a brute force scan.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
System and method for balancing computational load across a plurality of processors
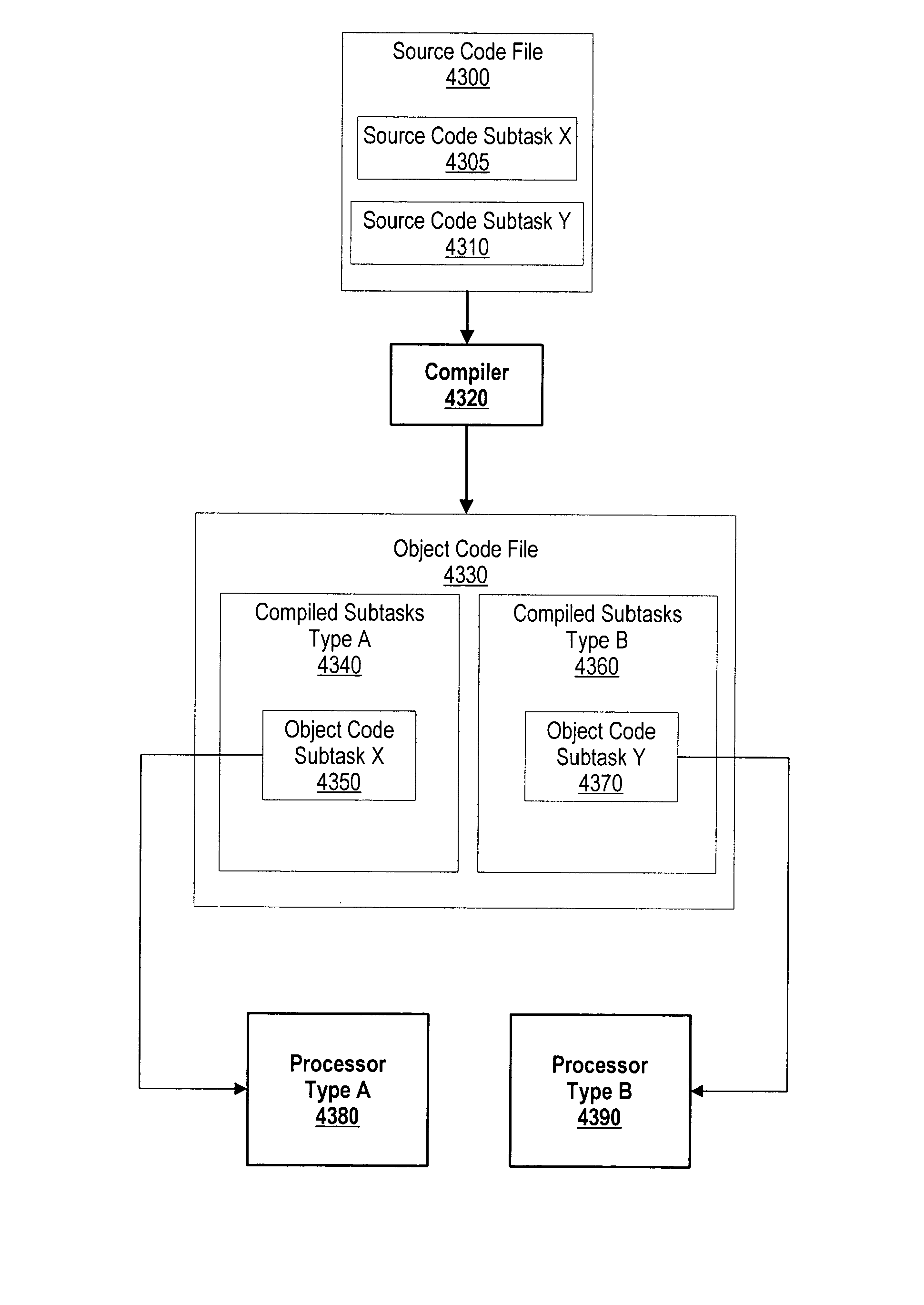
InactiveUS20050081182A1Resource allocationSpecific program execution arrangementsBrute forceObject code
A system and method for balancing computational load across a plurality of processors. Source code subtasks are compiled into byte code subtasks whereby the byte code subtasks are translated into processor-specific object code subtasks at runtime. The processor-type selection is based upon one of three approaches which are 1) a brute force approach, 2) higher-level approach, or 3) processor availability approach. Each object code subtask is loaded in a corresponding processor type for execution. In one embodiment, a compiler stores a pointer in a byte code file that references the location of a byte code subtask. In this embodiment, the byte code subtask is stored in a shared library and, at runtime, a runtime loader uses the pointer to identify the location of the byte code subtask in order to translate the byte code subtask.
Owner:IBM CORP
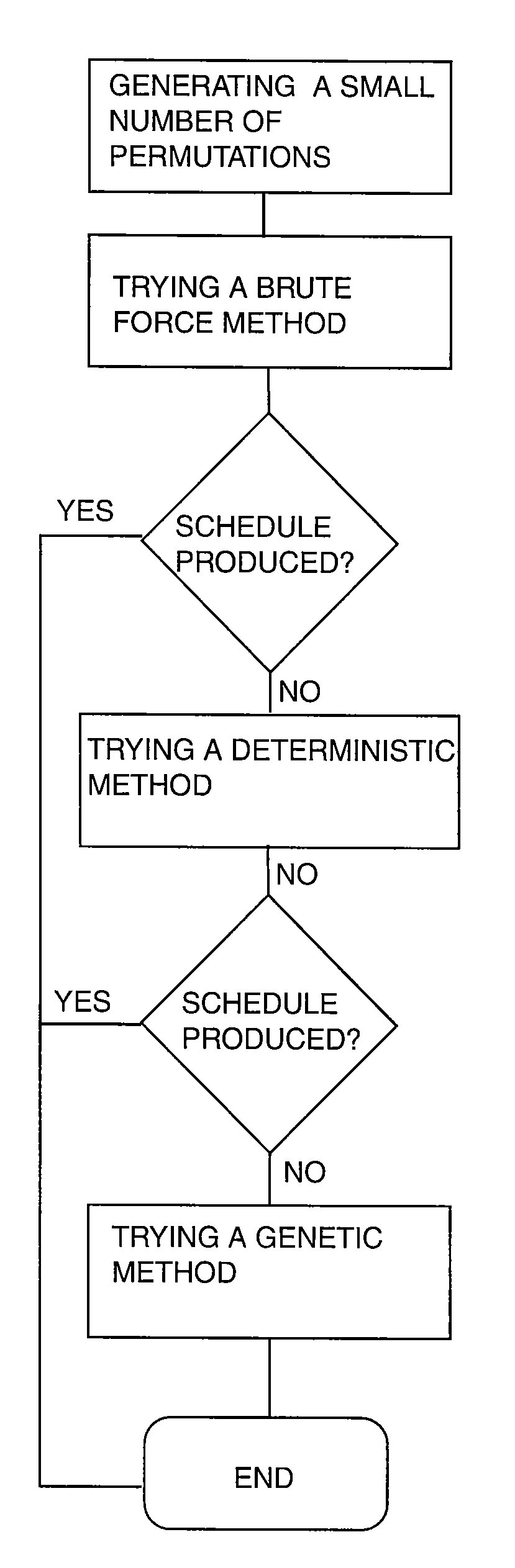
System for scheduling multiple time dependent events
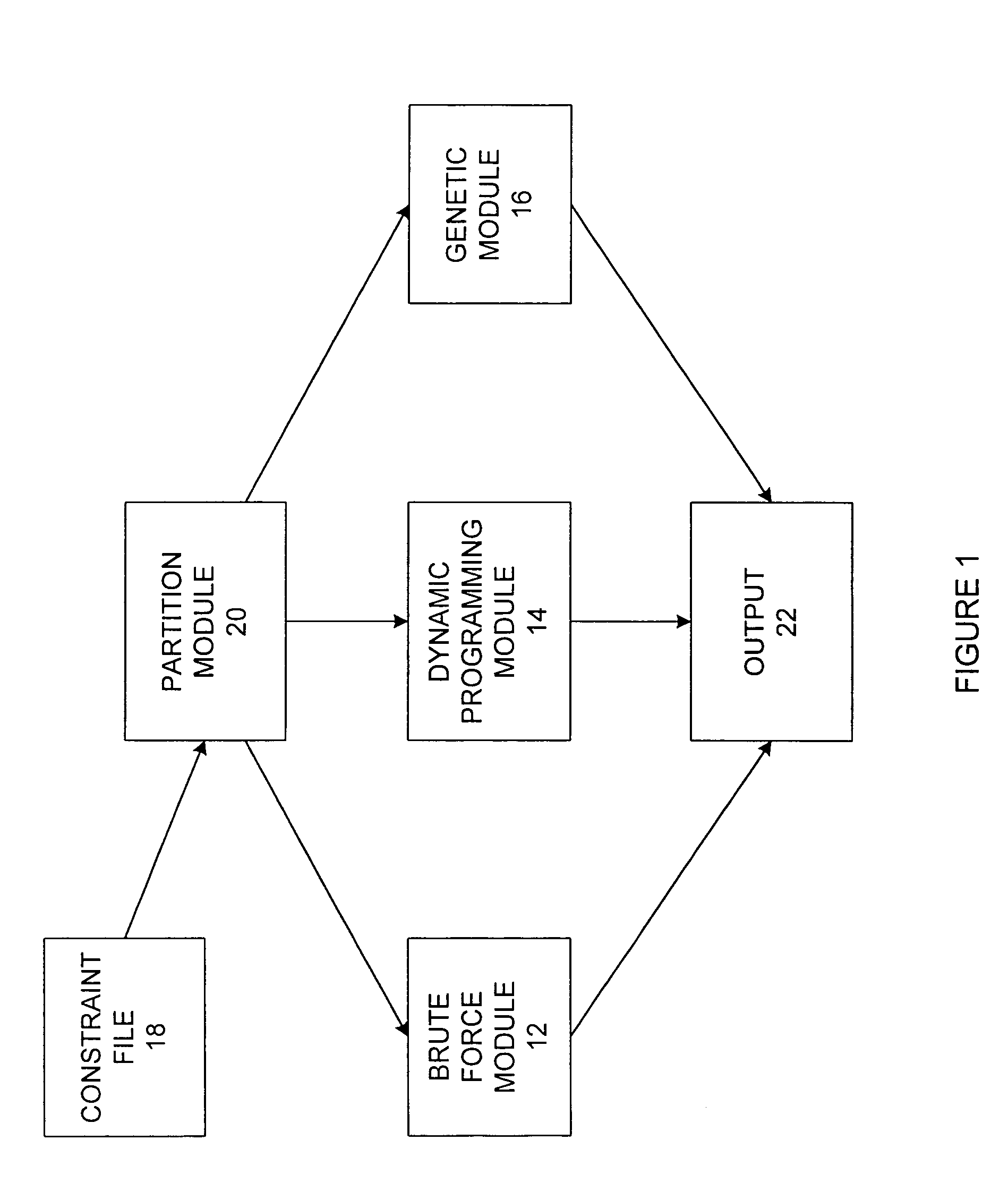
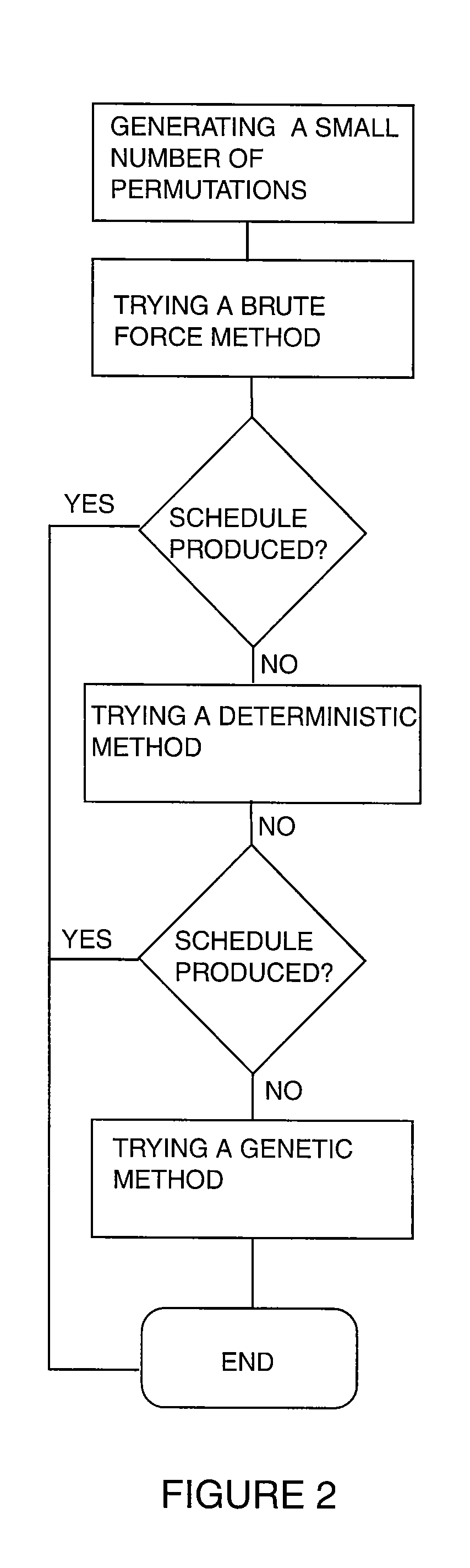
InactiveUS7246075B1Reduce the amount requiredSignificant memory savingResourcesSpecial data processing applicationsTime scheduleBrute force
A scheduling system for choosing the most appropriate heuristic for solving time-dependant scheduling problems. The invention includes a means for selecting the most appropriate heuristic method for generating a schedule from an enumerative (“brute force”) method, a dynamic programming method, and a genetic method. The invention further includes a hashing function that is capable of detecting duplicate solutions generated by the dynamic programming module and a height-balanced binary tree for providing search insertion and deletion operations.
Owner:MAGNOLIA CONSULTING INC
System and method for compiling source code for multi-processor environments
A system and method for compiling source code for multi-processor environments is presented. Source code is compiled which creates an object file whereby the object file includes multiple object code subtasks. Source code subtasks are compiled into object code subtasks using one of three approaches which are 1) a lowbrow approach, 2) a brute force approach, and 3) a program directive approach. Each object code subtask is formatted to run on a particular processor type with a particular architecture, such as a microprocessor-based architecture or a digital signal processor-based architecture. During runtime, each object code is loaded onto its corresponding processor type for execution.
Owner:IBM CORP
Secure Authentication Systems and Methods
InactiveUS20080016551A1Digital data processing detailsUser identity/authority verificationBrute forceInternet privacy
Systems and methods are provided for authentication by combining a Reverse Turing Test (RTT) with password-based user authentication protocols to provide improved resistance to brute force attacks. In accordance with one embodiment of the invention, a method is provided for user authentication, the method including receiving a username / password pair associated with a user; requesting one or more responses to a first Reverse Turing Test (RTT); and granting access to the user if a valid response to the first RTT is received and the username / password pair is valid.
Owner:INTERTRUST TECH CORP
Method and apparatus for quantum vortex implosion propulsion and species
InactiveUS20050109879A1Improve effective utilizationEasy constructionPower plant arrangements/mountingRadiation/particle handlingBrute forceFuel efficiency
System for converting high frequency quantum electrodynamic radiation energy and at least one atom through cavity vacuum fluctuations and converting same into a superconductive electrical implosion propulsion energy from zero point energy at a frequency that is amenable to conversion to electrical and implosive propulsion and superconductive energy extracted within an environment having a desired voltage and a reversed waveform such that the emitted energy returns into the system to be recycled. In an externally winged craft comprising a selectively shaped vacuum cohesive fuselage and means for providing lift and propulsion for an aircraft generating an enormous electrostatic vortex lifting force when energized in conjunction with the quantum electrodynamic vortex implosion propulsion system and power plant maximizing fuel efficiencies including the extraction of usable energy from the vacuum of space. Actually riding on or in the shock waves verses the brute force disruption of the environment's equilibrium, as is the case with conventional modes of transportation or aircraft design.
Owner:PATTERSON ROBERT A
Efficient and safe data deduplication method and efficient and safe data deduplication system based on user perception
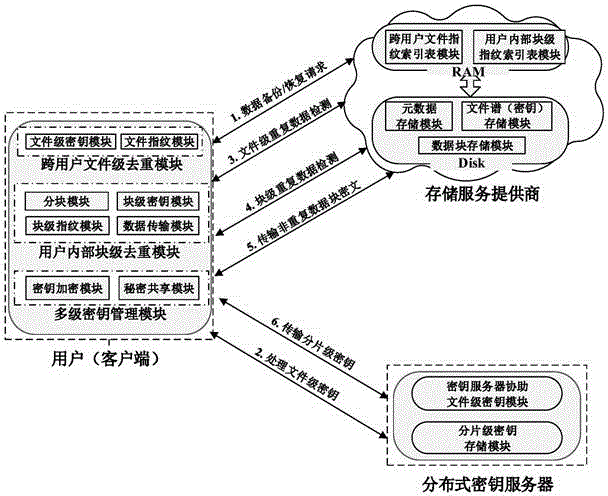
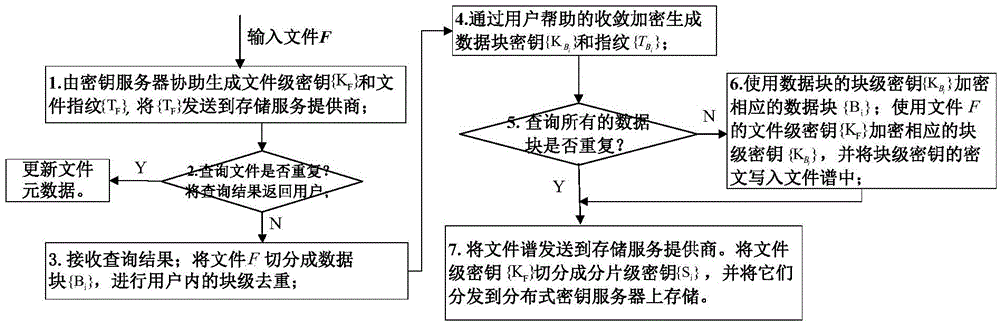
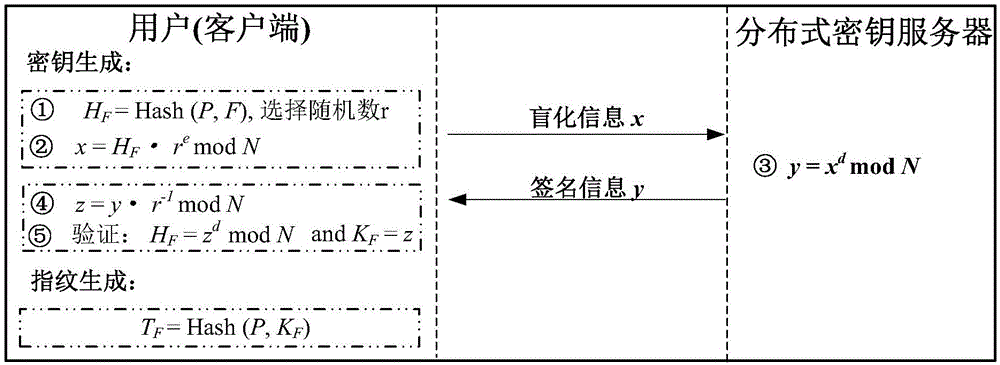
ActiveCN104917609AResistance to brute force attacksGuaranteed confidentialityKey distribution for secure communicationSpecial data processing applicationsBrute forceConfidentiality
The invention provides an efficient and safe data deduplication method based on user perception, which comprises the steps that a client adopts key server assisted Hash-based convergence encryption to carry out file-level data deduplication across users; if duplication does not exists in files, user assisted convergence encryption is adopted to carry out block-level deduplication inside the users; and multilevel key management is adopted, a file-level secret key is used to encrypt a block-level secret key, the file-level secret key is segmented into fragment-level secret keys by using secret sharing, and the fragment-level secret keys are stored in a distributed key server. The invention further provides an efficient and safe data deduplication system based on user perception. According to the invention, random information is added through adopting key server assisted Hash-based convergence encryption in a file level and adopting user assisted convergence encryption in a block level, thereby enabling file-level secret keys and block-level secret keys of users to be randomized, being capable of effectively resisting brute force attacks of opponents, and ensuring the data confidentiality and the safety of the users; and the multilevel key management scheme is adopted to ensure the safety of secret keys, and the secret key space overhead is reduced.
Owner:HUAZHONG UNIV OF SCI & TECH
Crinkle-resistant finishing protective agent and method for crinkle-resistant finishing of fabrics
InactiveCN1963012AGood orientationStrong retention rateFibre treatmentLiquid/gas/vapor textile treatmentWrinkle skinBrute force
The invention discloses a wrinkle-resistant collating protective agent, and it includes the following components : polybasic carboxylic acid 40-120g / l, accelerant 20-80g / l, softening agent 10-50g / l, penetrating agent 1-3g / l, polyethylene glycol 40-200g / l, water 547-889g / l; the method used to wrinkle-resisting and collating the fabric includes the following steps : soaking and rolling the fabric in wrinkle-resistant collating liquid respectively twice, the liquid pickup rate is 65 -75%, predrying for 3-5 minutes in 80 DEG C, then baking it for 2 minutes 150-190 degree C, washing with water, drying. The invention improves the loss of ripping strength of collating fabric and the hand touch of collating cloth; the resiliency of collated fabric, the brute force reserve rate, dyeing K / S values are improved substantially, the control of process is simple, and the raw materials origin of auxiliary agent is wide and cheap.
Owner:DONGHUA UNIV
Methods and systems for unilateral authentication of messages
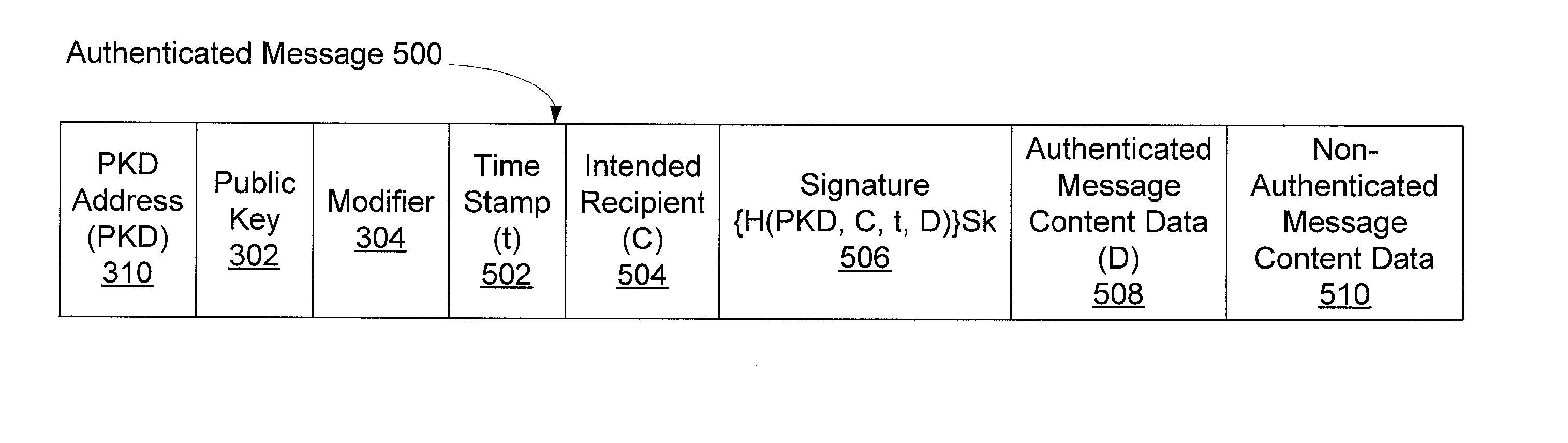
InactiveUS7134019B2Optimization mechanismUser identity/authority verificationSecret communicationBrute forceAuthentication
Disclosed is an authentication mechanism that enables an information recipient to ascertain that the information comes from the sender it purports to be from. This mechanism integrates a private / public key pair with selection by the sender of a portion of its address. The sender derives its address from its public key, for example, by using a hash of the key. The recipient verifies the association between the address and the sender's private key. The recipient may retrieve the key from an insecure resource and know that it has the correct key because only that key can produce the sender's address in the message. The hash may be made larger than the sender-selectable portion of the address. The recipient may cache public key / address pairs and use the cache to detect brute force attacks and to survive denial of service attacks. The mechanism may be used to optimize security negotiation algorithms.
Owner:MICROSOFT TECH LICENSING LLC
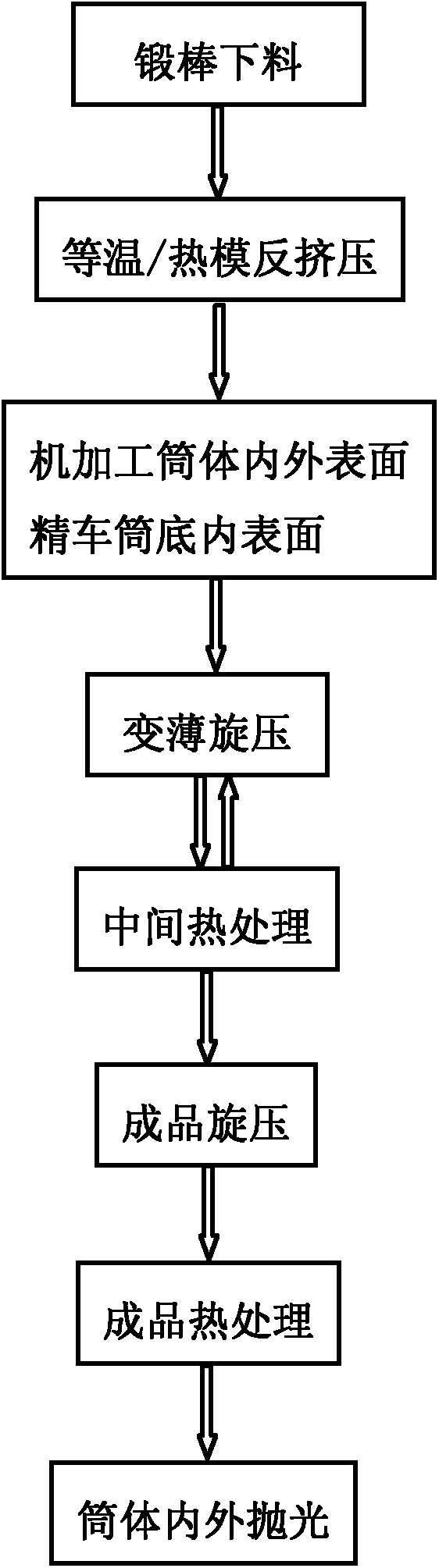
Machining method of high-quality large-diameter thin-wall metal barrel body
The invention relates to a machining method of a high-quality large-diameter thin-wall barrel body. The machining method comprises the following steps. Firstly, isothermy or hot die anti-extrusion technology is utilized, and anti-extrusion is performed on an alloy forging rod. Secondly, machining is performed on the inner and outer surfaces of a spinning barrel billet, and finish turning is performed on the inner surface of the barrel bottom of the barrel billet. Thirdly, multi-pass brute force thinning spinning is performed on the machined spinning barrel billet, and the spinning is hot spinning or cold spinning. Fourthly, intermediate heat treatment is performed on a spinning semi-finished product, and the intermediate heat treatment is annealing or solution treatment. Fifthly, the third step and the fourth step are performed repeatedly and alternatively so that finished product spinning is performed. Sixthly, scouring and cleaning are performed on the barrel body, and finished product heat treatment is performed. Seventhly, polishing of the inner and outer surfaces of the barrel body after heat treatment in the sixth step is performed, and a finished product barrel body is obtained. By adoption of the machining method of the high-quality large-diameter thin-wall barrel body to machine a large-diameter thin-wall metal barrel body without welding lines, organization is even and fine, comprehensive performance is high, the process is short, product additional values are high, and good application and popularizing prospects and certain economic and social benefits are achieved.
Owner:有研金属复材技术有限公司
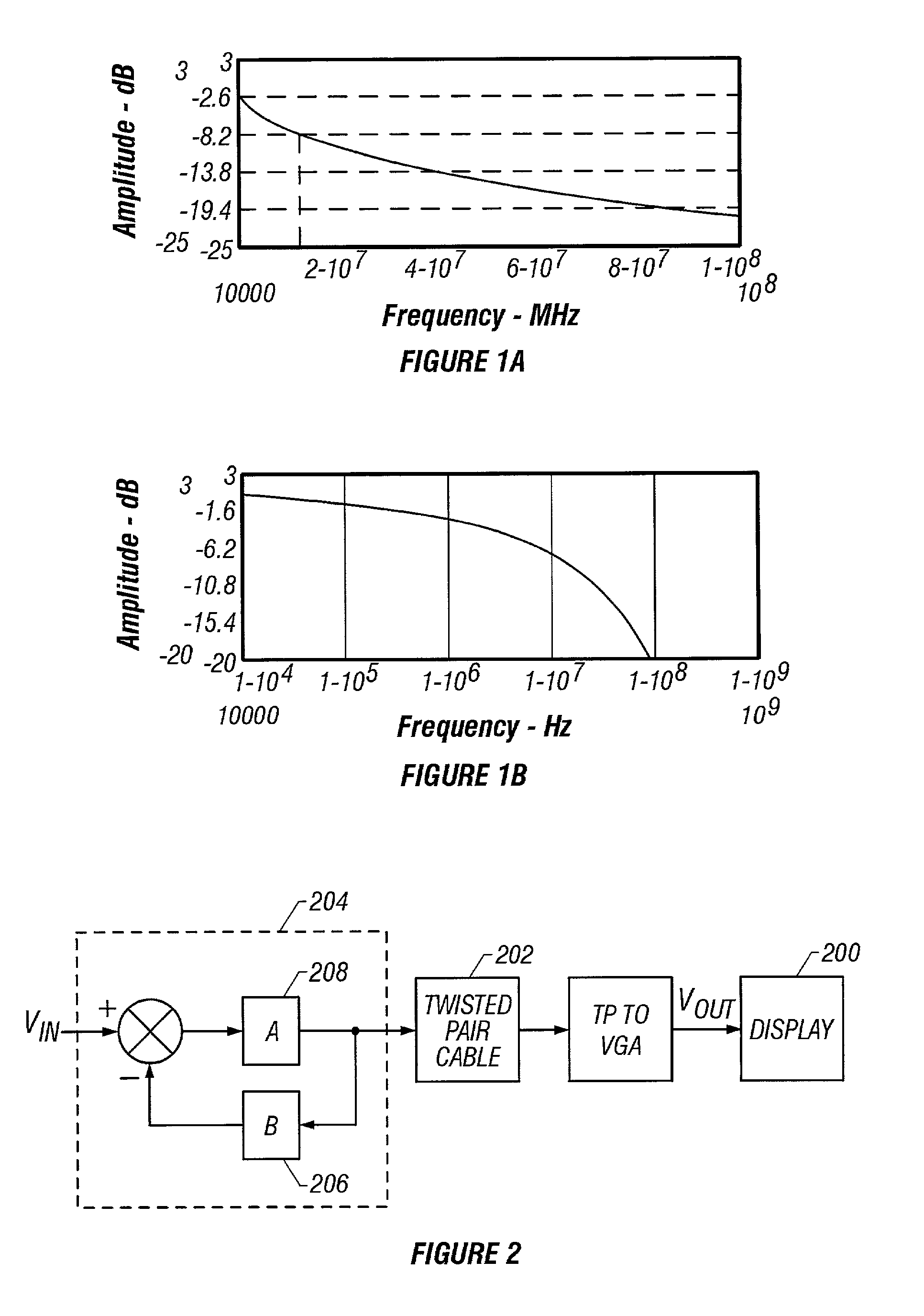
Method and apparatus for equalizing video transmitted over twisted pair cable
ActiveUS7047556B2Enhancing and improving quality of high-resolutionGood cost advantageTelevision system detailsTransmission control/equlisationBrute forceTwisted pair
A apparatus and apparatus for compensating for video insertion loss due to transmission over long twisted pair cable lines is presented. Transmission of video over twisted pair cable is advantageous because of its superior cost advantage over coaxial cable. However, twisted pair cables have significant loss characteristics at the higher frequencies (i.e., broadband) compared to coaxial cables. At a transmitter station, the video signal is amplified in the high frequency region for possible skin effect losses thereby brute forcing the high frequency components to the receiving station. At the receiver station, the video signal is further compensated for diffusion line and skin effect losses. The total skin effect compensation applied in both the transmitter and receiver stations is such that the square root of frequency characteristics of skin effect losses is compensated for. Thus, at the receiving station, the high frequency compensation added at the transmitter to brute force the high frequency components to the receiving station may be removed if found excessive. Additionally, compensation is included to adjust for skew that may occur because of irregularities between the various twisted pairs used to transmit the individual video components. Non-minimum phase type filters are used to inject delay into the faster arriving signals so that they may coincide in phase with later arriving signals resulting in a true reproduction of the video.
Owner:RGB SYST INC
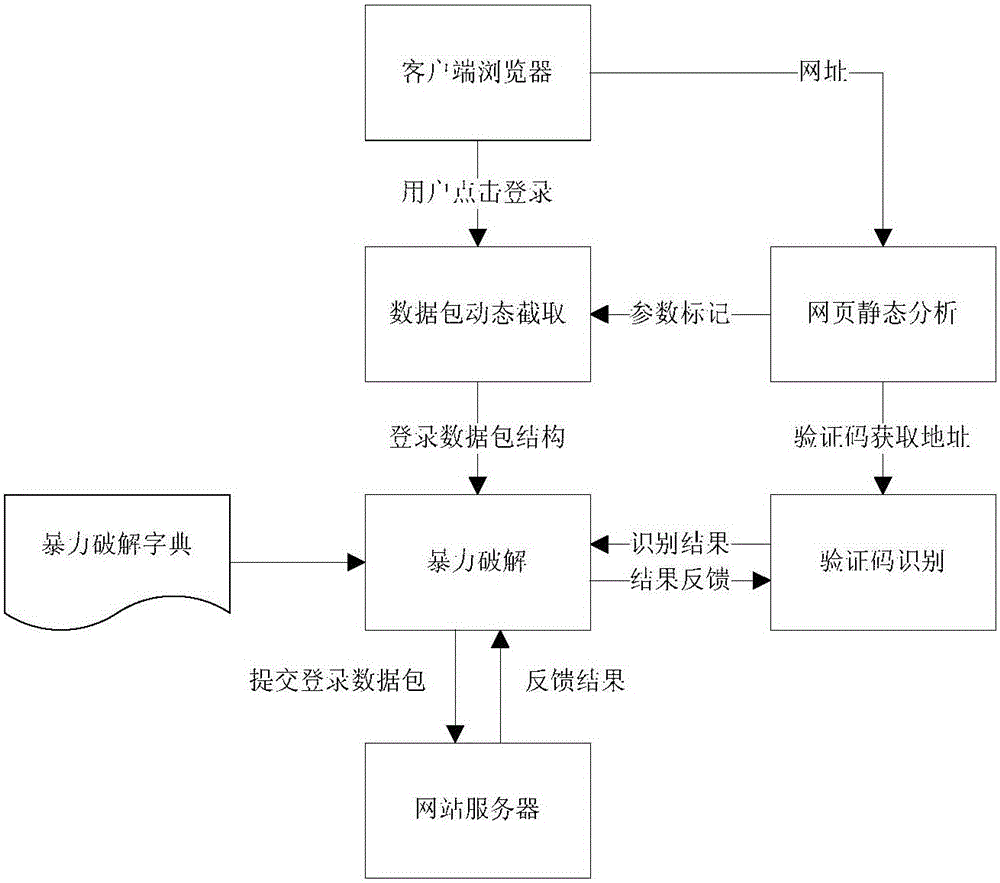
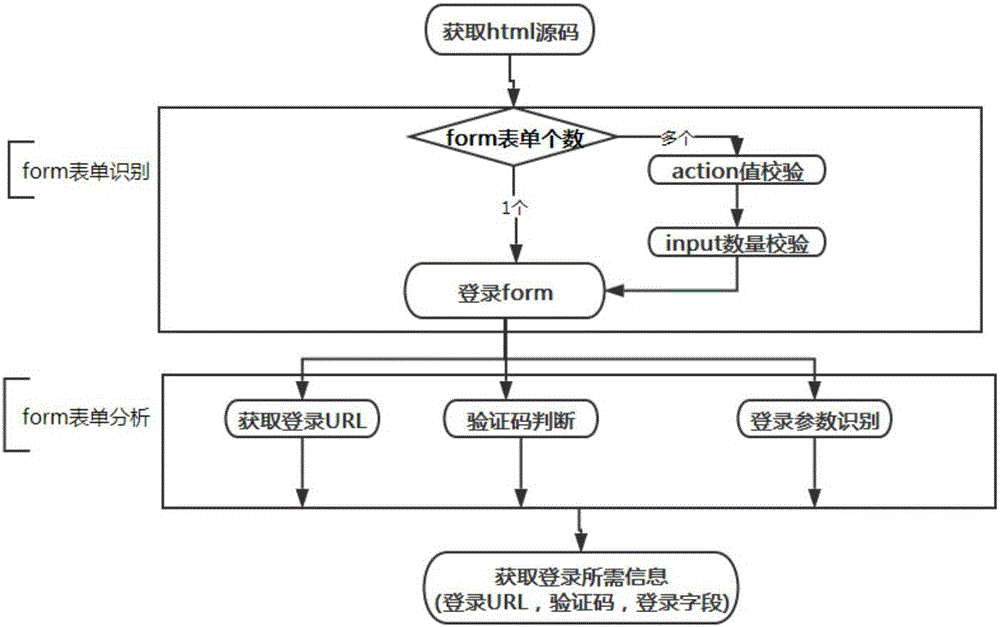
Website login brute force crack method and system capable of identifying verification code
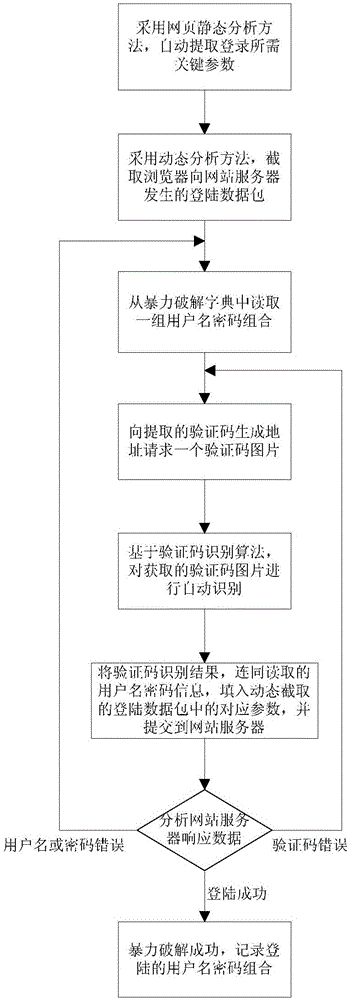
InactiveCN105844140ARealize automatic identificationHigh degree of automationDigital data authenticationPlatform integrity maintainanceBrute forceNetwork packet
The invention provides a website login brute force crack method and system capable of identifying a verification code. The method comprises the steps of 1, through static webpage analysis, extracting information required for website login; 2, through dynamic webpage analysis, intercepting a login data package submitted to a website server by a client browser; 3, reading a group of user names and passwords from a brute force crack dictionary; 4, obtaining a verification code picture; 5, identifying the obtained verification code picture; 6, filling corresponding parameters in the login data package intercepted in the step 2 with a verification code identification result as well as the user names and the passwords read in the step 3, and submitting the replaced login data package to the website server; and 7, analyzing a website server response, if it is prompted that the verification code is wrong, returning to the step 4; if it is prompted that the user name or the password is wrong, returning to the step 3; and if it is prompted that the login succeeds, recording the user name and the password by which the login succeeds. According to the method and system, a website with a verification code login function can be subjected to automated security testing.
Owner:STATE GRID CORP OF CHINA +2
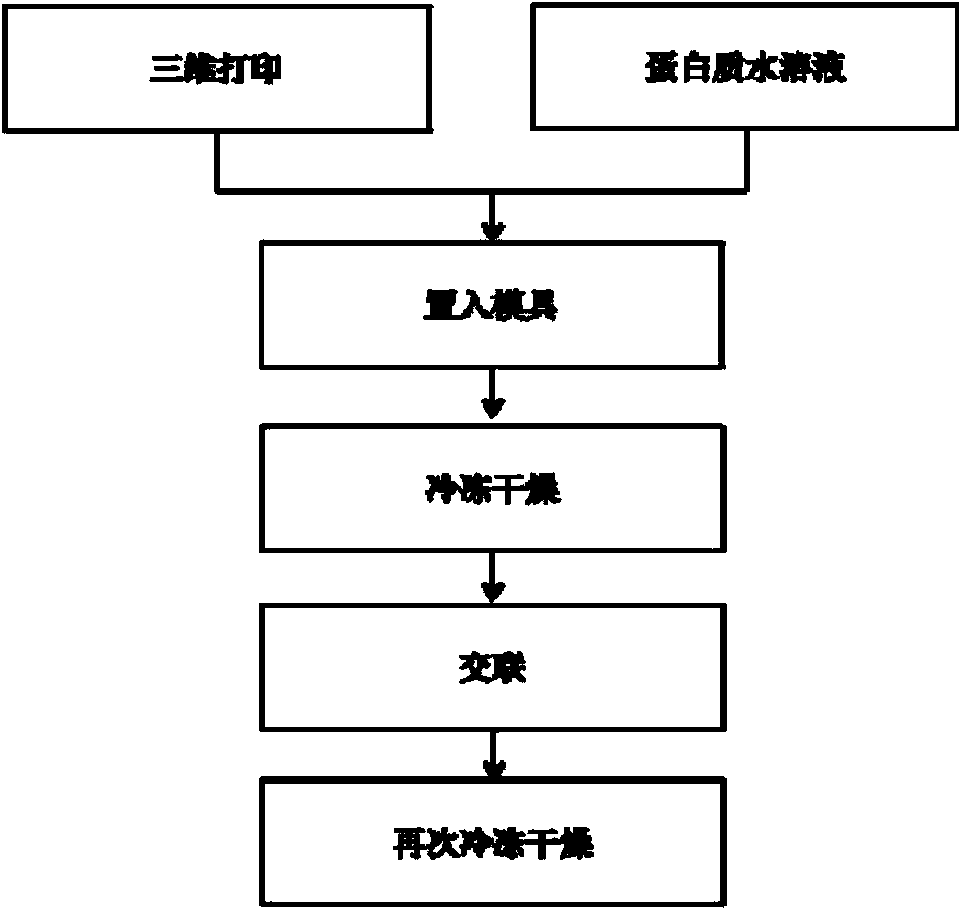
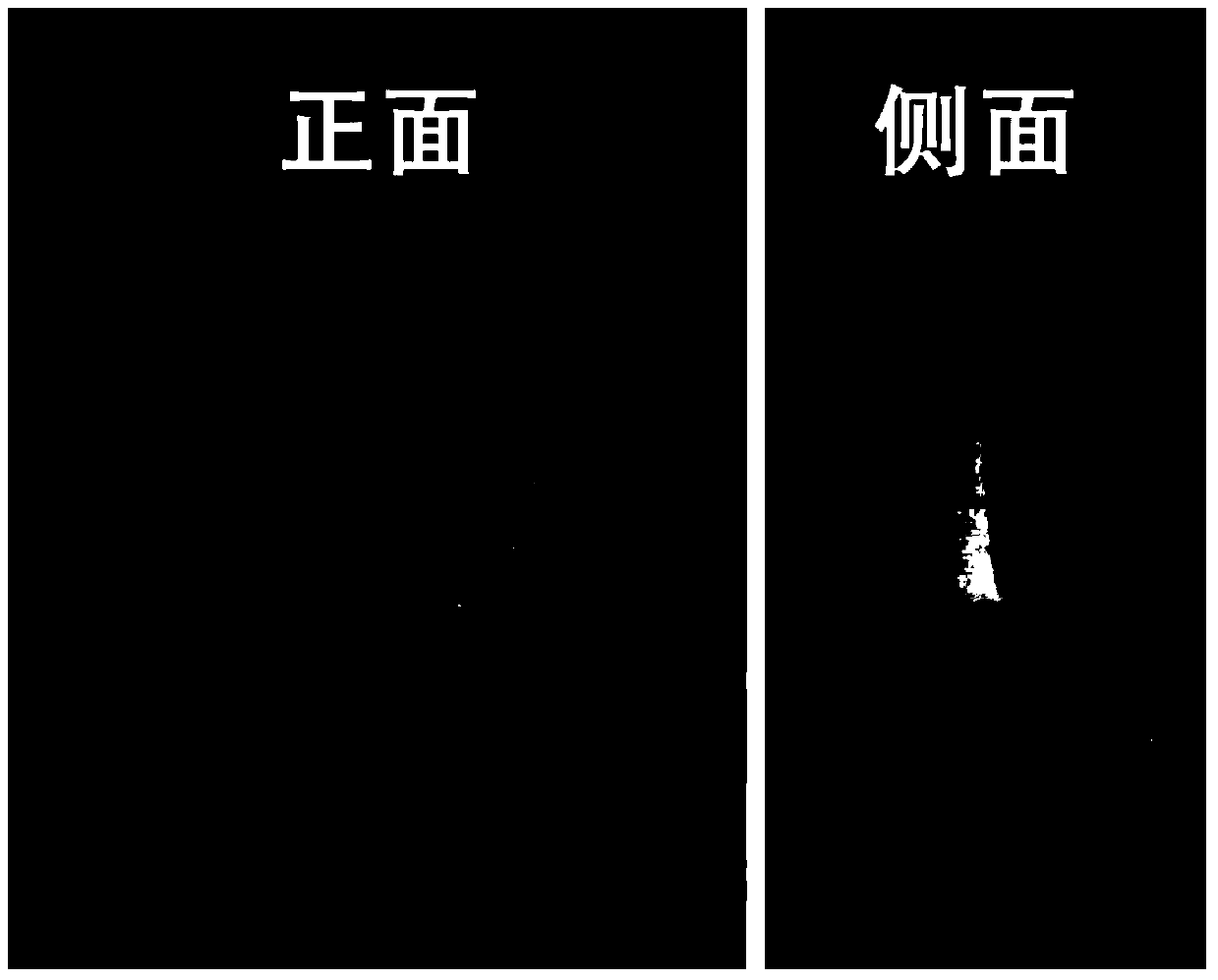
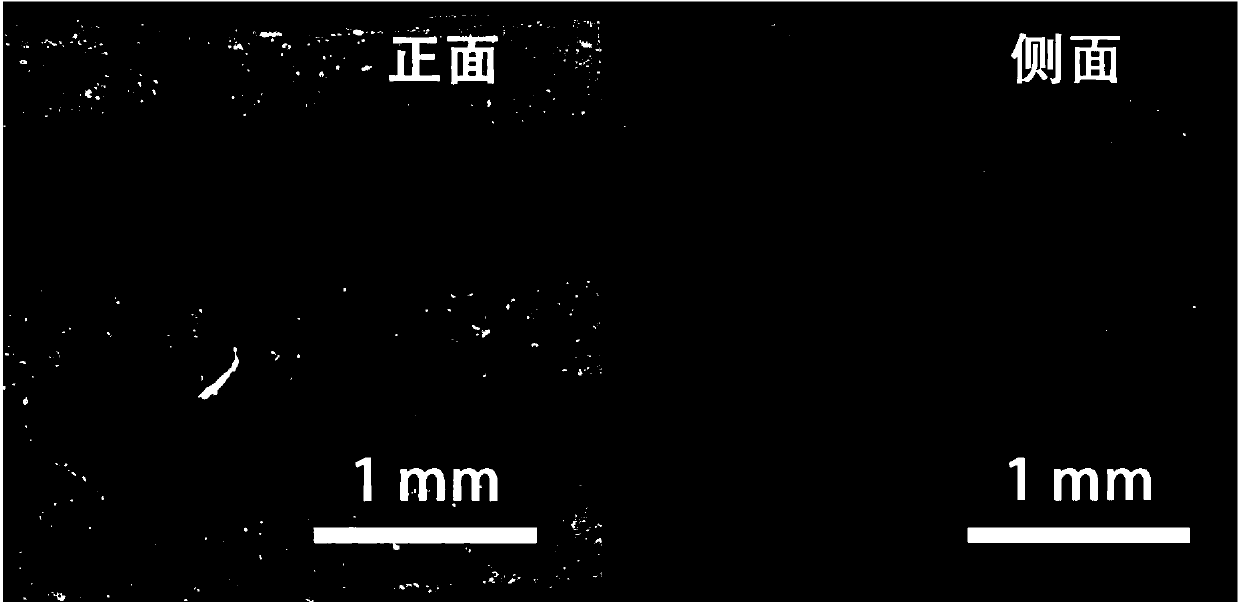
Three-dimensional scaffold material for bone tissue repair and preparation method thereof
The invention relates to a three-dimensional scaffold material for bone tissue repair and a preparation method thereof. The three-dimensional scaffold material consists of a three-dimensional printing polymer framework with an interpenetrating macroporous structure and a protein material which serves as a filling material and has a microporous structure. The preparation method comprises the following steps: 1) preparing a polymer three-dimensional framework by a three-dimensional printer; 2) preparing an aqueous solution of protein; 3) carrying out freeze drying; and 4) adding a crosslinking agent, washing with water and then carrying out freeze drying again to obtain the product. The three-dimensional scaffold material provided by the invention is simple to operate, high in stability, free from organic solvents in the whole course and green and safe. The prepared bone tissue scaffold is good in mechanical property. The polymer in the scaffold is tightly combined with proteins. The polymer scaffold can provide an enough brute force while the protein part can provide more cell adhesion sites to benefit penetrative growth of cells, thereby promoting tissue regeneration.
Owner:DONGHUA UNIV
Silk fibroin gel microneedle system and manufacturing method thereof
ActiveCN103800998ASimple methodDoes not affect biocompatibilityMicroneedlesMedical devicesBrute forceBiocompatibility Testing
The invention discloses a silk fibroin gel microneedle system and a manufacturing method of the silk fibroin gel system microneedle system. Silk fibroin solution with the mass concentration between 3 percent to 15 percent is processed through ultrasonic oscillation and then is poured on a polydimethylsiloxane film needle hole die array obtained through laser boring, dies are placed in a vacuum drying box and vacuumized, the solution is made to enter holes, the vacuum degree is kept, the dies are dried to constant weight, and then the silk fibroin gel microneedle system is obtained. The microneedle system is an insoluble gel microneedle and has certain brute force to puncture into the skin, the microneedle system swells after making contact with body fluid in the skin, and medicine in the microneedle system is released. The gel microneedle system is good in biocompatibility, easy to prepare, moderate in condition and capable of biodegradation, and the system can be used in the aspects of cosmetology, transdermal drug absorption devices and the like.
Owner:PHARSUN MEDICAL BIOTECHNICS (SHANGHAI) CO LTD
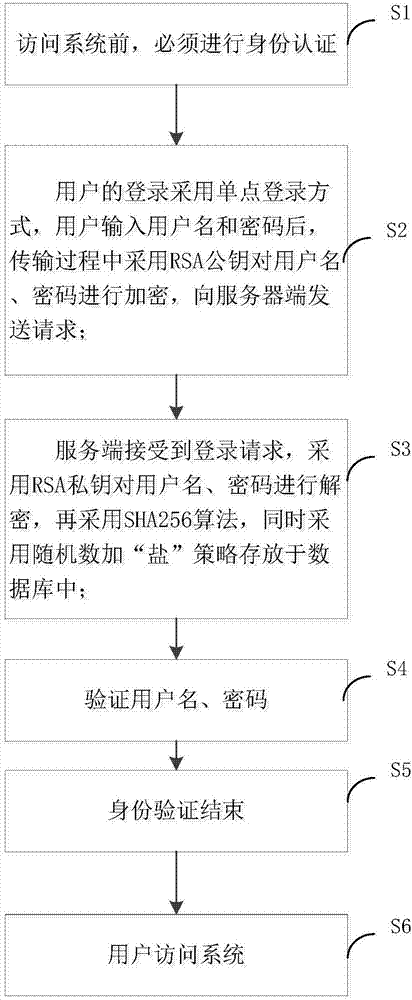
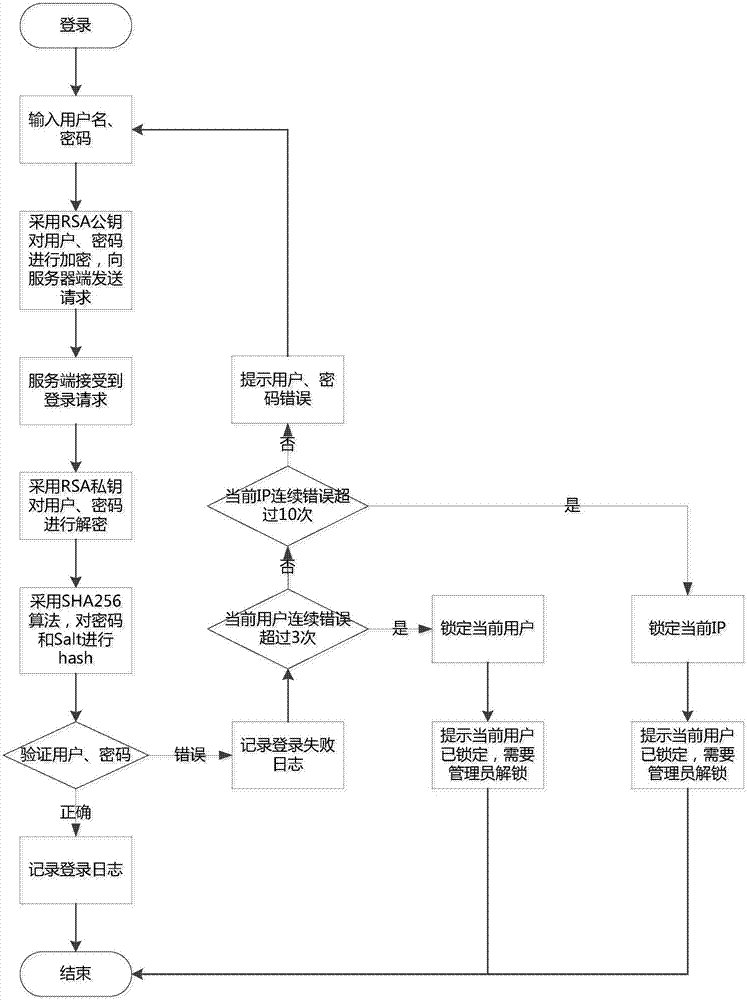
Cloud platform identity identification method
The invention provides a cloud platform identity identification method. The cloud platform identity identification method comprises the following steps that before a system is accessed, identity authentication must be conducted; a single sign-on mode is adopted as the sign-on mode of a user, after the user inputs a user name and a password, the user name and the password are encrypted through an RSA public key in the transmission process, and a request is sent to a server side; the server side receives the sign-on request, and the user name and the password are decrypted through an RSA private key and then stored in a database through an SHA256 algorithm and a random number salting strategy; the user name and the password are verified; identity authentication is finished; the user accesses the system. According to the cloud platform identity identification method, data encryption is conducted on the user name and the password which are input by the user through RSA asymmetric encryption (the public key and the private key), therefore, it is guaranteed that ciphertext of each request cannot be repeated, and plaintext transmission and brute force cracking of the password are avoided; and by adopting the sha256 algorithm, it is guaranteed that same data cannot be repeated or reversely operated after being encrypted, and then the user identity authentication security is greatly improved.
Owner:北京海顿中科技术有限公司
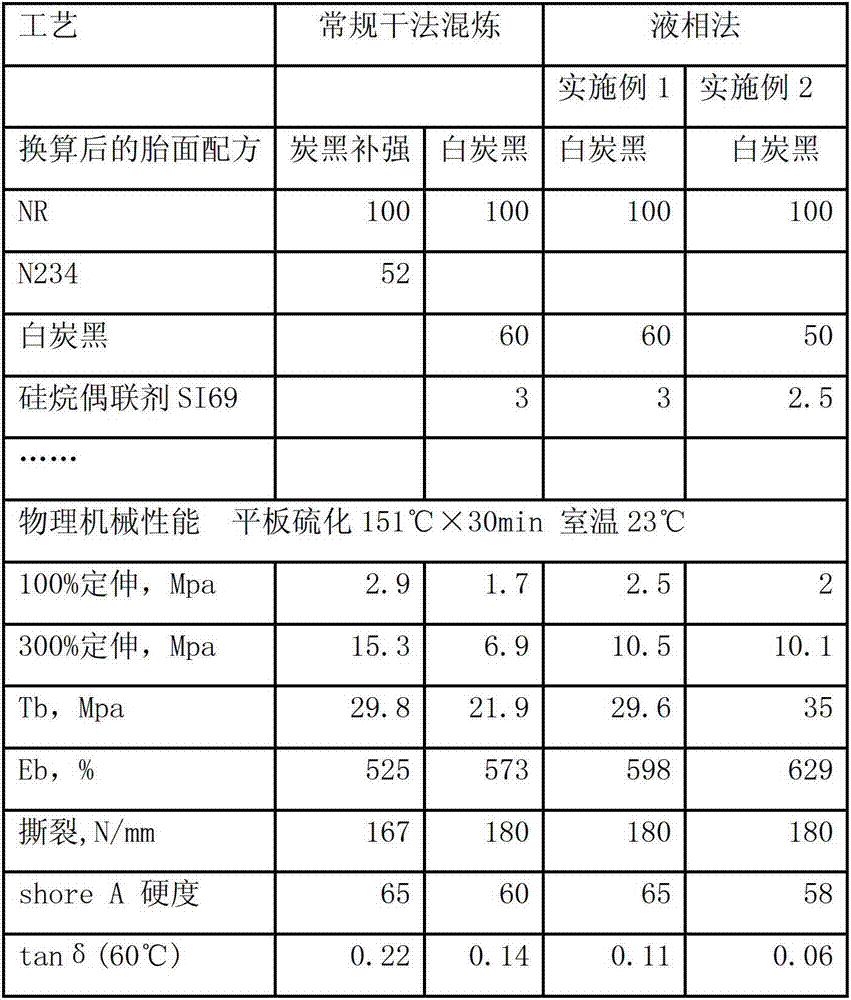
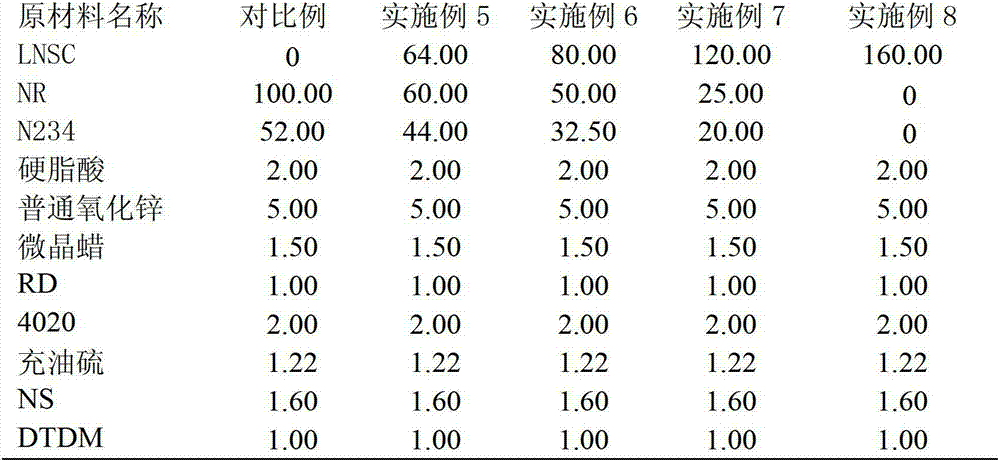
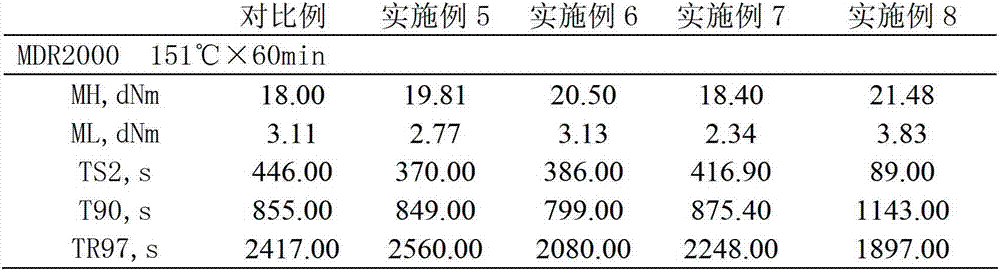
Preparation method for liquid phase stirring and mixing of white carbon black and natural rubber
ActiveCN102775654APreserve the status quoKeep strongSpecial tyresRolling resistance optimizationHysteresisBrute force
The invention relates to the production field of tire rubber sizing materials, in particular to a method for mixing liquid state white carbon black and liquid state natural rubber in a liquid phase. The preparation method for liquid phase stirring and mixing of the white carbon black and the natural rubber comprises the steps of (1) preparing slurry; (2) mixing; (3) solidifying, dehydrating, washing and stoving. The method adopts liquid-liquid high speed stirring and mixing to effectively preserve original states of natural rubber macromoleculars, effectively preserves brute force of the natural rubber and substantially promotes brute force and abrasive resistance of mixed glue. Brute force of sizing materials mixed by using the method is substantially promoted, and themogenesis and hysteresis loss are obviously reduced. The mixed glue produced by the method can be singly used and can also be blended with the natural rubber, rubber polymer, natural rubber carbon black rubber master batch and rubber polymer carbon black rubber master batch according to certain proportion. According to the method, the liquid state white carbon black and the liquid state natural rubber are mixed directly, the process is simple, the land occupation is small, the equipment investment is low, and dust pollution does not exist in a production process.
Owner:ZHONGCE RUBBER GRP CO LTD
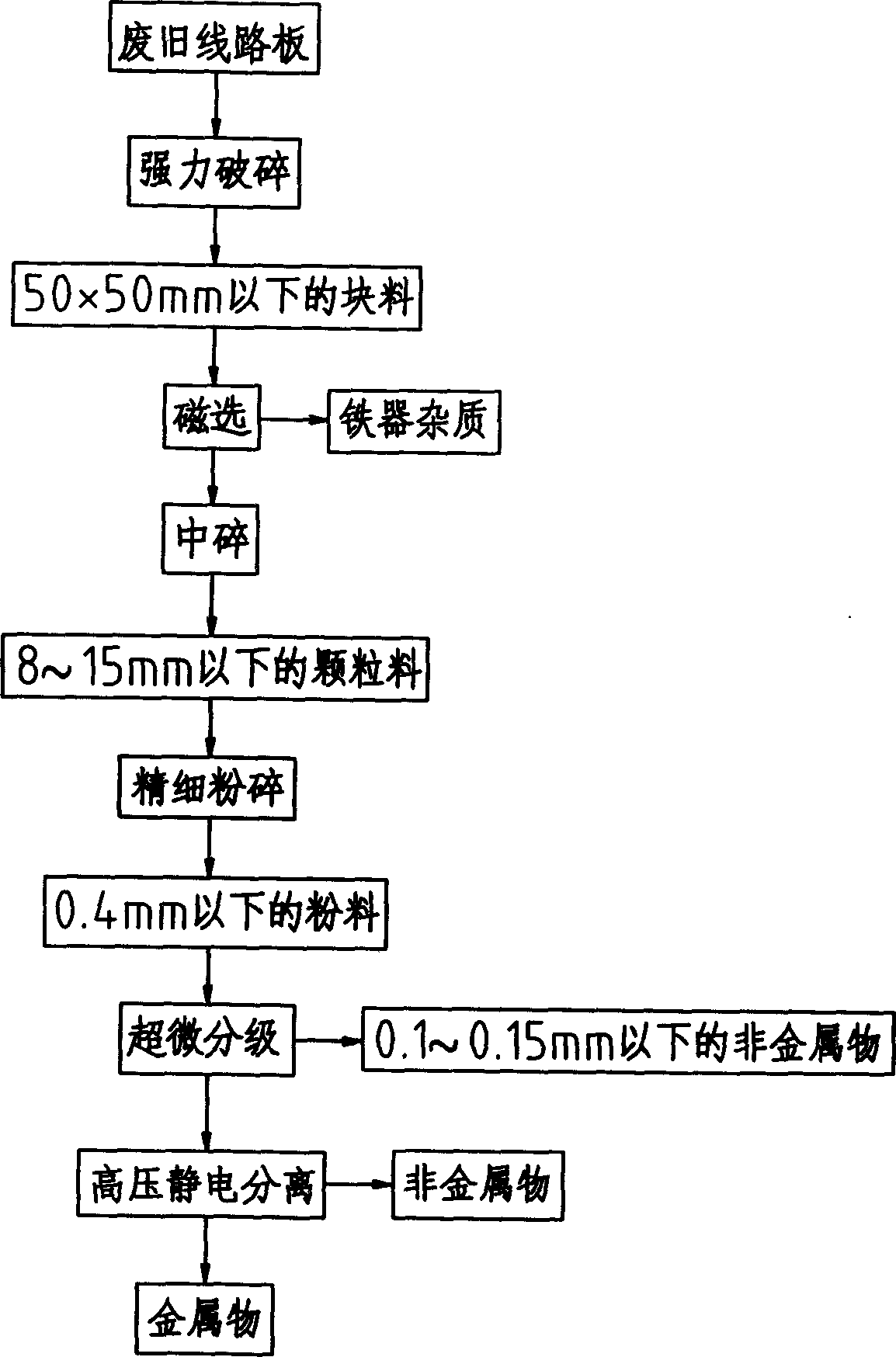
Grinding recovery treatment technology of waste electron wiring board and its equipment
InactiveCN1786222AGood dissociationEasy to separateSolid waste disposalProcess efficiency improvementBrute forceElectrostatic separation
The invention relates to a worn-out electronic circuit plate mechanical disintegration and electrostatic separation recovery processing technique and its using equipment. The processing steps include the following steps: crushing worn-out electronic circuit plate; intermediate crushing after removing iron; fine crushing; dividing part nonmetal matter by ultra-micro classifier; sending to high voltage electrostatic separator to from finished product. The equipment includes brute force crusher, magnetic separator, intermediate crusher, fine crusher, ultra-micro classifier, and high voltage electrostatic separator. Its advantages are good crushing dissociation, good reclaiming effect, low energy consumption, long using life and no secondary pollution.
Owner:浙江丰利粉碎设备有限公司
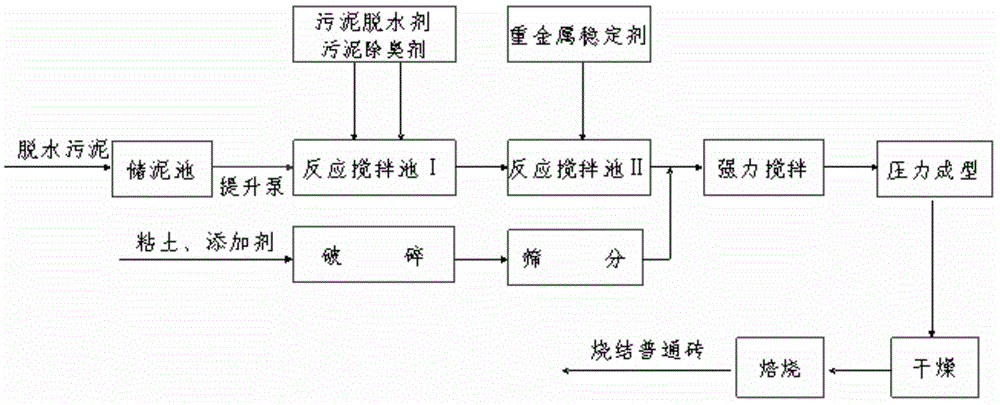
Novel sludge brick making technique
ActiveCN104649650AShorten the preprocessing processImprove utilization rateCeramic materials productionClaywaresTunnel kilnBrick
The invention discloses a novel sludge brick making technique which comprises the following steps that municipal sludge is subjected to dewatering conditioning and desodoration treatment; heavy metal is controlled; treated sludge pug, clay and an additive are blended to form a material; the material is fed into a brute force extrusion mixer to be mixed fully, and is ground and homogenized by brute force roll grinding and aged; the aged brick making pug is fed into an adobe making workshop to be subjected to compression moulding for adobe making; the moulded adobes are fed into a drying room to be dried; and the dried adobes are placed in a back stage of a tunnel kiln to be sintered. According to the technique, the sludge from a sewage plant is mixed with the raw clay directly, so that energy resources consumed due to sludge drying are saved; targeted improvement measures are put forwards to solve the problems of sludge dewatering, odor control, heavy metal stabilization, etc.; the quality performance and the strength grade of sludge bricks are improved by methods of optimizing a sludge blending ratio and feeding the additive, etc.; the reduction, harmlessness, reclamation and industrialization treatment goals on the municipal sludge are realized; and the sludge bricks, serving as a product, have objective economic benefits.
Owner:XIAN LISHENG SLUDGE TREATMENT +1
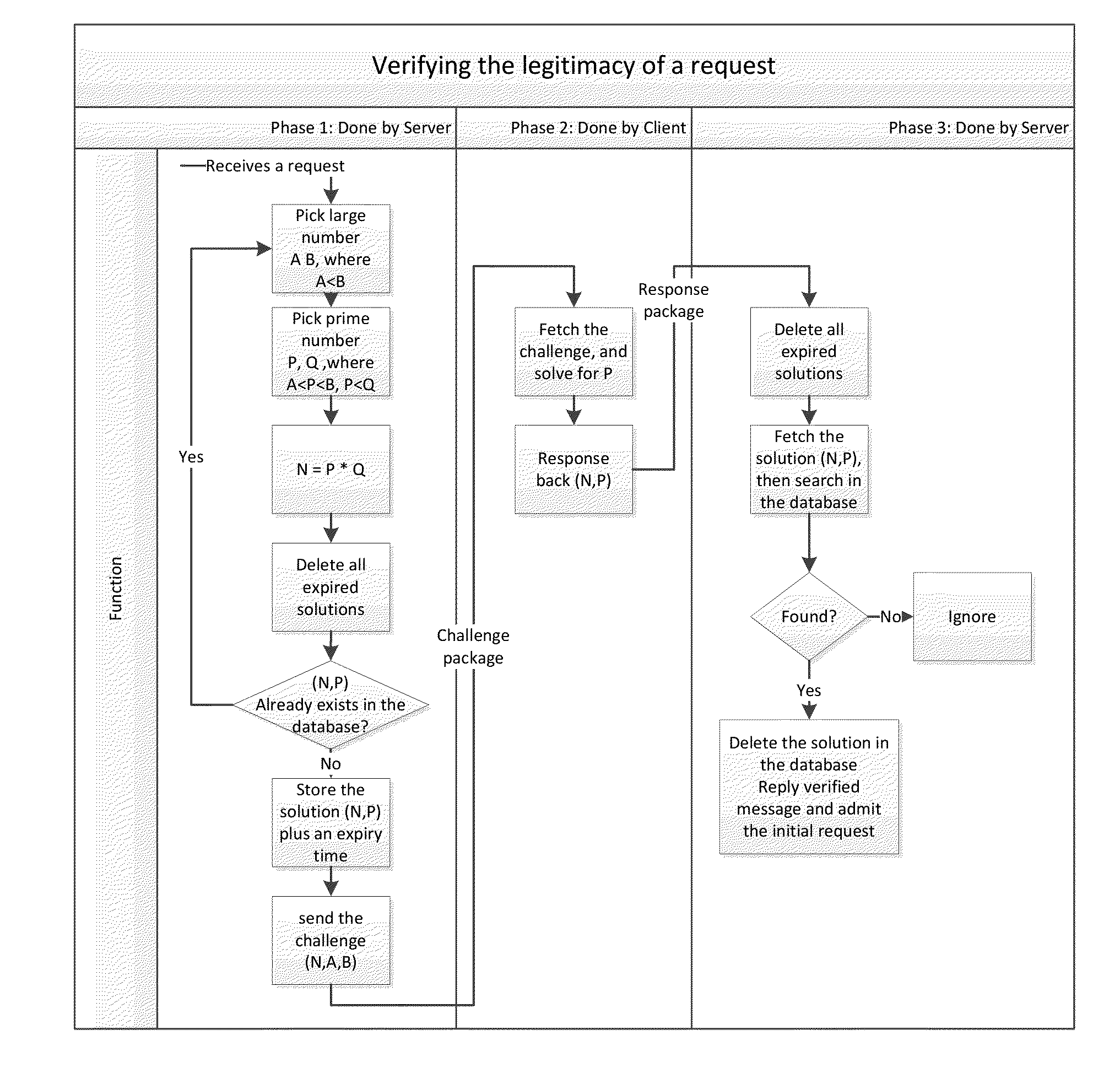
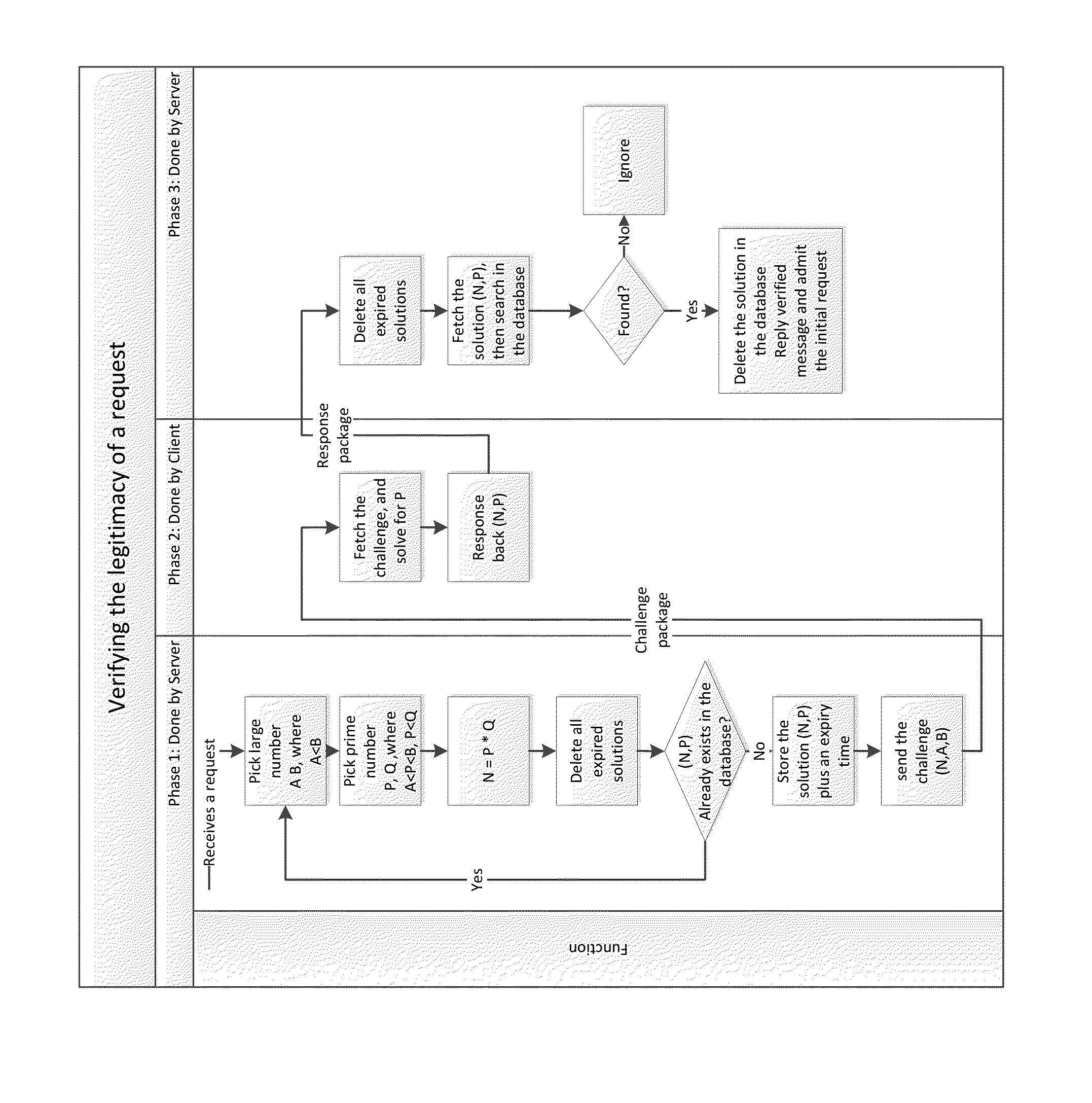
System and method for verifying the legitimacy of requests sent from clients to server
InactiveUS20140380418A1Preventing brute force attack against passwordImprove reliabilityDigital data processing detailsMultiple digital computer combinationsBrute forceComputation complexity
Disclosed herein are method and system that can be used for: preventing brute force attacks against passwords; preventing denial of service attacks by flooding; restricting bots from spamming emails, registering resources, and collecting sensitive information; and possibly in other challenge-response tests. It also can be used to replace CAPTCHA in some situations, with advantages of better reliability and spares human participation during the process. This present invention considers a request as legitimate when the requesting client has paid certain amount of computation resource required by the server, in exchange for the server to admit the request. It performs a challenge-response test. The subject challenged is the sincerity of the client to make that request, which is measured by computation resources the client willing to spend in exchange for the service provided by the server. The invention also gives a method to control and guarantee the computation complexity of the challenge problem of the test.
Owner:WANG HAOXU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com