Patents
Literature
1243 results about "Mutual authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
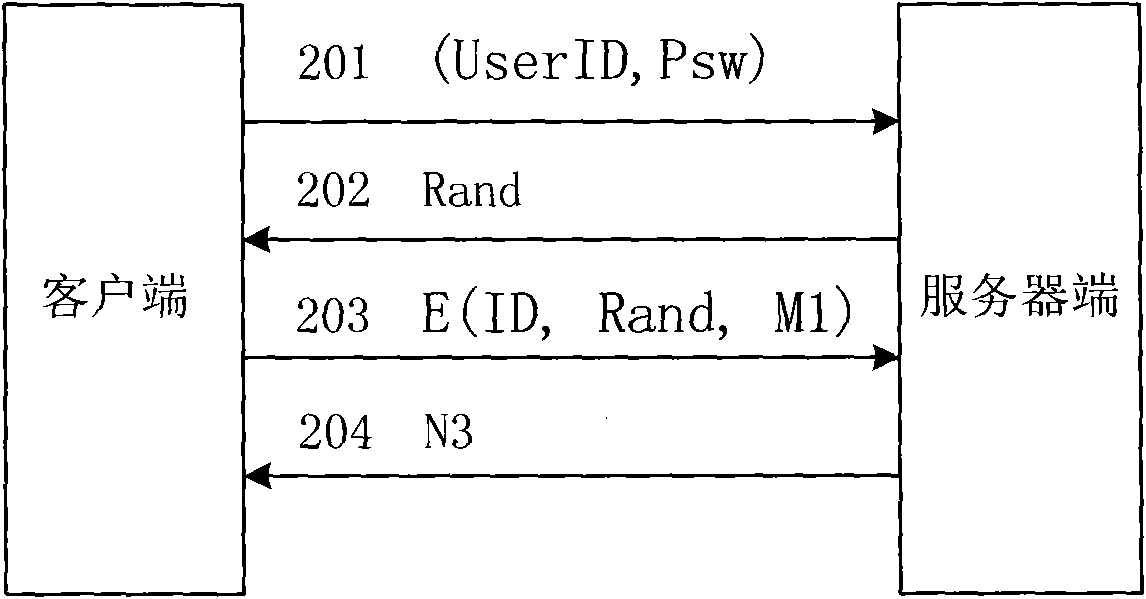
Mutual authentication or two-way authentication refers to two parties authenticating each other at the same time, being a default mode of authentication in some protocols (IKE, SSH) and optional in others (TLS).
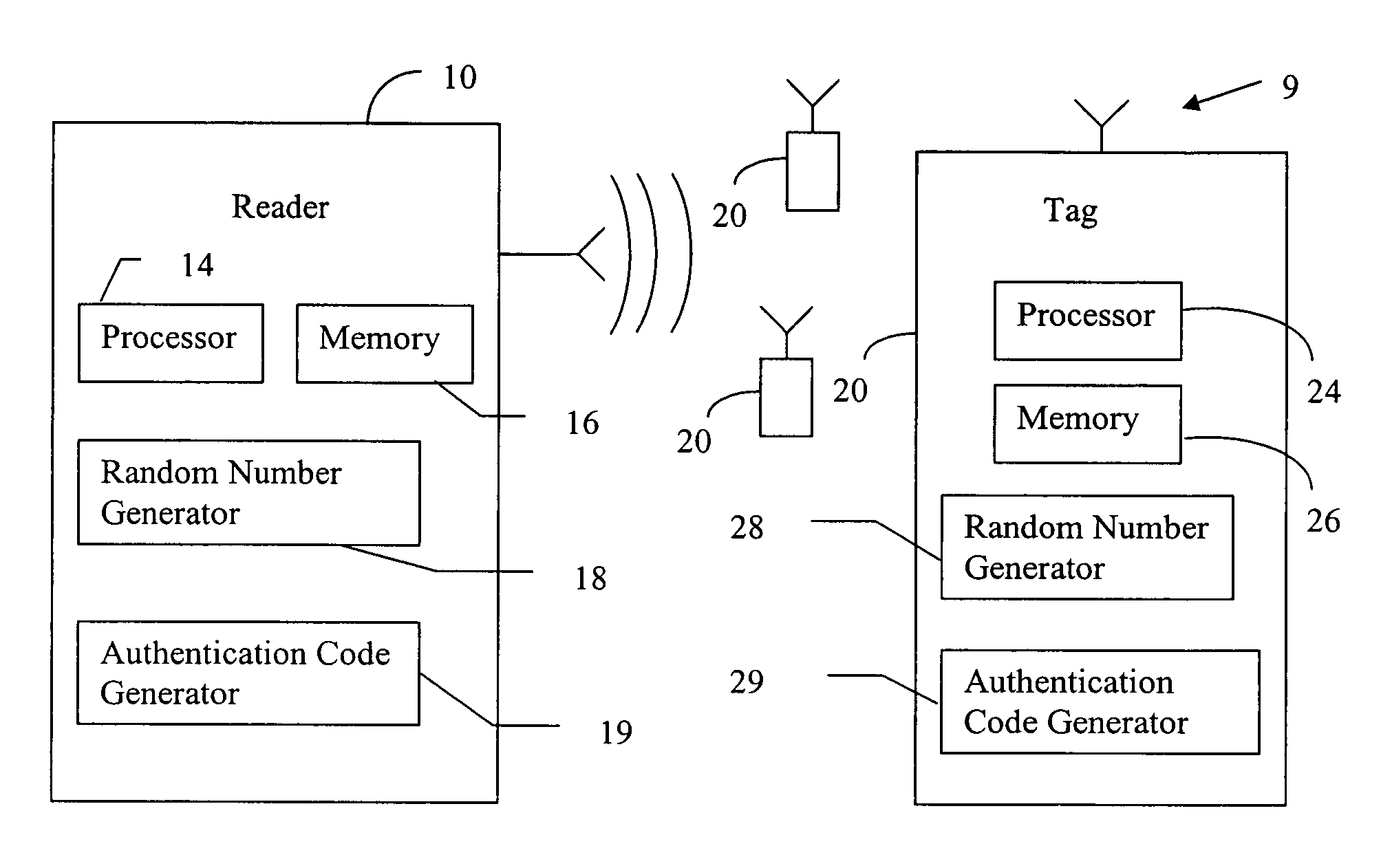
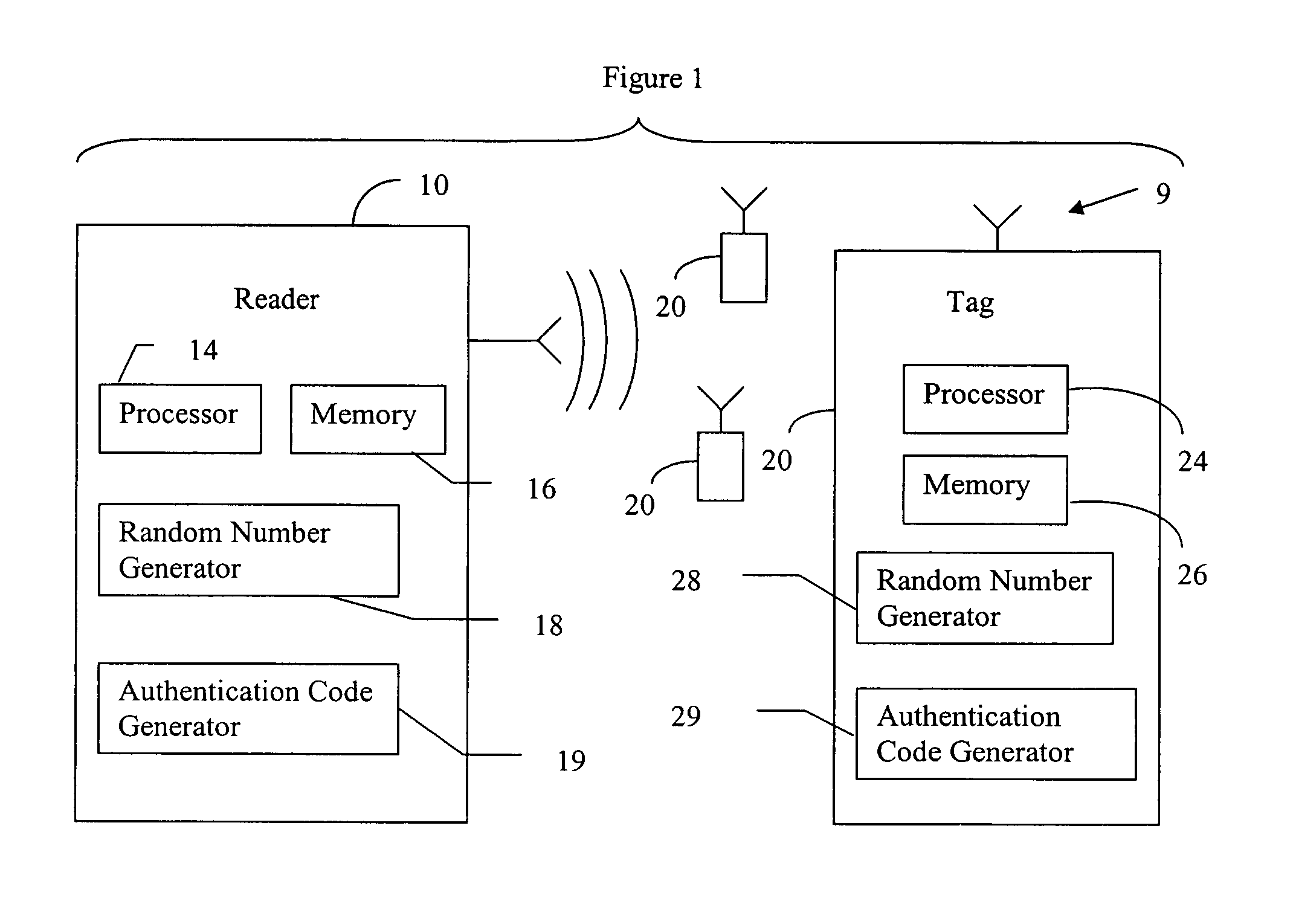
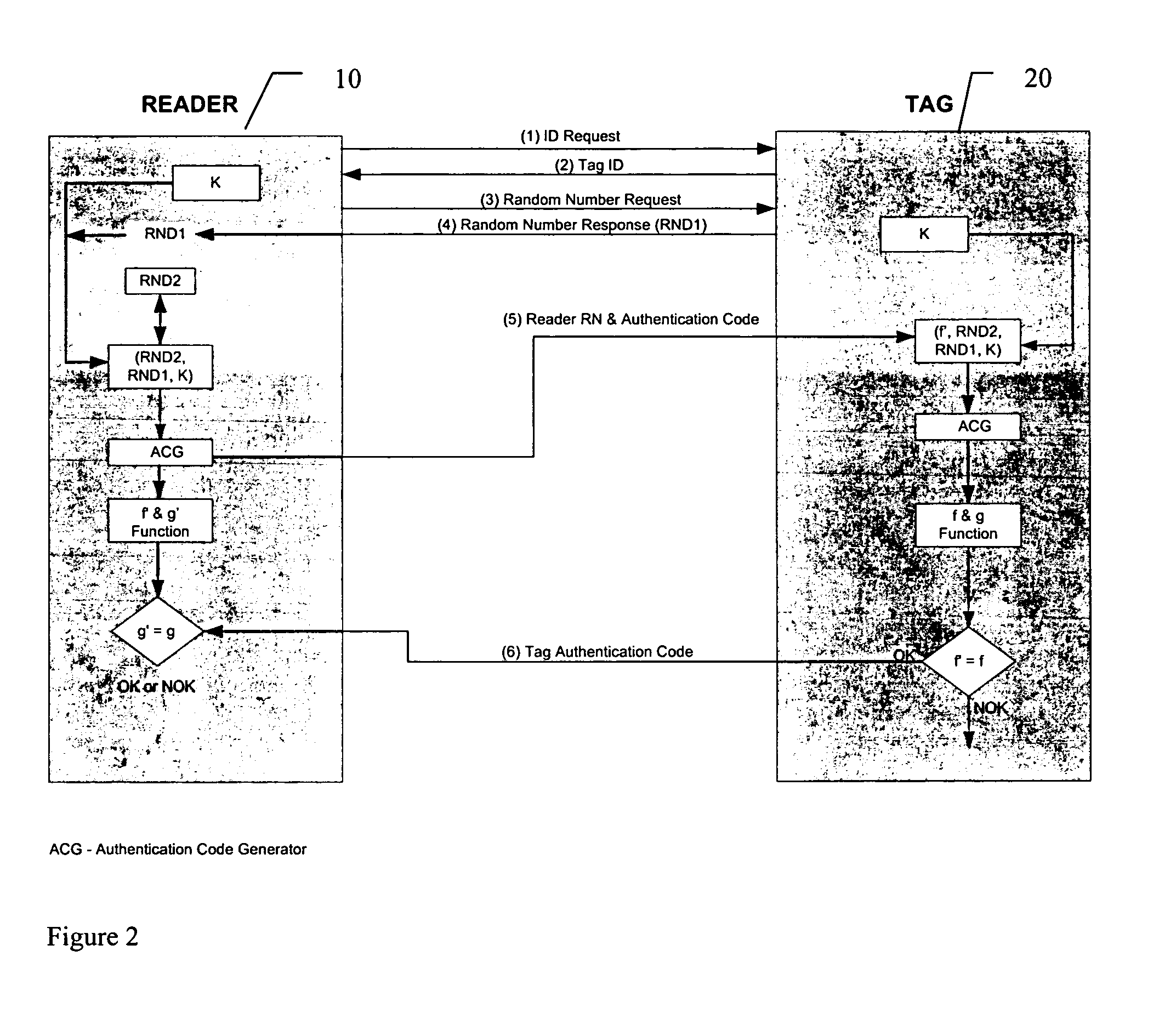
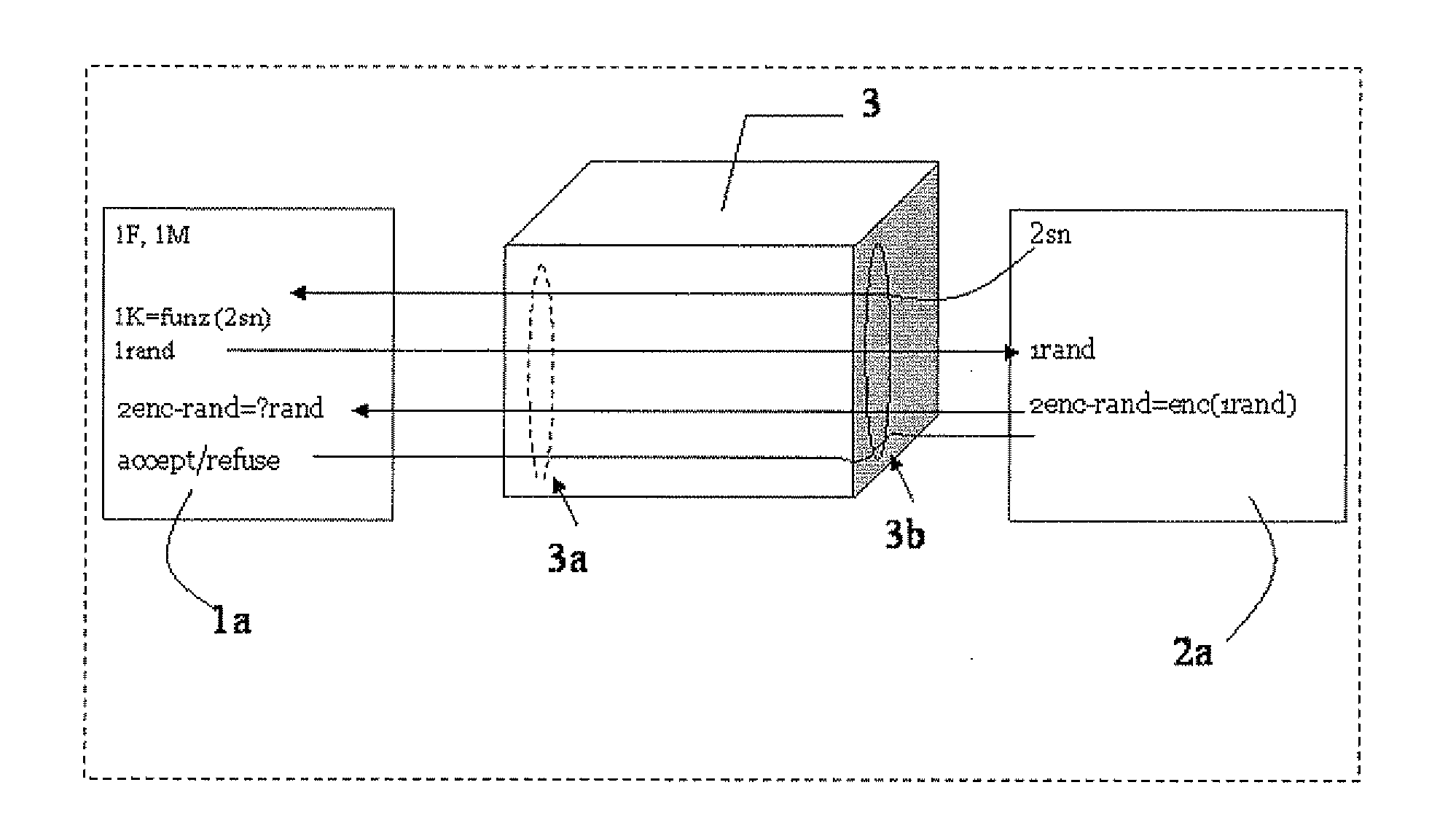
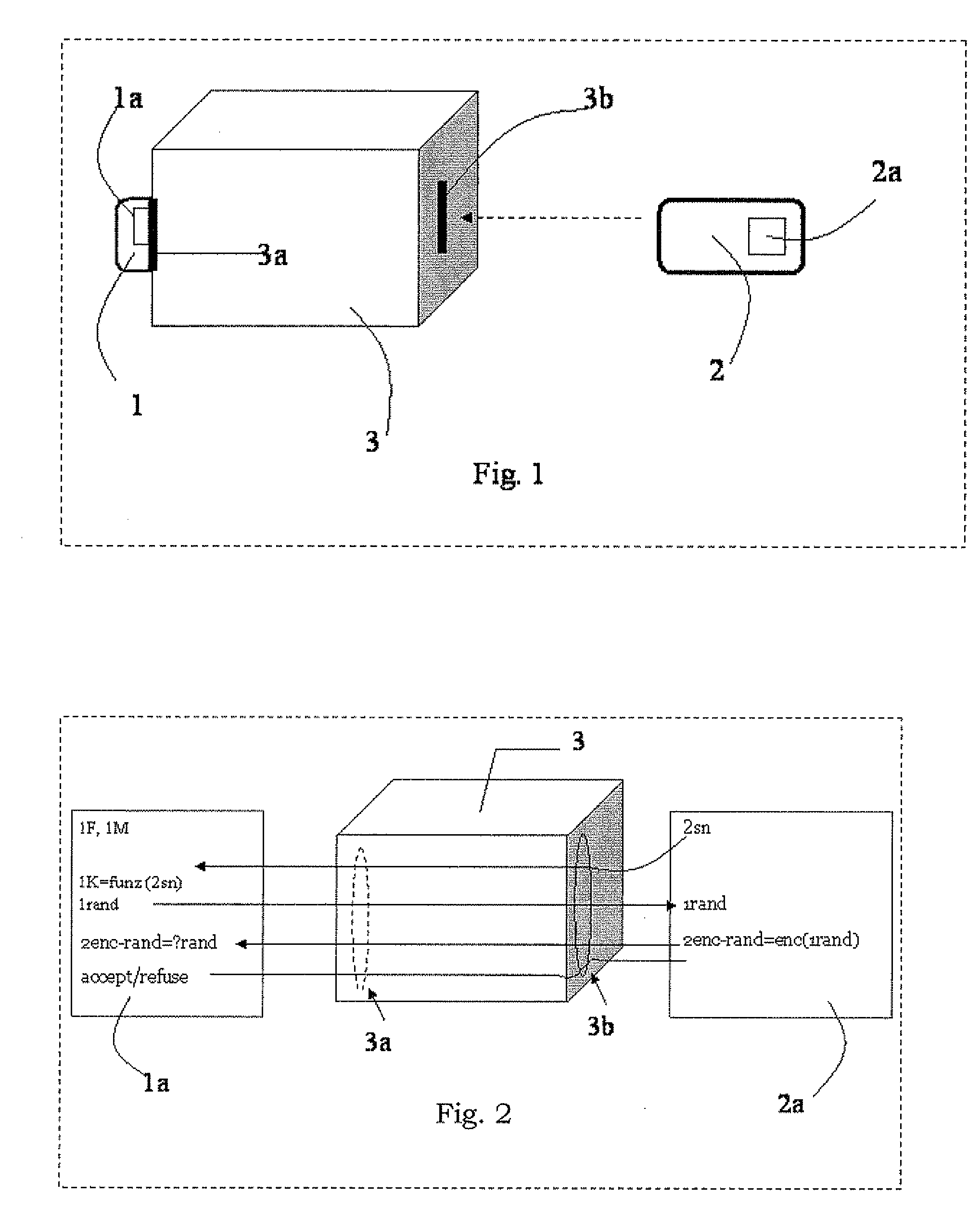
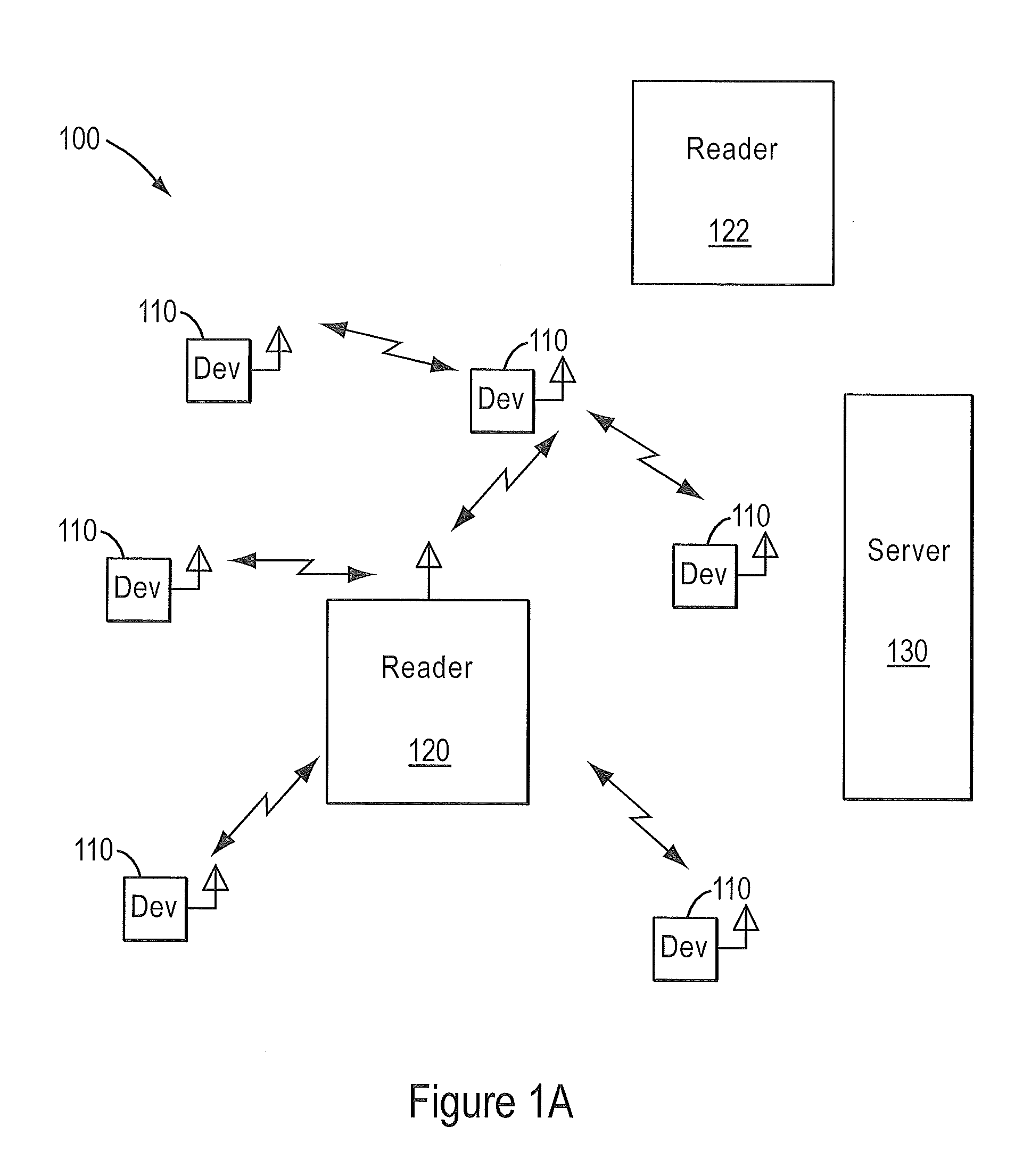
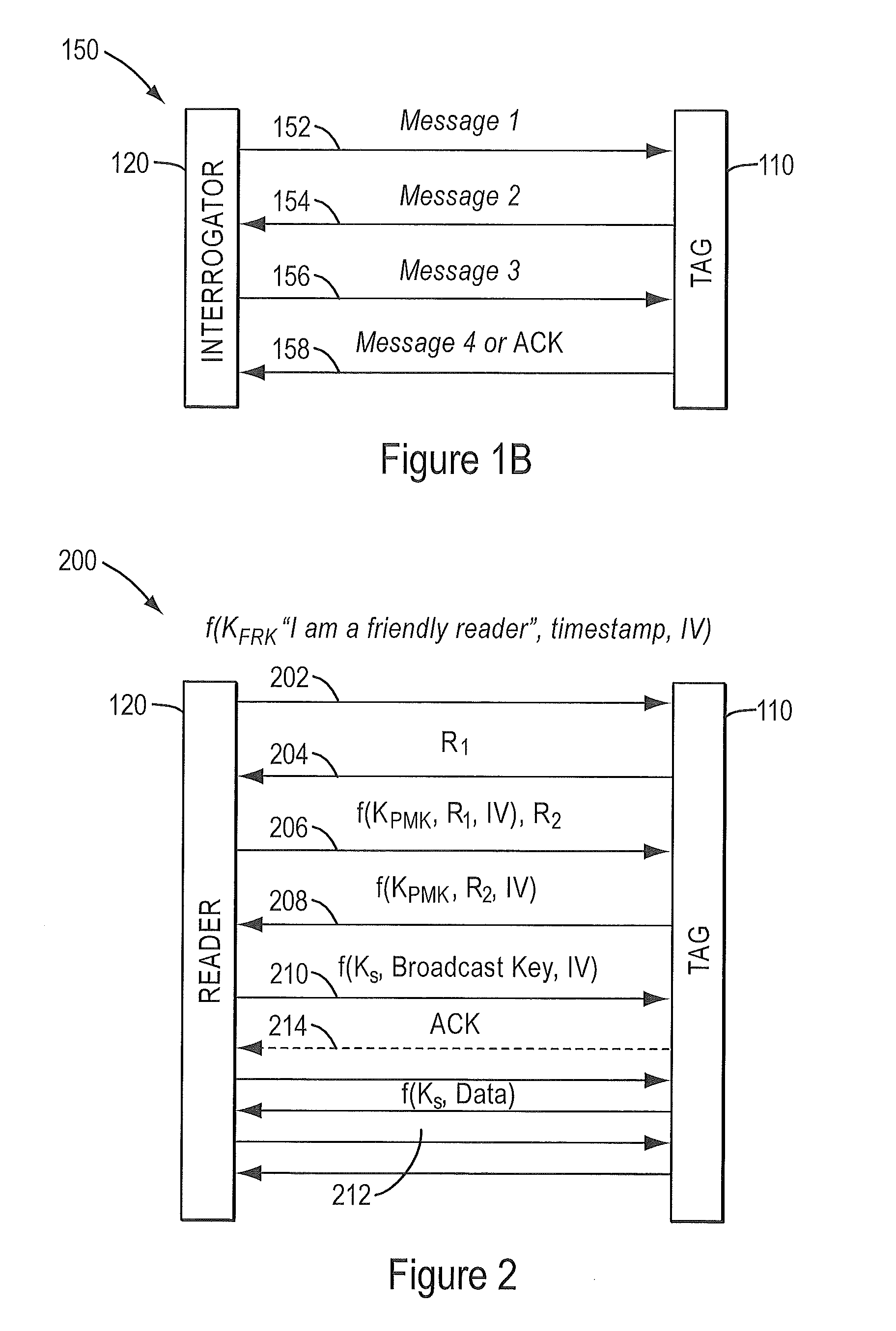
RFID mutual authentication verification session
ActiveUS7450010B1Privacy can be assuredElectric signal transmission systemsDigital data processing detailsMutual authenticationComputer security
Owner:AMTECH SYST
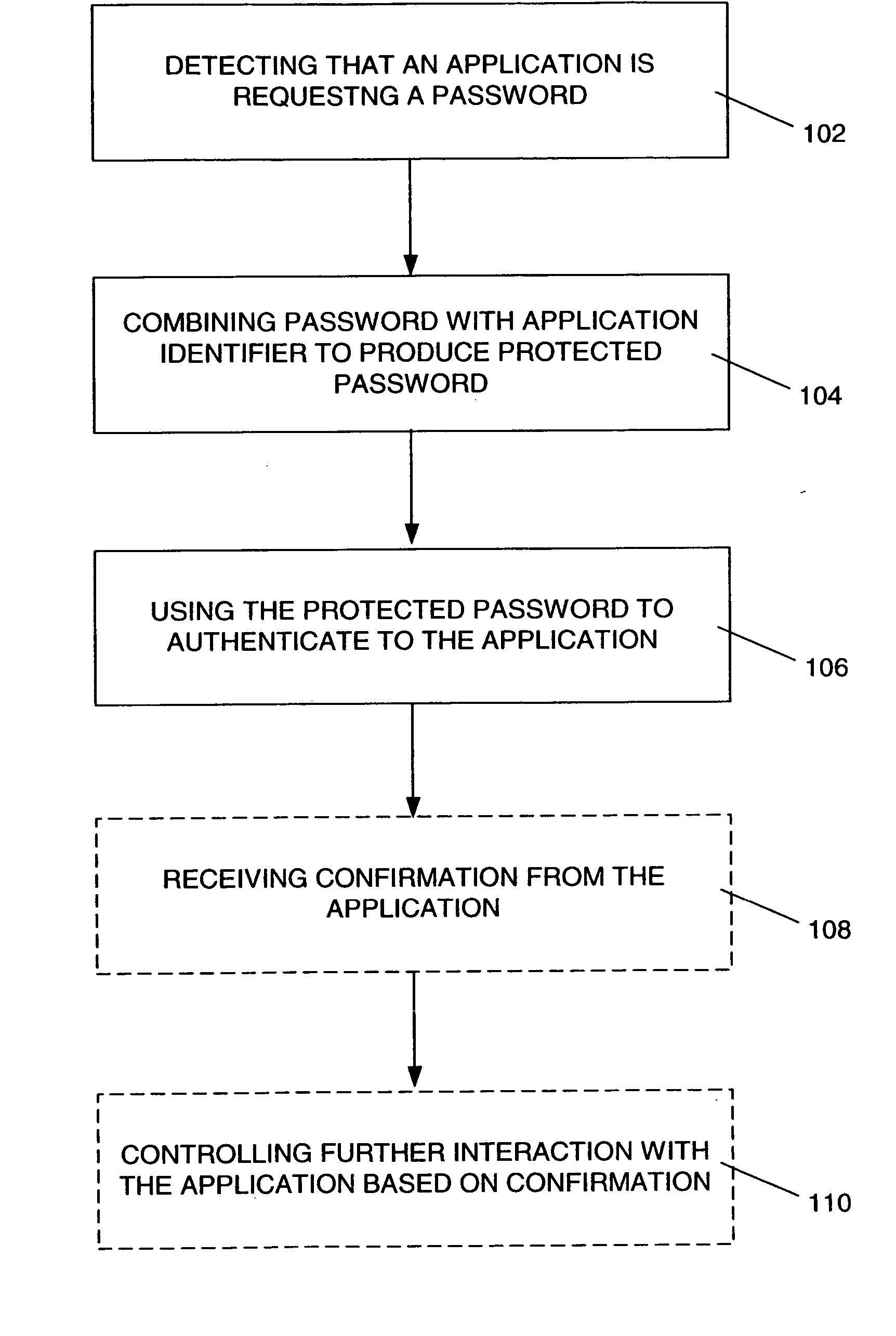
Password-protection module
ActiveUS20060041759A1Key distribution for secure communicationDigital data processing detailsMutual authenticationPassword protection
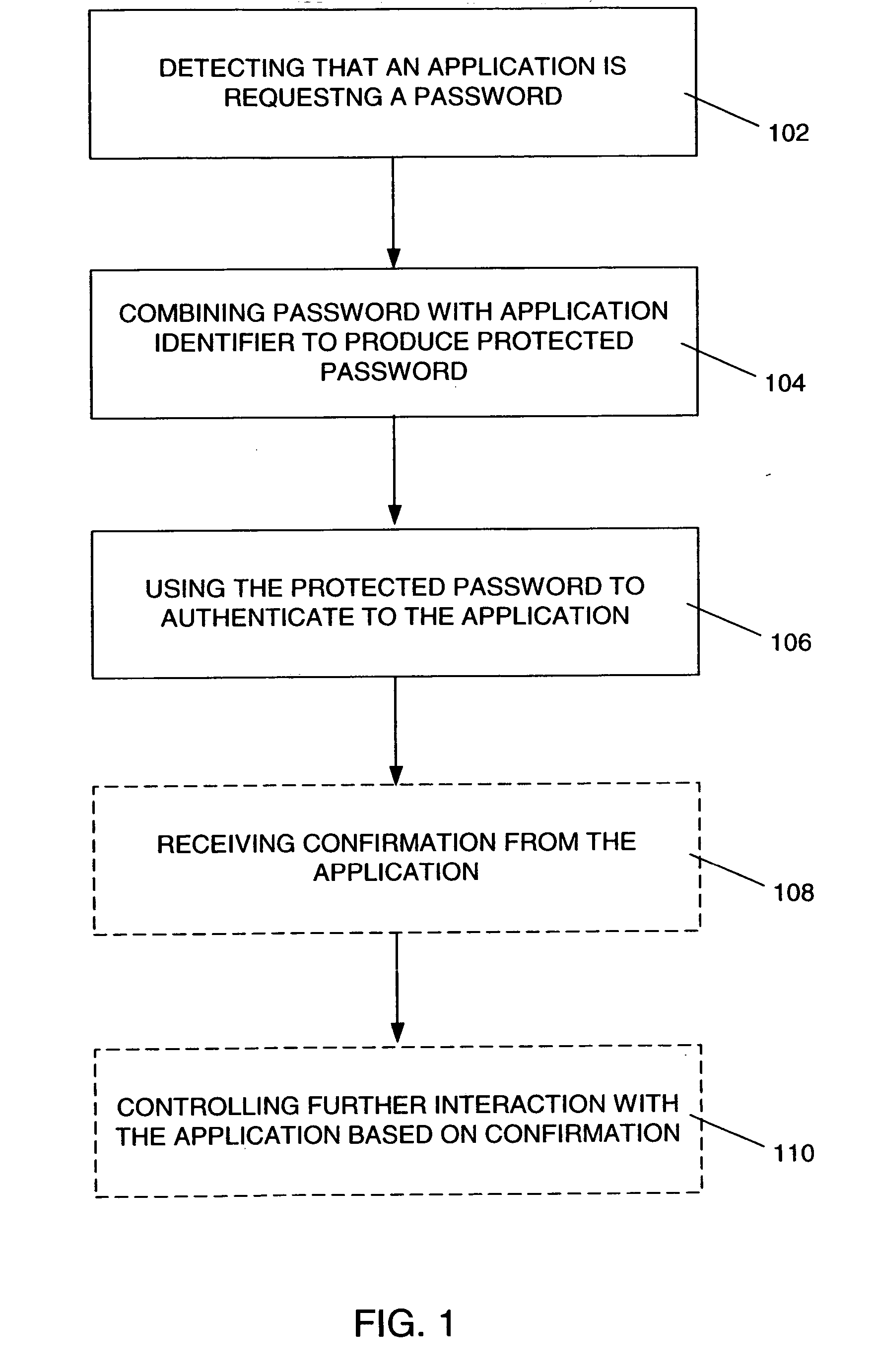
A method of protecting a password being used to establish interaction between a user and an application includes detecting a request for the password from the application by receiving a notification from the user indicating the request. The method further includes combining the password with information identifying the application, so as to produce a protected password, and authenticating to the application using the protected password. The method may also include a mutual authentication capability between user and the application.
Owner:EMC IP HLDG CO LLC
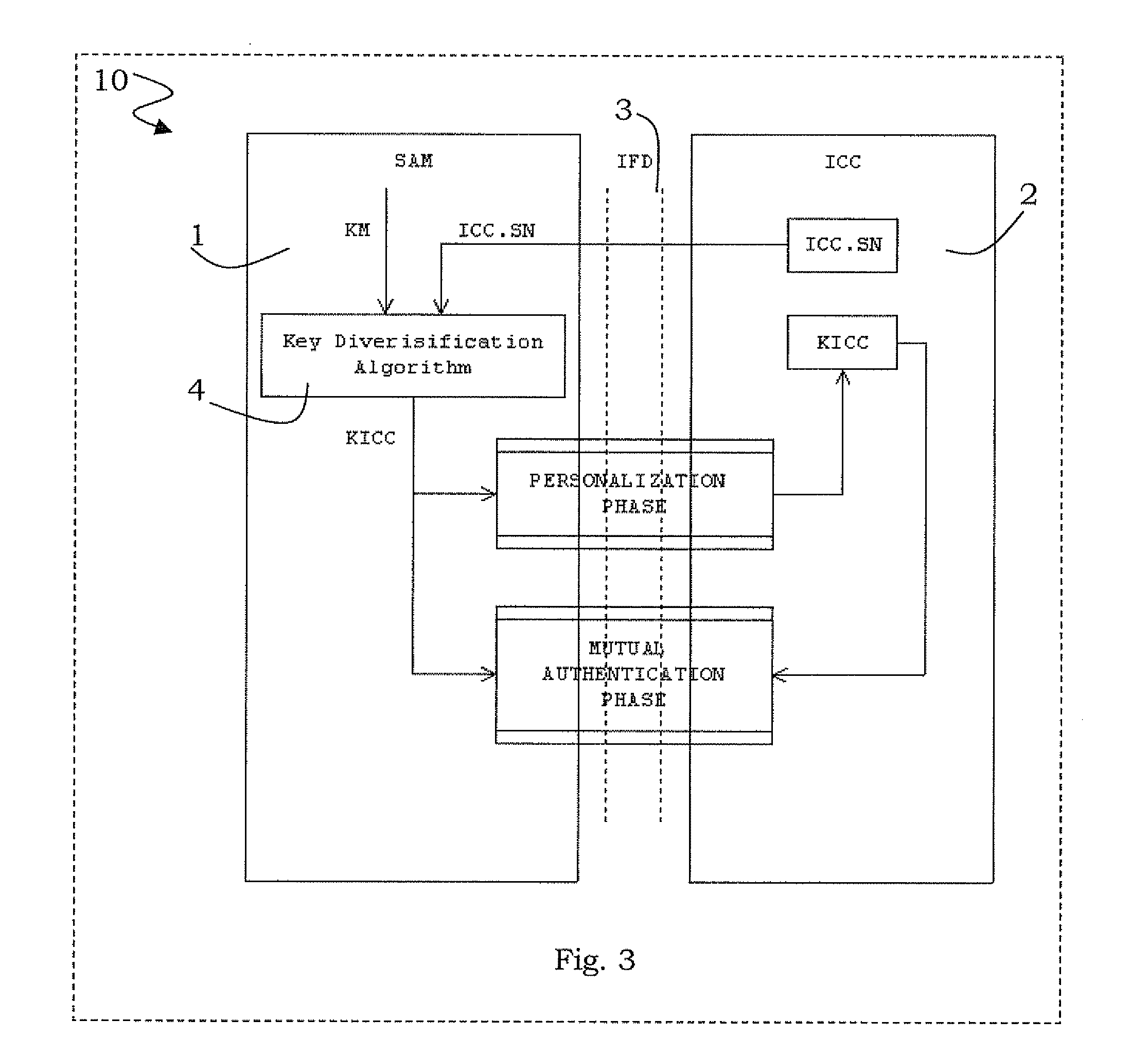
Method for key diversification on an IC card
InactiveUS20080008315A1Shorten the timeNon-time consuming and non-computational intensive operationsAcutation objectsUser identity/authority verificationCommunication interfaceMaster key
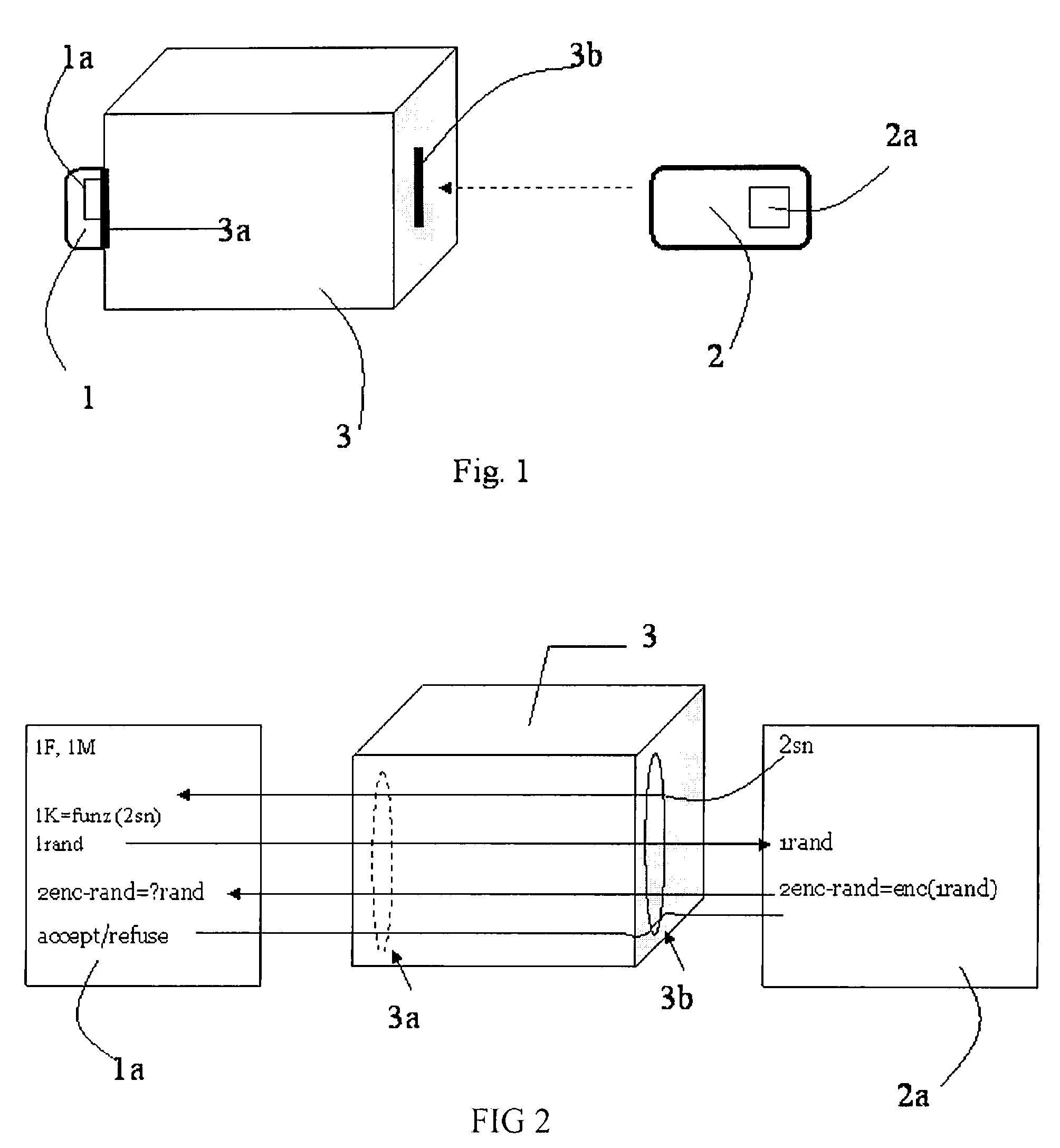
Key diversification is performed during a mutual authentication between a SAM integrated circuit (IC) card storing a master key, and a user IC card storing an identification number. The user IC card is connected to the SAM IC card through a communications interface. The key diversification includes deriving sub keys from the master key, and computing ciphered strings through corresponding cryptographic computations on a string obtained by an elaboration on the identification number with the sub keys. A diversification key is generated by linking together a combination of bytes of the ciphered strings.
Owner:STMICROELECTRONICS INT NV
Method for mobile security context authentication
ActiveUS20140096215A1Easy to solveDigital data processing detailsMultiple digital computer combinationsMobile securityMobile electronics
The present invention is a system and a method for improving the authentication security across a network from a mobile electronic computing device in the context of one or more users, devices, sites / sessions, servers, locations, proximity, motion and / or behavioral attributes within a defined session lifecycle. The authentication method and system utilizes a strong, elegant, private, definitive and real-time, triangulated verification, which requires mutual authentication between the parties.
Owner:LIVE ENSURE LTD
Methods and apparatus for awarding prizes based on authentication of computer generated outcomes using coupons
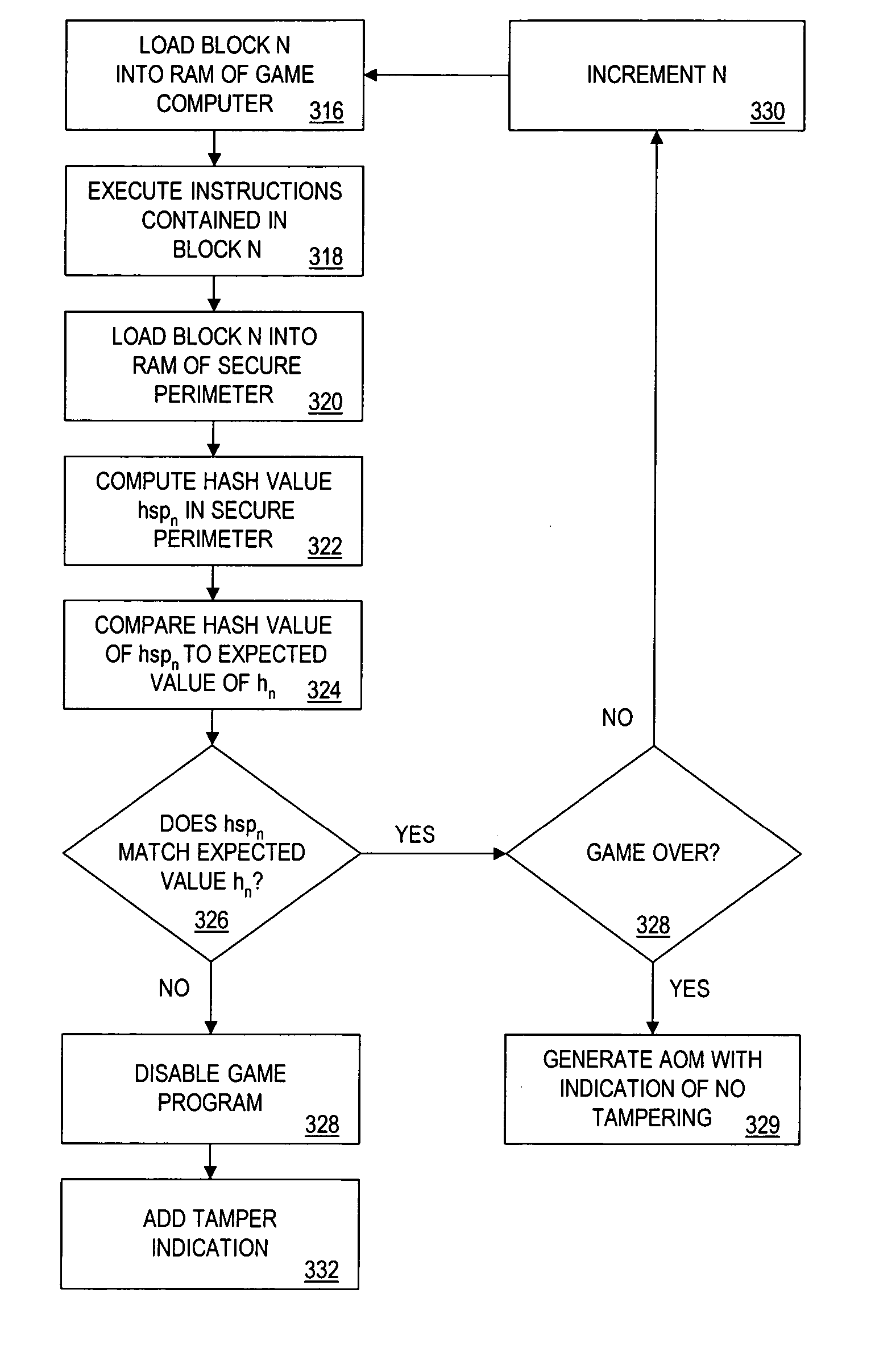
The present invention provides authentication of computer generated game or test results (“outcomes”), and a system by which persons who play games or take tests on a game or testing computer, respectively, may submit the outcomes of the games or tests to a central authority having at least one central computer, and have the central computer “certify” those outcomes as being accurately reported and fairly achieved. This certification of the computer generated result constitutes a “remote-auditing” of the activity taking place on the game computer. In one application, the system enables computer generated game tournaments in which players play the games on game computers and compete against each other by submitting the outcomes for those tournament games to the central computer, which certifies the outcomes and rates and ranks the players. In another application, the system provides for players of computer games to obtain a certified ranking and rating without participation in a tournament. In other embodiments, the system provides for self-authentication and certification of outcomes for games played on the game computer itself, or for mutual-authentication and certification of such outcomes on any other game computer in the system.
Owner:INVENTOR HLDG
Mutual authentication security system with detection and mitigation of active man-in-the-middle browser attacks, phishing, and malware and other security improvements.
ActiveUS20170346851A1Multiple keys/algorithms usagePublic key for secure communicationWeb sitePhishing
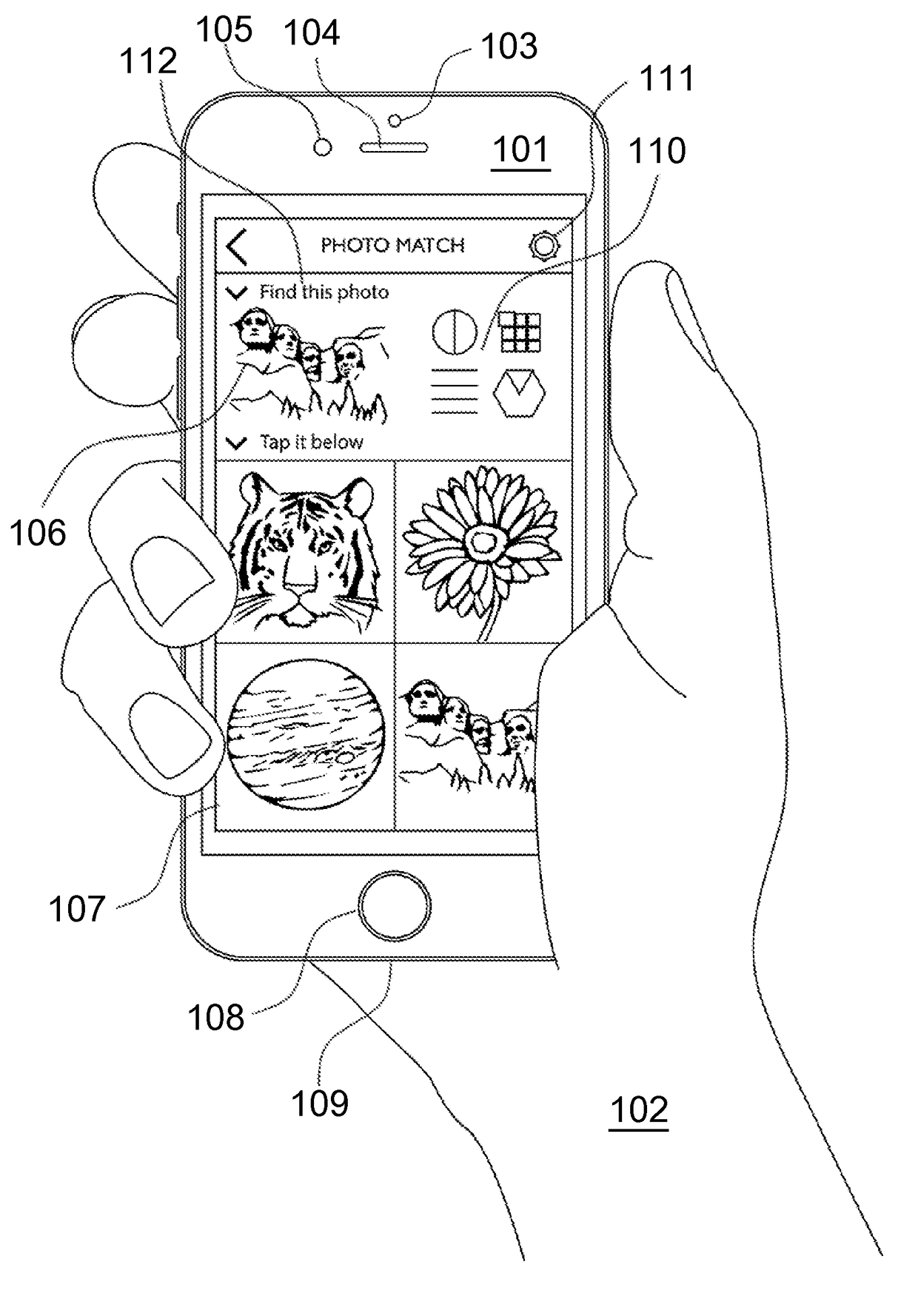
A strong, unified and comprehensive new computer security and authentication solution is disclosed. It is ideal for everyday users, and invents faster and easier enrollments, faster usage, easier usage, numerous aspects of stronger security including token based rapid mutual-authentication with protection against phishing, MitM, malware and user carelessness, secure resilience against token loss or theft, continuing protection in harsh situations, non-repudiation benefits, biometric encryption, code self-defenses, improved deployment, lower costs, new revenue opportunities, and more. One aspect's flow, visually-enforced mutual-authentication is: customer visits protected web site's login page, gets identified via Cookies, site displays one random photograph on said page, triggers customer's smartphone to automatically show a grid of random photos, one of which matches the login page photo, and customer taps it to login. Disclosed techniques teach how to block fraudulent sites and activity by preventing these producing any matching photo the customer can tap.
Owner:DRAKE CHRISTOPHER NATHAN TYRWHITT
Method and system of providing authentication of user access to a computer resource via a mobile device using multiple separate security factors
ActiveUS20160261411A1Easy to rememberPromote cloningKey distribution for secure communicationCryptography processingComputer resourcesPassword
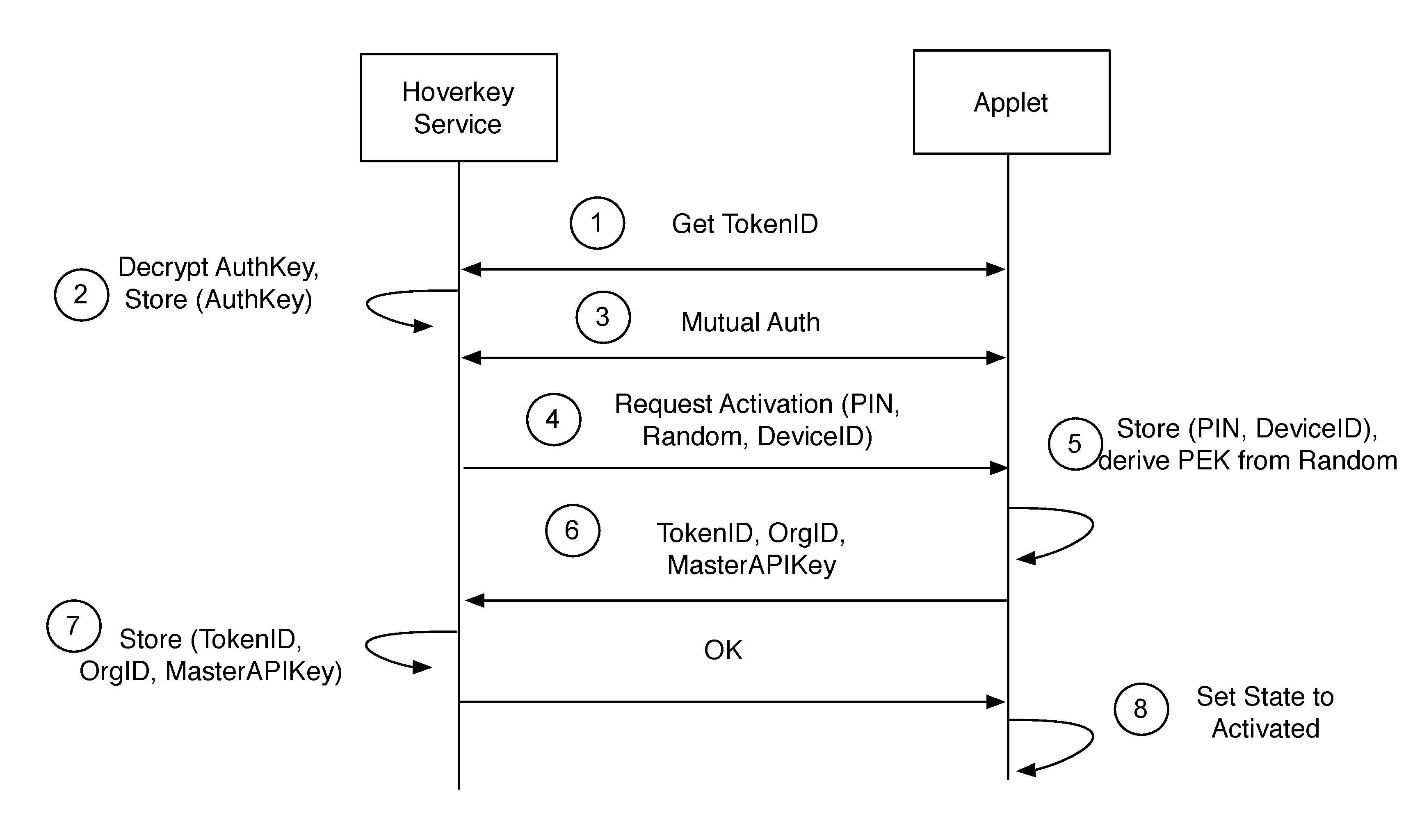
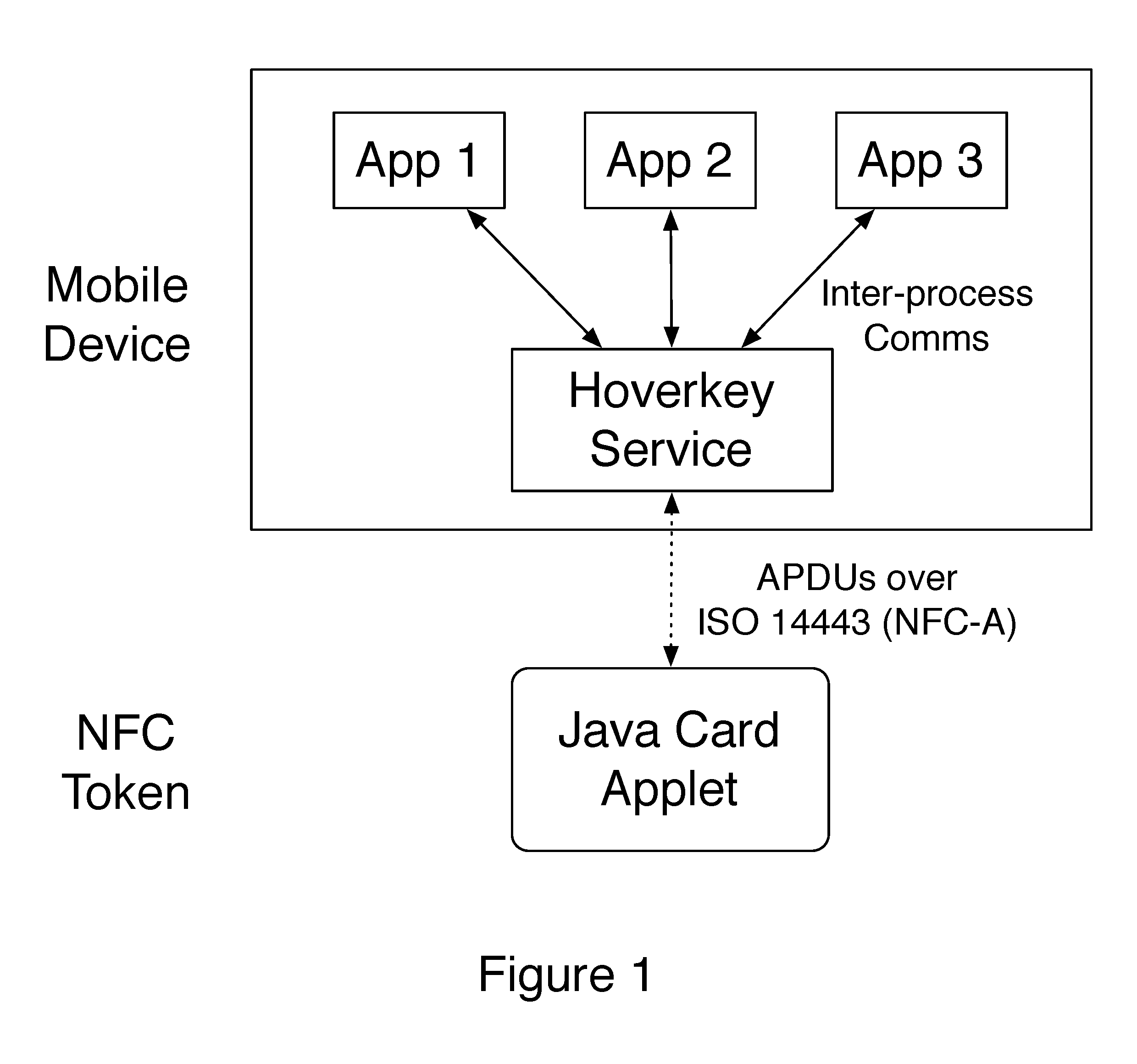
A method and system of authenticating a computer resource such as an application or data on a mobile device uses a contactless token to provide multi-factor user authentication. User credentials are stored on the token in the form of private keys, and encrypted data and passwords are stored on the device. When an application user requires access to the resource an encrypted password is transmitted to and decrypted on the token using a stored key. An unencrypted data encryption key or password is then transmitted back to the device under the protection of a cryptographic session key which is generated as a result of strong mutual authentication between the device and the token.
Owner:HOVERKEY
Method for Session Key Derivation in an IC Card
ActiveUS20080008322A1Shorten the timeAcutation objectsKey distribution for secure communicationCommunication interfaceMaster key
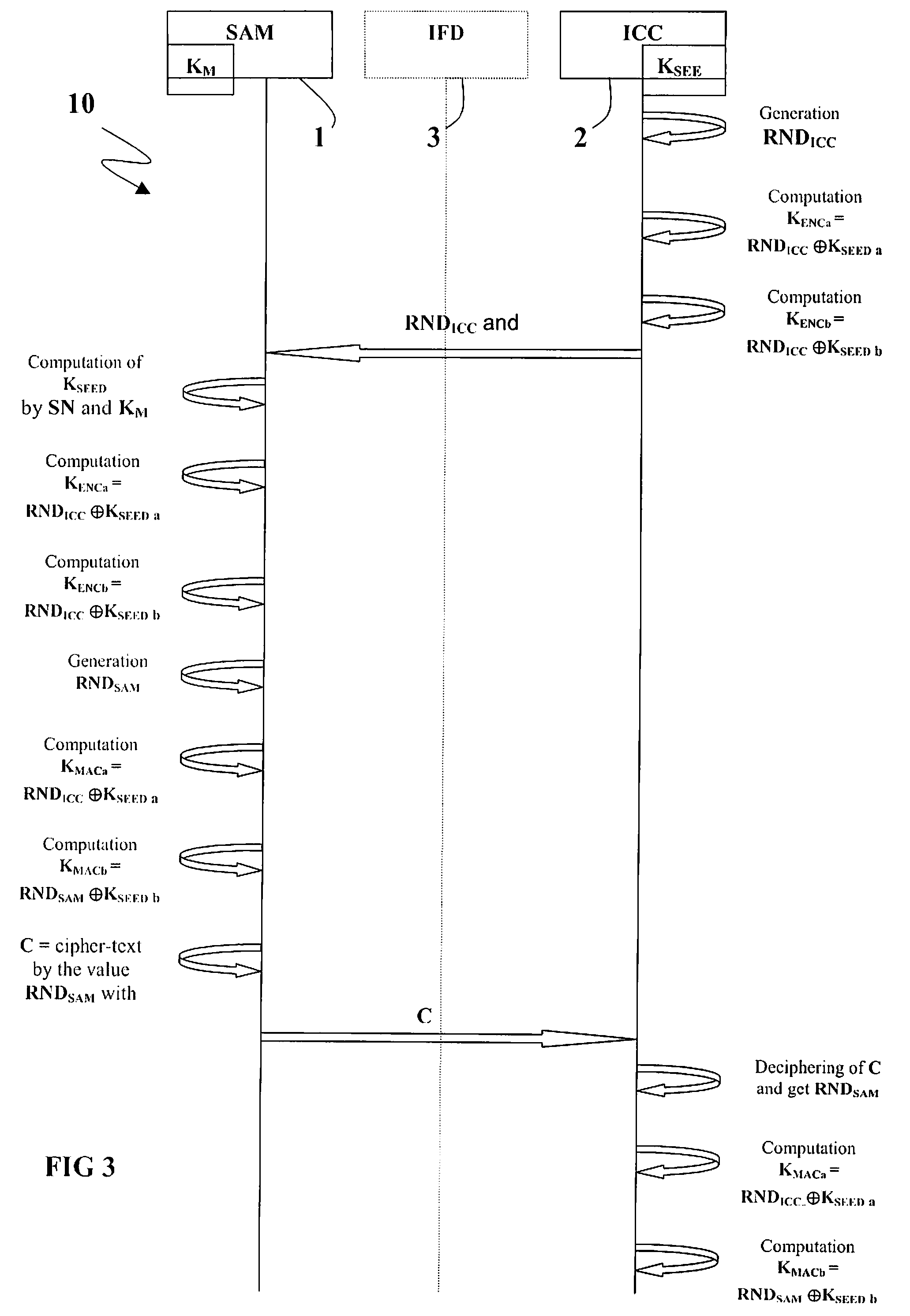
A key session derivation is provided during a mutual authentication between a master IC card storing a master key, and a user IC card storing a key-seed. The master IC card and the user IC card are connected through a communication interface for a communication session. A first random number associated to the user IC card is generated. First and second sub keys are derived from the key-seed. First and second session sub keys are respectively derived through the first sub key in combination with the first random number, and through the second sub key in combination with the first random number. The first and second session sub keys are joined in at least a session key for the communication session.
Owner:STMICROELECTRONICS INT NV
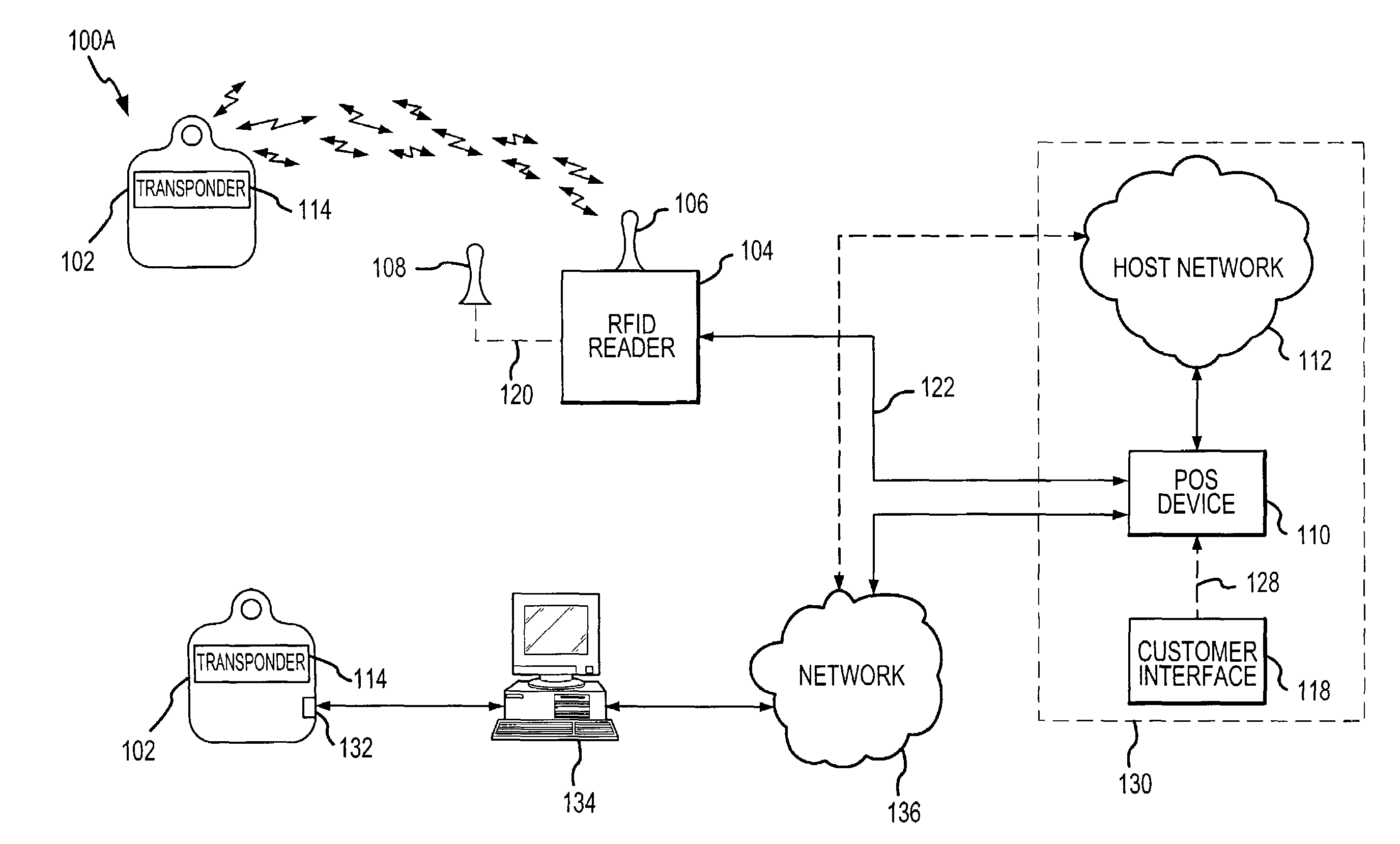
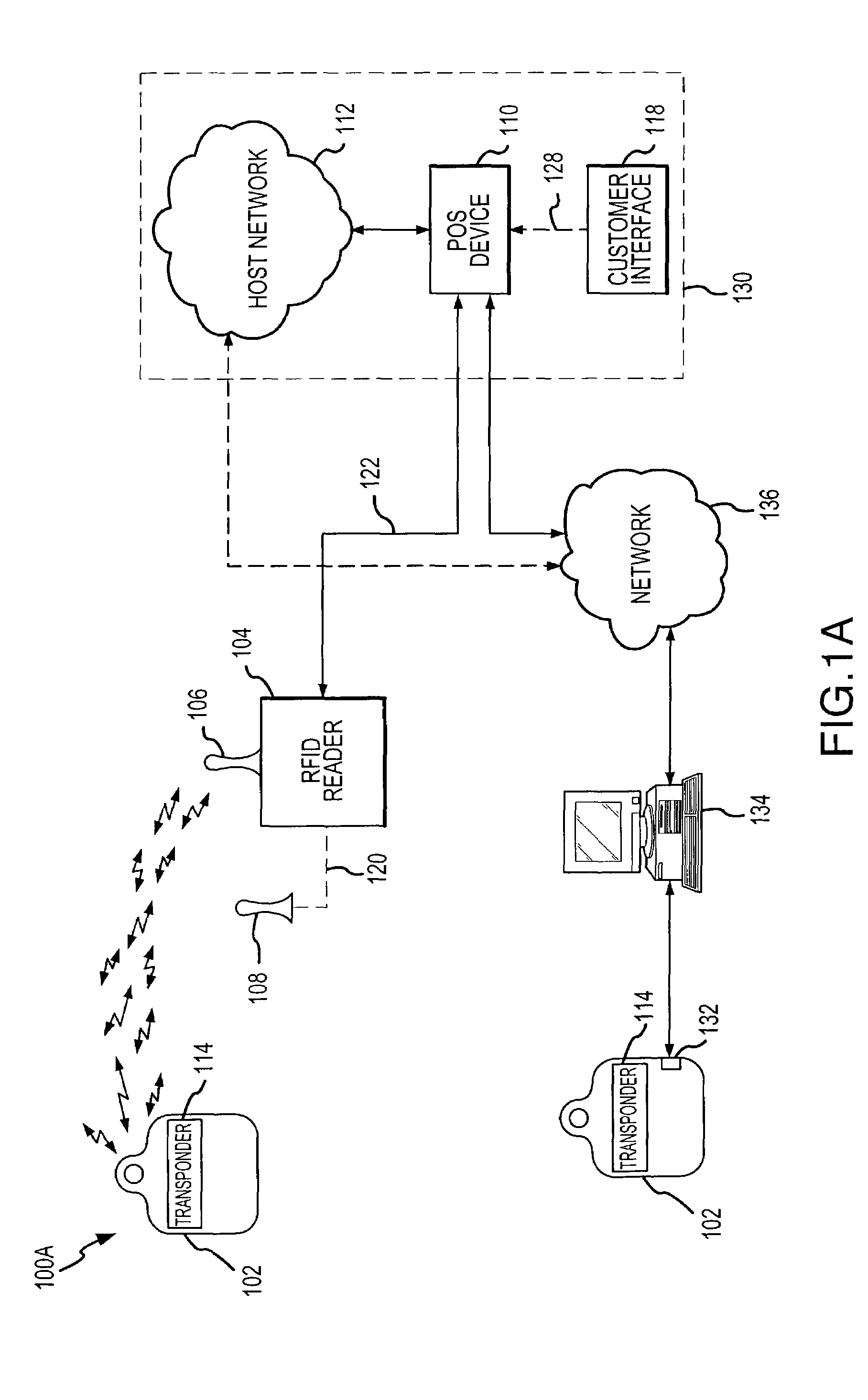
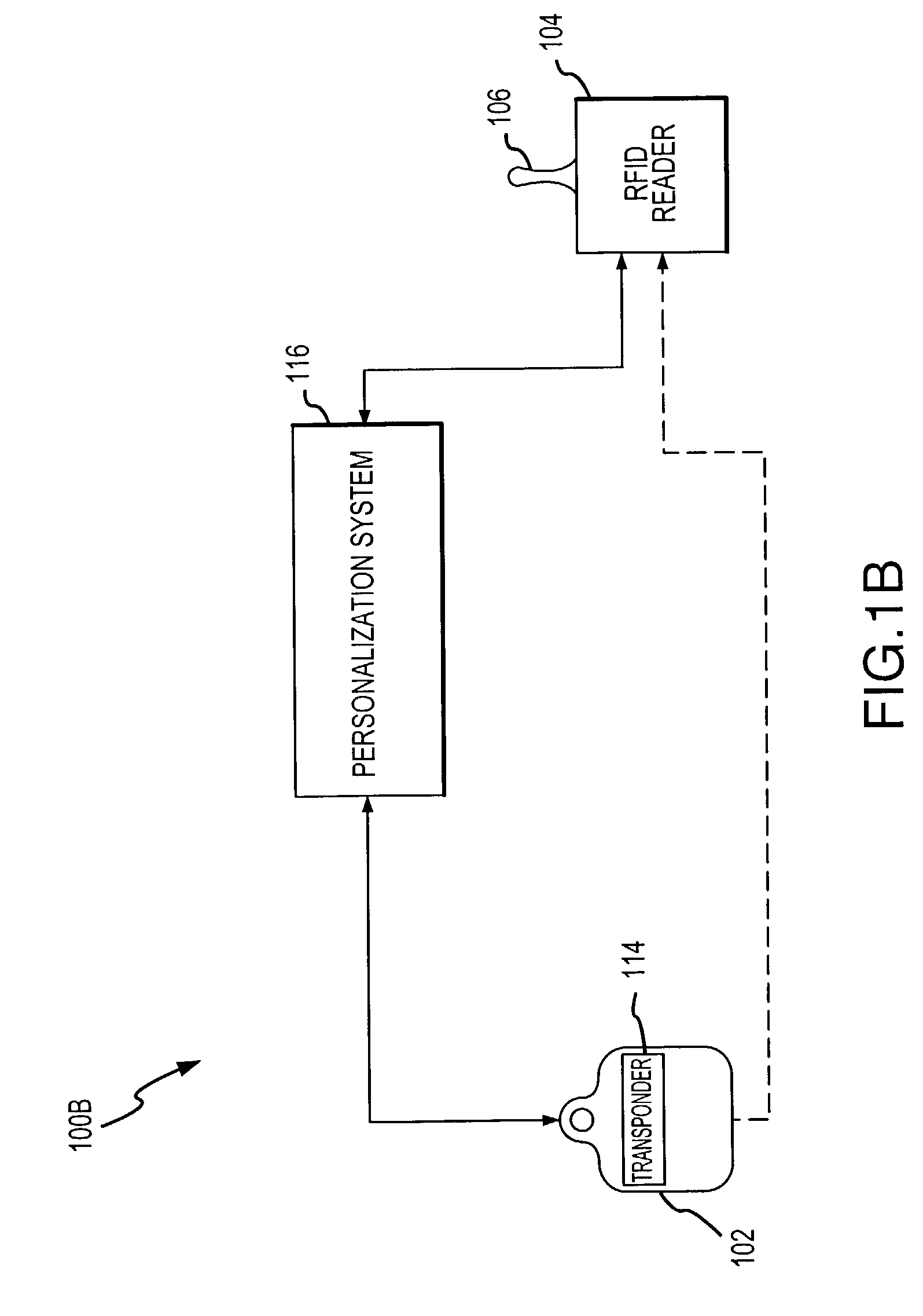
System and method for payment using radio frequency identification in contact and contactless transactions
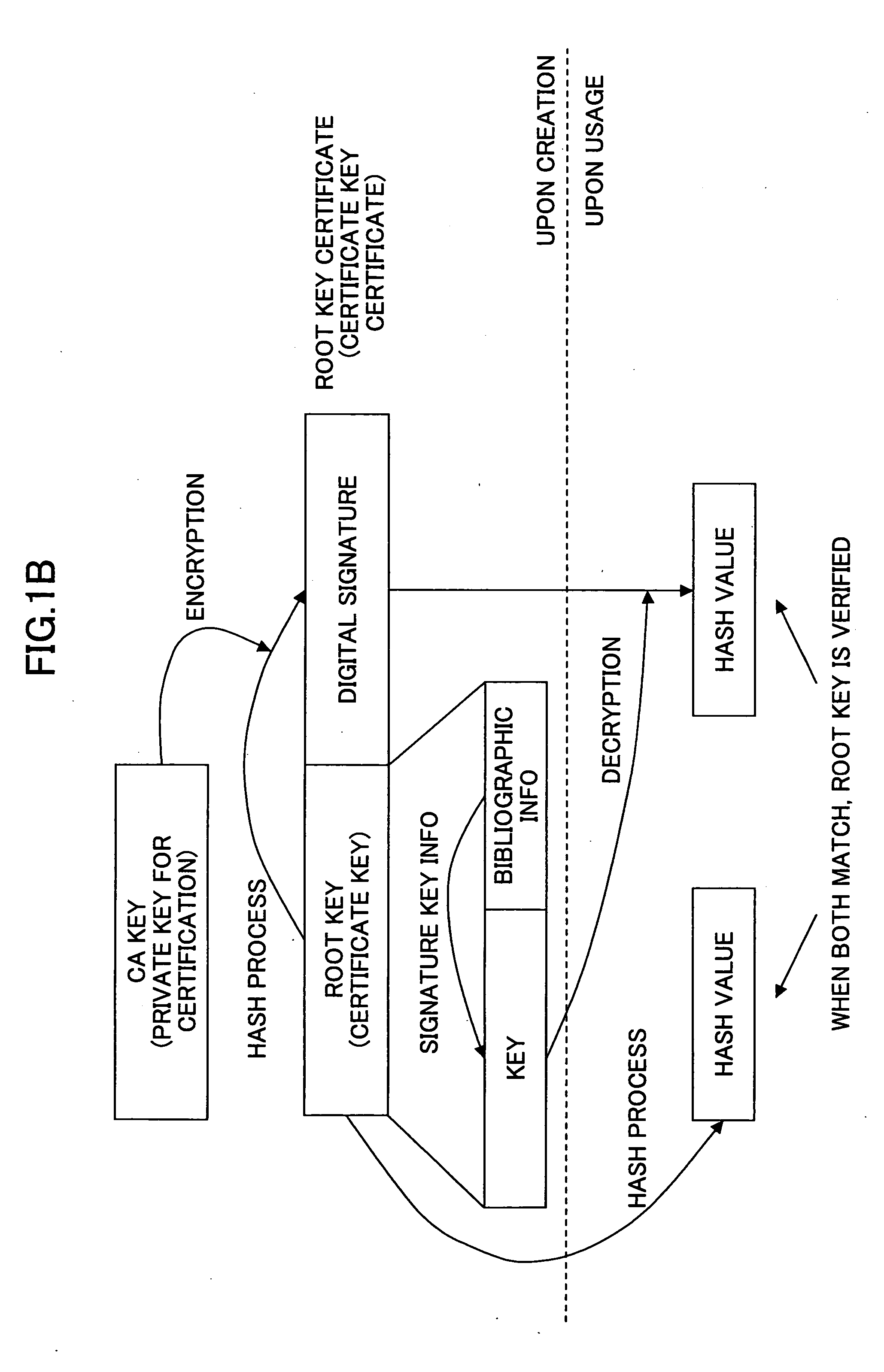
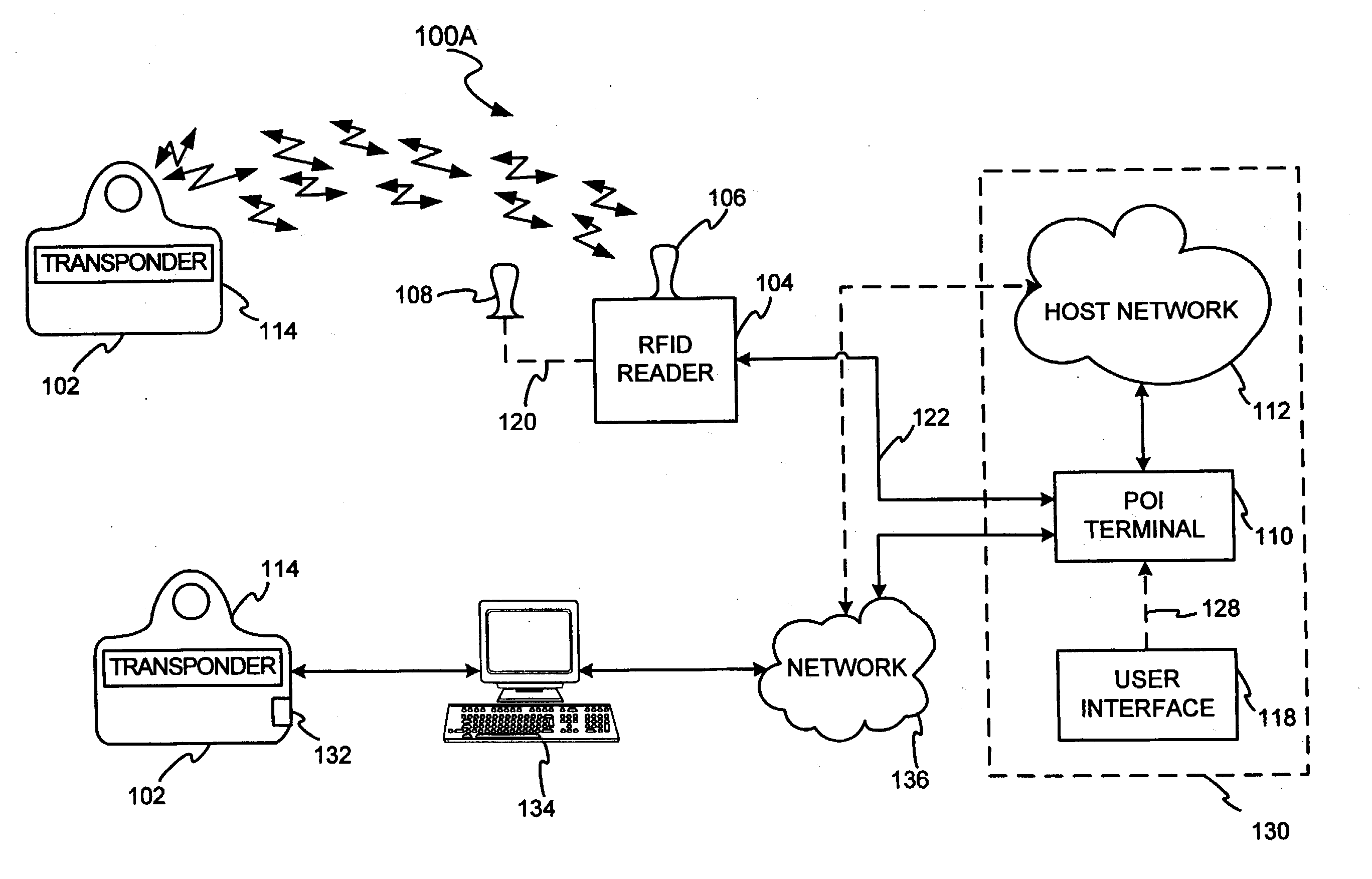
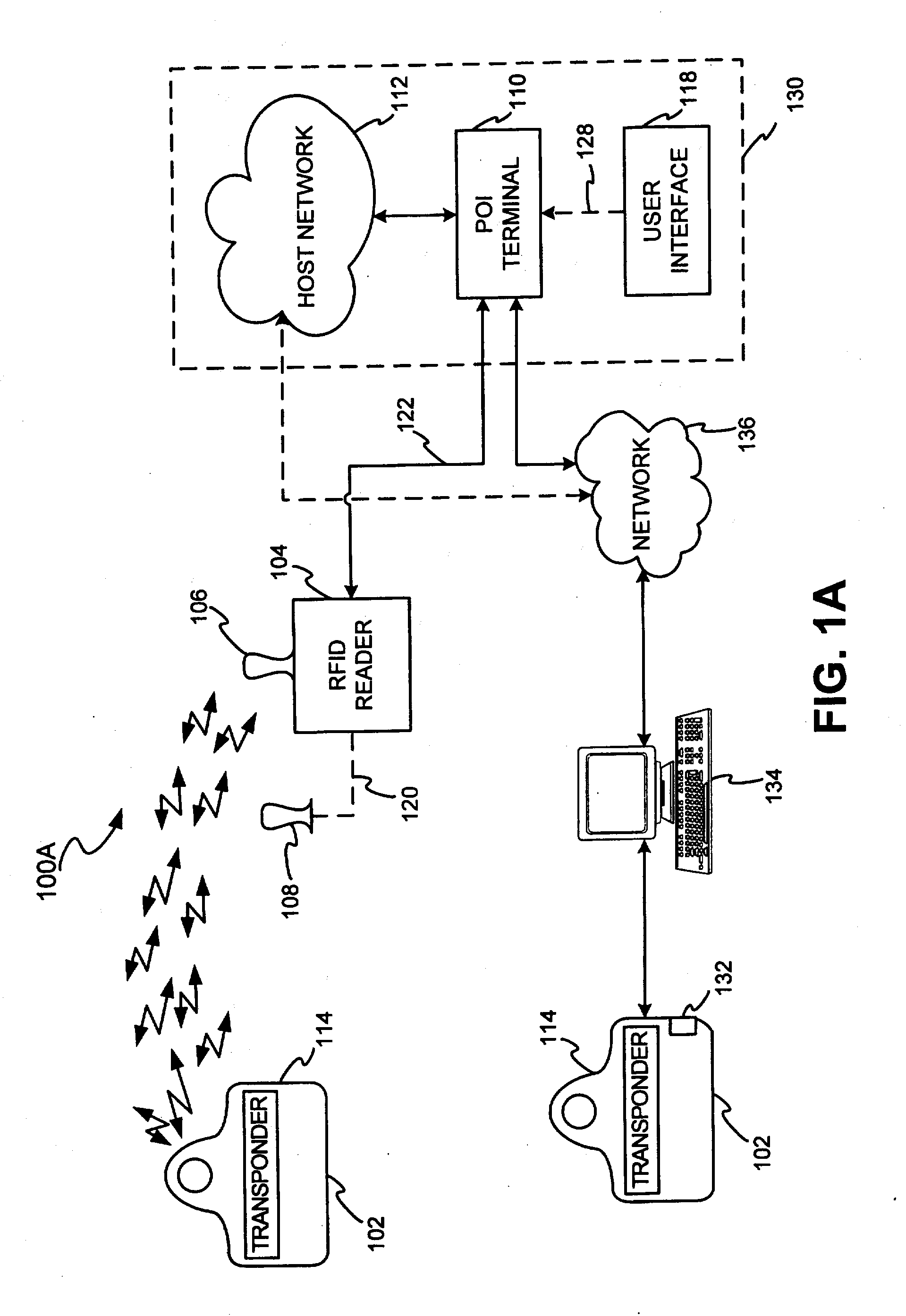
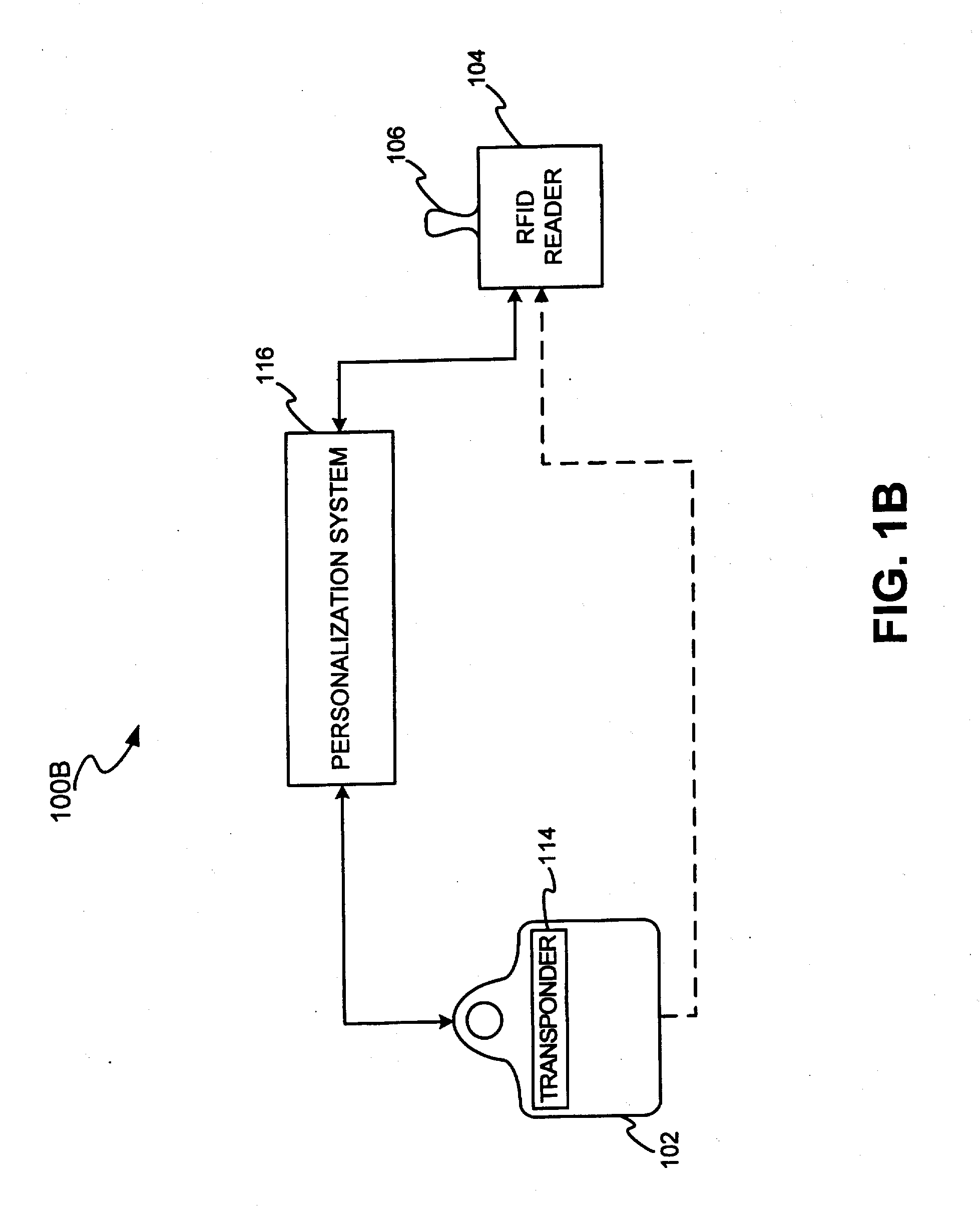
InactiveUS7239226B2Easy to completeElectric signal transmission systemsMultiple keys/algorithms usagePersonalizationFinancial transaction
A transponder-reader payment system includes a fob including a transponder, and a RFID reader for interrogating the transponder. The system may further include a personalization system for populating onto the fob and RFID reader identifying information and security and authentication keys which may be used during mutual authentication of the fob and the reader and for completing a transaction. In exemplary operation, the fob and RFID reader may be personalized, the fob may be presented to the RFID reader for interrogation, the fob and reader may engage in mutual authentication, and fob identifying information may be provided to the reader for transaction completion. In another exemplary embodiment, operation of the transponder-reader payment system may be controlled by an activation circuit. Further, the fob may be responsive to multiple interrogation signals.
Owner:LIBERTY PEAK VENTURES LLC
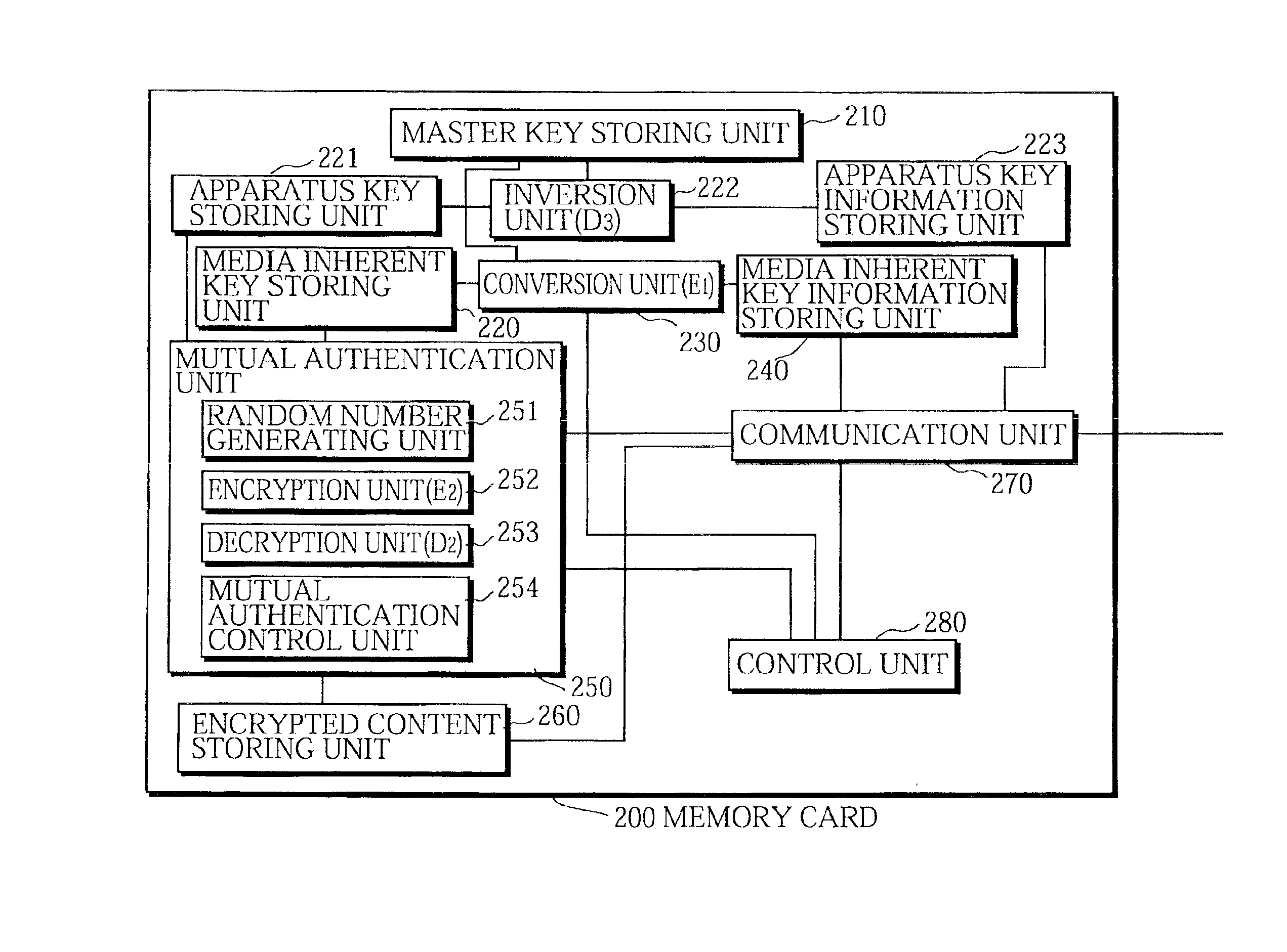
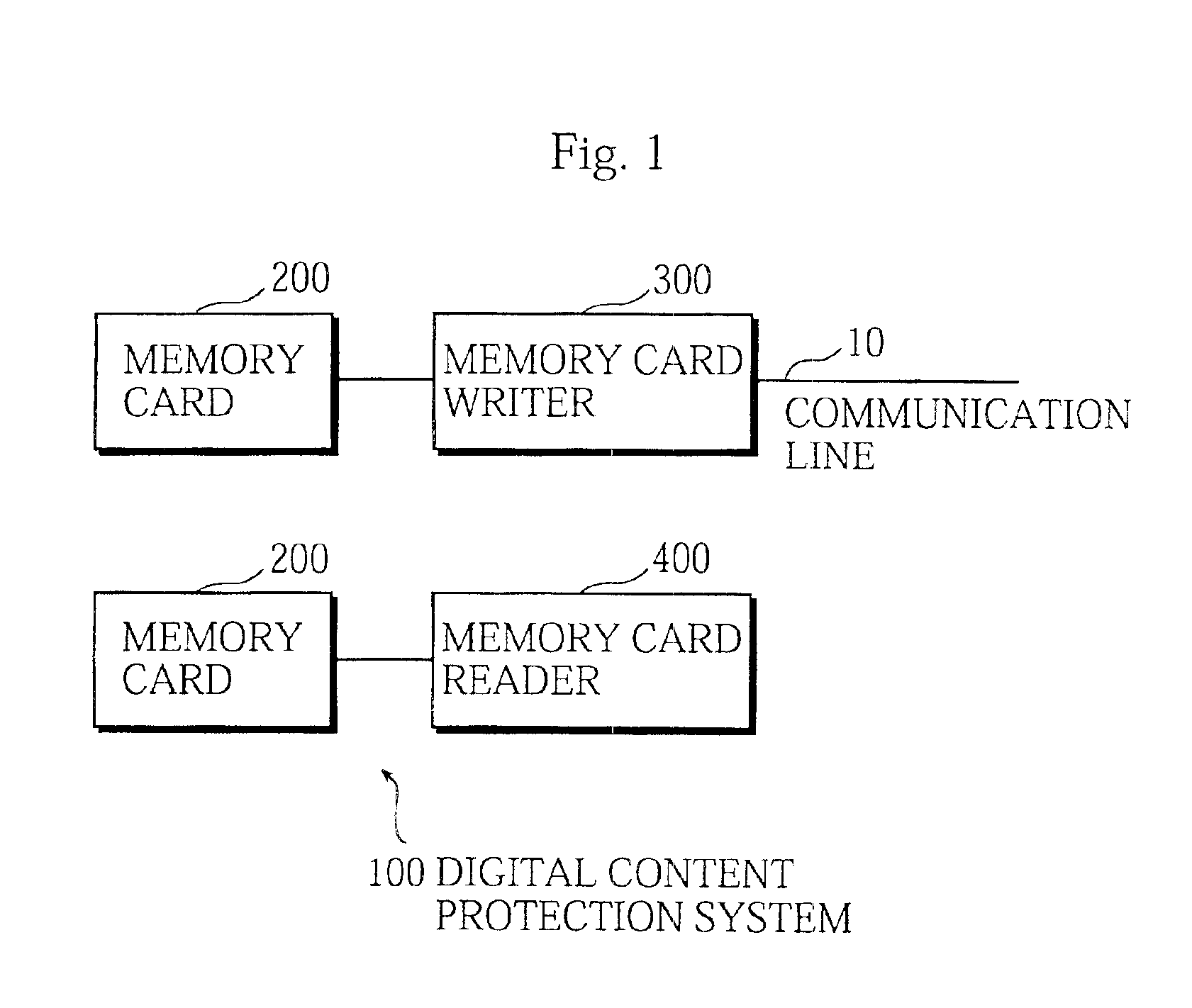
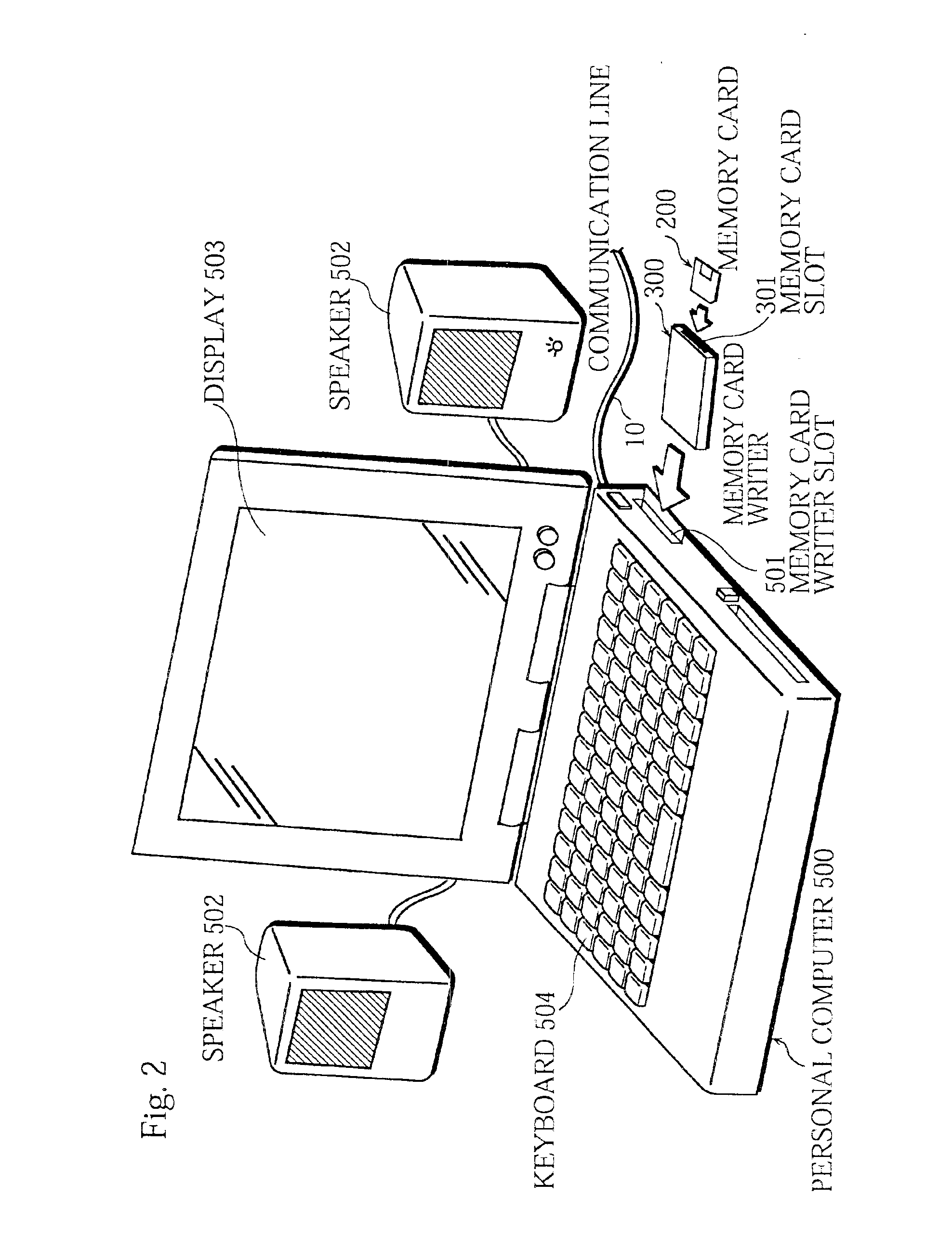
Digital content protection system
InactiveUS6859535B1Reduce scaleDigital data processing detailsUser identity/authority verificationDigital contentMediaFLO
The media inherent key storing unit 220 prestores an inherent key Ki, the conversion unit 230 generates an encrypted inherent key Ji from the inherent key read from the media inherent key storing unit 220, the random number generating unit 331 generates a random number R1, the encryption unit 252 generates an encrypted random number S1, the decryption unit 333 generates a random number R′1 from the encrypted random number R1, and the mutual authentication control unit 334 compares the random number R′1 with the random number R1 and, if the random number R′1 matches the random number R1, judges that the memory card 200 is an authorized device. If the memory card 200 and the memory card writer have successfully authenticated each other, the memory card writer encrypts a content using a decrypted inherent key. If the memory card 200 and the memory card reader have successfully authenticated each other, the memory card reader decrypts an encrypted content using the decrypted inherent key.
Owner:PANASONIC CORP
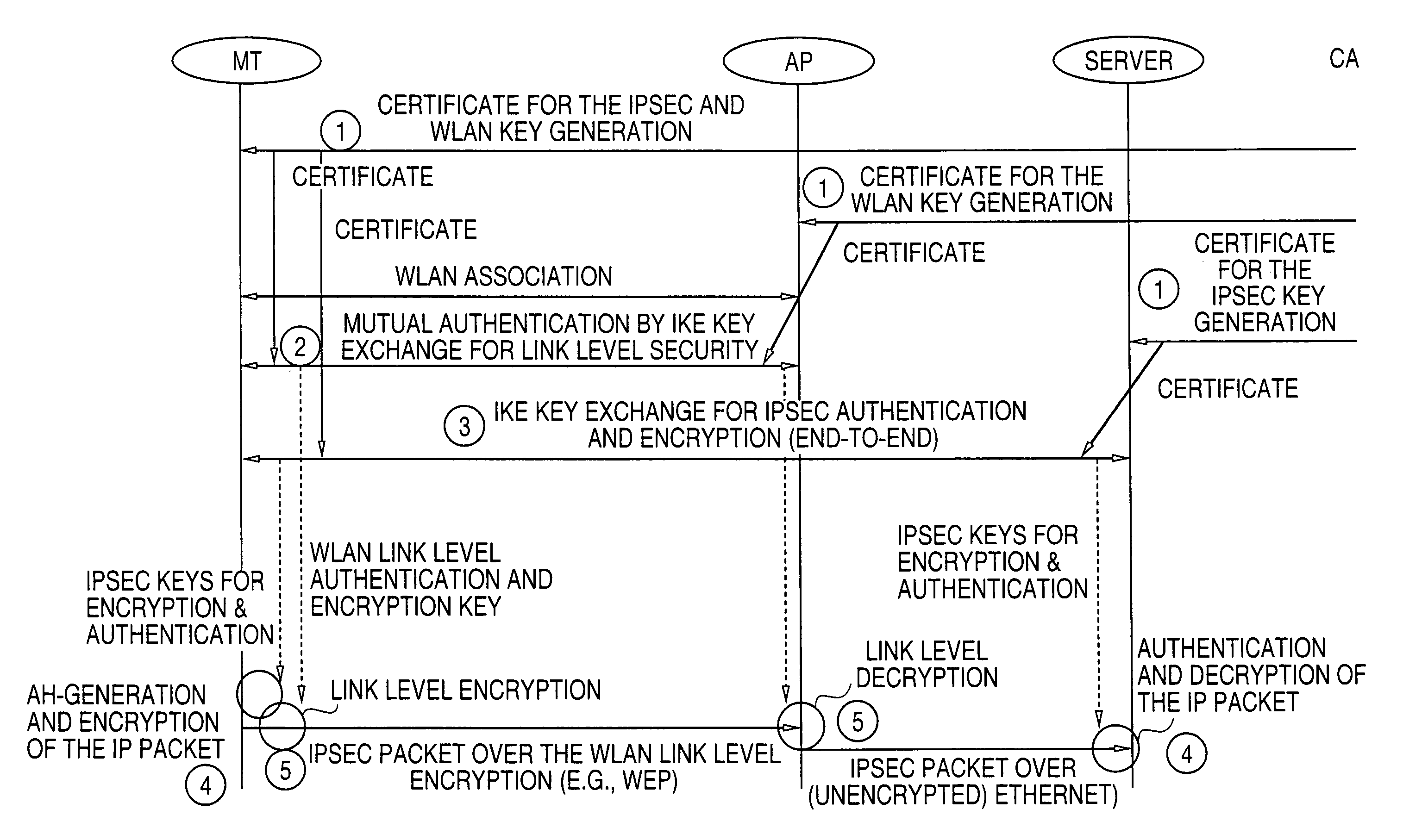
Key management methods for wireless LANs
InactiveUS7028186B1Work lessImprove securityUser identity/authority verificationNetwork topologiesSecurity functionMutual authentication
The security keys in the mobile terminals and access points of a wireless local area network (WLAN) are created, utilized and managed for a communication session between a mobile terminal and access point. Both the WLAN link level security protection and IP security functions of the network use the same Internet Key Exchange (IKE) key management protocol and use certificates in the same certificate hierarchy. When the mobile terminals associates with the network, it uses the IKE protocol with private keys and certificates to generate WLAN link level keys with the access point and provide mutual authentication.
Owner:CORE WIRELESS LICENSING R L
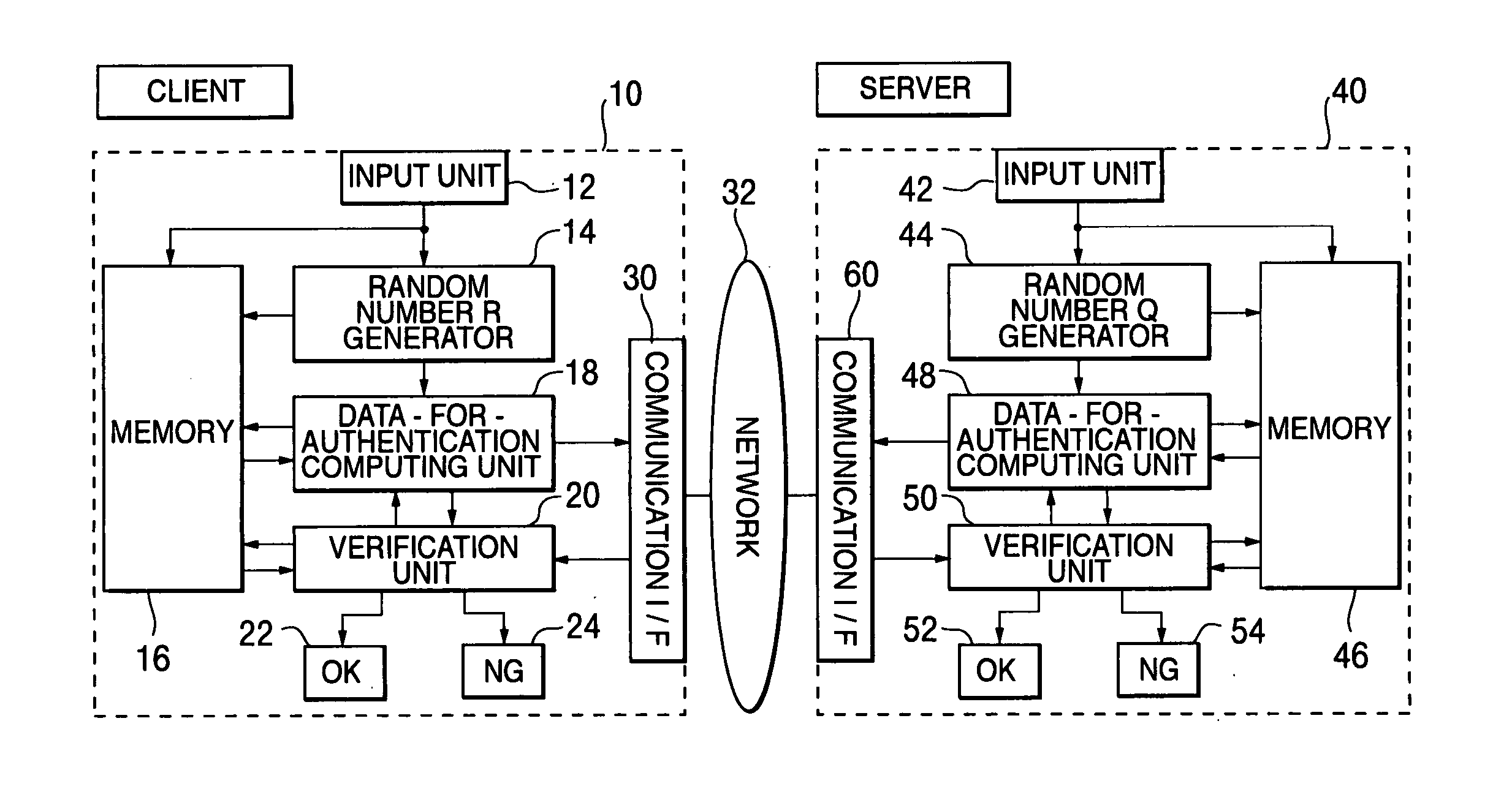
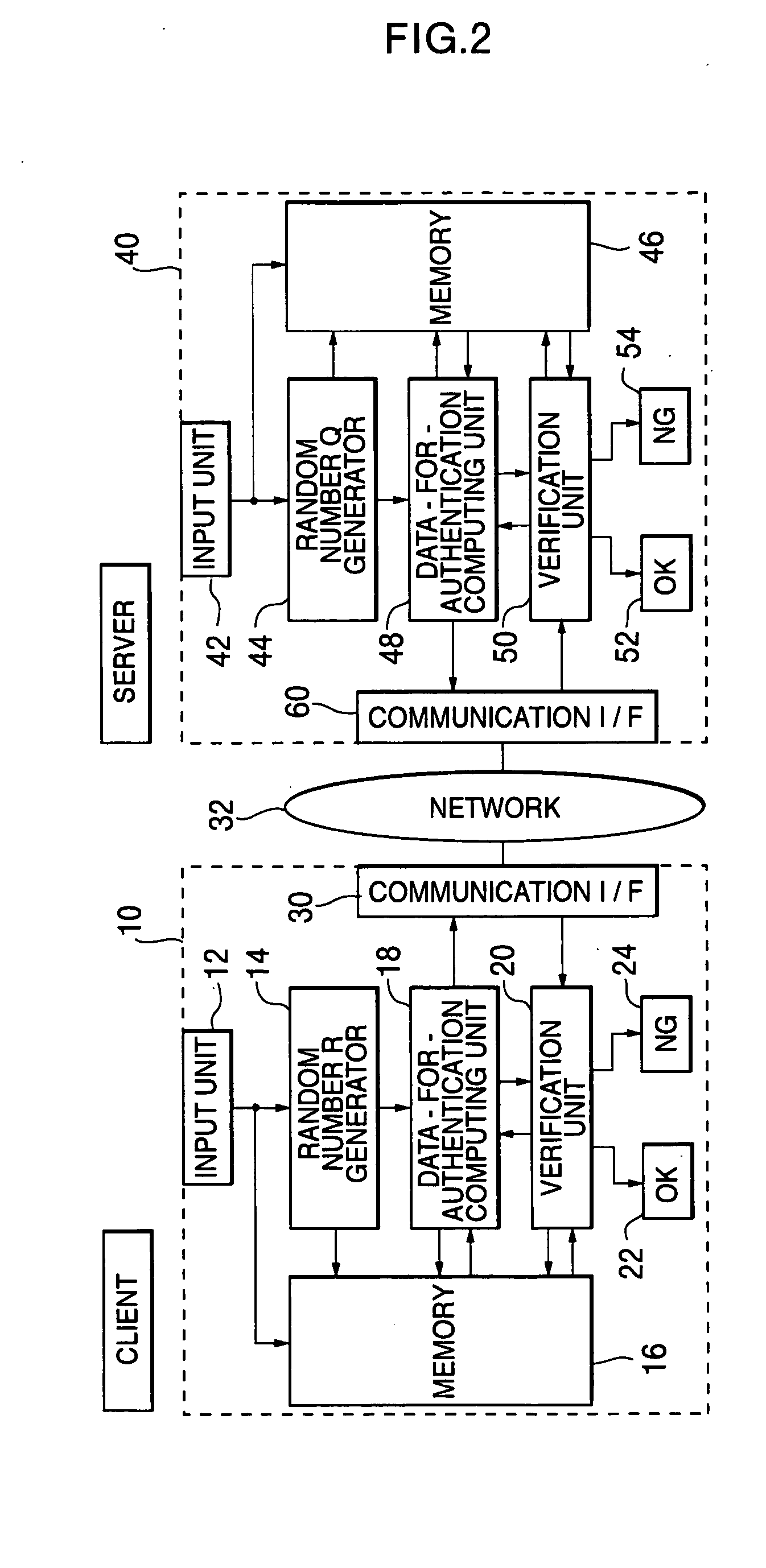
Inter-authentication method and device
InactiveUS20060143453A1Improve securityImprove convenienceUser identity/authority verificationCommunication unitOne-way function
An objective of the present invention is to obtain a mutual authentication method in which mutual authentication is carried out securely and conveniently. In order to achieve the above objective, in the mutual authentication process, a private key K0, being an initial value, is stored in a client and a server (Pc0, Ps0). The client generates a random number R, calculates secret data C and authentication data A, and transmits the data items to the server (Pc1). The server receives the authentication data A and the secret data C from the client, and generates a random number Q, calculates secret data S, and authentication data B and returns the data items, as well as updating the private key K0 with a private key K1 (Ps1). The client receives from the server the authentication data B and the secret data S, generates the random number R, calculates secret data C2, authentication data A2, and returns the data items to the server, and updates the private key K0 with the private key K1(Pc2). The client and the server check whether or not validity is established (Psm+1, Pcm+1). Further in the authentication method above, there is a method for generating a onetime ID, assuming that the onetime ID is identification information usable just one time in the authentication between a plurality of devices or application. In each of the devices or applications which carries out the authentication, a variable shared key which changes per predefined communication unit requiring the authentication is generated, a function value of one-way function is obtained in which the variable shared key is used as an argument, a onetime ID hard to tap and superior in security is generated based on the function value, and the onetime ID is utilized.
Owner:PSD +1
Method and system for providing single sign-on service
InactiveUS20090119763A1Possible to useDigital data processing detailsUser identity/authority verificationWeb serviceInternet privacy
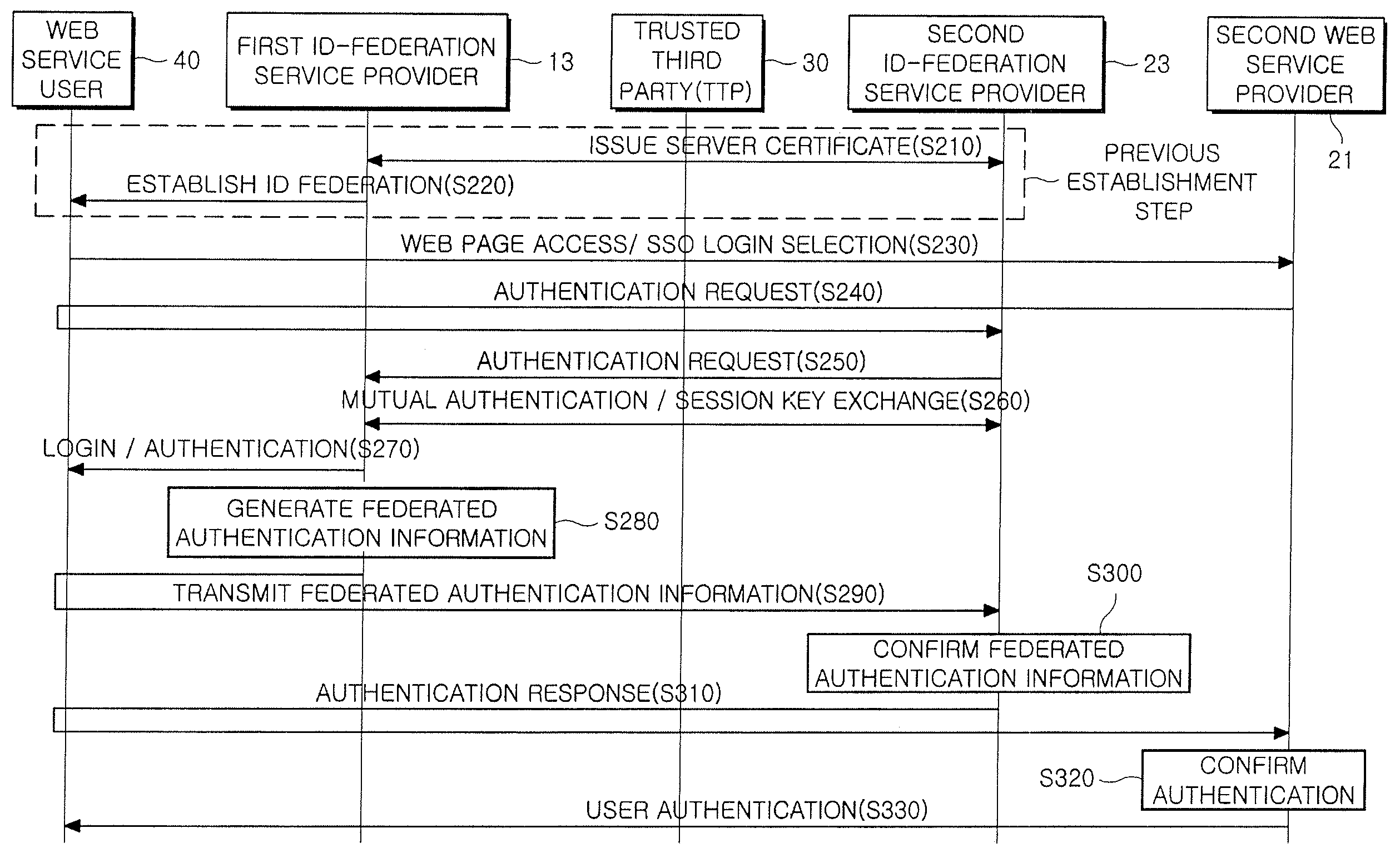
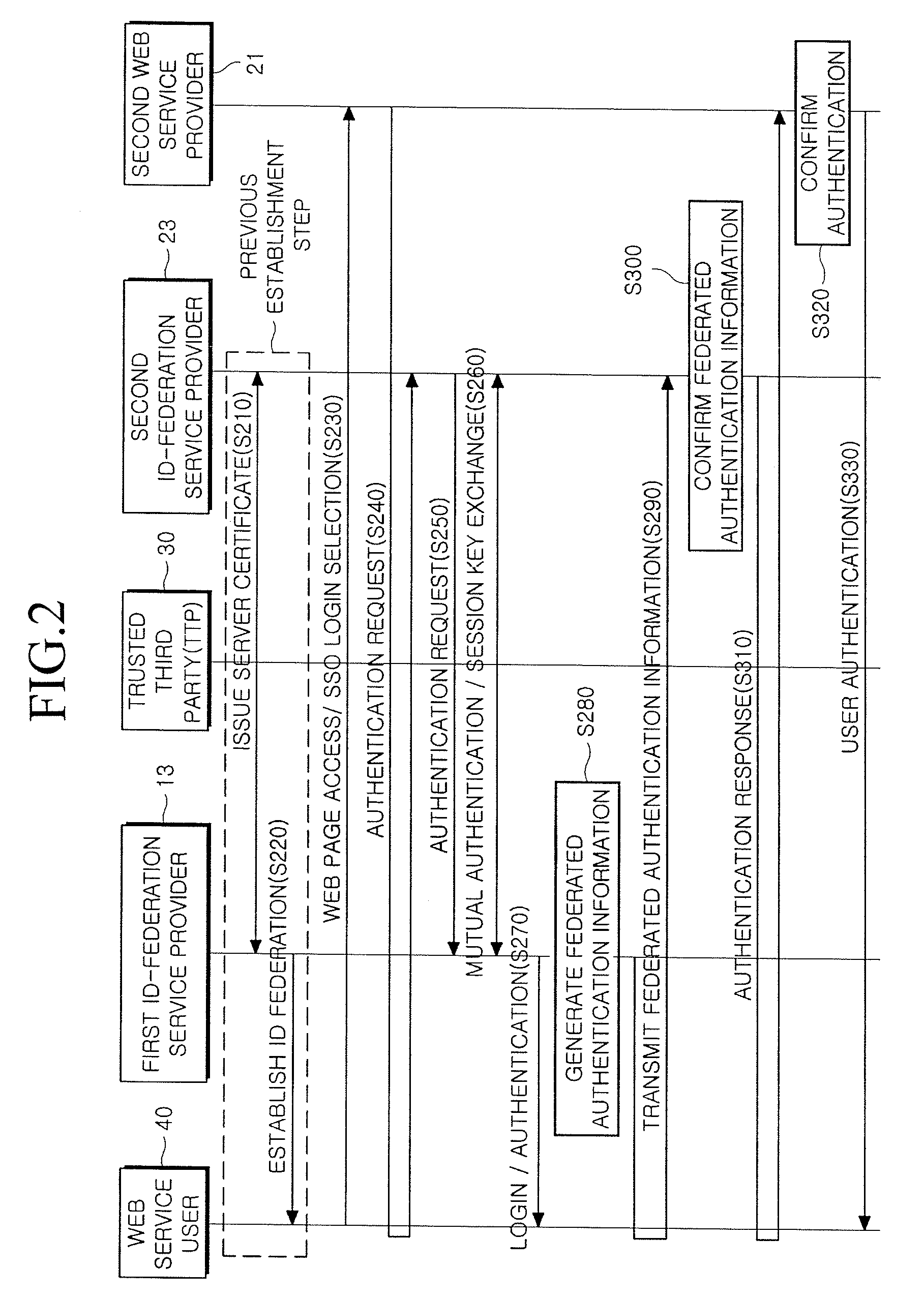
Provided is a method and system for providing an SSO service enabling the use of Web services in different trusted domains through a one-time authentication process. In the method, mutual authentication information is issued from a trusted third party to each of ID-federation service providers managing each of trusted domains, and an ID federation established between the ID-federation service provider and a user in the trusted domain of the ID-federation service provider. The first ID-federation service provider managing the first trusted domain, to which the user belongs to, is confirmed when a Web service provider in the second trusted domain receives a login request from the user in the first trusted domain. User authentication and mutual authentication arc performed between the first ID-federation service provider and a second ID-federation service provider managing the second trusted domain. The Web service provider authenticates the user in the first trusted domain and provides a corresponding Web service.
Owner:ELECTRONICS & TELECOMM RES INST
RFID security and mobility architecture
InactiveUS20110291803A1Secure distributionSupport mobilityMultiplex system selection arrangementsSubscribers indirect connectionEncryptionMutual authentication
A method of communication between RFID devices that includes mutually authenticating the RFID devices is disclosed. Once mutual authentication is completed, one or more encrypted messages based on the encryption scheme can be exchanged between the RFID devices.
Owner:SAVI TECH INC
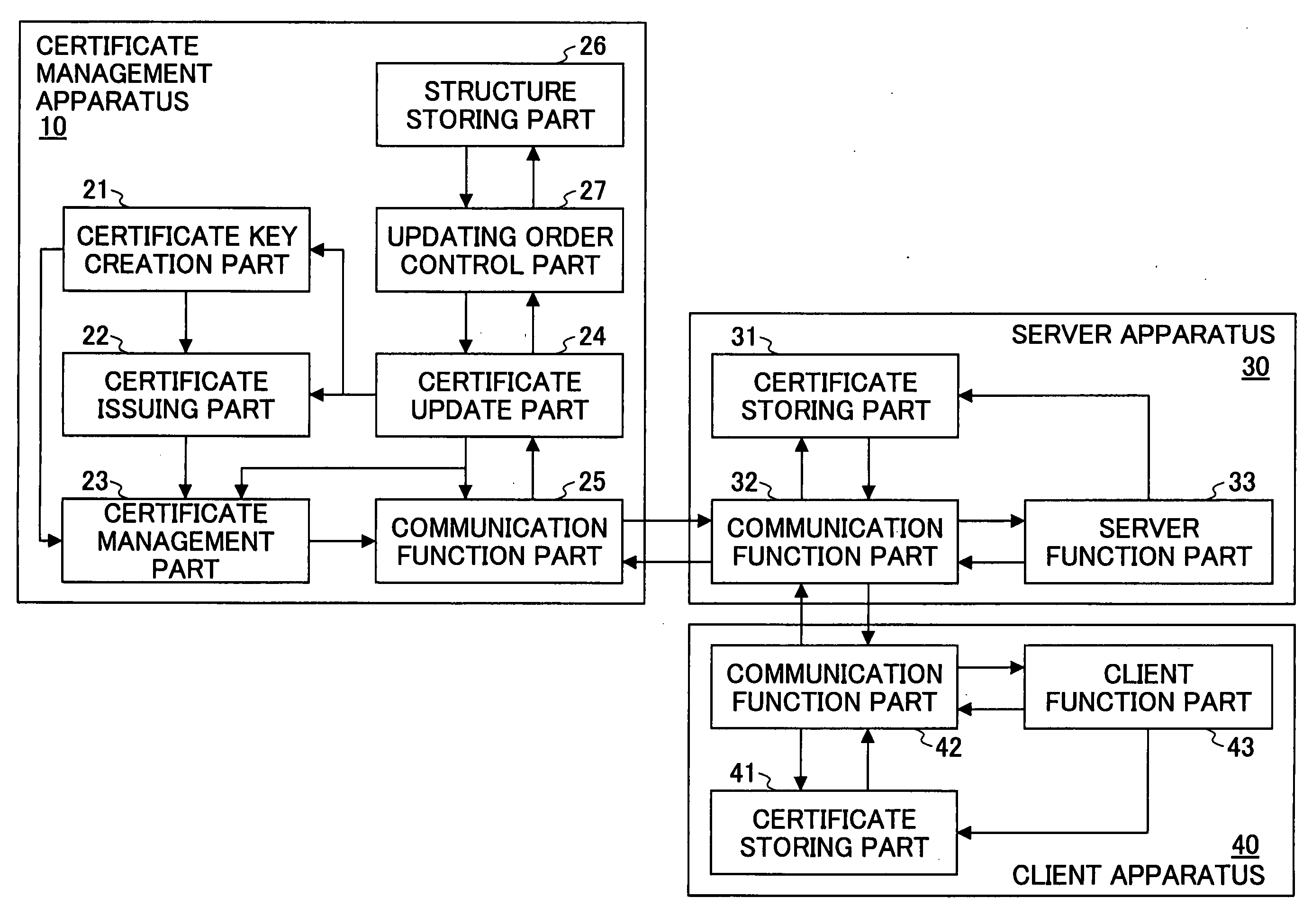
Digital certificate management system, digital certificate management apparatus, digital certificate management method, update procedure determination method and program
ActiveUS20050033957A1Authentication securitySecurity updateKey distribution for secure communicationMultiple keys/algorithms usageClient server systemsClient-side
In a digital certificate management system, a client / server system is connected to a digital certificate management apparatus capable of communicating with clients and servers. Mutual authentication is performed between the clients and the servers by using digital certificates and communications are performed over a communication channel established based on mutual authentication. The digital certificate management apparatus includes a certification key update part updating a server certification key used for mutual authentication and stored in each of the clients that become communication parties of one of the servers. The certification key updating part includes a key obtaining part, a certificate obtaining part, and first and second transmission parts. The second transmission part performs an operation of transmitting the new server certificate to each of the servers after there are responses, indicating that the new server certification key is received, from all of the clients that become communication parties of the server.
Owner:RICOH KK
Method and system for tracking user performance
InactiveUS20050033619A1Easy to useDigital data processing detailsCash registersTask completionSkill sets
A system and method for using RFID technology to track resource performance and task completion is disclosed. In one exemplary embodiment, a fob and an RFID reader may engage in mutual authentication. Where the RFID reader and the fob successfully mutually authenticate, the fob may transmit to the RFID reader information identifying the resource”s performance tracking account to which the fob is associated. The RFID reader may receive and forward the information to facilitate performance tracking. In one exemplary embodiment, the RFID reader may forward the information to a point of interaction terminal for transaction completion. In another exemplary embodiment, the fob completes tasks via a computer interface. In still another exemplary embodiment, the fob resource and / or a manager access to a resource engine, wherein the resource engine may be used to automatically grade, track, score, and assign resources based on resource skills and skill sets.
Owner:LIBERTY PEAK VENTURES LLC
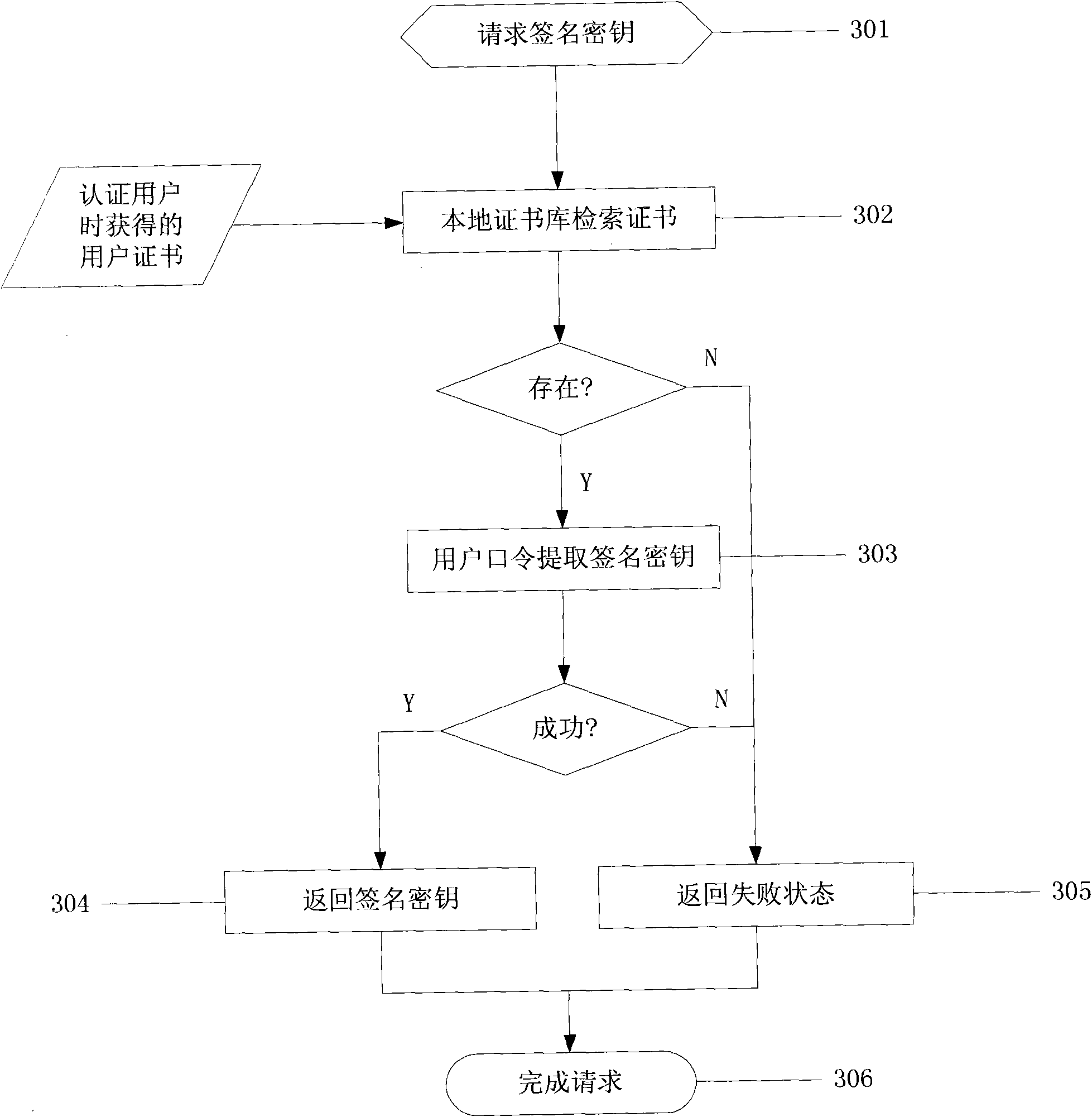
Methods and systems for remote password reset using an authentication credential managed by a third party
ActiveUS20080046982A1Digital data processing detailsUser identity/authority verificationThird partyPassword
Embodiments of the present invention provide a secure remote password reset capability. In some embodiments, an exemplary method provides a remote reset of a password associated with a token in a computer system having a security server. A token-based authentication process is activated by connecting the token to the security server. A server-based authentication process is initiated in the security server by activating a password reset process in a security client. The server-based authentication process communicates with the token-based authentication process over a secure channel. An authentication credential is managed by a third party agent that supplies a query and the authentication credential as a correct response to the query to the security server. A prompt provided by the password reset process collects the authentication credential and a new password. After the authentication credential is validated mutually authentication is performed between the security server and the token. The token is updated with the new password based on a successful result of the mutual authentication.
Owner:RED HAT
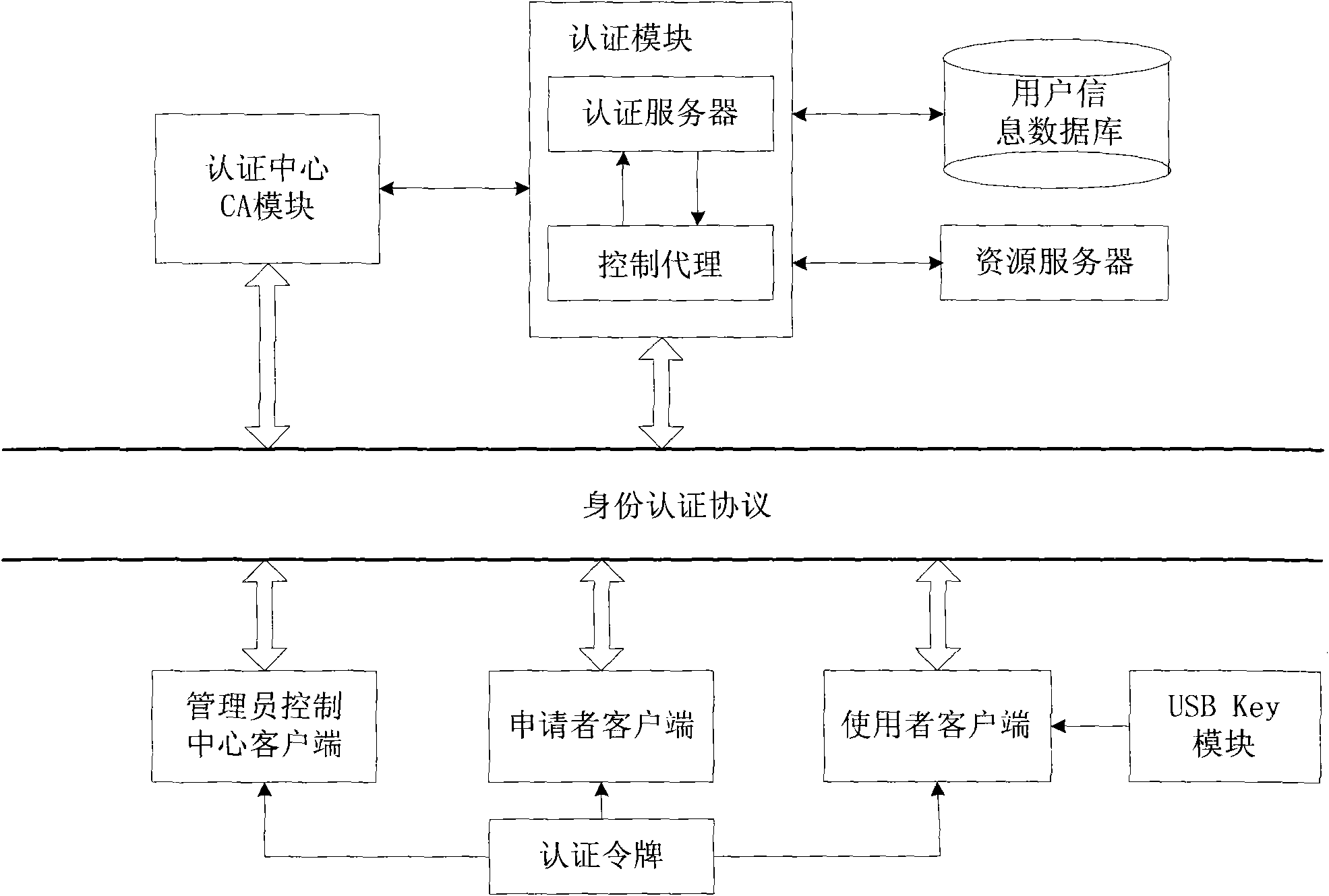
Network identity authentication system and method
InactiveCN101674304AEnsure safetyAchieve separationUser identity/authority verificationConfidentialityAuthentication server
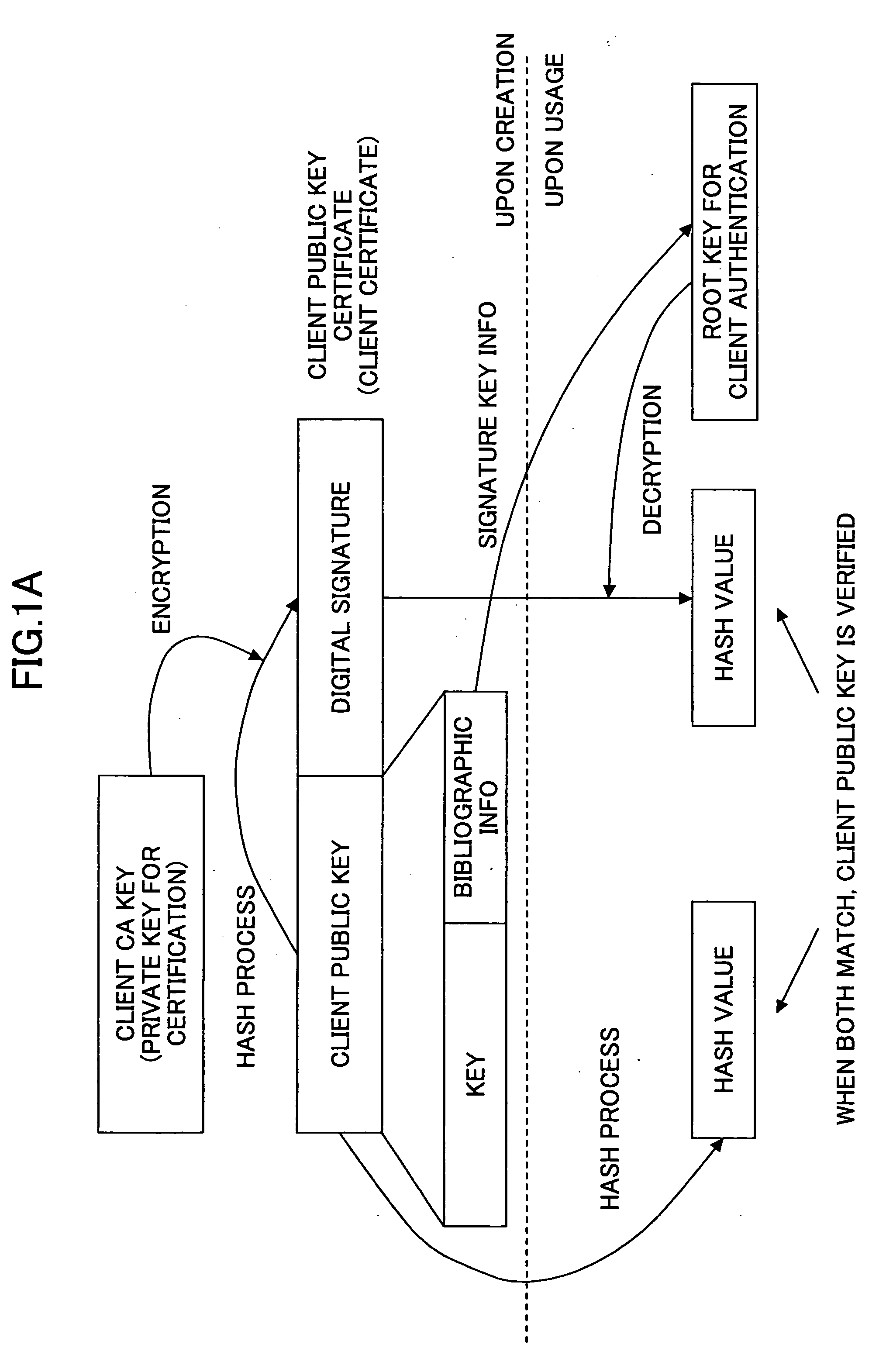
The invention relates to an identity authentication system and an authentication method. The identity authentication system comprises an authentication center CA module, an authentication module, a client side and a USB Key module, wherein the authentication center CA module is responsible for the functions of application, examination and approval, issuing, updating and revocation of a certificate; the authentication module respectively carries out the generation of a digital envelope and the authentication of a digital certificate to the client side and a server side; the client side mainly realizes the management of the system and the clients; and the USB Key module mainly provides a medium for storing the digital certificate and a user private key to the user. The invention adopts a digital envelope technology, and can meet the high-confidentiality requirement of data transmission; an authentication token is used for sending a request to the authentication server by the client sidefor authentication and realizing the security of the authentication process; and the client side and the authentication server respectively carry out the generation of the digital envelope and the digital certificate, thus being capable of realizing the mutual authentication between the client side and the authentication server.
Owner:ZHEJIANG NORMAL UNIVERSITY
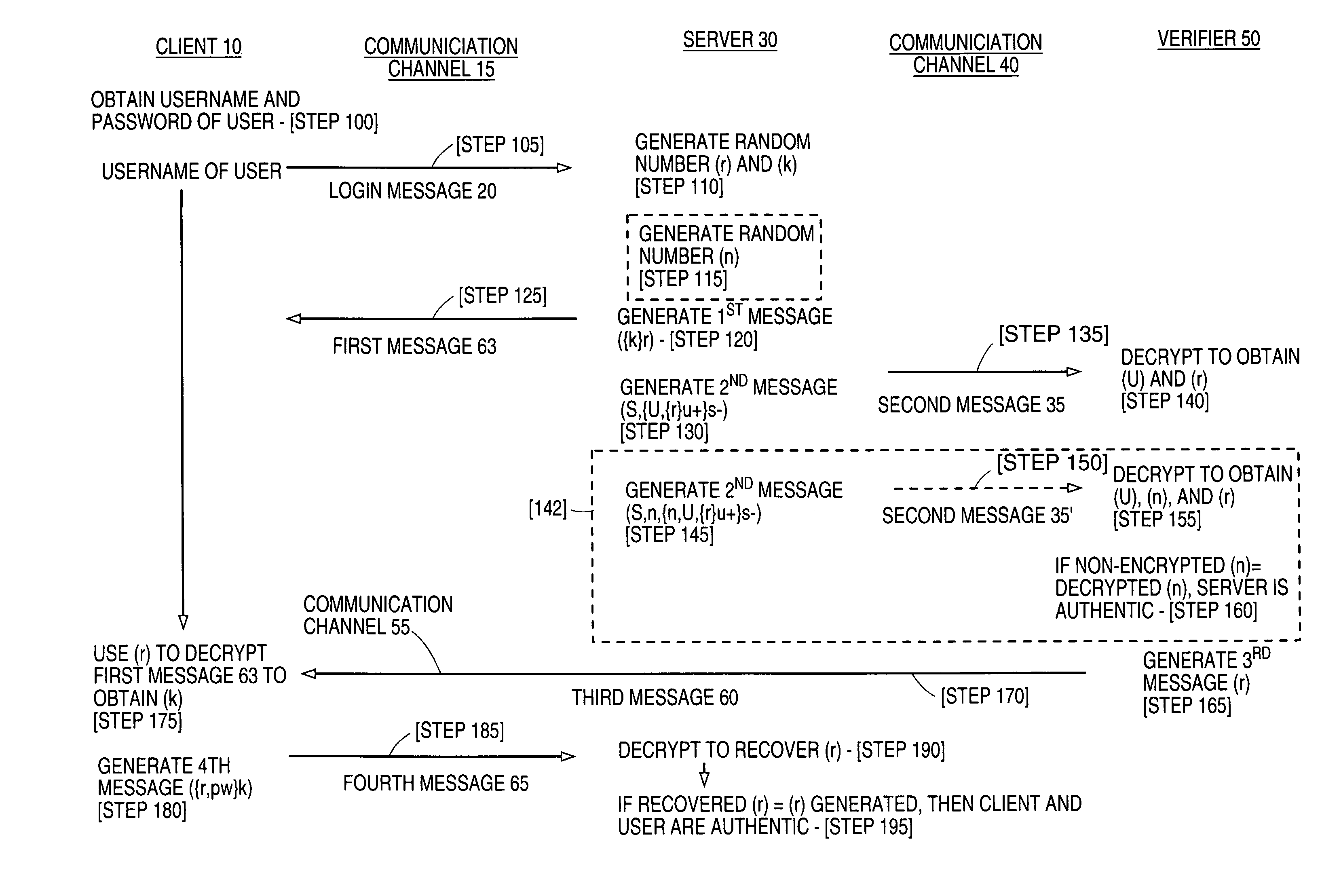
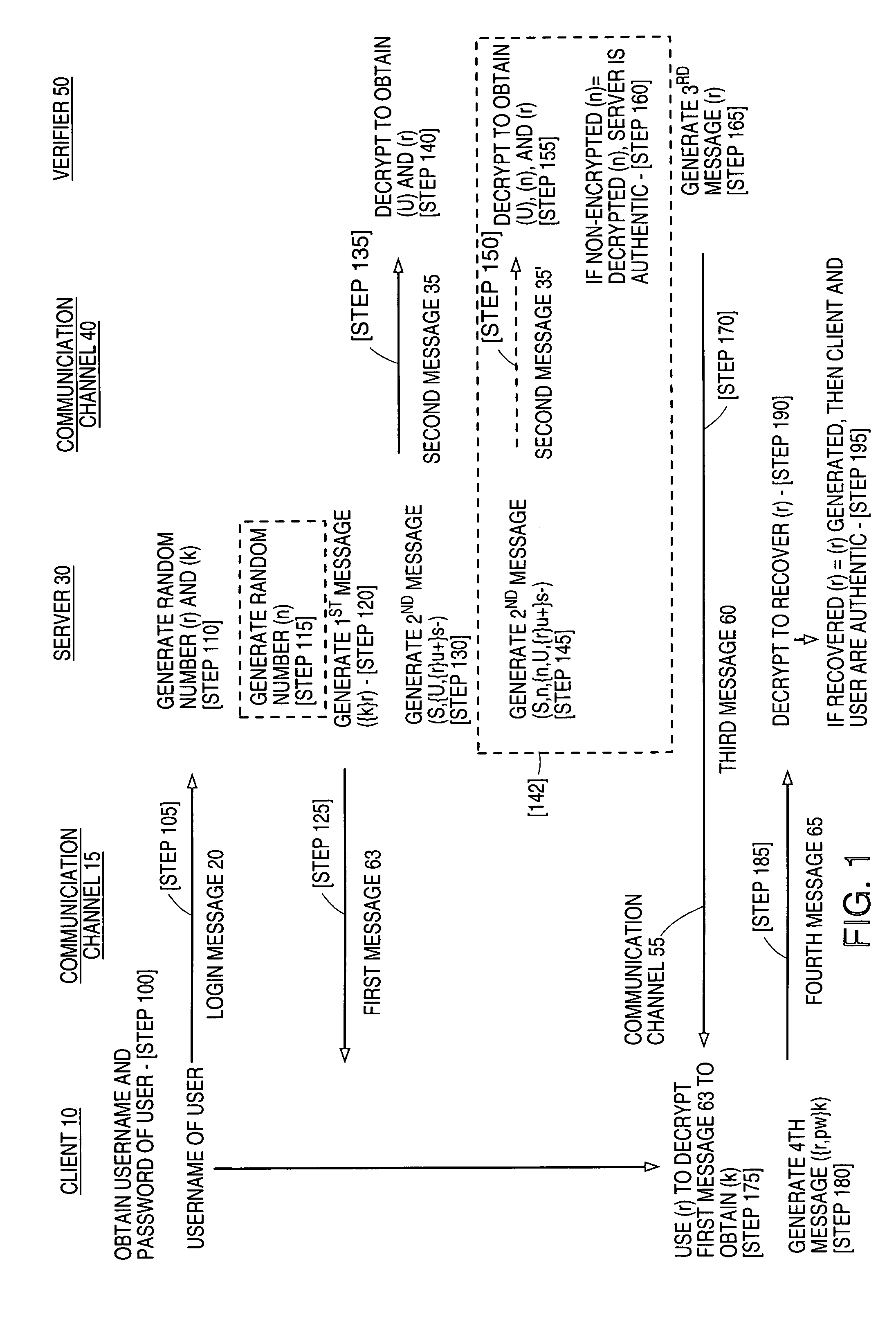
Strong mutual authentication of devices
InactiveUS7020773B1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesCommunications systemClient-side
The present invention relates to a method for enabling strong mutual authentication between two computers in a communication system. A user from a client attempts to gain access to a server. The server transmits a first key encrypted by a second key to the client and a second key encrypted by a user's private key to a verifier. The verifier uses the user's login information to obtain the user's private key, which the verifier uses to obtain the second key. The verifier transmits the second key to the client and the client decrypts the first key with the second key. The client then transmits the second key encrypted by the first key to the server. If the received second key is the same as the generated second key, the client is authenticated to the server.
Owner:CITRIX SYST INC
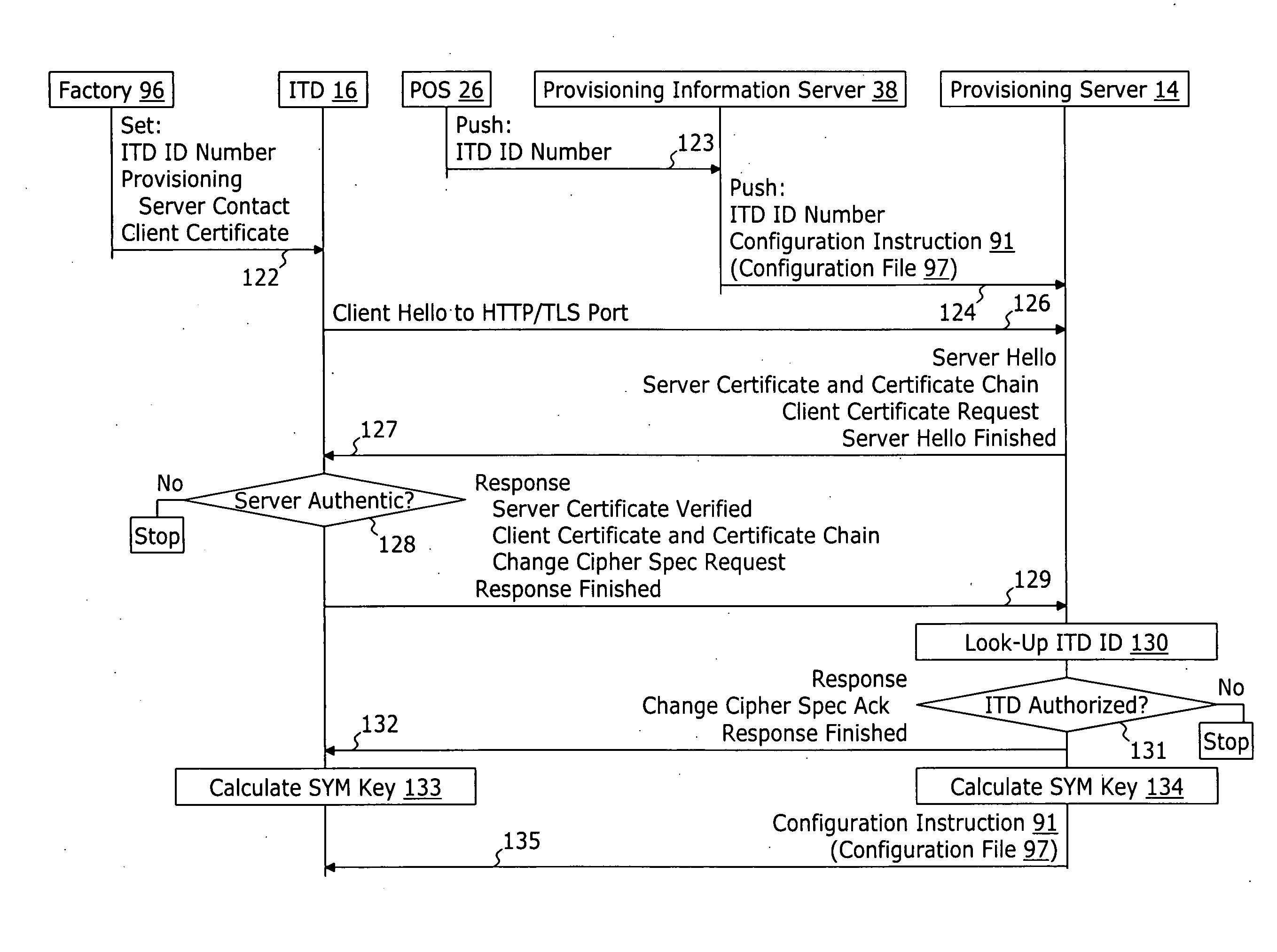
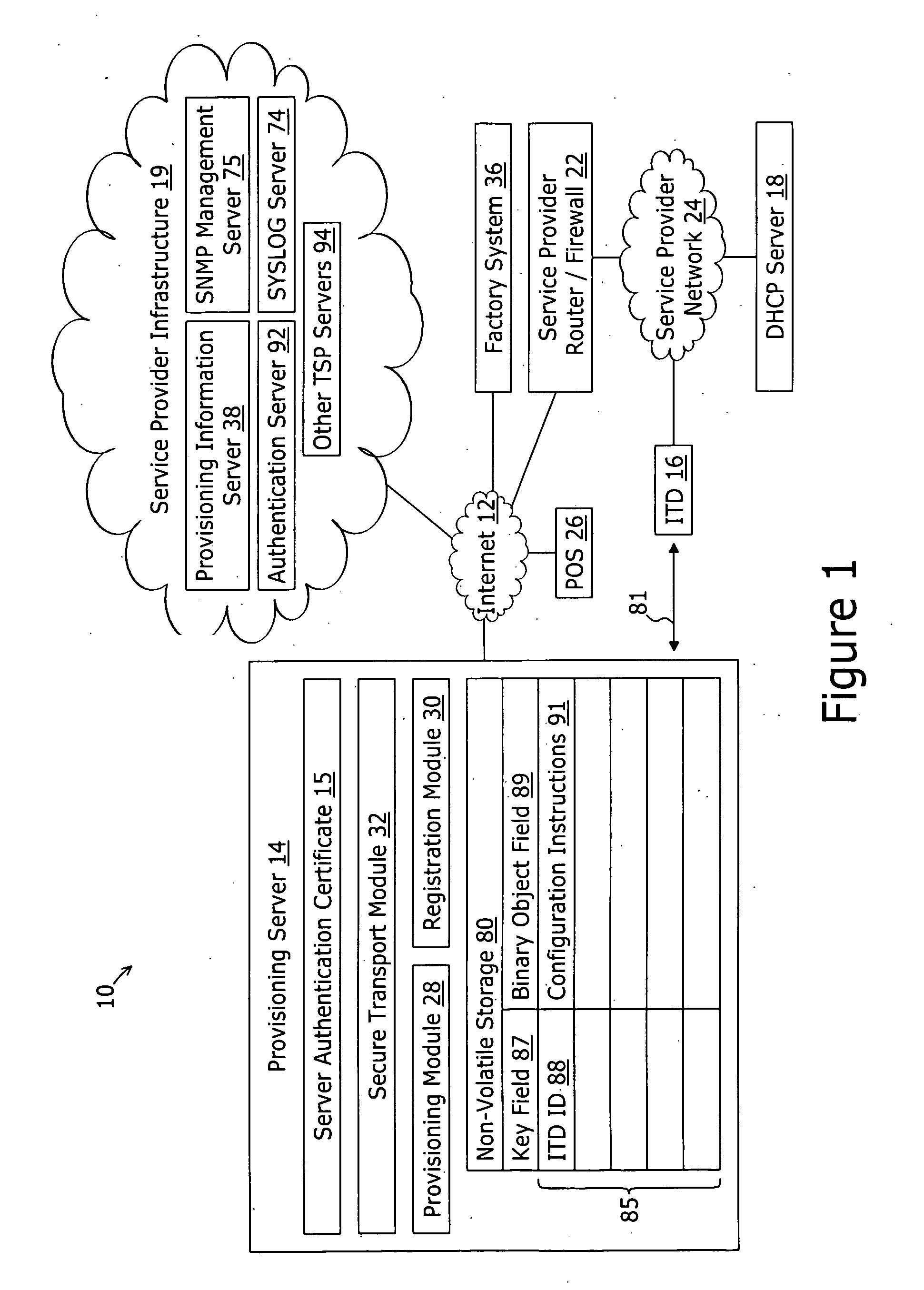
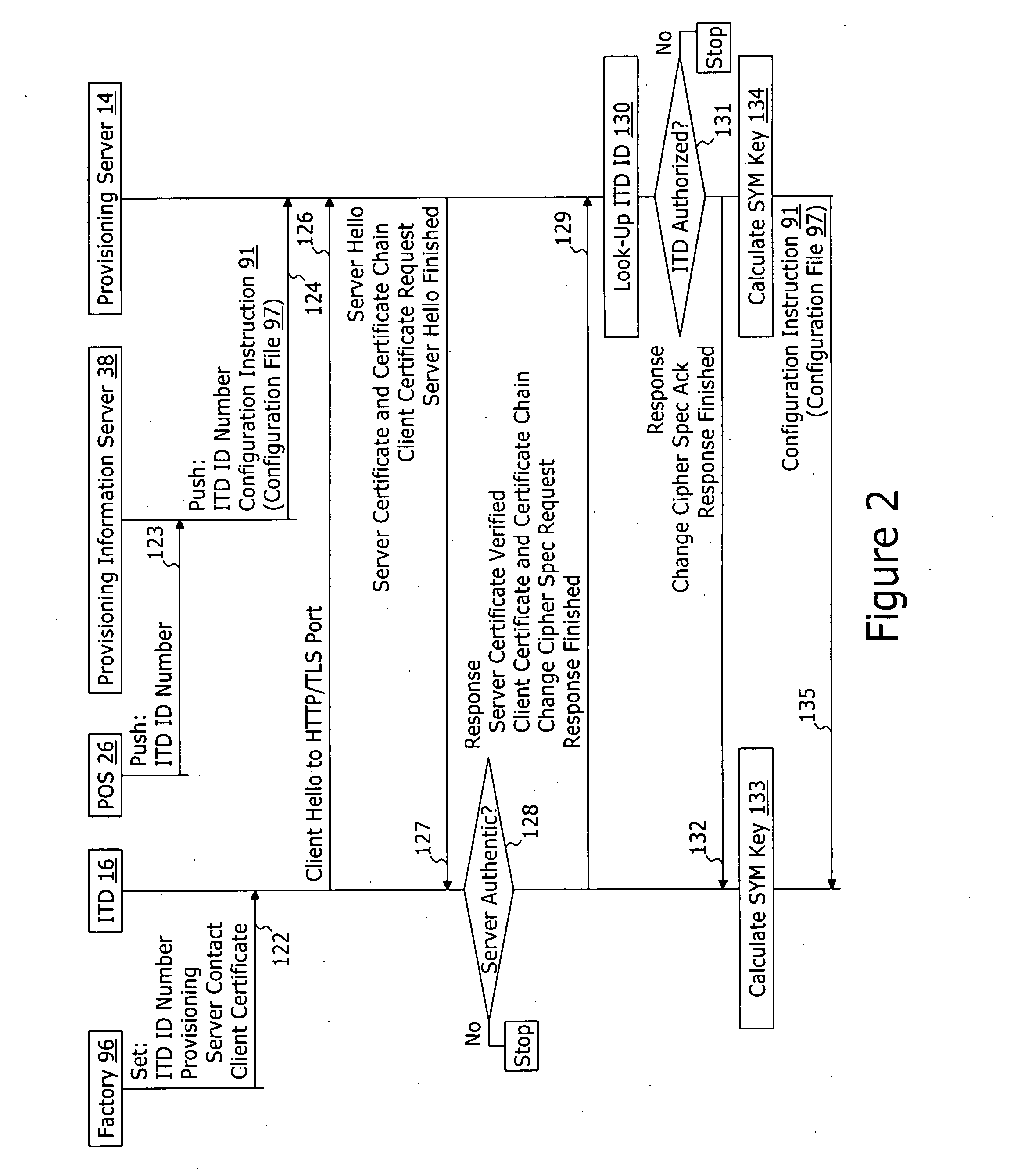
System and method for securely providing a configuration file over and open network
ActiveUS20060174018A1User identity/authority verificationUnauthorized memory use protectionDomain nameNetwork connection
A method for securely provisioning a device for operation within a service provider infrastructure over an open network comprises the device establishing physical and data link layer network connections for communication on at least a subnet of the open network and obtaining a network configuration data such as an IP address and a subnet mask from a provisioning server that responds to a network configuration broadcast request. A device establishes a secure hypertext transport protocol connection to a first provisioning server that corresponds to one of: i) and IP address and port number; and ii) a fully qualified domain name stored in a non-volatile memory of the device. After mutual authentication, the first provisioning server provides at least one of: i) a configuration file; and ii) identification of a second provisioning server and a cipher key through the secure connection. If the first provisioning server provided identification of a second provisioning server, the device establishes a transport connection to the identified second provisioning server. The second provisioning server provides an encrypted file which, when decrypted using the cipher key yields the configuration information needed by the device for operation with the service provider infrastructure.
Owner:INOMEDIA
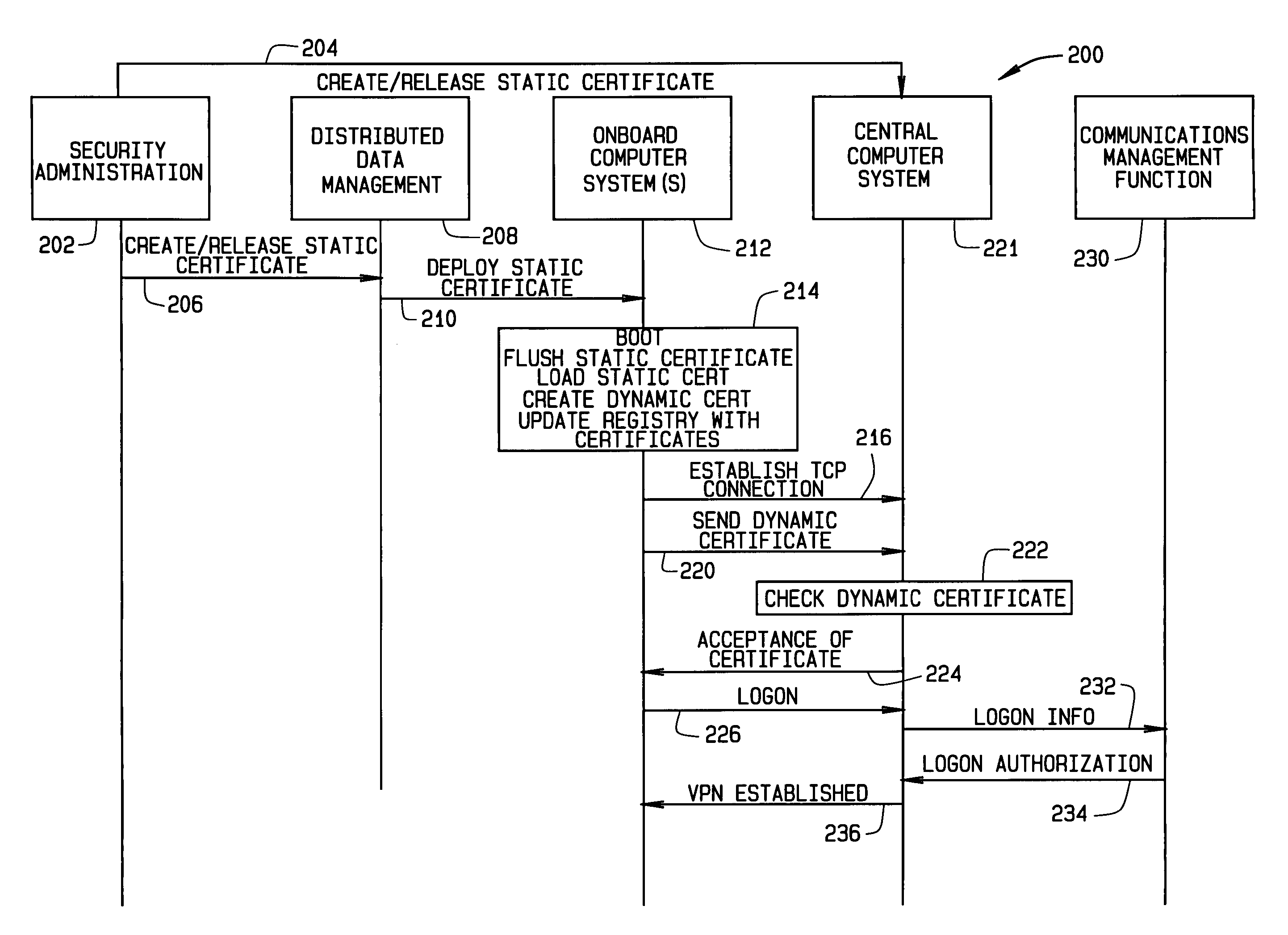
Security certificate management
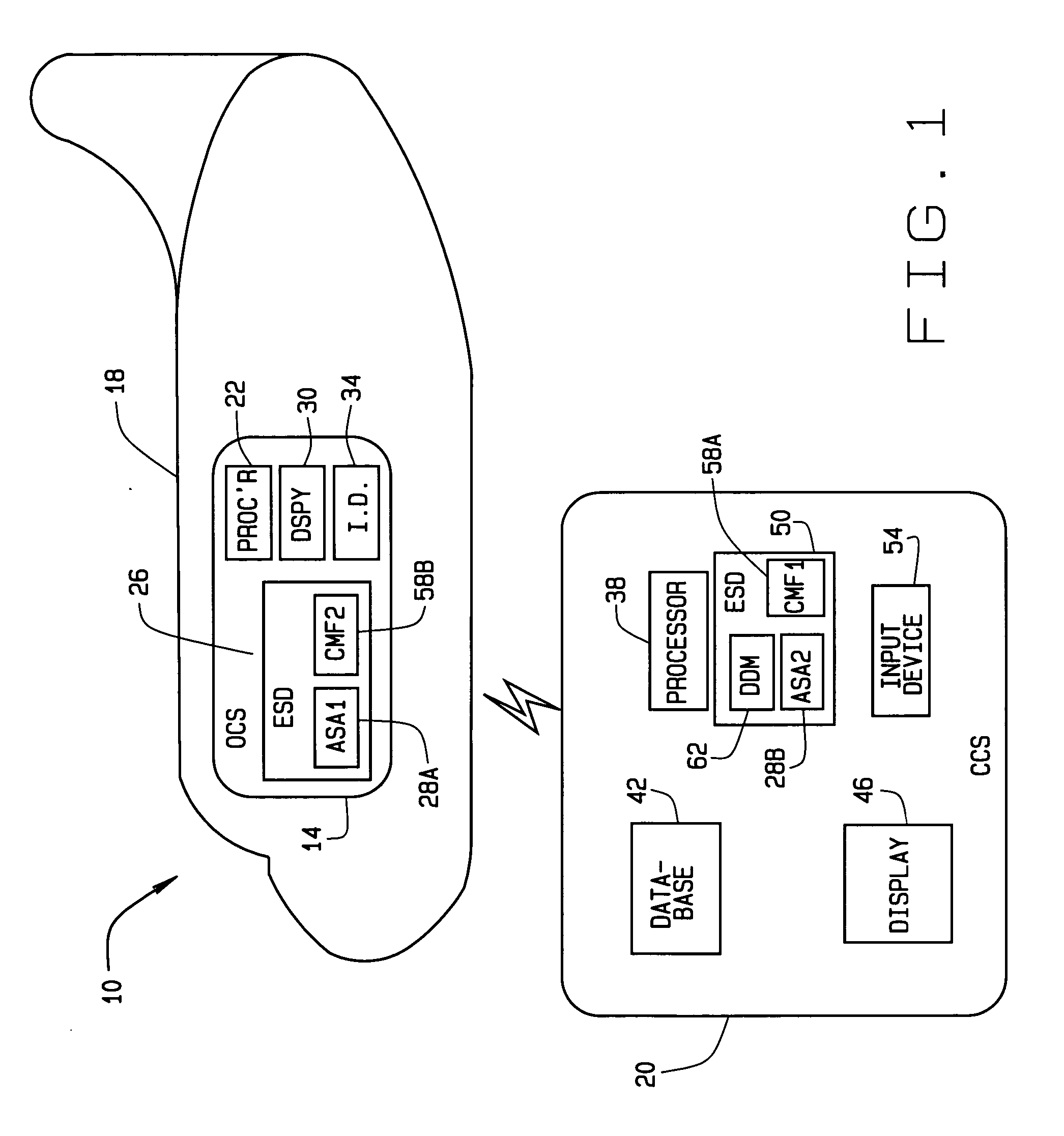
ActiveUS20070028095A1User identity/authority verificationDigital data authenticationOnboard computerMutual authentication
A system and method for establishing a mutually authenticated secure link between a mobile platform system and a remote system is provided. An onboard computer system (OCS) generates a dynamic certificate and digitally signs the dynamic certificate with a static certificate. The dynamic certificate is transmitted to a remote central computer system (CCS). The CCS verifies that the dynamic certificate is from a trusted source and sends a return dynamic certificate electronically signed with the static certificate to the OCS. The OCS verifies the return dynamic certificate is from the CCS, thereby establishing a mutually authenticated secure link between the OCS and the CCS.
Owner:THE BOEING CO
Secure network gateway
InactiveUS20060053290A1Limited in functionallyLimited in participant reachFinanceUser identity/authority verificationComputer scienceAuthorization
A secure gateway is disclosed which facilitates communication between a first network and a second network through an intermediate network. The secure gateway, when operated in conjunction with at least one other secure gateway, supports secure peer to peer connectivity with integral security features such as mutual authentication, authorization specific access, and end to end auditing. An authorized service can be served securely through this gateway, across the open network, to a known requester, without fear of compromising the security or privacy of the server's or requesters networks.
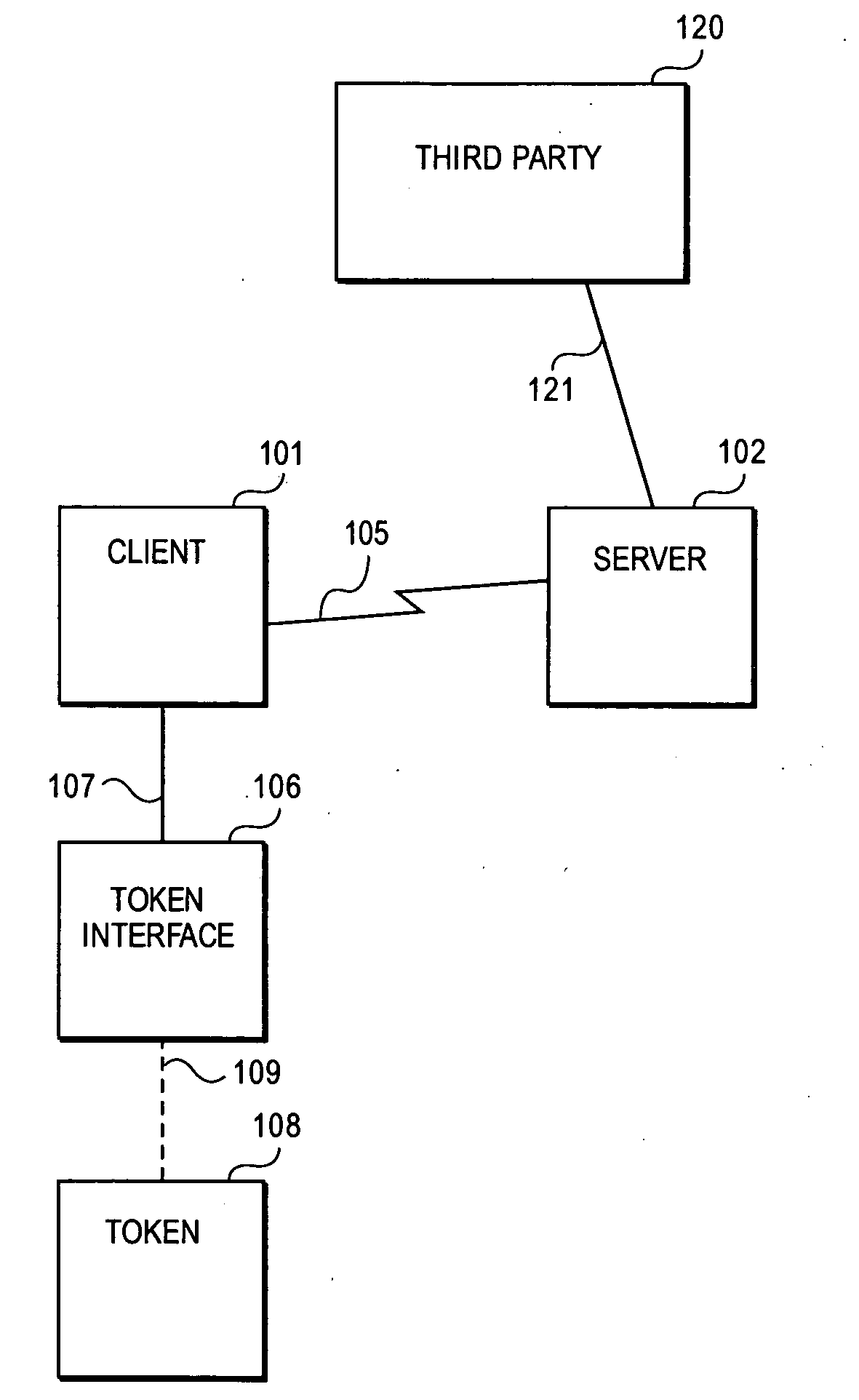
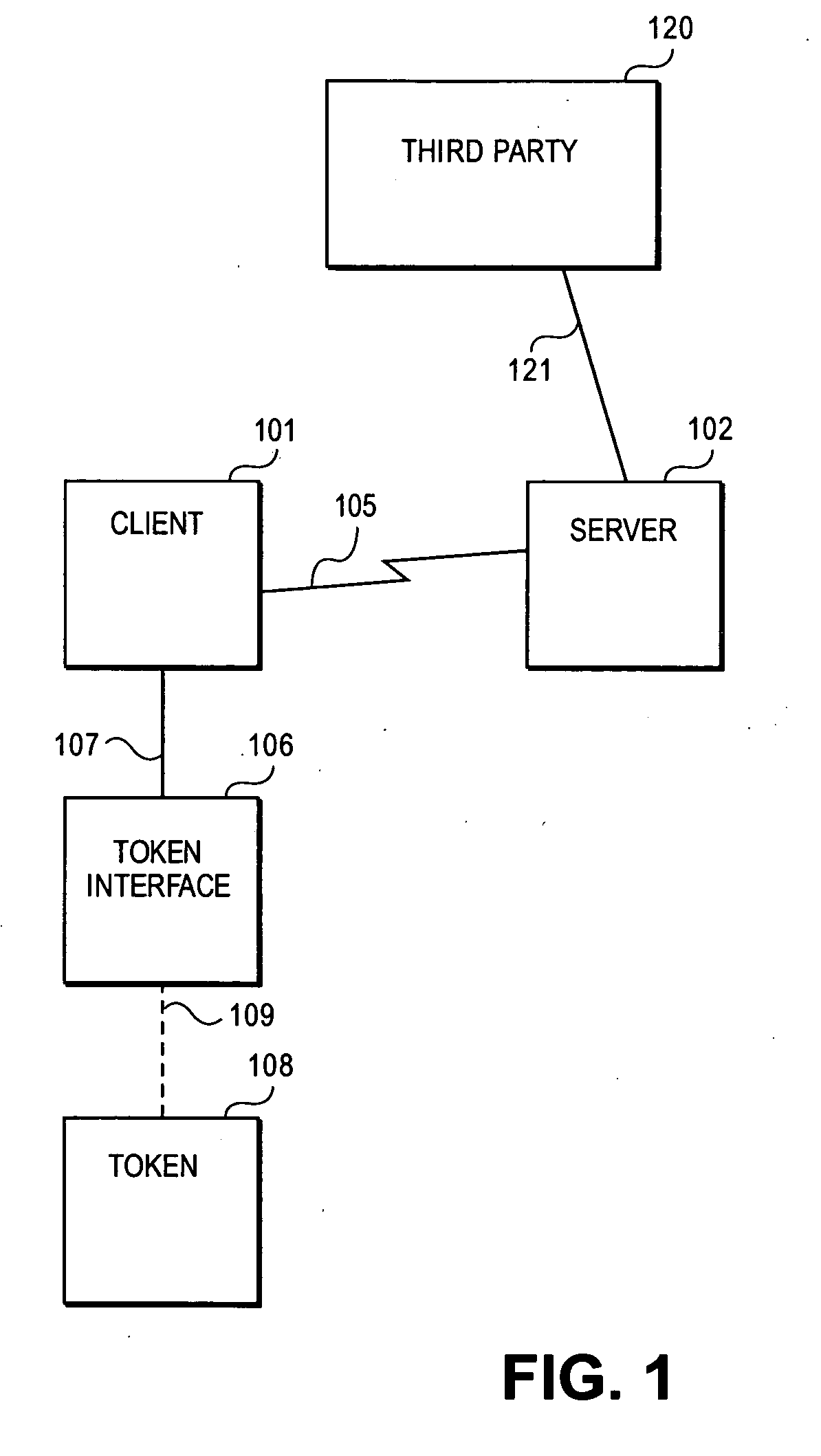
Owner:RANDLE WILLIAM M +1
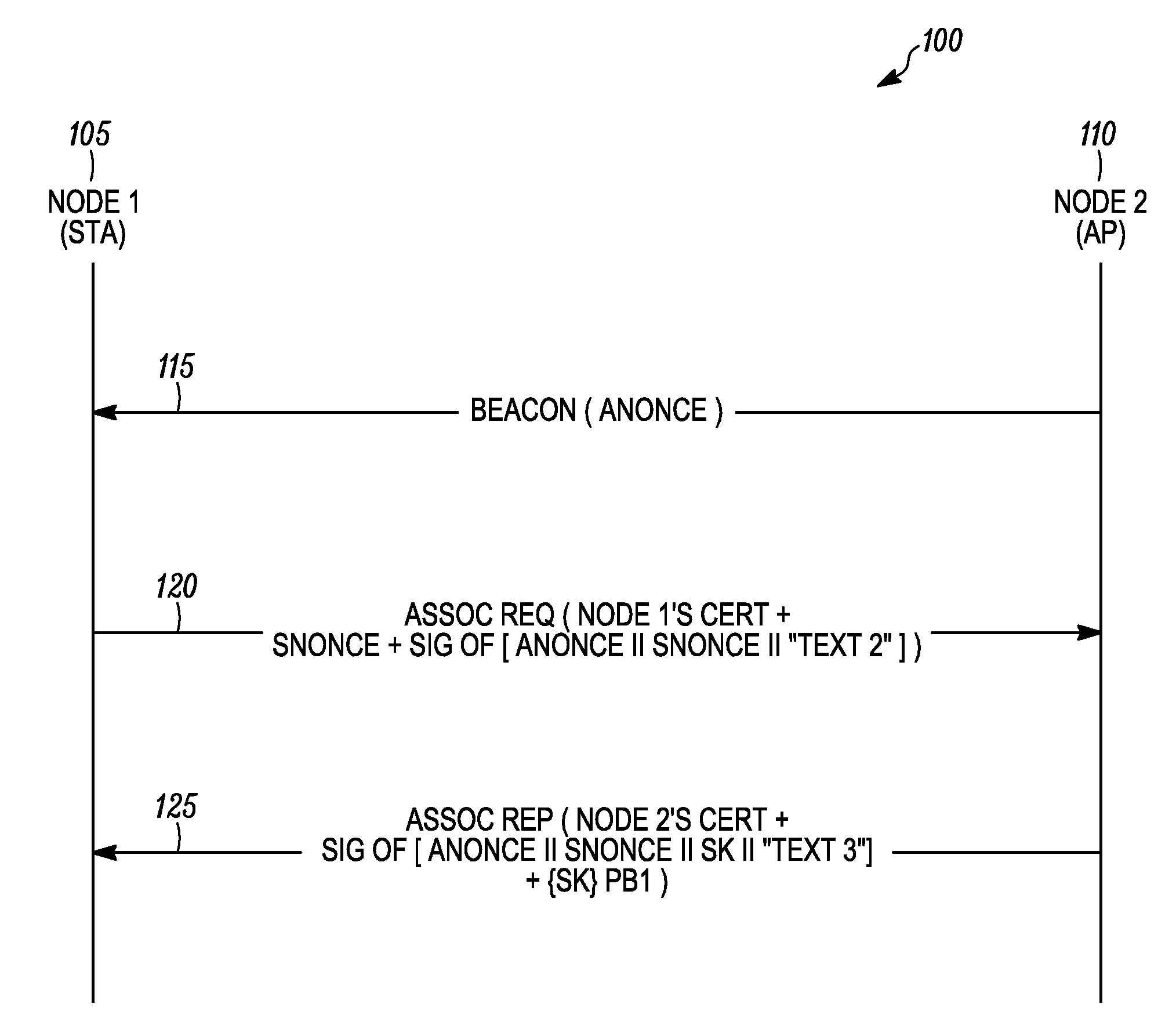
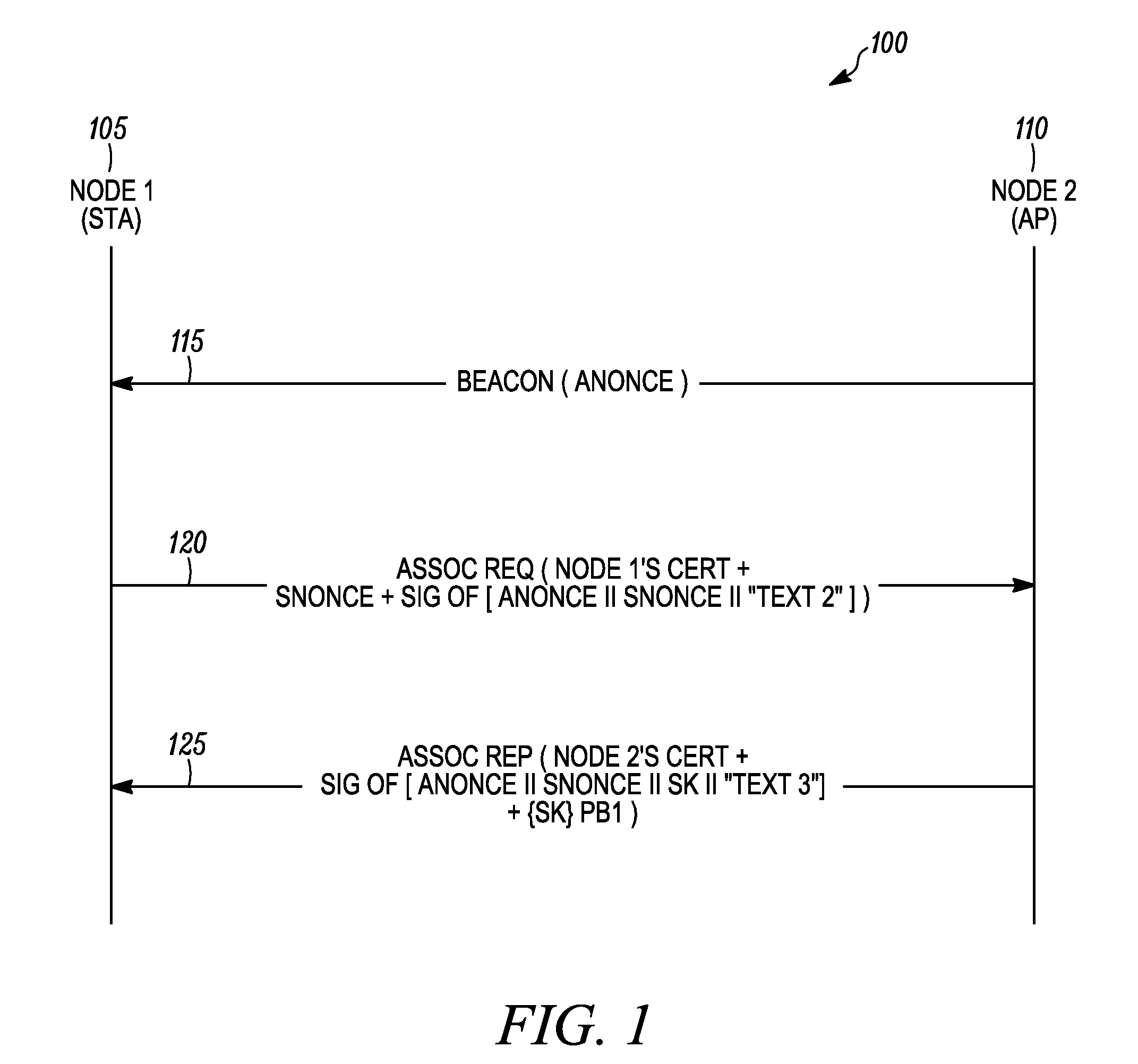
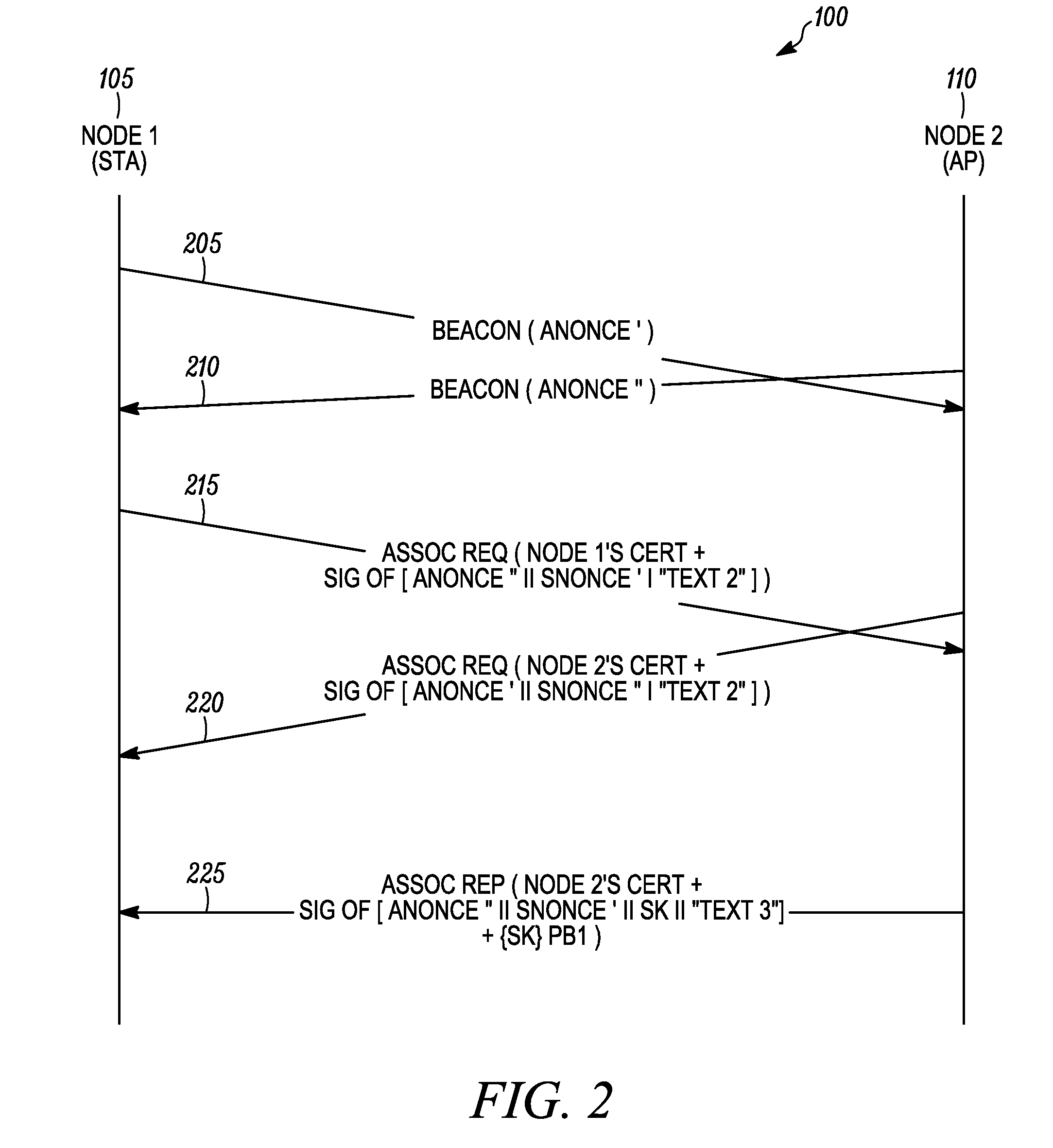
Method and system for mutual authentication of nodes in a wireless communication network
ActiveUS20090217043A1Multiple keys/algorithms usageUser identity/authority verificationWireless communication systemsMutual authentication
A method as provided enables mutual authentication of nodes in a wireless communication network. The method includes processing at a first node a beacon message received from a second node, wherein the beacon message comprises a first nonce value (step 405). An association request message comprising a certificate of the first node, a first signed block of authentication data, and a second nonce value is then transmitted from the first node to the second node (step 410). The second node can then verify a signature of the certificate of the first node and verify a signature of the first signed block of authentication data. An association reply message received from the second node is then processed at the first node (step 415), whereby the first node verifies a signature of a certificate of the second node and verifies a signature of a second signed block of authentication data.
Owner:ARRIS ENTERPRISES LLC
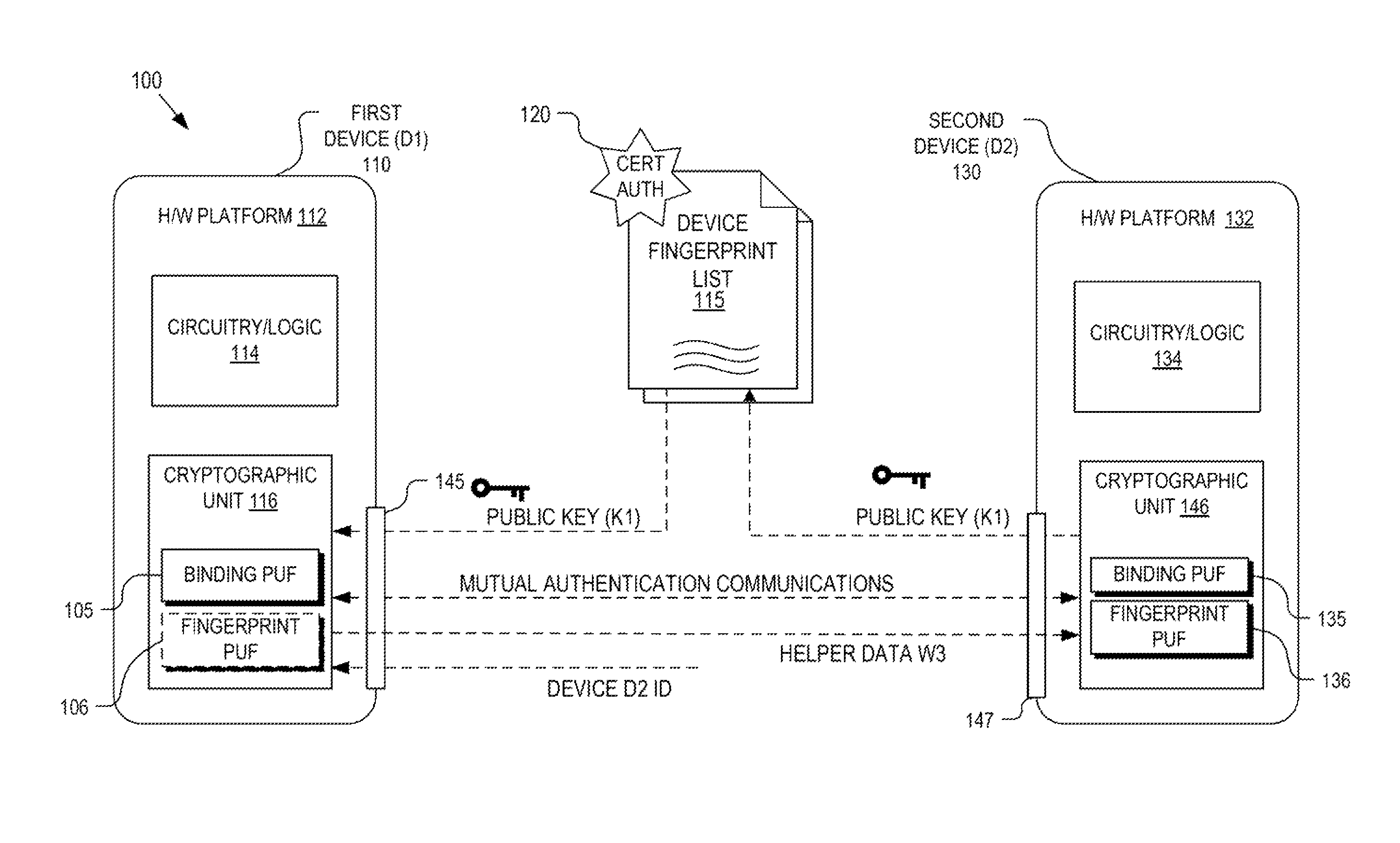
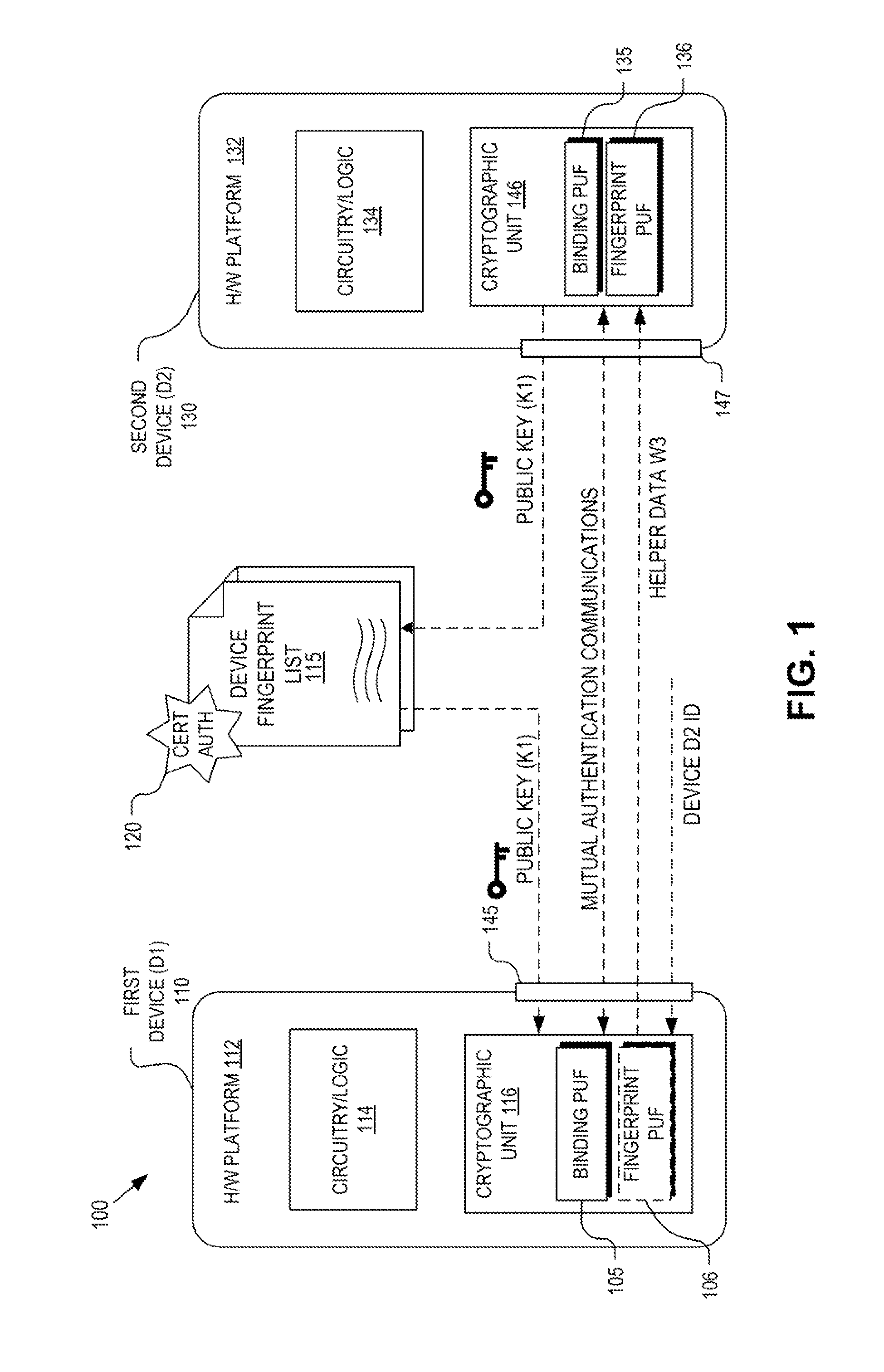
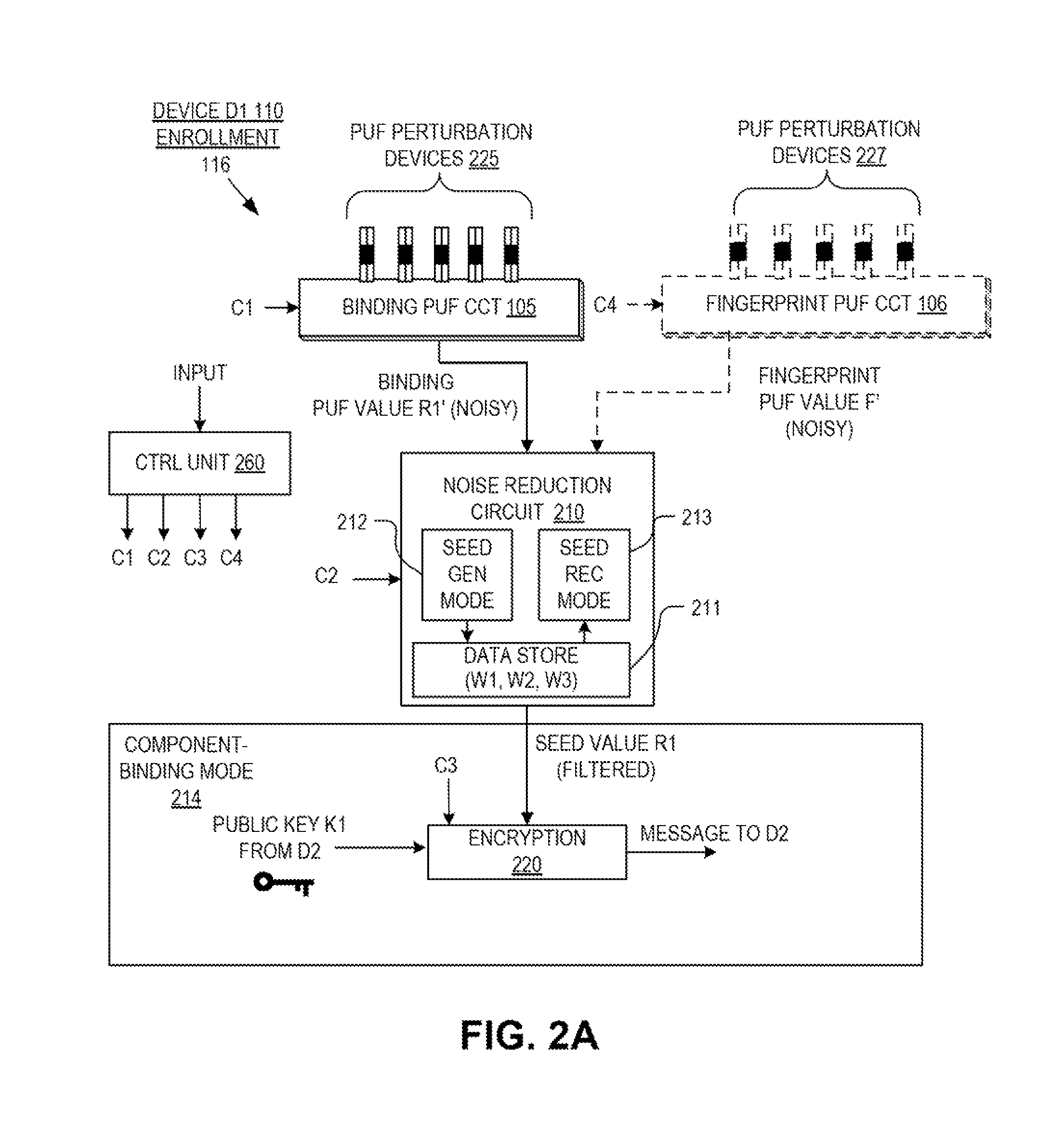
Hardware device binding and mutual authentication
ActiveUS8667265B1Digital data authenticationSecuring communicationComputer hardwarePhysical unclonable function
Detection and deterrence of device tampering and subversion by substitution may be achieved by including a cryptographic unit within a computing device for binding multiple hardware devices and mutually authenticating the devices. The cryptographic unit includes a physically unclonable function (“PUF”) circuit disposed in or on the hardware device, which generates a binding PUF value. The cryptographic unit uses the binding PUF value during an enrollment phase and subsequent authentication phases. During a subsequent authentication phase, the cryptographic unit uses the binding PUF values of the multiple hardware devices to generate a challenge to send to the other device, and to verify a challenge received from the other device to mutually authenticate the hardware devices.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
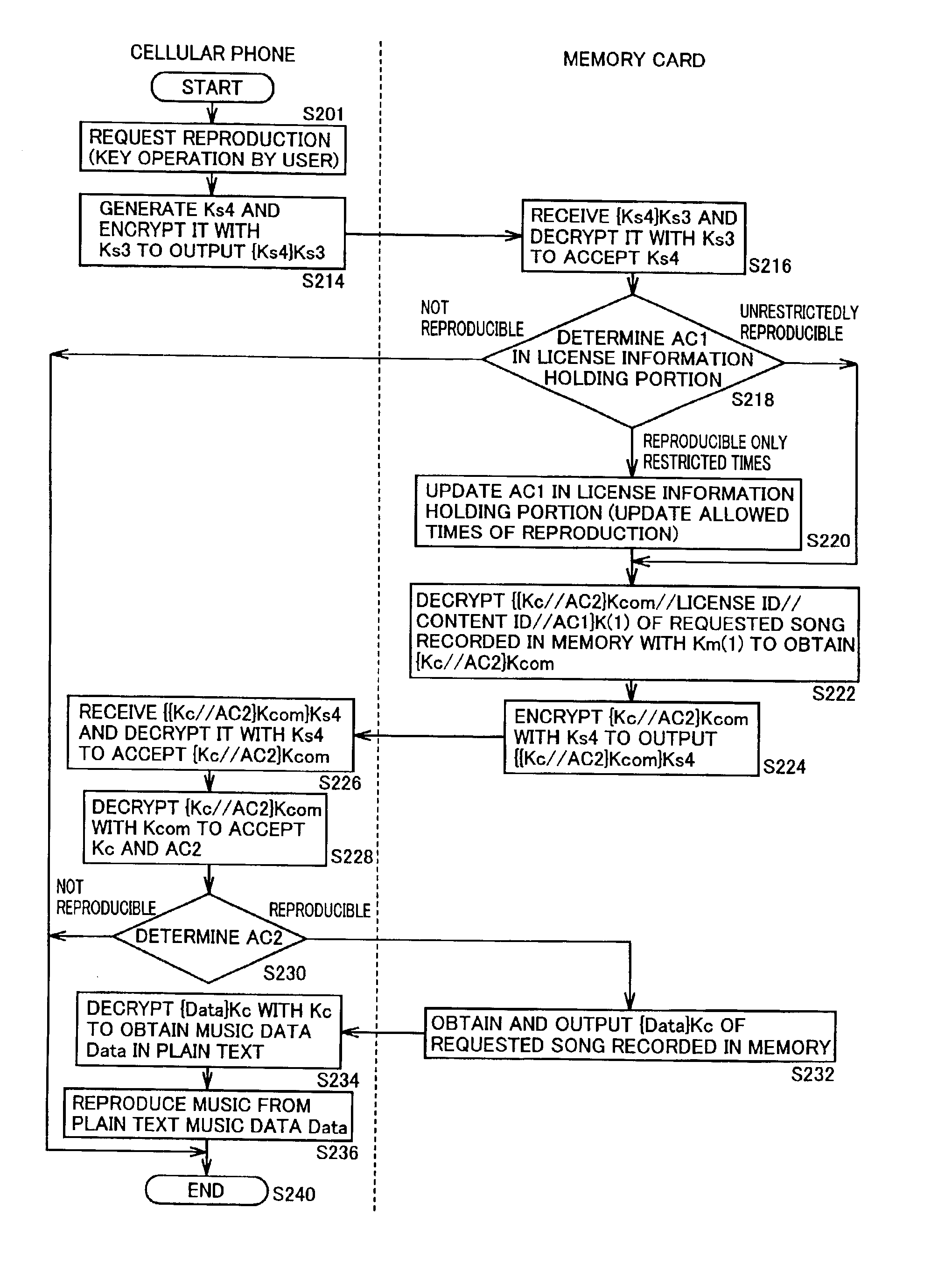
Device for reproducing data
InactiveUS6898708B2Improve data securityEasy to handleCordless telephonesKey distribution for secure communicationMemory cardsLicense
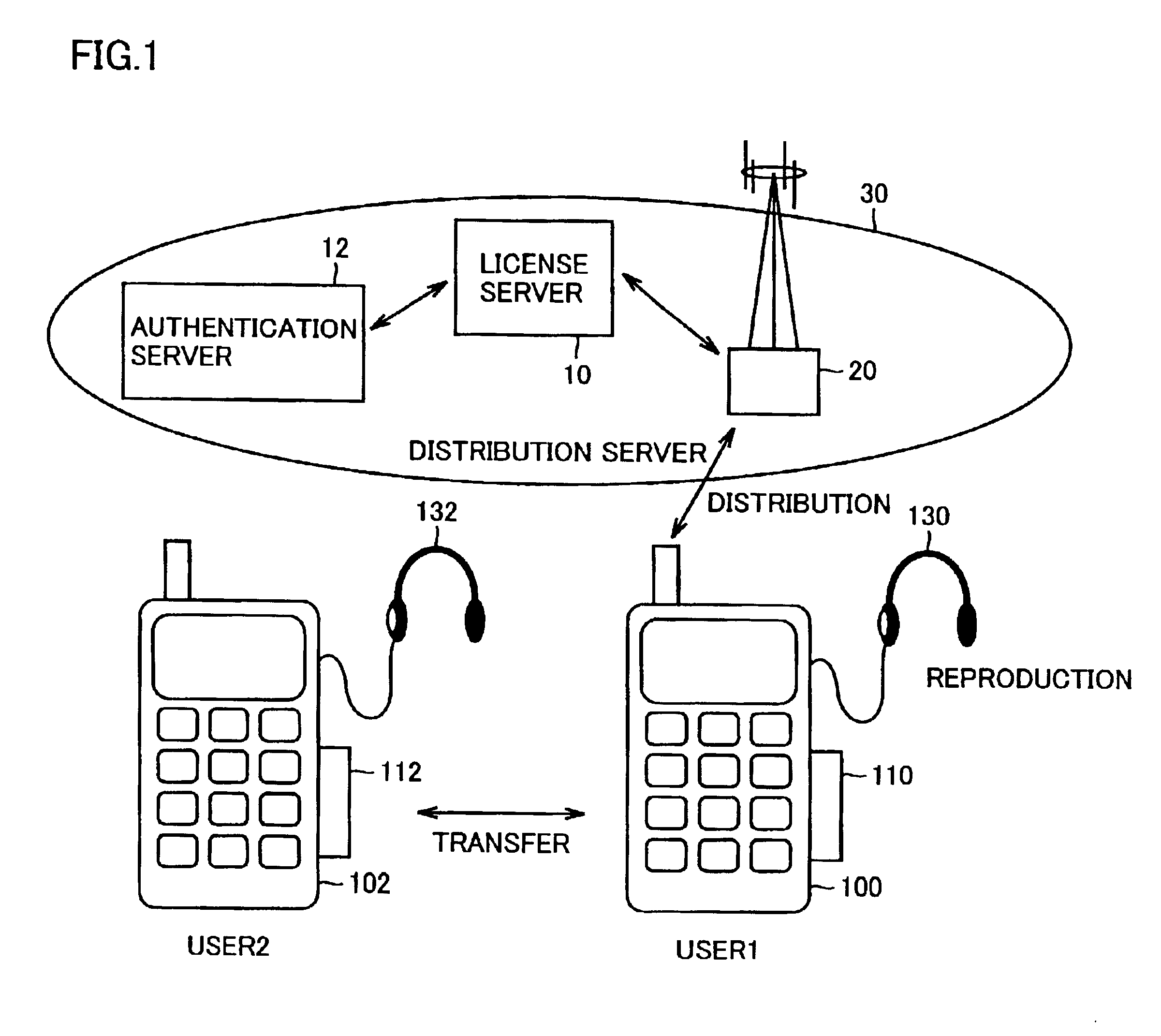
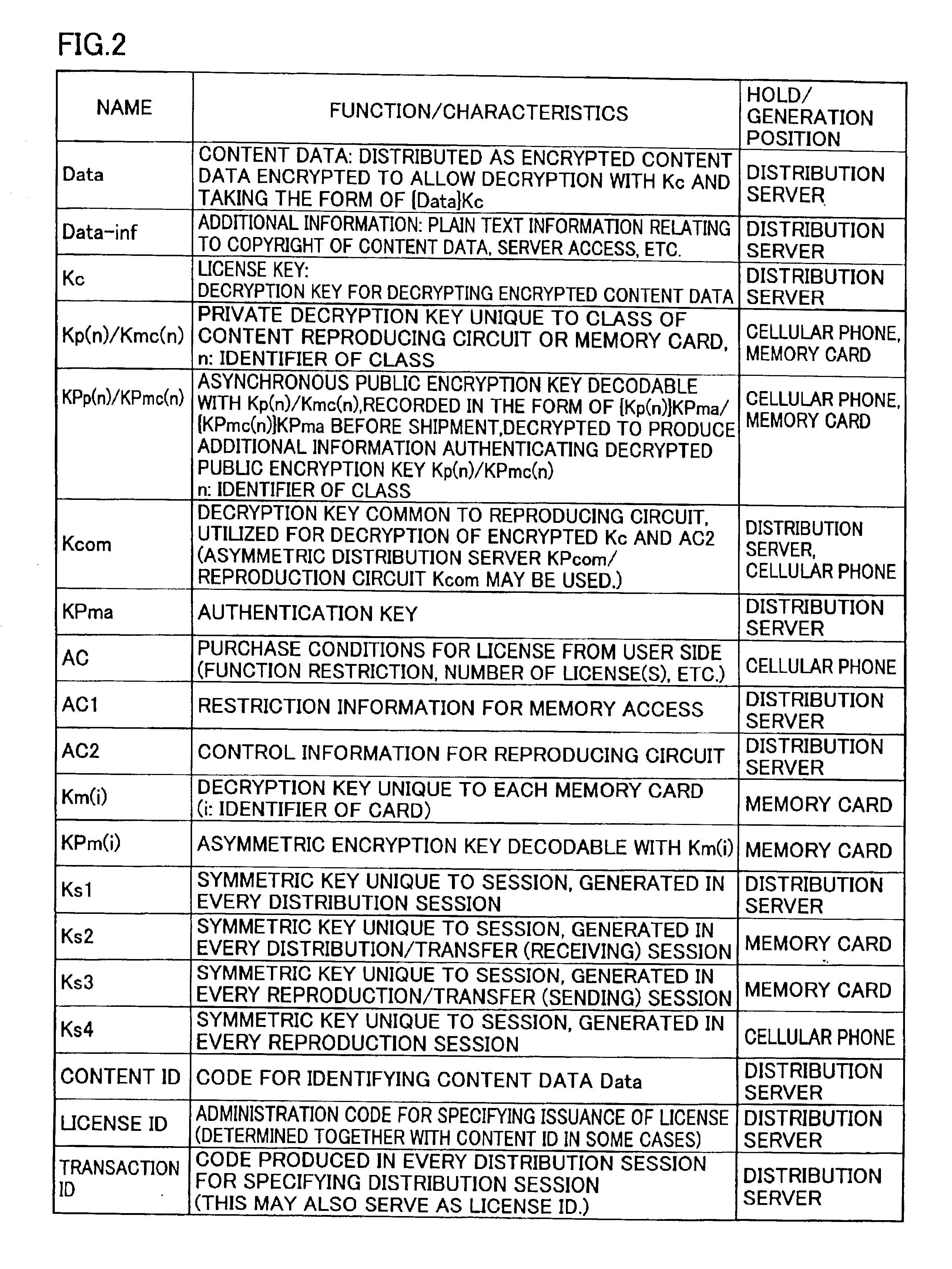
A cellular phone (100) stores encrypted content data and encrypted license key distributed thereto in a memory card (110). The cellular phone (100) and the memory card (110) collectively perform a part of mutual authentication processing upon power-on. The encrypted license key (Kc) read from the memory card (110) is decrypted by a first decryption processing portion (1510) with a session key (Ks4), and is further decrypted by a second decryption processing portion (1514) with a system symmetric key (Kcom) for extraction. A third encryption processing portion (1516) decrypts the encrypted content data read from memory card (110) with the license key (Kc) to reproduce content data (Data).
Owner:SANYO ELECTRIC CO LTD +1
Device authentication system
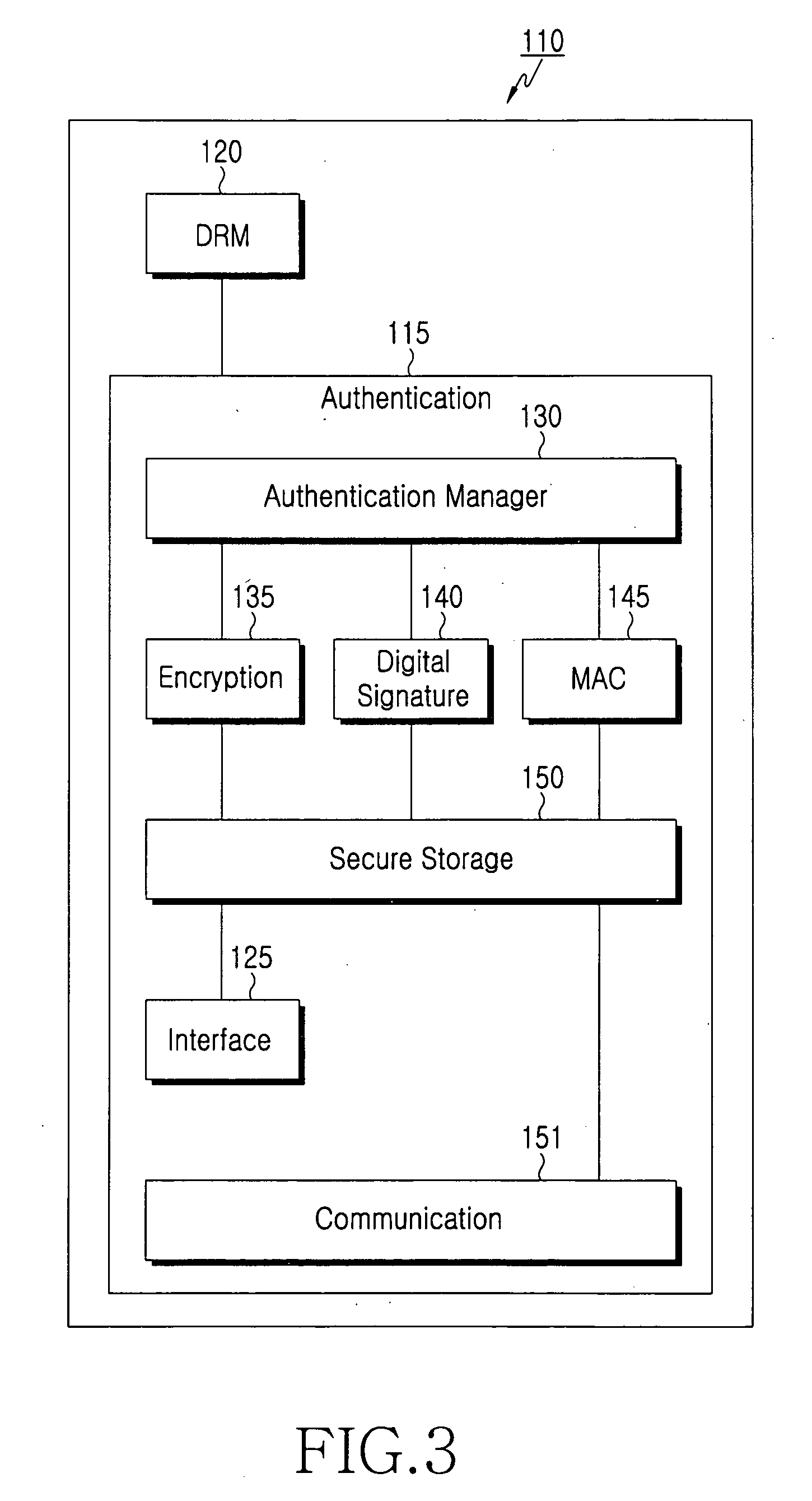
InactiveUS20070083750A1Commonly usedKey distribution for secure communicationUser identity/authority verificationAuthentication serverAuthentication system
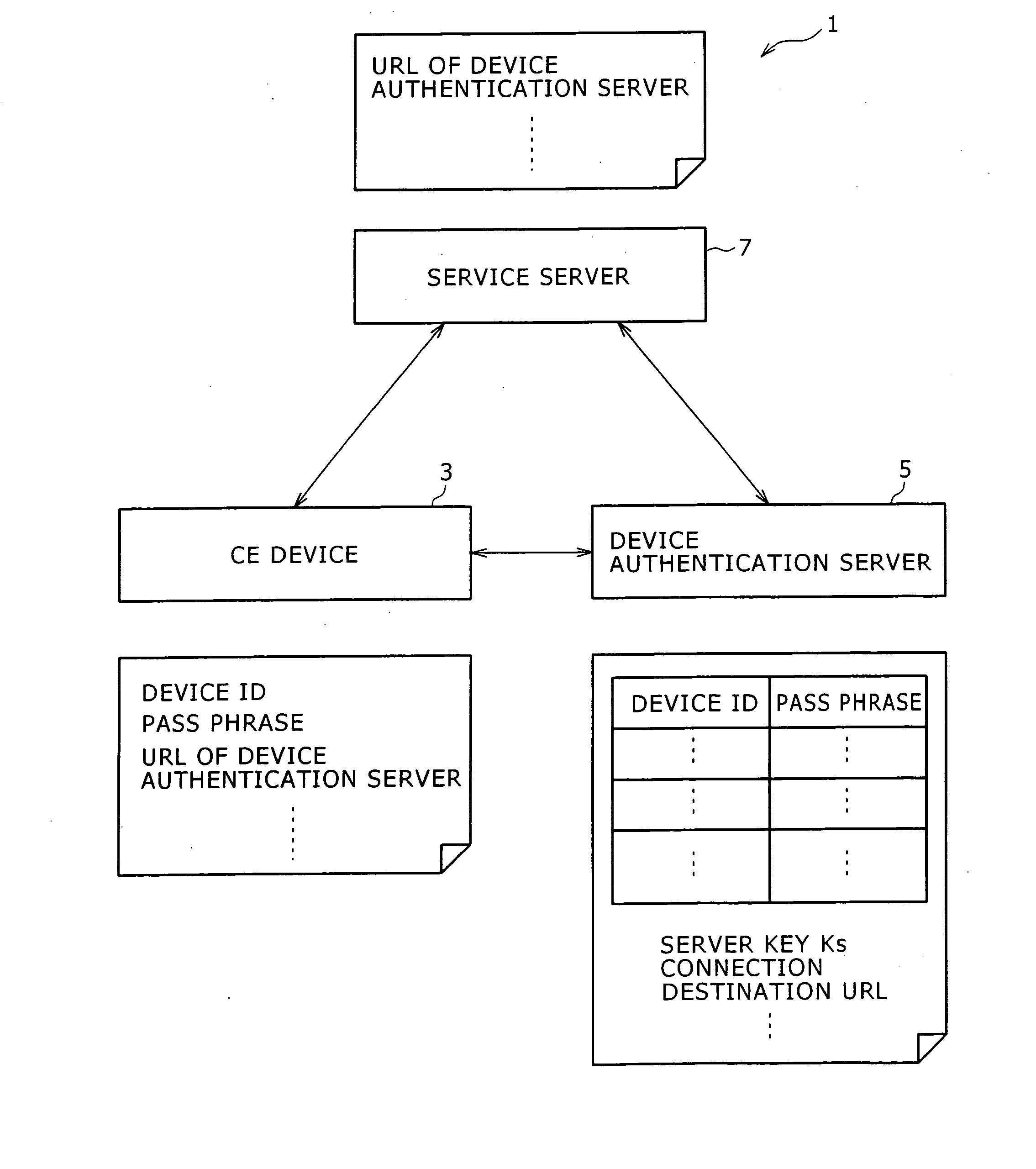
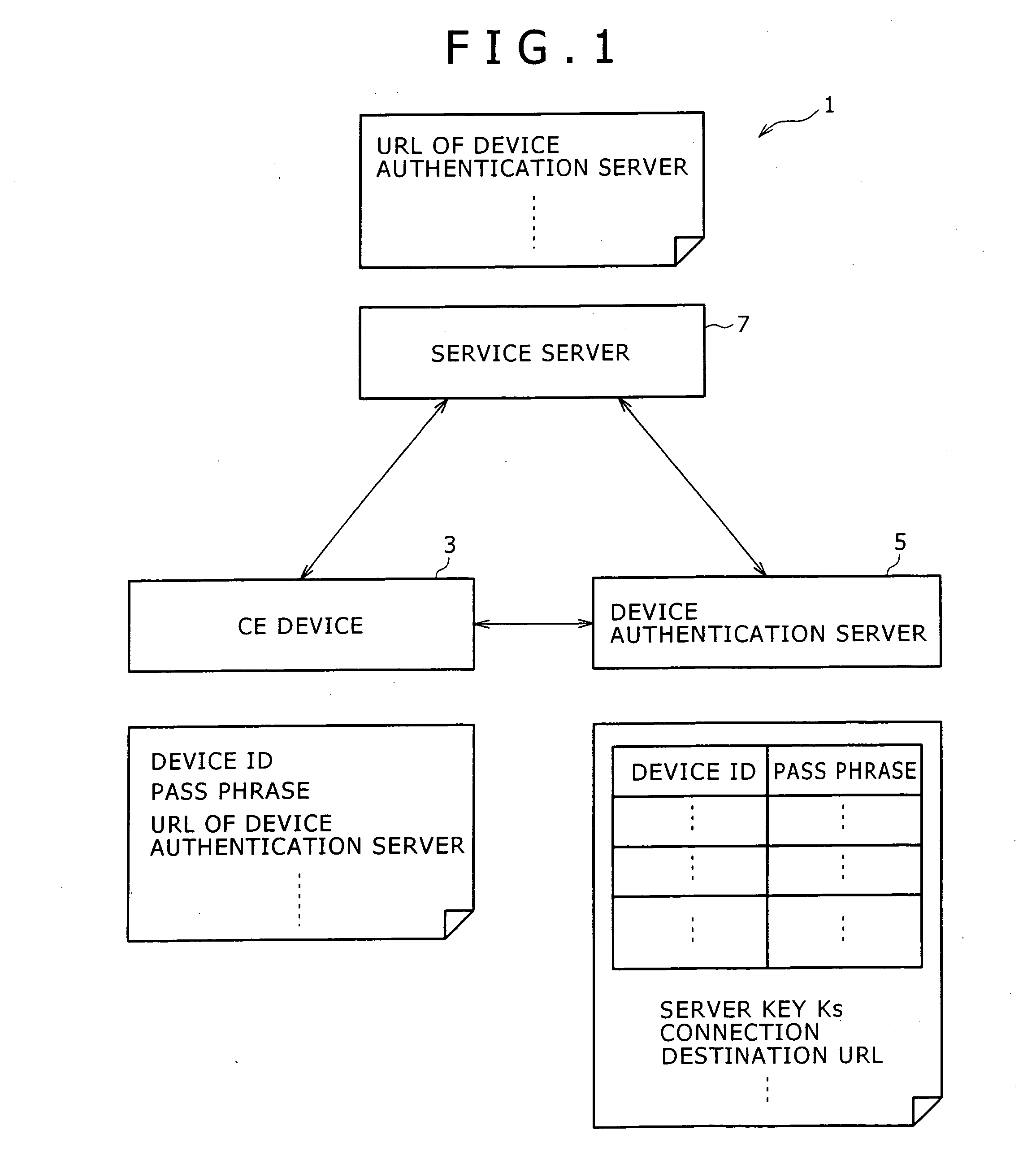
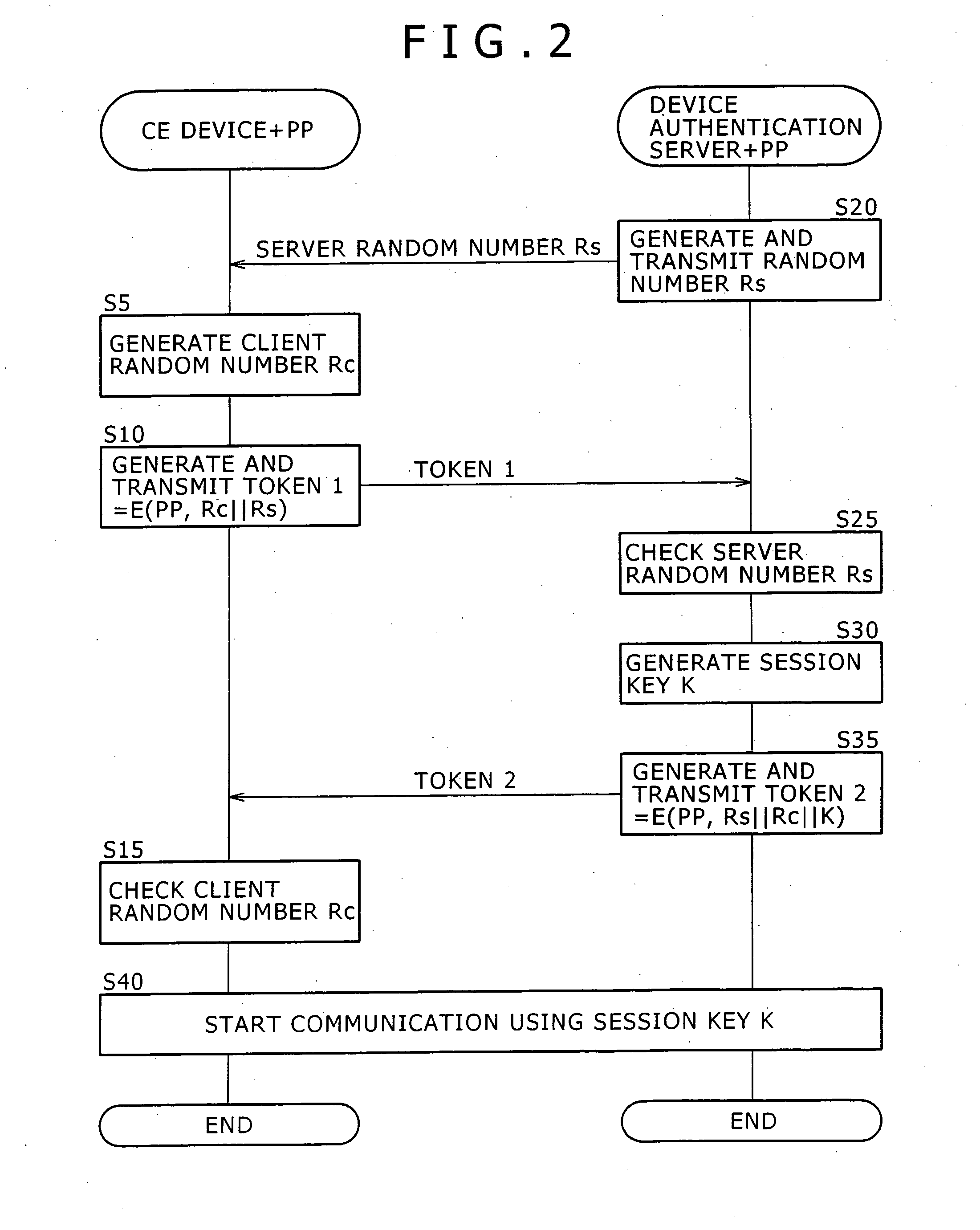
Disclosed herein is a device authentication system capable of authenticating devices efficiently using the common key system. When a CE device requests service offerings from a service server, the service server in turn requests the CE device to be authenticated by a device authentication server. Given the request, the CE device causes the device authentication server to perform device authentication on that device and transmits the result of the device authentication to the service server. Upon receipt of the device authentication result from the CE device, the service server causes the device authentication server to check that the authentication has been performed correctly and then starts offering services to the CE device. The CE device and device authentication server share a pass phrase, and each of the two parties checks that the other party indeed retains the pass phrase for mutual authentication.
Owner:SONY CORP
Secure intra-and inter-domain handover
ActiveUS20070064647A1Fast and secure handoverConnection securityNetwork traffic/resource managementUnauthorised/fraudulent call preventionHandoff controlFast handover
To achieve a secure and fast handover in a distributed mobile communication environment (10), the control functionality is lying at the borderline between wireless and wire-bound communication network elements, and it is proposed to, firstly, execute a mutual authentication between a mobile device (26) and a new access point (14) using security context information previously transmitted to the new access point. Then, after successful mutual authentication, a handover will be executed from the current access point (12) to the new access point (14).
Owner:NTT DOCOMO INC
Protected mutual authentication over an unsecured wireless communication channel
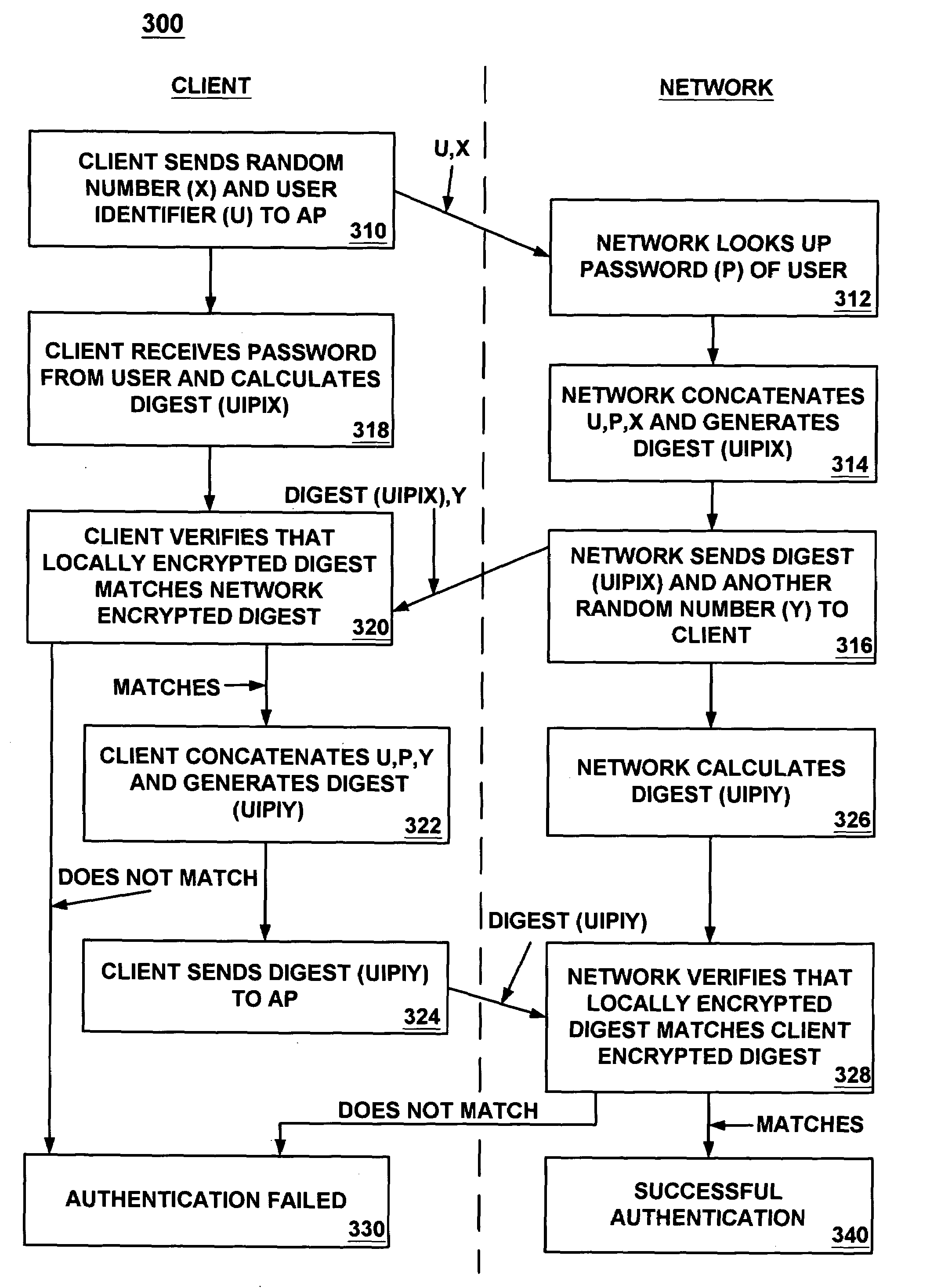
InactiveUS7024690B1Digital data processing detailsUser identity/authority verificationHash functionPassword
A process for mutual authentication of users and networks over an unsecured wireless communication channel. In one embodiment, sensitive information (e.g., passwords) is not communicated over the unsecured channel. Rather, hashed representations of user identifiers, passwords, etc., and randomly generated numbers are communicated between the client and the network during the log-in process. The representations may be encrypted with a one-way hash function such that it is not computationally feasible for an eavesdropper to decrypt. In one embodiment, the representation may be generated based on the user identifier, password and / or MAC address of a wireless LAN card.
Owner:VALTRUS INNOVATIONS LTD +1
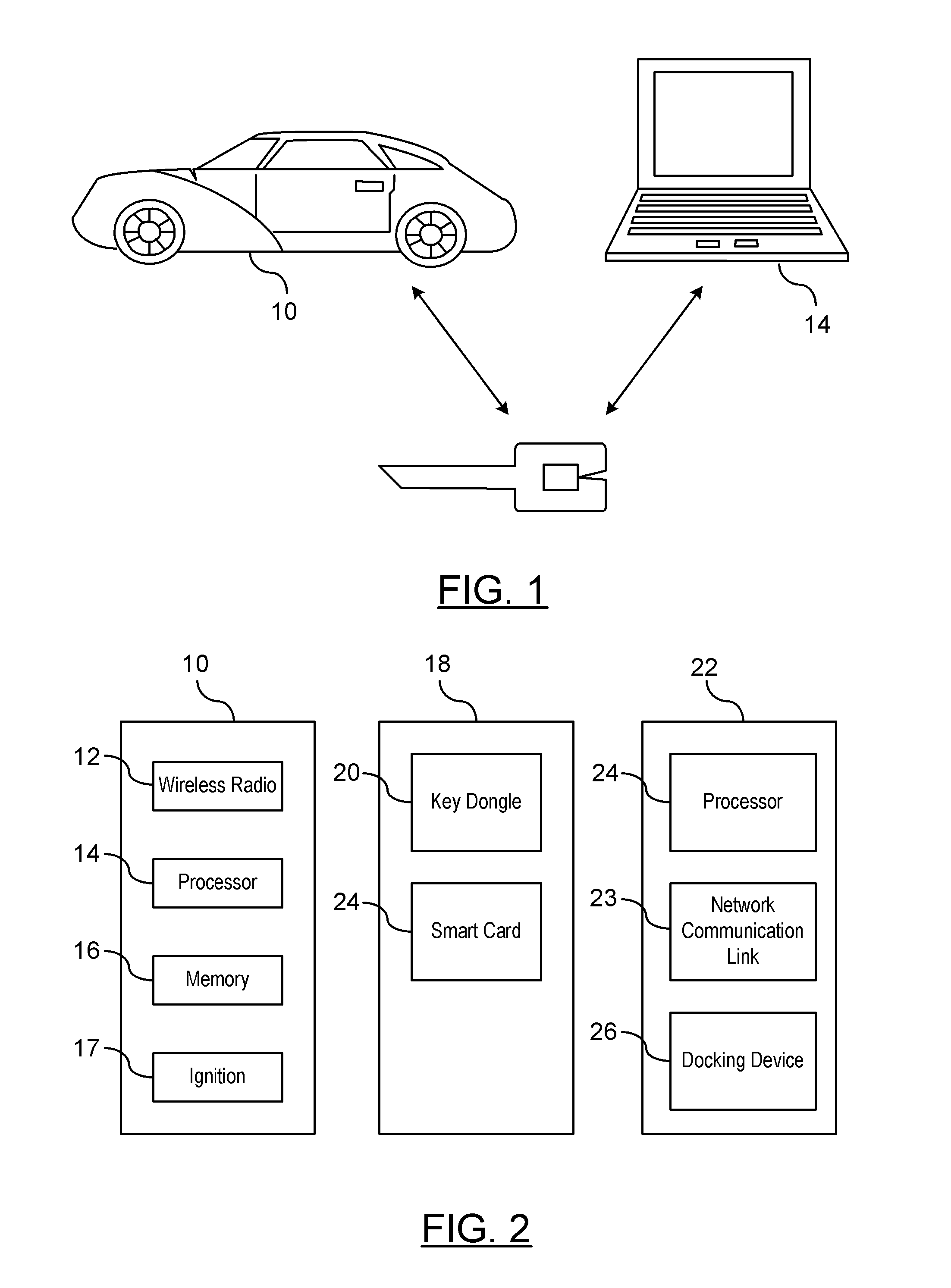
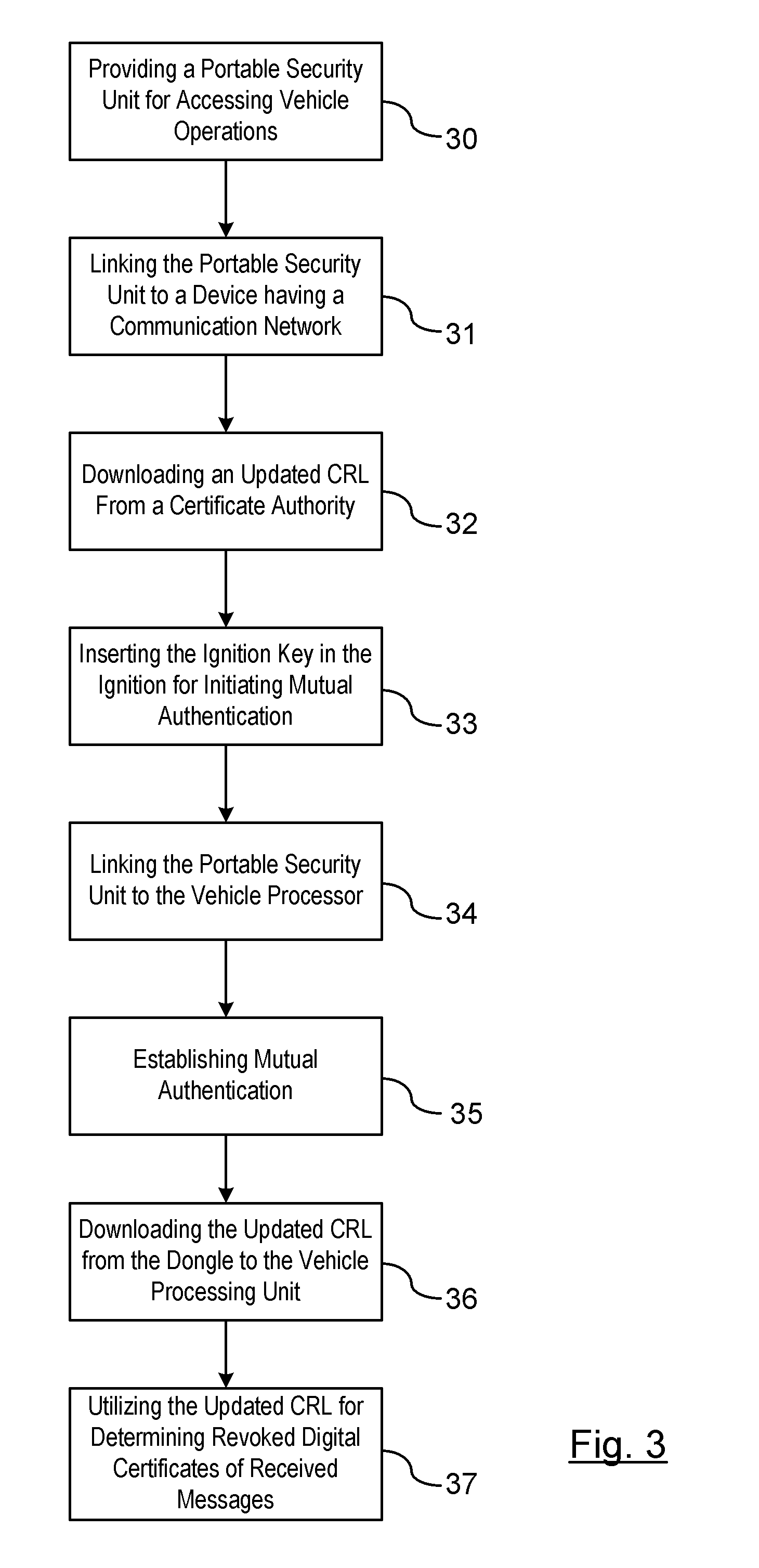
Threat mitigation in a vehicle-to-vehicle communication network
Owner:GM GLOBAL TECH OPERATIONS LLC
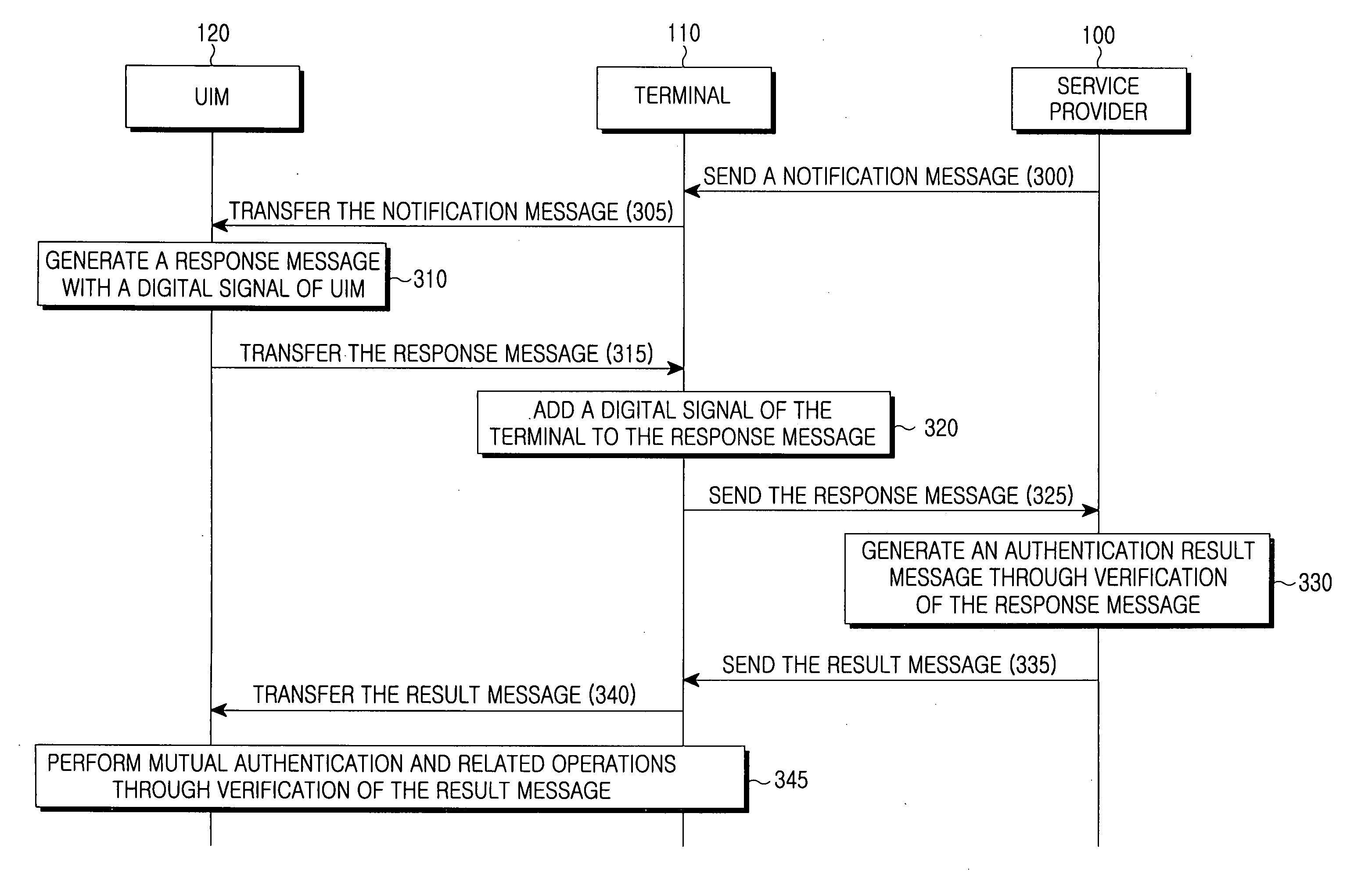
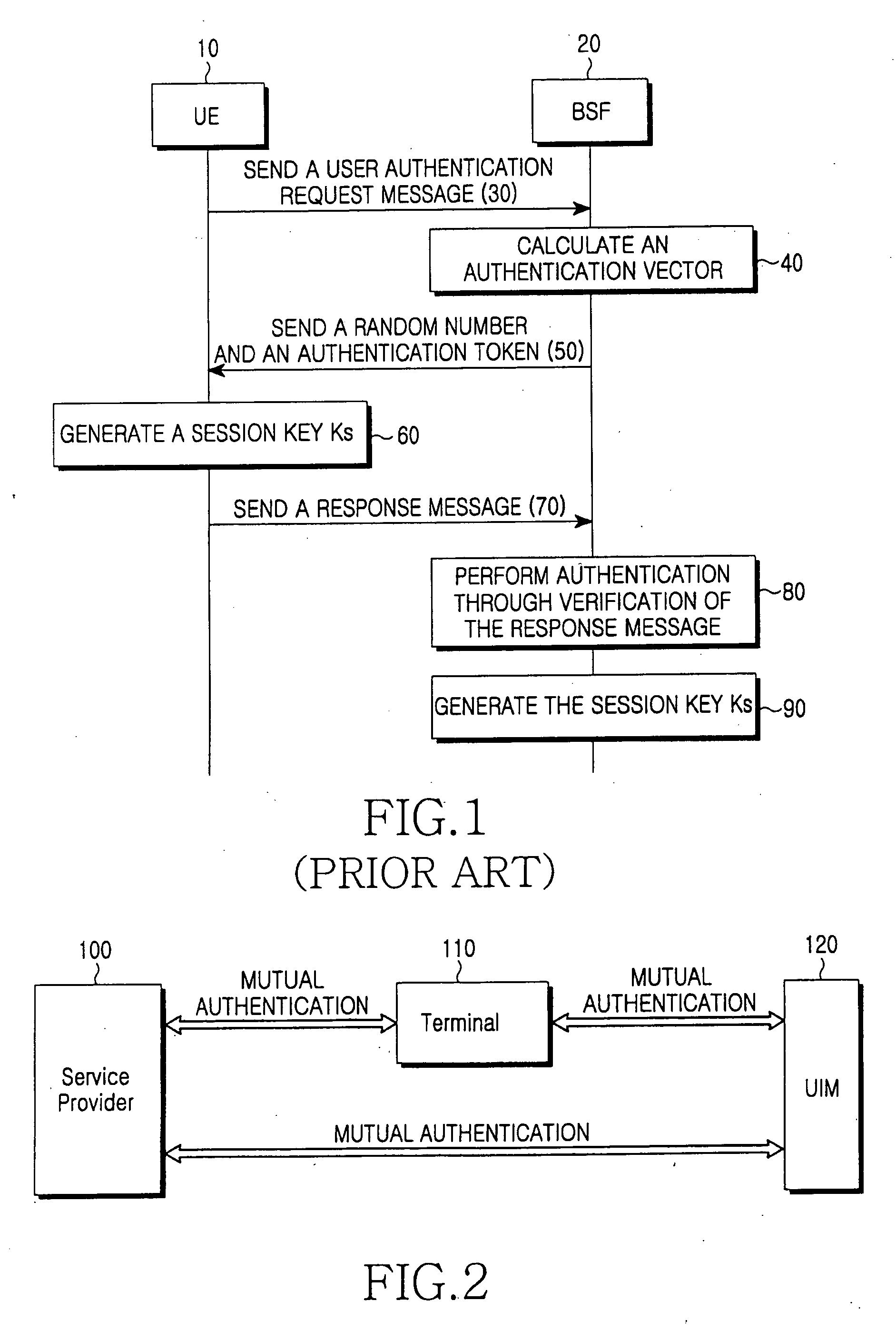
Method for inclusive authentication and management of service provider, terminal and user identity module, and system and terminal device using the method
ActiveUS20060281442A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPublic key authenticationNetworked system
Disclosed are a method and a system for mutual inclusive authentication between a service provider, a terminal and a user identity module. The authentication system is configured in a structure that can interact with a public key infrastructure of the current network security environment and can be independently used in a specific network system. The inclusive authentication method is divided into public key authentication and symmetric key authentication. Mutual authentication can be made between a service provider, a terminal and a user identity module using any of the two authentication schemes. Then a user can access content on any terminal device using the content license based on the user's identity.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com