Patents
Literature
7115 results about "Common key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
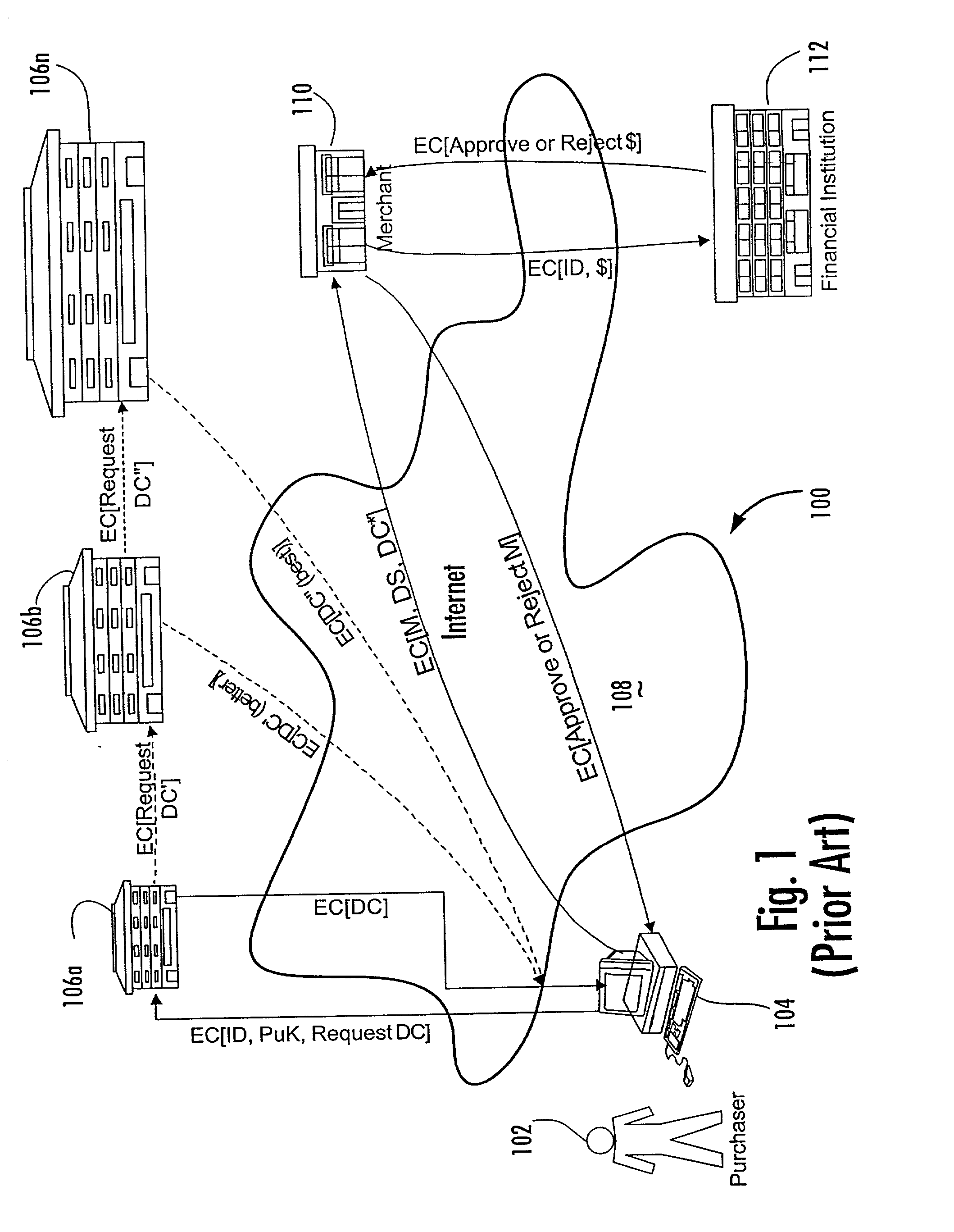
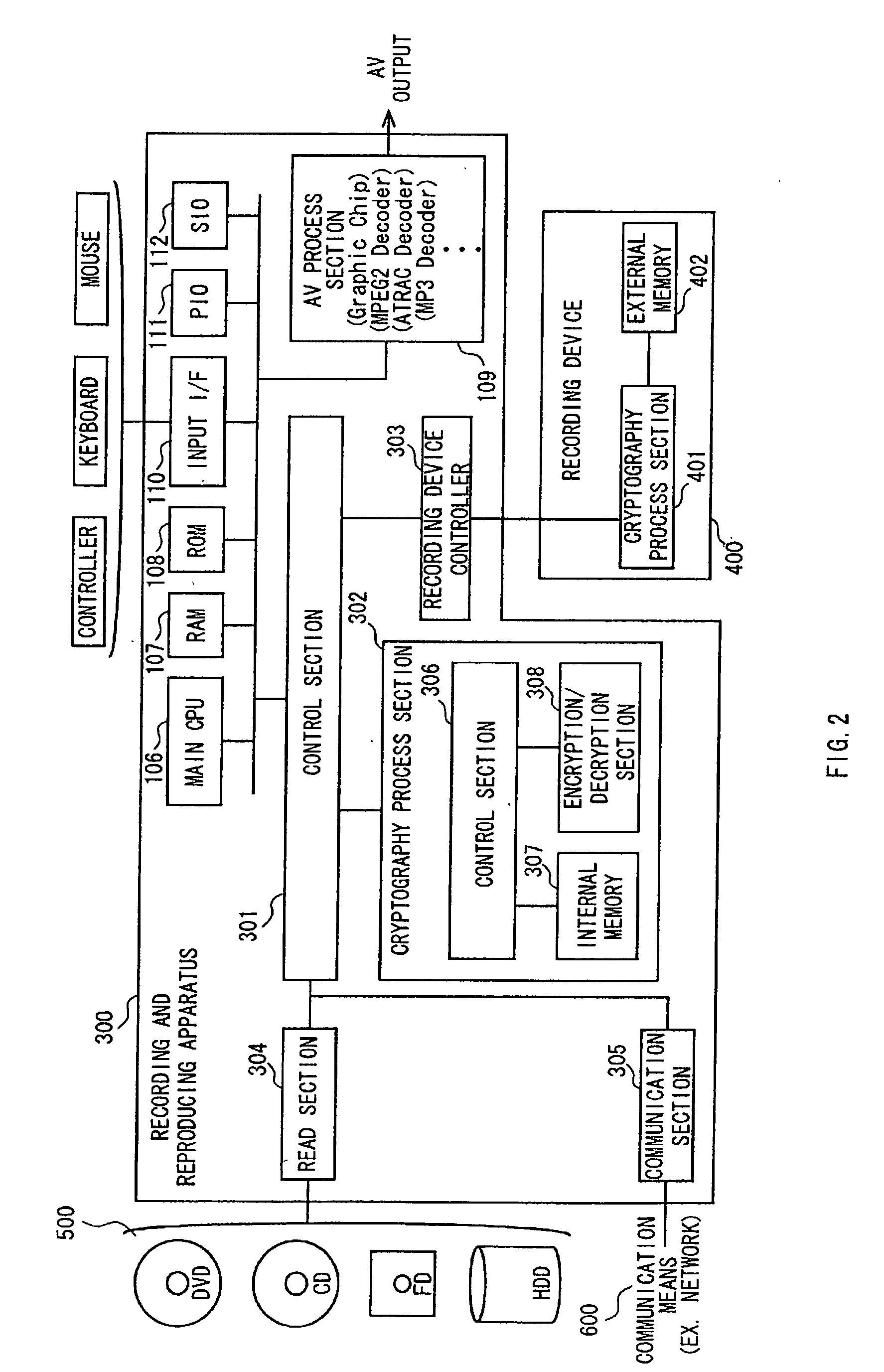
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
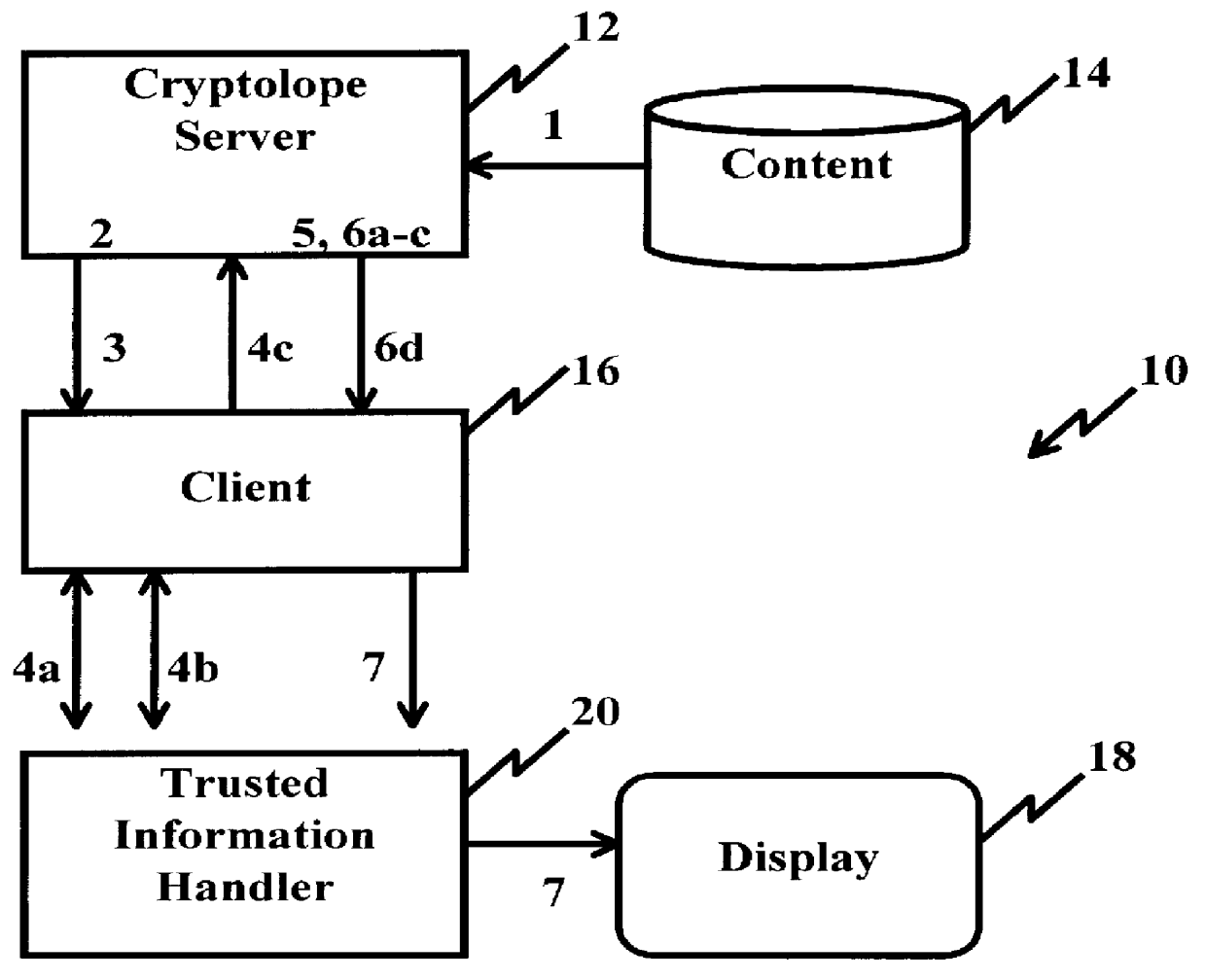
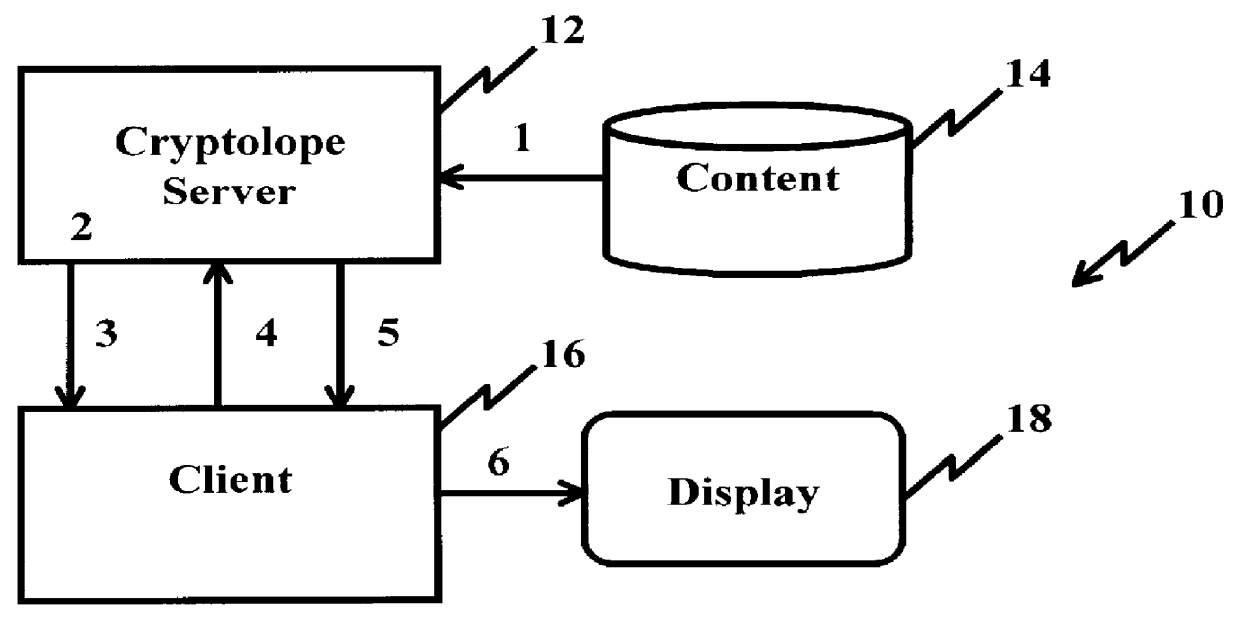
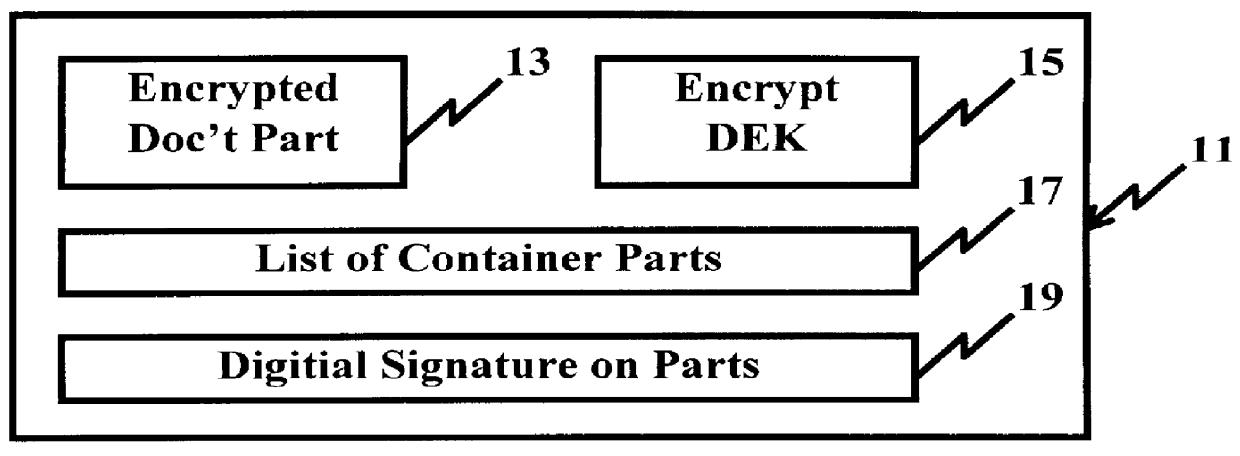
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
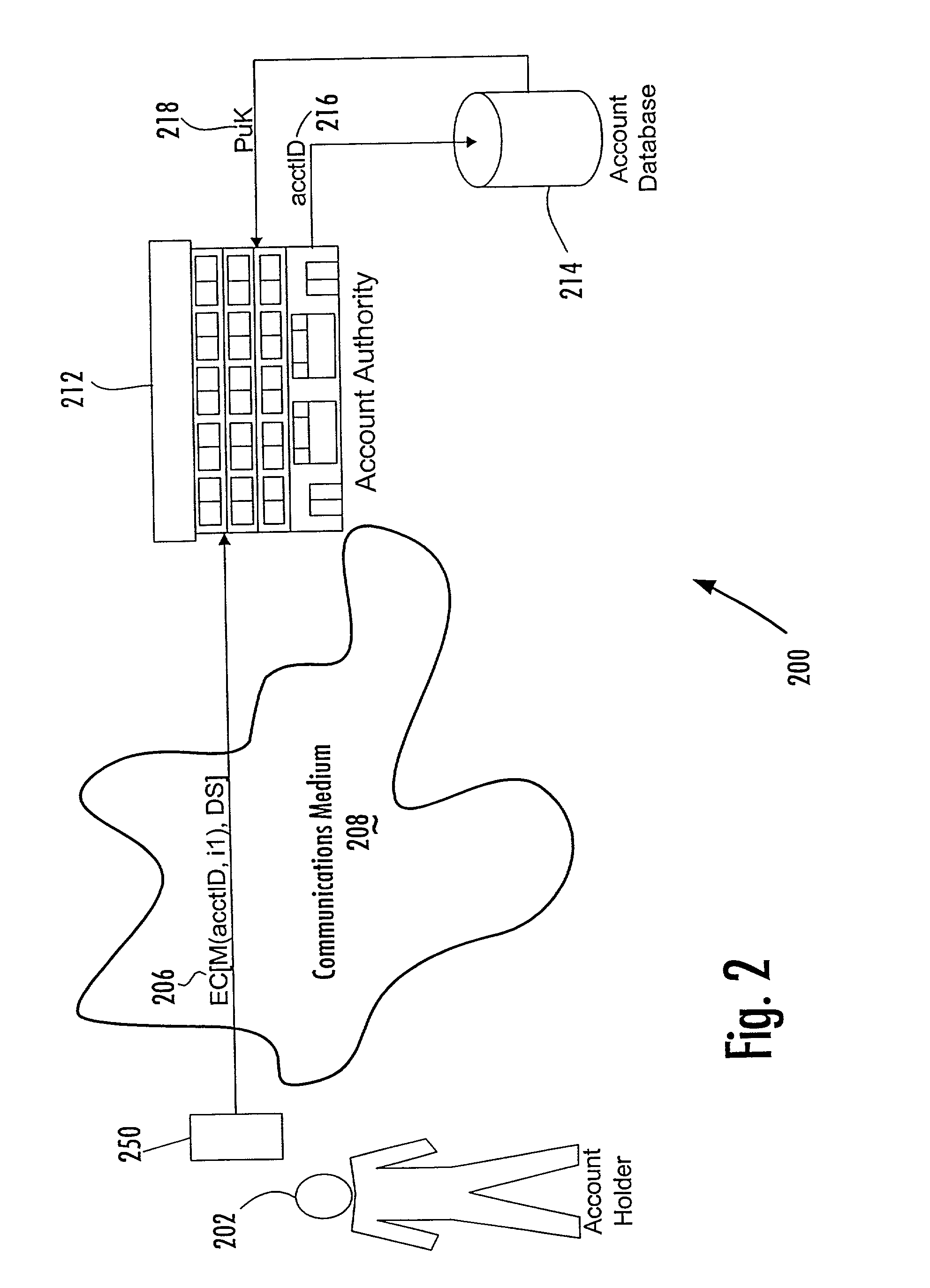
Account-based digital signature (ABDS) system
InactiveUS20020026575A1Key distribution for secure communicationFinanceDigital signatureElectronic communication
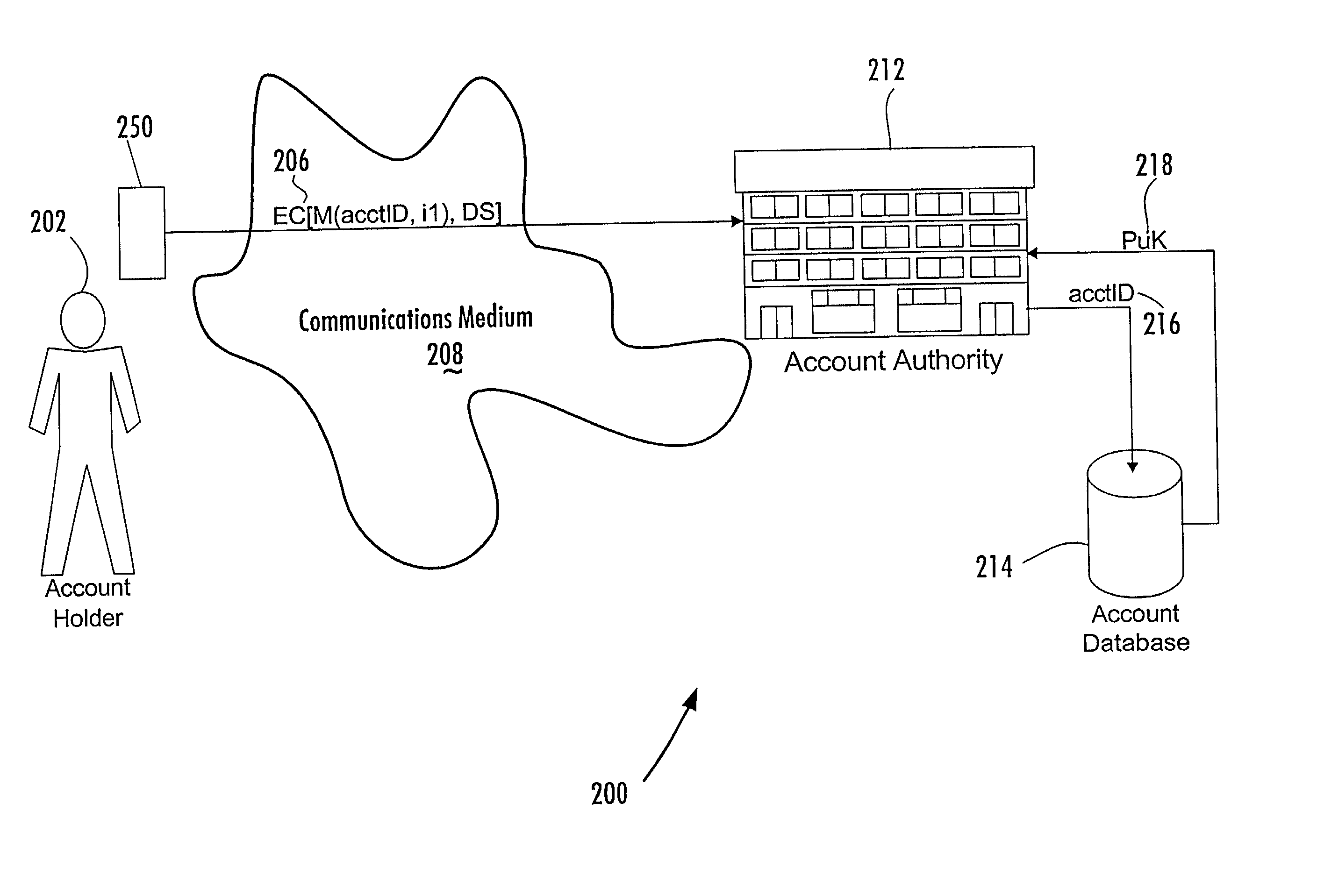
A method of authenticating an entity by a receiving party with respect to an electronic communication that is received by the receiving party and that includes both a unique identifier associated with an account maintained by the receiving party and a digital signature for a message regarding the account, consists of the steps of, before receipt of the electronic communication, first associating by the receiving party a public key of a public-private key pair with the unique identifier and, thereafter, only conducting message authentication using the digital signature received by the receiving party in the electronic communication and the public key associated with the account identifier.
Owner:FIRST DATA
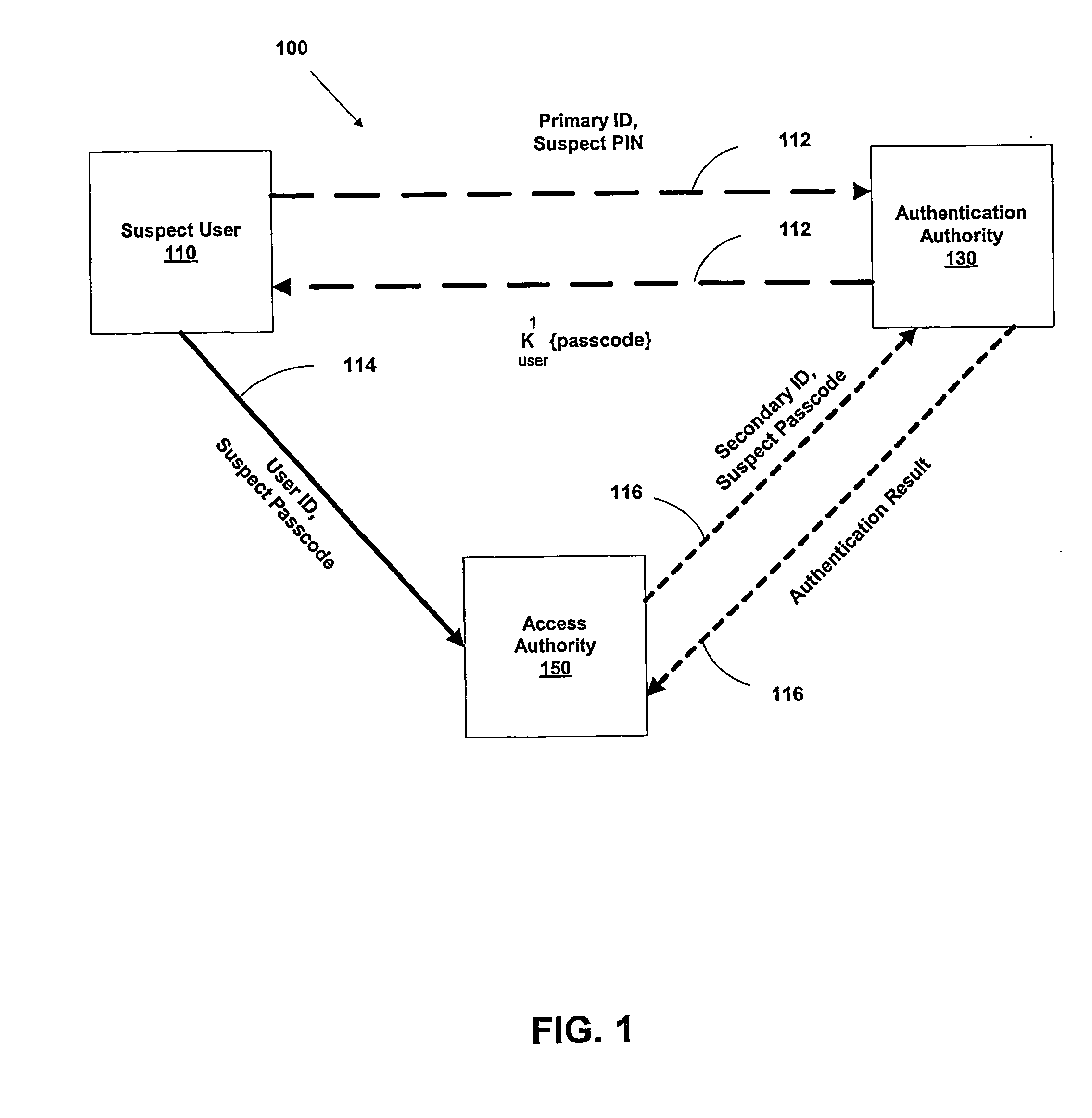
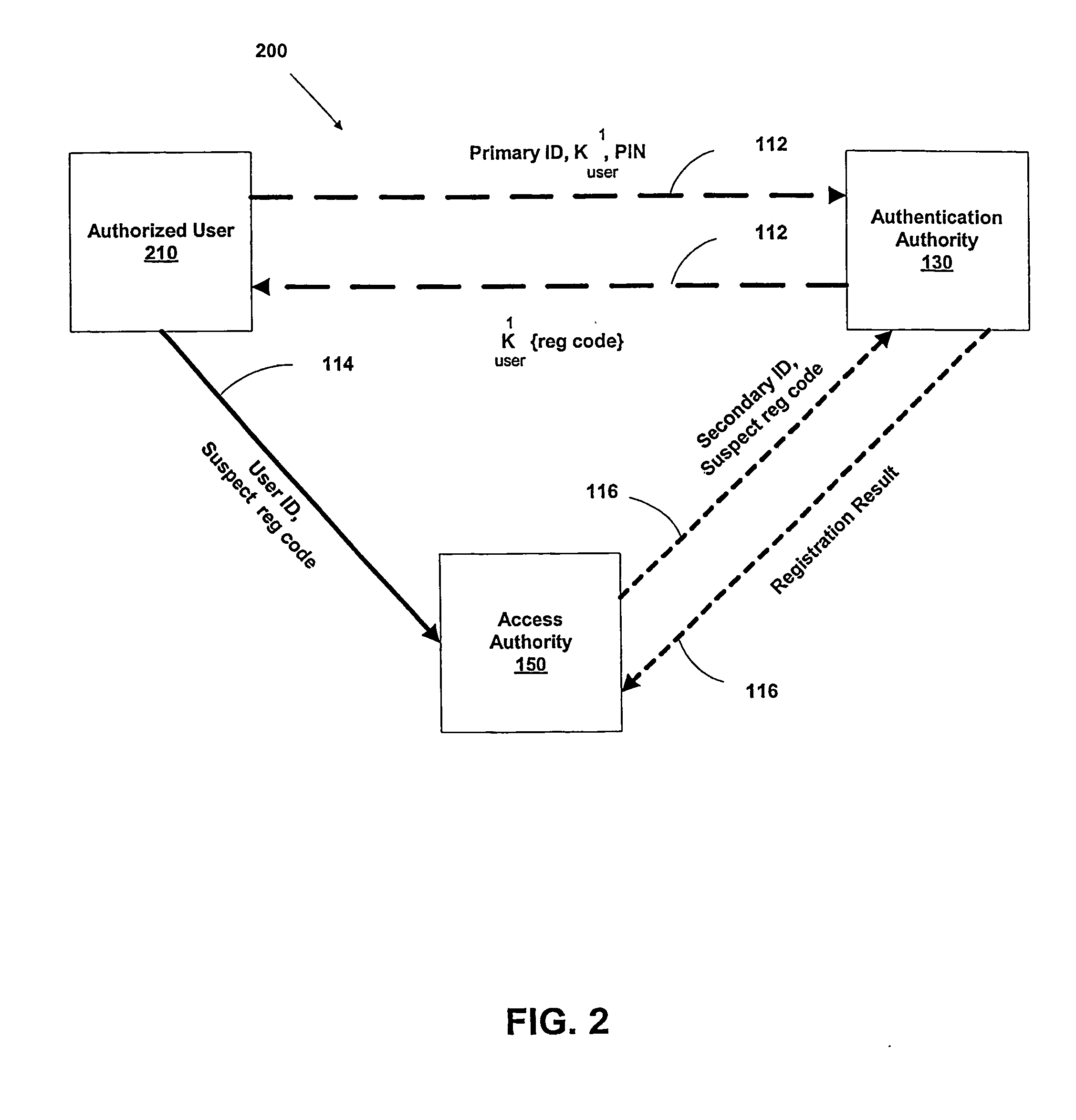
Multi-factor authentication system
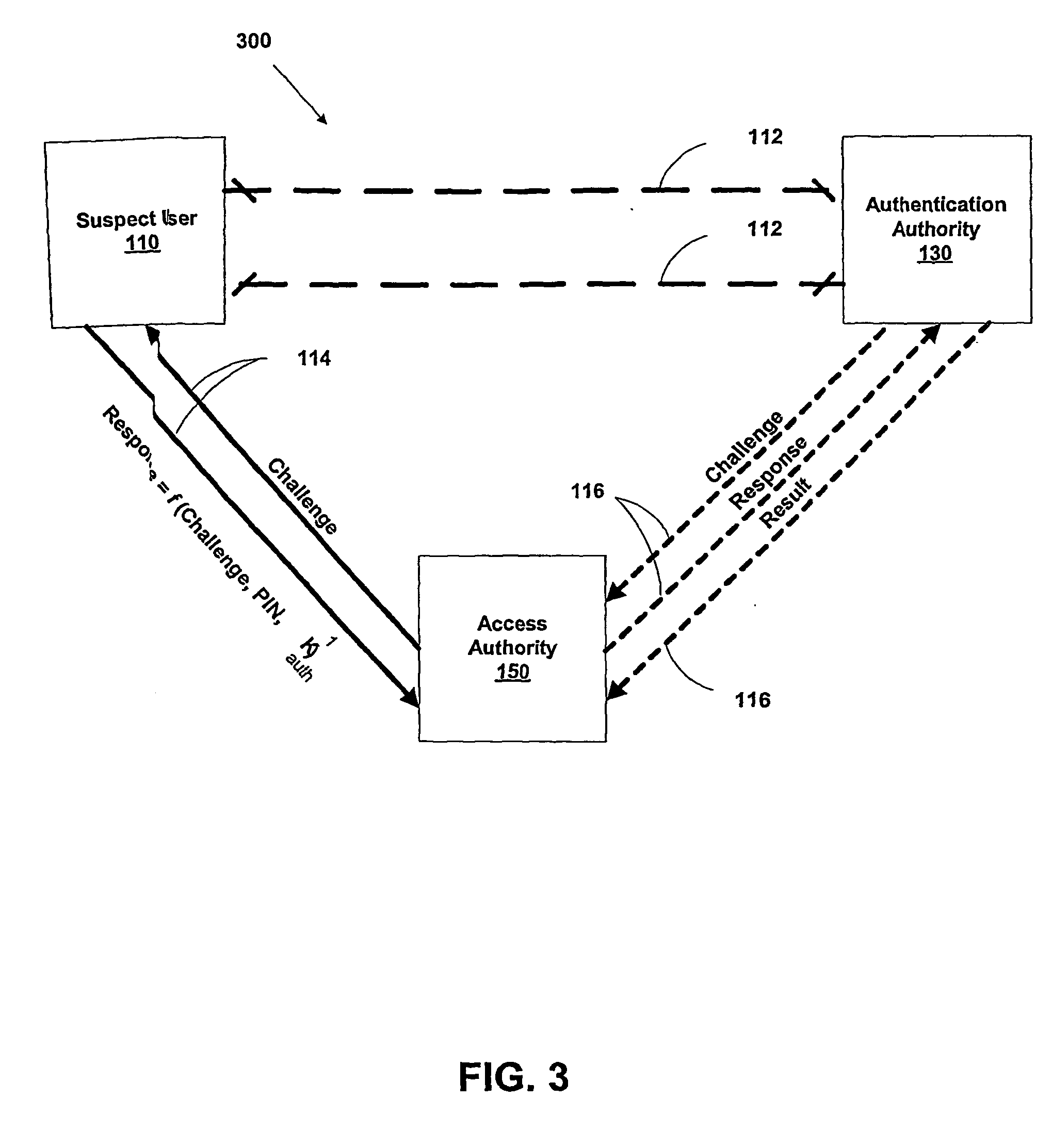
InactiveUS20040187018A1Easy to understandUser identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
A suspect user (110) seeks access to a network resource from an access authority (150) utilizing a passcode received from an authentication authority (130). Initially, an ID of a device is bound with a PIN, the device ID is bound with a private key of the device, and the device ID is bound with a user ID that has been previously bound with a password of an authorized user. The device ID is bound with the user ID by authenticating the user ID using the password. Thereafter, the suspect user communicates the device ID and the PIN from the device over an ancillary communications network (112); the authentication authority responds back over the ancillary communications network with a passcode encrypted with the public key of the device; and the suspect user decrypts and communicates over a communications network (114) the passcode with the user ID to the access authority.
Owner:KARETEK HLDG LLC
Secure online music distribution system
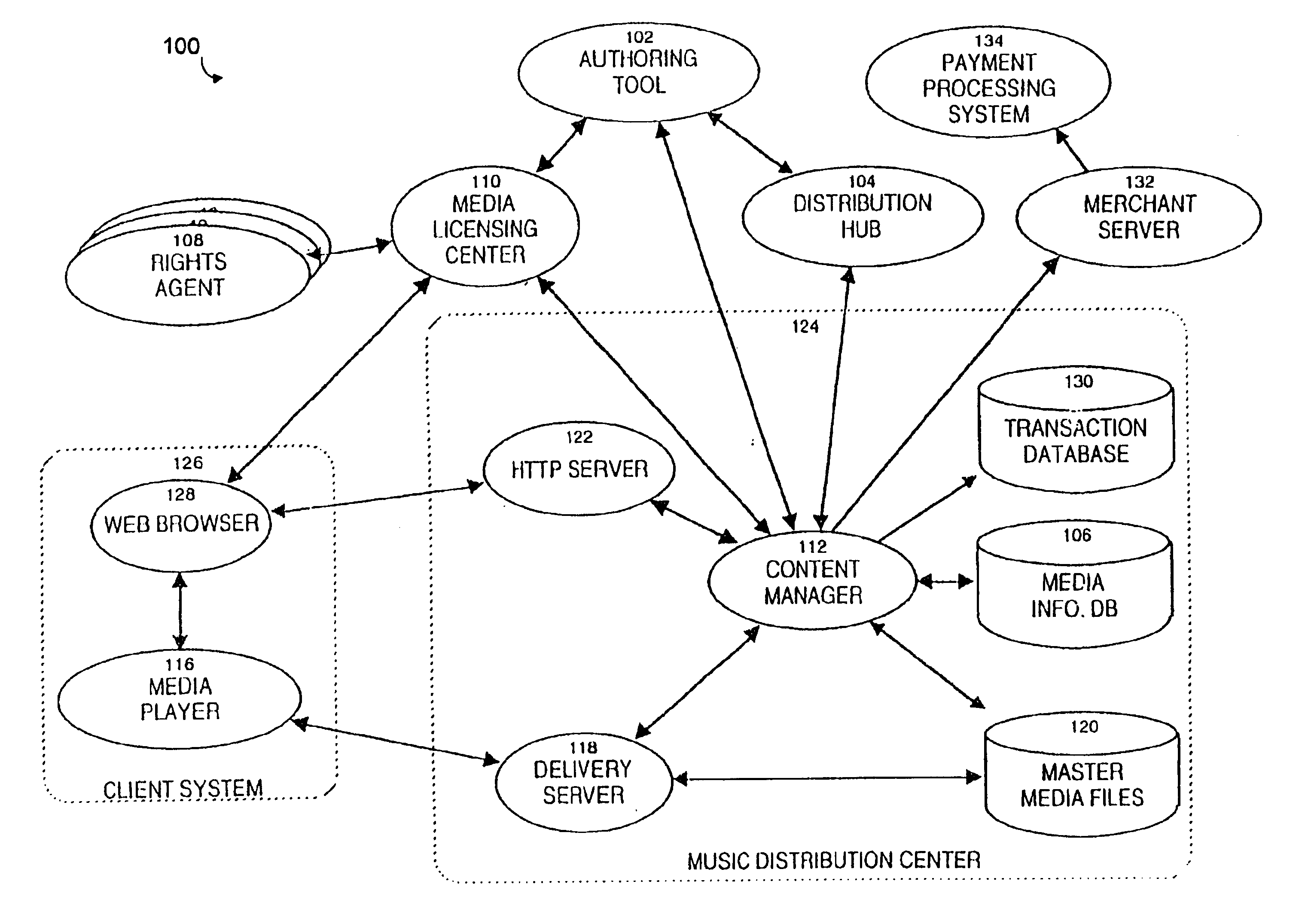
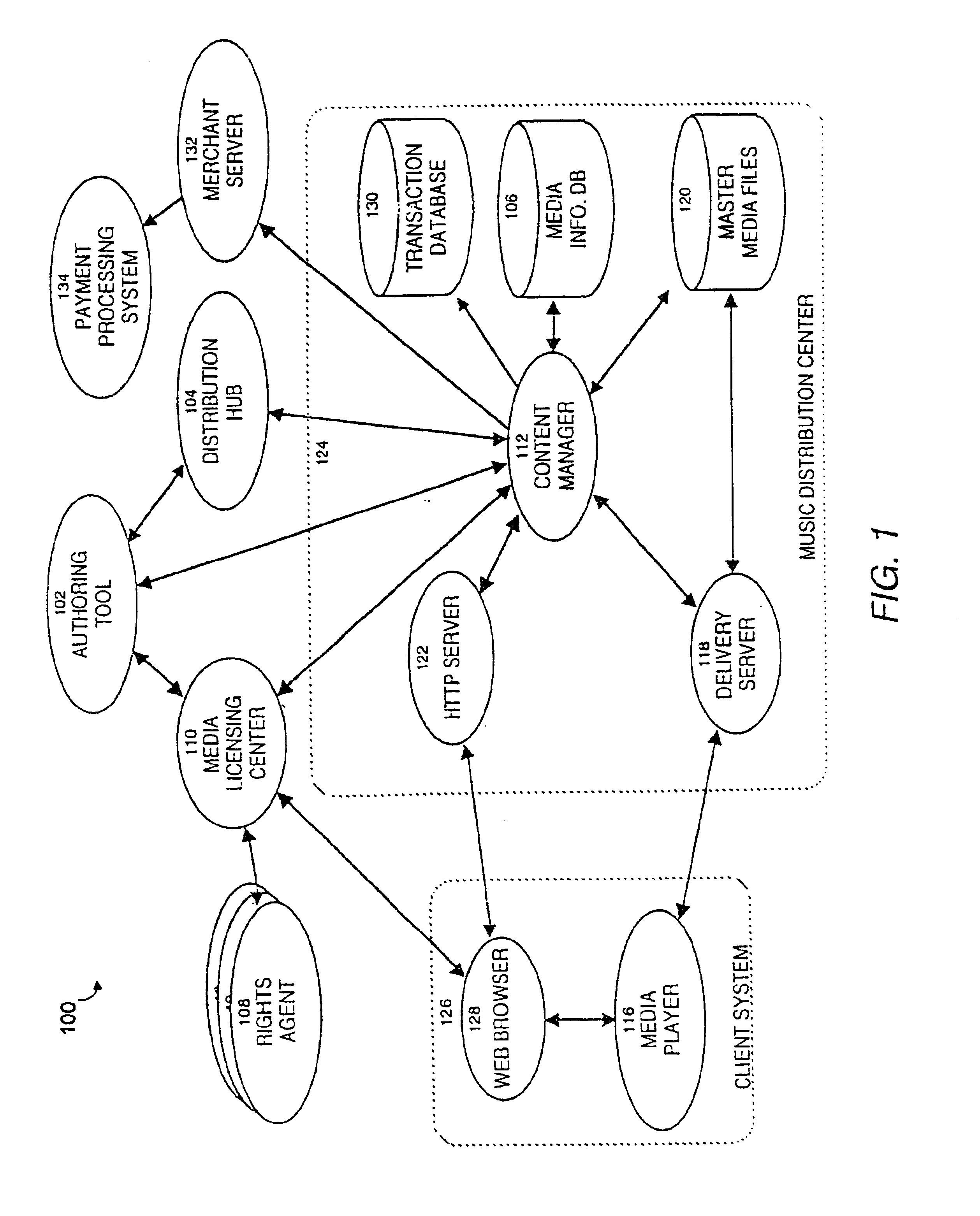
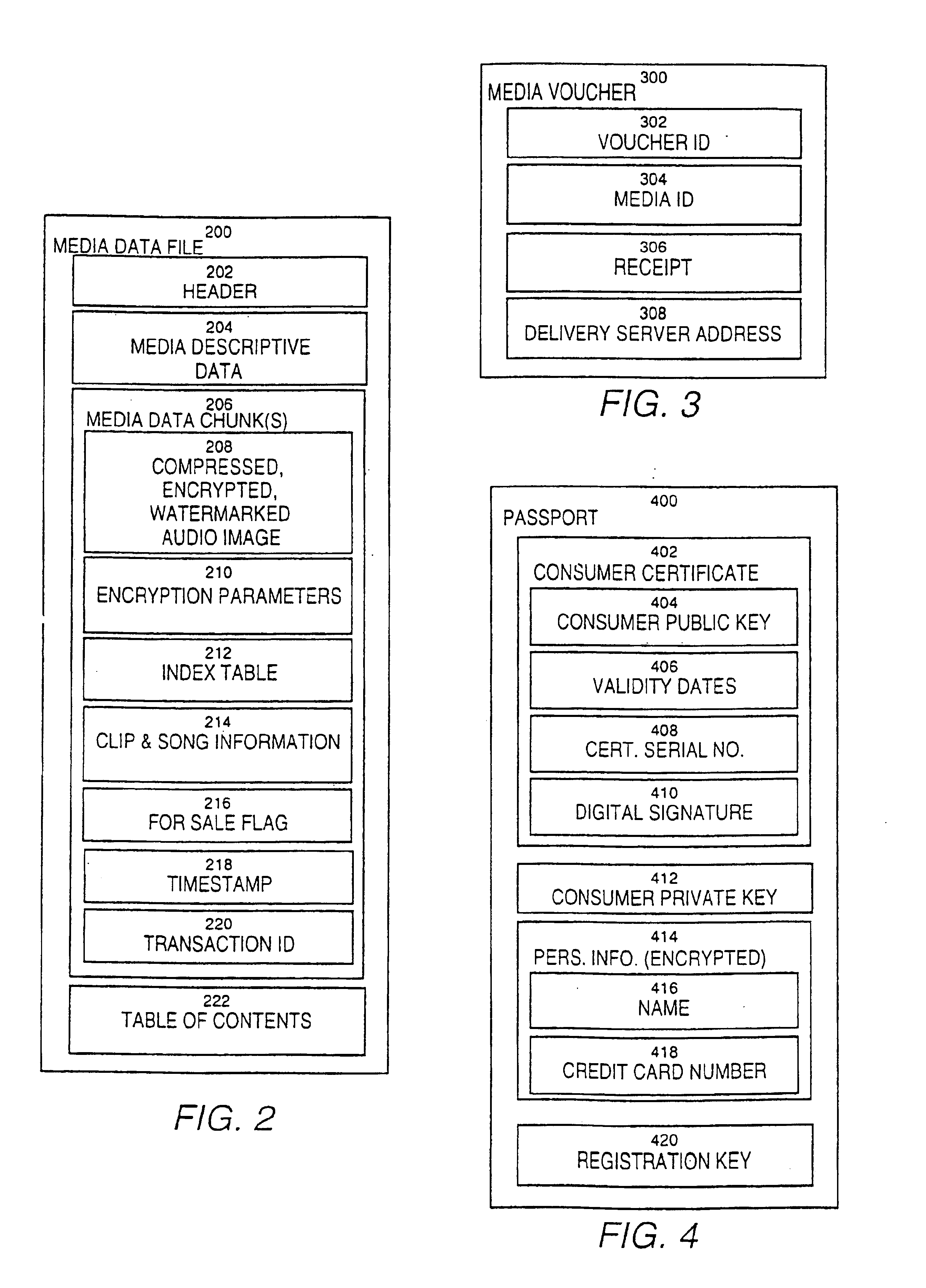
InactiveUS6868403B1Ease of useFlexibilityReservationsPayment architectureCredit cardClient server systems
A computer implemented online music distribution system provides for the secure delivery of audio data and related media, including text and images, over a public communications network. The online music distribution system provides security through multiple layers of encryption, and the cryptographic binding of purchased audio data to each specific purchaser. The online music distribution system also provides for previewing of audio data prior to purchase. In one embodiment, the online music distribution system is a client-server system including a content manager, a delivery server, and an HTTP server, communicating with a client system including a Web browser and a media player. The content manager provides for management of media and audio content, and processing of purchase requests. The delivery server provides delivery of the purchased media data. The Web browser and HTTP server provide a communications interface over the public network between the content manager and media players. The media player provides for encryption of user personal information, and for decryption and playback of purchased media data. Security of purchased media data is enhanced in part by the use of a personal, digital passport in each media player. The digital passport contains identifying information that identifies the purchaser, along with confidential information, such as credit card number, and encryption data, such as the media player's public and private keys. The media player encryption data is used to encrypt purchased media data, which is decrypted in real time by the media player. The media player also displays confidential information, such as the purchaser's credit card number, during playback.
Owner:MICROSOFT TECH LICENSING LLC
Secured peer-to-peer network data exchange
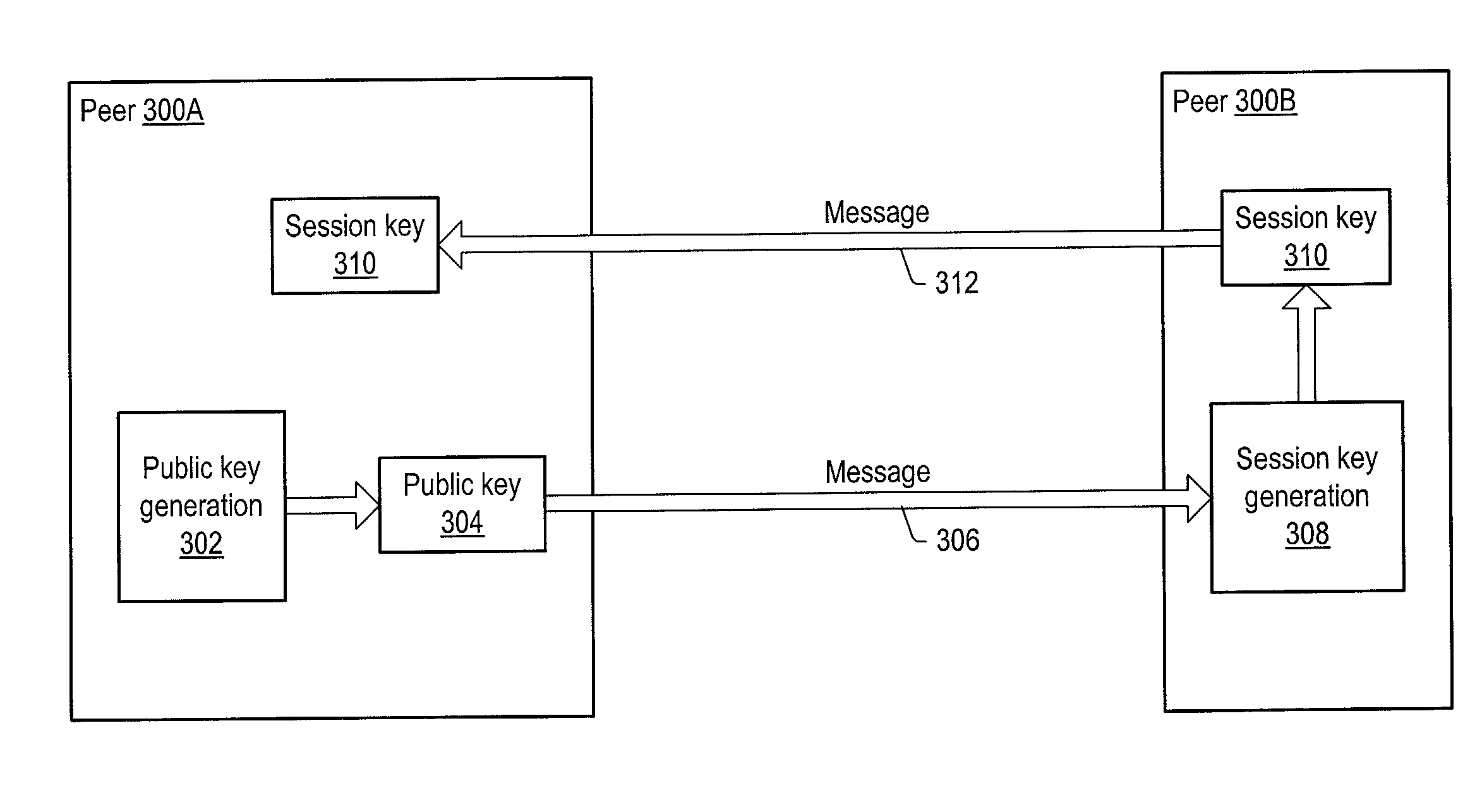
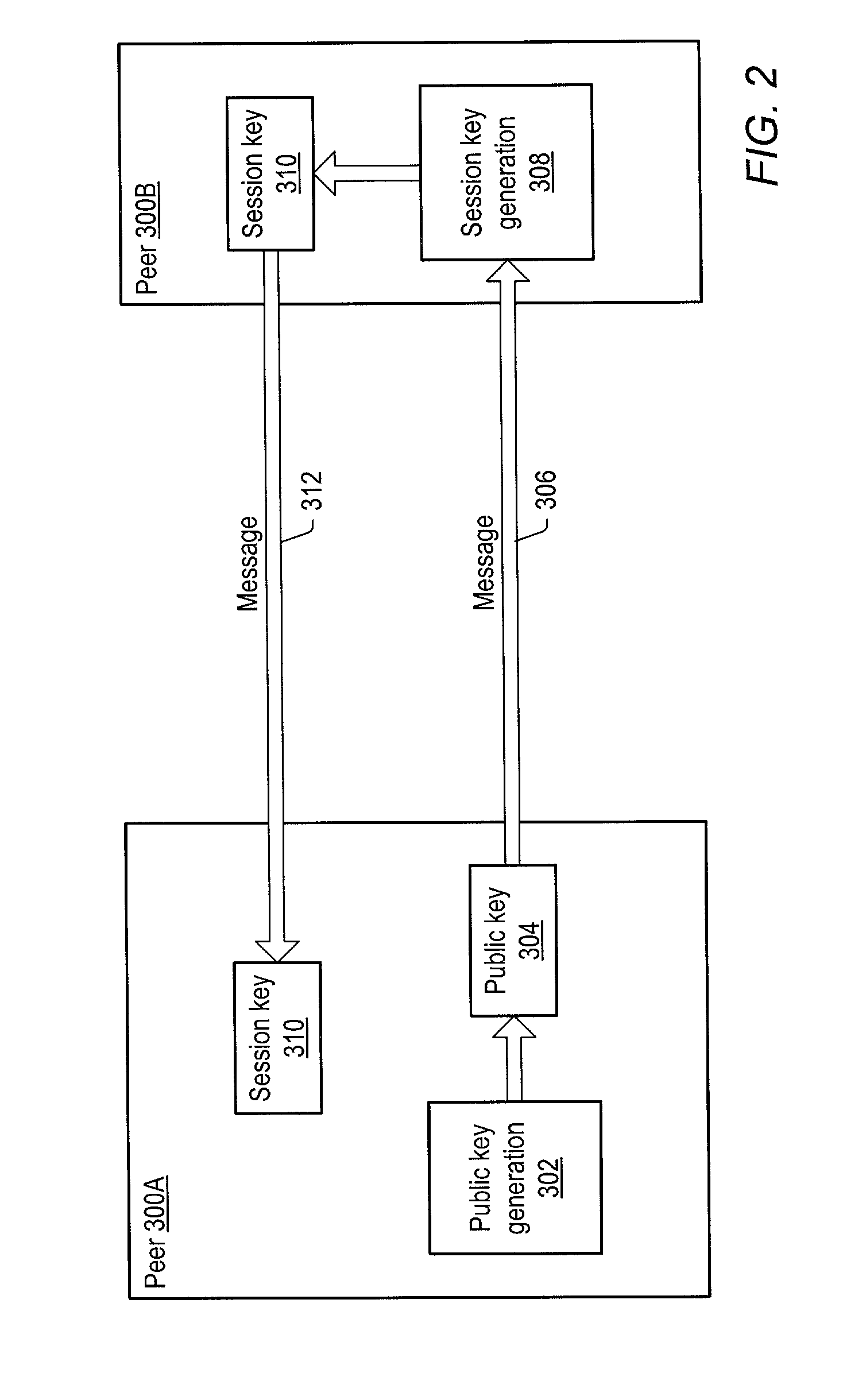
ActiveUS20030163697A1Key distribution for secure communicationPublic key for secure communicationGroup sessionPeer-to-peer
A system and method for providing secure exchange of messages between peers in peer groups. Embodiments may be used to provide secured sessions between peers in the peer-to-peer network. Embodiments may also be used to provide secured group sessions among a plurality of peers. A first peer may generate and send a public key to a second peer. The second peer may generate a session key from the public key. The second peer may send the session key to the first peer, or alternatively to two or more peers in a group session. The session key may be secured when sending. Messages and / or other data exchanged between the two peers may be encrypted and decrypted using the session key.
Owner:ORACLE INT CORP
Provision of secure communications connection using third party authentication
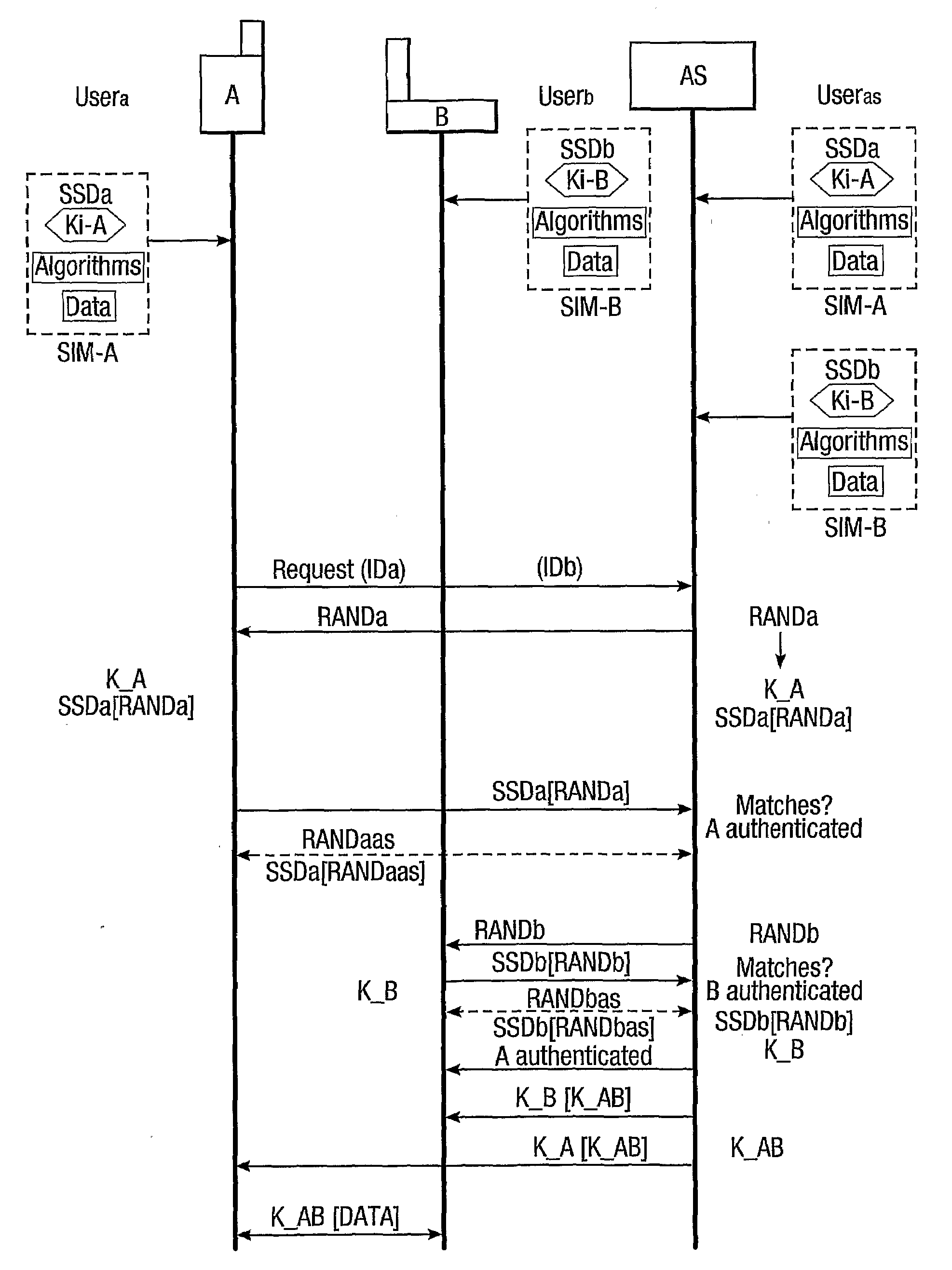
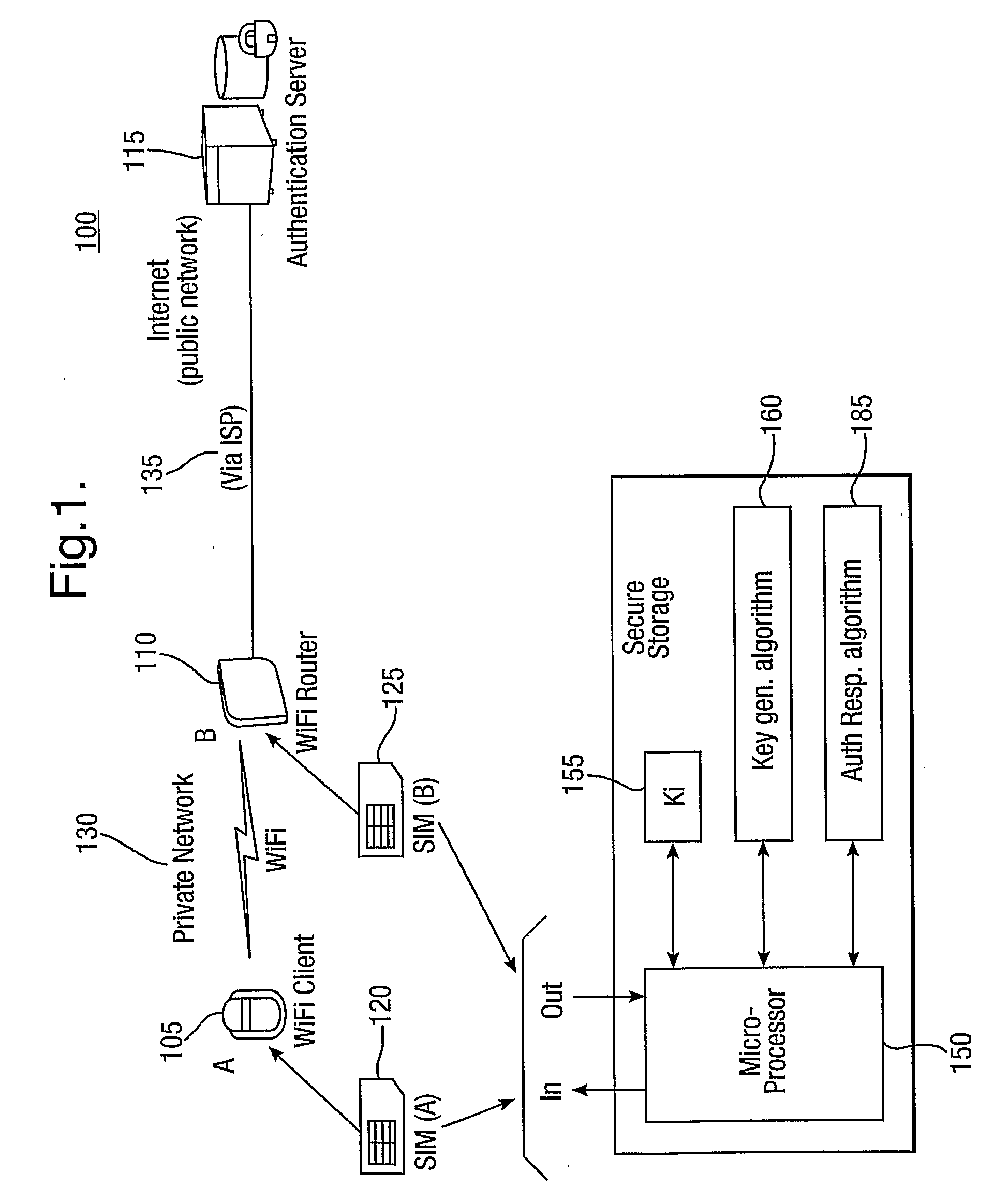
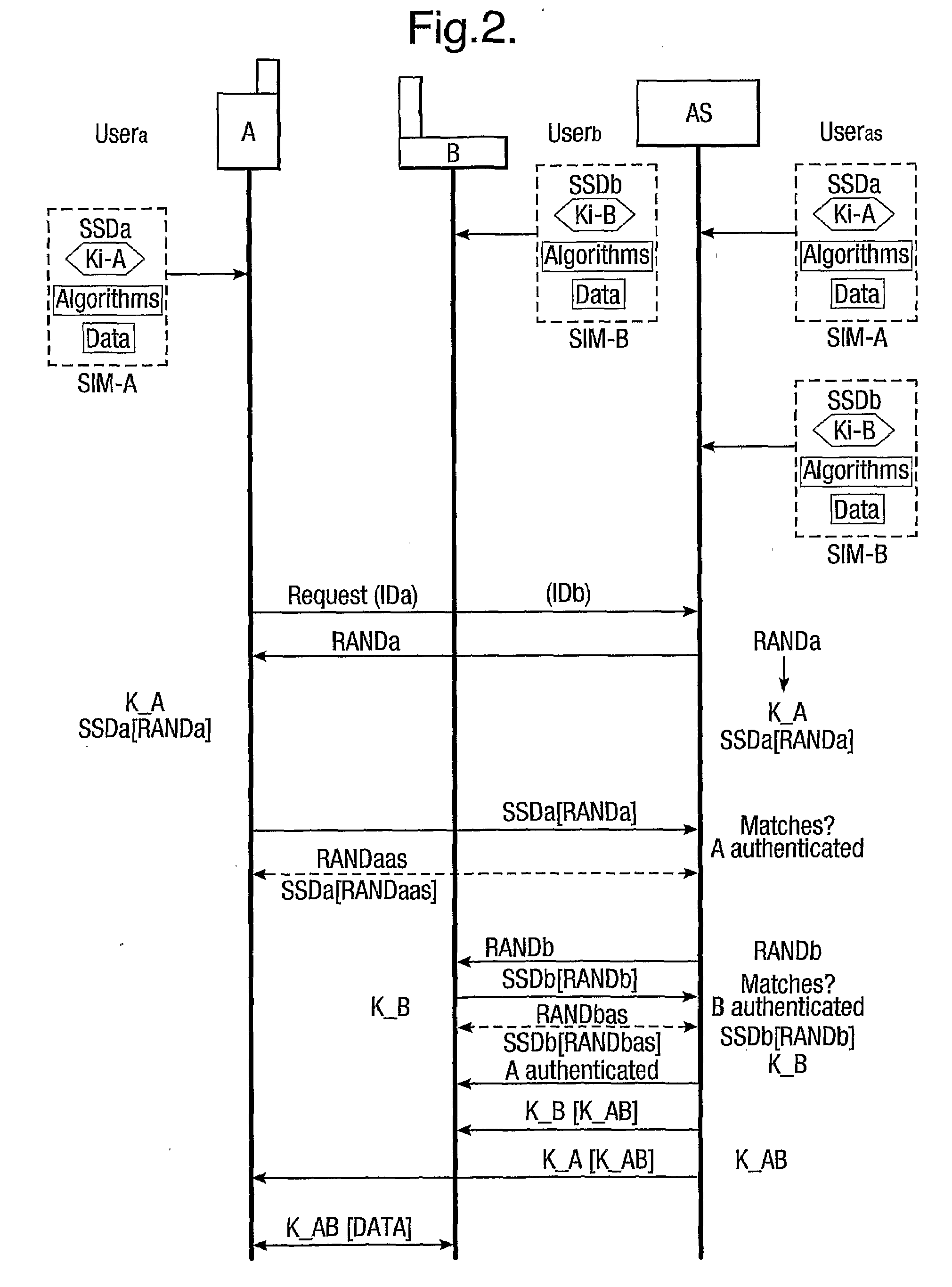
ActiveUS20090287922A1Connection securityCommunication securityKey distribution for secure communicationUser identity/authority verificationThird partySecure communication
The present invention relates to communications, and in particular though not exclusively to forming a secure connection between two untrusted devices. The present invention provides a method of securely connecting a first device (A) to a second device (B) using a third party authentication server (AS) coupled to the second device, the first device and the authentication server both having first device shared secret data (SSDa) and the second device and the authentication server both having second device shared secret data (SSDb). The method comprises receiving a request from the first device at the authentication server; the authentication server and the first device both generating a first device key (K_A) using the first device shared secret data in response to a first device random number (RANDa) sent from the authentication server to the first device; the authentication server and the second device both generating a second device key (K_B) using the second device shared secret data in response to a second device random number (RANDb) sent from the authentication server to the second device; and the authentication server securely forwarding to the second device (B) and the first device (A) a common key (K_AB) using the second and first device keys (K_B, K_A).
Owner:BRITISH TELECOMM PLC
Data authentication system
InactiveUS20020169971A1Efficient verificationPossibility of leakageTelevision system detailsMultiple keys/algorithms usageKey storageMaster key
A data processing apparatus a data processing method efficiently ascertain that data are valid, prevent encryption processing key data from leaking, eliminate illegal use of contents data, restrict contents utilization, apply a different plurality of data formats to contents and efficiently execute reproduction processing of compressed data. The verification process of partial data is executed by collating the integrity partial data as check values for a combination of partial data of a content, and the verification process of the entirety of the combination of partial data is executed by collating partial-integrity-check-value-verifying integrity check values that verify the combination of the partial integrity check values. Master keys to generate individual keys necessary for a process of such as data encryption are stored in the storage section and keys are generated as required. An illegal device list is stored in the header information of a content and referred to when data is used. Keys specific to a data processing apparatus and common keys are stored and the keys are selectively used according to the content use restriction. Plural content blocks are coupled, and at least a part of the content blocks is applied to an encryption process by an encryption key Kcon, then encryption key data that is the encryption key Kcon encrypted by an encryption key Kdis is stored in the header section. A content data is made of compression data and an expansion processing program or a combination of types of compression programs and the reproducing apparatus can determine an expansion program applicable to a compressed content.
Owner:SONY CORP
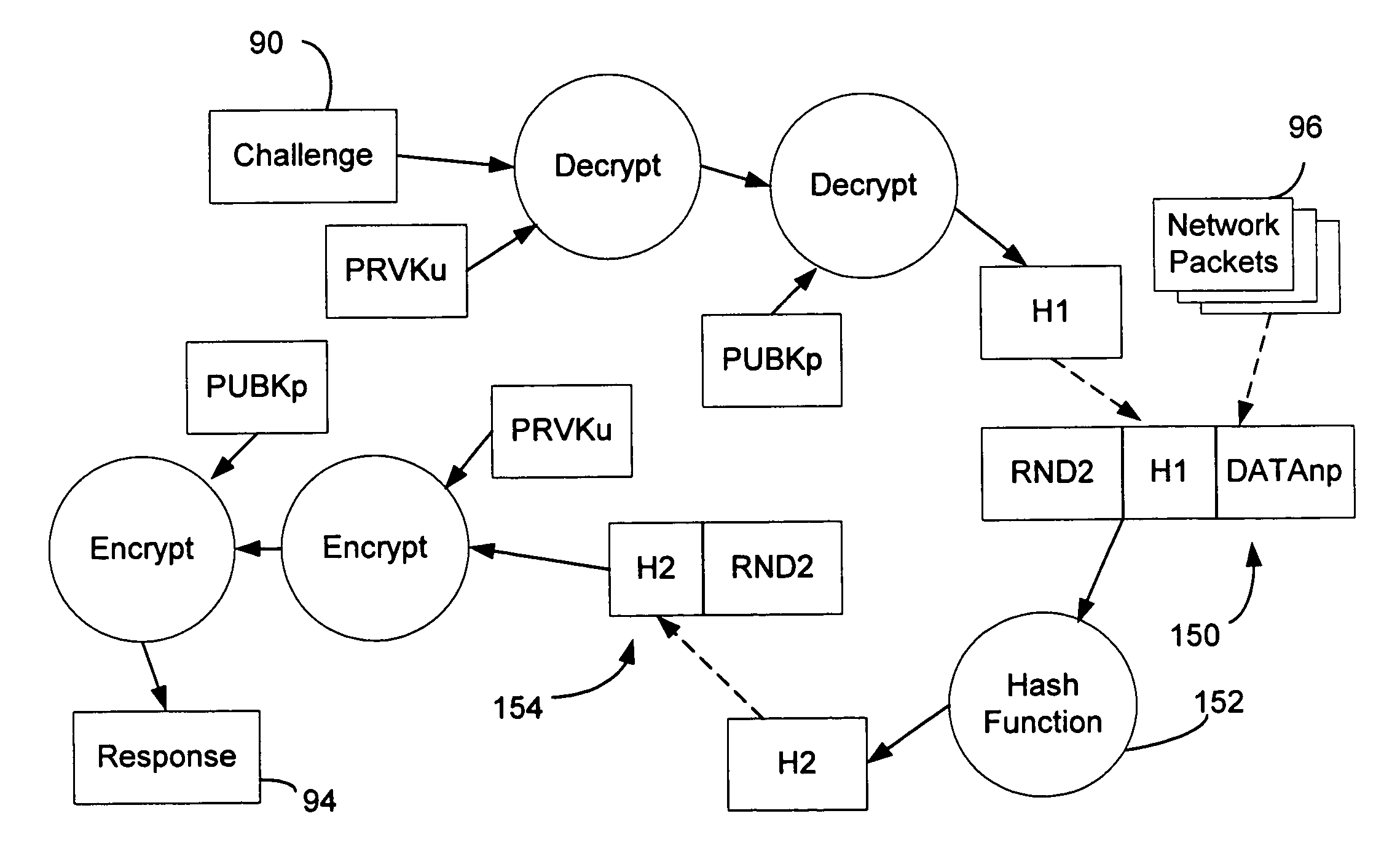
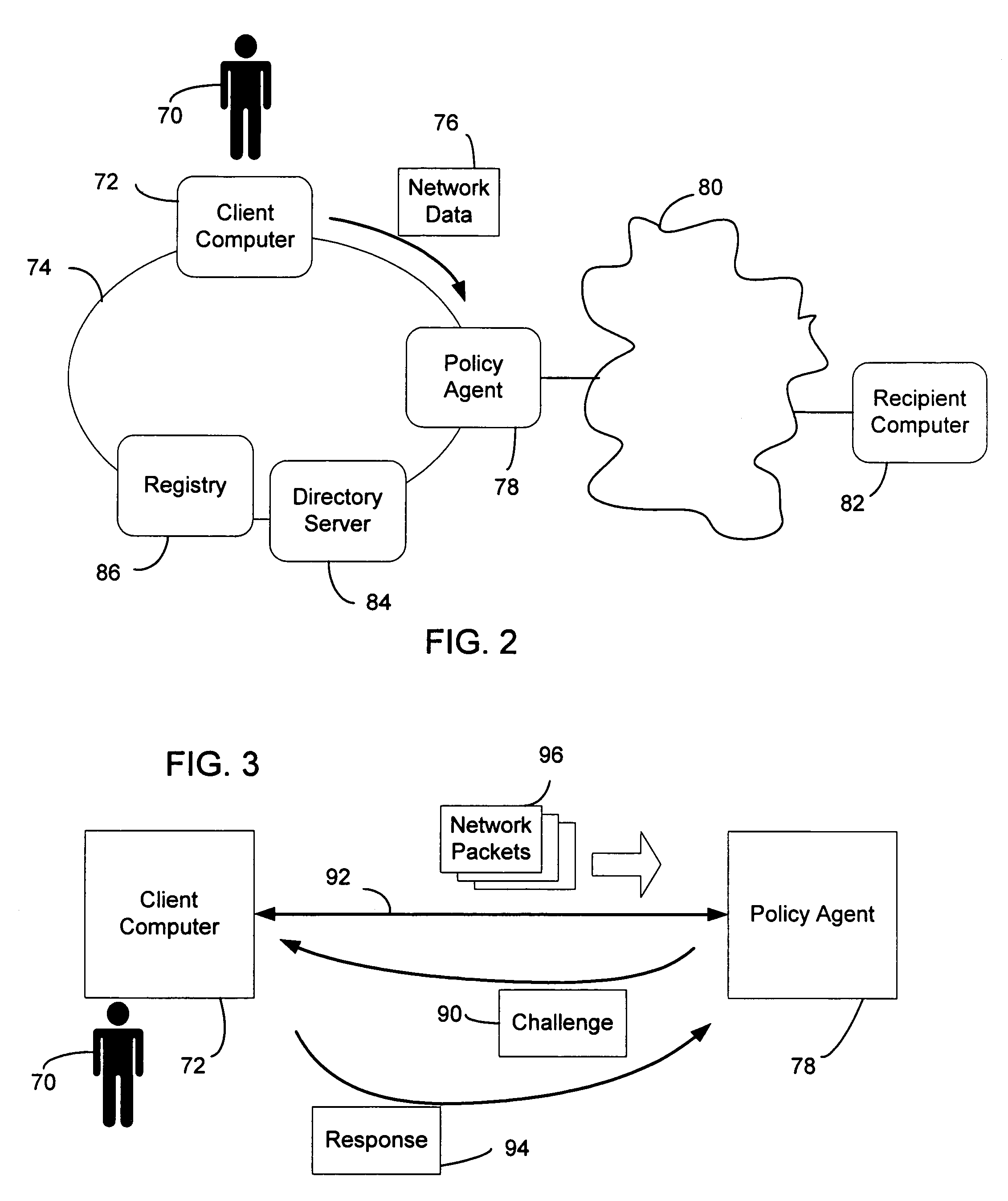
System and method of user authentication for network communication through a policy agent
InactiveUS7039713B1Digital data processing detailsComputer security arrangementsData connectionUser authentication
A policy agent of a network performs an out-of-band user authentication process to verify the identity of a user of a client computer and associates the network data received from the client computer with the user. When the client computer initiates a network data connection to or through the policy agent, the policy agent sends an encrypted challenge to the client computer. The challenge is encrypted with a private key of the policy agent. When the client computer receives the challenge, it decrypts the challenge and prepares a message digest value based on the challenge and the network data sent by the user. The message digest value is then encrypted with the private key of the user to form a response, and the response is sent to the policy agent. The policy agent decrypts the response with the public key of the user to obtain the message digest value and calculates a digest value based on the challenge and the received network data. The policy agent then compares the calculated digest value with the decrypted digest value. A match between the two digest values indicates that the user is successfully authenticated and that the received network data are associated with the user. The policy agent may then apply network policies based on the credentials of the authenticated user.
Owner:MICROSOFT TECH LICENSING LLC
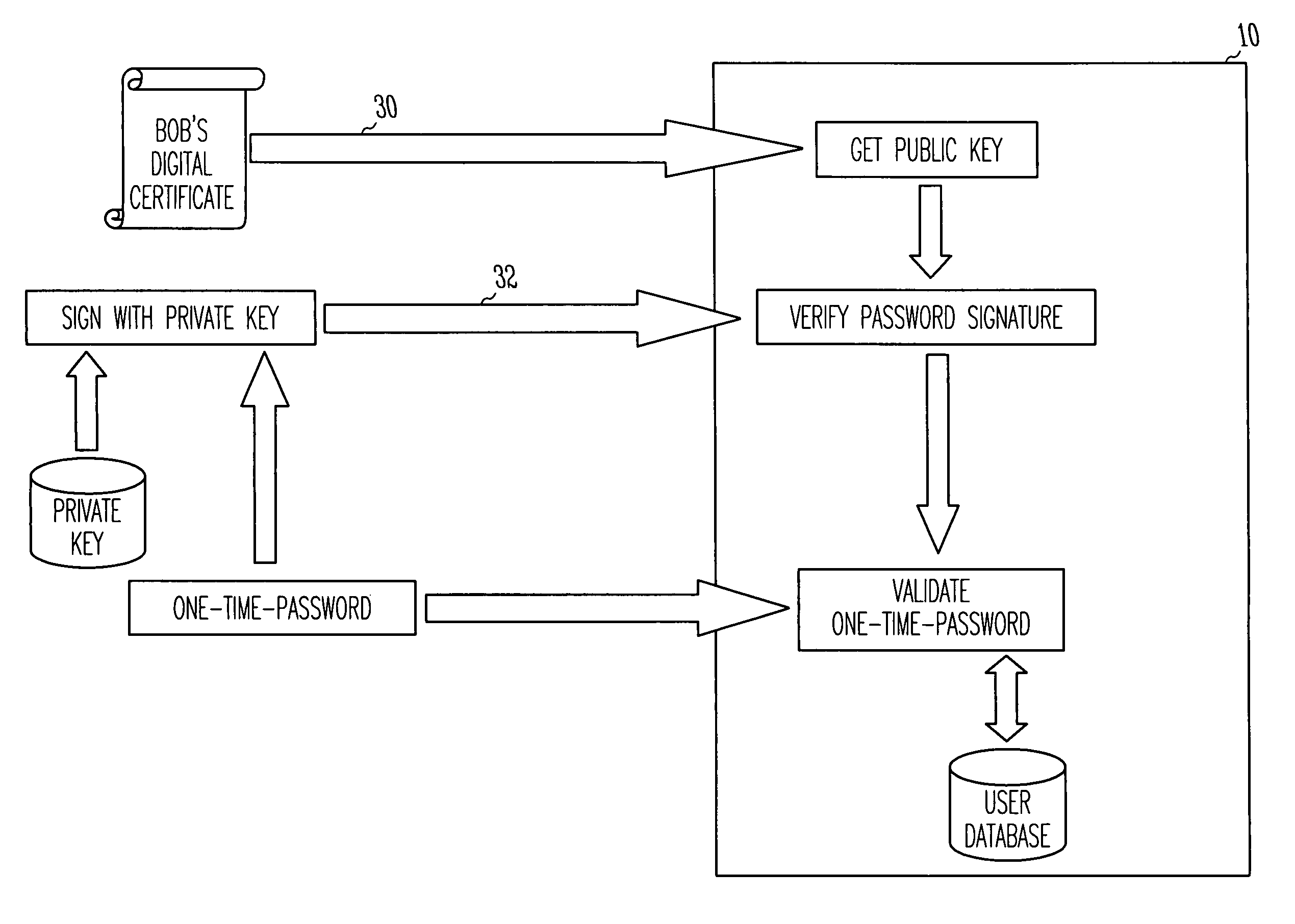
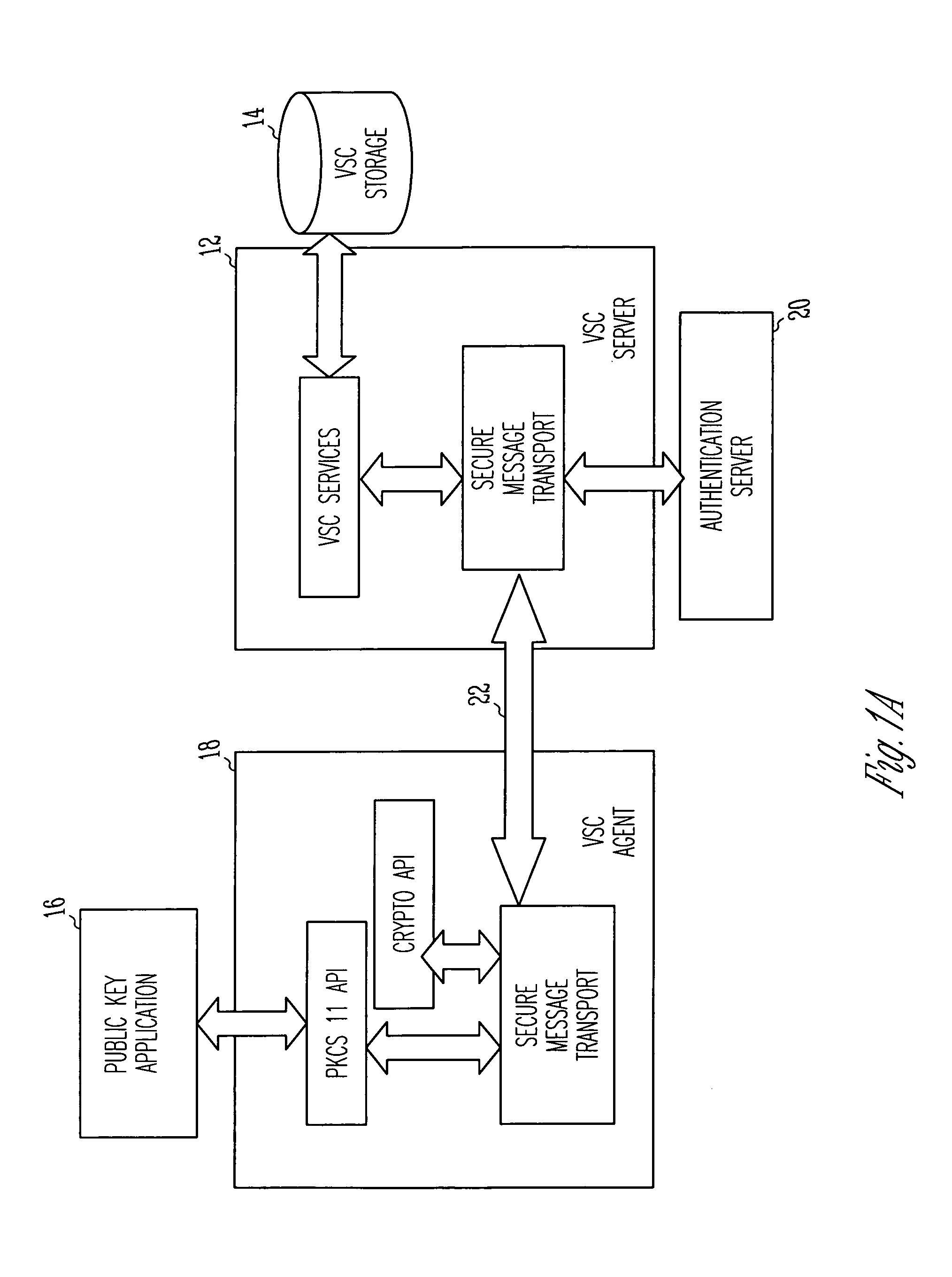
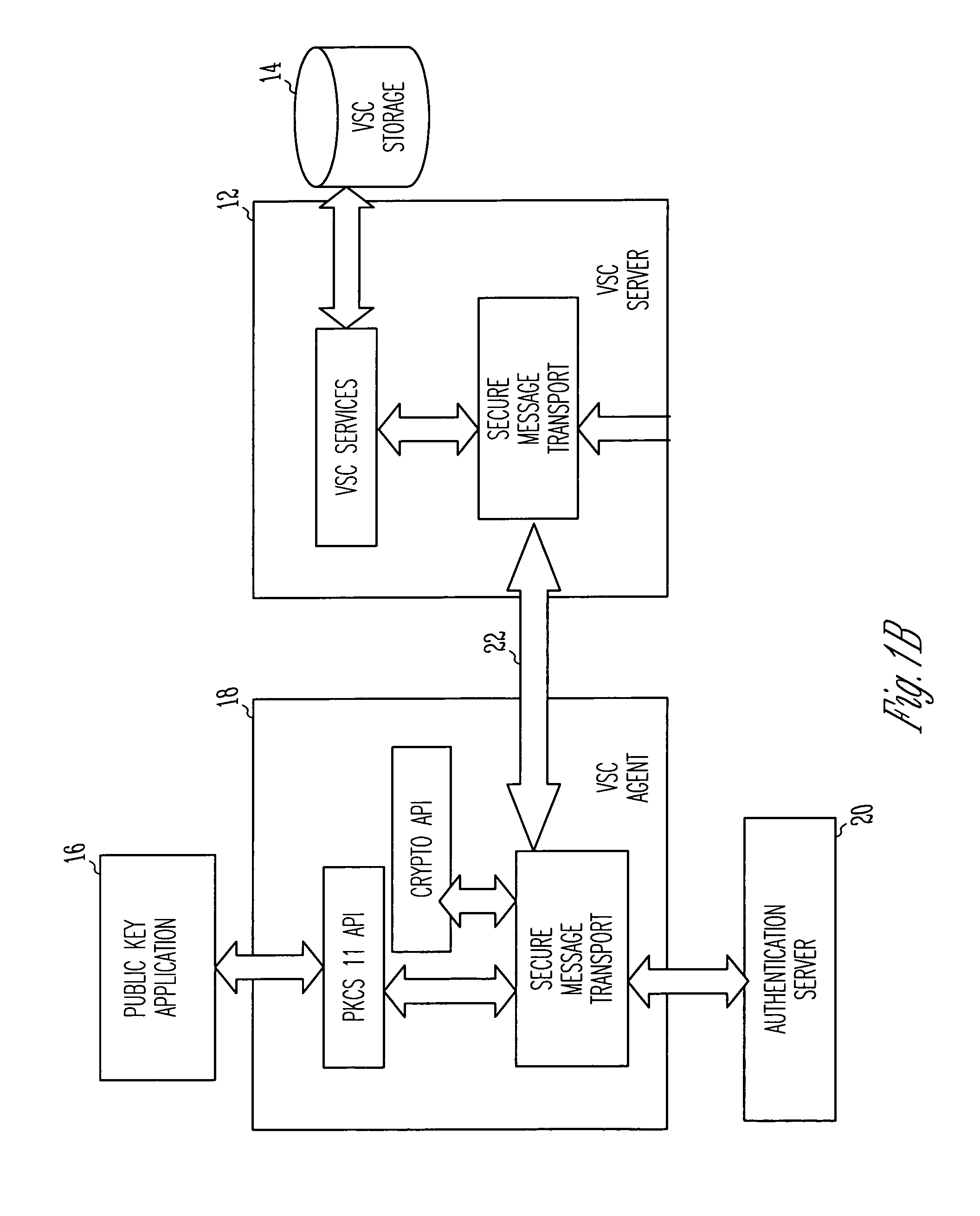
Virtual smart card system and method
InactiveUS7085931B1Digital data processing detailsUser identity/authority verificationPublic key authenticationComputerized system
A public key authentication system and method for use in a computer system having a plurality of users. The system includes a virtual smart card server, storage connected to the virtual smart card server, and a virtual smart card agent connected to the virtual smart card server. The storage includes a plurality of virtual smart cards, wherein each virtual smart card is associated with a user and wherein each smart card includes a private key. The virtual smart card agent authenticates the user and accesses the authenticated user's virtual smart card to obtain the user's private key.
Owner:SAFENET DATA SECURITY ISRAEL
Data privacy
ActiveUS8412837B1Public key for secure communicationComputer security arrangementsTokenization (data security)Coding decoding
In some embodiments, techniques for data security may include encoding and decoding unreadably encoded data, such as data encrypted with a public key or tokenized. In some embodiments, techniques for data security may include distributing an encrypted private key. In some embodiments, unreadable data may be encrypted and / or decrypted using time-varying keys.In some embodiments, techniques for data security may include combining information and a policy, and encoding the combined information and policy, wherein encrypting the combined information and policy is performed using a public key, or via tokenization.In some embodiments, techniques for data security may include receiving data, wherein the data has been encoded, decoding the data, determining a first datum and a second datum, wherein the first datum and the second datum are associated with the decoded data, and determining a policy, wherein the policy is associated with the first datum.
Owner:ROSKIND JAMES A DR
System and method for facilitating blockchain-based validation
InactiveUS20170344988A1Key distribution for secure communicationDigital data information retrievalFinancial transactionSmart contract
In certain embodiments, blockchain-based validation of a bearer of a private key used to register a record on a blockchain may be facilitated. In some embodiments, reference information associated with a user and with a blockchain record may be obtained. The reference information may be based on a blockchain address associated with the user and with the record. The blockchain address may be based on a public key corresponding to a private key used to register the record, where the keys are a key pair associated with the user. A smart contract may be caused to be generated based on the reference information and provided on a blockchain. The smart contract may be configured to automatically validate a transaction using the public key. A notification indicating that the user registered the record may be obtained responsive to the smart contract validating a transaction signed using the private key.
Owner:UBS BUSINESS SOLUTIONS AG
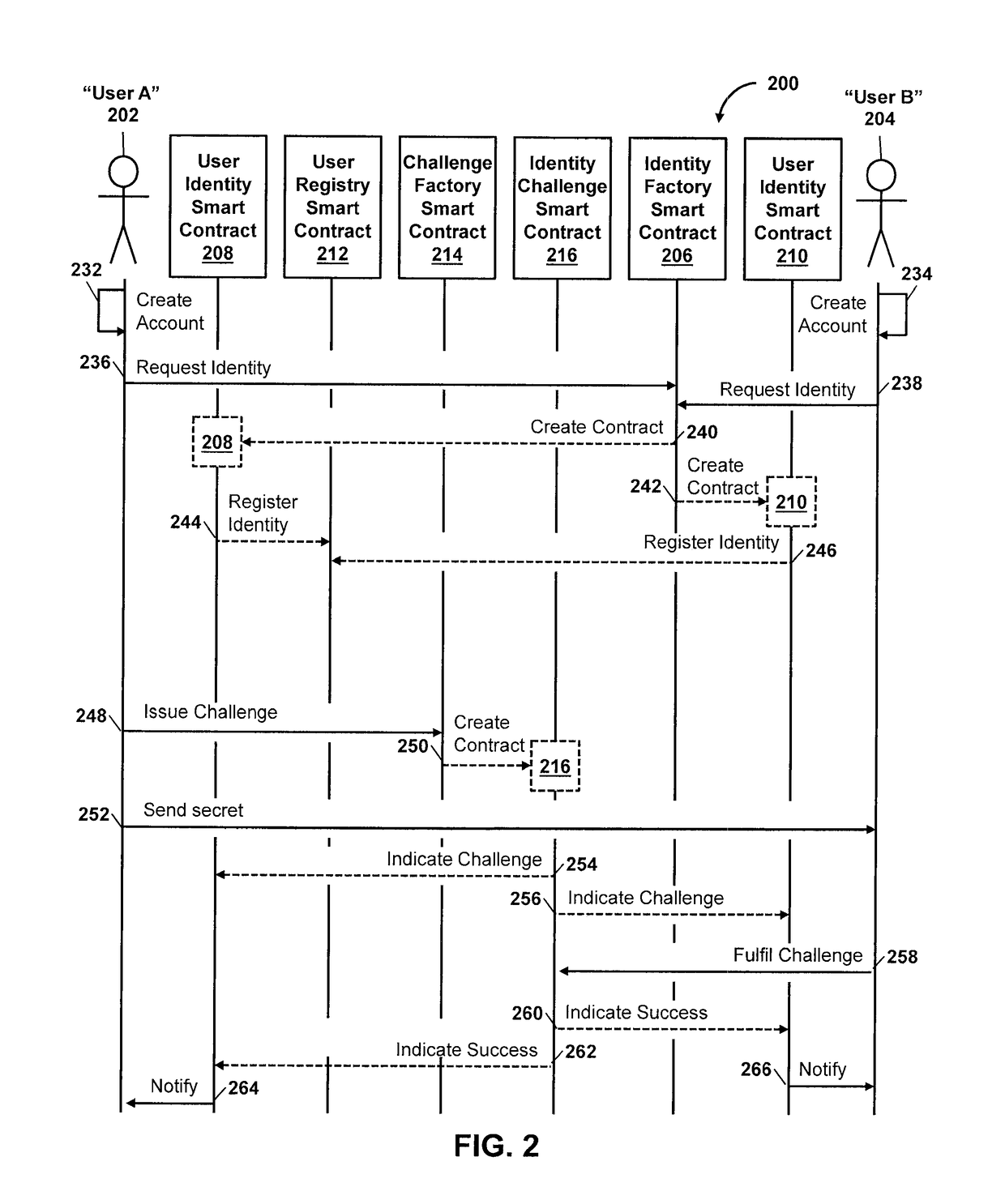
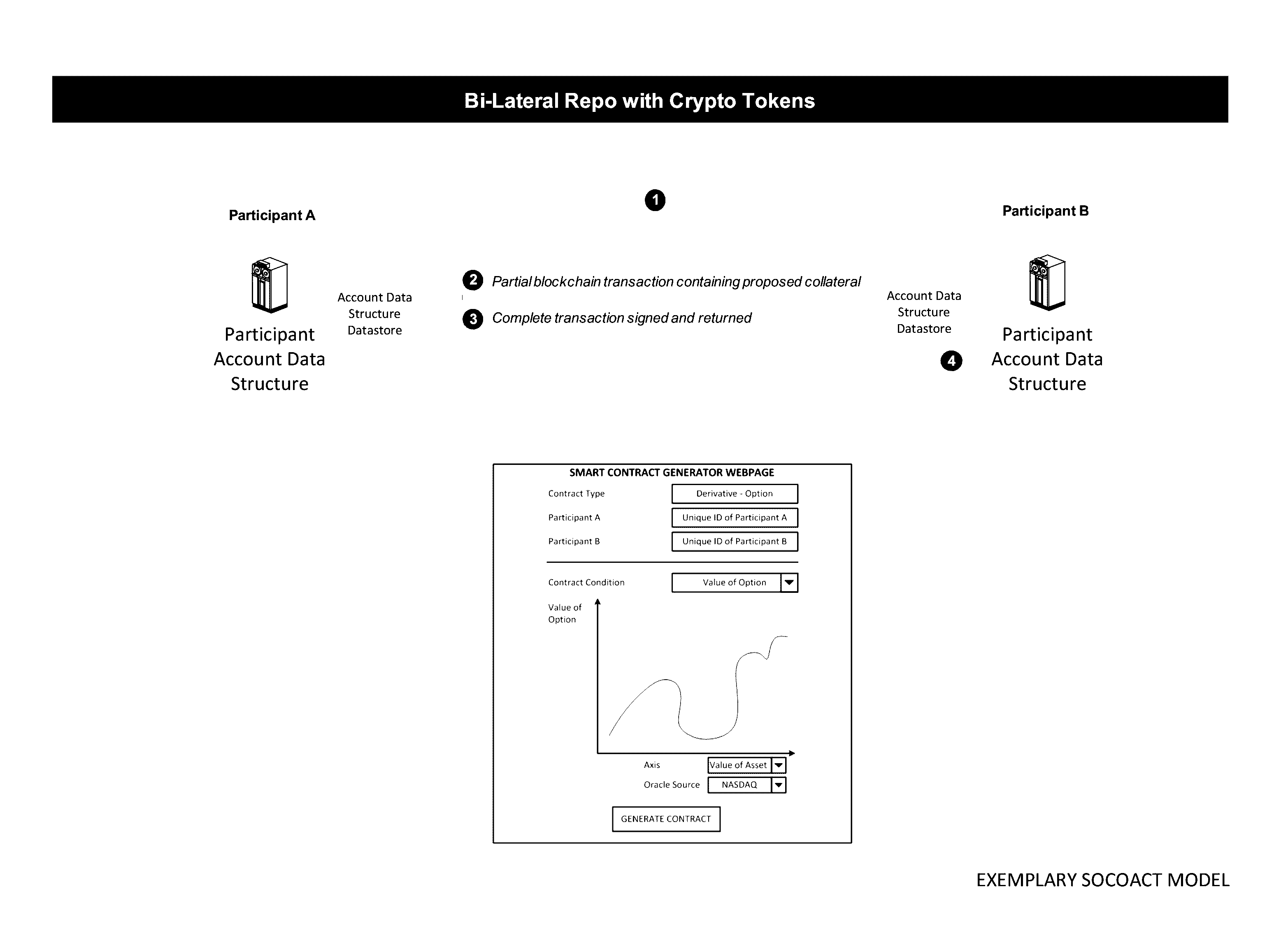
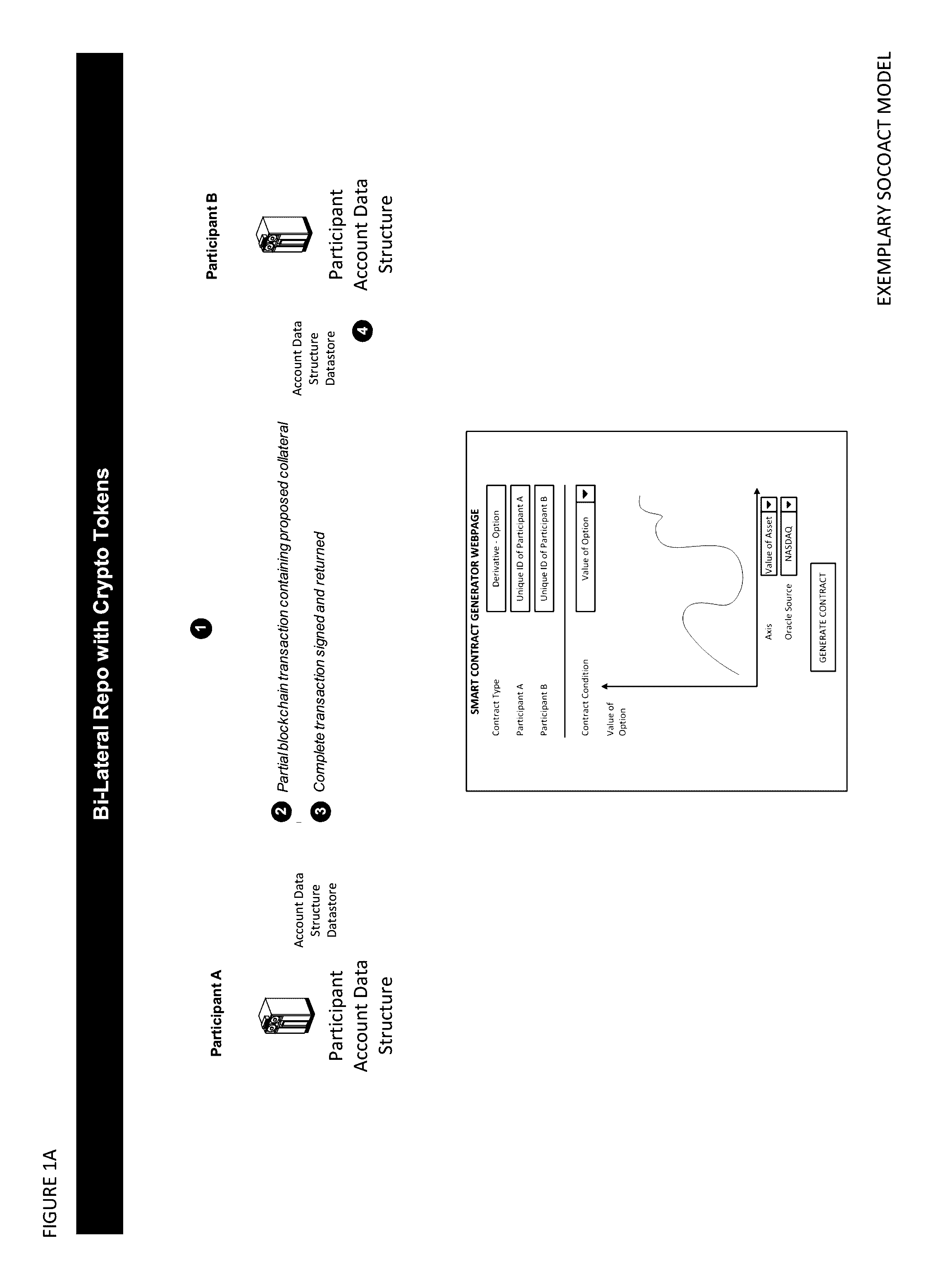
Crypto Key Recovery and Social Aggregating, Fractionally Efficient Transfer Guidance, Conditional Triggered Transaction, Datastructures, Apparatuses, Methods and Systems
InactiveUS20170048209A1Multiple keys/algorithms usageCryptography processingData structureKey recovery
The Crypto Key Recovery and Social Aggregating, Fractionally Efficient Transfer Guidance, Conditional Triggered Transaction, Datastructures, Apparatuses, Methods and Systems (“SOCOACT”) transforms MKADSD generation request, trigger event message inputs via SOCOACT components into transaction confirmation, recovery notification outputs. A multiple key account data structure datastore (MKADSD) generation request may be obtained from a user. A set of crypto public keys for a MKADSD may be determined. The MKADSD may be instantiated in a socially aggregated blockchain datastructure using the determined set of crypto public keys. A crypto recovery private key may be associate with the MKADSD and trigger event recovery settings for the MKADSD may be set. A trigger event message associated with the MKADSD may be obtained and recovery settings associated with a trigger event may be determined. The crypto recovery private key may be retrieved and a recovery action may be facilitated.
Owner:FMR CORP
Method and system for determining presence of probable error or fraud in a data set by linking common data values or elements
ActiveUS7373669B2Easy to operateEfficient and methodicalFinanceDigital data processing detailsFistData set
Owner:THE 41ST PARAMETER
Targeted secure printing
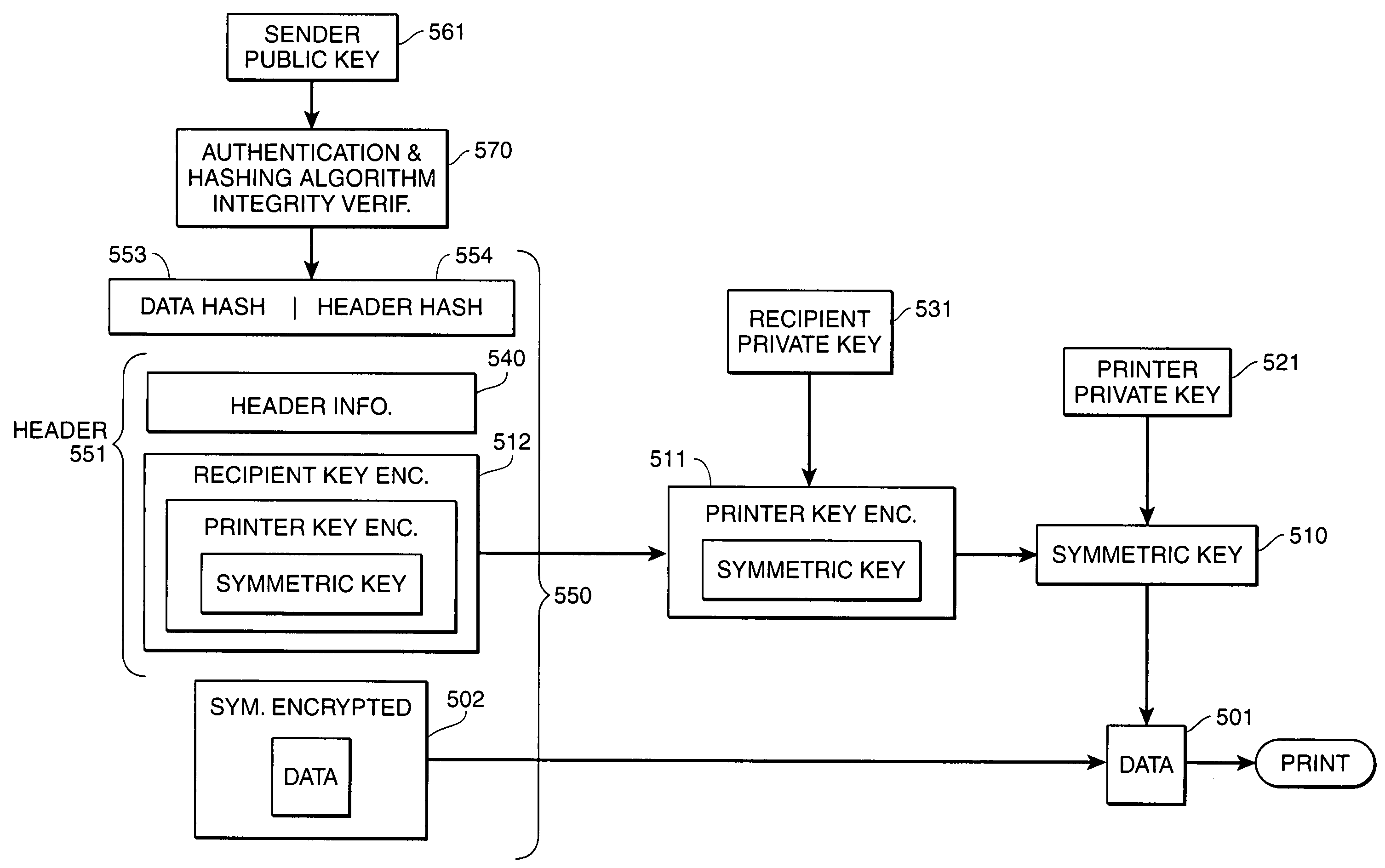
InactiveUS7003667B1Key distribution for secure communicationDigital data processing detailsSecure transmissionOutput device
Secure transmission of data to an intended image output device, wherein the data can be used to generate an image at the intended image output device in the presence of an intended recipient. The data is encrypted using a first key. The first key is then encrypted using a second key and a third key. The second key is a public key of a first private key / public key pair, a private key of the first private key / public key pair being primarily in the sole possession of the intended image output device. The third key is a public key of a second private key / public key pair, a private key of the second private key / public key pair being primarily in the sole possession of the intended recipient of the image. The encrypted data and the twice-encrypted first key are transmitted to the intended image output device. The twice-encrypted first key is then decrypted by using the private keys of the second and first key pairs, respectively, which are primarily in the sole possession of the intended recipient device and the intended image output device, respectively. The data is then decrypted and printed at an image output device.
Owner:CANON KK
Authentication method to enable servers using public key authentication to obtain user-delegated tickets
InactiveUS6643774B1Key distribution for secure communicationData taking preventionPublic key authenticationDelegation model
A method, system, and computer-readable code for delegating authority in a public key authentication environment from a client to a server machine or process, in order that the server machine or process can then securely access resources and securely perform tasks on behalf of the client. The authority is delegated by obtaining tickets (or other equivalent representation of user credentials) from a private key system, such as the Kerberos system, where the tickets identify a user's access rights or privileges. The present invention provides several alternative techniques with which this delegation model can be implemented. In these techniques, the client does not directly access the private key system.
Owner:IBM CORP
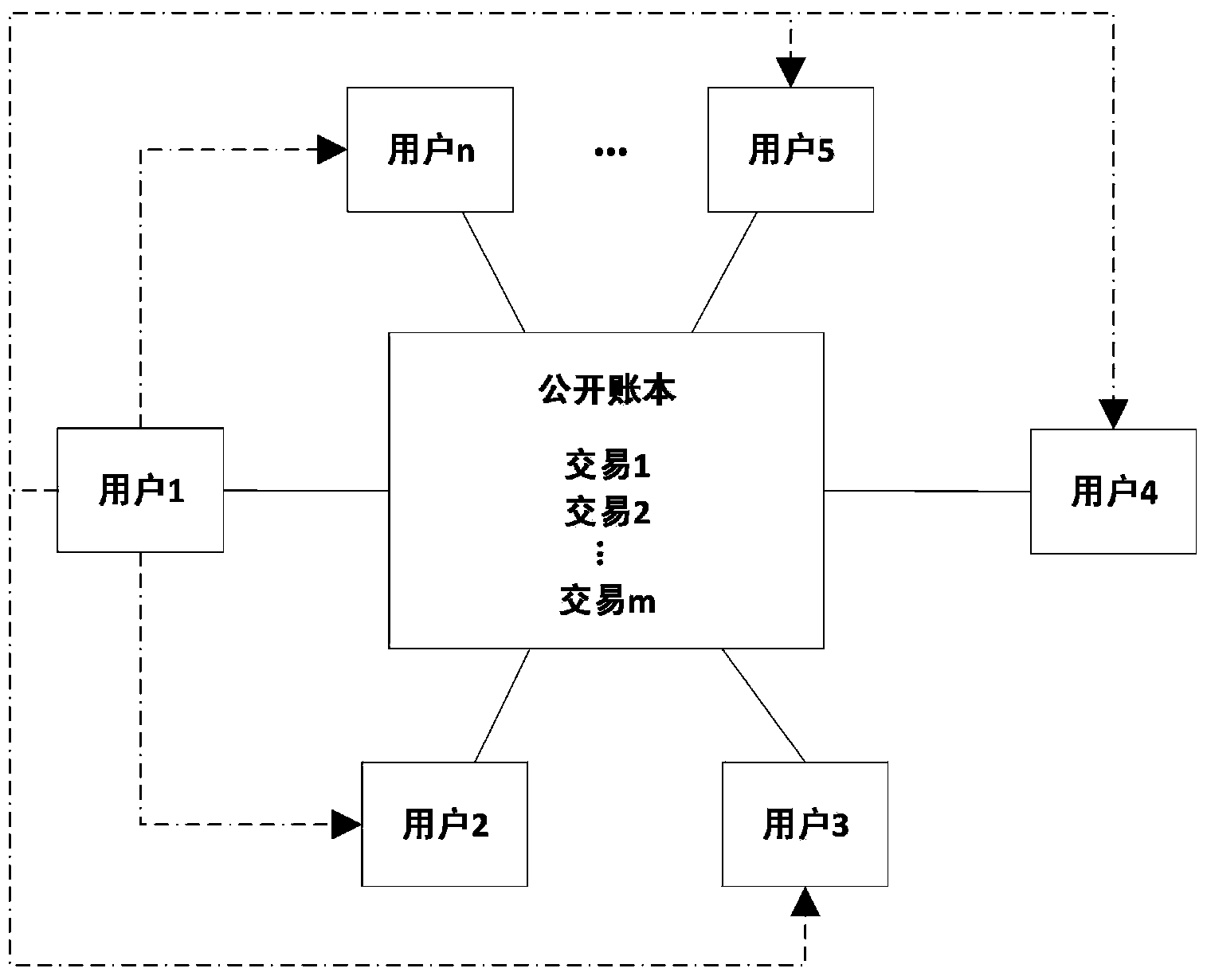
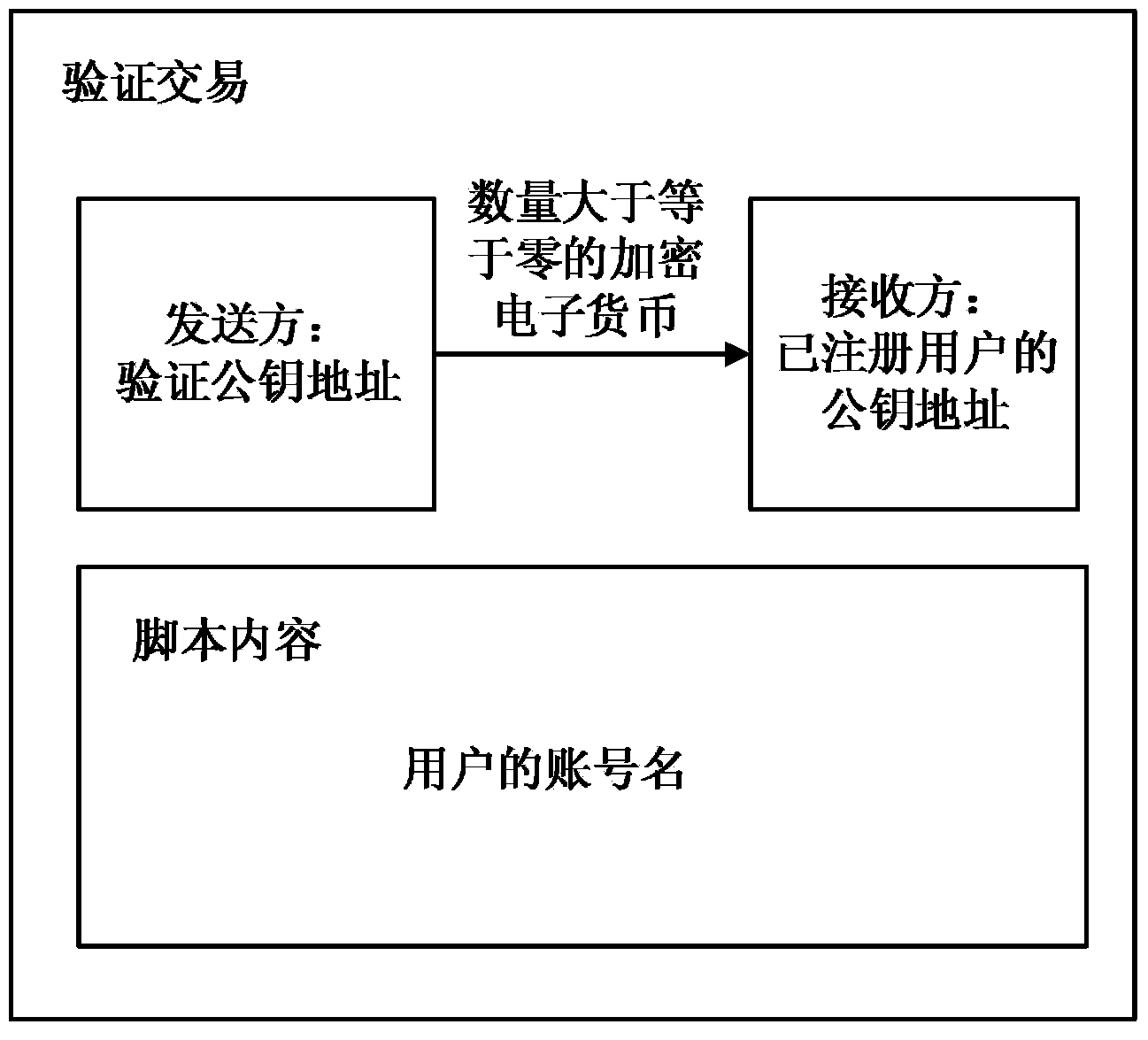
User public key address binding, searching and verifying method and system based on crypto currency open account book technology
ActiveCN104320262AImprove convenienceImprove securityUser identity/authority verificationPayment architectureDigital currencyDependability
The invention discloses a user public key address binding, searching and verifying method and system based on the crypto currency open account book technology. The user public key address binding, searching and verifying method is characterized by comprising the following steps that (1) verification public key addresses are published to users in a crypto currency network; (2) an account name registration request of one user is received, and the public key address of the user is received; (3) crypto currency is sent to the public key address of the crypto currency of the registered user through a private key address corresponding to the verification public key address and used as a verification transaction, and it is set that additional information or script content of the verification transaction contains the account number of the user, wherein the amount of the crypto currency is greater than or equal to zero; (4) query requests from other users in the crypto currency network are received, and the public key address of the registered user is fed back according to the query requests. The user public key address binding, searching and verifying method and system can substantially improve the availability, convenience, safety and reliability of crypto currency transactions, and protect the users against economic losses caused by the situation that the public key addresses are tampered with and used illegally.
Owner:安徽中科晶格技术有限公司
Secure PKI Communications for "Machine-to-Machine" Modules, including Key Derivation by Modules and Authenticating Public Keys
ActiveUS20150095648A1Extend battery lifeImprove efficiencyKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareDigital signature
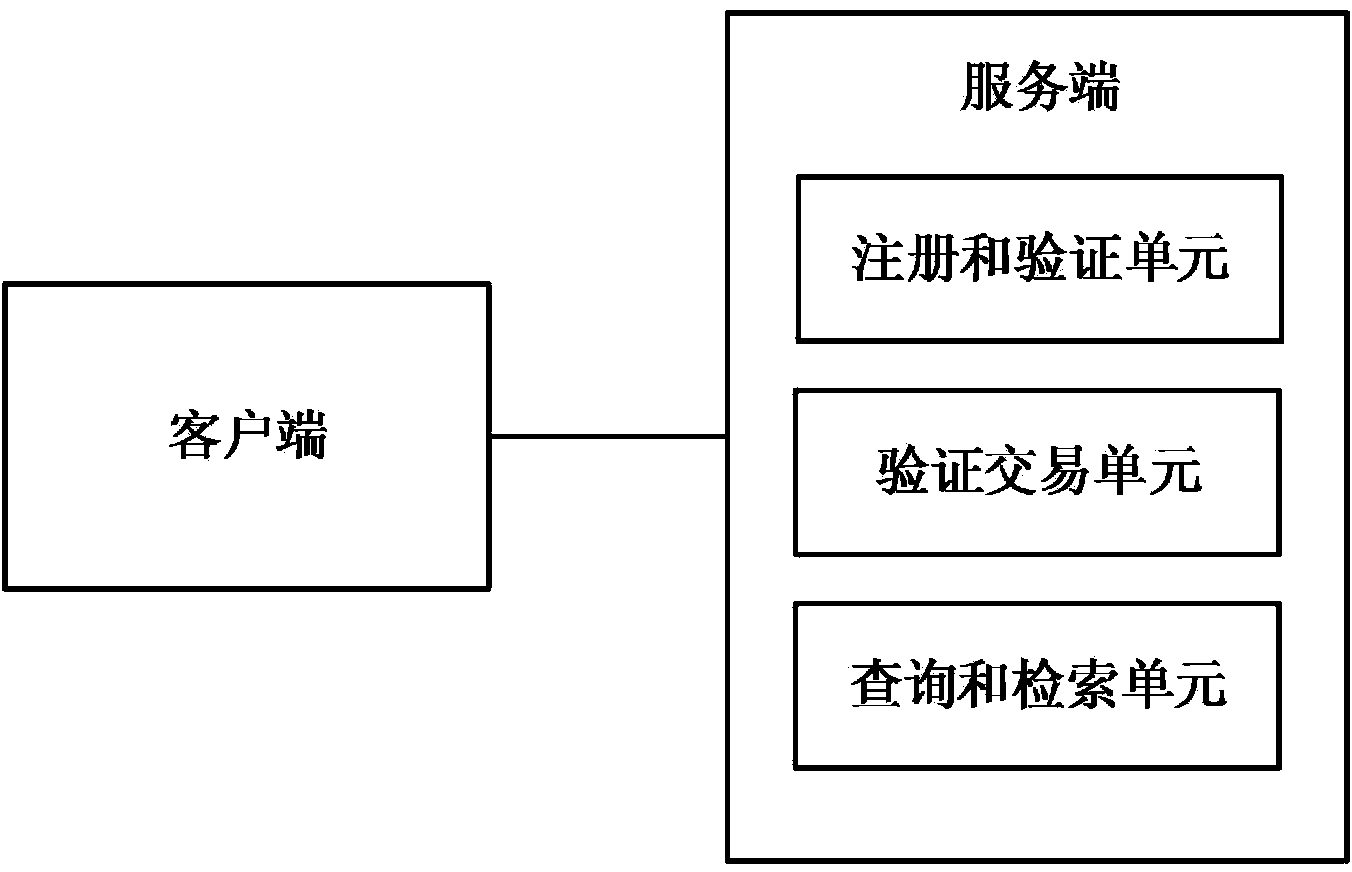
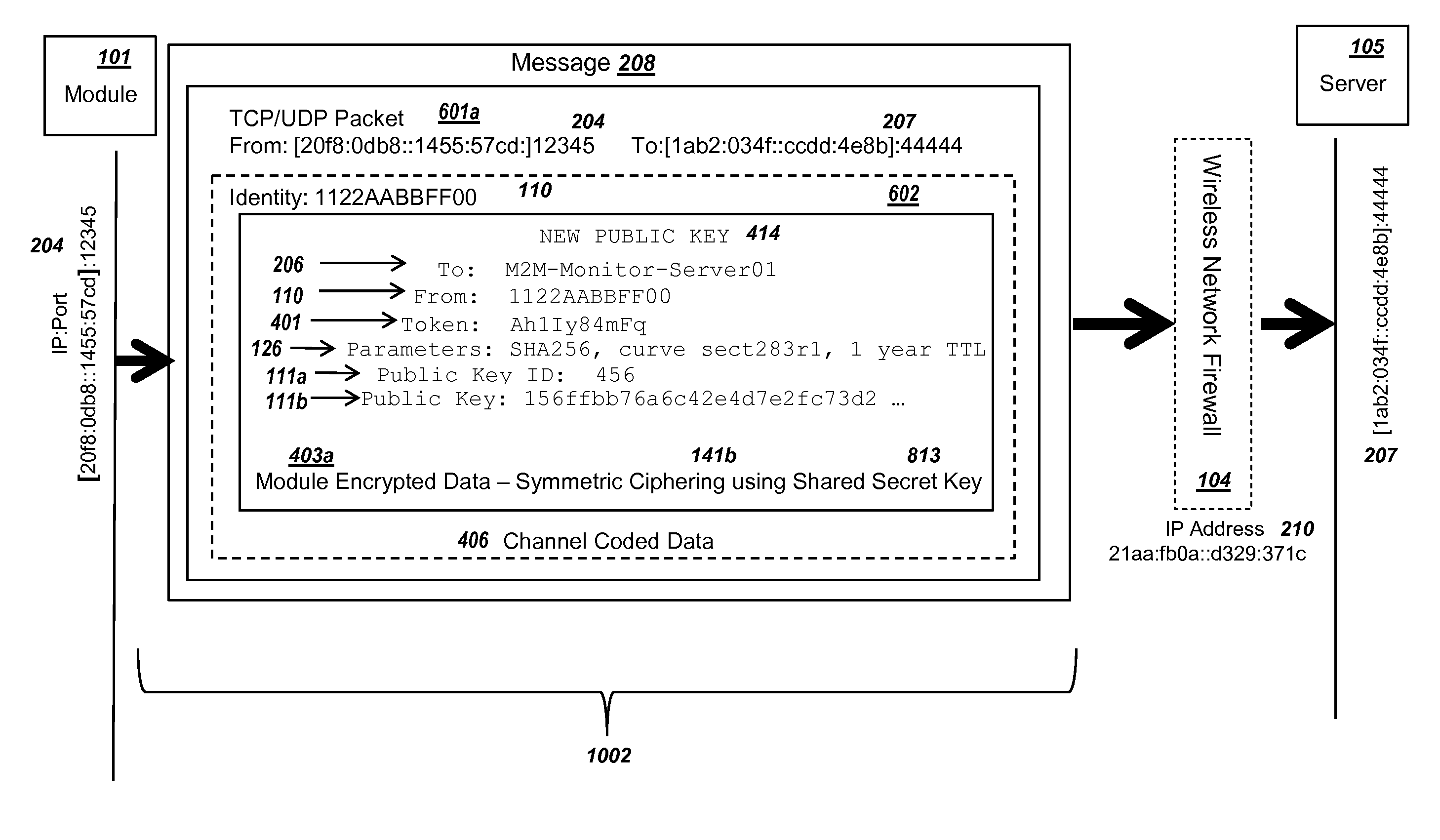
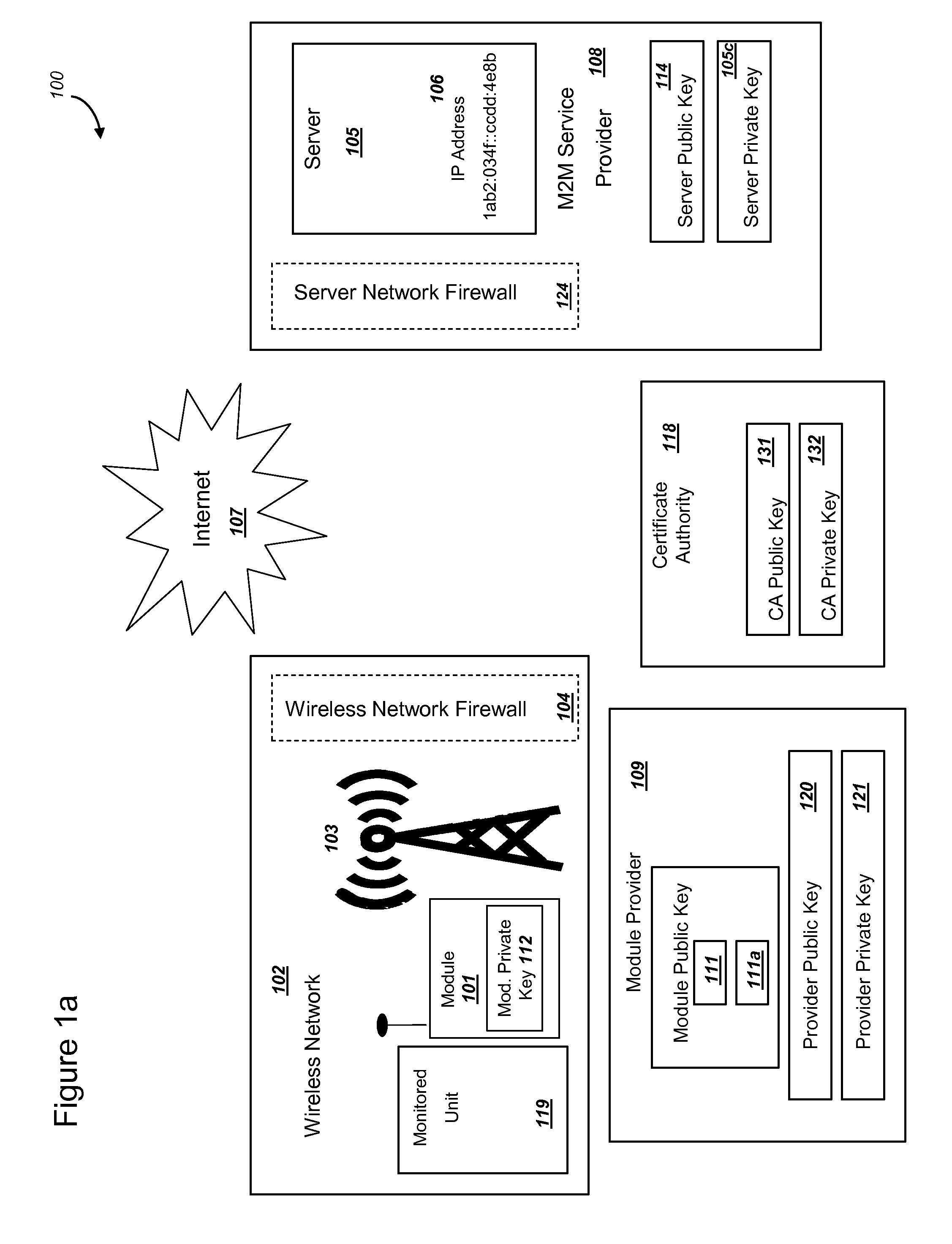
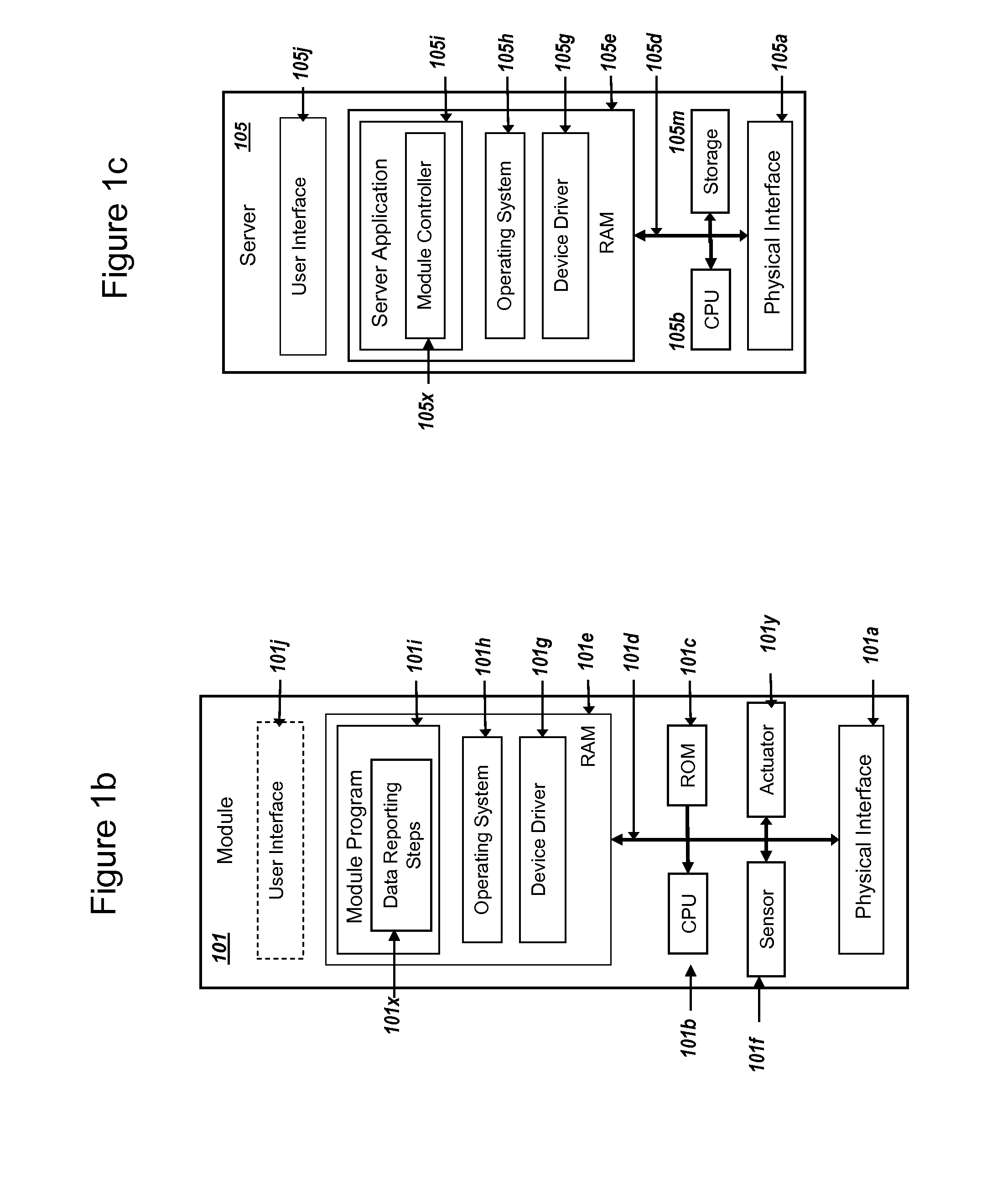
Methods and systems are provided for efficient and secure “Machine-to-Machine” (M2M) between modules and servers. A module can communicate with a server by accessing the Internet, and the module can include a sensor and / or actuator. The module and server can utilize public key infrastructure (PKI) such as public keys to encrypt messages. The module and server can use private keys to generate digital signatures for datagrams sent and decrypt messages received. The module can internally derive pairs of private / public keys using cryptographic algorithms and a set of parameters. A server can use a shared secret key to authenticate the submission of derived public keys with an associated module identity. For the very first submission of a public key derived the module, the shared secret key can comprise a pre-shared secret key which can be loaded into the module using a pre-shared secret key code.
Owner:NETWORK 1 TECH +1
Modifying message data and generating random number digital signature within computer chip
InactiveUS20020016913A1Improve privacyUser identity/authority verificationUnauthorized memory use protectionElectronic communicationDigital signature
A method of generating a digital signature within a computer chip includes receiving data representing a message, and generating a digital signature for the message by modifying the message data with additional data, calculating a hash value of the modified message, and encrypting the hash value using a private key of a public-private key pair. The additional data includes data prestored within content searchable memory of the computer chip and a verification status of the computer chip. The verification status is identified out of a plurality of predefined verification statuses as a function of verification data input into the computer chip and data prestored within the computer chip. An identified verification status is used by one entity in determining risk regarding an electronic communication from another entity, especially where the electronic communication comprises a request and a digital signature generated by the computer chip.
Owner:FIRST DATA
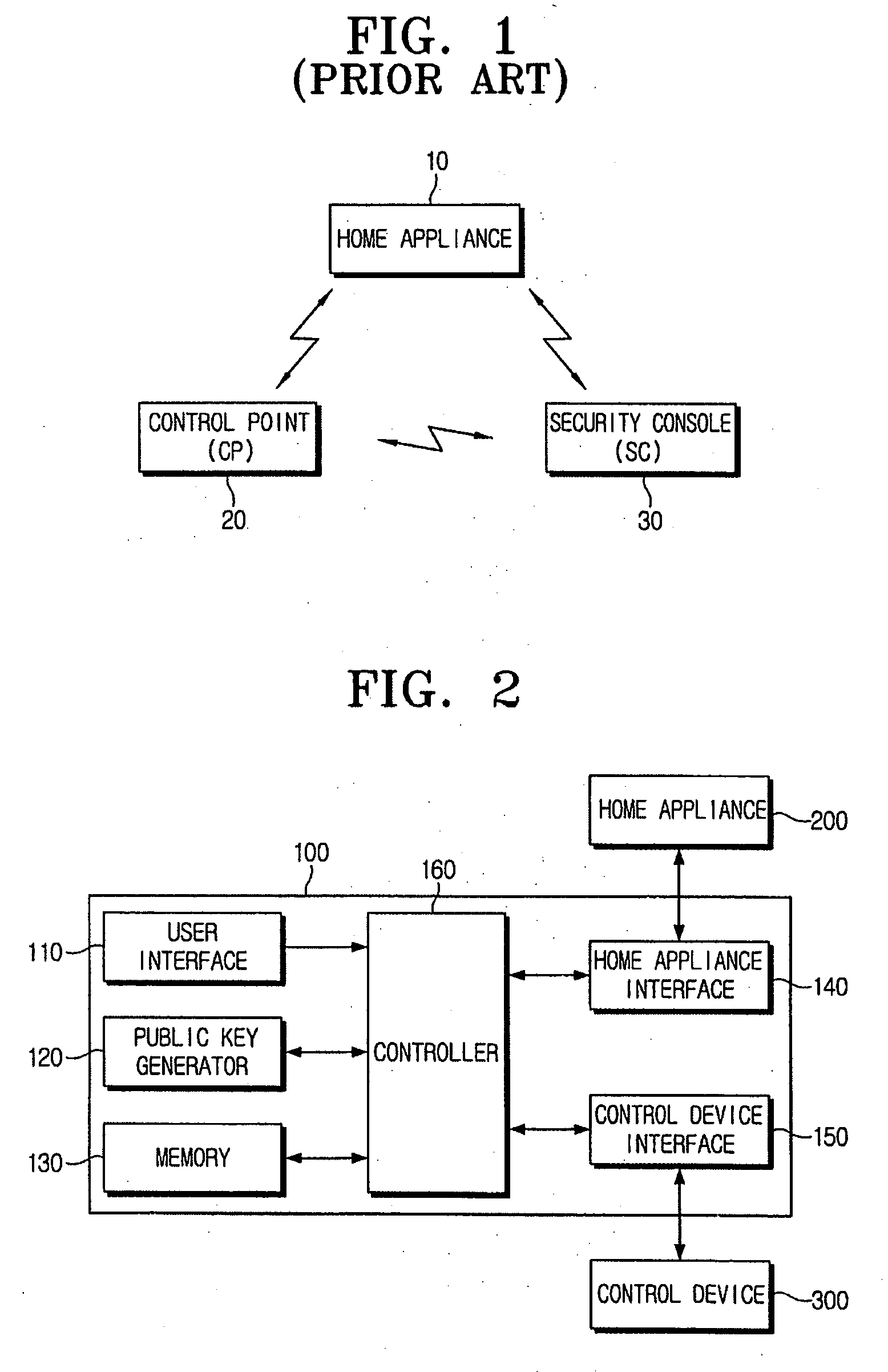
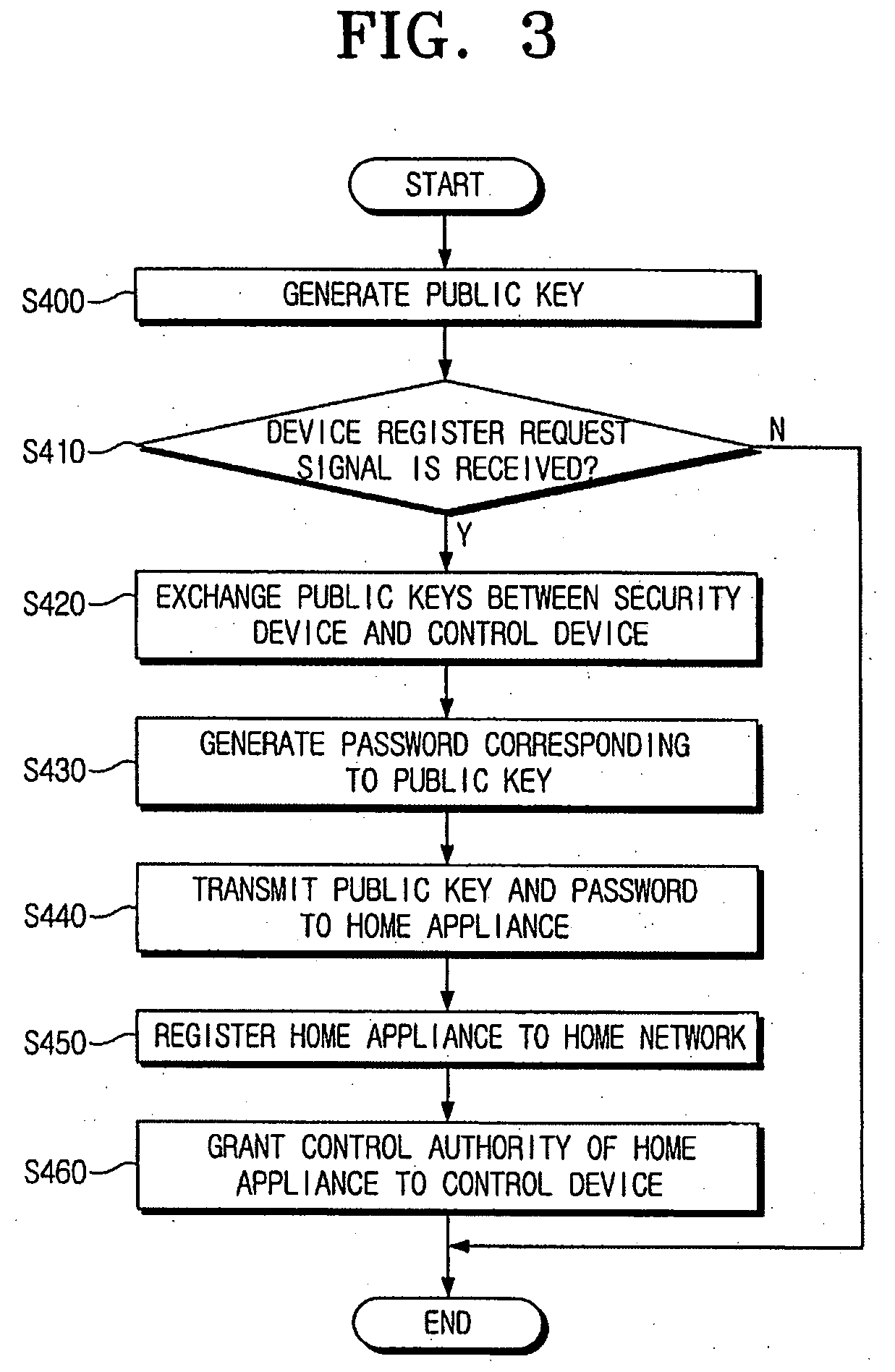
Security device for home network and security configuration method thereof
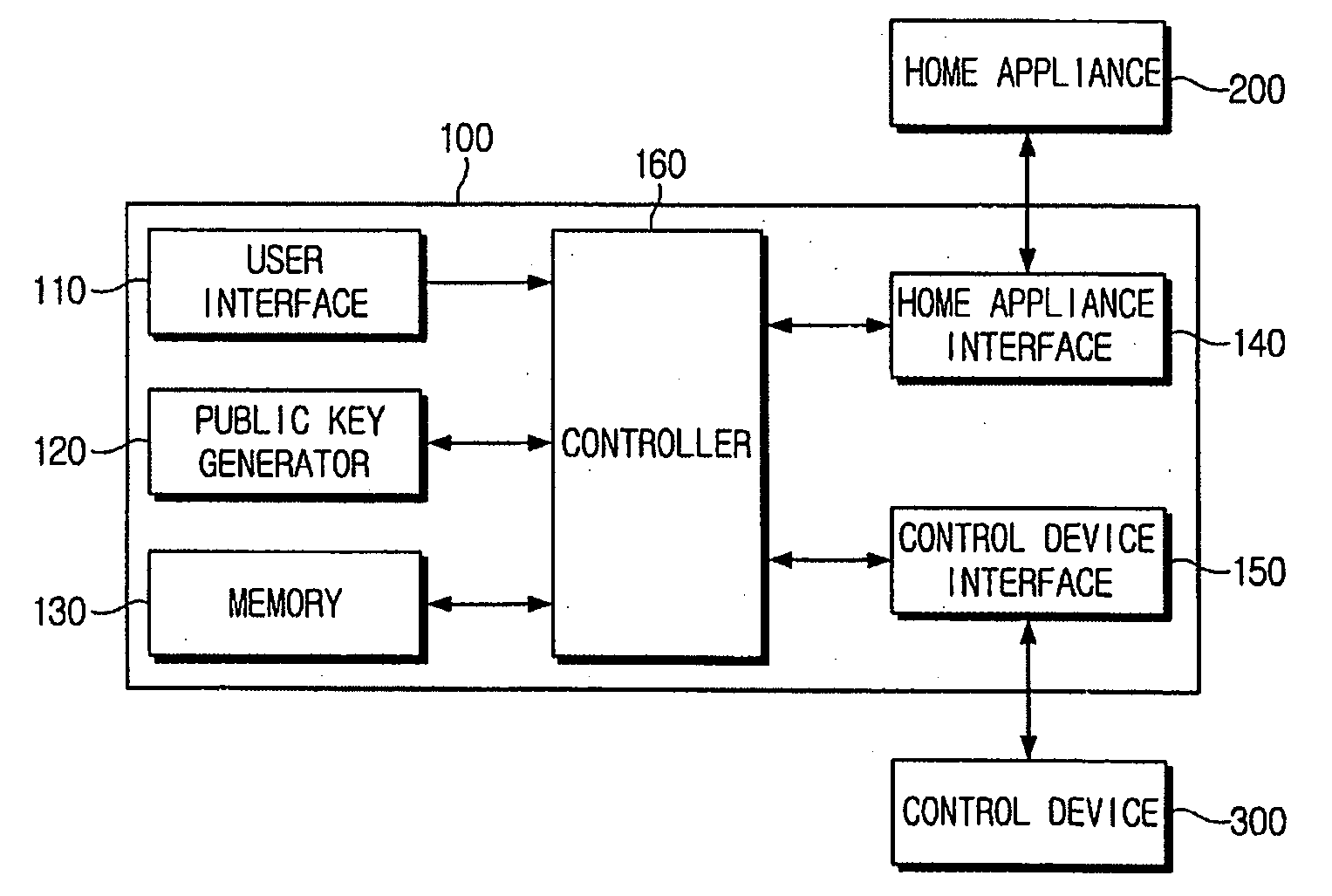
InactiveUS20060129837A1Public key for secure communicationSubstation remote connection/disconnectionDevice registerPassword
A security device for a home network and a security configuration method thereof. The security device for the home network includes a user interface to send at least one request signal that includes a device register request signal to register a home appliance to the home network; a public key generator to generate a public key and a password used for security configuration of the home network; a home appliance interface to interface with the home appliance; and a controller to control the home appliance interface to transmit the public key and the password to the home appliance, and the controller to control to register the home appliance to the home network according to a service discovery protocol when the device register request signal is received from the user interface. Accordingly, the security configuration of the home network can be facilitated.
Owner:SAMSUNG ELECTRONICS CO LTD
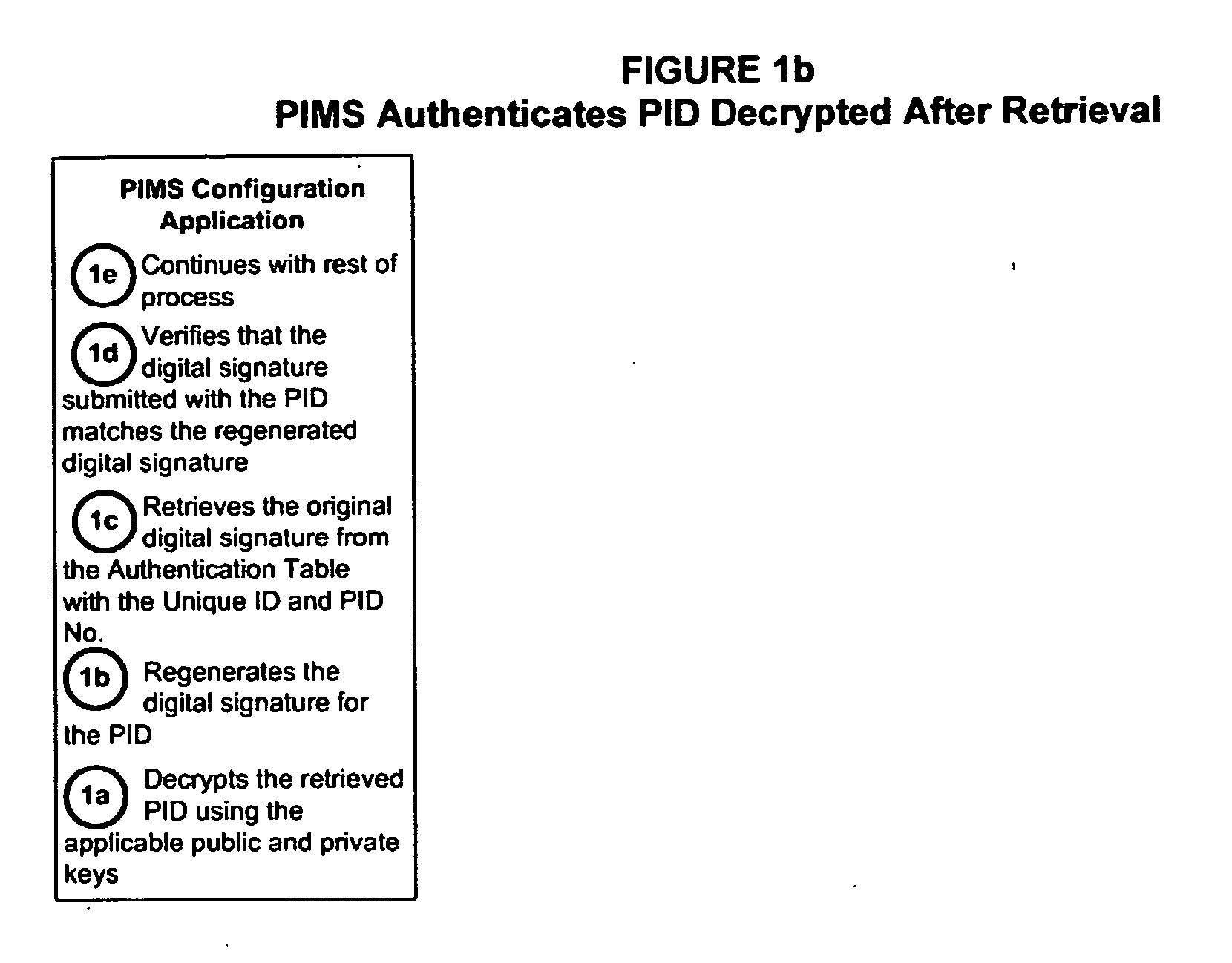
Personal identity data management
InactiveUS20060034494A1Public key for secure communicationUser identity/authority verificationSocial Security numberSmart card
Systems, methods and apparatus for personal identity data management permit individuals to manage their criminal background, credit history, employment, demographic and educational information, for example, to establish their credentials and to help protect their good names. All access to this personal identity data, including the biometrics that uniquely establish the individuals' identity, is under the personal control of the individuals, with access limited to others only with their specific authorization. The subject systems, methods and apparatus include at least two separate archives that store encrypted data about individuals that can be accessed only via the individuals' biometrics specific to the archives and unique Identification Numbers. The Identification Numbers are encrypted when they are associated with the individuals' demographic data, which includes their names, Social Security Numbers and the Unique Identifiers assigned by the system to each of the individuals. Public / private key encryption is used to encrypt the Personal Identity Data maintained in the archives and the Identification Numbers maintained in a Personal Identity Management Service configuration application server that links the rest of the system to the archives. To permit the private keys to be securely retained for use in regenerating a. Smartcard in case of loss or damage, separate segments of the private key are stored on different servers each of which requires submittal of a different biometric, which must match the biometric associated with the private key segment.
Owner:NAT BACKGROUND DATA
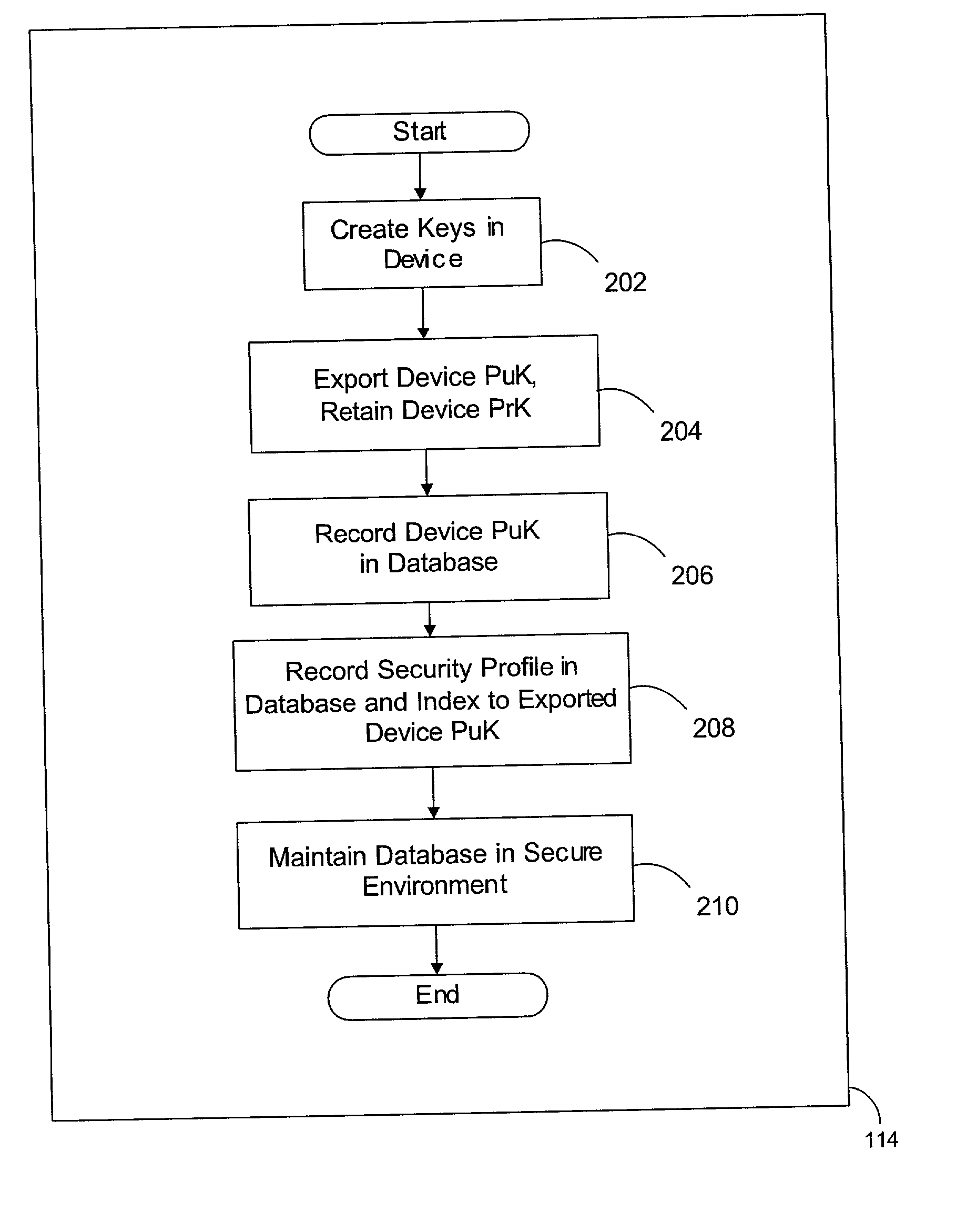
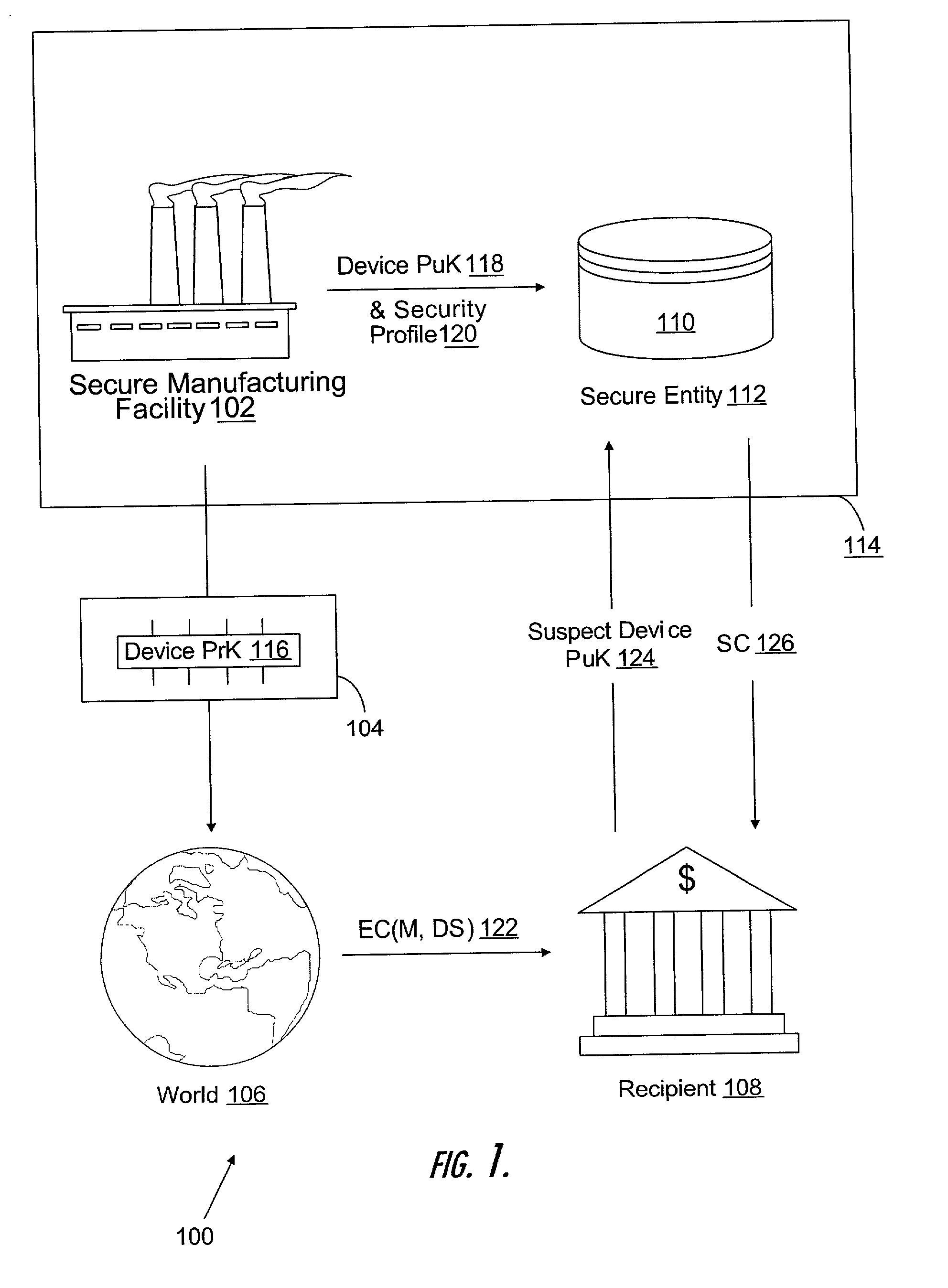
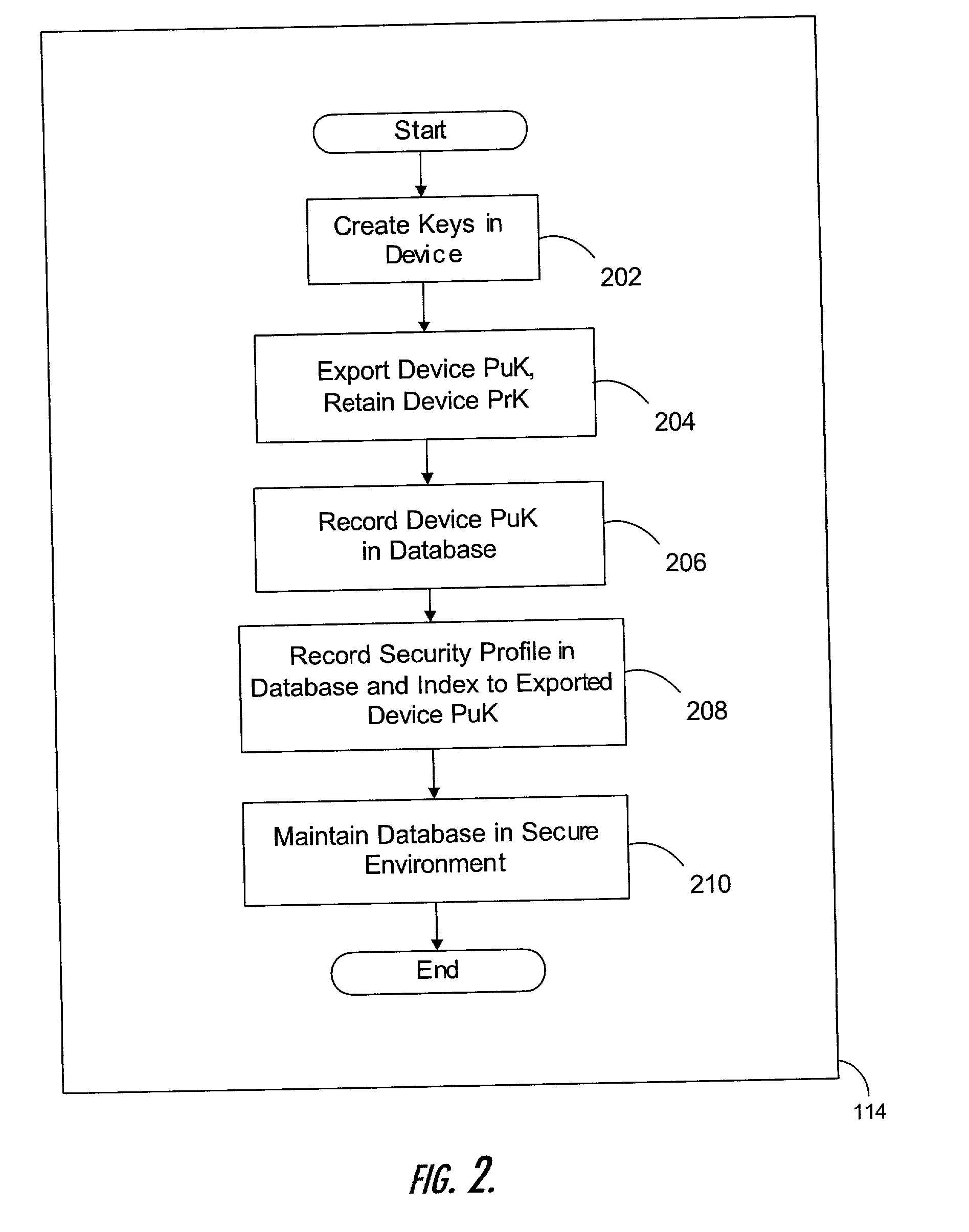
Manufacturing unique devices that generate digital signatures
InactiveUS20020023217A1User identity/authority verificationUnauthorized memory use protectionThird partyDigital signature
A method of manufacturing devices that generate digital signatures such that each device may be reliably and uniquely identified includes creating a public-private key pair within each device during manufacture; exporting only the public key from the device; retaining the private key within the device against the possibility of divulgement thereof by the device; and securely linking said exported public key with other information within the environment of the manufacture of the device, whereby each device is securely bound with its respective public key. A database of PuK-linked account information of users is maintained. The PuK-linked account information for each user includes a public key of such a device; information securely linked with the public key during manufacture; and third-party account identifiers, each of which identifies an account to a third-party of the user maintained with the third-party that has been associated with the user's public key by the third-party.
Owner:FIRST DATA
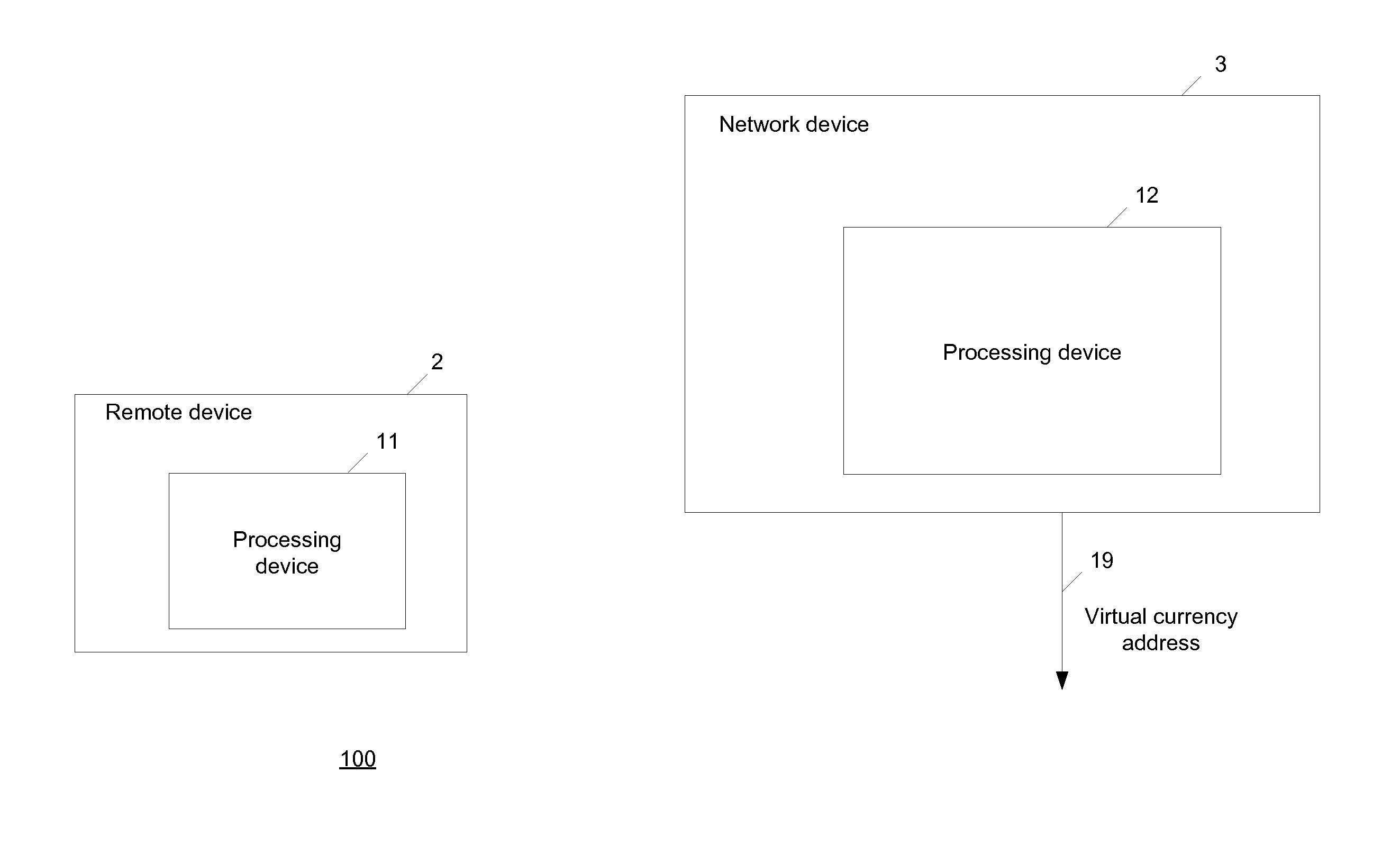
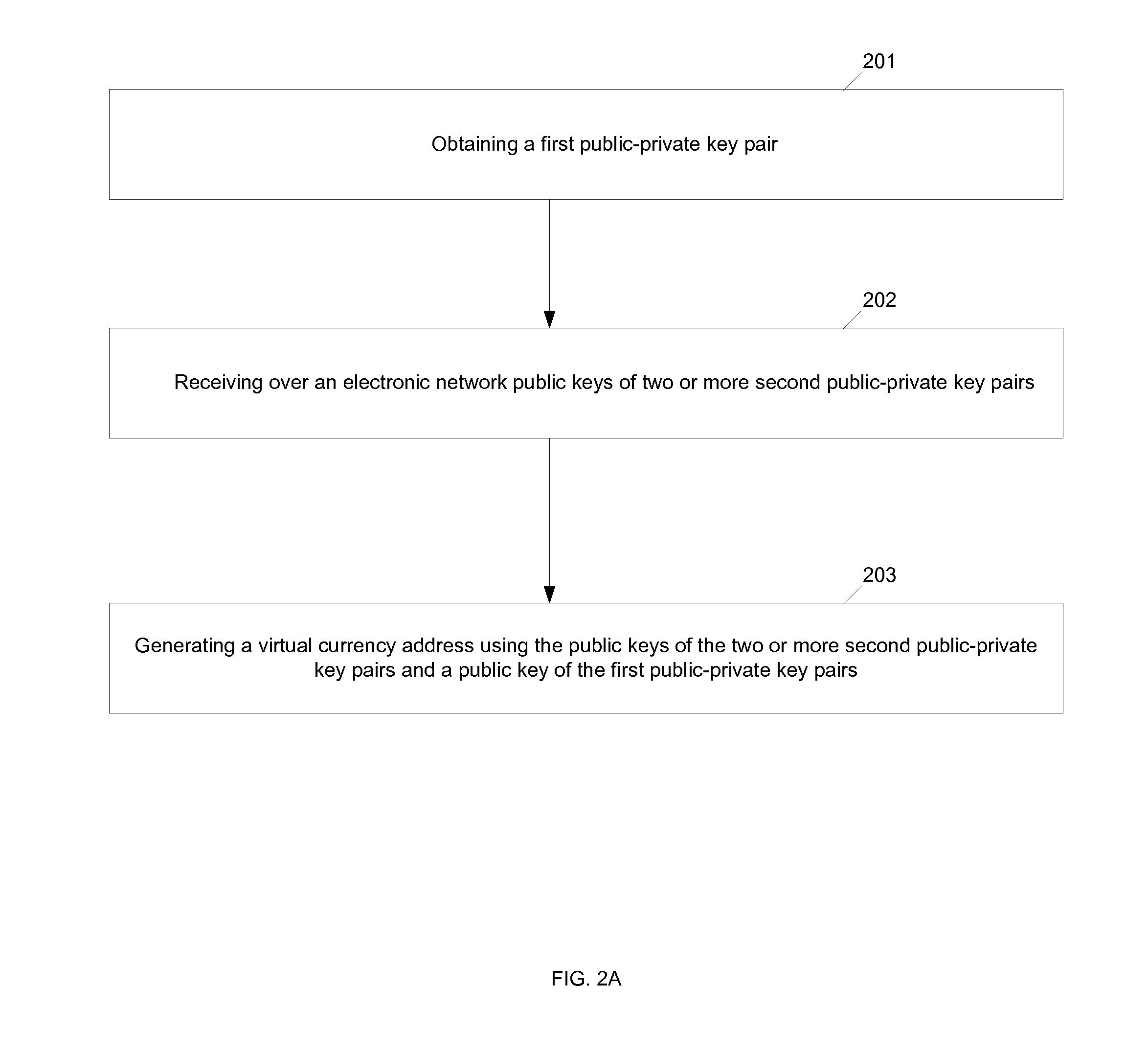
Virtual currency address security
In an example, a network device is configured to generate a first public-private key pair. The network device is configured to receive, over an electronic network, public keys of two or more second public-private key pairs. The network device is configured to generate a digital currency address using the public keys of the two or more second public-private key pairs and a public key of the first public-private key pair.
Owner:BITGO
Federated identity management with decentralized computing platforms
ActiveUS20200067907A1Key distribution for secure communicationDigital data protectionInternet privacyEngineering
Provided is a process that establishes user identities within a decentralized data store, like a blockchain. A user's mobile device may establish credential values within a trusted execution environment of the mobile device. Representations of those credentials may be generated on the mobile device and transmitted for storage in association with an identity of the user established on the blockchain. Similarly, one or more key-pairs may be generated or otherwise used by the mobile device for signatures and signature verification. Private keys may remain resident on the device (or known and input by the user) while corresponding public keys may be stored in associated with the user identity on the blockchain. A private key is used to sign representations of credentials and other values as a proof of knowledge of the private key and credential values for authentication of the user to the user identity on the blockchain.
Owner:HYPR CORP
Data Integrity and Non-Repudiation
ActiveUS20080045342A1Reduce boot timeImprove loading timeUnauthorized memory use protectionHardware monitoringComputer hardwareData integrity
Disclosed is a system and method that uses digital signature technology to authenticate the contents of one or more manifests located on a storage device. Each manifest contains a list of file records, where each record contains the name of a file stored on the storage device, and a signature value derived from the contents of the file. At boot time, the gaming machine first authenticates the contents of the manifest and then authenticates the contents of the files using the signature value stored in the manifest. Files are verified using the signature, as they are needed, during the boot up of the operating system and throughout normal operation. This method reduces the boot time of the gaming machine and eliminates the need to check digital signatures for each individual file or over the entire contents of a non-secure media. Similarly, a method of adding authentication ability to legacy software components without necessarily altering the legacy software components is disclosed. Introduction of a stronger authentication algorithm, or when a private key has been compromised would normally require the software component to be re-built to support the new algorithm or private / public key pair; however, a method is disclosed where algorithms and key pairs may be changed and applied to legacy software without having to re-built, re-test, re-sign, or re-submit the component to regulatory agencies for approval. Also disclosed is a system and method of establishing a trusted environment containing a gaming operating system and associated authentication module, file system drivers, and / or network drivers that may be used to in the process of authenticating contents of one or more manifests located on a storage device.
Owner:LNW GAMING INC
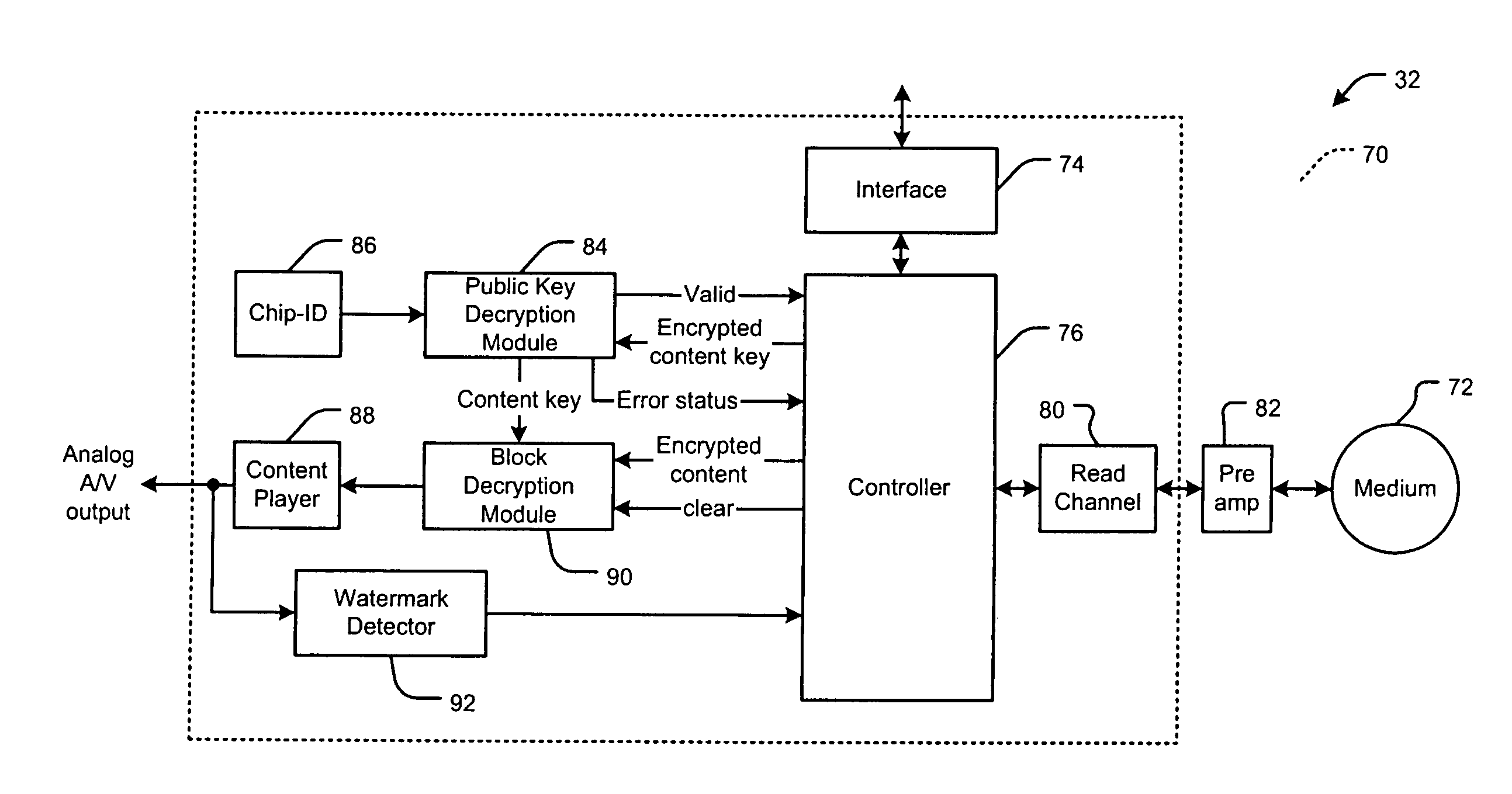
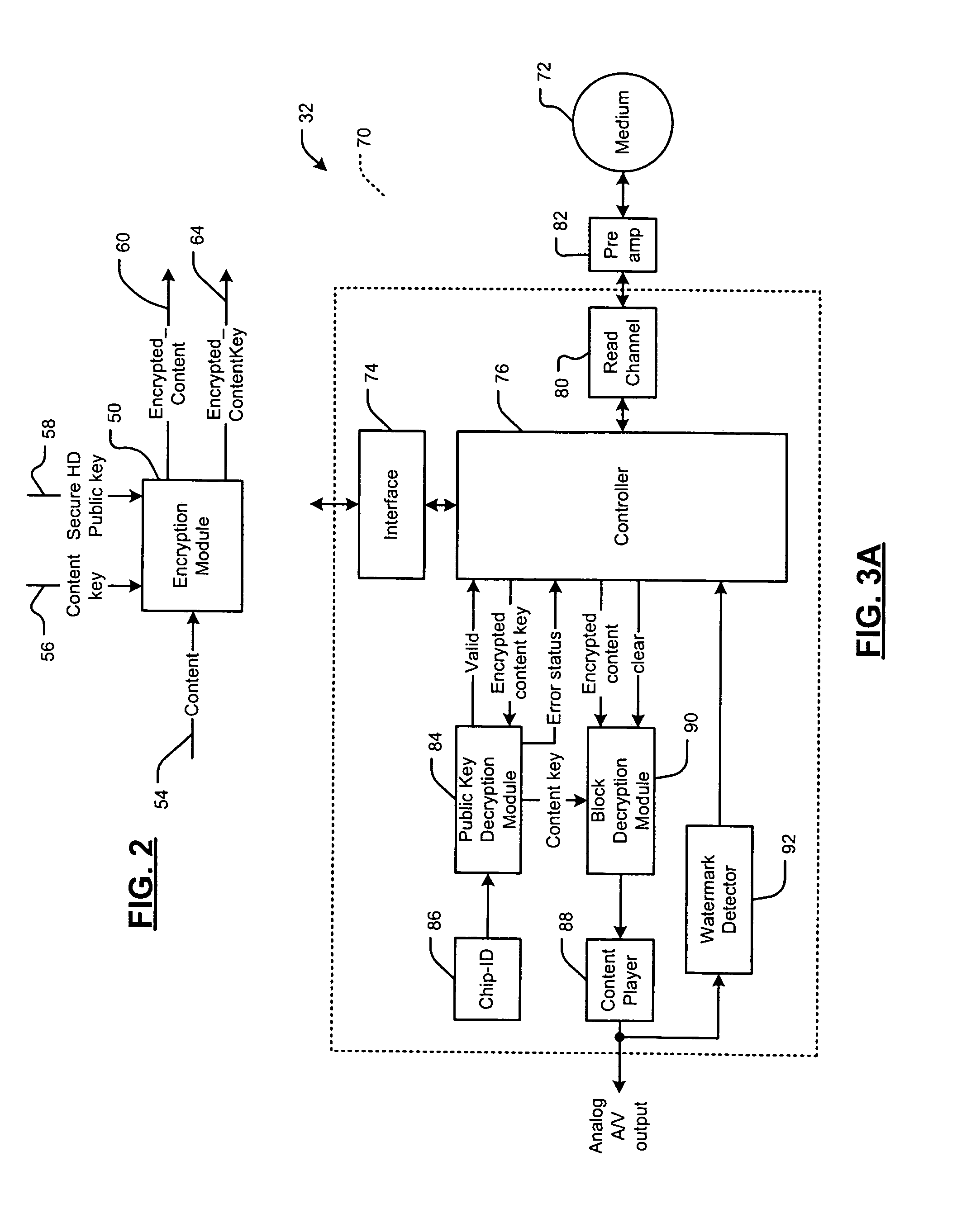
Secure digital content distribution system and secure hard drive
ActiveUS7647507B1Unauthorized memory use protectionHardware monitoringHard disc driveDigital content
A secure hard drive comprises a storage medium that stores encrypted digital content and corresponding encrypted content keys. A public key decryption module receives one of the encrypted content keys from the storage medium and decrypts the encrypted content key using a private key to generate a content key. A block decryption module receives the encrypted digital content corresponding to the one of the encrypted content keys from the storage medium and the content key from the public key decryption module and decrypts the encrypted content using the content key. The storage medium is a magnetic storage medium. The public key decryption module and the block decryption module are implemented by a system on chip (SOC). A content player receives the decrypted digital content from the block decryption module and generates at least one of an analog output signal and a digital output signal.
Owner:MARVELL ASIA PTE LTD
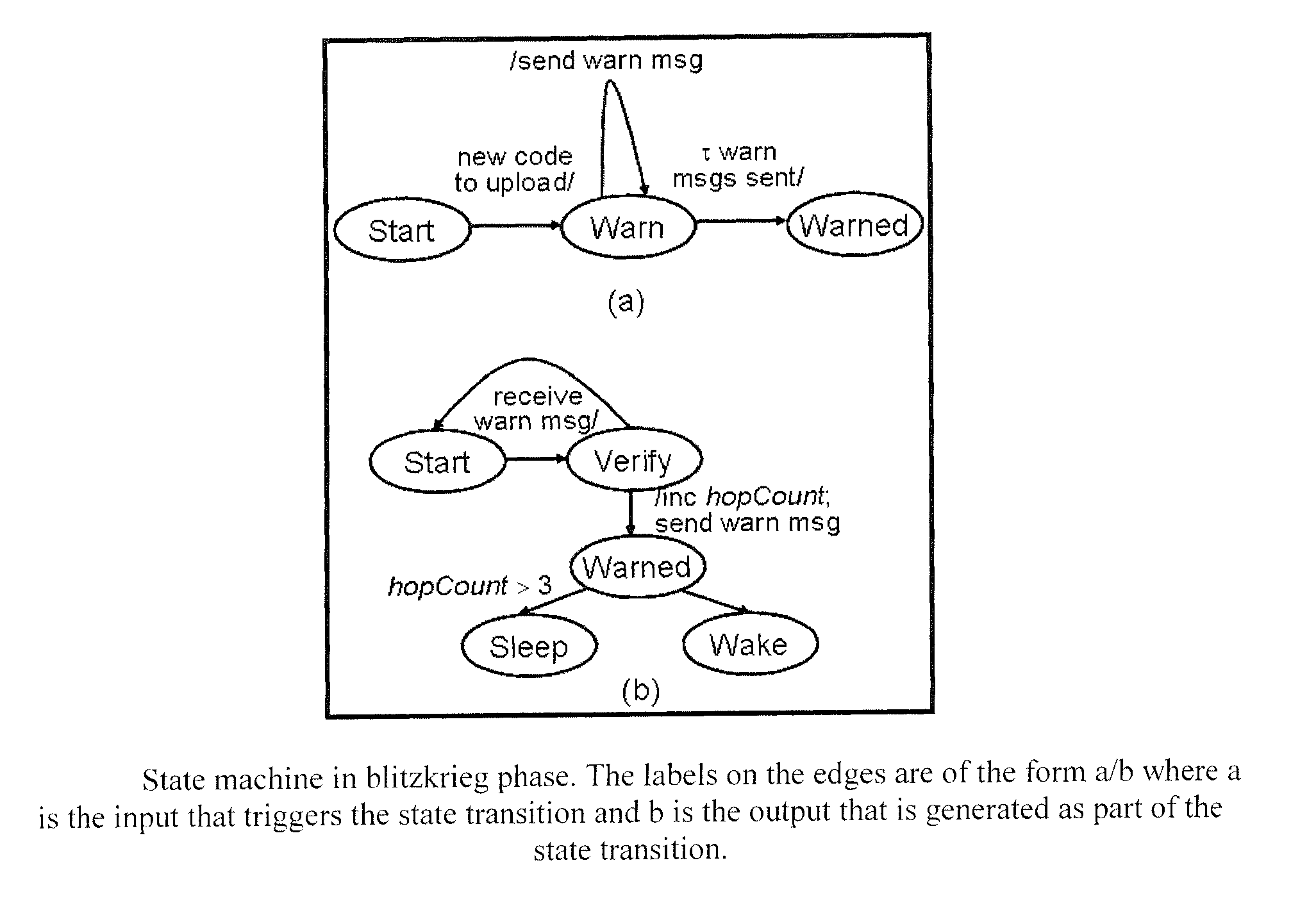
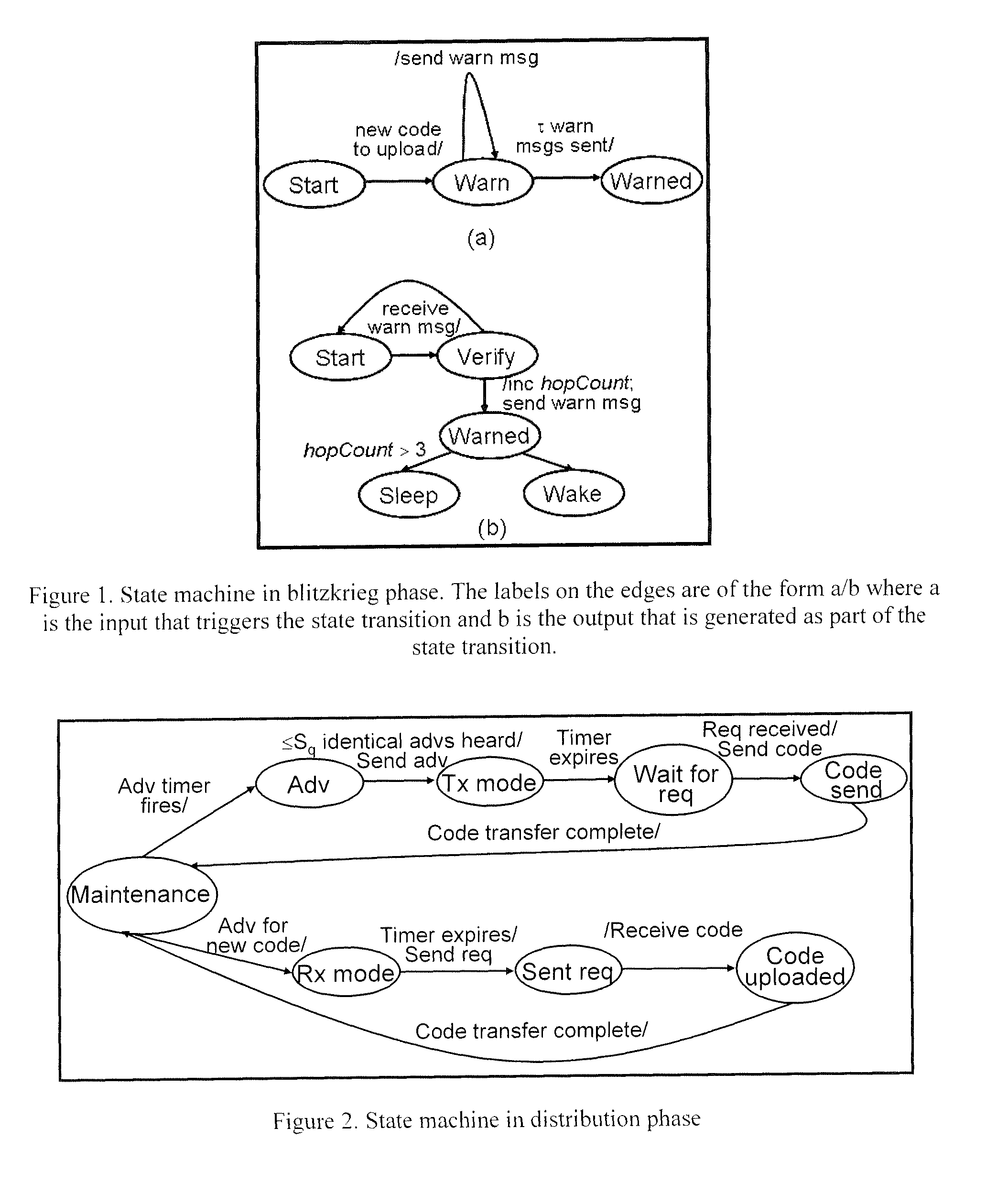
Protocol for secure and energy-efficient reprogramming of wireless multi-hop sensor networks
ActiveUS8107397B1Energy efficient ICTKey distribution for secure communicationTopology informationReprogramming
A protocol for optimizing the energy for code upload to sensors in a wireless sensor network and speeding up the dissemination if multiple sources of code are available. Energy optimization is achieved by equipping each node with limited non-local topology information, which it uses to determine the time when it can go to sleep since code is not being distributed in its vicinity. Another aspect of the invention is a protocol that facilitates secure upload of code in the wireless sensor network. The secure communication protocol divides the sensor field into control groups each with a control node, and manages data exchange between nodes within a control group through the mediation of a control head which provides the common key. The keys are refreshed periodically and the control nodes are changed periodically to enhance security. The protocol facilitates secure communication between sensor nodes despite the compromise of any number of other nodes in the network.
Owner:PURDUE RES FOUND INC
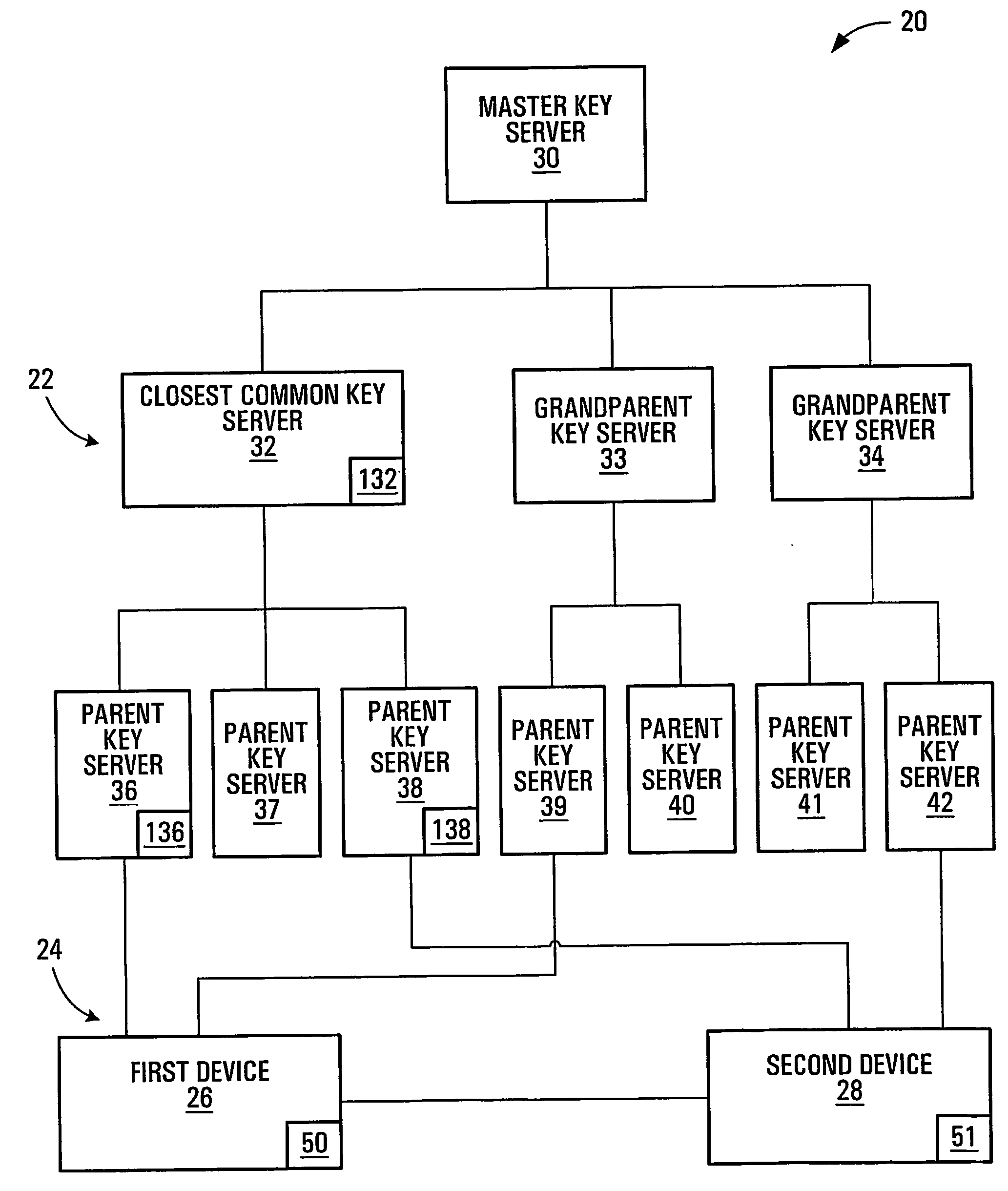
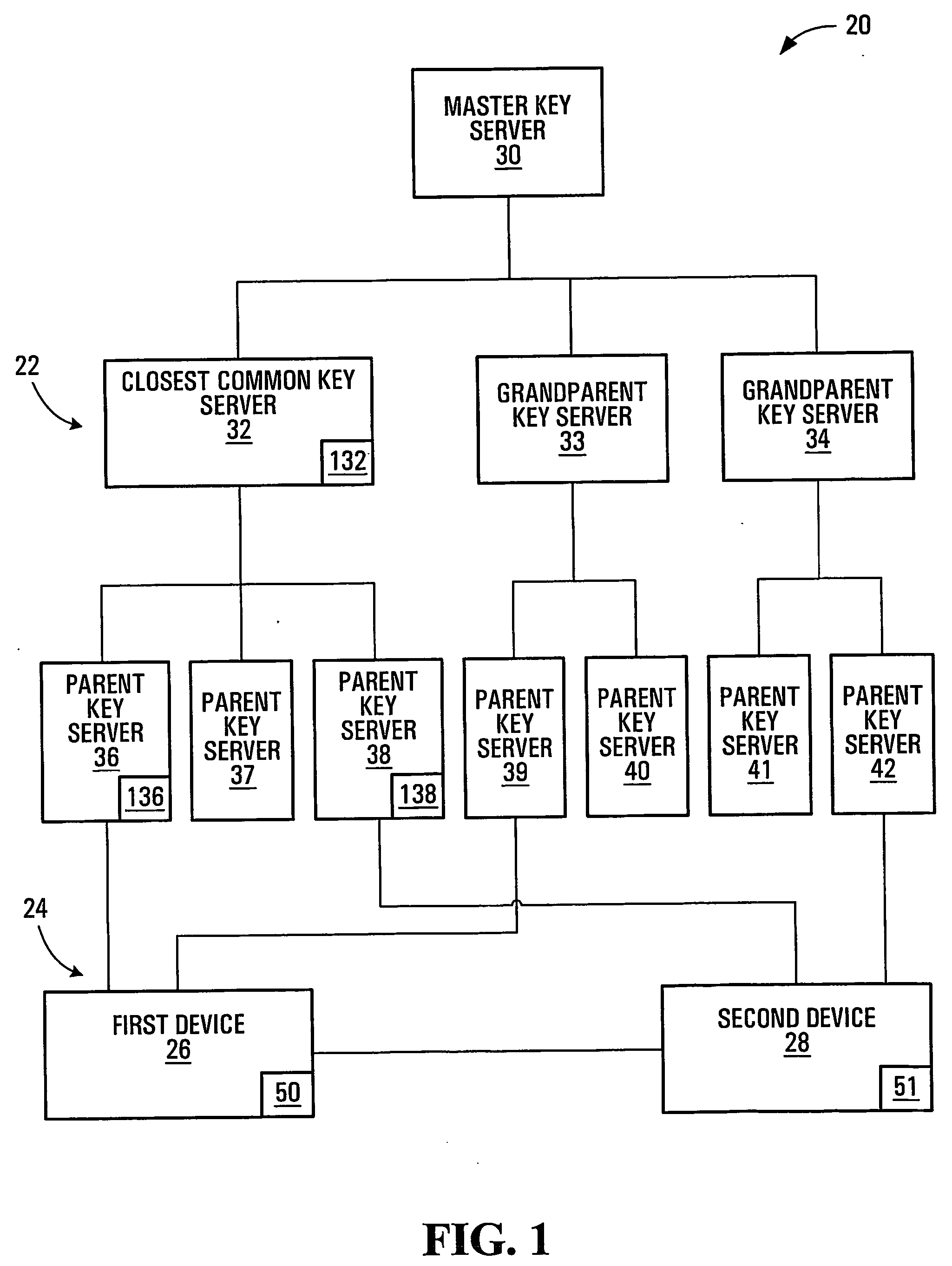
Session key distribution methods using a hierarchy of key servers
InactiveUS20050125684A1Facilitates secure communicationFacilitate communicationKey distribution for secure communicationPublic key for secure communicationSecure communicationKey server
Methods, apparatuses, media and signals for facilitating secure communication between a first device and a second device are disclosed. One method includes automatically identifying a common key server potentially accessible by both the first and second devices, and obtaining a secure private key from the common key server, for use in encrypting communications between the first and second devices. Identifying may include identifying as the common key server, a key server at an intersection of a first communication path defined between a first key server having a previously established relationship with the first device and a master key server, and a second communication path defined between a second key server having a previously established relationship with the second device and the master key server. Obtaining may include obtaining a plurality of private keys and blending the keys to produce a final private session key.
Owner:SCHMIDT COLIN MARTIN
Method for implementing safe storage system in cloud storage environment
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
Remote access vpn mediation method and mediation device
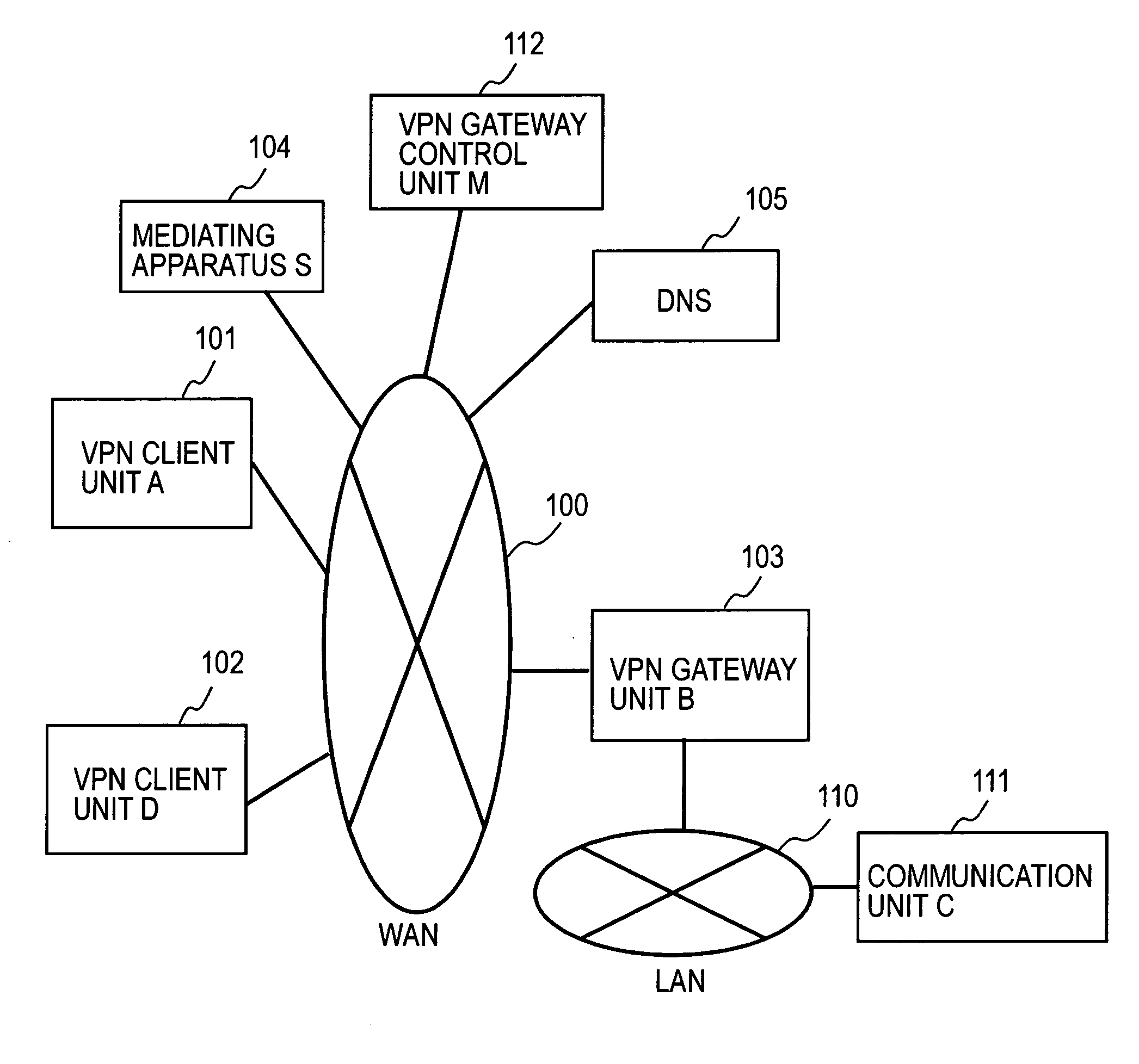
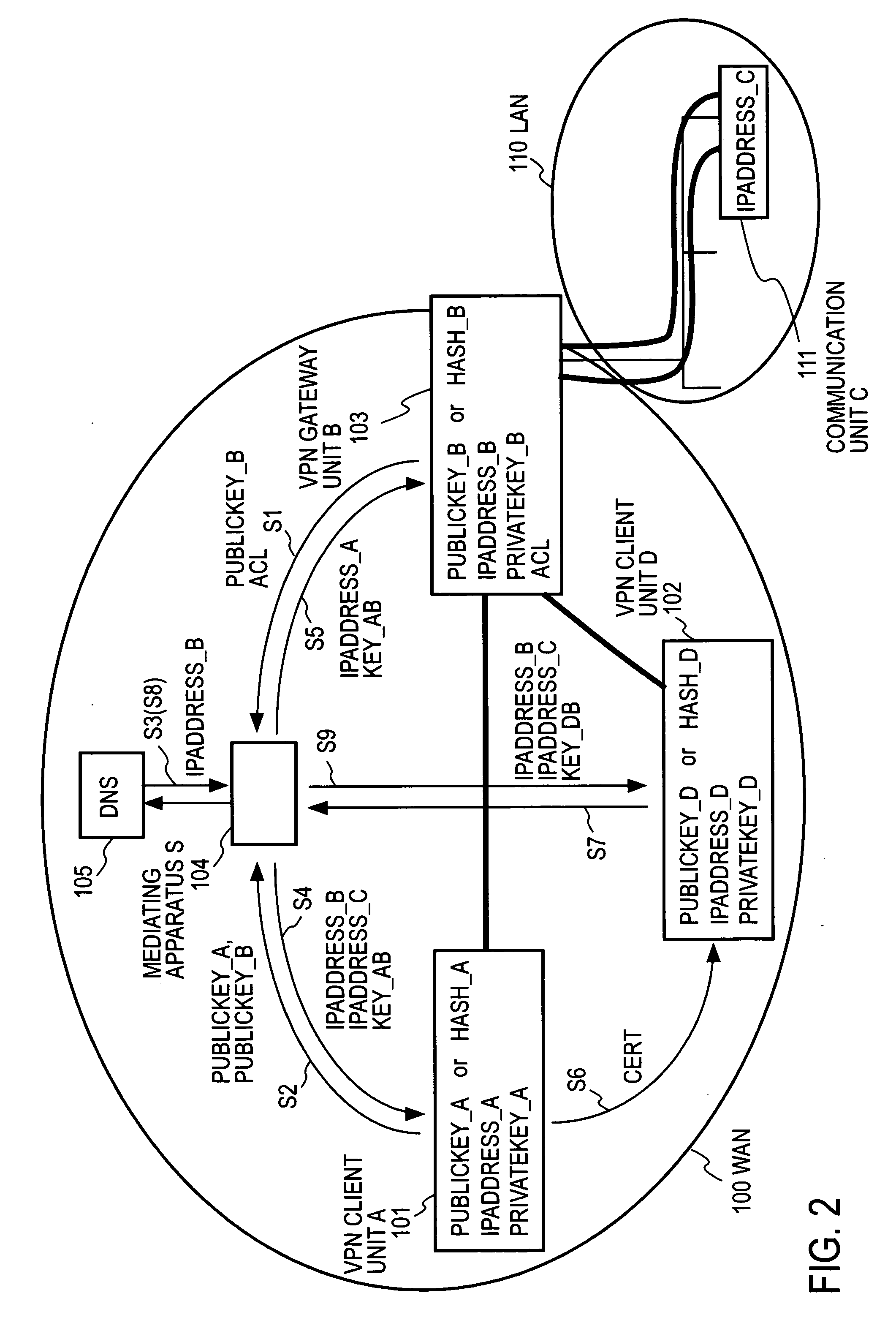
InactiveUS20060143702A1Secure distributionKey distribution for secure communicationDigital data processing detailsPrivate IPCommunication unit
A mediating apparatus is provided on an IP network, and stores an access control list (ACL) retained in a VPN gateway unit. The mediating apparatus: receives a retrieval request from a VPN client unit; acquires a private IP address of a communication unit by reference to ACL; searches DNS to acquire therefrom an IP address of the VPN gateway unit; generates a common key that is used for authentication between the VPN client unit and the VPN gateway unit and for encrypted communication therebetween; sends the IP address of the VPN gateway unit, the private IP address of the communication unit, and the common key to the VPN client unit; and sends the IP address of the VPN client unit and the common key to the VPN gateway unit.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Self-authentication communication device and device authentication system
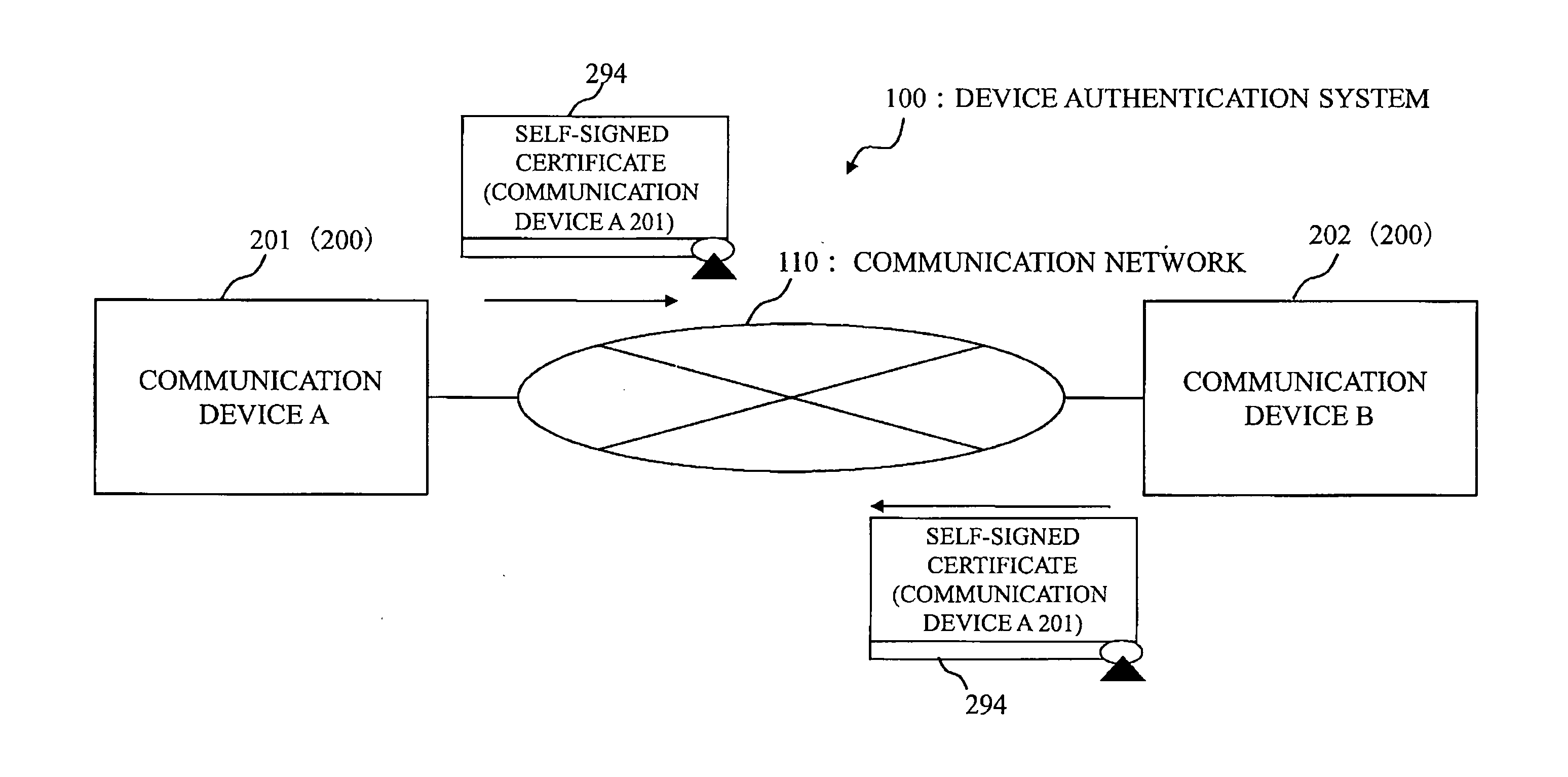
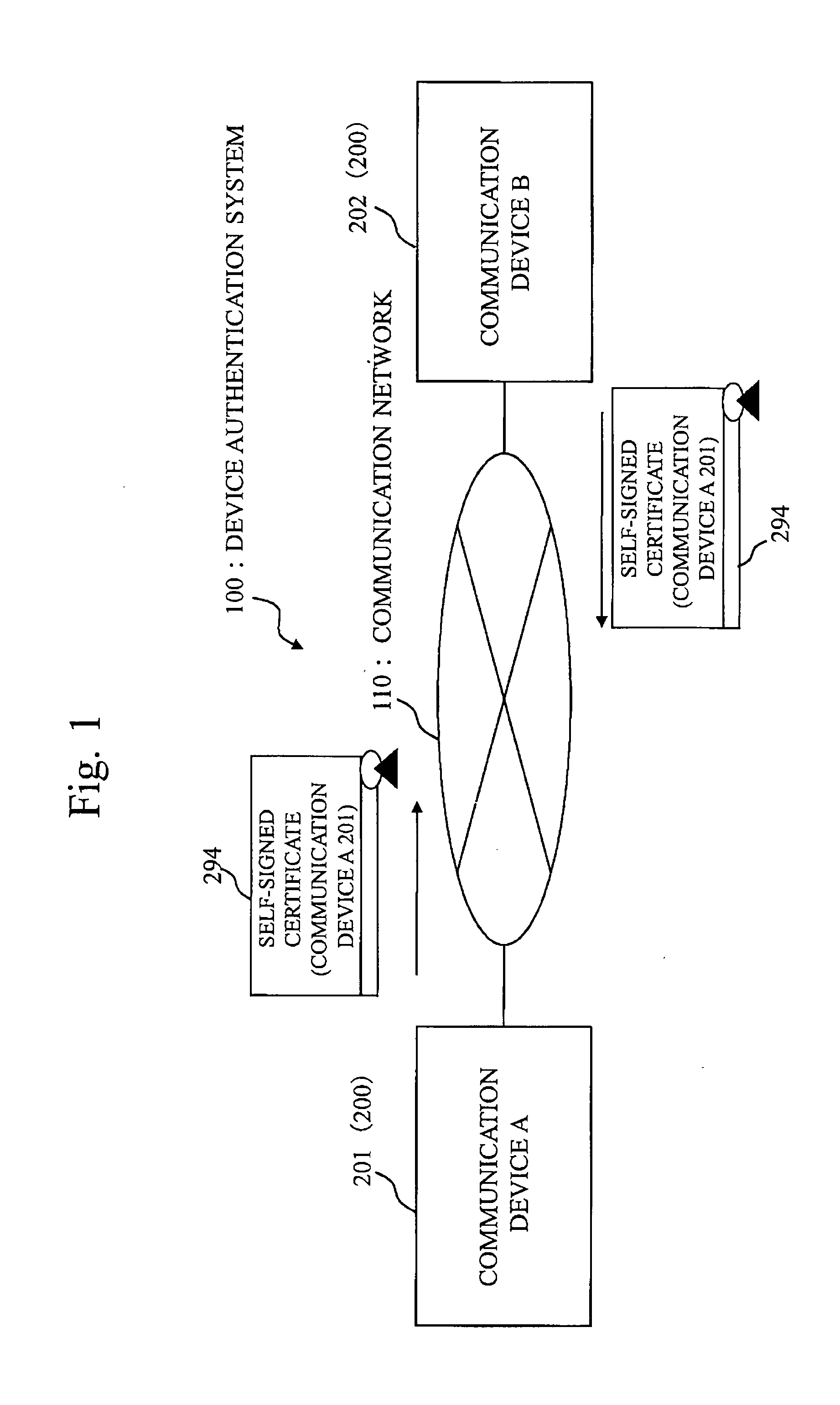
InactiveUS20120036364A1Public key for secure communicationUser identity/authority verificationExpiration dateSecure communication
In a system where a communication device performs secure communication by using a digital certificate, to enable a device of a communication party to verify that a self certificate is certainly generated by a device indicated on the self certificate even if the self certificate is not delivered offline in advance. Based on a master key and a public parameter, a communication device generates an ID-based encryption private key for which a device unique ID is used as a public key. Then, the communication device generates the digital signature of an RSA public key as a ID-based encryption signature by using the ID-based encryption private key. Then, the communication device generates an RSA self signature for the RSA public key, an expiration date, a host name, the device unique ID, and the ID-based encryption signature as the target. Then, the communication device generates a self-signed certificate to include the ID-based encryption signature and the RSA self signature.
Owner:MITSUBISHI ELECTRIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com