Method for implementing safe storage system in cloud storage environment
A secure storage and cloud storage technology, applied in transmission systems, electrical components, etc., can solve problems such as dissemination, security storage system performance is not optimistic, and specific versions are required
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
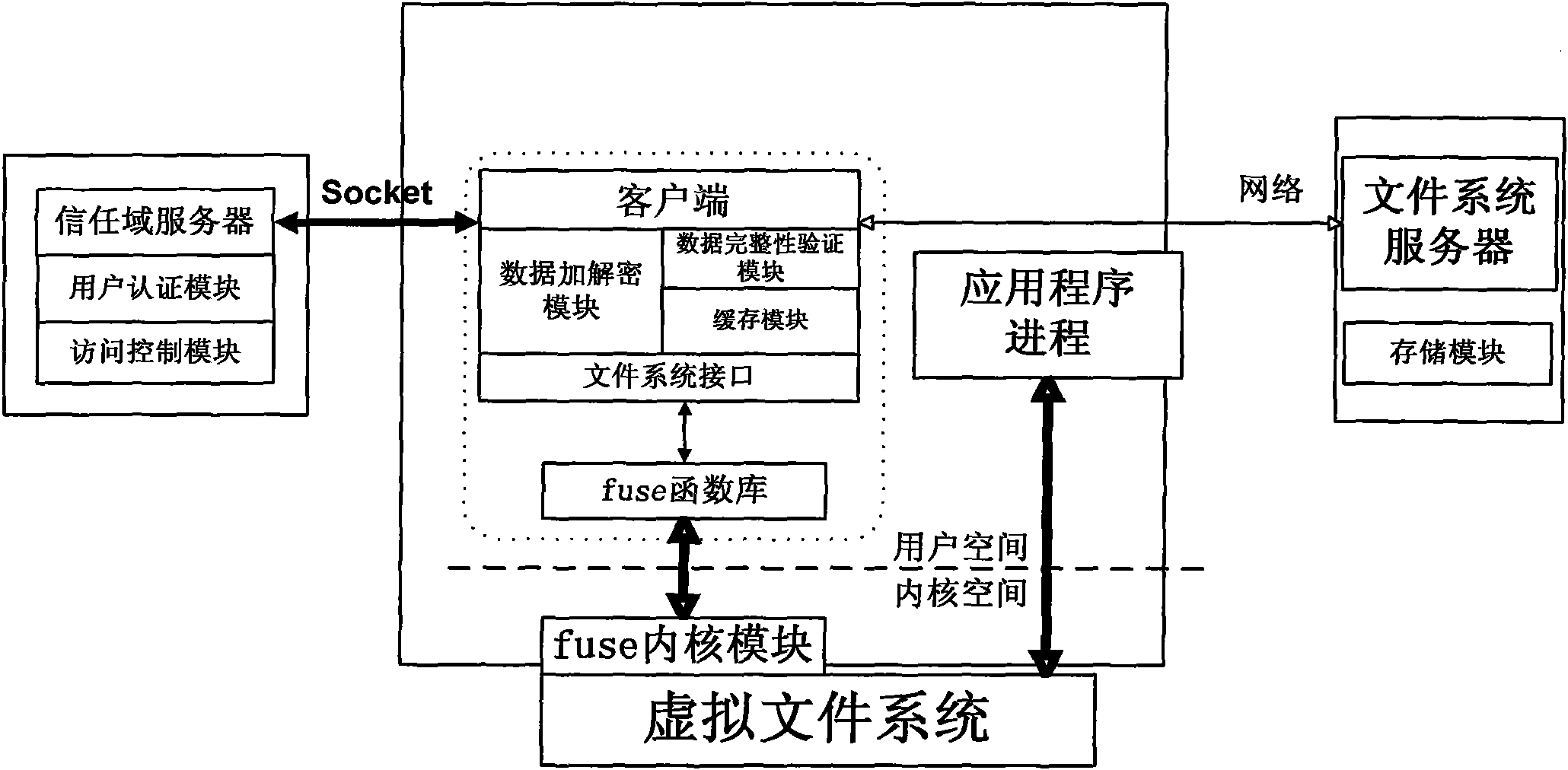
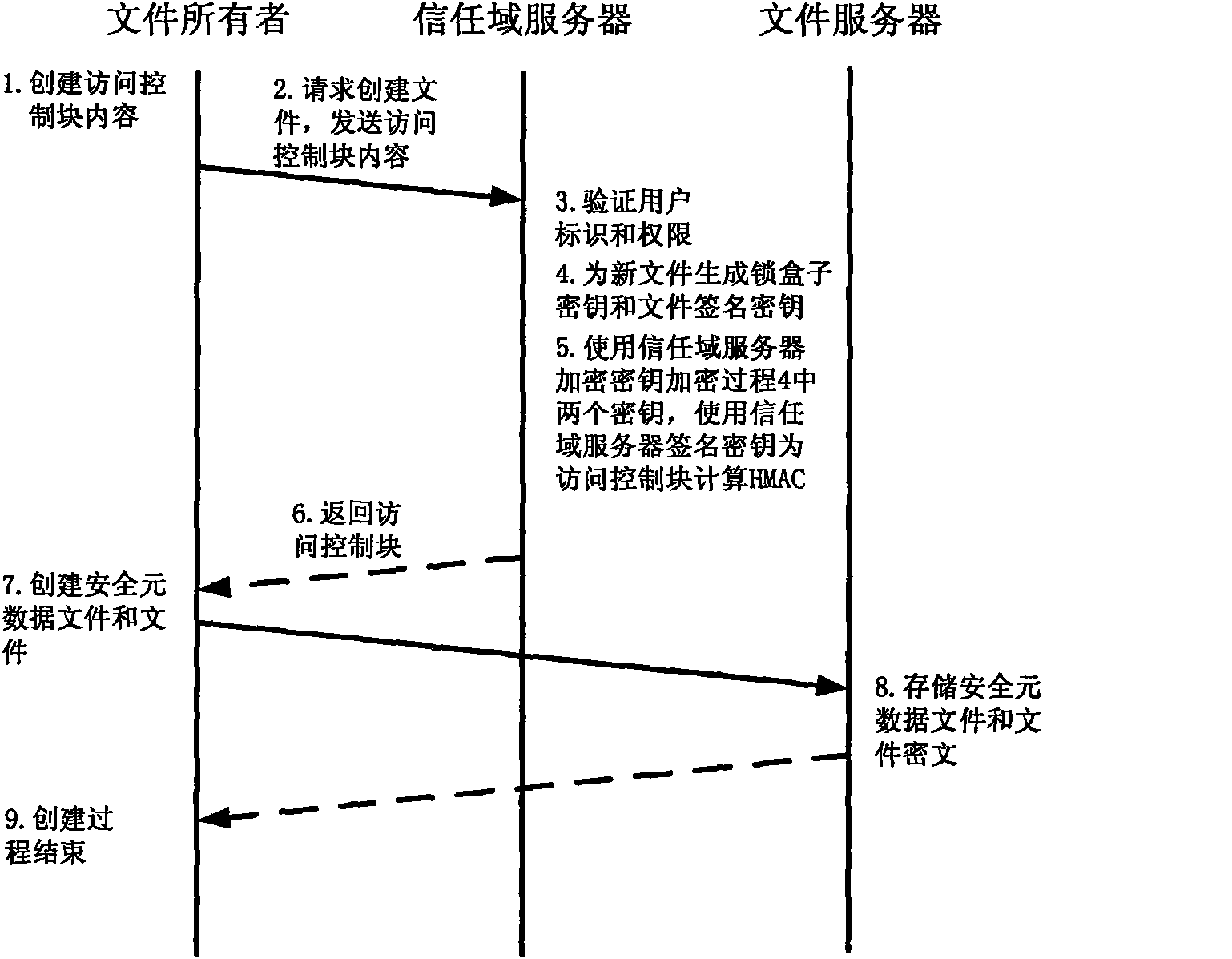
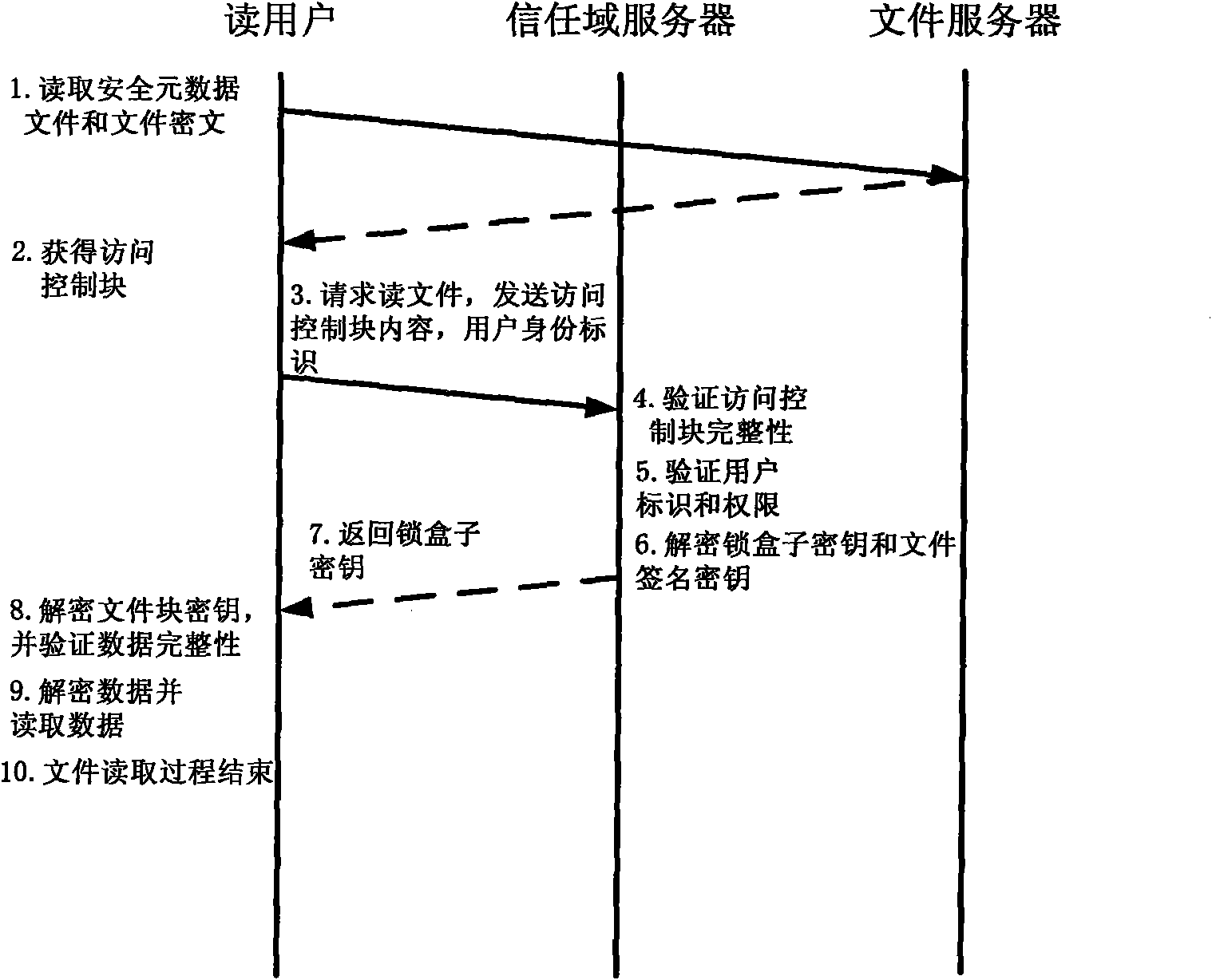
[0069] Step 1: The user applies to obtain the user ID: the user ID is the unique identity of the user in the system, and the file owner and the trust domain server both use the user ID to determine the user's identity and determine its access rights; in order to securely and effectively To identify the identities of subjects in the system (including trust domain servers and users), so that the system can establish a mutual trust relationship between operating users, the system needs a secure user identity identification mechanism independent of the underlying storage system. In this system, the public key infrastructure (PKI, Public Key Infrastructure) is used to provide user identification for the system through digital certificates. A digital certificate is an electronic document issued to a subject by a fair and authoritative organization. The document records the name of the subject, the serial number of the certificate, the name of the issuer, the validity period of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com