Patents
Literature
588 results about "Disk encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
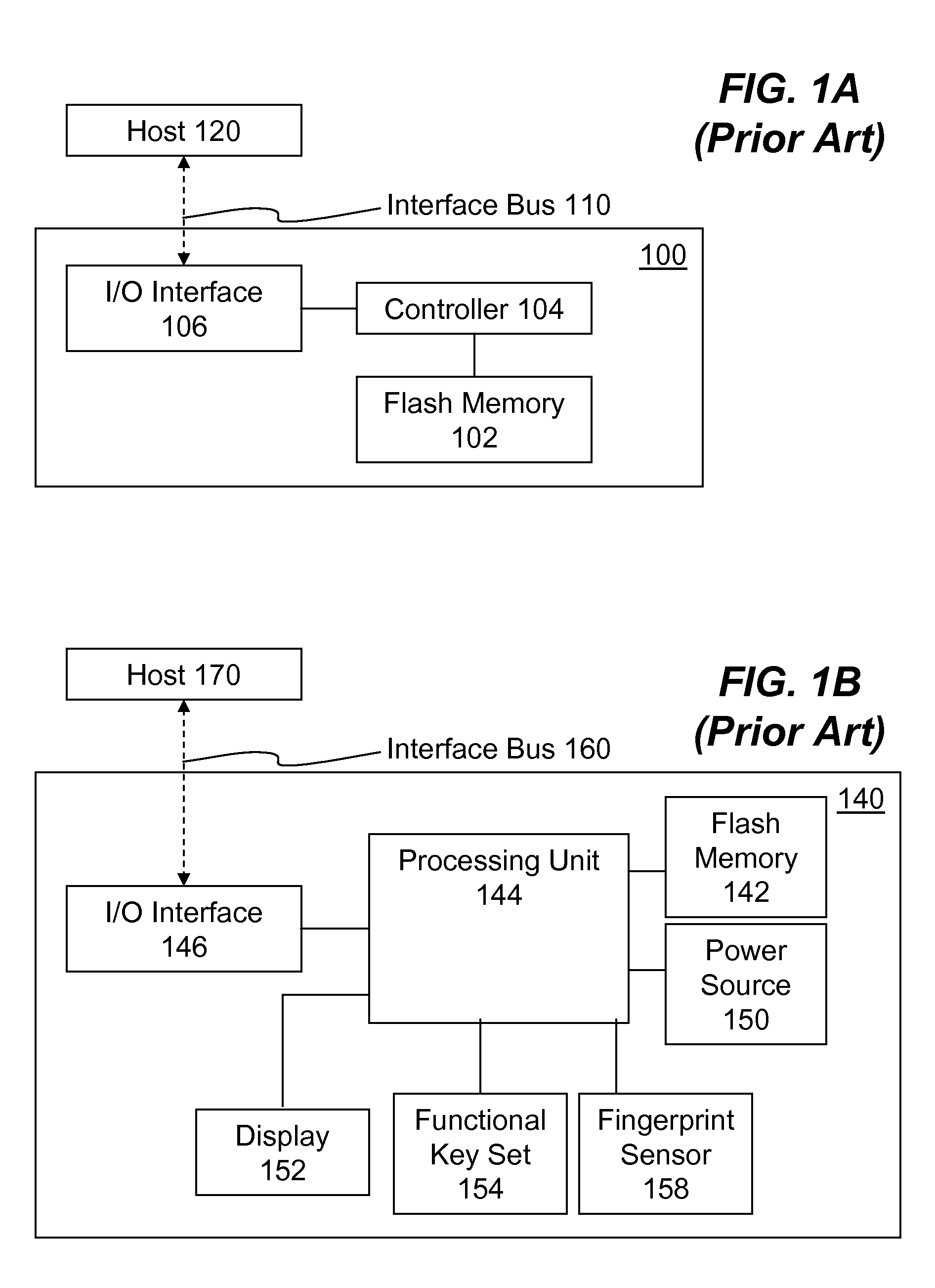
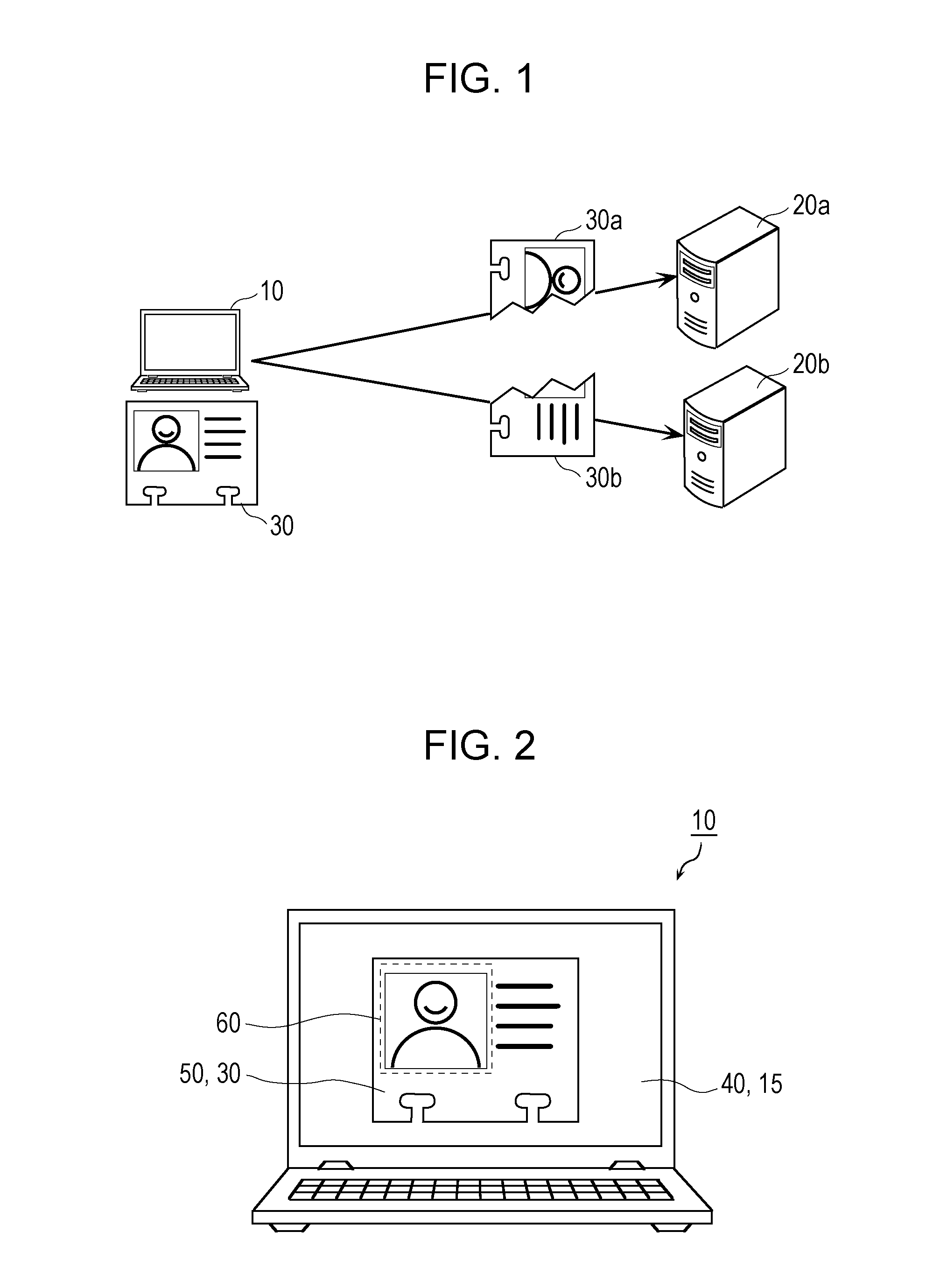
Disk encryption is a technology which protects information by converting it into unreadable code that cannot be deciphered easily by unauthorized people. Disk encryption uses disk encryption software or hardware to encrypt every bit of data that goes on a disk or disk volume. It is used to prevent unauthorized access to data storage.
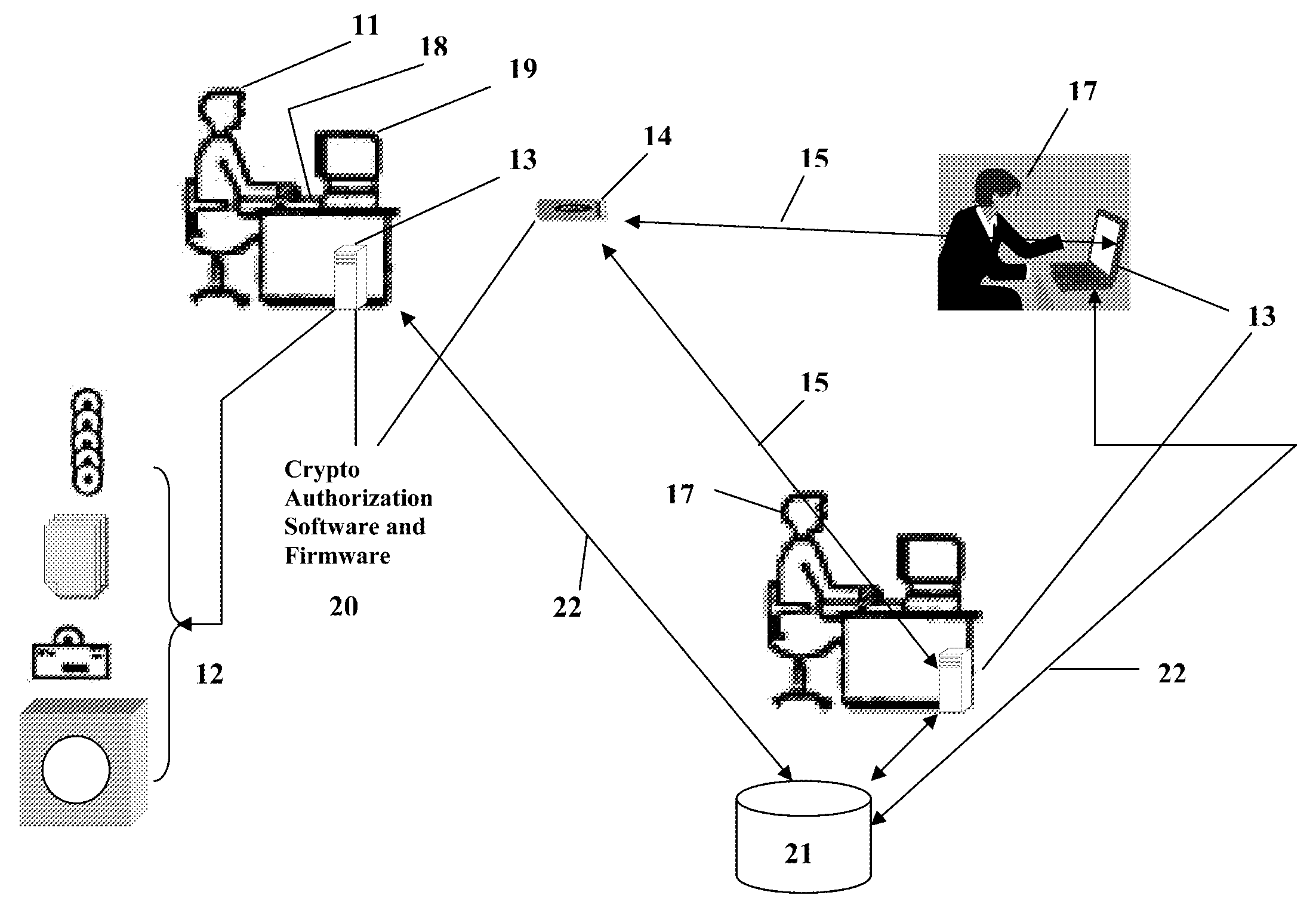
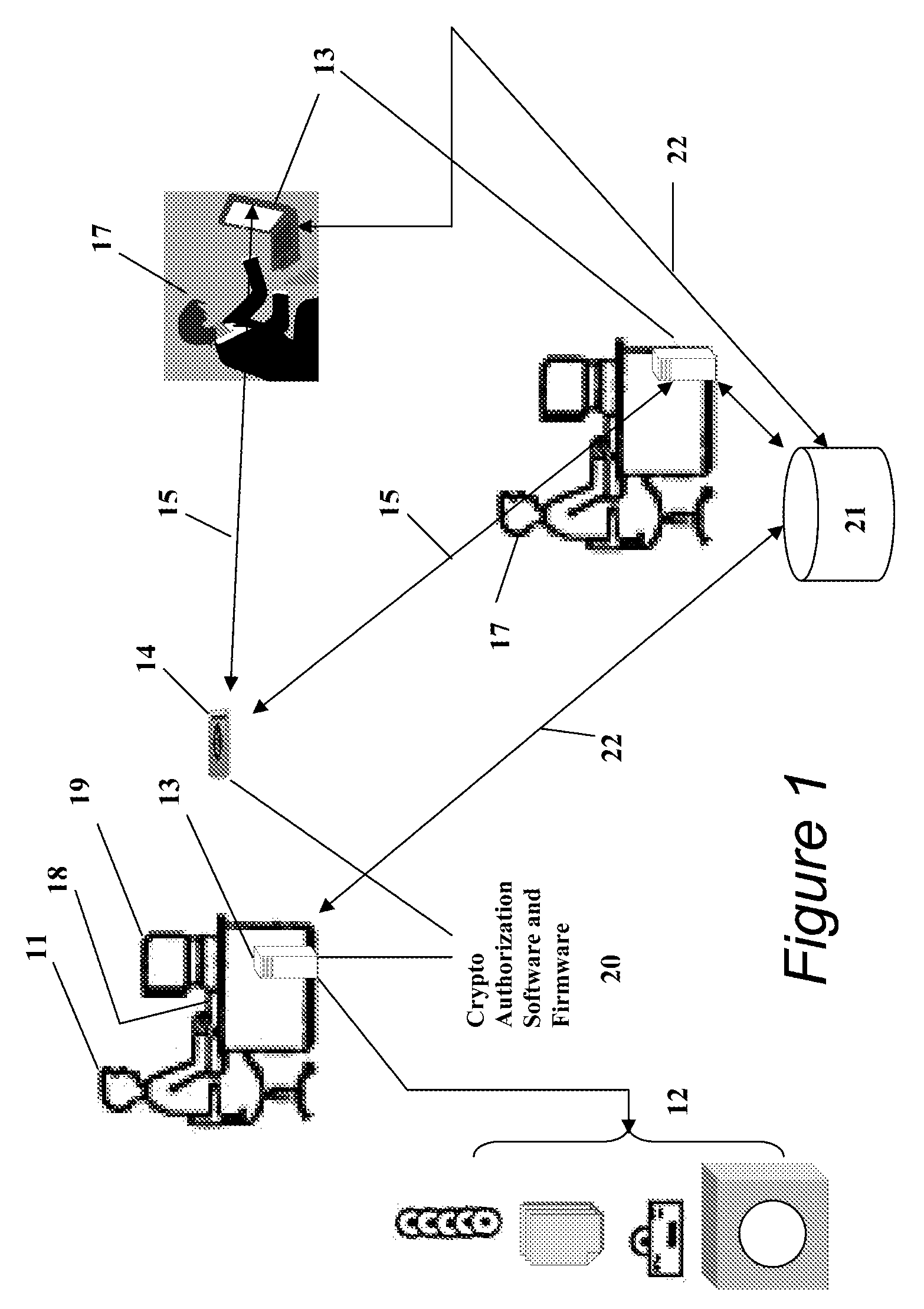
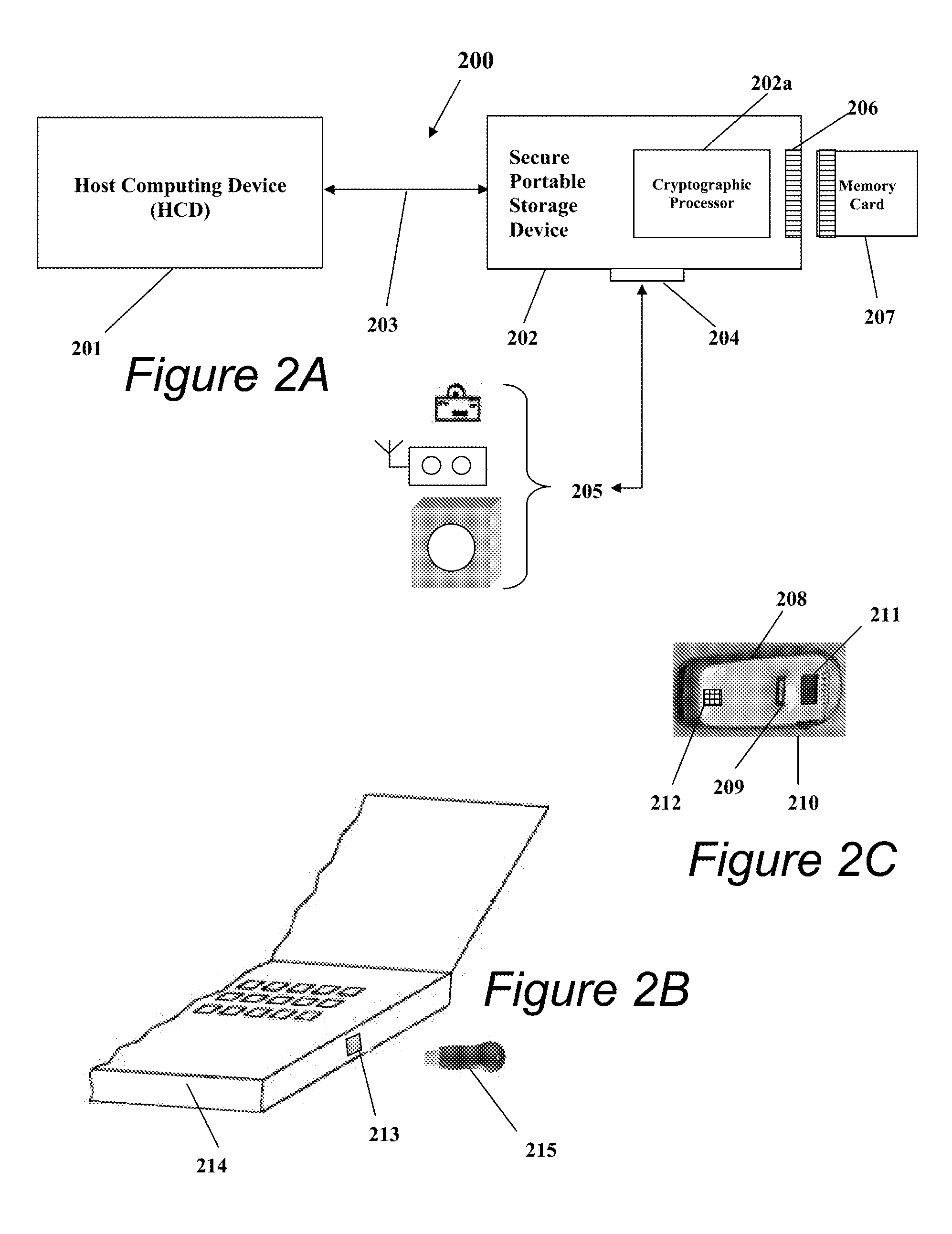
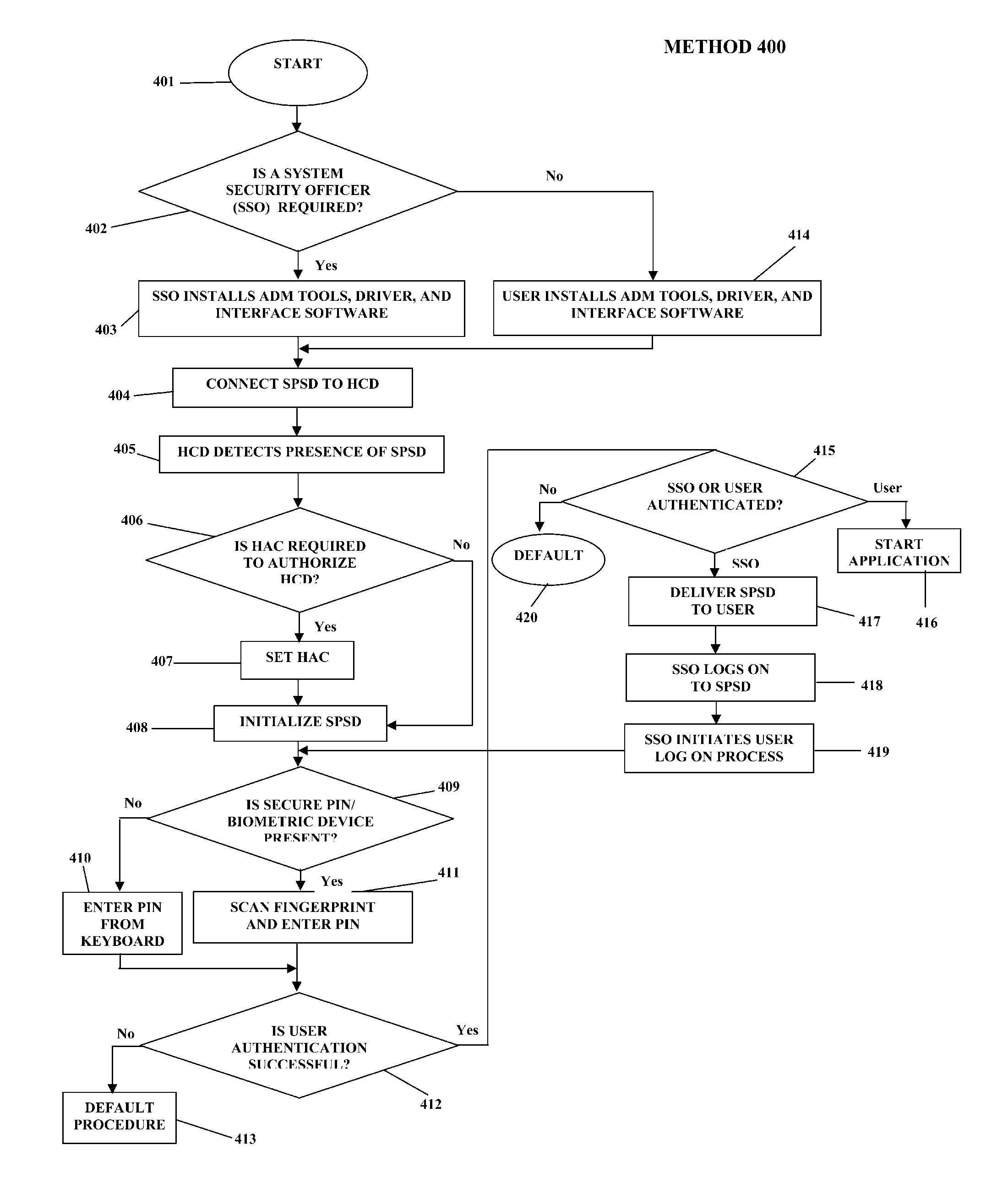
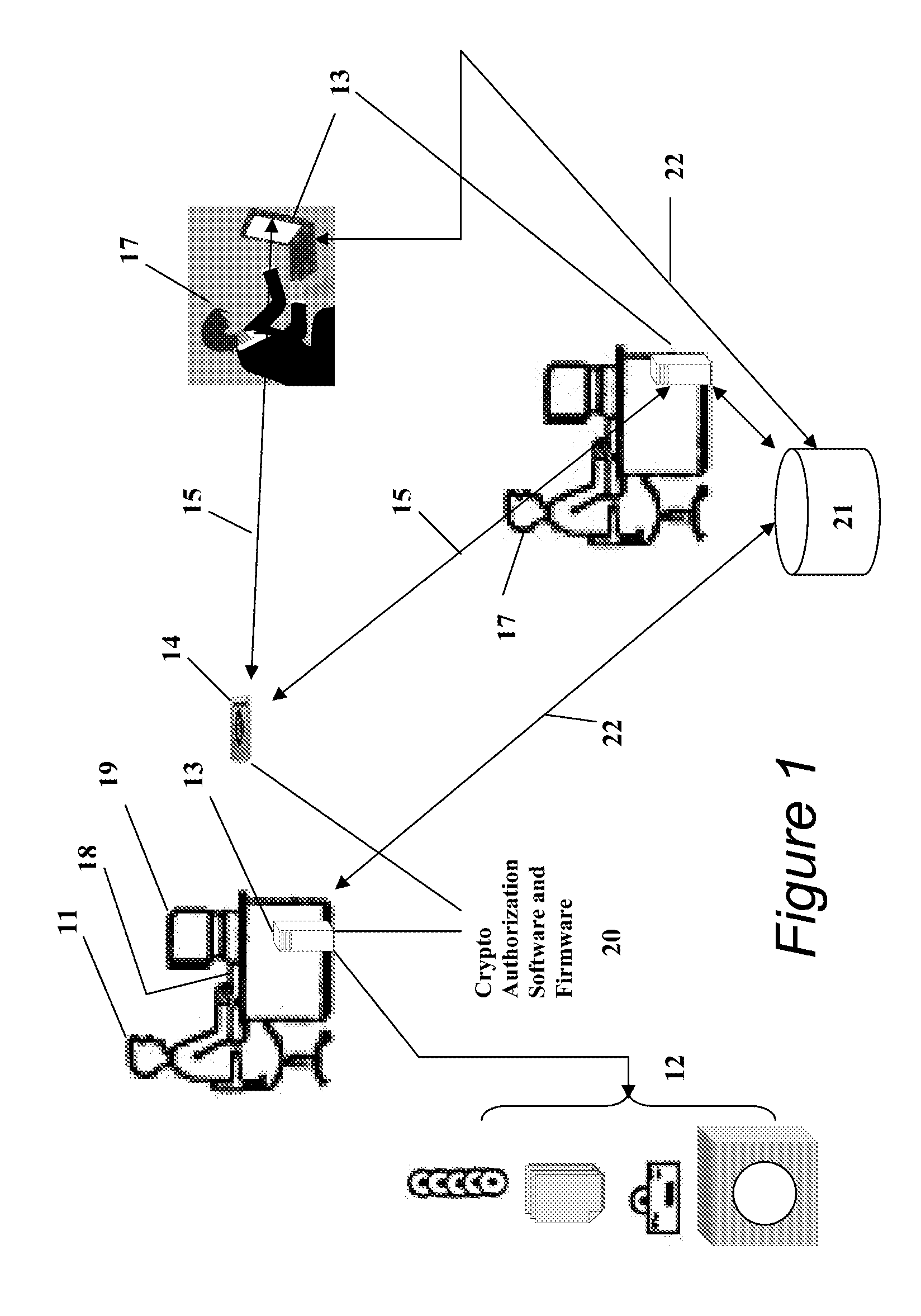
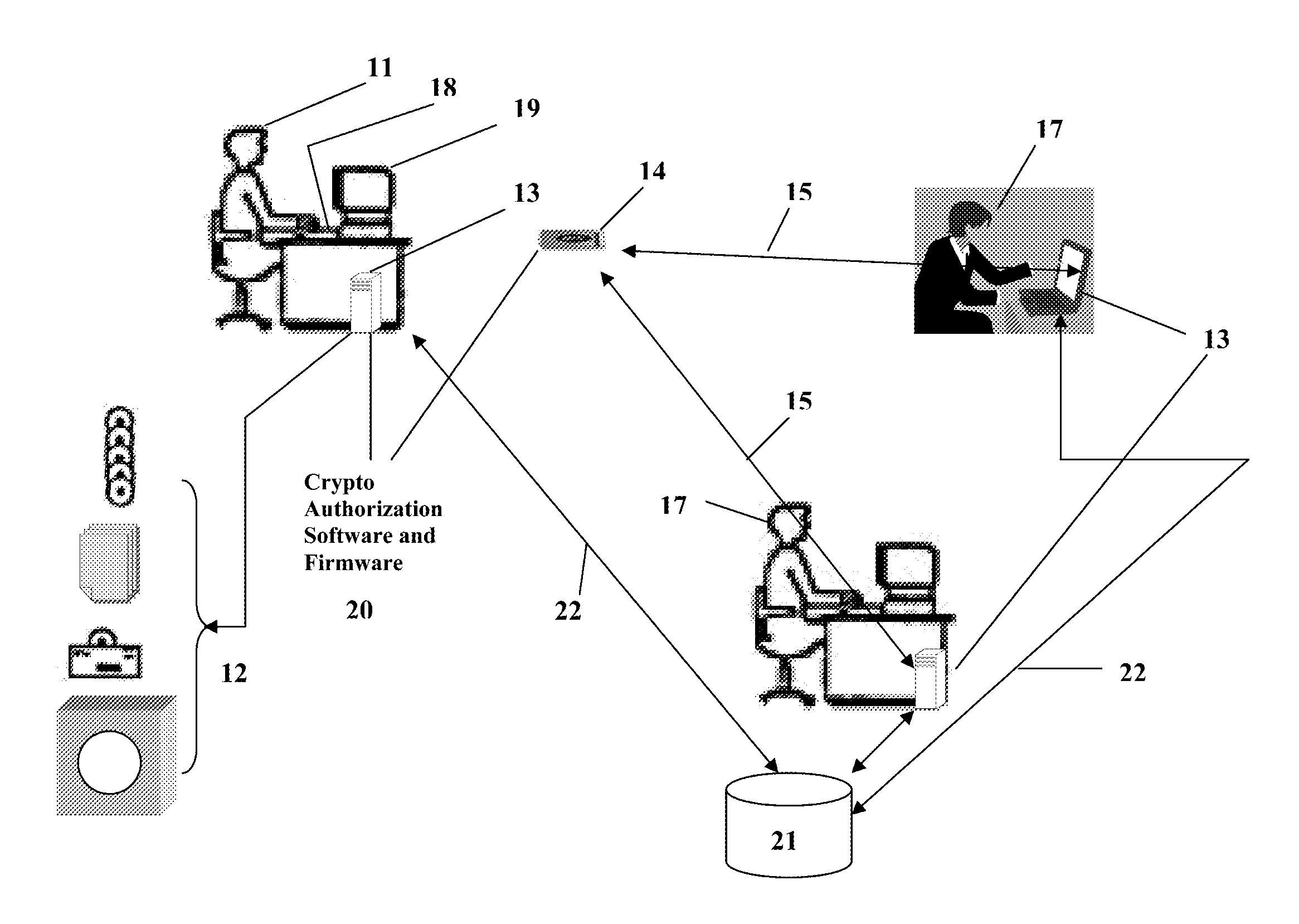
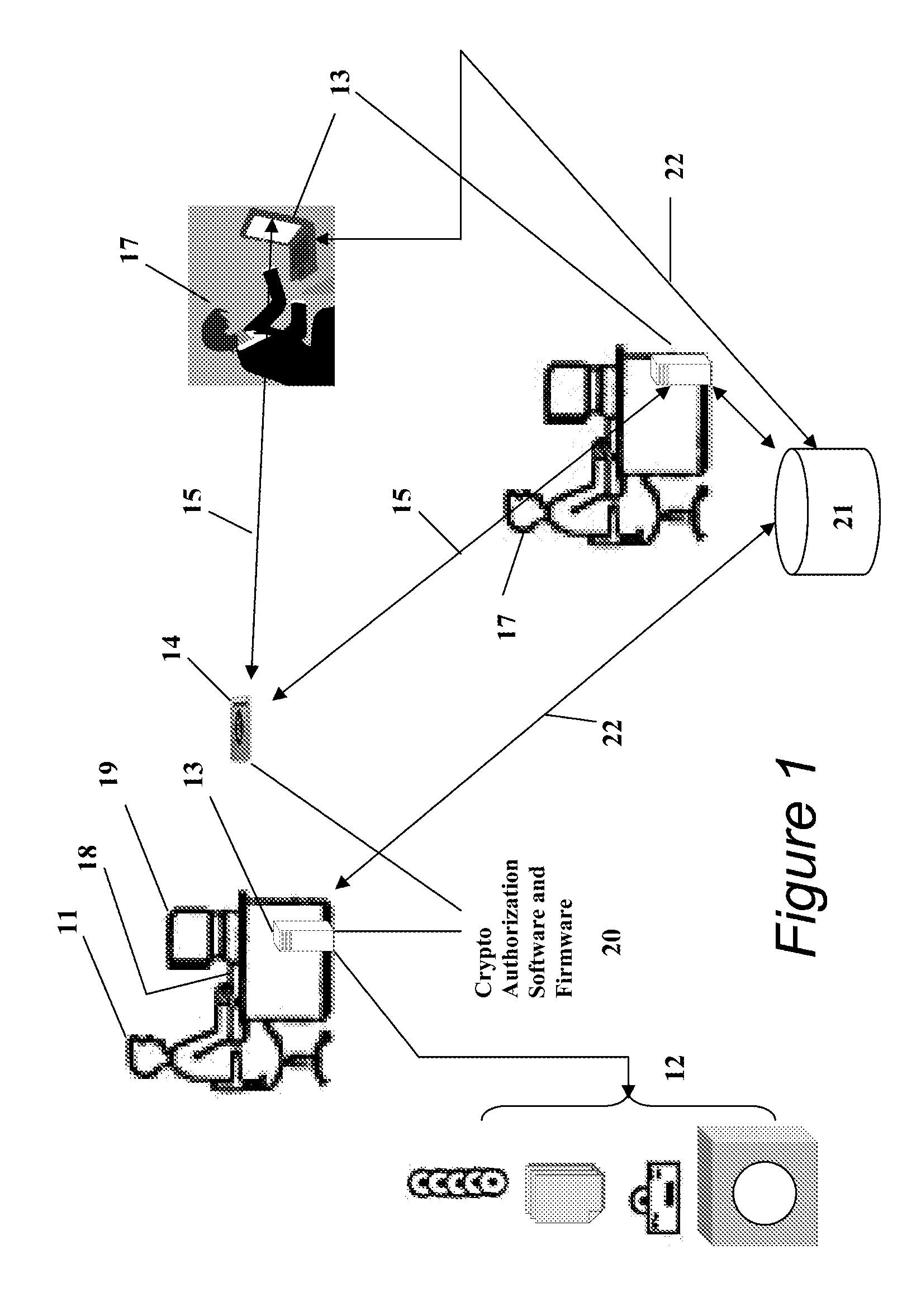
Portable Data Encryption Device with Configurable Security Functionality and Method for File Encryption
InactiveUS20080263363A1Mitigates and eliminates vulnerabilityUser identity/authority verificationInternal/peripheral component protectionComputer hardwarePlaintext
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
Portable data encryption device with configurable security functionality and method for file encryption
ActiveUS9049010B2Mitigates and eliminates vulnerabilityKey distribution for secure communicationUser identity/authority verificationPlaintextComputer hardware
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
Combined hardware and software based encryption of databases
InactiveUS6963980B1Increase flexibilityImprove performanceUser identity/authority verificationUnauthorized memory use protectionTamper proof hardwareRelational database
A relational database system for encryption of individual data elements comprising a encryption devices of at least two different types, the types being tamper-proof hardware and software implemented. The encryption processes of the system are of at least two different security levels, differing in the type of encryption device holding the process keys for at least one of the process key categories and also differing in which type of device executing the algorithm of the process. Each data element to be protected is assigned an attribute indicating the usage of encryption process of a certain security level.
Owner:PROTEGRITY CORP
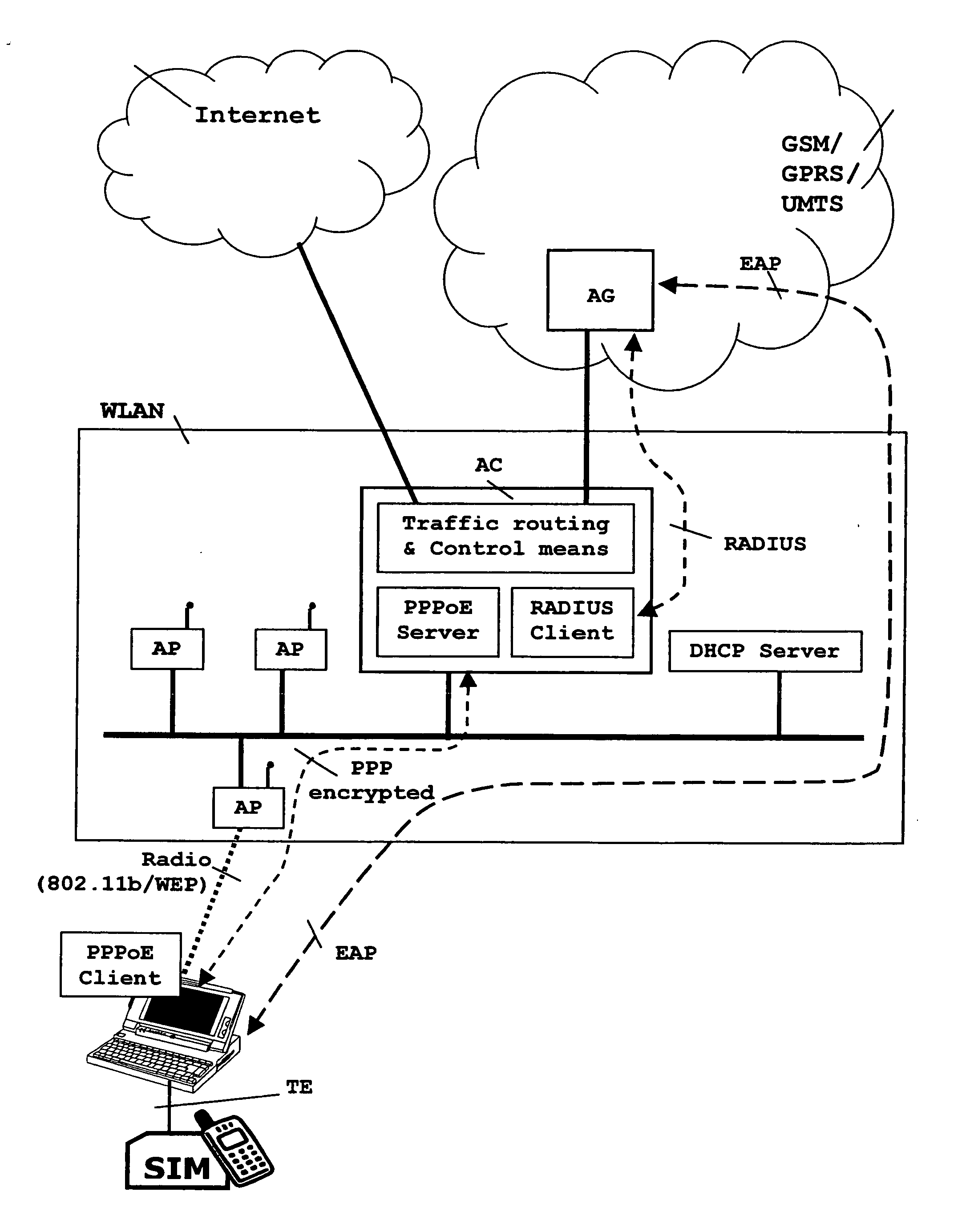
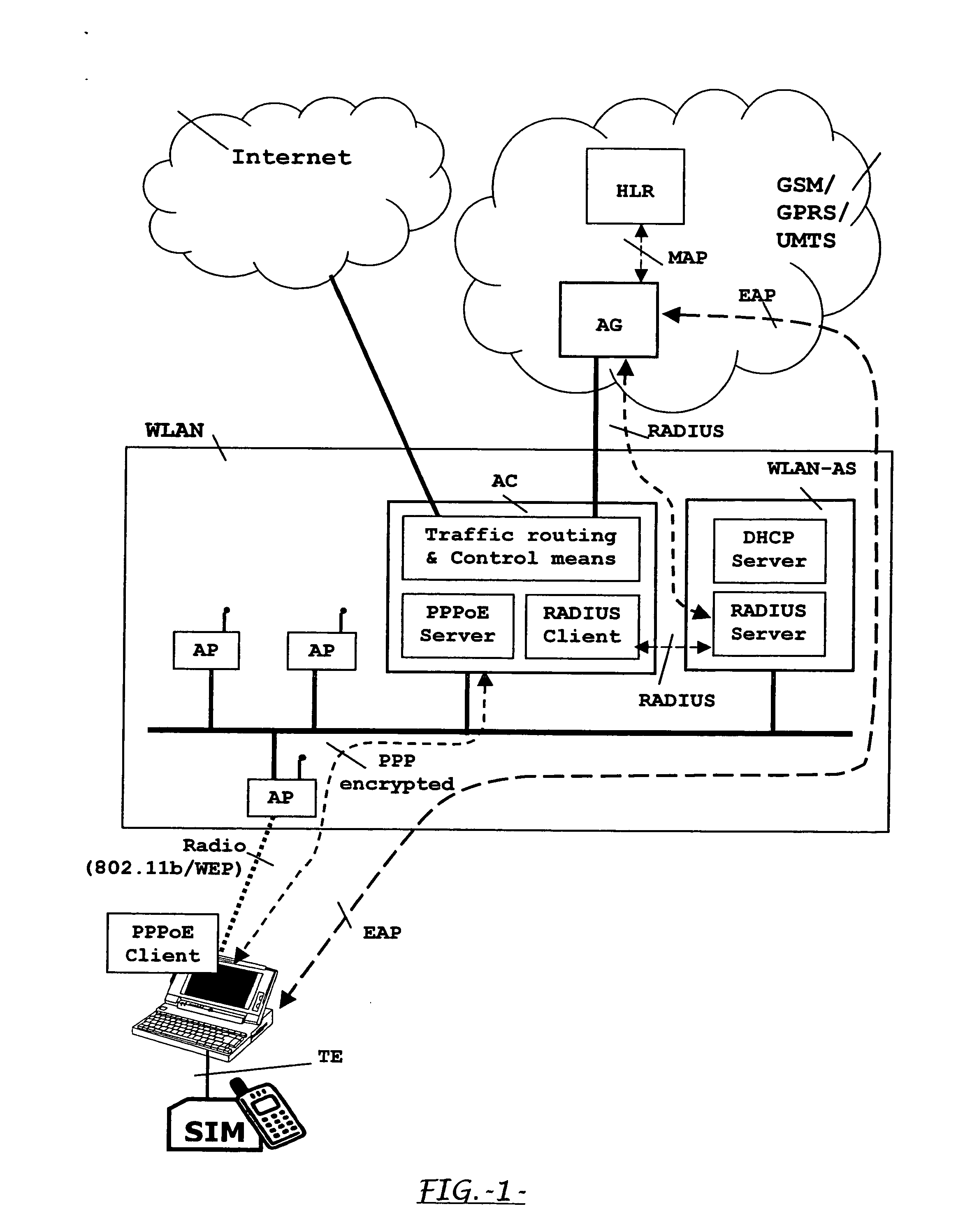
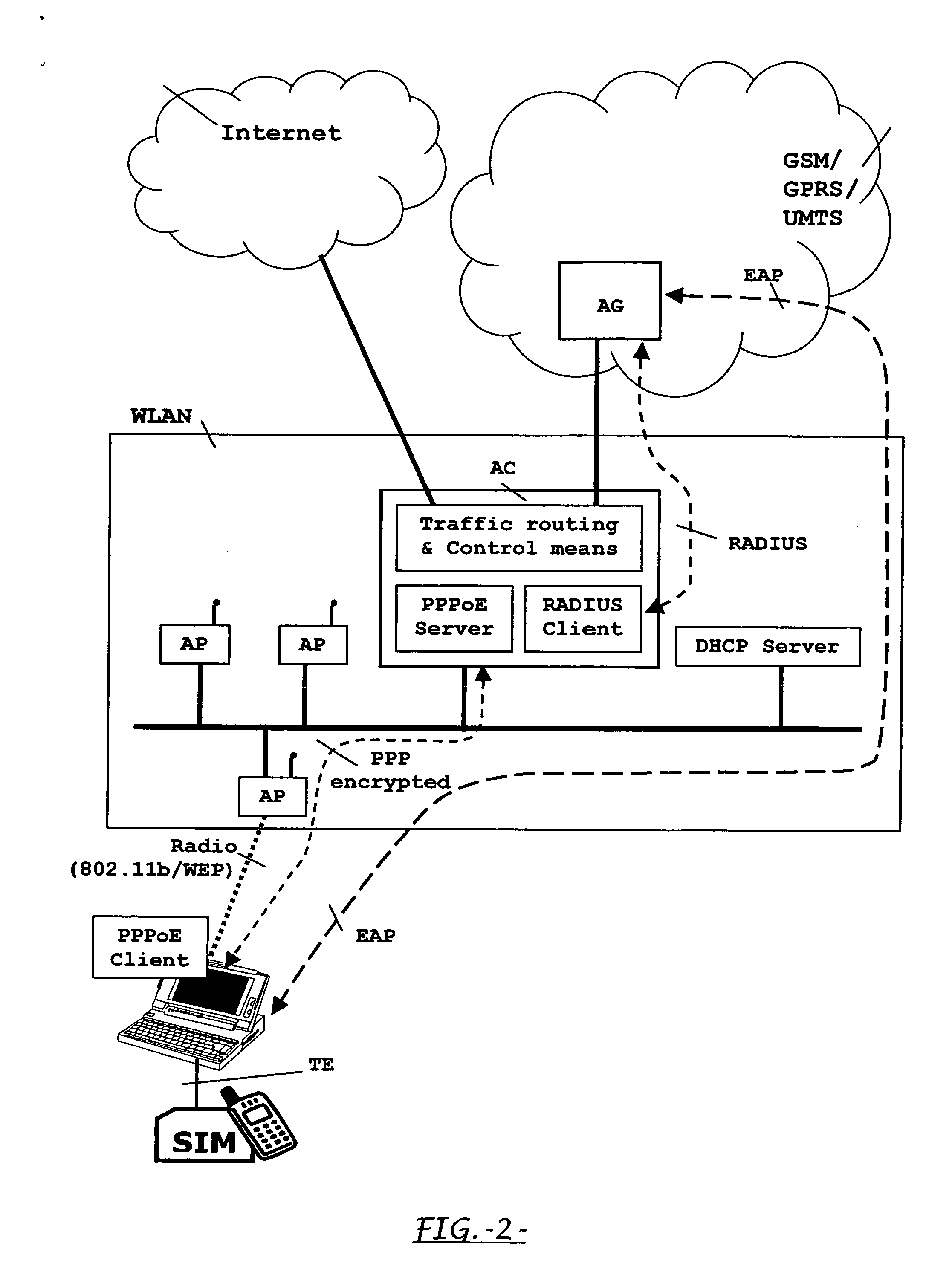
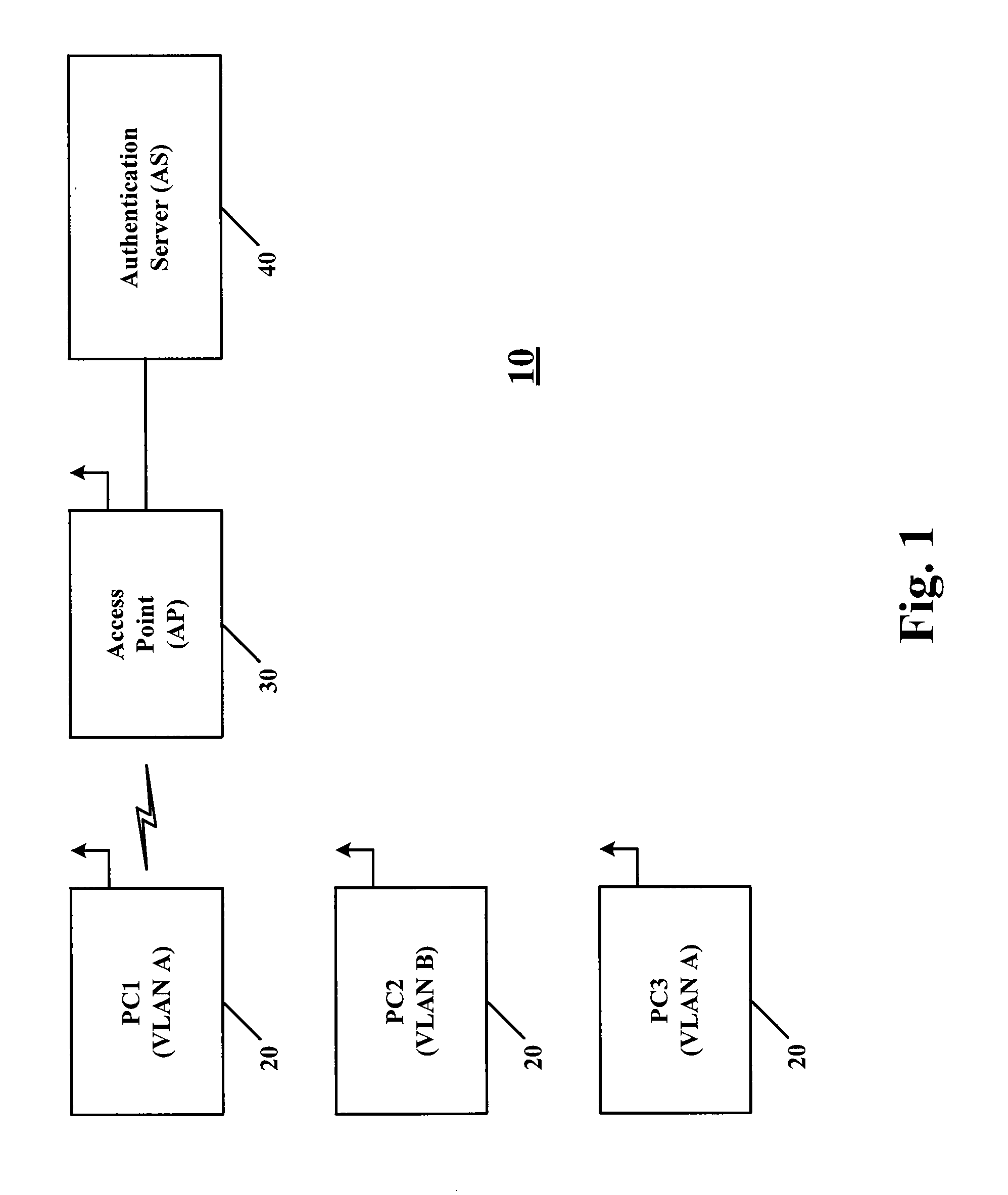
System, apparatus and method for sim-based authentication and encryption in wireless local area network access
ActiveUS20060052085A1Low costUnauthorised/fraudulent call preventionEavesdropping prevention circuitsRADIUSAuthentication
The invention refers to a system, apparatus and method for carrying out a SIM-based authentication of a user accessing a WLAN, without having provided yet an IP connectivity, along with a layer-2 encryption mechanism for protecting the path between the Terminal Equipment and the Mobile network. Therefore, the invention provides a method for establishing a PPP-tunnelling for AKA dialogues between the terminal and an Access Controller for accessing the mobile network owning the SIM. The invention also provides an Access Controller (AC) comprising a Point-to-Point over Ethernet (PPPOE) server for tunnelling AKA dialogues from a PPP-client installed in the terminal for the same purpose, and also comprising a Traffic Router and a RADIUS-client. The AC thus including a RADIUS-client is interposed between a RADIUS-proxy accessed from the access points (AP) in the WLAN and the mobile network where SIM-based authentication is carried out.
Owner:TELEFON AB LM ERICSSON (PUBL)
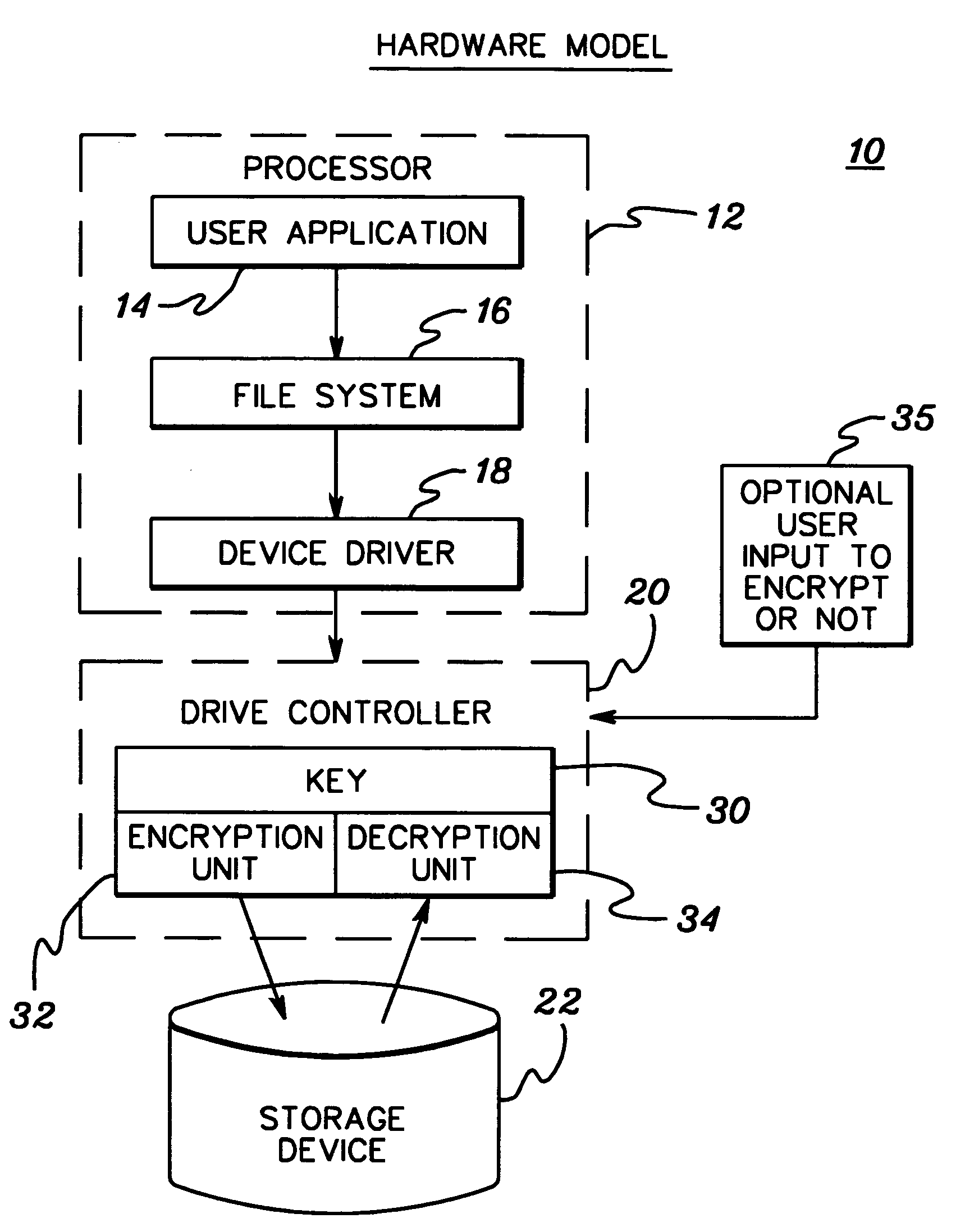
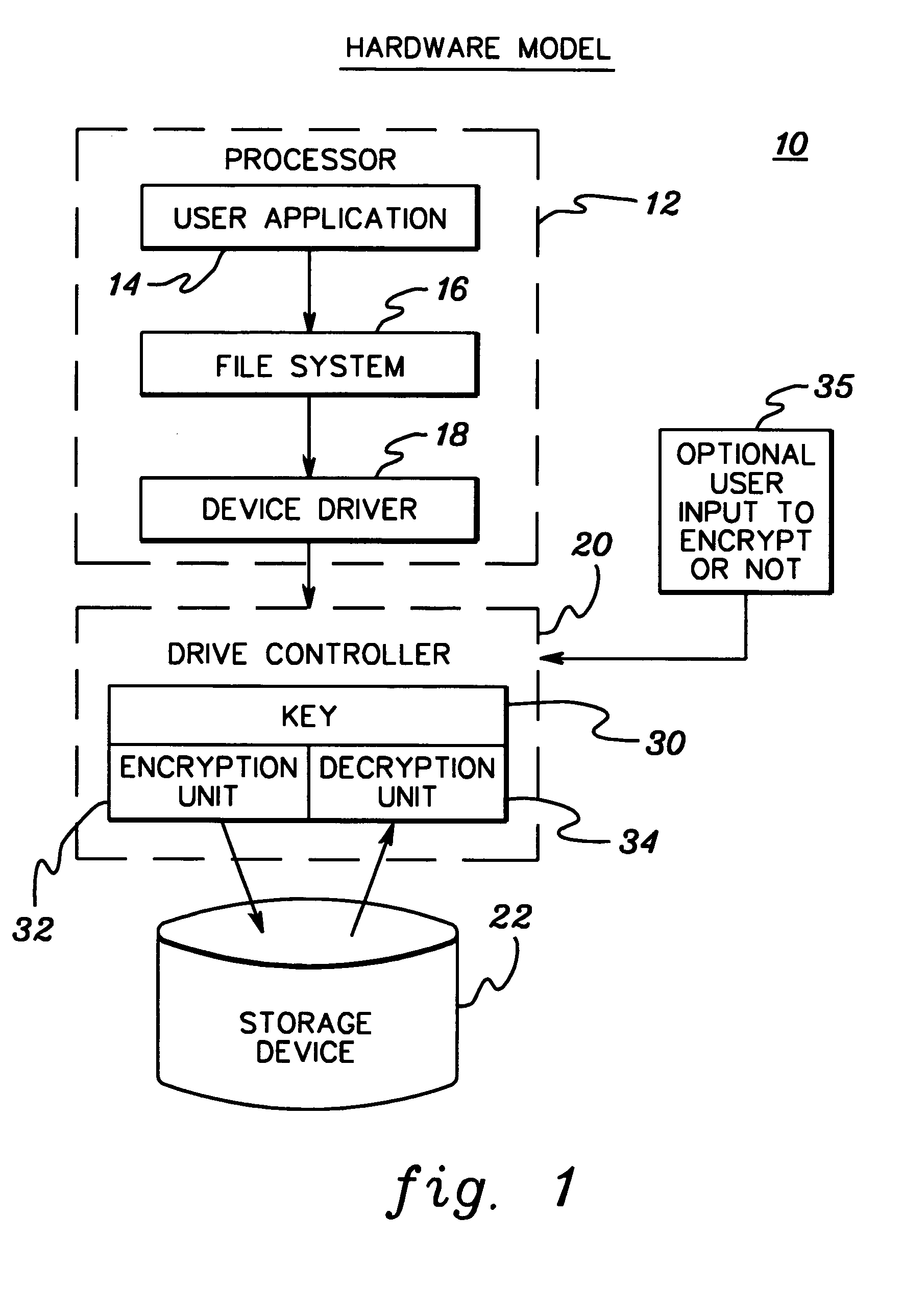
Encryption/decryption of stored data using non-accessible, unique encryption key
InactiveUS7278016B1Guaranteed usageKey distribution for secure communicationDigital computer detailsHard disc driveFloppy disk
Encryption and decryption of data stored from a computing system to a storage medium is disclosed wherein the processing employs a non-accessible encryption key that is unique to the computing system. The unique encryption key can be embedded in non-removable hardware of the computing system or generated, e.g., from identification numbers ascertained from non-removable hardware of the computing system. Processing includes establishing the unique encryption key, encrypting data using the unique encryption key and storing the encrypted data to the storage medium without storing the unique encryption key on the storage medium. The storage medium can comprise any non-removable or removable storage medium, including for example a computer hard drive, floppy diskette, or recordable compact disk.
Owner:RPX CORP
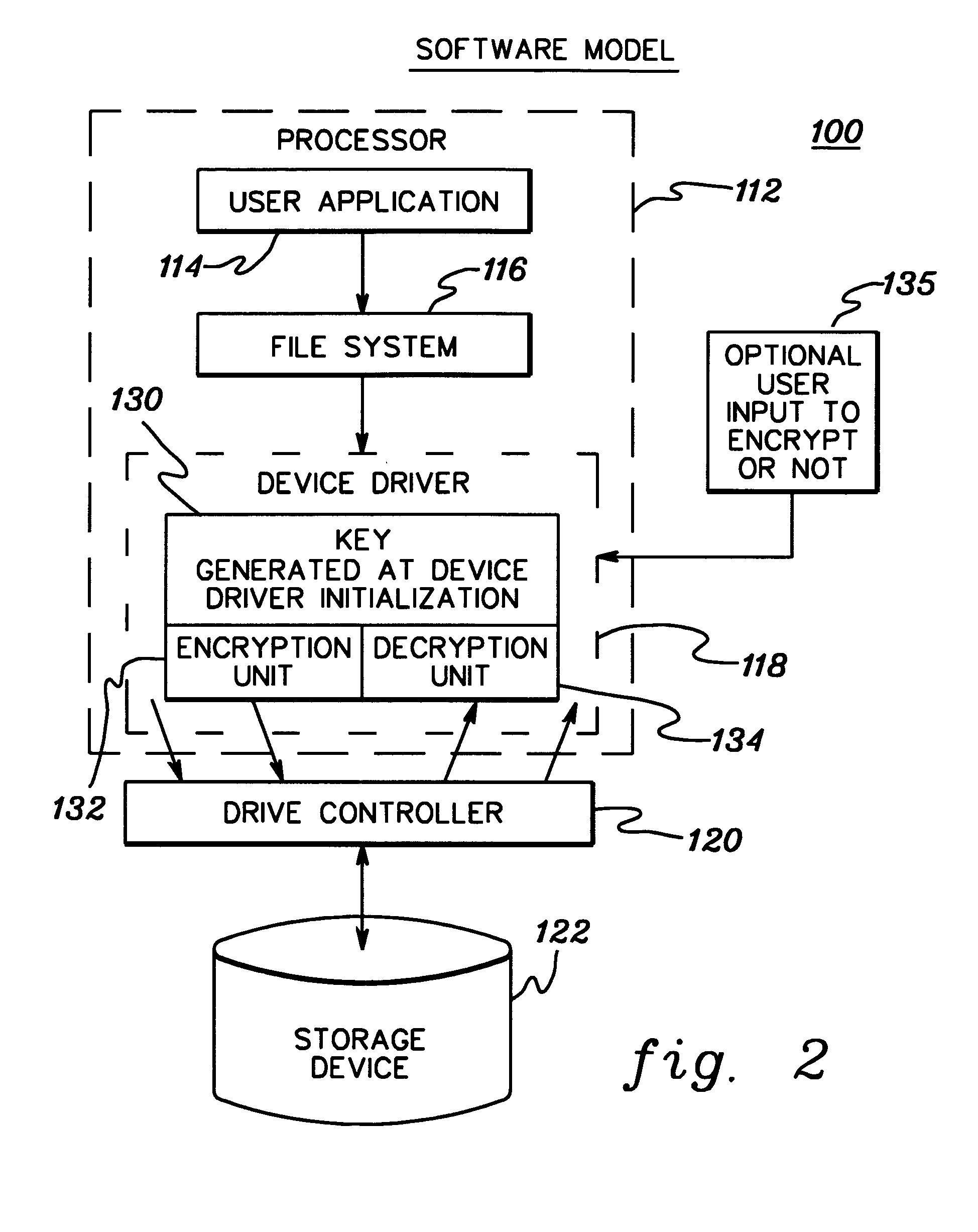
Transparent encryption and decryption with algorithm independent cryptographic engine that allows for containerization of encrypted files
InactiveUS6981141B1Digital data processing detailsInternal/peripheral component protectionComputer hardwareContainerization
An encryption method that is largely transparent to a user is accomplished by intercepting a change document or open document command, carrying out an encryption or decryption process, and then completing the command on an encrypted or decrypted file. The encryption method can be used in a wide variety of environments, such as an individual computer program, a database or electronic messaging over the Internet. The encryption method can select from a plurality of encryption algorithms. The encryption method can also allow just a portion of a document to be encrypted, placed in a container, and then be represented by an object linking and embedding (“OLE”) container object or other representation supported by the file.
Owner:RPX CORP
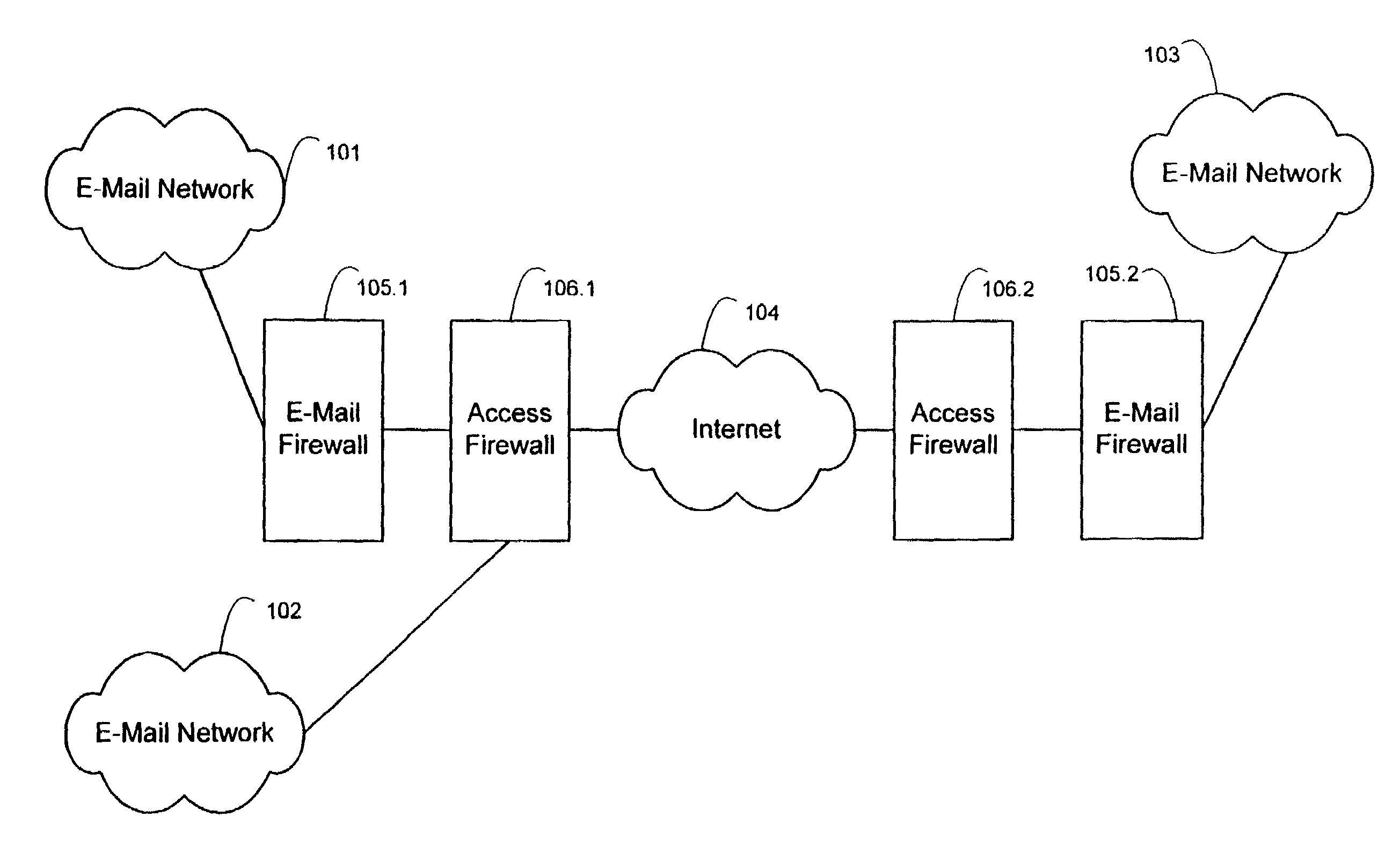
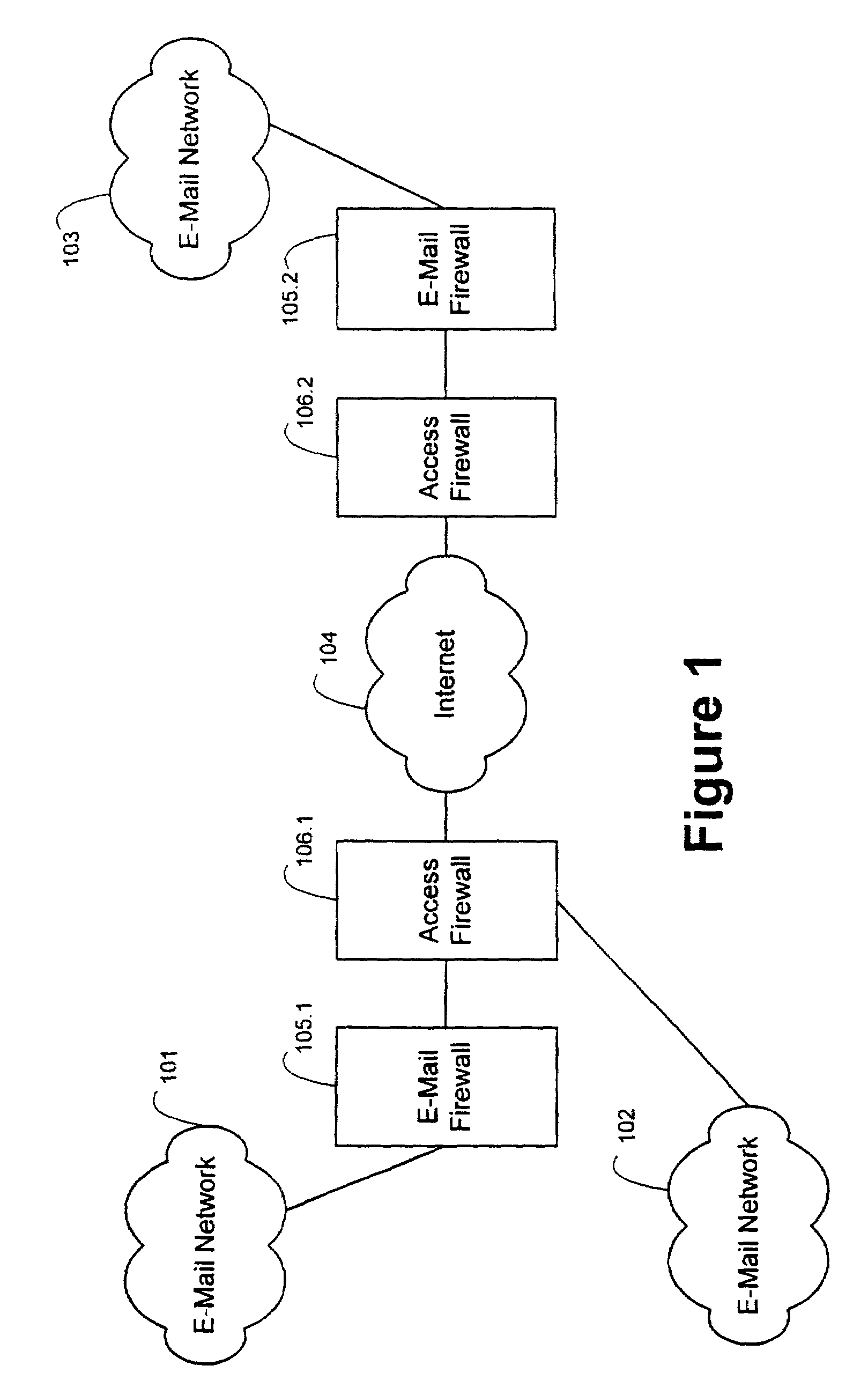
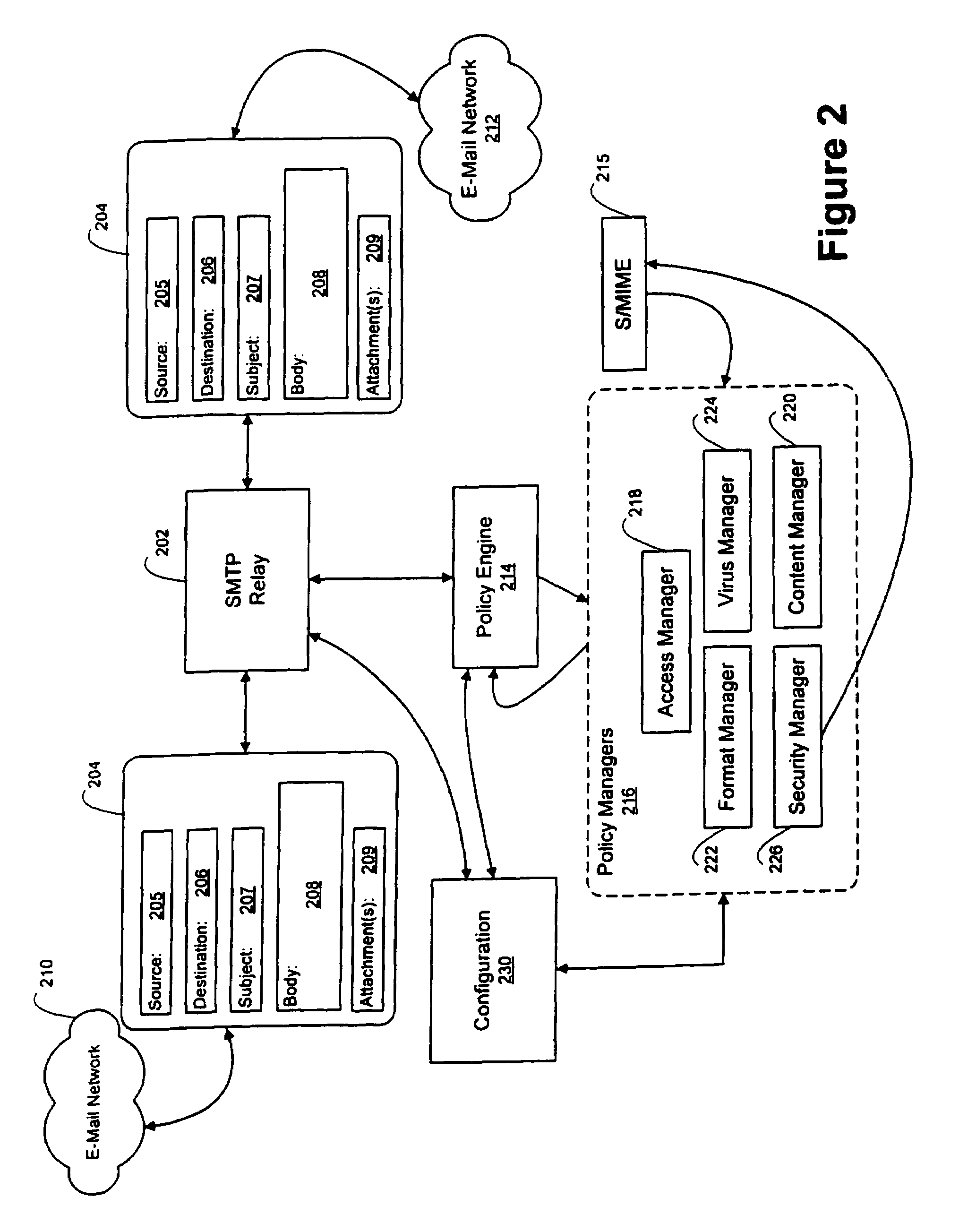
E-mail firewall with stored key encryption/decryption
InactiveUS7162738B2Easy to controlKey distribution for secure communicationMemory loss protectionVirusContent management
An e-mail firewall (105) applies policies to e-mail messages (204) between a first site and a plurality of second sites in accordance with a plurality of administrator selectable policies (216). The firewall comprises a simple mail transfer protocol (SMTP) relay (202) for causing the e-mail messages (204) to be transmitted between the first site and selected ones of the second sites. A plurality of policy managers (216) enforce administrator selectable policies. The policies, such as encryption and decryption policies, comprise at least a first source / destination policy (218), at least a first content policy (202) and at least a first virus policy (224). The policies are characterized by a plurality of administrator selectable criteria (310), a plurality of administrator selectable exceptions (312) to the criteria and a plurality of administrator selectable actions (314, 316, 322) associated with the criteria and exceptions. The policy managers comprise an access manager (218) for restricting transmission of e-mail messages (204) between the first site and the second sites in accordance with the source / destination policy (218). The policy managers (216) further comprise a content manager (220) for restricting transmission of e-mail messages (204) between the first site and the second sites in accordance with the content policy (220), and a virus manager (224) for restriction transmission of e-mail messages (204) between the first site and the second sites in accordance with the virus policy (224).
Owner:TUMBLEWEED COMM CORP
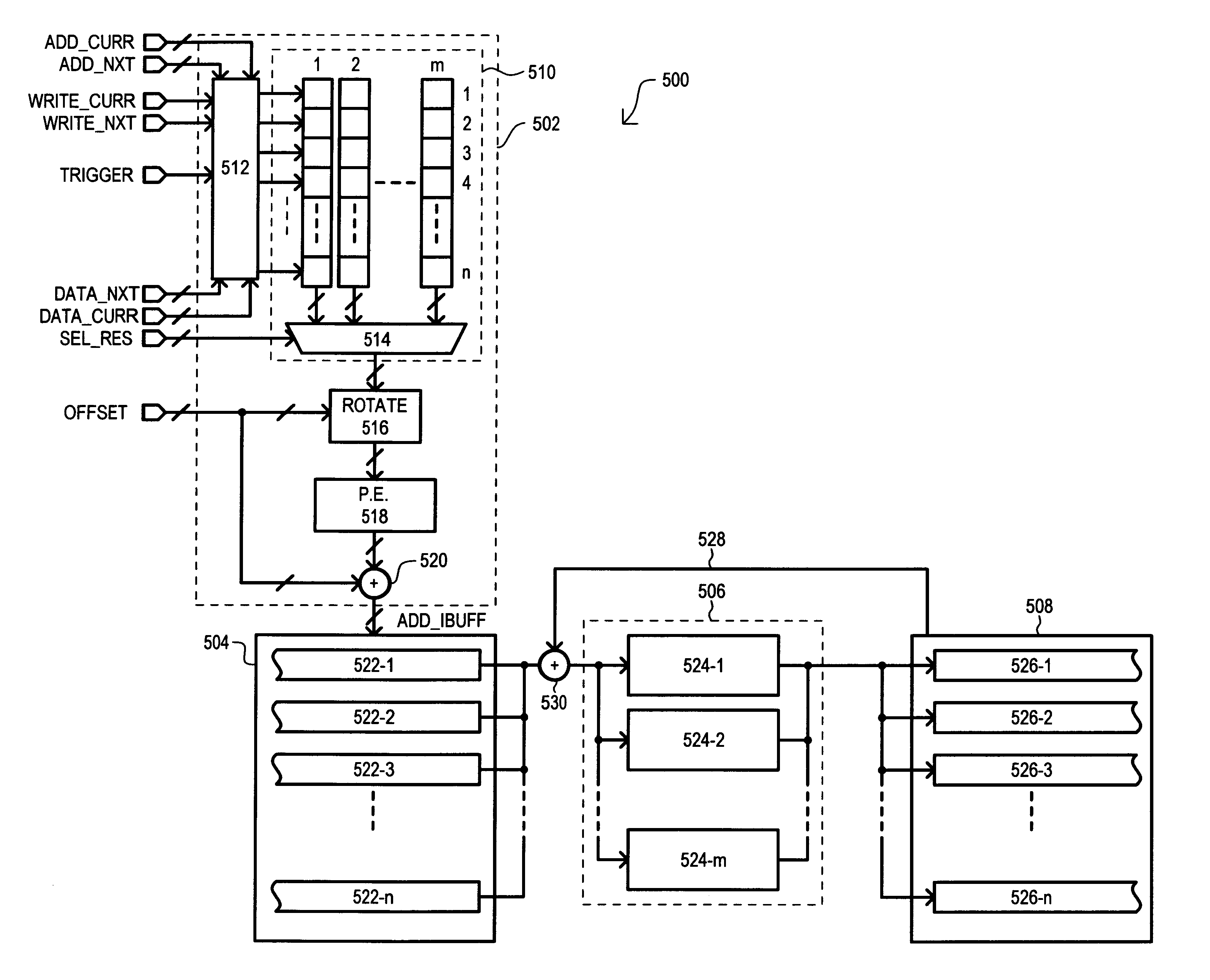
High throughput system for encryption and other data operations
InactiveUS6870929B1Encryption apparatus with shift registers/memoriesPublic key for secure communicationMultiplexerData operations
According to one embodiment, an encryption system (500) includes an input buffer (504) that can provide data blocks from different contexts (522-1 to 522-n) to a selected encryption circuit (524-1 to 524-m) according to a scheduling section (502). A scheduling section (502) can include a register array (510) having rows that each correspond to a context and columns that correspond to an encryption circuit. Each register array (510) row can store one “hot” bit that designates a context with a particular encryption circuit. A column can be selected by a multiplexer (514) and its values prioritized and encoded by a priority encoder (518) to generate an address that results in the selection of a data block from a particular context. Priority may be varied by shifting a column value with a rotate circuit (516) according to an offset value (OFFSET).
Owner:JUMIPER NETWORKS INC
Efficient volume encryption
InactiveUS20120216052A1Unauthorized memory use protectionHardware monitoringComputerized systemComputer science
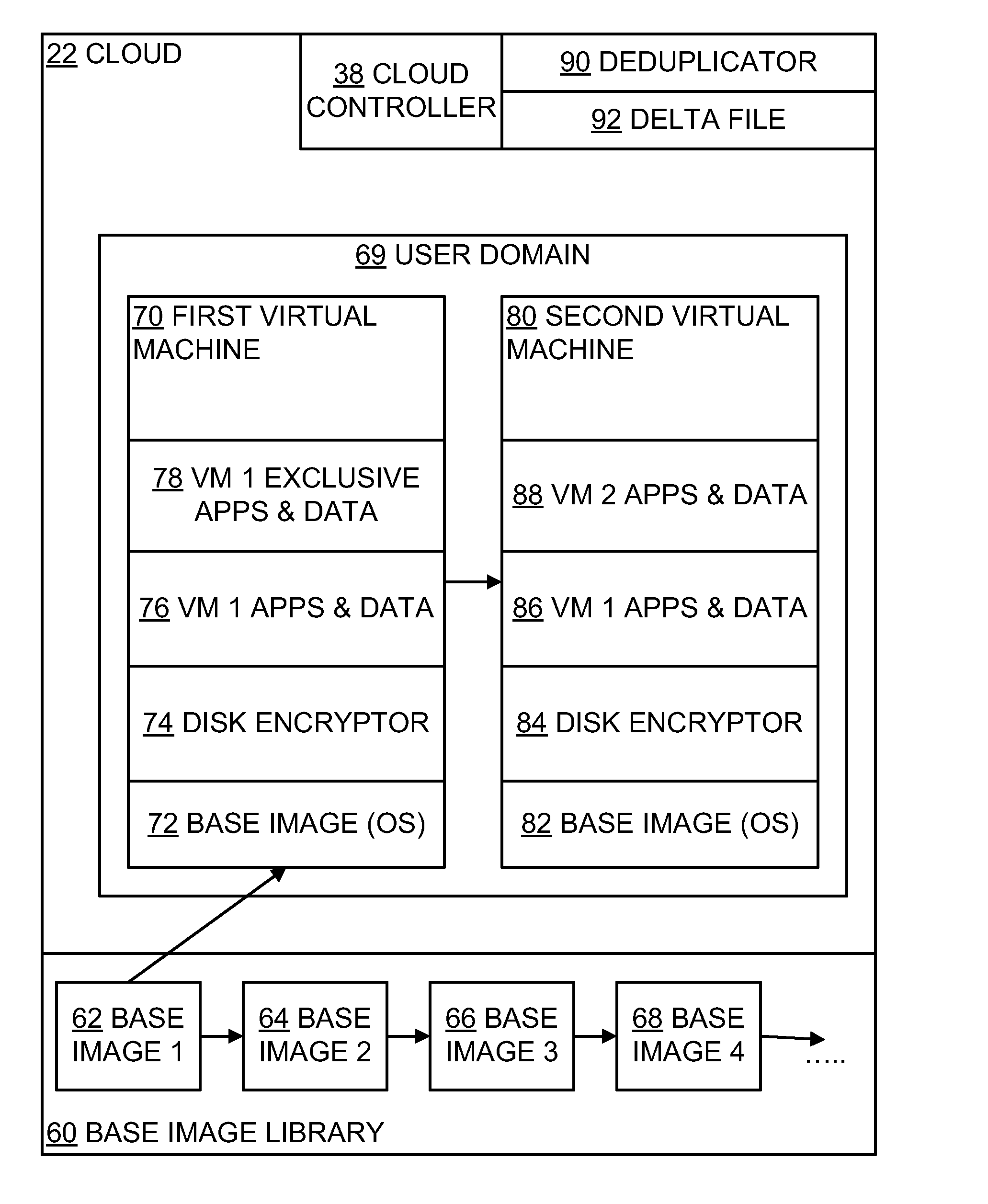
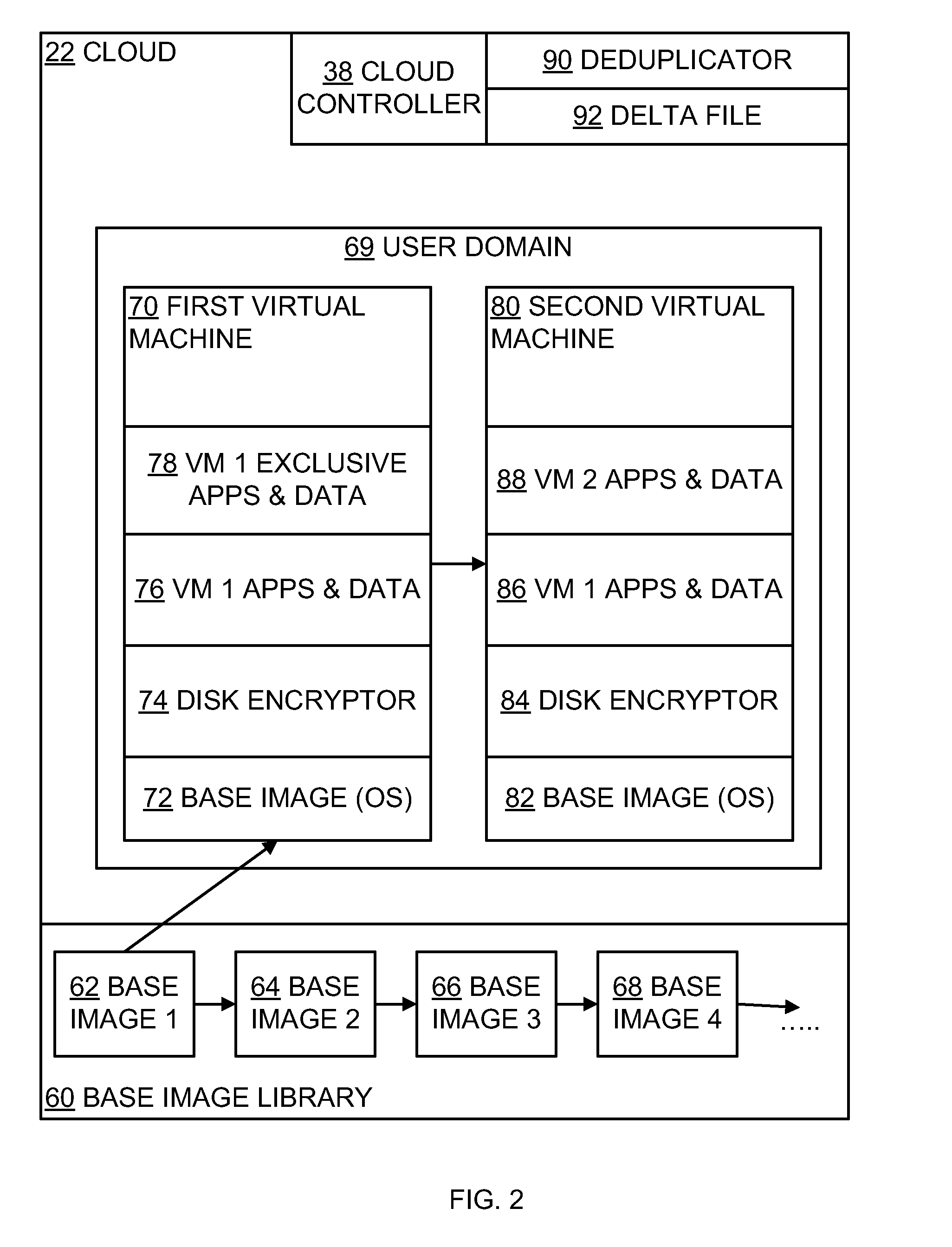
A computer system comprises a first region including a base image in the form of machine readable code stored on a non-volatile storage medium, a second region including a machine image in the form of machine readable code stored on a non-volatile storage medium, and a deduplicator. The second region machine image comprises a base part sufficiently similar to the base image for deduplication, and a part special to the second region machine image. The first region base image and the second region machine image are deduplicated by the deduplicator. The second region special part is encrypted by full disk encryption using a key not available to the first region. Methods of, and computer programs for, implementing such a system are described.
Owner:SAFENET
Network partitioning using encryption
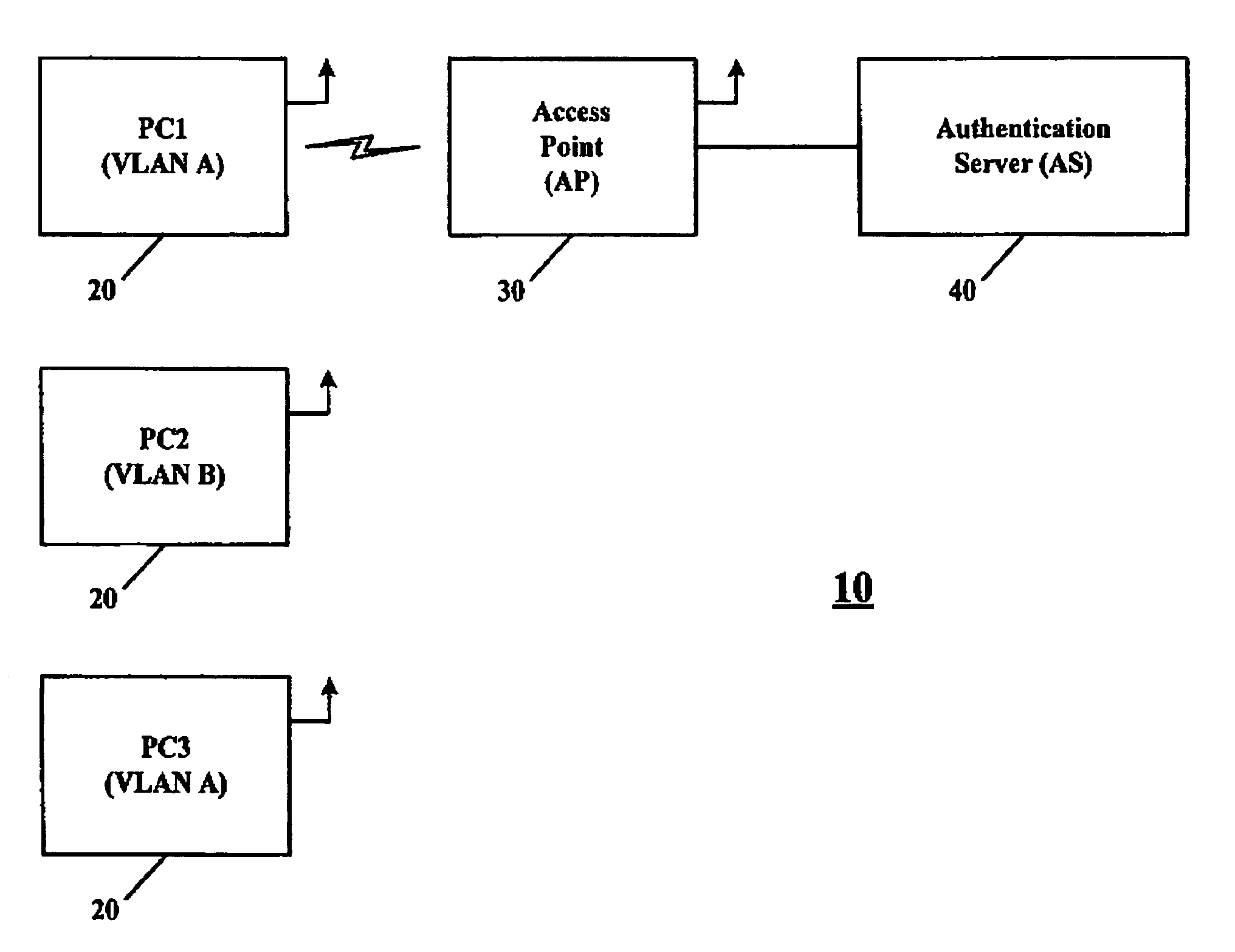
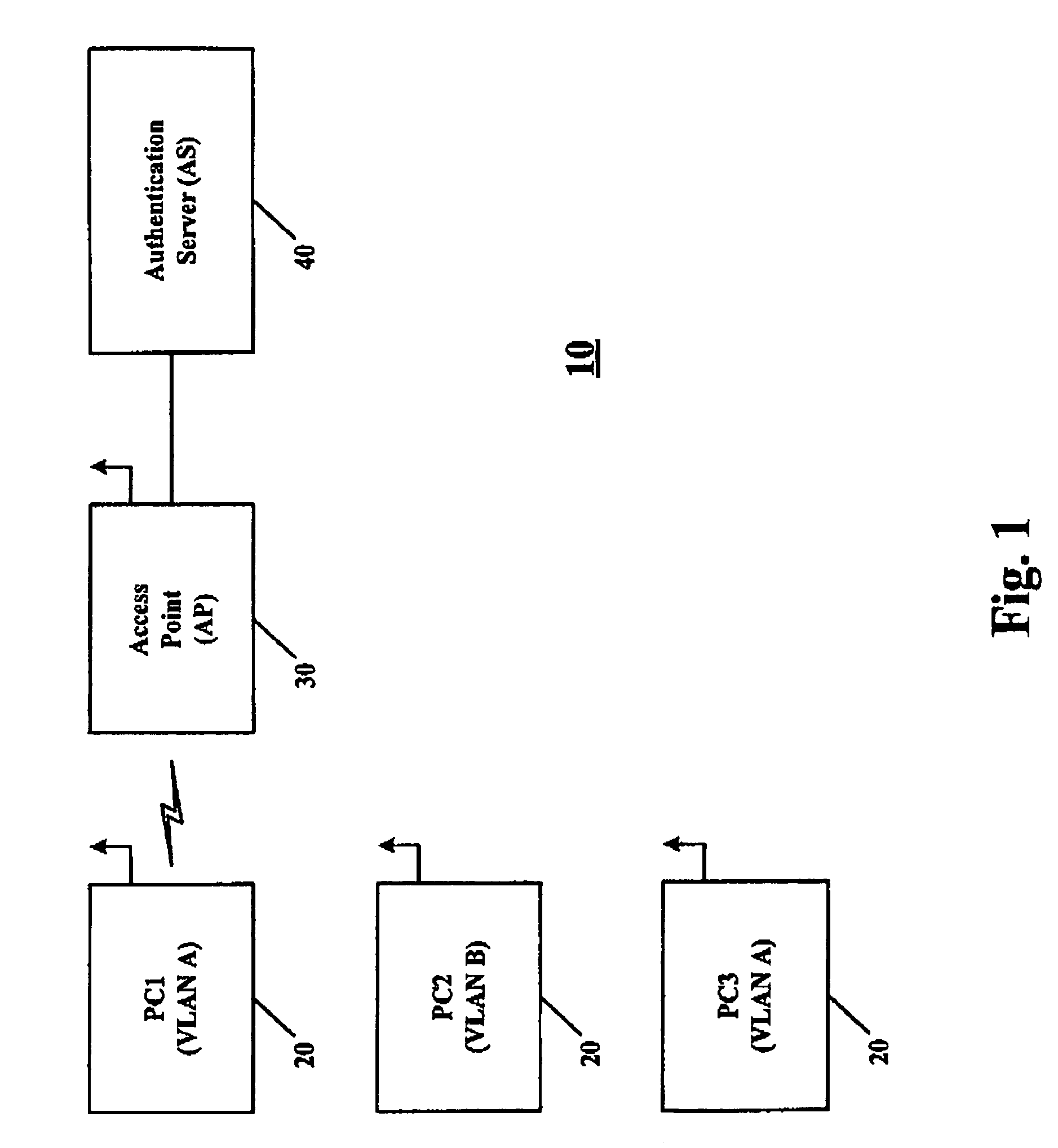
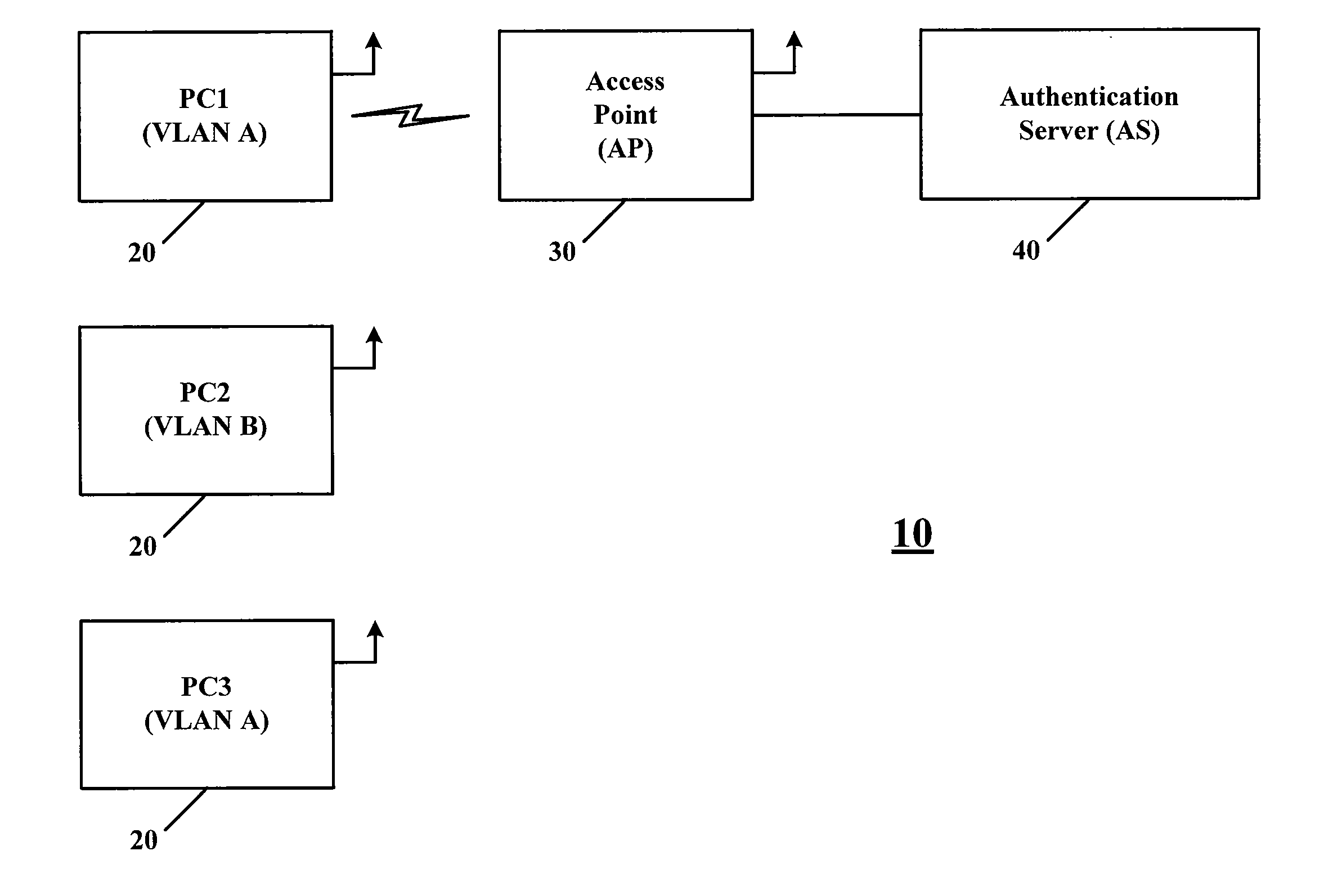
InactiveUS7194622B1Change the environmentSuitable environmentSecret communicationSecuring communicationVirtual LANEncryption
A system for providing a Virtual Local Area Network (VLAN) by use of an encryption states or encryption keys for identifying a VLAN. A table of data including a VLAN and an associated encryption state or key is provided for assignment of encryption states or keys, for devices in a wireless local area network.
Owner:CISCO TECH INC
Network partitioning using encryption
InactiveUS20070121565A1Key distribution for secure communicationRadio/inductive link selection arrangementsVirtual LANEncryption
In an example embodiment, a system for providing a Virtual Local Area Network (VLAN) by use of encryption states or encryption keys for identifying a VLAN. A table of data including a VLAN and an associated encryption state or key is provided for assignment of encryption states or keys, for devices in a wireless local area network.
Owner:CISCO TECH INC
Systems and methods for security hardening of data in transit and at rest via segmentation, shuffling and multi-key encryption
ActiveUS20150310219A1Hardening securityHardening confidentialityKey distribution for secure communicationMultiple keys/algorithms usageContextual integrityComputerized system
Systems and methods for security hardening of a file in transit and at rest via segmentation, shuffling and multi-key encryption are presented. The method including segmenting at a first computer system a file into a plurality of file segments, and encrypting the plurality of file segments using a plurality of encryption keys in order to generate a corresponding plurality of encrypted file segments, wherein each file segment of the plurality of file segments is encrypted using a respective encryption key of the plurality of encryption keys. Additionally included is bidirectional data transformation of a file by obfuscating at a first computer system digital values of the file in order to generate corresponding obfuscated digital values of the file, wherein the obfuscated digital values of the file retain their contextual integrity and referential integrity
Owner:TOPIA TECH
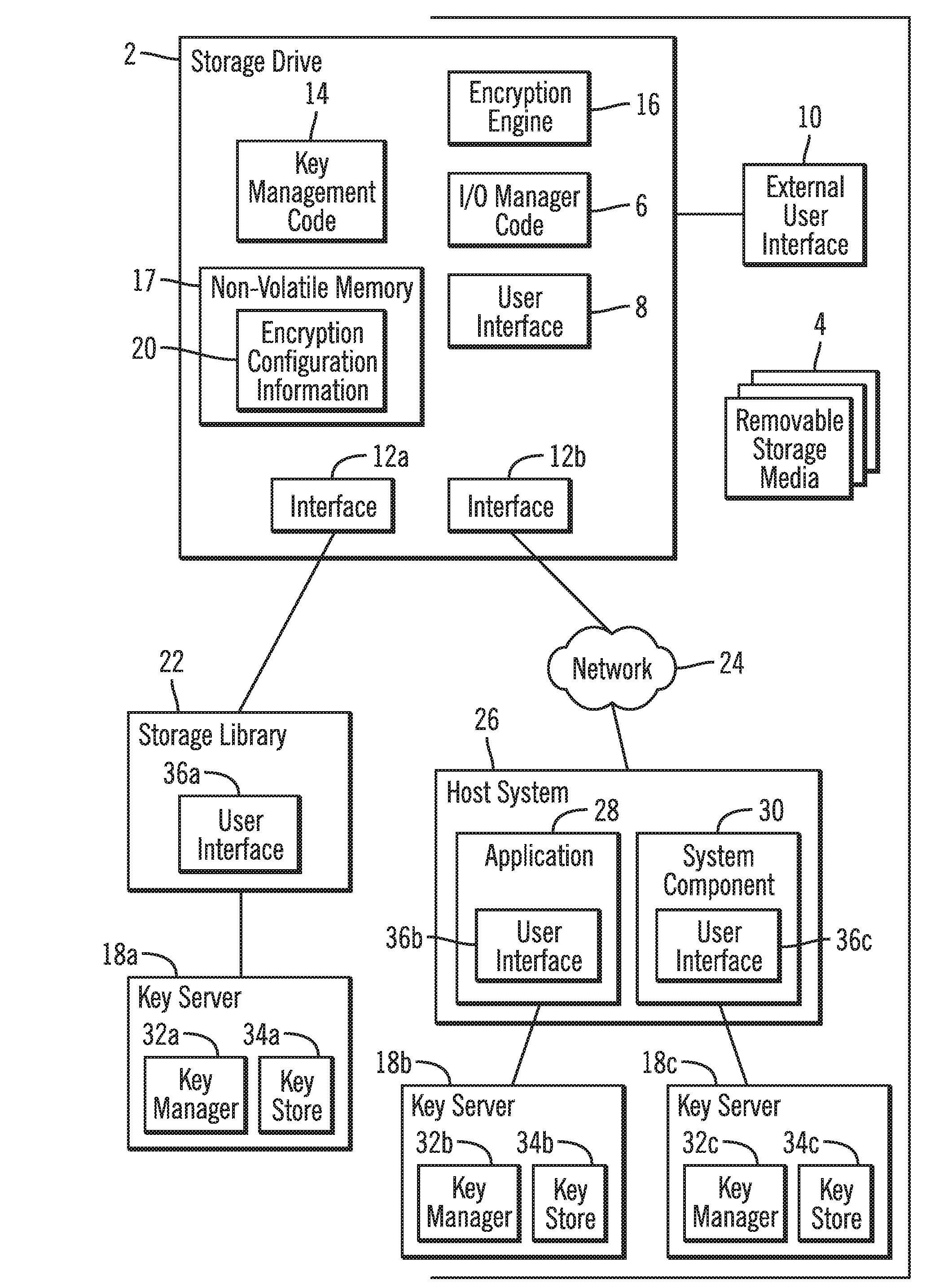
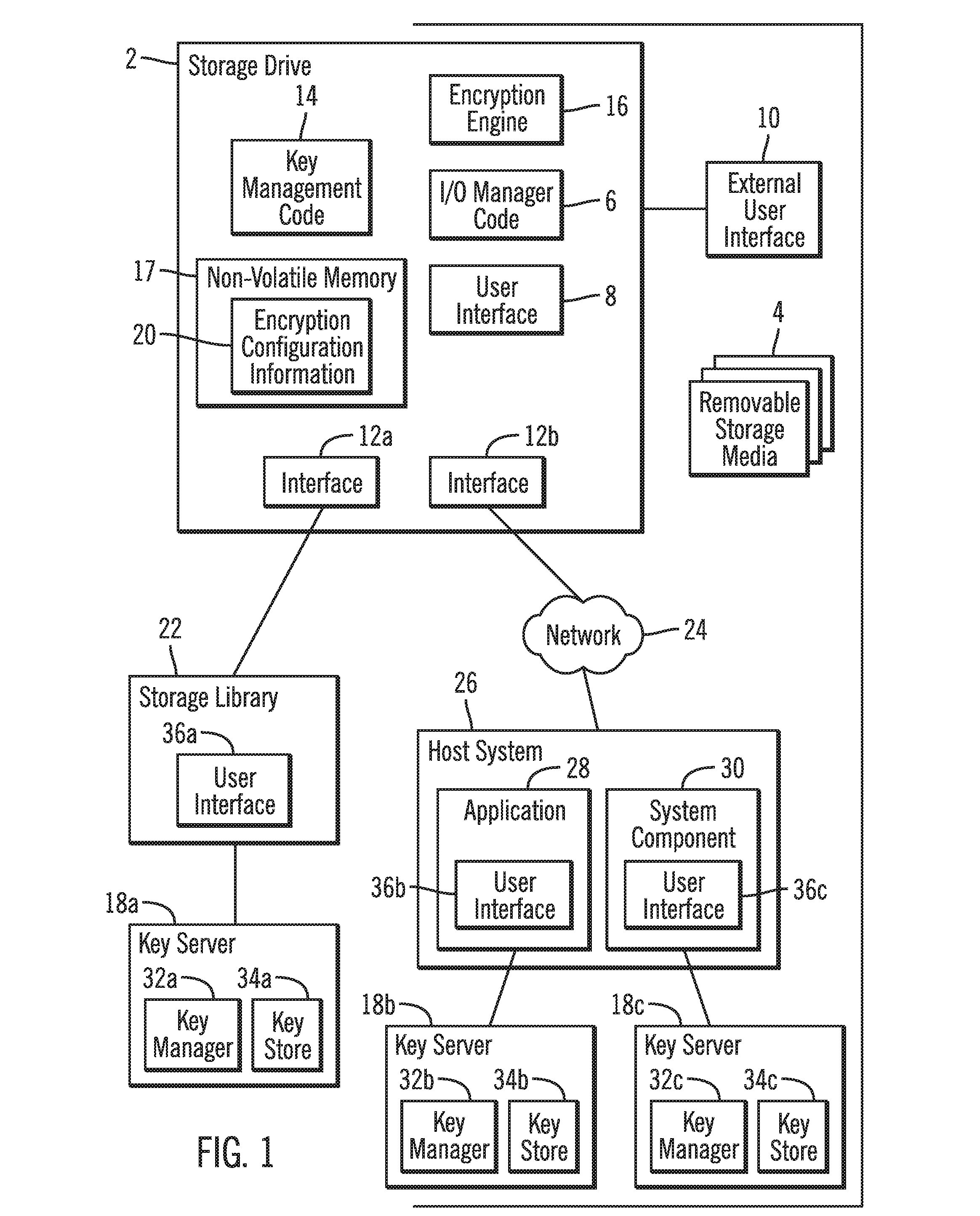
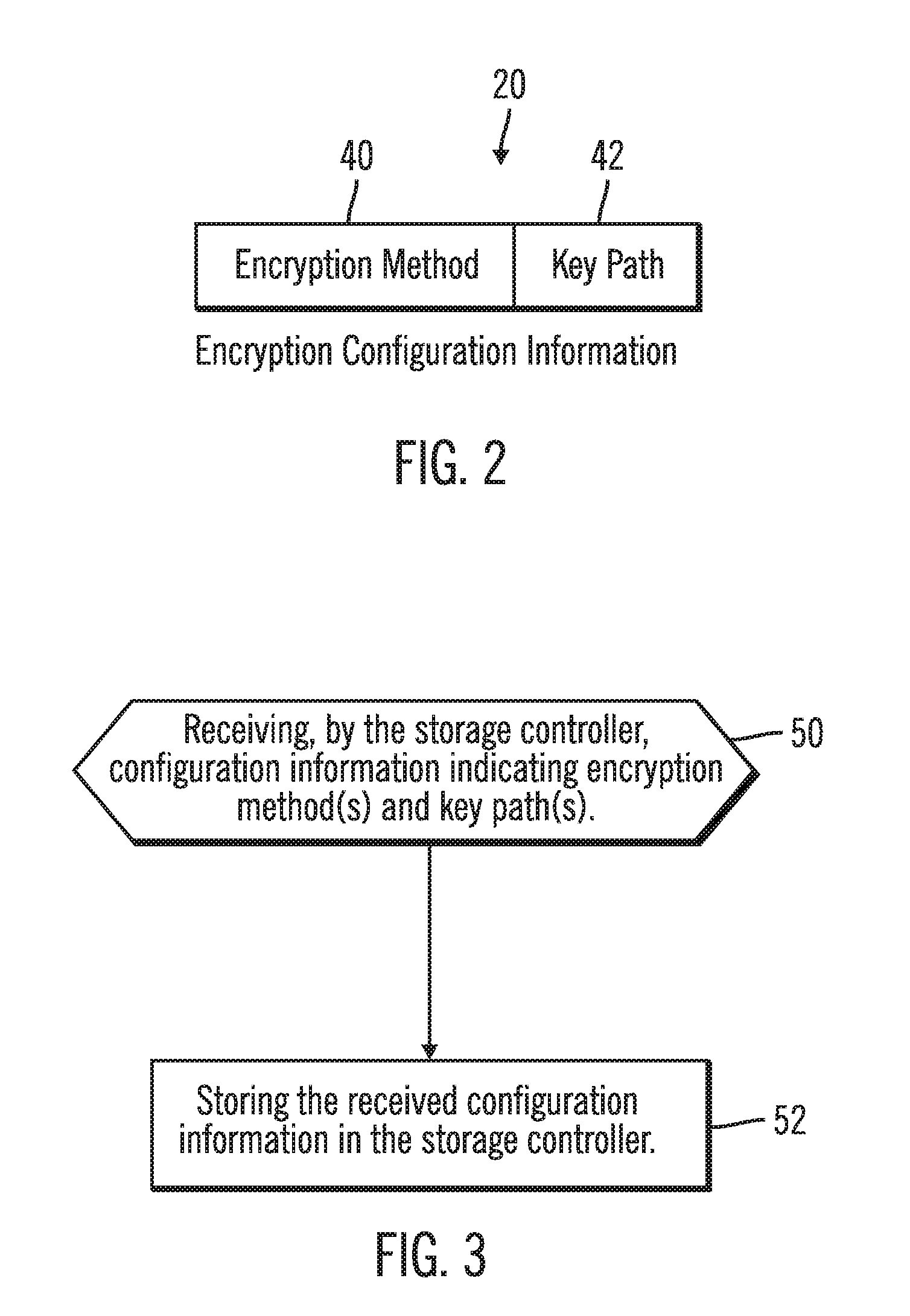
Configuring a storage drive to communicate with encryption and key managers
ActiveUS20080065882A1Unauthorized memory use protectionHardware monitoringData operationsRemovable media
Provided are a method, system, and article of manufacture for configuring a storage drive to communicate with encryption and key managers. A storage drive receives a request to access a coupled removable storage media for drive operations. The storage drive obtains encryption status for the coupled removable storage media from an encryption manager. The storage drive determines from the obtained encryption status whether to encrypt the coupled removable storage media to access. The storage drive obtains at least one key from a key manager in response to determining to encrypt with respect to the coupled removable storage media. The storage drive performs data operations using the at least one key to encrypt data.
Owner:IBM CORP
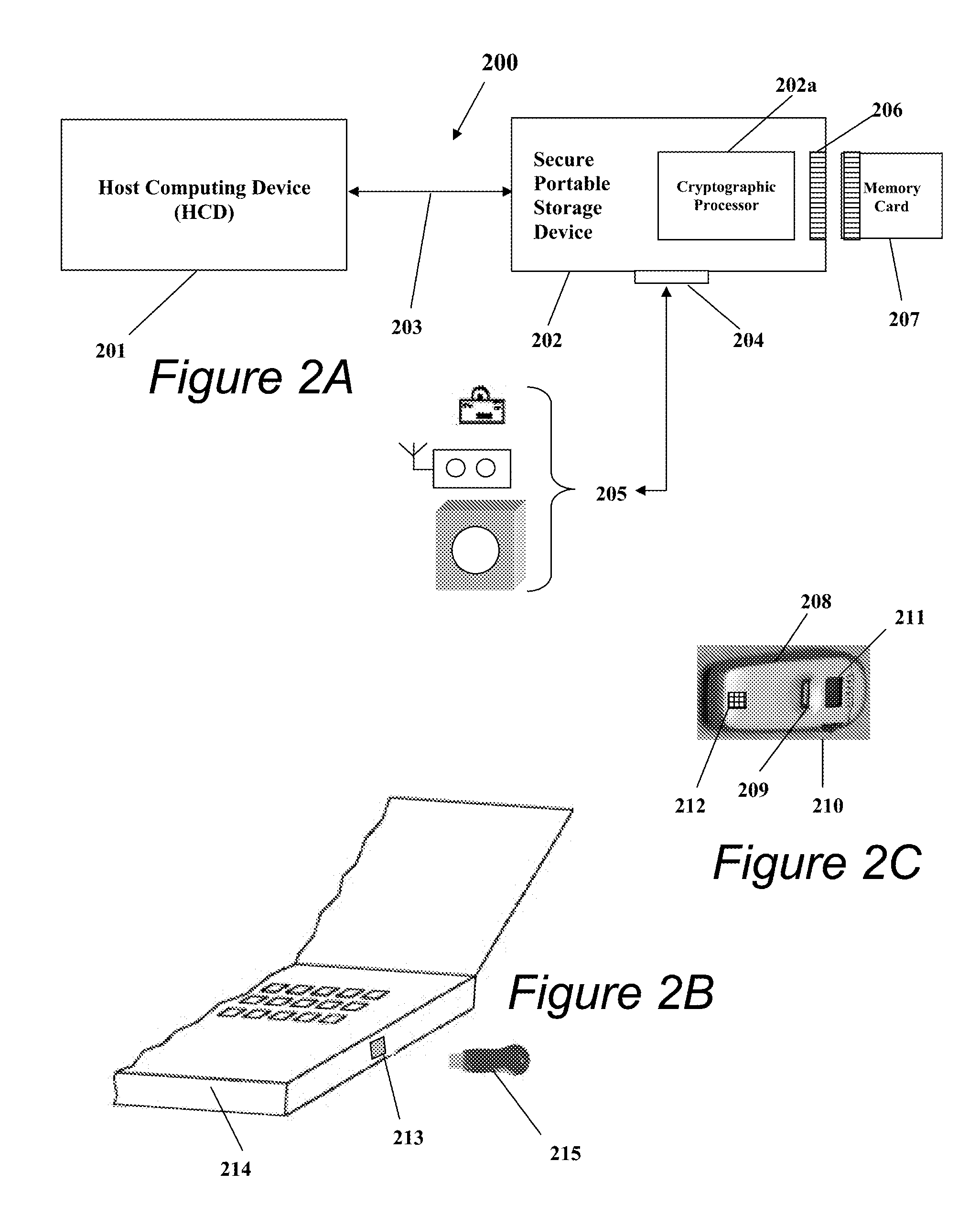
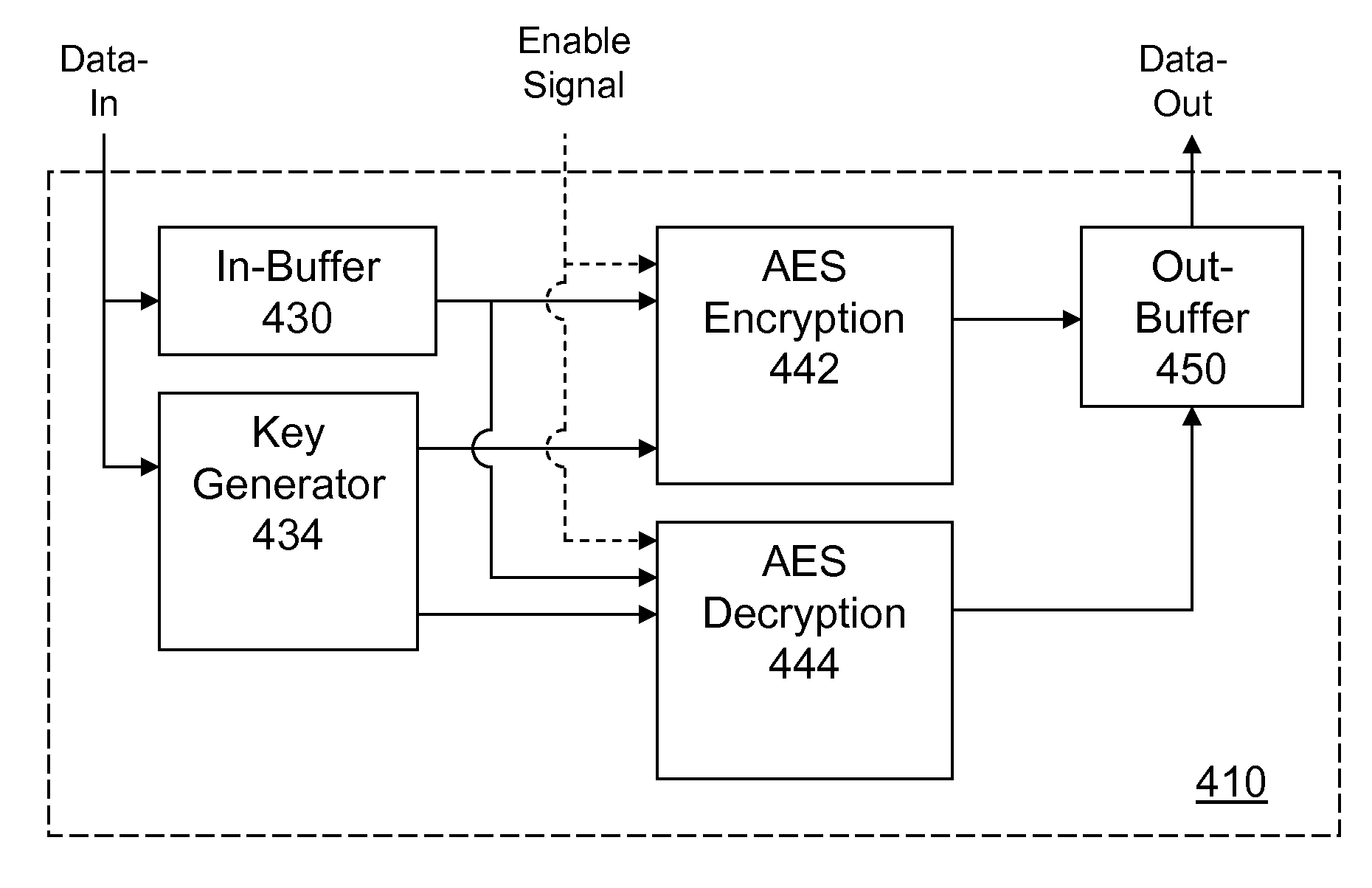
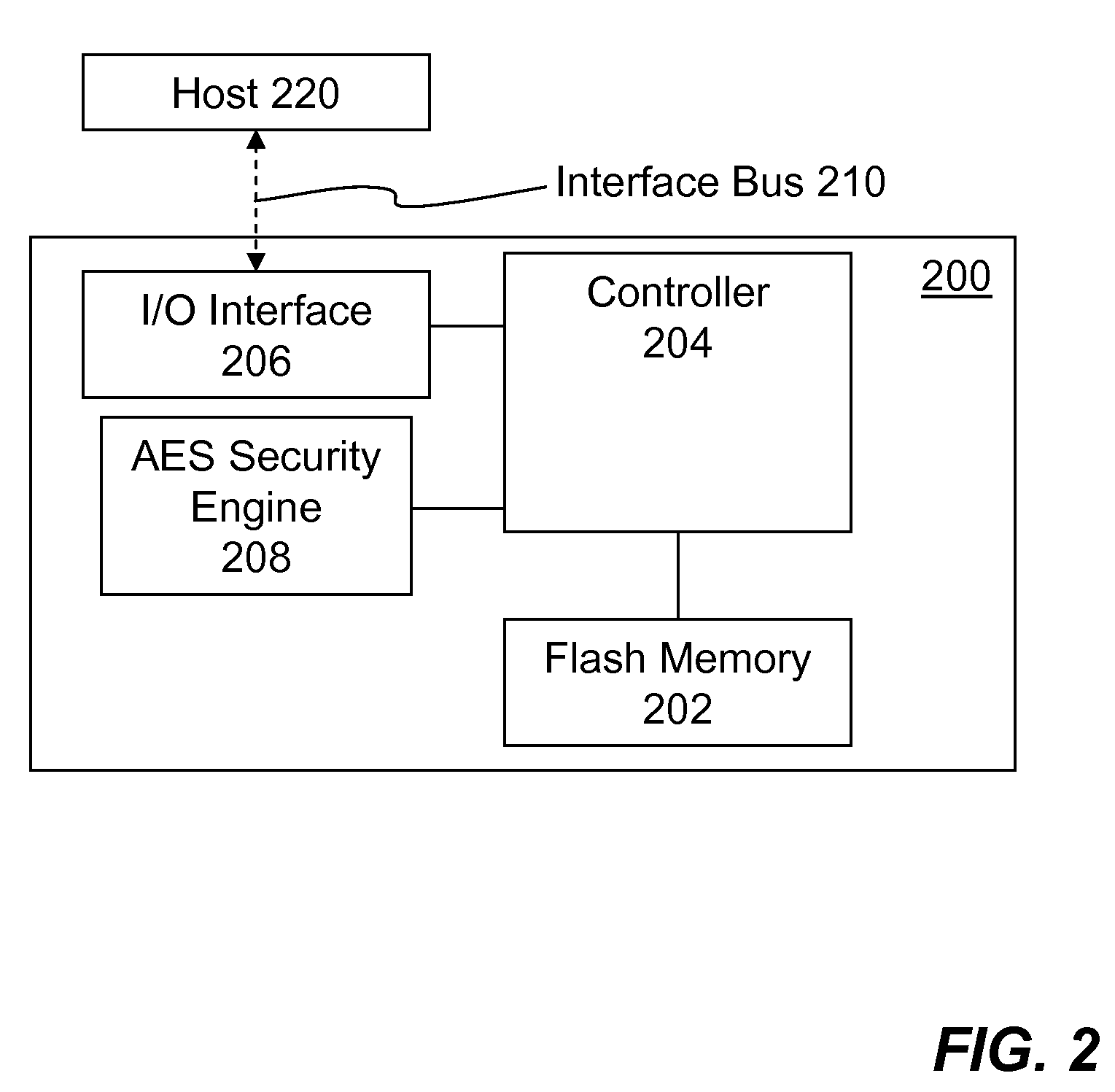
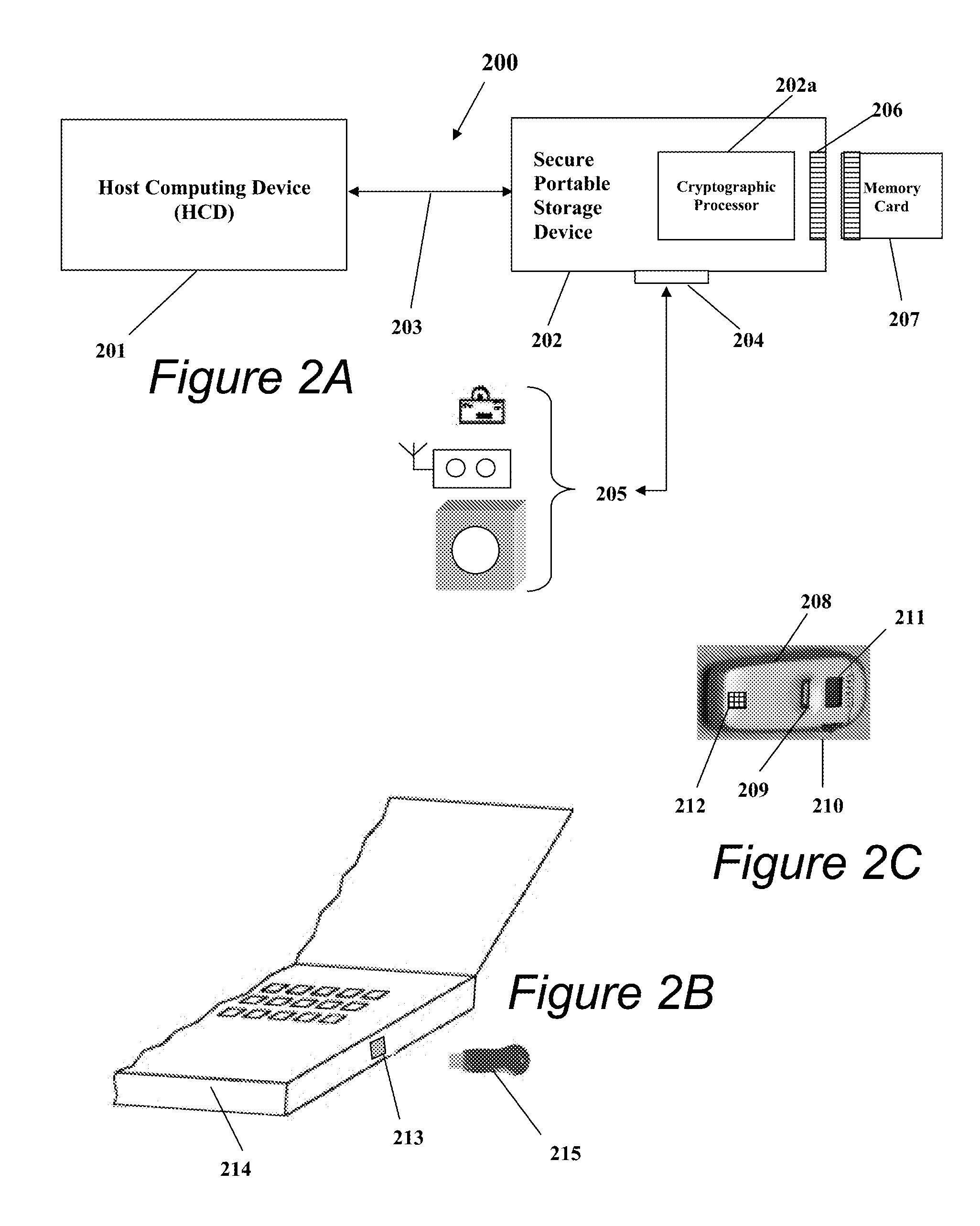
Portable Electronic Storage Devices with Hardware Security Based on Advanced Encryption Standard
InactiveUS20080192928A1Improve securityUnauthorized memory use protectionInternal/peripheral component protectionKey sizeAdvanced Encryption Standard
Portable electronic storage devices with hardware based security are described. According to one exemplary embodiment of the present invention, a portable electronic storage device (PESD) comprises a security engine integrated thereon. The security engine is configured to provide data encryption, data decryption, and encryption / decryption key (referred to as a key) generation according to a security standard (e.g., Advance Encryption Standard (AES)). AES is a symmetric encryption algorithm processing data in block of 128 bits. Under the influence of a key, a 128-bit data block is encrypted by transforming the data block in a unique way into a new data block of the same size. AES is symmetric sine the same key is used for encryption and the reverse transformation (i.e., decryption). The only secret necessary to keep for security is the key. AES may use different key-lengths (i.e., 128-bit, 192-bits and 256-bits).
Owner:SUPER TALENT ELECTRONICS
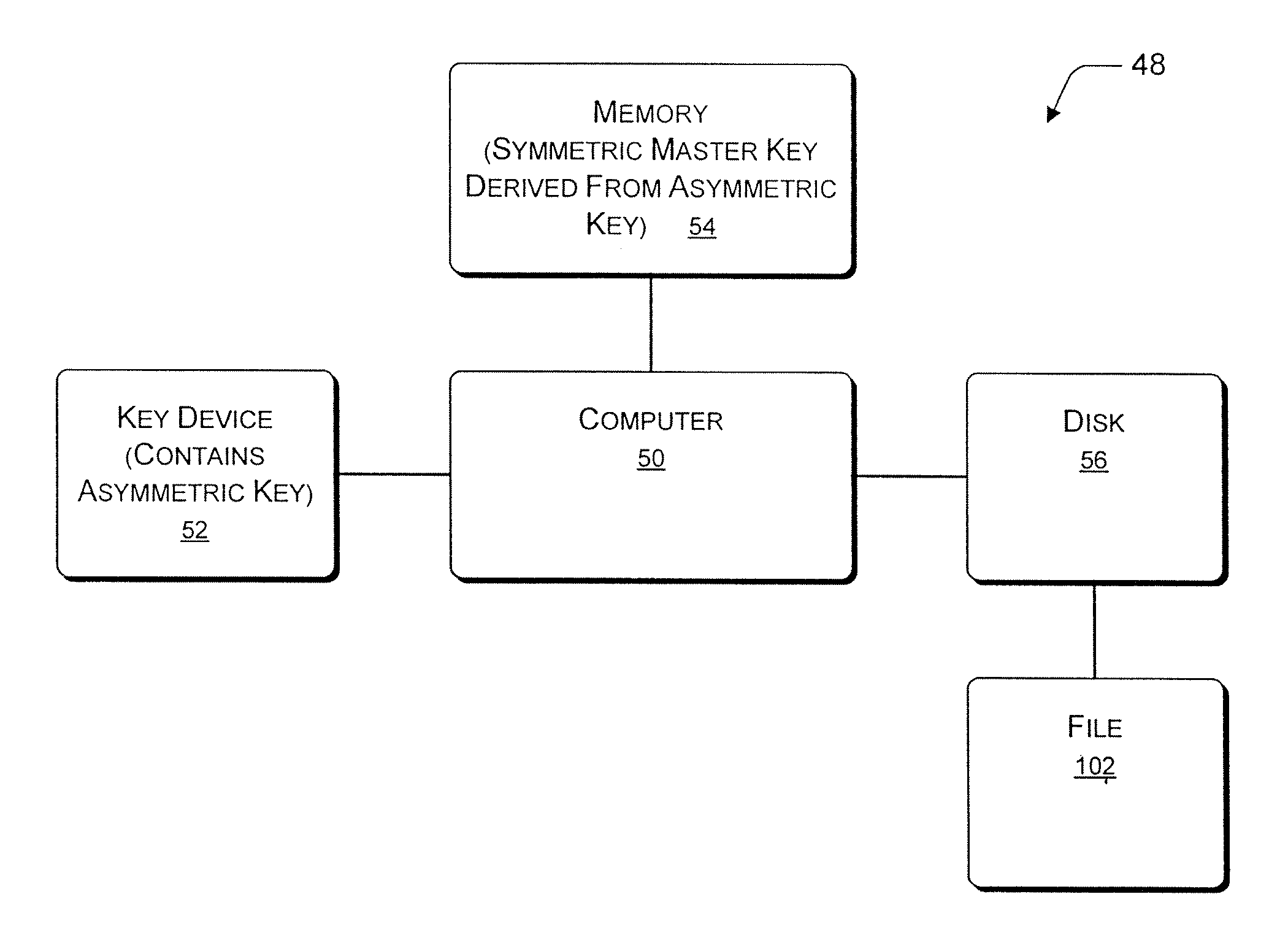
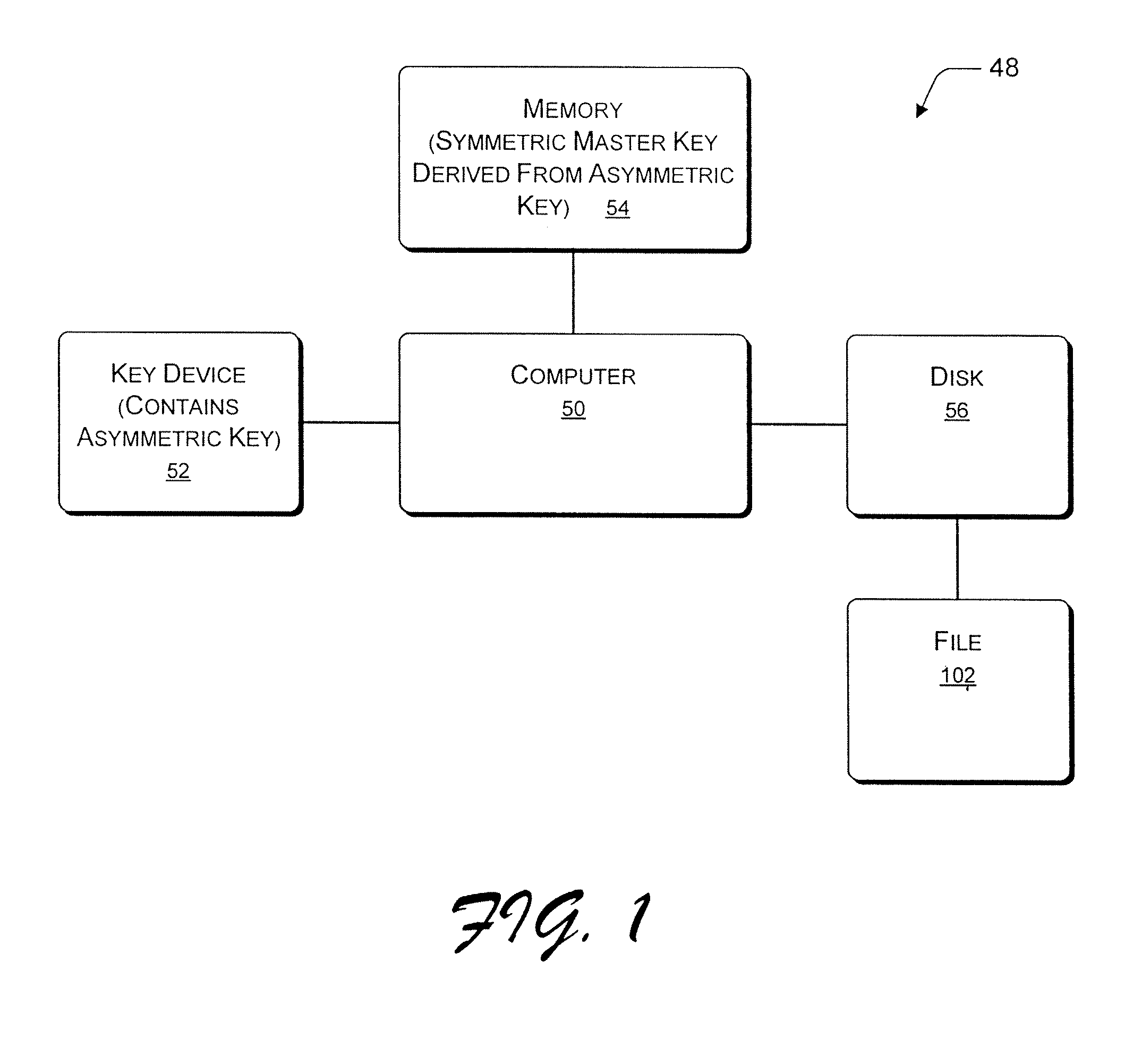
Deriving a symmetric key from an asymmetric key for file encryption or decryption
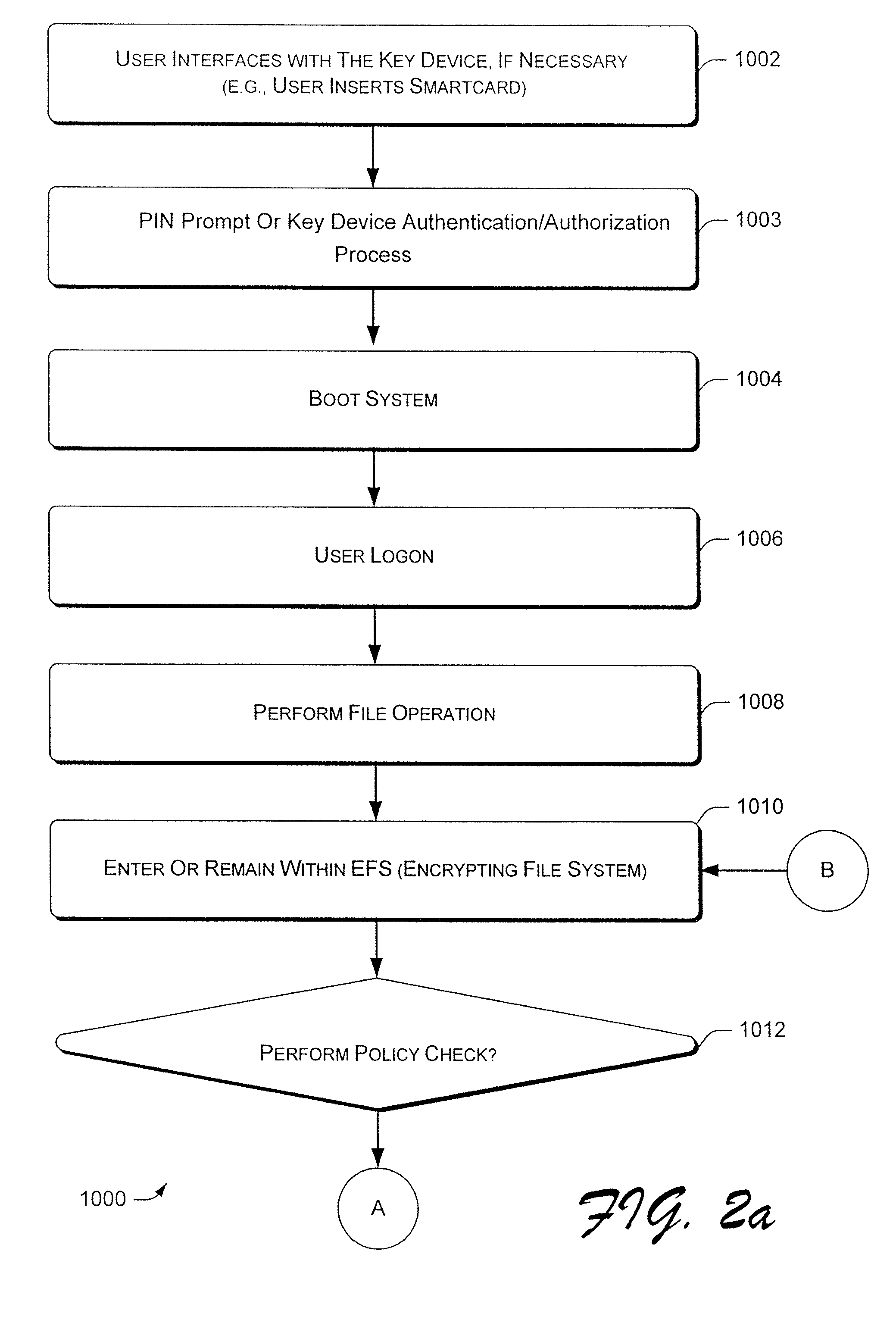
InactiveUS7382883B2Efficient and effectiveKey distribution for secure communicationPublic key for secure communicationMaster keyComputer memory
One aspect relates to a process and associated device that provides a private key of an asymmetric key pair in a key device. A symmetric master key is derived from the private key of the asymmetric key pair. The symmetric master key is stored in a computer memory location. The symmetric master key is used to encrypt or decrypt a file encryption key. The file encryption key can encrypt or decrypt files. In another aspect, the user can still access the files even if a user deactivates the key device by encrypting or decrypting the file encryption key directly from the symmetric master key.
Owner:MICROSOFT TECH LICENSING LLC
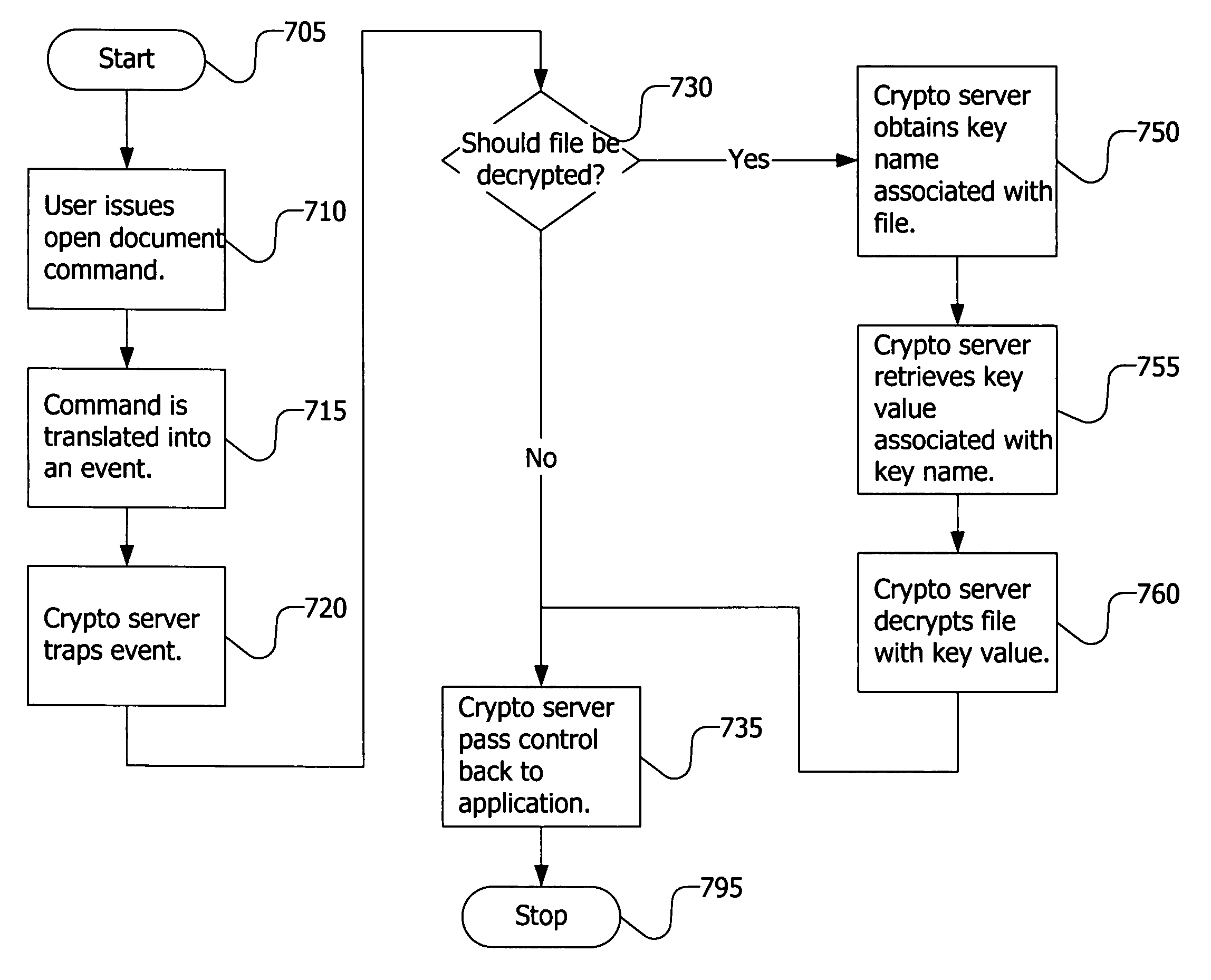
System and method for file encryption and decryption
InactiveUS20080104417A1Public key for secure communicationUser identity/authority verificationData decryptionDisk encryption
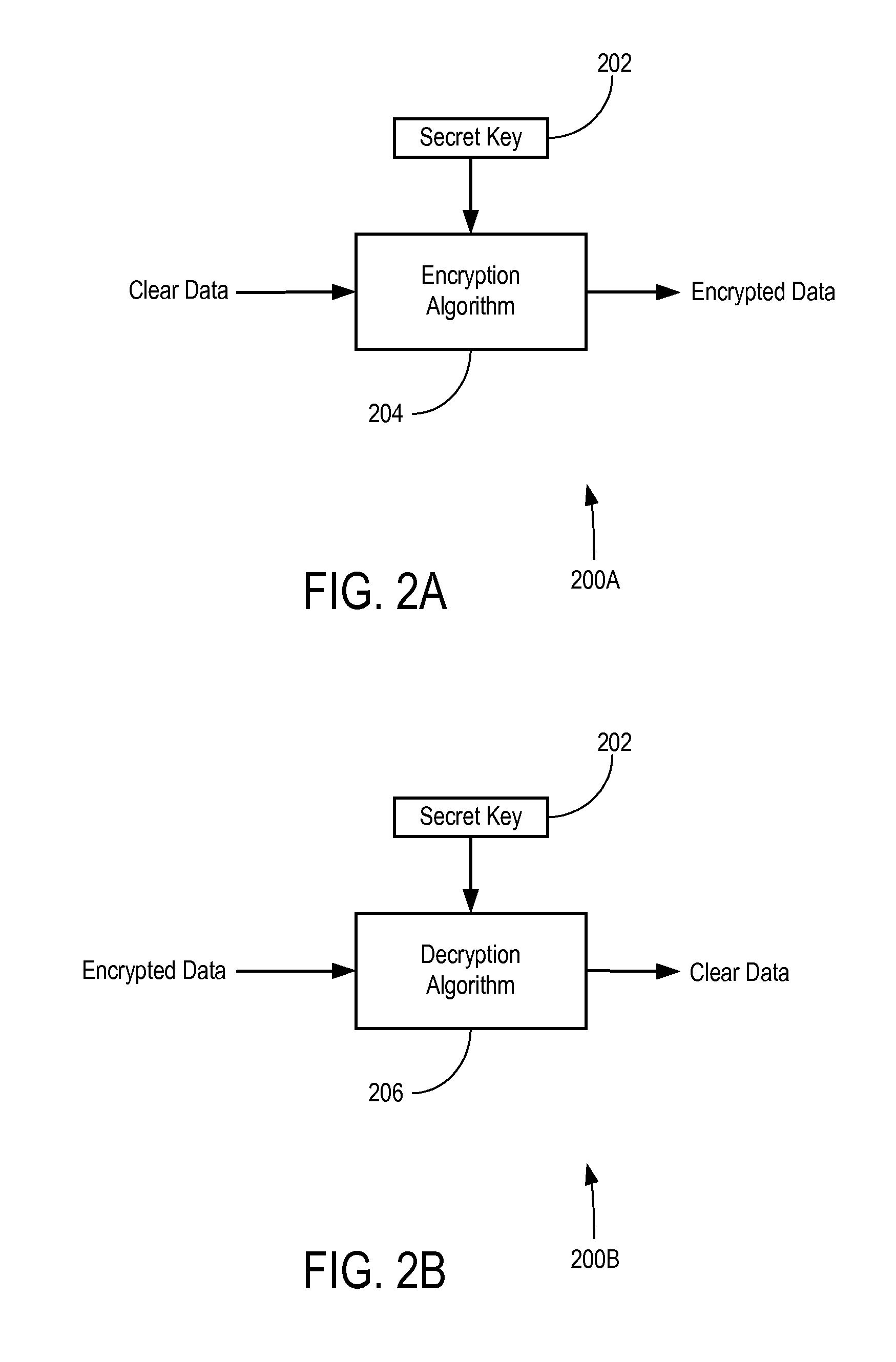
There is disclosed a system and method for file encryption and decryption. In an embodiment, a method of encrypting a file on backup media involves encrypting clear data using a data encryption key applied to a data encryption algorithm and outputting encrypted data; storing the encrypted data on the backup media; encrypting the data encryption key using a reference cryptographic key applied to a key encryption algorithm and outputting an encrypted data encryption key; and storing the encrypted data encryption key and reconstitution data in a header of the backup media. The encrypted data may be subsequently decrypted by identifying the reference cryptographic key using the reference cryptographic key name; applying the reference cryptographic key to a key decryption algorithm to decrypt the encrypted data encryption key; and applying the decrypted data encryption key to a data decryption algorithm to decrypt the encrypted data.
Owner:IBM CORP
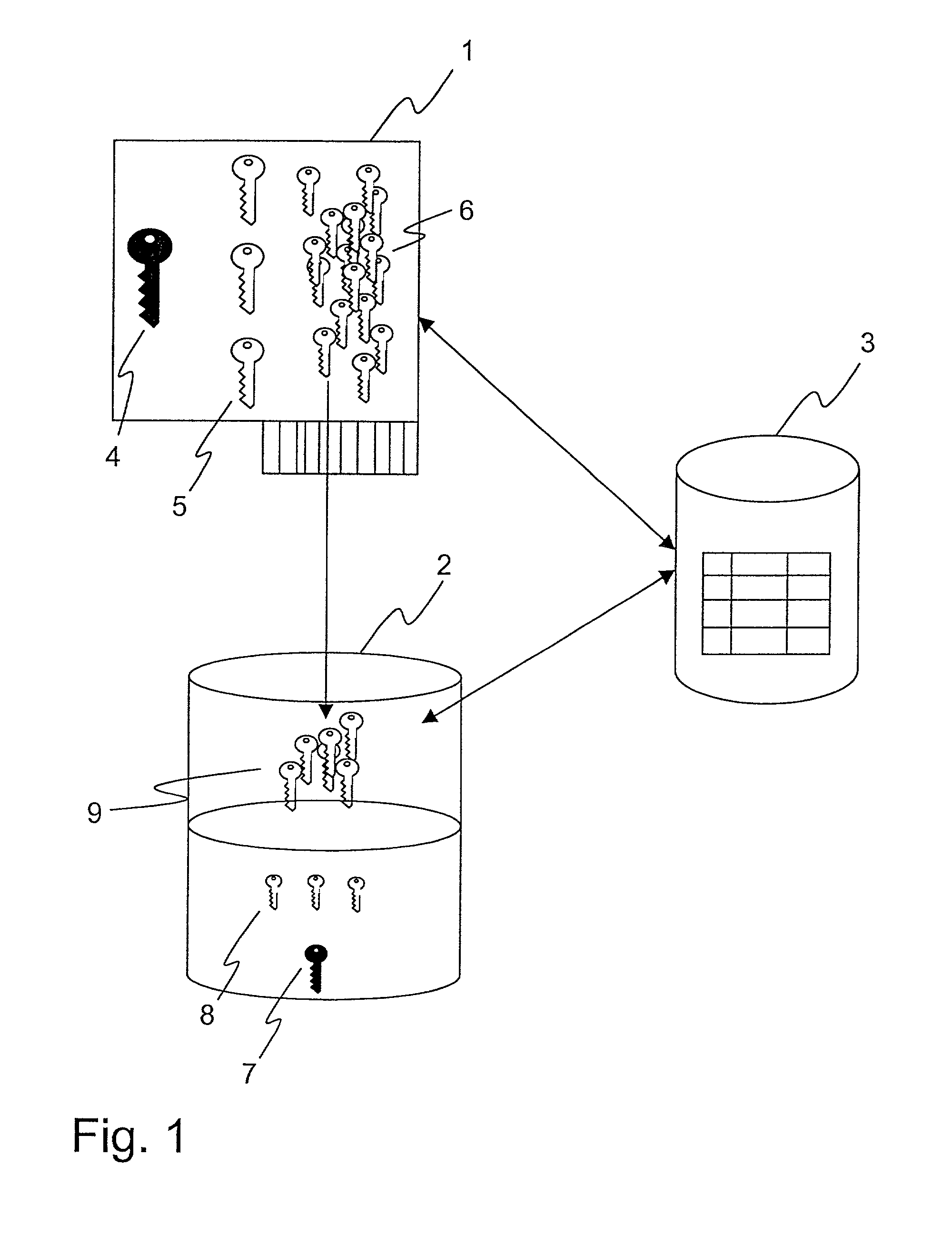
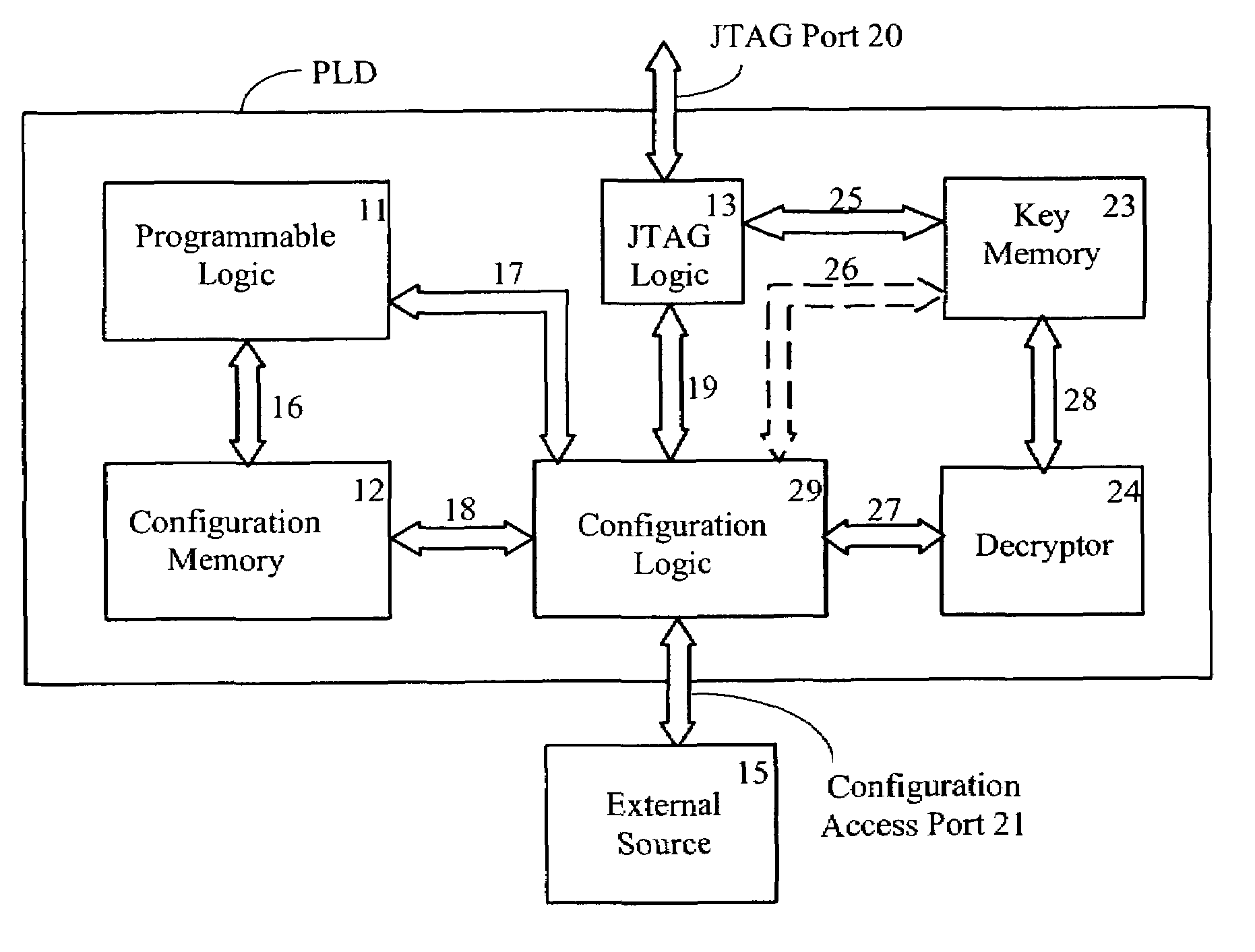
Encryption key for multi-key encryption in programmable logic device
InactiveUS6957340B1Multiple keys/algorithms usageUnauthorized memory use protectionProgrammable logic deviceEncryption
It is sometimes desirable to protect a design used in a PLD from being copied. If the design is stored in a different device from the PLD and read into the PLD through a bitstream, an unencrypted bitstream could be observed and copied as it is being loaded. According to the invention, a bitstream for configuring a PLD with an encrypted design includes unencrypted words for controlling loading of the configuration bitstream and encrypted words that actually specify the design.
Owner:XILINX INC
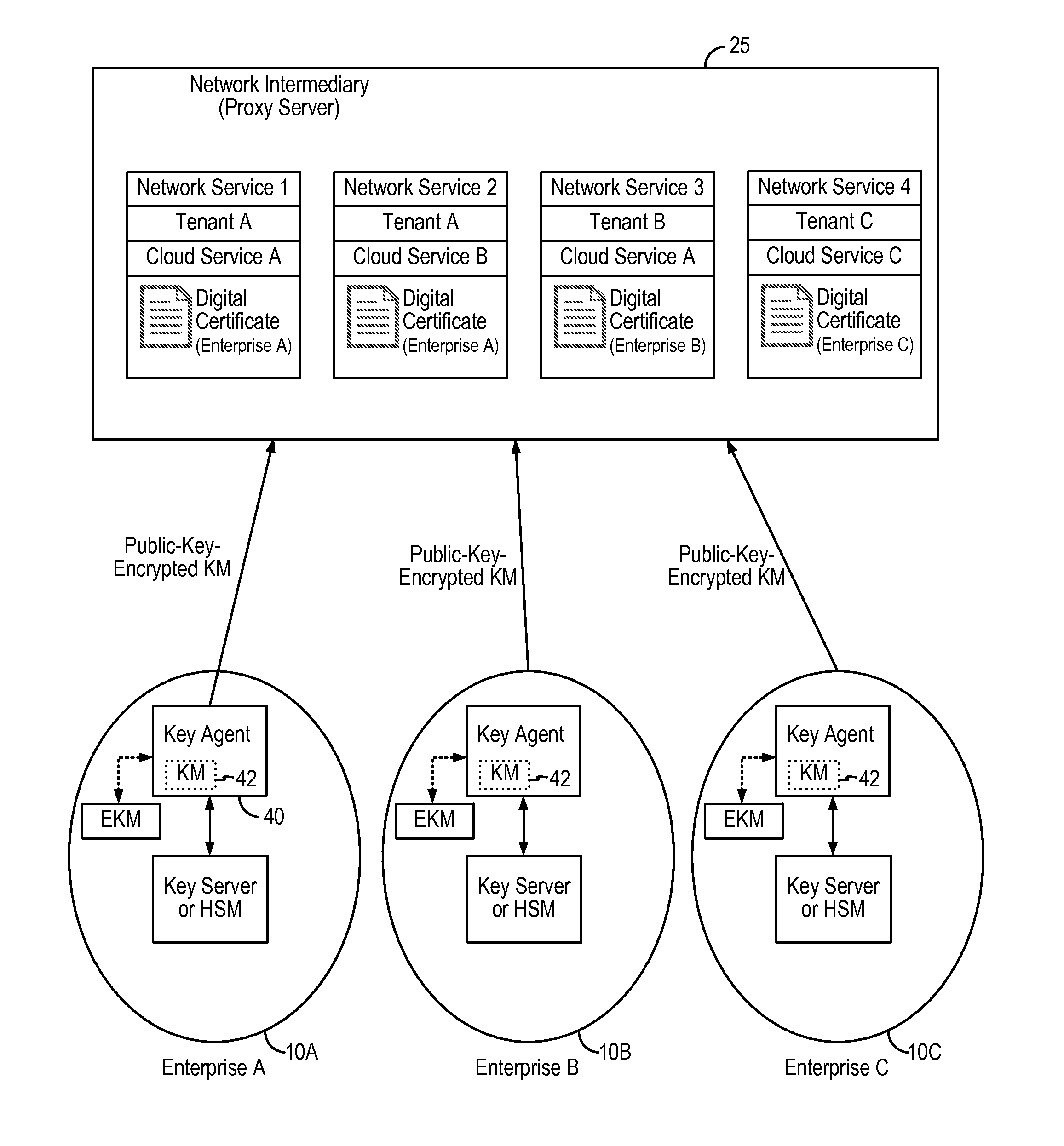
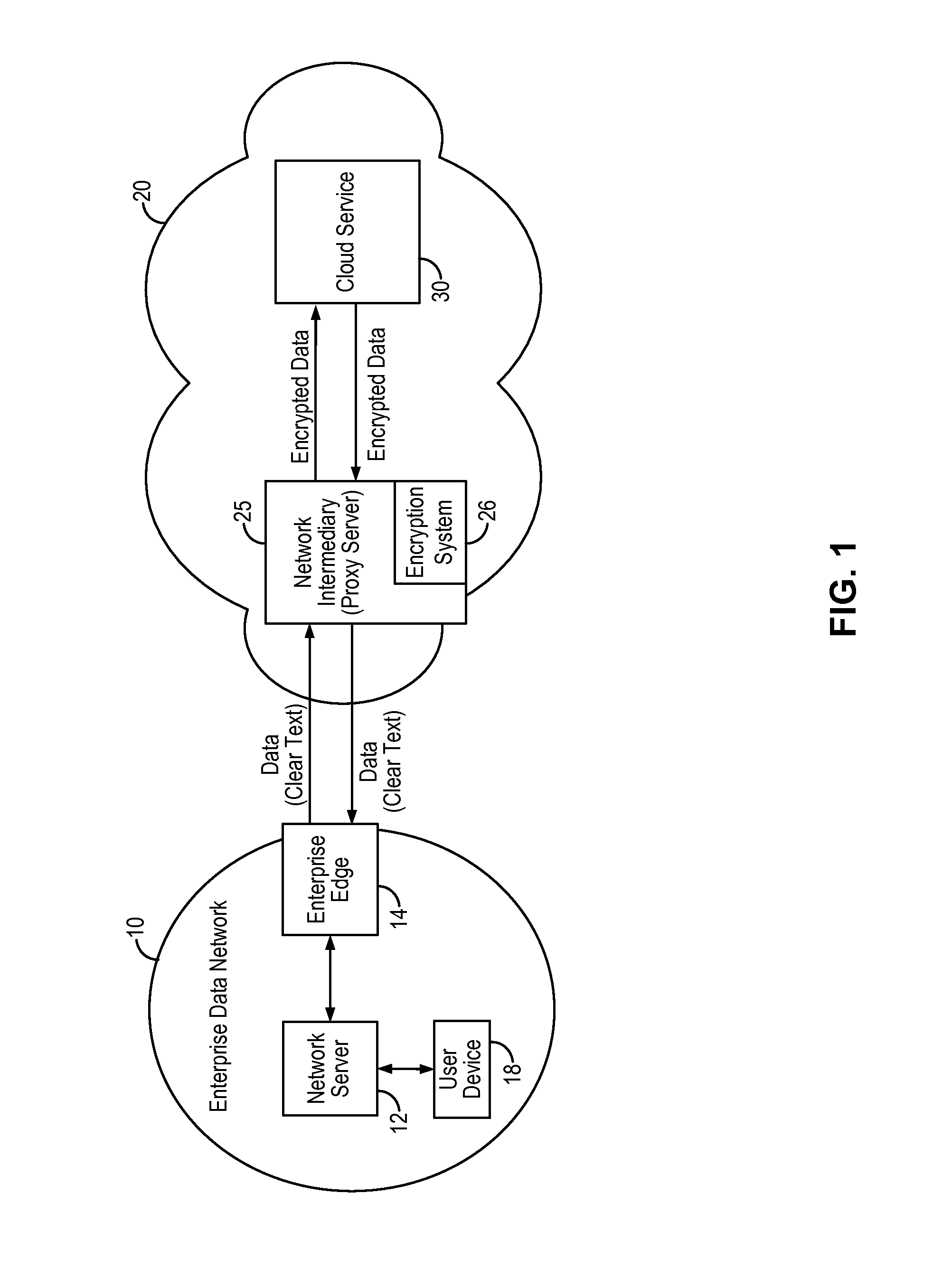
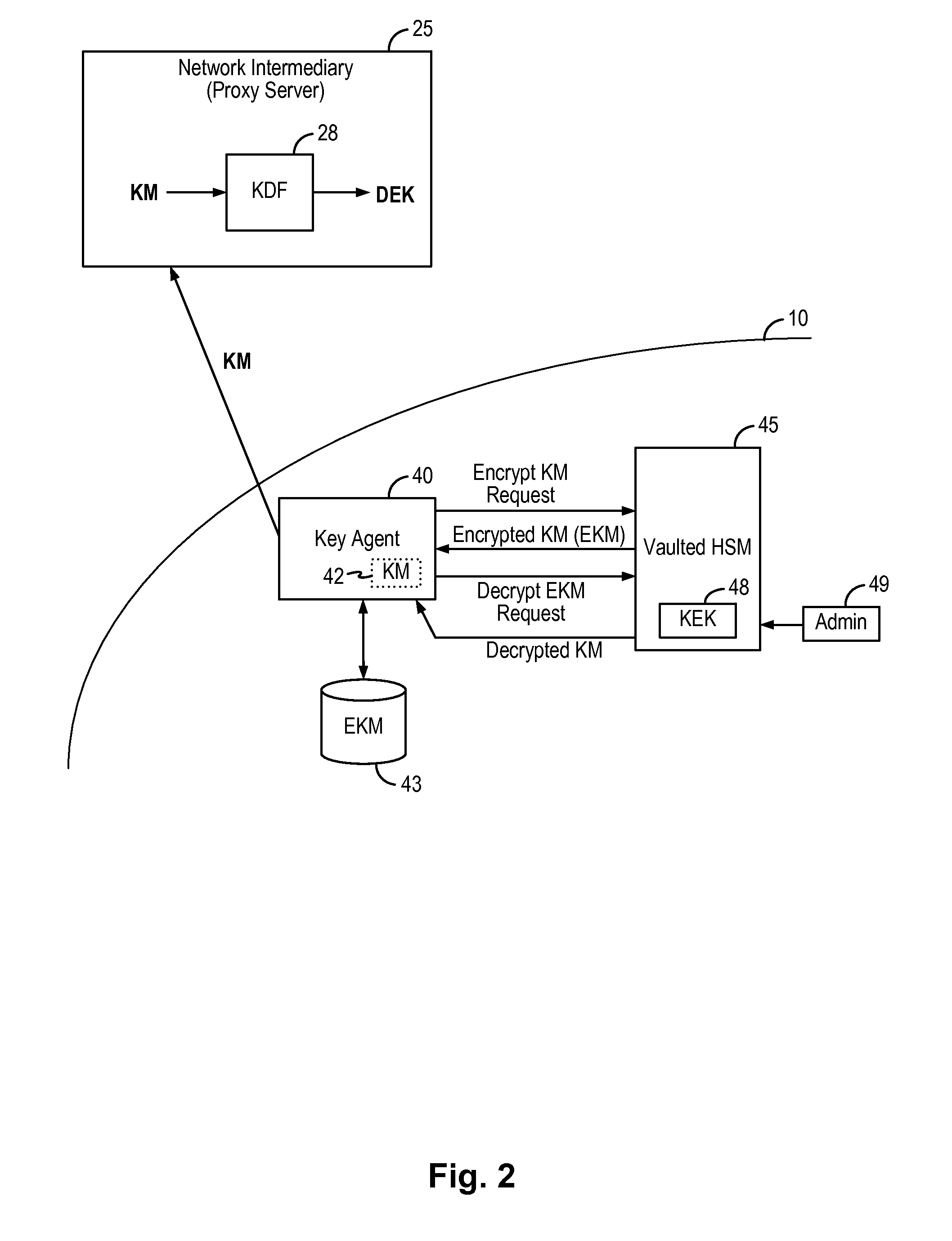
Encryption in the cloud using enterprise managed keys
An encryption key management system and method implements enterprise managed encryption key for an enterprise using encryption for cloud-based services. In some embodiments, the enterprise deploys a key agent on the enterprise data network to distribute encryption key material to the network intermediary on a periodic basis. The network intermediary receives the encryption key material from the enterprise and stores the encryption key material in temporary storage and uses the received encryption key material to derive a data encryption key to perform the encryption of the enterprise's data. In this manner, the enterprise can be provided with the added security assurance of maintaining and managing its own encryption key while using cloud-based data storage services. The encryption key management system and method can be applied to ensure that the enterprise's one or more encryption keys do not leave the enterprise's premises.
Owner:SKYHIGH SECURITY LLC
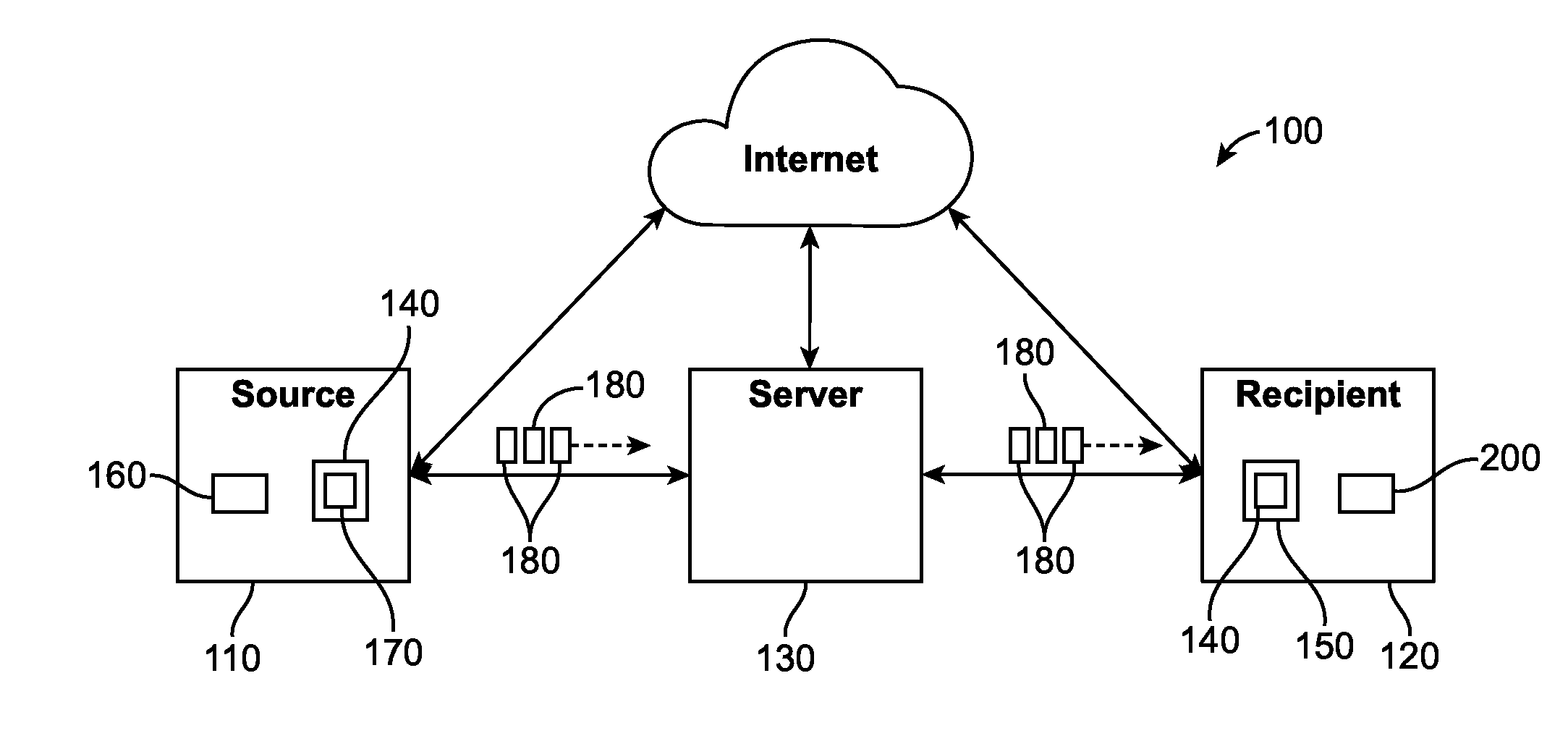
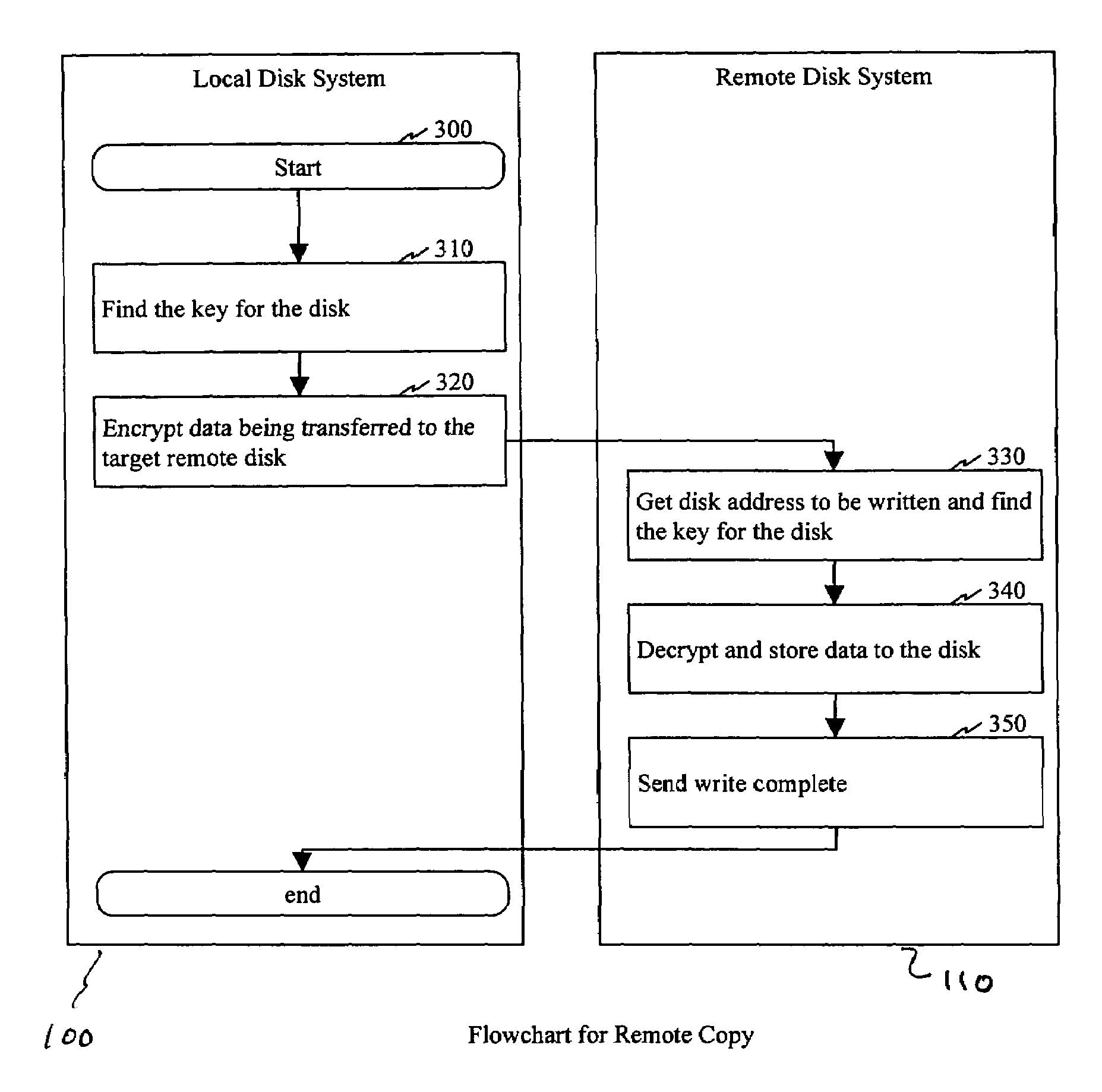
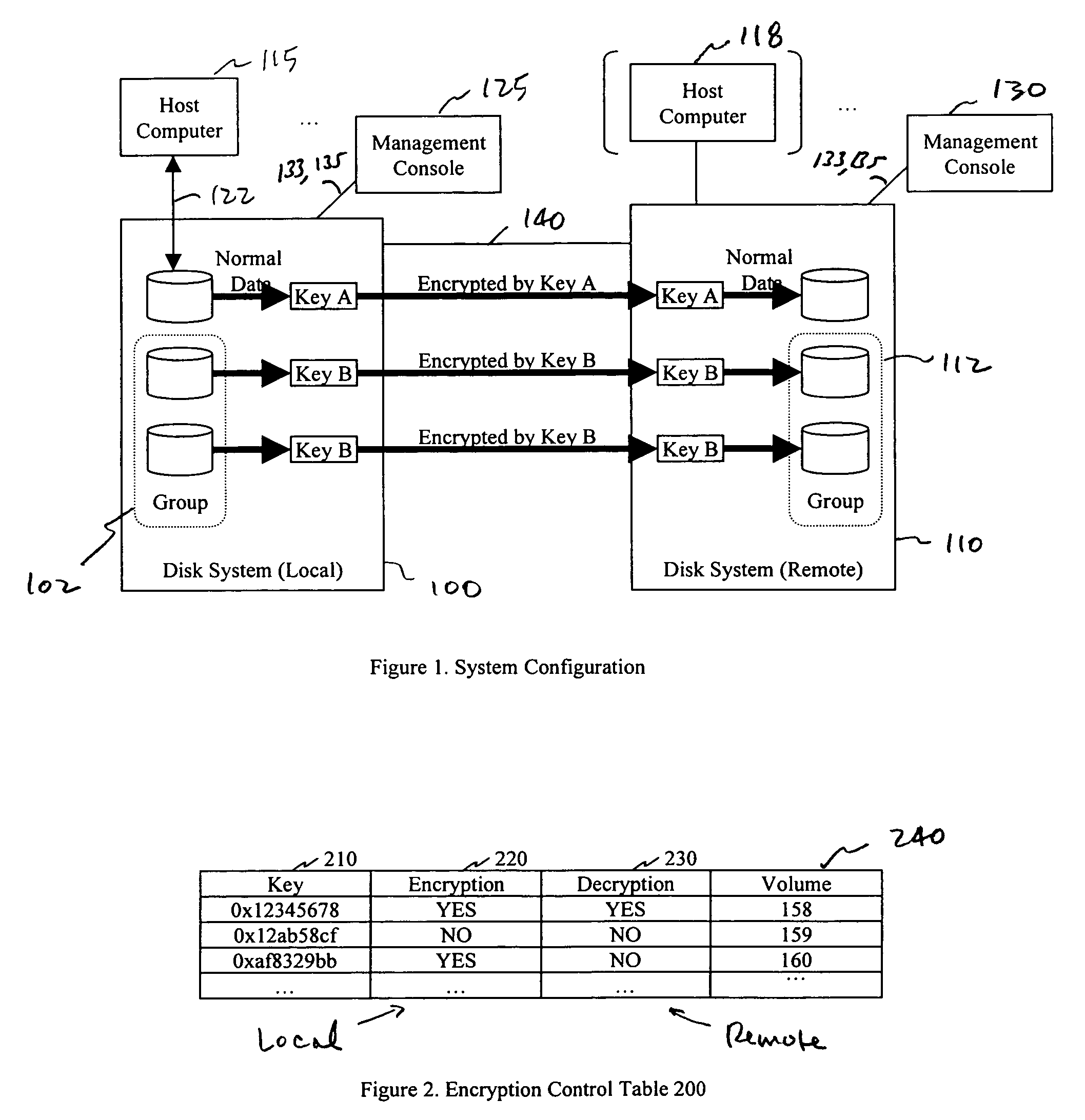
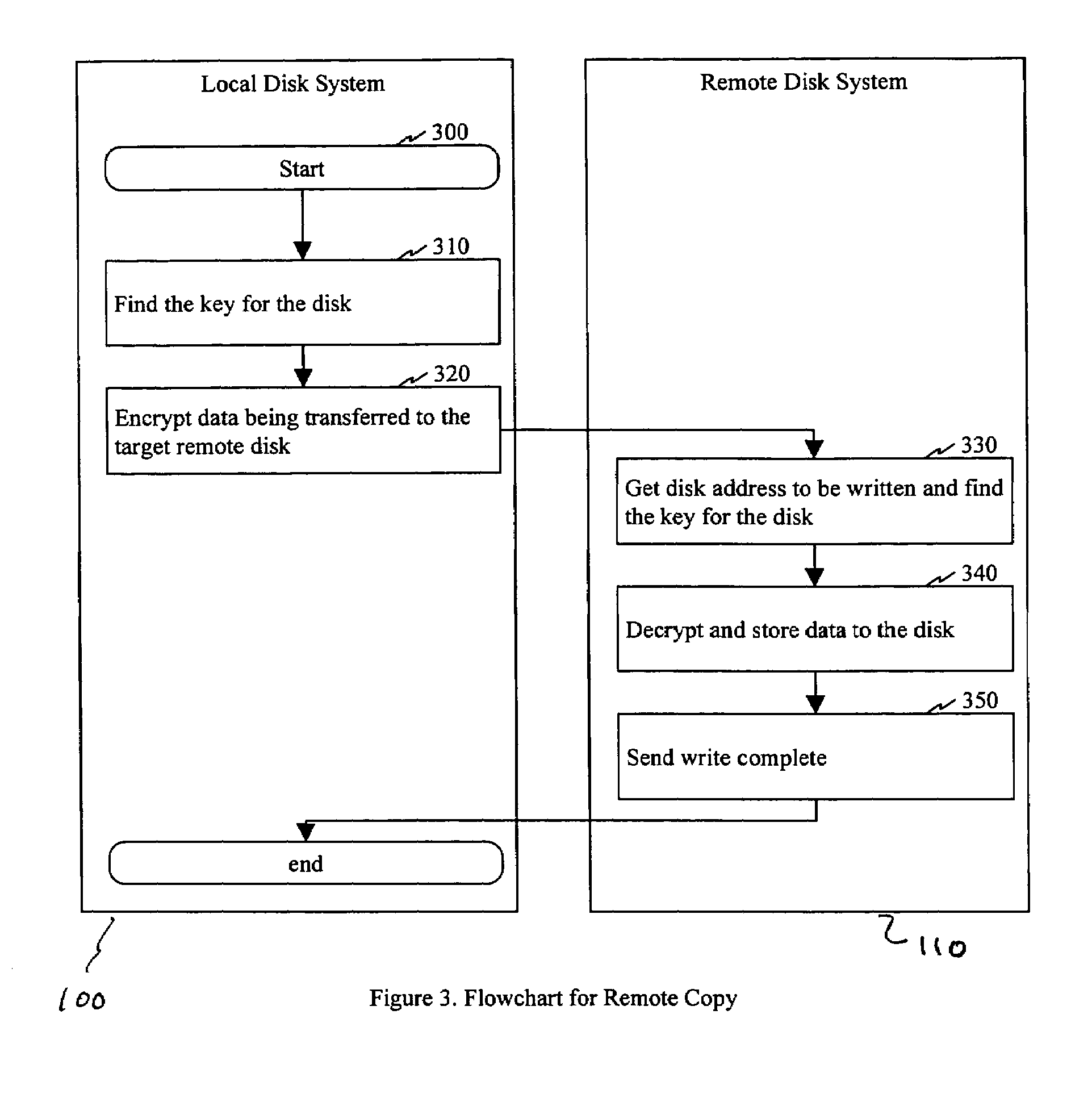
Method and apparatus for encryption and decryption in remote data storage systems
InactiveUS7240197B1Improve securityPrivacy can be assuredKey distribution for secure communicationInput/output to record carriersControl dataComputer science
In a storage system having local and remote disk systems, a system is described for selectively controlling the security of data on a volume by volume basis, for transparently exchanging encryption keys between the local and remote disk systems, and for controlling when encryption is used in the storage of data.
Owner:HITACHI LTD
Method for encryption or decryption using finite group operations
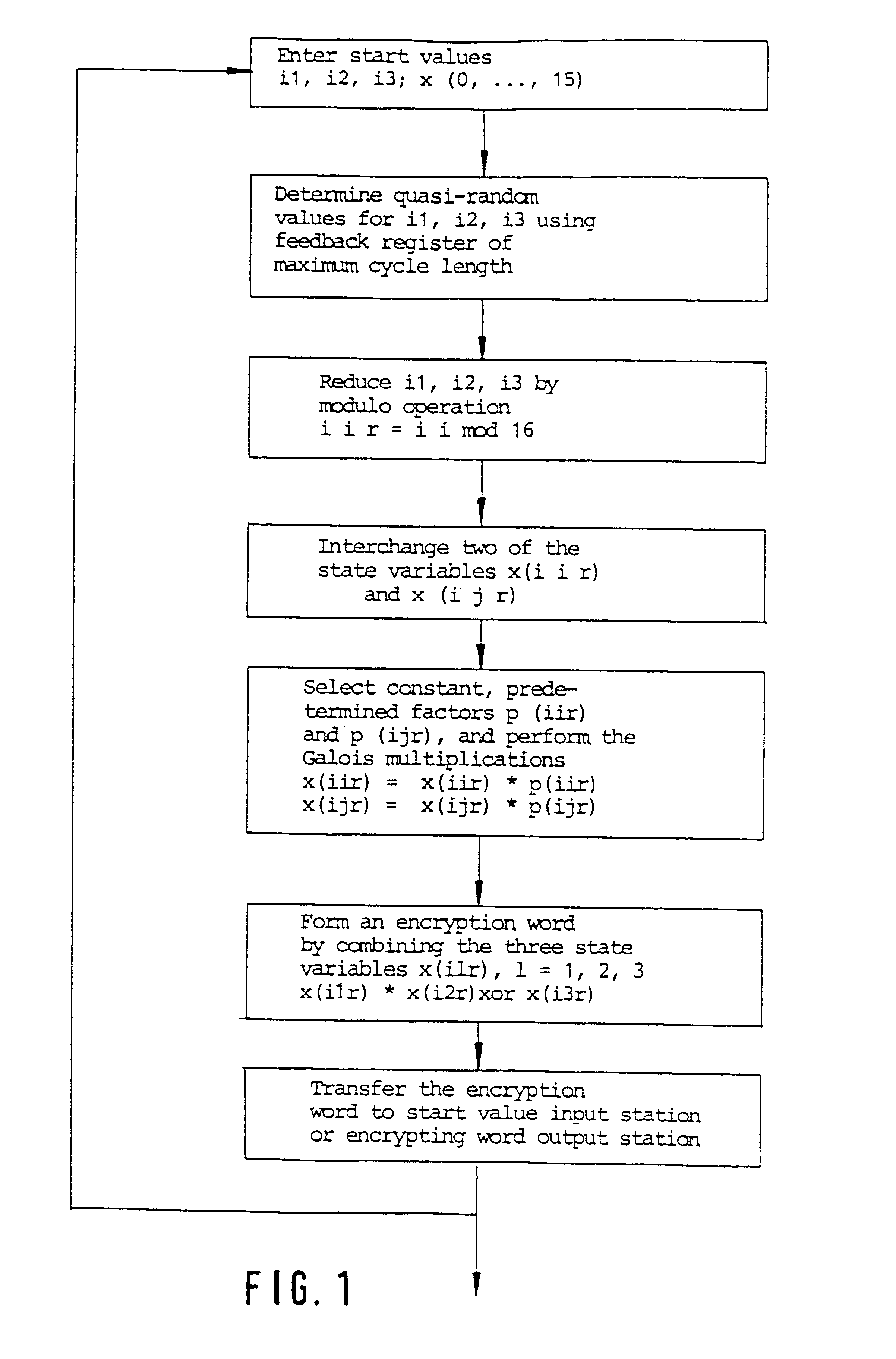
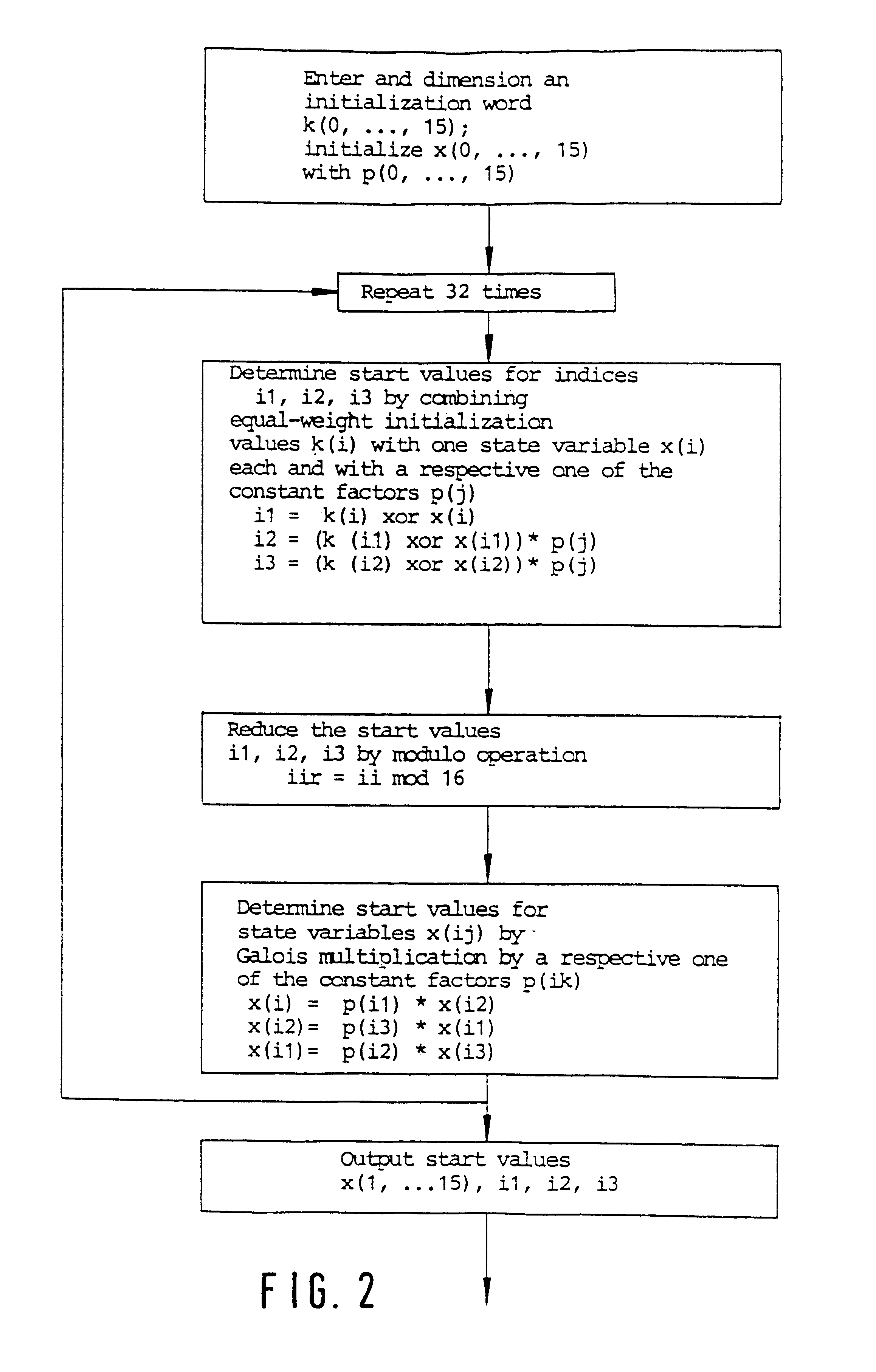
InactiveUS6314187B1Decryption is difficultLow costSecret communicationAnalogue-digital convertersComputer hardwareGroup operation
The invention relates to a method for encrypting or decrypting a sequence of successive data words in a data communications device, the method comprising executing an algorithm in which a sequence of quasi-random encryption words is generated from predetermined start values by performing operations in a finite group, and in which a respective one of the encryption words is combined with a respective one of the data words.
Owner:MICRONAS INTERMETTAL GMBH
Portable Data Encryption Device with Configurable Security Functionality and Method for File Encryption
ActiveUS20130046993A1Mitigates and eliminates vulnerabilityUser identity/authority verificationUnauthorized memory use protectionComputer hardwarePlaintext
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
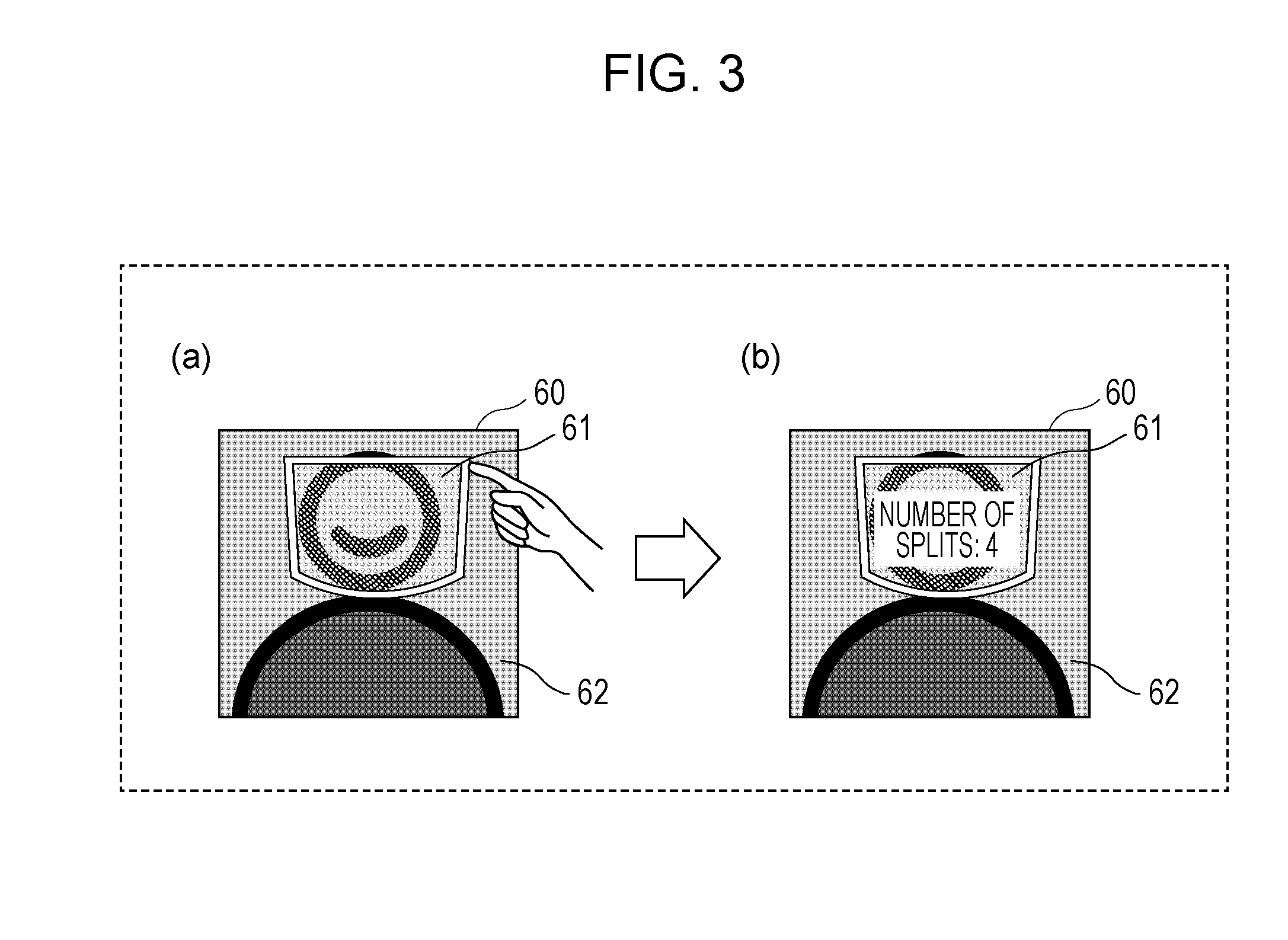
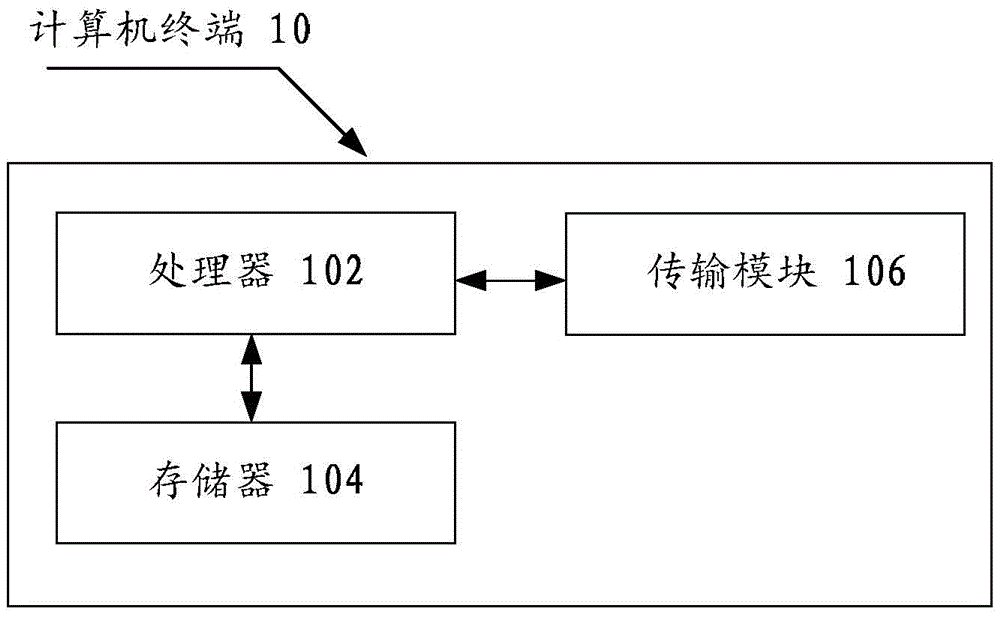
Encryption method, encryptor, and encryption system for encrypting electronic data by splitting electronic data
ActiveUS20160119134A1Improve confidentialityEasy to implementKey distribution for secure communicationUser identity/authority verificationXML EncryptionElectronic data
An encryption method includes displaying encryption target data on a display screen as an image, performing first acceptance in which designation of an at least partial region of the displayed image is accepted, performing second acceptance in which designation regarding splitting of the designated at least partial region is accepted, and splitting data that is included in the encryption target data and corresponds to the designated at least partial region in accordance with the designation regarding the splitting under a secret sharing scheme.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
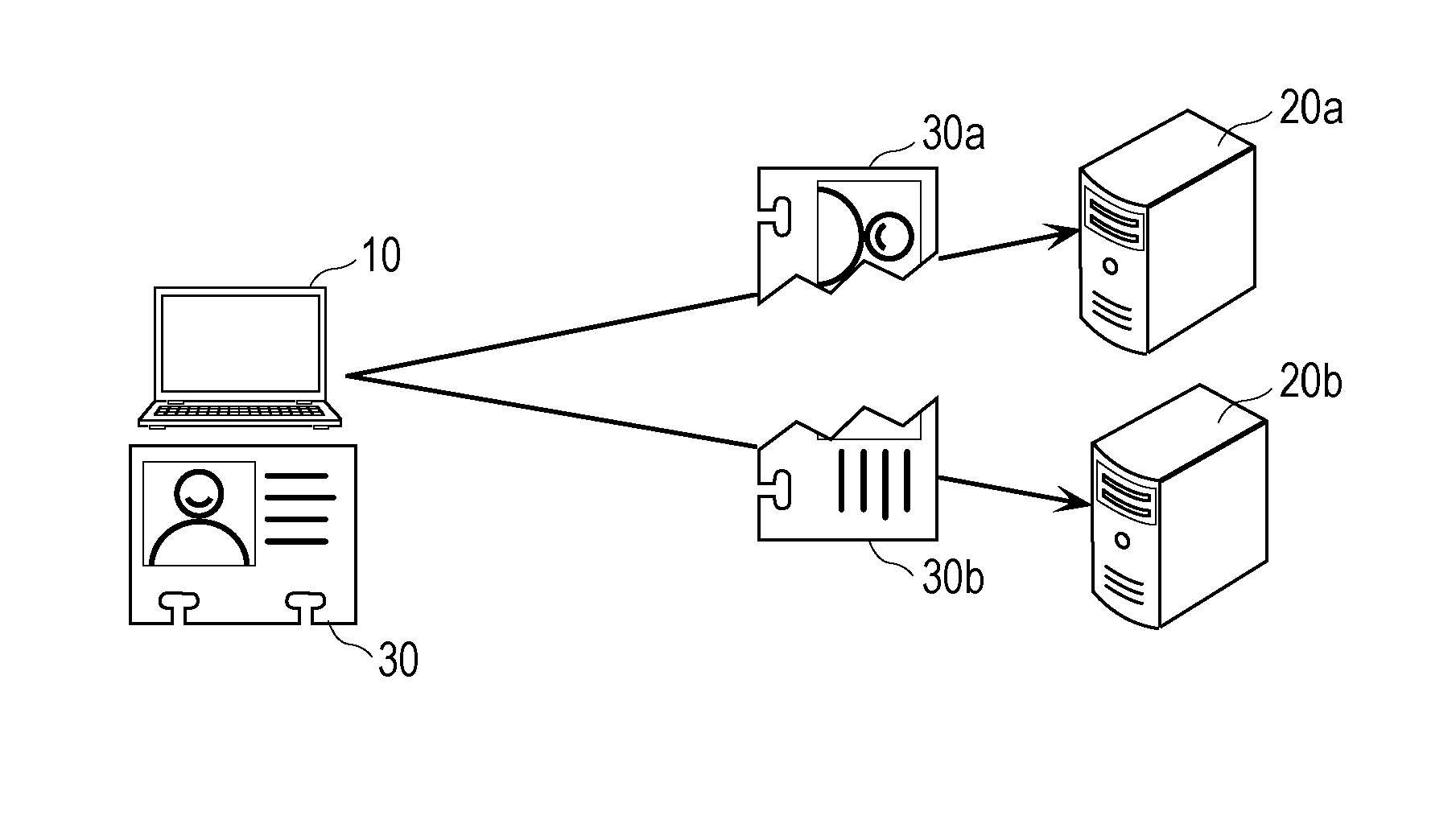
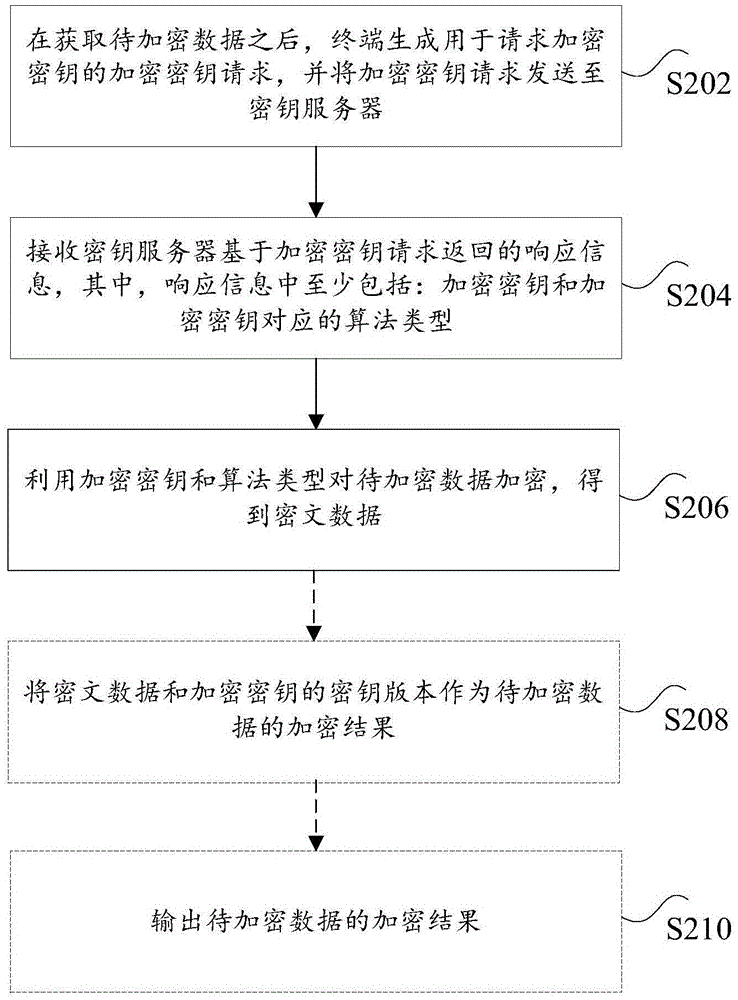
Methods and apparatuses for data encryption and decryption, method and apparatus for processing secret key request, and data encryption and decryption system
The application discloses methods and apparatuses for data encryption and decryption, a method and apparatus for processing a secret key request, and a data encryption and decryption system. The data encryption method includes: after to-be-encrypted data is obtained, a terminal generates an encryption key request used for requesting an encryption key and sends the encryption key request to a secret key server; response information returned by the secret key server based on the encryption key request is received, wherein the response information at least comprises the encryption key and the algorithm type corresponding to the encryption key; and the to-be-encrypted encryption data is encrypted by employing the encryption key and the algorithm type to obtain encrypted data. According to the method, the technical problem of high leakage risk of sensitive data of the encryption method is solved.
Owner:ALIBABA GRP HLDG LTD
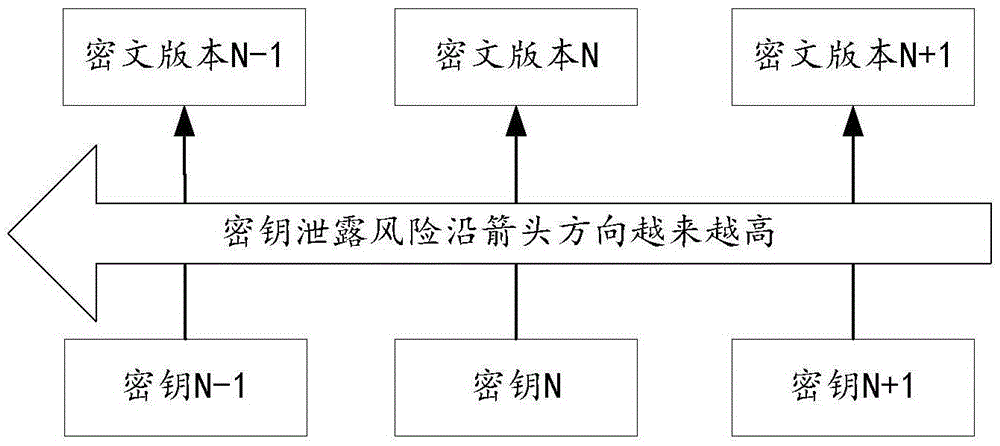
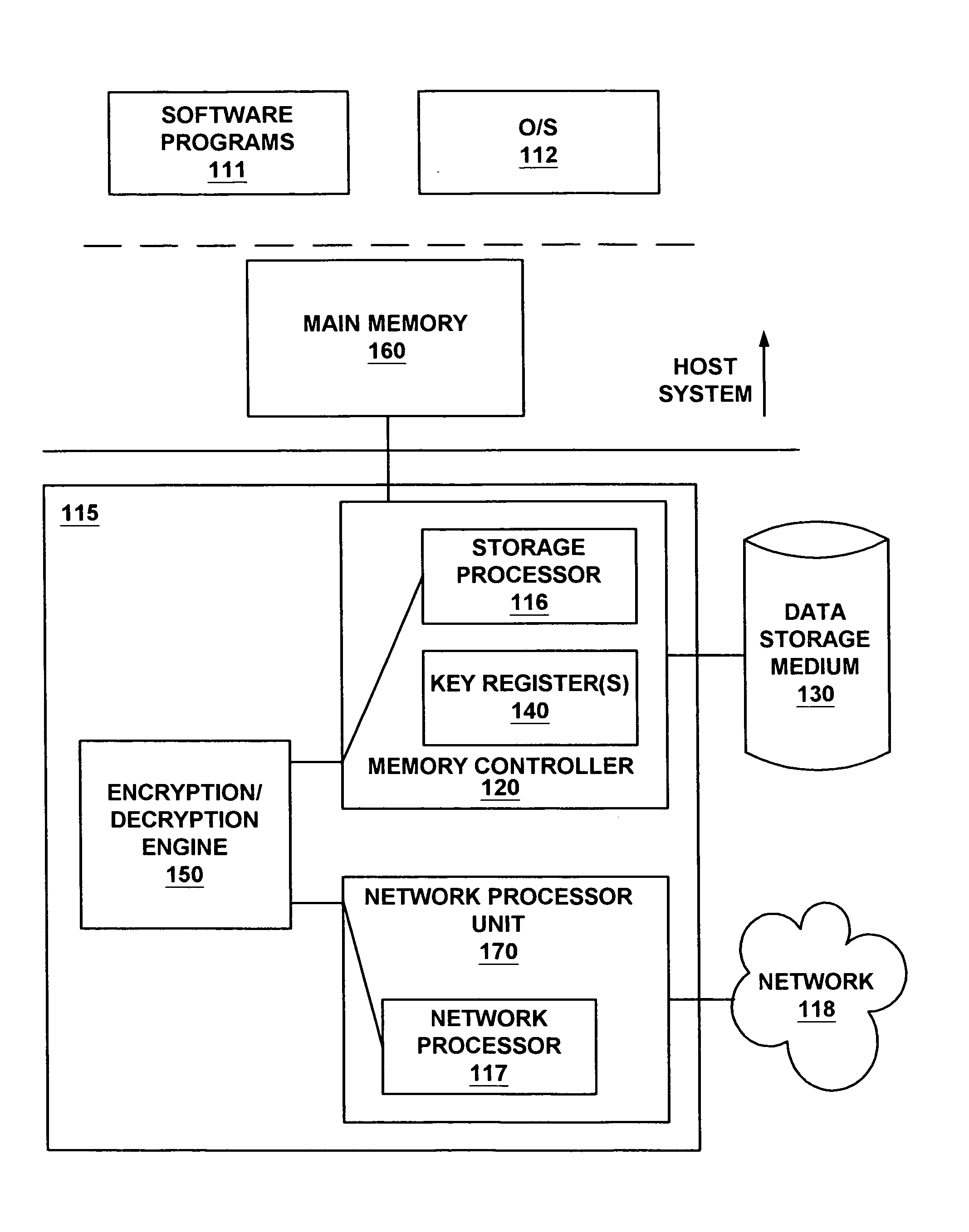
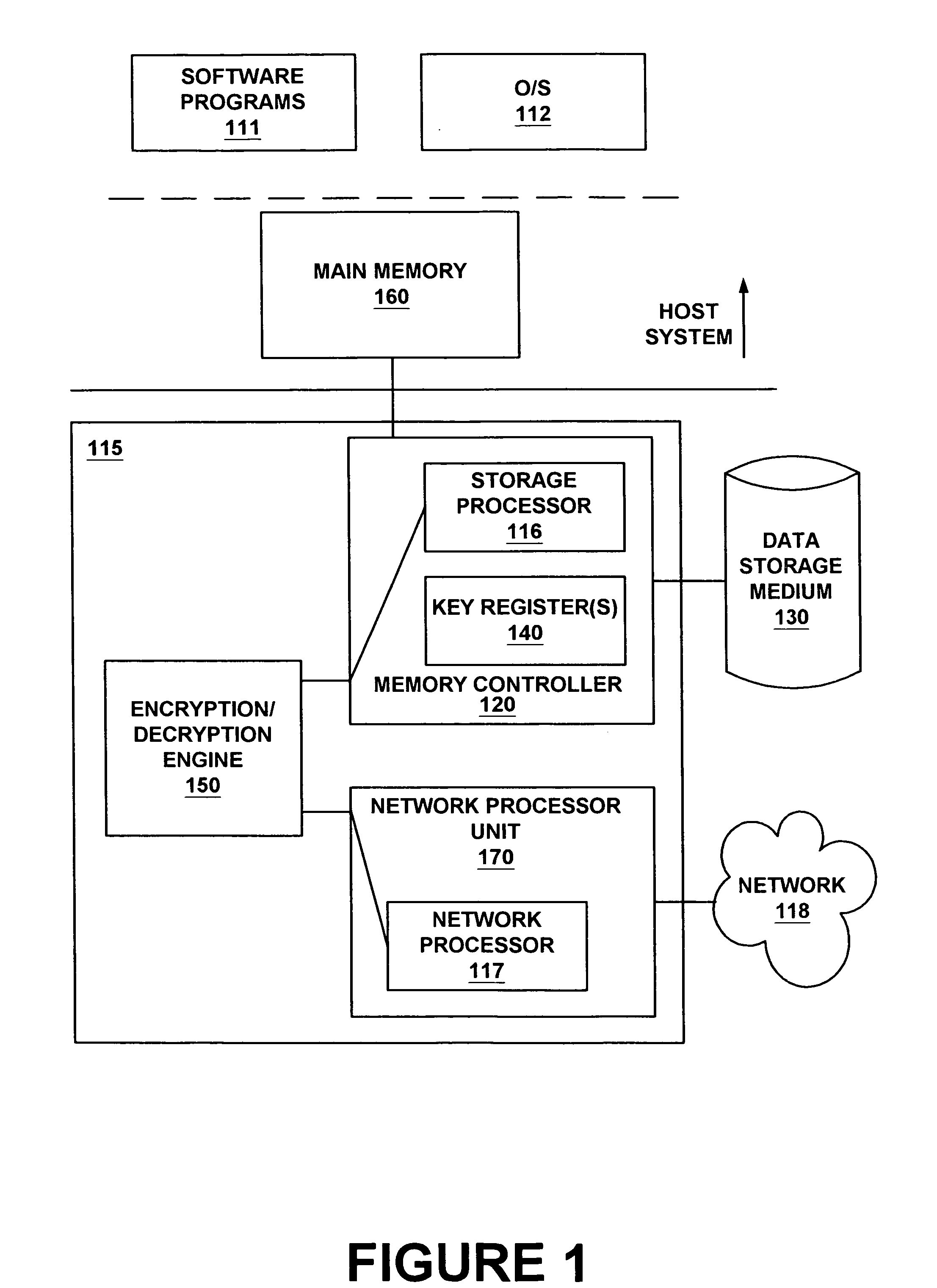
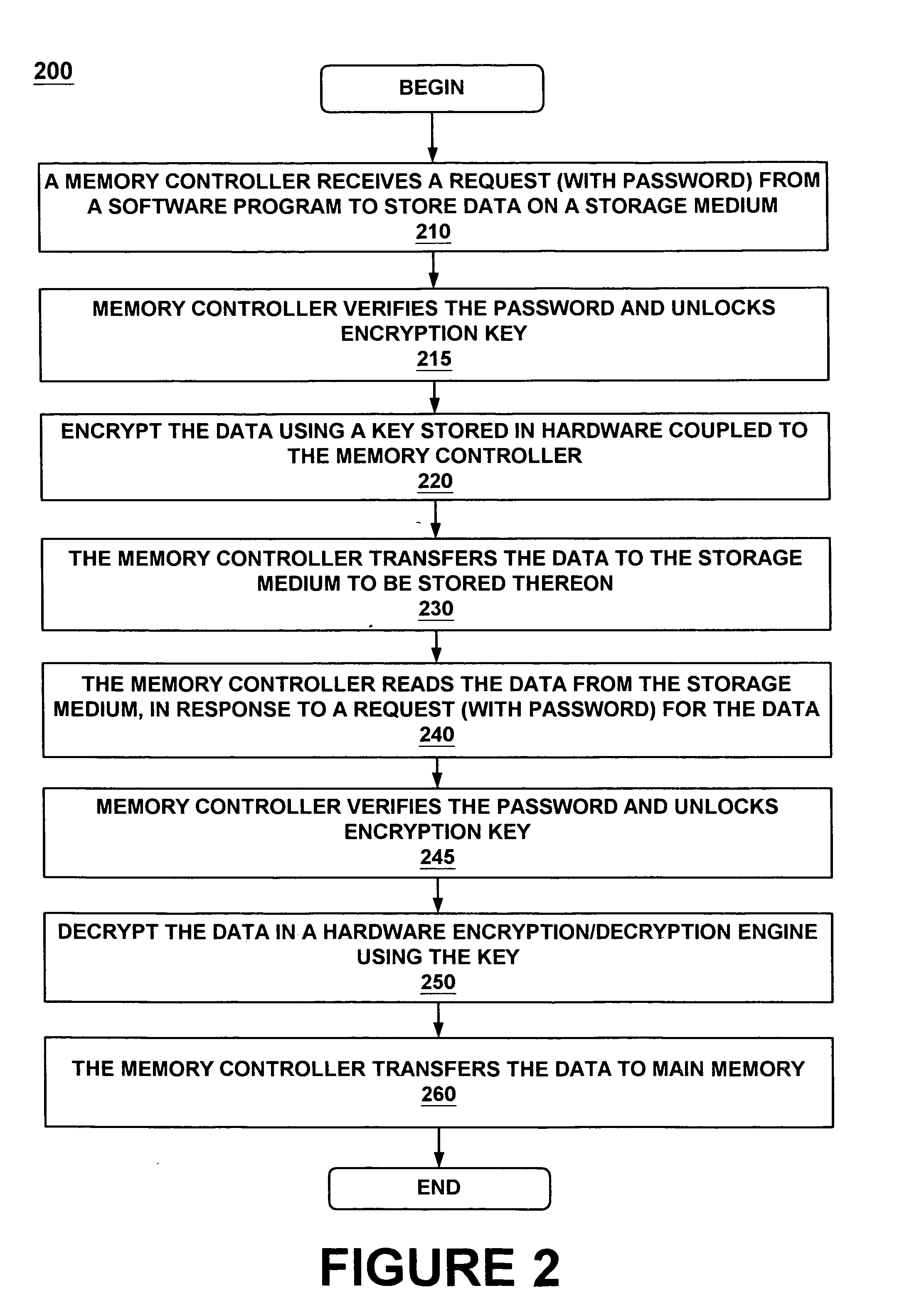
System and method for transparent disk encryption
InactiveUS20070180515A1Digital data processing detailsUnauthorized memory use protectionComputer hardwareOperational system
A data storage system providing transparent encryption. The data storage system has a hardware encryption / decryption engine and a register coupled to the hardware encryption / decryption engine. The register is for securely storing a key for encrypting and decrypting data. The key may not be read from outside the data storage system. More specifically, the key may not be read by the operating system. The user does not have access to the encryption key, but may have a password that is passed to a controller coupled to the encryption / decryption engine. The controller verifies the password and causes data received from main memory to be encrypted by the hardware encryption / decryption engine using the key. The controller also transfers the encrypted data to the data storage device.
Owner:NVIDIA CORP
Data encryption mobile storage management method based on virtual disk
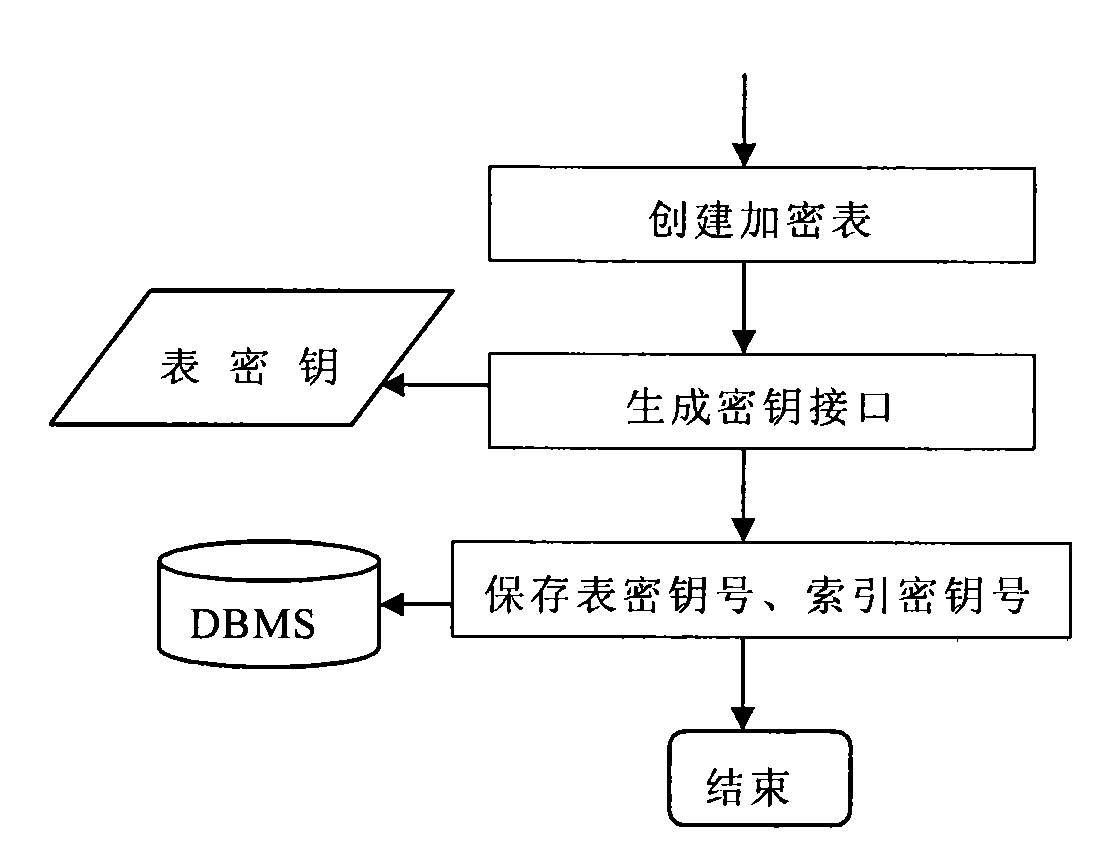
ActiveCN103065102AProtection securityEasy to manageInternal/peripheral component protectionSoftware simulation/interpretation/emulationComputer moduleStorage management
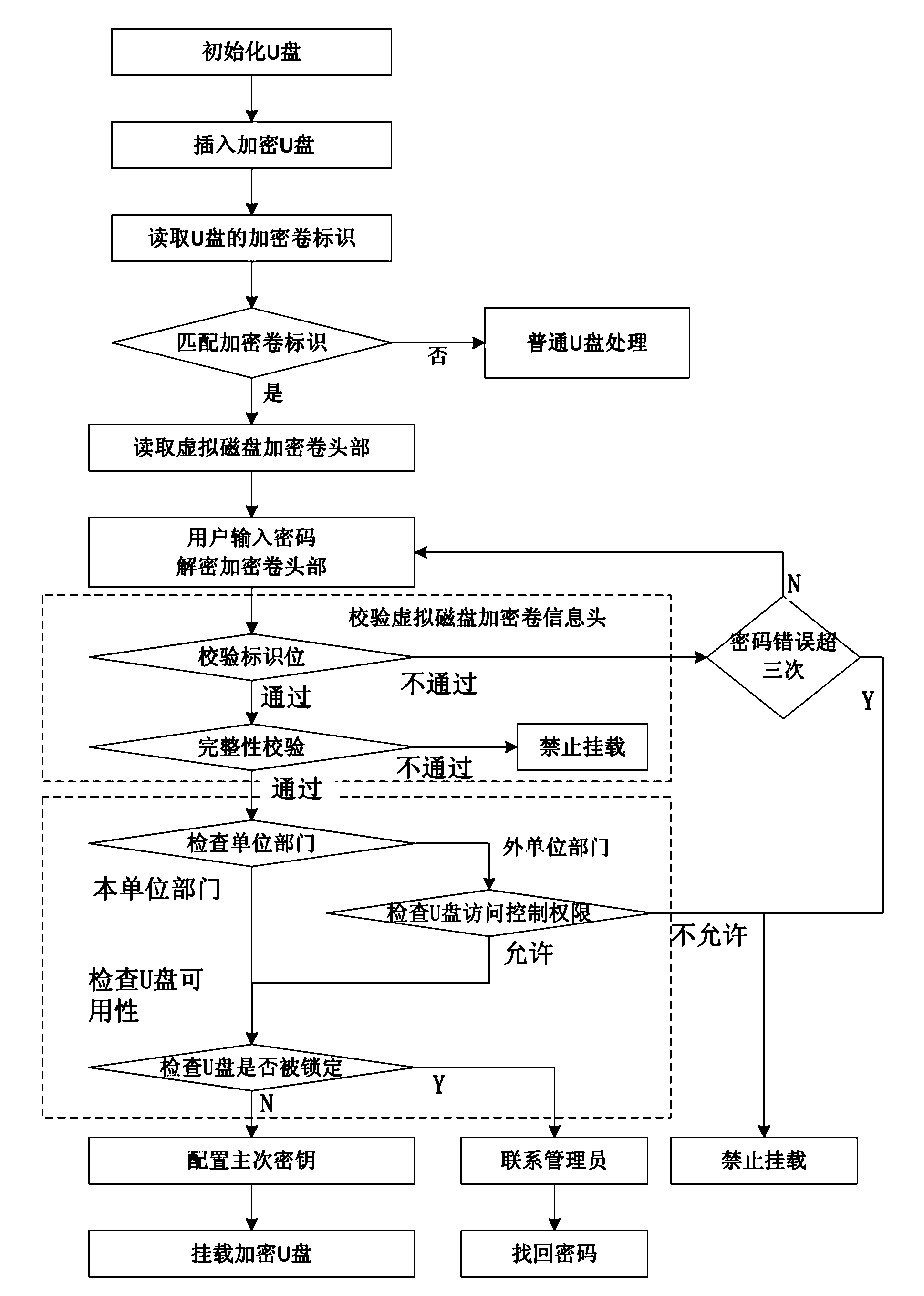
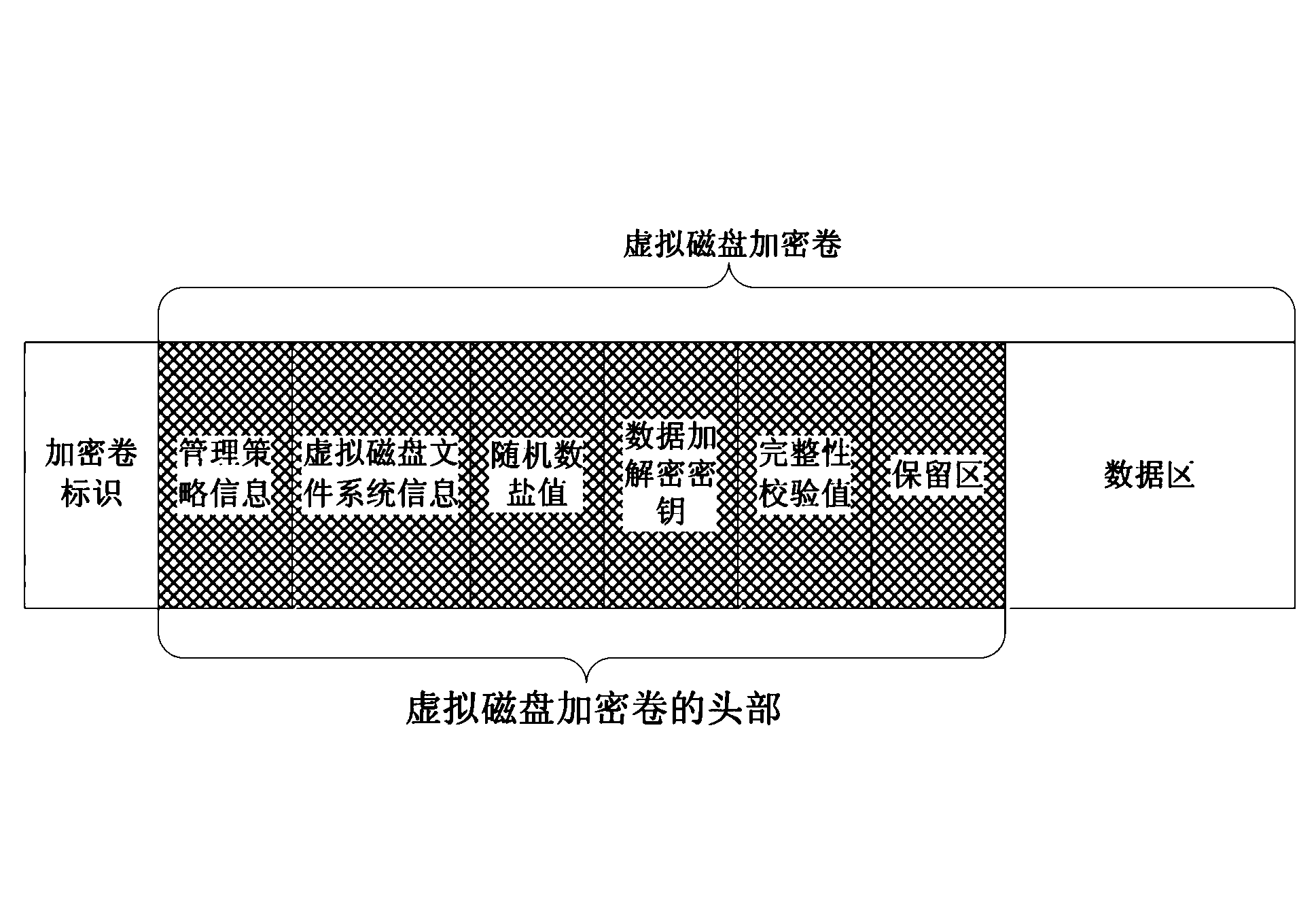
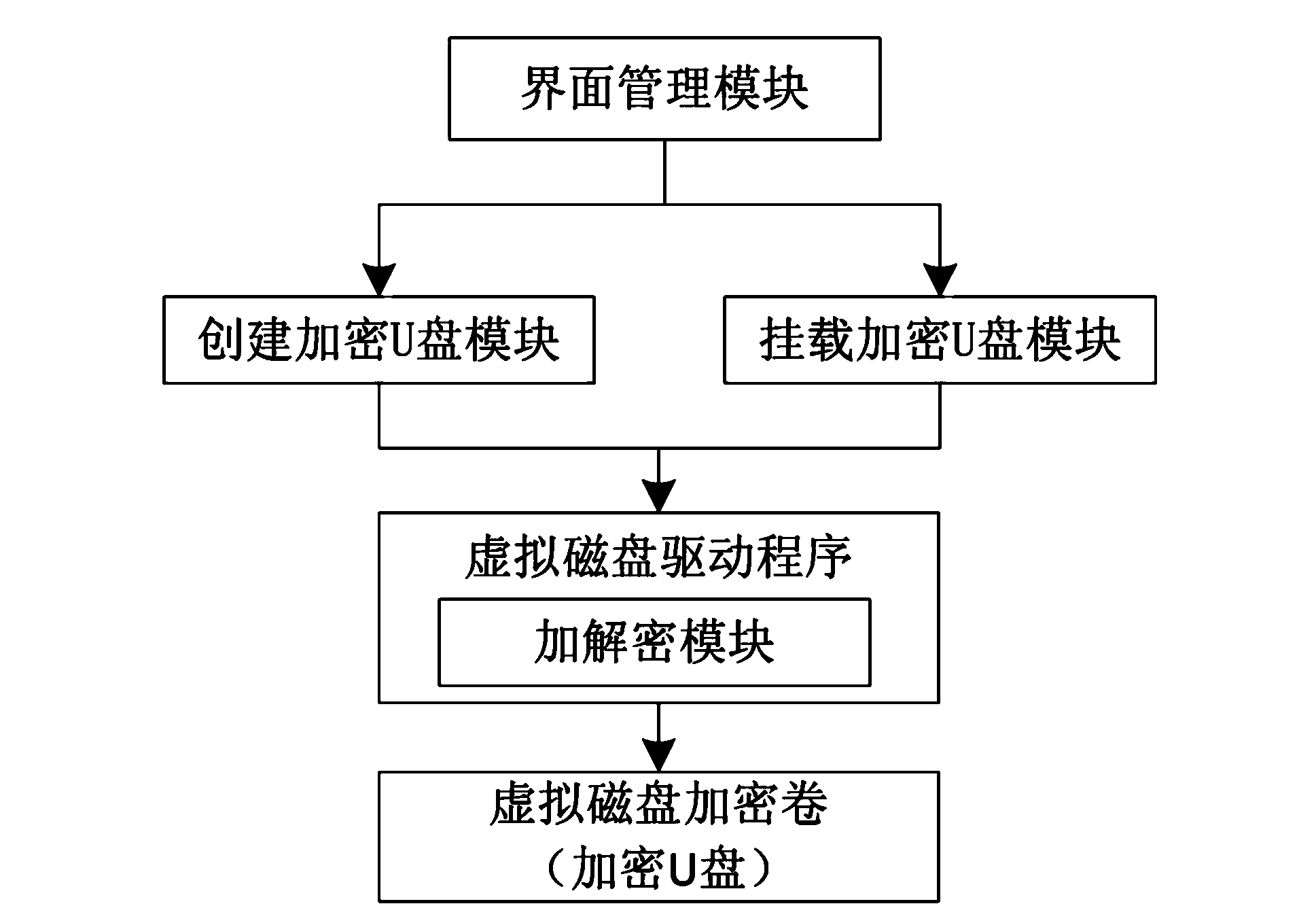
The invention discloses a data encryption mobile storage management method based on a virtual disk. The method includes the following steps: 1) writing an encryption roll identification in the head portion of the mobile storage device and building a virtual magnetic disc encryption roll in the mobile storage device; 2) checking the encryption roll identification when the mobile storage device is inserted in a designated computer and processing as a common mobile storage device if the encryption roll identification is not correct and executing the next step otherwise; 3) checking encryption roll information head of the virtual disc according to a mounting command and executing the next step if the check passes; 4) mounting the encryption roll of the virtual disk, calling virtual disk drive program with an encryption and decryption module to read and write the virtual disk encryption roll, enabling the encryption and decryption module to encrypt and decrypt in real time automatically and finally automatically unloading the virtual disk encryption roll when discharging the mobile storage device. The method has the advantages of being safe and reliable in information storage, flexible in security policy configuration, capable of simply and conveniently managing the portable storage device and high-efficient and transparent in data encryption and decryption processing.
Owner:NAT UNIV OF DEFENSE TECH
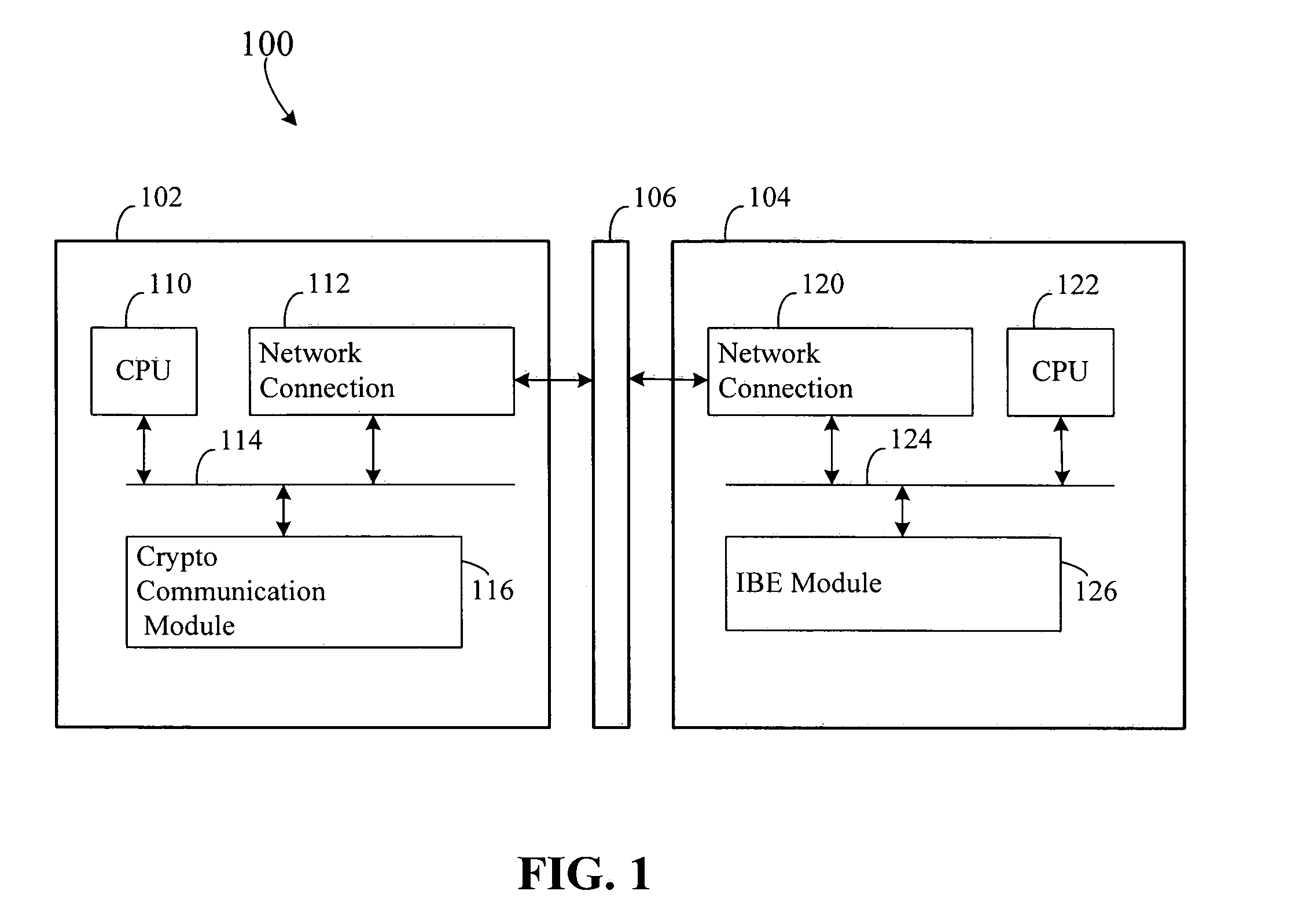
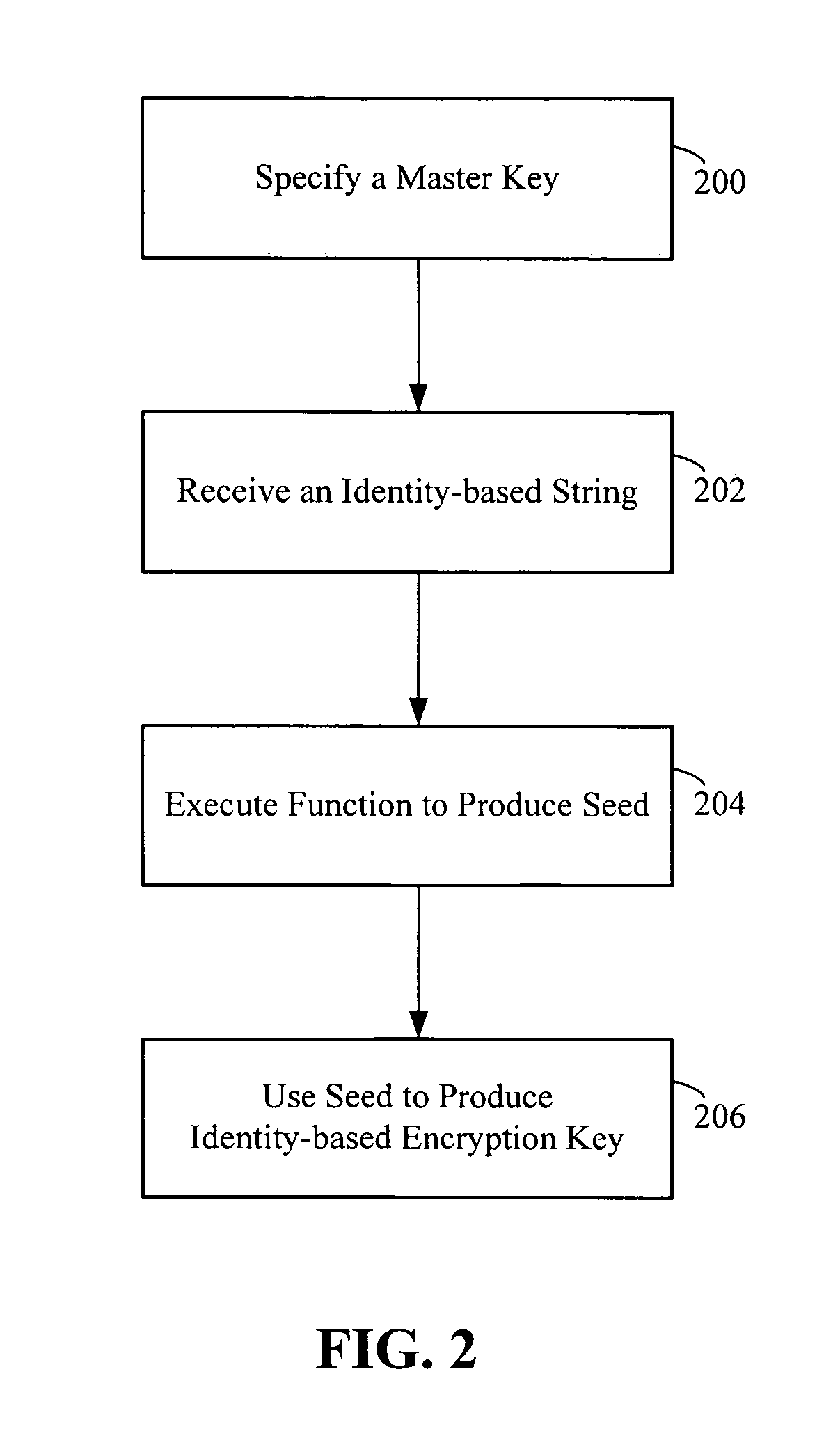
Apparatus and method for identity-based encryption within a conventional public-key infrastructure
InactiveUS7657037B2Avoid security issuesKey distribution for secure communicationDigital data processing detailsMaster keyPublic key cryptosystem
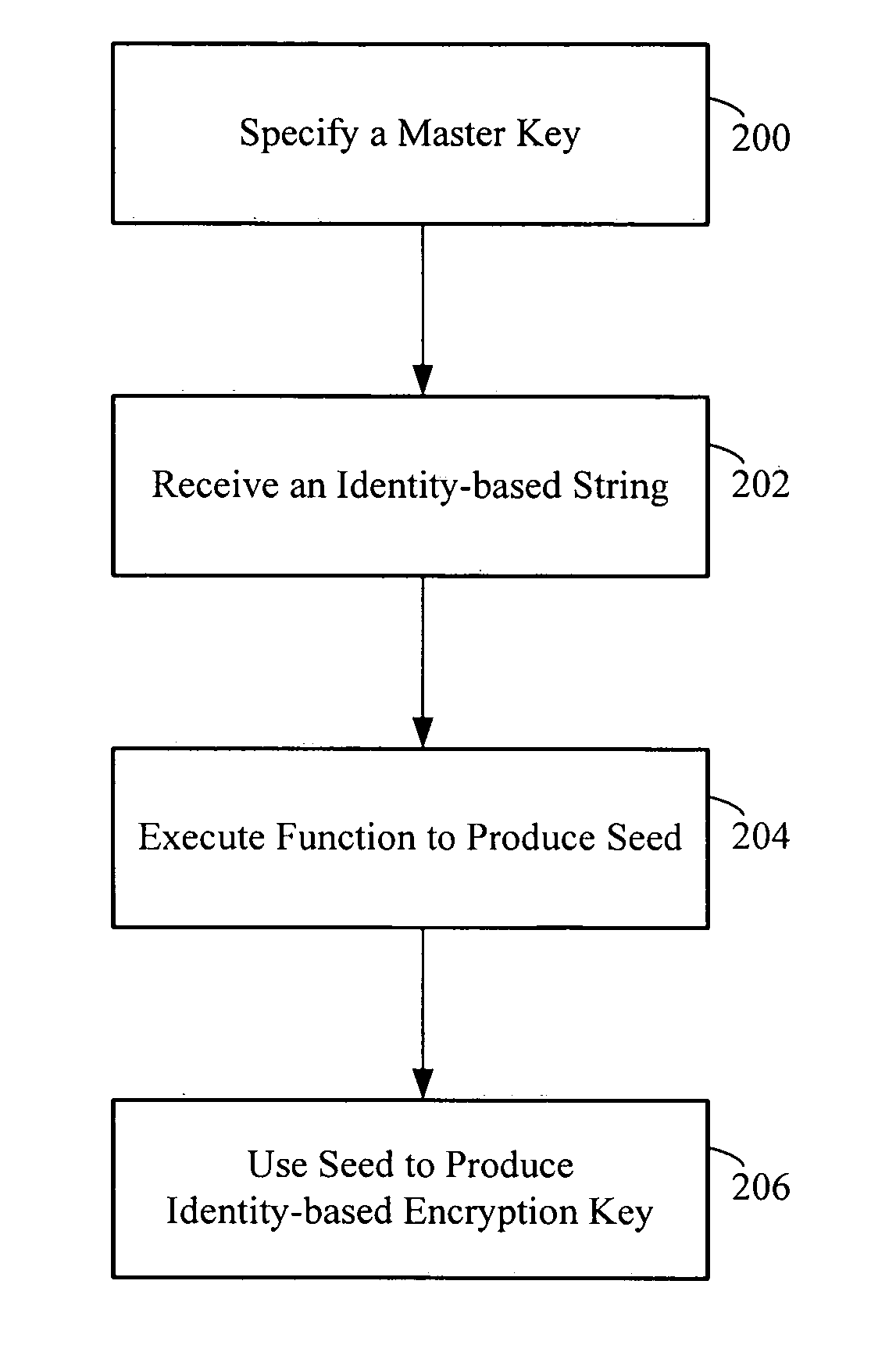
A computer readable medium storing executable code to generate an identity-based encryption key includes executable code to specify a master key, receive an identity-based string and execute a function that processes the master key and the identity-based string to produce a seed. The seed is then used to produce an identity-based encryption key interoperable with a deployed public key cryptosystem.
Owner:CA TECH INC
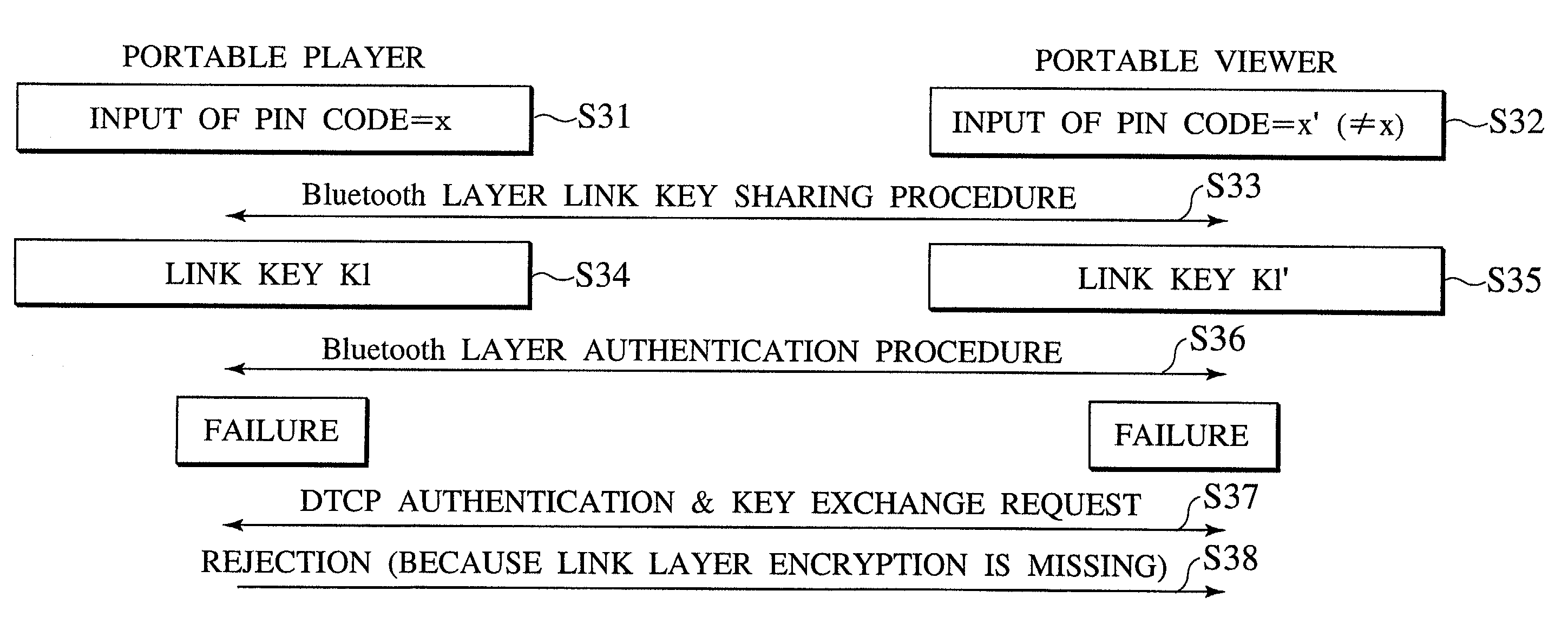
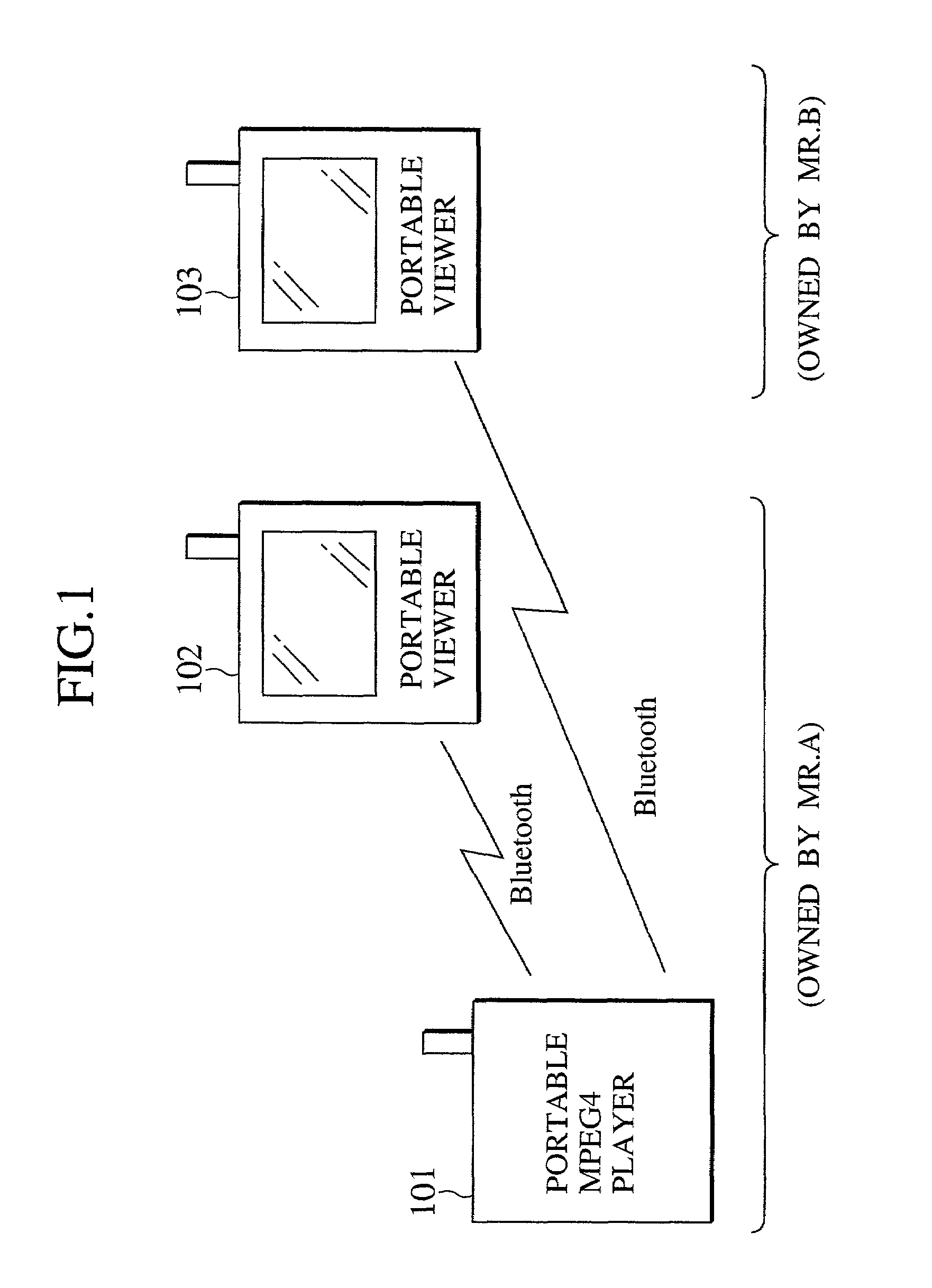
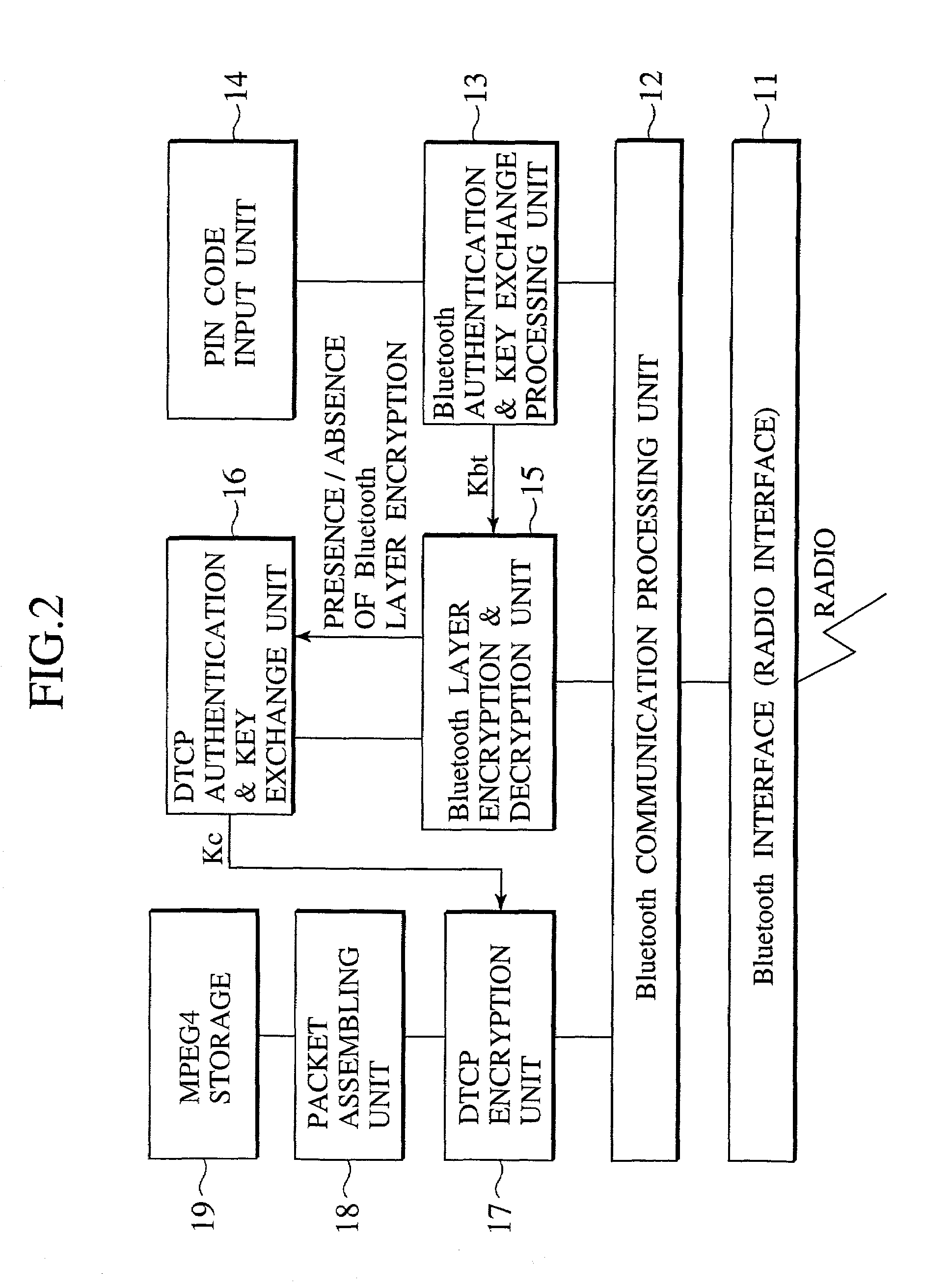
Scheme for transferring copyright protected contents data using radio link layer authentication/encryption
ActiveUS7324644B2Key distribution for secure communicationDigital data processing detailsComputer hardwareKey exchange
Between a transmitting device and a receiving device, a first authentication and key exchange procedure depending on a radio link layer network is carried out, and then a whole or a part of a second authentication and key exchange procedure depending on the copyright protected contents data is carried out by using the cipher communication using a first encryption key that is shared between the transmitting device and the receiving device by the first authentication and key exchange procedure, so that the contents data transfer by the cipher communication using a second encryption key can be carried out only between legitimate pair of the transmitting device and the receiving device that can successfully complete the first authentication.
Owner:KK TOSHIBA
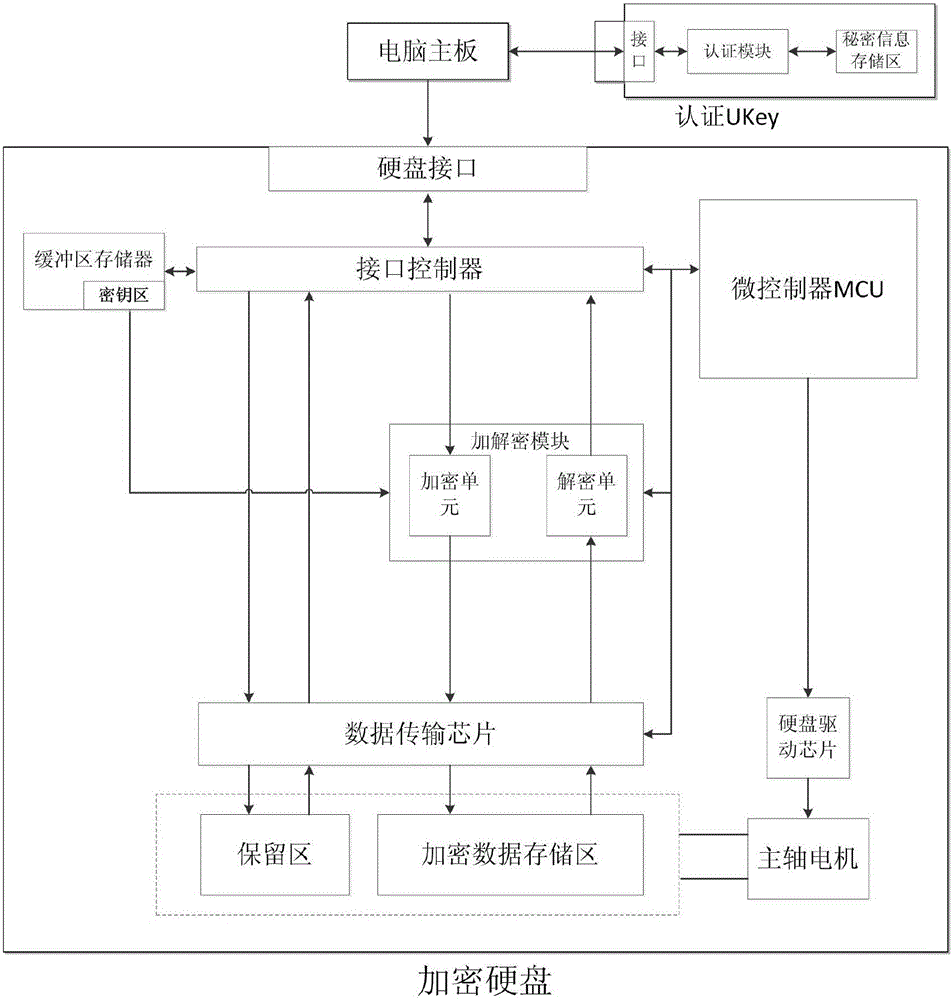
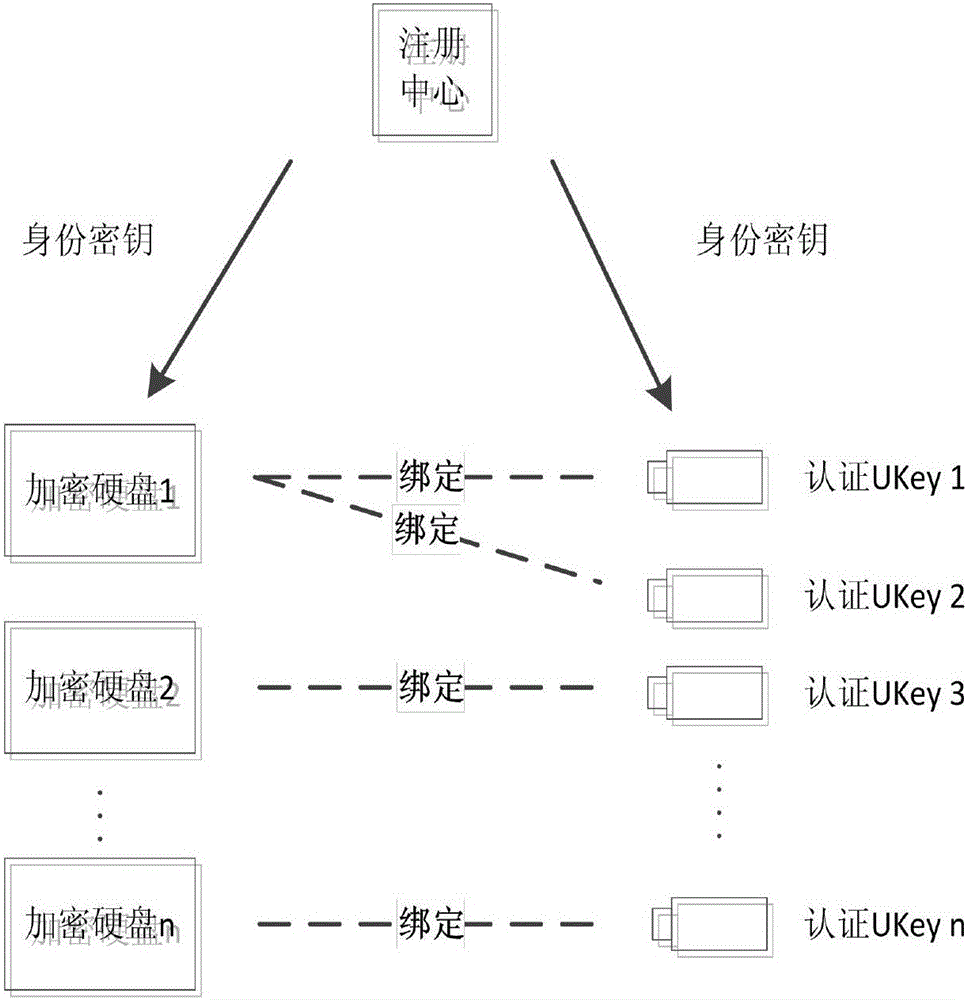
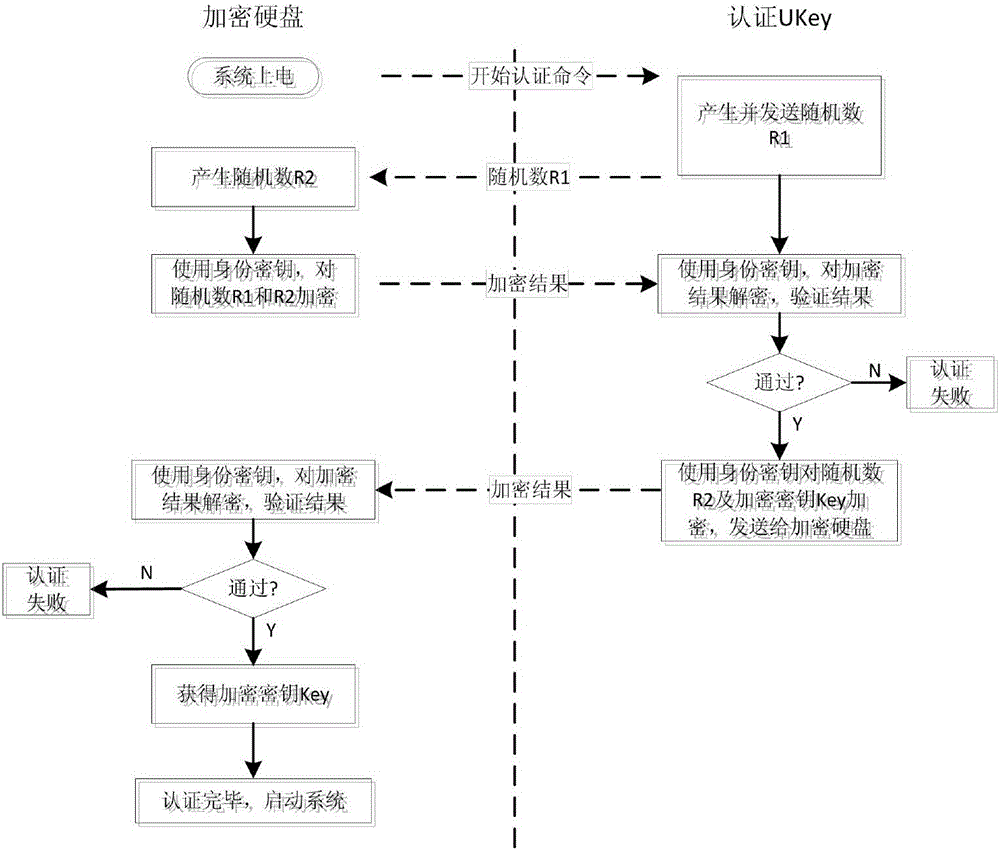
System and method for full disk encryption based on hardware
InactiveCN104951409APrevent theftPerformance is not affectedUnauthorized memory use protectionElectricityDisk encryption theory
The invention discloses a system and method for full disk encryption based on hardware. The method comprises the following steps: (1) performing registration and binding on a blank encryption hard disk of a host and a certification UKey through a registration center; storing a certification program and an identity key to a reserved area of the encryption hard disk; storing the identity key, an encryption Key and the certification program through the UKey; (2) prior to electrification of the host, inserting the UKey in the host; (3) after electrification, executing encryption hard disk and UKey mutual authentication; (4) after the authentication is successful, through the encryption hard disk, storing the Key obtained from the UKey in a buffer area memory undergoing power down loss; through an encryption and decryption module, using the Key to decrypt data and starting an operating system of the host; and (5) after the operating system is started, through the encryption and decryption module, utilizing the Key to decrypt read data, encrypt read-in data and then store the read-in data to an encrypted data storage area of the encryption hard disk. The system and method for full disk encryption based on the hardware greatly improves hard disk data security.
Owner:INST OF INFORMATION ENG CAS
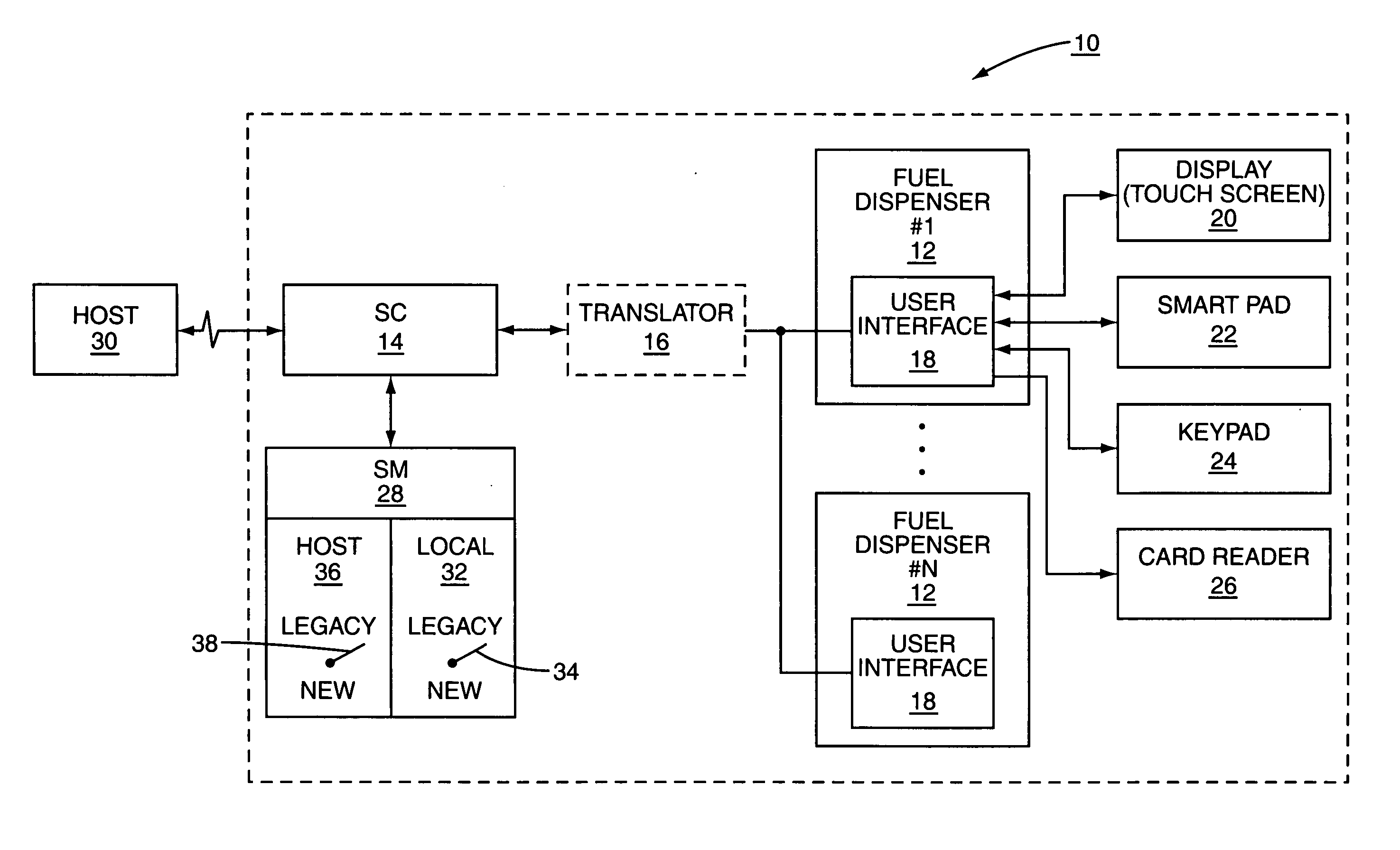
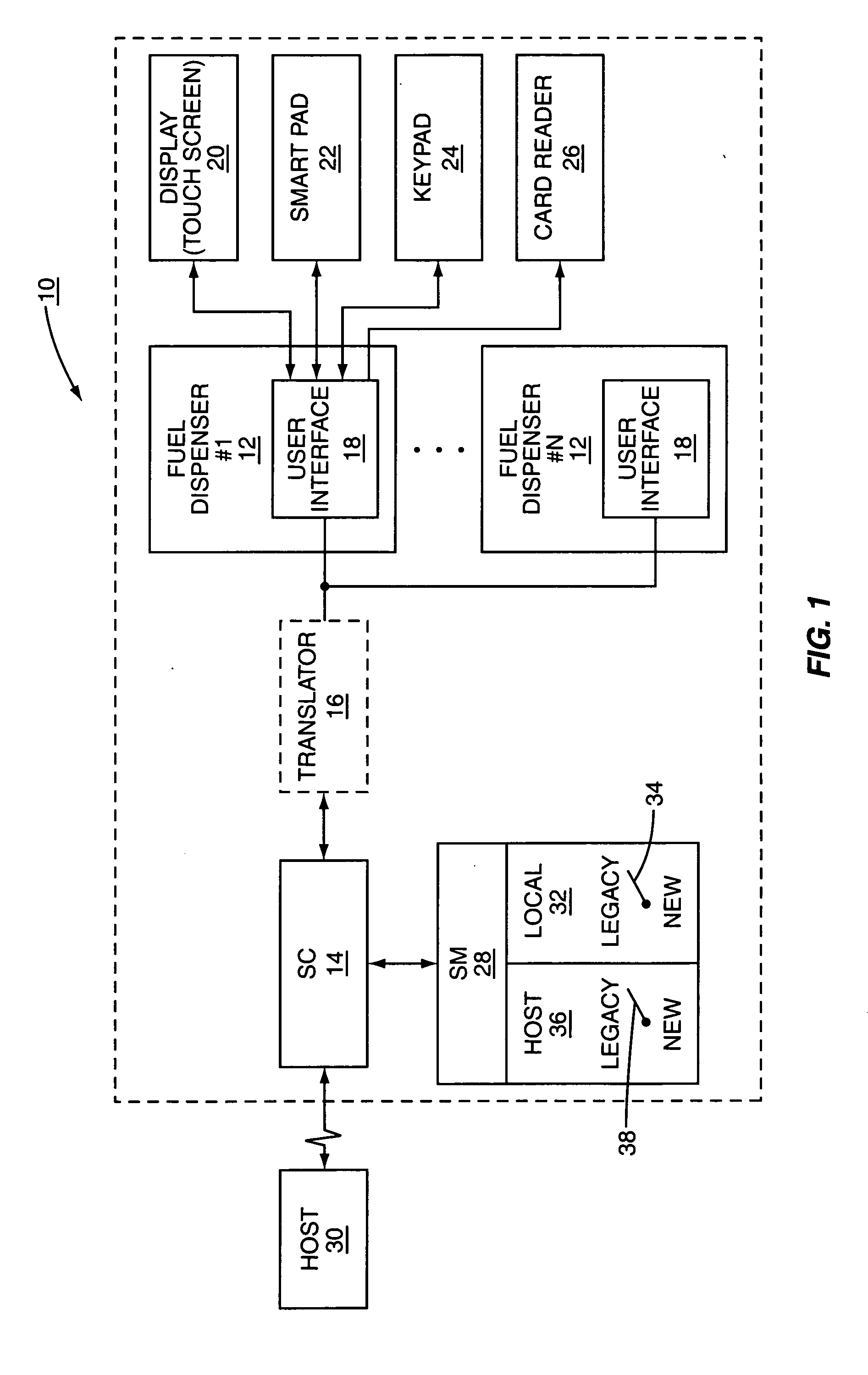
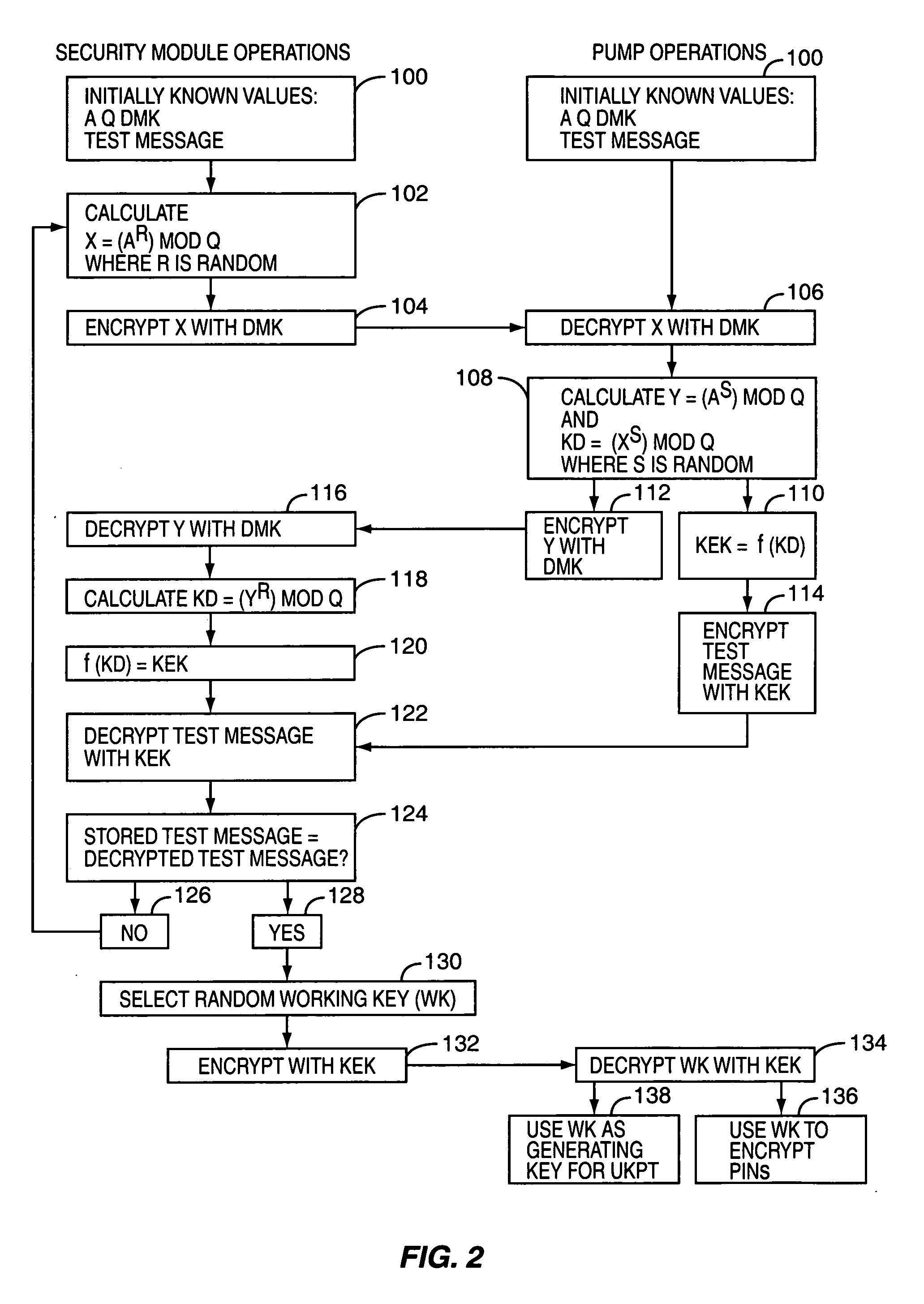
Encryption system and method for legacy devices in a retail environment
A security module used in a retail establishment has two zones of operation. The first zone uses a first encryption scheme between data entry point devices, such as a PIN keypad and the security module. The second zone uses a second encryption scheme between the security module and the host network computer. Both the local encryption scheme and the host encryption scheme may be selectively and independently switched from a legacy encryption scheme to a new encryption scheme to accommodate evolving encryption requirements.
Owner:GILBARCO
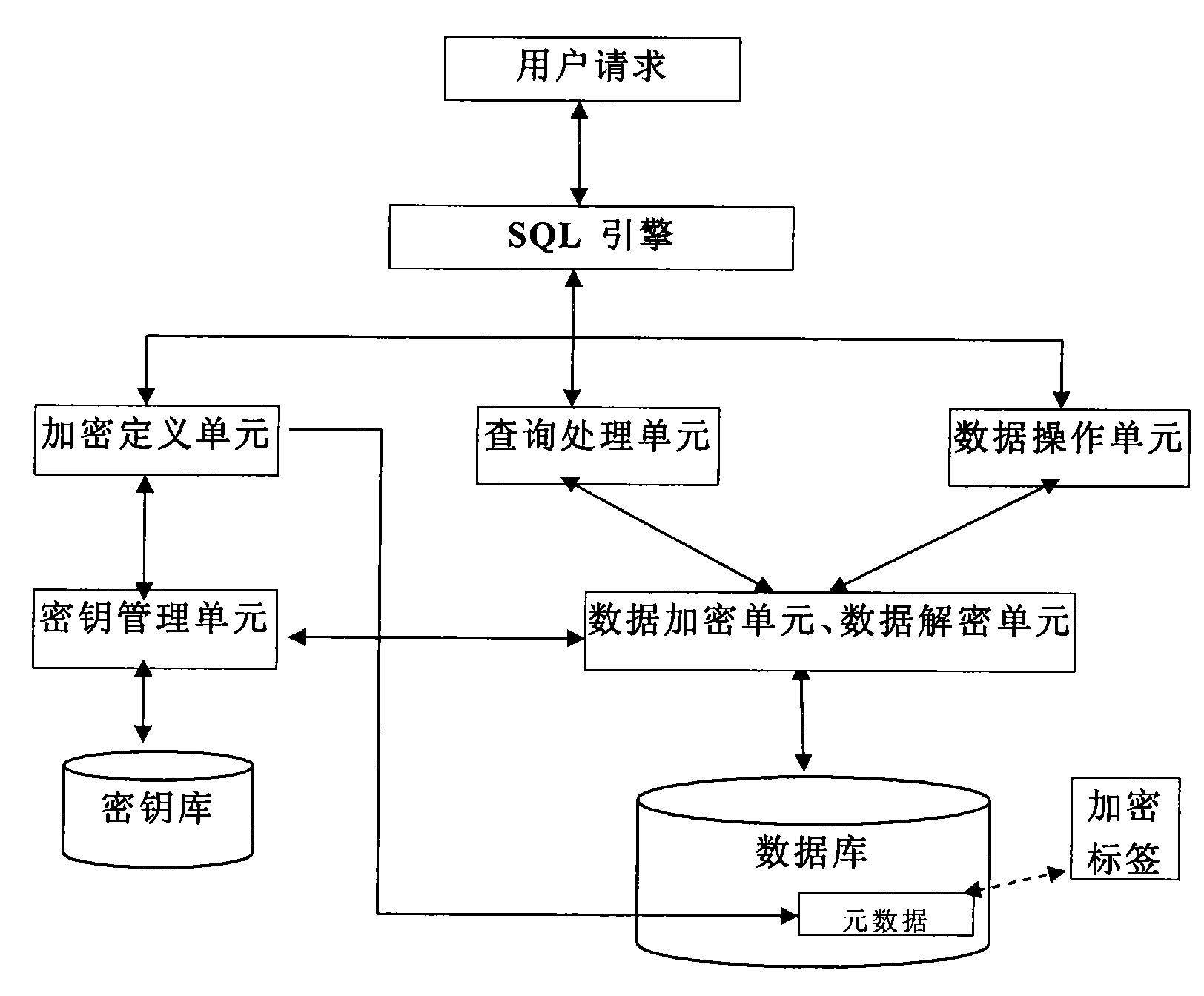
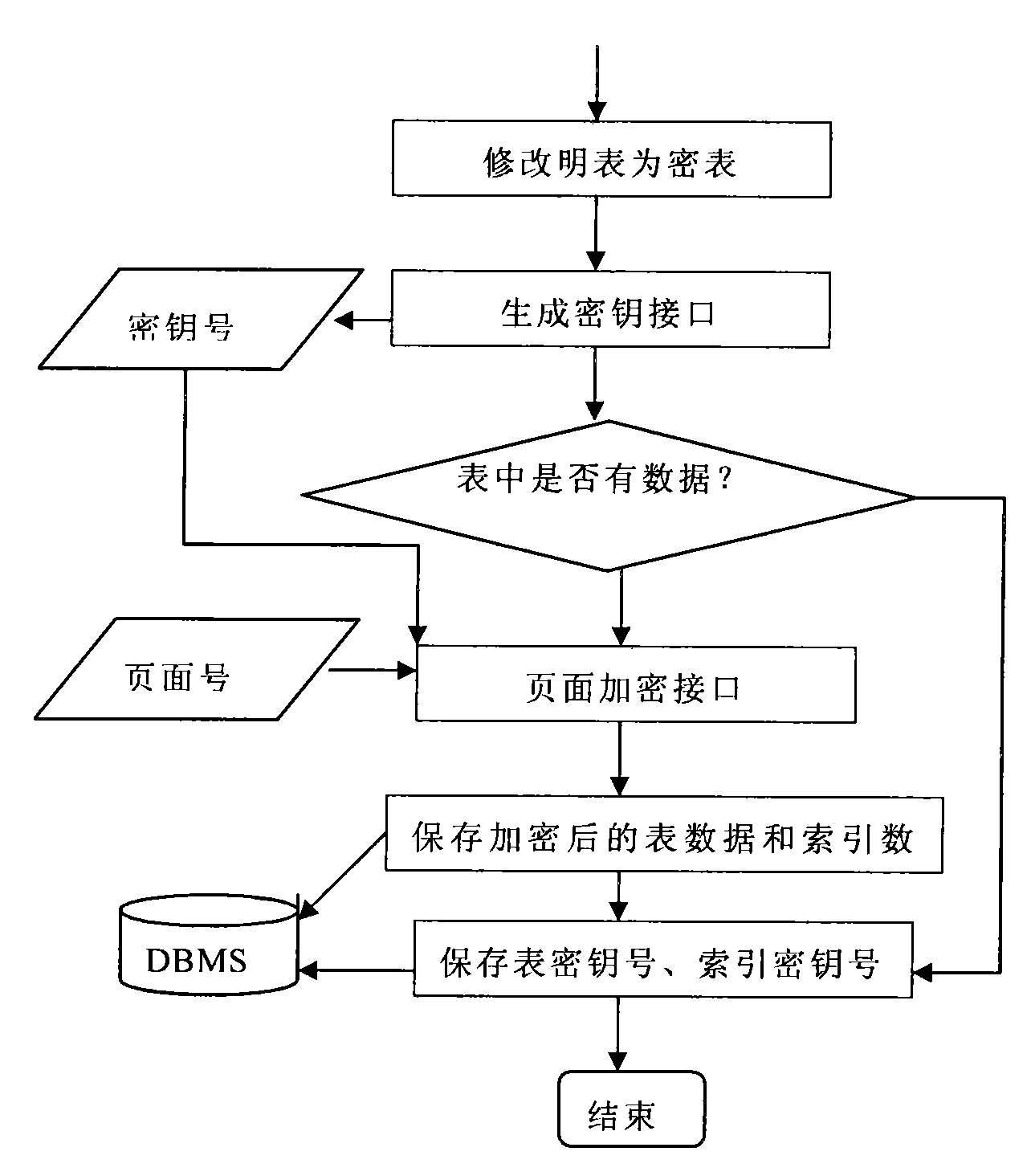
Database management system kernel oriented data encryption/decryption system and method thereof
InactiveCN101587479AReduce the burden onNot easy to be stolenSpecial data processing applicationsData operationsClient-side
The invention discloses a database management system kernel oriented data encryption / decryption system and a concrete method for performing encryption / decryption processing on data in a database by utilizing the same. The data encryption / decryption system comprises user request interface units which are distributed at clients and an encryption definition unit, an inquiry processing units, a data operation unit, a key management unit, a data decryption unit, a data encryption unit and a key database which are distributed at a server end. The system and the method realize the storage and the encryption of data in a database management system kernel. When the retrieval with a key is performed on the data in the database, the prior optimization strategy of the database can still be used, so the high-performance retrieval with the key can be provided.
Owner:北京人大金仓信息技术股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com