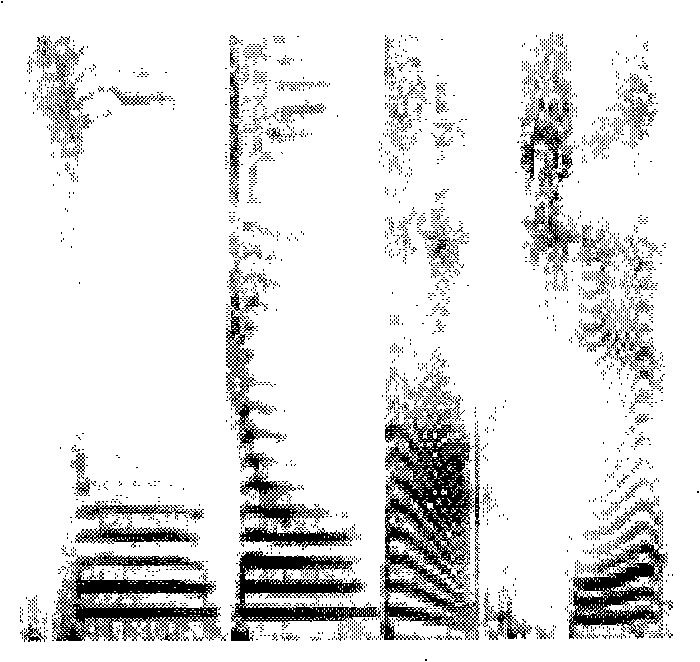Patents
Literature
452results about How to "Not easy to be stolen" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
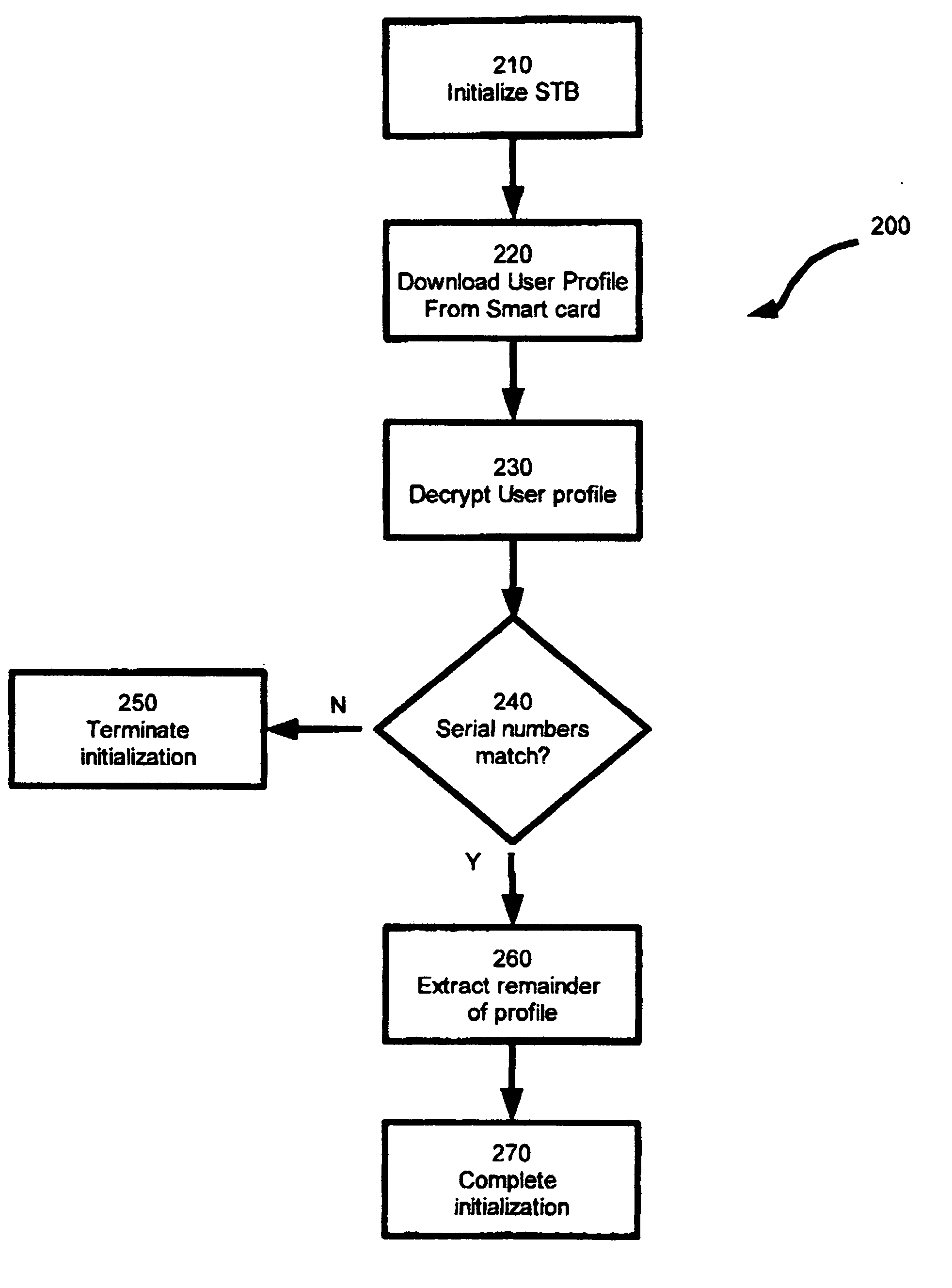
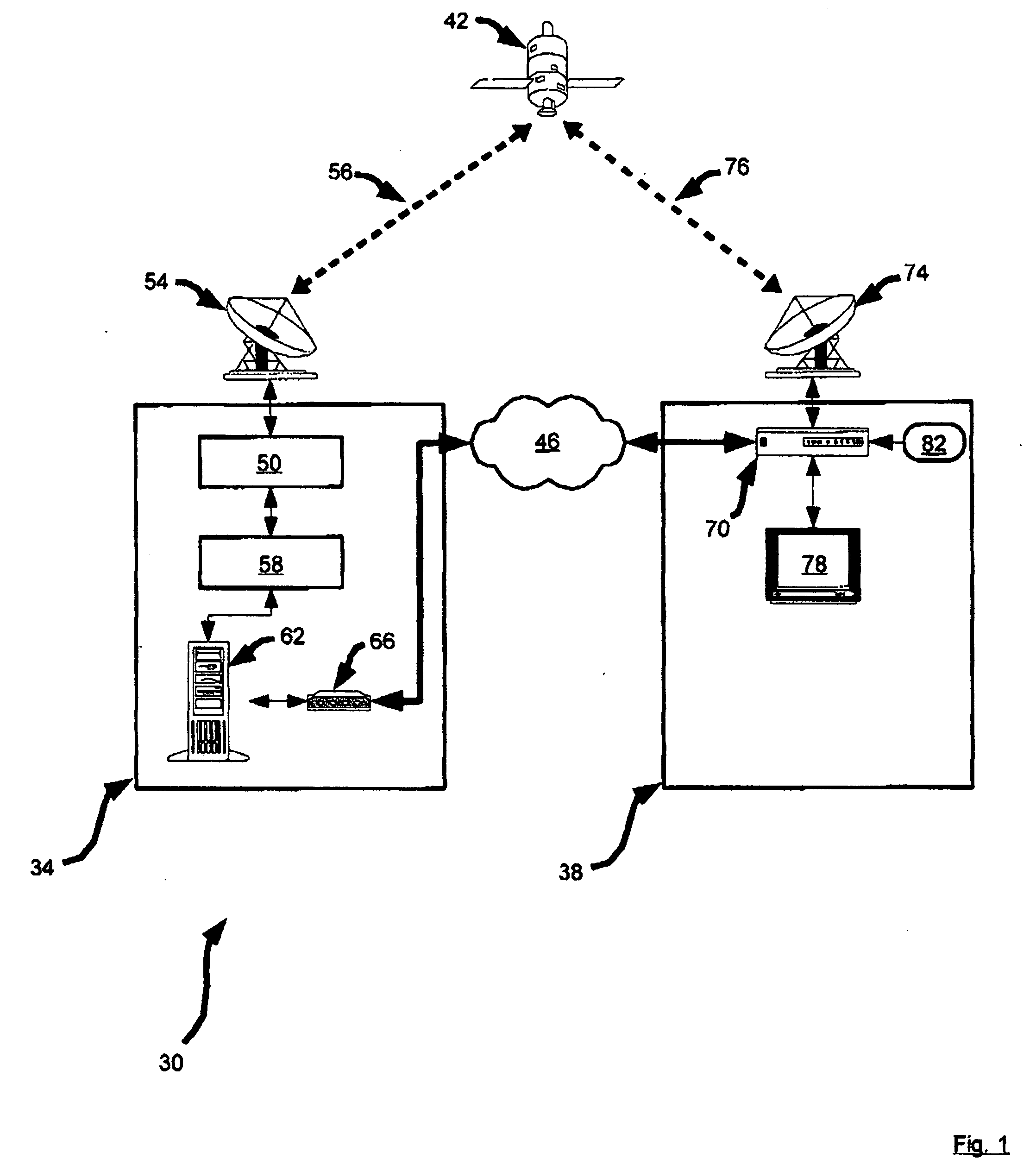
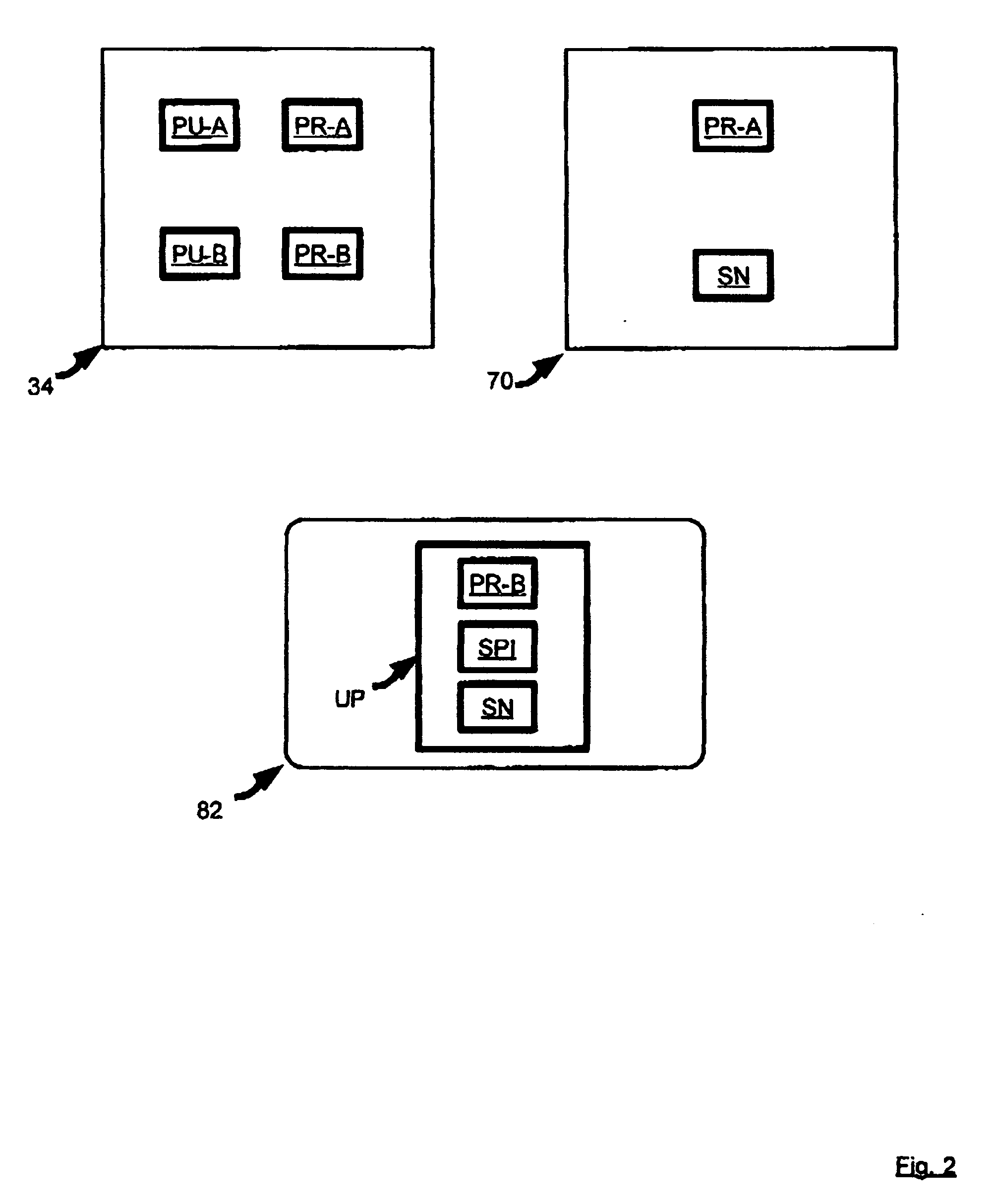
System and method for secure broadcast
InactiveUS20050050333A1Reduce the possibilityNot easy to be stolenTelevision system detailsBroadcast with distributionSecure communicationTelevision system
A novel system and method for secure communication is provided. In an embodiment, a satellite pay-tv system is provided that includes a head end office that broadcasts programming to one or more subscriber stations via satellite. The subscriber station includes a set top box operable to receive a smart card. The subscriber station is configured to only receive programming if the smart card contains a serial number that corresponds with the serial number of the subscriber station. Methods are provided for updating the smart card profile.
Owner:BCE
Securing device for table device
InactiveUS8413943B1Not always easyNot easy to be stolenPicture framesDomestic mirrorsEngineeringElectrical and Electronics engineering
Owner:ABA UFO INT CORP
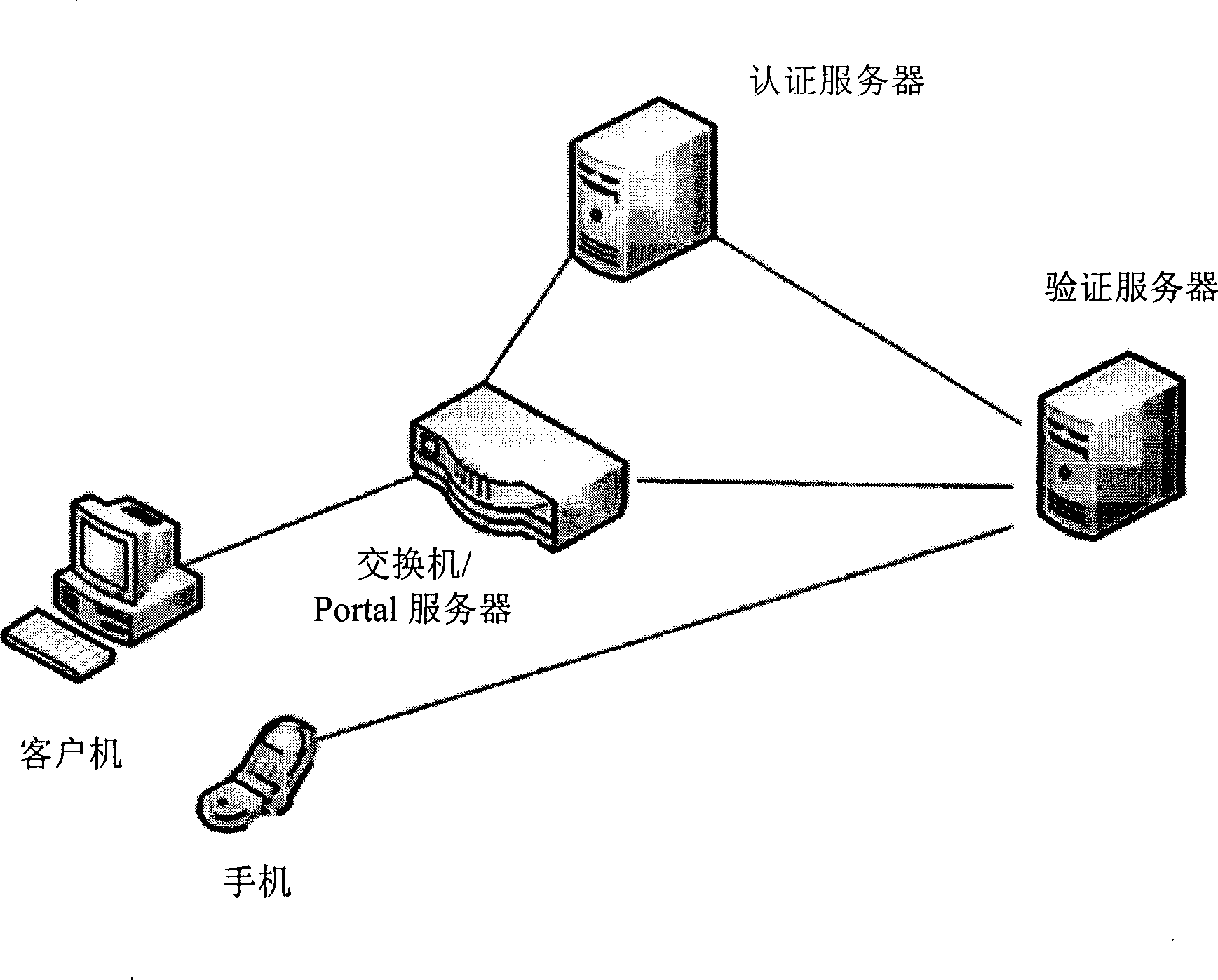
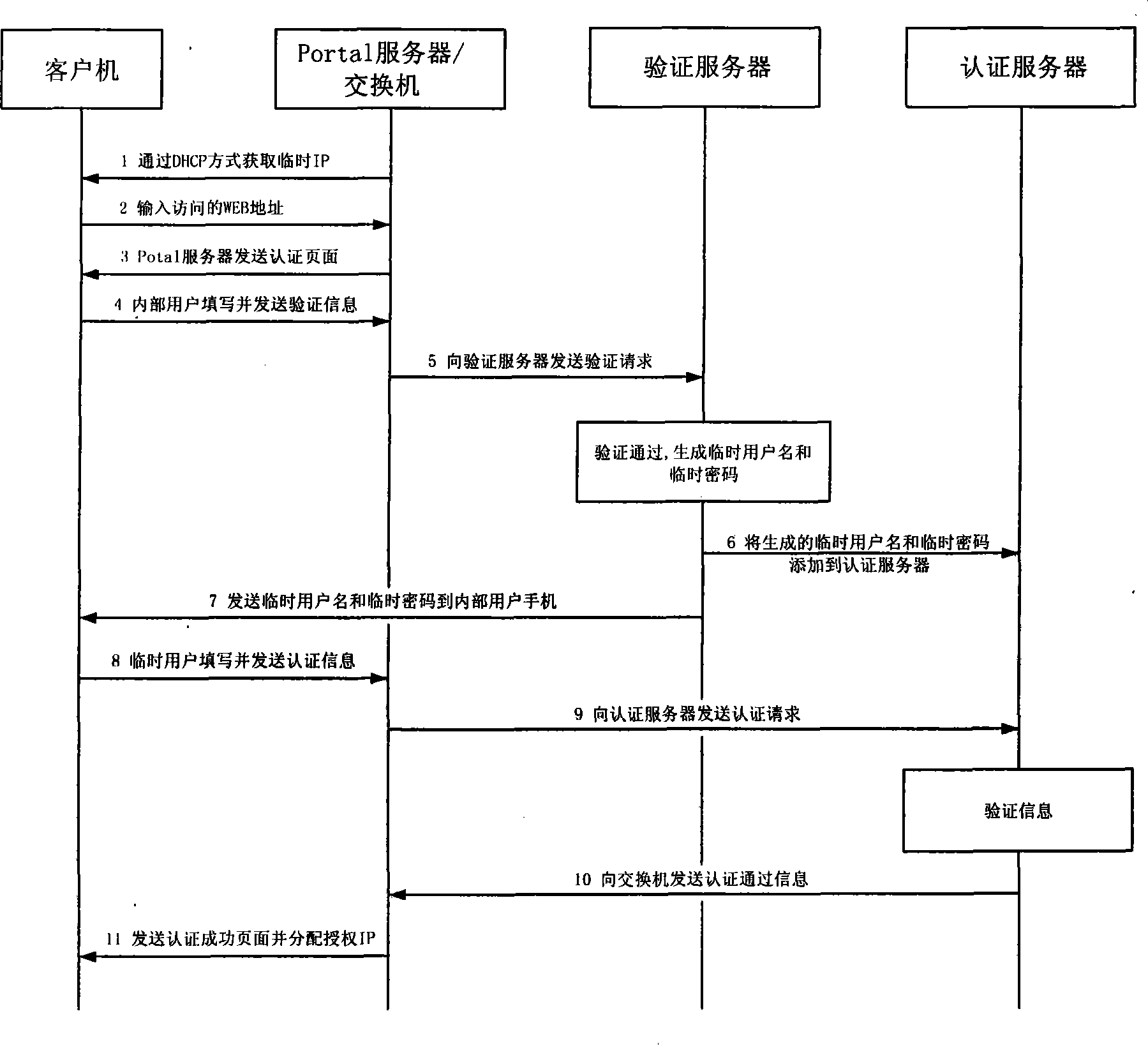
Method for local area network access authentication of casual user
ActiveCN101369893ASimple and standardized management processNot easy to be stolenUser identity/authority verificationData switching by path configurationManagement processAuthentication server
The invention relates to a method for implementing a user access authentication in a local area network, especially to a method for implementing a casual user access authentication in a public local area network. Firstly an internal user applies a casual user name and a key for the casual user through the authentication of a authentication server, the authentication server dynamically generates the casual user name and the key, then the casual user name and the key are stored in a user list of the authentication server, simultaneously the casual user name and the key are transmitted to a mobile phone of the internal user, the casual user uses the casual user name and the key for access authentication, and visits the authorized network resource after the authentication of the authentication server. The method of the invention adopts a double-factor and strong authentication system, the internal user is authenticated once, and the casual user is authenticated twice. The method can greatly improves the system safety, the casual user name and the key are all dynamically generated which are not easy to steal with high safety, and the management process for the casual user is simple and standard.
Owner:CHINA MOBILE GROUP DESIGN INST
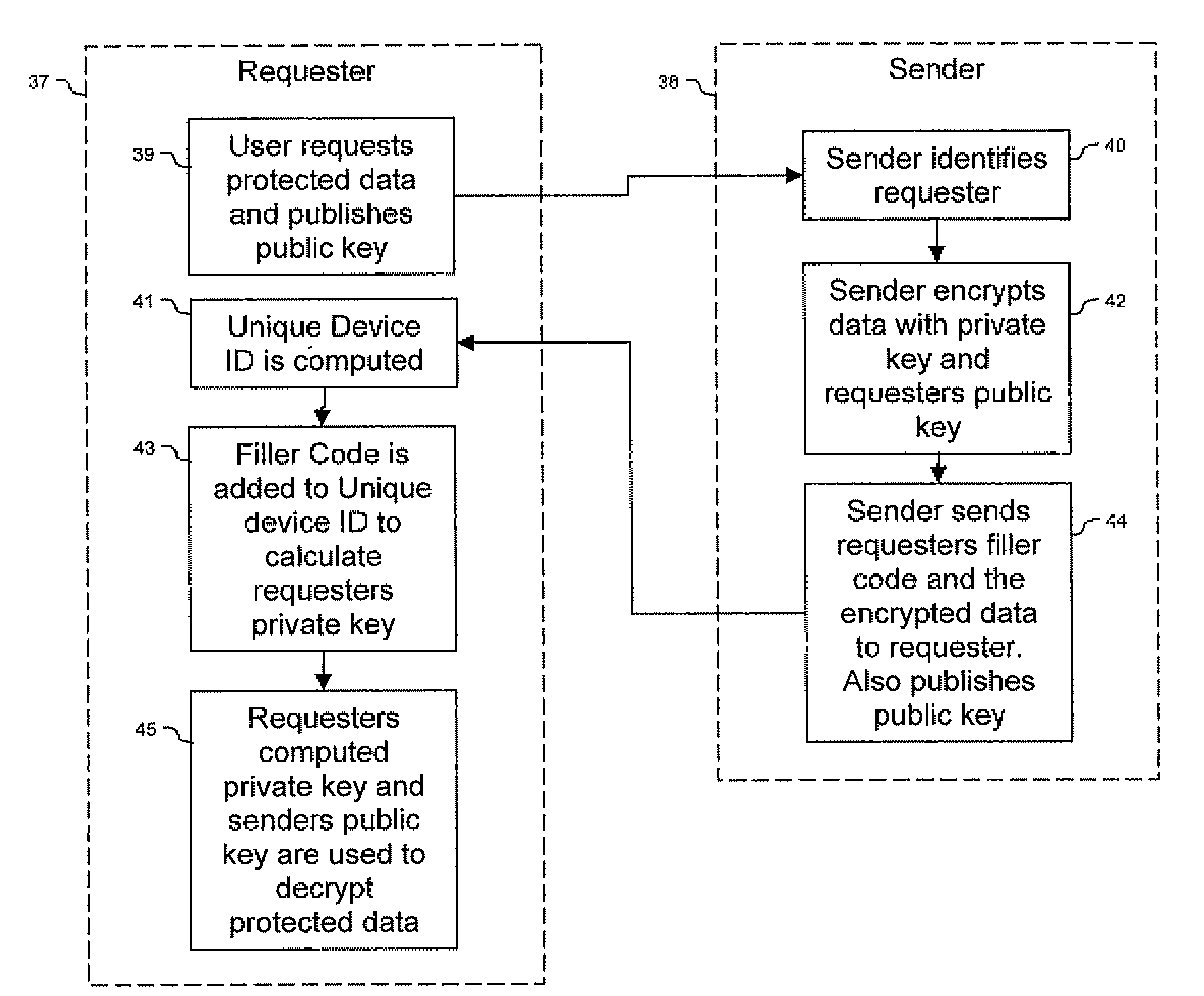
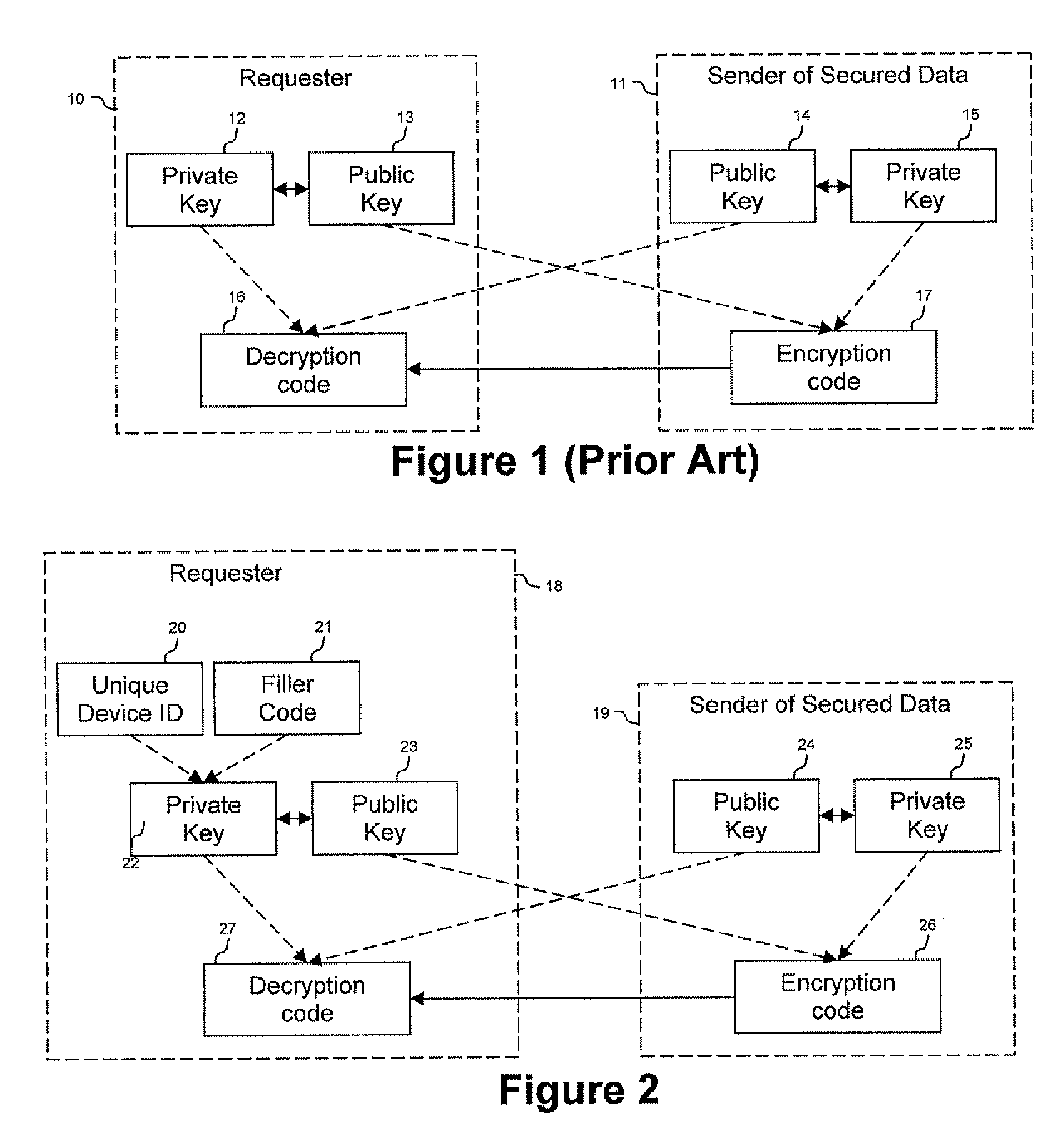
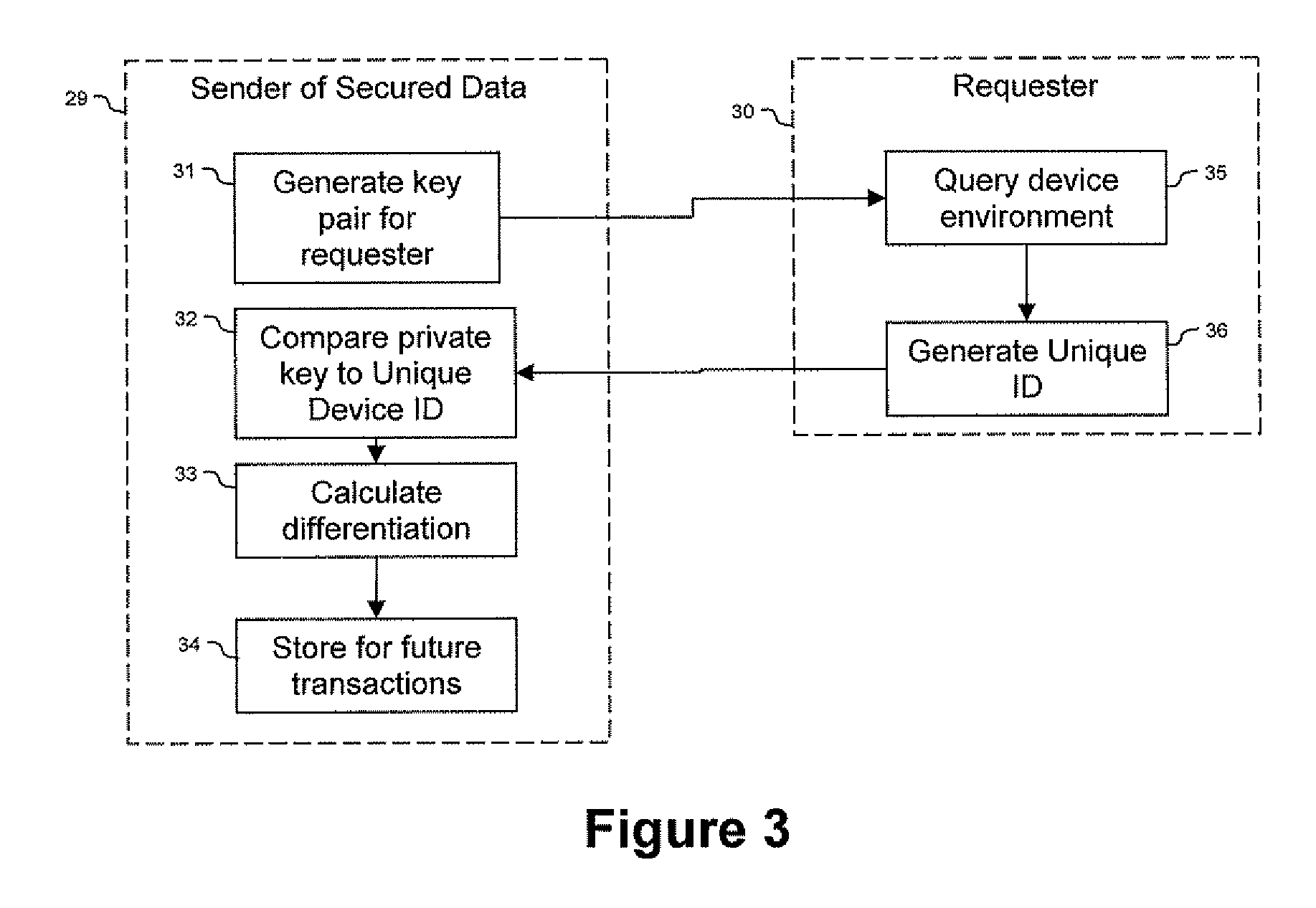
System and Method for Device Bound Public Key Infrastructure
ActiveUS20090150674A1Not easy to copyNot easy to be stolenDigital data processing detailsUser identity/authority verificationSecure communicationUnique device identifier
Techniques are provided secured communication of data, such as in the context of a public key infrastructure (PKI). In one embodiment, the technique may involve using a private key that is bound to the device requesting the secure data, thereby making it harder for someone to copy, steal or fake. The private key may be generated by adding a filler code to a unique device identifier. The identifier may be based on at least one user-configurable parameter and at least one non-user-configurable parameter of the device.
Owner:DEVICE AUTHORITY LTD
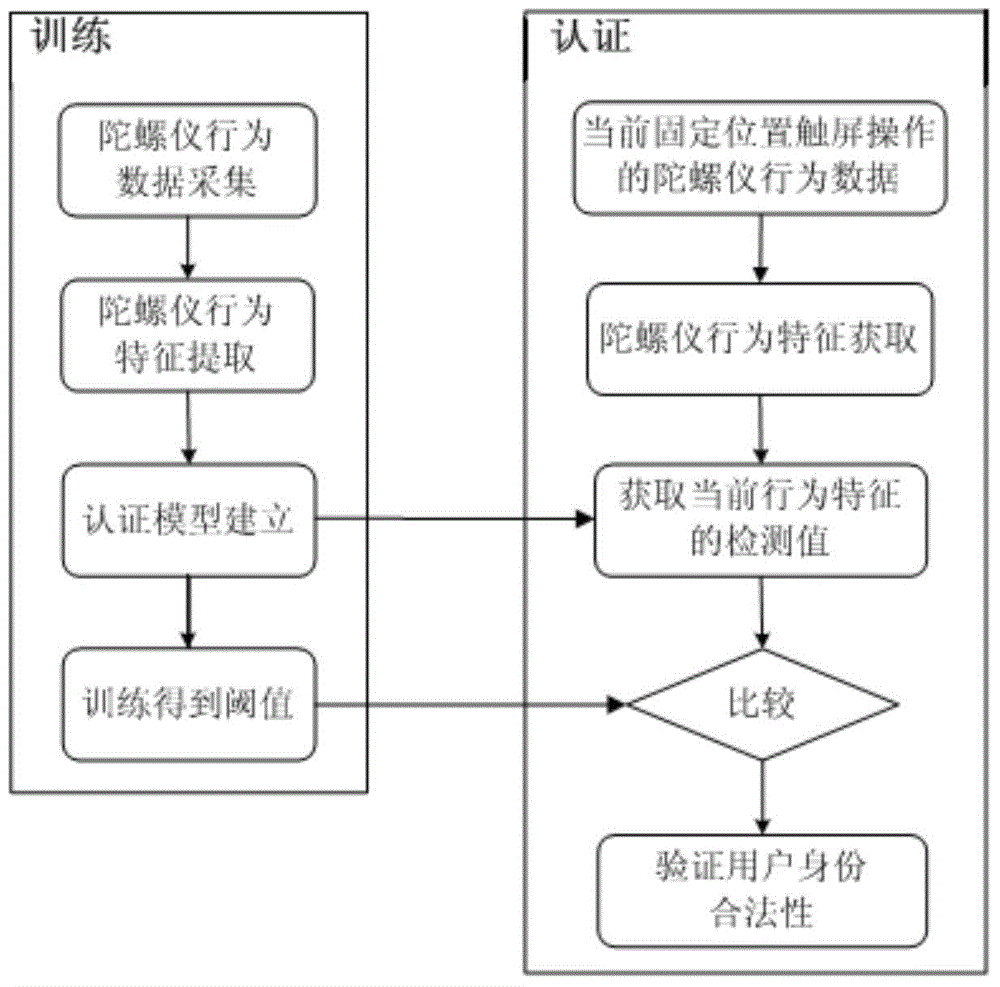
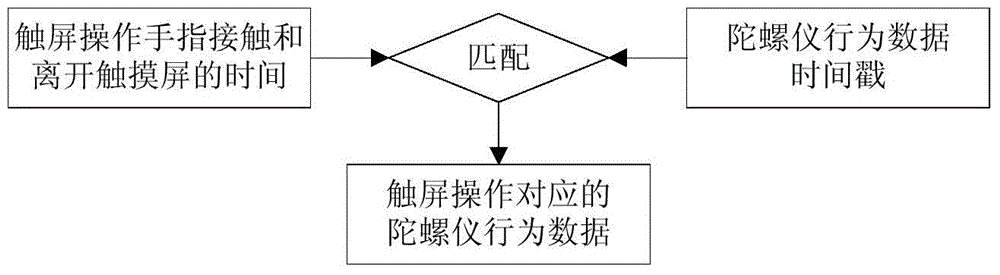
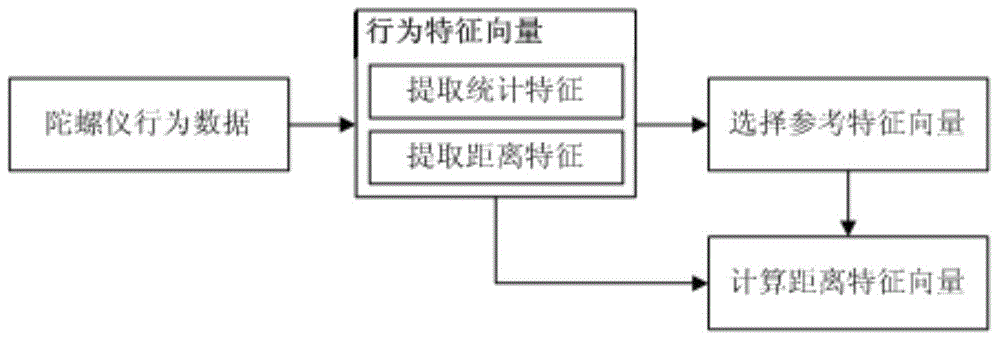
Smart phone user identity authentication method based on gyroscope behavior characteristics
ActiveCN104408341ANot easy to steal and counterfeitEasy to operateInput/output for user-computer interactionDigital data authenticationSmart phoneMobile phone
The invention discloses a smart phone user identity authentication method based on gyroscope behavior characteristics. The method comprises the following steps: extracting sensor behavior data corresponding to different operation events according to time information of screen touch operation by analyzing gyroscope behavior data generated during screen touch operation of a smart phone user to generate sensor behavior characteristics; establishing an identity authentication model of the user based on the behavior characteristics; performing identity authentication on the smart phone user. The method disclosed by the invention has the advantages that the method is easy to operate, and any additional equipment does not need to be added; the behavior characteristics of the mobile phone user in an authentication process are described by using gyroscope operation behaviors on the basis of not changing the user habit to lay a basis for user identity judgment, so that smear attack and observation attack can be effectively prevented, and extensive safety and adaptability are achieved.
Owner:XI AN JIAOTONG UNIV
Emblem for motor vehicle
Owner:DECOMA GERMANY
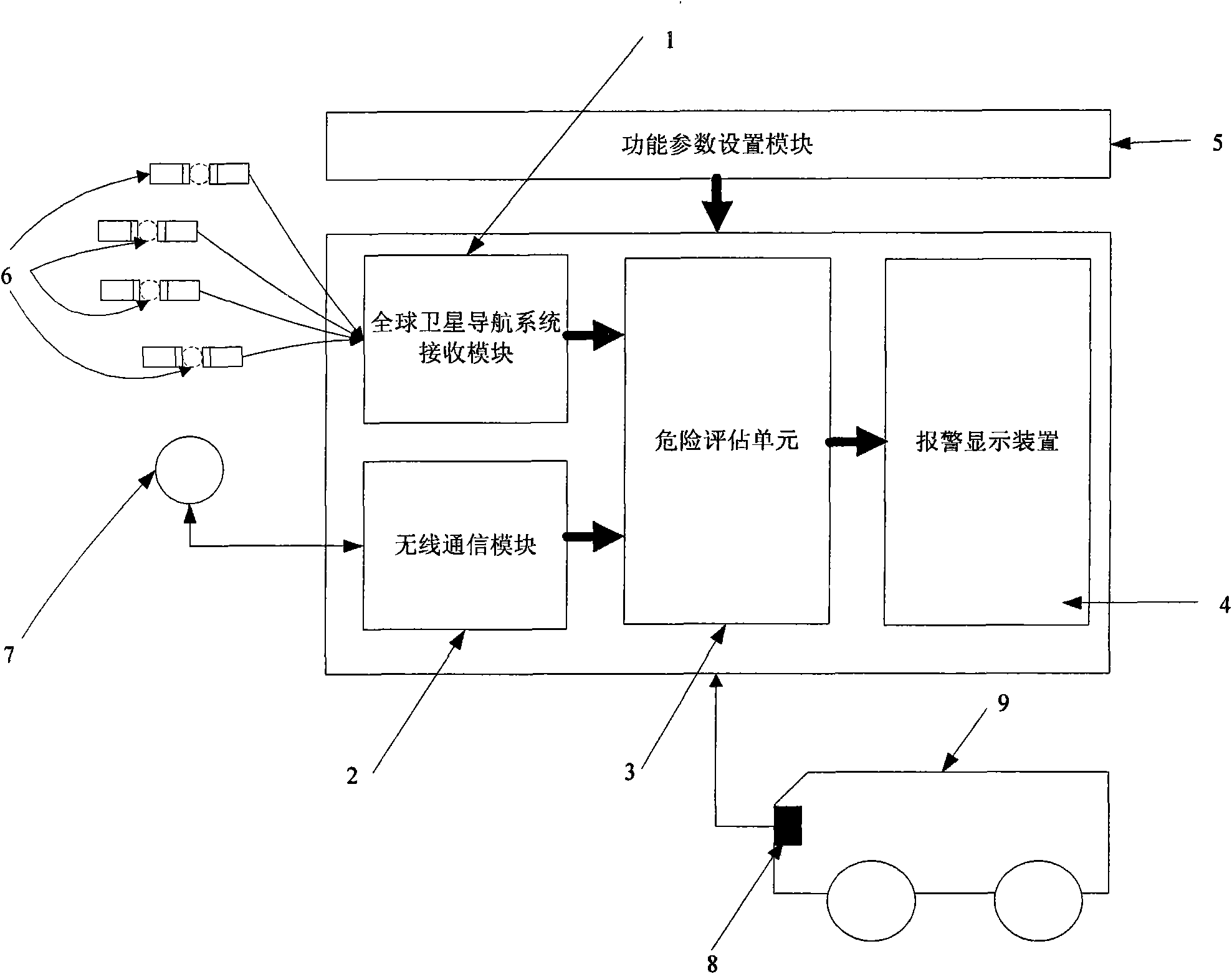
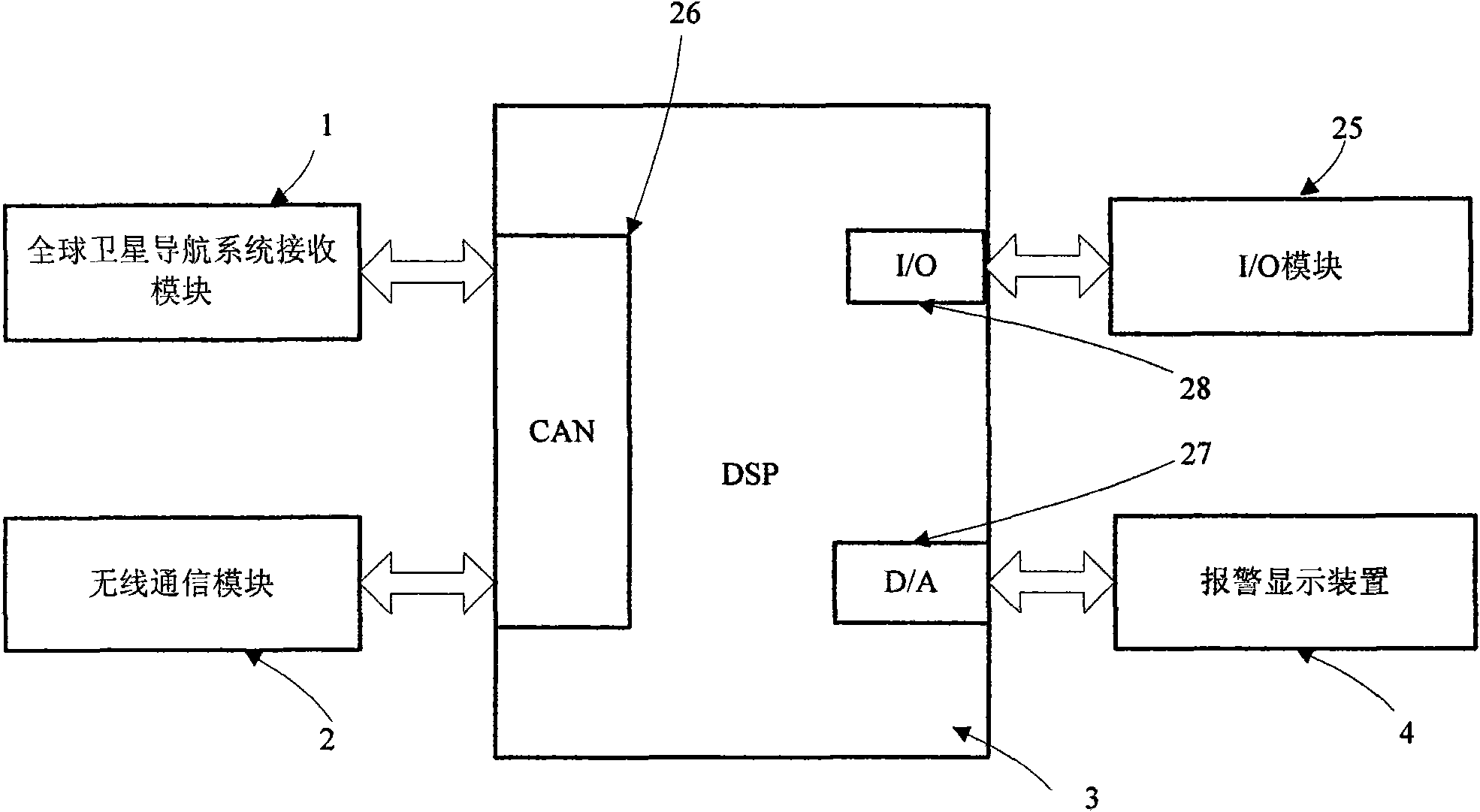
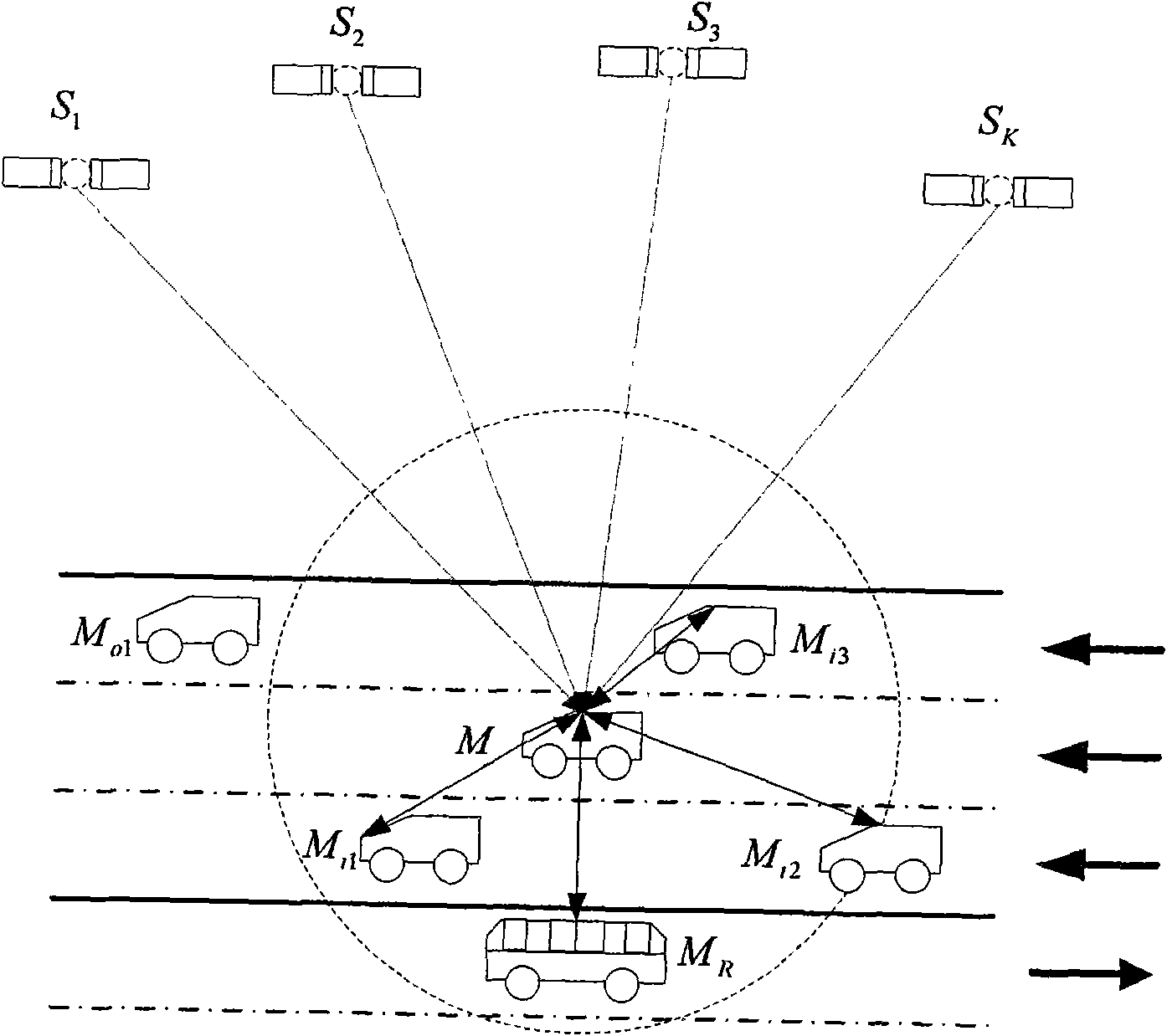
Early warning method when automobile closes at high speed and early warning device
InactiveCN101625797AEfficient use ofLower performance requirementsAnti-collision systemsPosition fixationDisplay deviceEngineering
The invention discloses an early warning method when an automobile closes at high speed and an early warning device. The method comprises the following steps: when the automobile drives at high speed, a navigation signal of a global navigation satellite system defines drive parameter information of the automobile, wireless net receives the drive parameter information of circumambient automobiles, the two drive parameter information are sent into a danger assessment unit, and the danger assessment unit judges whether the danger is existed to send an early warning signal. The device comprises a receiving module of the global navigation satellite system, a warless communication module, the danger assessment unit and a warning display device. The invention is the early warning method when the automobile closes at high speed and the early warning device, having simple and compact structure, low cost, convenient installation, wide application range and high safety.
Owner:NAT UNIV OF DEFENSE TECH
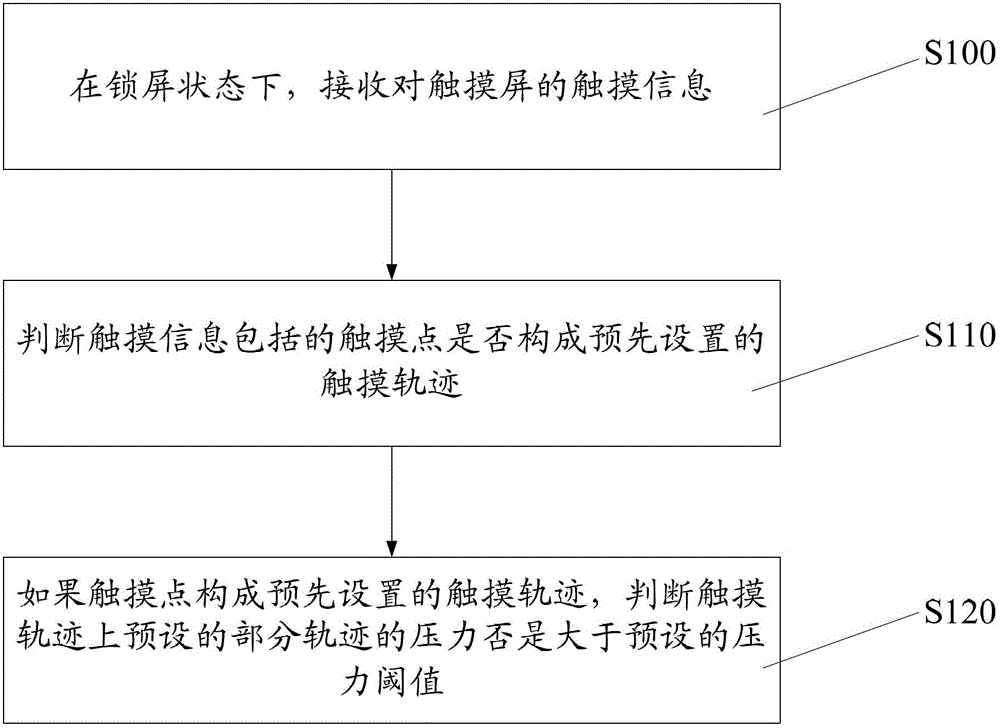
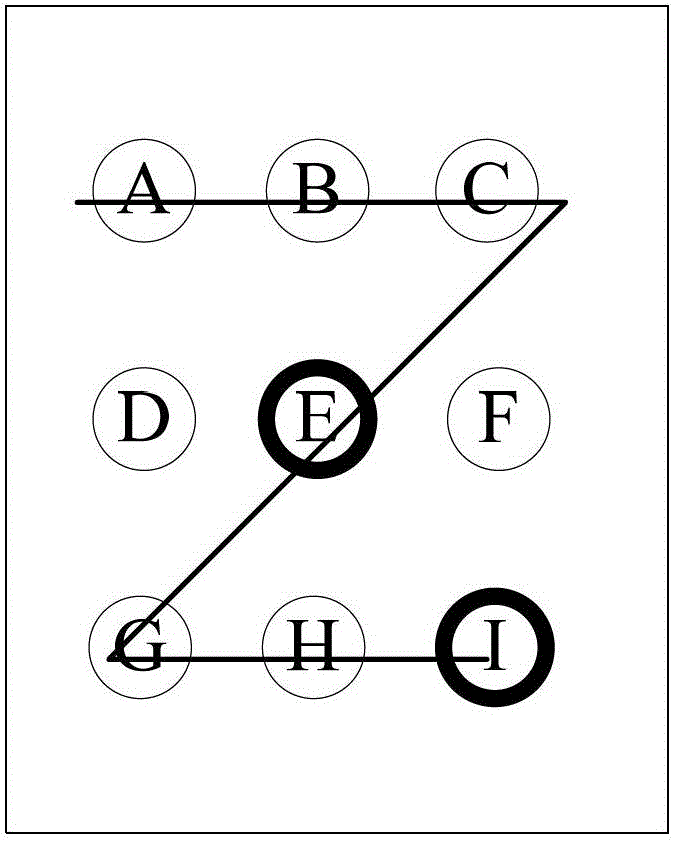
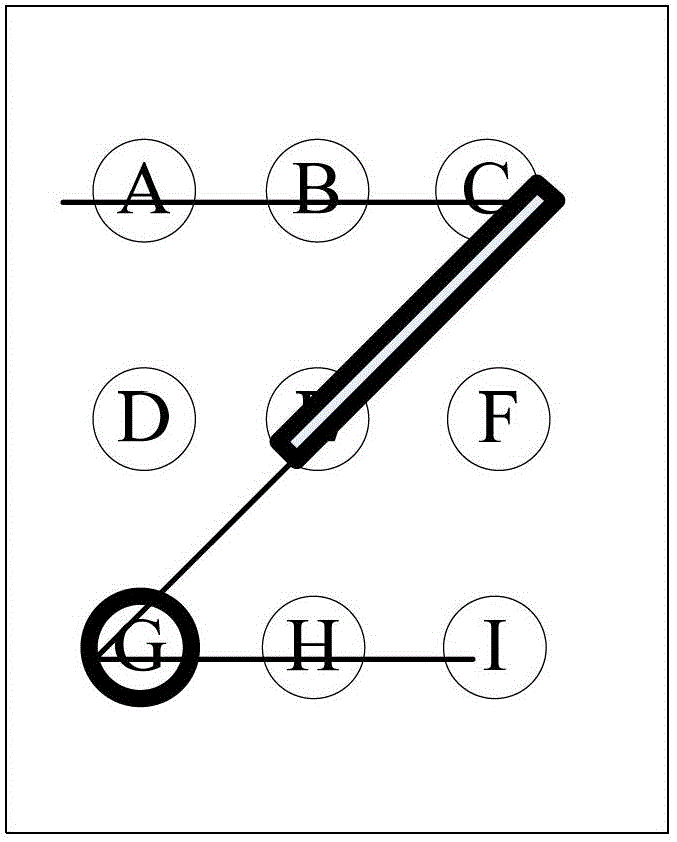
Unlocking method and device of touch screen
InactiveCN102722283AUnlocking Information ConfidentialityEasy to useInput/output processes for data processingPressure amplitudeTouchscreen
The embodiment of the invention provides an unlocking method of a touch screen. The unlocking method comprises the following steps of: A, receiving touch information on the touch screen in a screen lock state; and B, when judging that a preset touch track is constructed by touch points included in the touch information and when judging that the pressure amplitude of a part of track preset on the touch track is matched with the preset pressure amplitude, unlocking the touch screen. The embodiment of the invention also provides an unlocking device of the touch screen. By arranging the unlocking information as the touch track and applying pressure value information to the touch track, the unlocking information of the touch screen has higher security, and the system is safer in use.
Owner:北京中自投资管理有限公司
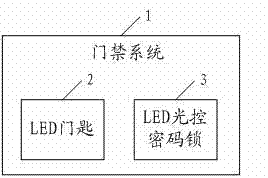
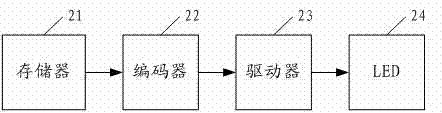
Entrance guard method, entrance guard system, light-emitting diode (LED) door key and LED light-operated trick lock
InactiveCN102542640ANot easy to be stolenEasy to useElectric permutation locksIndividual entry/exit registersPasswordEngineering
An embodiment of the invention discloses an entrance guard system, which comprises a light-emitting diode (LED) door key and an LED light-operated trick lock. The LED door key is used for enabling pre-stored password data to be converted into LED visible light signals which are sent to the LED light-operated trick lock for requesting for unlocking the LED light-operated trick lock. The LED light-operated trick lock is used for receiving the LED visible light signals emitted by the LED door key and enabling the LED visible light signals to be restored to the password data. The LED light-operated trick lock is further used for carrying out unlocking or maintaining current state according to the password data. The embodiment further discloses the LED door key, the LED light-operated trick lock and the entrance guard method. The entrance guard method, the entrance guard system, the LED door key and the LED light-operated trick lock can reduce energy consumption and are favorable to energy conservation.
Owner:KUANG CHI INST OF ADVANCED TECH
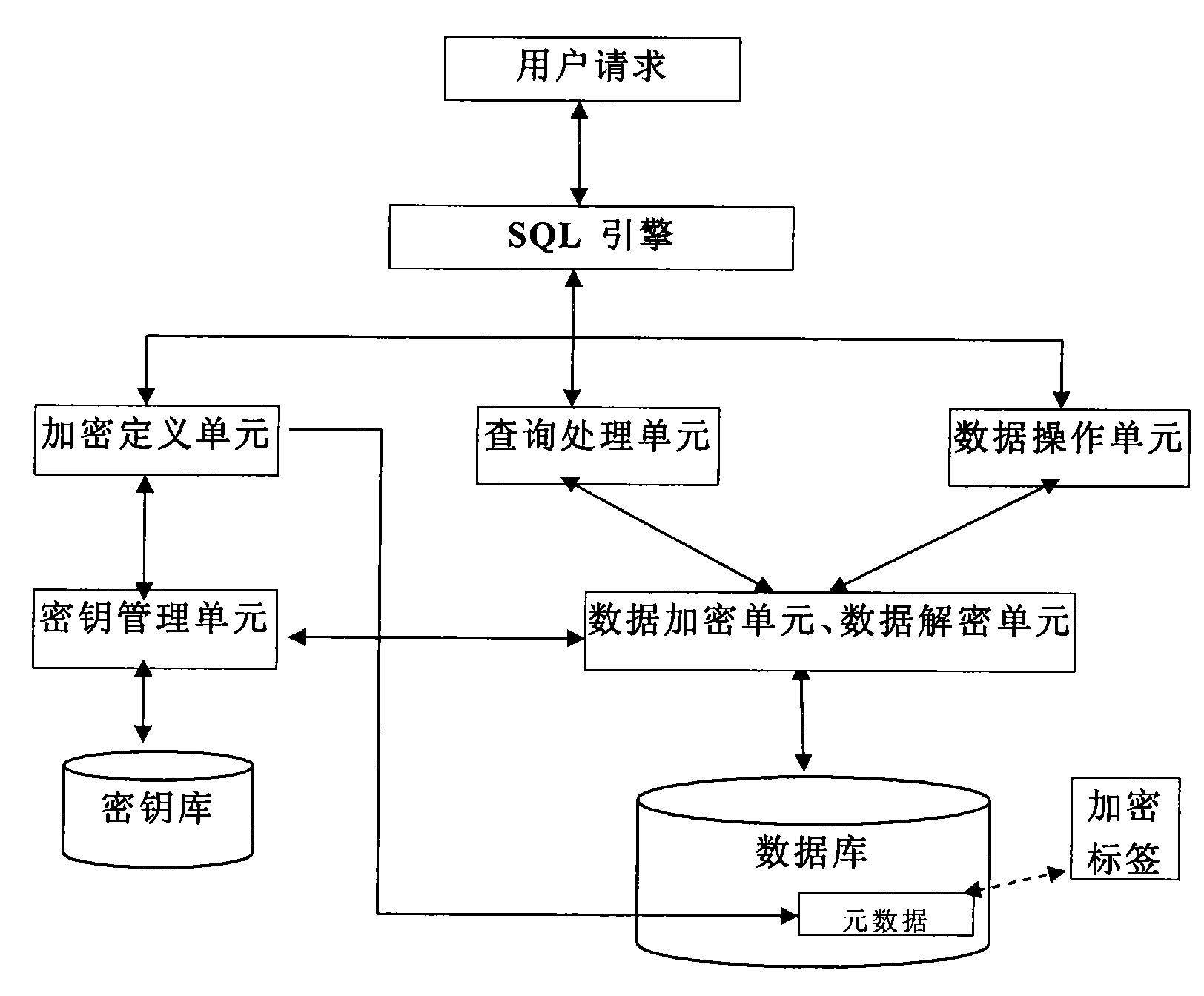
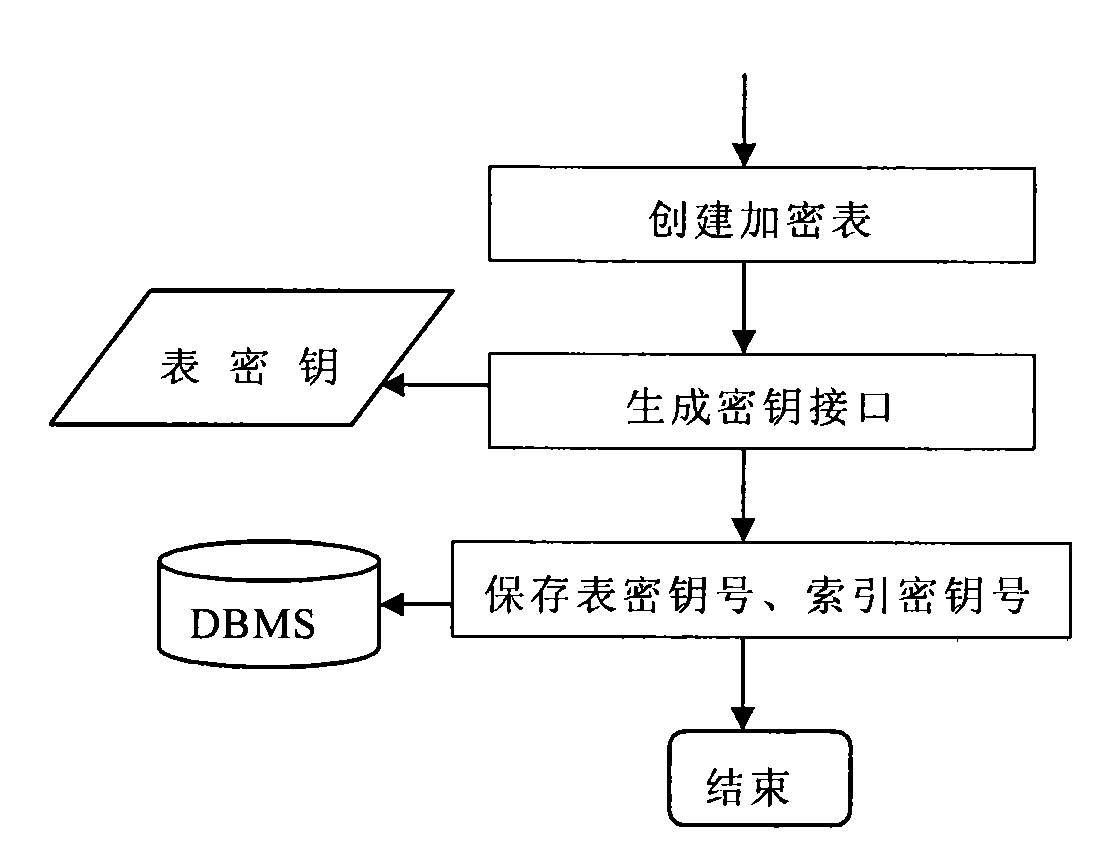
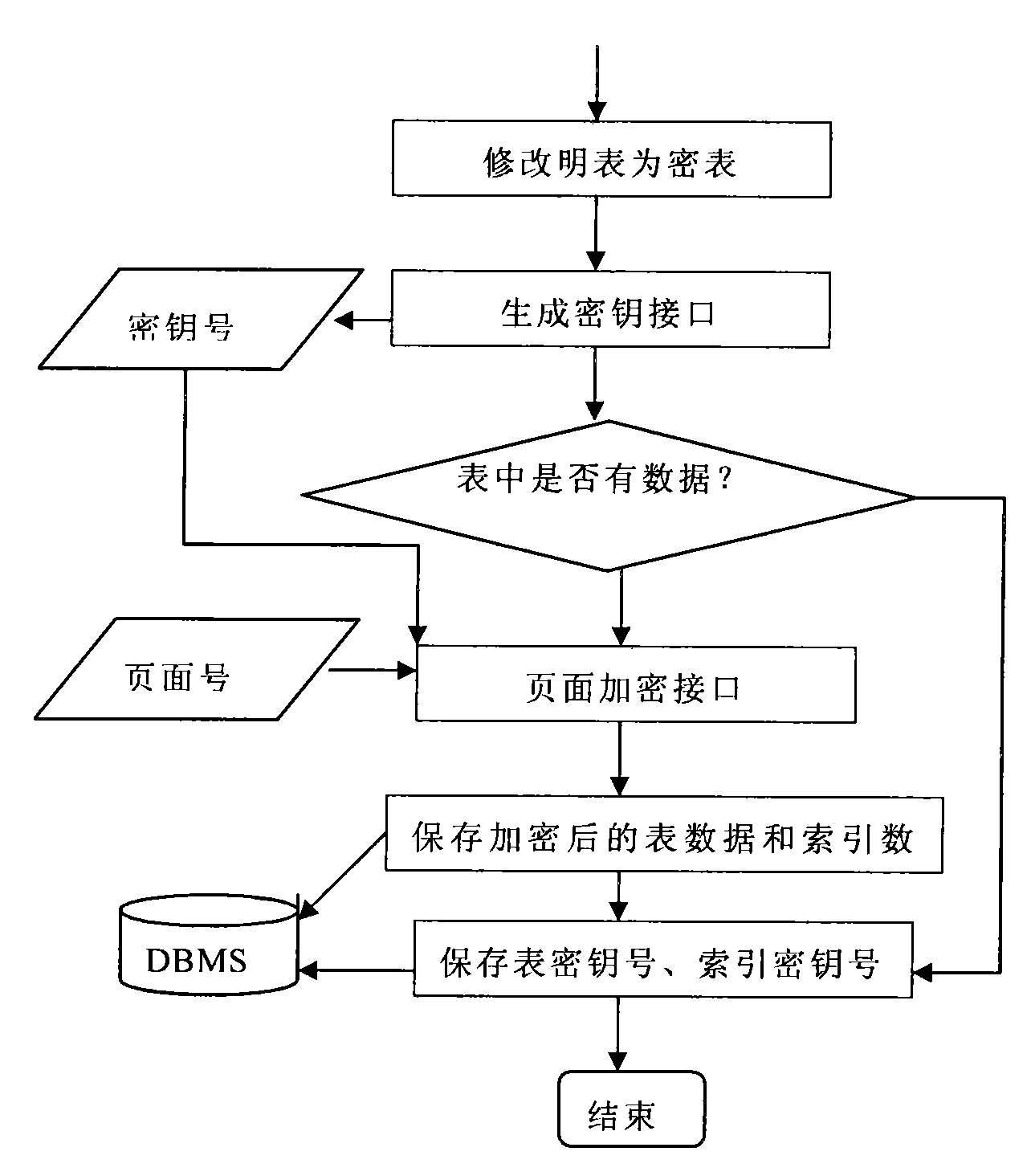
Database management system kernel oriented data encryption/decryption system and method thereof
InactiveCN101587479AReduce the burden onNot easy to be stolenSpecial data processing applicationsData operationsClient-side
The invention discloses a database management system kernel oriented data encryption / decryption system and a concrete method for performing encryption / decryption processing on data in a database by utilizing the same. The data encryption / decryption system comprises user request interface units which are distributed at clients and an encryption definition unit, an inquiry processing units, a data operation unit, a key management unit, a data decryption unit, a data encryption unit and a key database which are distributed at a server end. The system and the method realize the storage and the encryption of data in a database management system kernel. When the retrieval with a key is performed on the data in the database, the prior optimization strategy of the database can still be used, so the high-performance retrieval with the key can be provided.
Owner:北京人大金仓信息技术股份有限公司
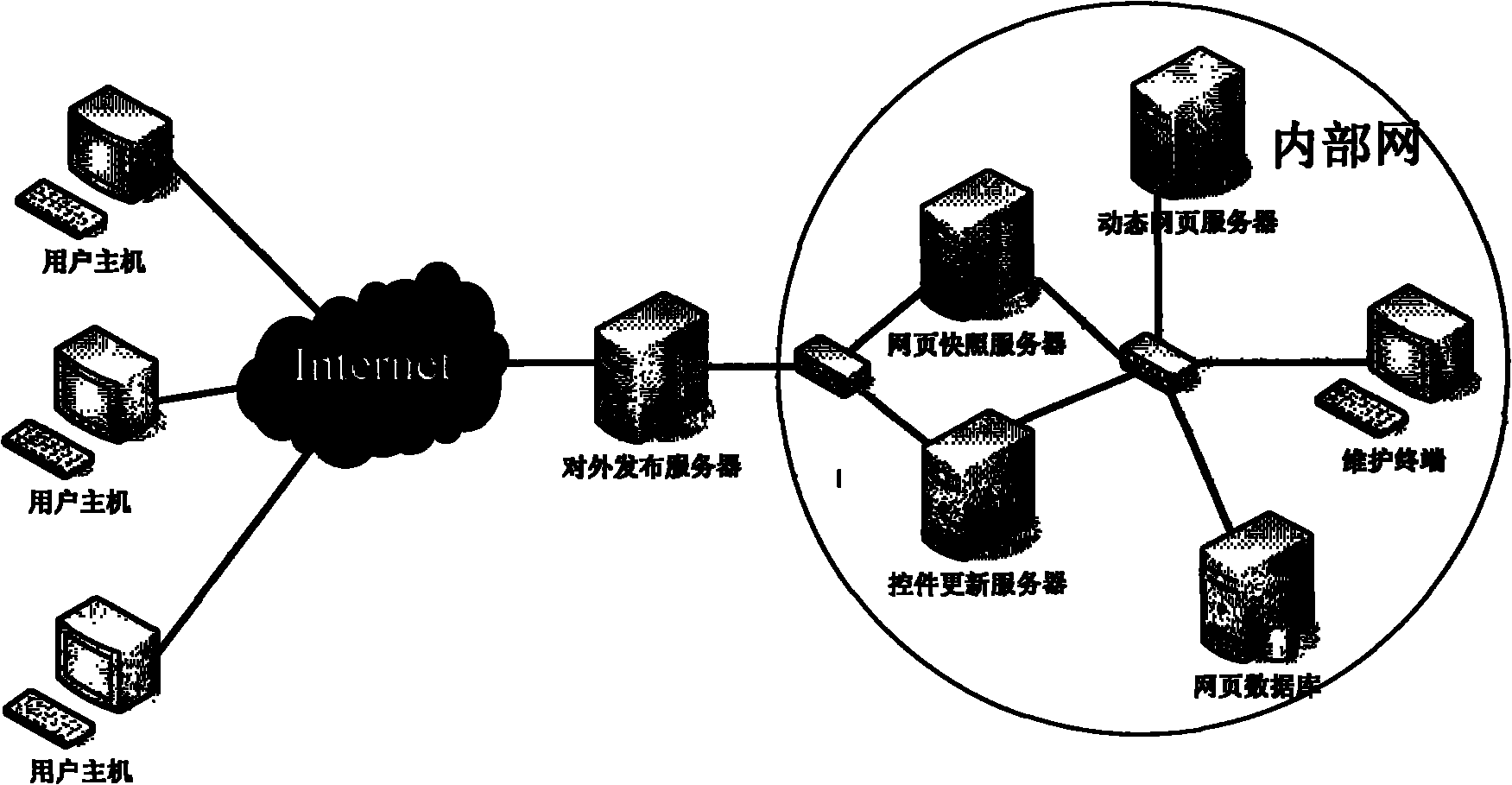
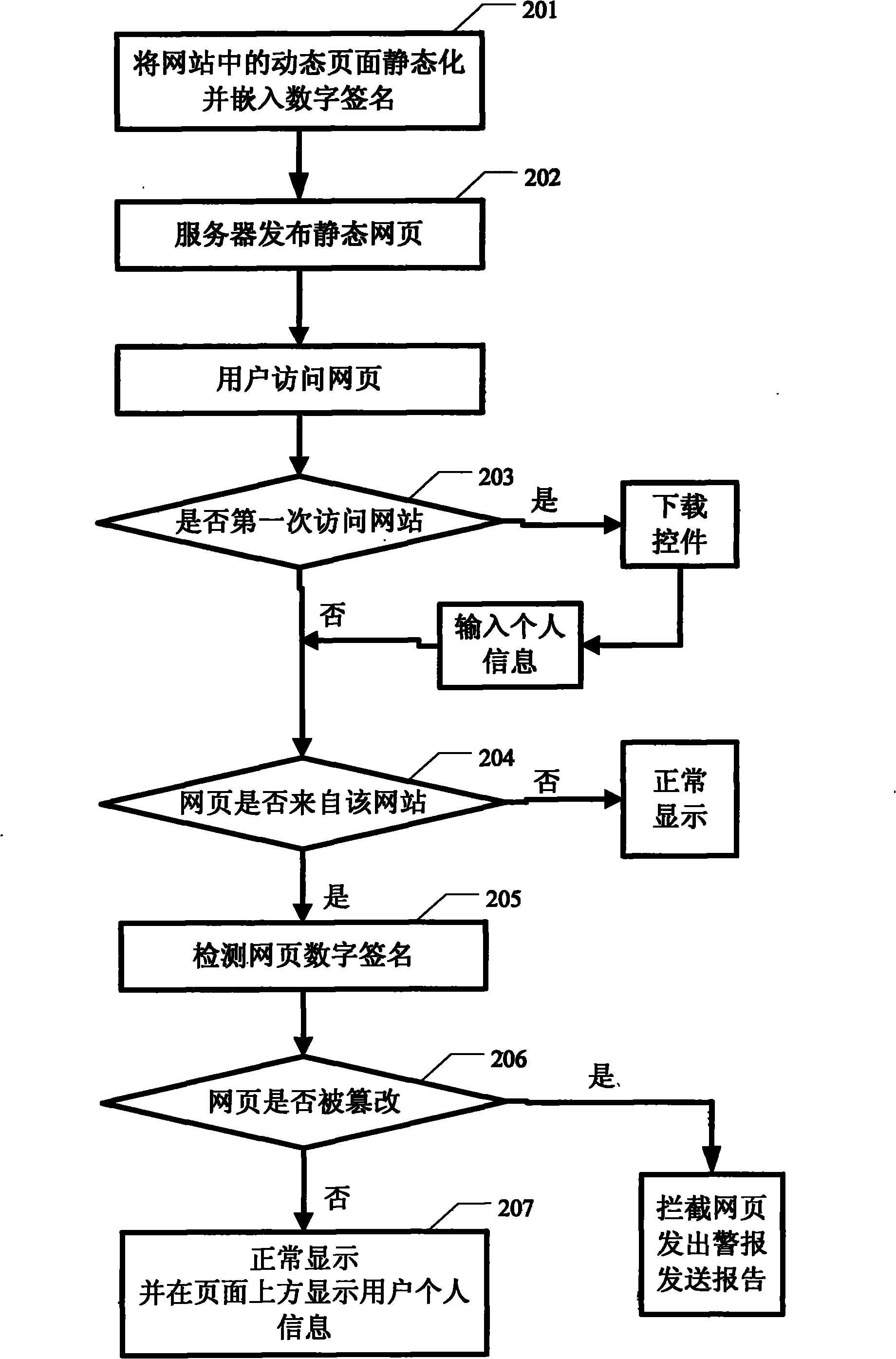
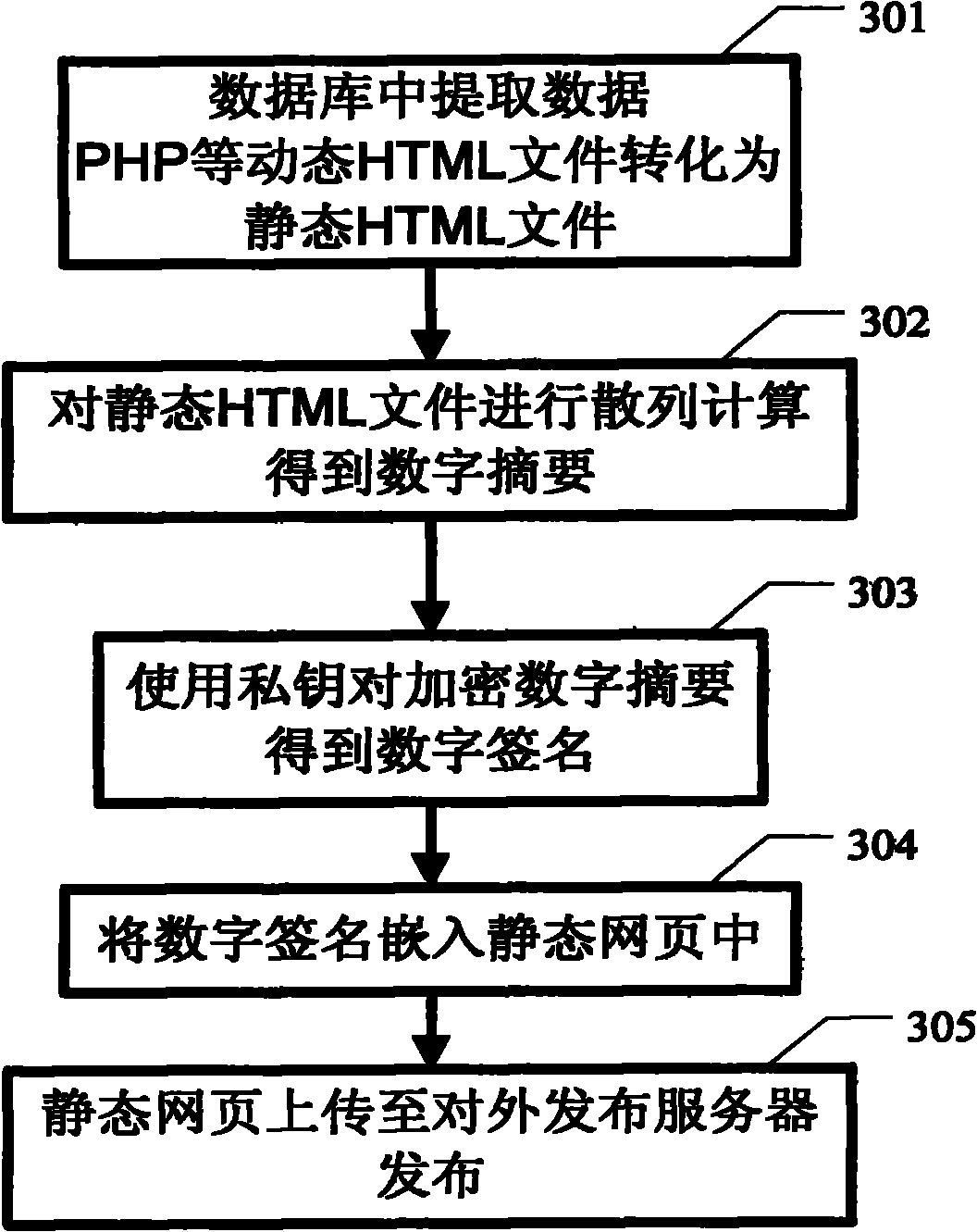
Anti-counterfeiting method for web page
ActiveCN102110198AEffective interceptionEasy to embedPlatform integrity maintainanceSpecial data processing applicationsWeb siteDigital signature
The invention provides an anti-counterfeiting method for a web page. The method comprises the following steps of: changing the dynamic web page in a website into a static web page, and embedding a concealed digital signature into the web page; when a user browses the web page, automatically loading a browser plug-in provided by the website, and inputting personal information during installing the plug-in; detecting whether the web page is from the website, detecting the digital signature of the web page from the website and judging whether the web page is the original web page by the plug-in; directly intercepting the non-original web page and giving an alarm by the plug-in; displaying the personal information input by the user at the same time of displaying the original web page on a browser; and when the user will log in the website and discovers the personal information is not correctly displayed, determining that the current website is a counterfeited angling website. By the method, the problem that most methods depending on known rule bases lack defense capacity on novel angling attacks and latest angling websites in the prior art is solved.
Owner:BEIJING SAFE CODE TECH
Digital watermark production and recognition method used for audio document
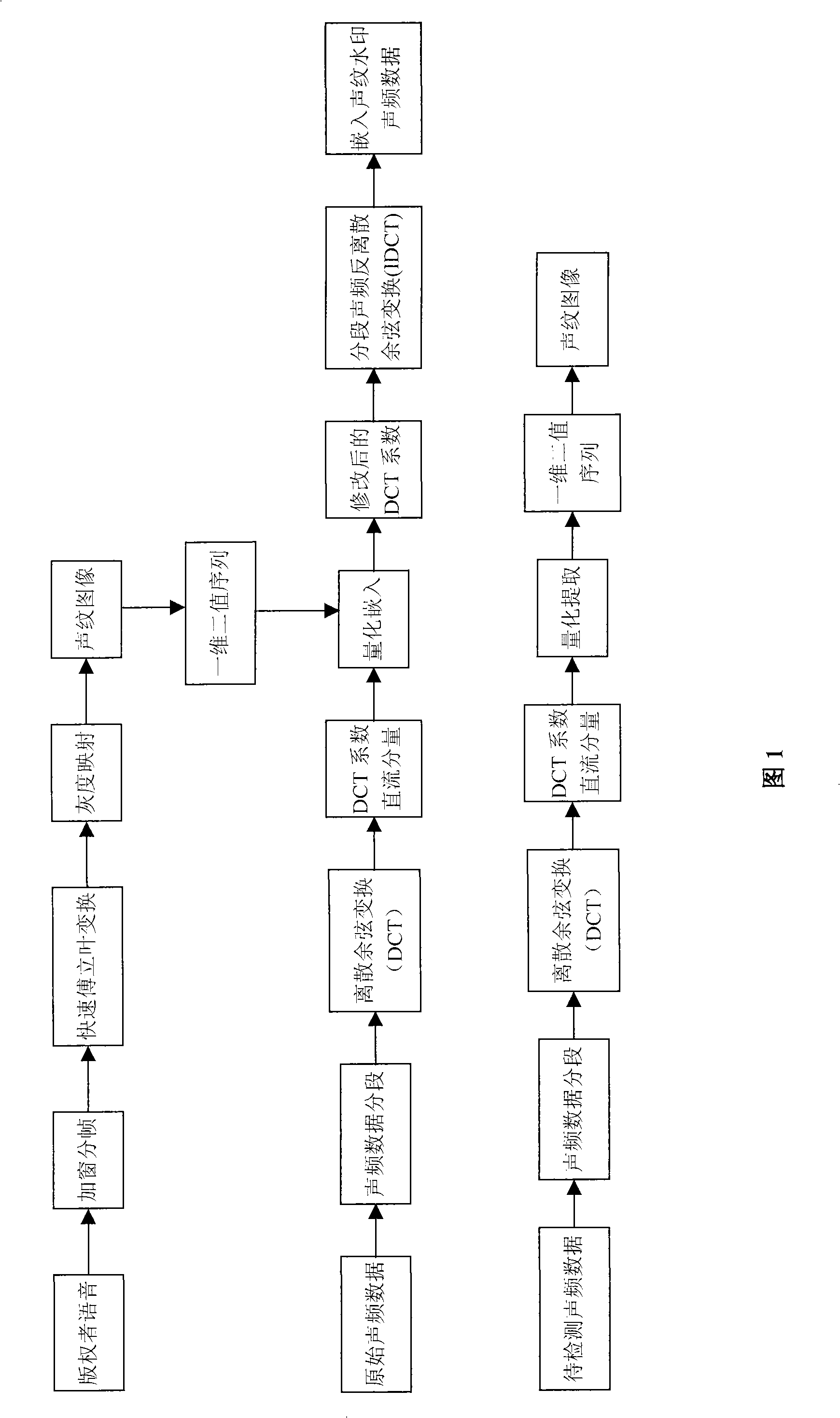
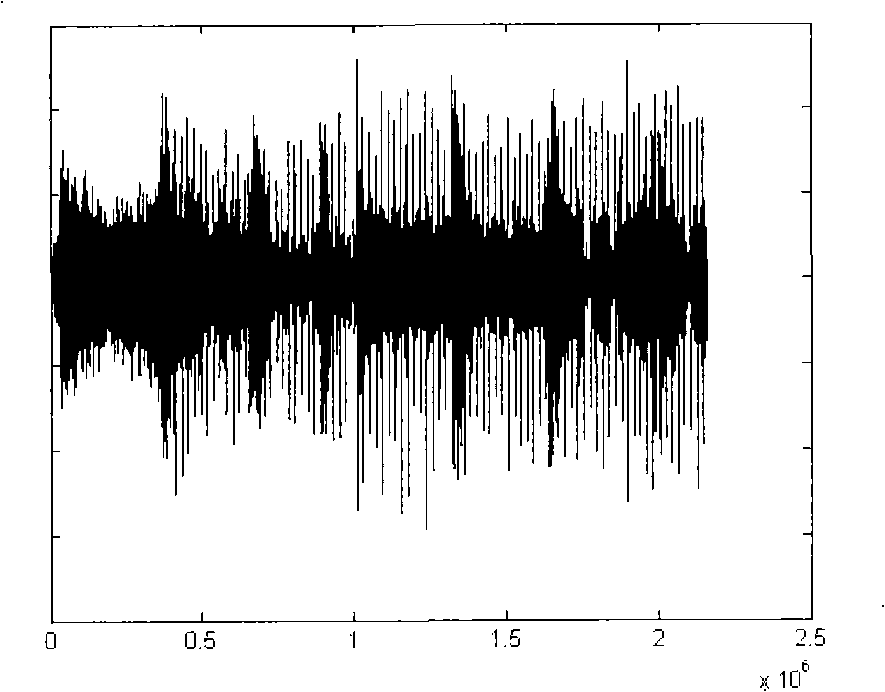
InactiveCN101345054AGuaranteed robustnessSolve the problem of copyright certificationSpeech analysisFrequency spectrumDigital watermarking
The invention discloses a digital watermark manufacture method and a recognition method used for audio files. The watermark is added in the audio digital file to be processed and taken as copyright marking information; the method of the invention is characterized in that the watermark is realized by adopting converted voiceprint information and comprises the steps as follows: a section of speech signals with copyright identification is colleted and a voiceprint watermark image is gained; the speech signal is converted into one-dimensional two-value sequence group; the gray-scale value of each matrix unit is presented by adopting an eight-bit binary number; the audio file where the watermark is to be inserted is divided into sections; frequency domain transformation is respectively carried out to each audio section so as to obtain the frequency spectrum file; a bit of one-dimensional two-value sequence group watermark data is embedded into each section of the frequency spectrum file; the embedding method is a method used for quantitatively modifying the frequency spectrum file coefficient; reverse conversion is carried out so as to obtain the audio data of the embedded watermark; the audio data is combined with the audio data which is processed so as to obtain the audio digital file with the digital watermark. Reverse separation operation is carried out during the recognition process. The method of the invention effectively solves the copyright verification problem of the digital audio product.
Owner:SUZHOU UNIV
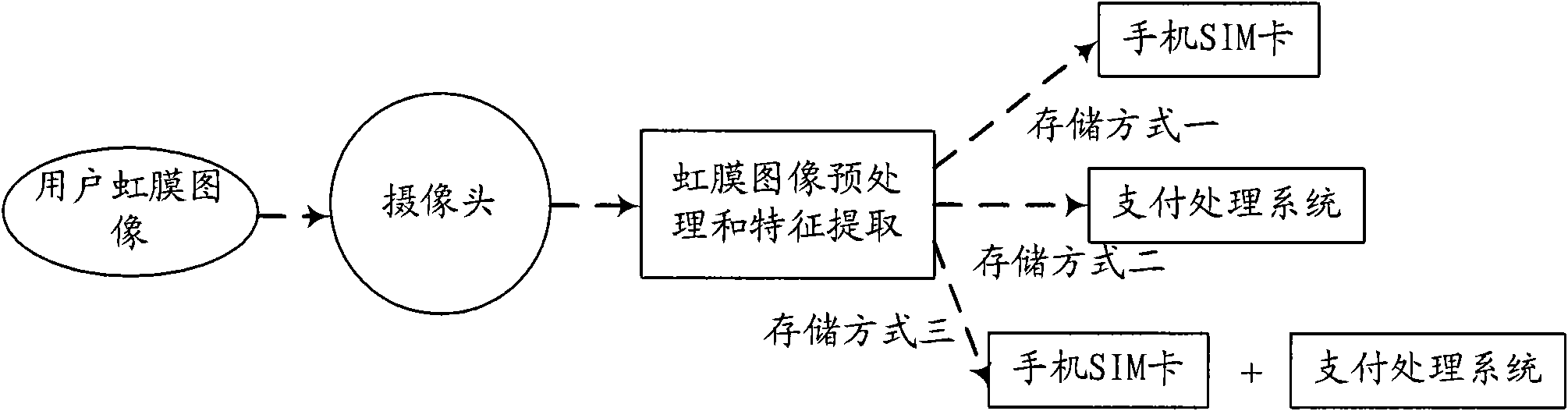
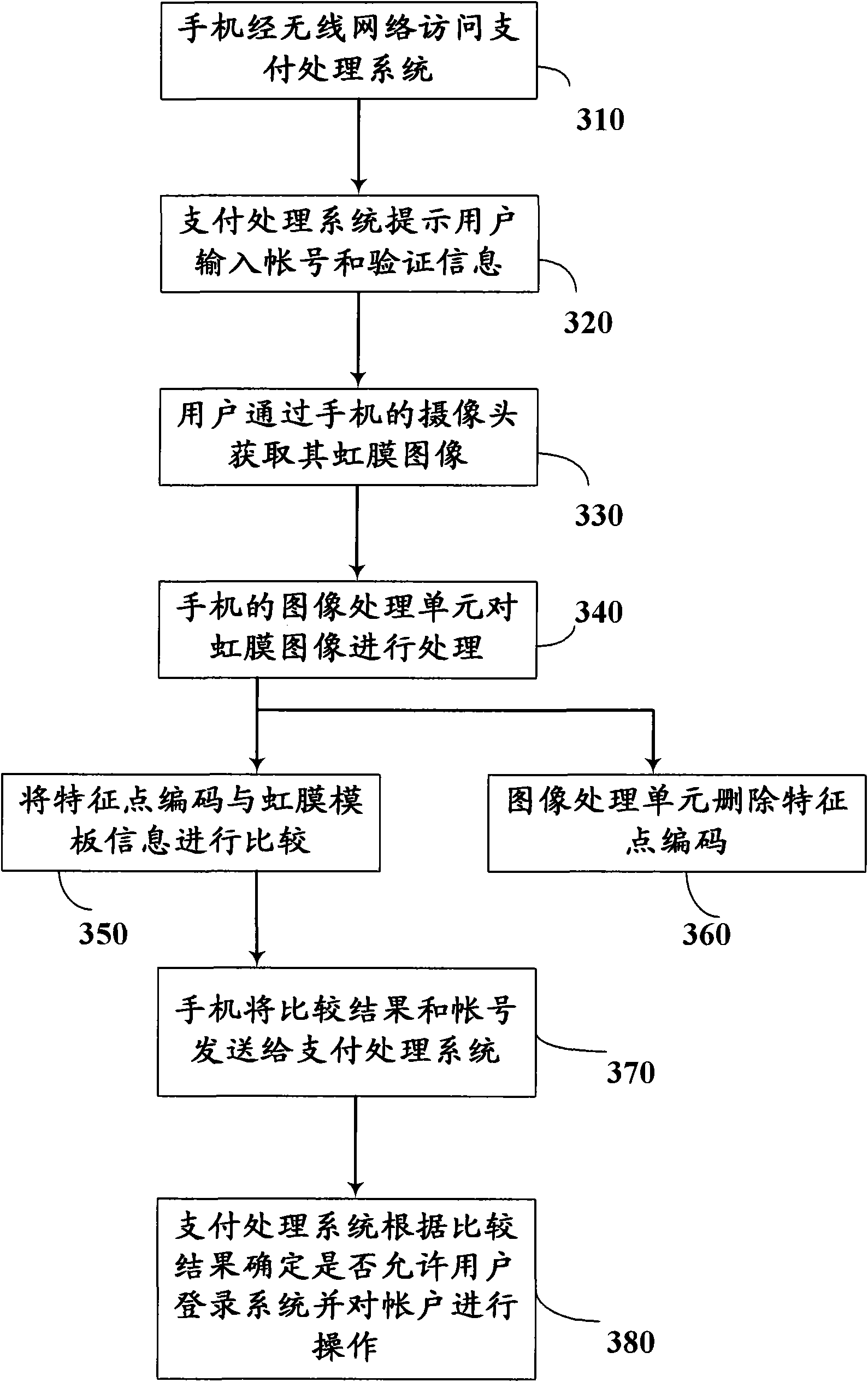
Mobile payment method and equipment for implementing same
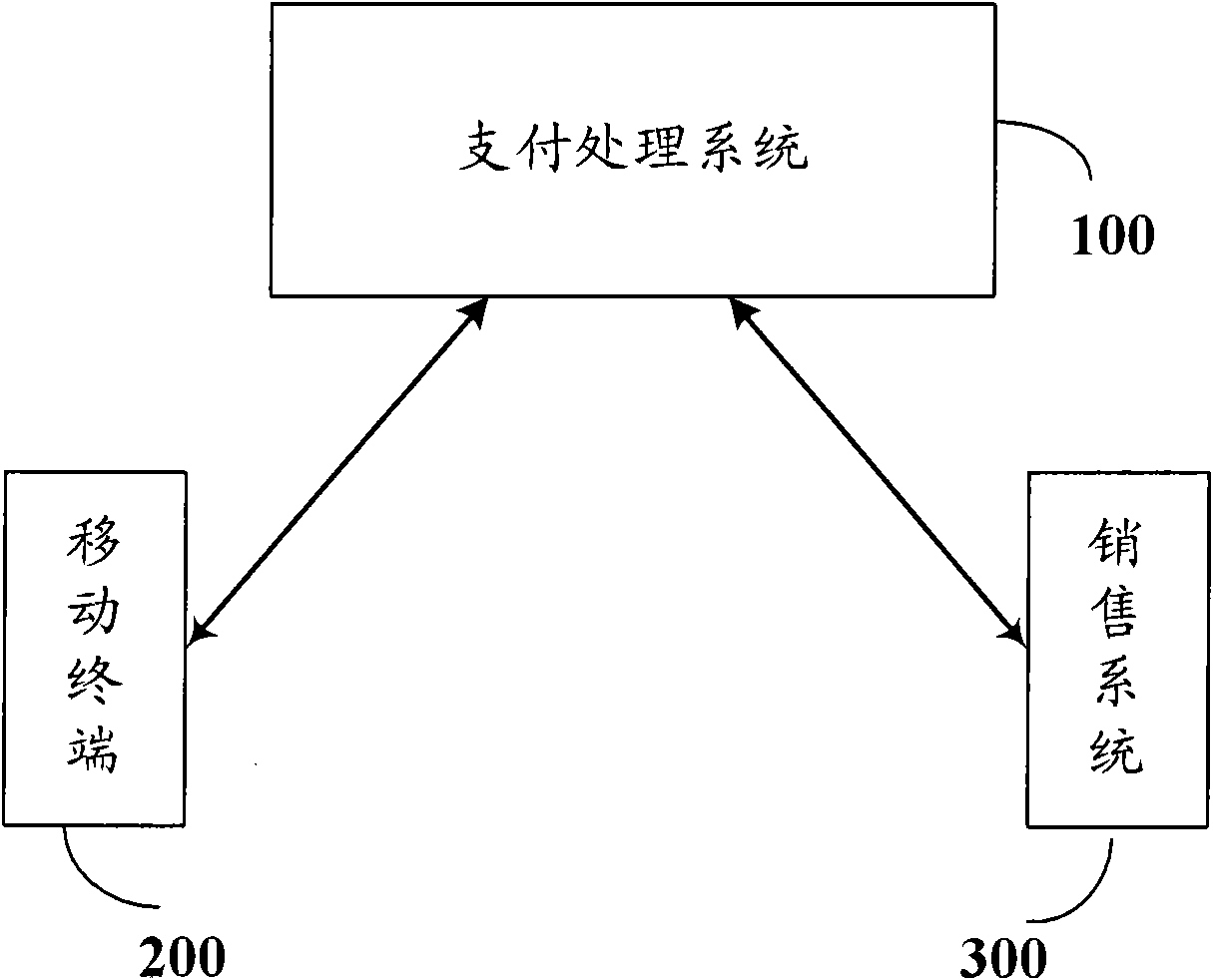
InactiveCN102314731AHigh precisionImprove stabilityComplete banking machinesCharacter and pattern recognitionPasswordIris image
The invention relates to an electronic payment technology, in particular to a mobile payment method, and a mobile terminal and a payment processing system for implementing the mobile payment method. According to the invention, the mobile payment method comprises the following steps of: acquiring an iris image of a user by using the mobile terminal which is provided with an image acquisition unit; determining the identity of the user according to the acquired iris image; and with the payment processing system, performing payment processing by using a judgment result. Compared with the conventional mobile payment method, the embodiment of the invention has the advantages that: by using iris information as the authentication information of the identity of the user, the safety of the payment service of a mobile phone is greatly improved; and by using the iris information, the burden on password memorization of the user is eliminated. In the embodiment of the invention, the safety capacity of a smart card technology is fully utilized in the processing of the iris information. Moreover, a camera serves as the standard hardware configuration of the mobile terminal such as the mobile phone, so system hardware can be less modified by using the iris information, stead of password inputting.
Owner:CHINA UNIONPAY
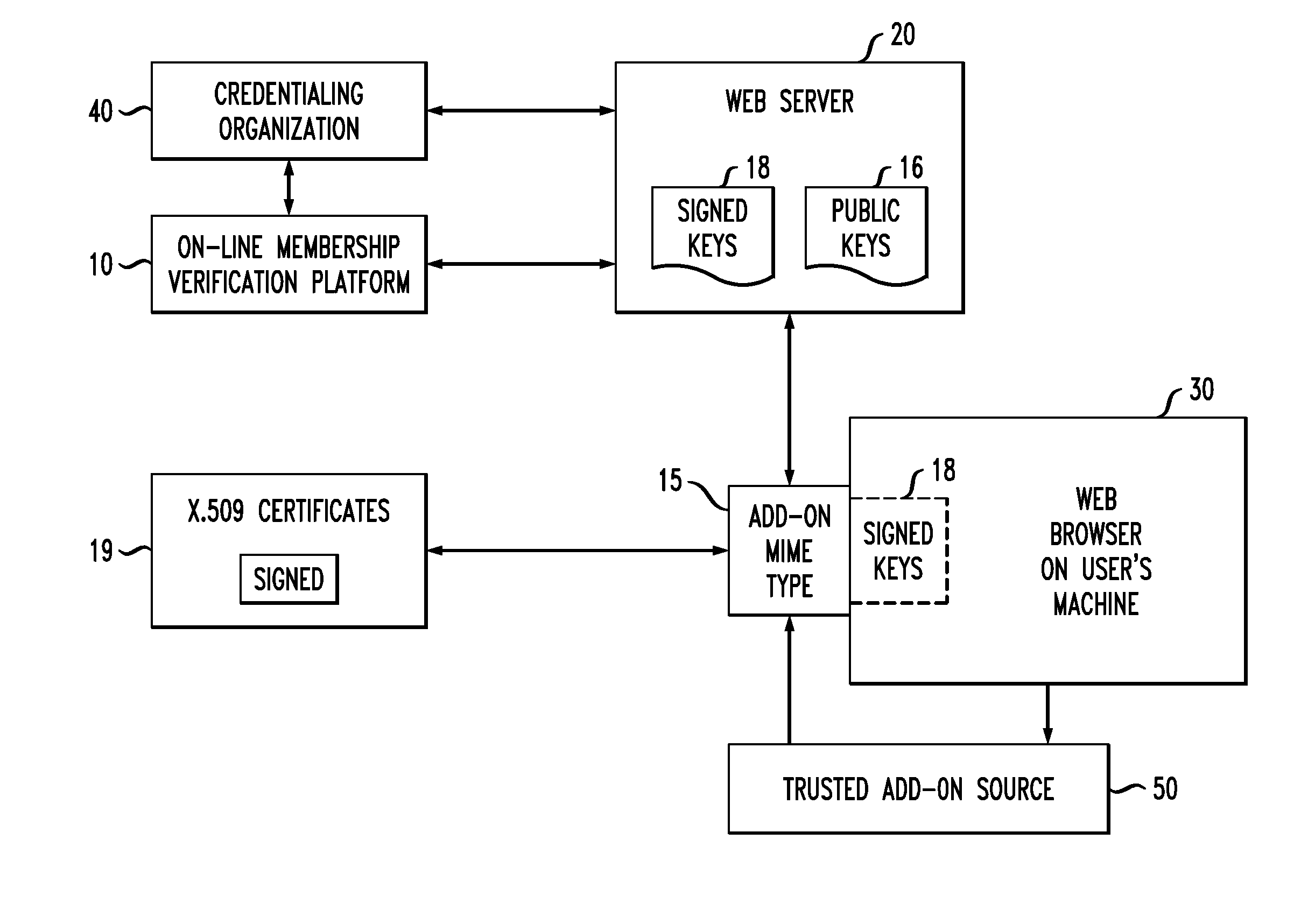
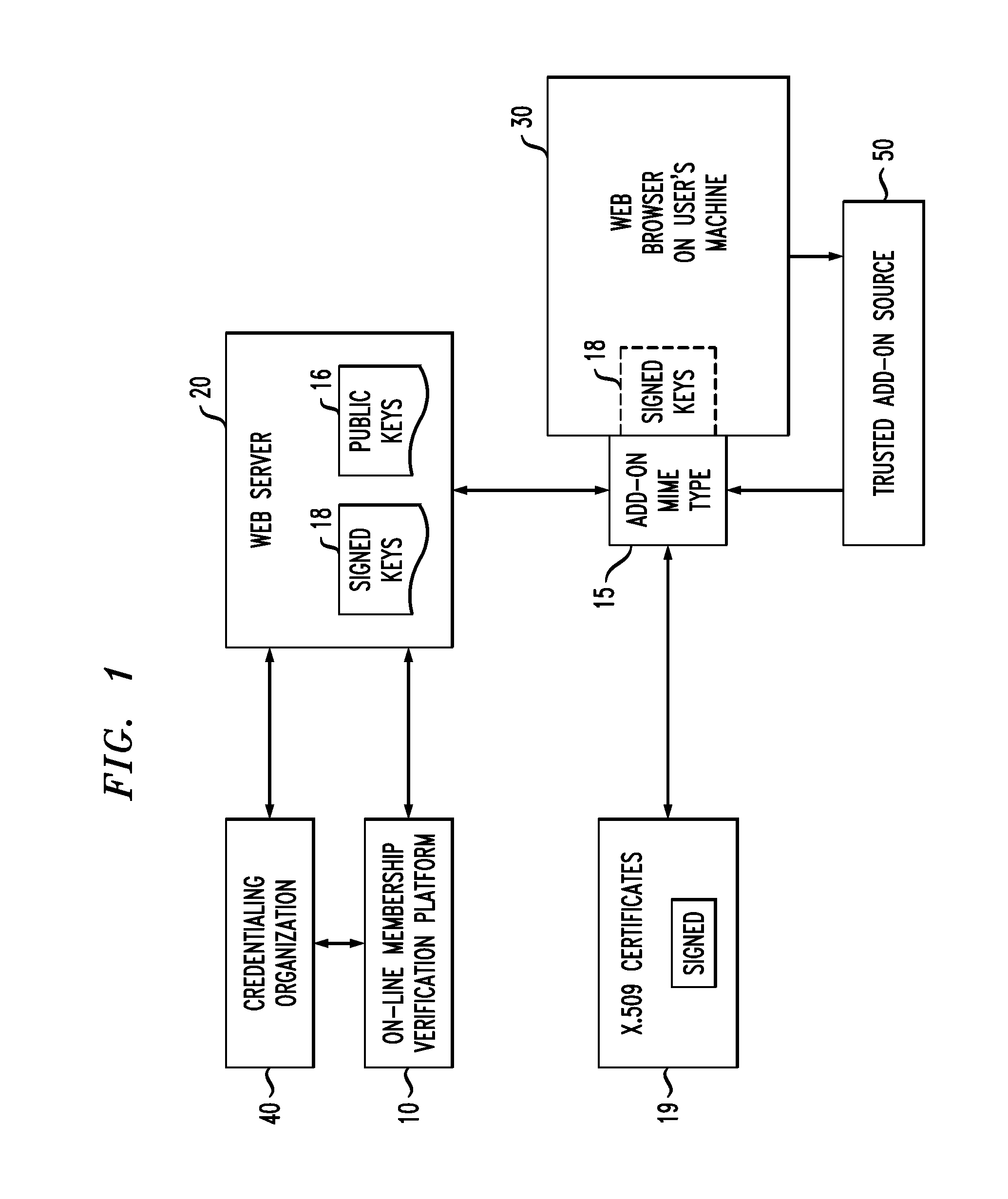
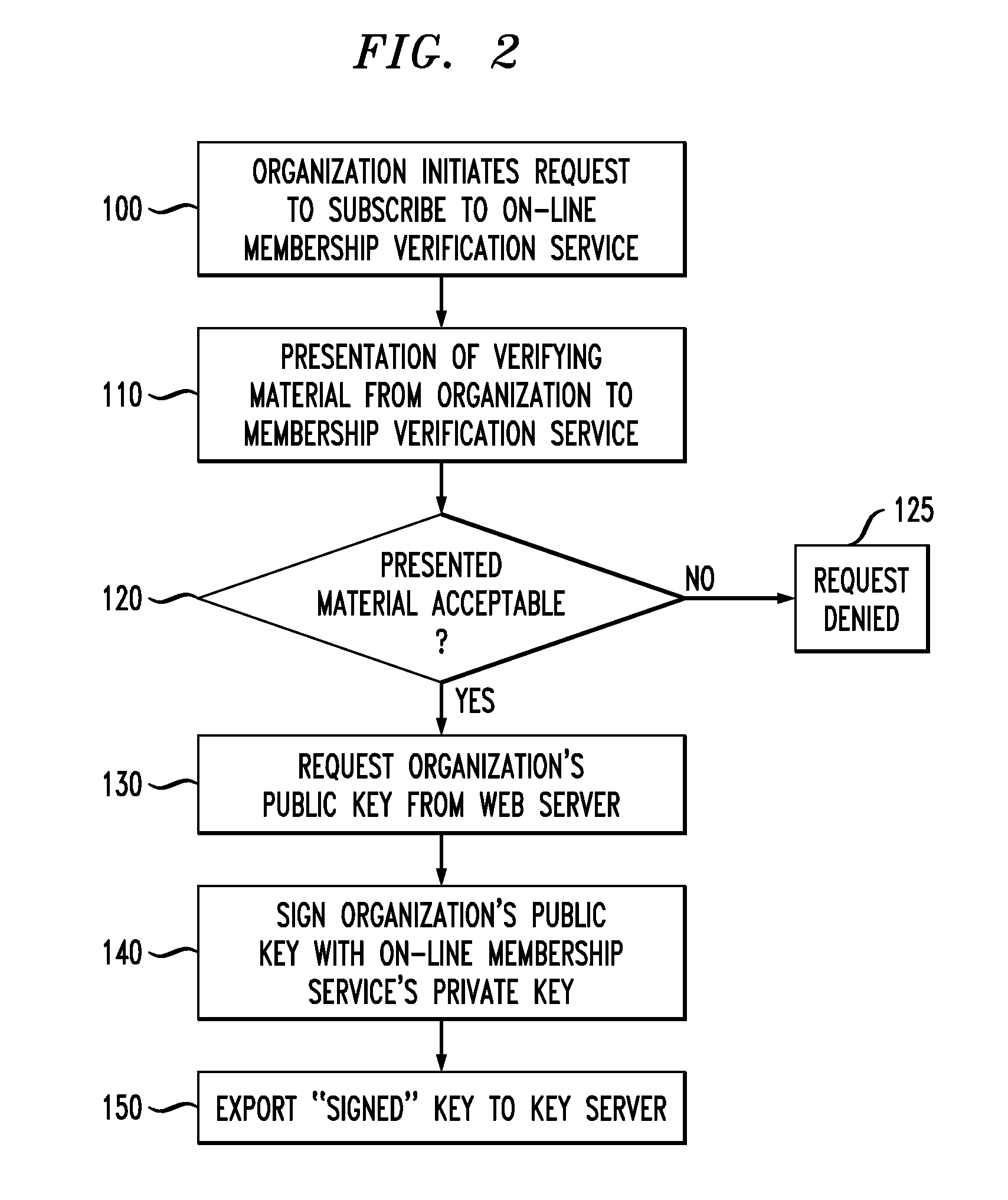
On-Line Membership Verification
ActiveUS20110010553A1Difficult to forgeNot easy to be stolenKey distribution for secure communicationDigital data processing detailsWeb siteNon-repudiation
A system and method of providing on-line verification of various credentials without requiring second site authentication utilizes protocols and cryptography to assure customers (generally referred to hereinafter as “users”) that they are dealing with a person (or organization) that can present multiple, non-repudiable proof of their identification. The system is launched directly from the user's browser such that certificate verification is performed “locally”, without needing to go out and obtain information from a second web site. The system is based upon the creation of a new MIME (i.e. Multipurpose Internet Mail Extensions) type that is employed by the user's browser and utilizes public keys associated with the credentialing organizations in combination with a public key of the verification organization.
Owner:CAHN ROBERT S
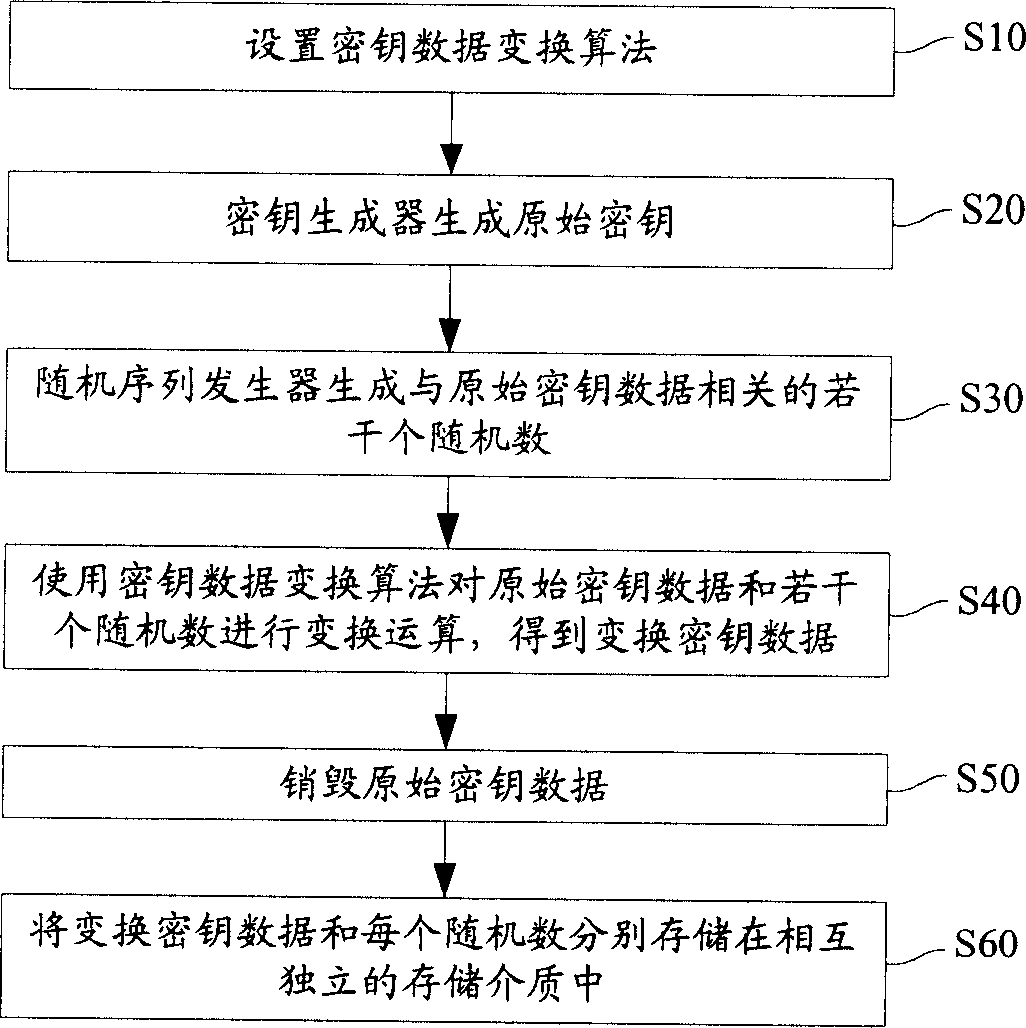
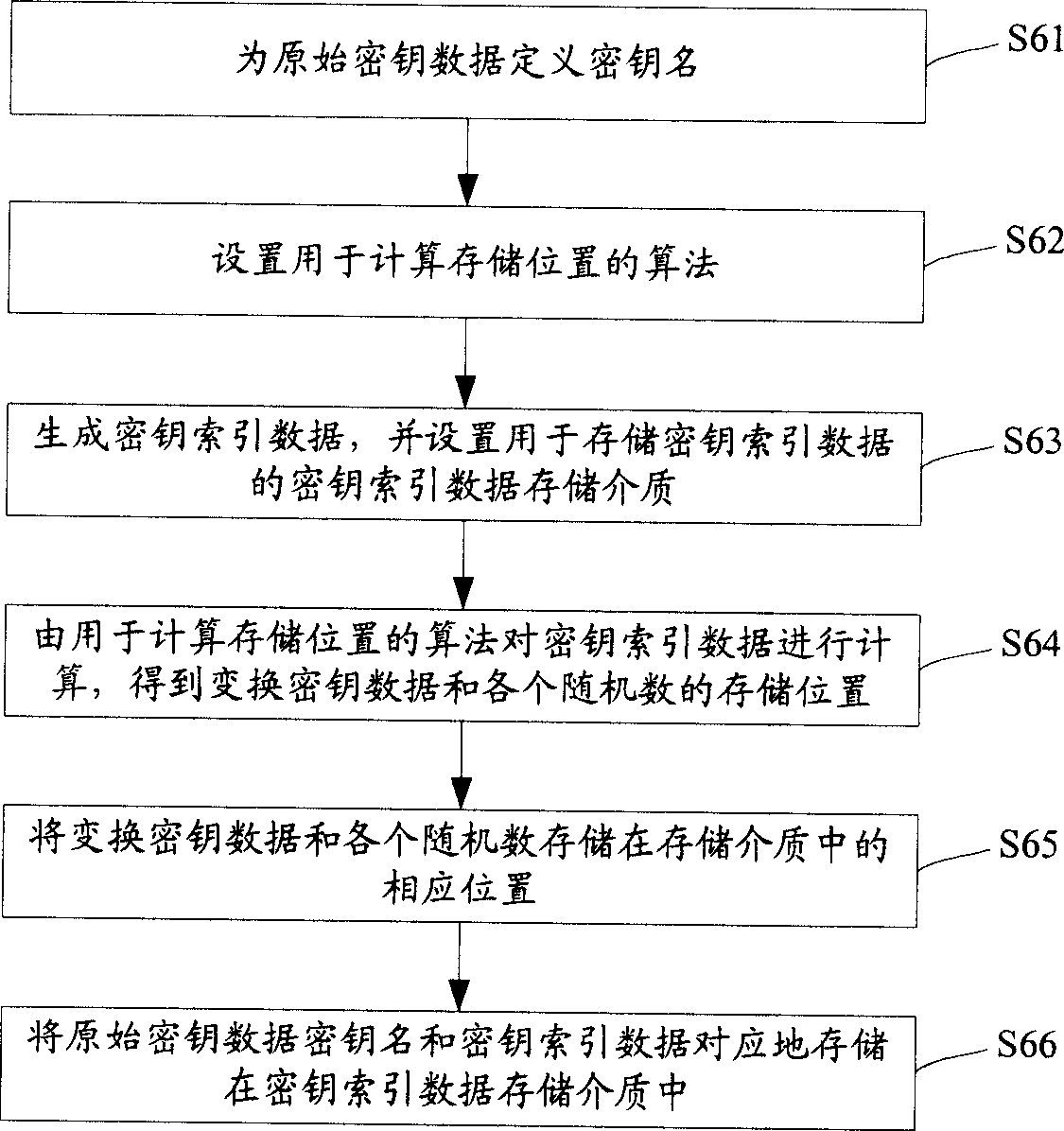
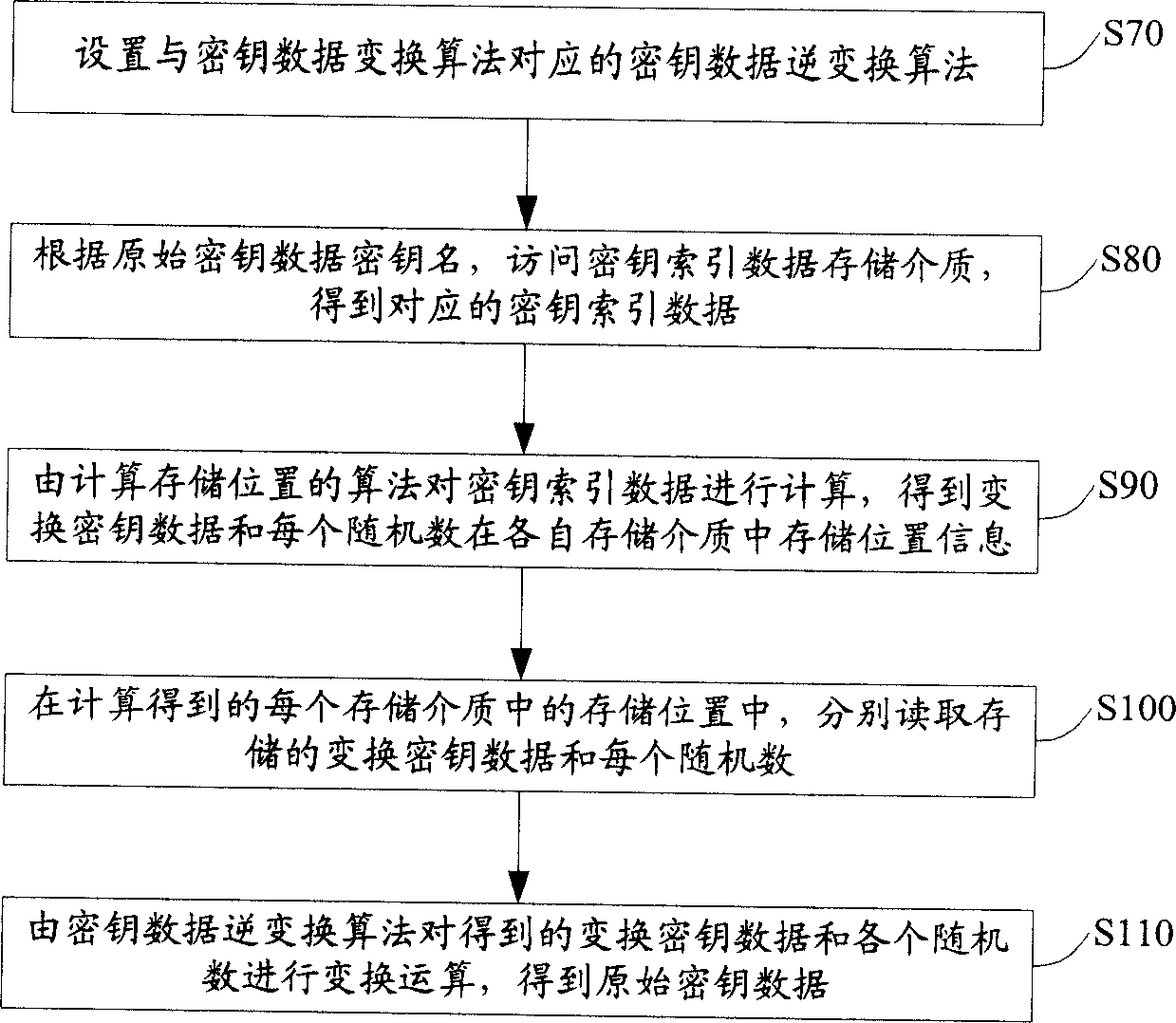
Method for storing cipher key
InactiveCN1697372ANot easy to leak and theftHigh security mechanismSynchronising transmission/receiving encryption devicesKey generatorKey storage
The method includes steps: setting up transformation algorithm for cipher key data in advance; generating original cipher key data by cipher key generator, random sequence generator generates several pieces of random numbers correlated to the original cipher key data at same time; carrying out transformation operation for original cipher key data and correlated several pieces of random numbers by using transformation algorithm for cipher key data setup before; storing up transformed cipher key data and each random number correlated to original cipher key data in storage media independent to each other. Comparing with prior art, the invention lowers complexity of cipher key storage step in cipher key management procedure, and raises security mechanism in storing cipher key.
Owner:HUAWEI TECH CO LTD
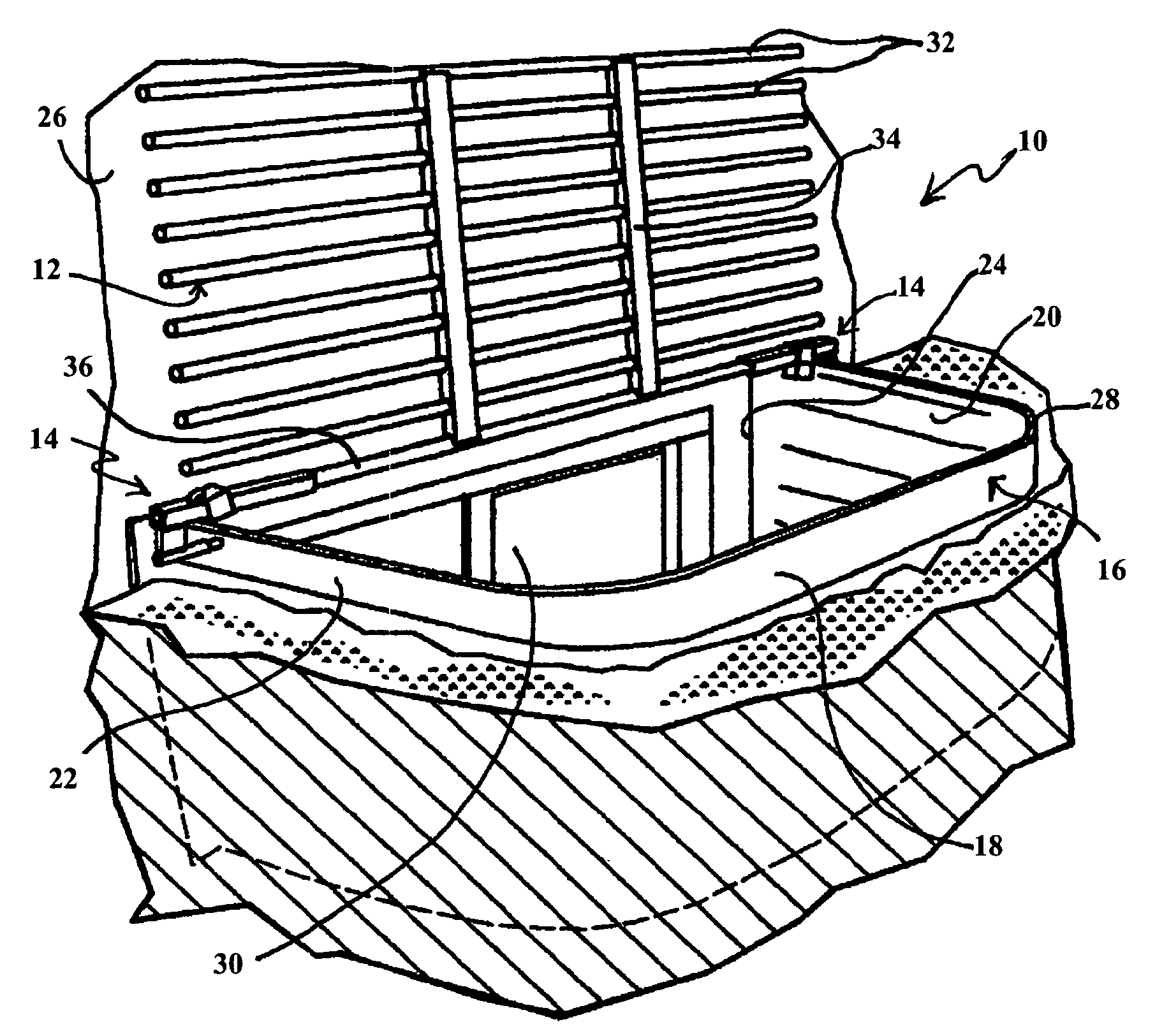
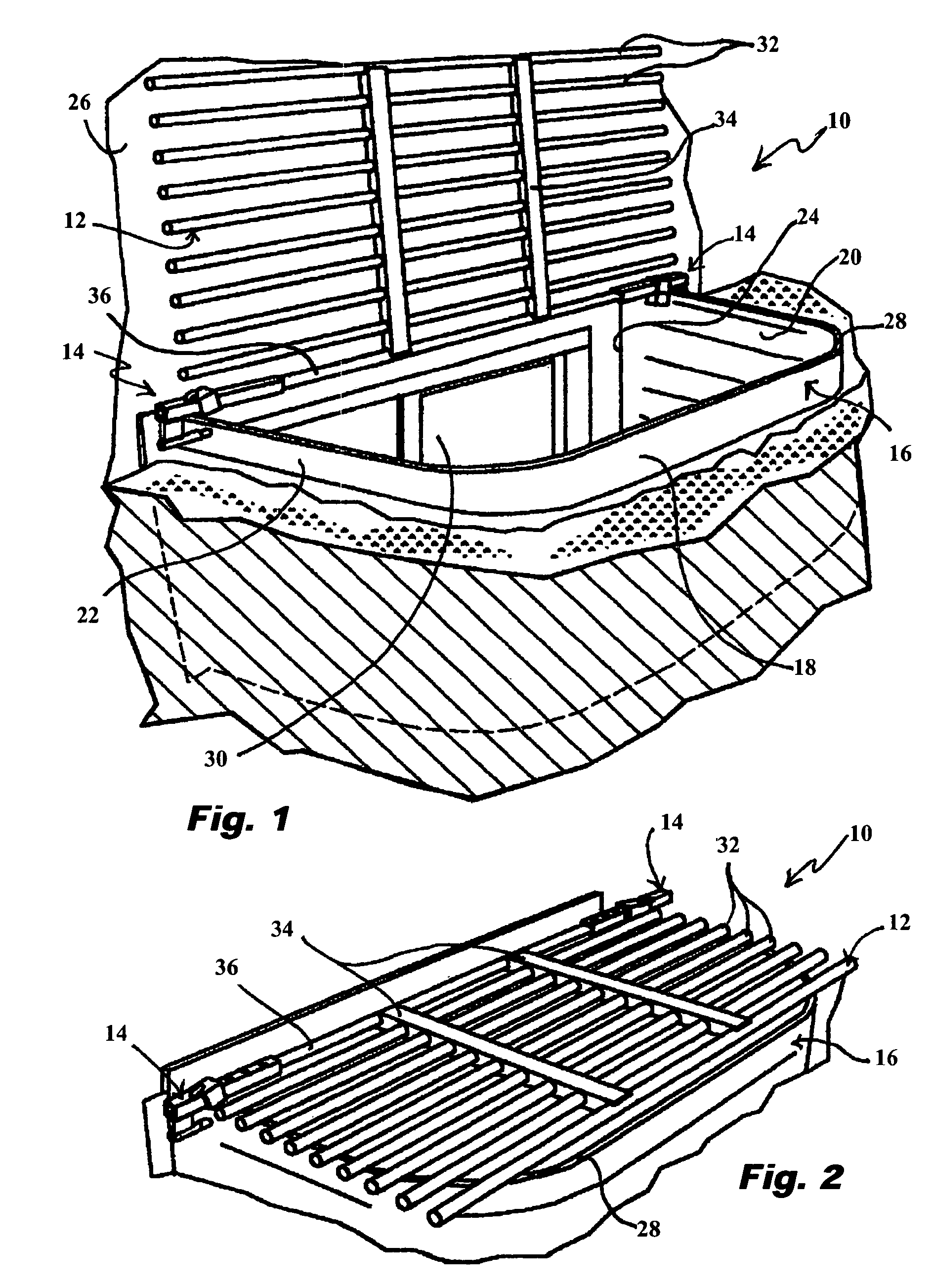
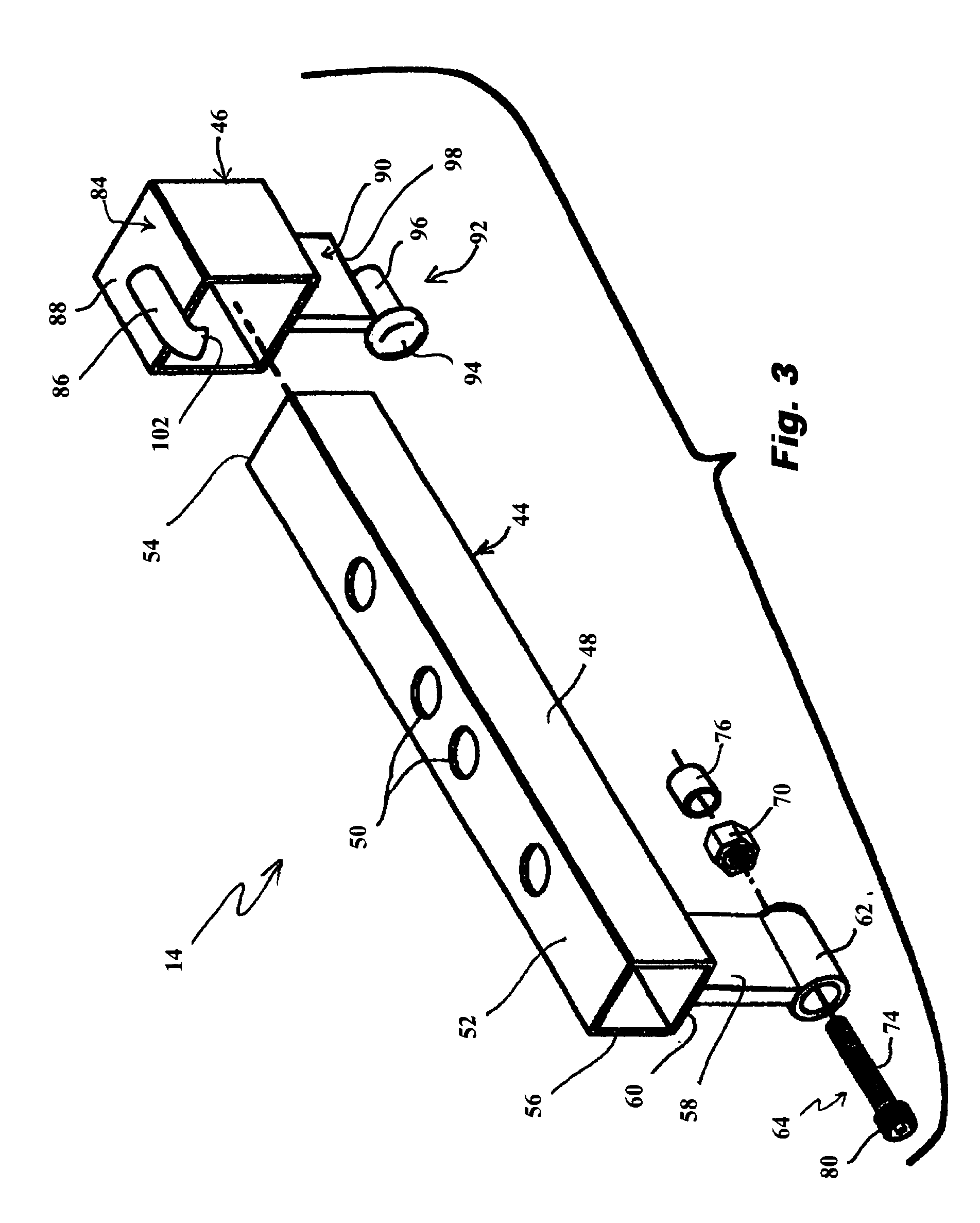
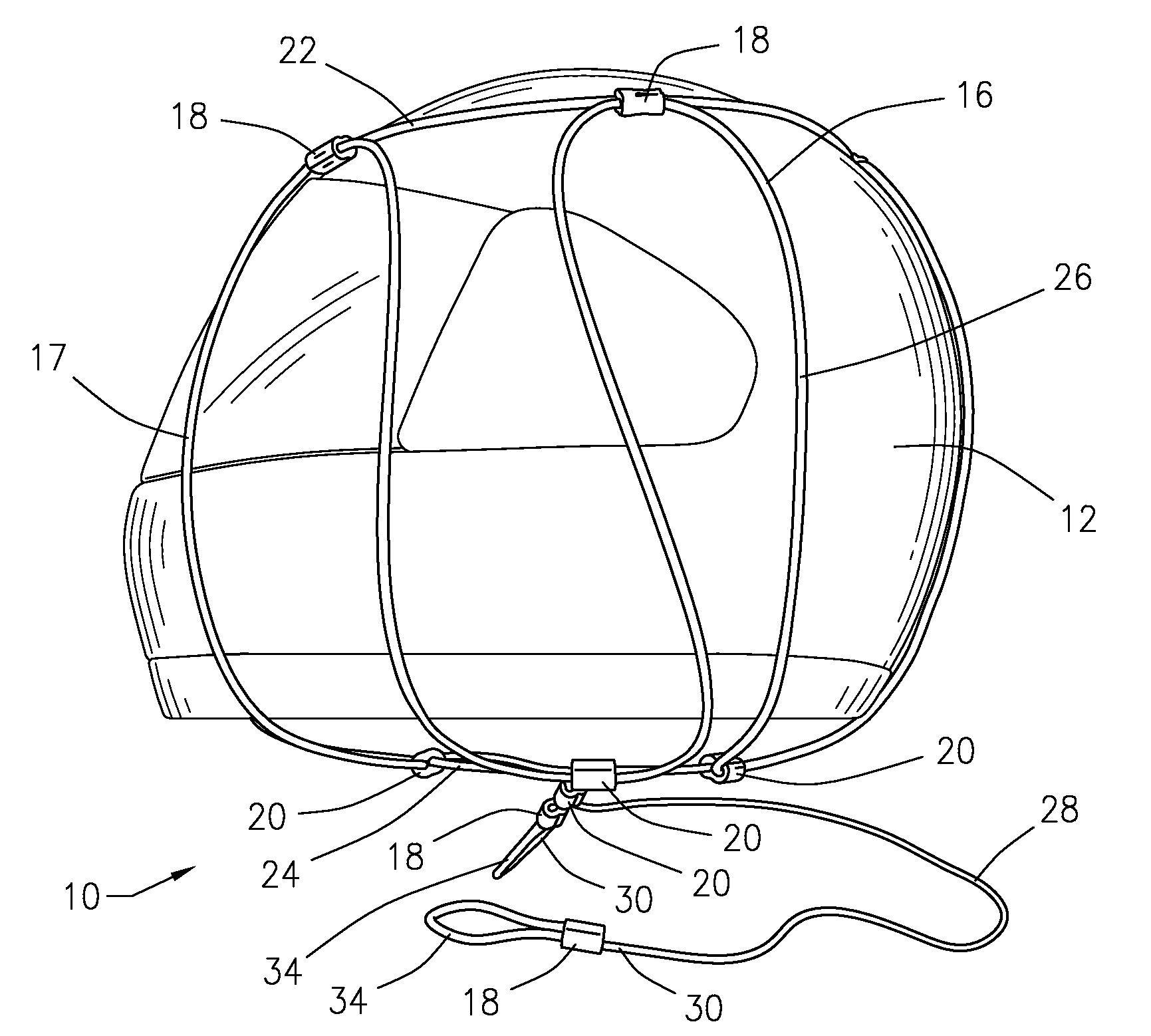
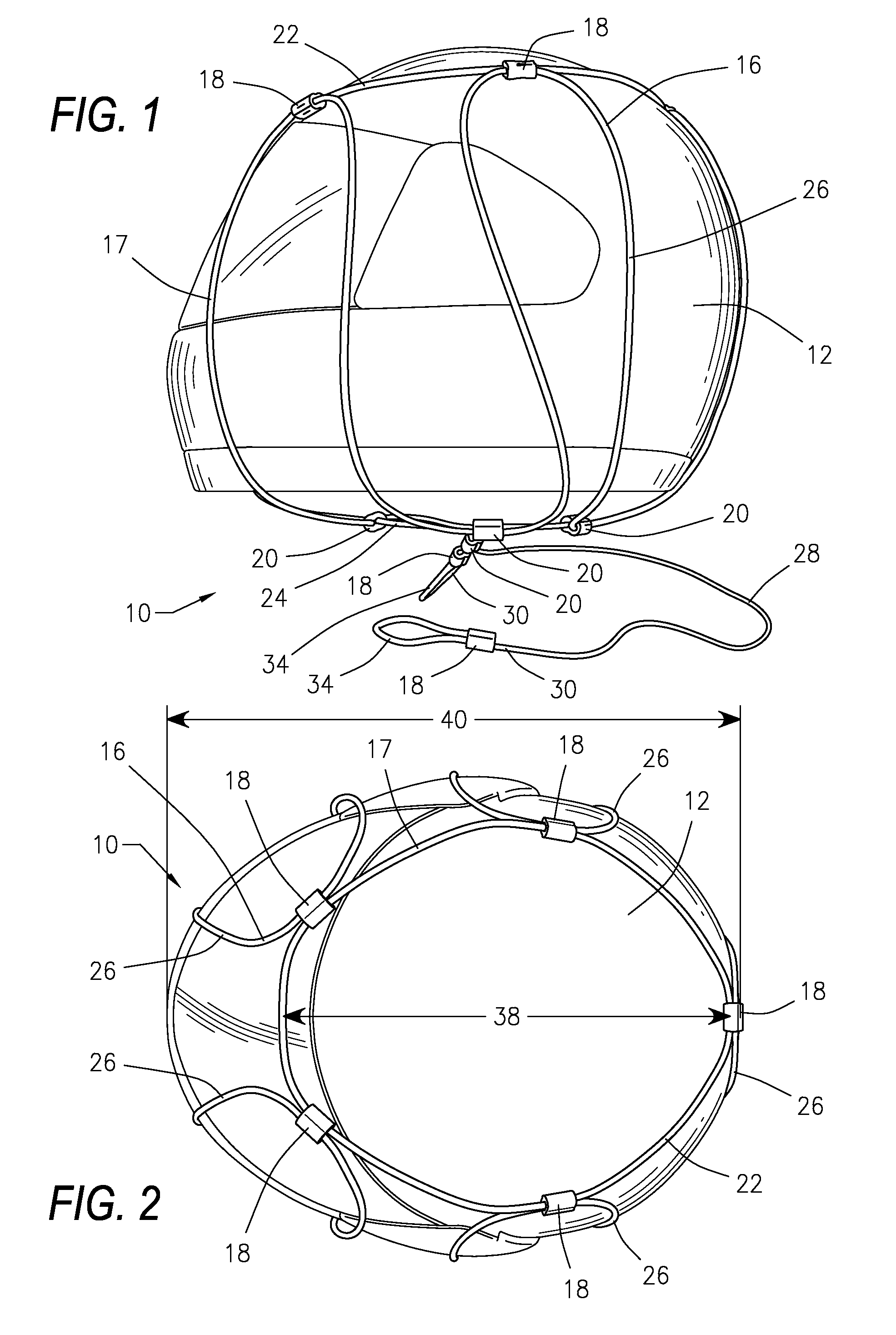
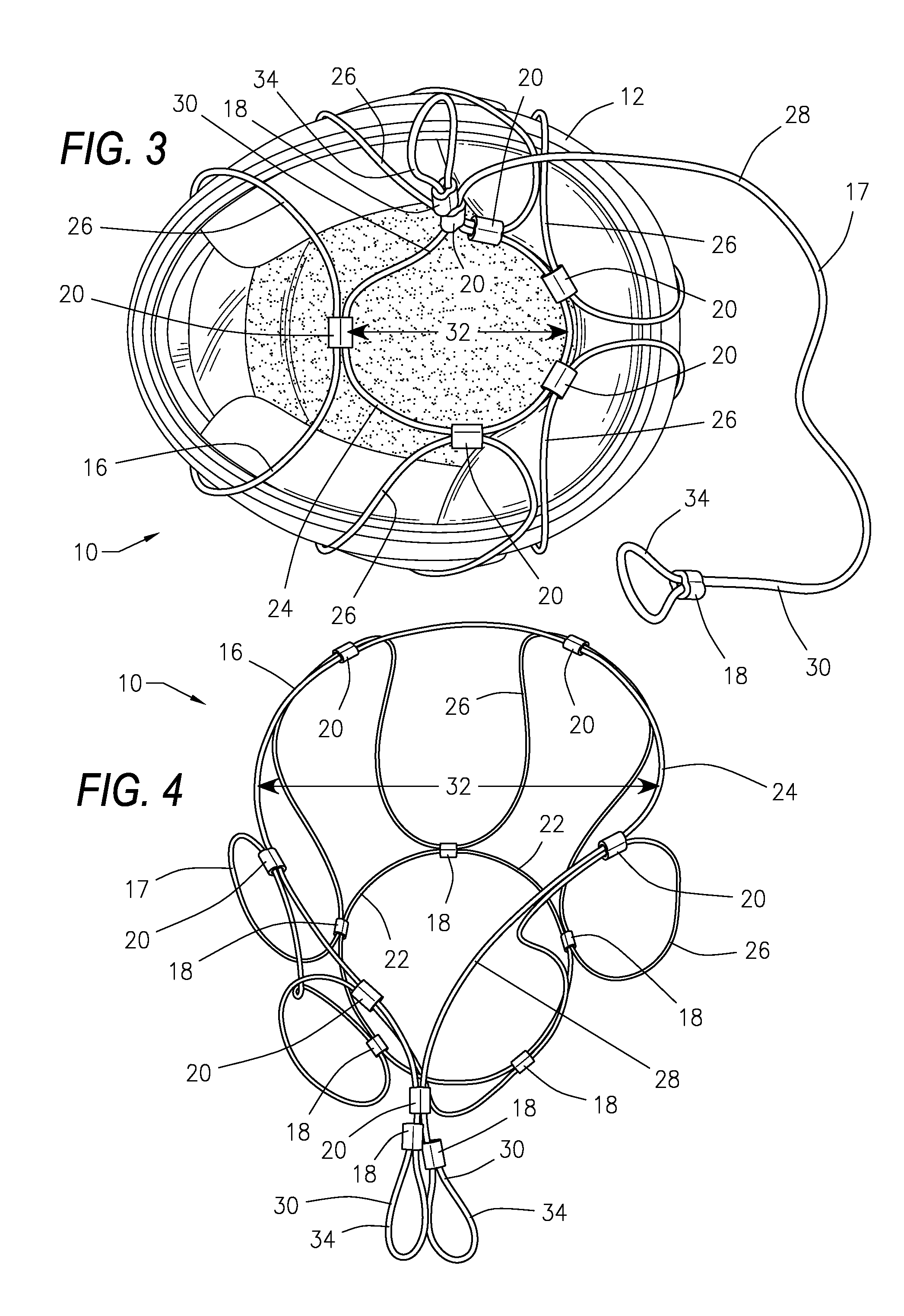
Window well covering system
InactiveUS7444784B2Improved window well covering systemPrevent removalBuilding roofsShutters/ movable grillesCovering systemEngineering
A system for temporally or permanently securing a removable window well cover or grid over a window well at, for example, a construction site is disclosed using adjustable mounts. The window well cover or grid may be pivoted open and closed without having to fully remove the window well cover from the opening of the window well. The adjustable mounts may include a grid sleeve unit slideably attached to the window well cover, and a lock keeper slideably mounted on the grid sleeve unit. In one aspect, the adjustable mounts include theft-deterring features that inhibit unauthorized removal of the window well cover from the window well.
Owner:SAFE T RAIL
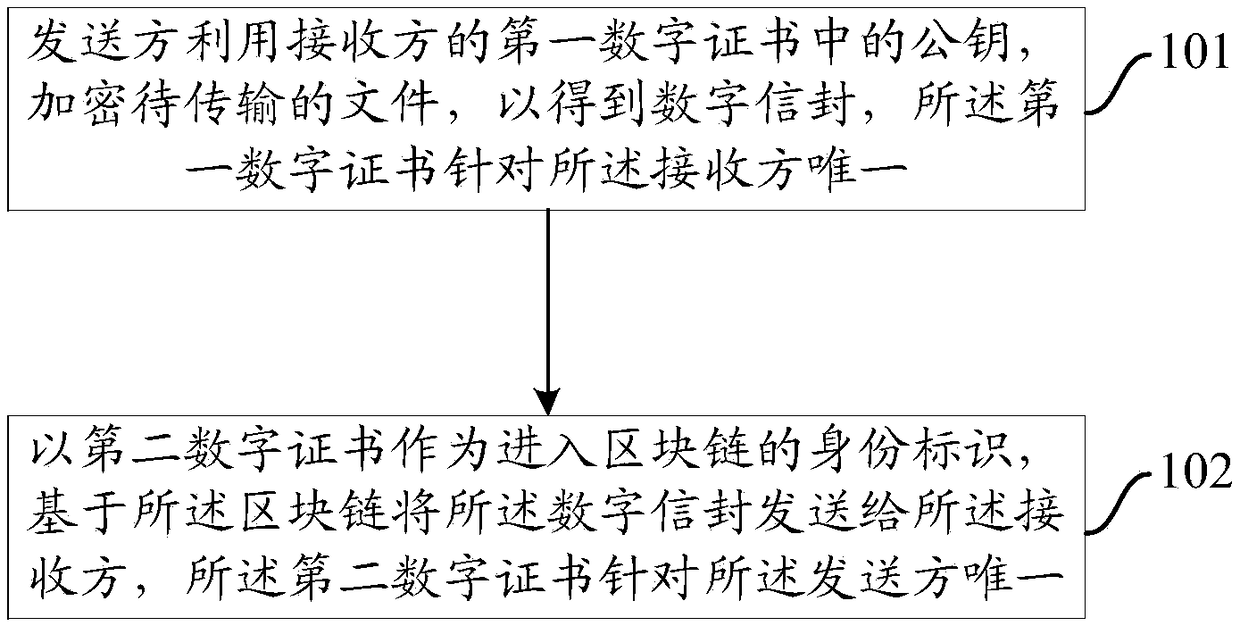
File transmission method, device and system based on block chain
InactiveCN108566395ANot easy to be stolenKey distribution for secure communicationFile transmissionBlockchain
The invention provides a file transmission method, device and system based on a block chain. A sender encrypts a to-be-transmitted file by utilizing a public key in a unique digital certificate of a receiver to obtain a digital envelope; and the sender uses an own unique digital certificate as the identity identifier for entering a block chain, and sends the digital envelope to the receiver basedon the block chain. Correspondingly, the receiver uses the own digital certificate as the identity identifier for entering the block chain, receives the digital envelope sent by the sender based on the block chain, and uses a private key in the own digital certificate to decrypt the digital envelope to obtain a to-be-received file. Both the sender and the receiver of the file use the digital certificate as the identity identifier for entering the block chain, the file is transferred on the block chain in a digital envelope form, and only the receiver with the corresponding digital certificatecan decrypt the file. Files are transmitted between the sender and the receiver based on the block chain, so that the files cannot be easily stolen by others.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
An underwater communication system based on continuous variable quantum key distribution and method realization method thereof
InactiveCN109039610ANot easy to be stolenEasy to detectKey distribution for secure communicationPhotonic quantum communicationBeam splitterHomodyne detection
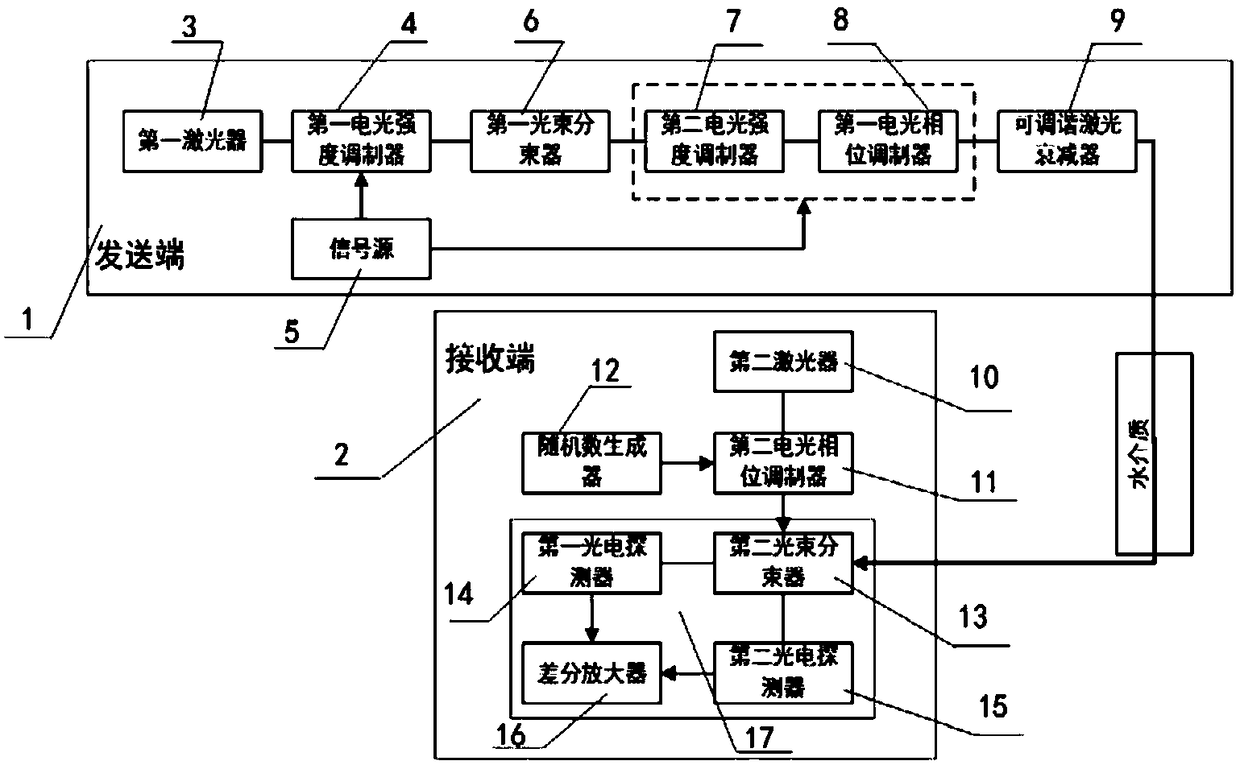
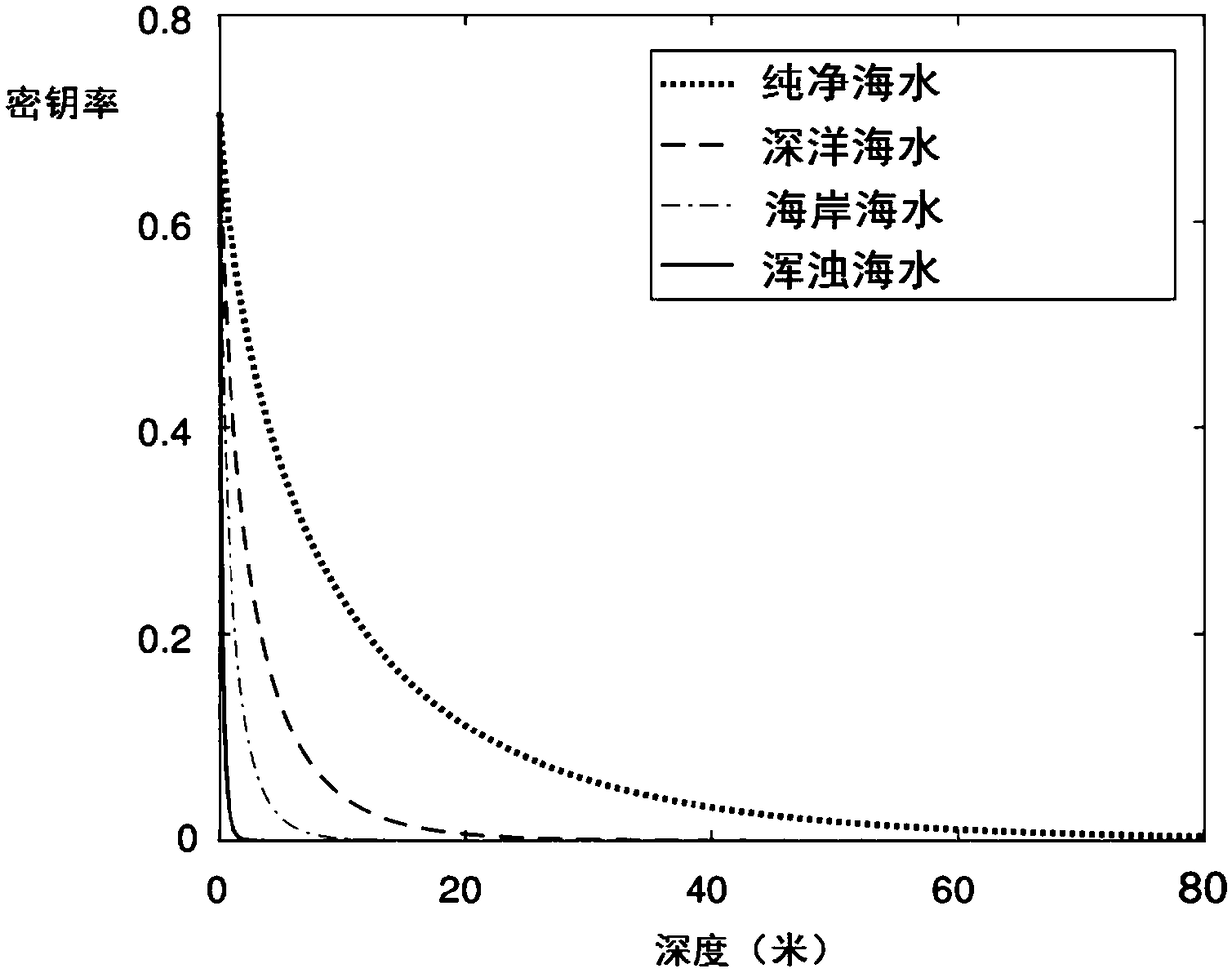
The invention discloses an underwater communication system based on continuous variable quantum key distribution and a realization method thereof, belonging to the technical field of free space quantum communication. The optical signal is outputted to the receiving end through the cooperation of a first laser, a first electro-optic intensity modulator, a signal source, a first beam splitter, a second electro-optic intensity modulator, a first electro-optic phase modulator and a tunable laser attenuator at the transmitting end; The second laser generates local oscillation light, which is modulated by the second electro-optical phase modulator, the local oscillation light and the optical signal outputted from the transmitting end enter the homodyne detector for detection, and finally the security key is established within the effective distance. The invention applies the continuous variable quantum key distribution technology to the underwater optical communication system, the optical signal is not easy to be stolen by a third party, and the safe underwater communication system is realized. Heterodyne detection is used to filter the ambient stray light, which also achieves good detection effect in the daytime and the environment with background light.
Owner:CENT SOUTH UNIV
Method, apparatus, and system for providing a security check
ActiveUS20150341333A1Not easy to be stolenAvoid possibilityDigital data processing detailsUser identity/authority verificationUnique identifierSecurity check
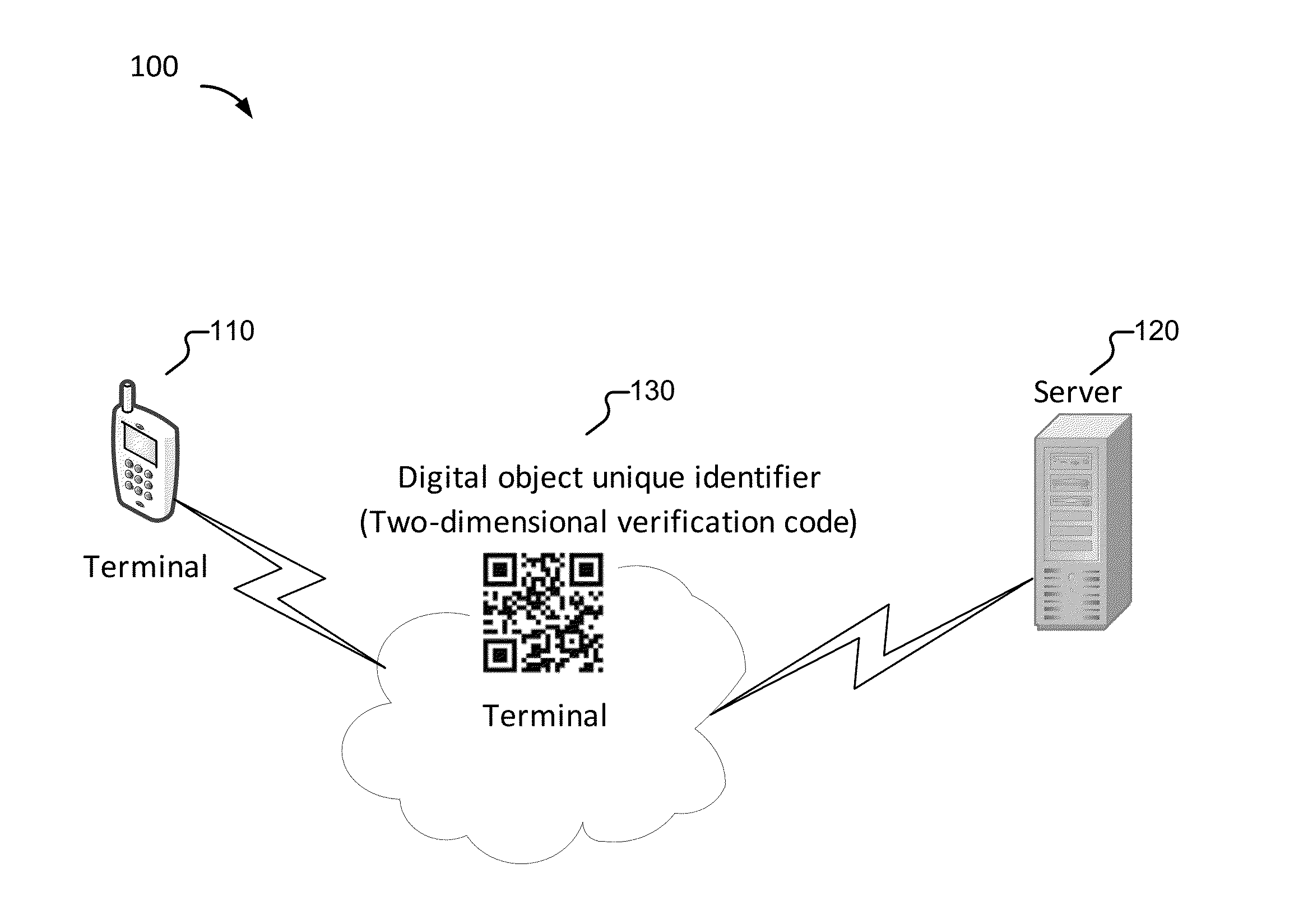
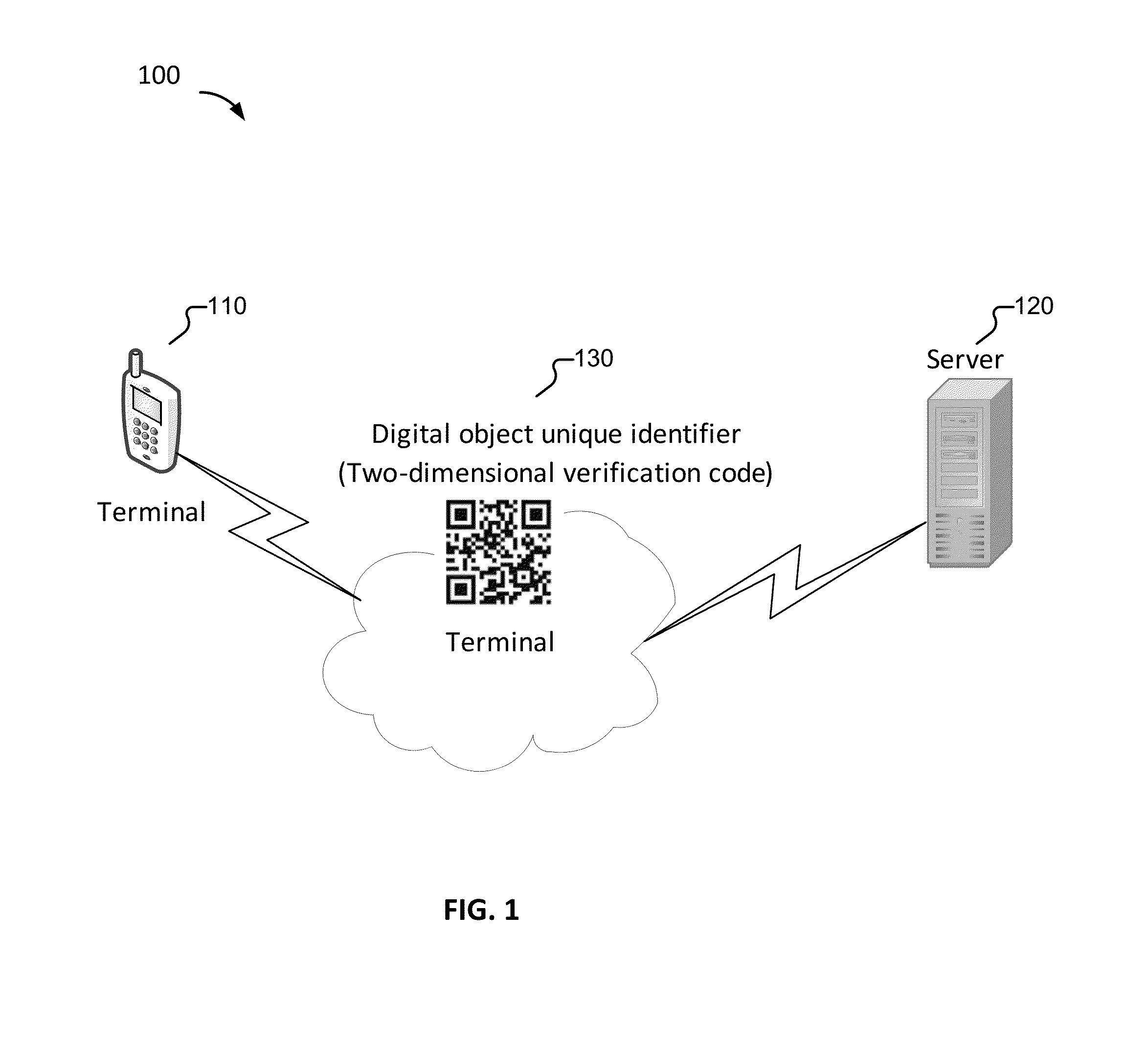
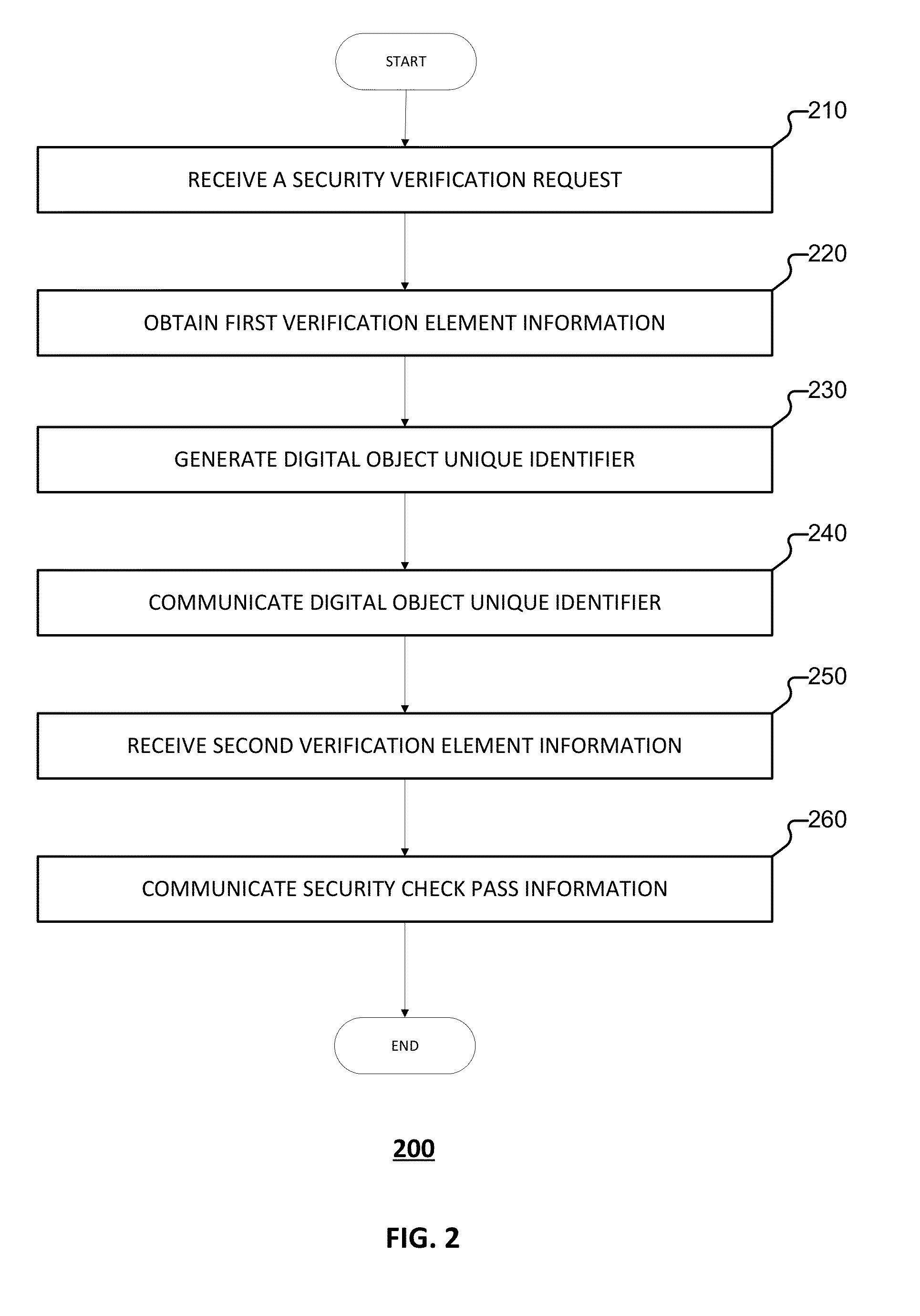
Embodiments of the present application relate to a method, apparatus, and system for providing a security check. The method includes receiving a security verification request sent from a terminal, obtaining first verification element information based at least in part on the security verification request, generating a digital object unique identifier based at least in part on the first verification element information, sending the digital object unique identifier to the terminal, receiving second verification element information from the terminal, and in the event that the first verification element information and the second verification element information are consistent, sending security check pass information to the terminal.
Owner:ADVANCED NEW TECH CO LTD
Fingerprint identification and authentication circuit of mobile terminal
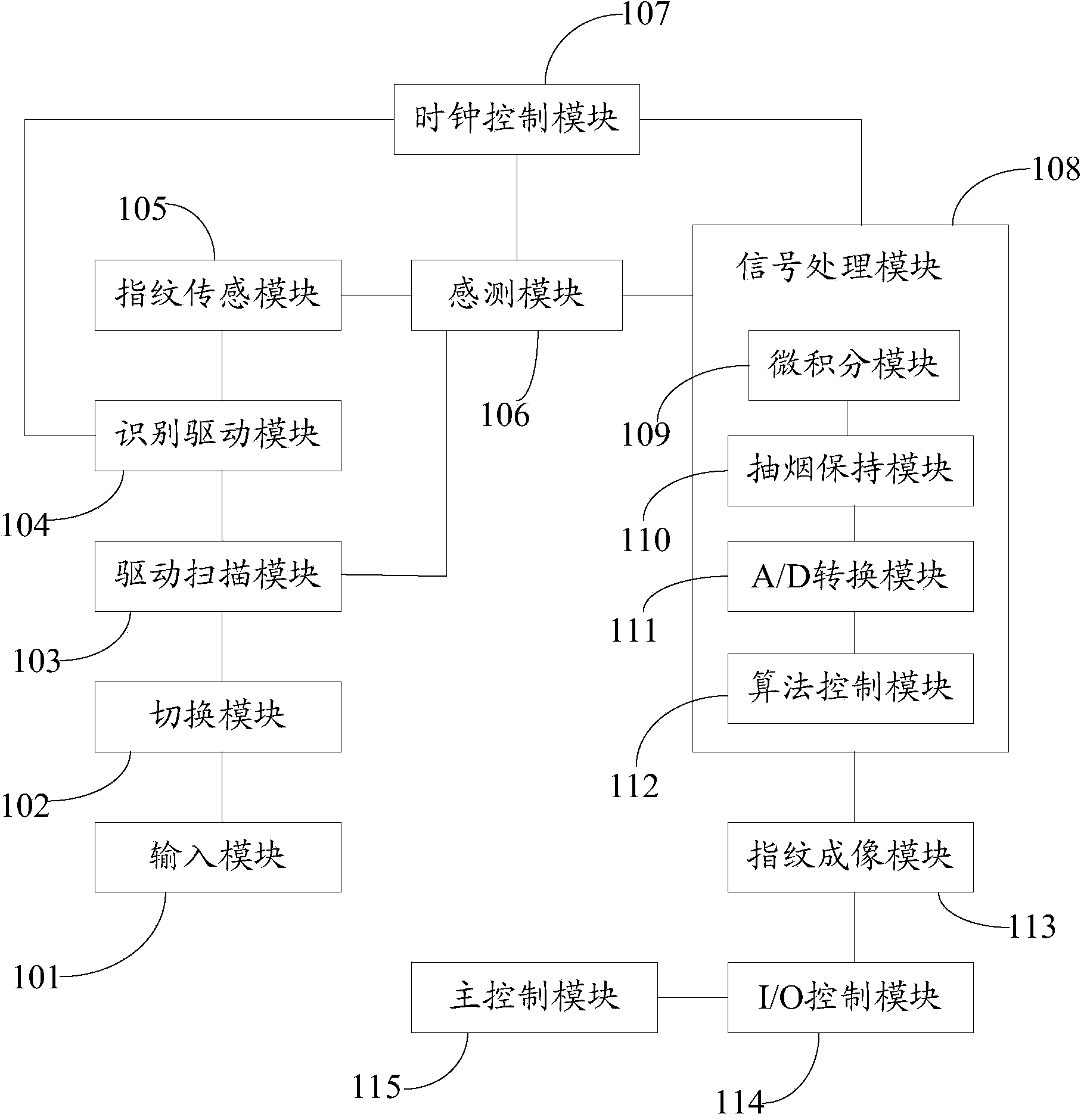
InactiveCN104298911AUniqueness guaranteedNot easy to be stolenDigital data authenticationFingerprintInput/output
A fingerprint identification and authentication circuit of a mobile terminal is used for identifying fingerprints of a user when the mobile terminal enters procedures requiring authentication. The fingerprint identification and authentication circuit comprises an inputting module, a switching module, a scanning driving module, an identification driving module, a fingerprint sensing module, a sensing module, a signal processing module, a clock control module, a fingerprint imaging module, an I / O (input / output) control module and a master control module; and when the mobile terminal enters the procedures requiring authentication, a touch command inputted by a user is received, and a touch mode of the mobile terminal is switched into the fingerprint sensing module. A fingerprint image inputted by the user is acquired and is compared to a pre-stored fingerprint image, if the fingerprint image is consistent to the pre-stored fingerprint image, the user is permitted to enter the procedures requiring authentication, and if the fingerprint image is not consistent to the pre-stored fingerprint image, the user is forbidden from entering the procedures requiring authentication. Fingerprints belong to biological characteristics and are unique. After the fingerprints serve as procedure entering conditions, the user does not need to memorize an account and a corresponding password, and data of the account and the password are not easy to steal.
Owner:NANCHANG OUFEI BIOLOGICAL IDENTIFICATION TECH +3
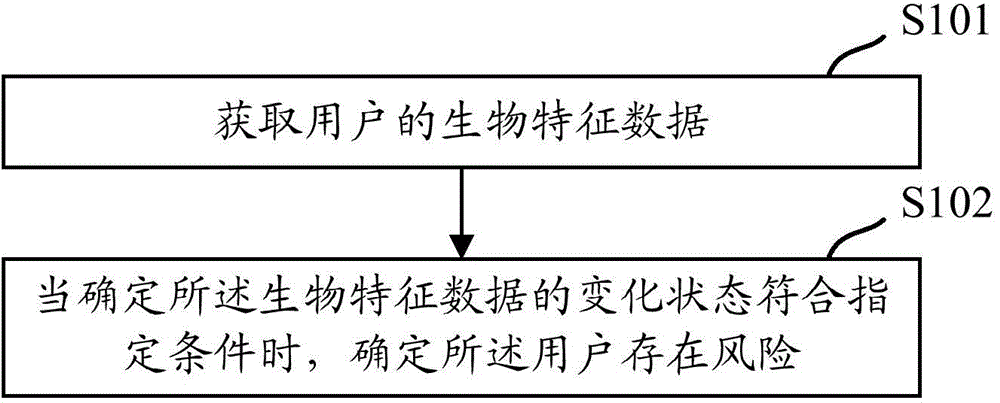
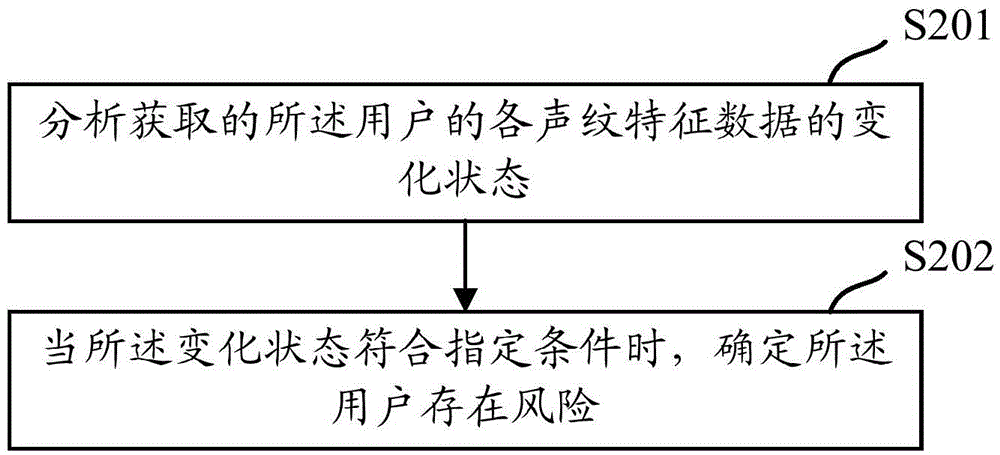
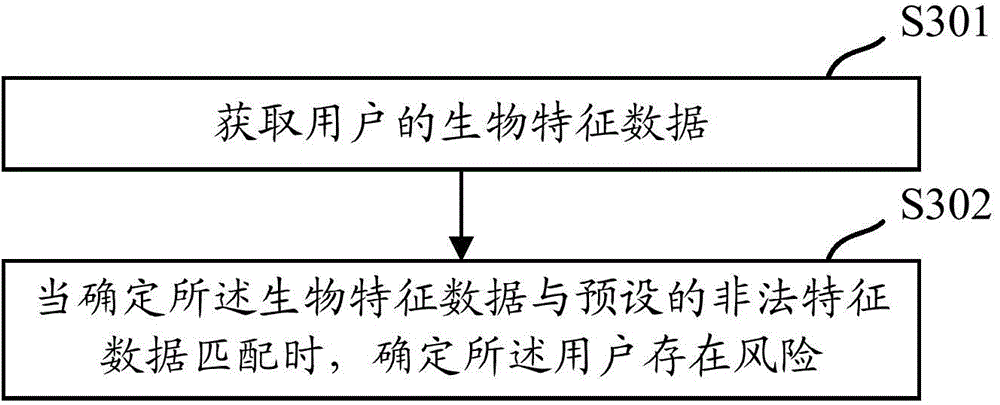
Method and device for identifying risk of user
The invention discloses a method, device and system for identifying the risk of a user. The method includes the following steps that: the biological characteristic data of the user are obtained; and when it is determined that the change state of the biological characteristic data accords with a specified condition, it is determined that a risk exists on the user. With the above method adopted, before business interaction with the current user is carried out, or in a business process, not only can the personal information of the user be verified, but also the change state of the biological characteristic data of the user can be analyzed, and / or the biological characteristic data can be subjected to matching, so that whether a risk exists on the user can be determined; and since the biological characteristic data have little possibility of being stolen, reliability is high, and therefore, the safety of a subsequent business process can be improved.
Owner:ADVANCED NEW TECH CO LTD
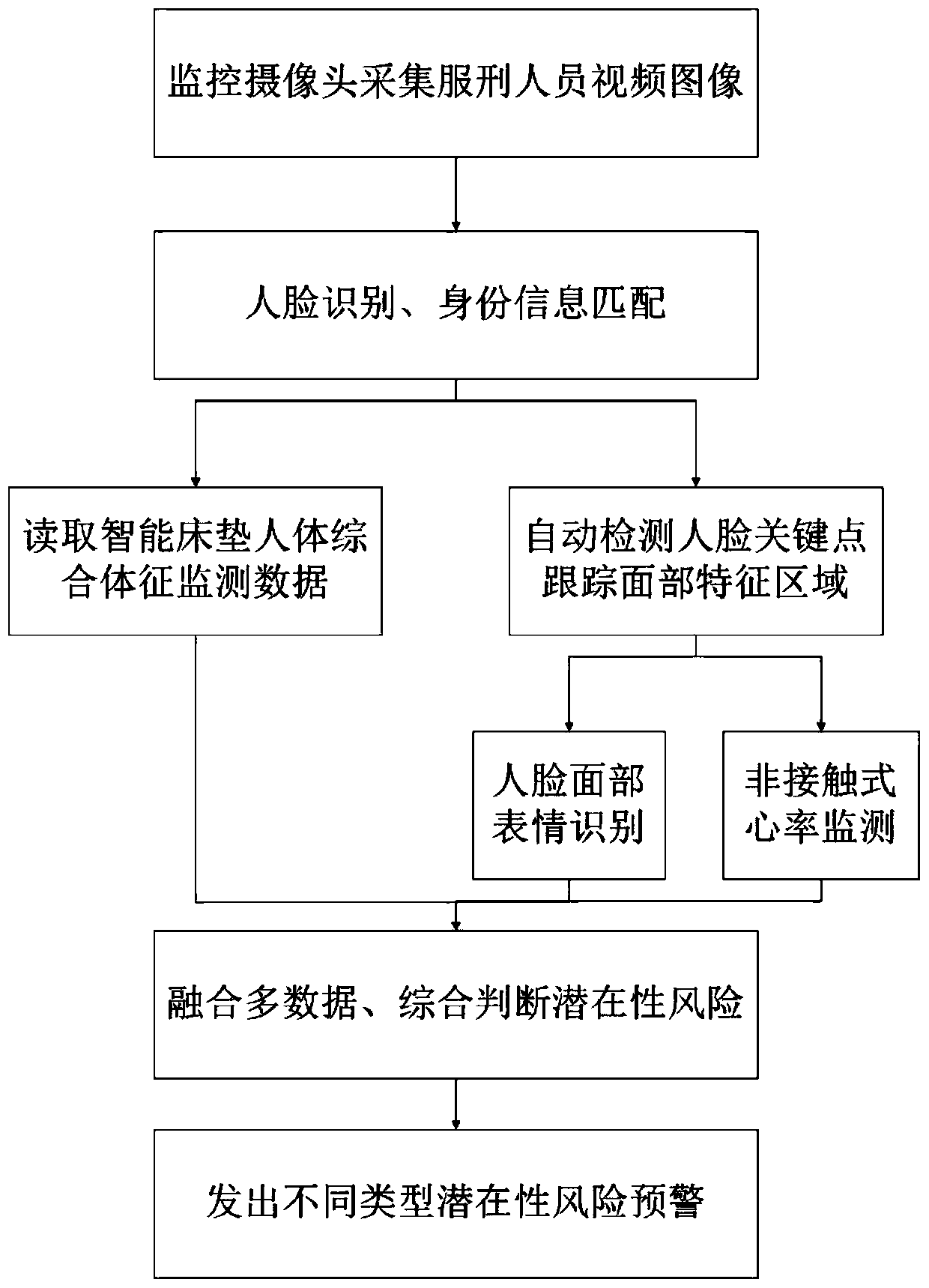
Prisoner physical sign monitoring method and device based on combination of video and device
ActiveCN110458101APrivacy protectionNot easy to be stolenNeural architecturesMeasuring/recording heart/pulse rateVideo monitoringDisease risk
The invention discloses a prisoner physical sign monitoring method and device based on combination of a video and a device, and the method comprises the following steps: recognizing the facial expression features and types of prisoners from a video frame through obtaining the current monitoring video of the prisoners; tracking a face feature area in real time through video monitoring, and meanwhile, a vital sign monitoring device detecting the heart rate of prisoners; and judging whether the prisoner has a potential disease risk or an abnormal behavior or not by combining the heart rate of theprisoner during rest and the facial expression characteristics and heart rate of the prisoner recognized from the video. Compared with traditional intelligent monitoring equipment, the method has higher stability and accuracy, can improve the accuracy of pre-judgment of potential risks and pre-judgment of sudden diseases existing in prison prisoners, and sends out early warning in time.
Owner:NANJING UNIV OF POSTS & TELECOMM
Anti-theft device for helmet
InactiveUS8087270B1Improve portabilityPrevent theftSnap fastenersAnti-theft cycle devicesMotorcycle helmetsElectrical and Electronics engineering
An anti-theft device in the form of a cage created from high security steel cable for use with a motorcycle helmet to secure the helmet to a motorcycle in order to prevent the helmet from being stolen when the helmet is not in use. The cage opens via a draw string type opening to capture the helmet therein and closes to prevent the helmet from being removed from the cage. A closure cable forms the draw string type closure for the cage and has a closure cable loop at each of its free ends so that the closure cable can be wrapped around the motorcycle and the ends secured together with a standard lock to secure the device and the captured helmet to the motorcycle. The device can be folded to store in a small storage space when not in use and the cable may be plastic coated or uncoated.
Owner:GRUVER ENTERPRISES
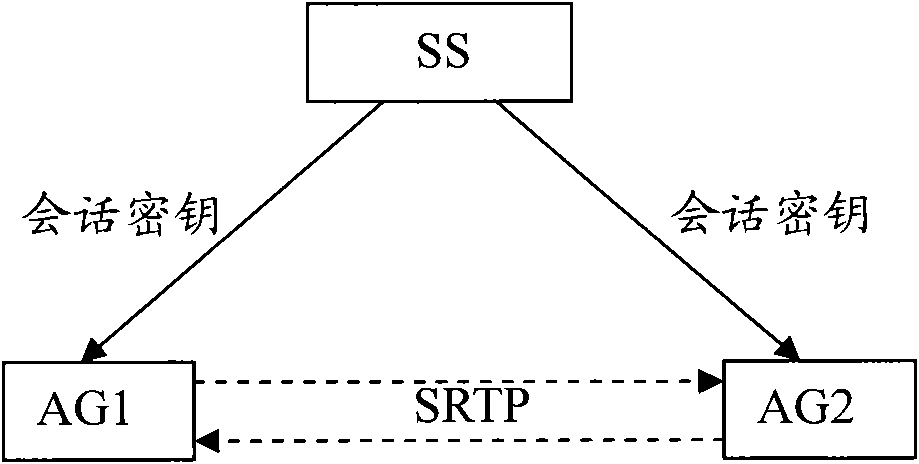
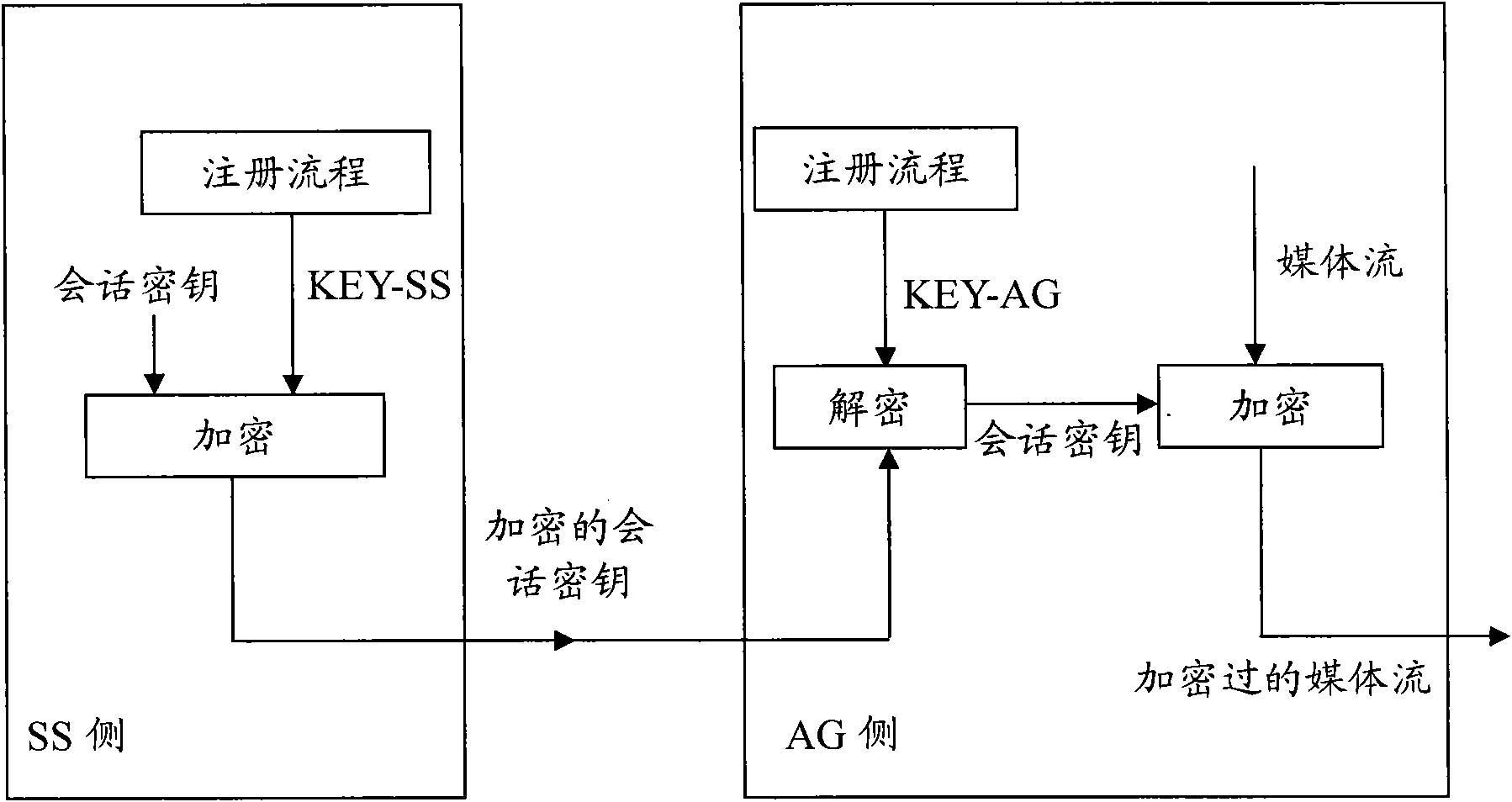
Method and device for safely consulting session key
InactiveCN101790160ANot easy to be stolenImprove securityKey distribution for secure communicationSecurity arrangementSoft switchSession key
The invention relates to a method for safely consulting a session key, comprising the following steps of: respectively acquiring a sharing key by an access gateway and a soft switch after the access gateway successfully registers to the soft switch, and respectively storing the sharing key in the access gateway and the soft switch; distributing the session key to sessions by using the soft switch according to the request of the access gateway before the registered access gateway carries out the session each time, and encrypting the session key distributed each time by using the sharing key, and then transmitting the encrypted session key to the access gateway; decrypting the encrypted session key by using the sharing key after the access gateway receives the encrypted session key each time so that the session key is acquired. The invention also provides a device for safely consulting the session key. The invention can further ensure the security of voice conversation when ensuring the security of the key, and has easy implementation.
Owner:ZTE CORP
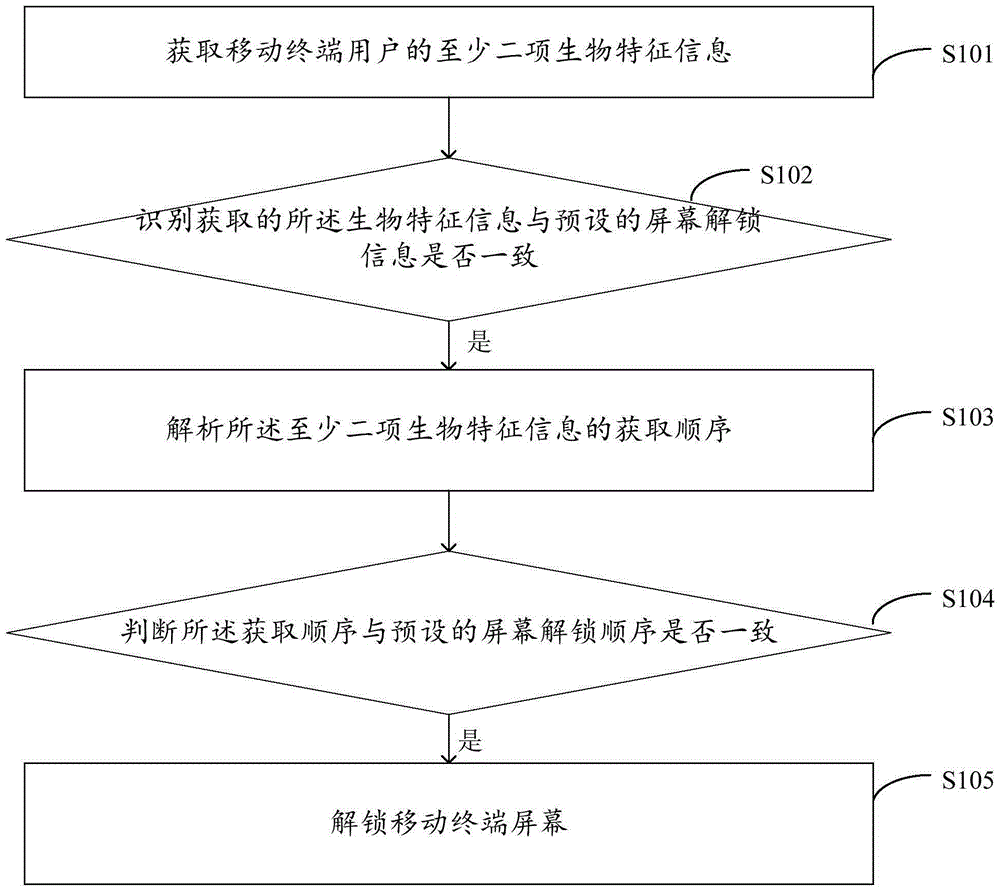
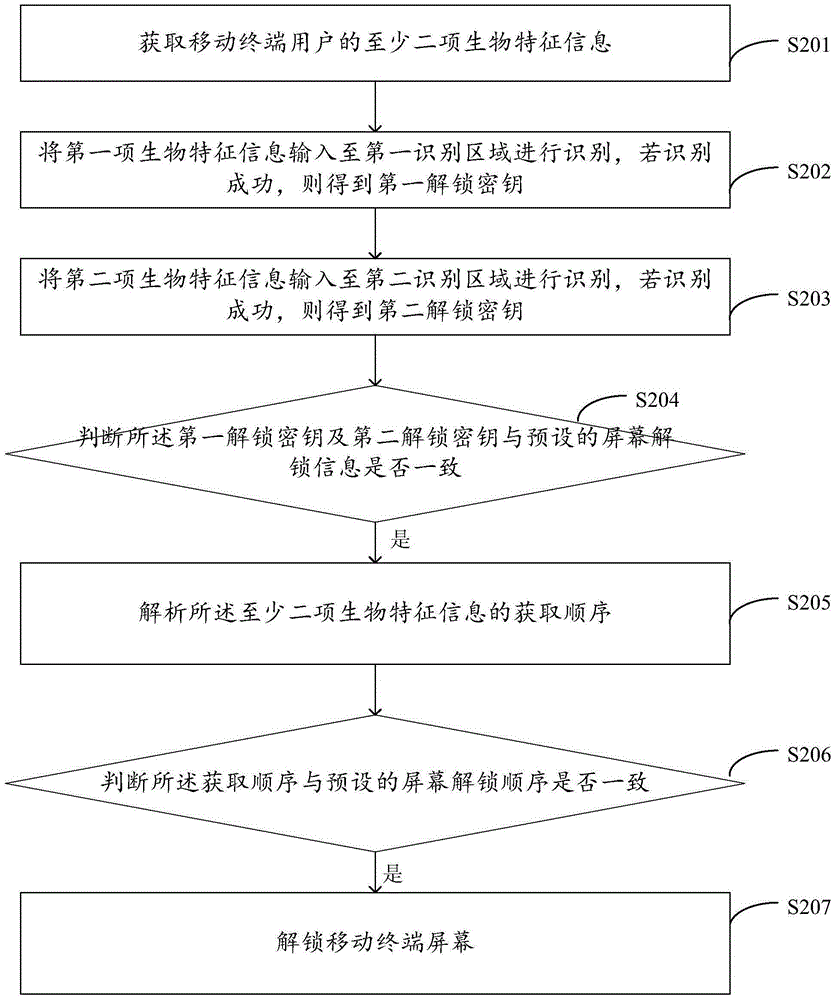
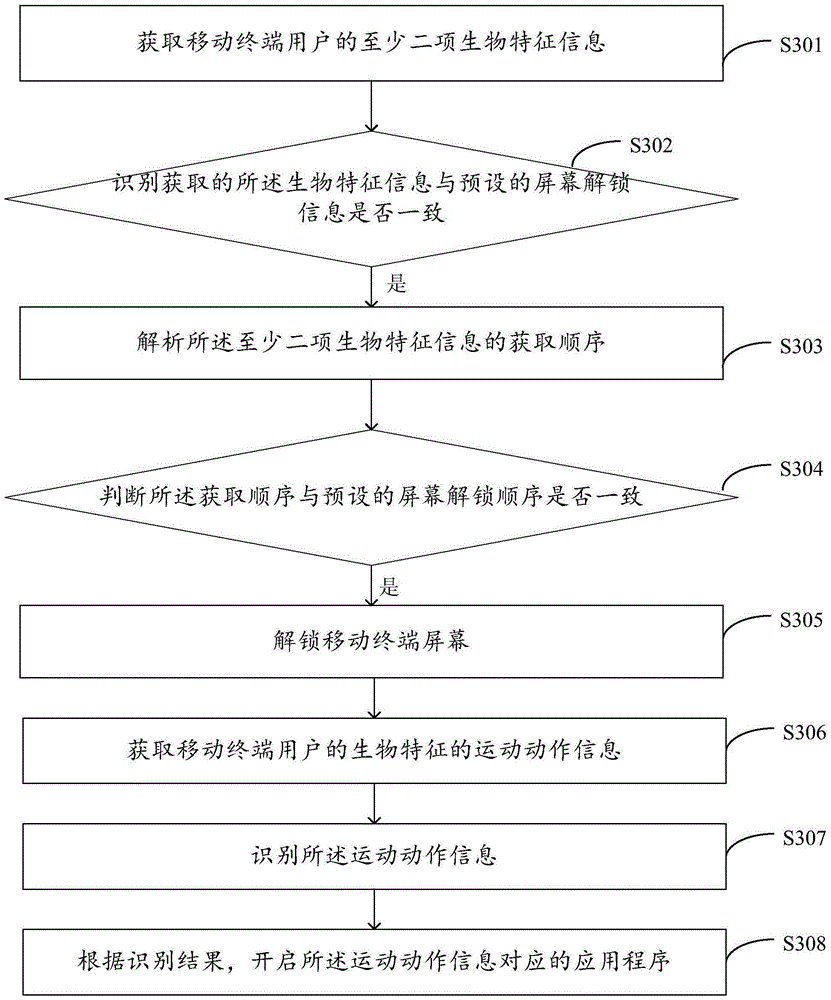
Unlocking method and device of mobile terminal
InactiveCN105205380AImprove user experienceImprove securityDigital data authenticationPasswordHuman–computer interaction
The invention provides an unlocking method and device of a mobile terminal. The method comprises the steps of: acquiring at least two pieces of biological feature information of a user of the mobile terminal; identifying whether the acquired biological feature information is consistent with preset screen unlocking information; if yes, analyzing an acquiring sequence of the at least two pieces of biological feature information; judging whether the acquiring sequence is consistent with a preset screen unlocking sequence; if yes, unlocking a screen of the mobile terminal. The unlocking method and device are very high in safety and convenience; since the biological feature information is unique biological feature (eyeball, voice, fingerprint and the like) of the user of the mobile terminal, the biological feature information is not easy to be stolen, the problem of forgetting an unlocking password does not exist and use experience of the user is greatly improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
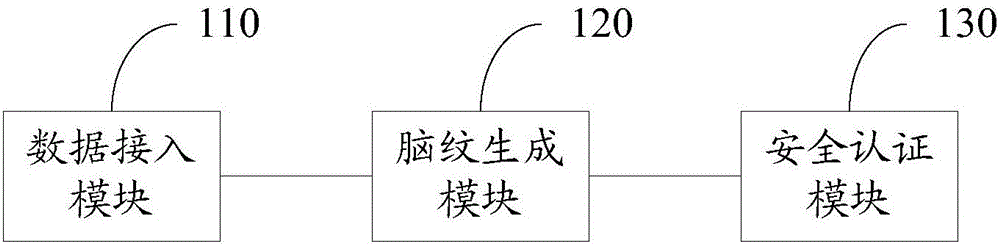
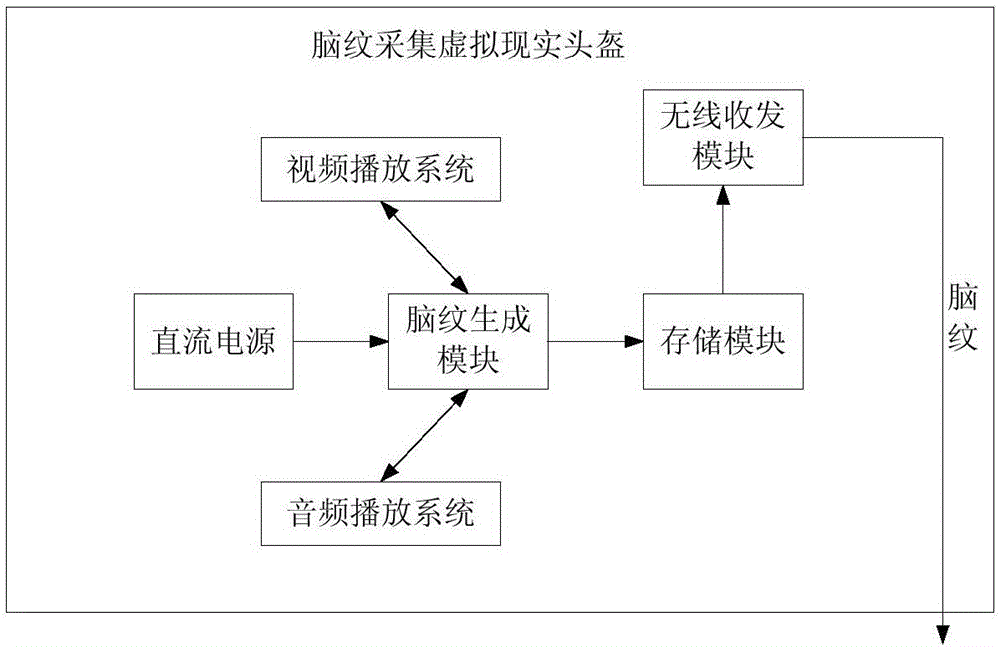
Security certification system based on virtual reality helmet brain grain collection
ActiveCN106503517ANot easy to be stolenNot easy to copy and abuseDigital data authenticationUnder-stimulationSecure authentication
The invention discloses a security certification system and method based on virtual reality helmet brain grain collection. The system comprises a data access module, a brain grain generation module and a security certification module, wherein the data access module generates a first brain grain feature parameter corresponding to identity information of a user according to a preset brain grain local database; the brain grain generation module acquires a second brain grain feature parameter generated under stimulation to the user based on audio and video signals; the security certification module compares the first brain grain feature parameter with the second brain grain feature parameter, and carries out recognition and security certification on the identity of the user according to a comparison result. The security certification system solves the problem that no brain grain collection-based security certification system is provided at the present in the prior art, and has the advantage that a brain grain password is not liable to steal, copy and abuse; under an extreme condition, if the brain grain password is leaked, the user can reset the brain grain password conveniently.
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC
Cable subsurface buoy real-time internal wave monitoring device installed on ocean platform
InactiveCN102305703ANot easy to be stolenNot easy to loseElectric signal transmission systemsSubsonic/sonic/ultrasonic wave measurementSurface oceanReal-time data
The invention discloses a cable subsurface buoy real-time internal wave monitoring device. The device comprises a power supply, an industrial personal computer, a steel cable, a customized cable and a plurality of internal wave measurement probes, wherein the plurality of internal wave measurement probes are all composed of conductivity temperature depth systems and current needles, the customized cable is connected with the power supply and the industrial personal computer respectively, the plurality of internal wave measurement devices are arranged on the customized cable, and spaces are kept among the plurality of internal wave measurement devices, the customized cable is fixed on the steel cable, one end of the steel cable is fixed on a deck of a ocean platform and the other end is movably connected with a weight, and the customized cable is fixed on the deck of the ocean platform by an inclined steel cable. According to the invention, the internal wave monitoring device is constructed based on the ocean platform, so that the cable subsurface buoy real-time internal wave monitoring device installed on ocean platform is not easy to steal and lose, the safety of the measurement device is ensured; the real-time power supply of the measurement device and real-time data collection can be achieved; and compared with a self-contained subsurface buoy internal wave monitoring device, the cable subsurface buoy real-time internal wave monitoring device installed on ocean platform is greatly improved in the timeliness of data.
Owner:CHINA NAT OFFSHORE OIL CORP +2
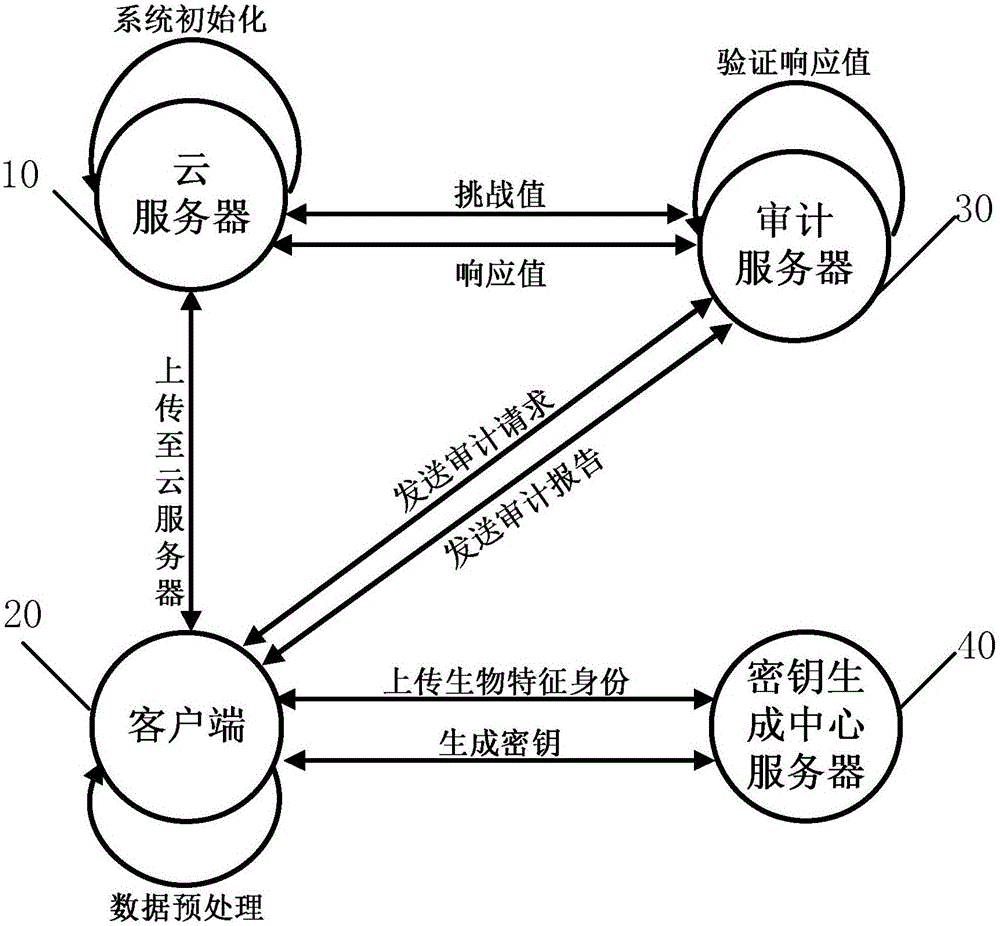
Cloud data integrity verification method and system based on biological characteristics
The invention relates to the technical field of network security, in particular to a cloud data integrity verification method and system based on biological characteristics. The method comprises: the system is initialized and generates public parameters; a client uploads biological characteristic identity, and a key generation central server generates keys for a user; the client uploads files and tags to a cloud server; an auditing server transmits a challenge value to the cloud server, the cloud server computes a response value by utilizing the challenge value, user data and the tag and transmits the response value to the auditing server, and the auditing server verifies the validity of the response value in order to check whether the cloud server completely saves the data of the client. According to the cloud data integrity verification method and system based on the biological characteristics, complex key management load of the traditional verification protocol is simplified, and the system complexity is reduced; and meanwhile, fault tolerance, which the cloud data integrity auditing scheme based on identity does not have, is provided, so that the practicability is better. The invention further relates to a system of the cloud data integrity verification method based on the biological characteristics.
Owner:SHAANXI NORMAL UNIV
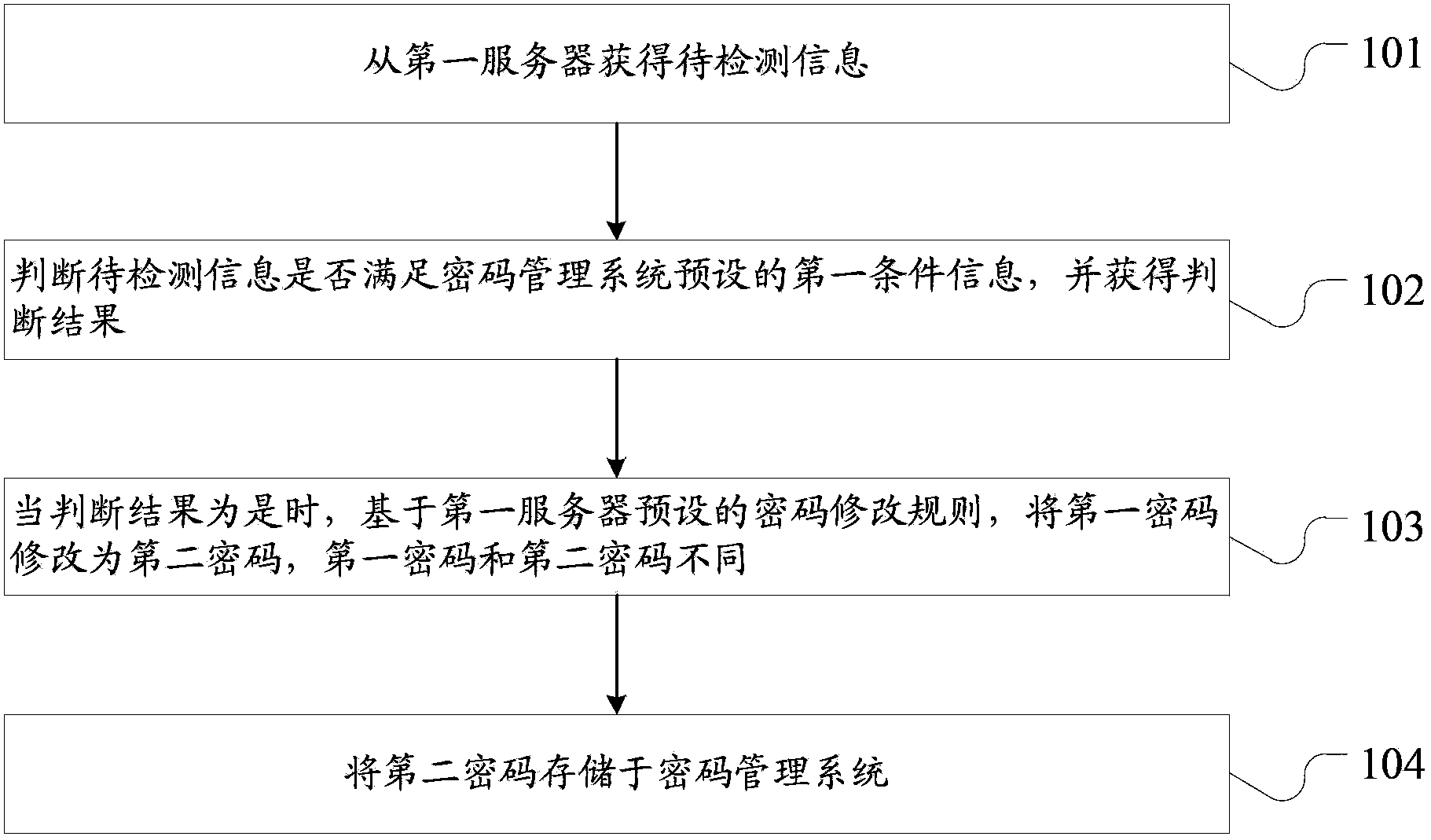
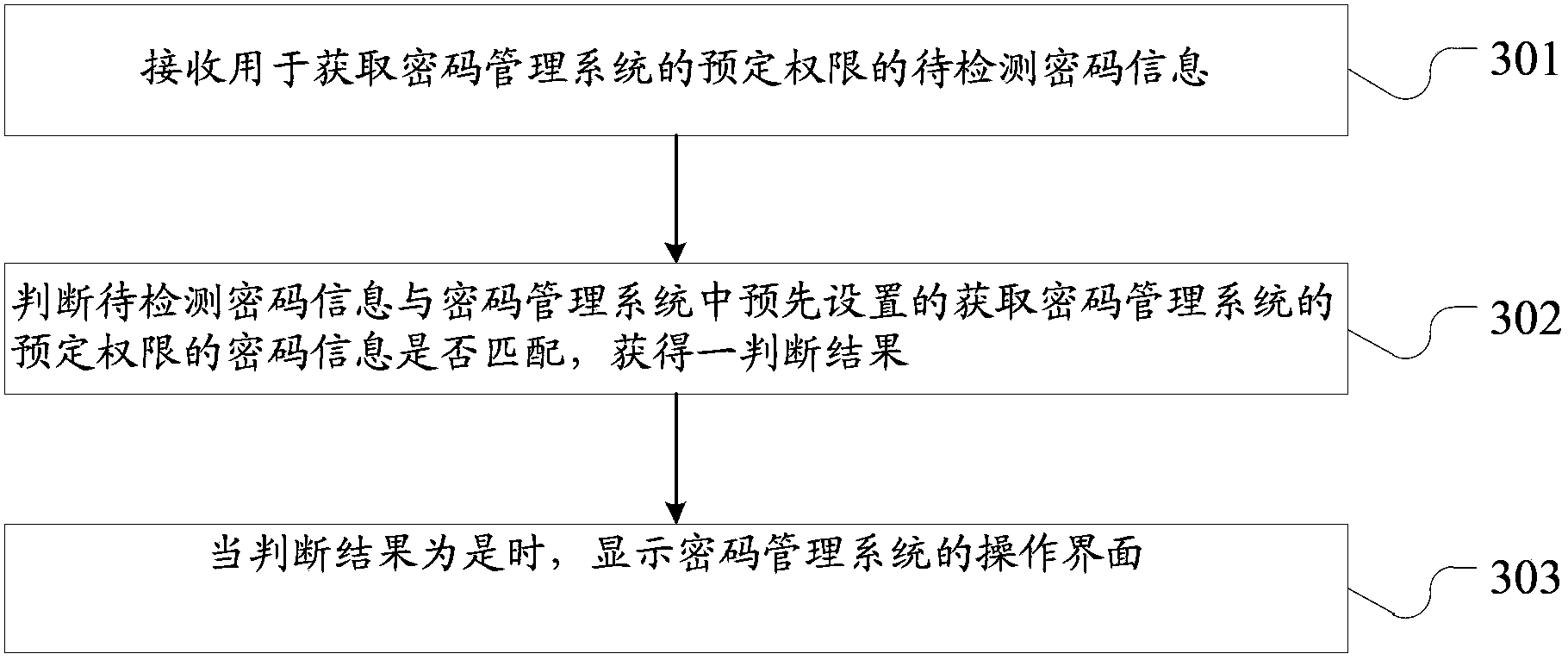
Data processing method and password management system
The invention provides a data processing method and a password management system. The data processing method is applied to the password management system. The password management system stores at least one password which contains a first password, the at least one password is used for being combined with the information of at least one account corresponding to the at least one password, the preset permission of at least one server is acquired, the first password is used for being combined with the information of the corresponding first account, and the preset permission of the first server is acquired, wherein the at least one server comprises a first server. The data processing method comprises the steps that information to be detected is obtained from the first server; whether the information to be detected meets the first condition information preset by the password management system is judged, and a judged result is acquired; when the judged result is yes, based on a password modification rule preset by the first server, the first password is modified into a second password, and the first password is different from the second password; the second password is stored in the password management system.
Owner:LENOVO (BEIJING) LTD
Bike tie down bar
InactiveUS8474767B1Maximize tie-strap angleIncrease the angleCurtain suspension devicesFlexible elementsPick-up truckEngineering
A tie-down bar apparatus and method for securing Cargo onto the bed of trailer or full-size, mid-size, or small pick-up truck comprising an adjustable telescoping support bar having a main body and two ends, the main body of the telescoping support bar has at least one tie-down ring is connected to the main body for securing one or more pieces of cargo including recreational vehicles, the main body of the telescoping support bar has two elongated arm which are positioning inside each end of the main body, to create the telescoping effect so that the support bar can be adjusted to match the size of the width of a vehicle's bed. Wherein a user will install said pair of connectors to the vehicle thereby securely attaching said telescoping support bar to the bed of vehicle. Wherein a user will place one or more pieces of cargo into said bed of the vehicle and then utilize one or more restraining means for securing said cargo in an upright position by connecting said restraining means to both the tie-down rings and to the cargo.
Owner:BIKE TITE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com