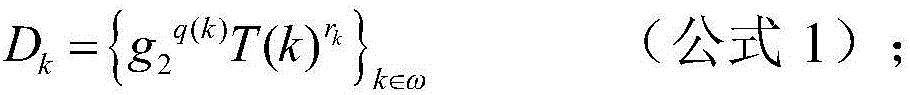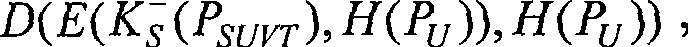Patents
Literature
124results about How to "Not easy to forget" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
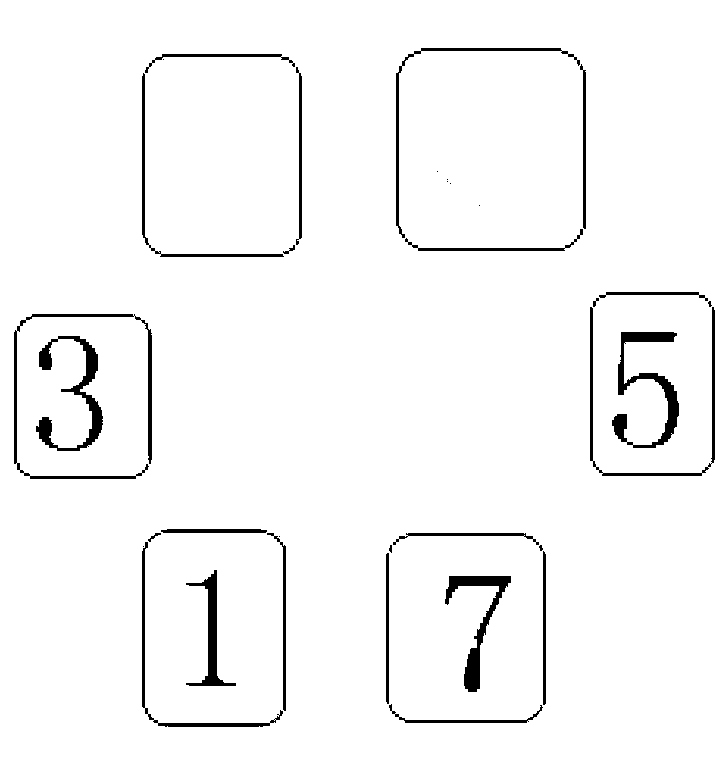
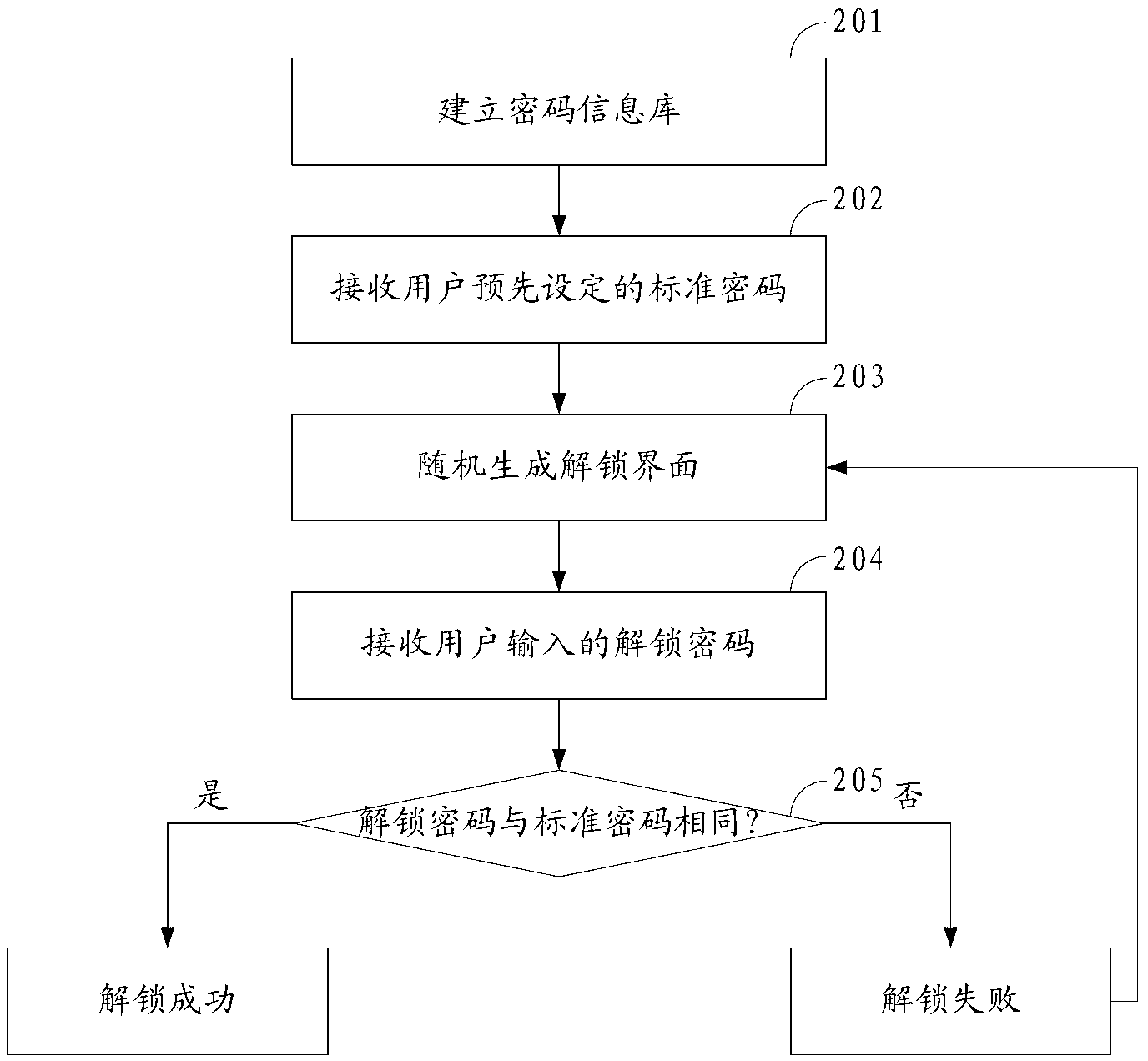
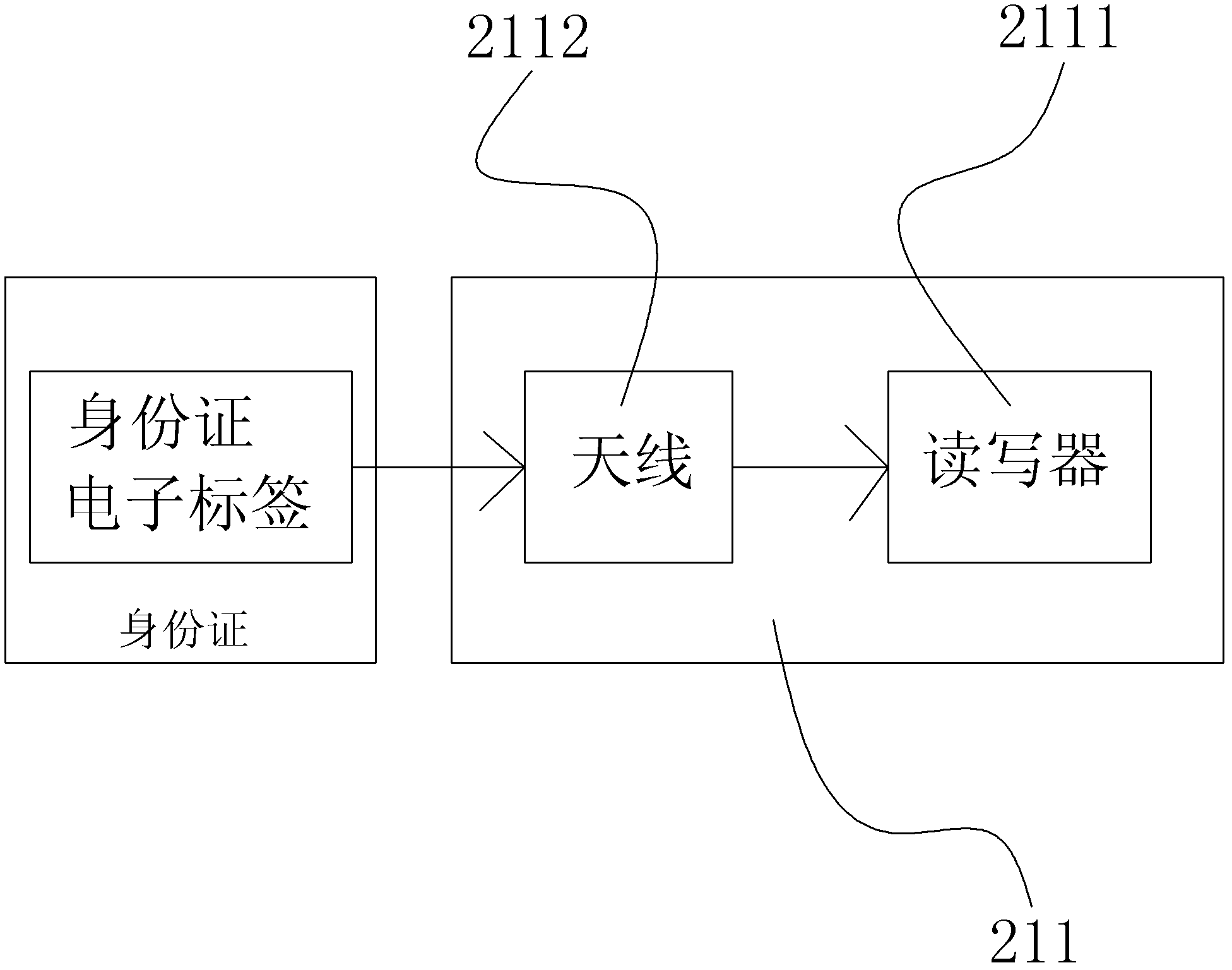
Password authentication method and device
ActiveCN103200011AAvoid crackingNot easy to forgetUser identity/authority verificationPasswordUser input
The invention discloses a password authentication method and a password authentication device, and in the password authentication implementation process, the password is difficult to be exposed, and is more safe and reliable. The method comprises the steps of receiving a standard password preset by users, wherein the standard password consists of characteristic values of a plurality of identification information; generating a plurality of identification information randomly on a touch screen when deblocking command is received, and recording the corresponding relationship between the position information of the identification information on the touch screen and the characteristic values of the identification information; acquiring the position information clicked on the touch screen, acquiring the characteristic values of the plurality of corresponding identification information according to a plurality of position information clicked by users, and forming a deblocking password input by users through the characteristic values of the plurality of identification information; and judging whether the deblocking password is identical to the standard password, if so, confirming that deblocking is successful, and if not, confirming that delocking is failed. The invention also discloses a password authentication device.
Owner:上海榕安科技有限公司
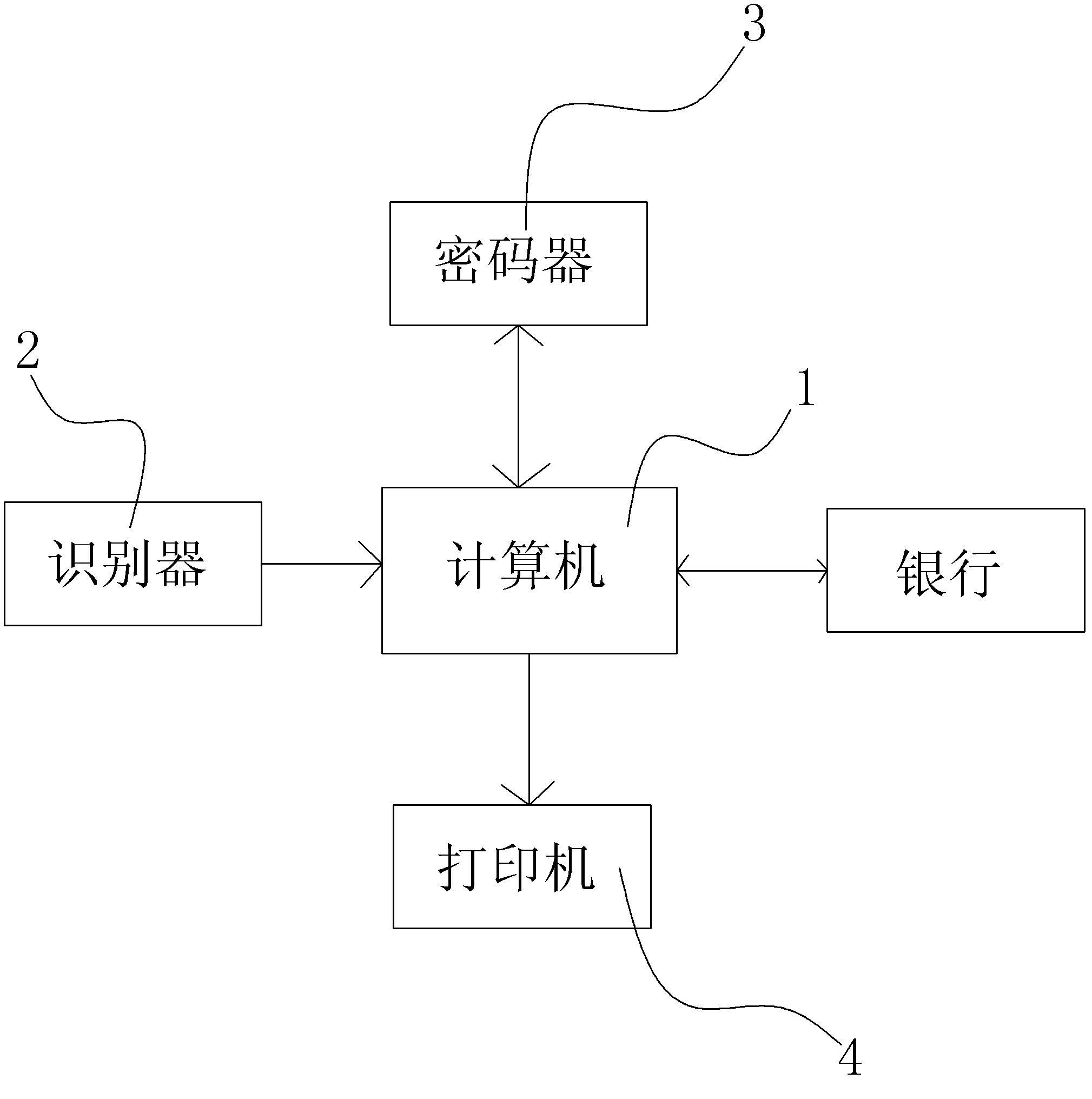
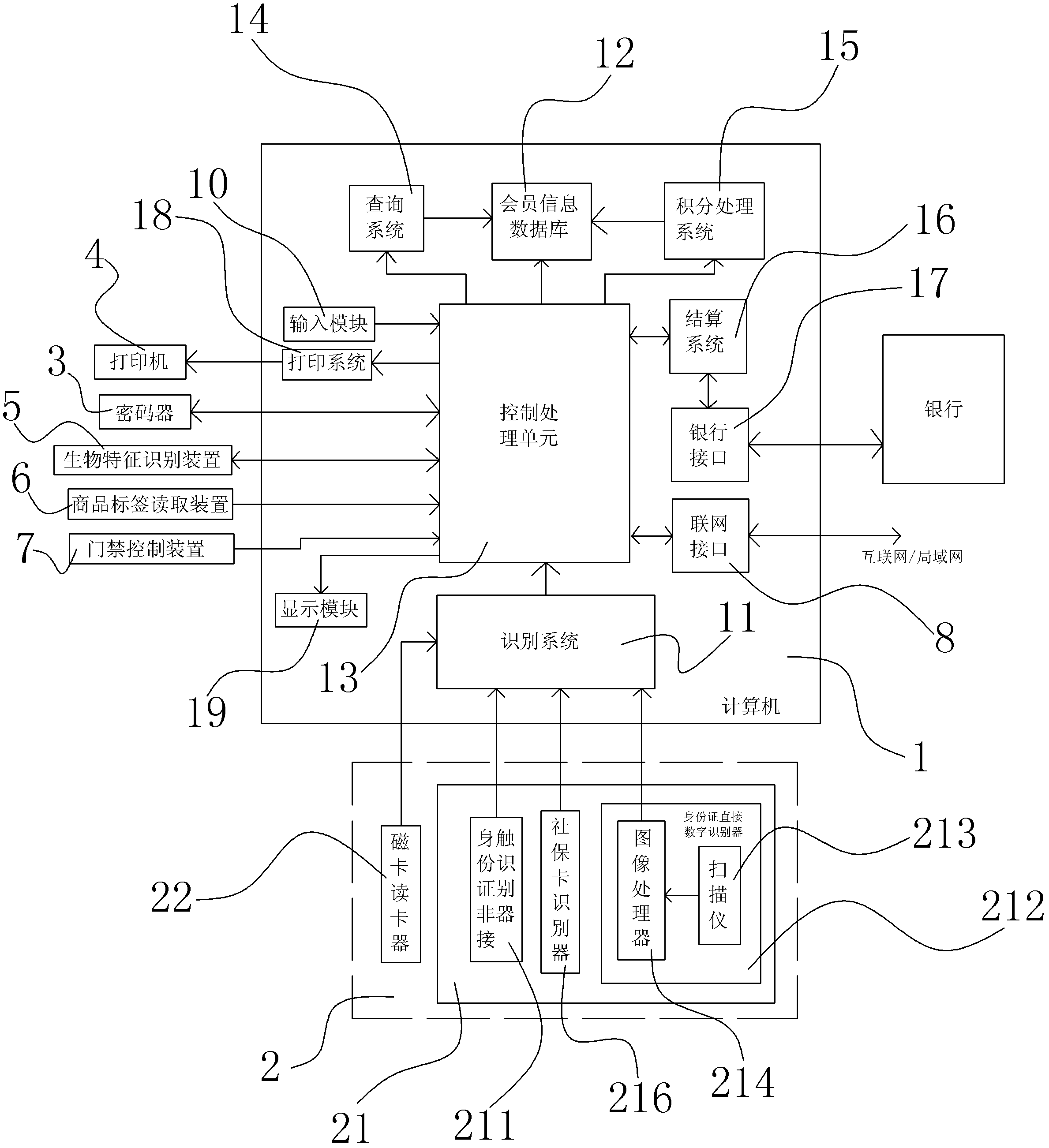
Member function system based on identity card recognition function
ActiveCN102567860AEasy to verify authenticityImprove securitySensing record carriersResourcesIdentity recognitionIdentification device
The invention discloses a member function system based on an identity card recognition function. The system comprises a computer and a recognizer, wherein the recognizer comprises an identity recognition device; the computer comprises a recognition system, a member information database and a control processing unit; the recognition system is connected with the identity recognition device to receive data of the identity recognition device; and the control processing unit is respectively connected with the member information database and the recognition system to communicate and process information. Through the system, the recognition and entry functions of member cards and members can be automatically realized by directly using identity cards, and a phenomenon that multiple member cards are inconvenient to carry or forgotten to be carried is avoided; and the system has good adaptability, can be separately used or used with other member and integrating systems, does not require to reform the conventional system much, can reduce the waste of social resources, is convenient for a user to consume and carry, and saves national resources.
Owner:黄启迪
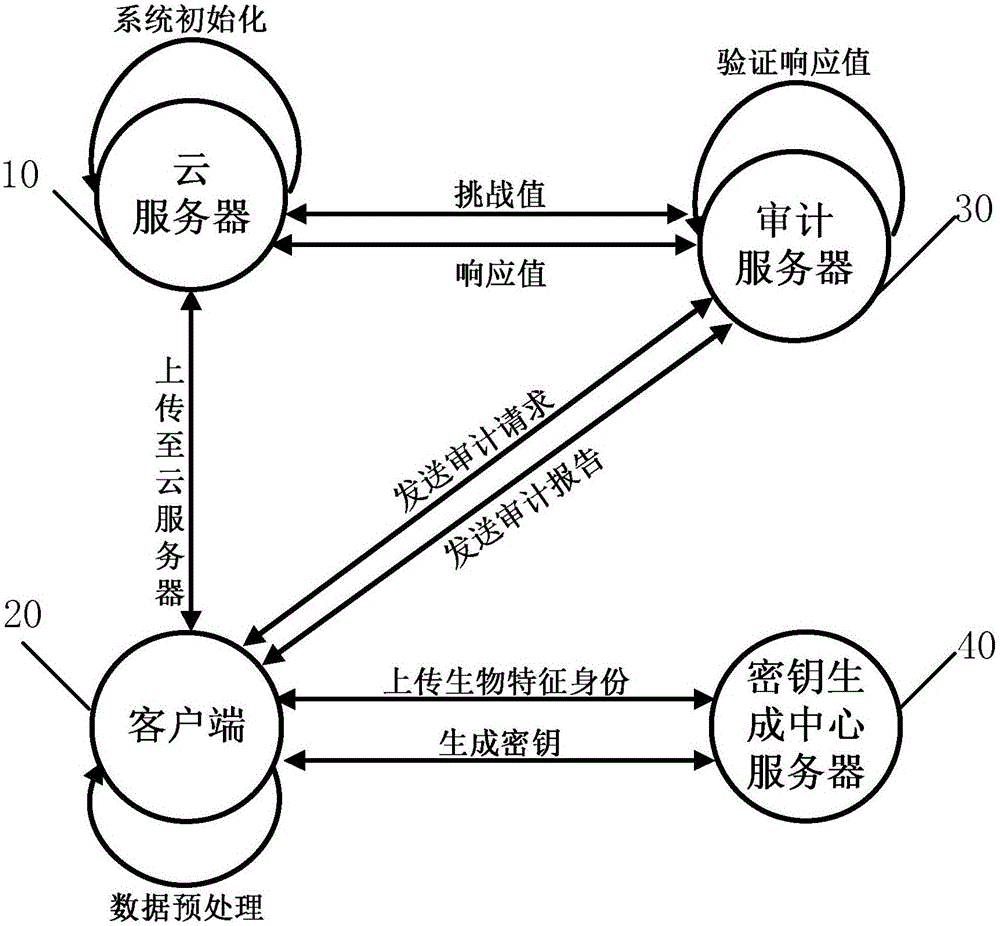
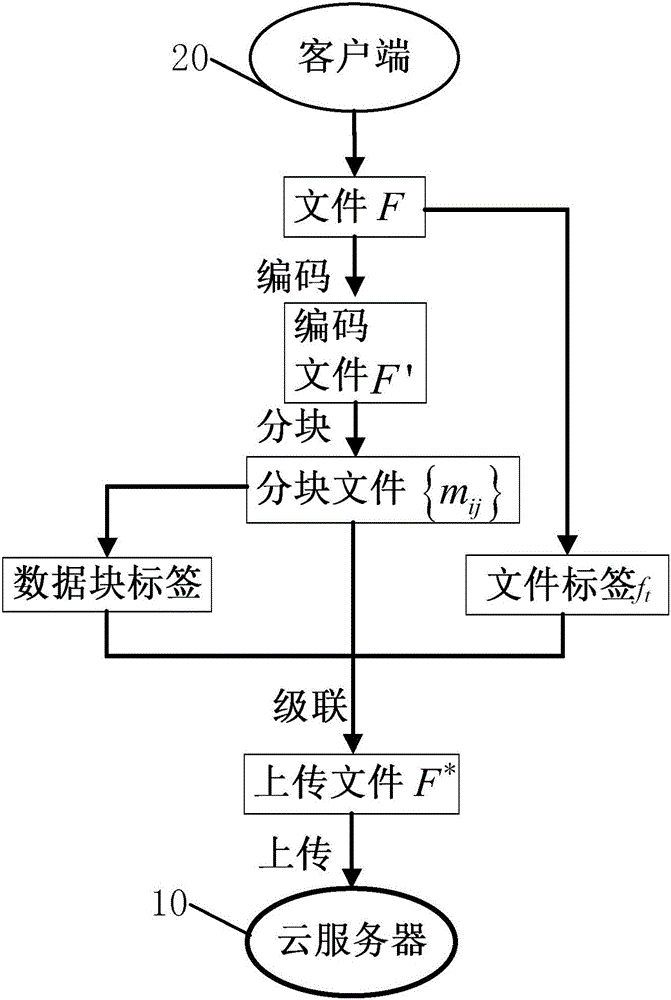
Cloud data integrity verification method and system based on biological characteristics
The invention relates to the technical field of network security, in particular to a cloud data integrity verification method and system based on biological characteristics. The method comprises: the system is initialized and generates public parameters; a client uploads biological characteristic identity, and a key generation central server generates keys for a user; the client uploads files and tags to a cloud server; an auditing server transmits a challenge value to the cloud server, the cloud server computes a response value by utilizing the challenge value, user data and the tag and transmits the response value to the auditing server, and the auditing server verifies the validity of the response value in order to check whether the cloud server completely saves the data of the client. According to the cloud data integrity verification method and system based on the biological characteristics, complex key management load of the traditional verification protocol is simplified, and the system complexity is reduced; and meanwhile, fault tolerance, which the cloud data integrity auditing scheme based on identity does not have, is provided, so that the practicability is better. The invention further relates to a system of the cloud data integrity verification method based on the biological characteristics.
Owner:SHAANXI NORMAL UNIV
Digital content protection method ciphered by biological characteristic
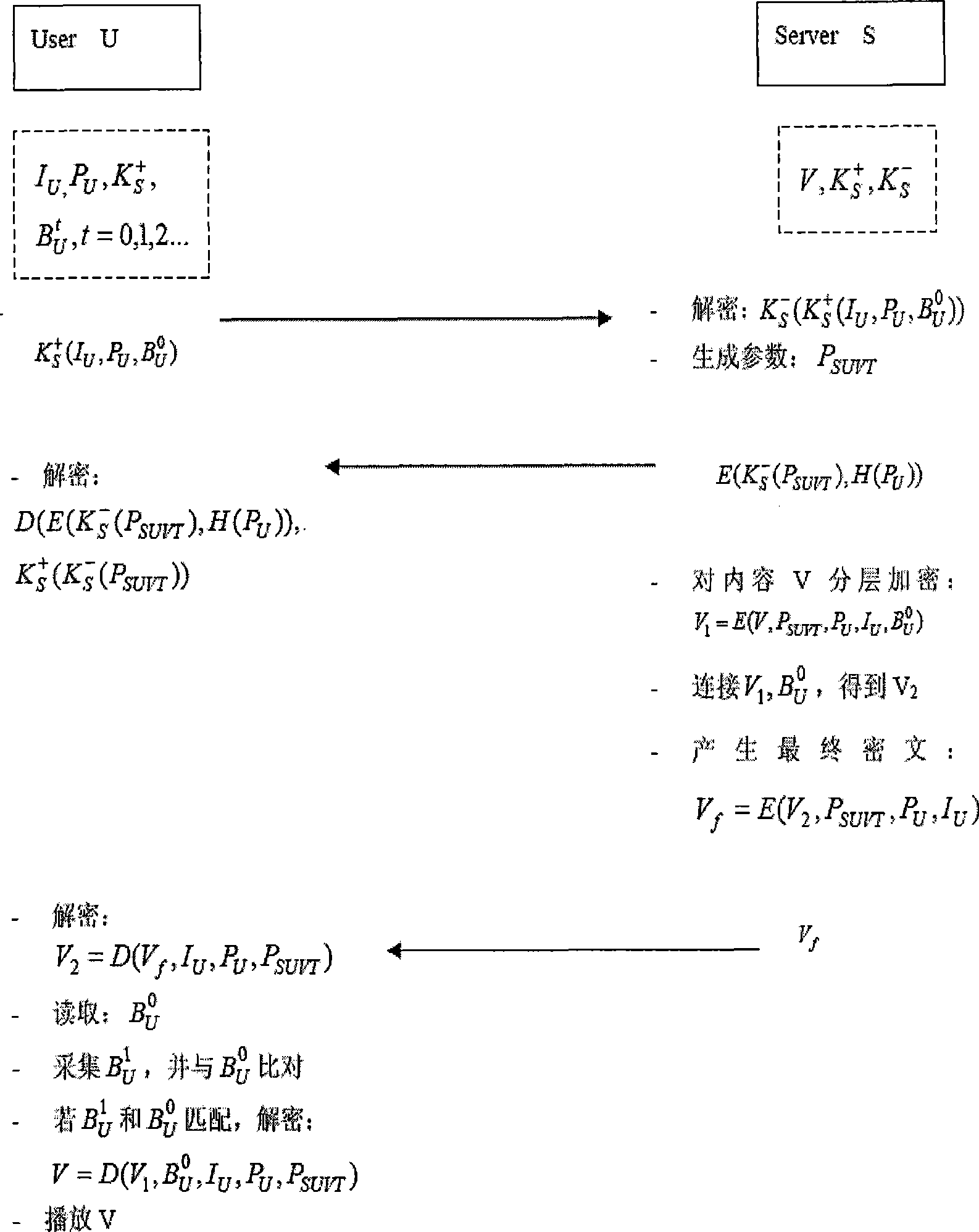
InactiveCN101383701AWill not limit playbackNot easy to forgetKey distribution for secure communicationPublic key for secure communicationDigital contentNumber content
The invention relates to an encrypted digital content guard method adopting biological characteristic, which belongs to the technical field of information security. The invention adopts the guard proposal that biometrics characteristics of a user is used to encrypt digital multimedia content, the guard proposal is based on the biometrics data of the user and one layered encryption and decryption plan, uses the combination of a symmetric key system and an asymmetric system, and prevents the illegal sharing of the keys through using the biometrics data as the keys. The proposal includes two communication bodies, i.e. a multimedia server S and a user U, the U receives and broadcasts a multimedia file V stored in the S. When the communication starts, the user sends the self biometrics characteristics to the server, the server uses the biometrics characteristics to encrypt the multimedia content which is then sent to the user, when the biometrics characteristics of the user matches with encrypted keys, the multimedia content can be watched, thereby the guard of the multimedia content is realized.
Owner:BEIJING UNIV OF TECH
Method and device for outputting bar code of password
InactiveCN101702192AWide choiceAvoid lostDigital data authenticationSubstation equipmentChinese charactersPassword
The invention relates to a method for outputting a bar code of a password by using a cell phone or a display screen. In the invention, a corresponding conversion program of characters, numbers and bar codes is provided; the password is outputted by using the cell phone of the display screen in a bar code mode; and the bar code is received by using a common camera or a photoelectric bar code reader and is identified by the conversion program, wherein the bar code can be a one-dimensional bar code or a two-dimensional bar code. Because the two-dimensional bar code can be used to identify Chinese characters, letters and the like, the invention can widen the password selection range of any users, that is to say, Chinese characters, letters and the like can be used as characters or methods of password input. By the method for outputting the bar code of the password, the user can input the password just by adopting the cell phone or the display screen when entering various equipment requiring password input, and a program internally set in the cell phone or the display screen converts the password into the bar code.
Owner:姚珍汉
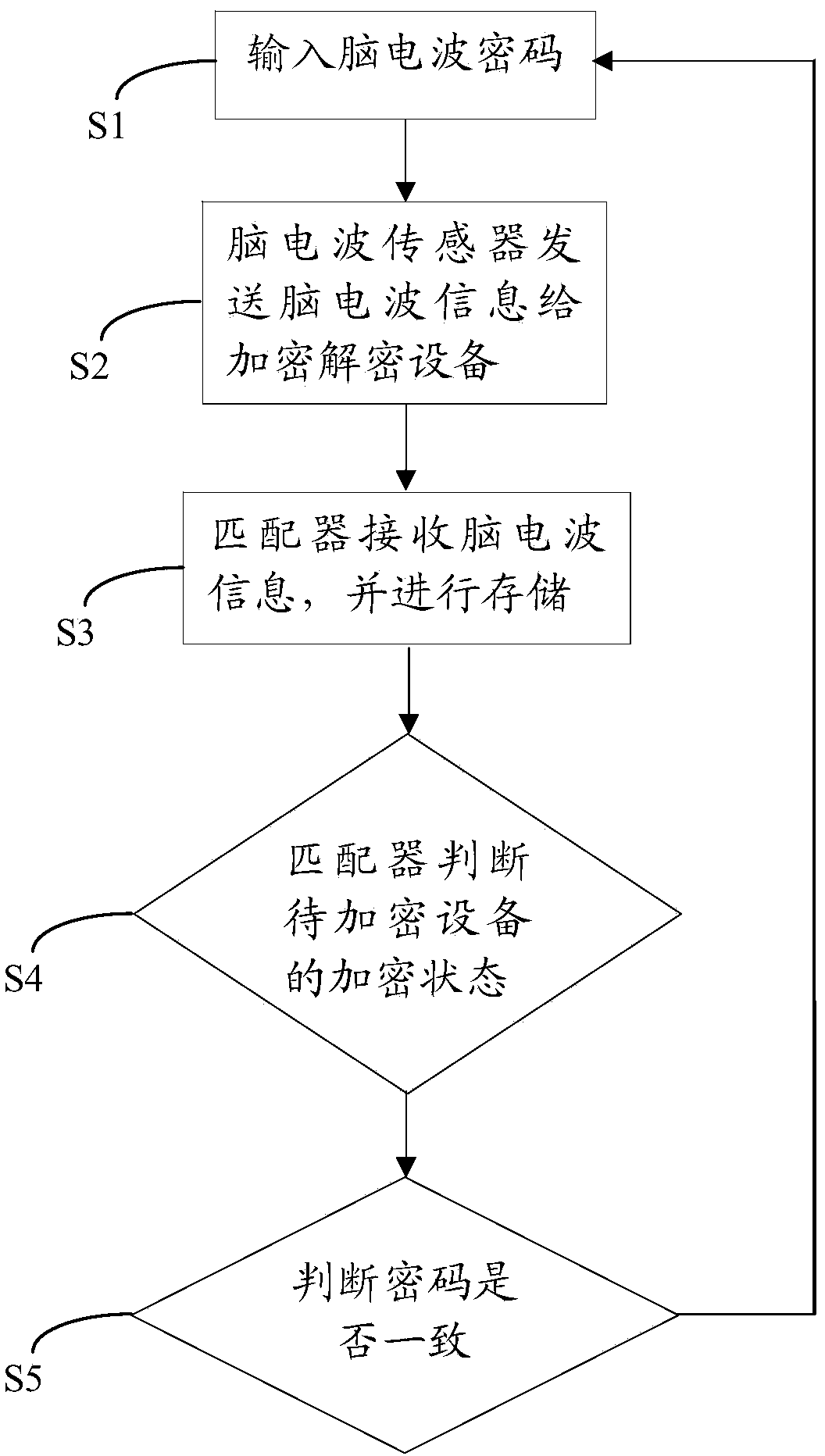
Coded lock based on brain-computer switching technique and encryption and decryption method of coded lock
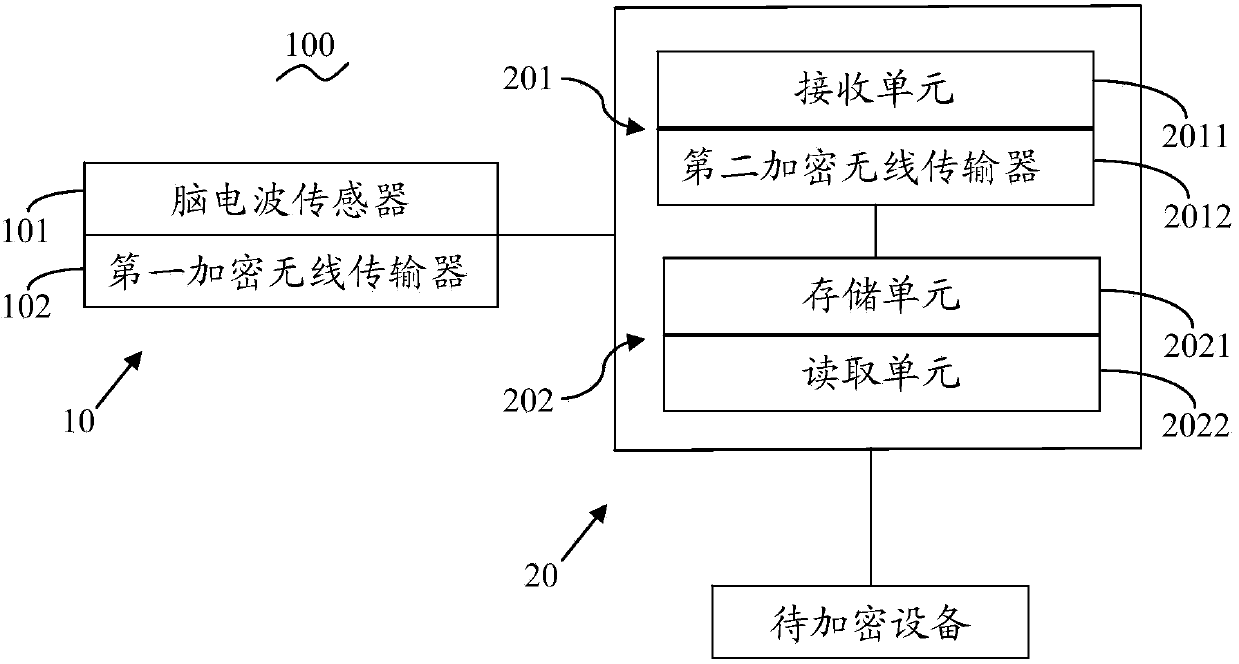
ActiveCN103810780ABig breakthroughImprove securityDigital data authenticationIndividual entry/exit registersComputer hardwarePassword
The invention discloses a coded lock based on a brain-computer switching technique and an encryption and decryption method of the coded lock. The coded lock comprises dressing equipment, encryption and decryption equipment and a code memory, wherein the dressing equipment comprises a shell matched with a human head; an internal space is formed by the shell; a brain wave sensor and a first encryption wireless transmitter are arranged inside the internal space; the brain wave sensor comprises a sensing unit and a signal transmission unit; the encryption and decryption equipment comprises a receiver and a matcher; the receiver comprises a receiving unit and a second encryption wireless transmitter; one end of the matcher is electrically connected with the receiving unit; an interface matched with equipment to be encrypted is arranged at the other end of the matcher; the matcher comprises a storing unit and a reading unit; the code memory is arranged in the equipment to be encrypted. The coded lock provided by the invention has the relatively high security, can provide the great convenience for the disable and the unschooled when passwords are set, and has the advantages of being simple to operate, convenient to use and wide in application.
Owner:SUZHOU UNIV
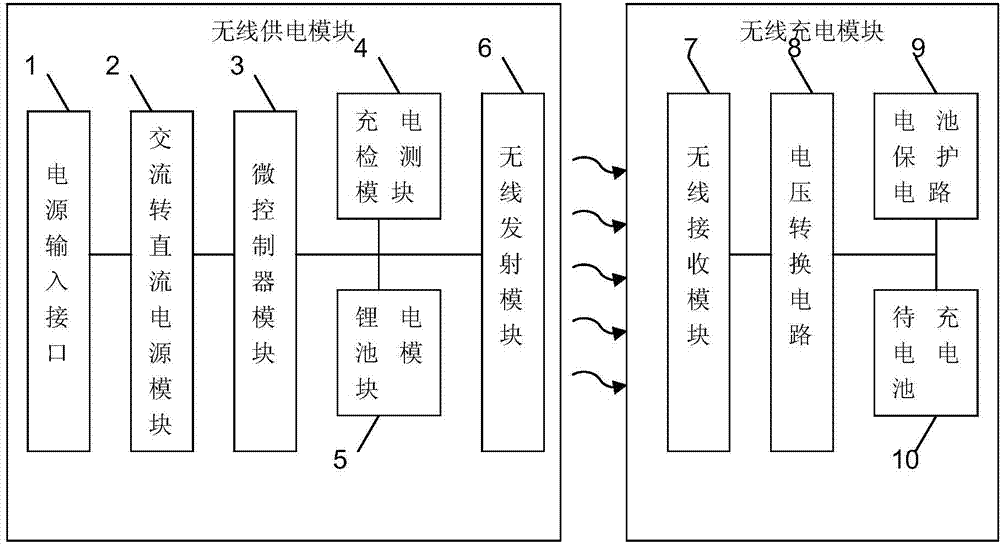
Wearable wireless charger baby
InactiveCN104779657AHigh degree of intelligenceReduce volumeBatteries circuit arrangementsElectromagnetic wave systemElectrical batteryEngineering
The invention discloses a wearable wireless charger baby which comprises a wireless power supply module and a wireless charge module, wherein a charge detection module is adopted to detect whether equipment to be charged is in a charge area of the wearable wireless charger baby or not; if the equipment to be charged is in the charge area of the wearable wireless charger baby, the lithium battery of a wireless transmitting module is adopted to supply power to enable a transmitting coil to generate and output radio frequency according to the result of the charge detection module; an energy conversion circuit in a wireless receiving module is adopted to receive electromagnetic signals transmitted from the wireless transmitting module and to convert the electromagnetic signals into alternative current; a voltage conversion circuit is adopted to receive generated alternative current and convert the alternative current into direct current; a battery protecting circuit is adopted to prevent the situation that a battery is damaged by situations such as over charge, over current and short circuit. Due to the adoption of a telescopic elastic band and double additional elliptical buckles, the wearable wireless charger baby disclosed by the invention can be worn on arms, wrists and legs or suspended above other articles, is convenient to carry over, and further has the advantages of wide wireless charge range, high intelligent degree, small size, simplicity in operation and the like.
Owner:HANGZHOU DIANZI UNIV
Application process of fingerprint identification technology on POS machine, imprinter and cash dispenser
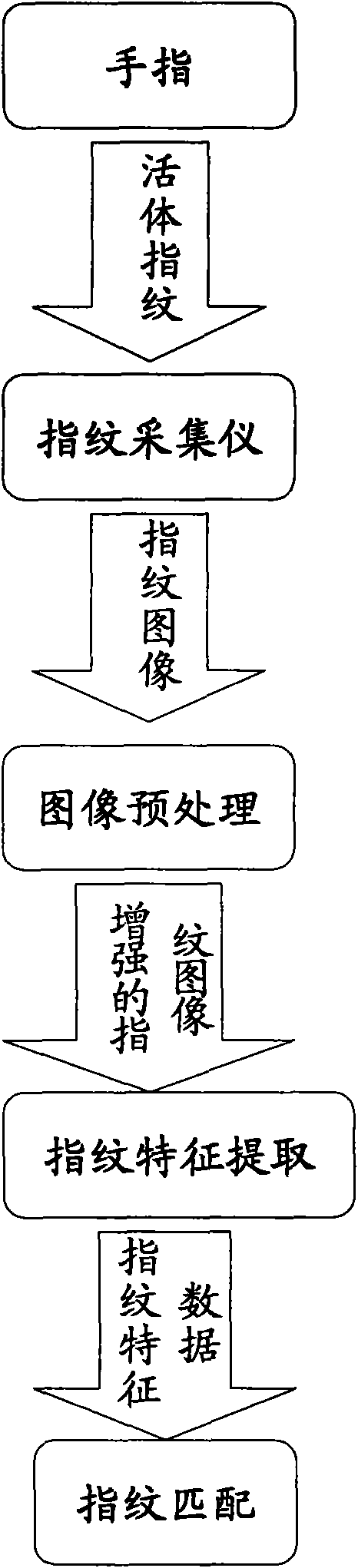
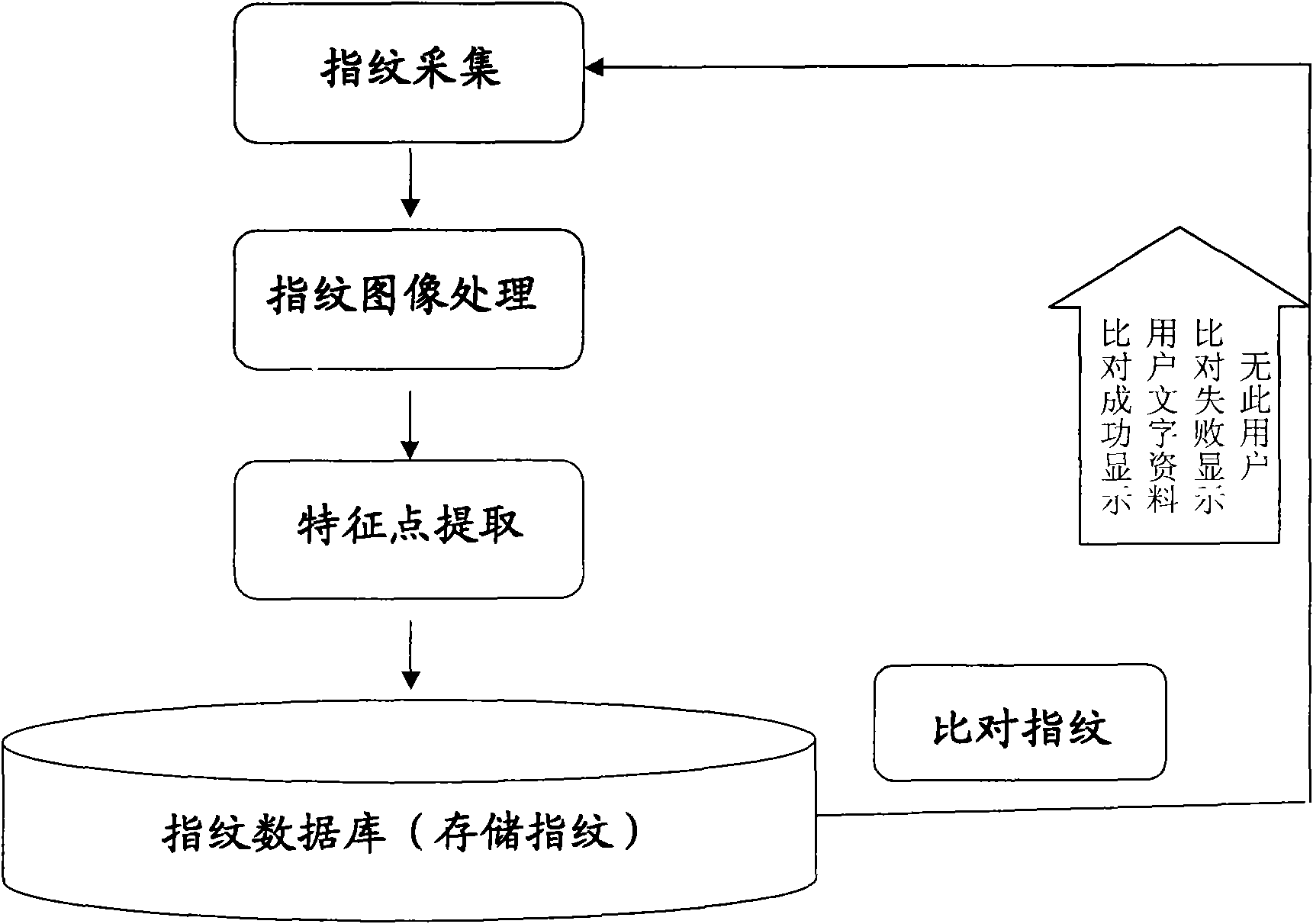
InactiveCN101556713ANot easy to forgetNot easy to loseCharacter and pattern recognitionSpecial data processing applicationsCredit cardPattern recognition
An application process of fingerprint identification technology on a POS machine, an imprinter and a cash dispenser mainly comprises fingerprinting, fingerprint image preprocessing, characteristic point extraction, characteristic point storage, integrates the characteristics of individual fingerprints into the information of the individual data of a credit card so as to bind with the information of the individual data. The fingerprint comparison comprises fingerprint collection, fingerprint image preprocessing, and characteristic point extraction, carries out feather matching on the extracted characteristic points and the stored characteristic points, and finally outputs and shows the comparison results. The invention has the advantages that the fingerprint identification technology is applied to the POS machine, the imprinter and the cash dispenser, has two major functions of fingerprint registration and fingerprint comparison, the individual fingerprint identification technology and the image conversion technology are used for realizing the transmission process of the image data and ensuring the non-losing and non-damaging of the characteristic information of the fingerprint; the implicative information is more obvious, is difficult to be forgotten or lost, forged or stolen, and carried about, is safe, convenient and fast in utilization.
Owner:FUSHUN JINDAO TECH
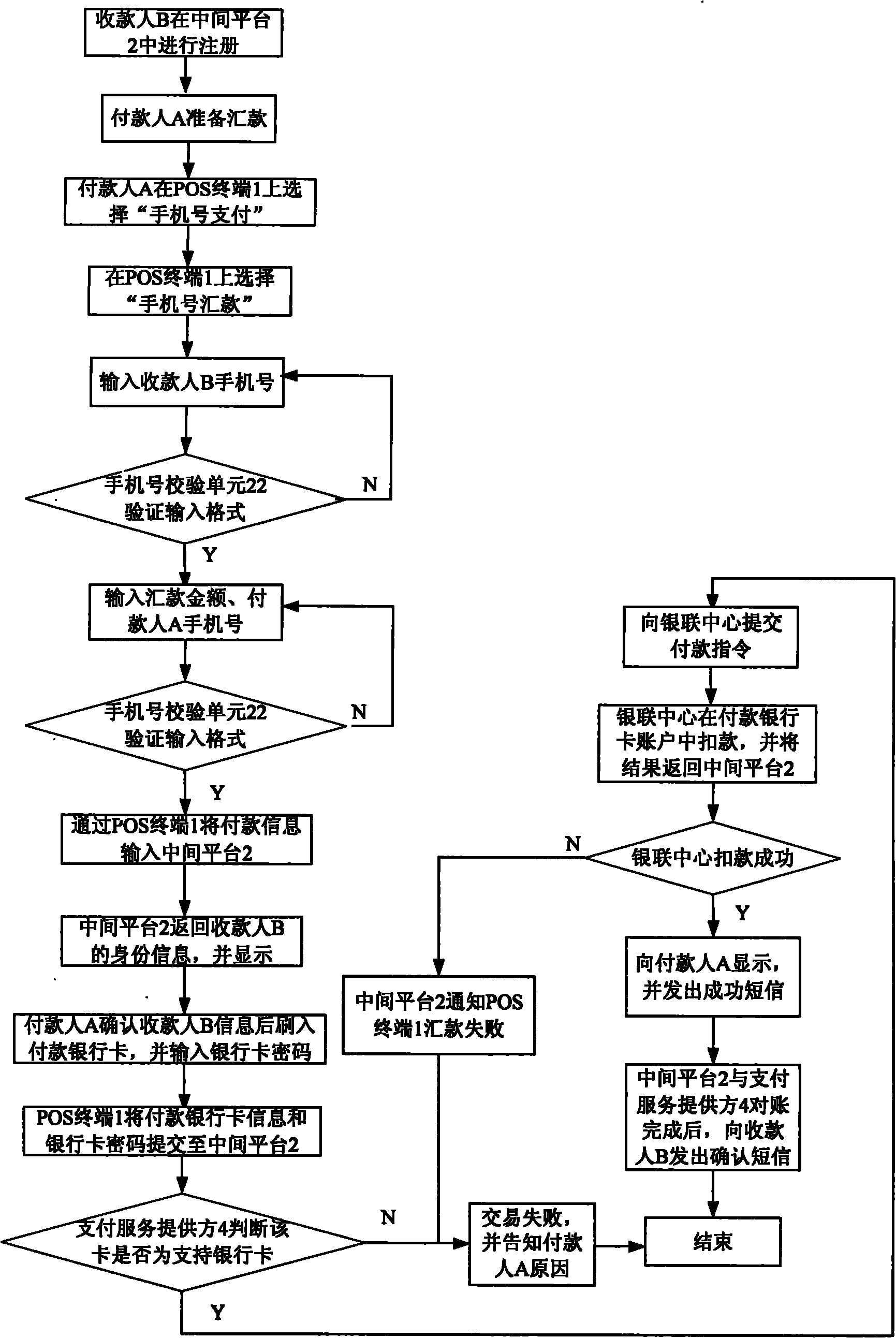
Phone number payment platform, payment trading system and method thereof
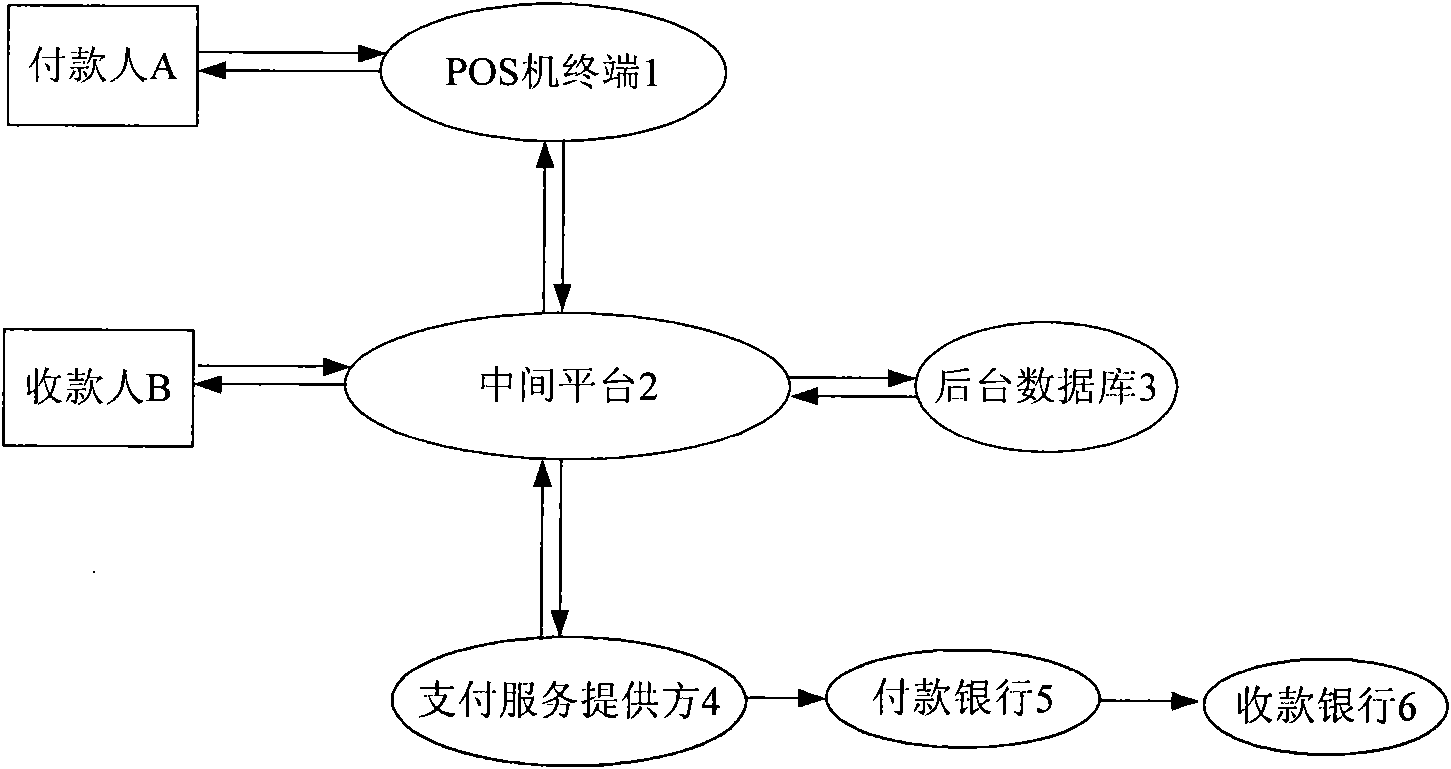
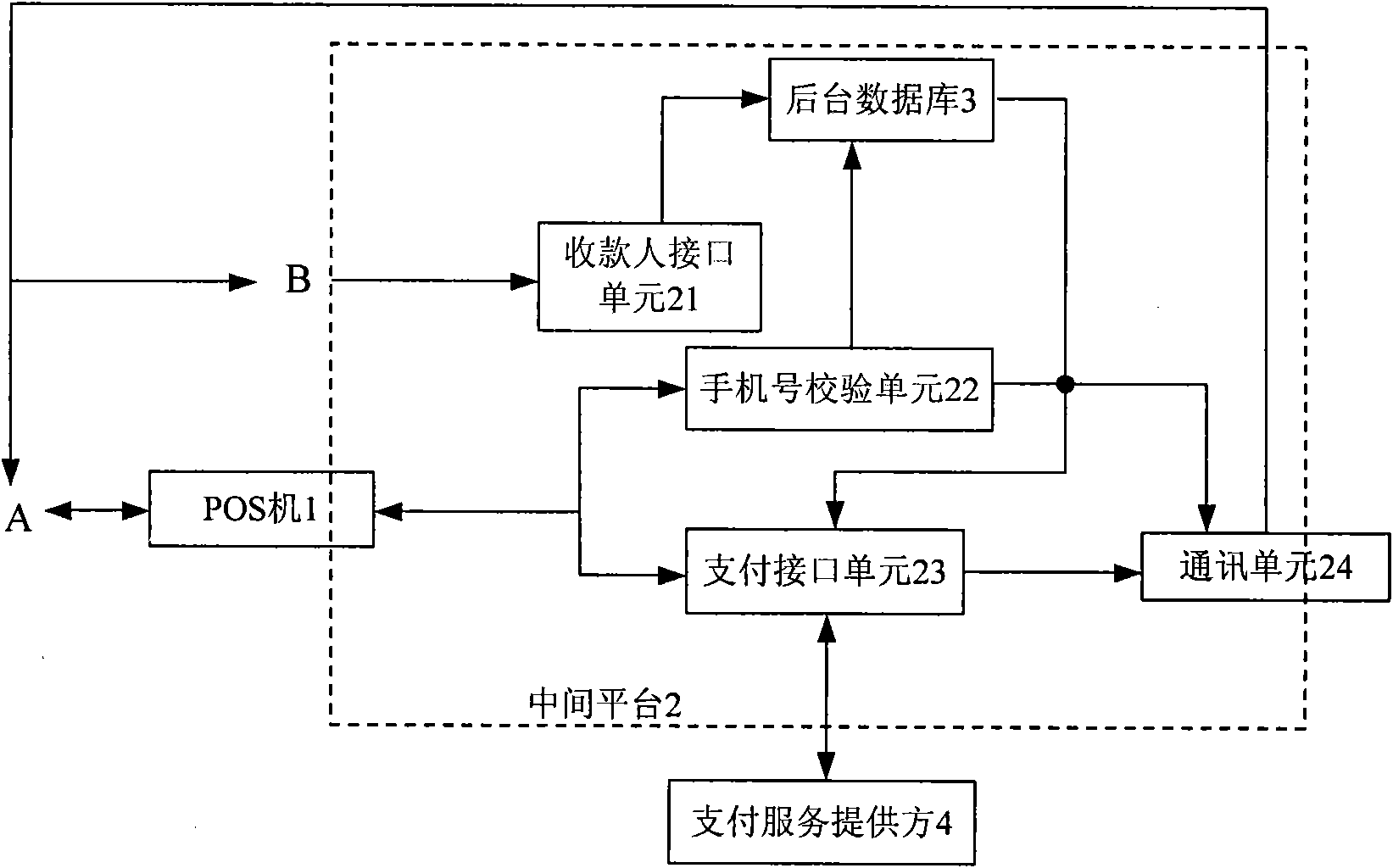
InactiveCN101976403ANot easy to confuseNot easy to forgetPayment architecturePaymentService provision
The invention relates to a phone number payment platform, a payment trading system and a method thereof. The invention comprises a POS machine terminal, a phone number payment platform and a background database, wherein the POS machine terminal is connected with the phone number payment platform by a fixed network; data in the phone number payment platform is stored in the background database, corresponding data is extracted from the background database according to requirement to carry out comparison and judgment; and the phone number payment platform is also connected with a payment service supplier by a unionpay special line. A payer inputs the phone number of a payee on the POS machine terminal and uses the phone number of the payee as a unique trading number, then the phone number payment platform can extract receiving bank card information bound with the phone number of the payee according to the payee registration information stored in the background database, inputs the paying bank card information, the bank card password, the receiving bank card information and the paying information to the payment service supplier and realizes the transfer from the paying bank to the receiving bank.
Owner:LAKALA PAYMENT CO LTD
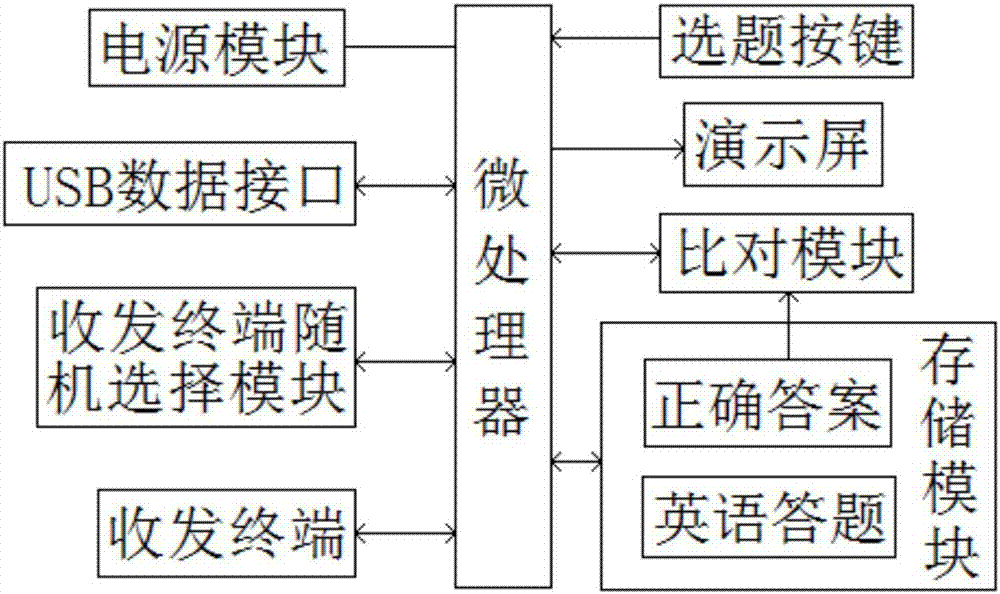
Circular feeding type English teaching demonstration device
InactiveCN107346617AIncrease interest in learningImprove learning effectElectrical appliancesComputer terminalComputer science
The invention provides a circular feeding type English teaching demonstration device which comprises a demonstrating screen, a plurality of transceiving terminals held by students, a microprocessor, a storage module, a comparison module, a question selecting button and a transceiving terminal random selecting module, wherein the demonstrating screen, the transceiving terminals, the storage module, the comparison module, the question selecting button and the transceiving terminal random selecting module are in signal connection to the microprocessor separately; the storage module is in signal connection to the comparison module; and the microprocessor is electrically connected to a power supply module. According to the device provided by the invention, can answering questions can be automatically circularly selected, answering students can be randomly selected and the answers fed back to the system by the students and the correct answers in the system can be displayed at the same time, so that the learning interest of the students can be motivated and the students are impressive to English knowledge and are unlikely to forget in the process of repeatedly circulating and randomly selecting students to answer. The interest of learning Engine by the students can be motivated, so that the English learning effect is favorably improved.
Owner:INNER MONGOLIA UNIV FOR THE NATITIES
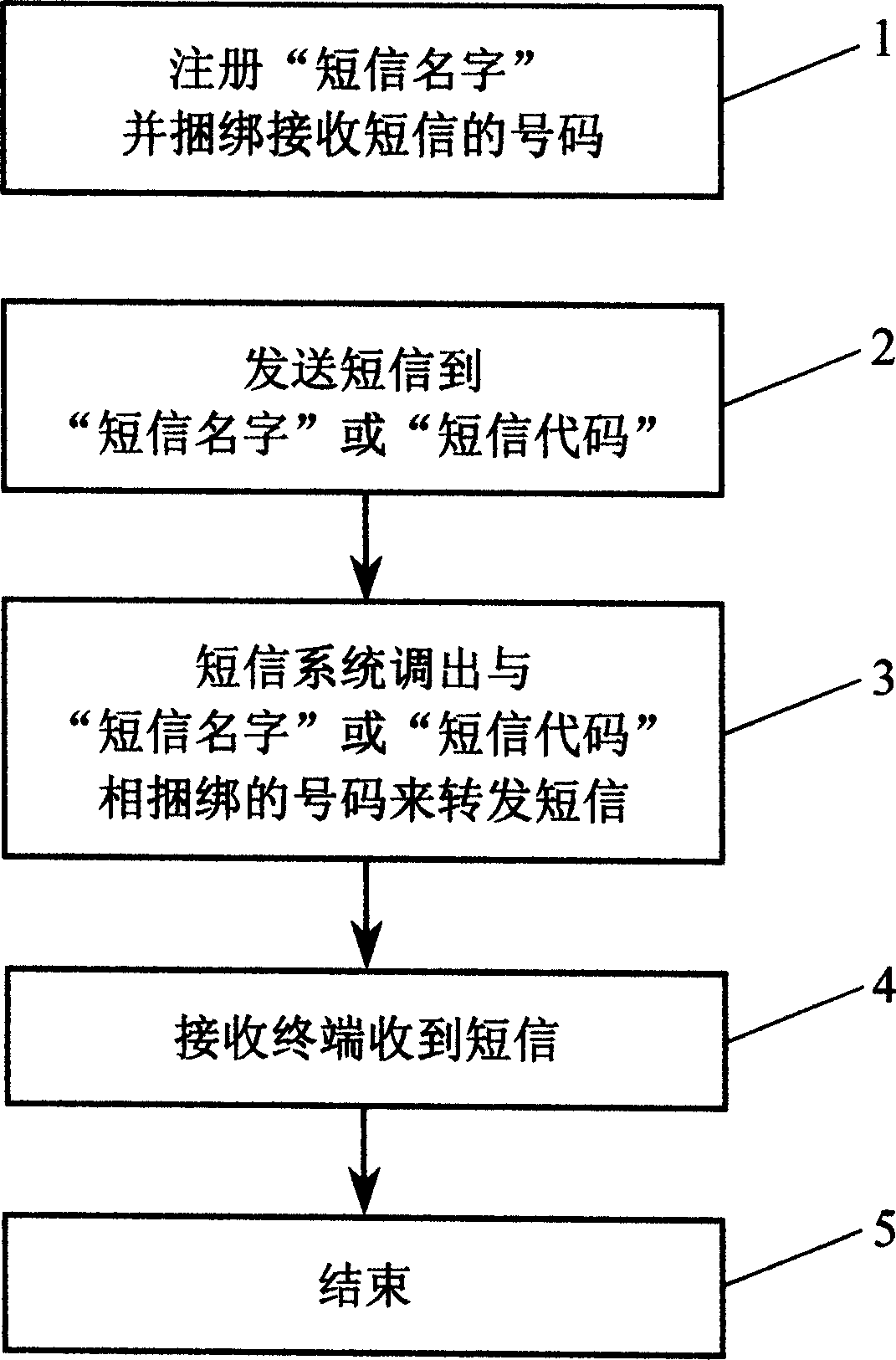
Note sending method with 'note name' instead of phone number
InactiveCN1992757ANot easy to forgetFacilitate communicationSpecial service for subscribersSubscriber signalling identity devicesComputer hardwareData bank
The invention relates to a message method which uses message name to replace phone number, wherein said method comprises that: first relating and storing the message name and the receiver number; when sending message to the message name or the message code converted from message name, message system receives message and distributes relative number from database, to send message to said number. With said invention, user only needs to send message to the registered message name.
Owner:周良勇
A ten-stroke ten-component classification method and Chinese character input method composed therefrom
InactiveCN1731327ASmall amount of memoryEasy to determineInput/output processes for data processingChinese charactersComputer graphics (images)
The invention relates to a font code and digital code general Chinese character input method re resolving project which is characterized in that it divides the stroke into ten strokes and the part into ten parts, then it uses them as core to design four font code and digital code general Chinese character input methods and uses the four input methods to form an integrated general Chinese character input method re resolving project of the denominator keyboard and the digital keyboard.
Owner:姜涛里
Infectious disease protective device
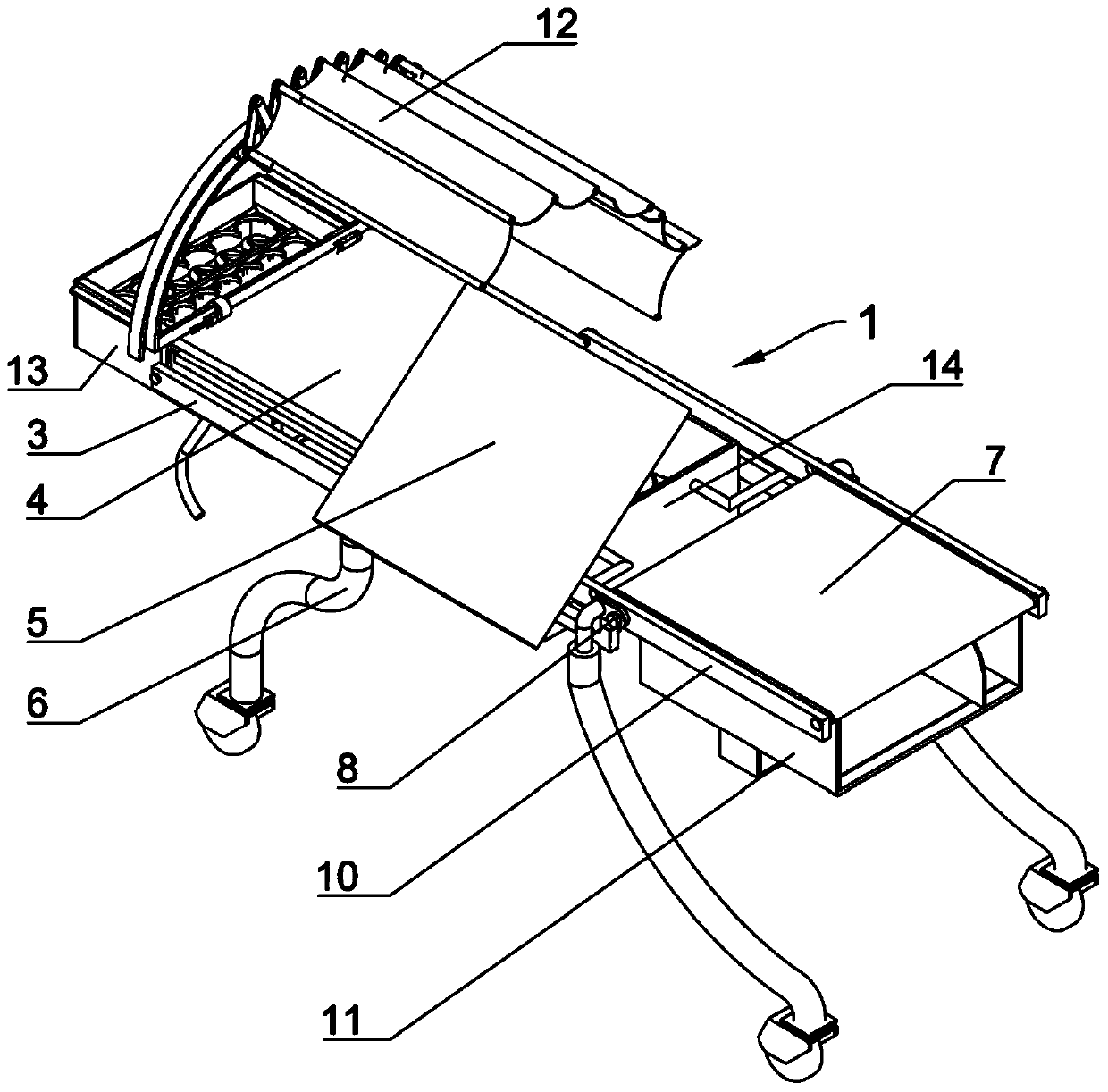
ActiveCN110123535ASolve the problem of inconvenient movingReduce the chance of contact infectionStretcherNursing bedsEngineeringUtilization rate
An infectious disease protective device is intended for effectively solving the problems that a patient with an infectious disease may propagate pathogens to air during coughing, the patient is inconvenient to transfer and a conventional infectious disease protective device has a single function. The infectious disease protective device comprises four support legs, first support bars, second support bars, a first support plate, a second support plate and a third support plate; the first support bars, the second support bars, the first support plate and the second support plate cooperate with one another to form a parallelepipedal frame; the frame, the first support plate, the second support plate and the third support plate form a bed after being horizontally arranged; after the frame is rotated, the frame, the first support plate, the second support plate and the third support plate form a cart; a linkage can be lifted and turned to drive the third support plate to lift and turn; a protective mechanism is arranged at the upper end of the first support plate. The infectious disease protective device is novel in structure and ingenious in concept, allows medical personnel to work more conveniently and more safely, and has a higher utilization rate.
Owner:THE FIRST AFFILIATED HOSPITAL OF ZHENGZHOU UNIV
Authentication method
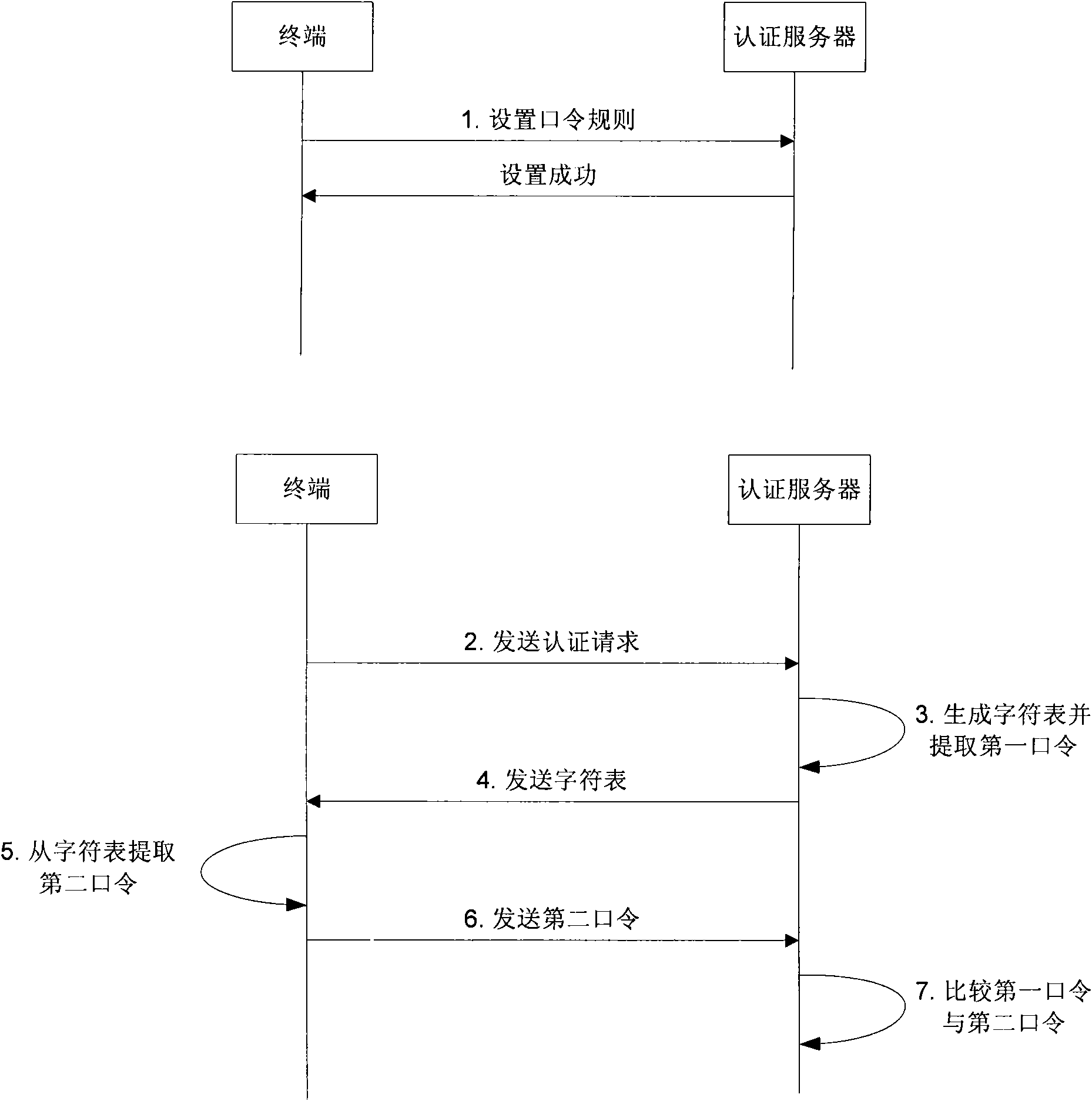
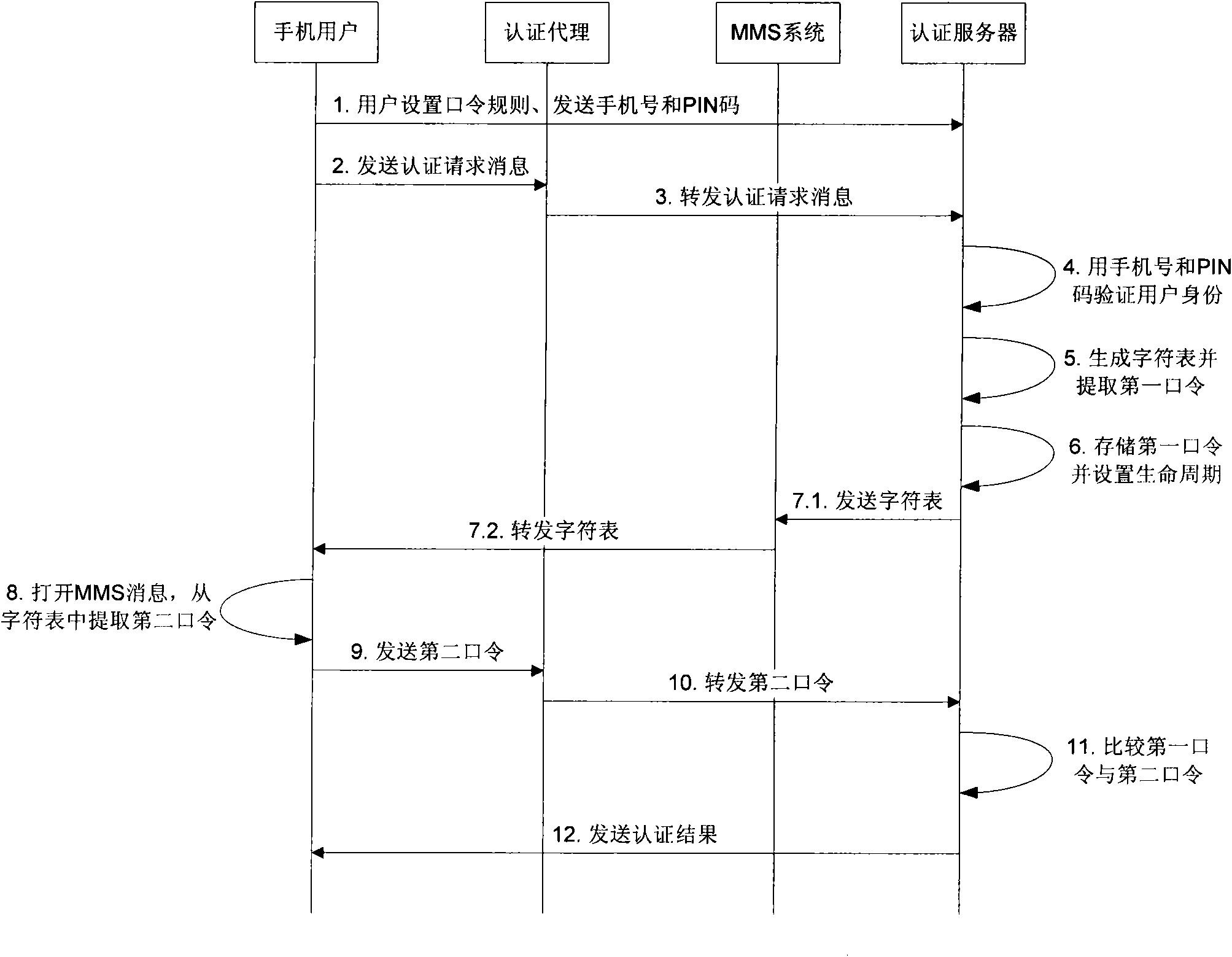
InactiveCN101640591ANot easy to forgetImprove securityUser identity/authority verificationComputer securityOne-time password
Owner:SIEMENS CHINA
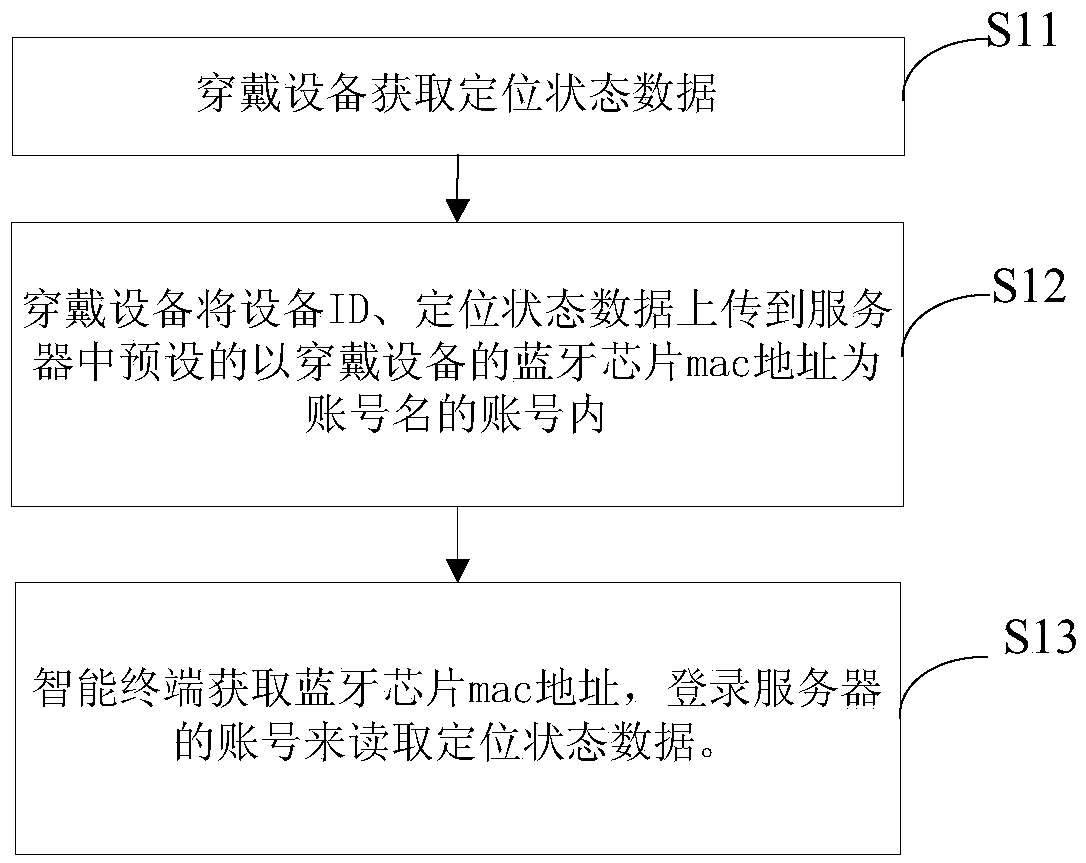
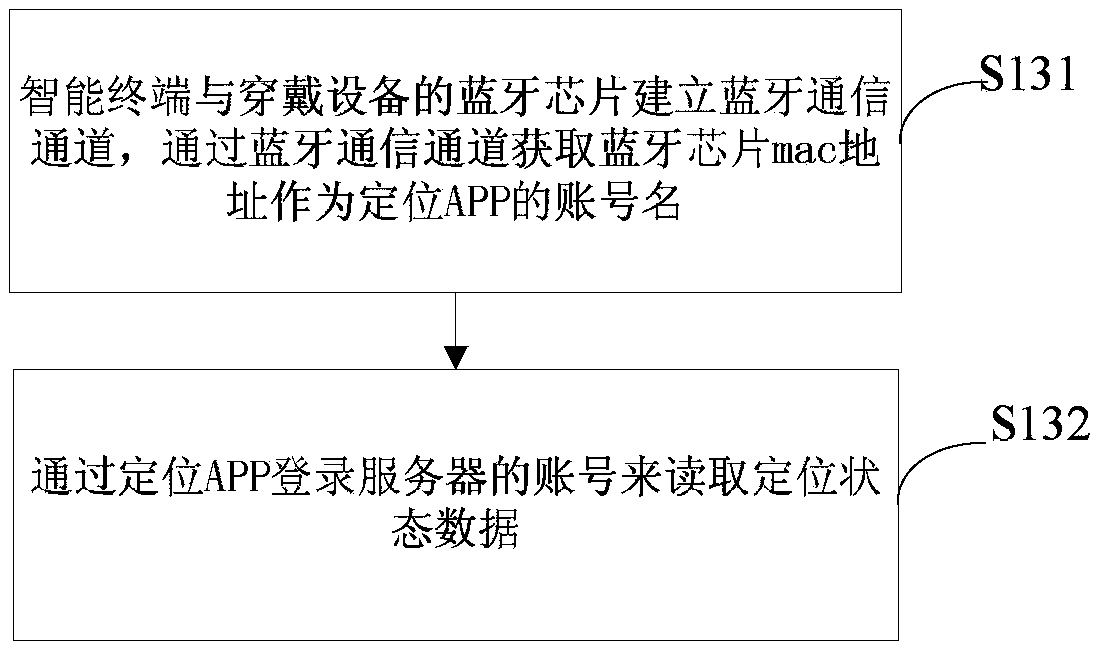
Positioning state data obtaining method and system of wearable device
InactiveCN105516890AImprove securityEasy accessWireless commuication servicesTransmissionEmbedded systemMAC address
The invention provides a positioning state data obtaining method and system of a wearable device. The positioning state data obtaining method of the wearable device comprises the following steps that the wearable device obtains positioning state data; the wearable device uploads the device ID and the positioning state data to a preset account in a server, the account takes the Bluetooth chip mac address of the wearable device as an account name; an intelligent terminal obtains the Bluetooth chip mac address and logs into the account of the server to read the positioning state data. According to the invention, the Bluetooth chip mac address of the wearable device is pre-stored in the server as the account name of the positioning state data; the Bluetooth chip mac address of the wearable device is pre-stored in the server, therefore account name coding is unnecessary, the account name can be easily obtained and cannot be easily forgotten; the Bluetooth chip mac address is obtained as the account name of the positioning APP through a Bluetooth communication channel, therefore the obtaining efficiency of the positioning state data of the wearable device is improved.
Owner:SHANGHAI DROI TECH CO LTD
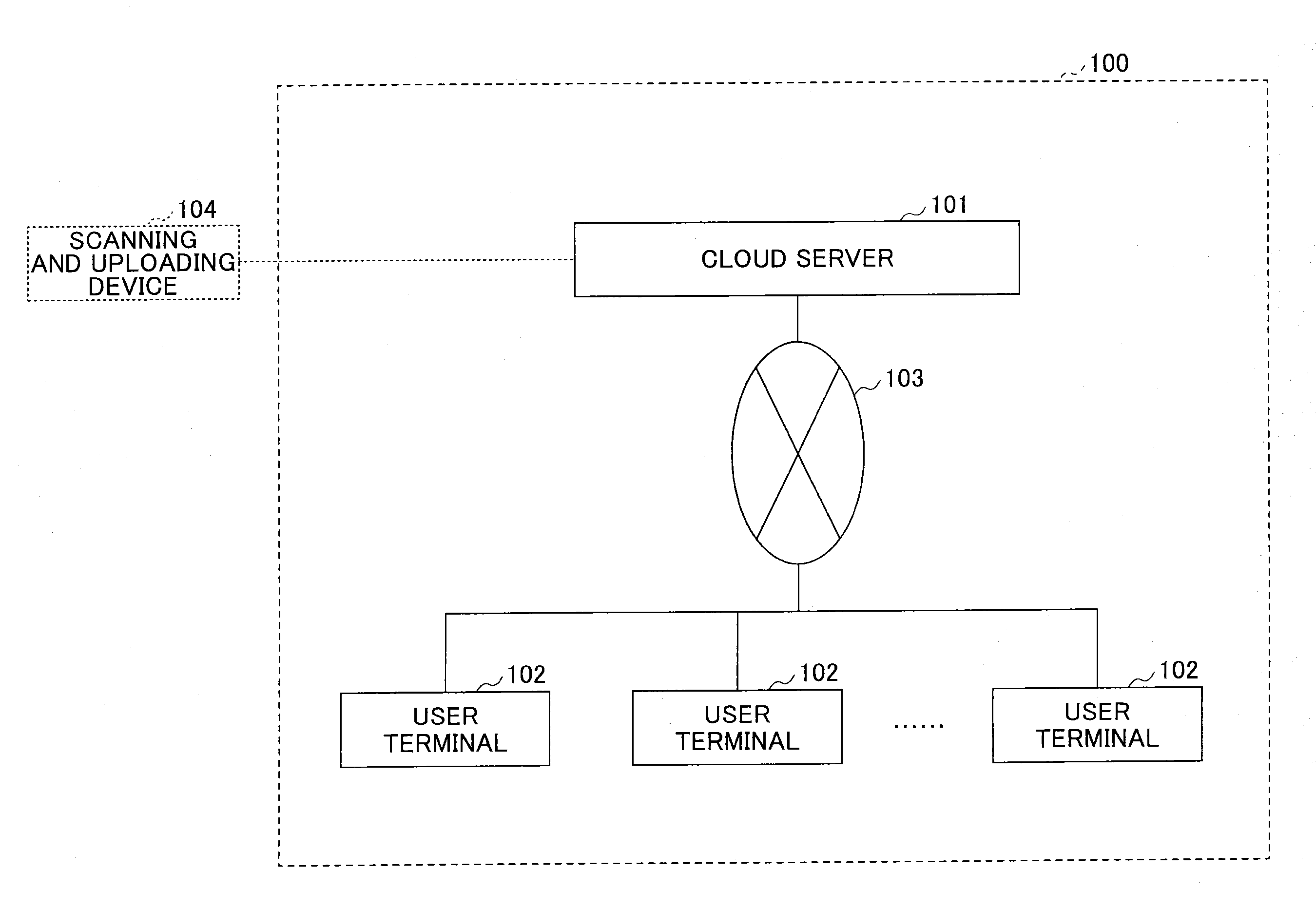
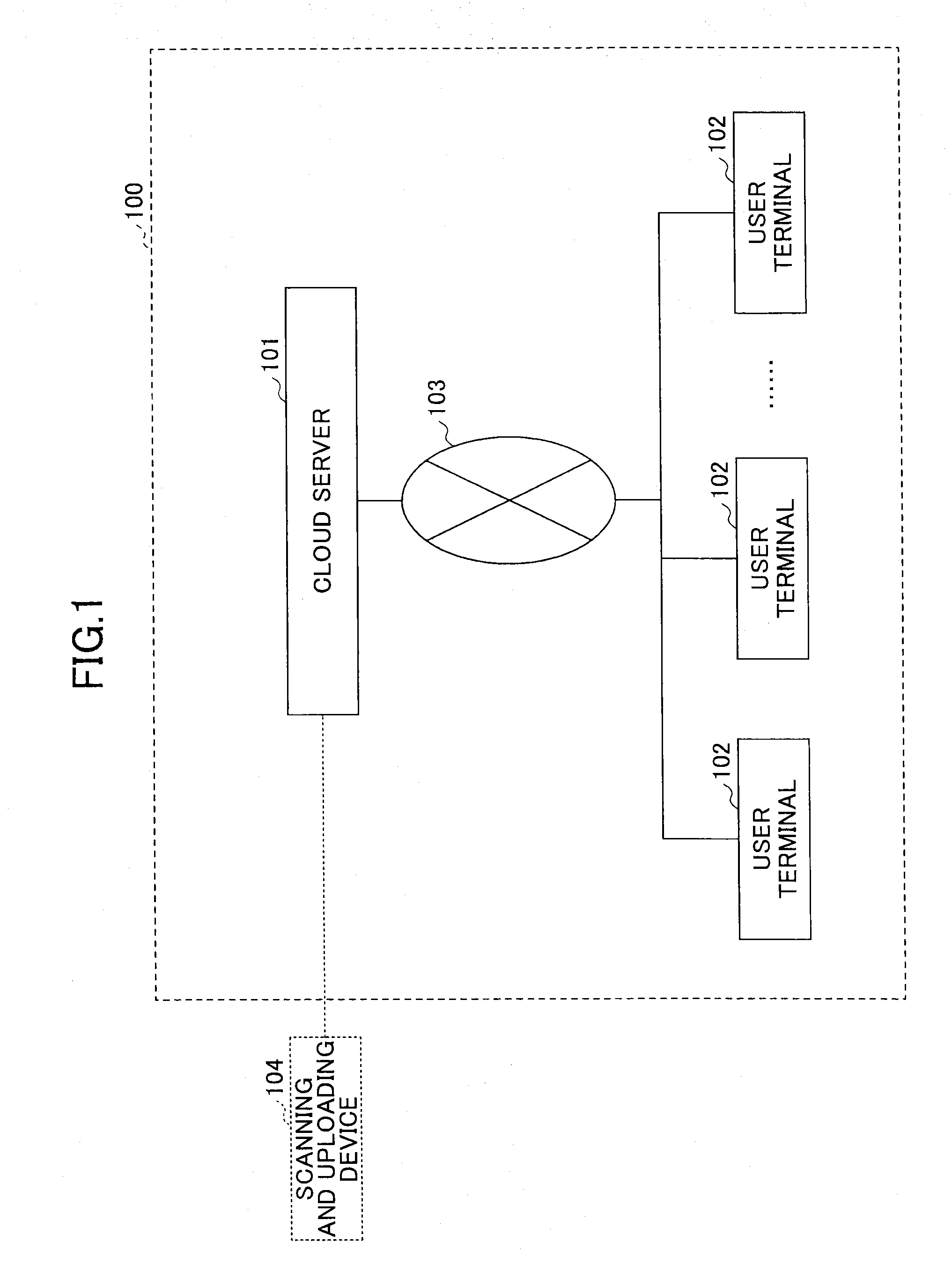
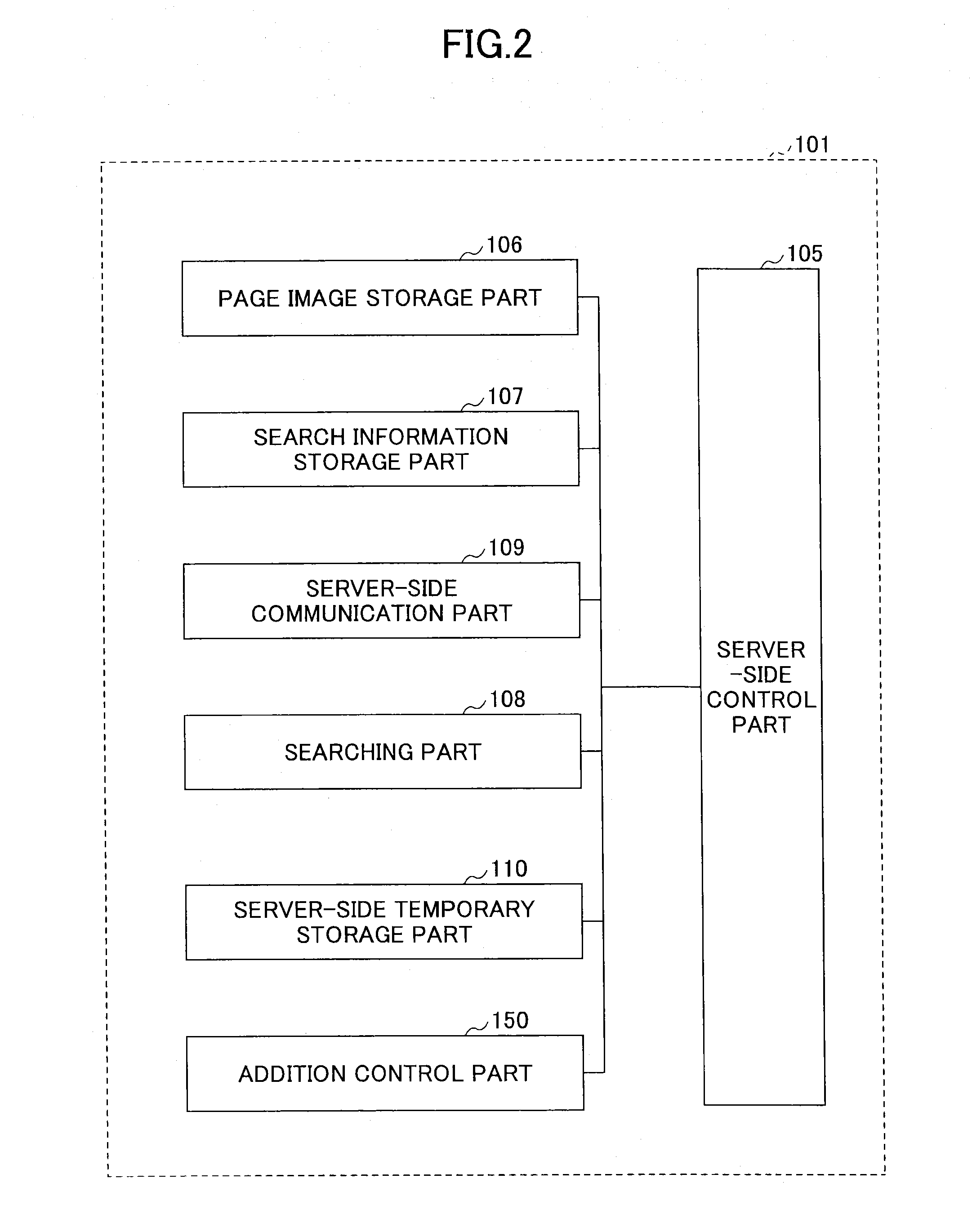
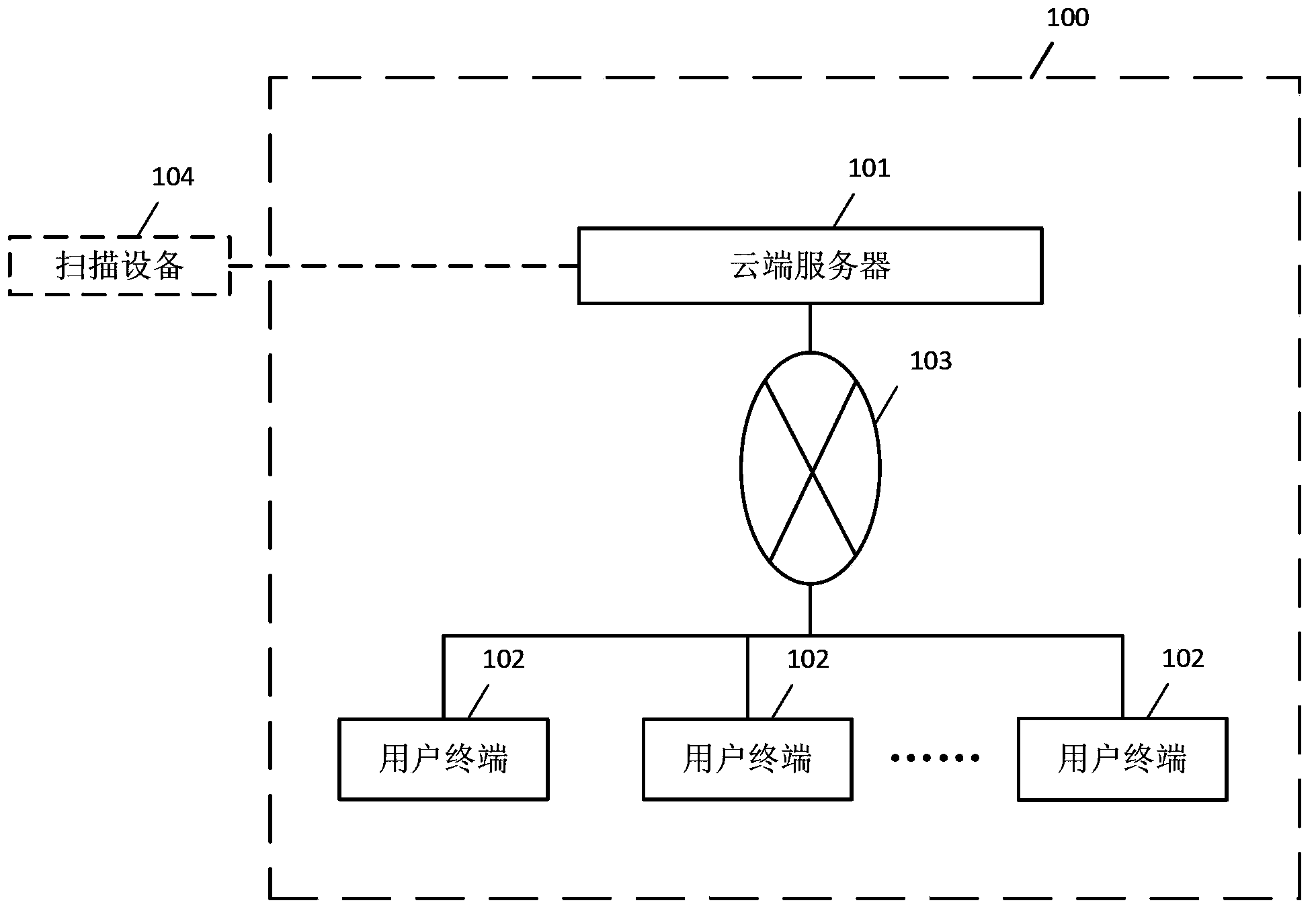
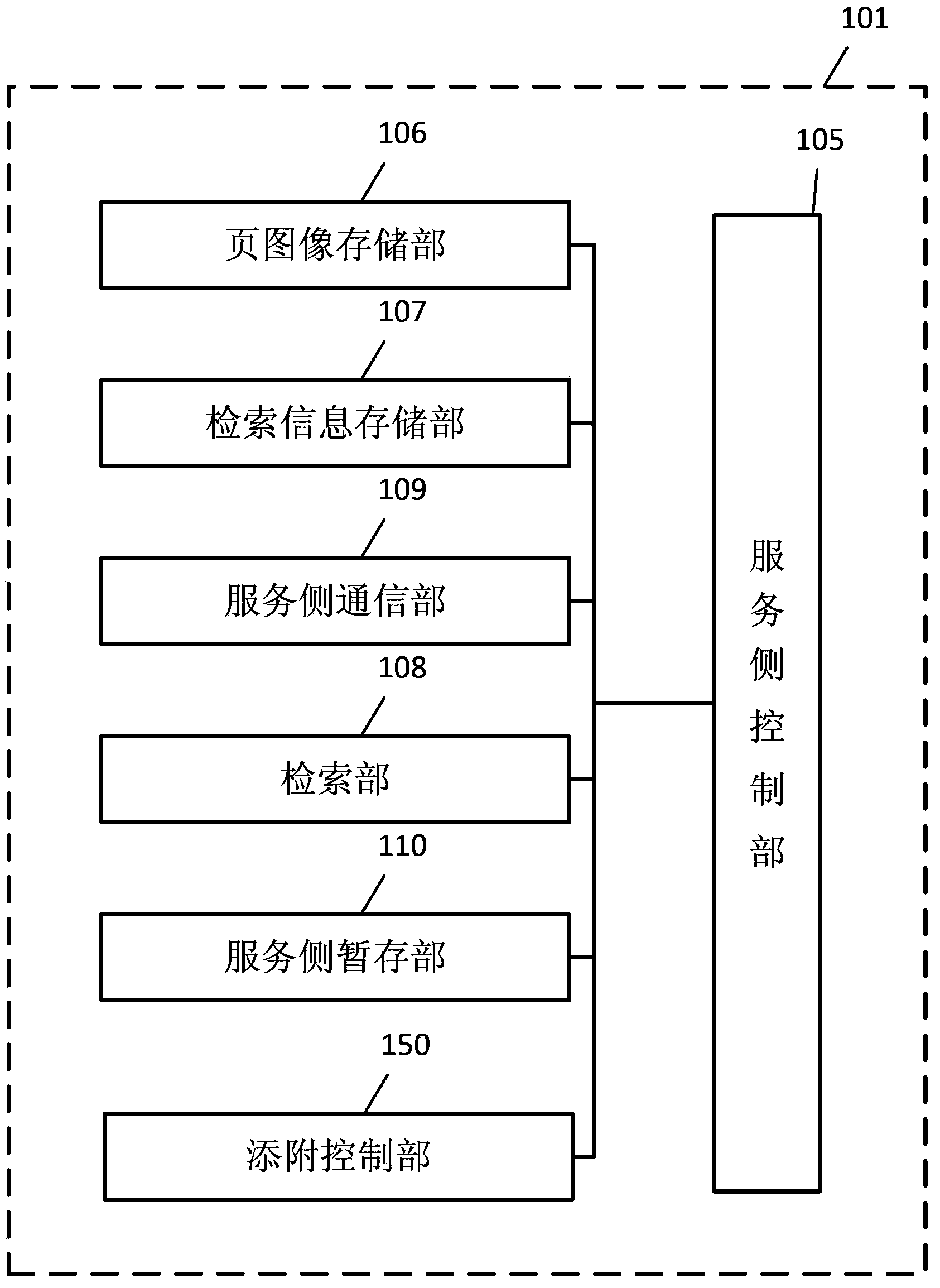
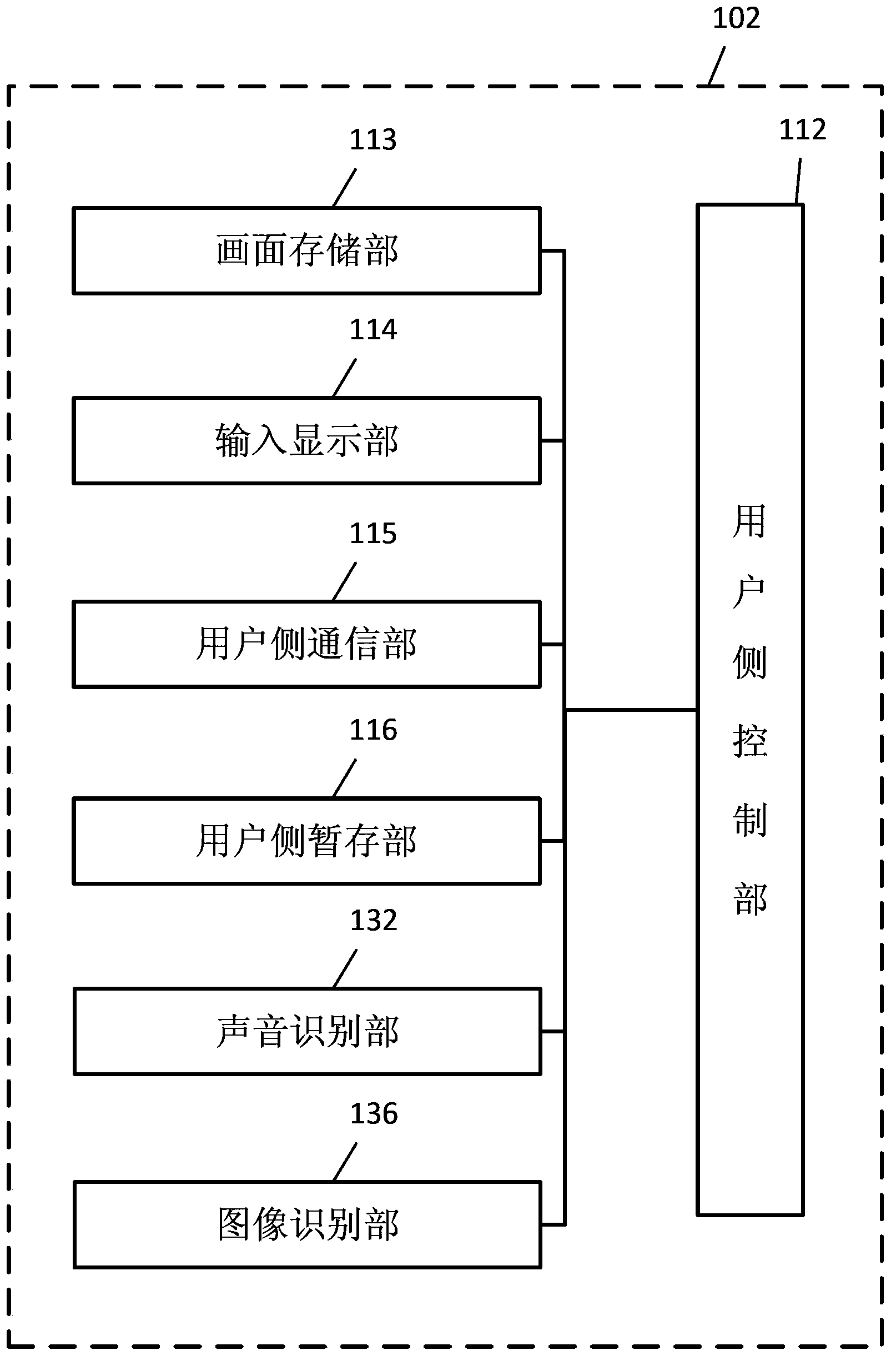
System for storing and searching image files, and cloud server
InactiveUS20150039643A1Improve search efficiencyImprove efficiencyDigital data processing detailsTransmissionCloud serverWorld Wide Web
A cloud server and a system for storing and searching image files configured to add search information for a search by a user to page images constituting an image file are disclosed. In the system for storing and searching the image files, an input display part of a user terminal displays a page image notification screen to make the user add the search information to the current displayed page image, a user-side communication part sends the search information and the current displayed page image to the cloud server, and an addition control part of the cloud server adds the search information to the corresponding page image.
Owner:RICOH KK
Portable wireless electronic communication terminal convenient to dial
InactiveCN103051758AEasy and intuitive to make callsEasy accessTelephone set constructionsKey pressingElectronic communication
The invention provides a portable wireless electronic communication terminal convenient to dial, which is truly of a mobilephone that is simple to dial and convenient to carry. The international patent classification number of the portable wireless electronic communication terminal convenient to dial is H04M 1 / 02. The old and the children have fewer contact persons, can not remember numbers, and are not good at looking up numbers from the mobilephone, and the existing mobile phone is inconvenient for the old and the children to carry. Aiming at the conditions, the portable wireless electronic communication terminal convenient to dial is simplified and the core calling function is emphasized, the numbers and images are preset in the mobilephone, then the special operation method comprises the steps: 1, pressing single main button for delay dialing or pressing an auxiliary button again for instant dialing, without digital buttons; and 2, displaying contact persons by images after the main button is pressed, pressing the main button to select next contact person within the delay waiting time. The old and the children frequently forget articles, so that the product can be made into a watch type or pocket watch type convenient to carry.
Owner:何守生
Networking-supportive electric energy measuring completion acceptance device
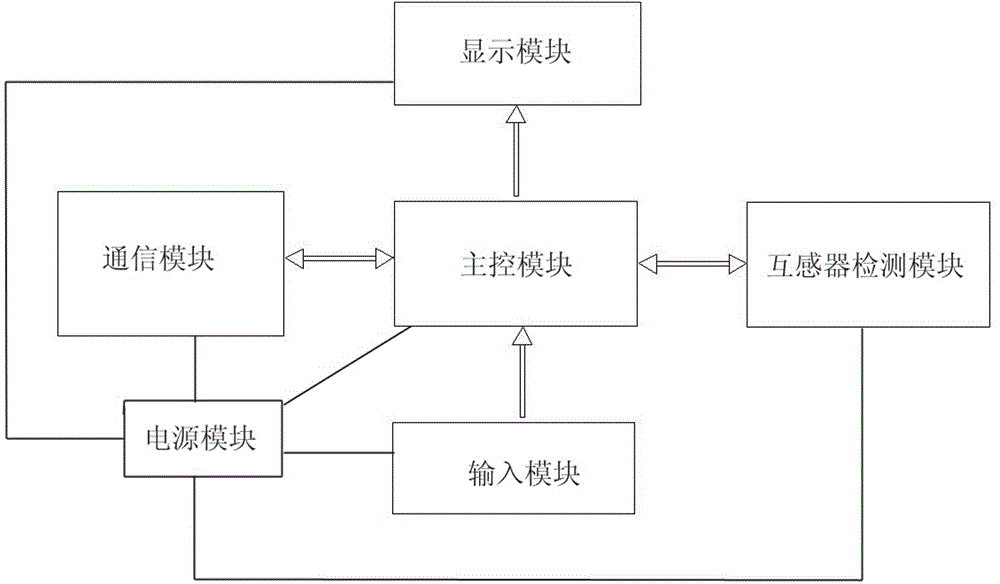
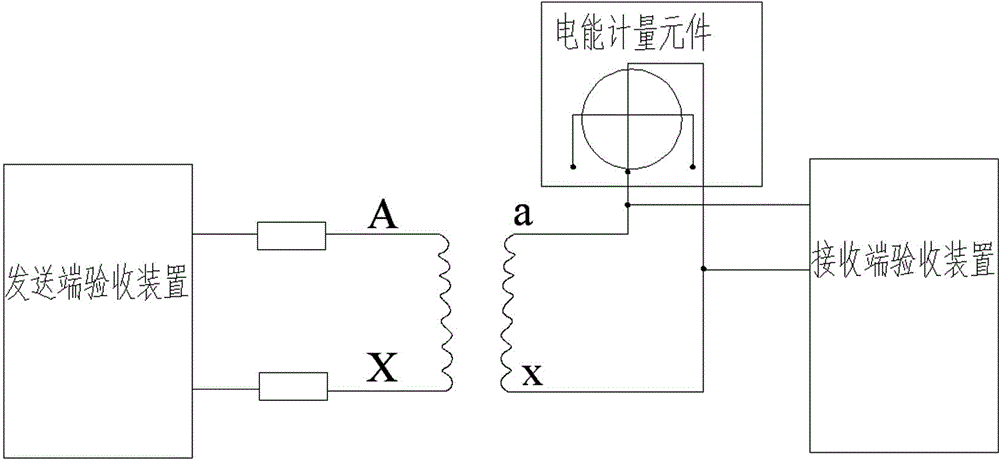
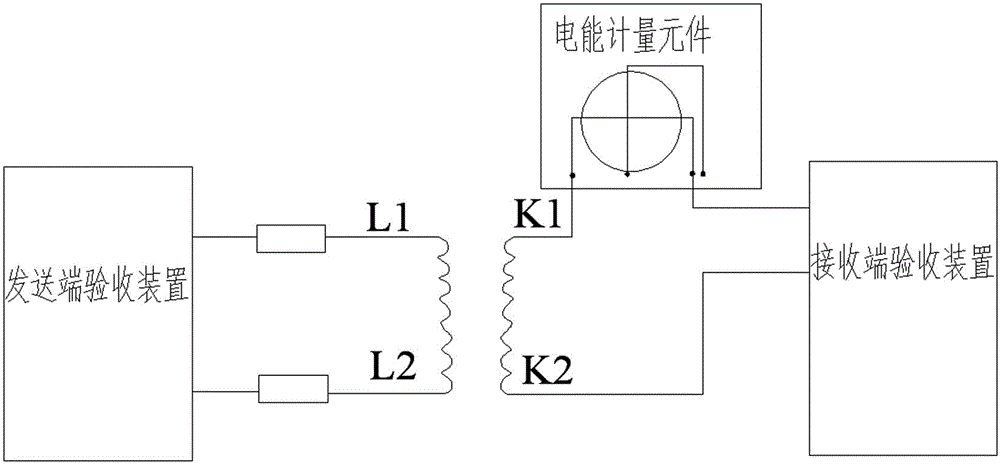
The invention relates to the technical field of electric energy measuring, in particular to a networking-supportive electric energy measuring completion acceptance device which is a wireless inspector aiming at safety and wiring correctness of an electric energy measuring device, especially an instrument used for correctness inspection under a power outage state. The networking-supportive electric energy measuring completion acceptance device comprises a body and a control circuit board, a display screen is arranged on the body, the control circuit board is mounted in the body, a power source module, a main control module, a transformer detection module, a communication module, an input module and a display module, the main control module is connected with the the transformer detection module, the communication module, the input module and the display module, the input module sends input signals to the main control module, the transformer detection module transmits detection signals to the main control module, the main control module transmits transformer polarity and transformation ratio information to the display module for displaying, and the power source module is connected with the main control module, the transformer detection module, the communication module, the input module and the display module.
Owner:STATE GRID CORP OF CHINA +2
Shape, sound, radical digital input method
InactiveCN1648831AFast typingDifficult to rememberInput/output processes for data processingChinese charactersComputer science
The configurational and phonetic radical digital Chinese character input method includes dividing each Chinese character into two parts including radical and etymon, taking the radical with most strokes as the coded radical, taking the first stroke code as the radical code, taking the first three stroke codes of the etymon, and taking the first pronunciation letter as the identifying code. The input method of the present invention has the advantages of less radicals, less duplication codes, easy learning, etc. and may be used widely.
Owner:覃祚剑
Work method of roller shutter door lock
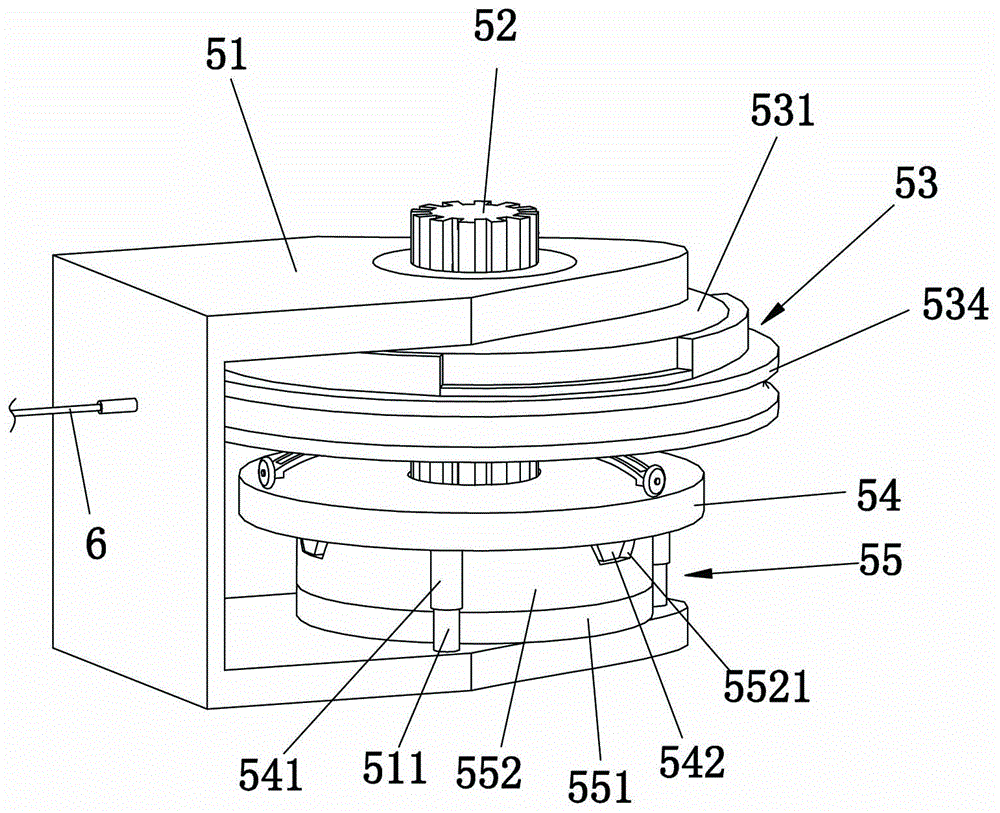
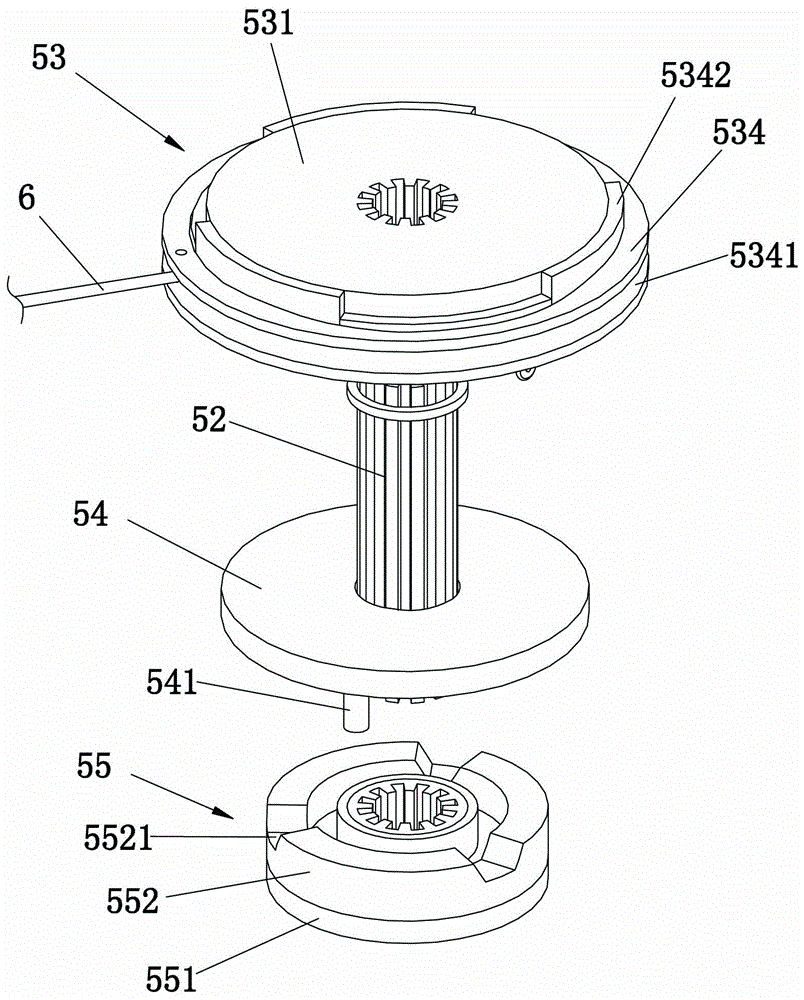
ActiveCN105888523AEasy to operateNot easy to forgetDoor/window protective devicesNon-mechanical controlsCircular discMotor drive
Owner:蔡为达
Cloud server and image storage and retrieval system
InactiveCN104346388AImprove retrieval efficiencyPersonalizeUser identity/authority verificationSpecial data processing applicationsPersonalizationComputer terminal
A cloud server and a system for storing and searching image files configured to add search information for a search by a user to page images constituting an image file are disclosed. In the system for storing and searching the image files, an input display part of a user terminal displays a page image notification screen to make the user add the search information to the current displayed page image, a user-side communication part sends the search information and the current displayed page image to the cloud server, and an addition control part of the cloud server adds the search information to the corresponding page image.
Owner:RICOH KK
Portable operating table on electricity marketing site
Disclosed is a portable operating table on an electricity marketing site. The portable operating table on the electricity marketing site is characterized by being provided with a foldable table body. The table body is formed by connecting a left table body and a right table body through a hinge. The left table body and the right table body are of hollow structures. Matrix-type insertion holes are respectively formed in the upper surface of the left table body and the upper surface of the right table body. An imporous writing area is arranged on the upper surface of the right table body at the same time. Rubber nails which are used for fixing operation tools on the electricity marketing site and installed in the insertion holes in an insertion mode are arranged on the table body. The portable operating table is conveniently used in working by electricity marketing workers, the related tools are prevented from being forgotten or lost or damaged, working resources are saved, and the working efficiency is remarkably improved.
Owner:STATE GRID CORP OF CHINA +1
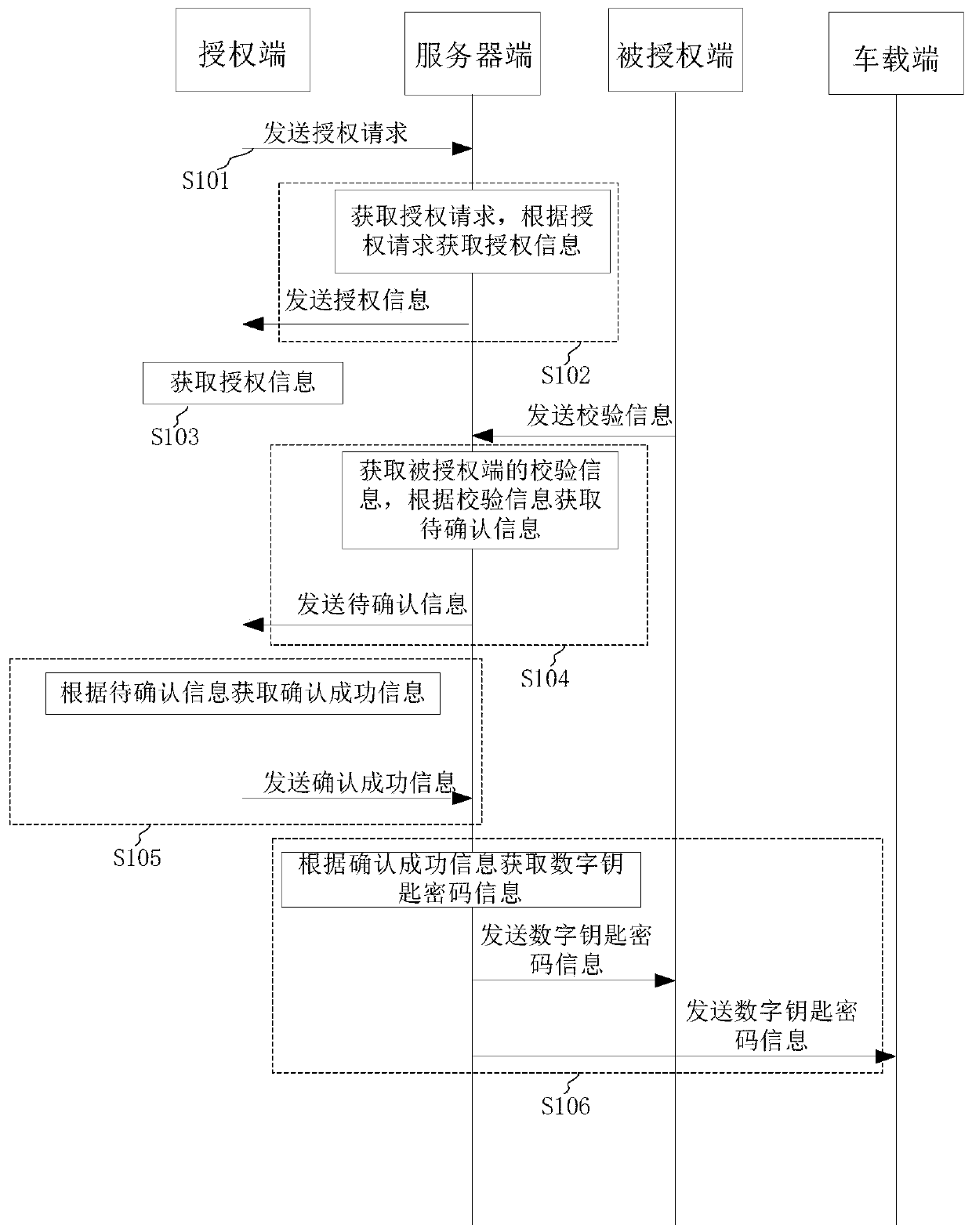
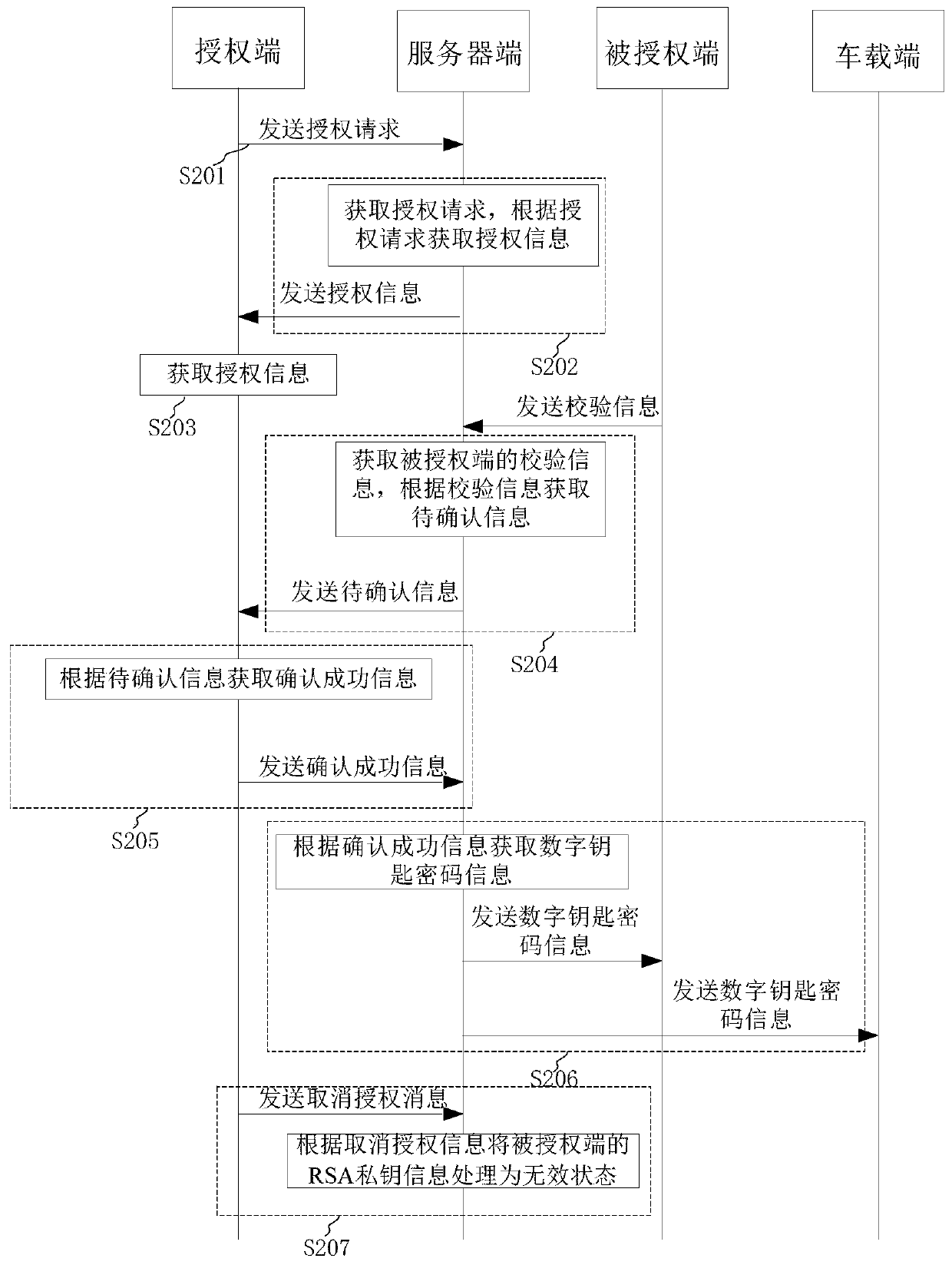
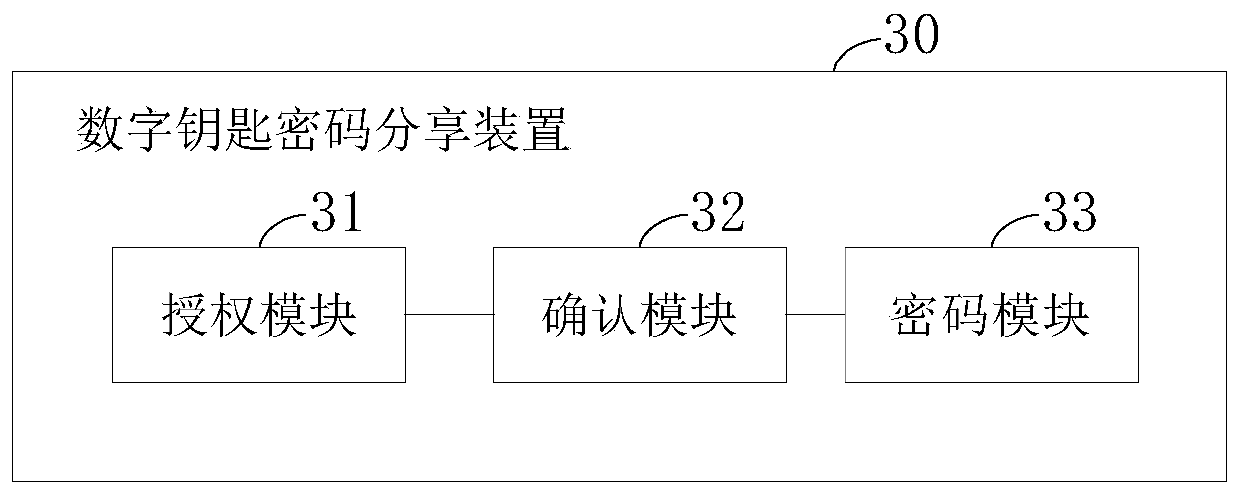
Digital key password sharing method and device
InactiveCN110808832ANot easy to forgetNot easy to loseKey distribution for secure communicationPublic key for secure communicationInternet privacyIn vehicle
The invention provides a digital key password sharing method and device, and the method comprises the steps: obtaining an authorization request of an authorization end, obtaining authorization information according to the authorization request, and transmitting the authorization information to the authorization end; obtaining verification information of the authorized end, obtaining to-be-confirmed information according to the verification information, and sending the to-be-confirmed information to the authorization end; and obtaining confirmation success information of the authorization end,obtaining digital key password information according to the confirmation success information, and sending the digital key password information to the authorized end and the vehicle-mounted end. The convenience of key sharing is improved.
Owner:南京酷沃智行科技有限公司
Input method of Chinese character stroke code
InactiveCN101303623AThe method of character splitting and code extraction is simpleEasy to learnSpecial data processing applicationsInput/output processes for data processingVertical barChinese characters
The invention provides a Chinese character stroke code inputting method; wherein, a Chinese character is considered to be composed of at least one line segment; the line segments are classified into three single-stroke codes, that is, a horizontal stroke code, a vertical stroke code and an oblique stroke code; wherein, the horizontal stroke code represents a horizontal stroke in Chinese characters, the vertical stroke code represents a vertical stroke and a hook stroke in Chinese characters, while the oblique stroke code represents a non-horizontal and non-vertical line segment in the Chinese characters; at least two single-stoke codes are combined to form a plurality of structural stroke codes, the structural stroke code includes a combined stroke code which is formed by connecting and crossing at least two single-stroke codes with each other and a matched stroke code which is formed by matching at least two single-stroke codes with each other; the single-stroke code, the combined stroke code and the matched stroke code are set on a computer key mapping according to different groups; the inputting method includes: a Chinese character to be input is split by using the structural stroke code and the single-stroke code; At most three stroke codes are selected from the split structure and the residual single-stroke codes; finally the Chinese character is input by clicking the keys corresponding to the stroke codes.
Owner:陈新伟
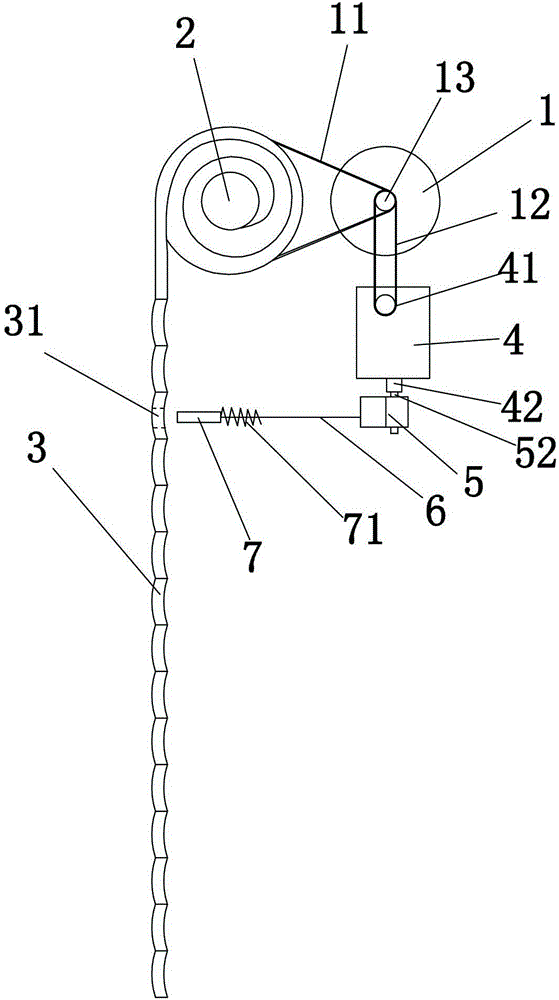
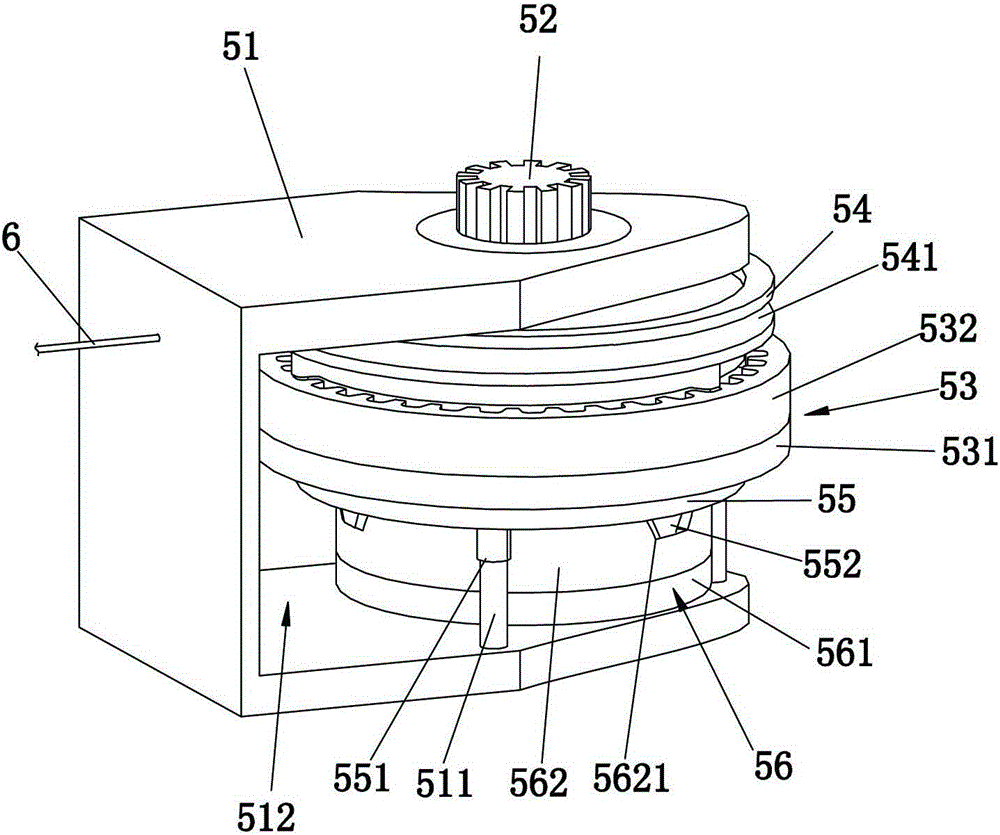
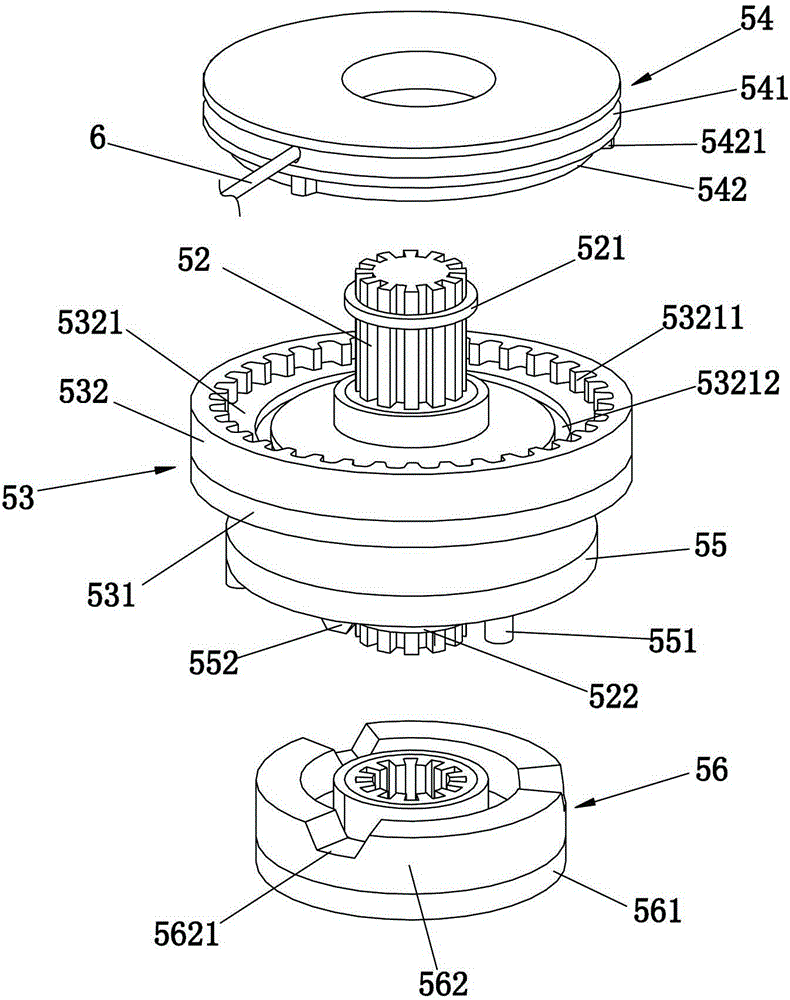
Roller shutter door lock and working principle thereof
ActiveCN105201300ADecentralization smoothlyWind evenlyDoor/window protective devicesNon-mechanical controlsPulp and paper industryClutch
The invention discloses a roller shutter door lock and a working principle thereof, and relates to the technical field of roller shutter doors. The roller shutter door lock comprises a lock cylinder, a spring enabling the lock cylinder to move towards a roller shutter door and lock the roller shutter door, an inhaul cable, a clutch device and a motor. One end of the inhaul cable is connected with the lock cylinder, and the other end of the inhaul cable is connected with the clutch device. The clutch device is driven by the motor to roll the inhaul cable, so that the lock cylinder and the roller shutter door are disengaged, and the roller shutter door is unlocked. After the motor stops, the inhaul cable rolled by the clutch device is stretched by the spring, so that the lock cylinder moves towards the roller shutter door, and the roller shutter door is locked. The roller shutter door lock and the working principle thereof have the advantages that additional operation is not needed when the roller shutter door is unlocked or locked, the operation of unlocking or locking the roller shutter door can be completed through the roller shutter door lock as long as the roller shutter door normally ascends and descends, operation is easy, and the anti-theft effect is good.
Owner:蔡为达
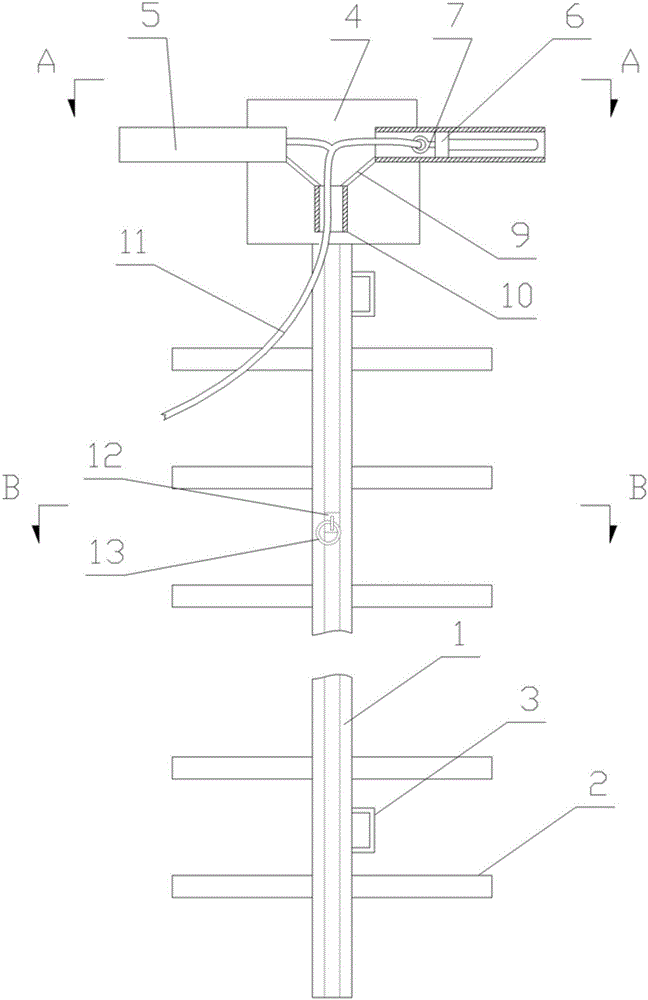
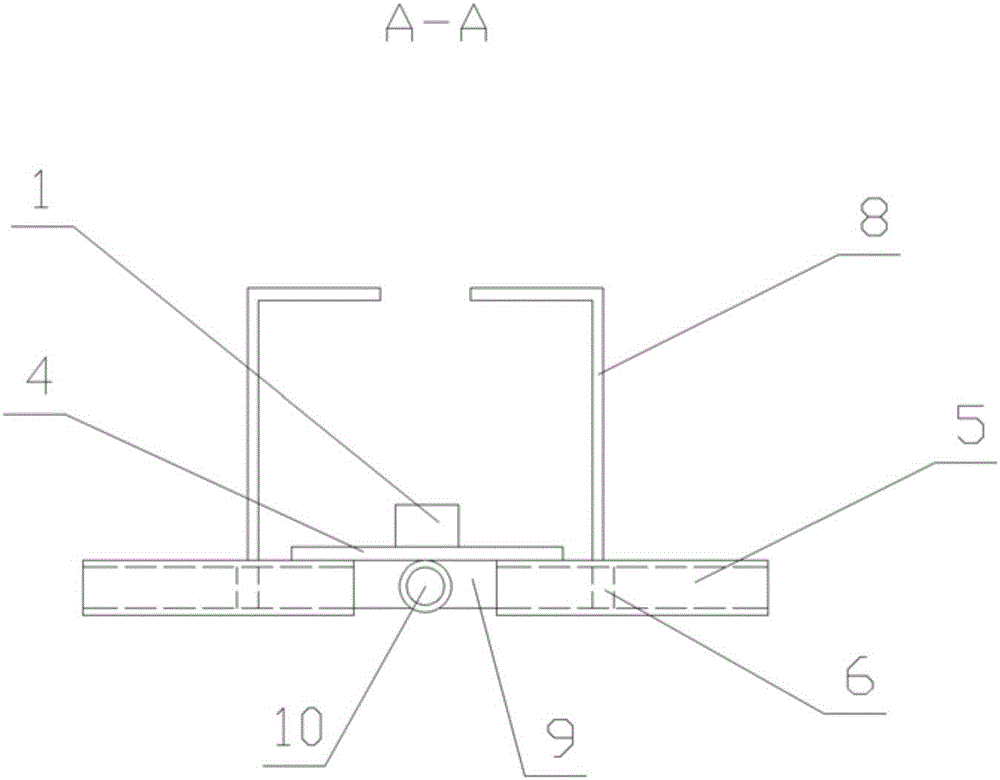
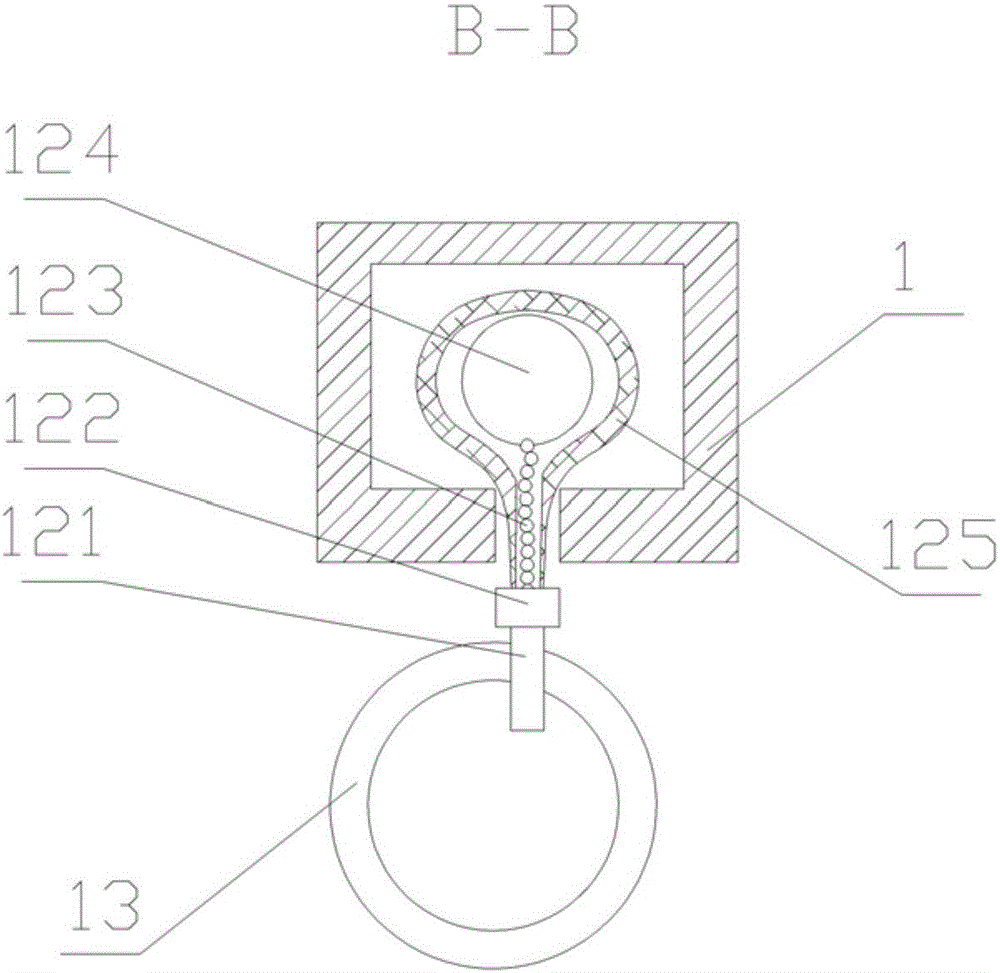
Climbing device with security mechanism
The invention relates to a climbing device with a security mechanism, comprising a ladder rod (1), a foot rod (2), a locking mechanism, a movable suspension ball (12) and a safety belt suspension ring (13), wherein the foot rod (2) is vertically mounted on the ladder rod (1); the ladder rod (1) is of a square metal tube structure with a through groove in the length direction; the movable suspension ball (12) comprises a half ring (121), a half ring seat (122), a stainless steel bead chain (123), a steel ball (124) and a rubber bag (125); the safety belt suspension ring (13) is arranged on the half ring (121) in a sleeved mode; the locking mechanism comprises a mounting plate (4), a sleeve (5), a slide block (6), a pull rope pull ring (7), a clamping post (8), a guide plate (9), a guide tube (10) and a pull rope (11); and the mounting plate (4) of the locking mechanism is fixedly mounted at the top of the ladder rod (1). The climbing device with the security mechanism disclosed by the invention has a simple structure, convenient use and good safety in climbing.
Owner:DATONG POWER SUPPLY COMPANY OF STATE GRID SHANXI ELECTRIC POWER
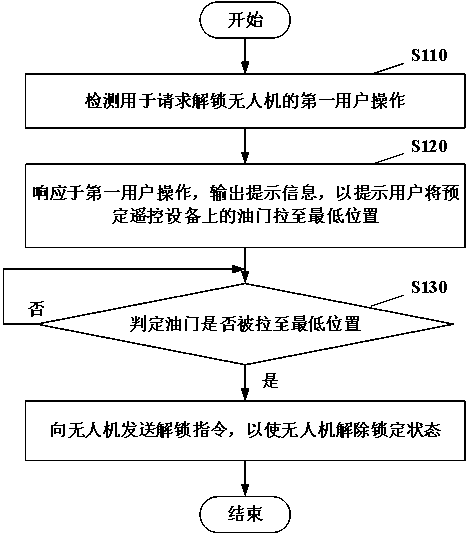
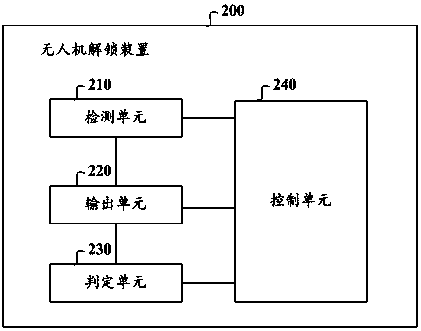
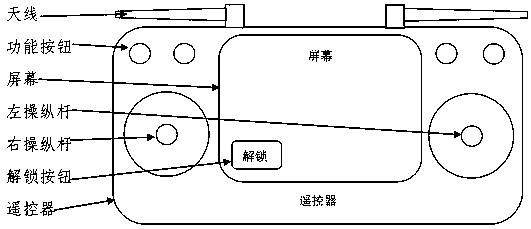
UAV unlocking method and device, storage medium and computing device
InactiveCN110070702ANot easy to forgetEasy to operateTransmission systemsSpeech recognitionRemote controlSafe operation
Embodiments of the invention provide a UAV unlocking method and device, a storage medium and a computing device. The UAV unlocking method comprises steps of detecting a first user operation requestingto unlock a UAV; in response to the first user operation, outputting prompt information, so as to prompt the user to pull an accelerator on a predetermined remote control device to a lowest position;determining whether the accelerator is pulled to the lowest position; and when the accelerator is pulled to the lowest position, sending an unlocking instruction to the UAV, so as to unlock the UAV.The UAV unlocking method is convenient and simple to operate, and permits unlocking when confirming that the accelerator is pulled to the lowest position after detecting the first user operation, thereby guaranteeing safe operation and preventing the UAV from unlocking when the accelerator is not in the lowest position.
Owner:江苏荣耀天翃航空科技有限公司
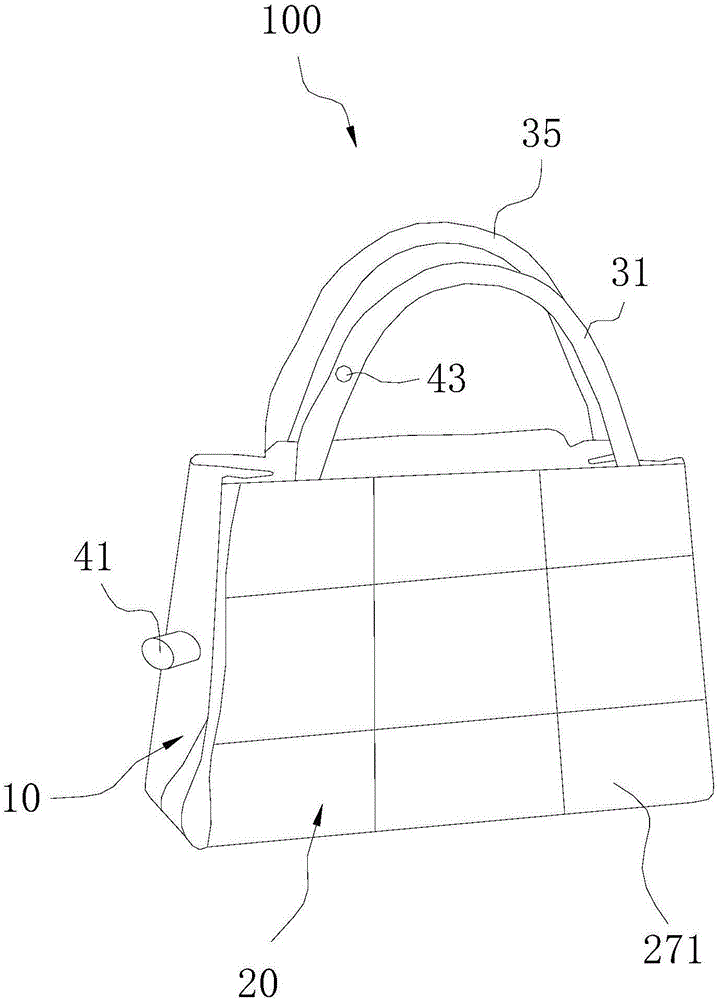
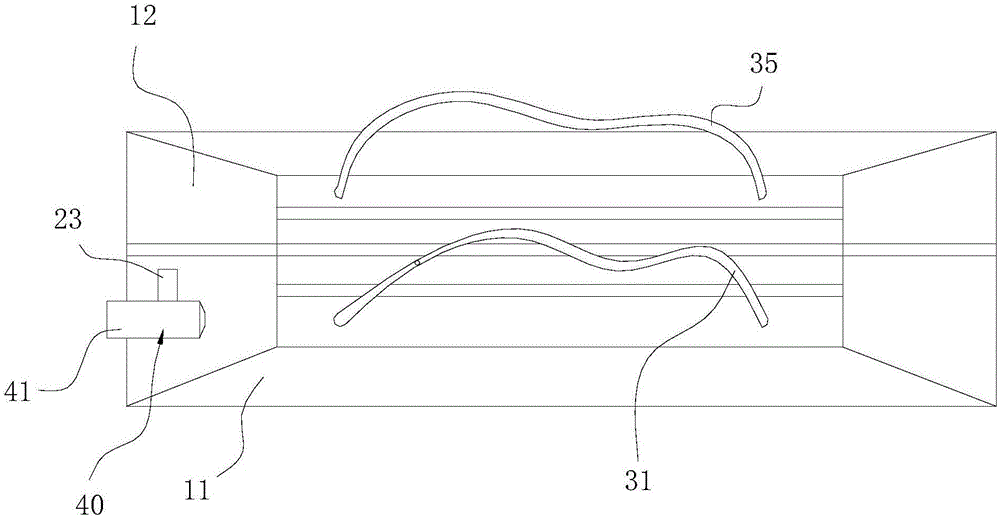
Flexible bag
The invention relates to a flexible bag which comprises an accommodating component, a display component, a first shoulder girdle, a second shoulder girdle, an illuminating component and a nameplate component, wherein the accommodating component comprises a first accommodating body and a second accommodating body which are parallel to each other; the display component comprises a power supply, a camera, a central controller and a plurality of display screens; the camera, the central controller and the display screens are all electrically connected with the power supply; the first shoulder girdle and the second shoulder girdle are respectively connected with the first accommodating body and the second accommodating body; the illuminating component comprises a lamp holder, a button and a cable; the nameplate component is arranged on one side of the second accommodating body away from the first accommodating body; the nameplate component comprises an installing frame and a plurality of display strips arranged on the installing frame in a rotating form; the installing frame is arranged around the surface periphery of the second accommodating body; the display strips are arranged in parallel. The flexible bag can realize the illuminating function and can show the nameplate or personalized signature.
Owner:惠州市大隆科技有限公司
Method for monitoring an air pressure in at least one tyre of a motor vehicle
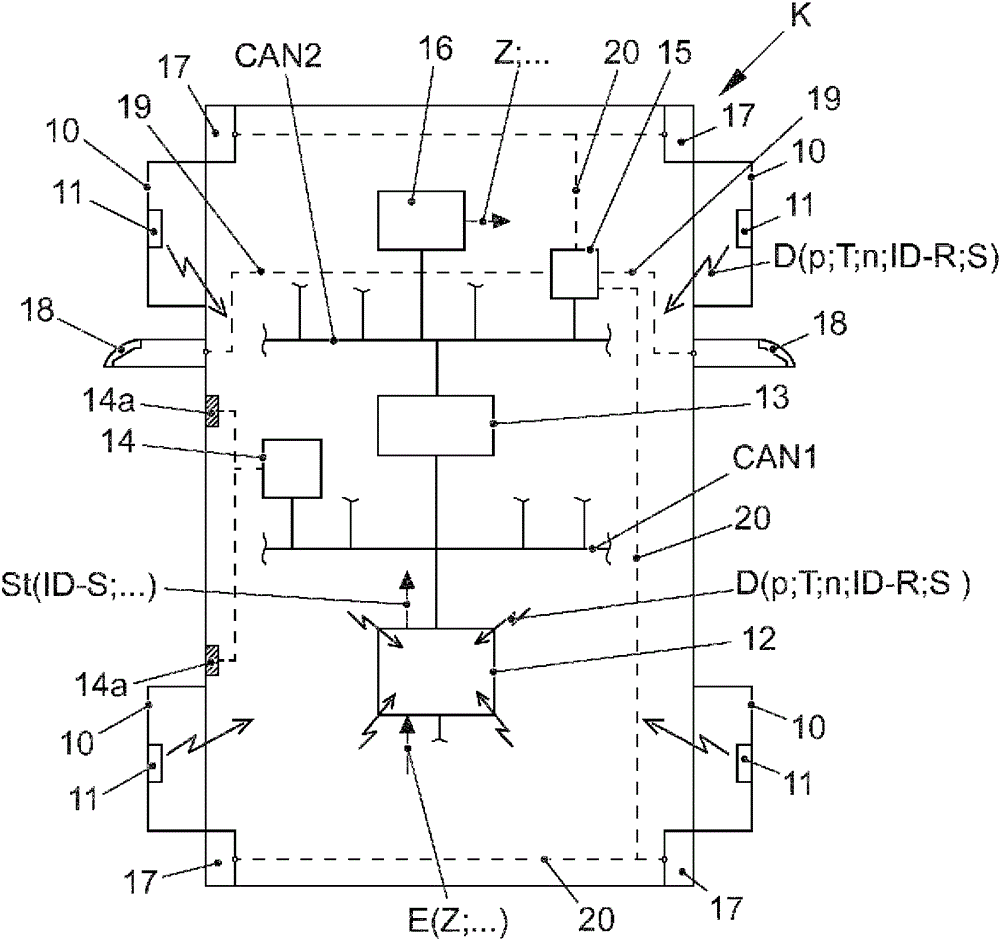
The invention relates to a method for monitoring an air pressure (p) in at least one tyre (10) of a motor vehicle (K), wherein at least one air pressure (p) in the tyre (10) is detected by means of at least one measuring electronics unit (11) present in the tyre (10) and data (D) is transmitted by the measuring electronics unit (11) to a control unit (12). Depending on the data (D), the control unit (12) activates components (14, 15) of the motor vehicle (K) to generate optical and / or acoustic signals. According to the invention, the control unit (12) is switched into an after-running mode for a defined period of time when an ignition of the motor vehicle (K) is shut off, in which mode the control unit (12) can continue to receive data (D) from the measuring electronics unit (11) and, depending on the data (D), can activate components (14, 15) of the motor vehicle (K) to generate optical and / or acoustic signals. This makes it possible for a vehicle driver to actively change a tyre pressure even with the ignition key removed, whereby a danger of theft and a load on the battery during such a process is reduced.
Owner:VOLKSWAGEN AG
Device for on-site payment and on-site payment method
PendingCN113554430AEnsure safetyNot easy to forgetFinancePayment protocolsComputer networkEngineering
The purpose of the present invention is to provide a device for on-site payment. The device at least enables a tandem networking collection, i.e., the device is capable of addressing pain points (e.g., not using a smartphone) faced by a payee (especially older people). According to the device, the payee at least does not need to be provided with networked communication equipment for on-site collection, and then does not need to pay networking fees, and the device can confirm collection by itself. The invention further provides an on-site payment method.
Owner:褚万青
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com