Coded lock based on brain-computer switching technique and encryption and decryption method of coded lock
An exchange technology, encryption and decryption technology, applied in the direction of instruments, digital data authentication, time register, etc., can solve the problems of monotonous password, easy to decipher, long and complex password combination, etc., to prevent peeping password behavior and strengthen security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
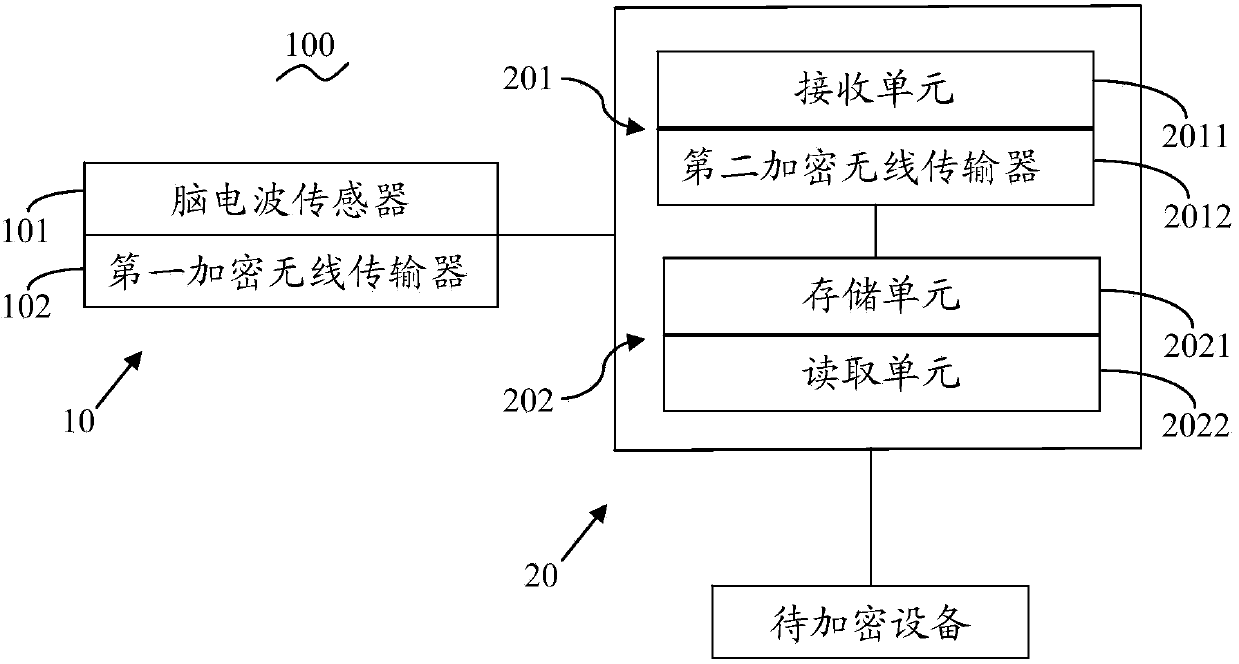
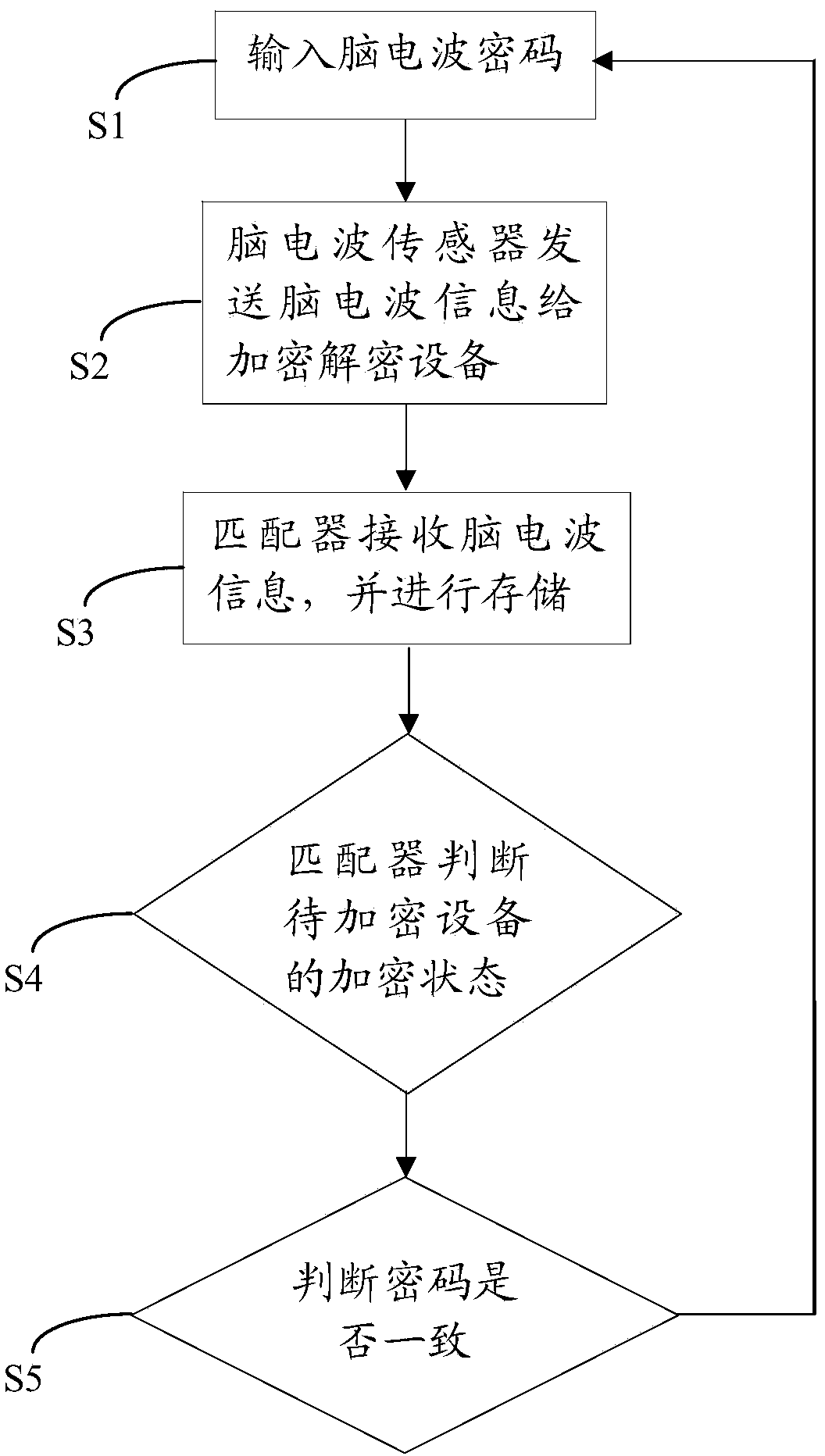
[0043] Such as figure 1 As shown, the combination lock 100 based on the brain-computer exchange technology of the present invention includes: a wearable device 10, the wearable device 10 includes a shell that matches the human head, and when people use the combination lock of the present invention, they need to wear the above-mentioned shell with the head on. Specifically, the above-mentioned casing has a shape similar to an earphone.
[0044]The outer shell is formed with an inner space, and the brainwave sensor 101 and the first encrypted wireless transmitter 102 are arranged in the inner space, and the brainwave sensor 101 and the first encrypted wireless transmitter 102 perform signal transmission. Wherein, the electroencephalogram sensor 101 specifically includes a sensing unit and a signal transmission unit, the above-mentioned sensing unit is used to sense and receive the brain wave information of the human body, and the signal transmission unit is used to transmit the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com